An Illustrated Guide To The Kaminsky DNS Vulnerability
User Manual: Pdf
Open the PDF directly: View PDF ![]() .
.
Page Count: 14

9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 1/14
SteveFriedl'sUnixwiz.netTechTips
AnIllustratedGuidetotheKaminskyDNSVulnerability
TableofContents
Terminology
FollowingasimpleDNSquery
What'sinaDNSpacket?
ResourceRecordTypes
Drillingdowntoarealquery
What'sinthecache?
Poisoningthecache
Shenanigans,Version1
Dan'sShenanigans
What'sthefix?
Summary
OtherReferences
ThebigsecuritynewsofSummer2008hasbeenDanKaminsky'sdiscoveryofaseriousvulnerabilityin
DNS.Thisvulnerabilitycouldallowanattackertoredirectnetworkclientstoalternateserversofhisown
choosing,presumablyforillends.
ThisallledtoamaddashtopatchDNSserversworldwide,and
thoughtherehavebeenmanywriteupsofjusthowthe
vulnerabilitymanifestsitself,wefelttheneedforoneinfar
moredetail.Hence,oneofourIllustratedGuides.
ThispapercovershowDNSworks:firstatahighlevel,thenby
pickingapartanindividualpacketexchangefieldbyfield.Next,
we'llusethisknowledgetoseehowweaknessesincommon
implementationscanleadtocachepoisoning.
Byfullyunderstandingtheissuesatplay,thereadermaybe
betterequippedtomitigatetherisksinhisorherown
environment.
WehopeeverybodywhorunsaDNSserverpatchessoon.
Terminology
BeforeweseehowDNSoperates,weneedtodefineafewtermstoknowwhotheplayersare,softwarewise.Thiswillbereview
formany,andinsomecasesweleaveoutsidedetailsthatanexpertwouldfindfaultwith.Omitteddetailswon'tmatterforan
understandingofthisissue.
zone
Thinkofthisasa"domain":acollectionofhostnames/IPpairsallmanagedtogether.
Ourserversoperateunixwiz.net,andalltheDNSrecordsthatgowithit—www.unixwiz.net,mvp.unixwiz.net,
cs.unixwiz.net,etc.—areallpartoftheunixwiz.netzone.
Thesubtledistinctioncomeswithsubdomains:sometimestheyarepartofthemainzone,sometimestheyareaseparate
zone,butnoneofthatmattersforthispaper.
Nameserver
ThisisserversoftwarethatanswersDNSquestions,suchas"WhatistheIPaddressforwww.unixwiz.net?".Sometimesa
nameserverknowstheanswerdirectly(ifit's"authoritative"forthezone),othertimesithastogoouttotheinternetandask
aroundtofindtheanswer(ifit'sarecursivenameserver).
Thereiswidevarietyofsoftwarethatperformsthisservice:BIND,PowerDNS,djbdns,andmanyothers.Theyallanswerthe
samequestionsmoreorlessthesameway,thoughtheminordifferencesmattersomeforthispaper.
AuthoritativeNameserver
Foreveryzone,somebodyhastomaintainafileofthehostnamesandIPaddressassociations("linux.unixwiz.netis
64.170.162.98",andsoon).Thisisgenerallyanadministrativefunctionperformedbyahuman,andinmostcasesone
machinehasthisfile.It'sthezonemaster.
Zoneswithmultiplepublicnameserversmakeadministrativearrangementstotransferthezonedataautomaticallyto
additionalslavenameservers,allofwhichareauthoritativeasfarastheoutsideworldisconcerned.Thedistinctionbetween
masterandslaveisunimportantforthispaper.
Resolver
ThisistheclientpartoftheDNSclient/serversystem:itasksthequestionsabouthostnames.Theresolverisusuallya
smalllibrarycompiledintoeachprogramthatrequiresDNSservices,anditknowsjustenoughtosendquestionstoanearby
nameserver.
OnLinux/UNIXsystems,thelocationoftheserverstoaskisfoundinthefile/etc/resolv.conf,andonWindowsit'spartof
theNetworkConnectionssetupinthecontrolpanel.ThisusuallyconsistsofalistofIPaddresses,eachofwhichexpectsto
findanameserverontheotherend.
Resolversareusuallyverysmallanddumb,relyingontheserverstodotheheavylifting.
RecursiveNameserver
Thisisanameserverthat'swillingtogooutontheinternetandfindtheresultsforzonesit'snotauthoritativefor,asa
servicetoitsclients.Notallnameserversareconfiguredtoproviderecursiveservice,orarelimitedtojusttrustedclients
(say,anISPmayprovidenameserviceonlytoitscustomers).
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 2/14
ResourceRecord
ThoughmostthinkofDNSasprovidinghostnametoIPmapping,thereareactuallyotherkindsofquestionswecanaskofa
nameserver,andthishighlightsthenotionthatDNSisreallyadatabaseof"resourcerecords".
ThemostcommontypeisanIPAddress(an"A"record),butotherrecordsexisttoo:NS(nameserver),MX(mailexchanger),
SOA(StartofAuthority),andsoon.
Delegation
Whenanameserverdoesn'thavethecontentsofazone,butknowshowtofindtheowner,it'ssaidtodelegateserviceof
thatzonetoanothernameserver.Informally,it'sapassthebuckmechanism:"Iknowthezoneyou'reaskingabout,goask
(hostname)forthedetails".
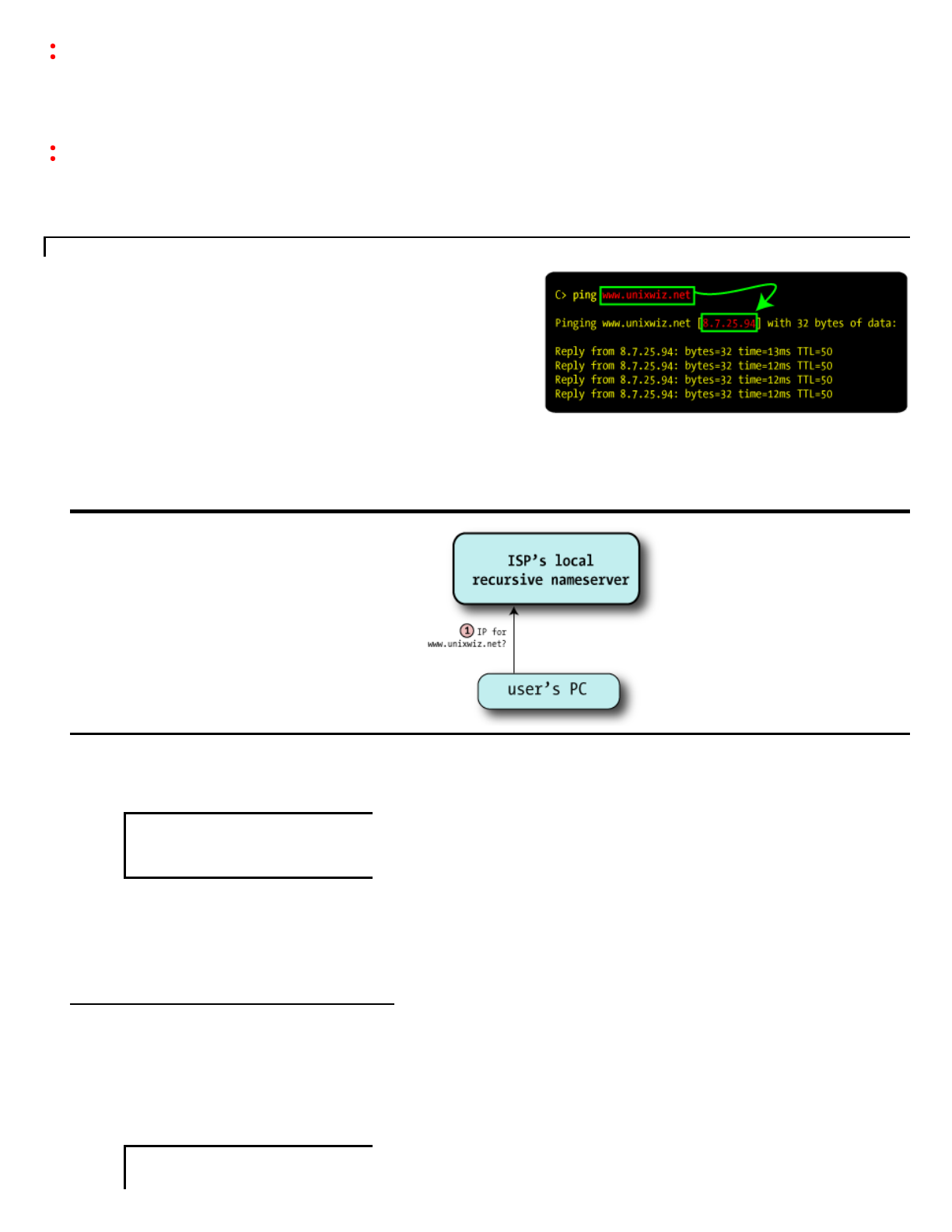
FollowingasimpleDNSquery
Withafewkeytermsdefined,we'llreviewhowasimplerecursivequery
worksintheabsenceofanybugsorshenanigans;thisformsthe
backgroundofwheretheexploitscanlaterbeapplied.
ThoughtheDNSpacketitselfhasmanyfields(eachofwhichis
important),we'reomittingthatdetailfornowinordertounderstandthe
highlevelflowofafullquery,fromtoptobottom.Visualizinghow
delegationbouncesrequestsfromoneservertoanotherisvitalto
understandingthevulnerabilitywillbeexploitedlater.
Wecan'treallytellbylookingatthequeryitselfwhatpromptedthe
queryinthefirstplace.Inthelogoofthissection,weseethattheuser
attemptedtopingourwebserver,andthepingprogramaskedthenameservertoperformthisnametoIPlookup.
