Sagem Wireless MA120 MA120 User Manual DOC MA
Sagem Wireless MA120 DOC MA
Contents
- 1. Installation Guide
- 2. Users Manual
Users Manual

2 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
Table of content
INTRODUCTION 6
INTERFACES PRESENTATION 7
MAN-MACHINE INTERFACE 7
ELECTRICAL INTERFACES 8
SETTING UP THE TERMINAL IP ADDRESS 9
ACCESS CONTROL PRESENTATION 10
IDENTIFICATION - AUTHENTICATION 10
“HIT OR NO HIT” RESULT COMMUNICATION 12
“PROXY” MODE 13
CONFIGURING A “CONNECTED” MORPHOACCESS 14
INTRODUCTION 14
NETWORK FACTORY SETTINGS 15
CONFIGURING A STANDALONE MORPHOACCESS 16
“USB” KEY ADMINISTRATION 16
PRINCIPLE 17
CHANGING A PARAMETER 18
CONFIGURATION INTERFACE 18
CONFIGURATION ORGANIZATION 18
“CONFIGURATION TOOL” 19
UPGRADING THE FIRMWARE 20
ACCESS CONTROL BY IDENTIFICATION 21
ACCESS CONTROL BY AUTHENTICATION (MA120 / MA110 ONLY) 22
CONTACTLESS AUTHENTICATION WITH TEMPLATES ON A CONTACTLESS CARD 23
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 3
CONTACTLESS AUTHENTICATION WITH TEMPLATES ON LOCAL DATABASE 24
CONTACTLESS AUTHENTICATION BASED ON CARD MODE 25
BYPASSING THE BIOMETRIC CONTROL IN AUTHENTICATION 26
MERGED MODE 27
MORPHOACCESS 220 320 COMPATIBILITY 28
PROXY MODE 29
RECOGNITION MODE SYNTHESIS 30
SETTING UP RECOGNITION MODE 31
TWO ATTEMPTS MODE 31
PARAMETERS 31
SETTING UP MATCHING PARAMETERS 32
RELAY ACTIVATION 33
LED IN ACTIVATION 34
LOG FILE 35
REMOTE MESSAGES 36
PRESENTATION 36
SUPPORTED PROTOCOLS 36
TAMPER SWITCH MANAGEMENT 37
ALARM ACTIVATION 37
EXAMPLES 38
MAN MACHINE INTERFACE 39
CONVENTION 39
IDENTIFICATION – WAITING FOR A FINGER 39
AUTHENTICATION – WAITING FOR A BADGE 39
FUSION - WAITING FOR A FINGER OR A BADGE 40
CONTROL OK 40
CONTROL FAILED 40
NO DATABASE OR EMPTY DATABASE 40
BIOMETRIC ACQUISITION, BAD PLACEMENT 41
USB KEY CAN BE REMOVED 41
SENSOR FAILED 41
4 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
NETWORK PARAMETERS 42
SECTION [BOOT PROTO] 42
SECTION [PARAMETERS] 42
TERMINAL INFORMATION 43
SECTION [INFO] (READ ONLY) 43
ADMINISTRATION PARAMETERS 44
SECTION [REMOTE MANAGEMENT TCP] 44
SECTION [TERMINAL] 44
ANNEX: CONTACTLESS MODES TABLE 45
ANNEX: REQUIRED TAGS ON CONTACTLESS CARD 46
FAQ 47
TERMINAL IP ADDRESS IS UNKNOWN OR TERMINAL IS NOT REACHABLE 47
SENSOR IS OFF 47
TERMINAL RETURNS ERRATIC ANSWERS TO PING REQUESTS 47
BIBLIOGRAPHY 48
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 5

I
IN
NT
TR
RO
OD
DU
UC
CT
TI
IO
ON
N
Congratulations for choosing the SAGEM MorphoAccess™ 1XX
Automatic Fingerprint Recognition Terminal.
MorphoAccess™ provides an innovative and effective solution for access
control or time and attendance applications using Fingerprint Verification
or/ and Identification.
Among a range of alternative biometric techniques, the use of finger
imaging has significant advantages: each finger constitutes an unalterable
physical signature which develops before birth and is preserved until
death. Unlike DNA, a finger image is unique to each individual - even
identical twins.
The MorphoAccess™ terminal integrates SAGEM image processing and
feature matching algorithms. This technology is based on lessons learned
during 20 years of experience in the field of biometric identification and the
creation of literally millions of individual fingerprint identification records.
We believe you will find the SAGEM MorphoAccess™ fast, accurate, easy
to use and suitable for physical access control or time and attendance.
To ensure the most effective use of your SAGEM MorphoAccess™, we
recommend that you read this User Guide totally.
6 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
I
IN
NT
TE
ER
RF
FA
AC
CE
ES
S
P
PR
RE
ES
SE
EN
NT
TA
AT
TI
IO
ON
N
M
Ma
an
n-
-m
ma
ac
ch
hi
in
ne
e
i
in
nt
te
er
rf
fa
ac
ce
e
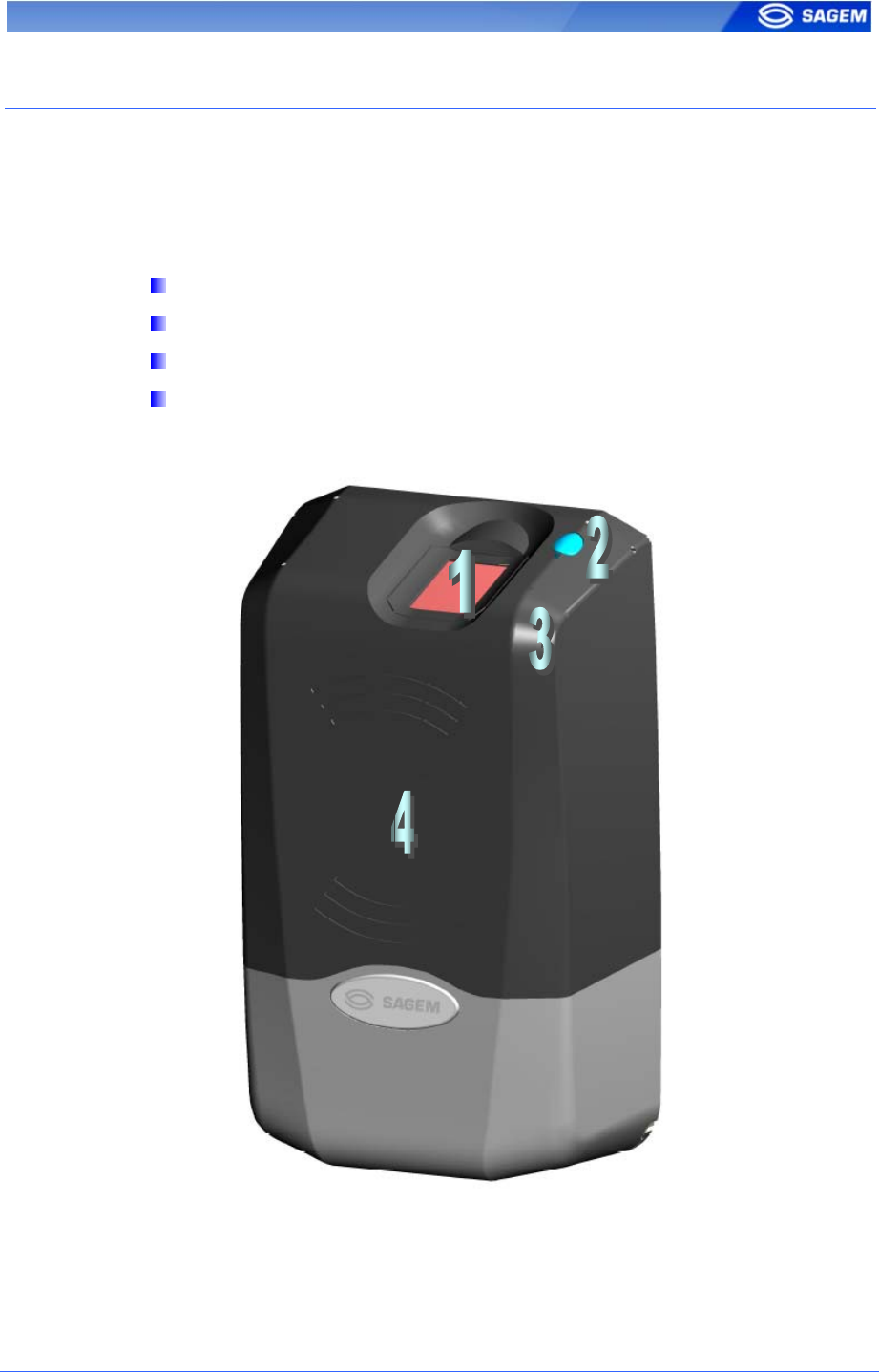
The MorphoAccess™ 1XX offers a simple and ergonomic man-machine
interface dedicated to access control based on fingerprint recognition:
A high quality optical scanner to capture fingerprints (1).
A multicolor led (8 colors) (2).
A multi-toned buzzer (3).
A MifareTM contactless reader on MA12X, to read reference
templates from a contactless card (4).
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 7

E
El
le
ec
ct
tr
ri
ic
ca
al
l
i
in
nt
te
er
rf
fa
ac
ce
es
s
The terminal offers multiple interfaces dedicated to administration and
control information:
A multiplexed Wiegand / Dataclock / RS485 output (5).
Two LED IN inputs to improve integration in an access control
system (6).
A relay to directly command an access (7).
A tamper switch (8).
An Ethernet interface (LAN 10 Mbps), allowing remote
management through TCP and sending control result through UDP (9).
A USB Host port dedicated to local configuration (10).
The MA1XX Installation Guide describes precisely each interface and
connection procedure.
8 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

