LINKSYS WRT310NV2 Wireless-N Gigabit Router User Manual WRT310N V10 UG C WEB
LINKSYS LLC Wireless-N Gigabit Router WRT310N V10 UG C WEB
LINKSYS >
User manual

USER GUIDE
Wireless-N Gigabit Router
Model: WRT310N

About This Guide
i
Wireless-N Gigabit Router
About
T
h
i
s
G
u
i
de
Icon Descri
p
tions
W
hile reading through the User Guide you may see
various icons that call attention to speci
f
ic items. Below is
a
description o
f
these icons
:
NOTE: Thi
s
c
h
ec
k m
a
rk in
d
i
cates
t
h
at
t
h
e
r
e
i
s
a note of interest and is something that
y
ou
sh
ou
ld
pa
y
specia
l
attention to w
h
i
l
e using t
h
e
p
roduct
.
WARNING: T
h
is exc
l
amation point in
d
icates
that there is a caution or warnin
g
and it is
s
omet
h
ing t
h
at cou
ld
d
amage
y
our propert
y
or
pro
d
uct
.
WEB: T
h
is g
l
o
b
e icon in
d
icates a notewort
hy
w
ebs
i
te
add
r
ess
o
r
e
-m
a
i
l
add
r
ess.
O
n
l
ine Res
ou
rce
s
W
e
b
site a
dd
resses in t
h
is
d
ocument are
l
iste
d
wit
h
out
h
ttp:// in
f
r
o
n
t
of
t
h
e
add
r
ess
because
m
ost
cu
rr
e
n
t
w
eb
b
rowsers do not require it. If you use an older web browser,
y
ou ma
y
h
ave to a
dd
h
ttp:/
/
in front of the web address
.
Resource Website
L
in
k
sys www.
l
in
k
sys.co
m
L
in
k
sys Internationa
l
www.
l
in
k
sys.com/internationa
l
G
l
ossar
y
www.
l
in
k
sys.com/g
l
ossar
y
N
etwor
k
Securit
y
www.
l
in
k
sys.com/securit
y
Copyright and Trademarks
L
in
k
s
y
s is a registere
d
tra
d
emar
k
o
r trademark o
f
Cisco Systems, Inc.
and/or its affiliates in the U.S. and
c
ertain ot
h
er countries. Cop
y
rig
h
t
© 2008 Cisco Systems, Inc. All rights
reserved. Other brands and
p
roduct
names are tra
d
emar
k
s or registere
d
trademarks o
f
their respective
holders.

Table of Contents
ii
Wireless-N Gigabit Router
Chapter 1: Product Overview 4
Front Panel..................................................4
Back Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
Placement Positions ............................................4
Chapter 2: Wireless Security Checklist 6
General Network Security Guidelines .................................6
Additional Security Tips . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Chapter 3: Advanced Conguration 7
Setup > Basic Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Setup > DDNS................................................11
Setup > MAC Address Clone.......................................12
Setup > Advanced Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
Wireless > Basic Wireless Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
Wireless > Wireless Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Wireless > Wireless MAC Filter......................................16
Wireless > Advanced Wireless Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Security > Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
Security > VPN Passthrough.......................................19
Access Restrictions > Internet Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Applications and Gaming > Single Port Forwarding........................21
Applications and Gaming > Port Range Forwarding . . . . . . . . . . . . . . . . . . . . . . .21
Applications & Gaming > Port Range Triggering . . . . . . . . . . . . . . . . . . . . . . . . . .22
Applications and Gaming > DMZ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
Applications and Gaming > QoS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Administration > Management.....................................25
Administration > Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
Administration > Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
Administration > Factory Defaults ...................................27
Administration > Firmware Upgrade . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
Status > Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
Status > Local Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
Status > Wireless Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
Appendix A: Troubleshooting 30
Appendix B: Specications 31
Appendix C: Warranty Information 32
Limited Warranty..............................................32
Exclusions and Limitations........................................32
Obtaining Warranty Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
Technical Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33

Table of Contents
iii
Wireless-N Gigabit Router
Appendix D: Regulatory Information 34
FCC Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34
FCC Radiation Exposure Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34
Safety Notices................................................34
Industry Canada Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34
Avis d’Industrie Canada..........................................35
Wireless Disclaimer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
Avis de non-responsabilité concernant les appareils sans l . . . . . . . . . . . . . . . . . .35
User Information for Consumer Products Covered by EU Directive 2002/96/EC on Waste
Electric and Electronic Equipment (WEEE) ..............................36
Appendix E: Software License Agreement 40
Software in Linksys Products . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Software Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40

Chapter 1 Product Overview
4
Wireless-N Gigabit Router
Ch
apter 1:
P
ro
d
uct Overview
T
hank
y
ou
f
or choosing the Links
y
s Wireless-N Gigabit
Router. The Router lets you access the Internet via a
wireless connection or through one of its four switched
p
orts. You can a
l
so use t
h
e Router to s
h
are resources, suc
h
a
s computers. A variety o
f
security
f
eatures help to protect
your data and your privacy while online. Security features
i
nclude WPA2 securit
y
, a State
f
ul Packet Inspection (SPI)
f
irewall and NAT technology. Con
f
iguring the Router is
easy using the provided browser-based utility
.
Front Panel
1, 2, 3, 4
(
Green/Blue)
T
hese numbered LEDs,
correspon
d
ing wit
h
t
h
e num
b
ere
d
ports on t
h
e
Router’s back panel, serve two purposes. The
LED is solidly lit when the Router is connected
to a device through that port. It
f
lashes to
i
ndicates network activity. Green indicates
Gigabit speeds, and blue indicates 10/100
spee
d
s
.
Wi-Fi Protected Setup Button
If
y
ou have
client devices, such as wireless ada
p
ters, that
support Wi-Fi Protecte
d
Setup, t
h
en
y
ou can
u
se Wi-Fi Protecte
d
Setup to automatica
lly
configure wireless security for your wireless
n
etwor
k
(s).
T
o use Wi-Fi Protected Setup, run the Setup
W
izard, or refer to the “Wireless > Basic Wireless
S
ettings” section of “Chapter 3: Advanced
Con
f
i
g
uration”.
Wi-Fi Protected Setup LED (Blue/Amber
)
I
t
l
ig
h
ts up
bl
ue w
h
en wire
l
ess securit
y
is
e
n
ab
l
ed.
Th
e
LED
f
l
as
h
es
b
l
ue
fo
r
t
w
o
m
inutes durin
g
Wi-Fi Protected Setup.
T
h
e LED
l
i
gh
ts up am
b
er i
f
t
h
e
r
e
i
s
a
n
e
rr
o
r
durin
g
the W
i
-
Fi Protected Setu
p
p
rocess. Make
sure t
h
e c
l
ient
d
evice supports W
i
-
Fi Protecte
d
S
etup. Wait until the LED is o
ff
, and then tr
y
again.
The LED flashes amber when a W
i
-
F
i Protecte
d
S
etup session is active, an
d
a secon
d
session
b
e
g
ins. The Router supports one session at a
time. Wait until the LED is off before starting the
n
ext Wi-Fi Protecte
d
Setup session
.
Wireless
(
B
l
ue
)
Th
e Wire
l
ess LED
l
ig
h
ts up
wh
e
n
t
h
e
wir
e
l
ess
featu
r
e
i
s
e
n
ab
l
ed.
I
f
t
h
e
LED
i
s flashing, the Router is actively sending or
r
eceiving
d
ata over t
h
e networ
k.
Internet
(
B
l
ue
)
T
h
e Internet LED
l
ig
h
ts up
w
h
en t
h
ere is a connection ma
d
e t
h
rou
gh
t
h
e
Internet port. A flashin
g
LED indicates networ
k
a
ctivit
y
over t
h
e Internet port
.
Power (Blue
)
The Power LED li
g
hts up and will
sta
y
on w
h
i
l
e t
h
e Router is powere
d
on. W
h
en
the Router
g
oes throu
g
h its sel
f
-dia
g
nostic
m
ode during every boot-up, this LED will flash.
Wh
en t
h
e
d
iagnostic is comp
l
ete, t
h
e LED wi
ll
b
e so
l
i
dly
l
it
.
B
a
c
k
P
a
ne
l
Internet
T
his Gigabit port is where you will
connect
y
our ca
bl
e or DSL Internet connection.
1, 2, 3, 4
Th
ese Giga
b
it ports (1, 2, 3, 4) connect
the Router to com
p
uters and other Ethernet
n
etwor
k
d
evices on your wire
d
networ
k
.
Reset
Th
ere are two wa
y
s to reset t
h
e Router’s
f
actory de
f
aults. Either press and hold the Reset
Button for approximately five seconds, or restore
the de
f
aults
f
rom Administratio
n
>
F
actor
y
De
f
aults in the Router’s web-based utility.
Power The Power port is where you will
connect t
h
e power a
d
apter
.
Placement Positions
Th
ere are two wa
y
s to p
hy
sica
lly
insta
ll
t
h
e Router. T
h
e
f
irst way is to place the Router horizontally on a surface.
Th
e secon
d
wa
y
is to mount t
h
e Router on a wa
ll.
Horizonta
l
P
l
acement
T
he Router has four rubber feet on its bottom panel. Place
t
h
e
R
oute
r
o
n
a
l
e
v
e
l
su
r
face
n
ea
r
a
n
e
l
ect
ri
ca
l
out
l
et.
Chapter 1 Product Overview
5
Wireless-N Gigabit Router
Wall-Mounting Placement
T
h
e
R
oute
r h
as
t
w
o
w
a
ll-m
ou
n
t
s
l
ots
o
n i
ts
botto
m
p
anel. The distance between the slots is 152 mm
(
6 inc
h
es
)
.
T
w
o
sc
r
e
w
s
a
r
e
n
eeded
to
m
ou
n
t
t
h
e
R
oute
r
.
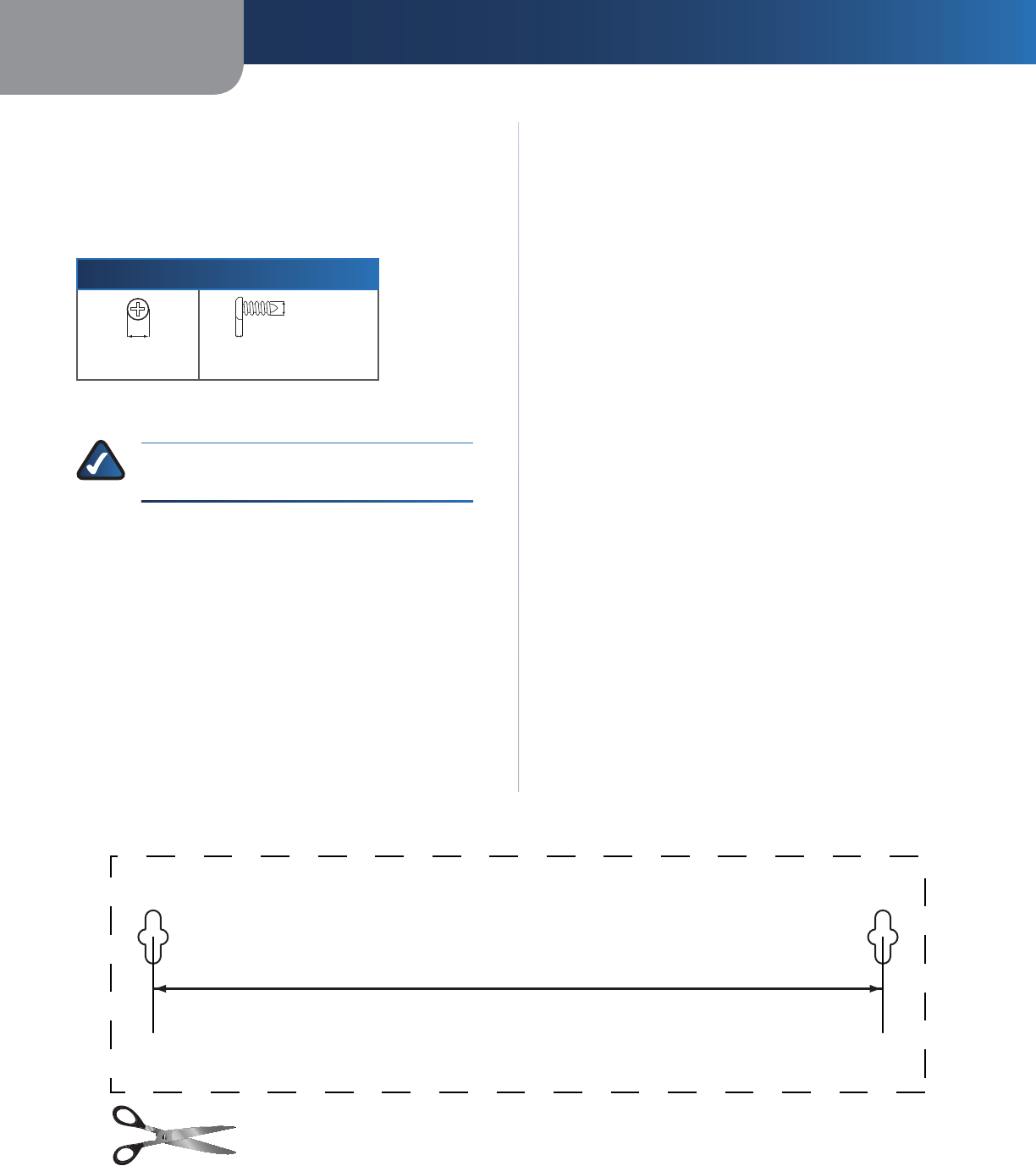
Suggested Mounting Hardware
2
.5-
3
.
0
m
m
4
-
5
mm
1
-
1
.
5
mm
N
ote: Mounting hardware illustrations are not
†
true to sca
l
e.
NOTE:
L
inks
y
s is not responsible
f
or damages
incurred by insecure wall-mounting hardware.
F
ollo
w
these
in
st
r
uct
i
o
n
s:
Determine where you want to mount the Router. Make
1.
s
ure that the wall
y
ou use is smooth, flat, dr
y
, and
s
turd
y
. Also make sure the location is within reach o
f
a
n
e
l
ect
ri
ca
l
out
l
et.
Dri
ll
two
h
o
l
es into t
h
e wa
ll
. Ma
k
e sure t
h
e
h
o
l
es are
2
.
152 mm (6 inc
h
es) apart
.
In
se
r
t
a
sc
r
e
w in
to
eac
h h
o
l
e
a
n
d
l
ea
v
e
3
mm
3.
(
0.12 inches) of its head ex
p
osed
.
Maneuver t
h
e Router so t
h
e wa
ll
-mount s
l
ots
l
ine up
4.
w
i
t
h
t
h
e
t
w
o
sc
r
e
w
s.
P
l
ace t
h
e wa
ll
-mount s
l
ots over t
h
e screws an
d
s
l
i
d
e5.
t
he Router down until the screws
f
it snugl
y
into the
wa
ll-m
ou
n
t
s
l
ots.
152 mm
W
a
ll
Mounting Temp
l
ate
Print t
h
is page at 100% size.
Cut a
l
on
g
t
h
e
d
otte
d
l
ine, an
d
p
l
ace on t
h
e wa
ll
to
d
ri
ll
precise spacin
g.

Chapter 2 Wireless Security Checklist
6
Wireless-N Gigabit Router
Ch
apter 2:
Wire
l
ess Securit
y
C
h
ec
kl
is
t
W
ire
l
ess networ
k
s are convenient an
d
eas
y
to insta
ll
, so
homes with hi
g
h-speed Internet access are adoptin
g
them
a
t a rapid pace. Because wireless networking operates by
sending in
f
ormation over radio waves, it can be more
v
u
ln
e
r
ab
l
e
to
in
t
r
ude
r
s
t
h
a
n
a
t
r
ad
i
t
i
o
n
a
l wir
ed
n
et
w
o
rk
.
Like signals from your cellular or cordless phones, signals
f
rom
y
our wireless network can also be intercepted. Since
you cannot physically prevent someone
f
rom connecting
to your wireless network, you need to take some additional
steps to
k
eep
y
our networ
k
secure.
1. Change the default wireless
network name or SSID
W
ireless devices have a default wireless network name
or Service Set Identi
f
ier (SSID) set b
y
the
f
actor
y
. This
i
s the name o
f
your wireless network, and can be up
to 32 characters in length. Linksys wireless products
use
l
in
k
s
y
s as the de
f
ault wireless network name. You
should chan
g
e the wireless network name to somethin
g
u
nique to distinguish your wireless network from other
wire
l
ess networ
k
s t
h
at ma
y
exist aroun
d
y
ou,
b
ut
d
o not
u
se personal in
f
ormation (such as your Social Security
n
umber) because this information may be available for
a
n
y
one to see when browsing
f
or wireless networks.
2. Change the default password
For wire
l
ess pro
d
ucts suc
h
as access points an
d
routers,
you will be asked
f
or a password when you want to change
their settings. These devices have a default password set
by
the
f
actor
y
. The Links
y
s de
f
ault password is a
d
mi
n
.
Hackers know these de
f
aults and may try to use them
to access your wireless device and change your networ
k
settings. To t
h
wart an
y
unaut
h
orize
d
c
h
anges, customize
the device’s password so it will be hard to
g
uess
.
3. Enable MAC address filtering
Linksys routers give you the ability to enable Media Access
Control (MAC) address filtering. The MAC address is a
u
nique series o
f
numbers and letters assigned to ever
y
n
etworkin
g
device. With MAC address
f
ilterin
g
enabled,
wireless network access is provided solely for wireless
devices with speci
f
ic MAC addresses. For example,
y
ou can
speci
f
y the MAC address o
f
each computer in your home
so that only those computers can access your wireless
n
etwor
k
.
4. Enable encryption
Encr
y
ption protects
d
ata transmitte
d
over a wire
l
ess
n
etwork. Wi-Fi Protected Access
(
WPA/WPA2
)
and Wired
Equivalency Privacy (WEP) offer different levels of security
f
or wireless communication
.
A
network encrypted with WPA/WPA2 is more secure
than a network encrypted with WEP, because WPA/WPA2
u
ses d
y
namic ke
y
encr
y
ption. To protect the in
f
ormation
a
s it passes over the airwaves, you should enable the
highest level of encryption supported by your networ
k
equ
i
pment.
W
EP is an older encryption standard and may be the
only option available on some older devices that do not
support WPA.
Genera
l
Networ
k
Securit
y
Gui
d
e
l
ine
s
W
ireless network security is useless if the underlying
n
etwor
k
is not secure.
Password protect all computers on the network and
s
i
ndividually password protect sensitive files
.
C
h
ange passwor
d
s on a regu
l
ar
b
asis
.
s
Install anti-virus so
f
tware and personal
f
irewall
s
software.
Disable
f
ile sharing (peer-to-peer). Some applications
s
m
ay open
f
ile sharing without your consent and/or
knowledge.
Additional Security Tip
s
Keep wireless routers, access points, or gateways away
s
f
rom exterior walls and windows
.
T
urn wire
l
ess routers, access points, or gatewa
y
s
s
o
ff
when they are not being used (at night, during
vacations)
.
Use strong passp
h
rases t
h
at are at
l
east eig
h
t c
h
aracters
s
i
n len
g
th. Combine letters and numbers to avoid usin
g
standard words that can be found in the dictionary.
WEB: F
o
r m
o
r
e
in
fo
rm
at
i
o
n
o
n wir
e
l
ess
s
ecurity, visit www.linksys.com/securit
y
Chapter 3 Advanced Configuration
7
Wireless-N Gigabit Router
Ch
apter 3:
A
dvanced Configuration
Af
ter setting up the Router with the Setup Wizard (located
on the CD-ROM), the Router will be ready
f
or use. However,
i
f you’d like to change its advanced settings, use the
Router’s we
b
-
b
ase
d
uti
l
it
y
. T
h
is c
h
apter
d
escri
b
es eac
h
web page o
f
the utility and each page’s key
f
unctions. You
can access the utility via a web browser on a computer
connecte
d
to t
h
e Router
.
T
he web-based utility has these main tabs: Setup,
W
ireless, Security, Access Restrictions, Applications &
Gaming, A
d
ministration, an
d
Status. A
dd
itiona
l
ta
b
s wi
ll
b
e available a
f
ter you click one o
f
the main tabs
.
NOTE: When first installing the Router, you
s
h
ou
ld
use t
h
e Setup Wizar
d
on t
h
e Setup
CD-ROM. I
f
y
ou want to con
f
igure advanced
settin
g
s, use this chapter to learn about the
we
b
-
b
ase
d
uti
l
it
y.
How to Access t
h
e We
b
-Base
d
Uti
l
it
y
T
o access the web-based utility, launch the web browser on
y
our computer, and enter the Router’s default IP address,
192
.
1
68.
1
.1
,
in the A
dd
r
ess
f
ield. Then, press
E
n
te
r
.
A
lo
g
in screen will appear. (Non-Windows XP users will
see a simi
l
ar screen.
)
Leave t
h
e
U
ser name field blank. The
f
irst time
y
ou open the Web-based utilit
y
, use the de
f
ault
p
assword
ad
mi
n
.
(You can set a new
p
assword from the
Ad
ministration ta
b
’s
Management
screen.) Click
t
OK
t
o
K
co
n
ti
n
ue.
L
o
g
in
S
creen
S
etu
p
> Basic Setu
p
T
he first screen that a
pp
ears is the
B
asic Setu
p
screen. This
all
ows
y
ou to c
h
ange t
h
e Router’s genera
l
settings.
S
etu
p
> Basic
S
etu
p
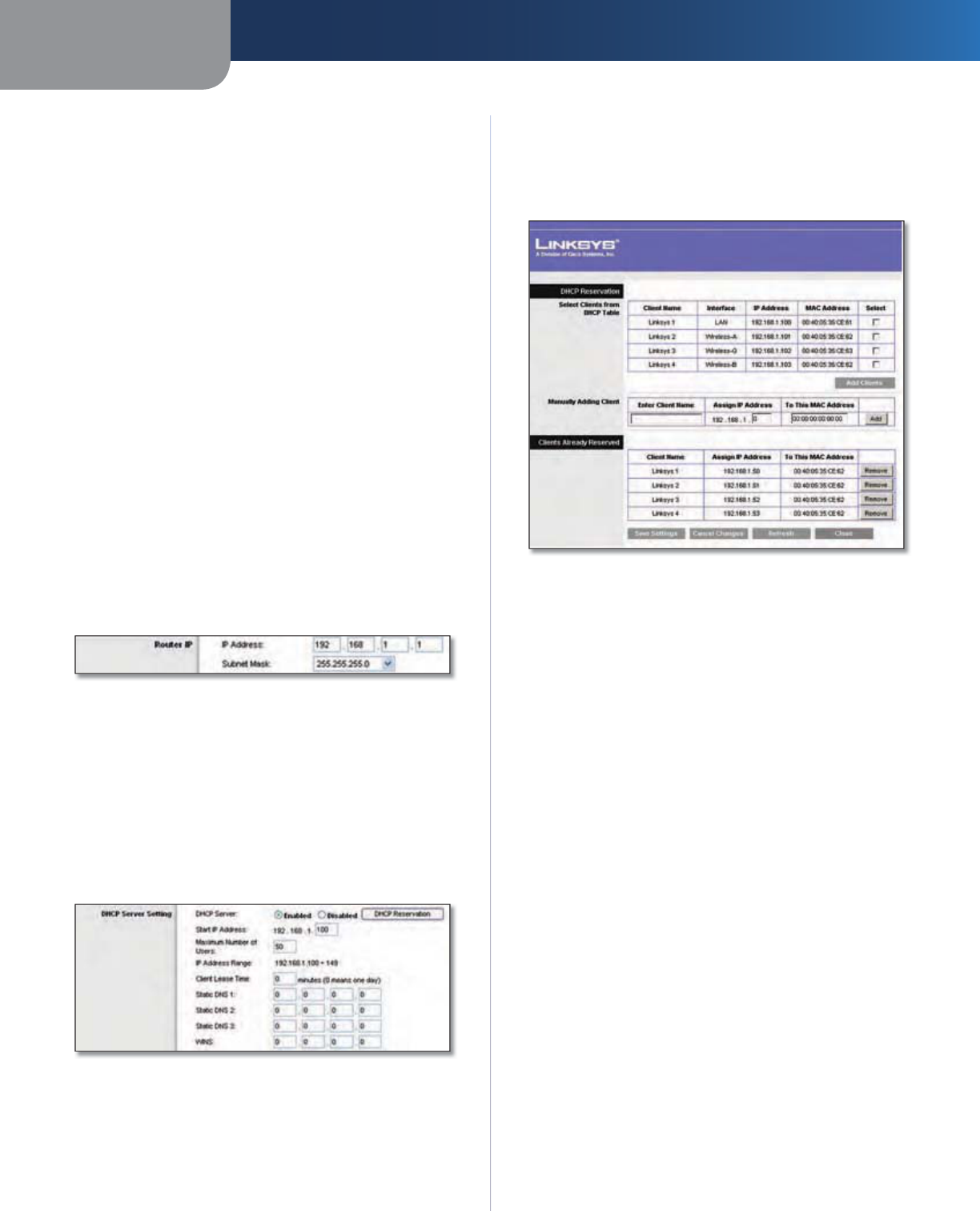
Internet Setu
p
T
he Internet Setup section configures the Router to your
Internet connection. Most o
f
this in
f
ormation can be
obtained through your ISP
.
I
nternet Connection T
y
p
e
S
elect the t
y
pe of Internet connection
y
our ISP provides
f
rom the drop-down menu. These are the available t
y
pes
:
A
utomatic Confi
g
uration - DHC
P
s
S
tatic IP
s
PPPo
E
s
PPTP
s
L2TP
s
T
e
l
stra Ca
ble
s
Automatic Con
f
iguration - DHC
P
B
y
de
f
ault, the Router’s Internet Connection T
y
pe is set
to
A
utomatic Confi
g
uration - DHC
P
, which should be
kept onl
y
if
y
our ISP supports DHCP or
y
ou are connecting
t
h
roug
h
a
dy
namic IP a
dd
ress. (T
h
is option usua
lly
app
l
ies
to cable connections.
)
I
nternet Connection Type > Automatic Configuration - DHC
P

Chapter 3 Advanced Configuration
8
Wireless-N Gigabit Router
S
t
a
tic I
P
I
f
you are required to use a permanent IP address to
connect to the Internet
,
select Static I
P
.
I
nternet
C
onnection T
y
pe >
S
tatic I
P
Internet IP Address This is the Router’s IP address, when
seen from the Internet. Your ISP will provide
y
ou with the
IP Address
y
ou need to speci
fy
here
.
Subnet Mask This is the Router’s Subnet Mask, as seen
by
users on t
h
e Internet (inc
l
u
d
ing
y
our ISP). Your ISP wi
ll
p
rovi
d
e
y
ou wit
h
t
h
e Su
b
net Mas
k.
Default Gateway Your ISP will provide you with the IP
a
ddress of the ISP server
.
DNS 1-3
Y
our ISP wi
ll
provi
d
e
y
ou wit
h
at
l
east one DNS
(Domain Name System) server IP address.
PPPoE
S
ome DSL-based ISPs use PPPoE (Point-to-Point Protocol
over Ethernet) to establish Internet connections. If
y
ou are
connecte
d
to t
h
e Internet t
h
rou
gh
a DSL
l
ine, c
h
ec
k
wit
h
your ISP to see if they use PPPoE. If they do, you will have
to ena
bl
e
P
PPo
E
.
Internet
C
onnection Type > PPPo
E
Username and Password
E
nter t
h
e Username an
d
Password provided by your ISP
.
Service Name If provided by your ISP, enter the Service
N
ame.
Connect on Demand: Max Idle Time You can confi
g
ure
the Router to cut the Internet connection after it has been
i
nactive
f
or a speci
f
ied period o
f
time (Max Idle Time). I
f
your Internet connection has been terminated due to
i
nactivit
y
, Connect on Deman
d
ena
bl
es t
h
e Router to
a
utomatica
lly
re-esta
bl
is
h
y
our connection as soon as
y
ou
a
ttempt to access the Internet a
g
ain. To use this option,
se
l
ect
C
onnect on Deman
d
. In t
h
e
M
ax I
dl
e Tim
e
field
,
enter the number o
f
minutes
y
ou want to have elapsed
b
efore your Internet connection terminates. The default
Max I
dl
e Time is 1
5
m
i
nutes
.
Keep Alive: Redial Period
If
you select this option,
t
he Router will periodically check your Internet
connection. I
f
y
ou are disconnected, then the Router
w
ill automatically re-establish your connection. To use
t
his o
p
tion, select
K
ee
p
Aliv
e
. In the Redial Perio
d
field,
d
y
ou speci
fy
how o
f
ten
y
ou want the Router to chec
k
t
h
e
In
te
rn
et
co
nn
ect
i
o
n
.
Th
e
defau
l
t
R
ed
i
a
l P
e
ri
od
i
s
30
seconds.
PP
T
P
Point-to-Point Tunneling Protocol (PPTP) is a service that
a
pp
l
ies to connections in Europe on
ly.
Internet
C
onnection Type > PPT
P
I
f
y
our ISP supports DHCP or
y
ou are connecting through
a
dynamic IP address, then select
Obta
in
a
n IP A
dd
r
ess
A
utomatica
lly
. If
y
ou are required to use a permanent IP
add
ress to connect to t
h
e Internet, t
h
en se
l
ect Speci
fy
an
IP A
dd
r
ess
.
Then confi
g
ure the followin
g:
Specify an IP Address
s
Th
is is t
h
e Router’s IP a
dd
ress
,
a
s seen
f
rom the Internet. Your ISP will provide
y
ou
w
ith the IP Address you need to specify here
.
Subnet Mask
s
T
h
is is t
h
e Router’s Su
b
net Mas
k,
as
seen b
y
users on the Internet (including
y
our ISP). Your
I
SP will provide you with the Subnet Mask
.
Default Gateway
s
Y
our ISP wi
ll
provi
d
e
y
ou wit
h
t
h
e
I
P
add
r
ess
of
t
h
e
I
S
P
se
rv
e
r
.
DNS 1-3
s
Your ISP will provide you with at least one
DNS (Domain Name S
y
stem) server IP a
dd
ress
.
PPTP Server IP Address
Y
our ISP will provide
y
ou with
t
h
e
IP
add
r
ess
o
f
t
h
e
PPTP
se
rv
e
r
.
Username and Password
E
nter t
h
e Username an
d
Password provided b
y
y
our ISP
.
Connect on Demand: Max Idle Time You can confi
g
ure
t
he Router to cut the Internet connection after it has been
i
nactive
f
or a speci
f
ied period o
f
time (Max Idle Time). I
f
y
our Internet connection has been terminated due to