Butitcouldhavejustaseasilybeenauserenteringhttp://www.unixwiz.netinabrowseraddressbar.Butit'snotimportantto
knowwhythename'sbeinglookedup,onlytoknowhowitlooksup.
1Theclient(notedas"User'sPC")makesa
requestforwww.unixwiz.net,andit's
routedtothenameserverprovidedbythe
user'sISP.ItrequeststheArecord,which
representsanIPaddress.
TheISP'snameserverknowsthatit'snot
authoritativeforunixwiz.net,soitcan't
lookitupinitslocalzonedatabase.Italso
doesn'tfindthenameititscacheof
recentlyseendata,soitknowsithastogo
outtotheinternettofinditforus.
2Allrecursivenameserversarepreconfigured
withalistof13rootservers,aselectionof
whichlookslike:
Roothints
A.ROOTSERVERS.NET.INA198.41.0.4
B.ROOTSERVERS.NET.INA192.228.79.201
C.ROOTSERVERS.NET.INA192.33.4.12
...
M.ROOTSERVERS.NET.INA202.12.27.33
ThankfullytheseIPaddressesdon'tchange
veryoften.
Thenameserverpicksoneatrandomand
sendsoffthequeryfortheArecordof
www.unixwiz.net;hereit'sgoingto
b.rootservers.net
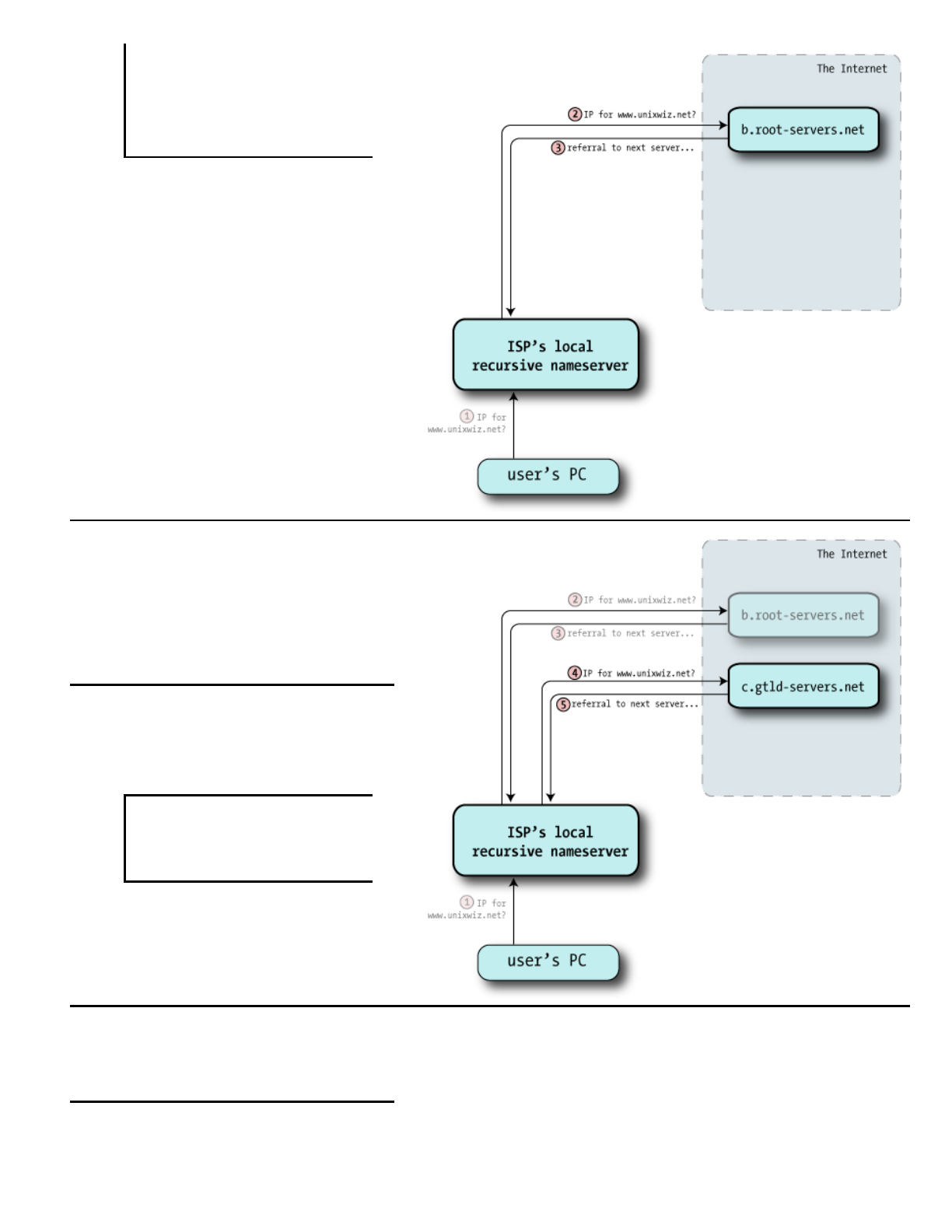
3Therootserverdoesn'tknowanythingabout
unixwiz.net,butishappytosendmethe
wayoftheGlobalTopLevelDomain(GTLD)
serversresponsibleforthe.netdomain.
ThisisintheformofNSrecordsofservers
morequalifiedtoanswerourquery:"Goask
theseguyshere'salist".
.NETreferrals
/*Authoritysection*/
NET.INNSA.GTLDSERVERS.NET.
INNSB.GTLDSERVERS.NET.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 3/14
INNSC.GTLDSERVERS.NET.
...
INNSM.GTLDSERVERS.NET.
/*Additionalsection"glue"records*/
A.GTLDSERVERS.net.INA192.5.6.30
B.GTLDSERVERS.net.INA192.33.14.30
C.GTLDSERVERS.net.INA192.26.92.30
...
M.GTLDSERVERS.net.INA192.55.83.30
ThoughtechnicallyweaskedonlyfortheNS
records,therootserversalsogiveustheIP
addressofeach:thisisknownas"glue"and
isprovidedtosaveusfromhavingtolookit
up.
4Withthehelpfulreferralfromtheroot
servers,thisnameserverchoosesoneofthe
authoritativeserversatrandom—here,
c.gtldservers.net—andsendsoffthe
samequery:"Iwastoldtoaskyou:what's
theArecordforwww.unixwiz.net?".
5TheGTLDserverdoesn'tknowthespecific
answertoourquery,butitdoesknowhow
togetuscloser.Liketherootservers,it
sendsbackareferral(asetofNSrecords)
thatarelikelytohavewhatweseek.
unixwiz.netreferral
/*Authoritysection*/
unixwiz.net.INNScs.unixwiz.net.
INNSlinux.unixwiz.net.
/*Additionalsection"glue"records*/
cs.unixwiz.net.INA8.7.25.94
linux.unixwiz.net.INA64.170.162.98
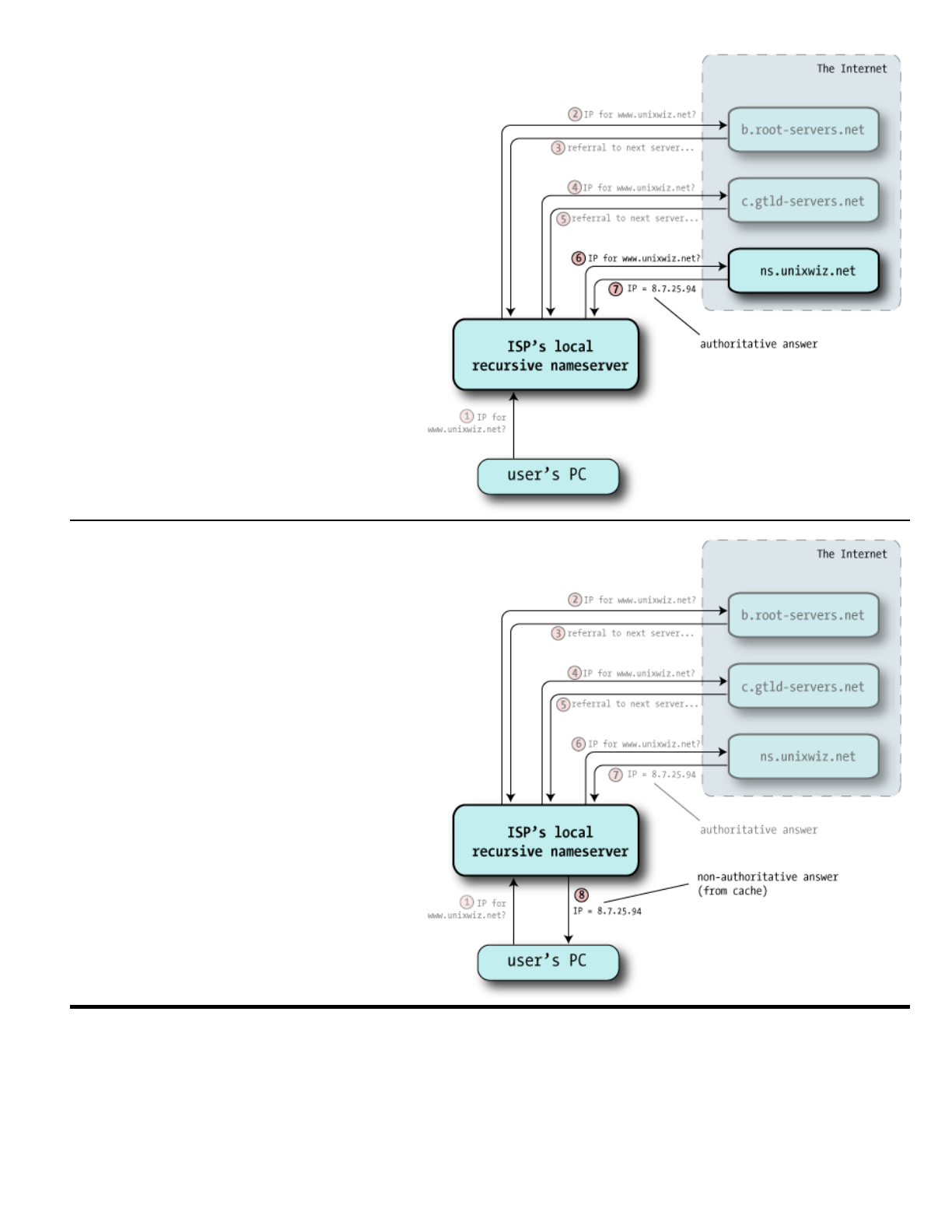
6Onceagaintherecursivenameserveris
followingachainofreferralsontheclient's
behalf,anditpicksoneofthenameservers
atrandomandsendsoffathirdquery(the
sameastheothertwo).
