TAF_Ver_1_Ref_Man_60459500C_Mar85 TAF Ver 1 Ref Man 60459500C Mar85
User Manual: Pdf TAF_Ver_1_Ref_Man_60459500C_Mar85
Open the PDF directly: View PDF ![]() .
.
Page Count: 226 [warning: Documents this large are best viewed by clicking the View PDF Link!]
60459500
CONTRPL DATA
TAF
VERSION 1
REFERENCE MANUAL
J0&K
CDC® OPERATING SYSTEM:
NOS 2
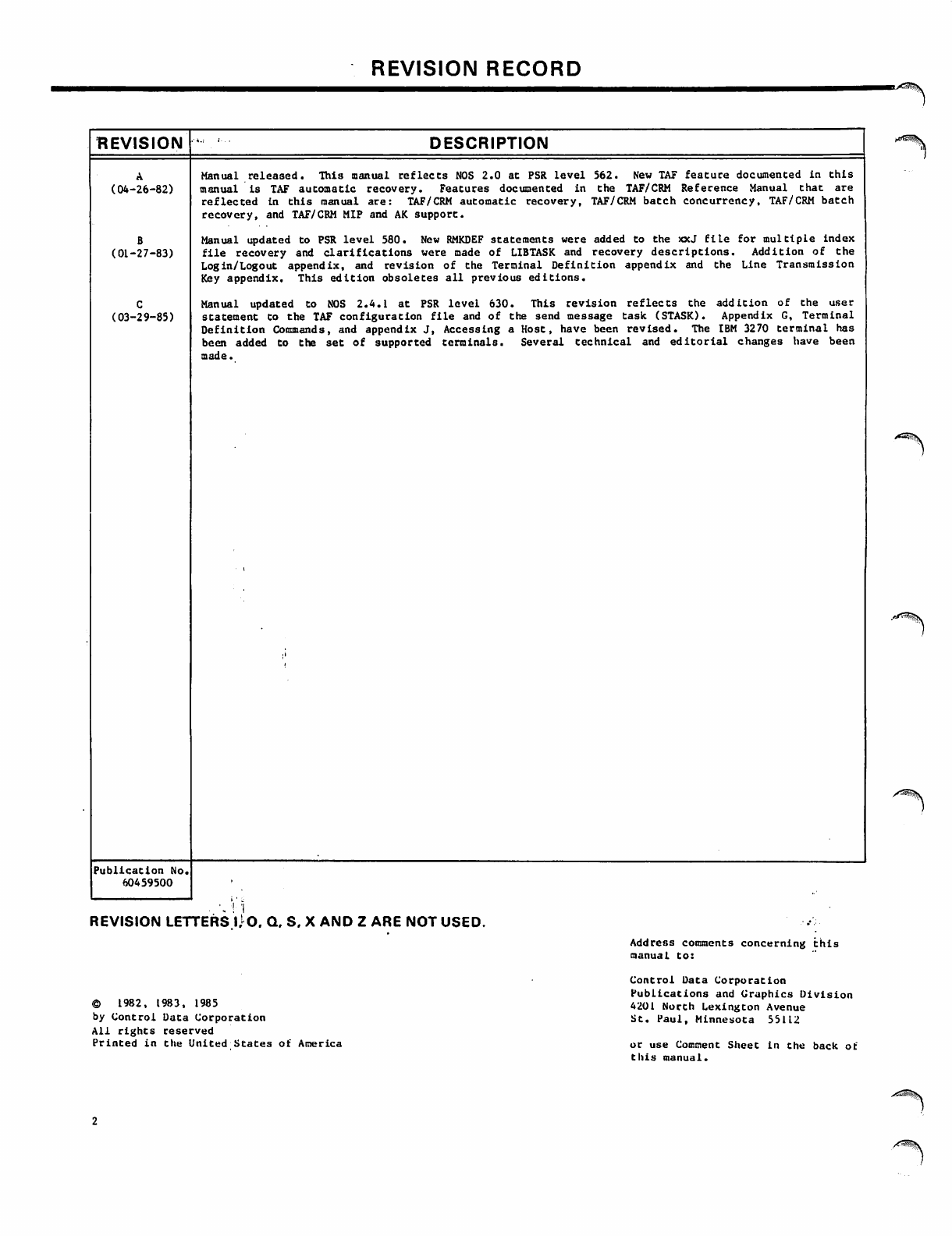
REVISION RECORD
b / ^ w
REVISION
(04-26-82)
B
(01-27-83)
(03-29-85)
Publication No.
60459500
DESCRIPTION
Manual released. This manual reflects NOS 2.0 at PSR level 562. New TAF feature documented in this
manual is TAF automatic recovery. Features documented in the TAF/CRM Reference Manual that are
reflected in this manual are: TAF/CRM automatic recovery, TAF/CRM batch concurrency, TAF/CRM batch
recovery, and TAF/CRM MIP and AK support.
Manual updated to PSR level 580. New RMKDEF statements were added to the xxJ file for multiple index
file recovery and clarifications were made of LIBTASK and recovery descriptions. Addition of the
Login/Logout appendix, and revision of the Terminal Definition appendix and the Line Transmission
Key appendix. This edition obsoletes all previous editions.
Manual updated to NOS 2.4.1 at PSR level 630. This revision reflects the addition of the user
statement to the TAF configuration file and of the send message task (STASK). Appendix G, Terminal
Definition Commands, and appendix J, Accessing a Host, have been revised. The IBM 3270 terminal has
been added to the set of supported terminals. Several technical and editorial changes have been
made.
REVISION LETTERS 1, O. Q, S. X AND Z ARE NOT USED.
Address comments concerning this
manual to:
© 1982, 1983, 1985
by Control Data Corporation
All rights reserved
Printed in che United States of America
Control Data Corporation
Publications and Graphics Division
4201 North Lexington Avenue
St. Paul, Minnesota 55112
or use Comment Sheet in che back of
this manual.
LIST OF EFFECTIVE PAGES
New features, as well as changes, deletions, and additions to information in this manual, are indicated by bars in the margins or by a dot
near the page number if the entire page is affected. A bar by the page number indicates pagination rather than content has changed.
PAGE REV
Front Cover
Inside Front
Cover
Title Page
2
3/4
5
6
7
8
9
10
1-1
1-2
1-3
1-4
1-5
2-1
2-2
2-3
2-4
2-5
2-6
2-7
2-8
2-9
2-10
2-11
2-12
2-13
2-14
2-15
2-16
2-17
2-18
2-19
2-20
2-21
2-22
2-23
2-24
2-25
2-26
2-27
2-28
2-29
2-30
2-30.1/2-30.2
2-31
2-32
2-33
2-34
2-35
2-36
2-37
2-38
2-39
2-40
2-41
PAGE REV
2-42
3-1
4-1
4-2
4-3
4-4
4-4.1/4-4.2
4-5
4-6
4-7
4-8
4-9
5-1
5-2
5-3
5-4
6-1
6-2
6-3
6-4
6-5
7-1
7-2
7-3
7-4
7-5
8-1
8-2
8-3
8-4
8-5
8-6
9-1
9-2
10-1
10-2
10-3
10-4
10-5
10-6
10-7
10-8
11-1
11-2
12-1
12-2
12-3
12-4
12-5
A-l
A-2
B-l
B-2
B-3
B-4
B-5
B-6
B-7
B-8
PAGE REV
B-9
B-10
B-ll
B-12
B-l 3
B-14
B-l 5
B-16
B-l 7
B-18
B-l 9
B-20
B-21
B-22
B-23
B-24
B-25
B-26
B-2 7
C-l
C-2
C-3
C-4
C-5
C-6
C-7
C-8
C-9
C-10
C-ll
C-l 2
D-l
E-l
E-2
F - l
F-2
F-3
F-4
F-5
G-l
G-2
G-3
G-4
G-5
G-6
G-7
G-8
G-9
G-10
G-ll
G-l 2
G-13
G-14
G-15
G-l 6
G-l 7
H-l
H-2
1-1
PAGE REV
J-l
J-2
J-3
J-4
J-5
J-6
J-7
J-8
J-9
J-10
J-ll
J-12
J-l 3
J-14
J-l 5
J-16
J-l 7
J-18
J-l 9
J-20
Index-1
Index-2
Index-3
Index-4
Comment
Sheet
Back Cover
...-;.
'1
PAGE REV
60459500 C 3/4
/^^%

J ^ * PREFACE
The CONTROL DATA® Transaction Facility (TAF),
Version 1.3, is a network host product. It is a
network application that requires the facilities of
the Network Access Method (NAM) and the 255x Series
Communications Control Program (CCP). TAF runs as a
subsystem of the Network Operating System (NOS),
Version 2, and may be used with COMPASS, FORTRAN, or
COBOL.
This manual documents the executive portion of TAF.
The three data managers available for use with TAF
are each documented in their respective reference
manuals. These are:
• CDC® CYBER Database Control System, Version
2 (CDCS)
• CDC TAF/CRM Data Manager Version 1 (CRM)
• CDC TOTAL Data Manager Version 2
Refer to the list of related publications for full
titles and publication numbers of the respective
manuals.
AUDIENCE
This manual is for the data administrator and
applications programmer. The data administrator
(DA) is a person or a group of people responsible
for installing and maintaining the transaction
subsystem. This person or group sets up the data
base and describes the relationships among the
various elements. The DA is concerned with the
internal design of the system and can modify many of
the system components to suit site requirements. An
applications programmer is a person who writes tasks
in FORTRAN, COBOL, or COMPASS to be used by the end
user (terminal operator). Using these tasks, the
terminal operator can access and update the data
base with little or no knowledge of TAF. New users
of TAF should consult the TAF I User's Guide as a
first source of information. It is an introductory
text for inexperienced users.
The user must be familiar with basic NOS operations
such as running a compilation job. The NOS 2
Reference Set, Volume 2, acquaints the new user with
the fundamentals of NOS. The NOS 2 Reference Set,
Volume 3, is for the high-level language applications
programmer who is already familiar with NOS. The
NOS 2 Reference Set, Volume 4, is for the COMPASS
applications programmer.
TERMINOLOGY AND CONVENTIONS
References in this manual to the transaction
subsystem imply every aspect of TAF. References to
the transaction executive imply the controlling
portion of TAF, the portion described in this
manual. References to FORTRAN imply either FORTRAN
Extended Version 4 or FORTRAN Version 5; TS mode is
not allowed (that is, the SEQ, TS, and OPT-O
parameters are not allowed on the FTN command).
References to COBOL imply Version 5.
Where brackets, [ ], are used in task request format
descriptions, they indicate optional parameters.
The term alphanumeric refers to any combination of
the letters A through Z and the numbers zero through
nine; special characters are not included.
Conventions for word formats are as follows:
• Crosshatching indicates a field is not used
by or is not applicable to TAF.
• Reserved fields may contain information
useful to TAF internal processing. The user
should not expect them to contain any partic
ular values.
• Fields labeled with mnemonics indicate that
a specific parameter must be inserted (gener
ally described after the word format).
• Fields with numeric identifiers indicate the
actual value that is used or returned for a
particular request.
Models 815, 825, 835, 845, and 855 of the CYBER 170
Computer Systems share many of the functional and
architectural attributes of the CYBER 180 computer
systems (models 810, 830, 835, 840, 845, 850, 855,
and 860). The term CYBER 180-class machines de
scribes these similar models collectively.
Extended memory for model 176 is large central
memory extended (LCME). Extended memory for models
865, 875 and CYBER 180-class machines is unified
extended memory (UEM). Extended memory for models
865 and 875 may also include either extended core
storage (ECS) or extended semiconductor memory
(ESM). Extended memory for all other NOS computer
systems is either ECS or ESM. ECS and ESM are the
only forms of extended memory that can be shared in
a linked shared device multimainframe complex and
can be accessed by a distributed data path (DDP).
In this manual, extended memory refers to all forms
of extended memory unless otherwise noted.
Programming information for the various forms of
extended memory can be found in the COMPASS 3
Reference Manual and in the appropriate computer
system hardware reference manual.
60459500 C
RELATED PUBLICATIONS
The following manuals contain additional information
for the user.
Publication
Control Data Publication Number
COBOL Version 5 Reference Manual 60497100
Common Memory Manager Version 1
Reference Manual 60499200
COMPASS Version 3 Reference
Manual 60492600
CYBER Database Control System
Version 2 Data Administration
Reference Manual 60485200
CYBER Database Control System
Version 2 Application Program
ming Reference Manual 60485300
CYBER Loader Version 1
Reference Manual 60429800
FORTRAN Extended Version 4
Reference Manual 60497800
FORTRAN Version 5 Reference
Manual 60481300
Network Products Network Access
Method Version I Network Defini
tion Language Reference Manual 60480000
Network Products
Network Access Method Version 1/
Communications Control Program
Version 3 Host Applicaton
Programming Reference Manual 60499500
NOS Version 2 Network Terminal
User's Instant 60459380
NOS Version 2 Installation
Handbook 60459320
NOS Version 2 Manual Abstracts 60485500
NOS Version 2 Operations
Handbook 60459310
CYBER Record Manager Advanced
Access Methods Version 2
Reference Manual 60499300
CYBER Record Manager Basic
Access Methods Version 1.5
Reference Manual 60495700
Network Products
Network Access Methods Version 1/
Communications Control Program
Version 3 Terminal Interfaces
Reference Manual 60480600
NOS Version 2 Reference Set,
Volume 1, Introduction to
Interactive Usage 60459660
Publication
Control Data Publication Number
NOS Version 2 Reference Set,
Volume 2, Guide to Systeo Usage 60459670
NOS Version 2 Reference Set,
Volume 3, System Commands 60459680
NOS Version 2 Reference Set,
Volume 4, Program Interface 60459690
NOS Version 2 Administration
Handbook 60459840
NOS Version 2 Analysis Handbook 60459300
TAF Version 1 User's Guide 60459520
TAF/CRM Data Manager
Version 1 Reference Manual 60459510
TOTAL - CDC Version 2
Reference Manual 76070300
The NOS 2 Manual Abstracts is a pocket-sized manual
containing brief descriptions of the contents and
intended audience of all NOS and NOS product manuals.
T h e a b s t r a c t s c a n b e u s e f u l i n d e t e r m i n i n g t h e
manuals of greatest interest to a particular user.
Control Data also publishes a Software Publications
Release History, publication number 60481000, of all
software manuals and revisions packets it has issued.
This history lists the revision level of a particular
manual that corresponds to the level of software
installed at the site.
These manuals are available through Control Data
sales offices or Control Data Literature Distribution
Services (308 North Dale, St. Paul, Minnesota 55103).
SUBMITTING COMMENTS
The last page of this manual is a comment sheet.
Please use it to give your opinion on the manual's
usablility, to suggest specific improvements, and to
report any errors. If the comment sheet has already
been used, you can mail you comments to:
Control Data Corporation
Publications and Graphics Division ARH219
4201 Lexington Avenue North
St. Paul, MN 55112
Additionally, 'if you have access to SOLVER, an
online facility for reporting problems, you can use
it to submit comments about the manual. Declare
your problem type as DOC and use NS2 as the product
identifier.
DISCLAIMER
This product is intended for use only as described in
this document. Control Data cannot be responsible
for the proper functioning of undescribed features
or parameters.
/^^K
60459500 C
J^V CONTENTS
1. INTRODUCTION l-l
On-Line Transaction Processing Advantages l-l
On-Line Transaction Processing Problems l-l
Batch Interface 1-3
Network Interface 1-3
Tasks 1-4
Transaction Processing 1-4
TAF Requests 1-4
Entering the Transaction Subsystem 1-4
Implementing an Application 1-5
Subcontrol Points 1-5
Multimainframe 1-5
Extended Memory 1-5
RERUN Request
RPUT and RGET Requests
RSECURE Request
SECURE Request
TSTAT Request
System Task Recovery Requests
CALLTRN Request
SRERUN Request
TINVOKE Request
WSTAT Request
3. ACCESS AND USE OF CDCS BY TASKS
2-32
2-33
2-34
2-35
2-37
2-38
2-38
2-40
2-40
2-41
3-1
2. TASK/TRANSACTION EXECUTIVE
INTERFACE
4. SYSTEM FILES 4-1
2-1
r
Communication Block
Requests
Data Manager Requests
Journal File Requests
Memory Dump Requests
System Requests
Memory Requests (COMPASS Only)
Message Requests
Task Scheduling Requests
CALLRTN Request
CALLTSK Request
NEWTRAN Request (COMPASS Only)
TRANCHK Request
Input/Output Requests
WAITINP Request
LOADCB Request
SETCHT Request
BLDABH Request
GETABH Request
TERMDEF Request
SEND Request
RELSCB Request
TSIM Request
TARO Request
I10 Request
BWAITINP Request (COMPASS Only)
TPSTAT Request (COMPASS Only)
BEGIN Request
Task Control Requests
CEASE Request
ITL Request
LOGT Request (COMPASS Only)
KPOINT Request
WAIT Request
Task Utility Requests
LOGIN Request
EXTRACT Request
INSERT Request
Application Recovery Requests
xxJ File 4-1
2-1 CRM Data Manager xxJ File 4-1
2-3 TOTAL Data Manager xxJ File 4-4
2-3 CDCS or No Data Manager xxJ File 4-4
2-3 Creating an xxJ File 4-4.1
2-3 Journal Files 4-5
2-3 System Journal File 4-5
2-3 Data Base Journal Files 4-5
2-4 Journal File Entry Header 4-5
2-4 JOURNL Request 4-5
2-4 TAF Configuration File 4-7
2-6 DMS Statement 4-7
2-7 DISPLAY Statement 4-7
2-8 NETWORK Statement 4-8
2-8 RECOVER Statement 4-8
2-9 K. Statement 4-8
2-10 User Statement 4-8
2-11 Communication Recovery File 4-8
2-12
2-14
2-16
2-17 5. BATCH/TRANSACTION SUBSYSTEM
2-23 INTERACTION 5-1
2-23
2-26 BTRAN Request 5-1
2-27 SUBMT Request 5-3
2-28
2-28
2-28
2-28 6. MEMORY DUMPS 6-1
2-28
2-29 Task Dump 6-1
2-29 DSDUMP Request 6-1
2-30 CMDUMP Request 6-3
2-30 K.DSDUMP Command 6-4
2-30.1 KTSDMP Utility 6-4
2-31 Task Dump Formats 6-4
2-31 TAF Dump 6-4
2-32 K.DUMP Command 6-5
2-32 K.DUMPLIM Command 6-5
60459500 C

7. APPLICATIONS INTERFACE FOR AUTOMATIC
RECOVERY
Purpose
Concepts
Named-Transactions and Run Units
Data Base Recovery
Transaction Recovery
Coding
Coding Structures for Data Base Recovery
Only
Transactions Using CRM
TAF Transactions Using CDCS
Coding Structures for Transaction Recovery
Transactions Using CRM
TAF Transactions Using CDCS
Terminal Recovery Considerations
CALLTSK without CEASE and RECOVERY
Multiple Data Manager Use
TOTAL Data Manager Use
8. DATA ADMINISTRATOR AND OPERATOR INTERFACE
FOR RECOVERY
Recovery Overview
Hardware Configuration Considerations
Installation
TAF K Display
Initial K Display
K.INT Command
K.ERO Command
K.REC Command
Restart K Display
TCF/CRF Recovery Considerations
TAF Configuration File
Communication Recovery File
Error Override
File Reformatting
Multiple Communication Recovery Files
Multimainframe Recovery
Recovery Processing Flow
TAF and System Failure
NAM Failure
Terminal Failure
CDCS Failure
Task Failure
TAF Termination
TAF Automatic Recovery Report
9. NETWORK FILES
7-1
7-1
7-1
7-1
7-1
7-1
7-2
7-2
7-2
7-2
7-3
7-3
7-3
7-4
7-5
7-5
7-5
8-1
10. TASK LIBRARY 10-1
LIBTASK Utility 10-1
Task Residency and Type 10-1
LIBTASK Command 10-2
Input Directives 10-5
Named-Transaction Input Directive 10-5
Task Input Directive 10-5
Scheduling Priority 10-7
Creating a New Task Library 10-7
Updating an Existing Task Library 10-7
Deleting a Task from a Task Library 10-7
Ignoring a Task in the Replacement File 10-8
11. REQUIRED SYSTEM TASKS AND TRANSACTIONS U-l
BTRAN Recovery Task (BTASK) 11-
Data Base Recovery Task (CTASK) 11-
Initial Task (ITASK) 11-
K Display Task (KDIS) 11-
Logout Task (LOGT) 11-
Message Abort (MSABT) 11-
Inactive Task (OFFTASK) 11-2
CDCS Rerun Task (RCTASK) 11-2
Run Unit Recovery Task (RTASK) 11-2
Terminal Network Description File
Network File Origination
8-1 Send Message Task (STASK) 11-2
8-2 System Message Task (SYSMSG) 11-2
8-2 Execute Named Task (XTASK) 11-2
8-2
8-2
8-2
XTRAN Transaction 11-2
8-3 12. ITASK SYSTEM TASK 12-1
8-3
8-3 Macros 12-1
8-3 TIMCNT Macro 12-1
8-3 TRAN Macro 12-1
8-3 STRAN Macro 12-1
8-3 ITASK Description 12-2
8-3 TAF-Originated Transactions 12-3
8-4 Conditions Requiring TAF-Originated
8-4 Transactions 12-3
8-4 Time Activation 12-3
8-4 K.IDLE Console Operator Command 12-3
8-5 Terminal Login 12-4
8-5 Terminal Break Conditions 12-4
8-5 Terminal Connection Broken 12-4
8-5 Network Normal Shutdown 12-4
8-5 Network Failure 12-4
8-6 Network Immediate Shutdown 12-4
Terminal Inactive 12-4
Logical Error 12-4
Block Not Delivered 12-5
9-1 Terminal Characteristic Change 12-5
Terminal Input Too Large 12-5
9-1 Terminal Type Ahead 12-5
9-1 User Status 12-5
/rfS^ly
A. CHARACTER SETS
B. DIAGNOSTIC MESSAGES
APPENDIXES
A-l D. SAMPLE COMMAND LIST STRUCTURES
B-l
COMPASS Task Command List Structure
FORTRAN Task Command List Structure
COBOL Task Command List Structure
D-l
D-l
D-l
D-l
C. GLOSSARY C-l E. FILES USED BY TAF E-l
• 8 60459500 C
Jffev
F. INSTALLATION OVERVIEW
G. TERMINAL DEFINITION COMMANDS
Introduction
Terminal Definition Command Format
Restrictions
Terminal Definition Commands
(AB) - Abort Output Block Character
(AR) - Automatic Character Recognition
(BF) - Blocking Factor
(BR) - Break Key as User Break 1
(BS) - Backspace Character
(Bl) - Interruption or User Break 1
Character
(B2) - Termination or User Break 2
Character
(CH) - Display Terminal Characteristics
(CI) - Carriage Return Idle Count
(CN) - Cancel Character
(CP) - Cursor Positioning after Input
(CT) - Network Control Character
(DL) - Delimiters for Single-Message
Transparent Input Mode
(EB) - End-of-Block Character
(EL) - End-of-Line Character
(EP) - Echoplex Mode
(FA) - Full-ASCII Input Mode
(HC) - Host Connection
(HD) - Display of Host Nodes
(HN) - Host Node Selection
(HS) - Host Selection
(IC) - Flow Control for Input Devices
(IN) - Input Device and Transmission Mode
(LI) - Line Feed Idle Count
(LK) - Lockout of Unsolicited Messages
(MS) - Message to Network Operator
(OC) - Flow Control for Output Devices
(OP) - Output Device Selection
(PA) - Parity Processing
(PG) - Page Waiting
(PL) - Page Length
(PW) - Page Width
(SE) - Special Editing Mode
(TC) - Terminal Class Command
(TM) - Terminating a Terminal-Host
Connection
(XL) - Multimessage Transparent Mode
JP^
F-l
G-l
G-l
G-l
G-2
G-2
G-3
G-3
G-3
G-3
G-4
G-4
G-4
G-4
G-4
G-5
G-5
G-5
G-5
G-6
G-7
G-7
G-7
G-8
G-8
G-9
G-9
G-9
G-9
G-10
G-10
G-10
G-ll
G-ll
G-ll
G-l 2
G-12
G-12
G-12
G-12
G-13
G-13
H. DELIMITING AND TRANSMITTING TERMINAL INPUT H-l
Physical End-of-Line (Line Feed) H-l
Logical End-of-Line (Carriage Return) H-l
Message Transmission H-l
I. DETECTION OF POTENTIALLY BLOCKED TASKS I-I
J. ACCESSING A HOST J-l
Brief Description of Access J-l
Step 1 - Gathering Information J-i
Step 2 - Setting Up Your Terminal J-l
Step 3 - Connecting Your Terminal to the
Network J-l
Step 4 - Identifying Your Terminal to the
Network J-3
Step 5 - Selecting a Host J-3
Step 6 - Connecting to the Selected Host J-3
Step 7 - Identifying Yourself and Your
Terminal to the Host J-4
Step 8 - Selecting a Network Application J-4
Detailed Description of Access J-4
Step 1 - Gathering Information J-4
Step 2 - Setting Up Your Terminal J-7
Step 3 - Connecting Your Terminal to the
Network J-8
Step 4 - Identifying Your Terminal to the
Network J-8
Procedure for Asynchronous Terminals J-8
Procedure for HASP Terminals J-9
Procedure for Mode 4 Terminals J-10
Procedure for Bisynchronous Terminals J-10
Step 5 - Selecting a Host J-10
Selecting a Host J-10
Selecting a Specific Host Path J-iI
Controlling the Display of Host Paths J—11
Step 6 - Connecting to the Selected Host J-13
Step 7 - Identifying Yourself and Your
Terminal to the Host J-13
Automatic Login J-14
Login Dialog J-14
Step 8 - Selecting a Network Application J-15
Automatic Connection J-15
Manual Connection J-15
Abbreviated Login and Application
Connection J-16
Switching to a Different Application J-16
Direct Switches J-16
Indirect Switches J-17
Dialog for Direct and Indirect Switches J-17
Restarting Login Identification J-17
Direct Restarts J-17
Indirect Restarts J-17
Secure Login Restarts J-17
Disconnecting from a Host J-18
Disconnecting with Application Commands J-18
Disconnecting with Host Commands J-18
Disconnecting with a Network Software
Command J-18
Reconnecting to a Host or Connecting
to a Different Host J-18
Disconnecting from One Host and
Connecting to a Different Host J-18
Interruptions J-19
Communicating with the Network Operator J-19
Receiving Messages J-19
Sending Messages J-19
Preventing Messages J-19
Suspensions of Communication J-19
Communication Failures J-19
Application Failures J-20
Disconnection from an Application
and/or Host J-20
Disconnection from the Network J-20
INDEX
0^ 60459500 C
FIGURES
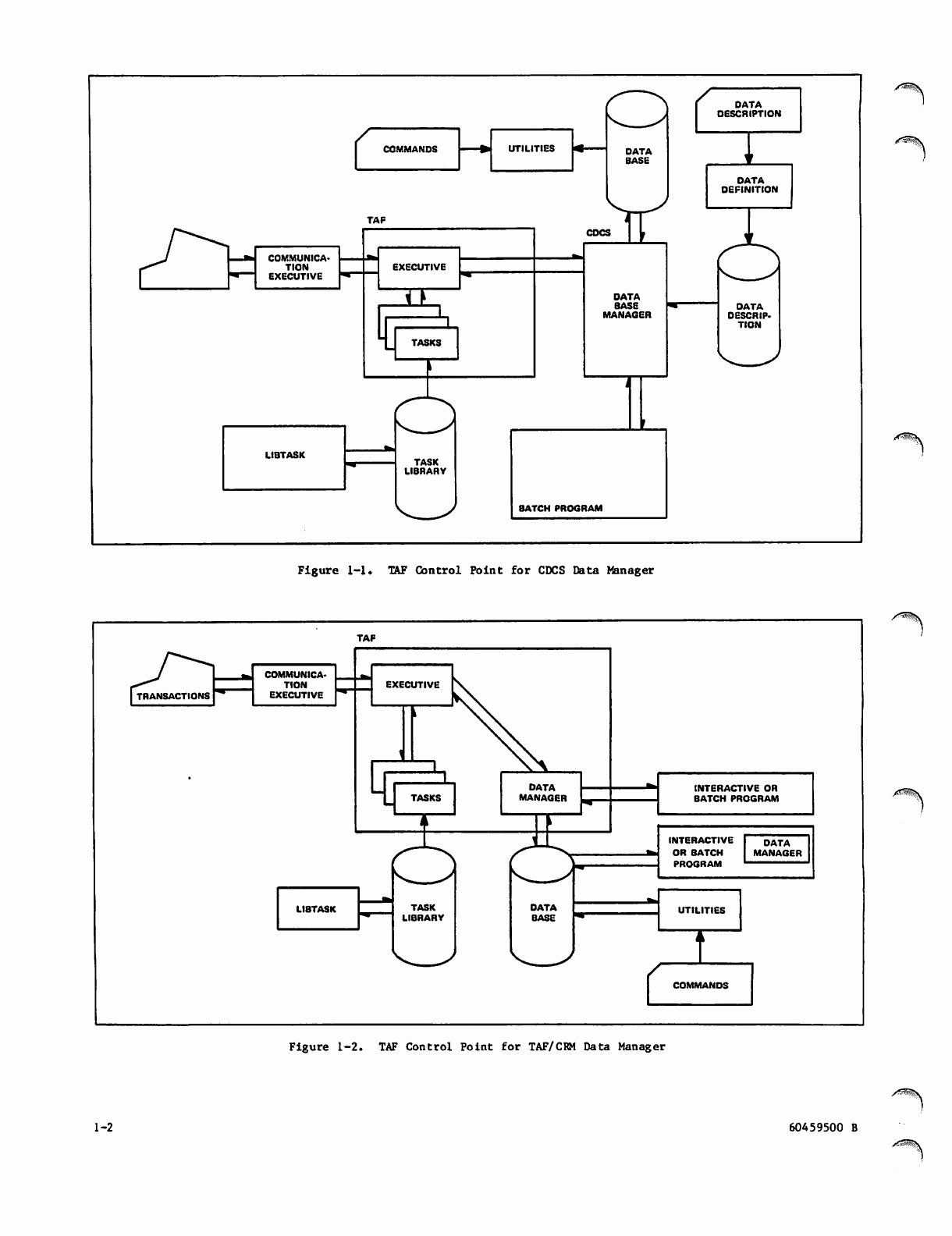
1-1 TAF Control Point for CDCS Data Manager
1-2 TAF Control Point for TAF/CRM
Data Manager
1-3 TAF Control Point for TOTAL
Data Manager
2-1 Communication Block Format
2-2 CALLRTN
2-3 CALLRTN (Chain)
2-4 CALLRTN (Multiple Chains)
2-5 CALLTSK with CEASE Request
2-6 CALLTSK without CEASE Request
2-7 NEWTRAN Parameter Table
2-8 TRANCHK Parameter Table
2-9 LOADCB Parameter Table
2-10 SETCHT Parameter Table
2-11 GETABH Parameter Table
2-12 TERMDEF Parameter Table
2-13 SEND Parameter Table
2-14 TSIM Parameter Table
2-15 TARO Parameter Table
2-16 IIO Parameter Table
2-17 ITL Parameter Table
4-1 Journal File (Buffered and
Nonbuffered Structure)
4-2 Journal File Entry Header
4-3 JOURNL Parameter Table
5-1 BTRAN Header Word
5-2 BTRAN Request
5-3 SUBMT Parameter Table
1-2 5-4
6-1
1-2 6-2
6-3
1-3 7-1
2-2
2-5 8-1
2-5
2-5 9-1
2-6
2-7 10-1
2-7 12-1
2-8 12-2
2-11 12-3
2-13 12-4
2-15
2-17 D-l
2-23 D-2
2-25 D-3
2-27 J-l
2-27 J-2
2-30 J-3
J-4
4-2 J-5
4-6 J-6
4-6 J-7
5-2 J-8
5-2 J-9
5-3
SUBMT Request 5-4
DSDUMP Parameter Table 6-3
CMDUMP Parameter Table 6-4
KTSDMP Format 6-5
Recoverable TAF Transaction
Using CDCS 7-4
Format of Part Three of the TAF
Automatic Recovery Report 8-6
Communication Between a Terminal Status
Table and a Communication Block 9-2
Task Library Report 10-4
Format of a TTOT Table Entry 12-1
Format of a TRANT Table Entry 12-2
Format of a TRANS Table Entry 12-2
Communication Block for TAF-
Originated Transactions 12-3
C O M PA S S C o m m a n d L i s t S t r u c t u r e D - l
FORTRAN Command List Structure D-l
COBOL Command List Structure D-l
Separate Acoustic Coupler J-2
Data Set Built into the Terminal J-2
Data Sets with Switches and Buttons J-2
Termina l with Built-in Acoust ic Couple r J-3
Interactive Display Console J-5
Interactive Printer Console J-5
Remote Batch Terminal J-6
Host Availability Display J-ll
Sample Login from an Asynchronous
Terminal J-13
TABLES
2-1 BLDABH Request Parameters
2-2 Application Block Header
2-3 COBOL SEND Request Parameters
2-4 FORTRAN SEND Request Parameters
2-5 COMPASS SEND Request Parameters
2-6 COMPASS SEND Parameter Interrelationships 2-24
2-7 TSAT Keyword Descriptions 2-39
2-8 WSTAT Keyword Descriptions 2-42
5-1 BTRAN Status Values 5-2
2-13 A-l
2-15
2-18 E-l
2-20 F-l
2-21 G-l
2-24 G-2
H-l
7-Bit ASCII Code Standard Print
63/64-Character Set
Files Used by TAF
Installation Overview
Default Terminal Definitions
Parameter Ranges for Terminal
Definition Commands
Default Message Delimiter and
Transmission Keys
A-l
E-l
F-2
G-l 5
G-16
H-2
/*S3l8v
• 1 0 60459500 C /iS|!X

INTRODUCTION
/fp^>,
J8*V
TAF is a network product that controls transaction
processing. Transaction processing consists of
taking an existing collection of information, called
a data base, and correcting old data or adding new
d a t a t o c r e a t e a n u p - t o - d a t e d a t a b a s e . S u c h a
correction or addition is called a transaction.
In a transaction processing system, the data base
must be efficiently structured and easily accessible
to the user. A data manager provides these features.
Control Data offers the following data managers for
use with TAF.
• The CYBER Database Control System (CDCS).
• The CYBER Record Manager (CRM). (TAF
supports only those features documented In
the TAF/CRM Data Manager 1 Reference Manual.)
• The TOTAL Data Manager.
All data managers can operate concurrently.
However, a single transaction can use only:
• CDCS and one other data manager,
or
• CDCS alone,
or
• One other data manager alone.
The most important feature of TAF is its efficient
system resource utilization. TAF's transaction
processing differs from other modes of operation in
that a task only contains application code.
Terminal communications are handled by one terminal
communications interface. Data base communications
are handled by one copy of a data base manager.
When tasks need to be loaded, they are simply copied
from a task library to a subcontrol point; none of
the normal overhead of loading is incurred.
The TAF control point contains application tasks as
subcontrol points. When a task completes, one of
the following occurs:
• I t m a y b e i m m e d i a t e l y r e u s e d b y o t h e r
waiting transactions (no reloading is
necessary).
• Another task may be loaded in its place.
• Other active tasks may be moved up in memory
and the remaining memory returned to the
system for use by non-TAF applications.
TAF will expand its memory to a maximum value as
needed.
Wh en th er e i s n o t ra n sa cti on acti vi ty, TAF size is
reduced to a small amount of memory. When input is
sensed, TAF rolls back in to service the request.
Figures 1-1, 1-2, and 1-3 summarize the TAF control
point and its operation.
T h e m a i n f u n c t i o n o f TA F i s o n - l i n e t r a n s a c t i o n
processing; that is, direct 'operator interface with
the data base through a terminal.
ON-LINE TRANSACTION PROCESSING
ADVANTAGES
Some advantages associated with on-line transaction
processing are:
• The operator submitting the data through TAF
can make immediate data corrections.
• The operator can verify that operations have
completed successfully. TAF allows the
operator to view additions or corrections to
the data base to verify their accuracy.
• The data base is updated in seconds. TAF
provides immediate updating capability,
which allows other transactions to make use
of the updated data base.
ON-LINE TRANSACTION PROCESSING
PROBLEMS
So me pro ble m s a ss o ci a te d with on-l ine tran sac tio n
processing and the methods that TAF uses to
alleviate them include the following.
• It is difficult to schedule and control
multiple jobs. TAF solves the problem of
multiple job control scheduling by using
subcontrol points. Like the operating
system that controls and schedules jobs to
control points (where they are processed),
TAF controls and schedules transaction
processing programs to portions of its
control point called subcontrol points.
Subcontrol points are protected from each
other by CYBER hardware memory protection.
• The terminal interface is complicated. TAF
minimizes terminal programming by using
simple input/output (I/O) commands that are
processed by the standard network terminal
interface.
60459500 A 1-1
COMMANDS DATA
BASE
D ATA
DESCRIPTION
TAF
COMMUNICA
TION
EXECUTIVE
TASKS
DATA
BASE
MANAGER
LIBTASK TASK
LIBRARY
BATCH PROGRAM
DATA
DEFINITION
^^
DATA
DESCRIP
TION
Figure 1-1. TAF Control Point for CDCS Data Manager
TAF
TRANSACTIONS
COMMUNICA
TION
EXECUTIVE
EXECUTIVE
TASK
LIBRARY
DATA
BASE
INTERACTIVE OR
BATCH PROGRAM
INTERACTIVE
OR BATCH
PROGRAM
DATA
MANAGER
cCOMMANDS
Figure 1-2. TAF Control Point for TAF/CRM Data Manager
1-2 60459500 B
yrfSS^S.
J^s
DATA
DESCRIPTION
TRANSACTIONS
COMMUNICA
TION
EXECUTIVE EXECUTIVE
TASK
LIBRARY OATA
BASE
DATA
MANAGER
BATCH PROGRAM
x rCOMMANOS
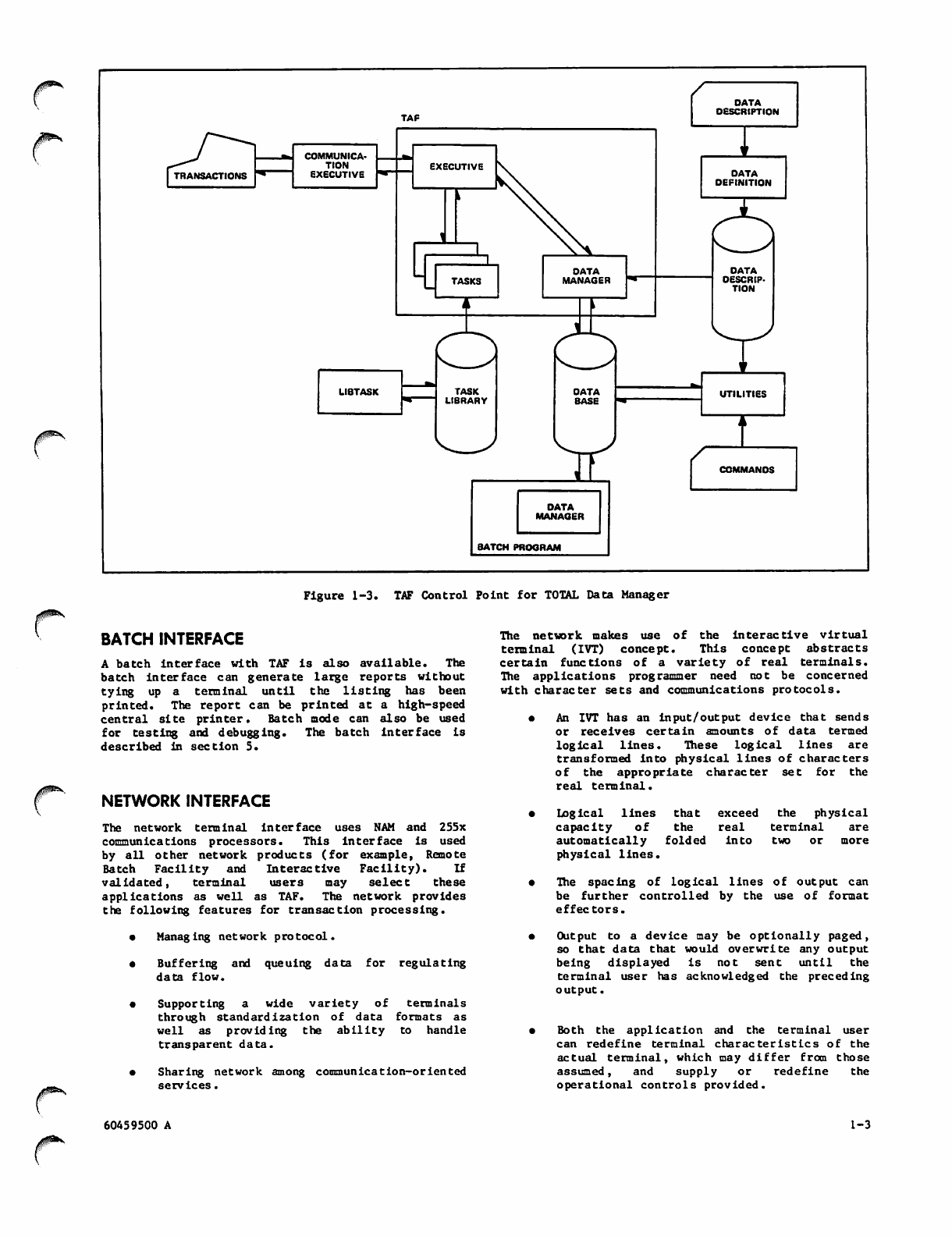
Figure 1-3. TAF Control Point for TOTAL Data Manager
^^v
BATCH INTERFACE
A batch interface with TAF is also available. The
batch interface can generate large reports without
tying up a terminal until the listing has been
printed. The report can be printed at a high-speed
central site printer. Batch mode can also be used
for testing and debugging. The batch interface is
described in section 5.
NETWORK INTERFACE
The network terminal interface uses NAM and 255x
communications processors. This interface is used
by all other network products (for example, Remote
Batch Facility and Interactive Facility). If
validated, terminal users may select these
applications as well as TAF. The network provides
the following features for transaction processing.
• Managing network protocol.
• Buffering and queuing data for regulating
data flow.
• Supporting a wide variety of terminals
through standardization of data formats as
well as providing the ability to handle
transparent data.
• Sharing network among communication-oriented
services.
60459500 A
The network makes use of the interactive virtual
terminal (IVT) concept. This concept abstracts
c e r t a i n f u n c t i o n s o f a v a r i e t y o f r e a l t e r m i n a l s .
The applications programmer need not be concerned
with character sets and communications protocols.
• An IVT has an input/output device that sends
or receives certain amounts of data termed
logical lines* These logical lines are
transformed into physical lines of characters
of the appropriate character set for the
real terminal.
• Logical lines that exceed the physical
capacity of the real terminal are
automatically folded into two or more
physical lines.
• The spacing of logical lines of output can
be fu r t her co n t rol l e d b y th e u s e o f fo rma t
effectors.
• Output to a device may be optionally paged,
so that data that would overwrite any output
being displayed is not sent until the
terminal user has acknowledged the preceding
output.
Both the application and the terminal user
can redefine terminal characteristics of the
actual terminal, which may differ from those
assumed, and supply or redefine the
operational controls provided.
1-3
When an application requires features not provided
by the IVT but known to exist on the connected real
terminal, the application may do one of the
following.
• Embed appropriate control characters in the
output text.
• Transfer data in transparent mode, in which
case all transforms are inhibited, and the
a p p l i c a t i o n h a s d i r e c t a c c e s s t o a n d
responsibility for all real terminal
features including the character set.
TASKS
The applications programmer implements a transaction
system by writing tasks. A task is a program with a
TAF interface that performs a specific function. A
single task or several tasks perform a sequence of
events called a transaction. Tasks can read and
update information on the user's data base. They
can send messages to terminals and receive input.
Tasks can also schedule other tasks to assist in
completing transactions.
Tasks that run under TAF can be written in COBOL,
FORTRAN, or COMPASS. A task differs from a normal
batch or interactive program in that it contains
calls to TAF commands and data manager commands and
m u s t h a v e a c o m m o n b l o c k ( r e f e r r e d t o a s t h e
communication block) defined. The communication
block is needed to receive terminal input and pass
data between tasks. (The communication block is
described in section 2.)
Binary copies of each task are stored in the task
library. The LIBTASK utility is used to place these
binary copies on the task library. Section 10
describes the task library and LIBTASK.
Tasks written in COBOL must be compiled with the TAF
parameter on the COBOL command. Tasks written in
FORTRAN must be compiled with the Z parameter on the
FORTRAN command (FORTRAN 4) or with DB=0 on the FTN5
command (FORTRAN 5).
TRANSACTION PROCESSING
After following the login procedures outlined in
appendix J, the user indicates the transaction to be
performed by entering a code that is assigned by the
system designers. Such a code could specify that a
user is entering a loan payment; another code would
be used to close out a loan, and so on. TAF receives
this Initial input and places it in a communication
block. This communication block is the means by
which the data is passed from a terminal to a task
or from task to task.
When a transaction is completed, the communication
block is released and can be used by other
tra nsactio ns.
After the communication block has been constructed,
TAF schedules an initial task (ITASK) to interpret
the code the user entered. Using this code, ITASK
requests TAF to schedule the appropriate task(s) to
process the transaction. The task scheduled may
also call other tasks to assist in completing the
transaction.
TAF REQUESTS
Communication between terminals and tasks is
accomplished by using TAF requests. Output can be
sent to a transaction terminal from the task by
u s i n g t h e S E N D r e q u e s t . W h e n t h i s r e q u e s t i s
processed, control passes to TAF. TAF extracts the
message from the task and passes it to the network.
The message is then transmitted to the transaction
terminal, and control passes back to the task for
additional processing.
When a task requires additional input from the
terminal, the WAITINP request is used. The task
performs a SEND request to send output to the
terminal, prompting the terminal operator for the
needed input. The WAITINP request is then
processed. Since the terminal operator takes
seconds to respond to the request, the task is
rolled out of central memory and the subcontrol
point and communication block are released. These
resources can then be used to process other
t r a n s a c t i o n s w h i l e t h e t e r m i n a l o p e r a t o r i s
responding. When TAF receives the requested input,
it places it into a new communication block, and the
task is rolled into an available subcontrol point.
The new communication block is passed to the task,
and the task continues processing.
Thes e and o ther re qu ests ar e f ur th er described in
sections 2 and 5.
ENTERING THE TRANSACTION SUBSYSTEM
The subsystem you will be accessing is the TAF
subsystem. There are various procedures for
accessing this transaction subsystem. These methods
are discussed in detail in appendix J. Using
appendix J, a coordinator of TAF activities at a
particular site who knows the types of users and
a p p l i c a t i o n s a t t h e s i t e c a n d e t e r m i n e t h e m o s t
desirable access procedures.
Because of the flexibility of the network and the
transaction subsystem, the procedure to access the
transaction subsystem can vary substantially from
site to site. Therefore, the coordinator of
transaction subsystem operations at each site should
provide each user, or terminal location, with a
detailed login procedure for that site.
The site should also provide information concerning
terminal characteristics. A variety of terminal
classes Is supported for use on the network with
1-4 60459500 C
J#*^
TAF. Each of these terminal classes has character
istics, which the analyst can change by modifying the
network files and which you can change by entering
terminal definition commands.
A discussion of the terminal characteristics, the
defaults for each terminal class, and the procedure
for changing these characteristics at a terminal is
included in appendix G.
IMPLEMENTING AN APPLICATION
T h e f o l l o w i n g s t e p s s p e c i f y t h e p r o c e d u r e f o r
implementing an application.
1. Review this manual.
2. Design the application including:
• Selection of the data manager (CDCS
and/or CRM, or TOTAL) to allow the
correct choice of file types, file
structure, and file interaction.
• Selection of recovery and backup
techniques, including journalizing
o f fi l e s .
Refer to the CYBER Database Control System 2
Reference Manuals, the TAF/CRM Data Manager
1 Reference Manual, or the TOTAL - CDC 2
Reference Manual for more information (publi
cation numbers are listed in the preface).
3. Describe and Install the data base using the
data manager. Refer to the appropriate data
manager reference manual for this procedure.
4 . Te s t l o a d t h e d a t a b a s e u s i n g t h e d a t a
manager commands (usually done in batch
mode).
5. Using the application design, write the
a p p l i c a t i o n t a s k s t o p r o c e s s t r a n s a c t i o n
input.
6. Optionally modify ITASK to reflect the
actual application. Tasks MSABT, LOGT, and
SYSMSG may also require modification.
(Refer to section 11.)
7. Build a task library. (Refer to section 10.)
8 . B u i l d a n x xJ fi le . ( R e f e r t o se c t i o n 4 . )
9. Build a network file, and use NDL to
configure terminals and establish login
sequences and terminal characteristics.
10. Build the TAF configuration file (TCF).
(Refer to section 4.)
Tasks reside at subcontrol points within the field
length of the transaction executive. Each task runs |
with its own exchange package, reference address
(relative to the transaction executive), and field
length (a subset of the field length of the trans
ac tio n exec uti v e) . A t a sk , t h ere for e , c an res ide in
any contiguous segment within the transaction execu
tive field length. Memory is allocated in 100g
word blocks located on even lOOg word boundaries
(for example, 32100g to 32200s). A subcontrol
point consists of one 120g word block of memory
for system use, followed by sufficient blocks to
contain an entire task.
The subcontrol point feature allows the transaction
executive to control each task. Some of the advant
ages associated with the subcontrol points are:
• Isolating one subcontrol point from other
subcontrol points and the transaction
executive. This means that no application
program can destroy the transaction
executive or circumvent system security.
• Blocking RA+1 requests from a subcontrol
point. No requests are allowed directly
fr om a su bc ont ro l p oint to NOS. A ny such
r e q u e s t s a r e i n t e r c e p t e d b y t h e s y s t e m
monitors, which return control to the
transaction executive. Thus, the only RA+l
requests a task can legally issue are those
processed by the transaction executive.
This includes requests to the data managers.
The transaction subsystem allows a maximum of 31
subcontrol points. An installation parameter sets
the number of subcontrol points that the transaction
executive initializes. When the transaction
executive is loaded, the operator can select a
number of subcontrol points other fhan this default
value. The number of subcontrol points must not be
less than 2 nor greater than 31. Once the
transaction subsystem is initialized, no change in
the number of subcontrol points is allowed. The
optimum number of subcontrol points is selected by
the site.
Each subcontrol point requires eight words of table
space. No space, other than a table entry, is
allocated for a subcontrol point unless it is
active. Each active subcontrol point has 11lg
words reserved, beginning at RA, similar to those
used for batch control points.
MULTIMAINFRAME
Under a multimalnframe configuration, the transaction
subsystem can be run on either or both mainframes.
However, a data base and J0UR0 file (section 4)
cannot be shared by the transaction subsystems.
Each subsystem must have a unique data base.
11. Test the system.
SUBCONTROL POINTS
The following discussion is intended for analysts
and may be omitted by the applications programmer.
EXTENDED MEMORY
TAP does not allow the use of your access to
extend ed m emory. However, th e TAF procedur e file
can declare data files and libraries as extended
memory-resident.
60459500 C 1-5

/^^%\
0^*- TASK/TRANSACTION EXECUTIVE INTERFACE
0^^
A task is isolated from th e data manager and the
remainder of the system by the transaction
executive. The isolation guarantees that errors in
a task do not propagate beyond the task. The
following types of requests constitute the interface
between the task and the transaction executive.
• Data manager requests
• Journal file requests
• Memory dump requests
• System requests
• Task scheduling requests
• Input/output requestst
• Task control requests
• Ta s k u t i l i t y r e q u e s t s
• Application recovery requests
• System recovery requests
Internally, a task performs a request by loading
address RA+1 of its subcontrol point. This activity
is not visible to the applications programmer who
uses the macros or calls given In this section. The
transaction executive uses the request parameters to
determine what processing is required by the task.
The address field and any fields in a parameter list
that reference an address contained within the task
are verified to ensure that the address referenced
is within the ta sk fie ld length.
Tasks communicate with each other and accumulate
input by using the communication block. The
communication block is discussed next, followed by
the types of requests.
the communication block (refer to the description of
m in figure 2-1). If the communication block is
passed between tasks in a transaction and overflow
data is present, other tasks in the transaction can
access this data with a LOADCB request.
If COBOL is used, the communication block must be
described in the COMMON-STORAGE SECTION. Shown here
is an example of such a description:
DATA DIVISION.
COMMON-STORAGE SECTION.
01 COMMUNICATION-BLOCK.
03 CB-HEADER-AREA-WORD-ZERO.
05 CB-OATA-BASE-NAME
05 CB-USER-TST-AREA
05 CB-TRANS SEQ-NUMBER
03 CB-HEADER-AREA-WORD-ONE.
05 CBHJSERNAME
05 CB-INPUT-STATUS-BYTE
05 CB-MESSAGE-WORD-COUNT
03 CB-MESSAGE-AREA
03 USER-AREA
03 CB-TRAILER-AREA.
05 FILLER
05 CB-PACKED-0ATE.
07 CB-YEAR
07 CB-M0NTH
07 CB-DAY
05 CB-PACKED-TIME.
07 CB-H0UR
07 CB-MINUTE
07 CB-SEC0ND
WORKING-STORAGE SECTION.
PIC X(2).
COMP-4 PIC 9C6).
COMP-4 PIC 9(6).
PIC X(7).
COMP-4 PIC 9.
COMP-4 PIC 99.
PIC X(570).
PIC X<90).
PIC X(4).
COMP-4 PIC 9.
COMP-4 PIC 9.
COMP-4 PIC 9.
COMP-4 PIC 9.
COMP-4 PIC 9.
COMP-4 PIC 9.
COMMUNICATION BLOCK
Communication between a chain of tasks is provided
by the communication block. The initial input or
the input from a terminal as a result of the WAITINP
request (refer to Input/Output Requests later in this
section) is also stored in the communication block.
The communication block can be used to pass parame
ters or data from task to task. The format of the
communication block is shown in figure 2-1. The
length of terminal input is not restricted by the
length of the communication block. The LOADCB re
quest is available to read extra input that overflows
T h i s w i l l b e r e f e r r e d t o i n t h e m a n u a l a s t h e
standard COBOL communication block because of the
correspondence between it and the fields shown and
described in figure 2-1. However, applications
programmers may find it convenient to use a more
abbreviated communication block when possible.
C O M P - 4 i s s p e c i fi e d f o r d a t a a r e a s i n t e n d e d f o r
numerical information. Refer to the COBOL 5 Refer
ence Manual for information on the relationship
between the number of digits specified in the
picture clause for COMP-4 data and the number of
bits reserved.
TThe standard CMR-supported, compiler-generated I/O calls from FORTRAN and COBOL are not allowed.
SORT verb is not supported.
The COBOL
J^ 60459500 B 2-1
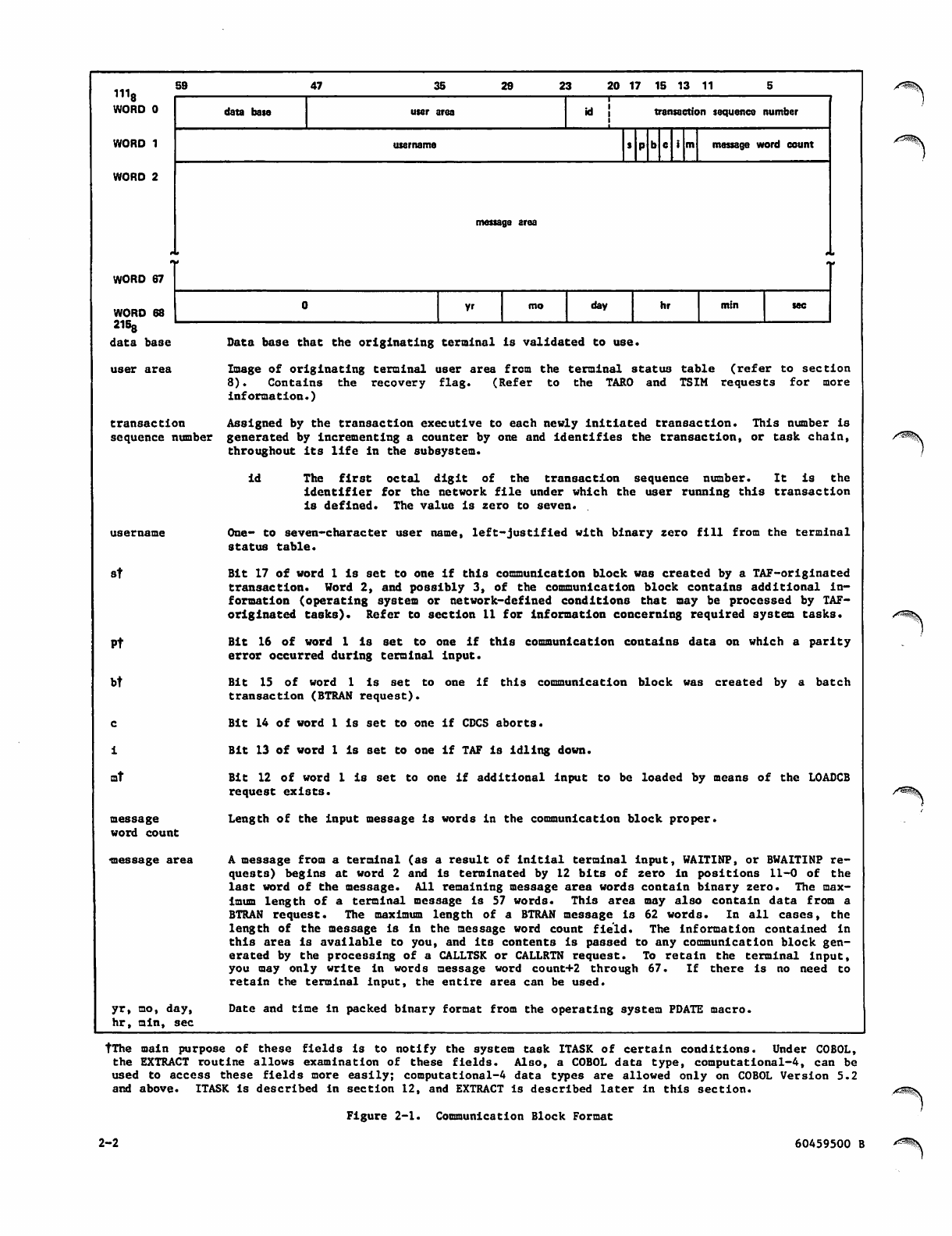
1118
WORD 0
WORD 1
WORD 2
59 4 7 3 5 2 9 2 3 2 0 17 15 13 1 1 5
data bate user area i d | t r a n s a c t i o n s e q u e n c e n u m b e r
i
usemame message word count
message area
WORD 67
WORD 68
215g
data base
user area
vr day hr min
Data base that the originating terminal is validated to use.
Image of originating terminal user area from the terminal status table (refer to section
8). Contains the recovery flag. (Refer to the TARO and TSIM requests for more
information.)
transaction Assigned by the transaction executive to each newly initiated transaction. This number is
sequence number generated by incrementing a counter by one and identifies the transaction, or task chain,
throughout its life in the subsystem.
id The first octal digit of the transaction sequence number. It is the
identifier for the network file under which the user running this transaction
is defined. The value is zero to seven. .
username
st
Pt
bt
c
i
mt
message
word count
•message area
yr, mo, day,
hr, min, sec
One- to seven-character user name, left-justified with binary zero fill from the terminal
status table.
Bit 17 of word 1 is set to one if this communication block was created by a TAF-originated
transaction. Word 2, and possibly 3, of the communication block contains additional in
formation (operating system or network-defined conditions that may be processed by TAF-
originated tasks). Refer to section 11 for information concerning required system tasks.
Bit 16 of word 1 is set to one if this communication contains data on which a parity
error occurred during terminal input.
Bit 15 of word 1 is set to one if this communication block was created by a batch
transaction (BTRAN request).
Bit 14 of word 1 is set to one if CDCS aborts.
Bit 13 of word 1 is set to one if TAF is idling down.
Bit 12 of word 1 is set to one if additional input to be loaded by means of the LOADCB
request exists.
Length of the input message is words in the communication block proper.
A message from a terminal (as a result of initial terminal input, WAITINP, or BWAITINP re
quests) begins at word 2 and is terminated by 12 bits of zero in positions 11-0 of the
last word of the message. All remaining message area words contain binary zero. The max
imum length of a terminal message is 57 words. This area may also contain data from a
BTRAN request. The maximum length of a BTRAN message is 62 words. In all cases, the
length of the message is in the message word count field. The information contained in
this area is available to you, and its contents is passed to any communication block gen
erated by the processing of a CALLTSK or CALLRTN request. To retain the terminal input,
you may only write in words message word count+2 through 67. If there is no need to
retain the terminal input, the entire area can be used.
Date and time in packed binary format from the operating system PDATE macro.
TThe main purpose of these fields is to notify the system task ITASK of certain conditions. Under COBOL,
the EXTRACT routine allows examination of these fields. Also, a COBOL data type, computational-4, can be
used to access these fields more easily; computational-4 data types are allowed only on COBOL Version 5.2
and above. ITASK is described in section 12, and EXTRACT is described later in this section.
Figure 2-1. Communication Block Format
2-2 60459500 B
If FORTRAN is used, the communication block must be
in the first block of labeled common.
If more data is input than can be contained in the
communication block, the LOADCB request may be used
to obtain the input.
REQUESTS
The following paragraphs describe the various types
of requests a task can make. They describe task
scheduling, input/output, task control, and task
utility requests and show the formats for making
these requests from tasks written in FORTRAN, COBOL,
and COMPASS.
COBOL Statements
ACCEPT x FROM DATE.
ACCEPT x FROM TIME.
ACCEPT item FROM TTY.
DISPLAY item UPON TTY.
These requests are described in detail in Volume 4
of the NOS 2 Reference Set, FORTRAN Extended 4
Reference Manual, FORTRAN 5 Reference Manual, and
the COBOL 5 Reference Manual. (Refer to the preface
for publication numbers.)
DATA MANAGER REQUESTS
A task can make data manager requests to one of the
data managers, (CDCS, CRM, or TOTAL) supported by
the transaction subsystem. (Refer to the preface
for a list of the publications that document these
data managers and the requests used.)
MEMORY REQUESTS (COMPASS ONLY)
Tasks can interrogate the status of and change their
central memory (CM) field length (FL) via the RA+1
requests MEM and RFL. The format of these calls is
doc ument ed f or t he MEMORY m acro in the NOS 2
Reference Set, Volume 4. The use of these requests
in TAF is restricted as follows:
JOURNAL FILE REQUESTS
A task can supplement automatic journal ing by
w r i t i n g d a t a o n a j o u r n a l fi l e . J o u r n a l fi l e s a n d
the journal requests are discussed in section 4.
MEMORY DUMP REQUESTS
These requests are discussed in section 6.
SYSTEM REQUESTS
System requests from transaction tasks are limited
to the following.
COMPASS Macros
ABORT
DATE x
ENDRUN
JDATE x
MEMORY (as described bel ow)
MESSAGE x (to console B display, line one
only)
PDATE x
RTTME x
TIME x
FORTRAN Functions and Subroutine Calls
DATE(x) or CALL DATE(x)
JDATE(x) or CALL JDATE(x)
TTME(x) or CALL TIME(x)
60459500 B
Me mo ry reques ts sho uld b e i ss ued w ith the
re c a ll ( r p a r ame t e r); ot h e rwi s e , c o ntr o l ma y
be returned before the request is processed.
There is an upper limit beyond which a task is
not allowed to increase its CM space; this
limit is referred to as the maximum task field
length (MFL). The MFL for each task is equal
to the task FL plus the value specified by the
EF LIBTASK directive for the task (refer to
section 10). If a task attempts to exceed
this value, it may be aborted (refer to docu
mentation of the MEMORY macro NA parameter in
the NOS 2 Reference Set, Volume 4).
Field length cannot be decreased to less than
the last word address of the default commun
ication block transfer address rounded up to
the nearest 100s«
A non-CM-resident task making a memory request
may be rolled out of CM if the request cannot
be satisfied initially.
Since a task making a memory request may be
rolled out, it may be desirable to free locked
data manager resources prior to the request.
Tasks will also be allowed to use the common memory
manager (CMM) with the following restrictions:
The processing performed by CMM for the task
must not result in CMM using the fast dynamic
loader or the task will be aborted.
• The preceding restrictions on use of MEM and
RFL requests apply.
Common memory manager requests are documented in
detail in the Common Memory Manager 1 Reference
Manual.
2-3

MESSAGE REQUESTS • NEWTRAN
COMPASS tasks can issue messages to the operator or
the JOURO file by using the RA+1 request MSG. The
function code determines the disposition of the
message. Function code zero causes the message to
be written to only the JOURO file. Function code
one causes the message to be placed in line one of
the B display.
FORTRAN termination messages are also written to the
JOURO file.
COBOL and FORTRAN tasks can issue messages to TAF's
dayfile by using the TMSG request. The tasks that
iss ue this request must reside in th e syst em t ask
library. TASKLX6
The TMSG request issues a message to TAF's dayfile.
The format is:
Initiates up to five new tasks (COMPASS
only).
• TRANCHK
Checks to see if a specific task is active
(COMPASS only).
1 NOTE |
If a list has either no tasks or more
than five tasks, TAF aborts the task
and issues the following error
message on the screen.
TASK REQUEST ARGUMENT ERROR
COBOL
ENTER TMSG USING message[.length].
message A 01-level data item containing
the dayfile message.
length A computational-l data item
specifying the length of the
message in characters. The
maximum length is 80 characters.
FORTRAN
CALL TMSG(message,length)
message The name of the array that
contains the dayfile message.
length An integer specifying the length
of the message in characters.
T h e m a x i m u m l e n g t h i s 8 0
characters.
TASK SCHEDULING REQUESTS
A task, including ITASK (refer to section 11), can
call in order a list of other tasks. This process
is referred to as task scheduling. The following
four requests can be used to schedule tasks.
• CALLRTN
Calls up to five tasks. Upon completion of
the called chain of tasks, returns control
to the calling task.
• CALLTSK
Calls up to five tasks. The task making the
call either ceases or continues to run,
allowing the new task chain to proceed
independently.
CALLRTN Request
The CALLRT N request is use d to request that t he
transaction executive schedule a task or series of
tasks, with control returning to the calling task
upon completion of the called tasks. A CALLRTN
request cannot be made while data manager requests
are outstanding. The current communication block is
passed to the called tasks and returned to the
caller when the caller is reinitiated. Upon return,
the caller begins execution immediately after the
CALLRTN request. Only the information in the
communication block may have changed. Return from
the called tasks to the caller takes place
automatically after the last called task ceases. A
task waiting for return may be temporarily rolled
from memory.
The format is:
COBOL
ENTER CALLRTN USING task! task2«..taskn.
task^ Parameter whose value Is a one-
to seven-character alphanumeric
task name. The tasks are
scheduled by CALLRTN in the
o r d e r s p e c i fi e d . F r o m o n e t o
five tasks can be specified.
FORTRAN
CALL CALLRTN(taskl,task2 taskn)
taski Parameter whose value is a one-
to seven-character alphanumeric
task name, left-justified with
either blank or binary zero fill
to a w o rd b o u ndar y. T h e t a s k s
are scheduled by CALLRTN in the
order specified. From one to
five tasks can be specified.
y*^^\
2-4 60459500 C
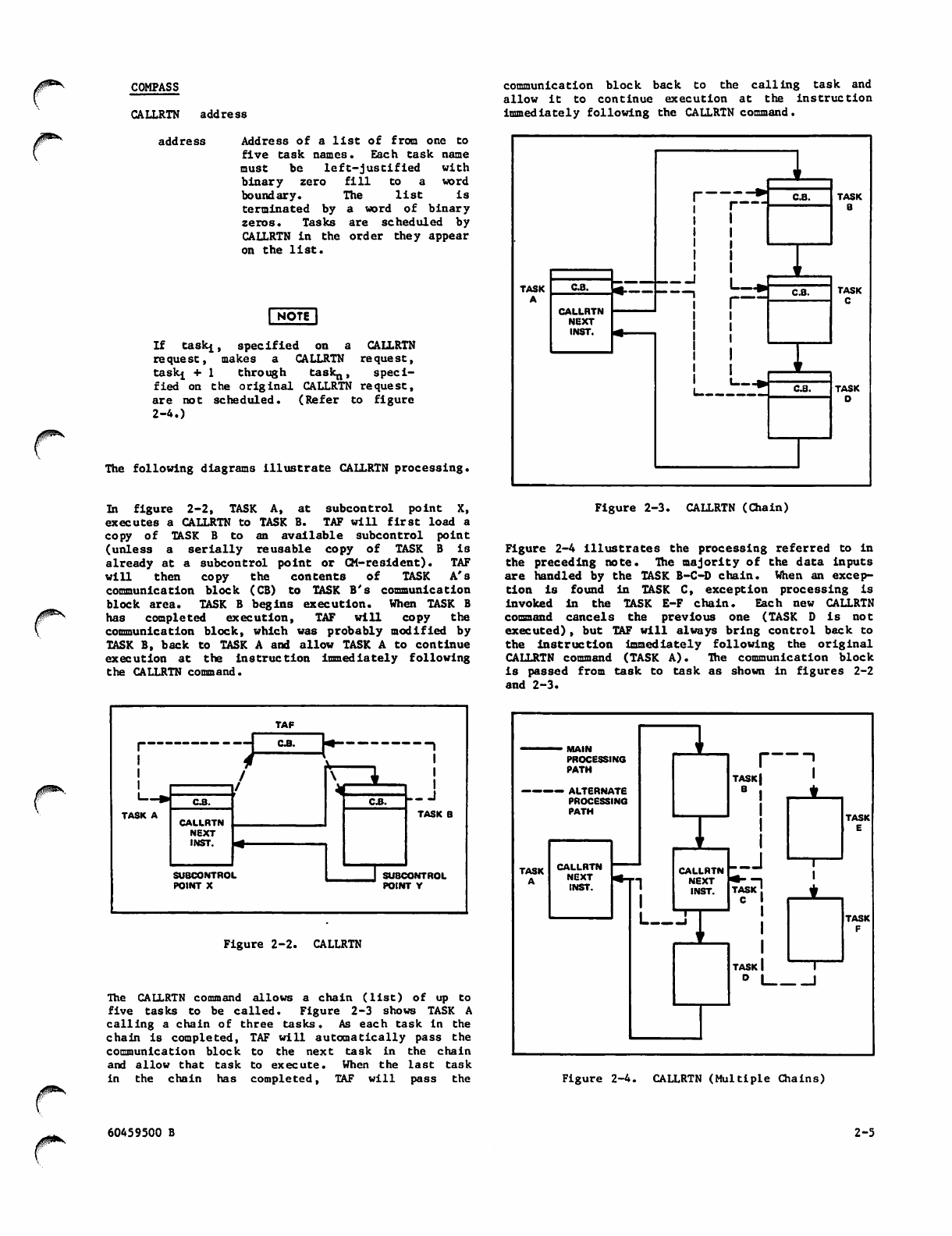
COMPASS
CALLRTN address
com m u n i c a t i on b l o c k b a c k to th e ca l l i n g t a s k an d
allow it to continue execution at the instruction
immediately following the CALLRTN command.
/^v
address Address of a list of from one to
five task names. Each task name
must be left-justified with
binary zero fill to a word
boundary. The list is
terminated by a word of binary
zeros. Tasks are scheduled by
CALLRTN in the order they appear
on the list.
("note"!
If taski, specified on a CALLRTN
request, makes a CALLRTN request,
taskj + 1 through task,,, speci
fied on the original CALLRTN request,
a r e n o t sc h e d u l e d . ( R e f e r t o fi g u r e
2-4.)
The following diagrams illustrate CALLRTN processing.
TASK
A
TASK
8
TASK
c
TASK
O
1
1
1
1
1
1
1
1
1 *
1—
I a >
1'
C B .
■— v . ,
C.B. #■C8.
CALLRTN
NEXT
INST.
CS.
JS»\
I n fi g u r e 2 - 2 , TA S K A , a t s u b c o n t r o l p o i n t X ,
executes a CALLRTN to TASK B. TAF will first load a
copy o f TA S K B to a n av a i l a b l e su b c o n t r o l po i n t
(unless a serially reusable copy of TASK B is
already at a subcontrol point or CM-resident). TAF
will then copy the contents of TASK A's
communication block (CB) to TASK B's communication
block area. TASK B begins execution. When TASK B
has completed execution, TAF will copy the
communication block, which was probably modified by
TASK B, back to TASK A and allow TASK A to continue
execution at the instruction immediately following
the CALLRTN command.
Figure 2-3. CALLRTN (Chain)
Figure 2-4 illustrates the processing referred to in
the preceding note. The majority of the data inputs
are handled by the TASK B-C-D chain. When an excep
tion is f o u n d i n TA S K C, exc e p t i o n pr o c e s s i n g i s
invoked in the TASK E-F chain. Each new CALLRTN
command cancels the previous one (TASK D is not
executed), but TAF will always bring control back to
the instruction immediately following the original
CALLRTN command (TASK A). The communication block
is passed from task to task as shown in figures 2-2
and 2-3.
TAF
1C B .
!1
14
/
1/
1
1 • »
TASK A TASK a
CS. CS.
CALLRTN
NEXT
INST.
SUBCONTRO
POINT X J SUMONTROL
POINT Y
Figure 2-2. CALLRTN
The CALLRTN command allows a chain (list) of up to
five tasks to be called. Figure 2-3 shows TASK A
calling a chain of three tasks. As each task in the
chain is completed, TAF will automatically pass the
communication block to the next task in the chain
and allow that task to execute. When the last task
in the chain has completed, TAF will pass the
MAIN
PROCESSING
PATH
> ALTERNATE
PROCESSING
PATH
TASK
A
CALLRTN
NEXT
INST.
TASK |
B .
CALLRTN
NEXT
INST.
i ^ r
L_J
task]
-1
I
_*_
TASK
E
TASK I
D I
TASK
F
Figure 2-4. CALLRTN (Multiple Chains)
/|P"v 60459500 B 2-5
CALLTSK Request
The CALLTSK request is used to request that the
transaction executive schedule a task or series of
tasks (task chain). Included in this request is a
parameter option that enables task branching or a
CEASE function to be performed after the call is
ho no re d. If t he tas k is not t o c ea se on thi s cal l,
a branching of the chain initiates a new chain that
is Independent of the original chain. The new chain
is assigned a new sequence number for unique
identification within the transaction subsystem
(figure 2-1). The number of branches allowed by a
transaction is controlled by an assembly constant
MAXBW. If a CALLTSK request without a CEASE request
is issued from a recoverable transaction, recovery
may be affected. Refer to CALLTSK without CEASE and
Recovery in section 7.
The format is:
code
COBOL
ENTER CALLTSK USING task code task1#. .tas^.
task Parameter whose value is a one-
Co seven-character alphanumeric
task name. This task is the
next task to call in the present
task chain (same sequence
number) if code is set to zero;
otherwise, it is the first task
o f a b r a n c h c h a i n ( t h e c a l l e d
task gets a different sequence
number and proceeds independently
of the calling task).
code Computational-l item whose value
i s n o n z e r o i f t h e c a l l i n g t a s k
is to continue after the
request, initiating an
independent task chain. If the
value of this parameter is zero,
t h e c a l l i n g t a s k c e a s e s a f t e r
this request. This parameter
must be specified.
task^ parameter whose value is a one-
to seven-character alphanumeric
t a s k na m e . Fr o m z e r o t o f o u r
t a s k s c a n b e s p e c i fi e d . Th e s e
tasks are scheduled after the
one specified in the task
parameter.
FORTRAN
CALL CALLTSK(task,code,taskj,..., task^
task Parameter whose value is a one-
to seven-character alphanumeric
t a s k n a m e , l e f t - j u s t i fi e d w i t h
either blank or binary zero fill
to a word boundary. This task
is th e ne xt t ask to ca ll i n t h e
present task chain (same
sequence number) if code is set
t o z e r o ; o t h e r w i s e , i t i s t h e
first task of a branch chain
(the called task gets a
different sequence number and
proceeds independently of the
calling task).
task*
Integer whose value is nonzero
i f t h e c a l l i n g t a s k i s t o c o n
tinue after the request, initiat
ing an independent task chain.
If the value of this parameter
is zero, the calling task ceas es
after this request. If not
specified, the default is zero.
Parameter whose value is a one-
to seven-character alphanumeric
t a s k n a m e , l e f t - j u s t i fi e d w i t h
e i t h e r b l a n k o r b i n a r y z e r o fi l l
to a word boundary. From zero
to four tasks can be specified.
These tasks are scheduled after
t h e o n e s p e c i fi e d i n t h e t a s k
parameter.
COMPASS
CALLTSK address,cease
address Address of a list of from one to
five task names. Each task name
oust be left-justified with bina
ry zero fill to a word boundary.
The list is terminated by a word
of binary zeros. CALLTSK sched
ules the tasks in the order they
appear on the list.
cease If specified, the calling task
ceases after this request. If
not specified, the calling task
continues after the request. In
this case the CALLTSK initiates
an independent task chain.
The following figures illustrate CALLTSK processing.
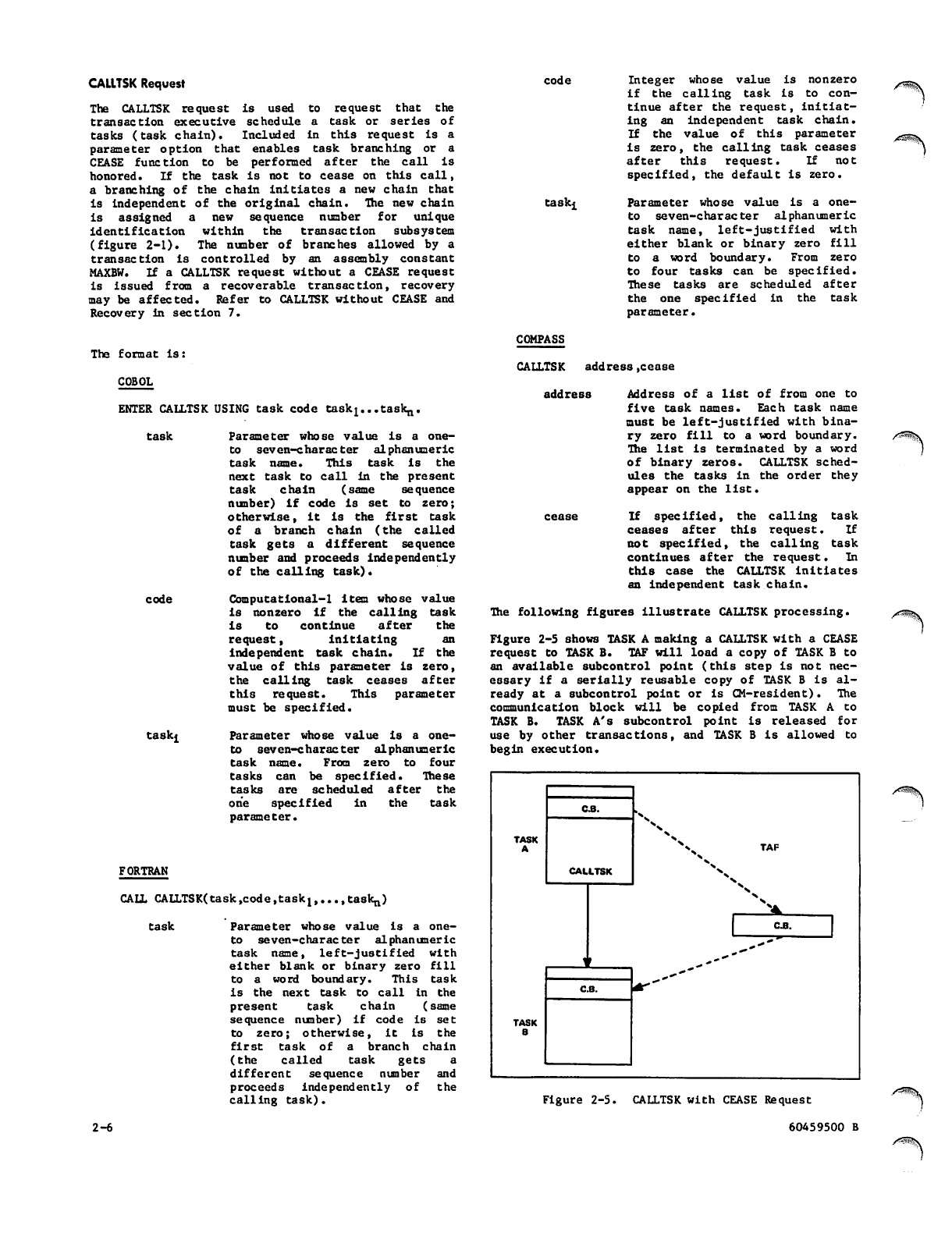
Figure 2-5 shows TASK A making a CALLTSK with a CEASE
request to TASK B. TAF will load a copy of TASK B to
an available subcontrol point (this step is not nec
essary if a serially reusable copy of TASK B is al
ready at a subcontrol point or is CM-resident). The
communication block will be copied from TASK A to
TASK B. TASK A's subcontrol point is released for
use by other transactions, and TASK B is allowed to
begin execution.
TASK
A
TASK
B
x s H T A F
X
CS.
CALLTSK
1'
Nx
C S .
^-
-l,«»*"
*****
CB.
2-6
Figure 2-5. CALLTSK with CEASE Request
60459500 B
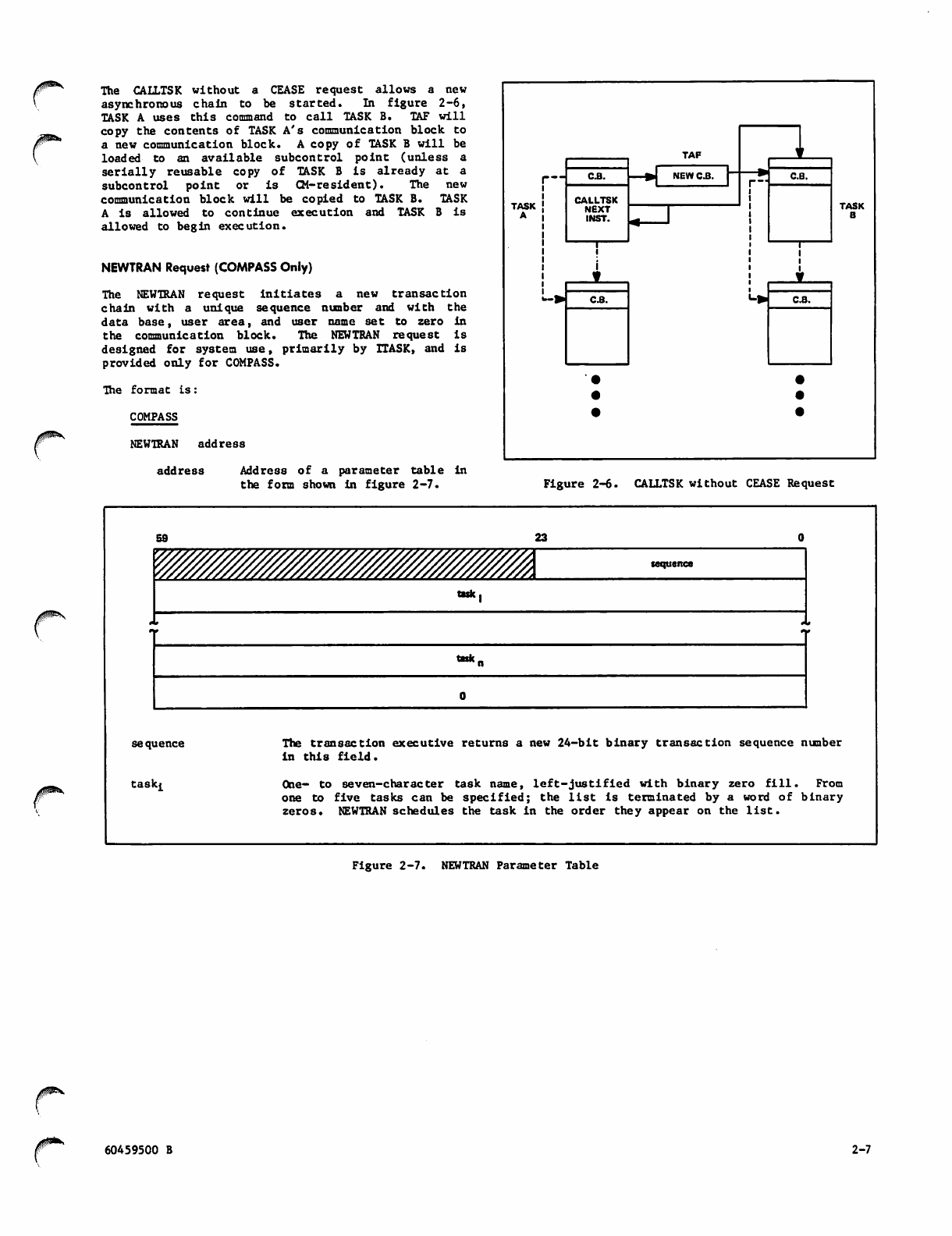
/$^N The CALLTSK without a CEASE request allows a new
asynchronous chain to be started. In figure 2-6,
TASK A uses this command to call TASK B. TAF will
copy the contents of TASK A's communication block to
a new communication block. A copy of TASK B will be
loaded to an available subcontrol point (unless a
serially reusable copy of TASK B is already at a
subcontrol point or is CM-resident). The new
communication block will be copied to TASK B. TASK
A is allowed to continue execution and TASK B is
allowed to begin execution.
NEWTRAN Request (COMPASS Only)
The NEWTRAN request initiates a new transaction
chain with a unique sequence number and with the
data base, user area, and user name set to zero in
the communication block. The NEWTRAN request is
designed for system use, primarily by ITASK, and is
provided only for COMPASS.
The format is:
COMPASS
NEWTRAN address
address Address of a parameter table in
the form shown in figure 2-7.
TASK
A
TAF
CS. NEW CB. r— CB.
CALLTSK
NEXT
INST.
I
TASK
B
Figure 2-6. CALLTSK without CEASE Request
J*5^
59 2 3 0
*
9
V/MMfr^^^^^^^^^^^, sequence
task|
* *
t #
task
0
seqt
tasl
jence The transaction executive returns a new 24-bit binary transaction sequence number
in this field.
One- to seven-character task name, left-justified with binary zero fill. From
one to five tasks can be specified; the list is terminated by a word of binary
zeros. NEWTRAN schedules the task In the order they appear on the list.
Figure 2-7. NEWTRAN Parameter Table
60459500 B 2-7
TRANCHK Request
The T RA NC HK request d et er mi nes th e status of a
transaction. This request is provided only for
COMPASS.
The format is:
COMPASS
TRANCHK address
address Address of a parameter table in
the form shown in figure 2-8.
BLDABH
Builds the application block header to use
different character types, terminal format
effectors, and auto input.
• GETABH
Returns the last application block header to
the task.
• TERMDEF
Defines the operational controls or format
of the terminal.
/■fSSsV
INPUT/OUTPUT REQUESTS
The following requests are associated with
input/output.
• WAITINP
Places terminal input data in the
communication block. Equivalent to a read
request.
• LOADCB
Reads data that overflowed the communication
block.
• SETCHT
Sets character type for terminal input.
• S E N D
Sends data to terminal. Equivalent to a
write request.
• RELSCB
Releases memory used for extra communication
blocks.
• T S I M
Reads terminal status table.
• TA R O
Writes into terminal status table.
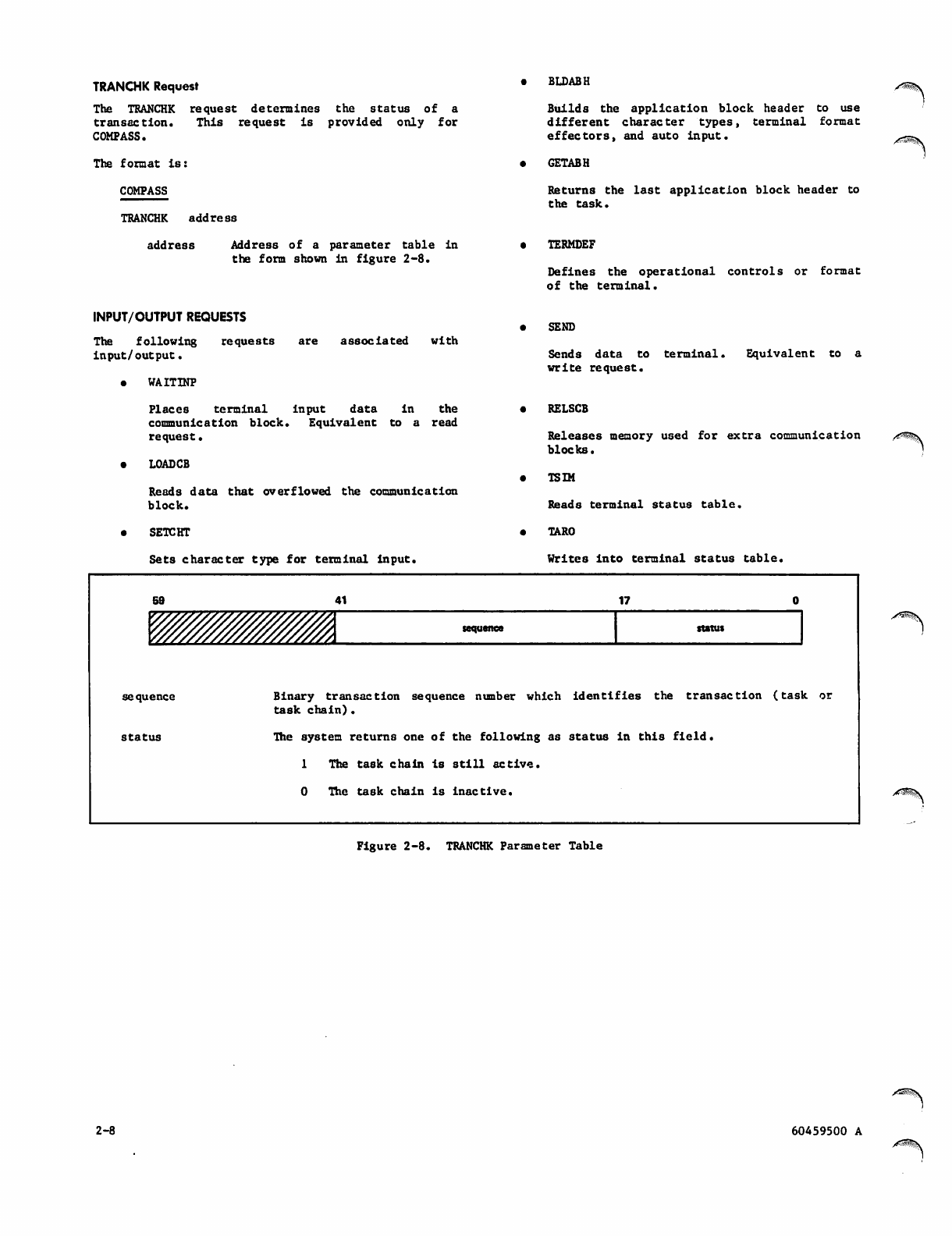
59 4 1 1 7
y///y////vyywyffiwZ'. sequence status
sequence Binary transaction sequence number which identifies the transaction
task chain).
( t a s k o r
st a t u s The system returns one of the following as status in this field.
1 The task chain is still active.
0 The task chain is Inactive.
,<?S^v
/ s l %
Figure 2-8. TRANCHK Parameter Table
2-8 60459500 A
no
Limits total number of requests (RA+1 calls)
a task can make.
BWAITINP
Specifies that terminal input data is to be
placed in a location in the task field length
that is not reserved for the communication
block.
TPSTAT
Returns a value indicating that the active
terminal subsystem is NAM.
BEGIN
When a WAITINP request is processed, all communica
tion blocks are released and the task is rolled out.
All data in the communication block, except the
transaction sequence number, will be lost, so the
user should save any data to be preserved prior to
the request. When input arrives from the terminal, a
new communication block is generated, and the task is
restarted. The new communication block will contain
the transaction sequence number associated with the
task prior to the WAITINP request. If the request
does not return a normal status, the information in
the communication block is meaningless.
The format is:
COBOL
ENTER WAITINP USING status time.
Specifies the area where the terminal trans
m i s s i o n i s to b e pl a c e d i n t h e t a s k fie l d
length. It does not return the communication
block to the first word address of the task
unless the task requests.
s t a t u s C o m p u t a t i o n a l - l i t e m t h a t t h e
system sets to indicate the sta
tus of the WAITINP request. Upon
completion of the request, status
has one of the following values.
J ^ ^
j^^\
WAITINP Request
The WAITINP request (wait for terminal input) reads
data from a terminal. Internally, this request in
forms the transaction executive that the next input
received from a terminal is to be passed directly to
t h e r eq u e s t i n g t a s k an d i s no t t o i n i t i a t e a ne w
transaction. The data entered is placed in the mes
sage area of the communication block. The data held
in the communication block prior to the WAITINP is
lost.
The first parameter is a data item or variable whose
value the system sets to indicate the reception of
terminal input or an error condition. An optional
second parameter of the request specifies a time
limit, after which processing of the transaction is
restarted even if no input has been received from
the terminal. time
NOTE
0 T h e r e q u e s t p r o c e s s e d
normally; terminal input
appears in the normal
input portion (begins in
t h e t h i r d w o r d ) o f t h e
communication block.
< 0 Another task is waiting
for input from the origi
nating terminal. The
WAITINP request must be
reissued if input is
desired.
> 0 The time delay elapsed
before input was received
from the terminal.
Computational-l item that con
tains the time limit, in decimal
s e c o n d s , t o w a i t f o r i n p u t . I f
not specified, the default is 480
seconds. The maximum value is
2048 seconds.
CM-resident tasks and tasks not asso
ciated with a terminal (batch origin)
are not permitted to make a WAITINP
request (task aborts).
At least one message (SEND) must be
sent to the terminal before making a
WAITINP request, and at least one SEND
request from the original task chain
must follow a message received follow
ing a WAITINP request.
No data manager requests may be active
when a task makes a WAITINP request.
All tasks that make WAITINP requests
mu st be e nte red in t he task libr ar y
with the scheduling queue limit set
to one. (Refer to section 10.)
WAITINP does not cause any data mana
ger cease requests to be Issued.
Therefore, any resources locked or
reserved by a transaction prior to a
WAITINP continue to be Locked or
reserved during and after the WAITINP.
FORTRAN
CALL WAITINP(status,time)
st a t u s Integer variable that the system
sets to indicate the status of
the WAITINP request. Upon com
pletion of the request, status
has one of the following values.
0 T h e r e q u e s t p r o c e s s e d
normally; terminal input
appears in the normal
Input portion (begins in
t h e t h i r d w o r d ) o f t h e
communication block.
< 0 Another task is waiting
for input from the origi
nating terminal. The
WAITINP request must be
reissued if input is
desired.
60459500 C 2-9

> 0 The time delay elapsed
before input was received
from the terminal.
time Integer time limit, in decimal
s e c o n d s , t o w a i t f o r i n p u t . I f
not specified, the default is
480 seconds. The maximum value
is 2048 seconds.
The overflow data can be requested as many times
d u r i n g a t r a n s a c t i o n a s d e s i r e d . E a c h t i m e , t h e
overflow data is transmitted as specified previously.
The format is:
COBOL
^^\
ENTER LOADCB USING buffer status r.
COMPASS
WAITINP time
time
buffer
status
Time limit, in decimal seconds,
to wait for input. If not
specified, the default is 480
seconds. The maximum value is
2048 seconds.
Status of the WAITINP macro is determined by the
following:
• Word 2 of the communication block contains 1
if the time delay elapsed before input wa s
received from the terminal.
• The X6 register contains a negative value if
an o t h er t a sk i s w a i t ing fo r in p u t f r o m t h e
originating terminal. The WAITINP request
must be reissued if input is desired. (Word
2 o f t h e c o m m u n i c a t i o n b l o c k s h o u l d b e
checked before X6 is checked.)
• The X6 register is set to zero if the request
processed normally; terminal input appears in
the normal input portion (begins in the third
word) of the communication block. (Word 2 of
the communication block should be checked
before X6 is checked.)
LOADCB Request
If the transaction input data exceeds the message
area of the communication block, bit 12 of word 1 of
the communication block (the i field) is set. The
LOADCB request loads the remainder of the input
message into a user-defined buffer. This buffer is
a single contiguous block of storage for all
additional communication blocks. No headers or
trailers appear In this area.
The maximum input size is determined by an installa
tion parameter.
The data that remains after the communication block
message area fills (referred to here as overflow
data) is transferred to the user-defined buffer. If
the LOADCB request is made with no data overflow (i
field not set) or if a RELSCB request was made prior
to the LOADCB request, no data is transferred and the
s t a t u s w o r d i s s e t t o z e r o . I f th e o v e r fl o w d a t a
consists of more words than will fit in the buffer,
the bu ffer is filled, an d th e status wor d is set to
a value greater than the number of words in the
buffer. If the overflow data can be contained in
the buffer, the overflow data is transferred to the
buffer, and the number of words transferred is set
in the status word.
A 01-level item identifying the
user-defined buffer area.
Computational-l item that the
system sets to indicate the
LOADCB equest status. The
significance of the value set
has been described earlier in
the LOADCB request description.
Computational-l item. If a non
zero value is entered for this
parameter, any message data that
overflows the LOADCB buffer spec
ified with the buffer parameter
is released (same as RELSCB).
FORTRAN
CALL L0ADCB(buffer,length,status,r)
b u f f e r A n a r r a y i d e n t i f y i n g t h e u s e r -
defined buffer area.
length Integer length of the array spec
ified with the buffer parameter
in words.
s t a t u s V a r i a b l e t h a t t h e s y s t e m s e t s t o
Indicate the LOADCB request
status. The significance of the
value set has been described
earlier in the LOADCB request
description. This value is also
returned as the value of the
function, if LOADCB is called as
a FORTRAN function.
r Integer variable. If a nonzero
value is entered for this param
eter, any message data that over
flows the LOADCB buffer specified
w i t h t h e b u f f e r p a r a m e t e r i s
released (same as RELSCB).
As stated in the description of the status
parameter, the LOADCB request can be referenced as a
FORTRAN function. The format of the function is
LOADCB(buffer,length,status ,r); the parameters are
the same as those already described. The value of
the function is the value of the status parameter.
COMPASS
LOADCB address
address Address of a parameter table in
the format shown in figure 2-9.
/ S ^ .
The LOADCB macro status is returned in the X6 regis
ter. The significance of the value returned has been
described earlier in the LOADCB request description.
2-10 60459500 B
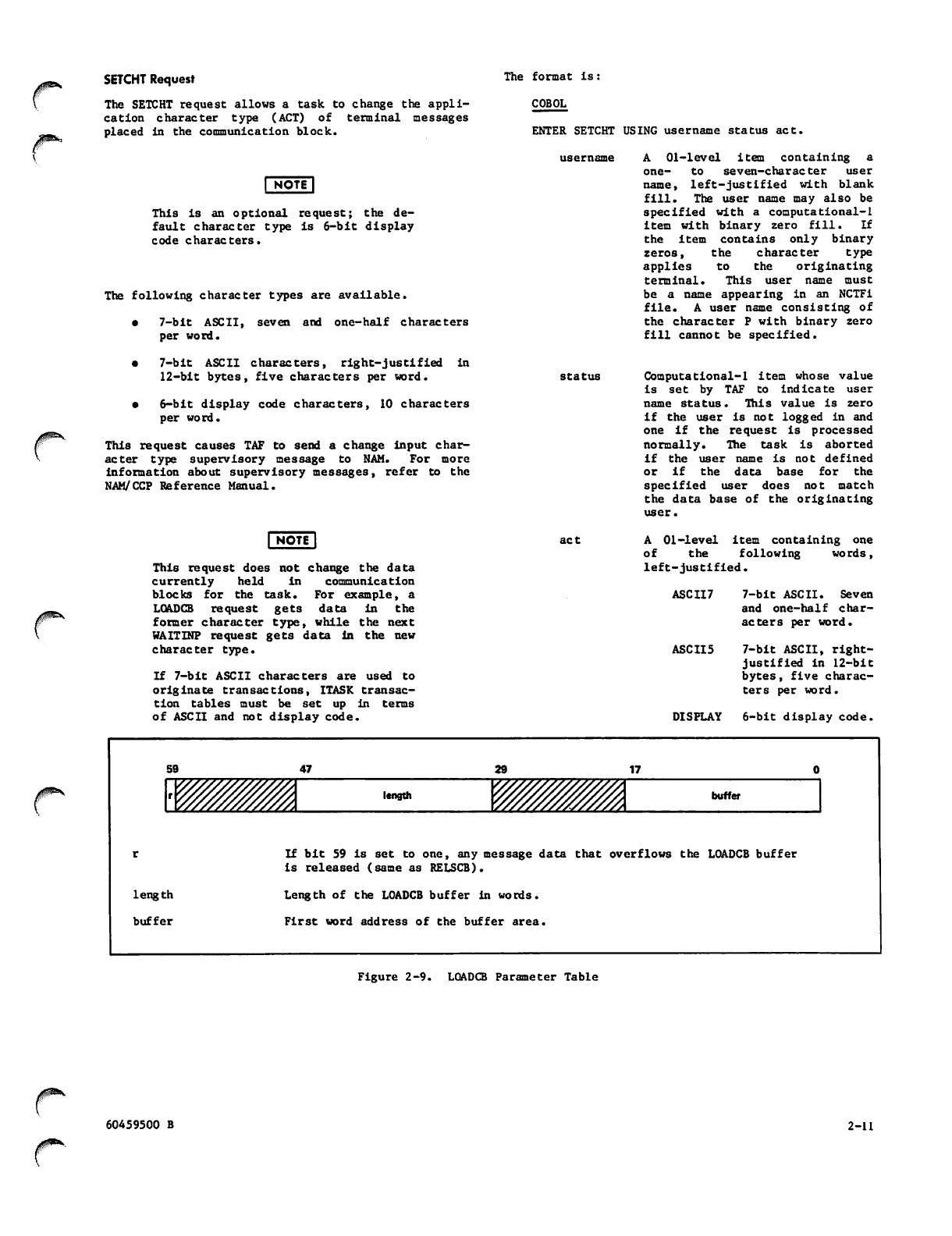
SETCHT Request
The SETCHT request allows a task to change the appli
cation character type (ACT) of terminal messages
placed in the communication block.
rNOTTI
This is an optional request; the de
fault character type is 6-bit display
code characters.
The following character types are available.
• 7-bit ASCII, seven and one-half characters
per word.
• 7 - b i t A S C I I c h a r a c t e r s , r i g h t - j u s t i f i e d i n
12-bit bytes, five characters per word.
• 6-bit display code characters, 10 characters
per word.
This request causes TAF to send a change input char
acter type supervisory message to NAM. For more
information about supervisory messages, refer to the
NAM/CCP Reference Manual.
The format is:
COBOL
ENTER SETCHT USING username status act.
username
st a t u s
NOTE act
This request does not change the data
currently held in communication
blocks for the task. For example, a
LOADCB request gets data in the
former character type, while the next
WAITINP request gets data in the new
character type.
If 7-bit ASCII characters are used to
originate transactions, ITASK transac
tion tables must be set up in terms
of ASCII and not display code.
A 0 1 - l e v e l i t e m c o n t a i n i n g a
one- to seven-character user
name, left-justified with blank
fill. The user name may also be
specified with a computational-l
item with binary zero fill. If
the item contains only binary
zeros, the character type
applies to the originating
terminal. This user name must
be a name appearing in an NCTFi
file. A user name consisting of
the character P with binary zero
fill cannot be specified.
Computational-l item whose value
is s e t by TAF t o in d i ca te use r
name status. This value is zero
if the user is not logged in and
one if the request is processed
normally. The task is aborted
if the user name is not defined
o r i f t h e d a t a b a s e f o r t h e
specified user does not match
the data base of the originating
user.
A 01-level item containing one
of the following words,
left-justified.
ASCII7 7-bit ASCII. Seven
and one-half char
acters per word.
A S C I I S 7 - b i t A S C I I , r i g h t -
j u s t i fi e d i n 1 2 - b i t
bytes, five charac
ters per word.
DISPLAY 6-bit display code.
59 4 7 2 9 17
rWatMlength '<M[MW/a buffer
r
lengt
bu ffe
h
r
If bit 59 is set to one, any message data
is released (same as RELSCB).
Length of the LOADCB buffer in words.
First word address of the buffer area.
that overflows the LOADCB buffer
Figure 2-9. LOADCB Parameter Table
60459500 B 2-11

FORTRAN
CALL SETCHT(username,status ,act)
status
act
One- to seven-character user
name, left-justified with zero
o r b l a n k fi l l . I f t h e t e r m i n a l
name is zero, the character type
applies to the originating termi
nal. This user name must be a
name appearing in an NCTFi file.
Unnormalized floating-point num
ber whose value specifies the
user name status. This value is
z e r o i f t h e us e r i s n o t l o g g e d
i n a n d o n e i f t h e r e q u e s t i s
processed normally.
The task is aborted if the user
name is not defined or if the
data base for the specified user
does not match the data base of
the originating user.
Parameter containing one of the
following words, left-justified
with binary zero or blank fill.
A S C I I 7 7 - b i t A S C I I , s e v e n
and one-half char
acters per word.
ASCII5 7-bit ASCII, right-
justified in 12-bit
bytes, five charac
ters per word.
DISPLAY 6-bit display code.
COMPASS
SETCHT address
address Address of a parameter table in
the form shown in figure 2-10.
BLDABH Request
The BLDABH request builds or modifies the application
block header (ABH). This header accompanies every
block passing between TAF and NAM, and thus is used
during communication between TAF and terminals. It
contains detailed information describing the block
it accompanies.
• Tr a ns p a r e n t mo d e s p e c i f i c a t i o n . Tr a n s p a r e n t
mode inhibits all data transforms and allows
the task direct access to the real terminal
fe at ure s.
• T e r m i n a l f o r m a t e f f e c t o r s p e c i f i c a t i o n .
Format effectors control printing (or the
cursor on display terminals).
• Auto-input mode specification. Auto-input
mode allows a fill in the form type of trans
action. This is provided since the first n
characters of a message output to the termi
nal via the SEND request (ABT=2 only) can be
used to form the first n characters of subse
quent input from the terminal. If n is
greater than 20, only the first 20 characters
are returned, followed by the entered text.
It is not necessary to use the BLDABH request before
every SEND. It is needed when a selectable param
eter on the ABH for the next SEND differs from a
setting on the ABH for the previous SEND. In other
wo r ds, a set t ing of a pa r a me t e r o nce se l ect e d b y
BLDABH stays In effect for that task unless changed
by a subsequent BLDABH request. If a task issues a
BLDABH request and then calls another task, the new
task must also issue a BLDABH request because the
request parameters are not passed to it. If a task
i s t o b e r e u s a b l e , t h e t a s k s h o u l d i n i t i a l i z e t h e
ABH if the default values have been changed.
D e f a u l t v a l u e s a r e s u p p l i e d o n t h e A B H . I f t h e
default values are the desired values, no BLDABH
request is required. Default values have been
selected to remain compatible with prior versions of
the transaction subsystem.
The format is:
COBOL
ENTER BLDABH USING fieldj value j.. .fie ldn valuen.
field£ A 01-level item containing a
three-character, left-justified
field for which a value is to be
set. field £ can be binary zero
or blank-filled. The possible
values are listed in table 2-1.
value£ A computational-l item whose
value is set for the correspond
ing fieldj. The fieldi and
value£ parameters must appear
in pairs. The possible values
a n d d e s c r i p t i o n s a r e l i s t e d i n
table 2-1.
.^^t\
(4"£fl?^V
This is an optional request. The
default application block header spec
ifies 6-bit display code characters,
nontransparent mode, no format effec
tors, and no auto input.
To use some of the NAM features, a task must use the
BLDABH request to modify the ABH. Some of the
features provided via the ABH are:
• Character type specification of messages sent
t o a t e r m i n al . Ei t h e r 7 - b i t A S C I I o r 6 - b i t
display code characters may be used.
FORTRAN
CALL BLDABH(field1,value1,...,fieldn,valuen)
fields Variable containing a three-
c h a r a c t e r , l e f t - j u s t i fi e d fi e l d
for which a value is to be set.
fieldj can be binary zero or
blank-filled. The possible
values are listed in table 2-1.
value £ Integer that is set for the
corresponding fieldj. The
fieldi and value^ parameters
must appear in pairs. The
possible values and descriptions
are listed in table 2-1.
2-12 604S9500 B
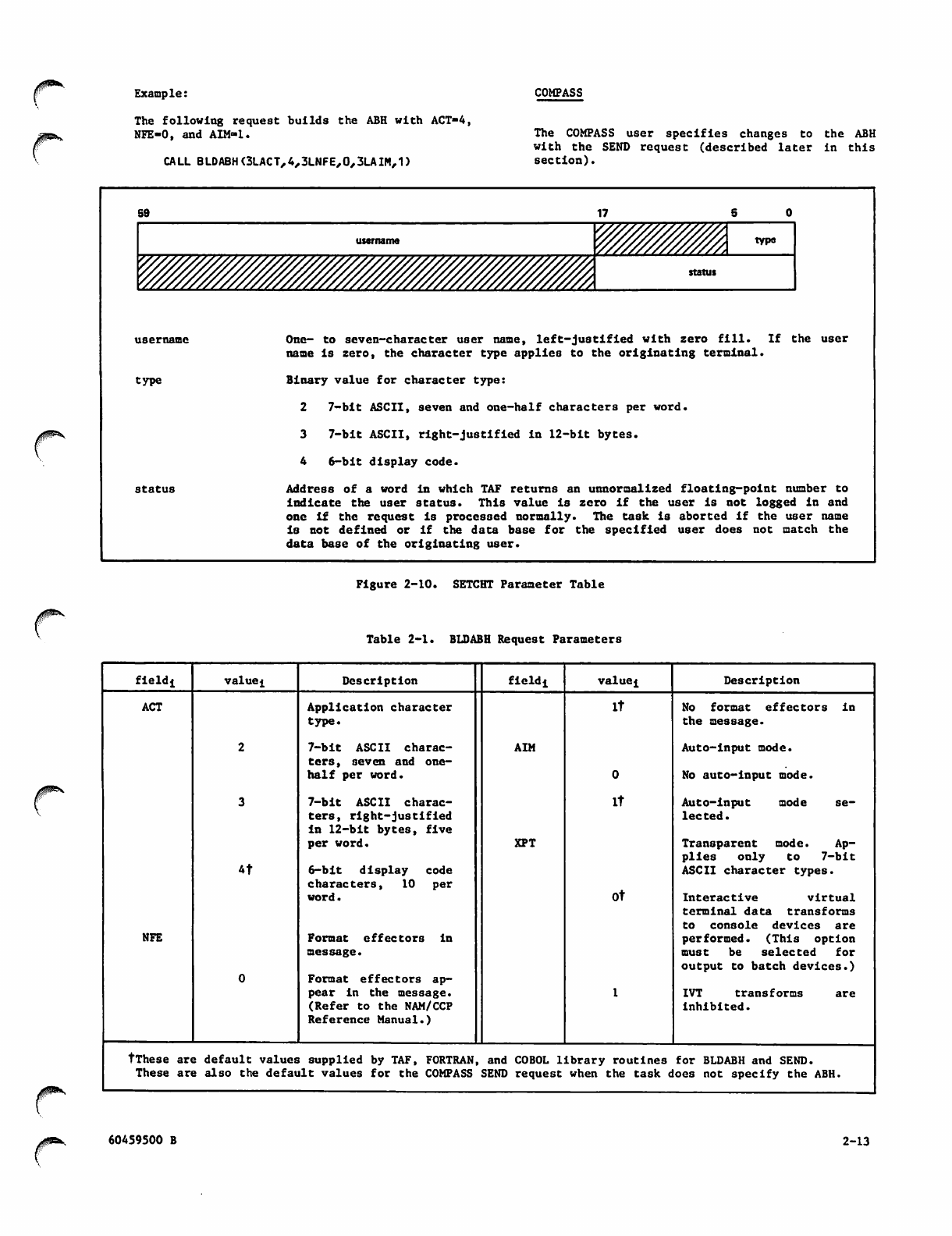
Example: COMPASS
The following request builds the ABH with ACT-4,
NFE-O, and AIM-1.
CALL BLDABH<3LACT,4,3LNFE,0,3LAIM,1)
The COMPASS user specifies changes to the ABH
with the SEND request (described later in this
section).
59 17 5 0
username S//0//A' ^ ^ type
ffl
mm mmmmm mstatus
username
type
status
One- to seven-character user name, left-justified with zero fill. If the user
name is zero, the character type applies to the originating terminal.
Binary value for character type:
2 7-bit ASCII, seven and one-half characters per word.
3 7 - b i t A S C I I , r i g h t - j u s t i fi e d i n 1 2 - b i t b y t e s .
4 6-bit display code.
Address of a word in which TAF returns an unnormalized floating-point number to
indicate the user status. This value is zero if the user is not logged in and
one if the request is processed normally. The task is aborted if the user name
is not defined or if the data base for the specified user does not match the
data base of the originating user.
JpSx.
Figure 2-10. SETCHT Parameter Table
Table 2-1. BLDABH Request Parameters
0&»i
fieldj valuej Description fieldi value£ Description
ACT Application character
type.
It No format effectors in
the message.
2 7-bit ASCII charac
ters, seven and one-
AIM Auto-input mode.
half per word. No auto-input mode.
3 7-bit ASCII charac
ters, right-justified
in 12-bit bytes, five
It Auto-input mode se
lected.
per word. XPT Tr a n s p a r e n t m o d e . A p
plies only to 7-bit
4t 6-bit display code
characters, 10 per
ASCII character types.
word. Ot Interactive virtual
termin al d ata tra nsforms
t o c o n s o l e d e v i c e s a r e
NFE F o r m a t e f f e c t o r s i n
message.
Format effectors ap
performed. (This option
m u s t b e s e l e c t e d f o r
output to batch devices.)
pear in the message. IVT transforms are
(Refer to the NAM/CCP inhibited.
Reference Manual.)
TThese ar<s default values supplied by TAF, FORTRAN, and COBOL library routines for BLDABH and SEND.
These ar<z also the defailit values for the COMPASS SEND request when the task d oes not specify the ABH.
0^- 60459500 B 2-13
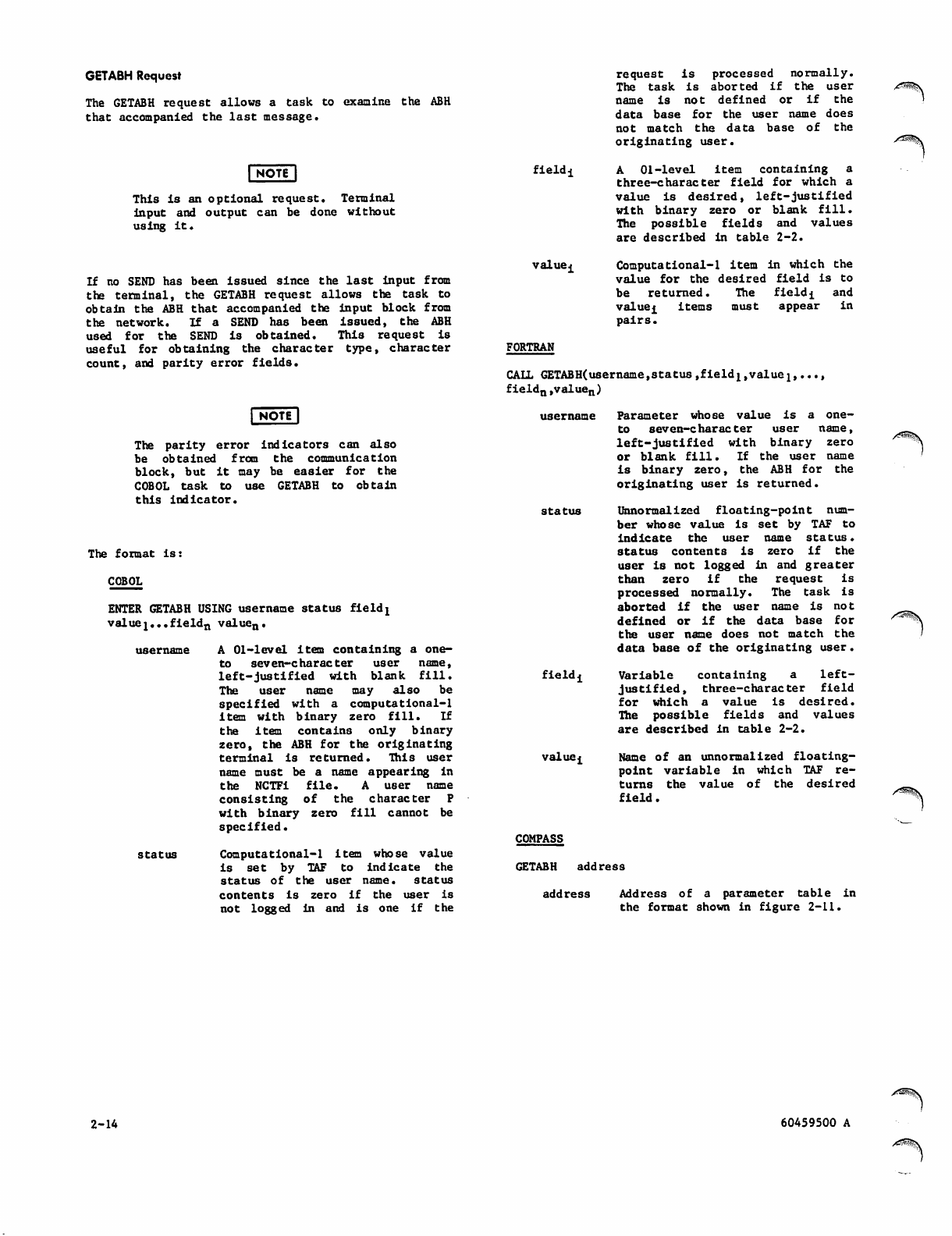
GETABH Request
The GETABH request allows a task to examine the ABH
that accompanied the last message.
NOTE
This is an optional request. Terminal
input and output can be done without
using it.
request is processed normally.
T h e t a s k i s a b o r t e d i f t h e u s e r
name is not defined or if the
data base for the user name does
n o t m atch t h e d a t a ba s e o f t h e
originating user.
fields A 01-level item containing a
three-character field for which a
value is desired, left-justified
with binary zero or blank fill.
The possible fields and values
are described in table 2-2.
/?Ǥ^v
If ro SEND has been issued since the last input from
the terminal, the GETABH request allows the task to
obtain the ABH that accompanied the input block from
the network. If a SEND has been issued, the ABH
u s e d f o r t h e S E N D i s o b t a i n e d . T h i s r e q u e s t i s
useful for obtaining the character type, character
count, and parity error fields.
("note"!
The parity error indicators can also
be obtained from the communication
block, but it may be easier for the
COBOL task to use GETABH to obtain
this indicator.
The format is:
COBOL
ENTER GETABH USING username status field}
value}...fleldn valuen.
username A 01-level item containing a one-
to seven-character user name,
left-justified with blank fill.
The user name may also be
specified with a computational-l
i t e m w i t h b i n a r y z e r o fi l l . I f
the item contains only binary
zero, the ABH for the originating
terminal is returned. This user
name must be a name appearing in
the NCTFi file. A user name
consisting of the character P
with binary zero fill cannot be
specified.
status Computational-l item whose value
is set by TAF to indicate the
status of the user name. status
c o n t e n t s i s z e r o i f t h e u s e r i s
no t log ge d i n a nd is o ne if t he
value^ Computational-l item in which the
va l u e f or t h e d e sired fi e l d i s t o
be returned. The fieldi and
value^ items must appear in
pairs.
FORTRAN
CALL GETABH(username,status,field},value},...,
fieldn,valuen)
username Parameter whose value is a one-
to seven-character user name,
left-justified with binary zero
or blank fill. If the user name
is b i n a ry z e r o , the A B H f or t h e
originating user is returned.
status Unnormalized floating-point num
ber whose value is set by TAF to
indicate the user name status,
status contents is zero if the
user is not logged in and greater
t h a n z e r o i f t h e r e q u e s t i s
processed normally. The task is
aborted if the user name is not
d e fi n e d o r i f t h e d a t a b a s e f o r
the user name does not match the
data base of the originating user.
fieldA Variable containing a left-
justified, three-character field
for which a value is desired.
The possible fields and values
are described in table 2-2.
value£ Name of an unnormalized floating
point variable in which TAF re
turns the value of the desired
field.
COMPASS
GETABH address
a d d r e s s A d d r e s s o f a p a r a m e t e r t a b l e i n
the format shown in figure 2-11.
2-14 60459500 A
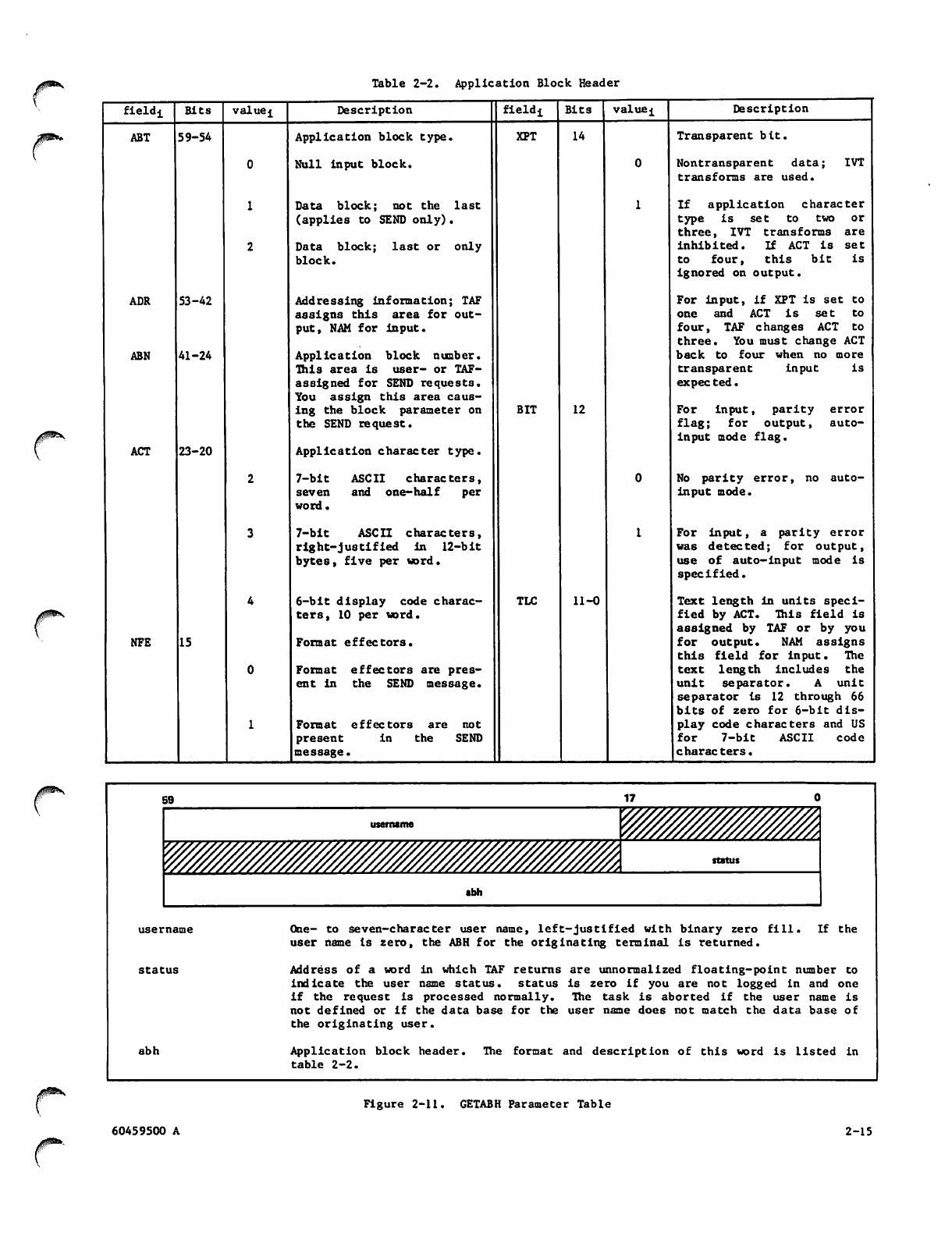
Table 2-2. Application Block Header
0$^*..
fieldi
ABT
ADR
ABN
ACT
Bits
59-54
53-42
41-24
23-20
NFE
value h
15
Description
Application block type.
Null input block.
Data block; not the last
(applies to SEND only).
Data block; last or only
block.
Addressing information; TAF
assigns this area for out
put, NAM for Input.
Application block number.
This area is user- or TAF-
assigned for SEND requests.
You assign this area caus
ing the block parameter on
the SEND request.
Application character type.
7-bit ASCII characters,
seven and one-half per
word.
7-bit ASCII characters,
right-justified in 12-bit
bytes, five per word.
6-bit display code charac
ters, 10 per word.
Format effectors.
Format effectors are pres
ent in the SEND message.
Format effectors are not
present in the SEND
message.
fieldi
XPT
BIT
TLC
Bits
14
12
value£
11-0
Description
Transparent bit.
Nontransparent data; IVT
transforms are used.
If application character
t y p e i s s e t t o t w o o r
three, IVT transforms are
inhibited. If ACT is set
t o f o u r , t h i s b i t i s
ignored on output.
For input, if XPT is set to
o n e a n d A C T i s s e t t o
four, TAF changes ACT to
three. You must change ACT
back to four when no more
transparent input is
expec ted.
For input, parity error
flag; for output, auto-
input mode flag.
No parity error, no auto-
input mode.
For input, a parity error
was detected; for output,
use of auto-inp ut m ode is
specified.
Text length in units speci
fie d by A C T. This fie l d i s
assigned by TAF or by you
for output. NAM assigns
t h i s fi e l d f o r i n p u t . T h e
text length includes the
unit separator. A unit
separator is 12 through 66
bits of zero for 6-bit dis
play code characters and US
for 7-bit ASCII code
characters.
59
username
st a t u s
abh
17
username ' # # %
Wvyytvyyyfvy J9Zf%% status
abh
One- to seven-character user name, left-justified with binary zero fill.
user name is zero, the ABH for the originating terminal is returned.
If th e
Address of a word in which TAF returns are unnormalized floating-point number to
indicate the user name status, status is zero if you are not logged in and one
if the request is processed normally. The task is aborted if the user name is
not defined or if the data base for the user name does not match the data base of
the originating user.
Application block header,
table 2-2.
The format and description of this word is listed in
jp>v
60459500 A
Figure 2-11. GETABH Parameter Table
2-15