Chapter 3 Advanced Configuration
9
Wireless-N Gigabit Router
i
nactivity, Connect on Demand enables the Router to
a
utomatica
lly
re-esta
bl
is
h
y
our connection as soon as
y
ou
a
ttempt to access the Internet a
g
ain. To use this option,
select
C
onnect on Deman
d
. In the
M
ax Idle Tim
e
field,
enter the number o
f
minutes
y
ou want to have elapsed
b
e
f
ore your Internet connection terminates. The de
f
ault
Max Idle Time is 1
5
minutes
.
Keep Alive: Redial Period
If
y
ou select this option, the
Router will periodically check your Internet connection. I
f
y
ou are disconnected, then the Router will automatically
r
e-esta
bl
is
h
y
our connection. To use t
h
is option, se
l
ect
Keep Aliv
e
.
In
t
h
e
Red
i
a
l P
e
ri
od
field, you specify how often
d
y
ou want the Router to check the Internet connection. The
de
f
ault value is 3
0
secon
d
s
.
L2TP
L2TP is a service t
h
at app
l
ies to connections in Israe
l
on
ly.
Internet Connection Type > L2TP
Server IP Address This is the IP address of the L2TP
S
erver. Your ISP wi
ll
provi
d
e
y
ou wit
h
t
h
e IP A
dd
ress
y
ou
n
eed to specify here
.
Username and Password
E
nter t
h
e Username an
d
Passwor
d
provi
d
e
d
by
y
our ISP
.
Connect on Demand: Max Idle Time You can confi
g
ure
the Router to cut the Internet connection after it has been
i
nactive
f
or a speci
f
ied period o
f
time (Max Idle Time). I
f
your Internet connection has been terminated due to
i
nactivit
y
, Connect on Deman
d
ena
bl
es t
h
e Router to
a
utomatica
lly
re-esta
bl
is
h
y
our connection as soon as
y
ou
a
ttempt to access the Internet a
g
ain. To use this option,
se
l
ect
C
onnect on Deman
d
. In t
h
e
M
ax I
dl
e Tim
e
field
,
enter the number o
f
minutes
y
ou want to have elapsed
b
efore your Internet connection terminates. The default
Max I
dl
e Time is 1
5
m
i
nutes
.
Keep Alive: Redial Period
If
y
ou select this option,
t
he Router will periodically check your Internet
connection. If
y
ou are disconnected, then the Router
w
i
ll
automatica
lly
re-esta
bl
is
h
y
our connection. To use
t
his o
p
tion, select
K
ee
p
Aliv
e
.
In
t
h
e
R
ed
i
a
l P
e
ri
od
field,
d
y
ou specif
y
how often
y
ou want the Router to chec
k
t
h
e
In
te
rn
et
co
nn
ect
i
o
n
.
Th
e
defau
l
t
R
ed
i
a
l P
e
ri
od
i
s
30
seco
n
ds.
T
e
l
str
a
C
able
T
elstra Cable is a service that a
pp
lies to connections in
A
ustralia only
.
I
nternet Connection Type > Telstra Cable
Server IP Address This is the IP address of the Heartbeat
S
erver. Your ISP wi
ll
provi
d
e
y
ou wit
h
t
h
e IP A
dd
ress
y
ou
n
eed to specify here
.
Username and Password
E
nter t
h
e Username an
d
Passwor
d
provi
d
e
d
by
y
our ISP
.
Connect on Demand: Max Idle Time You can confi
g
ure
the Router to cut the Internet connection after it has been
i
nactive
f
or a speci
f
ied period o
f
time (Max Idle Time). I
f
your Internet connection has been terminated due to
i
nactivit
y
, Connect on Deman
d
ena
bl
es t
h
e Router to
a
utomatica
lly
re-esta
bl
is
h
y
our connection as soon as
y
ou
a
ttempt to access the Internet a
g
ain. To use this option,
se
l
ect
C
onnect on Deman
d
. In t
h
e
M
ax I
dl
e Tim
e
field
,
enter the number o
f
minutes
y
ou want to have elapsed
b
efore your Internet connection terminates. The default
Max I
dl
e Time is 1
5
m
i
nutes
.
Keep Alive: Redial Period
If
y
ou select this option,
t
he Router will periodically check your Internet
connection. If
y
ou are disconnected, then the Router
w
i
ll
automatica
lly
re-esta
bl
is
h
y
our connection. To use
t
his o
p
tion, select
K
ee
p
Aliv
e
.
In
t
h
e
R
ed
i
a
l P
e
ri
od
field,
d
y
ou specif
y
how often
y
ou want the Router to chec
k
t
h
e
In
te
rn
et
co
nn
ect
i
o
n
.
Th
e
defau
l
t
R
ed
i
a
l P
e
ri
od
i
s
30
seco
n
ds.
Optiona
l
Setting
s
S
ome of these settings ma
y
be required b
y
y
our ISP. Verif
y
with
y
our ISP be
f
ore making an
y
changes
.
Optional Setting
s
Host Name and Domain Name These fields allow
y
ou to
suppl
y
a host and domain name
f
or the Router. Some ISPs,
u
sually cable ISPs, require these names as identification.
You ma
y
have to check with
y
our ISP to see if
y
our
b
roadband Internet service has been con
f
i
g
ured with a
Chapter 3 Advanced Configuration
10
Wireless-N Gigabit Router
host and domain name. In most cases, leaving these fields
bl
an
k
wi
ll
wor
k
.
MTU MTU is the Maximum Transmission Unit. It speci
f
ies
the largest packet size permitted for Internet transmission.
S
elect Manual i
f
y
ou want to manuall
y
enter the largest
p
acket size that is transmitted. To have the Router select
the best MTU for your Internet connection, keep the
de
f
ault setting,
A
uto
.
Size
W
h
e
n M
a
n
ua
l i
s
se
l
ected
in
t
h
e
MT
U
field, this option
U
i
s enabled. Leave this value in the 1200 to 1500 range. The
de
f
ault size depends on the Internet Connection T
y
pe
:
DHCP, Static IP, or Telstra:
s
1500
PPP
oE:
s
14
92
PPTP or L2TP:
s
146
0
Networ
k
Setup
Th
e Networ
k
Setup section c
h
anges t
h
e settings on t
h
e
n
etwork connected to the Router’s Ethernet ports. Wireless
setup is performed through the Wireless tab
.
R
outer I
P
Th
is presents
b
ot
h
t
h
e Router’s IP A
dd
ress an
d
Su
b
net
Mask as seen by your network
.
R
oute
r IP
D
H
C
P
S
erver
S
ettin
g
T
he settings allow
y
ou to con
f
igure the Router’s D
y
namic
Host Confi
g
uration Protocol (DHCP) server function. The
Router can be used as a DHCP server for
y
our network. A
DHCP server automaticall
y
assigns an IP address to each
computer on your network. If you choose to enable the
Router’s DHCP server option, ma
k
e sure t
h
ere is no ot
h
er
DHCP server on
y
our network.
DH
C
P
S
erver
S
ettin
g
DHCP Server
D
HCP is enabled by factory default. If you
al
rea
d
y
h
ave a DHCP server on your networ
k
, or you
d
on’t
want a DHCP server
,
t
h
en se
l
ect
D
isa
bl
e
d
(
no ot
h
er DHCP
f
eatures will be available)
.
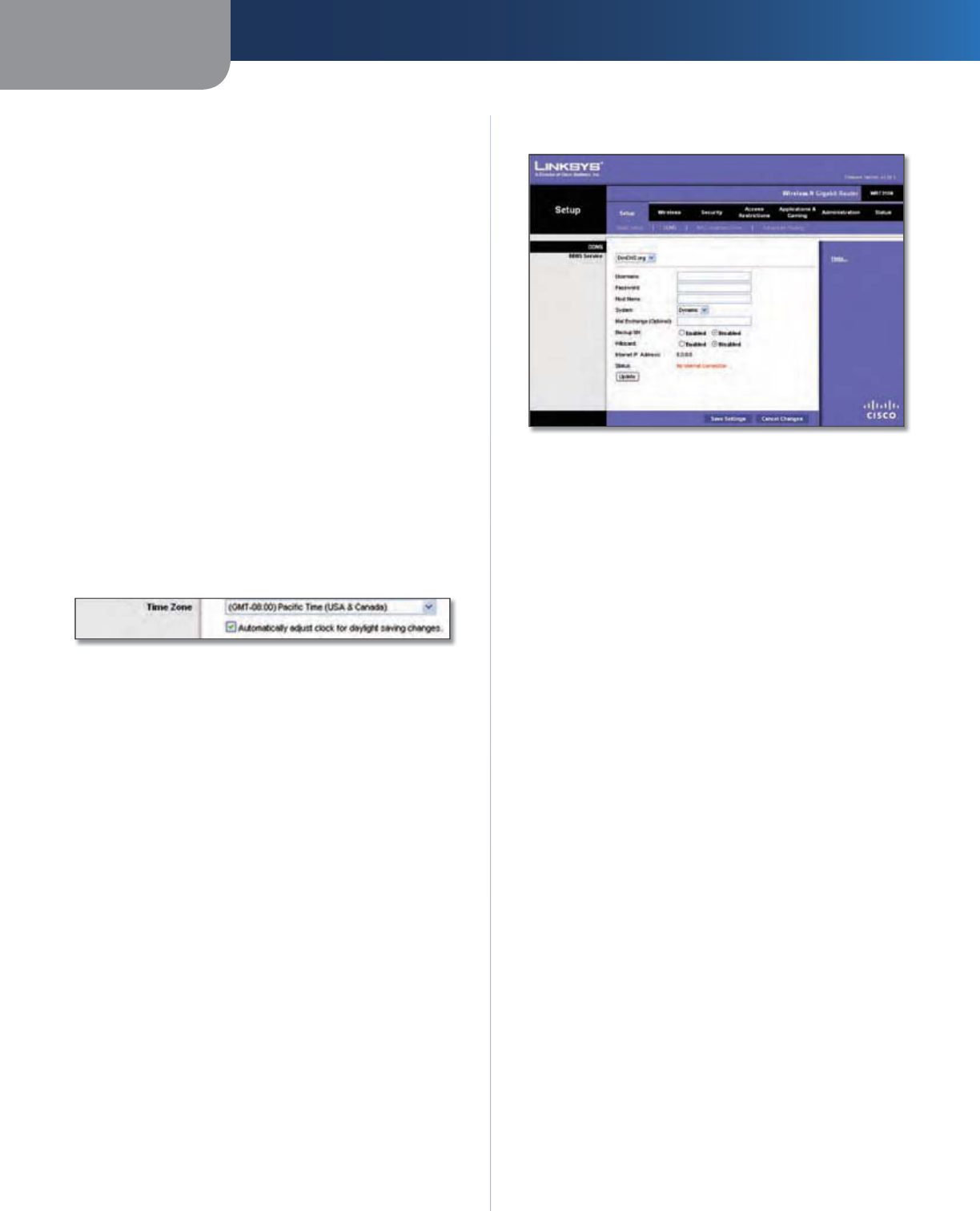
DHCP Reservation Click this button if you want to assign
a
f
ixed local IP address to a MAC address.
DH
C
P Reserv
a
ti
o
n
You will see a list o
f
DHCP clients with the
f
ollowin
g
i
nformation: Client Name
,
Interface
,
IP Address
,
and
MAC A
dd
ress.
DH
C
P R
ese
rv
at
i
o
n
Select Clients from DHCP Table
s
C
li
c
k
t
h
e
Se
l
ect
c
h
ec
k
bo
x
to
r
ese
rv
e
a
c
li
e
n
t
’
s
IP
add
r
ess.
Th
e
n
c
li
ck
Add
C
l
ients
.
Manually Adding Client
s
To manuall
y
assign an IP
a
ddress, enter the client’s name in the En
te
r
C
li
e
n
t
N
ame field. Enter the IP address
y
ou want it to have in
t
h
e
Assi
g
n IP Addres
s
f
i
e
l
d.
En
te
r i
ts
MA
C
add
r
ess
in
t
h
e
T
o
Thi
s
MA
C
A
dd
r
ess
fi
e
l
d.
Th
e
n
c
li
ck
Add
.
Clients Alread
y
Reserve
d
A
li
st
o
f DH
C
P
c
li
e
n
ts
a
n
d
t
h
e
ir fix
ed
l
oca
l IP
add
r
esses
will be displa
y
ed at the bottom of the screen. If
y
ou
want to remove a client
f
rom this list, clic
k
Re
m
o
v
e
.
C
li
c
kSave Settin
gs
to apply your changes, or clic
k
C
ance
l
C
h
anges to cance
l
y
our c
h
anges. To view t
h
e
m
ost up-to-date in
f
ormation, clic
k
Ref
r
esh
.
T
o
e
xi
t
t
hi
s
screen, click
C
l
ose
.
Start IP Address
E
nter a value for the DHCP server to
sta
r
t
wi
t
h wh
e
n i
s
suin
g
IP addresses. Because the Router’s
d
efault IP address is 192.168.1.1, the Start IP Address must
b
e 192.168.1.2 or greater,
b
ut sma
ll
er t
h
an 192.168.1.253.
The de
f
ault Startin
g
IP Address is
1
92
.
1
68.
1
.
1
00
.
Maximum Number of Users
E
n
te
r
t
h
e
m
a
xim
u
m
n
umber of PCs that
y
ou want the DHCP server to assign
I
P addresses to. This number cannot be
g
reater than 253.
Th
e
de
f
au
l
t
i
s
50
.
IP Address Range
D
ispla
y
ed here is the range of available
I
P
add
r
esses.
Chapter 3 Advanced Configuration
11
Wireless-N Gigabit Router
Client Lease Time
T
he Client Lease Time is the amount
o
f
time a network user will be allowed connection to the
Router with their current dynamic IP address. Enter the
a
mount of time, in minutes, that the user will be “leased
”
this d
y
namic IP address. A
f
ter the time is up, the user will
b
e automatically assigned a new dynamic IP address. The
default is
0
minutes, which means one day
.
Static DNS 1-3
T
h
e Domain Name S
y
stem (DNS) is
h
ow
t
h
e
In
te
rn
et
t
r
a
n
s
l
ates
do
m
a
in
o
r w
ebs
i
te
n
a
m
es
in
to
I
nternet addresses or URLs. Your ISP will provide you with at
l
east one DNS Server IP Address. I
f
y
ou wish to use another,
e
nter that IP Address in one o
f
these
f
ields. You can enter up
t
o three DNS Server IP Addresses here. The Router will use
t
hese
f
or quicker access to
f
unctioning DNS servers
.
WINS The Windows Internet Namin
g
Service (WINS)
m
anages each PC’s interaction with the Internet. If you
u
se a WINS server
,
enter t
h
at server’s IP A
dd
ress
h
ere.
O
therwise, leave this blank.
Time Setting
Time Zone
S
elect the time zone in which your networ
k
f
unctions
f
rom this drop-down menu. (You can even
a
utomatically adjust
f
or daylight saving time.
)
Time
S
etting
C
li
c
k
S
ave Settin
gs
to apply your changes, or clic
k
Ca
n
ce
l
Ch
ange
s
to cance
l
y
our c
h
anges
.
S
etu
p
> DDN
S
T
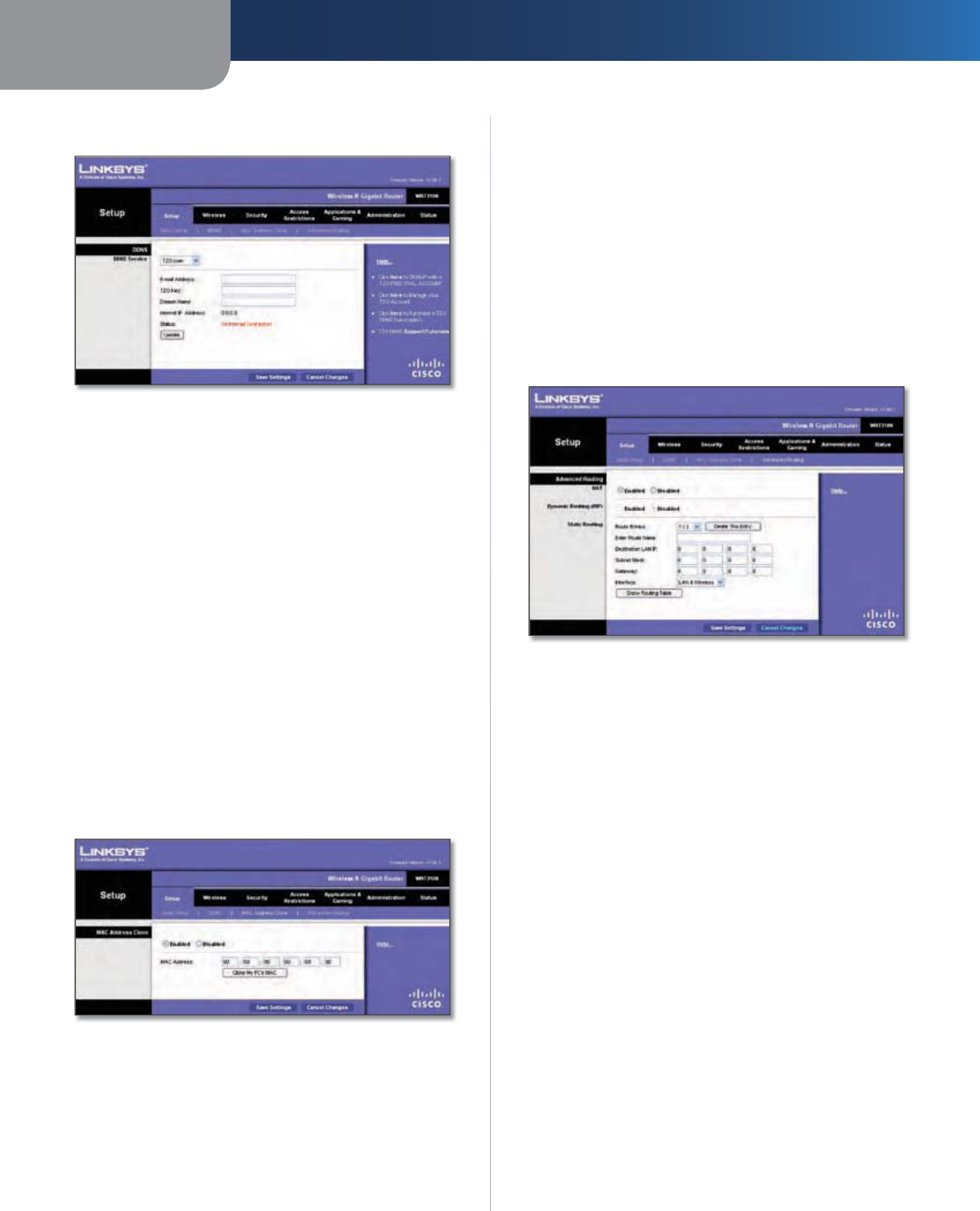
he Router offers a Dynamic Domain Name System (DDNS)
f
eature. DDNS lets
y
ou assign a fixed host and domain
n
ame to a d
y
namic Internet IP address. It is use
f
ul when
you are hosting your own website, FTP server, or other
server
b
e
h
in
d
t
h
e Router.
Be
f
ore
y
ou can use this
f
eature,
y
ou need to sign
up
for DDNS service with a DDNS service
p
rovider,
www.d
y
ndns.org or www.TZO.com. If
y
ou do not want to
u
se this
f
eature, keep the de
f
ault settin
g
,
D
i
sab
l
ed
.
DDN
S
D
DN
S
S
ervice
I
f
y
our DDNS service is provided b
y
D
y
nDNS.org, then
se
l
ect
D
ynDNS.or
g
from the drop-down menu. If your
DDNS service is provi
d
e
d
by
TZO, t
h
en se
l
ect TZO.co
m
.
T
h
e
featu
r
es
a
v
a
il
ab
l
e
o
n
t
h
e
DDN
S
screen will var
y
,
depending on which DDNS service provider you use.
D
y
nDN
S
.or
g
Setup > DDNS > DynDN
S
Username Enter the Username for
y
our DDNS account
.
Password Enter the Password
f
or
y
our DDNS account
.
Host Name
T
he is the DDNS URL assigned by the DDNS
serv
i
ce.
System
S
elect the D
y
nDNS service
y
ou use:
Dy
nam
i
c
,
Stat
i
c
, or
Custo
m
.
Th
e
de
f
au
l
t
se
l
ect
i
o
n i
s
D
ynami
c
.
Mail Exchange (Optional)
E
nter the address of
y
our mail
exchange server, so e-mails to
y
our D
y
nDNS address go to
your mail server.
Backup MX This feature allows the mail exchange server
to be a backup. To disable this
f
eature, keep the de
f
ault,
Di
sab
l
ed
.
To enable the feature, select En
ab
l
ed
.
If you
a
re not sure which setting to select, keep the default,
Di
sab
l
ed
.
Wildcard This settin
g
enables or disables wildcards
f
or
y
our host. For example, if
y
our DDNS address is
myplace.dyndns.or
g
and
y
ou enable wildcards, then
x
.myplace.dyndns.or
g
will work as well (x is the wildcard).
T
o disable wildcards, keep the default,
D
isa
bl
e
d
. To ena
bl
e
wildcards, select En
ab
l
ed
.
I
f
y
ou are not sure which setting
to select, kee
p
the default, Di
sab
l
ed
.
Internet IP Address T
h
e Router’s Internet IP a
dd
ress is
d
isp
l
a
y
e
d
h
ere. Because it is
dy
namic, it wi
ll
c
h
ange
.
Status Th
e
status
o
f
t
h
e
DDN
S
se
rvi
ce
co
nn
ect
i
o
n i
s
d
isp
l
a
y
e
d
h
ere.
Update
T
o manuall
y
trigger an update, click this button
.
C
li
c
k
S
ave Settin
gs
to apply your changes, or clic
k
Ca
n
ce
l
Ch
ange
s
to cance
l
y
our c
h
anges
.
Chapter 3 Advanced Configuration
12
Wireless-N Gigabit Router
T
ZO.co
m
Setu
p
> DDNS > TZO
E-mail Address, TZO Key, and Domain Name Enter the
settings o
f
the account
y
ou set up with TZO
.
Internet IP Address Th
e
R
oute
r’
s
In
te
rn
et
IP
add
r
ess
i
s
displayed here. Because it is dynamic, it will change
.
Status The status o
f
the DDNS service connection is
displayed here.
Update
T
o manually trigger an update, click this button
.
C
l
ic
k
S
ave Sett
i
ng
s
to app
ly
y
our c
h
anges, or c
l
ic
k
C
ance
l
C
han
g
e
s
to cancel your changes
.
S
etup > MAC Address Clone
A
MAC a
dd
ress is a 12-
d
igit co
d
e assigne
d
to a unique
p
iece o
f
hardware
f
or identi
f
ication. Some ISPs will require
you to register a MAC address in order to access the
Internet. I
f
y
ou do not wish to re-register the MAC address
with your ISP, you may assign the MAC address you have
currently registered with your ISP to the Router with the
MAC Address Clone
f
eature
.
S
etup > MAC Address Clone
MAC A
dd
ress C
l
on
e
Enabled/Disabled To
h
ave t
h
e MAC A
dd
ress c
l
one
d,
se
l
ect
En
ab
l
ed
.
MAC Address
E
nter the MAC Address re
g
istered with
y
our ISP
h
ere
.
Clone My PC’s MAC
Cl
i
ck
th
i
s
butto
n
to
clo
n
e
the
MA
C
a
ddress of the computer you are using
.
C
l
ic
k
S
ave Sett
i
ng
s
to app
ly
y
our c
h
anges, or c
l
ic
k
Cance
l
Ch
an
g
e
s
to cance
l
y
our c
h
anges
.
S
etup > Advanced Routin
g
Th
is screen is use
d
to set up t
h
e Router’s a
d
vance
d
f
unctions. Operating Mode allows
y
ou to select the
type(s) of advanced functions you use. Dynamic Routing
a
utomatica
lly
a
d
justs
h
ow pac
k
ets trave
l
on
y
our networ
k
.
S
tatic Routin
g
sets up a
f
ixed route to another networ
k
dest
in
at
i
o
n
.
S
etup > A
d
vance
d
Routing
Advanced Routin
g
NAT
Enabled/Disabled
If
this Router is hosting
y
our network’s
connection to the Internet, kee
p
the de
f
ault,
E
n
ab
l
ed
.
I
f
a
not
h
er router exists on
y
our networ
k
, se
l
ect Disa
bl
e
d
.
Wh
en t
h
e NAT setting is
d
isa
bl
e
d
,
dy
namic routing wi
ll
b
e
e
n
ab
l
ed.
Dy
namic Routing (RIP
)
Enabled/Disabled This feature enables the Router to
a
utomatica
lly
a
d
just to p
hy
sica
l
c
h
anges in t
h
e networ
k
’s
layout and exchange routing tables with the other router(s).
Th
e Router
d
etermines t
h
e networ
k
p
ac
k
ets’ route
b
ase
d
on the
f
ewest number o
f
hops between the source and
the destination. When the NAT settin
g
is enabled, the
D
y
namic Routing feature is automaticall
y
disabled. When
the NAT settin
g
is disabled, this
f
eature is available. Select
En
ab
l
ed
to use the Dynamic Routing feature
.
S
tatic Routing
A
static route is a pre-
d
etermine
d
pat
h
way t
h
at networ
k
i
n
f
ormation must travel to reach a speci
f
ic host or network.
Enter the information described below to set u
p
a new
static route.
Chapter 3 Advanced Configuration
13
Wireless-N Gigabit Router
Route Entries
T
o set u
p
a static route between the Router
a
nd another network, select a number
f
rom the drop
-
do
wn li
st.
C
li
c
k Delete This Entry
to
de
l
ete
a
stat
i
c
r
oute.
Enter Route Name Enter a name for the Route here,
u
sing a maximum o
f
25 alphanumeric characters
.
Destination LAN IP
T
h
e
D
est
in
at
i
o
n LAN IP i
s
t
h
e
add
r
ess
of the remote network or host to which you want to assign
a
stat
i
c route
.
Subnet Mask Th
e
Sub
n
et
M
as
k
dete
rmin
es
whi
c
h
p
ortion of a Destination LAN IP address is the networ
k
p
ortion, an
d
w
h
ic
h
portion is t
h
e
h
ost portion.
Gateway This is the IP address o
f
the gateway device that
a
llows for contact between the Router and the remote
n
etwor
k
or
h
ost
.
Interface This inter
f
ace tells you whether the Destination
IP Address is on the LAN & Wireles
s
(Ethernet and wireless
n
etwor
k
s
)
or t
h
e
WAN
(
Internet
)
.
C
li
c
k
S
how Routin
g
Tabl
e
to view the static routes you
have already set up
.
A
dvanced Routin
g
> Routin
g
Table
Routing Table
For eac
h
route
,
t
h
e Destination LAN IP a
dd
ress
,
Su
b
net
Mask, Gatewa
y
, and Inter
f
ace are displa
y
ed. Clic
k
R
e
fr
esh
to u
p
date the information. Clic
k
C
l
ose
to
e
xi
t
t
h
is screen
.
C
li
c
k
S
ave Sett
i
n
gs
to appl
y
y
our changes, or clic
k
Ca
n
ce
l
C
han
g
e
s
to cancel your changes
.
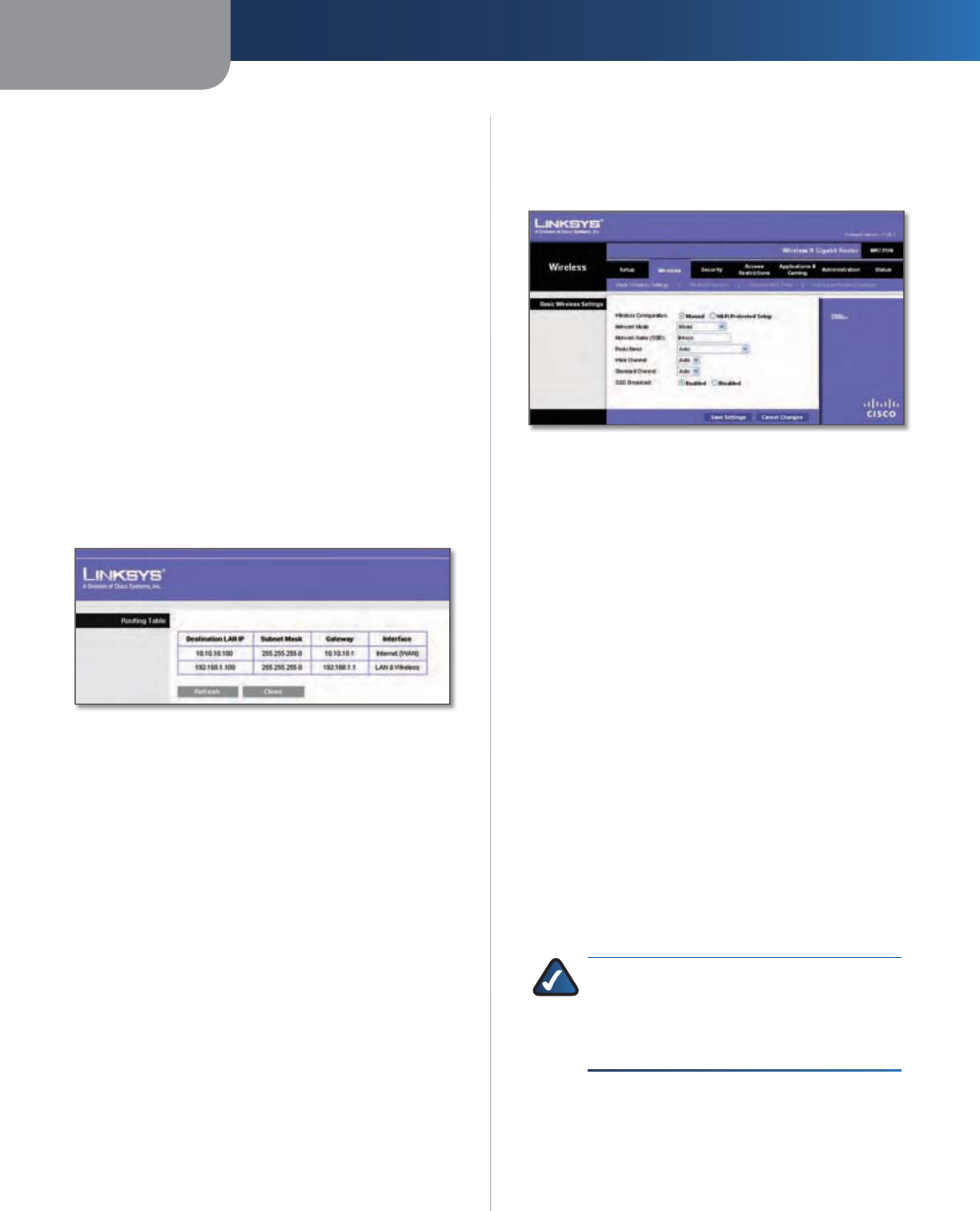
Wireless > Basic Wireless Settin
g
s
T
he basic settin
g
s
f
or wireless networkin
g
are set on this
sc
r
ee
n
.
T
here are two wa
y
s to configure the Router’s wireless
n
etwork(s), manual and Wi-Fi Protected Setup
.
W
i-Fi Protected Setup is a feature that makes it easy to set
u
p
y
our wireless network. If
y
ou have client devices, such
a
s wireless adapters, that support Wi-Fi Protected Setup,
then you can use Wi-Fi Protected Setup
.
Wireless Configuration
T
o manuall
y
configure
y
our
wire
l
ess networ
k
, se
l
ect
Ma
n
ual
.
Pr
oceed
to
the
“B
as
i
c
W
ireless Settin
g
s” section. To use Wi-Fi Protected Setup,
select Wi-Fi Protected Setu
p
. Proceed to the “Wi-Fi
Protecte
d
Setup” section
.
Basic Wire
l
ess Settin
gs
W
ireless > Basic Wireless Settin
g
s (Manual Setup)
Network Mode
F
rom t
h
is
d
rop-
d
own menu,
y
ou can
select the wireless standards running on
y
our network. I
f
you have Wireless-N, Wireless-G, and Wireless-B devices in
y
our network, keep the default setting, Mixe
d
.
If
y
ou have
onl
y
Wireless-G and Wireless-B devices in
y
our network,
se
l
ect
BG-Mix
ed
. If you have only Wireless-N devices,
se
l
ect Wire
l
ess-N On
ly
.
If
y
ou have onl
y
Wireless-G
devices, select
W
ireless-G Onl
y
. I
f
y
ou have onl
y
Wireless-
B devices, select
W
ireless-B Only
.
If you do not have any
wire
l
ess
d
evices in
y
our networ
k
, se
l
ect
D
isa
bl
e
d
.
Network Name (SSID) T
he
SS
ID i
s
the
n
et
w
o
r
k
n
a
m
e
shared amon
g
all points in a wireless network. The
S
SID must be identical for all devices in the wireless
net
w
o
r
k.
I
t
i
s
case
-
se
n
s
i
t
iv
e
a
n
d
m
ust
n
ot
e
x
ceed
3
2 characters (use any of the characters on the keyboard).
Make sure this setting is the same for all points in
y
our
wire
l
ess networ
k
. For a
dd
e
d
securit
y
,
y
ou s
h
ou
ld
c
h
ange
the default SSID
(
l
inksys) to a uni
q
ue name
.
Radio Band
F
or best performance in a network using
W
ire
l
ess-N, Wire
l
ess-G an
d
Wire
l
ess-B
d
evices,
k
eep t
h
e
default,
W
i
de
- 4
0
MHz
C
h
a
nn
e
l
.
F
o
r Wir
e
l
ess
-G
a
n
d
W
ire
l
ess-B networ
k
ing on
ly
, se
l
ect Stan
d
ar
d
- 20MHz
Cha
nn
el
.
I
f
y
ou are not sure which radio band to select,
kee
p
the default,
Auto
.
NOTE: If
y
ou select Wide - 40MHz Channel for
t
h
e Ra
d
io Ban
d
settin
g
, t
h
en Wire
l
ess-N can use
two channels: a primary one (Wide Channel)
an
d
a secon
d
ar
y
one (Stan
d
ar
d
C
h
anne
l
). T
h
is
will enhance Wireless-N per
f
ormance
.
Wide Channel
If
you selected Wide - 40MHz Channel
f
or
th
e Ra
d
io Ban
d
setting, t
h
en t
h
is setting wi
ll
b
e avai
l
a
bl
e
f
or
y
our primar
y
Wireless-N channel. Select an
y
channel
f
rom the drop-down menu. I
f
you are not sure which
c
hannel to select, kee
p
the default,
A
ut
o
.

