Netgear Prosafe Fvs124G Users Manual Reference For The Dual WAN VPN Gigabit Firewall
Netgear-Fvs124G-Quick-Reference-Guide netgear-fvs124g-quick-reference-guide
FVS124G to the manual 155a4157-6e89-4348-bf3c-b14dcd056bc9
2015-01-24
: Netgear Netgear-Prosafe-Fvs124G-Users-Manual-332071 netgear-prosafe-fvs124g-users-manual-332071 netgear pdf
Open the PDF directly: View PDF ![]() .
.
Page Count: 238 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Chapter 1 About This Manual
- Chapter 2 Introduction
- Chapter 3 Network Planning
- Chapter 4 Connecting the FVS124G to the Internet
- What You Will Need to Do Before You Begin
- Connecting the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
- Step 1: Physically Connect the VPN Firewall to Your Network (Required)
- Step 2: Log in to the VPN Firewall (Required)
- Step 3: Configure the Internet Connections to Your ISPs (Required)
- Step 4: Configure the WAN Mode (Required for Dual WAN)
- Step 5: Configure Dynamic DNS (If Needed)
- Step 6: Configure the WAN Options (If Needed)
- Chapter 5 LAN Configuration
- Chapter 6 Firewall Protection and Content Filtering
- Chapter 7 Virtual Private Networking
- Chapter 8 Router and Network Management
- Chapter 9 Troubleshooting
- Appendix A Technical Specifications
- Appendix B Network, Routing, Firewall, and Basics
- Appendix C Preparing Your Network
- Appendix D Virtual Private Networking
- Glossary

202-10085-01, March 2005
202-10085-01
March 2005
NETGEAR, Inc.
4500 Great America Parkway
Santa Clara, CA 95054 USA
Reference Manual for the
ProSafe VPN Firewall 25
with 4 Gigabit LAN and
Dual WAN Ports FVS124G

2
202-10085-01, March 2005
© 2005 by NETGEAR, Inc. All rights reserved.
Trademarks
NETGEAR is a trademark of Netgear, Inc.
Microsoft, Windows, and Windows NT are registered trademarks of Microsoft Corporation.
Other brand and product names are registered trademarks or trademarks of their respective holders.
Statement of Conditions
In the interest of improving internal design, operational function, and/or reliability, NETGEAR reserves the right to
make changes to the products described in this document without notice.
NETGEAR does not assume any liability that may occur due to the use or application of the product(s) or circuit
layout(s) described herein.
Federal Communications Commission (FCC) Compliance Notice: Radio Frequency Notice
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to
part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no
guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to
radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try
to correct the interference by one or more of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
EN 55 022 Declaration of Conformance
This is to certify that the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports is shielded
against the generation of radio interference in accordance with the application of Council Directive 89/336/EEC, Article
4a. Conformity is declared by the application of EN 55 022 Class B (CISPR 22).
Bestätigung des Herstellers/Importeurs
Es wird hiermit bestätigt, daß das FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports gemäß
der im BMPT-AmtsblVfg 243/1991 und Vfg 46/1992 aufgeführten Bestimmungen entstört ist. Das vorschriftsmäßige
Betreiben einiger Geräte (z.B. Testsender) kann jedoch gewissen Beschränkungen unterliegen. Lesen Sie dazu bitte die
Anmerkungen in der Betriebsanleitung.
Das Bundesamt für Zulassungen in der Telekommunikation wurde davon unterrichtet, daß dieses Gerät auf den Markt
gebracht wurde und es ist berechtigt, die Serie auf die Erfüllung der Vorschriften hin zu überprüfen.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-3
202-10085-01, March 2005
Certificate of the Manufacturer/Importer
It is hereby certified that the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports has been
suppressed in accordance with the conditions set out in the BMPT-AmtsblVfg 243/1991 and Vfg 46/1992. The operation
of some equipment (for example, test transmitters) in accordance with the regulations may, however, be subject to
certain restrictions. Please refer to the notes in the operating instructions.
Federal Office for Telecommunications Approvals has been notified of the placing of this equipment on the market
and has been granted the right to test the series for compliance with the regulations.
Voluntary Control Council for Interference (VCCI) Statement
This equipment is in the second category (information equipment to be used in a residential area or an adjacent area
thereto) and conforms to the standards set by the Voluntary Control Council for Interference by Data Processing
Equipment and Electronic Office Machines aimed at preventing radio interference in such residential areas.
When used near a radio or TV receiver, it may become the cause of radio interference.
Read instructions for correct handling.
Additional Copyrights
AES Copyright (c) 2001, Dr Brian Gladman <brg@gladman.uk.net>, Worcester, UK.
All rights reserved.
TERMS
Redistribution and use in source and binary forms, with or without modification, are permitted
subject to the following conditions:
1. Redistributions of source code must retain the above copyright notice, this list of
conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of
conditions and the following disclaimer in the documentation and/or other materials
provided with the distribution.
3. The copyright holder's name must not be used to endorse or promote any products
derived from this software without his specific prior written permission.
This software is provided 'as is' with no express or implied warranties of correctness or fitness
for purpose.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-4
202-10085-01, March 2005
Open SSL Copyright (c) 1998-2000 The OpenSSL Project. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions * are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions
and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of
conditions and the following disclaimer in the documentation and/or other materials
provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the
following acknowledgment: "This product includes software developed by the OpenSSL
Project for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to endorse or
promote products derived from this software without prior written permission. For written
permission, please contact openssl-core@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor may "OpenSSL"
appear in their names without prior written permission of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This
product includes software developed by the OpenSSL Project for use in the OpenSSL
Toolkit (http://www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR ITS
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young (eay@cryptsoft.com). This
product includes software written by Tim Hudson (tjh@cryptsoft.com).

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-5
202-10085-01, March 2005
MD5 Copyright (C) 1990, RSA Data Security, Inc. All rights reserved.
License to copy and use this software is granted provided that it is identified as the "RSA Data
Security, Inc. MD5 Message-Digest Algorithm" in all material mentioning or referencing this
software or this function. License is also granted to make and use derivative works provided
that such works are identified as "derived from the RSA Data Security, Inc. MD5
Message-Digest Algorithm" in all material mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either the merchantability of
this software or the suitability of this software for any particular purpose. It is provided "as is"
without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this documentation and/or
software.
PPP Copyright (c) 1989 Carnegie Mellon University. All rights reserved.
Redistribution and use in source and binary forms are permitted provided that the above
copyright notice and this paragraph are duplicated in all such forms and that any
documentation, advertising materials, and other materials related to such distribution and use
acknowledge that the software was developed by Carnegie Mellon University. The name of
the University may not be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTIBILITY AND FITNESS FOR A PARTICULAR PURPOSE.
Zlib zlib.h -- interface of the 'zlib' general purpose compression library version 1.1.4, March 11th,
2002. Copyright (C) 1995-2002 Jean-loup Gailly and Mark Adler.
This software is provided 'as-is', without any express or implied warranty. In no event will the
authors be held liable for any damages arising from the use of this software. Permission is
granted to anyone to use this software for any purpose, including commercial applications,
and to alter it and redistribute it freely, subject to the following restrictions:
1. The origin of this software must not be misrepresented; you must not claim that you wrote
the original software. If you use this software in a product, an acknowledgment in the
product documentation would be appreciated but is not required.
2. Altered source versions must be plainly marked as such, and must not be misrepresented
as being the original software.
3. This notice may not be removed or altered from any source distribution.
Jean-loup Gailly: jloup@gzip.org; Mark Adler: madler@alumni.caltech.edu
The data format used by the zlib library is described by RFCs (Request for Comments) 1950
to 1952 in the files ftp://ds.internic.net/rfc/rfc1950.txt (zlib format), rfc1951.txt (deflate format)
and rfc1952.txt (gzip format)

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-6
202-10085-01, March 2005
Product and Publication Details
Model Number: FVS124G
Publication Date: March 2005
Product Family: Router
Product Name: FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN
Ports
Home or Business Product: Business
Language: English
Publication Part Number: 202-10085-01

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-1
202-10085-01, March 2005
Contents
Chapter 1
About This Manual
Audience, Scope, Conventions, and Formats ................................................................1-1
How to Use This Manual ................................................................................................1-2
How to Print this Manual .................................................................................................1-3
Chapter 2
Introduction
Key Features of the VPN Firewall ..................................................................................2-1
Dual WAN Ports for Increased Reliability or Outbound Load Balancing ..................2-2
A Powerful, True Firewall with Content Filtering ......................................................2-2
Security ....................................................................................................................2-3
Autosensing Ethernet Connections with Auto Uplink ...............................................2-3
Extensive Protocol Support ......................................................................................2-4
Easy Installation and Management ..........................................................................2-4
Maintenance and Support ........................................................................................2-5
Package Contents ..........................................................................................................2-5
The Router’s Front Panel .........................................................................................2-6
The Router’s Rear Panel .........................................................................................2-7
The Router’s IP Address, Login Name, and Password ............................................2-8
Logging into the Router ............................................................................................2-9
Default Factory Settings .........................................................................................2-10
NETGEAR Related Products ........................................................................................2-11
Chapter 3
Network Planning
Overview of the Planning Process ..................................................................................3-1
Inbound Traffic .........................................................................................................3-1
Virtual Private Networks (VPNs) ..............................................................................3-1
The Rollover Case for Firewalls With Dual WAN Ports ............................................3-2
The Load Balancing Case for Firewalls With Dual WAN Ports ................................3-2

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-2
202-10085-01, March 2005
Inbound Traffic ................................................................................................................3-3
Inbound Traffic to Single WAN Port (Reference Case) ............................................3-3
Inbound Traffic to Dual WAN Port Systems .............................................................3-3
Inbound Traffic: Dual WAN Ports for Improved Reliability .................................3-4
Inbound Traffic: Dual WAN Ports for Load Balancing ........................................3-4
Virtual Private Networks (VPNs) .....................................................................................3-5
VPN Road Warrior (Client-to-Gateway) ...................................................................3-6
VPN Road Warrior: Single Gateway WAN Port (Reference Case) ....................3-6
VPN Road Warrior: Dual Gateway WAN Ports for Improved Reliability ............3-7
VPN Road Warrior: Dual Gateway WAN Ports for Load Balancing ...................3-8
VPN Gateway-to-Gateway .......................................................................................3-9
VPN Gateway-to-Gateway: Single Gateway WAN Ports (Reference Case) .....3-9
VPN Gateway-to-Gateway: Dual Gateway WAN Ports for Improved Reliability 3-10
VPN Gateway-to-Gateway: Dual Gateway WAN Ports for Load Balancing .... 3-11
VPN Telecommuter (Client-to-Gateway Through a NAT Router) ...........................3-12
VPN Telecommuter: Single Gateway WAN Port (Reference Case) ................3-12
VPN Telecommuter: Dual Gateway WAN Ports for Improved Reliability .........3-13
VPN Telecommuter: Dual Gateway WAN Ports for Load Balancing ...............3-14
Chapter 4
Connecting the FVS124G to the Internet
What You Will Need to Do Before You Begin .................................................................4-1
Cabling and Computer Hardware Requirements .....................................................4-3
Computer Network Configuration Requirements .....................................................4-3
Internet Configuration Requirements .......................................................................4-4
Where Do I Get the Internet Configuration Parameters? .........................................4-4
Record Your Internet Connection Information ..........................................................4-5
Connecting the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-6
Step 1: Physically Connect the VPN Firewall to Your Network (Required) ..............4-7
Step 2: Log in to the VPN Firewall (Required) .........................................................4-7
Step 3: Configure the Internet Connections to Your ISPs (Required) ......................4-8
Manually Configuring Your Internet Connection ..............................................4-12
Programming the Traffic Meter (if Desired) .....................................................4-13
Step 4: Configure the WAN Mode (Required for Dual WAN) .................................4-15
Rollover Setup .................................................................................................4-16

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-3
202-10085-01, March 2005
Load Balancing (and Protocol Binding) Setup .................................................4-17
Step 5: Configure Dynamic DNS (If Needed) .........................................................4-20
Step 6: Configure the WAN Options (If Needed) ....................................................4-23
Chapter 5
LAN Configuration
Using the LAN IP Setup Options ....................................................................................5-1
Configuring LAN TCP/IP Setup Parameters ............................................................5-2
Using the Firewall as a DHCP server .......................................................................5-4
Using Address Reservation ......................................................................................5-5
Multi Home LAN IPs .................................................................................................5-6
Configuring Static Routes ...............................................................................................5-6
Chapter 6
Firewall Protection and Content Filtering
Firewall Protection and Content Filtering Overview ........................................................6-1
Using Rules to Block or Allow Specific Kinds of Traffic ..................................................6-1
Services-Based Rules ..............................................................................................6-4
Inbound Rules (Port Forwarding) ......................................................................6-5
Outbound Rules (Service Blocking) .................................................................6-12
Customized Services .......................................................................................6-16
Quality of Service (QoS) Priorities ...................................................................6-18
Managing Groups and Hosts .................................................................................6-20
Using a Schedule to Block or Allow Specific Traffic ...............................................6-22
Time Zone ..............................................................................................................6-24
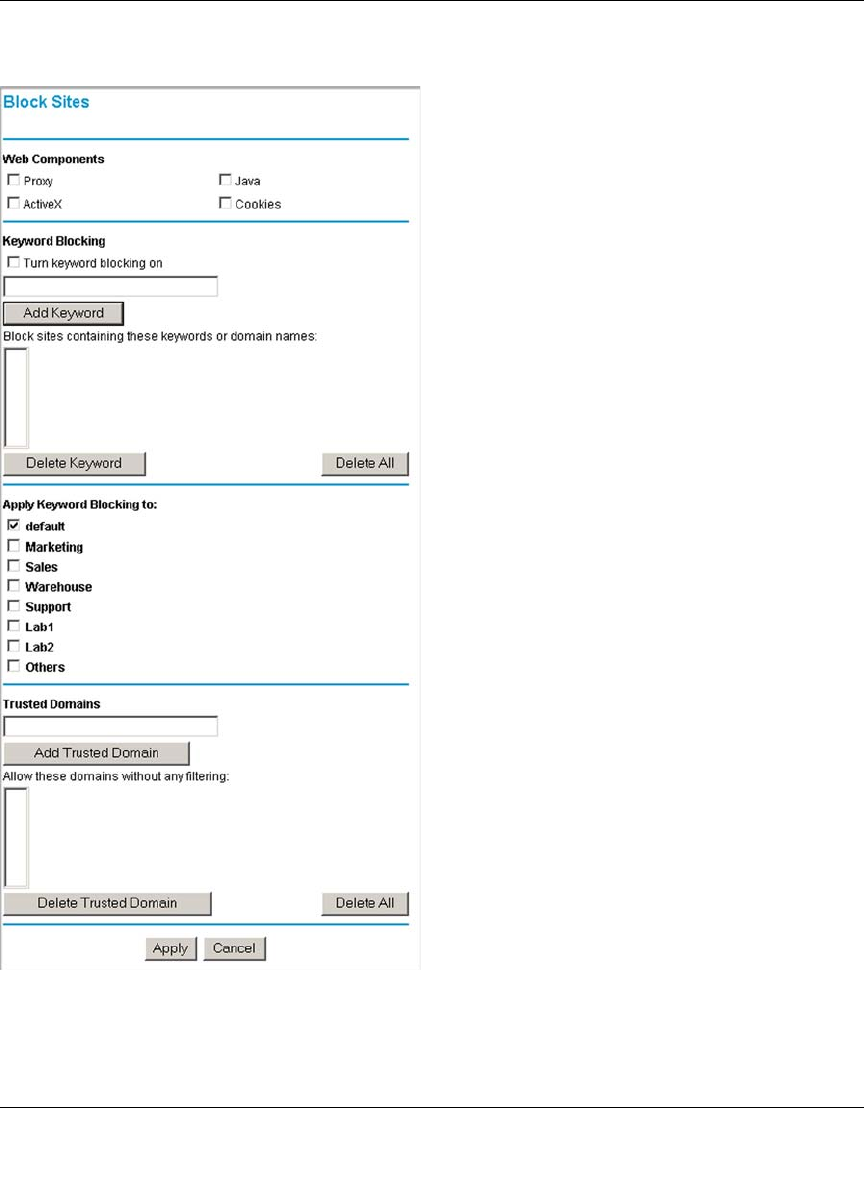
Block Sites ....................................................................................................................6-24
Source MAC Filtering ...................................................................................................6-27
Port Triggering ..............................................................................................................6-28
Getting E-Mail Notifications of Event Logs and Alerts ..................................................6-30
Syslog ....................................................................................................................6-33
Viewing Logs of Web Access or Attempted Web Access ......................................6-33
Administrator Information .............................................................................................6-35
Chapter 7
Virtual Private Networking
Dual WAN Port Systems .................................................................................................7-1
Rollover vs. Load Balancing Mode ...........................................................................7-1
Fully Qualified Domain Names .................................................................................7-2

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-4
202-10085-01, March 2005
Creating a VPN Connection: Between FVX538 and FVS124G ......................................7-5
Configuring the FVX538 ...........................................................................................7-5
Configuring the FVS124G ........................................................................................7-9
Testing the Connection ........................................................................................... 7-11
Creating a VPN Connection: Netgear VPN Client to FVS124G ................................... 7-11
Configuring the FVS124G ......................................................................................7-12
Configuring the VPN Client ....................................................................................7-12
Testing the Connection ...........................................................................................7-20
Chapter 8
Router and Network Management
Performance Management .............................................................................................8-1
Bandwidth Capacity .................................................................................................8-1
VPN Firewall Features That Reduce Traffic .............................................................8-2
Service Blocking ................................................................................................8-2
Block Sites .........................................................................................................8-4
Source MAC Filtering ........................................................................................8-4
VPN Firewall Features That Increase Traffic ...........................................................8-4
Port Forwarding .................................................................................................8-5
Port Triggering ...................................................................................................8-6
VPN Tunnels ......................................................................................................8-7
Using QoS to Shift the Traffic Mix ............................................................................8-7
Tools for Traffic Management ...................................................................................8-7
Administrator and Guest Access Authorization ..............................................................8-8
Changing the Passwords and Login Timeout ..........................................................8-8
Enabling Remote Management Access ...................................................................8-9
Command Line Interface ........................................................................................8-10
Event Alerts ..................................................................................................................8-11
WAN Port Rollover ................................................................................................. 8-11
Traffic Limits Reached ............................................................................................8-11
Login Failures and Attacks .....................................................................................8-12
Monitoring .....................................................................................................................8-14
Viewing VPN Firewall Status and Time Information ...............................................8-14
Firewall Status .................................................................................................8-14
Time Information ..............................................................................................8-16
WAN Ports ..............................................................................................................8-18

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-5
202-10085-01, March 2005
WAN Port Connection Status ...........................................................................8-18
Dynamic DNS Status .......................................................................................8-19
Internet Traffic Information ...............................................................................8-19
LAN Ports and Attached Devices ...........................................................................8-20
Known PCs and Devices .................................................................................8-20
DHCP Log .......................................................................................................8-22
Port Triggering Status ......................................................................................8-22
Firewall ...................................................................................................................8-23
VPN Tunnels ..........................................................................................................8-26
SNMP .....................................................................................................................8-27
Diagnostics .............................................................................................................8-27
Configuration File Management ...................................................................................8-29
Restoring and Backing Up the Configuration .........................................................8-30
Upgrading the Firewall Software ............................................................................8-30
Erasing the Configuration (Factory Defaults Reset) ...............................................8-31
Chapter 9
Troubleshooting
Basic Functioning ...........................................................................................................9-1
Power LED Not On ...................................................................................................9-1
LEDs Never Turn Off ................................................................................................9-2
LAN or Internet Port LEDs Not On ...........................................................................9-2
Troubleshooting the Web Configuration Interface ..........................................................9-3
Troubleshooting the ISP Connection ..............................................................................9-4
Troubleshooting a TCP/IP Network Using a Ping Utility .................................................9-5
Testing the LAN Path to Your Firewall ......................................................................9-5
Testing the Path from Your PC to a Remote Device ................................................9-6
Restoring the Default Configuration and Password ........................................................9-7
Problems with Date and Time .........................................................................................9-7
Appendix A
Technical Specifications
Appendix B
Network, Routing, Firewall, and Basics
Related Publications ...................................................................................................... B-1
Basic Router Concepts .................................................................................................. B-1
What is a Router? ................................................................................................... B-2

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-6
202-10085-01, March 2005
Routing Information Protocol ................................................................................... B-2
IP Addresses and the Internet ....................................................................................... B-2
Netmask .................................................................................................................. B-4
Subnet Addressing .................................................................................................. B-5
Private IP Addresses ............................................................................................... B-7
Single IP Address Operation Using NAT ....................................................................... B-8
MAC Addresses and Address Resolution Protocol ................................................. B-9
Related Documents ................................................................................................. B-9
Domain Name Server ............................................................................................ B-10
IP Configuration by DHCP ........................................................................................... B-10
Internet Security and Firewalls .................................................................................... B-10
What is a Firewall? .................................................................................................B-11
Stateful Packet Inspection ...............................................................................B-11
Denial of Service Attack ..................................................................................B-11
Ethernet Cabling ...........................................................................................................B-11
Category 5 Cable Quality ...................................................................................... B-12
Inside Twisted Pair Cables .................................................................................... B-13
Uplink Switches, Crossover Cables, and MDI/MDIX Switching ............................ B-14
Appendix C
Preparing Your Network
Preparing Your Computers for TCP/IP Networking ....................................................... C-1
Configuring Windows 95, 98, and Me for TCP/IP Networking ....................................... C-2
Install or Verify Windows Networking Components ................................................. C-2
Enabling DHCP to Automatically Configure TCP/IP Settings ................................. C-4
Selecting Windows’ Internet Access Method .......................................................... C-6
Verifying TCP/IP Properties .................................................................................... C-6
Configuring Windows NT4, 2000 or XP for IP Networking ............................................ C-7
Install or Verify Windows Networking Components ................................................. C-7
Enabling DHCP to Automatically Configure TCP/IP Settings ................................. C-8
DHCP Configuration of TCP/IP in Windows XP ..................................................... C-8
DHCP Configuration of TCP/IP in Windows 2000 ................................................ C-10
DHCP Configuration of TCP/IP in Windows NT4 .................................................. C-13
Verifying TCP/IP Properties for Windows XP, 2000, and NT4 .............................. C-15
Configuring the Macintosh for TCP/IP Networking ...................................................... C-16
MacOS 8.6 or 9.x .................................................................................................. C-16

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-7
202-10085-01, March 2005
MacOS X ............................................................................................................... C-16
Verifying TCP/IP Properties for Macintosh Computers ......................................... C-17
Verifying the Readiness of Your Internet Account ....................................................... C-18
Are Login Protocols Used? ................................................................................... C-18
What Is Your Configuration Information? .............................................................. C-18
Obtaining ISP Configuration Information for Windows Computers ....................... C-19
Obtaining ISP Configuration Information for Macintosh Computers ..................... C-20
Restarting the Network ................................................................................................ C-21
Appendix D
Virtual Private Networking
What is a VPN? ............................................................................................................. D-1
What Is IPSec and How Does It Work? ......................................................................... D-2
IPSec Security Features ......................................................................................... D-2
IPSec Components ................................................................................................. D-2
Encapsulating Security Payload (ESP) ................................................................... D-3
Authentication Header (AH) .................................................................................... D-4
IKE Security Association ......................................................................................... D-4
Mode ................................................................................................................. D-5
Key Management .................................................................................................... D-6
Understand the Process Before You Begin ................................................................... D-6
VPN Process Overview ................................................................................................. D-7
Network Interfaces and Addresses ......................................................................... D-7
Interface Addressing ......................................................................................... D-7
Firewalls ........................................................................................................... D-8
Setting Up a VPN Tunnel Between Gateways ........................................................ D-8
VPNC IKE Security Parameters .................................................................................. D-10
VPNC IKE Phase I Parameters ............................................................................. D-10
VPNC IKE Phase II Parameters ............................................................................ D-11
Testing and Troubleshooting ........................................................................................ D-11
Additional Reading ...................................................................................................... D-11
Glossary
List of Glossary Terms ........................................................................................Glossary-1
Numeric ..............................................................................................................Glossary-1
A .........................................................................................................................Glossary-2
B .........................................................................................................................Glossary-2

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-8
202-10085-01, March 2005
C .........................................................................................................................Glossary-3
D .........................................................................................................................Glossary-3
E .........................................................................................................................Glossary-4
G .........................................................................................................................Glossary-5
I ...........................................................................................................................Glossary-5
L ..........................................................................................................................Glossary-6
M .........................................................................................................................Glossary-7
P .........................................................................................................................Glossary-8
Q .........................................................................................................................Glossary-9
R .........................................................................................................................Glossary-9
S .........................................................................................................................Glossary-9
T .......................................................................................................................Glossary-10
U .......................................................................................................................Glossary-10
W ......................................................................................................................Glossary-10
About This Manual 1-1
202-10085-01, March 2005
Chapter 1
About This Manual
This chapter describes the intended audience, scope, conventions, and formats of this manual.
Audience, Scope, Conventions, and Formats
This reference manual assumes that the reader has basic to intermediate computer and Internet
skills. However, basic computer network, Internet, firewall, and VPN technologies tutorial
information is provided in the Appendices and on the Netgear website.
This guide uses the following typographical conventions:
This guide uses the following formats to highlight special messages:
This manual is written for the FVS124G VPN Firewall according to these specifications.:
Table 1-1. Typographical Conventions
italics Emphasis, books, CDs, URL names
bold User input
fixed Screen text, file and server names, extensions, commands, IP addresses
Note: This format is used to highlight information of importance or special interest.
Table 1-2. Manual Scope
Product Version FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN
Ports
Manual Publication Date March 2005
Note: Product updates are available on the NETGEAR, Inc. Web site at
http://kbserver.netgear.com/products/FVS124G.asp.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
1-2 About This Manual
202-10085-01, March 2005
How to Use This Manual
The HTML version of this manual includes the following:
• Buttons, and , for browsing forwards or backwards through the manual one page
at a time
• A button that displays the table of contents and an button. Double-click on a
link in the table of contents or index to navigate directly to where the topic is described in the
manual.
• A button to access the full NETGEAR, Inc. online knowledge base for the
product model.
• Links to PDF versions of the full manual and individual chapters.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
About This Manual 1-3
202-10085-01, March 2005
How to Print this Manual
To print this manual you can choose one of the following several options, according to your needs.
•Printing a Page in the HTML View.
Each page in the HTML version of the manual is dedicated to a major topic. Use the Print
button on the browser toolbar to print the page contents.
•Printing a Chapter.
Use the PDF of This Chapter link at the top left of any page.
– Click the PDF of This Chapter link at the top right of any page in the chapter you want to
print. The PDF version of the chapter you were viewing opens in a browser window.
Note: Your computer must have the free Adobe Acrobat reader installed in order to view
and print PDF files. The Acrobat reader is available on the Adobe Web site at
http://www.adobe.com.
– Click the print icon in the upper left of the window.
Tip: If your printer supports printing two pages on a single sheet of paper, you can save
paper and printer ink by selecting this feature.
•Printing the Full Manual.
Use the Complete PDF Manual link at the top left of any page.
– Click the Complete PDF Manual link at the top left of any page in the manual. The PDF
version of the complete manual opens in a browser window.
– Click the print icon in the upper left of the window.
Tip: If your printer supports printing two pages on a single sheet of paper, you can save
paper and printer ink by selecting this feature.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
1-4 About This Manual
202-10085-01, March 2005

Introduction 2-1
202-10085-01, March 2005
Chapter 2
Introduction
This chapter describes the features of the NETGEAR FVS124G ProSafe VPN Firewall 25 with 4
Gigabit LAN and Dual WAN Ports.
Key Features of the VPN Firewall
The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports with 4 port
switch connects your local area network (LAN) to the Internet through an external access device
such as a cable modem or DSL modem.
The FVS124G is a complete security solution that protects your network from attacks and
intrusions. Unlike simple Internet sharing firewalls that rely on Network Address Translation for
security, the FVS124G uses Stateful Packet Inspection for Denial of Service (DoS) attack
protection and intrusion detection. The FVS124G VPN Firewall provides you with multiple Web
content filtering options, plus browsing activity reporting and instant alerts -- both via e-mail.
Network administrators can establish restricted access policies based on time-of-day, Website
addresses and address keywords.
With minimum setup, you can install and use the firewall within minutes.
The FVS124G VPN Firewall provides the following features:
• 2 10/100 Mbps ports for an Ethernet connection to a WAN device, such as a cable modem or
DSL modem.
• Dual WAN ports provide for increased system reliability and provide load balancing.
• Support for up to 10 VPN tunnels.
• Easy, web-based setup for installation and management.
• URL keyword Content Filtering and Site Blocking Security.
• Quality of Service (QoS) support for traffic prioritization.
• Built in 4-port 10/100/1000 Mbps switch.
• Extensive Protocol Support.
• Login capability.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
2-2 Introduction
202-10085-01, March 2005
• Front panel LEDs for easy monitoring of status and activity.
• Flash memory for firmware upgrade.
Dual WAN Ports for Increased Reliability or Outbound Load
Balancing
The FVS124G VPN Firewall has two broadband WAN ports, WAN1 and WAN2, each capable of
operating independently at speeds of either 10 Mbps or 100 Mbps. The two WAN ports let you
connect a second broadband Internet line that can be configured on a mutually-exclusive basis to:
• Provide backup and rollover if one line is inoperable, ensuring you are never disconnected.
• Load balance, or use both Internet lines simultaneously for the outgoing traffic. The firewall
balances users between the two lines for maximum bandwidth efficiency.
See “Network Planning” on page 3-1 for the planning factors to consider when implementing the
following capabilities with dual WAN port gateways:
• Inbound traffic (e.g., port forwarding, port triggering)
• Virtual private networks
A Powerful, True Firewall with Content Filtering
Unlike simple Internet sharing NAT routers, the FVS124G is a true firewall, using stateful packet
inspection to defend against hacker attacks. Its firewall features include:
• DoS protection.
Automatically detects and thwarts DoS attacks such as Ping of Death, SYN Flood, LAND
Attack, and IP Spoofing.
• Blocks unwanted traffic from the Internet to your LAN.
• Blocks access from your LAN to Internet locations or services that you specify as off-limits.
• Logs security incidents.
The FVS124G will log security events such as blocked incoming traffic, port scans, attacks,
and administrator logins. You can configure the firewall to email the log to you at specified
intervals. You can also configure the firewall to send immediate alert messages to your email
address or email pager whenever a significant event occurs.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Introduction 2-3
202-10085-01, March 2005
• With its URL keyword filtering feature, the FVS124G prevents objectionable content from
reaching your PCs. The firewall allows you to control access to Internet content by screening
for keywords within Web addresses. You can configure the firewall to log and report attempts
to access objectionable Internet sites.
Security
The FVS124G VPN Firewall is equipped with several features designed to maintain security, as
described in this section.
• PCs Hidden by NAT
NAT opens a temporary path to the Internet for requests originating from the local network.
Requests originating from outside the LAN are discarded, preventing users outside the LAN
from finding and directly accessing the PCs on the LAN.
• Port Forwarding with NAT
Although NAT prevents Internet locations from directly accessing the PCs on the LAN, the
firewall allows you to direct incoming traffic to specific PCs based on the service port number
of the incoming request. You can specify forwarding of single ports or ranges of ports.
• Powerful Firewall Rules
Both inbound and outbound traffic can be controlled tightly by defining your own rules
regarding permitted users, services, protocols, schedules, and destinations.
Autosensing Ethernet Connections with Auto Uplink
With its internal 4-port 10/100/1000 switch, the FVS124G can connect to either a 10 Mbps
standard Ethernet network, a 100 Mbps Fast Ethernet network, or a 1000 Mbps Gigabit Ethernet.
Both the LAN and WAN interfaces are autosensing and capable of full-duplex or half-duplex
operation.
The firewall incorporates Auto UplinkTM technology. Each Ethernet port will automatically sense
whether the Ethernet cable plugged into the port should have a ‘normal’ connection such as to a
PC or an ‘uplink’ connection such as to a switch or hub. That port will then configure itself to the
correct configuration. This feature also eliminates the need to worry about crossover cables, as
Auto Uplink will accommodate either type of cable to make the right connection.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
2-4 Introduction
202-10085-01, March 2005
Extensive Protocol Support
The FVS124G VPN Firewall supports the Transmission Control Protocol/Internet Protocol (TCP/
IP) and Routing Information Protocol (RIP). For further information about TCP/IP, refer to
Appendix B, “Network, Routing, Firewall, and Basics.”
• IP Address Sharing by NAT
The FVS124G VPN Firewall allows several networked PCs to share an Internet account using
only a single IP address, which may be statically or dynamically assigned by your Internet
service provider (ISP). This technique, known as NAT, allows the use of an inexpensive
single-user ISP account.
• Automatic Configuration of Attached PCs by DHCP
The FVS124G VPN Firewall dynamically assigns network configuration information,
including IP, gateway, and domain name server (DNS) addresses, to attached PCs on the LAN
using the Dynamic Host Configuration Protocol (DHCP). This feature greatly simplifies
configuration of PCs on your local network.
• DNS Proxy
When DHCP is enabled and no DNS addresses are specified, the firewall provides its own
address as a DNS server to the attached PCs. The firewall obtains actual DNS addresses from
the ISP during connection setup and forwards DNS requests from the LAN.
• PPP over Ethernet (PPPoE)
PPPoE is a protocol for connecting remote hosts to the Internet over a DSL connection by
simulating a dial-up connection. This feature eliminates the need to run a login program such
as EnterNet or WinPOET on your PC.
Easy Installation and Management
You can install, configure, and operate the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit
LAN and Dual WAN Ports within minutes after connecting it to the network. The following
features simplify installation and management tasks:
• Browser-based management
Browser-based configuration allows you to easily configure your firewall from almost any
type of personal computer, such as Windows, Macintosh, or Linux. A user-friendly Setup
Wizard is provided and online help documentation is built into the browser-based Web
Management Interface.
• Smart Wizard
The FVS124G VPN Firewall automatically senses the type of Internet connection, asking you
only for the information required for your type of ISP account.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Introduction 2-5
202-10085-01, March 2005
•VPN Wizard
The FVS124G VPN Firewall includes the NETGEAR VPN Wizard to easily configure VPN
tunnels according to the recommendations of the Virtual Private Network Consortium (VPNC)
to ensure the VPN tunnels are interoperable with other VPNC-compliant VPN routers and
clients.
•SNMP
The FVS124G VPN Firewall supports the Simple Network Management Protocol (SNMP) to
let you monitor and manage log resources from an SNMP-compliant system manager. The
SNMP system configuration lets you change the system variables for MIB2.
• Diagnostic functions
The firewall incorporates built-in diagnostic functions such as Ping, Trace Route, DNS
lookup, and remote reboot.
• Remote management
The firewall allows you to login to the Web Management Interface from a remote location on
the Internet. For security, you can limit remote management access to a specified remote IP
address or range of addresses, and you can choose a nonstandard port number.
• Visual monitoring
The FVS124G VPN Firewall’s front panel LEDs provide an easy way to monitor its status and
activity.
Maintenance and Support
NETGEAR offers the following features to help you maximize your use of the FVS124G VPN
Firewall:
• Flash memory for firmware upgrade
• Free technical support seven days a week, twenty-four hours a day
Package Contents
The product package should contain the following items:
• FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports.
• AC power adapter (varies by region).
• Rubber feet.
• Category 5 (Cat 5) Ethernet cable.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
2-6 Introduction
202-10085-01, March 2005
•Resource CD for ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports,
including:
– This guide.
– Application Notes and other helpful information.
– ProSafe VPN Client Software - single user license.
• Warranty and Support Information Card.
If any of the parts are incorrect, missing, or damaged, contact your NETGEAR dealer. Keep the
carton, including the original packing materials, in case you need to return the firewall for repair.
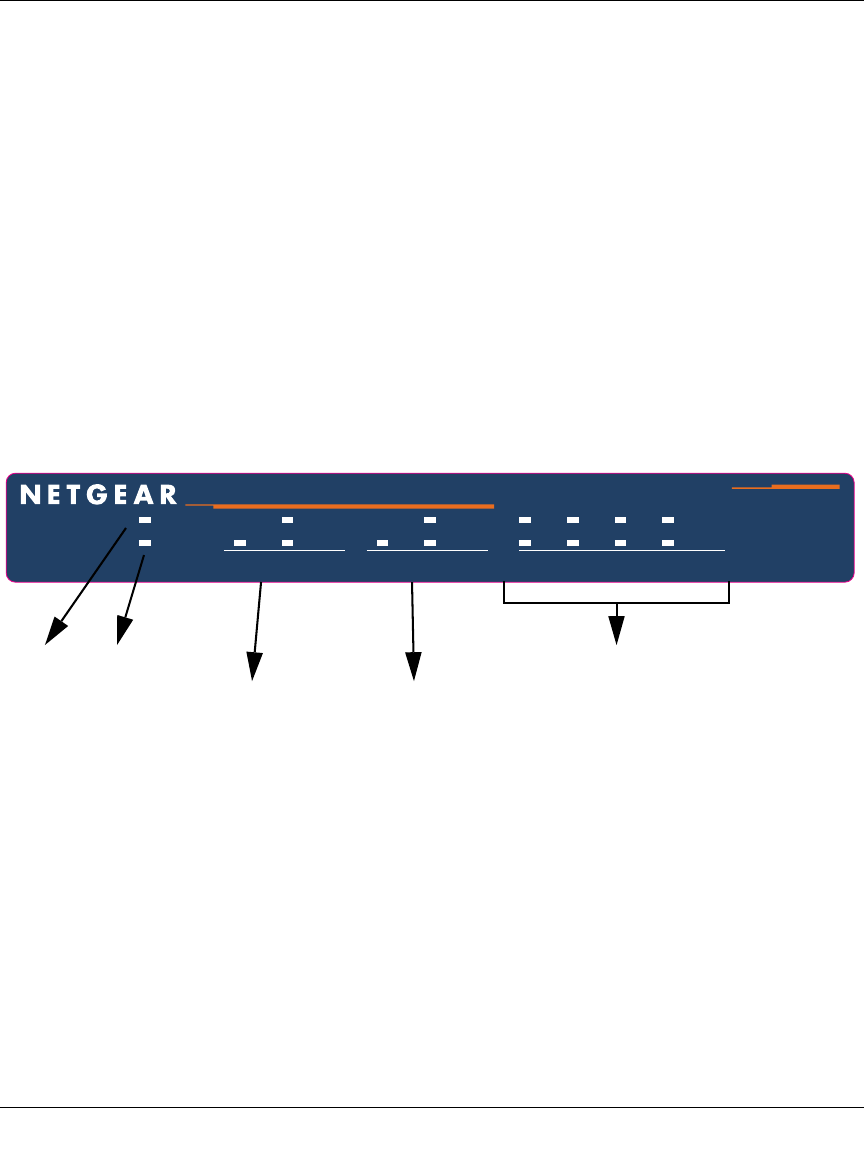
The Router’s Front Panel
The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports front panel
shown below contains the port connections, status LEDs, and the factory defaults reset button.
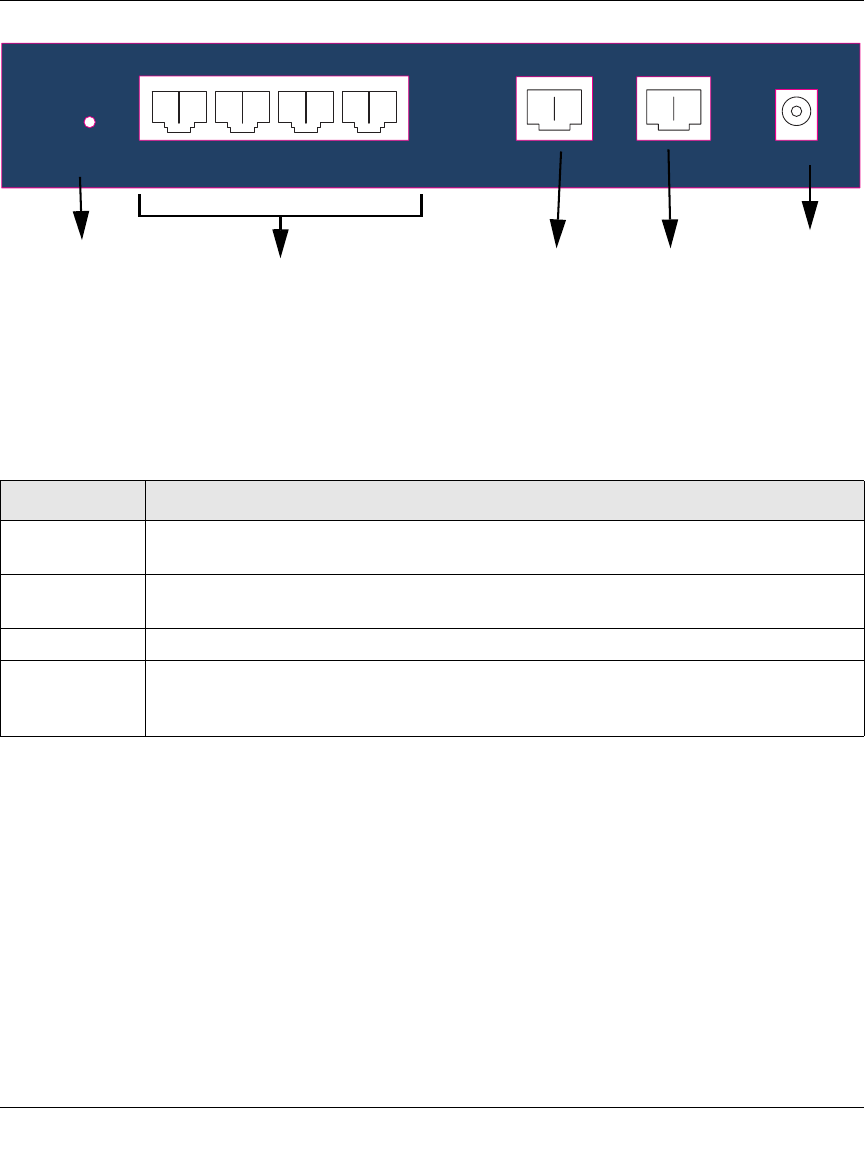
Figure 2-1: FVS124G Front Panel
You can use the LEDs to verify various conditions. Table 2-1 lists and describes each object on the
front panel of the firewall and its operation.
1
LAN
234
SPEED
LINK/ACT
ACTIVE
100
LINK/ACT
WAN2
ACTIVE
100
LINK/ACT
WAN1
TEST
PWR
MODEL FVS124G
ProSafe Dual WAN VPN Gigabit Firewall
PWR TEST
LED LED WAN1 Port
LEDs WAN2 Port
LEDs
Gigabit LAN
Port LEDs
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Introduction 2-7
202-10085-01, March 2005
The Router’s Rear Panel
The rear panel of the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN
Ports (Figure 2-2) contains the factory defaults reset button, LAN and WAN ports, and DC power
input connection.
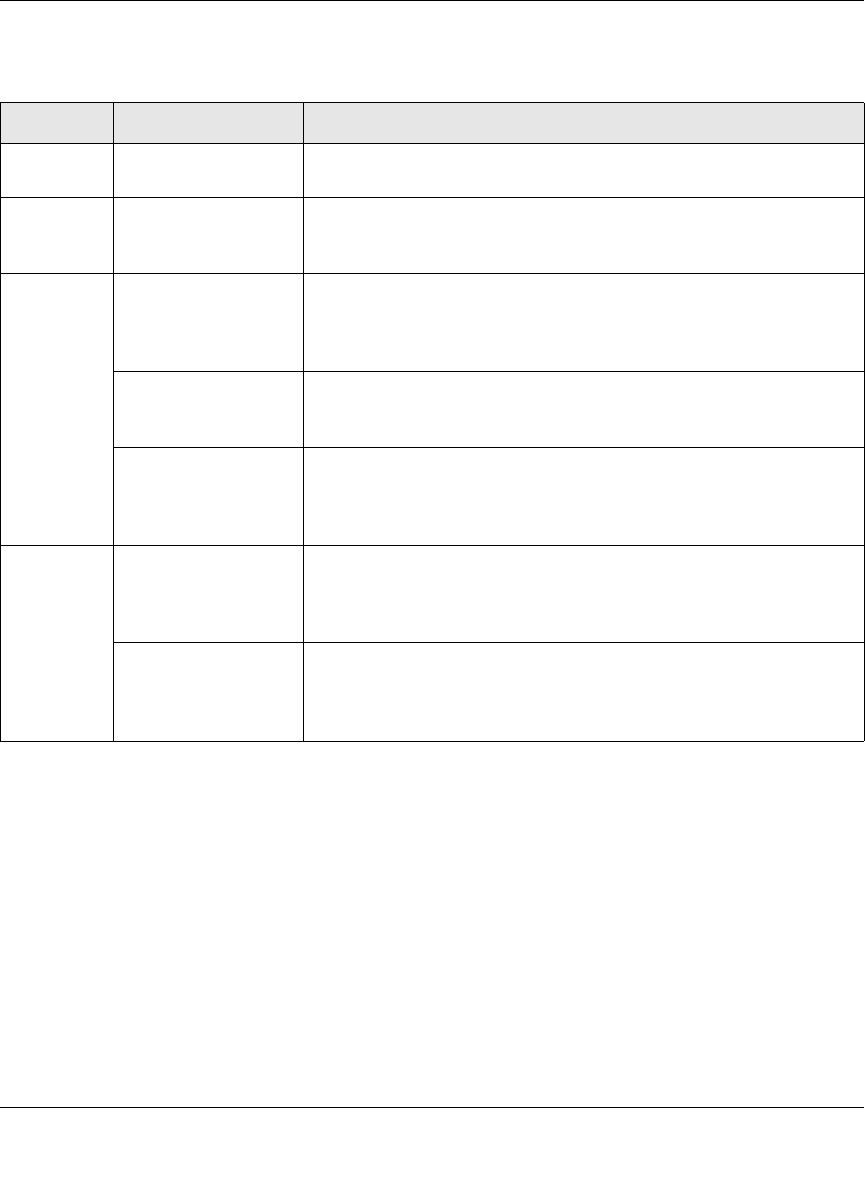
Table 2-1. FVS124G front panel
Object Activity Description
PWR LED On (Green)
Off Power is supplied to the firewall.
Power is not supplied to the firewall.
TEST LED On (Amber)
Blinking (Amber)
Off
Test mode: The system is initializing or the initialization has failed.
Writing to Flash memory (during upgrading or resetting to defaults).
The system has booted successfully.
WAN Port
LEDs Link/Act LED
On (Green)
Blinking (Green)
Off
The WAN port has detected a link with a connected Ethernet device.
Data is being transmitted or received by the WAN port.
The WAN port has no link.
100 LED
On (Green)
Off The WAN port is operating at 100 Mbps.
The WAN port is operating at 10 Mbps.
Active LED
On (Green)
On (Amber)
Off
The WAN port has a valid Internet connection.
The Internet connection is down or not being used.
The WAN port is either not enabled or has no link.
Gigabit LAN
Port LEDs Link/Act LED
On (Green)
Blinking (Green)
Off
The LAN port has detected a link with a connected Ethernet device.
Data is being transmitted or received by the LAN port.
The LAN port has no link.
Speed LED
On (Green)
On (Amber)
Off
The LAN port is operating at 1,000 Mbps.
The LAN port is operating at 100 Mbps.
The LAN port is operating at 10 Mbps.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
2-8 Introduction
202-10085-01, March 2005
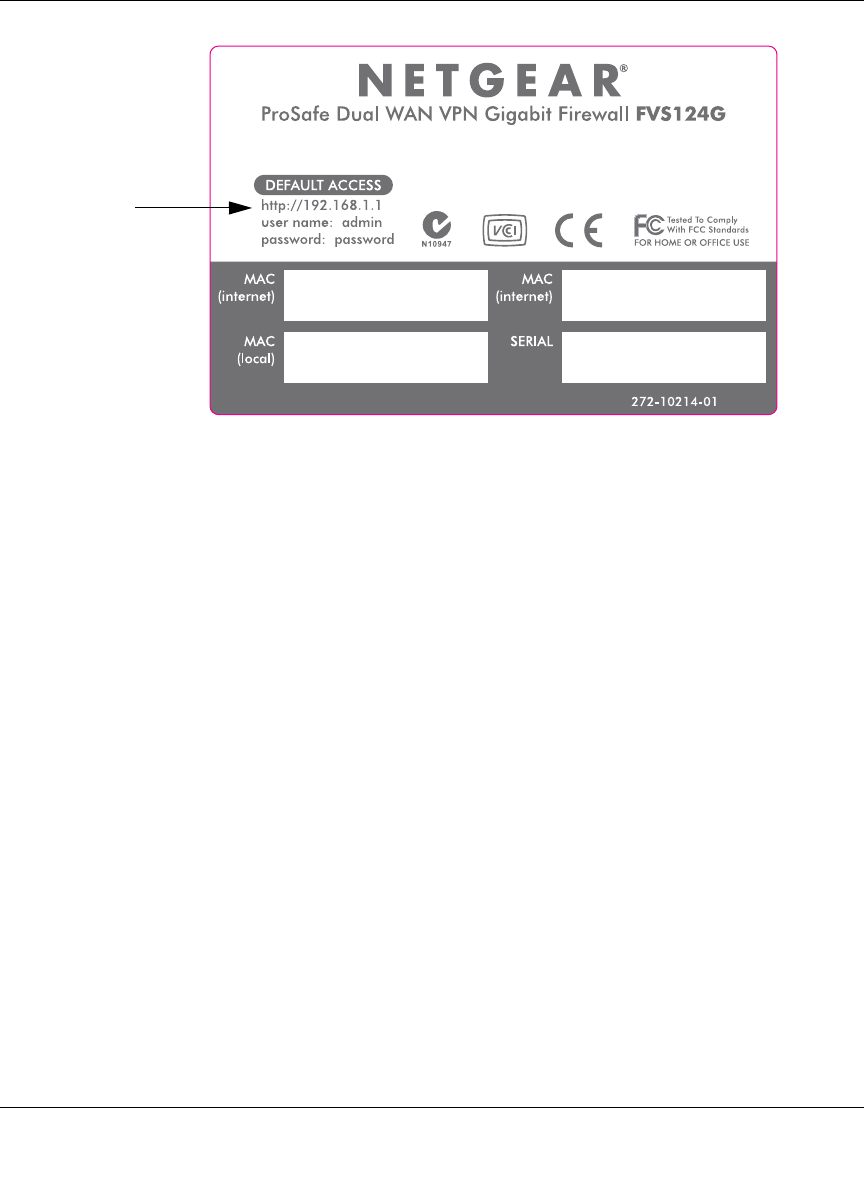
Figure 2-2: FVS124G Rear Panel
Viewed from left to right, the rear panel contains the following elements:
The Router’s IP Address, Login Name, and Password
Check the label on the bottom of the FVS124G’s enclosure if you forget the following factory
default information:
• IP Address: http://192.168.1.1 to reach the Web-based GUI from the LAN
•User name: admin
• Password: password
Table 2-2. FVS124G rear panel
Item Description
Factory Defaults
Button Factory Defaults reset push button (see “Default Factory Settings” on page 2-10 for the
factory defaults).
LAN Ports 4-port RJ-45 10/100/1000 Mbps Fast Ethernet Switch, N-way automatic speed
negotiation, auto MDI/MDIX.
WAN Ports Two RJ-45 WAN ports, N-way automatic speed negotiation, Auto MDI/MDIX.
AC Power
Adapter
Connection
12 VDC, 1.2A
Factory
Defaults
LAN
4 3 2 1 WAN2 WAN1 12VDC 1.2A
AC Power
Adapter
Factory
Defaults
Button Connection
WAN2 Port WAN1 Port
LAN Ports
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Introduction 2-9
202-10085-01, March 2005
Figure 2-3: FVS124G Bottom Label
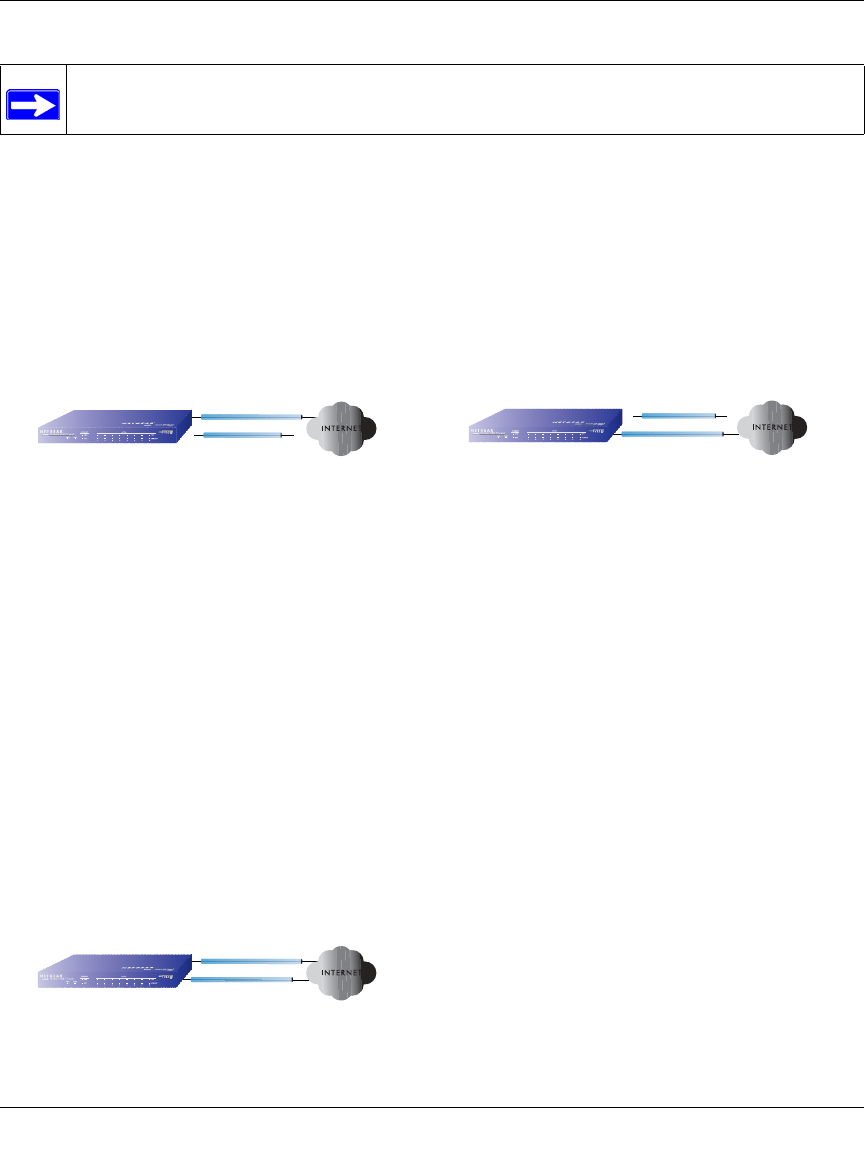
Logging into the Router
To log into the FVS124G once it is connected,
1. Open a Web browser.
2. Enter http://192.168.1.1 as the URL.
3. Once you get the login screen (Figure 2-4), enter the following information:
•admin for User Name
•password for Password
LAN IP Address
User Name
Password
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
2-10 Introduction
202-10085-01, March 2005
Figure 2-4: Login screen on the Web browser
Note: Read-only access is provided by logging in as username guest and default password
password.
Default Factory Settings
When you first receive your FVS124G, the default factory settings will be set as shown in
Table 2-1 below. You can restore these defaults with the Factory Defaults restore switch on the
front panel — see “The Router’s Front Panel” on page 2-6.
• Pressing this switch until the TEST LED blinks (approximately 10 seconds) causes the
firewall to restore all factory default settings and reboot.
• A shorter press and release causes the firewall to merely reboot.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Introduction 2-11
202-10085-01, March 2005
NETGEAR Related Products
NETGEAR products related to the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and
Dual WAN Ports are as follows:
• FA311 10/100 PCI Adapter
• FA511 10/100 32-bit CardBus Adapter
• GA311 10/100/1000 PCI Adapter
• FVL328 ProSafe VPN Firewall
• FVS318 ProSafe VPN Firewall 8
• FVS338 ProSafe VPN Firewall 50
• FVX538 ProSafe VPN Firewall 200
• FWG114P ProSafe 802.11g Wireless Firewall with USB Print Server
• NMS100 ProSafe Network Management System
• VPN01L and VPN05L ProSafe VPN Client Software
• WG302 ProSafe 802.11g Access Point
Table 2-1. Factory Default Settings
Feature Default
User Name (case sensitive) admin
Password (case sensitive) password
Built-in DHCP server DHCP server is enabled, issues addresses in the
default subnet
IP Configuration IP Address: 192.168.1.1
Subnet Mask: 255.255.255.0
Gateway: 0.0.0.0
Time Zone GMT
Time Zone Adjust for Daylight Saving TIme Enabled
SNMP Disabled

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
2-12 Introduction
202-10085-01, March 2005

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-1
202-10085-01, March 2005
Chapter 3
Network Planning
This chapter describes the factors to consider when planning a network using a firewall that has
dual WAN ports.
Overview of the Planning Process
The areas that require planning when using a firewall that has dual WAN ports include:
• Inbound traffic (e.g., port forwarding, port triggering)
• Virtual private networks (VPNs)
The two WAN ports can be configured on a mutually-exclusive basis to either:
• roll over for increased reliability, or
• balance the load for outgoing traffic.
These two categories of considerations interact to make the planning process more challenging.
Inbound Traffic
Unrequested incoming traffic can be directed to a PC on your LAN rather than being discarded.
The mechanism for making the IP address public depends on whether the dual WAN ports are
configured to either roll over or balance the loads. See “Inbound Traffic” on page 3-3 for further
discussion.
Virtual Private Networks (VPNs)
A virtual private network (VPN) tunnel provides a secure communication channel between either
two gateway VPN firewalls or between a remote PC client and gateway VPN firewall. As a result,
the IP address of at least one of the tunnel end points must be known in advance in order for the
other tunnel end point to establish (or re-establish) the VPN tunnel. See “Virtual Private Networks
(VPNs)” on page 3-5 for further discussion.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-2 Network Planning
202-10085-01, March 2005
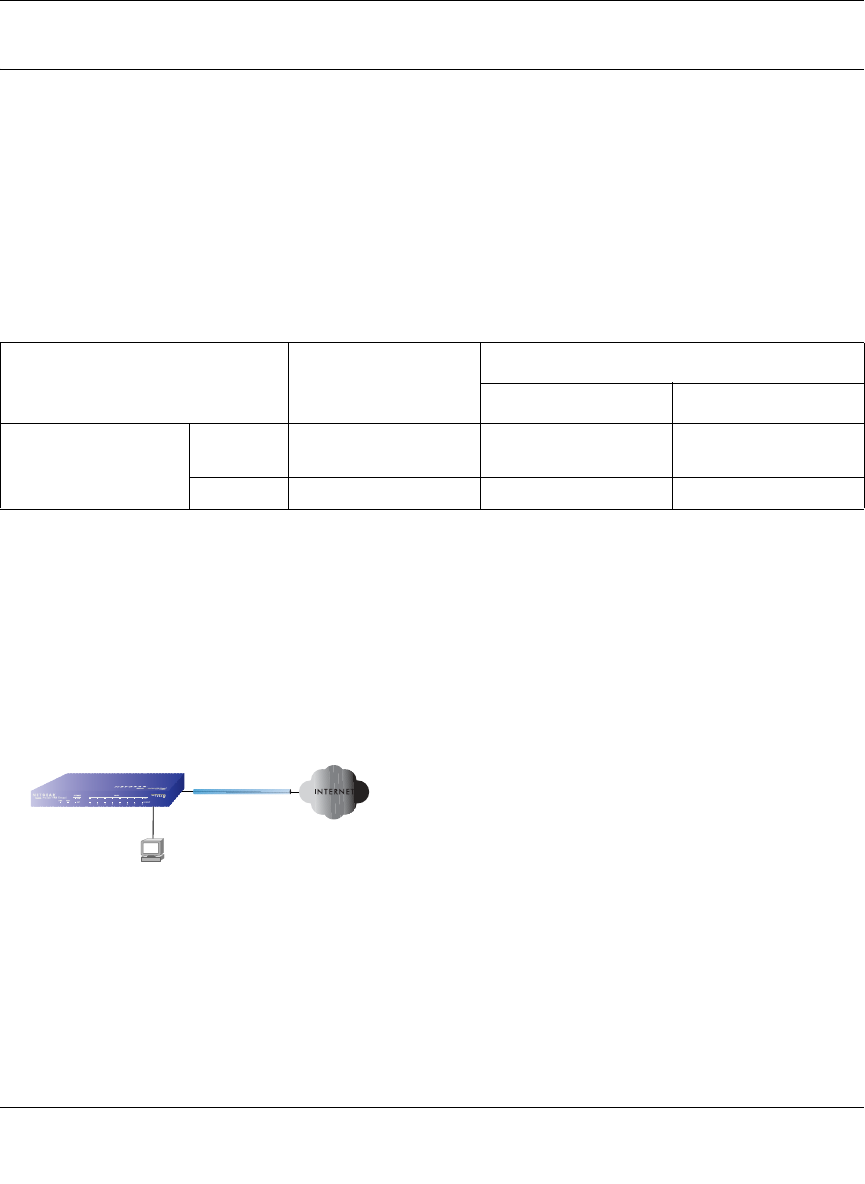
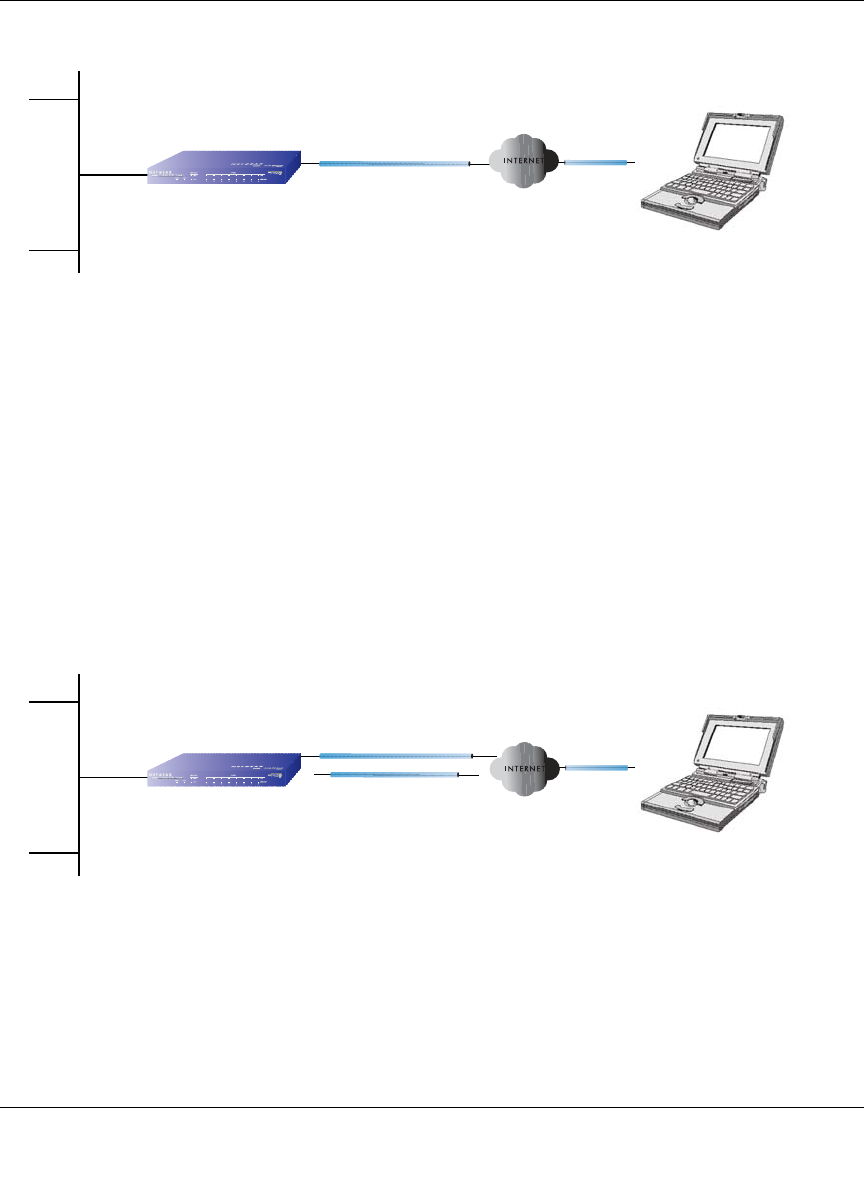
The Rollover Case for Firewalls With Dual WAN Ports
Rollover (Figure 3-1) for the dual WAN port case is different from the single gateway WAN port
case when specifying the IP address. Only one WAN port is active at a time and when it rolls over,
the IP address of the active WAN port always changes. Hence, the use of a fully-qualified domain
name is always required, even when the IP address of each WAN port is fixed.
Figure 3-1: Dual WAN ports before and after rollover
Features such as multiple exposed hosts are not supported when using dual WAN port rollover
because the IP addresses of each WAN port must be in the identical range of fixed addresses.
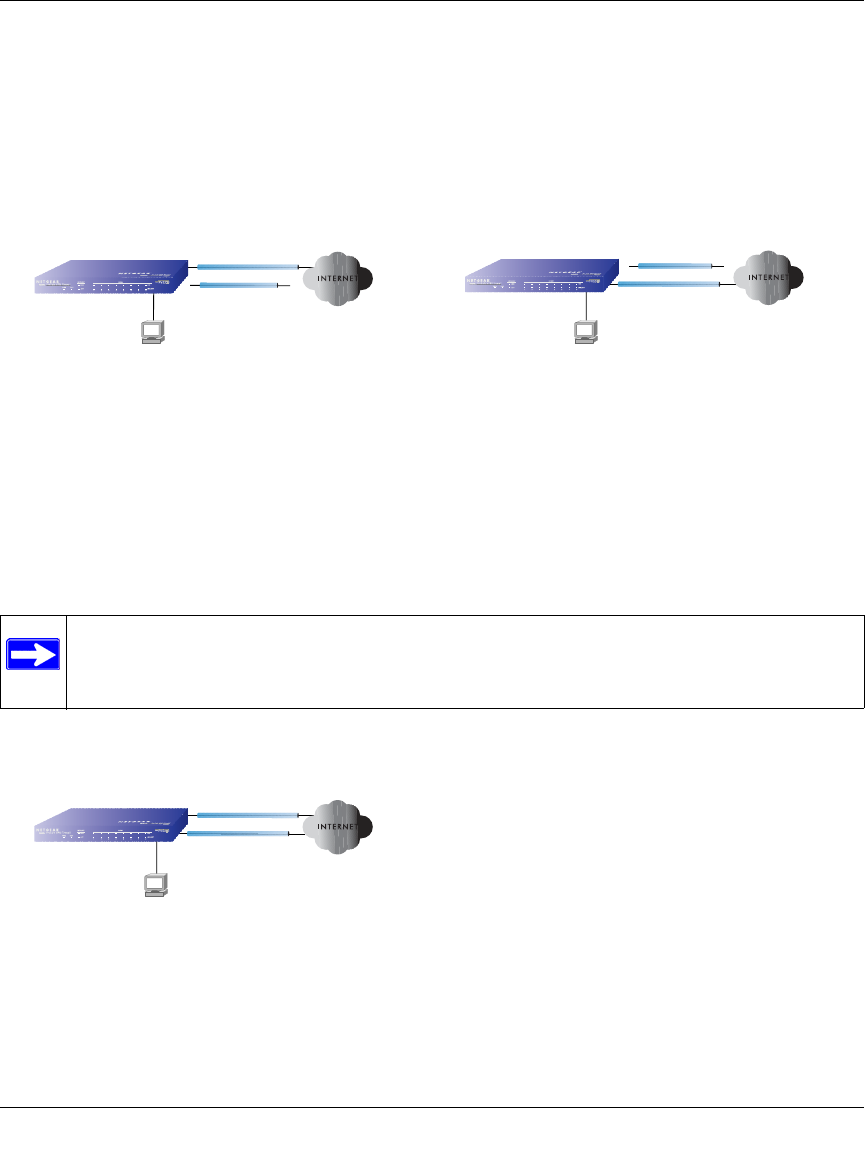
The Load Balancing Case for Firewalls With Dual WAN Ports
Load balancing (Figure 3-2) for the dual WAN port case is similar to the single WAN port case
when specifying the IP address. Each IP address is either fixed or dynamic based on the ISP:
fully-qualified domain names must be used when the IP address is dynamic and are optional when
the IP address is static.
Figure 3-2: Dual WAN ports for load balancing
Note: Once the gateway firewall WAN port rolls over, the VPN tunnel collapses and
must be re-established using the new WAN IP address.
Router
WAN1 port active
WAN1 IP
Dual WAN Ports (Before Rollover)
WAN2 IP (N/A)
WAN2 port inactive
Router
WAN1 port inactive
WAN1 IP (N/A)
Dual WAN Ports (After Rollover)
WAN2 IP
WAN2 port active
IP address of active WAN port changes after a rollover:
o use of fully-qualified domain names always required
o features requiring fixed IP address blocks not supported
XX
XX
Router
netgear1.dyndns.org
WAN1 IP
Dual WAN Ports (Load Balancing)
WAN2 IP
netgear2.dyndns.org
Use of fully-qualified domain names for IP addresses of WAN ports:
o required for dynamic IP addresses
o optional for fixed IP addresses
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-3
202-10085-01, March 2005
Inbound Traffic
Incoming traffic from the Internet is normally discarded by the firewall unless the traffic is a
response to one of your local computers or a service that you have configured in the Inbound Rules
menu. Instead of discarding this traffic, you can have it forwarded to one or more LAN hosts on
your network.
The addressing of the firewall’s dual WAN port depends on the configuration being implemented:
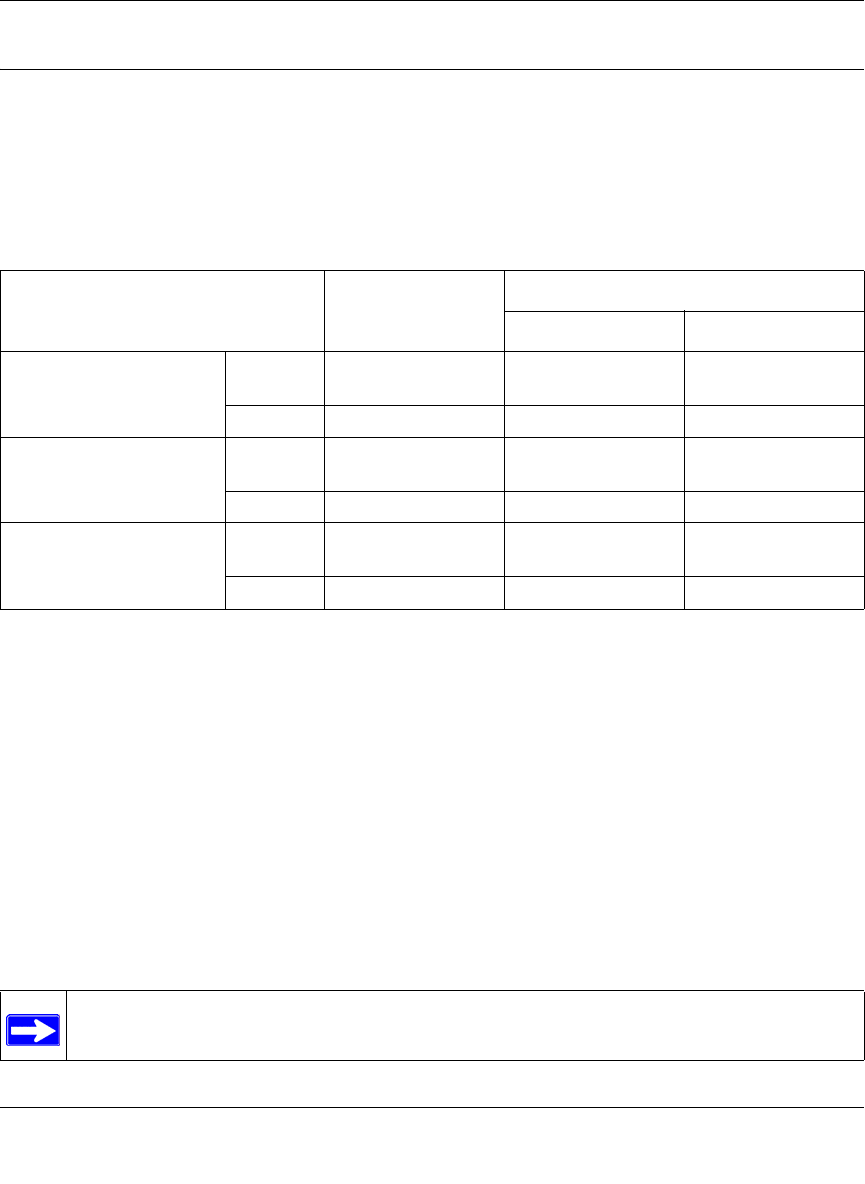
Inbound Traffic to Single WAN Port (Reference Case)
The Internet IP address of the firewall’s WAN port must be known to the public so that the public
can send incoming traffic to the exposed host when this feature is supported and enabled.
In the single WAN case (Figure 3-3), the WAN’s Internet address is either fixed IP or a
fully-qualified domain name if the IP address is dynamic.
Figure 3-3: Inbound traffic to single WAN port case
Inbound Traffic to Dual WAN Port Systems
The IP address range of the firewall’s WAN port must be both fixed and public so that the public
can send incoming traffic to the multiple exposed hosts when this feature is supported and enabled.
Table 3-1. IP addressing requirements for exposed hosts in dual WAN port systems
Configuration and
WAN IP address Single WAN Port
(reference case)
Dual WAN Port Cases
Rollover Load Balancing
Inbound traffic
• Port forwarding
• Port triggering
Fixed Allowed
(FQDN optional) FQDN required Allowed
(FQDN optional)
Dynamic FQDN required FQDN required FQDN required
Router
netgear.dyndns.org
WAN IP
IP address of WAN port:
FQDN is required for dynamic IP address and is optional for fixed IP address
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-4 Network Planning
202-10085-01, March 2005
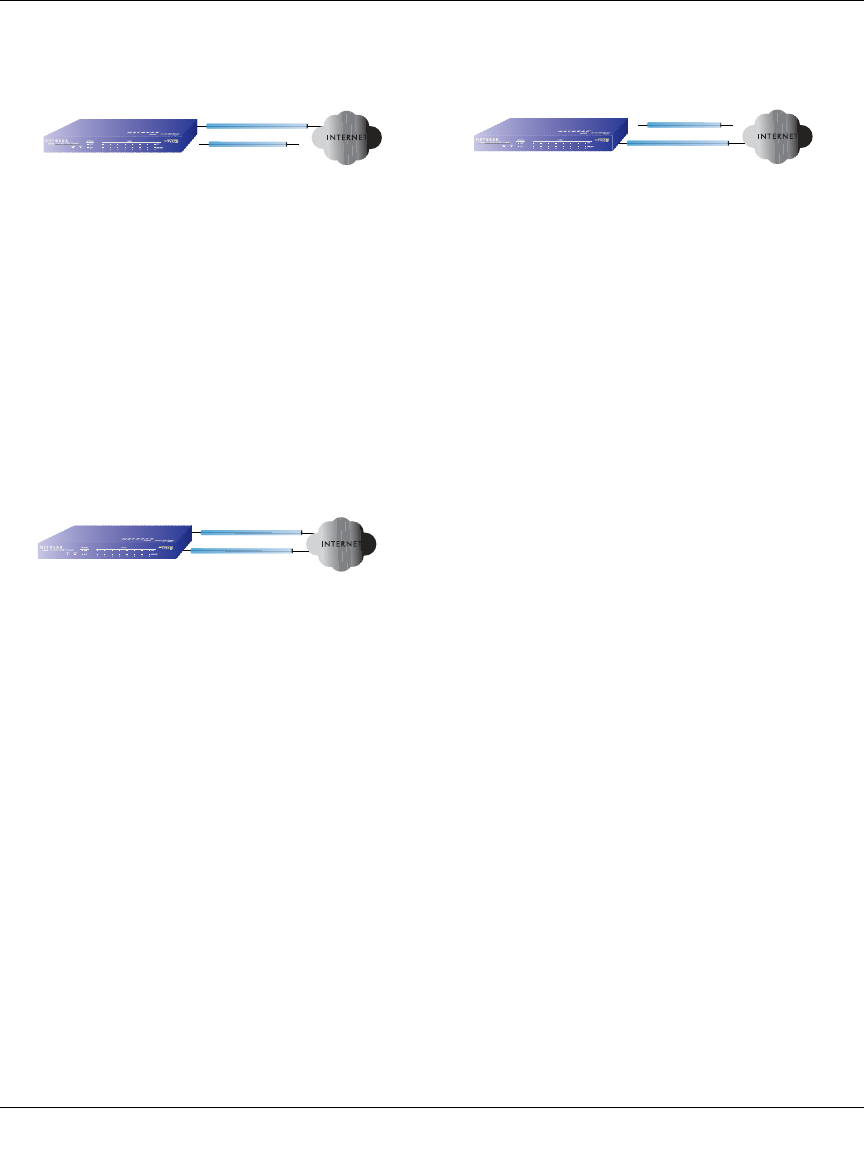
Inbound Traffic: Dual WAN Ports for Improved Reliability
In the dual WAN port case with rollover (Figure 3-4), the WAN’s IP address will always change at
rollover. A fully-qualified domain name must be used that toggles between the IP addresses of the
WAN ports (i.e., WAN1 or WAN2).
Figure 3-4: Inbound traffic to dual WAN ports, before and after rollover
Inbound Traffic: Dual WAN Ports for Load Balancing
In the dual WAN port case for load balancing (Figure 3-5), the Internet address of each WAN port
is either fixed if the IP address is fixed or a fully-qualified domain name if the IP address is
dynamic.
Figure 3-5: Inbound traffic to dual WAN ports for load balancing
Note: Load balancing is implemented for outgoing traffic and not for incoming traffic.
Consider making one of the WAN port Internet addresses public and keeping the other
one private in order to maintain better control of WAN port traffic.
Router
netgear.dyndns.org
WAN1 IP
Dual WAN Ports (Before Rollover)
WAN2 IP (N/A)
WAN2 port inactive
Router
WAN1 port inactive
WAN1 IP (N/A)
Dual WAN Ports (After Rollover)
WAN2 IP
netgear.dyndns.org
IP address of active WAN port changes after a rollover (use of fully-qualified domain names always required)
XX
XX
Router
netgear1.dyndns.org
WAN1 IP
Dual WAN Ports (Load Balancing)
WAN2 IP
netgear2.dyndns.org
IP addresses of WAN ports:
use of fully-qualified domain names
required for dynamic IP addresses
and optional for fixed IP addresses
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-5
202-10085-01, March 2005
Virtual Private Networks (VPNs)
When implementing virtual private network (VPN) tunnels, a mechanism must be used for
determining the IP addresses of the tunnel end points. The addressing of the firewall’s dual WAN
port depends on the configuration being implemented:
For the single gateway WAN port case, the mechanism is to use a fully-qualified domain name
(FQDN) when the IP address is dynamic and to use either an FQDN or the IP address itself when
the IP address is fixed. The situation is different when dual gateway WAN ports are used in a
rollover-based system.
• Rollover Case for Dual Gateway WAN Ports
Rollover (Figure 3-6) for the dual gateway WAN port case is different from the single gateway
WAN port case when specifying the IP address of the VPN tunnel end point. Only one WAN
port is active at a time and when it rolls over, the IP address of the active WAN port always
changes. Hence, the use of a fully-qualified domain name is always required, even when the IP
address of each WAN port is fixed.
Table 3-1. IP addressing requirements for VPNs in dual WAN port systems
Configuration and WAN IP address Single WAN Port
(reference case)
Dual WAN Port Cases
Rollover*
*All tunnels must be re-established after a rollover using the new WAN IP address.
Load Balancing
VPN Road Warrior
(client-to-gateway) Fixed Allowed
(FQDN optional) FQDN required Allowed
(FQDN optional)
Dynamic FQDN required FQDN required FQDN required
VPN Gateway-to-Gateway Fixed Allowed
(FQDN optional) FQDN required Allowed
(FQDN optional)
Dynamic FQDN required FQDN required FQDN required
VPN Telecommuter
(client-to-gateway through
a NAT router)
Fixed Allowed
(FQDN optional) FQDN required Allowed
(FQDN optional)
Dynamic FQDN required FQDN required FQDN required
Note: Once the gateway router WAN port rolls over, the VPN tunnel collapses and must
be re-established using the new WAN IP address.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-6 Network Planning
202-10085-01, March 2005
Figure 3-6: Dual gateway WAN ports before and after rollover
• Load Balancing Case for Dual Gateway WAN Ports
Load balancing (Figure 3-7) for the dual gateway WAN port case is the same as the single
gateway WAN port case when specifying the IP address of the VPN tunnel end point. Each IP
address is either fixed or dynamic based on the ISP: fully-qualified domain names must be
used when the IP address is dynamic and are optional when the IP address is static.
Figure 3-7: Dual gateway WAN ports for load balancing
VPN Road Warrior (Client-to-Gateway)
The following situations exemplify the requirements for a remote PC client with no firewall to
establish a VPN tunnel with a gateway VPN firewall:
• Single gateway WAN port
• Redundant dual gateway WAN ports for increased reliability (before and after rollover)
• Dual gateway WAN ports used for load balancing
VPN Road Warrior: Single Gateway WAN Port (Reference Case)
In the case of the single WAN port on the gateway VPN firewall (Figure 3-8), the remote PC client
initiates the VPN tunnel because the IP address of the remote PC client is not known in advance.
The gateway WAN port must act as the responder.
Gateway
netgear.dyndns.org
WAN1 IP
Dual WAN Ports (Before Rollover)
VPN Router WAN2 IP (N/A)
WAN2 port inactive
Gateway
WAN1 port inactive
WAN1 IP (N/A)
Dual WAN Ports (After Rollover)
VPN Router WAN2 IP
netgear.dyndns.org
IP address of active WAN port changes after a rollover (use of fully-qualified domain names always required)
XX
XX
Gateway
netgear1.dyndns.org
WAN1 IP
Dual WAN Ports (Load Balancing)
VPN Router WAN2 IP
netgear2.dyndns.org
IP addresses of WAN ports same as single
WAN port case (use of fully-qualified domain
names required for dynamic IP addresses
and optional for fixed IP addresses)
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-7
202-10085-01, March 2005
Figure 3-8: Single gateway WAN port case for VPN road warrior
The IP address of the gateway WAN port can be either fixed or dynamic. If the IP address is
dynamic, a fully-qualified domain name must be used. If the IP address is fixed, a fully-qualified
domain name is optional.
VPN Road Warrior: Dual Gateway WAN Ports for Improved Reliability
In the case of the dual WAN ports on the gateway VPN firewall (Figure 3-9), the remote PC client
initiates the VPN tunnel with the active gateway WAN port (port WAN1 in this example) because
the IP address of the remote PC client is not known in advance. The gateway WAN port must act
as a responder.
Figure 3-9: Dual gateway WAN ports, before rollover, for VPN road warrior
The IP addresses of the gateway WAN ports can be either fixed or dynamic, but a fully-qualified
domain name must always be used because the active WAN port could be either WAN1 or WAN2
(i.e., the IP address of the active WAN port is not known in advance).
Gateway A
bzrouter.dyndns.org
10.5.6.0/24
10.5.6.1
WAN IP WAN IP
LAN IP
Client B
FQDN 0.0.0.0
VPN Router
(at employer's
main office)
Road Warrior Example (Single WAN Port)
Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- optional for Fixed IP addresses
- required for Dynamic IP addresses
Gateway A
bzrouter.dyndns.org
10.5.6.0/24
10.5.6.1
WAN1 IP
WAN IP
LAN IP
Client B
0.0.0.0
VPN Router
(at employer's
main office)
Road Warrior Example
(Dual WAN Ports, Before Rollover)
Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- required for Fixed IP addresses
- required for Dynamic IP addresses
WAN2 port inactive
WAN2 IP (N/A)
XX