S
SE
ET
TT
TI
IN
NG
G
U
UP
P
T
TH
HE
E
T
TE
ER
RM
MI
IN
NA
AL
L
I
IP
P
A
AD
DD
DR
RE
ES
SS
S
The MorphoAccess™ can run in stand alone mode but a TCP/IP
connection is required to download records in the terminal and to
configure its recognition mode.
It is possible to specify standard TCP parameters: terminal network
address, network gateway and mask.
These parameters can be set using a USB mass storage key.
The complete procedure is described in section Configuring a “standalone”
MA1XX.
Once connected on the network, the MorphoAccess™ can be configured
using (for example) the.Configuration Tool.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 9

A
AC
CC
CE
ES
SS
S
C
CO
ON
NT
TR
RO
OL
L
P
PR
RE
ES
SE
EN
NT
TA
AT
TI
IO
ON
N
I
Id
de
en
nt
ti
if
fi
ic
ca
at
ti
io
on
n
-
-
a
au
ut
th
he
en
nt
ti
ic
ca
at
ti
io
on
n
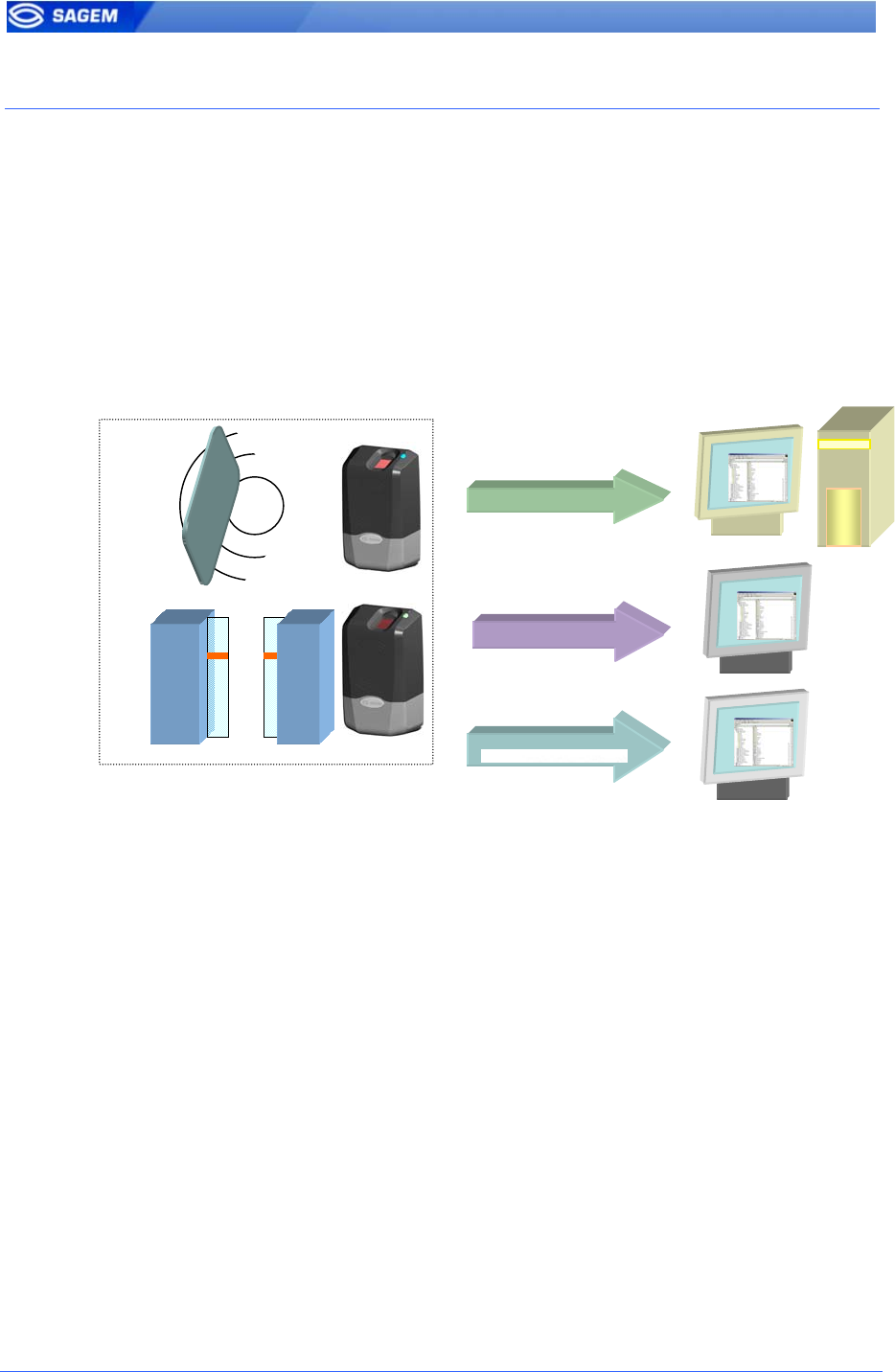
The MorphoAccess™ works according two biometric recognition modes:
identification or authentication. Both identification and authentication can
be activated (fusion mode).
Identification
The captured fingerprint is matched against a database – 1 vs. N.
Minutiae are stored in terminal local database. The terminal can store 500
users (2 fingers per user) in its local database.
In this mode the sensor will be always switched on, waiting for a finger.
The captured fingerprint is matched against the whole database.
Internal database
Users Templates
45641
45648
…
35631
…
12544
If the user is matched access is granted.
If the user is not recognized access is refused.
See section Access Control By Identification.
10 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
Authentication
The captured fingerprint is matched against a reference template – 1 vs. 1.
In authentication, user minutiae can be stored on a contactless card. It is
also possible to store minutiae in terminal local database.
Contactless card containing:
ID
Biometrics
If the user is matched access is granted.
If the user is not recognized access is refused.
See section Access Control By Authentication.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 11
“
“H
Hi
it
t
o
or
r
N
No
o
H
Hi
it
t”
”
r
re
es
su
ul
lt
t
c
co
om
mm
mu
un
ni
ic
ca
at
ti
io
on
n
If access is granted (the user has been recognized) the led lights green
and the buzzer emits a high-pitched “beep”.
If access is denied (the user has not been recognized) the led lights red
and the buzzer emits a low-pitched “beep”.
Control result:
RS485
Wiegand
Dataclock
UDP
Various messages or interfaces can be activated to send the control
result:
Relay
After a successful control the MorphoAccess™ relay may be activated
during a given period.
Wiegand Id Emission
The ID of the recognized user can be sent though the Wiegand output.
The format of the frame may be user defined.
Dataclock Id Emission
The ID of the recognized user can be sent though the Dataclock output.
Udp Id Emission
The ID of the recognized user can be sent though the Ethernet link using
UDP. The administrator may set the port.
RS485
Control information can be sent through RS485.
Local Diary (log)
A local file will store biometric logs.
12 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
“
“P
Pr
ro
ox
xy
y”
”
m
mo
od
de
e
Proxy Mode is not strictly speaking a recognition mode. In this mode, the
MorphoAccess™ works as “a slave” waiting for external orders such as:
Identification
Verification
Relay activation
Read data on a contactless card.
…
Proxy orders:
Identification
Verification
Relay activation
Read card
…
TCP IP
Section Remote Management gives more information about remote
management.
Please refer to MA100 Series Host System Interface for a complete
description of TCP orders possibilites.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 13
C
CO
ON
NF
FI
IG
GU
UR
RI
IN
NG
G
A
A
“
“C
CO
ON
NN
NE
EC
CT
TE
ED
D”
”
M
MO
OR
RP
PH
HO
OA
AC
CC
CE
ES
SS
S
I
In
nt
tr
ro
od
du
uc
ct
ti
io
on
n
A PC (typically a station with MEMSTM) connected to a MorphoAccess™
can manage the terminal. Available remote operations are:
Biometric template addition,
Control settings modification,
Configuration reading,
Local database deletion,
Record deletion,
Control diary downloading,
Firmware upgrade.
TCP IP
Remote management :
Change mode
Add template
Get configuration
…
The MorphoAccess™ works as a server waiting for PC request.
The PC will send biometric templates to the terminal and manage the local
database.
Please refer to MA100 Series Host System Interface for a complete
description of TCP administration. This document explains how to create a
database and store biometric records in this base.
14 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