Chapter 3 Advanced Configuration
14
Wireless-N Gigabit Router
Standard Channel
I
f you selected Wide - 40MHz Channel
or Standard - 20MHz Channel
f
or the Radio Band setting,
then this settin
g
will be available. Select the channel
f
or
W
ireless-N, Wireless-G, and Wireless-B networking. I
f
y
ou selected Wide – 40MHz Channel
f
or the Radio Band
setting, then the Standard Channel will be a secondary
channel for Wireless-N
.
SSID Broadcast W
h
en wire
l
ess c
l
ients surve
y
t
h
e
l
oca
l
a
rea
f
or wireless networks to associate with, they will
detect the SSID broadcast by the Router. To broadcast the
Router’s SSID, keep the de
f
ault setting,
E
na
bl
e
d
. I
f
y
ou
do not want to broadcast the Router’s SSID, then select
Disabled
.
C
l
ic
k
S
ave Sett
i
ng
s
to app
ly
y
our c
h
anges, or c
l
ic
k
C
ance
l
C
han
g
e
s
to cancel your changes
.
Wi-Fi Protected Setu
p
T
h
e
r
e
a
r
e
t
hr
ee
m
et
h
ods
a
v
a
il
ab
l
e.
Use
t
h
e
m
et
h
od
t
h
at
a
pplies to the client device you are configuring
.
Wireless > Basic Wireless Settings (Wi-Fi Protected Setup)
Wi-Fi Protected Setup > Con
g
ratulations
NOTE: Wi-Fi Protected Setup con
f
igures one
client device at a time. Re
p
eat the instructions
f
or each client device that su
pp
orts Wi-Fi
P
rotecte
d
Setup
.
M
eth
od
#1
Use this method i
f
your client device has a Wi-Fi Protected
S
etu
p
b
utton
.
C
l
ic
k
or press t
he
1.
Wi-Fi Protecte
d
Setup
b
utton on
t
h
e
c
li
e
n
t
de
vi
ce.
C
l
ic
k
t
h
e
2.
Wi
-
Fi Protecte
d
Setu
p
b
utton on t
h
is
s
c
reen.
Af
ter the client device has been con
f
i
g
ured, clic
k
3.
OK
.
Then refer back to your client device or its
documentation
f
or
f
urther instructions
.
M
eth
od
#
2
Use this method if your client device has a Wi-Fi Protected
S
etu
p
PIN num
b
er
.
En
te
r
the
PIN n
u
m
be
r in
the
1.
f
i
e
l
d
o
n
t
hi
s
sc
r
ee
n
.
C
li
c
k
2.
Re
g
iste
r
.
A
fter the client device has been configured, clic
k
3.
OK
.
Then re
f
er back to
y
our client device or its
docu
m
e
n
tat
i
o
n
fo
r
fu
r
t
h
e
r in
st
r
uct
i
o
n
s.
M
ethod #3
Use this method if your client device asks for the Router’s
PIN num
b
er.
Enter the PIN number listed on this screen. (It is also
1.
listed on the label on the bottom of the Router.
)
Af
ter the client device has been con
f
igured, clic
k
2
.
OK
.
Then re
f
er back to your client device or its
documentation for further instructions
.
Th
e Wi-Fi Protecte
d
Setup Status, Networ
k
Name (SSID),
S
ecurity, Encryption, and Passphrase are displayed at the
b
ottom of the screen
.
NOTE: I
f
y
ou have client devices that do not
support Wi-Fi Protected Setup, note the wireless
settings, and then manually configure those
cl
ient
d
evices
.
Wire
l
ess > Wire
l
ess Securit
y
T
he
Wireless Security
screen configures the security of
y
y
our wire
l
ess networ
k
. T
h
ere are six wire
l
ess securit
y
m
ode options supported by the Router: WPA Personal,
W
PA Enter
p
rise, WPA2 Personal, WPA2 Enter
p
rise, RADIUS,
a
nd WEP. (WPA stands
f
or Wi-Fi Protected Access
,
which
i
s a security standard stronger than WEP encryption. WEP
stands for Wired Equivalent Privacy, while RADIUS stands

Chapter 3 Advanced Configuration
15
Wireless-N Gigabit Router
f
or Remote Authentication Dial-In User Service.) These
six are brie
f
l
y
discussed here. For detailed instructions
on con
f
iguring wireless security
f
or the Router, re
f
er to
“
Chapter 2: Wireless Security.
”
Wire
l
ess Securit
y
S
ecurit
y
Mod
e
S
elect the security method for your wireless network. I
f
y
ou do not want to use wireless securit
y
, keep the de
f
ault,
Di
sab
l
ed
.
W
PA Pers
o
n
al
NOTE: I
f
y
ou are using WPA, alwa
y
s remember
that each device in your wireless network MUS
T
u
se t
h
e same WPA met
h
o
d
an
d
s
h
are
d
k
e
y
, or
else the network will not
f
unction properl
y.
Securit
y
Mo
d
e > WPA Persona
l
Passphrase
E
nter a Pass
p
hrase of 8-63 characters.
Key Renewal Enter a Ke
y
Renewa
l
perio
d
, w
h
ic
h
instructs
the Router how o
f
ten it should change the encr
y
ption ke
y
s.
T
he default Group Key Renewal period is
3600
seco
n
ds.
W
PA2 Persona
l
Securit
y
Mo
d
e > WPA2 Persona
l
Encryption WPA2 supports two encryption methods,
T
KIP an
d
AES, wit
h
dy
namic encr
y
ption
k
e
y
s. Se
l
ect t
h
e
t
y
pe o
f
algorithm, AE
S
or
T
KIP
o
r AE
S
.
Th
e
defau
l
t
i
s
TKIP
o
r AE
S
.
Passphrase
E
nter a Pass
p
hrase of 8-63 characters.
Key Renewal Enter a Ke
y
Renewa
l
perio
d
, w
h
ic
h
instructs
the Router how o
f
ten it should change the encryption keys.
T
he default Group Key Renewal period is
3
6
00
seconds.
WP
A Enterpris
e
T
his o
p
tion features WPA used in coordination with a
RADIUS server. (T
h
is s
h
ou
ld
on
ly
b
e use
d
w
h
en a RADIUS
server is connected to the Router.
)
S
ecurit
y
Mo
d
e > WPA Enterprise
RADIUS Server En
te
r
t
h
e
IP A
dd
r
ess
o
f
t
h
e
RADI
US
ser
v
er.
RADIUS Port Enter the port number o
f
the RADIUS
se
rv
e
r
.
Th
e
de
f
au
l
t
v
a
l
ue
i
s
18
1
2
.
Shared Secret
E
nter t
h
e
k
e
y
s
h
are
d
b
etween t
h
e Router
a
n
d
the
se
rv
e
r
.
Key Renewal Enter a Key Renewal period, which instructs
the Router how often it should change the encr
y
ption
ke
y
s. The de
f
ault Ke
y
Renewal period is
3600
seco
n
ds.
W
PA2 Enter
p
ris
e
T
his option
f
eatures WPA2 used in coordination with a
RADIUS server. (This should only be used when a RADIUS
server is connecte
d
to t
h
e Router.
)
S
ecurit
y
Mo
d
e > WPA2 Enterprise
Encryption
W
PA2 supports two encryption methods,
T
KIP an
d
AES, wit
h
d
ynamic encryption
k
eys. Se
l
ect t
h
e
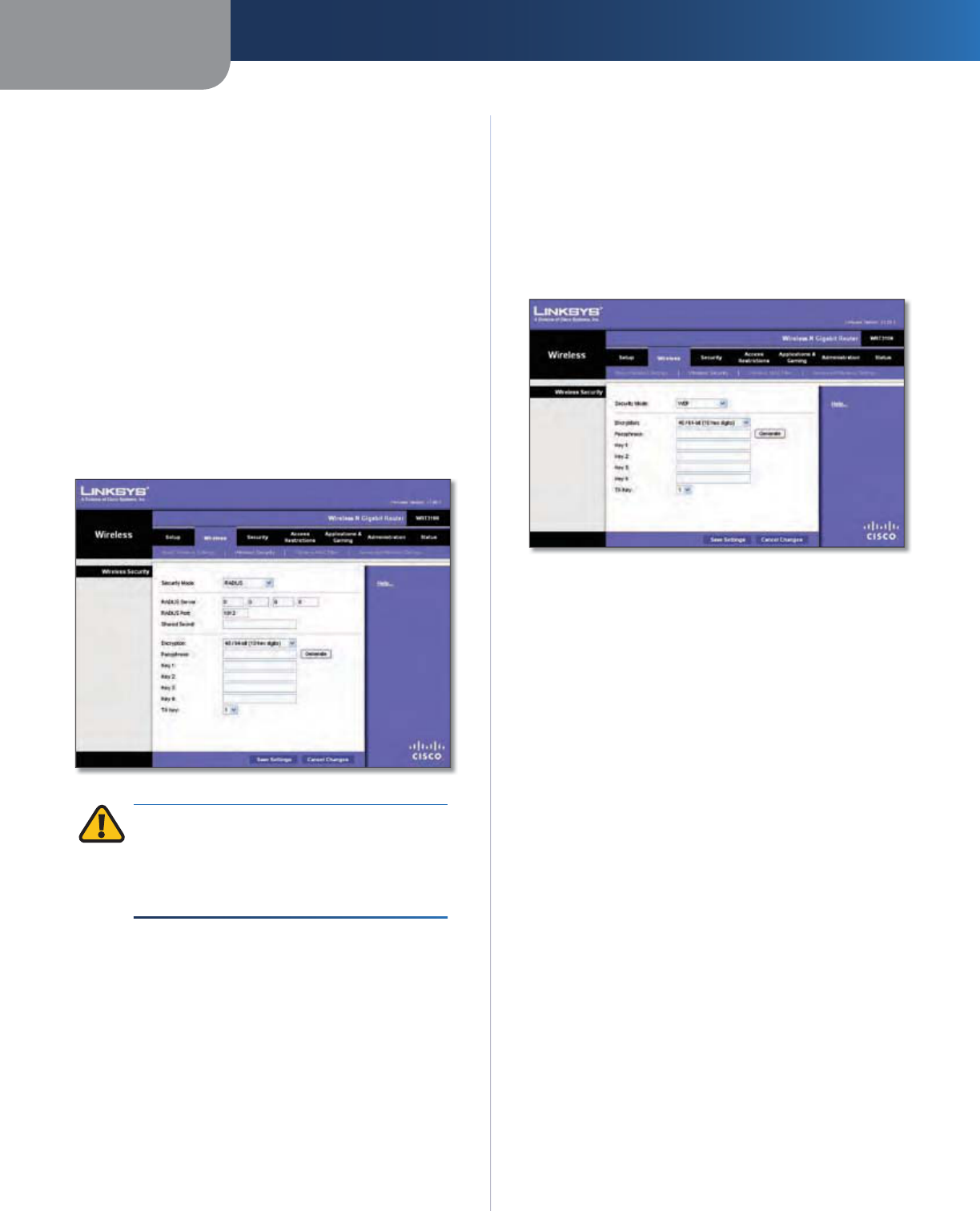
Chapter 3 Advanced Configuration
16
Wireless-N Gigabit Router
type of algorithm, AE
S
or
T
KIP or AES
.
The default is
TKIP
o
r AE
S
.
RADIUS Server En
te
r
t
h
e
IP A
dd
r
ess
of
t
h
e
RADI
US
server
.
RADIUS Port Enter the port number o
f
the RADIUS
se
rv
e
r
.
Th
e
defau
l
t
v
a
l
ue
i
s
18
1
2
.
Shared Secret
E
nter the key shared between the Router
a
n
d
t
h
e server
.
Key Renewal Enter a Key Renewal period, which instructs
the Router how often it should change the encryption
ke
y
s. The de
f
ault Ke
y
Renewal period is 3600 secon
d
s
.
RADI
US
T
his option
f
eatures WEP used in coordination with a
RADIUS server. (This should only be used when a RADIUS
server is connected to the Router.)
Security Mode > RADIUS
IMPORTANT: I
f
y
ou are using WEP encr
y
ption,
a
lways remember that each device in your
w
ire
l
ess networ
k
MUST use t
h
e same WEP
encr
y
ption met
h
o
d
an
d
encr
y
ption
k
e
y
, or e
l
se
y
our wireless network will not
f
unction properly.
RADIUS Server Enter the IP Address of the RADIUS
ser
v
er.
RADIUS Port Enter the
p
ort number o
f
the RADIUS
server. The default value is
18
1
2
.
Shared Secret
E
nter t
h
e
k
e
y
s
h
are
d
b
etween t
h
e Router
a
n
d
t
h
e
se
rv
e
r
.
Encryption Select a level of WEP encr
y
ption,
4
0/64
b
its (10
h
ex
d
i
g
its
)
or
104/128
b
its (26
h
ex
d
i
g
its
)
.
T
h
e
de
f
au
l
t
i
s
4
0/64 bits (10 hex di
g
its
)
.
Passphrase
E
nter a Passp
h
rase to automatica
lly
generate
W
EP
k
e
y
s. T
h
en c
l
ic
k
Ge
n
e
r
ate
.
Key 1-4
I
f you did not enter a Passphrase, enter the WEP
k
e
y
(s) manua
lly.
TX Key
S
elect which TX (Transmit) Key to use. The de
f
ault
i
s
1
.
W
E
P
W
EP is a basic encryption method, which is not as secure
a
s WPA.
Security Mode > WEP
Encryption Select a level of WEP encr
y
ption,
4
0/64
b
its (10
h
ex
d
i
g
its
)
or
104/128
b
its (26
h
ex
d
i
g
its
)
.
T
h
e
de
f
au
l
t
i
s
4
0/64 bits (10 hex di
g
its
)
.
Passphrase
E
nter a Passp
h
rase to automatica
lly
generate
W
EP
k
e
y
s. T
h
en c
l
ic
k
Ge
n
e
r
ate
.
Key 1-4
I
f you did not enter a Passphrase, enter the WEP
k
e
y
(s) manua
lly.
TX Key
S
elect which TX (Transmit) Ke
y
to use. The de
f
ault
is
1
.
C
l
ic
k
S
ave Sett
i
ng
s
to app
ly
y
our c
h
anges, or c
l
ic
k
C
ance
l
Ch
an
g
e
s
to cance
l
y
our c
h
anges
.
Wire
l
ess > Wire
l
ess MAC Fi
l
ter
Wireless access can be filtered b
y
using the MAC addresses o
f
t
h
e wire
l
ess
d
evices transmitting wit
h
in
y
our networ
k
’s ra
d
ius
.
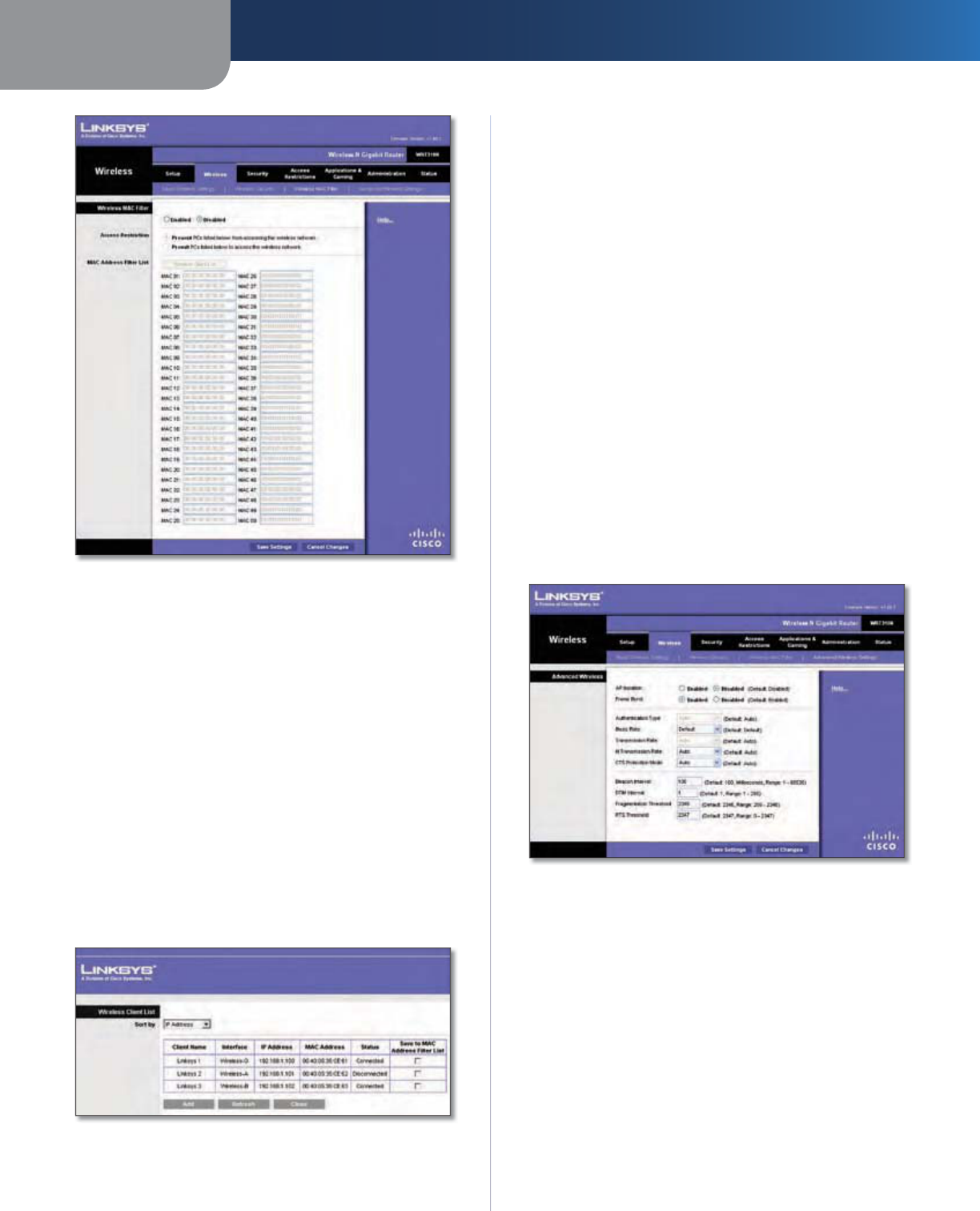
Chapter 3 Advanced Configuration
17
Wireless-N Gigabit Router
Wire
l
ess > Wire
l
ess MAC Fi
l
ter
Wire
l
ess MAC Fi
l
te
r
Enabled/Disabled
To
f
ilter wireless users b
y
MAC Address,
e
ither permittin
g
or blockin
g
access, select En
ab
l
ed
. I
f
you
d
o not wish to filter users by MAC Address, keep the default
s
ett
i
ng, Disa
bl
e
d
.
A
ccess Restricti
o
n
Prevent
Se
l
ect
t
hi
s
to block wireless access by MAC
A
ddress. This button is selected b
y
default
.
Permit
S
e
l
ect t
h
is to a
ll
ow wire
l
ess access
by
MAC
A
ddress. This button is not selected by de
f
ault
.
M
AC Address Filter List
Wireless Client List
Cl
ic
k
t
h
is to o
p
en t
h
eWire
l
ess C
l
ient
List
s
c
reen
.
t
W
ir
eless
Cl
i
e
n
t
Li
st
W
ir
eless
Cl
i
e
n
t
Li
st
T
his screen shows com
p
uters and other devices on
t
h
e wire
l
ess networ
k
. T
h
e
l
ist can
b
e sorte
d
b
y C
l
ient
Name
,
Inter
f
ace
,
IP Address
,
MAC Address
,
and Status.
Se
l
ect
Sa
v
e
to
MA
C
A
dd
r
ess
Fil
te
r Li
st
f
or any device
you want to a
dd
to t
h
e MAC A
dd
ress Fi
l
ter List. T
h
en
c
l
ic
k
A
dd
.
T
o retrieve the most u
p
-to-date in
f
ormation, clic
k
Refres
h
.
To exit t
h
is screen an
d
return to t
h
eWire
l
ess
MA
C
Fi
lter
screen, click
r
Close
.
MAC 01-50
E
n
te
r
t
h
e
MA
C
add
r
esses
of
t
h
e
de
vi
ces
w
h
ose wire
l
ess access you want to
bl
oc
k
or a
ll
ow
.
C
l
ic
k
S
ave Sett
i
ng
s
to app
ly
y
our c
h
anges, or c
l
ic
k
C
ance
l
C
han
g
e
s
to cancel your changes
.
Wireless > Advanced Wireless Setting
s
Th
is A
d
vance
d
Wire
l
ess Setting
s
screen is use
d
to set up
the Router’s advanced wireless
f
unctions. These settin
g
s
s
h
ou
ld
on
l
y
b
e a
d
juste
d
b
y an expert a
d
ministrator as
i
ncorrect settings can reduce wireless per
f
ormance
.
W
ire
l
ess > A
d
vance
d
Wire
l
ess Settings
A
d
v
a
nce
d
Wireles
s
AP Isolation
T
hi
s
i
so
l
ates
a
ll wir
e
l
ess
c
li
e
n
ts
a
n
d
wir
e
l
ess
devices on your network from each other. Wireless devices
wi
ll
b
e a
bl
e to communicate wit
h
t
h
e Router
b
ut not
with each other. To use this
f
unction, select
E
n
ab
l
ed
.
A
P
Isolation is disabled by default.
Frame Burst Ena
bl
ing t
h
is option s
h
ou
ld
provi
d
e
y
our
n
etwork with
g
reater per
f
ormance, dependin
g
on the
m
anufacturer of your wireless products. To use this option,
keep the de
f
ault, Ena
bl
e
d
. Ot
h
erwise
,
se
l
ect
D
isa
bl
e
d
.
Authentication Type Th
e
defau
l
t
i
s
set
to
A
uto
,
which
a
llows either Open System or Shared Key authentication
to
b
e use
d
. Wit
h
Open S
y
stem aut
h
entication, t
h
e sen
d
er
a
nd the recipient do NOT use a WEP key
f
or authentication.
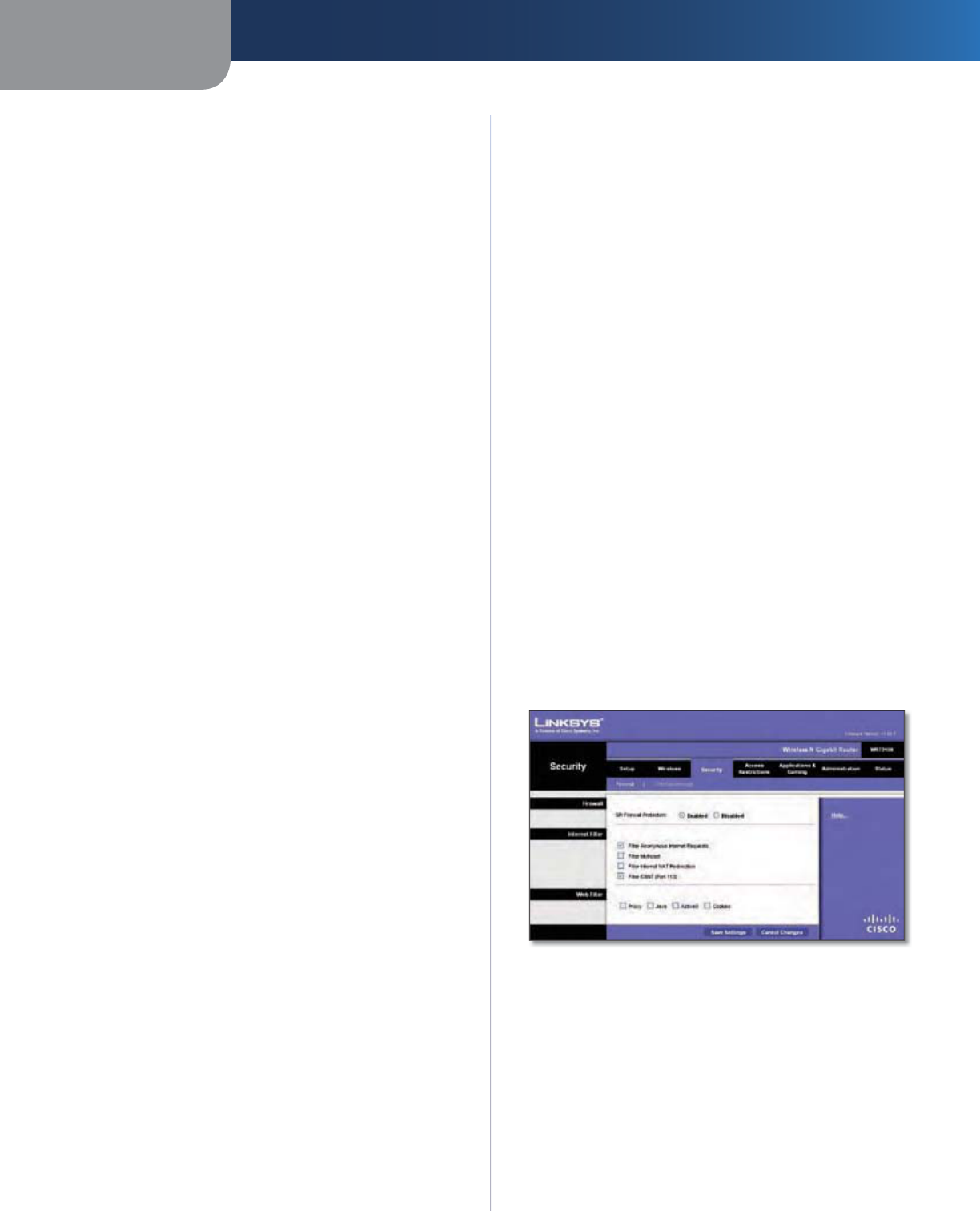
Chapter 3 Advanced Configuration
18
Wireless-N Gigabit Router
W
ith Shared Key authentication, the sender and recipient
u
se a WEP ke
y
f
or authentication. Select
Sh
are
d
Ke
y
to
only use Shared Key authentication
.
Basic Rate
T
he Basic Rate setting is not actually one rate
o
f
transmission but a series o
f
rates at which the Router
ca
n
t
r
a
n
s
mi
t.
Th
e
R
oute
r will
ad
v
e
r
t
i
se
i
ts
B
as
i
c
R
ate
to
t
h
e
other wireless devices in your network, so they know which
r
ates wi
ll
b
e use
d
. T
h
e Router wi
ll
a
l
so a
d
vertise t
h
at it wi
ll
a
utomatically select the best rate
f
or transmission. The
default setting is Defaul
t
,
when the Router can transmit
a
t a
ll
stan
d
ar
d
wire
l
ess rates (1-2M
b
ps, 5.5M
b
ps, 11M
b
ps,
1
8Mb
p
s, and 24Mb
p
s). Other o
p
tions are
1
-2Mb
ps
,
f
or
u
se with older wireless technology, and
All
,
when the
Router can transmit at a
ll
wire
l
ess rates. T
h
e Basic Rate
i
s not the actual rate o
f
data transmission. I
f
you want to
specify the Router’s rate of data transmission, configure
t
h
e Transmission Rate setting
.
Transmission Rate Th
e
r
ate
of
data
t
r
a
n
s
mi
ss
i
o
n
s
h
ou
l
d
b
e set depending on the speed of your wireless network.
You can select
f
rom a range o
f
transmission speeds, or
y
ou
ca
n
se
l
ect
A
uto
to have the Router automatically use the
f
astest
p
ossible data rate and enable the Auto-Fallbac
k
f
eature. Auto-Fallback will negotiate the best possible
connection speed between the Router and a wireless
client. The default is Auto
.
N Transmission Rate The rate o
f
data transmission
should be set depending on the speed o
f
y
our Wireless-N
n
etworkin
g
. You can select from a ran
g
e of transmission
spee
d
s, or
y
ou can se
l
ect
A
ut
o
to
h
ave t
h
e Router
a
utomaticall
y
use the
f
astest possible data rate and enable
the Auto-Fallback feature. Auto-Fallback will ne
g
otiate the
b
est possi
bl
e connection spee
d
b
etween t
h
e Router an
d
a
wir
e
l
ess
c
li
e
n
t.
Th
e
defau
l
t
i
s
A
uto
.
CTS Protection Mode
T
he Router will automatically
u
se CTS (C
l
ear-To-Sen
d
) Protection Mo
d
e w
h
en
y
our
W
ireless-N and Wireless-G products are experiencin
g
severe
p
roblems and are not able to transmit to the
Router in an environment with heav
y
802.11b traffic. This
f
unction boosts the Router’s abilit
y
to catch all Wireless
-
N and Wireless-G transmissions but will severely decrease
p
erformance. The default is
A
ut
o
.
Beacon Interval Enter a value between 1 and 65,535
m
illi
seco
n
ds.
Th
e
B
eaco
n In
te
rv
a
l v
a
l
ue
in
d
i
cates
t
h
e
f
requenc
y
interval of the beacon. A beacon is a packet
b
roadcast b
y
the Router to s
y
nchronize the wireless
net
w
o
rk
.
Th
e
de
f
au
l
t
v
a
l
ue
i
s
100
.
DTIM Interval T
h
is va
l
ue
,
b
etween 1 an
d
255
,
in
d
icates
the interval o
f
the Deliver
y
Tra
ff
ic Indication Message
(DTIM). A DTIM field is a countdown field informin
g
clients of the next window for listening to broadcast
a
nd multicast messa
g
es. When the Router has bu
ff
ered
b
roadcast or multicast messa
g
es for associated clients, it
sen
d
s t
h
e next DTIM wit
h
a DTIM Interva
l
va
l
ue. Its c
l
ients
h
ea
r
t
h
e
beaco
n
s
a
n
d
a
w
a
k
e
n
to
r
ece
iv
e
t
h
e
b
r
oadcast
a
nd multicast messages. The default value is
1
.
Fragmentation Threshold This value speci
f
ies the
m
aximum size for a packet before data is fra
g
mented
i
nto multiple packets. If
y
ou experience a high packet
error rate,
y
ou ma
y
s
l
ig
h
t
ly
increase t
h
e Fragmentation
T
hreshold. Settin
g
the Fra
g
mentation Threshold too low
m
a
y
result in poor network performance. Onl
y
minor
reduct
i
o
n
of
t
h
e
defau
l
t
v
a
l
ue
i
s
r
eco
mm
e
n
ded.
In m
ost
cases, it should remain at its default value o
f
23
4
6
.
RTS Threshold S
h
ou
ld
y
ou encounter inconsistent
d
ata
f
low, onl
y
minor reduction o
f
the de
f
ault value, 2
3
4
7
,
i
s
r
ecommended. If a network
p
acket is smaller than the
p
reset RTS t
h
res
h
o
ld
size, t
h
e RTS/CTS mec
h
anism wi
ll
n
ot
b
e ena
bl
e
d
. T
h
e Router sen
d
s Request to Sen
d
(RTS)
f
rames to a particular receivin
g
station and ne
g
otiates
the sending of a data frame. After receiving an RTS, the
wireless station responds with a Clear to Send (CTS)
f
rame
to acknowled
g
e the ri
g
ht to be
g
in transmission. The RTS
T
hreshold value should remain at its default value o
f
23
4
7
.
C
li
c
k
S
ave Settin
gs
to apply your changes, or clic
k
Ca
n
ce
l
Ch
ange
s
to cance
l
y
our c
h
anges
.
S
ecurit
y
> Firewa
ll
T
he Firewal
l
screen is used to configure a firewall that can
l
f
ilter out various t
y
pes o
f
unwanted tra
ff
ic on the Router’s
l
oca
l n
et
w
o
rk
.
Security > Firewal
l
Firew
a
l
l
SPI Firewall Protection To use firewall
p
rotection,
keep the default selection, Ena
bl
e
d
.
To turn off firewall
p
rotection, select
D
i
sab
l
ed
.
Internet Filte
r
Filter Anonymous Internet Requests
T
hi
s
featu
r
e
ma
k
es
i
t
m
o
r
e
d
iffi
cu
l
t
f
o
r
outs
i
de
use
r
s
to
w
o
rk
t
h
e
ir
wa
y
into
y
our network. This feature is selecte
d
b
y
default.

Chapter 3 Advanced Configuration
19
Wireless-N Gigabit Router
Deselect the feature to allow anonymous Internet
r
equests
.
Filter Multicast
M
ulticastin
g
allows
f
or multiple
transmissions to s
p
ecific reci
p
ients at the same time. I
f
m
u
l
ticasting is permitte
d
, t
h
en t
h
e Router wi
ll
a
ll
ow IP
m
ulticast packets to be
f
orwarded to the appropriate
computers. Select this feature to filter multicasting. This
f
eature is not selected b
y
de
f
ault
.
Filter Internet NAT Redirection
T
his
f
eature uses port
f
orwarding to block access to local servers from local
n
etworked computers. Select this
f
eature to
f
ilter Internet
NAT redirection. It is not selected by de
f
ault
.
Filter IDENT (Port 113)
T
his feature kee
p
s
p
ort 113 from
b
eing scanned b
y
devices outside o
f
y
our local network.
T
his
f
eature is selected by de
f
ault. Deselect this
f
eature to
disable it
.
We
b
Fi
l
ter
Proxy Use of WAN proxy servers may compromise the
Gatewa
y
’s securit
y
. Den
y
ing Prox
y
wi
ll
d
isa
bl
e access to
a
ny WAN proxy servers. Select this
f
eature to enable proxy
f
iltering. Deselect the feature to allow proxy acces
s
.
Java Java is a programming language
f
or websites. I
f
y
ou
deny Java, you run the risk o
f
not having access to Internet
sites created using this programming language. Select
this
f
eature to enable Java
f
iltering. Deselect the
f
eature
to allow Java usa
g
e
.
ActiveX
A
ctiveX is a programming language for websites.
I
f
y
ou den
y
ActiveX,
y
ou run the risk o
f
not having access to
Internet sites created usin
g
this pro
g
rammin
g
lan
g
ua
g
e.
S
elect this feature to enable ActiveX filtering. Deselect the
f
eature to allow ActiveX usage
.
Cookies
A
cookie is data stored on your computer and
u
sed by Internet sites when you interact with them. Select
this
f
eature to
f
ilter cookies. Deselect the
f
eature to allow
cookie usa
ge
.
Click
S
ave Setting
s
to apply your changes, or clic
k
C
ancel
Ch
ange
s
to cance
l
y
our c
h
anges
.
S
ecurity > VPN Passthroug
h
Th
eVPN Passt
h
roug
h
screen a
ll
ows
y
ou to ena
bl
e VPN
t
unnels usin
g
IPSec, PPTP, or L2TP protocols to pass throu
g
h
t
he Router’s firewall.
Security > VPN Passthrough
V
PN Passt
h
rou
gh
IPSec Passthrough
I
nternet Protoco
l
Securit
y
(IPSec) is
a
suite o
f
protocols used to implement secure exchan
g
e
of packets at the IP layer. To allow IPSec tunnels to pass
through the Router, keep the default, Ena
bl
e
d
.
PPTP Passthrough
P
oint-to-Point Tunne
l
in
g
Protoco
l
(PPTP) allows the Point-to-Point Protocol (PPP) to be
tunne
l
e
d
t
h
roug
h
an IP networ
k
. To a
ll
ow PPTP tunne
l
s to
p
ass throu
g
h the Router, keep the de
f
ault, En
abled
.
L2TP Passthrough
L
ayer 2 Tunneling Protocol is the
m
et
h
o
d
use
d
to ena
bl
e Point-to-Point sessions via t
h
e
Internet on t
h
e La
y
er 2
l
eve
l
. To a
ll
ow L2TP tunne
l
s to pass
throu
g
h the Router, keep the default, En
ab
l
ed
.
C
l
ic
k
S
ave Sett
i
ng
s
to app
ly
y
our c
h
anges, or c
l
ic
k
C
ance
l
Ch
an
g
e
s
to cance
l
y
our c
h
anges
.
Access Restr
i
ct
io
ns > Internet Access
Th
e
I
nternet
A
ccess screen a
ll
ows
y
ou to
bl
oc
k
or a
ll
ow
speci
f
ic kinds o
f
Internet usa
g
e and tra
ff
ic, such as Internet
a
ccess, desi
g
nated services, and websites durin
g
specific
d
a
y
s an
d
times
.
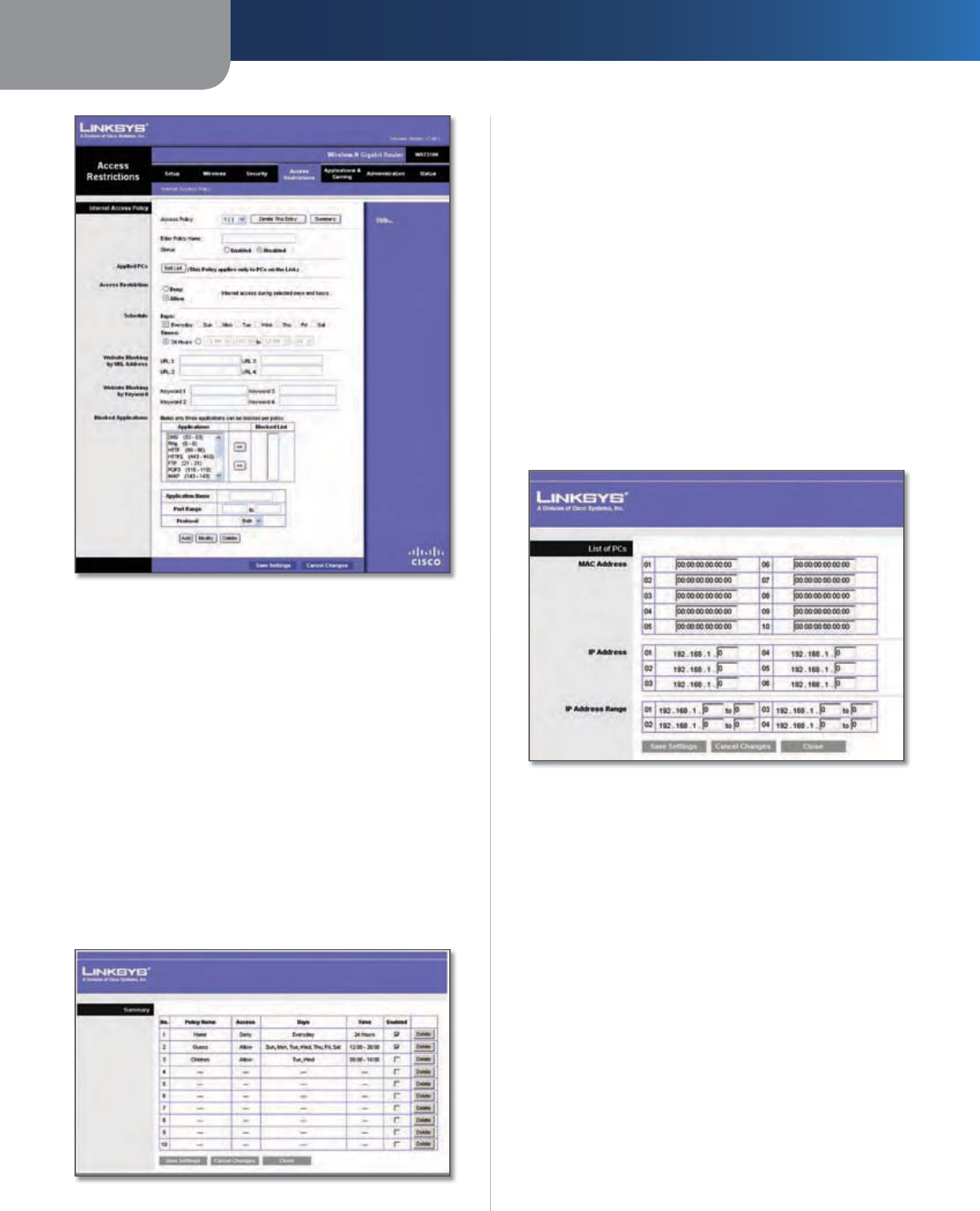
Chapter 3 Advanced Configuration
20
Wireless-N Gigabit Router
Access
R
estrictions > Internet Acces
s
Internet Access Polic
y
Access Policy Access can be managed by a policy. Use the
settings on this screen to establish an access policy (after
Save Sett
i
ngs is clicked). Selecting a polic
y
f
rom the drop
-
down menu will display that policy’s settings. To delete a
p
o
l
icy, se
l
ect t
h
at po
l
icy’s num
b
er an
d
c
l
ic
k
De
l
ete T
h
is
Po
l
ic
y
.
To view a
ll
t
h
e po
l
icies, c
l
ic
k
S
ummar
y
.
S
ummar
y
T
he policies are listed with the
f
ollowin
g
in
f
ormation: No.,
Po
l
ic
y
Name, Access, Da
y
s, Time, an
d
status (Ena
bl
e
d
). To
ena
bl
e a po
l
ic
y
, se
l
ect
E
n
abled
. To
d
e
l
ete a po
l
ic
y
, c
l
ic
k
D
e
l
ete
.
C
li
ck
S
ave Settin
g
s to save your changes, or clic
k
C
ance
l
C
h
anges to cance
l
your c
h
anges. To return to t
h
e
Internet Access Policy
screen, click
y
C
l
os
e
.
S
ummar
y
Status
P
olicies are disabled by default. To enable a policy,
select the polic
y
number
f
rom the drop-down menu, and
se
l
ect
En
ab
l
ed
.
T
o create a policy, follow steps 1-11. Repeat these steps to
create a
dd
itiona
l
po
l
icies, one at a time
.
Se
l
ect
a
n
u
m
be
r
f
r
o
m
t
h
e
1.
Access Policy
drop-down
y
m
enu
.
Enter a Polic
y
Name in the
f
ield provided.2
.
T
o enable this policy, select
3.
E
n
ab
l
ed
.
Click
4.
E
dit Lis
t
to select which PCs will be affected by
th
e po
l
ic
y
. T
h
e List o
f
PCs screen appears.
Y
ou can
select a PC by MAC address or IP address. You can also
enter a range of IP addresses if you want this policy to
a
ff
ect a group o
f
PCs. A
f
ter making
y
our changes, click
S
ave Sett
i
n
gs
to apply your changes, or click
Ca
n
ce
l
Changes to cancel your changes. Then click
C
lose
.
List o
f
PCs
S
elect the a
pp
ro
p
riate o
p
tion,
5.
D
en
y
o
rAll
o
w
,
d
epen
d
ing on w
h
et
h
er
y
ou want to
bl
oc
k
or a
ll
ow
Internet access
f
or the PCs
y
ou listed on the Li
st
of
P
Cs
sc
r
ee
n
.
Deci
d
e w
h
ic
h
d
a
y
s an
d
w
h
at times
y
ou want t
h
is po
l
ic
y
6.
to be en
f
orced. Select the individual da
y
s during which
the policy will be in effect, or select
E
veryda
y
.
Th
e
n
enter a range of hours and minutes during which the
p
olic
y
will be in e
ff
ect, or select 24
Hou
r
s
.
You can block websites with s
p
ecific URL addresses.
7.
Enter eac
h
URL in a separate
U
RL field.
You can also block websites using speci
f
ic ke
y
words.
8.
Enter each keyword in a separate
Keyword
field.
d

