LITE ON TECHNOLOGY WP300UP 802.11g Wireless Access Point / Workgroup Bridge User Manual WP 300U AP
LITE-ON Technology Corp. 802.11g Wireless Access Point / Workgroup Bridge WP 300U AP
Contents
- 1. AP mode User Manual
- 2. Bridge mode User Manual
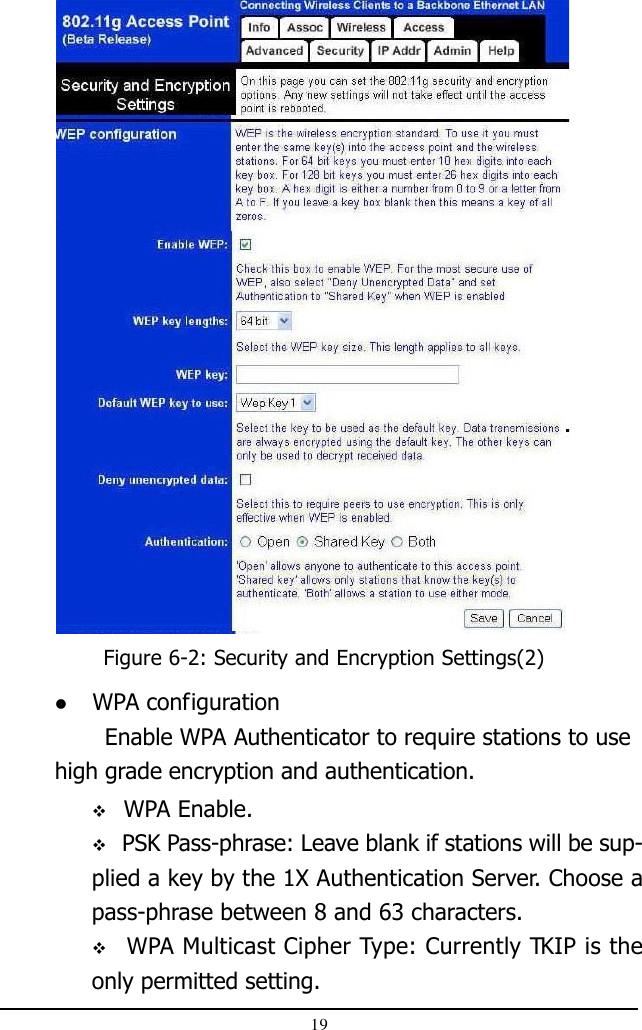
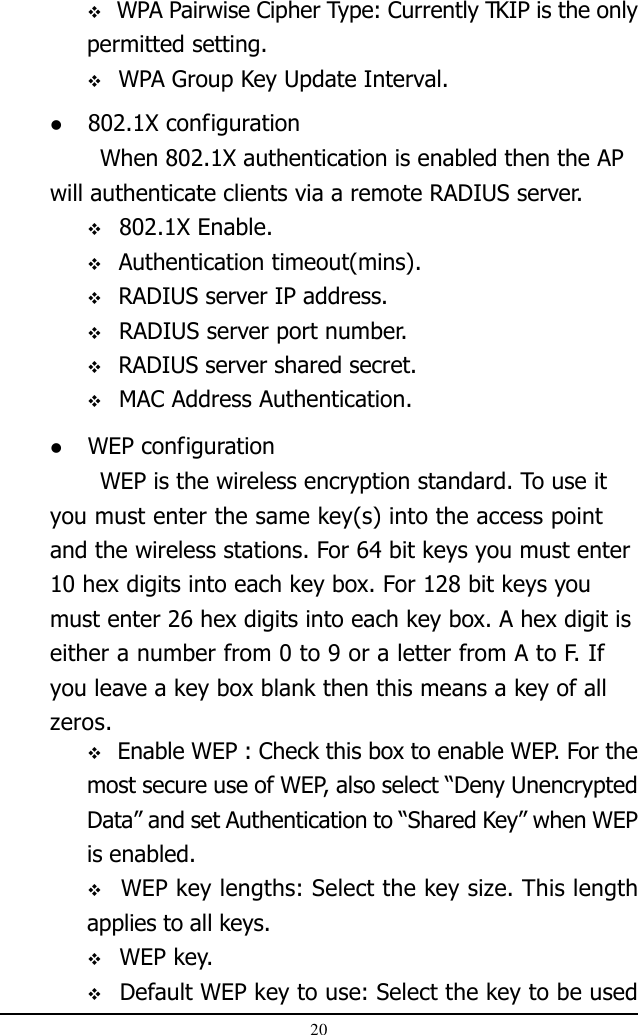
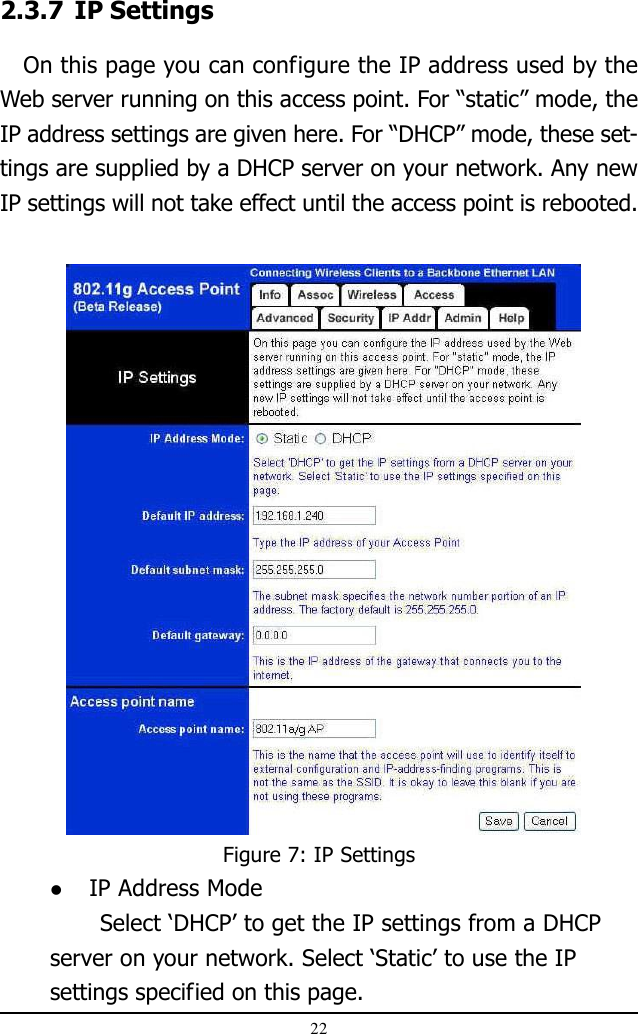
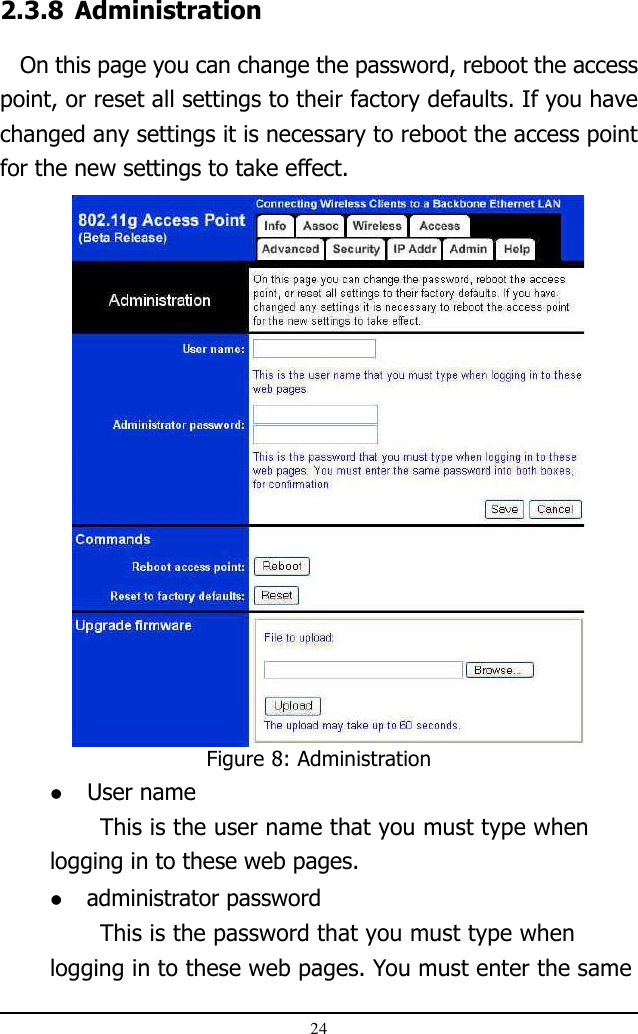
AP mode User Manual