NexAira 2400M-01 Wireless 802.11b/g/n Router User Manual
NexAira Inc. Wireless 802.11b/g/n Router
NexAira >
Users Manual

Introduction
Features
Package Contents
System
Requirements
Wi-Fi
Requirements
Hardware Setup
Wi-Fi Connection
Initial 3G/4G
Setup
Configuration
Basic Settings
Setup Wizard
Admin Password
Wi-Fi Settings
Interfaces
Cellular Datacard
Card Updates
Network Traffic
User Manual
Introduction
The BC2400M High Availability Router is a high-performance device that supports
wireless networking at home, work, or in a public place. Supports USB modems,
and Mini PCI-e Modules. The BC2400M High Availability Router works with both
EVDO and HSDPA technologies. The BC2400M High Availability Router supports
up to 300 Mbps Wi-Fi, and 100 Mbps Ethernet.
Features
NexWare’s quick and easy setup allows you to go where wires cannot, outside the
home or office. Fully compatible with the IEEE 802.11 b/g/n 2x2 mimo to provide a
wireless data transfer rate of up to 300 Mbps Wi-Fi 100 Mbps Ethernet. Backwards
compatible with the 802.11b IEEE standard. Operates in the Tx/Rx power
18dbm/Per Cell, indoors approx. 35-100 meters and outdoors up to 100-300
meters. Supports NAT with VPN pass-through. DHCP server enables all networked
computers to automatically receive IP addresses. Access Control for managing
users on the network. User-friendly configuration and diagnostic utilities.
Supports special applications that require multiple connections. Equipped with
two 10/100 Ethernet ports, one for LAN and one for WAN access, an Mini PCI-e
Module port, and a USB port for 3G/4G network connections. Connects multiple
computers to the Internet via a broadband EVDO, HSDPA network connection or
via cable/DSL connection. Please consult your service provider for more detailed
information on wireless network standards. Customizable 3G/4G Auto-Failover
with Anti-Flap. Virtual Router Redundancy Protocol (VRRP provides no single
point of failure). QoS (Quality of Service). Wireless Distribution System. Software
User Manual

Logout
Tool Box
Signal Strength
System Settings
Email
Notifications
System Log
Flash Firmware
Backup/Restore
Reset to Defaults
Reboot
License
Agreement
Advanced
Settings
DHCP
SNMP
Dynamic DNS
QoS
GPS
Security
Settings
Remote Admin
IPsec
SSH Server
definable Ethernet ports. 4G/WiMax Support.
NexWare’s quick and easy setup allows you to go where wires cannot, outside the
home or office.
Fully compatible with the IEEE 802.11 b/g/n 2x2 mimo to provide a wireless data
transfer rate of up to 300 Mbps Wi-Fi 100 Mbps Ethernet.
Backwards compatible with the 802.11b IEEE standard.
Operates in the Tx/Rx power 18dbm/Per Cell, indoors approx. 35-100 meters and
outdoors up to 100-300 meters.
Supports NAT with VPN pass-through.
DHCP server enables all networked computers to automatically receive IP
addresses.
Access Control for managing users on the network.
User-friendly configuration and diagnostic utilities.
Supports special applications that require multiple connections.
Equipped with two 10/100 Ethernet ports, one for LAN and one for WAN access,
an ExpressCard port, and a USB port for 3G/4G network connections.
Connects multiple computers to the Internet via a broadband EVDO, HSDPA
network connection or via cable/DSL connection. Please consult your service
provider for more detailed information on wireless network standards.
Customizable 3G/4G Auto-Failover with Anti-Flap.
Virtual Router Redundancy Protocol (VRRP provides no single point of failure).
QoS (Quality of Service).
Wireless Distribution System.
Software definable Ethernet ports.
4G/WiMax Support.
Package Contents
Important: Check the contents of the box first.
The BC2400M High Availability Router package should contain the items listed
below. If any of the items are missing, please contact your reseller.
(1) BC2400M High Availability Router

SHH Keys
Routing Settings
Routes
RIP
DMZ Host
VRRP
Internet Failover
Port Forwarding
UPnP
(1) CD-ROM
(1) RJ-45 Ethernet Cable
(1) USB Cable
(1) Switching 12V 1.25A Power Adapter
(2) WiFi External RP-SMA Antennas
(2) Ipex Coax Cables
Caution: Using a power supply with a different voltage rating other than the one
included with the BC2400M will cause damage and void the warranty for this
product.
System Requirements
Compatible with Mini PCI-e Module or USB 3G/4G modem card with activated
service. NOTE: Subject to terms available from your carrier.
Computer with Windows XP, Vista, Windows 7, Macintosh, or Linux-based
operating system with an integrated Ethernet adapter or Wireless Wi-Fi 802.11 G
interface. Internet Explorer, Firefox, Safari, and Google Chrome (for accessing
web-based configuration settings).
Wi-Fi Requirements
IEEE 802.11 b/g/n adapter. NOTE: Mini PCI-e Modules, and USB modems need to
be activated through your cellular service provider prior to insertion into the
BC2400M High Availability Router.
Hardware Setup
The BC2400M High Availability Router allows you to access your network using a

wireless connection from virtually anywhere within its operating range. Please
note that location placement of the router could affect the wireless signal and
range limits.
Typical ranges also vary depending on the types of materials and background RF
(Radio Frequency) noise present in your networking environment.
To maximize your wireless range, please follow these guidelines:
Choose the right location in your environment for the BC2400M High Availability
Router. The WLAN transmitters are radios; their signals radiate out from the
antenna, and degrade as they go through walls, floors, and obstacles like tubs full
of water (almost impenetrable), stone, or concrete. So for best reception, place
your router centrally to the rooms in which you expect to use WLAN the most.
Each wall or ceiling can reduce the BC2400M’s range by as much as 90 feet (27
meters). NOTE: The same considerations apply to your carrier’s 3G/4G broadband
carrier’s connection.
Keep your product away from electrical devices (such as microwaves, air
conditioners, cordless phones, refrigerators and televisions) that emit large
quantities of RFI (Radio Frequency Interference).
BC2400M High Availability Router Setup NOTE: DO NOT connect the BC2400M
to power before following the installation steps below!
Mini PCI-e Module or USB connection:
Insert an activated Mini PCI-e Module into the card slot and connect the two Ipex
Coax Cables per the diagram below.
Alternatively, insert an activated USB modem into the USB slot.
Ethernet connection:
Insert one end of an Ethernet cable into the LAN Port on the back panel of the
router. Insert the other end into an available Ethernet port of the network adapter
in the computer that will be used to configure the unit. LAN LED should be on
when connected. If not, check the connection between the router and computer.
LAN LED should be on when connected. If not, check the connection between the
router and computer.

NOTE: The BC2400M LAN Port is “Auto-MDI/MDIX”, so any standard
Ethernet cable will work.
Connect the power adapter to the receptor on the back panel of the router. Plug
the other end of the power adapter into a wall outlet or power strip. The LAN &
Wi-Fi LED will turn ON and occasionally flash, indicating that the unit is powered
on. The 3G/4G LED will flash and stabilize once a 3G/4G connection is established.
Upon completion of the boot-up cycle, the 3G light, LAN and Wi-Fi lights will be
on. Occational flashing may occur indicating normal activity.
NOTE: An Uninterruptible power supply (UPS) is recommended for power surges
and/or outages. At a minimum, a surge protector should always be used to
protect the equipment from being damaged by electrical spikes and transients.
Wi-Fi Connection:
If you are connecting wirelessly to the BC2400M High Availability Router, you
must ensure that the security settings on the connecting PC are the same as those
on the router.
By default, the router broadcasts a secure Wi-Fi signal with WPA-PSK encryption:
SSID / Wi-Fi Signal Name is set to NEXWARE###
(where ### equal the last three characters of the router’s MAC address).
Channel is set to channel 5(2.4GHz).
Security is set to WPA-PSK.
Key (password) is set to password
NOTE: It is recommended, for security reasons, that the security
settings on the router be changed during initial setup.
Please refer to your computer’s Wi-Fi adapter documentation for
additional information.
Initial 3G/4G Setup
Connecting to the Router Main Page for Installation and Configuration Settings