TERMDEF Request
The TERMDEF request can be used by a task to define
or modify terminal characteristics, where those of
the connected real terminal differ from the assump
tions made for the network's IVT model. This request
can also be used to tailor the operational controls
of the terminal.
I note"!
This is an optional request. Terminal
input and output can be done without
it . E a c h t e r m i n a l t h a t l ogs i n t o the
network is associated with a default
se t of t e rmi n al c har a cte r ist i cs. (R e
fer to appendix G.)
A complete list of terminal characteristics is pro
vided in the NAM/CCP Reference Manual and appendix G
of this manual. Characteristics that may be modified
include:
• Terminal physical page width.
• Number of physical lines on a terminal page.
• Specification of a character used to cancel
an input logical line in progress.
• Specification of a character to be used as a
break character. User breaks are sent to
the application task for processing.
• Set transparent input mode. This setting
exists for only one logical input line.
The format is:
COBOL
ENTER TERMDEF USING username status field}
field2...fieldn.
username A 01-level item containing a
one- to seven-character user
name, left-justified with blank
fill. The user name may also be
specified with a computational-l
item with binary zero fill. If
the item contains only binary
zero, the terminal definition
specified applies to the
originating terminal. This user
name must be a name appearing in
an NCTFi file. A user name
c o n s i s t i n g o f t h e c h a r a c t e r P
with binary zero fill cannot be
specified.
status Computational-l item that TAF
sets to indicate user name
status, status contents is zero
if the user is not logged in and
is one if the request is
processed normally. The task is
aborted if the user name is not
defined or if the user's data
b a s e do es n o t m a t c h the d a ta
base of the originating user.
fieldi A left-justified 01-level item
with binary zero or blank fill,
containing the characteristic
(for example, PW»60, PL»35, or
CN -2 B) . A maximum of 17 n on -
blank, nonbinary zero characters
i s a l l o w e d . T h e c h a r a c t e r i s t i c s
are described in the NAM/CCP
Reference Manual and appendix G
of this manual. If the NAM/CCP
Reference Manual specifies x or
h, a 6-bit display code alphanu
meric representation is required
(where x is a 7-bit ASCII charac
ter and h is a hexadecimal
character).
FORTRAN
CALL TERMDEF(username,status ,field},
fi e l d 2 , . . . , fi e l d n )
username Parameter whose value is a one-
to seven-character user name,
left-justified with binary zero
or blank fill. If the user name
i s z e r o , t h e t e r m i n a l d e fi n i t i o n
specified applies to the origi
nat ing termi nal. This user name
must be a name appearing in an
NCTFi file.
status Variable in which TAF places an
unnormalized floating-point num
ber to indicate user name status.
status contents is zero if the
user is not logged in and greater
than zero if the request is proc
essed normally. The task is
aborted if the user name is not
defined or if the data base for
the user does not match the data
base of the originating user.
fieldi A left-justified variable with
binary zero or blank fill, con
taining the characteristic (for
example, PW-60, PL=35, or CN=2B).
A maximum of 17 nonblank, non-
binary zero characters is
allowed. The characteristics
are described in the NAM/CCP
Reference Manual and appendix G
of this manual. If the NAM/CCP
Reference Manual specifies x or
h, a 6-bit display code alpha
numeric representation is
required (where x is a 7-bit
ASCII character and h is a
hexadecimal character).
Example:
The following request designates the page width
to be 60 characters, the page length to be 40
lines, and the plus character (ASCII representa
tion is 2B) to be the cancel character for user
USER5; it then assigns the status to variable
STATUS.
CALL TERMDEFC5HUSER5,STATUS,5LPW=60,
5LPL=40,5LCN=2B>
y£-»!S\
2-16 60459500 B
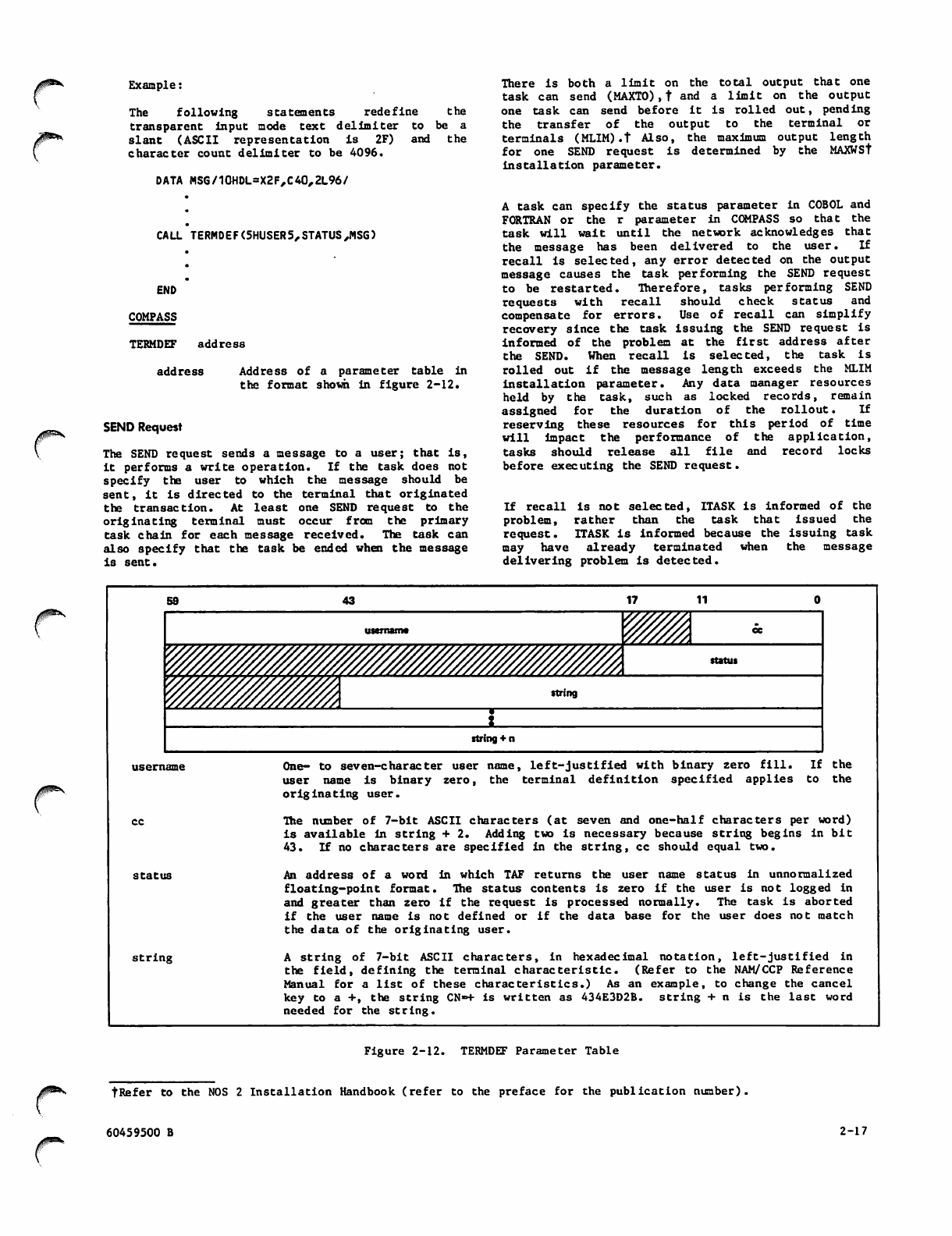
f^ Example:
The following statements redefine the
transparent input mode text delimiter to be a
slant (ASCII representation is 2F) and the
character count delimiter to be 4096.
DATA MSG/10HDL=X2F,C40,2L96/
CALL TERMDEF(5HUSER5,STATUS,MSG>
END
COMPASS
TERMDEF address
address Address of a parameter table in
the format shown in figure 2-12.
SEND Request
The SEND request sends a message to a user; that is,
it performs a write operation. If the task does not
specify the user to which the message should be
se nt , i t is direc te d t o the ter mi nal t hat o rig in at ed
the transaction. At least one SEND request to the
originating terminal must occur from the primary
task chain for each message received. The task can
also specify that the task be ended when the message
is sent.
There is both a limit on the total output that one
task can send (MAXTO), t and a limit on the output
one task can send before it is rolled out, pending
the transfer of the output to the terminal or
terminals (MLIM).t Also, the maximum output length
for one SEND request is determined by the MAXWSt
Installation parameter.
A task can specify the status parameter in COBOL and
FORTRAN or the r parameter in COMPASS so that the
task will wait until the network acknowledges that
the message has been delivered to the user. If
recall is selected, any error detected on the output
message causes the task performing the SEND request
to be restarted. Therefore, tasks performing SEND
requests with recall should check status and
compensate for errors. Use of recall can simplify
recovery since the task issuing the SEND request is
in f o r med of th e pr o b lem at th e fir s t a d d ress af t e r
the SEND. When recall is selected, the task is
rolled out if the message length exceeds the MLIM
installation parameter. Any data manager resources
held by the task, such as locked records, remain
assigned for the duration of the rollout. If
reserving these resources for this period of time
will impact the performance of the application,
tasks should release all file and record locks
before executing the SEND request.
If recall is not selected, ITASK is informed of the
problem, rather than the task that issued the
request. ITASK is informed because the issuing task
may have already terminated when the message
delivering problem is detected.
59 43 17 11
username //^
Wa ec
yyyyyyyyyyy
W, status
y/fflffl$y
WWk string
z
string + n
status
string
One- to seven-character user name, left-justified with binary zero fill. If the
user name is binary zero, the terminal definition specified applies to the
originating user.
The number of 7-bit ASCII characters (at seven and one-half characters per word)
is available in string + 2. Adding two is necessary because string begins in bit
43. If no characters are specified in the string, cc should equal two.
An address of a word in which TAF returns the user name status in unnormalized
floating-point format. The status contents is zero if the user is not logged in
and greater than zero if the request is processed normally. The task is aborted
if the user name is not defined or if the data base for the user does not match
the data of the originating user.
A s t r i n g o f 7 - b i t A S C I I c h a r a c t e r s , i n h e x a d e c i m a l no t a t i o n , le f t - j u s t i fi e d i n
the field, defining the terminal characteristic. (Refer to the NAM/CCP Reference
Manual for a list of these characteristics.) As an example, to change the cancel
key to a +, the string CN«*f is written as 434E3D2B. string + n is the last word
needed for the string.
Figure 2-12. TERMDEF Parameter Table
^^K tRefer to the NOS 2 Installation Handbook (refer to the preface for the publication number)
60459500 B 2-17
The format of the message on the terminal depends on
the terminal class and the format effectors in the
message. For example, on synchronous terminals the
cursor for entering the next message to the host
(upline) is always the first character of the line.
On asynchronous terminals the cursor follows the
last character of output; this assumes no format
effectors are in the message. The NAM/CCP Reference
Manual contains complete information on terminal
protocols.
The format is:
COBOL
ENTER "SEND" USING messageaddress username
cease-flag output-flag block status length.
The parameters are described in table 2-3.
FORTRAN
CALL SEND(messageaddress,length,username,
cease-flag.output-flag,block,status)
The parameters are described in table 2-4.
COMPASS
SEND address
address Address of a
the format
2-13. This
parameters in
be us ed wit h
table shows
b e t w e e n S E N D
Setting parameters
parameter table in
shown in figure
figure and the
table 2-5 should
table 2-6. This
interrela tionships
parameters.
shown in the
NOTE
top portion of table 2-6 results
in the corresponding events
shown in the bottom portion.
Under COBOL, SEND must be enclosed in
quotation marks, because SEND is a
reserved word for that compiler.
The entire four-word block must be present, even
if the last three words are not used.
Table 2-3. COBOL SEND Request Parameters (Sheet 1 of 2)
Parameter Data Type Value Description
messageaddress 01-level display item Data item containing the message to be sent. For 7-bit
ASCII character types, the message must have an end-of-
line byte of the single character US for all logical
lines. (Refer to the NAM/CCP Reference Manual for NAM
data formats.) The TAF SEND interface supplies end-of-
line bytes for 6-bit display code character types only.
username 01-level display item, Data item containing a one- to seven-character user
or computational-l name. If this parameter is omitted or specified as
C0MP-1 VALUE ZERO, the message is sent to the originat
ing terminal. This user name must be a name appearing
in the NCTFi file and must be validated for the same
data base as the sending task.t A user name consisting
of the character P with binary zero fill cannot be
specified. The user name can be binary zero or blank-
filled.
cease-flag Computational-l Task end flag.
0, omitted The task continues after the message is sent.
1 The task ends after the message is sent.
tTasks associate d with application identifier SY can SEND to any valid TAF user.
/^B5X
2-18 60459500 B
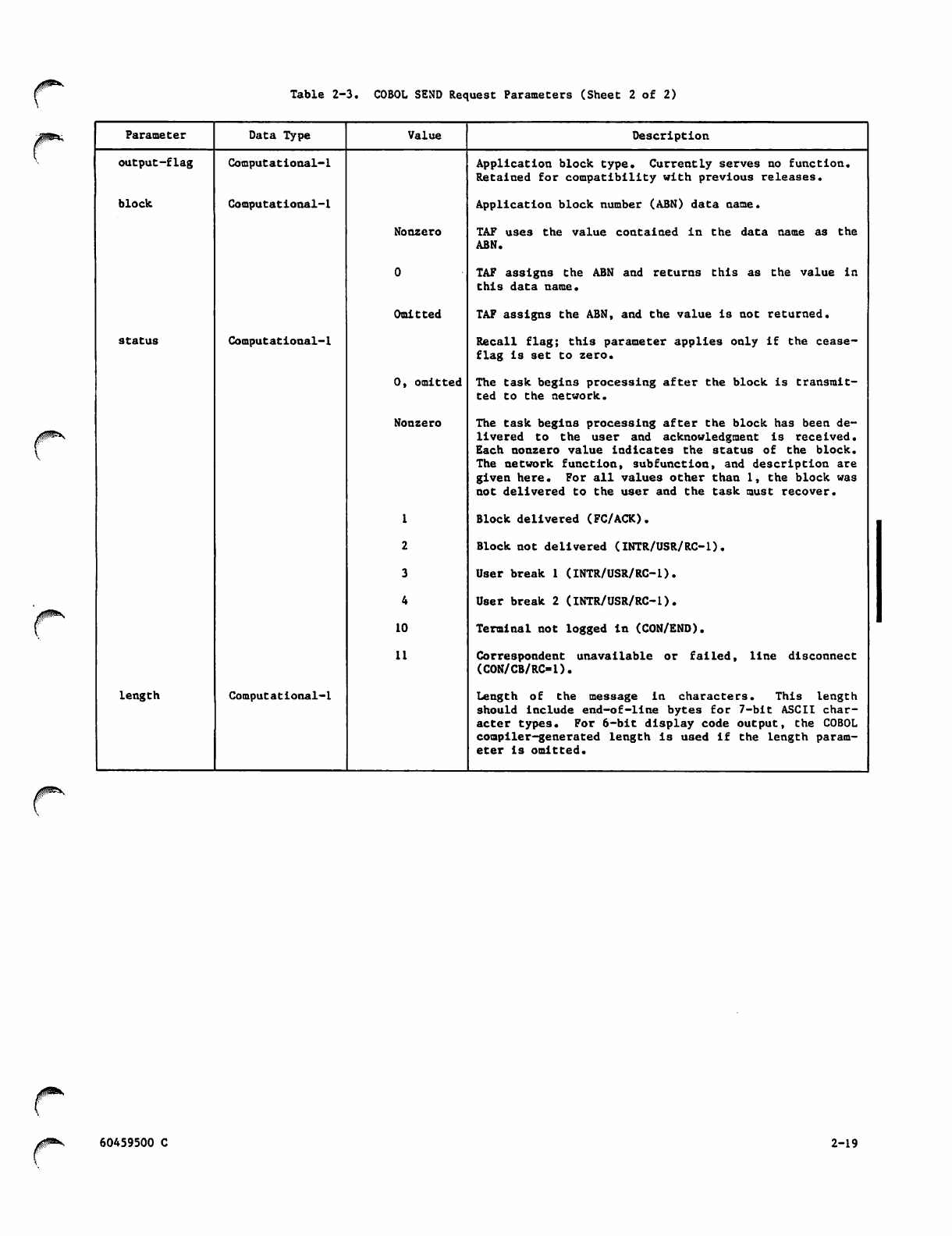
Table 2-3. COBOL SEND Request Parameters (Sheet 2 of 2)
Parameter Data Type Value Description
output-flag Computational-l Application block type. Currently serves no function.
Retained for compatibility with previous releases.
block Computational-l Application block number (ABN) data name.
Nonzero TAF uses the value contained in the data name as the
ABN.
0TAF assigns the ABN and returns this as the value in
this data name.
Omitted TAF assigns the ABN, and the value is not returned.
status Computational-l Recall flag; this parameter applies only if the cease-
flag is set to zero.
0, omitted The task begins processing after the block is transmit
ted to the network.
Nonzero The task begins processing after the block has been de
livered to the user and acknowledgment is received.
Each nonzero value indicates the status of the block.
The network function, subfunction, and description are
given here. For all values other than 1, the block was
not delivered to the user and the task must recover.
IBlock delivered (FC/ACK).
2Block not delivered (INTR/USR/RC-1).
3User break 1 (INTR/USR/RC-1).
4User break 2 (INTR/USR/RC-1).
10 Terminal not logged in (CON/END).
11 Correspondent unavailable or failed, line disconnect
(C0N/CB/RC-1).
length Computational-l Length of the message in characters. This length
should Include end-of-line bytes for 7-bit ASCII char
acter types. For 6-bit display code output, the COBOL
compiler-generated length is used if the length param
eter is omitted.
J^ 60459500 C 2-19
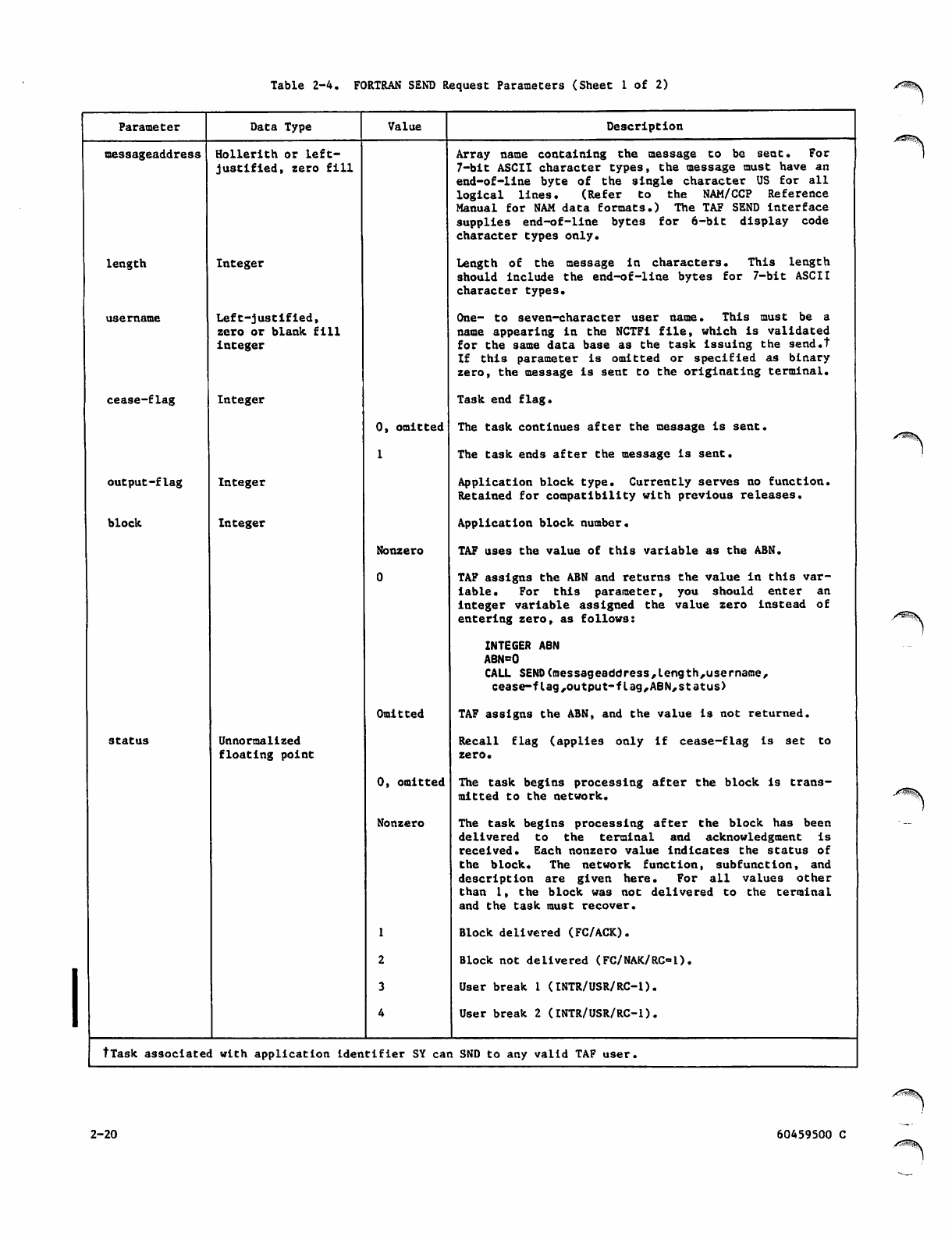
Table 2-4. FORTRAN SEND Request Parameters (Sheet 1 of 2)
Parameter Data Type Value Description
messageaddress Hollerith or left-
justified, zero fill
length
username
cease-flag
output-flag
block
Integer
Left-justified,
ze ro or bla nk fill
integer
Integer
Integer
Integer
st a t u s Unnormalized
floating point
0, omitted
1
Nonzero
0
Omitted
0, omitted
Nonzero
Array name containing the message to be sent. For
7-bit ASCII character types, the message must have an
en d - of- l i n e b y te o f t h e s i n gle ch a r act e r U S fo r a l l
l o g i c a l l i n e s . ( R e f e r t o t h e N A M / C C P R e f e r e n c e
Manual for NAM data formats.) The TAF SEND interface
supplies end-of-line bytes for 6-bit display code
character types only.
Length of the message in characters. This length
should include the end-of-line bytes for 7-bit ASCII
character types.
One- to seven-character user name. This must be a
name appearing in the NCTFi file, which is validated
for the same data base as the task issuing the send.t
If this parameter is omitted or specified as binary
zero, the message is sent to the originating terminal.
Task end flag.
The task continues after the message is sent.
The task ends after the message is sent.
Application block type. Currently serves no function.
Retained for compatibility with previous releases.
Application block number.
TAF uses the value of this variable as the ABN.
TAF assigns the ABN and returns the value in this var
iable. For this parameter, you should enter an
integer variable assigned the value zero instead of
entering zero, as follows:
INTEGER ABN
ABN=0
CALL SEND(messageaddress,length,username/
cease-flag,output-flag,ABN,status)
TAF assigns the ABN, and the value is not returned.
Recall flag (applies only if cease-flag is set to
zero.
The task begins processing after the block is trans
mitted to the network.
The task begins processing after the block has been
delivered to the terminal and acknowledgment is
received. Each nonzero value indicates the status of
the block. The network function, subfunction, and
description are given here. For all values other
than 1, the block was not delivered to the terminal
and the task must recover.
Block delivered (FC/ACK).
Block not delivered (FC/NAK/RC-l).
User break 1 (INTR/USR/RC-1).
User break 2 (INTR/USR/RC-1).
tTask associated with application identifier SY can SND to any valid TAF user.
2-20 60459500 C
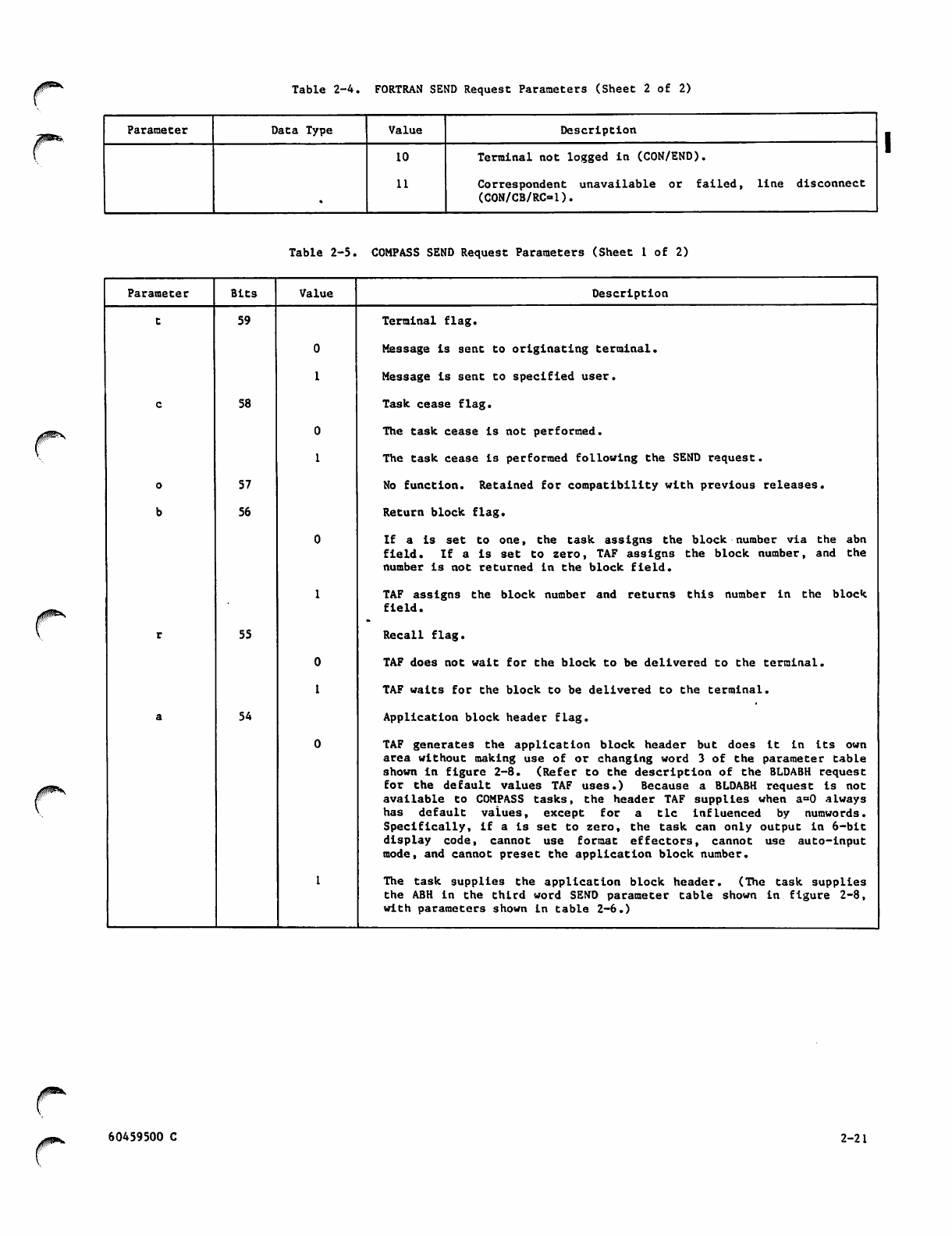
0^ Table 2-4. FORTRAN SEND Request Parameters (Sheet 2 of 2)
Parameter Data Type Value Description
10
11
Terminal not logged in (CON/END).
Correspondent unavailable or failed, line disconnect
(C0N/CB/RC-1).
Table 2-5. COMPASS SEND Request Parameters (Sheet I of 2)
Parameter Bits Value Description
t59 Terminal flag.
0Message is sent to originating terminal.
1Message is sent to specified user.
c58 Task cease flag.
0The task cease is not performed.
1The task cease is performed following the SEND request.
o57 No function. Retained for compatibility with previous releases.
b56 Return block flag.
0If a is set to one, the task assigns the block number via the abn
fie ld . I f a i s s et to zero, TA F a ss igns the b loc k num be r, a nd the
number is not returned in the block field.
1TAF assigns the block number and returns this number in the block
field.
r55 Recall flag.
0TAF does not wait for the block to be delivered to the terminal.
1TAF waits for the block to be delivered to the terminal.
a54 Application block header flag.
0TAF generates the application block header but does it in its own
area without making use of or changing word 3 of the parameter table
shown in figure 2-8. (Refer to the description of the BLDABH request
for the default values TAF uses.) Because a BLDABH request is not
available to COMPASS tasks, the header TAF supplies when a=0 always
has default values, except for a tic influenced by numwords.
Specifically, if a is set to zero, the task can only output in 6-bit
display code, cannot use format effectors, cannot use auto-input
mode, and cannot preset the application block number.
IThe task supplies the application block header. (The task supplies
the ABH in the third word SEND parameter table shown in figure 2-8,
with parameters shown in table 2-6.)
J^v 60459500 C 2-21
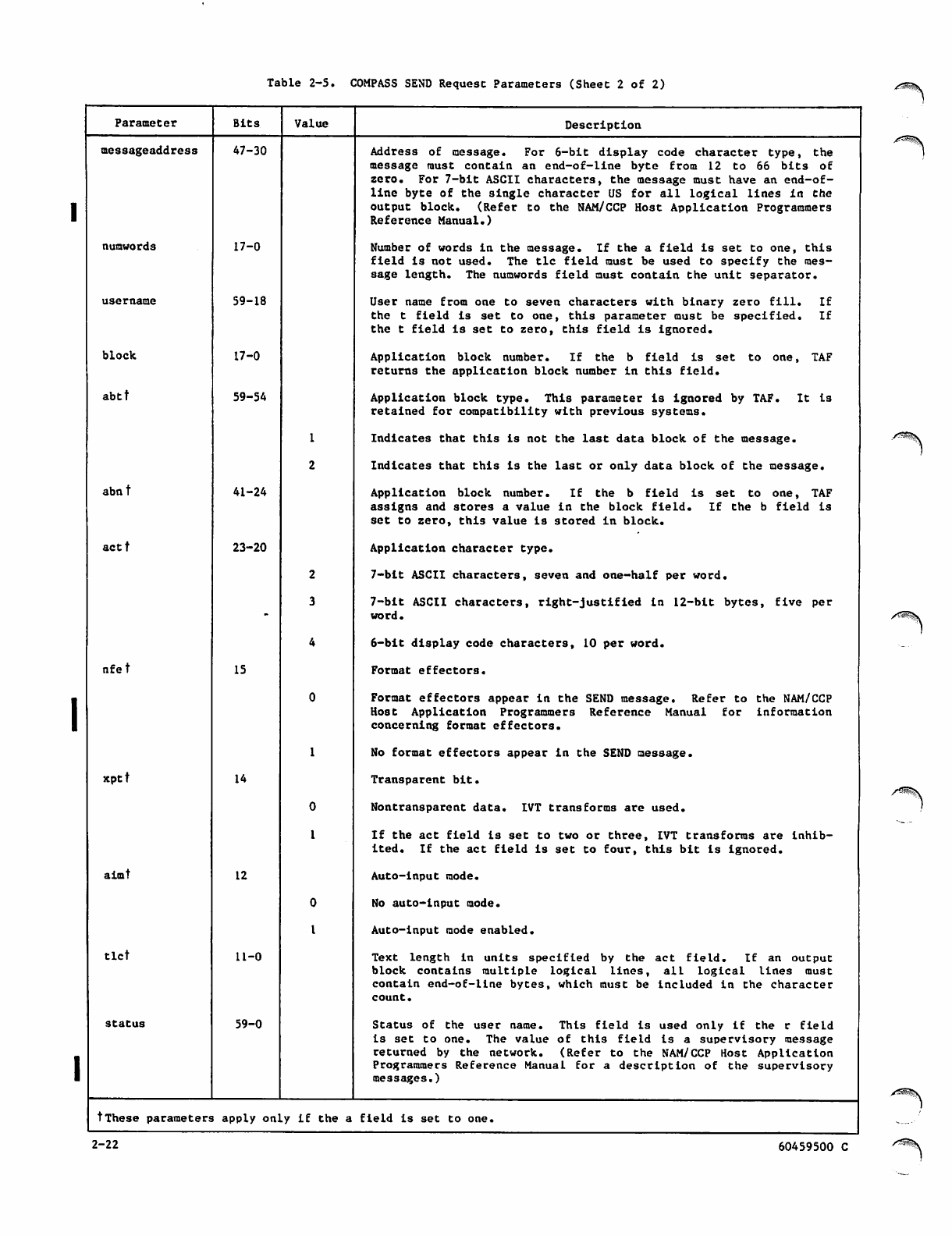
Table 2-5. COMPASS SEND Request Parameters (Sheet 2 of 2)
Parameter Bits Value Description
messageaddress 47-30 Address of message. For 6-bit display code character type, the
message must contain an end-of-line byte from 12 to 66 bits of
zero. For 7-bit ASCII characters, the message must have an end-of-
line byte of the single character US for all logical lines in the
output block. (Refer to the NAM/CCP Host Application Programmers
Reference Manual.)
numwords 17-0 Number of words in the message. If the a field is set to one, this
field is not used. The tic field must be used to specify the mes
sage length. The numwords field must contain the unit separator.
username 59-18 User name from one to seven characters with binary zero fill. If
the t field is set to one, this parameter must be specified. If
the t field is set to zero, this field is ignored.
block 17-0 Application block number. If the b field is set to one, TAF
returns the application block number in this field.
abtt 59-54 Application block type. This parameter is ignored by TAF. It is
retained for compatibility with previous systems.
1Indicates that this is not the last data block of the message.
2Indicates that this is the last or only data block of the message.
abn t 41-24 Application block number. If the b field is set to one, TAF
assigns and stores a value in the block field. If the b field is
set to zero, this value is stored in block.
actt 23-20 Application character type.
27-bit ASCII characters, seven and one-half per word.
-37-bit ASCII characters, right-justified in 12-bit bytes, five per
word.
46-bit display code characters, 10 per word.
nfet 15 Format effectors.
0Format effectors appear in the SEND message. Refer to the NAM/CCP
Host Application Programmers Reference Manual for information
concerning format effectors.
1No format effectors appear in the SEND message.
x p t t 14 Transparent bit.
0Nontransparent data. IVT transforms are used.
1If the act field is set to two or three, IVT transforms are inhib
ited. If the act field is set to four, this bit is ignored.
aimt 12 Auto-input mode.
0No auto-input mode.
IAuto-input mode enabled.
tlct 11-0 Te x t l e n g t h i n u n i t s s p e c i fi e d b y t h e a c t fi e l d . I f a n o u t p u t
block contains multiple logical lines, all logical lines must
contain end-of-llne bytes, which must be included in the character
count.
status 59-0 Status of the user name. This field is used only if the r field
is set to one. The value of this field Is a supervisory message
returned by the network. (Refer to the NAM/CCP Host Application
Programmers Reference Manual for a description of the supervisory
messages.)
tThese parameters apply onl.y if the a field is set to one.
2-22 60459500 C
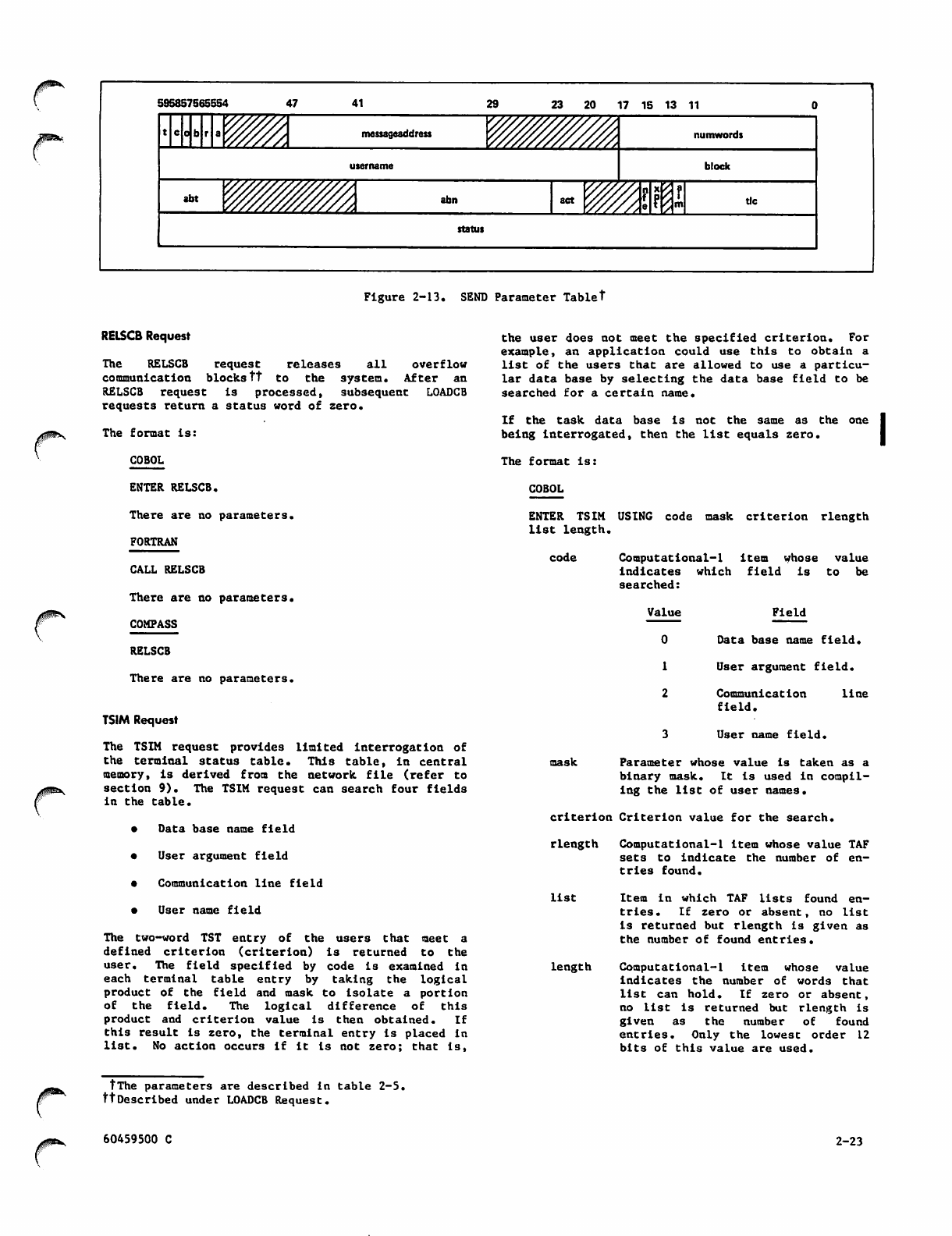
595857565554 4 7 4 1 2 9 2 3 2 0 1 7 1 5 1 3 1 1
messageaddress numwords
block
abt abn Vs
act
status
tic
Figure 2-13. SEND Parameter Tablet
r
RELSCB Request
The RELSCB request releases all overflow
communication blocks tt to the system. After an
RELSCB request is processed, subsequent LOADCB
requests return a status word of zero.
The format is:
COBOL
ENTER RELSCB.
There are no parameters.
FORTRAN
CALL RELSCB
There are no parameters.
COMPASS
RELSCB
There are no parameters.
TSIM Request
The TSIM request provides limited interrogation of
the terminal status table. This table, in central
memory, is derived from the network file (refer to
section 9). The TSIM request can search four fields
in the table.
• Data base name field
• User argument field
• Communication line field
• User name field
The two-word TST entry of the users that meet a
defined criterion (criterion) is returned to the
user. The field specified by code is examined in
each terminal table entry by taking the logical
product of the field and mask to isolate a portion
of the field. The logical difference of this
product and criterion value is then obtained. If
this result is zero, the terminal entry is placed in
list. No action occurs if it is not zero; that Is,
the user does not meet the specified criterion. For
example, an application could use this to obtain a
list of the users that are allowed to use a particu
lar data base by selecting the data base field to be
searched for a certain name.
If the task data base is not the same as the one
being interrogated, then the list equals zero.
The format is:
COBOL
ENTER TSIM USING code mask criterion rlength
list length.
code Computational-l item whose value
Indicates which field is to be
searched:
Value Field
0 Data base name field.
1 U s e r a r g u m e n t fi e l d .
2 Communication line
field.
3 User name field.
mask Parameter whose value is taken as a
binary mask. It is used in compil
ing the list of user names.
cri te ri on C ri te rion v alue f or the s ea rch.
rlength Computational-l item whose value TAF
sets to indicate the number of en
tries found.
list Item in which TAF lists found en
t r i e s . I f z e r o o r a b s e n t , n o l i s t
is returned but rlength is given as
the number of found entries.
length Computational-l item whose value
indicates the number of words that
list can hold. If zero or absent,
no list is returned but rlength is
given as the number of found
entries. Only the lowest order 12
bits of this value are used.
0^*- tThe parameters are described in table 2-5.
ttDescribed under LOADCB Request.
60459500 C 2-23
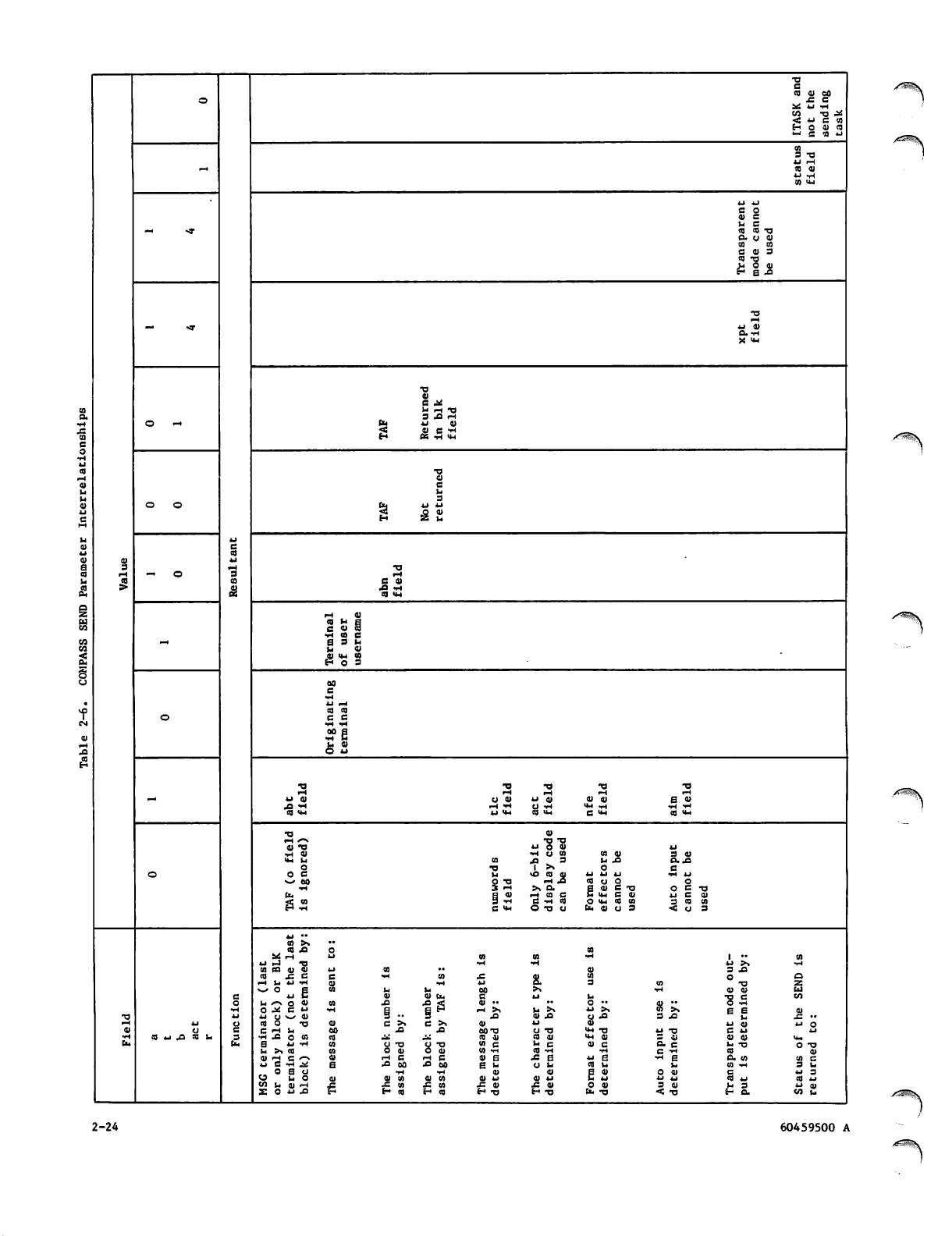
co <u eo
£c
S6 44 •h
Ui •o .*
<44 <o
H o 0)
'-' *j
mCO •o
au<u
03 CQ
aID
«j •o
44 9)
a. -h
e ^
bl i-( Xt
3 J H
e cu
ca m
5B
S2
CO •*-
0) •a
i-t tu
Ml
0
N^ eo ( 0 4 ) U ( J U
• H 4 3 C O u O
S-3 o n o
CO cu
u43
o
44 44
COa0) x<
U-l 0)
oU-l CO ca
u.
CO BQ 0) CU <->
O J > £ C « - H
CO 44 X co bl
4 4 C — I
C / J W C U i- i H co
., -< ■H<U 4 - 1 > ,
3 43 -,
ca CO
•H 44 CO ■o
u00 >. T4 CU cu
cu b. (- "8 5
E E
C/l
•s es C U • •
U > N 44 >, 8 ^ cu
43 CU 43 43 3 43 bi 4 = • •
c > . cu 44 <u 44 CU 4 4 O
43 eo-a cj -a u-t •o 4 4 X I C 4 4 44
CO it C O C U U-l cu 3 4) cu cu u*
o cu « c • - c cu O . C u -a O X I
« -rt CO -H ■wC - W CO cu
*3 B V 6 X B • h e O. <A C O c
43 00 E »- U b l ca CO ~4 3 b ,
•W <u cu CU O 91 4 4 3
cu ca CU 4J cu 44 44 4 J u CO 4J CO 44
x c a •e cu 4= CU cu 3 C U b i 3 44 CU
H t o H t > H TJ (h •o < X I H a . C / J b i
2-24 60459500 A
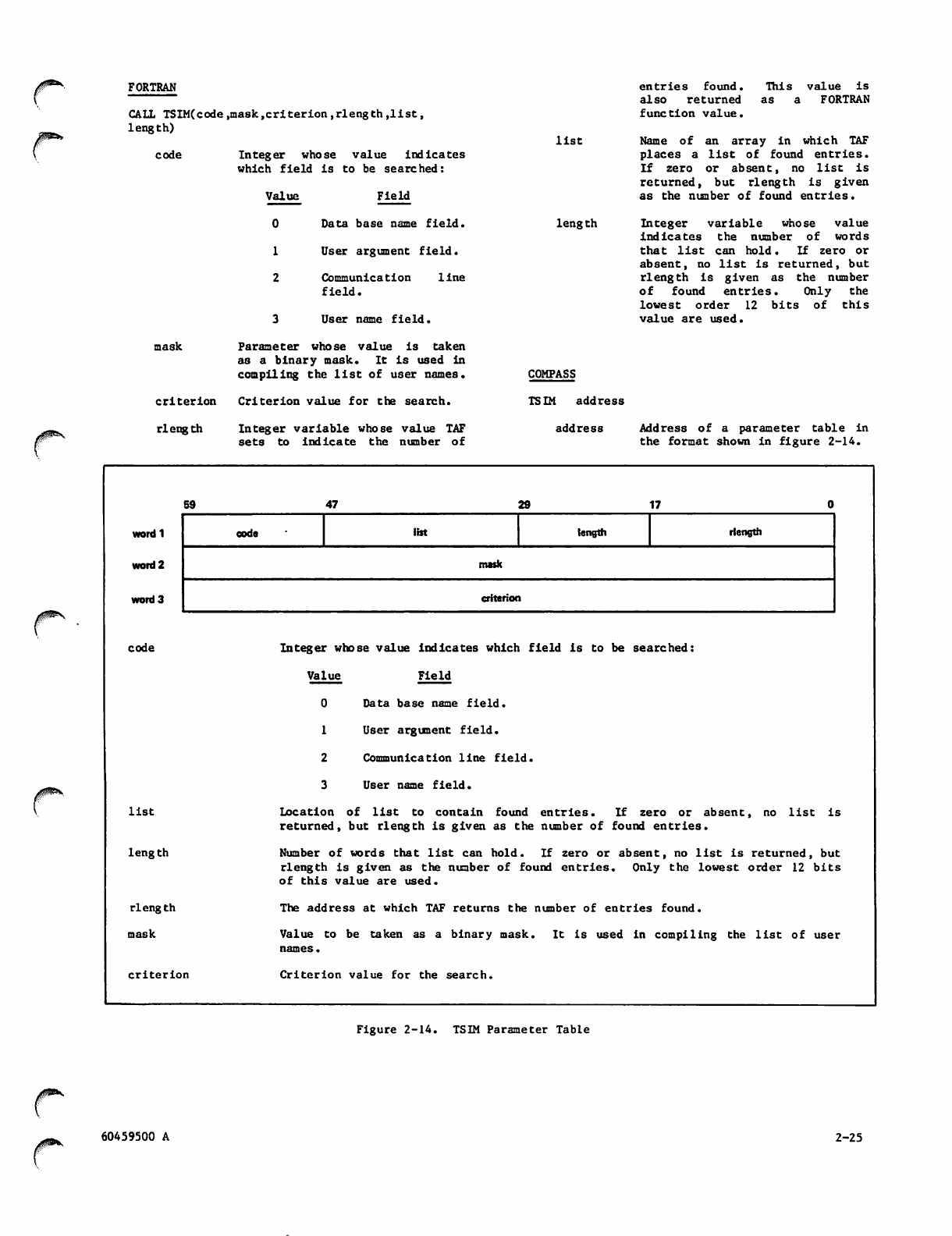
J^**- FORTRAN
CALL TSIM(code,mask,criterion,rlength,list,
length)
entries found,
a l s o r e t u r n e d
function value.
This value is
as a FORTRAN
code Integer whose value indicates
which field is to be searched:
Value Field
0 Data base name field.
1 User argument field.
2 Communication line
field.
3 User name field.
m a s k P a r a m e t e r w h o s e v a l u e i s t a k e n
as a binary mask. It is used in
compiling the list of user names.
c r i t e ri o n Cr i t e r io n va lu e fo r t h e s e a r c h .
r l e n g t h In t e g e r v a r i a b l e wh o s e v a l ue TA F
sets to indicate the number of
list
leng th
Name of an array in which TAF
places a list of found entries.
If zero or absent, no list is
r e t u r n e d , b u t r l e n g t h i s g i v e n
as the number of found entries.
Integer variable whose value
indicates the number of words
that list can hold. If zero or
absent, no list is returned, but
rl eng th i s g iv e n a s t he num ber
of found entries. Only the
l o w e s t o r d e r 1 2 b i t s o f t h i s
value are used.
COMPASS
T S I M a d d r e s s
address Address of a parameter table in
the format shown in figure 2-14.
wordl
word 2
word 3
code
59 47 29 17
code list length rlength
mask
criterion
list
length
rlength
mask
criterion
Integer whose value indicates which field is to be searched:
Value Field
0 Data base name field.
1 User argument field.
2 Communication line field.
3 U s e r n a m e fi e l d .
Location of list to contain found entries. If zero or absent, no list is
returned, but rlength is given as the number of found entries.
Number of words that list can hold. If zero or absent, no list is returned, but
rlength is given as the number of found entries. Only the lowest order 12 bits
of this value are used.
The address at which TAF returns the number of entries found.
Value to be taken as a binary mask. It is used in compiling the list of user
names.
Criterion value for the search.
Figure 2-14. TSIM Parameter Table
r60459500 A 2-25
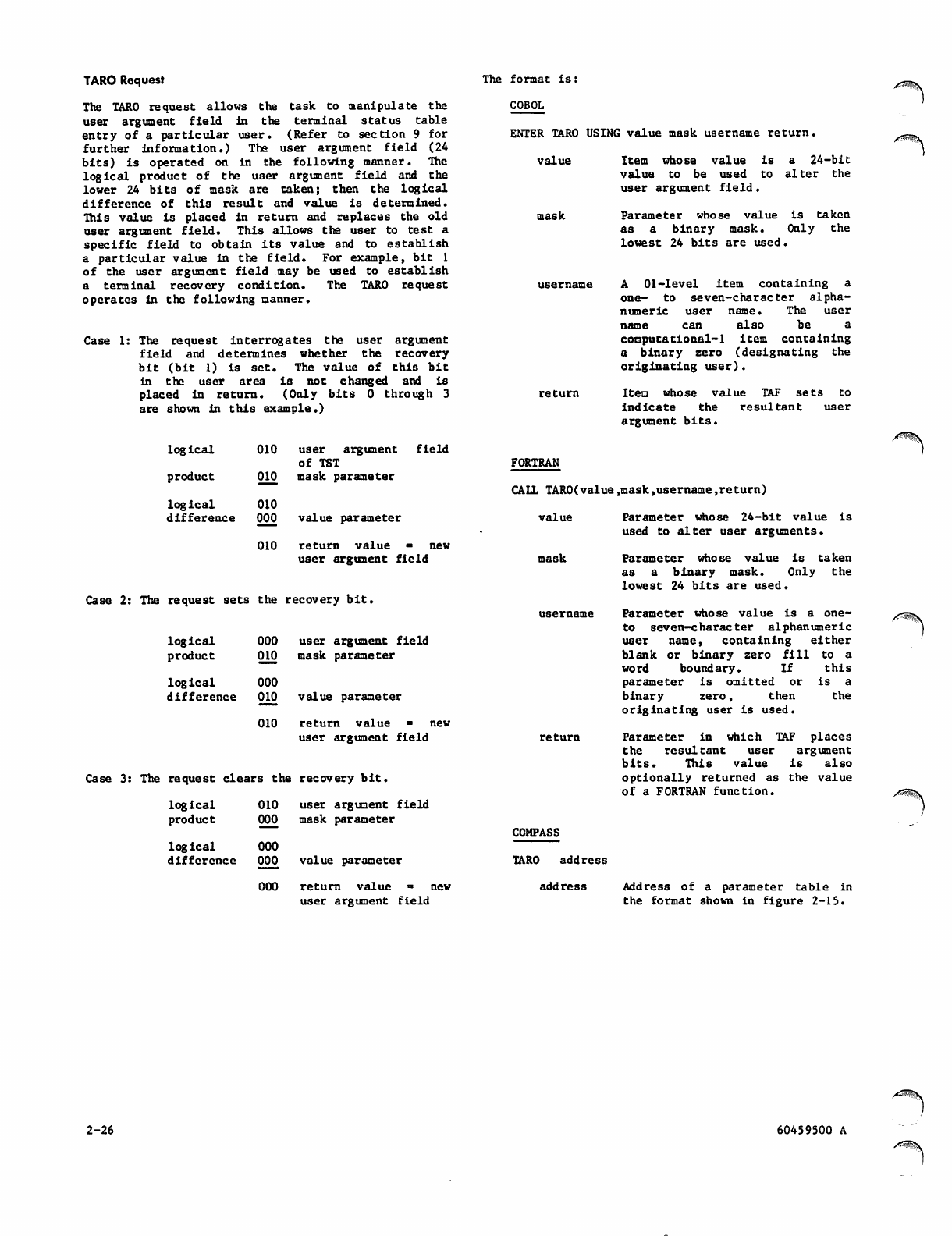
TARO Request
The TARO request allows the task to manipulate the
user argument field in the terminal status table
en tr y o f a p artic ul ar us er. (Re fe r to sec ti on 9 fo r
further information.) The user argument field (24
bi t s) is oper a te d on i n t h e f oll owi n g m ann er. Th e
logical product of the user argument field and the
lower 24 bits of mask are taken; then the logical
difference of this result and value is determined.
This value is placed in return and replaces the old
user argument field. This allows the user to test a
specific field to obtain its value and to establish
a particular value in the field. For example, bit 1
of the user argument field may be used to establish
a terminal recovery condition. The TARO request
operates in the following manner.
Case 1: The request interrogates the user argument
field and determines whether the recovery
bit (bit 1) is set. The value of this bit
in the user area is not changed and is
placed in return. (Only bits 0 through 3
are shown in this example.)
user argument field
of TST
mask parameter
log ical 010
product 010
logical
difference
010
000
010
value parameter
r e t u r n v a l u e ■ n e w
user argument field
Case 2: The request sets the recovery bit.
logical
product
logical
difference
000
010
000
plO
010
user argument field
mask parameter
value parameter
return value ■ n e w
user argument field
Case 3: The request clears the recovery bit.
logical
product
logical
difference
010
000
000
000
000
user argument field
mask parameter
value parameter
return value = new
user argument field
The format is:
COBOL
ENTER TARO USING value mask username return.
value Item whose value is a 24-bit
value to be used to alter the
user argument field.
mask Parameter whose value is taken
a s a b i n a r y m a s k . O n l y t h e
lowest 24 bits are used.
username A 01-level item containing a
o n e - t o s e v e n - c h a r a c t e r a l p h a
numeric user name. The user
n a m e c a n a l s o b e a
computational-l item containing
a binary zero (designating the
originating user).
return Item whose value TAF sets to
indicate the resultant user
argument bits.
FORTRAN
CALL TAR0(value,mask,username,return)
value Parameter whose 24-bit value is
used to alter user arguments.
Parameter whose value is taken
a s a b i n a r y m a s k . O n l y t h e
lowest 24 bits are used.
Parameter whose value is a one-
to seven-character alphanumeric
user name, containing either
blank or binary zero fill to a
word boundary. If this
p a r a m e t e r i s o m i t t e d o r i s a
binary zero, then the
originating user is used.
Parameter in which TAF places
the resultant user argument
bits. This value is also
optionally returned as the value
of a FORTRAN function.
mask
username
return
COMPASS
TARO address
address Address of a parameter table in
the format shown in figure 2-15.
2-26 60459500 A
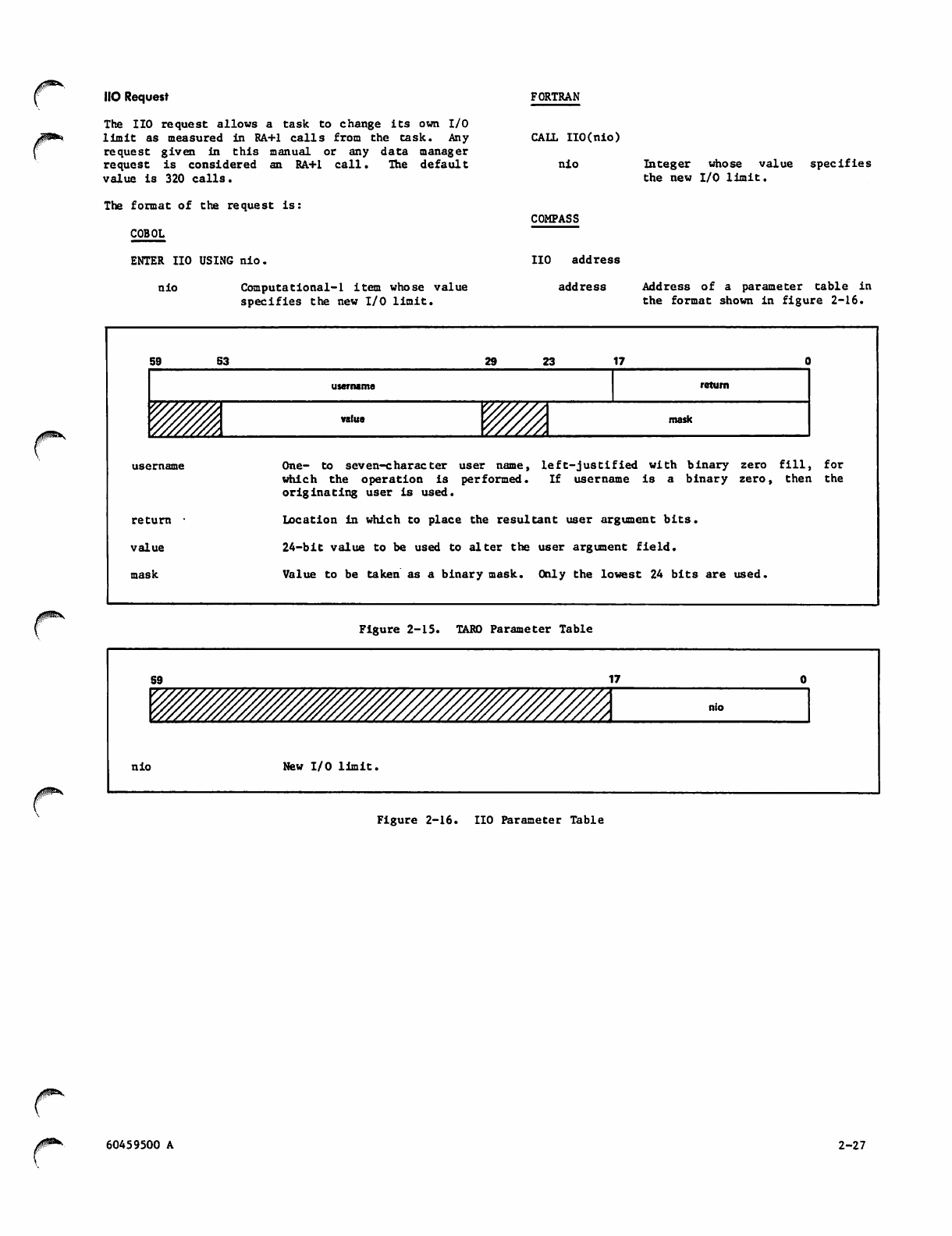
110 Request FORTRAN
The 110 request allows a task to change its own I/O
limit as measured in RA+1 calls from the task. Any
request given in this manual or any data manager
request is considered an RA+1 call. The default
value is 320 calls.
The format of the request is:
COBOL
ENTER 110 USING nio.
nio Computational-l item whose value
specifies the new I/O limit.
CALL 110(nio)
nio
COMPASS
110 address
address
I n t e g e r w h o s e v a l u e s p e c i fi e s
the new I/O limit.
Address of a parameter table in
the format shown in figure 2-16.
JPBK
59 53 29 23 17
username return
^w, value
tys/s
V/A mask
username
return •
value
mask
O n e - t o s e v e n - c h a r a c t e r u s e r n a m e , l e f t - j u s t i fi e d w i t h b i n a r y z e r o fi l l , f o r
which the operation is performed. If username is a binary zero, then the
originating user is used.
Location in which to place the resultant user argument bits.
24-bit value to be used to alter the user argument field.
Value to be taken as a binary mask. Only the lowest 24 bits are used.
j^v
Figure 2-15. TARO Parameter Table
59 17
wmmmmmmMmmm nio
nio New I/O limit.
Figure 2-16. 110 Parameter Table
60459500 A 2-27
BWAITINP Request (COMPASS Only)
The BWAITINP request allows a task to move data from
a terminal to a task field location. This location
has th e sa m e f o r m at a s th e c o m m unic a t i o n b l o ck
(refer to figure 2-1). The request is processed the
same as a WAITINP request, except that when the
terminal data is moved to the specified location, it
is moved to the area specified by the supplied
parameter (address), not the first word address of
the task (as In the WAITINP request). The first
word address is not changed by the execution of this
request.
The format is:
BWAITINP address
address Address of first word of the
storage area where the terminal
data is to be moved.
TAF does not pass this terminal data to tasks called
with the CALLTSK and CALLRTN requests.
TPSTAT Request (COMPASS Only)
The TPSTAT request is retained for compatibility
with previous releases of TAF. It was used to
enable a task to determine under which of two
terminal subsystems the task was running. Now, all
the tasks run under NAM. Therefore, the request
always returns a 1.
The format is:
TPSTAT address
address Address containing a 1 in bit 0
to indicate NAM is active.
The format is:
COBOL
ENTER BEGIN USING buffer.
buffer A 01-level item identifying the
user-defined buffer area.
FORTRAN
CALL BEGIN(buffer)
buffer
COMPASS
BEGIN address
address
A n a r r a y n a m e i d e n t i f y i n g t h e
user-defined buffer area.
Address of the user-defined
buffer area.
TASK CONTROL REQUESTS
These requests are used for task control.
• CEASE
End a task.
• I T L
Set a task time limit.
• L O G T
L o g a t e r m i n a l o u t o f TA F.
• KPOINT
Initiate execution of K display commands.
• W A I T
Suspend processing for a given amount of
time.
/<P**«iKJV
/"sa^v
BEGIN Request
The BEGIN request allows a task to specify the area
where the terminal input data is to be placed, If an
area other than the first word address of the task
field length is desired. It supports programming
languages that do not reserve the first word address
of the task for the common block that is used for
the communication block. The task must be Installed
in the appropriate task library with the (solicited)
input directive, because the default is
unsolicited. If task chains are involved, the
c a l l i n g ta s k m u s t is s u e a B E G I N r e q u e s t be f o r e
resuming execution of the original task, because the
calling task must be able to obtain the
communication block containing the returned data
from the called task. The returned communication
block in solicited mode is in the same form as in
unsolicited mode. Unless there is a specific need
for this request, its use is not recommended because
more execution overhead is required to support the
secondary load request.
CEASE Request
The CEASE request provides task end processing and
transaction completion processing. If a
predetermined task list exists for the chain (that
is, subsequent tasks have been requested for
scheduling, or the CEASE is a return from a CALLRTN
request), no special processing occurs on a CEASE
request from a task. However, if the request is
f r o m t h e fi n a l t a s k i n t h e c h a i n , t h e t r a n s a c t i o n
e x e c u t i v e r e l e a s e s a l l c o m m u n i c a t i o n b l o c k s an d
notifies the data manager that updated records
should be replaced on the data base. The one
exception to this procedure occurs if a task selects
an abnormal CEASE by use of an optional parameter.
A task that terminates in this manner is
automatically the final task in the chain. After an
abnormal CEASE occurs, all communication blocks are
released and records updated by the task but not yet
updated on the data base are not replaced on the
data base.
2-28 60459500 B
/P9**
The format is:
COBOL
ENTER CEASE USING a.
Computational-l item whose value
indicates the type of CEASE selected:
0
1
-1
217-1 > a > 1
Type of CEASE
Normal CEASE.
Abnormal CEASE with
out memory dump.
Normal CEASE and ter
minal remains locked.
Abnormal CEASE with
memory dump.t
-1 > a > -(217-1) Reserved for CDC.
Any other values produce undefined
results and should not be used.
217-1 > a > 1
Type of CEASE
Abnormal CEASE with
memory dump.t
-1 > a > -(217-1) Reserved for CDC.
Any other values produce undefined
results and should not be used.
ITL Request
The ITL request allows a task to set the time limit
for the task to a new value. The time limit is
expressed in exchange jump time units (that is, the
number of times a task executed its full time slice
without interruption). In addition, each call to
this function decreases the CPU priority of the task
by 1 until the lower limit of priority is reached to
ensure good s erv ice to other t ask s. The tim e limit
d e f a u l t v a l u e i s a p r o d u c t o f t w o i n s t a l l a t i o n
parameters. The released value is 1.12 CPU
seconds. If this is exceeded, the task aborts and
the message TIME LIMIT EXCEEDED is issued to the
terminal.
/pi£v
FORTRAN
CALL CEASE(a)
a Integer whose value indicates the type
of CEASE selected:
a T y p e o f C E A S E
0Normal CEASE.
IAbnormal CEASE with
out memory dump.
-1 Normal CEASE and ter
minal remains locked.
217-i > a > 1 Abnormal CEASE with
memory dump.t
-1 > a > -(217-1) Reserved for CDC.
Any other values produce undefined
results and should not be used.
The format is:
COBOL
ENTER ITL USING ntm.
ntm
FORTRAN
Computational-l item whose value
specifies the new time limit.
CALL ITL(nto)
ntm
COMPASS
Integer whose value specifies the
new time limit.
ITL address
address Address of a parameter table in
the format shown in figure 2-17.
COMPASS
CEASE
Integer whose value indicates the type
of CEASE selected:
0
1
-1
Type of CEASE
Normal CEASE.
Abnormal CEASE with
out memory dump.
Normal CEASE and ter
minal remains locked.
LOGT Request (COMPASS Only)
The LOGT request logs out a terminal from TAF and
returns it to nontransaction mode. The terminal can
then access other interactive applications. A
system task is provided using this request. (Refer
to System Tasks in section 11.)
The format is:
COMPASS
LOGT
There are no parameters.
tDumps are identified by the transaction subsystem user name or by the appropriate DSDUMP parameter (refer to
section 6).
60459500 C 2-29
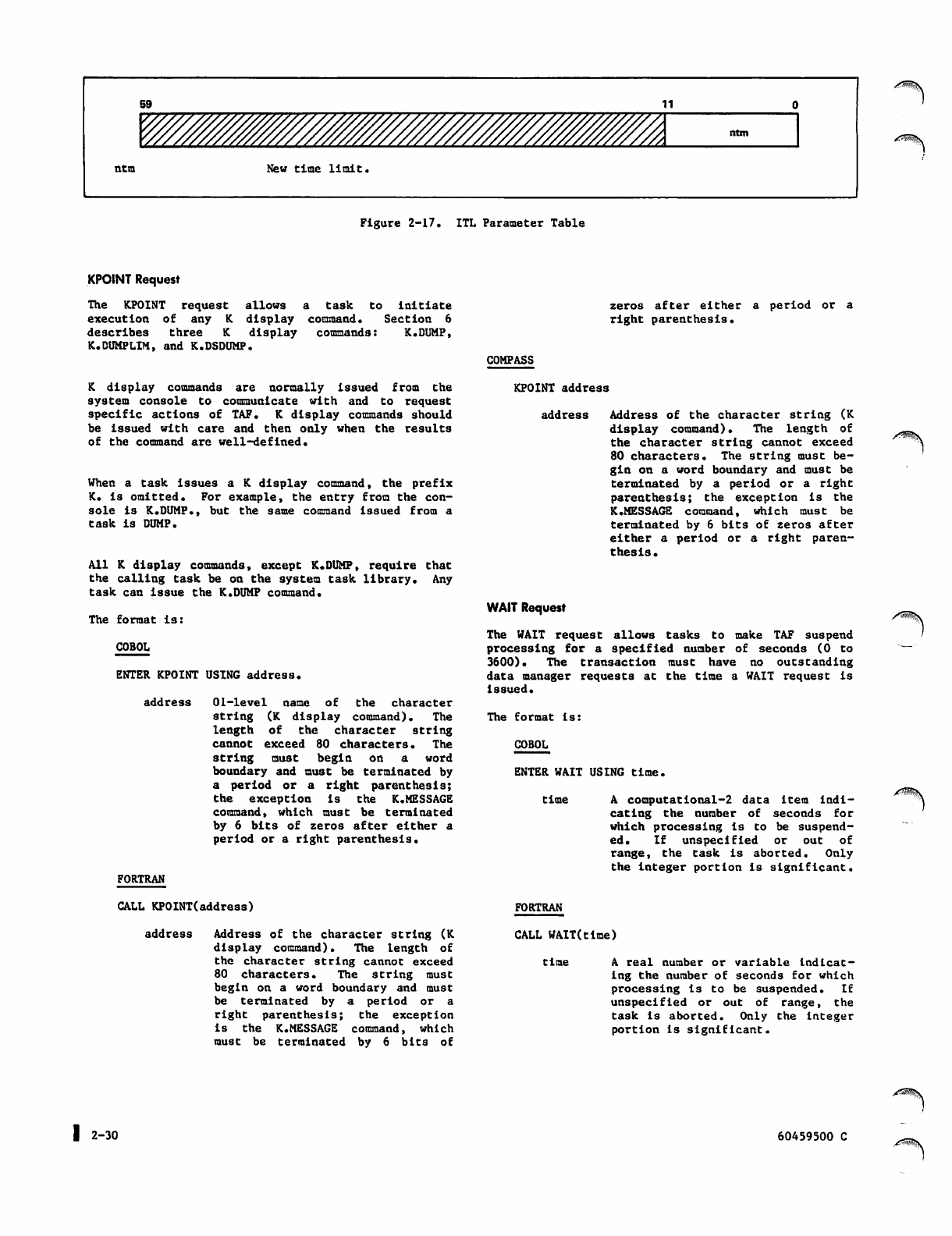
59 11
W^ WMMflftfo ntm
ntm New time limit.
Figure 2-17. ITL Parameter Table
KPOINT Request
The KPOINT request allows a task to initiate
execution of any K display command. Section 6
describes three K display commands: K.DUMP,
K.DUMPLIM, and K.DSDUMP.
zeros after either a period or a
right parenthesis.
COMPASS
K display commands are normally issued from the
system console to communicate with and to request
specific actions of TAF. K display commands should
be Issued with care and then only when the results
of the command are well-defined.
When a task issues a K display command, the prefix
K. is omitted. For example, the entry from the con
sole is K.DUMP., but the same command Issued from a
task is DUMP.
All K display commands, except K.DUMP, require that
the calling task be on the system task library. Any
task can issue the K.DUMP command.
The format is:
COBOL
ENTER KPOINT USING address.
address 01-level name of the character
string (K display command). The
length of the character string
cannot exceed 80 characters. The
string must begin on a word
boundary and must be terminated by
a period or a right parenthesis;
the exception is the K.MESSAGE
command, which must be terminated
by 6 bits of zeros after either a
period or a right parenthesis.
FORTRAN
KPOINT address
address Address of the character string (K
d i s p l a y c o m m a n d ) . Th e l e ng t h o f
the character string cannot exceed
80 characters. The string must be
gin on a word boundary and must be
terminated by a period or a right
parenthesis; the exception is the
K.MESSAGE command, which must be
terminated by 6 bits of zeros after
either a period or a right paren
thesis.
WAIT Request
The WAIT request allows tasks to make TAF suspend
processing for a specified number of seconds (0 to
360 0 ) . T h e t r an s ac t i on mu s t h a v e no o u t s t a n d i ng
data manager requests at the time a WAIT request is
issued.
The format is:
COBOL
ENTER WAIT USING time.
time A computational-2 data item indi
cating the number of seconds for
which processing is to be suspend
ed. If unspecified or out of
range, the task is aborted. Only
the Integer portion is significant.
/^H§s.
CALL KP0INT(address)
address Address of the character string (K
display command). The length of
the character string cannot exceed
80 characters. The string must
begin on a word boundary and must
be terminated by a period or a
right parenthesis; the exception
is the K.MESSAGE command, which
must be terminated by 6 bits of
FORTRAN
CALL WAIT(time)
time A real number or variable indicat
ing the number of seconds for which
processing is to be suspended. If
unspecified or out of range, the
ta sk is a bor ted . O nl y t he int eg er
portion is significant.
2-30 60459500 C /*«&.

COMPASS TASK UTILITY REQUESTS
WAIT address The following task utility requests provide capabili
ties for the FORTRAN and COBOL user, some of which
address The address of a word specifying the are difficult to do because they are at the bit
n u m b e r o f s e c o n d s ( N ) f o r w h i c h l e v e l ,
processing is to be suspended. The
word has the form 48/0,12/N. If • LOGIN
unspecified or out of range, the
task is aborted. Determine if a specified user is logged in.
• EXTRACT
Extract a bit string from a word.
• I N S E R T
Insert a bit string into a word.
j0^\
60459500 C 2-30.1/2-30.2 |

/P9**-
LOGiN Request
The LOGIN request allows a task to determine if a
specified user is logged in before it issues a SEND
request to that user. TAF aborts a task that issues
a SEND request without recall to a user who is not
logged in.
| NOTJ"|
It is possible for the receiving user
to log out after the task issues a
LOGIN request and before the task
issues a SEND request. Therefore, it
is recommended that the task issue
the SEND request soon after issuing
the LOGIN request.
EXTRACT Request
The EXTRACT request allows a task to extract a bit
st r i n g fr o m a wo r d a n d move i t to a n o ther w o r d,
right-justified. For instance, the EXTRACT request
can be us ed t o ch eck fields in th e te rmina l st atus
table or the communication block.
In the following request formats, if n is not within
the specified range, if bbp plus 1 minus n is less
than 0, or if there are any other errors in the
parameters, TAF aborts the task and issues the
following message.
TASK REQUEST ARGUMENT ERROR.
The format is:
COBOL
ENTER EXTRACT USING loci loc2 bbp n.
0$^
The format is:
COBOL
ENTER LOGIN USING username status.
username A one- to seven-character alpha
numeric user name, left-justi
fied. A binary zero specifies
the user associated with the
tran saction that is running.
status Address of the location to
contain the returned status.
The format of the returned
status is computational-l.
Values for status are:
0 User not logged in.
1 U ser lo g g ed i n.
FORTRAN
CALL LOGTN(username,status)
username A one- to seven-character alpha
numeric user name, left-justi
fied. Possible forms are nHf
and nLf (refer to the FORTRAN
Extended 4 Reference Manual). A
b i n a r y z e r o s p e c i fi e s t h e u s e r
associated with the transaction
that is running.
status Address of the location to
contain the returned status.
The format of the returned
status is integer. Values for
status are:
0 User not logged in.
1 U ser lo g g ed i n.
loci
loc2
bbp
Data name of the source field.
Any data type is allowed, loci
must begin on a word boundary.
Data name of the computational-l
destination field. The bit
string is right-justified in
this field.
Beginning bit position of field
l o c i ; t h i s i s t h e l e f t m o s t b i t
of the field. Bits are numbered
59 through 0.
Number of bits to extract; the
r a n g e o f v a l u e s f o r n i s 1 t o
59, inclusive. The format of n
must be computational-l.
FORTRAN
CALL EXTRACT(locl,loc2,bbp,n)
loci Name of the integer source field.
loc2 Name of the integer destination
field. The bit string is right-
justified in this field.
bbp Beginning bit position of field
l o c i ; t h i s i s t h e l e f t m o s t b i t
of the field. Bits are numbered
59 through 0.
n Number of bits to extract; the
r a n g e o f v a l u e s f o r n i s 1 t o
59, inclusive. n must be
integer type.
The COBOL STRING and UNSTRING statements also
provide capabilities for manipulating character-
aligned data. The EXTRACT request should be used
only when the use of these COBOL statements is
impossible or inconvenient.
j ^ y
60459500 A 2-31
INSERT Request APPLICATION RECOVERY REQUESTS
The INSERT request allows a task to insert a bit
string into a word. For instance, the INSERT
request can be used to set fields in the terminal
status table.
The following task requests are for use in
recoverable transactions. All are for use by
applicati ons tasks although s ome are also u sed by
system tasks.
In the following formats, if n is not within the
specified range, if bbp plus 1 minus n is less than
0, or if there are any other errors in the
parameters, TAF aborts the task and issues the
following message.
TASK REQUEST ARGUMENT ERROR.
The format is:
COBOL
RERUN
R e s t a r t s a r u n
terminal input.
RGET
unit using the initial
Retrieves data from
recovery file (CRF).
the communication
RPUT
Plac es data on the co mmunica tion recover y
file.
ENTER INSERT USING loci loc2 bbp n.
l o c i D a t a n a m e o f t h e c o m p u t a t i o n a l - l
source field. The bit string must
be right-justified in this field.
loc2 Data name of the destination field.
Any data type is allowed. loc2 must
begin on a word boundary.
bbp Beginning bit position of field
loc2; this is the leftmost bit of
the field. Bits are numbered 59
through 0.
n Number of bits to insert; the range
o f v a l u e s f o r n i s 1 t o 5 9 ,
inclusive. The format of n must be
computational-l.
FORTRAN
CALL INSERT(locl,loc2,bbp,n)
loci Name of the integer source field.
The - bit string must be
r i g h t - j u s t i fi e d i n t h i s fi e l d .
loc2
bbp
Name of
field.
the integer destination
Beginning bit position of field
loc2; this is the leftmost bit of
the field. Bits are numbered 59
through 0.
Number of bits to insert; the range
o f v a l u e s f o r n i s 1 t o 5 9 ,
inclusive, n must be integer type.
The COBOL STRING and UNSTRING statements also
provide capabilities for manipulating character-
aligned data. The INSERT request should be used
only when the use of these COBOL statements is
impossible or inconvenient.
RSECURE
Retrieves a message previously saved on the
communication recovery file by a SECURE
request.
SECURE
Signals the completion of a transaction's
work and saves a message on the recovery
file to be sent to the terminal when the run
unit ceases.
TSTAT
Returns the status of one or more specified
objects.
Refer to section 7 for an overview of the recovery
process from the applications programmer's
perspective. Refer to the applicable data manager
reference manual (CDCS, TAF/CRM, or TOTAL) for
requests associated with data base recovery.
RERUN Request
The RERUN request causes the initial terminal input
for a rerunnable run unit to be resubmitted to the
transaction system. The input comes from the
communication recovery file. The actions that occur
as a result of RERUN are:
1. T h e r eco v er y stat u s i s s e t t o z e ro so t hat
the recovery task will not be scheduled.
2. The restart status (TSTAT with keyword
RESTART) is set to one.
3. A term ina tio n i s p r oc e ss e d f or the run uni t
and ITASK is called to rerun the run unit.
Transactions using this request must take care to
avoid entering an infinite loop if the RERUN results
from an error condition.
/ < ^ s
2-32 60459500 A
The format is:
COBOL
ENTER RERUN USING status,
status A computational-l data item
wh ose v alu e i s s et by TAF to
indicate the status of the
request. The values are:
0 No errors.
29 Recovery is not in
stalled.
3 3 R u n u n i t i s n o t r e -
runnable.
FORTRAN
CALL RERUN (status)
status An integer variable in which
TAF will return a status. The
values are:
0 No errors.
29 Recovery is not in
stalled.
3 3 R u n u n i t i s n o t r e -
runnable.
RPUT and RGET Requests
The RPUT request allows a task to put application-
dependent data on the communication recovery file.
The RGET request allows the task to retrieve the
data placed on the recovery file by an RPUT. The
length of the data in each request and the number of
slots for data on the recovery file is specified at
TAF initialization on the RECOVER statement in the
TCF (refer to section 4). TAF maintains the data on
a user name basis. TAF does not modify the user
data unless the communication recovery file is
initialized. These requests may be used by any task
when TAF automatic recovery is installed.
The format is:
COBOL
ENTER "RPUT" USING message,index[.status .message-
length, act].
ENTER "RGET" USING message,index,status .message-
length(,act].
message An 01-level data item that
contains the message. This is
an input parameter for RPUT and
an output parameter for RGET.
index A computational-l data item
indicating the index for the
recovery record. Index 1
p o i n t s t o t h e fi r s t r e c o r d i n
user area of the communication
recovery file; index 2 points
to the second record in user
status
message-
length
act
a r e a o f t h e c o m m u n i c a t i o n
recovery file, and so on. This
parameter is input for both
RPUT and RGET. The maximum
value of index is the value of
the number parameter in the
RECOVER statement in the TCF.
A computational-l data item
wh o s e v a lue is se t by TAF to
i n d i c a t e t h e s t a t u s o f t h e
request. The values are:
0 No errors.
19 The index is outside of
the user recovery file
message area (RPUT
only).
20 No message (RGET only).
21 T h e m e s sag e do e s n o t
fit in the recovery
file message area (RPUT
only).
22 The message does not
fit in the user message
area (RGET only).
23 Incorrect application
character type (act).
2 8 T h e R G E T a c t i s n o t
equal to the RPUT act.
29 TAF automatic recovery
is not installed.
A computational-l data item
indicating the length of the
message in the message units
specified by the act parameter.
This parameter is required when
using message units other than
6-b i t di s p l a y c o d e . T his i s a n
input par ameter f or R PU T. Fo r
RGET, the user sets the message-
length of the area to receive
the message. Upon completion
of RGET, TAF places the length
o f t h e m e s s a g e i n m e s s a g e -
length.
A computational-l data item
indicating the application
character type. The type is
the same as for NAM. This is
an input parameter. The values
are:
2 7-bit ASCII characters,
seven and one-half per
word.
3 7-bit ASCII characters,
right-justified in 12-
bit bytes, five per
word.
4 6-bit display code char
acters, 10 per word.
This is the default
value.
60459500 B 2-33

FORTRAN
CALL RPUT(message,index,status.message-length
t.act])
CALL RGET(message,index,status ,message-length
[,act])
message
index
status
The name of an array that
contains the message. This is
an input parameter for RPUT and
output parameter for RGET.
An integer variable indicating
the index for recovery record.
I n d e x 1 p o i n t s t o t h e fi r s t
record in user area of the
c o m m u n i c a t i o n r e c o v e r y fi l e ;
i n d e x 2 p o i n t s t o t h e s e c o n d
record in user area of the
communication recovery file,
and so on. This parameter is
input for both RPUT and RGET.
The maximum value of index is
the value of the number
parameter in the RECOVER
statement in the TCF.
An integer variable whose value
is s e t b y TA F to in d i c a t e t h e
status of the request. The
values are:
act An integer variable indicating
the application character
type. The type is the same as
for NAM. This is an input
parameter. The values are:
2 7-bit ASCII characters,
seven and one-half per
word.
3 7-bit ASCII characters,
right-justified in 12-
bit bytes, five per
word.
4 6-bit display code
characters, 10 per
word. This is the
default value.
RSECURE Request
The RSECURE request allows a recovery task to obtain
a message previously saved on the communication
recovery file by a SECURE request. After obtaining
the message, the task would normally send the
message to the appropriate terminal. Any task may
use this request if automatic recovery has been
installed with TAF.
The format is:
0 No errors.
19 The index is outside of
the user recovery area.
20 No message (RGET only).
21 T h e m e s sag e do e s n o t
fit in the recovery
file message area (RPUT
only).
22 The message does not
fit in the user message
area (RGET only).
23 Incorrect application
character type (act).
2 8 T h e R G E T a c t i s n o t
equal to the RPUT act.
29 TAF automatic recovery
is not installed.
COBOL
ENTER "RSECURE" USING message,status ,
message-length ,ac t,format-effec tor,
transparent-mode.
message
st a t u s
An 01-level data item that
contains the message. This is
an output parameter.
A computational-l data item
whose v a l u e is se t by TAF t o
i n d i c a t e t h e s t a t u s o f t h e
request. The values are:
0 No errors.
20 No message.
2 2 T h e m e s s a g e d o e s n o t
fit in the user message
area.
29 Recovery
stalled.
is not in-
message- An integer variable indicating
length the length of message in the
message units specified by the
act parameter. This is an
input parameter for RPUT. For
RGET, the user sets the message-
length of the area to receive
the message . Up on c omp letion
of the request, TAF returns the
message-length as recorded on
the communication recovery file.
m e s s a g e - A c o m p u t a t i o n a l - l d a t a I t e m
length indicating the length of
message in the message units
specified by the act
parameter. Before issuing the
r e q u e s t , t h e u s e r s e t s t h e
message-length area in the
t a s k . U p o n c o m p l e t i o n o f t h e
request, TAF returns the
message-length as recorded on
the communication recovery file.
2-34 60459500 B
format-
effector
A computational-l data item
indicating the application
character type. The type is
the s a m e as fo r NAM. B e f o r e
issuing the request, the user
se t s t he a ct. Up on com p let i on
of the request, TAF returns the
act as recorded on the recovery
file. The values are:
2 7-bit ASCII characters,
seven and one-half per
word.
3 7-bit ASCII characters,
right-justified in 12-
bit bytes, five per
word.
4 6-bit display code
characters, 10 per
word. This is the
default value.
A computational-l data item
indicating format effector
usage. The values are:
0 F o r m a t eff e c t o r s appear
in the message.
1 No format effectors
appear in the message.
A computational-l data item
indicating transparent mode
usage. Default is nontranspar
ent mode. The values are:
0 Nontransparent data.
Interactive virtual
terminal transforms are
used.
1 T r a n s p a r e n t d a t a . I V T
transforms are inhib
ited.
FORTRAN
CALL RSECURE(message,status,message-length, act,
format-effector,transparent-mode)
message-
length
transpar
ent-mode
message
status
The name of an array that
contains the message. This is
an output parameter.
An integer variable whose value
Is set by TAF to indicate the
s t a t u s o f t h e r e q u e s t . T h e
values are:
0 No errors.
20 No message.
22 T h e m e s sag e do e s n o t
fit in the user message
area.
29 Recovery is not in
stalled.
act
An integer variable indicating
the length of the message in
message units specified by the
act parameter. Before issuing
the request, the user sets the
message-length area in the
t a s k . U p o n c o m p l e t i o n o f t h e
request, TAF returns the
message length as recorded on
the communication recovery file.
An integer variable indicating
the application character
type. The type is the same as
NAM. Before issuing the
request, the user sets the
act. Upon completion of the
request, TAF returns the act as
recorded on the recovery file.
The values are:
2 7-bit ASCII characters,
seven and one-half per
word.
3 7-bit ASCII characters,
right-justified in 12-
bit bytes, five per
word.
4 6-bit display code
characters, 10 per
word. This is the
default value.
An integer variable indicating
format effector usage. The
values are:
0 Format effectors appear
in the message.
1 No format effectors
appear in the message.
An integer variable indicating
transparent mode usage. The
values are:
0 Nontransparent data.
Interactive virtual
terminal transforms are
used.
1 Transparent data. IVT
transforms are inhib
ited.
SECURE Request
The SECURE request tells the transaction executive
tha t th e work of the ru n un it i s co mplete. All that
remains is to commit the data base and end the run
unit. The SECURE request includes a terminal
confirmation message. This message will be sent at
the run unit end time (normal CEASE). If the commit
request fails, the task may RERUN the run unit or
issue a CEASE request with abnormal termination. In
either case, the SECURE message will not be sent.
format-
effec tor
transpar
ent-mode
60459500 A 2-35
TAF records the message associated with SECURE on
p e r m a n e n t s t o r a g e s o t h a t t h e m e s s a g e c a n b e
d e l i v er e d in s p i t e o f s ys t e m or t e rm i n a l f a i l u re s .
If no failures occur, the message will be sent from
the task's SECURE message area. This means that the
SECURE, data base commit, and CEASE must occur in
the same task. TAF assumes that the message has
been acknowledged by the terminal operator when the
operator enters the next transaction input. The
SECURE message may appear twice if recovery is done
after a failure, but it is guaranteed to appear at
least once. TAF also saves the NAM application
block header with the message so that it will be
sent with the correct character type and mode. Only
the last SECURE message is saved per run unit. Any
t a s k ma y u s e t h i s re q u e s t i f r e c o v e r y h a s b e e n
installed with TAF; however, if the run unit is not
recoverable, the SECURE message will not be issued
to the terminal upon recovery (only at initial CEASE
time).
message-
length
act
A computational-l data item
indicating the length of the
message in the message units
specified by the act
parameter. This is an input
parameter. It is required when
the act parameter does not
specify display.
A computational-1 data item
indicating the application
character type. The type is
the same as for NAM. This is
an input parameter. The values
are:
2 7-bit ASCII characters,
seven and one-half per
word.
For a BTRAN run unit the message is recorded on the
communication recovery file but no message is sent
to the terminal/username. The RECOVER statement
maximumsize parameter specifies the message size
that can be recorded on the communication recovery
file.
The format of the message on the terminal depends on
the terminal class and the format effectors in the
message. Refer to the SEND request description
earlier in this section for more information.
The format is:
COBOL
ENTER "SECURE" USING message,statusf,message-
length,act ,format-effector .transparent-mode] .
format-
effec tor
7-bit ASCII characters,
right-justified in 12-
bit bytes, five per
word.
6-bit display code
characters, 10 per
word. This is the
default value.
A computational-l data item
indicating format effector
usage* This is an optional
parameter. It is necessary
o n l y i f f o r m a t e f f e c t o r s a r e
used. The default is no format
effectors. The values are:
message A 01-level data item that
contains the message. This is
an input parameter.
status A computational-l data item
wh o s e v a lue is se t by TAF to
indicate the status of the
request. The values are:
0 No errors.
21 The message is too
l a r g e t o fi t i n T A F ' s
communication recovery
file. Refer to the
RECOVER statement maxi
mumsize parameter.
23 Incorrect application
character type.
0 Format effectors appear
in the message.
1 No format effectors
appear in the message.
transpar- A computational-l data item
ent-mode indicating transparent mode
usage. This is an optional
parameter. It is necessary
only if transparent mode is
used. The default is
nontransparent mode. The
values are:
0 Nontransparent data.
Interactive virtual
terminal transforms are
used.
24 Incorrect format-
effector value.
25 Incorrect transparent-
mode value.
1 Transparent data. IVT
transforms are inhib
ited.
26 The message exceeds the
maximum length for SEND. FORTRAN
27 The message exceeds the
maximum length for a
run unit.
29 TAF automatic recovery
is not installed.
CALL SECURE (message,status,message-length
[ ,act,format-effector.transparent-mode])
message The name of an array that
contains the message. This is
an input parameter.
2-36 60459500 A
status An integer variable whose value
is set by TAF to indicate the
s t a t u s o f t h e r e q u e s t . T h e
values are:
0 No errors.
21 The message is too large
to fit in the communica
tion recovery file.
Refer to the RECOVER
statement maximumsize
parameter.
23 Incorrect application
character type.
24 Incorrect format effect
or value.
25 Incorrect transparent-
mode value.
26 The message exceeds the
maximum length for SEND.
27 The message exceeds the
maximum length for a
run unit.
transpar- An integer variable indicating
ent-mode transparent mode usage. This
is an optional parameter. It
is necessary only if
transparent mode is used. The
default is nontransparent
mode. The values are:
0 Nontransparent data.
Interactive virtual
terminal transforms are
used.
1 Transparent data. IVT
transforms are inhib
ited.
TSTAT Request
The TSTAT request returns information about the
current user or run unit. It is used by both system
tasks and applications (user) tasks.
The format is:
COBOL
J8*V
message-
length
act
29 TAF automatic recovery
is not installed.
An integer variable indicating
the length of the message in
the message units specified by
the act parameter. This is an
input parameter.
An integer variable indicating
the application character
type. The type is the same as
for NAM. This is an input
parameter. The values are:
2 7-bit ASCII characters,
seven and one-half per
word.
3 7-bit ASCII characters,
right-justified 12-bit
bytes, five per word.
6-bit display
characters, 10
word. This is
default value.
code
per
the
format- An integer variable indicating
effector format effector usage. This is
an optional parameter. It is
necessary only if format effec
tors are used. The default is
no format effectors. The
values are:
0 F o r m a t eff e c t o r s appear
in the message.
1 No format effectors
appear in the message.
ENTER "TSTAT** USING status .keyword j, value j,...,
keywordn,valuen.
status A computational-l data item
wh ose v alu e i s s et by TAF to
i n d i c a t e t h e s t a t u s o f t h e
request. The values are:
0 No errors.
12 The keyword speci
fied requires TAF
automatic recov
ery. TAF automatic
recovery is not
installed.
13 End of NEXT proc
essing.
14 USER is not defined
in the network file.
400+i keyword^ is invalid.
keyword ^ An 01-level item that contains
a one- to seven-character
keyword for which a value is
desired. The keyword must be
left-justified and blank-
filled. Refer to table 2-7 for
keyword definitions.
value^ A data item to which TAF returns
the value for the corresponding
keyword. The keyword^ and
value^ fields must appear in
pairs. For USER, NEXT, OLDID,
and NEWID usage is display. For
all other TSTAT keywords, usage
is computational-l.
60459500 A 2-37
FORTRAN TSTAT System Task Keywords
CALL TSTAT (status .keyword j, value j keyworda,
valuen)
status An integer variable whose value
is set by TAF to indicate the
status of the request. The
values are:
Keywords NEXT, STEP, TRAN, OLDID, NEWID are
used by BTASK to read sequentially the
communication recovery file to find batch
(BTRAN) run units that require rerunning.
BTASK uses the SRERUN request with username
to rerun BTRAN run units.
0 No errors.
12 The keyword speci
fi e d r e q u i r e s T A F
automatic recov
ery. TAF automatic
recovery is not
Installed.
13 End of NEXT proc
essing .
14 USER is not defined
in the ne two rk file.
400+i keywordi is invalid.
ke y w ord . £ A v a ria b le t hat co n tai n s a on e -
t o s e v e n - c h a r a c t e r l e f t - j u s -
t i fi e d k e y w o r d f o r w h i c h a
value is desired. The keyword
must be blank-filled. Refer to
table 2-7 for keyword
definitions.
value^ A variable field to which TAF
returns the value of the de
sired keyword. The keyword^
and valuer must appear in
pairs. For USER, NEXT, OLDID,
and NEWID valuer is character
d a t a . F o r a l l o t h e r T S T A T
keywords, valuer is an
integer.
Some TSTAT keywords (both as COBOL and FORTRAN
parameters) are meant for user tasks and others are
meant for system tasks, such as BTASK, CTASK, and
RTASK.
TSTAT User Task Keywords
• Keywords RESTART, OLDID, and NEWID are meant
for use by application tasks that use
multiple data manager begin-commit sequences
to determine If the run unit is in a
restarted state and, if so, where to begin
processing*
• Keywords STEP, TRAN, OLDIN, NEWID, CRM, and
CDCS are used by RTASK during terminal
l o g i n / r e l o g i n t o d e t e r m i n e i f a r u n u n i t
requires rerun. The SEQ (sequence number)
returned is the transaction sequence number
that was first assigned to the run unit.
RTASK can be either a system task or a user
task.
SYSTEM TASK RECOVERY REQUESTS
Applications programmers can skip this subsection
since all the requests documented here are available
only to system tasks (that is, tasks residing on the
system task library). Recovery requests that are for
use by both system tasks and application tasks are
documented under Application Recovery Requests ear
lier in this section. Refer to section 8 for an
overview of the recovery process from the data admin
istrator's perspective. Refer to the applicable data
manager reference manual (CDCS, TAF/CRM, or TOTAL)
for requests associated with data base recovery. The
following task requests are used by system tasks for
transaction recovery.
■ CALLTRN
Initiates a run unit*
• SRERUN
Resubmits initial terminal input for a rerun-
nable run unit.
• TINVOKE
Returns or specifies a system identifier for
begin-commit sequences in this job.
• W S TAT
Records information needed for recovery
processing.
CALLTRN Request
The CALLTRN request causes the initiation of a run
unit. It is available only to the system task ITASK.
The actions that occur as a result of CALLTRN are:
1. ITASK ceases. If an error condition is de
tected, an error message is issued to the
terminal via MSABT.
2. The initial terminal input is logged on the
CRF if the transaction is recoverable. The
transaction will not be scheduled for execu
tion until this circular input-output (CIO)
operation is complete.
3. If the transaction initiated is recoverable,
the commitment history of the previous recov
erable run unit for this user is released.
2-38 60459500 B
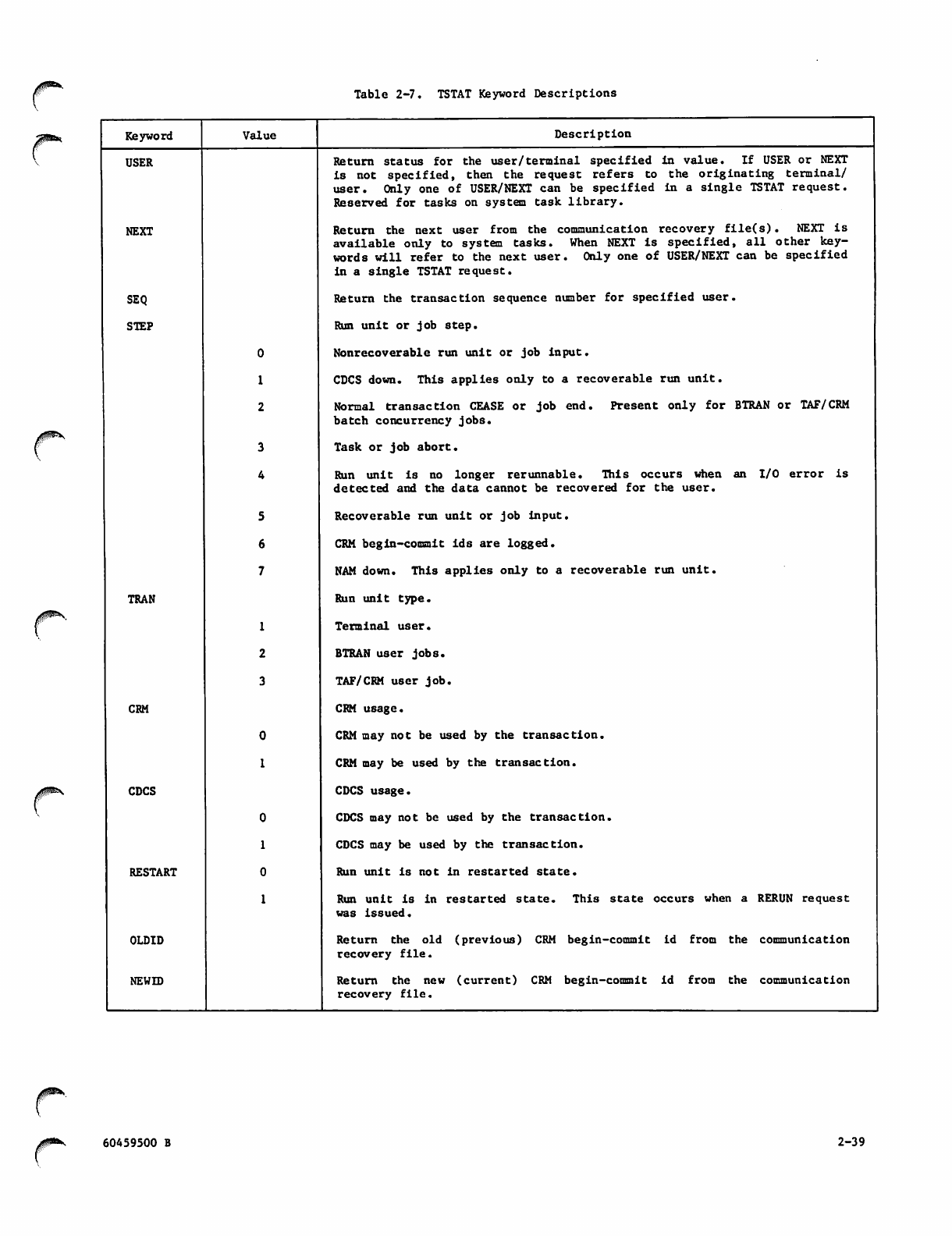
Table 2-7. TSTAT Keyword Descriptions
Keyword Value Description
USER
NEXT
SEQ
STEP
jgPN
TRAN
CRM
CDCS
RESTART
OLDID
NEWID
Return status for the user/terminal specified in value. If USER or NEXT
is not specified, then the request refers to the originating terminal/
user. Only one of USER/NEXT can be specified in a single TSTAT request.
Reserved for tasks on system task library.
Return the next user from the communication recovery file(s). NEXT is
available only to system tasks. When NEXT is specified, all other key
words will refer to the next user. Only one of USER/NEXT can be specified
in a single TSTAT request.
Return the transaction sequence number for specified user.
Run unit or job step.
Nonrecoverable run unit or job input.
CDCS down. This applies only to a recoverable run unit.
Normal transaction CEASE or job end. Present only for BTRAN or TAF/CRM
batch concurrency jobs.
Task or job abort.
Run unit is no longer rerunnable. This occurs when an I/O error is
detected and the data cannot be recovered for the user.
Recoverable run unit or job input.
CRM begin-commit ids are logged.
NAM down. This applies only to a recoverable run unit.
Run unit type.
Terminal user.
BTRAN user jobs.
TAF/CRM user job.
CRM usage.
CRM may not be used by the transaction.
CRM may be used by the transaction.
CDCS usage.
CDCS may not be used by the transaction.
CDCS may be used by the transaction.
Run unit is not in restarted state.
Run unit is in restarted state. This state occurs when a RERUN request
was issued.
Return the old (previous) CRM begin-commit id from the communication
recovery file.
Return the new (current) CRM begin-commit id from the communication
recovery file.
0^*.
60459500 B 2-39

