Lenovo Tc A51 8424 Users Manual User Guide
ThinkCentre 8425 19r0474
TC S51-8173 to the manual 3b7ea2e4-8d3b-ca94-fdf5-600acaec5910
2015-01-24
: Lenovo Lenovo-Tc-A51-8424-Users-Manual-329923 lenovo-tc-a51-8424-users-manual-329923 lenovo pdf
Open the PDF directly: View PDF ![]() .
.
Page Count: 60
- Contents
- Important safety information
- Chapter 1. Overview
- Chapter 2. Installing options
- Handling static-sensitive devices
- Installing external options
- Opening the cover
- Locating components
- Accessing system board components and drives
- Identifying parts on the system board
- Installing memory
- Installing PCI adapters
- Removing and replacing the battery
- Removing and replacing an optical drive
- Removing and replacing a diskette drive
- Installing security features
- Erasing a lost or forgotten password (clearing CMOS)
- Closing the cover and connecting the cables
- Chapter 3. Using the IBM Setup Utility
- Appendix A. Updating POST/BIOS
- Appendix B. Cleaning the mouse
- Appendix C. Manual modem commands
- Appendix D. Notices
- Index
ThinkCentre
™
User
Guide
Ty pe s
8424,
8425,
8428
Ty pe s
8171,
8172,
8173
ThinkCentre
™
User
Guide
Ty pe s
8424,
8425,
8428
Ty pe s
8171,
8172,
8173

Note
Before
using
this
information
and
the
product
it
supports,
be
sure
to
read
the
“Important
safety
information”
on
page
v
and
Appendix
D,
“Notices,”
on
page
41.
First
Edition
(April
2004)
©
Copyright
International
Business
Machines
Corporation
2004.
All
rights
reserved.
US
Government
Users
Restricted
Rights
–
Use,
duplication
or
disclosure
restricted
by
GSA
ADP
Schedule
Contract
with
IBM
Corp.

Contents
Important
safety
information
.
.
.
.
.
.v
Conditions
that
require
immediate
action
.
.
.
.
.v
General
safety
guidelines
.
.
.
.
.
.
.
.
.
.vi
Service
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.vi
Power
cords
and
power
adapters
.
.
.
.
.
.vi
Extension
cords
and
related
devices
.
.
.
.
. vii
Plugs
and
outlets
.
.
.
.
.
.
.
.
.
.
. vii
Batteries
.
.
.
.
.
.
.
.
.
.
.
.
.
. vii
Heat
and
product
ventilation
.
.
.
.
.
.
. viii
CD
and
DVD
drive
safety
.
.
.
.
.
.
.
. viii
Additional
safety
information
.
.
.
.
.
.
.
. viii
Lithium
battery
notice
.
.
.
.
.
.
.
.
.
.
.x
Modem
safety
information
.
.
.
.
.
.
.
.
.
.x
Laser
compliance
statement
.
.
.
.
.
.
.
.
.xi
Chapter
1.
Overview
.
.
.
.
.
.
.
.
.1
Information
resources
.
.
.
.
.
.
.
.
.
.
.1
Features
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.2
Available
options
.
.
.
.
.
.
.
.
.
.
.
.
.5
Specifications
.
.
.
.
.
.
.
.
.
.
.
.
.
.6
Supported
operating
positions
.
.
.
.
.
.
.
.7
Chapter
2.
Installing
options
.
.
.
.
.
.9
Handling
static-sensitive
devices
.
.
.
.
.
.
.
.9
Installing
external
options
.
.
.
.
.
.
.
.
.
.9
Locating
controls
and
connectors
on
the
front
of
your
computer
.
.
.
.
.
.
.
.
.
.
.
.10
Locating
connectors
on
the
rear
of
your
computer
11
Obtaining
device
drivers
.
.
.
.
.
.
.
.
.11
Opening
the
cover
.
.
.
.
.
.
.
.
.
.
.
.12
Locating
components
.
.
.
.
.
.
.
.
.
.
.13
Accessing
system
board
components
and
drives
.
.14
Identifying
parts
on
the
system
board
.
.
.
.
.15
Installing
memory
.
.
.
.
.
.
.
.
.
.
.
.16
Installing
PCI
adapters
.
.
.
.
.
.
.
.
.
.17
Removing
and
replacing
the
battery
.
.
.
.
.
.18
Removing
and
replacing
an
optical
drive
.
.
.
.19
Removing
and
replacing
a
diskette
drive
.
.
.
.20
Installing
security
features
.
.
.
.
.
.
.
.
.20
Identifying
security
locks
.
.
.
.
.
.
.
.
.21
Integrated
security
cable
.
.
.
.
.
.
.
.
.21
Rope
clip
.
.
.
.
.
.
.
.
.
.
.
.
.
.23
Cover
lock
.
.
.
.
.
.
.
.
.
.
.
.
.
.23
Password
protection
.
.
.
.
.
.
.
.
.
.23
Erasing
a
lost
or
forgotten
password
(clearing
CMOS)
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.24
Closing
the
cover
and
connecting
the
cables
.
.
.24
Chapter
3.
Using
the
IBM
Setup
Utility
25
Starting
the
IBM
Setup
Utility
program
.
.
.
.
.25
Viewing
and
changing
settings
.
.
.
.
.
.
.
.25
Exiting
from
the
IBM
Setup
Utility
program
.
.
.25
Using
passwords
.
.
.
.
.
.
.
.
.
.
.
.25
Password
considerations
.
.
.
.
.
.
.
.
.26
User
Password
.
.
.
.
.
.
.
.
.
.
.
.26
Administrator
Password
.
.
.
.
.
.
.
.
.26
IDE
Drive
User
Password
.
.
.
.
.
.
.
.26
IDE
Drive
Master
Password
.
.
.
.
.
.
.
.27
Setting,
changing,
and
deleting
a
password
.
.
.27
Using
Security
Profile
by
Device
.
.
.
.
.
.
.27
Selecting
a
startup
device
.
.
.
.
.
.
.
.
.
.28
Selecting
a
temporary
startup
device
.
.
.
.
.28
Changing
the
startup
device
sequence
.
.
.
.28
Advanced
settings
.
.
.
.
.
.
.
.
.
.
.
.28
Appendix
A.
Updating
POST/BIOS
.
.
.29
POST/BIOS
.
.
.
.
.
.
.
.
.
.
.
.
.
.29
Updating
(flashing)
BIOS
from
a
diskette
.
.
.
.29
Updating
(flashing)
BIOS
from
your
operating
system
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.29
Recovering
from
a
POST/BIOS
update
failure
.
.
.30
Appendix
B.
Cleaning
the
mouse
.
.
.31
Cleaning
an
optical
mouse
.
.
.
.
.
.
.
.
.31
Cleaning
a
mouse
with
a
ball
.
.
.
.
.
.
.
.31
Appendix
C.
Manual
modem
commands
.
.
.
.
.
.
.
.
.
.
.
.
.33
Basic
AT
commands
.
.
.
.
.
.
.
.
.
.
.33
Extended
AT
commands
.
.
.
.
.
.
.
.
.
.35
MNP/V.42/V.42bis/V.44
commands
.
.
.
.
.
.36
Fax
Class
1
commands
.
.
.
.
.
.
.
.
.
.37
Fax
Class
2
commands
.
.
.
.
.
.
.
.
.
.37
Voice
commands
.
.
.
.
.
.
.
.
.
.
.
.
.38
Appendix
D.
Notices
.
.
.
.
.
.
.
.
.41
Trademarks
.
.
.
.
.
.
.
.
.
.
.
.
.
.42
Index
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.43
©
Copyright
IBM
Corp.
2004
iii
iv
User
Guide

Important
safety
information
This
information
can
help
you
safely
use
your
IBM
®
personal
computer.
Follow
and
retain
all
information
included
with
your
IBM
computer.
The
information
in
this
document
does
not
alter
the
terms
of
your
purchase
agreement
or
the
IBM
Statement
of
Limited
Warranty.
Customer
safety
is
important
to
IBM.
Our
products
are
developed
to
be
safe
and
effective.
However,
personal
computers
are
electronic
devices.
Power
cords,
power
adapters,
and
other
features
can
create
potential
safety
risks
that
can
result
in
physical
injury
or
property
damage,
especially
if
misused.
To
reduce
these
risks,
follow
the
instructions
included
with
your
product,
observe
all
warnings
on
the
product
and
in
the
operating
instructions,
and
review
the
information
included
in
this
document
carefully.
By
carefully
following
the
information
contained
in
this
document
and
provided
with
your
product,
you
can
help
protect
yourself
from
hazards
and
create
a
safer
computer
work
environment.
Note:
This
information
includes
references
to
power
adapters
and
batteries.
In
addition
to
mobile
personal
computers,
IBM
ships
some
products
(such
as
speakers
or
monitors)
with
external
power
adapters.
If
you
have
such
a
product,
this
information
applies
to
your
product.
In
addition,
your
computer
product
may
contain
a
coin-sized
internal
battery
that
provides
power
to
your
system
clock
even
when
the
machine
is
unplugged,
so
the
battery
safety
information
applies
to
all
computers.
Conditions
that
require
immediate
action
Products
can
become
damaged
due
to
misuse
or
neglect.
Some
product
damage
is
serious
enough
that
the
product
should
not
be
used
again
until
it
has
been
inspected
and,
if
necessary,
repaired
by
an
authorized
servicer.
As
with
any
electronic
device,
pay
close
attention
to
the
product
when
it
is
turned
on.
On
very
rare
occasions,
you
might
notice
an
odor
or
see
a
puff
of
smoke
or
sparks
vent
from
your
machine.
Or
you
might
hear
sounds
like
popping,
cracking
or
hissing.
These
conditions
might
merely
mean
that
an
internal
electronic
component
has
failed
in
a
safe
and
controlled
manner.
Or,
they
might
indicate
a
potential
safety
issue.
However,
do
not
take
risks
or
attempt
to
diagnose
the
situation
yourself.
Frequently
inspect
your
computer
and
its
components
for
damage
or
wear
or
signs
of
danger.
If
you
have
any
question
about
the
condition
of
a
component,
do
not
use
the
product.
Contact
the
IBM
Support
Center
®
or
the
product
manufacturer
for
instructions
on
how
to
inspect
the
product
and
have
it
repaired,
if
necessary.
In
the
unlikely
event
that
you
notice
any
of
the
conditions
listed
below,
or
if
you
have
any
safety
concerns
with
your
product,
stop
using
the
product
and
unplug
it
from
the
power
source
and
telecommunication
lines
until
you
can
speak
to
the
IBM
Support
Center
for
further
guidance.
v
Power
cords,
plugs,
power
adapters,
extension
cords,
surge
protectors,
or
power
supplies
that
are
cracked,
broken
or
damaged.
v
Signs
of
overheating,
smoke,
sparks
or
fire.
©
Copyright
IBM
Corp.
2004
v

v
Damage
to
a
battery
(such
as
cracks,
dents,
creases),
discharge
from
a
battery,
or
a
buildup
of
foreign
substances
on
the
battery.
v
A
cracking,
hissing
or
popping
sound,
or
strong
odor
that
comes
from
the
product.
v
Signs
that
liquid
has
been
spilled
or
an
object
has
fallen
onto
the
computer
product,
the
power
cord
or
power
adapter.
v
The
computer
product,
the
power
cord
or
power
adapter
has
been
exposed
to
water.
v
The
product
has
been
dropped
or
damaged
in
any
way.
v
The
product
does
not
operate
normally
when
you
follow
the
operating
instructions.
Note:
If
you
notice
these
conditions
with
a
non-IBM
product
(such
as
an
extension
cord),
stop
using
that
product
until
you
can
contact
the
product
manufacturer
for
further
instructions,
or
until
you
get
a
suitable
replacement.
General
safety
guidelines
Always
observe
the
following
precautions
to
reduce
the
risk
of
injury
and
property
damage.
Service
Do
not
attempt
to
service
a
product
yourself
unless
instructed
to
do
so
by
the
IBM
Support
Center.
Use
only
an
IBM
authorized
service
provider
who
is
approved
to
repair
your
particular
product.
Note:
Some
parts
can
be
upgraded
or
replaced
by
the
customer.
These
parts
are
referred
to
as
Customer
Replaceable
Units,
or
CRUs.
IBM
expressly
identifies
CRUs
as
such,
and
provides
documentation
with
instructions
when
it
is
appropriate
for
customers
to
replace
those
parts.
You
must
closely
follow
all
instructions
when
performing
such
replacements.
Always
make
sure
that
the
power
is
turned
off
and
that
the
product
is
unplugged
from
any
power
source
before
you
attempt
the
replacement.
If
you
have
any
questions
or
concerns,
contact
the
IBM
Support
Center.
Power
cords
and
power
adapters
Use
only
the
power
cords
and
power
adapters
supplied
by
the
product
manufacturer.
Never
wrap
a
power
cord
around
the
power
adapter
or
other
object.
Doing
so
can
stress
the
cord
in
ways
that
can
cause
the
cord
to
fray,
crack
or
crimp.
This
can
present
a
safety
hazard.
Always
route
power
cords
so
that
they
will
not
be
walked
on,
tripped
over,
or
pinched
by
objects.
Protect
the
cord
and
power
adapters
from
liquids.
For
instance,
do
not
leave
your
cord
or
power
adapter
near
sinks,
tubs,
toilets,
or
on
floors
that
are
cleaned
with
liquid
cleansers.
Liquids
can
cause
a
short
circuit,
particularly
if
the
cord
or
power
adapter
has
been
stressed
by
misuse.
Liquids
can
also
cause
gradual
corrosion
of
the
power
cord
terminals
and/or
the
connector
terminals
on
the
adapter
which
can
eventually
result
in
overheating.
vi
User
Guide
Always
connect
power
cords
and
signal
cables
in
the
correct
order
and
ensure
that
all
power
cord
connectors
are
securely
and
completely
plugged
into
receptacles.
Do
not
use
any
power
adapter
that
shows
corrosion
at
the
ac
input
pins
and/or
shows
signs
of
overheating
(such
as
deformed
plastic)
at
the
ac
input
or
anywhere
on
the
power
adapter.
Do
not
use
any
power
cords
where
the
electrical
contacts
on
either
end
show
signs
of
corrosion
or
overheating
or
where
the
power
cord
appears
to
have
been
damaged
in
any
way.
Extension
cords
and
related
devices
Ensure
that
extension
cords,
surge
protectors,
uninterruptible
power
supplies,
and
power
strips
that
you
use
are
rated
to
handle
the
electrical
requirements
of
the
product.
Never
overload
these
devices.
If
power
strips
are
used,
the
load
should
not
exceed
the
power
strip
input
rating.
Consult
an
electrician
for
more
information
if
you
have
questions
about
power
loads,
power
requirements,
and
input
ratings.
Plugs
and
outlets
If
a
receptacle
(power
outlet)
that
you
intend
to
use
with
your
computer
equipment
appears
to
be
damaged
or
corroded,
do
not
use
the
outlet
until
it
is
replaced
by
a
qualified
electrician.
Do
not
bend
or
modify
the
plug.
If
the
plug
is
damaged,
contact
the
manufacturer
to
obtain
a
replacement.
Some
products
are
equipped
with
a
three-pronged
plug.
This
plug
fits
only
into
a
grounded
electrical
outlet.
This
is
a
safety
feature.
Do
not
defeat
this
safety
feature
by
trying
to
insert
it
into
a
non-grounded
outlet.
If
you
cannot
insert
the
plug
into
the
outlet,
contact
an
electrician
for
an
approved
outlet
adapter
or
to
replace
the
outlet
with
one
that
enables
this
safety
feature.
Never
overload
an
electrical
outlet.
The
overall
system
load
should
not
exceed
80
percent
of
the
branch
circuit
rating.
Consult
an
electrician
for
more
information
if
you
have
questions
about
power
loads
and
branch
circuit
ratings.
Be
sure
that
the
power
outlet
you
are
using
is
properly
wired,
easily
accessible,
and
located
close
to
the
equipment.
Do
not
fully
extend
power
cords
in
a
way
that
will
stress
the
cords.
Connect
and
disconnect
the
equipment
from
the
electrical
outlet
carefully
Batteries
All
IBM
personal
computers
contain
a
non-rechargeable
coin
cell
battery
to
provide
power
to
the
system
clock.
In
addition
many
mobile
products
such
as
Thinkpad
notebook
PCs
utilize
a
rechargeable
battery
pack
to
provide
system
power
when
in
portable
mode.
Batteries
supplied
by
IBM
for
use
with
your
product
have
been
tested
for
compatibility
and
should
only
be
replaced
with
IBM
approved
parts.
Never
attempt
to
open
or
service
any
battery.
Do
not
crush,
puncture,
or
incinerate
batteries
or
short
circuit
the
metal
contacts.
Do
not
expose
the
battery
to
water
or
other
liquids.
Only
recharge
the
battery
pack
strictly
according
to
instructions
included
in
the
product
documentation.
Important
safety
information
vii