Chapter 3 Advanced Configuration
21
Wireless-N Gigabit Router
You can filter access to various services accessed
9.
over t
h
e Internet
,
suc
h
as FTP or te
l
net. (You
can block up to three applications per policy.)
From t
h
e App
l
ications
l
ist, se
l
ect t
h
e app
l
ication
y
ou
w
a
n
t
to
b
l
oc
k
.
Th
e
n
c
li
c
k
t
h
e
>>
butto
n
to
m
o
v
e
i
t
to
the Blocked List. To remove an a
pp
lication from the
B
l
oc
k
e
d
List
,
se
l
ect it an
d
c
l
ic
k
t
h
e
<<
b
utton.
I
f
the application you want to block is not listed
10.
or you want to edit a service’s settings, enter the
a
pp
l
ication’s name in t
he
App
l
ication Nam
e
f
ield. Enter
i
ts ran
g
e in the
P
ort
R
an
ge
f
ields. Select its protocol
f
rom the
P
rotoco
l
drop-down menu. Then click
l
Add
.
T
o modi
f
y a service, select it
f
rom the
A
pplication list. Change its name, port range,
a
n
d
/or protoco
l
setting. T
h
en c
l
ic
k
M
odi
fy
.
T
o delete a service, select it from the A
pp
lication list.
Then click
Delete
k
.
C
li
c
k
11.
Save Sett
i
n
g
s to save the polic
y
’s settings. To
cancel the policy’s settings, clic
k
Cancel Chan
g
es
.
Applications and Gamin
g
> Sin
g
le Port
Forwar
d
in
g
T
he Single Port Forwarding screen allows you to customize
p
ort services
f
or common applications on this screen
.
When users send these types o
f
requests to your network via
the Internet, the Router will forward those re
q
uests to the
appropriate servers (computers). Be
f
ore using
f
orwarding,
y
ou should assign static IP addresses to the designated
s
ervers (use the DHCP Reservation feature on the Basic Setu
p
s
creen
)
.
A
pp
l
ications an
d
Gaming > Sing
l
e Port Forwar
d
in
g
Single Port Forwarding
Common a
pp
lications are available
f
or the
f
irst
f
ive
entries. Select the a
pp
ro
p
riate a
pp
lication. Then enter the
IP address o
f
the server that should receive these requests.
Se
l
ect
E
n
ab
l
ed
to activate this entry
.
For additional applications, complete the following fields
:
Application Name
E
nter t
h
e name
y
ou wis
h
to give t
h
e
a
pplication. Each name can be up to 12 characters
.
External Port Enter the external port number used by
t
h
e server or Internet app
l
ication. C
h
ec
k
wit
h
t
h
e Internet
app
lication documentation
f
or more in
f
ormation
.
Internal Port Enter the internal port number used by
t
h
e server or Internet app
l
ication. C
h
ec
k
wit
h
t
h
e Internet
a
pplication documentation
f
or more in
f
ormation
.
Protocol Select the
p
rotocol used for this a
pp
lication,
eit
h
e
r
T
C
P
or
U
DP
,
or
B
ot
h
.
To IP Address For each a
pp
lication, enter the IP address
of the PC that should receive the requests. If you assigned
a
static IP a
dd
ress to t
h
e PC, t
h
en
y
ou can c
l
ic
k
D
H
C
P
R
ese
rv
at
i
on
o
n
t
h
e
Basic
S
etu
p
screen to look u
p
its static
IP address.
Enabled For eac
h
app
l
ication, se
l
ect
E
na
bl
e
d
to ena
bl
e
p
ort
f
orwardin
g.
C
lick
S
ave Setting
s
to apply your changes, or clic
k
C
ancel
Ch
ange
s
to cance
l
y
our c
h
anges
.
App
l
ications an
d
Gaming > Port Range
Forwardin
g
Th
e Port Range Forwar
d
ing screen a
ll
ows
y
ou to set up
p
ublic services on your network, such as web servers,
f
t
p
servers, e-mail servers, or other s
p
ecialized Internet
app
l
ications. (Specia
l
ize
d
Internet app
l
ications are an
y
applications that use Internet access to per
f
orm
f
unctions
s
uch as videoconferencing or online gaming. Some Internet
applications ma
y
not require an
y
f
orwarding.
)
When users send these types o
f
requests to your network via
the Internet, the Router will forward those re
q
uests to the
appropriate servers (computers). Be
f
ore using
f
orwarding,
y
ou should assign static IP addresses to the designated
s
ervers (use the DHCP Reservation feature on the Basic Setu
p
s
creen
)
.
I
f
you need to
f
orward all ports to one computer, click the
D
M
Z
t
ab.
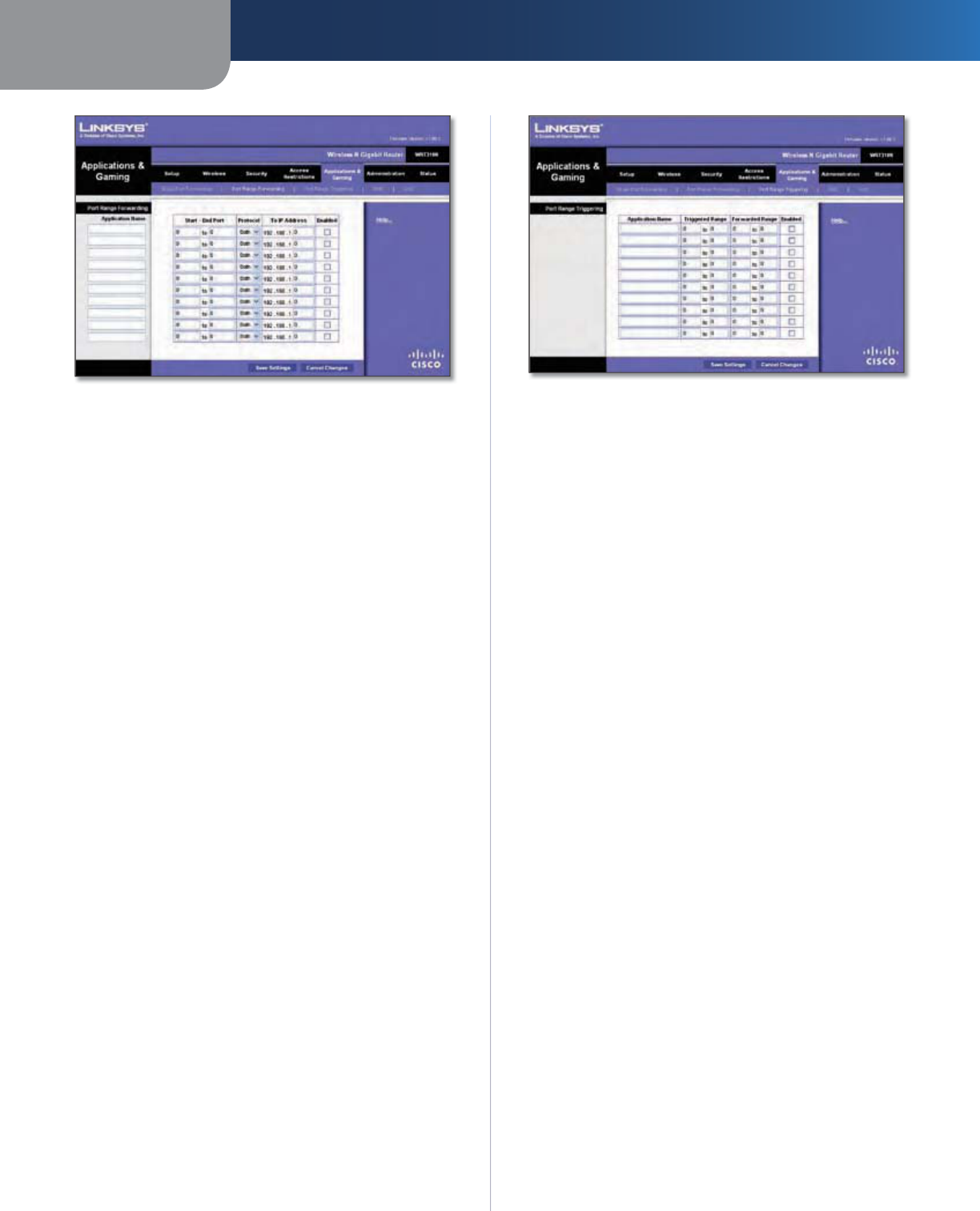
Chapter 3 Advanced Configuration
22
Wireless-N Gigabit Router
Applications and Gamin
g
> Port Ran
g
e Forwardin
g
Port Ran
g
e Forwar
d
in
g
T
o forward a
p
ort, enter the information on each line for
t
h
e criteria require
d.
Application Name
I
n this
f
ield, enter the name you
wis
h
to give t
h
e app
l
ication. Eac
h
name can
b
e up to 12
c
h
aracters
.
Start~End Port
E
nter the number or ran
g
e o
f
port(s)
u
se
d
b
y t
h
e server or Internet app
l
ications. C
h
ec
k
with the Internet application documentation
f
or more
i
n
fo
rm
at
i
o
n
.
Protocol Select the
p
rotocol used for this a
pp
lication,
e
i
ther
T
C
P
or
U
DP
,
or
Both
.
To IP Address For each a
pp
lication, enter the IP address
of the PC running the specific application. If
y
ou assigned
a
static IP a
dd
ress to t
h
e PC, t
h
en
y
ou can c
l
ic
k
D
H
C
P
R
ese
rv
at
i
on
o
n
t
h
e
Basic Setu
p
screen to look u
p
its static
IP a
dd
ress.
Enabled Se
l
ect Ena
bl
e
d
to enable port
f
orwarding
f
or
t
he applications you have de
f
ined
.
Cl
ic
k
S
ave Setting
s
to app
ly
y
our c
h
anges, or c
l
ic
k
C
ance
l
Ch
ange
s
to cance
l
y
our c
h
anges
.
App
l
ications & Gaming > Port Range
Tr
i
gger
i
ng
Th
e Port Range Triggerin
g
screen a
ll
ows t
h
e Router to
watch out
g
oin
g
data
f
or speci
f
ic port numbers. The IP
a
ddress of the computer that sends the matching data is
r
emem
b
ere
d
by
t
h
e Router, so t
h
at w
h
en t
h
e requeste
d
data returns throu
g
h the Router, the data is pulled bac
k
to the proper computer b
y
wa
y
of IP address and port
m
appin
g
ru
l
es
.
A
pp
l
ications an
d
Gaming > Port Range Triggerin
g
Port Range Triggering
Application Name Enter the application name o
f
the
tri
gg
er.
Triggered Range For eac
h
app
l
ication, enter t
h
e starting
a
nd ending port numbers o
f
the triggered port number
r
an
g
e. Check with the Internet application documentation
f
or the
p
ort number(s) needed
.
Forwarded Range For eac
h
app
l
ication, enter t
h
e startin
g
a
nd endin
g
port numbers of the forwarded port number
r
ange. C
h
ec
k
wit
h
t
h
e Internet app
l
ication
d
ocumentation
f
or the port number(s) needed
.
Enabled
Se
l
ect
En
ab
l
ed
to enable port tri
gg
erin
g
for the
a
pplications
y
ou have defined.
Cl
i
ck
S
ave Sett
i
n
gs
to app
ly
y
our c
h
anges, or c
l
ic
k
Ca
n
cel
C
han
g
e
s
to cancel your changes
.
Applications and Gaming > DMZ
T
he DMZ
f
eature allows one network computer to be
ex
p
osed to the Internet for use of a s
p
ecial-
p
ur
p
ose
service such as Internet gaming or videoconferencing.
DMZ hostin
g
f
orwards all the ports at the same time to
one PC. The Port Ran
g
e Forwardin
g
feature is more secure
b
ecause it on
ly
opens t
h
e ports
y
ou want to
h
ave opene
d
,
while DMZ hostin
g
opens all the ports o
f
one computer,
exposin
g
the computer to the Internet.
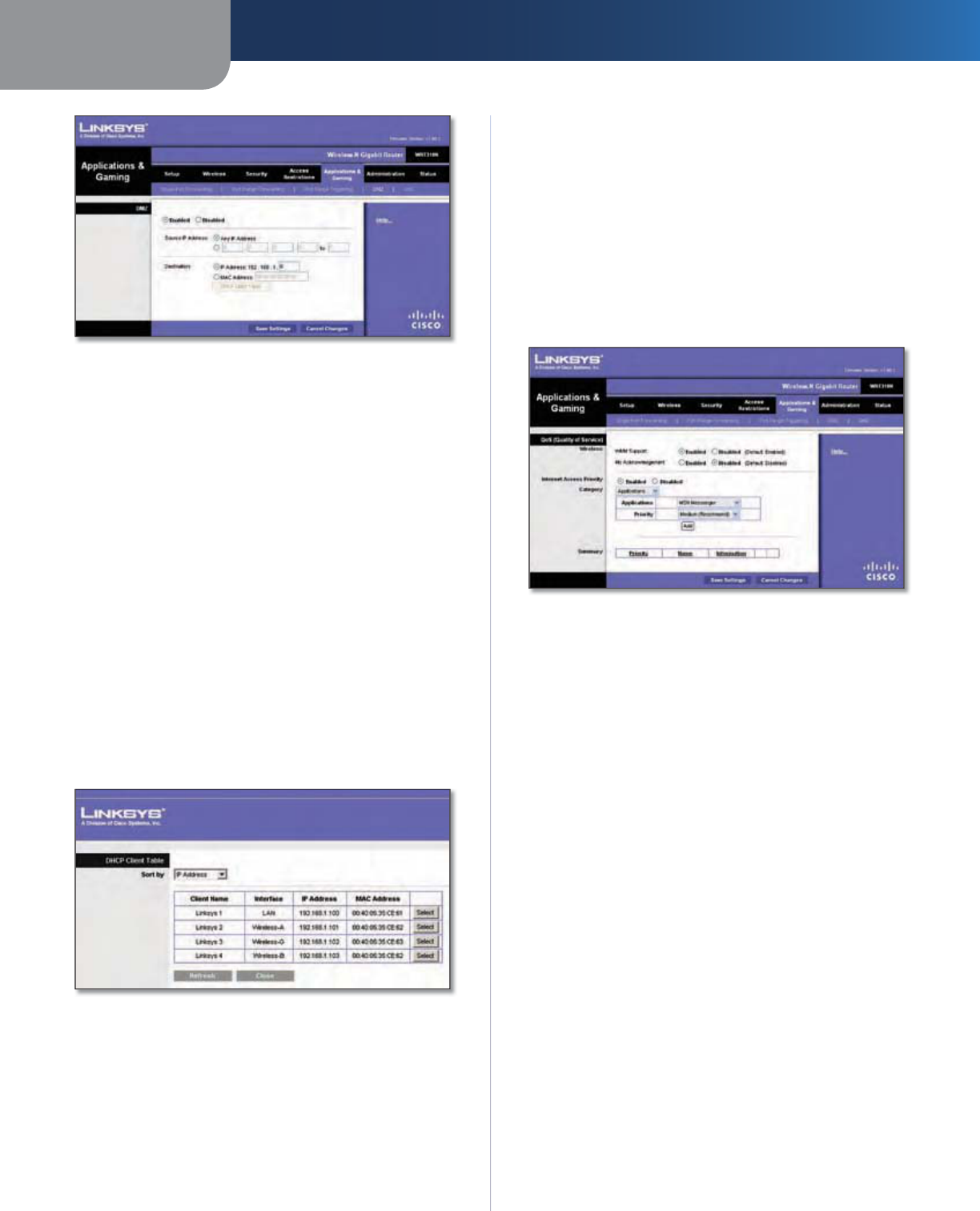
Chapter 3 Advanced Configuration
23
Wireless-N Gigabit Router
A
pp
l
ications an
d
Gaming > DM
Z
D
M
Z
A
ny PC whose port is being forwarded must have its DHCP
client function disabled and should have a new static IP
add
ress assigne
d
to it
b
ecause its IP a
dd
ress ma
y
c
h
ange
when usin
g
the DHCP
f
unction
.
Enabled/Disabled To
d
isa
bl
e DMZ
h
osting, se
l
ect
Disa
bl
e
d
.
To expose one PC, se
l
ect Ena
bl
e
d
.
T
h
en
con
f
i
g
ure the
f
ollowin
g
settin
g
s
:
Source IP Address If you want any IP address to be the
source
,
se
l
ect
A
n
y
IP A
dd
res
s
. I
f
y
ou want to speci
fy
an IP
a
ddress or ran
g
e o
f
IP addresses as the desi
g
nated source,
select and complete the IP address range fields
.
Destination
If
y
ou want to speci
fy
the DMZ host b
y
IP
a
ddress, select IP A
dd
r
ess
a
n
d
e
n
te
r
t
h
e
IP
add
r
ess
in
the field provided. If you want to specify the DMZ host
by
MAC a
dd
ress, se
l
ect MAC A
dd
ress an
d
enter t
h
e MAC
a
ddress in the
f
ield
p
rovided. To retrieve this in
f
ormation,
c
l
ic
k
D
HCP C
l
ient Ta
bl
e
.
D
MZ > DH
C
P
C
li
e
n
t
T
ab
l
e
D
HCP C
l
ient Ta
ble
Th
e DHCP C
l
ient Ta
bl
e
l
ists computers an
d
ot
h
er
devices that have been assigned IP addresses by the
Router. The list can be sorted by Client Name, Interface,
IP A
dd
ress, MAC A
dd
ress, an
d
Expire
d
Time (
h
ow muc
h
time is le
f
t
f
or the current IP address
)
. To select a DHCP
client, clic
k
Selec
t
.
To retrieve the most u
p
-to
-
d
ate
i
nformation, clic
k
R
efres
h
. To exit this screen and
r
eturn to t
h
e
D
M
Z
screen, click
Z
C
l
os
e
.
C
li
c
k
S
ave Sett
i
n
gs
to apply your changes, or clic
k
Ca
n
ce
l
C
hange
s
to cancel your changes
.
Applications and Gamin
g
> QoS
Quality o
f
Service (QoS) ensures better service to
high-priority types of network traffic, which may
i
nvo
l
ve
d
eman
d
ing, rea
l
-time app
l
ications, suc
h
as
videocon
f
erencin
g
.
A
pplications and Gamin
g
> QoS
Q
oS (Quality of Service
)
Wir
eless
You can configure the support and No Acknowledgement
settin
g
s in t
h
is section
.
WMM Support If you have other devices that support Wi
-
Fi Multimedia (WMM) on
y
our network, keep the default,
En
abled
.
Ot
h
erwise, se
l
ect Di
sabled
.
No Acknowledgement
I
f you want to disable the Router’s
A
cknowledgement feature, so the Router will not re-send
data i
f
an error occurs, then select En
abled
.
Ot
h
erwise,
kee
p
the default, Di
sab
l
ed
.
I
nternet Access
P
riority
In this section,
y
ou can set the bandwidth priorit
y
for a
variet
y
o
f
applications and devices. There are
f
our levels
p
riority: High, Medium, Normal, or Low. When you set
p
riorit
y
,
d
o not set a
ll
app
l
ications to Hig
h
,
b
ecause t
h
is wi
ll
de
f
eat the purpose o
f
allocatin
g
the available bandwidth.
If you want to select below normal bandwidth, select Low.
Depending on the application, a few attempts ma
y
be
n
eeded to set the appropriate bandwidth priorit
y.
Enabled/Disabled To use the QoS policies you have set,
keep the default, Ena
bl
e
d
. Ot
h
erwise
,
se
l
ect
D
isa
bl
e
d
.
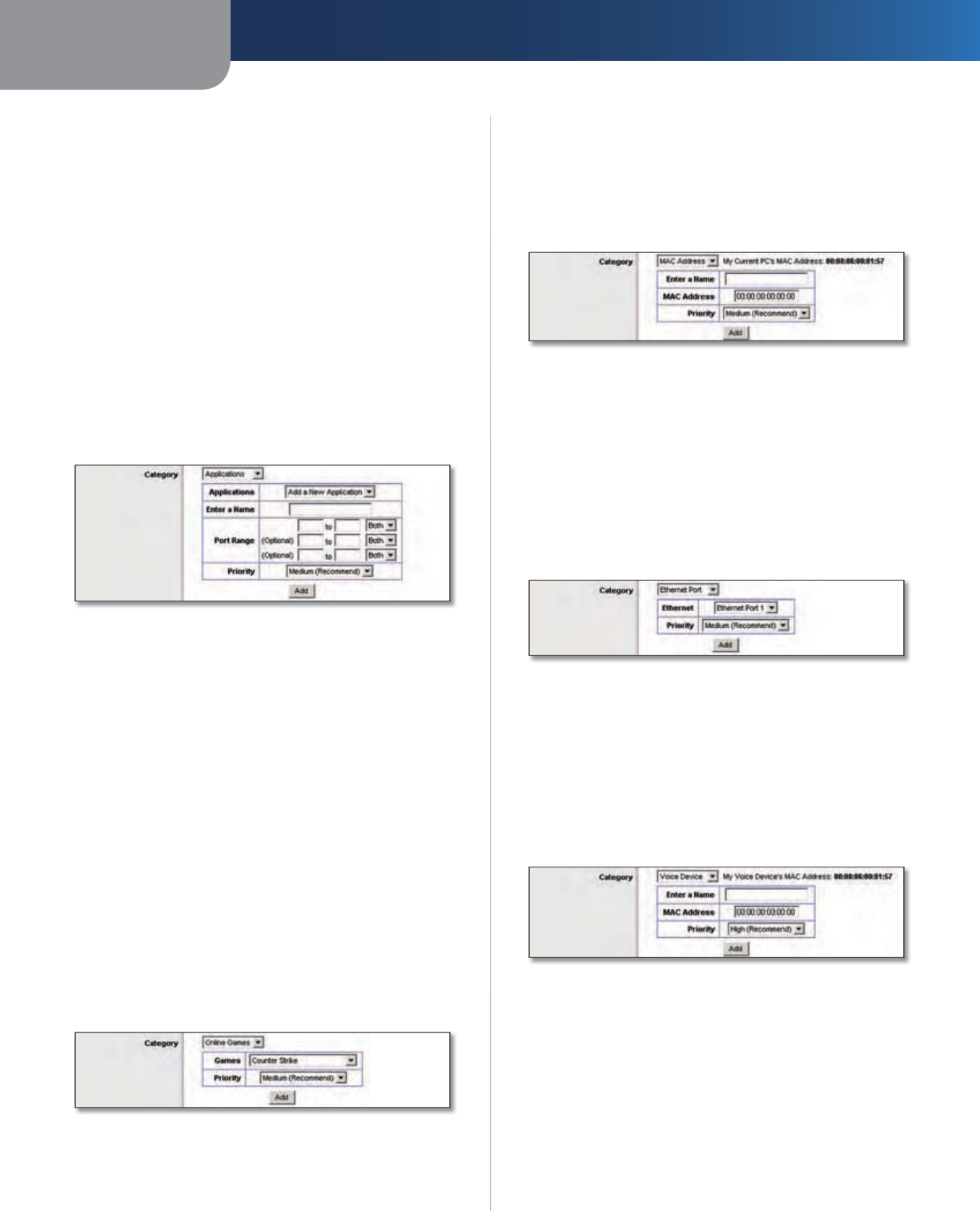
Chapter 3 Advanced Configuration
24
Wireless-N Gigabit Router
Categor
y
T
here are four categories available. Select one of the
f
ollowing: App
l
ications
,
On
l
ine Game
s
,
MAC A
dd
res
s
,
E
t
h
e
rn
et
P
o
r
t
, or V
o
i
ce
D
e
vi
ce
.
Pr
oceed
to
t
h
e
in
st
r
uct
i
o
n
s
for your selection
.
Application
s
Applications Select the appropriate application. If you
select Add a New Application,
f
ollow the Add a New
A
pplication instructions.
Priority
S
elect the appropriate priority:
H
ig
h
,
M
ediu
m
,
Norma
l
,
or
L
o
w
.
C
li
c
k
Add
to save your changes. Your new entry will appear
i
n the Summary list
.
Add
a New App
l
ication
Q
oS > A
dd
a New App
l
ication
Enter a Name Enter any name to indicate the name o
f
t
h
e entr
y.
Port Range Enter the port ran
g
e that the application will
b
e using. For example, if you want to allocate bandwidth
f
or FTP,
y
ou can enter 21-21. If
y
ou need services for an
a
pplication that uses
f
rom 1000 to 1250,
y
ou enter 1000
-
1
250 as your settings. You can have up to three ranges
to define for this bandwidth allocation. Port numbers
can range
f
rom 1 to 65535. Check
y
our application’s
documentation for details on the service
p
orts used.
S
elect the protocol T
CP
or
U
D
P
,
or select
Both
.
Priority
S
elect the appropriate priority: Hi
gh
,
Med
i
u
m
(
Recommen
d)
,
Norma
l
,
or
L
o
w
.
Cl
i
ck
Add
to save
y
our c
h
anges. Your new entr
y
wi
ll
appear
i
n the Summary list
.
Online Games
QoS > On
l
ine Game
s
Games
S
elect the appropriate
g
ame
.
Priority
S
elect the appropriate priority: Hig
h
,
M
edium
(
Recommen
d)
,
Norma
l
,
or
L
ow
.
C
li
c
k
Add
to save your changes. Your new entry will appear
i
n the Summary list
.
MAC Address
Q
oS > MAC Address
Enter a Name Enter a name for
y
our device
.
MAC Address
E
nter the MAC address o
f
y
our device
.
Priority
S
elect the appropriate priority: Hi
gh
,
Med
i
u
m
(
Recommen
d)
,
Norma
l
,
or
L
o
w
.
C
li
c
k
Add
to save
y
our changes. Your new entr
y
will appear
i
n the Summary list
.
Ethernet Por
t
Q
oS > Ethernet Por
t
Ethernet Se
l
ect t
h
e appropriate Et
h
ernet port
.
Priority
S
elect the appropriate priority: Hi
gh
,
Med
i
u
m
(
Recommen
d)
,
Norma
l
,
or
L
o
w
.
Cl
i
ck
Add
to save
y
our c
h
anges. Your new entr
y
wi
ll
appear
i
n the Summary list
.
V
oice Device
Q
oS > Voice Devic
e
Enter a Name Enter a name
f
or
y
our voice device
.
MAC Address
E
nter the MAC address o
f
your voice
device
.
Priority
S
e
l
ect t
h
e appropriate priorit
y
:
H
ig
h
(
Recommend
)
,
Med
i
um
,
No
rm
al
,
or
Lo
w
.
Click
A
d
d
to save your changes. Your new entry will appear
i
n t
h
e Summar
y
l
ist
.

Chapter 3 Advanced Configuration
25
Wireless-N Gigabit Router
S
ummar
y
T
his lists the QoS entries you have created for your
a
pp
l
ications an
d
d
evices
.
Priority
T
his column displays the bandwidth priority o
f
High, Medium, Normal, or Low
.
Name T
h
is co
l
umn
d
isp
l
a
y
s t
h
e app
l
ication,
d
evice, or
p
ort name.
Information This column displays the port range or
MAC address entered
f
or
y
our entr
y
. I
f
a pre-con
f
igured
a
pplication or
g
ame was selected, there will be no valid
entry shown in this section
.
Remove
Cl
ic
k
t
h
is
b
utton to remove an entr
y.
Edit
C
lick this button to make chan
g
es
.
Click
S
ave Setting
s
to apply your changes, or clic
k
C
ancel
Ch
ange
s
to cance
l
y
our c
h
anges
.
A
d
ministration > Management
T
he
Administration > Management
screen allows the
t
n
etwork’s administrator to manage speci
f
ic Router
f
unctions
f
or access and security
.
Administration > Management
Managemen
t
R
outer Access
T
o ensure the Router’s security, you will be asked for your
p
asswor
d
w
h
en
y
ou access t
h
e Router’s we
b
-
b
ase
d
uti
l
it
y
.
T
h
e
defau
l
t
i
s
ad
mi
n
.
Router Password Enter a new
p
assword for the Router
.
Re-enter to confirm
E
nter t
h
e passwor
d
again to
co
n
f
irm
.
Web Access
Web Utility Access HTTP (HyperText Transport Protocol)
i
s t
h
e communications protoco
l
use
d
to connect to servers
on the World Wide Web. HTTPS uses SSL
(
Secured Socket
Layer) to encrypt data transmitted for higher security.
S
e
l
ect
H
TT
P
or
H
TTP
S
.
H
TT
P
is the de
f
ault.
Web Utility Access via Wireless I
f
you are using the
Router in a public domain where you are giving wireless
a
ccess to
y
our guests,
y
ou can
d
isa
bl
e wire
l
ess access to
the Router’s web-based utility. You will only be able to
a
ccess the utility via a wired connection if you disable
the setting. Keep the de
f
ault,
E
na
bl
e
d
,
to a
ll
ow wire
l
ess
a
ccess to the utility, or select
D
i
sab
l
ed
to
b
l
oc
k wir
e
l
ess
a
ccess to the utility
.
R
em
o
te Access
Remote Management
T
o permit remote access o
f
the
Router,
f
rom outside the local network, select En
ab
l
ed
.
Otherwise, kee
p
the default, Disabled
.
Web Utility Access HTTP (H
y
perText Transport Protoco
l
)
i
s the communications protocol used to connect to servers
on the World Wide Web. HTTPS uses SSL (Secured Socket
La
y
er) to encr
y
pt data transmitted
f
or higher securit
y
.
Se
l
ect
H
TT
P
or
H
TTP
S
.
H
TT
P
i
s
t
h
e
defau
l
t.
Remote Upgrade If you want to be able to upgrade the
Router remotel
y
,
f
rom outside the local network, select
En
ab
l
ed
.
(You must have the Remote Mana
g
ement
f
eature enabled as well.) Otherwise, kee
p
the default,
Disa
bl
e
d
.
Allowed Remote IP Address
If
you want to be able to
a
ccess the Router from any external IP address, select
A
ny
IP A
dd
res
s
. I
f
y
ou want to speci
fy
an external IP address or
r
an
g
e o
f
IP addresses, then select the second option and
com
p
lete the fields
p
rovided
.
Remote Management Port Enter t
h
e port num
b
er t
h
at
will be open to outside access
.
NOTE: When you are in a remote location
an
d
wis
h
to manage t
h
e Router, enter
h
ttp://<Internet_IP_address>:por
t
or
h
tt
p
s://<Internet_IP_address>:
p
or
t
,
d
epen
d
ing on w
h
et
h
er
y
ou use HTTP or HTTPS.
E
nter the Router’s speci
f
ic Internet IP address in
p
lace of <Internet_IP_address>, and enter the
R
emote Management Port number in place o
f
the word port.
U
PnP
Universal Plug and Play (UPnP) allows Windows Me and XP
to automaticall
y
configure the Router for various Internet
a
pplications, such as
g
amin
g
and videocon
f
erencin
g.