7Unliketheotheranswers,thatmerely
passedthebuckontoothernameservers,
thisoneactuallyhaswhatwewerelooking
for:itprovidestheArecordfor
www.unixwiz.net.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 4/14
Inaddition,theresponseincludesaflag
saying"Thisisanauthoritativeresponse",
indicatingitcamefromthesourceoftruth
forthisdomain.
8Nowwithanswerinhand,theISP's
recursivenameserverhandsthatanswer
backtotheclient,andthatsatisfiesthe
entirequery.
Therecursivenameserveralsofilesaway
thisanswerintoitsowncacheincasethisor
someotherclientmakesthesamequery
later.
Butwe'llnotethatthereplytotheclient
doesn'tincludethe"authoritative"indicator.
Eventhoughitreceivedonefrom
cs.unixwiz.net,therecursivenameserver
can'tpretendtotheclientthatit'sactually
thesourceofauthority,soit'sconsidereda
nonauthoritativeanswer.
Thisproceduregoesonunderthehoodtrillionsoftimeeverydayovertheinternet.DNSisquitefast,sotheeightpacket
handshake(forthisparticularquery)routinelycompletesinjustasplitsecond.
ThisrevealsthedistributednatureofDNS:noonemachineknowseverything,buttheydoknowhowtofindeachothervia
delegation.
Asasidenote,nothingpreventsanynameserverfromhostinganyzone,includingthoseitdoesn'treallyown.Abadguycouldset
upanameserverandconfigureanauthoritativezoneforBankOfSteve.com,butithasnoeffectbecausenohigherlevel
nameservereverdelegatestoit.

9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 5/14
What'sinaDNSpacket?
Withagraspofthehighlevelexchangeswedigabitdeeperintowhat'sinsideaDNSpacket:thedetailsarerequiredto
understandcachepoisoningandthisrecentvulnerability.There'salotofdetailhere,butfortunatelymanyofthefieldsaren't
importantforanunderstandingoftheseissues.
TheillustrationontherightshowstheoverallstructureofasinglepacketofDNSdata,anditcanreflectaquestionpacketoran
answerpacket.We'vehighlightedsomeofthefieldsthataremostrelatedtothisexploit.
Source/DestinationIPaddress
ThesereflecttheIPaddressesofthemachinesthatsentand
shouldreceivethepacket.It'spossibletoforgethesource
address,butpointlesstoforgethedestination.
Analogintherealworld:onanenvelopesentintheUSMail,
youcanputanythingyouwantasthereturnaddress—the
sourceaddress—butifyoulieabouttherecipient,it'snot
goingtogowhereyouwant.
Source/Destinationportnumbers
DNSserverslistenonport53/udpforqueriesfromthe
outsideworld,sothefirstpacketofanyexchangealways
includes53astheUDPdestinationport.
Thesourceportvariesconsiderably(thoughnotenough,as
we'llfindshortly):sometimesit'salsoport53/udp,
sometimesit'safixedportchosenatrandombythe
operatingsystem,andsometimesit'sjustarandomport
thatchangeseverytime.
AsfarasDNSfunctionalityisconcerned,thesourceport
doesn'treallymatteraslongastherepliesgetroutedtoit
properly.Butthisturnsouttobethecruxoftheproblemat
hand.
QueryID
Thisisauniqueidentifiercreatedinthequerypacketthat's
leftintactbytheserversendingthereply:itallowsthe
servermakingtherequesttoassociatetheanswerwiththequestion.
Anameservermighthavemanyqueriesoutstandingatonetime—evenmultiplequeriestothesameserver—sothisQuery
IDhelpsmatchtheanswerswiththeawaitingquestions.
ThisisalsosometimescalledtheTransactionID(TXID).
QR(Query/Response)
Setto0foraquerybyaclient,1foraresponsefromaserver.
Opcode
Setbyclientto0forastandardquery;theothertypesaren'tusedinourexamples.
AA(AuthoritativeAnswer)
Setto1inaserverresponseifthisanswerisAuthoritative,0ifnot.
TC(Truncated)
Setto1inaserverresponseiftheanswercan'tfitinthe512bytelimitofaUDPpacketresponse;thismeanstheclientwill
needtotryagainwithaTCPquery,whichdoesn'thavethesamelimits.
RD(RecursionDesired)
Theclientsetsthisto1ifitwishesthattheserverwillperformtheentirelookupofthenamerecursively,or0ifitjustwants
thebestinformationtheserverhasandtheclientwillcontinuewiththeiterativequeryonitsown.Notallnameserverswill
honorarecursiverequest(rootservers,forinstance,won'teverperformrecursivequeries).
RA(RecursionAvailable)
Theserversetsthistoindicatethatitwill(1)orwon't(0)supportrecursion.
Z—reserved
Thisisreservedandmustbezero
rcode
Responsecodefromtheserver:indicatessuccessorfailure
Questionrecordcount
Theclientfillsinthenextsectionwithasingle"question"recordthatspecifieswhatit'slookingfor:itincludesthename
(www.unixwiz.net),thetype(A,NS,MX,etc.),andtheclass(virtuallyalwaysIN=Internet).

9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 6/14
Theserverrepeatsthequestionintheresponsepacket,sothequestioncountisalmostalways1.
Answer/authority/additionalrecordcount
Setbytheserver,theseprovidevariouskindsofanswerstothequeryfromtheclient:we'lldigintotheseanswersshortly.
DNSQuestion/Answerdata
Thisistheareathatholdsthequestion/answerdatareferencedbythecountfieldsabove.Thesewillbediscussedingreat
detaillater.
We'llseetheseinactionaswedisassembleoursamplequeryshortly.
ResourceRecordTypes
Ultimately,DNSisakindofdistributeddatabase,andeachqueryorresponseincludesa
name,atype,and(foraresponse)avalue.Theresourcetypesrepresentdifferent
purposes,andnounderstandingofDNSiscompletewithoutknowingaboutthem.
Therearedozensofresourcerecordtypes,thoughonlyafewareincommonusage.The
restareexperimental,obsolete,orserveobscurepurposesthatrarelycomeupinpractice.
CommonDNSResourceRecordTypes
Type Description
AThisisanIPAddressrecord,andisthemostobvioustypeofdata
supportedbyDNS.Indeed;manyusershavenoideathatDNSdeals
withanythingotherthanIPaddresses.
NS ThisdescribesaNameserverrecordresponsibleforthedomainasked
about.
MX TheMXrecordencodesthenameofaMailExchanger,asystem
responsibleforhandlingemailforthegivendomain.MultipleMXrecords
canbeprovidedforadomain(theyincludedwaytospecifypriority).
EmailserversoftwareisthemainconsumerofMXresourcerecords.
Curiously,themailexchangerforadomaindoesn'thavetobepartof
thatdomain;it'scommonforthemailserveratalargehostingoperation
tobeprimaryMXforthousandsofcustomerdomains.
SOA TheStartofAuthoritiesrecorddescribessomekeydataaboutthe
zoneasdefinedbythezoneadministrator(onthedomainmaster
machine).Itincludesthingssuchasthecontactaddressfortheadmin,
andtheamountoftimethatslavenameserversshouldhangontothe
zoneincasethemasterisunreachable.
CNAME TheCanonicalName,morecommonlyknownasanAlias,thisallows
providinganalternatenameforaresource.
TXT AgenericTextrecordthatprovidesdescriptivedataaboutdomain.
Theseareessentiallycomments,thoughsomeapplications(suchasSPF)
usethemforprogrammaticpurposes.
It'sgenerally(butnotuniversally)allowedthatonenamecanhavemultipleresourcerecords,evenmorethanoneofthesame
type.AcommonexamplewouldbeamachinehavingmultipleIPaddresses,bothofwhichareenteredinDNS:
www.example.com.INA192.168.1.3
www.example.com.INA192.168.7.149
Here,thenamewww.example.comhastwoIPaddressrecordsassociatedwithit,andbothwillbereturnedinanswertoanA
queryforthisname.Notethattheorderoftheaddressesastheyappearinthefilearenotmaintainedintheresponses:they're
usuallyshuffled.
We'llnotethattheINtokenmeanstheINternetclass,andthisisvirtuallytheonlyclassyou'lleverseeinpractice.Others(such
asChaosorHesiod)aredefinedbutareforspecializedandmostlyobsoletepurposes.