Battery
abuse
or
mishandling
can
cause
the
battery
to
overheat,
which
can
cause
gasses
or
flame
to
“vent”
from
the
battery
pack
or
coin
cell.
If
your
battery
is
damaged,
or
if
you
notice
any
discharge
from
your
battery
or
the
buildup
of
foreign
materials
on
the
battery
leads,
stop
using
the
battery
and
obtain
a
replacement
from
the
battery
manufacturer.
Batteries
can
degrade
when
they
are
left
unused
for
long
periods
of
time.
For
some
rechargeable
batteries
(particularly
Lithium
Ion
batteries),
leaving
a
battery
unused
in
a
discharged
state
could
increase
the
risk
of
a
battery
short
circuit,
which
could
shorten
the
life
of
the
battery
and
can
also
pose
a
safety
hazard.
Do
not
let
rechargeable
Lithium-Ion
batteries
completely
discharge
or
store
these
batteries
in
a
discharged
state.
Heat
and
product
ventilation
Computers
generate
heat
when
turned
on
and
when
batteries
are
charging.
Notebook
PCs
can
generate
a
significant
amount
of
heat
due
to
their
compact
size.
Always
follow
these
basic
precautions:
v
Do
not
leave
the
base
of
your
computer
in
contact
with
your
lap
or
any
part
of
your
body
for
an
extended
period
when
the
computer
is
functioning
or
when
the
battery
is
charging.
Your
computer
produces
some
heat
during
normal
operation.
Extended
contact
with
the
body
could
cause
discomfort
or,
potentially,
a
skin
burn.
v
Do
not
operate
your
computer
or
charge
the
battery
near
flammable
materials
or
in
explosive
environments.
v
Ventilation
slots,
fans
and/or
heat
sinks
are
provided
with
the
product
for
safety,
comfort,
and
reliable
operation.
These
features
might
inadvertently
become
blocked
by
placing
the
product
on
a
bed,
sofa,
carpet,
or
other
flexible
surface.
Never
block,
cover
or
disable
these
features.
CD
and
DVD
drive
safety
CD
and
DVD
drives
spin
discs
at
a
high
speed.
If
a
CD
or
DVD
is
cracked
or
otherwise
physically
damaged,
it
is
possible
for
the
disc
to
break
apart
or
even
shatter
when
the
CD
drive
is
in
use.
To
protect
against
possible
injury
due
to
this
situation,
and
to
reduce
the
risk
of
damage
to
your
machine,
do
the
following:
v
Always
store
CD/DVD
discs
in
their
original
packaging
v
Always
store
CD/DVD
discs
out
of
direct
sunlight
and
away
from
direct
heat
sources
v
Remove
CD/DVD
discs
from
the
computer
when
not
in
use
v
Do
not
bend
or
flex
CD/DVD
discs,
or
force
them
into
the
computer
or
their
packaging
v
Check
CD/DVD
discs
for
cracks
before
each
use.
Do
not
use
cracked
or
damaged
discs
Additional
safety
information
DANGER
Electrical
current
from
power,
telephone,
and
communication
cables
is
hazardous.
To
avoid
a
shock
hazard:
v
Do
not
connect
or
disconnect
any
cables
or
perform
installation,
maintenance,
or
reconfiguration
of
this
product
during
an
electrical
storm.
viii
User
Guide
v
Connect
all
power
cords
to
a
properly
wired
and
grounded
electrical
outlet.
v
Connect
to
properly
wired
outlets
any
equipment
that
will
be
attached
to
this
product.
v
When
possible,
use
one
hand
only
to
connect
or
disconnect
signal
cables.
v
Never
turn
on
any
equipment
when
there
is
evidence
of
fire,
water,
or
structural
damage.
v
Disconnect
the
attached
power
cords,
telecommunications
systems,
networks,
and
modems
before
you
open
the
device
covers,
unless
instructed
otherwise
in
the
installation
and
configuration
procedures.
v
Connect
and
disconnect
cables
as
described
in
the
following
table
when
installing,
moving,
or
opening
covers
on
this
product
or
attached
devices.
To
connect:
1.
Turn
everything
OFF.
2.
First,
attach
all
cables
to
devices.
3.
Attach
signal
cables
to
connectors.
4.
Attach
power
cords
to
outlet.
5.
Turn
device
ON.
To
disconnect:
1.
Turn
everything
OFF.
2.
First,
remove
power
cords
from
outlet.
3.
Remove
signal
cables
from
connectors.
4.
Remove
all
cables
from
devices.
DANGER
Le
courant
électrique
provenant
de
l’alimentation,
du
téléphone
et
des
câbles
de
transmission
peut
présenter
un
danger.
Pour
éviter
tout
risque
de
choc
électrique
:
v
Ne
manipulez
aucun
câble
et
n’effectuez
aucune
opération
d’installation,
d’entretien
ou
de
reconfiguration
de
ce
produit
au
cours
d’un
orage.
v
Branchez
tous
les
cordons
d’alimentation
sur
un
socle
de
prise
de
courant
correctement
câblé
et
mis
à
la
terre.
v
Branchez
sur
des
socles
de
prise
de
courant
correctement
câblés
tout
équipement
connecté
à
ce
produit.
v
Lorsque
cela
est
possible,
n’utilisez
qu’une
seule
main
pour
connecter
ou
déconnecter
les
câbles
d’interface.;
v
Ne
mettez
jamais
un
équipement
sous
tension
en
cas
d’incendie
ou
d’inondation,
ou
en
présence
de
dommages
matériels.
v
Avant
de
retirer
les
carters
de
l’unité,
mettez
celle-ci
hors
tension
et
déconnectez
ses
cordons
d’alimentation,
ainsi
que
les
câbles
qui
la
relient
aux
réseaux,
aux
systèmes
de
té
lécommunication
et
aux
modems
(sauf
instruction
contraire
mentionnée
dans
les
procédures
d’installation
et
de
configuration).
v
Lorsque
vous
installez,
que
vous
déplacez,
ou
que
vous
manipulez
le
présent
produit
ou
des
périphériques
qui
lui
sont
raccordés,
reportez-vous
aux
instructions
ci-dessous
pour
connecter
et
déconnecter
les
différents
cordons.
Important
safety
information
ix

Connexion:
1.
Mettez
les
unités
hors
tension.
2.
Commencez
par
brancher
tous
les
cordons
sur
les
unités.
3.
Branchez
les
câbles
d’interface
sur
des
connecteurs.
4.
Branchez
les
cordons
d’alimentation
sur
des
prises.
5.
Mettez
les
unités
sous
tension.
Déconnexion:
1.
Mettez
les
unités
hors
tension.
2.
Débranchez
les
cordons
d’alimentation
des
prises.
3.
Débranchez
les
câbles
d’interface
des
connecteurs.
4.
Débranchez
tous
les
câbles
des
unités.
Lithium
battery
notice
CAUTION:
Danger
of
explosion
if
battery
is
incorrectly
replaced.
When
replacing
the
battery,
use
only
IBM
Part
Number
33F8354
or
an
equivalent
type
battery
recommended
by
the
manufacturer.
The
battery
contains
lithium
and
can
explode
if
not
properly
used,
handled,
or
disposed
of.
Do
not:
v
Throw
or
immerse
into
water
v
Heat
to
more
than
100°C
(212°F)
v
Repair
or
disassemble
Dispose
of
the
battery
as
required
by
local
ordinances
or
regulations.
ATTENTION
Danger
d’explosion
en
cas
de
remplacement
incorrect
de
la
batterie.
Remplacer
uniquement
par
une
batterie
IBM
de
type
ou
d’un
type
équivalent
recommandé
par
le
fabricant.
La
batterie
contient
du
lithium
et
peut
exploser
en
cas
de
mauvaise
utilisation,
de
mauvaise
manipulation
ou
de
mise
au
rebut
inappropriée.
Ne
pas
:
v
Lancer
ou
plonger
dans
l’eau
v
Chauffer
à
plus
de
100°C
(212°F)
v
Réparer
ou
désassembler
Mettre
au
rebut
les
batteries
usagées
conformément
aux
règlements
locaux.
Modem
safety
information
To
reduce
the
risk
of
fire,
electrical
shock,
or
injury
when
using
telephone
equipment,
always
follow
basic
safety
precautions,
such
as:
v
Never
install
telephone
wiring
during
a
lightning
storm.
v
Never
install
telephone
jacks
in
wet
locations
unless
the
jack
is
specifically
designed
for
wet
locations.
v
Never
touch
uninsulated
telephone
wires
or
terminals
unless
the
telephone
line
has
been
disconnected
at
the
network
interface.
v
Use
caution
when
installing
or
modifying
telephone
lines.
x
User
Guide

v
Avoid
using
a
telephone
(other
than
a
cordless
type)
during
an
electrical
storm.
There
may
be
a
remote
risk
of
electric
shock
from
lightning.
v
Do
not
use
the
telephone
to
report
a
gas
leak
in
the
vicinity
of
the
leak.
Consignes
de
sécurité
relatives
au
modem
Lors
de
l’utilisation
de
votre
matériel
téléphonique,
il
est
important
de
respecter
les
consignes
ci-après
afin
de
réduire
les
risques
d’incendie,
d’électrocution
et
d’autres
blessures
:
v
N’installez
jamais
de
cordons
téléphoniques
durant
un
orage.
v
Les
prises
téléphoniques
ne
doivent
pas
être
installées
dans
des
endroits
humides,
excepté
si
le
modèle
a
été
conçu
à
cet
effet.
v
Ne
touchez
jamais
un
cordon
téléphonique
ou
un
terminal
non
isolé
avant
que
la
ligne
ait
été
déconnectée
du
réseau
téléphonique.
v
Soyez
toujours
prudent
lorsque
vous
procédez
à
l’installation
ou
à
la
modification
de
lignes
téléphoniques.
v
Si
vous
devez
téléphoner
pendant
un
orage,
pour
éviter
tout
risque
de
choc
électrique,
utilisez
toujours
un
téléphone
sans
fil.
v
En
cas
de
fuite
de
gaz,
n’utilisez
jamais
un
téléphone
situé
à
proximité
de
la
fuite.
Laser
compliance
statement
Some
IBM
Personal
Computer
models
are
equipped
from
the
factory
with
a
CD-ROM
drive
or
a
DVD-ROM
drive.
CD-ROM
drives
and
DVD-ROM
drives
are
also
sold
separately
as
options.
CD-ROM
drives
and
DVD-ROM
drives
are
laser
products.
These
drives
are
certified
in
the
U.S.
to
conform
to
the
requirements
of
the
Department
of
Health
and
Human
Services
21
Code
of
Federal
Regulations
(DHHS
21
CFR)
Subchapter
J
for
Class
1
laser
products.
Elsewhere,
these
drives
are
certified
to
conform
to
the
requirements
of
the
International
Electrotechnical
Commission
(IEC)
825
and
CENELEC
EN
60
825
for
Class
1
laser
products.
When
a
CD-ROM
drive
or
a
DVD-ROM
drive
is
installed,
note
the
following
handling
instructions.
CAUTION:
Use
of
controls
or
adjustments
or
performance
of
procedures
other
than
those
specified
herein
might
result
in
hazardous
radiation
exposure.
Removing
the
covers
of
the
CD-ROM
drive
or
DVD-ROM
drive
could
result
in
exposure
to
hazardous
laser
radiation.
There
are
no
serviceable
parts
inside
the
CD-ROM
drive
or
DVD-ROM
drive.
Do
not
remove
the
drive
covers.
Some
CD-ROM
drives
and
DVD-ROM
drives
contain
an
embedded
Class
3A
or
Class
3B
laser
diode.
Note
the
following
statement.
DANGER
Laser
radiation
when
open.
Do
not
stare
into
the
beam,
do
not
view
directly
with
optical
instruments,
and
avoid
direct
exposure
to
the
beam.
DANGER:
Important
safety
information
xi