Follow the steps below to access the Router and perform installation and
configure settings:
Open a web-browser on your computer connected to the router’s LAN port by an
Ethernet cable.
Enter the IP address of the BC2400M in the URL line of your web browser:
http://192.168.1.1
NOTE: If you have changed the router’s default IP address, enter that
address instead of the one above.
Type “admin” in the Password field. If you have changed the password, enter the
new one in this field. NOTE: Default Username is “root“.
Click “Login” button.
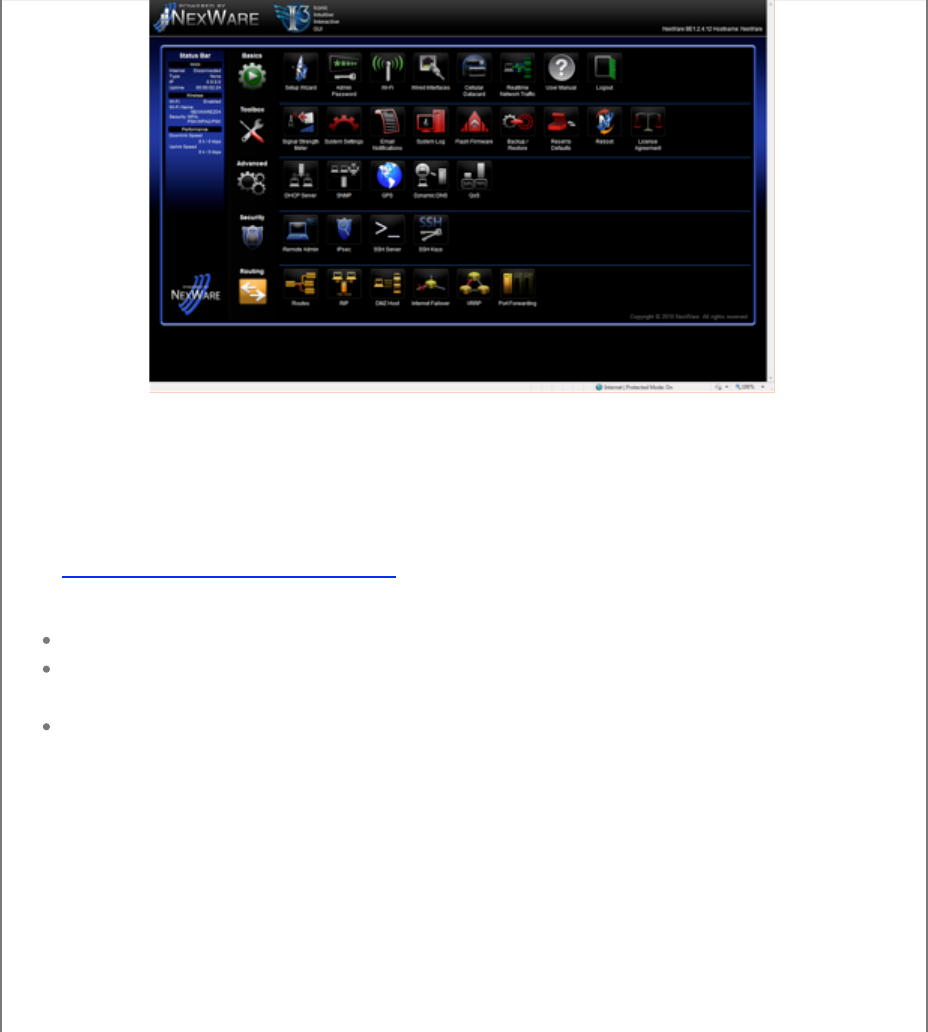
You will be greeted by the iconic home page.
Basic Settings
Setup Wizard
Select the Setup Wizard Icon. Select the Next button to proceed with the
indicated steps of the automated setup process.
1. Change your administration password.
It is recommended that the default password "admin" be replaced for security
reasons. Enter your new password and then re-enter to confirm.
Select next to retain any changes and move to the next step
2. Set up your Wired Internet connection.
During the boot up process of the router if your wide area network (WAN)
Ethernet cable is plugged into the WAN port of the router, the router will
automatically be connected to your ISP.
If your ISP requires you to setup the WAN as a PPPoE or PPTP, you will need to
enter your ISP’s required information into the proper fields.
PPPoE Typical entries include the Username and Password
PPTP Typical entries include the Username, Password, and the PPTP Server Name.
3. 3G/4G Internet Connection Setup.

During the boot up process of the router all compatible data cards or modules are
recognized and are setup automatically. No additional information is typically
required to complete the setup of your compatible 3G/4G data card or module. If
your ISP requires additional information to connect to their network, please refer
to their documentation for APN, PIN Code, Username, and Password. All data
entry fields may not be required to connect to your ISP’s network.
4. Configure your wireless settings.
This step allows you to change whether the Wi-Fi is enabled, the
channel on which the Wi-Fi is broadcast on, the name that is broadcast,
the mode, the encryption type, and the key (password) to access the
broadcasted Wi-Fi signal.
Disable only if you do not want anyone accessing the router wirelessly.
Change channel if other wireless devices are interfering with the router.
Change the Network Name (ESSID) to whatever name you wish to be
broadcasted.
Hiding the ESSID does not disable the Wi-Fi signal and should not be thought of
as security setting. Hiding the ESSID only eliminates the name from being
broadcasted.
Select the router's wireless operation mode. Provide, Independent, or Join. The
default setting is Provide (Access Point).
Change encryption type as necessary. Some wireless devices cannot connect to all
encryption modes. The default setting is WPA-PSK. Other typical choices include
WEP (ASCII or Hex), WPA=PSK, or WPA2-PSK. Additional available settings require
additional software or hardware not included with this router.
Change Key (password). We suggest that this setting be changed. This setting
controls the require Key or password to access your wireless signal.
Select Next to retain any changes and move to the Completion page and select
Finish.
Admin Password
You can change the router's administrative password. (default = admin).
Wi-Fi Settings

Here you can change whether the Wi-Fi is enabled, the channel on which the Wi-Fi
is broadcast on, the name that is broadcast, the wireless mode, the encryption
type, the key (password) to access the broadcasted Wi-Fi signal, and enable
Wireless Distribution System (WDS).
Disable only if you do not want anyone accessing the router wirelessly.
Change channel if other wireless devices are interfering with the router.
Change the router’s Wireless Mode. Choose from six settings, b, g, or n and mixes.
Routing mode is factory set to Provide (Access Point).
Choose to hide the ESSID.
Change the Network Name (ESSID) to whatever name you wish to be
broadcasted.
Change security and encryption type as necessary. Some wireless devices cannot
connect to all security modes.
Change Key (password). We suggest that this setting be changed.
Choose to enable MAC Address filtering, then select filter policy and create the
address list.
You can change the router's administrative password. (default = admin).
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.
WDS: Wireless Distribution System (WDS) is a feature that allows multiple access
points of the same physical radio type to be bridged together as one common
Wi-Fi network. Because the same physical radio type must be used, this feature
only operates with other Nexaira routers. The following configuration options are
available:
BSSID: Your router supports up to four WDS clients. Enter the BSSID (MAC address
listed on the bottom label of the router, also listed under LAN on the Wired
Interfaces page) of the other devices to be connected to via WDS.
NOTE: External WiFi antennas selection is on System Setting page. Router
configuration must use internal WiFi antennas if using a Mini PCI-e Module, as the
Module requires use of the two RP-SMA Female connectors on Rear of Router.
Default configuration is for Internal WiFi Antennas.

Interfaces
Here you can review WAN, and LAN status as well as change Local Network, and
WAN Ethernet settings.
The IP address is the address of the router. It is also your local network’s gateway
address which is used by all LAN hosts to access the Internet through the WAN
connection.
The Netmask is used to determine the number of sub networks that can be
connected to the router.
The IP Gateway (optional) field is and advanced and optional setting that available
if your local network has a gateway that is different than the router's LAN IP
address.
DNS Server (optional) allows you to specify a DNS server for LAN hosts to use if
your WAN connection does not supply a valid server address, or if not-peer DNS
Server information is required or chosen under Cellular Datacard settings.
Change WAN port into a second LAN port.
Enable IP Pass-through mode to have one client have the WAN IP. All router
functions are disabled.
Enable or disable the router’s ability to connect to the internet through a WAN
Ethernet connection.
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”
Network Traffic
The Network Traffic status screen shows current traffic status of active interfaces,
such as the LAN, the connected Datacard, and the WAN.
Cellular Datacard
Enable or disable the router’s ability to access the Internet through a datacard.
Select Service type: UMTS/GPRS, CDMA (default), or EV-DO.
Insert Access Point (APN), PIN code, Username, and Password as indicated by your

3G/4G wireless provider. (default = admin).
Select to use the Peer DNS or an optional location. Input DNS Server information
in Wired Interfaces.
Enable Keep-Alive to determine it the connection is up. Router well reinitialize
connection if connection is down.
Input time (in seconds) of inactivity until link is disconnected.
NOTE: Settings are auto-populated when an activated compatible datacard is
inserted.
Card Updates
Datacard activation, updates and network information.
Logout
This feature will log you out of administrative mode. You will be returned to the
login screen.
Tool Box
Signal Strength Meter
This feature displays feedback to determine the optimal position of the antenna
or router, to aquire the best signal strength.
System Settings
View system resource information such as load, memory usage, system time, and
system up time. Configure the router Hostname and Time zone for logging
timestamp. Additionally, selection of internal or external WiFi antennas is
performed on the page. Note if using a Mini PCI-e 3G/4G Modules internal WiFi
antennas must be selected. This allows the external RP-SMA female jacks on rear
of board to be used for the modules required external antennas.