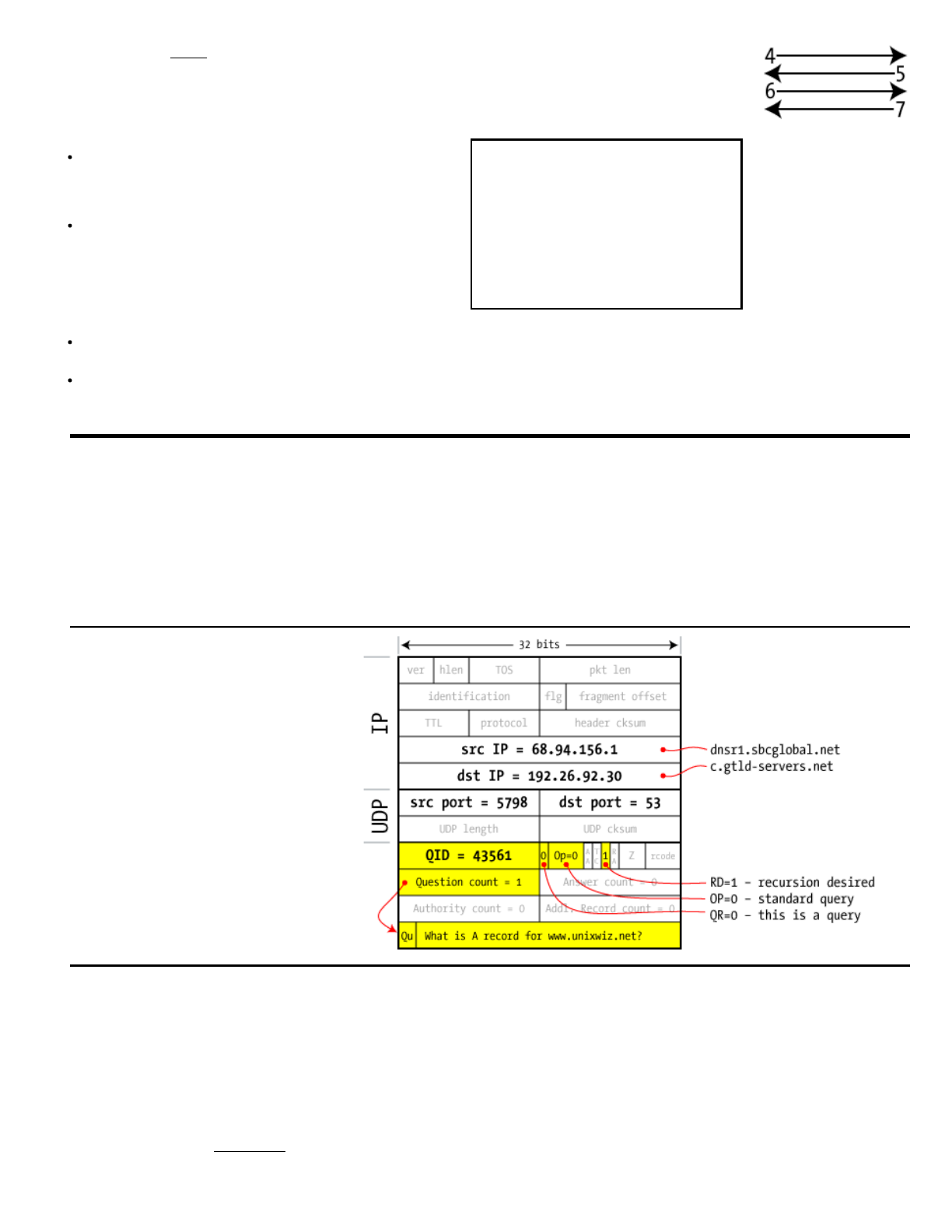
Drillingdowntoarealquery
Recallingourqueryexchangeabove,we'regoingtostudysteps4through7insomedetail:theyaremostrepresentativeofthe
DNSnameresolutionprocesswithoutaddingduplicativesteps.
Ultimately,DNSisakindofdistributeddatabase,anditcanlookupmuchmorethanjustanIPaddress:therearemultiple
resourcerecordtypesinvolvedinaquery,andonecan'tunderstandthepacketstructurewithoutknowingtheirdistinctions.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 7/14
ContrivedData!
Inthisexamplewe'reshowinga
hypotheticalpackettraceforourownISP's
recursivenameserver,butthisisamade
upexample.
Wecertainlyhavenowaytoactuallysniff
therealtrafficcomingandgoingfrom
theirserver,butwe'llnotethatasofthis
writing,AT&Thadpatchedthisserverto
avoidthisvulnerability.
We'llnotethatnoteverydetailispredictableevenwhentheprotocolisfullyunderstood:nameservers
havesomelatitudeinhowtheyaccomplisharesolution,soafewalternativesareavailable.We'rejust
choosingonecommonpaththroughthisprocess.
Inthisexample,we'reusingthenameserverofourownISP—dnsr1.sbcglobal.net—(referredtoas
dnsr1)asthelocalrecursivenameserver,andwe'llfindafewthingsincommonforallofthem.
Ineverycase,theQuestionsectionisthesame:"Whatis
theArecordforwww.unixwiz.net?".Thisquestionis
alsorepeatedintheanswer—mainlyasaconvenience—
soit'sseenincommonineverypacketwelookat.
TheISP'snameserverusuallysetstheRD=1flag
(RecursionDesired)ontheoddchancethattheotherend
iswillingtodotheheavyliftingandgofindthisanswer
forus.Mosttoplevelnameserversareunwillingtodo
this,sotheygiveusthebestinformationtheyhaveand
setRA=0flag(RecursionUnavailable)toletusknowthat
wehavetodotheworkourselves.
Inthisexample,thesourceUDPportnumberforallqueriesfromourISP'snameserveristhesame.It'sacommonpractice
fornameserversoftwaretorequestarandomportfromtheoperatingsystematstartup,thenuseitforeveryquery.
WeobservethattheQueryIDincrementsbyoneeachtimeitsendsanewquery.
Sowiththisinformationinhand,let'swalkthroughthestepsindetailandseehowour"simple"queryisactuallyresolved.
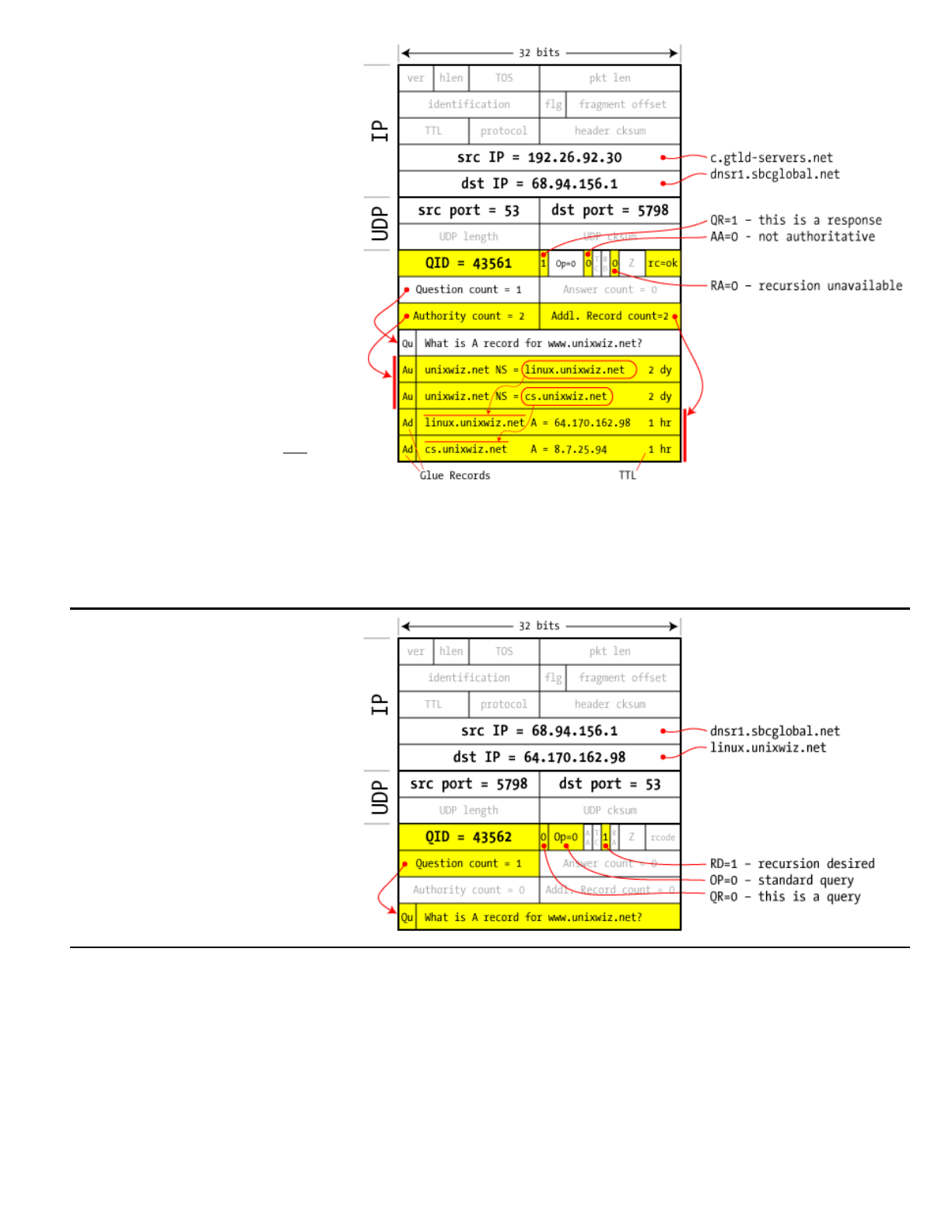
2&3 InthisstepourISP's
nameserverqueriedaroot
serverforwww.unixwiz.net,
anditrepliedwithalistof
globaltopleveldomain
serversthatknewaboutthe
.nethierarchy.Fromthis
delegation,theISP's
nameserverchoseoneat
random(c.gtldservers.net),
asshowninstep4.
(notillustrated)
4
client
to
server
Thednsr1serveratourISP
grabsoneoftheGTLD
nameserversreceivedfroma
rootserver(instep3)and
firesoffasecondquery.This
isessentiallythesameasthe
first;theQuestionisaboutthe
Arecordwww.unixwiz.net.
Becausethisisaquery—not
aresponse—the
answer/authorities/additional
recordsfieldsareblank(as
shownwithacountofzero).
