SECUTECH SOLUTIONS UNIMATETOKEN UniMate USB/TRRS PKI Token User Manual
SECUTECH SOLUTIONS PTY LTD UniMate USB/TRRS PKI Token Users Manual
Users Manual

UNIMATE & UNITOKEN
PRO MANUAL
VERSIO N 3.0

I
The data and information contained in this document cannot be altered without the express
written permission of SecuTech Solution Inc. No part of this document can be reproduced or
transmitted for any purpose whatsoever, either by electronic or mechanical means.
The general terms of trade of SecuTech Solution Inc. apply. Diverging agreements must be
made in writing.
Copyright © SecuTech Solution Inc. All rights reserved.
WINDOWS is a registered trademark of Microsoft Corporation.
The WINDOWS-logo is a reg istered t rad emark (TM) of Microsoft Corporation.
Software License
The software and the enclosed documentation are copyright-protected. By installing the
software, you agree to the conditions of the licensing agreement.
Licensing Agreement
SecuTech Solution Inc. (SecuTech for short) gives the buyer the simple, exclusive and non -
transferable licensing right to use the software on one individual computer or networked
computer system (LAN). Copying and any other form of reproduction of the software in full or
in part as well as mixing and linking it with others is prohibited. The buyer is authorized to make
one single copy of the software as backup. SecuTech reserves the right to change or improve
the software without notice or to replace it with a new development. SecuTech is not obliged to
inform the buyer of changes, improvements or new developmen ts or t o make these available to
him. A legally binding promise of certain qualities is not given. SecuTech is not responsible for
damage unless it is the result of deliberate action or negligence on the part of SecuTech or its
aids and assistants. SecuTech accepts no responsibility of any kind for indirect, accompanying or
subsequent damage.


IV
Table of Contents
PART 1 AN OVERVIEW O F UNI MA TE & UNI TOKEN 2
CHAPTER 1: UNIMA TE & UNITO KEN DEVICE 2
1 .1 Features 2
1 .2 Sp ecification s 3
CHAPTER 2: UNIMA TE & UNITO KEN SOFTW A RE 3
2 .1 UniMate & UniToken driver installation 3
2 .2 The PKCS#11 and MS-CAPI Modules of UniToken 4
2 .3 Token API 4
2 .4 Supported Platforms 4
CHAPTER 3: SECURI TY 5
3 .1 Key 5
3 .2 Data transmission 7
3 .3 Factory Default Settings 7
PART 2 UNI MA TE & UNITO KEN SDK 7
CHAPTER 4: SDK OVERVIEW 7
4 .1 Driver installation 8
4 .2 Redistribution Package 8
4 .3 Console 12
4 .4 M onitor 42
PART 3 APPLYING DIGITAL CERTIFICA TES 55
CHAPTER 1: APPLYING DIGITAL CERTIFICATES 55
1 .1 Applying VeriSign Certificates 55
1 .2 Applying Microsoft Certificates 56
1 .3 Using Digi tal Certi fi cates 58
PART 4 DEVELO PER S GUI DE 59
1 .1 Device Initialization 59
CHAPTER 1: PKCS11 APPLICATION 59
1 .2 Introduction 59
1 .3 Supported PKCS#11 Algorithms and APIs 61
1 .4 UniMate & UniToken PKCS#11 Function Library 62
1 .5 Samples 65

V
CHAPTER 2: M S-CAPI APPLICATIONS 67
2 .1 Introduction 67
2 .2 Supported Algorithms and APIs 68
2 .3 Samples 69
2 .4 UniMate & UniToken API 72

2 of 72
Part 1 An Overview of UniM ate &
UniToken
UniMate & UniToken, h ereinafter referred to as Token, is an in fo rmatio n secu ri ty
product based on CCID technology. It is a secure container for digital credentials.
Advanced processor and secure memory are built in the Token device to guarantee the
secu ri ty fo r ex changing , sto ring and handling electronic information.
Token has achieved an effective rights management and can provide a highly -secu red
file system. A built-in computing engine accomplishes fast and efficient information
processing.
Token supports PKI applications and provides Token API for secondary development.
Abundant samples bring ease to integrations.
Chapter 1: UniM ate & UniToken Device
1.1 Features
Key features of UniM ate & UniToken device:
Globally unique hardware ID
Customized software ID
Smartcard-based
3 of 72
On-board encryption
Two levels of PIN managemen t mechanism
A secure file system
Large memory up to 64K
Stylish and cute case
Lead free
1.2 Specifications
Dimensions 57×16×8 mm
Weight 9g
M in. Operating Voltage 5V
Current Consumption <= 50 mA
Operation Temperature 0℃ to 70℃
Storage Temperature -10℃ to 85℃
Humidity Rate 0-70% without condensation
Casing Tamper-evident M etal
M emory Data Retention At least 10 years
M emory Cell Rewriters At least 100,000 times
Chapter 2: UniM ate & UniToken
Software
2.1 UniM ate & UniToken driver installation
4 of 72
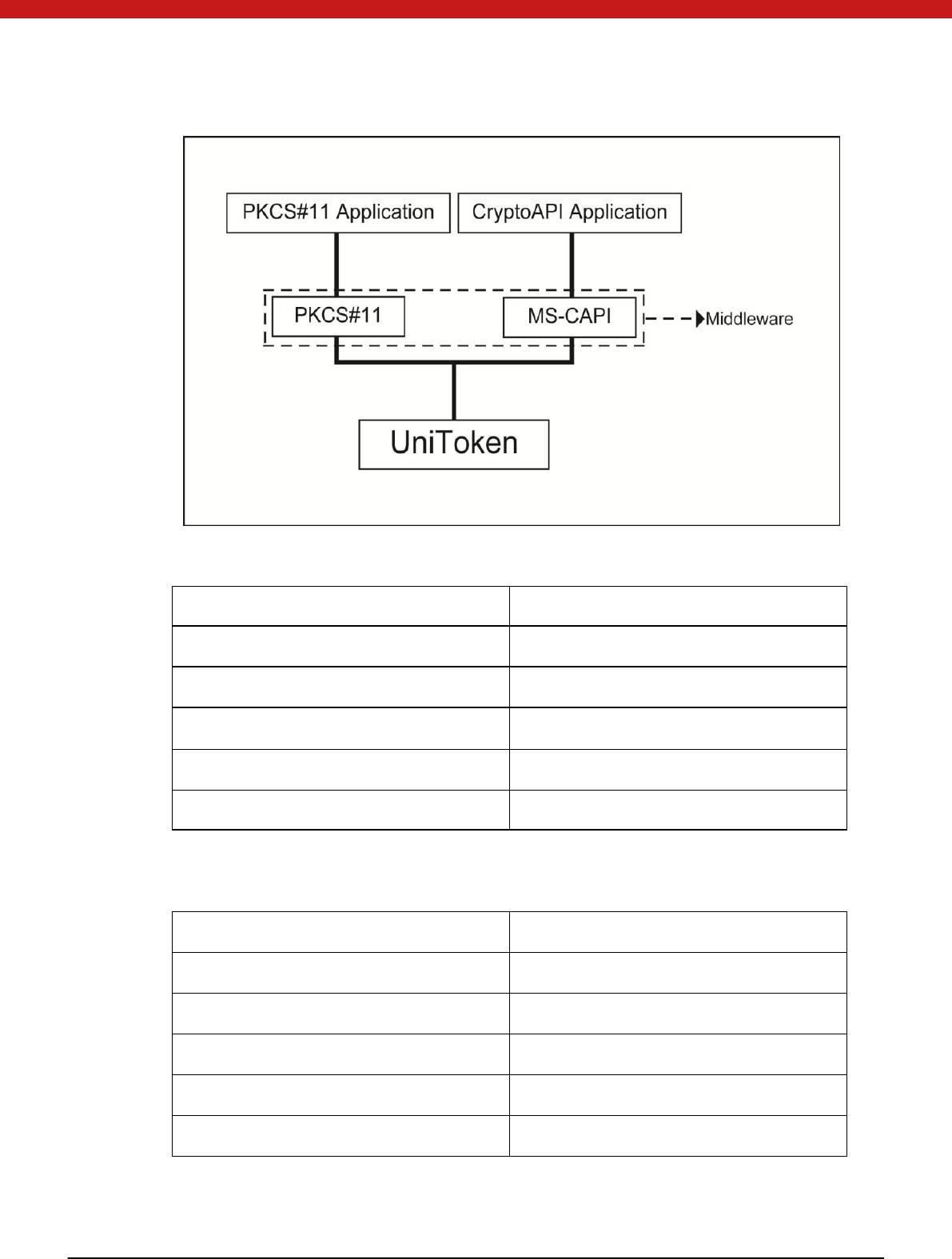
2.2 The PKCS#11 and M S-CAPI M odules of
UniToken
PKCS#11 module of Token is implemented according to PKCS#11 standards V.2.20,
which is a DLL file for C language running on Windows operating system. M S-CAPI
Module of UniToken is implemented in line with MS-CAPI standard.
These two modules can be used in cooperation with each other, i.e. the certificate
applied with PKCS#11 can be used by MS-CAPI module of Token, and vice versa.
2.3 Token API
Token provides a set of Token API, which allows users to manage one or several Token
hardware keys, i.e. operation of Token attributes, permission, built -in algorithms and
secure file system. Please install Token API package or Token full package to enable
these features.
2.4 Supported Platforms
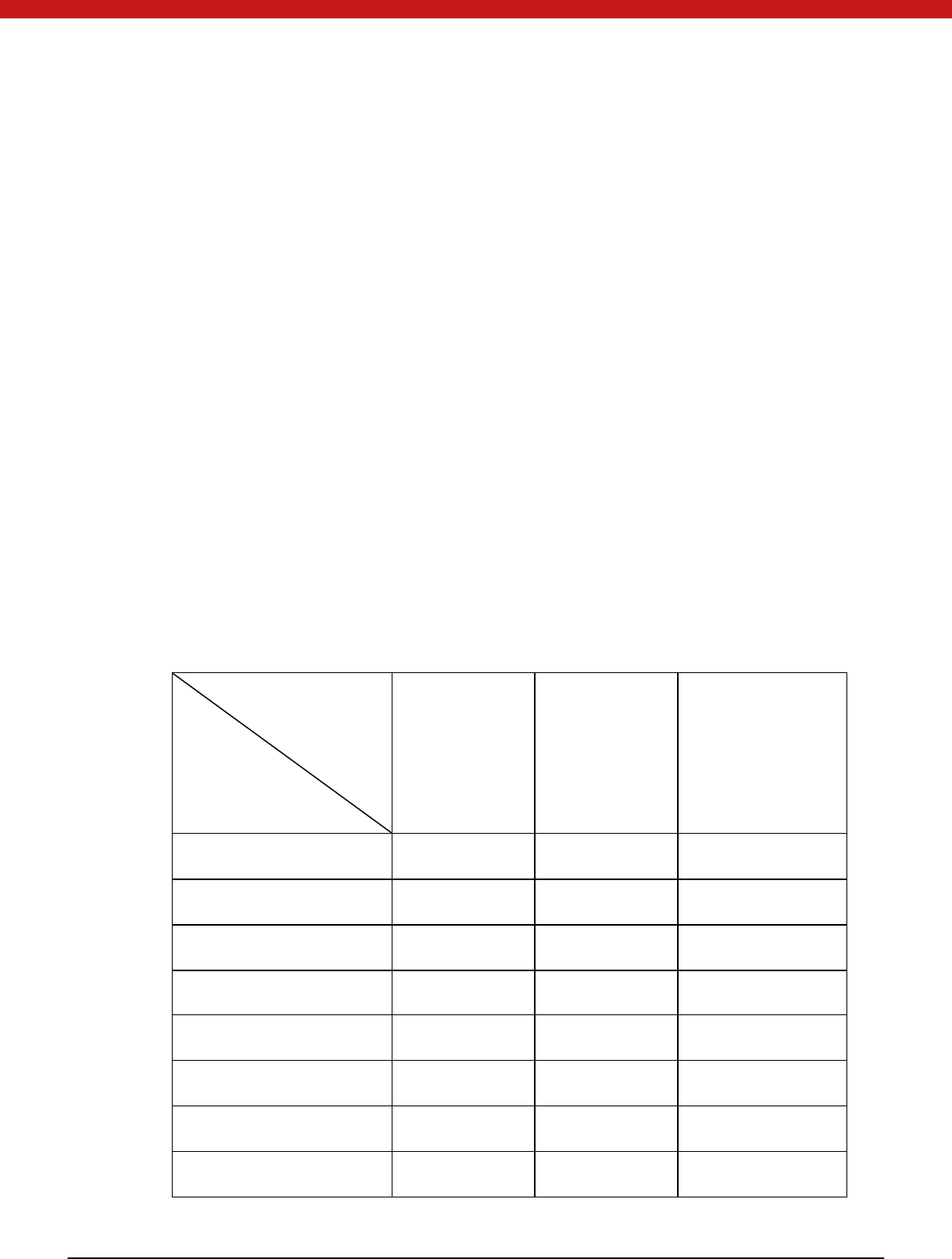
Table 1.3: Supported Platforms
Components
OS
UniMate Flex UniMate STD UniToken PRO
Windows 2000 √ √ √
Windows 2003 √ √ √
Windows XP √ √ √
Windows Vista √ √ √
Windows 7 √ √ √
Windows 2008 √ √ √
Windows 2012 √ √ √
Windows 8 √ √ √
5 of 72
iOS √
Android √
Chapter 3: Security
Security is the most important part in Token system, which involves in identification
and verification method, including not only the file access permission control
mechanism inside the token, but also the information confidential control inside the
token. The security attribute means the current state of the device when the card is
reset or after the token finished some commands.
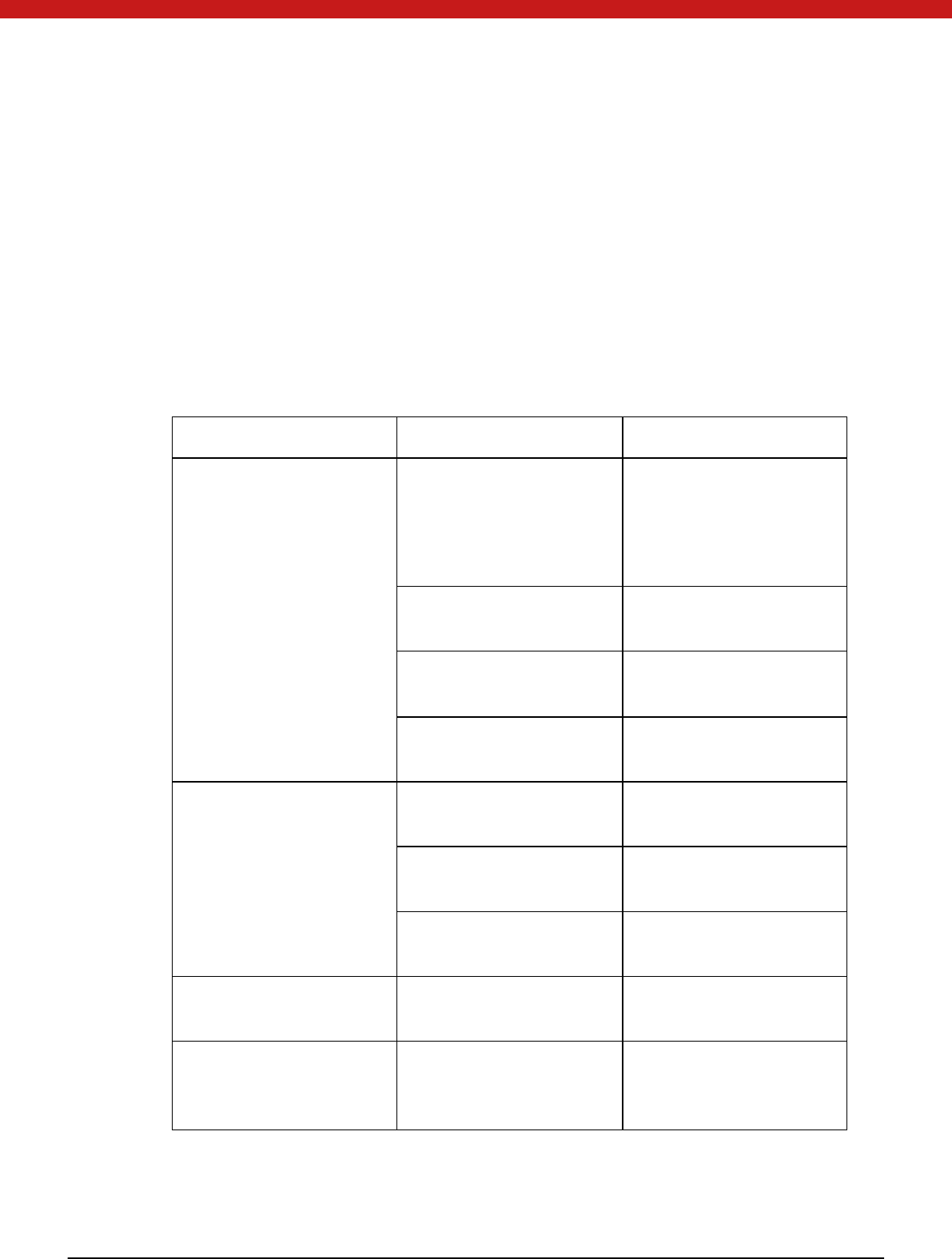
3.1 Key
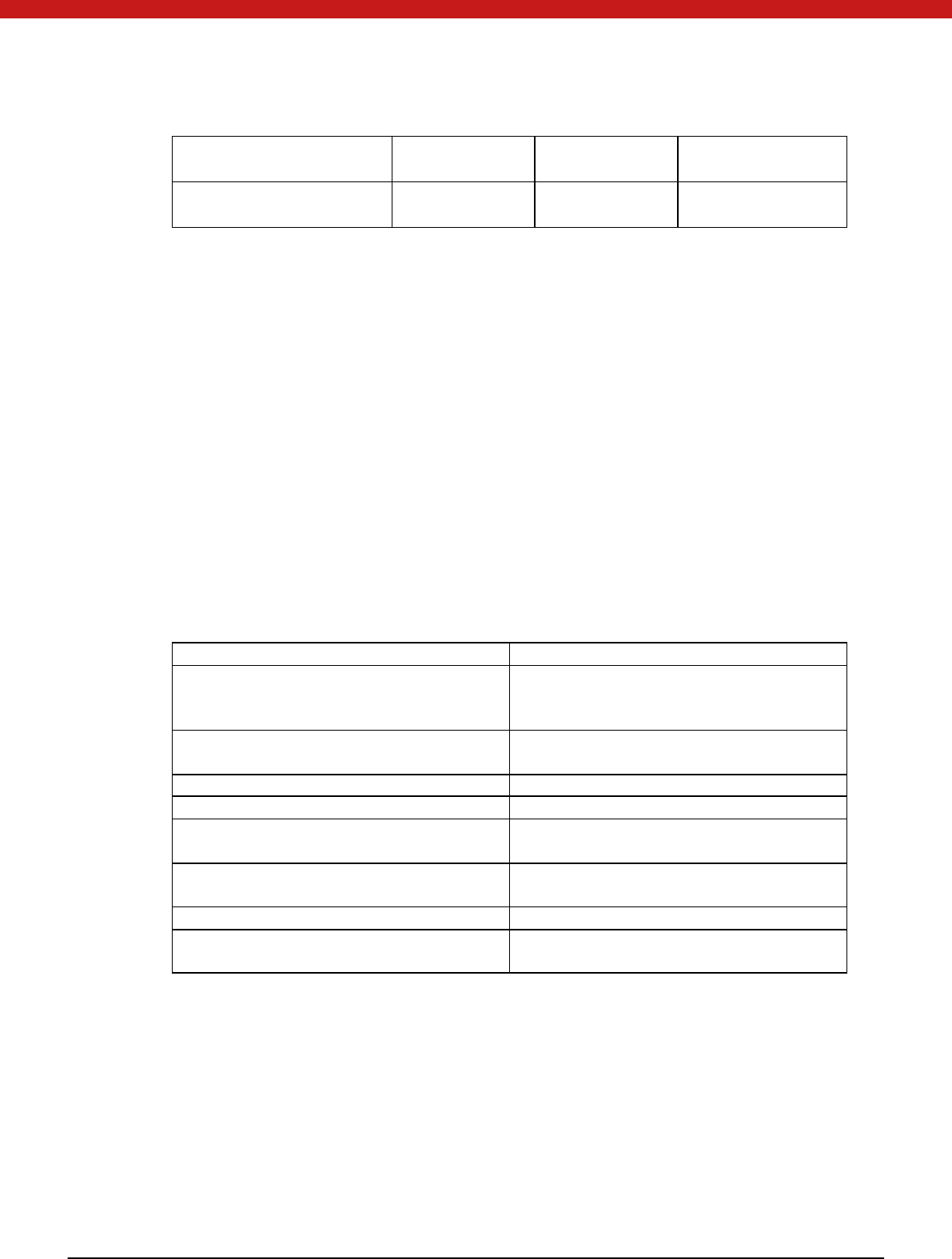
The following table describes different key types and use
Key Type Use
Transmission Key
Ensure the security during the card
initialization, and provide encryption and
decryption.
PIN
Directory level authentication. control
differet users’ read ad write perissio
PIN unlock key Used to unlock PIN
PIN reload key used to reload PIN
External authentication key Token
uses this key to authenticate the
exte rnal enti ty
Internal authentication key External entity uses this key to authenticate
the token device.
M aster key Used to secure transmission
Block encryption/ decry ption key Provide encryption/decryption for exte rnal
enti ty.
Transmission key: a 16-byte key that every device must have only one transmission
key
PIN: a personal identification number based on directory. The PIN is firstly hashed and
then stored in the device
PIN unlock key: a 16-byte key is used in unlock function. Its function is that encrypts
PIN and calculates M AC of the cipher text as a key.
6 of 72
PIN reload key: not used in this version and will add this function in the following
version.
External authentication key: a 16-byte key that used for external authentication. The
first 8-byte is the key1 and key3.
Internal authentication key: a 16-byte key that used for internal authentication. The
first 8-byte is the key1 and key3.
The block encryption/decryption key: used to specified algorithm, length is from 8-
byte to 16-byte. Currently the supported algorithms are DES (ECB, CBC), TDES (ECB,
CBC), AES (EBC, CBC).
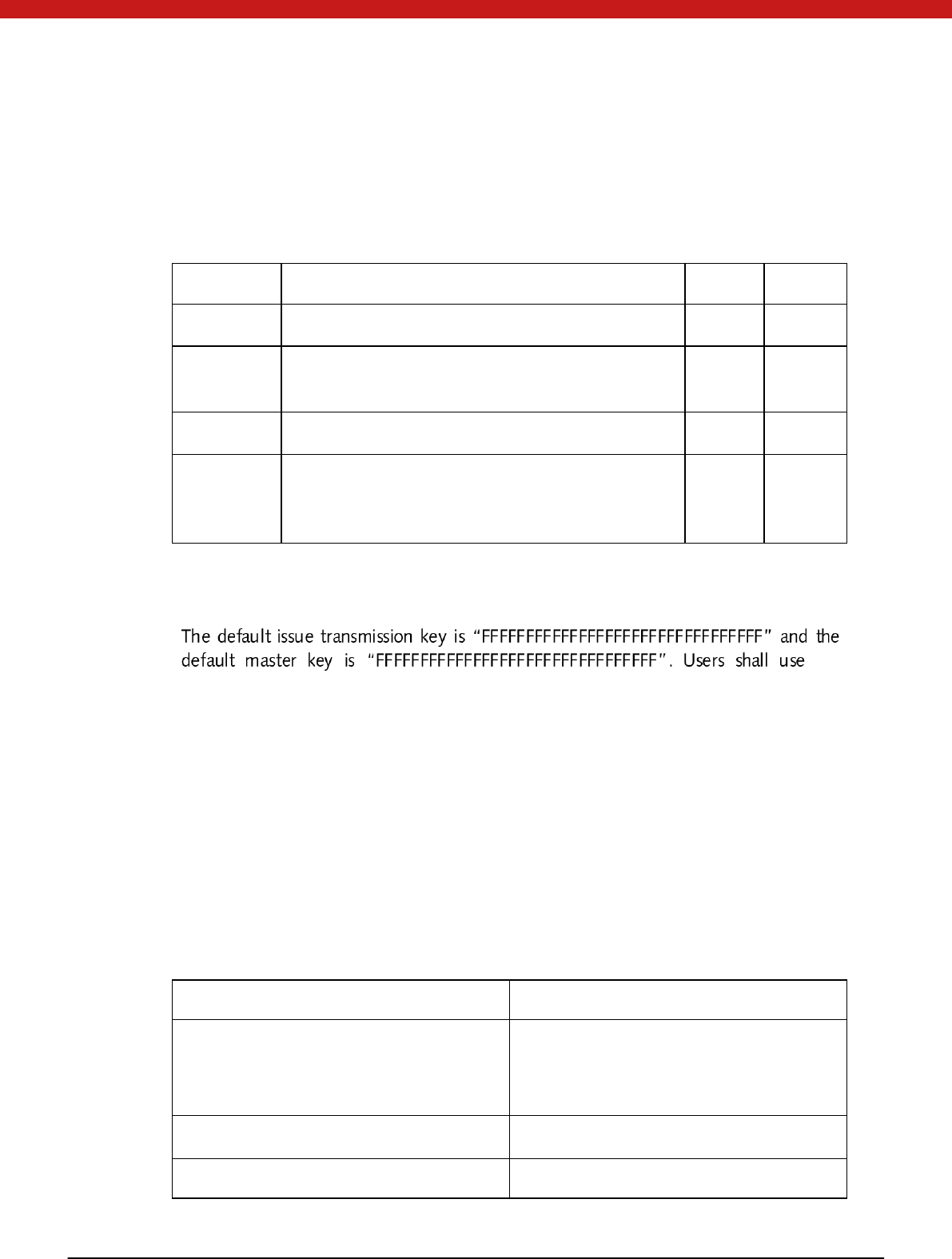
Authentication type Key type Use method and algorithm
Access permission
au t hen ti cation
Transmission key Comparison in plaintext
Ex ternal au then ti cati on (fo r
examp le, format device in
user state)
PIN
Ex ternal au th en ti cation
(TDES)
Extern authentication key
Ex ternal au th en ti cation
(TDES)
In ternal au then ti cati on key In ternal au th en ti cation
(TDES)
Cipher text transmission Transmission key TDES encryption (use DES
in M AC)
Master key TDES encryption (use DES
in M AC)
PIN unlock key TDES encryption (use DES
in M AC)
PIN reload key TDES encryption (use DES
in M AC)
Provide encryption
operation for external
en t i ty
Encryption key
Depending on
implemented encryption
algo ri thm s.
7 of 72
3.2 Data transmission
Data transmission means data transmitted between host machine and device, including
4 transmission modes.
M ode Definition Security Integrity
Plaintext Data is transferred directly without any process × ×
Plaintext
with MAC
Plaintext and M AC of the plaintext are transferred
together
× √
Cipher Plaintext is encrypted before transferred √ ×
Cipher with
M AC
Data is encryp ted and calculate the M AC o f th e
encrypted data, and then transferred the cipher
text and M AC
√ √
3.3 Factory Default Settings
the
master key to create and delete file.
Part 2 UniM ate & UniToken SDK
Chapter 4: SDK Overview
Table1.6 Token SDK Contents
Components Description
Include Declaration of the standardized
identifiers and interface of PKCS #11,
CSP and Token API.
Libraries Token libraries
Documents M anual for Token PRO and API

8 of 72
reference
Integration Guides Instruction about integration Token
with other soft ware
Redists Redistribution packages for developers
and end users
Samples Samples for CSP, PKCS and Token
API
W indows CCID Driver Token Drivers
4.1 Driver installation
driver to make Token work. For some old versions, such like Windows VISTA and XP,
driver must be installed to make the system recognise the device.
After inserting Token to a computer, from Control Panel→ Hardware and Sound →
Device M anager, open the Device manager.
From the hardware list find the unknown device, update the driver, the driver is in the
SDK\windows CCID Driver.
4.2 Redistribution Package
Token provides two different redistribution packages for developers and end users
respectively. Both the package provide Token PKI installation package. If you want to
use the PKI application, you must install it.
Installation
Token PKI package can be found in the redist folder of Token PRO SDK.
For developers package
Double click the icon to run the install shield wizard, and follow the illustration
belo w:
9 of 72
In this section, user name and company name are required. And cl
10 of 72
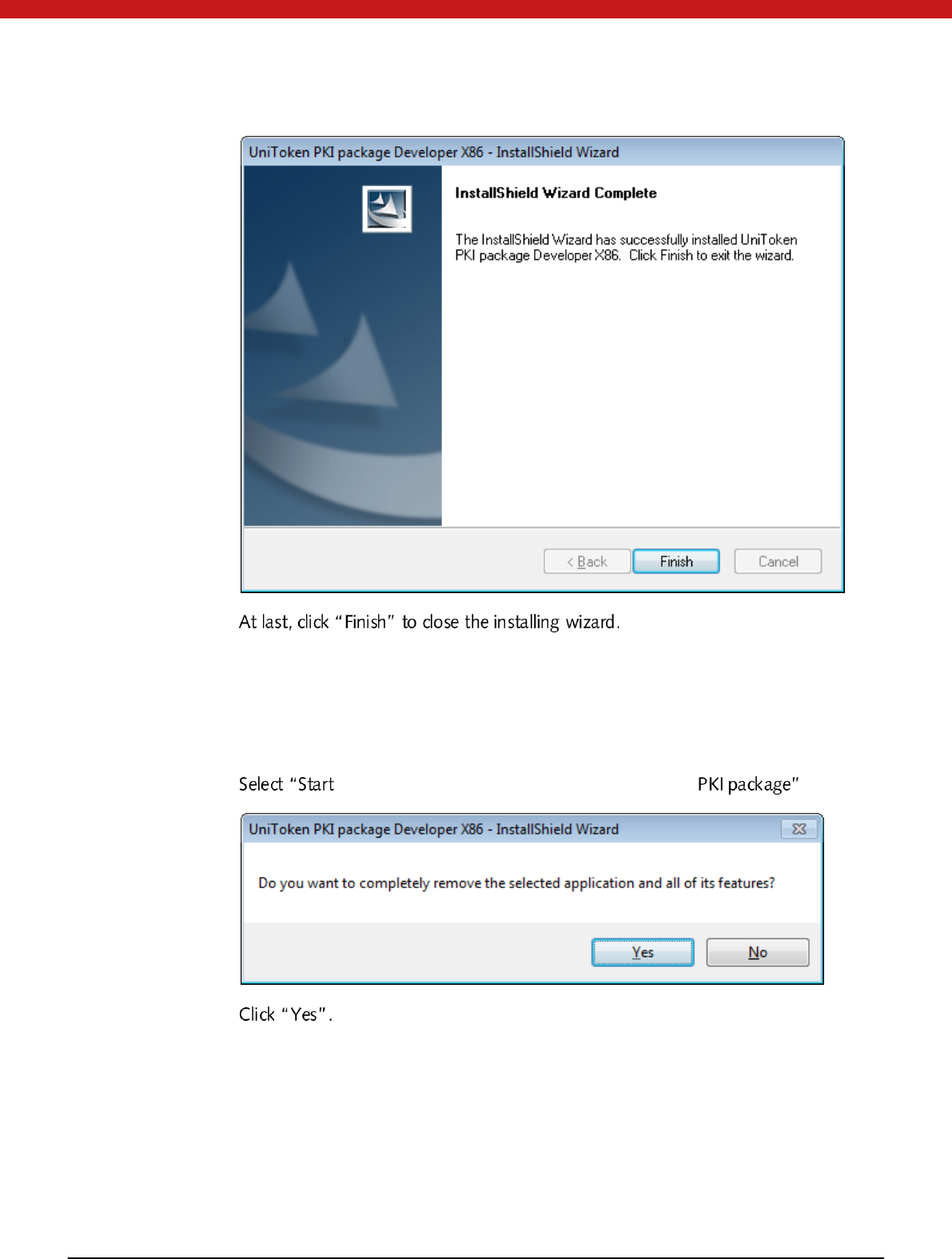
11 of 72
Uninstallation
To uninstall the software, there are two ways: start menu and control panel.