The format is:
COBOL
ENTER CALLTRN USING tname.
31 username is not in the
network file.
tname
FORTRAN
01-level data item containing a
one- to seven-character trans
action name.
CALL CALLTRN(tname)
tname An integer containing a one- to
seven-character transaction
name, left-justified with blank
fill.
SRERUN Request
The SRERUN request causes the initial terminal input
for a rerunnable run unit to be resubmitted to the
transaction subsystem. The input is retrieved from
the communication recovery file. The actions that
occur as result of SRERUN are:
• T h e r e c o v e r y s t a t u s i s s e t t o ze r o s o th a t
the recovery task will not be scheduled.
• The restart status (TSTAT with keyword
RESTART) is set to one.
• The SRERUN is done without requesting run
unit termination.
The format is:
COBOL
ENTER SRERUN USING status[.username].
status A computational-l data item in
which TAF will return a
status. The values are:
0 No errors.
29 Recovery not installed.
31 username not in network
file.
33 Run unit not rerunnable.
username 01-level data item containing a
o n e - t o s e v e n - c h a r a c t e r u s e r
n a m e . I f t h i s p a r a m e t e r I s
omitted, the rerun applies to
the user name under which the
current task is running.
FORTRAN
CALL SRERUN(status[,username])
status An integer in which TAF will
return a status. The values
are:
0 No errors.
29 Recovery is not in
stalled.
33 Run unit
rerunnable.
is not
username A variable containing a one- to
seven-character user name, left-
justified and blank-filled. If
this parameter is omitted, the
rerun applies to the originating
user.
TINVOKE Request
The TINVOKE request returns a system identifier to
be used for all begin-commit sequences in the job or
task. For TAF, this system identifier is the trans
action sequence number. Optionally, for the recovery
case, the job or task may supply an old system iden
tifier. This establishes the task or job as a
continuation of a previous task or job.
The format is:
COBOL
ENTER TINVOKE USING status,new-system-id,
old-system-id.
status A computational-l item in which
TAF will return a status* The
values are:
0 Request successful.
32 old-system-id unknown.
new-system-id A computational-l item in which
TAF will return a system identi
fi e r t o b e u s e d f o r a l l b e g i n -
commit sequences in the job or
task.
old-system-id A computational-l item in which
the task or job supplies the
old system identifier that
establishes the task or job as
a continuation of the old one.
FORTRAN
CAIi TINVOKE(status.new-system-id,old-system-id)
status An integer variable in which
TA F w i l l r e t u r n a s t a t u s . T h e
values are:
0 Request successful.
32 old-system-id unknown.
new-system-id An integer in which TAF will
return a system identifier to
be used for all begin-commit
sequences in the task or job.
old-system-id An integer in which the task or
job supplies the old system
identifier that establishes the
program as a continuation of a
previous one.
/tf^&sjV
/_C^v
2-40 60459500 A
WSTAT Request
The WSTAT request records information needed for
recovery processing on the communication recovery
file or TAF system tables. WSTAT is used by system
task CTASK.
The format is:
COBOL
ENTER "WSTAT" USING status .keyword!.valuet,...,
keywordn,valuen.
status A computational-l item whose
value is set by TAF to indicate
the status of th e request. The
values are:
0 No errors.
29 Keyword specified
requires TAF auto
matic recovery. TAF
a u t o m a t i c re c o v e r y
is not installed.
30 End of NEXT process
ing.
31 USER is not defined
in the network file.
FORTRAN
CALL WSTAT(status.keywordi,valuei,.
valuen)
,keywordn,
st a t u s
keyword^
An inte ger wh os e valu e i s s et
b y TA F t o g i v e t h e s t a t u s o f
the request. The values are:
0 No errors.
29 Keyword specified
requires TAF auto
matic recovery. TAF
a u t o m a t i c r e c o v e r y
is not installed.
30 E n d o f NE X T p r o cess
ing.
31 USER is not defined
in the network file.
400+i keyword^ is invalid.
A variable containing a one- to
seven-character keyword for
w h i c h a v a l u e i s s p e c i fi e d .
The keyword must be left-
justified and blank-filled.
Refer to table 2-8 for keyword
definitions.
400+i keyword^ is invalid.
keyword^ An 01-level item containing a
one- to seven-character keyword
for which a value is speci
fied. The keyword must be left-
justified and blank-filled. Re
f e r t o t a b l e 2 - 8 f o r k e y w o r d
definitions.
v a l u e ^ A c o m p u t a t i o n a l - l i t e m t h a t c o n
tains the value for the desired
keyword. The keyword^ and
valuej fields must appear in
pairs.
value£ Integer that contains the value
of the preceding keyword. The
keyword j and value j_ must
appear in pairs.
The WSTAT keywords (both for COBOL and FORTRAN param
eters) are given in table 2-8. All keywords neces
sary for recovery processing for a user name must be
specified in the WSTAT request. For instance, CTASK
makes a TSTAT request specifying NEXT, SEQ, STEP,
TRAN, CRM, and CDCS followed by a WSTAT with SEQ,
TRAN, CRM, CDCS, OLDID, NEWID, USER, and STEP. Any
keyword not specified retains the value associated
with it on the previous WSTAT request.
60459500 B 2-41
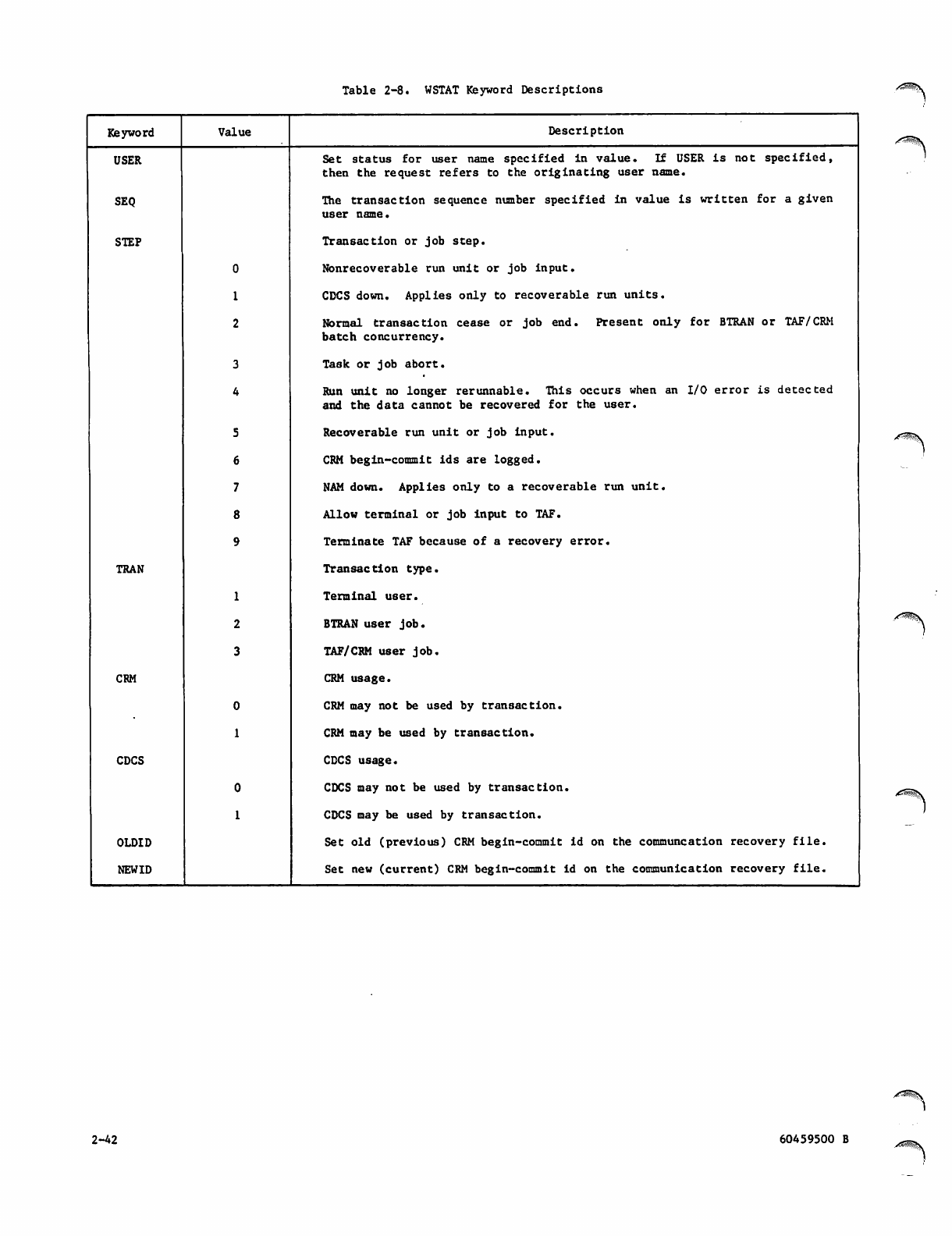
Ta b l e 2 - 8 . W S TAT K e y w or d D e s cr i pt i on s
Keyword Value Description
USER Set status for user name specified in value. If USER is not specified,
then the request refers to the originating user name.
SEQ The transaction sequence number specified in value is written for a given
user name.
STEP Transaction or job step.
0 Nonrecoverable run unit or job input.
1 CDCS down. Applies only to recoverable run units.
2 Normal transaction cease or job end. Present only for BTRAN or TAF/CRM
batch concurrency.
3 Task or job abort.
4 Run unit no longer rerunnable. This occurs when an I/O error is detected
and the data cannot be recovered for the user.
5 Recoverable run unit or job input.
6CRM begin-commit ids are logged.
7 NAM down. Applies only to a recoverable run unit.
8Allow terminal or job input to TAF.
9 Terminate TAF because of a recovery error.
TRAN Transaction type.
1 Terminal user.
2 BTRAN user job.
3TAF/CRM user job.
CRM CRM usage.
0 CRM may not be used by transaction.
1CRM may be used by transaction.
CDCS CDCS usage.
0CDCS may not be used by transaction.
1 CDCS may be used by transaction.
OLDID Set old (previous) CRM begin-commit id on the communcation recovery file.
NEWID Set new (current) CRM begin-commit id on the communication recovery file.
y^$w$?V
2-42 60459500 B
J ^ v ACCESS AND USE OF CDCS BY TASKS
The CYBER Database Control System can be used alone
or with one other data manager (CRM or TOTAL) in the
same transaction. If a task is to use CDCS, the
CDCS reference manuals listed in the preface should
be consulted for information on how to set up the
data base (schema, subschema, master directory, and
files). This data base is associated with CDCS and
the files will be at the control point of CDCS
during execution. Tasks can use the CDCS verbs for
data b as e acce ss pro vi ded th at the y are c ompiled
with the appropriate subschema relating them to a
CDCS data base.
In the following, xx represents the two-character
da ta base i den ti fier.
A TAF application (known by the xx identifier in the
TCF) is linked to a CDCS data base by means of the
subschemas used in the tasks associated with the
application (these are the tasks on xxTASKL). All
tasks in a transaction must use the same subschema
or a fatal task error (detected by CDCS) will occur.
A transaction will be considered to be connected to
CDCS if it has successfully issued a request to CDCS
and the terminate request to CDCS has not been
completed. (A CDCS terminate request from other
than the last task in a chain will be ignored.) If
the last task in the chain does not issue a CDCS
terminate request, one will be issued automatically
when the last task completes.
A task will abort if it attempts to use CDCS when
CDCS is not present in the system or if CDCS aborts
while a transaction is connected to it. If a task
aborts while it is connected to CDCS, TAF will issue
an abnormal termination notice to CDCS for the task
(unless the abort originated with CDCS).
Refer to sections 7 and 8 for information regarding
recoverable transactions and CDCS/transaction aborts.
The following TAF files are associated with an
application using CDCS:
TCF
xxJ
xxTASKL
xxJORl
XXJ0R2
xxJ0R3
Required.
Required unless all tasks are on
system task library.
Optional.
The possibility of a deadlock involving CDCS and
another data manager (TOTAL or CRM) exists. For
instance, if task X locks some resources under one
data manager and then tries to lock other resources
under another data manager that task Y initially
locked, then the two tasks may be deadlocked if task
Y tries to lock any of the resources locked by task
X. It is the responsibility of the installation,
applications programmers, and the data administrator
to prevent these situations from occurring. Such
deadlocks can be prevented by locking resources in a
specified order only, for example, lock in data
manager A resources first, then data manager B
resources, and so forth.
RESTRICT clauses cause tasks to automatically
request additional central memory. All of the
advice and requirements relevant to a task
requesting that its FL be increased apply when
RESTRICT clause processing is used (refer to Memory
Requests, section 2).
JlP^V
60459500 A 3-1

SYSTEM FILES
<#ffiv
0^**
This section is intended for the data administrator
and can be omitted by the applications programmer.
This section discusses four topics: the xxJ file,
journal files, the TAF configuration file, and the
communication recovery file.
An xxJ file is associated with each data base and
has the following functions.
• Defines the user's user name, password, and
optional user index.
• Defines optional journal files.
• Defines optional device residence for the
task library and some files specific to the
in di vid ua l d ata m ana ge rs (r efe r to the xxJ
file descriptions that follow).
Up to three journal files can be specified optionally
to su pplement t he system journalizing. A task c an
write to one of the journal files by using the JOURNL
request.
TCF, the TAF configuration file, defines the data
bases associated with a data manager, defines the
network files and communication recovery files to be
used, and may contain K display commands.
■A procedure file (TAFxxxx) is used to initialize TAF.
Commands may be added to it for recovery or to estab
lish the operating environment. For example, com
mands that attach journal files (xxJORn) and data
base files can be included In this file. Refer to
the NOS 2 Installation Handbook for more information
(refer to the preface for the publication number).
xxJ FILE
An indirect access permanent file, xxJ, where xx is
the data base name, is required for each data base.
If additional journal files are needed, they are de
fined in the xxJ file. The xxJ file Is saved under
the transaction subsystem user name. The file is in
job command format and varies depending on the data
manager used.
NOTE
The transaction subsystem user name
should be under the control of a data
administrator. The applications pro
grammer sh ou ld not hav e a cc es s to
this name.
CRM DATA MANAGER xxJ FILE
If data base recovery is to be used, the user speci
fied on the USER statement must be able to read the
xxJ file. This can be done by granting read permis
sion to that user or by making the file public.
The structure of the xxJ file (when using the CRM
Data Manager) is shown as follows.
xxJ
USER(username,password,
familyname)t
BRF,number
xxJORl,devlcetype,filetype.
xxJ0R2.devicetype, filetype.,
xxJ0R3 ,devicetype,filetype.
xxTASKL,PN~packname,
R-device.
CRM(xxpfnl,type.mode,users,
locks,mrl,pkl.hash,rec,fwi,
packname,device)
IXN(xxpfxn,naky,packname,
device)
AKY(akn,ako,akl)
AKY(akn,ako,akl)
RMKDEF(xxpfn1,rkw,rkp.kl,0,
kf ,ks,kg,kc,nl,ie,ch)
RMKDEF(xxpfnl,rkw,rkp,kl.O,
kf,ks,kg.kc.nl,le,ch)
CRM(xxpfnn,type,mode,users,
locks,mrl,pkl.hash,rec,
fwi, packname.device)
IXN(xxpfxn,naky.packname,
device)
AKY(akn,ako,akl)
AKY(akn,ako,akl)
RMKDEF(xxpfnn,rkw,rkp,kl,
O.kf,ks,kg,kc.nl,le.ch)
RMKDEF(xxpfnn,rkw,rkp,kl,
O.kf,ks,kg,kc,nl,ie,ch)
Required.
Optional,
One CRM statement
for each file.
tThis is the username, password, and familyname where all data base files and index files described In the
following CRM and IXN statements are located.
60459500 C 4-1
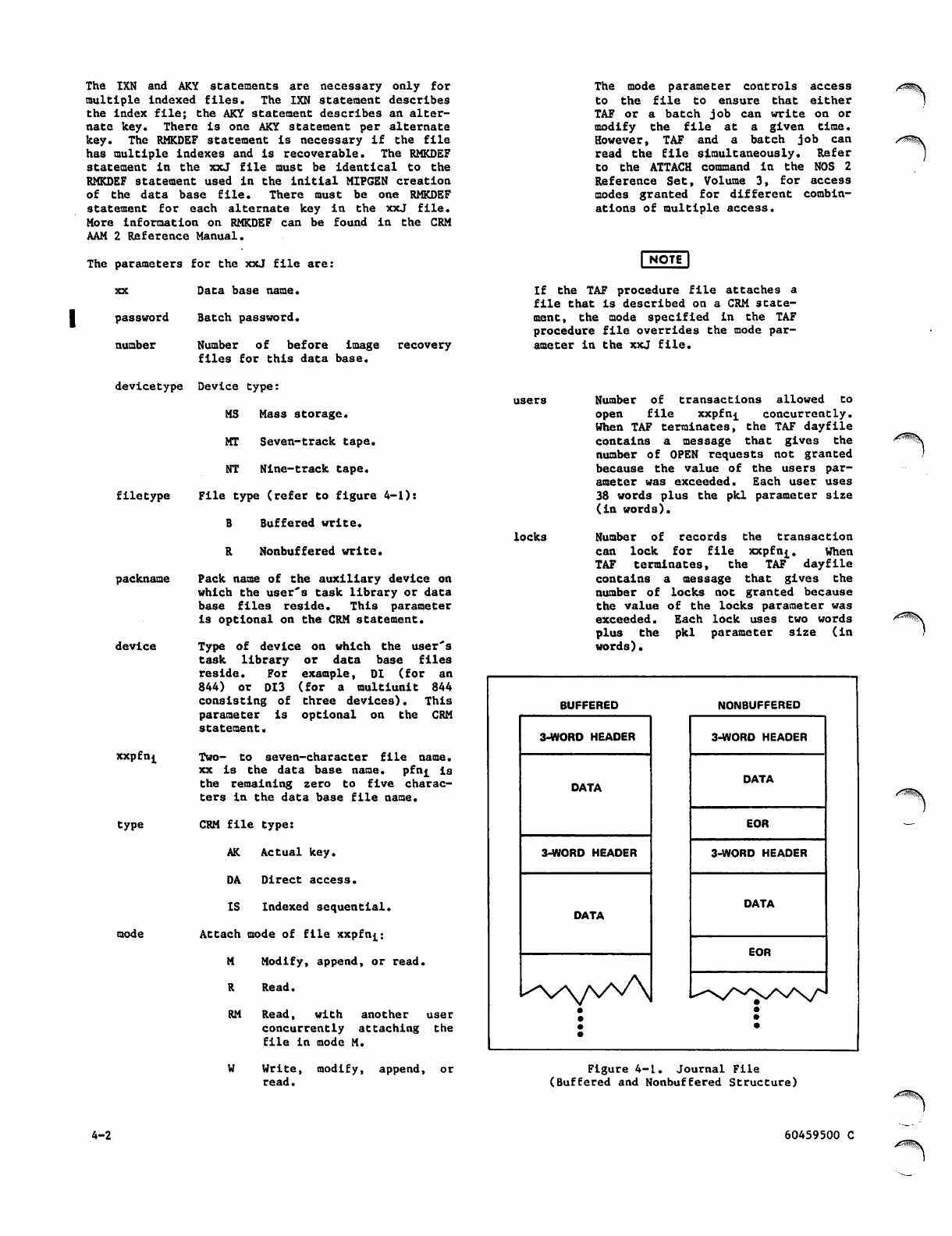
The IXN and AKY statements are necessary only for
multiple indexed files. The IXN statement describes
the index file; the AKY statement describes an alter
nate key. There is one AKY statement per alternate
key. The RMKDEF statement is necessary if the file
has multiple indexes and is recoverable. The RMKDEF
statement in the xxJ file must be identical to the
RMKDEF statement used in the initial MIPGEN creation
of the data base file. There must be one RMKDEF
statement for each alternate key in the xxJ file.
More information on RMKDEF can be found in the CRM
AAM 2 Reference Manual.
The parameters for the xxJ file are:
xx Data base name.
I password Batch password.
number Number of before image recovery
files for this data base.
The mode parameter controls access
to the file to ensure that either
TAF or a batch job can write on or
m o d i f y t h e fi l e a t a g i v e n t i m e .
However, TAF and a batch job can
read the file simultaneously. Refer
to the ATTACH command in the NOS 2
Reference Set, Volume 3, for access
modes granted for different combin
ations of multiple access.
NOTE
If the TAF procedure file attaches a
file that is described on a CRM state
ment, the mode specified in the TAF
procedure file overrides the mode par
ameter in the xxJ file.
devicetype
filetype
packname
device
xxpfn^
type
mode
Device type:
MS Mass storage.
MT Seven-track tape.
NT Nine-track tape.
File type (refer to figure 4-1)i
B Buffered write.
locks
RNonbuffered write.
Pack name of the auxiliary device on
which the user's task library or data
b a s e fi l e s r e s i d e . T h i s p a r a m e t e r
is optional on the CRM statement.
Type of device on which the user's
task library or data base files
reside. For example, DI (for an
8 4 4 ) o r D I 3 ( f o r a m u l t i u n i t 8 4 4
consisting of three devices). This
parameter is optional on the CRM
statement.
Two- to seven-character file name.
xx is the data base name. pfn^ is
the remaining zero to five charac
ters in the data base file name.
CRM file type:
AK Actual key.
DA Direct access.
IS Indexed sequential.
Attach mode of file xxpfn^;
M Modify, append, or read.
R Read.
RM Read, with another user
concurrently attaching the
file in mode M.
W Write, modify, append, or
read.
Number of transactions allowed to
open file xxpfn^ concurrently.
When TAF terminates, the TAF dayfile
contains a message that gives the
number of OPEN requests not granted
because the value of the users par
ameter was exceeded. Each user uses
38 words plus the pkl parameter size
(In words).
Number of records the transaction
c a n l o c k f o r fi l e x x p f n * ; . W h e n
TAF terminates, the TAF dayfile
contains a message that gives the
number of locks not granted because
the value of the locks parameter was
exceeded. Each lock uses two words
plus the pkl parameter size (in
words).
BUFFERED NONBUFFERED
3-WORD HEADER 3-WORD HEADER
DATA DATA
EOR
3-WORD HEADER 3-WORD HEADER
DATA
DATA
EOR
•
•
•
•
•
•
•
./S^jjk
Fi gu re 4-1. Jou rn al Fi le
(Buffered and Nonbuffered Structure)
4-2 60459500 C >f5il!\

/P8^
mrl
pkl
hash
Number specifying the maximum record
length (in characters) for file
xxpfn^.
Number specifying
characters of the
file xxpfn^.t
the length in
primary key for
One- to seven-character indirect
access file that contains the binary
code of the hashing routine for file
xxpfnj.. This indirect access file
must be stored under the username
parameter on the USER statement.
The entry point for the hashing rou
tine must be this file name (hash).
If this parameter is omitted, CRM
uses the hashing routine supplied
with CRM. This parameter applies
only for CRM direct access files.
File recoverability.
R T h i s fi l e i s r e c o v e r a b l e .
N This file is not recoverable.
When rec is not specified, N
is assumed.
NOTE
Adding recoverable files to the data
base that has a record or key length
larger than any previously specified
re co verab le fil e c auses rec ove ry file
validation errors during TAF initial
ization. Before image recovery files
need to be recreated and after image
recovery files need to be dumped to
tape (via DMREC) and recreated. To
ensure full data base recoverability,
recoverable files should only be added
to the data base following a normal
termination of TAF.
fwi Forced write indicator. When the
forced write indicator is OFF, the
modified data file buffers are writ
ten to disk when space is needed.
When the forced write indicator is
ON, all data file buffers that are
modified in core are written to disk
immediately. If fwi is not speci
fied, the forced write indicator is
set to OFF.
Y Sets forced write ON for this
file.
N Sets forced write OFF for
t h i s fi l e .
x x p f x n P e r m a n e n t fi l e n a m e o f t h e i n d e x
file; must begin with the two-letter
application identifier xx.
naky
akn
ako
atcl
rkw
rkp
kl
kf
ks
kg
kc
Number of alternate keys in the index
file.
Alternate key number. Alternate key
description statements for one data
base file must be ordered in a con
tinuous sequence by alternate key
number. For a detected key, this is
the only parameter present in the
statement.
Alternate key offset. The position
in the record of the first character
of the alternate key. This corre
sponds to the key offset parameter
used on data manager requests access
ing the record by this key. The
first position in the record is char
acter position number one (not zero).
Length of
characters.
alternate key in
Relative word in the record in which
the alternate key begins, counting
from 0; required.
Relative beginning character position
within the relative key word (rkw),
counting from 0; required.
Number of characters in the key, 1
to 255; required.
Required to mark position for the
reserved field.
Key format; required.
0 or S Symbolic.
1 o r I In t e g e r.
2 or U Unco Hated symbolic.
3 or P Purge alternate key defi
nition from the index.
S u b s t r u c t u r e f o r e a c h p r i m a r y k e y
list in the index; optional.
U Unique (default).
I Indexed sequential; recom
mended for efficiency in
processing.
F First-in, first-out.
Length in characters of the repeating
group in which the key resides.
Number of occurrences of the repeat
ing group; zero for T-type records,
and a number for a repeating group
embedded within the record.
tThe user can specify octal numbers and decimal numbers by using a postradix of B or D, respectively.
Decimal is the default.
/#*N 60459500 C 4-3
nl
ie
ch
Null suppression; a null value is
all spaces (symbolic key) or all
zeros (integer key):
0 Null values
(default).
are indexed
N Null values are not indexed.
Include/exclude sparse control char
acter:
I Include alternate key value
if the record contains a
sparse control character.
E Exclude alternate key value
if the record contains a
sparse control character.
Characters that qualify as sparse
control characters; up to 36 letters
and digits can be specified as a
cha ra cter stri ng .
n User index (obtained from site
analyst).
devicetype Device type:
MS Mass storage.
MT Seven-track tape.
NT Nine-track tape,
filetype File type (refer to figure 4-1):
B Buffered write.
R N o n b u f f e r e d w r i t e .
packname Pack name of the auxiliary device on
which the user's task library
(xxTASKL) or data sets will reside.
device Type of device on which the user's
file will reside [for example, DI
( f o r 8 4 4 ) o r D I 3 ( f o r a m u l t i u n i t
844 consisting of three devices)].
TOTAL DATA MANAGER xxJ FILE
The following shows the structure of the xxJ file
when using the TOTAL Data Manager.
xxJ
USER(username,password,familyname)t
UI»n.
xxJORl.devicetype,filetype.
xxJ0R2.devicetype,filetype.
xxJ0R3.devicetype,filetype.
xxTASKL,PN-packname,R-device.
NL.
LG,PN=packnarae,R-device.
aaaa,PNapackname,R-device
Optional.
Either the NL
statement or the
LG statement must
be selected. PN
and R parameters
are optional. NL
causes TOTAL to
not log recovery
data. LG causes
TOTAL to log re
covery data.
PN and R parame
ters are optional.
zzzz,PNapackname,R-device
The parameters for the xxJ file are:
xx Data base name.
password Batch password.
Four-character data set names.
CDCS OR NO DATA MANAGER xxJ FILE
If an application uses CDCS and one of the other data
managers (CRM or TOTAL)-, then the xxJ file should be
structured as specified for the other data manager.
If an application accesses only the CDCS Data Manager
or no data manager, the structure of the xxJ file is
as follows:
xxJ
USER(username,password,familyname)t
xxJORl,devicetype,filetype.
xxJ0R2,devicetype,filetype. Optional.
xxJ0R3.devicetype,filetype.
xxTASKL,PN-packname,R-device
The parameters are:
Parameter Description
xx Application (data base) name.
password Batch password,
devicetype Device type:
MS Mass storage.
MT Seven-track tape.
NT Nine-track tape.
tTAF locates the data base using the familyname parameter in the procedure file that initializes TAF and the
username and password parameters in the xxJ file. The username, password, and familyname parameters are
used for validation.
/<5SR^\
4-4 60459500 C

filetype File type (refer to figure 4-1): CREATING AN xxJ FILE
B Buffered write. To enter an xxJ file, the data administrator can run
a batch job to create and save the file under the
R Nonbuffered write. transaction subsystem user name. This can also be
done at a terminal through IAF. (Refer to the NOS 2
packname Pack name of the auxiliary device on Reference Set, Volume 1, for IAF operating
which the user's task library instructions.)
resides.
device Type of device on which the user's
task library resides.
/0&< 60459500 C 4-4.1/4-4.2 |

/^!j\
0^\
0^\
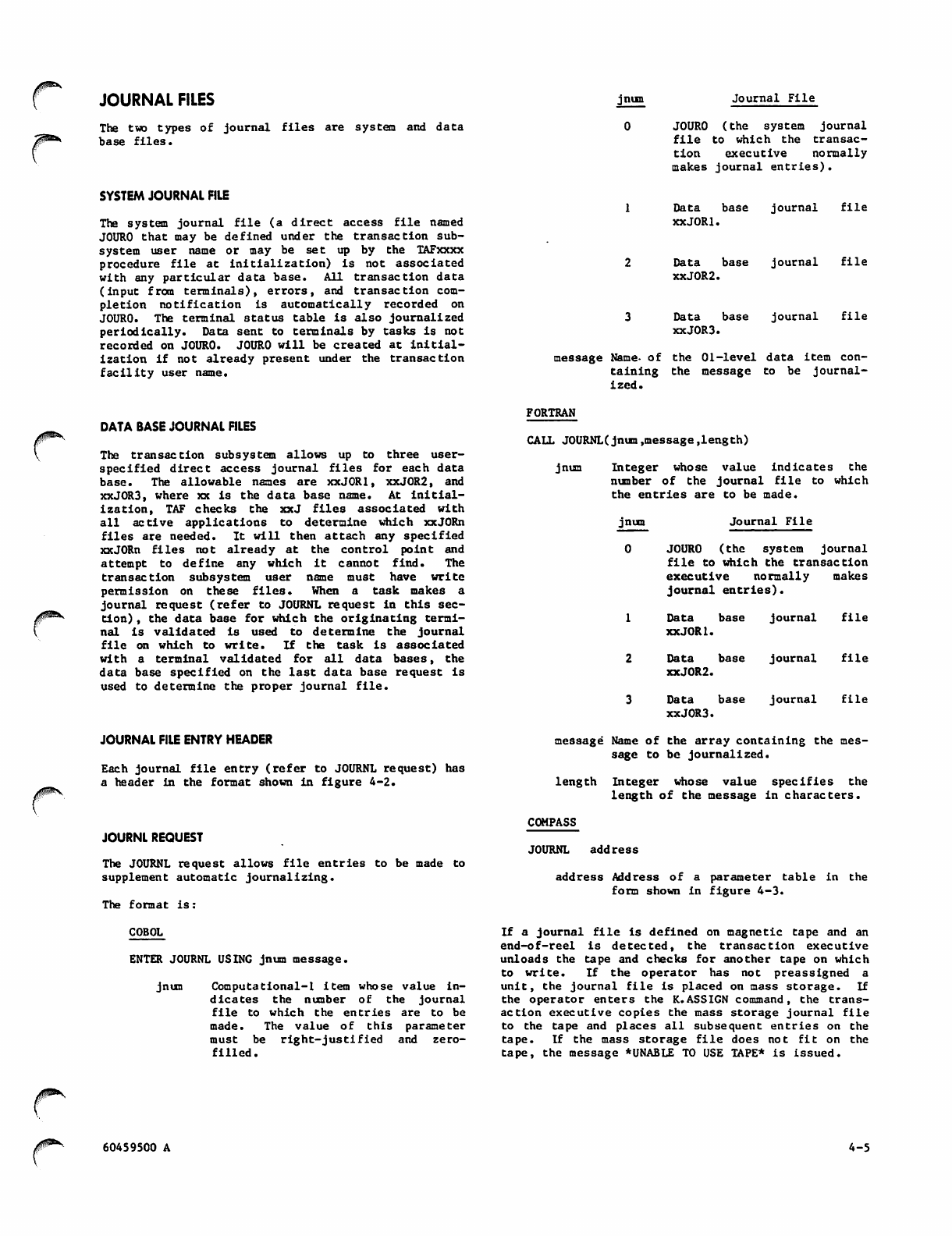
JOURNAL FILES
The two types of journal files are system and data
base files.
SYSTEM JOURNAL FILE
The system journal file (a direct access file named
JOURO that may be defined under the transaction sub
system user name or may be set up by the TAFxxxx
procedure file at initialization) is not associated
with any particular data base. All transaction data
(input from terminals), errors, and transaction com
pletion notification is automatically recorded on
JOURO. The terminal status table is also journalized
periodically. Data sent to terminals by tasks is not
recorded on JOURO. JOURO will be created at initial
ization if not already present under the transaction
facility user name.
jnum Journal File
JOURO (the system journal
fi l e t o w h i c h t h e t r a n s a c
tion executive normally
makes journal entries).
Data base journal file
xxJORl.
Data base journal file
xxJ0R2.
Data base
xxJ0R3.
journal file
message Name- of the 01-level data item con
taining the message to be journal
ized.
DATA BASE JOURNAL FILES
The transaction subsystem allows up to three user-
specified direct access journal files for each data
base. The allowable names are xxJORl, xxJ0R2, and
xxJ0R3, where xx is the data base name. At initial
ization, TAF checks the xxJ files associated with
all active applications to determine which xxJORn
files are needed. It will then attach any specified
xxJORn files not already at the control point and
attempt to define any which it cannot find. The
transaction subsystem user name must have write
pe r m i s s i o n on t h e s e fil e s . Wh e n a ta s k m a k es a
journal request (refer to JOURNL request in this sec
tion) , the data base for which the originating termi
nal is validated is used to determine the journal
fi l e o n w h i c h t o w r i t e . I f t h e t a s k i s a s s o c i a t e d
with a terminal validated for all data bases, the
data base specified on the last data base request is
used to determine the proper journal file.
JOURNAL FILE ENTRY HEADER
Each journal file entry (refer to JOURNL request) has
a header In the format shown in figure 4-2.
JOURNL REQUEST
The JOURNL request allows file entries to be made to
supplement automatic journalizing.
The format is:
FORTRAN
CALL JOURNL(jnum.message,length)
jnum Integer whose value indicates the
nu m be r of t h e j our n al fil e t o whic h
the entries are to be made.
Journal File
JOURO (the system journal
file to which the transaction
executive normally makes
j ournal en tr ie s).
Data base
xxJORl.
Data base
xxJ0R2.
Data base
xxJ0R3.
journal
journal
journal
fi l e
fi l e
file
message Name of the array containing the mes
sage to be journalized.
l e n g t h I n t e g e r w h o s e v a l u e s p e c i fi e s t h e
length of the message in characters.
COMPASS
JOURNL address
address Address of a parameter table in the
form shown in figure 4-3.
COBOL
ENTER JOURNL USING jnum message.
jnum Computational-l item whose value in
dicates the number of the journal
file to which the entries are to be
made. The value of this parameter
must be right-justified and zero-
filled.
If a journal file is defined on magnetic tape and an
end-of-reel is detected, the transaction executive
unloads the tape and checks for another tape on which
t o w r i t e . I f t h e o p e r a t o r h a s n o t p r e a s s i g n e d a
unit, the journal file is placed on mass storage. If
the operator enters the K.ASSIGN command, the trans
action executive copies the mass storage journal file
to the tape and places all subsequent entries on the
tape. If the mass storage file does not fit on the
tape, the message * UNABLE TO USE TAPE* is issued.
j f * K 60459500 A 4-5
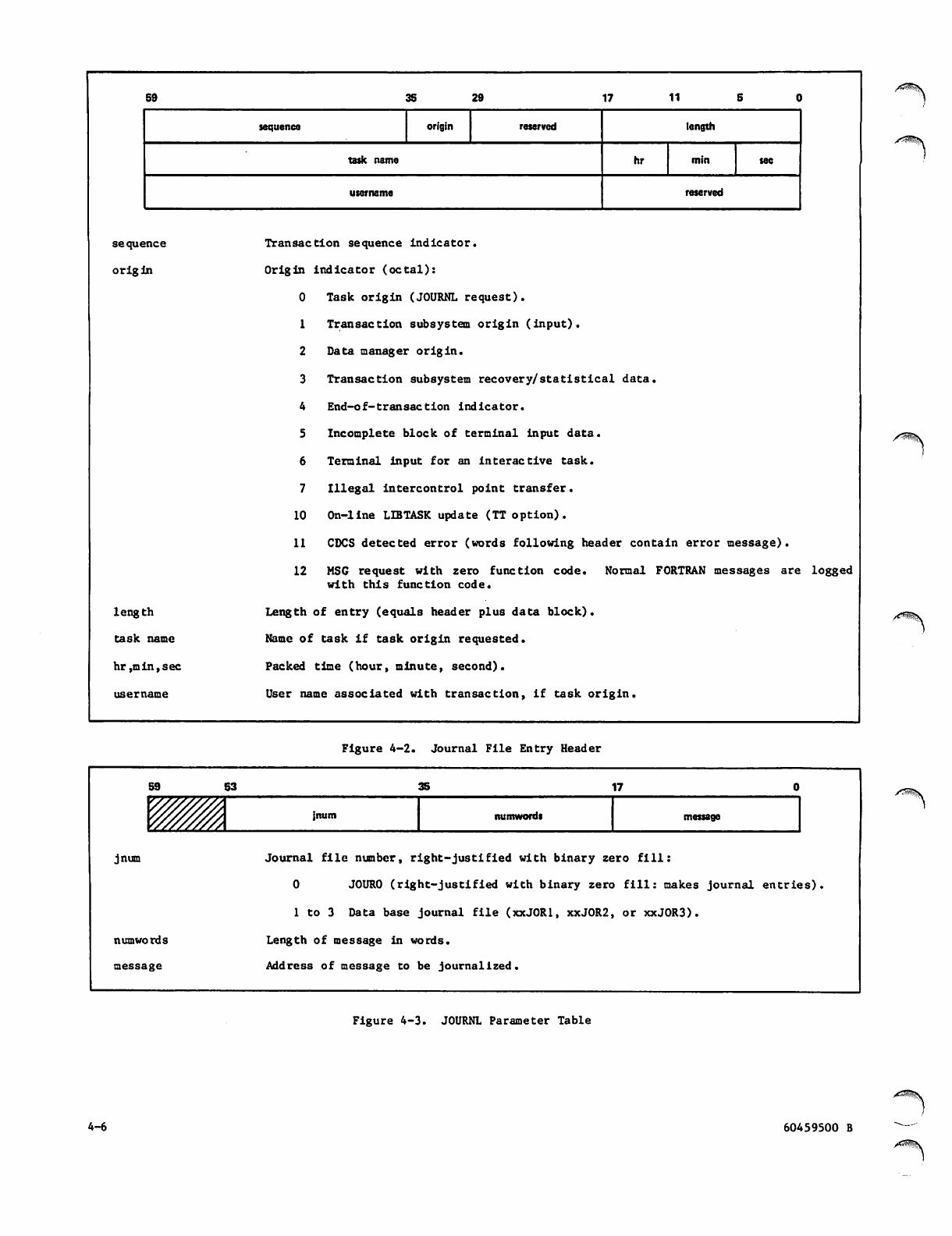
59 35 29 17 11
sequence origin reserved length
task name hr min see
username reserved
sequence
origin
length
task name
hr,min, sec
username
Transaction sequence indicator.
Origin indicator (octal):
0 Task origin (JOURNL request).
1 Transaction subsystem origin (input).
2 Data manager origin.
3 Transaction subsystem recovery/statistical data.
4 End-of-transaction indicator.
5 Incomplete block of terminal input data.
6 Terminal input for an interactive task.
7 Illegal intercontrol point transfer.
10 On-line LIBTASK update (TT option).
11 CDCS detected error (words following header contain error message).
12 MSG request with zero function code. Normal FORTRAN messages are logged
with this function code.
Length of entry (equals header plus data block).
Name of task if task origin requested.
Packed time (hour, minute, second).
User name associated with transaction, if task origin.
y^SSN
Figure 4-2. Journal File Entry Header
59 53 3 5 1 7 0
'////
m> jnum numwords message
jnum Journal file number, right-justified with binary zero fill:
0 JOURO (right-justified with binary zero fill: makes journal entries).
1 to 3 Data base journal file (xxJORl, xxJOR2, or xxJ0R3).
numwords Length of message in words.
message Address of message to be journalized.
/*tWsv
Figure 4-3. JOURNL Parameter Table
4-6 60459500 B
TAF CONFIGURATION FILE
The TAF configuration file is a required indirect
access permanent file saved under the transaction
facility user name. This file is used during TAF
initialization and recovery. If it is not local
when the TAFREC command is reached, TAFREC will
attempt to get it from TAF's user index. The TCF
has the following format:
USER,UN,PW,FM.
DMS ,datamanager,switen,xxj,
XX 2 , . . . , 2CKfi.
NETWORK,ID-i,FM-faraily,
UN-username.
RECOVER,ID-i,MS»maximumsize,
NM-number.
TABCON.n
DISPLAY,status.
K. command Rvalue i ,
K. commandnsvalue(i
At least one of
each required.
Required or not
allowed (refer to
statement de
scription.
Required for
b a t c h c o n c u r
rency. Refer to
the TAF/CRM Data
Manager Reference
Manual.
Optional.
OFF Data bases specified
on the same statement
are not made available
for TAF processing.
xxi Data base identifier. Must not
be duplicated on the same or
any other active DMS statement.
For the CRM Data Manager, it is
the two-letter data base name.
For the TOTAL Data Manager, this
parameter has the format:
xxyyyy
which is the data base name (the
DBMODt file name) specified in
the DATA-BASE-NAMEt statement
of the DBDLt statements, xx is
the unique TAF data base name
and yyyy is any combination of
four alphanumeric characters.
A separate DMS statement for CDCS (OTHER) is not
necessary if CDCS is to be used in conjunction with
another data manager.
The TCF file must contain at least one DMS statement
and each DMS statement with status set to ON must
have at least one data base identifier or TAF will
abort.
The maximum number of data bases that may be associ
ated with one data manager is specified by the in
stallation parameter MAXDB. This value is 25 unless
it is altered by the user's site.
jgp*v
DMS STATEMENT
DMS statements on the TCF are used to specify the
data managers to be loaded by TAF and the applica
tions (data bases) to be associated with each data
manager.
The format is:
DMS.datamanager.switch.xxj,xx2,...,xxn.
data
manager
r
switch
Name of the data manager. Must
be CRM, TOTAL, or OTHER. The
same data manager can be speci
fied on any number of DMS state
ments. Use the datamanager
value OTHER for specifying an
application that is either not
associated with a data manager
or is associated only with the
CDCS Data Manager.
Data manager status.
ON or OFF.
Mus t be
ON The specified data
manager (TOTAL or CRM)
will be loaded. The
data bases specified
on the same statement
are to be made avail
able for TAF process
ing. These data bases
are referred to as
active.
The maximum length of each DMS statement is 160 6-bit
display code characters.
DISPLAY STATEMENT
The DISPLAY statement on the TCF controls whether or
not the TAF K display will appear at the consoLe dur
ing initialization and recovery. However, an error
in a K display command causes TAFREC to issue an
error message and bring up the K display for correc
tions regardless of the DISPLAY statement. The
format is:
DISPLAY,status.
status A variable having one of the
following values.
ON K display will appear
at the console during
initialization and
recovery to enable the
operator to make
changes at those times.
O F F K d i s p l a y w i l l n o t
appear at the console
during Initialization
and recovery.
4m<- tRefer to the TOTAL - CDC 2 Reference Manual for a detailed description.
60459500 C 4-7
NETWORK STATEMENT
The NETWORK statements on the TCF declare the
network files (NCTFi) TAF uses to determine the
users allowed to access TAF. There must be at least
one and a maximum of eight NETWORK statements. The
format is:
NETWORK,ID-i,FM-familyname,UN=username.
i An integer specifying a unique
network file identifier. The
range is zero to seven. This
identifier is used in
constructing the name of the
network file (NCTFi).
familyname The family name under which the
network file exists. If the
familyname parameter is not
specified, the default family
name is used.
TAF will use. The name of the corresponding CRF is
ZZCRFi. The CRF resides under the same family and
user name as the corresponding network file.
K. STATEMENT
Any K display commands that can be issued under the
initial K display can appear in the TCF. Values
specified in the TCF become the default values in
place of the installation defaults (refer to the K
display utilities in the NOS 2 Analysis Handbook for
t h e i n s t a l l a t i o n d e f a u l t v a l u e s ) . I f t h e o p e r a t o r
changes any of these values during initialization,
those changes remain in effect if TAF is restarted
in recovery mode.
If K display commands are used in the TCF, they must
appear consecutively.
/^^^Sv
The user name under which the
network file exists. If the
username parameter is not
specified, the TAF user name is
used.
RECOVER STATEMENT
The RECOVER statement on the TCF declares the set of
files TAF is to use when in recovery mode. This
directive is required if TAF is assembled with
recovery, but it is not allowed if TAF is assembled
without recovery.
The format is:
RECOVER,ID-i,MS-maximumsize,NM-number.
1 An integer specifying a unique
recovery file id. The range is
zero to seven. This id is the
id used in constructing the
name of the communication
recovery file (ZZCRFi). Only
one id may be specified per
RECOVER statement. The id must
match an id specified in a
NETWORK statement.
maximumslze An integer specifying the maxi
mum size of the message, in
words, that TAF will record on
the communication recovery file.
The default Is 57. Maximum is
installation parameter MAXWS.
This is the maximum message
size for the RPUT and SECURE
requests.
number An integer specifying the maxi
mum number of user messages that
can be recorded on the communi
cation recovery file via the
RPUT request. The default Is
zero, the maximum is 10.
Each RECOVER statement specifies a recovery id. This
id determines the communication recovery file that
USER STATEMENT
The USER statement on the TCF specifies the user
name under which TAF is to run. This user name
should be defined through MODVAL to have the same
user index as defined by the installation parameter
TRUI. Only one USER statement is allowed in the
TCF. The format is as follows:
USER,UN,PW,FM.
or
ACCOUNT,UN,PW.FM.
Parameter Description
U N T h e u s e r n a m e u n d e r w h i c h T A F i s t o
run.
P W T h e b a t c h p a s s w o r d f o r t h e u s e r n a m e .
F M T h e f a m i l y u n d e r w h i c h TA F i s t o r u n .
The USER statement should be the first statement in
the TCF.
COMMUNICATION RECOVERY FILE
A communication recovery file is a file TAF uses to
maintain recovery information about recoverable
t r a n s a c t i on s . N ew C R F s a r e cr e a t e d an d e xis t i n g
CRFs are reinitialized at initialization time by
using the K.INT command (refer to section 8). There
can be up to eight of these files (named CRFO,
CRF1,...,CRF7).
Each one corresponds to a network file having the
same Identifier (NCTFO, NCTFI,....NCTF7). For every
user description statement in a network file, there
Is a user entry in the corresponding CRF. These
entries are added and deleted as follows:
• New user entries are added to a CRF by
adding a user description statement to the
corresponding network file.
• User entries are removed from a CRF by
removing the user description statement from
the corresponding network file.
4-8 60459500 C
TRANSACTION FACILITY (TAF) K DISPLAYS
The following commands control operation of the TAF Subsystem. Initiate the TAF Subsystem
by using the TAFffff command before issuing these commands.
INITIATING TAF K DISPLAY
When the transaction executive is brought to a control point, the message
REQUEST *K* DISPLAY appears at the control point if a DISPLAY,ON command is specified
in the TAF configuration file. Respond with the entry:
K,TAF.
Any of the following initialization commands can then be entered. If no values are to be
changed, enter the command:
K.END.
Values are decimal unless otherwise indicated.
Command
K.BFL=n.
K.CMB=n.
K.ECS=n.
K.EFL=n.
K.END.
Description
Changes the starting and minimum field length allocated by TAF to
CRM (200008 < n < 100000s). Default is 700008.
Changes the maximum number of communication blocks allowed to the
TAF Subsystem (7 < n <^ 40). Default is 40.
Sets the extended memory field length to be used by the transaction
executive; n is octal thousands of words. Default is 0.
Changes the maximum additional central memory field length made
available to CRM for buffers and capsules (0 < n < 100000s).
Default is 0.
Ends input of the transaction executive initialization parameters.
Initialization is completed when the TAF K display appears.
8-68 60459300 D
Command
K.ER0=CRF,op.
Description
Specifies whether to override certain I/O and logic errors when
processing the communication recovery files (CRF).
K.GO.
K.INT=typ,fileid,
NO
YES
op Description
Aborts if I/O or logic errors are encountered while
processing the communication recovery files. This is
the default setting.
I/O or logic errors encountered on a run unit header
record result in the loss of that run unit with no
indication to the terminal user. The loss is noted on
the recovery report.
I/O or logic errors encountered on a message record
within a run unit result in a loss of that run unit. A
status field is set in the run unit header, allowing TAF
to inform the terminal user of the run unit loss.
I/O or logic errors encountered on the CRF header record
result in an unconditional abort of the TAF Subsystem.
Ends input of the transaction executive initialization parameters.
Initialization is complete when the TAF K display appears.
Specifies which communication recovery files (CRF) are to be
initialized. This is the only way to initialize a CRF. Files
specified on a RECOVER command in the TAF configuration file and
specified in this command are initialized. Files specified on a
RECOVER command but not specified in this command are used for
recovery.
This command also specifies whether CYBER record manager (CRM) data
base recovery files are initialized or recovered. For CRM recovery
files, this command is valid regardless of TAF assembly parameters.
HE
CRF
CRM
Description
Communication recovery files. This parameter is valid
only if the installation parameter IPTAR equals 1.
CYBER Record Manager after-image and before-image
r e c o v e r y fi l e s .
60459300 D 8-69
Command D e sc r i Dt i o n
fileid Description
n A d i g i t f r o m 1 t o 7 t h a t d e fi n e s a C R F t o b e
initialized. The digit corresponds to the ID parameter
on the RECOVER command in the TAF configuration file.
This parameter is not valid for CRM recovery files.
ALL If typ is CRF, all communication recovery files defined
by RECOVER commands in the TAF configuration file are
initialized. If typ is CRM, all CRM recovery files are
initialized.
NOTE
This parameter must be used with caution
when typ is CRM since the CRM update history
currently on the after-image recovery files
is lost.
K.MFL=n.
K.REC=a.
NONE If typ is CRF, communication recovery files are
initialized; all communication recovery files specified
in RECOVER commands in the TAF configuration file are
recovered. If typ is CRM, all CRM data bases are
recovered based on information in the existing recovery
files. No CRM recovery files are initialized. This
fileid is the default for both typ=CRF and typ=CRM.
Sets the maximum field length to be used by the transaction
executive (40000 < n <_ 376600). Default is 376600.
Specifies whether to set the recovery bit in the user area of each
terminal status table entry (YES or NO). If YES, the user recovery
bit is set. If NO, the value of the user recovery bit is not
changed from what it was before the command was issued. Default is
NO.
K.SCP=n.
K.STOP.
K.TFL=n.
K.TLF=filename,
Changes the number of subcontrol points (2 <^ n < 31). Default is 31
Aborts the TAF Subsystem initialization unconditionally.
Changes the value used as the upper bound for TARGET. This is the
amount of memory CRM uses for data and index blocks
(100008 <n< 100000s). Default is 30000s. F°r more
information, refer to the CYBER Record Manager Advanced Access
Methods Version 2 Reference Manual.
Changes the name of the system task library file (any valid file
name). Default is TASKLIB.
y?5^3K
8-70 60459300 D
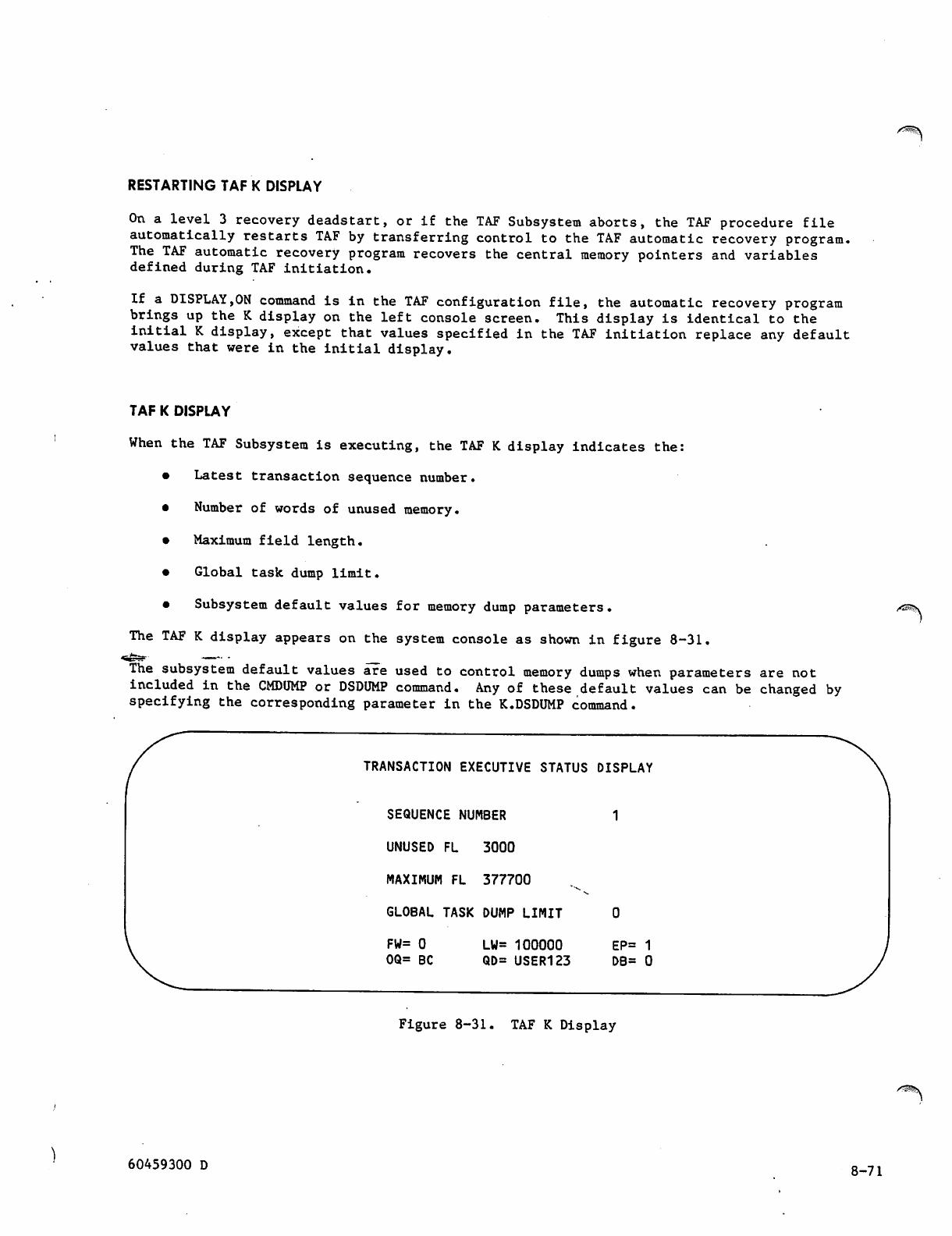
RESTARTING TAF K DISPLAY
On a level 3 recovery deadstart, or if the TAF Subsystem aborts, the TAF procedure file
automatically restarts TAF by transferring control to the TAF automatic recovery program.
The TAF automatic recovery program recovers the central memory pointers and variables
defined during TAF initiation.
If a DISPLAY,ON command is in the TAF configuration file, the automatic recovery program
brings up the K display on the left console screen. This display is identical to the
initial K display, except that values specified in the TAF initiation replace any default
values that were in the initial display.
TAF K DISPLAY
When the TAF Subsystem is executing, the TAF K display indicates the:
• Latest transaction sequence number.
• Number of words of unused memory.
• Maximum field length.
• Global task dump limit.
• Subsystem default values for memory dump parameters.
The TAF K display appears on the system console as shown in figure 8-31.
/i^iSSv
The subsystem default values are used to control memory dumps when parameters are not
included in the CMDUMP or DSDUMP command. Any of these default values can be changed by
specifying the corresponding parameter in the K.DSDUMP command.
TRANSACTION EXECUTIVE STATUS DISPLAY
SEQUENCE NUMBER 1
UNUSED FL 3000
MAXIMUM FL 377700
GLOBAL TASK DUMP LIMIT 0
FW= 0
0Q= BC
LW= 100000
QD= USER123
EP= 1
DB= 0
Figure 8-31. TAF K Display
60459300 D 8-71
/$ S \
The default parameter values for the CMDUMP and DSDUMP commands are given on the TAF K
display shown in figure 8-31.
Parameter Description
DB This parameter is not used. It is retained for compatibility with
previous releases of NOS.
EP Exchange package:
0 Do not dump the exchange package.
1 Dump the exchange package.
FW First word address of the task memory to be dumped.
L W L a s t w o r d a d d r e s s o f t h e t a s k m e m o r y t o b e d u m p e d .
OQ Output queue:
BC Local batch.
RB Remote batch.
PF Permanent file.
QD Queue destination:
User name (if OQ=BC).
Equipment identifier (if OQ«RB).
Permanent file name (if OQ=PF).
TAF K-DISPLAY COMMANDS
When the transaction executive is at its control point, the following commands can be
entered from the system console or submitted from tasks using the KPOINT request. Any task
can issue the K.DUMP command. Only tasks that reside on the system task library can issue
the other K-display commands. (Refer to the TAF Reference Manual for additional information
on the KPOINT request and the system task library.)
Command Description
K.ASSIGN,est. Assigns a magnetic tape unit to be used for a journal file, est is
the EST ordinal of the tape unit. The first form of the command
or makes unit est available for the transaction executive to assign to
the next tape journal file that encounters end of reel. Two tape
K.ASSIGN,est,db,n. units may be preassigned. If a tape has not been preassigned in
this manner, an end-of-reel on a journal file causes subsequent
en t r ie s f o r tha t fi le to be p l ace d o n dis k .
/$BN
8-72 60459300 D

0!&$£\
Command
K.DEBUG.
K.DR0P,n.
Description
The second form of the command forces journal file n (n=l, 2, or 3)
for data base db, defined as a tape file, from disk to tape. The
transaction executive copies the data from the disk journal file to
tape est and places all subsequent entries for that file on the
tape. This command is necessary after the transaction executive
i n i t i a l i z a t i o n t o a s s i g n t a p e u n i t s to t h e t a p e jo u r n a l fi l e s o r
after an end-of-reel on a tape journal file when no tape had been
preassigned to the transaction executive. All data residing on the
disk for"the tape journal file must fit on the tape assigned by this
command or the transaction executive will unload the tape and issue
the message *UNABLE TO USE TAPE*.
Turns on the application interface program (AIP) debug option', which
logs all messages on trace file ZZZZZDN. Use this command only when
TAF is installed with the DEBUG option.
Drops an executing task at subcontrol point n.
K.DSDUMP,FW=addr, Allows you to modify the standard system default parameters
LW=addr,EP=pkg, controlling memory dumps. The command does"not directly cause a
OQ=outq,QD=qdest, dump. Rather, it sets default values to be used when a subsequent
DB=db. CMDUMP request is received or when abort conditions occur. Refer to
TAF K Display, earlier in this sectrton, for explanations-of the
parameters•
K.DUMP,fwa,lwa. Dumps all or part of the field length of the Transaction Facility
from the first word address (fwa) to the last word address (lwa) of
the area to be dumped. The default value for fwa is 0 and for lwa
is 377777s. The default base is octal. If no parameters are
specified, the entire field length is dumped. The output is routed
to a printer that has an ID of 0.
Unlike other K-display commands, the K.DUMP command can be issued
from any task. Other K-display commands can be issued by tasks only
if they are on the system task library (refer to the TAF Reference
Manual).
Since secure information may be contained in a dump of the
Transaction Facility, the following safeguards have been set up to
protect dumped information; however, the installation must take the
ultimate responsibility for the protection of dumped information.
• The global task dump limit (GTDL) can be set by the
K.DUMPLIM command to limit the number of times the K.DUMP
command can be issued from tasks. The initial value of the
GTDL is 0 (zero), so the K.DUMP command is disabled from use
by a task by default.
• For all dumps of the Transaction Facility, whether you
initiated it or a task did, a one-page header precedes the
dump. This header page indicates the output is secure and
should be given only to the TAF central site systems analyst
• When the Transaction Facility is dumped, the message TAF
FIELD LENGTH DUMP RELEASED is issued to the system dayfile,
the Transaction Facility dayfile, and line one of the
control point.
604 59 300 D 5-73

M&\
Command
K.DUMPLIM,n. Sets GTDL to value n
GTDL is set to 0.
Description
(0 <^ n < 9999999). If n is not specified, the
The GTDL is the number of times the K.DUMP command can be issued
from tasks. This value is displayed on the TAF K display shown in
figure 8-31. The initial value of the GTDL is 0. When the GTDL is
0, no dumps of the Transaction Facility can occur from tasks. Thus,
the K.DUMP command is disabled from tasks by default.
To enable the K.DUMP command for tasks, issue the K.DUMPLIM command
to set the GTDL to a value greater than zero. Each time a task
Issues a K.DUMP command, the GTDL is decreased by one until it
equals zero. When the first K.DUMP command is issued from a task
with the GTDL equal to zero, the message
GLOBAL TASK DUMP LIMIT EXHAUSTED
is issued to the Transaction Facility dayfile, the system dayfile,
and line one of the control point. Also, the message
DUMPS LOST
is displayed on the K display in place_of the value of the GTDL.
This message remains until the value of GTDL is set to a value
greater than or equal to zero. The K.DUMPLIM command should be used
with care in system tasks, since this might allow unauthorized users
to alter the GTDL.
K.IDLE. Idles down the transaction control point. Once idle down has been
initiated, no new transactions will be permitted but currently
executing transactions will be allowed to finish.
K.JEND,db,n.
K.MAXFL,n.
Forces end-of-reel processing (writes an EOI and rewinds the file)
on tape journal file n of data base db. If n is not a tape journal
file, the command is ignored.
Alte r s the transacti o n executive max i m u m field length. The
transaction executive does not attempt to obtain more than n words
of storage. This command is rejected if the value for n is more
than 376600s or less than tne field length currently required for
TAF.
K. MESSAGE, TN=b.
message.
K.NODEBUG.
Directs the transaction executive to send message to a terminal
specified by terminal name b.
Turns off the application interface program (AIP) debug option,
which logs all messages on trace file ZZZZZDN. Use this command
only when TAF is installed with the DEBUG option.
8-74 60459300 D

Command
K.OFFTASK,a,db.
K.ONTASK.a,db.
K.ROLLTIM,nnnnnn.
Description
Disables the use of task a, where a is the task name in the data
base db task library directory (dbTASKL). The data base name db is
not specified for tasks in the system task library.
Reverses the effect of a previous OFFTASK command for the specified
task a in the data base db task library directory (dbTASKL). The
data base name db is not specified for tasks in the system task
li b ra r y (TA S KL I B) .
Changes the amount of time that TAF will retain its field length
between communication input messages; nnnnnn is specified in units
of milliseconds. Refer to the installation parameter ITRTL in the
NOS 2 Installation Handbook.
K.SWITCH. Causes the console K display to change to a display listing all
allowable console commands. When K.SWITCH is entered a second time,
the normal display returns. This command activates task KDIS and
forces TAF to remain rolled in.
K.TBCON,nn.
K.TST,TN=a,DB=db,
U=nnnn,UL=mmmm,
NN=b.
Changes the number of TAF/CRM batch concurrency users; nn is less
than or equal to the value specified on the TBCON command in TAF's
configuration file (TCF).
Changes entries in the termin al status table for terminal a. The
following entries can be changed: data base name db, user area
upper 12 bits (nnnn), user area lower 12 bits (mmmm), and new
terminal name b. The changes do not affect the network and
simulation files. Do not use this command if the terminal is logged
in.
<£**?\
60459300 D 8-75
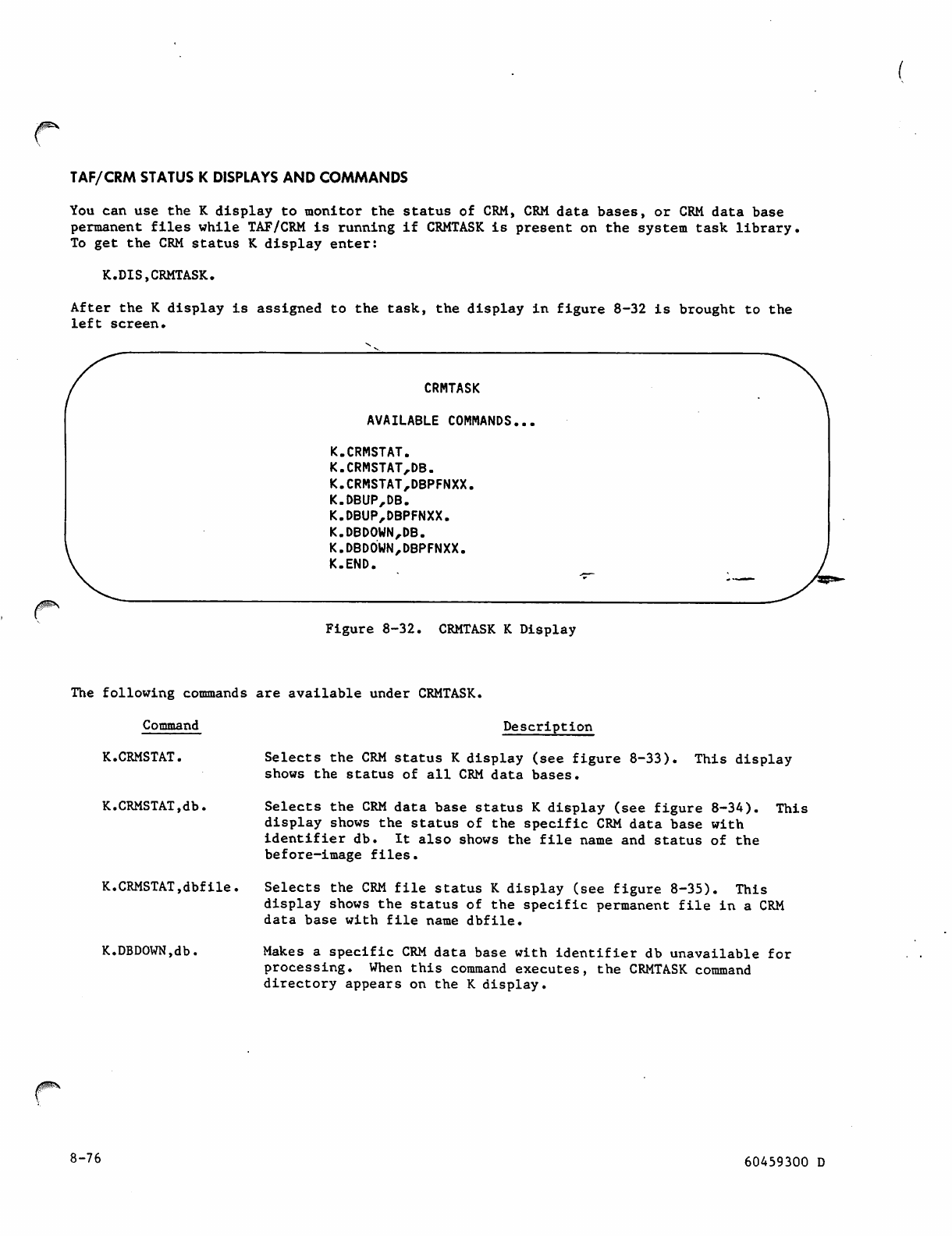
TAF/CRM STATUS K DISPLAYS AND COMMANDS
You can use the K display to monitor the status of CRM, CRM data bases, or CRM data base
permanent files while TAF/CRM is running if CRMTASK is present on the system task library.
To get the CRM status K display enter:
K.DIS,CRMTASK.
After the K display is assigned to the task, the display in figure 8-32 is brought to the
left screen.
CRMTASK
AVAILABLE COMMANDS,
K.CRMSTAT.
K.CRMSTAT,DB.
K.CRMSTAT,DBPFNXX.
K.DBUP,DB.
K.DBUP,DBPFNXX.
K.DBDOWN,DB.
K.DBDOWN,DBPFNXX.
K.END.
Figure 8-32. CRMTASK K Display
The following commands are available under CRMTASK.
Command
K.CRMSTAT.
Description
Selects the CRM status K display (see figure 8-33). This display
shows the status of all CRM data bases.
K.CRMSTAT,db. Selects the CRM data base status K display (see figure 8-34). This
display shows the status of the specific CRM data base with
identifier db. It also shows the file name and status of the
before-image files.
K.CRMSTAT,dbfile.
K.DBDOWN.db.
Selects the CRM file status K display (see figure 8-35). This
display shows the status of the specific permanent file in a CRM
data base with file name dbfile.
Makes a specific CRM data base with identifier db unavailable for
processing. When this command executes, the CRMTASK command
directory appears on the K display.
8-76 60459300 D
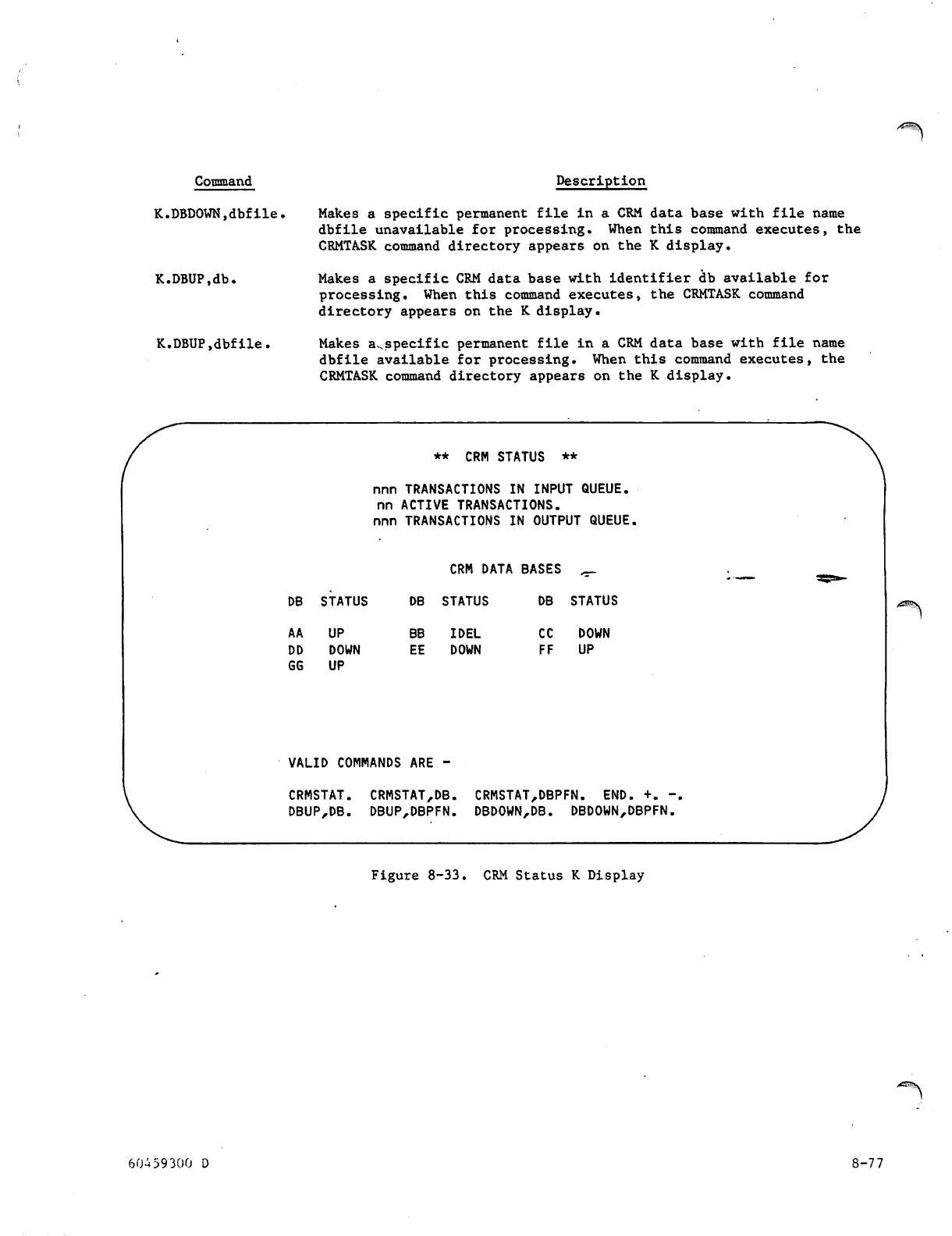
/^a&%
Command
K.DBDOWN,dbfile.
K.DBUP.db.
K. DBUP,dbfile.
Description
Makes a specific permanent file in a CRM data base with file name
dbfile unavailable for processing. When this command executes, the
CRMTASK command directory appears on the K display.
Makes a specific CRM data base with identifier db available for
processing. When this command executes, the CRMTASK command
directory appears on the K display.
Makes a^specific permanent file in a CRM data base with file name
dbfile available for processing. When this command executes, the
CRMTASK command directory appears on the K display.
** CRM STATUS **
nnn TRANSACTIONS IN INPUT QUEUE,
nn ACTIVE TRANSACTIONS,
nnn TRANSACTIONS IN OUTPUT QUEUE,
CRM DATA BASES ,_
D B S T A T U S D B S T A T U S D B S T A T U S
AA UP BB IDEL CC DOWN
DD DOWN EE DOWN FF UP
GG UP
VALID COMMANDS ARE -
CRMSTAT. CRMSTAT,DB. CRMSTAT,DBPFN. END. +. ■
DBUP,DB. DBUP,DBPFN. DBDOWN,DB. DBDOWN,DBPFN,
/^$\
Figure 8-33. CRM Status K Display
60459300 D 5-7 7
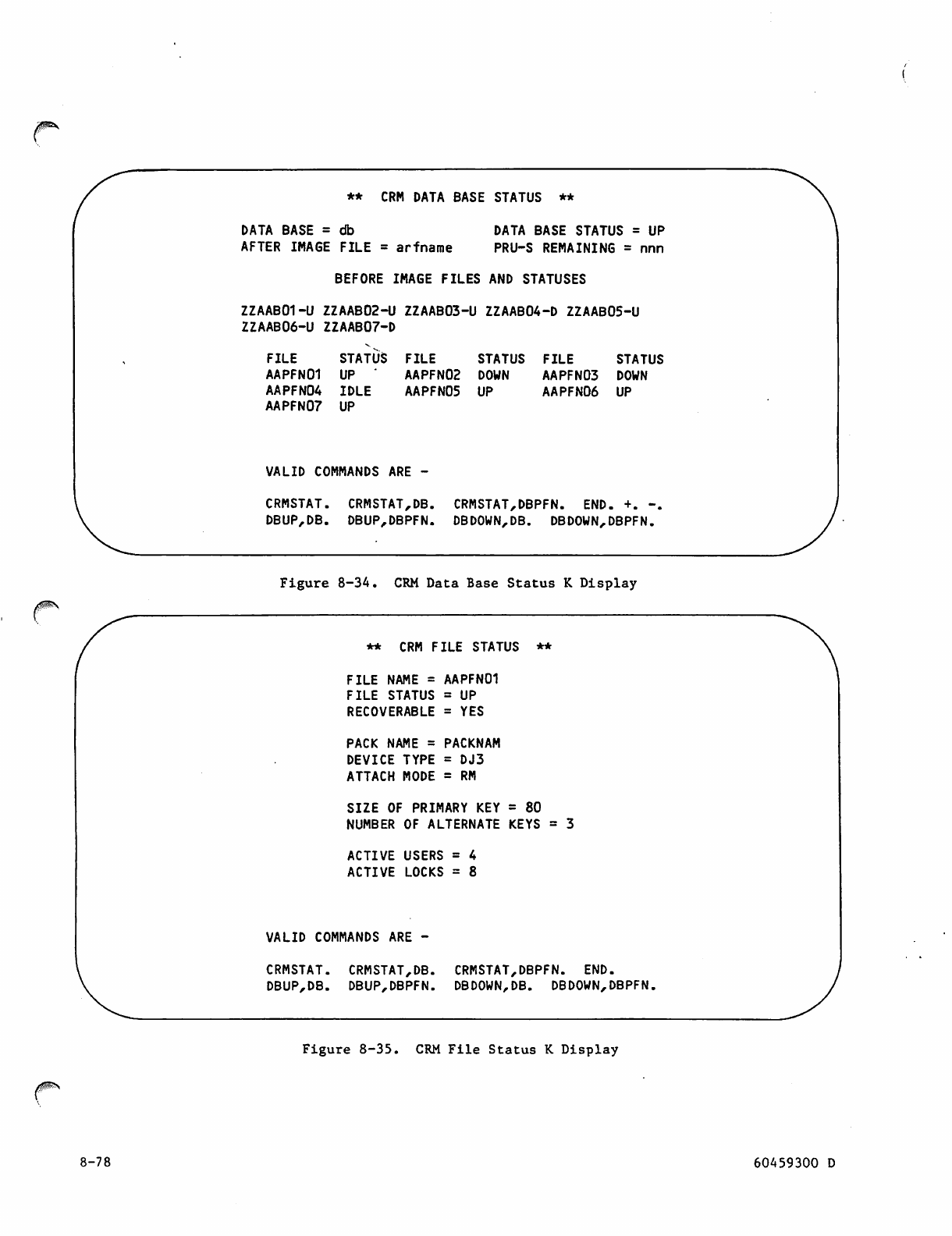
** CRM DATA BASE STATUS **
DATA BASE = db
AFTER IMAGE FILE = arfname
DATA BASE STATUS = UP
PRU-S REMAINING = nnn
BEFORE IMAGE FILES AND STATUSES
ZZAAB01-U ZZAAB02-U ZZAAB03-U ZZAAB04-D ZZAAB05-U
ZZAAB06-U ZZAAB07-D
FILE STATUS FILE STATUS FILE STATUS
AAPFN01 UP ' AAPFN02 DOWN AAPFN03 DOWN
AAPFN04 IDLE AAPFN05 UP AAPFN06 UP
AAPFN07 UP
VALID COMMANDS ARE -
CRMSTAT. CRMSTAT,DB. CRMSTAT,DBPFN. END. +. ■
DBUP,DB. DBUP,DBPFN. DBDOWN,DB. DBDOWN,DBPFN.
Figure 8-34. CRM Data Base Status K Display
** CRM FILE STATUS **
FILE NAME = AAPFN01
FILE STATUS = UP
RECOVERABLE = YES
PACK NAME = PACKNAM
DEVICE TYPE = DJ3
ATTACH MODE = RM
SIZE OF PRIMARY KEY = 80
NUMBER OF ALTERNATE KEYS = 3
ACTIVE USERS = 4
ACTIVE LOCKS = 8
VALID COMMANDS ARE -
CRMSTAT. CRMSTAT,DB. CRMSTAT,DBPFN. END.
DBUP,DB. DBUP,DBPFN. DBDOWN,DB. DBDOWN,DBPFN,
Figure 8-35. CRM File Status K Display
8-78 60459300 D

For the CRM status and CRM data base status displays, if all the information does not fit on
one screen, you can bring up additional pages by entering the following command.
K.+ .
To return to the first page of the display, enter the following command.
K.-.
At any time you can return to the initial CRMTASK K display (figure 8-32) by entering the
following command.
K.MENU.
To end CRM status K-display processing, enter the following command.
K.END.
^2$!\
60459300 D 8-79

Each user entry in a CRF contains space for initial To reduce the number of user messages and/or the
transaction input, RPUT messages, and a SECURE mes- message size, the CRF must be reinitialized using
sage. Two important CRF attributes are the number the K.INT command (refer to section 8).
of messages, number, that a recoverable run unit may
record on the file and the maximum size of these Under certain circumstances a CRF is reformatted
messages, maximumsize. The values for these param- during recovery. Refer to section 8 for details.
eters are given in the RECOVER statement in the TCF.
r
60459500 C 4-9

/^I\
/■^tv
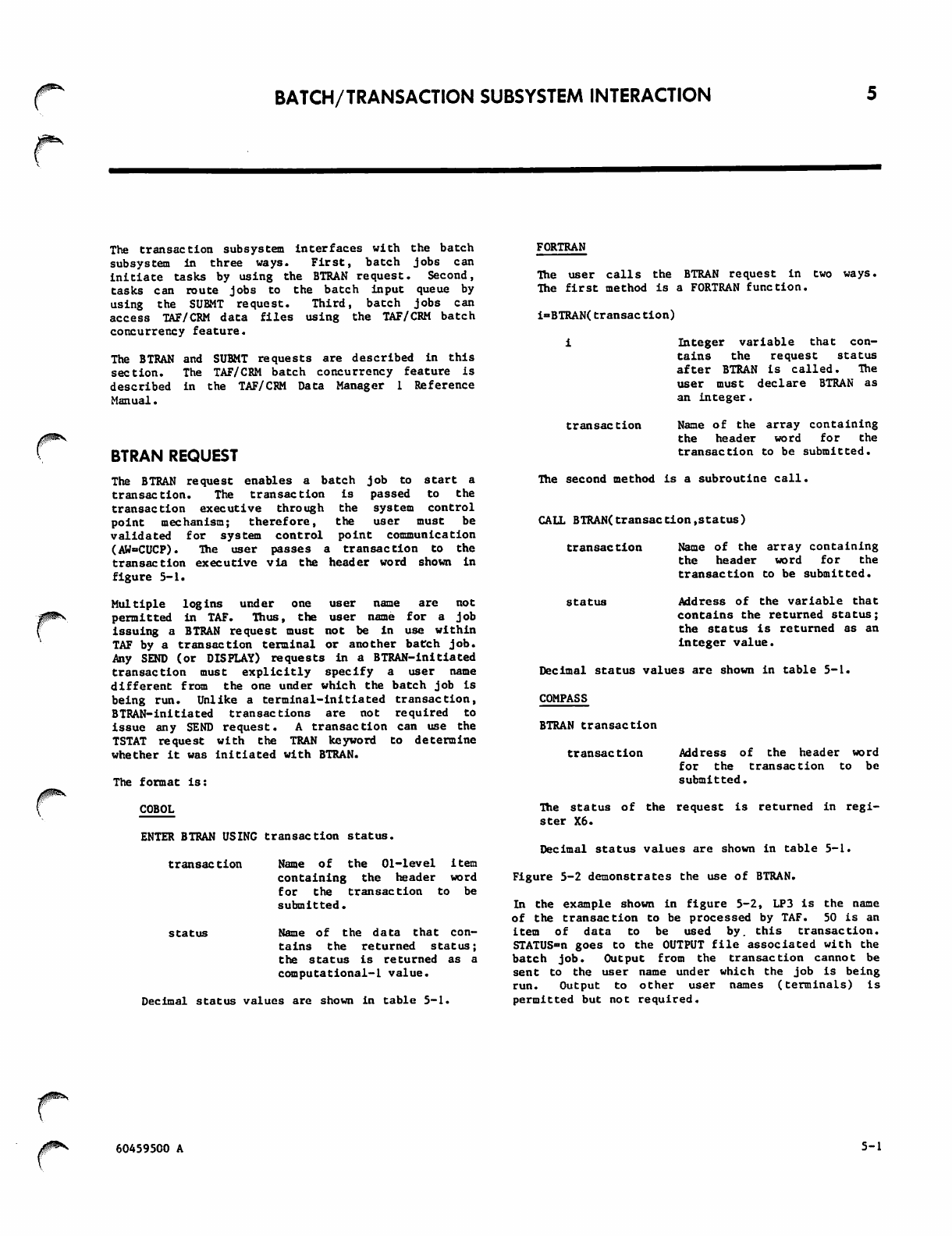
BATCH/TRANSACTION SUBSYSTEM INTERACTION
r
The transaction subsystem interfaces with the batch
subsystem in three ways. First, batch jobs can
initiate tasks by using the BTRAN request. Second,
tasks ca n ro ute jobs to the batch input q ueue by
using the SUBMT request. Third, batch jobs can
access TAF/CRM data files using the TAF/CRM batch
concurrency feature.
The BTRAN and SUBMT requests are described in this
section. The TAF/CRM batch concurrency feature is
described in the TAF/CRM Data Manager 1 Reference
Manual.
BTRAN REQUEST
The BTRAN request enables a batch job to start a
transaction. The transaction is passed to the
transaction executive through the system control
point mechanism; therefore, the user must be
validated for system control point communication
(AW°CUCP). The user passes a transaction to the
transaction executive via the header word shown in
figure 5-1.
Multiple logins under one user name are not
permitted in TAF. Thus, the user name for a job
issuing a BTRAN request must not be in use within
TAF by a transaction terminal or another batch job.
Any SEND (or DISPLAY) requests in a BTRAN-initiated
transaction must explicitly specify a user name
different from the one under which the batch job is
being run. Unlike a terminal-initiated transaction,
BTRAN-initiated transactions are not required to
issue any SEND request. A transaction can use the
TSTAT request with the TRAN keyword to determine
whether it was initiated with BTRAN.
The format is:
COBOL
ENTER BTRAN USING transaction status.
Name of the 01-level item
containing the header word
for the transaction to be
submitted.
Name of the data that con
tains the returned status;
the status is returned as a
computational-l value.
Decimal status values are shown in table 5-1.
t ran sac tion
status
FORTRAN
The user calls the BTRAN request in two ways.
The first method is a FORTRAN function.
i=BTRAN(transaction)
transaction
Integer variable that con
tains the request status
after BTRAN is called. The
user must declare BTRAN as
an integer.
Name of the array containing
the header word for the
transaction to be submitted.
The second method is a subroutine call.
CALL BTRAN(transaction,status)
transae tion
status
Name of the array containing
the header word for the
transaction to be submitted.
Address of the variable that
contains the returned status;
the status is returned as an
integer value.
Decimal status values are shown in table 5-1.
COMPASS
BTRAN transaction
transae tion Address of the header word
for the transaction to be
submitted.
The status of the request is returned in regi
ster X6.
Decimal status values are shown in table 5-1.
Figure 5-2 demonstrates the use of BTRAN.
In the example shown in figure 5-2, LP3 is the name
of the transaction to be processed by TAF. 50 is an
i t e m o f d a t a t o b e u s e d b y. t h i s t r a n s a c t i o n .
STATUS»n goes to the OUTPUT file associated with the
batch job. Output from the transaction cannot be
sent to the user name under which the job is being
run. Output to other user names (terminals) is
permitted but not required.
j^^. 60459500 A 5-1
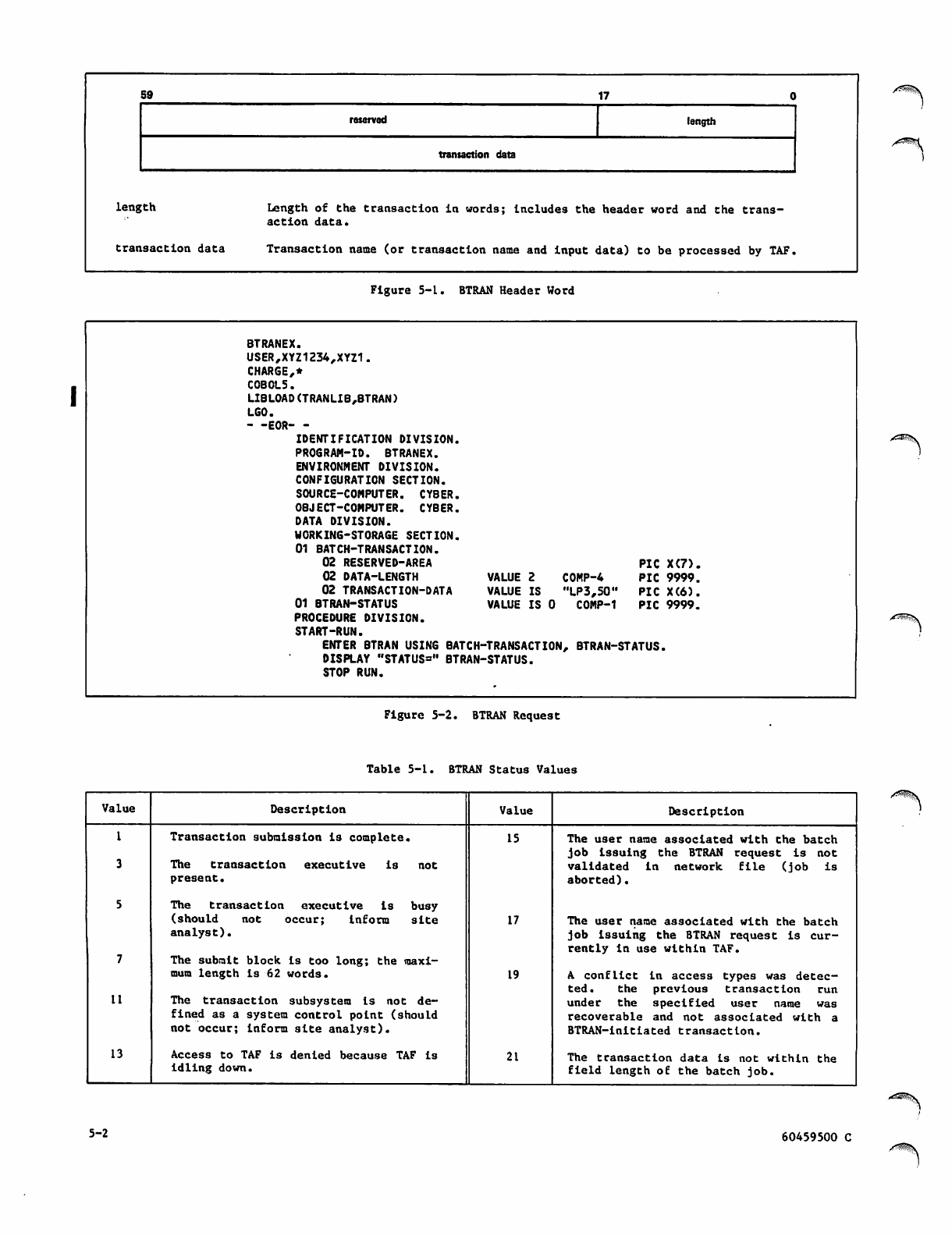
59 1 7 0
reserved length
transaction data
length
transaction data
Length of the transaction in words; Includes the header word and the trans
action data.
Transaction name (or transaction name and input data) to be processed by TAF.
>£3$!%>t
Figure 5-1. BTRAN Header Word
BTRANEX.
USER,XYZ1234,XYZ1.
CHARGE,*
C0B0L5.
LIBLOAD(TRANLIB,BTRAN)
LGO.
- - E O R - -
IDENTIFICATION DIVISION.
PROGRAM-ID. BTRANEX.
ENVIRONMENT DIVISION.
CONFIGURATION SECTION.
SOURCE-COMPUTER. CYBER.
OBJECT-COMPUTER. CYBER.
DATA DIVISION.
WORKING-STORAGE SECTION.
01 BATCH-TRANSACTION.
02 RESERVED-AREA
02 DATA-LENGTH
02 TRANSACTION-DATA
01 BTRAN-STATUS
PROCEDURE DIVISION.
START-RUN.
ENTER BTRAN USING BATCH-TRANSACTION, BTRAN-STATUS.
DISPLAY "STATUS*" BTRAN-STATUS.
STOP RUN.
PIC X<7)
VALUE 2 C O K P - 4 PIC 9999
VALUE I S " L P 3 , 5 0 " PIC X(6)
VALUE IS 0 COMP-1 PIC 9999
Figure 5-2. BTRAN Request
Table 5-1. BTRAN Status Values
Value Description Value Description
ITransaction submission is complete. 15 The user name associated with the batch
3T h e t r a n s a c t i o n e x e c u t i v e i s n o t job issuing the BTRAN request is not
validated in network file (job is
present. aborted).
5T h e t r a n s a c t i o n e x e c u t i v e I s b u s y
(should not occur; inform site 17 The user name associated with the batch
7
analyst).
The submit block is too long; the maxi
job issuing the BTRAN request is cur
rently in use within TAF.
mum length is 62 words. 19 A conflict in access types was detec
11 The transaction subsystem is not de
fined as a system control point (should
not occur; inform site analyst).
ted, the previous transaction run
under the specified user name was
recoverable and not associated with a
BTRAN-initiated transaction.
13 Access to TAF is denied because TAF i3
idling down. 21 The transaction data is not within the
field length oE the batch job.
5-2 60459500 C
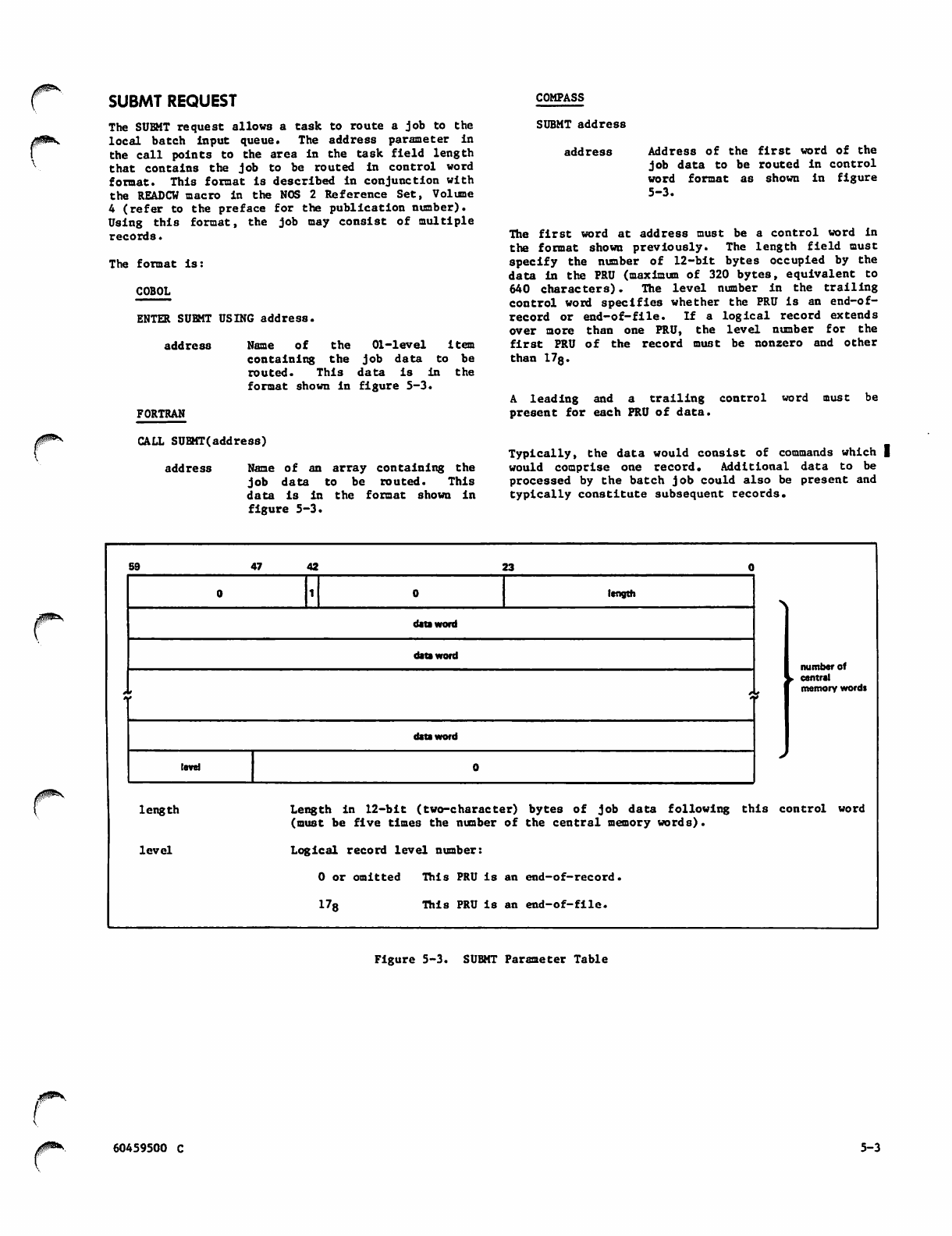
SUBMT REQUEST
The SUBMT request allows a task to route a job to the
local batch input queue. The address parameter in
the call points to the area in the task field length
that contains the job to be routed in control word
format. This format is described in conjunction with
the READCW macro in the NOS 2 Reference Set, Volume
4 (refer to the preface for the publication number).
Using this format, the job may consist of multiple
records.
The format is:
COBOL
ENTER SUBMT USING address.
address Name of the 01-level item
containing the job data to be
routed. This data is in the
format shown in figure 5-3.
COMPASS
SUBMT address
FORTRAN
address Address of the first word of the
job data to be routed in control
word format as shown in figure
5-3.
The first word at address must be a control word in
the format s hown p re viously. The le ngth fi el d mu st
specify the number of 12-bit bytes occupied by the
data in the PRU (maximum of 320 bytes, equivalent to
640 characters). The level number in the trailing
control word specifies whether the PRU is an end-of-
record or end-of-file. If a logical record extends
over more than one PRU, the level number for the
first PRU of the record must be nonzero and other
than 173.
A leading and a trailing control word must be
present for each PRU of data.
CALL SUBMT(address)
a d d re s s N a m e o f an a r r a y c o n t a i n i n g t h e
job data to be routed. This
data is in the format shown in
figure 5-3.
Typically, the data would consist of commands which |
wou l d co m pris e on e re c o rd. A d d i t iona l da t a to be
processed by the batch job could also be present and
typically constitute subsequent records.
59 » 7 4 2 2 3
4
0 1 0 Itngth
data word
number of
y central
, memory word*
data word
p 4
data word
lave)
length
level
Length in 12-bit (two-character) bytes of job data following
(must be five times the number of the central memory words).
Logical record level number:
0 or omitted This PRU is an end-of-record.
17g This PRU is an end-of-file.
this control word
Figure 5-3. SUBMT Parameter Table
60459500 C 5-3
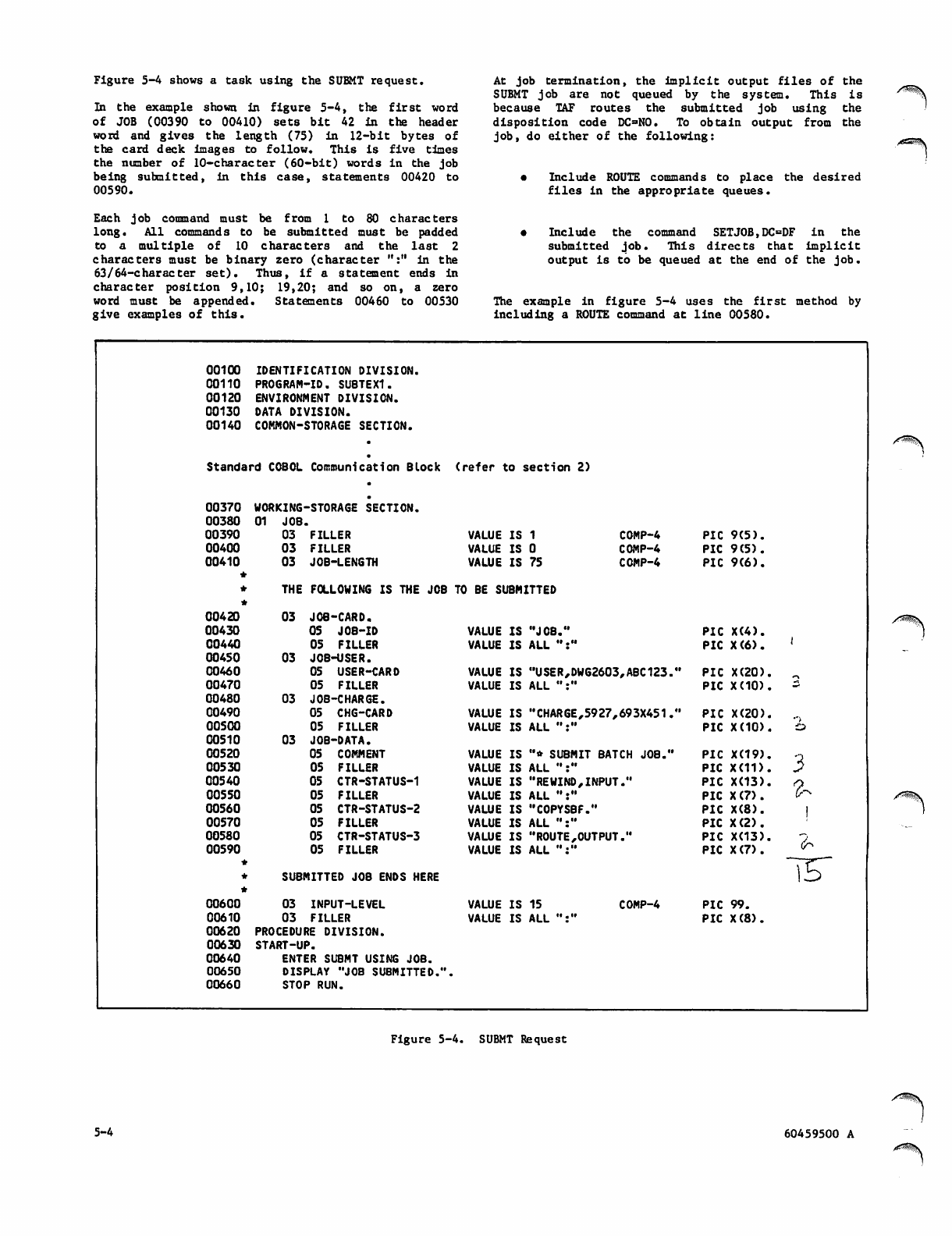
Figure 5-4 shows a task using the SUBMT request.
In the example shown in figure 5-4, the first word
of JOB (00390 to 00410) sets bit 42 in the header
word and gives the length (75) in 12-bit bytes of
the card deck images to follow* This is five times
the number of 10-character (60-bit) words in the job
being submitted, in this case, statements 00420 to
00590.
At job termination, the implicit output files of the
SUBMT job are not queued by the system. This is
because TAF routes the submitted job using the
disposition code DCaN0. To obtain output from the
job, do either of the following:
Include ROUTE commands to place the desired
files in the appropriate queues.
/ J 5 W ^ k
Each job command must be from 1 to 80 characters
long. All commands to be submitted must be padded
to a multiple of 10 characters and the last 2
characters must be binary zero (character ":" in the
63/64-character set). Thus, if a statement ends in
character position 9,10; 19,20; and so on, a zero
word must be appended. Statements 00460 to 00530
give examples of this.
• Include the command SETJOB,DC=DF in the
submitted job. This directs that implicit
output is to be queued at the end of the job.
The example in figure 5-4 uses the first method by
including a ROUTE command at line 00580.
00100 IDENTIFICATION DIVISION.
00110 PROGRAM -ID. SUBTEX1.
00120 ENVIRONMENT DIVISION.
00130 DATA DIVISION.
00140 COMMON-STORAGE SECTION.
Standard COBOL Com munication Block ( r e f e r t o !s e c t i o n 2 )
00370 WORKING -STORAGE SECTION.
00380 0 1 J O B
00390 03 FILLER VALUE IS 1 COMP-4 PIC 9(5).
00400 03 FILLER VALUE IS 0 C O M P - 4 PIC 9(5).
00410 03 JOB-LENGTH VALUE IS 75 COMP-4 PIC 9(6).
*THE FOLLOWING IS THE JOB TO BE SUBMITTED
00420 03 JOB-CARD.
00430 0 5 J O B - I D VALUE IS "JOB." PIC X(4).
00440 0 5 F I L L E R VALUE IS A L L " : " PIC X(6).
00450 03 JOB-USER.
00460 05 USER-CARD VALUE IS "USER,DWG2603,ABC123." PIC X(20).
00470 0 5 F I L L E R VALUE IS A L L " : " PIC X(10).
00480 03 JOB-CHARGE.
00490 05 CHG-CARD VALUE IS "CHARGE,5927,693X451." PIC X(20).
00500 0 5 F I L L E R VALUE IS A L L " : " PIC X(10).
00510 03 JOB-DATA.
00520 05 COMMENT VALUE IS "* SUBMIT BATCH J08." PIC X(19).
00530 0 5 F I L L E R VALUE IS A L L " : " PIC X ( 1 1 ) .
00540 05 CTR-STATUS-1 VALUE IS "REWIND,INPUT." PIC X(13). 2-
00550 05 FILLER VALUE IS A L L " : " PIC X(7).
00560 05 CTR-STATUS-2 VALUE IS "C0PYSBF." PIC X(8).
00570 0 5 F I L L E R VALUE IS A L L " : " PIC X(2).
00580 05 CTR-STATUS-3 VALUE IS "R0UTE,0UTPUT." PIC X<1 3 ) . /L
00590 0 5 F I L L E R VALUE IS A L L " : " PIC X(7). <r>
*
*SUBMITTED JOB ENDS HERE 15"
00600 03 INPUT-LEVEL VALUE IS 15 COMP-4 PIC 99.
00610 03 FILLER VALUE IS A L L " : " PIC X(8).
00620 PROCEDURE DIVISION.
00630 START-UP.
00640 ENTER SUBMT USING JOB.
00650 DISPLAY "JOB SUBMITTED."
00660 STOP RUN.
Figure 5-4. SUBMT Request
5-4 60459500 A
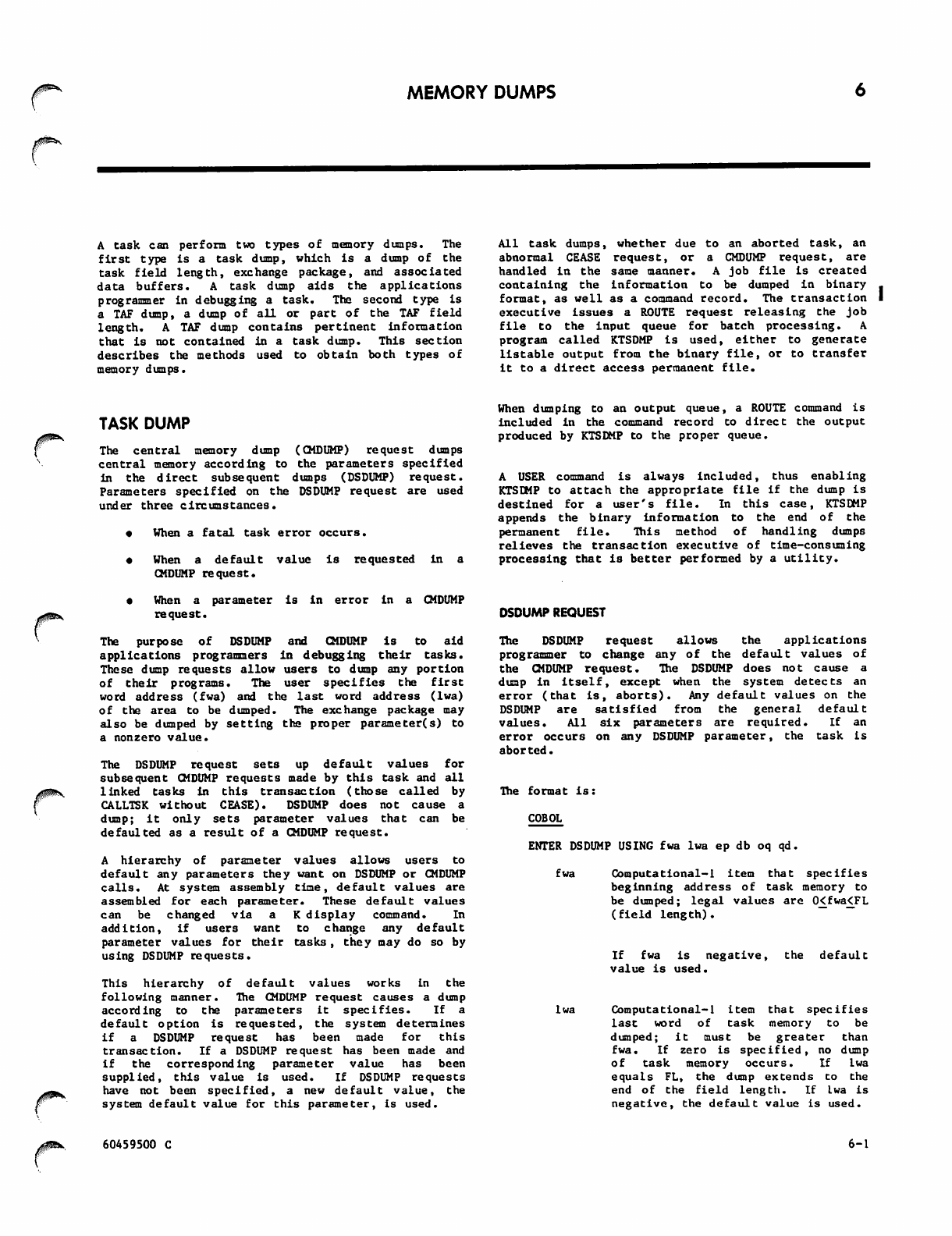
MEMORY DUMPS
A task can perform two types of memory dumps. The
first type is a task dump, which is a dump of the
task field length, exchange package, and associated
data buffers. A task dump aids the applications
programmer in debugging a task. The second type Is
a TAF dump, a dump of all or part of the TAF field
length. A TAF dump contains pertinent information
that is not contained in a task dump. This section
describes the methods used to obtain both types of
memory dumps.
All task dumps, whether due to an aborted task, an
abnormal CEASE request, or a CMDUMP request, are
handled in the same manner. A job file is created
containing the information to be dumped in binary
format, as well as a command record. The transaction
executive issues a ROUTE request releasing the job
fi l e t o t h e i n p u t q u e u e f o r b a t c h p r o c e s s i n g . A
program called KTSDMP is used, either to generate
listable output from the binary file, or to transfer
it to a direct access permanent file.
r
TASK DUMP
The central memory dump (CMDUMP) request dumps
central memory according to the parameters specified
in the direct subsequent dumps (DSDUMP) request.
Parameters specified on the DSDUMP request are used
under three circumstances.
• When a fatal task error occurs.
• When a default value is requested in a
CMDUMP request.
• When a parameter is in error in a CMDUMP
request.
The purpose of DSDUMP and CMDUMP is to aid
applications programmers in debugging their tasks.
These dump requests allow users to dump any portion
of their programs. The user specifies the first
word address (fwa) and the last word address (lwa)
of the area to be dumped. The exchange package may
also be dumped by setting the proper parameter(s) to
a nonzero value.
The DSDUMP request sets up default values for
subsequent CMDUMP requests made by this task and all
linked tasks in this transaction (those called by
CALLTSK without CEASE). DSDUMP does not cause a
dump; it only sets parameter values that can be
defaulted as a result of a CMDUMP request.
A hierarchy of parameter values allows users to
default any parameters they want on DSDUMP or CMDUMP
calls. At system assembly time, default values are
assembled for each parameter. These default values
can be changed via a K display command. In
addition, if users want to change any default
parameter values for their tasks, they may do so by
using DSDUMP requests.
T h i s h i e r a r c h y o f d e f a u l t v a l u e s w o r k s i n t h e
following manner. The CMDUMP request causes a dump
according to the parameters it specifies. If a
default option is requested, the system determines
if a DSDUMP request has been made for this
transaction. If a DSDUMP request has been made and
if the corresponding parameter value has been
supplied, this value is used. If DSDUMP requests
have not been specified, a new default value, the
system default value for this parameter, is used.
When dumping to an output queue, a ROUTE command is
included in the command record to direct the output
produced by KTSDMP to the proper queue.
A USER command is always included, thus enabling
KTSDMP to attach the appropriate file if the dump is
destined for a user's file. In this case, KTSDMP
appends the binary information to the end of the
permanent file. This method of handling dumps
relieves the transaction executive of time-consuming
processing that is better performed by a utility.
DSDUMP REQUEST
The DSDUMP request allows the applications
programmer to change any of the default values of
the CMDUMP request. The DSDUMP does not cause a
dump in itself, except when the system detects an
error (that is, aborts). Any default values on the
DSDUMP are satisfied from the general default
values* All six parameters are required. If an
error occurs on any DSDUMP parameter, the task is
aborted.
The format is:
COBOL
ENTER DSDUMP USING fwa lwa ep db oq qd.
fwa Computational-1 item that specifies
beginning address of task memory to
be dumped; legal values are 0<fwa<FL
(field length).
If fwa is negative,
value is used.
the default
lwa Computational-l item that specifies
last word of task memory to be
dumped; it must be greater than
fwa. If zero is specified, no dump
of task memory occurs. If lwa
equals FL, the dump extends to the
end of the field length. If lwa is
negative, the default value is used.
60459500 C 6-1

ep
db
oq
qd
Computational-l item that specifies
exchange package option.
0 Do not dump exchange package.
> 0 Dump exchange package.
< 0 Use default value.
Performs no function. Retained for
compatibility with previous releases.
Computational-l item that specifies
output queue option.
< 0 Use default value (refer to
following note).
0 Dump to local batch output
queue.
1 Dump to remote batch output
queue*
2 Dump to user permanent file
defined under data base user
number.
Queue destination option; value
depends on oq selection.
oq
0
qd
Printer id, specified as a
computational-l number. If
negative, use default value
(refer to following note).
U s e r ' A valid name
number specified in
display-coded,
Direct left-justified
access ▶characters
permanent with either
file name blank or
binary zero
.fill.
| NOTE |
If either oq or qd is negative, the
default value will be used for both,
regardless of the option selected for
the other.
FORTRAN
CALL DSDUMP(fwa,lwa,ep,db ,oq,qd)
fwa Octal integer that specifies the be
ginning address of task memory to be
dumped; legal values are zero<fwa<FL
(field length). -
If fwa is negative, the default
value is used.
lwa Octal integer that specifies the
last word of task memory to be
dumped; must be greater than fwa.
ep
db
oq
qd
I f z e r o i s s p e c i fi e d , n o d u m p o f
task memory occurs. If lwa equals
FL, the dump extends to the end of
the field length. If lwa is
negative, the default value is used.
Integer that specifies the exchange
package option.
0 Do not dump exchange package.
> 0 Dump exchange package.
< 0 Use default value.
Performs no function. Retained for
compatibility with previous releases.
Output queue option.
< 0 Use default value (refer to
following note).
0 Dump to local batch output
queue.
1 Dump to remote batch queue.
2 Dump to user permanent file
defined under data base user
number.
Queue destination option;
depends on oq selection.
value
oq qd
0 Integer specifying printer
id. If negative, use
default value (refer to
following note).
1User v A valid name
name 1 specified in
1 display-coded,
1 left-justified
Direct [characters with
access 1 either blank or
permanent 1 binary zero
file name >' fi l l .
| NOTE |
I f ei t h e r o q o r q d i s n e g a ti v e , t h e
default value will be used for both,
regardless of the option selected for
the other.
COMPASS
DSDUMP address
address Address of a parameter table. The
table has the form shown in figure
6-1.
6-2 60459500 A y^^&fSV
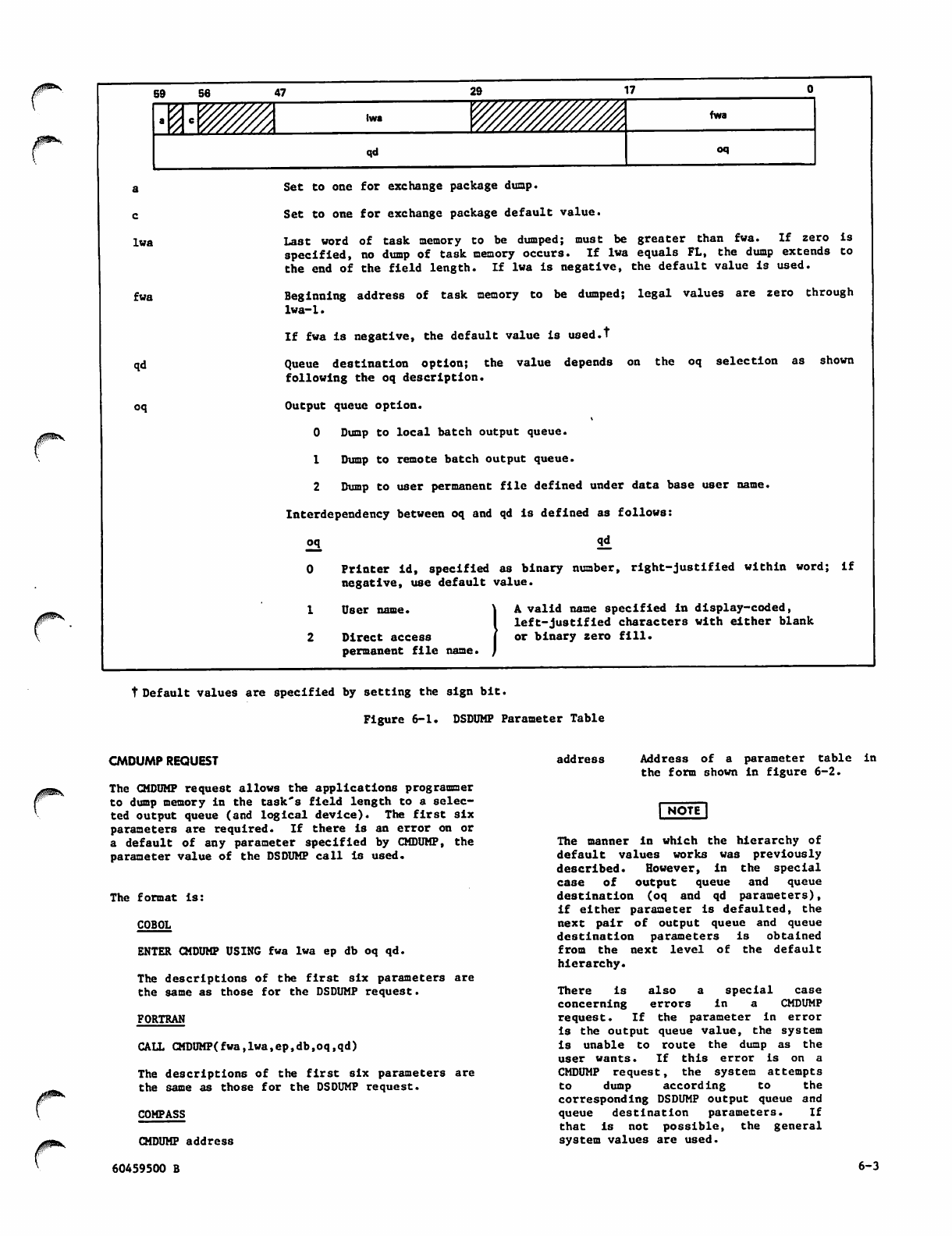
5 9 5 6 47 29 17
agc'ft//,7//A lwa 'Mttttfr'WM, fwa
qd oq
a
c
lwa
fwa
qd
oq
Set to one for exchange package dump.
Set to one for exchange package default value.
Last word of task memory to be dumped; must be greater than fwa. If zero is
specified, no dump of task memory occurs. If lwa equals FL, the dump extends to
the end of the field length. If lwa Is negative, the default value is used.
Beginning address of task memory to be dumped; legal values are zero through
lwa-1.
If fwa is negative, the default value is used.t
Queue destination option; the value depends on the oq selection as shown
following the oq description.
Output queue option.
0 Dump to local batch output queue.
1 Dump to remote batch output queue.
2 Dump to user permanent file defined under data base user name.
Interdependency between oq and qd is defined as follows:
oq
0
1
2
qd
Printer id, specified as binary number, right-justified within word; if
negative, use default value.
User name.
Direct access
permanent file name.
A valid name specified in display-coded,
left-justified characters with either blank
or binary zero fill.
t Default values are specified by setting the sign bit.
Figure 6-1. DSDUMP Parameter Table
/0^
CMDUMP REQUEST
The CMDUMP request allows the applications programmer
to dump memory in the task's field length to a selec
ted output queue (and logical device). The first six
parameters are required. If there is an error on or
a default of any parameter specified by CMDUMP, the
parameter value of the DSDUMP call is used.
The format is:
COBOL
ENTER CMDUMP USING fwa lwa ep db oq qd.
The descriptions of the first six parameters are
the same as those for the DSDUMP request.
FORTRAN
CALL CMDUMP(fwa,lwa,ep,db,oq,qd)
The descriptions of the first six parameters are
the same as those for the DSDUMP request.
COMPASS
CMDUMP address
60459500 B
address Address of a parameter table in
the form shown in figure 6-2.
1 note!
The manner in which the hierarchy of
default values works was previously
described. However, in the special
case of output queue and queue
destination (oq and qd parameters),
if either parameter is defaulted, the
next pair of output queue and queue
destination parameters is obtained
from the next level of the default
hierarchy.
There is also a special case
concerning errors in a CMDUMP
request. If the parameter in error
is the output queue value, the system
is unable to route the dump as the
user wants. If this error is on a
CMDUMP request, the system attempts
to dump according to the
corresponding DSDUMP output queue and
queue destination parameters. If
that is not possible, the general
system values are used.
6-3
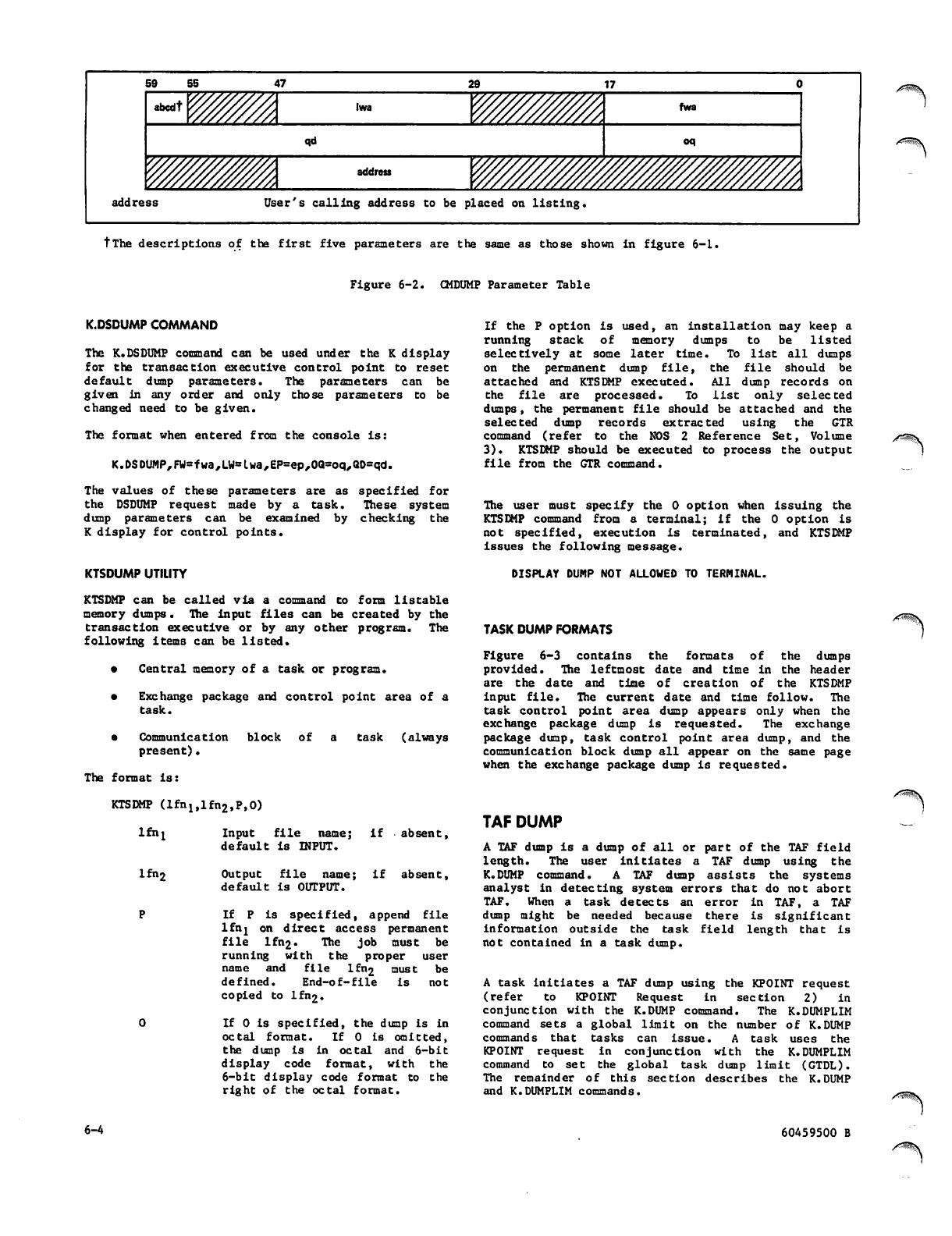
5 9 5 5
address
47 29 17
abcdt lwa W//////////// fwa
qd oq
^^i^ address mmmmmmmm
User's calling address to be placed on listing.
/SSSSV
TThe descriptions of the first five parameters are the same as those shown in figure 6-1.
Figure 6-2. CMDUMP Parameter Table
K.DSDUMP COMMAND
The K.DSDUMP command can be used under the K display
for the transaction executive control point to reset
default dump parameters. The parameters can be
given in any order and only those parameters to be
changed need to be given.
The format when entered from the console is:
K.DSDUMP,FW=fwa,LW=lwa,EP=ep/OQ=oq/QD=qd.
The values of these parameters are as specified for
the DSDUMP request made by a task. These system
dump parameters can be examined by checking the
K display for control points.
KTSDUMP UTILITY
KTSDMP can be called via a command to form lis table
memory dumps. The input files can be created by the
transaction executive or by any other program. The
following items can be listed.
Central memory of a task or program.
Exchange package and control point area of a
task.
Communica tion
pre se nt).
block of a task (always
The format is:
KTSDMP (lfn.1,lfn2,P,0)
l f t H Input file name; if absent,
default is INPUT.
lfn2 O u t p u t fi l e n a m e ;
default is OUTPUT.
if absent,
I f P i s s p e c i fi e d , a p p e n d fi l e
lfnj on direct access permanent
file lfn2. The job must be
running with the proper user
name and file lfn2 must be
defined. End-of-file is not
copied to lfn2.
If 0 is specified, the dump is in
o c t a l f o r m a t . I f 0 i s o m i t t e d ,
the dump is in octal and 6-bit
display code format, with the
6-bit display code format to the
right of the octal format.
6-4
If the P option is used, an installation may keep a
running stack of memory dumps to be listed
selectively at some later time. To list all dumps
on the permanent dump file, the file should be
attached and KTSDMP executed. All dump records on
the file are processed. To list only selected
dumps, the permanent file should be attached and the
selected dump records extracted using the GTR
command (refer to the NOS 2 Reference Set, Volume
3). KTSDMP should be executed to process the output
file from the GTR command.
The user must specify the 0 option when issuing the
KTSDMP command from a terminal; if the 0 option is
not specified, execution is terminated, and KTSDMP
issues the following message.
DISPLAY DUMP NOT ALLOWED TO TERMINAL.
TASK DUMP FORMATS
Figure 6-3 contains the formats of the dumps
provided. The leftmost date and time in the header
are the date and time of creation of the KTSDMP
i n p u t fi l e . T h e c u r r e n t d a t e a n d t i me f o l l o w. T h e
task control point area dump appears only when the
exchange package dump is requested. The exchange
package dump, task control point area dump, and the
communication block dump all appear on the same page
when the exchange package dump is requested.
TAF DUMP
A TAF dump is a dump of all or part of the TAF field
length. The user initiates a TAF dump using the
K.DUMP command. A TAF dump assists the systems
analyst in detecting system errors that do not abort
TAF. Whe n a task detects an error in TAF, a TAF
dump might be needed because there is significant
information outside the task field length that is
not contained in a task dump.
A task initiates a TAF dump using the KPOINT request
(refer to KPOINT Request in section 2) in
conjunction with the K.DUMP command. The K.DUMPLIM
command sets a global limit on the number of K.DUMP
c o m m a n d s t h a t ta sks c a n i s s u e . A ta s k us e s t h e
KPOINT request in conjunction with the K.DUMPLIM
command to set the global task dump limit (GTDL).
The remainder of this section describes the K.DUMP
and K.DUMPLIM commands.
60459500 B
/r5sts
/<"*8fV
KTSDMP-taskname yy///mm/dd.hh.mm.ss. yy/mm/dd .hh.mm.ss.
EXCHANGE PACKAGE.
Exchange package dump
TASK CONTROL POINT AREA.
Task control point area dump
COMMUNICATION BLOCK DUMP FROM fwa TO lwa
PROGRAM taskname SEQUENCE number ADDRESS xxxx
Communication block dump
KTSDMP-taskname yy/mm/dd.hh.mm .ss. yy/mm/dd.hh.mm.ss.
DUMP FROM fwa TO lwa
Memory dump
KTSDMP-taskname yy/mm/dd.hh.mm.ss . yy/mm/dd.hh.mm .ss.
DUMP FROM fwa TO lwa
Memory dump
KTSDMP-taskname yy/mm/dd.hh.mm.ss. yy/mm/dd.hh .mm .ss .
Figure 6-3. KTSDMP Format
jifMfiffl^^
K.DUMP COMMAND
The K.DUMP command initiates a 'dump of all or part
of TAF. The user can specify the first word address
(fwa) and the last word address (lwa) of the memory
to be dumped.
The command formats when issued from a task are:
DUMP,fwa,lwa.
or
DUMP,lwa.
or
DUMP.
fwa Octal address of the first word of
memory to be dumped; legal values
are 0<fwa<lwa. The default is
zero . T h i s pa r a m e t e r ca n n o t be
used unless the lwa parameter is
also used.
lwa Octal address of the last word of
memory to be dumped; legal values
are fwa<lwa<377777. The default
is 377777.
If both parameters are omitted, the entire field
length is dumped. The output of the dump is routed
to a printer that has an identifier of zero. A
header page precedes the dump; it lists the date and
time of the dump and the name of the task that
issued the dump. Also listed are the instructions
that the dump be given to the TAF central site
systems analyst.
K.DUMPLIM COMMAND
The K.DUMPLIM command sets the GTDL. The GTDL
specifies the number of K.DUMP commands that tasks
can issue.
The command format when issued from a task is:
DUMPLIM.n.
n The decimal number of TAF dumps
that tasks can issue. The
default is zero. The maximum
value is 9999999. The user
specifies octal by using a
postradix of B.
The ini t i a l va l u e fo r th e GT D L is ze r o . Wh e n th e
GTDL is zero, no TAF dumps from tasks are allowed.
The GTDL must be set to a value greater than zero
for TAF dumps from tasks to occur. Each TAF dump
(where the task does not abort) causes the GTDL to
be decreased by one. This command does not affect
the execution of task dumps.
JS^K
60459500 A 6-5