TheQueryIDvaluewas
takenasthenextIDavailable
fromthisserver'sinternal
counter.
5
server
to
client
TheGTLDserverweasked
doesn'tknowthespecific
answertoourquestion,butit
knowswheretoask:it
respondswithaseriesofNS
recordsthatshouldknowhow
tohandleourrequest.They
showupintheAuthorities
sectionascs.unixwiz.netand
linux.unixwiz.net.
We'regivenhostnamesofthe
nameserversweoughtto
contact,butrealnetwork
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 8/14
connectionsareonlymadeby
IPaddress:howdowelook
theseup?Avoidingwhatwould
clearlybeachickenandegg
problem,theGTLD
nameserverprovidesnotonly
thehostnamesofthe
authoritativeservers,but
theirIPaddressestoo.
TheseareprovidedasA
recordsinthe"Additional
Records"section,andare
knownas"gluedata".
Becausethisnameservercan't
giveusthefinalanswer,it
setstheAA=0flag
(AuthoritativeAnswer)tozero,
indicatingthatsomebodyelse
knowstherealstoryandwe
havetokeepaskingaround.
Butarelatednote:dnsr1isa
verybusynameserver,having
perhapshundredsofqueries
outstandingeverysecond.
Howdoesitknowthatthis
replypacketisaresponseto
thatspecificpendingrequest?
Theansweris:bymatchingon
theQueryID.InboundDNS
packetsthatdon'thavea
waitingQueryIDareignored.
TheTTLisaTimeToLive,
discussedlater.
6
client
to
server
Instep5wereceivedtwo
nameserversthatare
purportedtoknowmoreabout
theunixwiz.netdomain,so
onemorequeryiscreatedthat
asksthesamequestion—
again!—ofthesejustlearned
nameservers.
Thisrequestisreallyno
differentfromtheprevious
queries,thoughitdoes
incrementtheQueryIDbyone
beforesendingitoff.Theidea
isthatwekeepfollowingthese
delegationsuntilweactually
getarealanswer,nota
referral.
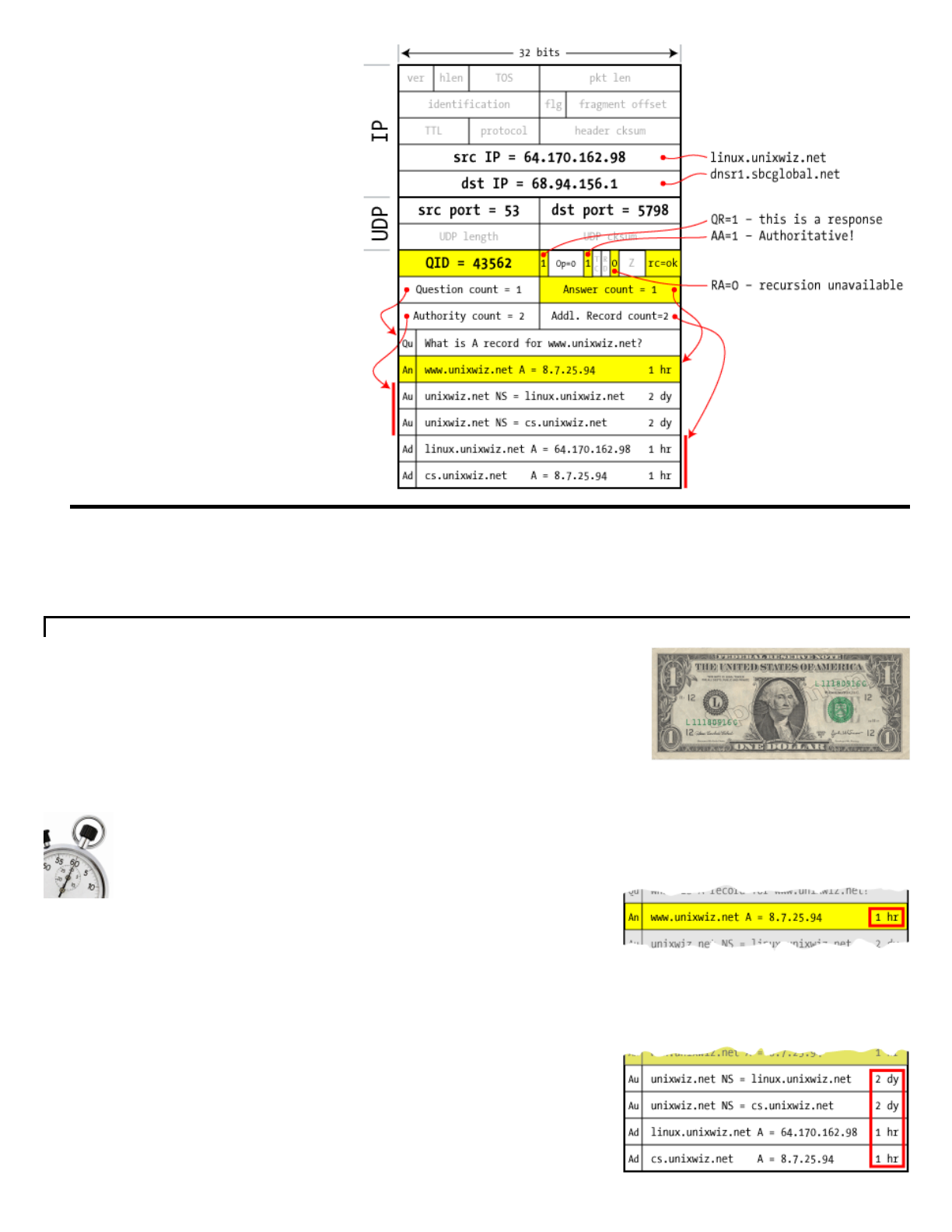
7
server
to
client
Andatlasttheanswercomes!
Unlikethepreviousreplies,
thisonehasanswer
count=1,anditcarriesanA
recordwiththeIPaddressto
satisfyourquery.
Inaddition,thisresponsehas
theAA=1flagset,which
indicatesthatit'san
authoritativeanswer(aka
"fromthehorse'smouth").If
ananswerisprovidedbutwith
AA=0,weassumeit'sfromthe
server'scache.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 9/14
Theansweralsoincludesthe
authorityandglueinformation,
butthistimeallwe'rereally
interestedinistheanswer
itself.Andthenameserver
usedtheQueryIDof43562
tomatchthisreplytothe
pendingrequest.
Asnotedpreviously,thesetransactionstypicallyoccurveryrapidlyacrosstheinternet,andtheuserisnormallyunawarethatso
muchisgoingonunderthehoodonhisbehalf.
Butlocalperformanceisfurtherenhancedbyuseofalocalcacheintherecursivenameservers:thisisanimportantpartofthe
domainnamesystem,andgetsusonestepclosertooursecurityissue.
What'sinthecache?
IntheDNSlookupswe'veseensofar,theISP'sresolvingnameserverhasgoneoutand
fullyresolvedeachnamefromscratch,relyingonnopriorknowledgeexceptthebuiltin
roothints.
Butinpracticethisfullroadtripisnotnecessary:oncewegetanauthoritativeanswerfor
agivenname,wecansaveitinalocalcachetousetosatisfyfuturequeriesdirectly.
Themoreclientsservicedbyanameserver,themorebenefitofthecache:theworkof
thefullnameresolutionsisspreadoutoverthewholeclientbase.Itmaywellrequire
quiteabitofmemoryinthenameserver,buttheamountsofRAMrequiredarepeanuts
comparedwiththebenefits.
TheTimeToLive
WhenaDNSanswerisstoredinthelocalcache,itcan'tkeepitforever:thiscouldleadtoterriblystaledatathat
effectivelybreaksthedomainsinvolved.
Fortunately,therecursivenameserverdoesn'thavetheburdenof
guessinghowlongtocachethings:theadministratorofthezone
specifiesthisinformationforeveryresourcerecord.ThisisknownasaTimeTo
Live(TTL),andit'salifetimemeasuredinseconds.
ATTLcanbeashortasafewminutes,oraslongasaweekormore:thisisentirely
determinedbytheadministratorofthezone.