Start M enu:
-All Programs-SecuTech-Token-Uninstall Token
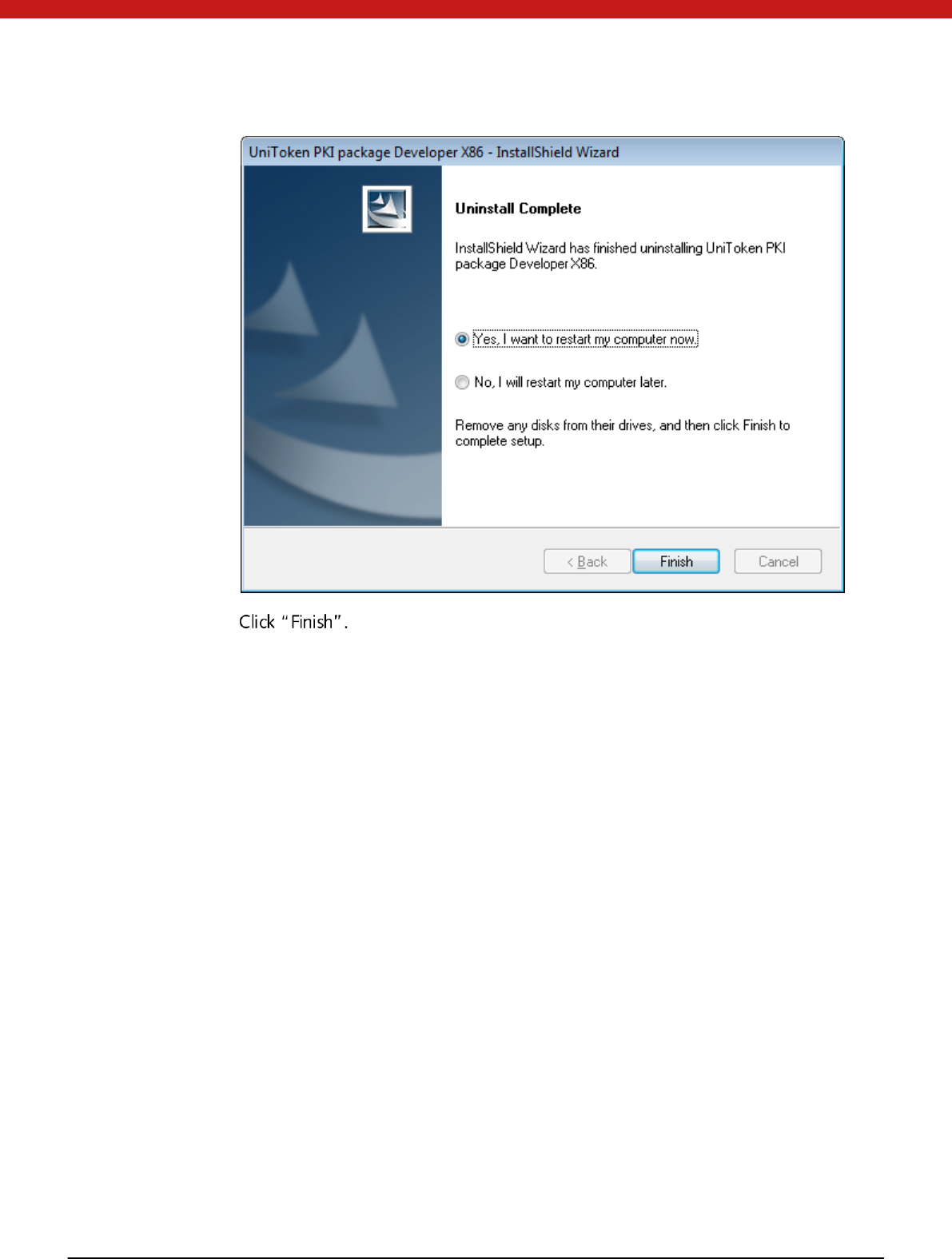
12 of 72
4.3 Console
Token Console is used to manage devices, set user permission as well as control file
system and certificates.
4.3.1 Check Token information
1. Start Console.exe and insert your device
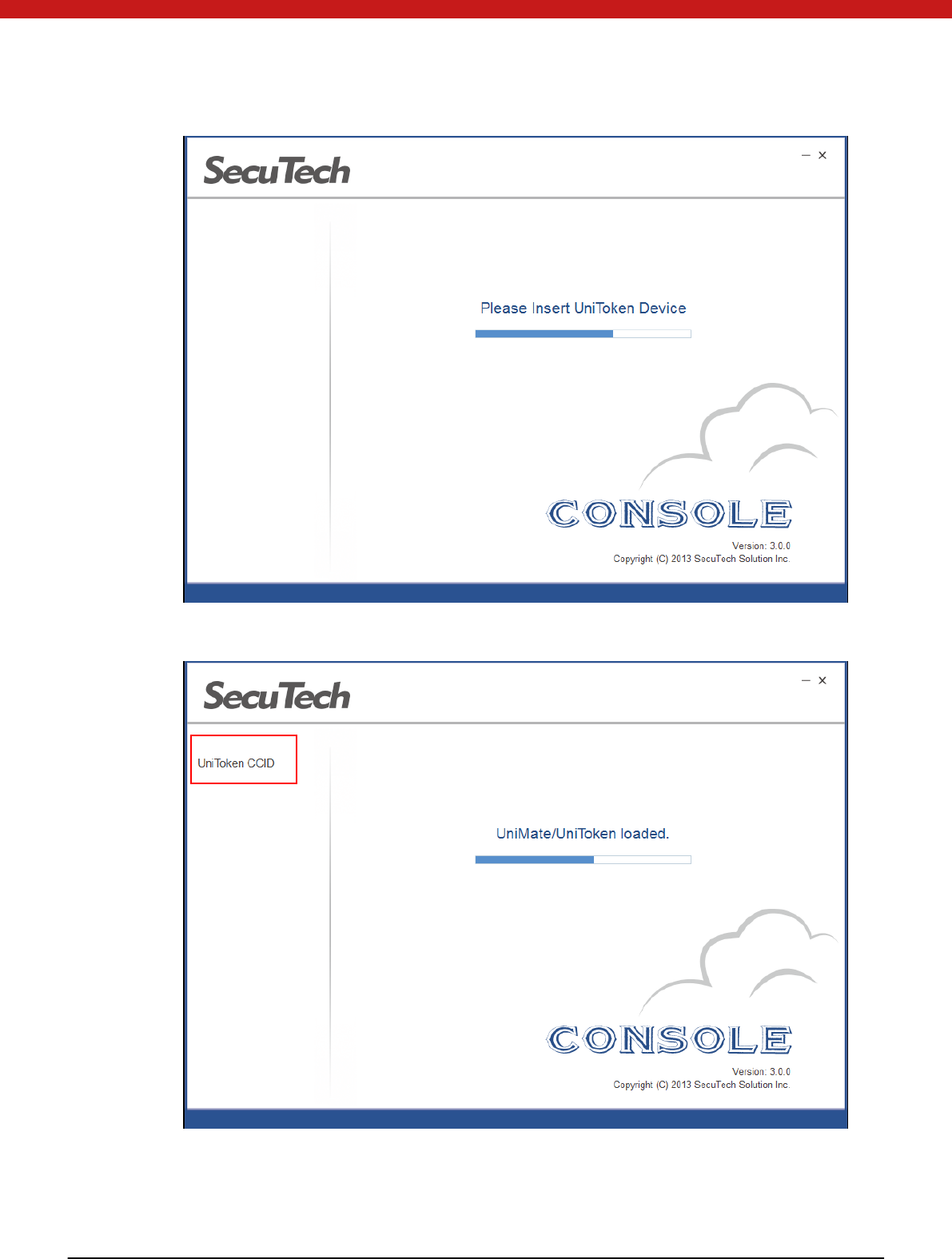
13 of 72
The devide name will appear on the left side of the page.
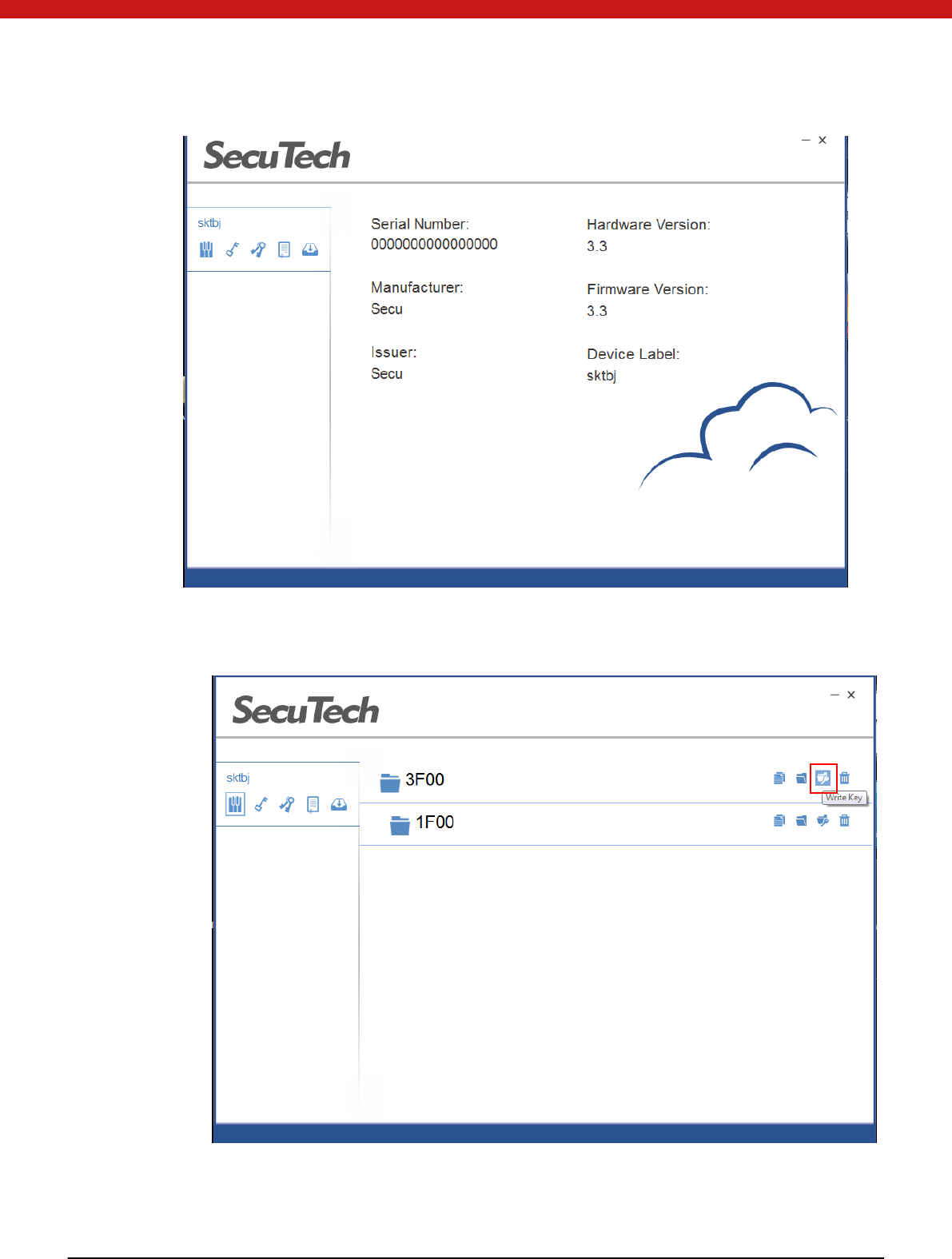
2. Click on the name of the device to check the device information.
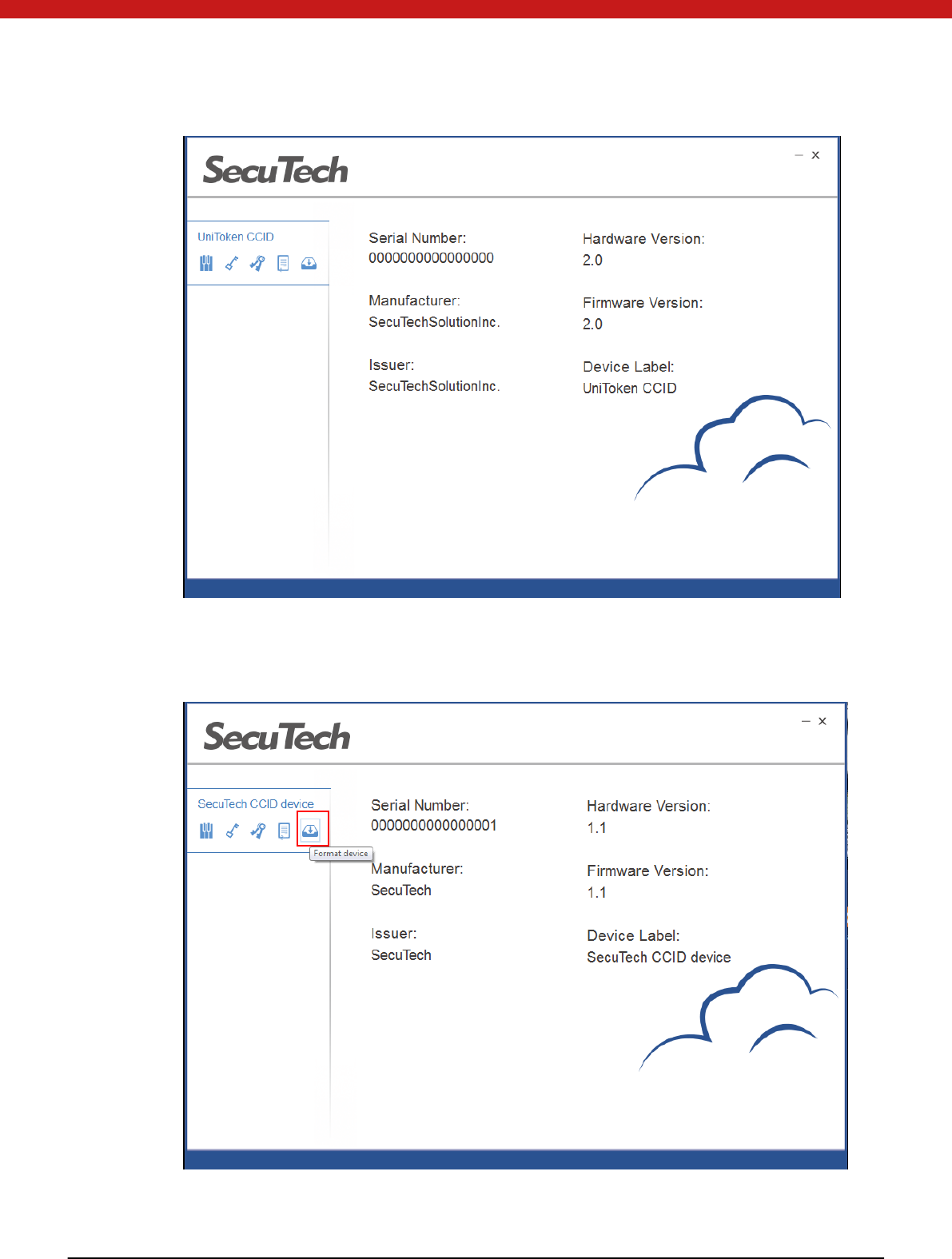
14 of 72
4.3.2 Initialize Token
1. On the main page, select the Token from the list.
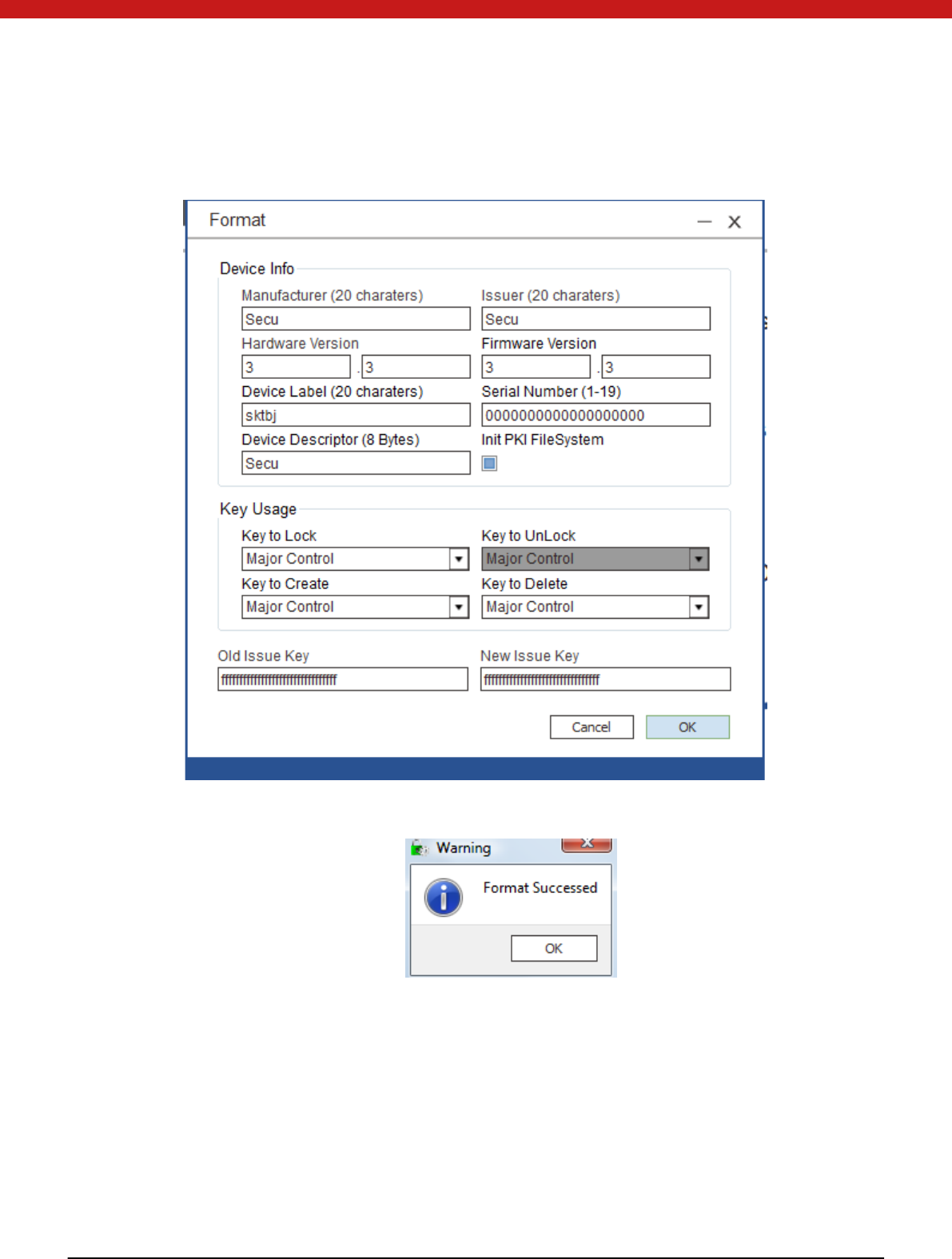
15 of 72
2. On the left side, click on the initialization icon . In the pop up page, fill the
in fo rmation , configure the key usage and input old issue key and set new issue key.
3. Click on O K to start initialization.
After the token is initialized successfully, a message page will pop up. Click on O K to
return the main page.
16 of 72
4.3.3 Change Key
1. Write a key for the folder by clicking on the writhe key icon.
2. In the pop up page, select the key usage, input the key value, the maximum
at temp ts and input the master key of the folder.
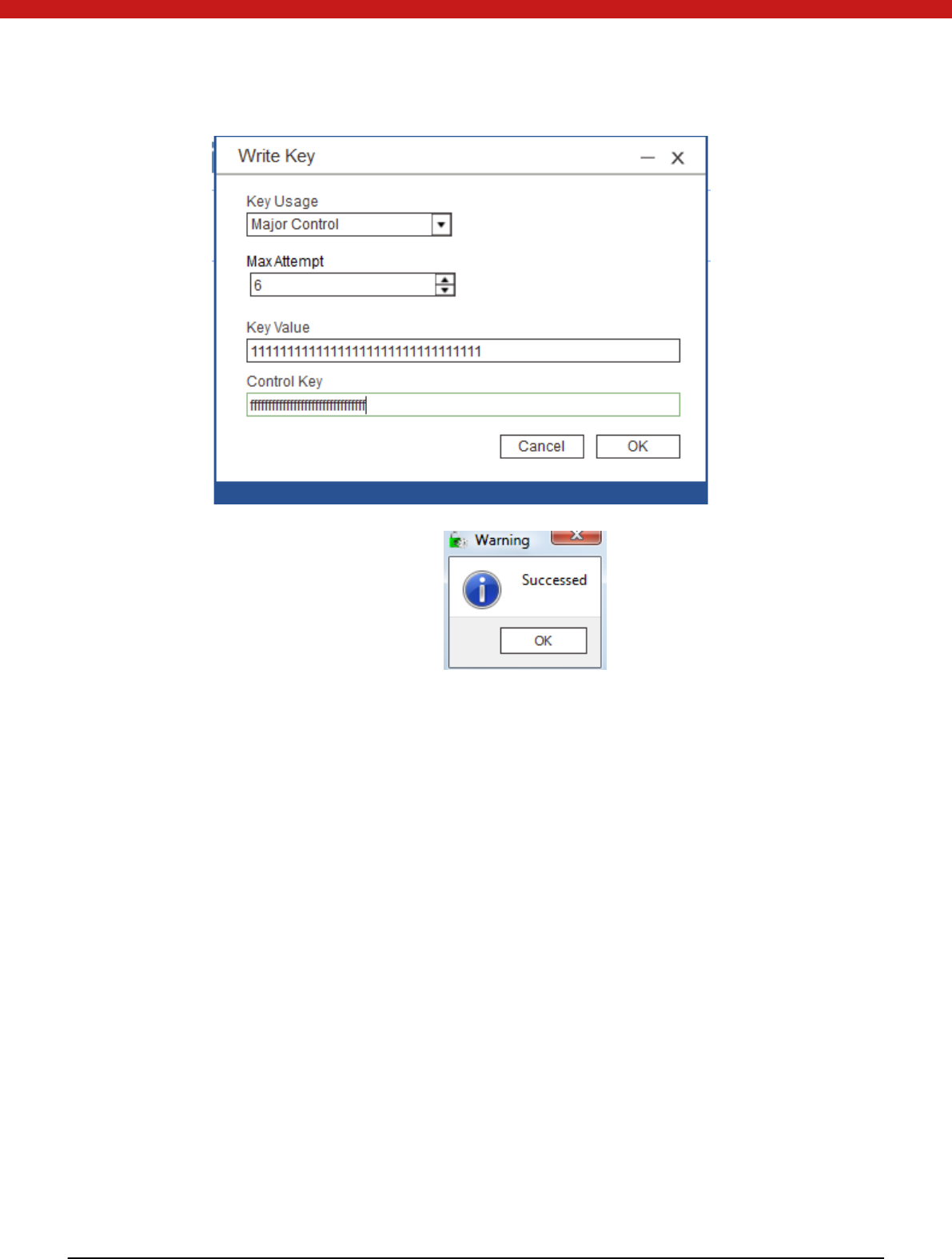
17 of 72
3. Click on OK
4.3.4 Create folder (max 3 level)
1. Click on the create folder icon
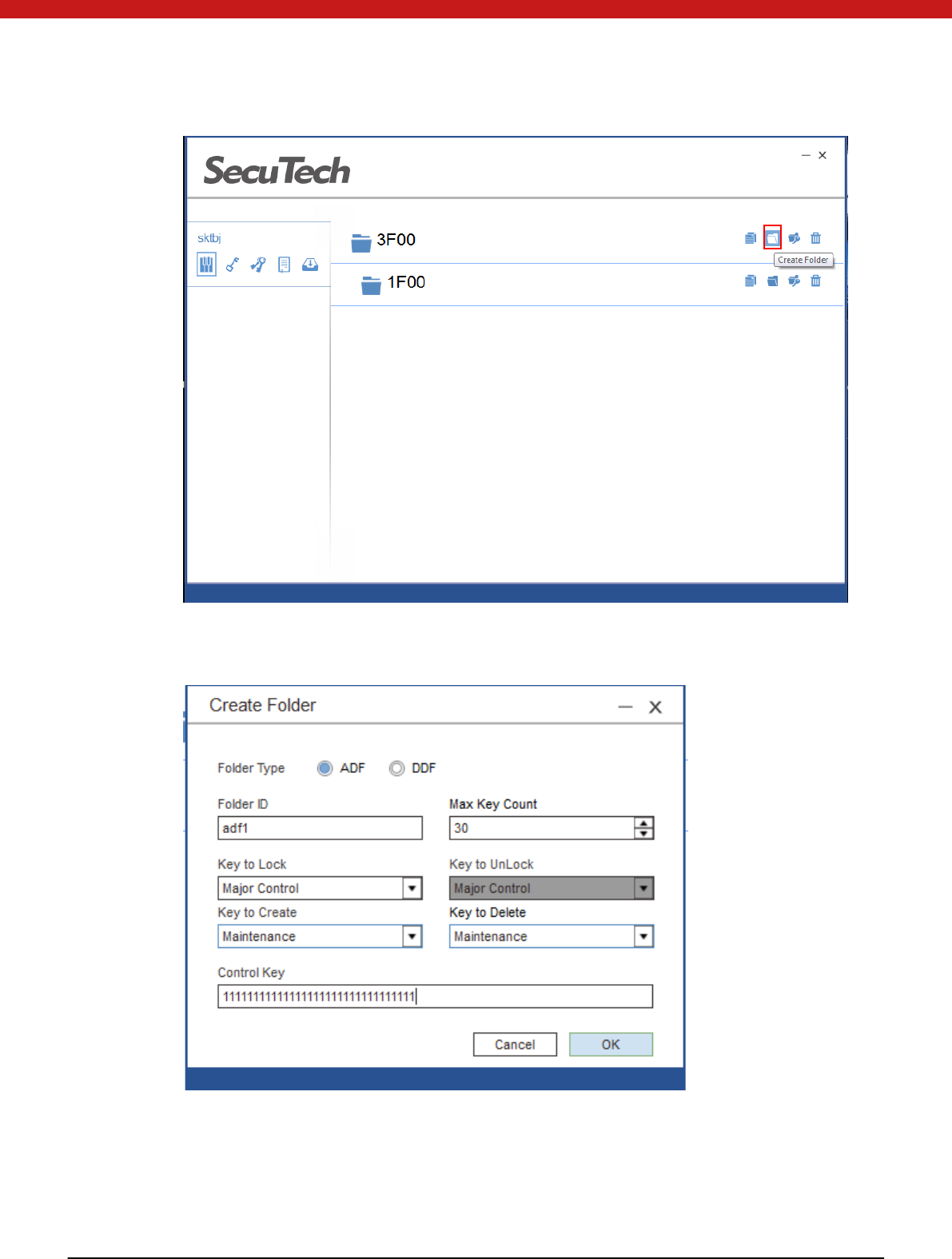
18 of 72
2. In the pop up page, select folder type, input name, create delete key t ype, and
input the key of the upper folder.
3. Click on OK, and the new folder will appear in the selected folder.
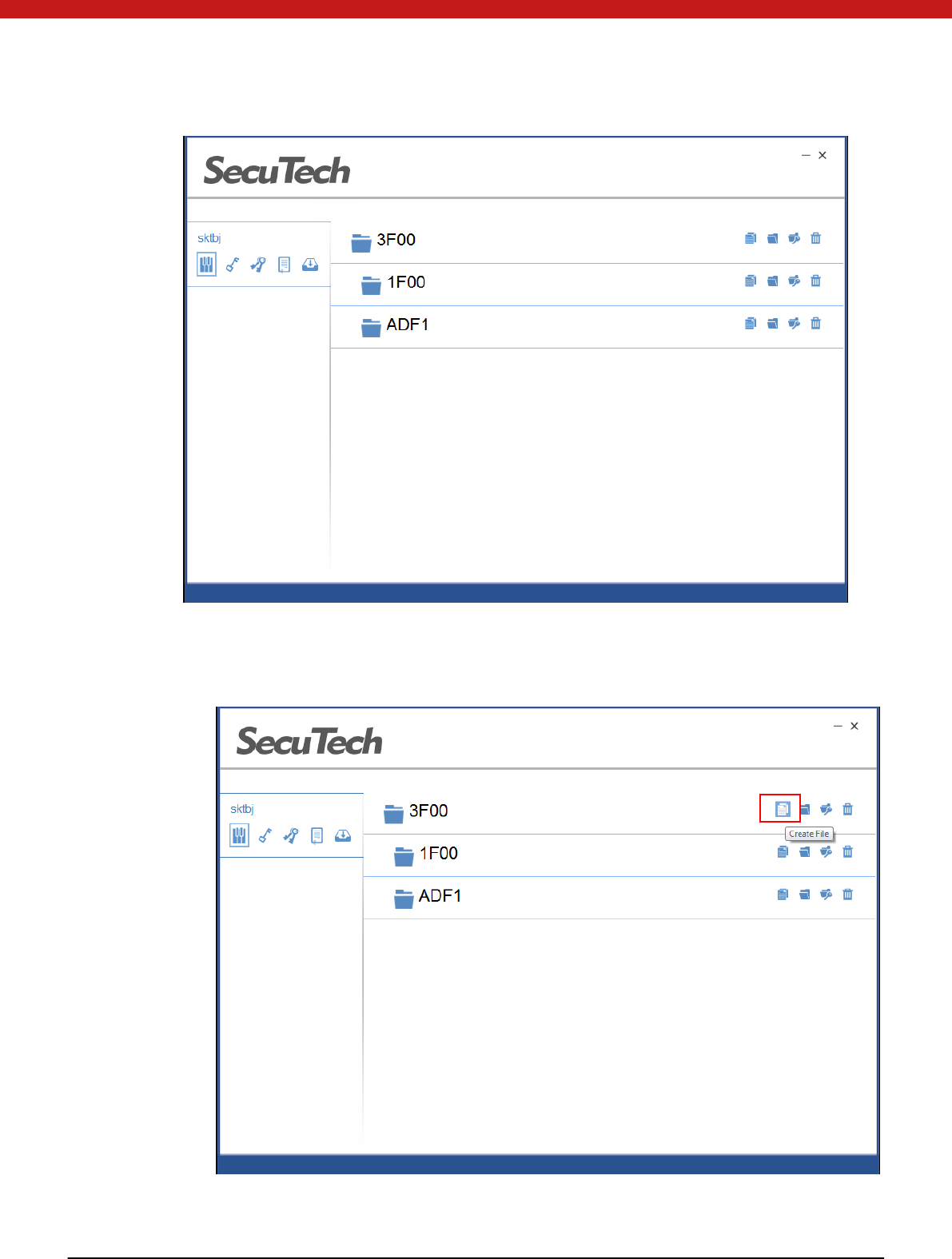
19 of 72
4.3.5 Create file
Click on the create file icon under the selected folder.