N
Ne
et
tw
wo
or
rk
k
f
fa
ac
ct
to
or
ry
y
s
se
et
tt
ti
in
ng
gs
s
By default the terminal IP address is 134.1.32.214. This address can be
changed through Ethernet or with a USB mass storage key.
The default server port is 11010.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 15
C
CO
ON
NF
FI
IG
GU
UR
RI
IN
NG
G
A
A
S
ST
TA
AN
ND
DA
AL
LO
ON
NE
E
M
MO
OR
RP
PH
HO
OA
AC
CC
CE
ES
SS
S
“
“U
US
SB
B”
”
k
ke
ey
y
a
ad
dm
mi
in
ni
is
st
tr
ra
at
ti
io
on
n
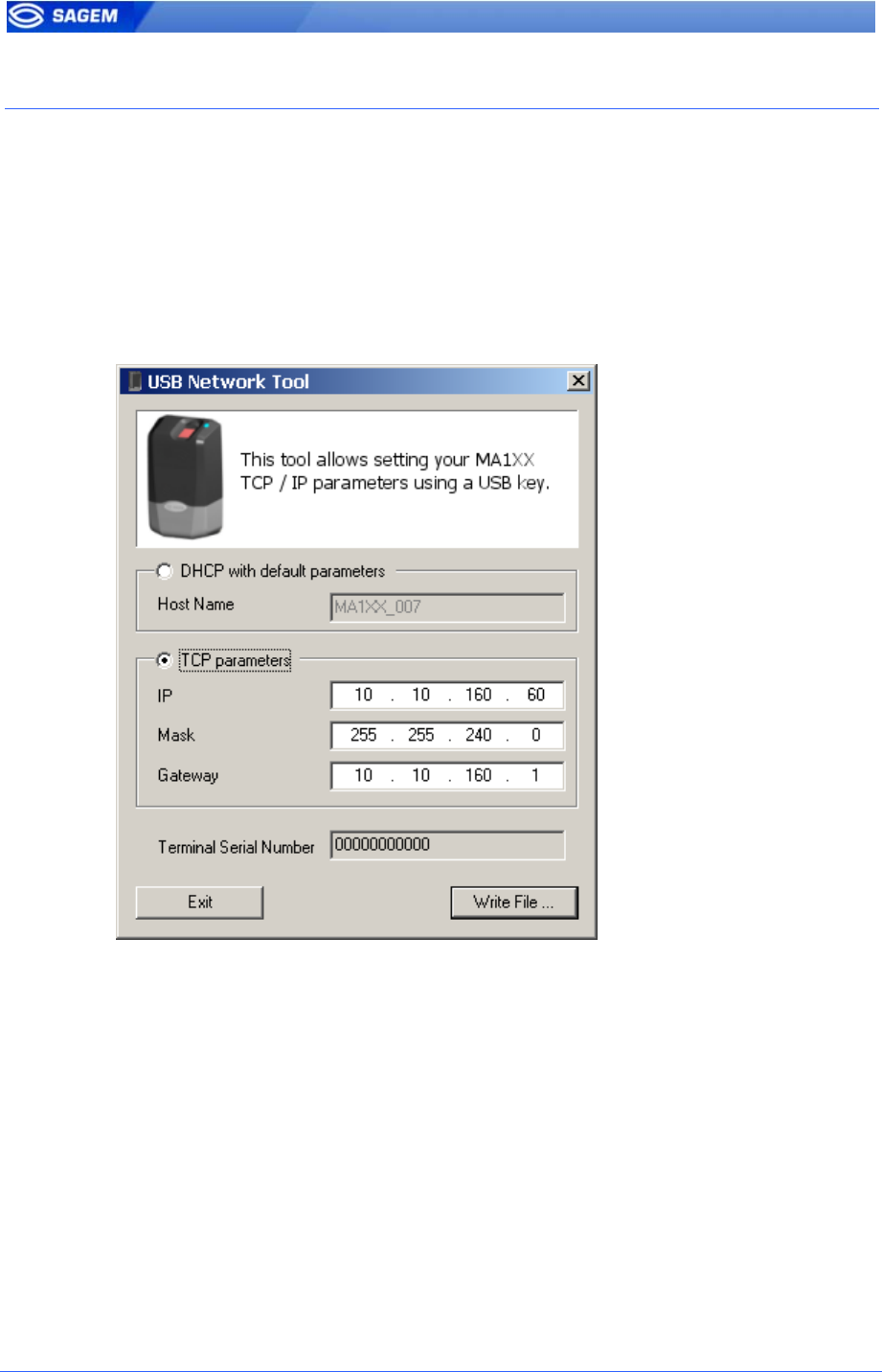
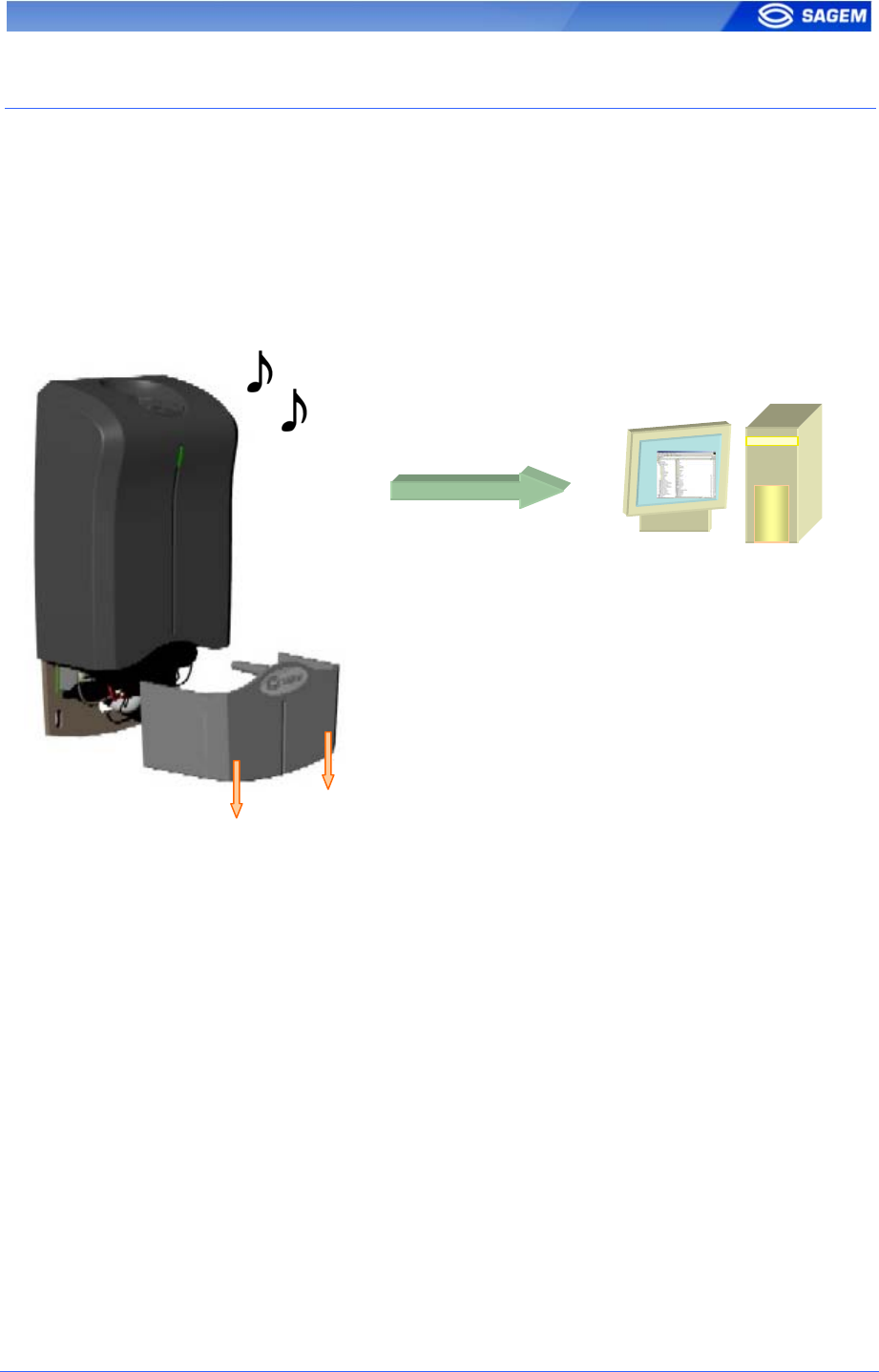
MA100 series have no keyboard, no screen. However it is possible to
change TCP/IP parameters without connecting the terminal on a network.
This operation only requires a standard USB Mass Storage Key (FAT16).
A dedicated PC application, USB Network Configuration Tool, allows
writing these new parameters on the key.
Please refer to MA100 Series USB Network Tool User Guide.
16 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
P
Pr
ri
in
nc
ci
ip
pl
le
e
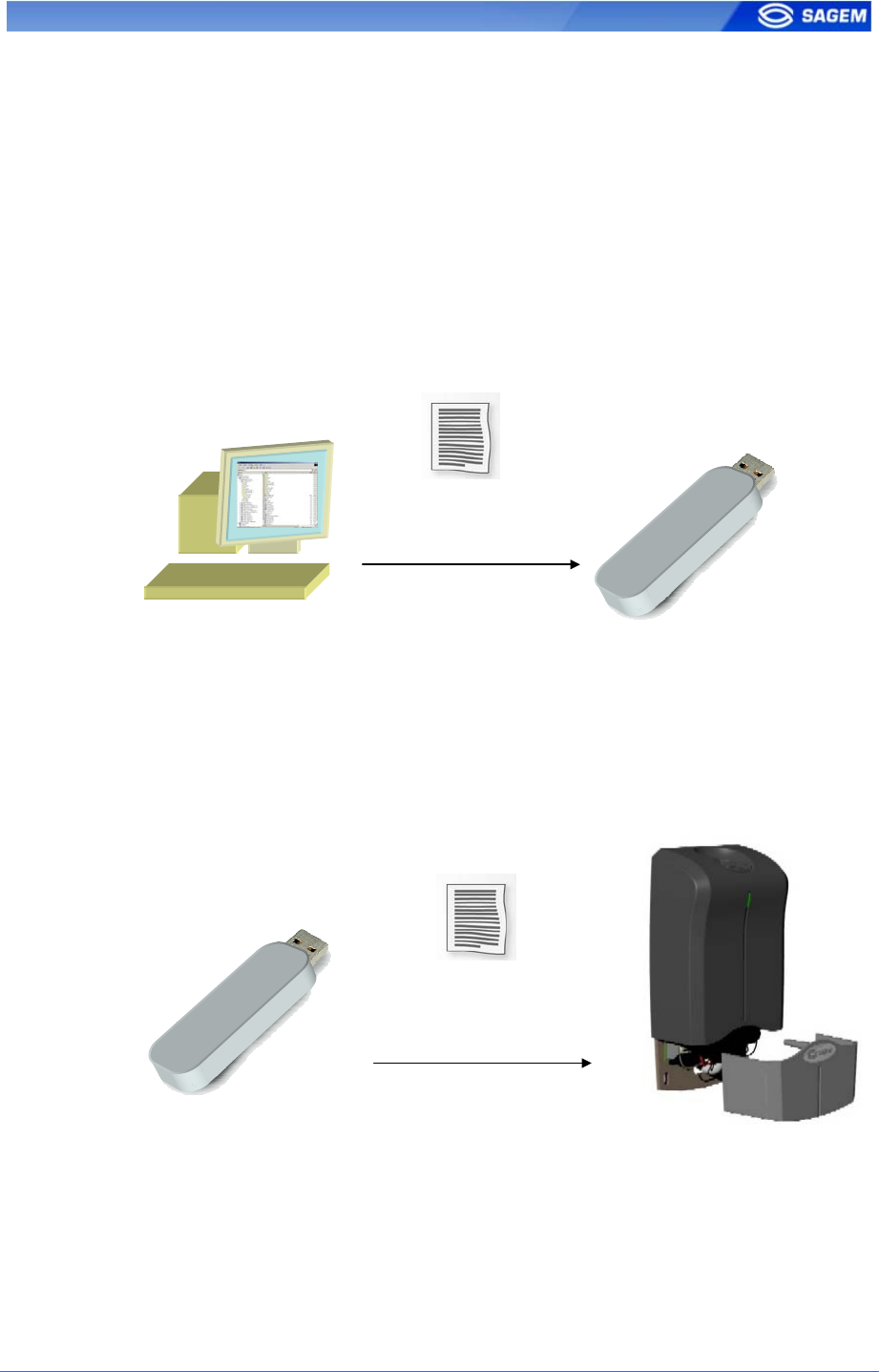
This feature is available to change network parameters (IP address, mask
and gateway).
Store a file on a USB Key
The administrator creates a configuration file on a PC using the USB
Network Configuration Tool. This configuration file contains new network
parameters. This file must be stored on a USB Mass Storage Key.
Configuration File:
network parameters
Apply changes on a “stand alone” MorphoAccess
The lower protection of the MorphoAccess must be removed to give
access to the USB Host Interface of the terminal. The terminal must be
powered on.
When the USB key is inserted in the MorphoAccess USB interface, the
configuration file is read: Ethernet parameters are applied.
Configuration File:
network parameters
At the end of the process a low-pitched “beep” indicates that the key can
be removed.
Please refer to USB Network Configuration Tool User Guide for more
information about this procedure.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 17

