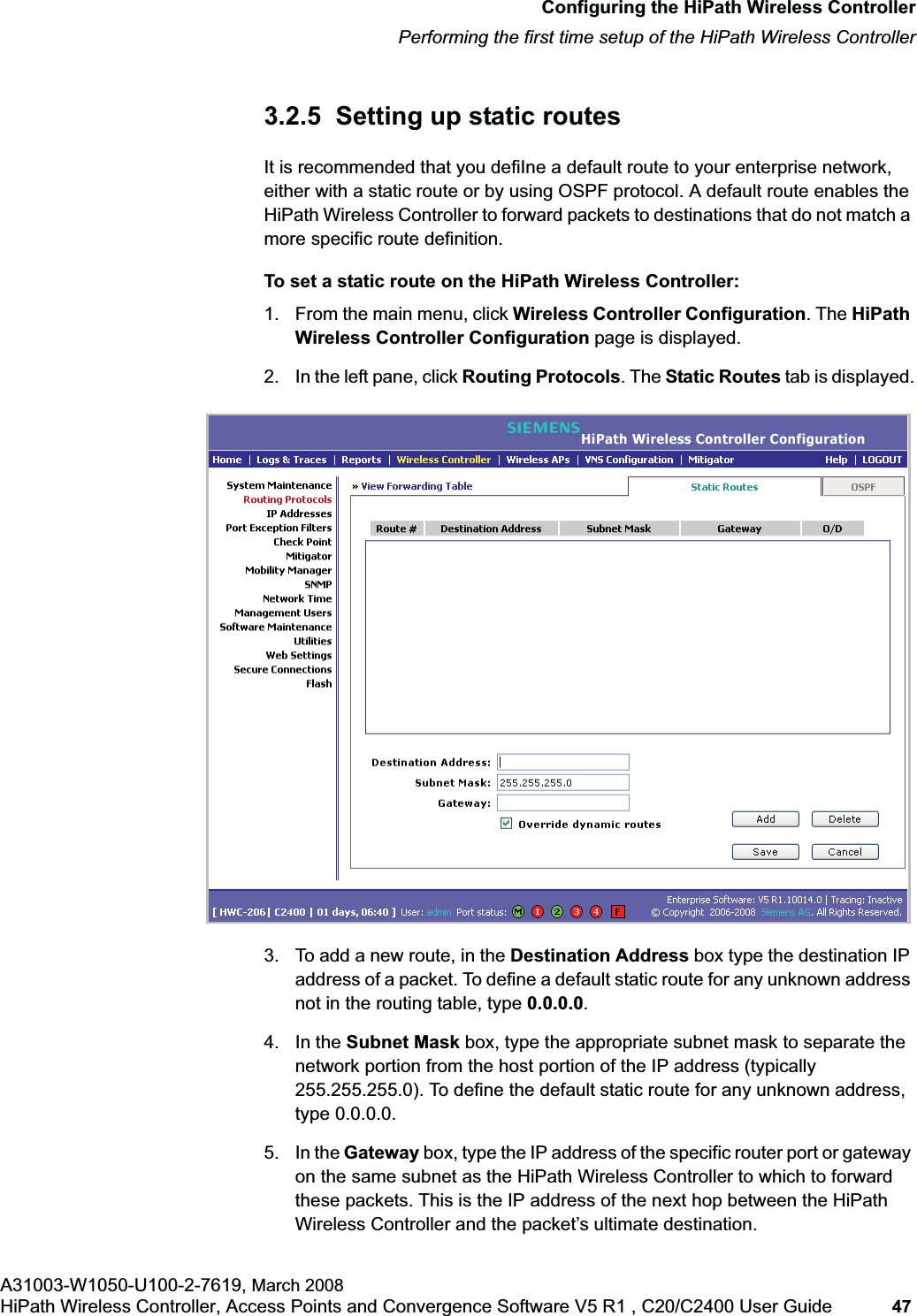
Siemens Communications AP36V1B HiPath Wireless AP, Altitude 450, Altitude 451 User Manual Part 1
Siemens Communications, Inc. HiPath Wireless AP, Altitude 450, Altitude 451 Part 1
Contents
- 1. User Manual Part 1
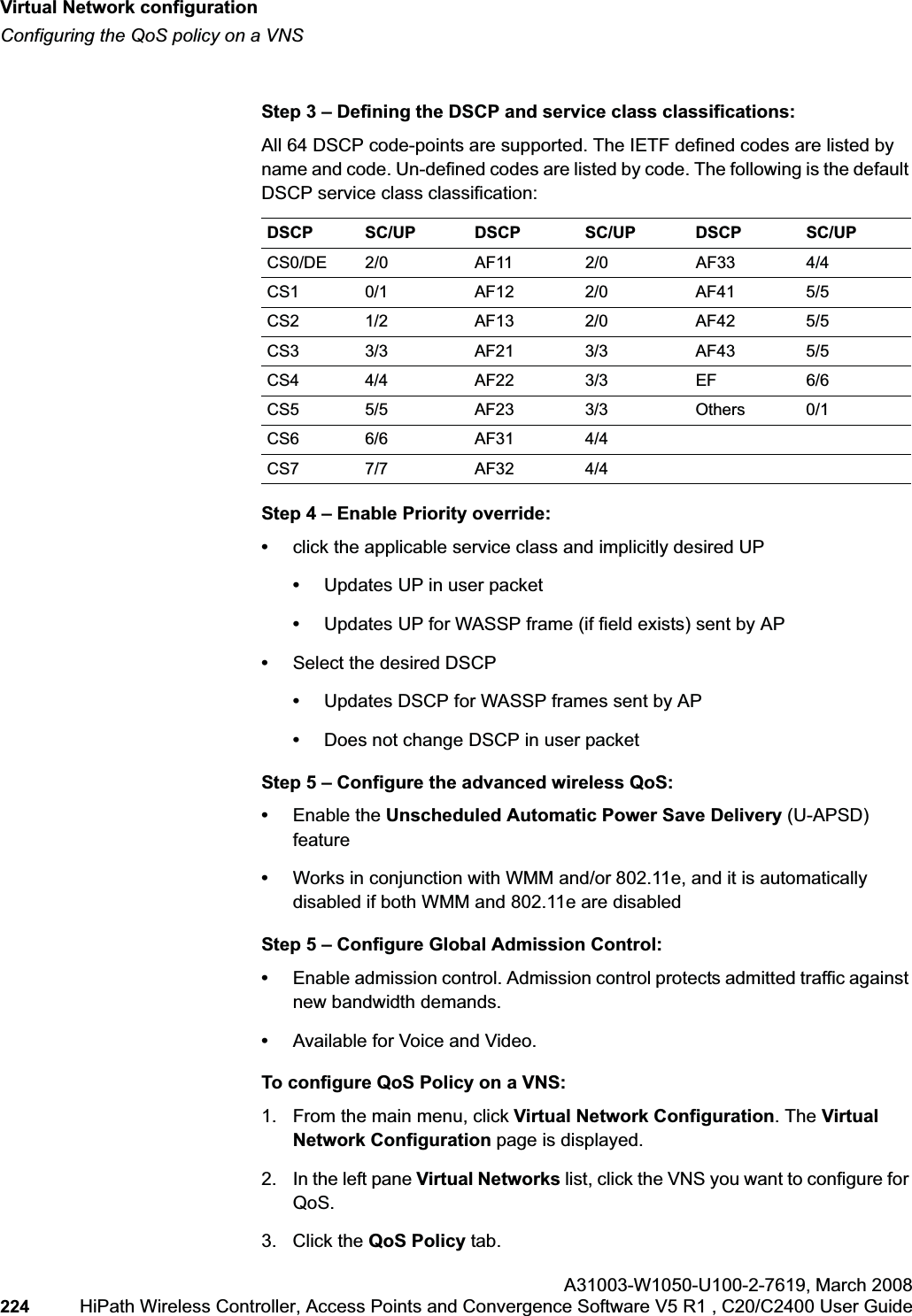
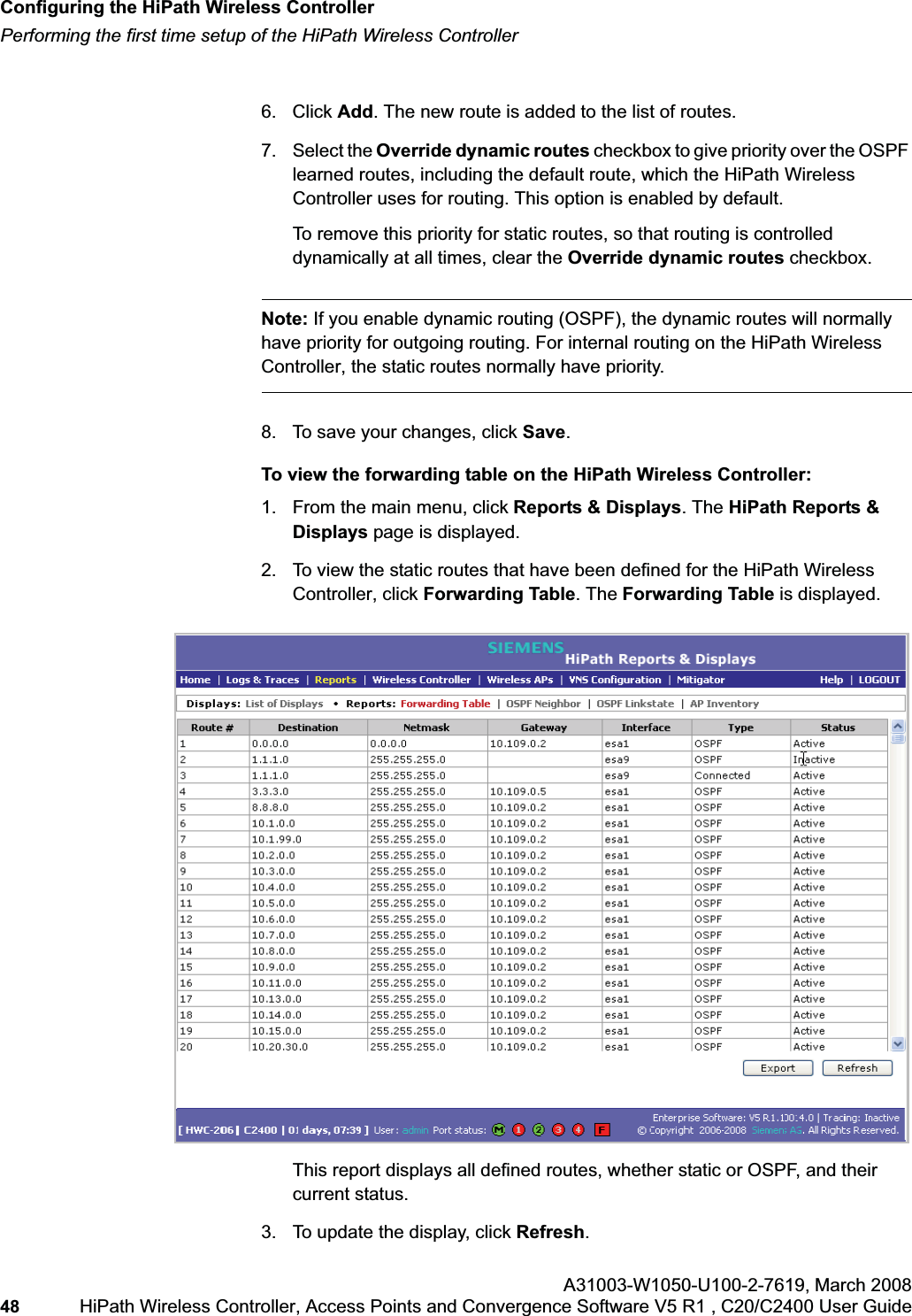