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-8 Network Planning
202-10085-01, March 2005
After a rollover of the gateway WAN port (Figure 3-10), the previously inactive gateway WAN
port becomes the active port (port WAN2 in this example) and the remote PC client must
re-establish the VPN tunnel. The gateway WAN port must act as the responder.
Figure 3-10: Dual gateway WAN ports, after rollover, for VPN road warrior
The purpose of the fully-qualified domain name in this case is to toggle the domain name of the
gateway firewall between the IP addresses of the active WAN port (i.e., WAN1 and WAN2) so that
the remote PC client can determine the gateway IP address to establish or re-establish a VPN
tunnel.
VPN Road Warrior: Dual Gateway WAN Ports for Load Balancing
In the case of the dual WAN ports on the gateway VPN firewall (Figure 3-11), the remote PC
initiates the VPN tunnel with the appropriate gateway WAN port (i.e., port WAN1 or WAN2 as
necessary to balance the loads of the two gateway WAN ports) because the IP address of the
remote PC is not known in advance. The chosen gateway WAN port must act as the responder.
Figure 3-11: Dual gateway WAN ports (load balancing case) for VPN road warrior
Gateway A
WAN1 port inactive
10.5.6.0/24
10.5.6.1
WAN1 IP (N/A)
WAN IP
LAN IP
Client B
0.0.0.0
VPN Router
(at employer's
main office)
Road Warrior Example
(Dual WAN Ports, After Rollover)
Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- required for Fixed IP addresses
- required for Dynamic IP addresses
bzrouter.dyndns.org
WAN2 IP
Remote PC must re-establish VPN tunnel after a rollover
XX
Gateway A
bzrouter1.dyndns.org
10.5.6.0/24
10.5.6.1
WAN1 IP
WAN IP
LAN IP
Client B
0.0.0.0
VPN Router
(at employer's
main office)
Road Warrior Example
(Dual WAN Ports, Load Balancing)
Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- optional for Fixed IP addresses
- required for Dynamic IP addresses
bzrouter2.dyndns.org
WAN2 IP
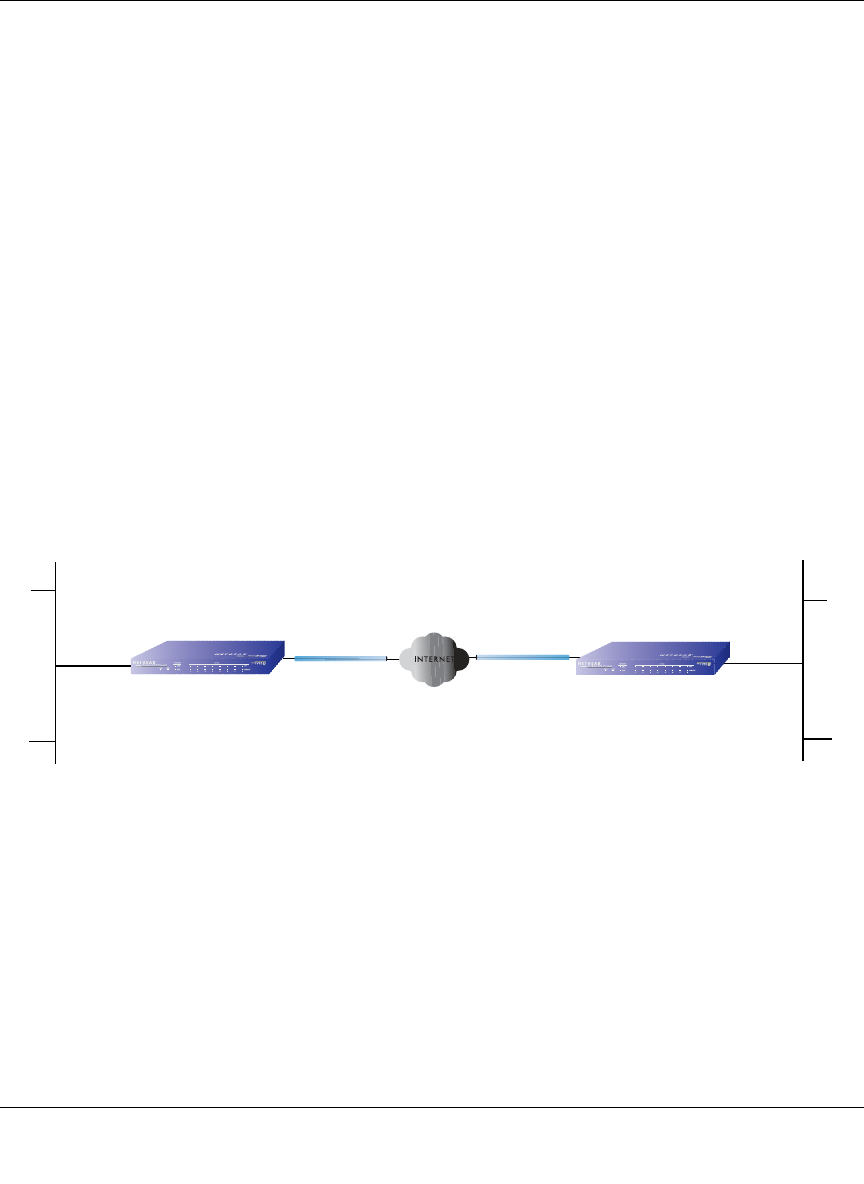
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-9
202-10085-01, March 2005
The IP addresses of the gateway WAN ports can be either fixed or dynamic. If an IP address is
dynamic, a fully-qualified domain name must be used. If an IP address is fixed, a fully-qualified
domain name is optional.
VPN Gateway-to-Gateway
The following situations exemplify the requirements for a gateway VPN firewall to establish a
VPN tunnel with another gateway VPN firewall:
• Single gateway WAN ports
• Redundant dual gateway WAN ports for increased reliability (before and after rollover)
• Dual gateway WAN ports used for load balancing
VPN Gateway-to-Gateway: Single Gateway WAN Ports (Reference Case)
In the case of single WAN ports on the gateway VPN firewalls (Figure 3-12), either gateway WAN
port can initiate the VPN tunnel with the other gateway WAN port because the IP addresses are
known in advance.
Figure 3-12: Single gateway WAN ports case for gateway-to-gateway VPN tunnels
The IP address of the gateway WAN ports can be either fixed or dynamic. If an IP address is
dynamic, a fully-qualified domain name must be used. If an IP address is fixed, a fully-qualified
domain name is optional.
Gateway A
22.23.24.25
FQDN
netgear.dyndns.org
10.5.6.0/24 172.23.9.0/24
172.23.9.1
10.5.6.1
WAN IP WAN IP LAN IP
LAN IP
Gateway B
Gateway-to-Gateway Example (Single WAN Ports)
Fully-Qualified Domain Names (FQDN)
- optional for Fixed IP addresses
- required for Dynamic IP addresses
VPN Router
(at office A)
VPN Router
(at office B)
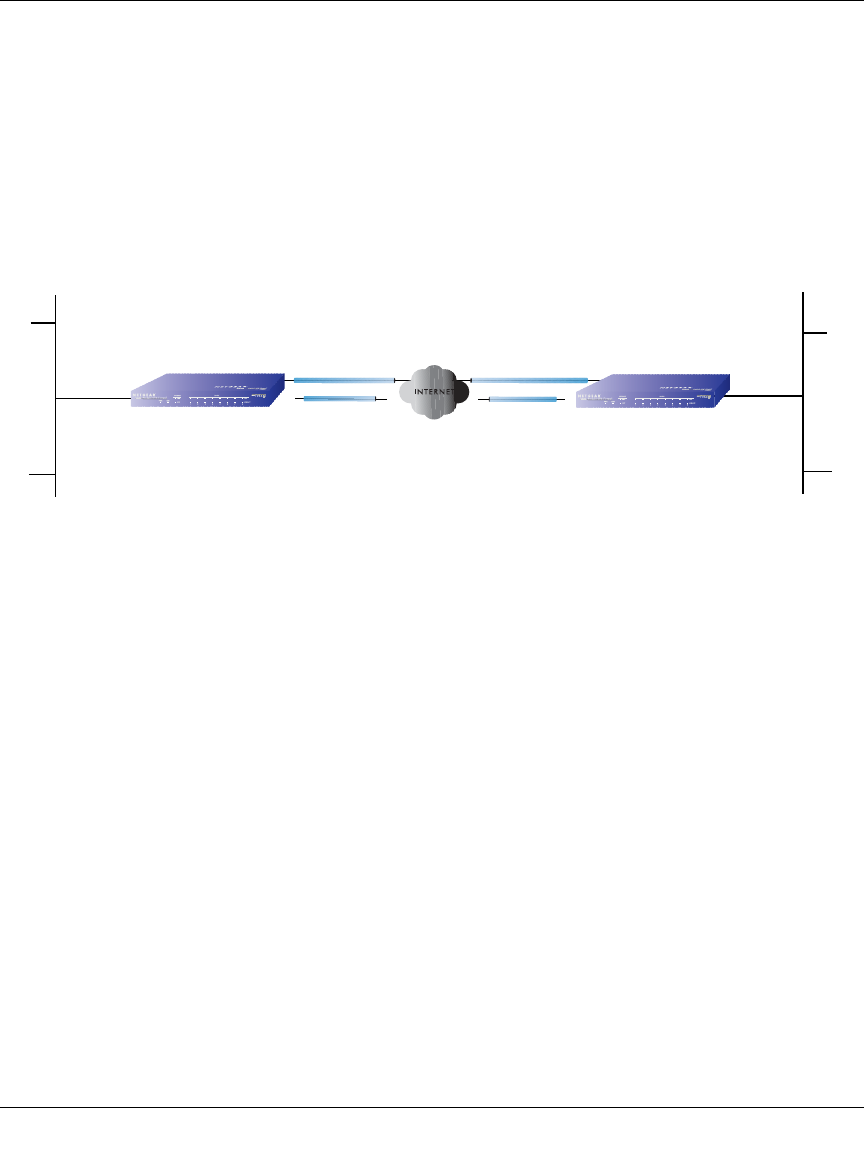
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-10 Network Planning
202-10085-01, March 2005
VPN Gateway-to-Gateway: Dual Gateway WAN Ports for Improved Reliability
In the case of the dual WAN ports on the gateway VPN firewall (Figure 3-13), either of the
gateway WAN ports at one end can initiate the VPN tunnel with the appropriate gateway WAN
port at the other end as necessary to balance the loads of the gateway WAN ports because the IP
addresses of the WAN ports are known in advance. In this example, port WAN_A1 is active and
port WAN_A2 is inactive at Gateway A; port WAN_B1 is active and port WAN_B2 is inactive at
Gateway B.
Figure 3-13: Dual gateway WAN ports, before rollover, for gateway-to-gateway VPN tunnels
The IP addresses of the gateway WAN ports can be either fixed or dynamic, but a fully-qualified
domain name must always be used because the active WAN ports could be either WAN_A1,
WAN_A2, WAN_B1, or WAN_B2 (i.e., the IP address of the active WAN port is not known in
advance).
After a rollover of a gateway WAN port (Figure 3-14), the previously inactive gateway WAN port
becomes the active port (port WAN_A2 in this example) and one of the gateway VPN firewalls
must re-establish the VPN tunnel.
Gateway A
netgearB.dyndns.org
netgearA.dyndns.org
10.5.6.0/24 172.23.9.0/24
172.23.9.1
10.5.6.1
WAN_A1 IP WAN_B1 IP
LAN IP
LAN IP
Gateway B
Gateway-to-Gateway Example
(Dual WAN Ports, Before Rollover)
Fully-Qualified Domain Names (FQDN)
- required for Fixed IP addresses
- required for Dynamic IP addresses
VPN Router
(at office A)
VPN Router
(at office B)
WAN_B2 IP (N/A)
WAN_A2 IP (N/A)
WAN_A2 port inactive WAN_B2 port inactive
XX
XX
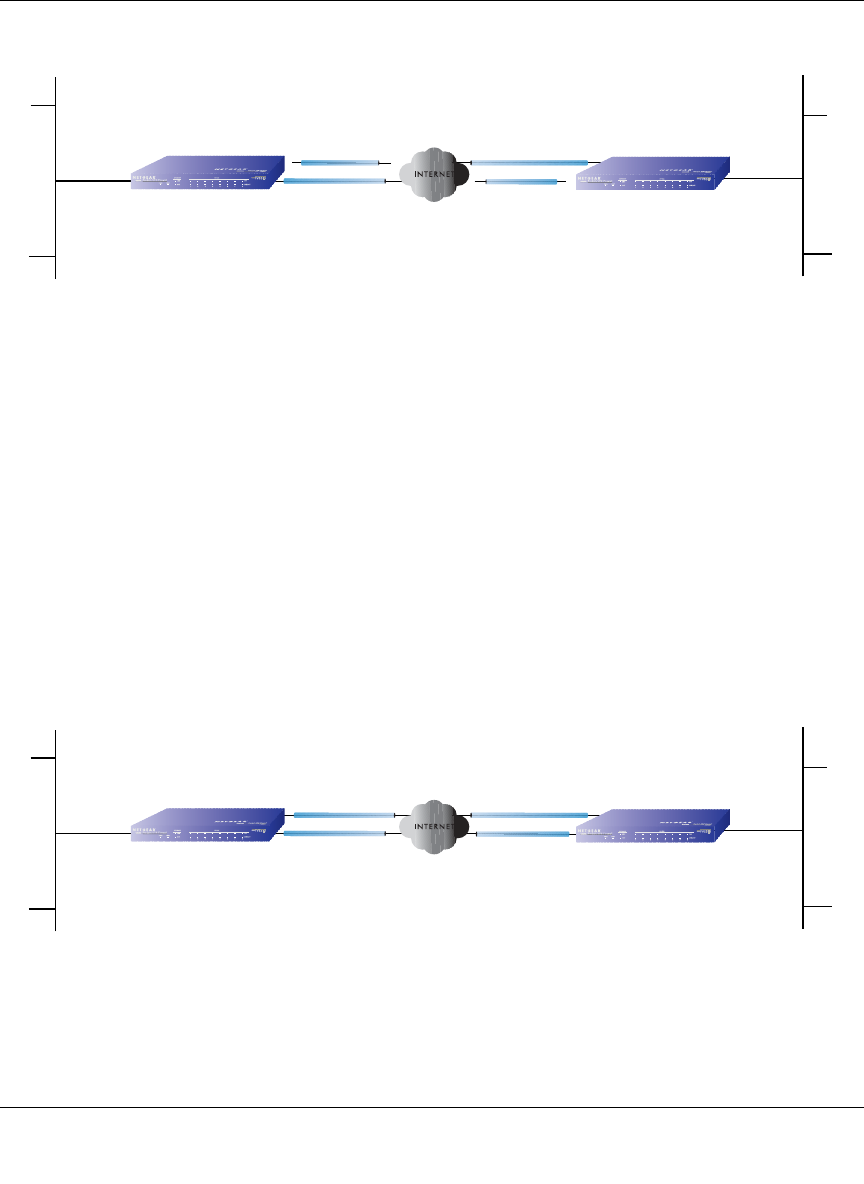
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-11
202-10085-01, March 2005
Figure 3-14: Dual gateway WAN ports, after rollover, for gateway-to-gateway VPN tunnels
The purpose of the fully-qualified domain names is this case is to toggle the domain name of the
failed-over gateway firewall between the IP addresses of the active WAN port (i.e., WAN_A1 and
WAN _A2 in this example) so that the other end of the tunnel has a known gateway IP address to
establish or re-establish a VPN tunnel.
VPN Gateway-to-Gateway: Dual Gateway WAN Ports for Load Balancing
In the case of the dual WAN ports on the gateway VPN firewall (Figure 3-15), either of the
gateway WAN ports at one end can be programmed in advance to initiate the VPN tunnel with the
appropriate gateway WAN port at the other end as necessary to manage the loads of the gateway
WAN ports because the IP addresses of the WAN ports are known in advance.
Figure 3-15: Dual gateway WAN ports (load balancing case) for gateway-to-gateway VPN
tunnels
Gateway A
netgearB.dyndns.org
WAN_A1 port inactive
10.5.6.0/24 172.23.9.0/24
172.23.9.1
10.5.6.1
WAN_A1 IP (N/A) WAN_B1 IP
LAN IP
LAN IP
Gateway B
Gateway-to-Gateway Example
(Dual WAN Ports, After Rollover)
Fully-Qualified Domain Names (FQDN)
- required for Fixed IP addresses
- required for Dynamic IP addresses
VPN Router
(at office A)
VPN Router
(at office B)
WAN_B2 IP (N/A)
WAN_A2 IP
netgear.dyndns.org WAN_B2 port inactive
One of the gateway routers must re-establish VPN tunnel after a rollover
XX
XX
Gateway A
22.23.24.25
netgear1.dyndns.org
10.5.6.0/24 172.23.9.0/24
172.23.9.1
10.5.6.1
WAN_A1 IP WAN_B1 IP
LAN IP
LAN IP
Gateway B
Gateway-to-Gateway Example
(Dual WAN Ports, Load Balancing)
Fully-Qualified Domain Names (FQDN)
- optional for Fixed IP addresses
- required for Dynamic IP addresses
VPN Router
(at office A)
VPN Router
(at office B)
WAN_B2 IP
WAN_A2 IP
netgear2.dyndns.org 22.23.24.26
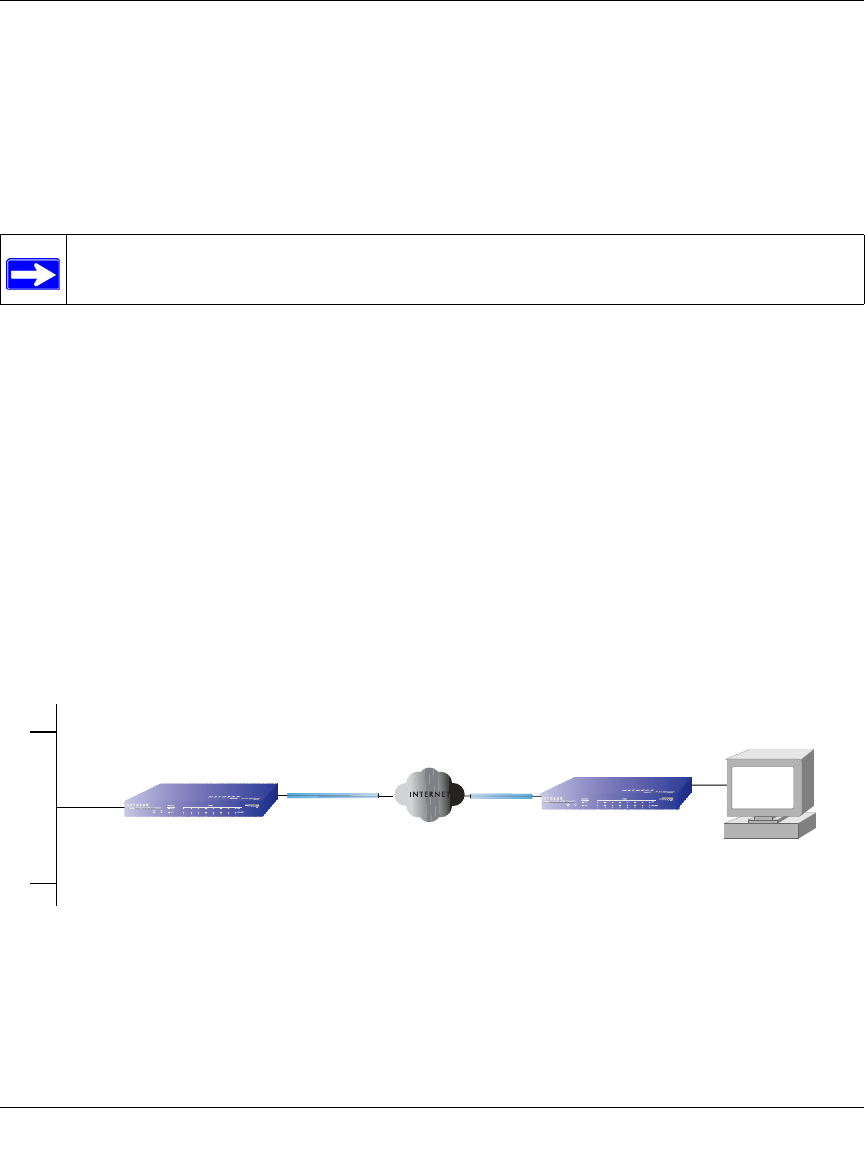
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-12 Network Planning
202-10085-01, March 2005
The IP addresses of the gateway WAN ports can be either fixed or dynamic. If an IP address is
dynamic, a fully-qualified domain name must be used. If an IP address is fixed, a fully-qualified
domain name is optional.
VPN Telecommuter (Client-to-Gateway Through a NAT Router)
The following situations exemplify the requirements for a remote PC client connected to the
Internet with a dynamic IP address through a NAT router to establish a VPN tunnel with a gateway
VPN firewall at the company office:
• Single gateway WAN port
• Redundant dual gateway WAN ports for increased reliability (before and after rollover)
• Dual gateway WAN ports used for load balancing
VPN Telecommuter: Single Gateway WAN Port (Reference Case)
In the case of the single WAN port on the gateway VPN firewall (Figure 3-16), the remote PC
client at the NAT router initiates the VPN tunnel because the IP address of the remote NAT router
is not known in advance. The gateway WAN port must act as the responder.
Figure 3-16: Single gateway WAN port case for VPN telecommuter
The IP address of the gateway WAN port can be either fixed or dynamic. If the IP address is
dynamic, a fully-qualified domain name must be used. If the IP address is fixed, a fully-qualified
domain name is optional.
Note: The telecommuter case presumes the home office has a dynamic IP address and
NAT router.
Gateway A
bzrouter.dyndns.org
10.5.6.0/24
10.5.6.1
WAN IP WAN IP
LAN IP
Client B
FQDN 0.0.0.0
VPN Router
(at employer's
main office)
Telecommuter Example (Single WAN Port)
NAT Router B
NAT Router
(at telecommuter's
home office) Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- optional for Fixed IP addresses
- required for Dynamic IP addresses
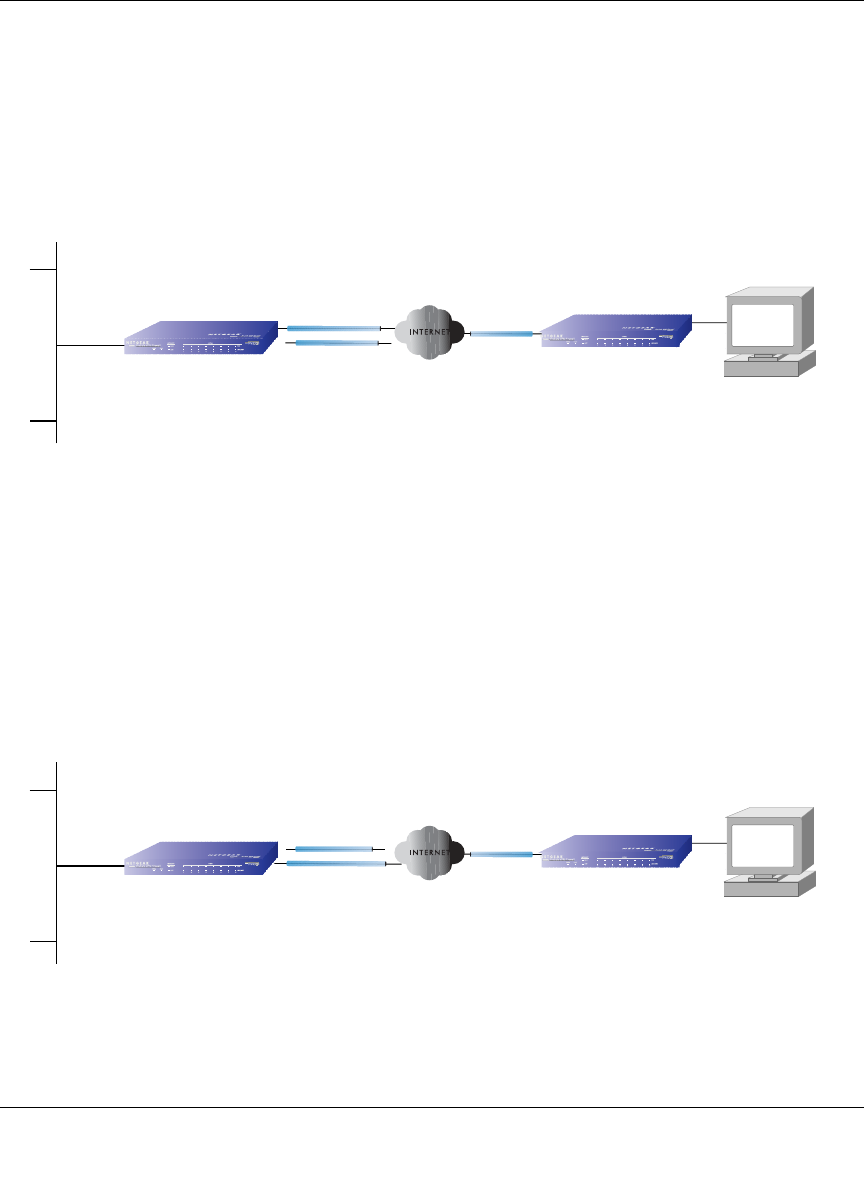
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network Planning 3-13
202-10085-01, March 2005
VPN Telecommuter: Dual Gateway WAN Ports for Improved Reliability
In the case of the dual WAN ports on the gateway VPN firewall (Figure 3-17), the remote PC
client initiates the VPN tunnel with the active gateway WAN port (port WAN1 in this example)
because the IP address of the remote NAT router is not known in advance. The gateway WAN port
must act as the responder.
Figure 3-17: Dual gateway WAN ports, before rollover, for VPN telecommuter
The IP addresses of the gateway WAN ports can be either fixed or dynamic, but a fully-qualified
domain name must always be used because the active WAN port could be either WAN1 or WAN2
(i.e., the IP address of the active WAN port is not known in advance).
After a rollover of the gateway WAN port (Figure 3-18), the previously inactive gateway WAN
port becomes the active port (port WAN2 in this example) and the remote PC must re-establish the
VPN tunnel. The gateway WAN port must act as the responder.
Figure 3-18: Dual gateway WAN ports, after rollover, for VPN telecommuter
Gateway A
WAN2 port inactive
10.5.6.0/24
10.5.6.1
WAN1 IP
WAN IP
LAN IP
Client B
0.0.0.0
VPN Router
(at employer's
main office)
Telecommuter Example
(Dual WAN Ports, Before Rollover)
NAT Router B
NAT Router
(at telecommuter's
home office) Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- required for Fixed IP addresses
- required for Dynamic IP addresses
WAN2 IP (N/A)
bzrouter1.dyndns.org
XX
Gateway A
bzrouter2.dyndns.org
10.5.6.0/24
10.5.6.1
WAN1 IP (N/A)
WAN IP
LAN IP
Client B
0.0.0.0
VPN Router
(at employer's
main office)
Telecommuter Example
(Dual WAN Ports, After Rollover)
NAT Router B
NAT Router
(at telecommuter's
home office) Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- required for Fixed IP addresses
- required for Dynamic IP addresses
WAN2 IP
WAN1 port inactive
Remote PC must re-establish VPN tunnel after a rollover
XX
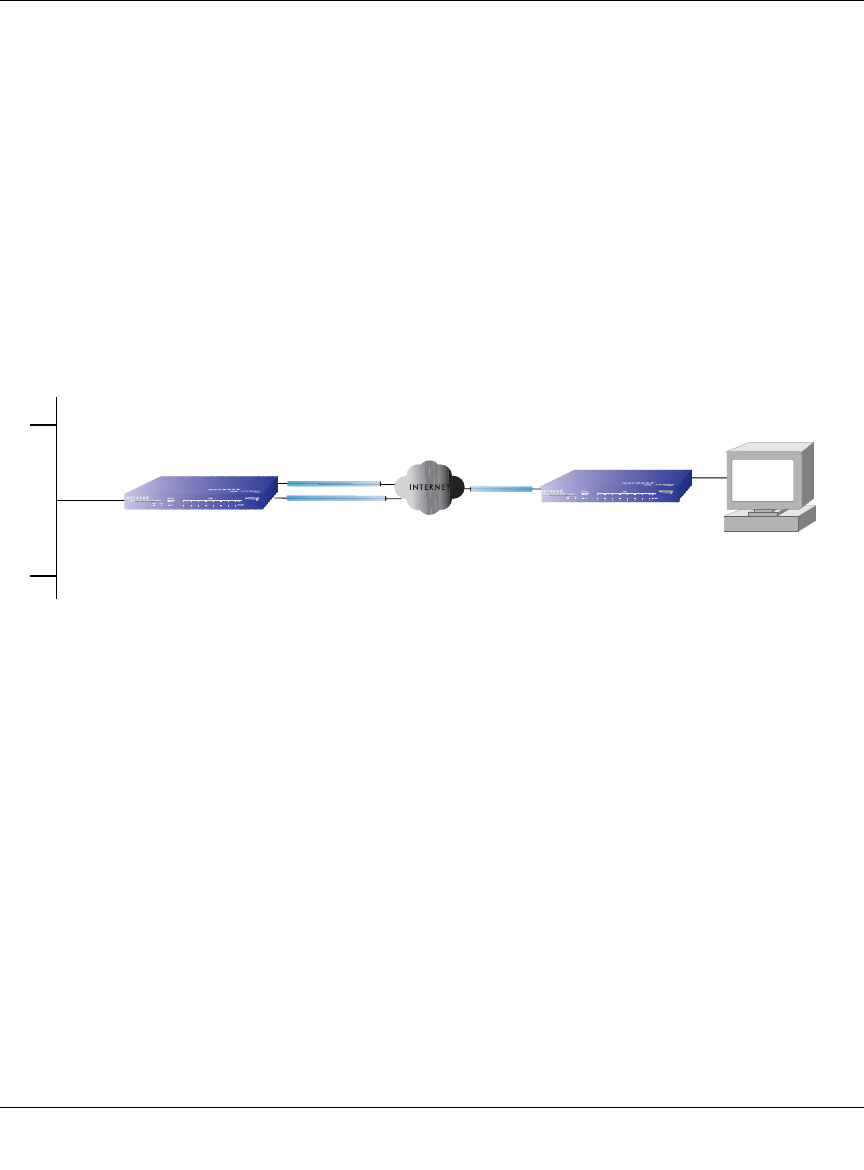
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
3-14 Network Planning
202-10085-01, March 2005
The purpose of the fully-qualified domain name is this case is to toggle the domain name of the
gateway router between the IP addresses of the active WAN port (i.e., WAN1 and WAN2) so that
the remote PC client can determine the gateway IP address to establish or re-establish a VPN
tunnel.
VPN Telecommuter: Dual Gateway WAN Ports for Load Balancing
In the case of the dual WAN ports on the gateway VPN firewall (Figure 3-19), the remote PC
client initiates the VPN tunnel with the appropriate gateway WAN port (i.e., port WAN1 or WAN2
as necessary to balance the loads of the two gateway WAN ports) because the IP address of the
remote NAT router is not known in advance. The chosen gateway WAN port must act as the
responder.
Figure 3-19: Dual gateway WAN ports (load balancing case) for VPN telecommuter
The IP addresses of the gateway WAN ports can be either fixed or dynamic. If an IP address is
dynamic, a fully-qualified domain name must be used. If an IP address is fixed, a fully-qualified
domain name is optional.
Gateway A
bzrouter2.dyndns.org
10.5.6.0/24
10.5.6.1
WAN1 IP
WAN IP
LAN IP
Client B
0.0.0.0
VPN Router
(at employer's
main office)
Telecommuter Example
(Dual WAN Ports, Load Balancing)
NAT Router B
NAT Router
(at telecommuter's
home office) Remote PC
(running NETGEAR
ProSafe VPN Client)
Fully-Qualified Domain Names (FQDN)
- optional for Fixed IP addresses
- required for Dynamic IP addresses
WAN2 IP
bzrouter1.dyndns.org

Connecting the FVS124G to the Internet 4-1
202-10085-01, March 2005
Chapter 4
Connecting the FVS124G to the Internet
This chapter describes how to connect the WAN ports of the FVS124G VPN Firewall to the
Internet.
What You Will Need to Do Before You Begin
The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports is a powerful
and versatile solution for your networking needs. But to make the configuration process easier and
to understand all of the choices available to you, you need to think through the following items
before you begin:
1. Plan your network
a. Determine whether you are going to use one or both WAN ports. For one WAN port, you
may need a fully qualified domain name either for convenience or if you have a dynamic
IP address.
b. If you are going to use both WAN ports, determine whether you are going to use them in
rollover mode for increased system reliability or load balancing mode for maximum
bandwidth efficiency. See Chapter 3, “Network Planning for more information. Your
decision has the following implications:
• Fully qualified domain name
– For rollover mode, you are going to need a fully qualified domain name to
implement features such as exposed hosts and virtual private networks.
– For load balancing mode, you may still need a fully qualified domain name either
for convenience or if you have a dynamic IP address.
• Protocol binding
– For rollover mode, protocol binding does not apply.
– For load balancing mode, you need to decide which protocols you want to bind to
a specific WAN port if you are going to take advantage of this option (you will
make these selections in “Step 4: Configure the WAN Mode (Required for Dual
WAN)” on page 4-15).
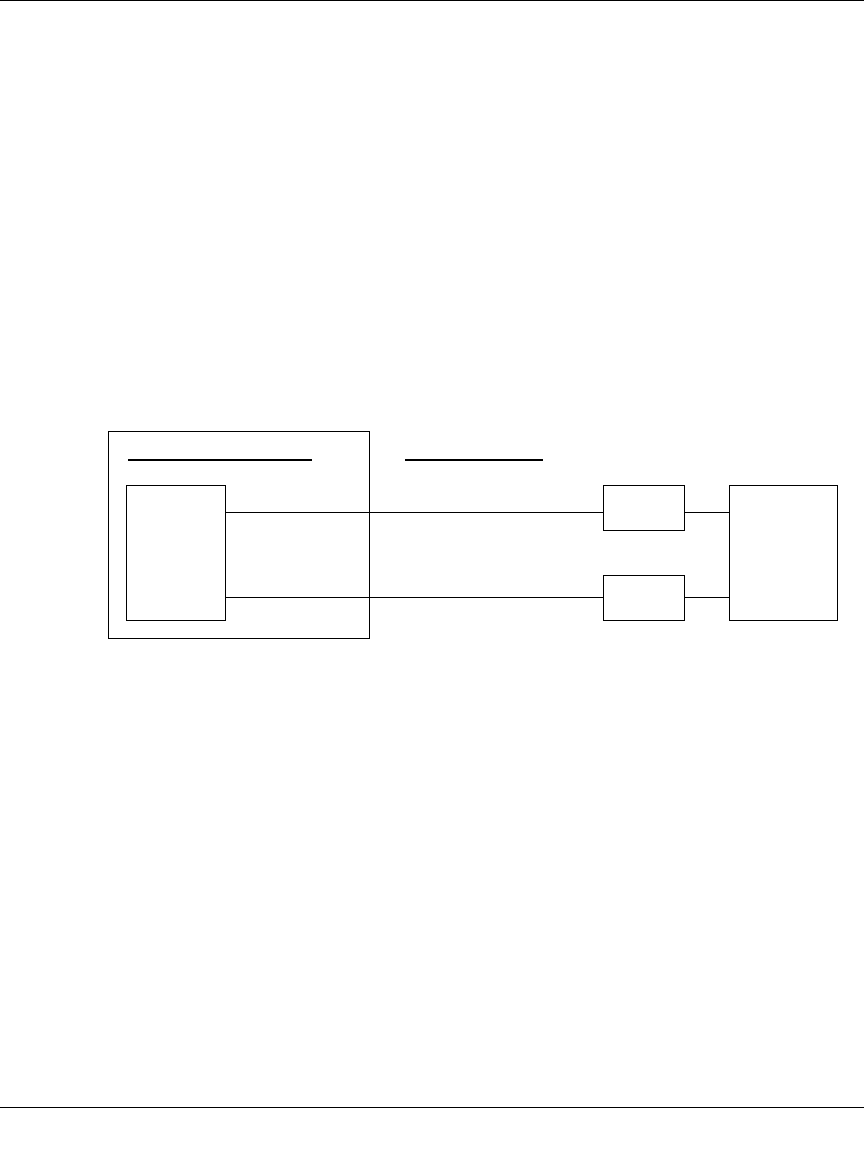
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-2 Connecting the FVS124G to the Internet
202-10085-01, March 2005
– You can also add your own service protocols to the list (see “Services-Based
Rules” on page 6-4 for information on how to do this).
2. Set up your accounts
a. Have active Internet services such as that provided by cable or DSL broadband accounts
and locate the Internet Service Provider (ISP) configuration information.
• In this document, the WAN side of the network is presumed to be provisioned as
shown in Figure 4-1 with two ISPs connected to the FVS124G VPN Firewall through
separate physical facilities.
Each FVS124G WAN port must be configured separately, however, whether you are
using a separate ISP for each WAN port or are having the traffic of both WAN ports
routed through the same ISP. You will need your ISP information for “Step 3:
Configure the Internet Connections to Your ISPs (Required)” on page 4-8.
Figure 4-1: Postulated WAN provisioning used in this document
• If your ISPs charge by the amount of bandwidth you use each month, you may want to
consider setting up a traffic meter to keep track of your traffic (see “Programming the
Traffic Meter (if Desired)” on page 4-13 if you want to do this).
b. Contact a Dynamic DNS Service and set up your fully qualified domain names if you need
or want them. You will need your fully qualified domain names for “Step 5: Configure
Dynamic DNS (If Needed)” on page 4-20.
3. Plan your network management approach
• The FVS124G VPN Firewall is capable of being managed remotely, but this feature must
be enabled locally after each factory default reset.
You are strongly advised to change the default password password to something that is
more secure at the time you enable remote management.
FVS124G
ISP 1
ISP 2
Internet
WAN port 1
WAN port 2
customer premises
physical facility 1
physical facility 2
route diversity
firewall

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-3
202-10085-01, March 2005
You make these selections during “Step 2: Log in to the VPN Firewall (Required)” on
page 4-7.
• There are a variety of WAN options you can choose when the factory default settings are
not applicable to your installation. These include enabling a WAN port to respond to a
ping and setting MTU size, port speed, and upload bandwidth. You will make these
choices in “Step 6: Configure the WAN Options (If Needed)” on page 4-23.
4. Prepare to physically connect the firewall to cable or DSL modems and a computer. You will
do this in “Step 1: Physically Connect the VPN Firewall to Your Network (Required)” on
page 4-7.
Cabling and Computer Hardware Requirements
To use the FVS124G VPN Firewall on your network, each computer must have an installed
Ethernet Network Interface Card (NIC) and an Ethernet cable. If the computer will connect to your
network at 100 Mbps, you must use a Category 5 (CAT5) cable such as the one provided with your
firewall.
Computer Network Configuration Requirements
The FVS124G includes a built-in Web Configuration Manager. To access the configuration menus
on the FVS124G, your must use a Java-enabled web browser program that supports HTTP uploads
such as Microsoft Internet Explorer or Netscape Navigator. NETGEAR recommends using
Internet Explorer or Netscape Navigator 4.0 or above. Free browser programs are readily available
for Windows, Macintosh, or UNIX/Linux.
For the initial connection to the Internet and configuration of your firewall, you will need to
connect a computer to the firewall that is set to automatically get its TCP/IP configuration from the
firewall via DHCP.
Note: For help with DHCP configuration, please refer to Appendix C, “Preparing Your Network.
The cable or DSL modem broadband access device must provide a standard 10 Mbps (10BASE-T)
or 100 Mbps (100BASE-Tx) Ethernet interface.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-4 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Internet Configuration Requirements
Depending on how your ISPs set up your Internet accounts, you will need one or more of these
configuration parameters to connect your firewall to the Internet:
• Host and Domain Names
• ISP Login Name and Password
• ISP Domain Name Server (DNS) Addresses
• Fixed IP Address which is also known as Static IP Address
Where Do I Get the Internet Configuration Parameters?
There are several ways you can gather the required Internet connection information.
• Your ISPs provide all the information needed to connect to the Internet. If you cannot locate
this information, you can ask your ISPs to provide it or you can try one of the options below.
• If you have a computer already connected using the active Internet access account, you can
gather the configuration information from that computer.
— For Windows 95/98/ME, open the Network control panel, select the TCP/IP entry for the
Ethernet adapter, and click Properties. Record all the settings for each tab page.
— For Windows 2000/XP, open the Local Area Network Connection, select the TCP/IP entry
for the Ethernet adapter, and click Properties. Record all the settings for each tab page.
— For Macintosh computers, open the TCP/IP or Network control panel. Record all the
settings for each section.
• You may also refer to the FVS124G Resource CD for the NETGEAR Router ISP Guide which
provides Internet connection information for many ISPs.
Once you locate your Internet configuration parameters, you may want to record them on the page
below.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-5
202-10085-01, March 2005
Record Your Internet Connection Information
Print this page. Fill in the configuration parameters from your Internet Service Provider (ISP).
ISP Login Name: The login name and password are case sensitive and must be entered exactly as
given by your ISP. For AOL customers, the login name is their primary screen name. Some ISPs
use your full e-mail address as the login name. The Service Name is not required by all ISPs. If
you connect using a login name and password, then fill in the following:
Login Name: ______________________________ Password: ____________________________
Service Name: _____________________________
Fixed or Static IP Address: If you have a static IP address, record the following information. For
example, 169.254.141.148 could be a valid IP address.
Fixed or Static Internet IP Address: ______.______.______.______
Gateway IP Address: ______.______.______.______
Subnet Mask: ______.______.______.______
ISP DNS Server Addresses: If you were given DNS server addresses, fill in the following:
Primary DNS Server IP Address: ______.______.______.______
Secondary DNS Server IP Address: ______.______.______.______
Host and Domain Names: Some ISPs use a specific host or domain name like CCA7324-A or
home. If you haven’t been given host or domain names, you can use the following examples as a
guide:
• If your main e-mail account with your ISP is aaa@yyy.com, then use aaa as your host name.
Your ISP might call this your account, user, host, computer, or system name.
• If your ISP’s mail server is mail.xxx.yyy.com, then use xxx.yyy.com as the domain name.
ISP Host Name: _________________________ ISP Domain Name: _______________________
Fully Qualified Domain Name: Some organizations use a fully qualified domain name (FQDN)
from a dynamic DNS service provider for their IP addresses.
Dynamic DSN Service Provider: ______________________ FQDN: _______________________

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-6 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Connecting the FVS124G ProSafe VPN Firewall 25 with 4
Gigabit LAN and Dual WAN Ports
This section provides instructions for connecting the FVS124G VPN Firewall. Also, the Resource
CD for ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports included with your
firewall contains an animated Installation Assistant to help you through this procedure.
There are six major steps to connecting your firewall:
1. Connect the firewall physically to your network (required)
You physically connect the cables during this step and then make sure the test lights are
working OK.
2. Log in to the firewall (required)
You log in to the firewall to enter the information needed in the remaining steps. You can also
change your password and enable remote management at this time if you want.
3. Configure the Internet connections to your ISPs (required)
You connect to your ISPs during this step. You can program the WAN traffic meters at this
time if you want also.
4. Configure the WAN mode (required for dual WAN)
You select either rollover mode or load balancing (on a mutually exclusive basis) during this
step. For load balancing, you can also select the protocol bindings if you want.
5. Configure dynamic DNS on the WAN ports (if needed)
You set up your fully qualified domain names during this step.
6. Configure the WAN options (if needed)
You can optionally enable each WAN port to respond to a ping during this step. You can also
optionally change the factory default MTU size, port speed, and uplink bandwidth.
Follow the steps below to connect your firewall to your network.
You can also refer to the Resource CD included with your firewall which contains an animated
Installation Assistant to help you through this procedure.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-7
202-10085-01, March 2005
Step 1: Physically Connect the VPN Firewall to Your Network
(Required)
1. Turn off your computer and Cable or DSL Modem.
2. Disconnect the Ethernet cable from your computer which connects to your cable or DSL
modem.
3. Connect the Ethernet cables from your cable or DSL modems to the WAN1 and WAN2
Internet ports on the FVS124G.
4. Connect the Ethernet cable which came with the firewall from a Local port on the firewall to
your computer.
Note: The FVS124G VPN Firewall incorporates Auto UplinkTM technology. Each LOCAL
Ethernet port will automatically sense if the cable should have a normal connection or an
uplink connection. This feature eliminates the need to worry about crossover cables because
Auto Uplink will make the right connection either type of cable.
5. Now, turn on your computer. If software usually logs you in to your Internet connection, do
not run that software or cancel it if it starts automatically.
6. Verify the following:
• When your turn the firewall on, the power light goes on.
• The firewall’s local lights are lit for any computers that are connected to it.
• The firewall’s Internet light is lit, indicating a link has been established to the cable or
DSL modem.
See “The Router’s Front Panel” on page 2-6 for a description of lights on the front panel and
their meaning.
Step 2: Log in to the VPN Firewall (Required)
Note: To connect to the firewall, your computer needs to be configured to obtain an IP address
automatically via DHCP. If you need instructions on how to do this, please refer to Appendix C,
“Preparing Your Network.
1. Connect to the firewall by typing http://192.168.1.1 in the address field of Internet Explorer or
Netscape® Navigator.
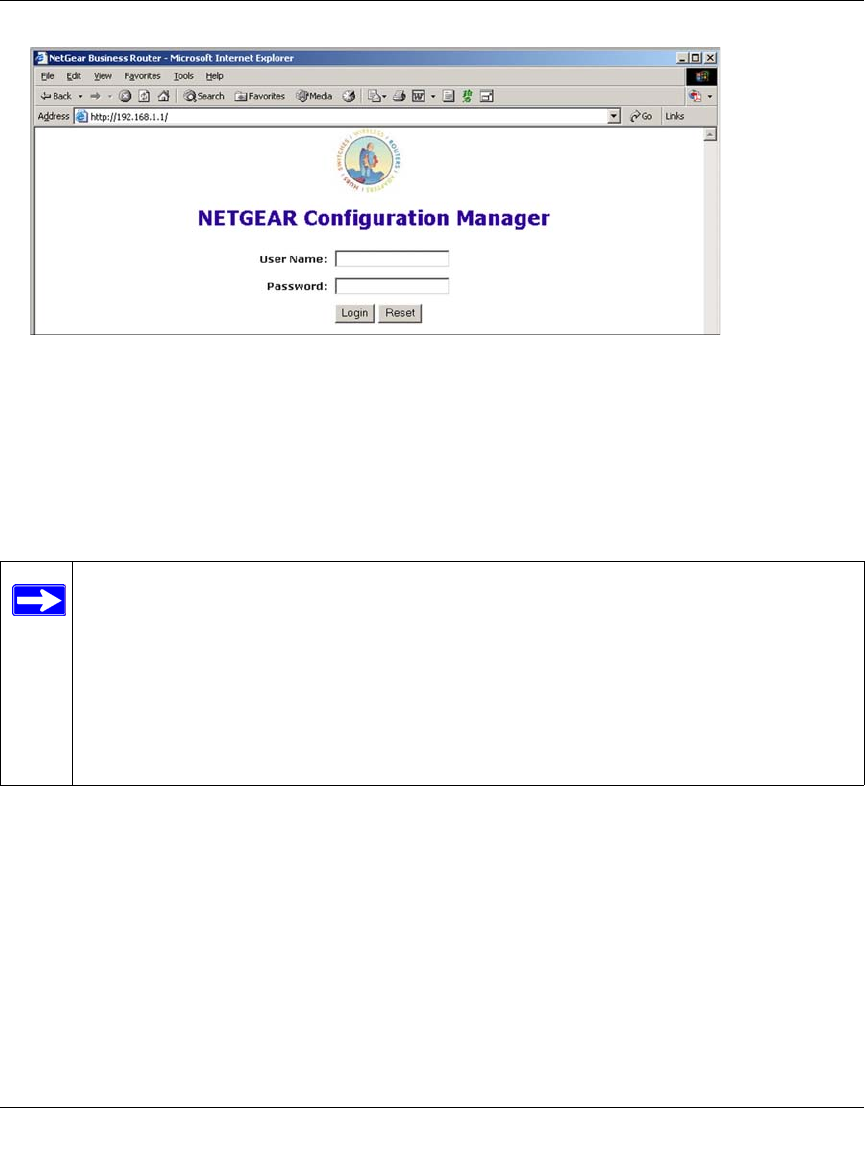
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-8 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Figure 4-2: Login screen on the Web browser
2. For security reasons, the firewall has its own user name and password. When prompted, enter
admin for the firewall user name and password for the firewall password, both in lower case
letters.The firewall user name and password are not the same as any user name or password
you may use to log in to your Internet connection.
Step 3: Configure the Internet Connections to Your ISPs
(Required)
The steps to configure the Internet connections to your ISPs are to configure WAN port 1 first and
then configure WAN port 2 second.
1. The steps to configure WAN port 1 are as follows:
a. You should now be connected to the firewall. If you do not see the WAN1 ISP Settings
screen shown in Figure 4-3, click the WAN1 ISP link directly under WAN Setup on the
upper left of the main menu.
Note: You might want to enable remote management at this time so that you can log in
remotely in the future to manage the firewall. See “Enabling Remote Management
Access” on page 8-9 for more information. Remote management enable is cleared with
a factory default reset.
Whenever you enable remote management, you are strongly advised to change your
password. See “Changing the Passwords and Login Timeout” on page 8-8 for the
procedure on how to do this.
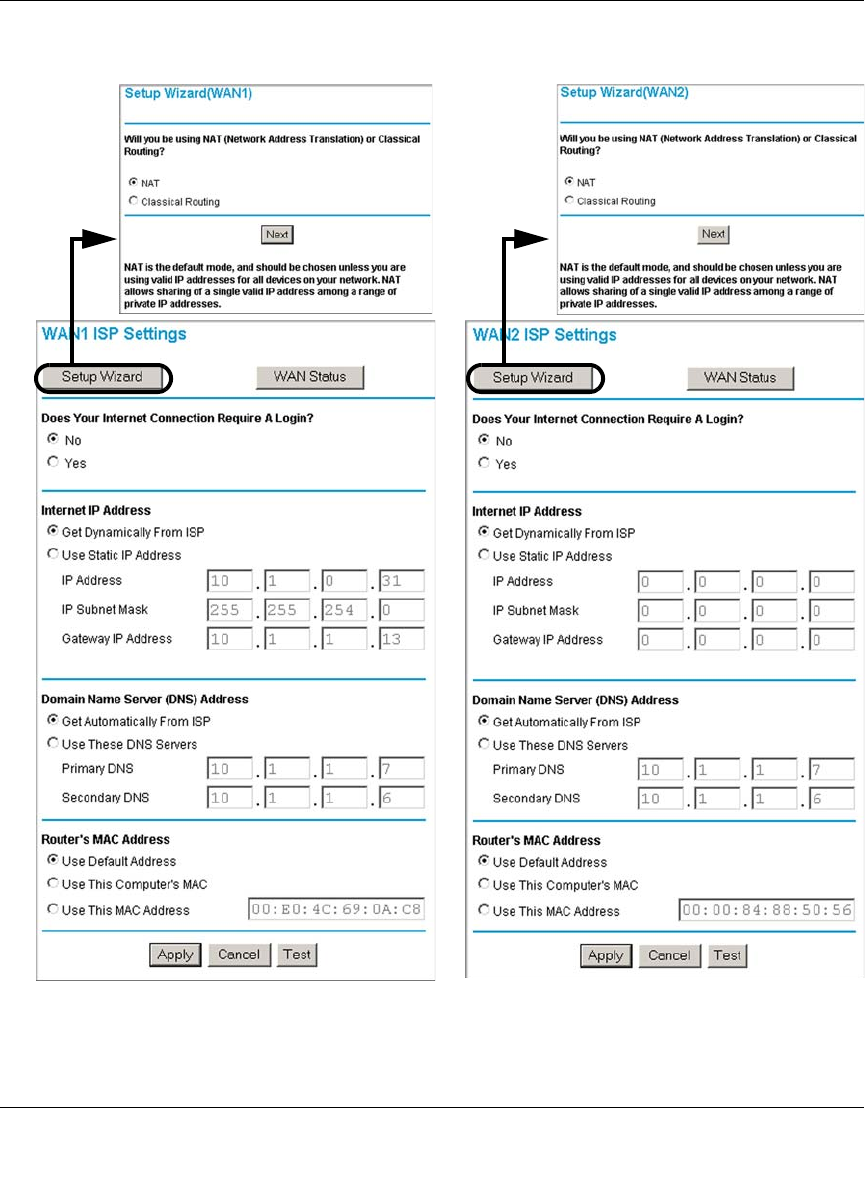
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-9
202-10085-01, March 2005
Figure 4-3: WAN1 and WAN2 Basic Settings and Setup Wizard Screens
WAN1 screens WAN2 screens
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-10 Connecting the FVS124G to the Internet
202-10085-01, March 2005
b. Click Setup Wizard on the WAN1 ISP Settings screen to get the Setup Wizard (WAN1)
screen.
c. Click Next and follow the steps in the WAN1 Setup Wizard for inputting the configuration
parameters from your ISP1 to connect to the Internet.
Note: If you choose not to use the Setup Wizard, you can manually configure your
Internet connection settings by following the procedure “Manually Configuring Your
Internet Connection” on page 4-12.
Unless your ISP automatically assigns your configuration automatically via DHCP, you
will need the configuration parameters from your ISP as you recorded them previously in
“Record Your Internet Connection Information” on page 4-5.
d. When the firewall successfully detects an active Internet service, the firewall’s Active
LED goes on. The Setup Wizard reports which connection type it discovered, and displays
the appropriate configuration menu. If the Setup Wizard finds no connection, you will be
prompted to check the physical connection between your firewall and the cable or DSL
line. The options are:
e. Set up the traffic meter for ISP1 if desired. See “Programming the Traffic Meter (if
Desired)” on page 4-13.
Table 4-1. Internet connection methods
Connection Method Data Required
PPPoE Login (Username, Password).
PPTP Login (Username, Password), Local IP, and PPTP Server IP.
DHCP (Dynamic IP) No data is required.
Fixed IP IP address and related data supplied by your ISP.
Note: At this point of the configuration process, you are now connected to the Internet
through WAN port 1. But you must complete the configuration process outlined in this
chapter to get the complete functionality of the dual WAN interface.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-11
202-10085-01, March 2005
2. The steps to configure WAN port 2 are as follows:
a. Repeat the above steps to set up the parameters for ISP2. Start by clicking the WAN2 ISP
link directly under WAN Setup on the upper left of the main menu to get the WAN2 ISP
Settings screen shown in Figure 4-3. Next click Setup Wizard on the WAN2 ISP Settings
screen to get the Setup Wizard (WAN2) screen. Then click Next and follow the steps in the
WAN2 Setup Wizard for inputting the configuration parameters from your ISP2 to connect
to the Internet.
b. Set up the traffic meter for ISP2 if desired. See “Programming the Traffic Meter (if
Desired)” on page 4-13.
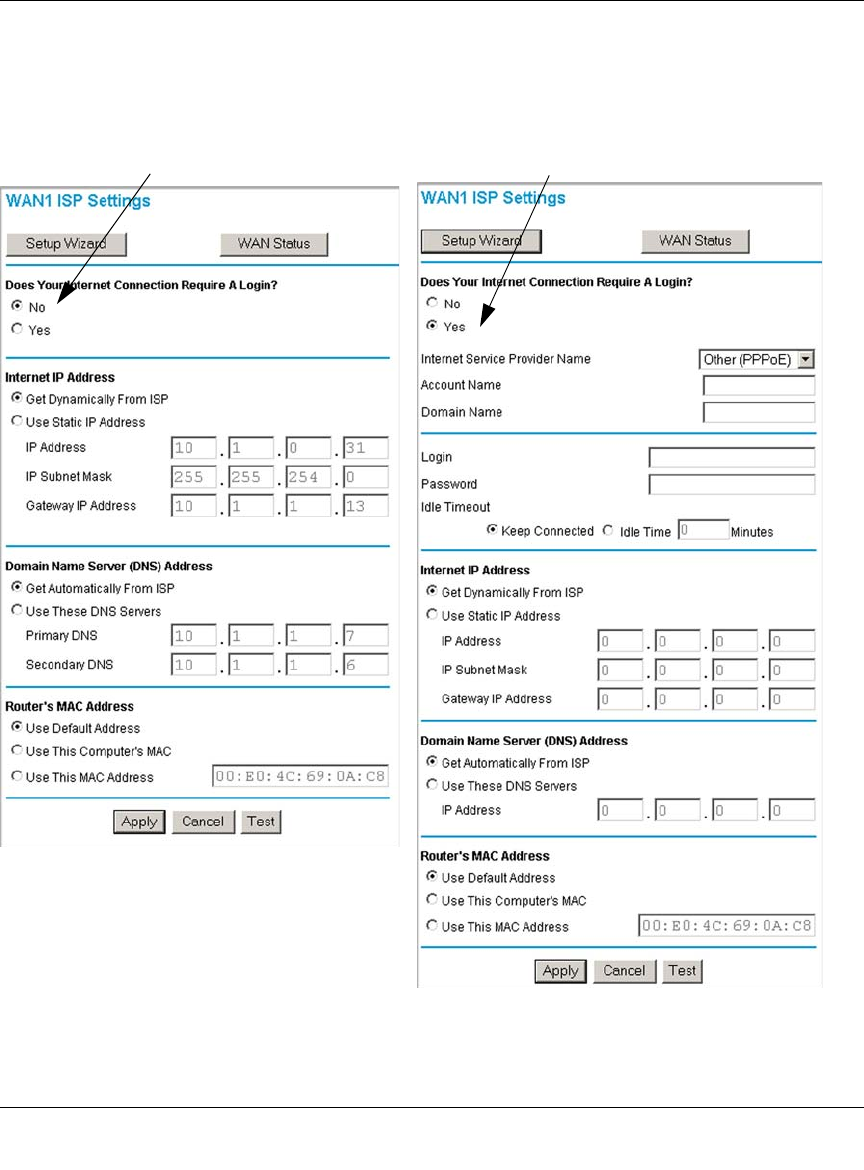
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-12 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Manually Configuring Your Internet Connection
You can manually configure your firewall using the menu below if you do not want to allow the
Setup Wizard to determine your configuration as described in the previous sections.
Figure 4-4: Browser-based configuration WAN ISP Settings menus (WAN1 ISP shown)
ISP Does Not Require Login ISP Does Require Login
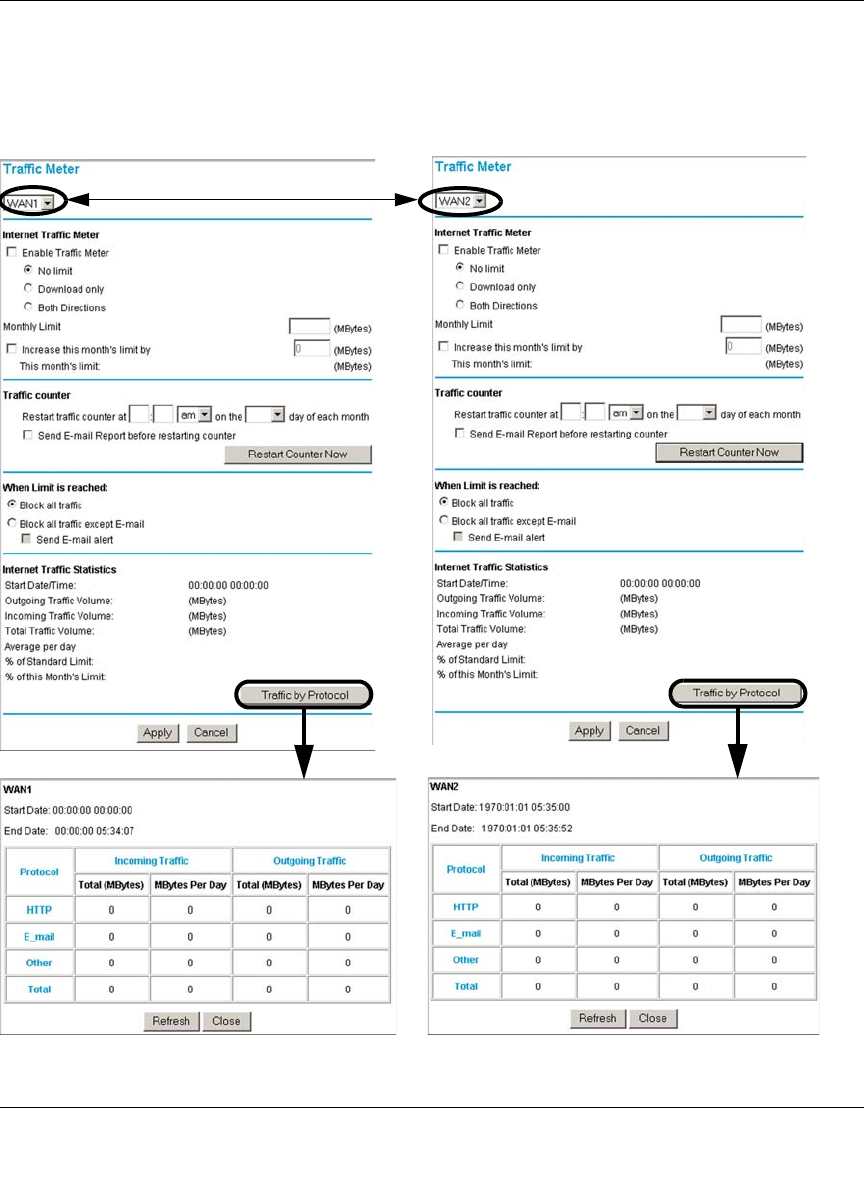
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-13
202-10085-01, March 2005
Programming the Traffic Meter (if Desired)
From the Main Menu of the browser interface, under WAN Setup, click Traffic Meter. You will get
the screens shown in Figure 4-5. Fill out the information described in Table 4-1.
Figure 4-5: Traffic Meter screens