C
CH
HA
AN
NG
GI
IN
NG
G
A
A
P
PA
AR
RA
AM
ME
ET
TE
ER
R
C
Co
on
nf
fi
ig
gu
ur
ra
at
ti
io
on
n
i
in
nt
te
er
rf
fa
ac
ce
e
Terminal parameters are stored in files. These files can be retrieved and
modified through TCP/IP using ILV commands. For more information
about remote management please refer to MA100 Series Host System
Interface.
C
Co
on
nf
fi
ig
gu
ur
ra
at
ti
io
on
n
o
or
rg
ga
an
ni
iz
za
at
ti
io
on
n
The terminal contains four files:
app.cfg.
adm.cfg.
bio.cfg.
net.cfg
The app.cfg file contains the application settings, adm.cfg contains
administration parameters, bio.cfg the biometric sensor settings and
net.cfg Ethernet parameters.
Parameter path has the following structure file_name/section/parameter.
For example the relay activation is driven by the app/relay/enabled
parameter.
18 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
“
“C
Co
on
nf
fi
ig
gu
ur
ra
at
ti
io
on
n
t
to
oo
ol
l”
”
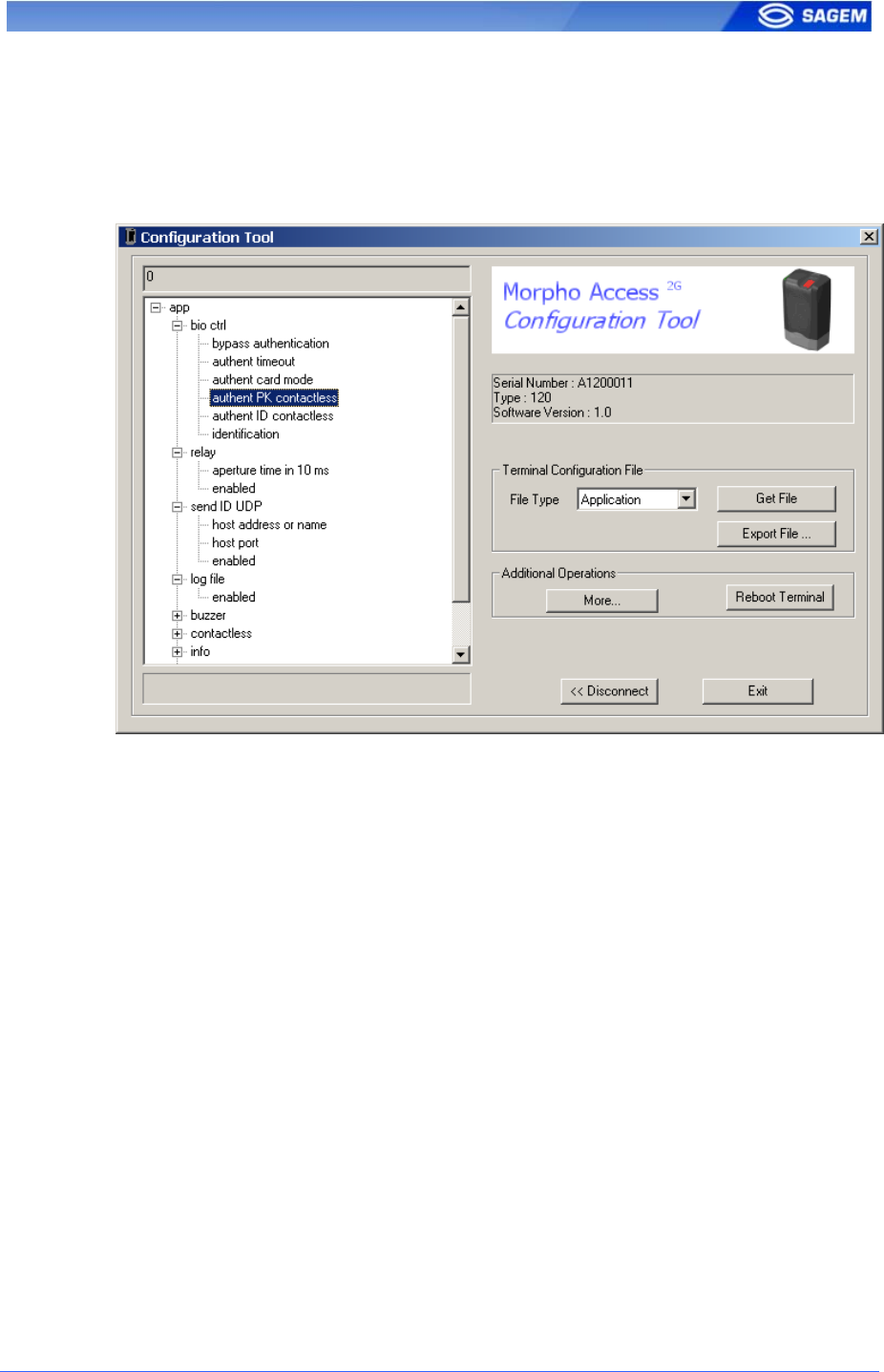
The Configuration Tool allows changing these parameters. This program
is an illustration of utilization of the TCP API. Please refer to Configuration
Tool User Guide for more information about this program.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 19

U
UP
PG
GR
RA
AD
DI
IN
NG
G
T
TH
HE
E
F
FI
IR
RM
MW
WA
AR
RE
E
It is possible to upgrade your MorphoAccess™ firmware. Two packages
type are available. One dedicated to terminal system, another one
dedicated to biometric library.
Use the MA1XX Downloader to upgrade your terminal system.
Use the MA1XX BioLoader to upgrade your terminal biometric library.
Please refer to the MA100 Series Upgrade Tools User Guide for more
information about upgrade procedures.
20 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

A
AC
CC
CE
ES
SS
S
C
CO
ON
NT
TR
RO
OL
L
B
BY
Y
I
ID
DE
EN
NT
TI
IF
FI
IC
CA
AT
TI
IO
ON
N
Access control by identification
app/bio ctrl/identification 1
To configure MorphoAccess™ terminal in this mode, set the parameter
app/bio ctrl/identification at 1.
After starting the MorphoAccess™ terminal waits for fingerprint detection
in identification mode.
If the identification is successful, the terminal triggers the access or returns
the corresponding ID to central security controller. The ID can be sent
through various interfaces. Please refer to MA100 Series Remote
Messages Specification for a complete description of “hit” and “no hit”
messages.
A relay can also be activated.
Once the person's identification is done, the terminal automatically loops
back and waits for a new finger.
At least one fingerprint must be stored in the local database. The terminal
can store 500 users with 2 fingerprints each.
If the terminal is running in identification mode with an empty database,
the sensor is off and the led flashes “yellow”.
Set app/bio ctrl/identification at 0 to disable the sensor (Proxy Mode).
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 21