System Log
View System Log file.
Email Notifications
Enable Email Notifications for certain router events.
Choose to truncate system logs to the last 50 lines.
Choose to be notified on: Boot-up, Interface Failover, and Interface Up/Down .
Input the name, Mail Domain, the To Address, the Mail Hub, Mail Port, Username,
and Password.
Select Email Now to send the system log to the specified location now.
Flash Firmware
Browse and select the firmware upgrade file from a selected location.
Choose to keep current or overwrite with new firmware configuration.
Select Flash Firmware to flash selected firmware file.
Router will upload selected file, flash the new firmware, and reboot to the login
screen upon completion.
Backup Settings
Create a backup file of current settings to a selected location.
Restore: Select a previously saved backup file by browsing to the file location and
then clicking “Restore backup”.
Reset to Defaults
This feature will reset the router to factory defaults.
Reboot
This feature will Reboot the router.
License Agreement
Nexaira, Inc.
Software License Agreement
Important: Please read this license agreement (this "Agreement") carefully before
using the software provided with the router (the "Software"). If you disagree with
any of these terms, do not use the router and the software.
1. License Grant. Subject to the terms and conditions of this Agreement, Nexaira
hereby grants you a non-exclusive, worldwide, non-transferable, perpetual,
revocable license to: (i) internally use the Software (in object code only) solely in
accordance with any user documentation (the "Documentation") for operating
the router provided with the Software; and (ii) internally use the Documentation
solely in connection with the use of the Software and the router.
2. Restriction. You acknowledge that the Software, including the structure,
organization, and source code of the Software, contains valuable trade secrets of
Nexaira. Accordingly, except as expressly permitted under this Agreement, you
agree not to: (i) sublicense, rent, lease, or otherwise transfer the Software to any
third party; (ii) modify, alter, translate, or create derivative works of the Software;
(iii) reverse engineer, decompile, disassemble, or otherwise attempt to derive the
source code for the Software; (iv) use the Software to control any other
instrument, computing hardware, or peripherals other than the Router; or (v) use
or copy the Software for any purpose except as permitted under Section 1.
3. Open Source. The Software includes third party codes, which are licensed to
you pursuant to the terms and conditions referenced in Exhibit A (the "Open
Source Codes").
4. Proprietary Rights. The Software, the Documentation, and all intellectual
property rights therein, are the exclusive property of Nexaira and its suppliers. All
rights in and to the Software not expressly granted to you are reserved by Nexaira
and its suppliers. This Agreement does not grant you title to the Software or title
to any copies of the Software, or an ownership of any intellectual property rights

in the Software.
5. Warranty. Except as provided in the standard warranty policy of Nexaira or
another supplier from whom you obtained the router, the Software and the
Documentation are provided “AS IS” without any warranty. Open Source Codes are
provided “AS IS” without any warranty. Nexaira disclaims all other warranties of
any kind, express, implied, or statutory, including any implied warranties of
merchantability, fitness for a particular purpose, title, and non-infringement of
third party rights. Nexaira does not warrant that the operation of the Software will
be uninterrupted or error free.
6. Limitation of Liability. In no event will Nexaira be liable for any incidental,
consequential, special, exemplary, or indirect damages (including lost profits and
lost data) arising from or relating to this Agreement or the Software, even if
Nexaira has been advised of the possibility of such damages. Nexaira’s total,
cumulative liability in connection with this Agreement and the Software, whether
in contract or tort or otherwise, will not exceed the amount of fees received by
Nexaira in consideration for licensing the Software or selling the router if you
purchased the router directly from Nexaira. In no event will suppliers be liable for
any direct, incidental, consequential, special, exemplary, or indirect damages
(including lost profits and lost data) arising from or relating to this Agreement or
the Open Source Codes. This section shall be given full effect even if the
warranties provided in Section 5 is deemed to have failed of its essential purpose.
7. Term and Termination. This Agreement is effective until terminated by either
party pursuant to this Section. You may terminate this Agreement for convenience
by notice to Nexaira. Nexaira may terminate this Agreement effective immediately
by providing a notice to you if you are in material breach of this Agreement and
do not cure such breach within twenty (20) days after receiving notice thereof
from Nexaira. Upon termination of this Agreement, you must immediately cease
all use of the Software.
8. Governing Law and Venue. This Agreement shall be governed by the laws of
the State of California without regard to conflicts of law principles that would
require the application of the laws of any other state. The United Nations
Convention on Contracts for the International Sale of Goods does not apply to this
Agreement. Any action or proceeding arising from or relating to this Agreement

must be brought in a federal court in the Southern District of California or in a
state court in San Diego County, California, and each party irrevocably submits to
the jurisdiction and venue of any such court in any such action or proceeding.
9. General. You acknowledge that any actual or threatened breach of Section 2
will constitute immediate, irreparable harm to Nexaira for which monetary
damages would be an inadequate remedy, and that injunctive relief is an
appropriate remedy for such breach. You will not export or re-export the Software
in violation of the U.S. Export Administration regulations or other applicable laws
and regulations. You may not assign or transfer any of the rights or obligations
under this Agreement to any third party without the prior written consent of
Nexaira, except in connection with the transfer of the router. Any attempted
transfer in violation of the foregoing will be null and void. The Software and
Documentation are "commercial items" as that term is defined at 48 C.F.R. 2.101,
consisting of "commercial computer software" and "commercial computer
software documentation" as such terms are used in 48 C.F.R. 12.212. Consistent
with 48 C.F.R. 12.212 and 48 C.F.R. 227.7202-1 through 227.7202-4, all U.S.
Government end users acquire the Software and Documentation with only those
rights set forth therein. All waivers must be in writing. A party’s failure to exercise
any of its rights under this Agreement shall not constitute a waiver or forfeiture of
any such rights nor of any other rights. If any provision of this Agreement is
unenforceable or invalid pursuant to any applicable law, such unenforceability or
invalidity will not render this Agreement unenforceable or invalid as a whole, and
such unenforceable or invalid provision will be changed and interpreted so as to
best accomplish the objectives of such provision within the limits of applicable
law or applicable court decisions. This Agreement represents the entire
agreement between you and Nexaira as to the matters set forth herein and
integrates all prior discussions and understanding between us. This Agreement
may be modified only by a binding written instrument entered into by you and
Nexaira.
Exhibit A (Open Source Codes)
The Software includes third party codes that are licensed to you pursuant to the
license agreements listed below:
GNU GENERAL PUBLIC LICENSE

Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc., 51 Franklin Street, Fifth
Floor, Boston, MA 02110-1301 USA Everyone is permitted to copy and distribute
verbatim copies of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share
and change it. By contrast, the GNU General Public License is intended to
guarantee your freedom to share and change free software--to make sure the
software is free for all its users. This General Public License applies to most of the
Free Software Foundation's software and to any other program whose authors
commit to using it. (Some other Free Software Foundation software is covered by
the GNU Lesser General Public License instead.) You can apply it to your programs,
too.
When we speak of free software, we are referring to freedom, not price. Our
General Public Licenses are designed to make sure that you have the freedom to
distribute copies of free software (and charge for this service if you wish), that you
receive source code or can get it if you want it, that you can change the software
or use pieces of it in new free programs; and that you know you can do these
things.
To protect your rights, we need to make restrictions that forbid anyone to deny
you these rights or to ask you to surrender the rights. These restrictions translate
to certain responsibilities for you if you distribute copies of the software, or if you
modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee,
you must give the recipients all the rights that you have. You must make sure that
they, too, receive or can get the source code. And you must show them these
terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you
this license which gives you legal permission to copy, distribute and/or modify the
software.
Also, for each author's protection and ours, we want to make certain that

everyone understands that there is no warranty for this free software. If the
software is modified by someone else and passed on, we want its recipients to
know that what they have is not the original, so that any problems introduced by
others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to
avoid the danger that redistributors of a free program will individually obtain
patent licenses, in effect making the program proprietary. To prevent this, we have
made it clear that any patent must be licensed for everyone's free use or not
licensed at all.
The precise terms and conditions for copying, distribution and modification
follow.
GNU GENERAL PUBLIC LICENSE TERMS AND CONDITIONS FOR COPYING,
DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice
placed by the copyright holder saying it may be distributed under the terms of
this General Public License. The "Program", below, refers to any such program or
work, and a "work based on the Program" means either the Program or any
derivative work under copyright law: that is to say, a work containing the Program
or a portion of it, either verbatim or with modifications and/or translated into
another language. (Hereinafter, translation is included without limitation in the
term "modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not covered by
this License; they are outside its scope. The act of running the Program is not
restricted, and the output from the Program is covered only if its contents
constitute a work based on the Program (independent of having been made by
running the Program). Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as
you receive it, in any medium, provided that you conspicuously and appropriately
publish on each copy an appropriate copyright notice and disclaimer of warranty;
keep intact all the notices that refer to this License and to the absence of any
warranty; and give any other recipients of the Program a copy of this License
along with the Program.

