Option OGLH-V2E Multimode GSM/GPRS/EDGE/UMTS/HSDPA PCMCIA CARD User Manual Manual UK
Option NV Multimode GSM/GPRS/EDGE/UMTS/HSDPA PCMCIA CARD Manual UK
Option >
Contents
- 1. User Manual
- 2. User Manual 2
- 3. Safety Manual
- 4. Users Manual
User Manual


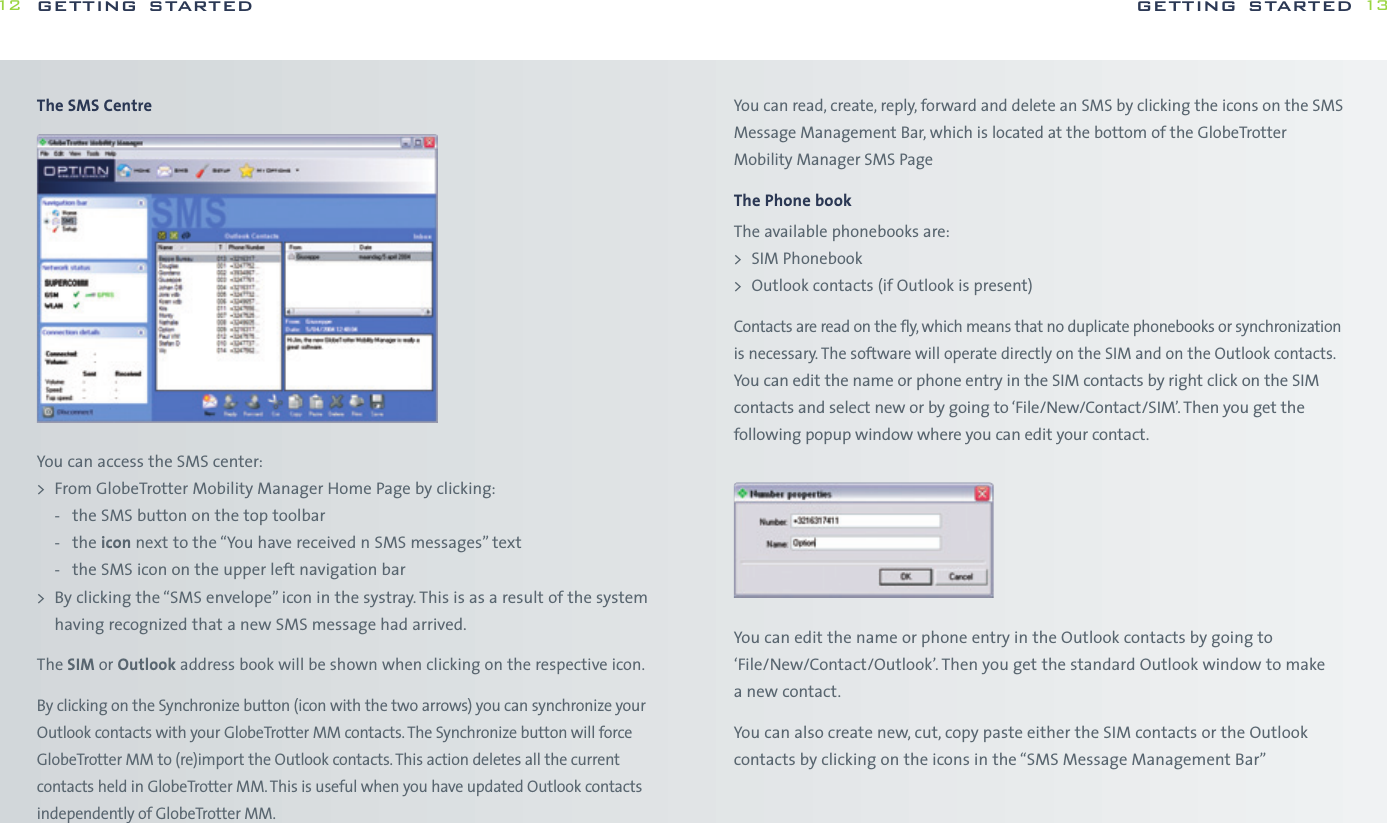
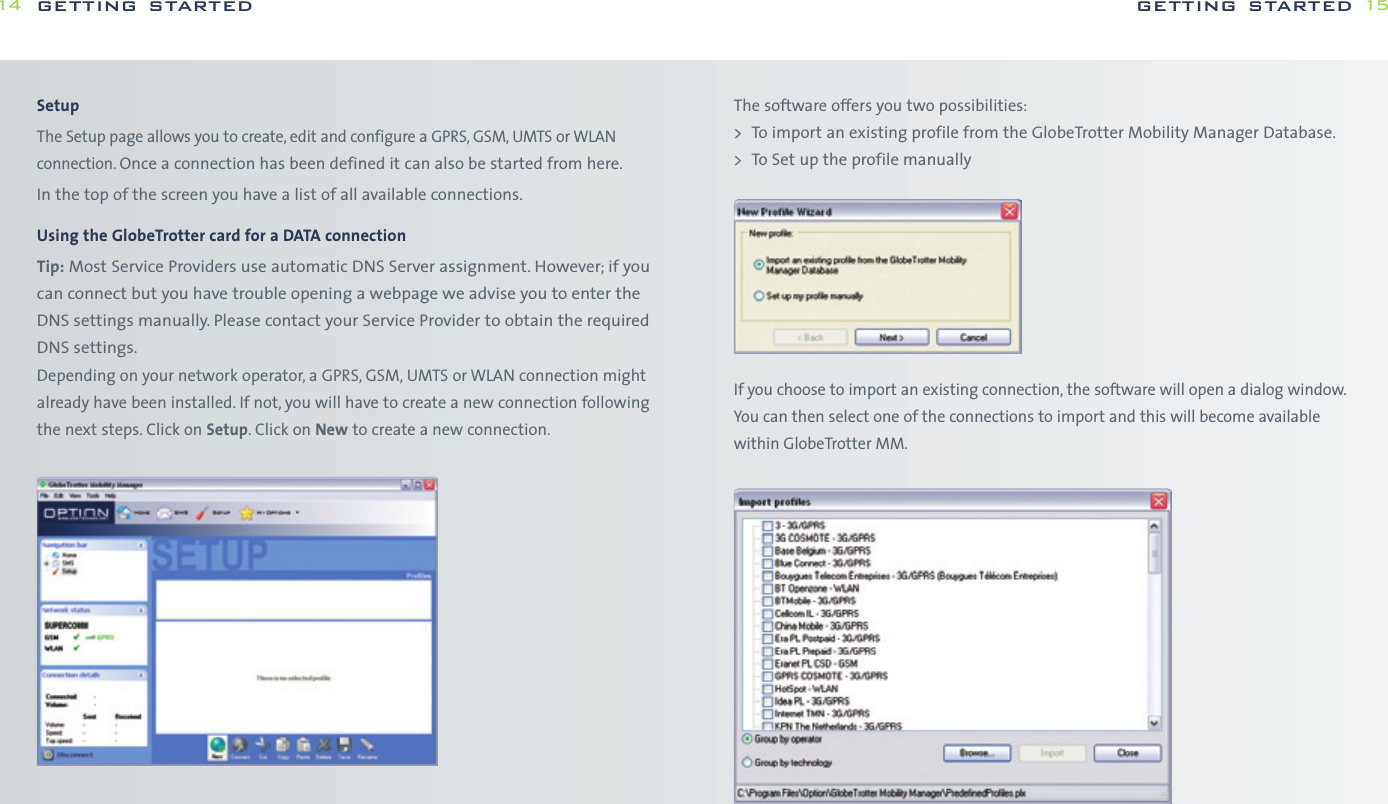
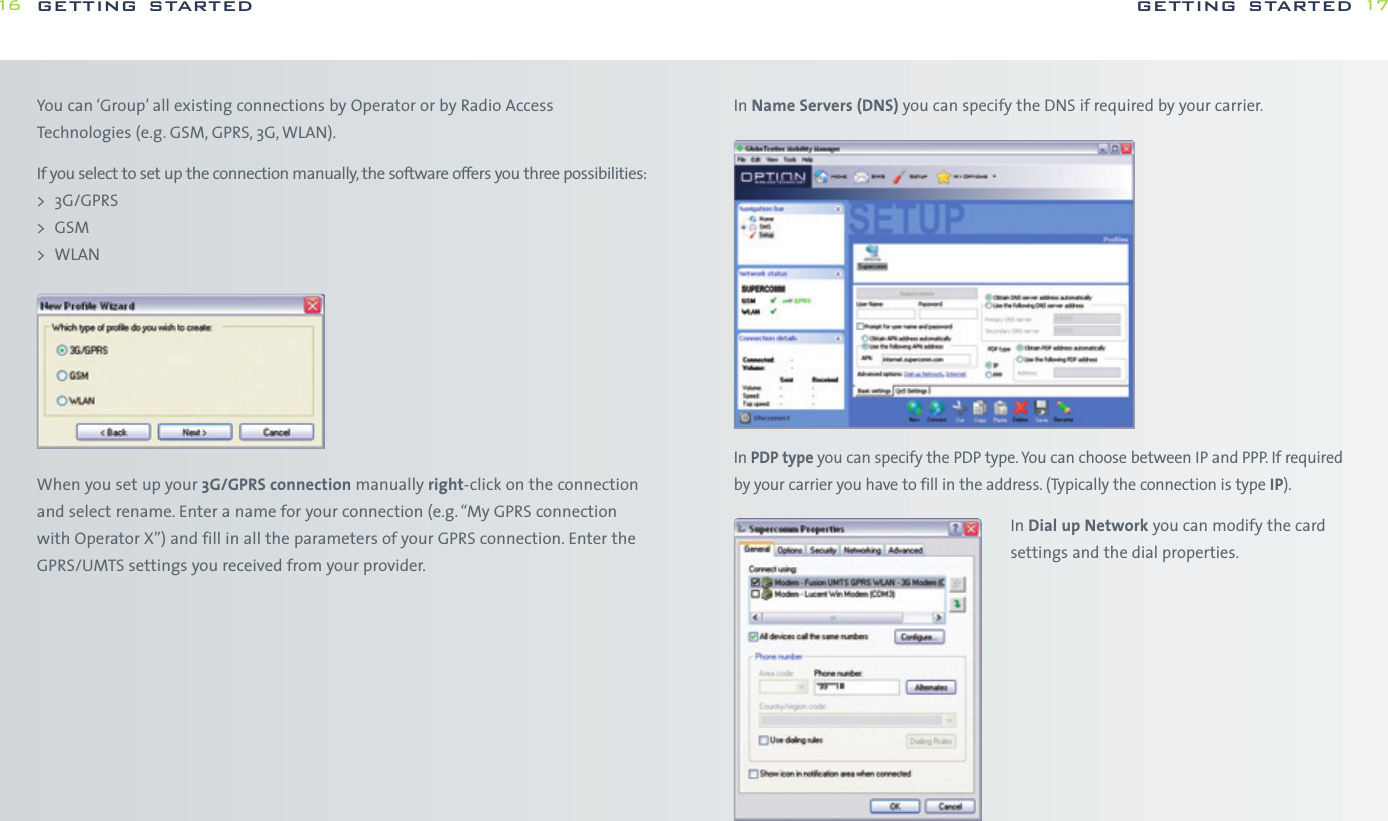
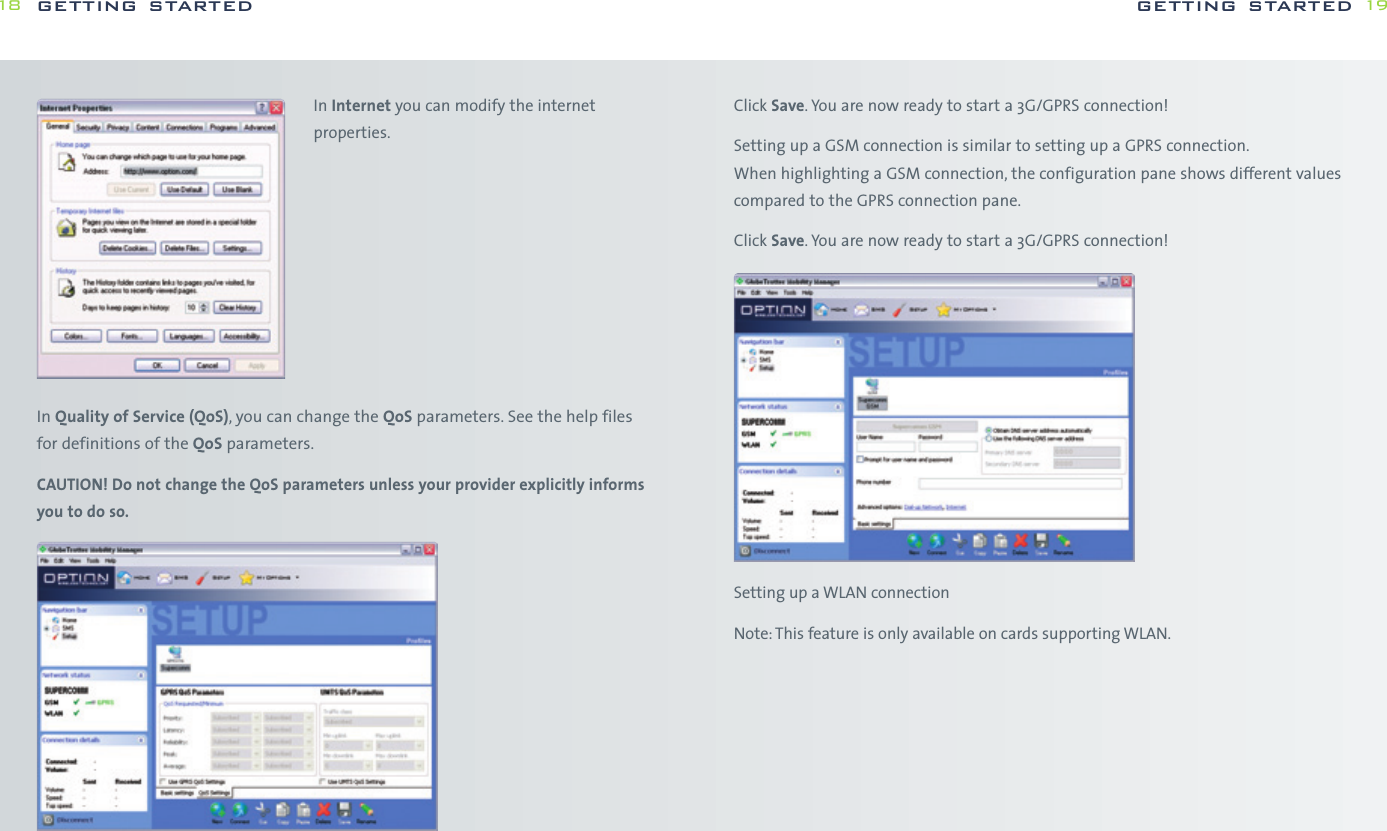
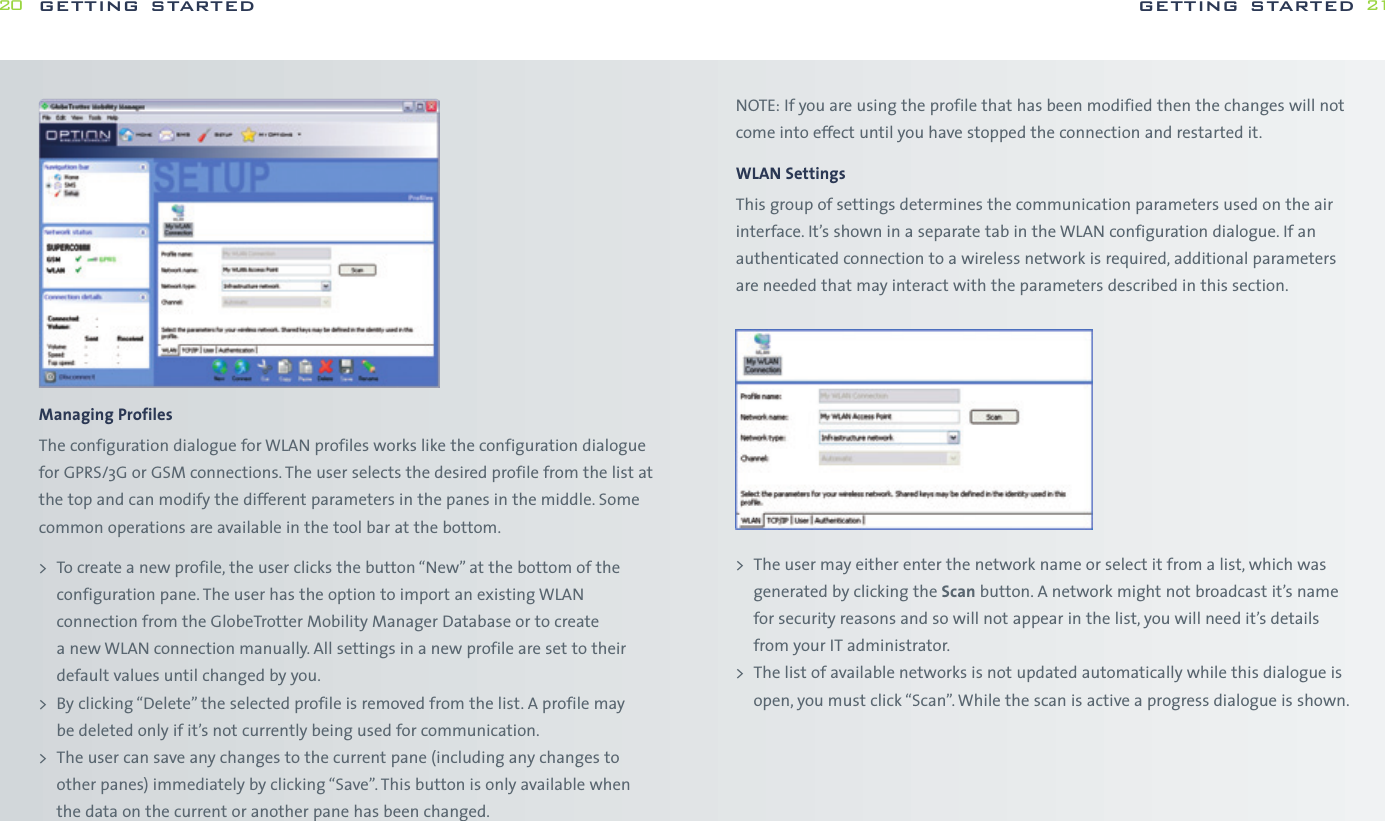
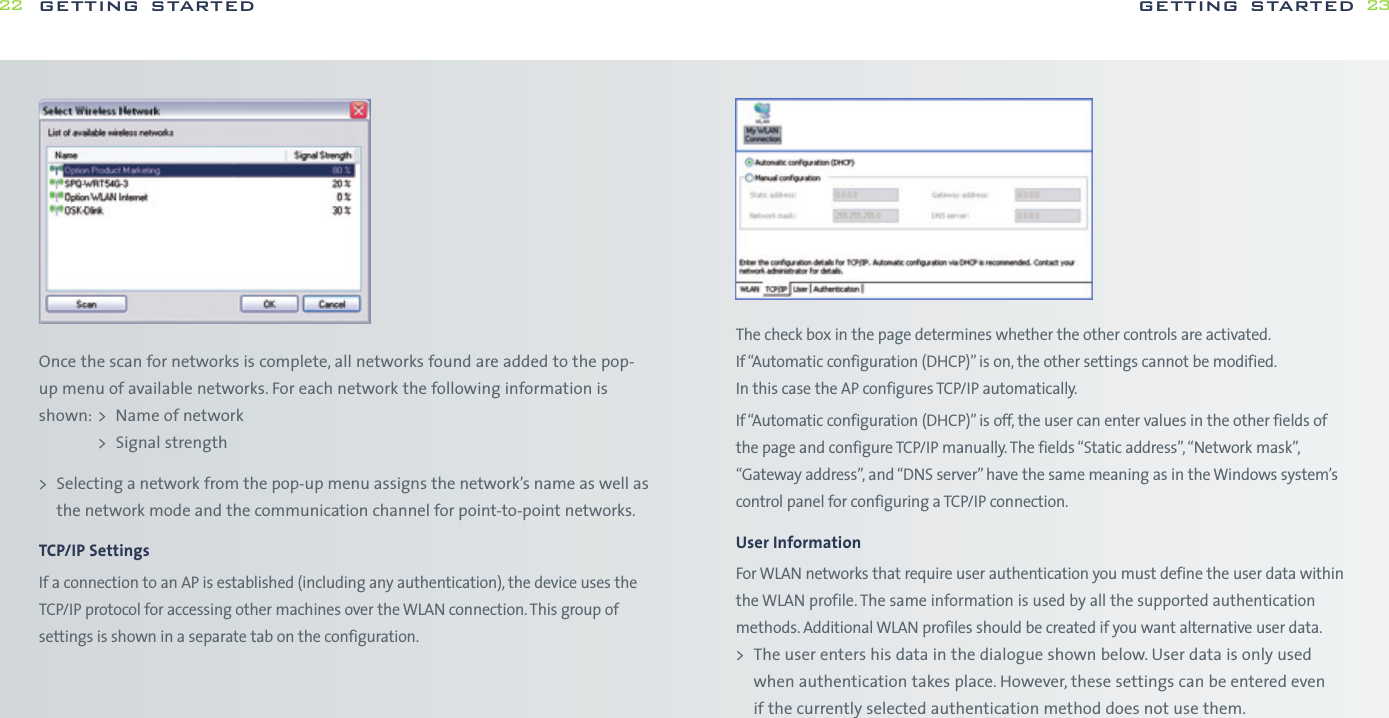
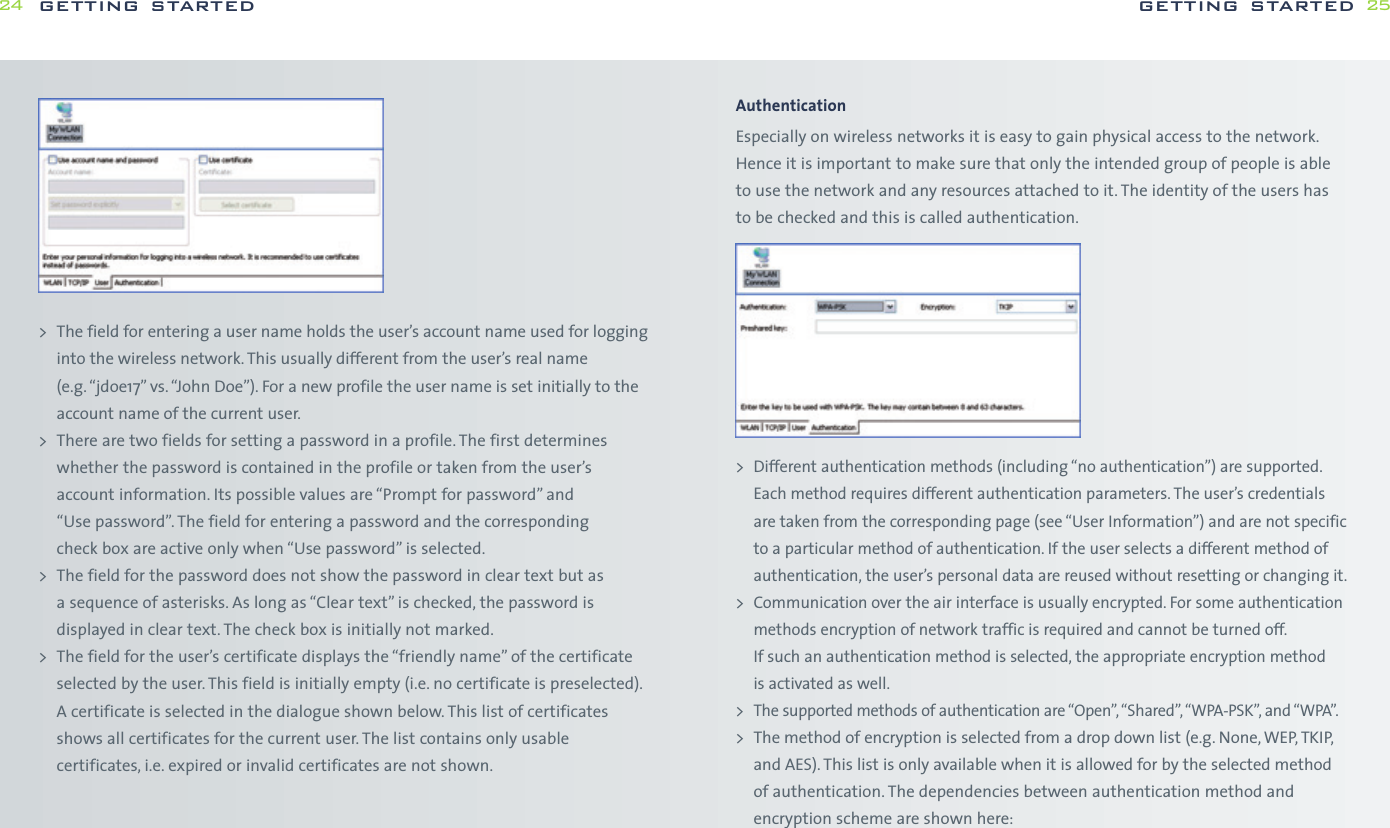