A
AC
CC
CE
ES
SS
S
C
CO
ON
NT
TR
RO
OL
L
B
BY
Y
A
AU
UT
TH
HE
EN
NT
TI
IC
CA
AT
TI
IO
ON
N
(
(M
MA
A1
12
20
0
/
/
M
MA
A1
11
10
0
O
ON
NL
LY
Y)
)
Various recognition modes can be applied depending on the templates
localization, the required security level.
These modes can be combined with a local identification (fusion mode).
Following modes are available:
Contactless authentication with templates on card:
Captured fingerprints are matched against templates read on the card
(PK). Identifier and fingerprints must be stored on the card.
Contactless authentication with templates on local database:
Captured fingerprints are matched against templates read from the local
database. Only the identifier is required on the card.
Contactless authentication based on card mode:
Depending on the card mode either templates are read on the card or
the control can be bypassed (visitor mode). The “card mode” tag must
be stored on the card.
Please refer to MA100 Series Contactless Card Specification for a
complete description of card structure and access mode.
It is also possible to skip the biometric control: in this case the terminal
acts as a badge reader.
22 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
C
Co
on
nt
ta
ac
ct
tl
le
es
ss
s
a
au
ut
th
he
en
nt
ti
ic
ca
at
ti
io
on
n
w
wi
it
th
h
t
te
em
mp
pl
la
at
te
es
s
o
on
n
a
a
c
co
on
nt
ta
ac
ct
tl
le
es
ss
s
c
ca
ar
rd
d
Contactless authentication with templates (PK) on card
app/bio ctrl/authent PK contactless 1
MorphoAccessTM 110 or 120 can work in contactless authentication mode:
the user presents its card, the terminal reads the reference biometric
templates (PK) on the card and launches a biometric control based on the
read templates.
In this case the card will contain the user identifier and biometric
templates: no local database is required.
To change the parameter value use the Set Registry Key ILV command,
or directly the Configuration Tool.
To enable this mode set app/bio ctrl/authent PK contactless to 1.
To disable this mode set app/bio ctrl/authent PK contactless to 0.
Required tags on card
ID CARD
MODE PK1 PK2 PIN BIOPIN
authent PK contactless Yes No Yes Yes No No
Card structure is described in MA100 Series Contactless Card
Specification.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 23
C
Co
on
nt
ta
ac
ct
tl
le
es
ss
s
a
au
ut
th
he
en
nt
ti
ic
ca
at
ti
io
on
n
w
wi
it
th
h
t
te
em
mp
pl
la
at
te
es
s
o
on
n
l
lo
oc
ca
al
l
d
da
at
ta
ab
ba
as
se
e
Contactless authentication with templates on local database
app/bio ctrl/authent ID contactless 1
The user identifier can be used as an index in the local database of the
MorphoAccess™: in this case the reference biometric templates are
stored in the local database.
The content of the “ID” tag must match with the user identifier in the
terminal database.
To enable this mode set app/bio ctrl/authent ID contactless to 1.
To disable this mode set app/bio ctrl/authent ID contactless to 0.
Required tags on card
ID CARD
MODE PK1 PK2 PIN BIOPIN
authent ID contactless Yes No No No No No
Card structure is described in MA100 Series Contactless Card
Specification.
24 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
C
Co
on
nt
ta
ac
ct
tl
le
es
ss
s
a
au
ut
th
he
en
nt
ti
ic
ca
at
ti
io
on
n
b
ba
as
se
ed
d
o
on
n
c
ca
ar
rd
d
m
mo
od
de
e
Contactless authentication with card mode
app/bio ctrl/authent card mode 1
In this mode the card “decides” on the control progress.
The “CARD MODE” tag is required. This tag can take two values:
• PKS [0x02]: user identifier, template 1 and template 2 are required
on the card. Biometric authentication is triggered with biometric
templates.
• ID_ONLY [0x01]: only the user identifier is required. There is no
biometric control, the control is immediately positive. This feature
is usefull for visitor requiring an access without enrollment. But it is
still possible to store templates on the card.
To enable this mode set app/bio ctrl/authent card mode to 1.
To disable this mode set app/bio ctrl/authent card mode to 0.
Required tags on card
If CARD MODE tag value is ID_ONLY.
ID CARD
MODE PK1 PK2 PIN BIOPIN
authent card mode (ID_ONLY) Yes Yes No No No No
If CARD MODE tag value is PKS.
ID CARD
MODE PK1 PK2 PIN BIOPIN
authent card mode (PKS) Yes Yes Yes Yes No No
Card structure is described in MA100 Series Contactless Card
Specification.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 25

B
By
yp
pa
as
ss
si
in
ng
g
t
th
he
e
b
bi
io
om
me
et
tr
ri
ic
c
c
co
on
nt
tr
ro
ol
l
i
in
n
a
au
ut
th
he
en
nt
ti
ic
ca
at
ti
io
on
n
In this mode only the user id is required on the card. This flag must be
combined with an authentication mode. Activating this flag means that the
biometric verification is bypassed.
When combined “authent ID contactless” the MorphoAccess™ verifies that
the identifier read on the card is present on the local database before
granting the access.
Disabling biometric control, but ID must be present in the local database
app/bio ctrl/bypass authentication 1
app/bio ctrl/authent ID contactless 1
When combined “authent PK contactless” the MorphoAccess™ allways
authorizes the access: the MorphoAccess™ works as a “simple” MifareTM
or iCLASS™ card reader.
Disabling biometric control, access is allways granted
app/bio ctrl/bypass authentication 1
app/bio ctrl/authent PK contactless 1
To bypass biometric control set app/bio ctrl/bypass authentication to 1.
To enable biometric control set app/bio ctrl/bypass authentication to 0.
Required tags on card
ID CARD
MODE PK1 PK2 PIN BIOPIN
bypass authentication Yes No No No No No
26 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
M
Me
er
rg
ge
ed
d
m
mo
od
de
e
This mode is the fusion of identification mode and contactless
authentication without database mode.
So this mode allows:
Running an identification if user places his finger (operation identical to
identification mode),
Running a contactless authentication if user places his contactless card
(operation identical to contactless authentication without database
mode).
If there is no database contactless card presentation is still possible.
This mode is activated by enabling one contactless mode and
identification.
Merged mode
app/bio ctrl/identification 1
And
app/bio ctrl/authent PK contactless
app/bio ctrl/authent card mode
0 or 1
0 or 1
Required tag on card depends on the authentication mode.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 27
M
Mo
or
rp
ph
ho
oA
Ac
cc
ce
es
ss
s
2
22
20
0
3
32
20
0
c
co
om
mp
pa
at
ti
ib
bi
il
li
it
ty
y
These tables present parameter equivalence between MA320/220 family
and MA120 family.
Merged mode (/cfg/Maccess/Admin/mode 5 on 220 and 320) is activated
when app/bio ctrl/identification is set to 1.
MA 220 320 MA 120
Contactless authentication with ID on card, template in local database
/cfg/Maccess/Admin/mode 4 app/bio ctrl/authent ID contactless 1
Contactless authentication: Card mode
/cfg/Maccess/Contactless/without
DB mode 0
/cfg/Maccess/Admin/mode 3 or
app/bio ctrl/authent card mode 1
/cfg/Maccess/Admin/mode 5
(merged mode)
app/bio ctrl/identification 1
Contactless authentication: Biometric verification
/cfg/Maccess/Contactless/without
DB mode 2
/cfg/Maccess/Admin/mode 3 or
app/bio ctrl/authent PK contactless 1
/cfg/Maccess/Admin/mode 5
(merged mode)
app/bio ctrl/identification 1
Contactless authentication: ID “only”, no biometric verification
/cfg/Maccess/Contactless/without
DB mode 1
/cfg/Maccess/Admin/mode 3 or
app/bio ctrl/authent PK contactless 1
app/bio ctrl/bypass authentication 1
/cfg/Maccess/Admin/mode 5
(merged mode)
app/bio ctrl/identification 1
28 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