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-14 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Table 4-1. Traffic meter
Parameter Description
Enable Traffic Meter Check this if you wish to record the volume of Internet traffic passing through the
Router's WAN1 or WAN2 port.WAN1 or WAN2 can be selected through the drop
down menu, the entire configuration is specific to each wan interface.
• No Limit - If this is selected specified restriction will not be applied when traffic limit
is reached.
• Download only - If this is selected the specified restriction will be applied to the
incoming traffic only
• Both Directions - If this is selected the specified restriction will be applied to both
incoming and outgoing traffic only
Enable Monthly Limit Use this if your ISP charges for additional traffic. If enabled, enter the monthly
volume limit and select the desired behavior when the limit is reached.
Note: Both incoming and outgoing traffic are included in the limit.
Increase this
month's limit Use this to temporarily increase the Traffic Limit if you have reached the monthly
limit, but need to continue accessing the Internet. Check the checkbox and enter the
desired increase. (The checkbox will automatically be cleared when saved so the
increase is only applied once.)
This month's limit This displays the limit for the current month.
Restart traffic
counter This determines when the traffic counter restarts. Choose the desired time and day of
the month.
Restart Counter Now Click this button to restart the Traffic Counter immediately.
Send E-mail Report
before restarting
counter
If checked, an E-mail report will be sent immediately before restarting the counter.
You must configure the E-mail screen in order for this function to work (see “Getting
E-Mail Notifications of Event Logs and Alerts” on page 6-30).
When limit is
reached Select the desired option:
• Block all traffic - all access to and from the Internet will be blocked.
• Block all traffic except E-mail - Only E-mail traffic will be allowed. All other traffic will
be blocked.
• If using this option, you may also select the Send E-mail alert option. You must
configure the E-mail screen in order for this function to work.
Internet Traffic
Statistics This displays statistics on Internet Traffic via the WAN port. If you have not enabled
the Traffic Meter, these statistics are not available.
Traffic by Protocol Click this button if you want to know more details of the Internet Traffic. The volume
of traffic for each protocol will be displayed in a sub-window.Traffic counters are
updated in MBytes scale, counter starts only when traffic passed is at least 1MB.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-15
202-10085-01, March 2005
Step 4: Configure the WAN Mode (Required for Dual WAN)
The dual WAN ports of the FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual
WAN Ports can be configured on a mutually exclusive basis for either rollover for increased
system reliability or load balancing for maximum bandwidth efficiency.
•Rollover (Auto-Rollover) Mode—In this mode, the selected WAN interface is made primary
and the other is the rollover link. As long as the primary link is up, all traffic is sent over the
primary link. Once the primary WAN interface goes down, the rollover link is brought up to
send the traffic.
Traffic will automatically roll back to the original primary link once the original primary link
is back up and running again.
•Load Balancing Mode—In this mode the router distributes the outbound traffic equally
among the WAN interfaces that are functional.
For both alternatives, you must also set up Network Address Translation (NAT):
• NAT—NAT is the technology which allows all PCs on your LAN to share a single Internet IP
address. From the Internet, there is only a single device (the Router) and a single IP address.
PCs on your LAN can use any "private" IP address range, and these IP addresses are not
visible from the Internet.
– The Router uses NAT to select the correct PC (on your LAN) to receive any incoming
data.
– If you only have a single Internet IP address, you MUST use NAT.
• Classical Routing—In this mode, the Router performs Routing, but without NAT. To gain
Internet access, each PC on your LAN must have a valid Internet IP address.
If your ISP has allocated many IP addresses to you, and you have assigned one of these
addresses to each PC, you can choose Classical Routing. Otherwise, selecting this method will
not allow Internet access through this Router.
To learn the status of the WAN ports, you can view the Router Status page (see “Firewall Status”
on page 8-14) or look at the LEDs on the front panel (see “The Router’s Front Panel” on page 2-6).
Note: Scenarios could arise when load balancing needs to be bypassed for certain traffic
or applications. Here the traffic needs to go on a specific WAN interface. This is done
with the protocol binding rules of that WAN interface. The rule should match the desired
traffic.
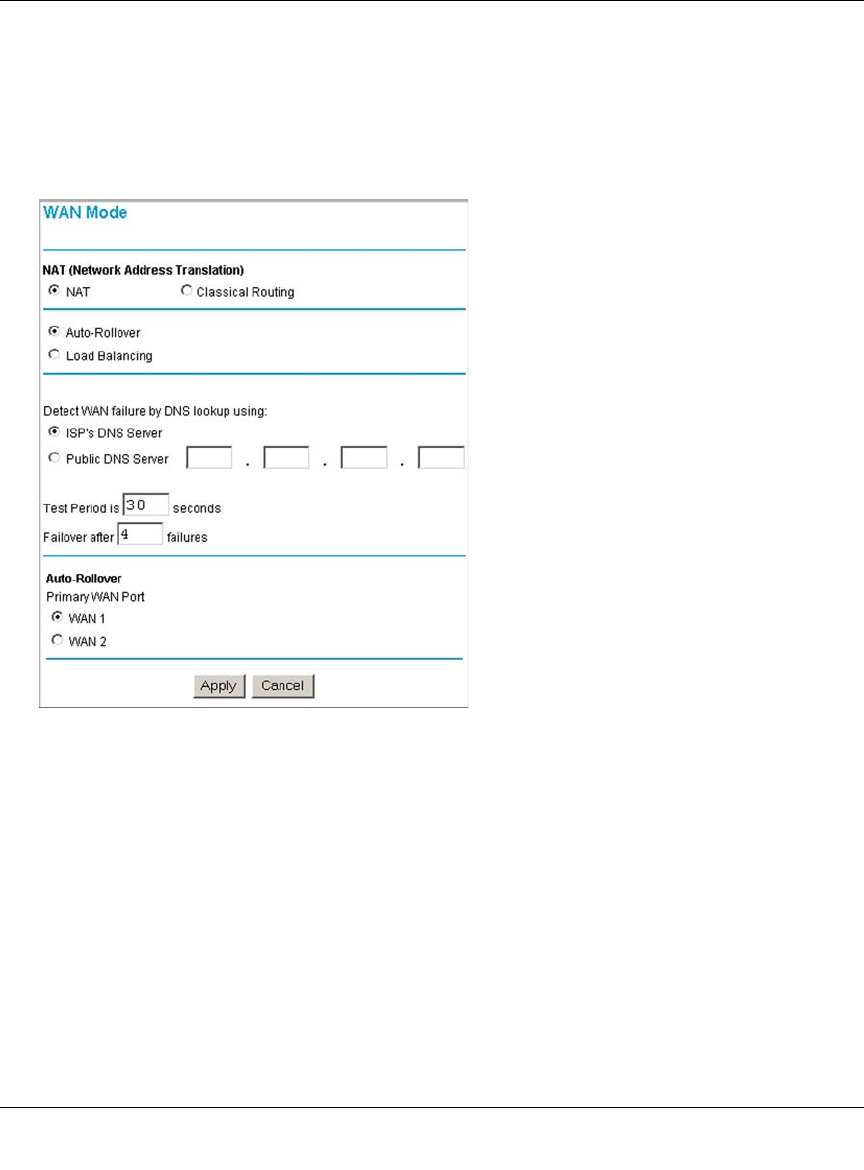
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-16 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Rollover Setup
Perform the following steps to configure the dual WAN ports for rollover:
1. Click the WAN Mode link directly under Setup on the upper left of the main menu to invoke
the WAN Mode Auto-Rollover screen shown in Figure 4-6.
Figure 4-6: WAN Mode screen for auto-rollover
Fill out the screen using the following parameter definitions:
• Detection of WAN failure—WAN failure is detected using DNS queries to the DNS
server. For each WAN interface, DNS queries are sent to the configured DNS server. If the
DNS replies are not received, the corresponding WAN interface is considered down.
– ISP DNS Server—In this case, DNS queries are sent to the DNS server configured on
the WAN ISP pages (see “Step 3: Configure the Internet Connections to Your ISPs
(Required)” on page 4-8).
– Public DNS Server—The user is also given an option, to enter any Public DNS
server.DNS queries are sent to this server through the WAN interface being
monitored.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-17
202-10085-01, March 2005
• Test Period—DNS query is sent periodically after every test period. The minimum test
period is 30 seconds.
• Maximum Failures—The WAN interface is considered down after the configured number
of DNS queries have failed to elicit a DNS reply from the configured DNS server. The
minimum number of failed DNS queries is four. The rollover link is brought up after this.
The minimum time to roll over after the primary WAN interface fails is two minutes (i.e., 30
second minimum test period times a minimum of four tests).
2. Once a rollover occurs, an alert will be generated (see “Getting E-Mail Notifications of Event
Logs and Alerts” on page 6-30). You should then get the failed WAN interface restored and
then force traffic back on the original primary WAN interface by reapplying the WAN Mode
menu shown in Figure 4-6.
Load Balancing (and Protocol Binding) Setup
Perform the following steps to configure the dual WAN ports for load balancing and protocol
binding on outbound traffic:
1. Select Load Balancing on the screen shown in Figure 4-6 to invoke the WAN Mode Load
Balancing screen shown in Figure 4-7.
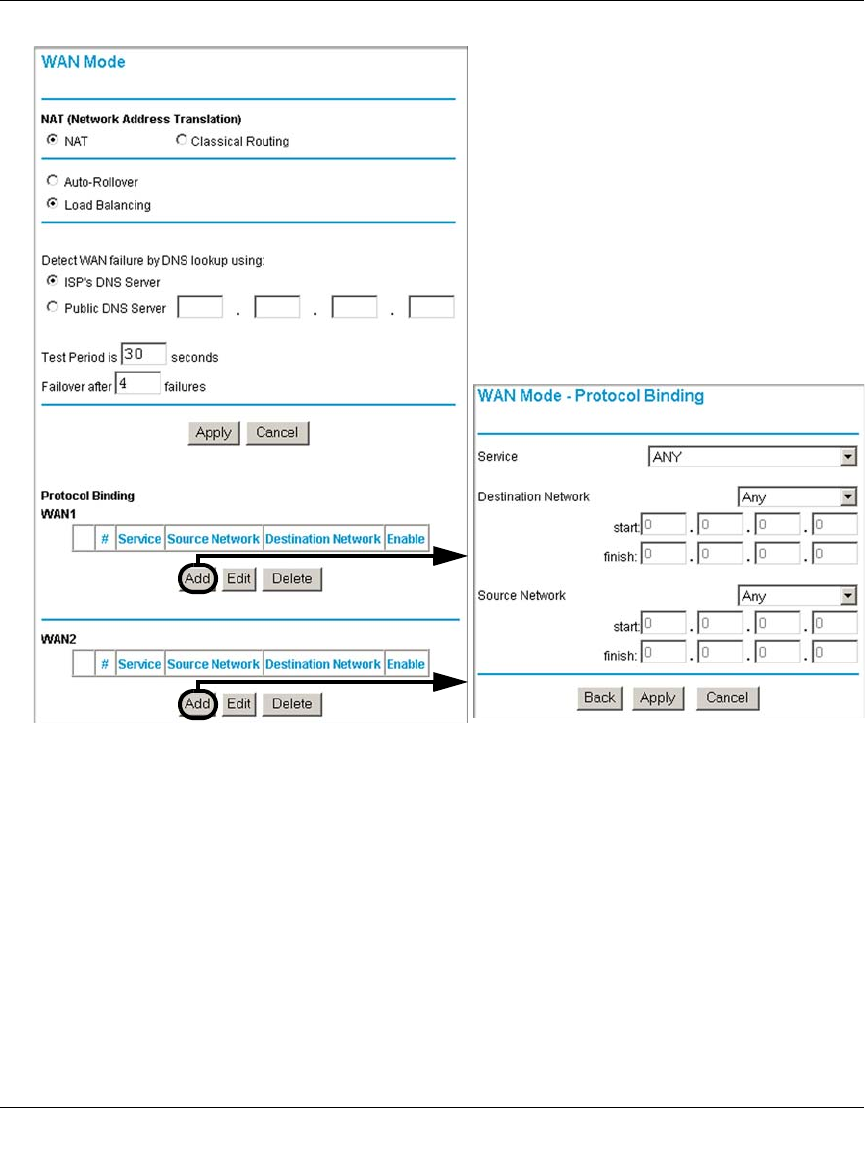
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-18 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Figure 4-7: WAN Mode screen for load balancing and protocol binding
Fill out the screen using the following parameter definitions:
• Detection of WAN failure—WAN failure is detected using DNS queries to the DNS
server. For each WAN interface, DNS queries are sent to the configured DNS server. If the
DNS replies are not received, the corresponding WAN interface is considered down.
– ISP DNS Server—In this case, DNS queries are sent to the DNS server configured on
the WAN ISP pages (see “Step 3: Configure the Internet Connections to Your ISPs
(Required)” on page 4-8).
– Public DNS Server—The user is also given an option to enter any Public DNS server.
DNS queries are sent to this server through the WAN interface being monitored.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-19
202-10085-01, March 2005
• Test Period—DNS query is sent periodically after every test period. The minimum test
period is 30 seconds.
• Maximum Failures—The WAN interface is considered down after the configured number
of DNS queries have failed to elicit a DNS reply from the configured DNS server. The
minimum number of failed DNS queries is four.
The minimum time for a WAN interface to be classified as having failed is two minutes (i.e.,
30 second minimum test period times a minimum of four tests). All traffic then stops on that
WAN port. Traffic that is not bound by protocol to the failed WAN port is then sent to the
working WAN port. If the total traffic on the working WAN port exceeds its bandwidth, then
congestion occurs.
Once a WAN interface fails, an alert will be generated (see “Getting E-Mail Notifications of
Event Logs and Alerts” on page 6-30). You must then get the failed WAN interface restored
before it can carry traffic again by reapplying the WAN Mode menu shown in Figure 4-10.
2. Click Add in the appropriate WAN interface section of the WAN Mode Load Balancing screen
to invoke the WAN Mode Protocol Bonding screen (if protocol binding is needed). Fill out the
screen using the following parameter definitions:
• Service—Select the desired Services or applications to be covered by this rule. If the
desired service or application does not appear in the list, you must define it using the
Services menu (see “Services-Based Rules” on page 6-4).
• Source Network—These settings determine which computers on your network are
affected by this rule. Select the desired options:
– Any—All PCs and devices on your LAN.
– Single address—Enter the required address and the rule will be applied to that
particular PC.
– Address range —If this option is selected, you must enter the start and finish fields.
– Groups—Select the Group you wish this rule to apply to. You can use the Network
Database screen to assign PCs to Groups.
• Destination Network—These settings determine which Internet locations are covered by
the rule, based on their IP address. Select the desired option:
– Any—All Internet IP address are covered by this rule.
– Single address—Enter the required address in the start fields.
– Address range—If this option is selected, you must enter the start and finish fields.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-20 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Step 5: Configure Dynamic DNS (If Needed)
If your network has a permanently assigned IP address, you can register a domain name and have
that name linked with your IP address by public Domain Name Servers (DNS). However, if your
Internet account uses a dynamically assigned IP address, you will not know in advance what your
IP address will be, and the address can change frequently. In this case, you can use a commercial
dynamic DNS service, which allows you to register an extension to its domain, and restores DNS
requests for the resulting FQDN to your frequently-changing IP address.
which will allow you to register your domain to their IP address, and will forward traffic directed
to your domain to your frequently-changing IP address.
• For rollover mode, you are going to need a fully qualified domain name to implement features
such as exposed hosts and virtual private networks regardless of whether you have a fixed or
dynamic IP address.
• For load balancing mode, you may still need a fully qualified domain name either for
convenience or if you have a dynamic IP address.
The firewall contains a client that can connect to a dynamic DNS service provider. To use this
feature, you must select a service provider and obtain an account with them. After you have
configured your account information in the firewall, whenever your ISP-assigned IP address
changes, your firewall will automatically contact your dynamic DNS service provider, log in to
your account, and register your new IP address.
Perform the following steps to configure Dynamic DNS:
1. If you haven’t already, log in to the firewall at its default LAN address of http://192.168.1.1
with its default user name of admin, default password of password, or using whatever
password and LAN address you have chosen for the firewall.
2. From the Main Menu of the browser interface, under WAN Setup, click on Dynamic DNS.
a. Rollover Mode: You will get the screen shown in Figure 4-8 with AUTO_ROLLOVER
shown in the pulldown.
b. Load Balancing Mode: Select WAN1 or WAN2 in the pulldown shown in Figure 4-8 to
invoke the appropriate WAN interface to program.
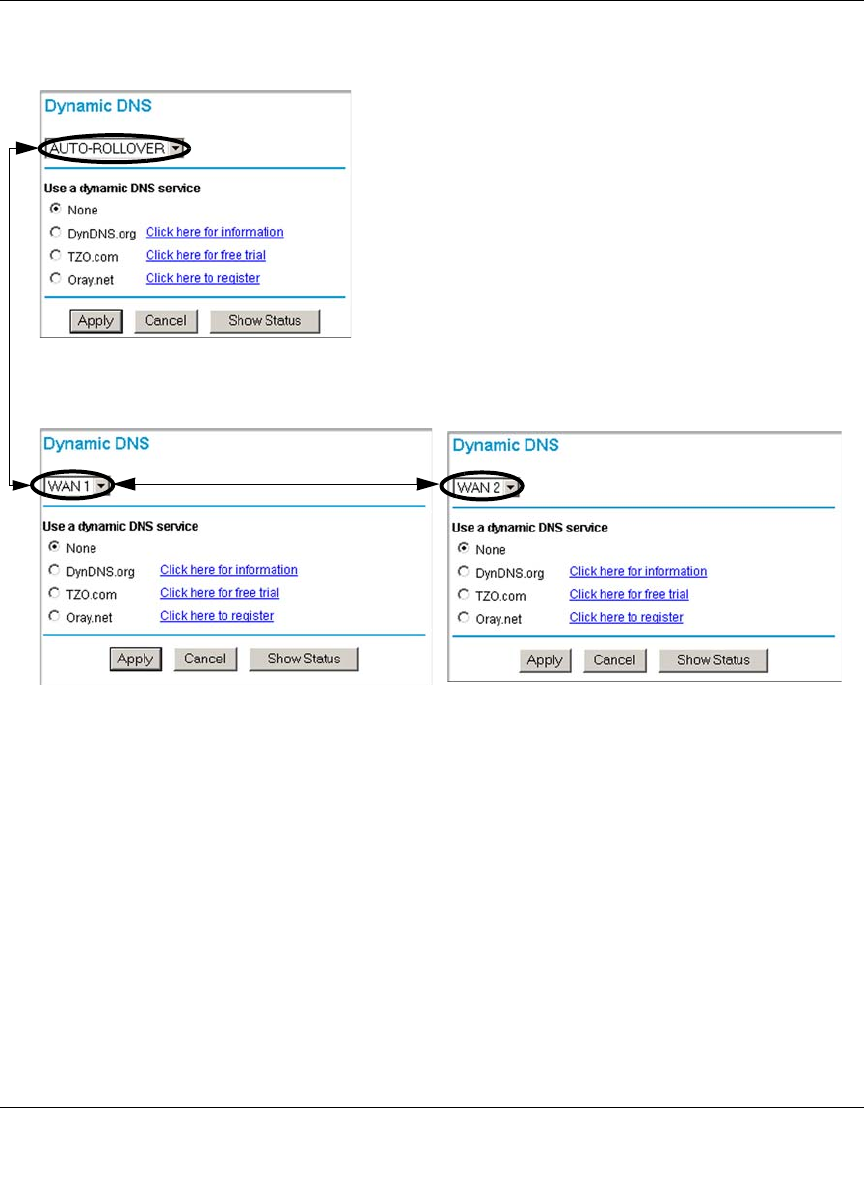
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-21
202-10085-01, March 2005
Figure 4-8: Dynamic DNS screens
Dynamic DNS screen for rollover mode
Dynamic DNS screens for load balancing mode
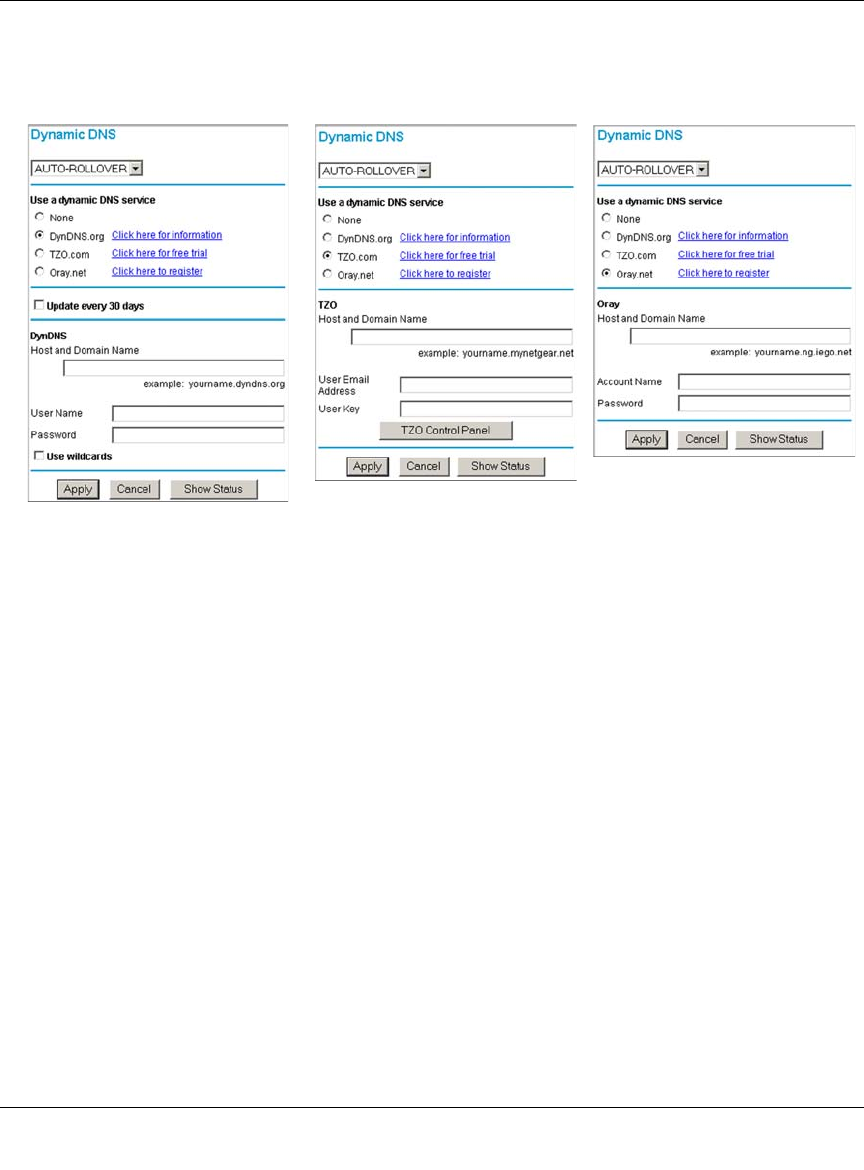
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-22 Connecting the FVS124G to the Internet
202-10085-01, March 2005
Each DNS service provider requires its own parameters (Figure 4-9).
Figure 4-9: Dynamic DNS service provider screens
3. Access the website of one of the dynamic DNS service providers whose names appear in the
‘Select Service Provider’ box, and register for an account.
For example, for dyndns.org, go to www.dyndns.org.
4. Select the Use a dynamic DNS service check box.
5. Select the name of your dynamic DNS Service Provider.
6. Type the entire FQDN name that your dynamic DNS service provider gave you,
such as myName.dyndns.org.
7. Type the user name for logging into your dynamic DNS account.
8. Type the password (or key) for your dynamic DNS account.
9. If your dynamic DNS provider allows the use of wildcards in resolving your URL, you may
select the Use wildcards check box to activate this feature.
For example, the wildcard feature will cause *.yourhost.dyndns.org to be aliased to the same
IP address as yourhost.dyndns.org
10. Click Apply to save your configuration.
DynDNS Service Screen TZO Service Screen Oray Service Screen
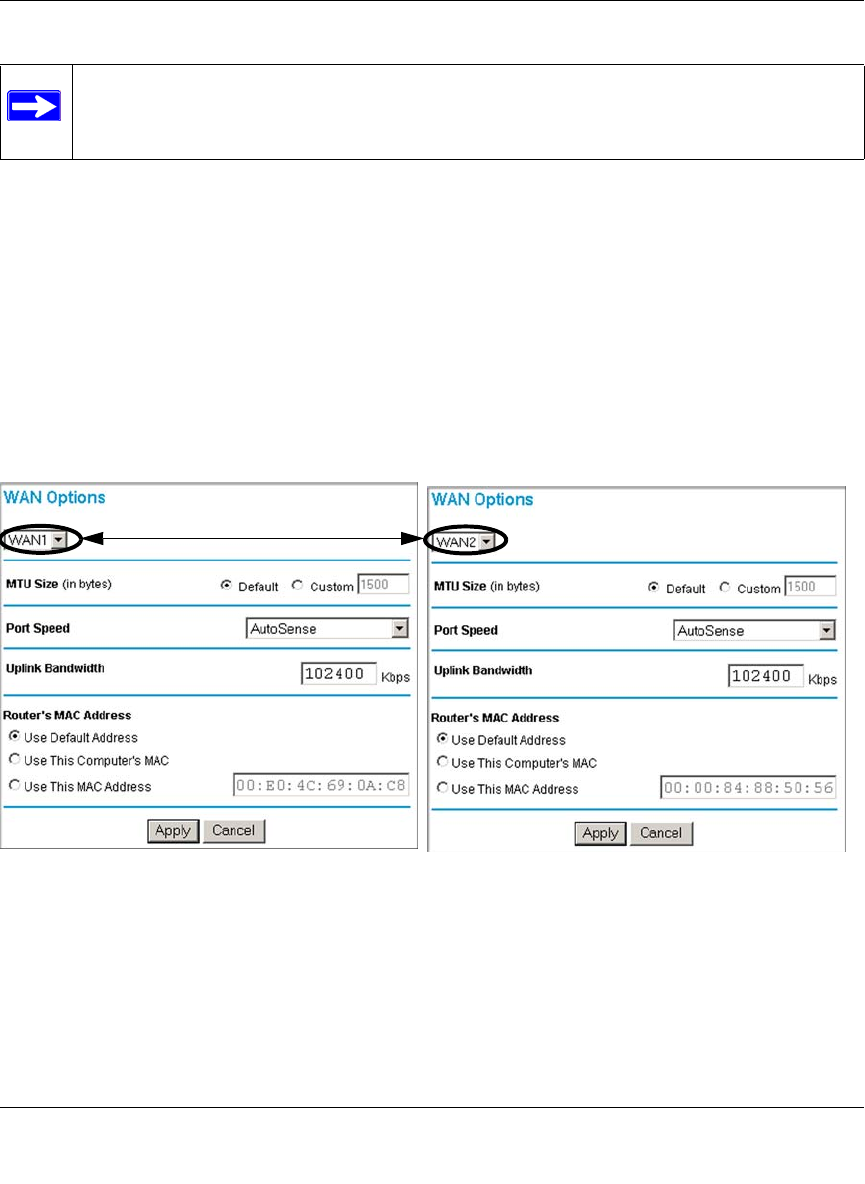
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Connecting the FVS124G to the Internet 4-23
202-10085-01, March 2005
Step 6: Configure the WAN Options (If Needed)
Perform the following steps to configure the WAN options:
1. If you haven’t already, log in to the firewall at its default LAN address of http://192.168.1.1
with its default user name of admin, default password of password, or using whatever
password and LAN address you have chosen for the firewall.
2. From the Main Menu of the browser interface, under WAN Setup, click on Options. You will
get the WAN1 screen shown in Figure 4-10 and can get the WAN2 screen from there using the
pulldown.
Figure 4-10: WAN Options Screens
3. Edit the default information you want to change.
• MTU Size—The normal MTU (Maximum Transmit Unit) value for most Ethernet
networks is 1500 Bytes, or 1492 Bytes for PPPoE connections. For some ISPs you may
need to reduce the MTU. But this is rarely required, and should not be done unless you are
sure it is necessary for your ISP connection.
Note: If your ISP assigns a private WAN IP address such as 192.168.x.x or 10.x.x.x, the
dynamic DNS service will not work because private addresses will not be routed on the
Internet.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
4-24 Connecting the FVS124G to the Internet
202-10085-01, March 2005
• Port Speed—In most cases, your router can automatically determine the connection speed
of the Internet (WAN) port. If you cannot establish an Internet connection and the Internet
LED blinks continuously, you may need to manually select the port speed.
If you know that the Ethernet port on your broadband modem supports 100BaseT, select
100M; otherwise, select 10M. Use the half-duplex settings unless you are sure you need
full duplex.
• Uplink Bandwidth—Set Uplink Bandwidth as per your requirements. You need to select a
value between 28 kbps to 100 Mbps that represents the maximum speed of your upstream
(outbound) connection. If you are unsure, leave it at the default value of 102,400 kbps. It
will depend on your WAN connection type and ISP.
• Router's MAC Address—Each computer or router on your network has a unique 32-bit
local Ethernet address. This is also referred to as the computer's MAC (Media Access
Control) address. Usually, select Use default address.
If your ISP requires MAC authentication, then select either Use this Computer's MAC
address to have the router use the MAC address of the computer you are now using or Use
This MAC Address to manually type in the MAC address that your ISP expects.
The format for the MAC address is XX:XX:XX:XX:XX:XX. If you select Use This MAC
Address and type in a MAC address, do not then select Use this Computer's MAC address
or your entry will be overwritten.
Note: Respond To Ping On Internet Port—If you want the router to respond to a 'Ping' from
the Internet, see the Respond To Ping On Internet Port checkbox on the Rules menu
(Figure 6-1 on page 6-2).

LAN Configuration 5-1
202-10085-01, March 2005
Chapter 5
LAN Configuration
This chapter describes how to configure the advanced features of your FVS124G ProSafe VPN
Firewall 25 with 4 Gigabit LAN and Dual WAN Ports. These features can be found under the
Advanced heading in the Main Menu of the browser interface.
• LAN Setup
•Static Routes
Using the LAN IP Setup Options
The LAN IP Setup menu allows configuration of LAN IP services such as DHCP and RIP. From
the Main Menu of the browser interface, under Advanced, click on LAN IP Setup to view the LAN
IP Setup menu, shown below.
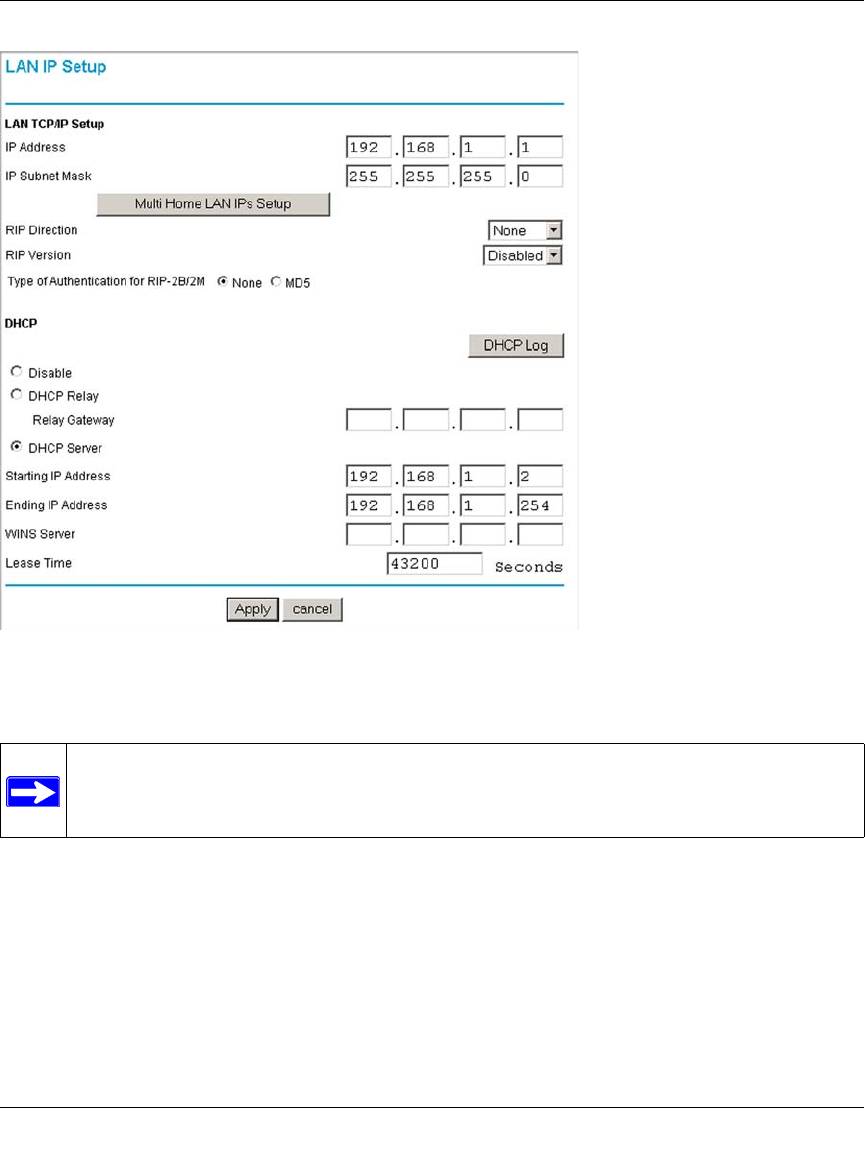
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
5-2 LAN Configuration
202-10085-01, March 2005
Figure 5-1: LAN IP Setup menu
Configuring LAN TCP/IP Setup Parameters
LAN TCP/IP Setup—The default values are suitable for most users and situations. These are
advanced settings that you may configure if you are a network administrator. RIP is applicable if
your network contains multiple routers.
• IP Address: Type the IP address of your router (factory default: 192.168.1.1).
Note: Once you have completed the LAN IP setup, all outbound traffic is allowed and all
inbound traffic is discarded. To change these traffic rules, refer to Chapter 6, “Firewall
Protection and Content Filtering.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
LAN Configuration 5-3
202-10085-01, March 2005
• IP Subnet Mask: The subnet mask specifies the network number portion of an IP address. Your
router will automatically calculate the subnet mask based on the IP address that you assign.
Unless you are implementing subnetting, use 255.255.255.0 as the subnet mask (computed by
the router).
• RIP Direction: RIP (Routing Information Protocol, RFC 2453) allows a router to exchange
routing information with other routers. The RIP Direction selection controls how the router
sends and receives RIP packets. Both is the default.
– When set to Both or Out Only, the router will broadcast its routing table periodically.
– When set to Both or In Only, it will incorporate the RIP information that it receives.
– When set to None, it will not send any RIP packets and will ignore any RIP packets
received.
• RIP Version: This controls the format and the broadcasting method of the RIP packets that the
router sends. (It recognizes both formats when receiving.) By default, this is set for RIP-1.
– RIP-1 is universally supported. RIP-1 is probably adequate for most networks, unless you
have an unusual network setup.
– RIP-2 carries more information. Both RIP-2B and RIP-2M send the routing data in RIP-2
format.
– RIP-2B uses subnet broadcasting.
– RIP-2M uses multicasting.
Note: Multicasting can reduce the load on non-router machines because they do not listen
to the RIP multicast address and will not receive the RIP packets. However, if one router
uses multicasting, then all routers on your network must use multicasting. For RIP-2B and
RIP-2M you can select the type of authentication as NONE or MD5. If MD5 is selected,
additional parameters need to be entered.
Use router as DHCP server—By default, the router will function as a DHCP (Dynamic Host
Configuration Protocol) server, providing TCP/IP configuration for all computers connected to the
router's LAN. If another device on your network will be the DHCP server, or if you will manually
configure all devices, select the Disable option under DHCP configuration. Select the DHCP
Relay option to configure the router as a DHCP relay.
• DHCP Log - Click this button to see the IP addresses which have been allocated by the DHCP
Server to PCs and other DHCP clients.
• Starting IP Address - This box specifies the first of the contiguous addresses in the IP address
pool. 192.168.1.2 is the default start address.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
5-4 LAN Configuration
202-10085-01, March 2005
• Ending IP Address - This box specifies the last of the contiguous addresses in the IP address
pool. 192.168.1.254 is the default ending address.
• WINS Server - This box can specify the Windows NetBios Server IP if one is present in your
network.
• Lease Time - This box specifies the Lease time to be given to the DHCP Clients.
Using the Firewall as a DHCP server
By default, the firewall will function as a DHCP (Dynamic Host Configuration Protocol) server,
allowing it to assign IP, DNS server, WWS Server, and default gateway addresses to all computers
connected to the firewall's LAN. The assigned default gateway address is the LAN address of the
firewall. IP addresses will be assigned to the attached PCs from a pool of addresses specified in
this menu. Each pool address is tested before it is assigned to avoid duplicate addresses on the
LAN.
For most applications, the default DHCP and TCP/IP settings of the firewall are satisfactory. See
“IP Configuration by DHCP” on page B-10 for an explanation of DHCP and information about
how to assign IP addresses for your network.
If another device on your network will be the DHCP server, or if you will manually configure the
network settings of all of your computers, clear the ‘Use firewall as DHCP server’ check box.
Otherwise, leave it checked.
Specify the pool of IP addresses to be assigned by setting the Starting IP Address and Ending IP
Address. These addresses should be part of the same IP address subnet as the firewall’s LAN IP
address. Using the default addressing scheme, you should define a range between 192.168.1.2 and
192.168.1.253, although you may wish to save part of the range for devices with fixed addresses.
The firewall will deliver the following parameters to any LAN device that requests DHCP:
• An IP Address from the range you have defined
• Subnet Mask
• Gateway IP Address (the firewall’s LAN IP address)
Note: If you change the LAN IP address of the firewall while connected through the
browser, you will be disconnected. You must then open a new connection to the new IP
address and log in again.
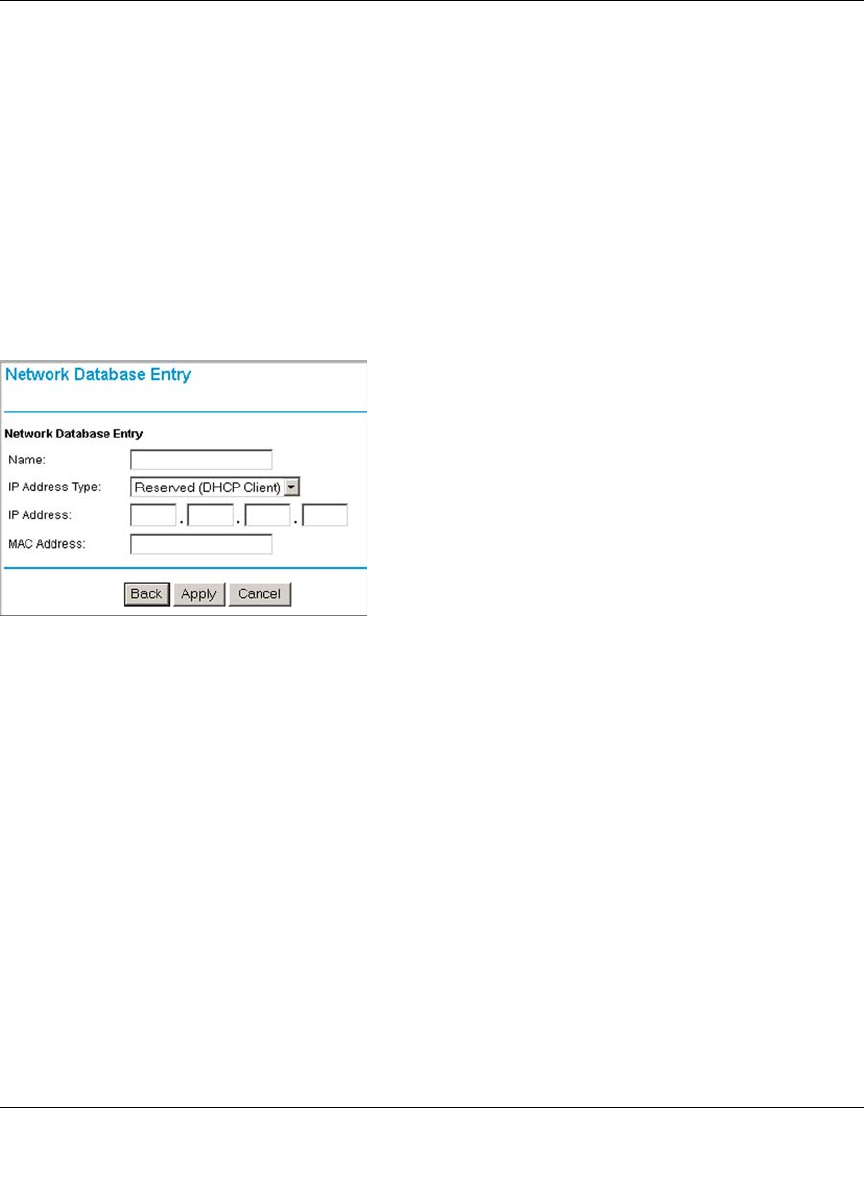
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
LAN Configuration 5-5
202-10085-01, March 2005
• Primary DNS Server (if you entered a Primary DNS address in the Basic Settings menu;
otherwise, the firewall’s LAN IP address)
• Secondary DNS Server (if you entered a Secondary DNS address in the Basic Settings menu)
• WINS Server (if you entered a Secondary DNS address in the Basic Settings menu)
Using Address Reservation
When you specify a reserved IP address for a PC on the LAN, that PC will always receive the
same IP address each time it access the firewall’s DHCP server. Reserved IP addresses should be
assigned to servers that require permanent IP settings.
Figure 5-2: Groups and Hosts Entry screen
To reserve an IP address, use the Groups and Hosts Entry screen (see “Managing Groups and
Hosts” on page 6-20).
Note: The reserved address will not be assigned until the next time the PC contacts the firewall's
DHCP server. Reboot the PC or access its IP configuration and force a DHCP release and renew.
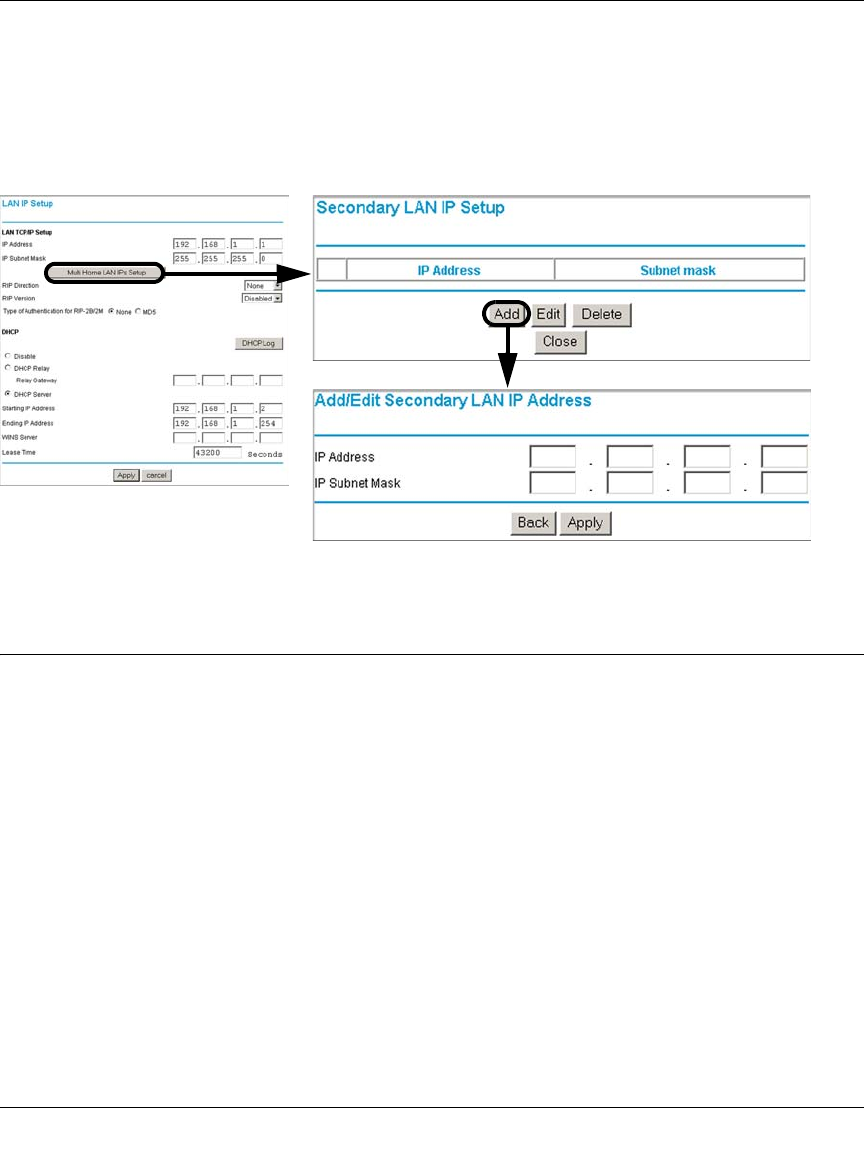
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
5-6 LAN Configuration
202-10085-01, March 2005
Multi Home LAN IPs
Click Multi Home LAN IPs Setup on the LAN IP Setup screen (see Figure 5-1) to invoke the
Secondary LAN IP Setup screens. This allows the firewall to act as a gateway to additional logical
subnets on your LAN. You can assign the firewall an IP address on each additional logical subnet.
Figure 5-3: Secondary LAN IP Setup screens
Configuring Static Routes
Static Routes provide additional routing information to your firewall. Under normal
circumstances, the firewall has adequate routing information after it has been configured for
Internet access, and you do not need to configure additional static routes. You must configure
static routes only for unusual cases such as multiple firewalls or multiple IP subnets located on
your network.
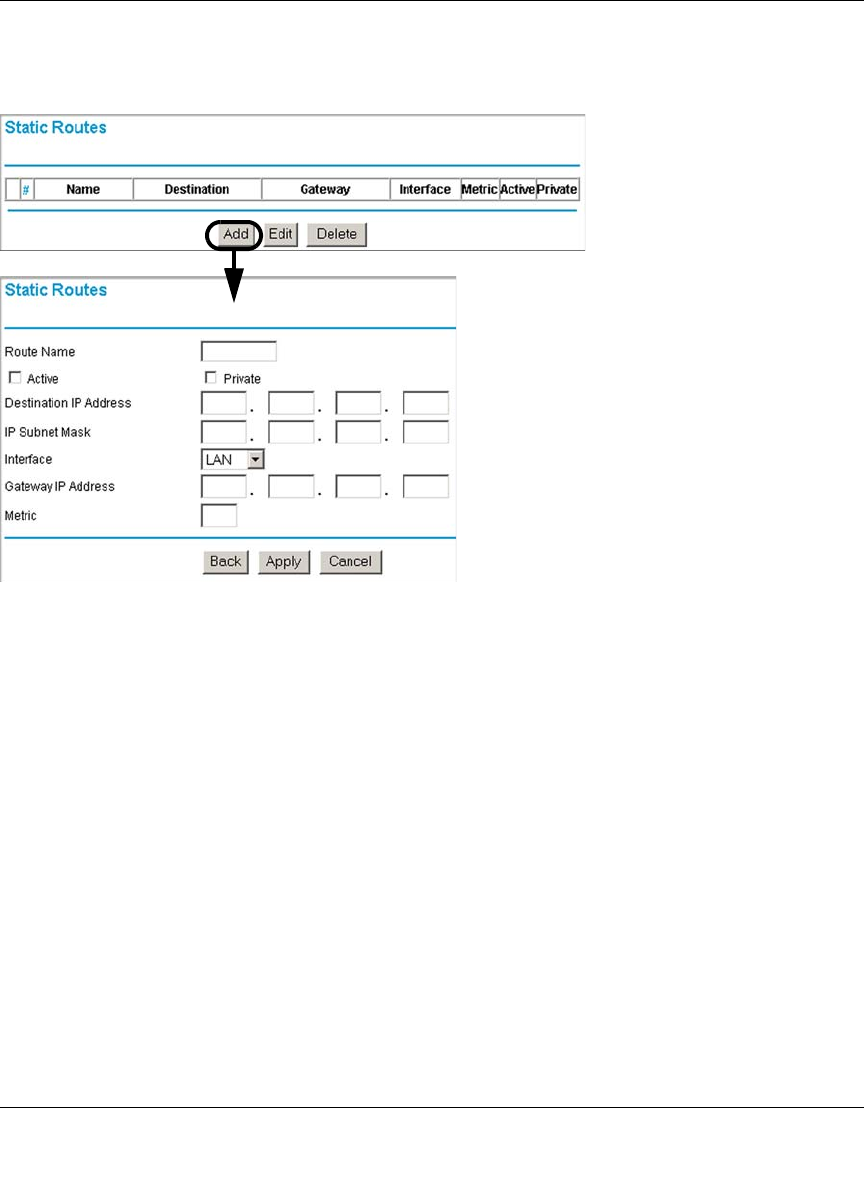
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
LAN Configuration 5-7
202-10085-01, March 2005
From the Main Menu of the browser interface, under Advanced, click on Static Routes to view the
Static Route menu, shown below.
Figure 5-4. Static Routes Summary Table and Add screens
To add or edit a Static Route:
1. Click the Add button to open the Add/Edit Menu, shown below.
2. Type a route name for this static route in the Route Name box under the table.
(This is for identification purpose only.)
3. Select Private if you want to limit access to the LAN only. The static route will not be reported
in RIP.
4. Select Active to make this route effective.
5. Type the Destination IP Address of the final destination.
6. Type the IP Subnet Mask for this destination.
If the destination is a single host, type 255.255.255.255.
7. Type the Gateway IP Address, which must be a firewall on the same LAN segment as the
firewall.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
5-8 LAN Configuration
202-10085-01, March 2005
8. Type a number between 1 and 15 as the Metric value.
This represents the number of firewalls between your network and the destination. Usually, a
setting of 2 or 3 works, but if this is a direct connection, set it to 1.
9. Click Apply to have the static route entered into the table.
As an example of when a static route is needed, consider the following case:
• Your primary Internet access is through a cable modem to an ISP.
• You have an ISDN firewall on your home network for connecting to the company where you
are employed. This firewall’s address on your LAN is 192.168.1.100.
• Your company’s network is 134.177.0.0.
When you first configured your firewall, two implicit static routes were created. A default route
was created with your ISP as the gateway, and a second static route was created to your local
network for all 192.168.1.x addresses. With this configuration, if you attempt to access a device on
the 134.177.0.0 network, your firewall will forward your request to the ISP. The ISP forwards your
request to the company where you are employed, and the request will likely be denied by the
company’s firewall.
In this case you must define a static route, telling your firewall that 134.177.0.0 should be accessed
through the ISDN firewall at 192.168.1.100.
In this example:
• The Destination IP Address and IP Subnet Mask fields specify that this static route applies to
all 134.177.x.x addresses.
• The Gateway IP Address fields specifies that all traffic for these addresses should be
forwarded to the ISDN firewall at 192.168.1.100.
• A Metric value of 1 will work since the ISDN firewall is on the LAN.
• Private is selected only as a precautionary security measure in case RIP is activated.
Firewall Protection and Content Filtering 6-1
202-10085-01, March 2005
Chapter 6
Firewall Protection and Content Filtering
This chapter describes how to use the content filtering features of the FVS124G ProSafe VPN
Firewall 25 with 4 Gigabit LAN and Dual WAN Ports to protect your network. These features can
be found by clicking on the Content Filtering heading in the Main Menu of the browser interface.
Firewall Protection and Content Filtering Overview
The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports provides you
with Web content filtering options, plus browsing activity reporting and instant alerts via e-mail.
Parents and network administrators can establish restricted access policies based on time-of-day,
web addresses and web address keywords. You can also block Internet access by applications and
services, such as chat or games.
A firewall is a special category of router that protects one network (the “trusted” network, such as
your LAN) from another (the “untrusted” network, such as the Internet), while allowing
communication between the two.
A firewall incorporates the functions of a NAT (Network Address Translation) router, while
adding features for dealing with a hacker intrusion or attack, and for controlling the types of traffic
that can flow between the two networks. Unlike simple Internet sharing NAT routers, a firewall
uses a process called stateful packet inspection to protect your network from attacks and
intrusions. NAT performs a very limited stateful inspection in that it considers whether the
incoming packet is in response to an outgoing request, but true Stateful Packet Inspection goes far
beyond NAT.
Using Rules to Block or Allow Specific Kinds of Traffic
Firewall rules are used to block or allow specific traffic passing through from one side to the other.
Inbound rules (WAN to LAN) restrict access by outsiders to private resources, selectively allowing
only specific outside users to access specific resources. Outbound rules (LAN to WAN) determine
what outside resources local users can have access to.
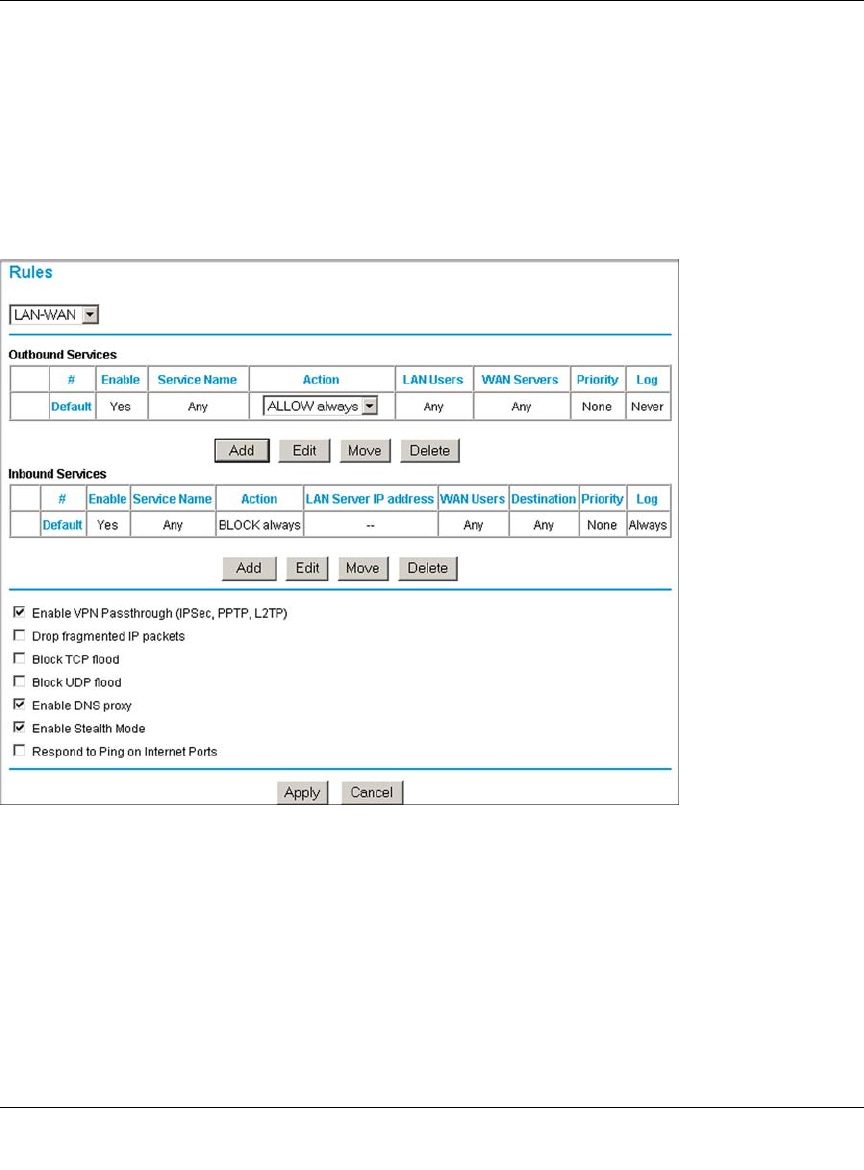
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-2 Firewall Protection and Content Filtering
202-10085-01, March 2005
A firewall has two default rules, one for inbound traffic and one for outbound. The default rules of
the FVS124G are:
• Inbound: Block all access from outside except responses to requests from the LAN side.
• Outbound: Allow all access from the LAN side to the outside.
These default rules are shown in the Rules table of the Rules menu (under Security on the main
menu) in Figure 6-1:
Figure 6-1: Rules menu
You may define additional rules that will specify exceptions to the default rules. By adding custom
rules, you can block or allow access based on the service or application, source or destination IP
addresses, and time of day.
You can also tailor these rules to your specific needs (see “Administrator Information” on
page 6-35).