![while WPA-PSK is more secure without the need for a dedicated authentication server.WPAOn the WPA settings pane, the user selects the method of authentication used whenthe device communicates with a RADIUS server. RADIUS servers are typically used in acorporate environment.> The method of authentication is selected from the “Main Protocol” pop-up menu.The following bullets describe in more detail additional parameters that mightbe necessary for the different methods:-EAP/LEAP This protocol does not use any additional parameters.-EAP/PEAP This protocol uses certificates for authentication. By setting the appropriatecheck box, the user may request a verification of the server’s certificate.-EAP/SIM This protocol does not use any additional parameters. The user’s SIMmust be present when he wants to attach to a WLAN network. Usually the user enters the SIM-PIN when the main application is started.If the user did not enter the SIM-PIN when the main application started,the main application prompts the user for the SIM-PIN using the usual dialog for entering a SIM. The main application can simply check whetherthe SIM-PIN is needed when the user tries to open a connection withEAP/SIM as its authentication method and prompt the users as appropriate.-EAP/TokenCard This protocol does not need any additional parameters.-EAP/TLS This protocol uses certificates for authentication. The user must selecta personal certificate for this method to work. If there is no certificate selected,this triggers a warning. The only additional parameter for this method iswhether the server’s certificate should be verified.-EAP/TLS This protocol uses a certificate for authentication.All connections can be started from the GlobeTrotter MM controller icon