Chapter 3 Advanced Configuration
26
Wireless-N Gigabit Router
UPnP If you want to use UPnP, keep the default setting,
Ena
bl
e
d
.
Ot
h
erwise
,
se
l
ect Disa
bl
e
d
.
Allow Users to Configure
K
eep the de
f
ault, En
ab
l
ed
,
i
f you want to be able to make manual changes to the
Router while using the UPnP
f
eature. Otherwise, select
Di
sab
l
ed
.
Allow Users to Disable Internet Access
S
elect Enabled
,
if
y
ou want to be able to prohibit an
y
and all Internet
connections. Otherwise, keep the de
f
ault settin
g
,
Disabled
.
B
ac
k
u
p
an
d
Restore
Backup Configurations
T
o
b
ac
k
up t
h
e Router’s
con
f
i
g
uration settin
g
s, click this button and
f
ollow the on
-
screen instructions
.
Restore Configurations
T
o restore t
h
e Router’s
con
f
i
g
uration settin
g
s, click this button and
f
ollow the on
-
screen instructions. (You must have previously backed up
the Router’s con
f
iguration settings.
)
C
li
c
k
S
ave Settin
gs
to apply your changes, or clic
k
Ca
n
ce
l
C
hange
s
to cancel your changes
.
Administration > Lo
g
T
he Router can keep logs o
f
all tra
ff
ic
f
or your Internet
connection.
A
dministration > Lo
g
L
o
g
Log
T
o disable the Log function, select Disa
bl
e
d
.
T
o
m
onitor tra
ff
ic between the network and the Internet,
kee
p
the default, En
ab
l
ed
.
W
ith logging enabled, you can
c
h
oose to view temporar
y
l
ogs
.
View Log
T
o view the lo
g
s, clic
k
Vi
ew Lo
g
.
Log > View Log
L
og
Type
s
S
e
l
ect
I
ncoming Log
,
Outgoing Log
,
Securit
y
L
og
,
or
D
HCP C
l
ient Log
.
<Type> Log
s
The Incoming Log will display a
t
emporar
y
log of the source IP addresses and
d
estination port numbers
f
or the incomin
g
Internet
t
ra
ff
ic. The Outgoing Log will display a temporary
l
og of the local IP addresses, destination URLs/IP
add
resses
,
an
d
s
ervice/port numbers
f
or the out
g
oin
g
Internet traffic. The Security log will display the login
i
nformation for the web-based utility. The DHCP
Cl
ient Log wi
ll
d
isp
l
a
y
t
h
e LAN DHCP server status
i
n
fo
rm
at
i
o
n
.
Cl
ic
k
S
ave t
h
e Log to save this information to a file
o
n
y
our PC’s
h
ar
d
d
rive. C
l
ic
k
Ref
r
es
h to up
d
ate t
h
e
l
o
g
. Clic
k
C
l
ea
r
to
c
l
ea
r
a
ll
t
h
e
inf
o
rm
at
i
o
n
t
h
at
i
s
d
isp
l
a
y
e
d
.
Cl
i
ck
Save Sett
i
n
g
s to app
ly
y
our c
h
anges, or c
l
ic
k
Ca
n
cel
C
han
g
es to cancel your changes
.
Administration > Diagnostics
Th
e
d
iagnostic tests (Ping an
d
Traceroute) a
ll
ow
y
ou to
check the connections o
f
your network devices, including
connection to t
h
e Internet
.
Ad
ministration > Diagnostics
Chapter 3 Advanced Configuration
27
Wireless-N Gigabit Router
Diagnostics
P
in
g
Tes
t
T
he Pin
g
test checks the status o
f
a connection.
IP or URL Address Enter the address of the PC whose
connection
y
ou wis
h
to test
.
Packet Size Enter the packet size you want to use. The
default is
32
bytes.
Times to Ping
E
nter man
y
times
y
ou wis
h
to test it.
Start to Ping To run the test, click this button. The
P
in
g
Test
screen will show if the test was successful. Click
t
C
lose
to return to t
h
eDiagnostic
s
s
c
reen.
D
iagnostics >
P
in
g
T
raceroute
T
est
T
he Traceroute test tests the performance of a
co
nn
ectio
n
.
IP or URL Address En
te
r
t
h
e
add
r
ess
o
f
t
h
e
P
C
wh
ose
connection
y
ou wis
h
to test
.
Start to Traceroute
T
o run the test, click this button. The
Traceroute Test
screen will show if the test was successful.
t
C
l
ic
k
Cl
os
e
to return to t
h
eDiagnostic
s
s
c
reen.
Diagnostics > Tracerout
e
Administration > Factory De
f
ault
s
Th
e
A
dministration > Factor
y
De
f
ault
s
screen a
ll
ows
y
ou
to restore the Router’s con
f
iguration to its
f
actory de
f
ault
settings.
A
dministration > Factory Default
s
NOTE: Do not restore the factory defaults unless
y
ou are having di
ff
iculties with the Router and
have exhausted all other troubleshootin
g
m
easures. Once t
h
e Router is reset, you wi
ll
h
ave
to re-enter all o
f
y
our con
f
iguration settings
.
Factory De
f
ault
s
Restore All Settings To reset t
h
e Router’s settings to t
h
e
de
f
ault values, click this button and then
f
ollow the on
-
screen instructions. Any settings you
h
ave save
d
wi
ll
b
e
lost when the de
f
ault settings are restored
.
A
d
ministration > Firmware Upgra
d
e
Th
eFirmware Upgra
d
e screen a
ll
ows you to upgra
d
e t
h
e
R
outer’s
f
irmware. Do not upgrade the
f
irmware unless
y
ou are experiencing problems with the Router or the new
firmware has a feature you want to use.
Ad
ministration > Firmware Upgra
d
e
NOTE: The Router may lose the settings you
have customized. Before
y
ou upgrade its
f
irmware, write down all o
f
y
our custom settings.
A
fter you upgrade its firmware, you will have to
re
-
enter all of
y
our configuration settings
.
Chapter 3 Advanced Configuration
28
Wireless-N Gigabit Router
Firmware Upgrad
e
Be
f
ore up
g
radin
g
the
f
irmware, download the Router’s
f
irmware upgrade file from the Linksys website,
www.links
y
s.com. Then extract the
f
ile
.
Please select a file to upgrade the firmware
C
li
ck
B
rowse and select the extracted firmware upgrade file
.
Start to Upgrade A
f
ter
y
ou have selected the
appropriate file, click this button, and f
o
ll
o
w
t
h
e
o
n-
sc
r
ee
n
f
f
i
nstructions.
S
tatus > Route
r
T
h
e
Router
screen displays information about the Router
r
a
nd its current settings
.
Status > Router
Router In
f
ormatio
n
Firmware Version
T
hi
s
i
s
t
h
e
v
e
r
s
i
o
n n
u
m
be
r
of
t
h
e
R
oute
r’
s
cu
rr
e
n
t
firmw
a
r
e.
Current Time
Th
is s
h
ows t
h
e time set on t
h
e Router
.
Internet MAC Address
T
his is the Router’s MAC Address,
a
s seen by your ISP
.
Host Name
I
f required b
y
y
our ISP, this was entered on
t
h
e
Basic
S
etu
p
screen.
Domain Name
I
f required by your ISP, this was entered
on t
h
eBasic Setu
p
s
c
reen.
Internet Connect
i
o
n
T
his section shows the current network information
stored in the Router. The in
f
ormation varies dependin
g
on
the Internet connection type selected on the
B
asic Setu
p
s
c
reen.
C
li
c
kR
ef
r
esh
to update the on-screen in
f
ormation
.
S
tatus > Local Network
Th
e
L
oca
l
Networ
k
screen displays information about the
k
local, wired network
.
Status
> L
oca
l N
et
w
o
rk
Loca
l
Networ
k
Local MAC Address The MAC address of the Router’s
local, wired inter
f
ace is displa
y
ed here
.
Router IP Address
T
his shows the Router’s IP address, as
i
t appears on
y
our
l
oca
l
networ
k.
Subnet Mask Thi
s
s
h
o
w
s
t
h
e
Sub
n
et
M
as
k
of
t
h
e
R
oute
r
.
DH
C
P
S
erve
r
DHCP Server Th
e
status
of
t
h
e
R
oute
r’
s
DH
C
P
se
rv
e
r
f
unction is displayed here
.
Start IP Address
F
or the range of IP addresses used b
y
d
evices on
y
our
l
oca
l
networ
k
, t
h
e starting IP a
dd
ress is
s
h
o
wn h
e
r
e.
End IP Address For the range of IP addresses used b
y
d
evices on
y
our
l
oca
l
networ
k
, t
h
e en
d
ing IP a
dd
ress is
s
h
o
wn h
e
r
e.
DHCP Clients Table
C
lick this button to view a list of PCs
that are usin
g
the Router as a DHCP server
.
D
H
C
P
C
li
e
n
ts
T
ab
l
e

Chapter 3 Advanced Configuration
29
Wireless-N Gigabit Router
D
HCP Client Tabl
e
T
he DHCP Client Table lists com
p
uters and other
d
evices t
h
at
h
ave
b
een assigne
d
IP a
dd
resses
by
t
h
e
Router. The list can be sorted by Client Name, Inter
f
ace,
IP Address, MAC Address, and Ex
p
ired Time (how
m
uch time is le
f
t
f
or the current IP address
)
. To remove
a
DHCP client, click
De
l
ete
. To retrieve the most u
p
-to-
date information
,
clic
k
R
efres
h
. To exit this screen and
r
eturn to t
h
e
L
oca
l
Networ
k
s
creen
,
c
l
ic
k
C
l
os
e
.
S
t
a
t
u
s > Wire
l
ess Netw
o
r
k
T
he Wireless Networ
k
screen displays information about
k
y
our wire
l
ess networ
k
.
Status
> Wir
e
l
ess
Wireless Netw
o
r
k
MAC Address The MAC address of the Router’s local,
wireless interface is displa
y
ed here
.
Mode
D
isp
l
a
y
e
d
h
ere is t
h
e wire
l
ess mo
d
e use
d
by
t
h
e
net
w
o
rk
.
Network Name (SSID)
D
ispla
y
ed here is the name of the
wire
l
ess networ
k
, w
h
ic
h
is a
l
so ca
ll
e
d
t
h
e SSID
.
Radio Band
S
hown here is the Radio Band settin
g
se
l
ecte
d
on t
h
eBasic Wire
l
ess Settings
s
c
reen
.
Wide Channel Shown here is the Wide Channel settin
g
se
l
ected
o
n
t
h
e
Basic Wireless Settin
g
s
sc
r
ee
n
.
Standard Channel S
h
own
h
ere is t
h
e Stan
d
ar
d
C
h
anne
l
settin
g
selected on the
B
asic Wireless Settin
gs
screen.
Security Displayed here is the wireless security method
u
se
d
by
t
h
e Router.
SSID Broadcast Displa
y
ed here is the status o
f
the SSID
Br
oadcast
f
eatu
r
e.
Appendix A Troubleshooting
30
Wireless-N Gigabit Router
A
ppen
d
ix A:
Trou
bl
es
h
ootin
g
Y
our computer cannot connect to t
h
e Internet.
Follow these instructions until your computer can connect
to the Internet
:
Ma
k
e sure t
h
at t
h
e Router is powere
d
on. T
h
e Power
s
LED should be
g
reen and not
f
lashin
g.
If the Power LED is flashing, then power off all o
f
s
y
our networ
k
d
evices, inc
l
u
d
ing t
h
e mo
d
em, Router,
a
nd computers. Then power on each device in the
f
ollowing order:
Ca
bl
e or DSL mo
d
e
m
1.
Route
r
2.
Com
p
uter
3.
C
h
ec
k
t
h
e ca
bl
e connections. T
h
e computer s
h
ou
ld
s
b
e connected to one o
f
the ports numbered 1-4 on
the Router, and the modem must be connected to the
Internet port on t
h
e Router
.
The modem does not have an Ethernet
p
ort
.
T
he modem is a dial-u
p
modem for traditional dial-u
p
service. To use t
h
e Router,
y
ou nee
d
a ca
bl
e/DSL mo
d
em
a
nd hi
g
h-speed Internet connection
.
Y
ou cannot use the DSL service to connect manuall
y
to
t
h
e Internet
.
Af
ter you have installed the Router, it will automatically
connect to your Internet Service Provider (ISP), so you no
l
onger nee
d
to connect manua
lly.
The DSL tele
p
hone line does not t into the Router’s
I
nternet
p
ort
.
Th
e Router
d
oes not rep
l
ace
y
our mo
d
em. You sti
ll
nee
d
your DSL modem in order to use the Router. Connect the
tele
p
hone line to the DSL modem, and then insert the
setup CD into
y
our computer. C
l
ic
k
S
etup and
f
ollow the
o
n
-
sc
r
ee
n
i
n
st
r
uctio
n
s.
When
y
ou double-click the web browser,
y
ou are
prompted
f
or a username and password. I
f
you want to
g
et rid o
f
the prompt,
f
ollow these instructions
.
Launch the web browser and perform the following steps
(these steps are speci
f
ic to Internet Explorer but are similar
f
or other browsers
):
Se
l
ect
1.
T
oo
l
s
>
Internet O
p
tion
s
.
C
l
ic
k
t
h
e2
.
C
onnect
i
on
s
ta
b
.
Se
l
ect
3.
Ne
v
e
r
d
i
a
l
a
co
nn
ect
i
on
.
C
li
c
k
4.
OK
.
The Router does not have a coaxial port
f
or the cable
co
nn
ectio
n
.
T
he Router does not replace your modem. You still need
y
our ca
bl
e mo
d
em in or
d
er to use t
h
e Router. Connect
y
our cable connection to the cable modem, and then
i
nsert the setup CD into your computer. Clic
k
Setu
p
a
n
d
f
ollow the on
-
s
creen
i
nstruct
i
ons
.
The computer cannot connect wirelessly to the network
.
M
a
k
e
su
r
e
t
h
e
wir
e
l
ess
n
et
w
o
rk n
a
m
e
o
r
SS
ID i
s
t
h
e
sa
m
e
on both the computer and the Router. If
y
ou have enabled
wireless securit
y
, then make sure the same securit
y
m
ethod and key are used by both the computer and the
Router.
Y
ou need to modi
f
y the settings on the Router
.
O
p
en the web browser (for exam
p
le, Internet Ex
p
lorer or
Firefox)
,
and enter the Router’s IP address in the address
f
ield
(
the de
f
ault IP address is
1
92
.
1
68.
1
.1
)
. When
p
rom
p
ted, enter the
p
assword to the Router (the default is
a
d
mi
n
). C
l
ic
k
t
h
e appropriate ta
b
to c
h
ange t
h
e settings
.
WEB: If your questions are not addressed here,
refer to the Links
y
s website,
w
ww.
l
in
k
s
y
s.co
m

Appendix B Specifications
31
Wireless-N Gigabit Router
A
ppen
d
ix B:
Sp
ecifications
Mo
d
e
l
W
RT310N
Sta
n
da
r
ds
Dra
f
t 802.11n, 802.11
g
, 802.11b
,
802.3, 802.3u, 802.3a
b
Ports Power
,
Internet
,
an
d
Et
h
erne
t
Butto
n
s
Reset, Wi-Fi Protected Setu
p
LE
D
s Ethernet (1-4), Wi-Fi Protecte
d
S
etup, Wire
l
ess, Internet, Power
Cabling Typ
e
C
AT
5e
Number of Antenna
s
3
Max. Rate
d
RF power: 17.5
d
Bm +/- 1.5
dB
UPnP able
/
cert
Ab
l
e
S
ecurity Feature
s
W
E
P
, W
P
A, W
P
A
2
S
ecurit
y
Ke
y
Bits
1
28-Bi
t
Environmental
D
im
e
n
s
i
o
n
s
7
.
9
5
" x
6.3
" x 1
.3
4
"
(202 x 160 x 34 mm
)
W
ei
ght
1
3.40 oz (0.38
kg)
Po
w
er
12V
Certicatio
n
FCC
,
CE
,
IC-03
,
Wi-F
i
O
peratin
g
Temp
.
3
2 to 104°F
(
0 to 40°C
)
S
tora
g
e Temp. -4 to 140°F (-20 to 60°C)
Operating Humi
d
it
y
1
0 to 85% Noncon
d
ensin
g
S
torage Humi
d
it
y
5
to 90% Noncon
d
ensin
g
* Th
e
R
oute
r h
as
t
w
o
m
a
in
a
n
te
nn
as.
Specications are subject to change without notice.
Appendix C Warranty Information
32
Wireless-N Gigabit Router
A
ppen
d
ix C:
Warrant
y
Informatio
n
Limited Warrant
y
Linksys warrants this Linksys hardware product against
defects in materials and workmanshi
p
under normal
u
se
f
or the Warrant
y
Period, which begins on the date o
f
p
urchase by the original end-user purchaser and lasts
f
or
the
p
eriod s
p
ecified below
:
One (1)
y
ear
f
or new produc
t
s
Ninety (90) days
f
or re
f
urbished produc
t
s
T
his limited warranty is non-transferable and extends only
to t
h
e origina
l
en
d
-user purc
h
aser. Your exc
l
usive reme
dy
a
nd Linksys’ entire liability under this limited warranty
will be for Linksys, at its option, to (a) repair the product
with new or re
f
urbished parts, (b) replace the product
with a reasonably available equivalent new or re
f
urbished
Linksys product, or (c) refund the purchase price of the
p
ro
d
uct
l
ess an
y
re
b
ates. An
y
repaire
d
or rep
l
acement
p
roducts will be warranted
f
or the remainder o
f
the
original Warranty Period or thirty (30) days, whichever is
l
onger. A
ll
pro
d
ucts an
d
parts t
h
at are rep
l
ace
d
b
ecome
the property o
f
Linksys
.
Exclusions and Limitations
T
his limited warrant
y
does not appl
y
i
f
: (a) the product
a
ssembly seal has been removed or damaged, (b) the
p
roduct has been altered or modified, except by Linksys, (c)
t
h
e pro
d
uct
d
amage was cause
d
by
use wit
h
no
n
-
Lin
k
s
y
s
p
roducts, (d) the product has not been installed, operated,
r
e
p
aired, or maintained in accordance with instructions
supp
l
ie
d
by
Lin
k
s
y
s, (e) t
h
e pro
d
uct
h
as
b
een su
b
jecte
d
to
a
bnormal physical or electrical stress, misuse, negligence,
or accident, (f) the serial number on the Product has been
a
ltered, de
f
aced, or removed, or (g) the product is supplied
or licensed
f
or beta, evaluation, testin
g
or demonstration
p
urposes for which Linksys does not charge a purchase
p
rice or license
f
ee
.
A
LL
SO
FTWARE PR
O
VIDED BY LINK
S
Y
S
WITH THE
PRODUCT, WHETHER FACTORY LOADED ON THE
PR
O
DU
C
T
O
R
CO
NTAINED
O
N MEDIA A
CCO
MPANYING
T
HE PRODUCT, IS PROVIDED “AS IS” WITHOUT WARRANTY
OF ANY KIND. Without limiting the foregoing, Linksys does
n
ot warrant that the operation o
f
the product or so
f
tware
will be uninterrupted or error
f
ree. Also, due to the
continual development of new techniques for intruding
u
pon an
d
attac
k
ing networ
k
s, Lin
k
s
y
s
d
oes not warrant
that the product, so
f
tware or any equipment, system or
n
etwork on which the
p
roduct or software is used will be
f
ree o
f
vulnerabilit
y
to intrusion or attack. The product
m
ay include or be bundled with third party so
f
tware or
service offerings. This limited warranty shall not apply to
such third part
y
so
f
tware or service o
ff
erings. This limited
warranty does not guarantee any continued availability
of a third party’s service for which this product’s use or
operat
i
on ma
y
requ
i
re.
TO
THE EXTENT N
O
T PR
O
HIBITED BY LAW, ALL IMPLIED
W
ARRANTIES AND CONDITIONS OF MERCHANTABILITY
,
S
ATI
S
FA
C
T
O
RY
Q
UALITY
O
R FITNE
SS
F
O
R A PARTI
C
ULAR
P
U
RP
OS
E ARE LIMITED T
O
THE D
U
RATI
O
N
O
F THE
W
ARRANTY PERIOD. ALL OTHER EXPRESS OR IMPLIED
CO
NDITI
O
N
S,
REPRE
S
ENTATI
O
N
S
AND WARRANTIE
S,
IN
C
LUDING, BUT N
O
T LIMITED T
O
, ANY IMPLIED
W
ARRANTY OF NON-INFRINGEMENT
,
ARE DISCLAIMED.
S
ome
j
uris
d
ictions
d
o not a
ll
ow
l
imitations on
h
ow
l
ong
a
n implied warranty lasts, so the above limitation may not
a
pply to you. This limited warranty gives you specific legal
r
ig
h
ts, an
d
y
ou ma
y
a
l
so
h
ave ot
h
er rig
h
ts w
h
ic
h
var
y
by
j
urisdiction
.
T
O THE EXTENT NOT PROHIBITED BY LAW
,
IN NO EVEN
T
W
ILL LINK
S
Y
S
BE LIABLE F
O
R ANY L
OS
T DATA
,
REVENUE
O
R PR
O
FIT,
O
R F
O
R
S
PE
C
IAL, INDIRE
C
T,
CO
N
S
E
Q
UENTIAL,
INCIDENTAL OR PUNITIVE DAMAGES
,
REGARDLESS OF THE
T
HEORY OF LIABILITY
(
INCLUDING NEGLIGENCE
),
ARISING
OU
T
O
F
O
R RELATED T
O
THE
US
E
O
F
O
R INABILITY T
O
USE THE PRODUCT (INCLUDING ANY SOFTWARE)
,
EVEN
IF LINK
S
Y
S
HA
S
BEEN ADVI
S
ED
O
F THE P
OSS
IBILITY
O
F
SUC
H DAMAGE
S.
IN N
O
EVENT WILL LINK
S
Y
S
’ LIABILITY
EXCEED THE AMOUNT PAID BY YOU FOR THE PRODUCT.
T
he
f
oregoing limitations will appl
y
even i
f
an
y
warrant
y
or remedy provided under this limited warranty
f
ails o
f
i
ts essential purpose. Some jurisdictions do not allow
the exclusion or limitation o
f
incidental or consequential
damages, so the above limitation or exclusion may not
a
pply to you
.
Obtaining Warranty Service
I
f
you have a question about your product or experience a
p
roblem with it, please go to
www.linksys.com/support
ypp
where
y
ou will
f
ind a variet
y
o
f
online support tools and
i
n
f
ormation to assist you with your product. I
f
the product
p
roves defective during the Warranty Period, contact
Links
y
s Technical Support
f
or instructions on how to
obtain warranty service. The telephone number
f
or Linksys
T
echnical Support in your area can be found in the product
User Gui
d
e an
d
at
www.linksys.com
y
. Have
y
our pro
d
uct
serial number and proo
f
o
f
purchase on hand when callin
g
.
A
DATED PROOF OF ORIGINAL PURCHASE IS RE
Q
UIRED
T
O PROCESS WARRANTY CLAIMS. I
f
y
ou are requested to
r
eturn your product, you will be given a Return Materials
A
uthorization (RMA) number. You are res
p
onsible for
p
roper
ly
pac
k
aging an
d
s
h
ipping
y
our pro
d
uct to Lin
k
s
y
s
a
t your cost and risk. You must include the RMA number
a
nd a copy of your dated proof of original purchase when
r
eturning
y
our pro
d
uct. Pro
d
ucts receive
d
wit
h
out a RMA
n
umber and dated proo
f
o
f
ori
g
inal purchase will be