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-3
202-10085-01, March 2005
Note: This feature is for Advanced Administrators only! Incorrect configuration will cause serious
problems.
Outbound Services—This lists all existing rules for outbound traffic. If you have not defined any
rules, only the default rule will be listed. The default rule allows all outgoing traffic.
• To create a new outbound service rule:
a. Click the Add button. It does not matter which radio button is selected.
The Outbound Service screen will be displayed (see “Outbound Rules (Service Blocking)”
on page 6-12). This screen has its own help file.
b. Complete the Outbound Service screen, and save the data. The new rule will be listed in
the table when you return to this screen.
• To make changes to an existing outbound service rule:
a. Click the check box at the beginning of the row and click Apply to disable or Enable the
policy.
b. Click the radio button next to an row in the table.
c. Click the button for the desired actions:
– Edit - to make any changes to the rule definition. The Outbound Service screen will be
displayed (see “Outbound Rules (Service Blocking)” on page 6-12) with the data for
the selected rule.
– Move - to move the selected rule to a new position in the table. You will be prompted
for the new position.
– Delete - to delete the selected rule.
Inbound Services—This lists all existing rules for inbound traffic. If you have not defined any
rules, only the default rule will be listed. The default rule blocks all inbound traffic.
• To create a new inbound service rule:
a. Click the Add button. It does not matter which radio button is selected.
The Inbound Service screen will be displayed (see “Inbound Rules (Port Forwarding)” on
page 6-5). This screen has its own help file.
b. Complete the Inbound Service screen and save the data. The new rule will be listed in the
table when you return to this screen.
• To make changes to an existing inbound service rule:
a. Click the radio button next to an row in the table.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-4 Firewall Protection and Content Filtering
202-10085-01, March 2005
b. Click the button for the desired actions:
– Edit - to make any changes to the rule definition. The Inbound Service screen will be
displayed (see “Inbound Rules (Port Forwarding)” on page 6-5) with the data for the
selected rule.
– Move - to move the selected rule to a new position in the table. You will be prompted
for the new position.
– Delete - to delete the selected rule.
Attack Checks—These check boxes allows you to enable check on various attacks. Select the
appropriate checkbox to enable them.
• VPN Passthrough: Enable this to pass the VPN traffic without any filtering, specially used
when this box is between two VPN tunnel end points.
• Drop fragmented IP packets: Enable this to drop the fragmented IP packets.
• UDP Flooding: Enable this to limit the number of UDP sessions created from one LAN
machine.
• TCP Flooding: Enable this to protect the router from Syn flood attack.
• Enable DNS Proxy: Enable this to allow the incoming DNS queries.
• Enable Stealth Mode: Enable this to set the firewall to operate in stealth mode.
• Respond To Ping On Internet Ports—If you want the router to respond to a 'Ping' from the
Internet, click this check box. This can be used as a diagnostic tool. You shouldn't check this
box unless you have a specific reason to do so.
Services-Based Rules
The rules to block traffic are based on the traffic’s category of service.
• Inbound rules (port forwarding)—Inbound traffic is normally blocked by the firewall unless
the traffic is in response to a request from the LAN side. The firewall can be configured to
allow this otherwise blocked traffic.
• Outbound rules (service blocking)—Outbound traffic is normally allowed unless the firewall
is configured to disallow it.
• Customized services—Additional services can be added to the list of services in the factory
default list. These added services can then have rules defined for them to either allow or block
that traffic.
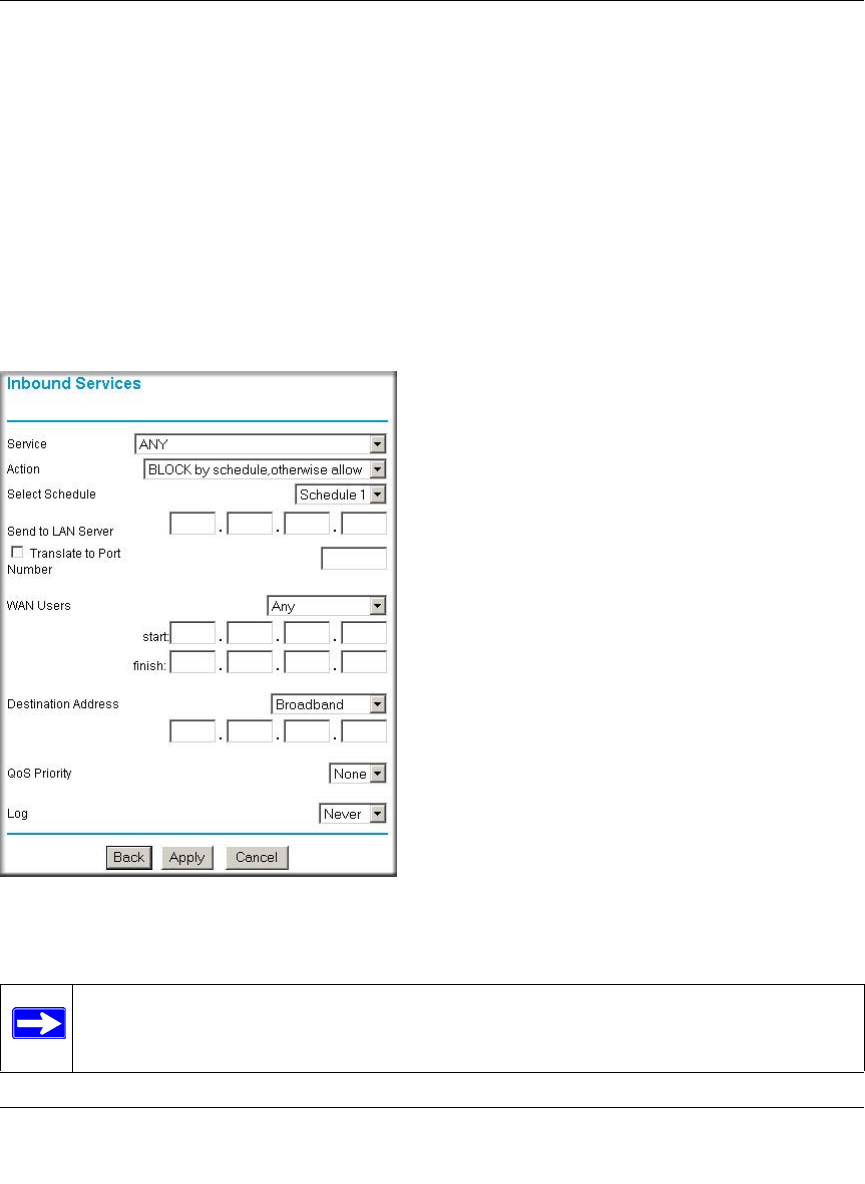
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-5
202-10085-01, March 2005
• Quality of service (QoS) priorities—Each service at its own native priority that impacts its
quality of performance and tolerance for jitter or delays. You can change this QoS priority if
desired to change the traffic mix through the system.
Inbound Rules (Port Forwarding)
Because the FVS124G uses Network Address Translation (NAT), your network presents only one
IP address to the Internet and outside users cannot directly address any of your local computers.
However, by defining an inbound rule you can make a local server (for example, a web server or
game server) visible and available to the Internet. The rule tells the firewall to direct inbound
traffic for a particular service to one local server based on the destination port number. This is also
known as port forwarding.
Figure 6-2: Add Inbound Service Rules screen
Note: See “Port Triggering” on page 6-28 for yet another way to allow certain types of
inbound traffic that would otherwise be blocked by the firewall.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-6 Firewall Protection and Content Filtering
202-10085-01, March 2005
Table 6-1. Inbound Services
Item Description
Services Select the desired Service or application to be covered by this rule. If the desired
service or application does not appear in the list, you must define it using the
Services menu (see “Customized Services” on page 6-16).
Action Select the desired action for packets covered by this rule:
• BLOCK always
• BLOCK by schedule, otherwise Allow
• ALLOW always
• ALLOW by schedule, otherwise Block
Note: Any inbound traffic which is not allowed by rules you create will be blocked by
the Default rule.
Select Schedule Select the desired time schedule (i.e., Schedule1, Schedule2, or Schedule3) that will
be used by this rule.
• This drop down menu gets activated only when "BLOCK by schedule, otherwise
Allow" or "ALLOW by schedule, otherwise Block" is selected as Action.
• Use schedule page to configure the time schedules.
LAN users These settings determine which computers on your network are affected by this rule,
based on their IP address. Select the desired IP Address in this field.
WAN Users These settings determine which Internet locations are covered by the rule, based on
their IP address. Select the desired option:
• Any - All Internet IP address are covered by this rule.
• Single address - Enter the required address in the start fields.
• Address range - If this option is selected, you must enter the start and finish fields.
Destination Address These settings determine the destination IP address for this rule which will be
applicable to incoming traffic, this rule will be applied only when the destination IP
address of the incoming packet matches the IP address of the WAN interface
selected or Specific IP address entered in this field.Selecting ANY enables the rule
for any IP in destination field.similarly WAN1 and WAN2 corresponds to respective
wan interfaces.
QoS Priority This setting determines the priority of a service, which in turn, determines the quality
of that service for the traffic passing through the firewall. By default, the priority
shown is that of the selected service. The user can change it accordingly. If the user
does not make a selection (i.e, leaves it as None), then the native priority of the
service will be applied to the policy. +5 is the highest priority. See “Quality of Service
(QoS) Priorities” on page 6-18.
Log This determines whether packets covered by this rule are logged. Select the desired
action:
• Always - always log traffic considered by this rule, whether it matches or not. This is
useful when debugging your rules.
• Never - never log traffic considered by this rule, whether it matches or not.
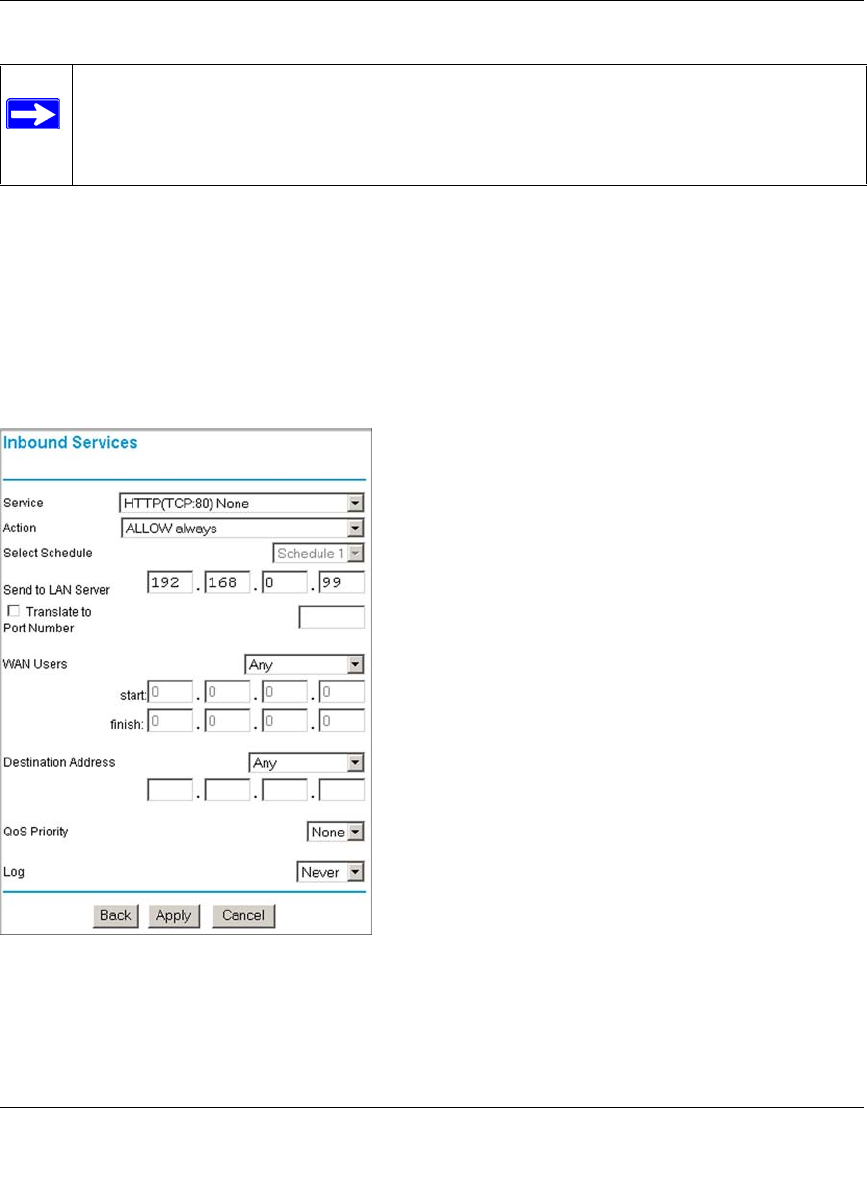
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-7
202-10085-01, March 2005
Remember that allowing inbound services opens holes in your FVS124G VPN Firewall. Only
enable those ports that are necessary for your network.
Inbound Rule Example: A Local Public Web Server
If you host a public web server on your local network, you can define a rule to allow inbound web
(HTTP) requests from any outside IP address to the IP address of your web server at any time of
day. This rule is shown in Figure 6-3:
Figure 6-3: Rule example: a local public web server
Note: Some residential broadband ISP accounts do not allow you to run any server
processes (such as a Web or FTP server) from your location. Your ISP may periodically
check for servers and may suspend your account if it discovers any active services at
your location. If you are unsure, refer to the Acceptable Use Policy of your ISP.
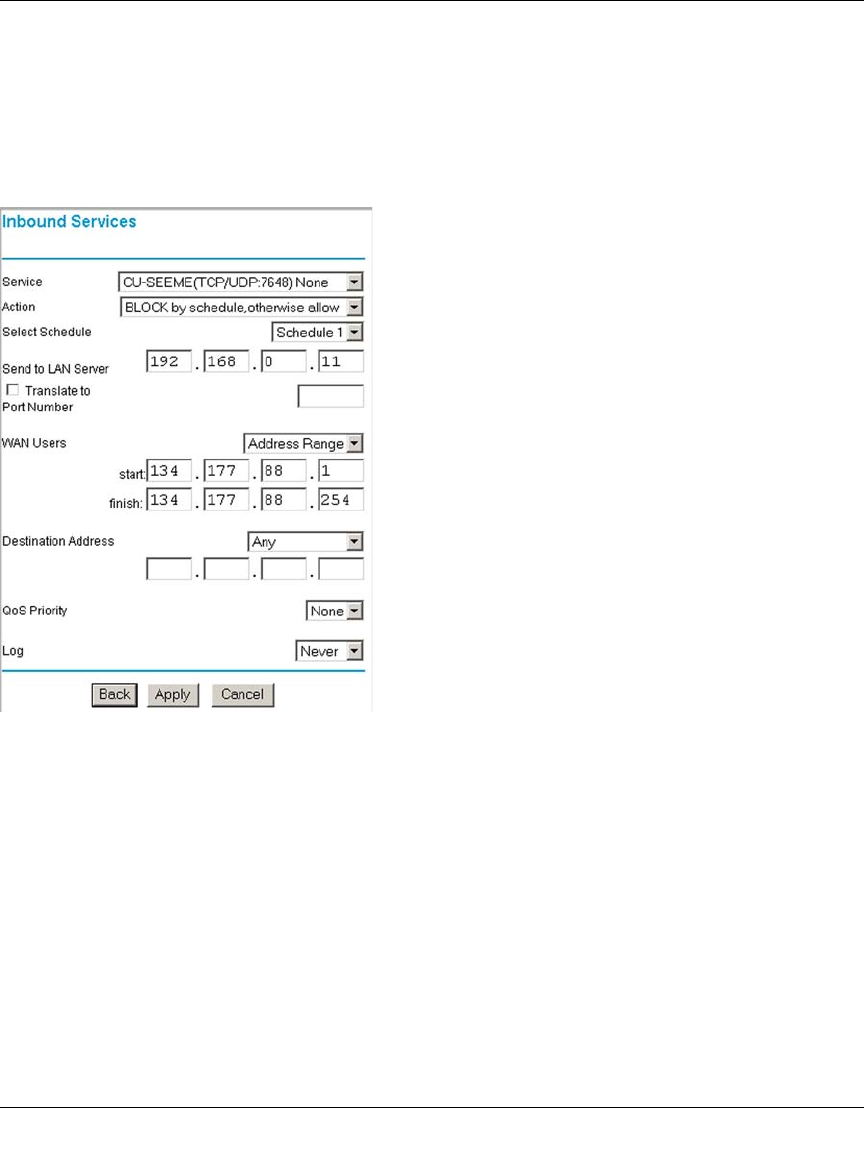
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-8 Firewall Protection and Content Filtering
202-10085-01, March 2005
Inbound Rule Example: Allowing Videoconference from Restricted Addresses
If you want to allow incoming videoconferencing to be initiated from a restricted range of outside
IP addresses, such as from a branch office, you can create an inbound rule. In the example shown
in Figure 6-4, CU-SeeMe connections are allowed only from a specified range of external IP
addresses.
Figure 6-4: Rule example: videoconference from restricted addresses
Inbound Rule Example: One-to-One NAT Mapping
This application note describes how to configure multi-NAT to support multiple public IP
addresses on one WAN interface of a NETGEAR FVS124G ProSafe VPN Firewall 25 with 4
Gigabit LAN and Dual WAN Ports. By creating an inbound rule, we will configure the firewall to
host an additional public IP addresses and associate this address with a web server on the LAN.
This procedure was developed and tested using:
• Netgear FVS124G VPN Firewall with version 1.0 firmware
– WAN1 IP address is 10.1.0.118
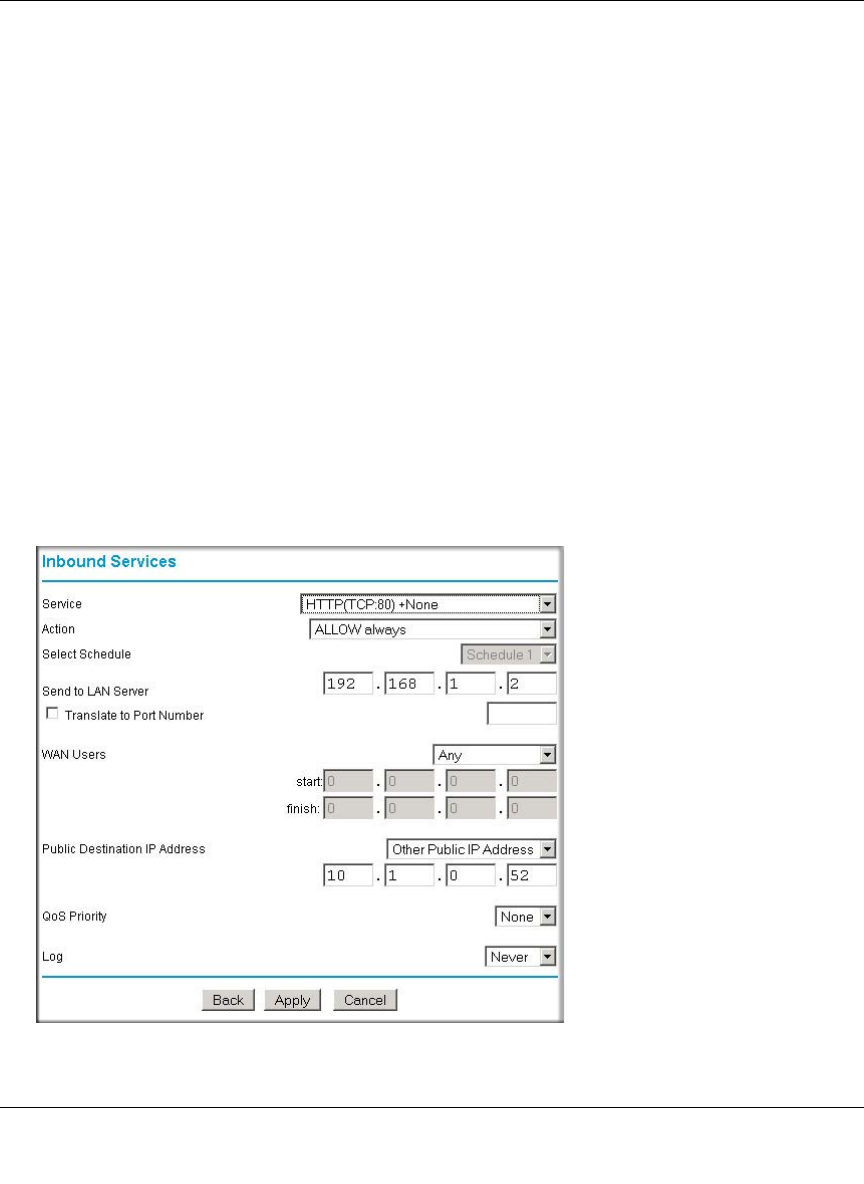
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-9
202-10085-01, March 2005
– LAN IP address subnet is 192.168.1.1 255.255.255.0
• Web server PC on the firewall's LAN
– LAN IP address is 192.168.1.2
– Access to Web server is (simulated) public IP address 10.1.0.52
IP Address Requirements—If you arrange with your ISP to have more than one public IP address
for your use, you can use the additional public IP addresses to map to servers on your LAN. One of
these public IP addresses will be used as the primary IP address of the router. This address will be
used to provide Internet access to your LAN PCs through NAT. The other addresses are available
to map to your servers.
To configure the FVS124G for additional IP addresses:
1. Go to the Rules menu.
2. If your server is to be on your LAN, select "LAN-WAN".
3. Click the Add button to create an Inbound Services rule.
4. In the Add/Edit menu (see Figure 6-5), select the HTTP service for a web server.
Figure 6-5: Rule example: one-to-one NAT mapping
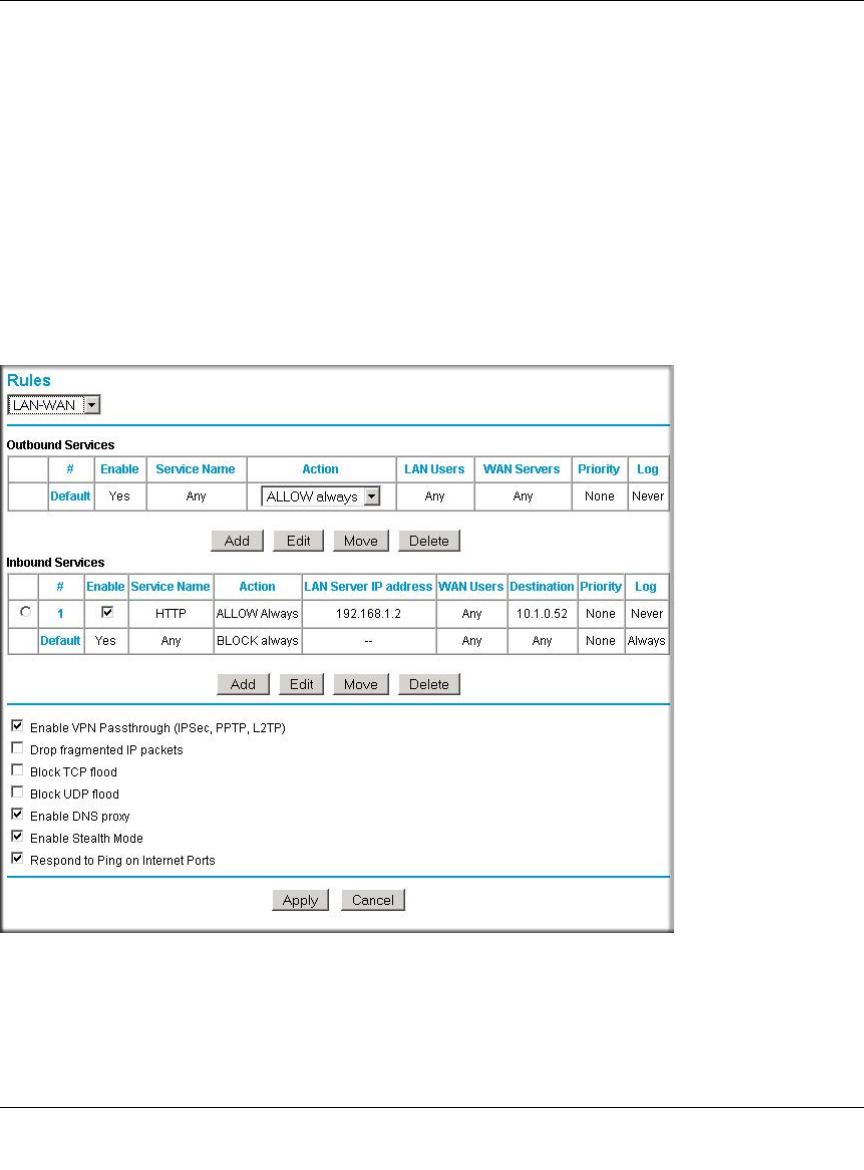
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-10 Firewall Protection and Content Filtering
202-10085-01, March 2005
5. Select Action "ALLOW always".
6. For Send to LAN Server, enter the local IP address of your web server PC.
7. For Public Destination IP Address, choose "Other Public IP Address."
8. Enter one of your public Internet addresses that will be used by clients on the Internet to reach
your web server.
9. Click Apply.
Your rule will now appear in the Inbound Services table of the Rules menu (see Figure 6-6). This
rule is different from a normal inbound port forwarding rule in that the Destination box contains an
IP Address other than your normal WAN IP Address.
Figure 6-6: Rule example: one-to-one NAT mapping on inbound services
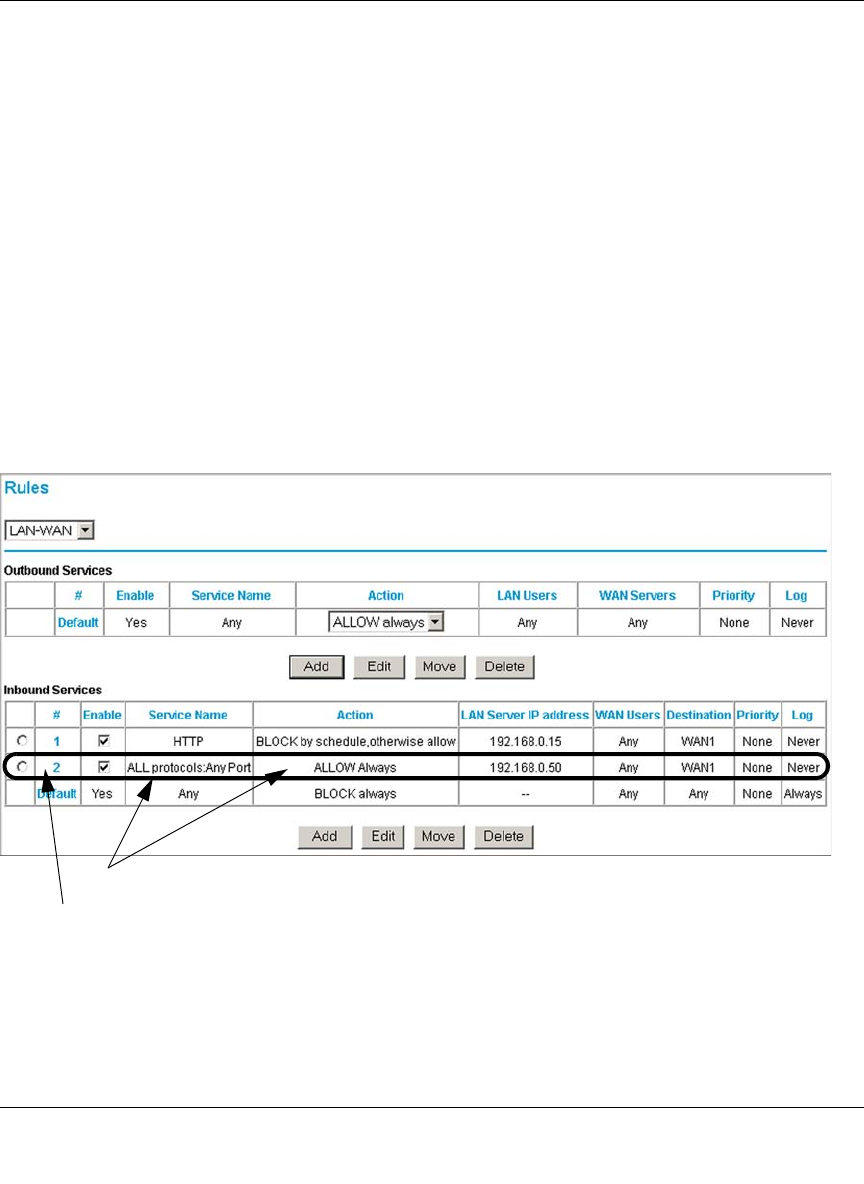
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-11
202-10085-01, March 2005
To test the connection from a PC on the Internet, type http://<IP_address>, where <IP_address>
is the public IP address you have mapped to your web server. You should see the home page of
your web server.
Inbound Rule Example: Exposed Host
Specifying an exposed host allows you to set up a computer or server that is available to anyone on
the Internet for services that you haven't defined. To expose one of the PCs on your LAN as this
host, do the following (see Figure 6-7):
1. Create an inbound rule that allows all protocols.
2. Place the rule below all other inbound rules.
Note: For security, NETGEAR strongly recommends that you avoid creating an exposed host.
When a computer is designated as the exposed host, it loses much of the protection of the firewall
and is exposed to many exploits from the Internet. If compromised, the computer can be used to
attack your network.
Figure 6-7: Rule example: exposed host
1. Select All protocols and ALLOW Always (or Allow by Schedule)
2. Place rule below all other inbound rules

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-12 Firewall Protection and Content Filtering
202-10085-01, March 2005
Considerations for Inbound Rules
• If your external IP address is assigned dynamically by your ISP, the IP address may change
periodically as the DHCP lease expires. Consider using the Dyamic DNS feature in the
Advanced menus so that external users can always find your network.
• If the IP address of the local server PC is assigned by DHCP, it may change when the PC is
rebooted. To avoid this, use the Reserved IP address feature in the LAN IP menu to keep the
PC’s IP address constant.
• Local PCs must access the local server using the PCs’ local LAN address (192.168.0.99 in this
example). Attempts by local PCs to access the server using the external WAN IP address will
fail.
Outbound Rules (Service Blocking)
The FVS124G allows you to block the use of certain Internet services by PCs on your network.
This is called service blocking or port filtering.
Figure 6-8: Add Outbound Service Rules screen

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-13
202-10085-01, March 2005
Note: See “Source MAC Filtering” on page 6-27 for yet another way to block outbound
traffic from selected PCs that would otherwise be allowed by the firewall.
Table 6-1. Outbound Services
Item Description
Services Select the desired Service or application to be covered by this rule. If the desired
service or application does not appear in the list, you must define it using the
Services menu (see “Customized Services” on page 6-16).
Action Select the desired action for outgoing connections covered by this rule:
• BLOCK always
• BLOCK by schedule, otherwise Allow
• ALLOW always
• ALLOW by schedule, otherwise Block
Note: Any outbound traffic which is not blocked by rules you create will be allowed by
the Default rule.
ALLOW rules are only useful if the traffic is already covered by a BLOCK rule. That
is, you wish to allow a subset of traffic that is currently blocked by another rule.
Select Schedule Select the desired time schedule (i.e., Schedule1, Schedule2, or Schedule3) that will
be used by this rule.
• This drop down menu gets activated only when "BLOCK by schedule, otherwise
Allow" or "ALLOW by schedule, otherwise Block" is selected as Action.
• Use schedule page to configure the time schedules (see “Using a Schedule to
Block or Allow Specific Traffic” on page 6-22).
LAN users These settings determine which computers on your network are affected by this rule.
Select the desired options:
• Any - All PCs and devices on your LAN.
• Single address - Enter the required address and the rule will be applied to that
particular PC.
• Address range - If this option is selected, you must enter the start and finish fields.
• Groups- Select the Group you wish this rule to apply to. You can use the Network
Database screen to assign PCs to Groups. See “Managing Groups and Hosts” on
page 6-20.
WAN Users These settings determine which Internet locations are covered by the rule, based on
their IP address. Select the desired option:
• Any - All Internet IP address are covered by this rule.
• Single address - Enter the required address in the start fields.
• Address range - If this option is selected, you must enter the start and finish fields.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-14 Firewall Protection and Content Filtering
202-10085-01, March 2005
QoS Priority This setting determines the priority of a service, which in turn, determines the quality
of that service for the traffic passing through the firewall. By default, the priority
shown is that of the selected service. The user can change it accordingly. If the user
does not make a selection (i.e, leaves it as None), then the native priority of the
service will be applied to the policy. +5 is the highest priority. See “Quality of Service
(QoS) Priorities” on page 6-18.
Log This determines whether packets covered by this rule are logged. Select the desired
action:
• Always - always log traffic considered by this rule, whether it matches or not. This is
useful when debugging your rules.
• Never - never log traffic considered by this rule, whether it matches or not.
Table 6-1. Outbound Services
Item Description
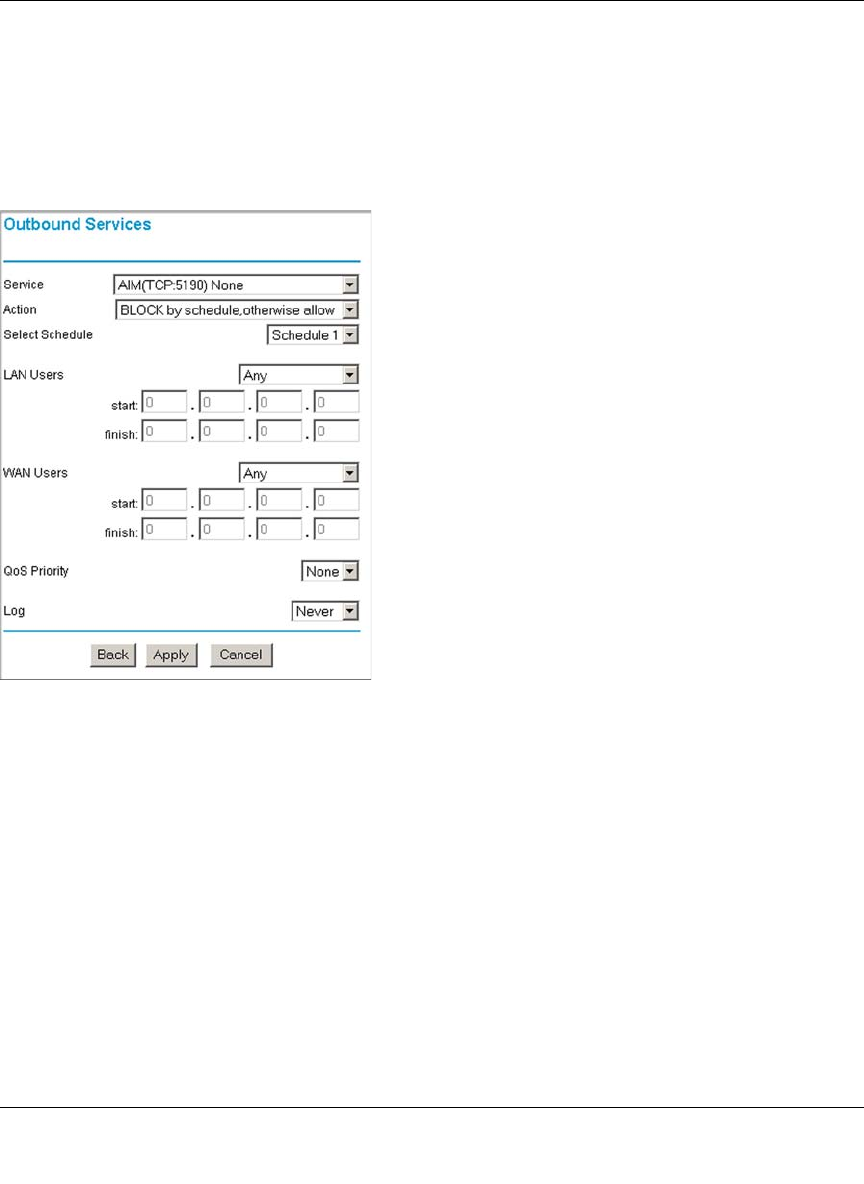
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-15
202-10085-01, March 2005
Outbound Rule Example: Blocking Instant Messenger
If you want to block Instant Messenger usage by employees during working hours, you can create
an outbound rule to block that application from any internal IP address to any external address
according to the schedule that you have created in the Schedule menu. You can also have the
firewall log any attempt to use Instant Messenger during that blocked period.
Figure 6-9: Rule example: Blocking Instant Messenger
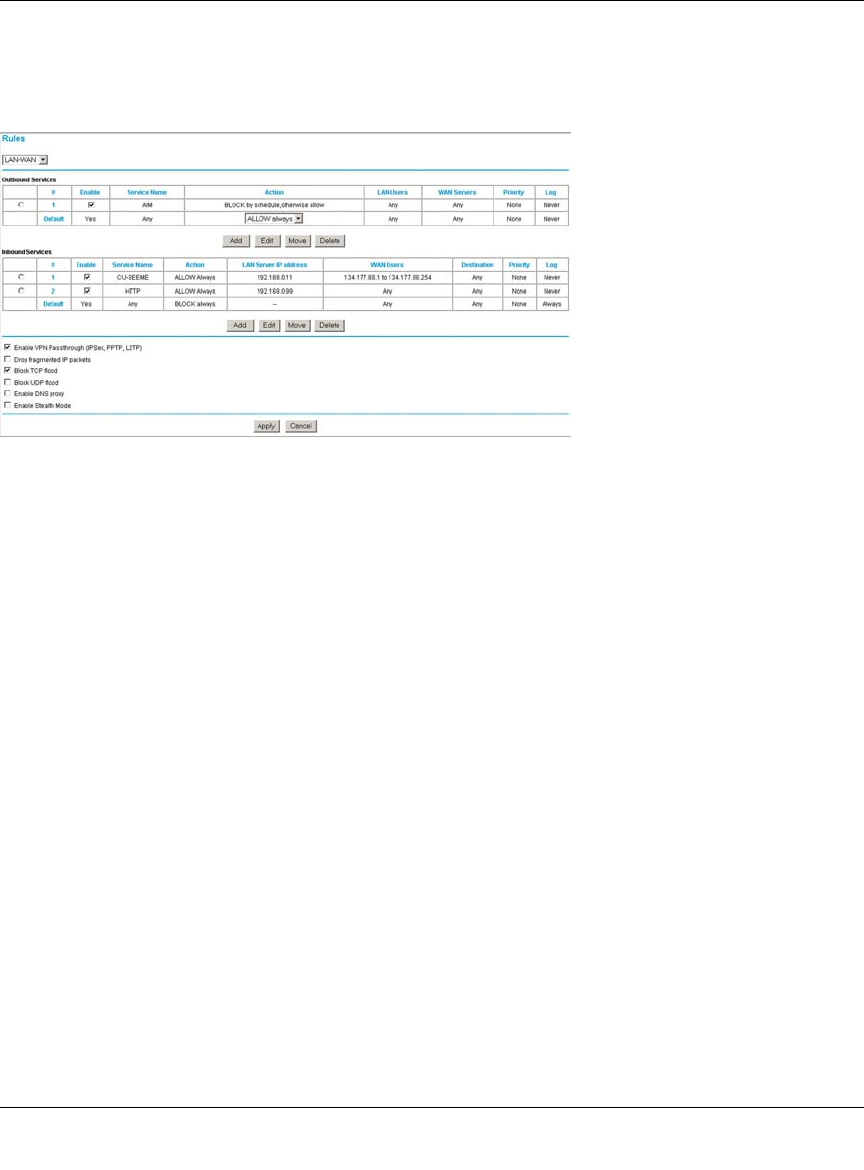
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-16 Firewall Protection and Content Filtering
202-10085-01, March 2005
Order of Precedence for Rules
As you define new rules, they are added to the tables in the Rules menu, as shown in Figure 6-10:
Figure 6-10: Rules table with examples
For any traffic attempting to pass through the firewall, the packet information is subjected to the
rules in the order shown in the Rules Table, beginning at the top and proceeding to the default rules
at the bottom. In some cases, the order of precedence of two or more rules may be important in
determining the disposition of a packet. The Move button allows you to relocate a defined rule to a
new position in the table.
Customized Services
Services are functions performed by server computers at the request of client computers. For
example, Web servers serve web pages, time servers serve time and date information, and game
hosts serve data about other players’ moves. When a computer on the Internet sends a request for
service to a server computer, the requested service is identified by a service or port number. This
number appears as the destination port number in the transmitted IP packets. For example, a packet
that is sent with destination port number 80 is an HTTP (Web server) request.
The service numbers for many common protocols are defined by the Internet Engineering Task
Force (IETF) and published in RFC1700, “Assigned Numbers.” Service numbers for other
applications are typically chosen from the range 1024 to 65535 by the authors of the application.
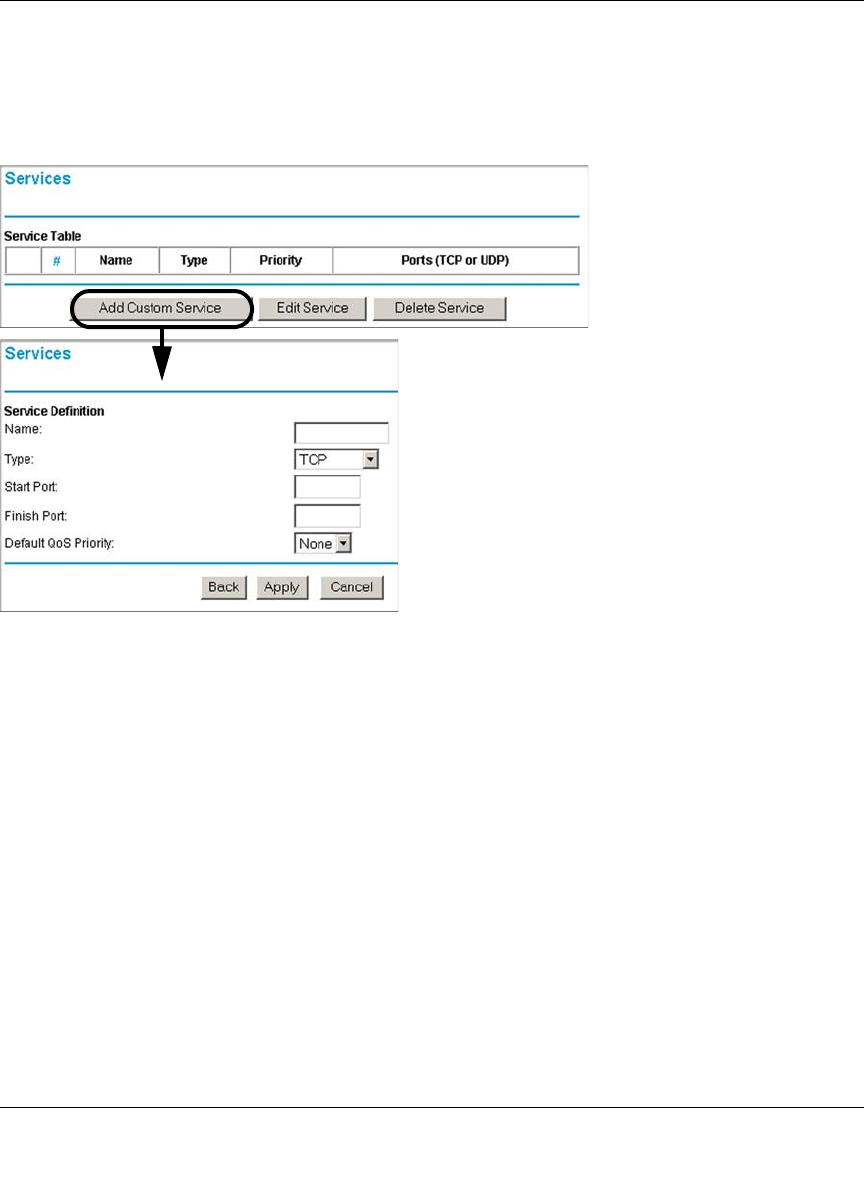
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-17
202-10085-01, March 2005
Although the FVS124G already holds a list of many service port numbers, you are not limited to
these choices. Use the Services menu to add additional services and applications to the list for use
in defining firewall rules. The Services menu shows a list of services that you have defined, as
shown in Figure 6-11:
Figure 6-11: Services and Add Custom Service screens
To define a new service, first you must determine which port number or range of numbers is used
by the application. This information can usually be determined by contacting the publisher of the
application or from user groups of newsgroups. When you have the port number information, go
the Services menu and click on the Add Custom Service button. The Add Services menu will
appear, as shown in Figure 6-11.
To add a service:
1. Enter a descriptive name for the service so that you will remember what it is.
2. Select whether the service uses TCP or UDP as its transport protocol.
If you can’t determine which is used, select both.
3. Enter the lowest port number used by the service.
4. Enter the highest port number used by the service.
If the service only uses a single port number, enter the same number in both fields.
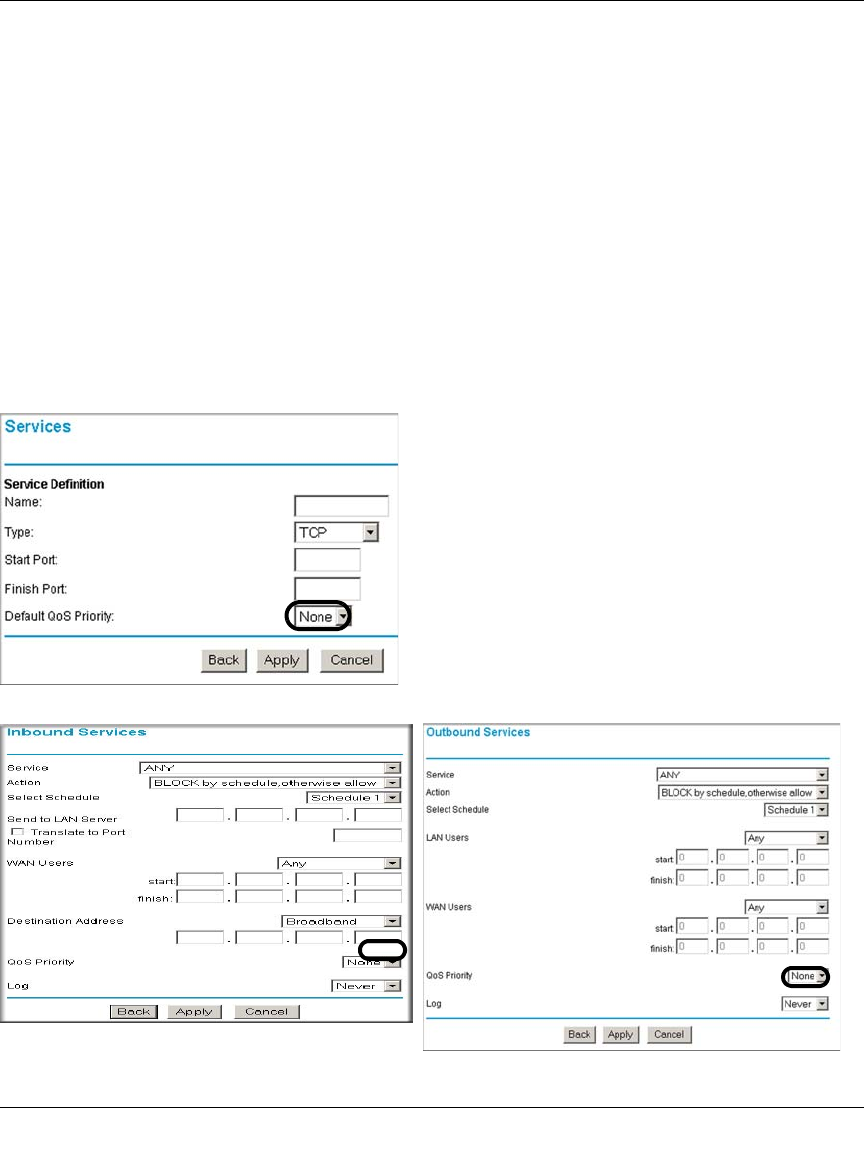
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-18 Firewall Protection and Content Filtering
202-10085-01, March 2005
5. Click Apply.
The new service will now appear in the Services menu, and in the Service name selection box in
the Rules menu.
Quality of Service (QoS) Priorities
This setting determines the priority of a service, which in turn, determines the quality of that
service for the traffic passing through the firewall. The user can change this priority:
• At the services definition screen for customized services
• On the inbound rules screen
• On the outbound rules screen
Figure 6-12: Setting and Overriding QoS priorities
Inbound Rules Add Screen Outbound Rules Add Screen
Services Add Screen
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-19
202-10085-01, March 2005
The QoS priority definition for a service determines the queue that is used for its traffic passing
through the FVS124G VPN Firewall as follows:
Example 1 (priority unchanged): If the native ToS setting for a service is 3 and the Netgear QoS
setting for this service is None, then the traffic for this service is placed in the queue that handles
priority 3 traffic. The priority of this service through the FVS124G VPN Firewall has not changed.
Example 2 (priority increased): If the native ToS setting for a service is 3 and the Netgear QoS
setting for this service is 4, then the traffic for this service is placed in the queue that handles
priority 4 traffic rather than the queue that handles priority 3 traffic. The priority of this service
through the FVS124G VPN Firewall has been increased.
Example 3 (priority decreased): If the native ToS setting for a service is 3 and the Netgear QoS
setting for this service is 2, then the traffic for this service is placed in the queue that handles
priority 2 traffic rather than the queue that handles priority 3 traffic. The priority of this service
through the FVS124G VPN Firewall has been decreased.
Table 6-2. Traffic queue to be used for a service
Native ToS Setting*
*IEEE 802.1D-1998 (formerly 802.1p) standard.
Netgear QoS Setting†
†Specifies which output queue in the FVS124G to use for that service’s traffic. The three type-of-service bits in the traffic
frame remain unchanged.
None65432
7 (highest) 765432
6 665432
5 565432
4 465432
3 365432
2 265432
1 (default) 1 6 5 4 3 2
0 (lowest) 065432

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-20 Firewall Protection and Content Filtering
202-10085-01, March 2005
Managing Groups and Hosts
The Network Database is an automatically-maintained list of all known PCs and network devices.
PCs and devices become known by the following methods:
• DHCP Client Requests—By default, the DHCP server in this Router is enabled, and will
accept and respond to DHCP client requests from PCs and other network devices. These
requests also generate an entry in the Network Database. Because of this, leaving the DHCP
Server feature (on the LAN screen) enabled is strongly recommended.
• Scanning the Network—The local network is scanned using standard methods such as arp.
This will detect active devices which are not DHCP clients. However, sometimes the name of
the PC or device cannot be accurately determined, and will be shown as Unknown.
Advantages of the Network Database are as follows:
• Generally, you do not need to enter either IP address or MAC addresses. Instead, you can just
select the desired PC or device.
• No need to reserve an IP address for a PC in the DHCP Server. All IP address assignments
made by the DHCP Server will be maintained until the PC or device is removed from the
database, either by expiry (inactive for a long time) or by you.
• No need to use a Fixed IP on PCs. Because the address allocated by the DHCP Server will
never change, you don't need to assign a fixed IP to a PC to ensure it always has the same IP
address.
• MAC-level Control over PCs. The Network Database uses the MAC address to identify each
PC or device. So changing a PC's IP address does not affect any restrictions on that PC.
• Group and Individual Control over PCs
– You can assign PCs to Groups and apply restrictions to each Group using the Firewall
Rules screen (see “Services-Based Rules” on page 6-4).
– You can also select the Groups to be covered by the Block Sites feature (see “Block Sites”
on page 6-24).
– If necessary, you can also create Firewall Rules to apply to a single PC (see “Source MAC
Filtering” on page 6-27). Because the MAC address is used to identify each PC, users
cannot avoid these restrictions by changing their IP address.
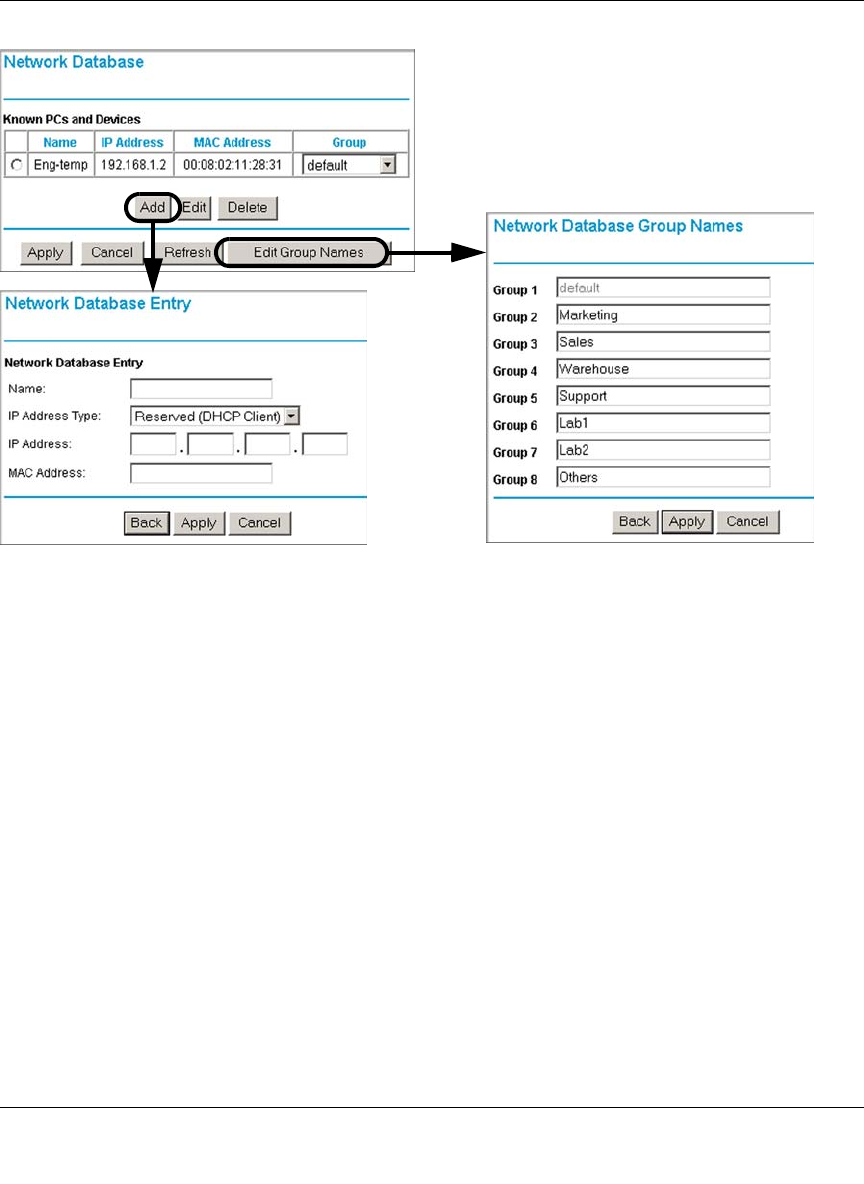
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-21
202-10085-01, March 2005
Figure 6-13: Groups and Hosts screens

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-22 Firewall Protection and Content Filtering
202-10085-01, March 2005
Using a Schedule to Block or Allow Specific Traffic
If you enabled content filtering in the Block Sites menu, or if you defined an outbound rule to use
a schedule, you can set up a schedule for when blocking occurs or when access is restricted. The
firewall allows you to specify when blocking will be enforced by configuring the Schedule tab
shown below:
Table 6-3. Groups and hosts
Item Description
Known PCs and
Devices This table lists all current entries in the Network Database. For each PC or device,
the following data is displayed.
• Radio button—Use this to select a PC for editing or deletion.
• Name—The name of the PC or device. Sometimes, this can not be determined,
and will be listed as Unknown. In this case, you can edit the entry to add a
meaningful name.
• IP Address—The current IP address. For DHCP clients, where the IP address is
allocated by the DHCP Server in this device, this IP address will not change. Where
the IP address is set on the PC (as a fixed IP address), you may need to update
this entry manually if the IP address on the PC is changed.
• MAC Address—The MAC address of the PC. The MAC address is a low-level
network identifier which is fixed at manufacture.
• Group—Each PC or device must be in a single group. The Group column indicates
which group each entry is in. By default, all entries are in the Default group (the D
column.)
Operations • Group Assignment —You can select a group for any entry by selecting the desired
group from the drop down menu in the Group column. Click Apply
• Adding a new Entry—If a PC is not connected, using a fixed IP, or a different LAN
segment, it may not be listed. In this case, you can add it by clicking the Add
button.
• Editing an Entry—You can edit an entry by selecting its radio button, and clicking
the Edit button.
• Deleting an Entry—If a PC or device has been removed from your network, you can
delete it from the database by selecting its radio button, and clicking the Delete
button.
• Edit Group Names—The Group names can be edited by clicking Edit Group
Names button. By default the group names are Default, Marketing, Sales,
Warehouse, Support, Lab1, Lab2, and Others.
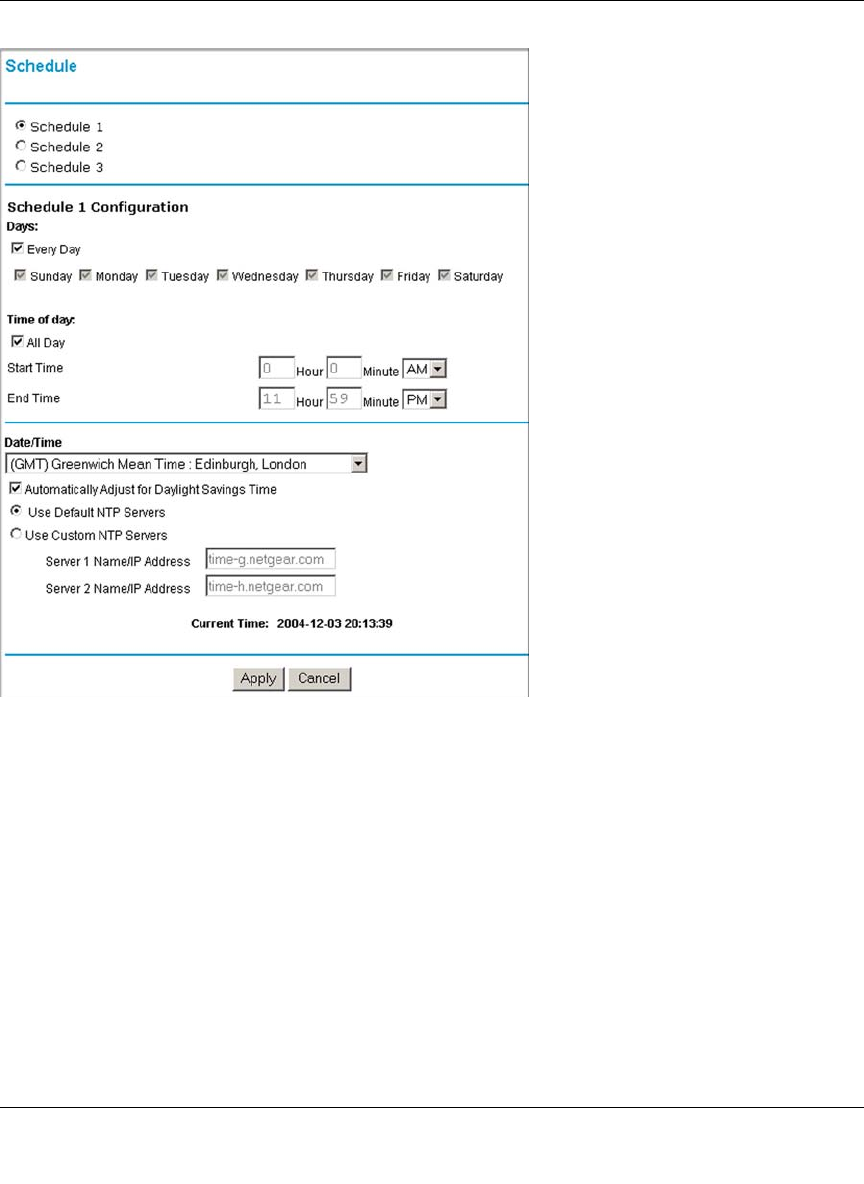
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-23
202-10085-01, March 2005
Figure 6-14: Schedule menu
To invoke rules and block keywords or Internet domains based on a schedule, select Every Day or
select one or more days. If you want to limit access completely for the selected days, select All
Day. Otherwise, if you want to limit access during certain times for the selected days, type a Start
Blocking time and an End Blocking time.
Note: Note: Enter the values as 24-hour time. For example, 10:30 am would be 10 hours and 30
minutes and 10:30 pm would be 22 hours and 30 minutes.
Be sure to click Apply when you have finished configuring this menu.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-24 Firewall Protection and Content Filtering
202-10085-01, March 2005
Time Zone
The FVS124G VPN Firewall uses the Network Time Protocol (NTP) to obtain the current time
and date from one of several Network Time Servers on the Internet. In order to localize the time
for your log entries, you must specify your Time Zone:
• Time Zone. Select your local time zone. This setting will be used for the blocking schedule
and for time-stamping log entries.
• Daylight Savings Time. Check this box for daylight savings time.
Note: If your region uses Daylight Savings Time, you must manually select Adjust for
Daylight Savings Time on the first day of Daylight Savings Time, and unselect it at the
end. Enabling Daylight Savings Time will add one hour to the standard time.
Be sure to click Apply when you have finished configuring this menu.
Block Sites
If you want to reduce incoming traffic by preventing access to certain sites on the Internet, you can
use the VPN firewall's content and Web component filtering feature. By default, this feature is
disabled; all requested traffic from any Web site is allowed. When users try to access a blocked
site, they will get a message: Blocked by NETGEAR.
• Keyword (and domain name) blocking—You can specify up to 32 words that, should they
appear in the website name (i.e., URL) or in a newsgroup name, will cause that site or
newsgroup to be blocked by the VPN firewall.
You can apply the keywords to one or more groups. Requests from the PCs in the groups for
which keyword blocking has been enabled will be blocked. Blocking does not occur for the
PCs that are in the groups for which keyword blocking has not been enabled.
You can bypass keyword blocking for trusted domains by adding the exact matching domain
to the list of Trusted Domains. Access to the domains on this list by PCs even in the groups for
which keyword blocking has been enabled will still be allowed without any blocking.
• Web component blocking—You can block the following Web component types: Proxy, Java,
ActiveX, and Cookies. Sites on the Trusted Domains list are still subject to Web component
blocking when the blocking of a particular Web component has been enabled.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-26 Firewall Protection and Content Filtering
202-10085-01, March 2005
Keyword application examples:
• If the keyword "XXX" is specified, the URL <http://www.badstuff.com/xxx.html> is blocked,
as is the newsgroup alt.pictures.XXX.
• If the keyword “.com” is specified, only websites with other domain suffixes (such as .edu or
.gov) can be viewed.
• If you wish to block all Internet browsing access, enter the keyword “.”.
Table 6-4. Block Sites
Item Description
Web Component
Blocking Select Proxy, Java, ActiveX and Cookies to enable respective content filtering.
Example: By enabling Java filtering *.java files will be blocked.
Note: Keywords are always blocked.
To block keywords or
Internet domains: • Select the Turn keyword blocking on check box.
• Type a keyword or domain name in the Add Keyword box, click Add Keyword
button. The word or domain name appears in the list below. Any number of domain
names and keywords can be added to the list.
• To delete a keyword or domain name: Select the word or domain name in the list,
click Delete Keyword button.
• To delete all keywords: Click Delete All button to delete all the Keywords from the
list.
Groups Select the groups specified below the Apply Keyword blocking to tab to enable
keyword blocking for those groups. The Request from the PC's that are in the group
for which Keyword filtering is enabled will undergo the Filtering process. Otherwise
the filtering does not apply. See “Managing Groups and Hosts” on page 6-20.
Trusted Domains • In the Trusted Domains box, enter the exact matching domain name for which the
keyword filtering will be bypassed.
Example: Enter www.netgear.com to bypass URL keyword filtering for this
domain. The domains in this list will be allowed without any filtering, web
component filtering still applies.
Click on Add Trusted Domains button. The domain name appears in the list below.
Any number of domain names can be added to the list.
• To delete a Domain name: Select the word or domain name in the list. Click Delete
Trusted Domain button.
• To delete all domain names: Click Delete All button.
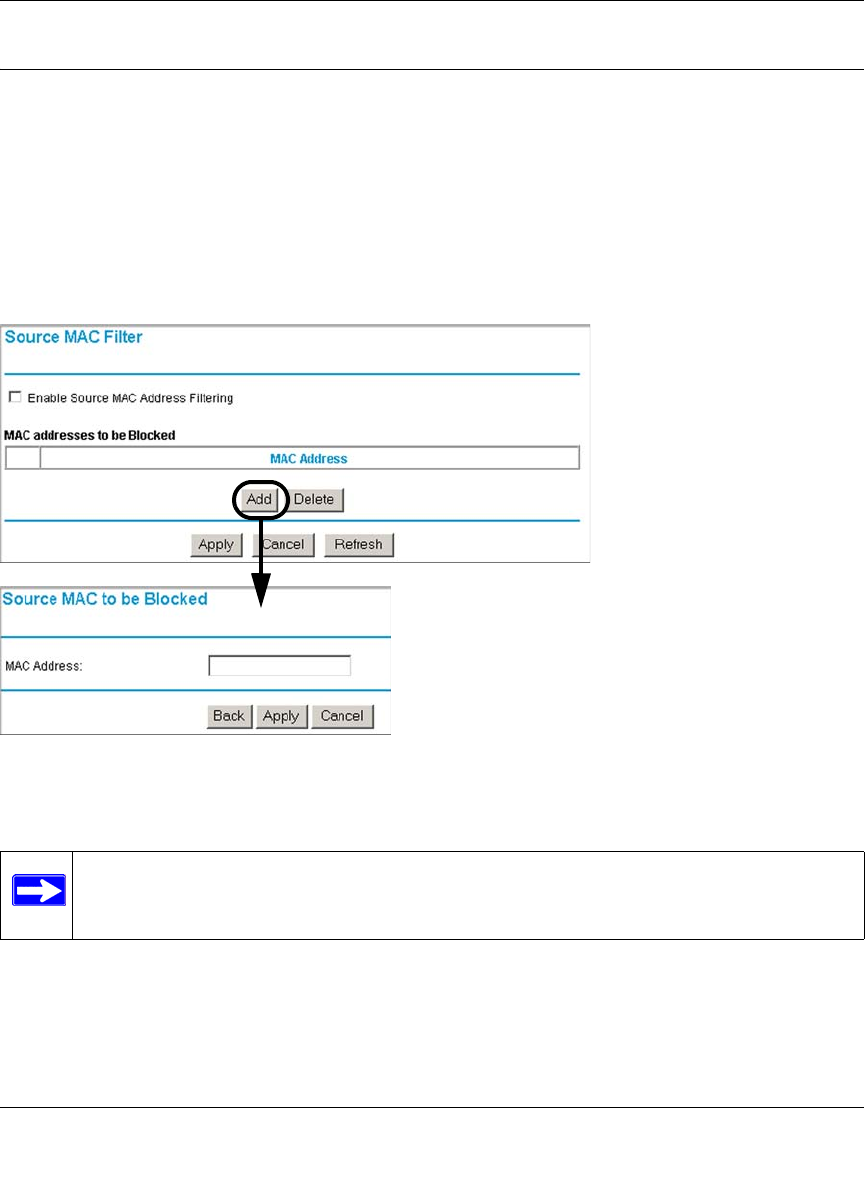
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-27
202-10085-01, March 2005
Source MAC Filtering
Source MAC Filter will drop the Internet-bound traffic received from the PCs with the specified
MAC address.
• By default, the source MAC address filter is disabled. All the traffic received from PCs with
any MAC address is allowed by default.
• When enabled, Internet-bound traffic will be dropped from the PCs that have the configured
MAC addresses.
Figure 6-16: Source MAC Filter screens
Note: For additional ways of restricting outbound traffic, see “Outbound Rules (Service
Blocking)” on page 6-12.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-28 Firewall Protection and Content Filtering
202-10085-01, March 2005
Port Triggering
Port triggering allows some applications to function correctly that would otherwise be partially
blocked by the firewall. Using this feature requires that you know the port numbers used by the
Application.
Once configured, operation is as follows:
• A PC makes an outgoing connection using a port number defined in the Port Triggering table.
• This Router records this connection, opens the additional INCOMING port or ports associated
with this entry in the Port Triggering table, and associates them with the PC.
• The remote system receives the PCs request and responds using the different port numbers that
you have now opened.
• This Router matches the response to the previous request, and forwards the response to the PC.
Without Port Triggering, this response would be treated as a new connection request rather
than a response. As such, it would be handled in accordance with the Port Forwarding rules.
• Only 1 PC can use a Port Triggering application at any time.
Table 6-5. Source MAC address filter
Item Description
Activation • Enable the source MAC filter by ticking the check box.
• Press APPLY.
Add • Now add the MAC Addresses from which the traffic should be dropped by clicking
on ADD button.
Each time one MAC Address entry can be added.
MAC Address input should be entered with ':' separator. A valid MAC address will
have 0 to 9 and A to F.
Example: 00:e0:4c:69:0a:11
• Press APPLY.
Now the traffic from the specified MAC addresses will be dropped.
Disable • To Disable Source MAC Filter, uncheck Source MAC Filter Enable check box.
The list of the MAC Addresses can be kept in the database.
• If the filter has to be avoided for a specific MAC address in the database, select the
MAC address entry and click on Delete button.
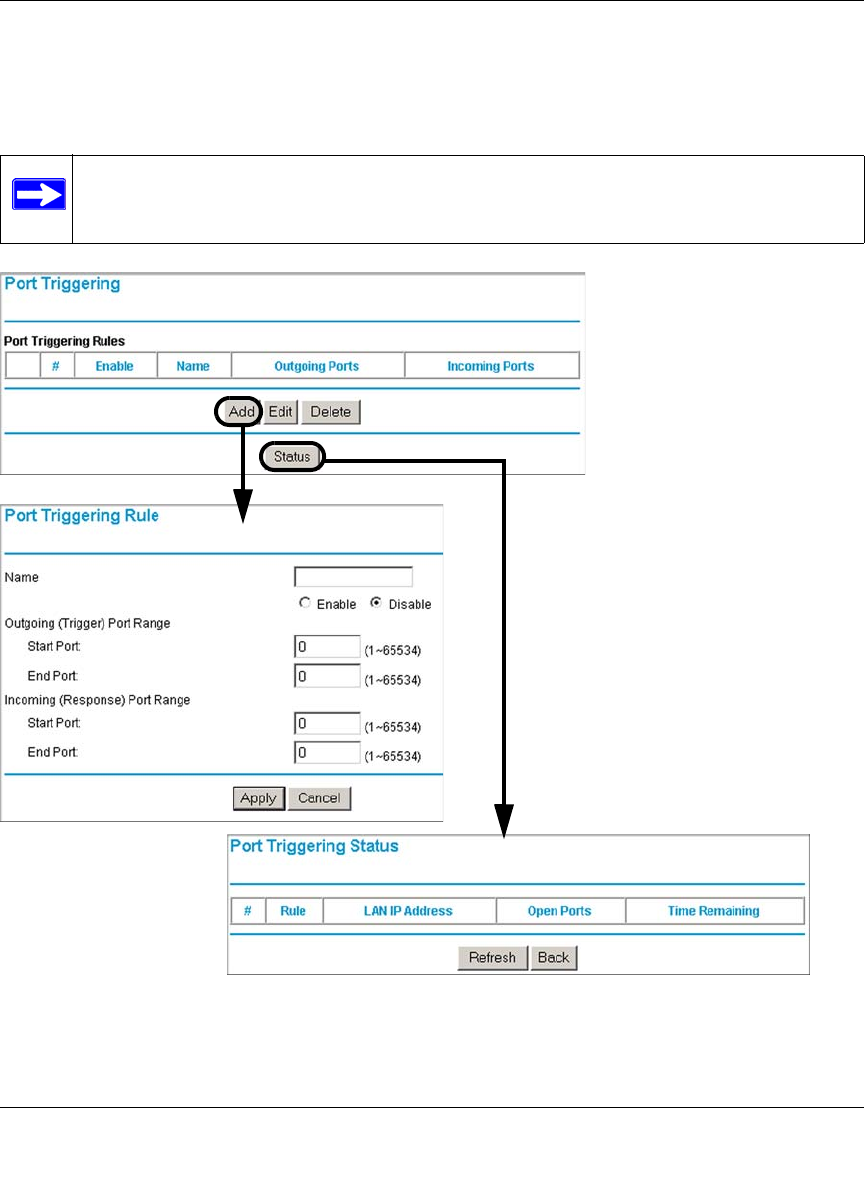
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-29
202-10085-01, March 2005
• After a PC has finished using a Port Triggering application, there is a Time-out period before
the application can be used by another PC. This is required because this Router cannot be sure
when the application has terminated.
Figure 6-17: Port Triggering screens
Note: For additional ways of allowing inbound traffic, see “Inbound Rules (Port
Forwarding)” on page 6-5.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-30 Firewall Protection and Content Filtering
202-10085-01, March 2005
Getting E-Mail Notifications of Event Logs and Alerts
Your router will log security-related events such as denied incoming service requests, hacker
probes, and administrator logins, according to your settings on this screen.
If you have set up content filtering on the Block Sites page (see “Block Sites” on page 6-24), you
can also log when someone on your network tried to access a blocked site.
In order to receive logs and alerts by e-mail, you must provide your e-mail information in the
E-Mail Logs subheading:
Table 6-6. Port Triggering
Item Description
Port Triggering
Rules • Enable - Indicates if the rule is enabled or disabled. Generally, there is no need to
disable a rule unless it interferes with some other function such as Port Forwarding.
• Name - The name for this rule.
• Outgoing Ports - The port or port range for outgoing traffic. An outgoing connection
using one of these ports will trigger this rule.
• Incoming Ports - The port or port range used by the remote system when it
responds to the outgoing request. A response using one of these ports will be
forwarded to the PC which triggered this rule.
Adding a new Rule • To add a new rule, click the Add and enter the following data on the resulting
screen.
• Name - enter a suitable name for this rule (e.g., the name of the application)
• Enable/Disable - select the desired option.
• Outgoing (Trigger) Port Range - enter the range of port numbers used by the
application when it generates an outgoing request.
• Incoming (Response) Port Range - enter the range of port numbers used by the
remote system when it responds to the PC's request.
Modifying or Deleting
an existing Rule: • Select the desired rule by clicking the radio button beside the rule.
• Click Edit or Delete as desired.
Checking Operation
and Status To see which rules are currently being used, click the Status button. The following
data will be displayed:
• Rule - the name of the Rule.
• LAN IP Address - The IP address of the PC currently using this rule.
• Open Ports - the Incoming ports which are associated the this rule. Incoming traffic
using one of these ports will be sent to the IP address above.
• Time Remaining - The time remaining before this rule is released, and thus
available for other PCs. This timer is restarted whenever incoming or outgoing
traffic is received.
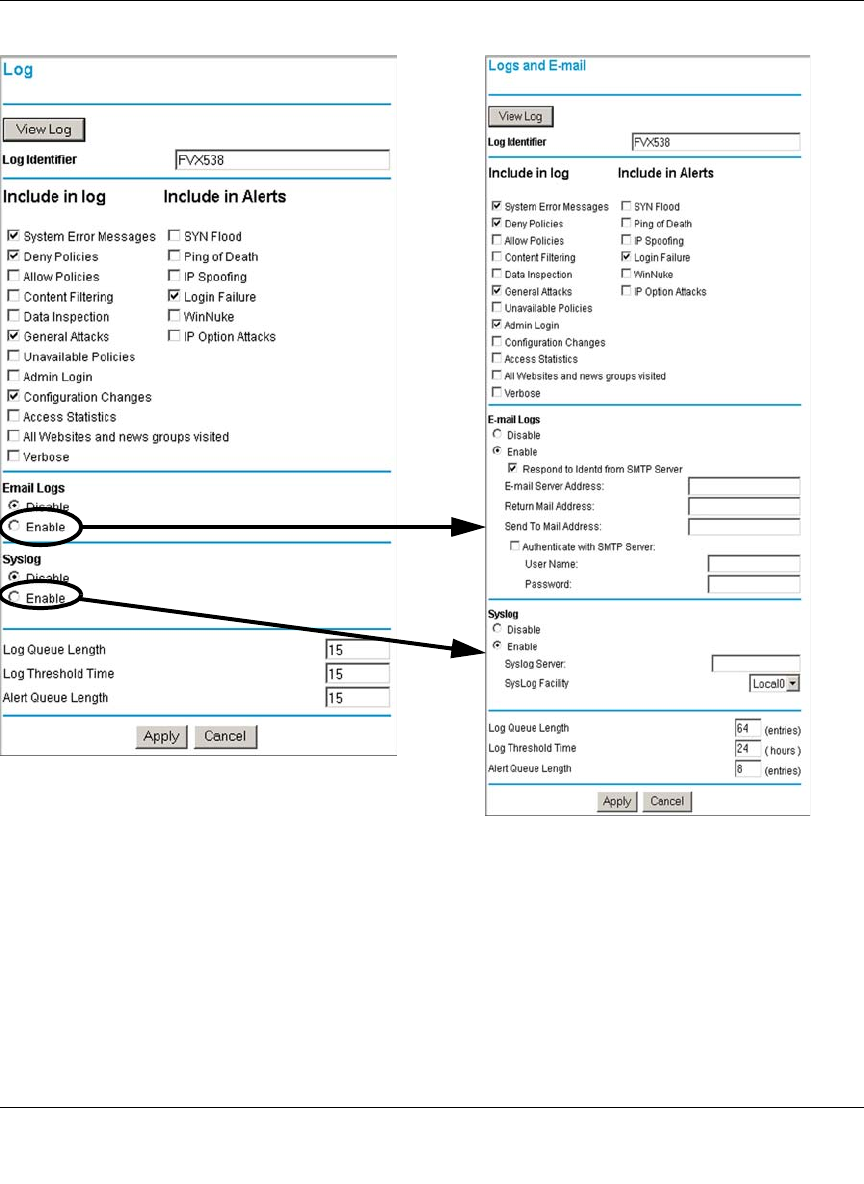
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-31
202-10085-01, March 2005
Figure 6-18: Logs and E-mail screens
Click on View Log button to view various log messages generated by the Router.
• In view log window To delete all log entries: Click Clear Log.
• To see the most recent entries: Click Refresh.
• To E-mail the log messages now: Click Send Log.
Log Identifier is a mandatory field to identify the log messages. This ID appended to log messages.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-32 Firewall Protection and Content Filtering
202-10085-01, March 2005
Items to include in the log:
• Use these checkboxes to determine which events are included in the log. Selecting all events
will increase the size of the log, so it is good practice to disable any events which are not really
required.
• Selecting an event under Include In Log will enable logging of messages pertaining to that
event. Ex: Selecting Admin Login, will enable generation of log messages whenever Admin
logs in.
• Selecting an event under Include In Alerts will enable logging of messages pertaining to that
event. This category typically contains Internet Attack events. Ex: Selecting SYN Flood, will
enable generation of Alert messages whenever SYN Flood occurs.
Emailing logs:
• If you have Email Logs enabled, you'll receive these logs in an Email message.
• To receive alerts and logs by e-mail you have to enable Email Logs option.
– In the Respond to Identd from SMTP Server check this box to respond to IDENT protocol.
– In the Email Server address Enter E-mail outgoing SMTP mail server of your ISP (for
example, 172.16.1.10).
– If you leave this box blank, no alerts or logs will be sent to you.
– In the Return Email Address box, type the user's e-mail address.
– In the Log / Alert Email box, type the e-mail address where the logs and alerts will be sent.
Use a full e-mail address (for example, ChrisXY@myISP.com).
– In the Authenticate with SMTP server Check this box to enable authentication for alerts
and logs.
– In the User Name Box, fill the user name for SMTP authentication.
– In the Password Box, fill the password for SMTP authentication.
Syslog—Enable or disable as required:
• Disable - Select this if you don't have a Syslog server.
• Enable - Syslog server IP address - If your Syslog server has a fixed IP address, select this
option, and enter the IP address of your Syslog server and select appropriate syslog facility.
Message length and frequency:
• In the Log Queue Length box, set the logs queue length.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-33
202-10085-01, March 2005
• In the Log Threshold Time box, set the logs Threshold time.
• In the Alert Queue Length box, set the alerts queue length.
Click Apply to have your changes take effect.
Syslog
You can configure the firewall to send system logs to an external PC that is running a syslog
logging program. Enter the IP address of the logging PC and click the Enable Syslog checkbox.
Logging programs are available for Windows, Macintosh, and Linux computers.
Viewing Logs of Web Access or Attempted Web Access
The firewall will log security-related events such as denied incoming and outgoing service
requests, hacker probes, and administrator logins.
• If you enable content filtering in the Block Sites menu, the Log page will also show you when
someone on your network tried to access a blocked site.
• If you enabled e-mail notification, you'll receive these logs in an e-mail message.
• If you don't have e-mail notification enabled, you can view the logs here.
An example is shown in Figure 6-19. Log entries are described in Table 6-7 and log action buttons
are described in Table 6-8.
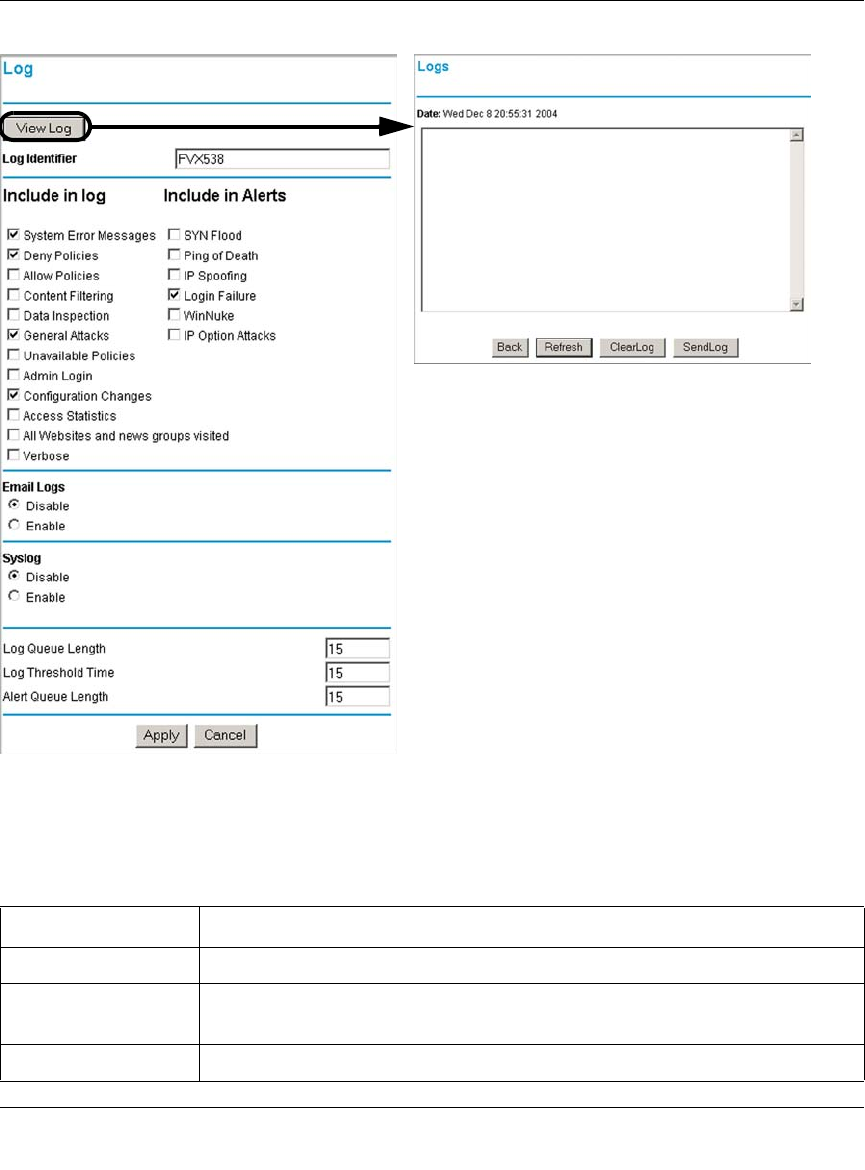
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-34 Firewall Protection and Content Filtering
202-10085-01, March 2005
Figure 6-19: Firewall Logs menu
Table 6-7. Log entry descriptions
Field Description
Date and Time The date and time the log entry was recorded.
Description or
Action The type of event and what action was taken if any.
Source IP The IP address of the initiating device for this log entry.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Firewall Protection and Content Filtering 6-35
202-10085-01, March 2005
Administrator Information
Consider the following operational items:
1. As an option, you can enable remote management if you have to manage distant sites from a
central location (see “Enabling Remote Management Access” on page 8-9).
2. Although rules (see “Using Rules to Block or Allow Specific Kinds of Traffic” on page 6-1) is
the basic way of managing the traffic through your system, you can further refine your control
with the following optional features of the FVS124G VPN Firewall:
– Groups and hosts (see “Managing Groups and Hosts” on page 6-20)
– Services (see “Services-Based Rules” on page 6-4)
– Schedules (see “Using a Schedule to Block or Allow Specific Traffic” on page 6-22)
– Block sites (see “Block Sites” on page 6-24)
– Source MAC filtering (see “Source MAC Filtering” on page 6-27)
– Port triggering (see “Port Triggering” on page 6-28)
Source port and
interface The service port number of the initiating device, and whether it originated
from the LAN or WAN
Destination The name or IP address of the destination device or website.
Destination port and
interface The service port number of the destination device, and whether it’s on the
LAN or WAN.
Table 6-8. Log action buttons
Field Description
Refresh Click this button to refresh the log screen.
Clear Log Click this button to clear the log entries.
Send Log Click this button to email the log immediately.
Table 6-7. Log entry descriptions
Field Description