- 2. User Manual Part 2
- 3. User's Guide
- 4. User's guide
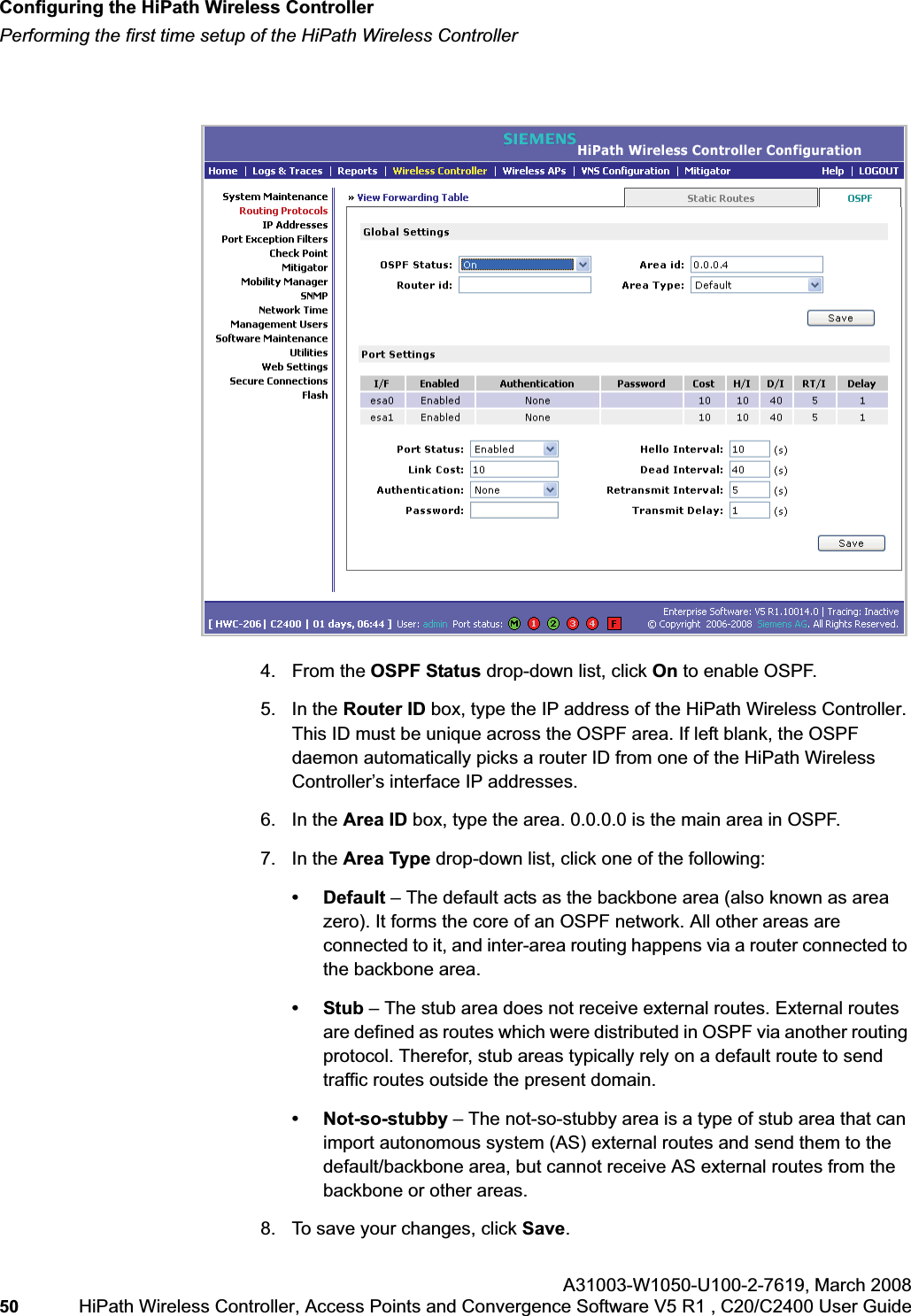
- 5. users guide
User Manual Part 1







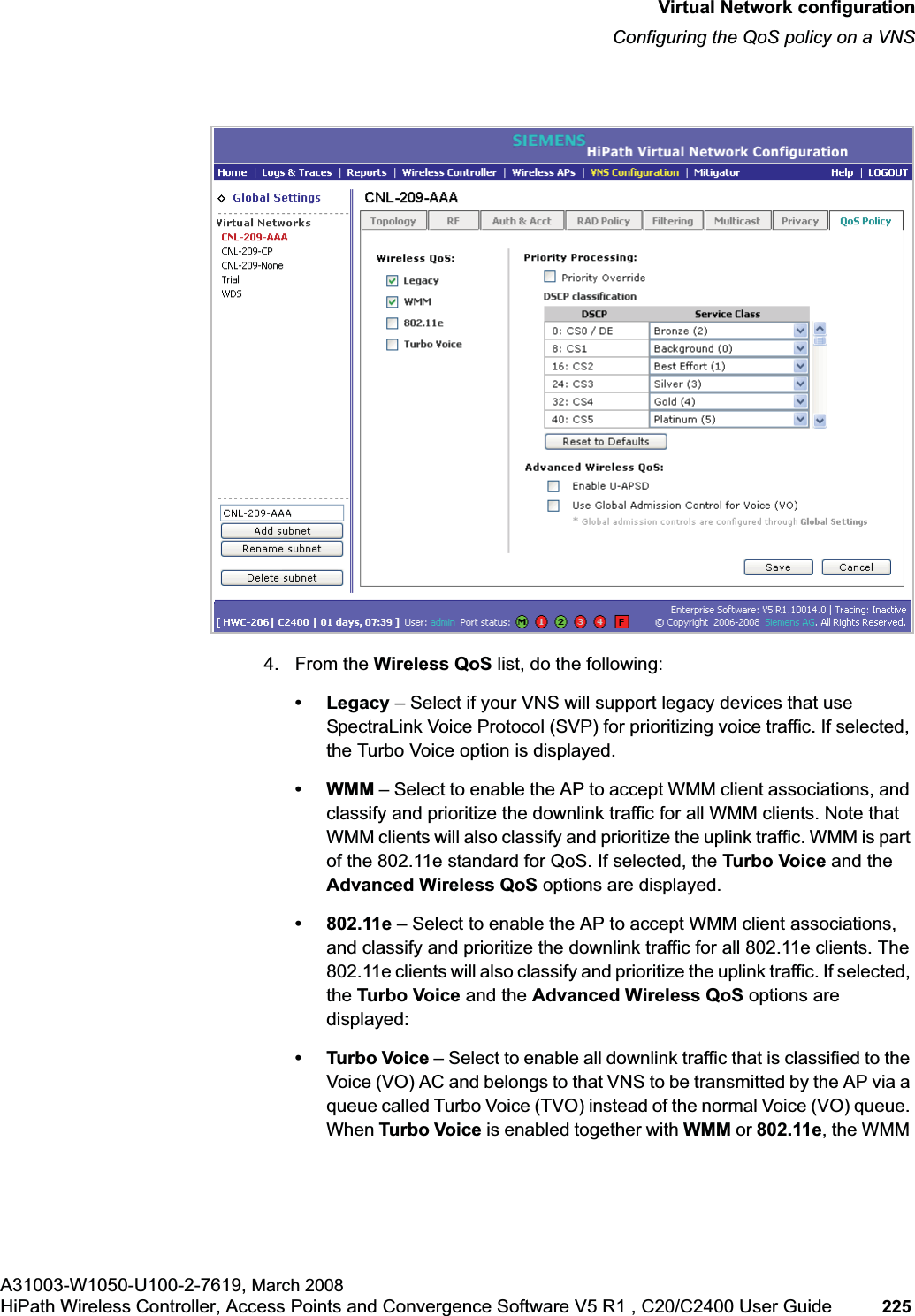
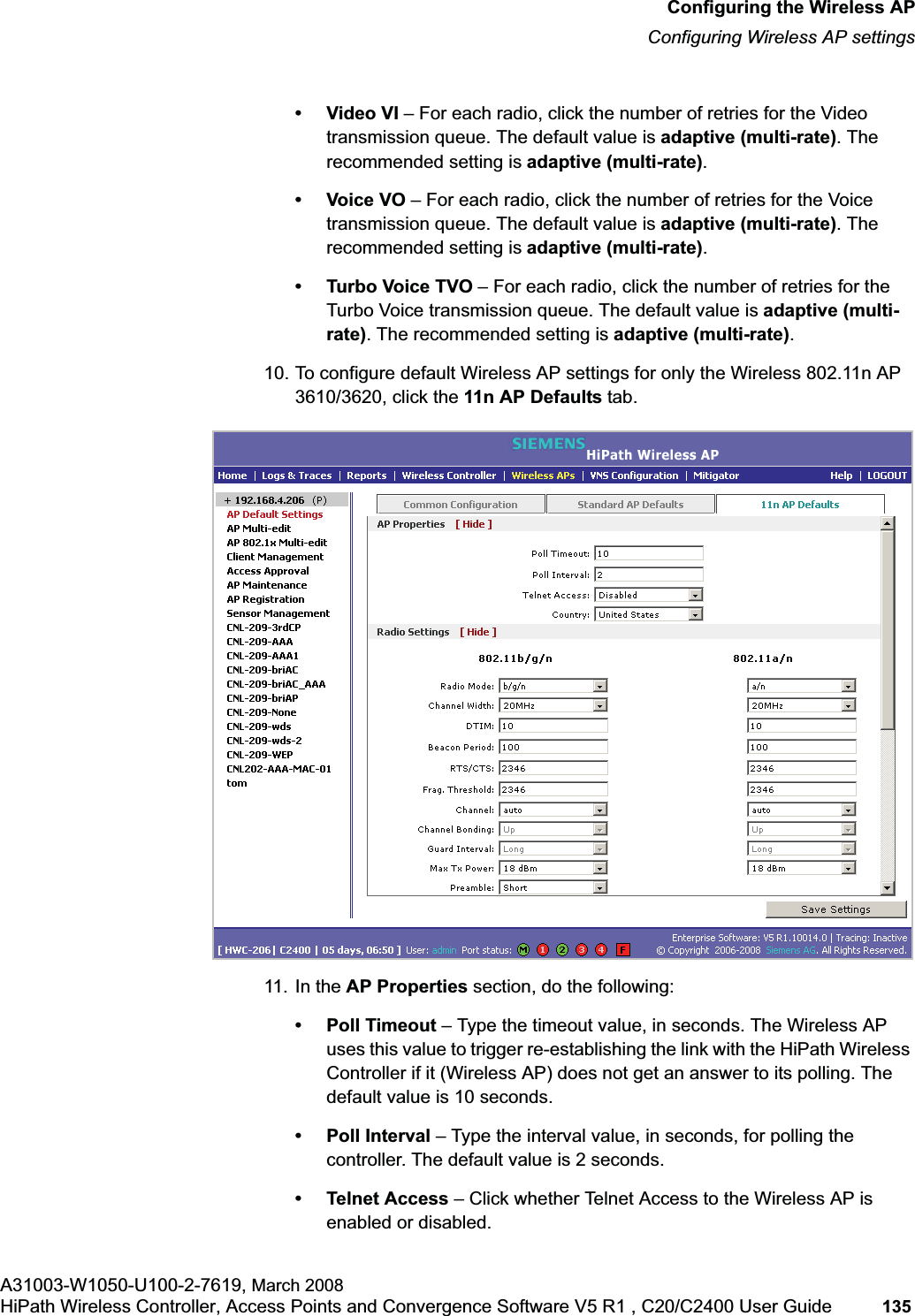
![hwc_pref.fmAbout this GuideDocumentation feedbackA31003-W1050-U100-2-7619, March 