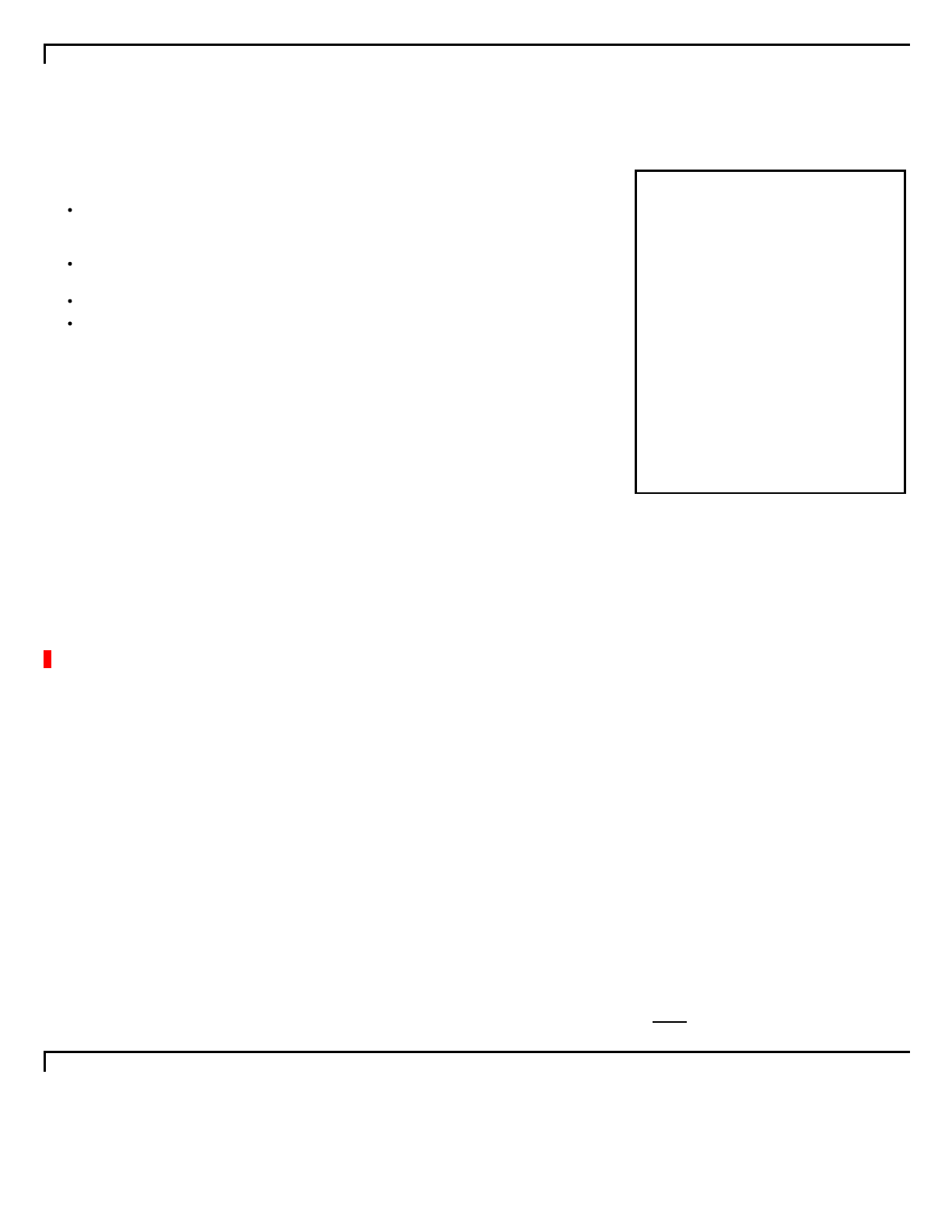
InourfinalStep7answerabove(withsnippettotheright),weseetheTTLofonehourfortheArecordinwww.unixwiz.net.All
clientrequestsforthisresourcerecordinthenexthourwillbesatisfiedimmediately,fromthecache.Butonceitexpires,it's
removedfromcacheandthenextrequestwillforceafulllookupfromscratch.
Butit'snotjusttheArecordthat'scached;alltheotherauthoritydata(theNSdata
plusassociatedglueArecords)arrivewiththeirownTTLs,andarealsocached.This
meansthatafulllookupforasingleresourcerecordcouldwellfillthecachewitha
halfdozenassociatedrecordsormore.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 10/14
Thisisnot"phishing"
ThoughDNScachepoisoninghassimilar
endresultstophishing—gettingauserto
believeabadsiteisgenuine—it'snotthe
samething.
Withphishing,abogusURLisusedto
referencethemaliciousserver,butit's
disguisedtolookliketherealhostname
(usuallywithabitofcleverHTMLorCSS).
Anattentiveusercanusuallydetectthis
misdirectionbyexaminingtheURLsor
hostnamescarefully.
WithDNScachepoisoning,thevery
natureofDNSitselfhasbeensubverted
suchthathostnametoIPlookupscanno
longerbetrusted.Thehostnamesbeing
visitedaregenuine,butthey'rebeing
routedtothebadserver:thiscan'tbe
detectedbyinspectionoflinksorHTML
sourcecode.
Poisoningthecache
WithagoodunderstandingofaproperlyfunctioningDNS,it'stimetoseewherethingsbreak.Cachepoisoningiswherethebad
guymanagestoinjectbogusdataintoarecursivenameserver'scache,causingittogiveoutthatbadinformationtounsuspecting
localclients.
It'snotsosimpleasjustsendingrandomDNSpacketstoanameserver,asDNSonlyacceptsresponsestopendingqueries;
unexpectedresponsesaresimplyignored.
Howdoesanameserverknowthatanyresponsepacketis"expected"?
TheresponsearrivesonthesameUDPportwesentitfrom:otherwisethe
networkstackwouldnotdeliverittothewaitingnameserverprocess(it'sdropped
instead).
TheQuestionsection(whichisduplicatedinthereply)matchestheQuestionin
thependingquery.
TheQueryIDmatchesthependingquery
TheAuthorityandAdditionalsectionsrepresentnamesthatarewithinthesame
domainasthequestion:thisisknownas"bailiwickchecking".
Thispreventsns.unixwiz.netfromreplyingwithnotonlytheIPaddressof
www.unixwiz.net,butalsofraudulentinformationabout(say)
BankOfSteve.com.
Ifalloftheseconditionsaresatisfied,anameserverwillacceptapacketasagenuine
responsetoaquery,andusetheresultsfoundinside.Thisincludescachinganswers,as
wellasvalidauthorityandadditionaldatafoundtheretoo.
ButifthebadguycanpredictandforgeaDNSresponsepacketthat'sjustright,hecan
causeallkindsofshenanigansforthevictims.
Thebadguynormallyfirstchooseshisvictimbyfindinganameserverhebelievesvulnerabletopoisoning:alloftheclientsof
thatDNSservergettounwittinglyridethevictimtrainaswell.
Thenhefindsatargetdomain,onehewishestotakeover.Hisintentistofoolthevictimsintovisitinghisownmaliciouswebsite
insteadoftherealdeal:bygettingwww.goodsite.comtoresolvetothebadguy'sIPaddress,theuser'strafficvisitsthebad
guy'swebsiteinsteadofthegoodone.
Wenotedthatunexpectedpacketsweresimplydropped,soabadguyneednotgeteverythingrighteverytime:sendingmany
packetsattemptingtoguesssomeofthekeyparametersislikelytoprovefruitfulwithenoughattempts.
GuessingtheQueryID
Inoldnameservers(andinourdetailedpackettraceexample),theQueryIDsimplyincrementsbyoneoneachoutgoingrequest,
andthismakesiteasytoguesswhatthenextonewillbeaslongasaninterlopercanseeasinglequery.
Weprobablycan'tdirectlyaskthenameserverforitsqueryID,butwecanprovokeitintotellingus:
1.Badguyasksthevictimnameservertolookupanameinazoneforanameserverhecontrols(perhapstest.badguy.com).
Hemightquerytheserverdirectly,ifitpermitsrecursionfromhislocation,orhemightconvinceausertolookupaname—
perhapsbyincludingthetesthostnameonawebpage.
2.Victimnameserverreceivestherequestandmakestheusualroundstoresolvethenamestartingattherootservers.Here,
we'veputtherootandGTLDserversinthesamecategorytoseparatethemfromthebadguy'snameserver.
3.Eventually,thevictimnameserverwillbedirectedtothebadguy'snameserver:afterall,it'sauthoritativeforbadguy.com.
4.Badguymonitorsthislookupoftest.badguy.combysniffingtheIPtrafficgoingtohisownmachine,orperhapsevenwith
acustommodificationtothenameserversoftware,andfromthisdiscoversthesourceportandQueryIDused.
Aha!
AtthispointheknowsthelastqueryIDandsourceportusedbythevictimnameserver.
Butthethoughtfulmightwonder:sowhat?Thishasn'tpoisonedanythingyet,andthere'snoneedtoengageinDNSshenanigans
forbadguy.comanyway.Afterall,thebadguyisalreadyauthoritativeforhisownzone.
Trueenough,butthiswasonlythefirststep:thenextoneengagesinDNSshenanigansforotherdomains.
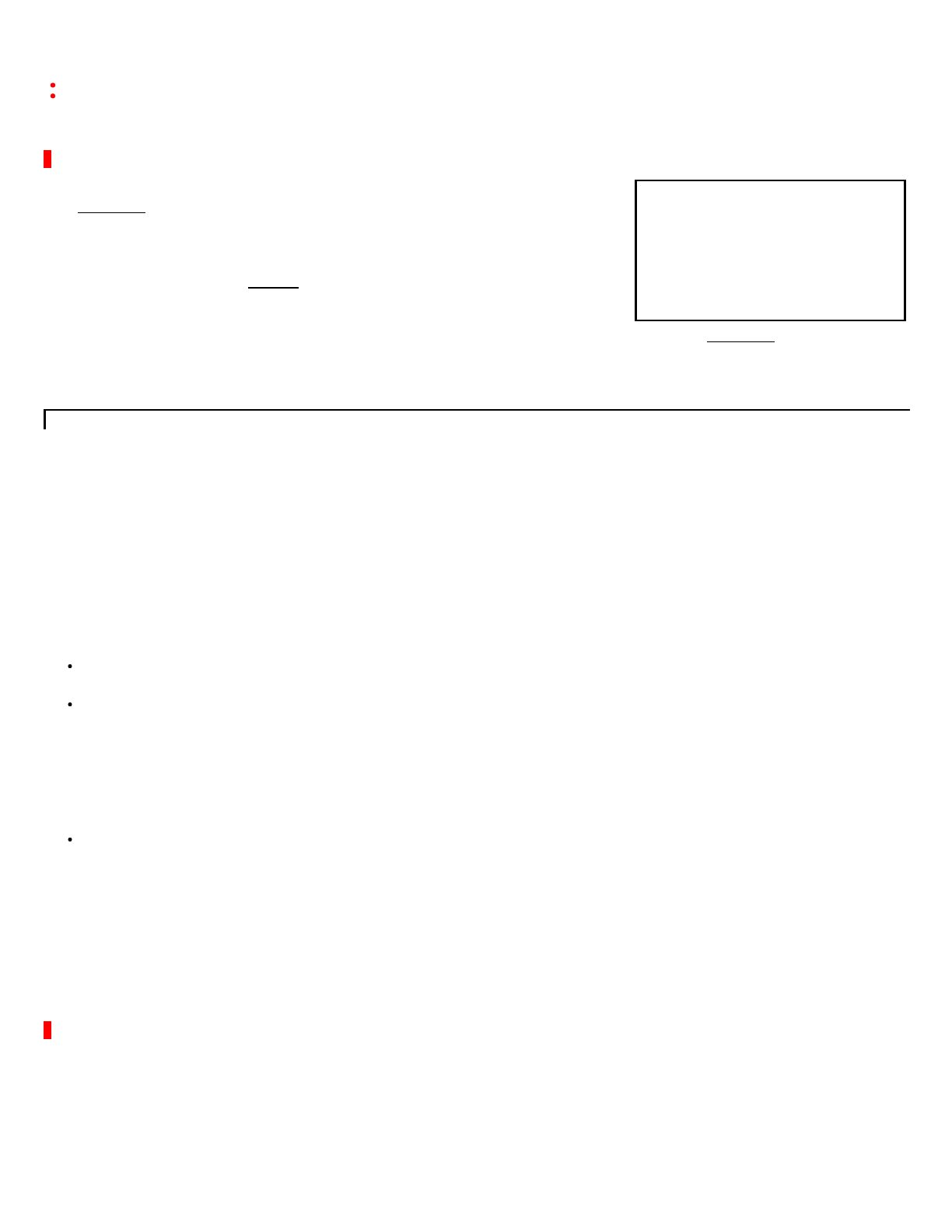
Shenanigans,Version1
WiththeabilitytoeasilypredictaqueryID,andsinceourvictimnameserveralwayssendsqueriesfromthesameUDPport,it
shouldbeeasyenoughtocausesometrouble.