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
6-36 Firewall Protection and Content Filtering
202-10085-01, March 2005
Virtual Private Networking 7-1
202-10085-01, March 2005
Chapter 7
Virtual Private Networking
This chapter describes how to use the virtual private networking (VPN) features of the FVS124G
VPN Firewall. VPN tunnels provide secure, encrypted communications between your local
network and a remote network or computer.
Tip: When using dual WAN port networks, use the VPN Wizard to configure the basic parameters
and them edit the VPN and IKE Policy screens for the various VPN scenarios.
Dual WAN Port Systems
The dual WAN ports in the FVS124G VPN Firewall can be configured for either rollover mode for
increased system reliability or load balancing mode for optimum bandwidth efficiency. This WAN
mode choice then impacts how the VPN features have to be configured.
Rollover vs. Load Balancing Mode
Refer to “Virtual Private Networks (VPNs)” on page 3-5 for an overview of the IP addressing
requirements for VPN in the two WAN modes.
Table 7-1. IP addressing requirements for VPNs in dual WAN port systems
Configuration and WAN IP address Rollover Mode*
*All tunnels must be re-established after a rollover using the new WAN IP address.
Load Balancing Mode
VPN Road Warrior
(client-to-gateway) Fixed FQDN required Allowed (FQDN optional)
Dynamic FQDN required FQDN required
VPN Gateway-to-Gateway Fixed FQDN required Allowed (FQDN optional)
Dynamic FQDN required FQDN required
VPN Telecommuter
(client-to-gateway through
a NAT router)
Fixed FQDN required Allowed (FQDN optional)
Dynamic FQDN required FQDN required
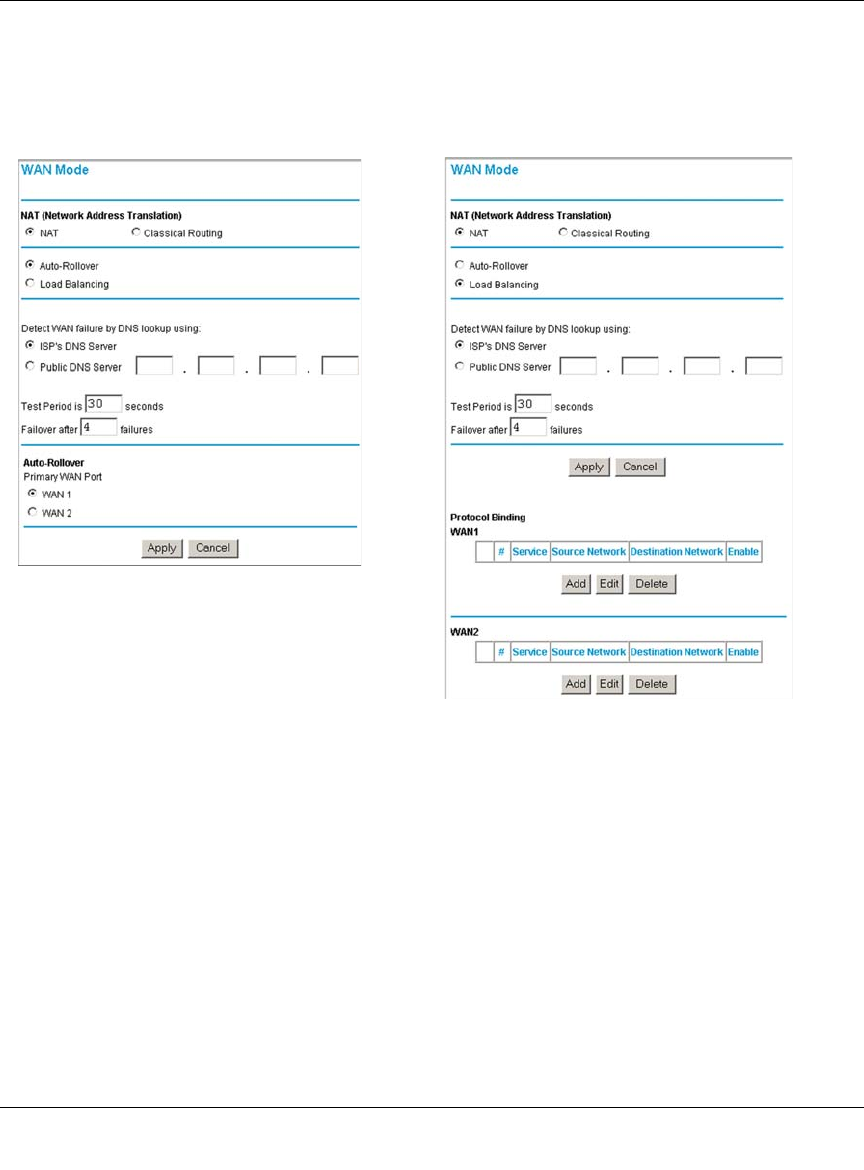
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-2 Virtual Private Networking
202-10085-01, March 2005
Figure 7-1 shows the setup screens for the selected WAN mode. This setup is accomplished in
“Step 4: Configure the WAN Mode (Required for Dual WAN)” on page 4-15.
Figure 7-1: WAN Mode Setup screens
Fully Qualified Domain Names
The use of fully qualified domain names is:
• Mandatory when the WAN ports are in rollover mode (Figure 7-2)
• Mandatory when the WAN port are in load balancing mode and the IP addresses are dynamic
(Figure 7-3)
• Optional when the WAN ports are in load balancing mode the IP addresses are static
(Figure 7-3)
Rollover Mode Setup Screen Load Balancing Mode Setup Screen
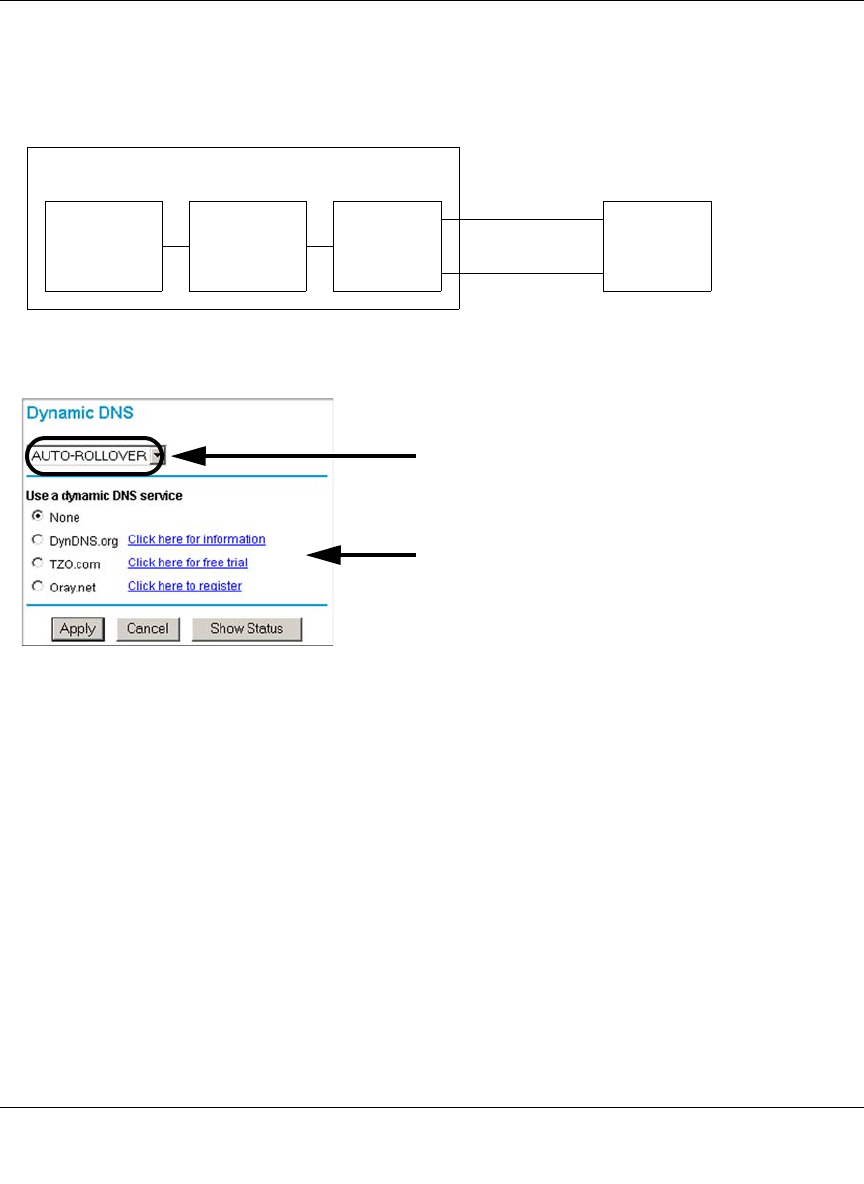
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-3
202-10085-01, March 2005
See “Step 5: Configure Dynamic DNS (If Needed)” on page 4-20 for how to select and configure
the Dynamic DNS service.
Figure 7-2: Functional operation of FVS124G WAN ports for rollover mode
Rest of
FVS124G
Functions
FVS124G
WAN Port
Functions
FVS124G
Rollover
Control
FVS124G Firewall
WAN 1 Port
WAN 2 Port Internet
FQDN required
FVS124G Functional Block Diagram
Dynamic DNS screen
Same FQDN setup for BOTH WAN ports
Select Dynamic DNS service
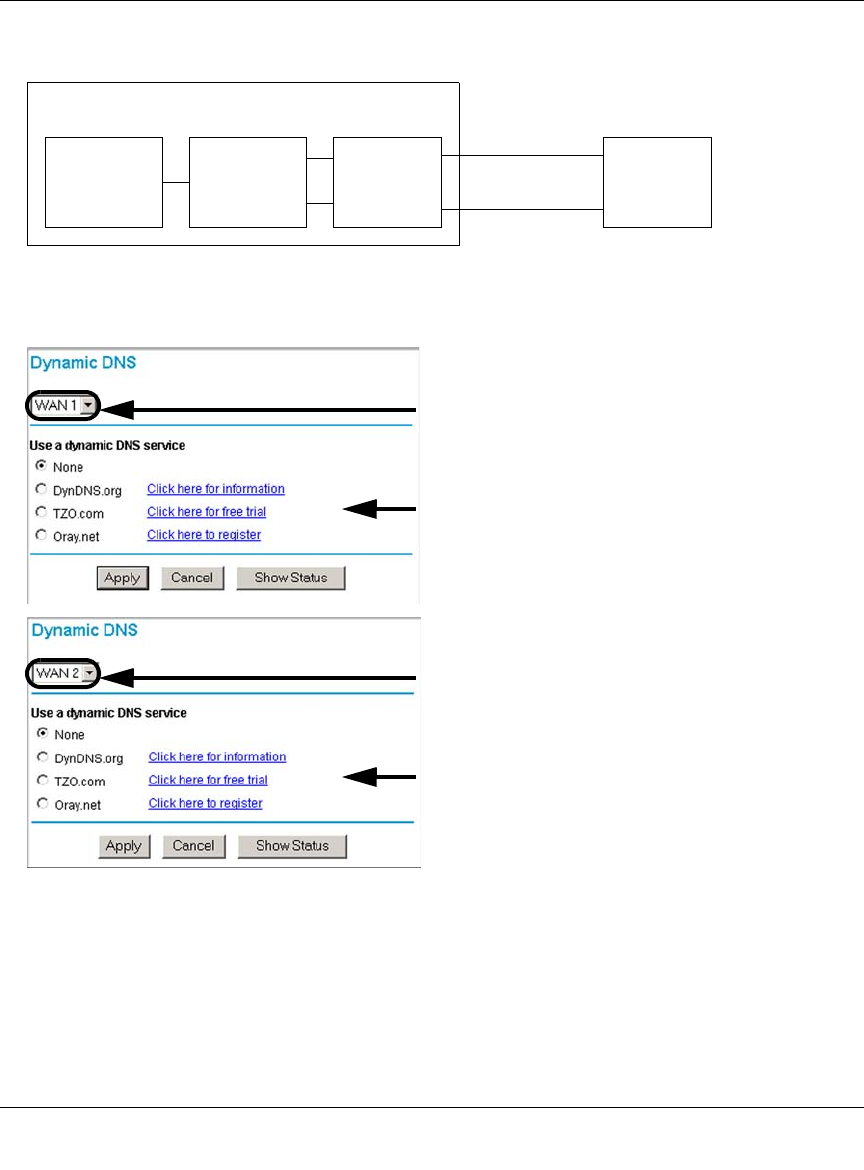
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-4 Virtual Private Networking
202-10085-01, March 2005
Figure 7-3: Functional operation of FVS124G WAN ports for load balancing mode
Rest of
FVS124G
Functions
FVS124G
WAN Port
Functions
Load
Balancing
Control
FVS124G Firewall
WAN 1 Port
WAN 2 Port Internet
FQDN required (dynamic IP addresses)
FVS124G Functional Block Diagram
Dynamic DNS screens
FQDN setup for WAN1 port
Select Dynamic DNS service
FQDN optional (static IP addresses)
Select Dynamic DNS service
FQDN setup for WAN2 port
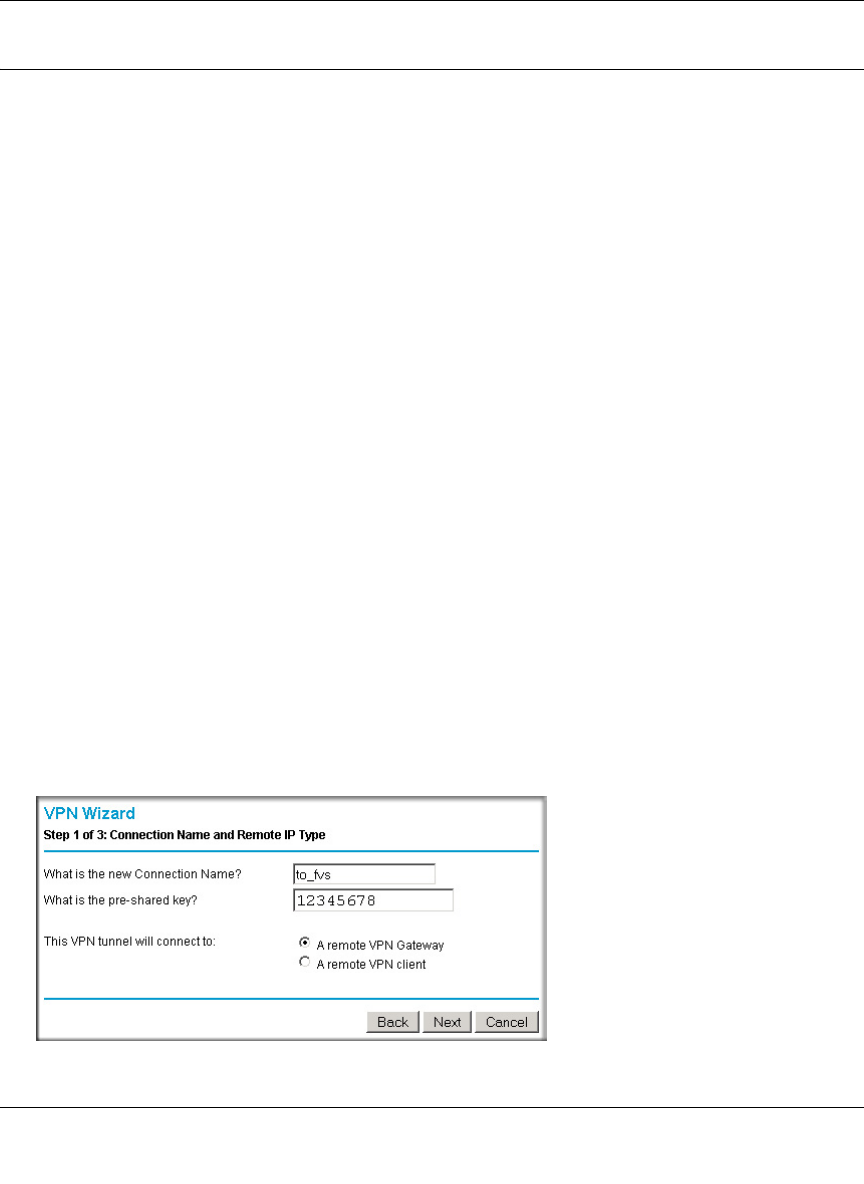
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-5
202-10085-01, March 2005
Creating a VPN Connection: Between FVX538 and FVS124G
This section describes how to configure a VPN connection between a NETGEAR FVX538 VPN
Firewall and a NETGEAR FVS124G VPN Firewall.
Using each firewall's VPN Wizard, we will create a set of policies (IKE and VPN) that will allow
the two firewalls to connect from locations with fixed IP addresses. Either firewall can initiate the
connection.
This procedure was developed and tested using:
• Netgear FVX538 VPN Firewall with version 1.6.11 firmware
– WAN1 IP address is 10.1.0.118
– LAN IP address subnet is 192.168.1.1 255.255.255.0
• Netgear FVS124g VPN Firewall with version 1.0 firmware
– WAN IP address is 10.1.1.150
– LAN IP address subnet is 192.168.2.1 255.255.255.0
Configuring the FVX538
1. Select the VPN Wizard
2. Give the client connection a name, such as to_fvs.
3. Enter a value for the pre-shared key.
4. Select 'a remote VPN gateway'.
Figure 7-4: VPN Wizard start page
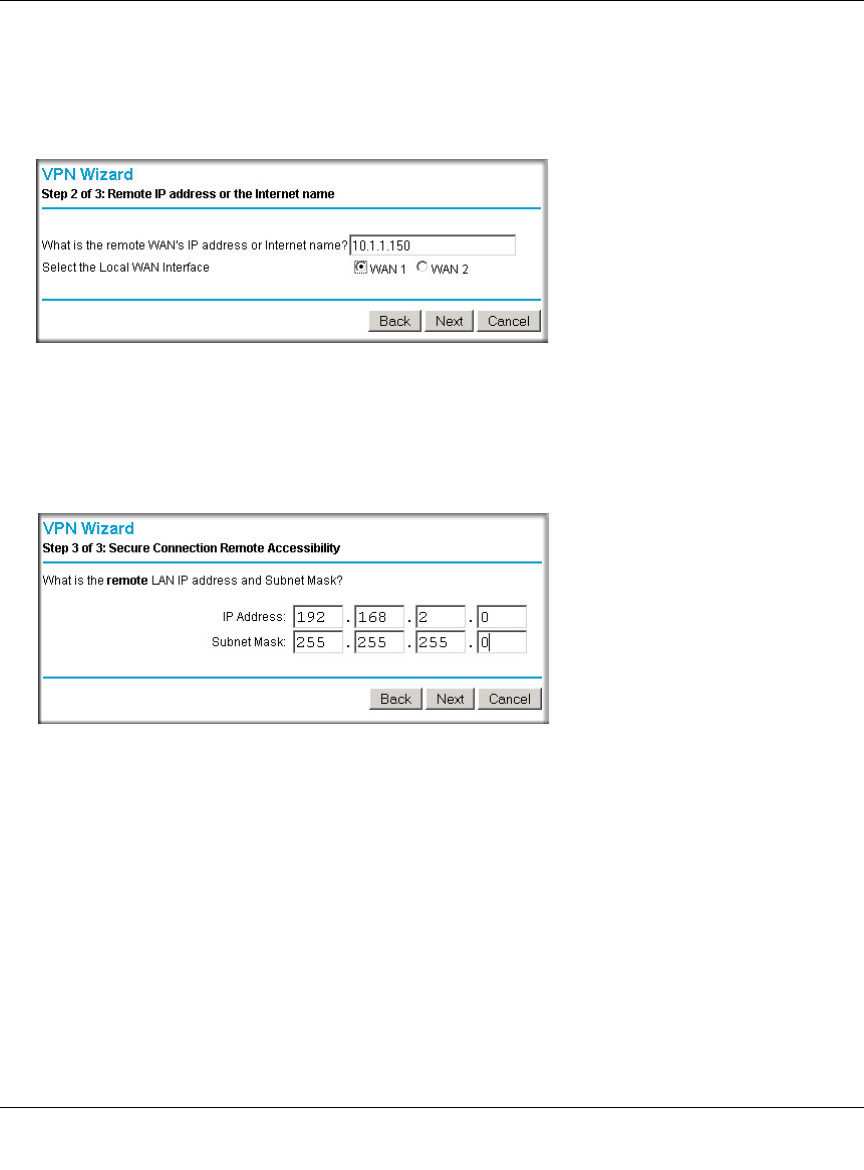
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-6 Virtual Private Networking
202-10085-01, March 2005
5. Click Next.
6. Enter the WAN IP address of the remote FVS124G.
7. Click WAN1 to bind this connection to the WAN1 port.
Figure 7-5: WAN IP address of remote FVS124G
8. Click Next.
9. Enter the LAN IP address and subnet mask of the remote FVS124G.
Figure 7-6: LAN IP address and subnet mask of remote FVS124G
10. Click Next.
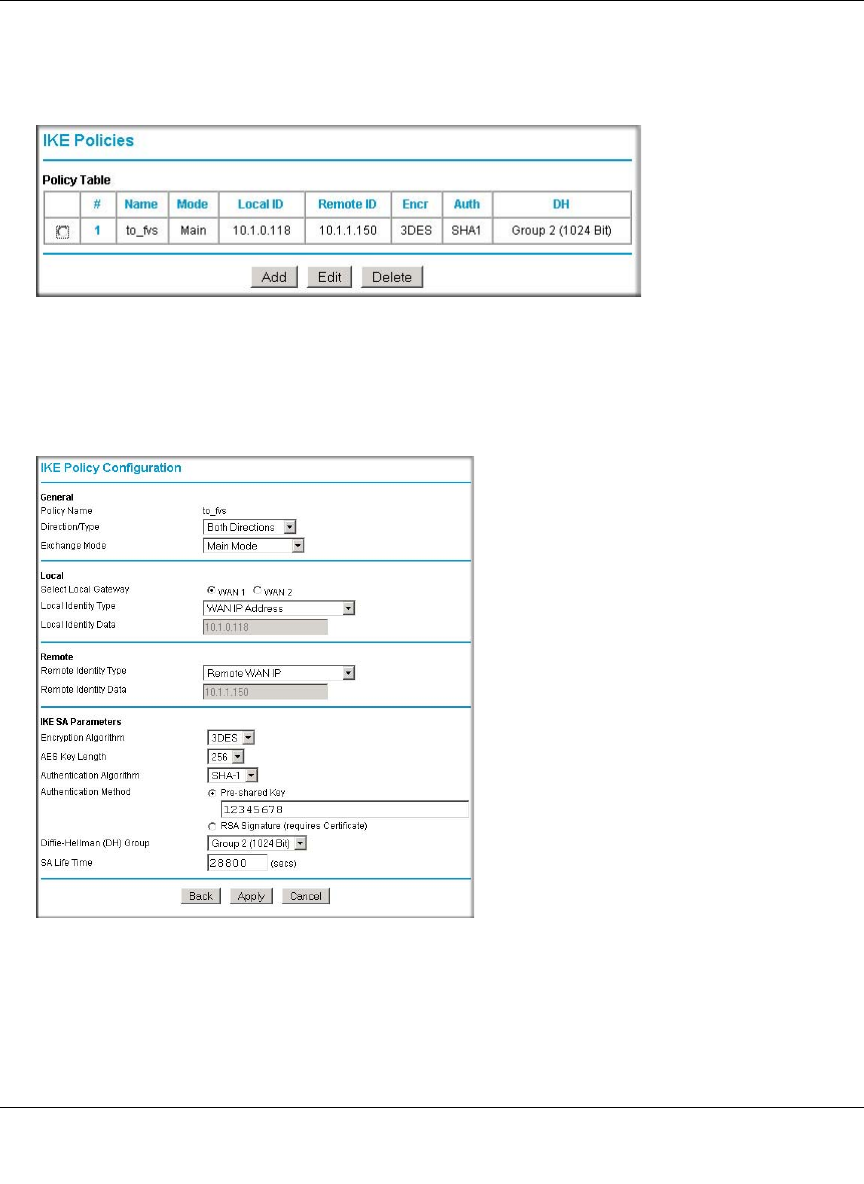
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-7
202-10085-01, March 2005
11. Click Done to create the 'to_fvs' IKE and VPN policies.
In the IKE Policies menu, the 'to_fvs' IKE policy will appear in the table.
Figure 7-7: IKE Policies
12. You can view the IKE parameters by selecting 'to_fvs' and clicking Edit. It should not be
necessary to make any changes.
Figure 7-8: FVX538-to-FVS124G IKE screen
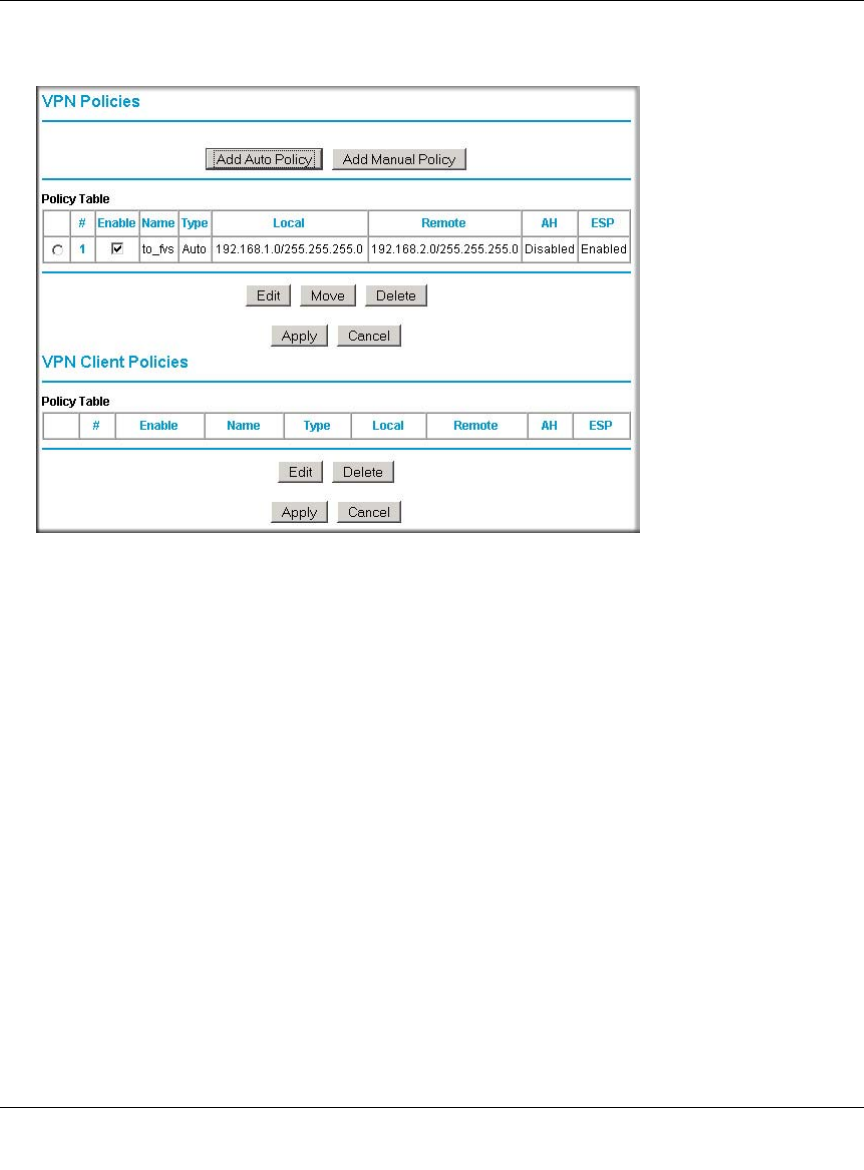
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-8 Virtual Private Networking
202-10085-01, March 2005
13. In the VPN Policies menu, the 'to_fvs' VPN policy will appear in the table.
Figure 7-9: FVX538 VPN Policies screen
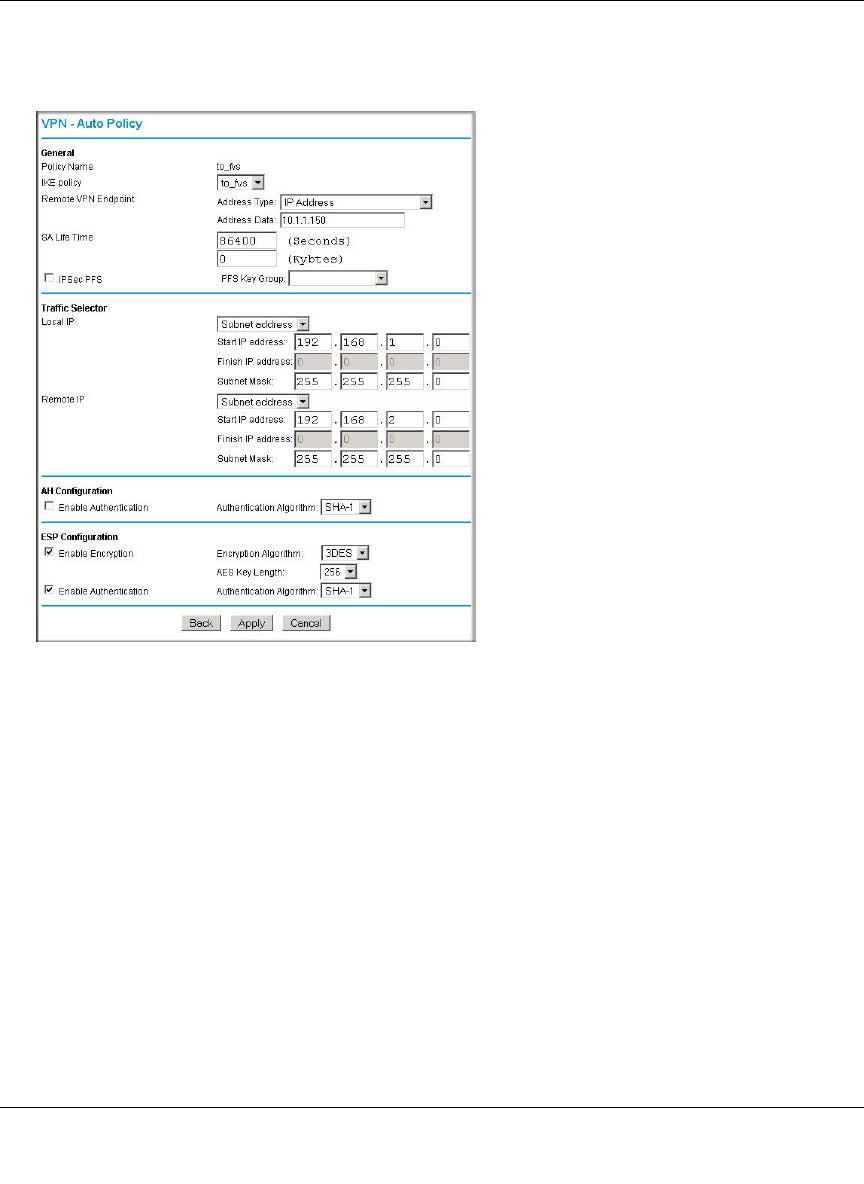
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-9
202-10085-01, March 2005
14. You can view the VPN parameters by selecting 'to_fvs' and clicking Edit. It should not be
necessary to make any changes.
Figure 7-10: FVX538-to-FVS124G VPN screen
Configuring the FVS124G
1. Select the VPN Wizard
2. Give the client connection a name, such as to_fvx.
3. Enter a value for the pre-shared key.
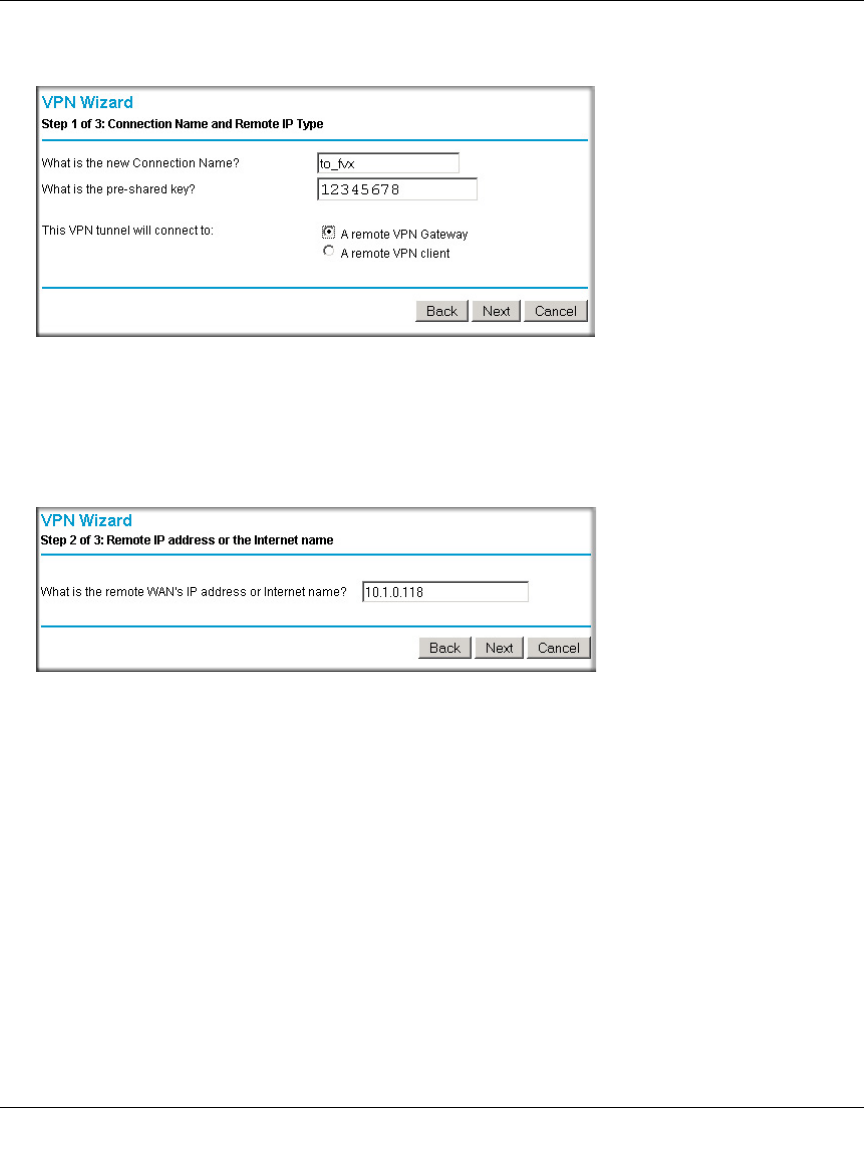
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-10 Virtual Private Networking
202-10085-01, March 2005
4. Select 'a remote VPN gateway'.
Figure 7-11: VPN Wizard start page
5. Click Next.
6. Enter the WAN IP address of the remote FVX538.
Figure 7-12: WAN IP address of remote FVX538
7. Click Next.
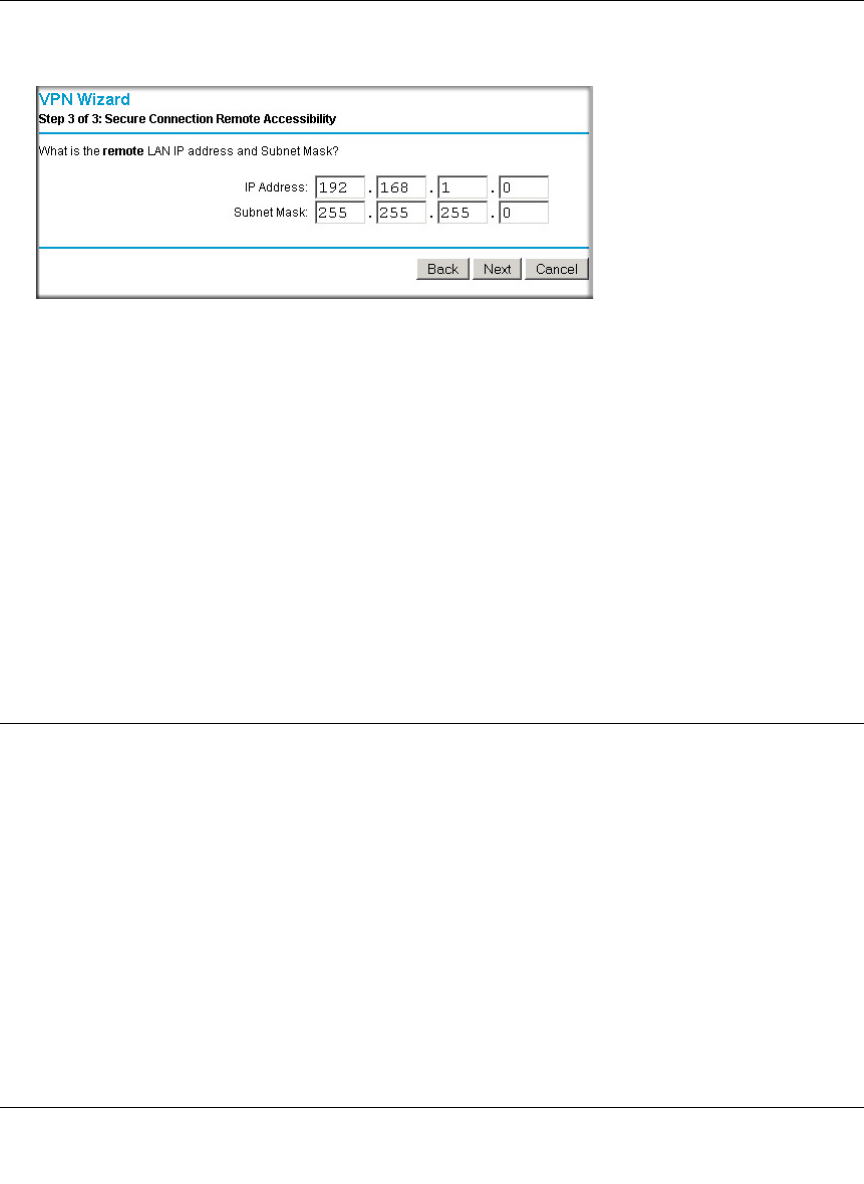
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-11
202-10085-01, March 2005
8. Enter the LAN IP address and subnet mask of the remote FVX538.
Figure 7-13: LAN IP address and subnet mask of remote FVX538
9. Click Next.
10. Click Done to create the 'to_fvx' IKE and VPN policies.
Testing the Connection
1. From a PC on either firewall's LAN, try to ping a PC on the other firewall's LAN. Establishing
the VPN connection may take several seconds.
2. For additional status and troubleshooting information, view the VPN log and status menu in
the FVX538 or FVS124G.
Creating a VPN Connection: Netgear VPN Client to FVS124G
This section describes how to configure a VPN connection between a Windows PC and the
FVS124G VPN Firewall.
Using the FVS124G's VPN Wizard, we will create a single set of policies (IKE and VPN) that will
allow up to 50 remote PCs to connect from locations in which their IP addresses are unknown in
advance. The PCs may be directly connected to the Internet or may be behind NAT routers. If more
PCs are to be connected, an additional policy or policies must be created.
Each PC will use Netgear's VPN Client. Since the PC's IP address is assumed to be unknown, the
PC must always be the Initiator of the connection.
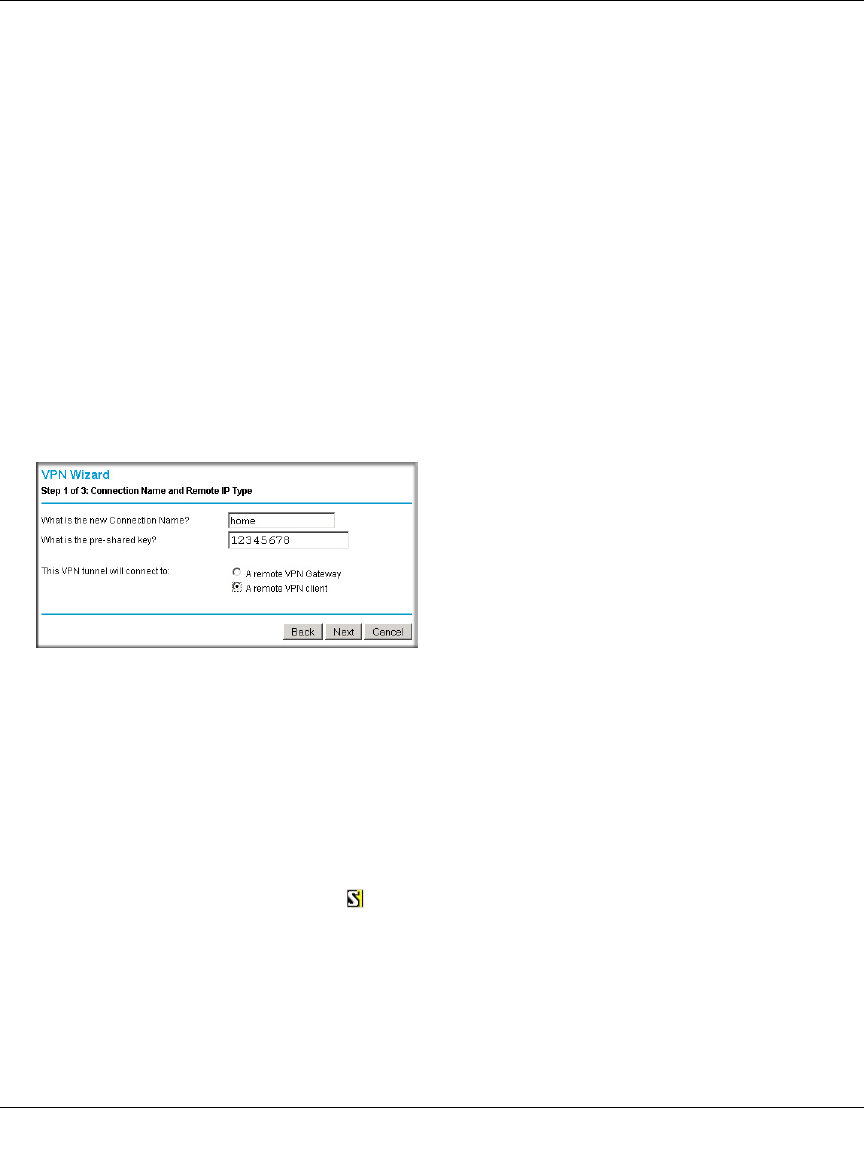
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-12 Virtual Private Networking
202-10085-01, March 2005
This procedure was developed and tested using:
• Netgear FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports with
version 1.0 firmware
• Netgear VPN Client version 10.3.5 (Build 6)
• NAT router: Netgear FR114P with version 1.5_09 firmware
Configuring the FVS124G
1. Select the VPN Wizard
2. Give the client connection a name, such as home.
3. Enter a value for the pre-shared key.
4. Select 'a remote VPN client'.
Figure 7-14: VPN Wizard
5. Click Next to go to the summary page.
6. Click Done to create the 'home' IKE and VPN policies.
Configuring the VPN Client
1. Right-click on the VPN client icon in your Windows toolbar and select the Security Policy
Editor.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-13
202-10085-01, March 2005
2. In the upper left of the Policy Editor window, click the New Document icon to open a New
Connection.
Figure 7-15: New Client Connection screen
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-14 Virtual Private Networking
202-10085-01, March 2005
3. Give the New Connection a name, such as to_FVS.
Figure 7-16: New connection named
4. In the Remote Party Identity section, select ID Type of IP Subnet.
5. Enter the LAN IP Subnet Address and Subnet Mask of the FVS124G's LAN.
6. Select 'Connect using Secure Gateway Tunnel'.
7. Under ID Type, select 'Domain Name' and 'Gateway IP Address'.
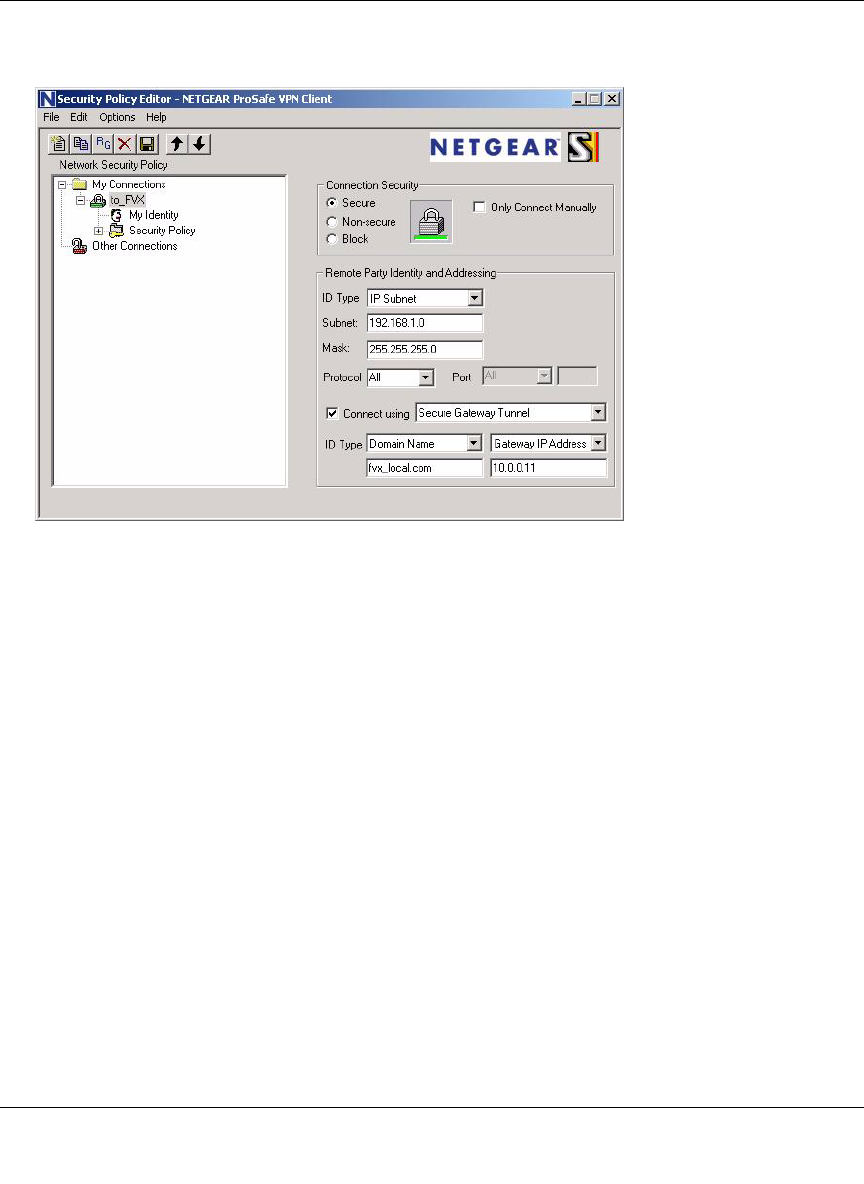
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-15
202-10085-01, March 2005
8. For Domain Name, enter 'fvs_local.com' and enter the WAN IP Address of the FVS124G.
Figure 7-17: Remote client info
9. In the left frame, click on My Identity.
10. Select Certificate = None.
11. Under ID Type, select 'Domain Name'.
The value entered under Domain Name will be of the form '<name><XY>.fvs_remote.com',
where each user must use a different variation on the Domain Name entered here. The <name>
is the policy name used in the FVS124G configuration. In this example, it is 'home'. X and Y
are an arbitrary pair of numbers chosen for each user.
Note: X may not be zero!
In this example, we have entered home11.fvs_remote.com. Up to fifty user variations can be
served by one policy.
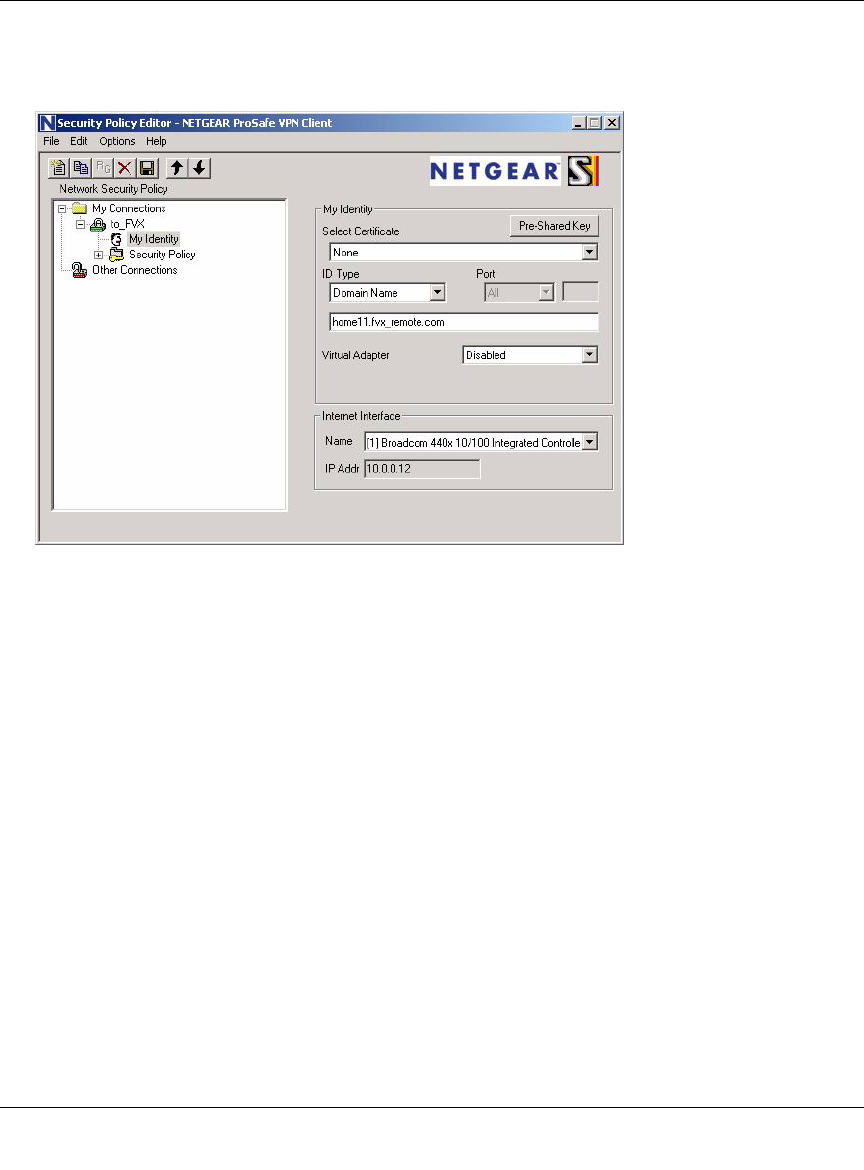
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-16 Virtual Private Networking
202-10085-01, March 2005
12. Leave Virtual Adapter disabled, and select your computer's Network Adapter. Your current IP
address will appear.
Figure 7-18: My Identity screen
13. Before leaving the My Identity menu, click the Pre-Shared Key button.
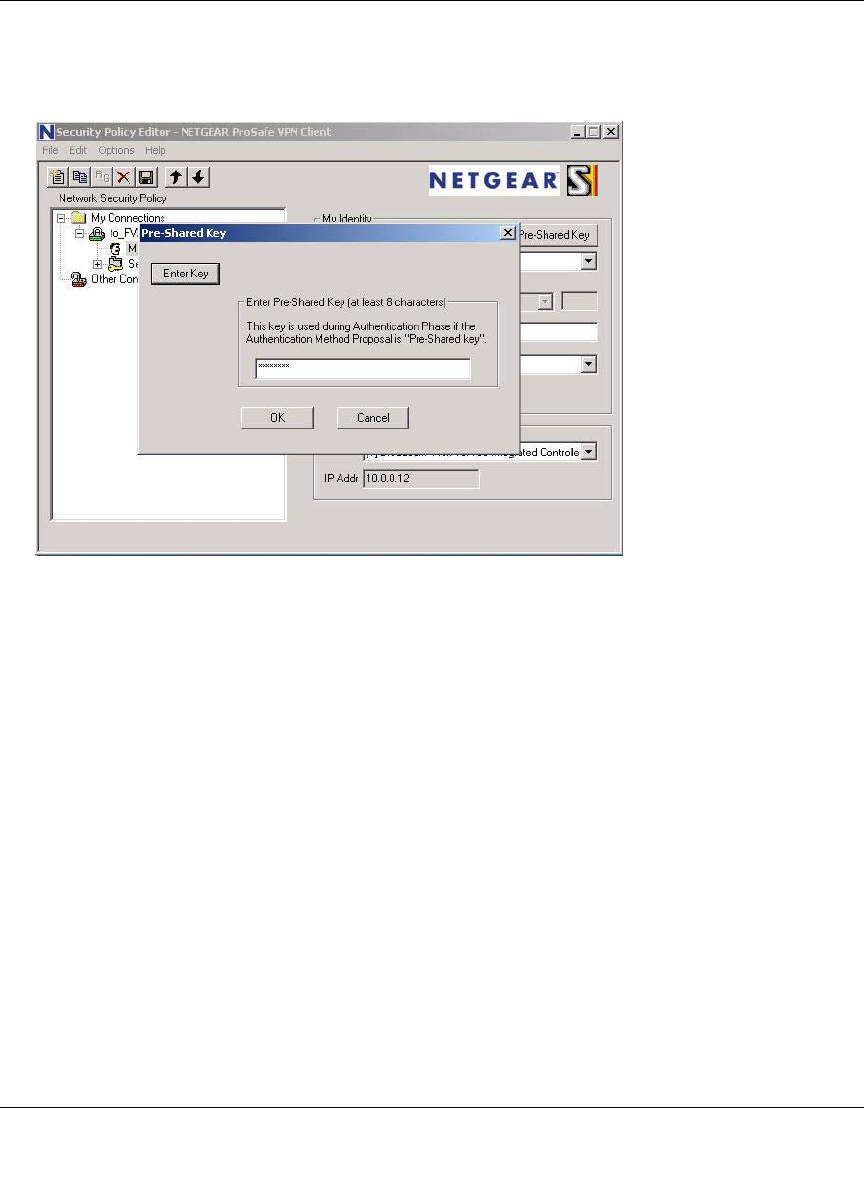
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-17
202-10085-01, March 2005
14. Click Enter Key, type your preshared key, and click OK.
This key will be shared by all users of the FVS124G policy "home".
Figure 7-19: Pre-shared key
15. In the left frame, click on Security Policy.
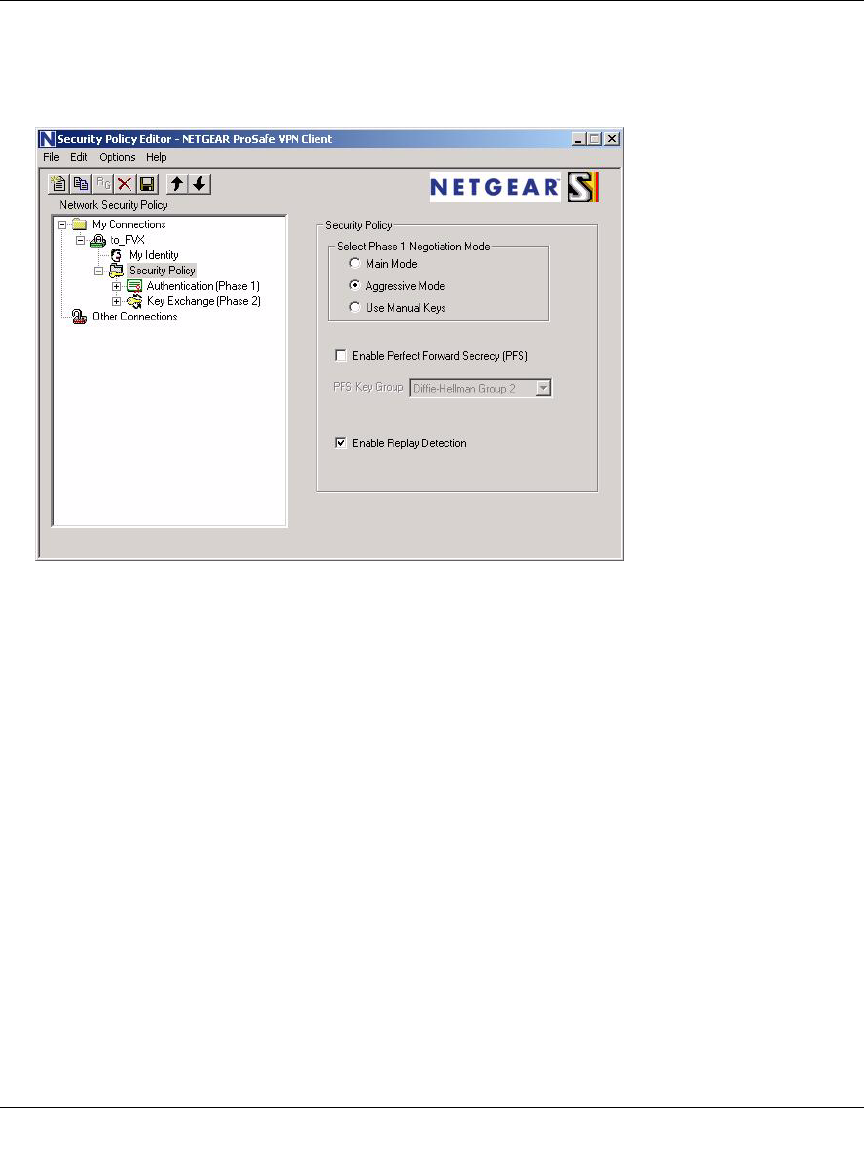
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-18 Virtual Private Networking
202-10085-01, March 2005
16. Select Phase 1 Negotiation Mode = Aggressive Mode.
PFS should be disabled, and Replay Detection should be enabled.
Figure 7-20: Client Security Policy screen
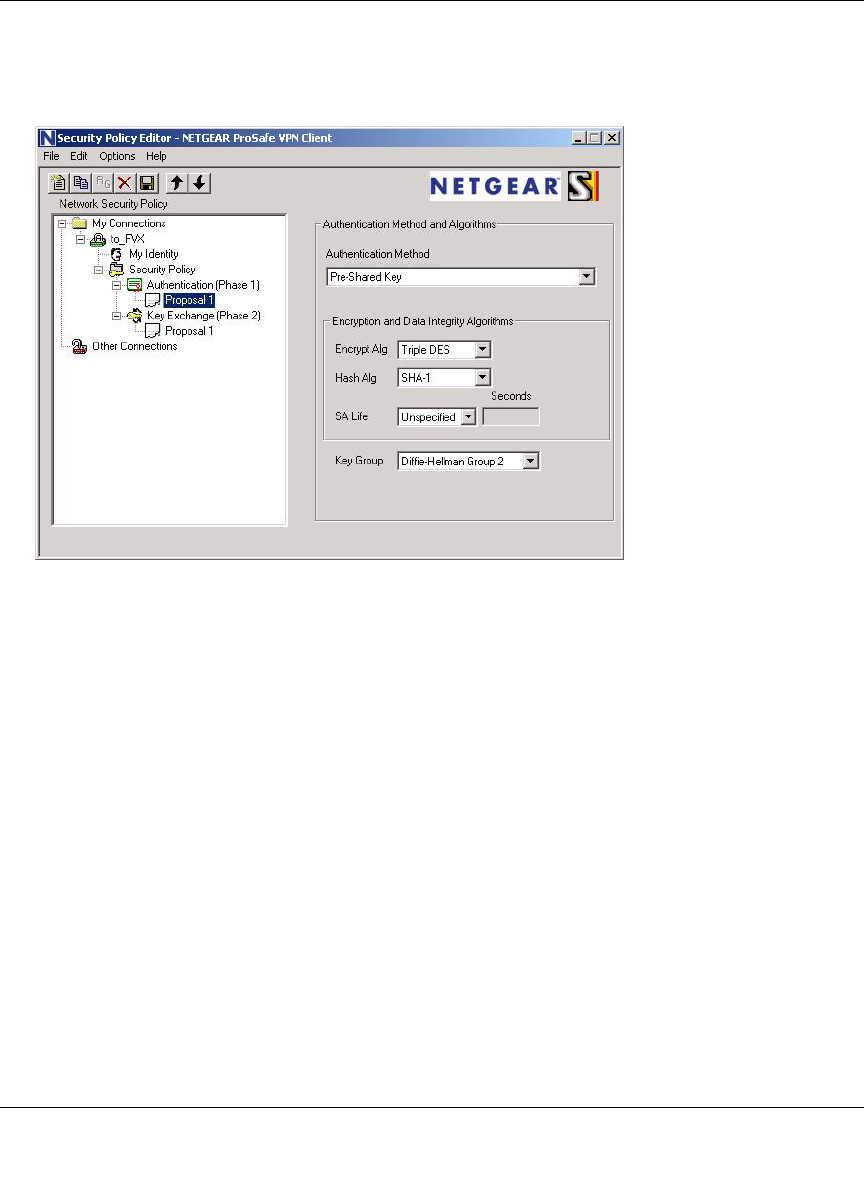
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-19
202-10085-01, March 2005
17. In the left frame, expand Authentication and select Proposal 1.
Compare with the figure below. No changes should be necessary.
Figure 7-21: Client Authorization screen
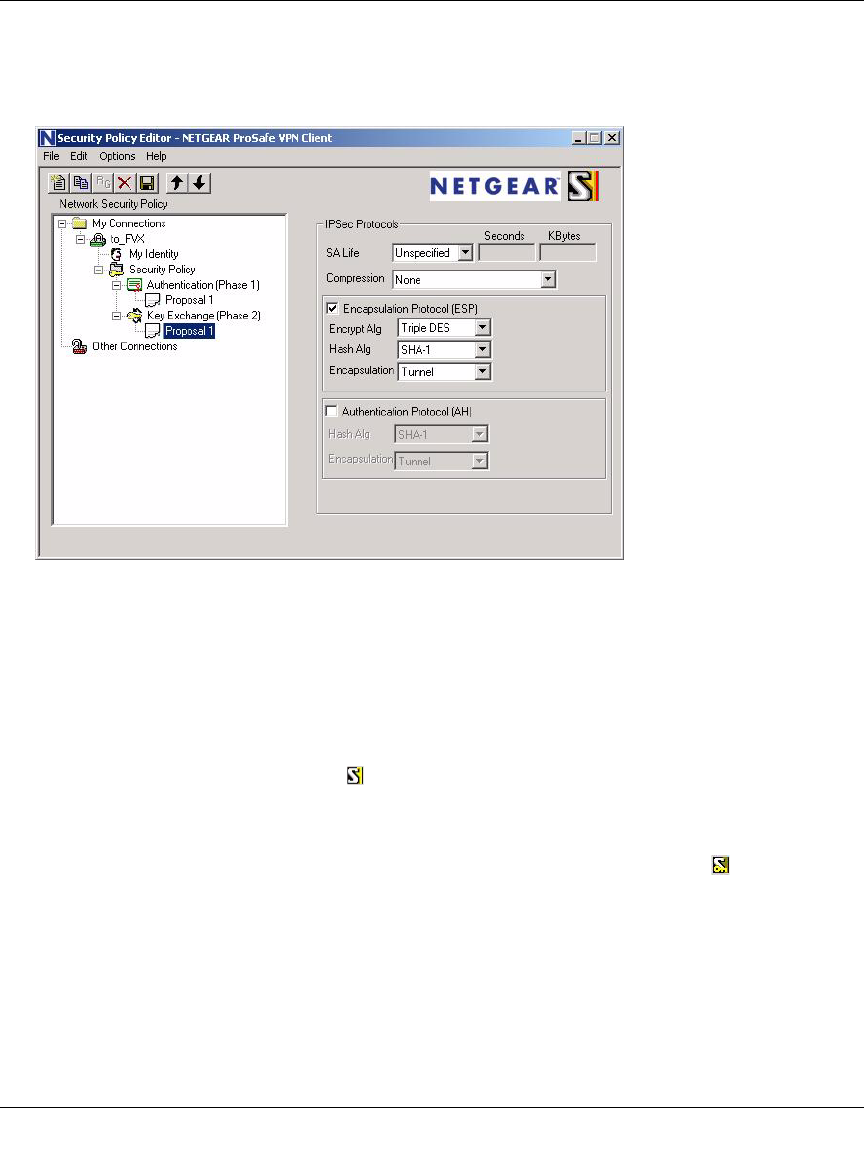
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-20 Virtual Private Networking
202-10085-01, March 2005
18. In the left frame, expand Key Exchange and select Proposal 1.
Compare with the figure below. No changes should be necessary.
Figure 7-22: Client Key Exchange screen
19. In the upper left of the window, click the disk icon to save the policy.
Testing the Connection
20. Right-click on the VPN client icon in your Windows toolbar and select "Connect...", then
"My Connections\to_FVS".
Within 30 seconds you should receive a message "Successfully connected to My
Connections\to_FVS" and the VPN client icon in the toolbar should say On:
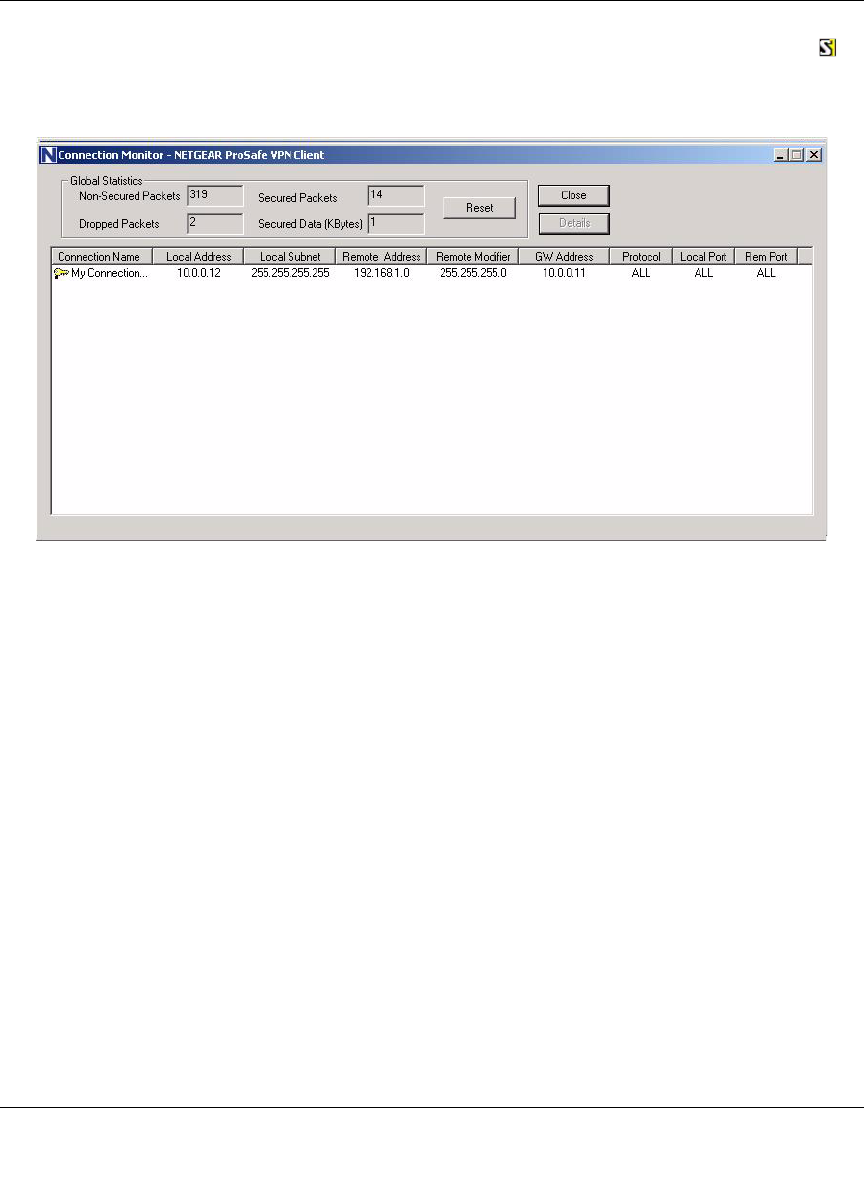
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking 7-21
202-10085-01, March 2005
21. For additional status and troubleshooting information, right-click on the VPN client icon in
your Windows toolbar and select "Connection Monitor" or "Log Viewer", or view the VPN
log and status menu in the FVS124G.
Figure 7-23: Client Connection Monitor screen

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
7-22 Virtual Private Networking
202-10085-01, March 2005