Certains
modèles
d’ordinateurs
personnels
sont
équipés
d’origine
d’une
unité
de
CD-ROM
ou
de
DVD-ROM.
Mais
ces
unités
sont
également
vendues
séparément
en
tant
qu’options.
L’unité
de
CD-ROM/DVD-ROM
est
un
appareil
à
laser.
Aux
État-Unis,
l’unité
de
CD-ROM/DVD-ROM
est
certifiée
conforme
aux
normes
indiquées
dans
le
sous-chapitre
J
du
DHHS
21
CFR
relatif
aux
produits
à
laser
de
classe
1.
Dans
les
autres
pays,
elle
est
certifiée
être
un
produit
à
laser
de
classe
1
conforme
aux
normes
CEI
825
et
CENELEC
EN
60
825.
Lorsqu’une
unité
de
CD-ROM/DVD-ROM
est
installée,
tenez
compte
des
remarques
suivantes:
ATTENTION:
Pour
éviter
tout
risque
d’exposition
au
rayon
laser,
respectez
les
consignes
de
réglage
et
d’utilisation
des
commandes,
ainsi
que
les
procédures
décrites.
L’ouverture
de
l’unité
de
CD-ROM/DVD-ROM
peut
entraîner
un
risque
d’exposition
au
rayon
laser.
Pour
toute
intervention,
faites
appel
à
du
personnel
qualifié.
Certaines
unités
de
CD-ROM/DVD-ROM
peuvent
contenir
une
diode
à
laser
de
classe
3A
ou
3B.
Tenez
compte
de
la
consigne
qui
suit:
DANGER
Rayonnement
laser
lorsque
le
carter
est
ouvert.
Évitez
toute
exposition
directe
des
yeux
au
rayon
laser.
Évitez
de
regarder
fixement
le
faisceau
ou
de
l’observer
à
l’aide
d’instruments
optiques.
xii
User
Guide
Chapter
1.
Overview
Thank
you
for
selecting
an
IBM
®
computer.
Your
computer
incorporates
many
of
the
latest
advances
in
computer
technology
and
can
be
upgraded
as
your
needs
change.
Instructions
for
installing
external
and
internal
options
are
included
in
this
publication.
When
adding
an
option,
use
these
instructions
along
with
the
instructions
that
come
along
with
the
option.
Information
resources
The
Quick
Reference
that
comes
with
your
computer
provides
information
for
setting
up
your
computer,
starting
the
operating
system,
troubleshooting,
and
notices.
Access
IBM
provides
a
link
to
more
information
about
your
computer.
Click
Start
→
Access
IBM.
If
you
have
Internet
access,
the
most
up-to-date
manuals
for
your
computer
are
available
from
the
World
Wide
Web.
To
access
this
information,
point
your
browser
to:
http://www.ibm.com/pc/support
Type
your
machine
type
and
model
number
in
the
Quick
Path
field,
and
click
Go.
©
Copyright
IBM
Corp.
2004
1
Features
This
section
provides
an
overview
of
the
computer
features
and
preinstalled
software.
System
summary
The
following
information
covers
a
variety
of
models.
For
a
listing
of
features
for
your
specific
model,
go
to
Chapter
3,
“Using
the
IBM
Setup
Utility,”
on
page
25.
Microprocessor
v
Intel
Pentium
®
4
processor
with
HyperThreading
Technology
v
Intel
Pentium
4
processor
v
Intel
®
Celeron
™
processor
v
Internal
cache
(size
varies
by
model
type)
Memory
Support
for
two
184-pin
dual
inline
memory
modules
(DIMMs).
Each
DIMM
socket
can
support
up
to
1
GB
of
PC2700
double
data
rate
(DDR)
synchronous
dynamic
random
access
memory
(SDRAM)
for
a
system
maximum
of
2
GB.
Internal
drives
v
3.5-inch,
half-inch
(slim)
diskette
drive
v
Hard
disk
drive
v
CD-ROM,
DVD-ROM,
DVD-ROM/CD-RW
Combo,
CD-RW,
or
Rambo
III,
IV
DVD-RAM
Multi-Burner
optical
drive
(some
models)
Video
subsystem
Intel
Graphics
Media
Accelerator
900
with
dual
display
support
Audio
subsystem
The
integrated
AC’97
audio
controller
provides
four
audio
connectors.
v
Microphone
and
headphone
connectors
on
the
front
panel
v
Line-in
and
line-out
connectors
on
the
rear
panel
v
Mono
internal
speaker
Connectivity
v
10/100/1000
Mbps
integrated
Intel
Ethernet
controller
that
supports
the
Wake
on
LAN
feature
(some
models)
v
Peripheral
Component
Interconnect
(PCI)
V.90
Data/Fax
modem
(some
models)
System
management
features
v
Remote
Program
Load
(RPL)
and
Dynamic
Host
Configuration
Protocol
(DHCP)
v
Wake
on
LAN
v
Wake
on
Serial
port
(RS232)
from
ACPI
S1,
S3,
and
S5
v
Wake
on
USB
from
ACPI
S1
and
S3
v
Wake
on
PS/2
Keyboard/Mouse
from
ACPI
S1
and
S3
v
Remote
Administration
v
Automatic
power-on
startup
2
User
Guide
v
System
Management
(SM)
BIOS
and
SM
software
v
Ability
to
store
POST
hardware
test
results
Input/output
features
v
1
PCI
Slot
v
1
PCI
Express
x1
slot
with
support
for
PCI-e
DVI-D
Connection
Adapter
v
25-pin
Parallel
Port
v
Two
9-pin
serial
connectors
v
Eight
USB
2.0
connectors
(two
on
front
panel
and
six
on
rear
panel)
v
PS/2
®
mouse
connector
v
PS/2
keyboard
connector
v
Ethernet
connector
v
VGA
monitor
connector
v
Two
audio
connectors
(line-in
and
line-out)
on
rear
panel
v
Two
audio
connectors
(microphone
and
headphone)
on
front
panel
Expansion
v
One
132-bit
PCI
slot
v
One
PCI
Express
x1
slot
with
support
for
PCI-e
DVI-D
Connection
Adapter
v
Two
DIMM
memory
connectors
Power
v
225
Watt
power
supply
with
manual
voltage
selection
switch
v
Automatic
50/60
Hz
input
frequency
switching
v
Advanced
Power
Management
support
v
Advanced
Configuration
and
Power
Interface
(ACPI)
support
Security
features
The
IBM
Embedded
Security
Subsystem
(ESS)
is
a
security
subsystem
included
on
IBM
ThinkCentre
PCs.
It
consists
of
a
dedicated
Hardware
Security
Module
built
on
to
the
motherboard
and
Client
Security
Software,
a
free,
web-downloaded
application.
ESS
provides
the
following
security
values
by
enhancing
the
security
of:
v
data
stored
on
the
PC
by
providing
an
encryption
application
(File
and
Folder
Encryption)
or
encryption
products
from
ISVs
(such
as
products
from
Utimaco
Safeware)
v
digital
certificates
and
other
digital
identity
information
stored
on
a
PC
v
VPN
products
from
Cisco,
Check
Point
and
3Com
by
increasing
the
protection
around
login
credentials
these
products
use
v
customer
network
by
providing
unique
machine
identifiers
for
PCs
in
the
network
(by
associating
certificates
with
the
built-in
Hardware
Security
Module)
Other
security
features
include:
v
User
and
administrator
passwords
v
Support
for
the
addition
of
a
cable
lock
such
as
a
Kensington
lock
v
Knockout
holes
for
installing
a
rope
clip
(U-bolt)
v
Optional
keylock
on
top
cover
v
Startup
sequence
control
Chapter
1.
Overview
3
v
Startup
without
diskette
drive,
keyboard,
or
mouse
v
Diskette
and
hard
disk
I/O
control
v
Serial
and
parallel
port
I/O
control
v
Security
profile
by
device
IBM
preinstalled
software
Your
computer
comes
with
preinstalled
software.
An
operating
system,
device
drivers
to
support
built-in
features,
and
other
support
programs
are
included.
4
User
Guide

Operating
systems
(preinstalled)
(varies
by
model)
Note:
Not
all
countries
or
regions
will
have
these
operating
systems.
v
Microsoft
®
Windows
®
XP
Home
v
Microsoft
Windows
XP
Professional
Available
options
The
following
are
some
available
options:
v
External
options
–
Parallel
port
devices,
such
as
printers
and
external
drives
–
Serial
port
devices,
such
as
external
modems
and
digital
cameras
–
Audio
devices,
such
as
external
speakers
for
the
sound
system
–
USB
devices,
such
as
printers,
joysticks,
and
scanners
–
Security
devices,
such
as
a
cable
lock
–
Monitors
v
Internal
options
–
System
memory,
called
dual
inline
memory
modules
(DIMMs)
–
Peripheral
component
interconnect
(PCI)
adapters
–
PCI
Express
x1
adaptors
–
CD-ROM,
DVD-ROM,
or
CD-RW
drive,
hard
disk
drive,
diskette
drive,
and
other
removable
media
drives
For
the
latest
information
about
available
options,
see
the
following
World
Wide
Web
pages:
v
http://www.ibm.com/pc/us/options/
v
http://www.ibm.com/pc/support/
You
can
also
obtain
information
by
calling
the
following
telephone
numbers:
v
Within
the
United
States,
call
1-800-IBM
SERV
(1-800-426-7378),
your
IBM
reseller,
or
IBM
marketing
representative.
v
Within
Canada,
call
1-800-565-3344
or
1-800-IBM-4YOU.
v
Outside
the
United
States
and
Canada,
contact
your
IBM
reseller
or
IBM
marketing
representative.
Chapter
1.
Overview
5

Specifications
This
section
lists
certain
specifications
for
your
computer.
For
the
latest
specification
information,
see
the
User
Guide
for
your
computer
model
and
type
at:
http://www.ibm.com/pc/support/
Dimensions
Width:
12.2
inches
(310
mm)
Height:
3.35
inches
(85
mm)
Depth:
14.1
inches
(358
mm)
Weight
Minimum
configuration
as
shipped:
7.3
kg
(16
lbs)
Maximum
configuration:
8.5
kg
(18.7
lbs)
Environment
Air
temperature:
Operating
at
0
-
3000
ft
(914.4
m):
10°
to
35°C
(50°
to
95°F)
Operating
at
3000
ft
-
7000
ft
(2134
m):
10°
to
32°C
(50°
to
89.6°F)
Non-operating:
10°
to
43°C
(50°
to
110°F)
Humidity:
Operating:
8%
to
80%
Non-operating:
8%
to
80%
Transit:
8%
to
90%
Maximum
altitude:
7000
ft
(2133.6
m)
Electrical
input
Input
voltage:
Low
range:
Minimum:
100
V
ac
Maximum:
127
V
ac
Input
frequency
range:
50–60
Hz
Voltage
switch
setting:
115
V
ac
High
range:
Minimum:
200
V
ac
Maximum:
240V
ac
Input
frequency
range:
50–60
Hz
Voltage
switch
setting:
230
V
ac
Input
kilovolt-amperes
(kVA)
(approximate):
Minimum
configuration
as
shipped:
0.09
kVA
Maximum
configuration:
0.23
kVA
Heat
output
(approximate)
in
British
thermal
units
(Btu)
per
hour:
Minimum
configuration:
205.8
Btu/hr
(60
watts)
Maximum
configuration:
548.8
Btu/hr
(160
watts)
Airflow
Approximately
14
cubic
feet
(0.45
cubic
meters)
per
minute
Acoustical
noise-emission
values
Note:
In
this
computer,
fan
speed
is
controlled
by
temperature,
configuration,
and
software.
Actual
noise-emission
values
might
be
different
from
the
stated
values
depending
on
the
number
of
fans
and
the
speed
of
the
fans.
Average
sound-pressure
levels
for
computers
with
a
microprocessor
that
runs
at
or
below
2.8
GHz:
At
operator
position
-
0.5
meters:
Idle:
30
dBA
Operating:
34
dBA
At
bystander
position
-
1
meter
(3.3
ft):
Idle:
26
dBA
Operating:
29
dBA
Declared
(upper
limit)
sound-power
levels:
Idle:
4.0
bels
Operating:
4.3
bels
Average
sound-pressure
levels
for
computers
with
a
microprocessor
that
runs
at
greater
than
2.8
GHz:
At
operator
position
-
0.5
meters:
Idle:
31
dBA
Operating:
34
dBA
At
bystander
position
-
1
meter
(3.3
ft):
Idle:
26
dBA
Operating:
29
dBA
Declared
(upper
limit)
sound-power
levels:
Idle:
4.0
bels
Operating:
4.3
bels
Note:
These
levels
were
measured
in
controlled
acoustical
environments
according
to
the
procedures
specified
by
the
American
National
Standards
Institute
(ANSI)
S12.10
and
ISO
7779
and
are
reported
in
accordance
with
ISO
9296.
Actual
sound-pressure
levels
in
a
given
location
might
exceed
the
average
values
stated
because
of
room
reflections
and
other
nearby
noise
sources.
The
declared
sound-power
levels
indicate
an
upper
limit,
below
which
a
large
number
of
computers
will
operate.
6
User
Guide
Supported
operating
positions
To
provide
proper
air
flow
to
internal
components,
you
must
position
your
computer
in
one
of
the
positions
as
illustrated
below.
Chapter
1.
Overview
7
8
User
Guide