APPLICATIONS INTERFACE FOR AUTOMATIC RECOVERY
This section describes automatic recovery as it
affects task writing. Recovery-related information
applicable to the applications programmer is covered.
Additional information of interest to the system in
stallation and maintenance personnel can be found in
section 8 of this manual.
PURPOSE
The purpose of the TAF automatic recovery feature is
to enable site personnel to design TAF transactions
that can recover quickly and predictably from system
failures, and maintain the data base in a consistent
state across failures* Terminal operators will be
able to determine the status of transactions upon re
covery so the possibility of issuing a double update
to the data base or of missing a data base update is
greatly reduced. The recovery will be automatic in
the sense that TAF and the data manager will deter
mine which data base updates to roll back, and which
transactions to restart upon initialization after a
failure. Site personnel need only select recovery
mode when bringing TAF back up.
CONCEPTS
There are two basic components to automatic recovery:
da t a b a s e r e cov e ry a nd t ran s a cti o n r e cov e r y. D ata
base recovery ensures that the data base is always in
a consistent and known state, even if a failure occurs
during a run unit. Transaction recovery automatically
reruns recoverable run units that were active at the
time of a failure. It also guarantees that the termi
nal operator will receive a confirmation message when
the run unit completes.
NAMED-TRANSACTIONS AND RUN UNITS
A transaction is a task or a series of linked tasks*
The linking can be internal to the tasks using the
CALLTSK and/or CALLRTN requests, or external to the
tasks using the LIBTASK /tname directive. Refer to
section 10 for a complete description of this direc
tive. Transactions defined using the /tname directive
are referred to as named-transact ions. In most dis
cussions in this section and throughout this manual,
it is not necessary to distinguish between the coding
that comprises a transaction and the execution of that
code. However, when the distinction is important, the
execution of a transaction is referred to as a run
unit. The terms executing transaction, running trans
action, and run unit can be used interchangeably. A
run unit is recoverable only if it is the execution of
a named-transaction and the RC parameter was specified
when the named-transaction was defined. There are
differen ce s in te rm in ol og y betw ee n CDCS an d TA F.
What is referred to as a transaction in TAF is always
called a run unit in CDCS. The processing bounded by
the begin statement (DB$BEG or BEGTRAN) and the commit
statement (DB$CMT or COMMITRAN) is referred to as a
transaction in CDCS. Each of these transactions has
an id supplied within the application.
DATA BASE RECOVERY
Automatic data base recovery is available to
transactions using the CDCS and/or the TAF/CRM Data
Managers. Data base recovery is based on the
concept of a begin-commit sequence. A begin-commit
sequence is a portion of a transaction, designated
by the programmer, that contains one or more data
base updates that are to be treated as a unit.
Should a failure occur during a recoverable run
unit, data base recovery ensures that all the
updates within a begin-commit sequence are performed
or that none of them are. It also provides a means
by which the transaction can determine which
begin-commit sequences had successfully completed
prior to failure so that on restart, the transaction
can avoid performing those updates a second time.
Data base begin-commit sequences are identified in a
transaction by placing a data base BEGIN request at
the beginning of the sequence and a data base COMMIT
request at the end of the sequence. (The BEGIN and
COMMIT requests have different forms depending on
the data manager and source language being used.)
The data base BEGIN request includes a parameter for
assigning an identifier to the begin-commit
sequence. This identifier (selected by the
programmer) is preserved across failures and can be
retrieved upon restart to enable the transaction to
determine how far processing had gone prior to
failure. The data base COMMIT request tells the
data manager that the updates are to be made
permane n t . A fa i l u r e be f o r e a d a t a ba s e CO M M I T
causes all updates for this sequence to be rolled
back. This means that the data base is returned to
the state it was in at the time the BEGIN for this
s e q u en c e wa s is s u e d . I f a f ai l u r e o c cu r s af t e r a
da t a b a se C OM M IT, a ll u pda t es f or t he co m mit t ed
sequence are retained. A transaction can terminate
an update sequence without committing the updates by
issuing a data base FREE request.
TRANSACTION RECOVERY
Transaction recovery restarts recoverable run units
that were active at the time of a system or terminal
failure. Transaction recovery also uses the concept
of a begin-commit sequence. With transaction
recovery, the BEGIN is implicit in the initiation of
any recoverable run unit. The transaction COMMIT is
specified with a SECURE request indicating that the
work of the transaction is complete. The SECURE
request should immediately precede the last data
base commit request in the transaction.
When a recoverable run unit is initiated from a
terminal or a batch job (via a BTRAN request), TAF
logs the initial input on the communication recovery
file. If a failure occurs during the run unit, auto
matic recovery takes place when TAF is subsequently
brought back up. At that time the data base recovery
ro ut in e i s c al le d i n t o r es to re the data base to a
consistent state.
60459500 B 7-1
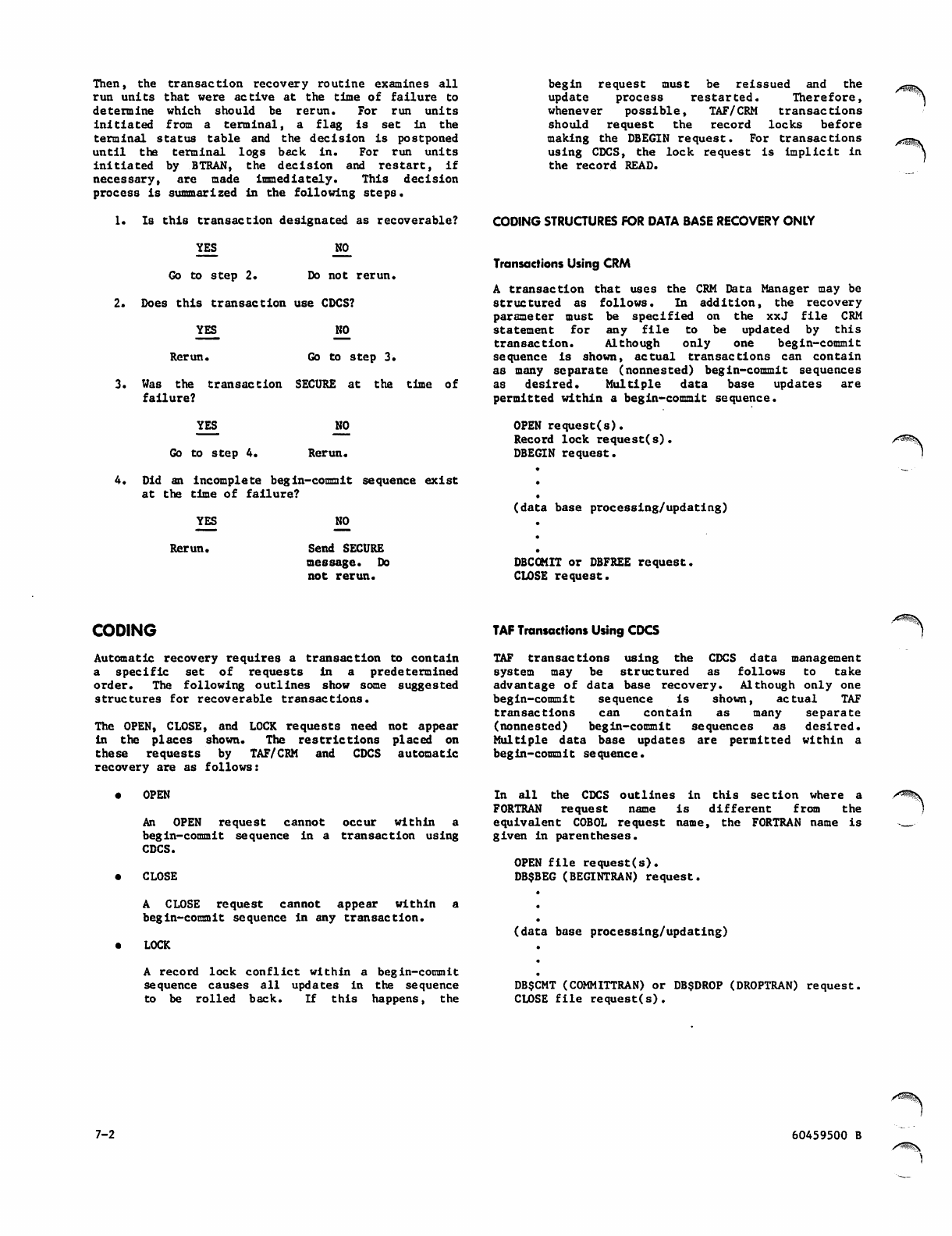
Then, the transaction recovery routine examines all
run units that were active at the time of failure to
determine which should be rerun. For run units
initiated from a terminal, a flag is set in the
terminal status table and the decision is postponed
u n t i l t h e t e r m i n a l l o g s b a c k i n . F o r r u n u n i t s
initiated by BTRAN, the decision and restart, if
necessary, are made Immediately. This decision
process is summarized in the following steps.
1. Is this transaction designated as recoverable?
YES NO
Go to step 2. Do not rerun*
2. Does this transaction use CDCS?
Y E S N O
Rerun. Go to step 3.
3. Was the t ransacti on SECU RE a t th e ti me o f
failure?
YES
Go to step 4.
NO
Rerun.
4. Did an incomplete begin-commit sequence exist
at the time of failure?
YES
Rerun.
NO
Send SECURE
message. Do
not rerun.
begin request must be reissued and the
update process restarted. Therefore,
whenever possible, TAF/CRM transactions
should request the record locks before
making the DBEGIN request. For transactions
using CDCS, the lock request is implicit in
the record READ.
CODING STRUCTURES FOR DATA BASE RECOVERY ONLY
Transactions Using CRM
A transaction that uses the CRM Data Manager may be
structured as follows. In addition, the recovery
parameter must be specified on the xxJ file CRM
statement for any file to be updated by this
transaction. Although only one begin-commit
sequence is shown, actual transactions can contain
as many separate (nonnested) begin-commit sequences
as desired. Multiple data base updates are
permitted within a begin-commit sequence.
OPEN request(s).
Record lock request(s).
DBEGIN request.
(data base processing/updating)
DBCOMIT or DBFREE request.
CLOSE request.
CODING
Automatic recovery requires a transaction to contain
a specific set of requests in a predetermined
order. The following outlines show some suggested
structures for recoverable transactions.
The OPEN, CLOSE, and LOCK requests need not appear
in the places shown. The restrictions placed on
these requests by TAF/CRM and CDCS automatic
recovery are as follows:
• O P E N
A n O P E N r e q u e s t c a n n o t o c c u r w i t h i n a
begin-commit sequence in a transaction using
CDCS.
• CLOSE
A C L O S E r e q u e s t c a n n o t a p p e a r w i t h i n a
begin-commit sequence in any transaction.
• L O C K
TAF Transactions Using CDCS
TAF transactions using the CDCS data management
system may be structured as follows to take
advantage of data base recovery. Although only one
begin-commit sequence is shown, actual TAF
transactions can contain as many separate
(nonnested) begin-commit sequences as desired.
Multiple data base updates are permitted within a
begin-commit sequence.
In all the CDCS outlines in this section where a
F O R T R A N r e q u e s t n a m e i s d i f f e r e n t f r o m t h e
equivalent COBOL request name, the FORTRAN name is
given in parentheses.
OPEN file request(s).
DB$BEG (BEGINTRAN) request.
(data base processing/updating)
A record lock conflict within a begin-commit
sequence causes all updates in the sequence
to be rolled back. If this happens, the DB$CMT (COMMITTRAN) or DBSDROP (DROPTRAN) request,
CLOSE file request(s).
7-2 60459500 B
/^Ss!\
CODING STRUCTURES FOR TRANSACTION RECOVERY (data base processing)
/P^K.
.jgSP^s
J^&K
Transactions Using CRM
Recoverable transactions using the CRM Data Manager
can be divided into two categories: single
begin-commit sequence transactions and multiple
begin-commit sequence transactions. A single
begin-commit sequence transaction needs only to
include a SECURE request immediately before the
COMMIT request. If a failure occurs before the
COMMIT request is successfully executed, the data
base will automatically be rolled back and the
transaction rerun at recovery time. A multiple
begin-commit sequence transaction must first
determine if recovery is in progress. If it is, the
transaction must then discover which was the last
successfully committed begin-commit sequence and
begin processing with the following begin-commit
sequence. For this purpose, the data base BEGIN
requests require a user-supplied identifier to be
included as part of the request. All identifiers
used within a single transaction must be unique for
the restart point to be unambiguous.
Single Begin-Commit Sequence Transaction
OPEN files.
Record lock request(s).
DBEGIN request.
(data base processing)
SECURE request.
DBCOMIT request.
CLOSE request,
transaction CEASE
terminal.
SECURE message is sent to
In the preceding transaction, if a failure
interrupts processing any time prior to the DBCOMIT
request, TAF automatic recovery reruns the
transaction from the beginning. If a failure
interrupts processing after the DBCOMIT request,
automatic recovery only sends the SECURE message to
the terminal.
Multiple Begin-Commit Sequence Transaction
OPEN files.
TSTAT request using keywords RESTART, OLDID.
If RESTART value is zero or OLDID value is
blank, begin processing at SEQN1.
If OLDID is SEQN1
begin processing at SEQN2.
If OLDID IS SEQN(n-l)
begin processing at SEQNn.
Processing Module(s)
SEQN1.
Record lock request(s).
DBEGIN request, begin-commit id = SEQN1.
Perform processing module(s).
DBCOMIT request.
SEQN2.
Record lock request(s).
DBEGIN request, begin-commit id = SEQN2.
Perform processing module(s).
DBCOMIT request.
SEQN3.
SEQNn.
Record lock request(s).
DBEGIN request, begin-commit id = SEQNn.
Perform processing module(s).
SECURE request.
DECOMIT request.
CLOSE files.
transaction CEASE — SECURE message is sent to
terminal.
TAF Transactions Using CDCS
A recoverable TAF transaction using CDCS must first
determine if recovery is in progress. If it is, the
TAF transaction must determine the last successfully
committed begin-commit sequence. This is necessary
even for single begin-commit sequence transactions
because all recoverable run units using CDCS are
rerun during recovery regardless of whether the last
begin-commit sequence was successfully committed.
The failure may have occurred after the COMMIT
request and before the transaction CEASE. Rerunning
from the start would cause a double update for the
transaction. The transaction must begin processing
at the first begin-commit sequence following the
last successful COMMIT. If the final begin-commit
sequence was successfully committed prior to
failure, the transaction need only retrieve and send
the SECURE message to the terminal.
Figure 7-1 shows the structure of a recoverable,
multiple begin-commit sequence transaction that uses
CDCS. The decision process that determines where to
begin during recovery is shown in expanded form for
clarity. The use of subscripted variables for
begin-commit ids would allow for condensed code in
the case of a large number of begin-commit sequences.
CDCS applications programmers should be aware of
some terminology differences between TAF automatic
recovery documentation and CDCS automatic recovery
documentation. The term transaction in CDCS
documentation refers to what TAF documentation calls
a b e g i n - c o m m i t s e q u e n c e ; t h a t i s , a l l p r o c e s s i n g
starting with a data base begin request and ending
with the corresponding data base commit request.
Similarly, CDCS documentation uses the term
transaction-id to refer to what TAF documentation
calls the begin-commit id.
JS^**"
60459500 A 7-3
OPEN file(s).
TSTAT request, Keyword RESTART.
If RESTART value is zero (If not being recovered.)
DBSGTID (ASSIGNID) request (Get new RESTART-id.)
RPUT request (Save new RESTART-id on CRF.)
begin processing at SEQN1. (Skip to first begin-commit sequence.)
ELSE
RGET request. (Retrieve old RESTART-id from CRF)
DB$ASK (FINDTRAN) request. (Get Id of last committed begin-commit
If the begin-commit id is blank sequence. This also assigns the old
begin processing at SEQN1. RESTART-id to this transaction.)
If the begin-commit id is SEQN1
begin processing at SEQN2.
IF the begin-commit id is SEQN2
If the begin-commit id is SEQN(n-l)
begin processing at SEQNn.
If the begin-commit id is SEQNn or **********
begin processing at WRAP-UP.
Processing Module(s)
(data base processing/updating)
SEQN1.
DB$BEG (BEGINTRAN) request, begin-commit id * SEQN1.
Perform processing module(s).
DB$CMT (COMMITRAN) request.
SEQN2.
SEQNn.
DB$BEG (BEGINTRAN) request, begin-commit id - SEQNn.
Perform processing module(s).
SECURE request.
DB$CMT (COMMITRAN) request.
RESTART-value equal to zero.
WRAP-UP.
If RESTART value is not zero
RSECURE request (Retrieve SECURE message from CRF.)
SEND request. (Send SECURE message to terminal.)
CLOSE request(s).
Transaction cease.
Figure 7-1. Recoverable TAF Transaction Using CDCS /*^$^\
TERMINAL RECOVERY CONSIDERATIONS
If a communication subsystem, TAF, or system failure
occurs, an application cannot assume that the termi
nal contains any particular set of data. The last
message may not have been transferred to the termi
nal, or the terminal operator may not have noticed
the message. Also, login procedures or terminal
failures may destroy the screen.
Terminal recovery is also dependent upon the type of
terminal and the form used on the terminal. On hard
cop y term inals, the termin al m ay not n eed al l th e
data resent. In fact resending the data may spoil
the form. O n c at ho de ray tub es (C RTs) , the d ata
entered by the operator may need to be sent after
recovery to indicate what still needs specification.
Applications must design their terminal dialog so
that the operator has no doubts about the state of
the run unit by sending a final message via SECURE
indicating unmistakably that the run unit was suc
cessfully completed. The transaction system guaran
tees that the operator will see this message in all
cases when the run unit completed successfully;
otherwise, the operator might reenter the transaction
causing a double update of the data base.
Applications that require many terminal interactions
must reconstruct the screen from the data base upon
recovery.
7-4 60459500 B

CALLTSK WITHOUT CEASE AND RECOVERY
A CALLTSK without CEASE starts a new run unit. This
n e w r u n u n i t i s n o t r e c o v e r a b l e . I t w i l l b e
restarted only if the calling task is part of a
recoverable run unit and the task makes the CALLTSK
request again upon restart.
Care is necessary when using SECURE, RSECURE, RPUT,
and RGET from run units initiated by CALLTSK without
CEASE. Such run units may write or read the same
recovery data being written or read by the
originating run unit.
MULTIPLE DATA MANAGER USE
Correct recovery cannot be assured for nested or
overlapping begin-commit sequences using both CDCS
and CRM. A transaction may use both CDCS and CRM
provided that begin-commit sequences are neither
nested nor overlapping.
TOTAL DATA MANAGER USE
The TOTAL Data Manager does not use the concept of
begin-commit for data base recovery. Applications
using this data manager, however, may Implement data
base recovery using current TOTAL features and TAF
automatic recovery. If TAF automatic recovery is
installed, such tasks may use any of the requests
described in section 2 of this manual, including the
application recovery requests.
During recovery, transactions that do not use CRM or
CDCS and that were active at the time of failure are
rerun unless the SECURE request data resides on the
communication recovery file. If the SECURE message
is present, the transaction is not rerun but the
SECURE message is sent to the terminal.
j#^
60459500 A 7-5


DATA ADMINISTRATOR AND OPERATOR INTERFACE FOR RECOVERY
/P^^-.
^>v
This section contains recovery information of inter
est to persons responsible for the installation and
maintenance of the transaction subsystem.
RECOVERY OVERVIEW
The TAF recovery package consists of two major compo
nents: transaction recovery and data base recovery.
Data base recovery can be further subdivided into the
automatic component and the batch component. The
integrated system works like this:
A transaction is declared to be recoverable when it
is added to the application task library. The data
managers (CRM and CDCS) provide methods of declaring
data files recoverable. Upon initiation of a recov
erable transaction, ITASK schedules the transaction
via a CALLTRN request. Then the original input (that
is, the transaction name and all unsolicited data) is
logged to the communication recovery file before the
transaction begins execution. The transaction must
indicate to the data manager that it wishes to open
a begin-commit sequence by making a data base BEGIN
request. When the transaction requests to update a
data file, the following occurs.
• The record as read from the data file (the rec
ord In this state is called the before image)
is logged to a before image recovery file, also
known as the before image log file.
• The record is processed by the transaction.
• The updated record (called the after image) is
logged to an after image recovery file when the
program makes a write, rewrite, or delete re
quest. The updated record is also written to
the d ata file at this time.
After an update or a series of updates, the transac
tion Indicates to the data manager that it wishes to
close the begin-commit sequence by making a data base
COMMIT request. If the transaction does not intend
to open another begin-commit sequence, it indicates
to TAF that its work is done by issuing a SECURE re
quest just prior to the COMMIT request. TAF logs a
message associated with the SECURE request to the CRF
and sends this message to the terminal when the final
transaction CEASE request is processed.
If a failure occurs prior to the BEGIN request, the
data base is unaffected and the transaction is re
started upon recovery using the original data logged
on the CRF.
If a failure occurs between the BEGIN and COMMIT
requests, the data manager rolls back the data base
by applying the before images from the before image
recovery file (BRF) to the affected data files. The
data base is then in the same state as it was at the
beginning of the begin-commit sequence. The trans
action is restarted upon recovery using the data on
the CRF.
60459500 A
If a fa i lu r e o cc u rs af ter the COM MIT r equ est , t he
data base is not rolled back, all updates become per
manent when the COMMIT is processed. Whether the
transaction is restarted depends upon the data mana
ger being used. CDCS transactions are restarted if a
failure occurs any time prior to the final transac
tion CEASE request. CRM transactions are rerun un
less both a COMMIT and SECURE request have been suc
cessfully issued. The applications tasks must be de
signed to handle cases where restart can occur after
a COMMIT has been successfully executed. Refer to
section 7 for some suggested transaction structures.
A B R F fi l e i s u s e d r e p e a t e d ly b y th e a p p l i c a t io n.
Only the before images for the current begin-commit
sequence need to be saved so each new begin-commit
sequence can overwrite the previous one.
An after image recovery file (ARF) is continuous.
New after images are written sequentially until the
file is full. At that time, logging is switched to
a second ARF while the after images from the first
ARF are dumped to tape.
The ARF files are not used for automatic recovery.
They provide a backup in case a CRF, BRF, or data
file becomes damaged. If this happens, the data ad
ministrator can use batch recovery to reload the data
file(s) from the dump tape and apply, after images
from an ARF dump, thus restoring the data base to a
correct state as of any desired point in time.
The function performed by each of the recovery compo
nents are as follows.
• Transaction recovery
- Logs the initial input to the CRF.
- Logs and sends the SECURE message.
- R est a rts re cov e rab l e t r ans a cti o ns a fte r a
failure.
• Data base recovery
- Automatic component
. Rolls back updates in uncommitted
begin-commit sequences.
. Logs before images to the BRF.
• Logs after images to the ARF.
. Switches after image logging when an
ARF is full and submits a batch job to
dump the full ARF to tape.
- Batch component
. Dumps full ARFs to tape.
. Dumps data files to tape upon request.
8-1
• Restores data base files from data file
and ARF tapes.
• Maintains a directory of dumped files.
The nomenclature used here is specific to the TAF/CRM
Data Manager. CDCS automatic recovery uses similar
concepts but different terminology. The details
associated with data base recovery are documented in
the respective data manager reference manuals. The
remainder of this section covers the details of
transaction recovery.
HARDWARE CONFIGURATION CONSIDERATIONS
Recovery cannot succeed if failures affect more than
one component of the recovery system. For example,
if a single hardware failure destroys both the recov
ery files and the data base, there is no recovery
other than to restore the data base from a backup
copy (file dump). For this reason, the data base
files, the communication recovery files, the before
image recovery files, and the after image recovery
fi l e s s h o u l d b e a s s i g n e d t o p h y s i c a l l y s e p a r a t e
de v i c e s . A l s o , th e b a c ku p d i r e c t o r y fi l e f o r b a t c h
recovery should not reside on the same device as the
ARFs.
The dump tape storage area should be physically
separate from the area housing the disk drives.
Automatic recovery also depends on the integrity of
single input/output operations. An on-line motor-
generator is essential to ensure that disk operations
underway at the time of a power failure have time to
complete correctly.
Performance improvements through the use of multiple
CRFs and BRFs (TAF/CRM only) will be realized only if
each additional file resides on a separate device.
INSTALLATION
A procedure file for TAF initialization and recovery
is presented in the NOS 2 Installation Handbook.
Transaction recovery is enabled or disabled by the
installation parameter IPTAR. If IPTAR is set to
one, transaction recovery is enabled; if IPTAR is set
to zero, transaction recovery is disabled.
If recovery is disabled, these requests will not be
honored in recovery mode:
CALLTRN
RERUN
RGET
RPUT
RSECURE
SECURE
TINVOKE
TSTAT
WSTAT
For logging of input on CRF.
Except for keywords USER and NEXT.
Except for keywords STEP (=8 or =9)
and USER.
A number of other installation parameters have an
effect on recovery. Refer to the NOS 2 Installation
Handbook for details.
TAF K DISPLAY
INITIAL K DISPLAY
Three K display commands are available to perform
recovery-related functions: K.INT, K.ERO, and K.REC.
K.INT Command
The K.INT command specifies which recovery file(s)
are to be initialized. This is the only means of
initalizing a CRF. Files listed on a RECOVER state
ment in the TCF and on this command will be initial
ized. Files listed on a RECOVER statement but not on
this command will be used for recovery. The INT com
mand also specifies whether CRM data base recovery
files (ARFs and BRFs) are to be initialized or recov
ered. When used for CRM recovery files, this command
is valid regardless of TAF installation options.
The format is:
K. INT-type,fileid
type File type. The options are:
CRF
CRM
Command relates to the
communication recovery
file. This option valid
only if installation
parameter IPTAR » 1.
Command relates
recovery files.
to CRM
fileid File identifier. The options are:
digits
0-7
ALL
. E a c h d i g i t i n t h e s t r i n g
specifies a CRF to be
initialized. The digit
corresponds to the id
parameter on the RECOVER
s t a t e m e n t i n t h e T C F.
This option is not valid
if type is CRM.
If type is CR F, all CRFs
listed In TCF RECOVER
statements are to be
initialized. If type is
CRM, all CRM after image
recovery files are to be
initialized.
NOTE
This option must be used with caution
as the CRM data base update history
currently residing on the recovery
files will be lost.
NONE If type is CRF, no CRF is
to be initialized (all
CRFs listed in TCF RECOVER
sta temen ts a re t o be re
covered) . If type is CRM,
no CRM recovery files will
be initialized. NONE is
the default for both
values of type.
X^&SK
8-2 60459500 C

K.ERO Command
The K.ERO command specifies whether to override
certain I/O or logical errors encountered during
processing of the communication recovery file(s).
The format is:
K. ERO»CRF ,o ption
option Error override option.
NO or YES.
Must be
NO Abort if I/O or logical er
rors are encountered when
processing the communication
recovery file(s). This is
the default.
YES I/O or logical errors en
countered on a run unit
header record will result in
the loss of that run unit
w i t h n o i n d i c a t i o n t o t h e
terminal user. The loss
will be noted on the recov
ery report.
I / O o r l o g i c a l e r r o r s e n
countered on a message rec
ord within a run unit will
result in a loss of that run
unit. However, a status in
dicator would be set in the
run unit header that would
enable the terminal user to
be informed.
If DISPLAY,ON is selected in the TCF, the K display
is issued. This display is identical to the initial
K display except that if any values were changed at
initialization, the changed values are retained on
the restarted K display. This does not apply to
K.INT and K.ERO commands. Changed values for these
commands are not retained after TAFREC completes.
(This prevents inadvertent initialization of
recovery files in a recovery situation).
TCF/CRF RECOVERY CONSIDERATIONS
TAF CONFIGURATION FILE
The TCF contains several recovery-related items.
• The RECOVER statement indicates the CRF
identifier (z er o t o seven) an d t he size and
number of messages that can be written to
the CRF.
• Default K display values can be changed by
placing K display commands in the TCF.
• The DISPLAY statement provides the option of
having the K display brought up at
i n i t i a l i z a t i o n a n d r e c o v e r y t o a l l o w t h e
operator to override any of the default
values.
Details on these statements are given with the TCF
description in section 4.
I/O or logical errors en
countered on the CRF header
record will result in uncon
ditional abort of TAF.
K.REC Command
The K.REC command sets the user recovery bit in the
terminal status ta ble . The f orm at is:
K.REC-nnn
n n n R e c o v e r y o p t i o n . M u s t b e Y E S o r
NO.
YES Set the user recovery bit in
the terminal status table.
NO Do not change the present
setting of the user recovery
bit.
The use of multiple CRFs is indicated by multiple
RE CO VER s tat em ents in the TCF. E ach R ECO VE R
statement corresponds to a separate CRF. For each
RECOVER statement there must be a corresponding
NETWORK statement. Refer to Use of Multiple
Communication Recovery Files in this section and
Communication Recovery File in section 4.
COMMUNICATION RECOVERY FILE
Error Override
Certain errors on the CRF file(s) can be overridden
by us i n g t h e K. ERO K d i s p lay c omma n d ( r e f er t o
Initial K Display in this section). Input/output
errors on the CRF encountered during the running of
t r a n s a c t i o n s c a u s e TA F t o a b o r t an d TA F R E C t o
attempt recovery of all readable data from the CRF.
J8^
RESTART K DISPLAY
The K display that TAF formats at initialization will
be displayed only if a DISPLAY statement with the ON
parameter selected appears in the TCF. Refer to sec
tion 4 for details on the DISPLAY statement. If the
K display is brought up, the operator makes any
desired changes and types K.GO or K.END to resume
processing. K.STOP will abort TAFREC.
On a level 3 deadstart, or if TAF aborts , the TAF
procedure file automatically restarts TAF by trans
ferring control to TAFREC. TAFREC recovers the low
CM pointers and variables that were defined at TAF
initialization via the initial K display.
File Reformatting
TAF recovery processing reformats the CRF under the
following circumstances.
• If the number of user messages per recovery
unit is increased in the number parameter on
the RECOVER statement.
• If the size of user messages per recovery
unit is increased in the maximumsize
parameter on the RECOVER statement.
• If a new user is added to or deleted from
the corresponding network file.
60459500 C 8-3
The RECOVER statement cannot be used to reduce the
number or size of the user messages. The only way
to reduce either of these is to reinitialize the CRF
using the K.INT command.
To reformat ZZCRFi, TAF creates a permanent file
named ZZCRFAi and writes the reformatted CRF to it.
When the reformat is complete, the old CRF (ZZCRFi)
i s p u r g e d a n d t h e n e w C R F ( Z Z C R FA i ) h a s i t s
permanent file name changed to ZZCRFi.
Multiple Communication Recovery Files
Up to eight CRFs may be active simultaneously. Each
CRF must have a unique identifier. Once a CRF has
been initialized with a given id, it must be brought
up with the same id. If this is not done, recovery
will fail. Advantages of using multiple CRFs are:
• The input/output associated with the CRFs is
spread out across several disks. This
improves performance.
• Mul timainf rame recovery becomes possible.
Refer to Mul timainf rame Recovery in this
sec tion.
MULTIMAINFRAME RECOVERY
The guidelines in this subsection pertain to sites
running TAF on several mainframes. These guidelines
are applicable if the ability to recover transaction
processing for a downed mainframe on an alternate
mainframe is desired.
• Make certain that the network (NCTFi) and
C R F ( C R F i ) fi l e i d e n t i fi e r s ( i ) o n e a c h
mainframe are unique among all mainframes.
• Allocate unique data base names to all
applications across all mainframes.
• Allocate recovery-related files to shared
mass storage.
• Define unique terminal user names across all
mainframes.
• When a mainframe goes down, IDLE TAF on the
mainframe that is to run the downed
applications, t
• Restart TAF with a TCF file that contains
RECOVER statements for the recovery ids of
both mainframes*
• When the downed mainframe is repaired, IDLE
TAF on the recovery mainframe. Then bring
TAF up independently on the two mainframes
with the original TCFs.
RECOVERY PROCESSING FLOW
TAF AND SYSTEM FAILURE
Following a TAF or operating system failure, the TAF
initialization procedure brings TAF up in recovery
mode. During recovery mode initialization, TAFREC
and TAF perform the following functions:
• Sets the K di sp la y v alu es to t ho se in effe ct
prior to failure.
• I d e n t i f i e s th e u s e r s tha t w e r e acti v e a t the
time of failure. Active users will have the
recovery flag (word 1, bits 0 and 53) set in
the terminal status table (TST).
• Reformats the CRF if necessary (refer to
File Reformatting under Communication
Recovery File in this sec tion).
• Prepares the TAF automatic recovery report.
• Initializes the transaction sequence number
count.
• Schedules CTASK to move begin-commit ids
from BRF to CRF.
BTASK is scheduled to determine which users active
at the time of failure were running recoverable
BTRAN-initiated transactions. BTASK calls CTASK to
recover these transactions.
Recovery for transactions being run from interactive
terminals is postponed until the terminal logs in.
When a terminal logs in, TAF checks the recovery
flag (word 1, bit 53) in the terminal status table.
If the recovery flag is set, RTASK is scheduled
instead of ITASK. RTASK performs these functions:
• If the run unit is not recoverable, RTASK
sends READY to the terminal and ceases.
• If a recoverable transaction is no longer
rerunnable, RTASK sends a message telling
the terminal operator
1. that recovery has occurred,
2. that the recoverable transaction
will not be rerun automatically, and
3. to enter the next input.
Th i s s itu ati on o cc u rs whe n a n inpu t /o u tpu t
error occurred on the communication recovery
file. Terminal operators should be
instructed to inform the data administrator
if this occurs since batch recovery will be
necessary to restore the data base.
• If the transaction SECURE request and a
TAF/CRM COMMIT request have been
successfully executed, RTASK sends the
terminal confirmation message, and ceases.
The terminal confirmation message was stored
on the CRF as a result of the transaction
SECURE request.
• If none of the preceding is true, RTASK
calls CTASK.
CTASK requests a new transaction sequence number and
returns the begin-commit history to TAF/CRM. CTASK
then makes a RERUN request. The RERUN request turns
off the recovery status, retrieves terminal input
from the CRF, and schedules ITASK using the new
sequence number and original terminal input. ITASK
processes the input as if it had come from the
terminal.
tlf CDCS has been running on both mainframes and interfacing with TAF, CDCS must be dropped on the functional
mainframe or recovery of CDCS data bases will not be possible.
8-4 60459500 C /<Sfev

J^v NAM FAILURE
I f NA M f a i l s , TA F c o n t i n u e s ru n n i ng . T h e r o ll o u t
table is searched to suspend transactions that were
initiated by an interactive terminal and are waiting
for input (the wait time in the rollout table is set
to zero). All other active transactions continue to
run. When a running transaction issues a network re
quest , it is suspended if recoverable and the request
is issued to the original terminal (without recall In
the case of SEND). If the transaction is not recov
erable, it is terminated. Suspended transactions are
processed as follows:
• A terminal-login-delay flag is set in the
terminal status table to prevent terminal
login until the next step is completed.
• CTASK is scheduled to recover the data base
associated with the transaction and to issue
a WSTAT request to clear the delay flag.
• At the time the terminal logs in, RTASK is
scheduled either to send the SECURE message
or to rerun the transaction.
TAF wil l period ica lly attem pt reconnec tio n to N AM.
When NAM becomes available, terminal operators will
have to go through the login dialog required for the
terminal. Upon terminal reconnection to TAF, TAF
issues an appropriate message to tell the terminal
operator the current state of the terminal work.
When CDCS is again accepting requests, TAF will
rerun those recoverable run units whose processing
was suspended, as previously described.
TASK FAILURE
TAF does the following when a task fails:
• TAF sends a failure or end run unit message
to the data manager. The data manager rolls
back updates in any incomplete being-commit
sequences.
TAF l o gs t he rea s on for th e f a ilu r e i n t h e
journal file.
TAF calls system task MSABT. The Control
Data-furnished version of MSABT sends a
m e s s a g e e x p l a i n i n g th e e r r o r c o n d i t i o n to
t h e te r mi n a l . Si t e s ma y m o d if y M S AB T t o
meet special requirements.
TAF reloads the task if the task has other
run units queued on it or is central memory-
resident.
Run units aborted because task failures are
not rerun. Failure of the logged in
terminal, NAM, or CDCS does not cause a task
failure for a recoverable run unit.
jP1^
TERMINAL FAILURE
Processing for an individual terminal failure is the
same as described for NAM abort.
CDCS FAILURE
If CDCS fails, TAF continues running. When TAF
detects a CDCS abort, it does the following to run
units using CDCS:
• If the run unit is recoverable, its proces
sing is suspended and an informative message
is issued. The terminal operator may wait
for the run unit to be automatically rerun
when CDCS becomes available, or may enter a
new transaction. In the latter case, the
run unit will not be rerun when CDCS becomes
available.
• I f t h e r u n u n i t i s n o t r e c o v e r a b l e , i t i s
aborted and an error message is issued to
the originating terminal.
TAF sets a flag in the CRF for suspended run units
waiting to use CDCS.
TAF, on a periodic basis, will check to see if CDCS
is running and ready for transaction processing.
TAF TERMINATION
TAF goes through termination processing when:
• The computer operator or terminal operator
forces execution of a K.IDLE request.
• The computer operator enters IDLE,TAF.
• TAF (Including any data manager in its field
length) fails.
• A l e v e l 3 deads t a r t oc c u r s .
When TAF receives a K.IDLE or IDLE,TAF command, TAF
tells ITASK with an idle message. ITASK then:
• Tells terminal users entering a new
transaction that shutdown is occurring.
• P r o h i bits new t r a nsact i o n s fr o m st a r ting.
When no more transactions are running (no
communication blocks are reserved), TAF does an
ENDRUN to give control to TAF2. TAF2 tells the data
manager(s) about shutdown and records a shutdown
status on the CRF. When TAF is subsequently brought
up, no recovery takes place since all users were
inactive at termination.
/fS^V 60459500 B 8-5
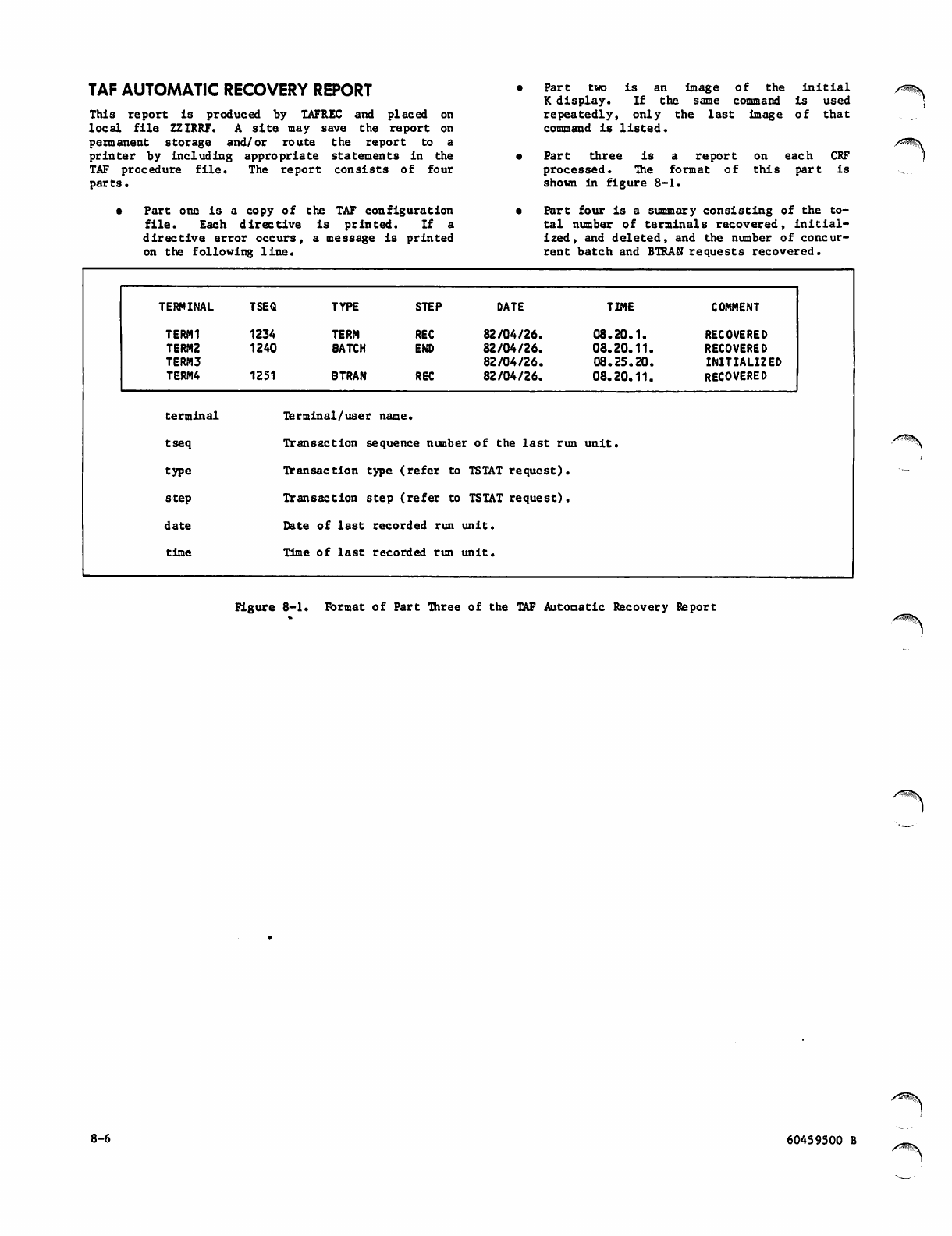
TAF AUTOMATIC RECOVERY REPORT
This report is produced by TAFREC and placed on
local file ZZIRRF. A site may save the report on
permanent storage and/or route the report to a
printer by including appropriate statements in the
TAF procedure file. The report consists of four
parts.
• Part one is a co py o f the TAF con figurati on
file. Each directive is printed. If a
directive error occurs, a message is printed
on the following line.
Part two is an image of the initial
K display. If the same command is used
repeatedly, only the last image of that
command is listed.
Part three is a report
processed. The format of
shown in figure 8-1.
on eac h CRF
t h i s p a r t i s
Part four is a summary consisting of the to
tal number of terminals recovered, initial
ized, and deleted, and the number of concur
rent batch and BTRAN requests recovered.
/*^%\
TERMINAL TSEQ TYPE STEP DATE TIME COMMENT
TERM1 1234 TERM REC 82/04/26. 08.20.1. RECOVERED
TERM2 1240 BATCH END 82/04/26. 08 .20.11. RECOVERED
TERM3 82/04/26. 08.25.20. INITIALIZED
TERM4 1251 BTRAN REC 82/04/26. 08.20.11. RECOVERED
terminal
tseq
type
step
date
time
Terminal/user name.
Transaction sequence number of the last run unit,
Transaction type (refer to TSTAT request).
Transaction step (refer to TSTAT request).
Date of last recorded run unit.
Time of last recorded run unit.
</^^V
Figure 8-1. Format of Part Three of the TAF Automatic Recovery Report
8-6 60459500 B
NETWORK FILES
Applications programmers should determine whether an
analyst is preparing the network files. If so,
applications programmers can skip this section.
Before any transaction processing can be done, the
terminal configuration must be defined to the
transaction executive. This is done by the terminal
ne t wo r k d esc rip t io n file (ne t wor k fi le) .
A simple set of terminal network file directives
follows:
//DIAL.
/AJ0HNSN,TT=*ID,DB=8C,
UA=16117711B.
/BJOHNSN,TT=*ID,DB=BC,
UA=00007700B.
/XYZ1,TT=*ID,DB=8C.
The NAM local configuration file is also needed to
describe the terminal configuration. This file is
described in the Network Products NAM 1 Network
Definition Language Reference Manual.
TERMINAL NETWORK DESCRIPTION FILE
A terminal network description file consists of
directives that describe users and their data
bases. The directives needed consist of the //DIAL
directive and user directives.
The format is:
//DIAL.
User directives must follow the //DIAL directive.
User directives have the form:
/username,parameter-string.
username A user name that is used to log
into the network and TAF (or is
specified in the local configura
tion file for automatic login).
User names must be unique across
all network files, even if they
reside on different families.
T h e p o s s i b l e e l e m e n t s o f t h e p a r a m e t e r s t r i n g ,
separated by commas, are:
TT=>*ID Transaction terminal type.
DB=aa
UA=n
Two-character name of the data base
to be accessed by 'the user. Only
one data base can be associated with
a user name.
Contents of the user argument area in
the communication block. n ranges
from 0 through 16777215. Default is
zero. User area contents can be ex
amined and changed by tasks. The
appropriate initial value is site
dependent. Bit 0 is the default
task recovery bit.
NETWORK FILE ORIGINATION
When an error-free network description is ready, an
analyst should create a system file called NCTFi
( w h e r e i i s t h e n e t w o r k fi l e i d e n t i fi e r ) f r o m t h e
terminal network description file.
A typical way to originate an NCTFi file follows.
First, the user establishes a set of network
description statements as a local fil e.
NCTF.
USER,username,password,familynaae.
' CHARGE,chargenuraber,projectnumber. or (*)
COPYBR,INPUT,NET.
SAVE,NET .
end-of-record
Network description statements
e n d - o f - fi l e
Then the user enters the following at the system
console.
X.DIS.
USER,username,password,familyname.
CHARGE,chargenumber,projectnumber.
GET,NET.
SUI,377777.
DEFINE,NCTFi/CT=PU.
COPY,NET,NCTFi,V.
RETURN,NCTFi,NET.
This creates a direct access public file called NCTFi
under the system user index 377777. NCTFi is used to
generate terminal status table entries.
Figure 9-1 illustrates a terminal status table entry.
Each line gives the user name and its associated data
base, read and update securities, and user area
value.
When a run unit originates from a terminal, the
transaction executive uses the appropriate entry in
the terminal status table to construct words 0 and 1
of the communication block.
After the network file is originated, it must be up
dated to reflect changes, and the transaction execu
tive must be reinitia lized t o re cognize the new in
formation.
60459500 C 9-1
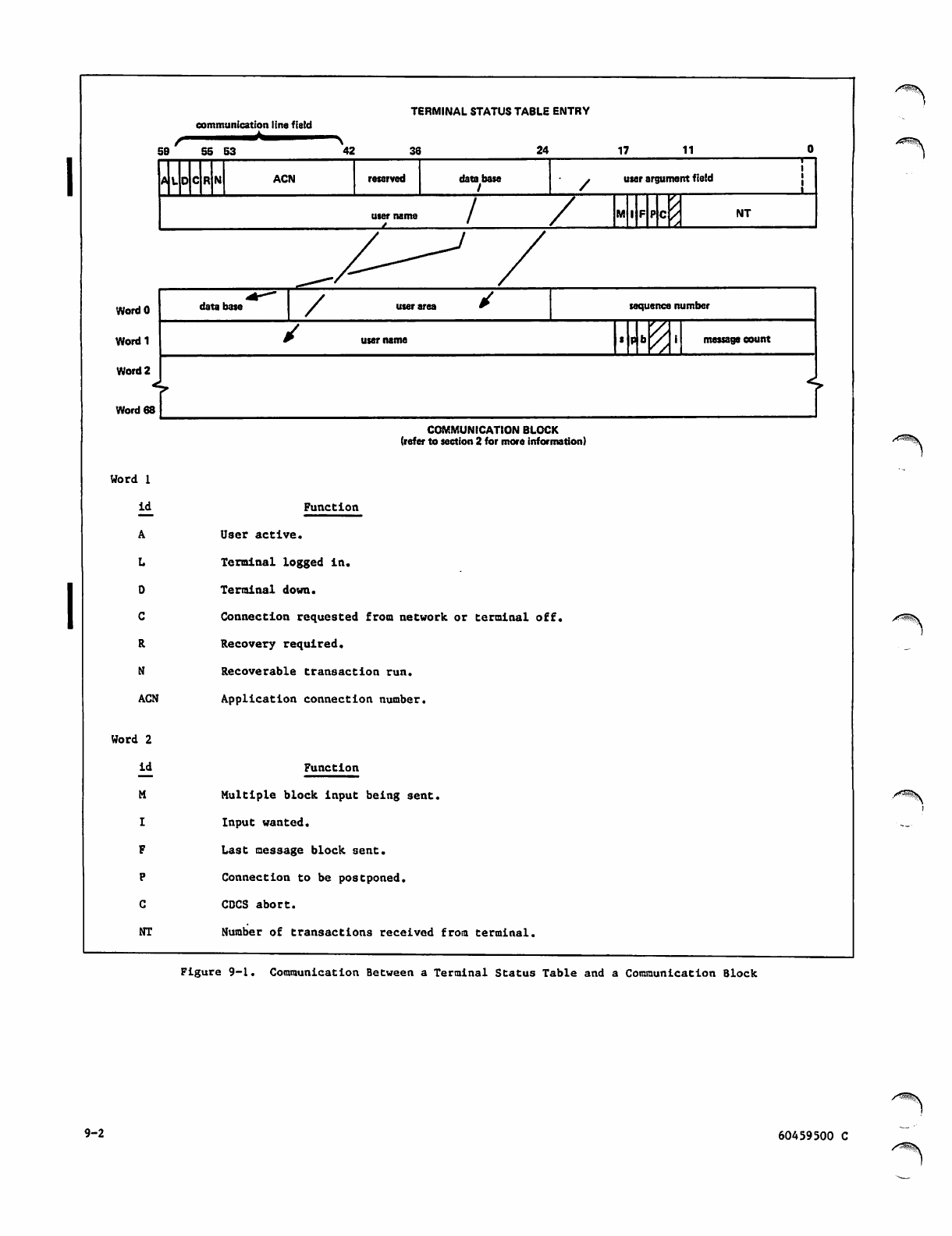
TERMINAL STATUS TABLE ENTRY
59
communication line field
A
55 53 42 38 24 17 11
WordO
Wordl
Word 2
Word 68
■t
Word 1
id
A
L
D
C
R
N
ACN
ACN reserved database
/user argument field
/ / IF NT
database sequence number
*g' message count
COMMUNICATION BLOCK
(refer to section 2 for more information)
Function
User active.
Terminal logged in.
Terminal down.
Connection requested from network or terminal off.
Recovery required.
Recoverable transaction run.
Application connection number.
Word 2
id Function
MMultiple block input being sent.
IInput wanted.
FLast message block sent.
PConnection to be postponed.
CCDCS abort.
NT Number of transactions received from terminal.
^ r ^ t ^ v
/*S§\
Figure 9-1. Communication Between a Terminal Status Table and a Communication Block
9-2 60459500 C

TASK LIBRARY 10
A task library contains all of the named-transactions
and tasks that may be requested by a user group with
in the transaction subsystem. The task library is
created by the LIBTASK utility.
A task library file is a direct access permanent
file with no password that must be created with a
D E F I N E c o m m a n d b e f o r e a l i b r a r y c r e a t i o n r u n
occurs. However, it does not have to be attached by
the user unless the DA option is specified (refer to
L I B TA S K c o m m a n d ) . T h e t r a n s a c t i o n s u b s y s t e m
simultaneously supports one system task library and,
optionally, one task library for each data base.
The system task library, called TASKLIB by default,
may be renamed at the site's option. It is defined
under the transaction subsystem user name and given
write permission to that user name. The name
TASKLIB may also be changed using the K display
command K.TLF. (Refer to the NOS 2 Operator/Analyst
Handbook.)
A user task library must be named xxTASKL where xx
is the name of the data base with which the library
is associated. It must be defined under the data
base user name, and explicit write permission must
be granted to the transaction subsystem user name to
access the file.
During initialization, TAF attempts to attach a
l i b r a r y f o r e a c h i n i t i a l i z e d d a t a b a s e . T h e x x J
file is accessed to determine the user name needed
to attach the library. When a scheduling request is
received, the transaction subsystem searches for the
named-transaction or task first in the associated
data base library, if one exists, and then in the
system library. Transaction ' and task names,
therefore, need be unique only within a given task
library. The only exception to this procedure is
the initial task, ITASK, which is always loaded from
the system library.
LIBTASK UTILITY
The LIBTASK utility creates a new library, adds new
named-transactions and tasks to an existing library,
deletes named-transactions and tasks from an
existing library, replaces tasks in an existing
library, and compacts an existing library by
removing inactive records. Named-transactions and
tasks may be added or deleted while the transaction
subsystem is running, because tasks are added as a
new file a t t h e en d of th e li b r a r y. T h e l i b r a r y i s
a multifile file. The transaction executive
attempts to read a new library directory if the
LIBTASK command contains the TT option. Thus, on
line update of any task library is allowed.
If the library is modified while the transaction
subsystem is running and the user wants the new
directory used, the user number and password of the
LIBTASK user are passed to the transaction
s u b s y s t e m f o r v a l i d a t i o n . T h i s i s d o n e b y
intercontrol point communication, which is also used
to check if the tra nsac tion subsystem is running if
t h e C R o r P R op t i o n i s se l e c t e d . Th e r e f o r e , t h e
first USER command in the job must have permission
to do intercontrol point communication. (Refer to
the NOS 2 System Maintenance Reference Manual for
the use of MODVAL to alter permissions.) The
LIBTASK run Issues an error message and does not
update the library if the validation fails. The
task binaries to be added or replaced are in ABS or
OVL format produced by the CYBER Loader.
TASK RESIDENCY AND TYPE
An important option of LIBTASK enables the user to
specify the residency and type of tasks on the task
l i b r a r y . A t a s k c a n r e s i d e o n c e n t r a l m e m o r y,
extended memory, or mass storage. This can be
s p e c i fi e d w i t h t h e C a n d E o p t i o n s o n L I B TA S K
d i r e c t i v e s .
A task can be of either reusable or nonreusable
type. A reusable task must be written so that it is
reinitializing. A reinitializing task (program)
does not modify program areas that the program
considers constant; if it does, it resets
(reinitializes) these areas upon reentry. Multiple
requests for a reusable task can be queued together;
this is p art ly unde r the control of the person wh o
sets up the task library and partly under the
control of the transaction executive. The queuing
of m ul ti pl e r eq ue st s occurs in an i nt er na l list, t he
requested task list (RTL). Each entry in this list
represents a scheduling request for a copy of a
task. There may be multiple entries in the RTL list
for a given task. The LIBTASK queue limit input
directive can be used to specify the maximum number
of transactions that can be queued against one
en try. W he n t h e t ra nsa cti on exe cu tiv e s che dul es a
cop y of a task from the RTL lis t, i t pi cks an RTL
entry and forces all of the multiple requests queued
for that RTL entry to use the same copy of the task.
It is generally possible to have multiple copies of
a g iv e n t ask in e x ecu tio n a t the sam e t i me (n ote
that this does not apply to CM-resident tasks).
Additional application control of task scheduling is
provided by the Q LIBTASK option in the input
directives.
A n o n r e u s abl e t ask i s n o t a r e i n i t i al i z i n g tas k ; a
new copy of the task must be loaded from the task
library for each transaction.
60459500 C 10-1

The task type can be specified with the D option on
L I B T A S K d i r e c t i v e s . T h e q u e u e l i m i t c a n b e
specified with the QL option.
If a task is specified as central memory-resident
and reusable, it is loaded to a subcontrol point
when TAF is initialized and, unless the task aborts,
remains at that subcontrol point to service
transactions as long as TAF is running. If the task
aborts, another copy of it will be loaded. It is a
single copy task. No additional copies of this task
are loaded to process requests after queue limit has
been reached.
LIBTASK COMMAND
The LI BTASK co mm an d has t wo formats. The fi rs t
format allows specification of the file containing
input directive statements; this format is:
LIBTASK(Pl,P2,...,Pn>
The second format specifies that input directive
statements are included in this LIBTASK command.
This format is:
LIBTASKtPi.pj,...,Z,...,Pn);dx;d2;...;dn.
; Unique delimiter that does not occur
in any d^ input directives. This
delimiter does not have to be a
semicolon.
dj Input directive statement (refer to
Input Directives in this sec tion).
The input directives on a LIBTASK command remain in
eff e c t for a ta s k in a n existing t a s k library u n t i l
the task is specified in a subsequent LIBTASK
command; that is, the most recent input directives
(including default input directives) for a task take
precedence over earlier input directives. However,
t h i s is n o t tr u e f o r a t a s k t h a t is n o t in a t a s k
library; in this case, the first input directives
(including default input directives) take precedence.
For example, you specify the following command:
LIBTASK(p1,p2,P3,...,pn);*T1 DL.
This command logically deletes task Tl. If you
specify task Tl in a subsequent LIBTASK command and
do not specify DL, the task is activated (by
default).
The LIBTASK com and cannot exceed 80 characters.
The parameters (pf) for either format can be in
any order and are:
Parame ter Description
I Specifies the file containing input
directives. The file is not rewound
b e f o r e p r o c e s s i n g . A l l d i r e c t i v e s
that do not refer to a task name
pre sent on the B file or P file are
ignored. Options are:
I File is COMPILE.
Parameter
I=lfn
1-0
Description
File is specified by
you.
/Sa^V
No directive
exists.
fi l e
Omitted Default file is INPUT.
Specifies the file containing task
binaries to be added to the library.
These may be tasks already existing
i n t h e l i b r a r y or t h e y m a y b e n e w
ones. The file is rewound before
processing. Options are:
B File is LGO.
B-lfn F i l e i s s p e c i fi e d b y
you.
B-0 No binary file exists.
Omitted Default file is LGOB.
Specifies the file on which output is
written. Options are:
L File is OUTPUT.
L-lfn File is specified by
you.
L«0 No output is written.
Omitted Default file is OUTPUT.
Specifies the name of a direct access
permanent file to be used as the
library file. The file is required.
Options are:
P
P-lfn
P-0
Omitted
File is TASKLIB.
File is specified by
you.
No old library file
exists.
Default
TASKLIB.
fi l e is
Specifies a newly defined direct ac
cess permanent file to be written as
the new library file. Use of this
option eliminates the complete copy
o f t h e P fi l e t o a s c r a t c h fi l e o n
the PR option, thus significantly
reducing the purge time for long
libraries. The P file is not purged.
Options are:
N File is TASKLIB.
N»lfn File is specified by
you.
Omitted Default file is the
file specified by P.
J^'^Wt^\
10-2 60459500 B /^S\
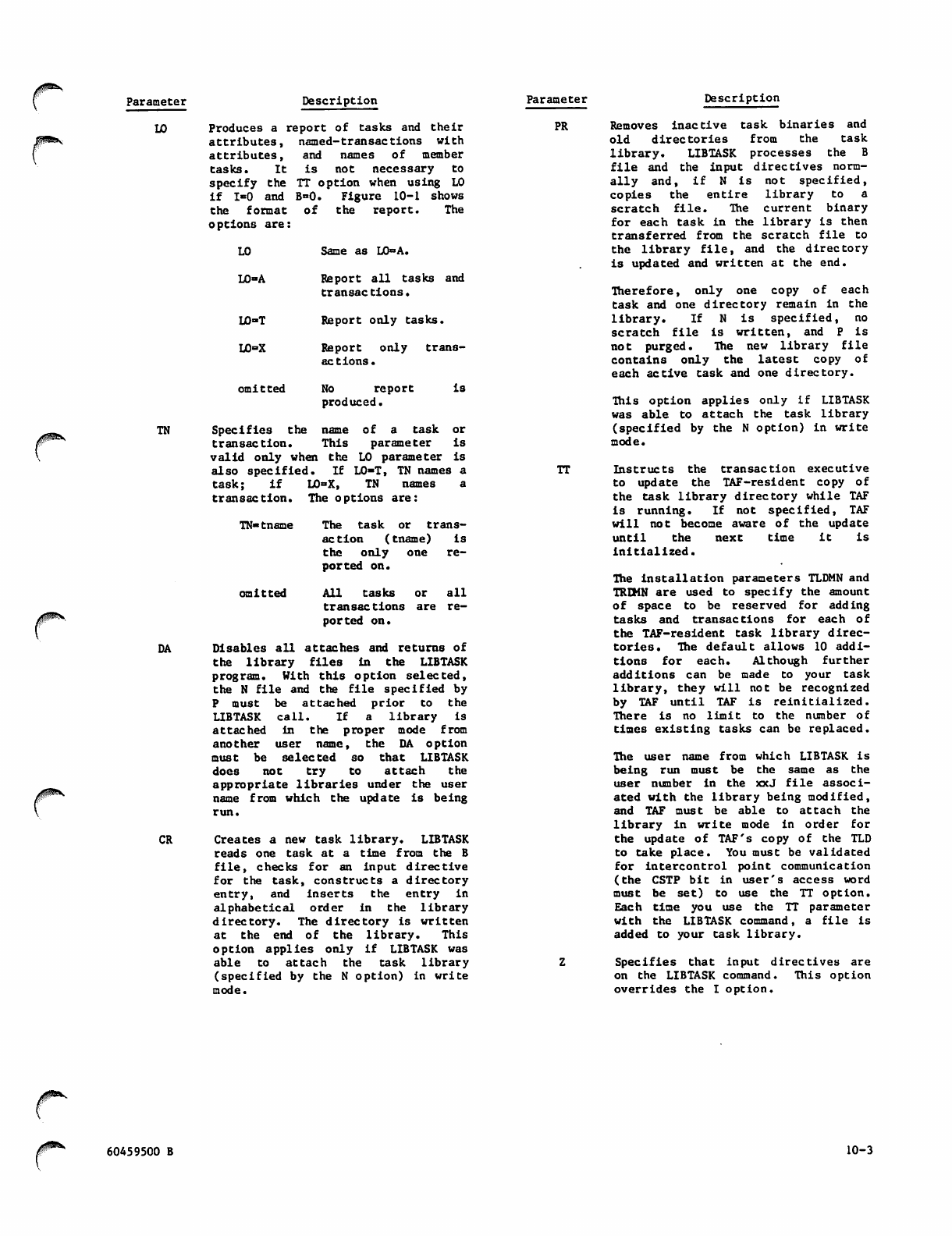
J^ Parameter
LO
TN
DA
CR
Description
Produces a report of tasks and their
attributes, named-transactions with
attributes, and names of member
tasks. It is not necessary to
specify the TT option when using LO
if I»0 and B=0. Figure 10-1 shows
t h e f o r m a t o f t h e r e p o r t . T h e
options are:
LO Same as LO»A.
LO=A Report all tasks and
transae tions.
LO«T Report only tasks.
LO=X Report only trans
actions.
omitted No report
produced.
is
Specifies the name of a task or
transaction. This parameter is
valid only when the LO parameter is
also specified. If LO-T, TN names a
task; if LO=X, TN names a
transaction. The options are:
TN*tname The task or trans
action (tname) is
the only one re
ported on.
omitted All tasks or all
transactions are re
ported on.
Disables all attaches and returns of
the library files in the LIBTASK
program. With this option selected,
the N file and the file specified by
P must be attached prior to the
LIBTASK call. If a library is
a t t a c h e d i n t h e pr o p e r m o d e f r o m
another user name, the DA option
must be selected so that LIBTASK
does not try to attach the
appropriate libraries under the user
name from which the update is being
run.
Creates a new task library. LIBTASK
reads one task at a time from the B
file, checks for an input directive
for the task, constructs a directory
e n t r y , a n d i n s e r t s t h e e n t r y i n
alphabetical order in the library
d i r e c t o r y. T h e d i r e c t o r y i s w r i t t e n
at the end of the library. This
option applies only if LIBTASK was
able to attach the task library
(specified by the N option) in write
mode.
Parameter
PR
TT
Description
Removes inactive task binaries and
old directories from the task
library. LIBTASK processes the B
file and the input directives norm
ally and, if N is not specified,
copies the entire library to a
scratch file. The current binary
for each task in the library is then
transferred from the scratch file to
the library file, and the directory
is updated and written at the end.
Therefore, only one copy of each
task and one directory remain in the
library. If N is specified, no
s c r a t c h fi l e i s w r i t t e n , a n d P i s
not purged. The new library file
contains only the latest copy of
each active task and one directory.
This opt ion applies only i f LIBTASK
wa s able to atta c h t h e t ask li bra r y
(specified by the N option) in w rit e
mode.
Instructs the transaction executive
to update the TAF-resident copy of
the task library directory while TAF
is running. If not specified, TAF
will not become aware of the update
until the next time it is
initialized.
The installation parameters TLDMN and
TREMN are used to specify the amount
of space to be reserved for adding
tasks and transactions for each of
the TAF-resident task library direc
tories. The default allows 10 addi
tions for each. Although further
additions can be made to your task
li bra ry, th e y w il l not be rec ogn i ze d
by TAF until TAF is reinitialized.
Th e re is n o l i mi t to t h e n umb e r o f
times existing tasks can be replaced.
The user name from which LIBTASK is
being run must be the same as the
user number in the xxJ file associ
ated with the library being modified,
and TAF must be able to attach the
library in write mode in order for
the update of TAF's copy of the TLD
to take place. You must be validated
for intercont rol point communication
(the CSTP bit in user's access word
must be set) to use the TT option.
Each time you use the TT parameter
with the LIBTASK command, a file is
added to your task library.
Specifies that input directives are
on the LIBTASK command. This option
overrides the I option.
/$PV
60459500 B 10-3
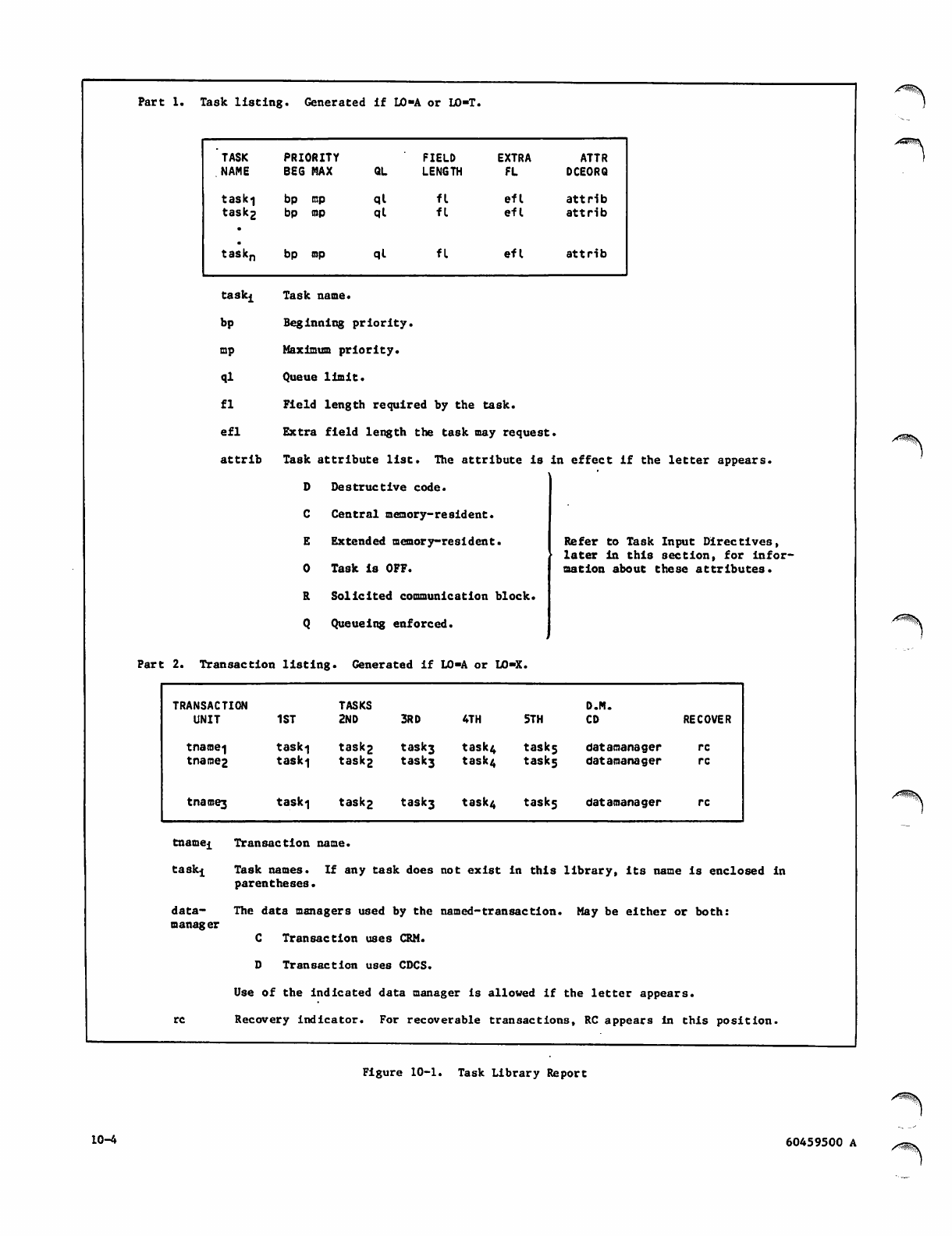
Part 1. Task listing. Generated if LO-A or LO-T.
TASK PRIORITY FIELD EXTRA ATTR
NAME BEG MAX QL LENGTH FL DCEORQ
taski bp mp ql flefl a t t r i b
taskg bp mp ql flefl a t t r i b
taskn bp mp ql flefl a t t r i b
taski Task name.
bp Beginning priority.
mp Maximum priority.
ql Queue limit.
fl Field length required by the task.
e fl E x t r a fi e l d l e n g t h t h e t a s k m a y r e q u e s t .
attrib Task attribute list. The attribute is in effect if the letter appears.
D Destructive code.
C Central memory-resident.
E Extended memory-resident.
0 Task is OFF.
R Solicited communication block.
Q Queueing enforced.
Part 2. Transaction listing. Generated if LO-A or LO-X.
Refer to Task Input Directives,
later in this section, for infor
mation about these attributes.
TRANSACTION
UNIT 1ST
TASKS
2ND 3RD 4TH 5TH
D.M.
CD RECOVER
tnamei
tnamej
taski
taski
task2
taskg
task3
task3
task/;
task/;
tasks
tasks
datamanager
datamanager
re
re
tname3 taski task2 task3 task/; tasks datamanager re
tnamei Transaction name.
taski
data-
manager
Task names. If any task does not exist in this library, its name is enclosed in
parentheses.
The data managers used by the named-transaction. May be either or both:
C Transaction uses CRM.
D Transaction uses CDCS.
Use of the indicated data manager is allowed if the letter appears.
Recovery indicator. For recoverable transactions, RC appears in this position.
/^8^S\
Figure 10-1. Task Library Report
10-4 60459500 A
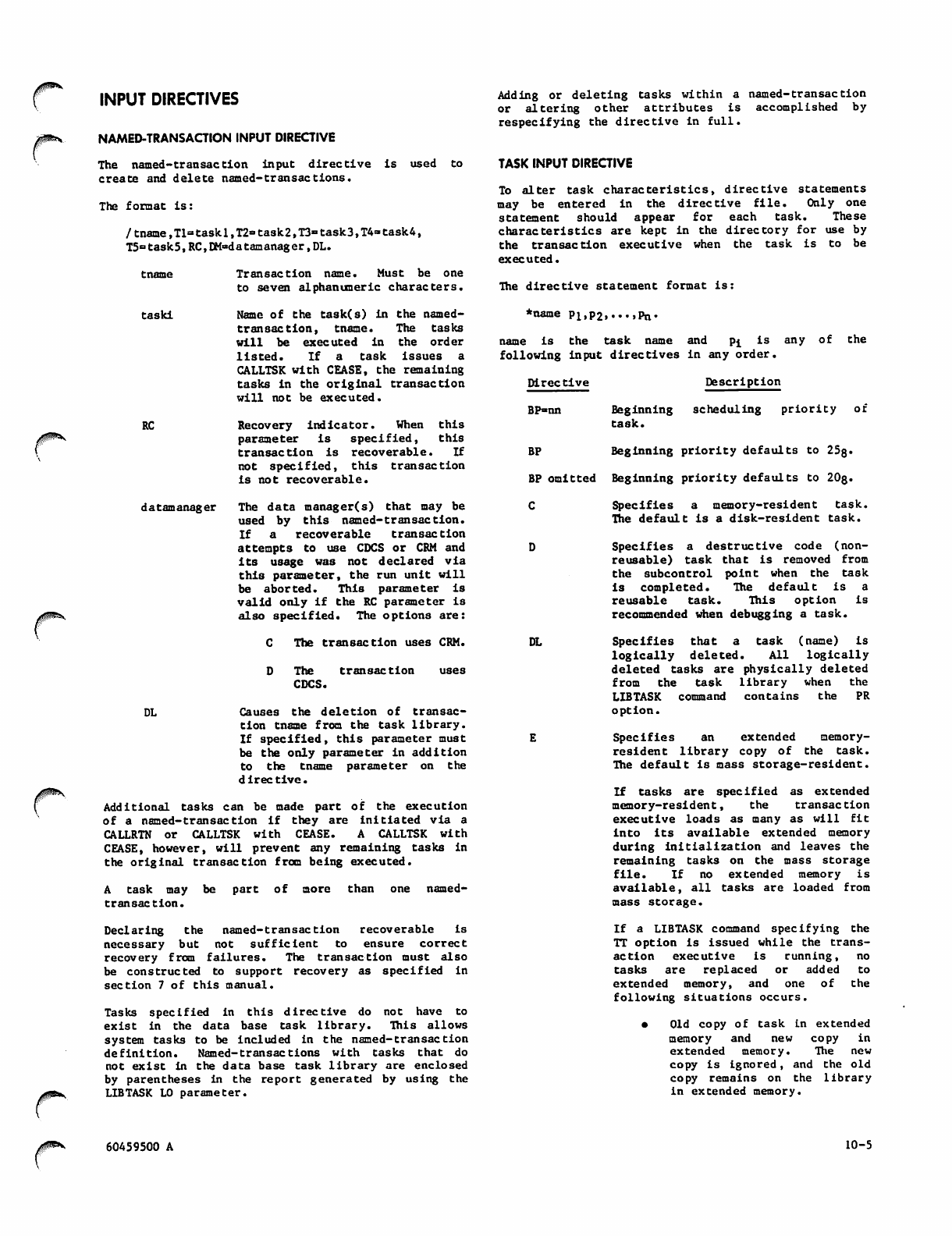
INPUT DIRECTIVES
J0^*\
NAMED-TRANSACTION INPUT DIRECTIVE
The named-transaction input directive is used to
create and delete named-transactions.
The format is:
/ tname, Tl=« task 1, T2- task2, T3- task3, T4- task4,
T5-task5,RC,DM»datamanager,DL.
t n a m e T r a n s a c t i o n n a m e . M u s t b e o n e
to seven alphanumeric characters.
taski Name of the task(s) in the named-
transaction, tname. The tasks
will be executed in the order
listed. If a task issues a
CALLTSK with CEASE, the remaining
tasks in the original transaction
will not be executed.
RC Recovery indicator. When this
parameter is specified, this
transaction is recoverable. If
not specified, this transaction
is not recoverable.
datamanager The data manager(s) that may be
used by this named-transaction.
If a recoverable transaction
attempts to use CDCS or CRM and
its usage was not declared via
this parameter, the run unit will
be aborted. This parameter is
valid only if the RC parameter is
also specified. The options are:
C The transaction uses CRM.
D The transaction uses
CDCS.
DL Causes the deletion of transac
tion tname from the task library.
If specified, this parameter must
be the only parameter in addition
to the tname parameter on the
d irec tive.
Additional tasks can be made part of the execution
of a named-trans action if they are initiated via a
CALLRTN or CALLTSK with CEASE. A CALLTSK with
CEASE, however, will prevent any remaining tasks in
the original transaction from being executed.
A task may be part of more than one named-
transaction.
Declaring the named-transaction recoverable is
necessary but not sufficient to ensure correct
recovery from failures. The transaction must also
be co nstructed to sup por t recove ry as spe cified in
section 7 of this manual.
Tasks specified in this directive do not have to
exist in the data base task library. This allows
system tasks to be included in the named-transaction
d e fi n it i o n . N a m e d - t r a n s a c t i o n s w it h ta s k s th a t do
not exist in the data base task library are enclosed
by parentheses in the report generated by using the
LIBTASK LO parameter.
Adding or deleting tasks within a named-transaction
o r a l t e r i n g o t h e r a t t r i b u t e s i s a c c o m p l i s h e d b y
respecifying the directive in full.
TASK INPUT DIRECTIVE
To alter task characteristics, directive statements
m a y b e e n t e r e d i n t h e d i r e c t i v e fi l e . O n l y o n e
statement should appear for each task. These
characteristics are kept in the directory for use by
th e t r ans a c t i o n exe c u t i v e whe n t h e t a s k is to b e
executed.
The directive statement format is:
*name Pi,P2 Pn«
n a m e i s t h e t a s k n a m e a n d p ^ i s a n y o f t h e
following input directives in any order.
Directive Description
BP-nn Beginning scheduling priority of
task.
B P B e g i n n i n g p r i o r i t y d e f a u l t s t o 2 5 g .
BP omitted Beginning priority defaults to 20g.
C Specifies a memory-resident task.
The default is a disk-resident task.
D Specifies a destructive code (non-
reusable) task that is removed from
the subcontrol point when the task
is completed. The default is a
reusable task. This option is
recommended when debugging a task.
DL Specifies that a task (name) is
logically deleted. All logically
deleted tasks are physically deleted
from the task library when the
LI BTASK comm an d c ont ai n s the PR
option.
Specifies an extended memory-
resident library copy of the task.
The default is mass storage-resident.
If tasks are specified as extended
memory-resident, the transaction
executive loads as many as will fit
into its available extended memory
during initialization and leaves the
remaining tasks on the mass storage
file. If no extended memory is
available, all tasks are loaded from
mass storage.
If a LIBTASK command specifying the
TT option is issued while the trans
action executive is running, no
tasks are replaced or added to
extended memory, and one of the
following situations occurs.
• Old copy of task in extended
memory and new copy in
e x t e n d e d m e m o r y. T he n e w
copy is ignored, and the old
copy remains on the library
in extended memory.
60459500 A 10-5

Directive Description Directive Description
• Old copy not in extended
memory and new copy in
extended memory. The new
copy is used but is read
from mass storage.
• Old copy in extended memory
and new copy not in extended
memory. The new copy is
loaded from mass storage.
E F - e fl S p e c i fi e s t h e m a x i m u m a m o u n t b y
which a task will be allowed to
increase its initial field length,
efl is assumed to be octal unless it
contains an 8 or 9 or is followed by
a trailing D. The default value is
z e r o . E F w i l l be i n c r e a s e d t o th e
next multiple of lOOg if it is not
already such a multiple. The maximum
field length allowed for the task is
(initial task FL) + efl. The value
of efl can range from 0 to 300000g.
IG Specifies that a task (name) In the
file specified with the B option is
ignored.
MP»nn Maximum scheduling priority of task
(for future use in aging tasks).
MP Maximum priority defaults to 50g.
MP omitted Maximum priority defaults to 40g.
0 Sets task to OFF; requests for the
task are routed to the OFF TASK
routine (refer to OFFTASK in section
11). The default is ON.
Q Specifies that queuing is to be
forced, described as follows. This
option alters the normal scheduling
priority of the task (refer to
Scheduling Priority) as follows:
1. When there are no active copies
of the task, the first copy of
the task is scheduled as usual
(refer to Scheduling Priority).
A n a c t i v e t a s k i s a c o p y o f a
task which is both:
• At a subcontrol point or
rolled out.
• In the process of
handling a transaction
or has transactions
queued against it (the
co py ).
If a LIBTASK function specifying the
TT parameter is issued while the
transaction executive is running and
an attempt is made to change the Q
attribute of a task on a library in
use by TAF, then the Q attribute
change will not affect TAF schedul
ing until the executive is
reinitialized.
This parameter is not applicable to
CM-resident tasks.
QL-n Specifies the number of requests, up
to a maximum of five, that can be
queued for an RTL entry for a task.
If a task uses a large amount of
m e m o r y and e x ecu t e s ra p id l y, pe r
formance is not degraded if requests
are queued. In this case, multiple
copies of the task require too much
memory. If a task does a large
amount of I/O, then performance is
degraded if requests are queued. In
this case, multiple copies of the
task enhance performance.
QL Queue entry limit defaults to five.
QL omitted Queue entry limit defaults to three.
R Specifies that the FL assigned to a
CM-resident task is to be reduced to
the Initial load value each time the
transaction is run. The default is
no reduce. Non-CM-resident tasks
are always started with their
initial load value.
2. While t here are fr om one to s ix
active copies of the task in
TAF, another copy of the task is
not scheduled until the number
of transactions queued against
its RTL entries equals or
exceeds the queue limit
specified by the QL directive.
When a n RTL entry is used to
schedule a task, it is released
and made available for
requesting the scheduling of
other tasks.
3. When the number of active copies
of the task equals seven,
additional copies of the task
will not be scheduled. This
applies ev en if the q ue ue lim it
is 1 .
SC Sets the task communication block
load status to solicited. This
means you must request the
communication block and supply a
valid address (using the BEGIN
request) after the task is initi
ated. The default is unsolicited.
All directives for one task must appear on the same
line. The following situation will result in only
Pj being recognized as an input directive for
TASKI.
*TASK1 pj.
*TASK1 p2.
*TASK1 pn,
Improper way to specify
input directives.
/<3SS|y
10-6 60459500 B
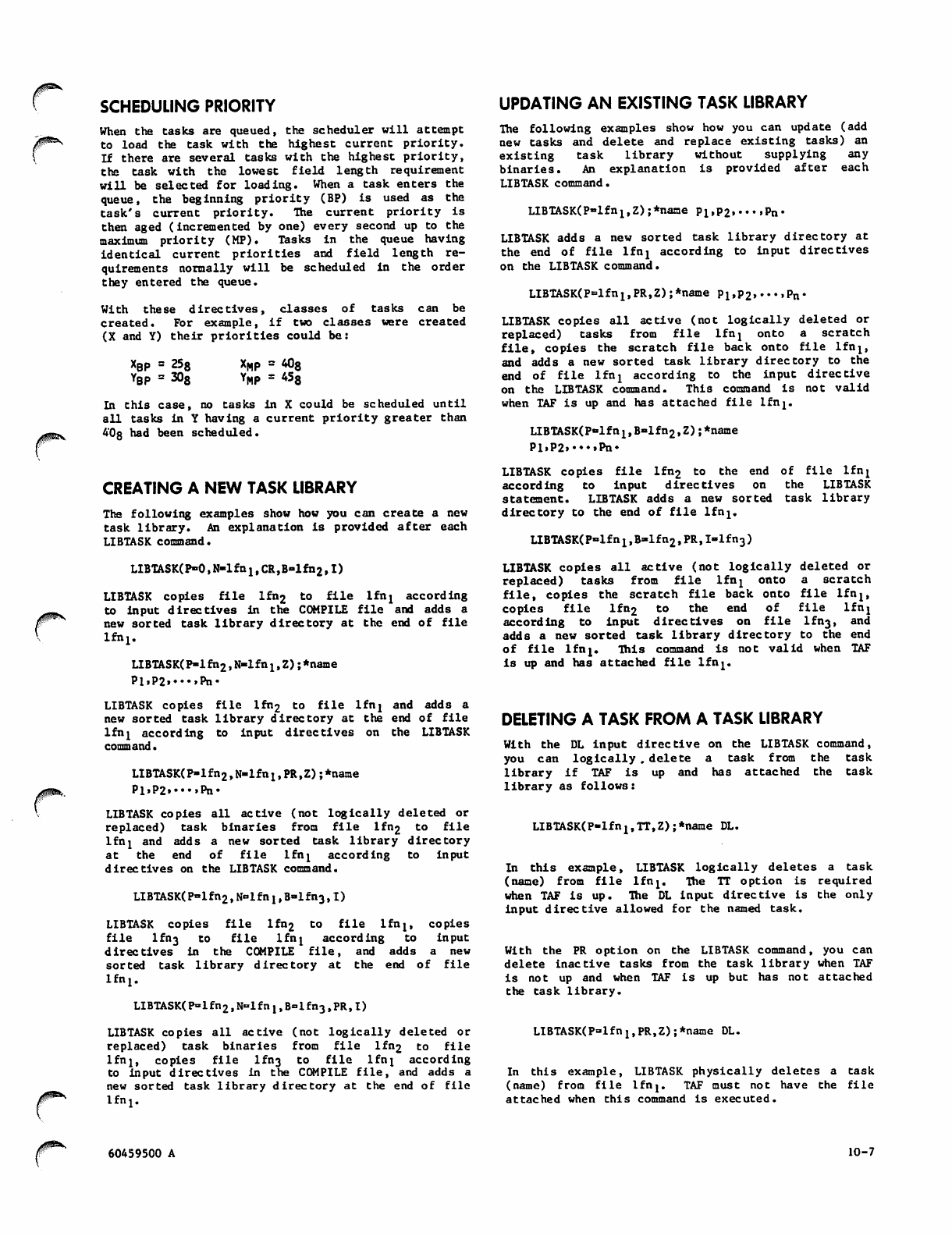
00$^**,
SCHEDULING PRIORITY
When the tasks are queued, the scheduler will attempt
to load the tas k w it h t h e h ig h es t c urr ent prio ri ty.
If there are several tasks with the highest priority,
the task with the lowest field length requirement
will be selected for loading. When a task enters the
queue, the beginning priority (BP) is used as the
task's current priority. The current priority is
then aged (incremented by one) every second up to the
maximu m pr iority (MP). Tasks in t he q ueue having
identical current priorities and field length re
quirements normally will be scheduled in the order
they entered the queue.
With these directives, classes of tasks can be
created. For example, if two classes were created
(X and Y) their priorities could be:
XBP = 25g
YBP = 308
XMP = 408
YMP = *58
In this case, no tasks in X could be scheduled until
all tasks in Y having a current priority greater than
40s had been scheduled.
CREATING A NEW TASK LIBRARY
The following examples show how you can create a new
task library. An explanation is provided after each
LIBTASK command.
LIBTASK(P»0,N-lfn !,CR,B-lfn2,1)
LIBTASK copies file lfn2 to file lfnj according
to input directives in the COMPILE file and adds a
new sorted task library directory at the end of file
lfnj.
LIBTASK(P-lfn2,N-lfh1,Z);*name
PliP2»»*»»Pn«
L I B TA S K c o p i e s fi l e l f n 2 t o fi l e l f n j a n d a d d s a
new sorted task library directory at the end of file
lfni according to input directives on the LIBTASK
command.
LIBTASK( P-lfn2,N-lfnj,PR,Z);*name
PlfP2»*'*»Pn«
LIBTASK copies all active (not logically deleted or
replaced) task binaries from file lfn2 to file
lfn} and adds a new sorted task library directory
at the end of file lfnj according to input
directives on the LIBTASK command.
LIBTASK(P=lfn2,N=lfn1,B-lfn3,I)
LIBTASK copies file lfn2 to file lfnj, copies
file lfn3 to file lfnj according to input
directives in the COMPILE file, and adds a new
sorted task library directory at the end of file
lfnj.
LIBTASK(P=lfn2,N=lfni,B=lfn3,PR,I)
LIBTASK copies all active (not logically deleted or
replaced) task binaries from file lfn2 to file
lfnj, copies file lfn3 to file lfnj according
to input directives in the COMPILE file, and adds a
new sorted task library directory at the end of file
lfn^
60459500 A
UPDATING AN EXISTING TASK LIBRARY
The following examples show how you can update (add
new tasks and delete and replace existing tasks) an
existing task library without supplying any
binaries. An explanation is provided after each
LIBTASK command.
LIBTASK(P-lfn1,Z);*name Pi,p2 Pn •
LIBTASK adds a new sorted task library directory at
the end of file lfn! according to input directives
on the LIBTASK command.
LIBTASK(P=lfn1,PR,Z);*name Pi,p2»•••»Pn«
LIBTASK copies all active (not logically deleted or
replaced) tasks from file lfnj onto a scratch
file, copies the scratch file back onto file lfnj,
and adds a new sorted task library directory to the
end of file lfn! according to the input directive
on the LIBTASK command. This command is not valid
when TAF is up and has attached file lfn!.
LIBTASK(P«lfni,B-lfn2,Z);*name
Pl»P2»'»»»Pn»
L I B TA S K c o p i e s fi l e l f n 2 t o t h e e n d o f fi l e l f n t
according to input directives on the LIBTASK
statement. LIBTASK adds a new sorted task library
di r e cto r y to t h e e n d of fi l e lf n!.
LIBTASK(P«lfn!,B»lfn2,PR,I-lfn3)
LIBTASK copies all active (not logically deleted or
replaced) tasks from file lfn! onto a scratch
file, copies the scratch file back onto file lfn!,
copies file lfn2 to the end of file lfnj
according to input directives on file lfn3, and
adds a new sorted task library directory to the end
of file lfn!. Tnis command is not valid when TAF
is up and has attached file lfn!.
DELETING A TASK FROM A TASK LIBRARY
With the DL input directive on the LIBTASK command,
you can logically . delete a task from the task
l i b r a r y i f TA F i s u p a n d h a s a t t a c h e d t h e t a s k
library as follows:
LIBTASK(P-lfn!,TT,Z);*name DL.
In this example, LIBTASK logically deletes a task
( n a m e ) f r o m f i l e l f n ! . T n e * T ° P t i o n i s r e q u i r e d
when TAF is up. The DL input directive is the only
input directive allowed for the named task.
With the PR option on the LIBTASK command, you can
delete inactive tasks from the task library when TAF
is not up and when TAF is up but has not attached
the task library.
LIBTASK(P=lfn!,PR,Z);*name DL.
In this example, LIBTASK physically deletes a task
(name) from file Ifn^ TAF must not have the file
attached when this command is executed.
10-7

IGNORING A TASK IN THE REPLACEMENT FILE In this example, LIBTASK skips a binary task (name) ^
on file lfn2 when copying file lfn2 to file I
With the IG input directive on the LIBTASK command, lfn!. The IG input directive is the only input
the user can tell LIBTASK to ignore a task binary in directive allowed for the named task.
the replacement file specified with the B option as -*=^s
follows: )
LIBTASK(P-lfn1,B=lfn2,Z);*name IG.
10"8 60459500 A

0^**- REQUIRED SYSTEM TASKS AND TRANSACTIONS 11
The applications programmer should be aware of the
functions of these tasks but may omit the detailed
information contained in this and section 12.
ITASK recognizes the transaction code EX., which is
used to call the system transaction XTRAN. This
special transaction code is reserved for XTRAN.
Several system tasks are required with every
application: BTRAN recovery task (BTASK), data base
recovery task (CTASK), initial task (ITASK),
K display director (KDIS), logout transaction
terminal (LOGT), message abort (MSABT), inactive
task (OFFTASK), CDCS rerun task (RCTASK), run unit
recovery task (RTASK), system message (SYSMSG), and
execute named tasks (XTASK). Each must reside on
the system task library of every transaction
system. Limited versions of these system tasks are
supplied by Control Data; however, modifications to
t h e s e t a s k s a r e o f t e n n e c e s s a r y f o r s p e c i fi c
applications. One additional system task, CRMTASK,
is required if the TAF/CRM Data Manager is used.
Refer to the TAF/CRM Data Manager 1 Reference Manual
for information on CRMTASK.
Directions for installing these tasks are contained
in the TAF Installation section of the NOS 2 Instal
lation Handbook.
BTRAN RECOVERY TASK (BTASK)
BTASK recovers rerunnable BTRAN run units. BTASK
must be installed on the TAF system library.
DATA BASE RECOVERY TASK (CTASK)
CTASK helps TAF/CRM recover the data base during TAF
initialization, terminal failure, and NETWORK
failure. CTASK must be installed on the TAF system
library.
INITIAL TASK (ITASK)
The primary functions of ITASK are analyzing
terminal input and TAF-originated transactions. If
the TAF-originated transaction field is set in the
communication block (figure 2-1), TTASK uses a table
to initiate the processing routine associated with
that type of transaction. Otherwise, TTASK examines
three characters, starting with the first character
of the input message. The first of these three
characters is the transaction code; the other two
comprise the sub transaction code entered from a
terminal.
("NOTE"!
Because TTASK schedules tasks, care
must be taken to avoid entering an
infinite loop when a task calls TTASK.
TTASK is described in more detail in section 12.
K DISPLAY TASK (KDIS)
KDIS is a system task scheduled by the transaction
executive when the K.SWITCH command is entered by
the console operator. KDIS requests the K display
and displays a complete list of K display commands.
The K display commands are discussed in the NOS 2 I
Analysis Handbook. |
LOGOUT TASK (LOGT)
This task logs a terminal out of TAF. However, the
task does not log the terminal off the computer
system. The task sends a message, END OF
TRANSACTION SESSION; performs a LOGT request; and
performs a CEASE request. The terminal is then
available for login to TAF or other network
applications.
MESSAGE ABORT (MSABT)
Message abort (MSABT) is a system task that sends
error messages to the originating terminal when a
transaction is terminated due to a system-detected
error. MSABT checks for error codes that were
placed in the communication block by the transaction
executive or the initial task. When an error code
is detected, MSABT sends the appropriate error
message and initiates an abnormal CEASE function.
MSABT is scheduled in the same manner as other tasks.
If the TOTAL Data Manager is used, MSABT must be
modified to perform a FREEX command. This ensures
that TOTAL records are released if a task aborts.
Error messages issued by MSABT are described in
appendix B.
00*. 60459500 C 11-1