Router and Network Management 8-1
202-10085-01, March 2005
Chapter 8
Router and Network Management
This chapter describes how to use the network management features of your FVS124G ProSafe
VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports. These features can be found by
clicking on the appropriate heading in the Main Menu of the browser interface.
The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports offers many
tools for managing the network traffic to optimize its performance. You can also control
administrator access, be alerted to important events requiring prompt action, monitor the firewall
status, perform diagnostics, and manage the firewall configuration file.
Performance Management
Performance management consists of controlling the traffic through the FVS124G VPN Firewall
so that the necessary traffic gets through when there is a bottleneck and either reducing
unnecessary traffic or rescheduling some traffic to low-peak times to prevent bottlenecks from
occurring in the first place. The FVS124G VPN Firewall has the necessary features and tools to
help the network manager accomplish these goals.
Bandwidth Capacity
At 1.5 Mbps, the WAN ports will support the following traffic rates:
• Load balancing mode: 3 Mbps (two WAN ports at 1.5 Mbps each)
• Rollover mode: 1.5 Mbps (one active WAN port at 1.5 Mbps)
As a result and depending on the traffic being carried, the WAN side of the firewall will be the
limiting factor to throughput for most installations.
Using the dual WAN ports in load balancing mode increases the bandwidth capacity of the WAN
side of the FVS124G VPN Firewall. But there is no backup in case one of the WAN ports fail. In
such an event and with one exception, the traffic that would have been sent on the failed WAN port
gets diverted to the WAN port that is still working, thus increasing its loading. The exception is
traffic that is bound by protocol to the WAN port that failed. This protocol-bound traffic is not
diverted.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-2 Router and Network Management
202-10085-01, March 2005
VPN Firewall Features That Reduce Traffic
Features of the VPN firewall that can be called upon to decrease WAN-side loading are as follows:
• Service blocking
• Block sites
• Source MAC filtering
Service Blocking
Note: This feature is for Advanced Administrators only! Incorrect configuration will cause serious
problems.
You can control specific outbound traffic (i.e., from LAN to WAN). Outbound Services lists all
existing rules for outbound traffic. If you have not defined any rules, only the default rule will be
listed. The default rule allows all outgoing traffic.
Each rule lets you specify the desired action for the connections covered by the rule:
•BLOCK always
• BLOCK by schedule, otherwise Allow
• ALLOW always
• ALLOW by schedule, otherwise Block
As you define your firewall rules, you can further refine their application according to the
following criteria:
• LAN users—These settings determine which computers on your network are affected by this
rule. Select the desired options:
– Any: All PCs and devices on your LAN.
– Single address: The rule will be applied to the address of a particular PC.
– Address range: The rule is applied to a range of addresses.
– Groups: The rule is applied to a Group (you use the Network Database to assign PCs to
Groups—see “Groups and Hosts” on page 8-3).
• WAN Users—These settings determine which Internet locations are covered by the rule, based
on their IP address.
– Any: The rule applies to all Internet IP address.
– Single address: The rule applies to a single Internet IP address.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-3
202-10085-01, March 2005
– Address range: The rule is applied to a range of Internet IP addresses.
• Services—You can specify the desired Services or applications to be covered by this rule. If
the desired service or application does not appear in the list, you must define it using the
Services menu (see “Services” on page 8-3).
• Schedule—You can specify whether the rule is to be applied on the Schedule 1, Schedule 2, or
Schedule 3 time schedule (see “Schedule” on page 8-3).
See “Using Rules to Block or Allow Specific Kinds of Traffic” on page 6-1 for the procedure on
how to use this feature.
Services
The Rules menu contains a list of predefined Services for creating firewall rules. If a service does
not appear in the predefined Services list, you can define the service. The new service will then
appear in the Rules menu's Services list.
See “Services-Based Rules” on page 6-4 for the procedure on how to use this feature.
Groups and Hosts
You can apply these rules selectively to groups of PCs to reduce the outbound or inbound traffic.
The Network Database is an automatically-maintained list of all known PCs and network devices.
PCs and devices become known by the following methods:
• DHCP Client Request—By default, the DHCP server in this Router is enabled, and will accept
and respond to DHCP client requests from PCs and other network devices. These requests also
generate an entry in the Network Database. Because of this, leaving the DHCP Server feature
(on the LAN screen) enabled is strongly recommended.
• Scanning the Network—The local network is scanned using standard methods such as arp.
This will detect active devices which are not DHCP clients. However, sometimes the name of
the PC or device cannot be accurately determined, and will be shown as Unknown.
See “Managing Groups and Hosts” on page 6-20 for the procedure on how to use this feature.
Schedule
If you have set firewall rules on the Rules screen, you can configure three different schedules (i.e.,
schedule 1, schedule 2, and schedule 3) for when a rule is to be applied. Once a schedule is
configured, it affects all Rules that use this schedule. You specify the days of the week and time of
day for each schedule.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-4 Router and Network Management
202-10085-01, March 2005
See “Using a Schedule to Block or Allow Specific Traffic” on page 6-22 for the procedure on how
to use this feature.
Block Sites
If you want to reduce traffic by preventing access to certain sites on the Internet, you can use the
VPN firewall's filtering feature. By default, this feature is disabled; all requested traffic from any
Web site is allowed.
• Keyword (and domain name) blocking—You can specify up to 32 words that, should they
appear in the website name (i.e., URL) or in a newsgroup name, will cause that site or
newsgroup to be blocked by the VPN firewall.
You can apply the keywords to one or more groups. Requests from the PCs in the groups for
which keyword blocking has been enabled will be blocked. Blocking does not occur for the
PCs that are in the groups for which keyword blocking has not been enabled.
You can bypass keyword blocking for trusted domains by adding the exact matching domain
to the list of Trusted Domains. Access to the domains on this list by PCs even in the groups for
which keyword blocking has been enabled will still be allowed without any blocking.
• Web component blocking—You can block the following Web component types: Proxy, Java,
ActiveX, and Cookies. Sites on the Trusted Domains list are still subject to Web component
blocking when the blocking of a particular Web component has been enabled.
See “Block Sites” on page 6-24 for the procedure on how to use this feature.
Source MAC Filtering
If you want to reduce outgoing traffic by preventing Internet access by certain PCs on the LAN,
you can use the source MAC filtering feature to drop the traffic received from the PCs with the
specified MAC addresses. By default, this feature is disabled; all traffic received from PCs with
any MAC address is allowed.
See “Source MAC Filtering” on page 6-27 for the procedure on how to use this feature.
VPN Firewall Features That Increase Traffic
Features that tend to increase WAN-side loading are as follows:
• Port forwarding
• Port triggering
• Exposed hosts

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-5
202-10085-01, March 2005
•VPN tunnels
Port Forwarding
The firewall always blocks DoS (Denial of Service) attacks. A DoS attack does not attempt to steal
data or damage your PCs, but overloads your Internet connection so you can not use it (i.e., the
service is unavailable). You can also create additional firewall rules that are customized to block or
allow specific traffic.
Note: This feature is for Advanced Administrators only! Incorrect configuration will cause serious
problems.
You can control specific inbound traffic (i.e., from WAN to LAN). Inbound Services lists all
existing rules for inbound traffic. If you have not defined any rules, only the default rule will be
listed. The default rule blocks all inbound traffic.
Each rule lets you specify the desired action for the connections covered by the rule:
•BLOCK always
• BLOCK by schedule, otherwise Allow
• ALLOW always
• ALLOW by schedule, otherwise Block
You can also enable a check on special rules:
• VPN Passthrough—Enable this to pass the VPN traffic without any filtering, specially used
when this firewall is between two VPN tunnel end points.
• Drop fragmented IP packets—Enable this to drop the fragmented IP packets.
• UDP Flooding—Enable this to limit the number of UDP sessions created from one LAN
machine.
• TCP Flooding—Enable this to protect the router from Syn flood attack.
• Enable DNS Proxy—Enable this to allow the incoming DNS queries.
• Enable Stealth Mode—Enable this to set the firewall to operate in stealth mode.
As you define your firewall rules, you can further refine their application according to the
following criteria:
• LAN users—These settings determine which computers on your network are affected by this
rule. Select the desired IP Address in this field.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-6 Router and Network Management
202-10085-01, March 2005
• WAN Users—These settings determine which Internet locations are covered by the rule, based
on their IP address.
– Any: The rule applies to all Internet IP address.
– Single address: The rule applies to a single Internet IP address.
– Address range: The rule is applied to a range of Internet IP addresses.
• Destination Address—These settings determine the destination IP address for this rule which
will be applicable to incoming traffic, this rule will be applied only when the destination IP
address of the incoming packet matches the IP address of the WAN interface selected or
Specific IP address entered in this field.Selecting ANY enables the rule for any IP in
destination field.similarly WAN1 and WAN2 corresponds to respective wan interfaces.
• Services—You can specify the desired Services or applications to be covered by this rule. If
the desired service or application does not appear in the list, you must define it using the
Services menu (see “Services” on page 8-3).
• Schedule—You can specify whether the rule is to be applied on the Schedule 1, Schedule 2, or
Schedule 3 time schedule (see “Schedule” on page 8-3).
See “Using Rules to Block or Allow Specific Kinds of Traffic” on page 6-1 for the procedure on
how to use this feature.
Port Triggering
Port triggering allows some applications to function correctly that would otherwise be partially
blocked by the firewall. Using this feature requires that you know the port numbers used by the
Application.
Once configured, operation is as follows:
• A PC makes an outgoing connection using a port number defined in the Port Triggering table.
• This Router records this connection, opens the additional INCOMING port or ports associated
with this entry in the Port Triggering table, and associates them with the PC.
• The remote system receives the PCs request and responds using the different port numbers that
you have now opened.
• This Router matches the response to the previous request and forwards the response to the PC.
Without Port Triggering, this response would be treated as a new connection request rather
than a response. As such, it would be handled in accordance with the Port Forwarding rules.
– Only one PC can use a Port Triggering application at any time.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-7
202-10085-01, March 2005
– After a PC has finished using a Port Triggering application, there is a time-out period
before the application can be used by another PC. This is required because the firewall
cannot be sure when the application has terminated.
See “Port Triggering” on page 6-28 for the procedure on how to use this feature.
VPN Tunnels
The VPN firewall permits up to 200 VPN tunnels at a time. Each tunnel requires extensive
processing for encryption and authentication.
See Chapter 7, “Virtual Private Networking” for the procedure on how to use this feature.
Using QoS to Shift the Traffic Mix
The QoS priority settings determine the priority and, in turn, the quality of service for the traffic
passing through the firewall. The QoS is set individually for each service.
• You can accept the default priority defined by the service itself by observing its QoS setting.
• You can override its default setting to give the service higher or lower priority than it
otherwise would have.
You will not change the WAN bandwidth used by changing any QoS priority settings. But you will
change the mix of traffic through the WAN ports by granting some services a higher priority than
others. The quality of a service is impacted by its QoS setting, however.
See “Quality of Service (QoS) Priorities” on page 6-18 for the procedure on how to use this
feature.
Tools for Traffic Management
The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports includes
several tools that can be used to monitor the traffic conditions of the firewall and control who has
access to the Internet and the types of traffic they are allowed to have. See “Monitoring” on
page 8-14 for a discussion of the tools.
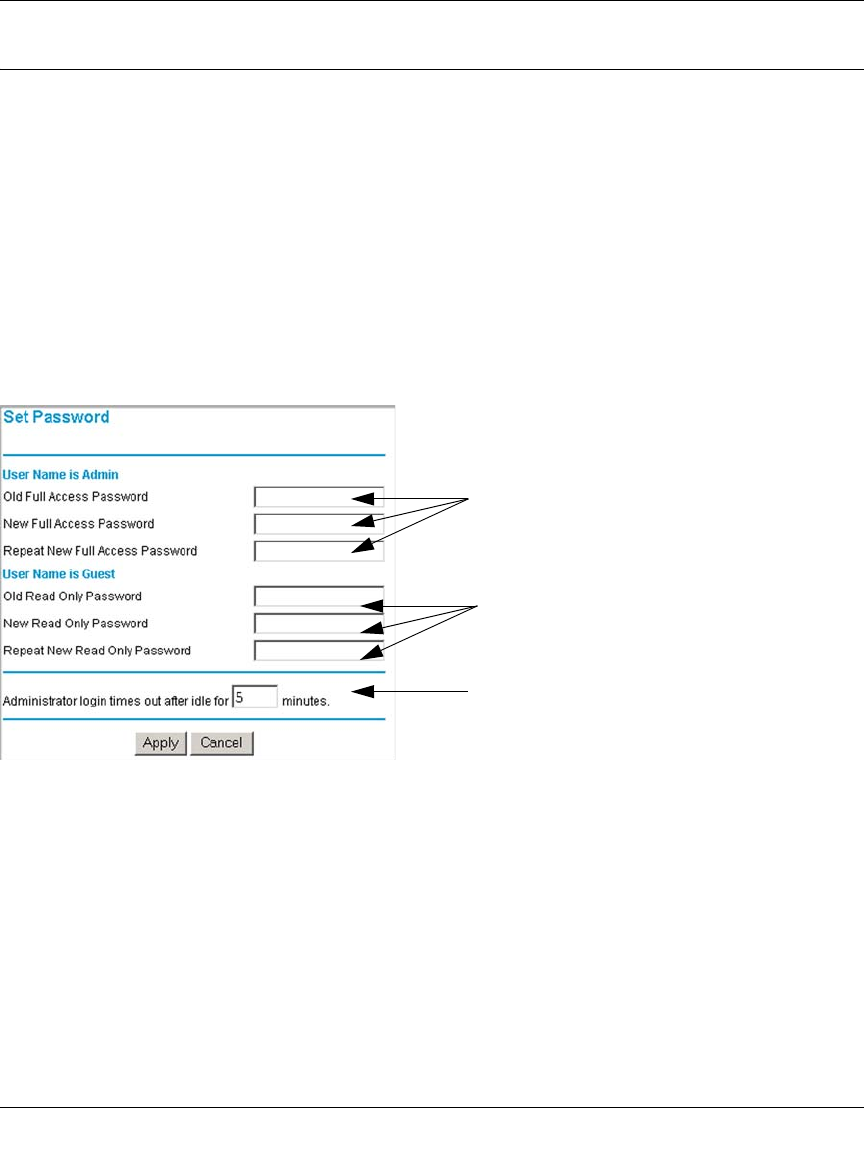
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-8 Router and Network Management
202-10085-01, March 2005
Administrator and Guest Access Authorization
You can change the administrator and guest passwords, administrator login timeout, and enable
remote management. Administrator access is read/write and guest access is read-only.
Changing the Passwords and Login Timeout
The default passwords for the firewall’s Web Configuration Manager is password. Netgear
recommends that you change this password to a more secure password.
From the main menu of the browser interface, under the Management heading, select Set Password
to bring up this menu.
Figure 8-1: Set Password menu
To change the password, first enter the old password, and then enter the new password twice. Click
Apply. To change the login idle timeout, change the number of minutes and click Apply.
Note: If you make the administrator login timeout value too large, you will have to wait a long
time before you are able to log back into the router if your previous login was disrupted (i.e., you
did not click Logout on the Main Menu bar to log out).
The password and timeout value you enter will be changed back to password and 5 minutes,
respectively, after a factory defaults reset.
Change administrator password
Change administrator login timeout
Change guest read-only password
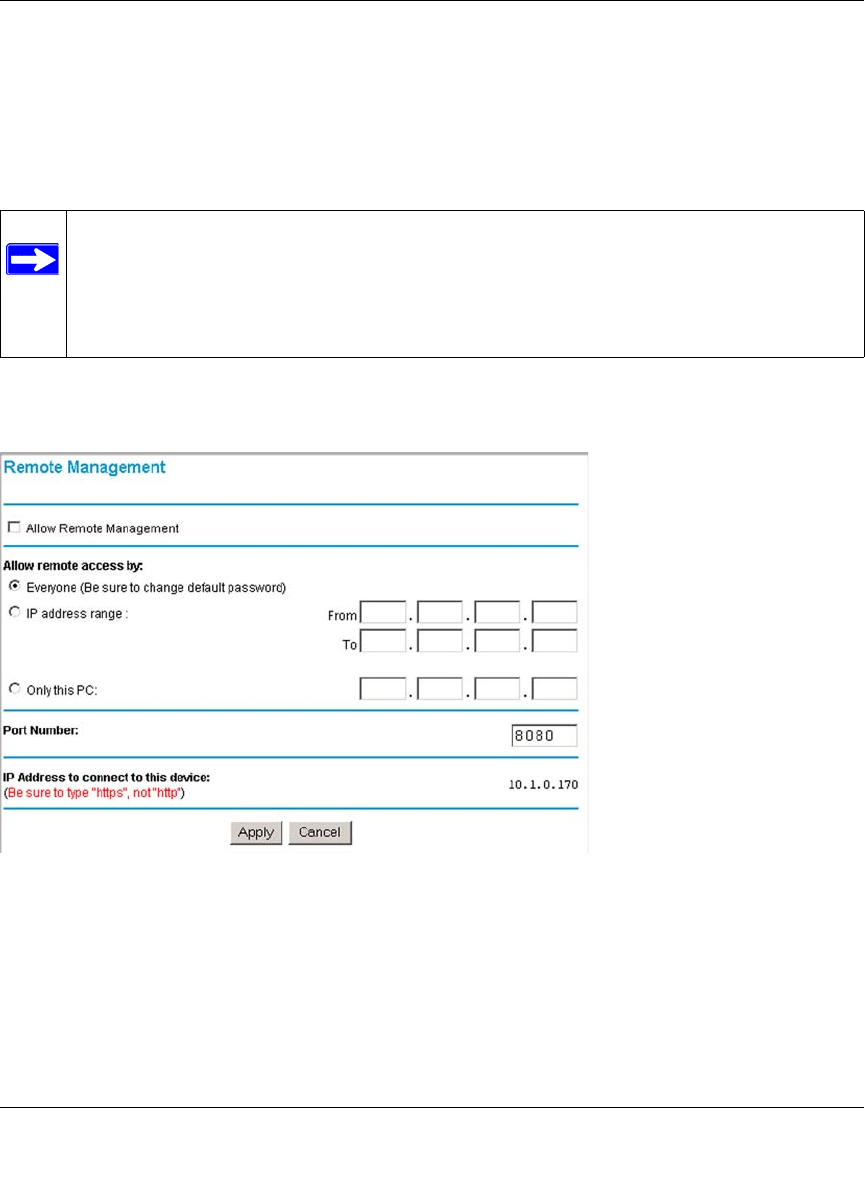
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-9
202-10085-01, March 2005
Enabling Remote Management Access
Using the Remote Management page, you can allow an administrator on the Internet to configure,
upgrade, and check the status of your FVS124G VPN Firewall. You must be logged in locally to
enable remote management (see “Step 2: Log in to the VPN Firewall (Required)” on page 4-7).
Figure 8-2 shows the Remote Management screen that is invoked by clicking Remote
Management under Management on the Main Menu bar.
Figure 8-2: Remote Management screen
To configure your firewall for Remote Management:
1. Select the Turn Remote Management On check box.
2. Specify what external addresses will be allowed to access the firewall’s remote management.
Note: For enhanced security, restrict access to as few external IP addresses as practical.
Note: Be sure to change the firewall's default configuration password to a very secure
password. The ideal password should contain no dictionary words from any language,
and should be a mixture of letters (both upper and lower case), numbers, and symbols.
Your password can be up to 30 characters. See “Changing the Passwords and Login
Timeout” on page 8-8 for the procedure on how to do this.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-10 Router and Network Management
202-10085-01, March 2005
a. To allow access from any IP address on the Internet, select Everyone.
b. To allow access from a range of IP addresses on the Internet, select IP address range.
Enter a beginning and ending IP address to define the allowed range.
c. To allow access from a single IP address on the Internet, select Only this PC.
Enter the IP address that will be allowed access.
3. Specify the Port Number that will be used for accessing the management interface.
Web browser access normally uses the standard HTTP service port 80. For greater security,
you can change the remote management web interface to a custom port by entering that
number in the box provided. Choose a number between 1024 and 65535, but do not use the
number of any common service port. The default is 8080, which is a common alternate for
HTTP.
4. Click Apply to have your changes take effect.
5. When accessing your firewall from the Internet, the Secure Sockets Layer (SSL) will be
enabled. You will enter https:// and type your firewall's WAN IP address into your browser,
followed by a colon (:) and the custom port number. For example, if your WAN IP address is
134.177.0.123 and you use port number 8080, type the following in your browser:
https://134.177.0.123:8080
The router’s remote login URL is https://IP_address:port_number or
https://FullyQualifiedDomainName:port_number.
If you do not use the SSL https://address, but rather use http://address, the FVS124G will
automatically attempt to redirect to https://address.
Note: The first time you remotely connect the FVS124G with a browser via SSL, you may get
a message regarding the SSL certificate. If you are using a Windows computer with Internet
Explorer 5.5 or higher, simply click Yes to accept the certificate.
Tip: If you are using a dynamic DNS service such as TZO, you can always identify the IP
address of your FVS124G by running TRACERT from the Windows Start menu Run option. For
example, tracert yourFVS124G.mynetgear.net and you will see the IP address your ISP
assigned to the FVS124G.
Command Line Interface
Note: The command line interface is not supported at this time. Check the Netgear Web site for
the latest status.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-11
202-10085-01, March 2005
You can access the command line interface (CLI) either by using telnet or by connecting a terminal
to the console port on the front of the unit.
To access the CLI from a communications terminal when the FVS124G VPN Firewall is still set to
its factory defaults (or use your own settings if you have changed them), do the following:
1. From the command line prompt, enter the following command:
telnet 192.168.1.1
2. Enter admin and password when prompted for the login and password information (or enter
guest and password to log in as a read-only guest).
Note: No password protection exists when using the console port to access the unit.
Any configuration changes made via the CLI are not preserved after a reboot or power cycle unless
the user issues the CLI save command after making the changes.
Event Alerts
You can be alerted to important events such as WAN port rollover, WAN traffic limits reached, and
login failures and attacks.
WAN Port Rollover
You can request an email alert when the WAN port rolls over if the WAN mode is configured for
rollover.
Traffic Limits Reached
Figure 8-3 shows the Internet Traffic screen that is invoked by clicking Internet Traffic under
WAN Setup on the Main Menu bar. The WAN1 and WAN2 ports are programmed separately. A
WAN port shuts down once its traffic limit is reached when this feature is enabled.
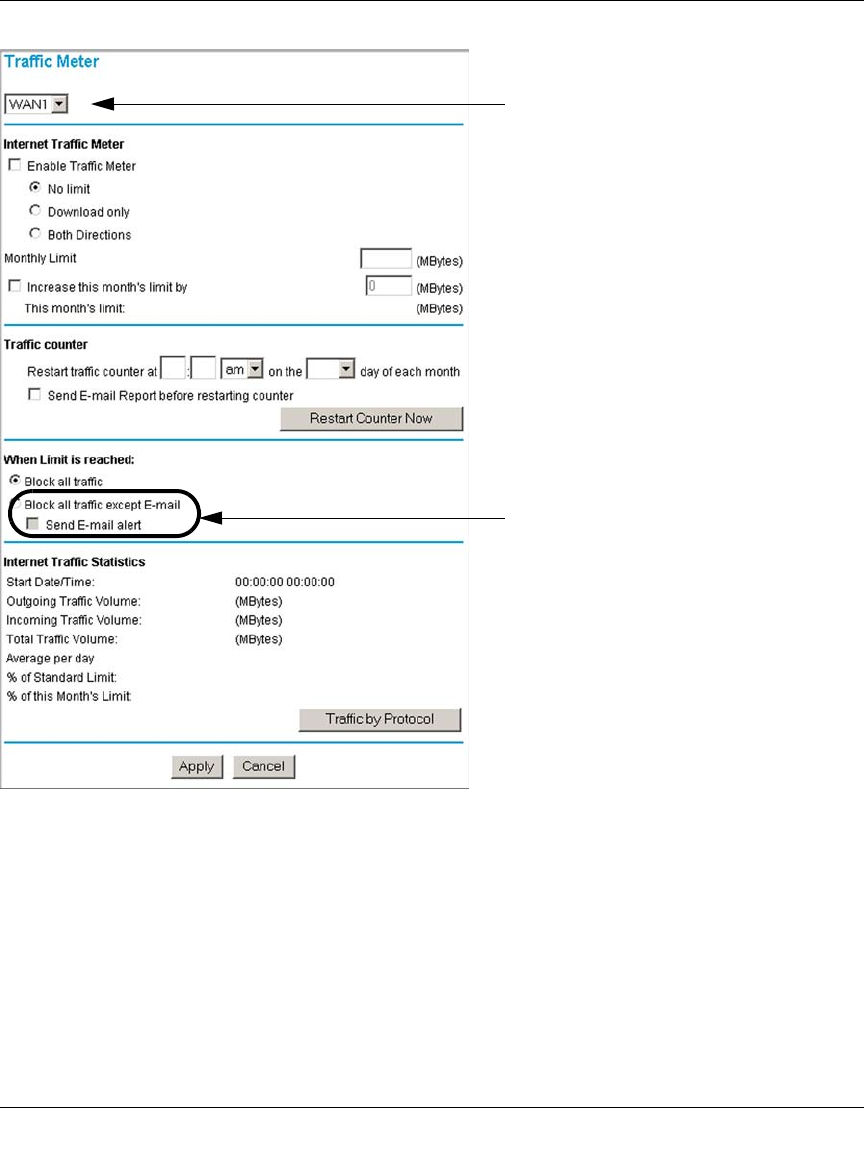
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-12 Router and Network Management
202-10085-01, March 2005
Figure 8-3: Traffic Limit Reached alert
Login Failures and Attacks
Figure 8-3 shows the Log screen that is invoked by clicking Logs and Email under Security on
the Main Menu bar.
WAN port shuts down once
the traffic limit is reached. An
email alert can be sent when
this shutdown happens.
Each WAN port is programmed
separately.
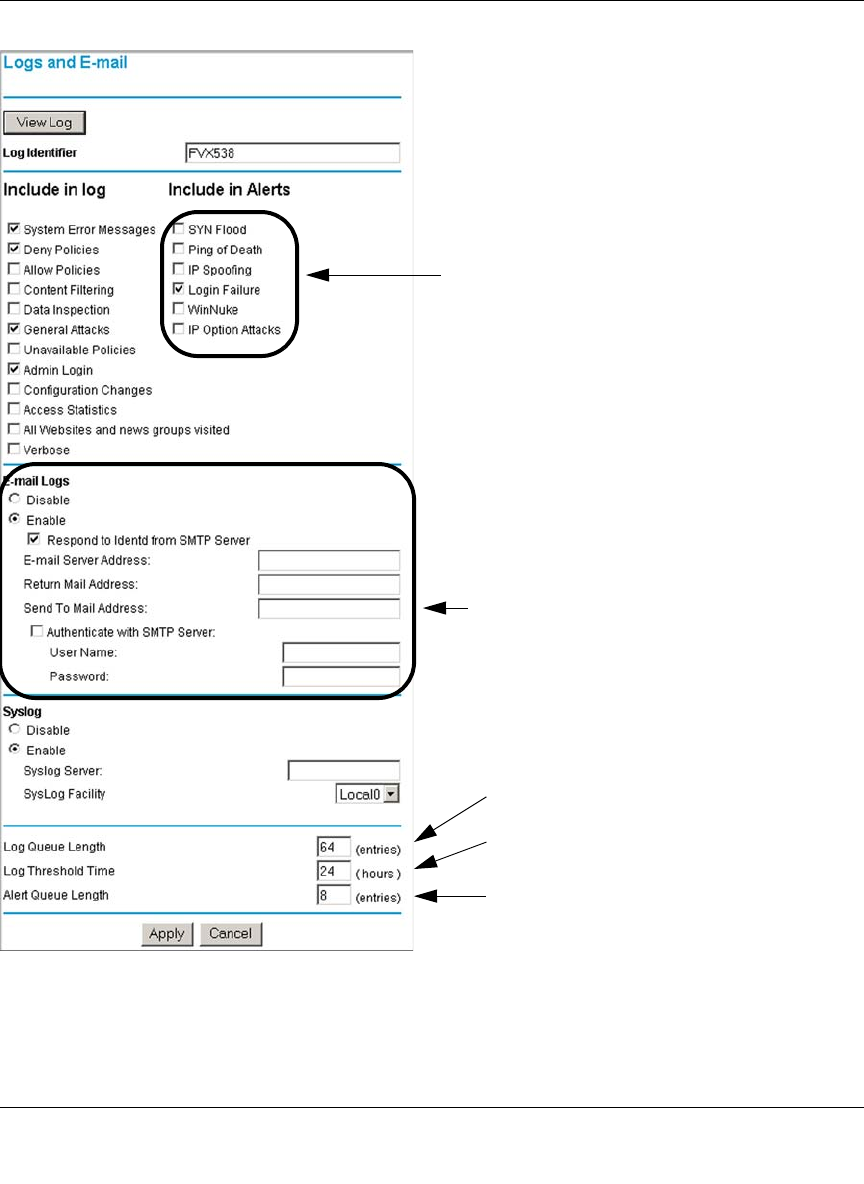
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-13
202-10085-01, March 2005
Figure 8-4: Logs and email screen
Select the types of alerts to email.
Enable email alerts.
Accumulate 64 messages before
sending a log email.
Accumulate 8 messages before
sending an alert email.
Wait 24 hours before sending
sending an email.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-14 Router and Network Management
202-10085-01, March 2005
Monitoring
You can view status information about the firewall, WAN ports, LAN ports, and VPN tunnels and
program SNMP connections.
Viewing VPN Firewall Status and Time Information
Firewall Status
The Router Status menu provides status and usage information. From the main menu of the
browser interface, click on Management, then select Router Status to view this screen.
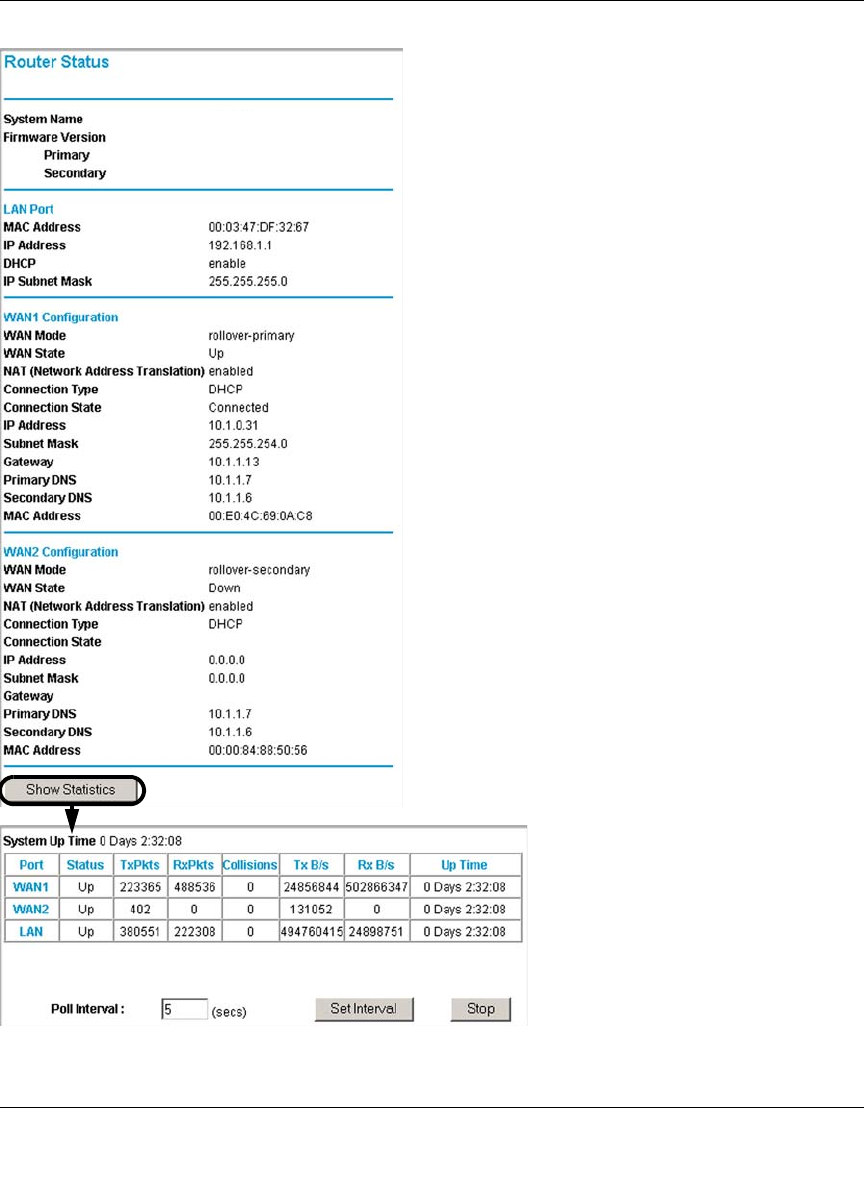
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-15
202-10085-01, March 2005
Figure 8-5: Router Status screen
FVS124G

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-16 Router and Network Management
202-10085-01, March 2005
Note: The Router Status page displays current settings and statistics for your router. As this
information is read-only, any changes must be made on other pages.
Time Information
Time information is found on the Schedules screen.
Table 8-1. Router Status
Item Description
System Name This is the Account Name that you entered in the Basic Settings page.
Firmware Version This is the current software the router is using. This will change if you upgrade your
router.
LAN Port Information These are the current settings for MAC address, IP address, DHCP role and Subnet
Mask that you set in the LAN IP Setup page. DHCP can be either Server or None.
WAN Port
Information This indicates whether NAT is Enabled or Disabled. It also displays the current
settings for MAC address, IP address, DHCP role and Subnet Mask that you set in
the Basic Settings page. DHCP can be either Client or None.
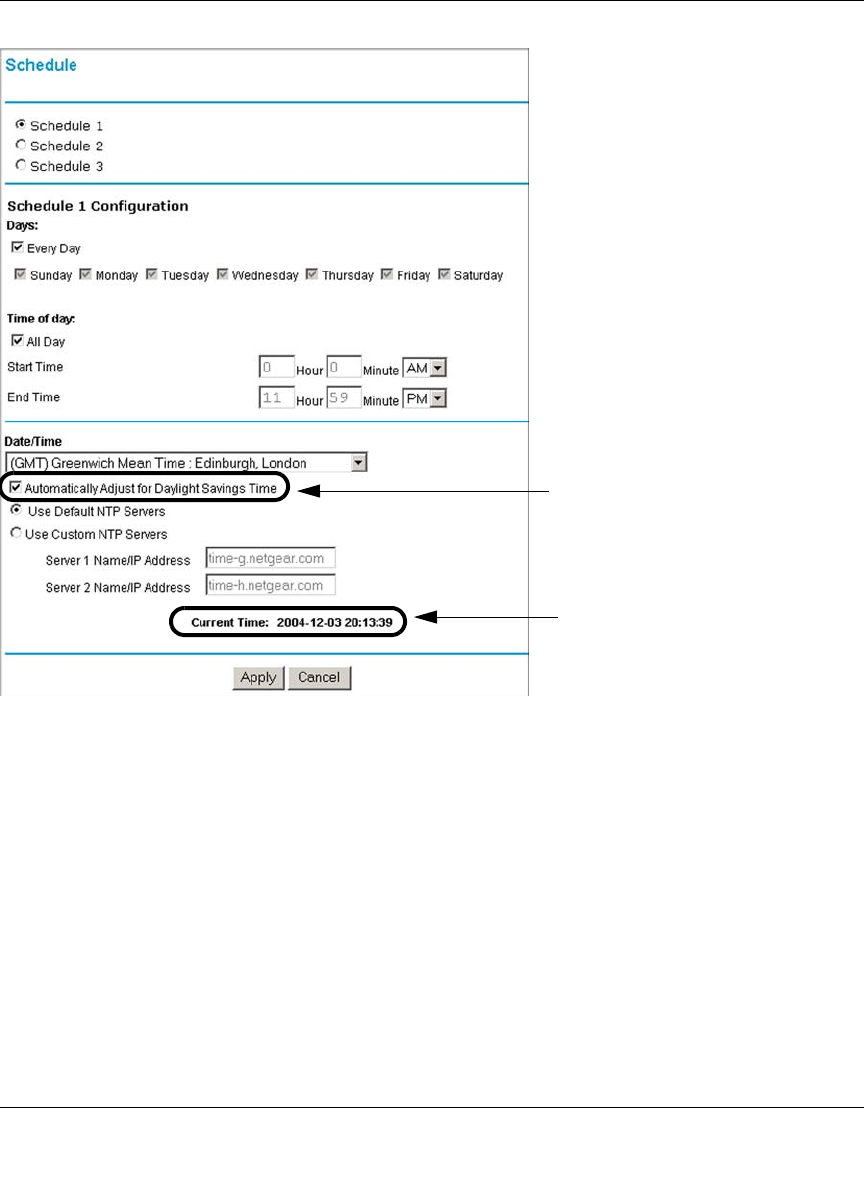
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-17
202-10085-01, March 2005
Figure 8-6: Time information on the Schedule screen
If supported for your region, you can check Automatically adjust for Daylight Savings Time.
Current date and time
Automatic adjustment
enable for daylight
savings time
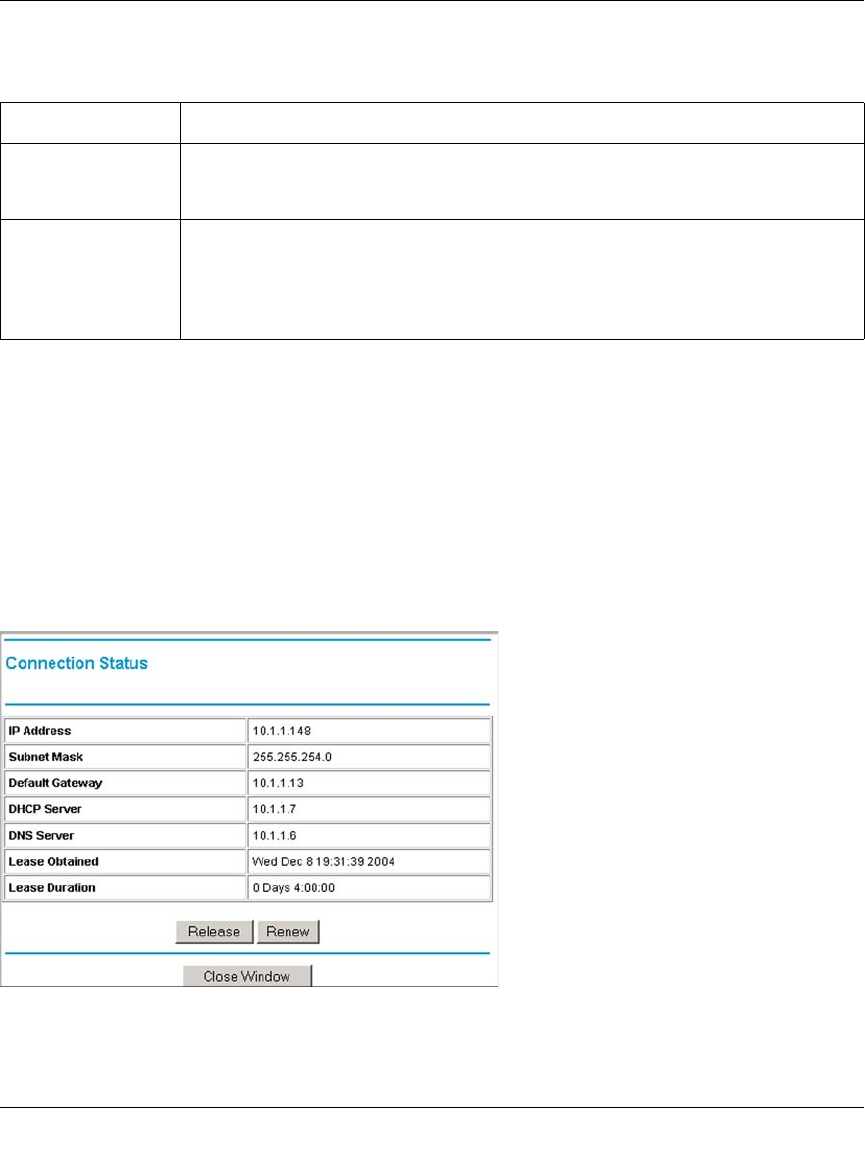
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-18 Router and Network Management
202-10085-01, March 2005
WAN Ports
You can monitor the status of the WAN connections, Dynamic DNS services, and Internet traffic
information.
WAN Port Connection Status
Invoke the Connection Status screen from WAN ISP Basic Settings screens by clicking on WAN
Status to view the current connection state of the WAN port.
Figure 8-7: Connection Status screen
Table 8-1. Current date and time
Item Description
Use Default NTP
Servers (Network
Time Protocol)
If enabled, the system clock is updated regularly by contacting a Default Netgear
NTP Server on the Internet.
Use Custom NTP
Servers If you prefer to use a particular NTP server, enable this and enter the name or IP
address of an NTP Server in the Server 1 Name/IP Address field. If required, you can
also enter the address of another NTP server in the Server 2 Name/IP Address
field.If you select this option and leave either Server 1 or Server 2 fields empty, they
get set to Default Netgear NTP servers
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-19
202-10085-01, March 2005
Dynamic DNS Status
Invoke the Dynamic DNS Status screen from Dynamic DNS screen by clicking Show Status to see
the current DDNS Status in a sub-window.
Figure 8-8: Dynamic DNS Status screen
Internet Traffic Information
The Internet Traffic screen provides the following information:
• Internet Traffic Statistics—This displays statistics on Internet Traffic via the WAN port. If you
have not enabled the Traffic Meter, these statistics are not available.
• Traffic by Protocol —Click this button if you want to know more details of the Internet
Traffic. The volume of traffic for each protocol will be displayed in a sub-window. Traffic
counters are updated in MBytes scale and the counter starts only when traffic passed is at least
1 MB
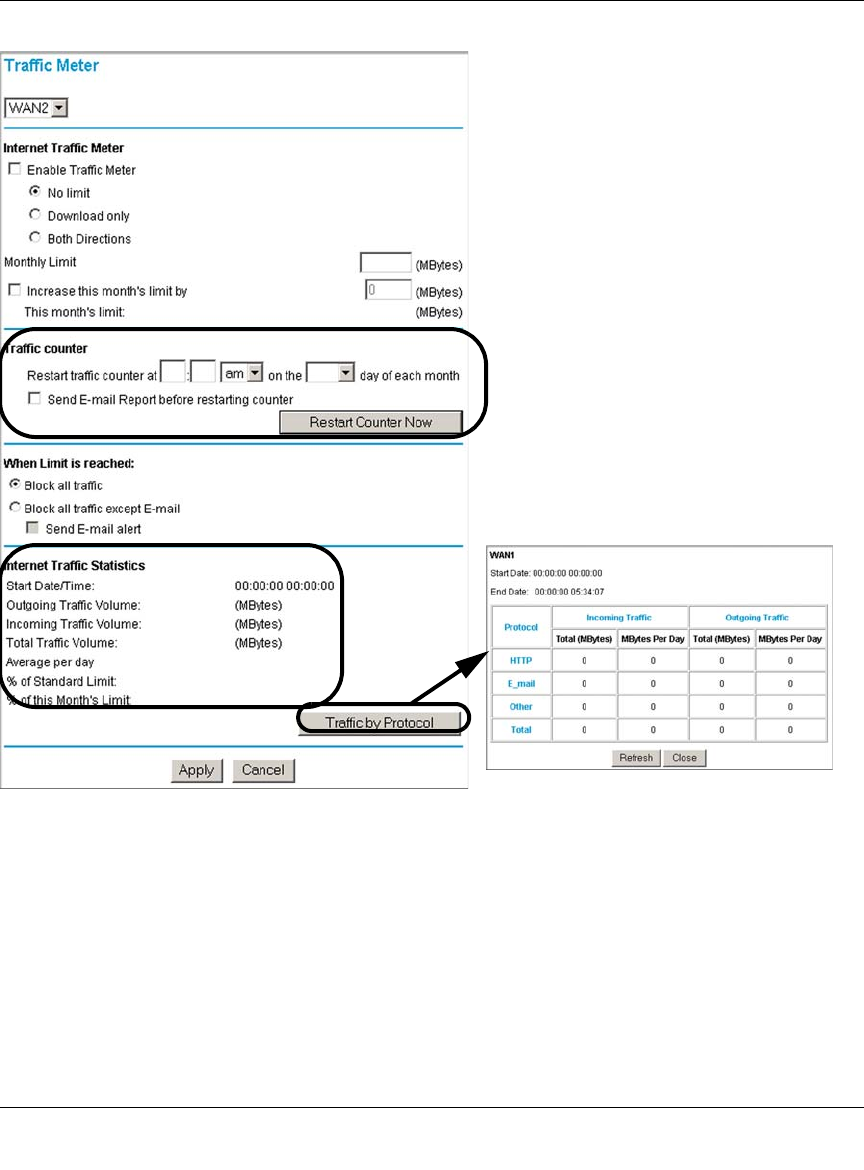
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-20 Router and Network Management
202-10085-01, March 2005
Figure 8-9: Internet Traffic information
LAN Ports and Attached Devices
Known PCs and Devices
The Attached Devices menu contains a table of all IP devices that the firewall has discovered on
the local network. From the Main Menu of the browser interface, under the Security heading,
select Groups and Hosts to view the table, shown below.
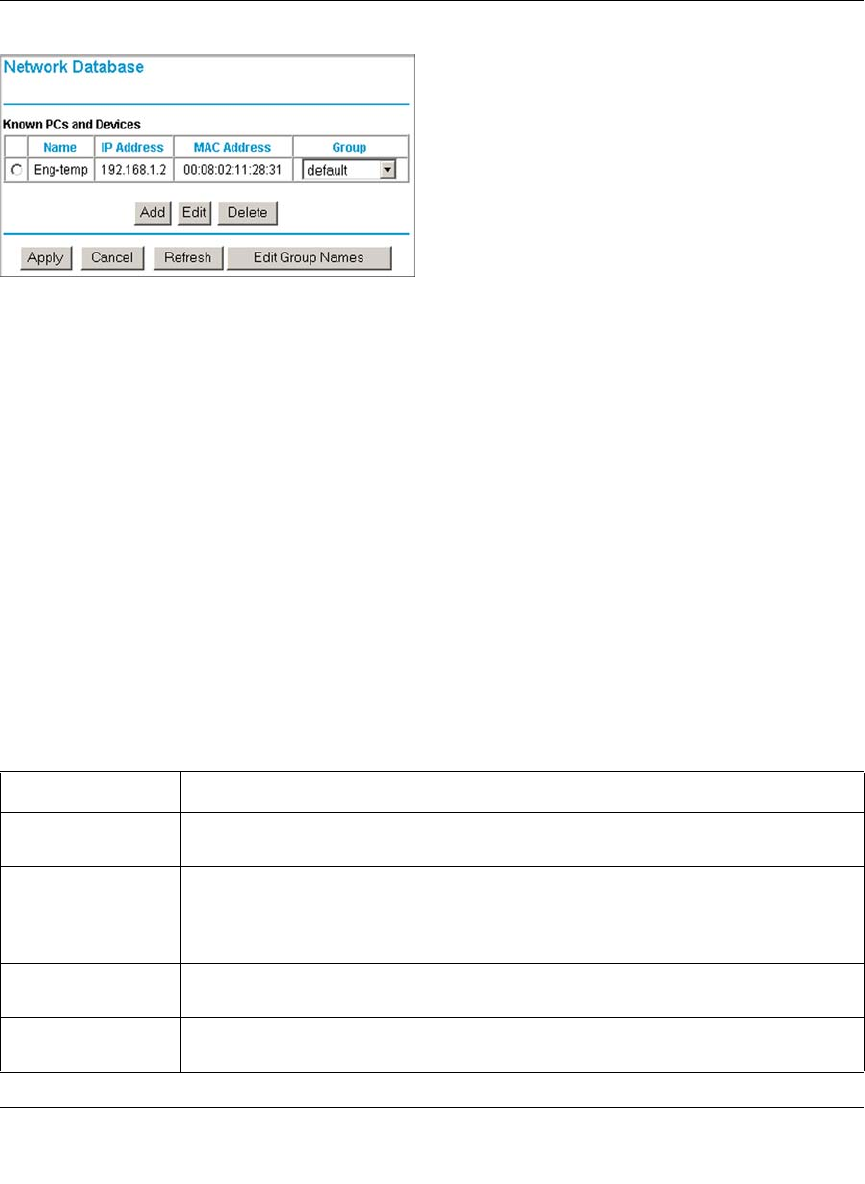
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-21
202-10085-01, March 2005
Figure 8-10: Network Database screen
The Network Database is an automatically-maintained list of all known PCs and network devices.
PCs and devices become known by the following methods:
• DHCP Client Requests—By default, the DHCP server in this Router is enabled, and will
accept and respond to DHCP client requests from PCs and other network devices. These
requests also generate an entry in the Network Database. Because of this, leaving the DHCP
Server feature (on the LAN screen) enabled is strongly recommended.
• Scanning the Network—The local network is scanned using standard methods such as arp.
This will detect active devices which are not DHCP clients. However, sometimes the name of
the PC or device cannot be accurately determined and will be shown as Unknown.
The Known PCs and Devices table lists all current entries in the Network Database. For each PC
or device, the following data is displayed.
Table 8-1. Known PCs and Devices table
Item Description
Name The name of the PC or device. Sometimes, this can not be determined, and will be
listed as Unknown. In this case, you can edit the entry to add a meaningful name.
IP Address The current IP address. For DHCP clients, where the IP address is allocated by the
DHCP Server in this device, this IP address will not change. Where the IP address is
set on the PC (as a fixed IP address), you may need to update this entry manually if
the IP address on the PC is changed.
MAC Address The MAC address of the PC. The MAC address is a low-level network identifier
which is fixed at manufacture.
Group Each PC or device must be in a single group. The Group column indicates which
group each entry is in. By default, all entries are in the Default group.
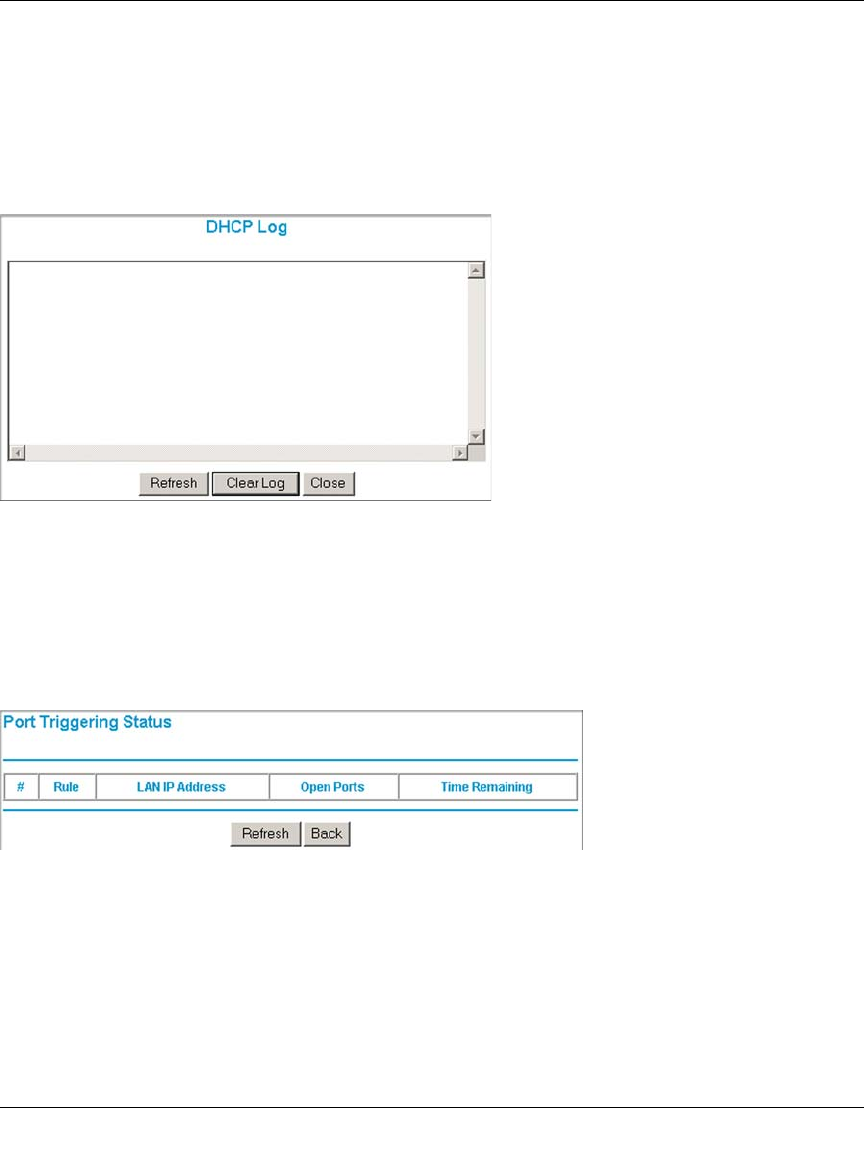
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-22 Router and Network Management
202-10085-01, March 2005
Note: If the firewall is rebooted, the table data is lost until the firewall rediscovers the devices. To
force the firewall to look for attached devices, click the Refresh button.
DHCP Log
You can view the DHCP log. Invoke the DHCP Log from LAN IP Setup screen.
Figure 8-11: DHCP Log
Port Triggering Status
You can view the status of port triggering. Invoke the Port Triggering Status screen from Port
Triggering screen.
Figure 8-12: Port Triggering Status screen

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-23
202-10085-01, March 2005
Firewall
You can view the log of the firewall activities.
Figure 8-3 shows the Log screen that is invoked by clicking Logs and Email under Security on
the Main Menu bar.
Table 8-1. Port Triggering Status data
Item Description
Rule The name of the Rule.
LAN IP Address The IP address of the PC currently using this rule.
Open Ports The Incoming ports which are associated the this rule. Incoming traffic using one of
these ports will be sent to the IP address above.
Time Remaining The time remaining before this rule is released, and thus available for other PCs.
This timer is restarted whenever incoming or outgoing traffic is received.
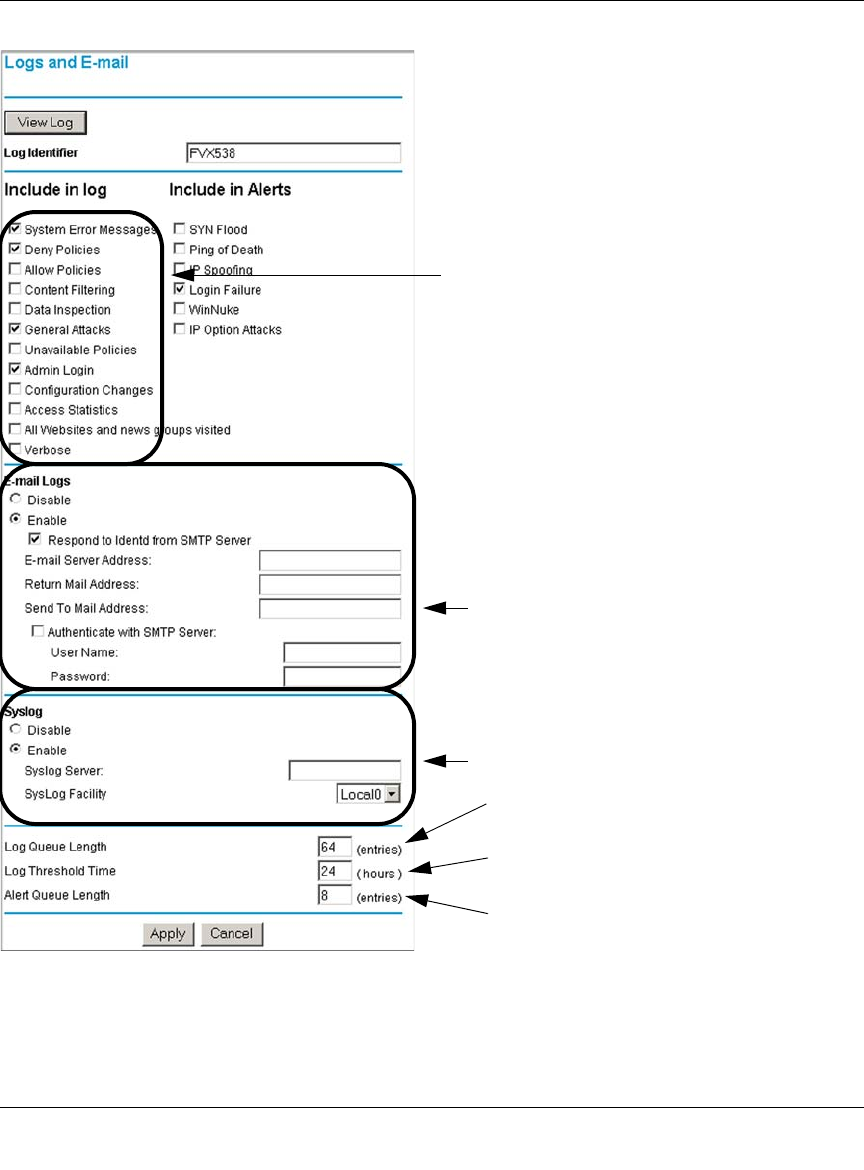
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-24 Router and Network Management
202-10085-01, March 2005
Figure 8-13: Logs and email screen
Select the types of logs to email.
Enable emailing of logs.
Enable system logs.
Accumulate 64 messages before
sending a log email.
Accumulate 8 messages before
sending an alert email.
Wait 24 hours before sending
sending an email.
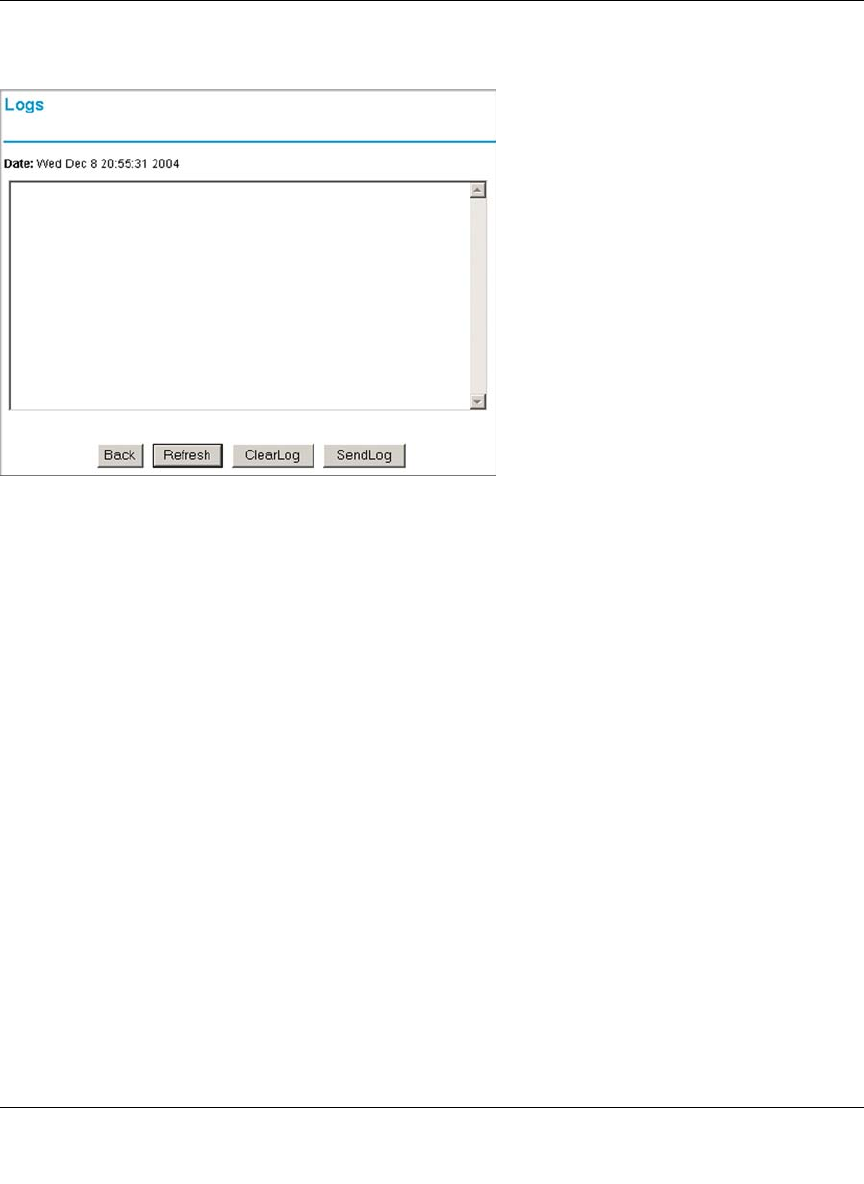
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-25
202-10085-01, March 2005
Invoke the Firewall Log screen from Logs and Email screen.
Figure 8-14: Firewall Log screen (invoked from Logs and Email screen)
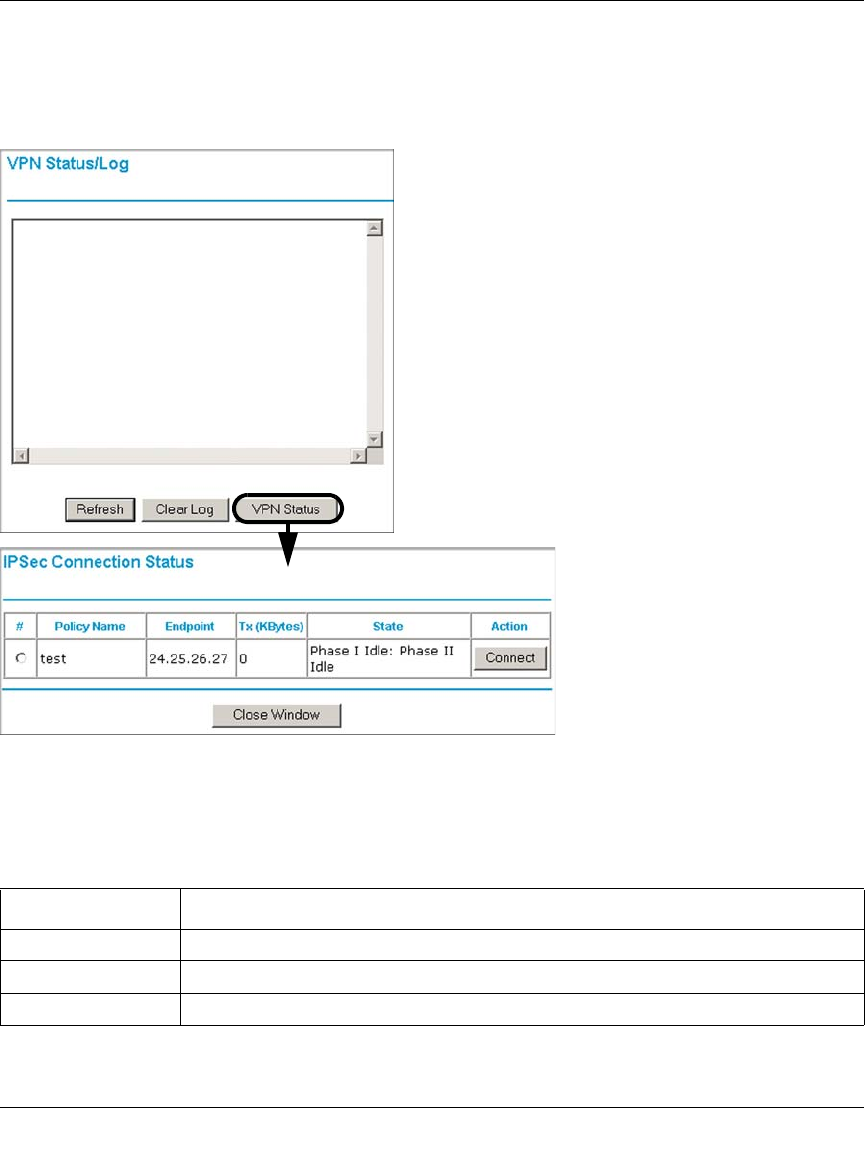
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-26 Router and Network Management
202-10085-01, March 2005
VPN Tunnels
You can view the status of the VPN tunnels.
Figure 8-15: VPN Status/Log and IPSec Connection Status screens
Table 8-1. VPN Status data
Item Description
Policy Name The name of the VPN policy associated with this SA.
Endpoint The IP address on the remote VPN Endpoint.
Tx (KBytes) The amount of data transmitted over this SA.
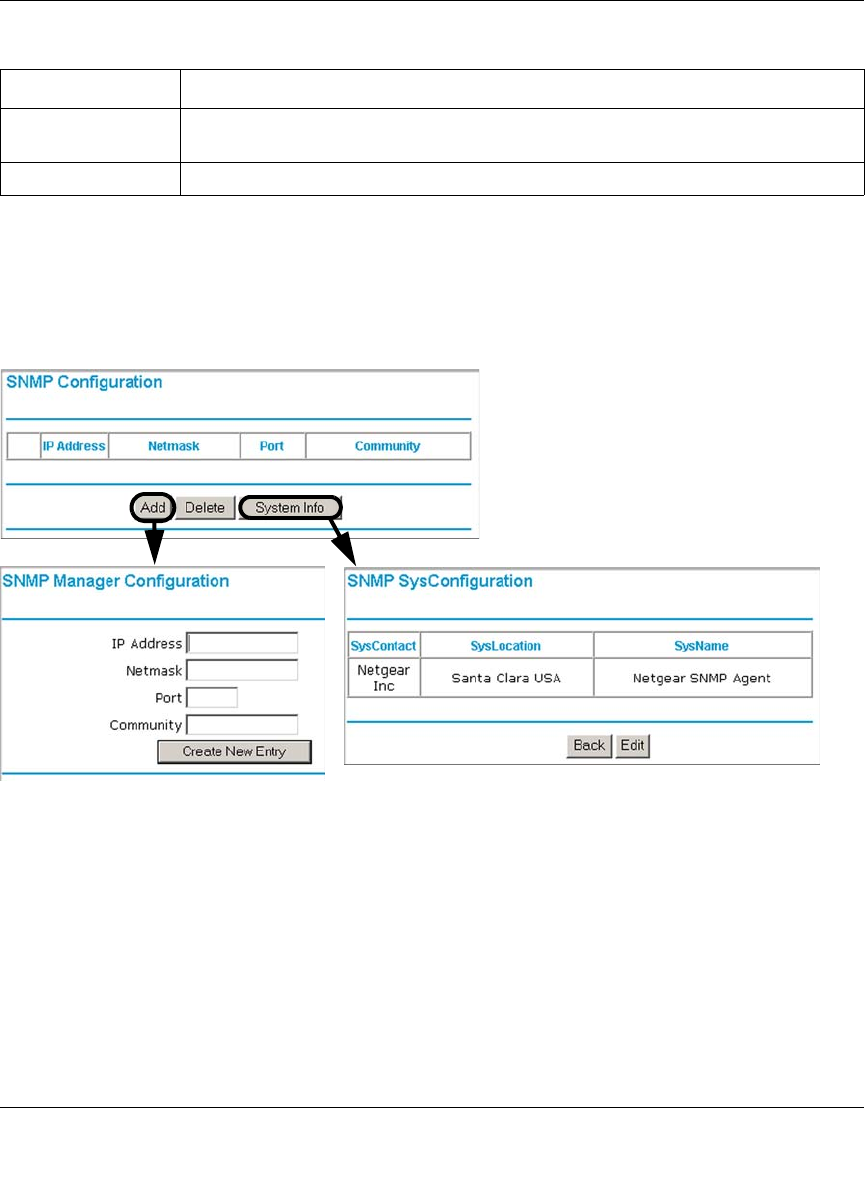
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-27
202-10085-01, March 2005
SNMP
SNMP lets you monitor and manage log resources from an SNMP-compliant system manager.
SNMP system configuration lets you change the system variables for MIB2.
Figure 8-16: SNMP Configuration screens
Diagnostics
You can perform diagnostics such as pinging an IP address, perform a DNS lookup, display the
routing table, reboot the firewall, and capture packets.
Note: For normal operation, diagnostics are not required.
State The current status of the SA.Phase 1 is Authentication phase and Phase 2 is Key
Exchange phase.
Action Use this button to terminate/build the SA (connection) if required.
Table 8-1. VPN Status data
Item Description
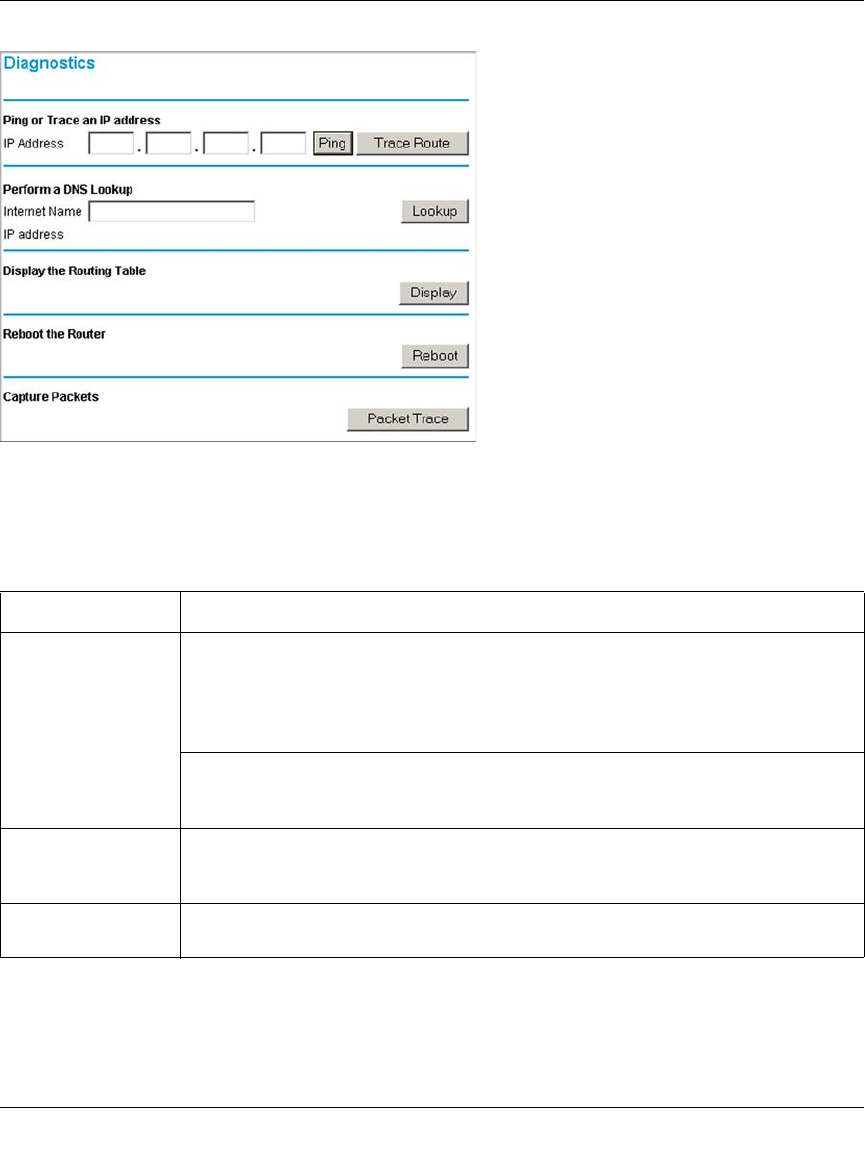
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-28 Router and Network Management
202-10085-01, March 2005
Figure 8-17: Diagnostics screen
Table 8-1. Diagnostics
Item Description
Ping or Trace an IP
address Ping—Use this to send a ping packet request to the specified IP address. This is
often used to test a connection. If the request times out (no reply is received), this
usually means the destination is unreachable. However, some network devices can
be configured not to respond to a ping. The ping results will be displayed in a new
screen; click Back to return to the Diagnostics screen.
Trace—Often called Trace Route, this will list all Routers between the source (this
device) and the destination IP address. The Trace Route results will be displayed in a
new screen; click Back to return to the Diagnostics screen.
Perform a DNS
Lookup A DNS (Domain Name Server) converts the Internet name (e.g. www.netgear.com) to
an IP address. If you need the IP address of a Web, FTP, Mail or other Server on the
Internet, you can do a DNS lookup to find the IP address.
Display the Routing
Table This operation will display the internal routing table. This information is used by
Technical Support and other staff who understand Routing Tables.
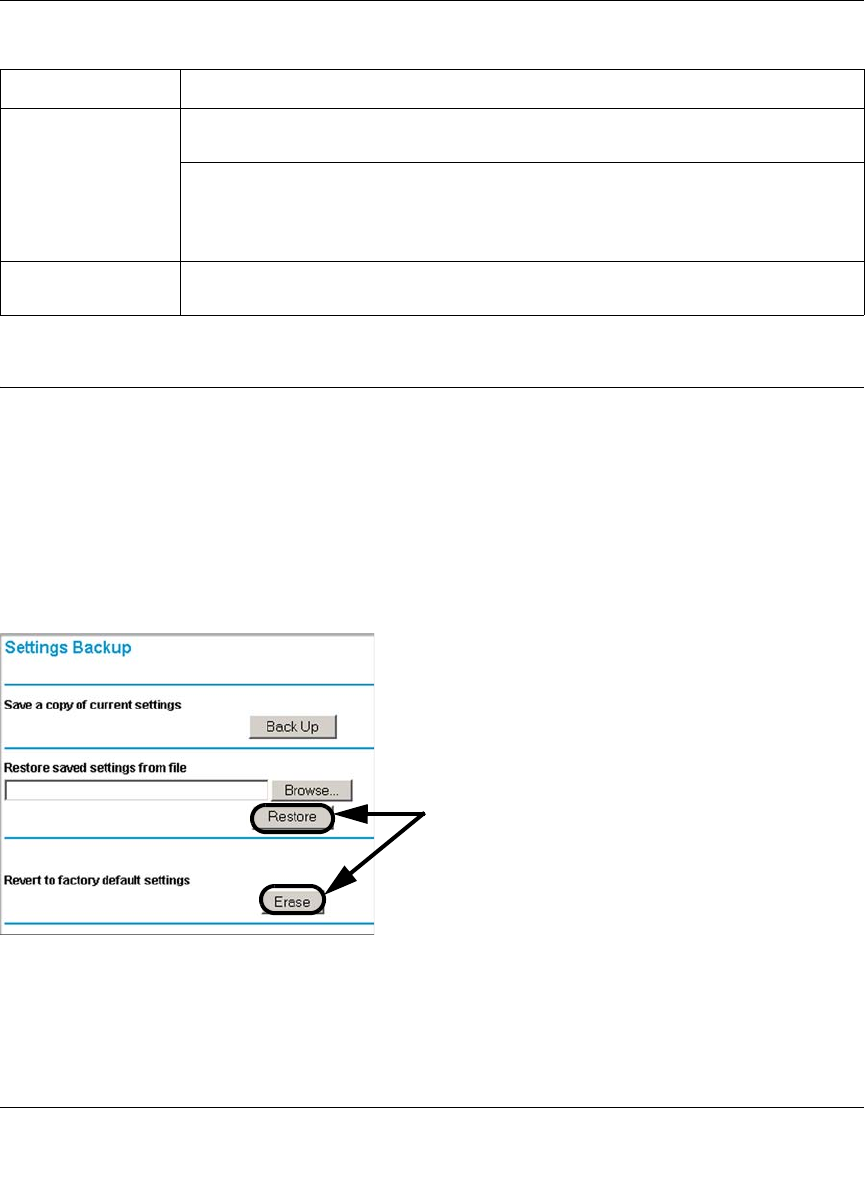
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-29
202-10085-01, March 2005
Configuration File Management
The configuration settings of the FVS124G VPN Firewall are stored within the firewall in a
configuration file. This file can be saved (backed up) to a user’s PC, retrieved (restored) from the
user’s PC, or cleared to factory default settings. You can also upgrade the firewall software with
the latest version from Netgear.
From the Main Menu of the browser interface, under the Management heading, select the Settings
Backup heading to bring up the menu shown below.
Figure 8-18: Settings Backup menu
The options are described in the following sections.
Reboot the Router Use this button to perform a remote reboot (restart). You can use this if the Router
seems to have become unstable or is not operating normally.
Note: Rebooting will break any existing connections either to the Router (such as this
one) or through the Router (for example, LAN users accessing the Internet).
However, connections to the Internet will automatically be re-established when
possible.
Packet Trace Click Packet Trace button to Select the interface and start the packet capture on that
interface.
Table 8-1. Diagnostics
Item Description
Be careful how you use these!