Chapter
2.
Installing
options
This
chapter
provides
instructions
for
installing
optional
memory,
PCI
adapters,
drives,
and
security
features.
When
installing
an
option,
use
these
instructions
along
with
the
instructions
that
come
with
the
option.
Important
Before
you
install
or
remove
any
option,
read
“Important
safety
information”
on
page
v.
These
precautions
and
guidelines
will
help
you
work
safely.
Handling
static-sensitive
devices
Static
electricity,
although
harmless
to
you,
can
seriously
damage
computer
components
and
options.
When
you
add
an
option,
do
not
open
the
static-protective
package
containing
the
option
until
you
are
instructed
to
do
so.
When
you
handle
options
and
other
computer
components,
take
these
precautions
to
avoid
static
electricity
damage:
v
Limit
your
movement.
Movement
can
cause
static
electricity
to
build
up
around
you.
v
Always
handle
components
carefully.
Handle
adapters
and
memory
modules
by
the
edges.
Never
touch
any
exposed
circuitry.
v
Prevent
others
from
touching
components.
v
When
you
install
a
new
option,
touch
the
static-protective
package
containing
the
option
to
a
metal
expansion-slot
cover
or
other
unpainted
metal
surface
on
the
computer
for
at
least
two
seconds.
This
reduces
static
electricity
in
the
package
and
your
body.
v
When
possible,
remove
the
option
and
install
it
directly
in
the
computer
without
setting
the
option
down.
When
this
is
not
possible,
place
the
static-protective
package
that
the
option
came
in
on
a
smooth,
level
surface
and
place
the
option
on
it.
v
Do
not
place
the
option
on
the
computer
cover
or
other
metal
surface.
Installing
external
options
This
section
shows
the
various
external
connectors
on
your
computer
to
which
you
can
attach
external
options,
such
as
external
speakers,
a
printer,
or
a
scanner.
For
some
external
options,
you
must
install
additional
software
in
addition
to
making
the
physical
connection.
When
adding
an
external
option,
use
the
information
in
this
section
to
identify
the
required
connector,
and
then
use
the
instructions
that
come
with
the
option
to
help
you
make
the
connection
and
install
any
software
or
device
drivers
that
are
required
for
the
option.
©
Copyright
IBM
Corp.
2004
9
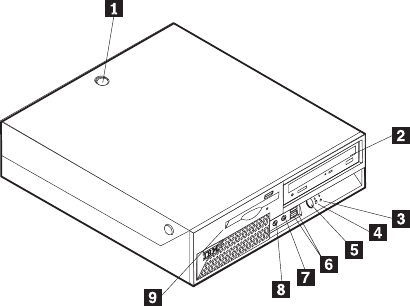
Locating
controls
and
connectors
on
the
front
of
your
computer
The
following
illustration
shows
locations
of
the
controls
and
connectors
on
the
front
of
your
computer.
1
Cover
keylock
(some
models)
6
USB
connectors
(2)
2
CD
or
DVD
drive
7
Microphone
connector
(line
in)
3
Hard
disk
drive
activity
indicator
8
Headphone
connector
(line
out)
4
Power-on
indicator
9
Diskette
drive
5
Power
button
10
User
Guide
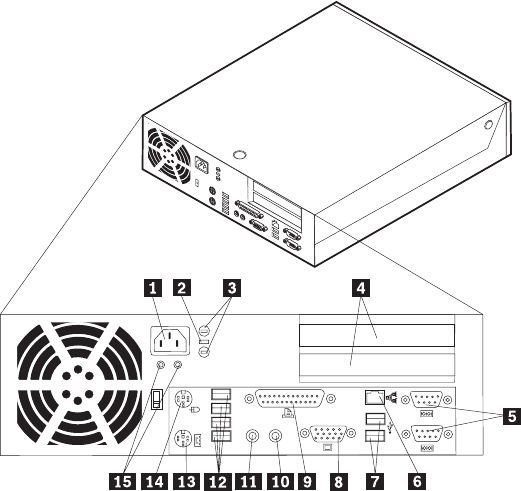
Locating
connectors
on
the
rear
of
your
computer
The
following
illustration
shows
locations
of
connectors
on
the
rear
of
your
computer.
1
Power
cord
connector
9
Parallel
connector
2
Cable
lock
latch
10
Audio
line-in
connector
3
Rope
clip
(U-bolt)
holes
11
Audio
line-out
connector
4
PCI
and
PCI
express
adapter
slots
12
USB
connectors
(4)
5
Serial
connectors
(2)
13
PS/2
keyboard
connector
6
Ethernet
connector
14
PS/2
mouse
connector
7
USB
connectors
(2)
15
LEDs
8
VGA
monitor
connector
Note:
Some
connectors
on
the
rear
of
your
computer
are
color-coded
to
help
determine
where
to
connect
the
cables.
Obtaining
device
drivers
You
can
obtain
device
drivers
for
operating
systems
that
are
not
preinstalled
at
http://www.ibm.com/pc/support/
on
the
World
Wide
Web.
Installation
instructions
are
provided
in
README
files
with
the
device-driver
files.
Chapter
2.
Installing
options
11
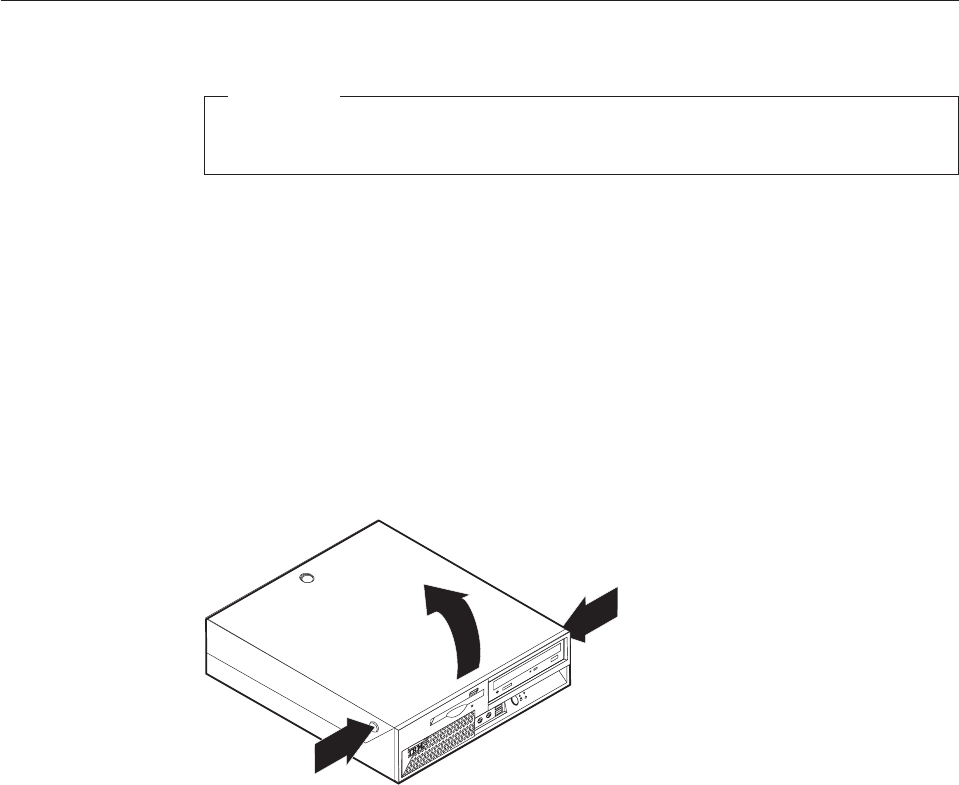
Opening
the
cover
Important
Read
“Important
safety
information”
on
page
v
and
“Handling
static-sensitive
devices”
on
page
9
before
opening
the
cover.
To
open
the
cover:
1.
Shut
down
your
operating
system,
remove
any
media
(diskettes,
CDs,
or
tapes)
from
the
drives,
and
turn
off
all
attached
devices
and
the
computer.
2.
Unplug
all
power
cords
from
electrical
outlets.
3.
Disconnect
all
cables
attached
to
the
computer.
This
includes
power
cords,
input/output
(I/O)
cables,
and
any
other
cables
that
are
connected
to
the
computer.
4.
Remove
the
floor
stand,
if
attached.
5.
If
a
cover
lock
is
installed,
unlock
the
cover.
6.
Press
inward
on
the
two
buttons
and
rotate
the
top
cover
upward
as
illustrated.
12
User
Guide
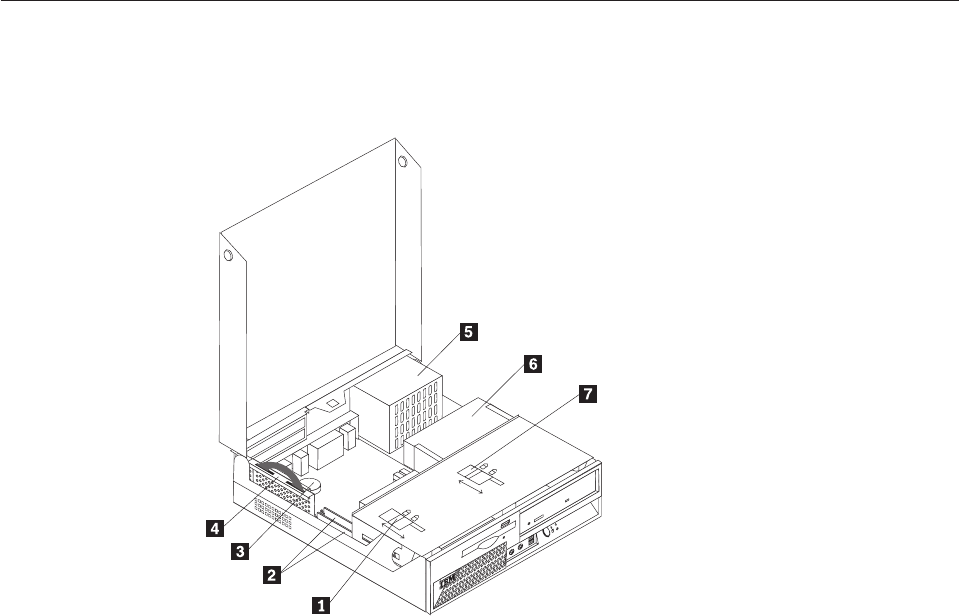
Locating
components
The
following
illustration
will
help
you
locate
the
various
components
in
your
computer.
1
Diskette
drive
lock
5
Power
supply
assembly
2
DIMM
(memory)
connectors
(2)
6
CD
or
DVD
drive
(hard
disk
drive
is
under
the
CD
drive)
3
Battery
7
CD
or
DVD
drive
lock
4
PCI
riser
Chapter
2.
Installing
options
13
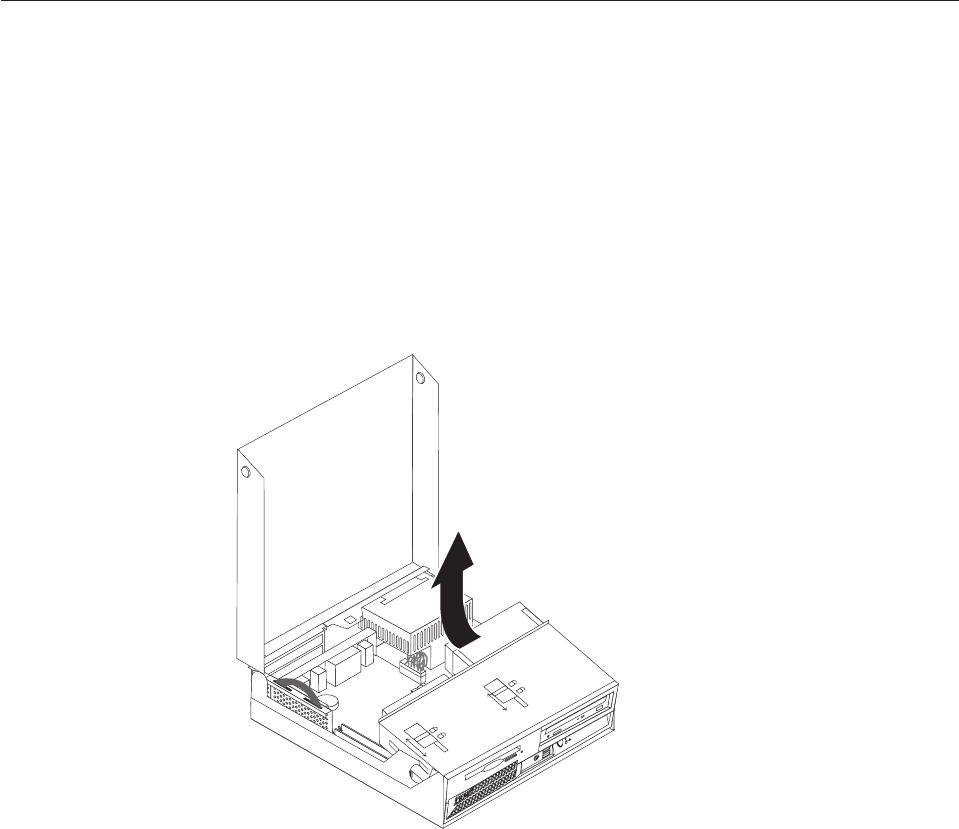
Accessing
system
board
components
and
drives
You
might
need
to
rotate
the
drive
bay
assembly
upward
and
remove
the
PCI
riser
and
adapters
to
access
system
board
components
such
as
memory,
the
battery,
the
Clear
CMOS/BIOS
recovery
jumper
and
to
access
the
drives.
To
access
system
board
components
and
the
drives:
1.
Turn
off
the
computer.
2.
Open
the
cover.
See
“Opening
the
cover”
on
page
12.
3.
Rotate
the
drive
bay
assembly
upward
as
illustrated.
Note:
Make
sure
you
note
the
location
of
any
cables
that
you
disconnect
from
the
drives
or
the
system
board.
4.
If
any
PCI
adapters
are
installed,
remove
the
PCI
riser
and
adapter
cards.
Do
not
remove
any
adapters
from
the
riser
card.
See
“Installing
PCI
adapters”
on
page
17.
14
User
Guide
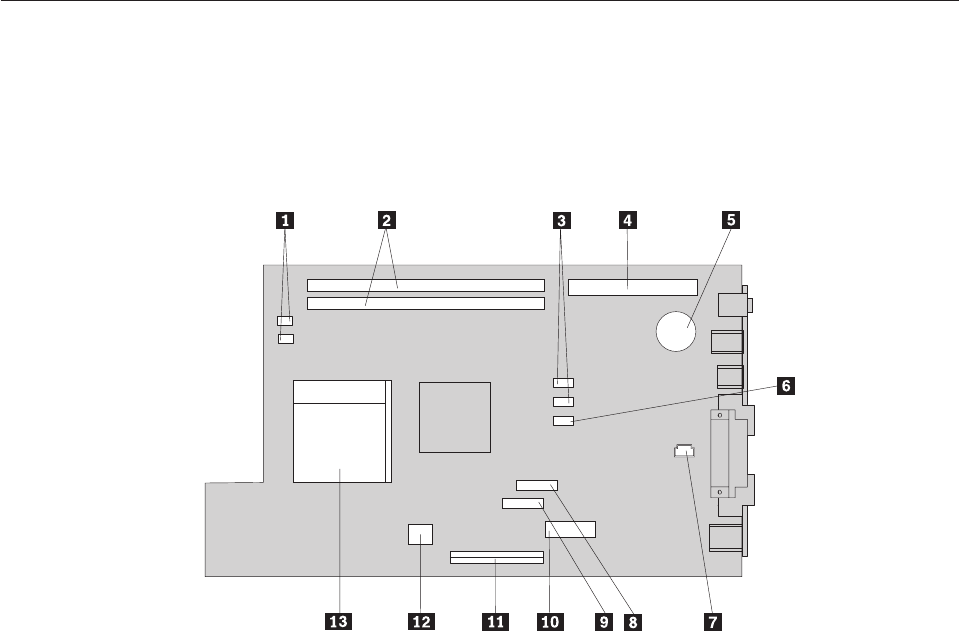
Identifying
parts
on
the
system
board
The
system
board
(sometimes
called
the
planar
or
motherboard)
is
the
main
circuit
board
in
your
computer.
It
provides
basic
computer
functions
and
supports
a
variety
of
devices
that
are
IBM-installed
or
that
you
can
install
later.
The
following
illustration
shows
the
locations
of
parts
on
the
system
board.
1
Fan
connectors
(2)
8
Diskette
drive
connector
2
Memory
DIMM
connectors
(2)
9
Power
button
and
front
LED
assembly
connector
3
SATA
IDE
hard
disk
drive
connectors
(2)
10
Power
supply
connector
4
Riser
connector
11
PATA
Primary
IDE
connector
(hard
disk
drive
and
CD-ROM
drive)
5
CMOS
Battery
12
Power
supply
connector
6
Clear
CMOS/BIOS
recovery
jumper
13
Microprocessor
7
Internal
speaker
connector
Chapter
2.
Installing
options
15
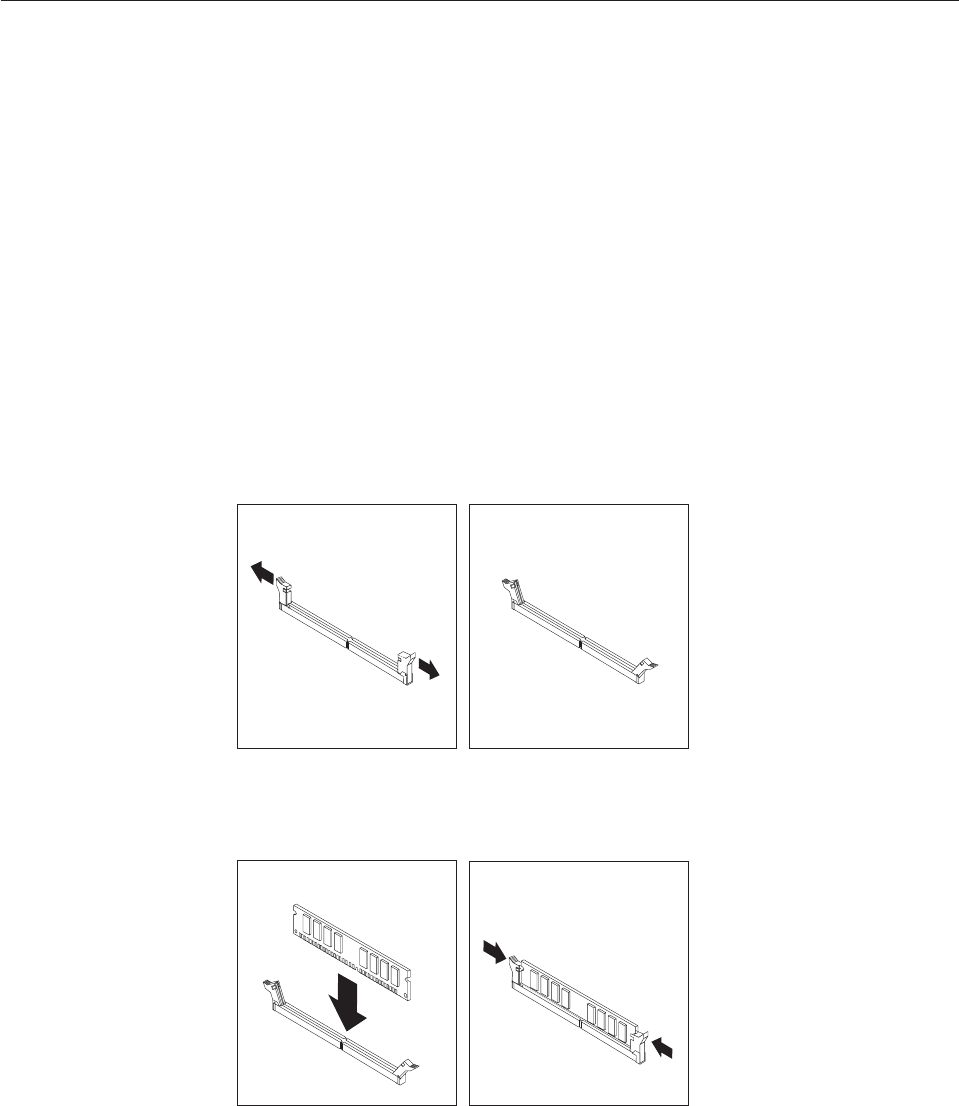
Installing
memory
Your
computer
has
two
connectors
for
installing
dual
inline
memory
modules
(DIMMs)
that
provide
up
to
a
maximum
of
2
GB
of
system
memory.
When
installing
memory,
the
following
rules
apply:
v
Use
2.5
V,
184-pin,
double
data
rate
synchronous
dynamic
random
access
memory
(DDR
SDRAM),
non-ECC
DIMMs.
v
Use
128
MB,
256
MB,
512
MB,
or
1
GB
DIMMs
(when
available)
in
any
combination.
Note:
Only
DDR
SDRAM
DIMMs
can
be
used.
To
install
DIMMs:
1.
Access
the
system
board.
See
“Accessing
system
board
components
and
drives”
on
page
14.
2.
Locate
the
DIMM
connectors.
See
“Identifying
parts
on
the
system
board”
on
page
15.
3.
Open
the
retaining
clips.
4.
Make
sure
the
notch
in
the
DIMM
aligns
with
the
tab
on
the
connector.
Push
or
insert
the
memory
module
straight
down
into
the
connector
until
the
retaining
clips
close.
5.
Replace
the
PCI
riser
and
adapters
if
it
was
removed.
6.
Place
the
drives
back
to
the
original
position.
7.
Replace
the
cover.
See
“Closing
the
cover
and
connecting
the
cables”
on
page
24.
16
User
Guide
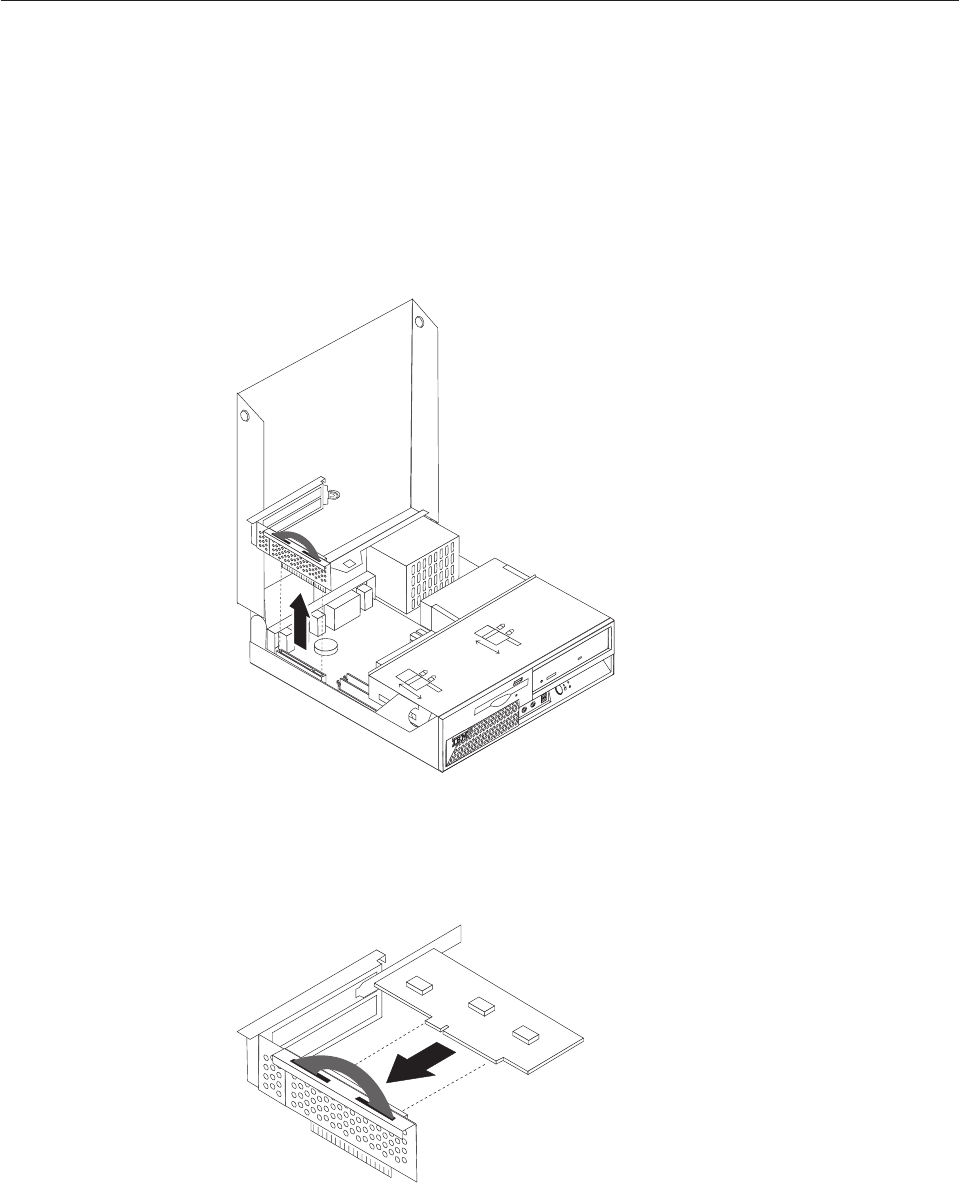
Installing
PCI
adapters
This
section
provides
information
and
instructions
for
installing
and
removing
PCI
adapters.
Your
computer
has
a
riser
card
with
one
PCI
expansion
slot
and
one
PCI
Express
x1
expansion
slot.
To
install
a
PCI
adapter:
1.
Open
the
cover.
See
“Opening
the
cover”
on
page
12.
2.
While
holding
the
left
rear
of
the
computer
chassis
down,
pull
upward
on
the
handle
provided,
to
remove
the
PCI
riser
and
any
adapters
that
are
currently
installed.
3.
Release
the
slot
cover
latch
and
remove
the
slot
cover
for
the
appropriate
expansion
slot.
4.
Remove
the
adapter
from
its
static-protective
package.
5.
Install
the
adapter
into
the
appropriate
slot
in
the
PCI
riser.
Note:
The
top
slot
is
for
the
PCI
adaptor
and
the
bottom
slot
is
for
the
PCI
express
adaptor.
Chapter
2.
Installing
options
17