You may charge a fee for the physical act of transferring a copy, and you may at
your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus
forming a work based on the Program, and copy and distribute such
modifications or work under the terms of Section 1 above, provided that you also
meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you
changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part
contains or is derived from the Program or any part thereof, to be licensed as a
whole at no charge to all third parties under the terms of this License.
c) If the modified program normally reads commands interactively when run, you
must cause it, when started running for such interactive use in the most ordinary
way, to print or display an announcement including an appropriate copyright
notice and a notice that there is no warranty (or else, saying that you provide a
warranty) and that users may redistribute the program under these conditions,
and telling the user how to view a copy of this License. (Exception: if the Program
itself is interactive but does not normally print such an announcement, your work
based on the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections
of that work are not derived from the Program, and can be reasonably considered
independent and separate works in themselves, then this License, and its terms,
do not apply to those sections when you distribute them as separate works. But
when you distribute the same sections as part of a whole which is a work based
on the Program, the distribution of the whole must be on the terms of this
License, whose permissions for other licensees extend to the entire whole, and
thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to
work written entirely by you; rather, the intent is to exercise the right to control
the distribution of derivative or collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the

Program (or with a work based on the Program) on a volume of a storage or
distribution medium does not bring the other work under the scope of this
License.
3. You may copy and distribute the Program (or a work based on it, under Section
2) in object code or executable form under the terms of Sections 1 and 2 above
provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code,
which must be distributed under the terms of Sections 1 and 2 above on a
medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third
party, for a charge no more than your cost of physically performing source
distribution, a complete machine-readable copy of the corresponding source
code, to be distributed under the terms of Sections 1 and 2 above on a medium
customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute
corresponding source code. (This alternative is allowed only for noncommercial
distribution and only if you received the program in object code or executable
form with such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making
modifications to it. For an executable work, complete source code means all the
source code for all modules it contains, plus any associated interface definition
files, plus the scripts used to control compilation and installation of the
executable. However, as a special exception, the source code distributed need not
include anything that is normally distributed (in either source or binary form) with
the major components (compiler, kernel, and so on) of the operating system on
which the executable runs, unless that component itself accompanies the
executable.
If distribution of executable or object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the source code
from the same place counts as distribution of the source code, even though third
parties are not compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as

expressly provided under this License. Any attempt otherwise to copy, modify,
sublicense or distribute the Program is void, and will automatically terminate your
rights under this License. However, parties who have received copies, or rights,
from you under this License will not have their licenses terminated so long as such
parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it.
However, nothing else grants you permission to modify or distribute the Program
or its derivative works. These actions are prohibited by law if you do not accept
this License. Therefore, by modifying or distributing the Program (or any work
based on the Program), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying the Program or
works based on it.
6. Each time you redistribute the Program (or any work based on the Program),
the recipient automatically receives a license from the original licensor to copy,
distribute or modify the Program subject to these terms and conditions. You may
not impose any further restrictions on the recipients' exercise of the rights
granted herein. You are not responsible for enforcing compliance by third parties
to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or
for any other reason (not limited to patent issues), conditions are imposed on you
(whether by court order, agreement or otherwise) that contradict the conditions
of this License, they do not excuse you from the conditions of this License. If you
cannot distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you may not
distribute the Program at all. For example, if a patent license would not permit
royalty-free redistribution of the Program by all those who receive copies directly
or indirectly through you, then the only way you could satisfy both it and this
License would be to refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under any particular
circumstance, the balance of the section is intended to apply and the section as a
whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other
property right claims or to contest validity of any such claims; this section has the

sole purpose of protecting the integrity of the free software distribution system,
which is implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed through that
system in reliance on consistent application of that system; it is up to the
author/donor to decide if he or she is willing to distribute software through any
other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a
consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in certain countries
either by patents or by copyrighted interfaces, the original copyright holder who
places the Program under this License may add an explicit geographical
distribution limitation excluding those countries, so that distribution is permitted
only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the
General Public License from time to time. Such new versions will be similar in
spirit to the present version, but may differ in detail to address new problems or
concerns.
Each version is given a distinguishing version number. If the Program specifies a
version number of this License which applies to it and "any later version", you have
the option of following the terms and conditions either of that version or of any
later version published by the Free Software Foundation. If the Program does not
specify a version number of this License, you may choose any version ever
published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs
whose distribution conditions are different, write to the author to ask for
permission. For software which is copyrighted by the Free Software Foundation,
write to the Free Software Foundation; we sometimes make exceptions for this.
Our decision will be guided by the two goals of preserving the free status of all
derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY

11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO
WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW.
EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS
AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF
ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE
PROGRAM IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME
THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY
MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE
TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE
PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A
FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF
SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF
SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use
to the public, the best way to achieve this is to make it free software which
everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest to attach them to
the start of each source file to most effectively convey the exclusion of warranty;
and each file should have at least the "copyright" line and a pointer to where the
full notice is found.
Copyright (C)
This program is free software; you can redistribute it and/or modify it under the
terms of the GNU General Public License as published by the Free Software

Foundation; either version 2 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY
WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS
FOR A PARTICULAR PURPOSE. See the GNU General Public License for more
details.
You should have received a copy of the GNU General Public License along with
this program; if not, write to the Free Software Foundation, Inc., 51 Franklin Street,
Fifth Floor, Boston, MA 02110-1301 USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this when it starts
in an interactive mode:
Gnomovision version 69, Copyright (C) year name of author Gnomovision comes
with ABSOLUTELY NO WARRANTY; for details type `show w'. This is free software,
and you are welcome to redistribute it under certain conditions; type `show c' for
details.
The hypothetical commands `show w' and `show c' should show the appropriate
parts of the General Public License. Of course, the commands you use may be
called something other than `show w' and `show c'; they could even be mouse-
clicks or menu items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your school, if
any, to sign a "copyright disclaimer" for the program, if necessary. Here is a
sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision' (which makes passes at compilers) written by James Hacker.
, 1 April 1989 Ty Coon, President of Vice
This General Public License does not permit incorporating your program into
proprietary programs. If your program is a subroutine library, you may consider it
more useful to permit linking proprietary applications with the library. If this is
what you want to do, use the GNU Lesser General Public License instead of this
License.

GNU LESSER GENERAL PUBLIC LICENSE Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc. 51 Franklin Street, Fifth
Floor, Boston, MA 02110-1301 USA Everyone is permitted to copy and distribute
verbatim copies of this license document, but changing it is not allowed.
[This is the first released version of the Lesser GPL. It also counts as the successor
of the GNU Library Public License, version 2, hence the version number 2.1.]
Preamble
The licenses for most software are designed to take away your freedom to share
and change it. By contrast, the GNU General Public Licenses are intended to
guarantee your freedom to share and change free software--to make sure the
software is free for all its users.
This license, the Lesser General Public License, applies to some specially
designated software packages--typically libraries--of the Free Software
Foundation and other authors who decide to use it. You can use it too, but we
suggest you first think carefully about whether this license or the ordinary General
Public License is the better strategy to use in any particular case, based on the
explanations below.
When we speak of free software, we are referring to freedom of use, not price. Our
General Public Licenses are designed to make sure that you have the freedom to
distribute copies of free software (and charge for this service if you wish); that you
receive source code or can get it if you want it; that you can change the software
and use pieces of it in new free programs; and that you are informed that you can
do these things.
To protect your rights, we need to make restrictions that forbid distributors to
deny you these rights or to ask you to surrender these rights. These restrictions
translate to certain responsibilities for you if you distribute copies of the library or
if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you
must give the recipients all the rights that we gave you. You must make sure that
they, too, receive or can get the source code. If you link other code with the
library, you must provide complete object files to the recipients, so that they can

relink them with the library after making changes to the library and recompiling it.
And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the library, and
(2) we offer you this license, which gives you legal permission to copy, distribute
and/or modify the library.
To protect each distributor, we want to make it very clear that there is no warranty
for the free library. Also, if the library is modified by someone else and passed on,
the recipients should know that what they have is not the original version, so that
the original author's reputation will not be affected by problems that might be
introduced by others.
Finally, software patents pose a constant threat to the existence of any free
program. We wish to make sure that a company cannot effectively restrict the
users of a free program by obtaining a restrictive license from a patent holder.
Therefore, we insist that any patent license obtained for a version of the library
must be consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the ordinary GNU
General Public License. This license, the GNU Lesser General Public License,
applies to certain designated libraries, and is quite different from the ordinary
General Public License. We use this license for certain libraries in order to permit
linking those libraries into non-free programs.
When a program is linked with a library, whether statically or using a shared
library, the combination of the two is legally speaking a combined work, a
derivative of the original library. The ordinary General Public License therefore
permits such linking only if the entire combination fits its criteria of freedom. The
Lesser General Public License permits more lax criteria for linking other code with
the library.
We call this license the "Lesser" General Public License because it does Less to
protect the user's freedom than the ordinary General Public License. It also
provides other free software developers Less of an advantage over competing
non-free programs. These disadvantages are the reason we use the ordinary
General Public License for many libraries. However, the Lesser license provides
advantages in certain special circumstances.