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-30 Router and Network Management
202-10085-01, March 2005
Restoring and Backing Up the Configuration
IMPORTANT! Once you start restoring settings or erasing the router, do NOT try to go online,
turn off the router, shutdown the computer or do anything else to the router until it finishes
restarting! This should only take a minute or so. When the Test light turns off, wait a few more
seconds before doing anything with the router.
The Restore and Backup options in the Settings Backup menu allow you to save and retrieve a file
containing your firewall’s configuration settings.
• To save your settings, select the Backup tab. Click the Backup button. Your browser will
extract the configuration file from the firewall and will prompt you for a location on your PC
to store the file. You can give the file a meaningful name at this time, such as pacbell.cfg.
• To restore your settings from a saved configuration file, enter the full path to the file on your
PC or click the Browse button to browse to the file. When you have located it, click the
Restore button to send the file to the firewall. The firewall will then reboot automatically.
An Alert page appears showing the status of restore operation.You need to manually restart the
router to make the restored settings effective.
IMPORTANT! Do not try to go online, turn off the router, shutdown the computer or do
anything else to the router until it finishes restarting! When the Test light turns off, wait a few
more seconds before doing anything with the router.
Upgrading the Firewall Software
The routing software of the FVS124G VPN Firewall is stored in FLASH memory, and can be
upgraded as new software is released by NETGEAR. Upgrade files can be downloaded from
Netgear's website. If the upgrade file is compressed (.ZIP file), you must first extract the binary
(.TRX) file before sending it to the firewall. The upgrade file can be sent to the firewall using your
browser.
Note: The Web browser used to upload new firmware into the FVS124G VPN Firewall must
support HTTP uploads. NETGEAR recommends using Microsoft Internet Explorer or Netscape
Navigator 3.0 or above.
From the Main Menu of the browser interface, under the Management heading, select the Router
Upgrade heading to display the menu shown below.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Router and Network Management 8-31
202-10085-01, March 2005
Figure 8-19: Router Upgrade menu
To upload new firmware:
1. Download and unzip the new software file from NETGEAR.
2. In the Router Upgrade menu, click the Browse button and browse to the location of the binary
image (.IMG) upgrade file
3. Click Upload.
Note: When uploading software to the FVS124G VPN Firewall, it is important not to interrupt
the Web browser by closing the window, clicking a link, or loading a new page. If the browser
is interrupted, it may corrupt the software. When the upload is complete, your firewall will
automatically restart. The upgrade process will typically take about one minute.
In some cases, you may need to reconfigure the firewall after upgrading.
Erasing the Configuration (Factory Defaults Reset)
It is sometimes desirable to restore the firewall to a known blank condition. This can be done by
using the Erase function, which will restore all factory settings. After an erase, the firewall's
password will be password, the LAN IP address will be 192.168.1.1, and the firewall's DHCP
client will be enabled.
• To erase the configuration and reset the router to the original factory default settings, click the
Erase button (see Figure 8-18).
IMPORTANT! Do not try to go online, turn off the router, shutdown the computer or do
anything else to the router until the router finishes restarting! When the Test light turns off,
wait a few more seconds before doing anything with the router.
You need to manually restart the router to make the default settings effective.After rebooting,
the router's password will be password, the LAN IP address will be 192.168.1.1 and the router
will act as a DHCP server on the LAN and act as a DHCP client to the Internet.
Be careful how you use this!

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
8-32 Router and Network Management
202-10085-01, March 2005
• To restore the factory default configuration settings without knowing the login password or IP
address, you must use the Default Reset button on the front panel of the firewall (see “The
Router’s Front Panel” on page 2-6). Also see “Restoring the Default Configuration and
Password” on page 9-7.
Troubleshooting 9-1
202-10085-01, March 2005
Chapter 9
Troubleshooting
This chapter gives information about troubleshooting your FVS124G ProSafe VPN Firewall 25
with 4 Gigabit LAN and Dual WAN Ports. After each problem description, instructions are
provided to help you diagnose and solve the problem.
Basic Functioning
After you turn on power to the firewall, the following sequence of events should occur:
1. When power is first applied, verify that the PWR LED is on.
2. After approximately 10 seconds, verify that:
a. The TEST LED is not lit.
b. The LAN port LEDs are lit for any local ports that are connected.
c. The Internet port LED is lit.
If a port’s LED is lit, a link has been established to the connected device. If a LAN port is
connected to a 100 Mbps device, verify that the port’s LED is green. If the port is 10 Mbps, the
LED will be amber.
If any of these conditions does not occur, refer to the appropriate following section.
Power LED Not On
If the Power and other LEDs are off when your firewall is turned on:
• Make sure that the power cord is properly connected to your firewall and that the power
supply adapter is properly connected to a functioning power outlet.
• Check that you are using the 12 V DC power adapter supplied by NETGEAR for this product.
If the error persists, you have a hardware problem and should contact technical support.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
9-2 Troubleshooting
202-10085-01, March 2005
LEDs Never Turn Off
When the firewall is turned on, the LEDs turns on for about 10 seconds and then turn off. If all the
LEDs stay on, there is a fault within the firewall.
If all LEDs are still on one minute after power up:
• Cycle the power to see if the firewall recovers.
• Clear the firewall’s configuration to factory defaults. This will set the firewall’s IP address to
192.168.1.1. This procedure is explained in “Restoring the Default Configuration and
Password” on page 9-7.
If the error persists, you might have a hardware problem and should contact technical support.
LAN or Internet Port LEDs Not On
If either the LAN LEDs or Internet LED do not light when the Ethernet connection is made, check
the following:
• Make sure that the Ethernet cable connections are secure at the firewall and at the hub or
workstation.
• Make sure that power is turned on to the connected hub or workstation.
• Be sure you are using the correct cable:
When connecting the firewall’s Internet port to a cable or DSL modem, use the cable that was
supplied with the cable or DSL modem. This cable could be a standard straight-through
Ethernet cable or an Ethernet crossover cable.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Troubleshooting 9-3
202-10085-01, March 2005
Troubleshooting the Web Configuration Interface
If you are unable to access the firewall’s Web Configuration interface from a PC on your local
network, check the following:
• Check the Ethernet connection between the PC and the firewall as described in the previous
section.
• Make sure your PC’s IP address is on the same subnet as the firewall. If you are using the
recommended addressing scheme, your PC’s address should be in the range of 192.168.0.2 to
192.168.0.254.
Note: If your PC’s IP address is shown as 169.254.x.x: Recent versions of Windows and
MacOS will generate and assign an IP address if the computer cannot reach a DHCP server.
These auto-generated addresses are in the range of 169.254.x.x. If your IP address is in this
range, check the connection from the PC to the firewall and reboot your PC.
• If your firewall’s IP address has been changed and you don’t know the current IP address,
clear the firewall’s configuration to factory defaults. This will set the firewall’s IP address to
192.168.1.1. This procedure is explained in “Restoring the Default Configuration and
Password” on page 9-7.
• Make sure your browser has Java, JavaScript, or ActiveX enabled. If you are using Internet
Explorer, click Refresh to be sure the Java applet is loaded.
• Try quitting the browser and launching it again.
• Make sure you are using the correct login information. The factory default login name is
admin and the password is password. Make sure that CAPS LOCK is off when entering this
information.
If the firewall does not save changes you have made in the Web Configuration Interface, check the
following:
• When entering configuration settings, be sure to click the APPLY button before moving to
another menu or tab, or your changes are lost.
• Click the Refresh or Reload button in the Web browser. The changes may have occurred, but
the Web browser may be caching the old configuration.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
9-4 Troubleshooting
202-10085-01, March 2005
Troubleshooting the ISP Connection
If your firewall is unable to access the Internet, you should first determine whether the firewall is
able to obtain a WAN IP address from the ISP. Unless you have been assigned a static IP address,
your firewall must request an IP address from the ISP. You can determine whether the request was
successful using the Web Configuration Manager.
To check the WAN IP address:
1. Launch your browser and select an external site such as www.netgear.com
2. Access the Main Menu of the firewall’s configuration at http://192.168.1.1
3. Under the Management heading, select Router Status
4. Check that an IP address is shown for the WAN Port
If 0.0.0.0 is shown, your firewall has not obtained an IP address from your ISP.
If your firewall is unable to obtain an IP address from the ISP, you may need to force your cable or
DSL modem to recognize your new firewall by performing the following procedure:
1. Turn off power to the cable or DSL modem.
2. Turn off power to your firewall.
3. Wait five minutes and reapply power to the cable or DSL modem.
4. When the modem’s LEDs indicate that it has reacquired sync with the ISP, reapply power to
your firewall.
If your firewall is still unable to obtain an IP address from the ISP, the problem may be one of the
following:
• Your ISP may require a login program.
Ask your ISP whether they require PPP over Ethernet (PPPoE) or some other type of login.
• If your ISP requires a login, you may have incorrectly set the login name and password.
• Your ISP may check for your PC's host name.
Assign the PC Host Name of your ISP account as the Account Name in the Basic Settings
menu.
• Your ISP only allows one Ethernet MAC address to connect to Internet, and may check for
your PC’s MAC address. In this case:
Inform your ISP that you have bought a new network device, and ask them to use the firewall’s
MAC address.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Troubleshooting 9-5
202-10085-01, March 2005
OR
Configure your firewall to spoof your PC’s MAC address. This can be done in the Basic
Settings menu. Refer to “Manually Configuring Your Internet Connection” on page 4-12.
If your firewall can obtain an IP address, but your PC is unable to load any web pages from the
Internet:
• Your PC may not recognize any DNS server addresses.
A DNS server is a host on the Internet that translates Internet names (such as www addresses)
to numeric IP addresses. Typically your ISP will provide the addresses of one or two DNS
servers for your use. You may configure your PC manually with DNS addresses, as explained
in your operating system documentation.
• Your PC may not have the firewall configured as its TCP/IP gateway.
Troubleshooting a TCP/IP Network Using a Ping Utility
Most TCP/IP terminal devices and firewalls contain a ping utility that sends an echo request packet
to the designated device. The device then responds with an echo reply. Troubleshooting a TCP/IP
network is made very easy by using the ping utility in your PC or workstation.
Testing the LAN Path to Your Firewall
You can ping the firewall from your PC to verify that the LAN path to your firewall is set up
correctly.
To ping the firewall from a PC running Windows 95 or later:
1. From the Windows toolbar, click on the Start button and select Run.
2. In the field provided, type Ping followed by the IP address of the firewall, as in this example:
ping 192.168.1.1
3. Click on OK.
You should see a message like this one:
Pinging <IP address> with 32 bytes of data
If the path is working, you see this message:
Reply from < IP address >: bytes=32 time=NN ms TTL=xxx

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
9-6 Troubleshooting
202-10085-01, March 2005
If the path is not working, you see this message:
Request timed out
If the path is not functioning correctly, you could have one of the following problems:
• Wrong physical connections
— Make sure the LAN port LED is on. If the LED is off, follow the instructions in “LAN
or Internet Port LEDs Not On” on page 9-2.
— Check that the corresponding Link LEDs are on for your network interface card and
for the hub ports (if any) that are connected to your workstation and firewall.
• Wrong network configuration
— Verify that the Ethernet card driver software and TCP/IP software are both installed
and configured on your PC or workstation.
— Verify that the IP address for your firewall and your workstation are correct and that
the addresses are on the same subnet.
Testing the Path from Your PC to a Remote Device
After verifying that the LAN path works correctly, test the path from your PC to a remote device.
From the Windows run menu, type:
PING -n 10 <IP address>
where <IP address> is the IP address of a remote device such as your ISP’s DNS server.
If the path is functioning correctly, replies as in the previous section are displayed. If you do not
receive replies:
— Check that your PC has the IP address of your firewall listed as the default gateway. If the
IP configuration of your PC is assigned by DHCP, this information will not be visible in
your PC’s Network Control Panel.
— Check to see that the network address of your PC (the portion of the IP address specified
by the netmask) is different from the network address of the remote device.
— Check that your cable or DSL modem is connected and functioning.
— If your ISP assigned a host name to your PC, enter that host name as the Account Name in
the Basic Settings menu.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Troubleshooting 9-7
202-10085-01, March 2005
— Your ISP could be rejecting the Ethernet MAC addresses of all but one of your PCs. Many
broadband ISPs restrict access by only allowing traffic from the MAC address of your
broadband modem, but some ISPs additionally restrict access to the MAC address of a
single PC connected to that modem. If this is the case, you must configure your firewall to
“clone” or “spoof” the MAC address from the authorized PC. Refer to “Manually
Configuring Your Internet Connection” on page 4-12.
Restoring the Default Configuration and Password
This section explains how to restore the factory default configuration settings, changing the
firewall’s administration password to password and the IP address to 192.168.1.1. You can erase
the current configuration and restore factory defaults in two ways:
• Use the Erase function of the firewall (see “Erasing the Configuration (Factory Defaults
Reset)” on page 8-31).
• Use the Default Reset button on the rear panel of the firewall. Use this method for cases when
the administration password or IP address is not known.
To restore the factory default configuration settings without knowing the administration password
or IP address, you must use the Default Reset button on the rear panel of the firewall.
1. Press and hold the Default Reset button until the Test LED turns on and begins to blink (about
10 seconds).
2. Release the Default Reset button and wait for the firewall to reboot.
Problems with Date and Time
The E-Mail menu in the Content Filtering section displays the current date and time of day. The
FVS124G VPN Firewall uses the Network Time Protocol (NTP) to obtain the current time from
one of several Network Time Servers on the Internet. Each entry in the log is stamped with the date
and time of day. Problems with the date and time function can include:
• Date shown is January 1, 2000. Cause: The firewall has not yet successfully reached a
Network Time Server. Check that your Internet access settings are configured correctly. If you
have just completed configuring the firewall, wait at least five minutes and check the date and
time again.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
9-8 Troubleshooting
202-10085-01, March 2005
• Time is off by one hour. Cause: The firewall does not automatically sense Daylight Savings
Time. In the E-Mail menu, check or uncheck the box marked “Adjust for Daylight Savings
Time”.

Technical Specifications A-1
202-10085-01, March 2005
Appendix A
Technical Specifications
This appendix provides technical specifications for the FVS124G ProSafe VPN Firewall 25 with 4
Gigabit LAN and Dual WAN Ports.
Network Protocol and Standards Compatibility
Data and Routing Protocols: TCP/IP, RIP-1, RIP-2, DHCP
PPP over Ethernet (PPPoE)
Power Adapter
Voltage and amperage: 12 VDC, 1.2A
Physical Specifications
Dimensions: 1.15 x 7.5 x 4.75 in.
Weight:
Environmental Specifications
Operating temperature: 0° to 40° C (32º to 104º F)
Operating humidity: 90% maximum relative humidity, noncondensing
Electromagnetic Emissions
Meets requirements of: FCC Part 15 Class B
VCCI Class B
EN 55 022 (CISPR 22), Class B

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
A-2 Technical Specifications
202-10085-01, March 2005
Interface Specifications
LAN: 10BASE-T or 100BASE-Tx, RJ-45
WAN: 10BASE-T or 100BASE-Tx

Network, Routing, Firewall, and Basics B-1
202-10085-01, March 2005
Appendix B
Network, Routing, Firewall, and Basics
This chapter provides an overview of IP networks, routing, and networking.
Related Publications
As you read this document, you may be directed to various RFC documents for further
information. An RFC is a Request For Comment (RFC) published by the Internet Engineering
Task Force (IETF), an open organization that defines the architecture and operation of the Internet.
The RFC documents outline and define the standard protocols and procedures for the Internet. The
documents are listed on the World Wide Web at www.ietf.org and are mirrored and indexed at
many other sites worldwide.
Basic Router Concepts
Large amounts of bandwidth can be provided easily and relatively inexpensively in a local area
network (LAN). However, providing high bandwidth between a local network and the Internet can
be very expensive. Because of this expense, Internet access is usually provided by a slower-speed
wide-area network (WAN) link such as a cable or DSL modem. In order to make the best use of the
slower WAN link, a mechanism must be in place for selecting and transmitting only the data traffic
meant for the Internet. The function of selecting and forwarding this data is performed by a router.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-2 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
What is a Router?
A router is a device that forwards traffic between networks based on network layer information in
the data and on routing tables maintained by the router. In these routing tables, a router builds up a
logical picture of the overall network by gathering and exchanging information with other routers
in the network. Using this information, the router chooses the best path for forwarding network
traffic.
Routers vary in performance and scale, number of routing protocols supported, and types of
physical WAN connection they support. The FVS124G ProSafe VPN Firewall 25 with 4 Gigabit
LAN and Dual WAN Ports is a small office router that routes the IP protocol over a single-user
broadband connection.
Routing Information Protocol
One of the protocols used by a router to build and maintain a picture of the network is the Routing
Information Protocol (RIP). Using RIP, routers periodically update one another and check for
changes to add to the routing table.
The FVS124G VPN Firewall supports both the older RIP-1 and the newer RIP-2 protocols.
Among other improvements, RIP-2 supports subnet and multicast protocols. RIP is not required
for most home applications.
IP Addresses and the Internet
Because TCP/IP networks are interconnected across the world, every machine on the Internet must
have a unique address to make sure that transmitted data reaches the correct destination. Blocks of
addresses are assigned to organizations by the Internet Assigned Numbers Authority (IANA).
Individual users and small organizations may obtain their addresses either from the IANA or from
an Internet service provider (ISP). You can contact IANA at www.iana.org.
The Internet Protocol (IP) uses a 32-bit address structure. The address is usually written in dot
notation (also called dotted-decimal notation), in which each group of eight bits is written in
decimal form, separated by decimal points.
For example, the following binary address:
11000011 00100010 00001100 00000111
is normally written as:
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-3
202-10085-01, March 2005
195.34.12.7
The latter version is easier to remember and easier to enter into your computer.
In addition, the 32 bits of the address are subdivided into two parts. The first part of the address
identifies the network, and the second part identifies the host node or station on the network. The
dividing point may vary depending on the address range and the application.
There are five standard classes of IP addresses. These address classes have different ways of
determining the network and host sections of the address, allowing for different numbers of hosts
on a network. Each address type begins with a unique bit pattern, which is used by the TCP/IP
software to identify the address class. After the address class has been determined, the software
can correctly identify the host section of the address. The follow figure shows the three main
address classes, including network and host sections of the address for each address type.
Figure 9-1: Three Main Address Classes
The five address classes are:
• Class A
Class A addresses can have up to 16,777,214 hosts on a single network. They use an eight-bit
network number and a 24-bit node number. Class A addresses are in this range:
1.x.x.x to 126.x.x.x.
• Class B
Class B addresses can have up to 65,354 hosts on a network. A Class B address uses a 16-bit
network number and a 16-bit node number. Class B addresses are in this range:
7261
C
lass A
N
etwork Node
C
lass B
C
lass C
Network Node
Network Node

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-4 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
128.1.x.x to 191.254.x.x.
• Class C
Class C addresses can have 254 hosts on a network. Class C addresses use 24 bits for the
network address and eight bits for the node. They are in this range:
192.0.1.x to 223.255.254.x.
• Class D
Class D addresses are used for multicasts (messages sent to many hosts). Class D addresses are
in this range:
224.0.0.0 to 239.255.255.255.
• Class E
Class E addresses are for experimental use.
This addressing structure allows IP addresses to uniquely identify each physical network and each
node on each physical network.
For each unique value of the network portion of the address, the base address of the range (host
address of all zeros) is known as the network address and is not usually assigned to a host. Also,
the top address of the range (host address of all ones) is not assigned, but is used as the broadcast
address for simultaneously sending a packet to all hosts with the same network address.
Netmask
In each of the address classes previously described, the size of the two parts (network address and
host address) is implied by the class. This partitioning scheme can also be expressed by a netmask
associated with the IP address. A netmask is a 32-bit quantity that, when logically combined (using
an AND operator) with an IP address, yields the network address. For instance, the netmasks for
Class A, B, and C addresses are 255.0.0.0, 255.255.0.0, and 255.255.255.0, respectively.
For example, the address 192.168.170.237 is a Class C IP address whose network portion is the
upper 24 bits. When combined (using an AND operator) with the Class C netmask, as shown here,
only the network portion of the address remains:
11000000 10101000 10101010 11101101 (192.168.170.237)
combined with:
11111111 11111111 11111111 00000000 (255.255.255.0)
Equals:
11000000 10101000 10101010 00000000 (192.168.170.0)
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-5
202-10085-01, March 2005
As a shorter alternative to dotted-decimal notation, the netmask may also be expressed in terms of
the number of ones from the left. This number is appended to the IP address, following a backward
slash (/), as “/n.” In the example, the address could be written as 192.168.170.237/24, indicating
that the netmask is 24 ones followed by 8 zeros.
Subnet Addressing
By looking at the addressing structures, you can see that even with a Class C address, there are a
large number of hosts per network. Such a structure is an inefficient use of addresses if each end of
a routed link requires a different network number. It is unlikely that the smaller office LANs would
have that many devices. You can resolve this problem by using a technique known as subnet
addressing.
Subnet addressing allows us to split one IP network address into smaller multiple physical
networks known as subnetworks. Some of the node numbers are used as a subnet number instead.
A Class B address gives us 16 bits of node numbers translating to 64,000 nodes. Most
organizations do not use 64,000 nodes, so there are free bits that can be reassigned. Subnet
addressing makes use of those bits that are free, as shown below.
Figure 9-2: Example of Subnetting a Class B Address
A Class B address can be effectively translated into multiple Class C addresses. For example, the
IP address of 172.16.0.0 is assigned, but node addresses are limited to 255 maximum, allowing
eight extra bits to use as a subnet address. The IP address of 172.16.97.235 would be interpreted as
IP network address 172.16, subnet number 97, and node number 235. In addition to extending
the number of addresses available, subnet addressing provides other benefits. Subnet addressing
allows a network manager to construct an address scheme for the network by using different
subnets for other geographical locations in the network or for other departments in the
organization.
7262
C
lass B
Network Subnet Node

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-6 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
Although the preceding example uses the entire third octet for a subnet address, note that you are
not restricted to octet boundaries in subnetting. To create more network numbers, you need only
shift some bits from the host address to the network address. For instance, to partition a Class C
network number (192.68.135.0) into two, you shift one bit from the host address to the network
address. The new netmask (or subnet mask) is 255.255.255.128. The first subnet has network
number 192.68.135.0 with hosts 192.68.135.1 to 129.68.135.126, and the second subnet has
network number 192.68.135.128 with hosts 192.68.135.129 to 192.68.135.254.
The following table lists the additional subnet mask bits in dotted-decimal notation. To use the
table, write down the original class netmask and replace the 0 value octets with the dotted-decimal
value of the additional subnet bits. For example, to partition your Class C network with subnet
mask 255.255.255.0 into 16 subnets (4 bits), the new subnet mask becomes 255.255.255.240.
The following table displays several common netmask values in both the dotted-decimal and the
masklength formats.
Note: The number 192.68.135.127 is not assigned because it is the broadcast address
of the first subnet. The number 192.68.135.128 is not assigned because it is the network
address of the second subnet.
Table 9-1. Netmask Notation Translation Table for One Octet
Number of Bits Dotted-Decimal Value
1 128
2 192
3 224
4 240
5 248
6 252
7 254
8 255
Table 9-2. Netmask Formats
Dotted-Decimal Masklength
255.0.0.0 /8
255.255.0.0 /16

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-7
202-10085-01, March 2005
Configure all hosts on a LAN segment to use the same netmask for the following reasons:
• So that hosts recognize local IP broadcast packets
When a device broadcasts to its segment neighbors, it uses a destination address of the local
network address with all ones for the host address. In order for this scheme to work, all devices
on the segment must agree on which bits comprise the host address.
• So that a local router or bridge recognizes which addresses are local and which are remote
Private IP Addresses
If your local network is isolated from the Internet (for example, when using NAT), you can assign
any IP addresses to the hosts without problems. However, the IANA has reserved the following
three blocks of IP addresses specifically for private networks:
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
Choose your private network number from this range. The DHCP server of the FVS124G VPN
Firewall is preconfigured to automatically assign private addresses.
Regardless of your particular situation, do not create an arbitrary IP address; always follow the
guidelines explained here. For more information about address assignment, refer to RFC 1597,
Address Allocation for Private Internets, and RFC 1466, Guidelines for Management of IP
Address Space. The Internet Engineering Task Force (IETF) publishes RFCs on its Web site at
www.ietf.org.
255.255.255.0 /24
255.255.255.128 /25
255.255.255.192 /26
255.255.255.224 /27
255.255.255.240 /28
255.255.255.248 /29
255.255.255.252 /30
255.255.255.254 /31
255.255.255.255 /32
Table 9-2. Netmask Formats
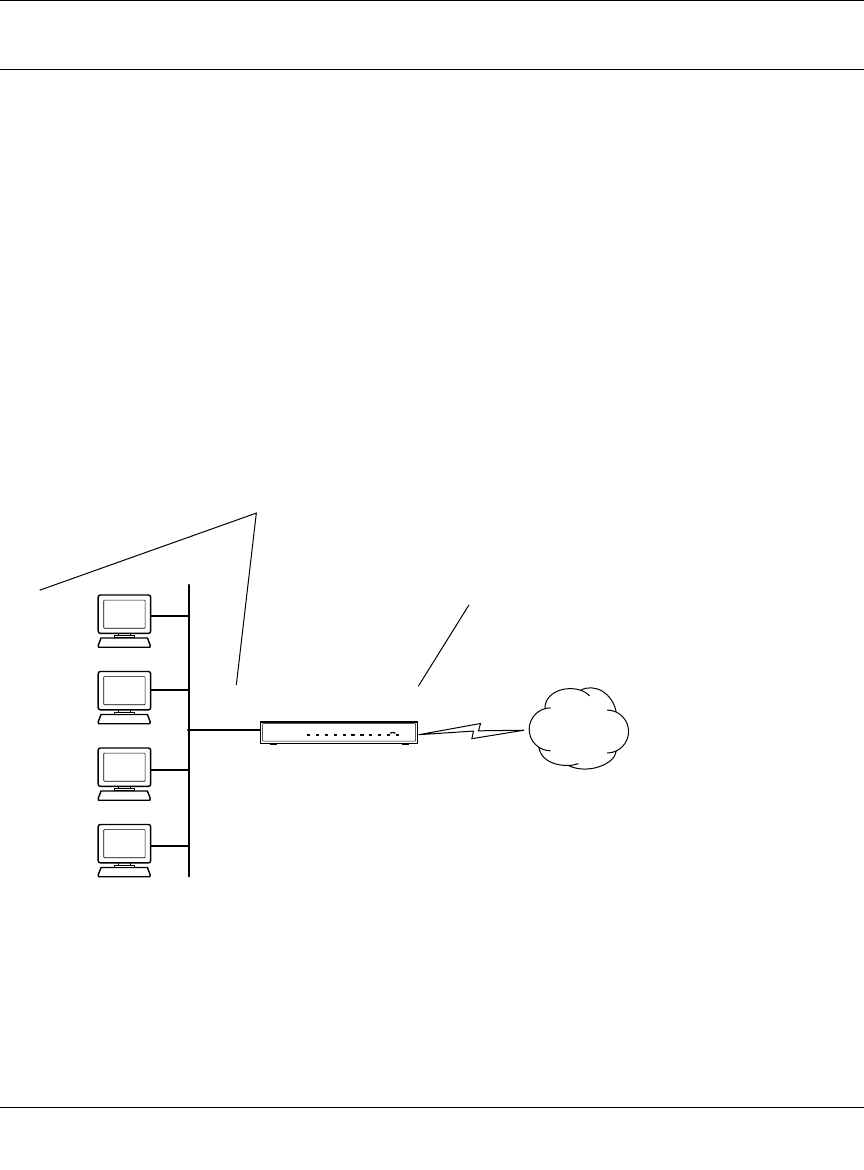
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-8 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
Single IP Address Operation Using NAT
In the past, if multiple PCs on a LAN needed to access the Internet simultaneously, you had to
obtain a range of IP addresses from the ISP. This type of Internet account is more costly than a
single-address account typically used by a single user with a modem, rather than a router. The
FVS124G VPN Firewall employs an address-sharing method called Network Address Translation
(NAT). This method allows several networked PCs to share an Internet account using only a single
IP address, which may be statically or dynamically assigned by your ISP.
The router accomplishes this address sharing by translating the internal LAN IP addresses to a
single address that is globally unique on the Internet. The internal LAN IP addresses can be either
private addresses or registered addresses. For more information about IP address translation, refer
to RFC 1631, The IP Network Address Translator (NAT).
The following figure illustrates a single IP address operation.
Figure 9-3: Single IP Address Operation Using NAT
7786EA
1
92.168.0.2
1
92.168.0.3
1
92.168.0.4
1
92.168.0.5
192.168.0.1 172.21.15.105
Private IP addresses
assigned by user
Internet
IP addresses
assigned by ISP

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-9
202-10085-01, March 2005
This scheme offers the additional benefit of firewall-like protection because the internal LAN
addresses are not available to the Internet through the translated connection. All incoming
inquiries are filtered out by the router. This filtering can prevent intruders from probing your
system. However, using port forwarding, you can allow one PC (for example, a Web server) on
your local network to be accessible to outside users.
MAC Addresses and Address Resolution Protocol
An IP address alone cannot be used to deliver data from one LAN device to another. To send data
between LAN devices, you must convert the IP address of the destination device to its media
access control (MAC) address. Each device on an Ethernet network has a unique MAC address,
which is a 48-bit number assigned to each device by the manufacturer. The technique that
associates the IP address with a MAC address is known as address resolution. Internet Protocol
uses the Address Resolution Protocol (ARP) to resolve MAC addresses.
If a device sends data to another station on the network and the destination MAC address is not yet
recorded, ARP is used. An ARP request is broadcast onto the network. All stations on the network
receive and read the request. The destination IP address for the chosen station is included as part of
the message so that only the station with this IP address responds to the ARP request. All other
stations discard the request.
Related Documents
The station with the correct IP address responds with its own MAC address directly to the sending
device. The receiving station provides the transmitting station with the required destination MAC
address. The IP address data and MAC address data for each station are held in an ARP table. The
next time data is sent, the address can be obtained from the address information in the table.
For more information about address assignment, refer to the IETF documents RFC 1597, Address
Allocation for Private Internets, and RFC 1466, Guidelines for Management of IP Address Space.
For more information about IP address translation, refer to RFC 1631, The IP Network Address
Translator (NAT).

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-10 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
Domain Name Server
Many of the resources on the Internet can be addressed by simple descriptive names such as
www.NETGEAR.com. This addressing is very helpful at the application level, but the descriptive
name must be translated to an IP address in order for a user to actually contact the resource. Just as
a telephone directory maps names to phone numbers, or as an ARP table maps IP addresses to
MAC addresses, a domain name system (DNS) server maps descriptive names of network
resources to IP addresses.
When a PC accesses a resource by its descriptive name, it first contacts a DNS server to obtain the
IP address of the resource. The PC sends the desired message using the IP address. Many large
organizations, such as ISPs, maintain their own DNS servers and allow their customers to use the
servers to look up addresses.
IP Configuration by DHCP
When an IP-based local area network is installed, each PC must be configured with an IP address.
If the PCs need to access the Internet, they should also be configured with a gateway address and
one or more DNS server addresses. As an alternative to manual configuration, there is a method by
which each PC on the network can automatically obtain this configuration information. A device
on the network may act as a Dynamic Host Configuration Protocol (DHCP) server. The DHCP
server stores a list or pool of IP addresses, along with other information (such as gateway and DNS
addresses) that it may assign to the other devices on the network. The FVS124G VPN Firewall has
the capacity to act as a DHCP server.
The FVS124G VPN Firewall also functions as a DHCP client when connecting to the ISP. The
firewall can automatically obtain an IP address, subnet mask, DNS server addresses, and a
gateway address if the ISP provides this information by DHCP.
Internet Security and Firewalls
When your LAN connects to the Internet through a router, an opportunity is created for outsiders
to access or disrupt your network. A NAT router provides some protection because by the very
nature of the process, the network behind the router is shielded from access by outsiders on the
Internet. However, there are methods by which a determined hacker can possibly obtain
information about your network or at the least can disrupt your Internet access. A greater degree of
protection is provided by a firewall router.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-11
202-10085-01, March 2005
What is a Firewall?
A firewall is a device that protects one network from another, while allowing communication
between the two. A firewall incorporates the functions of the NAT router, while adding features for
dealing with a hacker intrusion or attack. Several known types of intrusion or attack can be
recognized when they occur. When an incident is detected, the firewall can log details of the
attempt, and can optionally send email to an administrator notifying them of the incident. Using
information from the log, the administrator can take action with the ISP of the hacker. In some
types of intrusions, the firewall can fend off the hacker by discarding all further packets from the
hacker’s IP address for a period of time.
Stateful Packet Inspection
Unlike simple Internet sharing routers, a firewall uses a process called stateful packet inspection to
ensure secure firewall filtering to protect your network from attacks and intrusions. Since
user-level applications such as FTP and Web browsers can create complex patterns of network
traffic, it is necessary for the firewall to analyze groups of network connection states. Using
Stateful Packet Inspection, an incoming packet is intercepted at the network layer and then
analyzed for state-related information associated with all network connections. A central cache
within the firewall keeps track of the state information associated with all network connections.
All traffic passing through the firewall is analyzed against the state of these connections in order to
determine whether or not it will be allowed to pass through or rejected.
Denial of Service Attack
A hacker may be able to prevent your network from operating or communicating by launching a
Denial of Service (DoS) attack. The method used for such an attack can be as simple as merely
flooding your site with more requests than it can handle. A more sophisticated attack may attempt
to exploit some weakness in the operating system used by your router or gateway. Some operating
systems can be disrupted by simply sending a packet with incorrect length information.
Ethernet Cabling
Although Ethernet networks originally used thick or thin coaxial cable, most installations currently
use unshielded twisted pair (UTP) cabling. The UTP cable contains eight conductors, arranged in
four twisted pairs, and terminated with an RJ45 type connector. A normal straight-through UTP
Ethernet cable follows the EIA568B standard wiring as described below in Table B-1

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-12 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
.
Category 5 Cable Quality
Category 5 distributed cable that meets ANSI/EIA/TIA-568-A building wiring standards can be a
maximum of 328 feet (ft.) or 100 meters (m) in length, divided as follows:
20 ft. (6 m) between the hub and the patch panel (if used)
295 ft. (90 m) from the wiring closet to the wall outlet
10 ft. (3 m) from the wall outlet to the desktop device
The patch panel and other connecting hardware must meet the requirements for 100 Mbps
operation (Category 5). Only 0.5 inch (1.5 cm) of untwist in the wire pair is allowed at any
termination point.
A twisted pair Ethernet network operating at 10 Mbits/second (10BASE-T) will often tolerate low
quality cables, but at 100 Mbits/second (10BASE-Tx) the cable must be rated as Category 5, or
Cat 5, by the Electronic Industry Association (EIA). This rating will be printed on the cable jacket.
A Category 5 cable will meet specified requirements regarding loss and crosstalk. In addition,
there are restrictions on maximum cable length for both 10 and 100 Mbits/second networks.
Table B-1. UTP Ethernet cable wiring, straight-through
Pin Wire color Signal
1 Orange/White Transmit (Tx) +
2 Orange Transmit (Tx) -
3 Green/White Receive (Rx) +
4Blue
5 Blue/White
6 Green Receive (Rx) -
7 Brown/White
8Brown
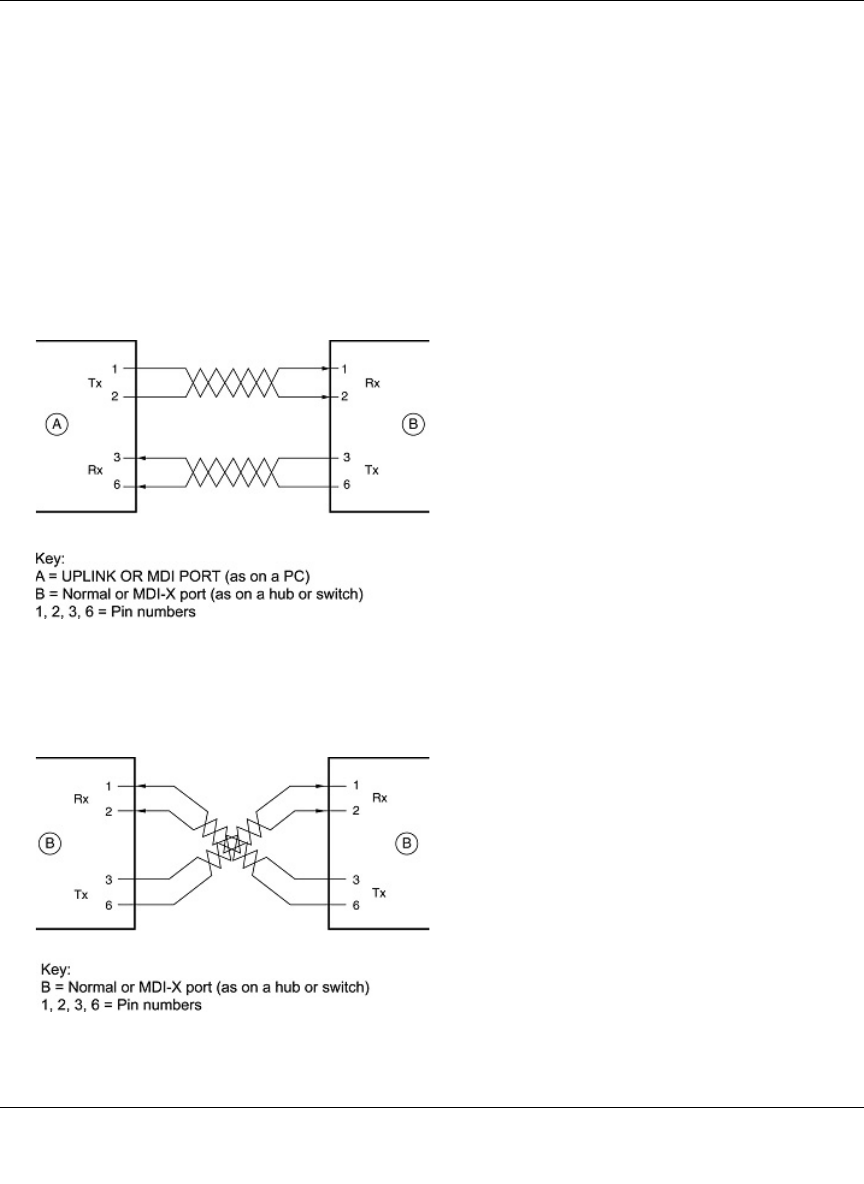
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-13
202-10085-01, March 2005
Inside Twisted Pair Cables
For two devices to communicate, the transmitter of each device must be connected to the receiver
of the other device. The crossover function is usually implemented internally as part of the
circuitry in the device. Computers and workstation adapter cards are usually media-dependent
interface ports, called MDI or uplink ports. Most repeaters and switch ports are configured as
media-dependent interfaces with built-in crossover ports, called MDI-X or normal ports. Auto
Uplink technology automatically senses which connection, MDI or MDI-X, is needed and makes
the right connection.
Figure B-1 illustrates straight-through twisted pair cable.
Figure B-1: Straight-Through Twisted-Pair Cable
Figure B-2 illustrates crossover twisted pair cable.
Figure B-2: Crossover Twisted-Pair Cable
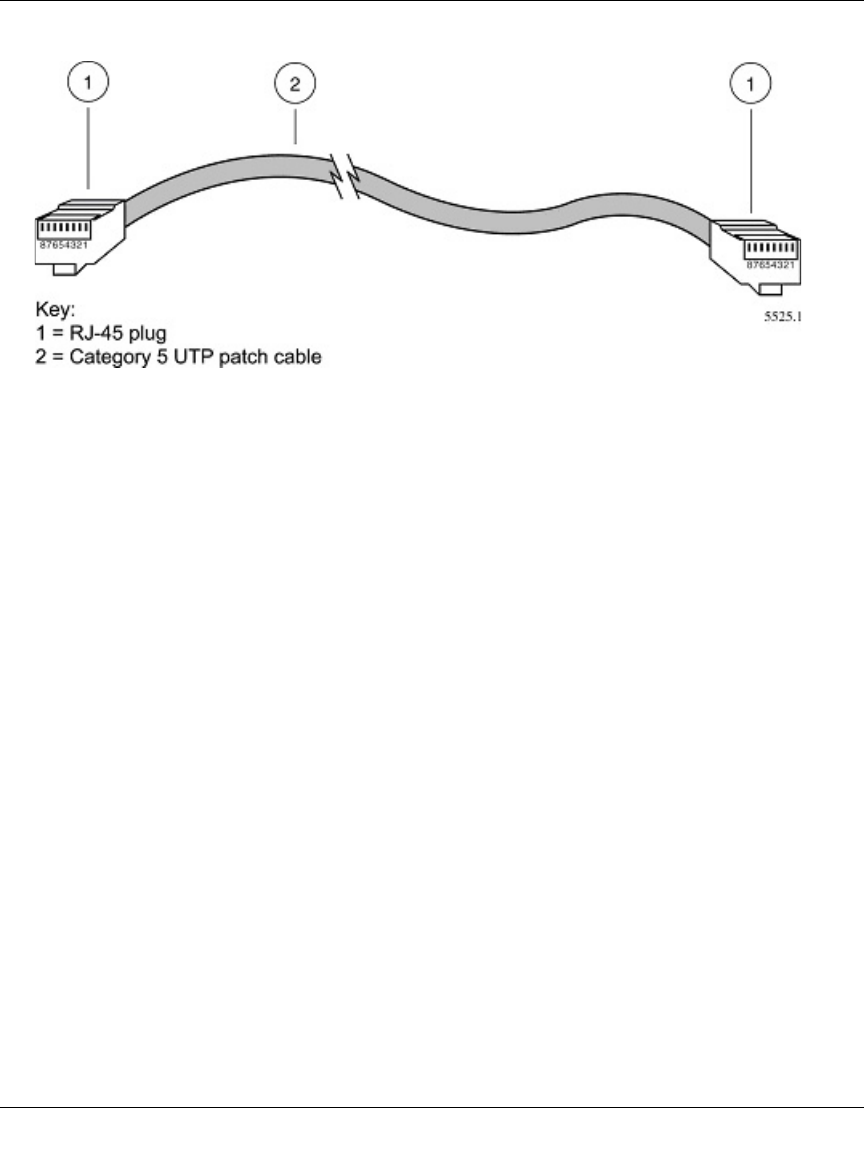
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-14 Network, Routing, Firewall, and Basics
202-10085-01, March 2005
Figure B-3: Category 5 UTP Cable with Male RJ-45 Plug at Each End
Note: Flat “silver satin” telephone cable may have the same RJ-45 plug. However, using telephone
cable results in excessive collisions, causing the attached port to be partitioned or disconnected
from the network.
Uplink Switches, Crossover Cables, and MDI/MDIX Switching
In the wiring table above, the concept of transmit and receive are from the perspective of the PC,
which is wired as Media Dependant Interface (MDI). In this wiring, the PC transmits on pins 1 and
2. At the hub, the perspective is reversed, and the hub receives on pins 1 and 2. This wiring is
referred to as Media Dependant Interface - Crossover (MDI-X).
When connecting a PC to a PC, or a hub port to another hub port, the transmit pair must be
exchanged with the receive pair. This exchange is done by one of two mechanisms. Most hubs
provide an Uplink switch which will exchange the pairs on one port, allowing that port to be
connected to another hub using a normal Ethernet cable. The second method is to use a crossover
cable, which is a special cable in which the transmit and receive pairs are exchanged at one of the
two cable connectors. Crossover cables are often unmarked as such, and must be identified by
comparing the two connectors. Since the cable connectors are clear plastic, it is easy to place them
side by side and view the order of the wire colors on each. On a straight-through cable, the color
order will be the same on both connectors. On a crossover cable, the orange and blue pairs will be
exchanged from one connector to the other.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Network, Routing, Firewall, and Basics B-15
202-10085-01, March 2005
The FVS124G VPN Firewall incorporates Auto UplinkTM technology (also called MDI/MDIX).
Each LOCAL Ethernet port will automatically sense whether the Ethernet cable plugged into the
port should have a normal connection (e.g. connecting to a PC) or an uplink connection (e.g.
connecting to a router, switch, or hub). That port will then configure itself to the correct
configuration. This feature also eliminates the need to worry about crossover cables, as Auto
UplinkTM will accommodate either type of cable to make the right connection.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
B-16 Network, Routing, Firewall, and Basics
202-10085-01, March 2005

Preparing Your Network C-1
202-10085-01, March 2005
Appendix C
Preparing Your Network
This appendix describes how to prepare your network to connect to the Internet through the
FVS124G ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports and how to verify
the readiness of broadband Internet service from an Internet service provider (ISP).
Preparing Your Computers for TCP/IP Networking
Computers access the Internet using a protocol called TCP/IP (Transmission Control Protocol/
Internet Protocol). Each computer on your network must have TCP/IP installed and selected as its
networking protocol. If a Network Interface Card (NIC) is already installed in your PC, then TCP/
IP is probably already installed as well.
Most operating systems include the software components you need for networking with TCP/IP:
•Windows
® 95 or later includes the software components for establishing a TCP/IP network.
• Windows 3.1 does not include a TCP/IP component. You need to purchase a third-party TCP/
IP application package such as NetManage Chameleon.
• Macintosh Operating System 7 or later includes the software components for establishing a
TCP/IP network.
• All versions of UNIX or Linux include TCP/IP components. Follow the instructions provided
with your operating system or networking software to install TCP/IP on your computer.
Note: If an ISP technician configured your computer during the installation of a
broadband modem, or if you configured it using instructions provided by your ISP, you
may need to copy the current configuration information for use in the configuration of
your firewall. Write down this information before reconfiguring your computers. Refer
to “Obtaining ISP Configuration Information for Windows Computers” on page C-19 or
“Obtaining ISP Configuration Information for Macintosh Computers” on page C-20 for
further information.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-2 Preparing Your Network
202-10085-01, March 2005
In your IP network, each PC and the firewall must be assigned a unique IP addresses. Each PC
must also have certain other IP configuration information such as a subnet mask (netmask), a
domain name server (DNS) address, and a default gateway address. In most cases, you should
install TCP/IP so that the PC obtains its specific network configuration information automatically
from a DHCP server during bootup. For a detailed explanation of the meaning and purpose of
these configuration items, refer to “Appendix B, “Network, Routing, Firewall, and Basics.”
The FVS124G VPN Firewall is shipped preconfigured as a DHCP server. The firewall assigns the
following TCP/IP configuration information automatically when the PCs are rebooted:
• PC or workstation IP addresses—192.168.0.2 through 192.168.0.254
• Subnet mask—255.255.255.0
• Gateway address (the firewall)—192.168.1.1
These addresses are part of the IETF-designated private address range for use in private networks.
Configuring Windows 95, 98, and Me for TCP/IP Networking
As part of the PC preparation process, you need to manually install and configure TCP/IP on each
networked PC. Before starting, locate your Windows CD; you may need to insert it during the
TCP/IP installation process.
Install or Verify Windows Networking Components
To install or verify the necessary components for IP networking:
1. On the Windows taskbar, click the Start button, point to Settings, and then click Control Panel.
2. Double-click the Network icon.
The Network window opens, which displays a list of installed components:
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-3
202-10085-01, March 2005
You must have an Ethernet adapter, the TCP/IP protocol, and Client for Microsoft Networks.
If you need to install a new adapter, follow these steps:
a. Click the Add button.
b. Select Adapter, and then click Add.
c. Select the manufacturer and model of your Ethernet adapter, and then click OK.
If you need TCP/IP:
a. Click the Add button.
b. Select Protocol, and then click Add.
c. Select Microsoft.
d. Select TCP/IP, and then click OK.
Note: It is not necessary to remove any other network components shown in the
Network window in order to install the adapter, TCP/IP, or Client for Microsoft
Networks.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-4 Preparing Your Network
202-10085-01, March 2005
If you need Client for Microsoft Networks:
a. Click the Add button.
b. Select Client, and then click Add.
c. Select Microsoft.
d. Select Client for Microsoft Networks, and then click OK.
3. Restart your PC for the changes to take effect.
Enabling DHCP to Automatically Configure TCP/IP Settings
After the TCP/IP protocol components are installed, each PC must be assigned specific
information about itself and resources that are available on its network. The simplest way to
configure this information is to allow the PC to obtain the information from a DHCP server in the
network.
You will find there are many similarities in the procedures for different Windows systems
when using DHCP to configure TCP/IP.
The following steps will walk you through the configuration process for each of these
versions of Windows.
Locate your Network Neighborhood icon.
• If the Network Neighborhood icon is on the Windows desktop, position your mouse
pointer over it and right-click your mouse button.
• If the icon is not on the desktop,
• Click Start on the task bar located at the bottom left of the window.
• Choose Settings, and then Control Panel.
• Locate the Network Neighborhood icon and click on it. This will open the Network
panel as shown below.
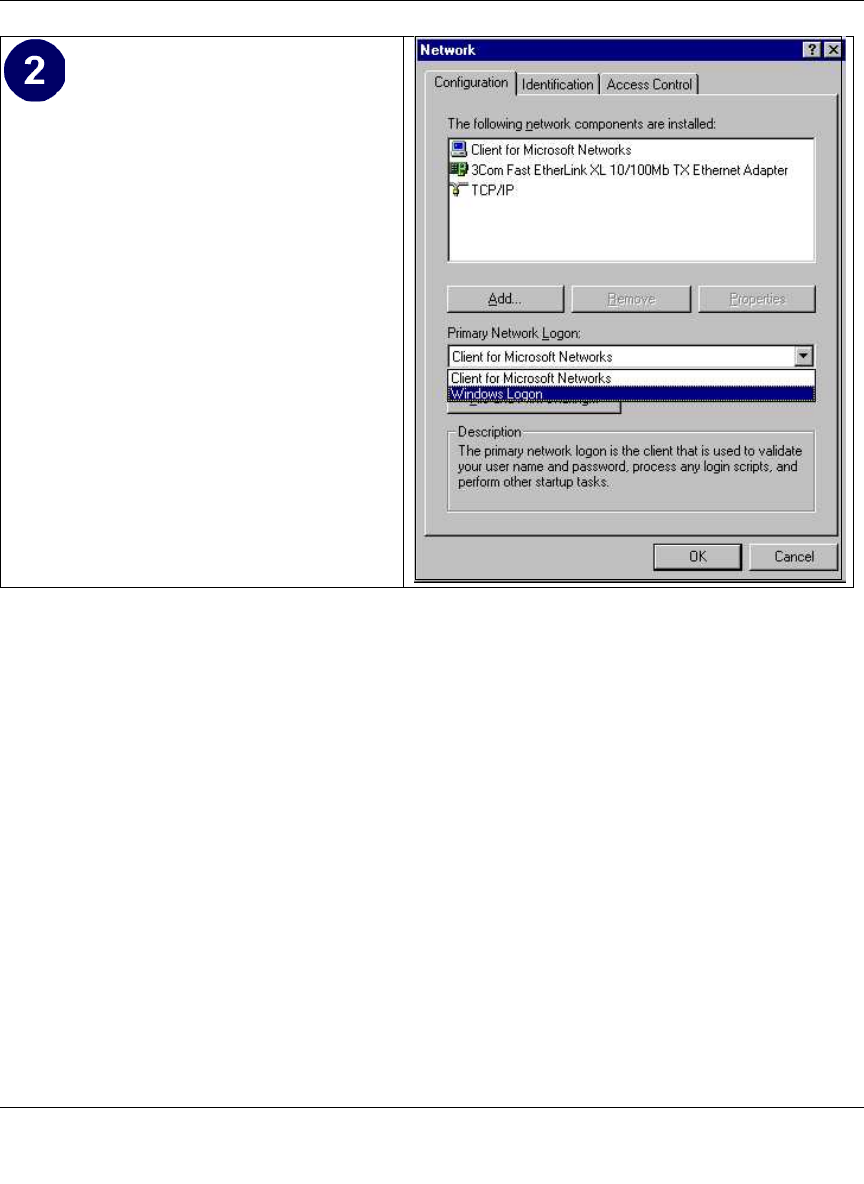
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-5
202-10085-01, March 2005
Verify the following settings as shown:
• Client for Microsoft Network exists
• Ethernet adapter is present
• TCP/IP is present
•Primary Network Logon is set to
Windows logon
Click on the Properties button. The
following TCP/IP Properties window will
display.
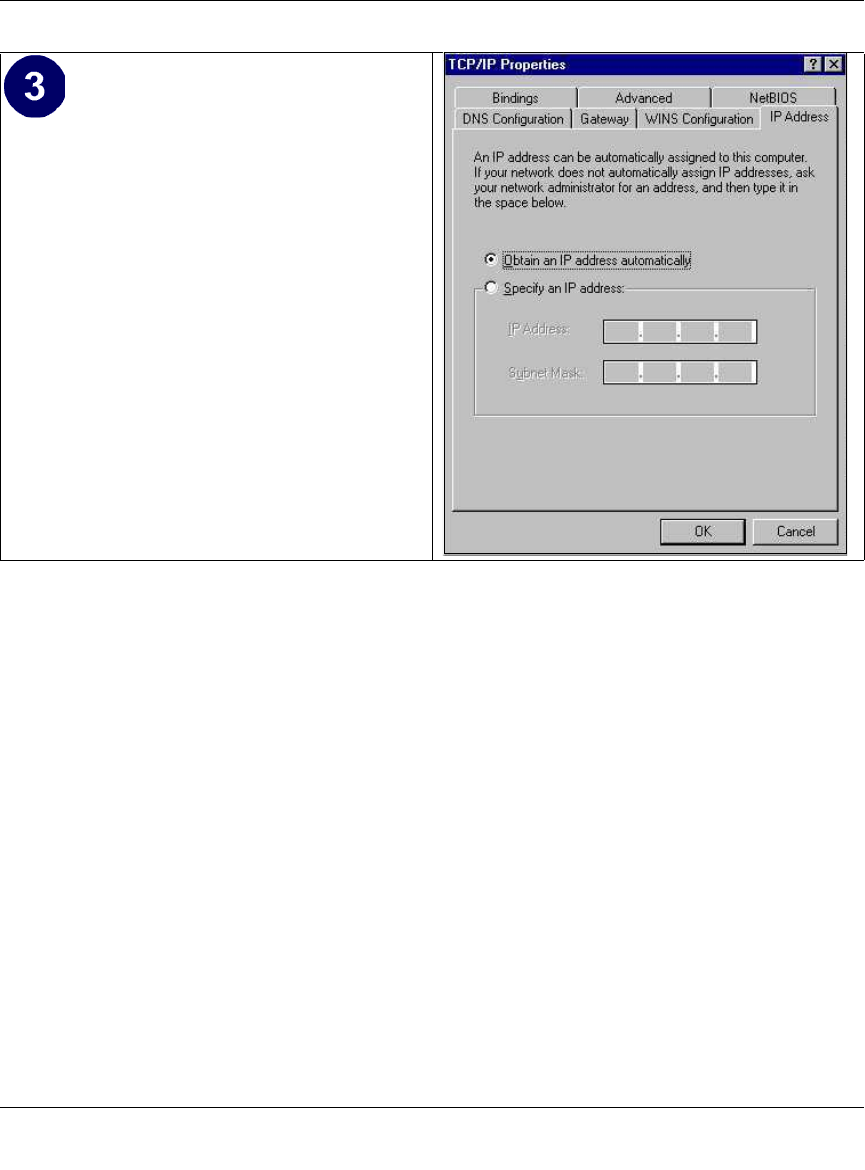
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-6 Preparing Your Network
202-10085-01, March 2005
Selecting Windows’ Internet Access Method
1. On the Windows taskbar, click the Start button, point to Settings, and then click Control Panel.
2. Double-click the Internet Options icon.
3. Select “I want to set up my Internet connection manually” or “I want to connect through a
Local Area Network” and click Next.
4. Select “I want to connect through a Local Area Network” and click Next.
5. Uncheck all boxes in the LAN Internet Configuration screen and click Next.
6. Proceed to the end of the Wizard.
Verifying TCP/IP Properties
After your PC is configured and has rebooted, you can check the TCP/IP configuration using the
utility winipcfg.exe:
1. On the Windows taskbar, click the Start button, and then click Run.
• By default, the IP Address tab is open on
this window.
• Verify the following:
Obtain an IP address automatically is
selected. If not selected, click in the radio
button to the left of it to select it. This
setting is required to enable the DHCP server
to automatically assign an IP address.
• Click OK to continue.
Restart the PC.
Repeat these steps for each PC with this
version of Windows on your network.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-7
202-10085-01, March 2005
2. Type winipcfg, and then click OK.
The IP Configuration window opens, which lists (among other things), your IP address, subnet
mask, and default gateway.
3. From the drop-down box, select your Ethernet adapter.
The window is updated to show your settings, which should match the values below if you are
using the default TCP/IP settings that NETGEAR recommends for connecting through a
router or gateway:
• The IP address is between 192.168.0.2 and 192.168.0.254
• The subnet mask is 255.255.255.0
• The default gateway is 192.168.1.1
Configuring Windows NT4, 2000 or XP for IP Networking
As part of the PC preparation process, you may need to install and configure
TCP/IP on each networked PC. Before starting, locate your Windows CD; you may need to insert
it during the TCP/IP installation process.
Install or Verify Windows Networking Components
To install or verify the necessary components for IP networking:
1. On the Windows taskbar, click the Start button, point to Settings, and then click Control Panel.
2. Double-click the Network and Dialup Connections icon.
3. If an Ethernet adapter is present in your PC, you should see an entry for Local Area
Connection. Double-click that entry.
4. Select Properties.
5. Verify that ‘Client for Microsoft Networks’ and ‘Internet Protocol (TCP/IP)’ are present. If
not, select Install and add them.
6. Select ‘Internet Protocol (TCP/IP)’, click Properties, and verify that “Obtain an IP address
automatically is selected.
7. Click OK and close all Network and Dialup Connections windows.
8. Then, restart your PC.
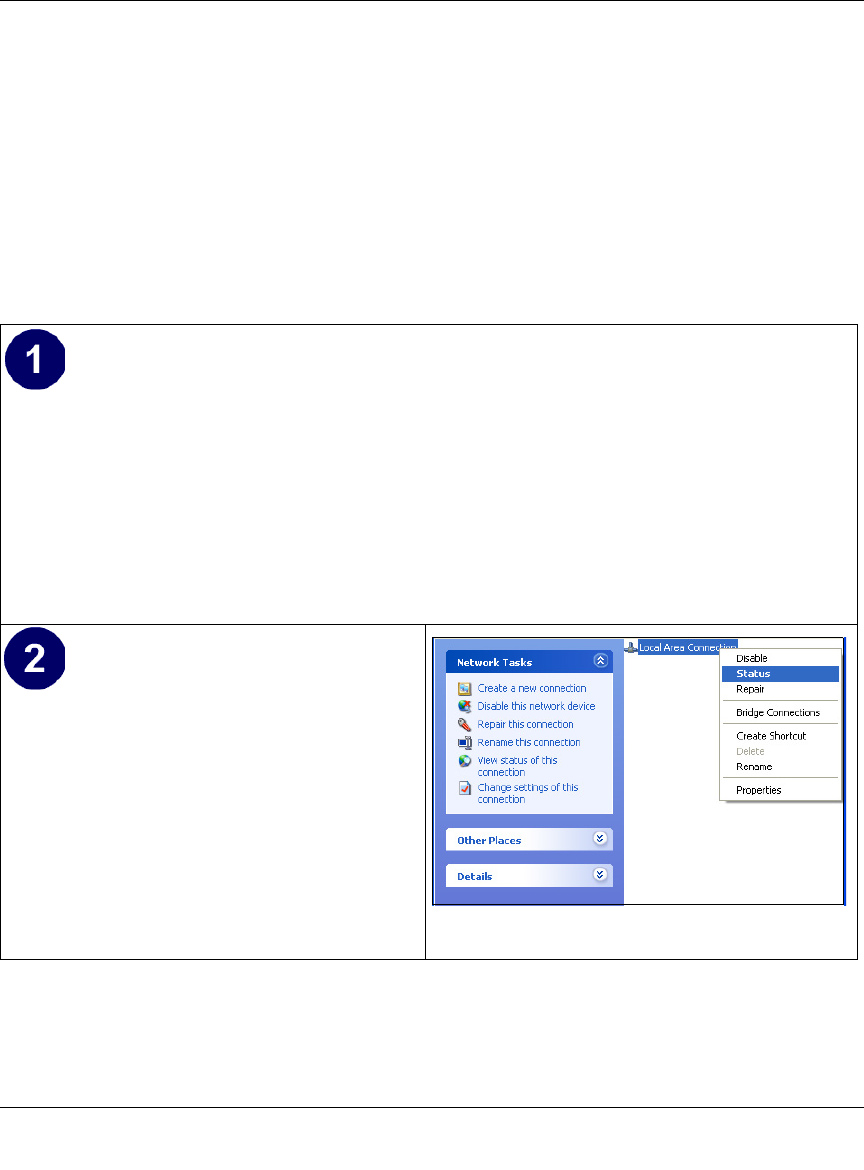
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-8 Preparing Your Network
202-10085-01, March 2005
Enabling DHCP to Automatically Configure TCP/IP Settings
You will find there are many similarities in the procedures for different Windows systems when
using DHCP to configure TCP/IP.
The following steps will walk you through the configuration process for each of these versions of
Windows.
DHCP Configuration of TCP/IP in Windows XP
Locate your Network Neighborhood icon.
• Select Control Panel from the Windows XP new Start Menu.
• Select the Network Connections icon on the Control Panel. This will take you to the next
step.
• Now the Network Connection window
displays.
The Connections List that shows all the
network connections set up on the PC,
located to the right of the window.
• Right-click on the Connection you will
use and choose Status.
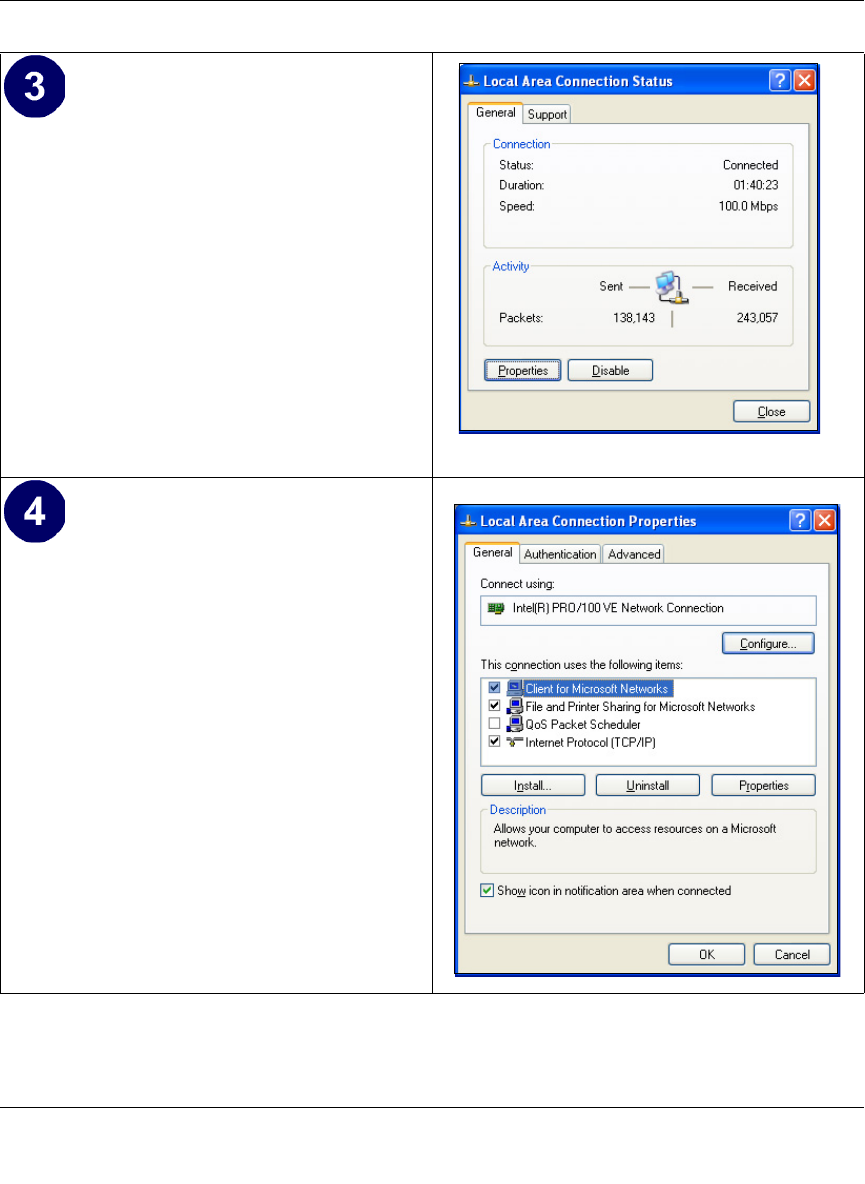
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-9
202-10085-01, March 2005
• Now you should be at the Local Area
Network Connection Status window. This
box displays the connection status, duration,
speed, and activity statistics.
• Administrator logon access rights are needed
to use this window.
• Click the Properties button to view details
about the connection.
• The TCP/IP details are presented on the
Support tab page.
• Select Internet Protocol, and click
Properties to view the configuration
information.
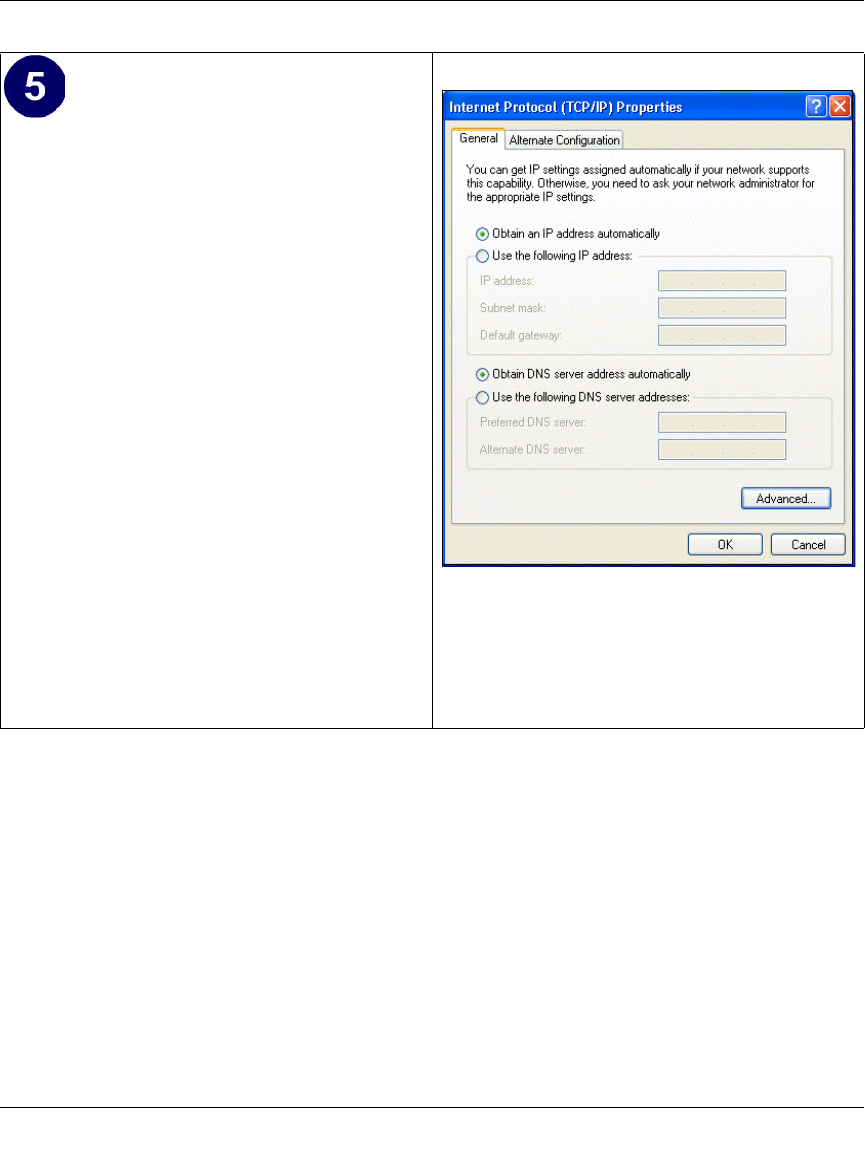
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-10 Preparing Your Network
202-10085-01, March 2005
DHCP Configuration of TCP/IP in Windows 2000
Once again, after you have installed the network card, TCP/IP for Windows 2000 is configured.
TCP/IP should be added by default and set to DHCP without your having to configure it.
However, if there are problems, follow these steps to configure TCP/IP with DHCP for Windows
2000.
• Verify that the Obtain an IP address
automatically radio button is selected.
• Verify that Obtain DNS server address
automatically radio button is selected.
• Click the OK button.
This completes the DHCP configuration of TCP/
IP in Windows XP.
Repeat these steps for each PC with this version
of Windows on your network.
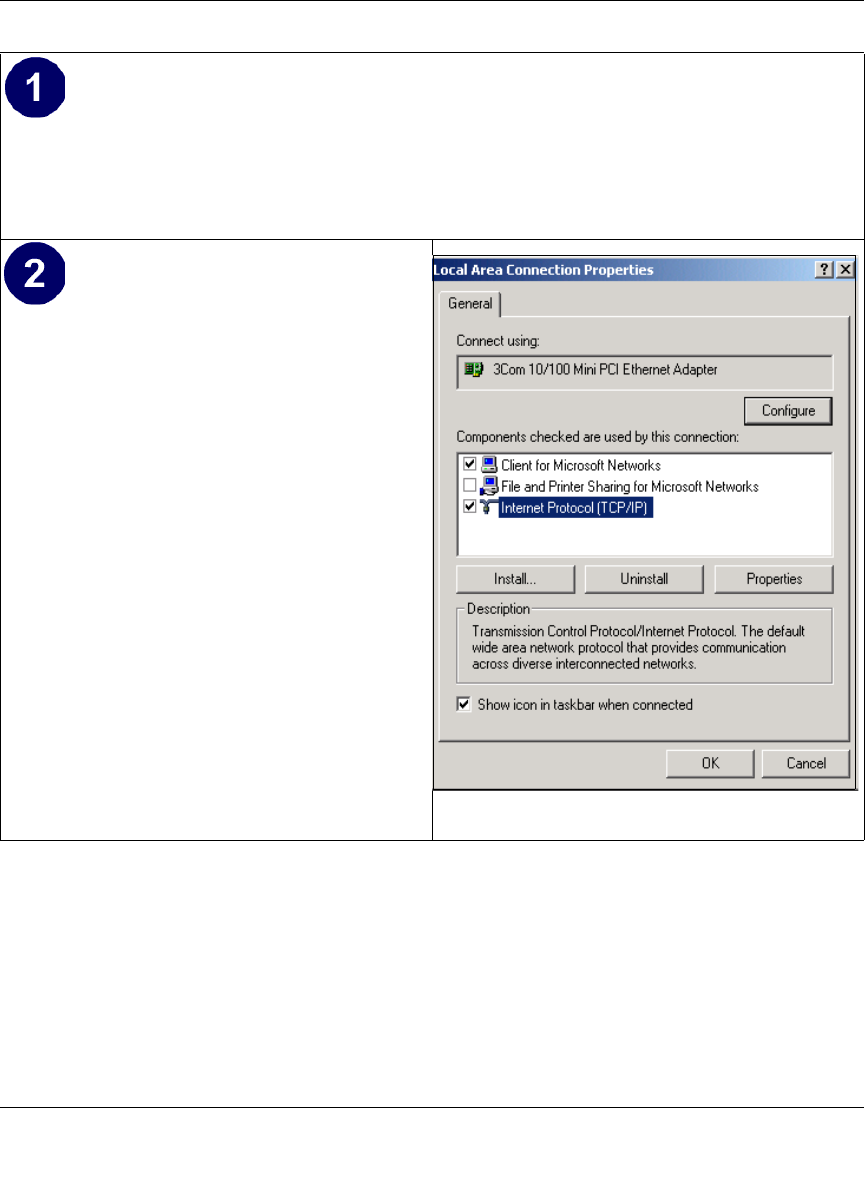
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-11
202-10085-01, March 2005
• Click on the My Network Places icon on the Windows desktop. This will bring up a window
called Network and Dial-up Connections.
• Right click on Local Area Connection and select Properties.
•The Local Area Connection Properties
dialog box appears.
• Verify that you have the correct Ethernet
card selected in the Connect using: box.
• Verify that at least the following two items
are displayed and selected in the box of
“Components checked are used by this
connection:”
• Client for Microsoft Networks and
• Internet Protocol (TCP/IP)
• Click OK.
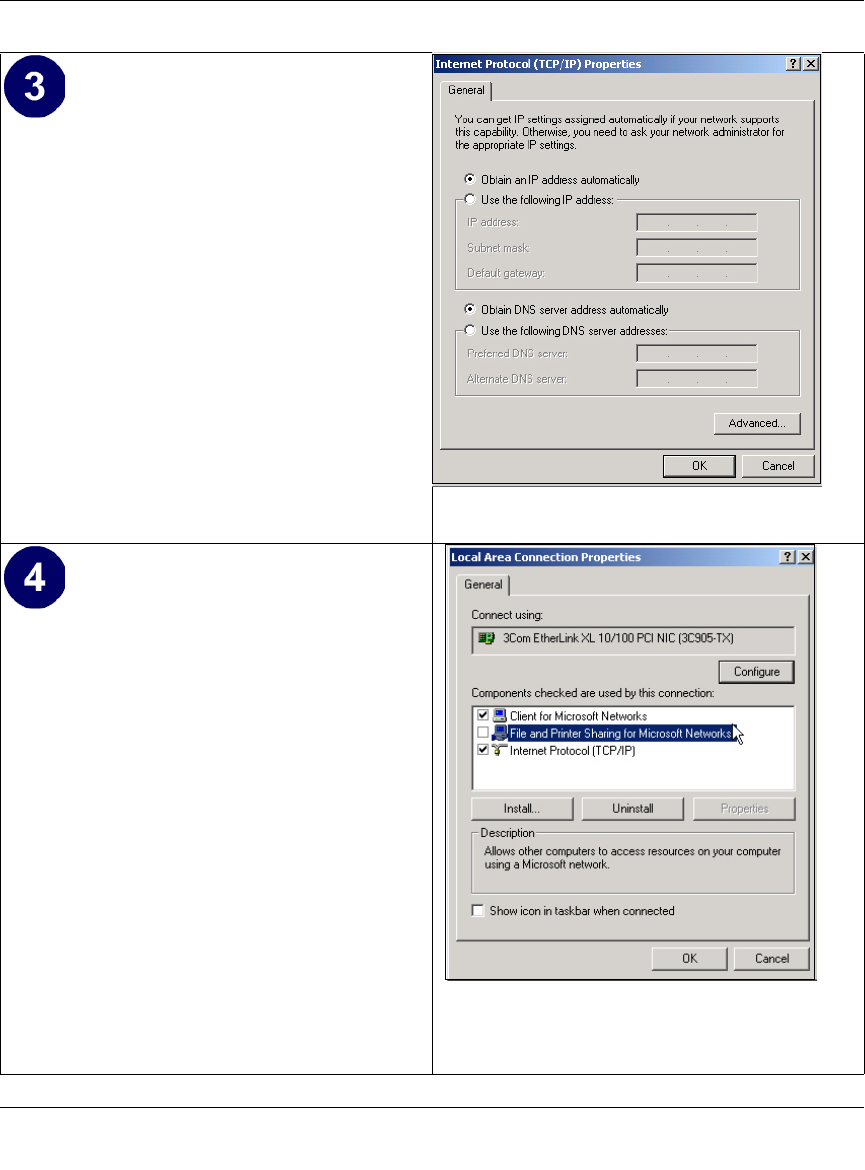
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-12 Preparing Your Network
202-10085-01, March 2005
• With Internet Protocol (TCP/IP) selected,
click on Properties to open the Internet
Protocol (TCP/IP) Properties dialogue box.
• Verify that
•Obtain an IP address automatically is
selected.
•Obtain DNS server address
automatically is selected.
• Click OK to return to Local Area
Connection Properties.
• Click OK again to complete the
configuration process for Windows 2000.
Restart the PC.
Repeat these steps for each PC with this version
of Windows on your network.
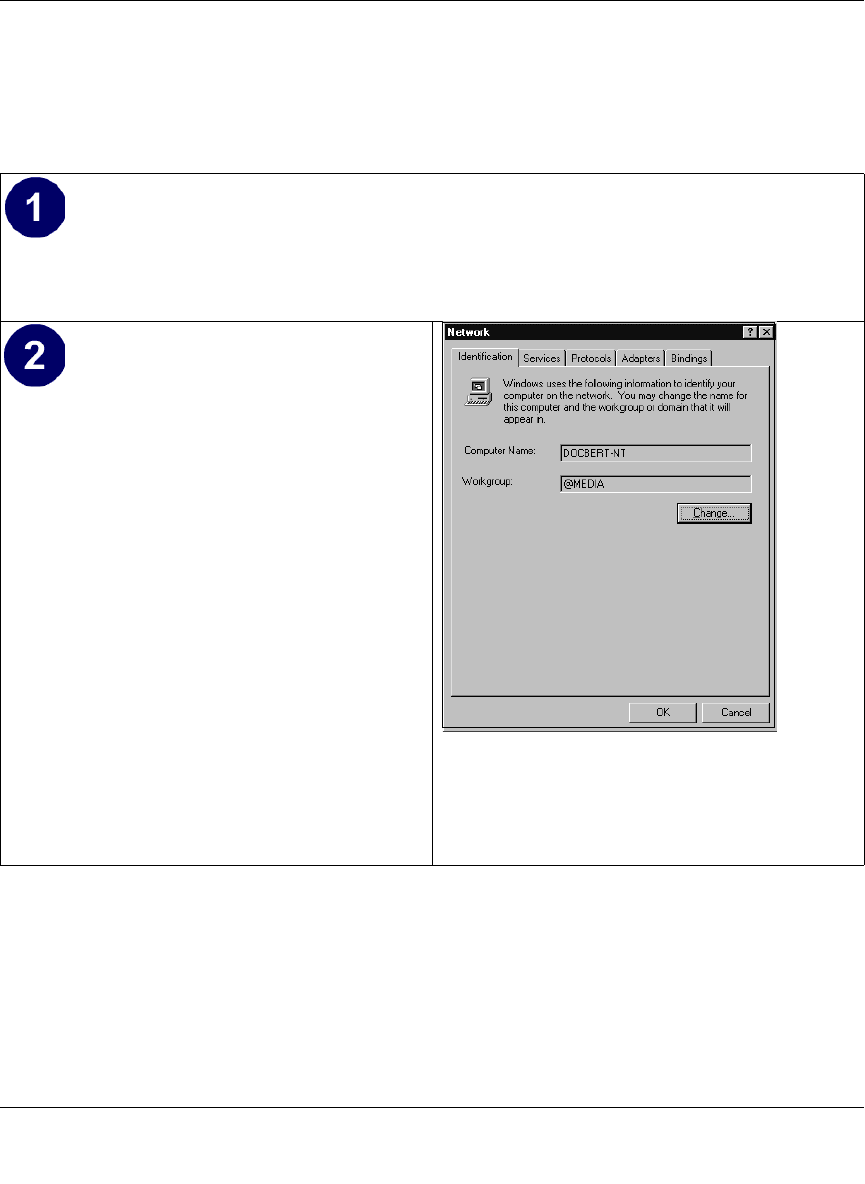
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-13
202-10085-01, March 2005
DHCP Configuration of TCP/IP in Windows NT4
Once you have installed the network card, you need to configure the TCP/IP environment for
Windows NT 4.0. Follow this procedure to configure TCP/IP with DHCP in Windows NT 4.0.
• Choose Settings from the Start Menu, and then select Control Panel.
This will display Control Panel window.
• Double-click the Network icon in the
Control Panel window.
The Network panel will display.
• Select the Protocols tab to continue.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-14 Preparing Your Network
202-10085-01, March 2005
• Highlight the TCP/IP Protocol in the
Network Protocols box, and click on the
Properties button.
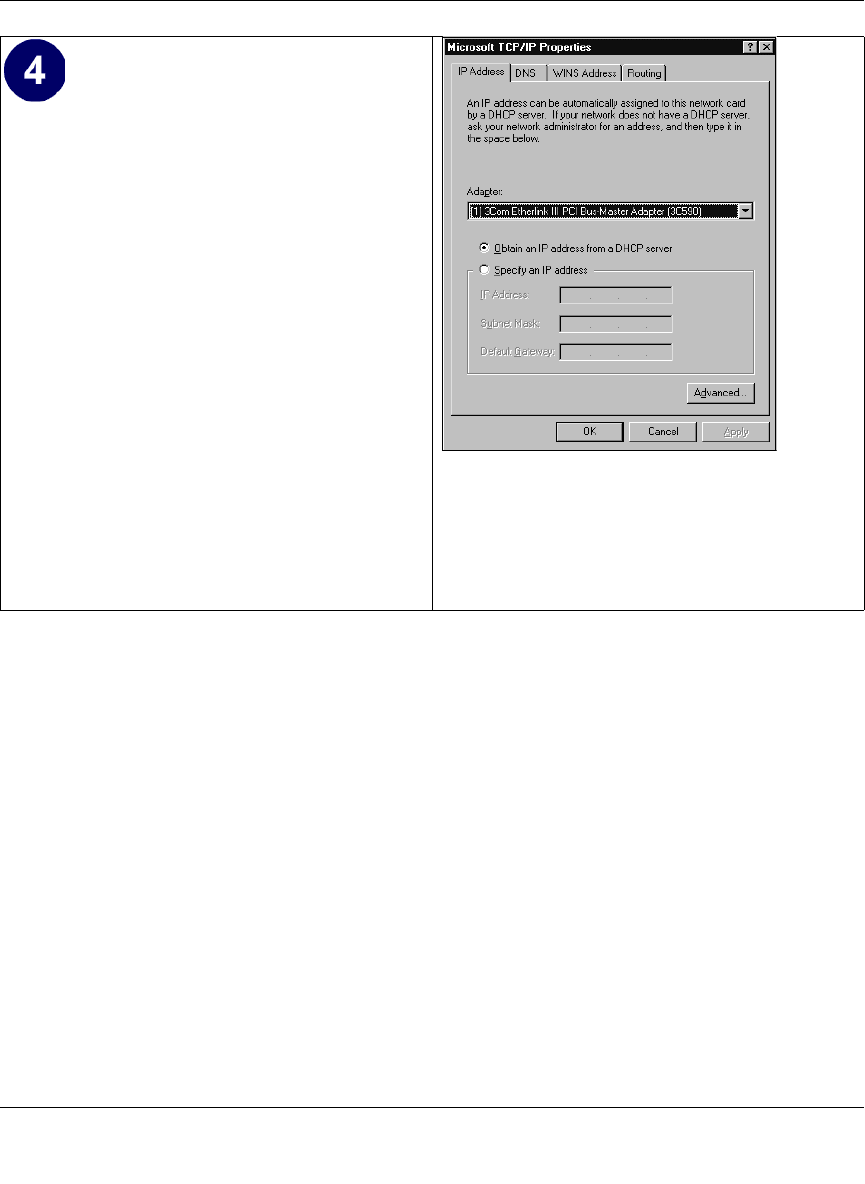
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-15
202-10085-01, March 2005
Verifying TCP/IP Properties for Windows XP, 2000, and NT4
To check your PC’s TCP/IP configuration:
1. On the Windows taskbar, click the Start button, and then click Run.
The Run window opens.
2. Type cmd and then click OK.
A command window opens
3. Type ipconfig /all
Your IP Configuration information will be listed, and should match the values below if you are
using the default TCP/IP settings that NETGEAR recommends for connecting through a
router or gateway:
• The IP address is between 192.168.0.2 and 192.168.0.254
• The subnet mask is 255.255.255.0
•The TCP/IP Properties dialog box now
displays.
• Click the IP Address tab.
• Select the radio button marked Obtain an IP
address from a DHCP server.
• Click OK. This completes the configuration
of TCP/IP in Windows NT.
Restart the PC.
Repeat these steps for each PC with this version
of Windows on your network.
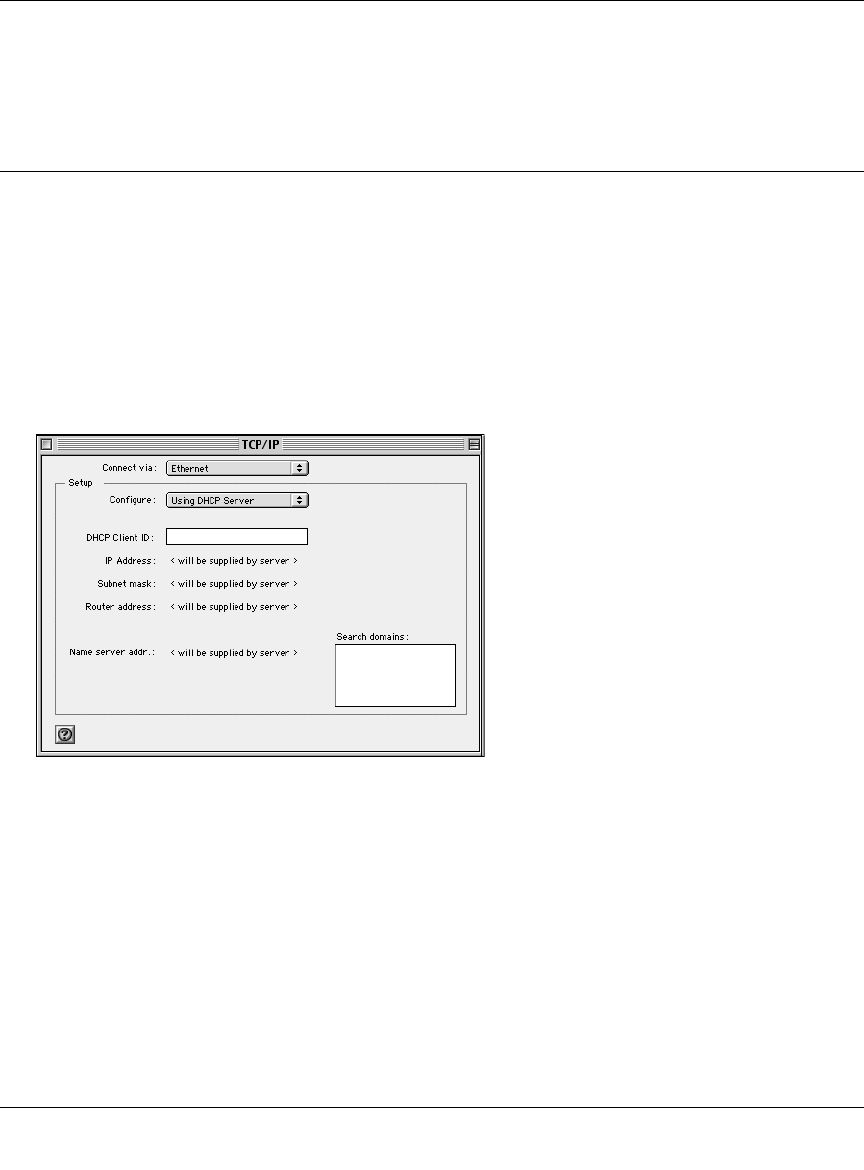
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-16 Preparing Your Network
202-10085-01, March 2005
• The default gateway is 192.168.1.1
4. Type exit
Configuring the Macintosh for TCP/IP Networking
Beginning with Macintosh Operating System 7, TCP/IP is already installed on the Macintosh. On
each networked Macintosh, you will need to configure TCP/IP to use DHCP.
MacOS 8.6 or 9.x
1. From the Apple menu, select Control Panels, then TCP/IP.
The TCP/IP Control Panel opens:
2. From the “Connect via” box, select your Macintosh’s Ethernet interface.
3. From the “Configure” box, select Using DHCP Server.
You can leave the DHCP Client ID box empty.
4. Close the TCP/IP Control Panel.
5. Repeat this for each Macintosh on your network.
MacOS X
1. From the Apple menu, choose System Preferences, then Network.
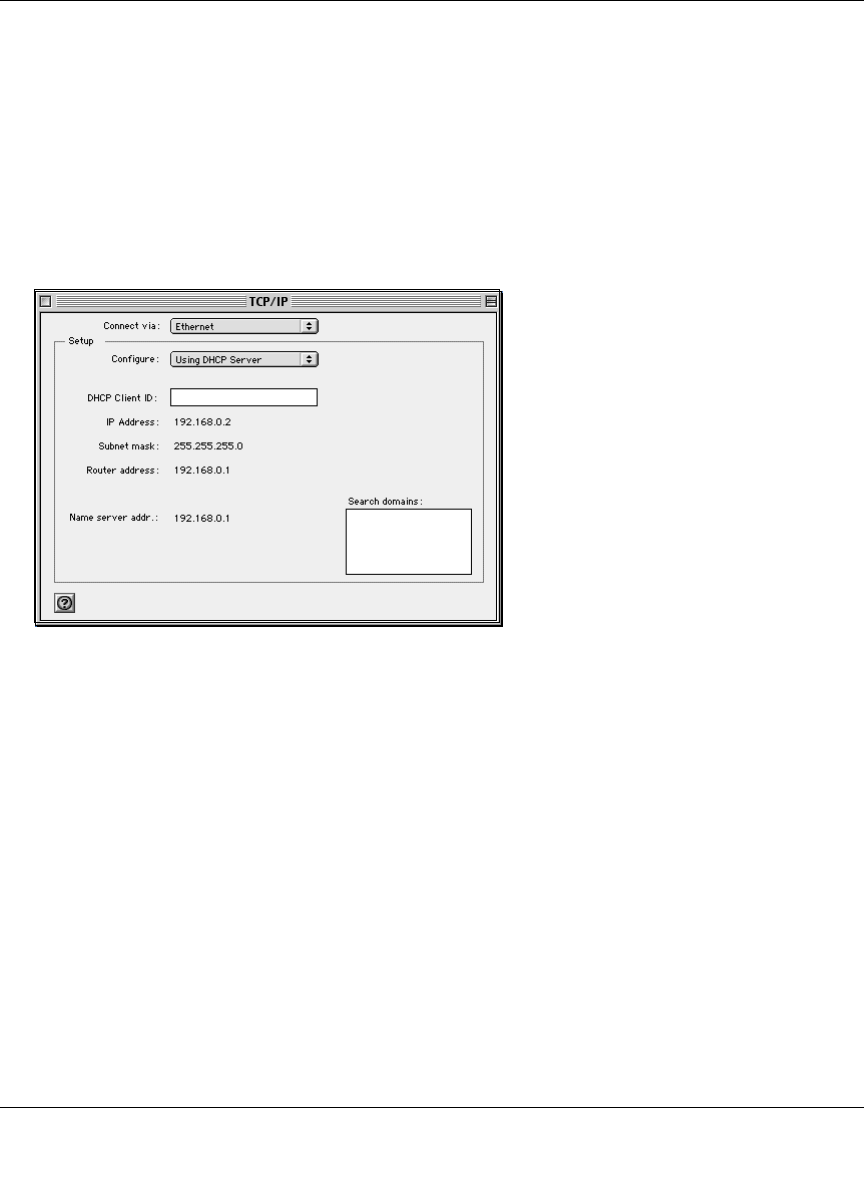
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-17
202-10085-01, March 2005
2. If not already selected, select Built-in Ethernet in the Configure list.
3. If not already selected, Select Using DHCP in the TCP/IP tab.
4. Click Save.
Verifying TCP/IP Properties for Macintosh Computers
After your Macintosh is configured and has rebooted, you can check the TCP/IP configuration by
returning to the TCP/IP Control Panel. From the Apple menu, select Control Panels, then TCP/IP.
The panel is updated to show your settings, which should match the values below if you are using
the default TCP/IP settings that NETGEAR recommends:
• The IP Address is between 192.168.0.2 and 192.168.0.254
• The Subnet mask is 255.255.255.0
• The Router address is 192.168.1.1
If you do not see these values, you may need to restart your Macintosh or you may need to switch
the “Configure” setting to a different option, then back again to “Using DHCP Server”.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-18 Preparing Your Network
202-10085-01, March 2005
Verifying the Readiness of Your Internet Account
For broadband access to the Internet, you need to contract with an Internet service provider (ISP)
for a single-user Internet access account using a cable modem or DSL modem. This modem must
be a separate physical box (not a card) and must provide an Ethernet port intended for connection
to a Network Interface Card (NIC) in a computer. Your firewall does not support a USB-connected
broadband modem.
For a single-user Internet account, your ISP supplies TCP/IP configuration information for one
computer. With a typical account, much of the configuration information is dynamically assigned
when your PC is first booted up while connected to the ISP, and you will not need to know that
dynamic information.
In order to share the Internet connection among several computers, your firewall takes the place of
the single PC, and you need to configure it with the TCP/IP information that the single PC would
normally use. When the firewall’s Internet port is connected to the broadband modem, the firewall
appears to be a single PC to the ISP. The firewall then allows the PCs on the local network to
masquerade as the single PC to access the Internet through the broadband modem. The method
used by the firewall to accomplish this is called Network Address Translation (NAT) or IP
masquerading.
Are Login Protocols Used?
Some ISPs require a special login protocol, in which you must enter a login name and password in
order to access the Internet. If you normally log in to your Internet account by running a program
such as WinPOET or EnterNet, then your account uses PPP over Ethernet (PPPoE).
When you configure your router, you will need to enter your login name and password in the
router’s configuration menus. After your network and firewall are configured, the firewall will
perform the login task when needed, and you will no longer need to run the login program from
your PC. It is not necessary to uninstall the login program.
What Is Your Configuration Information?
More and more, ISPs are dynamically assigning configuration information. However, if your ISP
does not dynamically assign configuration information but instead used fixed configurations, your
ISP should have given you the following basic information for your account:

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-19
202-10085-01, March 2005
• An IP address and subnet mask
• A gateway IP address, which is the address of the ISP’s router
• One or more domain name server (DNS) IP addresses
• Host name and domain suffix
For example, your account’s full server names may look like this:
mail.xxx.yyy.com
In this example, the domain suffix is xxx.yyy.com.
If any of these items are dynamically supplied by the ISP, your firewall automatically acquires
them.
If an ISP technician configured your PC during the installation of the broadband modem, or if you
configured it using instructions provided by your ISP, you need to copy the configuration
information from your PC’s Network TCP/IP Properties window or Macintosh TCP/IP Control
Panel before reconfiguring your PC for use with the firewall. These procedures are described next.
Obtaining ISP Configuration Information for Windows Computers
As mentioned above, you may need to collect configuration information from your PC so that you
can use this information when you configure the FVS124G VPN Firewall. Following this
procedure is only necessary when your ISP does not dynamically supply the account information.
To get the information you need to configure the firewall for Internet access:
1. On the Windows taskbar, click the Start button, point to Settings, and then click Control Panel.
2. Double-click the Network icon.
The Network window opens, which displays a list of installed components.
3. Select TCP/IP, and then click Properties.
The TCP/IP Properties dialog box opens.
4. Select the IP Address tab.
If an IP address and subnet mask are shown, write down the information. If an address is
present, your account uses a fixed (static) IP address. If no address is present, your account
uses a dynamically-assigned IP address. Click “Obtain an IP address automatically”.
5. Select the Gateway tab.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-20 Preparing Your Network
202-10085-01, March 2005
If an IP address appears under Installed Gateways, write down the address. This is the ISP’s
gateway address. Select the address and then click Remove to remove the gateway address.
6. Select the DNS Configuration tab.
If any DNS server addresses are shown, write down the addresses. If any information appears
in the Host or Domain information box, write it down. Click Disable DNS.
7. Click OK to save your changes and close the TCP/IP Properties dialog box.
You are returned to the Network window.
8. Click OK.
9. Reboot your PC at the prompt. You may also be prompted to insert your Windows CD.
Obtaining ISP Configuration Information for Macintosh
Computers
As mentioned above, you may need to collect configuration information from your Macintosh so
that you can use this information when you configure the FVS124G VPN Firewall. Following this
procedure is only necessary when your ISP does not dynamically supply the account information.
To get the information you need to configure the firewall for Internet access:
1. From the Apple menu, select Control Panels, then TCP/IP.
The TCP/IP Control Panel opens, which displays a list of configuration settings. If the
“Configure” setting is “Using DHCP Server”, your account uses a dynamically-assigned IP
address. In this case, close the Control Panel and skip the rest of this section.
2. If an IP address and subnet mask are shown, write down the information.
3. If an IP address appears under Router address, write down the address. This is the ISP’s
gateway address.
4. If any Name Server addresses are shown, write down the addresses. These are your ISP’s DNS
addresses.
5. If any information appears in the Search domains information box, write it down.
6. Change the “Configure” setting to “Using DHCP Server”.
7. Close the TCP/IP Control Panel.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Preparing Your Network C-21
202-10085-01, March 2005
Restarting the Network
Once you’ve set up your computers to work with the firewall, you must reset the network for the
devices to be able to communicate correctly. Restart any computer that is connected to the
FVS124G VPN Firewall.
After configuring all of your computers for TCP/IP networking and restarting them, and
connecting them to the local network of your FVS124G VPN Firewall, you are ready to access and
configure the firewall.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
C-22 Preparing Your Network
202-10085-01, March 2005

Virtual Private Networking D-1
202-10085-01, March 2005
Appendix D
Virtual Private Networking
There have been many improvements in the Internet including Quality of Service, network
performance, and inexpensive technologies, such as DSL. But one of the most important advances
has been in Virtual Private Networking (VPN) Internet Protocol security (IPSec). IPSec is one of
the most complete, secure, and commercially available, standards-based protocols developed for
transporting data.
What is a VPN?
A VPN is a shared network where private data is segmented from other traffic so that only the
intended recipient has access. The term VPN was originally used to describe a secure connection
over the Internet. Today, however, VPN is also used to describe private networks, such as Frame
Relay, Asynchronous Transfer Mode (ATM), and Multiprotocol Label Switching (MPLS).
A key aspect of data security is that the data flowing across the network is protected by encryption
technologies. Private networks lack data security, which allows data attackers to tap directly into
the network and read the data. IPSec-based VPNs use encryption to provide data security, which
increases the network’s resistance to data tampering or theft.
IPSec-based VPNs can be created over any type of IP network, including the Internet, Frame
Relay, ATM, and MPLS, but only the Internet is ubiquitous and inexpensive.
VPNs are traditionally used for:
•Intranets: Intranets connect an organization’s locations. These locations range from the
headquarters offices, to branch offices, to a remote employee’s home. Often this connectivity
is used for e-mail and for sharing applications and files. While Frame Relay, ATM, and MPLS
accomplish these tasks, the shortcomings of each limits connectivity. The cost of connecting
home users is also very expensive compared to Internet-access technologies, such as DSL or
cable. Because of this, organizations are moving their networks to the Internet, which is
inexpensive, and using IPSec to create these networks.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
D-2 Virtual Private Networking
202-10085-01, March 2005
•Remote Access: Remote access enables telecommuters and mobile workers to access e-mail
and business applications. A dial-up connection to an organization’s modem pool is one
method of access for remote workers, but is expensive because the organization must pay the
associated long distance telephone and service costs. Remote access VPNs greatly reduce
expenses by enabling mobile workers to dial a local Internet connection and then set up a
secure IPSec-based VPN communications to their organization.
•Extranets: Extranets are secure connections between two or more organizations. Common
uses for extranets include supply-chain management, development partnerships, and
subscription services. These undertakings can be difficult using legacy network technologies
due to connection costs, time delays, and access availability. IPSec-based VPNs are ideal for
extranet connections. IPSec-capable devices can be quickly and inexpensively installed on
existing Internet connections.
What Is IPSec and How Does It Work?
IPSec is an Internet Engineering Task Force (IETF) standard suite of protocols that provides data
authentication, integrity, and confidentiality as data is transferred between communication points
across IP networks. IPSec provides data security at the IP packet level. A packet is a data bundle
that is organized for transmission across a network, and includes a header and payload (the data in
the packet). IPSec emerged as a viable network security standard because enterprises wanted to
ensure that data could be securely transmitted over the Internet. IPSec protects against possible
security exposures by protecting data while in while in transit.
IPSec Security Features
IPSec is the most secure method commercially available for connecting network sites. IPSec was
designed to provide the following security features when transferring packets across networks:
•Authentication: Verifies that the packet received is actually from the claimed sender.
•Integrity: Ensures that the contents of the packet did not change in transit.
•Confidentiality: Conceals the message content through encryption.
IPSec Components
IPSec contains the following elements:
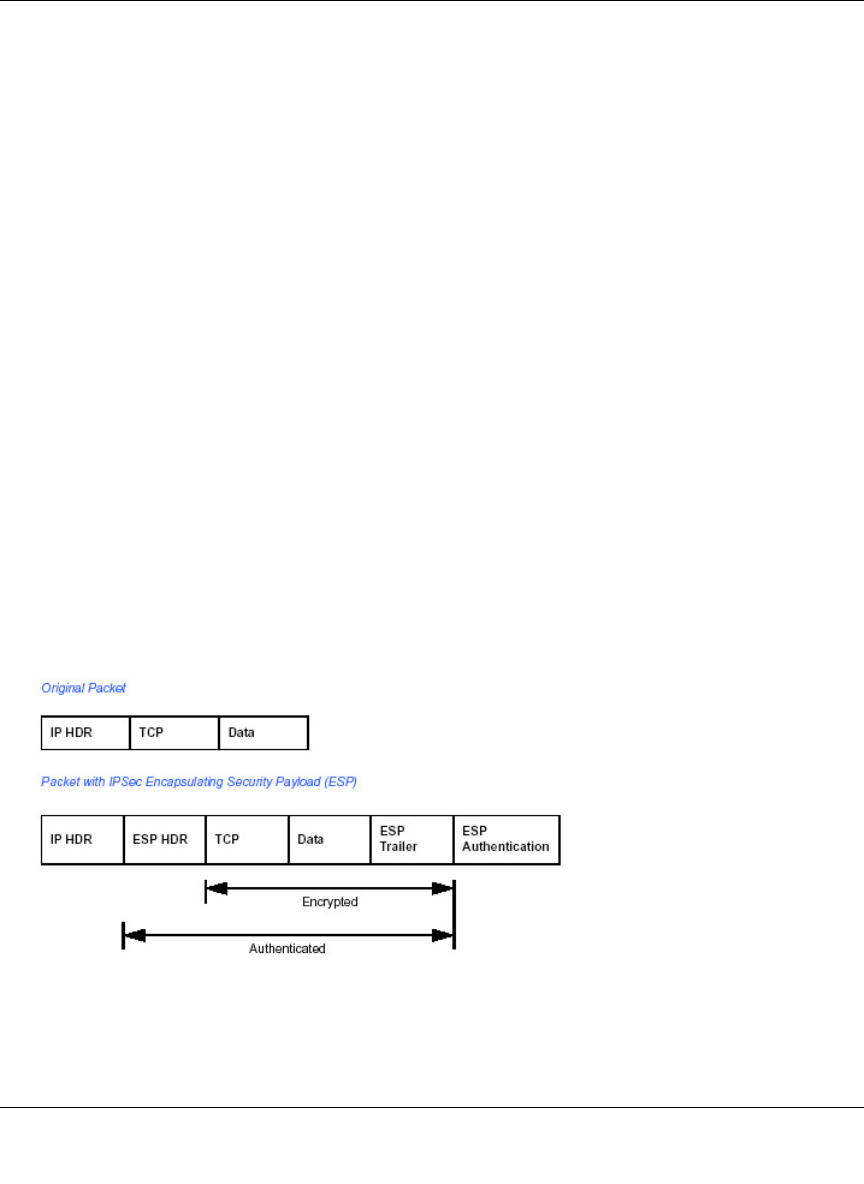
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking D-3
202-10085-01, March 2005
•Encapsulating Security Payload (ESP): Provides confidentiality, authentication, and
integrity.
•Authentication Header (AH): Provides authentication and integrity.
•Internet Key Exchange (IKE): Provides key management and Security Association (SA)
management.
Encapsulating Security Payload (ESP)
ESP provides authentication, integrity, and confidentiality, which protect against data tampering
and, most importantly, provide message content protection.
IPSec provides an open framework for implementing industry standard algorithms, such as SHA
and MD5. The algorithms IPSec uses produce a unique and unforgeable identifier for each packet,
which is a data equivalent of a fingerprint. This fingerprint allows the device to determine if a
packet has been tampered with. Furthermore, packets that are not authenticated are discarded and
not delivered to the intended receiver.
ESP also provides all encryption services in IPSec. Encryption translates a readable message into
an unreadable format to hide the message content. The opposite process, called decryption,
translates the message content from an unreadable format to a readable message. Encryption/
decryption allows only the sender and the authorized receiver to read the data. In addition, ESP has
an option to perform authentication, called ESP authentication. Using ESP authentication, ESP
provides authentication and integrity for the payload and not for the IP header.
Figure 9-4: Original packet and packet with IPSec Encapsulated Security Payload

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
D-4 Virtual Private Networking
202-10085-01, March 2005
The ESP header is inserted into the packet between the IP header and any subsequent packet
contents. However, because ESP encrypts the data, the payload is changed. ESP does not encrypt
the ESP header, nor does it encrypt the ESP authentication.
Authentication Header (AH)
AH provides authentication and integrity, which protect against data tampering, using the same
algorithms as ESP. AH also provides optional anti-replay protection, which protects against
unauthorized retransmission of packets. The authentication header is inserted into the packet
between the IP header and any subsequent packet contents. The payload is not touched.
Although AH protects the packet’s origin, destination, and contents from being tampered with, the
identity of the sender and receiver is known. In addition, AH does not protect the data’s
confidentiality. If data is intercepted and only AH is used, the message contents can be read. ESP
protects data confidentiality. For added protection in certain cases, AH and ESP can be used
together. In the following table, IP HDR represents the IP header and includes both source and
destination IP addresses.
Figure 9-5: Original packet and packet with IPSec Authentication Header
IKE Security Association
IPSec introduces the concept of the Security Association (SA). An SA is a logical connection
between two devices transferring data. An SA provides data protection for unidirectional traffic by
using the defined IPSec protocols. An IPSec tunnel typically consists of two unidirectional SAs,
which together provide a protected, full-duplex data channel.
The SAs allow an enterprise to control exactly what resources may communicate securely,
according to security policy. To do this an enterprise can set up multiple SAs to enable multiple
secure VPNs, as well as define SAs within the VPN to support different departments and business
partners.
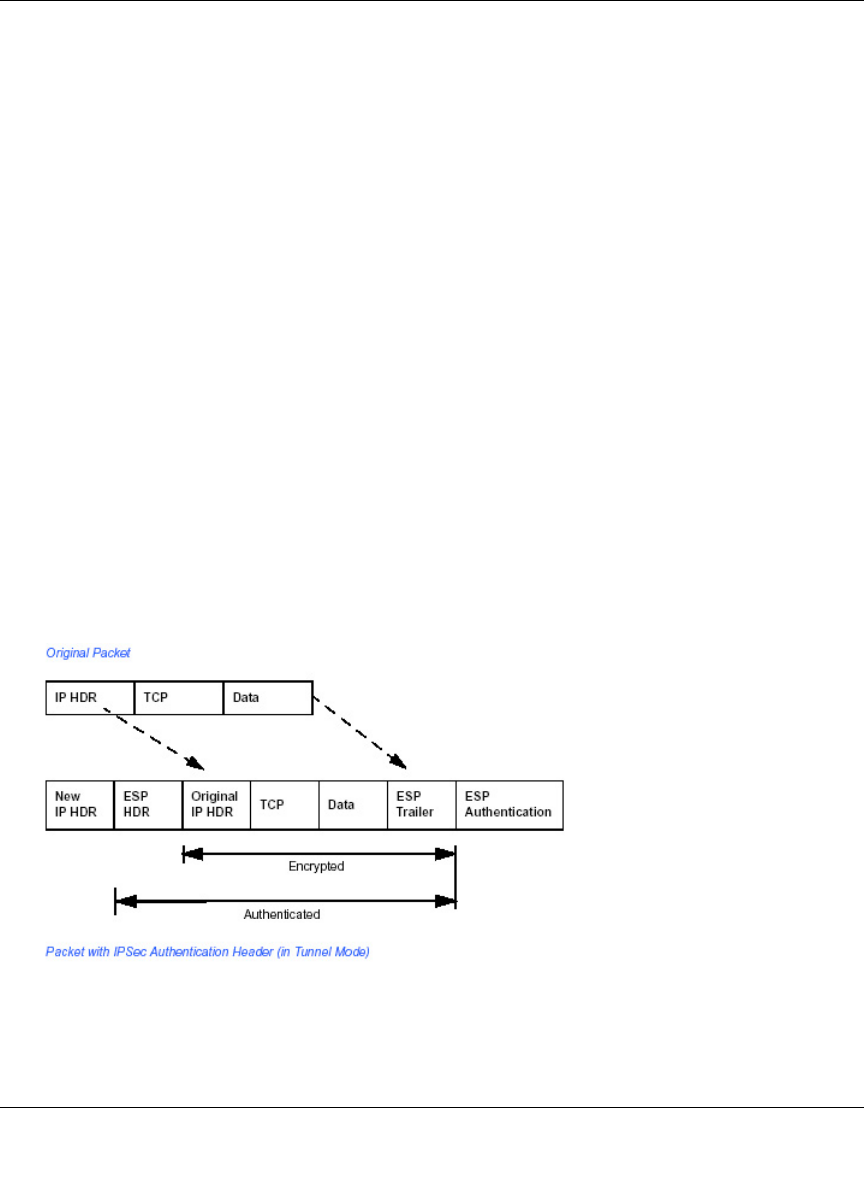
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking D-5
202-10085-01, March 2005
Mode
SAs operate using modes. A mode is the method in which the IPSec protocol is applied to the
packet. IPSec can be used in tunnel mode or transport mode. Typically, the tunnel mode is used for
gateway-to-gateway IPSec tunnel protection, while transport mode is used for host-to-host IPSec
tunnel protection. A gateway is a device that monitors and manages incoming and outgoing
network traffic and routes the traffic accordingly. A host is a device that sends and receives
network traffic.
•Transport Mode: The transport mode IPSec implementation encapsulates only the packet’s
payload. The IP header is not changed. After the packet is processed with IPSec, the new IP
packet contains the old IP header (with the source and destination IP addresses unchanged)
and the processed packet payload. Transport mode does not shield the information in the IP
header; therefore, an attacker can learn where the packet is coming from and where it is going
to. The previous packet diagrams show a packet in transport mode.
•Tunnel Mode: The tunnel mode IPSec implementation encapsulates the entire IP packet. The
entire packet becomes the payload of the packet that is processed with IPSec. A new IP header
is created that contains the two IPSec gateway addresses. The gateways perform the
encapsulation/decapsulation on behalf of the hosts. Tunnel mode ESP prevents an attacker
from analyzing the data and deciphering it, as well as knowing who the packet is from and
where it is going.
Note: AH and ESP can be used in both transport mode or tunnel mode.
Figure 9-6: Original packet and packet with IPSec ESP in Tunnel mode

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
D-6 Virtual Private Networking
202-10085-01, March 2005
Key Management
IPSec uses the Internet Key Exchange (IKE) protocol to facilitate and automate the SA setup and
the exchange of keys between parties transferring data. Using keys ensures that only the sender
and receiver of a message can access it.
IPSec requires that keys be re-created, or refreshed, frequently so that the parties can communicate
securely with each other. IKE manages the process of refreshing keys; however, a user can control
the key strength and the refresh frequency. Refreshing keys on a regular basis ensures data
confidentiality between sender and receiver.
Understand the Process Before You Begin
This TechNote provides case studies on how to configure a secure IPSec VPN tunnels. This
document assumes the reader has a working knowledge of NETGEAR management systems.
NETGEAR is a member of the VPN Consortium, a group formed to facilitate IPSec VPN vendor
interoperability. The VPN Consortium has developed specific scenarios to aid system
administrators in the often confusing process of connecting two different vendor implementations
of the IPSec standard. The case studies in this TechNote follow the addressing and configuration
mechanics defined by the VPN Consortium. Additional information regarding inter-vendor
interoperability may be found at http://www.vpnc.org/interop.html.
It is a good idea to gather all the necessary information required to establish a VPN before you
begin the configuration process. You should understand whether the firmware is up to date, all of
the addresses that will be necessary, and all of the parameters that need to be set on both sides. Try
to understand any incompatibilities before you begin, so that you minimize any potential
complications which may arise from normal firewall or WAN processes.
If you are not a full-time system administrator, it is a good idea to familiarize yourself with the
mechanics of a VPN. The brief description in this TechNote will help. Other good sources include:
• The NETGEAR VPN Tutorial – http://www.netgear.com/planetvpn/pvpn_2.html
• The VPN Consortium – http://www.vpnc.org/
• The VPN bibliography in “Additional Reading” on page D-11.
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking D-7
202-10085-01, March 2005
VPN Process Overview
Even though IPSec is standards-based, each vendor has its own set of terms and procedures for
implementing the standard. Because of these differences, it may be a good idea to review some of
the terms and the generic processes for connecting two gateways before diving into to the
specifics.
Network Interfaces and Addresses
The VPN gateway is aptly named because it functions as a “gatekeeper” for each of the computers
connected on the Local Area Network behind it.
In most cases, each Gateway will have a “public” facing address (WAN side) and a “private”
facing address (LAN side). These addresses are referred to as the “network interface” in
documentation regarding the construction of VPN communication. Please note that the addresses
used in the example.
Interface Addressing
This TechNote uses example addresses provided the VPN Consortium. It is important to
understand that you will be using addresses specific to the devices that you are attempting to
connect via IPSec VPN.
Figure 9-7: VPNC Example Network Interface Addressing
Gateway A
22.23.24.25
14.15.16.17
10.5.6.0/24 172.23.9.0/24
172.23.9.110.5.6.1
WAN IP WAN IP LAN IPLAN IP
Gateway B
VPNC Example
Network Interface Addressing
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
D-8 Virtual Private Networking
202-10085-01, March 2005
It is also important to make sure the addresses do not overlap or conflict. That is, each set of
addresses should be separate and distinct.
It will also be important to know the subnet mask of both gateway LAN Connections. Use the
worksheet in Appendix A to gather the necessary address and subnet mask information to aid in
the configuration and troubleshooting process.
Firewalls
It is important to understand that many gateways are also firewalls. VPN tunnels cannot function
properly if firewall settings disallow all incoming traffic. Please refer to the firewall instructions
for both gateways to understand how to open specific protocols, ports, and addresses that you
intend to allow.
Setting Up a VPN Tunnel Between Gateways
A SA, frequently called a tunnel, is the set of information that allows two entities (networks, PCs,
routers, firewalls, gateways) to “trust each other” and communicate securely as they pass
information over the Internet.
Table 9-1. WAN (Internet/Public) and LAN (Internal/Private) Addressing
Gateway LAN or WAN VPNC Example Address
Gateway A LAN (Private) 10.5.6.1
Gateway A WAN (Public) 14.15.16.17
Gateway B LAN (Private) 22.23.24.25
Gateway B WAN (Public) 172.23.9.1
Table 9-2. Subnet Addressing
Gateway LAN or WAN Interface Name Example Subnet Mask
Gateway A LAN (Private) Subnet Mask A 255.255.255.0
Gateway B LAN (Private) Subnet Mask B 255.255.255.0
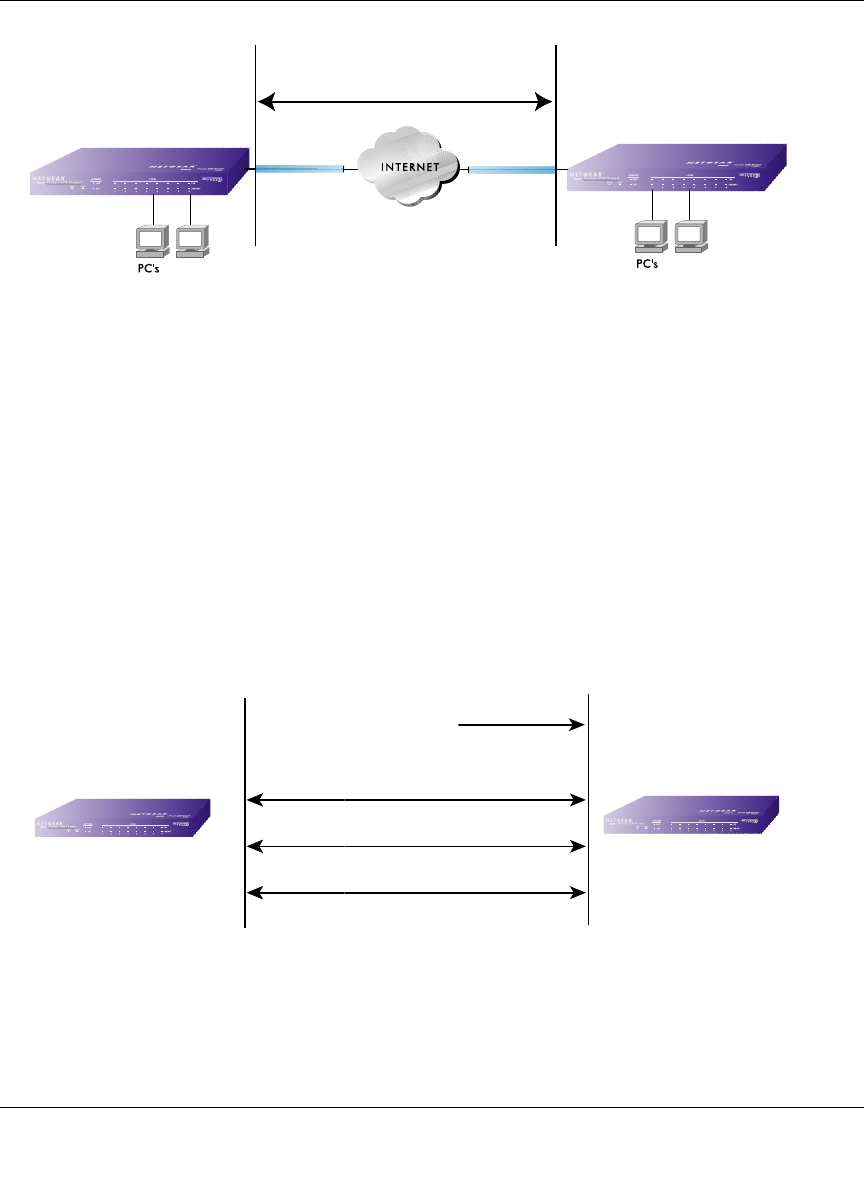
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking D-9
202-10085-01, March 2005
Figure 9-8: VPN Tunnel SA
The SA contains all the information necessary for gateway A to negotiate a secure and encrypted
communication stream with gateway B. This communication is often referred to as a “tunnel.” The
gateways contain this information so that it does not have to be loaded onto every computer
connected to the gateways.
Each gateway must negotiate its Security Association with another gateway using the parameters
and processes established by IPSec. As illustrated below, the most common method of
accomplishing this process is via the Internet Key Exchange (IKE) protocol which automates some
of the negotiation procedures. Alternatively, you can configure your gateways using manual key
exchange, which involves manually configuring each paramter on both gateways.
Figure 9-9: IPSec SA negotiation
1. The IPSec software on Host A initiates the IPSec process in an attempt to communicate
with Host B. The two computers then begin the Internet Key Exchange (IKE) process.
VPN Gateway A VPN Gateway B
VPN Tunnel
VPN Gateway
VPN Gateway
1) Communication
request sent to VPN Gateway
2) IKE Phase I authentication
3) IKE Phase II negotiation
4) Secure data transfer
5) IPSec tunnel termination
IPSec Security Association IKE
VPN Tunnel Negotiation Steps

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
D-10 Virtual Private Networking
202-10085-01, March 2005
2. IKE Phase I.
a. The two parties negotiate the encryption and authentication algorithms to use in the IKE
SAs.
b. The two parties authenticate each other using a predetermined mechanism, such as
preshared keys or digital certificates.
c. A shared master key is generated by the Diffie-Hellman Public key algorithm within the
IKE framework for the two parties. The master key is also used in the second phase to
derive IPSec keys for the SAs.
3. IKE Phase II.
a. The two parties negotiate the encryption and authentication algorithms to use in the IPSec
SAs.
b. The master key is used to derive the IPSec keys for the SAs. Once the SA keys are created
and exchanged, the IPSec SAs are ready to protect user data between the two VPN
gateways.
4. Data transfer. Data is transferred between IPSec peers based on the IPSec parameters and
keys stored in the SA database.
5. IPSec tunnel termination. IPSec SAs terminate through deletion or by timing out.
VPNC IKE Security Parameters
It is important to remember that both gateways must have the identical parameters set for the
process to work correctly. The settings in these TechNote examples follow the examples given for
Scenario 1 of the VPN Consortium.
VPNC IKE Phase I Parameters
The IKE Phase 1 parameters used:
•Main mode
•TripleDES
• SHA-1
• MODP group 1
• pre-shared secret of "hr5xb84l6aa9r6"
• SA lifetime of 28800 seconds (eight hours)

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Virtual Private Networking D-11
202-10085-01, March 2005
VPNC IKE Phase II Parameters
The IKE Phase 2 parameters used in Scenario 1 are:
•TripleDES
• SHA-1
• ESP tunnel mode
• MODP group 1
• Perfect forward secrecy for rekeying
• SA lifetime of 28800 seconds (one hour)
Testing and Troubleshooting
Once you have completed the VPN configuration steps you can use PCs, located behind each of
the gateways, to ping various addresses on the LAN-side of the other gateway.
You can troubleshoot connections using the VPN status and log details on the Netgear gateway to
determine if IKE negotiation is working. Common problems encountered in setting up VPNs
include:
• Parameters may be configured differently on Gateway A vs. Gateway B.
• Two LANs set up with similar or overlapping addressing schemes.
• So many required configuration parameters mean errors such as mistyped information or
mismatched parameter selections on either side are more likely to happen.
Additional Reading
•Building and Managing Virtual Private Networks, Dave Kosiur, Wiley & Sons; ISBN:
0471295264
•Firewalls and Internet Security: Repelling the Wily Hacker, William R. Cheswick and Steven
M. Bellovin, Addison-Wesley; ISBN: 0201633574
•VPNs A Beginners Guide, John Mains, McGraw Hill; ISBN: 0072191813
• [FF98] Floyd, S., and Fall, K., Promoting the Use of End-to-End Congestion Control in the
Internet. IEEE/ACM Transactions on Networking, August 1999.
Relevant RFCs listed numerically:
Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
D-12 Virtual Private Networking
202-10085-01, March 2005
• [RFC 791] Internet Protocol DARPA Internet Program Protocol Specification, Information
Sciences Institute, USC, September 1981.
• [RFC 1058] Routing Information Protocol, C Hedrick, Rutgers University, June 1988.
• [RFC 1483] Multiprotocol Encapsulation over ATM Adaptation Layer 5, Juha Heinanen,
Telecom Finland, July 1993.
• [RFC 2401] S. Kent, R. Atkinson, Security Architecture for the Internet Protocol, RFC 2401,
November 1998.
• [RFC 2407] D. Piper, The Internet IP Security Domain of Interpretation for ISAKMP,
November 1998.
• [RFC 2474] K. Nichols, S. Blake, F. Baker, D. Black, Definition of the Differentiated Services
Field (DS Field) in the IPv4 and IPv6 Headers, December 1998.
• [RFC 2475] S. Blake, D. Black, M. Carlson, E. Davies, Z. Wang, and W. Weiss, An
Architecture for Differentiated Services, December 1998.
• [RFC 2481] K. Ramakrishnan, S. Floyd, A Proposal to Add Explicit Congestion Notification
(ECN) to IP, January 1999.
• [RFC 2408] D. Maughan, M. Schertler, M. Schneider, J. Turner, Internet Security Association
and Key Management Protocol (ISAKMP).
• [RFC 2409] D. Harkins, D.Carrel, Internet Key Exchange (IKE) protocol.
• [RFC 2401] S. Kent, R. Atkinson, Security Architecture for the Internet Protocol.

Glossary -1
202-10085-01, March 2005
Glossary
List of Glossary Terms
Use the list below to find definitions for technical terms used in this manual.
Numeric
10BASE-T
IEEE 802.3 specification for 10 Mbps Ethernet over twisted pair wiring.
100BASE-Tx
IEEE 802.3 specification for 100 Mbps Ethernet over twisted pair wiring.
802.1x
802.1x defines port-based, network access control used to provide authenticated network access and
automated data encryption key management. The IEEE 802.1x draft standard offers an effective framework
for authenticating and controlling user traffic to a protected network, as well as dynamically varying
encryption keys. 802.1x uses a protocol called EAP (Extensible Authentication Protocol) and supports
multiple authentication methods, such as token cards, Kerberos, one-time passwords, certificates, and public
key authentication. For details on EAP specifically, refer to IETF's RFC 2284.
802.11a
IEEE specification for wireless networking at 54 Mbps operating in unlicensed radio bands over 5GHz.
802.11b
IEEE specification for wireless networking at 11 Mbps using direct-sequence spread-spectrum (DSSS)
technology and operating in the unlicensed radio spectrum at 2.4-2.5GHz.
802.11g
A soon to be ratified IEEE specification for wireless networking at 54 Mbps using direct-sequence
spread-spectrum (DSSS) technology and operating in the unlicensed radio spectrum at 2.4GHz. 802.11g is
backwards compatible with 802.11b.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-2 Glossary
202-10085-01, March 2005
A
Access Control List (ACL)
An ACL is a database that an Operating System uses to track each user’s access rights to system objects
(such as file directories and/or files).
Ad-hoc Mode
An 802.11 networking framework in which devices or stations communicate directly with each other,
without the use of an access point (AP). Ad-hoc mode is also referred to as peer-to-peer mode or an
Independent Basic Service Set (IBSS). Ad-hoc mode is useful for establishing a network where wireless
infrastructure does not exist or where services are not required.
ADSL
Short for asymmetric digital subscriber line, a technology that allows data to be sent over existing copper
telephone lines at data rates of from 1.5 to 9 Mbps when receiving data (known as the downstream rate) and
from 16 to 640 Kbps when sending data (known as the upstream rate). ADSL requires a special ADSL
modem. ADSL is growing in popularity as more areas around the world gain access.
ARP
Address Resolution Protocol, a TCP/IP protocol used to convert an IP address into a physical address (called
a DLC address), such as an Ethernet address. A host wishing to obtain a physical address broadcasts an ARP
request onto the TCP/IP network. The host on the network that has the IP address in the request then replies
with its physical hardware address. There is also Reverse ARP (RARP) which can be used by a host to
discover its IP address. In this case, the host broadcasts its physical address and a RARP server replies with
the host's IP address.
Auto Uplink
Auto UplinkTM technology (also called MDI/MDIX) eliminates the need to worry about crossover vs.
straight-through Ethernet cables. Auto UplinkTM will accommodate either type of cable to make the right
connection.
B
Bandwidth
The information capacity, measured in bits per second, that a channel could transmit. Bandwidth examples
include 10 Mbps for Ethernet, 100 Mbps for Fast Ethernet, and 1000 Mbps (I Gbps) for Gigabit Ethernet.
Baud
The signaling rate of a line, that is, the number of transitions (voltage or frequency changes) made per
second. Also known as line speed.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Glossary -3
202-10085-01, March 2005
Broadcast
A packet sent to all devices on a network.
C
Class of Service
A term to describe treating different types of traffic with different levels of service priority. Higher priority
traffic gets faster treatment during times of switch congestion
CA
A Certificate Authority is a trusted third-party organization or company that issues digital certificates used
to create digital signatures and public-private key pairs.
Cat 5
Category 5 unshielded twisted pair (UTP) cabling. An Ethernet network operating at 10 Mbits/second
(10BASE-T) will often tolerate low quality cables, but at 100 Mbits/second (10BASE-Tx) the cable must be
rated as Category 5, or Cat 5 or Cat V, by the Electronic Industry Association (EIA). This rating will be
printed on the cable jacket. Cat 5 cable contains eight conductors, arranged in four twisted pairs, and
terminated with an RJ45 type connector. In addition, there are restrictions on maximum cable length for both
10 and 100 Mbits/second networks.
Certificate Authority
A Certificate Authority is a trusted third-party organization or company that issues digital certificates used
to create digital signatures and public-private key pairs. The role of the CA in this process is to guarantee
that the individual granted the unique certificate is, in fact, who he or she claims to be. Usually, this means
that the CA has an arrangement with a financial institution, such as a credit card company, which provides it
with information to confirm an individual's claimed identity. CAs are a critical component in data security
and electronic commerce because they guarantee that the two parties exchanging information are really who
they claim to be.
D
DHCP
An Ethernet protocol specifying how a centralized DHCP server can assign network configuration
information to multiple DHCP clients. The assigned information includes IP addresses, DNS addresses, and
gateway (router) addresses.
DNS
Short for Domain Name System (or Service), an Internet service that translates domain names into IP
addresses. Because domain names are alphabetic, they're easier to remember. The Internet however, is really

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-4 Glossary
202-10085-01, March 2005
based on IP addresses. Every time you use a domain name, therefore, a DNS service must translate the name
into the corresponding IP address. For example, the domain name www.example.com might translate to
198.105.232.4. The DNS system is, in fact, its own network. If one DNS server doesn't know how to
translate a particular domain name, it asks another one, and so on, until the correct IP address is returned.
Domain Name
A descriptive name for an address or group of addresses on the Internet. Domain names are of the form of a
registered entity name plus one of a number of predefined top level suffixes such as .com, .edu, .uk, etc. For
example, in the address mail.NETGEAR.com, mail is a server name and NETGEAR.com is the domain.
DSL
Short for digital subscriber line, but is commonly used in reference to the asymmetric version of this
technology (ADSL) that allows data to be sent over existing copper telephone lines at data rates of from 1.5
to 9 Mbps when receiving data (known as the downstream rate) and from 16 to 640 Kbps when sending data
(known as the upstream rate).
ADSL requires a special ADSL modem. ADSL is growing in popularity as more areas around the world
gain access.
DSLAM
DSL Access Multiplexor. The piece of equipment at the telephone company central office that provides the
ADSL signal.
Dynamic Host Configuration Protocol
DHCP. An Ethernet protocol specifying how a centralized DHCP server can assign network configuration
information to multiple DHCP clients. The assigned information includes IP addresses, DNS addresses, and
gateway (router) addresses.
E
EAP
Extensible Authentication Protocol is a general protocol for authentication that supports multiple
authentication methods. EAP, an extension to PPP, supports such authentication methods as token cards,
Kerberos, one-time passwords, certificates, public key authentication and smart cards. In wireless
communications using EAP, a user requests connection to a WLAN through an AP, which then requests the
identity of the user and transmits that identity to an authentication server such as RADIUS. The server asks
the AP for proof of identity, which the AP gets from the user and then sends back to the server to complete
the authentication. EAP is defined by RFC 2284.
ESSID
The Extended Service Set Identification (ESSID) is a thirty-two character (maximum) alphanumeric key
identifying the wireless local area network.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Glossary -5
202-10085-01, March 2005
Ethernet
A LAN specification developed jointly by Xerox, Intel and Digital Equipment Corporation. Ethernet
networks transmit packets at a rate of 10 Mbps.
G
Gateway
A local device, usually a router, that connects hosts on a local network to other networks.
I
ICMP
See “Internet Control Message Protocol”
IEEE
Institute of Electrical and Electronics Engineers. This American organization was founded in 1963 and sets
standards for computers and communications.
IETF
Internet Engineering Task Force. An organization responsible for providing engineering solutions for TCP/
IP networks. In the network management area, this group is responsible for the development of the SNMP
protocol.
IKE
Internet Key Exchange. An automated method for exchanging and managing encryption keys between two
VPN devices.
Infrastructure Mode
An 802.11 networking framework in which devices communicate with each other by first going through an
Access Point (AP). In infrastructure mode, wireless devices can communicate with each other or can
communicate with a wired network. When one AP is connected to wired network and a set of wireless
stations it is referred to as a Basic Service Set (BSS). An Extended Service Set (ESS) is a set of two or more
BSSs that form a single subnetwork. Most corporate wireless LANs operate in infrastructure mode because
they require access to the wired LAN in order to use services such as file servers or printers.
Internet Control Message Protocol
ICMP is an extension to the Internet Protocol (IP) that supports packets containing error, control, and
informational messages. The PING command, for example, uses ICMP to test an Internet connection.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-6 Glossary
202-10085-01, March 2005
Internet Protocol
The method or protocol by which data is sent from one computer to another on the Internet. Each computer
(known as a host) on the Internet has at least one IP address that uniquely identifies it among all other
computers on the Internet. When you send or receive data (for example, an e-mail note or a Web page), the
message gets divided into little chunks called packets. Each of these packets contains both the sender's
Internet address and the receiver's address. Any packet is sent first to a gateway computer that understands a
small part of the Internet. The gateway computer reads the destination address and forwards the packet to an
adjacent gateway that in turn reads the destination address and so forth across the Internet until one gateway
recognizes the packet as belonging to a computer within its immediate neighborhood or domain. That
gateway then forwards the packet directly to the computer whose address is specified.
Because a message is divided into a number of packets, each packet can, if necessary, be sent by a different
route across the Internet. Packets can arrive in a different order than they were sent. The Internet Protocol
just delivers them. It's up to another protocol, the Transmission Control Protocol (TCP) to put them back in
the right order. IP is a connectionless protocol, which means that there is no continuing connection between
the end points that are communicating. Each packet that travels through the Internet is treated as an
independent unit of data without any relation to any other unit of data. (The reason the packets do get put in
the right order is because of TCP, the connection-oriented protocol that keeps track of the packet sequence in
a message.) In the Open Systems Interconnection (OSI) communication model, IP is in Layer 3, the
Networking Layer. The most widely used version of IP today is IP version 4 (IPv4). However, IP version 6
(IPv6) is also beginning to be supported. IPv6 provides for much longer addresses and therefore for the
possibility of many more Internet users. IPv6 includes the capabilities of IPv4 and any server that can
support IPv6 packets can also support IPv4 packets.
IP
See “Internet Protocol”
IP Address
A four-byte number uniquely defining each host on the Internet, usually written in dotted-decimal notation
with periods separating the bytes (for example, 134.177.244.57). Ranges of addresses are assigned by
Internic, an organization formed for this purpose.
ISP
Internet service provider.
L
LAN
See “Local Area Network”

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Glossary -7
202-10085-01, March 2005
Local Area Network
A communications network serving users within a limited area, such as one floor of a building. A LAN
typically connects multiple personal computers and shared network devices such as storage and printers.
Although many technologies exist to implement a LAN, Ethernet is the most common for connecting
personal computers and is limited to a distance of 1,500 feet. LANs can be connected together, but if
modems and telephones connect two or more LANs, the larger network constitutes what is called a WAN or
Wide Area Network.
M
MAC
(1) Medium Access Control. In LANs, the sublayer of the data link control layer that supports
medium-dependent functions and uses the services of the physical layer to provide services to the logical
link control (LLC) sublayer. The MAC sublayer includes the method of determining when a device has
access to the transmission medium. (2) Message Authentication Code. In computer security, a value that is a
part of a message or accompanies a message and is used to determine that the contents, origin, author, or
other attributes of all or part of the message are as they appear to be. (IBM Glossary of Computing Terms)
MAC address
The Media Access Control address is a unique 48-bit hardware address assigned to every network interface
card. Usually written in the form 01:23:45:67:89:ab.
Maximum Receive Unit
The size in bytes of the largest packet that can be sent or received.
Maximum Transmit Unit
The size in bytes of the largest packet that can be sent or received.
Mbps
Megabits per second.
MDI/MDIX
In cable wiring, the concept of transmit and receive are from the perspective of the PC, which is wired as a
Media Dependant Interface (MDI). In MDI wiring, a PC transmits on pins 1 and 2. At the hub, switch,
router, or access point, the perspective is reversed, and the hub receives on pins 1 and 2. This wiring is
referred to as Media Dependant Interface - Crossover (MDI-X).
MTU
The size in bytes of the largest packet that can be sent or received.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-8 Glossary
202-10085-01, March 2005
P
packet
A block of information sent over a network. A packet typically contains a source and destination network
address, some protocol and length information, a block of data, and a checksum.
Point-to-Point Protocol
PPP. A protocol allowing a computer using TCP/IP to connect directly to the Internet.
PPP
A protocol allowing a computer using TCP/IP to connect directly to the Internet.
PPPoA
PPPoA. PPP over ATM is a protocol for connecting remote hosts to the Internet over an always-on
connection by simulating a dial-up connection.
PPPoE
PPPoE. PPP over Ethernet is a protocol for connecting remote hosts to the Internet over an always-on
connection by simulating a dial-up connection.
PPP over ATM
PPPoA. PPP over ATM is a protocol for connecting remote hosts to the Internet over an always-on
connection by simulating a dial-up connection.
PPP over Ethernet
PPPoE. PPP over Ethernet is a protocol for connecting remote hosts to the Internet over an always-on
connection by simulating a dial-up connection.
PPTP
Point-to-Point Tunneling Protocol. A method for establishing a virtual private network (VPN) by embedding
Microsoft’s network protocol into Internet packets.
Protocol
A set of rules for communication between devices on a network.
PSTN
Public Switched Telephone Network.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Glossary -9
202-10085-01, March 2005
Q
QoS
See “Quality of Service”
Quality of Service
QoS is a networking term that specifies a guaranteed level of throughput. Throughput is the amount of data
transferred from one device to another or processed in a specified amount of time - typically, throughputs are
measured in bytes per second (Bps).
R
RADIUS
Short for Remote Authentication Dial-In User Service, RADIUS is an authentication system. Using
RADIUS, you must enter your user name and password before gaining access to a network. This
information is passed to a RADIUS server, which checks that the information is correct, and then authorizes
access. Though not an official standard, the RADIUS specification is maintained by a working group of the
IETF.
RFC
Request For Comment. Refers to documents published by the Internet Engineering Task Force (IETF)
proposing standard protocols and procedures for the Internet. RFCs can be found at www.ietf.org.
router
A device that forwards data between networks. An IP router forwards data based on IP source and
destination addresses.
S
SSID
A Service Set Identification is a thirty-two character (maximum) alphanumeric key identifying a wireless
local area network. For the wireless devices in a network to communicate with each other, all devices must
be configured with the same SSID. This is typically the configuration parameter for a wireless PC card. It
corresponds to the ESSID in the wireless Access Point and to the wireless network name. See also Wireless
Network Name and ESSID.
Segment
A section of a LAN that is connected to the rest of the network using a switch, bridge, or repeater.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-10 Glossary
202-10085-01, March 2005
Subnet Mask
Combined with the IP address, the IP Subnet Mask allows a device to know which other addresses are local
to it, and which must be reached through a gateway or router.
T
TCP/IP
The main internetworking protocols used in the Internet. The Internet Protocol (IP) used in conjunction with
the Transfer Control Protocol (TCP) form TCP/IP.
U
Universal Plug and Play
UPnP. A networking architecture that provides compatibility among networking technology. UPnP
compliant routers provide broadband users at home and small businesses with a seamless way to participate
in online games, videoconferencing and other peer-to-peer services.
UTP
Unshielded twisted pair is the cable used by 10BASE-T and 100BASE-Tx Ethernet networks.
W
WAN
See “Wide Area Network”
Web
Also known as World-Wide Web (WWW) or W3. An Internet client-server system to distribute information,
based upon the hypertext transfer protocol (HTTP).
WEB Proxy Server
A Web proxy server is a specialized HTTP server that allows clients access to the Internet from behind a
firewall. The proxy server listens for requests from clients within the firewall and forwards these requests to
remote Internet servers outside the firewall. The proxy server reads responses from the external servers and
then sends them to internal client clients.
WEP
Wired Equivalent Privacy is a data encryption protocol for 802.11b wireless networks. All wireless nodes
and access points on the network are configured with a 64-bit or 128-bit Shared Key for data encryption.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
Glossary -11
202-10085-01, March 2005
Wide Area Network
A WAN is a computer network that spans a relatively large geographical area. Typically, a WAN consists of
two or more local-area networks (LANs).
Wi-Fi
A trade name for the 802.11b wireless networking standard, given by the Wireless Ethernet Compatibility
Alliance (WECA, see http://www.wi-fi.net), an industry standards group promoting interoperability among
802.11b devices.
Windows Internet Naming Service
WINS. Windows Internet Naming Service is a server process for resolving Windows-based computer names
to IP addresses.
If a remote network contains a WINS server, your Windows PCs can gather information from that WINS
server about its local hosts. This allows your PCs to browse that remote network using the Windows
Network Neighborhood feature.
WINS
WINS. Windows Internet Naming Service is a server process for resolving Windows-based computer names
to IP addresses.
Wireless Network Name (SSID)
Wireless Network Name (SSID) is the name assigned to a wireless network. This is the same as the SSID or
ESSID configuration parameter.
WPA
Wi-Fi Protected Access (WPA) is a specification of standards-based, interoperable security enhancements
that increase the level of data protection and access control for existing and future wireless LAN systems.

Reference Manual for the ProSafe VPN Firewall 25 with 4 Gigabit LAN and Dual WAN Ports
-12 Glossary
202-10085-01, March 2005