INACTIVE TASK (OFFTASK)
This task is provided to give you control over an
i n t e r n a l c o n d i t i o n t h a t m i g h t b e t h e r e s u l t o f
o p e r a t i o n a l e r r o r. O F F TA S K i s s c h e d u l e d b y t h e
transaction executive when a request has been
received for an inactive task. The task may be
inactive or off due to the use of the K.OFFTASK
command or use of a LIBTASK directive when the task
was placed in the library. OFFTASK sends an error
message to the originating terminal and ceases
abnormally. It is expected that you will expand the
t a s k t o h a n d l e a n y s p e c i fi c c o n d i t i o n s t h a t m a y
exist when a transaction is interrupted by an
inactive task.
SEND MESSAGE TASK (STASK)
This task sends a message to the terminal and then
terminates. STASK is called from ITASK only when
ITASK is to terminate after sending a message to the
terminal.
SYSTEM MESSAGE TASK (SYSMSG)
This task sends K.MESSAGE-entered messages and
K display diagnostic messages to terminals. It
calls the subroutine in COMKCBT passing the user
argument bits. The word re turn ed is sent after the
message is sent.
/£ 5 S| v
CDCS RERUN TASK (RCTASK)
When CDCS becomes available after a failure, RCTASK
is activated. RCTASK determines which terminals
were effected by the CDCS failure and reruns their
transactions (if rerunnable).
RUN UNIT RECOVERY TASK (RTASK)
The recovery task RTASK is a Control Data-supplied
recovery task that will handle most transaction
application needs; however, some sites may wish to
modify RTASK to handle special requirements. The
following discussion will aid understanding of RTASK
in case a modification is required. RTASK must be
available to all applications. This implies that it
must be present on the TAF system task library
(TASKLIB) or en all of the data base task libraries.
It may be on the TASKLIB and any number of selected
data base task libraries. In this case, only those
applications without their own copy of RTASK will
use the version on TASKLIB.
After terminal disconnects, or NAM, TAF, and system
failures, the terminal must go through the login
pro c e d u r e s w it h TAF. T h e foll o w i n g s t e ps o u t l i n e
the decision process followed by RTASK. When a true
condition is encountered, the remaining steps are
skipped.
1. If the run unit Is not recoverable because
RC was not specified on the LIBTASK directive
for the named-transaction, RTASK sends the
message READY to the terminal.
2. If the run unit is not rerunnable because of
an I/O error encountered by TAFREC, RTASK
tells the terminal operator recovery has
occurred and to enter the next command.
3. If the run unit Is secure and the data base
i s c o m m i t t e d , RTA S K s e n d s t h e t e r m i n a l
confirmation (SECURE) message.
4. RTASK tells the terminal operator that
recovery has occurred, that the transaction
is being rerun, and reruns the transaction.
EXECUTE NAMED TASK (XTASK)
The execute named task (XTASK) is a special task
scheduler used to execute most named tasks. It will
not execute tasks by the names ITASK, KDIS, MSABT,
OFFTASK, SYSMSG, and XTASK. These are the names of
required system tasks. XTASK can be used to
schedule LOGT as a means of logging a terminal out
of transaction mode. XTASK is initiated via system
transaction XTRAN, described following the XTASK
description.
EX.task
EX.
task
Special three-character transaction
code which causes ITASK to schedule
XTRAN via a CALLTRN request. XTRAN
specifies XTASK as its only task.
One- to seven-character alphanumeric
t a s k n a m e , l e f t - j u s t i fi e d ( n o s p a c e
between EX. and task) with a
nonalphanumeric character terminator.
A site may want to delete the TRANS table entry of
STRAN (X.), XTASK in the TRANT table of ITASK, or
the system task XTASK altogether for security
reasons. XTASK was provided as a means of
scheduling tasks, and as an example of how a site
might use such a task. However, it may provide too
much flexibility, and therefore should be used with
discretion.
XTRAN TRANSACTION
Transaction XTRAN must be defined when the system
task library is created. XTRAN will be scheduled
when the three-character code EX. is entered from a
terminal. This transaction allows scheduling any
task in the local or system task library as
described under XTASK.
The characteristics of XTRAN are:
• Task name is XTASK.
• No data managers.
• N o t r e c o v e r a b l e .
sf^^X
11-2 60459500 C
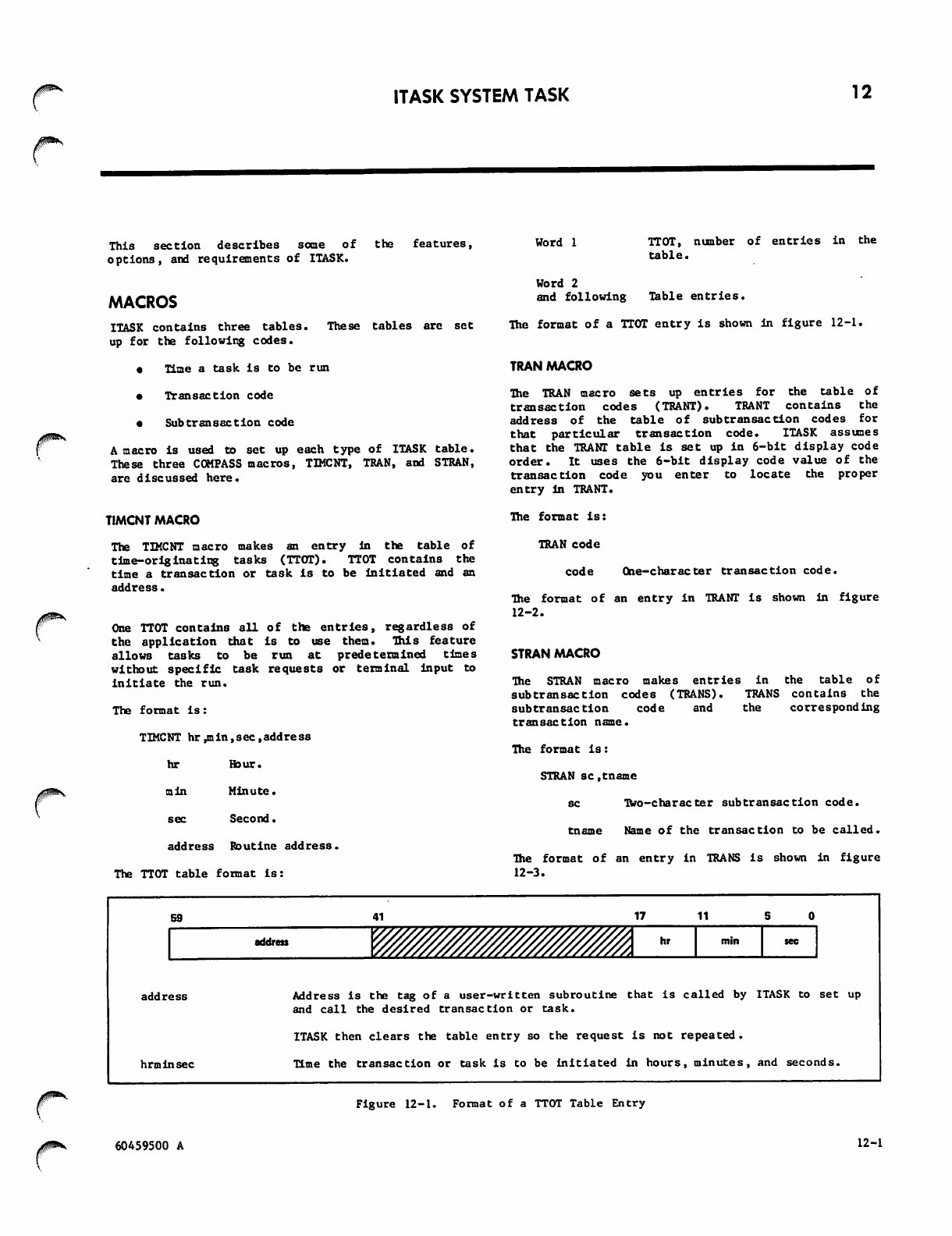
ITASK SYSTEM TASK 12
r
/0^*-
This section describes some of the features,
options, and requirements of ITASK.
MACROS
ITASK contains three tables. These tables are set
up for the following codes.
• Time a task is to be run
• Tr a n s a cti o n co d e
• Sub transaction code
A macro is used to set up each type of ITASK table.
These three COMPASS macros, TIMCNT, TRAN, and STRAN,
are discussed here.
TIMCNT MACRO
The TIMCNT macro makes an entry in the table of
time-originating tasks (TTOT). TTOT contains the
time a transaction or task is to be initiated and an
address.
One TTOT contains all of the entries, regardless of
the a p p l i c a ti o n t h a t is to u s e th e m . Th i s feature
allows tasks to be run at predetermined times
without specific task requests or terminal Input to
initiate the r u n .
The format is:
TIMCNT hr,min,sec,address
h r H o u r .
min Minute.
sec Second.
address Routine address.
The TTOT table format is:
Word 1 TTOT, number o f entries i n the
table.
Word 2
and following Ta ble en t rie s .
The format of a TTOT entry is shown in figure 12-1.
TRAN MACRO
Th e T R A N m a c r o s e t s u p en t r i es f o r t h e t a b l e o f
t r a n s a c t i o n c o d e s ( T R A N T ) . T R A N T c o n t a i n s t h e
address of the table of subtransaction codes for
that particular transaction code. ITASK assumes
that the TRANT table is set up in 6-bit display code
order. It uses the 6-bit display code value of the
transaction code you enter to locate the proper
entry in TRANT.
The format is:
TRAN code
co d e On e -ch a r a cte r tr a n sac t i o n c o d e.
The format of an entry in TRANT is shown in figure
12-2.
STRAN MACRO
T h e ST R A N m a c r o m a ke s en t r i e s i n t h e t a b l e o f
subtransaction codes (TRANS). TRANS contains the
subtransaction code and the corresponding
transaction name.
The format is:
STRAN sc,tname
sc Two-character subtransaction code.
tname Name of the transaction to be called.
The format of an entry in TRANS is shown in figure
12-3.
59 4 1 1 7 1 1 S 0
address 'wmmmmmm hr min sec
addr
hrmii
ess
tisec
Address is the tag of a user-written subroutine that is called by I
and call the desired transaction or task.
ITASK then clears the table entry so the request is not repeated.
Time the transaction or task Is to be initiated in hours, minutes, s
TASK to
nd secoi
set up
ids.
0^^ Figure 12-1. Format of a TTOT Table Entry
60459500 A 12-1
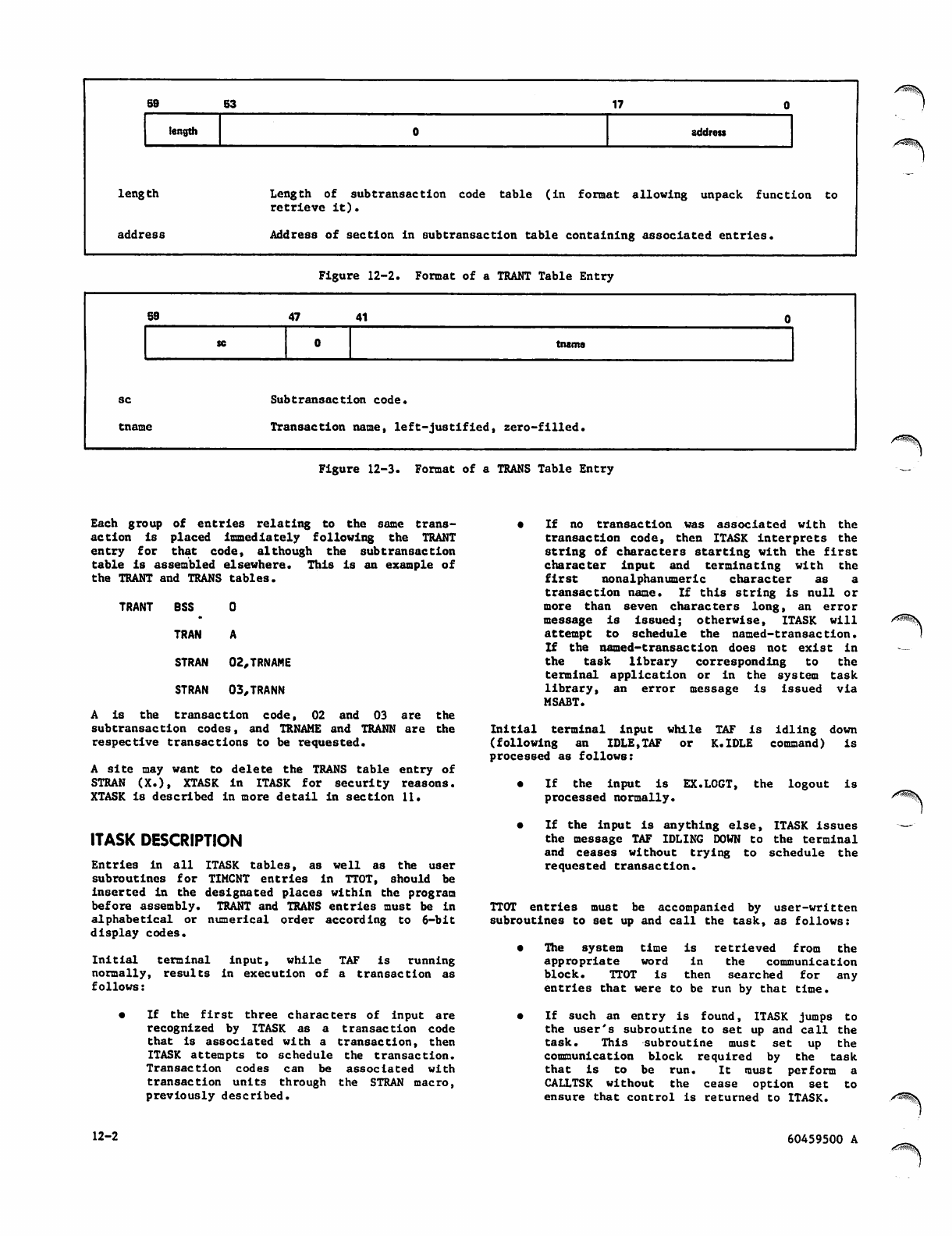
59 53 1 7 0
to
length address
length
address
Length of subtransaction code table (in format allowing unpack function
retrieve it).
Address of section in subtransaction table containing associated entries.
Figure 12-2. Format of a TRANT Table Entry
59 4 7 4 1
sc tname
sc
tname
Subtransaction code.
Transaction name, left-justified, zero-filled.
Figure 12-3. Format of a TRANS Table Entry
Each group of entries relating to the same trans
action is placed immediately following the TRANT
e n t r y f o r t h a t c o d e , a l t h o u g h t h e s u b t r a n s a c t i o n
table is assembled elsewhere. This is an example of
the TRANT and TRANS tables.
TRANT BSS
TRAN
STRAN 02,TRNAME
STRAN 03,TRANN
A is the transaction code, 02 and 03 are the
subtransaction codes, and TRNAME and TRANN are the
respective transactions to be requested.
A site may want to delete the TRANS table entry of
STRAN (X.), XTASK In ITASK for security reasons.
XTASK is described in more detail in section 11.
ITASK DESCRIPTION
E n t r i es i n a l l I TA SK t a b l e s , a s we l l a s t h e u s e r
subroutines for TIMCNT entries in TTOT, should be
inserted in the designated places within the program
before assembly. TRANT and TRANS entries must be in
alphabetical or numerical order according to 6-bit
display codes.
Initial terminal input, while TAF is running
normally, results in execution of a transaction as
follows:
• I f t h e f i r s t t h r e e c h a r a c t e r s o f i n p u t a r e
recognized by ITASK as a transaction code
that is associated with a transaction, then
ITASK attempts to schedule the transaction.
Transaction codes can be associated with
transaction units through the STRAN macro,
previously described.
• If no transaction was associated with the
transaction code, then ITASK interprets the
string of characters starting with the first
c h a r a c t e r i n p u t a n d t e r m i n a t i n g w i t h t h e
first nonalphanumeric character as a
transaction name. If this string is null or
more than seven characters long, an error
message is issued; otherwise, ITASK will
attempt to schedule the named-transaction.
If the named-transaction does not exist in
the task library corresponding to the
terminal application or in the system task
l i b r a r y , a n e r r o r m e s s a g e i s i s s u e d v i a
MSABT.
Initial terminal input while TAF is idling down
(following an IDLE,TAF or K.IDLE command) is
processed as follows:
• If the input is EX.LOGT, the logout is
processed normally.
• If the input is anything else, ITASK issues
the message TAF IDLING DOWN to the terminal
and ceases without trying to schedule the
requested transaction.
TTOT entries must be accompa nied by user-written
subroutines to set up and call the task, as follows:
• The system time is retrieved from the
a p p r o p r i a t e w o r d i n t h e c o m m u n i c a t i o n
b l o c k . T T O T i s t h e n s e a r c h e d f o r a n y
entries that were to be run by that time.
• If such an entry is found, ITASK jumps to
the user's subroutine to set up and call the
task. This subroutine must set up the
communication block required by the task
t h a t i s t o b e r u n . I t m u s t p e r f o r m a
C A L LT S K w i t h o u t t h e c e a s e op t i o n s e t to
ensure that control is returned to ITASK.
12-2 60459500 A
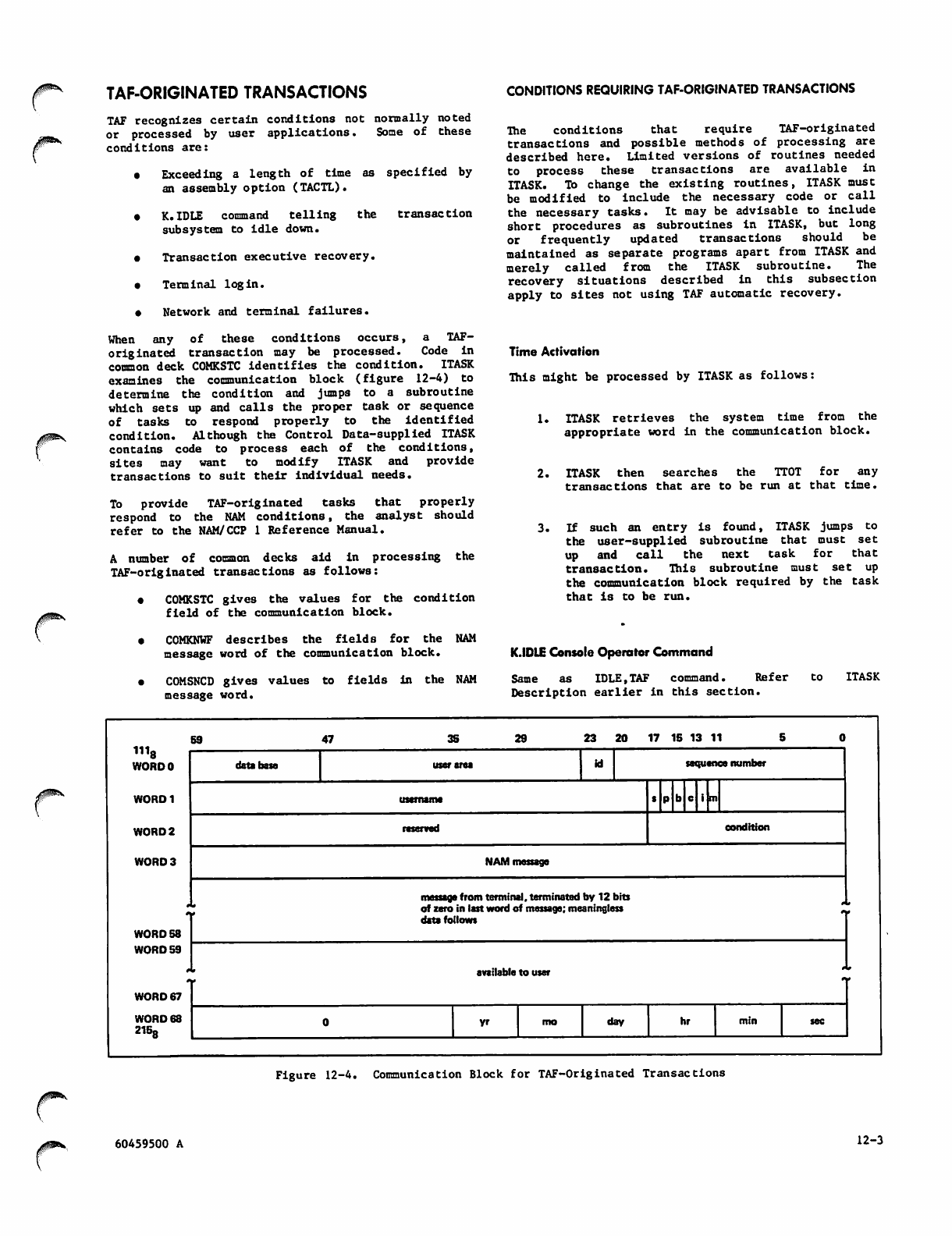
TAF-ORIGINATED TRANSACTIONS CONDITIONS REQUIRING TAF-ORIGINATED TRANSACTIONS
/0^**
^^v
TAF recognizes certain conditions not normally noted
or processed by user applications. Some of these
conditions are:
• Exceeding a length of time as specified by
an assembly option (TACTL).
• K.IDLE command telling
subsystem to idle down.
the transaction
• Transaction executive recovery.
• Terminal login.
• Network and terminal failures.
When any of these conditions occurs, a TAF-
originated transaction may be processed. Code in
common deck COMKSTC identifies the condition. ITASK
examines the communication block (figure 12-4) to
determine the condition and jumps to a subroutine
which sets up and calls the proper task or sequence
of tasks to respond properly to the identified
condition. Although the Control Data-supplied ITASK
contains code to process each of the conditions,
sites may want to modify ITASK and provide
transactions to suit their individual needs.
To provide TAF-originated tasks that properly
respond to the NAM conditions, the analyst should
refer to the NAM/CCP 1 Reference Manual.
A number of commo n decks ai d in proc essin g th e
TAF-originated transactions as follows:
• COMKSTC gives the values for the condition
field of the communication block.
• COMKNWF describes the fields for the NAM
message word of the communication block.
• COMSNCD gives values to fields In the NAM
message word.
The conditions that require TAF-originated
transactions and possible methods of processing are
described here. Limited versions of routines needed
to process these transactions are available in
TTASK. To change the existing routines, ITASK must
be modified to include the necessary code or call
the necessary tasks. It may be advisable to include
short procedures as subroutines in ITASK, but long
or frequently updated transactions should be
maintained as separate programs apart from ITASK and
merely called from the ITASK subroutine. The
r e c o v e r y s i t u a t i o n s d e s c r i b e d i n t h i s s u b s e c t i o n
apply to sites not using TAF automatic recovery.
Time Activation
This might be processed by ITASK as follows:
1 . I TA S K r e t r i e v e s t h e s y s t e m t i m e f r o m t h e
appropriate word in the communication block.
2. TTASK then searches the TTOT for any
transactions that are to be run at that time.
3. If su c h an en t ry I s f o u nd, I TASK ju m p s t o
the user-supplied subroutine that must set
up and call the next task for that
transaction. This subroutine must set up
the communication block required by the task
that is to be run.
K.IDLE Console Operator Command
Same as IDLE,TAF command. Refer to ITASK
De s cr i pti on ear l ier in t h is se cti on.
1118
WORDO
WORD1
WORD 2
WORD 3
WORD 58
WORD 59
WORD 67
WORD 68
2158
59 47 3 5 2 9 2 3 2 0 1 7 1 5 1 3 1 1 5 0
database user area id sequence number
user name i nft
reserved condition
NAM message
»message from terminal, terminated by 12 bits
of zero in last word of message; meaningless
data follows
t
i
available to user
0yr mo day hr min sec
Figure 12-4. Communication Block for TAF-Originated Transactions
60459500 A 12-3
Terminal Login Terminal Connection Broken
The application may want to prompt the terminal
user, set application character type, or go through
recovery procedures if the user has the recovery
field set in the user area of the terminal status
table. Upon terminal login, the NAM message word of
the communication block (figure 12-4) contains the
following information:
Significance
24
Block size of terminal.
Signifies a hardwired terminal if
s e t .
A connection may be broken because a line has been
disconnected. If a SEND with recall was active, the
task issuing the SEND rather than ITASK is notified
of the error. It may be desirable for the applica
tion to process these incomplete transactions. TAF
sets the recovery field in the terminal status table
user area. The application can save terminal output
on a data manager file and send it when the user
logs in again. The outstanding block limit speci
fied in the local configuration file determines how
many messages must be saved. (Refer to the Network
Products NAM 1 Network Definition Language Reference
Manual.)
/>^«i\
23-16 Terminal class.
15-8 Page width of terminal.
7-0 Page length of terminal.
Terminal Break Conditions
If some tasks perform SENDs without the recall flag
set, breaks can occur because of the following.
• User break keys.
• Output device not ready.
• Incorrectly formatted data.
For a user to resume processing after a terminal
break, the following must occur.
1. Terminal communication with NAM must be
reestablished. When the break occurs, NAM
places the supervisory message associated
with the break in the NAM message word of
the communication block. To restart
terminal communications, TAF must send a
reset supervisory message to NAM. The
individual application need not provide this
function. Upon the user task SEND request,
TAF issues the reset supervisory message
prior to honoring the SEND.
Network Normal Shutdown
TAF monitors task activity on communication blocks
gen e r a ted b y t e r m inal in p u t . W h e n a l l ta s k s h a v e
been completed and no tasks are performing WAITINP
requests, TAF sends end connection supervisory
messages to NAM for each logged-in user and performs
a NETOFF to end processing with the network. To
i n i t i a t e t h i s c o n d i t i o n , i t m a y b e d e s i r a b l e f o r
ITASK to notify users of the pending shutdown and
begin rejecting new transactions.
Network Failure
TAF sets the recovery field in the user area of the
terminal status table for all logged-in users. All
tasks performing WAITINP requests are scheduled.
The application, through ITASK, may want to begin
data base recovery.
Network Immediate Shutdown
TAF performs a NETOFF and sets the recovery field in
the user area of the terminal status table. The
application may want to begin recovery by processing
only transactions from batch input.
2. The user must resume interaction with the
application. The user application must
provide this break recovery. The following
description suggests one method.
ITASK and any recovery tasks can communicate
t h r o u g h t h e t e r m i n a l s t a t u s t a b l e u s e r
area. For instan ce, when ITASK initiates a
transaction, it could set a series of fields
in the TST to indicate important events in
the transaction. The recovery task could
examine the fields to determine what events
had occurred. Nonrecovery tasks could watch
a recovery field in the TST and CEASE to
allow the recovery task to proceed ir a
quiet environment. (TAF sets the recovery
field in the TST before calling ITASK.)
Terminal Inactive
NAM issues a terminal inactive supervisory message
when it detects that 10 minutes have elapsed without
message traffic over a connection. TAF passes the
tr ans a ct i on seq u en c e n umb e r o f a ny r un n ing , t a sk
using that user name to ITASK. The application may
want to log out the user after a period of time to
reduce line connect costs.
Logical Error
One of the application's tasks may have set up an
application block header or message block
incorrectly. If the task performed a SEND request
w i t h r e c a l l s e t , t h e t a s k , r a t h e r t h a n I TA S K , i s
no t i fied of th e e r ror.
12-4 60459500 A
J^*v
jfl^lfes^
Block Not Delivered
This occurs because of a system error. If the task
performed a SEND request with recall set, the task,
rather t ha n ITAS K, is notified o f the e rr or. B ef or e
scheduling ITASK, TAF sets the recovery field in the
user area of the TST. It may be desirable for the
application to recover by sending the lost block.
The application block number of the block that was
lost is returned in the NAM message word of the
communication block. Tasks may specify a block
number on the SEND or obtain the block number used
by TAF. Resending the lost block may cause the
block to be delivered out of sequence, if further
blocks had been sent following the lost block.
Terminal Characteristic Change
A NAM terminal characteristic supervisory message is
sent to ITASK when the terminal operator has
redefined the terminal class, page width, or page
length.
Terminal Input Too Large
The terminal operator sent a message longer than the
maximum input message size. TAF will not have
journalized the input.
TERMINAL TYPE AHEAD
The network allows terminal operator type-ahead. In
other words, the terminal operator can enter several
transactions without waiting for the response from
the first. The network ignores all type-ahead when
the terminal operator enters a user break 1 or user
break 2.
USER STATUS
The network allows a terminal user to make a status
request by typing:
ct (alpha)®
ct The network control character.
(alpha) Any alphabetic character.
TAF will right justify the character In word 3 of
the communication block and Initiate ITASK. At this
point a user-written routine In ITASK must take over
to perform whatever action is desired. The ITASK
reason code will Indicate a user status message.
J^*
60459500 C 12-5

0^,
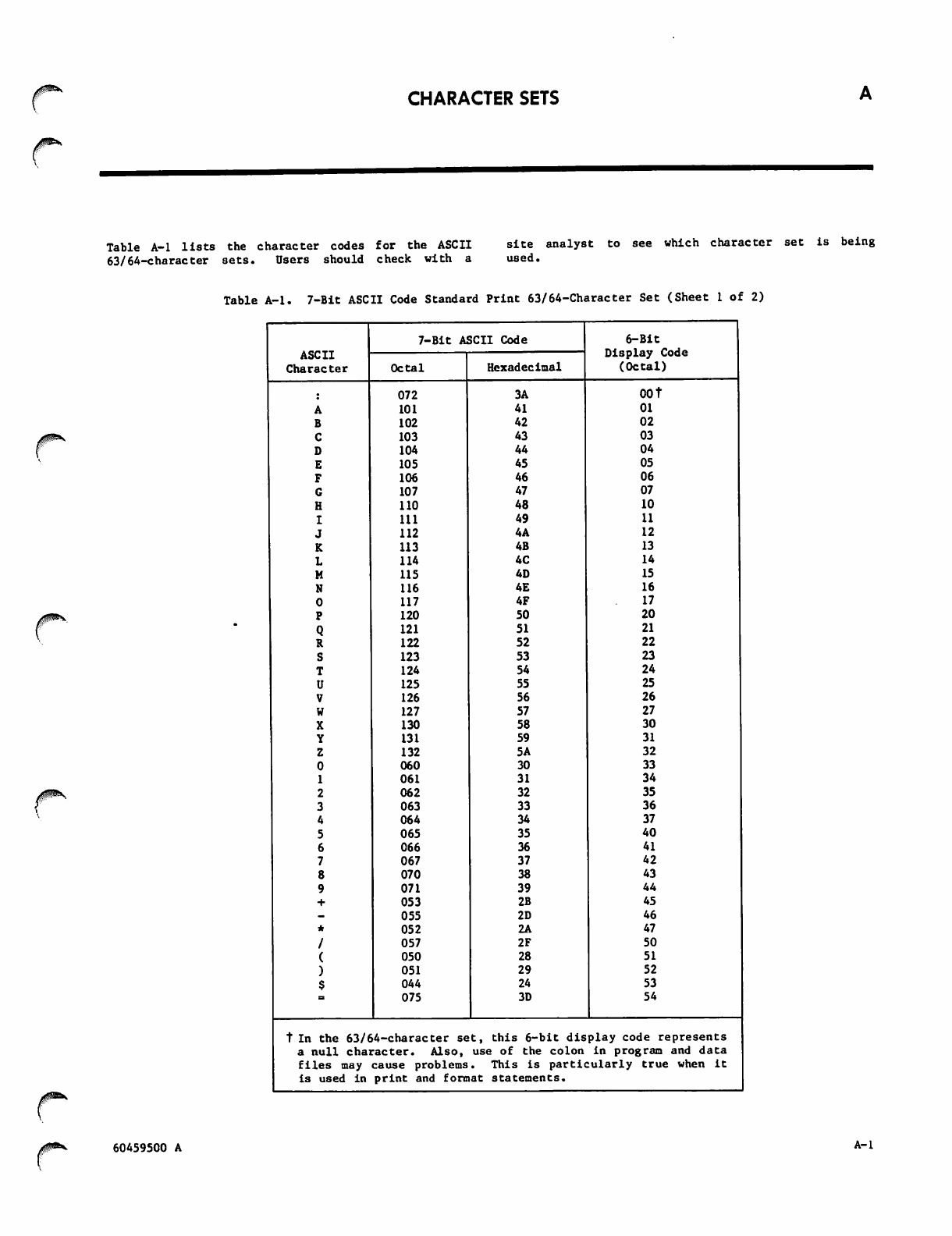
0^^ CHARACTER SETS
Ta b l e A - l li st s the c h a r a c t e r co d e s f o r the A S C I I
63/64-character sets. Users should check with a
s i t e a n a l y s t t o s e e w h i c h c h a r a c t e r s e t i s b e i n g
used.
Table A-l. 7-Bit ASCII Code Standard Print 63/64-Character Set (Sheet 1 of 2)
ASCII
Character
0mK
7-Bit ASCII Code
Octal
072
101
102
103
104
105
106
107
110
Ul
112
113
114
115
116
117
120
121
122
123
124
125
126
127
130
131
132
060
061
062
063
064
065
066
067
070
071
053
055
052
057
050
051
044
075
Hexadecimal
3A
41
42
43
44
45
46
47
48
49
4A
4B
4C
4D
4E
4F
50
51
52
53
54
55
56
57
58
59
5A
30
31
32
33
34
35
36
37
38
39
2B
2D
2A
2F
28
29
24
3D
6-Bit
Display Code
(Octal)
001
01
02
03
04
05
06
07
10
11
12
13
14
15
16
17
20
21
22
23
24
25
26
27
30
31
32
33
34
35
36
37
40
41
42
43
44
45
46
47
50
51
52
53
54
t In the 63/64-character set, this 6-bit display code represents
a null character. Also, use of the colon in program and data
files may cause problems. This is particularly true when it
is used in print and format statements.
60459500 A A-l
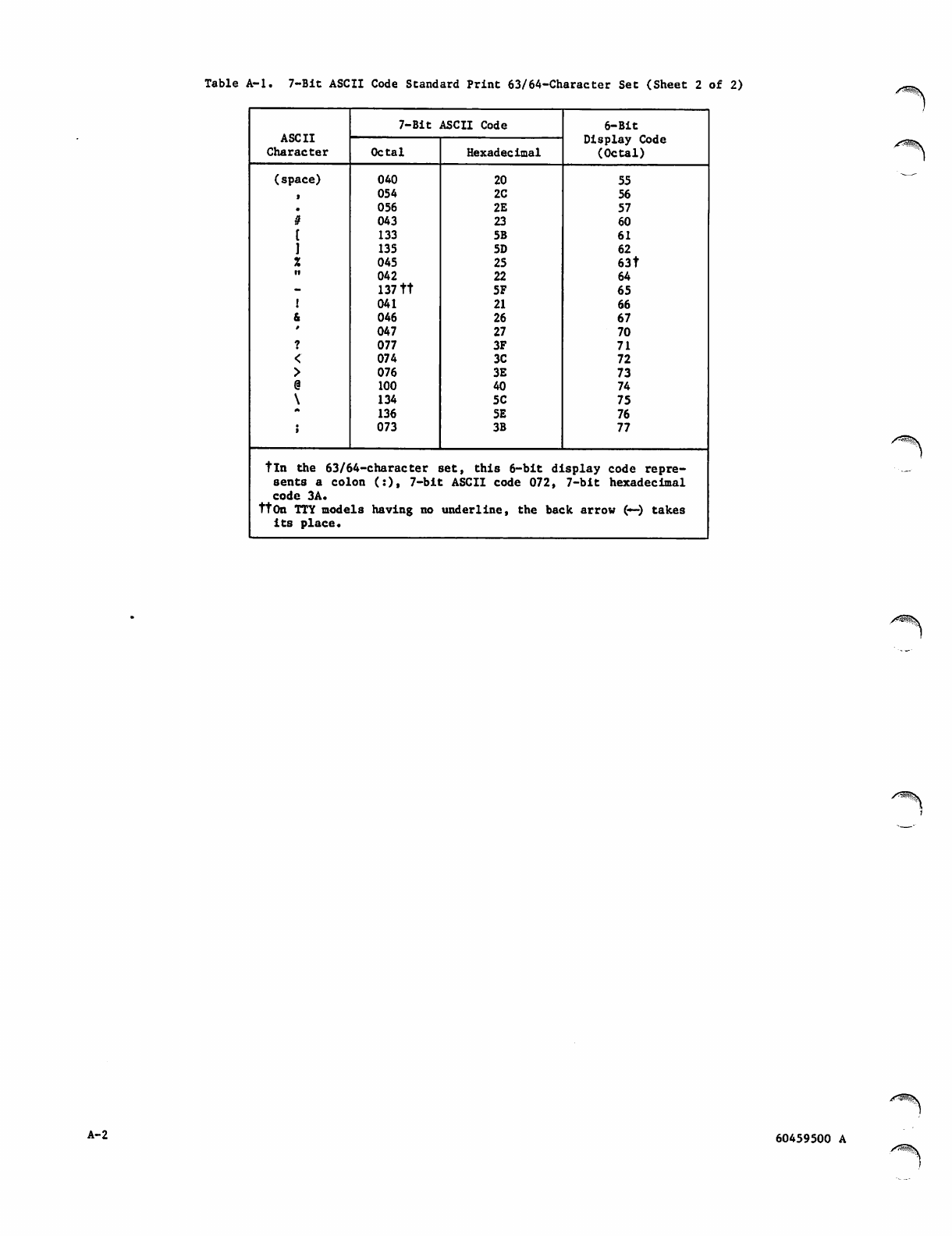
Table A-l. 7-Bit ASCII Code Standard Print 63/64-Character Set (Sheet 2 of 2)
ASCII
Character
7-Bit ASCII Code 6-Bit
Display Code
(Octal)
Octal Hexadecimal
(space)
>
i
l
]
X
ii
!
&
1
<
>
@
\
*
040
054
056
043
133
135
045
042
137 tt
041
046
047
077
074
076
100
134
136
073
20
2C
2E
23
5B
5D
25
22
5F
21
26
27
3F
3C
3E
40
5C
5E
3B
55
56
57
60
61
62
63t
64
65
66
67
70
71
72
73
74
75
76
77
tin the 63/64-character set, this 6-bit display code repre
sents a colon (:), 7-bit ASCII code 072, 7-bit hexadecimal
code 3A.
ttOn TTY models having no underline, the back arrow (—) takes
its place.
/<^V
/<^^\
A-2 60459500 A

DIAGNOSTIC MESSAGES B
This appendix contains an alphabetical listing of Lowercase letters are used within a message to
messages which may be important to the TAF identify variable fields. All messages beginning
programmer. Each message is followed by an with lowercase (variable) fields are listed
explanation of the message and/or the circumstances alphabetically according to the first nonvariable
causing it to be issued, the recommended action, and field after the messages that begin with nonvariable
the routine which issued the message. fields.
jpx
/ $ ^ K
60459500 A B_l
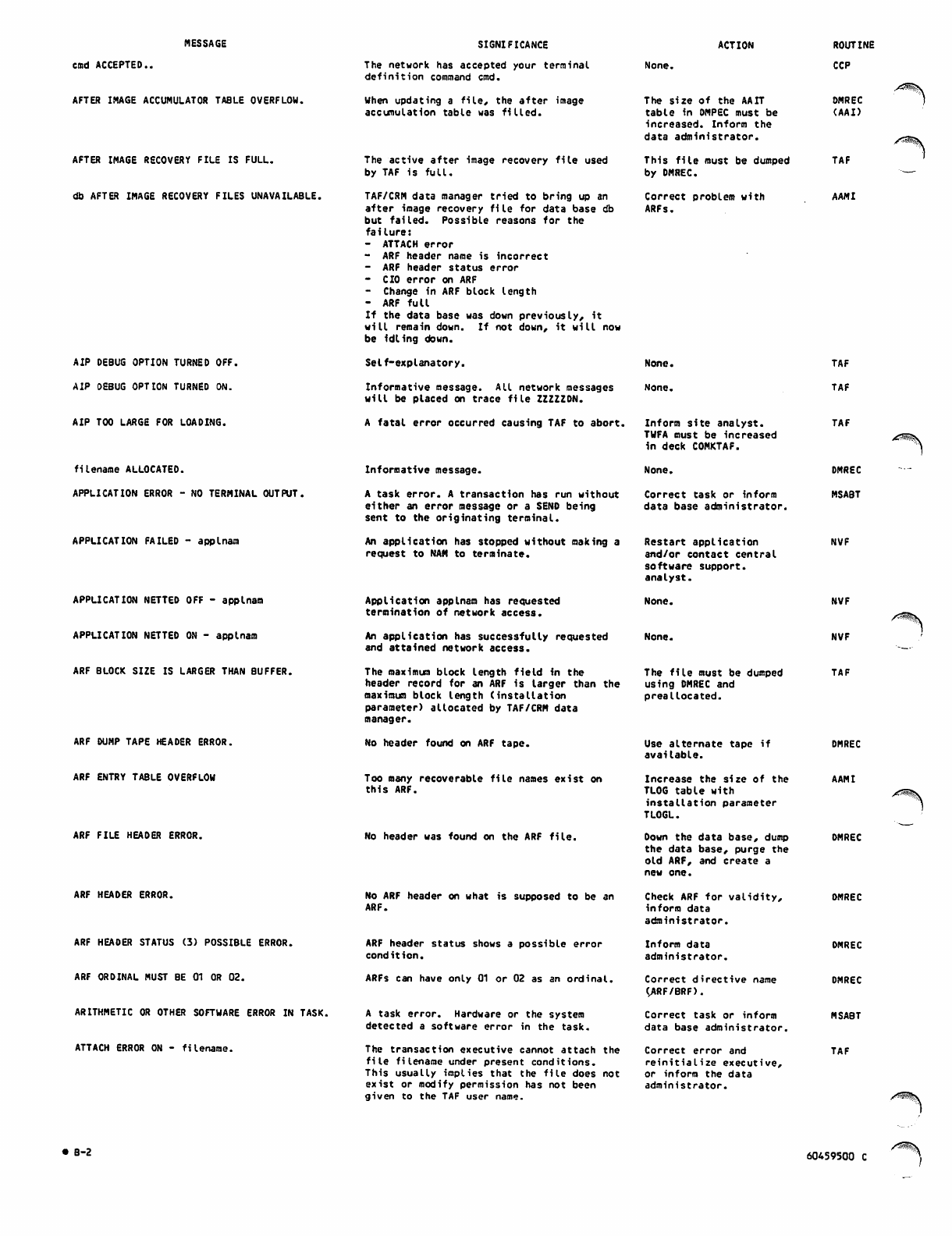
MESSAGE
cmd ACCEPTED..
AFTER IMAGE ACCUMULATOR TABLE OVERFLOW.
AFTER IMAGE RECOVERY FILE IS FULL.
db AFTER IMAGE RECOVERY FILES UNAVAILABLE.
AIP DEBUG OPTION TURNED OFF.
AIP DEBUG OPTION TURNED ON.
AIP TOO LARGE FOR LOADING.
filename ALLOCATED.
APPLICATION ERROR - NO TERMINAL OUTPUT.
APPLICATION FAILED - applnam
APPLICATION NETTED OFF - applnam
APPLICATION NETTED ON - applnam
ARF BLOCK SIZE IS LARGER THAN BUFFER.
ARF DUMP TAPE HEADER ERROR.
ARF ENTRY TABLE OVERFLOW
ARF FILE HEADER ERROR.
ARF HEADER ERROR.
ARF HEADER STATUS (3) POSSIBLE ERROR.
ARF ORDINAL MUST BE 01 OR 02.
ARITHMETIC OR OTHER SOFTWARE ERROR IN TASK.
ATTACH ERROR ON - filename.
SIGNIFICANCE
The network has accepted your terminal
d e fi n i t i o n c o m m a n d c m d .
W h e n u p d a t i n g a fi l e , t h e a f t e r i m a g e
accumulation table was filled.
T h e a c t i v e a f t e r i m a g e r e c o v e r y fi l e u s e d
b y TA F i s f u l l .
TAF/CRM data manager tried to bring up an
after image recovery file for data base db
but failed. Possible reasons for the
failure:
- ATTACH error
- ARF header name is incorrect
- ARF header status error
- CIO error on ARF
- Change in ARF block length
- ARF f ull
If the data base was down previously, it
will remain down. If not down, it will now
be idling down.
Self-explanatory.
Informative message. All network messages
will be placed on trace file ZZZZZDN.
A fatal error occurred causing TAF to abort.
Informative message.
A task error. A transaction has run without
either an error message or a SEND being
sent to the originating terminal.
An application has stopped without making a
request to NAM to terminate.
Application applnam has requested
termination of network access.
An application has successfully requested
and attained network access.
The maximum block length field in the
header record for an ARF is larger than the
maximum block length (installation
parameter) allocated by TAF/CRM data
manager.
No header found on ARF tape.
Too many recoverable file names exist on
this ARF.
No header was found on the ARF file.
No ARF header on what is supposed to be an
ARF.
ARF header status shows a possible error
condition.
ARFs can have only 01 or 02 as an ordinal.
A task error. Hardware or the system
detected a software error in the task.
The transaction executive cannot attach the
file filename under present conditions.
This usually implies that the file does not
exist or modify permission has not been
given to the TAF user name.
ACTION
None.
The size of the AAIT
table in OMPEC must be
increased. Inform the
data administrator.
This file must be dumped
by DMREC.
Correct problem with
ARFs.
None.
None.
Inform site analyst.
TWFA must be increased
in deck COMKTAF.
None.
Correct task or inform
data base administrator.
Restart application
and/or contact central
software support,
analyst.
None.
None.
The file must be dumped
using DMREC and
preallocated.
Use alternate tape if
available.
Increase the size of the
TLOG table with
installation parameter
TLOGL.
Down the data base, dump
the data base, purge the
old ARF, and create a
new one.
Check ARF for validity,
inform data
administrator.
Inform data
administrator.
Correct directive name
(ARF/BRF).
Correct task or inform
data base administrator.
Correct error and
reinitialize executive,
or inform the data
administrator.
ROUTINE
CCP
DMREC
(AAI)
.ysfesx
TAF
AAMI
TAF
TAF
TAF
DMREC
MSABT
NVF
NVF
NVF
DMREC
AAMI
DMREC
OMREC
DMREC
DMREC
MSA8T
TAF
• B-2 60459500 C
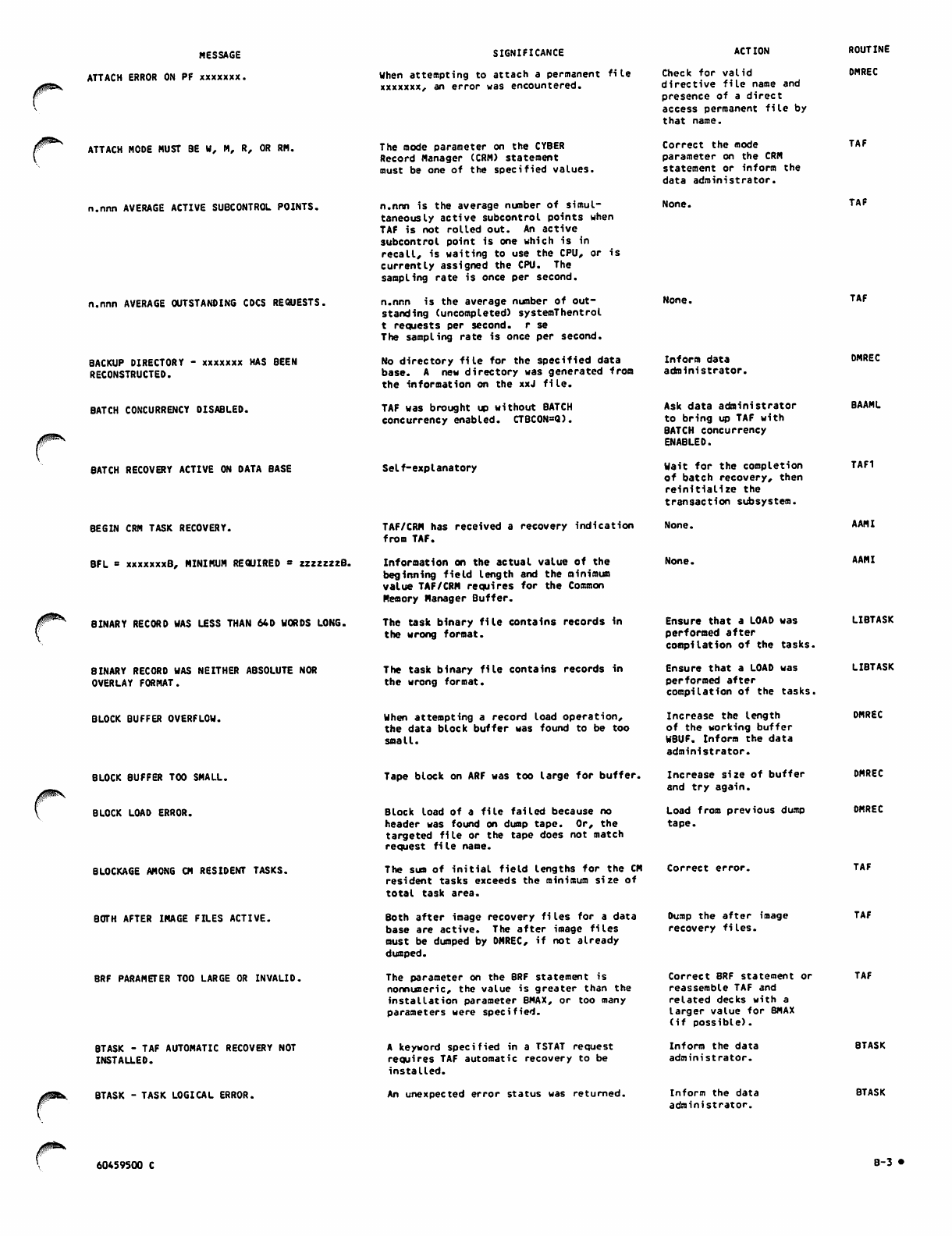
#^
JP*s
MESSAGE
ATTACH ERROR ON PF xxxxxxx.
ATTACH MODE MUST BE W, M, R, OR RM.
n.nnn AVERAGE ACTIVE SUBCONTROL POINTS.
n.nnn AVERAGE OUTSTANDING CDCS REQUESTS.
BACKUP DIRECTORY - xxxxxxx HAS BEEN
RECONSTRUCTED.
BATCH CONCURRENCY DISABLED.
BATCH RECOVERY ACTIVE ON DATA BASE
BEGIN CRM TASK RECOVERY.
BFL - xxxxxxxB, MINIMUM REQUIRED = zzzzzzzB.
BINARY RECORD WAS LESS THAN 64D WORDS LONG.
BINARY RECORD WAS NEITHER ABSOLUTE NOR
OVERLAY FORMAT.
BLOCK BUFFER OVERFLOW.
BLOCK BUFFER TOO SMALL.
BLOCK LOAD ERROR.
BLOCKAGE AMONG CM RESIDENT TASKS.
BOTH AFTER IMAGE FILES ACTIVE.
BRF PARAMETER TOO LARGE OR INVALID.
BTASK - TAF AUTOMATIC RECOVERY NOT
INSTALLED.
BTASK - TASK LOGICAL ERROR.
SIGNIFICANCE
When attempting to attach a permanent file
xxxxxxx, an error was encountered.
The mode parameter on the CYBER
Record Manager (CRM) statement
must be one of the specified values.
n.nnn is the average number of simul
taneously active subcontrol points when
TAF is not rolled out. An active
subcontrol point is one which is in
recall, is waiting to use the CPU, or is
currently assigned the CPU. The
sampling rate is once per second.
n.nnn is the average number of out
standing (uncompleted) systemThentrol
t requests per second, r se
The sampling rate is once per second.
No directory file for the specified data
base. A new directory was generated from
the information on the xxJ file.
TAF was brought up without BATCH
concurrency enabled. CTBCON=Q).
Self-explanatory
TAF/CRM has received a recovery indication
from TAF.
Information on the actual value of the
beginning field length and the minimum
value TAF/CRN requires for the Common
Memory Manager Buffer.
The task binary file contains records in
the wrong format.
The task binary file contains records in
the wrong format.
When attempting a record load operation,
the data block buffer was found to be too
small.
Tape block on ARF was too large for buffer.
Block load of a file failed because no
header was found on dump tape. Or, the
targeted f1le or the tape does not match
request file name.
The sum of initial field lengths for the CM
resident tasks exceeds the minimum size of
total task area.
Both after image recovery files for a data
base are active. The after image files
must be dumped by DMREC, if not already
dumped.
The parameter on the BRF statement is
nonnumeric, the value is greater than the
installation parameter BMAX, or too many
parameters were specified.
A keyword specified in a TSTAT request
requires TAF automatic recovery to be
installed.
An unexpected error status was returned.
ACTION
Check for valid
directive file name and
presence of a direct
access permanent file by
that name.
Correct the mode
parameter on the CRM
statement or inform the
data admini s trator.
None.
None.
Inform data
administrator.
Ask data administrator
to bring up TAF with
BATCH concurrency
ENABLED.
Wait for the completion
of batch recovery, then
reinitialize the
transaction subsystem.
None.
None.
Ensure that a LOAD was
performed after
compilation of the tasks.
Ensure that a LOAD was
performed after
compilation of the tasks.
Increase the length
of the working buffer
WBUF. Inform the data
administrator.
Increase size of buffer
and try again.
Load from previous dump
tape.
Correct error.
Dump the after image
recovery files.
Correct BRF statement or
reassemble TAF and
related decks with a
larger value for BMAX
(if possible).
Inform the data
administrator.
Inform the data
administrator.
ROUTINE
DMREC
TAF
TAF
TAF
DMREC
BAAML
TAF1
AAMI
AAMI
LIBTASK
LIBTASK
DMREC
DMREC
DMREC
TAF
TAF
8TASK
BTASK
60459500 C 8-3 •
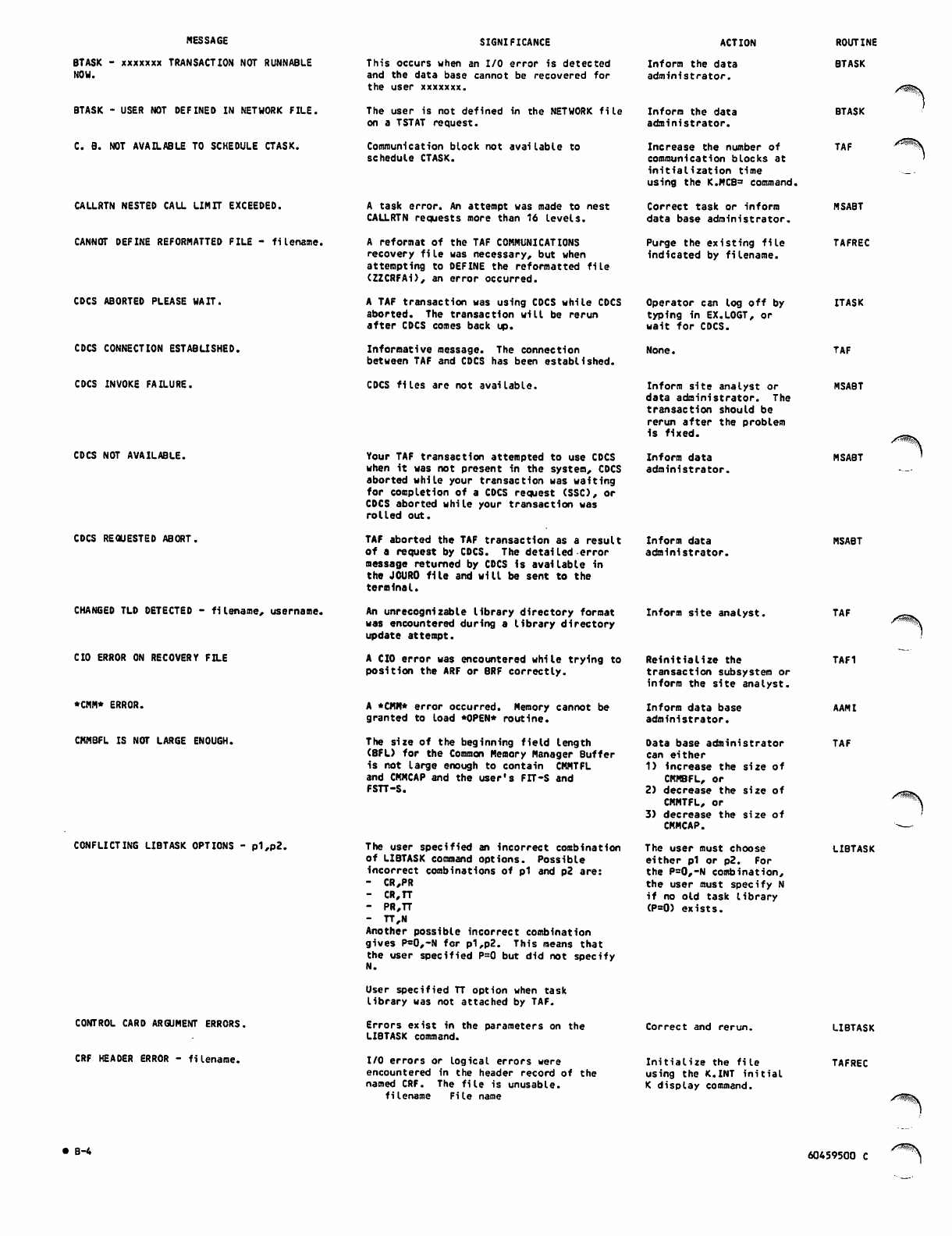
MESSAGE
BTASK - xxxxxxx TRANSACTION NOT RUNNABLE
NOW.
BTASK - USER NOT DEFINED IN NETWORK FILE.
C. B. NOT AVAILABLE TO SCHEDULE CTASK.
CALLRTN NESTED CALL LIMIT EXCEEDED.
CANNOT DEFINE REFORMATTED FILE - filename.
CDCS ABORTED PLEASE WAIT.
CDCS CONNECTION ESTABLISHED.
CDCS INVOKE FAILURE.
CDCS NOT AVAILABLE.
CDCS REQUESTED ABORT.
CHANGED TLD DETECTED - filename, username.
CIO ERROR ON RECOVERY FILE
*CMM* ERROR.
CMMBFL IS NOT LARGE ENOUGH.
CONFLICTING LIBTASK OPTIONS - p1,p2.
SIGNIFICANCE
This occurs when an I/O error is detected
and the data base cannot be recovered for
the user xxxxxxx.
The user is not defined in the NETWORK file
on a TSTAT request.
Communication block not available to
schedule CTASK.
A task error. An attempt was made to nest
CALLRTN requests more than 16 levels.
A reformat of the TAF COMMUNICATIONS
recovery file was necessary, but when
attempting to DEFINE the reformatted file
(ZZCRFAi), an error occurred.
A TAF transaction was using CDCS while CDCS
aborted. The transaction will be rerun
after CDCS comes back up.
Informative message. The connection
between TAF and CDCS has been established.
CDCS files are not available.
Your TAF transaction attempted to use CDCS
when it was not present in the system, CDCS
aborted while your transaction was waiting
for completion of a CDCS request (SSC), or
CDCS aborted while your transaction was
rolled out.
TAF aborted the TAF transaction as a result
of a request by CDCS. The detailed error
message returned by CDCS is available in
the JOURO file and will be sent to the
terminal.
An unrecognizable library directory format
was encountered during a library directory
update attempt.
A CIO error was encountered while trying to
position the ARF or BRF correctly.
A *CMM* error occurred. Memory cannot be
granted to load *OPEN* routine.
The size of the beginning field length
(8FL> for the Common Memory Manager Buffer
is not large enough to contain CMMTFL
and CKMCAP and the user's FIT-S and
FSTT-S.
The user specified an incorrect combination
of LIBTASK command options. Possible
incorrect combinations of p1 and p2 are:
- CR,PR
- CR,TT
- PR,TT
- T T, N
Another possible incorrect combination
gives P=0,-N for p1,p2. This means that
the user specified P=0 but did not specify
N.
ACTION
Inform the data
administrator.
Inform the data
administrator.
Increase the number of
communication blocks at
initialization time
using the K.MC8- command.
Correct task or inform
data base administrator.
Purge the existing file
indicated by filename.
Operator can log off by
typing in EX.LOGT, or
wait for CDCS.
None.
Inform site analyst or
data administrator. The
transaction should be
rerun after the problem
is fixed.
Inform data
administrator.
Inform data
administrator.
Inform site analyst.
Reinitialize the
transaction subsystem or
inform the site analyst.
Inform data base
administrator.
Data base administrator
can either
1) Increase the size of
CMMBFL, or
2) decrease the size of
CMMTFL, or
3) decrease the size of
CMMCAP.
The user must choose
either p1 or p2. For
the P=0,-N combination,
the user must specify N
if no old task libr ary
(P=0) exists.
ROUTINE
BTASK
BTASK
TAF
MSABT
TAFREC
ITASK
TAF
MSABT
MSA8T
MSABT
TAF
TAF1
AAMI
TAF
/?i^\
/*^5§k
LIBTASK
CONTROL CARD ARGUMENT ERRORS.
CRF HEADER ERROR - filename.
User specified TT option when task
library was not attached by TAF.
Errors exist in the parameters on the
LIBTASK command.
I/O errors or logical errors were
encountered in the header record of the
named CRF. The file is unusable,
filename File name
Correct and rerun.
Initialize the file
using the K.INT initial
K display command.
LIBTASK
TAFREC
• B - 4 60459500 C
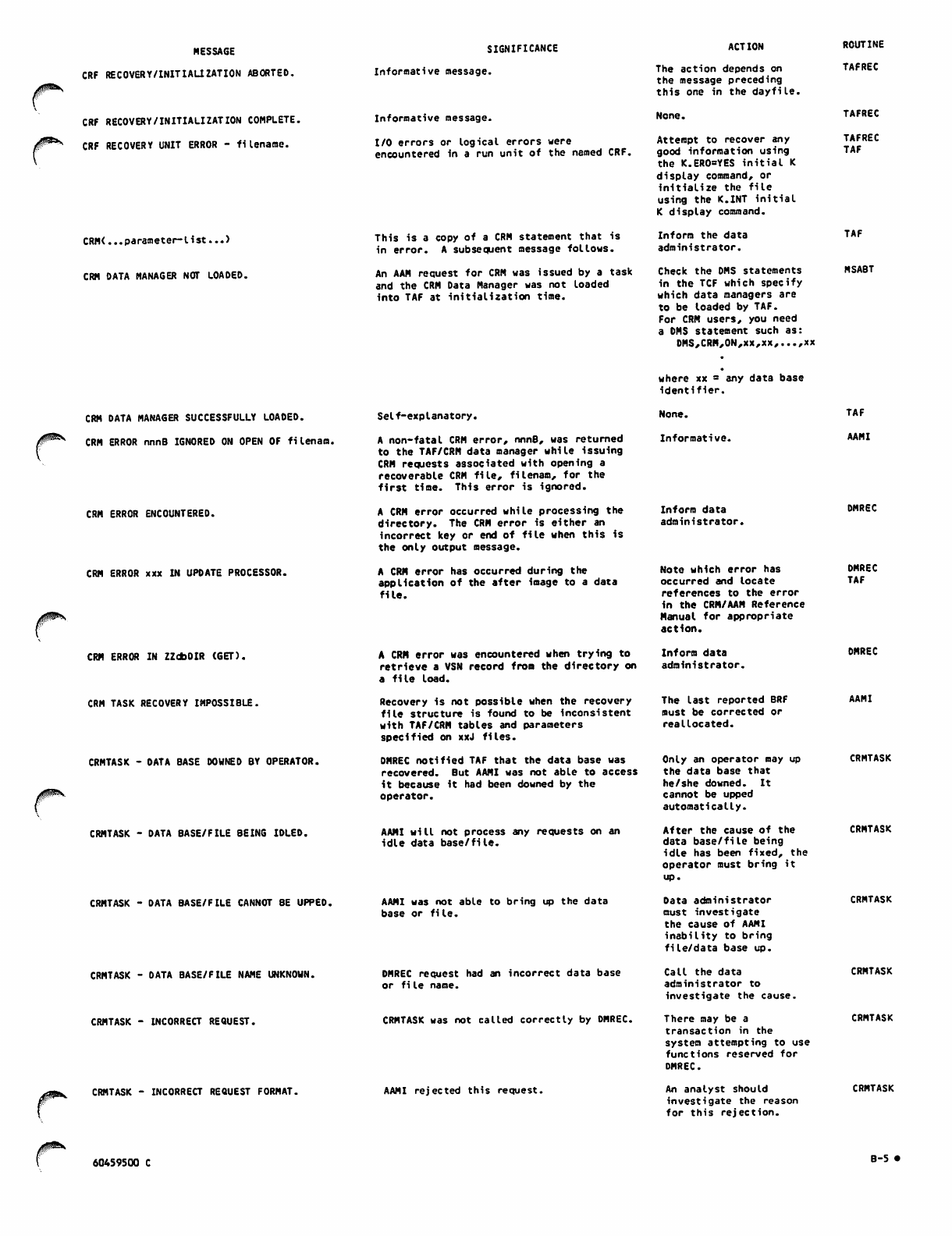
MESSAGE
CRF RECOVERY/INITIAUZATION ABORTED.
CRF RECOVERY/INITIALIZATION COMPLETE.
CRF RECOVERY UNIT ERROR - filename.
SIGNIFICANCE
CRM(...parameter-list...)
CRM DATA MANAGER NOT LOADED.
Informative message.
Informative message.
I/O errors or logical errors were
encountered in a run unit of the named CRF.
This is a copy of a CRM statement that is
in error. A subsequent message follows.
An AAM request for CRM was issued by a task
and the CRM Data Manager was not loaded
into TAF at initialization time.
ACTION ROUTINE
The action depends on TAFREC
the message preceding
this one in the dayfile.
None. TAFREC
Attempt to recover any TAFREC
good information using TAF
the K.ERO=YES initial K
display command, or
initialize the file
using the K.INT initial
K display command.
Inform the data TAF
administrator.
Check the DMS statements MSABT
in the TCF which specify
which data managers are
to be loaded by TAF.
For CRM users, you need
a DMS statement such as:
DMS,CRM,ON,xx,xx,...,xx
CRM DATA MANAGER SUCCESSFULLY LOAOED.
CRM ERROR nnnB IGNORED ON OPEN OF filenara.
CRM ERROR ENCOUNTERED.
CRM ERROR xxx IN UPDATE PROCESSOR.
^^N
CRM ERROR IN ZZdbOIR (GET).
CRM TASK RECOVERY IMPOSSIBLE.
CRMTASK - DATA BASE DOWNED BY OPERATOR.
CRMTASK - DATA BASE/FILE BEING IDLED.
CRMTASK - DATA BASE/FILE CANNOT BE UPPED.
CRMTASK - DATA BASE/FILE NAME UNKNOWN.
CRMTASK - INCORRECT REQUEST.
CRMTASK - INCORRECT REQUEST FORMAT.
Self-explanatory.
A non-fatal CRM error, nnnB, was returned
to the TAF/CRM data manager while issuing
CRM requests associated with opening a
recoverable CRM file, filenam, for the
first time. This error is ignored.
A CRM error occurred while processing the
directory. The CRM error is either an
incorrect key or end of file when this is
the only output message.
A CRM error has occurred during the
application of the after image to a data
file.
A CRM error was encountered when trying to
retrieve a VSN record from the directory on
a file load.
Recovery is not possible when the recovery
file structure is found to be inconsistent
with TAF/CRM tables and parameters
specified on xxJ files.
DMREC notified TAF that the data base was
recovered. But AAMI was not able to access
it because it had been downed by the
operator.
AAMI will not process any requests on an
idle data base/file.
AAMI was not able to bring up the data
base or fi le.
DMREC request had an incorrect data base
or file name.
CRMTASK was not called correctly by DMREC.
AAMI rejected this request.
where xx = any data base
identifier.
None.
Informative.
Inform data
administrator.
Note which error has
occurred and locate
references to the error
in the CRN/AAM Reference
Manual for appropriate
action.
Inform data
administrator.
The last reported BRF
must be corrected or
reallocated.
Only an operator may up
the data base that
he/she downed. It
cannot be upped
automatically.
After the cause of the
data base/file being
idle has been fixed, the
operator must bring it
up.
Oata administrator
must investigate
the cause of AAMI
inability to bring
file/data base up.
Call the data
administrator to
investigate the cause.
There may be a
transaction in the
system attempting to use
functions reserved for
DMREC.
An analyst should
investigate the reason
fo r t h i s re j e c t i on .
TAF
AAMI
DMREC
DMREC
TAF
DMREC
AAMI
CRMTASK
CRMTASK
CRMTASK
CRMTASK
CRMTASK
CRMTASK
60459500 C B-5 •
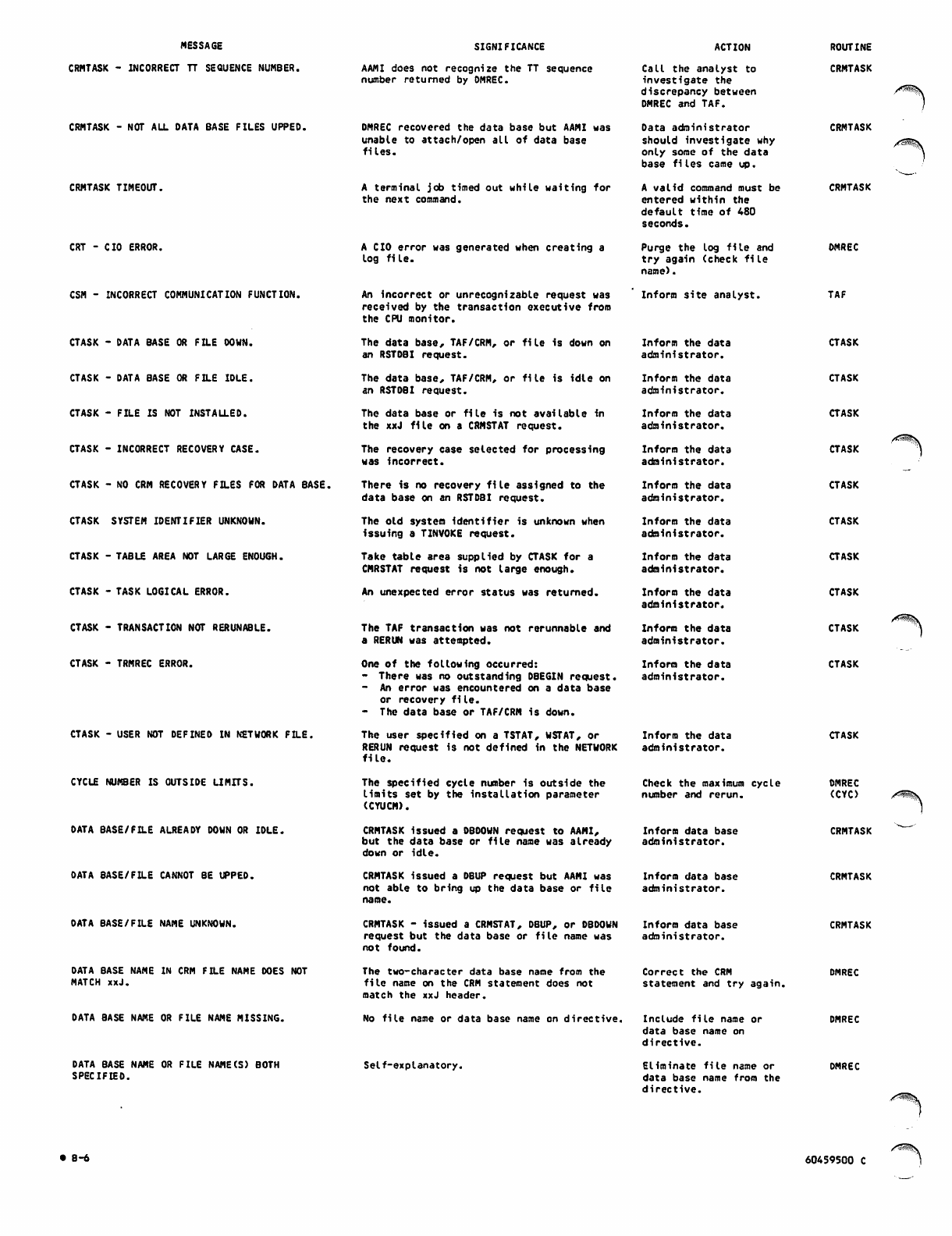
MESSAGE
CRMTASK - INCORRECT TT SEQUENCE NUMBER.
SIGNIFICANCE
AAMI does not recognize the TT sequence
number returned by DMREC.
ACTION
Call the analyst to
investigate the
discrepancy between
DMREC and TAF.
ROUTINE
CRMTASK
CRMTASK - NOT ALL DATA BASE FILES UPPED.
CRMTASK TIMEOUT.
DMREC recovered the data base but AAMI was
unable to attach/open all of data base
files.
A terminal job timed out while waiting for
the next command.
Data administrator CRMTASK
should investigate why
only some of the data
base files came up.
A valid command must be CRMTASK
entered within the
default time of 480
seconds.
CRT - CIO ERROR. A CIO error was generated when creating a
log file.
Purge the log file and
try again (check file
name).
DMREC
CSM - INCORRECT COMMUNICATION FUNCTION.
CTASK - DATA BASE OR FILE DOWN.
CTASK - DATA BASE OR FILE IDLE.
CTASK - FILE IS NOT INSTALLED.
CTASK - INCORRECT RECOVERY CASE.
CTASK - NO CRM RECOVERY FILES FOR DATA BASE.
CTASK SYSTEM IDENTIFIER UNKNOWN.
CTASK - TABLE AREA NOT LARGE ENOUGH.
CTASK - TASK LOGICAL ERROR.
An incorrect or unrecognizable request was
received by the transaction executive from
th e CPU monit o r.
The data base, TAF/CRM, or file is down on
an RSTDBI request.
The data base, TAF/CRM, or file is idle on
an RSTDBI request.
The data base or file is not available in
th e x xJ fil e on a CR M STAT r e ques t .
The recovery case selected for processing
was incorrect.
There is no recovery file assigned to the
data base on an RSTDBI request.
T h e o l d s y s t e m i d e n t i fi e r i s u n k n o w n w h e n
issuing a TINVOKE request.
Take tab l e a r e a s u p p l i e d b y C TA S K f o r a
CMRSTAT request is not large enough.
An unexpected error status was returned.
Inform site analyst.
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
TAF
CTASK
CTASK
CTASK
CTASK
CTASK
CTASK
CTASK
CTASK
CTASK - TRANSACTION NOT RERUNABLE.
CTASK - TRMREC ERROR.
CTASK - USER NOT DEFINED IN NETWORK FILE.
The TAF transaction was not rerunnable and
a RERUN was attempted.
One of the following occurred:
- There was no outstanding DBEGIN request.
- An error was encountered on a data base
or recovery file.
- The data base or TAF/CRM is down.
The user specified on a TSTAT, WSTAT, or
RERUN request is not defined in the NETWORK
fi l e .
Inform the data
administrator.
Inform the data
administrator.
Inform the data
administrator.
CTASK
CTASK
CTASK
CYCLE NUMBER IS OUTSIDE LIMITS. The specified cycle number is outside the
limits set by the installation parameter
(CYUCM).
Check the maximum cycle
number and rerun.
DMREC
(CYC)
DATA BASE/FILE ALREADY DOWN OR IDLE.
DATA BASE/FILE CANNOT BE UPPED.
CRMTASK issued a DBDOWN request to AAMI,
but the data base or file name was already
down or idle.
CRMTASK issued a DBUP request but AAMI was
not able to bring up the data base or file
name.
Inform data base
administrator.
Inform data base
administrator.
CRMTASK
CRMTASK
OATA BASE/FILE NAME UNKNOWN. CRMTASK - issued a CRMSTAT, DBUP, or DBDOWN
request but the data base or file name was
not found.
Inform data base
administrator.
CRMTASK
DATA BASE NAME IN CRM FILE NAME DOES NOT
MATCH xxJ.
DATA BASE NAME OR FILE NAME MISSING.
DATA BASE NAME OR FILE NAME(S) BOTH
SPECIFIED.
The two-character data base name from the
file name on the CRM statement does not
ma t c h t h e xx J h e a de r.
No file name or data base name on directive.
Self-explanatory.
Correct the CRM
statement and try again.
Include file name or
data base name on
directive.
Eliminate file name or
data base name from the
directive.
DMREC
DMREC
DMREC
• 8-6 60459500 C
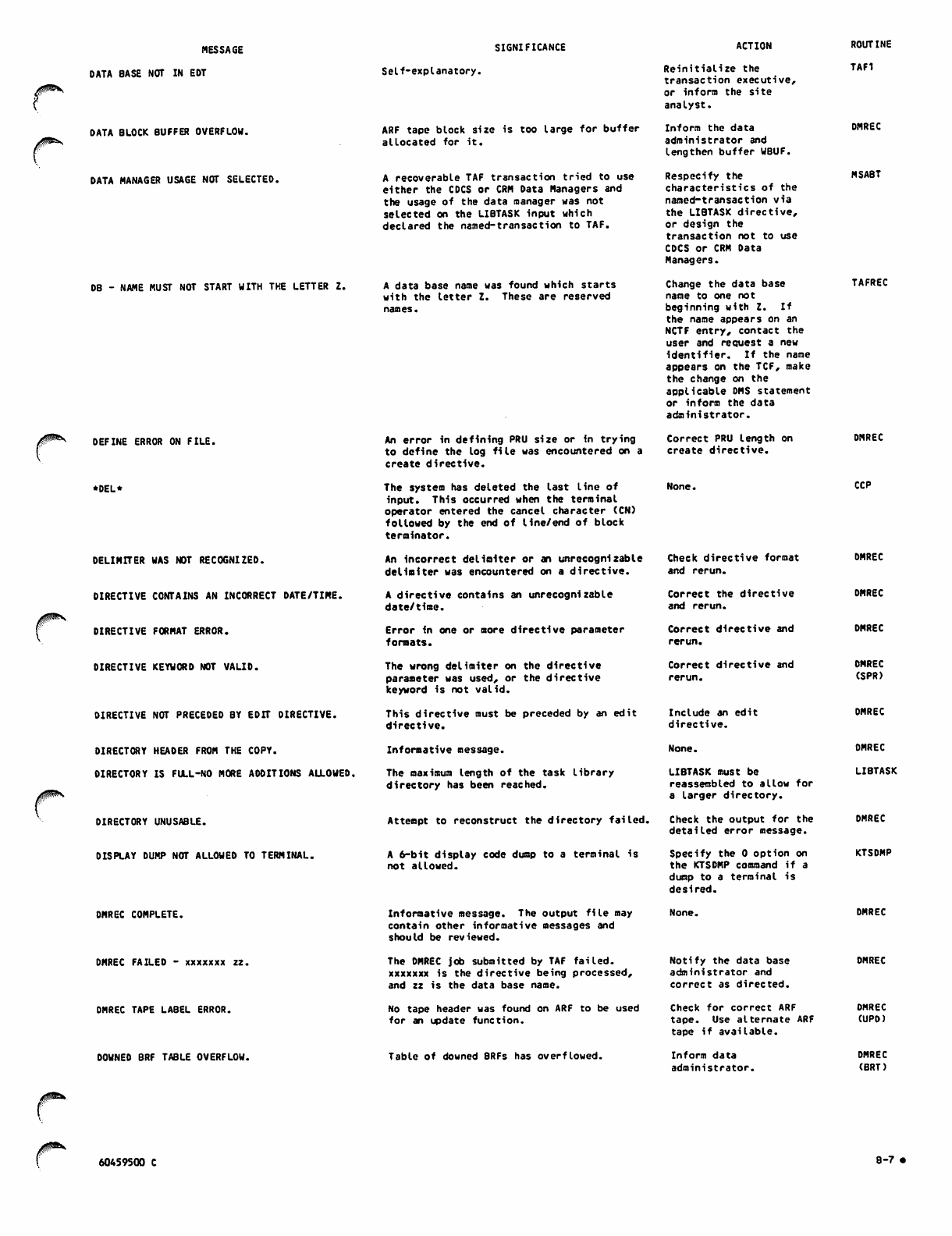
MESSAGE
DATA BASE NOT IN EOT
DATA BLOCK BUFFER OVERFLOW.
DATA MANAGER USAGE NOT SELECTED.
SIGNIFICANCE
Self-explanatory.
DB - NAME MUST NOT START WITH THE LETTER Z.
/^^ DEFINE ERROR ON FILE.
*DEL*
DELIMITER WAS NOT RECOGNIZED.
DIRECTIVE CONTAINS AN INCORRECT DATE/TIME.
DIRECTIVE FORMAT ERROR.
DIRECTIVE KEYWORD NOT VALID.
DIRECTIVE NOT PRECEDED BY EDIT DIRECTIVE.
DIRECTORY HEADER FROM THE COPY.
OIRECTORY IS FULL-NO MORE ADDITIONS ALLOWED.
DIRECTORY UNUSABLE.
DISPLAY DUMP NOT ALLOWED TO TERMINAL.
DMREC COMPLETE.
DMREC FAILED - xxxxxxx zz.
DMREC TAPE LABEL ERROR.
DOWNED BRF TABLE OVERFLOW.
ARF tape block size is too large for buffer
allocated for it.
A recoverable TAF transaction tried to use
either the CDCS or CRM Data Managers and
the usage of the data manager was not
selected on the LIBTASK input which
declared the named-transaction to TAF.
A data base name was found which starts
with the letter Z. These are reserved
names.
An error in defining PRU size or In trying
to define the log file was encountered on a
create dir e c t i v e.
The system has deleted the last line of
input. This occurred when the terminal
operator entered the cancel character (CN)
followed by the end of line/end of block
terminator.
An incorrect delimiter or an unrecognizable
delimiter was encountered on a directive.
A directive contains an unrecognizable
date/time.
Error in one or more directive parameter
formats.
The wrong delimiter on the directive
parameter was used, or the directive
keyword is not valid.
This directive must be preceded by an edit
directive.
Informative message.
The maximum length of the task library
directory has been reached.
Attempt to reconstruct the directory failed.
A 6-bit display code dump to a terminal is
not allowed.
Informative message. The output f1le may
contain other informative messages and
should be reviewed.
The DMREC job submitted by TAF failed,
xxxxxxx is the directive being processed,
and zz is the data base name.
No tape header was found on ARF to be used
for an update function.
Table of downed BRFs has overflowed.
ACTION
Reinitialize the
transaction executive,
or inform the site
analyst.
Inform the data
administrator and
lengthen buffer WBUF.
Respecify the
characteristics of the
named-transaction via
the LIBTASK directive,
or design the
transaction not to use
CDCS or CRM Data
Managers.
Change the data base
name to one not
beginning with Z. If
the name appears on an
NCTF entry, contact the
user and request a new
identifier. If the name
appears on the TCF, make
the change on the
applicable DMS statement
or inform the data
administrator.
Correct PRU length on
create directive.
None.
Check directive format
and rerun.
Correct the directive
and rerun.
Correct directive and
rerun.
Correct directive and
rerun.
Include an edit
directive.
None.
LIBTASK must be
reassembled to allow for
a larger directory.
Check the output for the
detailed error message.
Specify the 0 option on
the KTSDMP command if a
dump to a terminal is
desired.
None.
ROUTINE
TAF1
DMREC
MSABT
TAFREC
DMREC
CCP
DMREC
DMREC
DMREC
DMREC
(SPR)
DMREC
OMREC
LIBTASK
OMREC
KTSDMP
DMREC
Notify the data base DMREC
administrator and
correct as directed.
Check for correct ARF DMREC
tape. Use alternate ARF (UPD)
tape if available.
Inform data DMREC
administrator. (BRT)
J^"v
60459500 C 8-7 •
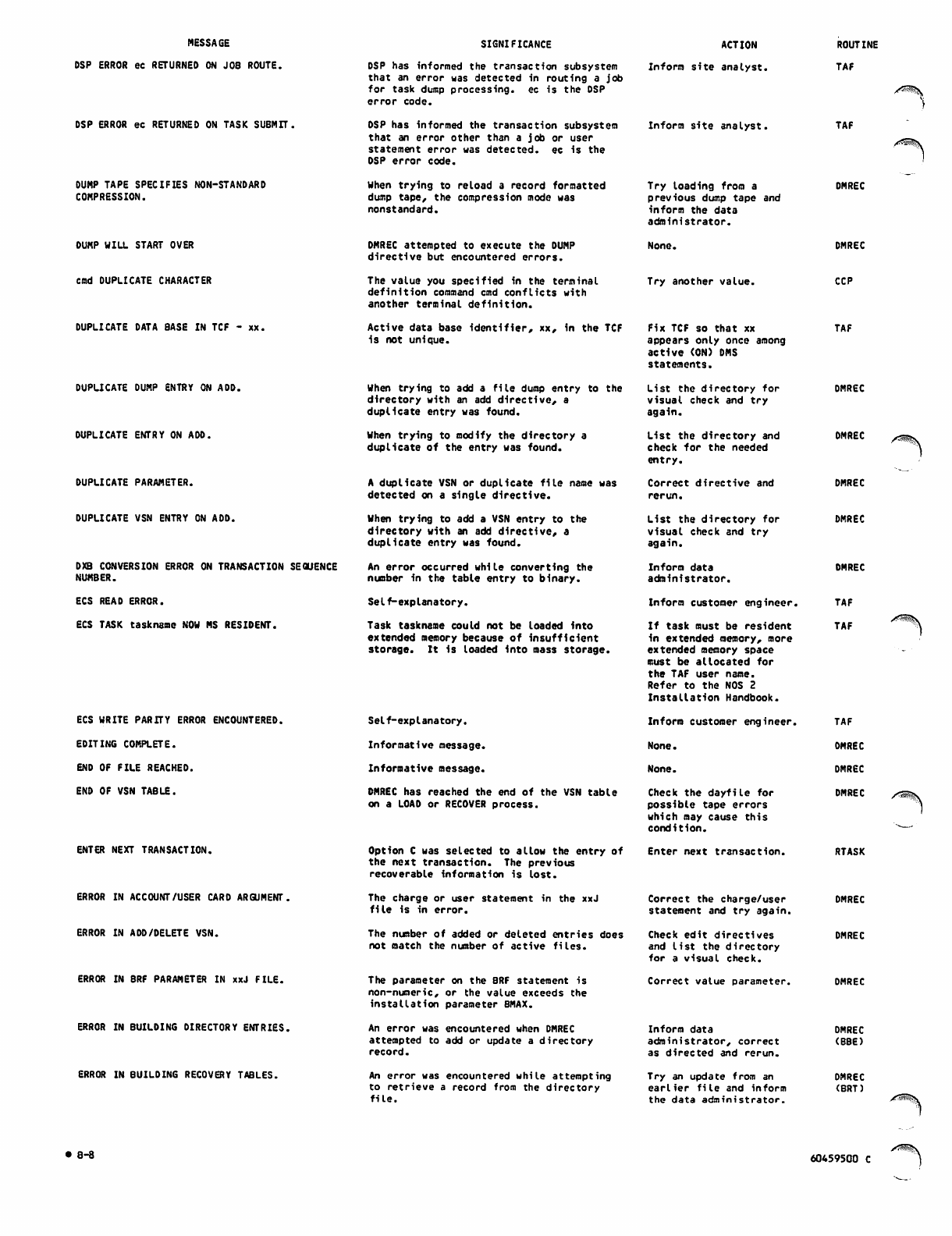
MESSAGE
DSP ERROR ec RETURNED ON J08 ROUTE.
DSP ERROR ec RETURNED ON TASK SUBMIT,
DUMP TAPE SPECIFIES NON-STANDARD
COMPRESSION.
DUMP WILL START OVER
cmd DUPLICATE CHARACTER
DUPLICATE DATA BASE IN TCF - xx.
DUPLICATE DUMP ENTRY ON ADD.
DUPLICATE ENTRY ON ADD.
DUPLICATE PARAMETER.
DUPLICATE VSN ENTRY ON ADD.
DXB CONVERSION ERROR ON TRANSACTION SEQUENCE
NUMBER.
ECS READ ERROR.
ECS TASK tasknsme NOW MS RESIDENT.
ECS WRITE PARITY ERROR ENCOUNTERED.
EDITING COMPLETE.
END OF FILE REACHED.
END OF VSN TABLE.
ENTER NEXT TRANSACTION.
ERROR IN ACCOUNT/USER CARD ARGUMENT.
ERROR IN ADD/DELETE VSN.
ERROR IN 8RF PARAMETER IN xxJ FILE.
ERROR IN BUILDING OIRECTORY ENTRIES.
ERROR IN BUILDING RECOVERY TABLES.
SIGNIFICANCE
DSP has informed the transaction subsystem
that an error was detected in routing a job
for task dump processing, ec is the DSP
error code.
DSP has informed the transaction subsystem
that an error other than a job or user
statement error was detected, ec is the
DSP error code.
When trying to reload a record formatted
dump tape, the compression mode was
nonstandard.
DMREC attempted to execute the DUMP
directive but encountered errors.
The value you specified in the terminal
definition command cmd conflicts with
another terminal definition.
Active data base identifier, xx, in the TCF
is not unique.
When trying to add a file dump entry to the
directory with an add directive, a
duplicate entry was found.
When trying to modify the directory a
duplicate of the entry was found.
A duplicate VSN or duplicate file name was
detected on a single directive.
When trying to add a VSN entry to the
directory with an add directive, a
duplicate entry was found.
An error occurred while converting the
number in the table entry to binary.
Self-explanatory.
Task taskname could not be loaded into
extended memory because of insufficient
storage. It Is loaded Into mass storage.
Self-explanatory.
Informative message.
Informative message.
DMREC has reached the end of the VSN table
on a LOAD or RECOVER process.
Option C was selected to allow the entry of
the next transaction. The previous
recoverable information is lost.
The charge or user statement in the xxJ
fi l e i s i n e r r o r.
The number of added or deleted entries does
not match the number of active files.
The parameter on the BRF statement is
non-numeric, or the value exceeds the
installation parameter BMAX.
An error was encountered when DMREC
attempted to add or update a directory
record.
An error was encountered while attempting
to retrieve a record from the directory
file.
ACTION
Inform site analyst.
Inform site analyst,
Try loading from a
previous dump tape and
inform the data
administrator.
None.
Try another value.
Fix TCF so that xx
appears only once among
active (ON) DMS
statements.
List the directory for
visual check and try
again.
List the directory and
check for the needed
entry.
Correct directive and
rerun.
List the directory for
visual check and try
again.
Inform data
administrator.
Inform customer engineer.
If task must be resident
in extended memory, more
extended memory space
must be allocated for
the TAF user name.
Refer to the NOS 2
Installation Handbook.
Inform customer engineer.
None.
None.
Check the dayfile for
possible tape errors
which may cause this
condition.
Enter next transaction.
Correct the charge/user
statement and try again.
Check edit directives
and list the directory
for a visual check.
Correct value parameter.
Inform data
administrator, correct
as directed and rerun.
Try an update from an
earlier file and inform
the data administrator.
ROUTINE
TAF
TAF
DMREC
DMREC
S^§\
CCP
TAF
DMREC
DMREC
DMREC
DMREC
DMREC
TAF
TAF
TAF
OMREC
DMREC
DMREC /-rSi§\
RTASK
DMREC
DMREC
DMREC
DMREC
(B8E)
DMREC
(BRT) ^eSSRv
• 8-8 60459500 C
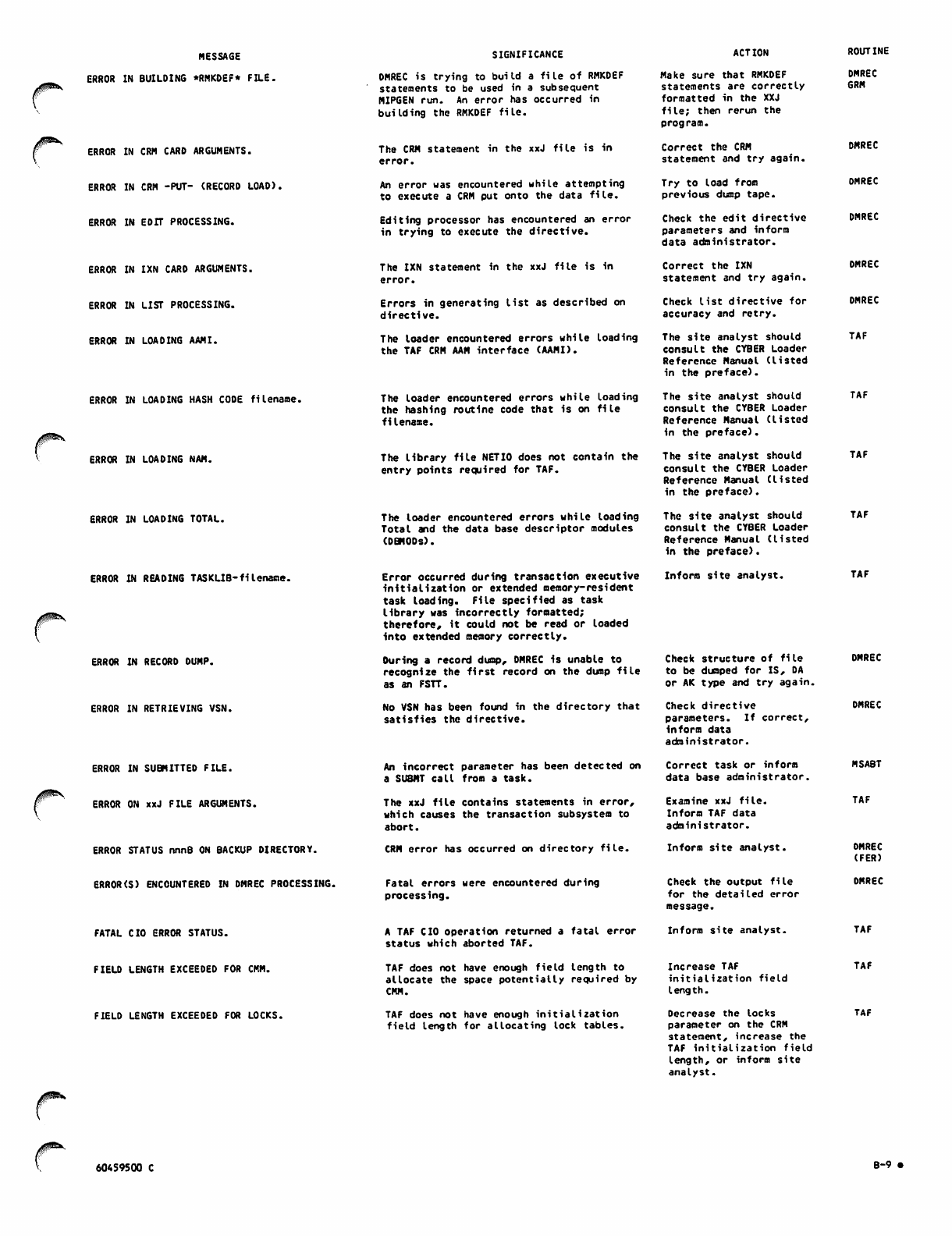
MESSAGE
ERROR IN BUILDING *RMKDEF* FILE.
ERROR IN CRM CARD ARGUMENTS.
ERROR IN CRM -PUT- (RECORD LOAD).
ERROR IN EDIT PROCESSING.
ERROR IN IXN CARD ARGUMENTS.
ERROR IN LIST PROCESSING.
ERROR IN LOADING AAMI.
ERROR IN LOADING HASH CODE filename.
ERROR IN LOADING NAM.
ERROR IN LOADING TOTAL.
ERROR IN READING TASKLIB-filename.
ERROR IN RECORD DUMP.
ERROR IN RETRIEVING VSN.
ERROR IN SUBMITTED FILE.
ERROR ON xxJ FILE ARGUMENTS.
ERROR STATUS nnnB ON BACKUP DIRECTORY.
ERROR(S) ENCOUNTERED IN OMREC PROCESSING.
FATAL CIO ERROR STATUS.
FIELD LENGTH EXCEEOED FOR CMM.
FIELD LENGTH EXCEEDED FOR LOCKS.
SIGNIFICANCE
DMREC is trying to build a file of RMKDEF
statements to be used in a subsequent
MIPGEN run. An error has occurred in
building the RMKDEF file.
The CRM statement in the xxJ file is in
error.
An error was encountered while attempting
to execute a CRM put onto the data file.
Editing processor has encountered an error
in trying to execute the directive.
The IXN statement in the xxJ file is in
error.
Errors in generating list as described on
directive.
The loader encountered errors while loading
the TAF CRM AAM interface (AAMI).
The loader encountered errors while loading
the hashing routine code that is on file
filename.
The library file NETIO does not contain the
entry points required for TAF.
The loader encountered errors while loading
Total and the data base descriptor modules
(DBMODs).
Error occurred during transaction executive
initialization or extended memory-resident
task loading. File specified as task
library was incorrectly formatted;
therefore, it could not be read or loaded
into extended memory correctly.
During a record dump, DMREC 1s unable to
recognize the first record on the dump file
as an FSTT.
No VSN has been found in the directory that
satisfies the directive.
An incorrect parameter has been detected on
a SUBMT call from a task.
The xxJ file contains statements in error,
which causes the transaction subsystem to
abort.
CRM error has occurred on directory file.
Fatal errors were encountered during
processing.
A TAF CIO operation returned a fatal error
status which aborted TAF.
TAF does not have enough field length to
allocate the space potentially required by
CMM.
TAF does not have enough initialization
field length for allocating lock tables.
ACTION
Make sure that RMKDEF
statements are correctly
formatted in the XXJ
file; then rerun the
program.
Correct the CRM
statement and try again.
Try to load from
previous dump tape.
Check the edit directive
parameters and inform
data admini s trator.
Correct the IXN
statement and try again.
Check list directive for
accuracy and retry.
The site analyst should
consult the CYBER Loader
Reference Manual (listed
in the preface).
The site analyst should
consult the CYBER Loader
Reference Manual (listed
in the preface).
The site analyst should
consult the CYBER Loader
Reference Manual (listed
in the preface).
The site analyst should
consult the CYBER Loader
Reference Manual (listed
in the preface).
Inform site analyst.
Check structure of file
to be dumped for IS, DA
or AK type and try again.
Check directive
parameters. If correct,
inform data
administrator.
Correct task or inform
data base administrator.
Examine xxJ file.
Inform TAF data
administrator.
Inform site analyst.
Check the output file
for the detailed error
message.
Inform site analyst.
Increase TAF
initialization field
length.
Decrease the locks
parameter on the CRM
statement, increase the
TAF initialization field
length, or inform site
analyst.
ROUTINE
DMREC
GRM
DMREC
OMREC
DMREC
DMREC
DMREC
TAF
TAF
TAF
TAF
DMREC
DMREC
MSABT
TAF
OMREC
(FER)
OMREC
TAF
TAF
60459500 C B-9 •
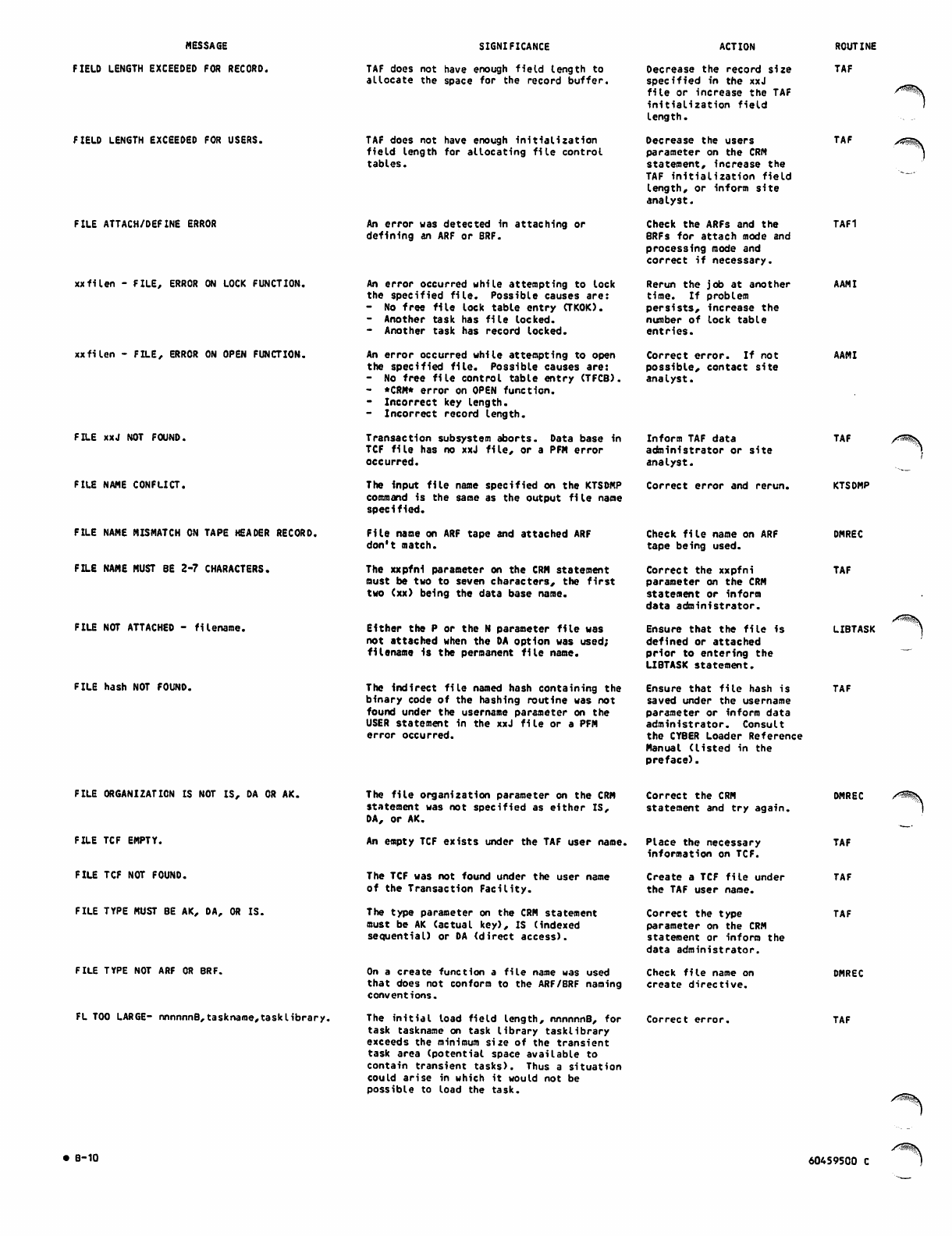
MESSAGE
FIELD LENGTH EXCEEDED FOR RECORD.
FIELD LENGTH EXCEEDED FOR USERS.
FILE ATTACH/DEFINE ERROR
xxfilen - FILE, ERROR ON LOCK FUNCTION.
xxfilen - FILE, ERROR ON OPEN FUNCTION.
FILE xxJ NOT FOUND.
FILE NAME CONFLICT.
FILE NAME MISMATCH ON TAPE HEADER RECORD.
FILE NAME MUST BE 2-7 CHARACTERS.
FILE NOT ATTACHED - filename.
FILE hash NOT FOUND.
SIGNIFICANCE
TAF does not have enough field length to
allocate the space for the record buffer.
TAF does not have enough initialization
field length for allocating file control
tables.
An error was detected in attaching or
defining an ARF or BRF.
An error occurred while attempting to lock
the specified file. Possible causes are:
- No free file lock table entry (TKOK).
- Another task has file locked.
- Another task has record locked.
An error occurred while attempting to open
the specified file. Possible causes are:
- No free file control table entry (TFCB).
- *CRM* error on OPEN function.
- Incorrect key length.
- Incorrect record length.
Transaction subsystem aborts. Data base in
TCF file has no xxJ file, or a PFM error
occurred.
The input file name specified on the KTSDMP
command is the same as the output f1le name
specified.
File name on ARF tape and attached ARF
don't match.
The xxpfni parameter on the CRM statement
must be two to seven characters, the first
two (xx) being the data base name.
Either the P or the N parameter file was
not attached when the DA option was used;
filename 1s the permanent file name.
The Indirect file named hash containing the
binary code of the hashing routine was not
found under the username parameter on the
USER statement in the xxJ file or a PFM
error occurred.
ACTION ROUTINE
Decrease the record size TAF
specified in the xxJ
file or increase the TAF
initialization field
length.
Decrease the users TAF
parameter on the CRM
statement, increase the
TAF initialization field
length, or inform site
analyst.
C h e c k t h e A R F s a n d t h e TA F 1
BRFs for attach mode and
processing mode and
co rrect if neces sary.
Rerun the job at another AAMI
time. If problem
persists, Increase the
number of lock table
en t ri e s .
Correct error. If not AAMI
possi b l e , conta c t site
analyst.
Inform TAF data TAF
administrator or site
analyst.
Correct error and rerun. KTSDMP
C h e c k fi l e n a m e o n A R F D M R E C
tape being used.
Correct the xxpfni TAF
parameter on the CRM
statement or inform
data admini s trator.
Ensure that the file is LIBTASK
defined or attached
prior to entering the
LIBTASK statement.
E n s u r e t h a t fi l e h a s h i s T A F
saved under the username
parameter or inform data
administrator. Consult
the CYBER Loader Reference
Manual (listed in the
preface).
/ ^ k
/^sSSs
FILE ORGANIZATION IS NOT IS, DA OR AK.
FILE TCF EMPTY.
FILE TCF NOT FOUND.
FILE TYPE MUST BE AK, DA, OR IS.
FILE TYPE NOT ARF OR BRF.
FL TOO LARGE- nnnnnnB,taskname,tasklibrary.
The file organization parameter on the CRM
statement was not specified as either IS,
DA, or AK.
An empty TCF exists under the TAF user name.
The TCF was not found under the user name
of the Transaction Facility.
The type parameter on the CRM statement
must be AK (actual key), IS (indexed
sequential) or DA (direct access).
On a create function a file name was used
that does not conform to the ARF/BRF naming
conventions.
The initial load field length, nnnnnnB, for
task taskname on task library taskiibrary
exceeds the minimum size of the transient
task area (potential space available to
contain transient tasks). Thus a situation
could arise in which it would not be
possible to load the task.
Correct the CRM
statement and try again.
Place the necessary
information on TCF.
Create a TCF f1le under
the TAF user name.
Correct the type
parameter on the CRM
statement or inform the
data admini s trator.
Check file name on
create directive.
Correct error.
DMREC
TAF
TAF
OMREC
/*-%m>%\
• 8-10 60459500 C )
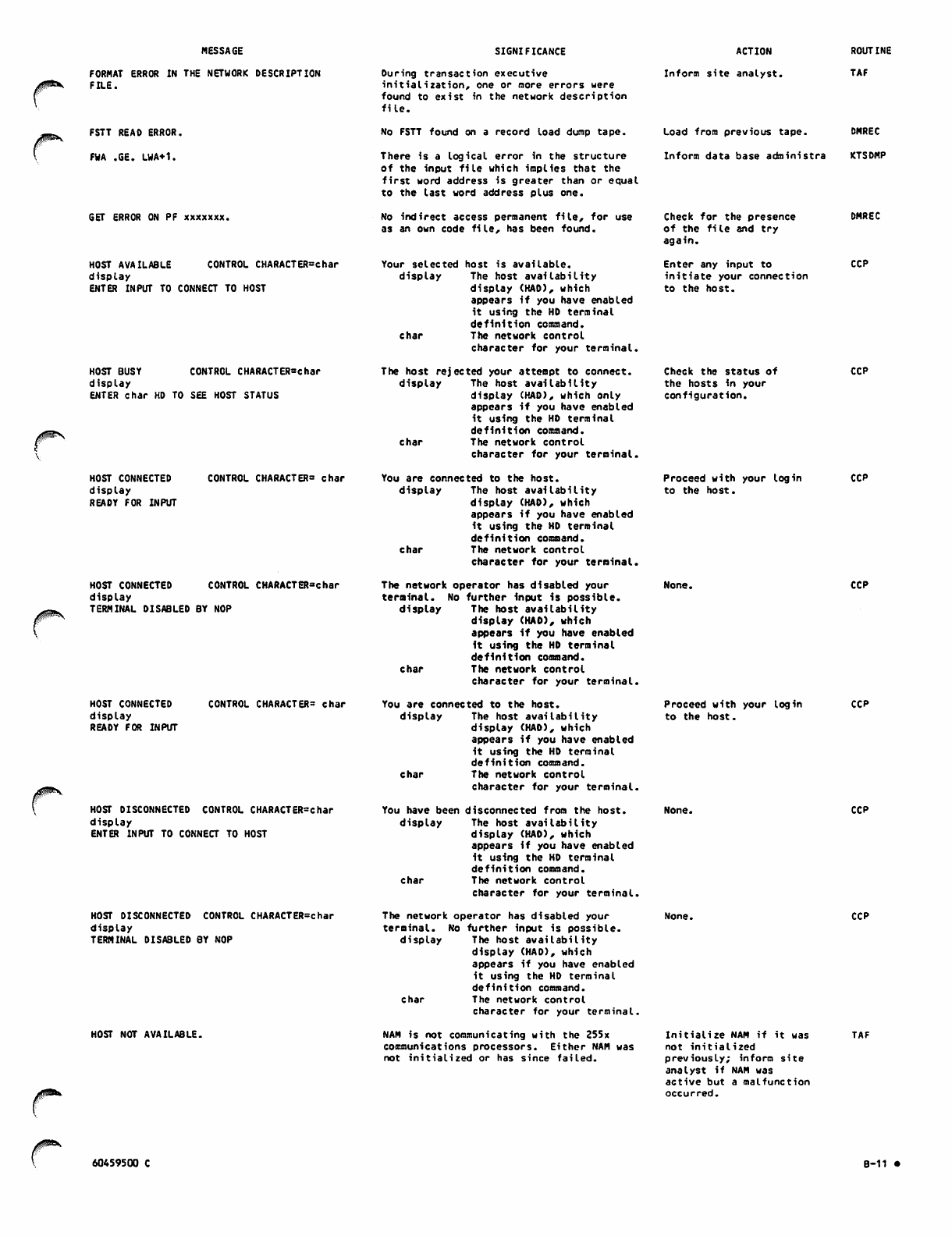
j0^z\
/gp«V
0^*
MESSAGE
FORMAT ERROR IN THE NETWORK DESCRIPTION
FILE.
FSTT READ ERROR.
FWA .GE. LWA+1.
GET ERROR ON PF xxxxxxx.
CONTROL CHARACTERSharHOST AVAILABLE
display
ENTER INPUT TO CONNECT TO HOST
HOST BUSY CONTROL CHARACTER=char
display
ENTER char HD TO SEE HOST STATUS
HOST CONNECTED
display
READY FOR INPUT
CONTROL CHARACTER- char
HOST CONNECTED
display
TERMINAL DISABLED BY NOP
CONTROL CHARACTERShar
HOST CONNECTED
display
READY FOR INPUT
CONTROL CHARACTERS char
HOST DISCONNECTED CONTROL CHARACTERShar
display
ENTER INPUT TO CONNECT TO HOST
HOST DISCONNECTED CONTROL CHARACTERS har
display
TERMINAL DISABLED 8Y NOP
HOST NOT AVAILABLE.
SIGNIFICANCE
During transaction executive
initialization, one or more errors were
found to exist in the network description
fi l e .
No FSTT found on a record load dump tape.
There is a logical error in the structure
of the input file which implies that the
first word address is greater than or equal
to the last word address plus one.
No indirect access permanent file, for use
as an own code file, has been found.
Your selected host is available.
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command.
char The network control
character for your terminal.
The host rejected your attempt to connect.
display The host availability
display (HAD), which only
appears if you have enabled
it using the HD terminal
definition command.
char The network control
character for your terminal.
You are connected to the host.
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command.
char The network control
character for your terminal.
The network operator has disabled your
terminal. No further input is possible,
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command,
char The network control
character for your terminal.
You are connected to the host.
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command.
char The network control
character for your terminal.
You have been disconnected from the host.
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command.
char The network control
character for your terminal.
The network operator has disabled your
terminal. No further input is possible,
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command,
c h a r T h e n e t w o r k c o n t r o l
character for your terminal.
NAM is not communicating with the 255x
communications processors. Either NAM was
not initialized or has since failed.
ACTION
Inform site analyst.
ROUTINE
TAF
Load from previous tape. DMREC
Inform data base administra KTSDMP
Check for the presence
of the file and try
again.
Enter any input to
initiate your connection
to the host.
Check the status of
the hosts in your
configuration.
Proceed with your login
to the host.
DMREC
CCP
CCP
CCP
None. CCP
Proceed with your login
to the host.
CCP
None. CCP
None. CCP
Initialize NAM if it was
not initialized
previously; inform site
analyst if NAM was
active but a malfunction
occurred.
TAF
c60459500 C B-11 •
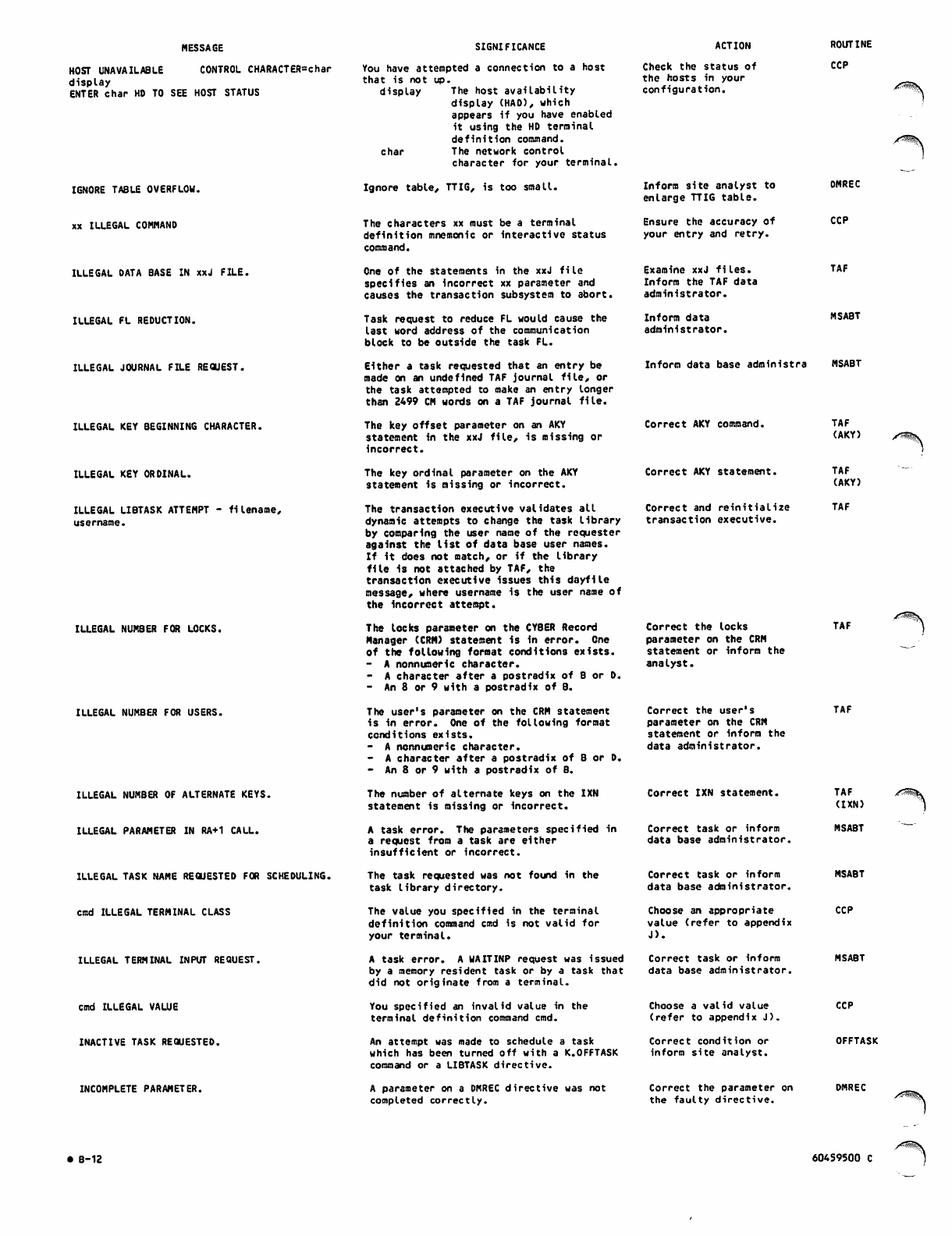
MESSAGE
HOST UNAVAILABLE CONTROL CHARACTERShar
display
ENTER char HD TO SEE HOST STATUS
IGNORE TABLE OVERFLOW,
xx ILLEGAL COMMAND
ILLEGAL DATA BASE IN xxJ FILE.
ILLEGAL FL REDUCTION.
ILLEGAL JOURNAL FILE REQUEST.
ILLEGAL KEY BEGINNING CHARACTER.
ILLEGAL KEY ORDINAL.
ILLEGAL LIBTASK ATTEMPT - filename,
username.
ILLEGAL NUM8ER FOR LOCKS.
ILLEGAL NUMBER FOR USERS.
ILLEGAL NUMBER OF ALTERNATE KEYS.
ILLEGAL PARAMETER IN RA+1 CALL.
ILLEGAL TASK NAME REQUESTED FOR SCHEDULING,
cmd ILLEGAL TERMINAL CLASS
ILLEGAL TERMINAL INPUT REQUEST.
cmd ILLEGAL VALUE
INACTIVE TASK REQUESTED.
INCOMPLETE PARAMETER.
SIGNIFICANCE
Yo u h a v e a t t e m p ted a connecti o n t o a h o s t
t h a t i s n o t u p .
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command,
char The network control
character for your terminal.
Ignore table, TTIG, is too small.
The characters xx must be a terminal
definition mnemonic or interactive status
command.
O n e o f t h e s t a t e m e n t s i n t h e x x J fi l e
specifies an incorrect xx parameter and
causes the transaction subsystem to abort.
Task request to reduce FL would cause the
last word address of the communication
b l o c k t o b e o u t s i d e t h e t a s k F L .
Either a task requested that an entry be
m a d e o n a n u n d e fi n e d TA F j o u r n a l fi l e , o r
the task attempted to make an entry longer
than 2499 CM words on a TAF journal file.
The key offset parameter on an AKY
statement in the xxJ file, is missing or
incorrect.
The key ordinal parameter on the AKY
statement is missing or incorrect.
The transaction executive validates all
dynamic attempts to change the task library
by comparing the user name of the requester
a g a i n s t t h e l i s t o f d a t a b a s e u s e r n a m e s .
If it does not match, or if the library
file 1s not attached by TAF, the
transaction executive issues this dayfile
message, where username is the user name of
the incorrect attempt.
The locks parameter on the CYBER Record
Manager (CRM) statement 1s In error. One
of the following format conditions exists.
- A nonnumeric character.
- A c h a r a c t e r a f t e r a p o s t r a d i x o f B o r D .
- A n 8 o r 9 w i t h a p o s t r a d i x o f B .
The user's parameter on the CRM statement
i s i n e r r o r. O n e o f t h e f o l l o w i n g f o r m a t
conditions exists.
- A nonnumeric character.
- A c h a r a c t e r a f t e r a p o s t r a d i x o f B o r D .
- A n 8 o r 9 w i t h a p o s t r a d i x o f B .
The number of alternate keys on the IXN
statement is missing or incorrect.
A t a s k e r r o r . T h e p a r a m e t e r s s p e c i fi e d i n
a request from a task are either
insufficient or incorrect.
The task requested was not found in the
t a s k l i b r a r y d i r e c t o r y .
The value you specified in the terminal
definition command cmd is not valid for
y o u r t e r m i n a l .
A task error. A WAITINP request was issued
b y a m e m o r y r e si d e nt t a s k or b y a t a s k th at
did not originate from a terminal.
You specified an invalid value in the
terminal definition command cmd.
An attempt was made to schedule a task
wh ich has bee n tu rned off with a K. OFFTA SK
command or a LIBTASK directive.
A parameter on a DMREC directive was not
completed correctly.
ACTION
Check the status of
the hosts in your
configuration.
ROUTINE
CCP
Inform site analyst to
enlarge TTIG table.
Ensure the accuracy of
your entry and retry.
Examine xxJ files.
Inform the TAF data
administrator.
Inform data
administrator.
Inform data base administra
Correct AKY command.
Correct AKY statement.
Correct and reinitialize
transaction executive.
Correct the locks
parameter on the CRM
statement or inform the
analyst.
Correct the user's
parameter on the CRM
statement or inform the
data admini s trator.
Correct IXN statement.
Correct task or inform
data base administrator.
Correct task or inform
data base administrator.
Choose an appropriate
value (refer to appendix
J).
Correct task or inform
data base administrator.
Choose a valid value
(refer to appendix J).
Correct condition or
inform site analyst.
Correct the parameter on
the faulty directive.
OMREC
CCP
TAF
MSABT
MSABT
TAF
(AKY)
TAF
(AKY)
TAF
TAF
TAF
TAF
(IXN)
MSABT
MSABT
CCP
MSABT
CCP
OFFTASK
DMREC
• B-12 60459500 C
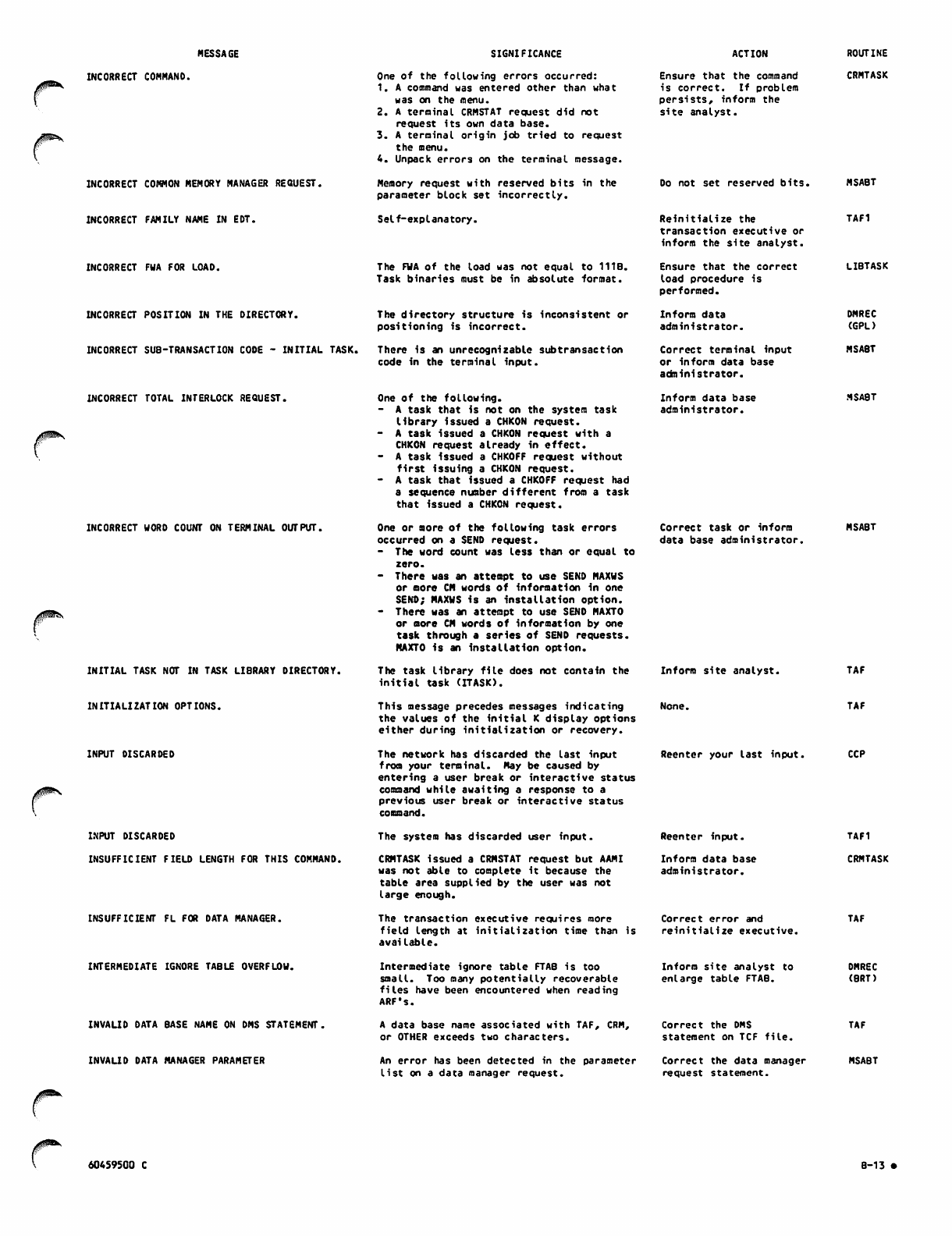
MESSAGE
INCORRECT COMMANO.
INCORRECT COMMON MEMORY MANAGER REQUEST.
INCORRECT FAMILY NAME IN EOT.
INCORRECT FWA FOR LOAD.
INCORRECT POSITION IN THE DIRECTORY.
INCORRECT SU8-TRANSACTI0N CODE - INITIAL TASK.
INCORRECT TOTAL INTERLOCK REQUEST.
INCORRECT WORD COUNT ON TERMINAL OUTPUT.
INITIAL TASK NOT IN TASK LI8RARY DIRECTORY.
INITIALIZATION OPTIONS.
INPUT DISCARDED
INPUT DISCAROED
INSUFFICIENT FIELD LENGTH FOR THIS COMMAND.
INSUFFICIENT FL FOR DATA MANAGER.
INTERMEDIATE IGNORE TABLE OVERFLOW.
INVALID DATA BASE NAME ON DMS STATEMENT.
INVALID DATA MANAGER PARAMETER
SIGNIFICANCE
One of the following errors occurred:
1. A command was entered other than what
was on the menu.
2 . A te r m i n a l C R M S TAT r e q u e s t di d r o t
request its own data base.
3. A terminal origin job tried to request
the menu.
4. Unpack errors on the terminal message.
Memory request with reserved bits in the
parameter block set incorrectly.
Self-explanatory.
The FWA of the load was not equal to 1118.
Task binaries must be in absolute format.
The directory structure is inconsistent or
positioning is incorrect.
There is an unrecognizable subtransaction
code in the terminal input.
One of the following.
- A t a s k t h a t i s n o t o n t h e s y s t e m t a s k
library issued a CHKON request.
- A task issued a CHKON request with a
C H K O N r e q u e s t al r e a d y i n ef f e c t .
- A task issued a CHKOFF request without
first issuing a CHKON request.
- A t a s k t h a t i s s u e d a C H K O F F r e q u e s t h a d
a s e q u e n c e n u m b e r d i f f e r e n t fr o m a ta s k
that issued a CHKON request.
One or more of the following task errors
occurred on a SEND request.
- The word count was less than or equal to
zero.
- There was an attempt to use SEND MAXWS
or m o r e CM w o r d s o f i n f or m a t io n i n o ne
SEND; MAXWS is an installation option.
- There was an attempt to use SEND MAXTO
or more CM words of information by one
task through a series of SEND requests.
MAXTO is an Installation option.
The task library file does not contain the
initial task (ITASK).
This message precedes messages indicating
the values of the initial K display options
either during initialization or recovery.
The network has discarded the last input
from your terminal. May be caused by
entering a user break or interactive status
command while awaiting a response to a
previous user break or interactive status
command.
The system has discarded user input.
CRMTASK issued a CRMSTAT request but AAMI
was not able to complete it because the
table area supplied by the user was not
large enough.
The transaction executive requires more
field length at initialization time than is
avallable.
Intermediate ignore table FTAB is too
small. Too many potentially recoverable
files have been encountered when reading
ARF's.
A data base name associated with TAF, CRM,
or OTHER exceeds two characters.
An error has been detected in the parameter
list on a data manager request.
ACTION
Ensure that the command
is correct. If problem
persists, inform the
site analyst.
Do not set reserved bits.
Reinitialize the
transaction executive or
inform the site analyst.
Ensure that the correct
load procedure is
performed.
Inform data
administrator.
Correct terminal input
or inform data base
administrator.
Inform data base
administrator.
ROUTINE
CRMTASK
Correct task or inform
data base administrator.
Inform site analyst.
None.
Reenter your last input.
Reenter input.
Inform data base
administrator.
Correct error and
reinitialize executive.
Inform site analyst to
enlarge table FTAB.
Correct the DMS
statement on TCF file.
Correct the data manager
request statement.
MSABT
TAF1
LIBTASK
DMREC
(GPL)
MSABT
MSABT
MSABT
TAF
TAF
CCP
TAF1
CRMTASK
TAF
OMREC
(BRT)
TAF
MSABT
/ # ^
60459500 C B-13 •
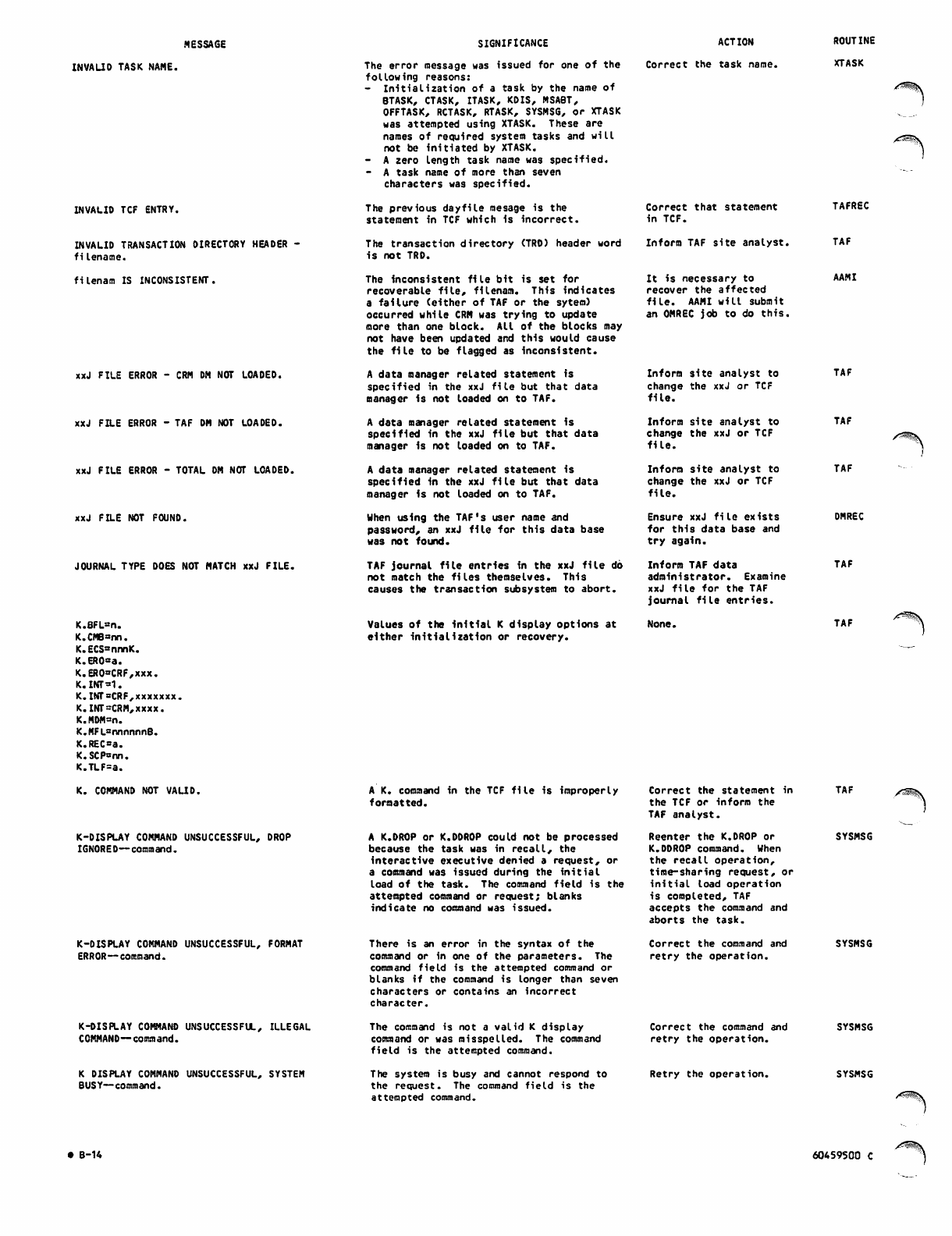
MESSAGE
INVALID TASK NAME.
INVAHO TCF ENTRY.
INVALID TRANSACTION DIRECTORY HEADER
filename.
filenam IS INCONSISTENT.
xxJ FILE ERROR - CRM DM NOT LOADED.
xxJ FILE ERROR - TAF DM NOT LOADED.
xxJ FILE ERROR - TOTAL DM NOT LOADED.
xx J FILE NOT FOUND.
JOURNAL TYPE DOES NOT MATCH xxJ FILE.
K.BFL=n.
K.CMB=nn.
K.£CS=nrmK.
K.ERO-a.
K.ERO=CRF,xxx.
K.INT=1.
K.INT=CRF,xxxxxxx.
K. INT =CRM, xxxx.
K.MDM=n.
K.MFL=nnnnnnB.
K.REC=a.
K.SCP=nn.
K.TLF=a.
K. COMMAND NOT VALID.
K-DISPLAY COMMAND UNSUCCESSFUL, DROP
IGNORED—-command.
K-DISPLAY COMMAND UNSUCCESSFUL, FORMAT
ERROR—command.
K-DISPLAY COMMAND UNSUCCESSFUL, ILLEGAL
COMMAND— comm and.
K DISPLAY COMMAND UNSUCCESSFUL, SYSTEM
BUSY—command.
SIGNIFICANCE
The error message was issued for one of the
following reasons:
- Initialization of a task by the name of
BTASK, CTASK, ITASK, KDIS, MSABT,
OFFTASK, RCTASK, RTASK, SYSMSG, or XTASK
was attempted using XTASK. These are
names of required system tasks and will
not be initiated by XTASK.
- A zero length task name was specified.
- A task name of more than seven
characters was specified.
The previous dayfile mesage is the
statement in TCF which is incorrect.
The transaction directory (TRD) header word
is not TRD .
The inconsistent file bit is set for
recoverable file, filenam. This indicates
a failure (either of TAF or the sytem)
occurred while CRM was trying to update
more than one block. All of the blocks may
not have been updated and this would cause
the file to be flagged as inconsistent.
A data manager related statement is
specified in the xxJ file but that data
manager 1s not loaded on to TAF.
A data manager related statement is
specified in the xxJ file but that data
manager 1s not loaded on to TAF.
A data manager related statement is
specified in the xxJ file but that data
manager 1s not loaded on to TAF.
When using the TAF's user name and
p a s s w o r d , a n x x J fi l e f o r t h i s d a t a b a s e
was not found.
TAF journal file entries in the xxJ file do
not match the files themselves. This
causes the transaction subsystem to abort.
Values of the initial K display options at
either initialization or recovery.
ACTION
C o r r e c t t h e t a s k n a m e .
ROUTINE
XTASK
A K. command in the TCF file is improperly
formatted.
A K.DROP or K.DDROP could not be processed
because the task was in recall, the
interactive executive denied a request, or
a command was issued during the initial
load of the task. The command field is the
attempted command or request; blanks
indicate no command was issued.
T h e r e i s a n e r r o r i n t h e s y n t a x o f t h e
command or in one of the parameters. The
co m mand fi eld is t he at t empt e d com m and o r
blanks if the command is longer than seven
c h a r a c t e r s o r c o n t a i n s a n i n c o r r e c t
character.
The command is not a valid K display
command or was misspelled. The command
fi e l d i s t h e a t t e m p t e d c o m m a n d .
The system is busy and cannot respond to
t h e r e q u e s t . T h e c o m m a n d fi e l d i s t h e
attempted command.
C o r r e c t t h a t s t a t e m e n t
in TC F.
Inform TAF site analyst.
I t i s n e c e s s a r y t o
recover the affected
file. AAMI will submit
an OMREC job to do this.
I n f o r m s i t e a n a l y s t t o
change the xxJ or TCF
file.
Inform site analyst to
change the xxJ or TCF
file.
I n f o r m s i t e a n a l y s t t o
change the xxJ or TCF
file.
Ensure xxJ file exists
for this data base and
try again.
Inform TAF data
administrator. Examine
x x J fi l e f o r t h e TA F
journal file entries.
None.
Correct the statement in
the TCF or inform the
TAF analyst.
Re ent er the K. DRO P or
K.DDROP command. When
the recall operation,
time-sharing request, or
initial load operation
is completed, TAF
accepts the command and
aborts the task.
Correct the command and
retry the operation.
Correct the command and
retry the operation.
Retry the operation.
TAFREC
TAF
AAMI
TAF
TAF
TAF
DMREC
TAF
TAF
TAF
SYSMSG
SYSMSG
SYSMSG
SYSMSG
• B- 1 4 60459500 C
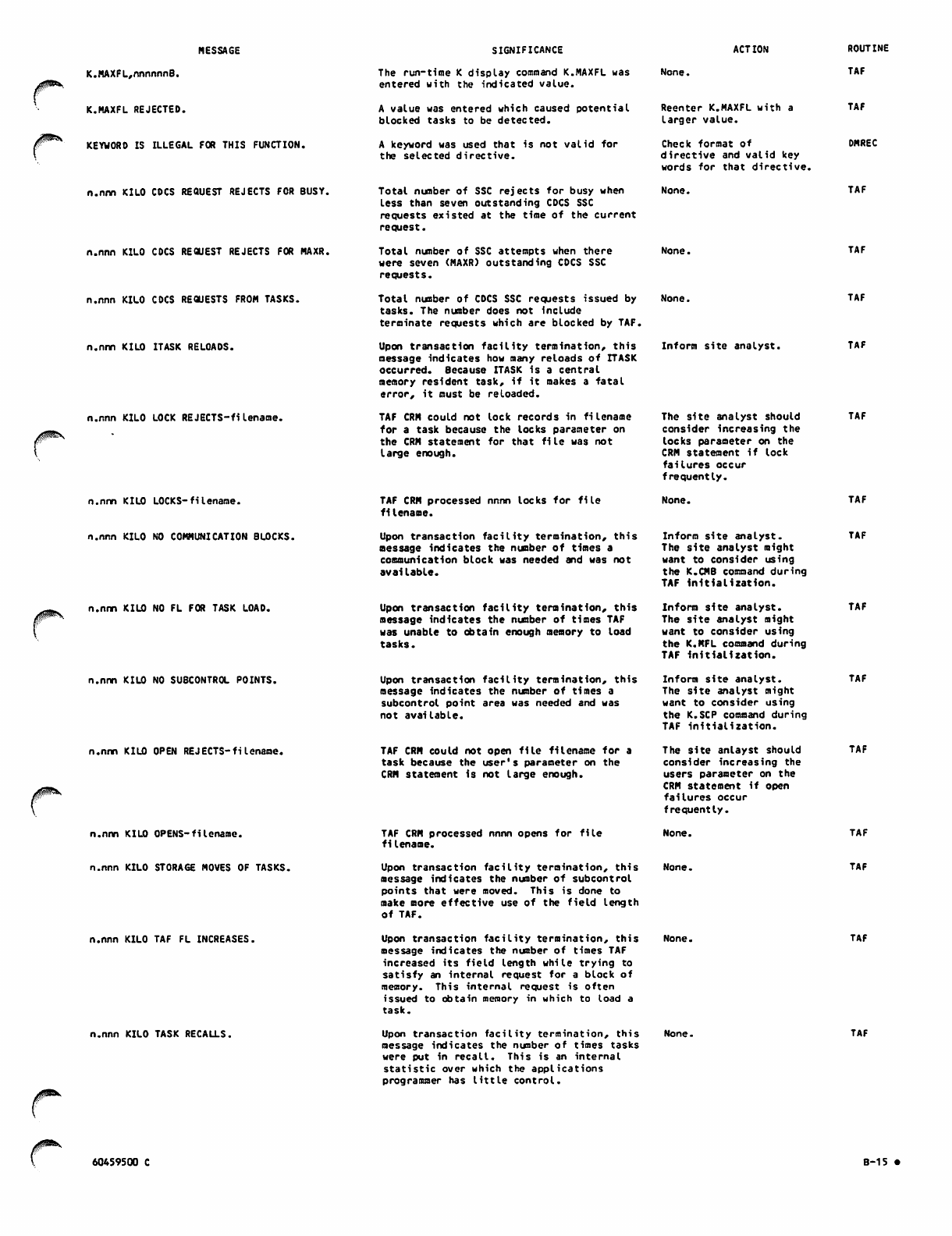
ji^s
j d P ^
MESSAGE
K.MAXFL,nnnnnnB.
K.MAXFL REJECTED.
KEYWORO IS ILLEGAL FOR THIS FUNCTION.
n.nnn KILO CDCS REQUEST REJECTS FOR BUSY.
n.nnn KILO CDCS REQUEST REJECTS FOR MAXR.
n.nnn KILO CDCS REQUESTS FROM TASKS,
n.nrm KILO ITASK RELOADS.
n.nnn KILO LOCK REJECTS-filename.
n.nnn KILO LOCKS-filename.
n.nnn KILO NO COMMUNICATION BLOCKS.
n.nm KILO NO FL FOR TASK LOAD.
n.nnn KILO NO SUBCONTROL POINTS.
n.nnn KILO OPEN REJECTS-filename.
n.nnn KILO OPENS-filename.
n.nnn KILO STORAGE MOVES OF TASKS.
n.nnn KILO TAF FL INCREASES.
SIGNIFICANCE
The run-time K display command K.MAXFL was None,
entered with the indicated value.
ACTION
n.nnn KILO TASK RECALLS.
A v a l u e w a s en t e r e d wh i c h c a u s e d p o t e n t i a l
blocked tasks to be detected.
A keyword was used that is not valid for
the selected directive.
Total number of SSC rejects for busy when
less than seven outstanding CDCS SSC
requests existed at the time of the current
request.
To t a l n u m b e r of SS C a t t e m p t s whe n t h e r e
were seven (MAXR) outstanding CDCS SSC
requests.
Total number of CDCS SSC requests issued by
tasks. The number does not include
terminate requests which are blocked by TAF.
Upon transaction facility termination, this
message indicates how many reloads of ITASK
occurred. Because ITASK is a central
memory resident task, if it makes a fatal
error, it must be reloaded.
TAF CRM could not lock records in filename
for a task because the locks parameter on
the CRM statement for that file was not
large enough.
TAF CRN processed nnnn locks for file
filename.
Upon transaction facility termination, this
message indicates the number of times a
communication block was needed and was not
available.
Upon transaction facility termination, this
message indicates the number of times TAF
was unable to obtain enough memory to load
tasks.
Upon transaction facility termination, this
message indicates the number of times a
subcontrol point area was needed and was
not available.
TAF CRM could not open file filename for a
task because the user's parameter on the
CRN statement is not large enough.
TA F C R N p rocess e d n n n n opens fo r fi l e
f1lename.
Upon transaction facility termination, this
message indicates the number of subcontrol
points that were moved. This is done to
m a k e m o r e e f f e c t i v e u s e o f t h e fi e l d l e n g t h
Of TA F.
Upon transaction facility termination, this
message indicates the number of times TAF
increased its field length while trying to
satisfy an internal request for a block of
memory. This internal request is often
issued to obtain memory in which to load a
task.
Upon transaction facility termination, this None,
message indicates the number of times tasks
were put in recall. This is an internal
statistic over which the applications
programmer has little control.
Reenter K.MAXFL with a
larger value.
Check format of
directive and valid key
w o r d s f o r t h a t d i r e c t i v e .
None.
None.
ROUTINE
TAF
TAF
OMREC
TAF
None.
Inform site analyst.
T h e s i t e a n a l y s t s h o u l d
consider increasing the
locks parameter on the
C R M st a t e m e n t i f l o c k
failures occur
frequently.
None.
Inform site analyst.
The site analyst might
want to consider using
the K.CMB command during
TAF Initialization.
Inform site analyst.
The site analyst might
want to consider using
the K.MFL command during
TAF initialization.
Inform site analyst.
The site analyst might
want to consider using
the K.SCP command during
TAF initialization.
T h e s i t e a n l a y s t s h o u l d
consider increasing the
users parameter on the
CRM statement if open
failures occur
frequently.
None.
None.
None.
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
60459500 C B-15 •
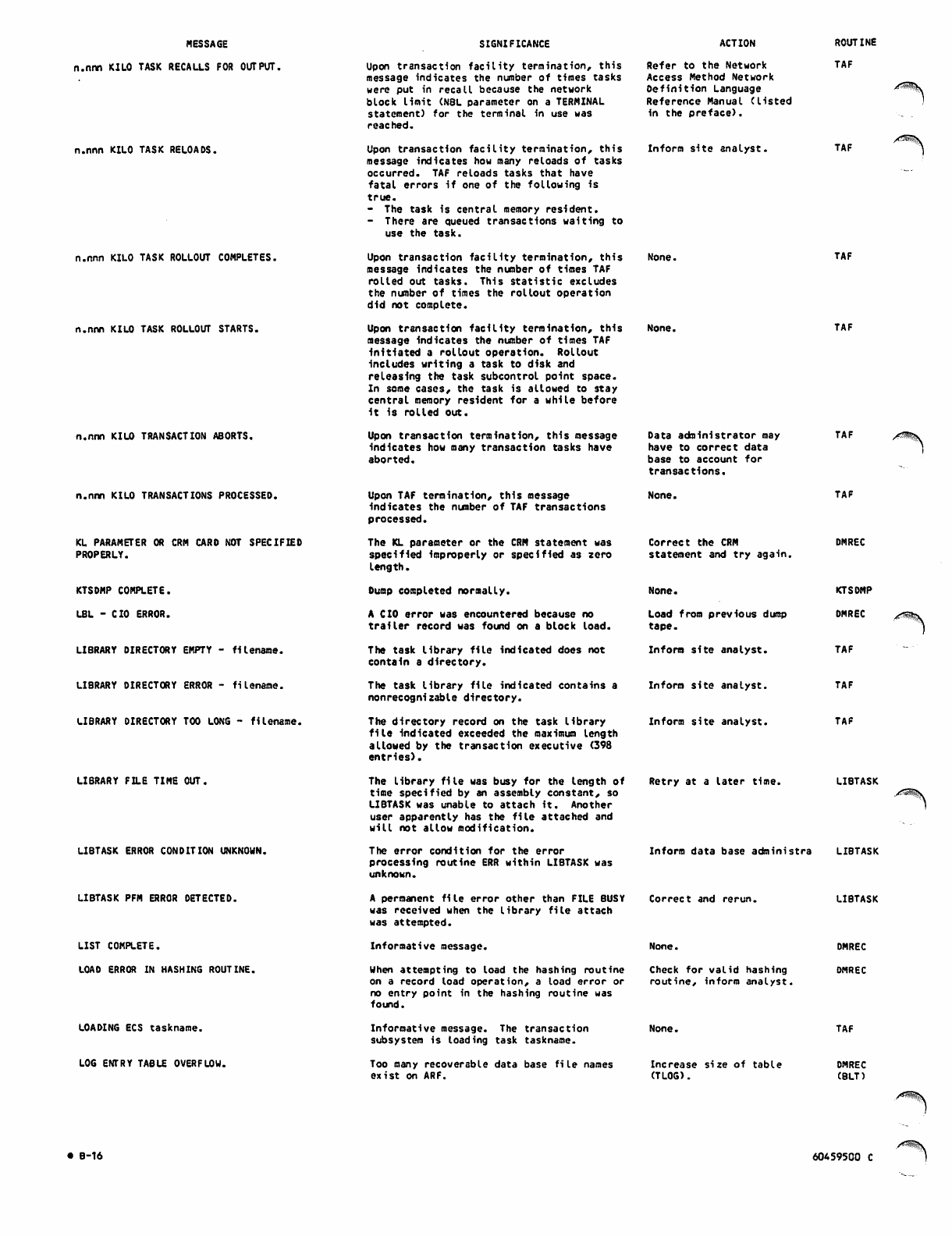
MESSAGE
n.nnn KILO TASK RECALLS FOR OUTPUT.
n.nnn KILO TASK RELOADS.
n.nnn KILO TASK ROLLOUT COMPLETES.
n.nnn KILO TASK ROLLOUT STARTS.
n.nnn KILO TRANSACTION ABORTS.
n.nnn KILO TRANSACTIONS PROCESSED.
KL PARAMETER OR CRM CARD NOT SPECIFIED
PROPERLY.
KTSDMP COMPLETE.
LBL - CIO ERROR.
LIBRARY DIRECTORY EMPTY - filename.
LIBRARY DIRECTORY ERROR - filename.
LIBRARY DIRECTORY TOO LONG - filename.
LIBRARY FILE TIME OUT.
LIBTASK ERROR CONDITION UNKNOWN.
LIBTASK PFM ERROR DETECTED.
LIST COMPLETE.
LOAD ERROR IN HASHING ROUTINE.
LOADING ECS taskname.
LOG ENTRY TABLE OVERFLOW.
SIGNIFICANCE
Upon transaction facility termination, this
message indicates the number of times tasks
were put in recall because the network
block limit (NBL parameter on a TERMINAL
statement) for the terminal in use was
reached.
Upon transaction facility termination, this
message indicates how many reloads of tasks
occurred. TAF reloads tasks that have
fatal errors if one of the following is
true.
- The task is central memory resident.
- There are queued transactions waiting to
use the task.
Upon transaction facility termination, this
message indicates the number of times TAF
rolled out tasks. This statistic excludes
the number of times the rollout operation
did not complete.
Upon transaction facility termination, this
message indicates the number of times TAF
initiated a rollout operation. Rollout
includes writing a task to disk and
releasing the task subcontrol point space.
In some cases, the task is allowed to stay
central memory resident for a while before
it is rolled out.
Upon transaction termination, this message
indicates how many transaction tasks have
aborted.
Upon TAF termination, this message
indicates the number of TAF transactions
processed.
The KL parameter or the CRN statement was
specified improperly or specified as zero
length.
Dump completed normally.
A CIO error was encountered because no
trailer record was found on a block load.
The task library file Indicated does not
contain a directory.
The task library file indicated contains a
nonrecognizable directory.
The directory record on the task library
file Indicated exceeded the maximum length
allowed by the transaction executive (398
entries).
The library file was busy for the length of
time specified by an assembly constant, so
LIBTASK was unable to attach it. Another
user apparently has the file attached and
will not allow modification.
The error condition for the error
processing routine ERR within LIBTASK was
unknown.
A permanent file error other than FILE BUSY
was received when the library file attach
was attempted.
Informative message.
When attempting to load the hashing routine
on a record load operation, a load error or
no entry point in the hashing routine was
found.
Informative message. The transaction
subsystem is loading task taskname.
Too many recoverable data base file names
exist on ARF.
ACTION
Refer to the Network
Access Method Network
Definition Language
Reference Manual (listed
in the preface).
Inform site analyst.
ROUTINE
TAF
TAF /^^\
None.
None.
TAF
TAF
Data administrator may
have to correct data
base to account for
transactions.
None.
Correct the CRM
statement and try again.
None.
Load from previous dump
tape.
Inform site analyst.
Inform site analyst.
Inform site analyst.
Retry at a later time.
Inform data base administra
Correct and rerun.
None.
Check for valid hashing
routine, inform analyst.
None.
Increase size of table
(TLOG).
TAF
TAF
DMREC
KTSDMP
DMREC
TAF
TAF
TAF
LIBTASK
LIBTASK
LIBTASK
DMREC
OMREC
TAF
OMREC
(8LT)
• B-16 60459500 C 1
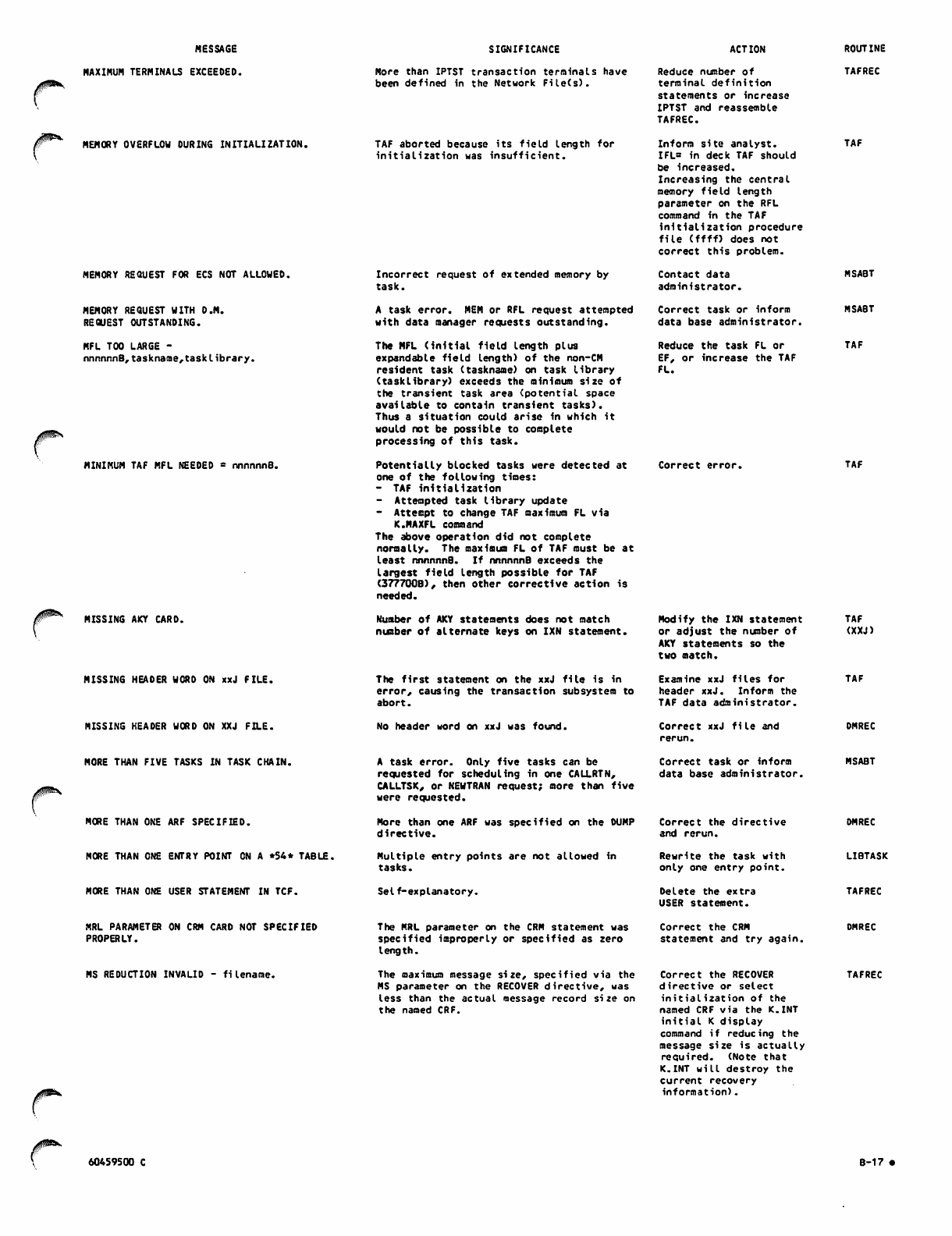
0^^
MESSAGE
MAXIMUM TERMINALS EXCEEDED.
MEMORY OVERFLOW DURING INITIALIZATION.
MEMORY REQUEST FOR ECS NOT ALLOWED.
MEMORY REQUEST WITH D.M.
REQUEST OUTSTANDING.
NFL TOO LARGE -
nnnnnnB,taskname,task library.
MINIMUM TAF MFL NEEDED = nnnnnnB.
J^v
yf$$ft\
MISSING AKY CARD.
MISSING HEADER WORD ON xxJ FILE.
MISSING HEAOER WORD ON XXJ FILE.
MORE THAN FIVE TASKS IN TASK CHAIN.
MORE THAN ONE ARF SPECIFIED.
MORE THAN ONE ENTRY POINT ON A *54* TABLE.
MORE THAN ONE USER STATEMENT IN TCF.
MRL PARAMETER ON CRM CARD NOT SPECIFIED
PROPERLY.
NS REDUCTION INVALID - filename.
SIGNIFICANCE
More than IPTST transaction terminals have
been defined in the Network File(s).
TAF aborted because its field length for
initialization was insufficient.
Incorrect request of extended memory by
task.
A task error. MEM or RFL request attempted
with data manager requests outstanding.
The MFL (initial field length plus
expandable field length) of the non-CN
resident task (taskname) on task library
(tasklibrary) exceeds the minimum size of
the transient task area (potential space
available to contain transient tasks).
Thus a situation could arise in which it
would not be possible to complete
processing of this task.
Potentially blocked tasks were detected at
one of the following times:
- TAF initialization
- Attempted task library update
- Attempt to change TAF maximum FL via
K.MAXFL command
The above operation did not complete
normally. The maximum FL of TAF must be at
least nnnnnnB. If nnnnnnB exceeds the
largest field length possible for TAF
(377700B), then other corrective action is
needed.
Number of AKY statements does not match
number of alternate keys on IXN statement.
The first statement on the xxJ file is in
error, causing the transaction subsystem to
abort.
No header word on xxJ was found.
A task error. Only five tasks can be
requested for scheduling in one CALLRTN,
CALLTSK, or NEWTRAN request; more than five
were requested.
More than one ARF was specified on the DUMP
directive.
Multiple entry points are not allowed in
tasks.
Self-explanatory.
The MRL parameter on the CRM statement was
specified improperly or specified as zero
length.
The maximum message size, specified via the
MS parameter on the RECOVER directive, was
less than the actual message record size on
the named CRF.
ACTION
Reduce number of
terminal definition
statements or increase
IPTST and reassemble
TAFREC.
Inform site analyst.
IFL- in deck TAF should
be increased.
Increasing the central
memory field length
parameter on the RFL
command in the TAF
initialization procedure
fi l e ( f f f f ) d o e s n o t
correct this problem.
Contact data
administrator.
Correct task or inform
data base administrator.
Reduce the task FL or
EF, or increase the TAF
FL.
Correct error.
Nod ify the IXN statement
or adjust the number of
AKY statements so the
two match.
Examine xxJ files for
header xxJ. Inform the
TAF data administrator.
Correct xxJ file and
rerun.
Correct task or inform
data base administrator.
Correct the directive
and rerun.
Rewrite the task with
only one entry point.
Delete the extra
USER statement.
Correct the CRN
statement and try again.
Correct the RECOVER
directive or select
initialization of the
named CRF via the K.INT
initial K display
command if reducing the
message size is actually
required. (Note that
K.INT will destroy the
current recovery
information).
ROUTINE
TAFREC
TAF
MSABT
MSABT
TAF
TAF
TAF
(XXJ)
TAF
DMREC
MSABT
DMREC
LIBTASK
TAFREC
DMREC
TAFREC
/0^~ 60459500 C B-17 •