in the taskbar.getting started 27OpenOpen authentication lets users attach to networks quickly as there is no access control and encryption may be turned off. The amount of configuration is thereforeminimal. This mode is ideal for an ad-hoc network created for instance during ameeting to exchange data or collaborate on a document. If encryption is set to“None”, the files for entering WEP keys are hidden.SharedShared authentication using WEP encryption provides weak security. If this methodhas been selected, the user can either enter four shared keys. You can choose if youwant a 40(64) bit [equivalent to 10 hexadecimal or 5 ASCII characters] or 104 (128)bit [equivalent to 26 hexadecimal or 13 ASCII characters] WEP key.> The user can enter up to four different WEP keys. All entered keys must be of the same length or the configuration is invalid. If the configuration is invalid,the triggers a warning.> The user can enter a key either as a sequence of hexadecimal digits or as a stringof characters as defined by the format buttons above the key fields.> As long as the user enters a key and the key’s length is not correct, an appropriatewarning is shown.WPA-PSKIf the user selects authentication via WPA-PSK, he has to enter a so-called pre-shared key. Such keys contain between 8 and 63 characters. The user mayenter these characters in an appropriate password field. The text of the key isshown masked unless the check box “Clear text” is turned on.Note WPA-PSK is a stronger encryption method than WEP, users are advised to useWPA-PSK whenever possible. The amount of configuration is essentially the same getting started26](https://usermanual.wiki/Option/OGLH-V2E.User-Manual/User-Guide-760019-Page-14.png)