Appendix C Warranty Information
33
Wireless-N Gigabit Router
r
ejected. Do not include any other items with the product
y
ou are returning to Links
y
s. De
f
ective product covered
b
y this limited warranty will be repaired or replaced and
r
eturned to you without charge. Customers outside o
f
the United States o
f
America and Canada are responsible
f
or all shippin
g
and handlin
g
char
g
es, custom duties,
VAT and other associated taxes and charges. Repairs or
r
ep
l
acements not covere
d
un
d
er t
h
is
l
imite
d
warrant
y
wi
ll
b
e subject to charge at Linksys’ then-current rates
.
Technical Suppor
t
Th
is
l
imite
d
warrant
y
is neit
h
er a service nor a support
contract. In
f
ormation about Linksys’ current technical
support offerings and policies (including any fees for
support services) can be
f
ound at:
www.linksys.com/suppor
ypp
t
.
T
his limited warranty is governed by the laws of the
juris
d
iction in w
h
ic
h
t
h
e Pro
d
uct was purc
h
ase
d
by
y
ou
.
Please direct all inquiries to: Linksys, P.O. Box 18558, Irvine,
CA 92623
.
Appendix D Regulatory Information
34
Wireless-N Gigabit Router
A
ppen
d
ix D:
R
egulator
y
Information
F
CC
S
tatemen
t
T
his device complies with Part 15 o
f
the FCC Rules.
Operation is subject to the following two conditions: (1)
T
his device ma
y
not cause harm
f
ul inter
f
erence, and (2) this
device must accept any inter
f
erence received, including
i
nterference that may cause undesired operation
.
Th
is pro
d
uct
h
as
b
een teste
d
an
d
comp
l
ies wit
h
t
h
e
speci
f
ications
f
or a Class B di
g
ital device, pursuant to Part
1
5 of the FCC Rules. These limits are designed to provide
r
easonable protection against harm
f
ul inter
f
erence in
a
residential installation. This equipment
g
enerates,
u
ses, and can radiate radio frequency energy and, if not
i
nsta
ll
e
d
an
d
use
d
accor
d
ing to t
h
e instructions, ma
y
cause
h
a
rm
fu
l in
te
r
fe
r
e
n
ce
to
r
ad
i
o
co
mm
u
ni
cat
i
o
n
s.
However, there is no guarantee that interference will not
occur in a particular installation. I
f
this equipment does
cause harm
f
ul inter
f
erence to radio or television rece
p
tion,
which is found by turning the equipment off and on, the
u
ser is encouraged to tr
y
to correct the inter
f
erence b
y
one or more o
f
the
f
ollowin
g
measures
:
Reorient or relocate the receiving antenn
a
s
Increase t
h
e separation
b
etween t
h
e equipment or
s
de
vi
ces
Connect the e
q
ui
p
ment to an outlet other than the
s
r
eceiver
’
s
Consult a dealer or an ex
p
erienced radio/TV technician
s
f
or assistanc
e
FCC Caution: An
y
changes or modi
f
ications not expressl
y
a
pproved by the party responsible
f
or compliance could
void the user’s authority to operate this equipment
.
FCC Radiation Exposure Statement
T
his equipment complies with FCC radiation exposure
limits set forth for an uncontrolled environment. This
equipment s
h
ou
ld
b
e insta
ll
e
d
an
d
operate
d
wit
h
m
inimum distance 20cm between the radiator and your
b
ody.
Th
is transmitter must not
b
e co-
l
ocate
d
or operating in
conjunction with any other antenna or transmitter. IEEE
802.11b or 802.11g operation of this product in the USA is
f
irmware-limited to channels 1 through 11
.
S
a
f
ety Notice
s
Caution: To reduce the risk o
f
f
ire, use onl
y
No.26 AWG
s
or lar
g
er telecommunication line cord
.
Do not use this
p
roduct near water, for exam
p
le, in a
s
wet
b
asement or near a swimming poo
l.
A
void usin
g
this product durin
g
an electrical storm.
s
T
here may be a remote risk of electric shock from
l
ig
h
tning
.
WARNING: T
h
is pro
d
uct contains
l
ea
d
,
k
nown
to the State of California to cause cancer, and
b
irth defects or other reproductive harm. Wash
hands a
f
ter handlin
g.
In
d
ustr
y
Cana
d
a Statement
Th
is C
l
ass B
d
igita
l
apparatus comp
l
ies wit
h
Cana
d
ian
I
C
E
S
-
003
a
n
d
R
SS
21
0.
Operation is subject to the following two conditions
:
T
his device ma
y
not cause interference an
d
1.
T
his device must accept an
y
inter
f
erence, including2
.
i
nterference that may cause undesired operation of the
d
evice. T
h
is
d
evice
h
as
b
een
d
esigne
d
to operate wit
h
a
n antenna havin
g
a maximum
g
ain o
f
2dBi. Antenna
having a higher gain is strictly prohibited per regulations
of Industr
y
Canada. The required antenna impedance
is
50
oh
m
s.
T
o reduce potential radio interference to other users,
t
h
e antenna t
y
pe an
d
its gain s
h
ou
ld
b
e so c
h
osen
that the EIRP is not more than re
q
uired for successful
commun
i
cat
i
on.
In
d
ustry Cana
d
a Ra
d
iation Exposure Statement
:
Th
is equipment comp
l
ies wit
h
IC ra
d
iation exposure
l
imits
set
f
orth
f
or an uncontrolled environment. This equipment
should be installed and o
p
erated with minimum distance
20cm
b
etween t
h
e ra
d
iator &
y
our
b
o
dy.
T
his transmitter must not be co-located or operatin
g
in
conjunction with any other antenna or transmitter
.
Appendix D Regulatory Information
35
Wireless-N Gigabit Router
Avis d’Industrie Canada
Cet appareil numérique de la classe B est con
f
orme aux
no
rm
es
NMB-
003
et
R
SS
21
0
du
Ca
n
ada.
L’utilisation de ce dis
p
ositif est autorisée seulement aux
con
d
itions suivantes
:
i
l ne doit pas produire de brouilla
g
e et
1.
i
l doit accepter tout brouillage radioélectrique reçu,
2.
m
ême si ce
b
roui
ll
age est suscepti
bl
e
d
e compromettre
le
f
onctionnement du dispositi
f
. Le dispositi
f
a été
conçu pour fonctionner avec une antenne ayant un gain
m
aximum
d
e 2
d
Bi. Les règ
l
ements
d
’In
d
ustrie Cana
d
a
i
n
te
r
d
i
se
n
t
st
ri
cte
m
e
n
t
l’
ut
ili
sat
i
o
n
d
’
a
n
te
nn
es
do
n
t
l
e
gain est supérieur à cette limite. L’impédance requise
d
e
l
’antenne est
d
e 50 o
h
ms.
Af
in de réduire le risque d’inter
f
érence aux autres
u
tilisateurs, le type d’antenne et son gain doivent
être choisis de
f
açon à ce que la puissance isotrope
r
ayonnée équivalente (p.i.r.e.) ne soit pas supérieure
a
u niveau re
q
uis
p
our obtenir une communication
satis
f
aisante
.
Avis
d
’In
d
ustrie Cana
d
a concernant
l
’exposition
a
ux radiofréquences
:
Ce matériel est conforme aux limites établies
p
ar IC
en matière d’exposition aux radio
f
réquences dans un
e
nvir
o
nn
e
m
e
n
t
n
o
n
co
n
t
r
ô
l
é.
Ce
m
até
ri
e
l
do
i
t
êt
r
e
in
sta
ll
é
et utilisé à une distance d’au moins 20 cm entre l’antenne
et
l
e corps
d
e
l
’uti
l
isateur.
L’émetteur ne doit
p
as être
p
lacé
p
rès d’une autre antenne
ou d’un autre émetteur
,
ou fonctionner avec une autre
a
ntenne ou un autre
é
metteur.
Wire
l
ess Disc
la
ime
r
T
he maximum
p
erformance for wireless is derived from
IEEE Standard 802.11 speci
f
ications. Actual per
f
ormance
can vary, including lower wireless network capacity,
data throughput rate, range and coverage. Performance
depends on man
y
f
actors, conditions and variables,
i
ncludin
g
distance
f
rom the access point, volume o
f
n
etwork traffic, building materials and construction,
operating s
y
stem used, mix o
f
wireless products used,
i
n
te
r
fe
r
e
n
ce
a
n
d
ot
h
e
r
ad
v
e
r
se
co
n
d
i
t
i
o
n
s.
Avis de non-responsabilité concernant les
a
ppareils sans fil
Les per
f
ormances maximales pour les réseaux sans
f
il
sont tirées des s
p
écifications de la norme IEEE 802.11.
Les per
f
ormances réelles peuvent varier, notamment
en
f
onction de la capacité du réseau sans
f
il, du débit
de la transmission de données, de la
p
ortée et de la
couverture. Les per
f
ormances dépendent de
f
acteurs,
conditions et variables multiples, en particulier de la
distance
p
ar ra
pp
ort au
p
oint d’accès, du volume du trafic
r
éseau
,
d
es matériaux uti
l
isés
d
ans
l
e
b
âtiment et
d
u
type de construction, du système d’exploitation et de la
combinaison de
p
roduits sans fil utilisés, des interférences
et de toute autre condition dé
f
avorable
.
Appendix D Regulatory Information
36
Wireless-N Gigabit Router
User In
f
ormation
f
or Consumer Products
Covered by EU Directive 2002/96/EC on
Waste E
l
ectric an
d
E
l
ectronic E
q
ui
p
ment
(
WEEE
)
T
his document contains important in
f
ormation
f
or users
with regards to the proper disposal and recycling o
f
Linksys products. Consumers are required to comply with
this notice
f
or all electronic products bearing the
f
ollowing
symbol
:
En
g
lish - Environmental Information for Customers in
th
e Euro
p
ean Unio
n
Euro
p
ean Directive 2002/96/EC re
q
uires that the e
q
ui
p
ment
bearing this s
y
mbol on the product and/or its packa
g
in
g
must
n
ot be disposed of with unsorted municipal waste. The s
y
mbol
i
ndicates that this product should be disposed of separatel
y
f
rom regular household waste streams. It is
y
our responsibilit
y
to
d
is
p
ose of this and other electric and electronic e
q
ui
p
ment via
d
esignated collection facilities appointed b
y
the government or
l
ocal authorities. Correct disposal and rec
y
cling will help prevent
p
otential ne
g
ative consequences to the environment and
h
uman health. For more detailed information about the dis
p
osal
o
f
y
our old equipment, please contact
y
our local authorities,
w
aste disposal service, or the shop where
y
ou purchased the
p
roduct.
Български (Bu
lg
arian) - Информация относно
о
пазването на околната с
р
еда за пот
р
ебители в
Ев
р
опе
й
ския съюз
Европейска директива 2002/96/EC изисква
у
редите, носещи
т
о
зи
с
имв
о
л върх
у
изделието и/или опаковката м
у
, да не
се изхвъ
р
ля т с несо
р
ти
р
ани битови отпадъци. Символът
обозначава, че изделието т
р
ябва да се изхвъ
р
ля отделно от
сметосъби
р
ането на обикновените битови отпадъци. Ваша
е отговорността този и др
у
гите електрически и електронни
у
реди да се изхвърлят в предварително определени от
държавните или общински органи специализирани п
у
нктове
за съби
р
ане. П
р
авилното изхвъ
р
ляне и
р
ецикли
р
ане
ще спомогнат да се предотвратят евент
у
ални вредни за
околната с
р
еда и зд
р
авето на населението последствия. За
по-под
р
обна ин
ф
о
р
мация относно изхвъ
р
лянето на вашите
стари
у
реди се обърнете към местните власти, сл
у
жбите за
сметосъбиране или магазина, от който сте зак
у
пили
у
реда.
C
eština
(
Czech
)
-
Informace o ochraně životního
prostře
d
í pro zá
k
azní
ky
v zemíc
h
Evrops
k
é uni
e
Evrops
k
á směrnice 2002/96/ES za
k
azuje, a
b
y zařízení označené
tímto sym
b
o
l
em na pro
d
u
k
tu ane
b
o na o
b
a
l
u
b
y
l
o
l
i
k
vi
d
ováno
s
netří
d
ěným
k
omuná
l
ním o
d
pa
d
em. Tento sym
b
o
l
u
d
ává,
ž
e
d
aný pro
d
u
k
t musí
b
ýt
l
i
k
vi
d
ován o
dd
ě
l
eně o
d
b
ěžné
h
o
k
omuná
l
ní
h
o o
d
pa
d
u. O
d
poví
d
áte za
l
i
k
vi
d
aci to
h
oto pro
d
u
k
tu
a
d
a
l
šíc
h
e
l
e
k
tric
k
ýc
h
a e
l
e
k
tronic
k
ýc
h
zařízení prostře
d
nictvím
u
rčenýc
h
s
b
ěrnýc
h
míst stanovenýc
h
v
l
á
d
ou ne
b
o místními
ú
řa
d
y. Správná
l
i
k
vi
d
ace a recy
kl
ace pomá
h
á pře
d
c
h
ázet
p
otenciálním negativním dopad
ů
m na životní prostředí a lidské
z
draví. Podrobnější in
f
ormace o likvidaci starého vybavení si
l
askavě vyžádejte od místních úřad
ů
, podniku zabývajícího se
l
ikvidací komunálních odpad
ů
nebo obchodu, kde jste produkt
z
a
k
oupi
l
i.
Dansk (Danish) - Miljøin
f
ormation
f
or kunder i E
U
EU-direktiv 2002/96/EF kræver, at udstyr der bærer dette symbol
på produktet o
g
/eller emballa
g
en ikke må bortskaffes som
u
sorteret kommunalt affald. S
y
mbolet bet
y
der, at dette produkt
s
kal bortskaffes adskilt fra det almindelige husholdningsaffald.
D
et er dit ansvar at bortska
ff
e dette og andet elektrisk og
el
e
k
tronis
k
u
d
styr via
b
estemte in
d
sam
l
ingsste
d
er u
d
peget
af
staten eller de lokale myndigheder. Korrekt bortska
ff
else
o
g genvinding vil hjælpe med til at undg
å
mulige skader for
m
i
l
jøet og mennes
k
ers sun
dh
e
d
. Konta
k
t ven
l
igst
d
e
l
o
k
a
l
e
m
yn
d
ig
h
e
d
er, renovationstjenesten e
ll
er
d
en
b
uti
k
,
h
vor
d
u
h
ar købt produktet, ang
å
ende mere detaljeret information om
b
ortska
ff
else a
f
dit gamle udstyr.
Deutsch
(
German
)
- Umweltinformation für Kunden
inner
h
a
lb
d
er Europäisc
h
en Unio
n
Die Europäisc
h
e Ric
h
t
l
inie 2002/96/EC ver
l
angt,
d
ass tec
h
nisc
h
e
Ausrüstung,
d
ie
d
ire
k
t am Gerät un
d
/o
d
er an
d
er Verpac
k
ung mit
d
iesem Sym
b
o
l
verse
h
en ist
,
nic
h
t zusammen mit unsortiertem
G
emeindeab
f
all entsorgt werden dar
f
. Das Symbol weist darau
f
h
in,
d
ass
d
as Pro
d
u
k
t von regu
l
ärem Haus
h
a
l
tmü
ll
getrennt
e
ntsorgt wer
d
en so
ll
te. Es
l
iegt in I
h
rer Verantwortung,
d
ieses
G
erät un
d
an
d
ere e
l
e
k
trisc
h
e un
d
e
l
e
k
tronisc
h
e Geräte ü
b
er
d
ie da
f
ür zuständigen und von der Regierung oder örtlichen
B
e
h
ör
d
en
d
azu
b
estimmten Samme
l
ste
ll
en zu entsorgen.
O
rdnungsgemä
ß
es Entsorgen und Recyceln trägt dazu bei,
p
otentielle negative Folgen
f
ür Umwelt und die menschliche
G
esundheit zu vermeiden. Wenn Sie weitere In
f
ormationen zur
E
ntsorgung I
h
rer A
l
tgeräte
b
enötigen, wen
d
en Sie sic
h
b
itte an
d
ie ört
l
ic
h
en Be
h
ör
d
en o
d
er stä
d
tisc
h
en Entsorgungs
d
ienste
od
er an
d
en Hän
dl
er,
b
ei
d
em Sie
d
as Pro
d
u
k
t erwor
b
en
h
a
b
en.
Appendix D Regulatory Information
37
Wireless-N Gigabit Router
Eesti
(
Estonian
)
- Keskkonnaalane informatsioon
Euroopa Lii
d
us asuvate
l
e
kl
ienti
d
e
le
Euroopa Liidu direktiivi 2002/96/E
Ü
nõuete kohaselt on
sea
d
mei
d
, mi
ll
e
l
on toote
l
või pa
k
en
d
i
l
k
äeso
l
ev süm
b
o
l
,
k
ee
l
atu
d
k
õrva
ld
a
d
a
k
oos sorteerimata o
l
mejäätmetega. See
süm
b
o
l
näita
b
, et too
d
e tu
l
e
k
s
k
õrva
ld
a
d
a era
ld
i tava
l
istest
o
l
mejäätmevoogu
d
est. O
l
ete
k
o
h
ustatu
d
k
õrva
ld
ama
k
äeso
l
eva
ja
k
a muu
d
e
l
e
k
tri- ja e
l
e
k
trooni
k
asea
d
me
d
riigi või
k
o
h
a
l
i
k
e
ametiasutuste poo
l
t ette nä
h
tu
d
k
ogumispun
k
ti
d
e
k
au
d
u.
Sea
d
mete
k
orre
k
tne
k
õrva
ld
amine ja ring
l
ussevõtt aita
b
vä
l
ti
d
a
võima
l
i
kk
e negatiivsei
d
tagajärgi
k
es
kk
onna
l
e ning inimeste
tervise
l
e. Vana
d
e sea
d
mete
k
õrva
ld
amise
k
o
h
ta täpsema
in
f
ormatsiooni saamiseks võtke palun ühendust kohalike
ametiasutustega, jäätmekäitlus
f
irmaga või kauplusega, kust te
toote osts
i
te.
Español (Spanish) - In
f
ormación medioambiental para
c
lientes de la Unión Euro
p
ea
La Directiva 2002/96/CE de la UE exi
g
e que los equipos que
ll
e
v
e
n
este
s
ím
bo
l
o
en el propio aparato
y
/o en su embalaje
no deben eliminarse
j
unto con otros residuos urbanos no
seleccionados. El símbolo indica
q
ue el
p
roducto en cuestión
debe se
p
ararse de los residuos domésticos convencionales con
vistas a su eliminación. Es responsabilidad su
y
a desechar este
y
cualesquiera otros aparatos eléctricos
y
electrónicos a través de
los puntos de recogida que ponen a su disposición el gobierno
y
las autoridades locales. Al desechar
y
reciclar correctamente estos
aparatos estará contribu
y
endo a evitar posibles consecuencias
negativas para el medio ambiente
y
la salud de las personas. Si
desea
obte
n
e
r inf
o
rm
ac
i
ó
n m
ás
deta
ll
ada
sob
r
e
l
a
e
limin
ac
i
ó
n
se
g
ura de su aparato usado, consulte a las autoridades locales,
al servicio de recogida
y
eliminación de residuos de su zona o
pre
g
unte en la tienda donde adquirió el producto.
ξ
λληνικά (Greek) - Στοιχεία περιβαλλοντικής
προστασίας για πελάτες εντός της Ευρωπαϊκής
Ένωσ
η
ς
Η Κοινοτικ
ή
Οδ
ηγ
ία 2002/96/EC απαιτεί ότι ο εξοπλισ
μ
ός ο οποίος
φ
έ
ρ
ει αυτό το σύ
μβ
ολο στο π
ρ
οϊόν και/
ή
στ
η
συσκευασία
του δεν π
ρ
έπει να απο
ρρ
ίπτεται
μ
αζί
μ
ε τα
μ
ικτά κοινοτικά
απο
ρρ
ί
μμ
ατα. Το σύ
μβ
ολο υποδεικνύει ότι αυτό το π
ρ
οϊόν θα
πρέπει να απορρίπτεται ξε
χ
ωριστά από τα συνήθη οικιακά
απο
ρρ
ί
μμ
ατα. Είστε υπεύθυνος
γ
ια τ
η
ν από
ρρ
ι
ψη
του πα
ρ
όντος
και άλλου
η
λεκτ
ρ
ικού και
η
λεκτ
ρ
ονικού εξοπλισ
μ
ού
μ
έσω των
καθο
ρ
ισ
μ
ένων ε
γ
καταστάσεων συ
γ
κέντ
ρ
ωσ
η
ς απο
ρρ
ι
μμ
άτων οι
οποίες παρέ
χ
ονται από το κράτος ή τις αρμόδιες τοπικές αρ
χ
ές.
Η σωστ
ή
από
ρρ
ι
ψη
και ανακύκλωσ
η
συ
μβ
άλλει στ
η
ν π
ρ
όλ
ηψη
πιθανών α
ρ
ν
η
τικών συνεπειών
γ
ια το πε
ρ
ι
β
άλλον και τ
η
ν υ
γ
εία.
Για περισσότερες πληροφορίες σ
χ
ετικά με την απόρριψη του
παλιού σας εξοπλισ
μ
ού, πα
ρ
ακαλώ επικοινων
ή
στε
μ
ε τις τοπικές
αρ
χ
ές, τις υπηρεσίες απόρριψης ή το κατάστημα από το οποίο
α
γ
ο
ρ
άσατε το π
ρ
οϊόν.
Français (French) - Informations environnementales
pour
l
es c
l
ients
d
e
l
’Union européenn
e
La
d
irective européenne 2002/96/CE exige que
l
’équipement
sur
l
eque
l
est apposé ce sym
b
o
l
e sur
l
e pro
d
uit et/ou son
em
b
a
ll
age ne soit pas jeté avec
l
es autres or
d
ures ménagères. Ce
sym
b
o
l
e in
d
ique que
l
e pro
d
uit
d
oit être é
l
iminé
d
ans un circuit
d
istinct
d
e ce
l
ui pour
l
es
d
éc
h
ets
d
es ménages. I
l
est
d
e votre
responsa
b
i
l
ité
d
e jeter ce matérie
l
ainsi que tout autre matérie
l
é
l
ectrique ou é
l
ectronique par
l
es moyens
d
e co
ll
ecte in
d
iqués
par
l
e gouvernement et
l
es pouvoirs pu
bl
ics
d
es co
ll
ectivités
territoriales. L’élimination et le recyclage en bonne et due
f
orme
ont pour but de lutter contre l’impact né
f
aste potentiel de ce
type
d
e pro
d
uits sur
l
’environnement et
l
a santé pu
bl
ique. Pour
plus d’in
f
ormations sur le mode d’élimination de votre ancien
équipement, veui
ll
ez pren
d
re contact avec
l
es pouvoirs pu
bl
ics
l
ocaux,
l
e service
d
e traitement
d
es
d
éc
h
ets, ou
l
’en
d
roit où vous
avez ac
h
eté
l
e pro
d
uit
.
Italiano (Italian) - In
f
ormazioni relative all’ambiente
p
er i clienti residenti nell’Unione Euro
p
e
a
La direttiva euro
p
ea 2002/96/EC richiede che le a
pp
arecchiature
contrasse
g
nate con questo simbolo sul
p
rodotto e/o
s
ull’imballa
gg
io non siano smaltite insieme ai rifiuti urbani
n
on differenziati. Il simbolo indica che
q
uesto
p
rodotto non
de
v
e
esse
r
e
s
m
a
l
t
i
to
in
s
i
e
m
e
a
i n
o
rm
a
li rifi
ut
i
do
m
est
i
c
i
.
È
r
es
p
onsabilità del
p
ro
p
rietario smaltire sia
q
uesti
p
rodotti sia
l
e altre a
pp
arecchiature elettriche ed elettroniche mediante
l
e specifiche strutture di raccolta indicate dal
g
overno o da
g
li
e
nti pubblici locali. Il corretto smaltimento ed il ricicla
gg
io
a
iuteranno a prevenire conse
g
uenze potenzialmente ne
g
ative
p
er l’ambiente e
p
er la salute dell’essere umano. Per ricevere
i
nformazioni più detta
g
liate circa lo smaltimento delle vecchie
a
pparecchiature in Vostro possesso, Vi invitiamo a contattare
g
li
e
nti
p
ubblici di com
p
etenza, il servizio di smaltimento rifiuti o il
n
e
g
ozio nel quale avete acquistato il prodotto.
Latviešu valoda (Latvian) - Ekoloģiska informācija
k
lientiem Eiropas Savienības jurisdikcij
ā
Dire
k
tīvā 2002/96/EK ir prasī
b
a,
k
a aprī
k
ojumu,
k
am pievienota
z
ī
me uz paša izstrādājuma vai uz tā iesaiņojuma, nedrīkst
i
zmest neš
ķ
irotā veidā kopā ar komunālajiem atkritumiem
(
tiem, ko rada vietēji iedzīvotāji un uz
ņ
ēmumi). Šī zīme nozīmē
t
o, ka šī ierīce ir jāizmet atkritumos tā, lai tā nenonāktu kopā ar
p
arastiem mā
j
saimniecības atkritumiem. Jūsu pienākums ir šo
u
n citas elektriskas un elektroniskas ierīces izmest atkritumos
,
i
zmantojot īpašus atkritumu savākšanas veidus un līdzek
ļ
us, ko
n
odrošina valsts un
p
ašvaldību iestādes. Ja izmešana atkritumos
u
n pārstrāde tiek veikta pareizi, tad mazinās iespē
j
amais
k
aitējums dabai un cilvēku veselībai. Sīkākas zi
ņ
as par
n
ovecojuša aprīkojuma izmešanu atkritumos jūs varat sa
ņ
emt
v
ietē
j
ā pašvaldībā, atkritumu savākšanas dienestā, kā arī veikalā,
k
ur iegādā
j
āties šo izstrādā
j
umu.
Appendix D Regulatory Information
38
Wireless-N Gigabit Router
Lietuvškai (Lithuanian) - Aplinkosaugos informaci
j
a,
sk
irta Europos Sąjungos vartotojam
s
Europos
d
ire
k
tyva 2002/96/EC numato,
k
a
d
įrangos,
k
uri ir
k
urios pa
k
uotė yra pažymėta šiuo sim
b
o
l
iu (įves
k
ite sim
b
o
l
į),
nega
l
ima ša
l
inti
k
artu su nerūšiuotomis
k
omuna
l
inėmis
atliekomis.
Š
is simbolis rodo, kad gaminį reikia šalinti atskirai
nuo
b
en
d
ro
b
uitinių at
l
ie
k
ų srauto. Jūs priva
l
ote užti
k
rinti,
k
a
d
ši ir
k
ita e
l
e
k
tros ar e
l
e
k
troninė įranga
b
ūtų ša
l
inama per tam
ti
k
ras naciona
l
inės ar vietinės va
ld
žios nustatytas at
l
ie
k
ų rin
k
imo
sistemas. Tin
k
amai ša
l
inant ir per
d
ir
b
ant at
l
ie
k
as,
b
us išvengta
galimos žalos aplinkai ir žmonių sveikatai. Daugiau in
f
ormacijos
apie jūsų senos įrangos ša
l
inimą ga
l
i patei
k
ti vietinės va
ld
žios
institucijos, at
l
ie
k
ų ša
l
inimo tarny
b
os ar
b
a par
d
uotuvės,
k
uriose
į
sigijote tą gamin
į
.
M
alti (Maltese) - In
f
ormazzjoni Ambjentali għal Klijenti
f
l-Un
j
oni Ewropea
Id-Direttiva Ewropea 2002/96/KE titlob li t-tagħmir li
j
kun fih is-
s
im
bo
l
u
fuq il-prodott u/
j
ew fuq l-ippakk
j
ar ma
j
istax
j
intrema
m
a’ skart muniċipali li ma ġiex isseparat. Is-simbolu
j
indika
l
i dan il-prodott għandu
j
intrema separatament minn ma’ l-
i
skart domestiku regolari. Hi
j
a responsabbiltà tiegħek li tarmi
d
an it-ta
g
ħmir u kull ta
g
ħmir ieħor ta’ l-elettriku u elettroniku
p
ermezz ta’ faċilita
j
iet ta’ ġbir appuntati apposta mill-gvern
j
ew
m
ill-awtorita
j
iet lokali. Ir-rimi b’mod korrett u r-riċiklaġġ
j
għin
j
ipprev
j
eni konsegwenzi negattivi potenz
j
ali għall-amb
j
ent u
g
ħas-saħħa tal-bniedem. Għal aktar informazz
j
oni dettal
j
ata
d
war ir-rimi tat-tagħmir antik tiegħek,
j
ekk
j
ogħġbok ikkuntatt
j
a
l
ill-awtorita
j
iet lokali tiegħek, is-servizzi għar-rimi ta’ l-iskart,
j
ew
i
l-ħanut minn fe
j
n xtra
j
t il-prodott.
M
ag
y
ar (Hungarian) - Körn
y
ezetvédelmi in
f
ormáció az
e
urópai uniós vásárlók számár
a
A 2002/96/EC számú európai uniós iránye
l
v meg
k
ívánja,
h
ogy
azo
k
at a termé
k
e
k
et, ame
l
ye
k
en, és/vagy ame
l
ye
k
csomago
l
ásán
az a
l
á
bb
i cím
k
e meg
j
elenik, tilos a többi szelektálatlan lakossági
h
u
ll
a
d
é
kk
a
l
együtt
k
i
d
o
b
ni. A cím
k
e azt je
l
ö
l
i,
h
ogy az a
d
ott
termék kidobásakor a szokván
y
os háztartási hulladékelszállítási
rendszerektõl elkülönített eljárást kell alkalmazni. Az
Ö
n
f
elelõssége, hogy ezt, és más elektromos és elektronikus
b
eren
d
ezéseit a
k
ormányzati vagy a
h
e
l
yi
h
atóságo
k
á
l
ta
l
kijelölt gyűjtõredszereken keresztül számolja
f
el. A meg
f
elelõ
hulladék
f
eldolgozás segít a környezetre és az emberi egészségre
potenciá
l
isan árta
l
mas negatív
h
atáso
k
mege
l
õzésé
b
en. Ha
elavult berendezéseinek
f
elszámolásához további részletes
in
f
ormációra van szüksége, kérjük, lépjen kapcsolatba a helyi
hatóságokkal, a hulladék
f
eldolgozási szolgálattal, vagy azzal
üz
l
ette
l
, a
h
o
l
a termé
k
et vásáro
l
ta.
Nederlands
(
Dutch
)
- Milieu-informatie voor klanten
in
d
e Europese Uni
e
De Europese Richtlijn 2002/96/EC schrij
f
t voor dat apparatuur die
is voorzien van
d
it sym
b
oo
l
op het product o
f
de verpakking,
niet mag wor
d
en ingezame
ld
met niet-gesc
h
ei
d
en
h
uis
h
ou
d
e
l
ij
k
a
f
val. Dit symbool gee
f
t aan dat het product apart moet worden
ingezameld. U bent zel
f
verantwoordelijk voor de vernietiging
van
d
eze en an
d
ere e
l
e
k
trisc
h
e en e
l
e
k
tronisc
h
e apparatuur via
d
e
daarvoor door de landelijke o
f
plaatselijke overheid aangewezen
inzame
l
ings
k
ana
l
en. De juiste vernietiging en recyc
l
ing van
d
eze apparatuur voor
k
omt moge
l
ij
k
e negatieve gevo
l
gen voor
het milieu en de gezondheid. Voor meer in
f
ormatie over het
vernietigen van uw ou
d
e apparatuur neemt u contact op met
de plaatselijke autoriteiten o
f
a
f
valverwerkingsdienst, o
f
met de
winkel waar u het product hebt aangescha
f
t.
Norsk (Norwegian) - Miljøin
f
ormasjon
f
or kunder i E
U
EU-direktiv 2002/96/EF krever at utstyr med følgende symbol
avbildet på produktet o
g
/eller paknin
g
en, ikke må kastes
s
ammen med usortert avfall. S
y
mbolet indikerer at dette
p
roduktet skal h
å
ndteres atskilt fra ordinær avfallsinnsamling
f
or husholdningsavfall. Det er ditt ansvar å kvitte deg med
d
ette produktet og annet elektrisk og elektronisk av
f
all via egne
i
nnsam
l
ingsor
d
ninger s
l
i
k
myn
d
ig
h
etene e
ll
er
k
ommunene
b
estemmer. Korrekt avfallsh
å
ndtering og gjenvinning vil
v
ære med p
å
å
forhindre mulige negative konsekvenser for
m
iljø og helse. For nærmere informasjon om h
å
ndtering av
d
et
k
asserte utstyret
d
itt,
k
an
d
u ta
k
onta
k
t me
d
k
ommunen,
e
n innsamlingsstasjon
f
or av
f
all eller butikken der du kjøpte
p
ro
d
u
k
tet.
Polski (Polish) - Informac
j
a dla klientów w Unii
Europejs
k
iej o przepisac
h
d
ot
y
cząc
y
c
h
oc
h
ron
y
ś
r
odo
wi
s
k
a
D
y
rekt
y
wa Europejska 2002/96/EC w
y
maga, ab
y
sprzęt
oznaczon
y
s
y
mbolem znajdując
y
m się na produkcie i/lub jego
o
pa
k
owaniu nie
b
y
ł
wyrzucany razem z innymi niesortowanymi
o
dpadami komunaln
y
mi. S
y
mbol ten wskazuje, że produkt
nie powinien
b
yć usuwany razem ze zwy
kł
ymi o
d
pa
d
ami z
g
ospo
d
arstw
d
omowyc
h
. Na Państwu spoczywa o
b
owiąze
k
w
yrzucania tego i innyc
h
urzą
d
zeń e
l
e
k
trycznyc
h
oraz
el
e
k
tronicznyc
h
w pun
k
tac
h
o
db
ioru wyznaczonyc
h
przez w
ł
a
d
ze
k
rajowe
l
u
b
l
o
k
a
l
ne. Poz
b
ywanie się sprzętu we w
ł
aściwy sposó
b
i
jego recy
kl
ing pomogą zapo
b
iec potencja
l
nie negatywnym
k
onse
k
wencjom
dl
a śro
d
owis
k
a i z
d
rowia
l
u
d
z
k
iego. W ce
l
u
u
zyskania szczegółowych in
f
ormacji o usuwaniu starego sprzętu,
prosimy zwrócić się
d
o
l
o
k
a
l
nyc
h
w
ł
a
d
z, s
ł
uż
b
oczyszczania
miasta
l
u
b
s
kl
epu, w
k
tórym pro
d
u
k
t zosta
ł
na
b
yty.
Appendix D Regulatory Information
39
Wireless-N Gigabit Router
Português (Portuguese) - Informação ambiental para
cl
ientes
d
a União Europei
a
A Directiva Europeia 2002
/
96
/C
E exige que o equipamento
que exi
b
e este sím
b
o
l
o no pro
d
uto e/ou na sua em
b
a
l
agem
n
ão seja e
l
imina
d
o junto com os resí
d
uos municipais não
s
epara
d
os. O sím
b
o
l
o in
d
ica que este pro
d
uto
d
eve ser
el
imina
d
o separa
d
amente
d
os resí
d
uos
d
omésticos regu
l
ares.
É
da sua responsabilidade eliminar este e qualquer outro
e
quipamento e
l
éctrico e e
l
ectrónico através
d
as insta
l
ações
d
e reco
lh
a
d
esigna
d
as pe
l
as autori
d
a
d
es governamentais ou
l
ocais. A e
l
iminação e recic
l
agem correctas aju
d
arão a prevenir
a
s consequências negativas para o am
b
iente e para a saú
d
e
h
umana. Para obter in
f
ormações mais detalhadas sobre a
f
orma de eliminar o seu equipamento antigo, contacte as
a
utori
d
a
d
es
l
ocais, os serviços
d
e e
l
iminação
d
e resí
d
uos ou o
e
sta
b
e
l
ecimento comercia
l
on
d
e a
d
quiriu o pro
d
uto.
Română (Romanian) - In
f
orma
ţ
ii de mediu pentru
c
lien
ţ
ii din Uniunea European
ă
Directiva euro
p
eană 2002/96/CE im
p
une ca echi
p
amentele care
p
rezintă acest simbol pe produs şi/sau pe ambala
j
ul acestuia să
nu fie casate împreună cu gunoiul mena
j
er municipal. Simbolul
indică fa
p
tul că acest
p
rodus trebuie să fie casat se
p
arat de
gunoiul menajer obişnuit. Este responsabilitatea dvs. să casa
ţ
i
acest produs
ş
i alte echipamente electrice
ş
i electronice prin
intermediul unită
ţ
ilor de colectare special desemnate de guvern
sau de autorită
ţ
ile locale. Casarea şi reciclarea corecte vor ajuta
la prevenirea poten
ţ
ialelor consecin
ţ
e negative asupra sănătă
ţ
ii
mediului şi a oamenilor. Pentru mai multe informa
ţ
ii detaliate
cu privire la casarea acestui echipament vechi, contacta
ţ
i
autorită
ţ
ile locale, serviciul de salubrizare sau magazinul de la
care a
ţ
i achizi
ţ
ionat produsul.
Slovenčina (Slovak) - In
f
ormácie o ochrane životného
prostredia pre zákazníkov v Európskej úni
i
Podľa európskej smernice 2002/96/ES zariadenie s t
ý
mto
sym
b
o
l
om na produkte a/alebo jeho balení nesmie by
ť
l
ikvidované spolu s netrieden
ý
m komunáln
y
m odpadom.
S
ymbol znamená, že produkt by sa mal likvidova
ť
oddelene
o
d bežného odpadu z domácností. Je vašou povinnos
ť
ou
l
ikvidova
ť
toto i ostatné elektrické a elektronické zariadenia
p
rostre
d
níctvom špecia
l
izovanýc
h
z
b
ernýc
h
zaria
d
ení určenýc
h
vl
á
d
ou a
l
e
b
o miestnymi orgánmi. Správna
l
i
k
vi
d
ácia a recy
kl
ácia
p
omôže zabráni
ť
prípadným negatívnym dopadom na životné
p
rostredie a zdravie
ľ
udí. Ak máte záujem o podrobnejšie
i
nformácie o likvidácii starého zariadenia, obrá
ť
te sa, prosím, na
m
iestne orgány, organizácie zao
b
erajúce sa
l
i
k
vi
d
áciou o
d
pa
d
ov
al
e
b
o o
b
c
h
o
d
, v
k
torom ste si pro
d
u
k
t za
k
úpi
l
i.
Slovenčina (Slovene) - Okol
j
ske informaci
j
e za stranke
v Evrops
k
i unij
i
Evrops
k
a
d
ire
k
tiva 2002/96/EC prepove
d
uje o
dl
aganje opreme,
označene s tem sim
b
o
l
om – na iz
d
e
lk
u in/a
l
i na em
b
a
l
aži – me
d
o
b
ičajne, nerazvrščene o
d
pa
dk
e. Ta sim
b
o
l
opozarja,
d
a je tre
b
a
iz
d
e
l
e
k
o
d
vreči
l
očeno o
d
preosta
l
i
h
gospo
d
injs
k
i
h
o
d
pa
dk
ov.
Vaša o
d
govornost je,
d
a to in preosta
l
o e
l
e
k
trično in e
l
e
k
trons
k
o
opremo o
d
nesete na pose
b
na z
b
ira
l
išča,
k
i ji
h
d
o
l
očijo
d
ržavne ustanove a
l
i
l
o
k
a
l
na uprava. S pravi
l
nim o
dl
aganjem
in reci
kl
iranjem
b
oste prepreči
l
i more
b
itne š
k
o
dl
jive vp
l
ive na
okolje in zdravje ljudi.
Č
e želite izvedeti več o odlaganju stare
opreme, se o
b
rnite na
l
o
k
a
l
no upravo, o
d
pa
d
a
l
i trgovino,
k
jer
ste iz
d
e
l
e
k
k
upi
l
i
.
Suomi (Finnish) - Ympäristöä koskevia tietoja EU
-
alueen asiakkaille
EU-direktiivi 2002/96/EY edell
y
ttää, että jos laitteistossa on tämä
s
y
mboli itse tuotteessa
j
a/tai sen pakkauksessa, laitteistoa
ei saa hävittää lajittelemattoman
y
hd
y
skuntajätteen mukana.
S
y
mboli merkitsee sitä, että tämä tuote on hävitettävä erillään
tavallisesta kotitalous
j
ätteestä. Sinun vastuullasi on hävittää
tämä elektroniikkatuote
j
a muut vastaavat elektroniikkatuotteet
vi
e
m
ä
ll
ä
tuote
ta
i
tuotteet
vir
a
n
o
m
a
i
ste
n m
ää
r
ää
m
ää
n
kerä
y
spisteeseen. Laitteiston oikea hävittäminen estää
mahdolliset kielteiset vaikutukset
y
mpäristöön ja ihmisten
terve
y
teen. Lisätietoja vanhan laitteiston oikeasta hävit
y
stavasta
saa paikallisilta viranomaisilta, jätteenhävit
y
spalvelusta tai siitä
m
yy
mälästä, josta ostit tuotteen.
Svenska (Swedish) - Miljöin
f
ormation
f
ör kunder i
Europeiska unione
n
Det europeis
k
a
d
ire
k
tivet 2002/96/EC
k
räver att utrustning me
d
d
enna symbol p
å
produkten och/eller förpackningen inte f
å
r
k
astas med osorterat kommunalt av
f
all. Symbolen visar att denna
produkt bör kastas efter att den avskiljts fr
å
n vanligt hush
å
llsavfall.
Det faller p
å
ditt ansvar att kasta denna och annan elektrisk och
e
lektronisk utrustning p
å
fastställda insamlingsplatser utsedda
av regeringen e
ll
er
l
o
k
a
l
a myn
d
ig
h
eter. Korre
k
t
k
assering oc
h
å
tervinning skyddar mot eventuella negativa konsekvenser
f
ör miljön och personhälsa. För mer detaljerad in
f
ormation om
k
assering av
d
in gam
l
a utrustning
k
onta
k
tar
d
u
d
ina
l
o
k
a
l
a
myndigheter, av
f
allshanteringen eller butiken där du köpte
pro
d
u
k
ten
.
WEB: For additional information,
p
lease visit
www.
l
in
k
s
y
s.com

