R F Technologies 30011534001 User Manual Hardware Overview
RF Technologies Inc Hardware Overview
Contents
- 1. Hardware Overview
- 2. Cell Controller Manual
- 3. Antenna Manual
Hardware Overview

PinPoint Corporation
System Hardware Introduction

FCC REGULATIONS
This system complies with Part 15 of the FCC Rules. Operation is subject to
the following two conditions: (1) this device may not cause harmful interference,
and (2) this device must accept any interference received, including interference
that may cause undesired operation.
WARNINGS
Changes or modifications not expressely approved by PinPoint Corporation
could void the users authority to operate the equipment.

Contents

Section 1: Introduction to the System
WELCOME
Welcome to the 3D-iD system. The 3D-iD system is an LPS (Local Positioning
System) designed to take asset and personnel tracking to the next level. Where
GPS supplies global, outdoor, positioning data, the 3D-iD LPS system provides
local, indoor and outdoor, positioning data. In addition, the system comes with a
variety of tools that enable you to track and monitor tagged assets in three-
dimensional space. The purpose of this manual is to introduce you to the sys-
tems technology and walk you through the an overview of its installation.
There are myriad applications for the technology applications which previous
technologies, due to their many limitations cannot address. In manufacturig
and distribution applications, the 3D-iD system can help shippers find containers
in shipping yards. In healthcare, it can be used to insure that hospitals can
keep track of their valuable assets, decreasing lost equipment and increasing
efficiency.
The 3D-iD system relies on a combination of hardware and software. Before
examining the systems operation, well take a brief look at the components that
make up the system. The two elements relevant to an end-user include:
· Tags that are attached to assets or people which are to be tracked
· A suite of software applications that present the user with information
about Tag locations and conditions.
The remaining elements, all of which have to be installed and configured,
include:
·The Antennas,
·The Cell Controllers
·The software infrastructure.
In this manual, well briefly explore each of these elements.

HOW THE 3D-ID SYSTEM WORKS:
The 3D-iD system is comprised of two basic parts, a hardware and a software
system. The combination of the two systems allows tags to be located, tracked
and secured throughout an installation site. The hardware side of the system
generates Tag Antenna Distance (TAD) data, while the software side of the sys-
tem converts that data to other forms, and presents it to the end-user.
The hardware side of the system consists of three parts: Tags, Antennas and
Cell Controllers.
Tags are the objects tracked they can be affixed to an asset or person,
allowing the system to track that asset or person.
Antennas are stationary devices from which TAD distances are meas-
ured. They are supplied with DC power via their coaxial cable connection
to a Cell Controller.
Cell Controllers are the brains of the hardware side of the system. They
coordinate the antennas and use the roundtrip time required for a radio
signal to travel from an antenna to a tag to calculate the distance
between the Tags and Antennas. This is what we call TAD (Tag-Antenna
Distance) data.
Once TAD data has been generated, it is forwarded to a ViewPoint Server on
the software side of the system. Which then converts that data into Location
and Alert data and publishes it to client applications.
Location (or LOC) data is data that indicates the Location (which are derived
from logical statements involving TAD variables) that a tag is in. A Location can
be a room, a wing or even an entire floor, depending on the configuration of the
system.
Alert (or ALR) data is data that is generated based on certain trigger events for
single tags or pairs of tags. There are two basic groups of alert conditions. The
first group, alerts associated with a single tag, can be set when a tag enters or
exits an area or when a tag remains within a certain location for a set period of
time. The second group, alerts associated with a pair of tags, can be triggered
when one tag enters an area without the other, when the two tags are near one
another or when the two tags are far from one another.

Detailed information about the ViewPoint Server is available in the Users
Manual. In brief, ViewPoints NT Services (which are programs that run in the
background on the server, and require no user input) receive the TAD data.
These services then use lookup tables created by the user when the software
system is setup to convert the TAD data into Location (LOC) and Alert (ALR)
data. The services then publish that data to various client applications which
end-users use to view specific data. The services can also publish data to a
Recorder service, which saves data to a database.
Combined, the hardware and software elements of the PinPoint system can
generate a wide variety of data based on the location of tags.