MESSAGE
MSABT CALL ERROR.
NAKY PARAMETER ON THE IXN CARD NOT SPECIFIED
PROPERLY.
NAM ERROR - ILLOGICAL ABT.
NAM ERROR - INCORRECT ABH.
NAM FUNCTION NOT FOUND.
NAM LOGICAL ERROR.
NAM NOT AVAILABLE.
NAM PHYSICAL ERROR EC=ec.
NAM REJECT.
NEED AT LEAST xx SUBCONTROL POINTS.
NETOFF COMPLETE.
NETON COMPLETE.
NETWORK FILE NOT FOUND - filename.
NETWORK SHUT DOWN DETECTED.
NM REDUCTION INVALID - filename.
NO ACCOUNT/USER CARD IN xxJ FILE.
NO ACCOUNT/USER CARD ON XXJ FILE.
NO ALTERNATE KEY SPECIFIED ON IXN CARD.
NO ARF DUMP ENTRIES - DUMP IGNORED.
NO ARF DUMP ENTRIES IN DIRECTORY.
SIGNIFICANCE
MSABT was called with an incorrect error
code.
The NAKY parameter is not specified
properly or of 2ero length.
The application block type (ABT) sent to
TAF by NAM is unrecognizable.
The application block header (ABH) sent to
TAF by NAM is unrecognizable.
TAF received a supervisory message from NAM
which had an unrecognizable primary or
secondary function code.
NAM sent TAF a message out of order or an
unrecognizable message.
Informative message indicating that TAF is
currently at a control point but NAM is
not. TAF transactions can be initiated
from batch only, or TAF-CRM data bases may
be accessed from batch or interactive jobs.
NAM has detected a physical error indicated
by error code ec.
During login processing, NAM rejected the
terminal.
There are more CN resident tasks defined
than subcontrol points. If non-CM resident
tasks exist, there must be at least one
more subcontrol point than there are CN
resident tasks.
Informative message indicating that TAF is
no longer communicating with NAN. NAN
initiated shutdown procedures prior to loss
of communications.
Informative message indicating that TAF is
communicating with NAN.
The network description file, NCTFI, could
not be found.
Self-explanatory.
The maximum number of user messages,
specified by the NM parameter on the
RECOVER directive, was less than the actual
number of user messages on the named CRF.
The USER statement in the xxJ file is not
present, causing the transaction subsystem
to abort.
No user statement exists on the xxJ file.
Self-explanatory.
When trying to build directory entries for
an ARF dump function, no ARF file was found.
A search of the directory for the targeted
VSNs of ARF tapes was unsuccessful.
ACTION
Inform data base
administrator.
Correct the IXN
statement and try again.
Contact Central Software
Support.
Contact Central Software
Support.
Contact Central Software
Support.
Contact Central Software
Support.
Bring NAM to a control
point, if desired.
Refer to the NAM
Reference Manual for the
meaning of this error
code.
Inform site analyst.
Reinitialize the
transaction executive
and assign more
subcontrol points, or
reduce the number of CM
resident tasks.
When NAN is available,
the central site console
operator command K.NAMON
can be used to resume
communications between
TAF and NAM.
None.
Check that correct
parameters were
specified on the NETWORK
directive corresponding
to filename.
None.
Correct the RECOVER
directive or select
initialization of the
named CRF via the K.INT
initial K display
command if reducing the
number of user messages
is actually required.
(Note that K.INT will
destroy the current
recovery information).
Add USER statement in
xxJ file. Inform the
TAF data administrator.
Correct the xxJ file and
rerun.
Correct the IXN
statement and try again.
Include ARF file name on
dump.
Check time and data or
VSN used to delineate
update.
ROUTINE
MSABT
DMREC
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAF
TAFREC
TAF
TAFREC
/ s ^ v
TAF
DMREC
(CXJ)
DMREC
DMREC
DMREC
• 8-18 60459500 C 1
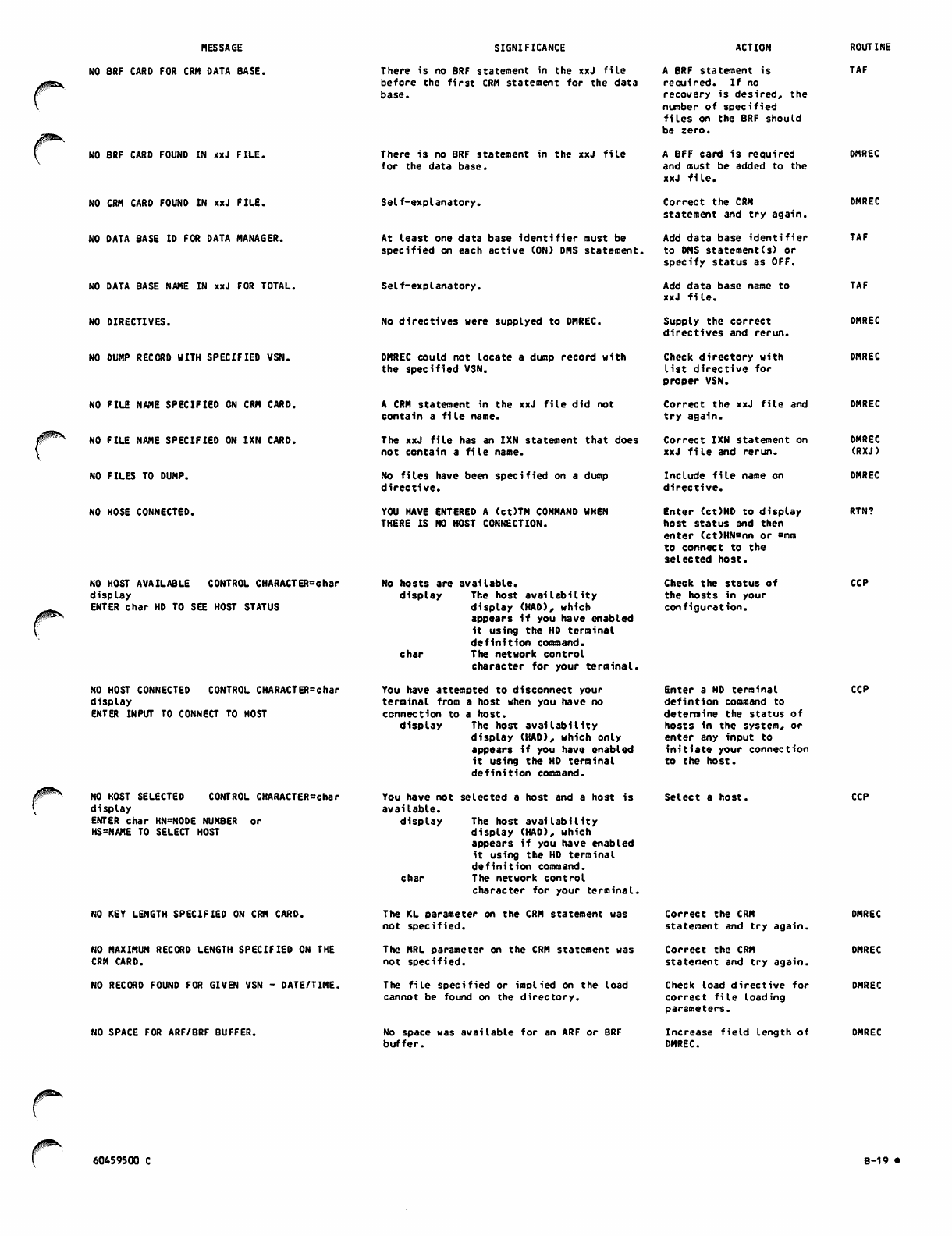
0r*«
NESSAGE
NO 8RF CARD FOR CRN DATA BASE.
NO BRF CARD FOUND IN xxJ FILE.
SIGNIFICANCE
There is no BRF statement in the xxJ file
before the first CRM statement for the data
base.
There is no BRF statement in the xxJ file
for the data base.
ACTION
A BRF statement is
r e q u i r e d . I f n o
recovery is desired, the
number of specified
files on the BRF should
be zero.
A BFF card is required
and must be added to the
xxJ file.
ROUTINE
TAF
DMREC
/^^
NO CRM CARD FOUND IN xxJ FILE.
NO DATA BASE ID FOR DATA MANAGER.
NO DATA BASE NAME IN xxJ FOR TOTAL.
NO DIRECTIVES.
NO DUMP RECORD WITH SPECIFIED VSN.
NO FILE NAME SPECIFIEO ON CRM CARD.
NO FILE NAME SPECIFIED ON IXN CARD.
Self-explanatory.
A t l e a s t o n e d a t a b a s e i d e n t i fi e r m u s t b e
s p e c i fi e d o n ea c h a c t i ve ( O N ) D M S s t a t e m e n t .
Self-explanatory.
No directives were supplyed to DMREC.
DMREC could not locate a dump record with
the specified VSN.
A C R M s t a t e m e n t in t h e x x J fi l e di d n o t
c o n t a i n a fi l e n a m e .
T h e x x J fi l e h a s a n I X N s t a t e m e n t th a t d o e s
not contain a file name.
Correct the CRN
statement and try again.
Add data base identifier
to DNS statement(s) or
s p e c i f y s t a t u s a s O F F.
Add data base name to
xxJ file.
S u p p l y t h e c o r r e c t
d i r e c t i v e s a n d r e r u n .
C h e c k d i r e c t o r y w i t h
list directive for
pro p e r V S N .
Correct the xxJ file and
try again.
Correct IXN statement on
xxJ file and rerun.
DMREC
TAF
DNREC
DMREC
DNREC
DMREC
(RXJ)
NO FILES TO DUMP. No files have been specified on a dump
directive.
Include file name on
directive.
DMREC
NO HOSE CONNECTED.
NO HOST AVAILABLE CONTROL CHARACTERShar
display
ENTER char HD TO SEE HOST STATUS
NO HOST CONNECTED CONTROL CHARACTERS har
display
ENTER INPUT TO CONNECT TO HOST
NO HOST SELECTED CONTROL CHARACTERshar
display
ENTER char HN=NOD6 NUMBER or
HS=NAME TO SELECT HOST
NO KEY LENGTH SPECIFIED ON CRM CARD.
NO MAXIMUM RECORD LENGTH SPECIFIED ON THE
CRM CARD.
NO RECORD FOUND FOR GIVEN VSN - DATE/TIME.
NO SPACE FOR ARF/BRF BUFFER.
YOU HAVE ENTERED A (ct)TM COMMAND WHEN
THERE IS NO HOST CONNECTION.
No hosts are available.
display The host availability
display (HAD), which
appears if you have enabled
it using the HD terminal
definition command.
char The network control
c h a r a c t e r f o r y o u r t e r m i n a l .
Yo u h a v e a t t e m p t e d t o d i s c o n n e c t y o u r
terminal from a host when you have no
connection to a host.
display The host availability
display (HAD), which only
appears if you have enabled
it using the HD terminal
definition command.
You have not selected a host and a host is
available.
display The host availability
display (HAD), which
appears if you have enabled
i t u s i n g t h e H D t e r m i n a l
definition command,
char The network control
c h a r a c t e r f o r y o u r t e r m i n a l .
The KL parameter on the CRM statement was
not specified.
The MRL parameter on the CRM statement was
not specified.
The file specified or implied on the load
cannot be found on the directory.
No space was available for an ARF or BRF
buffer.
Enter (ct)HD to display
host status and then
enter (ct)HN=nn or =mm
t o c o n n e c t t o t h e
selected host.
Check the status of
the hosts in your
configuration.
Enter a HD terminal
d e fi n t i o n c o m m a n d t o
determine the status of
h o s t s i n t h e s y s t e m , o r
enter any input to
initiate your connection
to the host.
Select a host.
Correct the CRM
statement and try again.
Correct the CRN
statement and try again.
Check load directive for
correct file loading
parameters.
Increase field length of
ONREC.
RTN?
CCP
CCP
CCP
DNREC
DNREC
DMREC
DMREC
60459500 C B-19 •
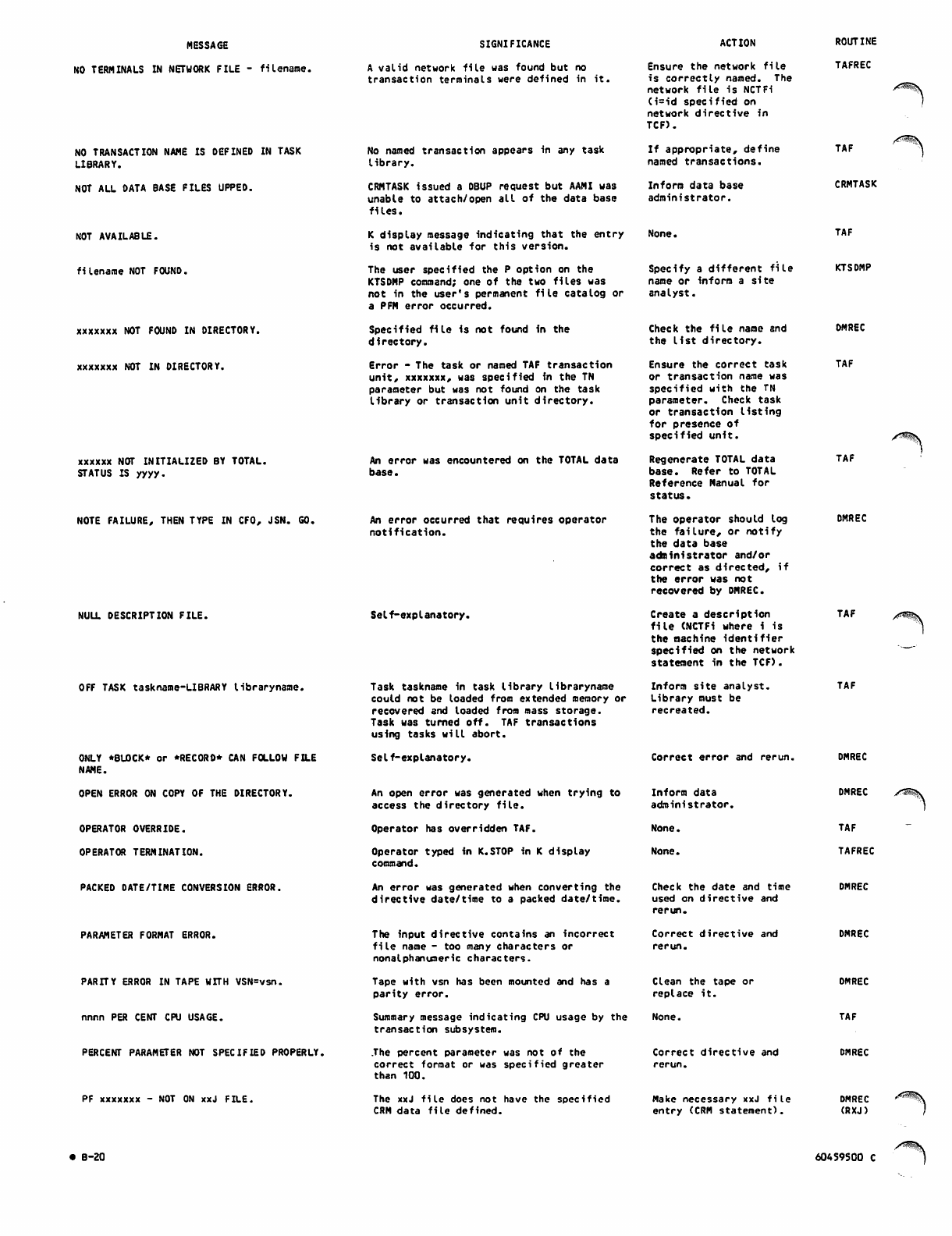
MESSAGE
NO TERMINALS IN NETWORK FILE - filename.
NO TRANSACTION NAME IS DEFINED IN TASK
LIBRARY.
NOT ALL DATA BASE FILES UPPED.
NOT AVAILA8LE.
filename NOT FOUND.
xxxxxxx NOT FOUND IN DIRECTORY,
xxxxxxx NOT IN DIRECTORY.
xxxxxx NOT INITIALIZED BY TOTAL.
STATUS IS yyyy.
NOTE FAILURE, THEN TYPE IN CFO, JSN. GO.
NULL DESCRIPTION FILE.
OFF TASK taskname-LIBRARY libraryname.
ONLY *8L0CK* or *RECORD* CAN FOLLOW FILE
NAME.
OPEN ERROR ON COPY OF THE DIRECTORY.
OPERATOR OVERRIDE.
OPERATOR TERMINATION.
PACKED OATE/TIME CONVERSION ERROR.
SIGNIFICANCE
A valid network file was found but no
transaction terminals were defined in
No named transaction appears in any task
library.
CRMTASK issued a DBUP request but AAMI was
unable to attach/open all of the data base
files.
K display message indicating that the entry
is not available for this version.
The user specified the P option on the
KTSDMP command; one of the two files was
not in the user's permanent file catalog or
a PFM error occurred.
Specified file 1s not found in the
directory.
Error - The task or named TAF transaction
unit, xxxxxxx, was specified in the TN
parameter but was not found on the task
library or transaction u n it directory.
An error was encountered on the TOTAL data
base.
An error occurred that requires operator
notification.
Self-explanatory.
Task taskname in task library libraryname
could not be loaded from extended memory or
recovered and loaded from mass storage.
Task was turned off. TAF transactions
using tasks will abort.
Self-explanatory.
An open error was generated when trying to
access the directory file.
Operator has overridden TAF.
Operator typed in K.STOP in K display
command.
An error was generated when converting the
directive date/time to a packed date/time.
ACTION
Ensure the network file
is correctly named. The
network file is NCTFi
(i=id speci fied on
network directive in
TCF).
If appropriate, define
named transactions.
Inform data base
administrator.
None.
Specify a different file
name or inform a site
analyst.
Check the file name and
the list directory.
Ensure the correct task
or transaction name was
specified with the TN
parameter. Check task
or transaction listing
for presence of
specified unit.
Regenerate TOTAL data
base. Refer to TOTAL
Reference Manual for
status.
The operator should log
the failure, or notify
the data base
administrator and/or
cor rec t a s di rec t ed , i f
the error was not
recovered by DMREC.
Create a description
file (NCTF1 where 1 is
the machine identifier
specified on the network
statement in the TCF).
Inform site analyst.
Library must be
recreated.
Correct error and rerun.
ROUTINE
TAFREC
TAF
CRMTASK
TAF
KTSDMP
DMREC
TAF
TAF
DMREC
TAF
DMREC
S^^\
Inform data
administrator.
DMREC X*^5\
None. TAF
None. TAFREC
Check the date and time
used on directive and
rerun.
DMREC
PARAMETER FORMAT ERROR.
PARITY ERROR IN TAPE WITH VSN=vsn.
nnnn PER CENT CPU USAGE.
PERCENT PARAMETER NOT SPECIFIED PROPERLY.
PF xxxxxxx - NOT ON xxJ FILE.
The input directive contains an incorrect
file name - too many characters or
nonalphanumeric characters.
Tape with vsn has been mounted and has a
parity error.
Summary message indicating CPU usage by the
transaction subsystem.
The percent parameter was not of the
correct format or was specified greater
than 100.
The xxJ file does not have the specified
CRM data file defined.
Correct directive and
rerun.
Clean the tape or
repla c e it.
None.
Correct directive and
rerun.
Make necessary xxJ file
entry (CRN statement).
DMREC
OMREC
TAF
OMREC
DMREC
(RXJ)
,<i*!t§\
• B-20 60459500 C )
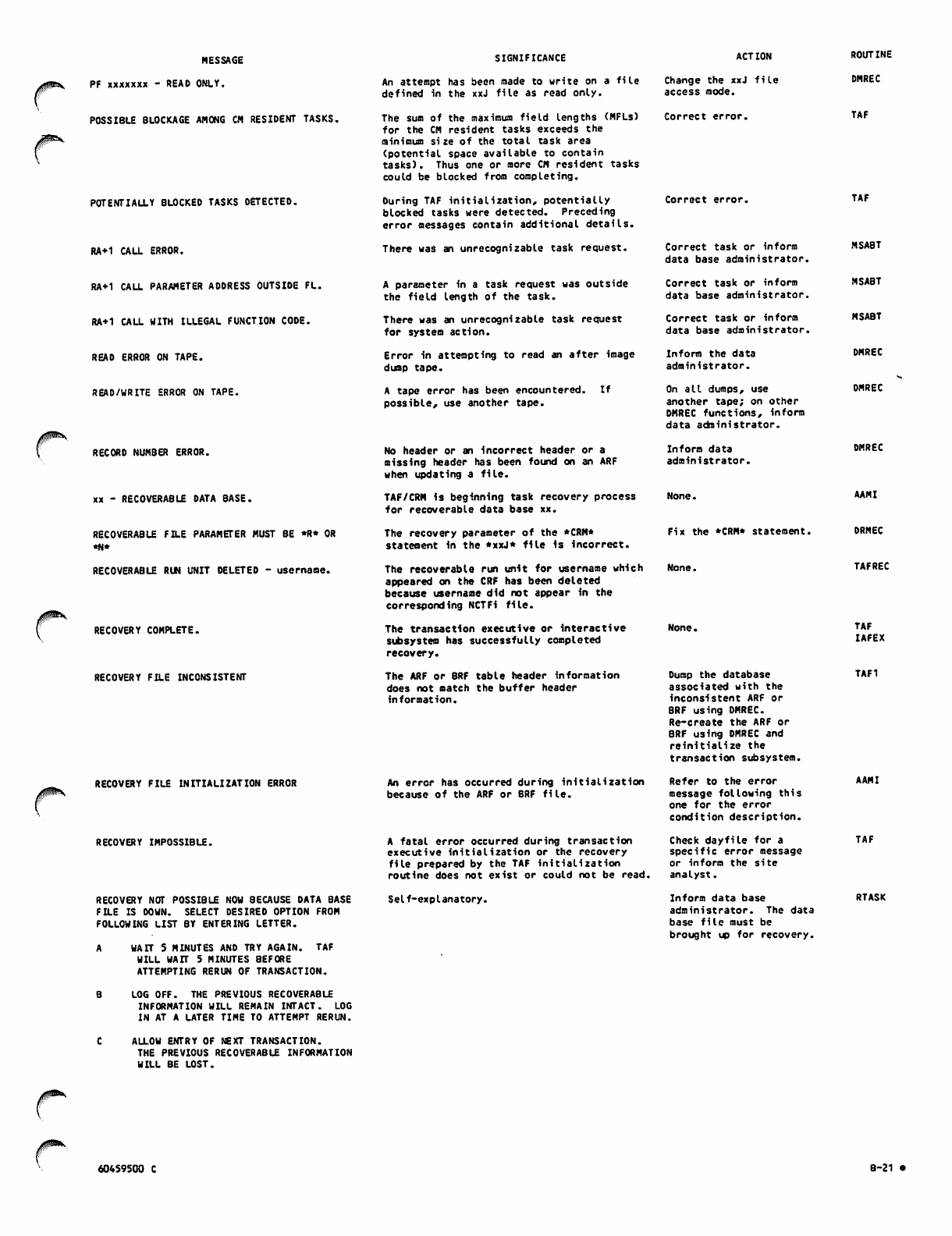
Jp^.
r
MESSAGE
PF xxxxxxx - READ ONLY.
POSSIBLE BLOCKAGE AMONG CM RESIDENT TASKS.
POTENTIALLY BLOCKED TASKS DETECTED.
RA+1 CALL ERROR.
RA+1 CALL PARAMETER AOORESS OUTSIOE FL.
RA+1 CALL WITH ILLEGAL FUNCTION CODE.
REAO ERROR ON TAPE.
READ/WRITE ERROR ON TAPE.
RECORD NUMBER ERROR.
xx - RECOVERABLE OATA 8ASE.
RECOVERABLE FILE PARAMETER MUST BE *R* OR
*N*
RECOVERABLE RUN UNIT DELETED - username.
RECOVERY COMPLETE.
RECOVERY FILE INCONSISTENT
RECOVERY FILE INITIALIZATION ERROR
RECOVERY IMPOSSIBLE.
RECOVERY NOT POSSIBLE NOW 8ECAUSE DATA BASE
FILE IS DOWN. SELECT DESIRED OPTION FROM
FOLLOWING LIST BY ENTERING LETTER.
A WA I T 5 MIN U T E S A N D TRY A G A I N . TA F
WILL WAIT 5 MINUTES BEFORE
ATTEMPTING RERUN OF TRANSACTION.
B LOG OFF. THE PREVIOUS RECOVERABLE
INFORMATION WILL REMAIN INTACT. LOG
IN AT A LATER TIME TO ATTEMPT RERUN.
C ALLOW ENTRY OF NEXT TRANSACTION.
THE PREVIOUS RECOVERABLE INFORMATION
WILL BE LOST.
SIGNIFICANCE
An attempt has been made to write on a file
d e fi n e d i n t h e x x J fi l e a s r e a d o n l y .
The sum of the maximum field lengths (MFLs)
for the CM resident tasks exceeds the
minimum size of the total task area
(potential space available to contain
tasks). Thus one or more CM resident tasks
could be blocked from completing.
During TAF initialization, potentially
blocked tasks were detected. Preceding
error messages contain additional details.
There was an unrecognizable task request.
A parameter in a task request was outside
the field length of the task.
There was an unrecognizable task request
f o r s y s t e m a c t i o n .
Error in attempting to read an after image
dump tape.
A tape error has been encountered. If
possible, use another tape.
No header or an incorrect header or a
missing he ader has been found on an A RF
when updating a file.
TAF/CRM is beginning task recovery process
for recoverable data base xx.
The recovery parameter of the *CRM*
statement in the *xxJ* file is incorrect.
The recoverable run unit for username which
appeared on the CRF has been deleted
because username did not appear in the
c o r r e s p o n d i n g N C T F i fi l e .
The transaction executive or interactive
subsystem has successfully completed
recovery.
The ARF or BRF table header information
does not match the buffer header
information.
An error has occurred during initialization
because of the ARF or BRF file.
A fatal error occurred during transaction
executive initialization or the recovery
file prepared by the TAF initialization
routine does not exist or could not be read.
Self-explanatory.
ACTION
Change the xxJ file
access mode.
Correct error.
Correct error.
Correct task or inform
data base administrator.
Correct task or inform
data base administrator.
Correct task or inform
data base administrator.
Inform the data
administrator.
On all dumps, use
another tape; on other
DMREC functions, inform
data administrator.
Inform data
administrator.
None.
Fix the *CRM* statement.
None.
None.
Dump the database
associated with the
inconsistent ARF or
BRF using DMREC.
Re-create the ARF or
BRF using DNREC and
reinitialize the
transaction subsystem.
Refer to the error
message following this
one for the error
condition description.
Check dayfile for a
specific error message
or inform the site
analyst.
Inform data base
administrator. The data
base file must be
brought up for recovery.
ROUTINE
DNREC
TAF
TAF
MSABT
MSABT
MSABT
DMREC
DMREC
DMREC
AAMI
ORMEC
TAFREC
TAF
IAFEX
TAF1
A AN I
TAF
RTASK
/P^
60459500 C B-21 •
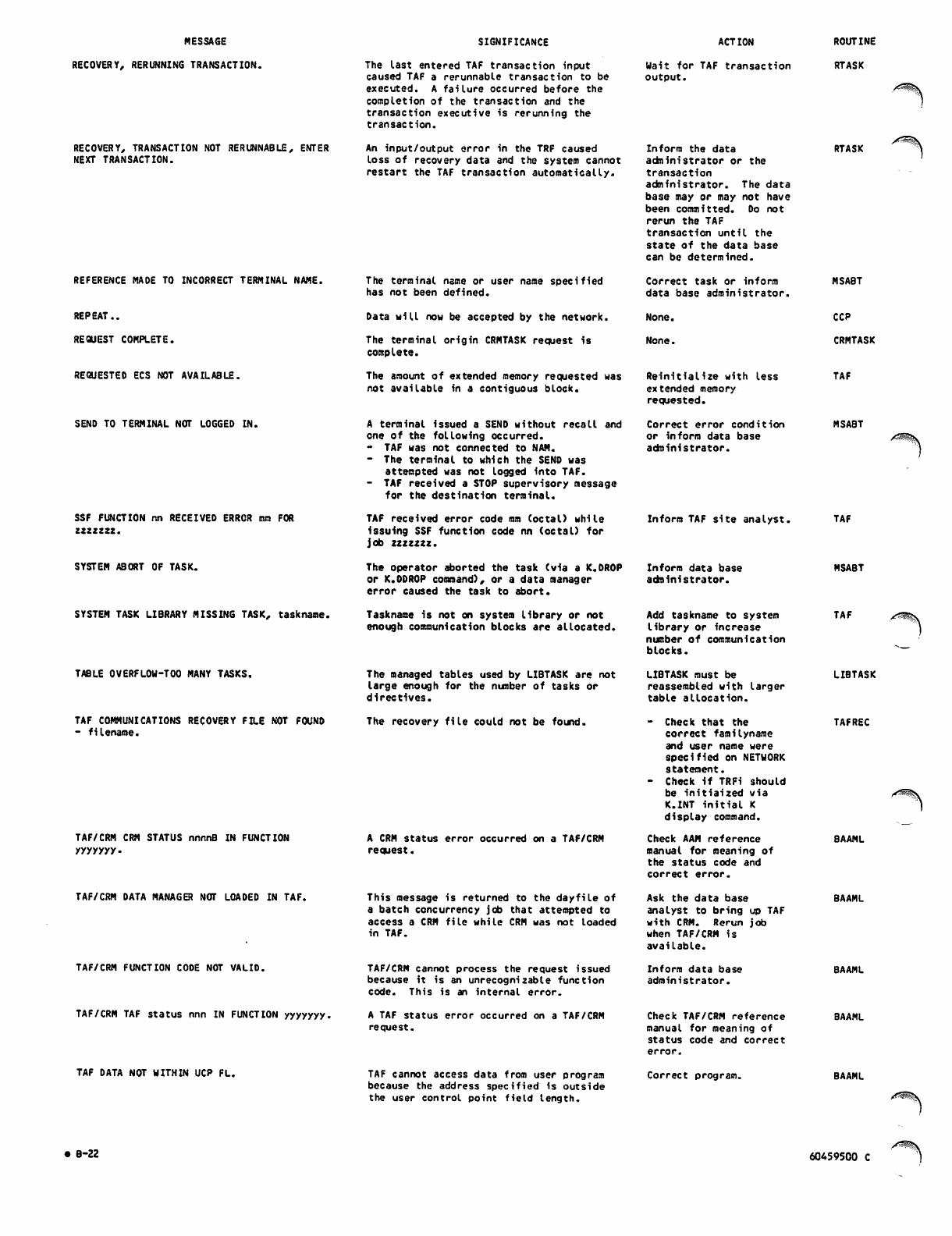
NESSAGE
RECOVERY, RERUNNING TRANSACTION.
RECOVERY, TRANSACTION NOT RERUNNABLE, ENTER
NEXT TRANSACTION.
REFERENCE MAOE TO INCORRECT TERMINAL NAME.
REPEAT..
REQUEST COMPLETE.
REQUESTEO ECS NOT AVAILABLE.
SEND TO TERMINAL NOT LOGGED IN.
SSF FUNCTION nn RECEIVED ERROR mm FOR
zzzzzzz.
SYSTEM ABORT OF TASK.
SYSTEM TASK LIBRARY MISSING TASK, taskname.
TABLE OVERFLOW-TOO MANY TASKS.
TAF COMMUNICATIONS RECOVERY FILE NOT FOUND
- filename.
TAF/CRM CRM STATUS nnnnB IN FUNCTION
yyyyyyy.
TAF/CRN DATA MANAGER NOT LOADED IN TAF.
TAF/CRM FUNCTION CODE NOT VALID.
TAF/CRM TAF status nnn IN FUNCTION yyyyyyy.
TAF DATA NOT WITHIN UCP FL.
SIGNIFICANCE
The last entered TAF transaction input
caused TAF a rerunnable transaction to be
executed. A failure occurred before the
completion of the transaction and the
transaction executive is rerunning the
transact i o n.
An input/output error in the TRF caused
loss of recovery data and the system cannot
restart the TAF transaction automatically.
The terminal name or user name specified
has not been defined.
Data will now be accepted by the network.
The terminal origin CRMTASK request is
complete.
The amount of extended memory requested was
not available in a contiguous block.
A terminal issued a SEND without recall and
one of the following occurred.
- TAF was not connected to NAN.
- The terminal to which the SEND was
attempted was not logged into TAF.
- TAF received a STOP supervisory message
for the destination terminal.
TAF received error code mm (octal) while
issuing SSF function code nn (octal) for
job zzzzzzz.
The operator aborted the task (via a K.DROP
or K.DDROP command), or a data manager
error caused the task to abort.
Taskname is not on system library or not
enough communication blocks are allocated.
The managed tables used by LIBTASK are not
large enough for the number of tasks or
directives.
The recovery file could not be found.
A CRN status error occurred on a TAF/CRM
request.
This message is returned to the dayfile of
a batch concurrency job that attempted to
access a CRM file while CRM was not loaded
in TAF.
TAF/CRM cannot process the request issued
because it is an unrecognizable function
code. This is an internal error.
A TAF status error occurred on a TAF/CRM
request.
TAF cannot access data from user program
because the address specified is outside
the user control point field length.
ACTION
Wait for TAF transaction
output.
Inform the data
administrator or the
transaction
administrator. The data
base may or may not have
been committed. Do not
rerun the TAF
transaction until the
state of the data base
can be determined.
Correct task or inform
data base administrator.
None.
None.
Reinitialize with
ex tended memory
requested.
less
Correct error condition
or inform data base
administrator.
Inform TAF site analyst.
Inform data base
administrator.
Add taskname to system
library or increase
number of communication
blocks.
LIBTASK must be
reassembled with larger
table allocation.
- Check that the
correct familyname
and user name were
specified on NETWORK
statement.
- Check if TRFi should
be initiaized via
K.INT initial K
display command.
Check AAM reference
manual for meaning of
the status code and
correct error.
Ask the data base
analyst to bring up TAF
with CRM. Rerun job
when TAF/CRN is
available.
Inform data base
administrator.
Check TAF/CRM reference
manual for meaning of
status code and correct
error.
Correct program.
ROUTINE
RTASK
RTASK
MSABT
CCP
CRMTASK
TAF
MSABT
TAF
MSABT
TAF
LIBTASK
TAFREC
8AAML
BAAML
BAAML
BAAML
BAAML
/f^^V
• 6-22 60459500 C )
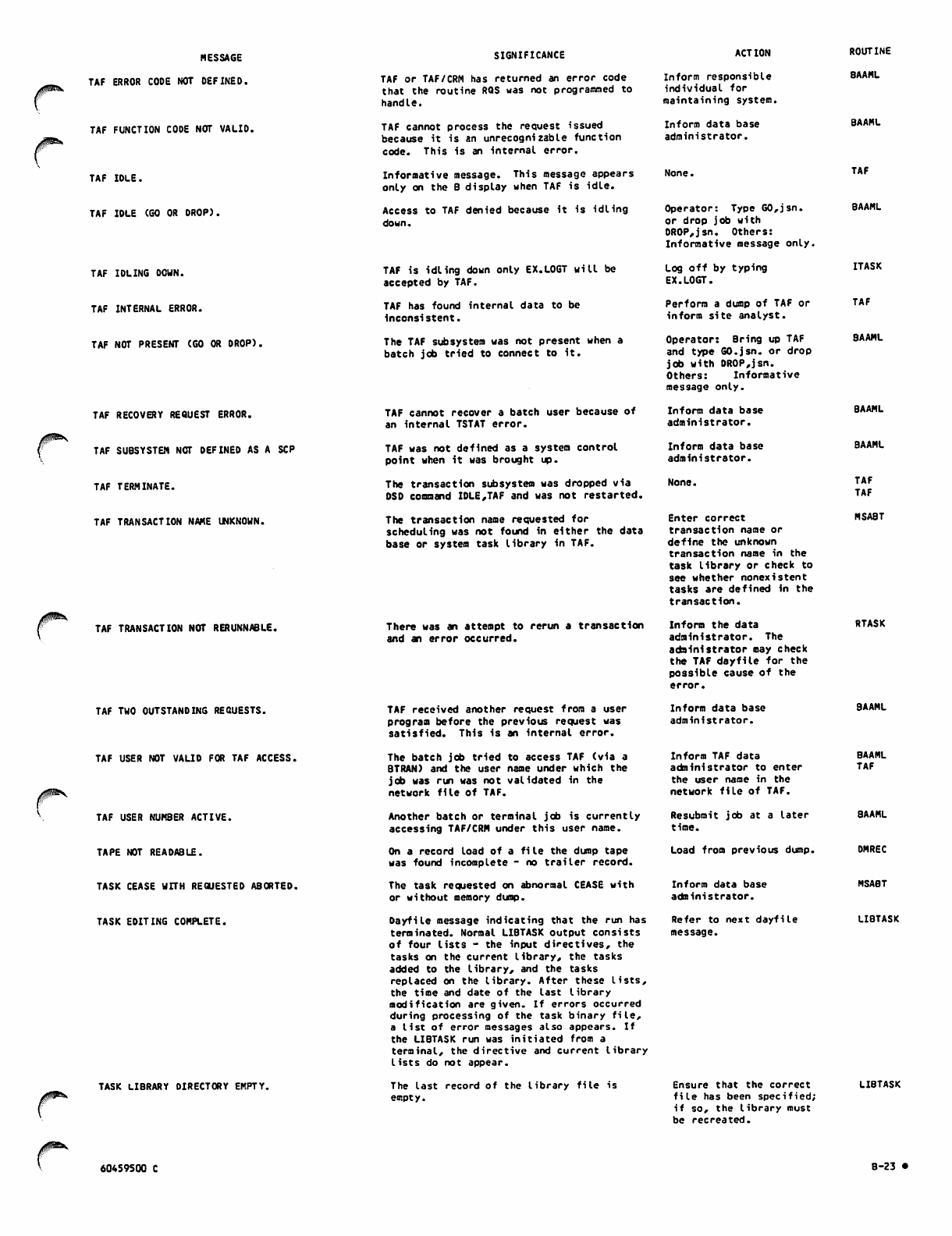
jpfifc.
MESSAGE
TAF ERROR CODE NOT DEFINED.
TAF FUNCTION CODE NOT VALID.
TAF IDLE.
TAF IDLE (GO OR DROP).
TAF IDLING DOWN.
TAF INTERNAL ERROR.
TAF NOT PRESENT (GO OR DROP).
TAF RECOVERY REQUEST ERROR.
TAF SUBSYSTEM NOT DEFINED AS A SCP
TAF TERMINATE.
TAF TRANSACTION NAME UNKNOWN.
j0^K
TAF TRANSACTION NOT RERUNNABLE.
TAF TWO OUTSTANDING REQUESTS.
TAF USER NOT VALID FOR TAF ACCESS.
TAF USER NUMBER ACTIVE.
TAPE NOT READABLE.
TASK CEASE WITH REQUESTED ABORTED.
TASK EDITING COMPLETE.
TASK LIBRARY DIRECTORY EMPTY.
604S9SO0 C
SIGNIFICANCE
TAF or TAF/CRM has returned an error code
that the routine RQS was not programmed to
handle.
TAF cannot process the request issued
because it is an unrecognizable function
code. This is an internal error.
Informative message. This message appears
only on the B display when TAF is idle.
Access to TAF denied because it is idling
down.
TAF is idling down only EX.LOGT will be
accepted by TAF.
TAF has found internal data to be
inconsistent.
The TAF subsystem was not present when a
batch job tried to connect to it.
TAF cannot recover a batch user because of
an internal TSTAT error.
TAF was not defined as a system control
point when it was brought up.
The transaction subsystem was dropped via
DSD command IDLE,TAF and was not restarted.
The transaction name requested for
scheduling was not found in either the data
base or system task library in TAF.
There was an attempt to rerun a transaction
and an error occurred.
TAF received another request from a user
program before the previous request was
satisfied. This is an internal error.
The batch job tried to access TAF (via a
BTRAN) and the user name under which the
job was run was not validated in the
network file of TAF.
Another batch or terminal job is currently
accessing TAF/CRM under this user name.
On a record load of a file the dump tape
was found incomplete - no trailer record.
The task requested on abnormal CEASE with
or without memory dump.
Dayfile message indicating that the run has
terminated. Normal LIBTASK output consists
of four lists - the input directives, the
tasks on the current library, the tasks
added to the library, and the tasks
replaced on the library. After these lists,
the time and date of the last library
modification are given. If errors occurred
during processing of the task binary file,
a list of error messages also appears. If
the LIBTASK run was initiated from a
terminal, the directive and current library
lists do not appear.
The last record of the library file is
empty.
ACTION
Inform responsible
individual for
maintaining system.
Inform data base
administrator.
None.
Operator: Type G0,jsn.
or drop job with
0ROP,jsn. Others:
Informative message only.
Log off by typing
EX. LOGT.
Perform a dump of TAF or
inform site analyst.
Operator: Bring up TAF
and type GO.jsn. or drop
job with DR0P,jsn.
Others: Informative
message only.
Inform data base
administrator.
Inform data base
administrator.
None.
Enter correct
transaction name or
define the unknown
transaction name in the
task library or check to
see whether nonexistent
tasks are defined in the
t r a n s a c t i o n .
Inform the data
administrator. The
administrator may check
the TAF dayfile for the
possible cause of the
error.
Inform data base
administrator.
Inform TAF data
administrator to enter
the user name in the
network file of TAF.
Resubmit job at a later
time.
Load from previous dump.
Inform data base
administrator.
Refer to next dayfile
message.
ROUTINE
BAANL
BAAML
TAF
BAAML
ITASK
TAF
8AAML
BAAML
BAAML
TAF
TAF
NSABT
RTASK
BAANL
BAAML
TAF
8AAML
OMREC
MSABT
LIBTASK
Ensure that the correct
file has been specified;
if so, the library must
be recreated.
LIBTASK
8-23 •
MESSAGE
TASK LIBRARY DIRECTORY EMPTY - libraryname.
TASK LIBRARY DIRECTORY ERROR - libraryname.
TASK LIBRARY DIRECTORY ERRORS.
TASK LIBRARY DIRECTORY TOO LONG.
TASK LIBRARY DIRECTORY TOO LONG
libraryname.
TASK NOT VALIDATED FOR REQUEST.
taskname - TASK RECOVERED,
taskname - TASK RECOVERY FAILED.
TASK REQUEST ARGUMENT ERROR.
TASK REQUESTED CEASE 8EF0RE DM FINISHED.
TASK TIME LIMIT.
nnn TASKS NOT LOADED INTO ECS.
TERMINAL DISABLED BY NOP.
TERMINAL NOT AVAILABLE.
TERMINAL TIMEOUT, OPTION B ASSUMED.
TERMINATION IN PROGRESS.
TLD OVERFLOW.
TN REQUIRES EITHER LO=T OR LO=X.
TOO MANY BRANCHES IN TASK CHAIN REQUESTED.
SIGNIFICANCE
The file specified as the task library
contains no recognizable directory. TAF
aborts.
Ta s k l i b r a r y l i b r a r y n a m e c o n t a i n s n o
recognizable directory. TAF aborts.
The first word of the last record on the
library file does not contain the directory
header.
T h e d i r e c t o r y i s t o o l o n g f o r t h e b u f f e r
allocated.
The length of the indicated task library
d i r e c t o r y e x c e e d s t h e l i m i t s p e c i fi e d b y
the installation parameter TLDMT.
O n e o f t h e f o l l o w i n g a c t i o n s h a s o c c u r r e d .
- The terminal operator initiated a TAF
t r a n s a c t i o n w h i c h t r i e d t o p e r f o r m a n
a c t i o n a s s o c i a t e d w i t h a d a t a b a s e f o r
which the terminal was not validated.
- A NEWTRAN request was issued by a task
not in the system task library (TASKLIB),
The specified task has been recovered.
The specified task recovery attempt has
failed.
A parameter error occurred in a request.
T h e ta s k r e q u e s t e d t o e n d b e f o r e t h e d a t a
manager completed all outstanding requests.
The task exceeded n time slices. The
length of the time slice is set by an
installation parameter. The number of time
slices, n, allowed for the execution of a
ta s k c an b e c h an g e d wi t h a t a s k I T L r e qu e s t.
An insufficient amount of extended memory
was available to load all tasks. The nnn
field is the number of tasks not loaded.
The network operator has disabled your
terminal. No further input is possible.
A n i n t e r a c t i v e u s e r h a s a t t e m p t e d t o l o g i n
with recovery outstanding on a batch
concurrency or BTRAN user
Sel f-explanatory.
The interactive subsystem has begun
dump/disconnect/recovery procedures due to
an abort or termination condition.
S p a c e i s r e s e r v e d a t i n i t i a l i z a t i o n t o
dynamically add tasks to the TAF resident
copy of each task directory. The number of
tasks is limited (default is 10) by the
installation parameter TLDL. This message
i n d i c a t e s t h a t m o r e t a s k s t h a n a l l o w e d ha v e
been added since the most recent TAF
initialization. The extra tasks will be
ignored by TAF until it is reinitialized.
The TN parameter was specified on the
LIBTASK command without a corresponding
L0=T or L0=X parameter.
Only three branches are allowed in the task
c h a i n ; mo r e t h a n t h r e e w e r e re q u e s t e d .
ACTION
Inform site analyst.
Task library libraryname
must be corrected and
TAF reinitialized.
Inform site analyst.
Task library must be
corrected.
Correct and rerun.
This may be altered by
changing an assembly
constant.
Si2e of task library
must be reduced or TAF
and LIBTASK must be
reassembled with TLDNT
increased.
Perform the appropriate
action.
- Inform the data
adm inistrat or. Set
up the terminal
name in the network
file to use the data
base. The system
data base (SY) may be
used.
- Put the task on
TASKLIB.
None.
Inform data
administrator.
Correct task or inform
data base administrator.
Correct task or inform
data base administrator.
Increase time slices or
inform data base
administrator.
Check extended memory
requested and
reinitialize with more
extended memory if
appropriate.
None.
Recover the batch
concurrency or BTRAN
user.
None.
None.
None.
ROUTINE
TAF
TAF
LIBTASK
LIBTASK
TAF
MSABT
AAMI
AAMI
MSABT
MSABT
MSABT
TAF
CCP
RTASK
RTASK
TAF
IAFEX
TAF
Specify correct
combination of list
option parameters.
Correct task or inform
data base administrator.
LIBTASK
MSABT
• B-24 60459500 C
MESSAGE
TOO MANY DATA BASE NAMES.
TOO MANY FILE NAMES OR VSN-S SPECIFIED.
TOO MANY FILES IN TOTAL DATA BASE.
TOO MANY NEW TRANSACTIONS ON TRANSACTION
DIRECTORY - filename.
TOO MANY RA+1 CALLS.
TOO MANY TAF JOURNAL FILES IN xxJ FILE.
TOTAL DATA MANAGER NOT LOADED.
TOTAL DATA MANAGER SUCCESSFULLY LOADED.
TOTAL DID NOT RECOVER PROPERLY
STATUS IS yyyy.
TRAN. SEQ. zzzzzzzzB with ID xxxxx MIGHT BE
BAD.
TRANSACTION DIRECTORY EMPTY.
TRANSACTION DIRECTORY EMPTY - filename.
TRANSACTION DIRECTORY ERROR.
TRANSACTION DIRECTORY ERROR - filename.
TRANSACTION DIRECTORY TOO LONG - filename.
TRANSACTION DIRECTORY TOO LONG.
TRANSACTION SESSION ENDED.
TT OPTION REQUIRES USER NUMBER.
UN=username NOT VALID ON FM=family.
UNABLE TO ATTACH TOTAL BINARIES.
SIGNIFICANCE
The number of data base names associated
wi t h one d a ta ma n ager v ia DM S s tat e ment s
exceeds the value of MAXDB.
The VSN or file name limit was exceeded on
a directive.
Self-explanatory.
Informative message. During an on line
update of a task library, TAF detected that
the transaction directory (TRD) was longer
than allowed (the number of new additions
exceeds installation parameter TRDMN).
Excess named TAF transaction definitions
will be discarded.
Only n monitor requests are allowed; more
than n occurred, where n 1s an assembly
constant.
More than three TAF journal files per data
base were specified, causing the
transaction subsystem to abort.
TOTAL data manager was called but has not
been loaded.
Self-explanatory.
An error status yyyy was returned on a
TOTAL FINAL call. Refer to Diagnostics in
the TOTAL Reference Manual for yyyy.
A BRF disk error has occurred and the
transaction sequence numbers listed in the
dayfile might contain errors.
Probable corruption of task library file.
Probable corruption of task library file.
Probable corruption of task library file.
Probable corruption of task library file.
Error — Too many transaction definitions
exist in the transaction directory.
Too many transactions exist in
named-transaction directory.
Option B was selected and TAF logged the
terminal off leaving the previous
recoverable inforraaton intact.
When updating a task library on-line (TT
option is specified on LIBTASK command),
the user name must be specified prior to
the LIBTASK command so the library
associated with that user name can be found.
Username on the specified familyname is
not valid. The user name and familyname
may not be defined or are incorrect in xxJ
fi l e .
File of TOTAL binaries is not under the
user index of the transaction subsystem or
a PFM error occurred.
ACTION
Decrease the number of
data base names
associated with the data
manager.
Check the installation
parameters TVSNL and
TDFNL for maximums.
Reduce the number of
entries in the TCF file
or increase TMAXFIL.
None. When TAF is next
initialized, the new
transaction definitions
will be included.
Inform site analyst.
Possibly a task is in a
loop.
Examine xxJ file for
xxJOR entries. Inform
the TAF data
administrator.
Inform data base
administrator.
None.
library. Make sure the
number of transactions
does not exceed
Installation parameter
TRDMT or reassemble TAF
and LIBTASK increasing
the size of the
installation parameter
TRDMT.
Either reduce number of
named-transactions
declared or contact TAF
site analyst.
Log in at a later time
to attempt rerun.
Specify user name via
USER or CHARGE command
before LI8TASK command
and rerun job.
Inform site analyst.
Correct error and
reinitialize transaction
executive, or inform
site analyst.
ROUTINE
TAF
DMREC
TAF
TAF
MSABT
TAF
MSABT
TAF
Correct error and TAF
reinitialize transaction TAF
executive.
Inform data base DMREC
administrator of the REC
error.
Regenerate task library. LIBTASK
Regenerate task library. TAF
Regenerate task library. LIBTASK
Regenerate task library. TAF
Regenerate task LIBTASK
LIBTASK
RTASK
LIBTASK
TAF
60459500 C B-25 •
MESSAGE
UNABLE TO ATTACH TOTAL D8M0D BINARIES.
UNKNOWN FILE FORMAT.
UNKNOWN NAMED TRANSACTION UNIT REQUESTED FOR
SCHEDULING.
UNRECOGNIZABLE CIO ERROR CODE.
UNRECOGNIZABLE HEADER TYPE.
USER STATEMENT DOES NOT APPEAR IN TCF.
USER STATEMENT NOT VALID ON FAMILY.
VALID LO OPTIONS ARE LO, LO=A, LO=T or LO=X.
VALID OPTIONS ARE A, B, OR C.
cmd VALUE INAPPROPRIATE
VSN ALREADY EXISTS.
VSN - xxxxxx ALREADY IN DIRECTORY.
VSN AND OATE/TIME CANNOT CO-EXIST ON LOAD
DIRECTIVE.
VSN ASSIGNED DOES NOT MATCH VSN REQUESTED.
VSN DOES NOT EXIST.
VSN IS NOT FIRST REEL.
VSN OR DATE/TIME NOT SPECIFIED.
VSN TABLE OVERFLOW.
W A I T. .
WAIT ING
WAITINP FROM MULTI QUEUED TASK.
WRONG ENTRY WHILE READING VSN ENTRIES.
WRONG VSN USED.
ZZdbAnn - ACTIVE ARF.
• 8-26
SIGNIFICANCE
One or more of the DBMOD files listed on
the TOTAL DMS statement in the TCF file
could not be attached under the user name
of the transaction subsystem or a PFM error
occurred.
There is a logical error In the structure
of the input file. It does not conform to
the established format rules.
The transaction name requested for
scheduling was incorrect.
Self-explanatory.
When interpreting ARF after image header
types, one has been found incorrect.
Self-explanatory.
The user name specified by the USER
statement is not valid on the family.
The LO parameter was specified on the
LIBTASK command with an incorrect list
option.
The option entered was not A, 8, or C.
The value you specified in the terminal
definition command cmd is not appropriate
for your terminal.
When attempting to use the edit/add
directives, the VSN specified was found to
already exist on the directory.
The VSN supplied for this operation was
found to already exist on the directory.
On a load directive the date/time keywords
cannot be used with VSN keyword.
The VSN assigned as a result of a DMREC ADO
subdirective does not agree with the VSN
specified on the subdirective.
When attempting to access a directory, the
specified VSN was not found on the
directory.
When attempting to modify a directory, the
specified VSN was not the first reel of th
s e t . the
When attempting to delete directory
entries, no VSN or date/time was specified.
Too many VSN entries were encountered for
this directive.
The network is unable to accept any further
data from your terminal. Oata that was
entered is discarded. This is normally a
temporary situation caused by buffer
shortages in the host or the network.
Option A was selected and TAF will wait 5
minutes before attempting a rerun of the
transact i o n.
A WAITINP request was issued by a task that
was scheduled to process more than one TAF
transaction or by a task that was called
with return.
The VSN record read from the directory has
an incorrect format.
Either the wrong VSN was used or no header
was found on ARF.
File ZZdbAnn is the active image recovery
file for data base db.
ACTION
Correct error and
reinitialize transaction
executive, or inform
site analyst.
None.
Enter the correct
transaction name.
Inform site analyst.
Inform data
administrator.
Add a USER statement to
the TCF.
Validate user on
specified family or
correct USER statement.
Specify one of the
following valid list
options LO, L0=A, LO=T
or LO=X.
Reenter a valid option.
Choose an appropriate
value (refer to appendix
J).
Continue processing.
Try another VSN.
Correct the directive
and rerun.
Correct the VSN conflict.
List the directory for
further Information.
Specify the first reel
of the multireel set.
Specify VSN or date/time
and rerun.
Check directive and
increase TVSN size if
necessary.
Wait for the REPEAT.,
message.
None.
Inform data
administrator.
Make sure the correct
ARF is being used and
retry.
Informative message.
ROUTINE
TAF
KTSDMP
ITASK
TAF
DMREC
TAFREC
TAFREC
LIBTASK
RTASK
CCP
DMREC
DMREC
DMREC
DMREC
DMREC
OMREC
DMREC
OMREC
(BVT)
CCP
RTASK
C o r r e c t t a s k o r i n f o r m M S A B T
data base administrator.
DMREC
OMREC
AAMI
/<!*5S%k
60459500 C

MESSAGE
ZZdbBnn - 8RF RECOVERY
FILE.
ZZdbOIR UNREADA8LE.
SIGNIFICANCE
TAF/CRM is beginning to roll back data base
updates from file ZZdbBnn.
When trying to expand a data file, an.
attempt to read the directory file failed.
ACTION
File name entry can be
restored by adding an
appropriate CRM
statement to the xxJ
fi l e .
Inform data
administrator.
ROUTINE
AAMI
DMREC
^ffP*\
60459500 C B-2? •

0 ^ \ I
j/^rX
^psv. GLOSSARY
AAM
Refer to Advanced Access Methods.
ABH
Refer to Application Block Header.
ABN
Refer to Application Block Number.
Absolute code
Code in which all required external references
have been satisfied. All addresses refer to
specific locations within the job field length.
ABT
Refer to Application Block Type.
ACN
Refer to Application Connection Number.
ACT
Refer to Application Character Type.
Actual Key
T h e p r i m a r y k e y f o r a r e c o r d i n a fi l e w i t h
actual key organization; indicates the storage
location of the record.
Actual Key (AK) File
A mass storage file in which each record is
stored at the location indicated by the primary
key. For initial actual key files, the primary
key must specify the block and record slot number
in which the record is stored. For extended
a c t u a l k e y fi l e s , t he p ri m a r y k e y is a r e c o r d
number that AAM converts to the storage location
of the record. Access is random or sequential.
Address
The location of a word in memory. The location
is designated by number or symbolic name.
Advanced Access Methods (AAM)
A file manager that processes indexed sequential,
direct access, and actual key file organizations,
and supports the Multiple Index Processor. Refer
to CYBER Record Manager.
After Image
A copy of a DMS-170 data base record after it
has been modified.
After Image Recovery File (ARF)
A file upon which TAF writes after images of
records in recoverable files when a request to
update such a record is processed within a
begin-commit sequence.
AK File
Refer to Actual Key File.
Alias
A data name used in a subschema in place of a
schema data name.
Alphabetic Character
A character belonging to the set of letters A
through Z and the space.
Alphanumeric
Consisting of alphabetic and/or numeric
characters only.
Alternate Key
A key, other than the primary key, by which an
indexed sequential, direct access, or actual key
file can be accessed.
ANSI
American National Standards Institute. An
organization that establishes standards for the
benefit of its member organizations.
Application
In TAF, a set of data files and the set of tasks
associated with those files.
Application
A program resident in a host computer that
provides an information storage, retrieval,
and/or processing service to a remote user via
the data communication network. IAF is an
example of an application.
Application Block Header (ABH)
A single 60-bit word description accompanying
every block passing between an application and
NAM.
Application Block Number (ABN)
A field in the application block header. An
application-assigned number used to identify a
particular data message block.
/0^ 60459500 B C-l

Application Block Type (ABT)
A field in the application block header defining
the accompanying block as either data or
supervisory, null or not null, and indicating if
this is the last block of a message.
Application Character Type (ACT)
A field in the application block header defining
the byte size of text characters.
Application Connection Number (ACN)
A number assigned by the communications
supervisor program to identify a particular
logical connection within an application.
Application Switching
The process of leaving the control of one
application and entering the control of another,
without going through another complete login
sequence.
supplied to NVF from the local configuration
file. Parameters supplied through automatic log
in configuration of a terminal suppress prompting
for the corresponding dialog entries and override
any entries made from the terminal. Automatic
login is required for terminals (passive devices)
incapable of conducting dialog with NVF.
Backup Directory
A direct access file automatically allocated and
maintained by DMREC. It contains information
about the data base, index and after image recov
ery files for an application. The file name is
ZZxxDIR where xx is the application identifier.
Backup Dump
A copy of all or selected portions of a data
base, which is produced on a regularly scheduled
basis for the explicit purpose of data base
recovery.
Batch Job
Area
A uniquely named DMS-170 data base subdivision
that contains data records; a file.
In st ructi on s a nd data sub mi tted as a c om ple te
unit without further user intervention. The job
can be punched on cards or created and submitted
from a terminal.
ARF Batch Mode
Refer to After Image Recovery File.
ASCII
American National Standard Code for Information
Interchange. The standard character set and
code used for information interchange between
systems.
ASCII Mode
Use of the American National Standard Code for
Information Interchange; a 128-character set.
It includes both uppercase and lowercase letters.
Assemble
To transform a COMPASS language program into a
form that the computer can execute directly.
During assembly, machine language operation
codes are substituted for COMPASS codes and
machine addresses for symbolic addresses.
COMPASS performs the assembly.
Attach
The process of making a permanent file
accessible to a job by specifying the proper
permanent file identification and passwords.
Auto Mode
Mode of entering information into a primary file
where the system automatically generates line
numbers. This allows you to correct, insert,
and delete lines easily because you can
reference each line by its line number.
Automatic Login
The process whereby one or more of the Network
Validation Facility login dialog parameters is
The state of a mode 4A terminal during which
batch data is transmitted from the terminal's
card reader to central files and/or from central
files to the terminal's line printer. Also, the
state of an asynchronous terminal during which
input transmission occurs on a block-by-block
basis.
Batch Test Facility
An absolute program residing on the CDCS system
library that allows CDCS to run at the same
control point as a user program.
Before Image
A copy of a DMS-170 data base record before it
has been modified.
Before Image Recovery File (BRF)
A file to which TAF/CRM writes the before images
of records in recoverable files when a request
to read such a record is processed from within a
begin-commit sequence.
Begin-commit sequence
A series of data base updates beginning with a
data base begin request and ending with a data
base commit or data base free request.
Beginning-of-Information (BOI)
The start of the first user record in a file.
Tape labels and system-supplied information,
such as an index block or control word, do not
affect beginning-of-information.
Binary File
Usually a noneditable file containing a pre
compiled program.
/*^S§\
C-2 60459500 A

J ^ '
J^fe*
B i t
An a b b r e v i ation o f bi n a r y di g i t . I t Is a si n g l e
digit, 0 or 1, In a binary number. Also used to
represent the smallest unit of information. A
central memory word (one storage location)
contains 60 bits.
Block
In the context of network communications, a por
tion or all of a message. A message is divided
into blocks to facilitate buffering, transmis
sion, error detection, and correction for vari
able length data streams.
During Input from a terminal, a block is a single
transmission comprising one or more lines of one
or more messages.
During input to an application, a block is a
single line comprising part or all of a message.
Terminal transmission blocks are divided into as
many application input blocks as needed to
provide one block of input per terminal input
line, until the message is completed.
During output to a terminal, a block is one or
more lines comprising one message.
BOI
BP
Refer to Beginning-of-information.
Beginning Priority.
BRF
Refer to Before Image Recovery File.
Called Task
A task which Is the object of a CALLTSK or a
CALLRTN request.
Calling Task
A task which executes a CALLSTK or a CALLRTN
request.
Carriage Control
The control exercised over the format of printed
output. The leftmost character of the data line
to be printed is the carriage control character.
Carriage control is also called format control.
CB
Communication Block.
CCP
Communications Control Program.
CDCS
Central Memory (CM)
The main storage device whose storage cells
(words) can be addressed by a computer program
and from which instructions and data can be
l o a d e d d i r e c t l y i n t o r e g i s t e r s f r o m w h i c h t h e
instructions can be executed or from which data
can be manipulated.
Character
Any alphabetic, numeric, or special symbol that
can be encoded. This term applies to the graphic
characters for an Input or output device, and to
uniquely encoded control characters used by a
terminal. Unless specified otherwise, characters
are ASCII 8-bit byte characters.
Charge Number
An alphanumeric identifier the installation uses
to allocate charges to individual users for
system usage.
CIO
Circular Input/Output
Close
A set of terminating operations performed on a
file when input and output operations are
complete. All files processed by the CYBER
Record Manager must be closed.
CM
Refer to Central Memory.
CMM
Common Memory Manager.
COBOL
Refer to CYBER Database Control System.
Common Business-Oriented Language. This higher
level language simplifies the programming of
business data applications.
Command
A sequence of words and characters that call a
system routine to perform a job step. The com
mand must conform to format specifications and
end with either a period or a right parenthesis.
A command is sometimes called a control
statement.
Communication Recovery File (CRF)
Files used for the automatic recovery feature.
Compile
To translate a program from a higher level pro
gramming language (for example, FORTRAN or BASIC)
into machine Instructions called object code.
60459500 B C-3

Concurrency Data Base Status Block
Simultaneous access to the same data in a data
base by two or more applications during a given
span of time.
Console
A terminal devoted to network control processing.
There may be three such terminals: the network
operator's (NOP) terminal, the local operator's
(LOP) terminal, and the network processing unit
console.
CRF
Refer to Communication Recovery File.
CRM
Refer to CYBER Record Manager.
CRT
Cathode Ray Tube.
CYBER Database Control System (CDCS)
The DMS-170 controlling module that provides the
interface between an application and a data base.
CYBER Loader
The utility that prepares programs for execution
by placing program instruction and data blocks
in central memory.
CYBER Record Manager (CRM)
A software product that allows a variety of
record types, blocking types, and file organiza
tions to be created and accessed. Products like
COBOL 5, FORTRAN Extended 4, FORTRAN 5, Sort/
Merge 4, Sort/Merge 5, ALGOL 5, and DMS 170 use
the CYBER Record Manager to manage execution
time input/output. Neither the input/output of
the operating system nor that of most of the
system utilities such as COPY or SKIFF is
implemented through the CYBER Record Manager.
All CYBER Record Manager file processing
requests ultimately pass through the operating
system input/output routines.
DA
Refer to Data Administrator.
Data Administrator (DA)
The individual who leads the design,
programming, implementation, and maintenance
efforts associated with a DMS-170 controlled
data base.
Data Base
A systematically organized, central pool of
information; organization is described by a
specific schema.
An area of memory defined within an application
to which CDCS returns information concerning the
status of operations on data base files and
relations. The status block is updated after
each CDCS operation.
Data Block
A block in which user records are stored in an
indexed sequential or actual key file. Data
blo ck s truct ure is d efined by th e us er, o r A AM
defaults are accepted. Contrast with Index
Block for indexed sequential files.
Data Description Language (DDL)
The language used to structure a DMS-170 schema
and subschema.
Data Management System
Refer to Database Management System.
Database Management System
A generalized computer program which handles the
mechanics of storing, updating, and accessing
data for multiple applications.
Dayfile
A chronological file created during job
execution which forms a permanent accounting and
j o b h i s t o r y r e c o r d . D a y fi l e m e s s a g e s a r e
generated by operator action or when commands
are processed. A copy of the dayfile is printed
with the output for each job. You must
explicitly request it in an interactive job.
DBREC
U t i l i t y u s e d t o p r e p a r e fi l e s f o r t r a n s a c t i o n
recovery using CDCS.
DDL
Refer to Data Description Language.
Deadlock
A situation that arises i n con current data base
access when two or more applications are contend
ing for a resource that is locked by one of the
other ones, and none of the programs can proceed
without that resource.
Deadstart
The process of initializing the system by
loading the operating system library programs
and any of the product set from magnetic tape or
d i s k . D e a d s t a r t r e c o v e r y i s r e i n i t i a l i z a t i o n
after system failure.
Default
A system-supplied option used when you do not
supply the option.
/?-$%&$!.
C-4 60459500 B

Delimiter
A character used to separate statement elements,
such as words and literal constants, or other
strings of text.
Device
The physical recording medium of random mass
storage, such as a disk pack.
Device Set
j0^^i
A group of rotating mass storage devices. No
device can belong to more than one device set.
Every file must be contained within one device
set, but can be on different devices in that
device set.
Direct Access File
A CYBER Record Manager file containing records
stored randomly in home blocks according to the
hashed value of the primary key in each record.
Files must be mass storage-resident. All
allocation for home blocks occurs when the file
is opened on its creation run. Access is random
or sequential. It may be attached to your job
a n d a l l c h a n g e s a r e m a d e o n t h e fi l e i t s e l f
rather than a temporary copy of the file.
Di rec tiv es
The instructions that supplement processing
defined by a command or by a program call for
execution of a utility function or member of a
product set. Directives do not appear in the
command record; they are usually In a separate
record of the file INPUT or a file referenced In
a command. Directives are required for execution
of FORM, the CREATE utility, and EDITLIB, among
others.
Disk
A unit composed of one or more flat, circular
plates with magnetic material on both sides that
is used to store large amounts of data or
programs.
Display Code
A 6-bit-dlsplay code set used to represent
alphanumeric and special characters.
Displays
Two console screens or a split screen used to
display system and job information, operator
messages, and contents of central memory.
Through the console keyboard, the operator can
control the operation of the system. The
displays are identified by alphabetic
characters; some used frequently are: job status
(B), system files (H), and dayfile messages (A).
Dump
A printed listing of the contents of the central
processor registers and a predetermined number
of words within central memory that pertain to a
job.
Dynamic Access
Access mode that allows a nonsequential file on
mass storage to be accessed randomly or
sequentially, depending on the format of the
access statement.
ECS
Refer to Extended Core Storage.
End-of-File (EOF)
A boundary within a sequential file, but not
necessarily the end of a file, that can be
referenced by name. The actual end of a named
file is d e fi n e d b y EO I . Fo r la b e l e d t a p e , E O F
and EOI (denoted by the E0F1 label) are the
same. For multifile tape files, EOF and EOI do
not correspond. In the product set manuals, an
end-of-file is also referred to as an
end-of-partition.
End-of-Information (EOI)
An indicator that marks the physical end of a
named file.
End-of-Record (EOR)
The terminator of a logical record. On a PRU
device, a short PRU or a zero-length PRU with a
level designator of 0 indicates EOR. On tapes
that are not PRU devices, an inter record gap
Indicates EOR.
EOF
Refer to End-of-File.
EOI
Refer to End-of-Inforraation.
EOR
Refer to End-of-Record.
ESM
Extended Semiconductor Memory.
Exchange Package
A t a b l e tha t c ont a i n s inf o r m a t i o n u s e d d u r i n g
job execution. It is printed as part of the
output when a job aborts.
Extended
A terra used in conjunction with indexed sequen
tial, direct access, and actual key files to
denote a specific type of Internal processing by
AAM and MIP. Processing is indicated by setting
the ORG FIT field to NEW.
Extended Core Storage (ECS)
Optional additional memory. ECS contains 60-bit
words; it has a large amount of storage and fast
transfer rates. ECS can be used only for program
and data storage, not for program execution.
Special hardware instructions exist for transfer
ring data between central memory and ECS.
60459500 C C-5

Extended Memory
An extension to central memory which is physi
cally located outside of the machine. Formerly
referred to as extended core storage (ECS) or
large central memory (LCM).
Family Name
Name of the permanent file storage device or set
of devices on which all of your permanent files
are stored. When you request a permanent file,
the system looks for it on this family (group) of
devices. Usually a system has only one family
of permanent file devices but it is possible to
have alternate families in the system. You
specify which family you are using when you log
in. Your family name is given to you by your
employer, instructor, or computer personnel.
Fast Dynamic Loader (FDL)
A f a c i l i t y t h a t p r o v i d e s f a s t l o a d i n g a n d
unloading of specially formatted code called
capsules. The amount of memory required for job
execution can be greatly reduced because
capsules can be easily loaded and unloaded as
needed, freeing memory for other uses.
FDL
Refer to Fast Dynamic Loader.
FE
Refer to Format Effector.
FET
Refer to File Environment Table.
Field Length (FL)
The area in central memory allocated to a
particular job; the only part of central memory
that a job can directly access. Also the number
of central memory words required to process a
job.
F i l e
A c o l l e c t i o n o f i n f o r m a t i o n r e f e r r e d t o b y a
file name (from one through seven characters,
either letters or numbers). You can create a
file at the terminal or retrieve a file from
permanent file storage for use during a terminal
session.
FILE Command
A command that supplies file information table
values after a source language program is
compiled or assembled but before the program is
executed. Basic file characteristics such as
organization, record type, and description can
be specified in the FILE command.
File Environment Table (FET)
A table within a program's field length through
which the program communicates with operating
system input/output routines. One FET exists
for each file in use by the program.
File Information Table (FIT)
A table through which a user program
communicates with the CYBER Record Manager. For
d i r e c t p r o c e s s i n g t h r o u g h C R M , a u s e r m u s t
initiate establishment of this table. All file
processing executes on the basis of information
i n t h i s t a b l e . T h e u s e r c a n s e t F I T fi e l d s
directly or use parameters in a file access call
that sets the fields indirectly. Some product
set members set the fields automatically for the
user.
File Organization
Defined by ORGANIZATION clause. Can be sequen
t i a l , i n d e x e d , r e l a t i v e , d i r e c t , a c t u a l - k e y, o r
word-address. Established at the time the file
is created and cannot change as long as the file
exists. Affects access mode, open mode, and for
mats of statements that can be used to manipulate
file records.
File Statement
Command for the CYBER Record Manager that
specifies parameters for the FIT at the time the
file is opened.
File Statistics Table (FSTT)
A table generated and maintained by the CYBER
Record Manager to collect statistics about each
direct access, indexed sequential, and actual key
file. The FSTT is a permanent part of a file
and contains information such as organization
type, size of blocks and the number of current
accesses.
FIT
Refer to File Information Table.
FL
Refer to Field Length.
Flag
A character or bit that signals the occurrence
or presence of a particular condition.
FORM
A general purpose file management utility for
manipulating records and creating and converting
files.
Format Effector (FE)
A control symbol used by certain protocols (for
instance, the HASP protocol).
FORTRAN
FORmula TRANslation. A language that solves
algebraic and scientific problems using symbols
and statements that closely resemble
mathematical notation.
FSE
Refer to Full Screen Editor.
/tf$^\
C-6 60459500 C

FSTT Input
jpsv
Refer to File Statistics Table.
Full Screen Editor
The editing facility that enables you to edit
files In a screen format or a llne-by-line
format.
GTDL
Global Task Dump Limit.
HAD
Host availability display.
Hashing
The method of using primary keys to search for
relative home block addresses of records in a
file with direct access storage structure.
Header
A word or set of words at the beginning of a
block, record, file, or buffer which contains
control information for that unit of data.
Host
Information flowing upline from the terminal to
the host computer.
Interactive
A mode of job processing in which the user
enters a command or input to an executing
program and receives an immediate response.
Interactive Access Facility (IAF)
An application that provides a terminal operator
with the i n t e r a ctive p r o c e s sing c a p a b i l i ty. The
interactive facility makes terminal input/output
and file input/output appear the same to an
executing program.
I/O
Input /O utput.
IS File
Refer to Indexed Sequential File.
Itemize
A utility routine that produces a listing of the
contents of a file or library.
A computer that executes applications.
IAF
IVT
Interactive Virtual Terminal.
0^
Refer to Interactive Access Facility.
Index
In t h e c o n t e x t of A A M , a s e r i e s of k e y s an d
pointers to records associated with the keys.
The system creates an index for AAM files which
re la te s a ltern at e r ec or d k ey s t o p ri mary keys,
using the file defined by the second
implementor-name of an ASSIGN clause.
In general context, a computer storage area or
register, the content of which represents the
identification of a particular element.
Index Block
For an indexed sequential file, a block with
ordered keys and pointers to data blocks and
other index blocks, forming a directory of the
records within a file.
Indexed Sequential (IS) File
A file organization in which the CYBER Record
Manager maintains records in sorted order by use
of a programmer-defined key, which need not be
within the record. Keys may be integer, floating
point, or symbolic; access Is random or sequen
tial. Files contain index blocks and data
blocks.
Indirect Access File
A NOS permanent file that you access by making a
temporary copy of the file (GET or OLD command).
You create or alter it by saving or substituting
the contents of an existing temporary file
(REPLACE or SAVE command).
Job
All co m p u t e r-re l a t e d a c t i v i ty a s s ocia t e d wi t h a
terminal session from login to logout. A batch
job consists of instructions and data submitted
as a complete unit.
Key
A group of contiguous characters or numbers the
user defines to identify a record in a CRM file.
LCME
Large Central Memory Extended.
LDSET
The loader directive used to control the
process under a variety of conditions.
load
LGO
The default name of the file to which language
processors write executable code during program
assembly or compilation.
Load Sequence
A sequence of load operations which encompasses
all of the loader's processing from the time that
no thi ng i s l oad ed unt il the ti me ex ec u ti o n b e
gins. It includes initialization, specification
of specified Loader requests, and the completion
of the load.
60459500 C C-7
Loader Multiple Index File
A software product that prepares programs for
execution by placing program instructions and
d a t a b l o c k s i n c e n t r a l m e m o r y a n d l i n k i n g
references In the program to the appropriate
external routines.
Local
Refers to data that exists only during the proc
essing of a single job and that can only be
accessed by that job.
Local Operator (LOP)
The network operator who monitors line, terminal,
and application activities in the network.
Login
The procedure used at an interactive terminal to
gain access to the system.
Logout
The procedure by which
session. You type BYE. you end terminal
LOP
Refer to Local Operator.
Macro
A sequence of source commands that are saved and
then assembled whenever needed through a macro
call.
Mass Storage
Magnetic disk or extended memory that can be
accessed randomly as well as sequentially.
Master Directory
A file containing information used by CDCS in
processing. This information consists of schema
and subschema tables, media parameters, and data
base procedure library and logging specifica
tions.
MFL
Maximum Field Length.
MIP
Refer to Multiple Index Processor.
MP
Maximum Priority.
Multifile Set
A tape file set having more than one tape file.
Multimainframe Operation
Operation that provides mechanisms by which more
than one computer can share mass storage devices.
An indexed sequential, direct access, or actual
key file that has alternate keys defined.
Multiple Index Processor (MIP)
A processor that allows AAM files to be accessed
by alternate keys.
NAM
Refer to Network Access Method.
NCT
Network Communication Table.
NCTF
Refer to Network Description File.
NDL
Refer to Network Definition Language.
Network Access Method (NAM)
A software package that provides a generalized
metho d of us ing a commun ic at ions n et work f or
switching, buffering, queuing, and transmitting
data. NAM is a set of Interface routines used
by a terminal servicing facility for shared
access to a network of terminals and other
applications, so that the facility program does
not need to support the physical structures and
protocols of a private communication network.
Network Definition Language (NDL)
The compiler-level language used to define the
network configuration file and local config
uration file contents.
Network Description File (NCTF)
File that must be present if the transaction
facility is used. The file is prepared by the
site analyst.
NOS
Network Operating System.
Numeric Character
Digits 0 through 9.
Object Code
The machine language version of a program that
has been translated (compiled) from source code
written in a higher level language.
Open
A set of preparatory operations performed on a
file before input and output can take place;
required for all CRM files.
/^S^v
| C - 8 60459500 C
Operating System Physical Record Unit (PRU)
Th e s e t o f s yst e m p rog ram s t h at co ntr ols th e
execution of computer programs and provides
scheduling, error detection, input/output
control, accounting, compilation, storage
assignment, and other related services.
Operation
A particular function performed on units of
data; for instance, opening or closing an area,
or storing or deleting a record.
Order Dependent
Used to describe items which must appear in a
specific order.
Order Independent
Used to describe items which need not appear in
any specific order. Parameters, particularly
those with keywords, may be order independent.
Output
Information flowing downline from host to
terminal.
Output File
The file on which the system writes information
to the user. Unless another file name is speci
fied, the output file is printed at the terminal.
Pack Name
A one- to seven-character name that identifies
the auxiliary device to be accessed In a
permanent file request.
Parameter
A vari able th at i s gi ven a speci fic v alu e fo r a
particular purpose or process.
Parity
In writing data, an extra bit is either set or
cleared in each byte so that every byte has
either an odd number of set bits (odd parity) or
a n e v e n n u m b e r o f s e t b i t s ( e v e n p a r i t y ) .
Parity is checked on a read for error detection
and possible recovery.
Password
A name or word entered during login to provide
extra security for your user name. A unique
password ensures that no one else can log into
the system using your user name and access your
files.
Permanent File
A file stored on mass storage. This file is
cataloged by the system so that its location and
identification are always known to the system.
Permanent files cannot be destroyed accidentally
during normal system operation. They are
protected by the system from unauthorized access
according to privacy controls specified by the
file owner.
60459500 C
The amount of information transmitted by a
single physical operation of a specified
device. For mass storage files, a PRU is 64
central memory words (640 characters); for
magnetic tape files, the size of the PRU depends
upon the tape format. A PRU that is not full of
user data is called a short PRU; a PRU that has
a level terminator but no user data is called a
zero-length PRU.
Primary Key
A key whose value uniquely Identifies a record
and d ete rmines t he location of the record in a
file. The primary key for a file must be
defined when the file is created and must be
used to update the file. Contrast with Alternate
Key.
Procedure
A user-defined set of instructions that are
referenced by name. The instructions consist of
procedure directives and system commands.
Procedure File
A file containing one or more procedures.
PRU
Refer to Physical Record Unit.
PSN
Packet-Switching Network.
Purge
To delete a permanent file from the system.
This enables releasing its mass storage space,
erasing its catalog entries, and so forth.
Queue
A sequence of blocks, tables, messages, and so
f o r t h . M o s t N P U q u e u e s a r e m a i n t a i n e d b y
leaving the queued elements in place and using
tables of pointers to the next queued element.
Most queues operate on a flrst-ln, first-out
basis. A series of workllst entries for a
specific terminal is an example of an NPU queue.
RA
Refer to Reference Address.
RAE
Refer to Reference Address.
Record
A unit of information. In the CYBER Record
Manager and its language processors, a record is
a unit of information produced by a single read
or write request. Eight different record types
exist within CRM. The user defines the
structure and characteristics of records within
a file by declaring a record format.
Other parts of the operating system and Its
products might have additional or different
definitions of records.
C - 9 |

Record Slot Number Rewind
The position of a record within a block in an
actual k ey file; sp ec ifi ed by th e low-order b its
of the primary key.
Record Type
The term record type can have one of several
meanings, depending on the context. The CYBER
Record Manager defines eight record types estab
lished by an RT field in the file information
ta bl e. Ta bl es output by the loa der a re cl assi
fied as record types such as text, relocatable,
or absolute, depending on the first few words of
the tables.
Recovery
A process that makes a data base useful after
some type of software or hardware failure has
occurred.
Reference Address (RA and RAE)
RA is the absolute central memory address that
is the starting, or zero, relative address
assigned to a program. Addresses within the
program are relative to RA. RA+1 is used as the
communication word between the user program and
monitor. RAE is the absolute extended memory
starting address assigned to the file.
Release System
A software system delivered to a customer. In
installing a system, the customer, but not an
individual applications programmer, can use
d e f a u l t v al u e s o r p a r a m e te r s th a t di ff e r f r om
the released system.
Relocatable Code
Code that can be loaded into any region of the
job field length. External references have not
yet been satisfied.
Request
A s t a t e m e n t t h a t i d e n t i fi e s a f u n c t i o n t o b e
p e r f o r m e d . Of t e n th e r e a r e item s u s e d b y or
resulting from the function that are required as
parameters in the request.
Reserved Word
An identifier that has a predefined meaning to a
compiler and must not appear In a source program
as a user-defined word or name.
R e s t a r t I d e n t i fie r F il e
Random permanent file used for a start
Identifier in recovery by CDCS.
Returned Value
The value returned from a procedure invoked as a
function, or the value returned by a buiLt-in
function.
An operation that positions a file at
beginning-of-information.
RMS
Refer to Rotating Mass Storage.
Rollback
The process of restoring a data base to a
previous state.
Rotating Mass Storage (RMS)
A disk storage device.
RTL
Requested Task List.
Satisfying External References
The process of searching one or more libraries
and loading programs that contain entry points
matching external references that are currently
unsatisfied.
Schema
A detailed description of the internal structure
of a data base.
Separator
A character used to separate parameters in a
command•
Sequential (SQ) File
A file in which records are accessed in the
order in which they occur. Any file can be
accessed sequentially. Sequential files must be
accessed sequentially because no key or address
is associated with each record in the files.
Source Code
Code input to the computer for later translation
into executable machine language instructions
(object code).
SQ File
Refer to Sequential File.
Stimulator
A collection of central memory and peripheral
processor programs which enters a hypothetical
work load Into the system to analyze the effects
of such a load on response time and system
r e l i a b i l i t y .
String
A sequence of contiguous characters or bits
treated as a unit.
y^^v
| C-10 60459500 C
J^*v Subschema
A detailed description of the portion of a data
base to be made available to one or more
applications.
Supervisory Message
A message block in the host not directly Involved
with the transmission of data, but which provides
information for establishing and maintaining an
environment for the communication of data between
the application and NAM, then through the network
to a destination or from a source. Supervisory
messages may be transmitted to an NPU in the
format of a service message.
TAF Configuration File (TCF)
A file created and maintained by the data admini
strator specifying which data managers are active
and the applications to be associated with each.
Task
A program to be executed under the transaction
subsystem. Tasks are stored in absolute binary
format on libraries which must be available to
the transaction subsystem.
Task Library Directory (TLD)
The directory on each task library which contains
information on the tasks in the library. TAF
makes its own copy of each TLD at initialization
and uses this copy to locate requested tasks.
TCF
Refer to TAF Configuration File.
Terminal
The equipment a person uses to communicate with
the computer.
Terminal Class
An NDL parameter describing the physical attri
butes of a group of similar terminals, in terms
of an archetype terminal for the group.
Terminal Session
Period between the time you physically connect
the terminal to the system in preparation for
login to the time you log out.
Text Mode
Mode of entering information Into a primary file
w i t h o u t sp eci f y i n g li ne n u m b e rs. I t is u s u a lly
used to create data files. If a file does not
contain line numbers, you can change lines by
using an editing facility such as the Full
Screen Editor.
Transaction
A task or a series of tasks executed as a unit
under the transaction subsystem. All tasks in a
transaction have the same transaction sequence
number. In CDCS, the term data base transaction
refers to the process which this manual calls a
begin-commit sequence.
Transaction Library Directory (TRD)
The directory on each task library which contains
information on the transactions in the library.
TAF makes its own copy of each TRD at initializa
tion and uses this copy to locate requested
transactions.
Transaction Name
The one to seven alphanumeric character name
given to a transaction created with the /tname
input directive from the LIBTASK utility.
Transaction Recovery File
Random permanent file used for before image
records necessary for recovery by CDCS.
Transaction Sequence Number
A unique number assigned by TAF to each transac
ti on. It I s u sed by TAF f or tas k i den tifi cat io n .
Transparent Mode
A software feature provided by the Network Access
Method and the network processing unit (NPU).
When transparent mode transmission occurs between
an application and a terminal the Network Access
Method does not convert data to or from 6-bit
display code, and the NPU does not edit the char
acter stream or convert the characters to or from
7-bit ASCII code. When no parity is in effect for
the terminal and transparent mode transmission
occurs, all seven bits of the character byte can
be used to represent characters In character sets
(such as EBCDIC).
TRD
Refer to Transaction Library Directory.
TST
Terminal Status Table.
TTOT
Table of Time-Originating Tasks.
UEM
Unified Extended Memory.
TLD UJN
Refer to Task Library Directory. User Job Name.
60459500 C C-l I