For example, on rare occasions, there may be a special need to encourage the
widest possible use of a certain library, so that it becomes a de-facto standard. To
achieve this, non-free programs must be allowed to use the library. A more
frequent case is that a free library does the same job as widely used non-free
libraries. In this case, there is little to gain by limiting the free library to free
software only, so we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free programs enables
a greater number of people to use a large body of free software. For example,
permission to use the GNU C Library in non-free programs enables many more
people to use the whole GNU operating system, as well as its variant, the
GNU/Linux operating system.
Although the Lesser General Public License is Less protective of the users'
freedom, it does ensure that the user of a program that is linked with the Library
has the freedom and the wherewithal to run that program using a modified
version of the Library.
The precise terms and conditions for copying, distribution and modification
follow. Pay close attention to the difference between a "work based on the library"
and a "work that uses the library". The former contains code derived from the
library, whereas the latter must be combined with the library in order to run.
GNU LESSER GENERAL PUBLIC LICENSE TERMS AND CONDITIONS FOR COPYING,
DISTRIBUTION AND MODIFICATION
0. This License Agreement applies to any software library or other program which
contains a notice placed by the copyright holder or other authorized party saying
it may be distributed under the terms of this Lesser General Public License (also
called "this License"). Each licensee is addressed as "you".
A "library" means a collection of software functions and/or data prepared so as to
be conveniently linked with application programs (which use some of those
functions and data) to form executables.
The "Library", below, refers to any such software library or work which has been
distributed under these terms. A "work based on the Library" means either the
Library or any derivative work under copyright law: that is to say, a work

containing the Library or a portion of it, either verbatim or with modifications
and/or translated straightforwardly into another language. (Hereinafter,
translation is included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for making
modifications to it. For a library, complete source code means all the source code
for all modules it contains, plus any associated interface definition files, plus the
scripts used to control compilation and installation of the library.
Activities other than copying, distribution and modification are not covered by
this License; they are outside its scope. The act of running a program using the
Library is not restricted, and output from such a program is covered only if its
contents constitute a work based on the Library (independent of the use of the
Library in a tool for writing it). Whether that is true depends on what the Library
does and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library's complete source
code as you receive it, in any medium, provided that you conspicuously and
appropriately publish on each copy an appropriate copyright notice and
disclaimer of warranty; keep intact all the notices that refer to this License and to
the absence of any warranty; and distribute a copy of this License along with the
Library.
You may charge a fee for the physical act of transferring a copy, and you may at
your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Library or any portion of it, thus
forming a work based on the Library, and copy and distribute such modifications
or work under the terms of Section 1 above, provided that you also meet all of
these conditions:
a) The modified work must itself be a software library.
b) You must cause the files modified to carry prominent notices stating that you
changed the files and the date of any change.
c) You must cause the whole of the work to be licensed at no charge to all third
parties under the terms of this License.
d) If a facility in the modified Library refers to a function or a table of data to be

supplied by an application program that uses the facility, other than as an
argument passed when the facility is invoked, then you must make a good faith
effort to ensure that, in the event an application does not supply such function or
table, the facility still operates, and performs whatever part of its purpose remains
meaningful.
(For example, a function in a library to compute square roots has a purpose that is
entirely well-defined independent of the application. Therefore, Subsection 2d
requires that any application-supplied function or table used by this function
must be optional: if the application does not supply it, the square root function
must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections
of that work are not derived from the Library, and can be reasonably considered
independent and separate works in themselves, then this License, and its terms,
do not apply to those sections when you distribute them as separate works. But
when you distribute the same sections as part of a whole which is a work based
on the Library, the distribution of the whole must be on the terms of this License,
whose permissions for other licensees extend to the entire whole, and thus to
each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to
work written entirely by you; rather, the intent is to exercise the right to control
the distribution of derivative or collective works based on the Library.
In addition, mere aggregation of another work not based on the Library with the
Library (or with a work based on the Library) on a volume of a storage or
distribution medium does not bring the other work under the scope of this
License.
3. You may opt to apply the terms of the ordinary GNU General Public License
instead of this License to a given copy of the Library. To do this, you must alter all
the notices that refer to this License, so that they refer to the ordinary GNU
General Public License, version 2, instead of to this License. (If a newer version
than version 2 of the ordinary GNU General Public License has appeared, then you
can specify that version instead if you wish.) Do not make any other change in
these notices.

Once this change is made in a given copy, it is irreversible for that copy, so the
ordinary GNU General Public License applies to all subsequent copies and
derivative works made from that copy.
This option is useful when you wish to copy part of the code of the Library into a
program that is not a library.
4. You may copy and distribute the Library (or a portion or derivative of it, under
Section 2) in object code or executable form under the terms of Sections 1 and 2
above provided that you accompany it with the complete corresponding
machine-readable source code, which must be distributed under the terms of
Sections 1 and 2 above on a medium customarily used for software interchange.
If distribution of object code is made by offering access to copy from a designated
place, then offering equivalent access to copy the source code from the same
place satisfies the requirement to distribute the source code, even though third
parties are not compelled to copy the source along with the object code.
5. A program that contains no derivative of any portion of the Library, but is
designed to work with the Library by being compiled or linked with it, is called a
"work that uses the Library". Such a work, in isolation, is not a derivative work of
the Library, and therefore falls outside the scope of this License.
However, linking a "work that uses the Library" with the Library creates an
executable that is a derivative of the Library (because it contains portions of the
Library), rather than a "work that uses the library". The executable is therefore
covered by this License. Section 6 states terms for distribution of such
executables.
When a "work that uses the Library" uses material from a header file that is part of
the Library, the object code for the work may be a derivative work of the Library
even though the source code is not. Whether this is true is especially significant if
the work can be linked without the Library, or if the work is itself a library. The
threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data structure layouts and
accessors, and small macros and small inline functions (ten lines or less in length),
then the use of the object file is unrestricted, regardless of whether it is legally a

derivative work. (Executables containing this object code plus portions of the
Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may distribute the object
code for the work under the terms of Section 6. Any executables containing that
work also fall under Section 6, whether or not they are linked directly with the
Library itself.
6. As an exception to the Sections above, you may also combine or link a "work
that uses the Library" with the Library to produce a work containing portions of
the Library, and distribute that work under terms of your choice, provided that the
terms permit modification of the work for the customer's own use and reverse
engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the Library is
used in it and that the Library and its use are covered by this License. You must
supply a copy of this License. If the work during execution displays copyright
notices, you must include the copyright notice for the Library among them, as
well as a reference directing the user to the copy of this License. Also, you must do
one of these things:
a) Accompany the work with the complete corresponding machine-readable
source code for the Library including whatever changes were used in the work
(which must be distributed under Sections 1 and 2 above); and, if the work is an
executable linked with the Library, with the complete machine-readable "work
that uses the Library", as object code and/or source code, so that the user can
modify the Library and then relink to produce a modified executable containing
the modified Library. (It is understood that the user who changes the contents of
definitions files in the Library will not necessarily be able to recompile the
application to use the modified definitions.)
b) Use a suitable shared library mechanism for linking with the Library. A suitable
mechanism is one that (1) uses at run time a copy of the library already present on
the user's computer system, rather than copying library functions into the
executable, and (2) will operate properly with a modified version of the library, if
the user installs one, as long as the modified version is interface-compatible with
the version that the work was made with.

c) Accompany the work with a written offer, valid for at least three years, to give
the same user the materials specified in Subsection 6a, above, for a charge no
more than the cost of performing this distribution.
d) If distribution of the work is made by offering access to copy from a designated
place, offer equivalent access to copy the above specified materials from the same
place.
e) Verify that the user has already received a copy of these materials or that you
have already sent this user a copy.
For an executable, the required form of the "work that uses the Library" must
include any data and utility programs needed for reproducing the executable
from it. However, as a special exception, the materials to be distributed need not
include anything that is normally distributed (in either source or binary form) with
the major components (compiler, kernel, and so on) of the operating system on
which the executable runs, unless that component itself accompanies the
executable.
It may happen that this requirement contradicts the license restrictions of other
proprietary libraries that do not normally accompany the operating system. Such
a contradiction means you cannot use both them and the Library together in an
executable that you distribute.
7. You may place library facilities that are a work based on the Library side-by-side
in a single library together with other library facilities not covered by this License,
and distribute such a combined library, provided that the separate distribution of
the work based on the Library and of the other library facilities is otherwise
permitted, and provided that you do these two things:
a) Accompany the combined library with a copy of the same work based on the
Library, uncombined with any other library facilities. This must be distributed
under the terms of the Sections above.
b) Give prominent notice with the combined library of the fact that part of it is a
work based on the Library, and explaining where to find the accompanying
uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute the Library except