P
PR
RO
OX
XY
Y
M
MO
OD
DE
E
This mode allows controlling the MorphoAccess™ remotely (the link is
Ethernet) using a set of biometric and databasing management function
interface access commands.
Identification and authentication must be disabled. It means that all control
must be turned off: the terminal becomes a “slave”.
Proxy mode
app/bio ctrl/identification 0
app/bio ctrl/authent PK contactless 0
app/bio ctrl/authent ID contactless 0
app/bio ctrl/authent card mode 0
Please refer to refer to MA100 Series Host System Interface: this
document explains how to manage a terminal on a TCP network.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 29
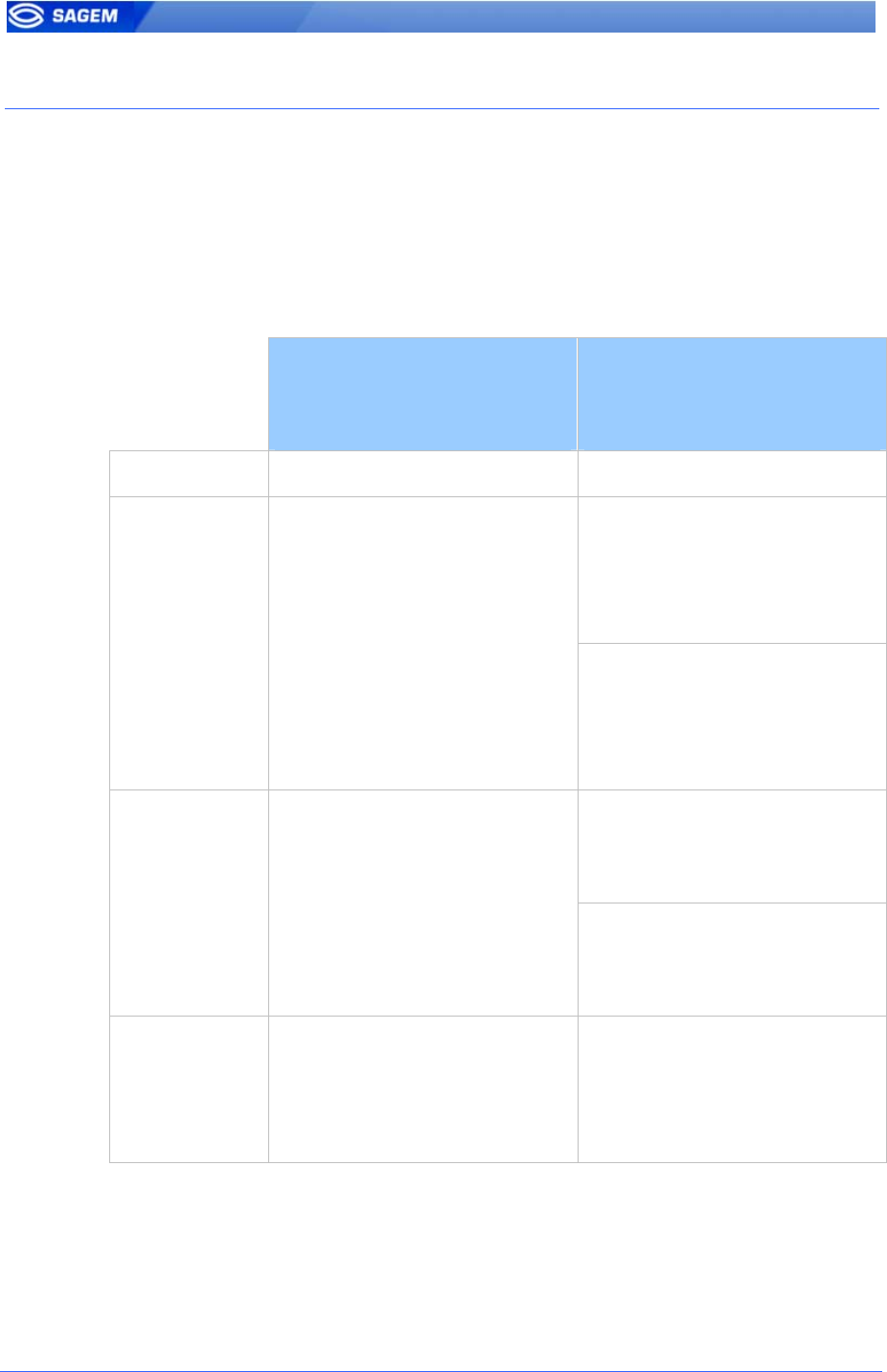
R
RE
EC
CO
OG
GN
NI
IT
TI
IO
ON
N
M
MO
OD
DE
E
S
SY
YN
NT
TH
HE
ES
SI
IS
S
The MA100 series operating mode is driven by:
• The authentication or identification mode required: Card Only, Card
+ Biometric, Biometric only
• Who defined the operating mode: Card or Terminal
Mode defined by Card
app/bio ctrl/authent card mode
1
Mode defined by Terminal
app/bio ctrl/authent card mode
0
Operating mode
ID in card
bypass authentication 1
authent ID contactless 1
Check ID on terminal
Authentication
Card only
(MA120/MA110)
ID in card
Card Mode Tag = ID_ONLY
ID in card
bypass authentication 1
authent PK contactless 1
No ID check on terminal
ID and BIO in card
bypass authentication 0
authent PK contactless 1
Authentication
Card
+ Biometric
(MA120/MA110)
ID and BIO in Card
Card Mode Tag = PKS
ID on card and BIO in terminal
bypass authentication 0
authent ID contactless 1
Identification
Biometric only
(MA1xx)
ID and BIO in termina
identification 1
30 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

S
SE
ET
TT
TI
IN
NG
G
U
UP
P
R
RE
EC
CO
OG
GN
NI
IT
TI
IO
ON
N
M
MO
OD
DE
E
T
Tw
wo
o
a
at
tt
te
em
mp
pt
ts
s
m
mo
od
de
e
If the recognition fails, it is possible to give a “second chance” to the user.
In identification mode if a bad finger is presented the user has 5 seconds
to present a finger again. The result is sent if this period expires or if the
user presents a finger again.
In authentication mode, if the user presents a bad finger, he can replace
his finger without presenting his card again. The result is sent only after
this second attempt.
It is possible to set the finger presentation timeout and to deactivate this
“two attempts mode”.
P
Pa
ar
ra
am
me
et
te
er
rs
s
This mode can be configured using the Configuration Tool for example.
By default the two attempts mode is activated.
Setting up the number of attempts
app/bio ctrl/nb attempts 1 (only one attempts)
2 (two attempts mode)
The period between two attempts in identification (two attempts mode) can
be modified.
Setting up the identification timeout
app/bio ctrl/identification timeout 5 (1-60)
In authentication mode a finger presentation period can be defined.
Setting up the authentication timeout
app/bio ctrl/authent timeout (1-60)
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 31