40
Appendix E Software License Agreement
Wireless-N Gigabit Router
A
ppendix E: Software
L
icense Agreemen
t
S
oftware in Linksys Product
s
T
his product
f
rom Cisco-Linksys LLC or
f
rom one o
f
its
a
ffiliates Cisco Systems-Linksys (Asia) Pte Ltd. or Cisco
-
Links
y
s K.K. (“Links
y
s”) contains so
f
tware (including
f
irmware) originating
f
rom Linksys and its suppliers
a
nd may also contain software from the open source
communit
y
. An
y
so
f
tware originating
f
rom Links
y
s and its
suppliers is licensed under the Linksys So
f
tware License
A
greement contained at Schedule 1 below. You may also
b
e prompted to review and accept that Links
y
s So
f
tware
License A
g
reement upon installation o
f
the so
f
twar
e
A
ny software from the open source community is licensed
u
nder the speci
f
ic license terms applicable to that so
f
tware
m
ade available by Linksys at
www.linksys.com/gpl
ygp
o
r
as
p
rovided for in Schedules 2, 3 and 4 below
.
W
here such speci
f
ic license terms entitle
y
ou to the source
code o
f
such so
f
tware, that source code is u
p
on re
q
uest
a
vailable at cost from Linksys for at least three years
f
rom the purchase date o
f
this product and ma
y
also be
a
v
a
il
ab
l
e
fo
r
do
wnl
oad
f
r
o
m
www.linksys.com/gpl
ygp
.
F
o
r
detailed license terms and additional information on
open source so
f
tware in Links
y
s products please look at
the Linksys public web site at:
www.linksys.com/gpl/
ygp
o
r
S
chedules 2, 3 or 4 below as a
pp
licable
.
BY D
O
WNL
O
ADING
O
R IN
S
TALLING THE
SO
FTWARE
,
O
R U
S
ING THE PR
O
DU
C
T
CO
NTAINING THE
SO
FTWARE,
YOU ARE CONSENTING TO BE BOUND BY THE SOFTWARE
LI
C
EN
S
E AGREEMENT
S
BEL
O
W. IF Y
O
U D
O
N
O
T AGREE T
O
A
LL
O
F THE
S
E TERM
S
, THEN Y
O
U MAY N
O
T D
O
WNL
O
AD,
INSTALL OR USE THE SOFTWARE. YOU MAY RETURN
UNUSED SOFTWARE
(
OR
,
IF THE SOFTWARE IS SUPPLIED
A
S PART OF ANOTHER PRODUCT, THE UNUSED PRODUCT
)
FOR A FULL REFUND UP TO 30 DAYS AFTER ORIGINAL
PUR
C
HA
S
E
,
S
UBJE
C
T T
O
THE RETURN PR
OC
E
SS
AND
P
O
LI
C
IE
S
O
F THE PARTY FR
O
M WHI
C
H Y
OU
P
U
R
C
HA
S
ED
S
UCH PRODUCT OR SOFTWARE
.
S
oftware Licenses
T
he so
f
tware Licenses applicable to so
f
tware
f
rom Linksys
a
re made available at the Linksys public web site at:
www.linksys.com
y
. For
y
our convenience o
f
re
f
erence, a
copy o
f
the Linksys So
f
tware License Agreement and the
m
ain open source code licenses used by Linksys in its
p
ro
d
ucts are containe
d
in t
h
e Sc
h
e
d
u
l
es
b
e
l
ow
.
Schedule 1 - Links
y
s So
f
tware License Agreemen
t
T
HI
S
LI
C
EN
S
E AGREEMENT I
S
BETWEEN Y
OU
AND
CISCO-LINKSYS LLC OR ONE OF ITS AFFILIATES CISCO
S
YSTEMS-LINKSYS
(
ASIA
)
PTE LTD. OR CISCO-LINKSYS
K.K.
(
“LINKSYS”
)
LICENSING THE SOFTWARE INSTEAD OF
CISCO-LINKSYS LLC. BY DOWNLOADING OR INSTALLING
T
HE
SO
FTWARE
,
O
R U
S
ING THE PR
O
DU
C
T
CO
NTAINING
T
HE
SO
FTWARE, Y
O
U ARE
CO
N
S
ENTING T
O
BE B
O
UND BY
T
HIS AGREEMENT. IF YOU DO NOT AGREE TO ALL OF THESE
T
ERM
S,
THEN Y
O
U MAY N
O
T D
O
WNL
O
AD
,
IN
S
TALL
O
R U
S
E
T
HE
SO
FTWARE
.
Y
OU
MAY RET
U
RN
U
N
US
ED
SO
FTWARE
(OR
,
IF THE SOFTWARE IS SUPPLIED AS PART OF ANOTHER
PRODUCT
,
THE UNUSED PRODUCT
)
FOR A FULL REFUND
UP T
O
30 DAY
S
AFTER
O
RIGINAL PUR
C
HA
S
E,
S
UBJE
C
T T
O
T
HE RETURN PROCESS AND POLICIES OF THE PARTY FROM
W
HI
C
H Y
O
U PUR
C
HA
S
ED
S
U
C
H PR
O
DU
C
T
O
R
SO
FTWARE
.
Li
ce
n
se
.Sub
j
ect to the terms and conditions o
f
this
A
greement, Linksys grants the original end user purchaser
o
f
the Links
y
s product containing the So
f
tware (“You”)
a
nonexclusive license to use the So
f
tware solely as
embedded in or (where authorized in the a
pp
licable
documentation)
f
or communication with such product.
T
his license may not be sublicensed, and is not trans
f
erable
except to a person or entity to which you transfer
ownership o
f
the complete Links
y
s product containing
the So
f
tware, provided you permanently trans
f
er all rights
u
nder this Agreement and do not retain any full or partial
copies o
f
the So
f
tware, and the recipient agrees to the
terms o
f
this A
g
reement
.
“
Software” includes, and this Agreement will apply to
(
a
)
the software of Links
y
s or its suppliers provided in or
with the applicable Links
y
s product, excluding technolog
y
f
rom the open source community, and (b) any upgrades,
u
pdates, bug fixes or modified versions (“Upgrades”) or
b
ackup copies o
f
the So
f
tware supplied to You b
y
Links
y
s
or an authorized reseller, provided you already hold a
valid license to the original software and have paid an
y
a
pplicable
f
ee
f
or the Up
g
rade.
Pr
otect
i
o
n
o
f Inf
o
rm
at
i
o
n
.
Th
e
So
f
t
w
a
r
e
a
n
d
d
ocumentation contain tra
d
e secrets an
d
/or cop
y
rig
h
te
d
m
aterials o
f
Links
y
s or its suppliers. You will not cop
y
or modify the Software or decompile, decrypt, reverse
engineer or disassemble the Software (except to the
extent expressl
y
permitted b
y
law notwithstanding this
p
rovision), and You will not disclose or make available
such trade secrets or cop
y
righted material in an
y
form
to an
y
third part
y
. Title to and ownership o
f
the So
f
tware
a
nd documentation and any portion thereof, will remain
so
l
e
ly
wit
h
Lin
k
s
y
s or its supp
l
iers
.
Collection and Processin
g
o
f
In
f
ormation
.
You a
g
ree that
Linksys and/or its affiliates may, from time to time, collect
a
nd process in
f
ormation about
y
our Links
y
s product and
/
or the So
f
tware and/or
y
our use o
f
either in order (i) to
enable Linksys to offer you Upgrades; (ii) to ensure that

41
Appendix E Software License Agreement
Wireless-N Gigabit Router
your Linksys product and/or the Software is being used in
a
ccordance with the terms o
f
this Agreement; (iii) to provide
i
mprovements to the way Linksys delivers technology to
you and to other Linksys customers; (iv) to enable Linksys
to compl
y
with the terms o
f
an
y
agreements it has with
a
ny third parties regarding your Linksys product and/or
S
oftware and/or (v) to enable Linksys to comply with all
a
pp
l
ica
bl
e
l
aws an
d
/or regu
l
ations, or t
h
e requirements
o
f
any regulatory authority or government agency.
Linksys and/ or its affiliates may collect and process
this in
f
ormation provided that it does not identi
fy
y
ou
p
ersonally. Your use o
f
your Linksys product and/or the
S
oftware constitutes this consent by you to Linksys and
/
or its a
ff
iliates’ collection and use o
f
such in
f
ormation and
,
f
or EEA customers, to the trans
f
er o
f
such in
f
ormation to a
location outside the EEA
.
So
f
tware Upgrades etc
.
I
f
the So
f
tware enables
y
ou to
r
eceive Upgrades, you may elect at any time to receive
these Upgrades either automatically or manually. If you
e
l
ect to receive Upgra
d
es manua
lly
or
y
ou ot
h
erwise
elect not to receive or be noti
f
ied o
f
any Upgrades, you
m
ay expose your Linksys product and/or the Software
to serious securit
y
threats and/or some
f
eatures within
your Linksys product and/or So
f
tware may become
i
naccessible. There may be circumstances where we
a
pp
ly
an Upgra
d
e automatica
lly
in or
d
er to comp
ly
wit
h
changes in legislation, legal or regulatory requirements
or as a result of requirements to comply with the terms
o
f
an
y
agreements Links
y
s has with an
y
third parties
r
egarding your Linksys product and/or the So
f
tware. You
will always be notified of any Upgrades being delivered
to
y
ou. The terms o
f
this license will appl
y
to an
y
such
Up
g
rade unless the Up
g
rade in question is accompanied
b
y a separate license, in which event the terms of that
l
icense wi
ll
app
ly.
O
p
en Source So
f
tware
.
The GPL or other o
p
en source
code incor
p
orated into the Software and the o
p
en source
license
f
or such source code are available
f
or
f
ree download
at
http://www.linksys.com/gpl
pygp
. I
f
You would like a copy
of the GPL or other o
p
en source code in this Software on a
CD, Links
y
s will mail to You a CD with such code for $9.99
p
lus the cost o
f
shippin
g
, upon request
.
Term and Termination. You may terminate this License
a
t an
y
time b
y
destro
y
ing all copies o
f
the So
f
tware
a
nd documentation. Your ri
g
hts under this License will
terminate immediately without notice from Linksys if You
f
ail to compl
y
with an
y
provision o
f
this Agreement
.
Limited Warrant
y.
The warranty terms and period
specified in the applicable Linksys Product User Guide
shall also appl
y
to the So
f
tware
.
Di
sc
l
a
im
e
r
of
Li
ab
ili
t
i
es
. IN N
O
EVENT WILL LINK
S
Y
S
O
R
ITS SUPPLIERS BE LIABLE FOR ANY LOST DATA
,
REVENUE
O
R PR
O
FIT
,
O
R F
O
R
S
PE
C
IAL
,
INDIRE
C
T
,
CO
N
S
E
Q
UENTIAL
,
IN
C
IDENTAL
O
R PUNITIVE DAMAGE
S
, REGARDLE
SS
O
F
CAUSE (INCLUDING NEGLIGENCE)
,
ARISING OUT OF
OR RELATED TO THE USE OF OR INABILITY TO USE THE
SO
FTWARE
,
EVEN IF LINK
S
Y
S
HA
S
BEEN ADVI
S
ED
O
F
T
HE P
OSS
IBILITY
O
F
SUC
H DAMAGE
S.
IN N
O
EVENT WILL
LINKSYS’ LIABILITY EXCEED THE AMOUNT PAID BY YOU
FOR THE PRODUCT. The
f
oregoing limitations will appl
y
even i
f
any warranty or remedy under this Agreement
f
ails
of its essential purpose. Some jurisdictions do not allow
the exclusion or limitation o
f
incidental or consequential
damages, so the above limitation or exclusion may not
a
pply to You.
E
xport. So
f
tware, including technical data, ma
y
be subject
to U.S. export control laws and re
g
ulations and/or export
or import regulations in other countries. You agree to
comp
ly
strict
ly
wit
h
a
ll
suc
h
l
aws an
d
regu
l
ations
.
U
.
S
. G
o
v
e
rnm
e
n
t
Use
r
s.
Th
e
Soft
w
a
r
e
a
n
d
docu
m
e
n
tat
i
o
n
qualify as “commercial items” as defined at 48 C.F.R. 2.101
a
n
d
48 C.F.R. 12.212. A
ll
Government users acquire t
h
e
S
o
f
tware and documentation with only those rights
herein that apply to non-governmental customers
.
Genera
l
Terms
.
T
h
is Agreement wi
ll
b
e governe
d
by
an
d
co
n
st
r
ued
in
acco
r
da
n
ce
wi
t
h
t
h
e
l
a
w
s
of
t
h
e
State
of
California, without reference to conflict of laws
p
rinci
p
les.
T
he United Nations Convention on Contracts
f
or the
International Sale o
f
Goods will not apply. I
f
any portion
of this Agreement is found to be void or unenforceable,
the remaining provisions will remain in
f
ull
f
orce and
e
ff
ect. This A
g
reement constitutes the entire a
g
reement
b
etween the
p
arties with res
p
ect to the Software and
supersedes an
y
con
f
licting or additional terms contained
i
n any purchase order or elsewhere
.
END OF SCHEDULE 1
Sc
h
e
dul
e
2
If this Linksys product contains open source software
licensed under Version 2 o
f
the “GNU General Public
Li
ce
n
se
”
t
h
e
n
t
h
e
li
ce
n
se
te
rm
s
be
l
o
w in
t
hi
s
Sc
h
edu
l
e
2
will apply to that open source software. The license terms
b
elow in this Schedule 2 are
f
rom the public web site at
http://www.gnu.org/copyleft/gpl.html
pggpygp
GNU GENERAL PUBLIC LICENS
E
Version 2
,
June 1991
Cop
y
right © 1989, 1991 Free So
f
tware Foundation, Inc.
5
1 Franklin Street, Fi
f
th Floor, Boston, MA 02110-1301,
US
A
Ever
y
one is permitte
d
to cop
y
an
d
d
istri
b
ute ver
b
atim
copies o
f
this license document, but chan
g
in
g
it is not
a
llowed
.
P
re
a
m
bl
e
T
he licenses
f
or most so
f
tware are designed to take awa
y
your
f
reedom to share and change it. By contrast, the
42
Appendix E Software License Agreement
Wireless-N Gigabit Router
GNU General Public License is intended to guarantee your
f
reedom to share and change
f
ree so
f
tware–to make sure
t
h
e
soft
w
a
r
e
i
s
f
r
ee
fo
r
a
ll i
ts
use
r
s.
Thi
s
G
e
n
e
r
a
l P
ub
li
c
License a
pp
lies to most of the Free Software Foundation’s
so
f
tware and to an
y
other program whose authors
commit to usin
g
it. (Some other Free So
f
tware Foundation
software is covered by the GNU Lesser General Public
License instea
d
.) You can app
ly
it to
y
our programs, too.
W
hen we speak o
f
f
ree so
f
tware, we are re
f
errin
g
to
f
reedom, not
p
rice. Our General Public Licenses are
designed to make sure that
y
ou have the
f
reedom to
distribute copies o
f
f
ree so
f
tware (and char
g
e
f
or this
service if you wish), that you receive source code or can
get it i
f
y
ou want it, that
y
ou can change the so
f
tware or
u
se pieces o
f
it in new
f
ree programs; and that you know
you can do these things.
T
o protect
y
our rig
h
ts, we nee
d
to ma
k
e restrictions t
h
at
f
orbid anyone to deny you these rights or to ask you to
surrender the rights. These restrictions translate to certain
r
esponsibilities
f
or
y
ou i
f
y
ou distribute copies o
f
the
so
f
tware, or i
f
you modi
f
y it.
For example, if you distribute copies of such a program,
whether gratis or
f
or a
f
ee,
y
ou must give the recipients
a
ll the rights that you have. You must make sure that they,
too, receive or can get the source code. And you must
s
h
ow t
h
em t
h
ese terms so t
h
e
y
k
now t
h
eir rig
h
ts.
W
e protect your rights with two steps: (1) copyright the
software, and (2) offer you this license which gives you
legal permission to cop
y
, distribute and/or modi
fy
the
soft
w
a
r
e.
A
lso, for each author’s
p
rotection and ours, we want to
m
a
k
e certain t
h
at ever
y
one un
d
erstan
d
s t
h
at t
h
ere is no
warranty
f
or this
f
ree so
f
tware. I
f
the so
f
tware is modi
f
ied
b
y someone e
l
se an
d
passe
d
on, we want its recipients
to
k
now t
h
at w
h
at t
h
e
y
h
ave is not t
h
e origina
l
, so t
h
at
a
ny problems introduced by others will not re
f
lect on the
origina
l
aut
h
ors’ reputations.
Finall
y
, an
y
f
ree program is threatened constantl
y
b
y
so
f
tware patents. We wish to avoid the dan
g
er that
r
edistributors of a free program will individually obtain
p
atent licenses, in e
ff
ect making the program proprietar
y
.
T
o prevent this, we have made it clear that any patent must
b
e licensed for everyone’s free use or not licensed at all.
T
he precise terms and conditions
f
or cop
y
ing, distribution
a
n
d
m
od
i
f
i
cat
i
o
n
fo
ll
o
w
.
TERMS AND C
O
NDITI
O
NS F
O
R C
O
PYING, DISTRIBUTI
O
N AND
MO
DIFICATI
ON
T
his License applies to any program or other wor
k
0.
w
h
ic
h
contains a notice p
l
ace
d
by
t
h
e cop
y
rig
h
t
holder saying it may be distributed under the terms
of this General Public License. The “Program”, below,
r
e
f
ers to an
y
such program or work, and a “wor
k
b
ased on the Pro
g
ram” means either the Pro
g
ram
or any derivative work under copyright law: that is
to sa
y
, a wor
k
containing t
h
e Program or a portion
o
f
it, either verbatim or with modi
f
ications and
/
or translated into another language. (Hereinafter,
trans
l
ation is inc
l
u
d
e
d
wit
h
out
l
imitation in t
h
e term
“
modi
f
ication”.) Each licensee is addressed as “you”.
A
ctivities ot
h
er t
h
an cop
y
ing,
d
istri
b
ution an
d
m
odi
f
ication are not covered by this License; they
a
re outside its scope. The act of running the Program
i
s not restricted, and the output
f
rom the Program is
covered only i
f
its contents constitute a work based on
the Program (independent of having been made by
r
unning t
h
e Program). W
h
et
h
er t
h
at is true
d
epen
d
s
on what the Pro
g
ram does.
You may copy and distribute verbatim copies of the
1.
Program’s source co
d
e as
y
ou receive it, in an
y
me
d
ium,
p
rovided that
y
ou conspicuousl
y
and appropriatel
y
p
ublish on each copy an appropriate copyright
n
otice and disclaimer of warrant
y
; keep intact all the
not
i
ces
t
h
at
r
efe
r
to
t
hi
s
Li
ce
n
se
a
n
d
to
t
h
e
abse
n
ce
of any warranty; and give any other recipients of the
Program a cop
y
of this License along with the Program.
You may charge a fee for the physical act of transferring
a
cop
y
, and
y
ou ma
y
at
y
our option offer warrant
y
p
rotection in exchan
g
e
f
or a
f
ee.
You may modify your copy or copies of the Program
2.
or an
y
portion of it, thus forming a work based on the
Program, and cop
y
and distribute such modi
f
ications
or work under the terms of Section 1 above,
p
rovided
that
y
ou also meet all of these conditions:
You must cause the modi
f
ied
f
iles to carr
y
a.
p
rominent notices stating that you changed the
f
iles and the date of an
y
change.
You must cause an
y
wor
k
t
h
at
y
ou
d
istri
b
ute or
b.
p
ublish, that in whole or in
p
art contains or is
derived from the Program or an
y
part thereof, to be
l
icense
d
as a w
h
o
l
e at no c
h
ar
g
e to a
ll
t
h
ir
d
parties
u
n
de
r
t
h
e
te
rm
s
o
f
t
hi
s
Li
ce
n
se.
43
Appendix E Software License Agreement
Wireless-N Gigabit Router
If the modified program normally reads commandsc.
i
nteractive
ly
w
h
en run,
y
ou must cause it, w
h
en
started runnin
g
f
or such interactive use in the most
ordinary way, to print or display an announcement
i
nc
l
u
d
ing an appropriate cop
y
rig
h
t notice an
d
a
notice that there is no warranty (or else, saying
that you provide a warranty) and that users may
r
e
d
istri
b
ute t
h
e program un
d
er t
h
ese con
d
itions,
a
nd telling the user how to view a copy o
f
this License. (Exception: if the Program itself is
i
nteractive
b
ut
d
oes not norma
lly
print suc
h
an
a
nnouncement, your work based on the Program
i
s not re
q
uired to
p
rint an announcement.)
T
hese requirements appl
y
to the modi
f
ied work as
a
wh
o
l
e.
I
f
i
de
n
t
i
f
i
ab
l
e
sect
i
o
n
s
of
t
h
at
w
o
rk
a
r
e
n
ot
derived from the Program, and can be reasonably
consi
d
ere
d
in
d
epen
d
ent an
d
separate wor
k
s in
themselves, then this License, and its terms, do not
a
pply to those sections when you distribute them as
separate wor
k
s. But w
h
en
y
ou
d
istri
b
ute t
h
e same
sections as
p
art o
f
a whole which is a work based on
the Program, the distribution of the whole must be on
the terms o
f
this License, whose permissions
f
or other
licensees extend to the entire whole, and thus to each
a
nd every part regardless of who wrote it.
T
hus, it is not the intent o
f
this section to claim rights
or contest your rights to work written entirely by you;
r
ather, the intent is to exercise the right to control the
distribution o
f
derivative or collective works based on
the Pro
g
ram.
In addition, mere aggregation of another work not
b
ase
d
on t
h
e Program wit
h
t
h
e Program (or wit
h
a
work based on the Pro
g
ram) on a volume o
f
a stora
g
e
or distribution medium does not bring the other wor
k
u
nder the scope o
f
this License.
You may copy and distribute the Program (or a
3.
work based on it, under Section 2) in object code or
executable form under the terms of Sections 1 and 2
a
bove provided that
y
ou also do one o
f
the
f
ollowing:
A
ccompany it with the complete corresponding
a.
m
ac
h
ine-rea
d
a
bl
e source co
d
e
,
w
h
ic
h
must
b
e
d
i
st
ri
buted
u
n
de
r
t
h
e
te
rm
s
of
Sect
i
o
n
s
1
a
n
d
2
a
bove on a medium customarily used for software
i
nterc
h
ange; or,
A
ccompan
y
it with a written o
ff
er, valid
f
or at least
b.
three years, to give any third party, for a charge
n
o more than
y
our cost of ph
y
sicall
y
performing
source distribution, a complete machine-readable
copy of the corresponding source code, to be
distributed under the terms of Sections 1 and 2
a
bove on a medium customaril
y
used
f
or so
f
tware
i
nterchan
g
e; or,
A
ccompany it with the information you received as
c.
to the offer to distribute corresponding source code.
(This alternative is allowed onl
y
f
or noncommercial
distribution and only if you received the program
i
n object code or executable form with such an
o
ff
er, in accord with Subsection b above.)
T
he source code for a work means the
p
referred form
of the work for making modifications to it. For an
executa
bl
e wor
k
, comp
l
ete source co
d
e means a
ll
the source code for all modules it contains, plus any
a
ssociated interface definition files, plus the scripts
u
sed to control compilation and installation o
f
the
executable. However, as a s
p
ecial exce
p
tion, the source
co
d
e
d
istri
b
ute
d
nee
d
not inc
l
u
d
e an
y
t
h
ing t
h
at is
n
ormall
y
distributed (in either source or binar
y
f
orm)
with the major components (compiler, kernel, and so
on) of the operating s
y
stem on which the executable
r
uns, unless that component itsel
f
accompanies the
e
x
ecutab
l
e.
If distribution of executable or object code is made
by
o
ff
ering access to cop
y
f
rom a designated place,
then offering equivalent access to copy the source
code from the same place counts as distribution o
f
t
h
e source co
d
e, even t
h
ou
gh
t
h
ir
d
parties are not
compelled to copy the source along with the object
co
d
e.
You ma
y
not cop
y
, modi
fy
, sublicense, or distribute
4.
the Program except as expressly provided under
this License. An
y
attempt otherwise to cop
y
, modif
y
,
su
bl
icense or
d
istri
b
ute t
h
e Pro
g
ram is voi
d
, an
d
wi
ll
a
utomatically terminate your rights under this License.
However, parties w
h
o
h
ave receive
d
copies, or rig
h
ts,
f
rom
y
ou under this License will not have their licenses
terminated so lon
g
as such parties remain in full
com
pl
iance.
You are not require
d
to accept t
h
is License, since
y
ou
5.
have not signed it. However, nothing else grants you
p
ermission to modify or distribute the Program or its
derivative works. These actions are prohibited b
y
law i
f
you do not accept this License. There
f
ore, by modi
f
ying
or
d
istri
b
uting t
h
e Program (or any wor
k
b
ase
d
on t
h
e
Program),
y
ou indicate
y
our acceptance o
f
this License
to do so, and all its terms and conditions
f
or copying,
distributing or modifying the Program or works based
on
i
t.
Each time you redistribute the Program (or any wor
k
6.
b
ase
d
on t
h
e Program), t
h
e recipient automatica
ll
y
r
eceives a license
f
rom the original licensor to cop
y
,
distribute or modi
f
y the Program subject to these
terms and conditions. You may not impose any further
r
estrictions on the recipients’ exercise o
f
the rights
g
ranted herein. You are not responsible
f
or en
f
orcin
g
comp
l
iance
b
y t
h
ir
d
parties to t
h
is License.
44
Appendix E Software License Agreement
Wireless-N Gigabit Router
If, as a consequence of a court judgment or allegation7
.
o
f
patent in
f
ringement or
f
or an
y
other reason (not
limited to patent issues), conditions are imposed on
you (whether by court order, agreement or otherwise)
that contradict the conditions o
f
this License, the
y
do
n
ot excuse you
f
rom the conditions o
f
this License. I
f
you cannot distribute so as to satisfy simultaneously
y
our o
bl
igations un
d
er t
h
is License an
d
an
y
ot
h
er
p
ertinent obligations, then as a consequence you
m
ay not distribute the Program at all. For example,
if
a patent license would not permit ro
y
alt
y
-
f
ree
r
edistribution o
f
the Program by all those who receive
copies directly or indirectly through you, then the only
wa
y
y
ou could satis
fy
both it and this License would be
to re
f
rain entirely
f
rom distribution o
f
the Program.
If any portion of this section is held invalid or
u
nen
f
orceable under an
y
particular circumstance,
the balance o
f
the section is intended to apply and
the section as a whole is intended to apply in other
c
i
rcumstances.
It is not the purpose o
f
this section to induce you to
i
nfringe any patents or other property right claims or
to contest validit
y
o
f
an
y
such claims; this section has
the sole purpose o
f
protecting the integrity o
f
the
f
ree
software distribution system, which is implemented
by
pu
bl
ic
l
icense practices. Man
y
peop
l
e
h
ave
m
ade
g
enerous contributions to the wide ran
g
e o
f
software distributed through that system in reliance
on consistent application o
f
that s
y
stem; it is up to
the author/donor to decide i
f
he or she is willin
g
to
distribute software through any other system and a
l
icensee cannot impose t
h
at c
h
oice.
T
his section is intended to make thoroughly clear
what is believed to be a conse
q
uence of the rest of this
L
i
cense.
I
f
the distribution and/or use o
f
the Pro
g
ram is
8.
r
estricted in certain countries either by patents or by
cop
y
righted interfaces, the original cop
y
right holder
who places the Program under this License ma
y
add an
explicit
g
eo
g
raphical distribution limitation excludin
g
t
h
ose countries, so t
h
at
d
istri
b
ution is permitte
d
on
ly
i
n or amon
g
countries not thus excluded. In such case,
this License incor
p
orates the limitation as if written in
the bod
y
of this License.
T
he Free So
f
tware Foundation ma
y
publish revised
9.
a
nd/or new versions of the General Public License
f
rom time to time. Such new versions will be similar in
spirit to the present version, but ma
y
di
ff
er in detail to
a
ddress new
p
roblems or concerns.
Eac
h
version is given a
d
istinguis
h
ing version num
b
er.
I
f
the Pro
g
ram speci
f
ies a version number o
f
this
License which applies to it and “any later version”, you
have the option of following the terms and conditions
either o
f
that version or o
f
an
y
later version published
b
y the Free Software Foundation. If the Program does
n
ot specify a version number of this License, you
m
a
y
c
h
oose an
y
version ever pu
bl
is
h
e
d
by
t
h
e Free
Soft
w
a
r
e
F
ou
n
dat
i
o
n
.
If you wish to incorporate parts of the Program into
10.
other
f
ree programs whose distribution conditions are
di
ff
erent, write to the author to ask
f
or permission. For
software which is copyrighted by the Free Software
Foundation
,
write to the Free So
f
tware Foundation
;
we
sometimes make exce
p
tions
f
or this. Our decision will
b
e guided by the two goals of preserving the free status
o
f
all derivatives o
f
our
f
ree so
f
tware and o
f
promoting
the sharing and reuse o
f
so
f
tware generally.
NO
WARRANTY
BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE,
1
1
.
T
HERE I
S
N
O
WARRANTY F
O
R THE PR
O
GRAM
,
T
O
THE
EXTENT PERMITTED BY APPLI
C
ABLE LAW
.
EX
C
EP
T
W
HEN OTHERWISE STATED IN WRITING THE COPYRIGH
T
H
O
LDER
S
AND
/O
R
O
THER PARTIE
S
PR
O
VIDE THE
PR
O
GRAM “A
S
I
S
” WITH
OU
T WARRANTY
O
F ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING,
BUT N
O
T LIMITED T
O,
THE IMPLIED WARRANTIE
S
O
F
MER
C
HANTABILITY AND FITNE
SS
F
O
R A PARTI
CU
LAR
PURPOSE. THE ENTIRE RISK AS TO THE
Q
UALITY AND
PERF
O
RMAN
C
E
O
F THE PR
O
GRAM I
S
WITH Y
O
U.
S
H
O
ULD THE PR
O
GRAM PR
O
VE DEFE
C
TIVE, Y
O
U
A
SSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR
O
R
CO
RRE
C
TI
O
N.
IN N
O
EVENT UNLE
SS
RE
Q
UIRED BY APPLI
C
ABLE LAW
O
R
12.
A
GREED TO IN WRITING WILL ANY COPYRIGHT HOLDER,
OR ANY OTHER PARTY WHO MAY MODIFY AND
/
OR
REDI
S
TRIBUTE THE PR
O
GRAM A
S
PERMITTED AB
O
VE,
BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY
GENERAL
,
SPECIAL
,
INCIDENTAL OR CONSEQUENTIAL
DAMAGE
S
ARI
S
ING
OU
T
O
F THE
US
E
O
R INABILITY T
O
USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO
LOSS OF DATA OR DATA BEING RENDERED INACCURATE
O
R L
OSS
E
S
SUS
TAINED BY Y
OU
O
R THIRD PARTIE
S
O
R
A
FAIL
U
RE
O
F THE PR
O
GRAM T
O
O
PERATE WITH ANY
OTHER PROGRAMS
),
EVEN IF SUCH HOLDER OR OTHER
PARTY HA
S
BEEN ADVI
S
ED
O
F THE P
OSS
IBILITY
O
F
SUC
H DAMAGE
S.
END OF TERMS AND CONDITION
S
END
O
F
SC
HED
U
LE
2
Sche
du
le
3
I
f
this Linksys product contains open source so
f
tware
licensed under Version 2.1 of the “GNU Lesser General Public
License” t
h
en t
h
e
l
icense terms
b
e
l
ow in t
h
is Sc
h
e
d
u
l
e 3
will apply to that open source so
f
tware. The license terms
b
elow in this Schedule 3 are from the
p
ublic web site at
http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
pgg gp
.
45
Appendix E Software License Agreement
Wireless-N Gigabit Router
GNU LESSER GENERAL PUBLIC LICENS
E
Version 2.1, February 199
9
Cop
y
right (C) 1991, 1999 Free So
f
tware Foundation, Inc.
5
1 Franklin Street, Fi
f
th Floor, Boston, MA 02110-1301,
US
A
Ever
y
one is permitte
d
to cop
y
an
d
d
istri
b
ute ver
b
atim
copies o
f
this license document, but chan
g
in
g
it is not
a
llowed
.
[
This is the
f
irst released version o
f
the Lesser GPL. It also
counts as the successor o
f
the GNU Library Public License,
version 2
,
hence the version number 2.1.
]
P
ream
bl
e
T
he licenses
f
or most so
f
tware are designed to take awa
y
your
f
reedom to share and change it. By contrast, the GNU
General Public Licenses are intended to guarantee your
f
reedom to share and change
f
ree so
f
tware—to make
su
r
e
t
h
e
soft
w
a
r
e
i
s
f
r
ee
fo
r
a
ll i
ts
use
r
s.
T
his license, the Lesser General Public License, a
pp
lies to
some speciall
y
designated so
f
tware packages—t
y
picall
y
li
b
r
a
ri
es
—
of
t
h
e
Fr
ee
Soft
w
a
r
e
F
ou
n
dat
i
o
n
a
n
d
ot
h
e
r
a
uthors who decide to use it. You can use it too
,
but we
suggest
y
ou
f
irst think care
f
ull
y
about whether this license
or the ordinary General Public License is the better strategy
to use in any particular case, based on the explanations
b
e
l
ow.
W
hen we speak o
f
f
ree so
f
tware, we are re
f
errin
g
to
f
reedom of use, not
p
rice. Our General Public Licenses
a
re designed to make sure that
y
ou have the
f
reedom
to distribute copies o
f
f
ree so
f
tware (and char
g
e
f
or this
service if you wish); that you receive source code or can
get it i
f
y
ou want it; that
y
ou can change the so
f
tware and
u
se pieces o
f
it in new
f
ree programs; and that you are
i
nformed that you can do these things
.
T
o protect
y
our rig
h
ts, we nee
d
to ma
k
e restrictions t
h
at
f
orbid distributors to deny you these rights or to ask you
to surrender these rights. These restrictions translate to
certain responsibilities
f
or
y
ou i
f
y
ou distribute copies o
f
the library or i
f
you modi
f
y it
.
For example, if you distribute copies of the library,
whether gratis or
f
or a
f
ee,
y
ou must give the recipients
a
ll the rights that we gave you. You must make sure that
they, too, receive or can get the source code. If you lin
k
ot
h
er co
d
e wit
h
t
h
e
l
i
b
rar
y
,
y
ou must provi
d
e comp
l
ete
object
f
iles to the recipients, so that they can relink them
with the library after making changes to the library and
r
ecompi
l
ing it. An
d
y
ou must s
h
ow t
h
em t
h
ese terms so
they know their rights
.
W
e protect your rig
h
ts wit
h
a two-step met
h
o
d
: (1) we
cop
y
right the librar
y
, and (2) we o
ff
er
y
ou this license,
which gives you legal permission to copy, distribute and
/
or modify the library
.
T
o protect each distributor, we want to make it very clear
that there is no warrant
y
f
or the
f
ree librar
y
. Also, i
f
the
library is modi
f
ied by someone else and passed on, the
r
ecipients should know that what they have is not the
origina
l
version, so t
h
at t
h
e origina
l
aut
h
or’s reputation
will not be a
ff
ected by problems that might be introduced
b
y ot
h
ers.
Finall
y
, so
f
tware patents pose a constant threat to the
existence o
f
any
f
ree program. We wish to make sure
that a company cannot effectively restrict the users o
f
a
f
ree program b
y
obtaining a restrictive license
f
rom a
p
atent holder. There
f
ore, we insist that any patent license
obtained for a version of the library must be consistent
with the
f
ull
f
reedom o
f
use speci
f
ied in this license
.
Most GNU so
f
tware, includin
g
some libraries, is covered
b
y t
h
e or
d
inary GNU Genera
l
Pu
bl
ic License. T
h
is
l
icense,
t
h
e GNU Lesser Genera
l
Pu
bl
ic License, app
l
ies to certain
desi
g
nated libraries, and is quite di
ff
erent
f
rom the
ordinary General Public License. We use this license for
certain
l
i
b
raries in or
d
er to permit
l
in
k
ing t
h
ose
l
i
b
raries
i
nto non-
f
ree pro
g
rams.
Wh
en a program is
l
in
k
e
d
wit
h
a
l
i
b
rary, w
h
et
h
er
staticall
y
or using a shared librar
y
, the combination o
f
the two is legally speaking a combined work, a derivative
of the original library. The ordinary General Public
License there
f
ore permits such linking onl
y
i
f
the entire
co
m
b
in
at
i
o
n
f
i
ts
i
ts
c
ri
te
ri
a
of
f
r
eedo
m
.
Th
e
L
esse
r G
e
n
e
r
a
l
Public License permits more lax criteria for linking other
co
d
e wit
h
t
h
e
l
i
b
rar
y.
We
ca
ll
t
hi
s
li
ce
n
se
t
h
e
“L
esse
r” G
e
n
e
r
a
l P
ub
li
c
Li
ce
n
se
b
ecause it does Less to
p
rotect the user’s freedom than
t
h
e or
d
inar
y
Genera
l
Pu
bl
ic License. It a
l
so provi
d
es
other
f
ree so
f
tware developers Less o
f
an advanta
g
e over
competing non-free programs. These disadvantages are
t
h
e reason we use t
h
e or
d
inar
y
Genera
l
Pu
bl
ic License
f
or many libraries. However, the Lesser license provides
ad
vantages in certain specia
l
circumstances
.
For examp
l
e, on rare occasions, t
h
ere ma
y
b
e a specia
l
n
eed to encoura
g
e the widest possible use o
f
a certain
library, so that it becomes a de-facto standard. To achieve
this, non-
f
ree programs must be allowed to use the librar
y
.
A
more
f
requent case is that a
f
ree library does the same
job as widely used non-free libraries. In this case, there is
little to gain b
y
limiting the
f
ree librar
y
to
f
ree so
f
tware
only, so we use the Lesser General Public License
.
In ot
h
er cases, permission to use a particu
l
ar
l
i
b
rar
y
in non
-
f
ree pro
g
rams enables a
g
reater number o
f
people to use
a
large body of free software. For example, permission to
u
se the GNU C Librar
y
in non-free programs enables man
y
m
ore peop
l
e to use t
h
e w
h
o
l
e GNU operating s
y
stem, as
well as its variant, the GNU/Linux operating system
.
Al
t
h
oug
h
t
h
e Lesser Genera
l
Pu
bl
ic License is Less
p
rotective o
f
the users’
f
reedom, it does ensure that the
u
ser of a program that is linked with the Library has the
46
Appendix E Software License Agreement
Wireless-N Gigabit Router
f
reedom and the wherewithal to run that program using a
m
odi
f
ied version o
f
the Librar
y.
T
he precise terms and conditions
f
or copying, distribution
a
nd modification follow. Pay close attention to the
di
ff
erence between a “work based on the librar
y
” and a
“
work that uses the library”. The
f
ormer contains code
derived from the library, whereas the latter must be
com
b
ine
d
wit
h
t
h
e
l
i
b
rar
y
in or
d
er to run
.
G
N
U
LE
SS
ER
G
ENERAL P
U
BLI
C
LI
C
EN
SE
TERMS AND CONDITIONS FOR COPYING
,
DISTRIBUTION AND
MO
DIFICATI
ON
T
his License Agreement applies to any so
f
tware library
0.
or other program which contains a notice placed by
t
h
e cop
y
rig
h
t
h
o
ld
er or ot
h
er aut
h
orize
d
part
y
sa
y
ing
i
t may be distributed under the terms o
f
this Lesser
General Public License (also called “this License”). Each
l
icensee is a
dd
resse
d
as “
y
ou”.
A
“library” means a collection o
f
so
f
tware
f
unctions
a
nd/or data prepared so as to be conveniently linked
with application programs (which use some o
f
those
f
unctions and data
)
to
f
orm executables
.
T
he “Library”, below, refers to any such software library
or wor
k
w
h
ic
h
h
as
b
een
d
istri
b
ute
d
un
d
er t
h
ese terms.
A
“work based on the Library” means either the Library
or any derivative work under copyright law: that is to
sa
y
, a work containing the Librar
y
or a portion o
f
it,
either verbatim or with modi
f
ications and
/
or translated
straightforwardly into another language. (Hereinafter,
trans
l
ation is inc
l
u
d
e
d
wit
h
out
l
imitation in t
h
e term
“
modi
f
ication”.
)
“
Source code” for a work means the
p
referred form o
f
the work
f
or making modi
f
ications to it. For a librar
y
,
com
p
lete source code means all the source code
f
or
a
ll modules it contains, plus any associated interface
de
f
inition
f
iles, plus the scripts used to control
compilation and installation o
f
the library
.
A
ctivities other than copying, distribution and
m
odi
f
ication are not covered b
y
this License; the
y
are
outside its scope. The act o
f
runnin
g
a pro
g
ram usin
g
the Library is not restricted, and output from such a
p
rogram is covered onl
y
i
f
its contents constitute a
work based on the Library (independent o
f
the use
of the Library in a tool for writing it). Whether that is
true
d
epen
d
s on w
h
at t
h
e Li
b
rar
y
d
oes an
d
w
h
at t
h
e
p
rogram that uses the Library does
.
You may copy and distribute verbatim copies of the
1.
Li
b
rar
y
’s comp
l
ete source co
d
e as
y
ou receive it, in
a
n
y
medium, provided that
y
ou conspicuousl
y
and
a
ppropriately publish on each copy an appropriate
cop
y
right notice and disclaimer of warrant
y
; keep
i
n
tact
a
ll
t
h
e
n
ot
i
ces
t
h
at
r
efe
r
to
t
hi
s
Li
ce
n
se
a
n
d
to
the absence of any warranty; and distribute a copy o
f
t
h
is License a
l
ong wit
h
t
h
e Li
b
rar
y.
You ma
y
charge a
f
ee
f
or the ph
y
sical act o
f
trans
f
erring
a
copy, and you may at your option offer warranty
p
rotection in exchange for a fee
.
You ma
y
modi
fy
y
our cop
y
or copies o
f
the Librar
y
or2
.
a
ny portion of it, thus forming a work based on the
Librar
y
, and cop
y
and distribute such modifications
or work under the terms o
f
Section 1 above, provided
that you also meet all of these conditions
:
T
he modified work must itself be a software
a)
l
i
b
rar
y
.
You must cause the files modified to carry
b)
p
rominent notices stating t
h
at
y
ou c
h
ange
d
t
h
e
f
iles and the date o
f
an
y
change
.
Y
ou
m
ust
cause
t
h
e
wh
o
l
e
o
f
t
h
e
w
o
rk
to
be
c
)
l
icense
d
at no c
h
arge to a
ll
t
h
ir
d
parties un
d
er t
h
e
te
rm
s
of
t
hi
s
Li
ce
n
se.
If a facility in the modified Library refers to a functiond
)
or a table of data to be supplied b
y
an application
p
rogram that uses the
f
acilit
y
, other than as an
a
rgument passed when the facility is invoked, then
y
ou must make a good faith effort to ensure that,
i
n t
h
e event an app
l
ication
d
oes not supp
ly
suc
h
f
unction or table, the facility still operates, and
p
erforms whatever part of its purpose remains
m
eanin
gf
ul.
(For example, a function in a library to compute
square roots
h
as a purpose t
h
at is entire
ly
we
ll-
de
f
ined independent o
f
the application. There
f
ore,
S
ubsection 2d requires that any application
-
supplied function or table used b
y
this function
m
ust be optional: i
f
the application does not suppl
y
i
t, the s
q
uare root function must still com
p
ute
square roots.
)
T
hese requirements appl
y
to the modi
f
ied work as
a
wh
o
l
e.
If i
de
n
t
ifi
ab
l
e
sect
i
o
n
s
o
f
t
h
at
w
o
rk
a
r
e
n
ot
derived from the Librar
y
, and can be reasonabl
y
considered independent and separate works in
themselves, then this License, and its terms, do
n
ot app
ly
to t
h
ose sections w
h
en
y
ou
d
istri
b
ute
them as separate works. But when
y
ou distribute
the same sections as
p
art of a whole which is a
work based on the Librar
y
, the distribution of the
whole must be on the terms o
f
this License, whose
p
ermissions for other licensees extend to the entire
w
h
o
l
e, an
d
t
h
us to eac
h
an
d
ever
y
part regar
dl
ess
of
wh
o
wr
ote
i
t.
47
Appendix E Software License Agreement
Wireless-N Gigabit Router
T
hus, it is not the intent of this section to claim
r
ig
h
ts or contest
y
our rig
h
ts to wor
k
written entire
ly
b
y you; rather, the intent is to exercise the right to
control the distribution of derivative or collective
wor
k
s
b
ase
d
on t
h
e Li
b
rar
y.
In addition, mere a
gg
re
g
ation o
f
another wor
k
n
ot based on the Library with the Library (or with
a
work based on the Librar
y
) on a volume o
f
a
stora
g
e or distribution medium does not brin
g
the
other work under the sco
p
e of this License
.
You ma
y
opt to appl
y
the terms o
f
the ordinar
y
GNU
3.
G
e
n
e
r
a
l P
ub
li
c
Li
ce
n
se
in
stead
of
t
hi
s
Li
ce
n
se
to
a
given copy of the Library. To do this, you must alter all
the notices that re
f
er to this License, so that the
y
re
f
er
to the ordinary GNU General Public License, version
2, instead of to this License. (If a newer version than
version 2 o
f
the ordinar
y
GNU General Public License
has appeared, then you can speci
f
y that version
i
nstead if you wish.) Do not make any other change in
t
h
ese notices
.
Once this change is made in a given copy, it is
i
rreversible for that copy, so the ordinary GNU General
Pu
bl
ic License app
l
ies to a
ll
su
b
sequent copies an
d
derivative works made
f
rom that copy
.
T
his option is useful when you wish to copy part of the
code o
f
the Librar
y
into a program that is not a librar
y.
You may copy and distribute the Library (or a portion
4.
or derivative of it, under Section 2) in object code or
executable
f
orm under the terms o
f
Sections 1 and
2 above provided that
y
ou accompan
y
it with the
complete correspondin
g
machine-readable source
code
,
which must be distributed under the terms o
f
S
ections 1 and 2 above on a medium customaril
y
used
f
or software interchan
g
e
.
I
f
distribution o
f
object code is made b
y
o
ff
ering
a
ccess to cop
y
f
rom a designated place, then o
ff
ering
equivalent access to copy the source code from the
same place satis
f
ies the requirement to distribute
the source code, even thou
g
h third parties are not
compelled to copy the source along with the object
co
d
e
.
A
program that contains no derivative o
f
any portion
5.
of the Library, but is designed to work with the Library
by
b
eing compi
l
e
d
or
l
in
k
e
d
wit
h
it, is ca
ll
e
d
a “wor
k
that uses the Librar
y
”. Such a work, in isolation, is not
a
derivative work of the Library, and therefore falls
outside the scope of this License
.
However, linking a “work that uses the Librar
y
” with
the Library creates an executable that is a derivative
of the Librar
y
(because it contains portions of the
Librar
y
), rather than a “work that uses the librar
y
”. The
executable is therefore covered by this License. Section
6
states terms for distribution of such executables
.
W
hen a “work that uses the Library” uses material from
a
header file that is part of the Librar
y
, the object code
f
or the work ma
y
be a derivative work o
f
the Librar
y
even thou
g
h the source code is not. Whether this is
true is especiall
y
significant if the work can be linked
without the Librar
y
, or i
f
the work is itsel
f
a librar
y
. The
threshold for this to be true is not precisely defined by
l
aw
.
I
f
such an object
f
ile uses onl
y
numerical parameters,
data structure layouts and accessors, and small macros
a
nd small inline functions (ten lines or less in length),
then the use o
f
the ob
j
ect
f
ile is unrestricted, regardless
of whether it is legally a derivative work. (Executables
containing this object code plus portions of the Librar
y
will still
f
all under Section 6.
)
Otherwise, if the work is a derivative of the Library, you
m
a
y
distribute the object code for the work under the
terms o
f
Section 6. An
y
executables containing that
work also fall under Section 6, whether or not they are
linked directl
y
with the Librar
y
itself
.
A
s an exception to the Sections above,
y
ou ma
y
also
6.
combine or link a “work that uses the Library” with the
Librar
y
to produce a work containing portions of the
Librar
y
, and distribute that work under terms o
f
y
our
choice,
p
rovided that the terms
p
ermit modification
of the work for the customer’s own use and reverse
en
g
ineerin
g
f
or debu
gg
in
g
such modi
f
ications
.
You must give prominent notice with each copy o
f
t
h
e wor
k
t
h
at t
h
e Li
b
rar
y
is use
d
in it an
d
t
h
at t
h
e
Li
b
rar
y
an
d
its use are covere
d
by
t
h
is License. You
m
ust supply a copy of this License. If the work during
execution
d
isp
l
a
y
s cop
y
rig
h
t notices,
y
ou must inc
l
u
d
e
the cop
y
right notice
f
or the Librar
y
among them, as
well as a reference directing the user to the copy of this
License. Also,
y
ou must do one of these things
:
A
ccompan
y
t
h
e wor
k
wit
h
t
h
e comp
l
ete
a)
correspondin
g
machine-readable source code
f
or the Library including whatever changes were
u
se
d
in t
h
e wor
k
(
w
h
ic
h
must
b
e
d
istri
b
ute
d
u
nder Sections 1 and 2 above); and, i
f
the wor
k
i
s an executa
bl
e
l
in
k
e
d
wit
h
t
h
e Li
b
rary, wit
h
t
h
e
comp
l
ete mac
h
ine-rea
d
a
bl
e “wor
k
t
h
at uses t
h
e
Library”, as object code and/or source code, so that
the user can modify the Library and then relin
k
to produce a modi
f
ied executable containing the
m
odi
f
ied Library. (It is understood that the user
who changes the contents of definitions files in the
Li
b
rar
y
wi
ll
not necessari
ly
b
e a
bl
e to recompi
l
e t
h
e
app
lication to use the modified definitions.
)
48
Appendix E Software License Agreement
Wireless-N Gigabit Router
Use a suitable shared library mechanism for linking
b)
wit
h
t
h
e Li
b
rar
y
. A suita
bl
e mec
h
anism is one t
h
at
(1) uses at run time a copy o
f
the library already
p
resent on the user’s computer system, rather than
cop
y
ing librar
y
f
unctions into the executable, and
(2) will operate properly with a modi
f
ied version o
f
the library, if the user installs one, as long as the
m
odi
f
ied version is inter
f
ace-compatible with the
v
e
r
s
i
o
n
t
h
at
t
h
e
w
o
rk w
as
m
ade
wi
t
h
.
A
ccompany the work with a written offer, validc
)
f
or at least three
y
ears, to give the same user the
m
aterials speci
f
ied in Subsection 6a, above,
f
or a
charge no more than the cost of performing this
d
istri
b
ution
.
I
f
distribution o
f
the work is made by o
ff
ering accessd
)
to copy from a designated place, offer equivalent
a
ccess to cop
y
the above speci
f
ied materials
f
rom
the same place.
Verify that the user has already received a copy o
f
e
)
t
h
ese materia
l
s or t
h
at
y
ou
h
ave a
l
rea
dy
sent t
h
is
user
a
c
op
y
.
For an executable, the re
q
uired form of the “work that
u
ses t
h
e Li
b
rar
y
” must inc
l
u
d
e an
y
d
ata an
d
uti
l
it
y
p
ro
g
rams needed
f
or reproducin
g
the executable
f
rom
i
t. However, as a s
p
ecial exce
p
tion, the materials to be
d
istri
b
ute
d
nee
d
not inc
l
u
d
e an
y
t
h
ing t
h
at is norma
lly
distributed (in either source or binary
f
orm) with the
m
ajor components (compiler, kernel, and so on) of the
operating s
y
stem on w
h
ic
h
t
h
e executa
bl
e runs, un
l
ess
that component itsel
f
accompanies the executable
.
It may happen that this requirement contradicts the
license restrictions o
f
other proprietar
y
libraries that
do not normally accompany the operating system.
S
uch a contradiction means you cannot use both
t
h
em an
d
t
h
e Li
b
rar
y
toget
h
er in an executa
bl
e t
h
at
you distribute
.
You may place library facilities that are a work based7
.
on t
h
e Li
b
rar
y
si
d
e-
by
-si
d
e in a sing
l
e
l
i
b
rar
y
toget
h
er
with other librar
y
f
acilities not covered b
y
this License,
a
nd distribute such a combined library, provided that
the separate distribution of the work based on the
Librar
y
and o
f
the other librar
y
f
acilities is otherwise
p
ermitted, and provided that you do these two
t
h
ings
:
A
ccompan
y
the combined librar
y
with a cop
y
o
f
the
a)
same work based on the Library, uncombined with
a
n
y
other librar
y
facilities. This must be distributed
u
n
de
r
t
h
e
te
rm
s
of
t
h
e
Sect
i
o
n
s
abo
v
e.
Give prominent notice with the combined library o
f
b)
the fact that part of it is a work based on the Librar
y
,
a
nd explaining where to
f
ind the accompan
y
ing
u
n
co
m
b
in
ed
f
o
rm
o
f
t
h
e
sa
m
e
w
o
rk
.
You may not copy, modify, sublicense, link with, or
8.
d
istri
b
ute t
h
e Li
b
rar
y
except as express
ly
provi
d
e
d
u
nder this License. An
y
attempt otherwise to cop
y
,
m
odify, sublicense, link with, or distribute the Library
i
s voi
d
, an
d
wi
ll
automatica
lly
terminate
y
our rig
h
ts
u
nder this License. However, parties who have received
copies, or rights, from you under this License will not
h
ave t
h
eir
l
icenses terminate
d
so
l
ong as suc
h
parties
r
emain in
f
ull compliance
.
You are not required to accept this License, since you
9.
h
ave not signe
d
it. However, not
h
ing e
l
se grants
y
ou
p
ermission to modi
fy
or distribute the Librar
y
or its
derivative works. These actions are prohibited by law i
f
y
ou do not accept this License. Therefore, b
y
modif
y
ing
or
d
istri
b
uting t
h
e Li
b
rar
y
(or an
y
wor
k
b
ase
d
on t
h
e
Library), you indicate your acceptance of this License
to do so, and all its terms and conditions for cop
y
ing,
distributing or modi
fy
ing the Librar
y
or works based
o
n i
t.
Eac
h
time
y
ou re
d
istri
b
ute t
h
e Li
b
rar
y
(or an
y
wor
k
1
0
.
b
ase
d
on t
h
e Li
b
rar
y
), t
h
e recipient automatica
lly
r
eceives a license from the original licensor to copy,
distribute, link with or modif
y
the Librar
y
subject
to t
h
ese terms an
d
con
d
itions. You ma
y
not impose
a
ny further restrictions on the recipients’ exercise o
f
t
h
e rig
h
ts grante
d
h
erein. You are not responsi
bl
e
f
or en
f
orcing compliance b
y
third parties with this
Li
ce
n
se.
If, as a consequence of a court judgment or allegation
1
1
.
o
f
patent in
f
ringement or
f
or an
y
other reason (not
limited to
p
atent issues), conditions are im
p
osed on
y
ou (w
h
et
h
er
by
court or
d
er, agreement or ot
h
erwise)
that contradict the conditions o
f
this License, the
y
do
n
ot excuse you from the conditions of this License. I
f
y
ou cannot distribute so as to satisf
y
simultaneousl
y
y
our o
bl
igations un
d
er t
h
is License an
d
an
y
ot
h
er
p
ertinent obligations, then as a consequence you may
n
ot distribute the Librar
y
at all. For example, if a patent
license would not permit ro
y
alt
y
-
f
ree redistribution o
f
the Library by all those who receive copies directly or
i
n
d
irect
ly
t
h
roug
h
y
ou, t
h
en t
h
e on
ly
wa
y
y
ou cou
ld
satis
fy
both it and this License would be to re
f
rain
entirely from distribution of the Library
.
If an
y
portion of this section is held invalid or
u
nen
f
orceable under an
y
particular circumstance,
the balance of the section is intended to apply, and
t
h
e section as a w
h
o
l
e is inten
d
e
d
to app
ly
in ot
h
er
ci
r
cu
m
sta
n
ces.
It is not the purpose of this section to induce you to
i
nfringe an
y
patents or other propert
y
right claims or
to contest validit
y
o
f
an
y
such claims; this section has
the sole purpose of protecting the integrity of the free
software distribution s
y
stem which is implemented
by
pu
bl
ic
l
icense practices. Man
y
peop
l
e
h
ave
m
ade
g
enerous contributions to the wide ran
g
e o
f