as expressly provided under this License. Any attempt otherwise to copy, modify,
sublicense, link with, or distribute the Library is void, and will automatically
terminate your rights under this License. However, parties who have received
copies, or rights, from you under this License will not have their licenses
terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not signed it.
However, nothing else grants you permission to modify or distribute the Library or
its derivative works. These actions are prohibited by law if you do not accept this
License. Therefore, by modifying or distributing the Library (or any work based on
the Library), you indicate your acceptance of this License to do so, and all its terms
and conditions for copying, distributing or modifying the Library or works based
on it.
10. Each time you redistribute the Library (or any work based on the Library), the
recipient automatically receives a license from the original licensor to copy,
distribute, link with or modify the Library subject to these terms and conditions.
You may not impose any further restrictions on the recipients' exercise of the
rights granted herein. You are not responsible for enforcing compliance by third
parties with this License.
11. If, as a consequence of a court judgment or allegation of patent infringement
or for any other reason (not limited to patent issues), conditions are imposed on
you (whether by court order, agreement or otherwise) that contradict the
conditions of this License, they do not excuse you from the conditions of this
License. If you cannot distribute so as to satisfy simultaneously your obligations
under this License and any other pertinent obligations, then as a consequence
you may not distribute the Library at all. For example, if a patent license would not
permit royalty-free redistribution of the Library by all those who receive copies
directly or indirectly through you, then the only way you could satisfy both it and
this License would be to refrain entirely from distribution of the Library.
If any portion of this section is held invalid or unenforceable under any particular
circumstance, the balance of the section is intended to apply, and the section as a
whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other
property right claims or to contest validity of any such claims; this section has the

sole purpose of protecting the integrity of the free software distribution system
which is implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed through that
system in reliance on consistent application of that system; it is up to the
author/donor to decide if he or she is willing to distribute software through any
other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a
consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in certain countries
either by patents or by copyrighted interfaces, the original copyright holder who
places the Library under this License may add an explicit geographical
distribution limitation excluding those countries, so that distribution is permitted
only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
13. The Free Software Foundation may publish revised and/or new versions of the
Lesser General Public License from time to time. Such new versions will be similar
in spirit to the present version, but may differ in detail to address new problems or
concerns.
Each version is given a distinguishing version number. If the Library specifies a
version number of this License which applies to it and "any later version", you have
the option of following the terms and conditions either of that version or of any
later version published by the Free Software Foundation. If the Library does not
specify a license version number, you may choose any version ever published by
the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free programs whose
distribution conditions are incompatible with these, write to the author to ask for
permission. For software which is copyrighted by the Free Software Foundation,
write to the Free Software Foundation; we sometimes make exceptions for this.
Our decision will be guided by the two goals of preserving the free status of all
derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY

15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER
PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER
EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE LIBRARY IS
WITH YOU. SHOULD THE LIBRARY PROVE DEFECTIVE, YOU ASSUME THE COST OF
ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY
MODIFY AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED ABOVE, BE LIABLE TO
YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE
LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A
FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER SOFTWARE), EVEN IF
SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF
SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Libraries
If you develop a new library, and you want it to be of the greatest possible use to
the public, we recommend making it free software that everyone can redistribute
and change. You can do so by permitting redistribution under these terms (or,
alternatively, under the terms of the ordinary General Public License).
To apply these terms, attach the following notices to the library. It is safest to
attach them to the start of each source file to most effectively convey the
exclusion of warranty; and each file should have at least the "copyright" line and a
pointer to where the full notice is found.
Copyright (C)
This library is free software; you can redistribute it and/or modify it under the

terms of the GNU Lesser General Public License as published by the Free Software
Foundation; either version 2.1 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful, but WITHOUT ANY
WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS
FOR A PARTICULAR PURPOSE. See the GNU Lesser General Public License for more
details.
You should have received a copy of the GNU Lesser General Public License along
with this library; if not, write to the Free Software Foundation, Inc., 51 Franklin
Street, Fifth Floor, Boston, MA 02110-1301 USA
Also add information on how to contact you by electronic and paper mail.
You should also get your employer (if you work as a programmer) or your school, if
any, to sign a "copyright disclaimer" for the library, if necessary. Here is a sample;
alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the library `Frob' (a library
for tweaking knobs) written by James Random Hacker.
, 1 April 1990 Ty Coon, President of Vice
That's all there is to it!
Advanced Settings
DHCP Settings
Here you can change whether the DHCP server is enabled, view current Active
Leases, and assign Static DHCP Leases to other devices.
Change first available lease number.
Change the total number of leases available.
Change the duration of an active lease (h = hours).
Assign Static DHCP leases to other devices.
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.