User Index VSN
A unique 17-bit identifier that is associated
with each user name. The user index is used by
the permanent file manager to identify the device
and catalog track for the user's files.
User Name
A system access word that must be supplied by
the user for validation purposes at login.
Utility
A program designed to help the user perform spe
cific functions such as permanent file mainte
nance, library maintanence, and file editing.
Virtual Terminal
A software concept for CCP that converts all
types of upline messages to one of two formats:
batch virtual terminal or interactive virtual
terminal. By this method, applications in the
host need only to be able to process data in IVT
or BVT format rather than in the multiplicity of
formats which real terminals use. Downline
me ssa g es fro m t h e h ost to r e al te rmi nal s a r e
converted from IVT or BVT to real terminal
format. The IVT/BVT processors are a part of
the NPU's network communications software.
Volume Serial Number (VSN)
A one- to six-character identifier that identi
fies the volume of magnetic tape for the opera
t o r .
Refer to Volume Serial Number.
Word
A group of bits (or 6-bit characters) between
boundaries imposed by the computer system. A
word is 60 bits in length. The bits are numbered
59 through 0, starting from the left. It is also
composed of five 12-bit bytes, numbered 0 through
4, from the left.
Working Storage Area
An area within the user's field length intended
for receipt of data from a file or transmission
of data to a file.
Write Mode
Allows a user to write, modify, append, read,
execute, or purge the file (modify permission
applies only to direct access files).
xx J Files
Files created and maintained by the data
administration which associates a particular
user with a particular application.
Zero-Length PRU
A PRU that contains system information, but no
user data. Under the CYBER Record Manager, a
zero-length PRU level of 17 is a partition bound
ary. Under NOS, a zero-length PRU defines EOF.
/^sffs^V
C-12 60459500 C
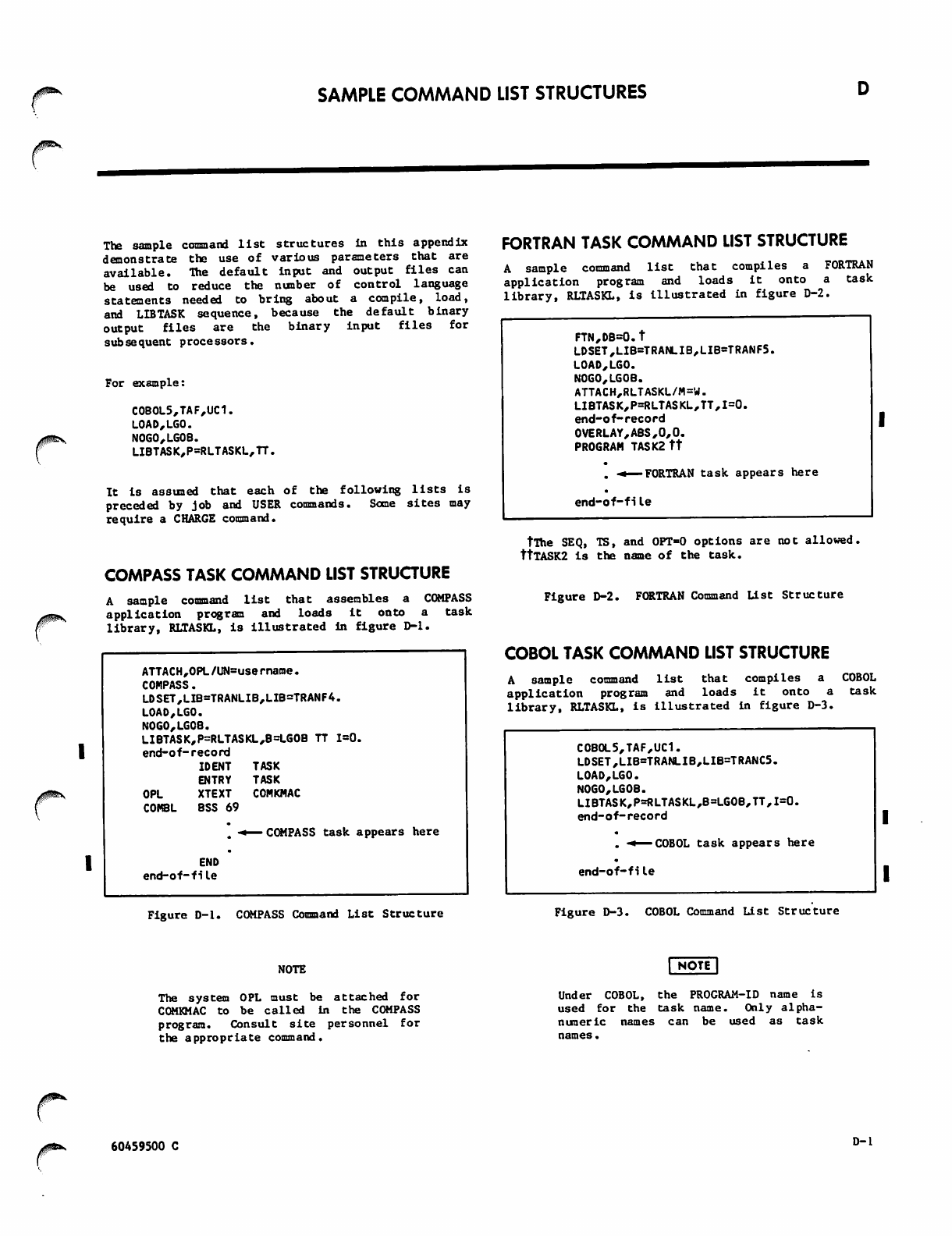
/#^- SAMPLE COMMAND LIST STRUCTURES
/fP^V
The sample command list structures in this appendix
demonstrate the use of various parameters that are
available. The default input and output files can
be used to reduce the number of control language
statements needed to bring about a compile, load,
and LIBTASK sequence, because the default binary
output files are the binary input files for
subsequent processors.
For example:
C0B0L5,TAF,UC1.
L0AD/LG0.
N0G0,LG0B.
LIBTASK,P=RLTASKL,TT.
It Is assumed that each of the following lists is
preceded by job and USER commands. Some sites may
require a CHARGE command.
COMPASS TASK COMMAND LIST STRUCTURE
A sample command list that assembles a COMPASS
a p p l i c a t i o n p r o g r a m a n d l o a d s I t o n t o a t a s k
library, RLTASKL, is illustrated in figure D-l.
FORTRAN TASK COMMAND LIST STRUCTURE
A sample command list that compiles a FORTRAN
application program and loads it onto a task
library, RLTASKL, is Illustrated in figure D-2.
FTN,DB=0.t
LDSET,LIB=TRANLIB,LIB=TRANF5.
L0AD,LG0.
N060,L60B.
ATTACH,RLTASKL/M=W.
LIBTASK,P=RLTASKL,TT,I=0.
end-of-record
OVERLAY,ABS,0,0.
PROGRAM TASK2 tt
FORTRAN task appears here
end-of-file
ATTACH,0PL/UN=use rname.
COMPASS.
LDSET,LIB=TRANLIB,LIB=TRANF4.
L0AD,lG0.
N0G0,LG0B.
LIBTASK,P=RLTASKL,B=LGOB TT 1=0.
e n d - o f - r e c o r d
IDENT
ENTRY
OPL XTEXT
C0K8L 8SS 69
END
end-of-file
TASK
TASK
COMKMAC
COMPASS task appears here
TThe SEQ, TS, and OPT-0 options are not allowed.
TtTASK2 is the name of the task.
Figure D-2. FORTRAN Command List Structure
COBOL TASK COMMAND LIST STRUCTURE
A sample command list that compiles a COBOL
application program and loads it onto a task
library, RLTASKL, is illustrated in figure D-3.
C0B0L5,TAF,UC1.
LDSET,LIB=TRANLIB,LIB=TRANC5.
L0AD,LG0.
N0GO,LG08.
LIBTASK,P=RLTASKL,B=LGOB,TT,I=0.
end-of-record
COBOL task appears here
e n d - o f - fi l e
Figure D-l. COMPASS Command List Structure F i g u r e D -3 . C OB OL Co mm an d L is t S tr u c t u r e
NOTE NOTE |
The system OPL must be attached for
COM KMAC to be called in the COMPASS
program. Consult site personnel for
the appropriate command.
Under COBOL, the PROGRAM-ID name is
used for the task name. Only alpha
numeric names c an b e used as tas k
names.
0^*
60459500 C D-l

/ * ^ < s \
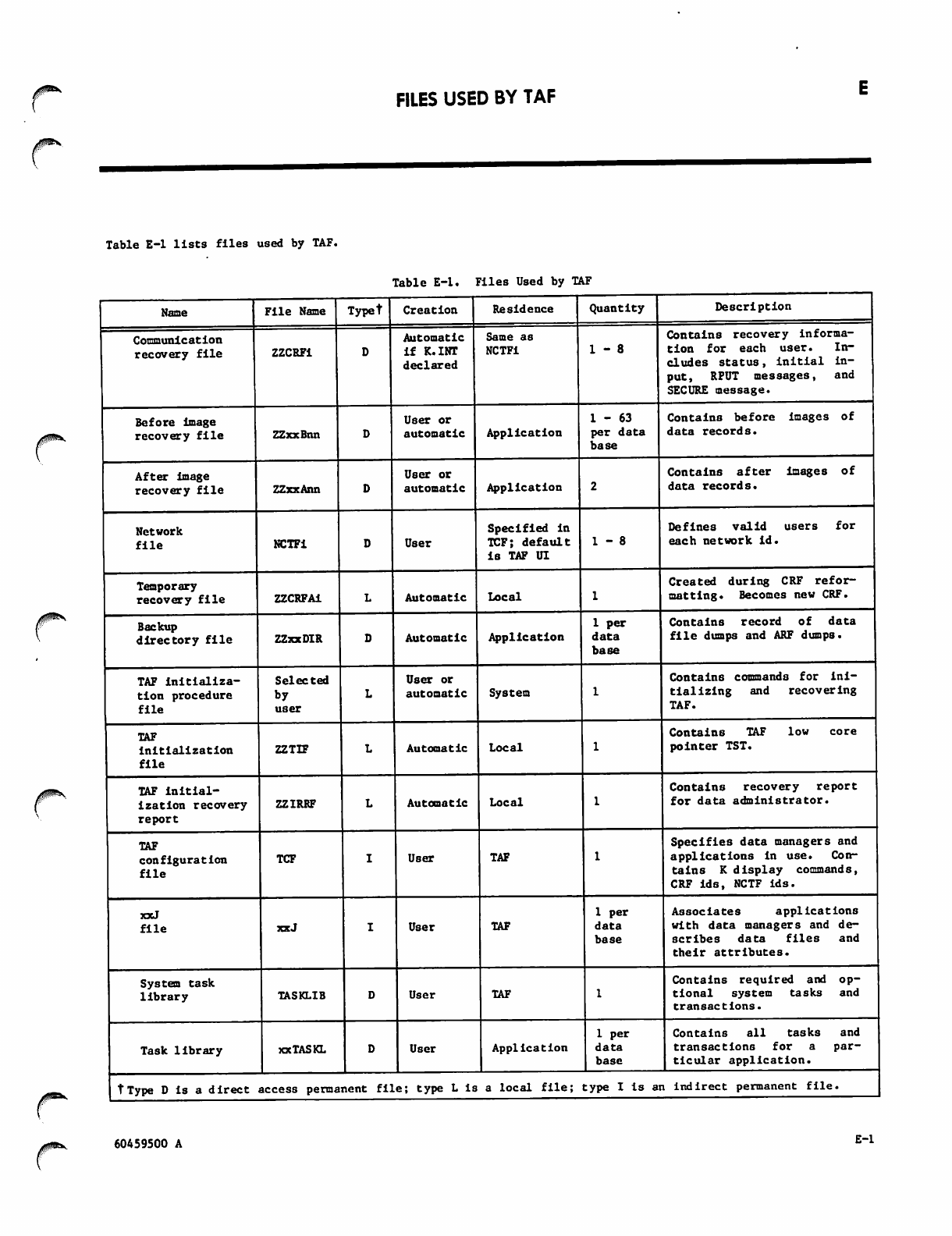
Jp^ FILES USED BY TAF
Table E-l lists files used by TAF.
08-^
Table E-l. Files Used by TAF
Name File Name Typet Creation Residence Quantity Description
Communication
recovery file ZZCRFi
Automatic
if K.INT
declared
Same as
NCTFi 1-8
Contains recovery informa
tion for each user. In
c l u d e s s t a t u s , i n i t i a l i n
put, RPUT messages, and
SECURE message.
Before image
recovery file ZZxxBnn
User or
automatic Application
1-63
per data
base
Contains before images of
data records.
After image
recovery file ZZxxAnn
User or
automatic Application
Contains after images of
data records.
Network
file NCTFi User
Sp e cifi e d i n
TCF; default
is TAF DT
1-8
Defines valid users for
each network id.
Temporary
recovery file ZZCRFAI Automatic Local
Created during CRF refor
matting. Becomes new CRF.
Backup
directory file ZZxxDIR Automatic Application
1 per
data
base
C o n t a i n s r e c o r d o f d a t a
file dumps and ARF dumps.
TAF I n i t ia liza
tion procedure
file
Selected
by
user
User or
automatic System
Contains commands for ini
tializing and recovering
TAF.
TAF
initialization
file
ZZTTF Automatic Local
Contains TAF low core
pointer TST.
TAF initial
ization recovery
report
ZZIRRF Automatic Local
Contains recovery report
for data administrator.
TAF
configuration
fi l e
TCF User TAF
Specifies data managers and
applications in use. Con
tains K display commands,
CRF ids, NCTF ids.
xxJ
fi l e xxJ User TAF
1 per
data
base
Associates applications
with data managers and de
scribes data files and
their attributes.
System task
library TASKLIB User TAF
Contains required and op
t i o n a l s y s t e m t a s k s a n d
transactions.
Task library xxTASKL User Application
1 per
data
base
Contains all tasks and
transactions for a par
ticular application.
tType D is a direct access perma nent file; type L is a l o c a l fi l e ; type I is ail indirect permanent file.
60459500 A E-l

In addition to the files described in table E-l, the SCRA-SCRZ _—
following reserved files are used by TAF. No task 0^,
or procedure file called by TAF can attach or use SCR1-SCR5 )
any file having one of these names. "-^-'
TROB
KTSROLL
MAP
OUTPUT
ZZZZZ.. (file names starting with five Zs)
RECOVER
0^^^\
; "1
E"2 60459500 B

INSTALLATION OVERVIEW
Table F-l is provided to aid the systems analyst and procedures detailed in the respective manuals. The
data administrator in performing TAF installation. complete name and publication number of each entry
It is a chronologically ordered outline of the in the Manual column follows the table.
ifjJ^V
60459500 A F_l
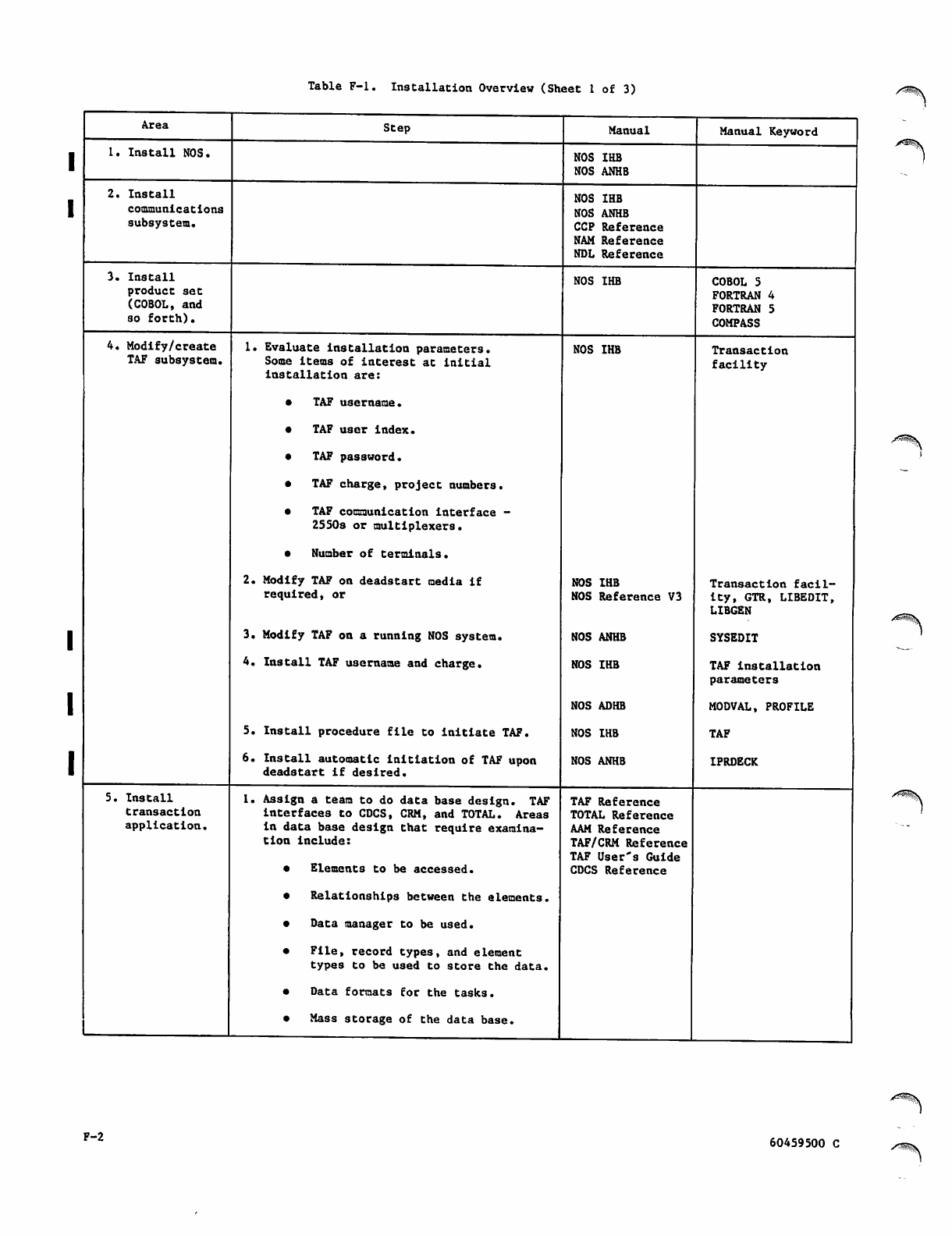
Table F-l. Installation Overview (Sheet I of 3)
Area
1. Install NOS.
2. Install
communications
subsystem.
3 . I n s t a l l
product set
(COBOL, and
so forth).
4. Modify/create
TAF subsystem.
Step
5 . I n s t a l l
transaction
application.
1. Evaluate installation parameters.
Some items of interest at initial
installation are:
TAF username.
TAF user index.
TAF password.
TAF charge, project numbers.
TAF communication interface
2550s or multiplexers.
• Num ber of terminals.
2. Modify TAF on deadstart media if
required, or
3. Modify TAF on a running NOS system.
4. Install TAF username and charge.
5. Install procedure file to initiate TAF.
6. Install automatic Initiation of TAF upon
deadstart if desired.
Manual
NOS IHB
NOS ANHB
NOS IHB
NOS ANHB
CCP Reference
NAM Reference
NDL Reference
NOS IHB
NOS IHB
1. Assign a team to do data base design. TAF
interfaces to CDCS, CRM, and TOTAL. Areas
in data base design that require examina
tion Include:
• Elements to be accessed.
• Relationships between the elements.
• Data manager to be used.
• File, record types, and element
types to be used to store the data.
• Data formats for the tasks.
• Mass storage of the data base.
NOS IHB
NOS Reference V3
NOS ANHB
NOS IHB
NOS ADHB
NOS IHB
NOS ANHB
Manual Keyword
COBOL 5
FORTRAN 4
FORTRAN 5
COMPASS
Transaction
facility
TAF Reference
TOTAL Reference
AAM Reference
TAF/CRM Reference
TAF User's Guide
CDCS Reference
Transaction facil
ity, GTR, LIBEDIT,
LIBGEN
SYSEDIT
TAF in s tal l a t ion
parameters
MODVAL, PROFILE
TAF
IPRDECK
F-2 60459500 C
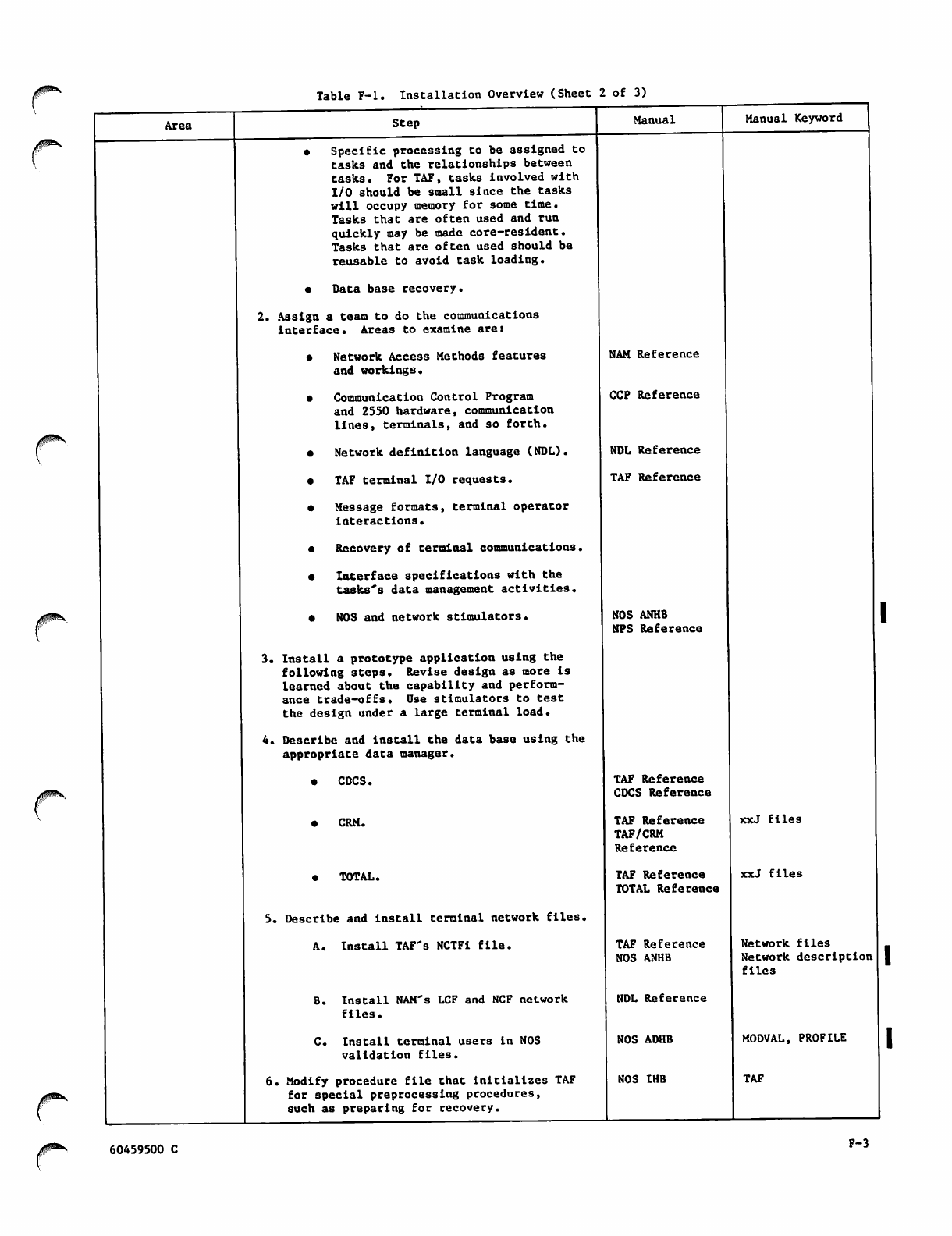
Table F-l. Installation Overview (Sheet 2 of 3)
Area
0^-
J^
Step
• Specific processing to be assigned to
tasks and the relationships between
tasks. For TAF, tasks involved with
I/O should be small since the tasks
will occupy memory for some time.
Tasks that are often used and run
quickly may be made core-resident.
Tasks that are often used should be
reusable to avoid task loading.
• Data base recovery.
2. Assign a team to do the communications
interface. Areas to examine are:
• Network Access Methods features
and workings.
• Communication Control Program
and 2550 hardware, communication
lines, terminals, and so forth.
• Network definition language (NDL).
• TAF termin al I /O reques ts.
• Message formats, terminal operator
interactions.
• Recovery of terminal communications.
• Interface specifications with the
tasks's data management activities.
• NOS and network stimulators.
3. Install a prototype application using the
following steps. Revise design as more Is
learned about the capability and perform
ance trade-offs. Use stimulators to test
the design under a large terminal load.
4. Describe and install the data base using the
appropriate data manager.
• CDCS.
• C R M .
• T O TA L .
5. Describe and install terminal network files,
A. Install TAF's NCTFi file.
B. Install NAM's LCF and NCF network
files.
C. Install terminal users in NOS
validation files.
6. Modify procedure file that initializes TAF
for special preprocessing procedures,
such as preparing for recovery.
Manual
NAM Reference
CCP Reference
NDL Reference
TAF Reference
NOS ANHB
NPS Reference
TAF Reference
CDCS Reference
TAF Reference
TAF/CRM
Reference
TAF Reference
TOTAL Reference
TAF Reference
NOS ANHB
NDL Reference
Manual Keyword
xxJ files
xxJ files
NOS ADHB
NOS IHB
Network files
Network description
files
MODVAL, PROFILE
TAF
60459500 C F-3
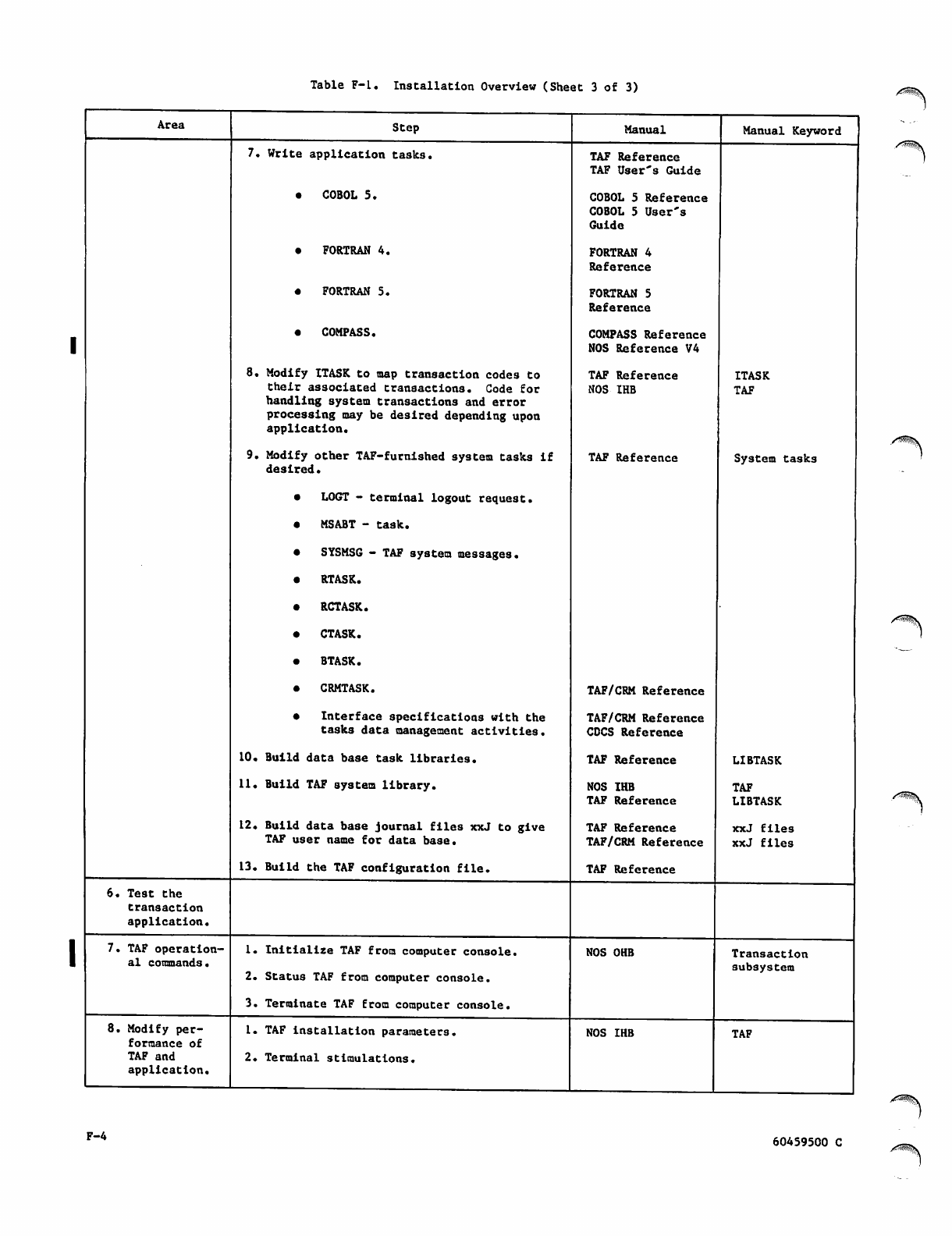
Table F-l. Installation Overview (Sheet 3 of 3)
Area
6. Test the
transaction
application.
7. TAF operation
al commands.
8. Modify per
formance of
TAF and
application.
Step
7. Write application tasks.
• COBOL 5.
FORTRAN 4.
FORTRAN 5.
COMPASS.
8. Modify ITASK to map transaction codes to
their associated transactions. Code for
handling system transactions and error
processing may be desired depending upon
application.
9. Modify other TAF-furnished system tasks if
desired.
LOGT - terminal logout request.
MSABT - task.
SYSMSG - TAF system messages.
RTASK.
RCTASK.
CTASK.
BTASK.
CRMTASK.
Interface specifications with the
tasks data management activities.
10. Build data base task libraries.
11. Build TAF system library.
12. Build data base journal files xxJ to give
TAF user name for data base.
13. Build the TAF configuration file.
1. Initialize TAF from computer console.
2. Status TAF from computer console.
3. Terminate TAF from computer console.
1. TAF installation parameters.
2. Terminal stimulations.
Manual
TAF Reference
TAF User's Guide
COBOL 5 Reference
COBOL 5 User's
Guide
FORTRAN 4
Reference
FORTRAN 5
Reference
COMPASS Reference
NOS Reference V4
TAF Reference
NOS IHB
TAF Reference
TAF/CRM Reference
TAF/CRM Reference
CDCS Reference
TAF Reference
NOS IHB
TAF Reference
TAF Reference
TAF/CRM Reference
TAF Reference
NOS OHB
NOS IHB
Manual Keyword
F-4
ITASK
TAF
System tasks
LIBTASK
TAF
LIBTASK
xxJ files
xxJ files
Transaction
subsystem
TAF
/*^i\
60459500 C
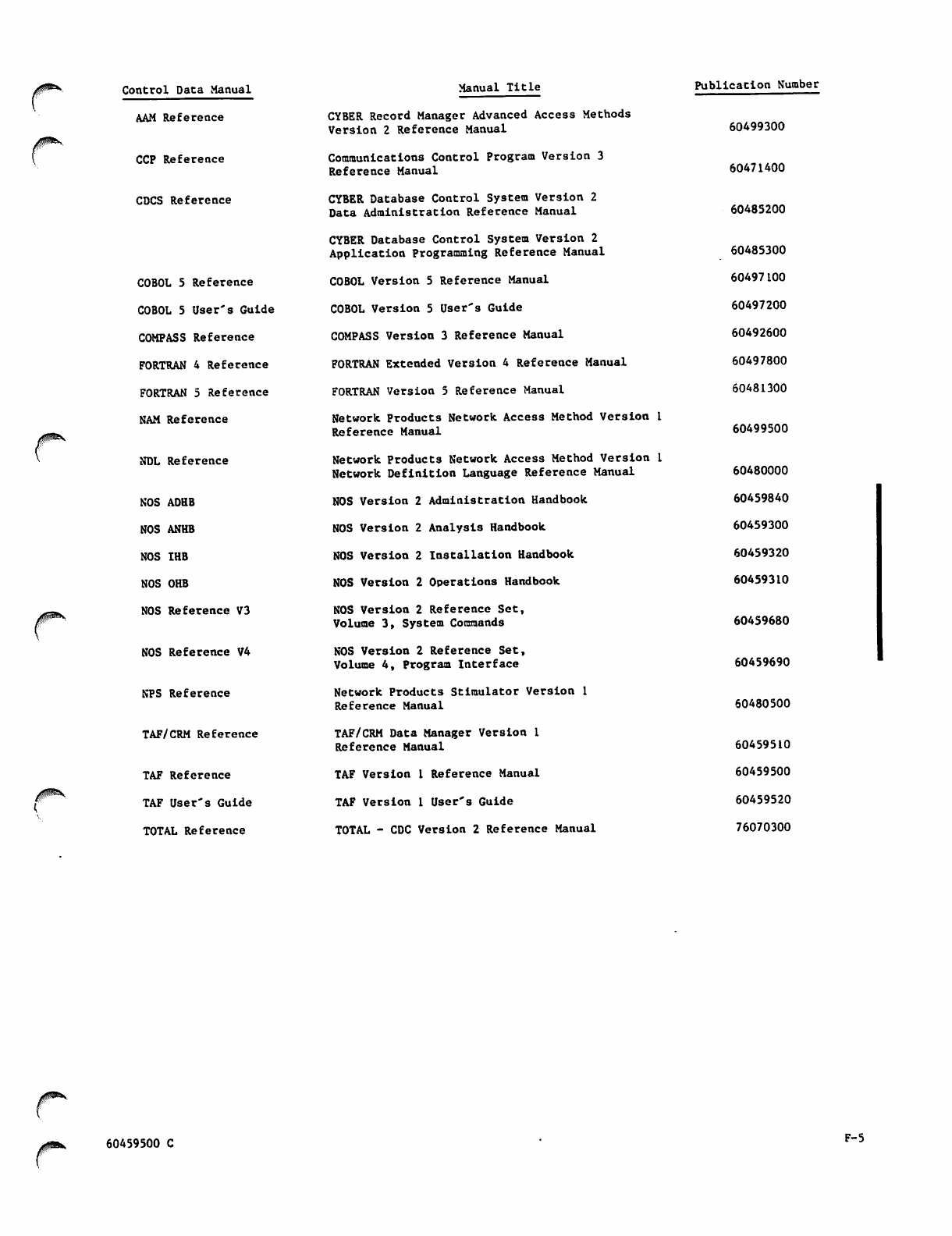
Control Data Manual Manual Title Publication Number
0^\
jf^y
AAM Reference
CCP Reference
CDCS Reference
COBOL 5 Reference
COBOL 5 User's Guide
COMPASS Reference
FORTRAN 4 Reference
FORTRAN 5 Reference
NAM Reference
NDL Reference
NOS ADHB
NOS ANHB
NOS IHB
NOS OHB
NOS Reference V3
NOS Reference V4
NPS Reference
TAF/CRM Reference
TAF Reference
TAF User's Guide
TOTAL Reference
CYBER Record Manager Advanced Access Methods
Version 2 Reference Manual
Communications Control Program Version 3
Reference Manual
CYBER Database Control System Version 2
Data Administration Reference Manual
CYBER Database Control System Version 2
Application Programming Reference Manual
COBOL Version 5 Reference Manual
COBOL Version 5 User's Guide
COMPASS Version 3 Reference Manual
FORTRAN Extended Version 4 Reference Manual
FORTRAN Version 5 Reference Manual
Network Products Network Access Method Version I
Reference Manual
Network Products Network Access Method Version 1
Network Definition Language Reference Manual
NOS Version 2 Administration Handbook
NOS Version 2 Analysis Handbook
NOS Version 2 Installation Handbook
NOS Version 2 Operations Handbook
NOS Version 2 Reference Set,
Volume 3, System Commands
NOS Version 2 Reference Set,
Volume 4, Program Interface
Network Products Stimulator Version 1
Reference Manual
TAF/CRM Data Manager Version 1
Reference Manual
TAF Version 1 Reference Manual
TAF Version 1 User's Guide
TOTAL - CDC Version 2 Reference Manual
60499300
60471400
60485200
60485300
60497100
60497200
60492600
60497800
60481300
60499500
60480000
60459840
60459300
60459320
60459310
60459680
60459690
60480500
60459510
60459500
60459520
76070300
r
60459500 C F-5

TERMINAL DEFINITION COMMANDS
/#*v
INTRODUCTION
The network, through which terminals access a host
and its applications (like TAF), can support many
types of terminals. All supported terminals are
grouped by the network into 18 standard terminal
classes. Each terminal class has specific operating
characteristics, also referred to as terminal
characteristics. These terminal characteristics,
taken together, make up a terminal definition and
are predefined by the network to closely match the
operating characteristics of actual terminals. The
network accepts changes to any of these terminal
definitions through terminal definition commands.
These commands specify one or more parameters, each
of which may give a new value to a terminal char
acteristic. Tables G-l and G-2 list these terminal
definitions, the default values, and possible values
for each of the 18 classes.
The tables use the following abbreviations when iden
tifying the terminal types for each terminal class:
Abbreviation
HASP
HAZ
POST
PRE
Tek
Terminal
Terminals using the Houston
A u t o m a t i c S p o o l i n g P r o g r a m
communication protocol.
Hazeltine.
HASP terminals that only sup
port postprint format control.
HASP terminals that only sup
por t prepr int for mat control.
Tektronix (teletypewriter emu
lation) •
istics of your terminal do not match those of its
assigned terminal class, you can change the values
of the terminal characteristics or even change the
terminal class by using the terminal definition
commands described in this appendix. You can enter
terminal definition commands any time the terminal
is connected to the network (refer to appendix J for
information on how to access a host).
When you use a terminal definition command to change
a value, that change remains in effect until the
terminal is disconnected from the network or another
terminal definition command is used to change the
value. Even application switching and logout do not
change the values of the terminal characteristics if
the terminal has not been disconnected from the
network. Disconnecting your terminal from the net
work (that is, disconnecting the phone and redialing
on dial-up terminals or turning a dedicated terminal
off and then on again) causes all terminal character
istics to be reset to site-defined default values.
The site defines these values using the Network
Definition Language (NDL).
You can also reset your terminal's characteristics
by entering the TC command. The TC command resets
your terminal characteristics to the default values
specified by the Communications Control Program
(CCP). Note that CCP-defined values may differ from
the site-defined NDL values.
It is also possible to change terminal definitions
using the TRMDEF command or by using control byte 16
fro m an In te ractive job . The TRMDEF command i s
described under Terminal Control Commands in the NOS
Reference Set, Volume 3, System Commands. Refer to
NOS Reference Set, Volume 4, Program Interface, for
information on control bytes.
TTY
UT
X.25
X3.64
Teletype.
User Terminal.
Terminals connected to a packet
switching network (PSN) using
the X.25 communication proto
col.
Terminals conforming to the
ANSI X3.64 standard.
When a terminal logs in to the network, either the
network assumes It to be of a certain terminal class
or assigns it a terminal class that resembles the
terminal's actual characteristics. If you do not
know the terminal class in use, you can enter the CH
command (described in this appendix) to ascertain
the terminal class and some of the characteristics
of your terminal. In either case, if the character-
TERMINAL DEFINITION COMMAND FORMAT
This section describes the general format of a
terminal definition command. The specific format of
each command appears later In this appendix.
General formats:
ct keyword-valuet
ct keywordj-valuei ct keyword2*value2
...ct keywordn»valuent
Parameter
ct
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command. Table G-l gives
tThe spaces shown are for clarity only. Do not include spaces when you enter a terminal definition command.
60459500 C G-l
Parameter Description
the default network control char
ac te r f or you r t er min al. t
keyword Represents a mnemonic associated
with a terminal characteristic.
value Specifies a particular value
a s s o c i a t e d w i t h t h e t e r m i n a l
definition mnemonic. Table G-2
g i v e s t h e r a n g e o f v a l u e s f o r
e a c h t e r m i n a l d e fi n i t i o n k e y
word. On some commands the
■value portion of the command is
optional and defaults to <-Y.
keyword^ Same as keyword.
value^ Same as value.
The second format allows you to make multiple ter
minal definitions in one line. If the line extends
beyond character position 54, the results are unpre
dictable. Also, if you change the network control
character ct in a concatenated group of commands,
the CT command does not take effect until the re
maining commands in the group have been processed.
As with all commands described in this manual, you
must press the message transmission key in order for
the system to process your command. Appendix K of
the NOS Reference Set, Volume 3, System Commands,
shows the default message transmission keys for the
various terminal classes. This appendix describes
how you can change the message transmission key
(refer to the EB and EL commands).
Example:
To change the page width of a 200 User Terminal,
enter these characters
ZPW-50
and press the SEND key. The X character is the
network control character, PW is the keyword
associated with page width, 50 is the new page width
for the terminal, and the SEND key is the message
transmission key for a 200 User Terminal.
RESTRICTIONS
You should not enter terminal definition commands
while output is in progress. The network may not be
able to perform such commands immediately.
The network presets all user-adjustable terminal
characteristics any time you establish a connection
to the network. The site administrators choose
these preset values. Additionally, when a terminal
is disconnected from the network and then recon
nected, the network resets any terminal character
istics you have changed to their preset values.
To enter a terminal definition command at asynch
ronous terminals from which you can enter more than
one line before transmitting (IN=»BK is specified).
the terminal definition command must be the last
input line in the transmission. If the input is from
paper tape (IN-PT is specified), the tape reader must
stop. Unpredictable results can occur if more input
follows the terminal definition command in the trans
mission block.
Characters or character codes you specify for the
value portion of terminal definition commands are
subject to the following restrictions:
• You cannot use the following ASCII charac
ters (or their character codes) in the value
portion of the AB, CN, BS, Bl, B2, CT, EB,
or EL commands:
any lowercase or uppercase alphabetic
character
any digit 0 through 9
NUL
SOH
STX
■
DEL
space
• The ASCII characters or character codes you
specify for the AB, BS, Bl, B2, CN, CT, EB,
and EL terminal definitions must all be
different, except that AB and CN can have
the same value and EB and EL may have the
same value.
• If output flow control is used, do not use
DCls and DC33 In the AB, CN, BS, Bl, B2, CT,
EB, or EL commands.
TERMINAL DEFINITION COMMANDS
This subsection describes the function and format of
each terminal definition command. The headings
consist of the command name (a two-character
mnemonic) followed by the terminal attribute it
defines. Generally, the format descriptions do not
show the default values or ranges of values since
th ey var y w i th te rm i na l clas s. Tab le s G-l an d G -2
show this information. If you are unable to find
the key on your keyboard that corresponds to a
particular character given in table G-l, consult the
documentation for your terminal.
This section refers to categories of terminal classes
to which commands apply. The categories are as
follows:
Category
Asynchronous
Mode 4
HASP
Bisynchronous
X.25 PSN
3270
Terminal Classes
1 through 8
10, 11, 12, 13, 15
9, 14
16, 17, 18
1, 2, 3, 5, 6, 7, 8
18
/■SSN
/^^%s
TYou must press the ATTN key on a 2741-compatible terminal before entering this character.
• G-2 60459500 C
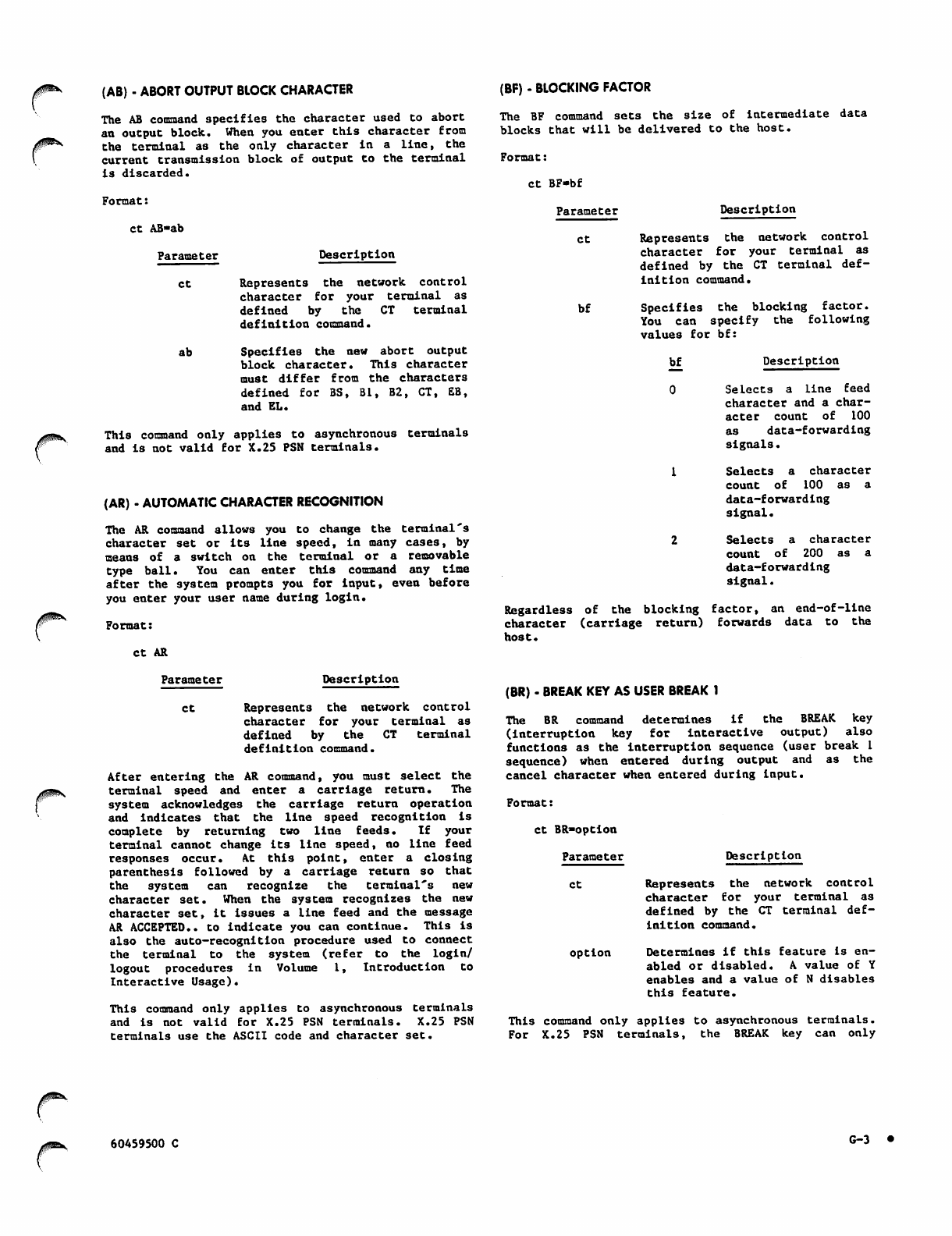
(AB) - ABORT OUTPUT BLOCK CHARACTER
The AB command specifies the character used to abort
an output block. When you enter this character from
the terminal as the only character in a line, the
current transmission block of output to the terminal
is discarded.
(BF) • BLOCKING FACTOR
Format:
ct AB-ab
Parameter
ct
ab
Description
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
Specifies t h e ne w abort o u t p u t
block character. This character
must differ from the characters
defined for BS, Bl, B2, CT, EB,
and EL.
This command only applies to asynchronous terminals
and is not valid for X.25 PSN terminals.
(AR) - AUTOMATIC CHARACTER RECOGNITION
The AR command allows you to change the terminal's
character set or Its line speed, in many cases, by
means of a switch on the terminal or a removable
type ball. You can enter this command any time
after the system prompts you for input, even before
you enter your user name during login.
Format:
ct AR
The BF command sets the size of intermediate data
blocks that will be delivered to the host.
Format:
ct BF-bf
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
bf Specifies the blocking factor.
You can specify the following
values for bf:
bf Description
0 Selects a line feed
character and a char
acter count of 100
as data-forwarding
signals.
1 Selects a character
c o u n t o f 1 0 0 a s a
data-forwarding
signal.
2 Selects a character
c o u n t o f 2 0 0 a s a
data-forwarding
signal.
Regardless of the blocking factor, an end-of-line
character (carriage return) forwards data to the
host.
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
After entering the AR command, you must select the
terminal speed and enter a carriage return. The
system a ckn owledges th e ca rri age return operation
and indicates that the line speed recognition is
complete by returning two line feeds. If your
terminal cannot change its line speed, no line feed
responses occur. At this point, enter a closing
parenthesis followed by a carriage return so that
the system can recognize the terminal's new
character set. When the system recognizes the new
character set, it issues a line feed and the message
AR ACCEPTED., to indicate you can continue. This is
also the auto-recognition procedure used to connect
the terminal to the system (refer to the login/
logout procedures in Volume 1, Introduction to
Interactive Usage).
This command only applies to asynchronous terminals
and is not valid for X.25 PSN terminals. X.25 PSN
terminals use the ASCII code and character set.
(BR) • BREAK KEY AS USER BREAK 1
The BR command determines if the BREAK key
(interruption key for interactive output) also
functions as the interruption sequence (user break I
sequence) when entered during output and as the
cancel character when entered during input.
Format:
ct BR-option
Parameter
ct
option
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Determines if this feature is en
abled or disabled. A value of Y
enables and a value of N disables
this feature.
This command only applies to asynchronous terminals.
For X.25 PSN terminals, the BREAK key can only
>^v
60459500 C G-3
function as the interruption sequence whether entered
during input or output.
(BS) • BACKSPACE CHARACTER
The BS command specifies the character used to
delete the previous input character.
Format:
ct BS«bs
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
bs Specifies the new backspace char
act e r. T h i s c h a r a cter mu s t di f
fer from the characters currently
defined for AB, Bl, B2, CN, CT,
EB, and EL.
It is possible to backspace only to the beginning of
the current physical line; additional backspaces are
disregarde d. When a page w idth of 0 is selected,
the network assumes a page width of 100 characters
for backspacing. If the page width is in the range
20 through 56, backspacing Into previous physical
lines is sometimes permitted.
This command only applies to asynchronous terminals
only.
(Bl) - INTERRUPTION OR USER BREAK 1 CHARACTER
The Bl command specifies the character that, when
entered as the only character in a logical line
(Interruption character followed by the message
transmission key), causes program interruption.
Format:
ct Bl-ubl
Parameter
ct
ubl
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Specifies the new user break 1
character. This character must
d i ff e r f r o m th e c h a ract e r s cu r
rently defined for AB, BS, B2,
CN, CT, EB, and BL.
The interruption sequence is discussed in section 17.
The BR command determines whether the BREAK key can
also function as the Bl character.
This command does not apply to bisynchronous 2780
and 3780 terminals.
(B2) - TERMINATION OR USER BREAK 2 CHARACTER
The B2 command specifies the character that, when
entered as the only character in a logical line (ter
mination character followed by the message transmis
sion key), causes program termination.
Format:
ct B2-ub2
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
u b 2 S p e c i fi e s t h e n e w u s e r b r e a k 2
character. This character must
differ from the characters cur
rently defined for AB, BS, Bl,
CN, CT, EB, and EL.
The termination sequence is discussed in section 17.
This command does not apply to bisynchronous 2780 and
3780 terminals.
(CH) • DISPLAY TERMINAL CHARACTERISTICS
The CH command displays some of the terminal's cur
rent characteristics.
Format:
ct CH
Parameter Description
c t R e p r e s e n t s t h e n e t w o r k c o n t r o l
character for your terminal as
defined by the CT terminal def
inition command.
The CH command produces a display in the following
format:
TC-tc,BS-bs,CN»cn,AB=ab,Bl-ubl,B2"ub2,EL«"el,EB=eb
where the variable portions appear as ASCII charac
ters If printable, mnemonics (for example, STX) If
nonprlntable, or N/A if the attribute is not appli
cable.
(Cl) • CARRIAGE RETURN IDLE COUNT
The CI command specifies the number of idle charac
ters to be inserted into the output stream after a
carriage return.
Format:
ct CI»ci
• G - 4 60459500 C
Parameter Description Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
ci Specifies the new carriage return
idle count. This value can be
from 0 to 99 or the string CA. A
value of CA restores the carriage
return idle count to the default
value.
When t he network p ro du ce s a c arriage re tu rn , th e
network outputs the specified number of idle charac
ters before outputting the next line. This allows
time for the carriage return function and ensures
that characters are not lost because of printing
attempts during the carriage return operation.
This command only applies to asynchronous terminals.
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
option Indicates whether to send a res
ponse to the terminal or not. A
value of Y indicates yes and N
indicates no.
This command applies only to asynchronous terminals
(except 2741s). If CP-Y and IN-KB are selected, the
system responds to the line feed key by sending a
carriage return and responds to an EL or EB charac
t e r b y s e n d i n g t h e c u r s o r p o s i t i o n i n g r e s p o n s e
specified by the EL or EB command. If IN=BK is
selected or you are at an X.25 PAD terminal, the
system responds only to the EB character by sending
the cursor positioning response selected by the EB
command.
jjKSBN. (CN) • CANCEL CHARACTER
The CN command specifies the character used to cancel
the logical line currently being input.
Format:
ct CN»CQ
(CT) • NETWORK CONTROL CHARACTER
The CT command specifies a network control character
for the terminal. When you enter this character as
the first character of a logical line, it signals
that what follows is a terminal definition command
or a special command that the network forwards to
your application with a preemptive status.
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
en Specifies the new cancel char
acter. This character must
differ from the characters
currently defined for BS, Bl,
B2, CT, EB, and EL.
When you enter the cancel character as the last
character in a line, the entire logical line in
progress is cancelled. The system responds to a
cancel line character by printing *DEL* on the next
line and positioning the carriage to the beginning
of a new line. The BR command determines whether
the BREAK key can also function as the CN character.
This command does not apply to bisynchronous 2780,
3270, and 3780 terminals.
(CP) - CURSOR POSITIONING AFTER INPUT
The CP command determines whether or not the system
sends the terminal a response to the line feed key,
the EL character, and the EB character.
Format:
ct CP»option
Format:
ct CT-char
Parameter
ct
char
Description
Represents the current network
control character for your ter
minal.
Specifies the new network con
trol character. This character
must differ from the characters
currently defined for AB, BS,
Bl, B2, CN, EB, and EL.
If you enter the CT command in a line with multiple
terminal definitions, the new value char does not
take effect until the complete line is processed.
(DL) - DELIMITERS FOR SINGLE-MESSAGE TRANSPARENT INPUT
MODE
The DL command specifies the delimiters that
terminate single-message transparent Input mode.
When you initiate transparent input mode (IN»X,
IN-XK, or IN»XP), the network reads your input and
sends it to the system without translation until it
encounters a delimiter. If your terminal's parity
is set to even, odd, or zero (PA=E, 0, or Z), the
parity bit is stripped (set to zero) before the
c h a r a c t e r s a r e s e n t t o t h e h o s t , a l t h o u g h n o
60459500 C G-5
t r a n s l a t i o n o c c u r s . I f y o u r t e r m i n a l ' s p a r i t y i s
set to none or ignore (PA=N or I), the parity bit is
not stripped. See the NAM/CCP Terminal Interfaces
Reference Manual for more information on transparent
input and parity. The first delimiter encountered
terminates transparent input mode.
Format:
ct DL»Xxx,Ccount,TO
Parameter
ct
Description
Xxx
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
Specifies the 2-digit hexadecimal
code (xx) of the character you
want as a delimiter. The network
does not send the character as
part of the input data. When you
specify a hexadecimal code above
7F, you must have previously set
your ter- minal's parity to none
(PA-N) or ignore (PA-I); other
wise the network cannot detect
t h e c o d e w h e n i t o c c u r s i n a
transparent mode message. If the
terminal's parity is set to none,
the 8-bit hexadecimal code input
from the terminal is matched
against the 8-bit hexadecimal
code specified as the delimiter
(xx). If the terminal's parity
is set to ignore, the bottom 7
bits of the terminal input are
matched against the bottom 7 bits
of the specified delimiter (xx).
Specifies a decimal value (count)
fr om 1 to 409 51 that f unc ti on s
as a character count delimiter.
Specifies that a timeout of be
tween 200 and 400 milliseconds
will be a transparent mode de
l i m i t e r .
You can select any of the three types of delimiters:
character delimiter (specify Xxx), character count
delimiter (specify Ccount), and timeout delimiter
(specify TO).
The parameter values for DL are order-independent
and optional. However, you must specify at least
one of the parameter values. You can omit trailing
commas if you do not specify all three types of
delimiters.
Entering this command with any number of new
delimiters cancels all transparent mode input
delimiters already in effect, including those
specified with the XL command.
The DL command applies only to asynchronous and mode
4 terminals. Terminal class 4 is configured with
the RETURN key as the only transparent mode
terminator and mode 4 terminals are configured with
Ccount
TO
the SEND or ETX key as their only transparent mode
terminator. For X.25 devices, the PAD forwarding
signal always acts as a transparent mode terminator
in addition to any other options selected.
(EB) • END-OF-BLOCK CHARACTER
The EB command defines the end-of-block character
and defines the cursor-positioning response to that
character. The EB character acts as the message
transmission key for terminals operating in block
mode (refer to the IN command).
Format:
ct EB-eb,cpr
Parameter
ct
eb
cpr
Description
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
Specifies the new end-of-block
character. You can specify the
following values for eb:
eb Description
char Selects the new EB
character. This
character must dif
fer from the charac
t e r s c u r r e n t l y d e
fined for AB, BS, Bl,
B2, CN, and CT.
EB Selects the default
end-of-block charac
ter or character se
quence .
EL Selects the current
logical end-of-line
character.
Specifies the cursor-positioning
response to the EB character.
You can specify the following
values for cpr:
cpr Description
CR Send a carriage re
turn to the terminal.
L F S e n d a l i n e f e e d t o
the terminal.
CL
NO
Send a carriage re
turn and a line feed
to the term inal.
Send no response.
The two EB parameters (EB=eb and cpr) are optional
and order-independent. If you omit one, the system
retains its previous value.
tThese values are valid within the network. However, unless changed during installation, the maximum logical
input line length in IAF (160 characters) limits you.
• G-6 60459500 C
This command is valid only for asynchronous ter
minals, except for paper tape devices and 2741 ter
minals. The end-of-block character for mode 4 ter
minals is ETX and is not changeable. The X.25 PAD
forw arding signal is th e default for X.25 PSN ter
minals and always acts as an end-of-block. If you
specify the char form of the eb parameter, it is only
effective if It occurs as the last character in a
packet sequence.
The CP command enables or disables the cursor-
positioning response specified by the cpr parameter.
(EL) • END-OF-LINE CHARACTER
T h e E L c o m m a n d d e fi n e s t h e l o g i c a l e n d - o f - l i n e
character (carriage return) and defines the cursor-
positioning response to that character. It also
defines the message transmission key for asynch
ronous terminals not operating in block mode (refer
to the IN command).
Format:
ct EL«el, cpr
Parameter
ct
el
/#**>
Description
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
Specifies the new logical end-of-
line character. You can specify
the following values for el:
el Description
char Selects the new EL
character. This
character must dif
fer from the charac
ters currently de
fi n e d f o r A B , B S ,
Bl, B2, CN, and CT.
EB Selects the current
end-of-block char
acter or character
sequence.
EL Selects the default
logical end-of-line
character.
cpr Description
CL Send a carriage re
turn and a line feed
to the term inal.
NO Send no response.
The two EL parameters (el and cpr) are optional and
order-Independent. If you omit one, the system
retains its previous value.
This command does not apply to 2741, HASP, 3270, and
bisynchronous 2780 and 3780 terminals; the cpr
par ame ter does not ap ply to m ode 4 or X.25 PSN
terminals; and the char specification does not apply
to mode 4 terminals.
The CP command enables or disables the cursor-
positioning response specified by the cpr parameter.
(EP) • ECHOPLEX MODE
The EP command enables or disables the echoing of
input characters back to the terminal.
Format:
ct EP-option
Parameter
ct
option
Description
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
Specifies whether to enable (Y)
or disable (N) input echoing.
Some terminals can perform their own character
echoing, such as terminals with a HALF/FULL duplex
sw i tch . I f the s wit c h i s i n t h e H A LF pos i tio n , s et
the EP value to N, and the terminal echoes the
input. If the switch is in the FULL position, set
the EP value to Y and the network echoes the input.
You can use the EP command and full-duplex mode as a
security measure. If you are in full-duplex mode
and EP is Y during login, the system echoes all of
your input except your password. This is not true,
however, if you enter your user name and password on
the same line.
This command only applies to asynchronous terminals
(except 2741s) but is not valid for X.25 PSN
terminals.
c p r S p e c i fi e s t h e c u r s o r - p o s i t i o n i n g
response to the EL character.
You can specify the following
values for cpr:
cpr
CR
LF
Description
Send a carriage re
turn to the terminal.
Send a line feed
the terminal.
to
(FA) • FULL ASCII INPUT MODE
The FA command enables or disables the full-ASCII
input mode.
Format:
ct FAdoption
60459500 C G-7
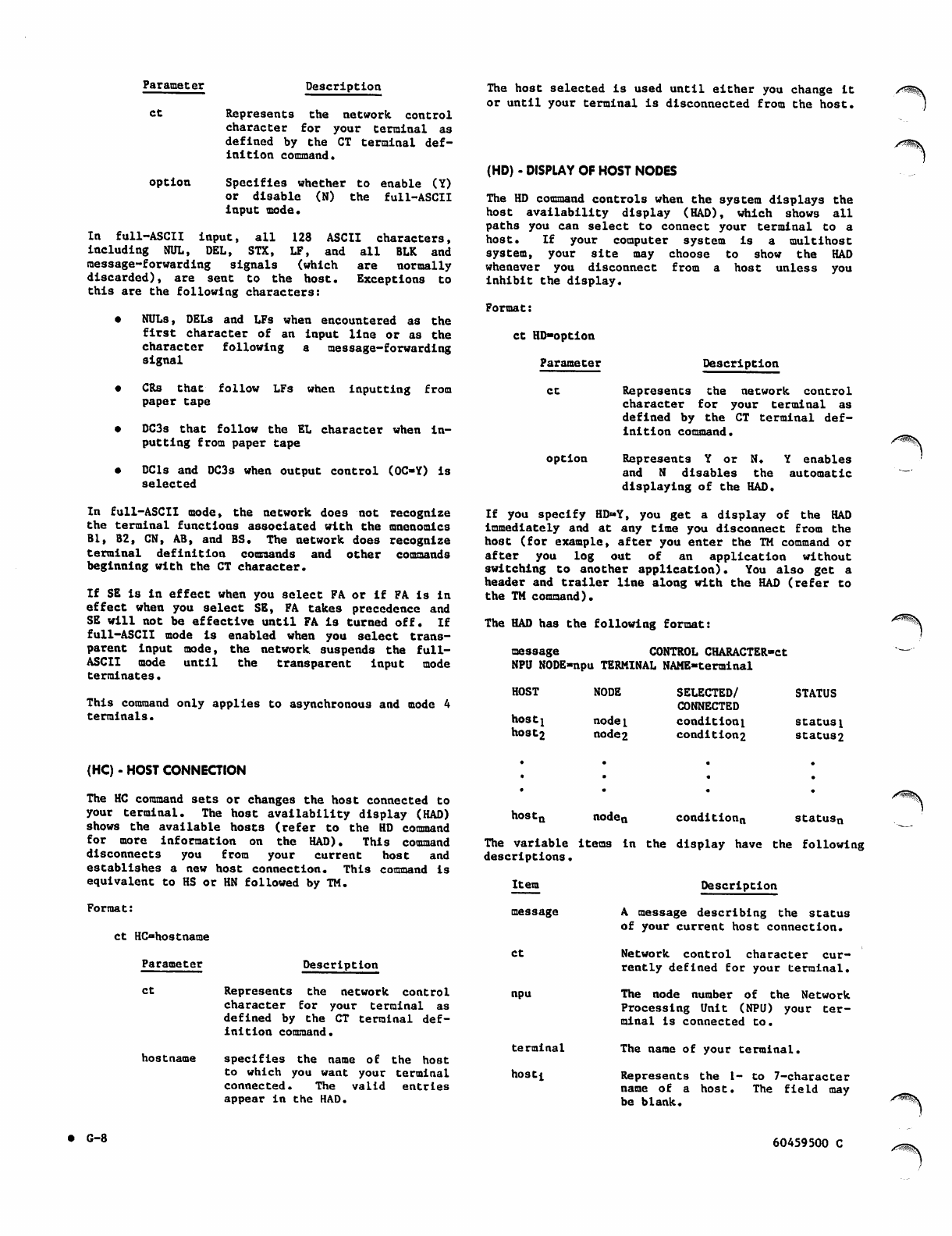
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
option Specifies whether to enable (Y)
or disable (N) the full-ASCII
input mode.
In full-ASCII input, all 128 ASCII characters,
including NUL, DEL, STX, LF, and all BLK and
message-forwarding signals (which are normally
discarded), are sent to the host. Exceptions to
this are the following characters:
• NULs, DELs and LFs when encountered as the
first character of an input line or as the
character following a message-forwarding
signal
• CRs that follow LFs when inputting from
paper tape
• DC3s that follo w t he EL c ha racte r whe n in
putting from paper tape
• DCls and DC3s when output control (OC-Y) is
selected
In full-ASCII mode, the network does not recognize
the terminal functions associated with the mnenomics
Bl, B2, CN, AB, and BS. The network does recognize
terminal definition commands and other commands
beginning with the CT character.
If SE is in effect when you select FA or if FA is in
effect when you select SE, FA takes precedence and
SE will not be effective until FA is turned off. If
full-ASCII mode Is enabled when you select trans
parent input mode, the network, suspends the full-
ASCII mode until the transparent input mode
terminates.
This command only applies to asynchronous and mode 4
terminals.
The host selected is used until either you change it
or until your terminal is disconnected from the host.
(HD) • DISPLAY OF HOST NODES
The HD command controls when the system displays the
host availability display (HAD), which shows all
paths you can select to connect your terminal to a
host. If your computer system is a multihost
system, your site may choose to show the HAD
whenever you disconnect from a host unless you
inhibit the display.
Format:
ct HD-option
Parameter
ct
option
Description
Represents Che network control
character for your terminal as
defined by the CT terminal def
inition command.
Represents Y or N. Y enables
and N disables the automatic
displaying of the HAD.
If you specify HD-Y, you get a display of the HAD
immediately and at any time you disconnect from the
host (for example, after you enter the TM command or
after you log out of an application without
switching to another application). You also get a
header and trailer line along with the HAD (refer to
the TM command).
The HAD has the following format:
message CONTROL CHARACTER»ct
NPU NODE-npu TERMINAL NAME-terminal
/'SjS^v
HOST NODE SELECTED/
CONNECTED
STATUS
host} nodei condltloni statusi
host 2 node 2 condition2 status2
(HC) • HOST CONNECTION
The HC command sets or changes the host connected to
your terminal. The host availability display (HAD)
shows the available hosts (refer to the HD command
for more information on the HAD). This command
disconnects you from your current host and
establishes a new host connection. This command is
equivalent to HS or HN followed by TM.
Format:
ct HC«hostname
Parameter
ct
hostname
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
specifies the name of the host
to which you want your terminal
connected. The valid entries
appear in the HAD.
host. noder conditionn statusr
The variable items In the display have the following
descriptions.
Description
ct
npu
terminal
host*;
A message describing the status
of your current host connection.
Network control character cur
rently defined for your terminal.
The node number of the Network
Processing Unit (NPU) your ter
minal is connected to.
The name of your terminal.
Represents the I- to 7-character
name of a host. The field may
be blank.
• G - 8 60459500 C
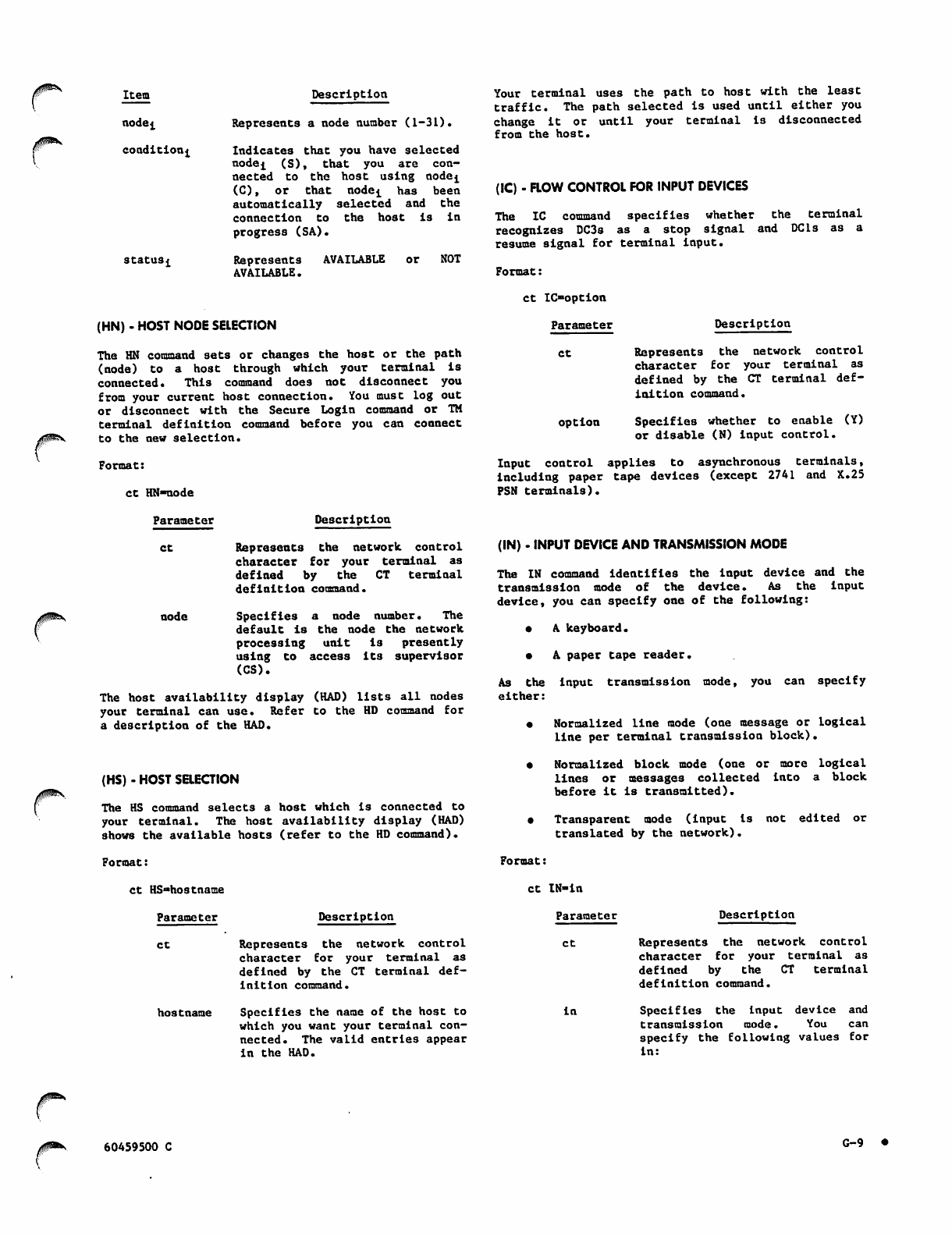
<(#Sv
r
Item
node^
condition^
Description
Represents a node number (1-31).
Indicates that you have selected
node^ (S), that you are con
nec te d to the h ost us ing no de^
(C), or that node^ has been
a u t o ma t i c al l y se l e c t e d an d t h e
connection to the host is in
progress (SA).
status£ Represents
AVAILABLE.
AVAILABLE or NOT
(HN) - HOST NOOE SELECTION
The HN command 3ets or changes the host or the path
( n o d e ) t o a h o s t t h r o u g h w h i c h y o u r t e r m i n a l i s
connected. This command does not disconnect you
from your current host connection. You must log out
or disconnect with the Secure Login command or TM
terminal definition command before you can connect
to the new selection.
Format:
Your terminal uses the path to host with the least
traffic. The path selected is used until either you
change it or until your terminal Is disconnected
from the host.
(IC) - FLOW CONTROL FOR INPUT DEVICES
The IC command specifies whether the terminal
recognizes DC3s as a stop signal and DC Is as a
resume signal for terminal input.
Format:
ct IC- opt io n
Parameter
ct
option
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Specifies whether to enable (Y)
or disable (N) input control.
ct HN-node
Input control applies to asynchronous terminals,
including paper tape devices (except 2741 and X.25
PSN terminals).
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
n o d e S p e c i fi e s a n o d e n u m b e r . T h e
default is the node the network
processing unit is presently
using to access its supervisor
(CS).
The host availability display (HAD) lists all nodes
your terminal can use. Refer to the HD command for
a description of the HAD.
(HS) - HOST SELECTION
The HS command selects a host which is connected to
your terminal. The host availability display (HAD)
shows the available hosts (refer to the HD command).
(IN) - INPUT DEVICE AND TRANSMISSION MODE
The IN command identifies the input device and the
transmission mode of the device. As the input
device, you can specify one of the following:
• A keyboard.
• A p ape r t ap e r ead er.
As the input transmission mode, you can specify
either:
• Normalized line mode (one message or logical
line per terminal transmission block).
• Normalized block mode (one or more logical
lines or messages collected Into a block
bef o r e it is tr a n s m i t t ed).
• Transparent mode (input Is not edited or
translated by the network).
Format: Format:
ct HS»ho3tname
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
hostname Specifies the name of the host to
which you want your terminal con
nected. The valid entries appear
in the HAD.
ct IN-in
Parameter
ct
in
Description
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
S p e c i fi e s t h e I n p u t de v i c e an d
transmission mode. You can
sp ec ify the fol lo win g v al u es for
I n :
60459500 C G-9
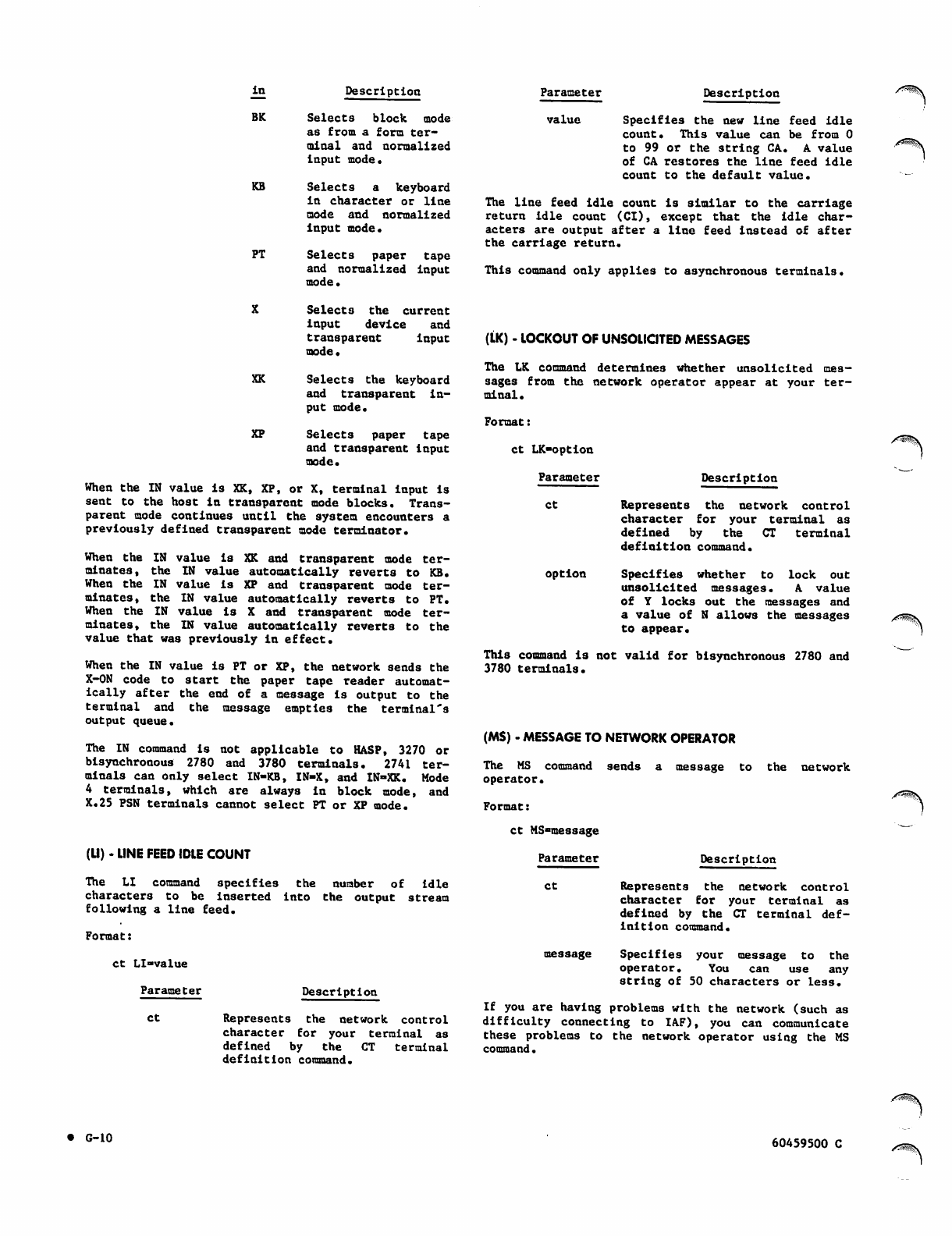
in Description
BK Selects block mode
as from a form ter
minal and normalized
input mode.
KB Selects a keyboard
in c h a r a c t e r or l i n e
mode and normalized
input mode.
PT Selects paper tape
and normalized input
mode.
Parameter Description
value Specifies the new line feed idle
count. This value can be from 0
to 99 or the string CA. A value
of CA restores the line feed idle
count to the default value.
The line feed idle count is similar to the carriage
return idle count (CI), except that the idle char
acters are output after a line feed instead of after
the carriage return.
This command only applies to asynchronous terminals.
X Selects the current
input device and
transparent input
mode.
XK Selects the keyboard
and transparent in
put mode.
XP Selects paper tape
and transparent input
mode.
When the IN value is XK, XP, or X, terminal input is
sent to the host in transparent mode blocks. Trans
parent mode continues until the system encounters a
previously defined transparent mode terminator.
When the IN value is XK and transparent mode ter
minates, the IN value automatically reverts to KB.
When the IN value is XP and transparent mode ter
minates, the IN value automatically reverts to PT.
When the IN value is X and transparent mode ter
minates, the IN value automatically reverts to the
value that was previously in effect.
When the IN value is PT or XP, the network sends the
X-ON code to start the paper tape reader automat
ically after the end of a message is output to the
terminal and the message empties the terminal's
output queue.
The IN command is not applicable to HASP, 3270 or
bisynchronous 2780 and 3780 terminals. 2741 ter
minals can only select IN-KB, IN-X, and IN-XK. Mode
4 terminals, which are always in block mode, and
X.25 PSN terminals cannot select PT or XP mode.
(LI) . LINE FEED IDLE COUNT
The LI command specifies the number of idle
characters to be inserted into the output stream
following a line feed.
Format:
ct LI»value
Parameter
ct
Description
Represents t he net wo rk co nt ro l
character for your terminal as
d e fi n e d b y t h e C T t e r m i n a l
definition command.
(LK) - LOCKOUT OF UNSOLICITED MESSAGES
The LK command determines whether unsolicited mes
sages from the network operator appear at your ter
minal.
Format:
ct LK-option
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
option Specifies whether to lock out
unsolicited messages. A value
of Y locks out the messages and
a value of N allows the messages
to appear.
This command is not valid for bisynchronous 2780 and
3780 terminals.
(MS) - MESSAGE TO NETWORK OPERATOR
The MS command sends a message to the network
operator.
Format:
ct MS«message
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
message Specifies your message to the
operator. You can use any
string of 50 characters or less.
If you are having problems with the network (such as
difficulty connecting to IAF), you can communicate
these problems to the network operator using the MS
command•
Jf-tmgK
• G-10 60459500 C
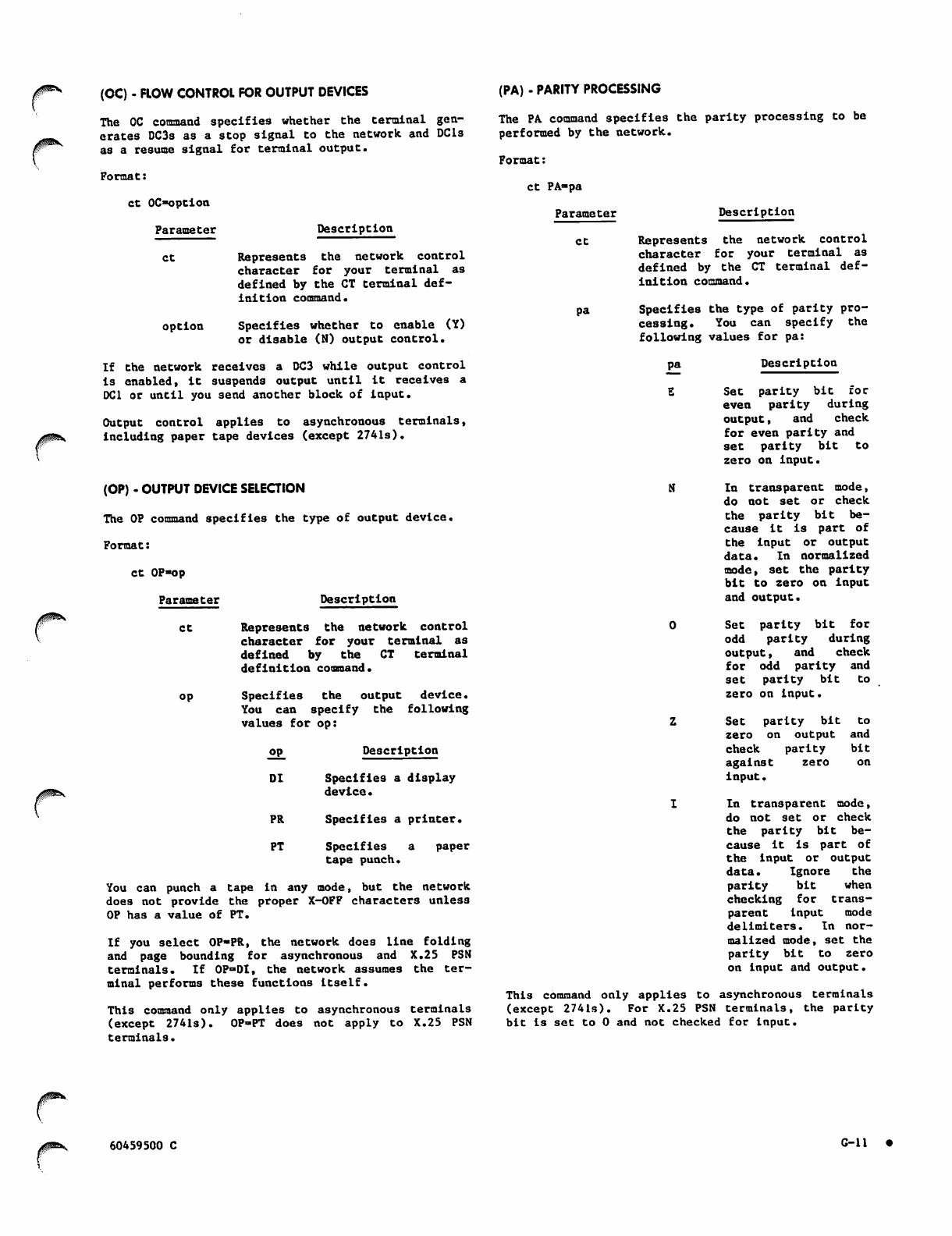
(OC) - FLOW CONTROL FOR OUTPUT DEVICES
The OC command specifies whether the terminal gen
erates DC3s as a stop signal to the network and DCls
as a resume signal for terminal output.
(PA) - PARITY PROCESSING
The PA command specifies the parity processing to be
performed by the network.
Format:
Format:
ct OC«option
Parameter
ct
option
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Specifies whether to enable (Y)
or disable (N) output control.
ct PA-pa
Parameter
ct
pa
If the network receives a DC3 while output control
is enabled, it suspends output until it receives a
DC1 or until you send another block of input.
Output control applies to asynchronous terminals,
including paper tape devices (except 2741s).
(OP) • OUTPUT DEVICE SELECTION
The OP command specifies the type of output device.
Format:
ct OP«op
Parameter
ct
op
Description
Represents the network control
character for your terminal as
defined by the CT terminal
definition command.
S p e c i fi e s t h e o u t p u t d e v i c e .
You can specify the following
values for op:
op Description
DI Specifies a display
device.
PR Specifies a printer.
PT Specifies a paper
tape punch.
You can punch a tape in any mode, but the network
does not provide the proper X-OFF characters unless
OP has a value of PT.
If you select OP-PR, the network does line folding
and page bounding for asynchronous and X.25 PSN
terminals. If OP=>DI, the network assumes the ter
minal performs these functions Itself.
This command only applies to asynchronous terminals
(except 2741s). OP-PT does not apply to X.25 PSN
terminals.
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Specifies the type of parity pro
cessing. You can specify the
following values for pa:
pa Description
E Set parity bit for
even parity during
output, and check
for even parity and
set parity bit to
zero on input.
N In transparent mode,
do not set or c hec k
t h e p a r i t y b i t b e
cause it is part of
the input or output
data. In normalized
mode, set the parity
bit to zero on input
and output.
0 Set parity bit for
odd parity during
output, and check
f o r o d d p a r i t y a n d
set parity bit to
zero on input.
Z Set parity bit to
zero on output and
check parity bit
against zero on
input.
1 In transparent mode,
do not set or check
t h e p a r i t y b i t b e
cause It is part of
the input or output
data. Ignore the
parity bit when
checking for trans
parent input mode
delimiters. In nor
malized mode, set the
parity bit to zero
on input and output.
This command only applies to asynchronous terminals
(except 2741s). For X.25 PSN terminals, the parity
bit is set to 0 and not checked for input.
J ^ V 60459500 C G-ll

(PG) • PAGE WAITING
The PG command enables or disables page waiting at
t h e t e r m i n a l d u r i n g o u t p u t . I f y o u e n a b l e p a g e
waiting, the terminal stops at the end of each
output page for your acknowledgement (a null input
line) before output continues.
Format:
ct PG-option
Parameter
ct
option
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Specifies whether to enable (Y)
or disable (N) page waiting.
Wh en you enter a n ul l i nput line to ge t t he ne xt
page of output, the null input line has no other
meaning.
Page waiting does not apply to bisynchronous 2780 or
3780 terminals or to HASP terminals.
(PL) - PAGE LENGTH
The PL command establishes the maximum number of
physical lines that can be printed as one page. If
OP h as a va l ue of P R , t he netw ork auto mat ic a ll y
positions the carriage to the top of the form after
PL lines have been output.
Format:
ct PL-pl
Parameter
ct
Pi
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Specifies the page length. You
can specify 0 or any value from
8 to 255. PL-0 selects an In
finitely long page.
The PL value must be nonzero if you want to enable
page waiting, since page waiting only occurs after
the number of lines defined by pl-1 are output.
Parameter Description
ct Represents the network control
character for your terminal as
defined by the CT term ina l de f
inition command.
p w S p e c i fi e s t h e p a g e w i d t h . Y o u
can specify a value of 0 or any
v a l u e f r o m 2 0 t o 2 5 5 . P W - 0
selects an infinitely long line.
(SE) - SPECIAL EDITING MODE
The SE command enables or disables the
editing variant of normalized input mode.
special
Format:
ct SE»option
Parameter
ct
option
Description
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Enables (Y) or disables (N)
special editing operations.
When special editing is in effect, any backspace
character entered is stored for transmission to the
host. Similarly, a line feed entry produces a
normal line feed operation at the terminal and the
network stores the line feed character code for
transmission to the host. A backspace followed by a
line feed causes the system to output a bell and an
exclamation point on an ASCII terminal or an in
verted caret (v) on an APL terminal below the last
character entered.
This command is only valid for asynchronous ter
minals but not for X.25 PSN terminals.
(TC) - TERMINAL CUSS COMMAND
The TC command specifies a terminal class for your
terminal. The terminal class associates your
terminal with a predefined set of terminal
characteristics. To effectively use a terminal
class, choose a terminal class whose default
terminal definition corresponds to the
characteristics of your terminal.
Format:
(PW) - PAGE WIDTH
The PW command establishes the maximum number of
characters that the terminal prints on one output
line. If OP has the value PR, the system automat
ic a lly st a rt s a ne w li ne a fte r p w ch ara c ter s h a ve
been output.
Format:
ct PW»pw
ct TC-tc
Parameter Description
c t R e p r e s e n t s t h e n e t w o r k c o n t r o l
character for your terminal as
defined by the CT terminal def
inition command.
tc Specifies the terminal class.
The value tc can be from 1 to 17.
• G-12 60459500 C
The following list associates terminal class values
with terminal types:
Parameter
ct
J 0 ^ L y
tc
I
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
Terminal Type
M33, M35, M37, M38 teletypes
CDC 713-10, 722, 751-1, 752, 756
CDC 721
IBM 2741
M40 teletypes
Hazeltine 2000
Terminals conforming to the ANSI
X3.64 standard (DEC VT100)
Tektronix 4010, 4014
HASP protocol, postprint format
control
200 User Terminal
CDC 714-30
CDC 711-10
CDC 714-10/20
HASP protocol, preprint format
control
CDC 734, 731-12, 732-12
IBM 2780
IBM 3780
IBM 3270
A terminal that is not shown as belonging to a ter
minal class may still be operational. The terminal
can be assigned to a terminal class having similar
characteristics and the terminal's definition can be
modified as necessary to correctly define the opera
tional characteristics of the terminal.
If your terminal is on an auto-recognition line and
Its terminal class is other than 1, 4, 10, or 13,
you can use the TC command to change its terminal
class to ensure proper operation.
If you include a TC command in a sequence of ter
minal definition commands, enter the TC command
first as It resets all other terminal character
istics.
(TM) - TERMINATING A TERMINAL-HOST CONNECTION
The TM command severs the connection between your
terminal and a host.
Format:
ct TM
Description
Represents the network control
character for your terminal as
defined by the CT command.
You can use the TM command if your application does
not respond to your input. The system responds to
the TM command in the following manner:
host status
had
prompt
CONTROL CHARACTER=ct
The variable items have the following descriptions:
Item
host status
ct
had
prompt
J®>^
Description
Indicates the status of the host
you have just specified or to
which you are/were connected.
You can get any one of the fol
lowing messages:
HOST AVAILABLE
HOST BUSY
HOST CONNECTED
HOST DISCONNECTED
HOST UNAVAILABLE
NO HOST AVAILABLE
NO HOST CONNECTED
NO HOST SELECTED
Represents the network control
character for your terminal as
defined by the CT command.
Represents the host availability
display (HAD). The HAD appears
only if you have enabled its
automatic display (refer to the
HD command).
Represents an action the system
wants you to take or a status
message. You can get any one of
the following prompts:
ENTER Ct HD TO SEE HOST
STATUS
ENTER Ct HN=NN TO SELECT HOST
ENTER INPUT TO CONNECT TO
HOST
INPUT DISCARDED
READY FOR INPUT
TERMINAL DISABLED BY NOP
(XL) - MULTIMESSAGE TRANSPARENT MODE
The network provides a transparent mode that allows
you to remain in transparent input mode even after
message blocks have been forwarded to the applica
tion. The XL command specifies the multimessage-
forwarding signal and the terminator for transparent
Input mode. If your terminal's parity Is set to
even, odd, or zero (PA-E, 0 or Z), the parity bit Is
stripped (set to zero) before the characters are
sent to the host, although no translation occurs.
If your terminal's parity Is set to none or ignore
(PA«N or I), the parity bit Is not stripped. See
the NAM/CCP Terminal Interfaces Reference manual for
more Information on transparent Input and parity.
60459500 C G-13
Format: Parameter Description
ct XL-Xxx,Ccount,TO,Yyy
Parameter Description
ct
Xxx
Ccount
TO
Yyy
Represents the network control
character for your terminal as
defined by the CT terminal def
inition command.
Selects the character with the
two-digit hexadecimal represen
tation xx as the messageforward-
ing signal. If you do not
specify a value yy, the occur
rence of two successive charac
ters defined by xx acts as a ter
minator for transparent input
mode. When you specify a hexa
decimal code above 7F, you must
have previously set your ter
minal's parity to none (PA-N) or
ignore (PA-I); otherwise the net
work cannot detect the code when
it occurs in a transparent mode
message.
Selects a decimal value from 1
to 40951 as a character count
that functions as a message-
forwarding signal.
Selects timeout as a transparent
input mode terminator.
Selects the character with the
two-digit hexadecimal represen
t a t i o n y y a s a t e r m i n a t o r f o r
transparent input mode when it
follows xx. When you specify a
hexadecimal code above 7F, you
must have previously set your
terminal's parity to none (PA-N)
or ignore (PA-I); otherwise the
network cannot detect the code
when it occurs in a transparent
mode message.
Yyy, If specified, must follow the Xxx parameter;
otherwise, it is ignored. The parameters are
otherwise order-independent. You must specify at
least one of Xxx or TO to select a transparent mode
terminator. When it immediately follows the
character defined by Xxx on input, the character
defined by yy terminates transparent input mode.
The characters defined by Xxx and Yyy can be
identical or you can omit Yyy. In either case, two
s u c c e s s i v e i n p u t c h a r a c t e r s d e fi n e d b y X x x a r e
required to terminate transparent mode.
The message-forwarding signals and mode terminators
are not sent to the host.
This command cancels all transparent mode termina
tors and delimiters defined by the DL command or a
previous XL command. You can select multimessage
transparent input mode by using the XL command in
conjunction with the IN command and selecting IN-X,
IN-XK, or IN-XP.
This command does not apply to HASP and bisynchro
nous terminals.
/SE8V
/^'SaSSs.
tThese values are valid with the network. However, unless changed during Installation, the maximum logical
input line length in IAF (160 characters) limits you. y/^S^V
• G-14 60459500 C
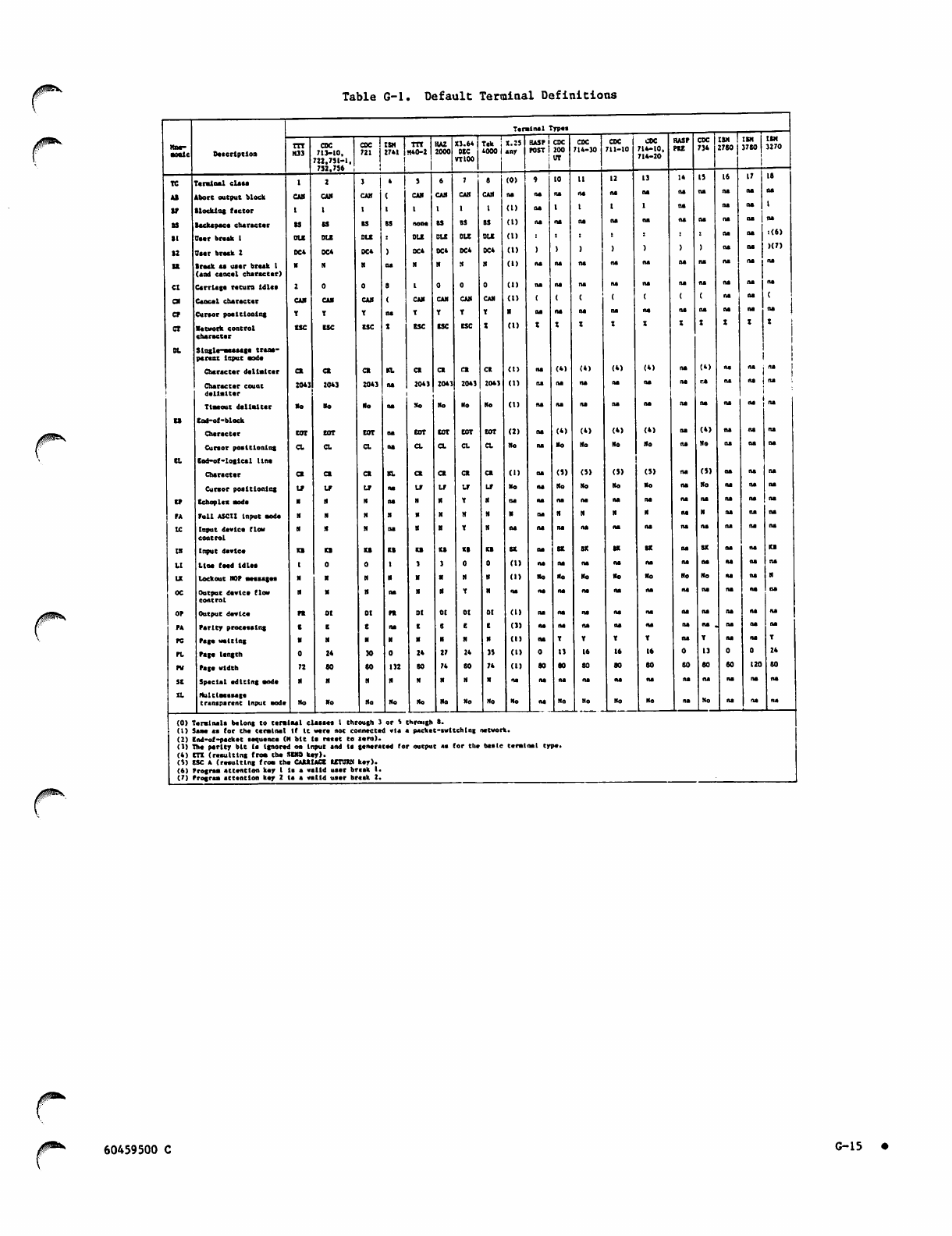
Table G-l. Default Terminal Definitions
/^PN
0^*-.
Naa-
eooic
Teratnel Types
Detcriptloa
TIT
Ml)
CDC
713-10.
722,731-1.
712,796
C D C ! I M
721 2741
TTt IhAZ
M40-2 2000
X3.64
occ
VT100
T e k j
4000 x.:7T
any
HASP 1 CDC
POST i 200
j UT
CDC
714-10
CDC
711-10
COC
714-10,
714-20
HASP
PRE
CDC
734
IBM !
2710
in
1780
UN
3270
TC
Al
W
as
Terminal clou
A b or t ou t p u t bl o c k
Slocking (actor
teckapace character
CAB
1
IS
CAM
I
SS
J i
CAN
1
IS IS
] 1
CAB
I
none
CAB
I
as
CAB
1
IS
CAB
I
IS
(0)
na
(I)
(I)
na
oa
na
10
na
I
na
11
na
I
na
12
na
1
na
1)
na
1
14
na
na
na
13
na
na
16
na
na
na
17
na
na
na
IS
na
I
na
!(6)
tl Oa.r break 1 ou ou ou OU su DU DU (I) na na
12 Our brack 1 OC* OCA OCA OCA 0C4 DC* oc* (l> na ae )<7)
a
CI
I r a a k a a u a . r b r e ak 1
(and cancel character)
Carriage renin tdlee
na
a
<l>
(1)
na
na
na
na
na na
na
na
na
na na
na
na
na
am
am
na
na
aCancel character CAB CAB CAB CAB CAB CAN CAB (I) na na
a
a
Conor paaltloalnt
Network control
character
(SC ISC ESC
aa
Xtsc ISC isc (I)
na
X
na
X
na
X
na
X
ne
X
na
X
na
X
na
X
ne
X
na
X
DL Slsgle-axaeaga treae-
nercot Input aoda
Character dallalcer Ct at CR KL Cl at Cl Cl (1) na (41 (4) (4) (4) ne (*) ne oa Z !
Character count
dellalter
: o * j 2043 204) na 204) 2041 204) 204) (1) na no na na ne na na na na
Timeout dellaiter Bo Bo Bo aa Bo No No No (1) na na na ne ne na na na
utad-of-block
Character COT tor tOT na COT COT COT COT (2) aa (4) (4) (4) (4) Oat (4) na na na
Cureor poaltlonlng CL CL na CL CL CL CL Bo na Bo No No Bo ft* No na na na
a. Cod-of-logical line
Character Cl Ct BL at at Ct Cl (1) na (3) (S> ()> (3) TU ()) na ne na
Conor poaltlonlng L» LP LP na if LP LP LT Bo na No No No Bo rt* No na na na
aCchoplcx aoda na na no na na na tu na na ne na
tu foil ASCII Input aoda na (l* aa na na
tc Input device (1cm
control
na aa na na na na na na na na am na
IB Input device Kl Kg Kl Kl Kl CK no CK BK ax MC aa BK na KB
It Line (oed tdlee (I) KM na na aa na aa na na na
Ulockout NOP aeeaatea (1) No No No Bo Bo No No na na ft
oc Output device (lew
control
na na
or O u t p u t de v i c e ft 01 01 rt DI 01 01 DI (I) na na na ae na oa na na «M na
PA rarity processing aa ()) na as na ne •» na n a . na oa na
PS
n.
feae waiting
fare length 24 30 24 27 24 33
(1)
(I)
aa
01) 16 16 16
aa
01)
na
0
na
024
fW hfe width 72 SO (0 1)2 to 74 CO 74 (I) SO ao SO SO to eo 80 60 120 ao
sc Special adltlRf aoda na na na na na na na na na ne na
IL rtolttaeesaie
transparent Input eode No Bo No No No No No No No na No No No No n. No na na na
(0) Teralnale belong to urelul claaece 1 th
(1) Sua a. (oc the tcralMt If It were not ec
( I ) C a d - o t - p a ck e t l ao u e n c e ( H b i t I t re e e t t o
(1) The portly bit 1. Ignored oa Input and to
(4) CTX (moulting (roa eh. SEND key).
(5) CSC A (reeuttlng (roa th. CAJUIUCI tfTUXN
(6) Prograa attention k«r 1 1. a valid eaar b
( 7 ) P r o g r a a a t t e n t i o n k e y 2 l e a «a t ! 4 ti a a r b
o u g h ) o f i
nnected via
t.ro).
generated fo
key).
a a k 1 .
c a k 2 .
through t.
i packet-swt
r o u t p u t a a
thing
o r t h *
networt
beele
k.
t.ral nal type.
60459500 C G-15
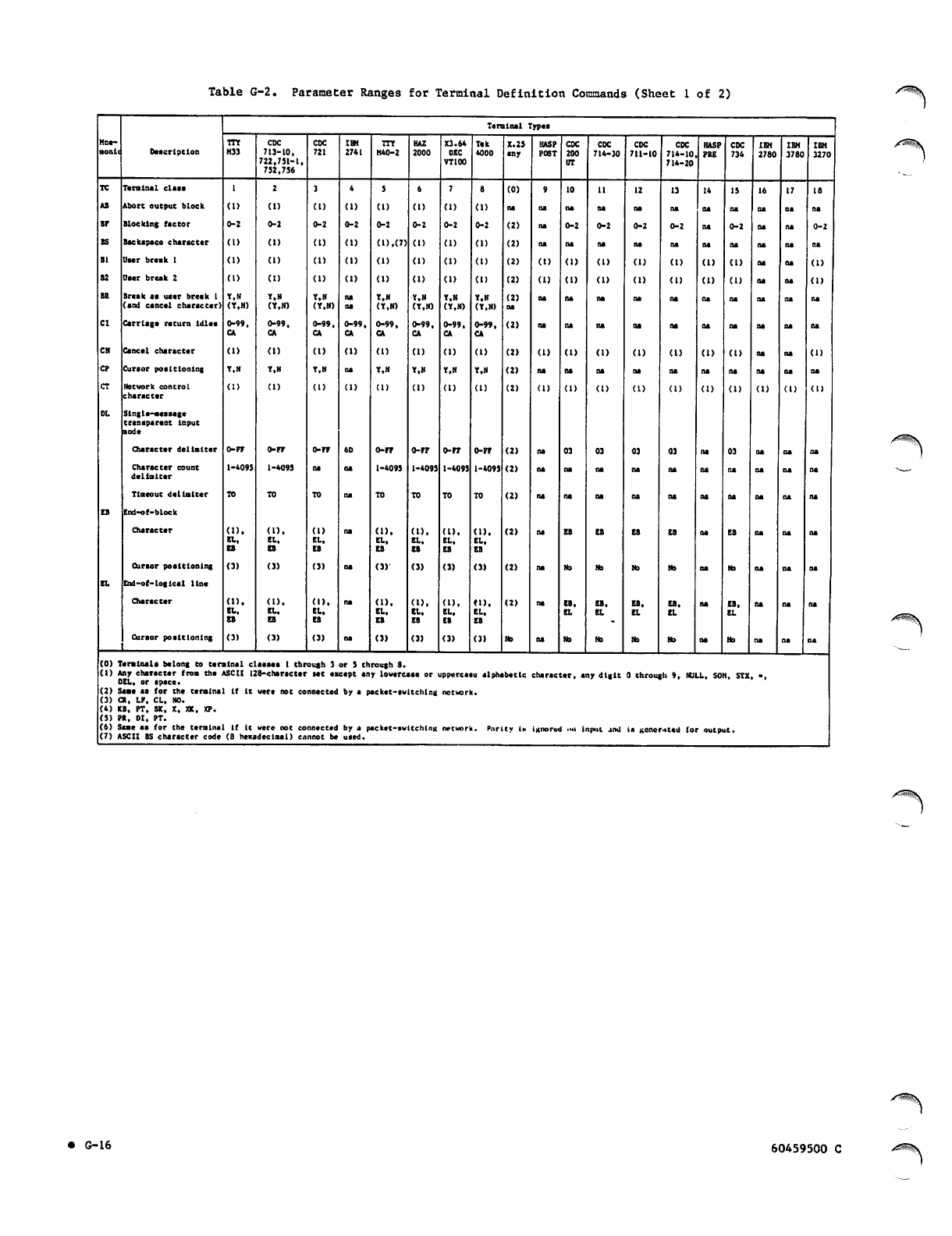
Table G-2. Parameter Ranges for Terminal Definition Commands (Sheet I of 2)
Kae-
Bonli
Terolnal Typea
Deacrlptlon
tty
N33
CDC
713-10,
722,751-1,
752,756
CDC
721
laM
2741
TTT
K40-2
HAZ
2000
X3.64
OEC
VT100
Te k
4000
X.25
any
HASP
POST
CDC
200
OT
CDC
714-30
CDC
711-10
CDC
714-10,
714-20
HASP
PRE
CDC
734
IBM
2780
IBM
3780
IBM
3270
TC Terminal claia (0) 10 11 12 13 14 IS 16 17 18
AB Abort output block (1) (1) (I) (1) (1) (I) (0 (1) na na na na na na aa na na oa na
BF Blocking factor 0-2 0-2 0-2 0-2 0-2 0-2 0-2 0-2 (2) na 0-2 C-2 0-2 0-2 na 0-2 na na 0-2
BS Backepaco character (1) (1) (I) (1) (0,(7) ( l > (I) (1) (2) ne na na na na aa na na na na
Bl User break 1 (1) (1) (I) (1) (1) (1) (1) ( t > (2) ( l > (1) (I) (1) (I) (1) (1) na na (D
B2 Ueer break 2 (1) (l) (1) (1) <n (O <1> (1) (2) (1) (1) (1> (1) (1) (1) (I) na na (1)
BR Brtak aa uaar break I
(and cancel character)
Y. N
(Y,N)
Y, N
(Y.N)
Y. N
(Y.N)
na
na
Y, N
(Y,N)
Y,N
(Y.N)
Y. N
(Y.N)
Y. N
(Y.N)
(2)
oa
na na na na na na na na na na
Cl Carriage re cum ldlea 0-99,
ca
0-99,
CA
0-99,
CA
0-99,
CA
0-99,
CA
0-99,
CA
0-99.
ca
0-99,
CA
(2) na na na na na na na na na na
CN Cancel character ( i > (1) ( l > (1) (1) (1) (1) ( l > (2) (1) (I) (1) (1) (1) (1) (1) na na (1)
CP Curaor poaltlonlng Y. N Y. N Y. N na Y.N Y.N Y,N Y.N (2) na na na na na na na na na na
CT Network control
character
(1) (1) <l> (1) (1) (1) u> (1) (2) (1) (1) ( l > (I) (1) (t) (1) (I) (I) (1)
DL Slngla-aeiMge
tranapareat Input
lode
Character dellatter 0-FF 0-FF 0-FF 6D 0-F F 0- FF 0- FF 0-FF (2> na 03 03 03 03 na 03 na na na
Character count
dellalter
1-4095 1-4095 na na 1-4093 1-4093 1-4093 1-4093 (2> na na oa na na na na na na oa
Tlstcout dellalter TO TO TO na TO TO TO TO (2) na na na na na na na ne na na
EB End-of-block
Character (1).
E l ,
EB
O ) .
EL,
EB
( l >
EL,
EB
na (1).
E l ,
EB
(I).
EL,
EB
(l>.
EL.
EB
(1),
ei.
EB
(2) na EB CB EB EB na EB na na na
Curaor poatclonlng (3> (3) (3) na (3) (3) (3) (3) (2) na No No H> No na No na na na
EL End-of-logleal line
Character <n,
EL,
SB
(t).
EL,
EB
Cl.
EB
na (1).
E l ,
»
(l>.
E l ,
EB
(I).
EL,
EB
(1).
EL,
EB
(2) na EB,
EL
EB,
El
EB.
El
EB,
EL
na CB,
EL
na na na
Curaor poaltlonlng <3) <3) (3) na (3) (3) (3) (3) No na No So No No na No na na na
(0) Teralnala belong to terminal claasea 1 thr
(1) Any character froa the ASCII 128-character
DEL, or space.
(2) Sab* aa (or Che terminal If It were not co
(3) CR, LF, CL, NO.
(4) KB, PT, BK, X, XK, XP.
(3) PK. DI, PT.
(6 ) S u e «■ for the teratnat If It were not co
(7) ASCII BS character code (8 he»;adcclaal) ca
ough 3
a c t »
nnected
nnected
nnot be
or 3 t h
ccpt an
by a p
by a p
uaed.
rough 8.
y lowereaae or
acket-awltchtng
acket-ewttchtnu.
ippercaea alphabetic
network.
artwork. Parity tr.
Chirac
ixtnret
ear, a
<»i i
iy digit
ifxil and
0 through 9, NULL. SOH, STX
ia Kcnorated (or output.
• ■•
• G-16 60459500 C >*^™^v
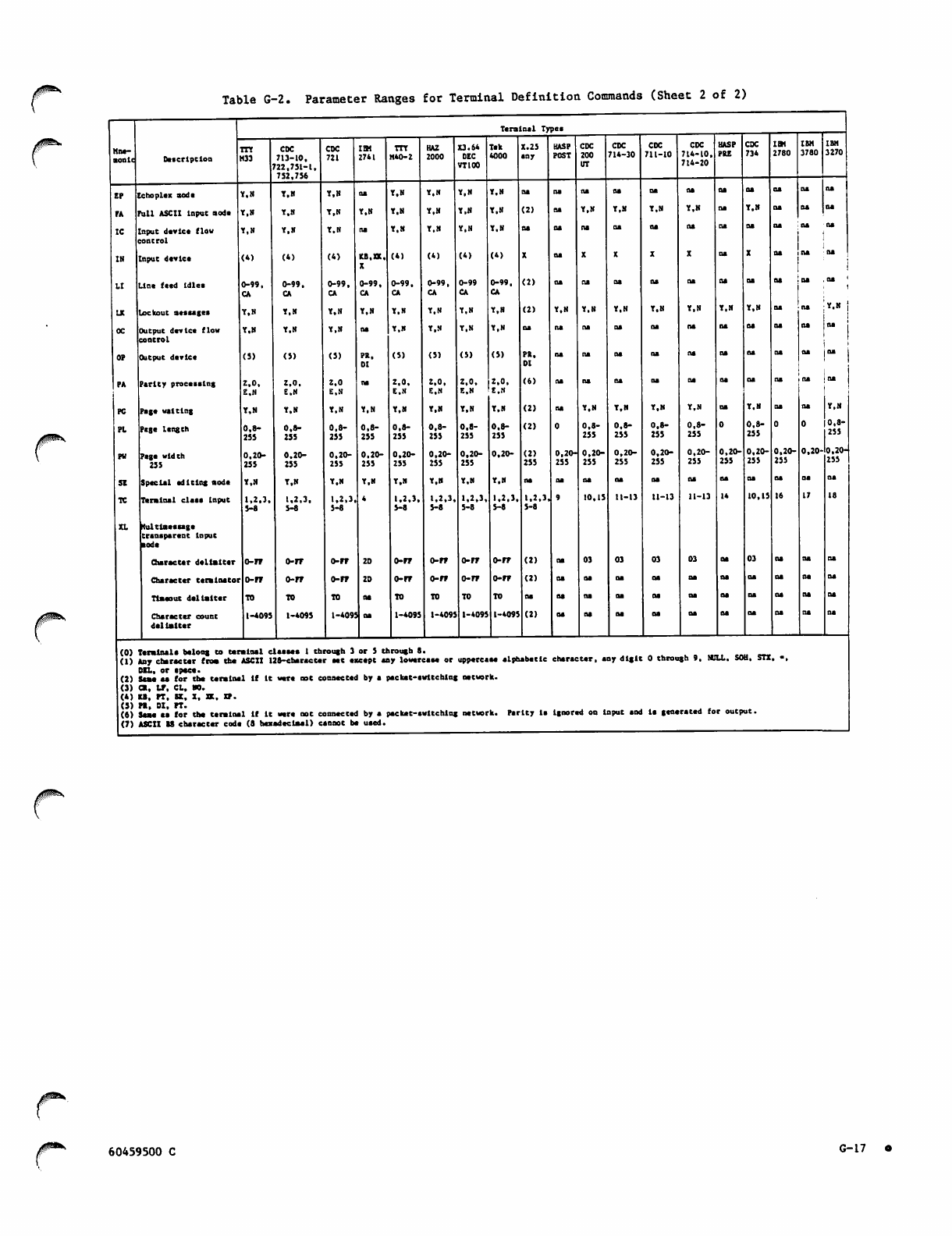
Table G-2. Parameter Ranges for Terminal Definition Commands (Sheet 2 of 2)
0$^.
Kne-
■onlc Deacrlptlon
Teralnal Typea
TTY
H33
CK
713-10,
722,751-1.
752,756
CDC
721
IBM
2741
TTT
H40-2
HAZ
2000
X3.&4
DEC
VT100
Tek
4000
X.25
any
HASP
POST
CDC
200
UT
CDC
714-30
CDC
711-10
CDC
714-10.
714-20
HASP
PRE
CDC
734
IBM
2780
IBM
3780
IBM
3270
EP Cchoplax aoda Y. N Y. N Y, N na Y. N Y. N Y. N Y. N na na na aa na na na na na na na
FA Full ASCII Input aode Y,N Y.N Y. N Y.N Y.N Y. N Y. N Y. N (2) na Y.N Y. N Y.N Y. N na Y. N na na na
IC Input device (low
control
Y, N Y. H Y. N na Y. N Y. N Y. N Y.N na na na na na na na na na na na
IN Input device (4) (4) (4) KB,XX.
X
(4) (4) (4) (4) na na na na na
LI Line feed ldlea 0-99,
CA
0-99.
CA
0-99,
CA
0-99,
CA
0-99.
CA
0-99,
CA
0-99
a0-99,
CA
(2) na na na na na oa na na na n a '
!
LK lockout aeaeagea Y.N Y. N Y. N Y. N Y.N Y.N Y. N Y. N (2) Y.N Y. N Y. H T. N Y. N Y. N Y. N na na Y . N j
OC Output device flow
c o n t r o l
Y.N Y. N Y. N na Y.N Y.N Y. N Y. N na na na na na na na na na na " i
OP Output device (5) (3) (5) PR,
DI
(5) (5) ( S ) (5) PR,
DI
na na na na na na na na na n. j
PA Parity processing Z.O,
E.N
Z.O.
E.N
Z.O
E.N
na Z.O.
E.N
Z.O,
E.N
Z.O.
E.N
Z.O.
E.H
(6) na na na na na na na na na na
PC Page waiting Y. N Y. N Y. N Y. N Y. N Y. N Y.N Y.N (2) na Y.N Y. N Y.N Y. N na Y. N na na Y. N
PL Page length 0 , 8 -
255
0 . 8 -
255
0 , 8 -
255
0,8-
255
0,8-
255
0.8-
255
0 , 8 -
255
0 , 8 -
255
(2) 0,8-
255
0 . 8 -
255
0,8-
255
0,8-
255
0.8-
255
0,8-
255
PW Page width
235
0.20-
255
0.20-
255
0,20-
255
0.20-
255
0,20-
255
0,20-
255
0,20-
255
0,20- (2)
255
0,20-
255
0,20-
255
0,20-
255
0,20-
255
0,20-
255
0,20-
255
0,20-
255
0,20-
255
0,20- 0,20-
255
SE Special editing aode Y.N T.N Y. N Y.N Y.N Y.N Y.N Y. N aa na na na na na na na na na na
TC Teralnal claaa Input 1,2.3.
5-8
1 . 2 . 3 ,
5-8
1 . 2 . 3 ,
5-8
1 . 2 . 3 ,
5-8
1 . 2 . 3 .
5-8
1 . 2 . 3 ,
5-8
1 . 2 . 3 .
5-8
1 . 2 . 3 ,
5-8
10,15 11-13 11-13 11-13 14 10,15 16 17 18
XL Kultlaeaeage
tranaparent Input
aode
Character dellalter 0-FF 0-FF O-FF 2D 0-FF 0-FF O-FF O-FF (2) na 03 03 03 03 oa 03 na na na
Character teralnator 0-FF 0-FF 0-FF 2D 0-F F 0-FF 0 -FF O-FF (2) na oa na oa aa na oa na na na
Timeout dellalter TO TO TO na TO TO TO TO na na na na oa na aa na na na na
Character count
dellalter
I-409S 1-4095 1-409! na 1-4095 1-4093 1-4095 1-4095 (2) oa na aa oa oa na na na na na
(0) Teralnala belong to uralnal claoeee I th
(1) Any character (roa the ASCII 128-eharacte
OIL, or apace.
(2) Saae aa (or the teralnel If It were not c
(3) CR, IF, CL, NO.
(4) KB. PT. BK, X, XK. XP.
(3) P I, D I, PT.
(6) Seae aa for the terminal If It were not c
(7) ASCII BS character code (8 bcxadeclaal) c
rough 3 or 5 through 8
r eat except any lower
onnccted by a packet-a
onnccted by a packet-a
annot be uaed.
eaae or upperca
witching networ
witching networ
ae alphabetic
k.
k . P a r i t y l a
character, any digit
Ignored on Input and
0 through 9, MILL. SOU, STX
la generated for output.
0^ 60459500 C G-17