49
Appendix E Software License Agreement
Wireless-N Gigabit Router
software distributed through that system in reliance
on consistent application o
f
that s
y
stem; it is up to
the author/donor to decide i
f
he or she is willin
g
to
distribute software through any other system and a
l
icensee cannot impose t
h
at c
h
oice
.
T
his section is intended to make thoroughly clear
what is believed to be a conse
q
uence of the rest of this
L
i
cense
.
I
f
the distribution and/or use o
f
the Library is restricted
12.
i
n certain countries either by patents or by copyrighted
i
nter
f
aces, the original cop
y
right holder who places
the Library under this License may add an explicit
geographical distribution limitation excluding those
countries, so t
h
at
d
istri
b
ution is permitte
d
on
ly
in or
a
mon
g
countries not thus excluded. In such case, this
License incor
p
orates the limitation as if written in the
b
od
y
o
f
this License
.
T
he Free So
f
tware Foundation may publish revised
13.
a
nd/or new versions of the Lesser General Public
License
f
rom time to time. Such new versions will be
similar in spirit to the present version, but may di
ff
er in
detail to address new
p
roblems or concerns.
Eac
h
version is given a
d
istinguis
h
ing version num
b
er.
I
f
the Library speci
f
ies a version number o
f
this License
which applies to it and “any later version”, you have the
option o
f
f
ollowing the terms and conditions either o
f
that version or o
f
an
y
later version published b
y
the Free
S
oftware Foundation. If the Library does not specify a
l
icense version num
b
er,
y
ou ma
y
c
h
oose an
y
version
ever published by the Free So
f
tware Foundation
.
If you wish to incorporate parts of the Library into
1
4
.
other free programs whose distribution conditions are
i
ncompatible with these, write to the author to ask
f
or
p
ermission. For software which is copyrighted by the
Free Software Foundation
,
write to the Free Software
Foundation; we sometimes make exceptions
f
or
this. Our decision will be guided by the two goals o
f
p
reserving the free status of all derivatives of our free
so
f
tware and o
f
promotin
g
the sharin
g
and reuse o
f
software generally.
NO WARRANT
Y
BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE,
1
5
.
T
HERE I
S
N
O
WARRANTY F
O
R THE LIBRARY
,
T
O
THE
EXTENT PERMITTED BY APPLI
C
ABLE LAW
.
EX
C
EP
T
W
HEN OTHERWISE STATED IN WRITING THE COPYRIGH
T
H
O
LDER
S
AND
/O
R
O
THER PARTIE
S
PR
O
VIDE THE
LIBRARY “AS IS” WITHOUT WARRANTY OF ANY KIND,
EITHER EXPRESSED OR IMPLIED, INCLUDING, BU
T
N
O
T LIMITED T
O,
THE IMPLIED WARRANTIE
S
O
F
MER
C
HANTABILITY AND FITNE
SS
F
O
R A PARTI
CU
LAR
PURPOSE. THE ENTIRE RISK AS TO THE
Q
UALITY AND
PERF
O
RMAN
C
E
O
F THE LIBRARY I
S
WITH Y
O
U.
S
H
O
ULD
T
HE LIBRARY PR
O
VE DEFE
C
TIVE, Y
O
U A
SS
UME THE
COST OF ALL NECESSARY SERVICING, REPAIR OR
CO
RRE
C
TI
O
N
.
IN N
O
EVENT UNLE
SS
RE
Q
UIRED BY APPLI
C
ABLE LAW
16.
O
R AGREED T
O
IN WRITING WILL ANY
CO
PYRIGH
T
HOLDER
,
OR ANY OTHER PARTY WHO MAY MODIFY
A
ND
/O
R REDI
S
TRIBUTE THE LIBRARY A
S
PERMITTED
A
BOVE, BE LIABLE TO YOU FOR DAMAGES,
INCLUDING ANY GENERAL
,
SPECIAL
,
INCIDENTAL OR
CO
N
S
E
Q
UENTIAL DAMAGE
S
ARI
S
ING
O
UT
O
F THE
USE OR INABILITY TO USE THE LIBRARY (INCLUDING
BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INA
CCU
RATE
O
R L
OSS
E
S
SUS
TAINED BY
Y
OU
O
R THIRD PARTIE
S
O
R A FAIL
U
RE
O
F THE LIBRARY
T
O OPERATE WITH ANY OTHER SOFTWARE
),
EVEN IF
SUC
H H
O
LDER
O
R
O
THER PARTY HA
S
BEEN ADVI
S
ED
O
F THE P
OSS
IBILITY
O
F
SUC
H DAMAGE
S.
END
O
F TERM
S
AND
CO
NDITI
O
N
S
END
O
F
SC
HED
U
LE
3
Sche
du
le 4
I
f
this Linksys product contains open source so
f
tware
licensed under the O
p
enSSL license
:
T
his product includes so
f
tware developed b
y
the
OpenSSL Pro
j
ect
f
or use in the OpenSSL Toolkit.
(
http://www.openssl.org/
ppg
).
T
his product includes cr
y
ptographic so
f
tware written b
y
Eric Young (eay@cryptso
f
t.com)
.
T
his product includes software written by Tim Hudson
(tjh@cr
y
ptso
f
t.com)
.
In addition, i
f
this Linksys product contains open
source software licensed under the O
p
enSSL license
t
h
en t
h
e
l
icense terms
b
e
l
ow in t
h
is Sc
h
e
d
u
l
e 3 wi
ll
a
pply to that open source so
f
tware. The license terms
b
elow in this Schedule 3 are from the
p
ublic web site at
http://www.openssl.org/source/license.html
ppg
.
T
he OpenSSL toolkit stays under a dual license, i.e. both
the conditions of the OpenSSL License and the original
S
SLea
y
license appl
y
to the toolkit. See below
f
or the
a
ctual license texts. Actually both licenses are BSD-style
Open Source licenses. In case of any license issues related
to OpenSSL p
l
ease contact openss
l
-core@openss
l
.org
.

50
Appendix E Software License Agreement
Wireless-N Gigabit Router
Op
enSSL License
Copyright © 1998-2007 The OpenSSL Project. All rights
r
eserved
.
Redistribution and use in source and binar
y
f
orms, with
or without modi
f
ication, are
p
ermitted
p
rovided that the
f
ollowing conditions are met
:
Redistributions o
f
source code must retain the above
1.
copyright notice, this list o
f
conditions and the
f
ollowing disclaimer
.
Redistributions in binar
y
f
orm must reproduce the2
.
a
bove copyright notice, this list o
f
conditions and the
f
ollowing disclaimer in the documentation and/or
ot
h
er materia
l
s provi
d
e
d
wit
h
t
h
e
d
istri
b
ution
.
A
ll advertisin
g
materials mentionin
g
f
eatures or
3.
u
se of this software must display the following
a
cknowledgment: “This product includes so
f
tware
developed by the OpenSSL Project
f
or use in the
O
p
enSSL Toolkit.
(
http://www.openssl.org/
ppg
)
”
Th
e names “OpenSSL Too
lk
it” an
d
“OpenSSL Pro
j
ect
”
4.
m
ust not be used to endorse or promote products
derived from this software without
p
rior written
p
ermission. For written permission, p
l
ease contact
openssl-core@openssl.or
g.
Products derived from this software may not be called
5.
“
OpenSSL” nor ma
y
“OpenSSL” appear in t
h
eir names
without prior written permission o
f
the OpenSSL
P
roject.
Redistributions o
f
an
y
f
orm whatsoever must retain
6.
the
f
ollowin
g
acknowled
g
ment: “This product includes
software developed by the OpenSSL Project for use in
t
h
e OpenSSL Too
lk
it
(
http://www.openssl.org/
ppg
)
”
T
HI
S
SO
FTWARE I
S
PR
O
VIDED BY THE
O
pen
SS
L PR
O
JE
CT
“
AS IS” AND ANY EXPRESSED OR IMPLIED WARRANTIES,
INCLUDING
,
BUT NOT LIMITED TO
,
THE IMPLIED
W
ARRANTIE
S
O
F MER
C
HANTABILITY AND FITNE
SS
F
O
R
A
PARTI
CU
LAR P
U
RP
OS
E ARE DI
SC
LAIMED
.
IN N
O
EVEN
T
S
HALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE
LIABLE F
O
R ANY DIRE
C
T, INDIRE
C
T, IN
C
IDENTAL,
S
PE
C
IAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING,
BUT NOT LIMITED TO
,
PROCUREMENT OF SUBSTITUTE
G
OO
D
S
O
R
S
ERVI
C
E
S
; L
OSS
O
F U
S
E, DATA,
O
R PR
O
FIT
S
;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY
,
WHETHER IN CONTRACT
,
S
TRICT LIABILITY, OR TORT
(
INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
T
HIS SOFTWARE
,
EVEN IF ADVISED OF THE POSSIBILITY OF
SUC
H DAMAGE
.
T
his product includes cryptographic software written by
Eric Young (ea
y
@cr
y
ptso
f
t.com). This product includes
so
f
tware written b
y
Tim Hudson (tjh@cr
y
ptso
f
t.com)
.
O
riginal SSLea
y
License
Copyright © 1995-1998 Eric Young (eay@cryptso
f
t.com)All
r
ights reserved.
Th
is pac
k
age is an SSL imp
l
ementation written
by
Eric
Young (eay@cryptso
f
t.com)
.
T
he im
p
lementation was written so as to conform with
Netscape
’
s SSL.
T
his library is
f
ree
f
or commercial and non-commercial
u
se as long as the following conditions are adhered to.
T
he
f
ollowing conditions appl
y
to all code
f
ound in this
distribution, be it the RC4, RSA, lhash, DES, etc., code; not
just the SSL code. The SSL documentation included with
t
h
is
d
istri
b
ution is covere
d
by
t
h
e same cop
y
rig
h
t terms
except that the holder is Tim Hudson (tjh@cryptso
f
t
.
com)
.
Cop
y
rig
h
t remains Eric Young’s, an
d
as suc
h
an
y
Cop
y
rig
h
t
not
i
ces
in
t
h
e
code
a
r
e
n
ot
to
be
r
e
m
o
v
ed.
If this package is used in a product, Eric Young should be
given attribution as the author o
f
the parts o
f
the librar
y
u
sed. This can be in the
f
orm o
f
a textual messa
g
e at
p
rogram startup or in
d
ocumentation (on
l
ine or textua
l
)
p
rovi
d
e
d
wit
h
t
h
e pac
k
age
.
Redistribution and use in source and binary
f
orms, with
or without modification, are
p
ermitted
p
rovided that the
f
ollowing conditions are met
:
R
ed
i
st
ri
but
i
o
n
s
of
sou
r
ce
code
m
ust
r
eta
in
t
h
e
1.
copyright notice, this list of conditions and the
f
ollowing disclaimer
.
Redistributions in binary
f
orm must reproduce the
2.
a
bove copyright notice, this list of conditions and the
f
ollowing disclaimer in the documentation and/or
other materials provided with the distribution
.
A
ll advertising materials mentioning features or
3.
u
se o
f
this so
f
tware must displa
y
the
f
ollowing
a
cknowled
g
ement:
“
This product includes cryptographic software written
by
Eric Young (ea
y
@cr
y
ptso
f
t.com)
”
T
he word ‘cryptographic’ can be le
f
t out i
f
the routines
f
rom the library being used are not cryptographic
r
e
l
ate
d
.
I
f
you include any Windows speci
f
ic code (or a derivative
4.
thereof) from the apps directory (application code)
y
ou must inc
l
u
d
e an ac
k
now
l
e
d
gement: “T
h
is pro
d
uct
i
ncludes so
f
tware written by Tim Hudson (tjh
@
cryptsoft.com)
”
T
HIS SOFTWARE IS PROVIDED BY ERIC YOUNG
“
AS IS
”
AND
A
NY EXPRE
SS
O
R IMPLIED WARRANTIE
S
, IN
C
LUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MER
C
HANTABILITY AND FITNE
SS
F
O
R A PARTI
C
ULAR
P
U
RP
OS
E ARE DI
SC
LAIMED
.
IN N
O
EVENT
S
HALL THE
AU
TH
O
R
O
R
CO
NTRIB
U
T
O
R
S
BE LIABLE F
O
R ANY
51
Appendix E Software License Agreement
Wireless-N Gigabit Router
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY,
OR CONSEQUENTIAL DAMAGES
(
INCLUDING
,
BUT NO
T
LIMITED T
O
, PR
OC
UREMENT
O
F
S
UB
S
TITUTE G
OO
D
S
O
R
S
ERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION
)
HOWEVER CAUSED AND ON ANY THEORY
O
F LIABILITY, WHETHER IN
CO
NTRA
C
T,
S
TRI
C
T LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
A
RI
S
ING IN ANY WAY
O
UT
O
F THE U
S
E
O
F THI
S
SO
FTWARE
,
EVEN IF ADVI
S
ED
O
F THE P
OSS
IBILITY
O
F
SUC
H DAMAGE
.
T
he license and distribution terms for any publicly available
version or derivative o
f
this code cannot be changed. i.e.
this code cannot simply be copied and put under another
distribution license [including the GNU Public License.
]
END
O
F
SC
HEDULE
4
8
100210B-ST