HOW THE HARDWARE WORKS:
The purpose of PinPoints 3D-iDs hardware system is to determine the distance
between tags and antennas. There are three elements involved in this process.
The first two are the tags and the antennas. The third is the cell controller,
which coordinates the actions of the tags and antennas and interprets their
signals.
Each tag is on (and detectable) for a very short period of time. Because this
on time is so brief - relative to the off times - the chances of two tags being
on at once are very remote. With this in mind, we can examine the Cell
Controllers operation. The Cell Controllers basic job is to record the amount of
time a radio signal takes to go between each antenna and the tag which is cur-
rently on and back. The Cell Controller can calculate the distance between a
single Antenna and a Tag from the transmission time and the speed of light.
The following is the procedure it follows for deriving the time needed for a radio
signal to travel between the Tag and the Antenna:
1. The Cell Controller sends an antenna a spread spectrum radio signal to
broadcast to the tags at 2.442GHz.
2. Whichever tag is on at that moment (assuming one is on and in range of
the antenna):
2.1. Receives the signal
2.2. Converts it to 5.770GHz
2.3. Modulates its unique serial number on the return signal
2.4. Retransmits the signal
3. The current antenna receives the signal and sends it back to the Cell
Controller.
4. The Cell Controller receives the signal and runs filters to remove multi-
path and then demodulates the signal.
5. The Cell Controller determines the delay between the sent and the
received message and then uses that to calculate the distance between
the tag and the antenna.
6. The newly created Tag Antenna Distance (TAD) data is then forwarded to
the Cell Controllers subscribers in the software system.
7. The Cell Controller then returns to step one, cycling the next antenna.
The Cell Controller cycle time is fast enough for every antenna on a Cell
Controller to detect a tag during that single tags on time.

8. By cycling constantly, the Cell Controller repeats the process for every
tag within reach of its antennas.
The 3D-iD tags are designed using L3RF technology. They are designed for
Long range, Long battery life and Low cost. In an open environment, a tag can
be seen at more than 100 feet. This is a far greater distance than traditional
RFID tracking technologies can offer. In addition, a tags battery typically lasts
over 1 year. With some configurations, a tags battery can last over 5 years.
What defines the tag as an L3RF device? The technology is proprietary, howev-
er, there are some interesting technologies involved.
Spread Spectrum Technology:
First and foremost, the system uses direct sequence spread spectrum technolo-
gy. Spread spectrum is used because the technology allows for clear transmis-
sion over long distances with little signal strength. In addition, spread spectrum
technology allows for the operation of many devices within a single frequency
range. This removes the impractical requirement that a frequency be set aside
soley for use of the 3D-iD system. Direct Sequence spread spectrum is used
because alternatives, such as frequency hopping spread spectrum, require sig-
nificantly more complex hardware and far greater system synchronization. This
hardware would complicate Tag, Antenna and Cell Controller design, raise main-
tenance costs, increase Tag weight and significantly increase the initial costs of
the system. For more details, see the www.pinpointco.com
Dual Frequency Technology:
The 3D-iD system also relies on a unique dual frequency architecture. The
Antennas send signals to the Tags at 2.442GHz. The Tags respond with a
5.770GHz signal. The dual frequency approach is used to remove the complex-
ities of separating modulated Tag responses from unmodulated radio reflections
when both lie within a single frequency. Take as an example a signal that is
broadcast by an antenna at one frequency when the antenna is listening at that
same frequency. Metal walls and other objects might bounce back a false
return signal that would be difficult to distinguish from a geniune Tag return sig-
nal. If the tag responds at another frequency, in this case, at 5.770GHz, its sig-
nal need only be separated from the surrounding noise - not from very similar
versions of itself.

While the 3D-iD system benefits from the strenths of L3RF technology, it must
be kept in mind that various factors can negatively influence the effectiveness of
the system. Shorter chirp rates - the rates at which the tag announces its
presence - will result in shorter battery lives. In addition, microwave ovens,
thick walls and metal surfaces - among other things - can significantly impact an
Antennas effective range.

RULE SETS
Abrief examination of rule sets is suggested before the installation overview is
begun. While the technician who carries out the site survey will define the loca-
tion rule set for the site, an understanding of what rule sets are is very impor-
tant.
Rule Sets define how the software side of the 3D-iD system interprets TAD data.
An end-user has very little use for TAD data in and of itself. For example, know-
ing how far a wheelchair is from a particular antenna is of little practical use to a
nurse sitting at a desk. Far more useful would be some sort of data indicated
which room a wheelchair is in - or perhaps simply an alert if a wheelchair goes
someplace it is not supposed to. Rule Sets, which are lookup tables of a sort,
were created to convert TAD data to more useful formats.
As previously mentioned, alert sets are used to convert TAD data into two other
forms of data.
The first of these is Location (or LOC) data. Location data is data that
indicates the Location (which are derived from logical statements involv-
ing TAD variables) that a tag is in. A Location can be a room, a wing or
even an entire floor, depending on the configuration of the system.
The second kind of data is Alert (or ALR) data. Alert data is generated
from Location data. Alert data is data that is generated based on certain
trigger events for single tags or pairs of tags. There are two basic
groups of alert conditions. The first group, alerts associated with a single
tag, can be set when a tag enters or exits an area or when a tag remains
within a certain location for a set period of time. The second group,
alerts associated with a pair of tags, can be triggered when one tag
enters an area without the other, when the two tags are near one another
or when the two tags are far from one another.
LOCATION DATA