6.
Position
the
adapter-slot-cover
latch
to
retain
the
adapters.
7.
Reinstall
the
PCI
riser
and
adapters.
8.
Close
the
cover.
See
“Closing
the
cover
and
connecting
the
cables”
on
page
24.
What
to
do
next:
v
To
work
with
another
option,
go
to
the
appropriate
section.
v
To
complete
the
installation,
go
to
“Closing
the
cover
and
connecting
the
cables”
on
page
24.
Removing
and
replacing
the
battery
Your
computer
has
a
special
type
of
memory
that
maintains
the
date,
time,
and
settings
for
built-in
features,
such
as
parallel-port
assignments
(configuration).
A
battery,
sometimes
called
the
CMOS
battery,
keeps
this
information
active
when
you
turn
off
the
computer.
The
battery
normally
requires
no
charging
or
maintenance
throughout
its
life;
however,
no
battery
lasts
forever.
If
the
battery
fails,
the
date,
time,
and
configuration
information
(including
passwords)
are
lost.
An
error
message
is
displayed
when
you
turn
on
the
computer.
Refer
to
“Lithium
battery
notice”
on
page
x
for
information
about
replacing
and
disposing
of
the
battery.
Important
Before
you
install
or
remove
any
component,
read
“Important
safety
information”
on
page
v.
These
precautions
and
guidelines
will
help
you
work
safely.
To
change
the
battery:
1.
Turn
off
the
computer
and
disconnect
the
power
cord
from
the
electrical
outlet
and
from
the
computer.
2.
Open
the
cover.
See
“Opening
the
cover”
on
page
12.
3.
Refer
to
“Identifying
parts
on
the
system
board”
on
page
15
and
locate
the
battery.
4.
Remove
the
PCI
riser
and
PCI
adapters
that
impede
access
to
the
battery.
5.
Remove
the
old
battery.
18
User
Guide
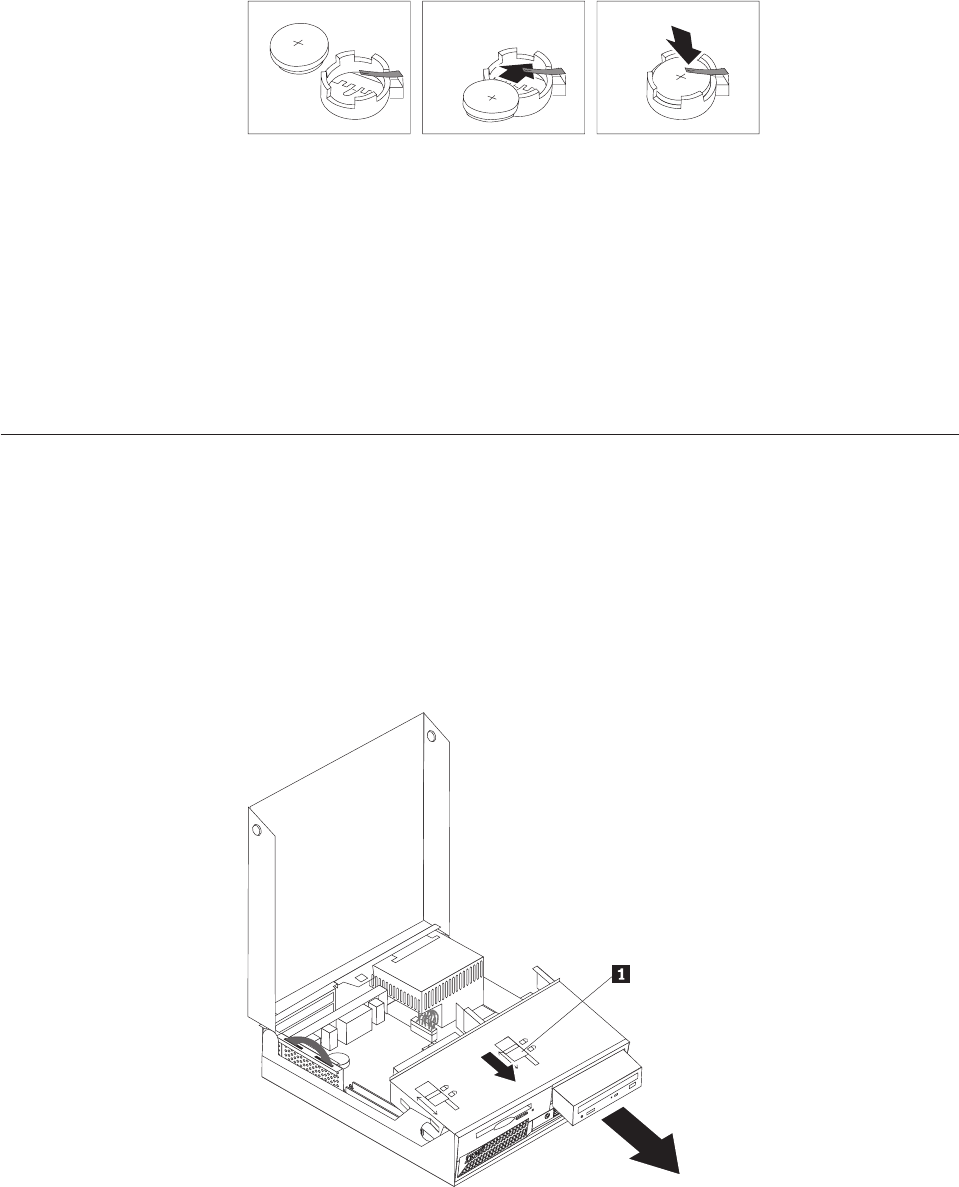
6.
Install
the
new
battery.
7.
Install
the
PCI
riser
and
adapters
if
removed.
8.
Replace
the
cover,
and
connect
the
cables.
See
“Closing
the
cover
and
connecting
the
cables”
on
page
24.
Note:
When
the
computer
is
turned
on
for
the
first
time
after
battery
replacement,
an
error
message
might
be
displayed.
This
is
normal
after
replacing
the
battery.
9.
Turn
on
the
computer
and
all
attached
devices.
10.
Use
the
IBM
Setup
Utility
program
to
set
the
date
and
time
and
any
passwords.
Removing
and
replacing
an
optical
drive
1.
Open
the
cover.
See
“Opening
the
cover”
on
page
12.
2.
Rotate
the
drive
bay
assembly
upward
to
gain
access
to
the
cable
connections.
See
“Accessing
system
board
components
and
drives”
on
page
14
and
“Locating
components”
on
page
13.
3.
Disconnect
the
signal
and
power
cables
from
the
drive.
4.
Slide
the
lock1to
the
unlocked
position.
5.
Open
the
door
at
the
front
of
the
drive
and
slide
it
out
the
front
of
the
computer.
6.
Install
the
new
drive
into
the
bay
from
the
front.
7.
Slide
the
lock
1to
the
locked
position
and
close
the
door
at
the
front
of
the
drive.
Chapter
2.
Installing
options
19
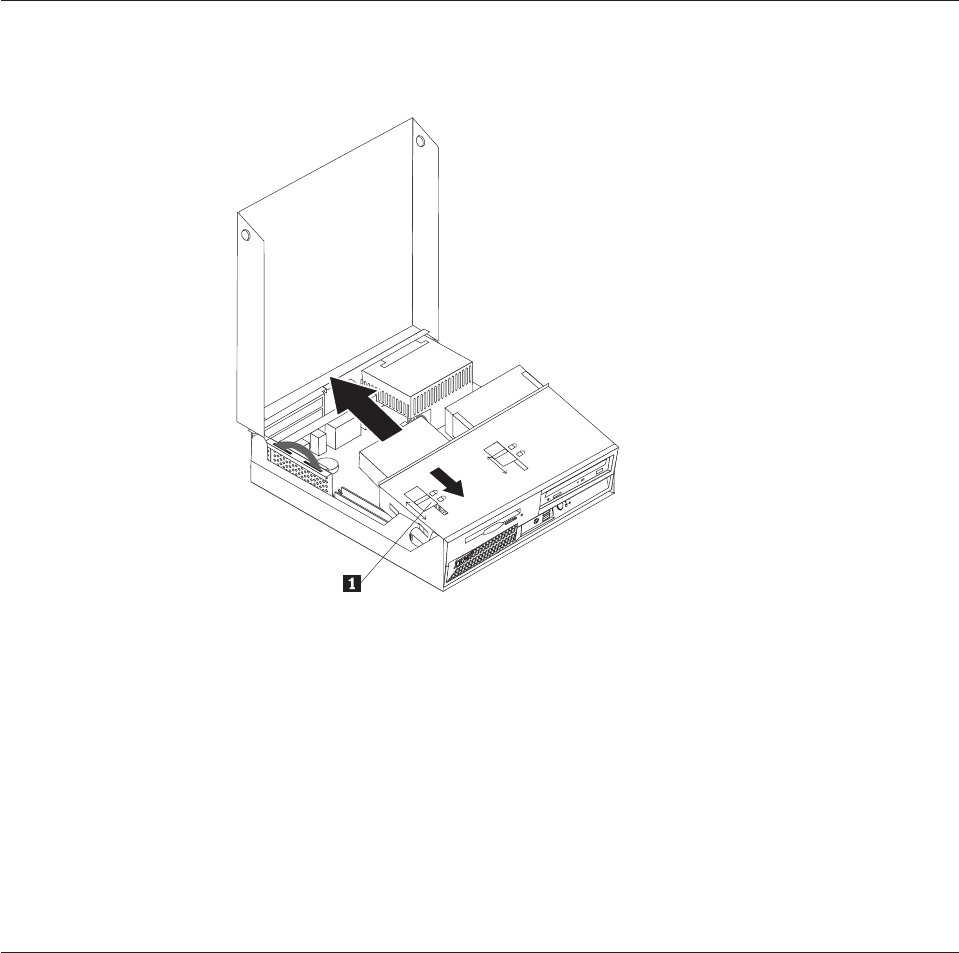
8.
If
you
are
replacing
an
existing
drive,
place
the
master/slave
jumper
on
the
drive
in
the
same
position
as
on
the
drive
being
replaced.
Also
refer
to
any
instructions
that
come
with
the
drive.
9.
Connect
the
signal
cable
and
power
cable
to
the
drive.
10.
See
“Closing
the
cover
and
connecting
the
cables”
on
page
24
to
finish
the
procedure.
Removing
and
replacing
a
diskette
drive
1.
Open
the
cover.
See
“Opening
the
cover”
on
page
12.
2.
Slide
the
lock1to
the
unlocked
position.
3.
Slide
the
drive
towards
the
rear
of
the
computer
far
enough
to
gain
access
to
the
flat
cable
connector
on
the
drive
and
disconnect
the
flat
cable
from
the
drive.
4.
Rotate
the
drive
bay
assembly
upward
and
remove
the
diskette
drive.
To
install
a
new
diskette
drive:
1.
Slide
the
new
drive
partially
into
the
bay
from
the
rear.
2.
Connect
the
flat
cable
to
the
new
drive.
3.
Slide
the
new
drive
completely
into
the
bay
and
slide
the
lock1to
the
locked
position.
4.
See
“Closing
the
cover
and
connecting
the
cables”
on
page
24
to
finish
the
procedure.
Installing
security
features
To
help
prevent
hardware
theft
and
unauthorized
access
to
your
computer,
several
security
lock
options
are
available.
The
following
sections
help
you
identify
and
install
the
various
types
of
locks
that
might
be
available
for
your
computer.
In
addition
to
physical
locks,
unauthorized
use
of
your
computer
can
be
prevented
by
a
software
lock
that
locks
the
keyboard
until
a
correct
password
is
typed
in.
20
User
Guide
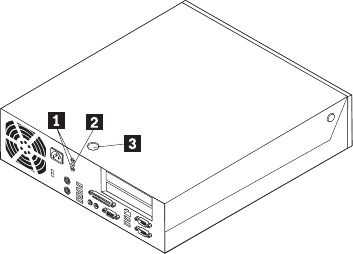
Make
sure
that
any
security
cables
you
install
do
not
interfere
with
other
computer
cables.
Identifying
security
locks
The
following
illustration
will
help
you
to
identify
the
various
types
of
security
locks
that
your
computer
might
have.
1
Holes
for
Rope
clip
(U-bolt)
2
Slot
for
integrated
cable
lock
(Kensington
lock)
3
Cover
lock
Integrated
security
cable
With
an
integrated
cable
lock
(sometimes
referred
to
as
the
Kensington
lock),
you
can
secure
your
computer
to
a
desk,
table,
or
other
non-permanent
fixture.
The
cable
lock
attaches
to
a
security
slot
at
the
rear
of
your
computer
and
is
operated
with
a
key.
This
is
the
same
type
of
lock
used
with
many
laptop
computers.
You
can
order
a
security
cable
directly
from
IBM.
Go
to
http://www.pc.ibm.com/support
and
search
on
Kensington.
Chapter
2.
Installing
options
21
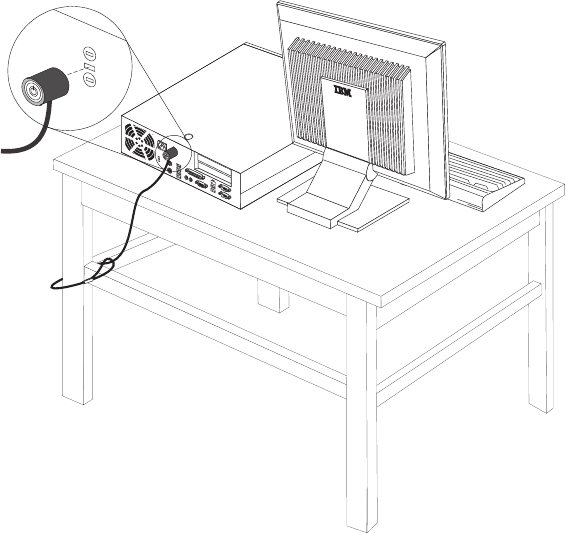
®
22
User
Guide
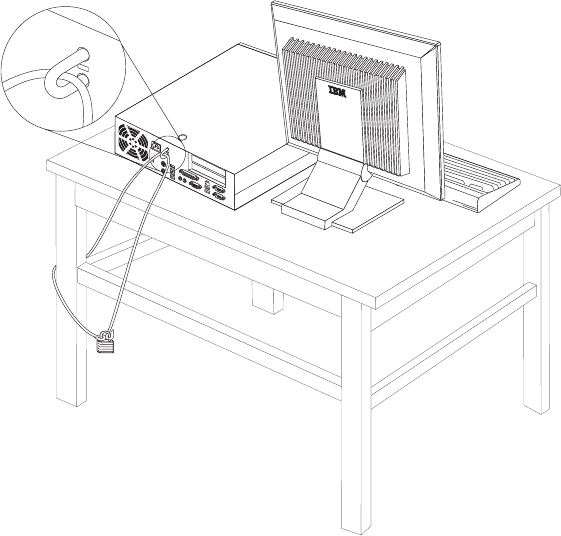
Rope
clip
Using
a
3/16
in
(5
mm)
security
rope
clip
(sometimes
referred
to
as
a
U-bolt),
a
steel
security
cable,
and
a
padlock
you
can
secure
your
computer
to
a
desk,
table,
or
other
non-permanent
fixture.
For
computers
designed
to
accommodate
the
rope
clip,
knockouts
at
the
rear
of
the
chassis
are
provided.
To
install
a
rope
clip:
1.
Remove
the
cover.
See
“Opening
the
cover”
on
page
12.
2.
Use
a
tool,
such
as
a
screwdriver,
to
remove
the
two
metal
knockouts.
3.
Insert
the
rope
clip
through
the
rear
of
the
chassis
and
install
the
nuts
using
either
an
adjustable
or
an
appropriate
sized
wrench.
4.
Replace
the
cover.
5.
Thread
the
security
cable
through
the
rope
clip
and
around
an
object
that
is
not
part
of
or
permanently
attached
to
the
building
structure
or
foundation,
and
from
which
it
cannot
be
removed;
then
fasten
the
cable
together
with
a
lock.
®
Cover
lock
Your
computer
comes
with
a
built-in
key
lock
or
a
provision
to
install
a
key
lock
such
as
those
provided
by
the
Illinois
Lock
Company.
The
mailing
address
is:
Illinois
Lock
Company
301
W.
Hintz
Road
Wheeling,
IL
60090-5754
USA
Password
protection
To
deter
unauthorized
use
of
your
computer,
you
can
use
the
IBM
Setup
Utility
program
to
set
a
password.
When
you
turn
on
your
computer
you
are
prompted
to
type
the
password
to
unlock
the
keyboard
for
normal
use.
Chapter
2.
Installing
options
23