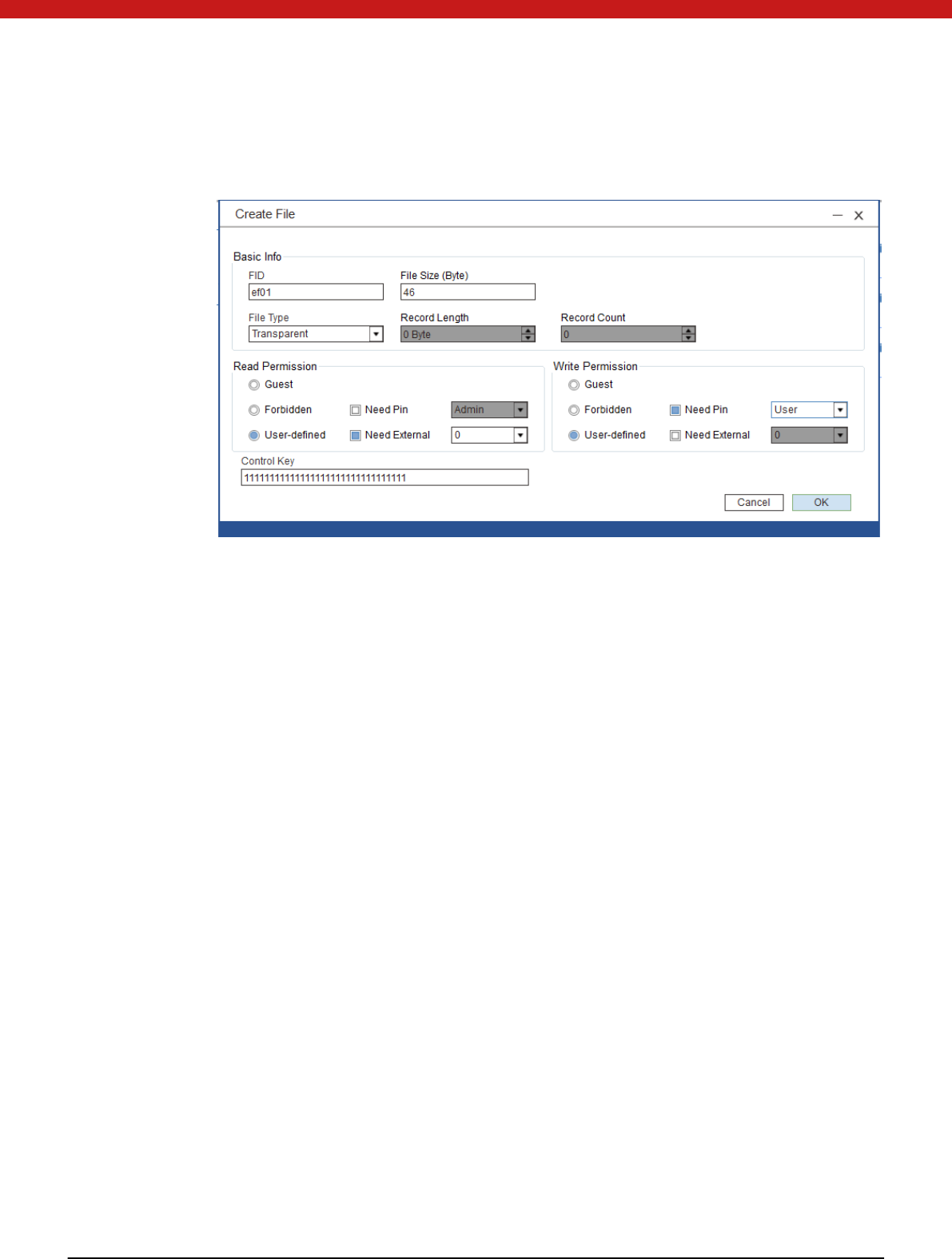
20 of 72
1. Fill the general information in the pop up page (file name must be EF01-EFFF) and
input file create key of the selected folder.
2. Click on OK, and the new file will appear in the selected folder.
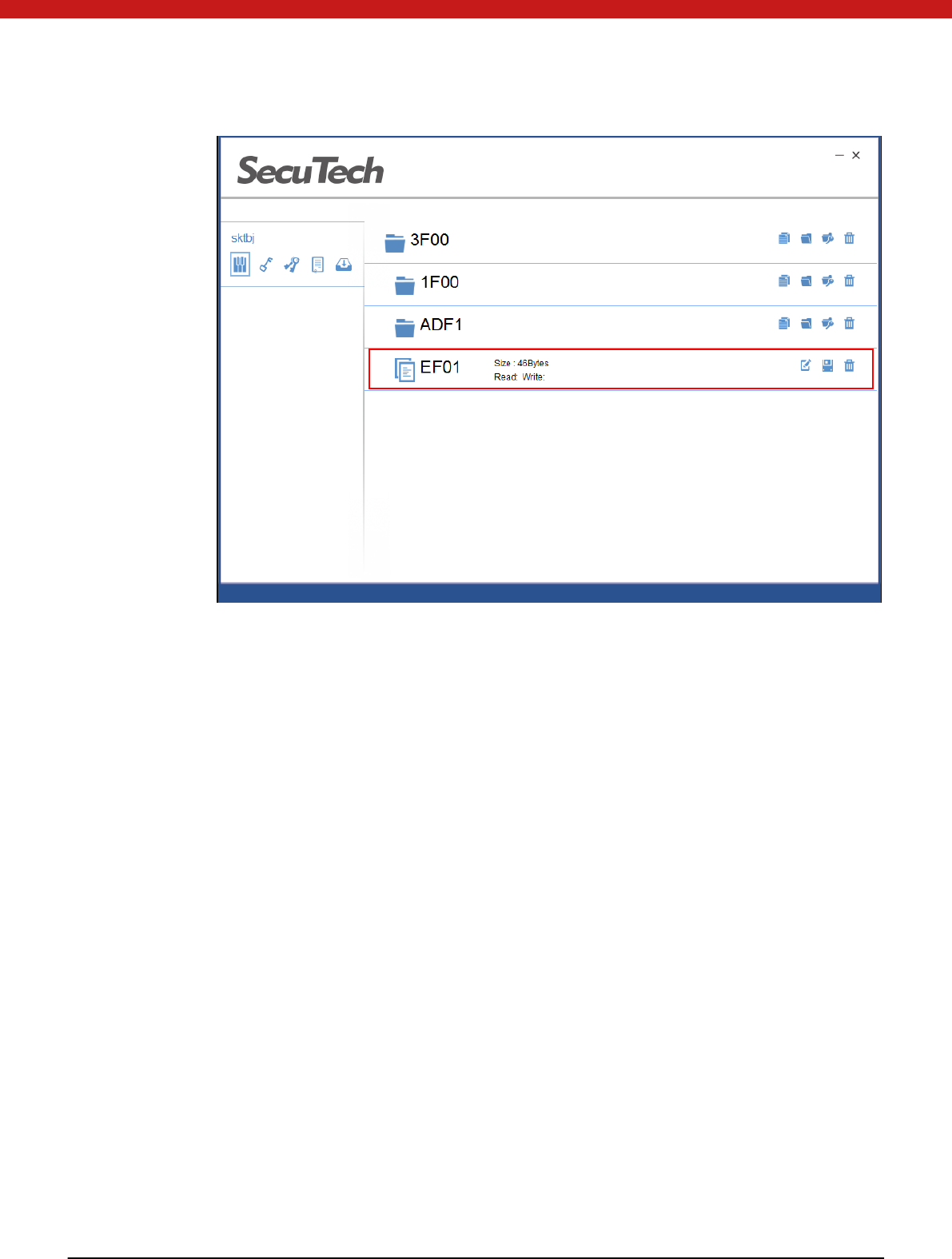
21 of 72
4.3.6 Read/write file
W rite file
1. Select the file and click on the update local file icon.
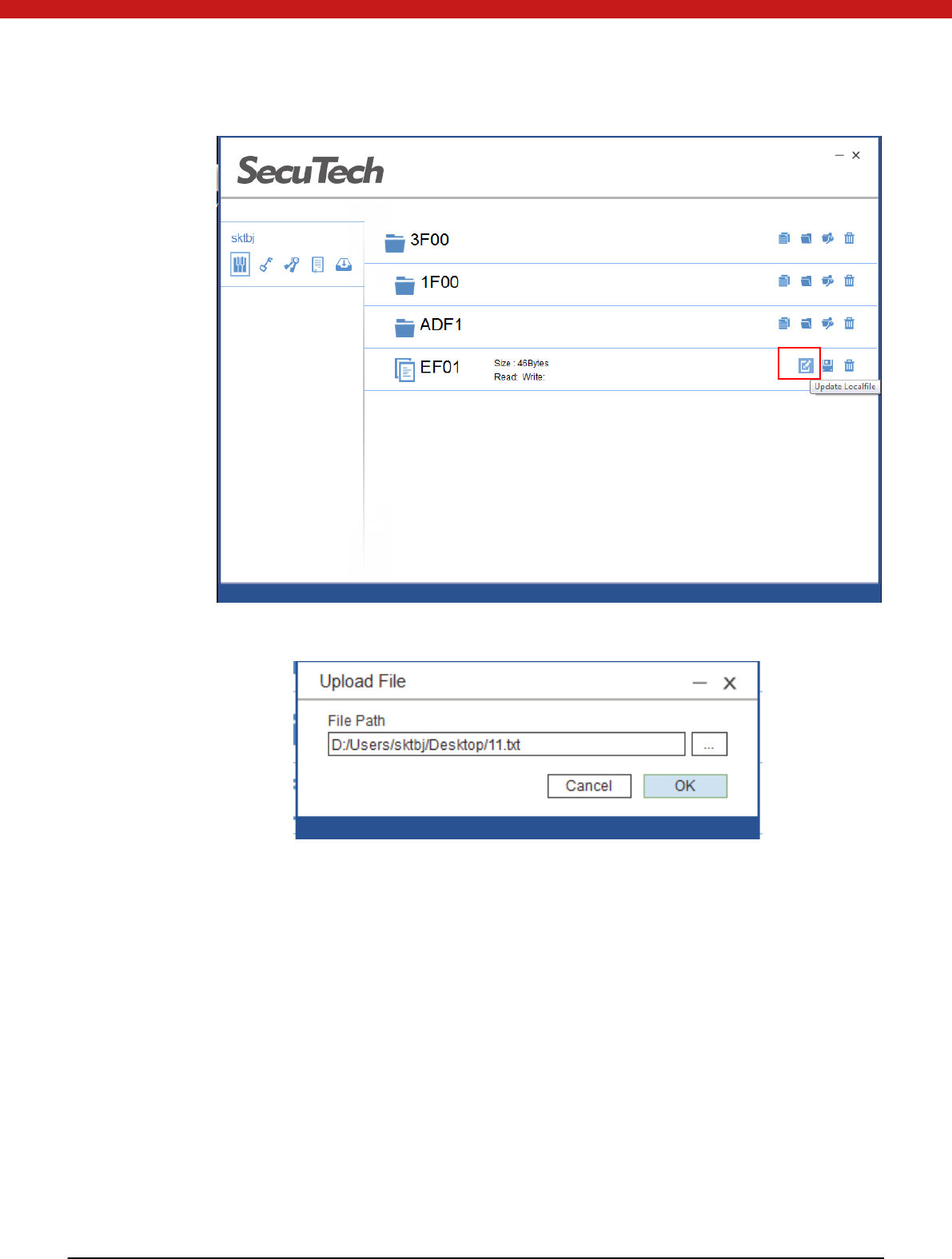
22 of 72
In the pop up page, select the file from you r PC
The token will authenticate the write right of the selected file according to the file
access right configured when the file is created.
Read File
1. Select the file and click on the Save to local icon.
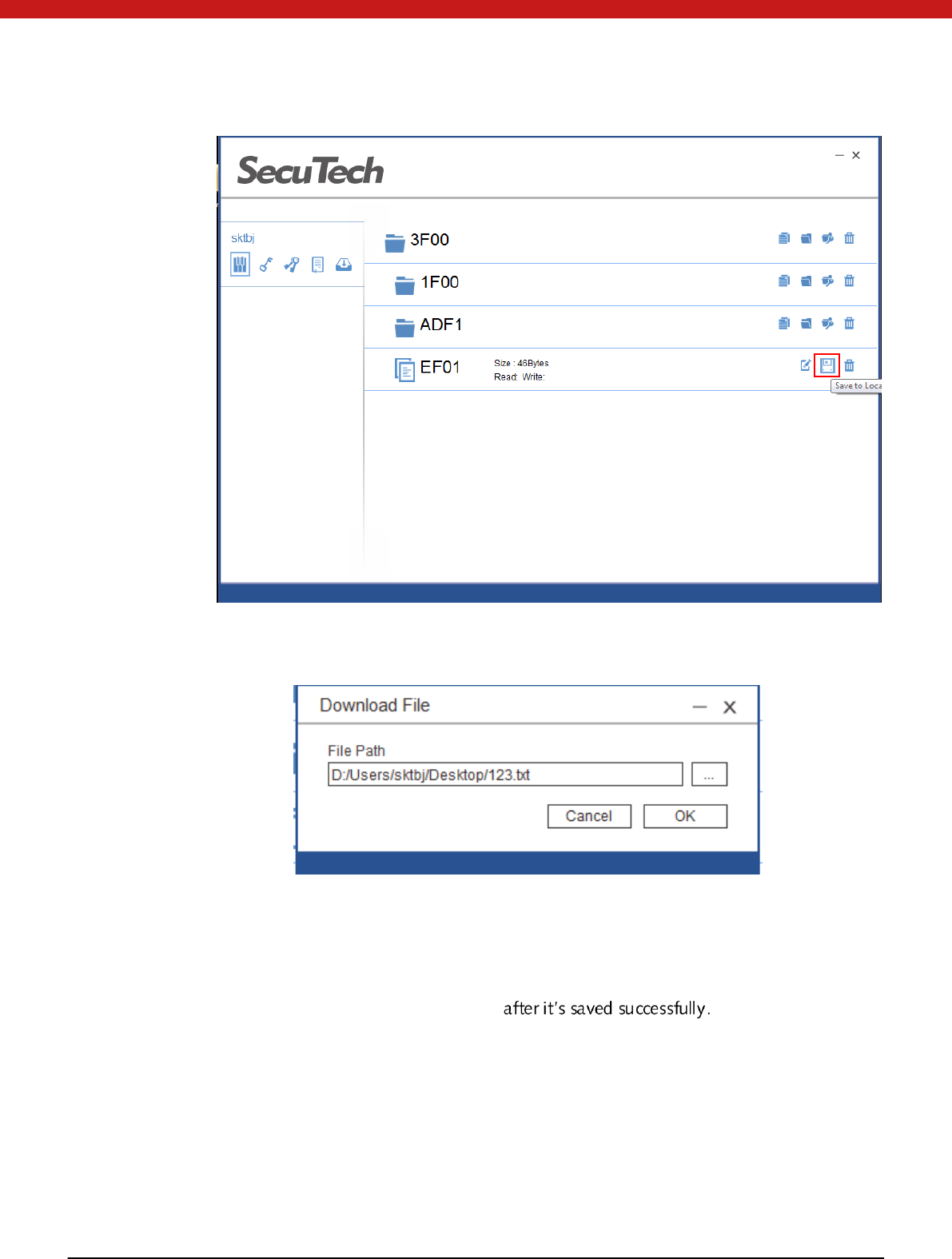
23 of 72
2. In the pop up page, input the directory and file name that the sel ected fil e to be
samed.
3. Click on OK to save the file in token to the local PC.
The token will authenticate the read right according to the access right configured
when the file is created.
The file will be found in your local PC
4.3.7 Delete file/ folder
Delete folder
1. Select the folder and click on the delete icon.
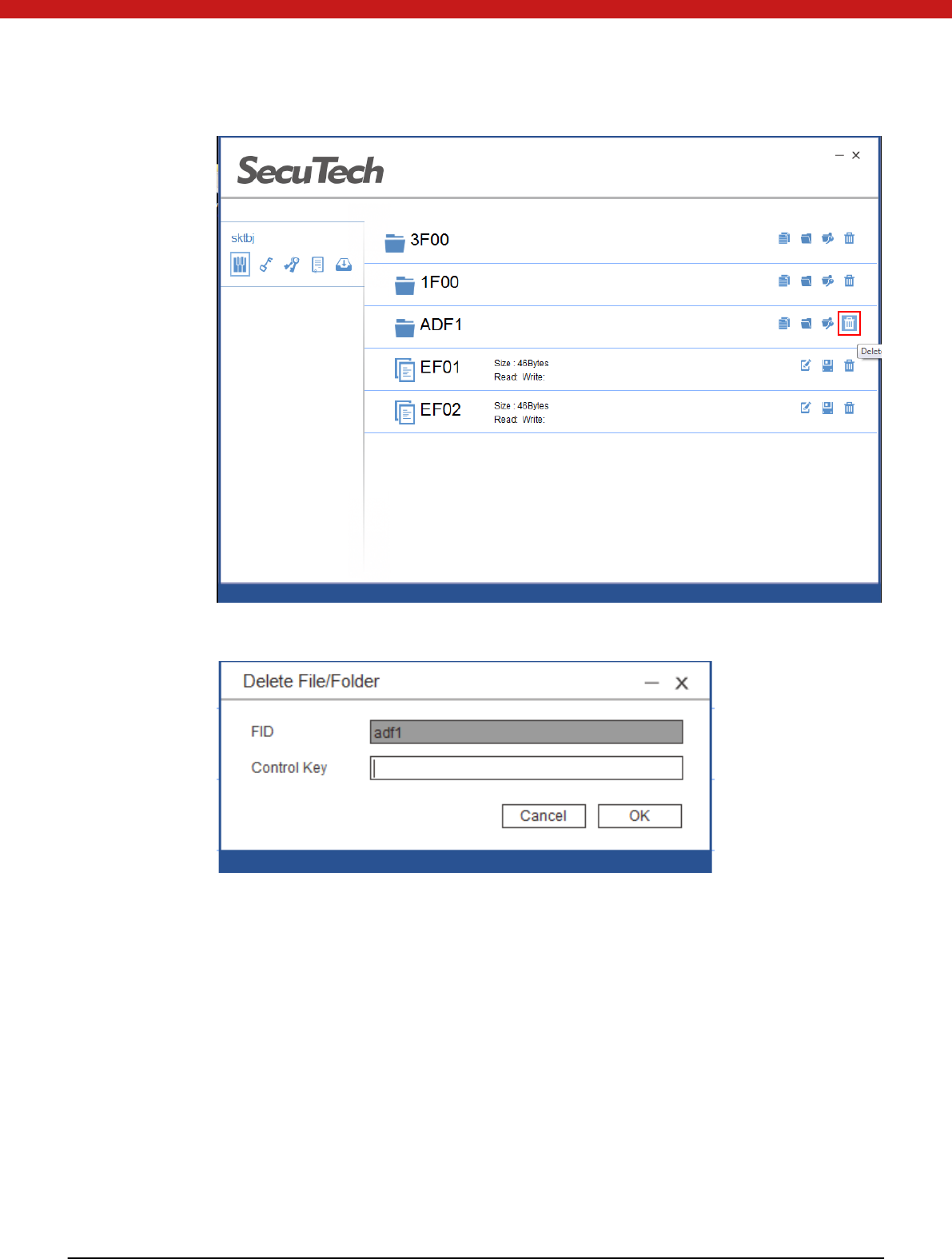
24 of 72
2. Input the key of the upper level of the selected file and click on O K
25 of 72
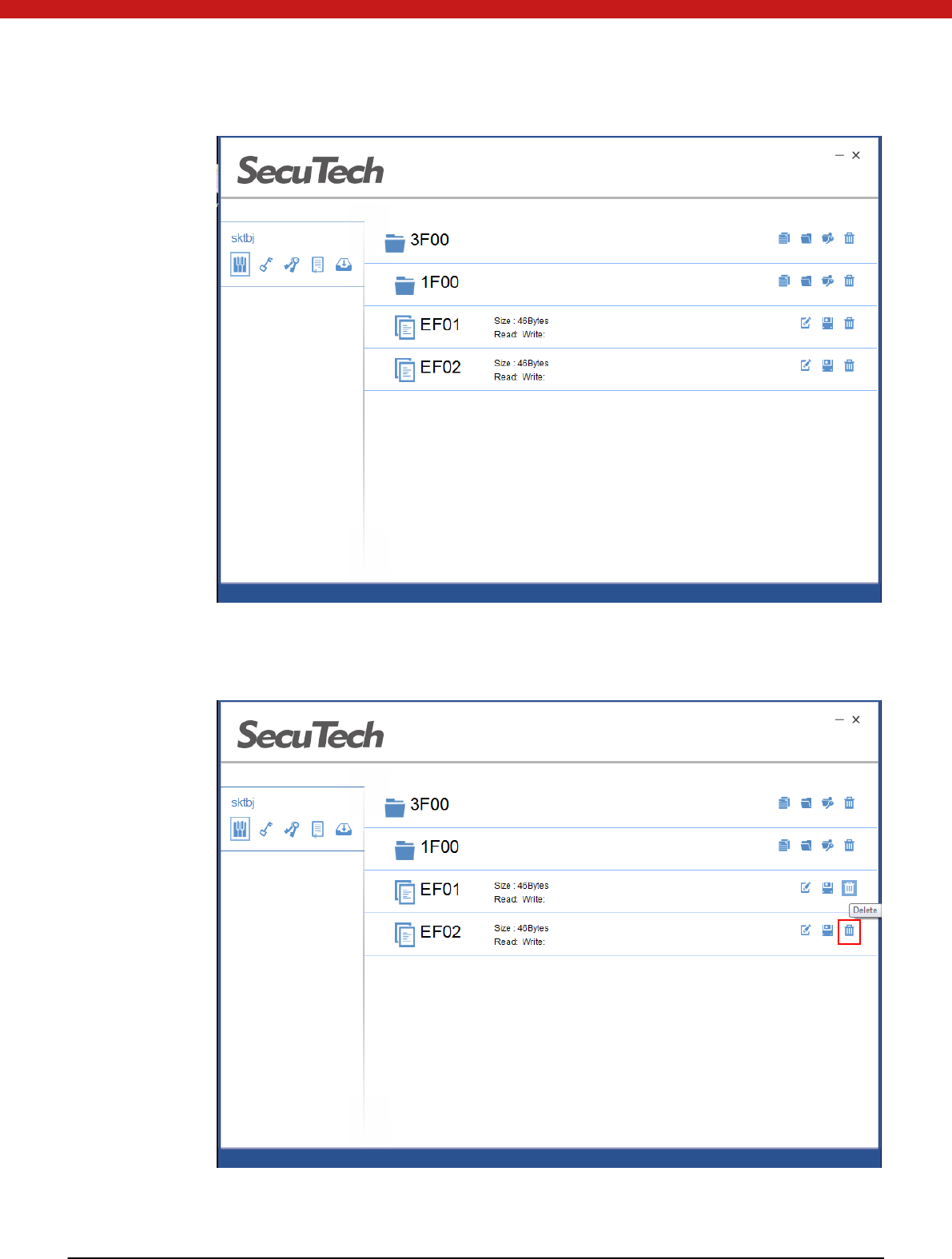
D elete f ile
1. Selet the file to be deleted, and click on the delete icon
2. In the pop up page input the key of the upper folder and click on OK.
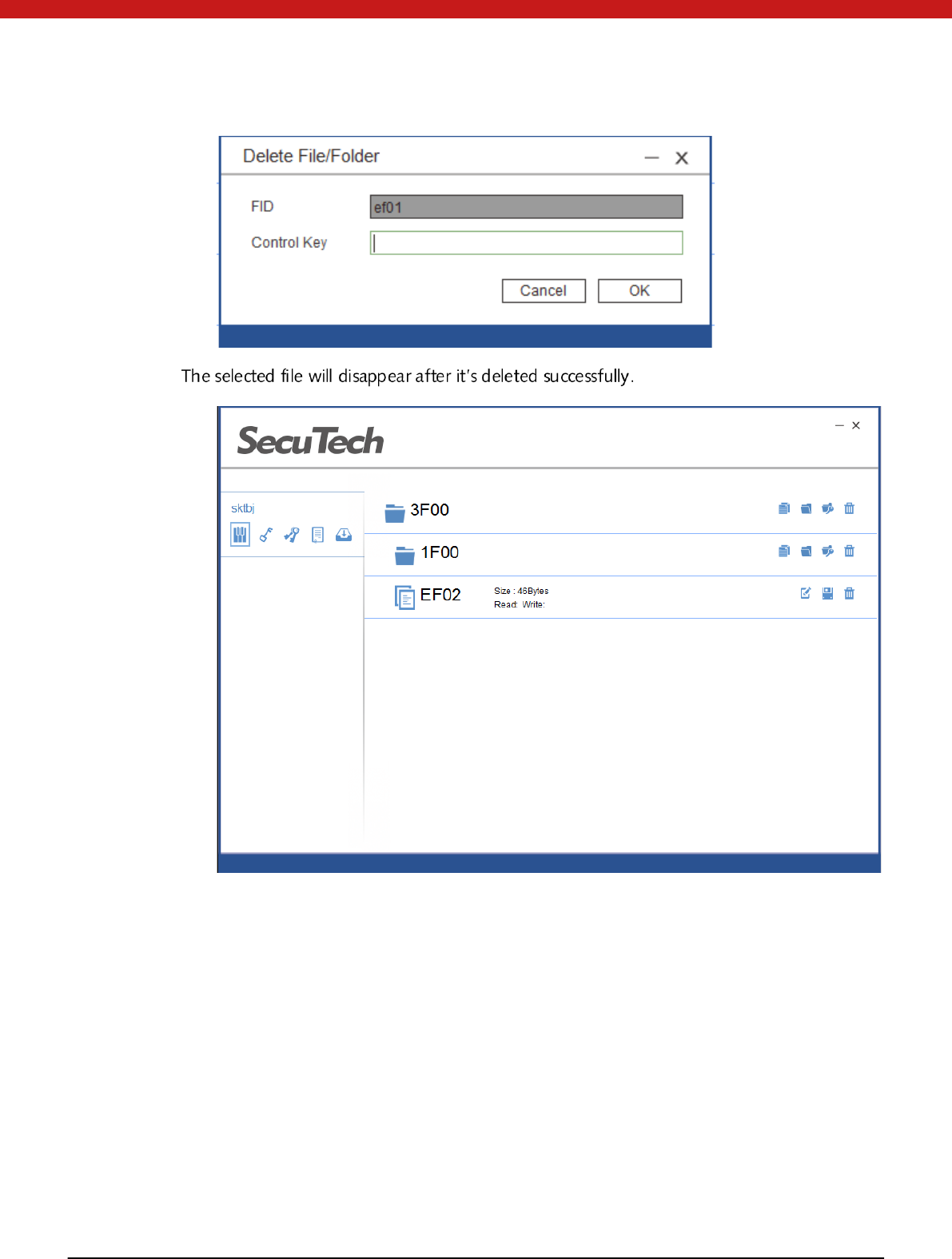
26 of 72
4.3.8 Symmetric Key
Click on the symmetric keys i con .