S
SE
ET
TT
TI
IN
NG
G
U
UP
P
M
MA
AT
TC
CH
HI
IN
NG
G
P
PA
AR
RA
AM
ME
ET
TE
ER
RS
S
Setting up matching threshold
bio/bio ctrl/matching th 1-10
The performances of a biometric system are characterized by two
quantities, the False Non Match Rate - FNMR - (Also called False Reject
Rate) and the False Match Rate - FMR - (Also called False Acceptance
Rate). Different trade-off are possible between FNMR and FMR depending
on the security level targeted by the access control system. When
convenience is the most important factor the FNMR must be low and
conversely if security is more important then the FMR has to be
minimized.
Different tuning are proposed in the MorphoAccess terminal depending on
the security level targeted by the system. The table below details the
different possibilities.
This parameter can be set to values from 1 to 10. This parameter specifies
how tight the matching threshold is. Threshold scoring values are
identified hereafter
1 Very few persons rejected FAR < 1%
2 FAR < 0.3%
3 Recommended value
(default value)
FAR < 0.1%
4 FAR < 0.03%
5 Intermediate threshold FAR < 0.01%
6 FAR < 0.001%
7 FAR < 0.0001%
8 FAR < 0.00001%
9 Very high threshold (few false
acceptances) Secure
application
FAR < 0.0000001%
10 High threshold for test purpose
only There are very few false
recognitions, and many rejections
32 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
R
RE
EL
LA
AY
Y
A
AC
CT
TI
IV
VA
AT
TI
IO
ON
N
If the control is successful, a relay may be activated to directly control a
door. This installation type offers a low security level.
Relay activation
app/relay/enabled 1
The relay aperture time can be defined and is set by default to 3 seconds
(i.e. 300).
Relay aperture time in 10 ms
app/relay/aperture time in 10 ms 300
( 50 to 60000 )
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 33
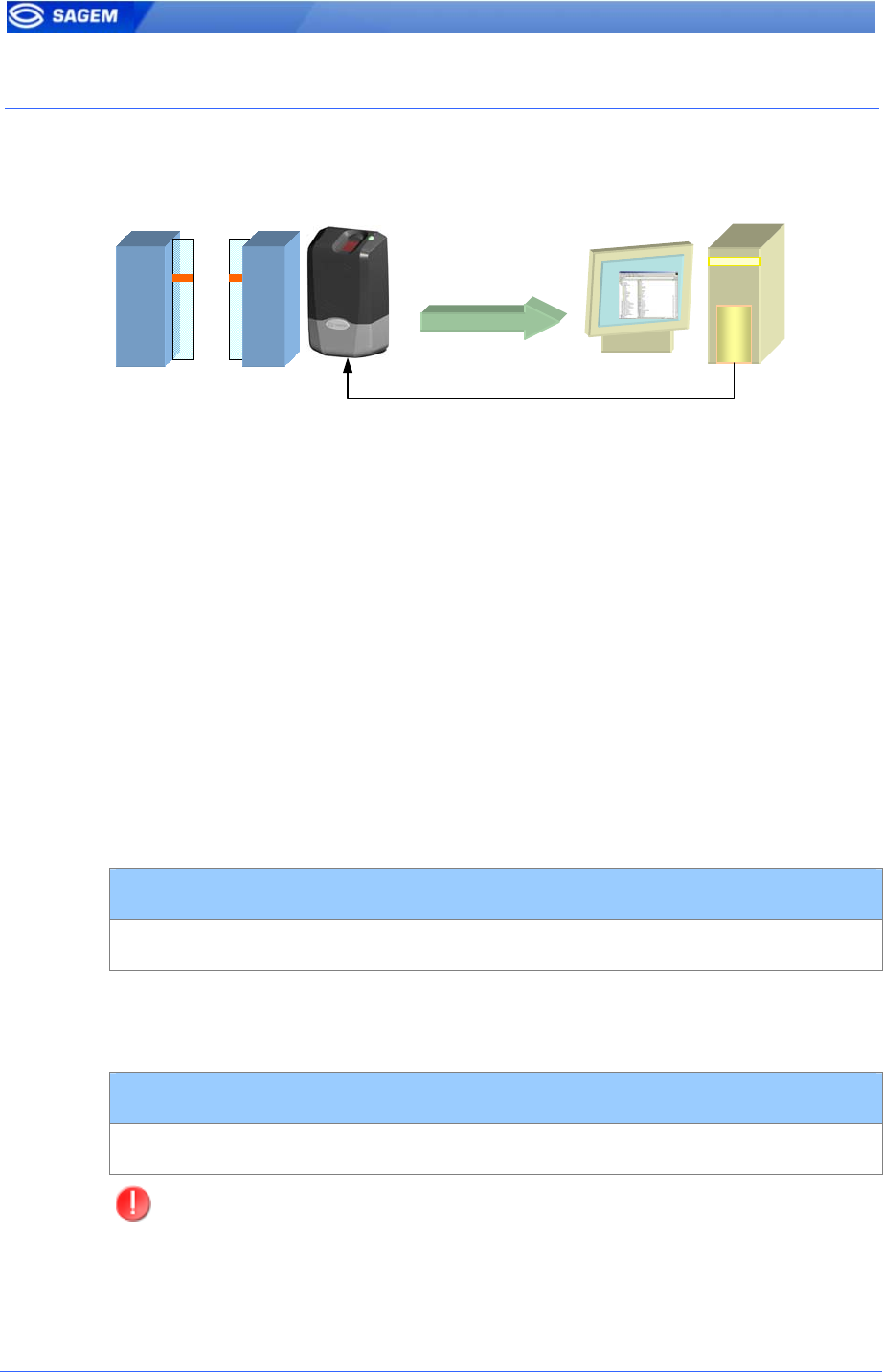
L
LE
ED
D
I
IN
N
A
AC
CT
TI
IV
VA
AT
TI
IO
ON
N
Use this signal to wait a controller “ACK” before granting the access.
User ID
LED1 to GND: Access authorized.
LED2 to GND: Access refused.
1- If the user is recognized the MA1XX sends the user identifier to the
controller.
2 - The MA1XX waits for a GND signal on LED1 or LED2. A timeout can
be defined.
3 - The controller checks the user rights.
4 - The controller sets LED1 to GND to authorize the access or sets LED2
to GND to forbid the access.
5 – The control restarts only when LED1 and LED2 are set to “1” again.
This feature improves integration in an access control system (ACS). The
ACS through LED IN signals validates result of biometric matching.
LED IN mode activation
app/led IN/enabled 1
When the ACS validates the control a timeout must be specified: it defines
the time during which the MorphoAccess™ will wait for an
acknowledgement signal from the ACS through LED IN signals
LED IN “acknowledgement timeout” in 10 ms
app/led IN/controller ack timeout 0 to 268435455
During the time LED1 or LED2 is set to GND the control DOES NOT
RESTART.
34 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
L
LO
OG
G
F
FI
IL
LE
E
MorphoAccessTM is logging its activities
app/log file/enabled 1
The MorphoAccess™ can log its biometric activities. It stores the result of
the command, the date and time, the matching mark, the execution time,
and the ID of the user.
It is possible to download the diary file. For more information on this
feature, refer to the MA100 Series Host System Interface.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 35
R
RE
EM
MO
OT
TE
E
M
ME
ES
SS
SA
AG
GE
ES
S
P
Pr
re
es
se
en
nt
ta
at
ti
io
on
n
The MorphoAccessTM terminal can send status messages in real time to a
controller by different means and through different protocols. This
information, called Remote Messages can be used, for instance to display
on an external screen the result of a biometric operation, the name or the
ID of the person identified…depending on the role of the controller in the
system.
UDP
RS485
The MA100 Series Remote Messages Specification describes the different
solutions offered by the MorphoAccess™ to dialog with a controller, and
how to make use of them.
S
Su
up
pp
po
or
rt
te
ed
d
P
Pr
ro
ot
to
oc
co
ol
ls
s
The terminal can send messages about the biometric operations
performed by the MorphoAccess™ to a controller through the following
protocols:
Wiegand
Dataclock
RS485
Ethernet (UDP)
36 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
T
TA
AM
MP
PE
ER
R
S
SW
WI
IT
TC
CH
H
M
MA
AN
NA
AG
GE
EM
ME
EN
NT
T
A
Al
la
ar
rm
m
a
ac
ct
ti
iv
va
at
ti
io
on
n
The MorphoAccess™ can detect that the back cover has been removed.
The device can send an alarm to the central controller in case of intrusion.
It can also play a sound alarm whilst sending the alarm.
Sound alarm
A
larm messa
g
e
•UDP
•RS485
•Wiegand
•Dataclock
To send an alarm on an output (UDP, Wiegand, Dataclock or RS485), the
corresponding interface must be activated otherwise no alarm will be sent.
Because Wiegand, Dataclock, and RS485 are multiplexed on the same
lines, only one of these protocols shall be enabled at one time, else priority
is given to Wiegand, then Dataclock, then RS485.
These keys are:
app/send ID wiegand/enabled
app/send ID dataclock/enabled
app/send ID RS485/enabled
app/send ID UDP/enabled
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 37
Tamper switch management feature is configured by setting the key
app/tamper alarm/level to an appropriate value.
Tamper Alarm Level
app/tamper alarm/level
0 No Alarm.
1 Send Alarm (No Sound Alarm).
2 Send Alarm and Activates Buzzer (Sound Alarm)
0-2
The key app/failure ID/alarm ID defines the value of the alarm ID to send
in Wiegand or Dataclock. This ID permits to distinguish between an user
ID and a error ID.
Tamper Alarm Level
app/failure ID/alarm ID 0- 65535
In Wiegand and Dataclock the alarm ID is sent like other Failure IDs, see
the documentation MA100 Series Remote Messages Specification for a
description of the packet format in UDP and RS-485.
E
Ex
xa
am
mp
pl
le
es
s
Example 1: Send an alarm ID (62221) in Wiegand, and play sound
warning, in case of intrusion detection.
To send an alarm in Wiegand, the key app/send ID wiegand/enabled must
be set to 1.and the key app/tamper alarm/level must be set to 2 (alarm and
buzzer.)
The key app/failure ID/alarm ID must be set to 62221 to link the intrusion
event to this identifier.
Example 2: Send an alarm in UDP quietly in case of intrusion
detection.
To send an alarm in UDP, the key app/send ID UDP/enabled must be set
to 1.
Then the key app/tamper alarm/level must be set to 1 (quiet alarm.)
38 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
M
MA
AN
N
M
MA
AC
CH
HI
IN
NE
E
I
IN
NT
TE
ER
RF
FA
AC
CE
E
C
Co
on
nv
ve
en
nt
ti
io
on
n
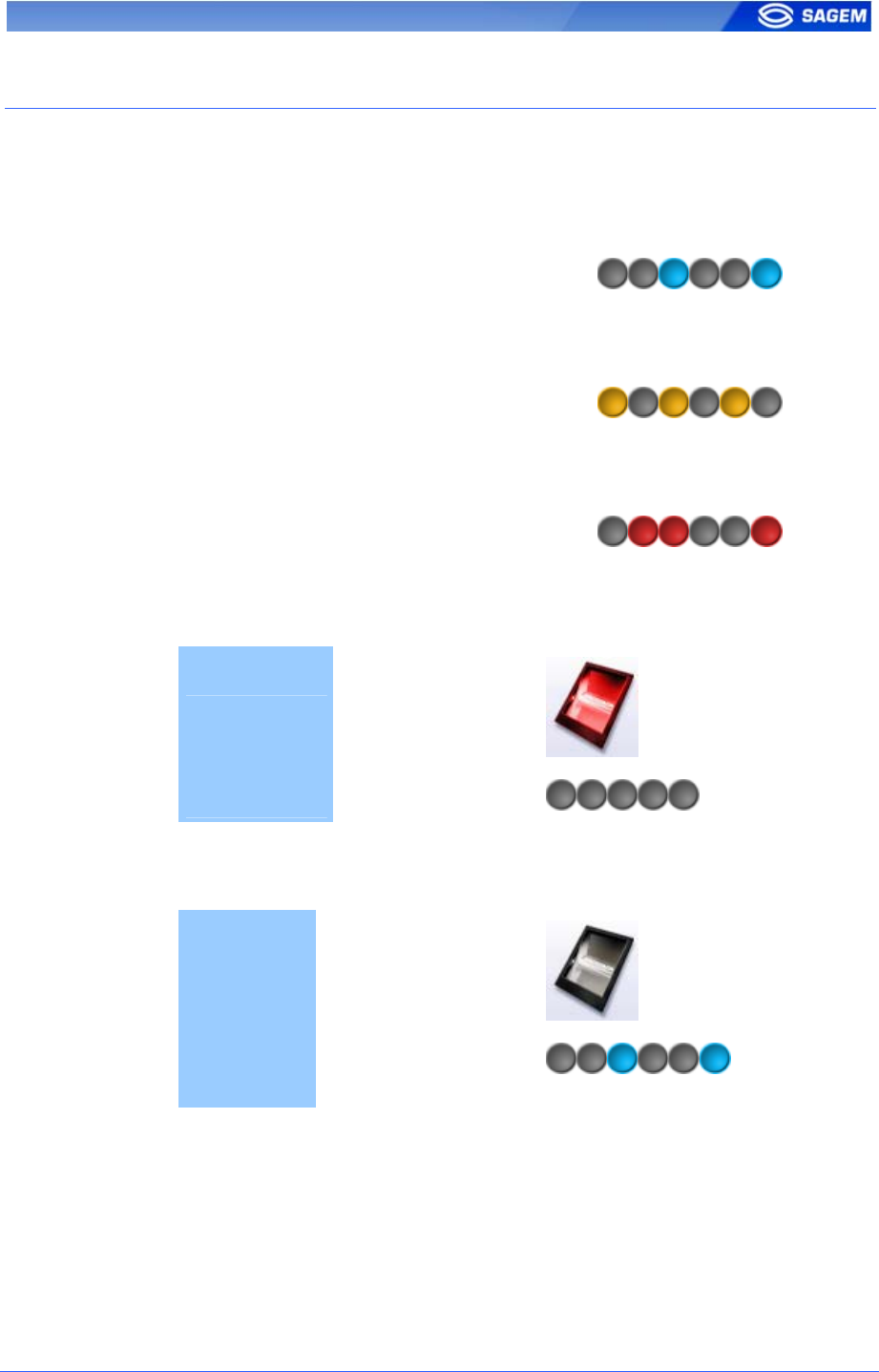
Intermittent “Pulse”: led is 1 second OFF, 0.05 second ON. For example:
Intermittent blue “Pulse”
Fast “Pulse”: led flashes quickly. The rhythm is the same than when a
hard drive works.
Fast orange “Pulse”
Slow intermittent “Pulse”. led is 1 second OFF, 1 second ON. For
example:
Slow intermittent red “Pulse”.
I
Id
de
en
nt
ti
if
fi
ic
ca
at
ti
io
on
n
–
–
w
wa
ai
it
ti
in
ng
g
f
fo
or
r
a
a
f
fi
in
ng
ge
er
r
Sensor ON
Led OFF
A
Au
ut
th
he
en
nt
ti
ic
ca
at
ti
io
on
n
–
–
w
wa
ai
it
ti
in
ng
g
f
fo
or
r
a
a
b
ba
ad
dg
ge
e
Sensor OFF
Led Intermittent blue
“Pulse”
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 39
F
Fu
us
si
io
on
n
-
-
w
wa
ai
it
ti
in
ng
g
f
fo
or
r
a
a
f
fi
in
ng
ge
er
r
o
or
r
a
a
b
ba
ad
dg
ge
e
Sensor ON
Led Intermittent blue
“Pulse”
C
Co
on
nt
tr
ro
ol
l
O
OK
K
Sensor ON
Led Green 1 second
Buzzer ON 0.1 second - High-
pitched
C
Co
on
nt
tr
ro
ol
l
f
fa
ai
il
le
ed
d
Sensor ON
Led Red 1second
Buzzer ON 0.7 second - Low-
pitched
N
No
o
d
da
at
ta
ab
ba
as
se
e
o
or
r
e
em
mp
pt
ty
y
d
da
at
ta
ab
ba
as
se
e
Sensor OFF
Led Slow intermittent
orange “Pulse”.
40 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
B
Bi
io
om
me
et
tr
ri
ic
c
a
ac
cq
qu
ui
is
si
it
ti
io
on
n,
,
b
ba
ad
d
p
pl
la
ac
ce
em
me
en
nt
t
Sensor ON
Led Fast intermittent
orange “Pulse”.
U
US
SB
B
k
ke
ey
y
c
ca
an
n
b
be
e
r
re
em
mo
ov
ve
ed
d
Sensor - -
Led Fast intermittent blue
“Pulse”.
Buzzer ON 0.7 second - Low-
pitched
S
Se
en
ns
so
or
r
f
fa
ai
il
le
ed
d
Sensor OFF
Led Slow intermittent red
“Pulse”.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 41