TAD data is converted to LOC data by means of a Location Rule Set. The first
kind of Rule Set is called a Location Rule Set. A Location Rule Set works by
reading in TAD data and testing it against a list of user-defined statements.
Each statement is associated with a Location. These statements are descrip-
tions of locations in terms of TAD data. For example, a basic statement, in plain
english, might read A tag is in this location if it is within 10 feet of Antenna 2 on
Cell Controller 1 and more than 20 feet from Antenna 3 on Cell Controller 1.
A very common type of Location statement is called the closest to statement.
Just like a tag can be said to be in a location because it is less than 15 feet
from a certain antenna, it can also be said to be in a location if it is closest to a
particular antenna. This can allow for a very simple definition of locations. A
basic closest to statement might read A tag is in this location if it is closest to
Antenna 2 on Cell Controller 1. Please note, a tag is assigned to the location
associated with the first statement in the list that is true.
The Location Rule Set statements can make use of a standard array of boolean
and functional operators. Without exploring the actual syntax, these statements
include and, or, not, parenthetical and closest to statements. All behave as they
would normally be expected to.
Asyntax reference for Location Rule Sets is available in the ViewPoint Users
Manual.
ALERT DATA
An Alert Rule Set is used to convert Location Data to Alert Data. The idea
behind Alert data is quite simple. When Tag location data matches certain con-
ditions, an Alert will be fired. There is no need to define conditions before
installing the system. Doing so might be counterproductive, as many of the
Alerts depend on the assets the tags themselves are attached to. But, it is
important to have a general idea about what kinds of alerts will be created. The
details of Alerts pertain to the types of Locations that should be created -- and,
by extension, on where antenna should be placed.
For reference, there are 8 Alert Types, 4 of which are Single Tag Alert Types
and 4 of which are Paired Tag Alert Types:
Single Tag Alert Types

Entry: The Entry Alert is triggered when the associated Tag enters a par-
ticular location.
Exit: The Exit Alert is triggered when the associated Tag exits a particular
location.
Stationary: The Stationary Alert is triggered when the associated Tag
remains in the indicated location for a set period of time.
TimeOut: The Timeout alert is fired when a Tag was last heard from in
the indicated location, but has not been heard from in any location for a
set period of time. Any subsequent chirp from this Tag in any location
clears this Alert.
Paired Tag Alert Types
Escort: The Escort Alert is triggered when the tag selected first in the
pair enters a particular location without the second tag.
Pair: The Pair Alert is triggered when either tag enters a particular loca-
tion without the other.
Friend: The Friend Alert is triggered when two tags within a particular
location are separated by more than a set distance.
Foe: The Foe Alert is triggered when two tags within a particular location
are nearer than a set distance from each other.

Section 2: Installation Planning
CUSTOMER CONSULTATION
The first step in setting up a 3D-iD Installation is the customer consultation. A
customers needs must be assessed before any hardware placement work can
begin. There is a series of questions that must be answered before work can
proceed. The following are the questions which must be answered:
WHAT TYPE OF COVERAGE IS REQUIRED?
There are several basic types of coverage. These include:
Portal Coverage
Which is coverage of entrances and exits
Zonal Coverage
Which is coverage of certain locations, or zones
Tracking Coverage
Which is the fullest type of coverage allowing the tracking of real time
movement.
Antennas can be placed much more sparingly if portal coverage is all that
is required. Greater antenna density will be required if broader coverage
is necessary.
WHERE IS COVERAGE REQUIRED?
Once the type of coverage has been assessed, it is generally a good idea to lay
out where coverage is actually required. Working from a floorplan, required
locations can be drawn. For example, if laying out portal coverage, locations
should be drawn around entrances and exits. The technicians carrying out the
site survey and antenna layout procedure can then use the Locations drawn on
the floorplan as a road map for antenna placement.

WHAT TYPES OF ASSETS ARE TO BE TAGGED, AND FOR WHAT PURPOSE?
There is a tradeoff between a tags reporting rates and the amount of time
required to track them. In a situation where there are 500 tags, each reporting
every second, and all within the domain of a single cell controller, the Cell
Controller will have a difficult time tracking the tags quickly. If, however, those
500 tags are reporting in every 3 seconds the Cell Controller will be able to see
all of them far more quickly. Tags can be set to report at a variety of intervals.
For assets which need to be closely monitored, like notebook computers, faster
reporting will probably be required. If an asset does not need to be closely
monitored, the Cell Controller will have an easier time tracking tags if the tag
reporting time is larger. The tag reporting time is technically referred to as its
chirp time. More detailed documentation on chirp times and how they affect Cell
Controller behavior is available in the Tag Specification in Section 3 of this man-
ual.
ARE THE CLIENT SYSTEMS ABLE TO RUN THE VIEWPOINT CLIENT SOFTWARE?
The client systems must be running with the minimum characteristics described
in the Equipment Descriptions and Specifications.
ISTHE INFRASTRUCTURE PREPARED FOR THE 3D-ID COMPONENTS?
Agreat deal of infrastructure work can be done later in the process. But it
should be understood that existing ethernet and power drops, as well as prede-
fined routes which are setup for cabling can greatly simplify the installation pro-
cedure.