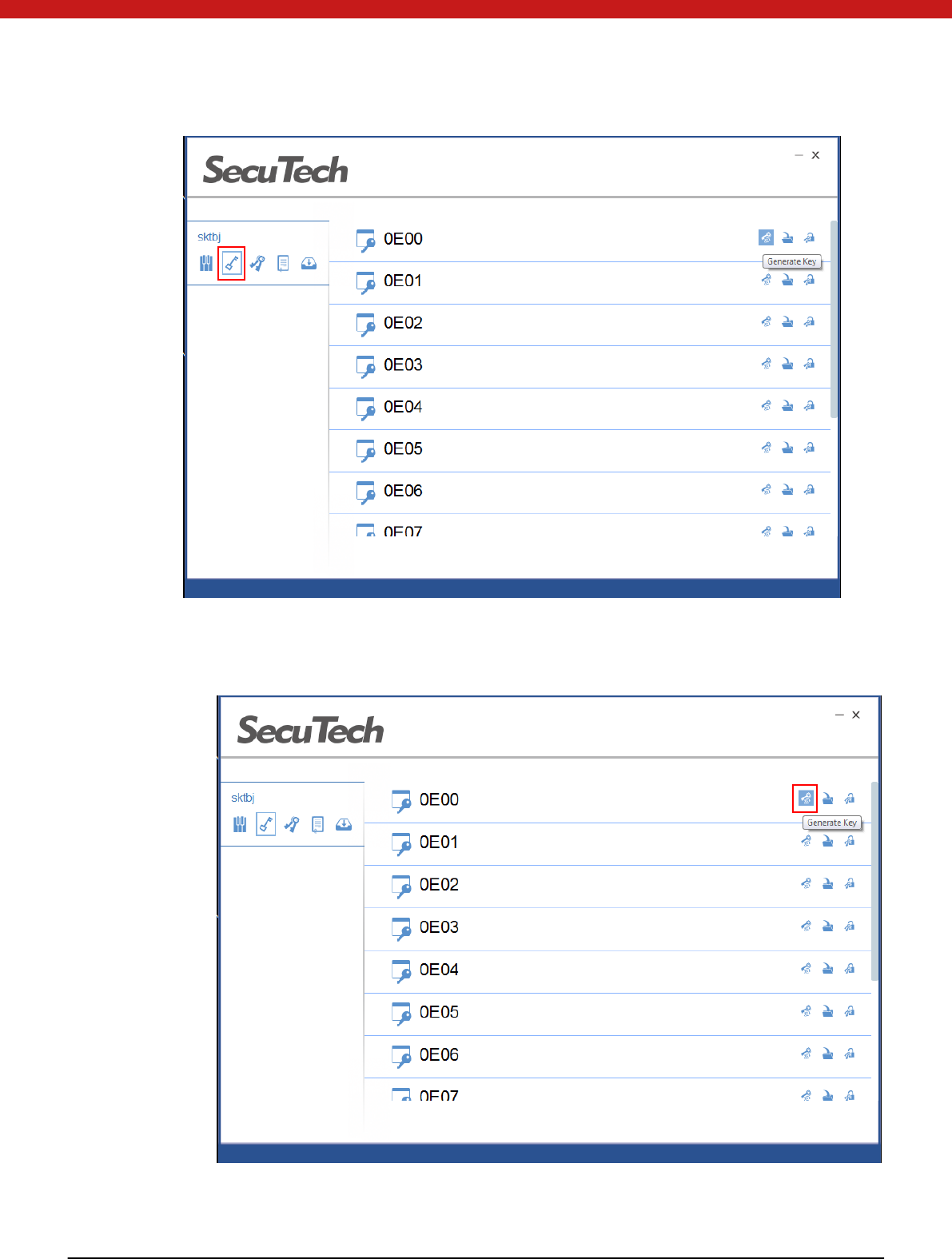
27 of 72
Generate Key
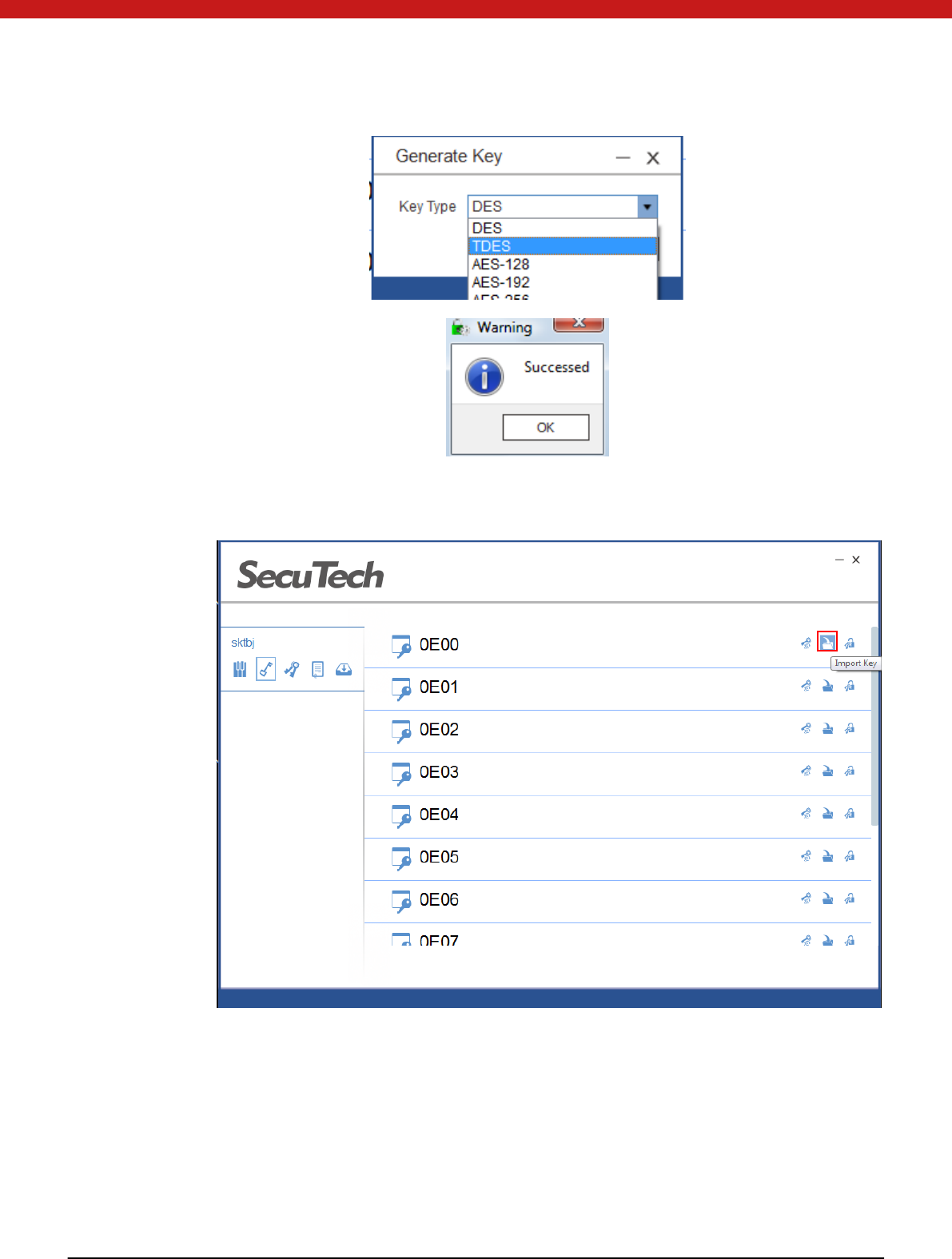
1. Select a key file from the list and click on the generate key icon
2. In the pop up page, select key type and click on OK.
28 of 72
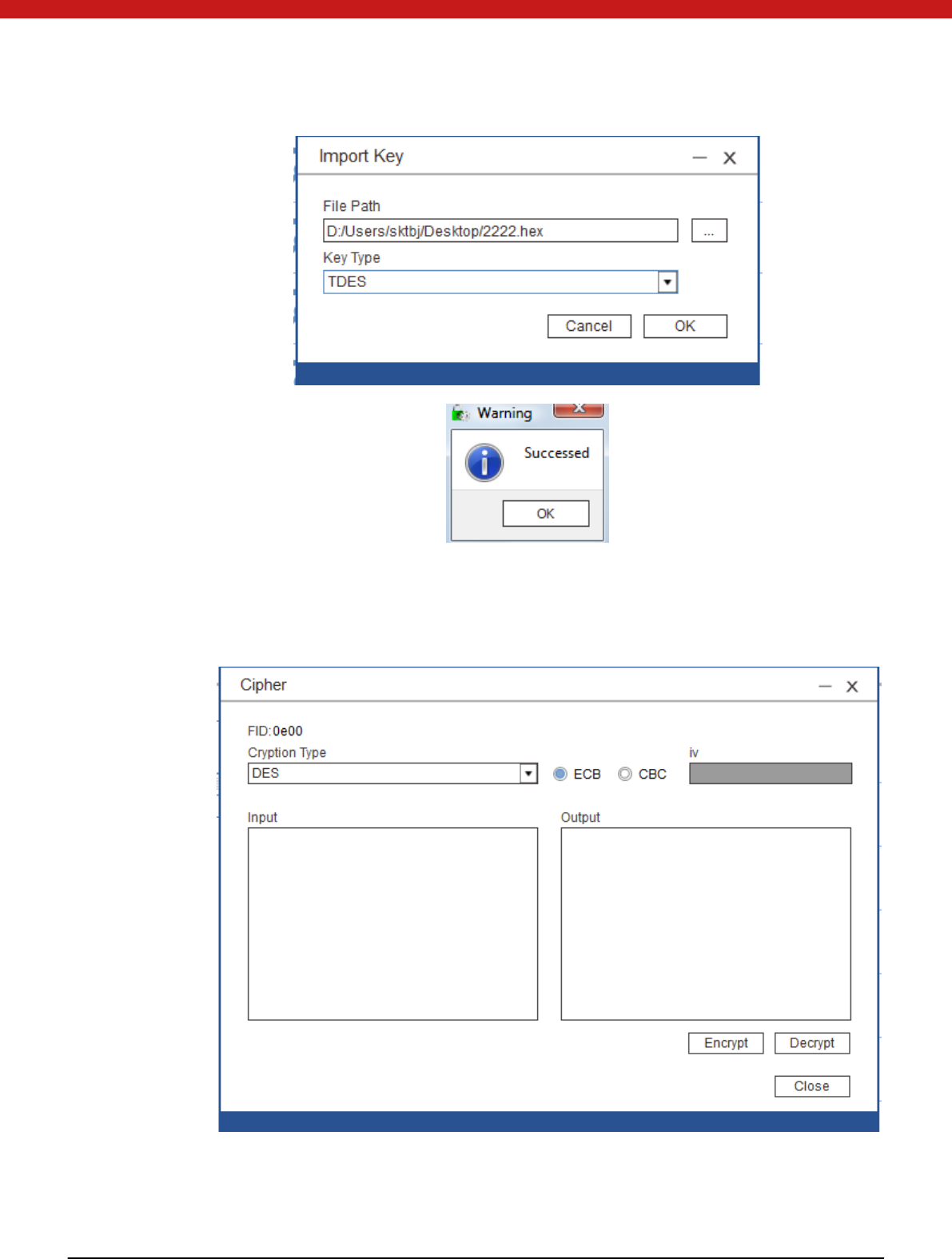
Import Key
1. Select a key file and click on the import key icon.
2. In the pop up page, find your key file and select key type. Click on OK.
29 of 72
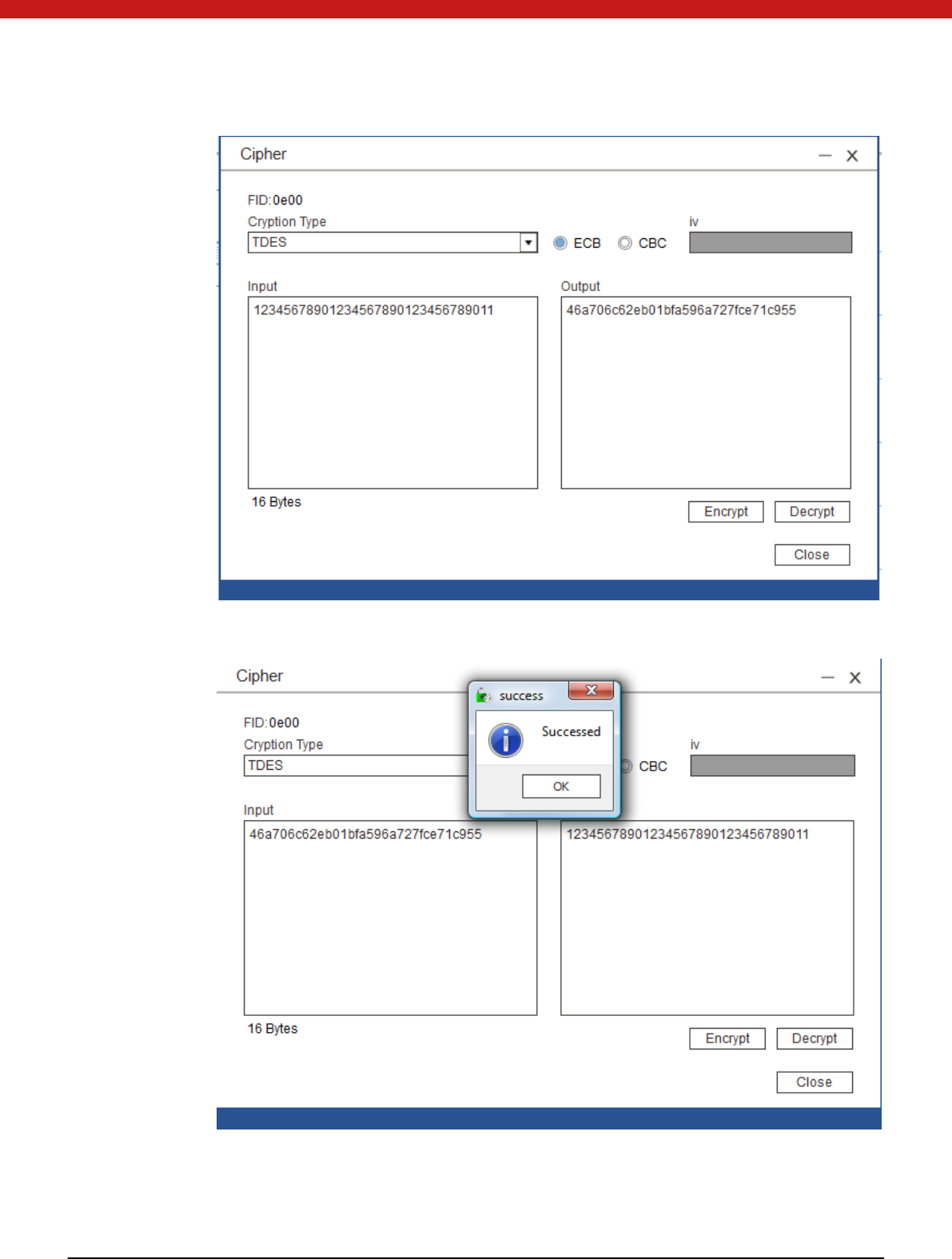
Encrypt/ decrypt
Select the key file to be used to encrypt/decrypt. (ensure a key has been stored in
the selected key file and key type)
Select the algo ri thm and input the data in HEX to be encrypted/decrypted. Click
on the encrypt/decrypt button.
30 of 72
Result will display in the output box.
31 of 72
4.3.9 Asymmetric Key
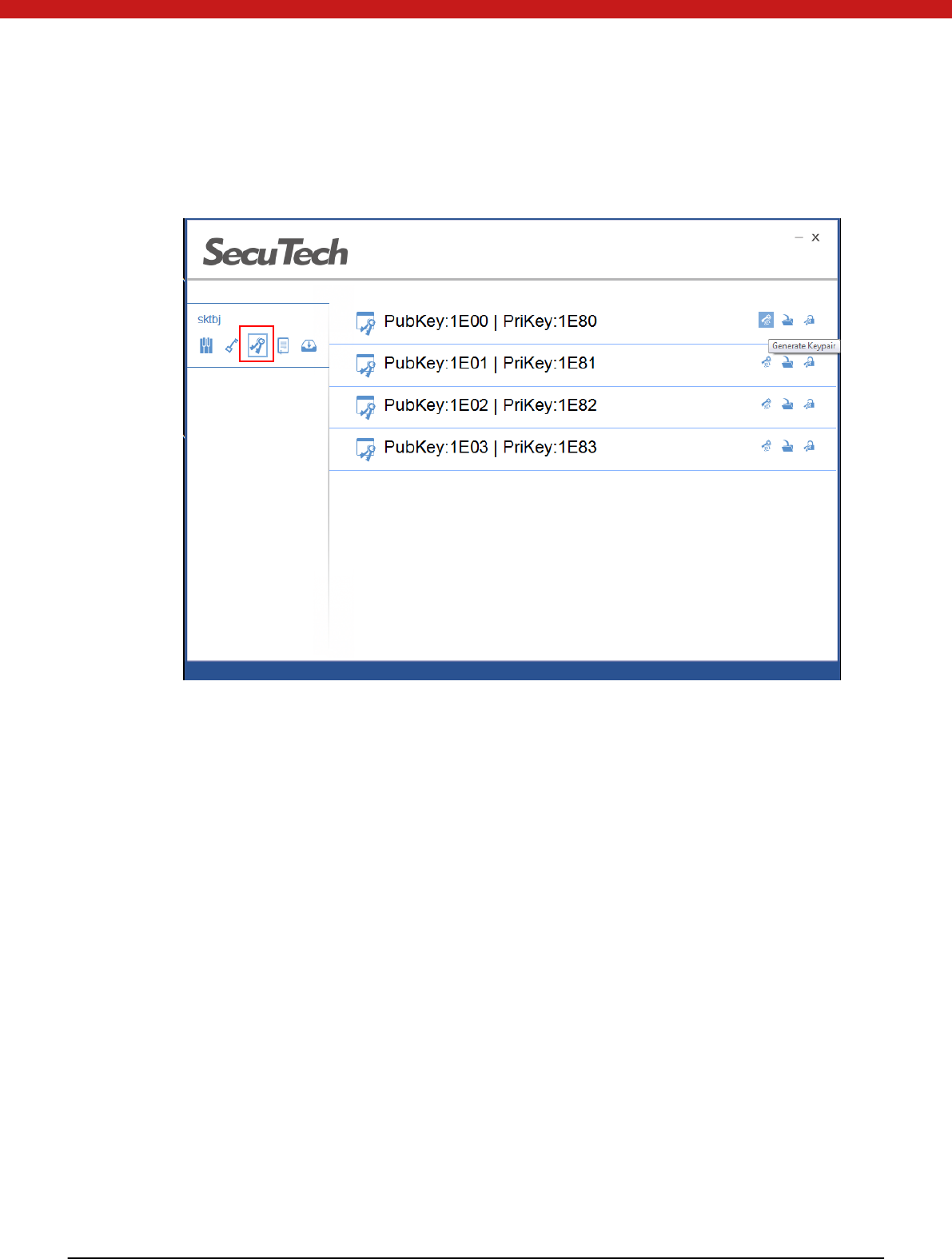
Select the symmetric key pair i co n
Generate key
1. Select a key file from the list and click on the generate key icon.
32 of 72
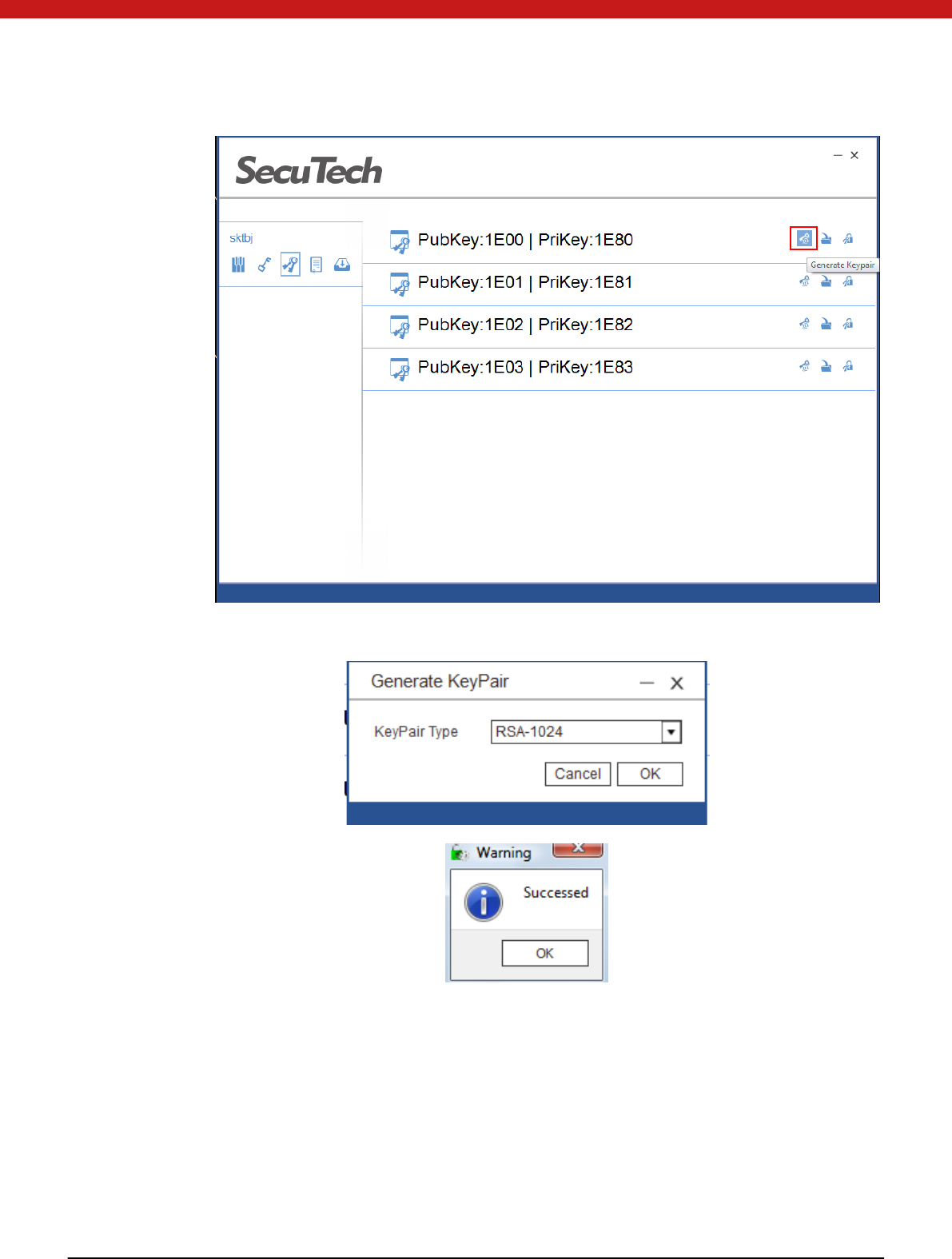
2. In the pop up page select key pair type and click on OK
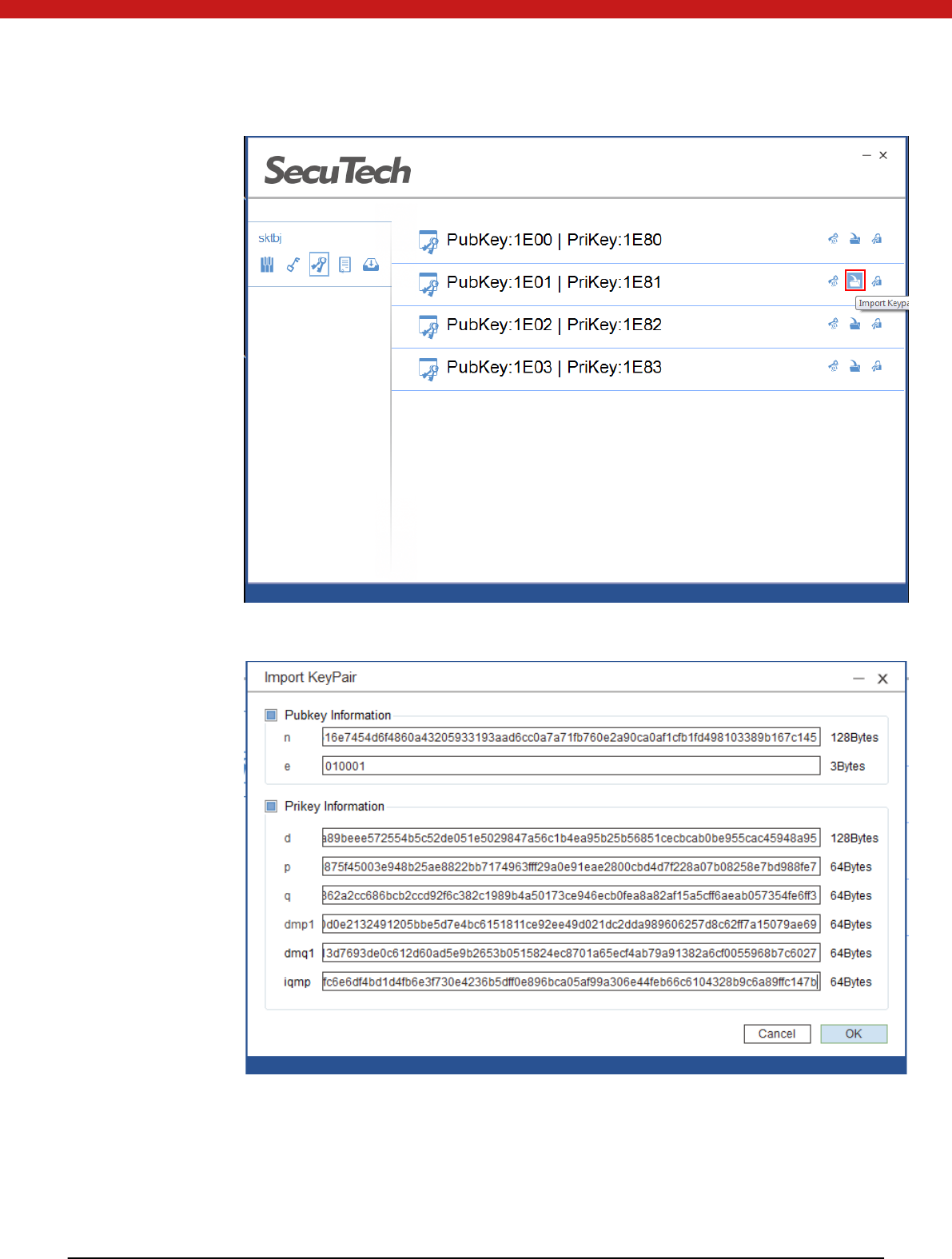
Import Key Pair
1. Select key file and click on the import icon.
33 of 72
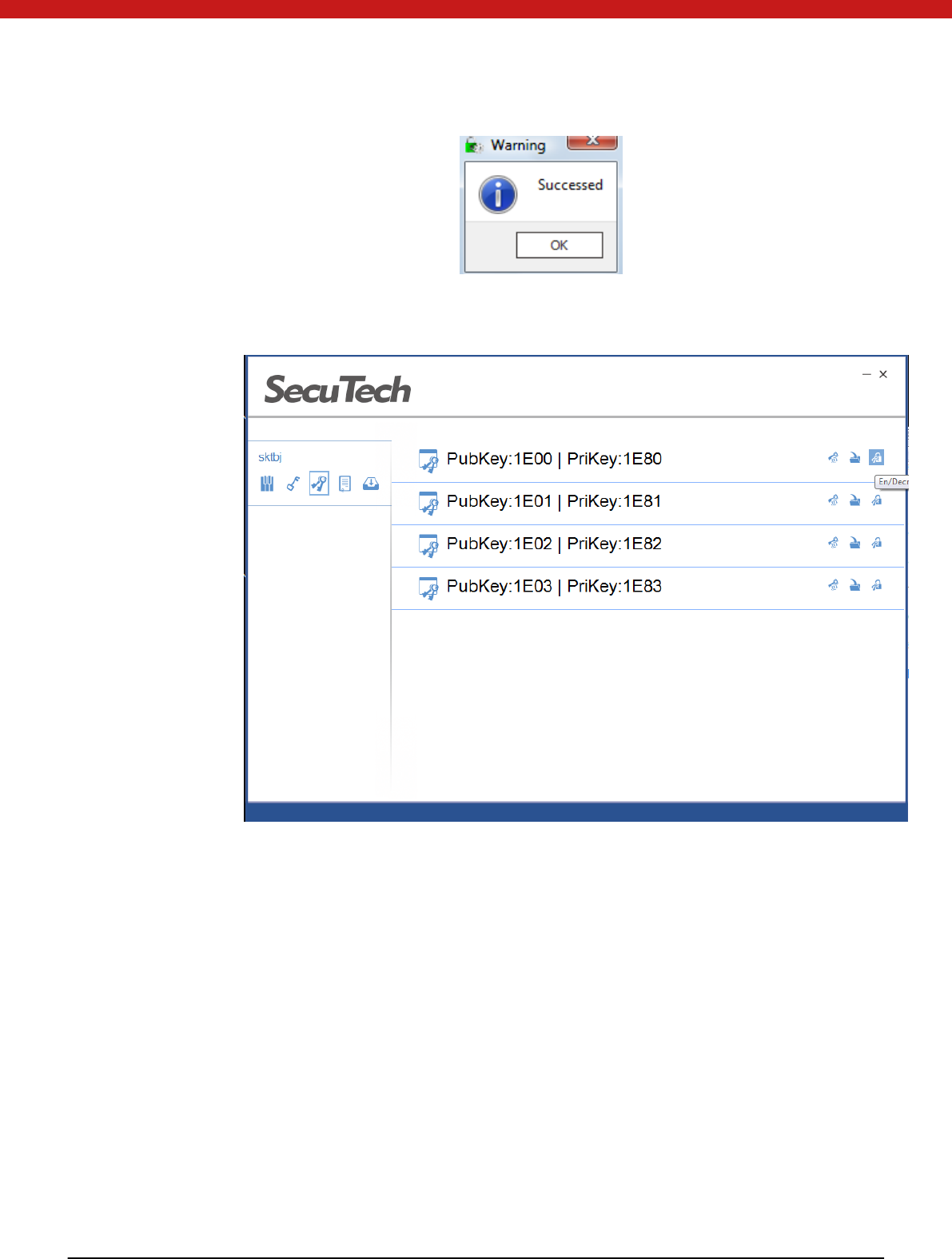
2. In the pop up page, input the correct key, and click on O K
34 of 72
Encrypt/ decrypt
1. Select the key file
2. Select encrypt
Input data in HEX to be encrypted and click on run.
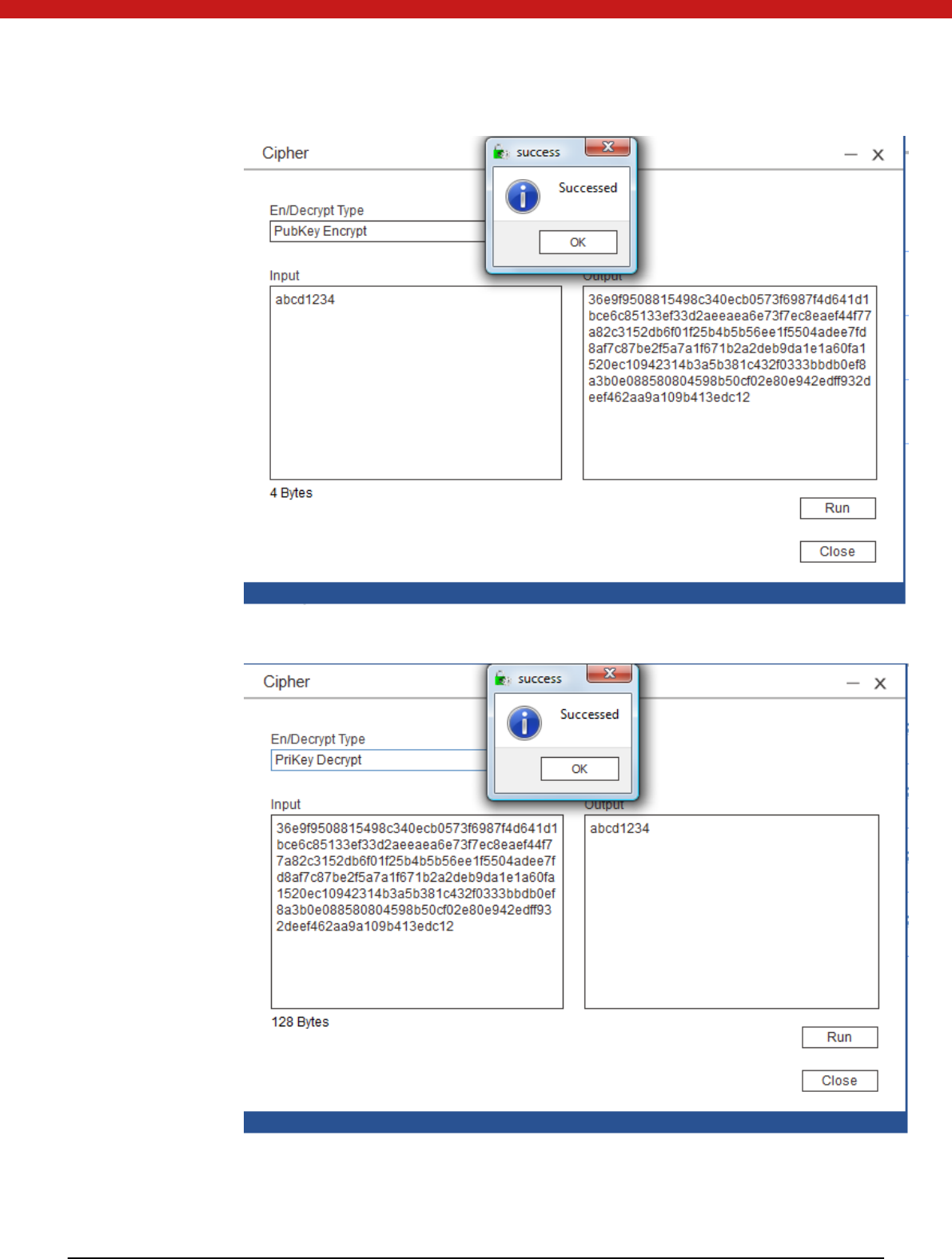
35 of 72
In the same procedure, select decrypt and click on run to decrypt.