Inthisillustration,we'llattempttopoisonaparticularnameserverwithafraudulentIPforalegitimatebankingwebsite,
www.BankOfSteve.com.Thebadguy'sintentionistogetalloftheISP'scustomerstovisithisownmalicioussiteinsteadofthe
realoneoperatedbytheBank.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 11/14
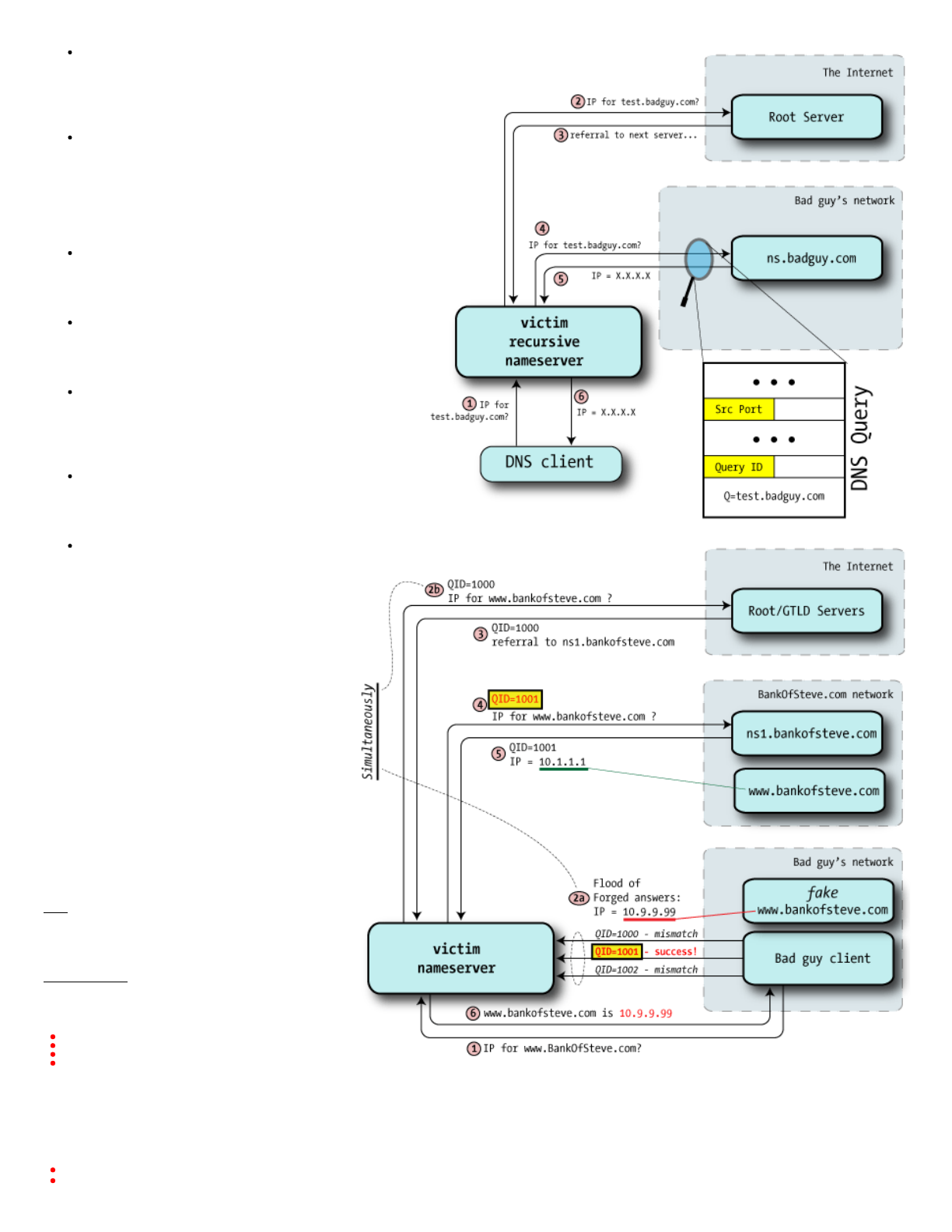
Step1—BadguysendsaDNSquerytothe
victimnameserverforthehostnameitwishesto
hijack.Thisexampleassumesthatthevictim
nameserverallowsrecursivequeriesfromthe
outsideworld.
Step2a—Knowingthatthevictimwillshortly
beaskingns1.bankofsteve.com(asdirected
fromtheroot/GTLDservers)foranIPaddress,
thebadguystartsfloodingthevictimwith
forgedDNSreplypackets.Allpurporttobefrom
ns1.bankofsteve.com,butincludetheanswer
withtheIPofbadguy'sfraudulentwebserver.
Steps2b&3—Root/GTLDserversprovide
referraltons1.bankofsteve.com.Thismaybe
multiplequeries,butwe'reshowingjustonefor
simplicity.
Step4—victimnameserverasks
ns1.bankofsteve.comfortheIPaddressof
www.bankofsteve.com,anditusesqueryID
1001(onehigherthanthepreviousquery).
Step5—therealnameserverprovidesa
legitimateresponsetothisquery,with
QID=1001.Butifthebadguyhassuccessfully
matchedthequeryIDinthestep2aflood,this
legalreplyarrivestoolateandisignored.Oops.
Step6—WiththebogusIPaddress(ofthebad
guy'swebserver)incacheitprovidesthis
poisonedanswertotherequestingDNSclient.
Boom.
Step7(notillustrated)—futureDNS
clientsaskingfor
www.bankofsteve.comwillreceive
thesamefraudulentanswer.
Theruleis:firstgoodanswerwins.Mostof
theforgedanswersaredroppedbecausethe
QueryIDdoesn'tmatch,butifjustonein
theflurryoffakeresponsesgetsitright,the
nameserverwillaccepttheansweras
genuine.
Andbecausethatsatisfiestherequest,the
realanswerthatarriveslaterisdropped,
becausethequeryisnolongerpending.
Inanycase,oncethebadguygetsthe
answerfromthevictim'snameserver,the
matterisclosed,andhecanstopflooding
thevictim.
We'llnotethateventhoughthisillustrates
tryingtobeatjustthereplyfrom
ns1.bankofsteve.com,ourforgedDNS
trafficcouldactuallymatchthequeryIDof
anyofthepriorsteps.
Thisincludesmatchinganearlierreplyfrom
therootserverortheGTLD(.com)server:
ifthequeryIDmatches,ourfake
authoritativewins,andpollutesthecache.
Thisisarace,butonlytheattackerknows
it'splaying.
Thenamecan'talreadybeinthe
cache
Ifwww.bankofsteve.comisalready
inthevictimnameserver'scache,alloftheexternalqueriesareavoided,andthere'ssimplynowaytopoisonitinthis
manner.
Ifthebadguystillwantstopoisonthatparticularhostname,hehastowaitforittoexpirefromcache(asdeterminedbythe
TTL).
ThebadguyhastoguessthequeryID
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 12/14
Isitrandom?
Oldernameserversusedaterriblerandom
numberalgorithmthatallowedabadguy
topredictthenextQueryIDgivenan
existingone,andthiswasusedby
attackerstocommitcachepoisoning.
Modernsoftwareusesrealrandomnumber
algorithmsthatdon'tfallforthis.
Thisismadeeasywith(nowobsolete)nameserversthatincrementtheQueryIDbyoneeachtime—evenabusy
nameserverhasafairlysmallrangetoguessfrom.
Thebadguyhastobefasterthantherealnameserver
Ifthevictimnameserverandtherealnameserveraretopologicallyclose(networkwise),thenthesteps2/3and4/5may
completesoquicklythatthebadguyhasatoosmallwindowtoexploit.
Mitigations
AnobviousmitigationhereistorandomizetheQueryID.
WithsequentialQueryIDs,thebadguyhasafairlylimitedrangeofguessesrequired
onceheobservesasinglecurrentQueryID.IfheseesQID=999,thenhemayfloodwith
QIDs10001029inanattempttomakeatleastonematch.
Experiencehasshownthisisaneasywindowtobeat.
ButifthenameserverchoosesrandomQueryIDs,thentheattackerhasthefull16bit
pooltochoosefrom—that's64kvalues—andthisisamuchhardertargettohitinthe
narrowwindowoftimewhilethevictimisgoingthroughtheroutineresolutionsteps.
Thoughforging20packetsinroutinenameresolutiontimeisstraightforwardenough,doingsowiththousandsofpacketsisa
muchmoresubstantialchallenge.