INITIAL SITE SURVEY
Once the customers requirements have been examined, a site survey can be
carried out. While we will briefly explain what the survey is and why it is done,
referral to a PinPoint technician for your actual site survey is highly recommend-
ed. As the process is extremely complicated, our technicians are very practiced
at it and effective at quickly and accurately completing it.
A site survey is carried out in order to ensure that assets will be tracked in the
areas where they must be tracked. Working from the customers coverage
requirements, the placement and direction of antennas must be precisely deter-
mined. Correctly placed antennas will allow for easier location and alert config-
uration.
The initial site survey involves setting up a test 3D-iD system and extensively
testing various possible antenna positions to ensure that tags can be seen by
antennas where coverage is required. In determining which antenna positions
to test many factors are taken into account. Among them,
·The effects of metal surfaces such white boards or metal equipment on
RF signals.
·The effects of microwave ovens and other RF emitters.
· The types of wall construction at a facility. Wall Construction can and will
affect the visibility of Tags by Antennas. Standard drywall constructions
do not drastically affect Antenna performance. However, cinderblock,
firewalls, hard plaster and many older style constructions will stop the
Antenna signal.
·Holes in walls (such as doors or windows) that may more easily permit
the transit of RF signals.
While the site survey is being carried out, the exact locations of every antenna
and Cell Controller are chosen. In addition, the strength of the antennas sig-
nals and the signal to noise threshold used to filter the tags return signals are
set for each antenna. When placing Cell Controllers and Antennas, care is
taken to ensure that they are within cabling length of each other.
Once the site survey is complete, the installer will have available a floorplan
detailing the placement of every antenna, Cell Controller and Server (although
there is greater leeway in Server placement). With this information in hand, the
actual installation of the 3D-iD elements can proceed.

PHYSICAL INSTALLATION
The physical installation of the 3D-iD system involves the placement of 4 com-
ponents. These include, as mentioned in the Installation Planning section, the
Antennas, Cell Controllers and Servers. In addition, tags must be attached to
assets. While extensive documentation on the actual installation of all of these
elements is available in the packaging for each element, a brief explanation of
the installation process is included below. It is generally suggested that the ele-
ments of the 3D-iD system be installed in the following order:
1. Antennas
2. Cell Controllers
3. Antenna/Cell Controller Cabling
4. Tags
5. 3D-iD Server
6. ViewPoint (Client) Software Installations
ANTENNAS
1. Attach the base of the antenna mount to
the wall where the antenna should be
placed. In situations where the antenna is
to be mounted in other types of locations,
such as under a drop ceiling, additional
mounting creativity might be required.
2. Attach the antenna to the mount, and
align it in the manner determined by the
technician during the site survey.
3. The antenna must be installed so that there is at least a 6 inch gap
between it and any possible contact with people. Failure to install it in
this fashion may invalidate the users
license to operate this product.

CELL CONTROLLERS
1. Place the Cell Controller in the location
determined earlier.
2. Ensure that the Cell Controller has ade-
quate ventilation.
3. Attach the power and network cabling to
the Cell Controller.
ANTENNA/CELL CONTROLLER CABLING
For each Cell Controller/Antenna combination:
1. String cable from the Cell Controller towards the Antenna. Leave 1-2 feet
of cable at the Cell Controller. In order to avoid bends or kinks which
will cripple the accuracy of antenna readings - do not attach the cable to
the Cell Controller.
2. Coil the extra cabling near the antenna to allow for easier movement of
the antenna should the need arise.
3. Connect the cable to both the Cell Controller and the Antenna
4. Label the cable at both ends for future ref-
erence. A potential labeling scheme could
be based on the Cell Controller Antenna
port that the Antenna is connected to.
TAGS
1. PinPoint 3D-iD tags should be mounted
securely and fixed to the asset. Since the
tags antenna is not omni-directional, try to make certain it is always fac-
ing the same way as the asset moves throughout the facility.
2. Make certain that access to the removable battery cover plate on the tag
is maintained.
3. Tags must always be mounted with THE BATTERY SIDE FACE DOWN
AGAINST THE ASSET. The top of the tag contains the antenna struc-
tures, and it is essential that this side stay facing up in order to ensure
strong broadcast and reception of RF signals.