Sign
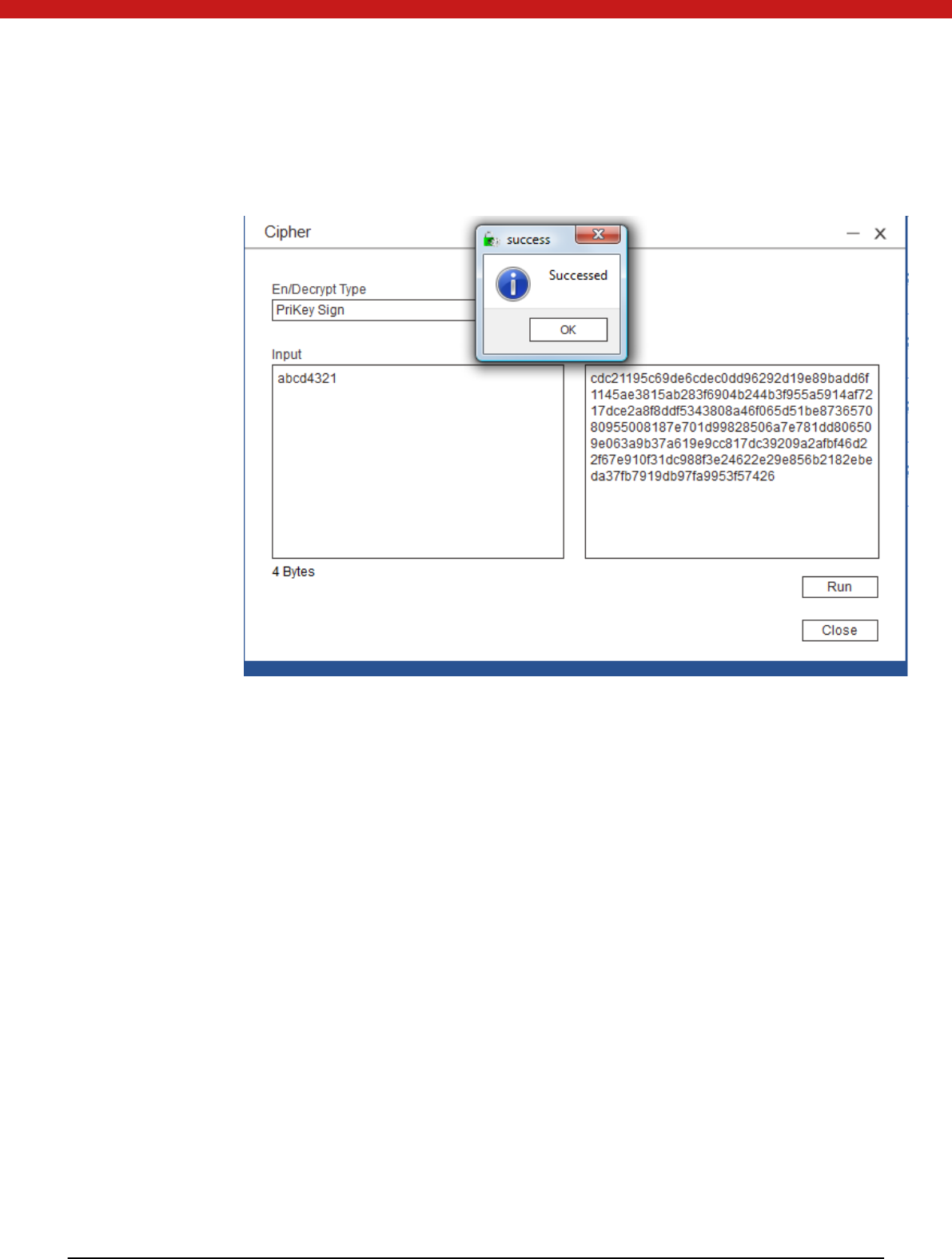
36 of 72
Select sign
Input data in HEX to be signed and click on run.
Veri fy signatu re
Input the signature, select verify signature and click on run.
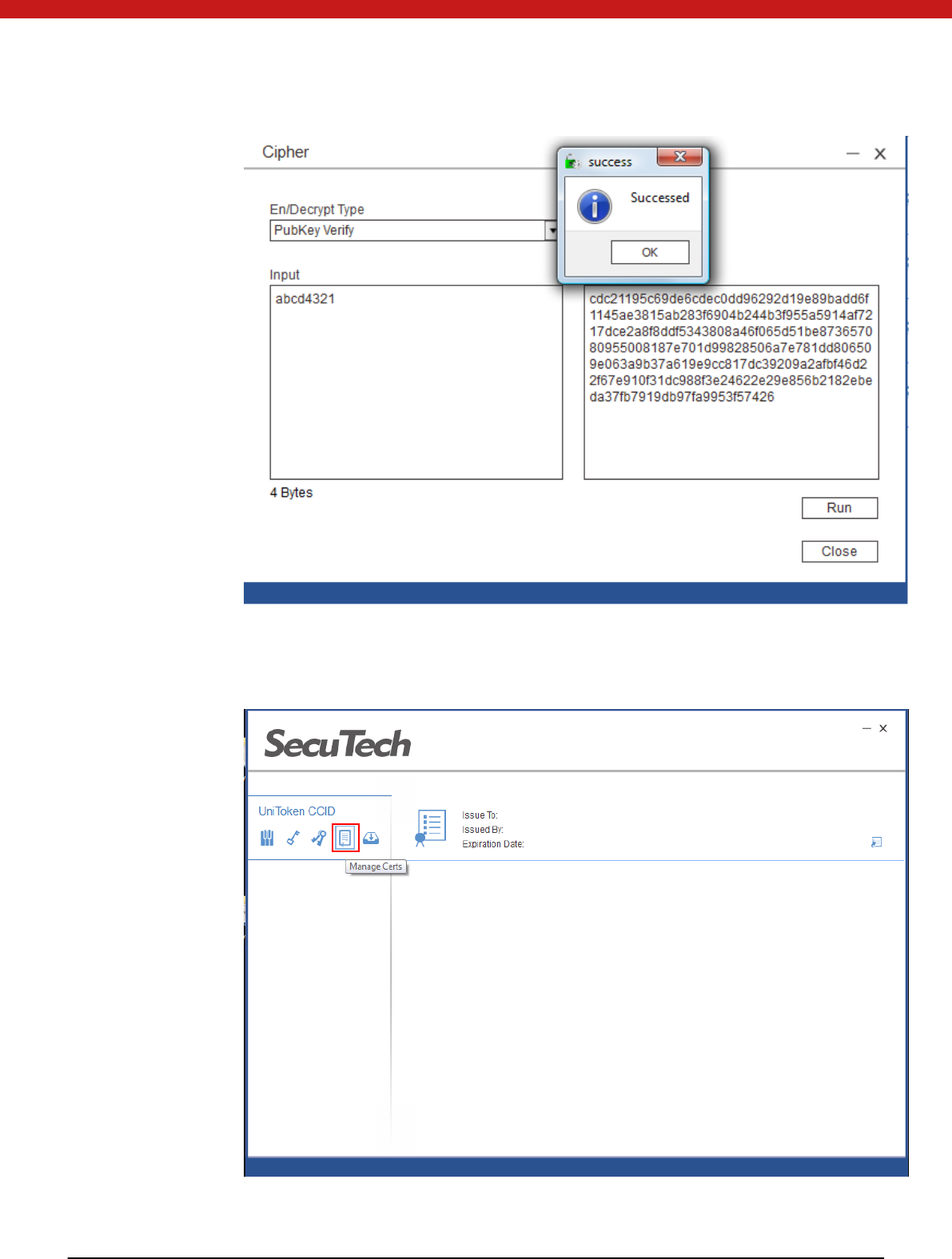
37 of 72
4.3.10 Change certifiate
Click on manage cert s icon.
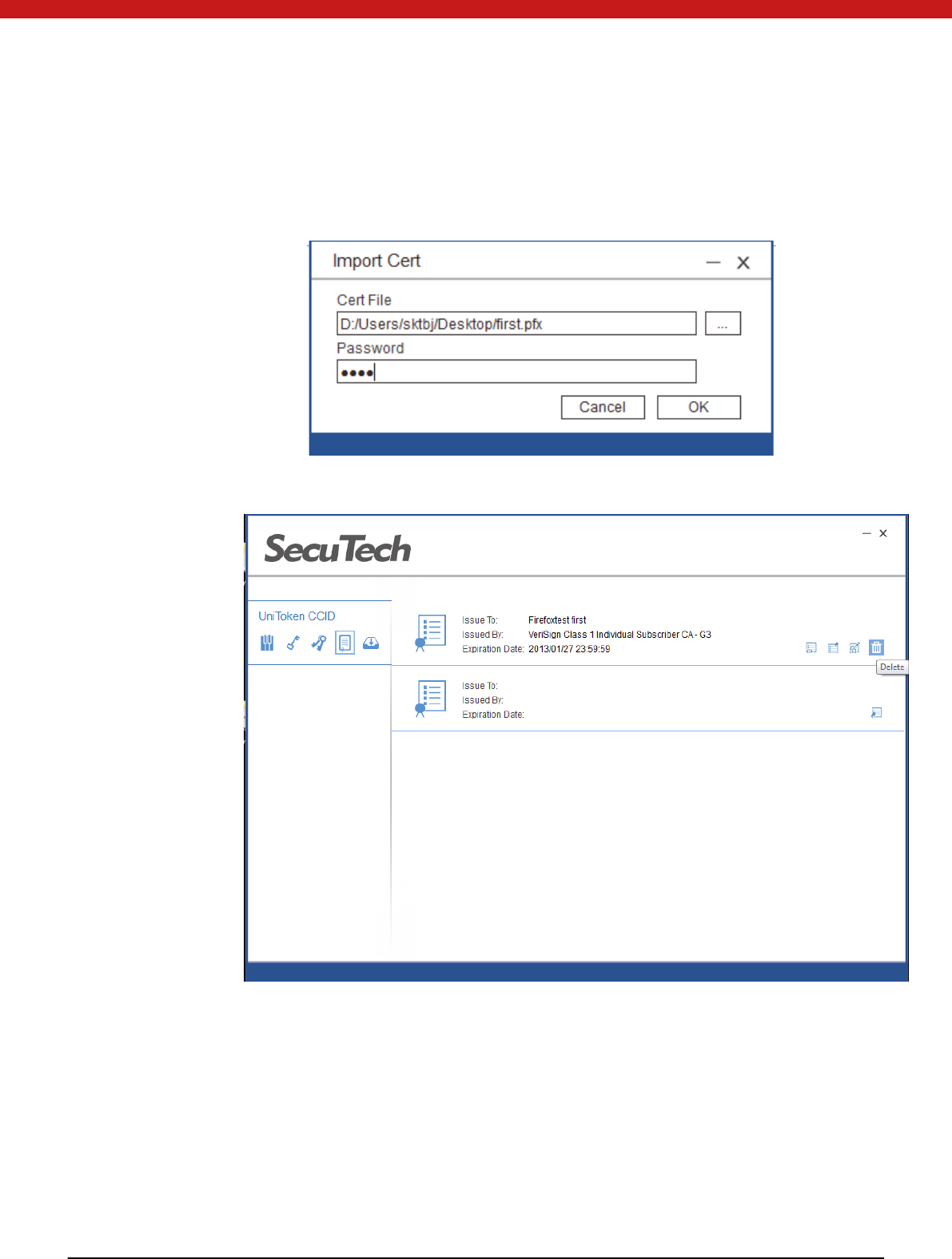
38 of 72
Import certificate
Click on import certs and select the certificate to be imported and input the
password to the certificate.
Click on OK to import the certificate.
View certificate
Click on the view certs and the cert i fi cate in fo rmat ion will display in the pop
up page.
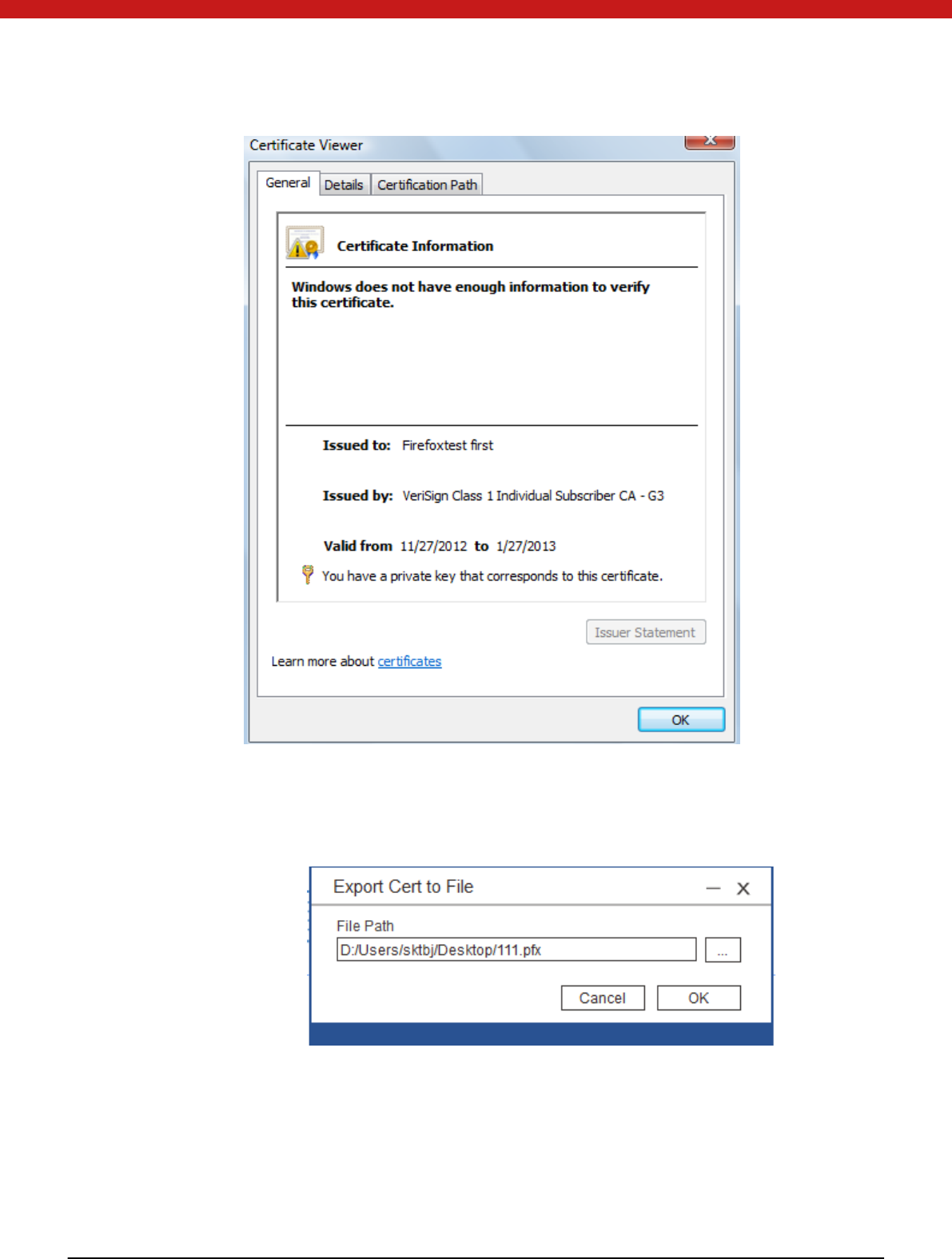
39 of 72
Expo rt cert i fi cate
Click on the export certs and specified the directory that the certificate to be
saved.
Click on OK and the certificate will be saved to the directory.
Sign by a certificate
Click on the sign icon and select hash algorithm.
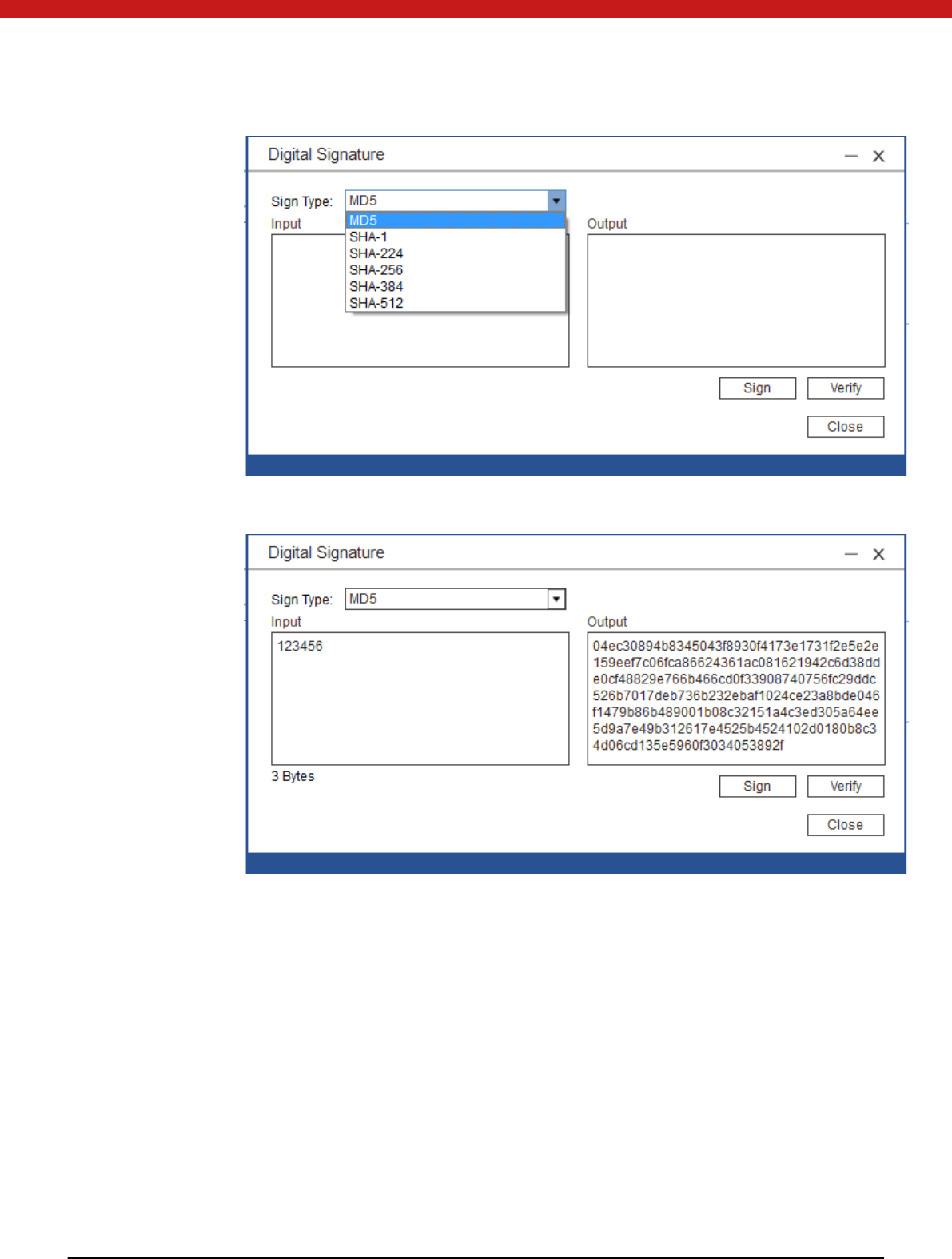
40 of 72
Input data in HEX and click on sign.
Veri fi cati on
In this page, click on verify to verify a signature signed by this certificate.
Delet e cert i fi cate
Click on the delete icon
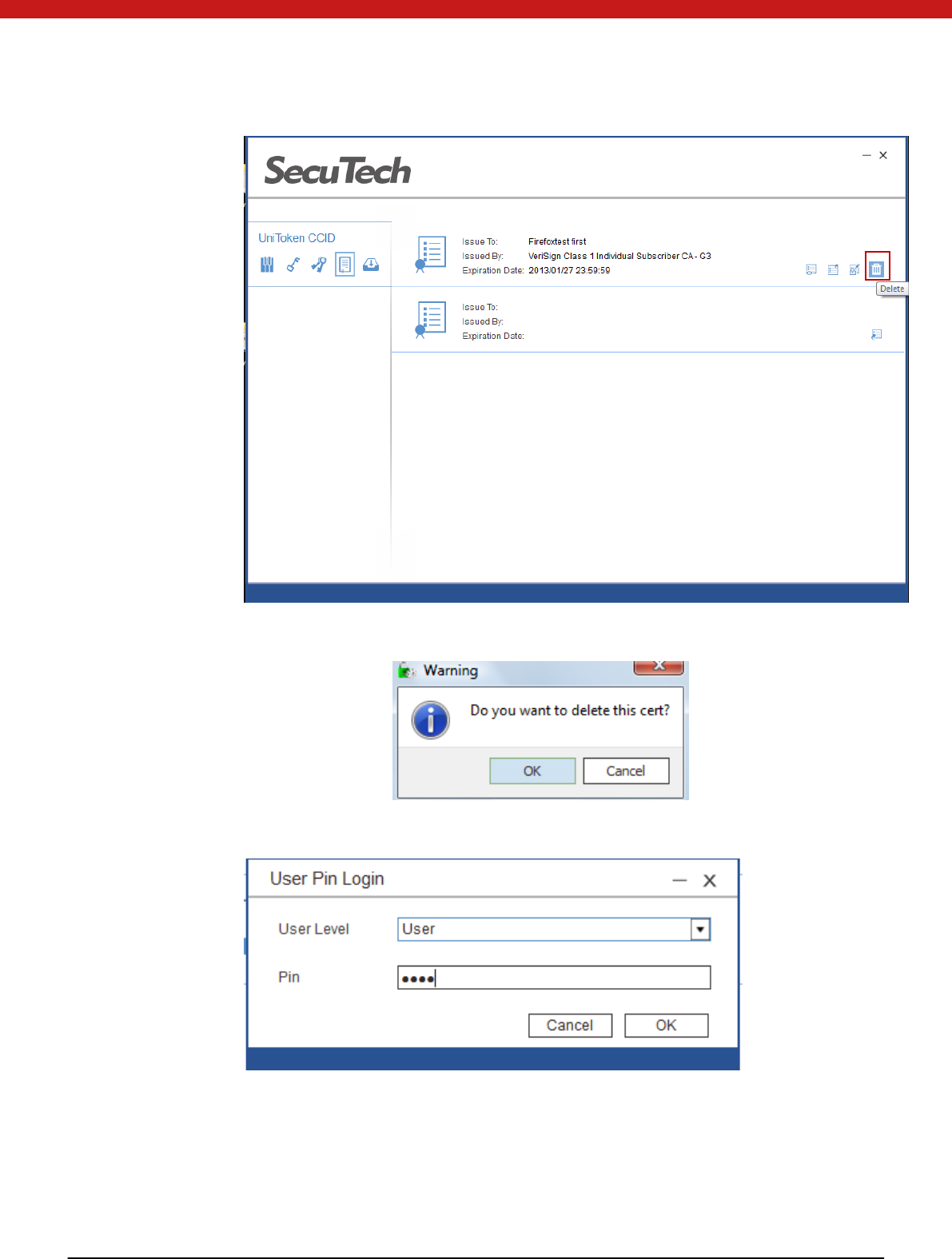
41 of 72
Click on OK
Click on OK and in the pop up page input user PIN.
Click on OK to delete the certificate.
42 of 72
4.4 Monitor
UniToken Monitor is used to view the detailed information of certificates imported into
the UniToken and register or unregister certificates. Here, it also provides a way to
change User PIN.
4.4.1 Monitor device
Start UniTokenM onitor.exe and insert token.
Unplug device
4.4.2 Operation
1. Start Monitor.exe and select a target device.
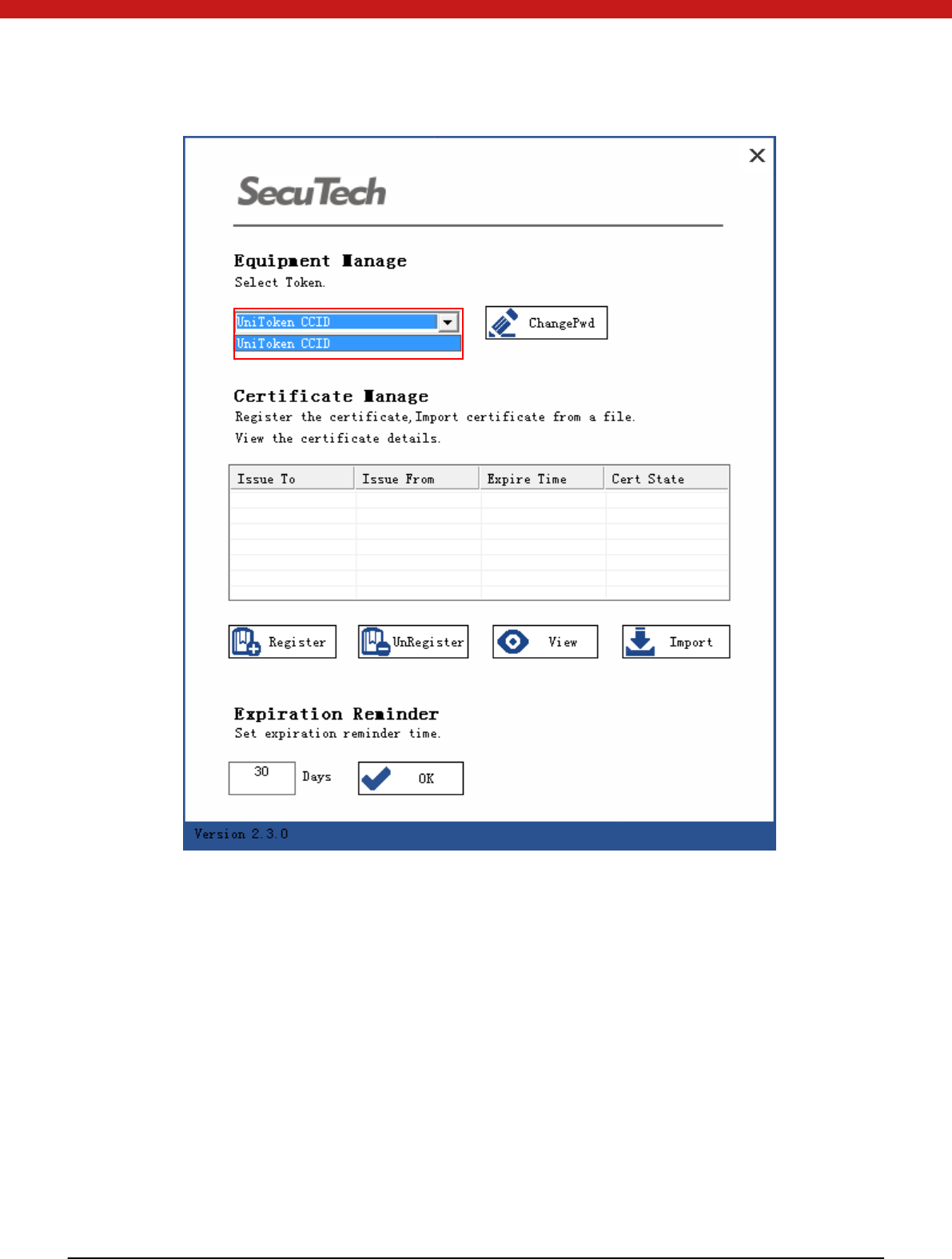
43 of 72
Change password
Click on ChangePwd, and in the pop up window input old password and new
password.
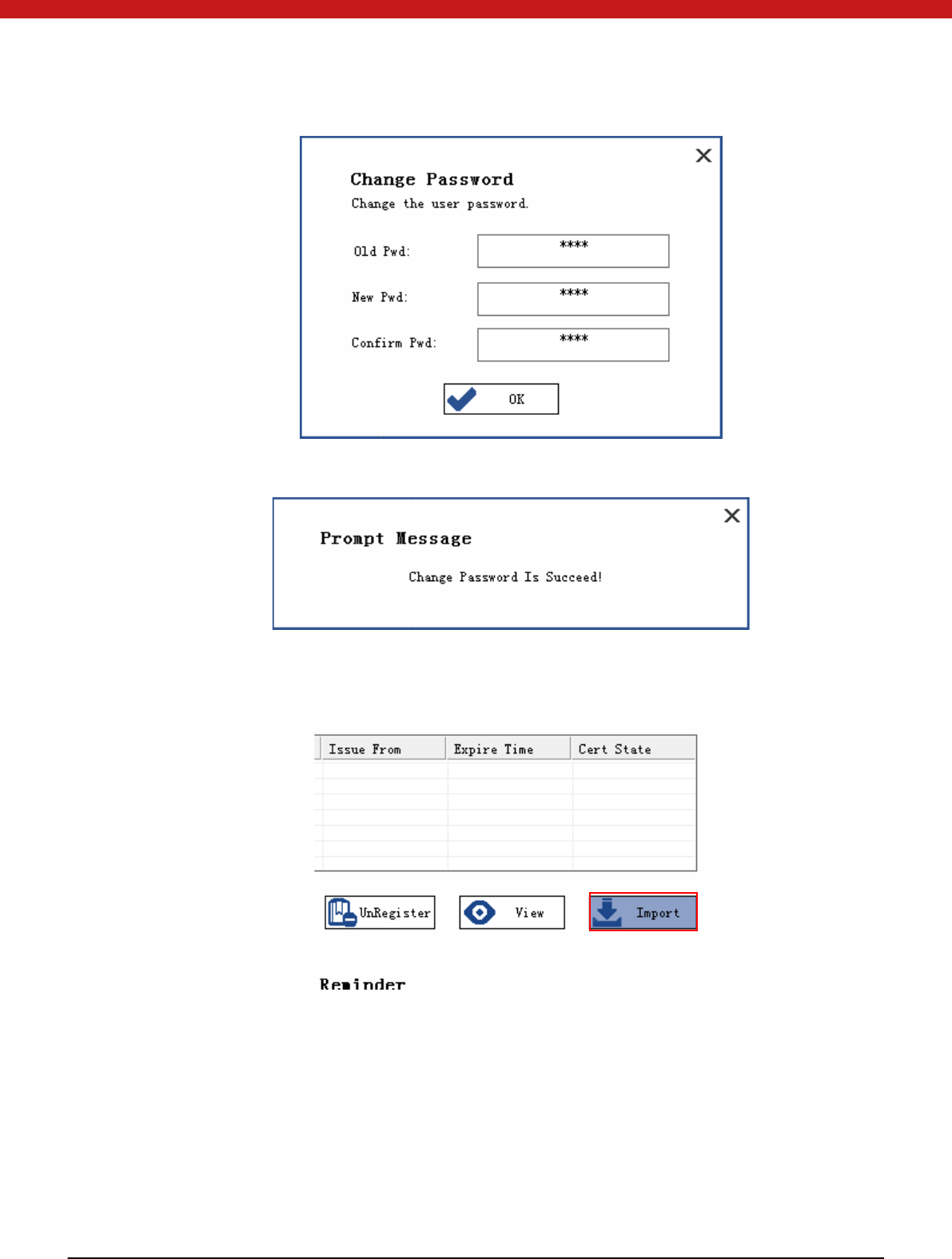
44 of 72
Click on OK
Import certificate
Click on the import.
In the pop up page, input user password and click on login.