SotruerandomizationofQueryIDsraisesthebarquiteabit.
Dan'sShenanigans
Sofarwe'veseenhowtopoisonasinglerecord,butthishaslessimpactthanexpected:it'sjustonerecord,andmanyproperties
requiremultiplehostnamestooperate,andit'shardertohackthemall.
DanKaminskyfoundanapproachthat'sdramaticallymoreeffectivethanthis,anditcausedquiteafurorinthesecurity
community.Thegeneralapproachisthesameasthesimpleapproachshownabove,butthekeydifferenceisthenatureofthe
forgedpayload.
Inthesimpleexample,ourintentionwastopoisonthefinalanswer,theArecordwiththeIPaddress,butwhatDandiscoveredis
thatwecangouponelevelandhijacktheauthorityrecordsinstead.
Beforeundertakingtheattack,thebadguyconfiguresanameserverthat'sauthoritativeforthebankofsteve.comzone,including
whateverresourcerecordshelikes:Arecords,MXforemail,etc.
There'snothingstoppinganybodyfromconfiguringhisownnameservertobeauthoritativeforanydomain,butit'spointless
becausetherootserverswon'tpointtoit:it'sgotanswers,butnobodyeverasksitaquestion.
Step1—badguyclientrequestsarandomnamewithinthetargetdomain(www12345678.bankofsteve.com),
somethingunlikelytobeincacheevenifotherlookupsforthisdomainhavebeendonerecently.
Step2a—Asbefore,thebadguysendsastreamofforgedpacketstothevictim,butinsteadofArecordsaspartofan
Answer,itinsteaddelegatestoanothernameserverviaAuthorityrecords."Idon'tknowtheanswer,butyoucanaskover
there".
Theauthoritydatamaywellcontainthe"real"bankofsteve.comnameserverhostnames,butthegluepointsthose
nameserversatbadguyIPs.Thisisthecrucialpoisoning,becauseaQueryIDmatchmeansthatthevictimbelievesthat
badguy'snameserversareauthoritativeforbankofsteve.com.
Thebadguynowownstheentirezone.
Curiously,therestofthestepsdon'tmatter:thepointofthisprocesswastofakeoutthevictimintothinkingthatbadguy
runsthedomaininquestion,andthatwouldhavebeensuccessfulinthisstep.
Onceoneofthevictim'squerieshasbeenpoisoned—itcouldbeanyinthechain—alltherestaredirectedtobadguy's
servers.
Thisisadevastatingattack:byowningtheentiretargetdomain,thebadguycontrolsessentiallyeverythingwithrespecttothat
resolvingnameserver.Hecanredirectwebvisitorstohisownservers(imagineredirectinggoogle.com),hecanrouteemailtohis
ownserversviaservingupbogusMXrecords.
ThebadguywilltypicallysetaveryhighTTLinthepoisoningresponsessothatthevictimwillkeepthebogusdataincacheas
longaspossible.
Flurryofqueries
Ourexamplehasshownasinglequerybeinghijacked,butthisisunlikelytobesuccessful:becauseofQueryIDrandomization,it's
notlikelythatthatthebadguywillmanagetogetahitintheshorttimerequiredtomatchon64kIDs.
Instead,thebadguyissuesaflurryofqueries,eachforadifferentrandomnameunderthemaindomain.Thefirstrequestcaused
thenameservertoperformtheusualrootfirstresolution,butiteventuallycachesthevalidns1.bankofsteve.comvalues.
Subsequentquerieswithinthisdomaingodirectlytothatnameserver,skippingtherootsteps.
Butthenextrequestforadifferentrandomname(whichcertainlywon'tbeincache)causesanimmediatequerytothevalidns1
server.Thebadguythenthrowsafloodofforgeddataatthevictimaboutthatsecondrandomname,thoughtheoddshereare
stillprettylong.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 13/14
DJBWasRight
Onenameserverisnotableforhaving
gottenboththequeryidandsourceport
randomnessrightfromthestart:DJBDNS
bythelegendaryDanielJ.Bernstein.
Thoughlongalightningrodfor
controversy,he'sclearlywalkedthewalk
onsecurity:there'sbeenjustoneminor
securityvulnerabilityinDJBDNS.
Justforthesakeofdiscussion,let'sassume
thatthebadguycangenerate50forged
repliesforeachrandomnamequerybefore
therealreplyarrivesfromthereal
nameserver.Thisappearstobeaverysmall
chance,butwhenrepeatedoverandover—
andrunfromautomatedtools—successby
thebadguyislikely.
It'sbeenreportedthatsuccesscan
commonlybeachievedin10seconds.
Goingforthetop
Ourexampleshaveallfocusedonhijacking
anenddomain,butthesametechniques
candothesamethingupalevel:taking
over.COM,.NET,orthelike.
BypoisoningtheAuthorityrecordsfor.COM
andthelike,thevictimnameserverwill
routeallDNSlookupstothebadguy's
nameservers.Thiseffectivelyhijacksall
namesunderthattoplevel,including
domainshedidn'tactuallyrequest.This
givesagreatdealofflexibilityeventhough
itmaywellrequiresubstantialcomputing
andnetworkresourcestoservethefloodof
requeststhatthishijackingmustgenerate.
What'sthefix?
Thisallsoundsawful:howdoesonefixthis?
Ashasbeenalludedtoseveraltimes,it's
thesmallspace—just16bits—ofthe
QueryIDthatmakesthisattackpossible.
Thoughcertainlyonemightwishtoincrease
thatIDtosomethinglarger(perhaps32
bits),it'ssimplynotpossibledothatinthe
shorttermbecauseitwouldbreakDNSon
theinternet:thefieldsarewhattheyare,
andtheycan'tbechangedcasually.
Butanadditionalsourceofrandomnessisrequirednevertheless,andthat'sbeendonebyrandomizingthesourceport.Rather
thanusejustasingleUDPport,whichistrivialtodiscover,amuchlargerrangeofportsisallocatedbythenameserverandthen
usedrandomlywhenmakingoutboundqueries.
Asonewouldimagine,thenameserverwouldkeeptrackofwhichsourceportwasusedforeachquery:repliesarrivingonthe
wrongportwouldbediscardedjustasiftheQueryIDfailedtomatch.
Microsoft'supdatedDNSserverissaidtopreallocate2,500UDPportstousefortheserandomqueries,andfordiscussionwe'll
roundthisdowntoanevenpoweroftwo:211=2,048.Thisyieldsthismuchlargertransactionspace:
Increasingthesearchspacefrom64kto134Mprovidesfarbetteroddsforthegoodguys.
Wepresumethateachnameserverprovidesawayofsettinghowlargeofapooltouseforthesesourceports,aswellasawayof
excludingcertainportnumbersknowntoberequiredforotherpurposes.
9/14/2017 An Illustrated Guide to the Kaminsky DNS Vulnerability
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html 14/14
Home StephenJ.Friedl SoftwareConsultant OrangeCounty,CAUSA
Summary
ThishasbeenanexceptionallyseriousvulnerabilitybecauseitunderminestheveryfaithinDNS:thisisatthecoreoftheinternet.
Mostexpertsbelievethatifyoucan'ttrustDNS,allelseislost,andwe'reofthissamemind.
Thereisfarmoredetailaboutthisvulnerabilitythanwecanpresenthere,andwe'llurgethereadertoconsultotherresources
(especiallyDan'spresentation).
Butwecanincludeafew(ahem)randomnotesaboutthismatterthatdidn'tseemtofitinelsewhere,andseemimportantand/or
interestingenoughtoincludeinthispaper.
Patchyourservers:Toolsexisttomakeexploitinaboxavailabletoevenlowskilledbadguys.
Authoritativeonlynameserversarenotvulnerablebecausetheyhavenocachetopoison,butwe'dbesurprisedifnosmall
numberof"authonly"nameserversactuallyprovidedrecursiveservicetoatleastsomeclients.
AnameserverneednotbedirectlyvisibletotheInternettobeexploitable.Byconvincingausertovisitaparticularweb
page,itcantriggerachainofeventsthatreliablyleadtopoisoning.
EvenpatchedserversmaystillbevulnerableifaninterveningfirewallperformsPortAddressTranslationinawaythatun
randomizesthesourceports.
It'sbeensuggestedthatDNSSECorIPv6aresolutionstothisproblem,butthisisonlyintheory.Bothofthesetechnologies
havetobefullyrolledouttobeeffective,andthisislikelyyearsaway,atbest.
TheSecureSocketsLayer(SSL)isonlyapartialprotectionagainstbeingredirectedtomaliciouswebsites.Puttingupafake
BankOfSteve.comwebsitewillhavethewrongSSLcertificatename(whichisawarningtotheuserwho'spayingattention),
butthegreatmajorityofusersskiprightthroughthosewarnings.
ButthebadguycansubvertevenSSL:sincemanyCertificateAuthoritiesvalidateauser'scontroloveradomainbysending
email,hijackingamailserverbyattackingthecertvendor'sresolvingDNS,thismaywellmeanthatanattackercanobtaina
fullyvalidcertificateforthetargetdomain.
Thisisveryscary.
References
DanKaminsky'sBlackHatpresentation(PowerPoint)—Excellentreading.
DNSandBIND,O'Reilly—ThedefinitivebookonDNS.
TCP/IPIllustrated,Volume1:TheProtocols,W.RichardStevens—thedefinitivebookonTCP/IP.
BIND(BerkeleyInternetNameDomain)—Themostpopularnameserver,withalonghistoryofsecurityissues.
DJBDNSnameserver—Alwaysanattitude,butneverasecurityvulnerability.
MindOfRootpodcast#63—interviewedregardingtheDNSvulnerability
DNSCachePoisoningatWikipedia
AdobeIllustratorCS3™—theexcellentsoftwareusedtomaketheallthediagramsinthispaper.
Yes,thistookalongtimetowrite.
Firstpublished:2008/08/07