3D-ID SERVER
The 3D-iD Server is perhaps the most complex element to install. Detailed
information is available on the ViewPoint installation process with the ViewPoint
documentation. The below is a greatly (perhaps too much so) simplified Server
installation process. Once you have located an appropriate PC for a primary
server and it has been placed on the same subnet as the Cell Controllers:
1. Both DHCP and IIS must be loaded and configured.
2. The 3D-iD server software must be installed on the system.
3. The Configurator application must be run which involves such proce-
dures as defining the rule sets.
4. Afterwards, the ViewPoint Control Panel must be run on the system in
order to define and start the services that will be running on the server.
5. Once the primary server is setup, start up the Cell Controllers that are on
the same subnet as the primary server. When you turn on each Cell
Controller you will be greeted by one of three beep patterns:
-An ascending scale indicates that the Cell Controller is working
properly.
- A high-low (daa-dum) tone indicates that something is wrong with
the Cell Controllers network connection (is DHCP configured cor-
rectly).
- A Beethovens fifth (daa-dum-dum-dum) indicates that something
is wrong with the Cell Controllers hardware.
There can be additional servers beyond the primary server. These servers host
services, but not the Configurator database. In most large scale installa-
tions, these additional servers are suggested for load balancing reasons.
It is also suggested, for network traffic reasons, that these additional
servers be running on the same subnet as the primary 3D-iD server. See
the ViewPoint Users Manual for information on installing these servers.
VIEWPOINT (CLIENT) APPLICATIONS
To load the client systems simply:
1. Run the ViewPoint Setup program, install the end-user applications.
2. Configure each of the end-user applications by specifying the services
they should connect to.

INSTALLATION VERIFICATION
There are tools that can be used to test whether an installation is functioning
correctly. The bulk of those tools are accessible through software. Detailed
assistance with those tools is available in the software documentation.
However, a summary follows below.
Cell Controller Waveform Viewer this Cell Controller based applet,
accessible from the Configurator, displays waveform data from the Cell
Controllers antennas. It can be used to verify that the antennas are
hooked up and operating correctly. An X-Window viewer such as Xceed
is required to use this utility.
TADView this application can be used to verify that the Cell Controller
is properly broadcasting TAD data. It can also be used to test TADder
Service broadcasts.
Location Viewer this application can be used to verify the functioning
of Location Services.
Alert Viewer this application can be used to verify the correct function-
ing of Alert Services.


Section 3. Equipment Descriptions and Specifications
TAGS
The tag is one of three key elements in the PinPoint 3D-iD hardware system.
PinPoint 3D-iD Tags are radio frequency
tags that are mounted onto assets or
people that are to be tracked. Each tag
contains a 2-structure antenna in the
opposite configuration of the PinPoint
3D-iD Antenna, but at 500 milliwatts of
power. The tags 5.8 GHz broadcast pro-
vides the Cell Controller with a distance
measurement from a given antenna, and
allows the ViewPoint application to dis-
play the location of the tagged item.
Tags can be mounted on flat or curved surfaces using PinPoints tag mounting
kits. Tags are available in asset design or as personnel tags.
TAG DETECTION
Time to See Specific tag
0.0
5.0
10.0
15.0
20.0
25.0
30.0
35.0
40.0
0
50
100
150
200
250
300
350
400
450
500
Tags in Range of Cell Controller
Seconds
Average
90.0%
99.0%
99.9%
A Tags chirp length is 2.3ms. While a Tag is chirping, it is responding to incom-
ing signals. A Tag can only
be detected by an antenna
only while it is chirping.
Tags chirp asynchronously,
meaning they are not syn-
chronized to the reader or
to each other. To prevent
two Tags from continuously
chirping in synchronization,
the chirping interval
includes a randomized off-
set, utilizing a function that
incorporates the Tags ID.
The combination of the off-
set and the very short 2.3 millisecond Tag signals minimize the number of Tag
collisions. There is a possibility that Tag reads will be lost due to collisions,
particularly if there are large numbers of Tags in range of a given Cell Controller.
A Tags chirp interval (the period at which it repeats its chirp) can be set if nec-
essary. A variety of chirping intervals are supported in the T20 tag. The default
chirp interval is 3 seconds. Alternatively, chirp intervals of 0.5, 1, 2, 3, 4, 5, 10,
15, 20, 30, 45, or 60 sec-
onds can be set in the fac-
tory, in accordance with
end-user requirements.
Faster chirp rates mean
Tags will be detected more
rapidly. On the other hand,
Tags with faster chirp rates
have shorter battery lives.
Generally, chirp intervals
are set lower for critical
hardware and higher for for
larger, less mobile or less
critical assets such as
desks.
Time to See All Tags
0.0
10.0
20.0
30.0
40.0
50.0
60.0
0
50
100
150
200
250
300
350
400
450
500
Tags in Range of Cell Controller
Seconds
Average
90.0%
99.0%
99.9%
Time to See Specific Tag (99%)
0.0
5.0
10.0
15.0
20.0
25.0
30.0
35.0
40.0
0
75
150
225
300
375
450
Tags in Range of Cell Controller
Seconds
1 sec tag
3 sec tag