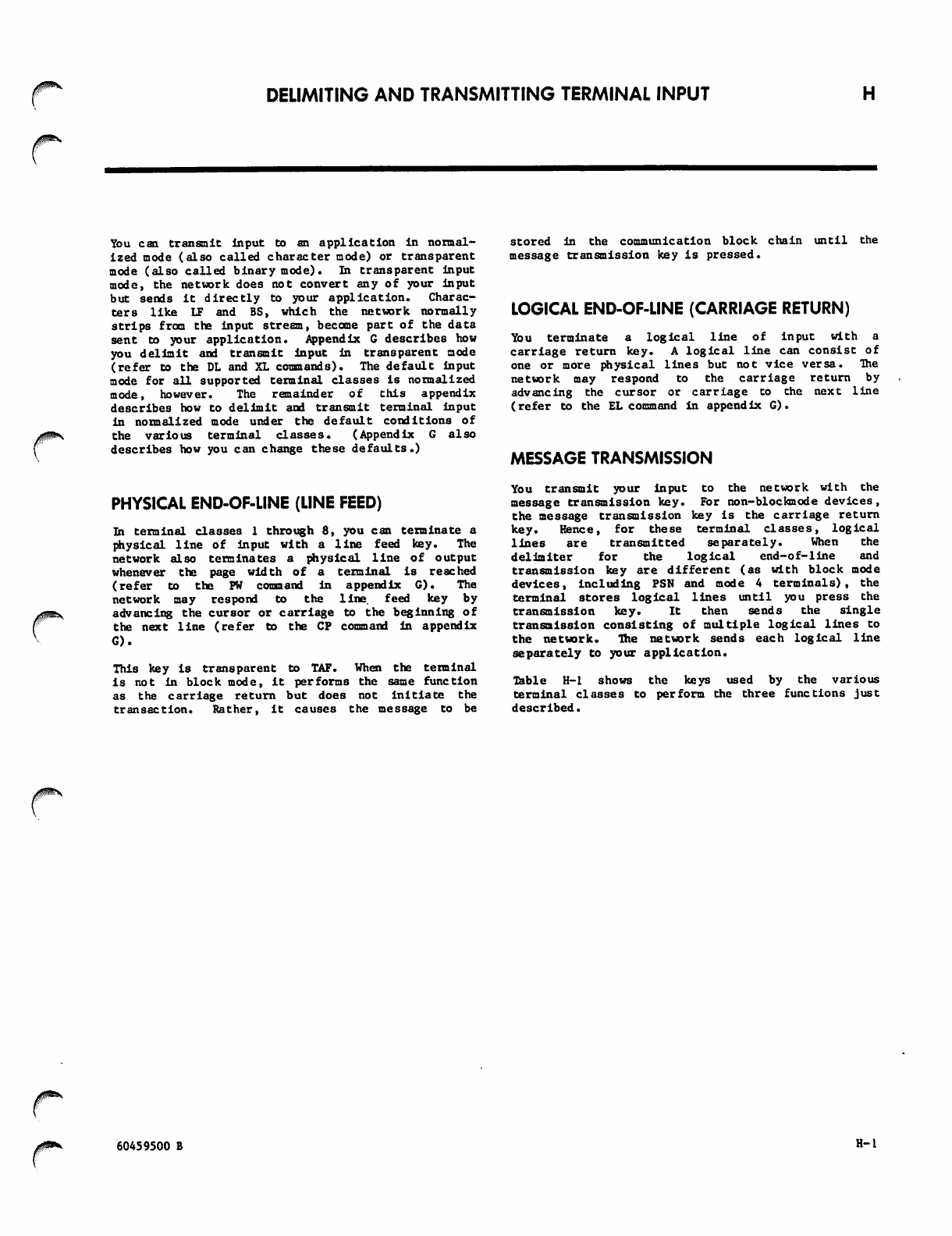
DELIMITING AND TRANSMITTING TERMINAL INPUT
/0^
0^\
/ ^ S V
You can transmit input to an application in normal
ized mode (also called character mode) or transparent
mode (also called binary mode). In transparent input
mode, the network does not convert any of your input
but sends it directly to your application. Charac
ters like LF and BS, which the network normally
strips from the input stream, become part of the data
sent to your application. Appendix G describes how
you delimit and transmit input in transparent mode
(refer to the DL and XL commands). The default input
mode for all supported terminal classes is normalized
mode, however. The remainder of this appendix
describes how to delimit and transmit terminal input
in normalized mode under the default conditions of
t h e v a r i o u s t e r m i n a l c l a s s e s . ( A p p e n d i x G a l s o
describes how you can change these defaults.)
stored in the communication block chain until the
message transmission key is pressed.
LOGICAL END-OF-LINE (CARRIAGE RETURN)
You terminate a logical line of input with a
carriage return key. A logical line can consist of
one or more physical lines but not vice versa. The
network may respond to the carriage return by
advancing the cursor or carriage to the next line
(refer to the EL command in appendix G).
MESSAGE TRANSMISSION
PHYSICAL END-OF-LINE (LINE FEED)
In terminal classes 1 through 8, you can terminate a
physical line of input with a line feed key. The
network also terminates a physical line of output
whenever the page width of a terminal is reached
( r e f e r t o t h e P W c o n n a n d i n a p p e n d i x G ) . T h e
network may respond to the line, feed key by
advancing the cursor or carriage to the beginning of
the next line (refer to the CP command in appendix
G).
This key is transparent to TAF. When the terminal
is not in block mode, it performs the same function
as the carriage return but does not initiate the
transaction. Rather, it causes the message to be
You transmit your input to the network with the
message transmission key. For non-blocks ode devices,
the message transmission key is the carriage return
key. Hence, for these terminal classes, logical
lines are transmitted separately. When the
delimiter for the logical end-of-line and
transmission key are different (as with block mode
devices, including PSN and mode 4 terminals), the
terminal stores logical lines until you press the
transmission key. It then sends the single
transmission consisting of multiple logical lines to
the network. The network sends each logical line
separately to your application.
Table H-l shows the keys used by the various
terminal classes to perform the three functions just
described.
60459500 B H-l
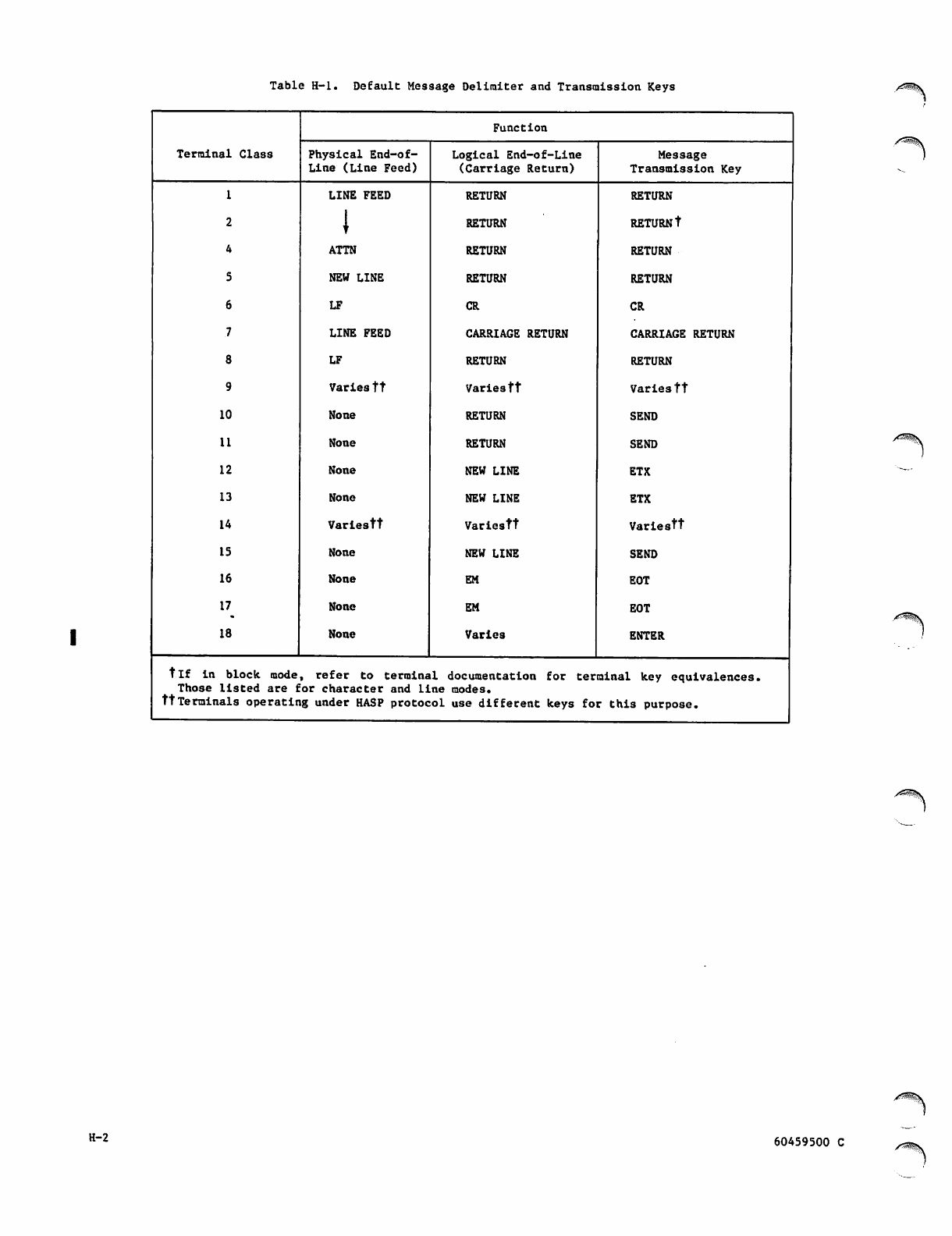
Table H-l. Default Message Delimiter and Transmission Keys
Terminal Class
Function
Physical End-of-
Line (Line Feed)
Logical End-of-Line
(Carriage Return)
Message
Transmission Key
1LINE FEED RETURN RETURN
2JRETURN RETURNt
4ATTN RETURN RETURN
5NEW LINE RETURN RETURN
6LF CR CR
7LINE FEED CARRIAGE RETURN CARRIAGE RETURN
8LF RETURN RETURN
9Varies tt Va r i e s t t V a r i e s t t
10 None RETURN SEND
11 None RETURN SEND
12 None NEW LINE ETX
13 None NEW LINE ETX
14 Variestt Variestt Variestt
15 None NEW LINE SEND
16 None EM EOT
17 None EM EOT
18 None Varies ENTER
tlf in block mode, refer to terminal documentation for terminal key equivalences.
Those listed are for character and line modes,
tt Terminals operating under HASP protocol use different keys for this purpose.
H-2 60459500 C
DETECTION OF POTENTIALLY BLOCKED TASKS
/pPNv
0^\
TAF prevents situations from occuring in which the
execution of a task is blocked because it is
impossible under the circumstances to obtain the
needed central memory space for the task, whether
for an initial load or a memory increase. Several
terms will be defined to aid in the description of
how potentially blocked tasks are detected:
• Minimum size of the total task area
The total task area is the CM in which TAF
will schedule tasks. It includes the space
o c c u p i e d b y C M - r e s i d e n t t a s k s . T h e a r e a
extends from the first word address into
which tasks can be loaded to the maximum
fiel d le n g t h o f TA F. T h e si z e of th i s a r e a
fluctuates if the TAF/CRM Data Manager is
used. The minimum size of this area occurs
when the TAF/CRM buffer takes on its maximum
size.
• Minimum size of the transient task area
The transient task area is that portion of
the total task area not occupied by
CM-resident tasks. The minimum size of this
area is defined to be the minimum size of
th e to t a l t a s k a r ea m i nus t he s u m o f th e
MFLs of all CM-resident tasks.
One or more tasks will be considered to be
potentially blocked under the following
circumstances.
• If the initial field lengths of the
CM-resident tasks are so large that they all
couldn not be loaded together.
• If the sum of the MFLs for the CM-resident
tasks exceeds the minimum size of the total
task area.
• If the MFL of a non-CM-resident task exceeds
the minimum size of the transient task area.
Following are the situations when potentially
blocked tasks are detected and the actions that are
taken.
• At TAF initialization. Potentially blocked
tasks result in TAF being aborted.
• W h e n TA F i s inf o r m e d , vi a th e LI B TA S K T T
option, of the update of a task library
attached by TAF and the library contains
potentially blocked tasks, the update will
be rejected.
• When an attempt is made to reduce the MFL of
TAF via the K.MAXFL command to a value that
r e s u l t s i n p o t e n t i a l l y b l o c k e d t a s k s , t h e
command will be rejected.
The preceding checking assumes that the maximum
field length of TAF is set (by default, via K.MFL,
or via K.MAXFL commands) to a value that can be
attained.
j^HPn,
60459500 A I - 1

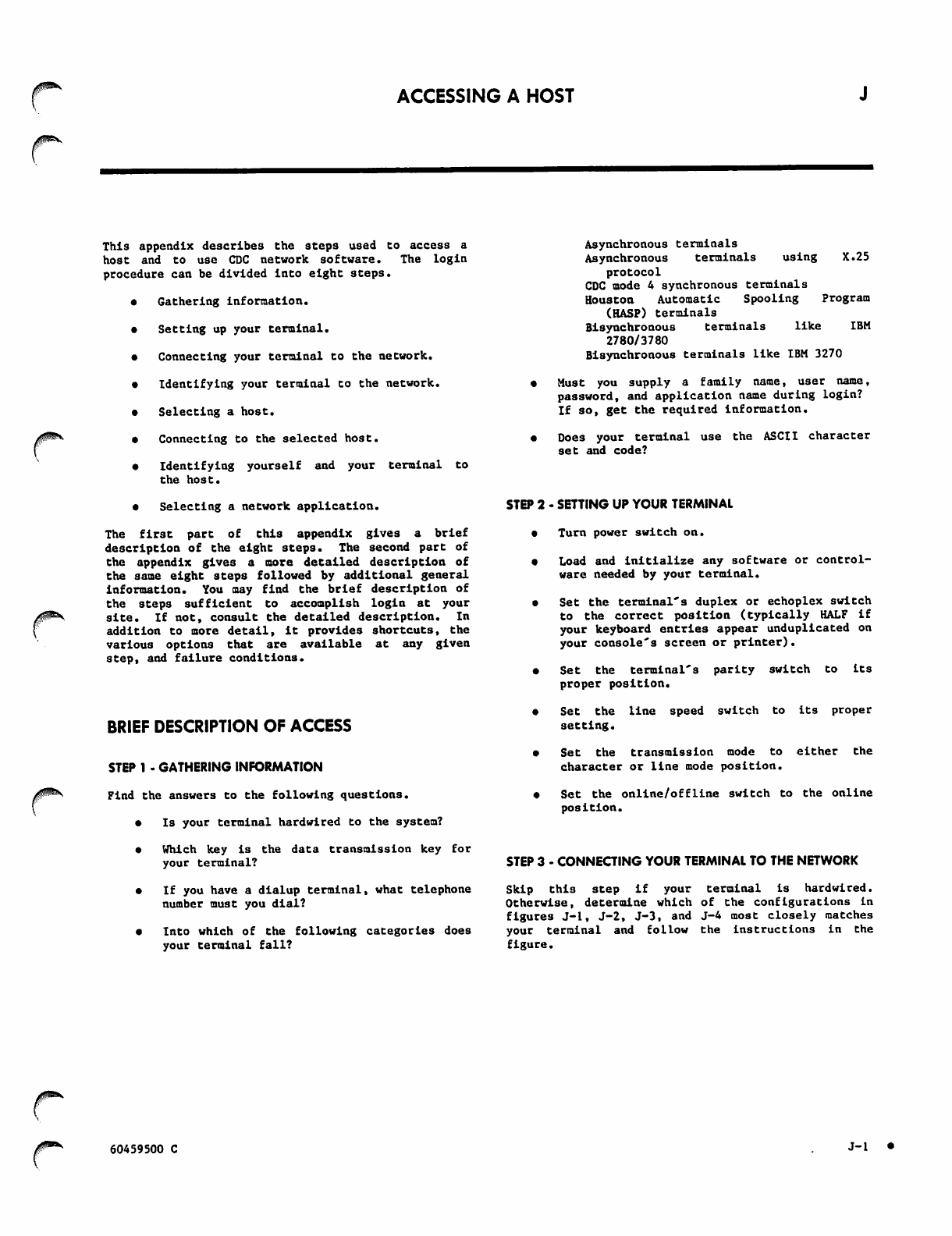
J^v ACCESSING A HOST
/ifls^K
This appendix describes the steps used to access a
host and to use CDC network software. The login
procedure can be divided into eight steps.
Gathering information.
Setting up your terminal.
Connecting your terminal to the network.
Identifying your terminal to the network.
Selecting a host.
Connecting to the selected host.
Identifying yourself and your terminal to
the host.
• Selecting a network application.
The first part of this appendix gives a brief
description of the eight steps. The second part of
the appendix gives a more detailed description of
the same eight steps followed by additional general
information. You may find the brief description of
the steps sufficient to accomplish login at your
site. If not, consult the detailed description. In
addition to more detail, it provides shortcuts, the
various options that are available at any given
step, and failure conditions.
BRIEF DESCRIPTION OF ACCESS
STEP 1 • GATHERING INFORMATION
Find the answers to the following questions.
• Is your terminal hardwired to the system?
• Which key is the data transmission key for
your terminal?
• If you have a dialup terminal, what telephone
number must you dial?
• Into which of the following categories does
your terminal fall?
Asynchronous terminals
Asynchronous terminals using X.25
protocol
CDC mode 4 synchronous terminals
Houston Automatic Spooling Program
(HASP) terminals
Bisynchronous terminals like IBM
2780/3780
Bisynchronous terminals like IBM 3270
• Must you supply a family name, user name,
password, and application name during login?
If so, get the required information.
• Does your terminal use the ASCII character
set and code?
STEP 2 - SETTING UP YOUR TERMINAL
• Turn power switch on.
• Load and initialize any software or control-
ware needed by your terminal.
• Set the terminal's duplex or echoplex switch
to the correct position (typically HALF if
your keyboard entries appear unduplicated on
your console's screen or printer).
• Set the terminal's parity switch to its
proper position.
• Set the line speed switch to its proper
setting.
• Set the transmission mode to either the
character or line mode position.
• Set the online/offline switch to the online
position.
STEP 3 • CONNECTING YOUR TERMINAL TO THE NETWORK
Skip this step if your terminal is hardwired.
Otherwise, determine which of the configurations in
figures J-l, J-2, J-3, and J-4 most closely matches
your terminal and follow the instructions in the
figure.
60459500 C J-l
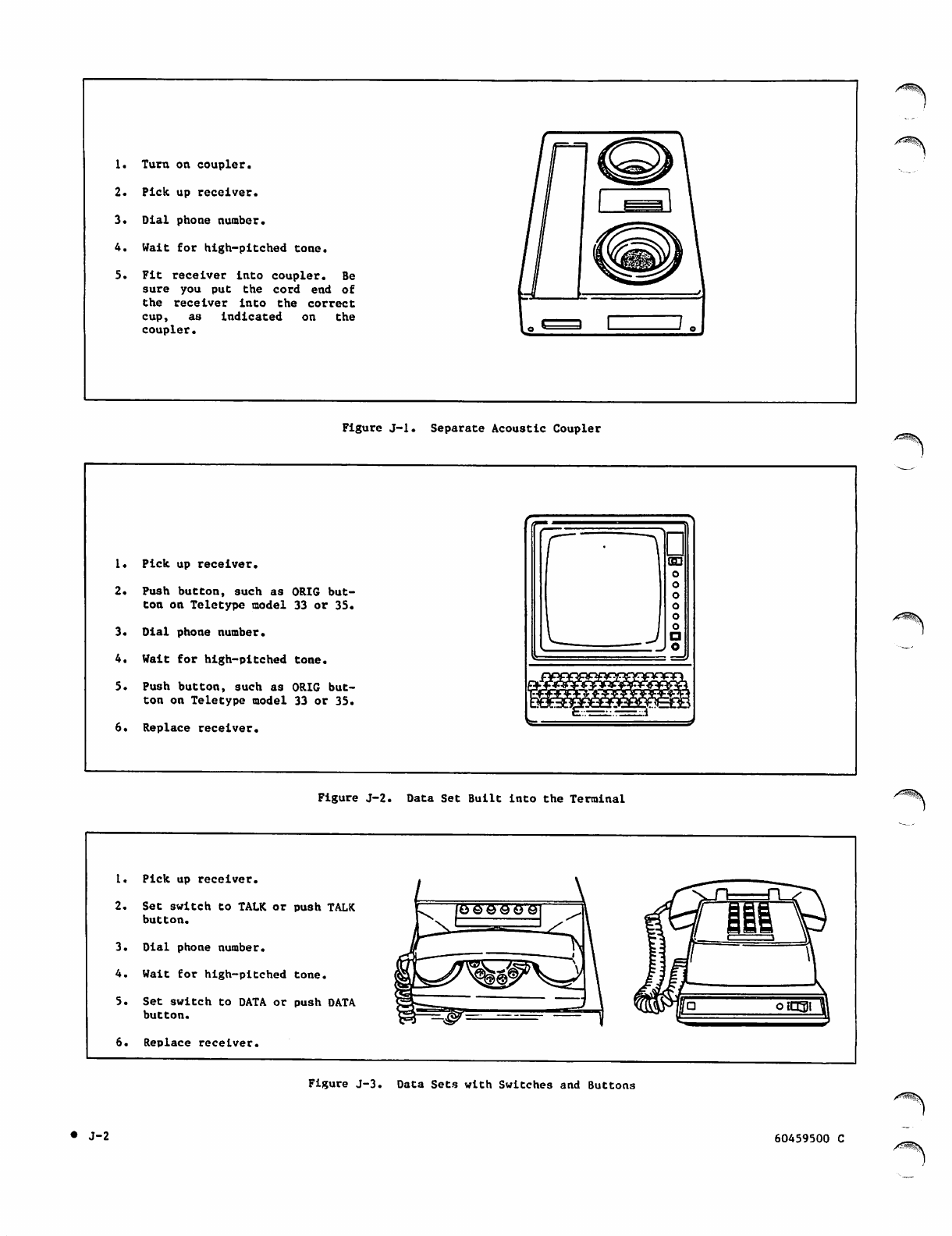
1.
2.
3.
4.
5.
Turn on coupler.
Pick up receiver.
Dial phone number.
Wait for high-pitched tone.
Fit receiver into coupler. Be
sure you put the cord end of
the receiver into the correct
cup, as indicated on the
coupler.
&\
l\w\
lo^^=" 1 ( .
/C="*iS!v
Figure J-l. Separate Acoustic Coupler
1. Pick up receiver.
2. Push button, such as ORIG but
ton on Teletype model 33 or 35.
3. Dial phone number.
4. Wait for high-pitched tone.
5. Push button, such as ORIG but
ton on Teletype model 33 or 35.
6. Replace receiver.
__J
S3
o
o
o
o
o
o
□
o
Figure J-2. Data Set Built Into the Terminal
1. Pick up receiver.
2. Set switch to TALK or pu3h TALK
button.
3. Dial phone number.
4. Wait for high-pitched tone.
5. Set switch to DATA or push DATA
button.
6. Replace receiver.
Figure J-3. Data Sets with Switches and Buttons
• J - 2 60459500 C / £ ^ v
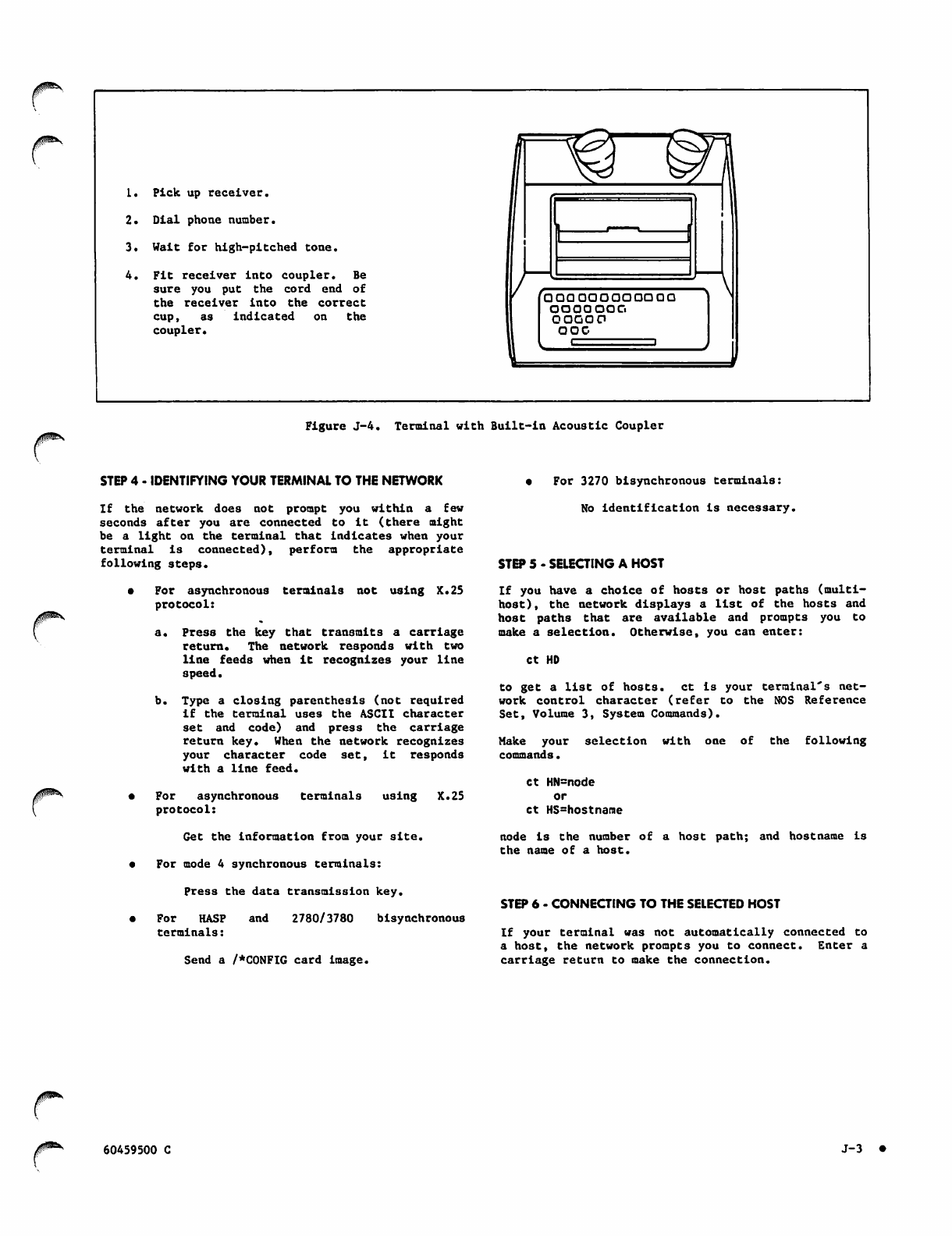
1. Pick up receiver.
2. Dial phone number.
3. Wait for high-pitched tone.
4. Fit receiver into coupler. Be
sure you put the cord end of
the receiver into the correct
cup, as indicated on the
coupler.
000 000000000
oaaaoac.
OOQOO
ooc
Figure J-4. Terminal with Built-in Acoustic Coupler
STEP 4 - IDENTIFYING YOUR TERMINAL TO THE NETWORK
If th e ne two r k do es n o t p r ompt yo u wi thi n a few
seconds after you are connected to it (there might
be a light on the terminal that indicates when your
t e r m i n a l i s c o n n e c t e d ) , p e r f o r m t h e a p p r o p r i a t e
following steps.
• F o r a s yn c h r o n o u s te r m i n a l s no t u s i n g X. 2 5
protocol:
a. Press the key that transmits a carriage
return. The network responds with two
line feeds when it recognizes your line
speed.
b. Type a closing parenthesis (not required
if the terminal uses the ASCII character
set and code) and press the carriage
return key. When the network recognizes
your character code set, it responds
with a line feed.
• For asynchronous terminals using X.25
protocol:
Get the Information from your site.
• For mode 4 synchronous terminals:
Press the data transmission key.
• F o r H A S P a n d 2 7 8 0 / 3 7 8 0 b i s y n c h r o n o u s
terminals:
Send a /*C0NFIG card image.
• For 3270 bisynchronous terminals:
No identification is necessary.
STEP 5 - SELECTING A HOST
If you have a choice of hosts or host paths (multi-
host), the network displays a list of the hosts and
host paths that are available and prompts you to
make a selection. Otherwise, you can enter:
ct HD
to get a list of hosts, ct is your terminal's net
work control character (refer to the NOS Reference
Set, Volume 3, System Commands).
Make your selection with one of the following
commands *
ct HN=node
or
ct HS=hostnarae
node is the number of a host path; and hostname is
the name of a host.
STEP 6 • CONNECTING TO THE SELECTED HOST
If your terminal was not automatically connected to
a host, the network prompts you to connect. Enter a
carriage return to make the connection.
0^ 60459500 C J-3
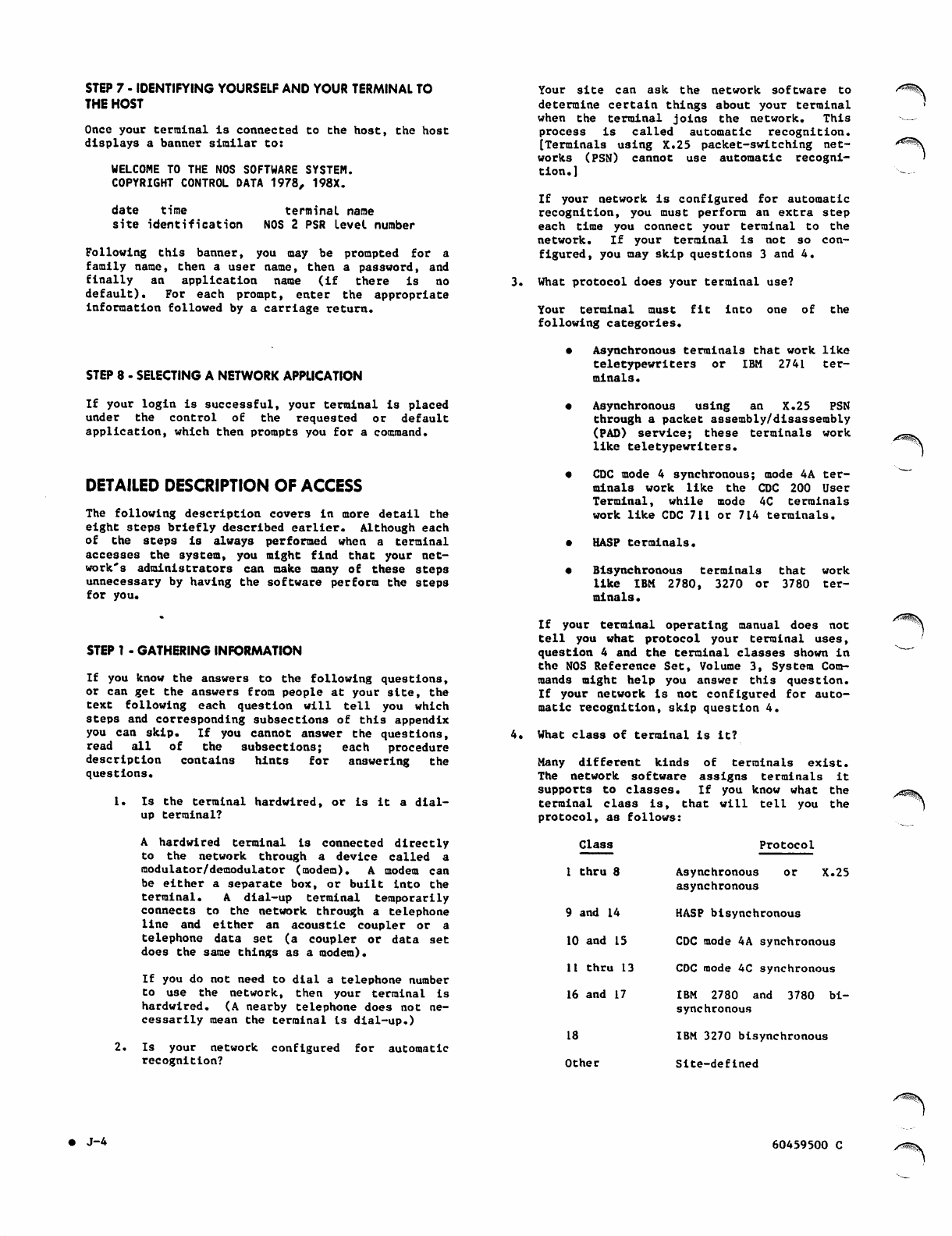
STEP 7 ■ IDENTIFYING YOURSELF AND YOUR TERMINAL TO
THE HOST
Once your terminal is connected to the host, the host
displays a banner similar to:
WELCOME TO THE NOS SOFTWARE SYSTEM.
COPYRIGHT CONTROL DATA 1978, 198X.
date time terminal name
site identification NOS 2 PSR Level number
Following this banner, you may be prompted for a
family name, then a user name, then a password, and
finally an application name (if there is no
default). For each prompt, enter the appropriate
Information followed by a carriage return.
STEP 8 • SELECTING A NETWORK APPLICATION
If your login is successful, your terminal is placed
under the control of the requested or default
application, which then prompts you for a command.
Your site can ask the network software to
determine certain things about your terminal
when the terminal joins the network. This
process is called automatic recognition.
[Terminals using X.25 packet-switching net
works (PSN) cannot use automatic recogni
t i o n . ]
If y ou r n et wo rk is configured f or aut om at ic
recognition, you must perform an extra step
each time you connect your terminal to the
n e t w o r k . I f y o u r t e r m i n a l i s n o t s o c o n
figured, you may skip questions 3 and 4.
3. What protocol does your terminal use?
Your terminal must fit Into one of the
following categories.
• Asynchronous terminals that work like
teletypewriters or IBM 2741 ter
minals.
• Asynchronous using an X.25 PSN
through a packet assembly/disassembly
(PAD) service; these terminals work
like teletypewriters.
DETAILED DESCRIPTION OF ACCESS
The following description covers in more detail the
eight steps briefly described earlier. Although each
of the steps is always performed when a terminal
accesses the system, you might find that your net
work's administrators can make many of these steps
unnecessary by having the software perform the steps
for you.
STEP 1 - GATHERING INFORMATION
If you know the answers to the following questions,
or can get the answers from people at your site, the
text following each question will tell you which
steps and corresponding subsections of this appendix
you can skip. If you cannot answer the questions,
r e a d a l l o f t h e s u b s e c t i o n s ; e a c h p r o c e d u r e
description contains hints for answering the
questions.
1. Is the terminal hardwired, or is it a dial-
up terminal?
A hardwired terminal is connected directly
to the network through a device called a
modulator/demodulator (modem). A modem can
be either a separate box, or built into the
terminal. A dial-up terminal temporarily
connects to the network through a telephone
line and either an acoustic coupler or a
telephone data set (a coupler or data set
does the same things as a modem).
If you do not need to dial a telephone number
to use the network, then your terminal is
hardwired. (A nearby telephone does not ne
cessarily mean the terminal is dial-up.)
2. Is your network configured for automatic
recognition?
• CDC mode 4 synchronous; mode 4A ter
minals work like the CDC 200 User
Terminal, while mode 4C terminals
work like CDC 711 or 714 terminals.
• HASP terminals.
• Bisynchronous terminals that work
like IBM 2780, 3270 or 3780 ter
minals .
If your terminal operating manual does not
te l l y o u w h a t p r oto c ol y our term i nal us e s,
question 4 and the terminal classes shown in
the NOS Reference Set, Volume 3, System Com
mands might help you answer this question.
If your network is not configured for auto
matic recognition, skip question 4.
4. What class of terminal is it?
Many different kinds of terminals exist.
The network software assigns terminals it
supports to classes. If you know what the
terminal class is, that will tell you the
protocol, as follows:
Class Protocol
1 thru 8 Asynchronous or X.25
asynchronous
9 and 14 HASP bisynchronous
10 and 15 CDC mode 4A synchronous
11 thru 13 CDC mode 4C synchronous
16 and 17 I BM 278 0 an d 3 7 80 bi
synchronous
18 IBM 3270 bisynchronous
Other Site-defined
/<K!§Sv
• J - 4 60459500 C /-SS^y
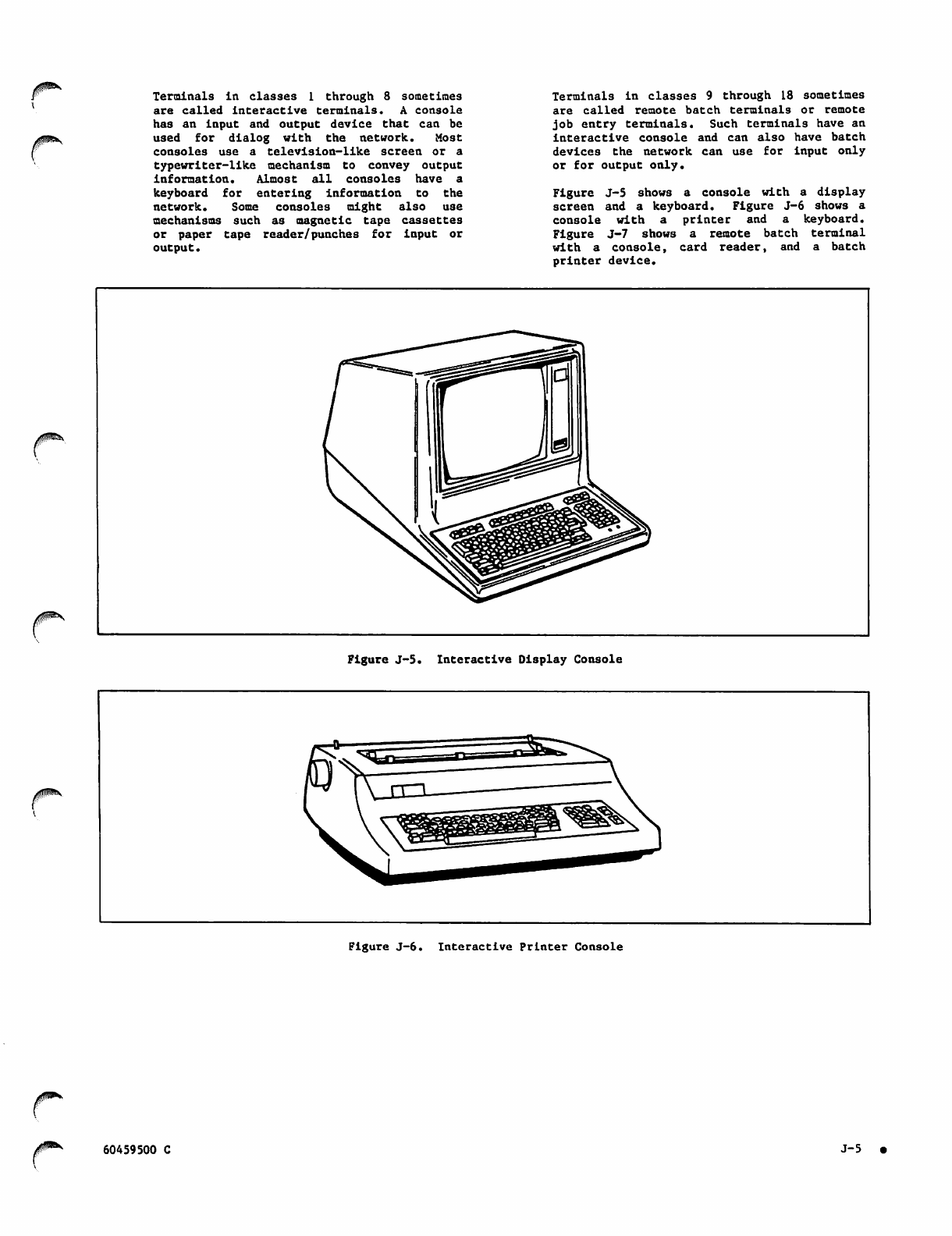
/a&Hn^
Terminals in classes 1 through 8 sometimes
are called interactive terminals. A console
has an input and output device that can be
used for dialog with the network. Most
consoles use a television-like screen or a
typewriter-like mechanism to convey output
information. Almost all consoles have a
keyboard for entering information to the
n e t w o r k . S o m e c o n s o l e s m i g h t a l s o u s e
mechanisms such as magnetic tape cassettes
or paper tape reader/punches for input or
output.
Terminals in classes 9 through 18 sometimes
are called remote batch terminals or remote
job entry terminals. Such terminals have an
interactive console and can also have batch
devices the network can use for input only
or for out put on ly.
Figure J-5 shows a console with a display
screen and a keyboard. Figure J-6 shows a
console with a printer and a keyboard.
Figure J-7 shows a remote batch terminal
with a console, card reader, and a batch
printer device.
Figure J-5. Interactive Display Console
^ms^fev
Figure J-6. Interactive Printer Console
60459500 C J - 5 •
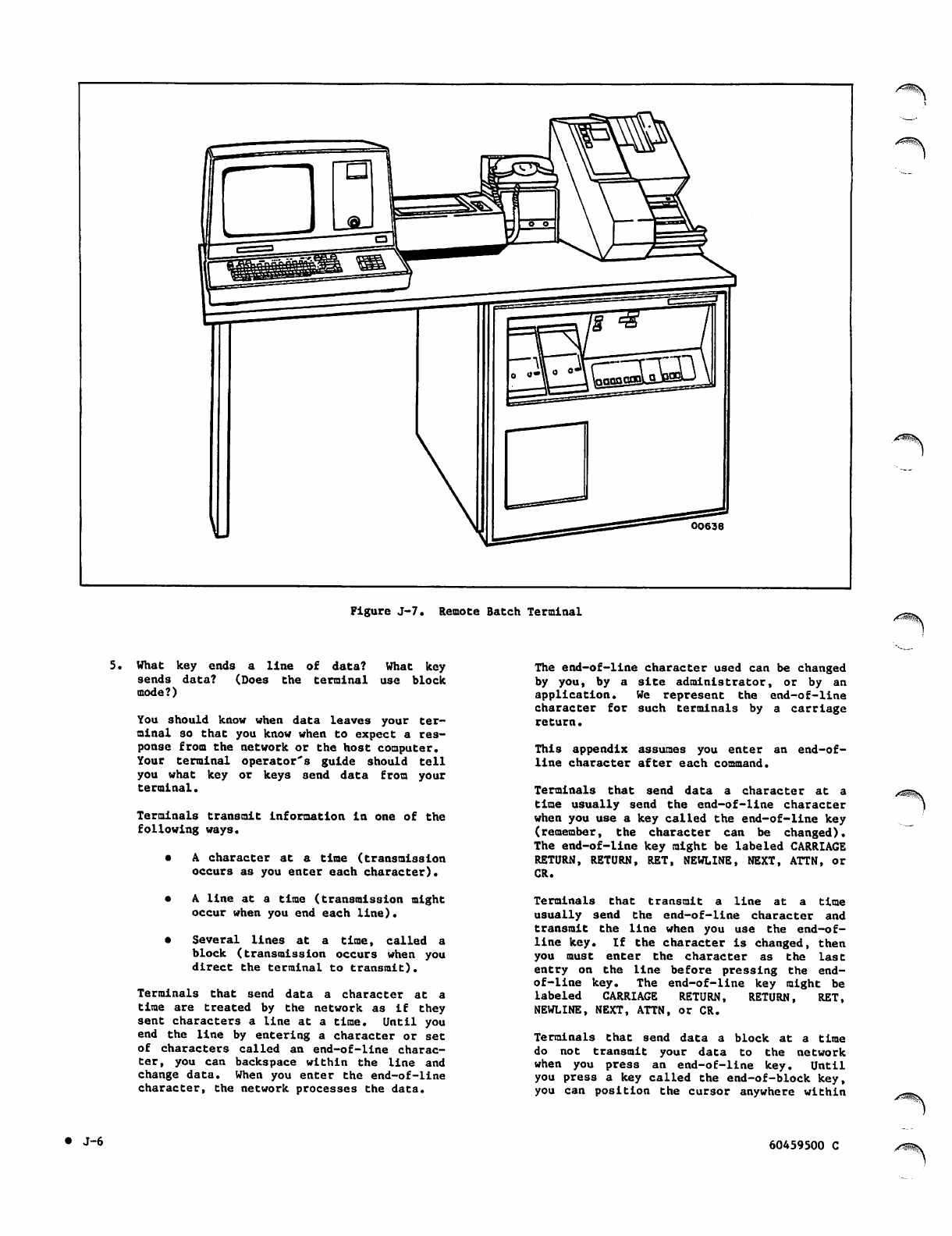
Figure J-7. Remote Batch Terminal
5 . W h a t ke y e n d s a l i n e o f d a t a ? W h a t k e y
sends data? (Does the terminal use block
mode?)
You should know when data leaves your ter
minal so that you know when to expect a res
ponse from the network or the host computer.
Your terminal operator's guide should tell
you what key or keys send data from your
terminal.
Terminals transmit information in one of the
following ways.
• A character at a time (transmission
occurs as you enter each character).
• A l in e a t a tim e ( tr an smiss io n m ig ht
occur when you end each line).
• Several lines at a time, called a
block (transmission occurs when you
direct the terminal to transmit).
Terminals that send data a character at a
time are treated by the network as if they
sent characters a line at a time. Until you
end the line by entering a character or set
of characters called an end-of-llne charac
ter, you can backspace within the line and
change data. When you enter the end-of-line
character, the network processes the data.
The end-of-line character used can be changed
b y y o u , by a si t e ad m i n i st r a t o r, o r b y a n
application. We represent the end-of-line
character for such terminals by a carriage
retu r n .
This appendix assumes you enter an end-of-
line character after each command.
Terminals that send data a character at a
time u su al ly s en d the e nd -o f- li ne characte r
when you use a key called the end-of-line key
(remember, the character can be changed).
The end-of-line key might be labeled CARRIAGE
RETURN, RETURN, RET, NEWLINE, NEXT, ATTN, or
CR.
Terminals that transmit a line at a time
usually send the end-of-line character and
transmit the line when you use the end-of-
line key. If the character is changed, then
you must enter the character as the last
entry on the line before pressing the end-
of-line key. The end-of-line key might be
labeled CARRIAGE RETURN, RETURN, RET,
NEWLINE, NEXT, ATTN, or CR.
Terminals that send data a block at a time
do not transmit your data to the network
when you press an end-of-line key. Until
you press a key called the end-of-block key,
you can position the cursor anywhere within
• J - 6 60459500 C

yflflP^y
any unsent line and change data. This key
might be labeled SEND, ETX, EOT, or XMIT.
When you press the end-of-block key, the
network processes each line of data as if it
had been transmitted one line at a time.
The network expects each block from a block
mode terminal to end with a character or set
of characters called the end-of-block indi
cator. The end-of-block indicator used can
be changed by you, by a site administrator,
or by an application program. We do not show
the end-of-block indicator in the examples.
Terminals that transmit a block at a time
usually send the end-of-block character and
transmit all lines in the block when you use
the end-of-block key. If the character is
changed, then you must enter the character
at the end of the last line before pressing
the end-of-block key.
Terminals that transmit blocks are sometimes
said to work in batch mode; do not confuse
this kind of batch mode operation with re
mote batch data transmissions. Remote batch
data transmissions are simply transmissions
of files from or to the host using batch de
vices, bypassing the terminal.
6. What telephone number is appropriate?
If your terminal is hardwired, you may skip
questions 6 and 7.
Your network might use a specific telephone
number for terminals that communicate at a
certain speed, for terminals operating in
block mode, or for all terminals using cer
tain protocols.
The telephone number you use determines
whether you need to complete some of the
procedures. If you do not know what numbers
you should use, get help from a site admin
i s t r a t o r .
7. Is your terminal automatically connected to
a host?
If it is, skip question 8.
8. What is the name or node number for the host
you need to use?
9. Will your terminal be automatically logged
in?
If so, skip question 10.
10. What is the family name, user name, and
password appropriate for you on the host
system you will be using?
You can get this information from site
administrators.
11. Is your terminal automatically connected to
a network application?
If so, you will not have to select an
application at login.
STEP 2 - SETTING UP YOUR TERMINAL
If your terminal is hardwired, you can probably skip
most of this subsection; hardwired terminals are
usually set up once and left in the appropriate
co nd it ion. Befor e u si ng this s ubsec ti on , r ev iew t he
applicable terminal operator's manual, which des
cribes the procedures for setting up your terminal.
If you a re u sing an X.25 termin al, follo w th e PAD
access procedures supplied by the packet-switching
network service.
Switch settings are important. The number, type,
settings, and names of switches vary from terminal
to terminal. Some terminals use buttons or toggles
for switches; others use software option selections
as switches.
If other people have used your terminal to connect
to the network, the switches should be set correctly;
do not change them. Directions for setting the
switches may be posted near your terminal.
Here is a suggested procedure to follow when setting
up your terminal:
1. Turn on the power switch.
2. Load and initialize any software or control-
ware needed by your terminal. You will find
detailed information on this task in your
terminal's operator manual.
3. Set the terminal's duplex or echoplex switch
to the correct position (use HALF if you are
not sure). If you wish to have the display
of your login password suppressed, you must
use full duplex. If nothing you enter
appears on your console after you connect to
the network, the network must display char
acters for your console. The NOS Reference
Set, Volume 3, System Commands describes how
to enable and disable character echoing by
the network (refer to the EP command).
4. Set the terminal's parity switch to the
proper position. If garbled output appears
at your console after you connect to the
network , the n e t w o r k m u s t use a di fferent
parity choice for your terminal. The NOS
Reference Set, Volume 3, System Commands
describes how to change parity use by the
network (see the PA command).
5. S e t th e li n e speed s w i t c h t o a s p e e d th a t
matches one associated with the telephone
numbers you were given. If you do not know
the line speed you should use, set the
switch to any position for X.25, mode 4
synchronous, or bisynchronous terminals; set
the switch to 30 characters per second (300
bits per second) for asynchronous terminals.
6. Set the transmission mode switch to either
the character or line mode position (you can
change it later if you have a block mode
terminal). For example: on a Viking 721,
select the CHAR option; on a CDC 751, set
the switch to the CHAR position; on a CDC
200 User Terminal, set the switch to the
LINE position.
#^
60459500 C J-7
7. Set the online/offline switch to the position
that permits online communications. For ex
ample: on a Viking 721, select the ON option
of the LINE setting; on a CDC 713, turn off
the LOCAL indicator switch; on a Teletype,
set the LINE/OFF/LOCAL switch to the LINE
position; on a CDC 200 User Terminal con
sole, set the ATTENDED/UNATTENDED switch to
the ATTENDED position.
You are now ready to connect your terminal to the
network.
• Connect to the selected host.
• Identify yourself and your terminal to the
host (log in).
• Select a network application.
The software usually sends you a message that helps
you decide which step comes next. If nothing
appears at your terminal within a few seconds, you
pr oba bly need to i de n ti fy the term ina l t o t he ne t
work.
STEP 3 - CONNECTING YOUR TERMINAL TO THE NETWORK STEP 4 • IDENTIFYING YOUR TERMINAL TO THE NETWORK
To begin communication, your terminal must be
physically connected to the network. If your
terminal is hardwired, skip the remainder of this
subsection; this subsection applies only to dial-up
terminals.
A dial-up terminal uses either an acoustic coupler
(asynchronous terminal) or a data set (asynchronous,
X.25, bisynchronous, or synchronous terminal) to
link itself to the network.
An acoustic coupler can be built into the terminal.
Figure J-4 shows a terminal with a built-in acoustic
coupler and gives directions to connect the terminal
to the network.
An acoustic coupler can also be separate from the
terminal. Figure J-l shows an acoustic coupler
separate from a terminal and gives directions to
connect the terminal to the network.
A data set can be built into the terminal. Figure
J-2 shows a terminal with a data set built in and
gives directions to connect the terminal to the
network.
A stand-alone data set can have either a switch
labeled TALK and DATA or individual buttons labeled
TALK and DATA. Figure J-3 shows both a data set
with switches and a data set with buttons and gives
directions to connect the terminal to the network.
Once you have established physical connection to the
net w o r k h a r d ware , yo u mi g ht n e e d t o Id e n tif y th e
terminal to the network software.
This identification procedure, called automatic
recognition, is not always needed. It does not
a p p l y to X . 2 5 t e r mi n a l s . I t d o es n o t a p p ly i f t h e
c o m m u n i c a t i o n l i n e u s e d b y y o u r t e r m i n a l is n o t
configured for automatic recognition.
If your terminal does not display any information
within a few seconds of physical connection, you
should complete one of the identification procedures
described in the following subsections. The pro
cedure you use depends on the terminal protocol,
which you can determine if you know the terminal's
type and/or class.
If yo u do not complete the iden tifi cat ion procedure
within the allowed time, the network disconnects a
dial-up terminal. Hang up the phone and redial the
number if you are using a dial-up terminal. You
must restart the procedure for a hardwired terminal.
Procedure for Asynchronous Terminals
For an asynchronous terminal, which belongs in
terminal classes 1 through 8, complete this pro
cedure within 1 minute:
After you dial the phone number, either you get a
h i g h - p i t c h t o n e o r a n o p e r a t o r a n s w e r s . I f a n
operator answers, ask for your terminal to be con
nected, wait for the tone, and then place the re
ceiver in the coupler or set the data set switch or
button to the on or data position. If you get a
busy signal, wait and redial or try another number.
If your terminal has an indicator (sometimes marked
DSR, DATA SET READY, or SYSTEM ACTIVE), it lights to
let you know that the terminal is connected to the
network. Wait approximately 2 seconds after the
light comes on before entering data.
You are now ready for the next step. You might need
to do one or all of the following:
• Identify your terminal to an X.25 network
(this appendix does not describe this pro
cedure).
• Identify your terminal to the CDC network.
• Select a host.
1. Wait about 2 seconds after the light that
indicates your terminal is connected to the
network comes on.
2 . P r e s s t h e c a r r i a g e r e t u r n k e y t o i d e n t i f y
the li ne spe ed use d b y your te rm in al . Th e
network software responds with two line
feeds.
3. If your terminal uses an APL, EBCD, or cor
respondence code character set, type a
closing parenthesis; if your terminal uses
an ASCII character set, you need not type in
anything.
4 . P r e s s t h e c a r r i a g e r e t u r n k e y t o i d e n t i f y
the character and code set used by the
terminal. The network software responds
with a line feed.
The software sends you a message that helps you
decide which step comes next. Turn to the sub
section appropriate for the next step you must
perform.
/&m$£\
• J - 8 60459500 C
Procedure for HASP Terminals Parameter Description
r
^ " f P f t y
>^^S\
HASP terminals belong either to terminal class 9 or
14. For automatic recognition of your HASP ter
minal, you might need to modify the signon block or
enter a special statement*
The first information transmitted by a HASP terminal
a f t e r i t i s c o n n e c t e d t o t h e n e t w o r k i s c a l l e d a
signon block. A terminal might handle signon block
transmission in one of several ways.
• Some terminals automatically transmit a sig
non block that begins with the characters:
/•SIGNON
The se eight char acters and t he i nformat ion
following them imitate the card required by
some IBM host systems for terminal identi
fication. This transmission can occur with
out your knowledge or Intervention if the
information is built into the firmware or
hardware.
• Some terminals require you to enter informa
tion for the signon block before they will
transmit anything to the network; however,
they only allow the block to contain infor
mation beginning with the eight characters
/*SIGNON. These characters and other infor
mation might be required as:
-A command from the console.
-A card read from any card reader.
-A card read from a specific card reader.
• S o me t e rmi n a l s r e q uir e yo u to e n t e r s i g non
block information before they will transmit
anything to the network, but the content of
the signon block is left up to you. Whether
the Information can be entered from the con
sole or from a card reader depends on the
terminal.
The network software cannot use information from a
/♦SIGNON card image. When such a card image is
received in a signon block, the signon block con
tents are discarded.
Instead, the network software uses a /*CONFIG state
ment for the automatic recognition procedure. You
can send the /*CONFIG statement in the signon block
when your terminal permits you to provide the con
tents of that block.
If the signon block does not contain the /*CONFtG
s t a t e m e n t a n d t h e t e r m i n a l m u s t u s e a u t o m a t i c
recognition, a prompt requesting that statement is
sent to the terminal console. When a prompt for the
st at ement appear s, ente r the sta tem en t t hr oug h a
card reader.
The format of the /*CONFIG statement is:
/*C0NFIG,t i,CO=co,CR=x,LP=x,CP=y,PL=z
Blanks are not allowed within the statement; a blank
ends parameter processing. The parameters, which
you can specify in any order, are:
ti Terminal type:
POST HASP postprint (de
fault); this is ter
minal class 9.
PRE HASP preprint; this
is terminal class 14.
C0=co Configuration ordinal, a decimal
integer from 1 to 255; the de
fault is 1. Use the configura
tion ordinal to select one of
several terminal definitions de
fined for the line that describes
a specific combination of addi
tional characteristics. Site ad
ministration personnel can tell
you the correct number to use*
CR=x Identifies available card
readers. The default i s 1.
LP=x Identifies available line
prin t e r s . T h e de f a u l t is 1.
CP=y Identifies available card
punches; y cannot equal z. The
default is 1.
PL=z Identifies available plotters; y
cannot equal z. No default
exists for z; you cannot omit
PL-z if you have a plotter.
x, y, or z is a list of numbers specified by either:
1 / 2 / . . . / 7
ALL (all numbers from 1 through 7)
The numbers you use for x, y, and z must match the
HASP stream numbers used for the corresponding de
vices within the workstation. Site administration
personnel should have this Information if you do not
know what numbers to use.
For example:
/*C0NFIG,PRE,C0=2,CR=2,LP=2/3,CP=4/PL=5
identifies your terminal as the second preprinting
workstation defined for the communication line,
having:
• A card reader and line printer on stream 2.
• Another printer on stream 3.
• A card punch on stream 4.
• A plotter on stream 5.
If no prompt for a /*C0NFIG statement appears, you
are ready for the next step.
The software se nds you a message tha t helps you
decide which step comes next. Turn to the
subsection appropriate for the next step you must
perform.
60459500 C J-9
Procedure for Mode 4 Terminals
Mode 4 terminals belong to terminal classes 10
through 13 and 15. For automatic recognition, press
the end-of-block key within 1 minute of physical con
nection.
You are ready for the next step. The software sends
you a message that helps you decide which step comes
next. Turn to the subsection appropriate for the
next step you must perform.
Procedure for Bisynchronous Terminals
Bisynchronous terminals belong to terminal classes
1 6 , 1 7 , a n d 1 8 . E n t e r a / * C 0 N F I G s t a t e m e n t t o
specify the type of terminal and the devices avail
able at it.
The format of the /*C0NFIG statement is:
/*C0NFIG,ti,C0=co,CR,LP*CP=y
Blanks are not allowed within the statement; a blank
ends parameter processing. The parameters, which you
can specify in any order, are as follows:
Parameter
ti
C0=co
CR
LP
CP=y
Description
Terminal type:
2780 IBM 2780 (default);
this is terminal
class 16.
3780 IBM 3780; this is
terminal class 17.
3270 IBM 3270; this is
terminal class 18.
The configuration ordinal, a
de c ima l i n teg e r f rom 1 thr o ugh
25 5 ; t h e d e f aul t is 1. U s e t h e
configuation ordinal to select
on e o f se v e r a l te r m i na l d e fi n i
tions defined for the line that
describes a specific combination
of additional characteristics.
Site personnel can tell you the
correct number to use.
Indicates an available card
reader; assumed if not specified.
Indicates an available line
printer; assumed if not spe
cified.
Indicates an available card
punch; assumed not to exist if
not specified. The »y portion is
not allowed for 2780; for 3270 or
3780, the y portion is required
and can be either 2 or 3 to cor
respond to the device selection
character DC2 or DC3.
For example:
/*C0NFIG,3780,C0=4,CR,LP,CP=2
identifes your terminal as a 3780 terminal having:
• A card reader and line printer*
• A card punch, which is selected by the char
acter code DC2.
If no prompt for a /*CONFIG statement appears, you
are ready for the next step.
The software expecting the next step sends you a
message which helps you decide which procedure comes
n e x t . Tu r n t o t h e s u b s e c t i o n a p p r o p r i a t e f o r t h e
next step you must perform.
STEP 5 • SELECTING A HOST
You might need to select the host, which runs the
software you want to use. This is not necessary if
your Installation personnel select a host path for
your terminal when the network is configured.
You can select or change a site-defined host path
after you connect your terminal to the network. The
host path selected is used until either you change
it o r un t i l yo u r te r m i n a l i s disc o n n e c t e d fr o m th e
network.
More than one host path can be available to each
host from a terminal. If one host path fails, you
can select an alternate route to the host.
Selecting a Host
You can select a host or override a site-defined host
selection with the following terminal definition com
mand.
ct HS=hostname
ct represents the network control character for your
terminal. For most asynchronous terminals this is
ESC or X,
Each host may be configured with a unique name.
This name (1 through 7 characters) is indicated by
hostname.
For example:
%HS=ARHN0S
would select the path with the least traffic to the
host called ARHNOS (Z represents your terminal's
network control character).
If you specify the name, your terminal uses the host
pa th w it h t h e l eas t t raf fic.
If you do not know the name you need, the host
availability display (HAD) can show you what names
are available. That display is described later in
this appendix.
Once you have selected your host, you are ready for
the next step.
• J - 1 0 60459500 C
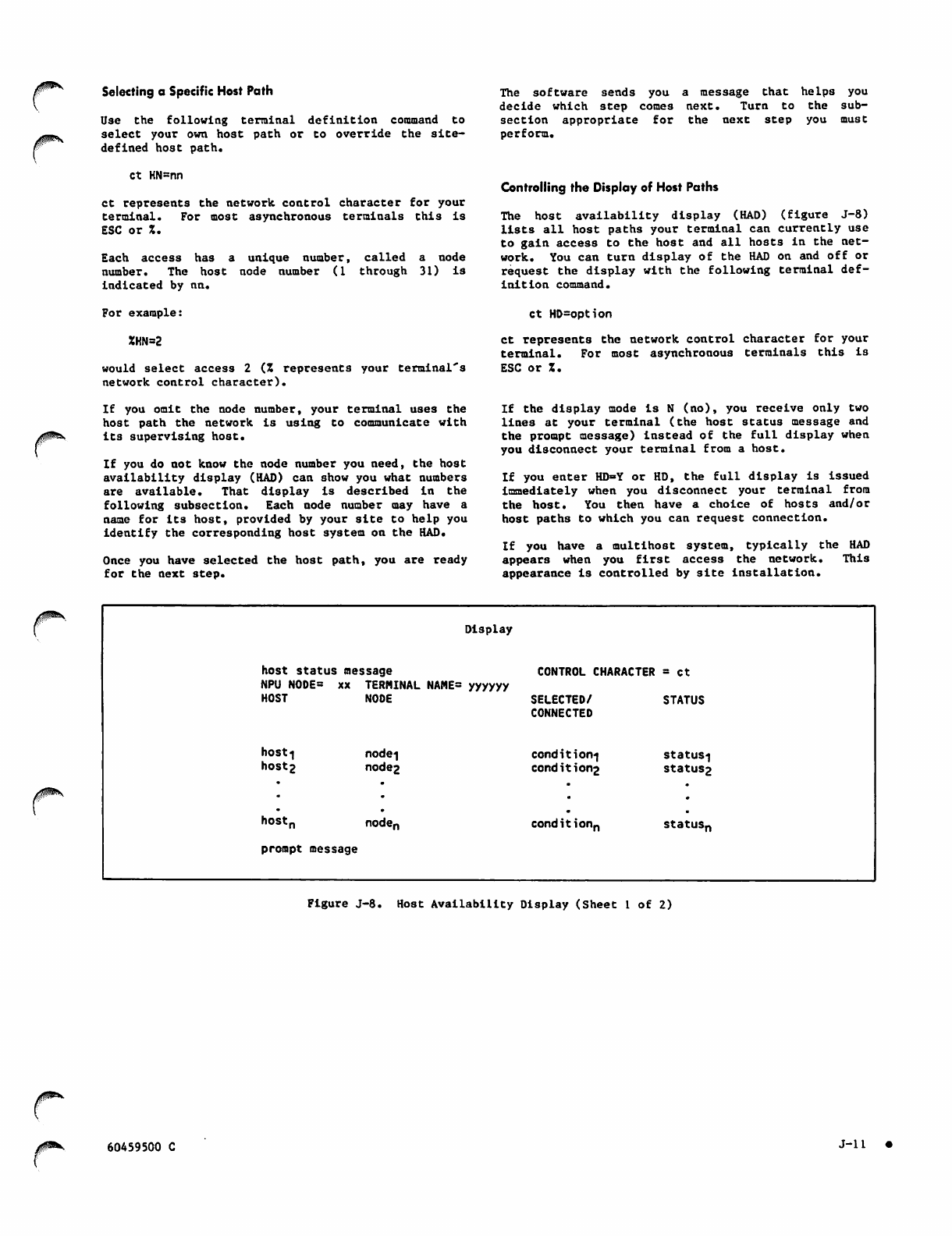
Selecting a Specific Host Path
Use the following terminal definition command to
select your own host path or to override the site-
defined host path.
ct HN=nn
ct represents the network control character for your
terminal. For most asynchronous terminals this is
ESC or X.
Each access has a unique number, called a node
number. The host node number (1 through 31) is
indicated by nn.
The software sends you a message that helps you
decide which step comes next. Turn to the sub
section appropriate for the next step you must
perform.
Controlling the Display of Host Paths
The host availability display (HAD) (figure J-8)
lists all host paths your terminal can currently use
to gain access to the host and all hosts in the net
work. You can turn display of the HAD on and off or
request the display with the following terminal def
inition command.
iggjSRay
For example:
%HN=2
would select access 2 (Z represents your terminal's
network control character).
If you omit the node number, your terminal uses the
host path the network is using to communicate with
its supervising host.
If you do not know the node number you need, the host
availability display (HAD) can show you what numbers
are available. That display is described in the
following subsection. Each node number may have a
name for Its host, provided by your site to help you
identify the corresponding host system on the HAD.
Once you have selected the host path, you are ready
for the next step.
ct HD=option
ct represents the network control character for your
terminal. For most asynchronous terminals this is
ESC or Z.
If the display mode Is N (no), you receive only two
lines at your terminal (the host status message and
the prompt message) instead of the full display when
you disconnect your terminal from a host.
If you enter HD=Y or HD, the full display is issued
immediately when you disconnect your terminal from
the host. You then have a choice of hosts and/or
host paths to which you can request connection.
If you have a multihost system, typically the HAD
appears when you first access the network. This
appearance is controlled by site installation.
Display
host status
NPU NODEs
HOST
message
xx TERMINAL
NODE
NAME= yyyyyy
CONTROL CHARACTER
SELECTED/
CONNECTED
= ct
STATUS
host-)
hosts
node-)
nodes
condition-)
conditions
status-)
statusj
hostn noden co nd it io nn statusn
prompt message
Figure J-8. Host Availability Display (Sheet 1 of 2)
/ f & i
60459500 C J-l I
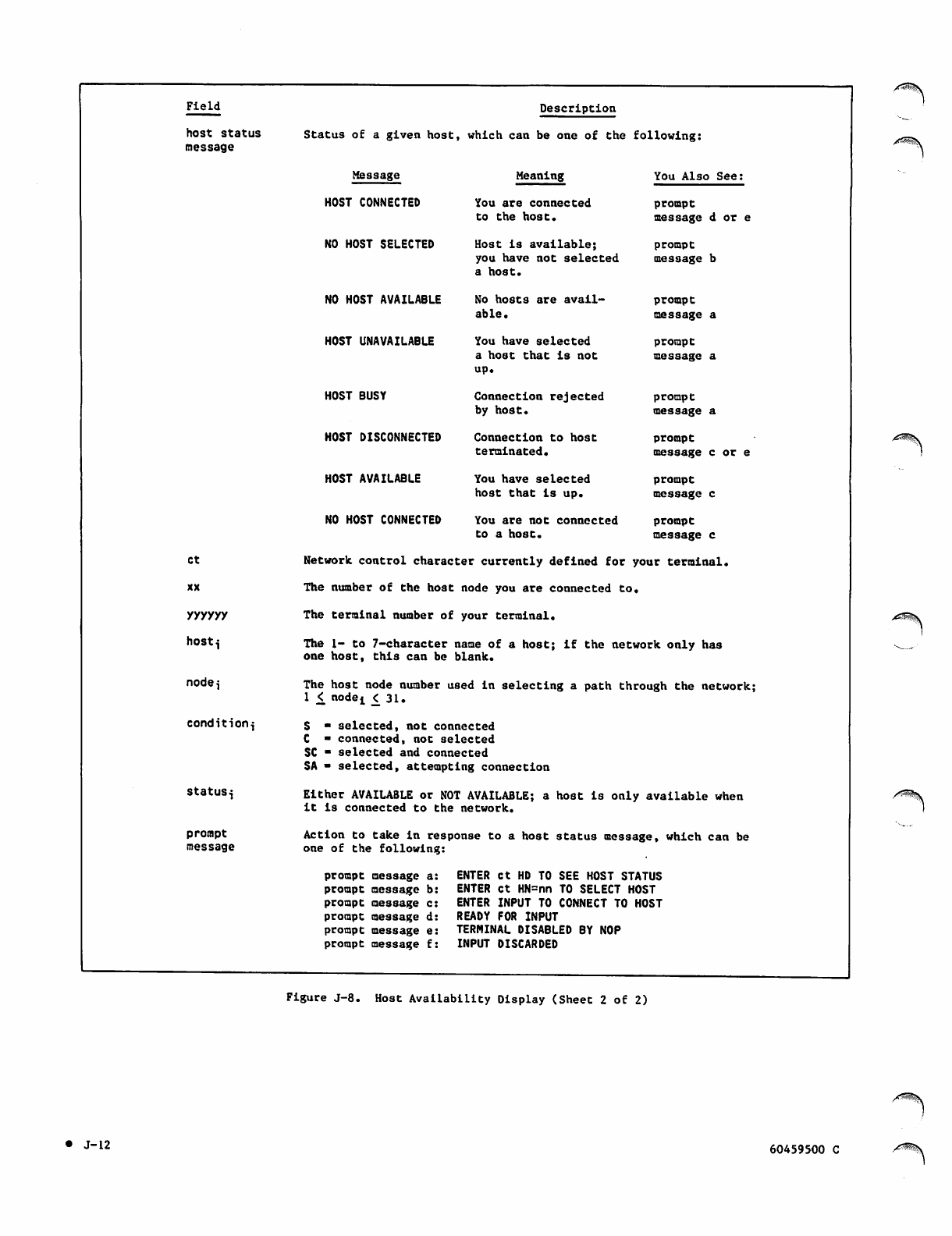
Field Description
host status
message
Status of a given host, which can be one of the following:
ct
xx
yyyyyy
host.;
node,
condition^
status;
prompt
message
Message
HOST CONNECTED
NO HOST SELECTED
NO HOST AVAILABLE
HOST UNAVAILABLE
HOST BUSY
HOST DISCONNECTED
HOST AVAILABLE
NO HOST CONNECTED
Meaning
You are connected
to the host.
Host is available;
you have not selected
a host.
No hosts are avail
able.
You have selected
a host that is not
up.
Connection rejected
by host.
Connection to host
terminated.
You have selected
host that is up.
You are not connected
to a host.
You Also See:
prompt
message d or e
prompt
message b
prompt
message a
prompt
message a
prompt
message a
prompt
message c or e
prompt
message c
prompt
message c
Network control character currently defined for your terminal.
The number of the host node you are connected to.
The terminal number of your terminal.
The 1- to 7-character name of a host; if the network only has
one host, this can be blank.
The host node number used in selecting a path through the network;
1 < node*; < 31.
S ■ selected, not connected
C - connected, not selected
SC ■ selected and connected
SA ■ selected, attempting connection
Either AVAILABLE or NOT AVAILABLE; a host is only available when
it is connected to the network.
Action to take In response to a host status message, which can be
one of the following:
prompt message a: ENTER Ct HD TO SEE HOST STATUS
prompt message b: ENTER ct HN=nn TO SELECT HOST
prompt message c: ENTER INPUT TO CONNECT TO HOST
prompt message d: READY FOR INPUT
prompt message e: TERMINAL DISABLED BY NOP
prompt message f: INPUT DISCARDED
Figure J-8. Host Availability Display (Sheet 2 of 2)
• J - 1 2 60459500 C
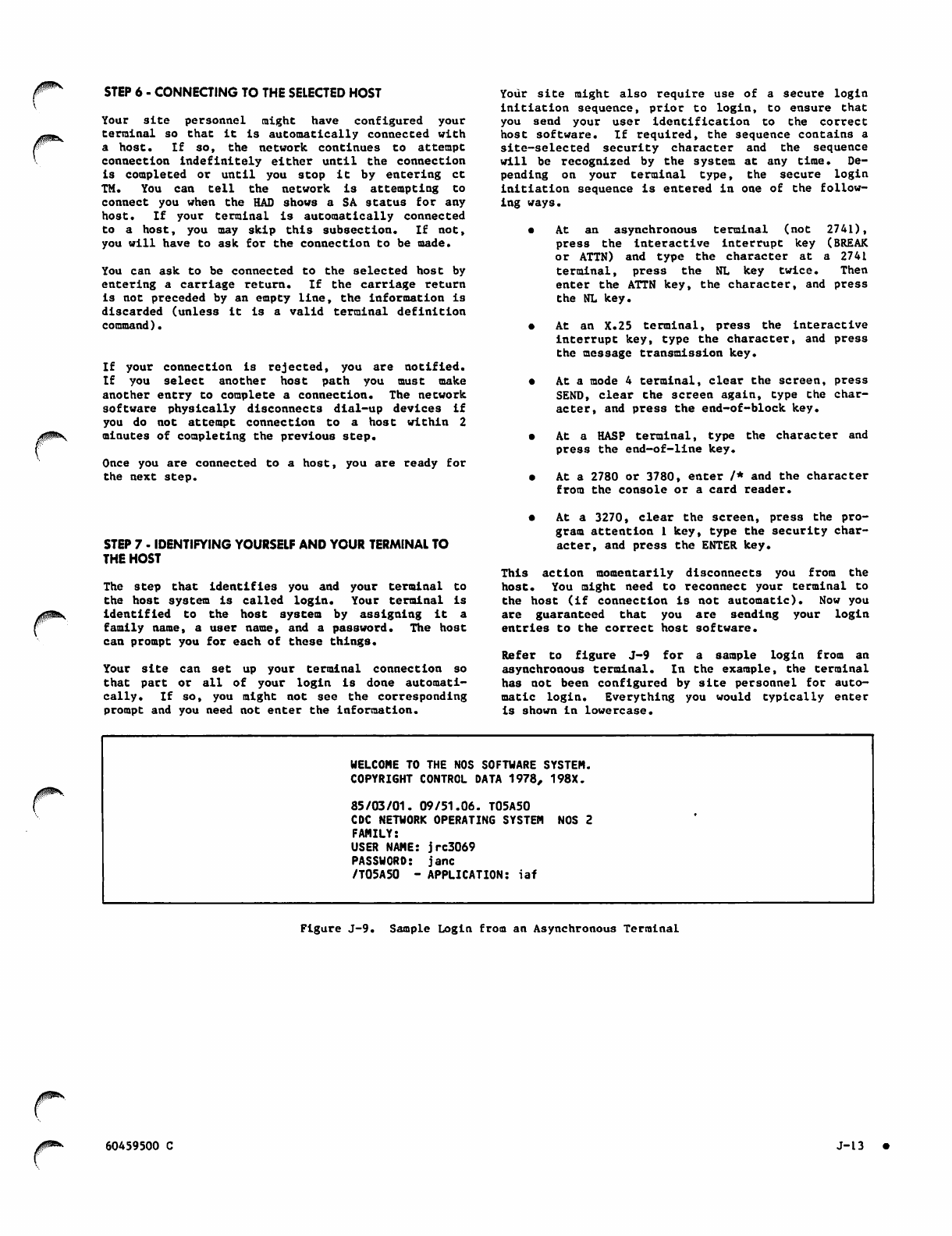
yUSfflJ^ STEP 6 • CONNECTING TO THE SELECTED HOST
Your site personnel might have configured your
terminal so that it is automatically connected with
a host. If so, the network continues to attempt
connection indefinitely either until the connection
is completed or until you stop it by entering ct
TM. You can tell the network is attempting to
connect you when the HAD shows a SA status for any
host. If your terminal is automatically connected
to a host, you may skip this subsection. If not,
you will have to ask for the connection to be made.
You can ask to be connected to the selected host by
entering a carriage return. If the carriage return
is not preceded by an empty line, the information is
discarded (unless it Is a valid terminal definition
command).
If your connection is rejected, you are notified.
If you select another host path you must make
another entry to complete a connection. The network
software physically disconnects dial-up devices if
you do not attempt connection to a host within 2
minutes of completing the previous step.
Once you are connected to a host, you are ready for
the next step.
Your site might also require use of a secure login
initiation sequence, prior to login, to ensure that
you send your user identification to the correct
host software. If required, the sequence contains a
site-selected security character and the sequence
will be recognized by the system at any time. De
pending on your terminal type, the secure login
initiation sequence is entered in one of the follow
ing ways.
• At an asynchronous terminal (not 2741),
press the interactive interrupt key (BREAK
or ATTN) and type the character at a 2741
terminal, press the NL key twice. Then
enter the ATTN key, the character, and press
the NL key.
• At an X.25 terminal, press the interactive
interrupt key, type the character, and press
the message transmission key.
• At a mode 4 terminal, clear the screen, press
SEND, clear the screen again, type the char
acter, and press the end-of-block key.
• At a HASP terminal, type the character and
press the end-of-line key.
• At a 2780 or 3780, enter /* and the character
from the console or a card reader.
STEP 7 • IDENTIFYING YOURSELF AND YOUR TERMINAL TO
THE HOST
Th e step th a t i d ent i fies yo u a n d y our te r min a l t o
the host system is called login. Your terminal is
identified to the host system by assigning it a
family name, a user name, and a password. The host
can prompt you for each of these things.
Your site can set up your terminal connection so
that part or all of your login is done automati
cally. If so, you might not see the corresponding
prompt and you need not enter the information.
• At a 3270, clear the screen, press the pro
gram attention 1 key, type the security char
acter, and press the ENTER key.
Th i s ac t i on m o m ent a r i l y d i s conn e c t s y o u fr o m t h e
host. You might need to reconnect your terminal to
the host (if connection is not automatic). Now you
are guaranteed that you are sending your login
entries to the correct host software.
Refer to figure J-9 for a sample login from an
asynchronous terminal. In the example, the terminal
has not been configured by site personnel for auto
matic login. Everything you would typically enter
is shown in lowercase.
j^p^H..
WELCOME TO THE NOS SOFTWARE SYSTEM.
COPYRIGHT CONTROL DATA 1978, 198X.
85/03/01. 09/51.06. T05A50
CDC NETWORK OPERATING SYSTEM
FAMILY:
USER NAME: jrc3069
PASSWORD: jane
/T05A50 - APPLICATION: iaf
NOS 2
Figure J-9. Sample Login from an Asynchronous Terminal
/#^- 60459500 C J-13

Automatic Login
The family name or user name assigned to your ter
minal for an automatic login can be:
• A mandatory value.
• A default value.
• A primary value.
If a mandatory value is assigned, you do not receive
a prompt and cannot use any other value.
If a default value is assigned, you are prompted and
you can either: enter an empty line as a response
to the system prompt if you want either the default
family or user name to apply, or respond to the
prompt with another value.
The default family name value assigned to your
terminal for automatic login can be different from
t h e d e f a u l t v a l u e u s e d b y t h e h o s t f o r a f a m i l y
name. You can override the login default even when
you do not know the system default; this procedure
is described in the following subsection.
If a primary value is assigned, you do not receive a
prompt the first time login occurs while you are
connected to the host. Subsequent logins (refer to
Restarting Login Identification) do prompt you. You
can override a primary value for user name by
entering a different value during an abbreviated
login. Abbreviated login is described in a later
subsection.
Login Dialog
Login begins when the system displays the following
lines.
WELCOME TO THE NOS SOFTWARE SYSTEM.
COPYRIGHT CONTROL DATA 1978, 198X.
Then a line appears with the date, time, and
terminal name; for example:
83/12/28. 15.23.58. TERM201
Next is a line your site supplies that identifies
the host system used; something similar to:
CDC NETWORK OPERATING SYSTEM NOS 2
The next line is either of the following prompts.
FAMILY:
This indicates that no mandatory or primary
family name has been assigned to your ter
minal. Enter the 1- to 7-character name of
the storage device that contains your per
manent files and press t he carri age return.
If you want to us e the default login family
name, just press the carriage return after
th e FAM I LY pr omp t appe a rs. You can a lso
enter a value of 0 to override a preassigned
login default family name and use the system
default family name. If you have no preas
signed default family name, carriage return
selects the system default family name.
USER NAME:
Thi3 indicates that no mandatory or primary
user name has been assigned to your terminal.
Enter the user name you were given. The user
name, which can contain any combination of
digits, letters, and asterisks, identifies
you as the terminal operator.
The next prompt appears only after a USER NAME
prompt has appeared. This final prompt is either:
PASSWORD:
PASSWORD:
XXXXXXX
The system attempts to preserve your password's
secrecy. If you have set your terminal at full
duplex (refer to the NOS Reference Set, Volume 3,
System Commands), your password will not be displayed
when you enter it. You will not see what you type
in. At some terminals, the network overprints
several characters on a line and asks you to type
your password on that line, as shown by the second
PASSWORD prompt. After creating this row of over-
struck characters, the cursor moves back to the
first character.
Enter the password currently associated with your
user name. If you must enter the user name, you
also must enter the password. No default exists for
a password.
J-14 60459500 C

y^PfeS
You must respond to each prompt within 2 minutes.
If you ta ke too lon g t o r es pon d, this mess ag e i s
displayed at your terminal.
TIMEOUT.
Your terminal is then disconnected from the host.
If you enter an unacceptable family name, user name,
or password, you receive either the following
message:
IMPROPER LOGIN, TRY AGAIN.
FAMILY:
if no mandatory family name is assigned to your
term in al , o r:
IMPROPER LOGIN, TRY AGAIN.
USER NAME:
if a mandatory family name is assigned. Reenter all
needed login information, beginning with the
requested parameter, regardless of when the error
occurred.
Yo u must s p e l l e a c h login e n t r y c o r r e c t l y. If yo u
make a mistake, such as typing the letter 0 for the
numeral 0 or the number 1 for the letter 1, your
login will not be successful. Try again when the
prompting sequence restarts.
You are allowed four consecutive chances to complete
the login procedure. If you make four unsuccessful
attempts to complete login, this message appears at
your terminal:
USER RETRY LIMIT.
Your terminal is then disconnected from the host.
If this happens, check the spelling of all of the
e n t r i e s . I f y o u s p e l l e d e v e r y t h i n g c o r r e c t l y ,
contact a site administrator.
When the family name, user name, and password are
accepted by the host, you must next connect your
terminal to an application, if there is no default
network application.
STEP 8 • SELECTING A NETWORK APPLICATION
Your s ite m ay be se t u p s o tha t you r ter mi na l i s
connected to the IAF application automatically. Or
your site may connect your terminal automatically to
another application, depending on the installation.
If so, you might not see the corresponding prompt.
If not, you must complete this step yourself.
You are allowed several chances to make a correct
ent ry. Ho wever, if y ou f ai l to connec t su cc essfu lly
after four consecutive attempts, your terminal is
automatically disconnected from the host. If this
happens, check the spelling of the name you used.
If the spelling was correct, contact a site
administrator.
Automatic Connection
Your host may permit you access only to one network
application, or an application can be connected
automatically. Your host site can configure your
connection for either possibility by preassigning an
automatic connection application name.
A preassigned automatic application connection can
be either mandatory or primary for the connection or
it c an be mandator y for t he use r. If ei th er y ou or
your connection has a preassigned mandatory appli
cation, you are not prompted, you are automatically
connected to that application, and you cannot use
any other application. If a mandatory application
program is not running in the host, you are logged
out and disconnected from that host.
If a primary value is assigned, you are not prompted
for the initial connection request after identifying
your terminal to the host, and connection to that
program occurs automatically. If that connection is
not successful or if you disconnect from that appli
cation program, you have a choice of actions; you can
select another application or disconnect from the
host.
To override a primary automatic application connec
tion on the first attempt to select an application,
name a different application in an abbreviated login
entry (described later in this appendix) following a
login prompt.
When a primary value is assigned, you are prompted
on subsequent attempts to select an application,
such as when you are switching applications. When
you are prompted to enter an application name and
you want to be connected to your primary applica
tion, enter an empty line as a response.
Manual Connection
This procedure begins when you see the following
prompting message.
terminalname - APPLICATION:
The terminalname variable on this line is the same
terminal name as the one on the first line of your
login sequence. If your terminal is automatically
logged into a network application, you do not
receive this prompt.
When you receive the APPLICATION prompt, enter the
letters and digits that identify the network appli
cation you want to access; for example, IAF for the
Interactive Facility. You can access CDC-written
applications from the following list that are in
stalled at your site:
• Remote Batch Facility (enter RBF).
• I n t e r a c t i v e F a c i l i t y ( e n t e r I A F ) .
• Transaction Facility (enter TAF).
• Terminal Verification Facility (enter TVF).
• Message Control System (enter MCS).
• PLATO (enter PNI, which stands for the
PLATO-NAM Interface).
Oth e r a pp licat i o n s , wr i t t en a t y o u r s i t e , migh t b e
available.
60459500 C J-15
You must respond to the prompt within 2 minutes. If
you take too long to respond, this message is
displayed at your terminal.
TIMEOUT.
Your terminal is then disconnected from the host.
You must spell your entry correctly. If you make a
mistake, such as typing the letter 0 for the numeral
0 or the letter 1 for the number 1, you receive the
following error message:
ILLEGAL APPLICATION, TRY AGAIN,
terminalname - APPLICATION:
The terminal name is indicated by terminalname. You
can also receive this message if your user name is
not permitted access to the application you named.
If you did not spell the name correctly, try again.
If you did spell the name correctly, disconnect your
terminal and contact a site administrator.
If you make four unsuccessful attempts to enter an
application name, this message appears at your ter
minal.
APPLICATION RETRY LIMIT.
Your terminal is then disconnected from the host.
This step is complete when the application you re
quest connects to your terminal. The application
you asked to use might print an identification line
next.
Whether the program sends such a message or not, you
can use commands recognized by that application. If
you need to disconnect your terminal from the appli
cation, the application probably has a command for
that purpose. If the program has no such command,
the subsection called Disconnecting from a Host des
cribes a command you can use.
To use the site-defined login default family name,
enter:
,RLS4525,PASS123,IAF
To o v e r r i d e y o u r s i t e - d e fi n e d l o g i n d e f a u l t f a m i l y
name with the host's default family name, enter:
0,RLS4525,PASS123,IAF
To use a login default family name and user name
defined by the site for your terminal, enter:
///IAF
To also use a default application name defined by
the site for your terminal, enter:
You can supply combined entries in response to the
FAMILY, USER NAME, and PASSWORD prompts. Although
you do not need to complete the remaining sequence
on the same line, you must enter the information in
the correct order: family name, user name, password,
and application (if there is no default). For
example:
FAMILY: systema
USER NAME: rls4525,pass123
terminalname - APPLICATION: iaf
If you supply a user/password combination that is
overridden by a mandatory specification, this mes
sage is displayed.
VOLUNTEERED USER/PASSWORD IGNORED.
If you offer an application name that is overridden
by a preassigned mandatory application, the follow
ing message is displayed.
VOLUNTEERED APPLICATION IGNORED.
y^s^s.
ABBREVIATED LOGIN AND APPLICATION CONNECTION
You can shorten the standard login and application
connection procedures by entering all of the re
quired information at once. For example, in res
ponse to the FAMILY prompt, you can enter the fol
lowing information on the same line.
FAMILY: familynanie,username,password,application
Separate all entries with a comma. The entries are
order-dependent. Use a comma to indicate any default
or unused entries.
You do not receive any of the remaining login selec
tion prompts if you use this abbreviated login pro
cedure, unless you omit a required entry or supply an
entry that is not recognized. Your password entry is
not protected by the system when you use an abbrevi
ated login procedure.
Here are some examples. To log In and connect to
the Interactive Facility application IAF with a
family name of SYSTEMA, a user name of RLS4525, and
a password of PASS123, enter:
SYSTEMA,RLS4525,PASS123,IAF
SWITCHING TO A DIFFERENT APPLICATION
Unless you have a mandatory network application
assigned for your terminal, you can transfer your
terminal's connection from the current application
to another application. There are two ways to do
this, depending on the commands used by the current
application.
Direct Switches
You can switch in one step by entering a switch com
mand recognized by the current application. The fol
lowing switch commands are recognized by CDC-written
network applications:
Application
RBF
IAF
MCS
Command
IAF
BYE,application
LOGIN,application
For example, if your terminal is connected to RBF,
y o u ca n g a in a c c e s s to I A F b y en t e r i ng t h e I A F
command.
y^v
• J - 1 6 60459500 C
Do not enter any more input until the application
acknowledges it has processed your switch command.
Otherwise, you may lose the input.
Indirect Switches
If your current application does not have a command
for a direct switch, you must disconnect your ter
minal from the current application with a command
r e c o g n i z e d b y t h a t a p p l i c a t i o n . T h e n y o u m u s t
request another application connection from the
host. The following disconnection commands are
recognized by CDC-written network applications:
Program Command
RBF END
IAF BYE,
MCS END
TAF EX.LOGT
TVF END
For example, you can switch your terminal connection
from RBF to an application other than IAF by
entering the END command. You then receive a prompt
for a new application name. Do not enter any more
input until the application acknowledges it has
processed your disconnection command. Otherwise,
you might lose the input.
Dialog for Direct and Indirect Switches
After disconnecting the application, the system in
dicates that a connection switch is in progress by
issuing this message.
application - CONNECT TIME hh.mm.ss.
The application that was just disconnected is In
dicated by application and the time that passed
while the terminal was connected to the program is
indicated by hh.mm.ss.
If you used a switch command, you receive an iden
tifying me ss ag e f ro m your ne w a pp li ca ti on . If yo u
used a disconnection command, you receive another
prompt for an application name.
terminalname - APPLICATION:
unless the terminal is permitted access to only one
application. If so, you are disconnected from the
host.
If you enter the name of another application in res
ponse to the APPLICATION prompt, you are connected
to that application.
RESTARTING LOGIN IDENTIFICATION
There are many reasons why you might want to restart
login identification and the subsequent application
connection. Perhaps you have several user names
available to you, each with permission to use dif
ferent host resources. Or perhaps someone else left
the terminal connected to an application you do not
need, and you do not want to use their user name.
There are three ways to restart login, depending on
the commands recognized by the current application
and installation options.
Direct Restarts
You can restart host identification by entering a
login command recognized by the current application.
The following login commands are recognized by CDC-
written network applications:
Application
RBF
IAF
MCS
Command
LOGIN
HELLO
LOGIN
For example, if your terminal is connected to IAF,
you can restart login by entering the HELLO command.
Do not enter any more input until the application
acknowledges it has processed your command. Other
wise, you may lose the input.
Indirect Restarts
If your current application does not have a command
for a direct switch, you must disconnect your ter
minal from the current program with a command rec
ognized by that application. Then you must request
restart of login from the host. The disconnection
commands recognized by CDC-written network applica
tion are described earlier in this section under
Switching to a Different Application.
For example, you can restart your terminal login from
RBF by entering the END command. You then receive a
prompt for a new application name. Do not enter any
more input until the application acknowledges it has
processed your disconnection command. Otherwise, you
might lose the input.
Secure Login Restarts
If your site has selected the secure login initiation
option and defined a security character, the sequence
may be entered at any time to immediately disconnect
from the current application and initiate the user
login procedure.
After entering the disconnection command, you receive
another prompt for an application name:
terminalname - APPLICATION:
unless the terminal is permitted access to only one
application program. If so, you are disconnected
from the host and can restart login by reconnecting.
If you receive the APPLICATION prompt, you use one
of the following commands to ask the host system to
restart login:
HELLO
LOGIN
60459500 C J-17

DISCONNECTING FROM A HOST
You might want to disconnect your terminal from a
host for several reasons, for example:
• You want to disconnect from the network
properly, without leaving behind an indica
tion that something went wrong; disconnecting
from a host is the first step in disconnect
ing from a CDC network.
• You are allowed access to more than one host
system, and you want to transfer your ter
minal's connection from the current host to
another host.
There are four ways to do this, depending on the
commands used by the current application.
Disconnecting with Application Commands
You can disconnect in one step by entering a host
disconnection command recognized by the current
application. The following host disconnection
commands a re rec og ni ze d b y CDC-written n et wo rk
applications:
The following host disconnection commands are valid
responses to the APPLICATION prompt on CDC host
systems:
8YE
LOGOUT
For example, you can disconnect your terminal from
RBF by entering the END command. You then receive a
prompt for a new application name and enter BYE.
Disconnecting with a Network Software Command
You normally end a connection with a host by using a
command to disconnect you from an application and/or
a command to log out of the host. Events might make
it impossible for you to do either. When this
happens, you can end your terminal's connection to
the host by entering this terminal definition
command.
Ct TM
ct represents the network control character. For
most asynchronous terminals this is ESC.
/T*®&?&\
Program
RBF
IAF
MCS
Command
LOGOUT or LOGOFF
BYE or LOGOUT or GOODBYE
BYE or LOGOUT
The network responds to your TM command with a new
host availablity display. You can use the TM com
mand if an application does not respond to your
entries.
For example, if your terminal is connected to IAF,
you can disconnect from the host by entering the BYE
command.
Disconnecting with Host Commands
If your current application does not have a command
for direct disconnection, you must first disconnect
your terminal from the current program with a com
mand recognized by that application. Then you must
request host disconnection from the host. Applica
tion disconnection commands are described earlier in
this section under Switching to a Different Applica
tion.
After disconnecting the application, the system in
dicates that a connection switch is in progress by
issuing this message:
application - CONNECT TIME hh.mm.ss.
The application that was just disconnected is indi
cated by application and the time that passed
while the terminal was connected to the program is
indicated by hh.mm.ss.
You then receive another prompt for an application
program name:
terminalname - APPLICATION:
unless the terminal is permitted access to only one
ap p li c ati on. If s o , y ou a re di sco nne c te d from th e
host anyway.
Reconnecting to a Host or Connecting to a Different Host
For a single host system, after your terminal is dis
connected from the host, this message is printed.
HOST DISCONNECTED. CONTROL CHARACTER = Ct
ct is the network control character,
is followed by the prompting message.
ENTER INPUT TO CONNECT TO HOST
This message
You can then attempt another connection to the same
host by sending any input you want. If you have a
m u l t i h o s t s y s t e m , t y p i c a l l y t h e H A D w i l l b e d i s
played between these two messages. To reach a dif
ferent host, you must complete the procedures for
Selecting a Host and Connecting to the Selected Host
described earlier in this appendix.
Disconnecting from One Host and Connecting to a Different
Host
You can disconnect from one host establish a connec
tion with another host using the single command
ct HC = hn
ct is the network control character, and hn is the
name of the desired host.
/^v
• J - 1 8 60459500 C ^*^v

/ptfev
INTERRUPTIONS
Events can sometimes interrupt your input or output.
These interruptions fall into two categories.
• Interruptions for communication with the
network operator.
• Temporary suspensions in communication.
Communicating with the Network Operator
The term network operator includes any operator who
has access to the network, including the host oper
ato r. Any n e twork op e r a t o r c a n se n d a n d re c e i v e
messages that involve you.
Receiving Messages
The network operator can send short messages to a
terminal. The message appears at your terminal in
this format.
FROM NOP message text
These messages can appear at any time a new line of
output is possible at your terminal. For example,
the network operator might want to Inform all con
nected terminals that communication is going to be
suspended intentionally with this message.
FROM NOP SHUTDOWN IN 5 MIN
Sending Messages
You can respond to such messages by entering the
following terminal definition command.
ct MS=message
ct represents the network control character,
most asynchronous terminals this is ESC.
For
The message text must not exceed 50 graphic charac
ters. Because the network operator can be located
at a terminal that does not support many special
characters, you should avoid characters not in the
ASCII 63-character subset described in appendix A of
the NOS Reference Set, Volume 2, Guide to System
Usage.
You can also begin dialog with the network operator.
Fo r ex a m p le, i f y o u ne e d t o us e a re m o t e b a t c h
printer that has been logically disabled, the entry:
%MS=PLEASE ENABLE LP=M4C555
causes the message PLEASE ENABLE LP-M4C555 to appear
at the network operator's terminal, prefixed by the
terminal name of your terminal. The Z character
represents the network control character for your
terminal.
Preventing Messages
S o m e t i m e s i t i s i m p o r t a n t t h a t o u t p u t t o y o u r
terminal does not include unplanned messages from
th e n etw ork ope r at or. Yo u c an pr ev ent deli ver y o f
messages from the network operator by locking them
out with the following terminal definition command.
ct LK=option
ct represents the network control character,
most asynchronous terminals this is ESC.
For
After you enter this command with the option Y, any
message to your terminal from the network operator
is discarded by the network software. Messages are
discarded until you again allow delivery by using
the command with the option N.
Site administrators can configure your terminal so
that messages are discarded as soon as the terminal
is connected to the network. A netw ork applicatio n
can also change the LK option in use.
Suspensions of Communication
Sometimes, message traffic in the network is so heavy
t h a t a l l s t o r a g e i s t e m p o r a r i l y u s e d u p . A l s o , a
host may be too busy to accept data. During these
times, the network software takes steps that tempor
arily stop input until enough output has occurred to
free additional storage.
Although storage may be low, sometimes the network
cannot prevent you from entering data. Therefore,
the network discards each message from your terminal
and sends this message to your terminal.
WAIT . .
When the following message appears, you can reenter
any information that was previously discarded.
REPEAT . .
If your terminal transmits more than one message at
a time, you must determine which information you
need to reenter. The application might have
commands that can help you determine which messages
it received.
Communication Failures
Events can occur that:
• Cause your application to fail.
• Disconnect your terminal from an application.
• Disconnect your terminal from the host.
• Disconnect your terminal from the network.
60459500 C J-19

Application Failures Disconnection from the Network
I f a n a p p l i c a t i o n f a i l s a f t e r y o u r t e r m i n a l i s
connected, this message is displayed.
APPLICATION FAILED.
application CONNECT TIME hh.mm.ss.
terminalname - APPLICATION:
The length of time your terminal was connected to
the application is specified by hh.mm.ss;
application is the name of the application; and
terminalname represents the terminal name the
n e t w o r k us es t o ide n t i f y th e t e r m i n a l . Yo u eith e r
can select another application or log out.
Disconnection from an Application and/or a Host
An application is Informed of two events that you
might want to take action on.
• Long periods of device inactivity.
• Pending network shutdown.
The network software informs an application if more
than 10 minutes have elapsed without any
communication between a device at your terminal and
the application. An application can:
• Ignore this time interval.
• Ask you for continued dialog.
• Disconnect from your terminal or from the
device with or without telling you.
The effect of device inactivity depends on the
application with which the device is currently
connected.
When shutdown of the network is pending, the network
operator can enter a command that informs all
applications of the pending event. Your application
might take actions that either result in connection
termination or application failure. It also might
send you a message to warn you of the event.
If you receive a message from an application
indicating that shutdown is pending, you should take
steps immediately to save all data or files you are
currently using. Then end connection with both the
application and the host as soon as possible.
The network informs you that it has lost
communication with the host software by displaying
the host status message:
HOST DISCONNECTED. CONTROL CHARACTER = Ct
followed by the prompting message:
ENTER INPUT TO CONNECT TO HOST
If you have a multihost system, the HAD will be
displayed between these two messages.
If you are at a dial-up terminal and you do not
attempt to connect to the same or a different host
within 2 minutes, your terminal is disconnected from
the network.
If communication between the network and the host
software resumes, you must connect to the host and
log in again but you do not need to access the net
work again (perform dial-up and auto-recognition pro
ce du re s). Th ese h ost com mu nicat io n f ai lu res o ccur
either when the host has been shut down or when hard
ware fails in the communication path between the net
work and the host.
All network software conditions (that is, parameters
that may be set with terminal definition commands)
ar e re t ain e d a c r oss ho s t d i s conn e c tio n ex cept fo r
transparent, full ASCII, and special edit input
modes. Refer to the NOS Reference Set, Volume 3,
System Commands for a discussion of these commands.
Failures in the communication path between the net
work hardware and your terminal are treated by the
network software as if your terminal had failed.
These failures can occur because of hardware prob
lems, or maybe because you entered an input charac
ter during output. If you hold the interactive out
put interrupt key down for too long, a communication
failure can occur. This key is identified in the NOS
Reference Set, Volume 3, System Commands.
There are several tests for communication failures.
If your terminal has a CTS, ON-LINE, or CARRIER in
dicator, the light goes out when a failure occurs.
At other terminals, if a failure has occurred, re
questing the host availability display produces no
response from the network.
Batch input and ouput devices associated with the
failed console stop running, and batch device con
nections are ended. The network software does not
distinguish between dial-up and hardwired terminals
when processing terminal failures.
Terminal failures require you to complete new access
and login procedures to resume communication with the
network. Terminal failures always cause disconnec
tion when the terminal is on a dial-up line.
yS^awSX
• J - 2 0 60459500 C
INDEX
jfflSSBSi^
Accessing a host J-l
Accessing transaction subsystem
ACT 2 -11
After image recovery file 8-1
AKY statement 4-1
Alternate keys 4-2
Application block header
Building 2-12
Examining 2-14
Modifying 2-12
Application character type 2-11
ARF 8-i
Attach mode 4-2
Audience 5
Auto-Input mode 1-3; 2-12
Automatic recovery
Description 7-1; 8-1
Report 8-4,6
Requests
Application 2-32
System 2-38
Backup directory file 8-2
Batch
I n t e r f a c e 1 - 3 ; 5 - 1
Subsystem interaction 5-1
Batch output 5-4
Batch recovery 8-1
Before image recovery file 8-1
Begin-commit identifier 7-1,3
Begin-commit sequence 7-1; 8-1
BEGIN request
1-4
Data base 7-•1,3; 8-1
TA F 2 - 2 8
BLDABH request 2-12
Blocked tasks I-•1
BRF 8-1
BTASK system task 8-4
BTRAN request 5-■I; 7-1
Build ABH 2-12
BWAITINP request 2-28
Call tasks 2-4
CALLRTN 2-4
CALLTRN request 2-38; 8-1
CALLTSK 7-4,5
CALLTSK request 2-6
CDCS 1-2; 3-1; 4-4; 7-1,3
CEASE request 2-28
Chain 2-4
Change ACT 2-11
Change CMDUMP request values
Change I/O Limit 2-28
Change task field length
Character sets * '
Character type
CLOSE requests
CMDUMP request
COMMIT requests
6-1
2-3;
A-l
2-11
7-2
6-3
7-1,3; 8-1
10-6
Commit updates 7-3
Communication block
Defined 2-1
Diagram 2-2
Dump 6-4
Load overflow data 2-10
Release overflow data 2-23
TAF-originated transactions 12-3,4
Communication recovery file
Description 4-1,8; 7-1; 8-1
Error override 8-3
Multiple 3-4
Reformat 8-3
User messages
Read 2-33
Write 2-33
Concurrent users 4-2
Confirmation message 2-35; 7-1
Create task library 10-7
Create xxJ file 4-4
CRF 4-1,8
C R M fi l e t y p e 4 - 2
CYBER Database Control System 1-1,2; 3-1; 4-4
CYBER Record Manager Data Manager 1-1,2; 4-1,2
Data base
Describe 9-1
J o u r n a l fi l e s 4 - 5
Maximum number of 4-7
Reco v e r y 7- 1 ; 8- 1
Data manager
Concurrency l-l; 3-1
Requests 2-3
xxJ files 4-1,4
Deadlocks 3-1
Define terminal characteristics 2-16
10-7
9-1
2-31
2-28
8-2
Delete tasks from task library
Describe users and data bases
Determine if user is logged In
Determine subsystem for task
D i a g n o s t i c s B - l
DIAL directive 9-1
Oisable transaction recovery
DISPLAY statement 4-7
DMS statement 4-7
DSDUMP request 6-1
Dump Communication block 6-4
Exchange package 6-4
TA F fi e l d l e n g t h 6 - 4
Ta s k fi e l d l e n g t h 6 - 3 , 4
E C S 5
End task 2-28
Entering transaction subsystem 1-4
E n t r y h e a d e r, j o u r n a l fi l e 4 - 5
ERO command 8-3
Error messages B-l
Establish system identifier 2-40
60459500 C Index-1

Examine ABH 2-14
Execute named task 11-2
Exe c u t i n g t r a n sact i o n 7- 1
Extend field length 2-3; 10-6
Extended core storage 1-5
Extended memory 5; 1-5
Extract bit string from word 2-31
EXTRACT request 2-31
File
CRM type 4-2
Definitions E-l
Descriptions E-l
I n d e x 4 - 2
Files
Journal 4-5
JOURO 4-5
NCTFI 4-8
Network 4-8; 9-1
Procedure 4-1
Recoverable 8-1
Recovery 4-8; 8-1
Re se rve d E-2
System 4-1
TCF 4-1,7; E-l
xxJ 4-1,2,4
xxJORn 4-4
xxTASKL 10-1
Force d write i n d i c a t o r 4 - 3
Format effectors 2-12,15
Free req ue st s 7 -1
FSE C-6
GETABH request 2-14
Global task dump limit
GTD L 6 -5
6-5
Hardware configuration 8-2
Ignore task in replacement file 10-8
110 request 2-28
Implement application 1-5
Index file 4-2
Initate a run unit 2-38
Initial task 1-3; U-l; 12-1
Initialize recovery files 8-2
Initiate new transaction chain 2-6
Input/output
Limit 2-28
Requests 2-8
Input overflow 2-10,23
Insert bit string into word 2-31
INSERT request 2-32
Installing TAF F-l
INT command 8-2
Interactive virtual terminal 1-3; 2-16
Interrogate TST 2-23
ITASK 1-4; 11-1; 12-1
IT L r e que st 2 -2 9
IVT 1-3; 2-16
IXN statement 4-2
Journal files 4-5
JOURNL request 4-5
JOURO file 4-5
• Index-2
K display commands 2-30; 4-8; 6-1,4; 8-2,3
K.DSDUMP command 6-4
K.DUMP command 6-5
K.DUMPLIM command 6-5
K.ERO command 8-3
8-2
8-3
4-8
K.INT command
K.REC command
K. statement
KDIS U-l
KPOINT request 2-30
H-l
KTSDMP utility/request 6-4
Libraries 10-1
LIBTASK command 10-2
LIBTASK input directives 10-5
LIBTASK utility/command 10-1
Line feed and transmission keys
List tasks on library 10-3
Load overflow blocks
LOADCB request 2-10
Lock conflict 7-2
LOGIN request 2-31
Login terminal to TAF
Logout task ll-l
Logout terminal from TAF 2-29; 11-1
LOGT request 2-29
LOGT system task 11-1
2-10
1-4
Macros 12-1
Manipulate user area of TST 2-26
Memory
Changing from tasks 2-3; 10-5
Dump requests 6-1
Dumps 6-1
Requests 2-3
Message abort 11-1
Modify ABH 2-12
Modify terminal characteristics 2-16
Move data from terminal to task 2-28
MSABT ll-l
Multlmainframe 1-5
Multimainframe recovery 8-4
Multiple indexed files 4-2
Multiple RECOVER statements 8-3
NAM 1-3; 12-3
Named-transaction 7-1; 10-5
NCTFi file 4-8
NDL 1-5
Network
Access Method 1-3; 12-3
Definition language 1-5
File origination 9-1
Files 4-8; 9-1
I n t e r f a c e 1 - 3
NETWORK statement 4-8; 8-3
NEWTRAN request 2-7
OFFTASK 11-2
On-line transaction processing
OPEN requests 7-2
Output from SUBMT jobs 5-4
Override 1/0 errors 8-3
l - l
60459500 C

Parameter
SEND request 2-18
Par ameter table 2-25
Procedure file 4-1,4
Put recovery data on CRF 2-33,41
RSECURE request 2-34
RTASK system task 8-4; 11-2
Complete 2-35
Initate 2-38
Running transaction 7-1
jgpss,
4-8; 8-2,3
8-1
8-5
RA+1 calls 1-5; 2-1
RC parameter 7-1
RCTASK system task 11-2
Read data from terminal 2-8
Read recovery data 2-33
Read SECURE message 2-34
Record data on journal file 4-5
Record lock conflict 7-2
Record locks 4-2
RECOVER statement
Recoverable files
Recovery
CDCS 7-1
CDCS failure
CRF file 8-3
Data base 7-1; 8-1
Disable 8-2
File identifier 4-8
F l a g 8 - 4
General 7-1; 8-1
Hardware configuration 8-2
Initialize files 8-2
K display commands 4-8; 8-2
Multimainframe 8-4
Multiple data manager tasks 7-5
NAM fai l u r e 8- 5
Override I/O errors 8-3
Overview 7-1; 8-1
Processing flow 8-4
Requests
Application 2-33
System 2-38
System failure 8-4
TAF/CRM Data Manager 7-1
TAF failure 8-4
Task failure 8-5
T C F fi l e 8 - 3
Terminal 7-4; 8-5
Transaction 7-1; 8-1
Recovery indicator 10-5
Application 2-32
System 2-38
Release overflow blocks 2-23
RELSCB request 2-23
Requests
Data manager 2-3
Input/output 2-8
Journal file 2-3; 4-5
Memory 2-3
Memory dump 6-1
Message 2-4
Recovery
Application 2-32
System 2-38
System 2-3
Task
Control 2-28
Scheduling 2-4
Utility 2-30
Rerun request 2-32
Reserved files E-2
RESTRICT clause processing 3-1
Resubmit terminal input 2-32,40
Retrieve recovery data 2-33
RGET request 2-33
RPUT request 2-33
Sample deck s tru ctu res D-l
Schedule tasks 2-4; 10-7
Scheduling priority 10-7
SECURE message
Acknowledge 2-36
BTRAN 2-36
Description 7-3; 8-1
R e t r i e v e 2 - 3 4
W r i t e 2 - 3 5
SECURE request 2-35; 7-1,3; 8-1
Send message task 11-2
Send message to user 2-17
SEND request 2-17
Set GTDL 6-5
Set system identifier 2-40
S e t t i m e l i m i t fo r t a s k 2 - 2 9
Set transaction sequence number 2-40
Set user recovery bit 8-3
SETCHT request 2-11
Specify communication block location 2-28
SRERUN request 2-40
Start transaction using batch job 5-1
Start update sequence 7-3
STASK 11-2
St a t us o f c u r ren t tr ansa c t ion 2- 3 7
Status of current user 2-37
S t a t u s o f t r a n s a c t i o n 2 - 8
STRAN macro 12-1
Subcontrol points 1-5
Submit batch job from task 5-3
Submitting comments 5
SUBMT request 5-3
Subtransaction codes 12-1
Supervisory messages 2-11
Suspend processing 2-30
SYSMSG 11-2
System
Files 4-1
J o u r n a l fi l e s 4 - 5
Requests 2-3
Ta s k l i b r a r y 1 0 - 1
Tasks ll-l
TABCON statement 4-7
Tables
Terminal status (TST) 9-2
TAF
Automatic recovery report 8-4,6
Configuration file 4-7; E-l
Control point 1-1,2
Installation F-l
Originated transactions 12-3
Procedure file 4-1,4
Termination 8-5
TAF/CRM Data Manager 7-1
TAFREC 8-4
TARO request 2-26
Task
Chain 2-4
Control requests 2-28
Defined 1-4; 2-1
Dump 6-1
Field length changes 2-3; 10-6
Library
60459500 C Index-3

Create 10-7
Defined 10-1
Delete task from 10-7
Ignore task in replacement file
List tasks 10-3
Update 10-7
Pause 2-30
Queue limit 10-6
Queuing 10-1,6,7
Residency 10-1
Scheduling priority 10-7
Scheduling requests 2-4
Type 10-1
U t i l i t y r e q u e s t s 2 - 3 0
Task library report 10-3,4
TASKLIB 10-1
Tasks
Blocked I-I
Call 2-4
End 2-29
Schedule 2-4; 10-7
Time-originating 12-1
TCF file 4-1,7; E-l
TERMDEF request 2-16
Terminal
Characteristics
Define 2-16; G-l
General 12-4,5
Modify 2-16; G-l
Definition commands G-l
Failure 7-4; 8-5
Network description file 9-1
Recovery 7-4
Status request 12-5
Status table
Figure of 9-2
I n t e r r o g a t e 2 - 2 3
Manipulate user area 2-26
Recovery bit 8-3
Terminology and conventions 5
TIMCNT macro 12-1
Time-originating tasks 12-1
TINVOKE request 2-40
TMSG request 2-4
TOTAL Data Manager 1-1,3; 4-4; 7-5
TOTAL task area 1-1
TPSTAT request 2-28
TRAN macro 12-1
TRANCHK request 2-8
TRANS 12-1
10-8
Transaction
Codes 12-1
Coding 7-2
Defined 1-1
Named 7-1
P r o c e s s i n g 1 - 4
Recovery 7-1; 8-1
Rerun 2-32
Subsystem
Entering 1-4
Interaction 5-1
TAF-originated 12-3
Transaction-Id 7-3
Transaction sequence number
Transient task area 1-1
Transparent mode 2-12
TRANT 12-1
2-2,40
TSIM request
T S T 9 - 2
TSTAT request
TTOT 12-1
Type ahead
2-23
2-37
12-5
Updating task library 10-7
User recovery bit 8-3
USER statement 4-8
User status 12-5
Wa i t f o r te r m i na l in p u t 2- 9
WAIT request 2-30
WAITINP request 2-9
Write data to CRF 2-33,41
WSTAT request 2-41
XTASK 11-2
XTRAN system transaction 11-2
xxJ files
CDCS Data Manager 4-4
Creating 4-4
CRM Data Manager 4-2
No data manager 4-4
TOTAL 4-4
xxJORn file 4-4
xxTASKL file 10-I
• I n d e x - 4 60459500 C

/0^^l COMMENT SHEET
MANUAL TITLE: CDC TAF Version 1 Reference Manual
PUBLICATION NO.: 60459500 REVISION: C
NAME_ -
COMPANY:
/gs\, o
/p**^
STREET ADDRESS:
CITY: .STATE: ZIP CODE:
This form is not intended to bo used as an order blank. Control Data Corporation welcomes your evaluation of
this manual. Please indicate any errors, suggested additions or deletions, or general comments below {please
include page number references).
D Please Reply D No Reply Necessary
NO POSTAGE STAMP NECESSARY IF MAILED IN U.S.A.
FOLD FOLD
FIRST CUSS
BUSINESS REPLY MAIL
PERMIT NO. 8241 MINNEAPOLIS, MINN.
POSTAGE WILL BE PAID BY
CONTROL DATA CORPORATION
Publications and Graphics Division
ARH219
4201 North Lexington Avenue
Saint Paul, Minnesota 55112
NO POSTAGE
NECESSARY
IF MAILED
IN THE
UNITED STATES
_i
<
FOLD
FOLD