Erasing
a
lost
or
forgotten
password
(clearing
CMOS)
This
section
applies
to
lost
or
forgotten
passwords.
For
more
information
about
lost
or
forgotten
passwords,
go
to
Access
IBM.
To
erase
a
forgotten
password:
1.
Refer
to
“Accessing
system
board
components
and
drives”
on
page
14.
2.
Locate
the
Clear
CMOS/BIOS
recovery
jumper
on
the
system
board.
See
“Identifying
parts
on
the
system
board”
on
page
15.
3.
Move
the
jumper
from
the
standard
position
(pins
1
and
2)
to
the
maintenance
or
configure
position
(pins
2
and
3).
4.
Install
the
PCI
riser
and
adapters
if
removed.
5.
Lower
the
drive
bay
assembly
and
reconnect
any
cables
that
were
disconnected.
6.
Close
the
cover
and
connect
the
power
cable.
See
“Closing
the
cover
and
connecting
the
cables.”
7.
Restart
the
computer,
leave
it
on
for
approximately
10
seconds,
and
then
turn
off
the
computer.
8.
Repeat
step
1.
9.
Move
the
CMOS/BIOS
recovery
jumper
back
to
the
standard
position
(pins
1
and
2).
10.
Reassemble
the
computer
and
close
the
cover.
See
“Closing
the
cover
and
connecting
the
cables.”
Closing
the
cover
and
connecting
the
cables
After
working
with
options,
you
need
to
install
any
removed
parts,
close
the
cover,
and
reconnect
cables,
including
telephone
lines
and
power
cords.
Also,
depending
on
the
option
that
is
installed,
you
might
need
to
confirm
the
updated
information
in
the
IBM
Setup
Utility
program.
To
close
the
cover
and
connect
cables
to
your
computer:
1.
Ensure
that
all
components
have
been
reassembled
correctly
and
that
no
tools
or
loose
screws
are
left
inside
your
computer.
2.
Clear
any
cables
that
might
impede
the
replacement
of
the
cover.
3.
Make
sure
the
drive
bay
assembly
is
lowered
and
that
the
drive
locks
are
both
in
the
locked
position.
Otherwise,
you
cannot
close
the
cover.
4.
Close
the
cover.
5.
If
a
cover
lock
is
installed,
lock
the
cover.
6.
If
your
computer
is
being
placed
in
the
vertical
position,
attach
the
floor
stand.
Attention:
To
prevent
overheating
and
possible
component
damage,
always
attach
the
floor
stand
when
placing
the
computer
in
the
vertical
position.
7.
Reconnect
the
external
cables
and
power
cords
to
the
computer.
See
“Locating
connectors
on
the
rear
of
your
computer”
on
page
11.
8.
To
update
the
configuration,
see
Chapter
3,
“Using
the
IBM
Setup
Utility,”
on
page
25.
24
User
Guide

Chapter
3.
Using
the
IBM
Setup
Utility
The
IBM
Setup
Utility
program
is
stored
in
the
electrically
erasable
programmable
read-only
memory
(EEPROM)
of
your
computer.
The
IBM
Setup
Utility
program
is
used
to
view
and
change
the
configuration
settings
of
your
computer,
regardless
of
which
operating
system
you
are
using.
However,
the
operating-system
settings
might
override
any
similar
settings
in
the
IBM
Setup
Utility
program.
Starting
the
IBM
Setup
Utility
program
To
start
the
IBM
Setup
Utility
program,
do
the
following:
1.
If
your
computer
is
already
on
when
you
start
this
procedure,
shut
down
the
operating
system
and
turn
off
the
computer.
2.
Turn
on
the
computer
and
look
for
the
following
prompt
on
the
logo
screen:
(To
interrupt
normal
startup,
press
Enter)
Press
Enter
when
you
see
the
prompt.
3.
When
the
Startup
Interrupt
Menu
displays,
press
F1.
Note:
If
a
user
password
or
an
administrator
password
has
been
set,
the
IBM
Setup
Utility
program
menu
is
not
displayed
until
you
type
your
password.
See
“Using
passwords”
for
more
information.
The
IBM
Setup
Utility
might
start
automatically
when
POST
detects
that
hardware
has
been
removed
or
new
hardware
has
been
installed
in
your
computer.
Viewing
and
changing
settings
The
IBM
Setup
Utility
program
menu
lists
items
that
identify
system
configuration
topics.
When
working
with
the
IBM
Setup
Utility
program
menu,
you
must
use
the
keyboard.
The
keys
used
to
perform
various
tasks
are
displayed
at
the
bottom
of
each
screen.
Exiting
from
the
IBM
Setup
Utility
program
When
you
finish
viewing
or
changing
settings,
press
Esc
to
return
to
the
IBM
Setup
Utility
program
menu
(you
might
have
to
press
Esc
several
times).
If
you
want
to
save
the
new
settings,
select
Save
Settings
or
Save
and
exit
the
Setup
Utility.
Otherwise,
your
changes
will
not
be
saved.
Using
passwords
By
using
the
IBM
Setup
Utility
program,
you
can
set
passwords
to
prevent
unauthorized
persons
from
gaining
access
to
your
computer
and
data.
The
following
types
of
passwords
are
available:
v
User
Password
v
Administrator
Password
v
IDE
Drive
User
Password
v
IDE
Drive
Master
Password
©
Copyright
IBM
Corp.
2004
25

You
do
not
have
to
set
any
passwords
to
use
your
computer.
However,
if
you
decide
to
set
any
passwords,
read
the
following
sections.
Password
considerations
If
you
are
setting
any
of
the
various
types
of
passwords
on
your
computer,
you
should
read
and
understand
the
following
information:
v
If
you
type
an
incorrect
password,
you
will
see
an
error
message.
If
you
type
an
incorrect
password
three
consecutive
times,
you
must
turn
the
computer
off
and
start
again.
v
If
you
set
both
a
User
Password
and
an
IDE
Drive
User
Password
to
the
same
string,
you
will
be
prompted
for
the
password
only
once
when
you
turn
on
your
computer.
v
Do
not
move
an
IDE
hard
disk
drive
to
another
computer
if
an
IDE
Drive
User
Password
has
been
set
unless
that
computer
also
supports
the
IDE
Drive
User
password.
v
If
your
computer
is
connected
to
a
local
area
network
(LAN),
Wake
on
LAN
will
not
work
unless
both
a
User
Password
and
an
IDE
Drive
User
Password
are
set
using
the
same
password.
User
Password
When
a
User
Password
is
set,
the
user
is
prompted
to
type
a
valid
password
each
time
the
computer
is
turned
on.
The
computer
cannot
be
used
until
a
valid
password
is
typed
from
the
keyboard.
Administrator
Password
Setting
an
Administrator
Password
deters
unauthorized
persons
from
changing
configuration
settings.
If
you
are
responsible
for
maintaining
the
settings
of
several
computers,
you
might
want
to
set
an
Administrator
Password.
After
you
set
an
Administrator
Password,
a
password
prompt
is
displayed
each
time
you
try
to
access
the
IBM
Setup
Utility
program.
If
both
the
user
and
administrator
passwords
are
set,
you
can
type
either
password.
However,
to
change
any
configuration
settings,
you
must
use
your
administrator
password.
IDE
Drive
User
Password
The
IDE
Drive
User
Password
is
used
to
protect
the
data
on
the
IDE
hard
disk
drive(s).
When
this
password
is
set,
you
are
prompted
to
type
a
valid
password
before
any
hard
disk
drive
can
be
used.
This
prompt
is
displayed
each
time
you
turn
on
your
computer.
If
your
computer
has
multiple
hard
disk
drives,
they
all
must
use
the
same
password.
Attention
If
an
IDE
Drive
User
Password
is
set
but
no
IDE
Drive
Master
Password
is
set,
there
is
no
recovery
in
the
event
that
the
IDE
Drive
User
Password
is
lost
or
forgotten.
The
hard
disk
drive
must
be
replaced.
See
“IDE
Drive
Master
Password”
on
page
27.
26
User
Guide

IDE
Drive
Master
Password
The
IDE
Drive
Master
Password
is
used
to
recover
use
of
the
hard
disk
drive
in
the
event
that
the
IDE
Drive
User
Password
is
lost
or
forgotten.
Only
the
person
who
knows
the
IDE
Drive
Master
password
can
reset
the
IDE
Drive
User
Password.
Attention
Make
sure
that
the
IDE
Drive
Master
password
is
stored
in
a
safe
place.
If
both
the
IDE
Drive
User
password
and
the
IDE
Drive
Master
password
are
lost
or
forgotten,
the
IDE
hard
disk
drive
must
be
replaced.
If
both
the
IDE
Drive
User
Password
and
the
IDE
Drive
Master
Password
are
to
be
set,
the
IDE
Drive
Master
Password
must
be
set
before
setting
the
IDE
Drive
User
Password.
Setting,
changing,
and
deleting
a
password
To
set,
change,
or
delete
a
password,
do
the
following:
Note:
A
password
can
be
any
combination
of
up
to
seven
characters
(A-
Z,
a-z,
and
0-9).
1.
Start
the
IBM
Setup
Utility
program
(see
“Starting
the
IBM
Setup
Utility
program”
on
page
25).
2.
From
the
IBM
Setup
Utility
program
menu,
select
Security.
3.
Select
Set
Passwords.
Read
the
information
displayed
on
the
right
side
of
the
screen.
Using
Security
Profile
by
Device
Security
Profile
by
Device
is
used
to
enable
or
disable
user
access
to
the
following
devices:
IDE
controller
When
this
feature
is
set
to
Disable,
all
devices
connected
to
the
IDE
controller
(such
as
hard
disk
drives
or
the
CD-ROM
drive)
are
disabled
and
will
not
be
displayed
in
the
system
configuration.
Diskette
Drive
Access
When
this
feature
is
set
to
Disable,
the
diskette
drive
cannot
be
accessed.
Diskette
Write
Protect
When
this
feature
is
set
to
Enable,
all
diskettes
are
treated
as
if
they
are
write-protected.
To
set
Security
Profile
by
Device,
do
the
following:
1.
Start
the
IBM
Setup
Utility
program
(see
“Starting
the
IBM
Setup
Utility
program”
on
page
25).
2.
From
the
IBM
Setup
Utility
program
menu,
select
Security.
3.
Select
Security
Profile
by
Device.
4.
Select
the
desired
devices
and
settings
and
press
Enter.
5.
Return
to
the
IBM
Setup
Utility
program
menu
and
select
Exit
and
then
Save
Settings
or
Save
and
exit
the
Setup
Utility.
Note:
If
you
do
not
want
to
save
the
settings,
select
Exit
the
Setup
Utility
without
saving.
Chapter
3.
Using
the
IBM
Setup
Utility
27