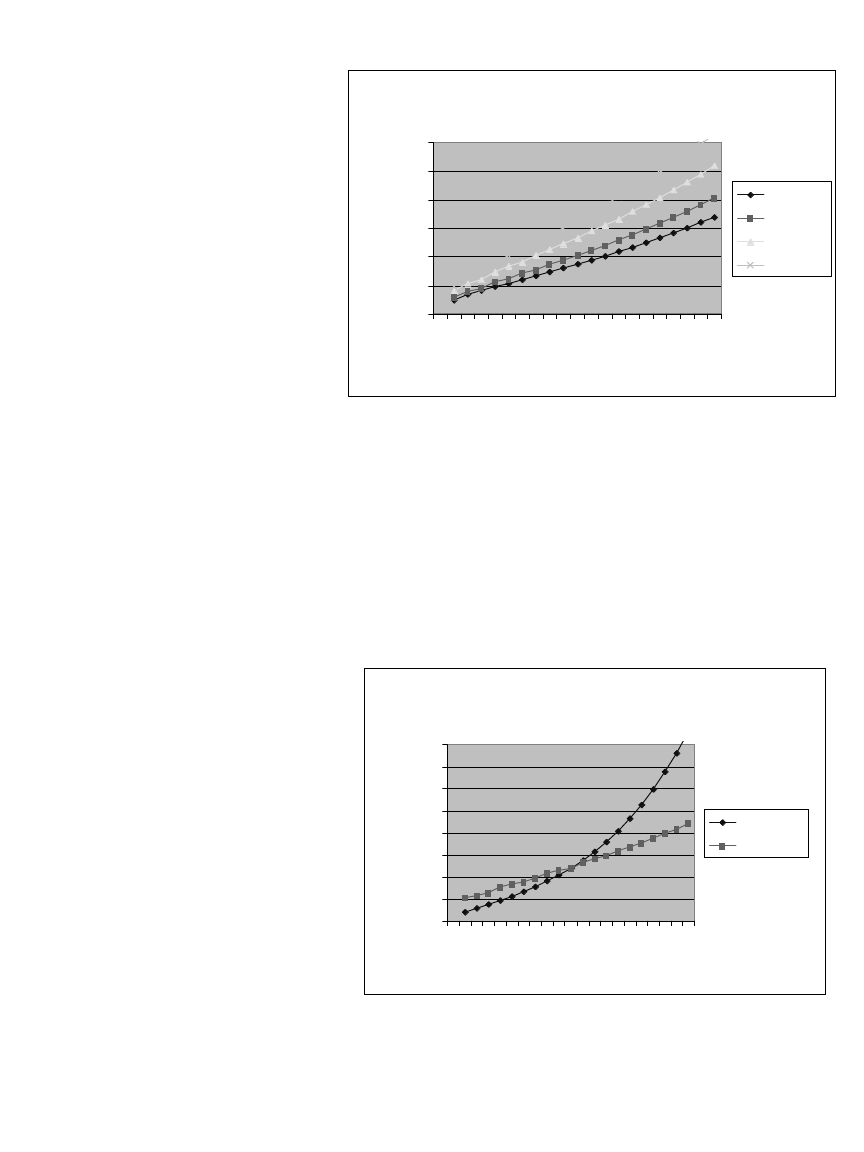
System performance depends on the number of Tags in range of individual cell
controllers, and whether the Tags chirp frequently or infrequently. For example,
if 50 Tags within range of a single Cell Controller are configured to chirp at the
default rate of 3 seconds, there is a 99% chance of seeing a specific tag within
5 seconds, and a 99% chance of seeing all Tags within 8 seconds. With 100
Tags, these values increase to 6 and 12 seconds, respectively.
The associated graphs provide performance estimates for various Tag popula-
tions within range of a single Cell Controller, up to 500 tags. Two graphs
assume the default of a 3-second tag, a third graph shows similar data with a 1-
second Tag. Most installations have a large number of Cell Controllers, with the
Tags divided among them. For example, if an installation has 750 Tags equally
divided among 10 Cell Controllers, system performance can be estimated based
on 75 Tags per cell controller. Increasing the number of Cell Controllers, or
decreasing the number of chirps per tag can increase system capacity.
With populations of 100 tags or fewer, performance can be substantially
improved by configuring tags to chirp more frequently. The third chart shows
performance of a tag that chirps once per second, compared with the default of
3 seconds. Note that 3-second tags perform better with tag populations of 300
or more, while 1-second tags are better at lower overall tag populations.
T20 BATTERY LIFE
The battery life of a T20 tag is over a year (1.2 years) with a tag that chirps
once every three seconds, which is the default. Configuring tags to chirp more
frequently then every three seconds reduces battery life roughly proportionally.
For example, a tag that chirps twice as frequently will have approximately half
the battery life.
Similarly, battery life may be extended by programming tags to chirp less fre-
quently. This is particularly a consideration for asset tracking applications. The
battery life roughly doubles by increasing the chirping interval from 3 to 20 sec-
onds.
The T20 is our most current tag model.
TAG READ RANGE AND ORIENTATION CONSIDERATIONS