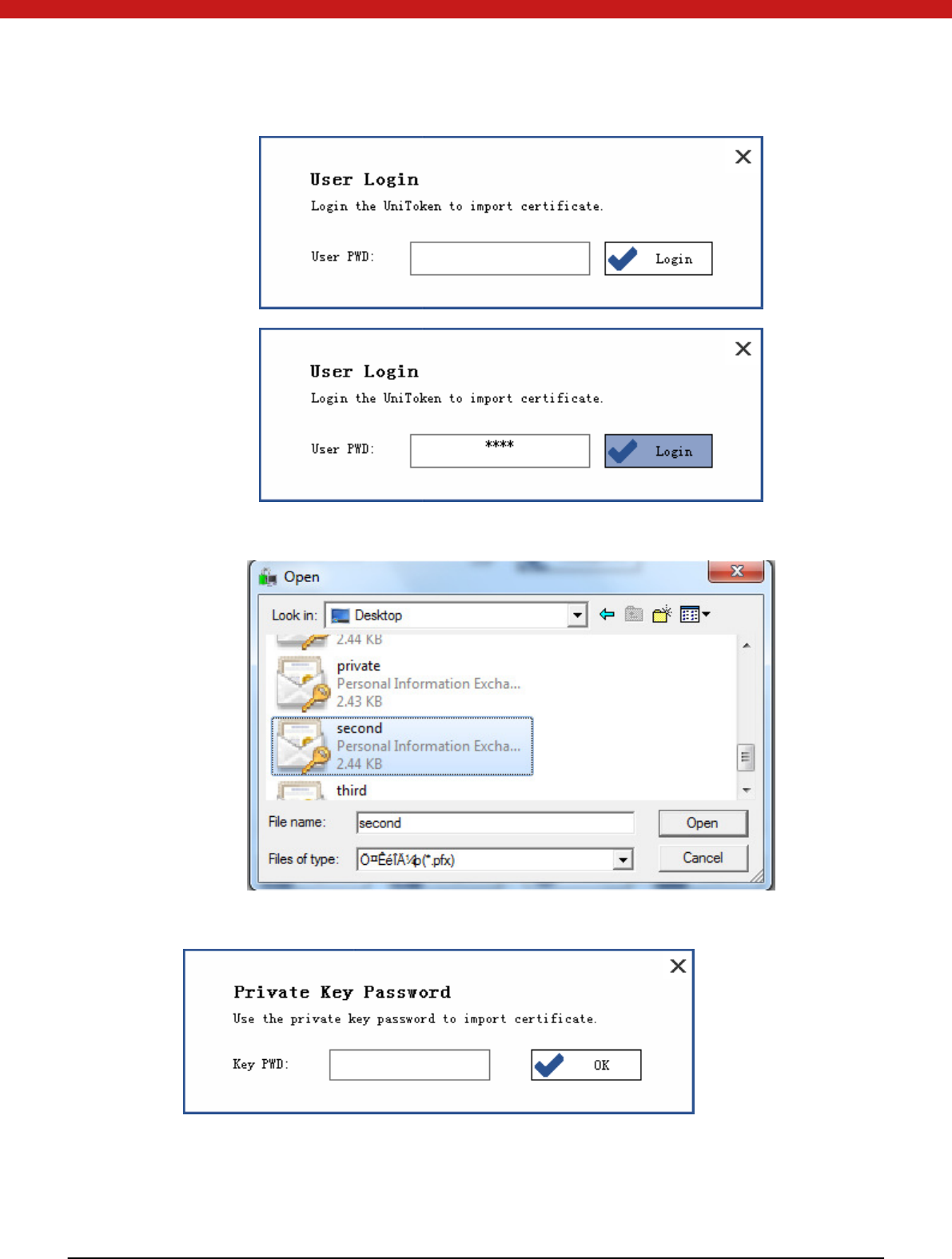
45 of 72
Find the certi fi cat e to be impo rted .
Enter the password to the certi fi cate.
Click on OK.
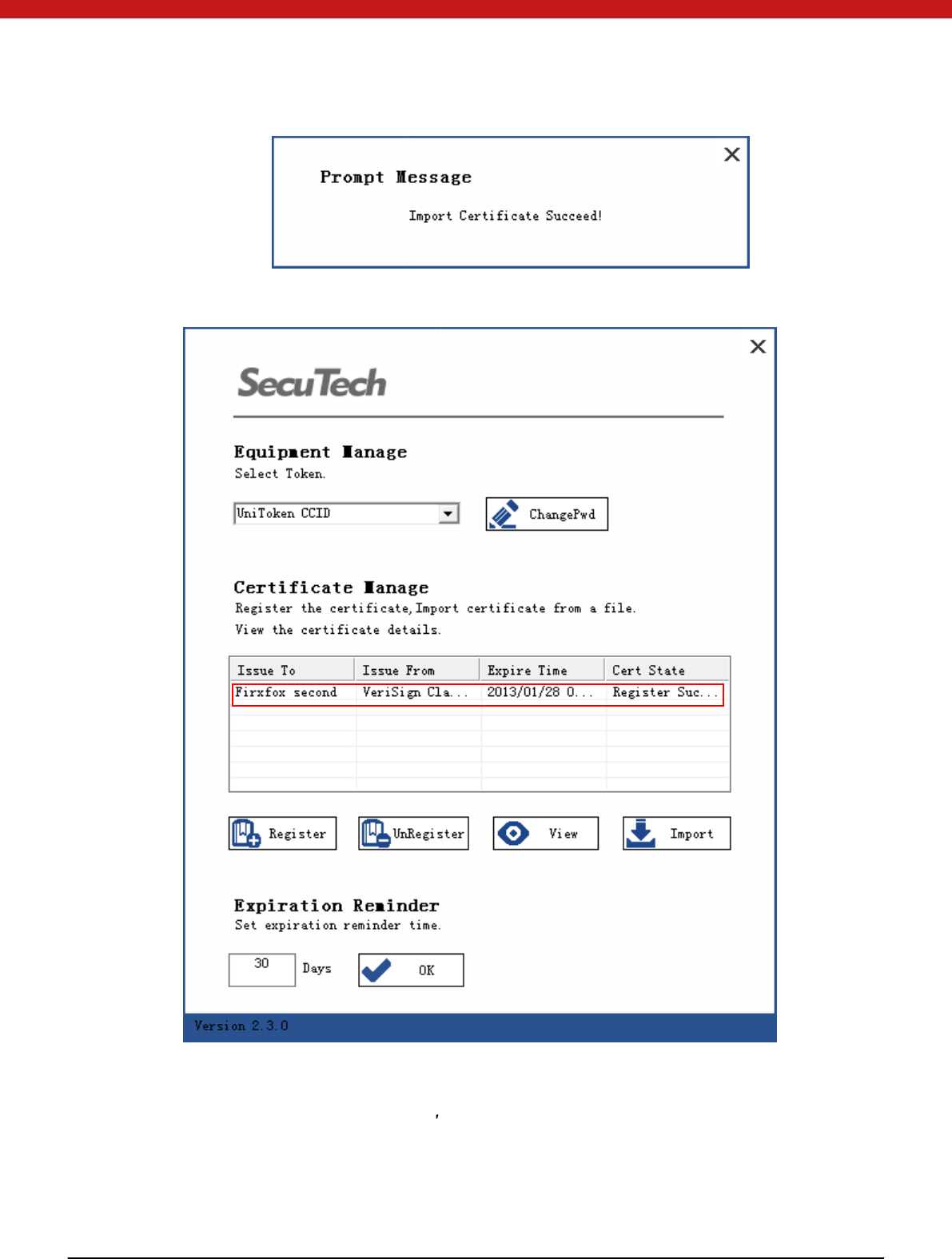
46 of 72
Certificate will display in the device.
Register certificate
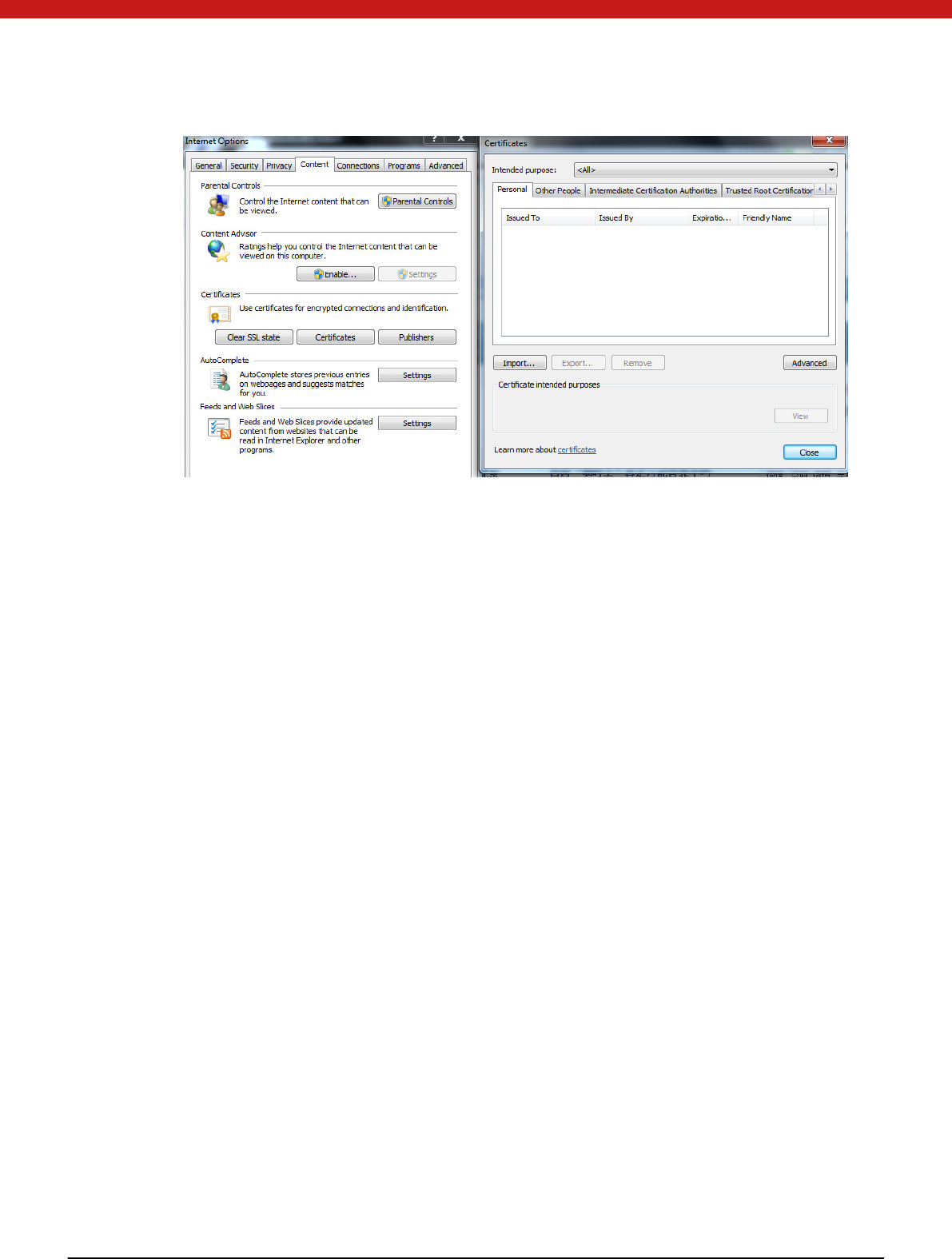
In IE-to ol -in tern et options-content-certificates check the registered certificates.
There is no certificate if it s first used.
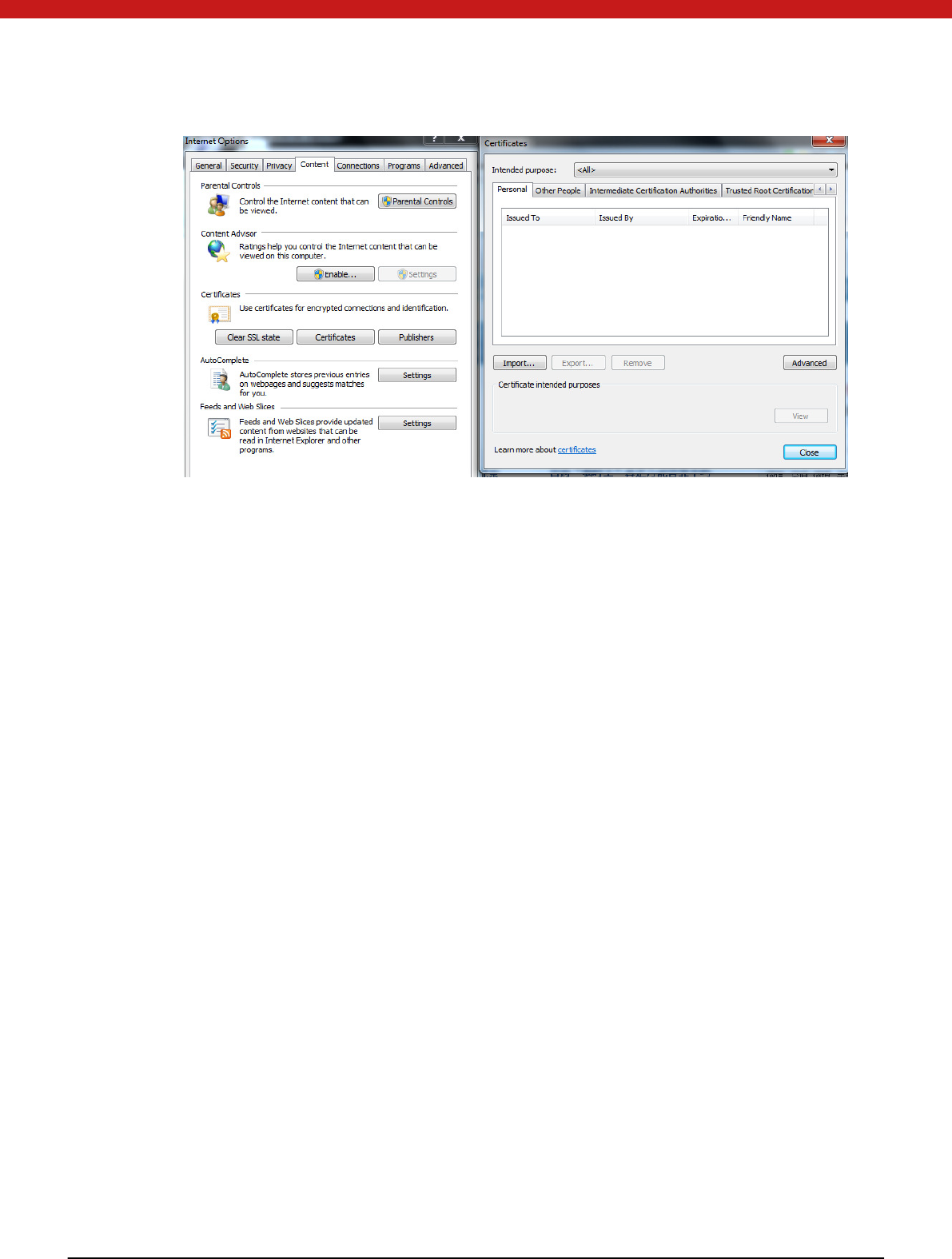
47 of 72
Select the certificate to be imported.
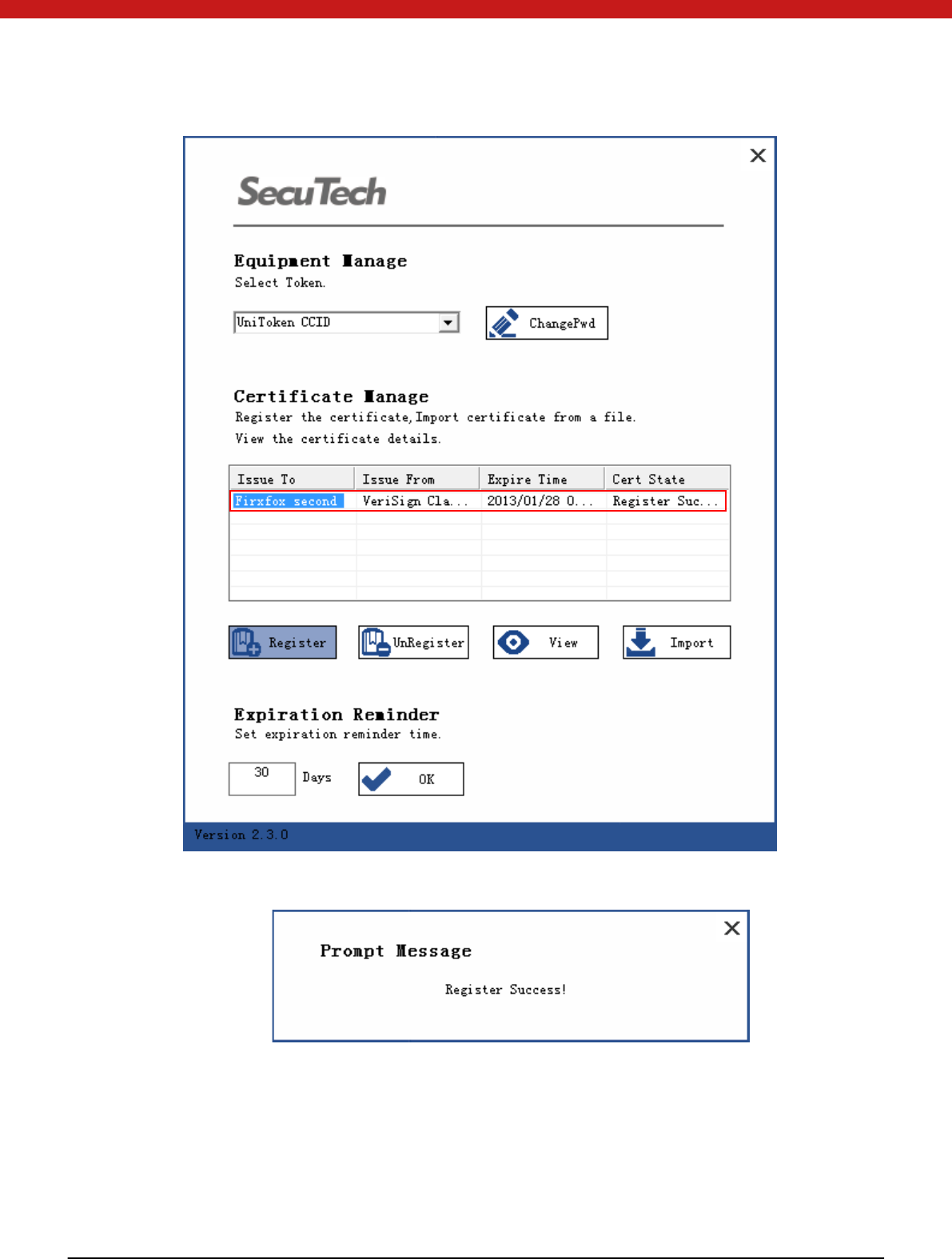
48 of 72
Click on Regi ster
Fro m IE-internet options-content-cert ifi cates, the regi st ered certi fi cate can be foun d .
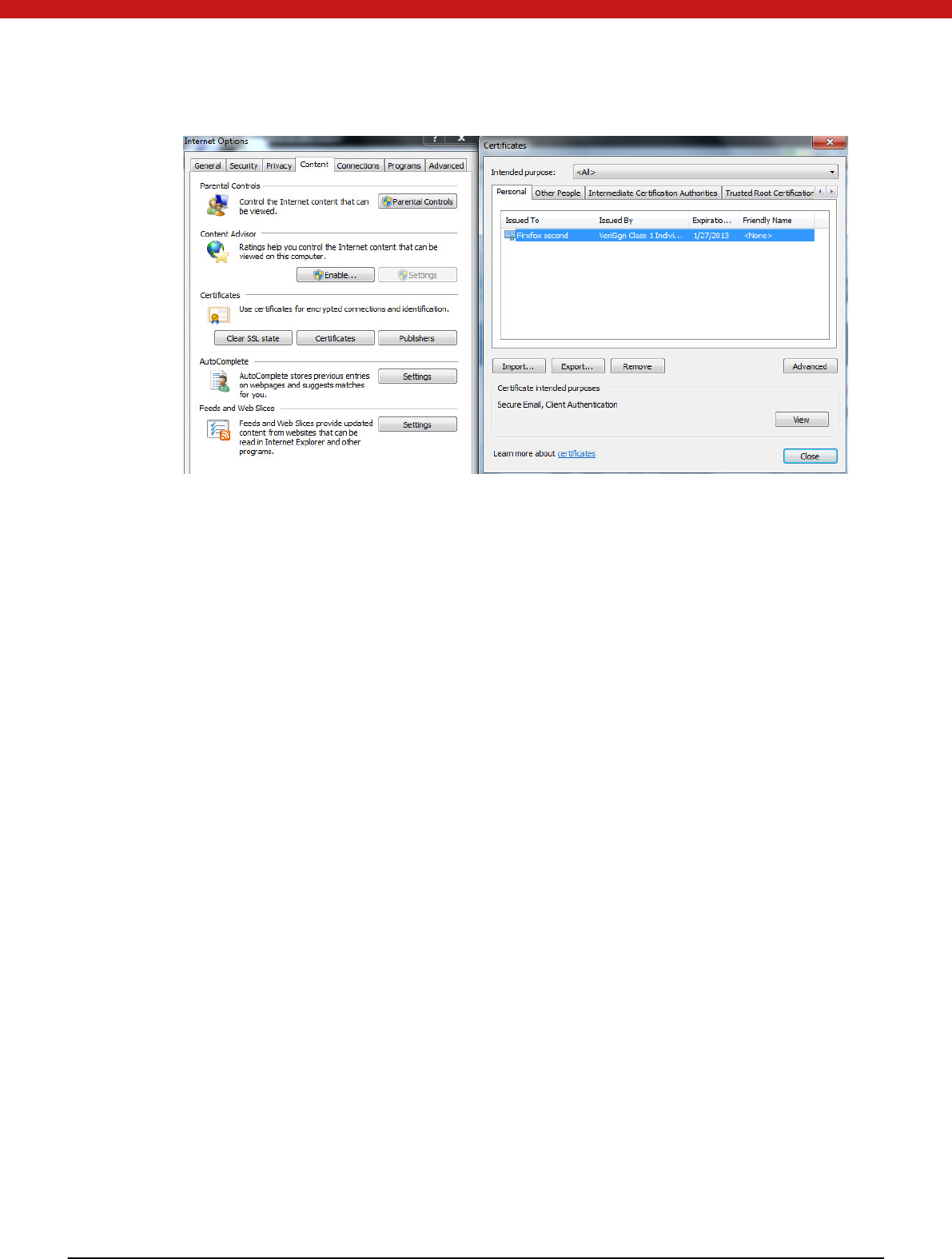
49 of 72
Unregister certificate
Select the certificate to be unregistered.
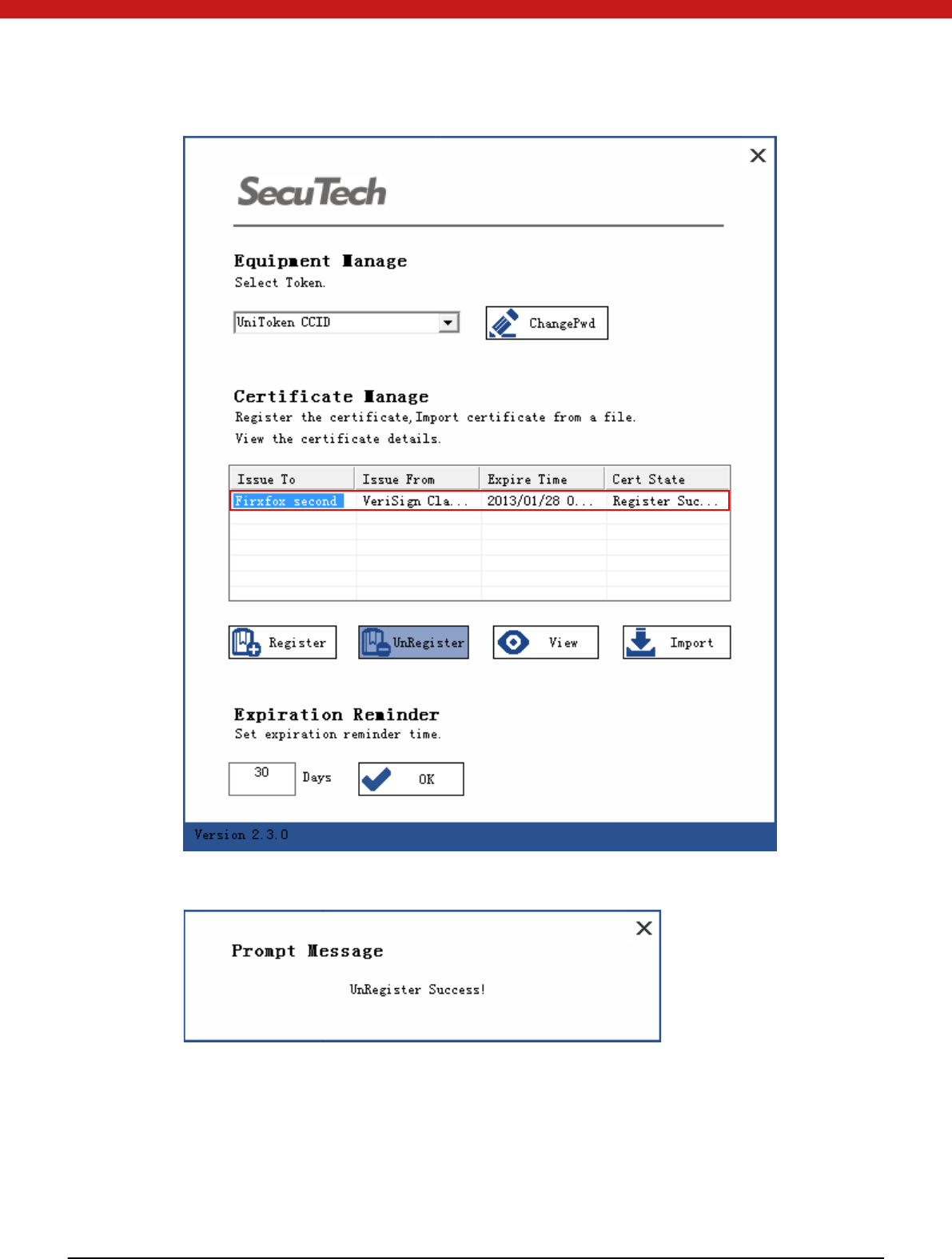
50 of 72
Click on Un regi ster
In IE-to ol -in tern et option-content-certi fi cates, the u n regi stered cert if i cat e i s rem oved .
51 of 72
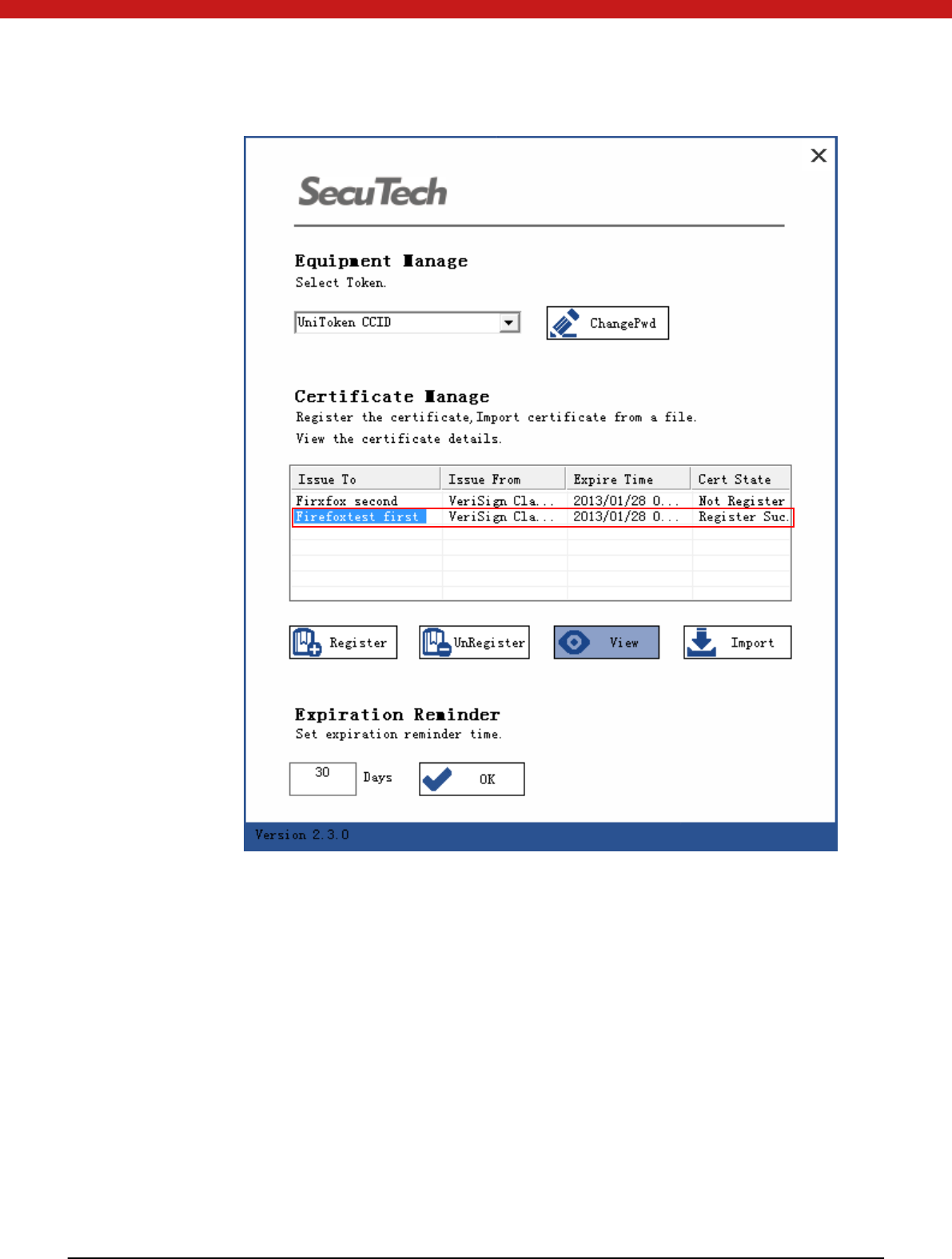
View certificate information
Select a certificate
52 of 72
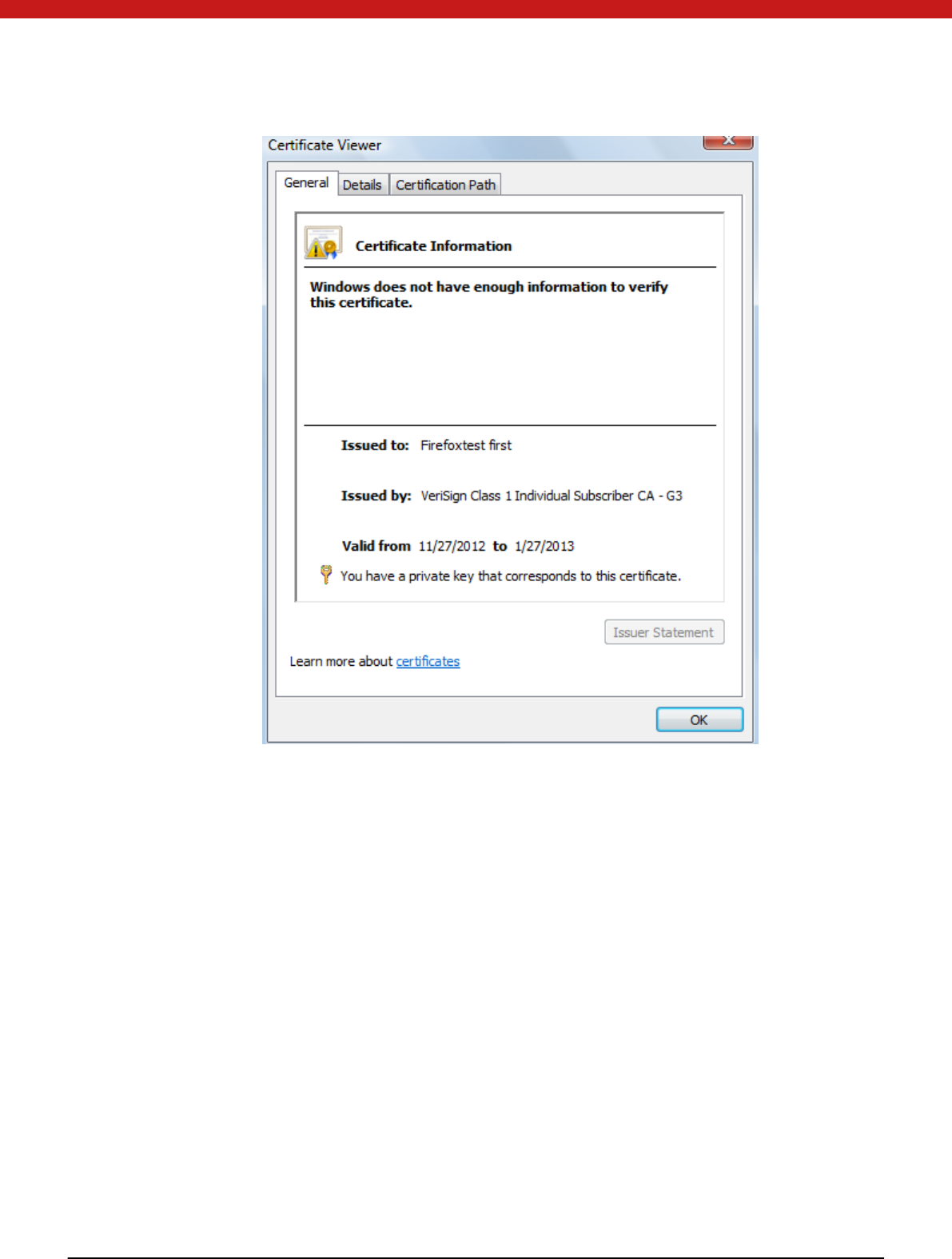
Click on view, and the certificate in fo rmat ion will display in the pop up page.