Selecting
a
startup
device
If
your
computer
does
not
start
up
(boot)
from
a
device
such
as
the
CD-ROM,
diskette,
or
hard
disk
as
expected,
use
one
of
the
following
procedures
to
select
a
startup
device.
Selecting
a
temporary
startup
device
Use
this
procedure
to
startup
from
any
boot
device.
Note:
Not
all
CDs,
hard
disks,
and
diskettes
are
startable
(bootable).
1.
Turn
off
your
computer.
2.
Turn
on
your
computer
and
look
for
the
following
prompt
on
the
logo
screen:
(To
interrupt
normal
startup,
press
Enter)
Press
Enter
when
you
see
the
prompt.
3.
When
the
Startup
Interrupt
Menu
displays,
press
F12.
4.
Select
the
desired
startup
device
from
the
Startup
Device
menu
and
press
Enter
to
begin.
Note:
Selecting
a
startup
device
from
the
Startup
Device
menu
does
not
permanently
change
the
startup
sequence.
Changing
the
startup
device
sequence
To
view
or
permanently
change
the
configured
startup
device
sequence,
do
the
following:
1.
Start
the
IBM
Setup
Utility
program
(see
“Starting
the
IBM
Setup
Utility
program”
on
page
25).
2.
Select
Startup.
3.
Select
Startup
Sequence.
See
the
information
displayed
on
the
right
side
of
the
screen.
4.
Select
the
devices
for
the
Primary
Startup
Sequence,
the
Automatic
Startup
Sequence,
and
the
Error
Startup
Sequence.
5.
Select
Exit
from
the
IBM
Setup
Utility
menu
and
then
Save
Settings
or
Save
and
exit
the
Setup
Utility.
If
you
have
changed
these
settings
and
want
to
return
to
the
default
settings,
select
Load
Default
Settings
on
the
Exit
menu.
Advanced
settings
On
some
computer
models
the
Advanced
settings
menu
includes
a
setting
to
Enable/Disable
HyperThreading.
This
feature
works
only
with
HyperThreading-aware
operating
systems
such
as
Microsoft
Windows
XP.
The
default
setting
for
HyperThreading
is
Enabled.
However,
if
you
select
Set
Defaults
and
are
using
an
operating
system
other
than
Windows
XP,
your
computer
performance
might
be
degraded.
Therefore,
you
should
always
set
HyperThreading
to
Disabled
unless
you
are
sure
your
operating
system
supports
HyperThreading.
28
User
Guide

Appendix
A.
Updating
POST/BIOS
This
appendix
contains
information
about
updating
POST/BIOS
and
how
to
recover
from
a
POST/BIOS
update
failure.
POST/BIOS
POST
and
BIOS
are
the
basic
layer
of
software
that
is
built
into
your
computer.
They
include
the
power-on
self-test
(POST),
the
basic
input/output
system
(BIOS)
code,
and
the
IBM
Setup
Utility
program.
POST
is
a
set
of
tests
and
procedures
that
is
performed
each
time
you
turn
on
your
computer.
BIOS
is
a
layer
of
software
that
translates
instructions
from
other
layers
of
software
into
electrical
signals
that
the
computer
hardware
can
understand.
You
can
use
the
IBM
Setup
Utility
program
to
view
and
change
the
configuration
and
setup
of
your
computer.
Your
computer
system
board
has
a
module
called
electrically
erasable
programmable
read-only
memory
(EEPROM,
also
referred
to
as
flash
memory).
You
can
easily
update
POST,
BIOS,
and
the
IBM
Setup
Utility
program
by
starting
your
computer
using
a
flash
update
diskette
or
by
running
a
special
update
program
from
your
operating
system.
IBM
might
make
changes
and
enhancements
to
the
POST/BIOS.
When
updates
are
released,
they
are
available
as
downloadable
files
on
the
World
Wide
Web
(see
the
Quick
Reference).
Instructions
for
using
the
POST/BIOS
updates
are
available
in
a
.txt
file
that
is
included
with
the
update
files.
For
most
models,
you
can
download
either
an
update
program
to
create
a
system-program-update
(flash)
diskette
or
an
update
program
that
can
be
run
from
the
operating
system.
Note:
You
can
download
a
self
starting
bootable
CD
image
(known
as
an
.iso
image)
of
the
diagnostics
program
from
http://www.ibm.com/pc/support
to
support
systems
without
a
diskette
drive.
Updating
(flashing)
BIOS
from
a
diskette
1.
Insert
a
POST/BIOS
update
(flash)
diskette
into
the
diskette
drive
(drive
A)
in
your
computer.
POST/BIOS
updates
are
available
at
http://www.ibm.com/pc/support/
on
the
World
Wide
Web.
2.
Turn
on
the
computer.
If
it
is
on
already,
you
must
turn
it
off
and
back
on
again.
The
update
begins.
Updating
(flashing)
BIOS
from
your
operating
system
Note:
Due
to
constant
improvements
being
made
to
the
IBM
Web
site,
Web
page
content
(including
the
links
referenced
in
the
following
procedure)
is
subject
to
change.
1.
From
your
browser,
type
http://www.pc.ibm.com/support
in
the
address
field
and
press
Enter.
2.
Locate
Downloadable
files
for
your
type
of
computer.
3.
Under
Select
your
product,
choose
your
machine
type
and
click
Go.
4.
In
Downloadable
file
by
category,
click
BIOS.
5.
Under
Download
files
-
BIOS
by
date,
click
your
machine
type.
©
Copyright
IBM
Corp.
2004
29

6.
Scroll
down
and
look
for
a
.txt
file
that
has
instructions
for
Flash
BIOS
update
from
the
operating
system.
Click
the
.txt
file.
7.
Print
these
instructions.
This
is
very
important
since
they
are
not
on
the
screen
after
the
download
begins.
8.
From
your
browser,
Click
Back
to
return
to
the
list
of
files.
Carefully
follow
the
printed
instructions
to
download,
extract,
and
install
the
update.
Recovering
from
a
POST/BIOS
update
failure
If
power
to
your
computer
is
interrupted
while
POST/BIOS
is
being
updated
(flash
update),
your
computer
might
not
restart
correctly.
If
this
happens,
perform
the
following
procedure
commonly
called
Boot-block
Recovery.
1.
Turn
off
the
computer
and
any
attached
devices,
such
as
printers,
monitors,
and
external
drives.
2.
Unplug
all
power
cords
from
electrical
outlets,
and
open
the
cover.
See
“Opening
the
cover”
on
page
12.
3.
Locate
the
Clear
CMOS/BIOS
Recovery
jumper
on
the
system
board.
See
“Identifying
parts
on
the
system
board”
on
page
15.
4.
If
necessary,
refer
to
“Accessing
system
board
components
and
drives”
on
page
14
to
gain
access
to
the
Clear
CMOS/BIOS
Recovery
jumper.
5.
Remove
any
cables
or
adapters
that
impede
access
to
the
Clear
CMOS/BIOS
Recovery
jumper.
6.
Move
the
jumper
from
the
standard
position
(pins
1
and
2)
to
pins
2
and
3.
7.
Replace
any
cables
or
adapters
that
were
removed.
8.
Close
the
cover.
See
“Closing
the
cover
and
connecting
the
cables”
on
page
24.
9.
Reconnect
the
power
cords
for
the
computer
and
monitor
to
electrical
outlets.
10.
Insert
the
POST/BIOS
update
(flash)
diskette
into
drive
A,
and
turn
on
the
computer
and
the
monitor.
11.
During
the
update
session
there
will
be
no
video.
You
will
hear
a
long
beep
when
recovery
is
completed.
Remove
the
diskette
from
the
diskette
drive,
and
turn
off
the
computer
and
monitor.
12.
Unplug
the
power
cords
from
electrical
outlets.
13.
Open
the
cover.
See
“Opening
the
cover”
on
page
12.
14.
Remove
any
cables
or
adapters
that
impede
access
to
the
Clear
CMOS/BIOS
Recovery
jumper.
15.
Replace
the
Clear
CMOS/BIOS
Recovery
jumper
to
its
original
position.
16.
Replace
any
cables
or
adapters
that
were
removed.
17.
Close
the
cover
and
reconnect
any
cables
that
were
disconnected.
18.
Turn
on
the
computer
to
restart
the
operating
system.
30
User
Guide
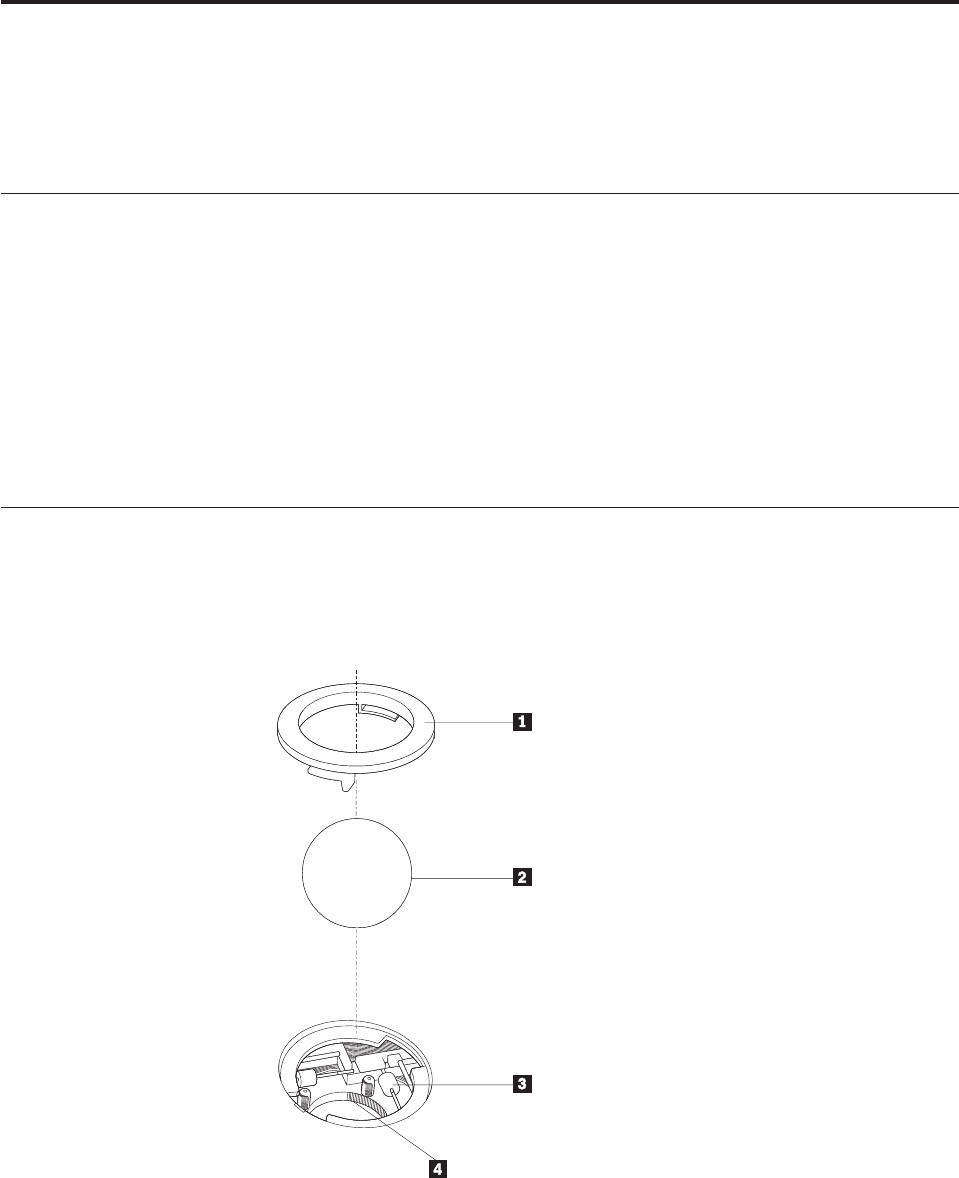
Appendix
B.
Cleaning
the
mouse
This
appendix
provides
instructions
on
how
to
clean
your
mouse.
The
procedure
will
be
different
depending
on
which
type
of
mouse
you
have.
Cleaning
an
optical
mouse
If
you
experience
some
problems
with
your
optical
mouse,
check
the
following:
1.
Turn
the
mouse
over
and
look
carefully
at
the
lens
area.
a.
If
there
is
a
smudge
on
the
lens,
gently
clean
the
area
with
a
plain
cotton
swab
or
plain
q-tip.
b.
If
there
is
some
debris
in
the
lens,
gently
blow
the
debris
away
from
the
area.
2.
Check
the
surface
you
are
using
the
mouse
on.
If
you
have
a
very
intricate
picture
or
pattern
beneath
the
mouse
it
is
difficult
for
the
digital
signal
processor
(DSP)
to
determine
changes
in
the
mouse
position.
Cleaning
a
mouse
with
a
ball
If
the
pointer
on
the
screen
does
not
move
smoothly
with
the
mouse,
you
might
need
to
clean
the
mouse.
Note:
The
following
illustration
might
be
slightly
different
from
your
mouse.
1
Retainer
ring
2
Ball
3
Plastic
rollers
4
Ball
cage
©
Copyright
IBM
Corp.
2004
31
To
clean
a
mouse
with
a
ball:
1.
Turn
off
your
computer.
2.
Turn
the
mouse
over,
with
the
top
side
down,
and
look
carefully
at
the
bottom.
Twist
the
retainer
ring1to
the
unlocked
position
to
remove
the
ball.
3.
Place
your
hand
over
the
retainer
ring
and
ball2,
and
then
turn
the
mouse
over,
top
side
up,
so
that
the
retainer
ring
and
ball
fall
out
into
your
hand.
4.
Wash
the
ball
in
warm,
soapy
water
then
dry
it
with
a
clean
cloth.
Blow
air
carefully
into
the
ball
cage4to
dislodge
dust
and
lint.
5.
Look
for
a
build
up
of
dirt
on
the
plastic
rollers3inside
the
ball
cage.
This
build
up
usually
appears
as
a
stripe
running
across
the
middle
of
the
rollers.
6.
If
the
rollers
are
dirty,
clean
them
by
using
a
cotton
swab
soaked
in
isopropyl
(rubbing)
alcohol.
Turn
the
rollers
with
your
finger
and
continue
swabbing
them
until
all
the
dirt
is
removed.
Be
sure
the
rollers
are
still
centered
in
their
channels
after
you
clean
them.
7.
Remove
any
fibers
from
the
swab
that
might
be
remaining
on
the
rollers.
8.
Replace
the
ball
and
the
retainer
ring.
9.
Turn
your
computer
back
on.
32
User
Guide
Appendix
C.
Manual
modem
commands
The
following
section
lists
commands
for
manually
programming
your
modem.
Commands
are
accepted
by
the
modem
while
it
is
in
Command
Mode.
Your
modem
is
automatically
in
Command
Mode
until
you
dial
a
number
and
establish
a
connection.
Commands
may
be
sent
to
your
modem
from
a
PC
running
communication
software
or
any
other
terminal
devices.
All
commands
sent
to
the
modem
must
begin
with
AT
and
end
with
ENTER.
All
commands
may
be
typed
in
either
upper
or
lower
case,
but
not
mixed.
To
make
the
command
line
more
readable,
spaces
may
be
inserted
between
commands.
If
you
omit
a
parameter
from
a
command
that
requires
one,
it
is
just
like
specifying
a
parameter
of
0.
Example:
ATH
[ENTER]
Basic
AT
commands
In
the
following
listings,
all
default
settings
are
printed
in
bold
text.
Command
Function
A
Manually
answer
incoming
call.
A/
Repeat
last
command
executed.
Do
not
precede
A/
with
AT
or
follow
with
ENTER.
D_
0
-
9,
A-D,
#
and
*
L
last
number
redial
P
pulse
dialing
Note:
Pulse
dialing
is
not
supported
for
Australia,
New
Zealand,
Norway,
and
South
Africa.
T
touch-tone
dialing
W
wait
for
second
dial
tone
,
pause
@
wait
for
five
seconds
of
silence
!
flash
;
return
to
Command
Mode
after
dialing
DS=n
Dial
one
of
the
four
telephone
numbers
(n=0-3)
stored
in
the
modem
non-volatile
memory.
E_
E0
Commands
are
not
echoed
E1
Commands
are
echoed
+++
Escape
Characters
-
Switch
from
Data
Mode
to
Command
Mode
(T.I.E.S.
Command)
H_
H0
Force
modem
on-hook
(hang
up)
©
Copyright
IBM
Corp.
2004
33
Command
Function
H1
Force
modem
off-hook
(make
busy)
Note:
H1
command
is
not
supported
for
Italy
I_
I0
Display
product-identification
code
I1
Factory
ROM
checksum
test
I2
Internal
memory
test
I3
Firmware
ID
I4
Reserved
ID
L_
L0
Low
speaker
volume
L1
Low
speaker
volume
L2
Medium
speaker
volume
L3
High
speaker
volume
M_
M0
Internal
speaker
off
M1
Internal
speaker
on
until
carrier
detected
M2
Internal
speaker
always
on
M3
Internal
speaker
on
until
carrier
detected
and
off
while
dialing
N_
Included
for
compatibility
only,
provides
no
effect
O_
O0
Return
to
Data
Mode
O1
Return
to
Data
Mode
and
initiate
an
equalizer
retrain
P
Set
Pulse
dial
as
default
Q_
Q0
Modem
sends
responses
Sr?
Read
and
display
value
in
register
r.
Sr=n
Set
register
r
to
value
n
(n
=
0-255).
T
Set
Tone
Dial
as
default
V_
V0
Numeric
responses
V1
Word
responses
W_
W0
Report
DTE
speed
only
W1
Report
line
speed,
error
correction
protocol,
and
DTE
speed.
W2
Report
DCE
speed
only
X_
X0
Hayes
Smartmodem
300
compatible
responses/blind
dialing.
X1
Same
as
X0
plus
all
CONNECT
responses/blind
dialing
X2
Same
as
X1
plus
dial
tone
detection
X3
Same
as
X1
plus
busy
detection/blind
dialing
X4
All
responses
and
dial
tone
and
busy
signal
detection
Z_
Z0
Reset
and
retrieve
active
profile
0
Z1
Reset
and
retrieve
active
profile
1
34
User
Guide