PinPoint T20 Tags can be read at a distance of 80 meters (250 feet) under ideal
conditions. This specification provides margin for the Tag to be read in a wide
variety of typical indoor conditions, such as through walls. Specifically, the Tag
is designed to be powerful enough to be read through sheet rock walls, but
lacks the power to be read through concrete and metal typically found in floor
construction. The ability to be read through walls allows Cell Controller anten-
nas to be placed in a hallway, and read the tags in adjacent offices. The inabili-
ty to be read through floors ensures that a Tags location will always be identi-
fied on the correct floor. This is consistent with many applications, where great
precision is not needed as long as the floor is correctly identified.
The Tags antenna is linearly polarized. In combination with the circularly polar-
ized Cell Controller antenna, the result is that the tag is insensitive to rotation
around the radial axis.
The T20 Tag is normally attached to assets or worn as a badge. Therefore, to
conserve power the Tags antenna is designed to emit power from the front of
the Tag only. The HPBW (Half Power Beam Width) is approximately 80 degrees
on the vertical axis, and 120 degrees on the horizontal axis. Multipath environ-
ments typical for indoor applications usually enable a Tag to be read at dis-
tances up to about 20 meters, even if the Tag is facing away from the Cell
Controllers antenna.
TECHNICAL SPECIFICATION
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) this device may not cause harmful interference,
and (2) this device must accept any interference received, including interference
that may cause undesired operation.
Tag Size: 2.5 x 3.5 x 0.75
Transmission Frequency: 5.774GHz
Reception Frequency: 2.884GHz
Survivable Temperature Range: -40°C (-38°F) to 70°C (158°F)
Operational Temperature Range: 0°C (32°F) to 50°C (122°F)
Effective Range: 3-120 from Antenna
Accuracy/Resolution:
System will locate tag within 10 of actual location 99% of the time.
Radiation Pattern: 180° radiation pattern from outer (Antenna) surface
Default Duty Cycle: 5 sec
Battery Life: 12 months at 5 second duty cycle

CELL CONTROLLERS
The Cell Controller acts as the brains for the PinPoint hardware system. The
PinPoint Cell Controller is an
active network peripheral, which
transmits and receives a radio
frequency signal through attached
antennas. This signal is returned
from a 3D-iD tag and translated
by the Cell Controller into Tag
Antenna Distance information
(TAD data). The translated TAD
data is then sent from the Cell
Controller to a server via stan-
dard TCP / IP over an Ethernet
LAN. Each PinPoint Cell
Controller can support up to 16
antennas and comes with a sin-
gle 10 / 100 BT network interface. The PinPoint Cell Controller acts as a DCHP
client; therefore receiving its networking addressing information from a DHCP
server across the LAN.
The Cell Controller is a Linux based system running proprietary software devel-
oped by PinPoint. The hardware
is a Pentium system with custom
PinPoint developed boards pro-
viding customized processing and
communications capabilities.
The Cell Controllers transmit and
receive signal strengths - as well
as other settings, can be altered
via the Cell Controller Interface,
which is in turn available through
the Configurator application. For
additional assistance, see the
Configurator application and its
accompanying documentation.