53 of 72
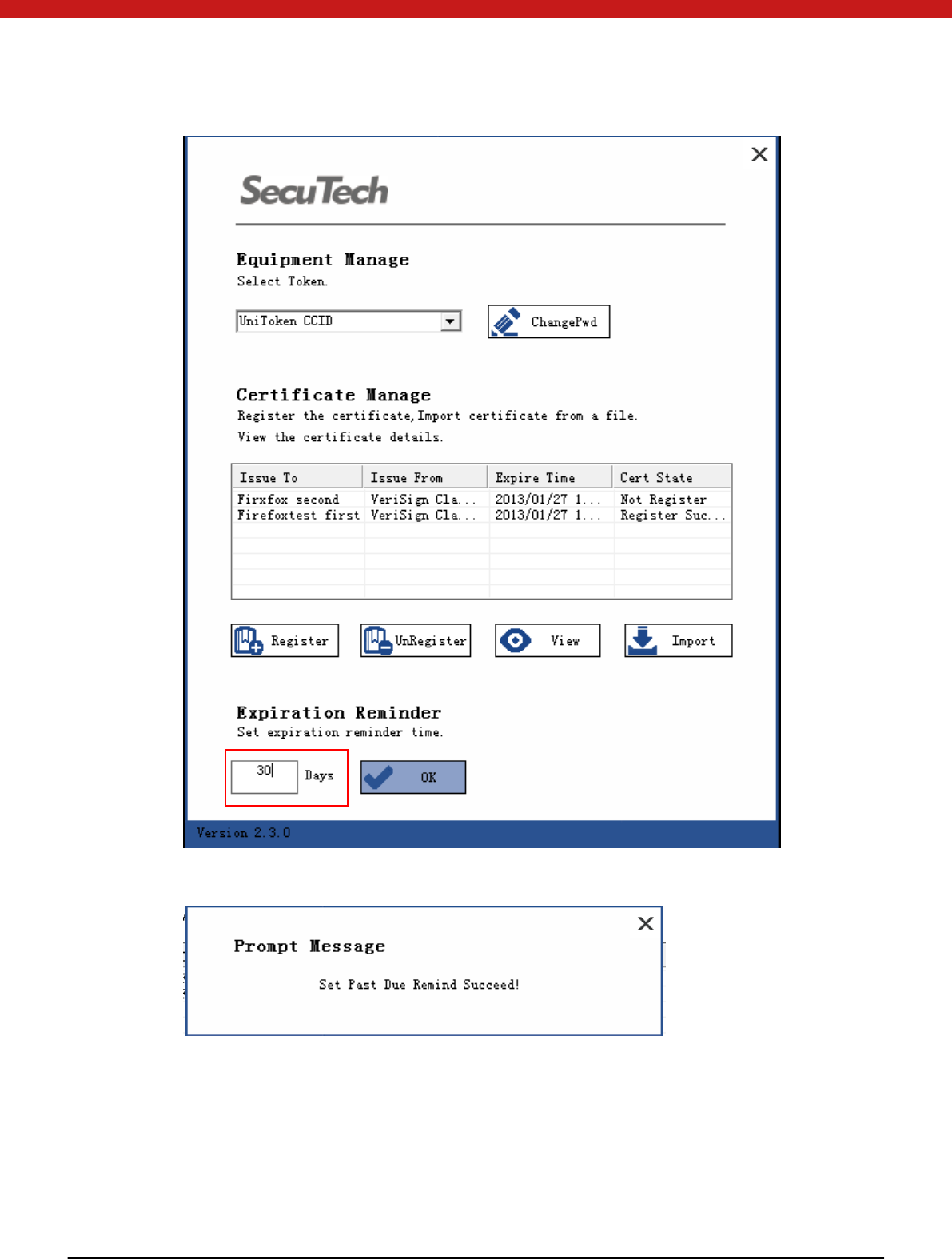
4.4.3 Expiration reminder
In onitor.exe, input ex pi ratio n remin der tim e
54 of 72
Click on OK
If a certificate expire date is less than the reminding date, a reminding message will
display shown as the following picture.
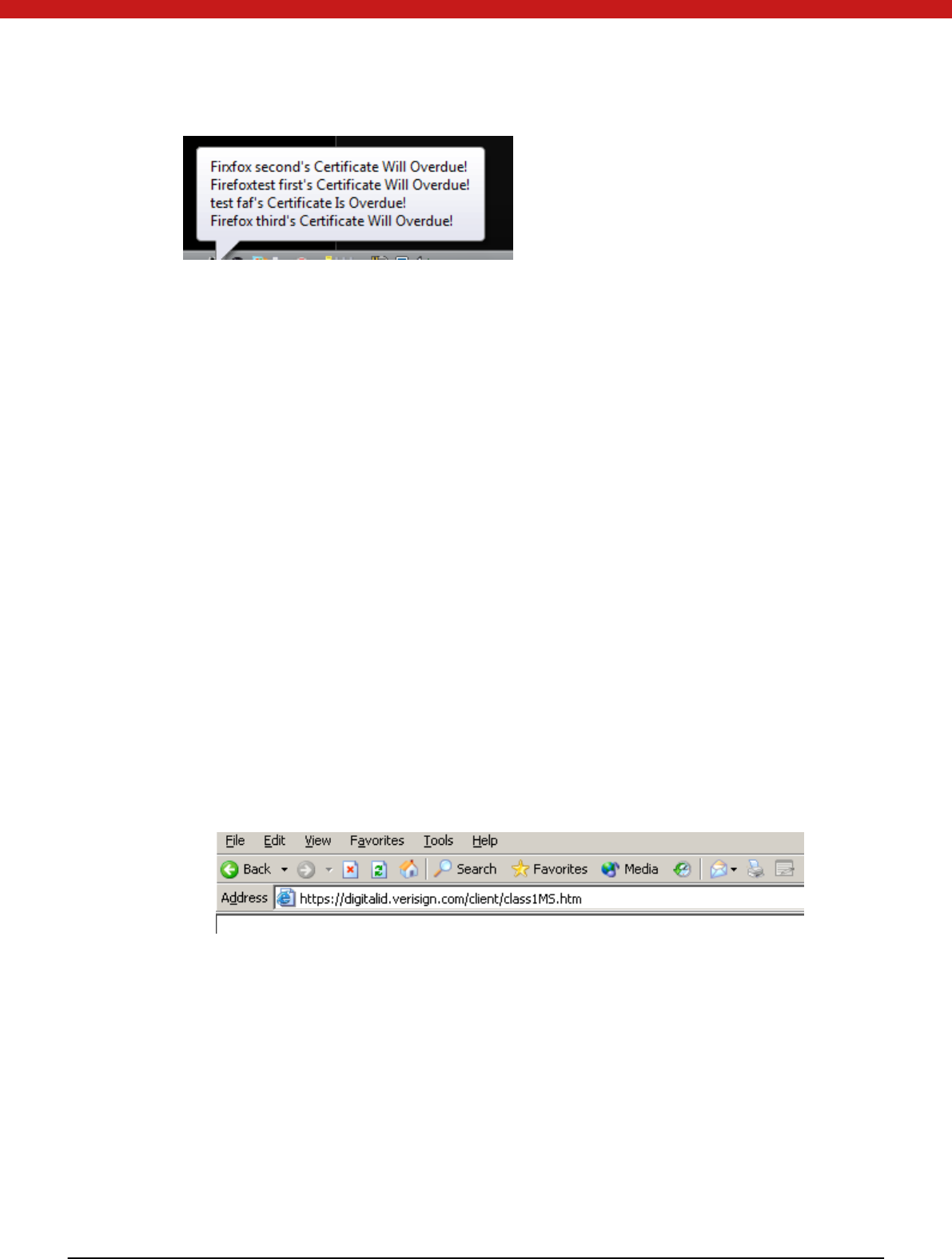
55 of 72
Part 3 Applying Digital Certificates
Chapter 1: Applying Digital Certificates
Token provides a perfect container for digital certificates. Token supports X.509 igital
certificates. Token PKI package is the middleware software, which provides digital
certificate usage. (See also 1.4.2)
Digital certificate is used to certify that the Token is the right device. Without it, any
op eration o f the Token is forbidden. In this part, we will introduce how to apply digital
certificates. We will take the VeriSign certificate and Microsoft Certificate for example.
1.1 Applying VeriSign Certificates
Insert one Token into USB port first, and start IE, type in
https://digitalid.verisign.com/client/class1MS.htm to open the certificate applying
page.
Th ere are fou r steps fo r app lying a certificate. The page provides comprehensible
instructions. It is easy to apply certificates by following the instructions step by step.
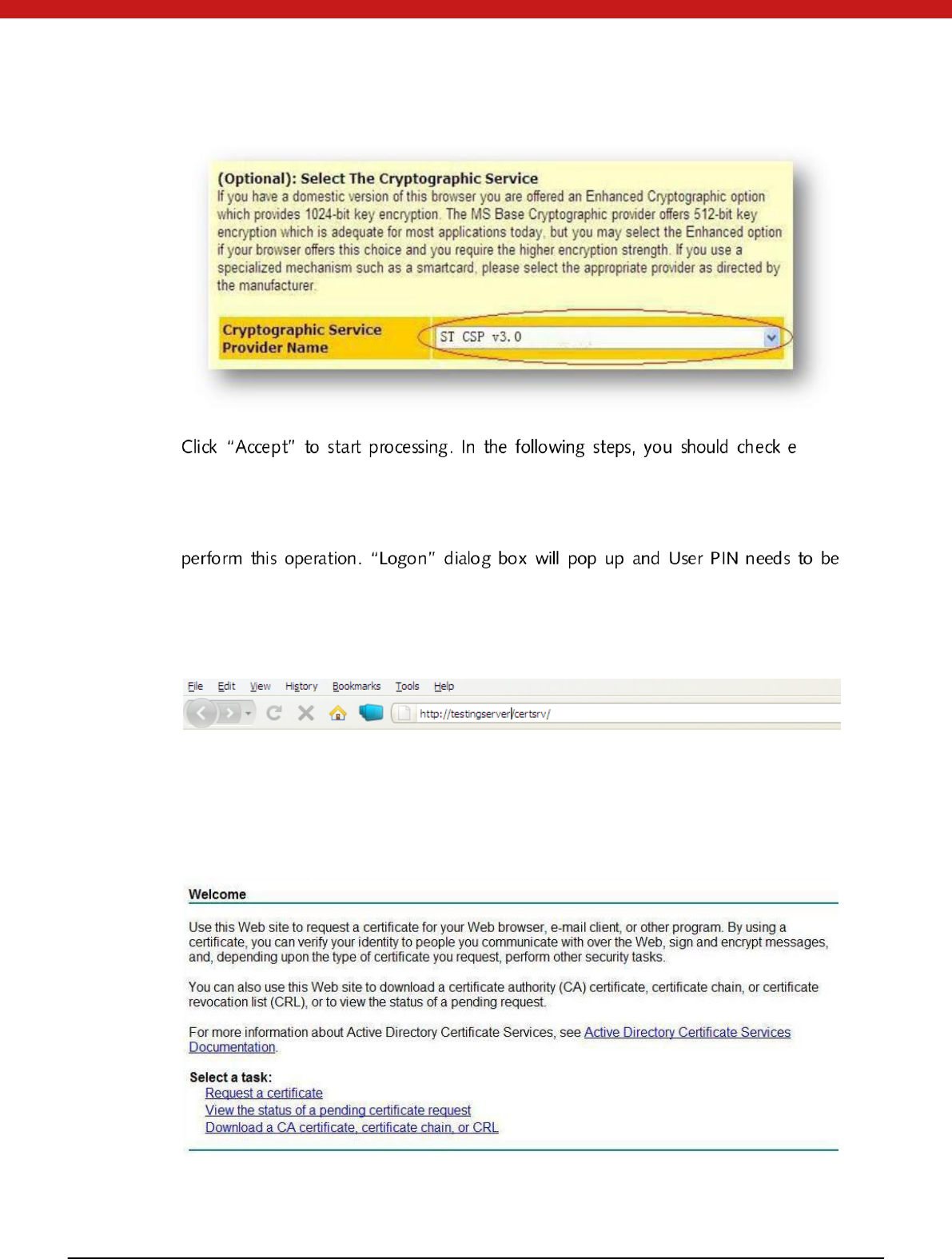
In parti cular, at the step o f co mplet e the en roll men t , aft er fil ling all th e in fo rm ation
required, select ST CSP v3.0 from the drop down list of Cryptographic Service Provider
Name.
56 of 72
-m ail ,
pick up digital ID and then install the digital ID according to the page tips. RSA
encryption key is generated in the Token.
If more than one Token are inserted in USB ports, please select the Token you want to
input.
1.2 Applying M icrosoft Certificates
Insert one Token into USB port first, and start IE to open M icrosoft certificate applying
page.
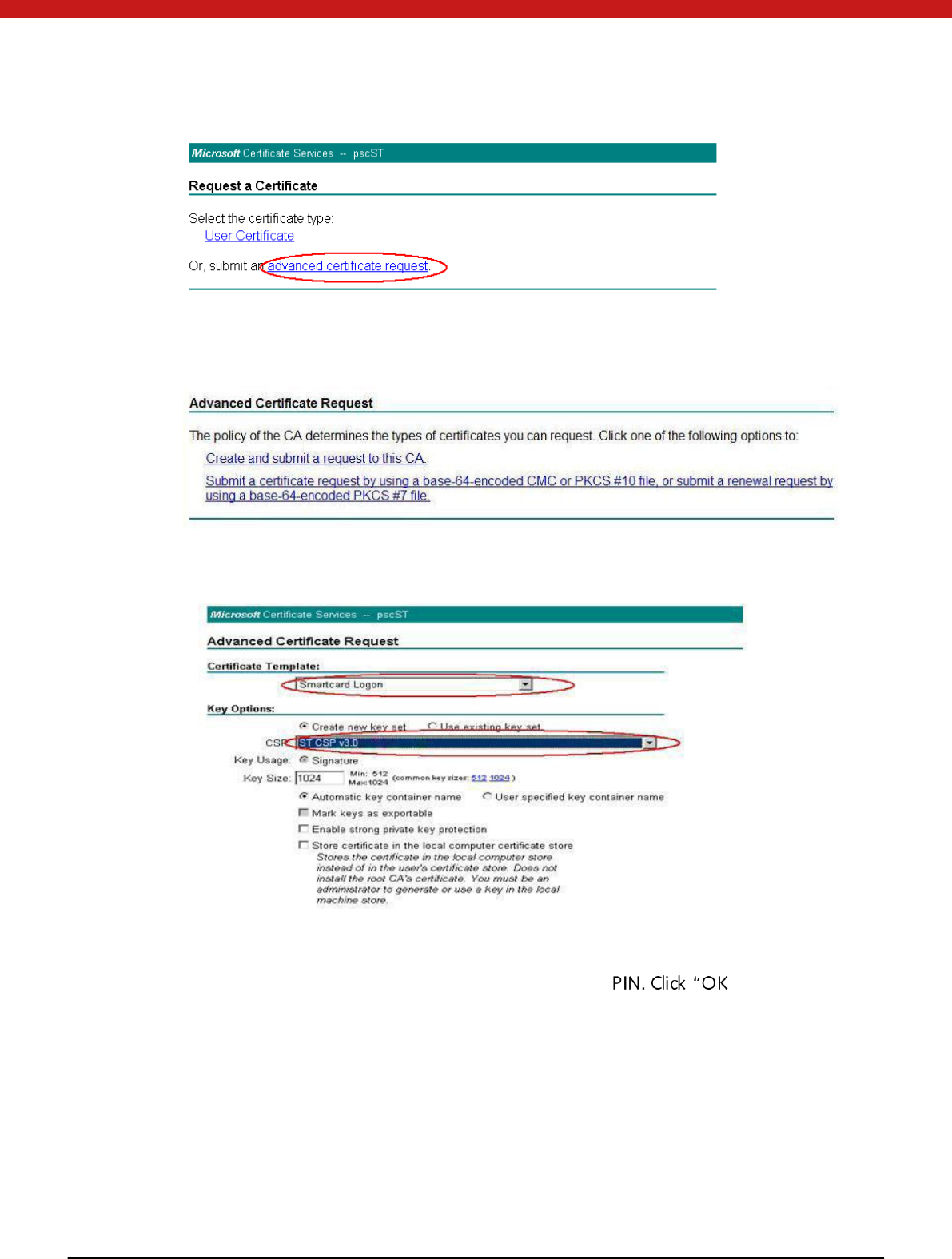
This is the home page of the certificate applying site. Firstly, you should click Request a
certificate.
And then, select advanced certificate request.
57 of 72
On the page of Advanced Certificate Request, select create and submit a request to
this CA.
For certificate template, select smartcard logon in the list; for CSP, select ST CSP v3.0
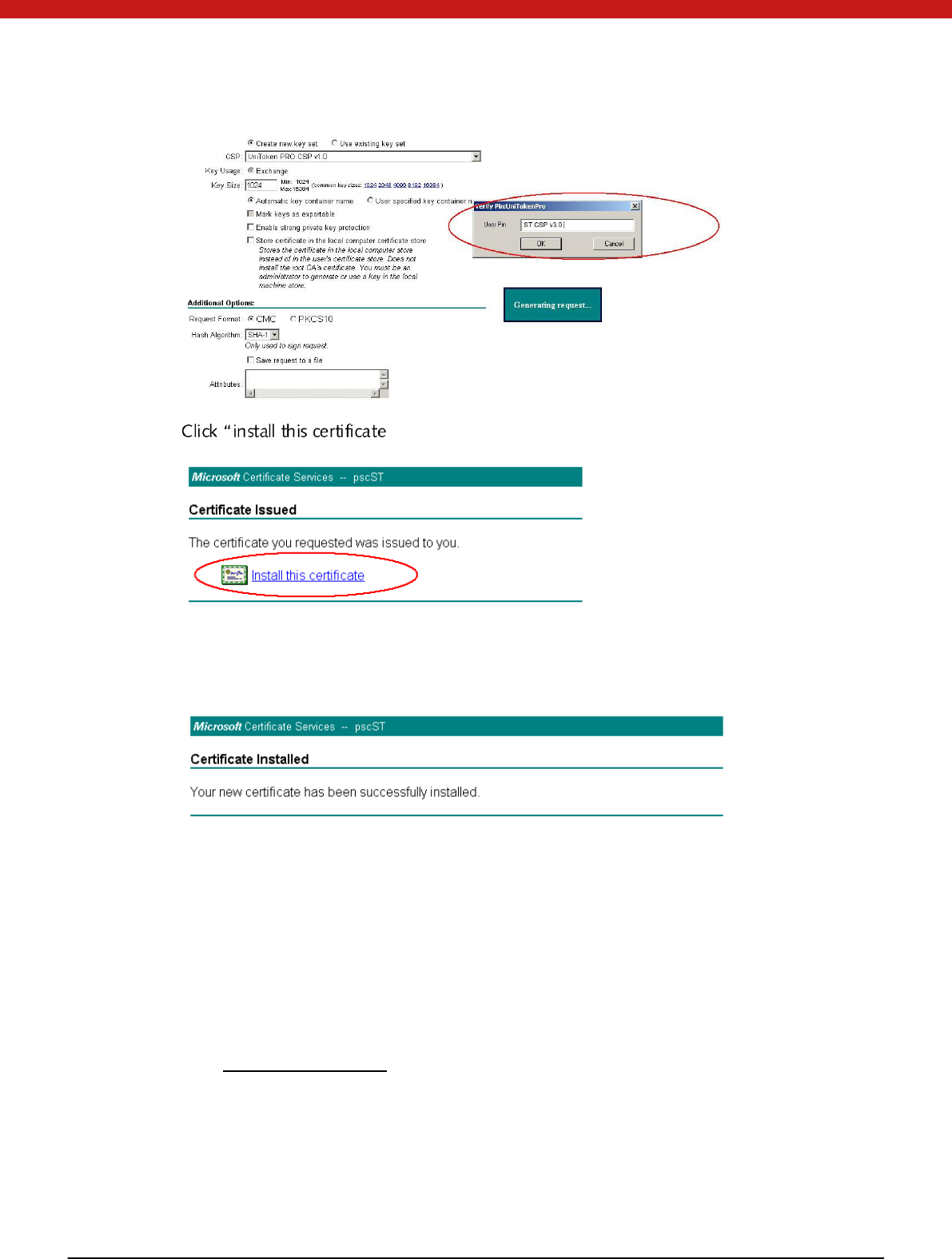
Then, a window will appear to ask you to type in Token ”. The system
will generate certificate automatically.
58 of 72
”for installation.
After installation, the system will prompt that certification has been successfully
installed.
1.3 Using Digital Certificates
SecuTech provides a series of solutions about the use of digital certificates, in the
aspects of IE, Outlook, PDF, Office and so on.
For the detailed instructions about that, please download relative integration guides
from www.eSecuTech.com.

59 of 72
Part 4 Developer’s Guide
Device Initialization
Token has b een PKI initialization at f actory . You can use CCID token in PKI application
the PKI application, you can use console in SDK\U ti li ties\Console\console.exe. To
complete the format operation, you need to provide transmission key, which
suggest security officer change this key to ensure the device security.
For the third party developers, we provide PKI initialization library and sample which can be
found in SDK\Libraries and SDK\Samples respectively.
Chapter 1: PKCS11 Application
1.2 Introduction
PKCS#11 is a Public-Key Cryptography Standard (PKCS) for public key cryptography,
developed by RSA Laboratories and includes both algorithm -specifi c and algo ri th m-
independent implementation standards. It is an industry standard that defines a
technology independent programming interface for cryptographic devices such as
smartcards and PCM CIA cards. This standard specifies an application program
in t erf ace (API), cal led Cryp to ki (Cryp tog raphi c Token In terface), to devi ces, either
physical or virtual, which hold cryptographic information (keys and other data) and
perform cryptographic functions. This API is used across many platforms and is
powerful enough for most security-related applications. SecuTech uses PKCS#11 as the
main API for Token programming. Token supports PKCS#11 application via Token
middleware.
60 of 72
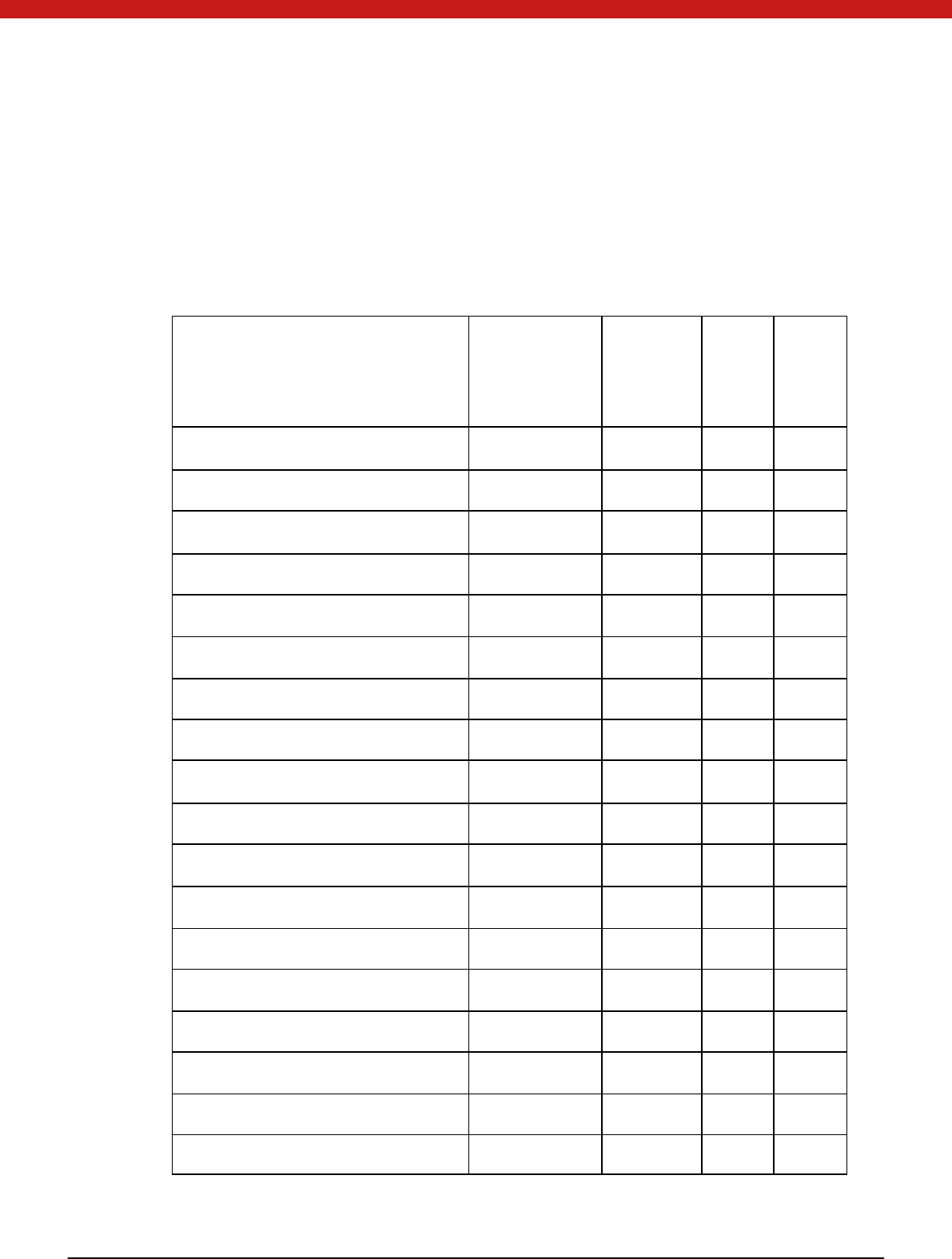
The following files are needed when developing the Token PKCS#11 applications.
Files Path
Cryptpki.h Provided by RSA
pkcs11.h Provided by RSA
Pkcs11f.h Provided by RSA
Pkcs11t.h Provided by RSA
uktp11.dll C:\ Windows\system32\
PKCS#11 module of Token supports the creation of the following objects:
Object Class Description
CKO _D ATA For data structures defined by application
CKO_SECRET_KEY For symmetric keys
CKO_CERTIFICATE For X.509 v3 certificates
CKO_PUBLIC_KEY For RSA/ DSA public key
CKO_PRIVATE_KEY For RSA/DSA private key All
61 of 72
All the object s listed in the above t able can be created with Token. The secu re storage
in Token is limited, so objects can only be created in memory but can NOT be stored in
the Token secure storage. Only encryption keys and permanently present data need to
be saved in the Token.
1.3 Supported PKCS#11 Algorithms and APIs
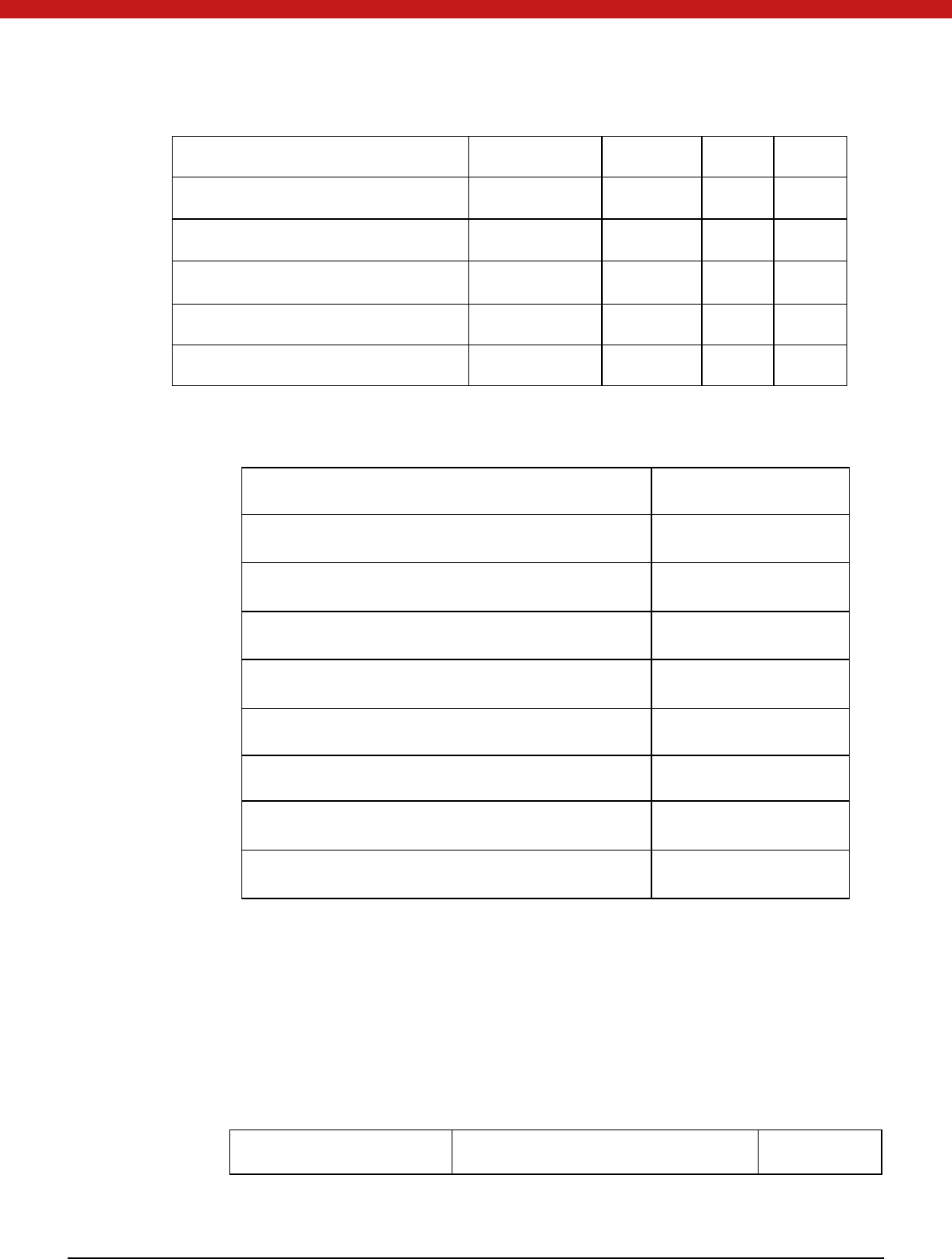
M echanisms Encrypt/ D ecry
pt
Sign/ Verif
y
Digest Genera
te
key/ pa
ir
CKM_RSA_PKCS_KEY_PAIR_GEN √
CKM_RSA_PKCS
CKM_DSA_KEY_PAIR_GEN √
CKM_DSA
CKM _RC2_KEY_GEN √
CKM _RC2_ECB
CKM _RC2_CBC
CKM _RC2_CBC_PAD
CKM _RC4_KEY_GEN √
CKM _RC4
CKM_DES_KEY_GEN √
CKM_DES_ECB
CKM _DES_CBC
CKM_DES3_KEY_GEN √
CKM _DES3_ECB
CKM _DES3_CBC
CKM _DES3_CBC_PAD
CKM _M D 2
62 of 72
CKM _M D 5
CKM _SHA_1
CKM_DH_PKCS_KEY_PAIR_GEN √
CKM_AES_KEY_GEN √
CKM_AES_CBC
CKM_AES_ECB
The table below lists all the key sizes in Token PKCS#11.