N
NE
ET
TW
WO
OR
RK
K
P
PA
AR
RA
AM
ME
ET
TE
ER
RS
S
These parameters can be changed using the Configuration Tool or by
implementing ILV commands.
Network parameters are stored in a file named “net.cfg”.
A change is applied after rebooting the terminal.
S
Se
ec
ct
ti
io
on
n
[
[b
bo
oo
ot
t
p
pr
ro
ot
to
o]
]
DHCP activated
0 NO
1 YES
S
Se
ec
ct
ti
io
on
n
[
[p
pa
ar
ra
am
me
et
te
er
rs
s]
]
host name
“MA-1234567890”
network address
“134.1.32.214” by default, static address.
network mask
“255.255.240.0“by default.
default gateway
“134.1.6.20“ by default.
42 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

T
TE
ER
RM
MI
IN
NA
AL
L
I
IN
NF
FO
OR
RM
MA
AT
TI
IO
ON
N
These parameters can be changed using the Configuration Tool or by
implementing ILV commands.
The “app.cfg” file contains information about your terminal configuration.
S
Se
ec
ct
ti
io
on
n
[
[i
in
nf
fo
o]
]
(
(r
re
ea
ad
d
o
on
nl
ly
y)
)
Type
120: MorphoAccess™ with local database and MifareTM contactless reader
110: MorphoAccess™ with local database and ICLASSTM contactless
reader
100: MorphoAccess™ with local database.
Minor
Software revision (minor)
Major
Software revision (major)
Release
Release version.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 43

A
AD
DM
MI
IN
NI
IS
ST
TR
RA
AT
TI
IO
ON
N
P
PA
AR
RA
AM
ME
ET
TE
ER
RS
S
The “app.cfg” file contains advanced parameter to modify the host port
and the connection mode. This parameter must not be changed.
S
Se
ec
ct
ti
io
on
n
[
[r
re
em
mo
ot
te
e
m
ma
an
na
ag
ge
em
me
en
nt
t
T
TC
CP
P]
]
Inactivity timeout
Must be set to 0.
Port
11010 by default, defines the socket server port.
S
Se
ec
ct
ti
io
on
n
[
[t
te
er
rm
mi
in
na
al
l]
]
Group
Must be set to 255.
44 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden
A
AN
NN
NE
EX
X:
:
C
CO
ON
NT
TA
AC
CT
TL
LE
ES
SS
S
M
MO
OD
DE
ES
S
T
TA
AB
BL
LE
E
Operation
Authent card
mode
Authent PK
contactless
Authent ID
contactless
Bypass
authentication
Authentication with templates in database
Read ID on contactless card.
Retrieve corresponding templates in database.
Biometric authentication using these templates.
Send ID if authentication is successfull.
0 0 1 0
Authentication with templates on card
Read ID and templates on contactless card.
Biometric authentication using these templates.
Send ID if authentication is successfull.
0 1 0 0
Card mode authentication
Read card mode, ID, templates (if required by card mode)
on contactless card.
If card mode is « ID only », send ID.
If card mode is « Authentication with templates on card »,
biometric authentication using templates read on card, then
send ID if authentication is successfull.
1 0 0 0
Authentication with templates in database – biometric
control disabled
Read ID on contactless card.
Check corresponding templates presence in database.
Send ID if templates are present.
0 0 1 1
Authentication with templates on card – biometric
control disabled
Read ID on contactless card.
Send ID.
0 1 0 1
Card mode authentication – biometric control disabled
Read card mode, ID, templates (if required by card mode)
on contactless card.
Whatever card mode, send ID.
1 0 0 1
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 45

A
AN
NN
NE
EX
X:
:
R
RE
EQ
QU
UI
IR
RE
ED
D
T
TA
AG
GS
S
O
ON
N
C
CO
ON
NT
TA
AC
CT
TL
LE
ES
SS
S
C
CA
AR
RD
D
Operation ID CARD
MODE PK1 PK2 PIN BIOPIN
A
uthentication with templates
in database Yes No No No No No
A
uthentication with templates
on card Yes No Yes Yes No No
Card mode authentication
(ID_ONLY) Yes Yes No No No No
Card mode authentication
(PKS) Yes Yes Yes Yes No No
Authentication with templates
in database – biometric control
disabled
Yes No No No No No
A
uthentication with templates
on card – biometric control
disabled
Yes No No No No No
Card mode authentication
(ID_ONLY) – biometric control
disabled
Yes Yes No No No No
Card mode authentication
(PKS) – biometric control
disabled
Yes Yes Yes Yes No No
46 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

F
FA
AQ
Q
T
Te
er
rm
mi
in
na
al
l
I
IP
P
a
ad
dd
dr
re
es
ss
s
i
is
s
u
un
nk
kn
no
ow
wn
n
o
or
r
t
te
er
rm
mi
in
na
al
l
i
is
s
n
no
ot
t
r
re
ea
ac
ch
ha
ab
bl
le
e
Use USB Network Configuration Tool to set a valid network address in
your terminal. See section Configuring a standalone MorphoAccess.
S
Se
en
ns
so
or
r
i
is
s
o
of
ff
f
Verify that the base contents at least one record.
Check that identification is enabled.
T
Te
er
rm
mi
in
na
al
l
r
re
et
tu
ur
rn
ns
s
e
er
rr
ra
at
ti
ic
c
a
an
ns
sw
we
er
rs
s
t
to
o
p
pi
in
ng
g
r
re
eq
qu
ue
es
st
ts
s
Check the subnet mask. Ask to your administrator the right value.
SAGEM Défense Sécurité document. Reproduction and disclosure forbidden 47

B
BI
IB
BL
LI
IO
OG
GR
RA
AP
PH
HY
Y
MA100 Series Installation Guide
This document describes terminal electrical interfaces and connection
procedures.
MA100 Series Standard Host Interface Specification
A complete description of remote management commands.
MA100 Series Remote Messages Specification
A description of the MA1XX communication interfaces.
MA100 Series Contactless Card Specification
This document describes the MA12X Contactless card feature.
MA100 Series Configuration Tool User Guide
Configuration Tool user guide , via Ethernet
MA100 Series USB Network Tool User Guide
Configuration Tool user guide , via USB key
MA100 Series Upgrade Tools User Guide
Upgrade Tool user guide about firmware upgrading procedures.
MA100 Series Configuration Guide
The complete description of terminal configuration files.
48 SAGEM Défense Sécurité document. Reproduction and disclosure forbidden

Siège social : Le Ponant de Paris
27, rue Leblanc - 75512 PARIS CEDEX 15 - FRANCE