SNMP
Simple Network Management Protocol (SNMP) is used in conjunction with a
network management system to monitor specified network devices for defined
events and activities. Those activities are defined in a Management Information
Base (MIB). Your router supports a light implementation of SNMP with a defined
MIB.
The following configuration options are available:
Enable Check Box: This box will enable or disable the SNMP feature.
TCP Port: Specify the TCP port you would like the SNMP server to listen on. The
default is 161.
UDP Port: Specify the UDP port you would like the SNMP server to listen on. The
default is 161.
Community Name: Specify the community name for your SNMP neighborhood.
Device Description: An optional field to give the device a description upon SNMP
query.
Location Name: An optional field to list the device's location.
Administrator Email: An optional field to input the network administrator's e-mail
contact information.
LAN, WAN, and 3G checkboxes: Enable or disable reporting of these interfaces
upon SNMP query.
Dynamic DNS
The Dynamic DNS feature enables the router to interface directly with DDNS
service providers to update your WAN IP address when it changes. Dynamic DNS
maps the name of your DDNS host to your current WAN IP address. Before you
enable Dynamic DNS, you need to register an account on one of the Dynamic DNS
servers listed in the Service field. To enable Dynamic DNS click the check box next
to Enable. Next enter the appropriate information about your Dynamic DNS
Server.
You have to define:
Service.
Hostname.
Username.
Password.
Additional controls of the Dynamic DNS server include:
Check for changed IP every – Enter numeric value.
Check-Time unit – Select a unit of time from the list.
Force update every – Enter numeric value.
Force-Time unit – Select a unit of time from the list.
Add additional entry(ies).
NOTE: This information is established when you register an account on
a Dynamic DNS server. After any changes, select ”Save” to retain.
System will refresh following, “Save”.
QoS
Quality of Service settings provide a mechanism to provide prioritization of
certain types of traffic over other types of traffic. Disable by default, QoS can be
enabled as necessary.
Downlink and Uplink speeds can be modified for either the Datacard or WAN
connections.
Prioritization. This section allows for the following choices:
Set Priority: Low, normal, express, or priority
Source address: Select from detected sources.
Target Address: Select detected targets.
Service: Select Service option.
P2P: Select Peer-to-Peer protocol.
Protocol: Select internet protocol.
Ports: Enter ports.
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.
GPS
BC2400M and RB2400M provided a rich GPS (Global Positioning System) function
when used with a compatible and certified GPS modem. The GPS is a receiver
which calculates its position by precisely timing the signals sent by GPS satellites
high above the Earth. Each satellite continually transmits messages that include:
The time the message was transmitted
Precise orbital information (the ephemeris)
The general system health and rough orbits of all GPS satellites (the almanac).
The receiver uses the messages it receives to determine the transit time of each
message and computes the distance to each satellite. These distances along with
the satellites' locations are used to compute the position of the receiver. The
BC2400M provides this position data in the KLM/KMZ format which is compatible
with Google.
Setup: controlling the GPS function and configuration on BC2400M and RB2400M
may be done via both the Web based i3GUI or CLI commands. Please reference
the BC2400M / RB2400M CLI manual for all CLI commands. Following are the Web
based GUI instruction for configuring the GPS.
The BC2400M and RB2400M support GPS on certified compatible modems only.
Please see the BC2400M and RB2400M compatibility chart at http://nexaira.com
/wireless-routers for the GPS certified compatible modems. Additionally, if a
modem is certified for GPS on the BC2400M and RB2400M, the GPS icon on the
GUI in the advanced section is displayed indicating GPS feature is available as
shown below.
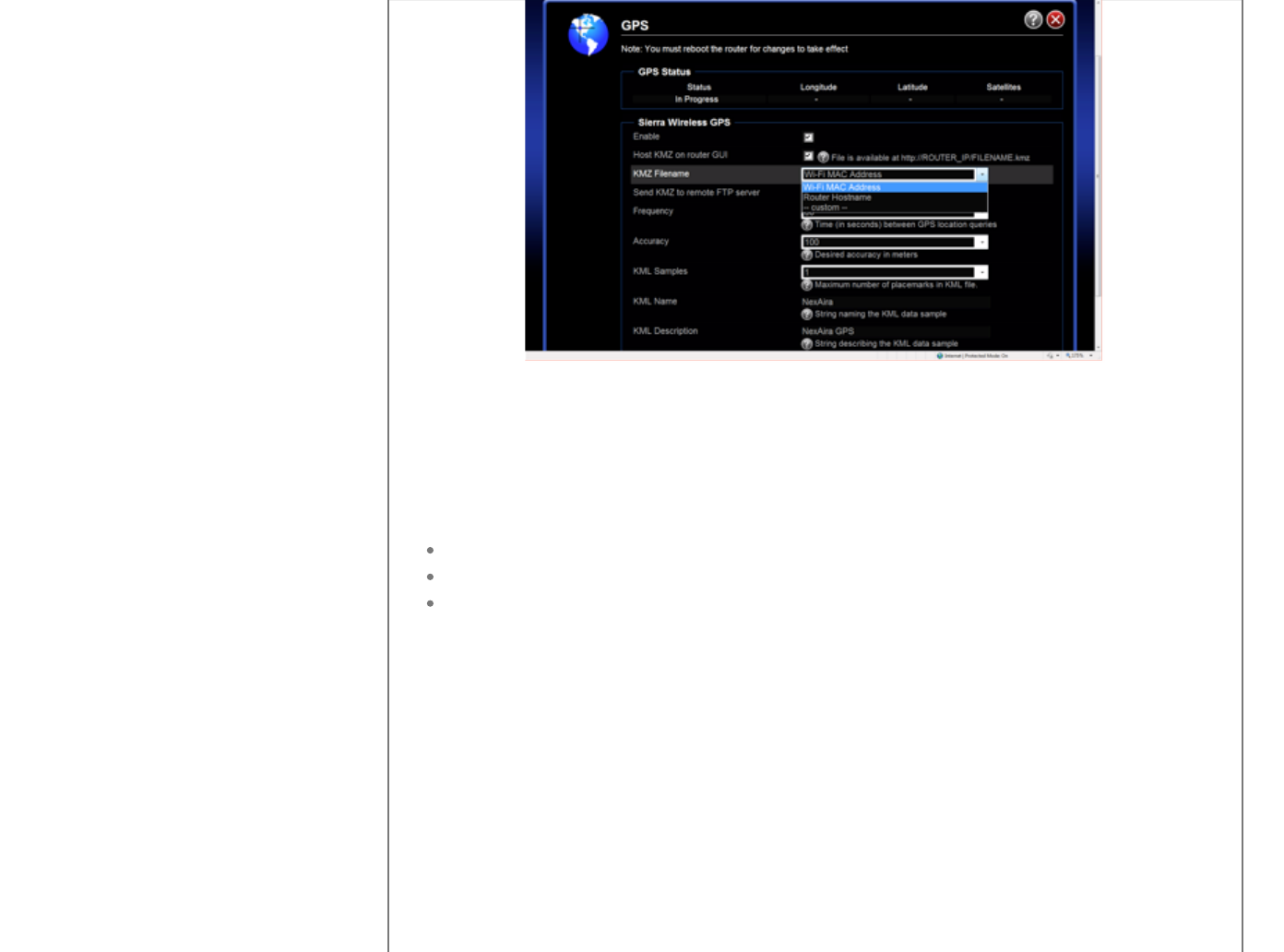
Configuraion Step 1: Select the GPS ICON and Selct Enable.
Configuration Step 2: Select to access GPS data locally by checking Host KMZ on
Router GUI
This will allow the KMZ file to be stored on the router and accessed at the
http://ROUTER_IP/FILENAME.kmz where FILENAME is defined as one of three
options:
WiFi MAC Address (which is the Default)
Router Host Name (Note; create a unique Router Hostname: located on the
Systems Page accessed from the Main GUI)
Custom Name
Configuration Step 3: Allows selection of using a remote GPS sever to store and
utilize the location information. The GPS data will always be sent in a KMZ
compressed file format. To enable check send KMZ to Remote FTP Server.
Upon selecting Remote FTP GPS Sever three additional entry fields appear the
remote server information:
FTP Server IP Address
FTP Sever Username
FTP Password
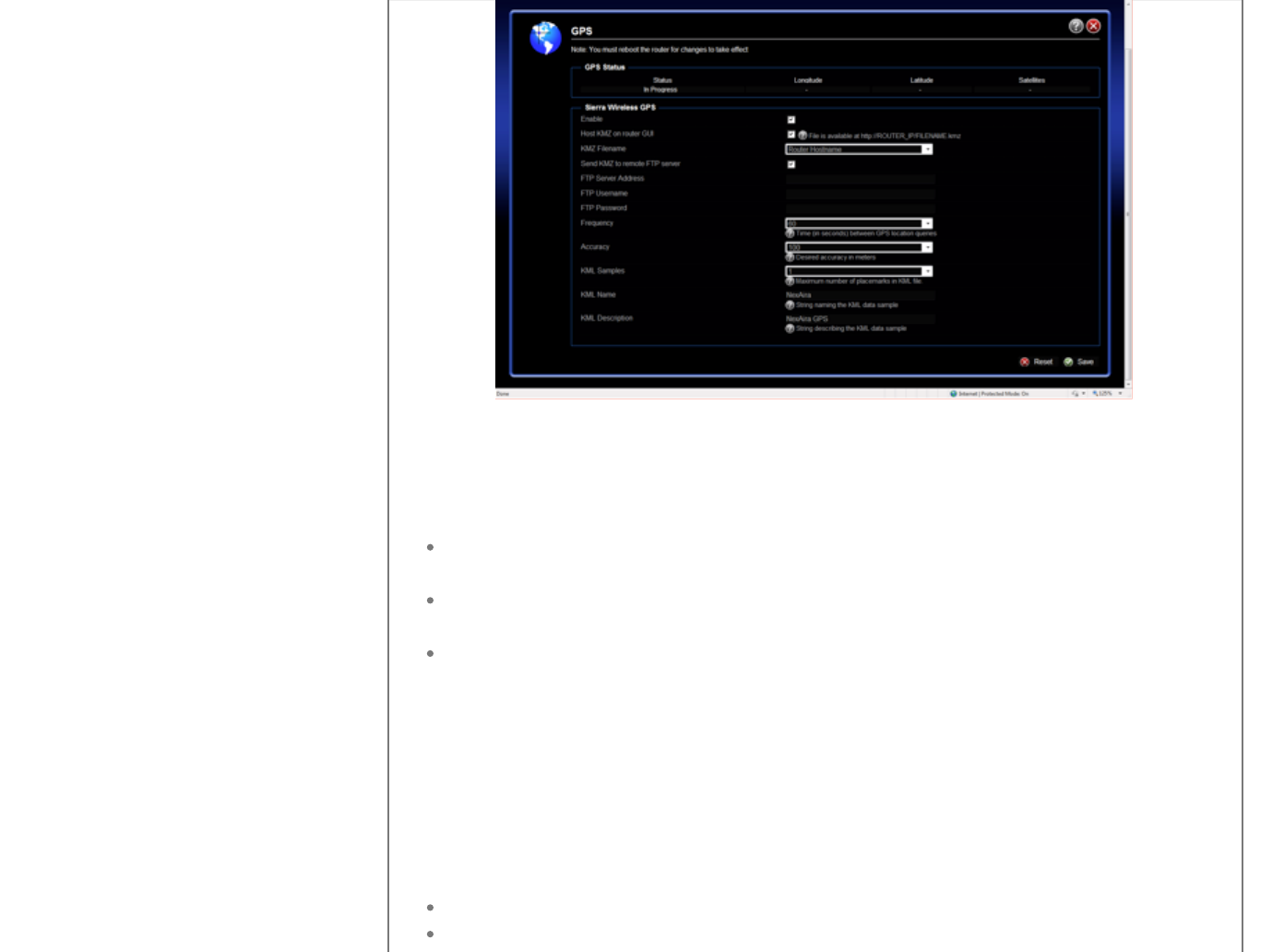
Configuration Step 4: allow for setting the sample interval and quantity which will
be stored and shipped in each KMZ file of information. This allows for longer time
buffering the GPS data for situations where the device may be out cellular service
yet still powered on and receiving GPS data.
Frequency is drop down box allows for sample storage every 10 seconds to once
an hour.
Accuracy setting 10 to 1000 meters will drive the GPS chipset to improve location
accuracy at the expense of delay and fewer samples.
KML Samples in a drop down box sets the maximum number of sample stored
and sent in each file.
Please note: the KMZ file storage is limited to 720 samples so as to not burden
the network when the GPS data sent to the FTP GPS server. However, at a
sample an hour that would provide about 30 days of GPS location data storage
given power remained on the device. This would maintain GPS data during
normal or extended cellular outages.
Configuration Step 5: Provides KML identities to the GPS Data
KML Name well be used to identify the Name TAG of the file
KML Description will be used to identify the Description Tag of the KML file
Configuration of the GPS modem is complete.
Security Settings
Remote Admin
This feature allows you to enable administrative remote access to the router. You
can choose the default port of 8080, or assign any other valid port.
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.
IPsec
IP Security (IPsec) is a suite of protocols for transmitting encrypted IP data
securely. This function is performed by authenticating and securing each packet
from source to destination. The BC2400M supports IPsec in tunnel mode, with
multiple configuration options for authentication and encryption. Two concurrent
IPsec tunnels utilizing AES encryption are supported in your router. The following
configuration options are available:
Enable Check Box: This checkbox will enable or disable the IPsec tunneling
feature.
Initiate Tunnel: Choose when tunnel is initiated.
WAN Interface: Choose the routing WAN interface.
Key Exchange Method:Choose encryption key exchange method.
Local LAN Network: Enter the Network and subnet in network prefix notation of
your LAN.
Remote WAN IP: Enter the public WAN IP address of the IPsec endpoint you wish
to connect to.
Remote LAN IP: Enter the LAN gateway IP address of the LAN you wish to connect
to.
Remote LAN Network: Enter the Network and subnet in network prefix notation
of the LAN you wish to connect to.
WAN IP Address: Your router’s public WAN IP address, either from Ethernet or