M echanisms Key Sizes
CKM _RSA_PKCS_KEY_PAIR_GEN 512~2048bits
CKM _DSA_KEY_PAIR_GEN 512~1024bits
CKM _RC2_KEY_GEN 1~128bits
CKM _RC4_KEY_GEN 1~256bits
CKM _DES_KEY_GEN 8bits
CKM _DES3_KEY_GEN 24bits
CKM _AES_KEY_GEN 16~32bits
CKM _DH_PKCS_KEY_PAIR_GEN 1~128bits
1.4 UniMate & UniToken PKCS#11 Function
Library
Token PKCS#11 library only implements the standard PKCS#11 APIs. Any other API
beyond PKCS#11 is not implemented. If such API is called, an error return code like
CKR_FUNCTION_NO_SUPPO RT will be returned.
Category Function Supported
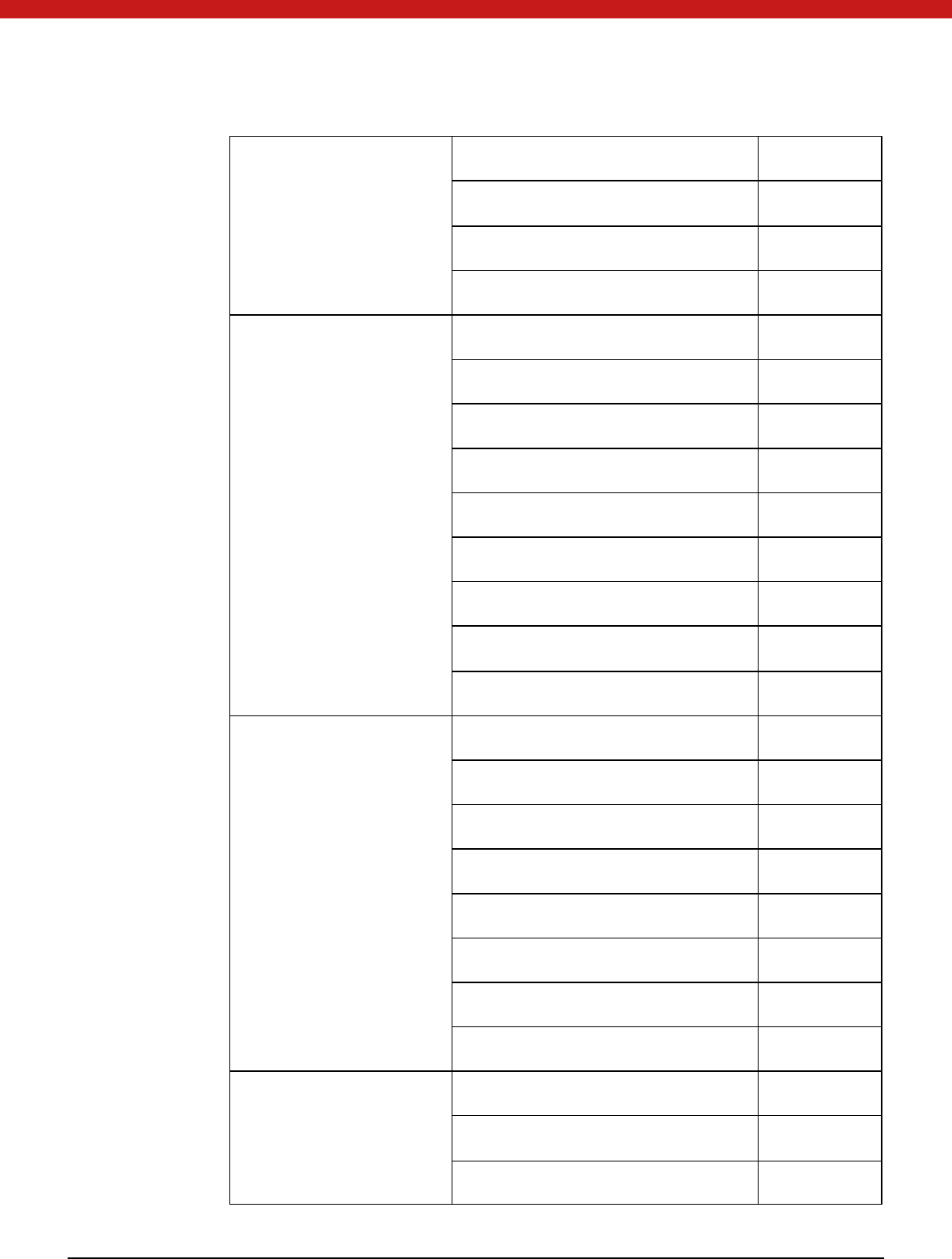
63 of 72
General Purpose Function
C_Initialize YES
C_Finalize YES
C_GetInfo YES
C_GetFunctionList YES
Slot and Token
Management Function
C_GetSlotList YES
C_GetSlotInfo YES
C_GetTokenInfo YES
C_WaitForSlotEvent YES
C_GetM echanismList YES
C_GetM echanismInfo YES
C_InitToken YES
C_InitPIN YES
C_SetPIN YES
Session M anagement
Function
C_OpenSession YES
C_CloseSession YES
C_CloseAllSessions YES
C_GetSessionInfo YES
C_GetOperationState YES
C_SetOperationState YES
C_Login YES
C_Logout YES
Objects M anagement
Function
C_CreateObject YES
C_CopyO bject NO
C_DestroyO bject YES
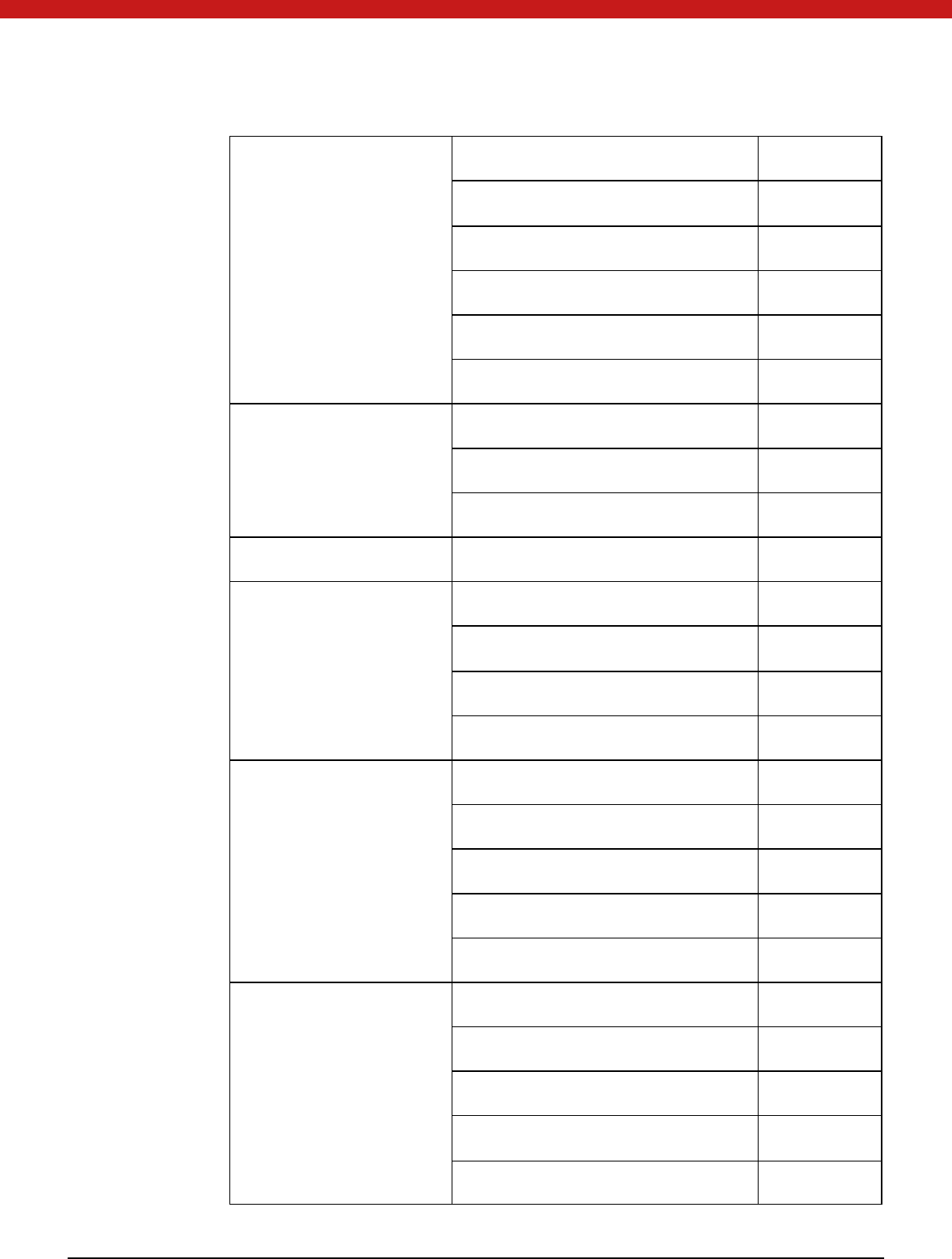
64 of 72
C_GetObjectSize YES
C_GetAttributeValue NO
C_SetAttributeValue YES
C_FindObjectsInit YES
C_FindO bjects YES
C_FindO bjectsFinal YES
Encryption Function C_EncryptInit YES
C_Encrypt YES
C_EncryptUpdate YES
C_EncryptFinal YES
Decryption Function C_DecryptInit YES
C_Decrypt YES
C_DecryptUpdate YES
C_DecryptFinal YES
Message Digesting Function C_DigestInit YES
C_Digest YES
C_DigestUpdate YES
C_DigestKey YES
C_DigestFinal YES
Signing and Hashing
Function (M AC)
C_SignInit YES
C_Sign YES
C_SignUpdate YES
C_SignFinal YES
C_SignRecoverInit YES
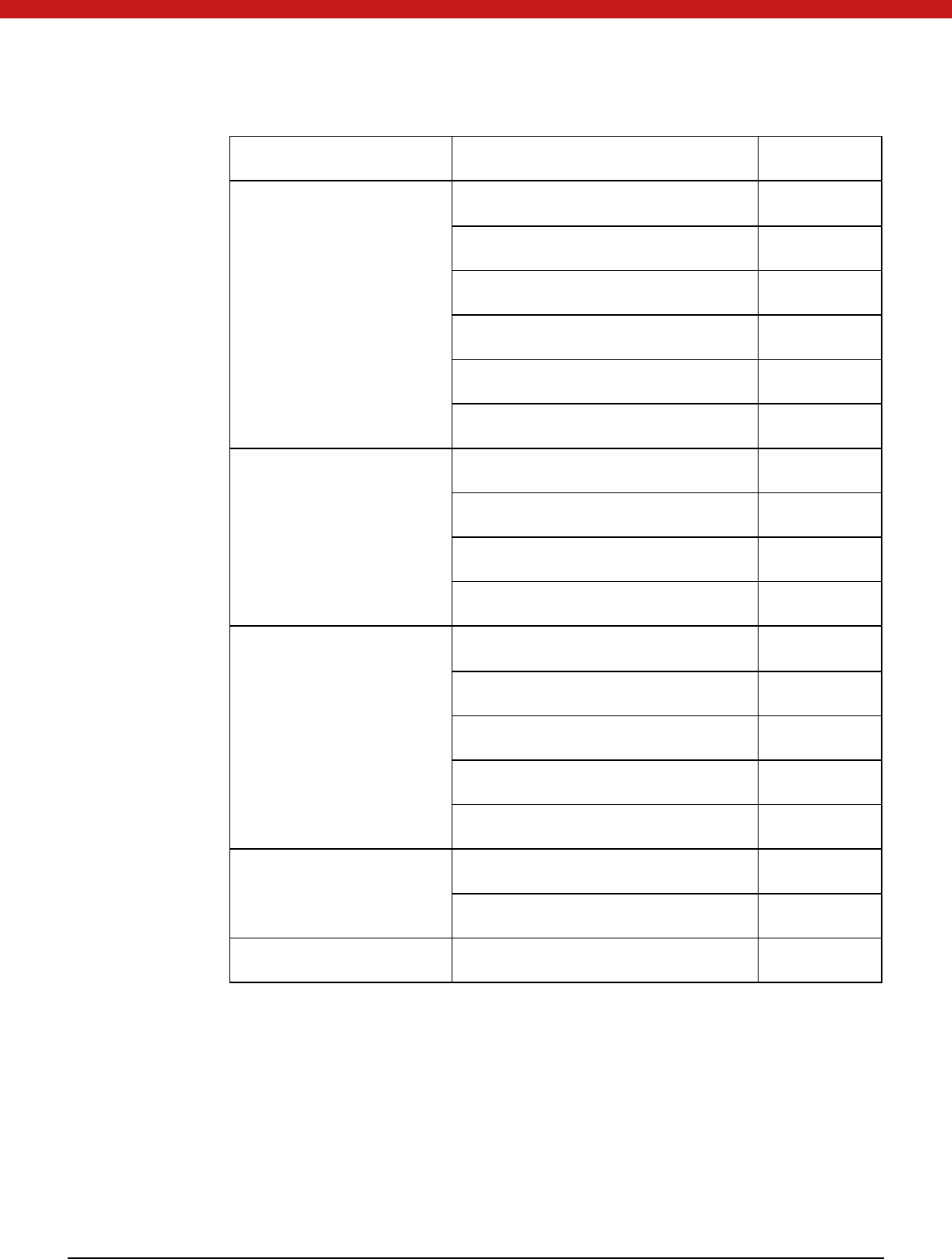
65 of 72
C_SignRecover YES
Functions for Verifying
Signatures and Hashing
(M AC)
C_VerifyInit YES
C_Verify YES
C_VerifyUpdate YES
C_VerifyFinal YES
C_VerifyRecoverInit YES
C_VerifyRecover YES
Dual-
purpose Cryptographic
Function
C_DigestEncryptUpdate YES
C_DecryptDigestUpdate YES
C_SignEncryptUpdate YES
C_DecryptVerifyUpdate YES
Key M anagement Function C_GenerateKey YES
C_GenerateKeyPair YES
C_WrapKey NO
C_UnwrapKey YES
C_DeriveKey NO
Random Number
Generation Function
C_SeedRandom YES
C_GenerateRandom YES
Callback Function YES
1.5 Samples
All the samples are implemented in C language, and they all support PKCS#11
standard v.
2.20. For this version, we provide the samples below:
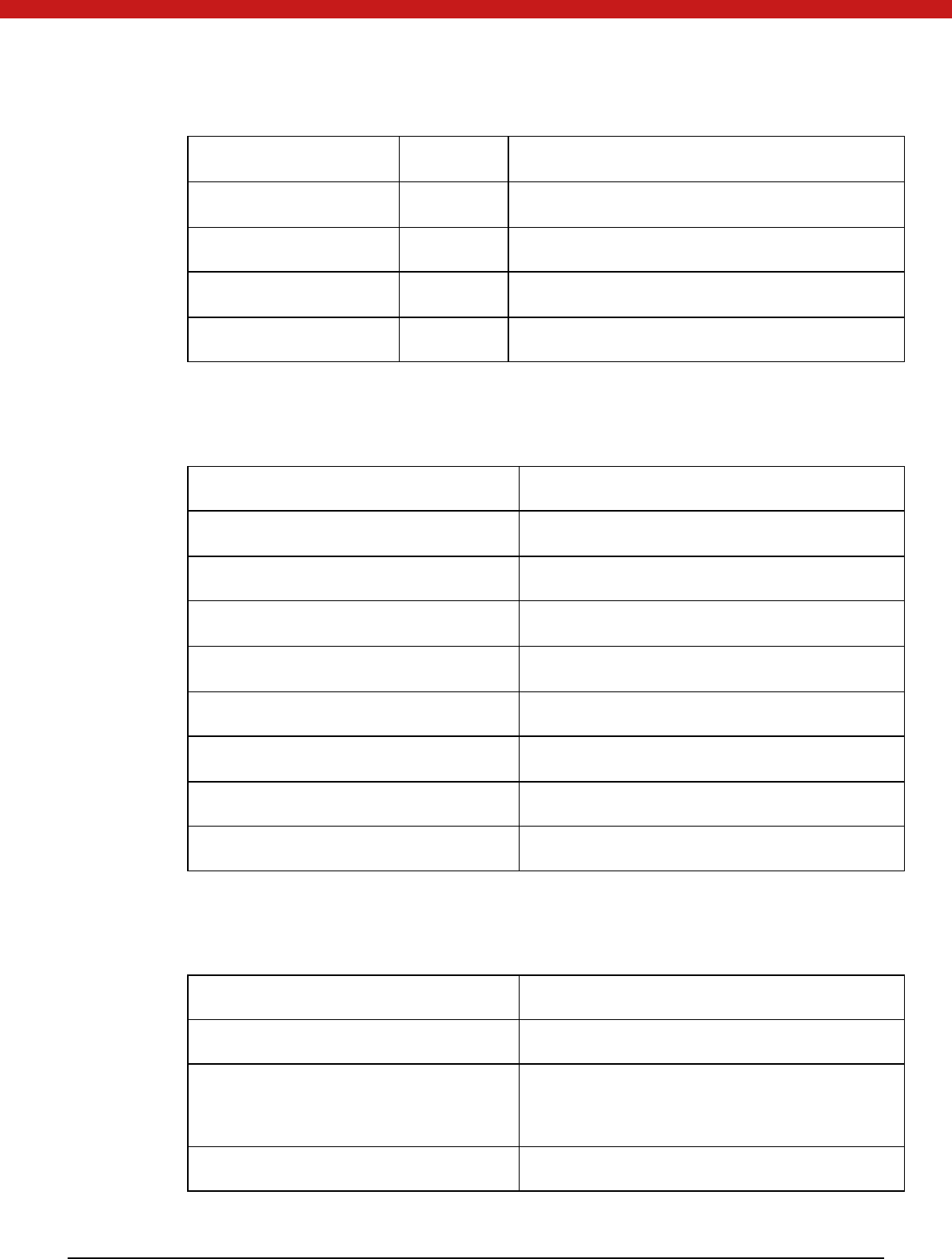
66 of 72
FUNCTIO N SAM PLE DESCRIPTIO N
To Initialize token Init Token The sample is used to initialize token.
To get token information TokenInfo The sample is used to get token information.
Encryption/ Decryption EDcrypt The sample is used to encrypt and decrypt data.
Sign verification SignVerify The sample is used for sign verification.
To initialize token
Path: SDK\sam ple\PKCS\InitToken\
STEPS FUNCTIO N
1. Initialize the PKCS#11 library C_Initialize
2. Get the slot list C_GetSlotList
3. Get token information C_GetTokenInfo
4. Initialize token C_InitToken
5. Open an session for token C_OpenSession
6. Log in C_Login
7. Initialize user PIN C_InitPIN
8. Log out C_C_Logout
To get token information
Path: SDK\sam ple\PKCS\TokenInfo\
STEPS FUNCTIO N
1. Initialize the PKCS#11 library C_Initialize
2. Get the information of PKCS#11
library
C_GetInfo
3. Get the slot list C_GetSlotList

67 of 72
4. Get the slot information C_GetSlotInfo
5. Get the token information C_GetTokenInfo
To verify signature
Path: SDK\sam ple\PKCS\SignVerify\
STEPS FUNCTIO N
1. Initialize the PKCS#11 library C_Initialize
2. Get the slot list C_GetSlotList
3. Open an session for token C_OpenSession
4. Log in C_ C_Login
5. If not found, generate key pair. C_GenerateKeyPair
6. Initialize a signature C_SignInit
7. Sign data C_Sign
8. Initialize verification C_VerifyInit
9. Verify signature C_Verify
Chapter 2: MS-CAPI Applications
2.1 Introduction
CAPI (Cryptographic Application Programming Interface), developed by Microsoft as
part of Microsoft Windows, is an interface to a library of functions software developers
can call upon for security and cryptography services. It is intended for use by
developers of applications for M S Windows platforms. CAPI allows multiple
cryptographic service providers (CSP) to coexist on the same computer and to be used
in the same application. It is also possible to associate a CSP with a particular
smartcard , so th at sm art card -enabled Windows applications will call the correct CSP.
M S W indows contains many helper functions that application developers may use to
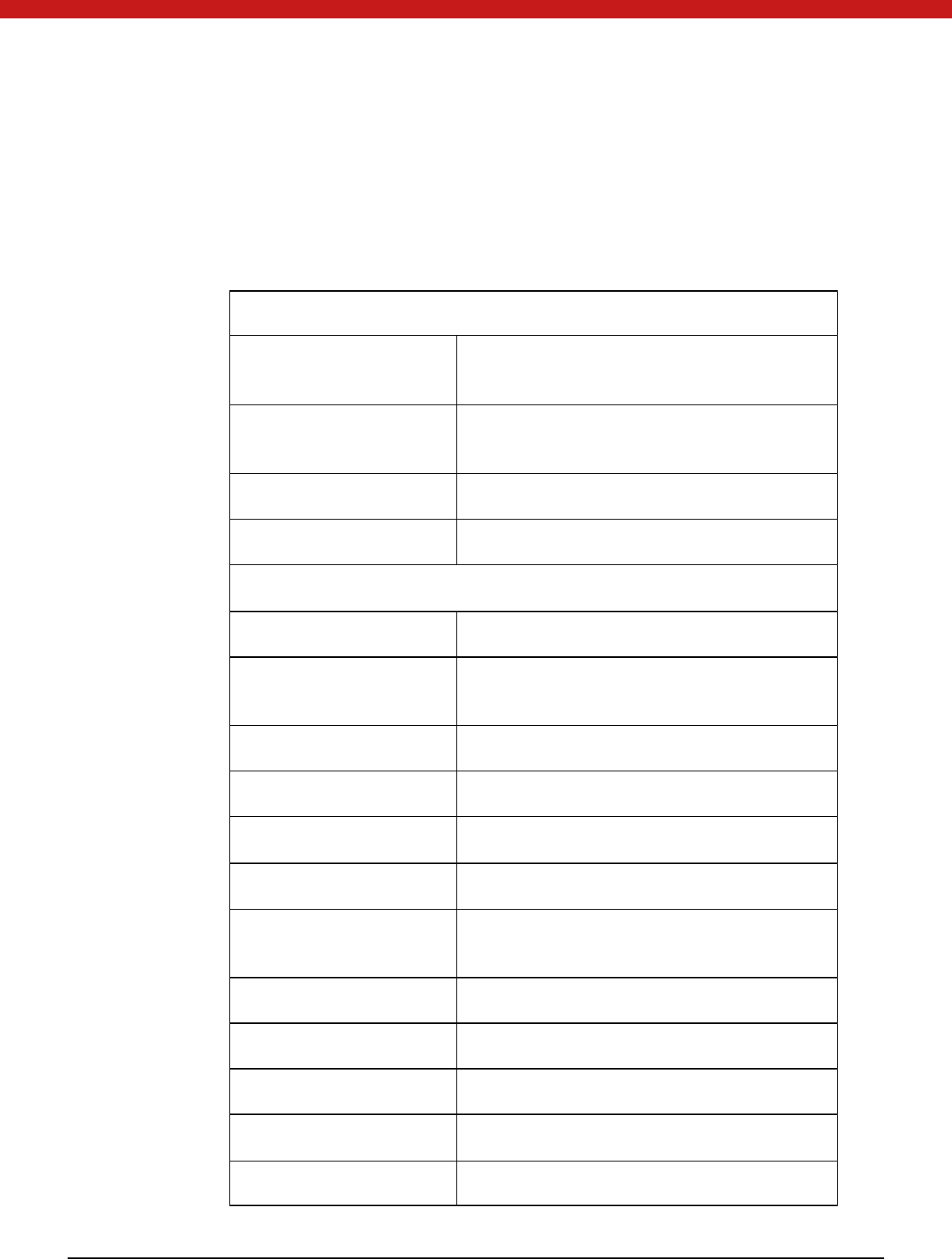
68 of 72
simplify code when working with cryptographic functions or with complicated data
stru ctu res (su ch as certificates). Choosing which API to use when developing
applications is dependent on the needs of the particular application.
2.2 Supported Algorithms and APIs
Connection Function
CPAcquireContext
Create a context and initialize access to CSP
which must be specified
CPReleaseContext
Release the context created in
CPAcquireContext and other resources
CPGetProvParam Return information related to CSP
CPSetProvParam Set parameters of CSP
Key to generate and exchange function
CPGenKey Generate key or key pair
CPDeriveKey
Derive a session key from a data hash and
guarantee the generated key different
CPSetKeyParam Set key attribute
CPGetKeyParam Get the attribute of encryption-operating key
CPExportKey Export key from container
CPImportKey Import the key to CSP container
CPDestroyKey Release key handle, after which the handle will
be
invalid and no access allowed
CPDuplicateKey Create a duplicate of key
CPGenRandom Generate random data
CPGetUserKey Get the enduring key pair from CSP container
Data encryption function
69 of 72
CPDecrypt Decrypt encrypted document
CPEncrypt Encrypt unencrypted document
CPCreateHash Create hashing objects and initialize them
CPDestroyHash Delete hashing objects handle
CPDuplicateHash Create a duplicate of hashing object
CPHashData Hash the input number
CPGetHashParam Get the computing result of hashing object
CPHashSessionKey
Hash a session key but no reveal of the key
value to application
CPSetHashParam Set the attribute of a hashing object
CPSignHash Sign a hashing object
CPVerifySignature Verify a digital signature
2.3 Samples
All the samples are implemented in C language, and they all support M S-CAPI
standard. For the standard, we provide the samples below:
Path: SDK\sam ple\CAPI
FUNCTIO N FILES DESCRIPTIO N
Algorithm algorithmTest.cpp
algorithmTest.h
The sample provides the operations on symmetric keys,
hashing and asymmetric keys.
Container kcsTest .cpp
kcsTest .h
The sample provides the operations on enumeration,
delete and creation of files.
Certificates listcerts.cpp
listcerts.h
The sample provides the operations on certificate list.
Algorithm sample
70 of 72
The samples include 3 functions:
int GenerateAlgTest(ULONG ulALG); int DeviceAlgTest(ULONG ulALG); int
RstTest(ULONG version);
GenerateAlgTest is used for DES key generation, encryption and decryption
op eration s.
STEPS FUNCTIO N
1.
Create a container CryptAcquireContext
2.
Retrieve parameters that govern the
operations of a CSP
CryptGetProvParam
3.
Generate a key CryptGenKey
4.
Data Encryption CryptEncrypt
5.
Data Decryption CryptDecrypt
DeviceAlgTest is used for key derivation, data encryption and decryption operations.
STEPS FUNCTIO N
1.
Create a container CryptAcquireContext
2.
Initiate the hashing of a stream of data CryptCreateHash
3. Add data to a specified hash object CryptHashData
4. Derive a key CryptDeriveKey
4.
Data Encryption CryptEncrypt
5.
Data Decryption CryptDecrypt
RstTest is used for RSA key generation, data encryption and decryption operations.
STEPS FUNCTIO N
1.
Create a container CryptAcquireContext
71 of 72
2.
Generate a key CryptGenKey
3. Data Encryption CryptEncrypt
4.
Data Decryption CryptDecrypt
Container Sample
The sample demonstrates how to enumerate, add and delete containers with int
kcsTest(ULONG ulActive) function.
For enumerating a container
STEPS FUNCTIO N
1.
Acquire a " VERIFYCONTEXT" handle CryptAcquireContext
2.
Enumerate the key containers CryptGetProvParam
3.
Acquire a handle to the key container found CryptAcquireContext
4.
Try to get a handle to the key pair CryptGetUserKey
5. Get key permissions CryptGetKeyParam
6.
Display key permissions
For adding a container
STEPS FUNCTIO N
1. Check whether the container already
exist s
CryptAcquireContext
2.
If not, create a container CryptAcquireContext
For deleting a container
STEPS FUNCTIO N
1.
Check whether the container already CryptAcquireContext
72 of 72
exist s
2. If there is, release the handle to the context CryptReleaseContext
3.
Delete the container CryptAcquireContext
List Certificate Sample
The sample demonstrates how to enumerate certificates with int listcerts(void) function
For enumerating certificates
STEPS FUNCTIO N
1.
Open a handle to the MY\ \ TokenStore certificate store CertO penStore
2.
Go over each and every certificate within the
certificate store
CertEnumCertificatesInStore
3.
Get and display the subject name from the certificate CertGetNameString
2.4 UniMate & UniToken API
(See also UniMate & UniToken API Reference in Token SDK\Documents\ )
About SecuTech

2 of 2
SecuTech Solution Inc. is a company specializing in data protection and strong authentication, providing
t o tal cu stomer sati sfact ion in secu ri ty sy stem s & serv i ces fo r ban ks, fin an cial i nsti tu i tion s & o th er i ndu stries.
Having extensive and in -depth experience within the information security market, SecuTech has drawn
-edge technologies, enables enterprises, financial institutions,
and government to safely adopt the economic benefits of mobile and cloud computing that are effective
against increasingly sophisticated cyber att acks.
www .eSecuTech.com SecuTech Solution Inc.
North America
1250 Boulevard Ren é-
Lévesque Ouest, #2200,
Mon treal, QC, H3B
4W8, Can ada
T: +1 -888-259-5825
F: + 1 -888-259-5825
ext.0
E:
INFO@eSecuTech .co m
China
Level 12, #67 Bei Si
Hu an Xi Lu,
Beijing, Chin a, 100080
T: +8610-8288 8834
F: + 8610-8288 8834
E: CN@eSecuTech.co m
APAC
Suite 5.14, 32 Delhi Rd,
No rth Ryd e,
NSW, 2113, Australia
T: 00612-9888 6185
F: 00612-9888 6185
E: AUS@eSecuTech.co m
EM EA
4 Cours Bayard 69002
Lyon, Fran ce
T: +33-042-6 00 -2810
F: +33-042-600-2810
M : +33-060-939 6463
E: Europ e@eSecuTech.co m
© Co pyright 20 12 SecuTech Sol ut ion I nc. All right s reserved. Reproduct ion in whole or in part wit h out writ t en per m ission f rom Secu Tech is prohi bit ed. SecuTech Token a nd t he Secu Tech l og o are
trademarks of SecuTech Inc. W indows a nd a ll ot her trademarks are properties of their respective owners. Features and specific at ions are subject t o cha nge w it ho ut not ice.