Extended
AT
commands
Command
Function
&C_
&C0
Force
Carrier
Detect
Signal
High
(ON)
&C1
Turn
on
CD
when
remote
carrier
is
present
&D_
&D0
Modem
ignores
the
DTR
signal
&D1
Modem
returns
to
Command
Mode
after
DTR
toggle
&D2
Modem
hangs
up,
returns
to
the
Command
Mode
after
DTR
toggle
&D3
Resets
modem
after
DTR
toggle
&F_
&F
Recall
factory
default
configuration
&G_
&G0
Guard
tone
disabled
&G1
Guard
tone
disabled
&G2
1800
Hz
guard
tone
&K_
&K0
Disable
flow
control
&K3
Enable
RTS/CTS
hardware
flow
control
&K4
Enable
XON/XOFF
software
flow
control
&K5
Enable
transparent
XON/XOFF
flow
control
&K6
Enable
both
RTS/CTS
and
XON/XOFF
flow
control
&M_
&M0
Asynchronous
operation
&P_
&P0
US
setting
for
off-hook-to-on-hook
ratio
&P1
UK
and
Hong
Kong
off-hook-to-on-hook
ratio
&P2
Same
as
&P0
setting
but
at
20
pulses
per
minute
&P3
Same
as
&P1
setting
but
at
20
pulses
per
minute
&R_
&R0
Reserved
&R1
CTS
operates
per
flow
control
requirements
&S_
&S0
Force
DSR
Signal
High
(ON)
&S1
DSR
off
in
command
mode,
on
in
on-line
mode
&T_
&T0
Ends
test
in
progress
&T1
Perform
Local
Analog
Loopback
Test
&T3
Perform
Local
Digital
Loopback
Test
&T4
Grant
Remote
Digital
Loopback
Test
request
by
remote
modem
&T5
Deny
Remote
Digital
Loopback
Test
request
&T6
Perform
a
Remote
Digital
Loopback
Test
&T7
Perform
a
Remote
Digital
Loopback
Test
and
Self-Test
&T8
Perform
Local
Analog
Loopback
Test
and
Self-Test
&V
&V0
Displays
Active
and
Stored
Profiles
Appendix
C.
Manual
modem
commands
35

Command
Function
&V1
Display
Last
Connection
Statistics
&W_
&W0
Stores
the
active
profile
as
Profile
0
&W1
Stores
the
active
profile
as
Profile
1
%E_
%E0
Disable
auto-retrain
%E1
Enable
auto-retrain
+MS?
Displays
the
current
Select
Modulation
settings
+MS=?
Displays
a
list
of
supported
Select
Modulation
options
+MS=a,b,c,e,f
Select
modulation
where:
a=0,
1,
2,
3,
9,
10,
11,
12,
56,
64,
69;
b=0-1;
c=300-56000;
d=300-
56000;
e=0-1;
and
f=0-1.
A,
b,
c,
d,
e,
f
default=12,
1,
300,
56000,
0,
0.
Parameter
“a”
specifies
the
modulation
protocol
desired
where:
0=V.21,
1=V.22,
2=V.22bis,
3=V.23,
9=V.32,
10=V.32bis,
11=V.34,
12=V.90,K56Flex,V.34......,56=K
56Flex,
V.90,V.34......,
64=Bell
103,
and
69=Bell
212.
Parameter
“b”
specifies
automode
operations
where:
0=automode
disabled,
1=
automode
enabled
with
V.8/V.32
Annex
A.
Parameter
“c”
specifies
the
minimum
connection
data
rate
(300-
56000).
Parameter
“d”
specifies
the
maximum
connection
rate
(300-56000);
Parameter
“e”
specifies
the
codec
type
(0=
Law,
and
1=A-Law).
Parameter
“f”
specifies
“robbed
bit”
signaling
detection
(0=detection
disabled
1=detection
enabled)
MNP/V.42/V.42bis/V.44
commands
Command
Function
%C_
%C0
Disable
MNP
Class
5
and
V.42bis
data
compression
%C1
Enable
MNP
Class
5
data
compression
only
%C2
Enable
V.42bis
data
compression
only
%C3
Enable
MNP
Class
5
and
V.42bis
data
compression
&Q_
&Q0
Direct
data
link
only
(same
as
\N1)
&Q5
V.42
data
link
with
fallback
options
&Q6
Normal
data
link
only
(same
as
\N0)
+DS44=0,
0
Disable
V.44
+DS44=3,
0
Enable
V.44
+DS44?
Current
values
+DS44=?
List
of
support
values
36
User
Guide
Fax
Class
1
commands
+FAE=n
Data/Fax
Auto
Answer
+FCLASS=n
Service
Class
+FRH=n
Receive
data
with
HDLC
framing
+FRM=n
Receive
data
+FRS=n
Receive
silence
+FTH=n
Transmit
data
with
HDLC
framing
+FTM=n
Transmit
data
+FTS=n
Stop
transmission
and
wait
Fax
Class
2
commands
+FCLASS=n
Services
class.
+FAA=n
Adaptive
answer.
+FAXERR
Fax
error
value.
+FBOR
Phase
C
data
bit
order.
+FBUF?
Buffer
size
(read
only).
+FCFR
Indicate
confirmation
to
receive.
+FCLASS=
Service
class.
+FCON
Facsimile
connection
response.
+FCIG
Set
the
polled
station
identification.
+FCIG:
Report
the
polled
station
identification.
+FCR
Capability
to
receive.
+FCR=
Capability
to
receive.
+FCSI:
Report
the
called
station
ID.
+FDCC=
DCE
capabilities
parameters.
+FDCS:
Report
current
session.
+FDCS=
Current
session
results.
+FDIS:
Report
remote
capabilities.
+FDIS=
Current
sessions
parameters.
+FDR
Begin
or
continue
phase
C
receive
data.
+FDT=
Data
transmission.
+FDTC:
Report
the
polled
station
capabilities.
+FET:
Post
page
message
response.
+FET=N
Transmit
page
punctuation.
+FHNG
Call
termination
with
status.
+FK
Session
termination.
+FLID=
Local
ID
string.
+FLPL
Document
for
polling.
+FMDL?
Identify
model.
+FMFR?
Identify
manufacturer.
Appendix
C.
Manual
modem
commands
37

+FPHCTO
Phase
C
time
out.
+FPOLL
Indicates
polling
request.
+FPTS:
Page
transfer
status.
+FPTS=
Page
transfer
status.
+FREV?
Identify
revision.
+FSPT
Enable
polling.
+FTSI:
Report
the
transmit
station
ID.
Voice
commands
#BDR
Select
Baud
Rate
#CID
Enable
Caller
ID
detection
and
reporting
format
#CLS
Select
Data,
Fax
or
Voice/Audio
#MDL?
Identify
Model
#MFR?
Identify
Manufacturer
#REV?
Identify
Revision
Level
#TL
Audio
output
transmit
level
#VBQ?
Query
Buffer
Size
#VBS
Bits
per
sample
(ADPCM
or
PCM)
#VBT
Beep
Tone
Timer
#VCI?
Identify
Compression
Method
#VLS
Voice
line
select
#VRA
Ringback
goes
away
timer
#VRN
Ringback
never
came
timer
#VRX
Voice
Receive
Mode
#VSDB
Silence
deletion
tuner
#VSK
Buffer
skid
setting
#VSP
Silence
detection
period
#VSR
Sampling
rate
selection
#VSS
Silence
deletion
tuner
#VTD
DTMF
tone
reporting
capability
#VTM
Enable
timing
mark
placement
#VTS
Generate
tone
signals
#VTX
Voice
transmit
mode
38
User
Guide
Attention
Switzerland
User:
If
your
Swisscom
phone
line
does
not
have
Taxsignal
switched
OFF,
modem
function
may
be
impaired.
The
impairment
may
be
resolved
by
a
filter
with
the
following
specifications:
Telekom
PTT
SCR-BE
Taximpulssperrfilter-12kHz
PTT
Art.
444.112.7
Bakom
93.0291.Z.N
Appendix
C.
Manual
modem
commands
39
40
User
Guide

Appendix
D.
Notices
IBM
may
not
offer
the
products,
services,
or
features
discussed
in
this
document
in
all
countries.
Consult
your
local
IBM
representative
for
information
on
the
products
and
services
currently
available
in
your
area.
Any
reference
to
an
IBM
product,
program,
or
service
is
not
intended
to
state
or
imply
that
only
that
IBM
product,
program,
or
service
may
be
used.
Any
functionally
equivalent
product,
program,
or
service
that
does
not
infringe
any
IBM
intellectual
property
right
may
be
used
instead.
However,
it
is
the
user’s
responsibility
to
evaluate
and
verify
the
operation
of
any
non-IBM
product,
program,
or
service.
IBM
may
have
patents
or
pending
patent
applications
covering
subject
matter
described
in
this
document.
The
furnishing
of
this
document
does
not
give
you
any
license
to
these
patents.
You
can
send
license
inquiries,
in
writing,
to:
IBM
Director
of
Licensing
IBM
Corporation
North
Castle
Drive
Armonk,
NY
10504-1785
U.S.A.
INTERNATIONAL
BUSINESS
MACHINES
CORPORATION
PROVIDES
THIS
PUBLICATION
“AS
IS”
WITHOUT
WARRANTY
OF
ANY
KIND,
EITHER
EXPRESS
OR
IMPLIED,
INCLUDING,
BUT
NOT
LIMITED
TO,
THE
IMPLIED
WARRANTIES
OF
NON-INFRINGEMENT,
MERCHANTABILITY
OR
FITNESS
FOR
A
PARTICULAR
PURPOSE.
Some
jurisdictions
do
not
allow
disclaimer
of
express
or
implied
warranties
in
certain
transactions,
therefore,
this
statement
may
not
apply
to
you.
This
information
could
include
technical
inaccuracies
or
typographical
errors.
Changes
are
periodically
made
to
the
information
herein;
these
changes
will
be
incorporated
in
new
editions
of
the
publication.
IBM
may
make
improvements
and/or
changes
in
the
product(s)
and/or
the
program(s)
described
in
this
publication
at
any
time
without
notice.
The
products
described
in
this
document
are
not
intended
for
use
in
implantation
or
other
life
support
applications
where
malfunction
may
result
in
injury
or
death
to
persons.
The
information
contained
in
this
document
does
not
affect
or
change
IBM
product
specifications
or
warranties.
Nothing
in
this
document
shall
operate
as
an
express
or
implied
license
or
indemnity
under
the
intellectual
property
rights
of
IBM
or
third
parties.
All
information
contained
in
this
document
was
obtained
in
specific
environments
and
is
presented
as
an
illustration.
The
result
obtained
in
other
operating
environments
may
vary.
IBM
may
use
or
distribute
any
of
the
information
you
supply
in
any
way
it
believes
appropriate
without
incurring
any
obligation
to
you.
Any
references
in
this
publication
to
non-IBM
Web
sites
are
provided
for
convenience
only
and
do
not
in
any
manner
serve
as
an
endorsement
of
those
Web
sites.
The
materials
at
those
Web
sites
are
not
part
of
the
materials
for
this
IBM
product,
and
use
of
those
Web
sites
is
at
your
own
risk.
©
Copyright
IBM
Corp.
2004
41

Trademarks
The
following
terms
are
trademarks
of
the
IBM
Corporation
in
the
United
States
or
other
countries
or
both:
IBM
PS/2
ThinkCentre
Wake
on
LAN
Intel,
Celeron,
and
Pentium
are
trademarks
of
Intel
Corporation
in
the
United
States,
other
countries,
or
both.
Microsoft,
Windows,
and
Windows
NT
are
trademarks
of
Microsoft
Corporation
in
the
United
States,
other
countries,
or
both.
Other
company,
product,
and
service
names
may
be
trademarks
or
service
marks
of
others.
42
User
Guide

Index
Special
characters
.iso
image
29
A
Access
IBM
1
adapter
installing
17
peripheral
component
interconnect
(PCI)
5
removing
and
replacing
17
slots
17
audio
subsystem
2
automatic
startup
sequence
28
B
battery,
changing
18
BIOS
settings
25
BIOS
updating
29
Boot-block
recovery
30
bootable
CD
image
29
C
cable
lock
20
cables,
connecting
24
changing
battery
18
startup
device
sequence
28
cleaning
mouse
31
closing
the
cover
24
components,
internal
13,
14
connectors
front
10
rear
11
cover
closing
24
lock
20
opening
12
D
device
drivers
11
DIMMs
16
diskette
drive,
removing
and
replacing
20
double
data
rate
(DDR)
memory
16
drives
installing
14
E
environment,
operating
6
error
startup
sequence
28
Ethernet
2
exiting
Setup
Utility
25
expansion
adapters
3
external
options
9
F
features
2
H
hard
disk
drive
security
25
hyper
threading
28
I
IBM
Setup
Utility
25
information
resources
1
input/output
(I/O)
features
3
installing
options
adapters
17
cable
lock
20
drives
14
memory
16
internal
drives
2
L
locating
components
13
M
memory
installing
16
removing
and
replacing
16
type
2
microprocessor
type
2
modem
commands
Basic
AT
33
Extended
AT
35
Fax
Class
1
37
Fax
Class
2
37
MNP/V.42/V.42bis/V.44
36
Voice
38
mouse
cleaning
31
N
noise
level
6
O
opening
the
cover
12
optical
drive,
removing
and
replacing
19
options
5
available
5
external
5
internal
5
©
Copyright
IBM
Corp.
2004
43
P
password
erasing
24
lost
or
forgotten
24
setting,
changing,
deleting
27
PCI
adapter
17
POST/BIOS
29
power
Advanced
Configuration
and
Power
Interface
(ACPI)
support
3
Advanced
Power
Management
support
3
features
3
primary
startup
sequence
28
R
recovering
from
a
POST/BIOS
update
failure
30
removing
and
replacing
adapters
17
battery
18
diskette
drive
20
memory
16
optical
drive
19
riser
card
17
S
security
cable
lock
20
features
3
hard
disk
drive
25
profile
by
device
27
selecting
startup
device
28
temporary
startup
device
28
software
4
specifications
6
startup
sequence
28
system
board
components,
accessing
14
connectors
15
identifying
parts
15
location
15
memory
5,
16
system
management
2
U
updating
BIOS
diskette
29
OS
29
updating
POST/BIOS
29
using
IBM
Setup
Utility
25
passwords
25
security
profile
by
device
27
V
video
subsystem
2
44
User
Guide

Part
Number:
19R0474
Printed
in
USA
(1P)
P/N:
19R0474