HARDWARE/SOFTWARE:
APinPoint 3D-iD Cell Controller (code named C20) includes:
4 x 4 switching antenna cards
a 10 / 100 BT network interface card
a power cord
and PinPoint 3D-iD Cell Controller Software version 1.0 or higher
TECHNICAL SPECIFICATION
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) this device may not cause harmful interference,
and (2) this device must accept any interference received, including interference
that may cause undesired operation.
Dimensions: 18 x 9 x 6
Range: 3 to 125 feet
Performance: Detect 1 tag in a population of:
100 4.6ms tags within 10 seconds 99% of the time
500 4.6ms tags within 30 seconds 99% of the time
Number of Antennas: Between 1 and 16
Required Antenna Cable Length: All cables must be exactly 100 long
Operational Temperatures: 10°C (50°F) - 35°C (95°F)
Survivable Temperatures: -40°C (-38°F) - 65°C (149°F)

ANTENNAS
The antenna actually broadcasts messages to the tags and receives the tags
responses. The antennas are designed to work exclusively with the PinPoint
3D-iD Cell Controller. The antenna is composed of 2 structures, one designed to
transmit and one to receive. The transmit
structure broadcasts a 2.4 GHz radio fre-
quency signal at 1 watt of power generat-
ed from the Cell Controller. When this
signal is picked up by a 3D-iD tag, the
tag responds with a 5.8 GHz signal
which is picked up by the receive struc-
ture on the antenna. Each antenna is
connected to the Cell Controller by a
dedicated piece of plenum or riser rated
coaxial cable. The coaxial also supplies
the AC needed to power the antenna.
The coaxial cable is connected to a dedicated port on one of the Cell
Controllers 4 x 4 multiplexing switching antenna cards.
Antennas can be mounted flush against walls with provided wall mounting hard-
ware, suspended above ceiling tiles or mounted on tripods.
TECHNICAL SPECIFICATION
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) this device may not cause harmful interference,
and (2) this device must accept any interference received, including interference
that may cause undesired operation.
Frequency: Tx: 2442 + 83.5 MHz
Rx: 5800 + 150 MHz
Power: 12 V DC (supplied from coaxial cable)
Radiation Pattern: Ellipto-conical (62° azimuth, 32° elevation)
Dimensions: 10 x 7x 2
Environment: -20°C 40°C (operating range)
5% - 95% humidity, no condensation
See Cell Controller/Antenna Data Sheets for details

VIEWPOINT SERVERS
TheViewPoint Server is an active network peripheral which uses Microsofts
DHCP server services to assign IP addresses to PinPoint cell controllers,
receive tag / antenna / distance (TAD) information from the cell controllers and
deliver TAD and alert data to client connected to the local area network. The
server uses standard TCP / IP protocol, and, unless a router is installed, must
be on the same LAN segment as the cell controller. The server runs the full
suite of the ViewPoint 3D-iD software, and PinPoints proprietary services,
Location Service, Alert Service, Tracker Service, Tadder Service and Broker
Service. The server is also where location rules sets, alert information, tag infor-
mation, Cell Controller and antenna profiles are stored and distributed.
SERVER SYSTEM: MINIMUM HARDWARE REQUIREMENTS:
Pentium 133 or better processor
Minimum of 128 MB of RAM
CD ROM drive
3.5 floppy disk drive
10 / 100 Ethernet adapter
500 MB of free HDD space
SERVER SYSTEM: MINIMUM SOFTWARE REQUIREMENTS:
Microsoft Windows NT Server version 4.0
Service Pack 3 or higher
TCP / IP protocol
Microsoft Internet Information Server
Microsoft DCHP Server
Microsoft Internet Explorer 4.0 or Netscape Navigator 4.0
NT Option Pack 4
Microsoft Access(optional)

VIEWPOINT CLIENTS
The ViewPoint Clients are Microsoft Windows 95, 98, 2000 or NT machines
connected to the local area network via TCP / IP protocol, and running the
ViewPoint 3D-iD Client software. 3D-iD clients will be able to track, locate and
secure tagged assets and people by running any of the client application
installed on the machine, these include:
Location Viewer which allows the user to view Tag Locations by area.
Finder which allows the user to search for Tags by Serial Number, by
Resource, by Tag Group, and by Location.
Alert Viewer which allows the user to monitor Alert Conditions as they
arise.
Floorplan Viewer which serves as a unified viewer of Tag Antenna
Distance, Location, and Alert data.
Tracker which allows the user to access historical Tag Location and Alert
data.
3D-iD clients can reside anywhere on the network, provided they have access
to the subnet where the server resides.
CLIENT SYSTEM: MINIMUM HARDWARE REQUIREMENTS:
Pentium 90 or better processor
Minimum of 32 MB RAM (64MB RAM for clients running NT Workstation 4.0)
CD ROM drive
3.5 floppy disk drive
10 / 100 Ethernet adapter
200 MB of free HDD space
CLIENT SYSTEM: MINIMUM SOFTWARE REQUIREMENTS:
Microsoft Windows 95, 98 or NT Workstation version 4.0 (Service Pack 3 or
higher)
TCP / IP protocol
Microsoft Internet Explorer 4.0 or Netscape Navigator 4.0


PinPoint Corporation
One Oak Park Bedford, MA 01730
http://www.pinpointco.com
phone: 781-687-9720
fax: 781-687-9730