3G/4G, should be entered here.
Integrity: Choose integrity type.
Encryption Algorithm: Choose encryption algorithm.
DH Group: Choose DH group
Strict Negotiation: Choose to use only above settings.
Pre-Shared Key: Enter your chosen PSK value in this field.
Add Entry: Choose to add an entry.
SSH Server
Enable remote shell access.
Choose the port.
Select connection criteria.
Allow SSH access remotely.
Choose to allow only listed IP addresses.
Choose to allow authentication.
SSH Keys
Here you can insert keys for Public-Key authentication (one per line.)
Routing Settings
Routes
Active IPv4-Routes
View current routes for the datacard, LAN, or WAN. Static IPv4 Routes.
Add entry. Adding an entry inserts fields which require additional information.
Interface: Set interface (LAN, datacard, or WAN).
Target: Select Target (Host-IP or Network).
IPv4-Netmask: Select IPv4-Netmask (only if target is a network).
IPv4-Gateway: Select IPv4-Gateway.
NOTE: After any changes, select ”Save” to retain. System will refresh

following, “Save”.
RIP
This feature allows use of RIP protocol over the selected RIP device.
RIP Version 1 or Version 2 can be selected.
Additional entries can also be added.
NOTE: After any changes, select ”Save” to retain. System will refresh
following, “Save”.
DMZ Host
DMZ allows all traffic to be forwarded to one host on the LAN provided there are
no other port forwarding rules that will effect that traffic.
Check the enable box
Type in the IP Address on LAN to be placed in DMZ.
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.
VRRP
Virtual Router Redundancy Protocol (VRRP) is an open source router redundancy
protocol as specified in RFC 3768. It is designed to provide gateway redundancy
across multiple routers on the same subnet. It is important to note that this
feature provides redundancy for routing functions only, and does not include
other LAN functions such as DHCP.
NOTE: After configuring VRRP, the router must be rebooted before VRRP takes
effect.
The following configuration options are available:
Enable Check Box: Enable or disable the VRRP feature.
ID: The ID value of the router, a range of 1 through 254.
Priority: This is the priority of the router in the VRRP chain; 254 is always master.

The higher the value, the higher the priority of the device.
IP Address: This is the virtual router IP address. By default it should match your
primary gateway's LAN IP address. All VRRP routers on the subnet must utilize the
same virtual router IP address.
Interval: This is the interval by which VRRP registration messages are sent via
broadcast and gratuitous ARP.
Internet Failover
Internet Failover is a feature that provides failover from your primary internet
connection, WAN, to your secondary internet connection when your primary
connection fails.
Choose to enable Internet Failover.
Choose Primary and Backup interfaces.
Choose to keep the backup connection alive .
Choose Failover and Switchback times.
Input Test IP names for connection testing.
Choose the number of seconds between each ping for connection testing.
NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.
Port Forwarding
Port forwarding allows a port or range of ports to be opened to inbound traffic.
That traffic is than forwarded to a LAN host on a specified port or range of ports.
Adding an entry will insert fields requiring additional information to configure this
feature.
Insert Name (optional).
Choose Protocol, TCP, UDP, or TCP + UDP.
Insert port number or range of ports (first-last) for external device.
Select internal IP-address.
Select internal port or range (optional).

NOTE: After any changes, select ”Save” to retain. System will refresh following,
“Save”.
UPnP
Enable UPnP to allow clients in the local network to automatically configure the
router.
©2011 Nexaira Inc.

NEX-BC-2400M
IC 7839B-2400M01
Industry Canada - Class B
This digital apparatus does not exceed the Class B limits for radio noise emissions from
digital apparatus as set out in the interference-causing equipment standard entitled
“Digital Apparatus,” ICES-003 of Industry Canada. Cet appareil numérique respecte les
limites de bruits radioélectriques applicables aux appareils numériques de Classe B
prescrites dans la norme sur le matérial brouilleur: “Appareils Numériques,” NMB-003
édictée par l’Industrie. (1) This device may not cause interference,and (2) this device
must accept any interference, including interference that may cause undesired operation
of the device." Under Industry Canada regulations, this radio transmitter may only
operate using an antenna of a type and maximum (or lesser) gain approved for the
transmitter by Industry Canada. To reduce potential radio interference to other users, the
antenna type and its gain should be so chosen that the equivalent isotropically radiated
power (e.i.r.p.) is not more than that necessary for successful communication. Sous la
réglementation d'Industrie Canada, ce transmetteur radio ne peut fonctionner en utilisant
une antenne d'un type et un maximum (ou moins) gain approuvées pour l'émetteur par
Industrie Canada. Pour réduire le risque d'interférence aux autres utilisateurs, le type
d'antenne et son gain doivent être choisis de manière que la puissance isotrope rayonnée
équivalente (PIRE) ne dépasse pas ce qui est nécessaire pour une communication réussie.
L'equipement est conforme aux limites d'exposition aux RF etablies pour un
environnement non controle. L'antenne (s) utilisee pour ce transmetteur ne doit pas etre
co-localises ou fonctionnant en conjonction avec une autre antenne ou transmetteur.
RF exposure warning:
The equipment complies with RF exposure limits set forth for an uncontrolled
environment. The antenna(s) used for this transmitter must not be co-located or operating
in conjunction with any other antenna or transmitter. This device is restricted to indoor
use due to its operation in the 5.15 to 5.25 GHz frequency range. IC requires this product
to be used indoors for the frequency range 5.15 to 5.25 GHz to reduce the potential for
harmful interference to co-channel Mobile Satellite systems. High power radars are
allocated as primary users of the 5.25 to 5.35 GHz and 5.65 to 5.85 GHz bands. These
radar stations can cause interference with and /or damage this device. Ce dispositif est
limite a une utilisation en interieur a cause de son fonctionnement dans la gamme 5.15 a
5.25 GHz. IC exige que ce produit soit utilise a l'interieur de la gamme de frequence 5,15
a 5,25 GHz pour reduire les risques d'interference nuisible a la co-canal systemes mobiles
par satellite. Radars a haute puissance sont designes comme utilisateurs principaux de
l'5,25 a 5,35 GHz et 5,65 a 5,85 GHz. Ces stations radar peut provoquer des interferences
avec et / ou endommager l'appareil.
Warning: This device complies with Industry Canada licence-exempt RSS standard(s).
Operation is subject to the following two conditions: (1) this device may not cause
interference, and (2) this device must accept any interference, including interference that
may cause undesired operation of the device.
IC Warning:
Le présent appareil est conforme aux CNR d'Industrie Canada applicables aux appareils radio exempts de licence.
L'exploitation est autorisée aux deux conditions suivantes :
(1) l'appareil ne doit pas produire de brouillage, et
(2) l'utilisateur de l'appareil doit accepter tout brouillage radioélectrique subi, même si le brouillage est susceptible
d'en compromettre le fonctionnement.
FCC YAZ-2400M-01
FCC 15b devices
This equipment has been tested and found to comply with the limits for a Class B digital
device, pursuant to part 15 of the FCC rules. These limits are designed to provide
reasonable protection against harmful interference in a residential installation. This
equipment generates, uses and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the
user is encouraged to try to correct the interference by one or more of the following
measures:
-Reorient or relocate the receiving antenna.
-Increase the separation between the equipment and receiver.
-Connect the equipment into an outlet on a circuit different from that to which the
receiver is connected.
-Consult the dealer or an experienced radio/TV technician for help
FCC Part 15.21 information for user
You are cautioned that changes or modifications not expressly approved by the party
responsible for compliance could void your authority to operate the equipment.
FCC part 15.19
This device complies with part 15 of the FCC rules.
Operation is subject to the following two conditions
(1) This device may not cause harmful interference and
(2) This device must accept any interference received, including interference that may
cause undesired operation for mobile devices without co-location condition ( the
transmitting antenna is installed or located more than 20cm away from the body of
user and near by person )
FCC RF Radiation Exposure Statement:
1. This Transmitter must not be co-located or operating in conjunction with any other
antenna or transmitter.
2. This equipment complies with FCC RF radiation exposure limits set forth for an
uncontrolled environment. This equipment should be installed and operated with a
minimum distance of 20 centimeters between the radiator and your body.