2008HiPath Wireless Controller, Access Points and Convergence Software V5 R1 , C20/C2400 User Guide 11 For example: Type https://<hwc-address>[:mgmt-port>]•The following notes are used to draw your attention to additional information:Note: Notes identify useful information, such as reminders, tips, or other ways to perform a task.Caution: Cautionary notes identify essential information, which if ignored can adversely affect the operation of your equipment or software.Warning: Warning notes identify essential information, which if ignored can lead to personal injury or harm.1.4 Documentation feedbackIf you have any problems using this document, please contact your next level of support:•Siemens employees should contact the interactive Customer Engagement Team (i-CET).•Customers should contact the Siemens Customer Support Center.When you call, please have the following information ready. This will help us to identify the document that you are referring to.•Title: HiPath Wireless Controller, Access Points and Convergence Software V5 R1 C20/C2400 User Guide•Part Number: A31003-W1050-U100-2-76191.5 Safety InformationDangers•Replace the power cable immediately if it shows any sign of damage. •Replace any damaged safety equipment (covers, labels and protective cables) immediately.•Use only original accessories or components approved for the system. Failure to observe these instructions may damage the equipment or even violate safety and EMC regulations.](https://usermanual.wiki/Siemens-Communications/AP36V1B.User-Manual-Part-1/User-Guide-936679-Page-11.png)











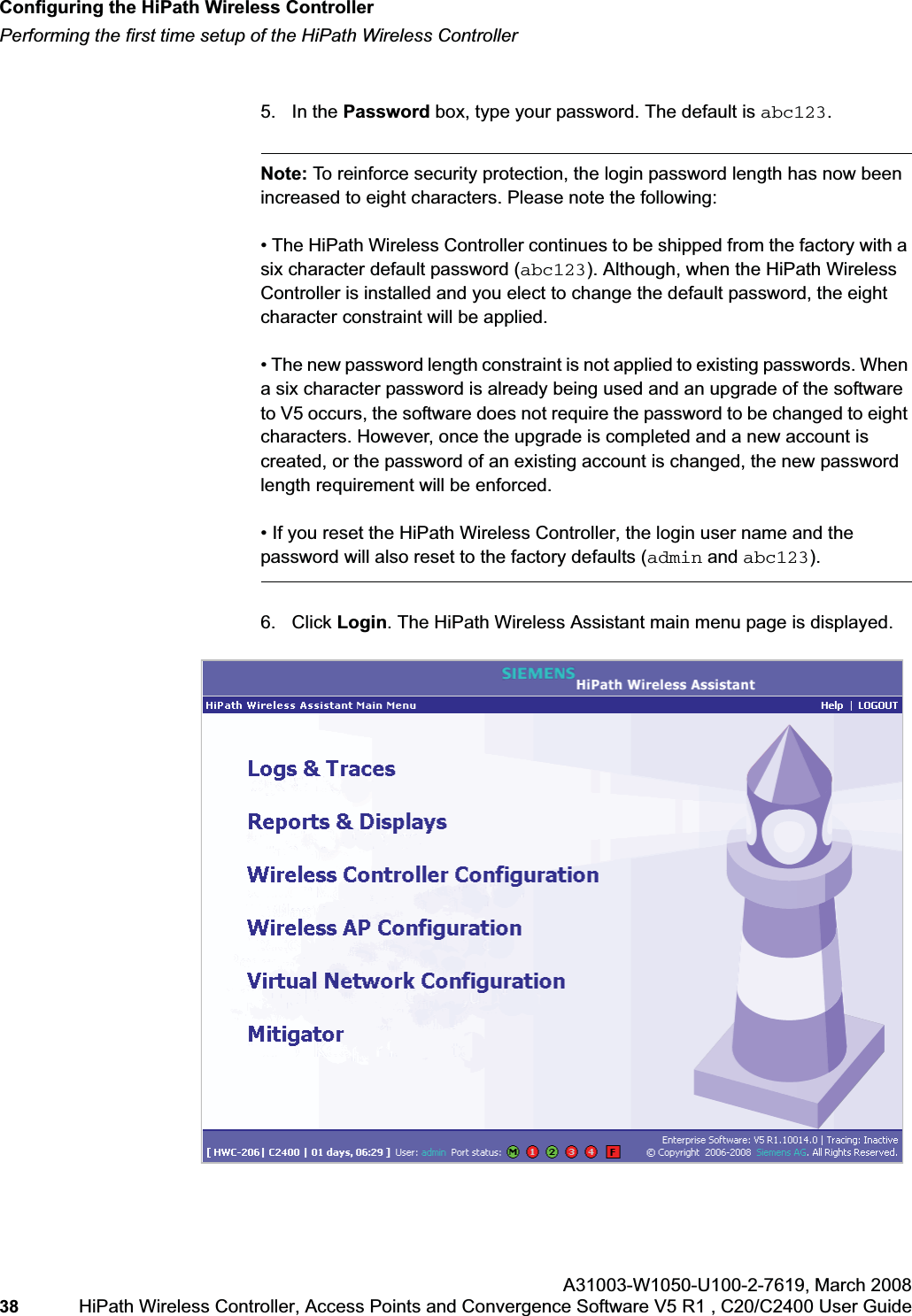
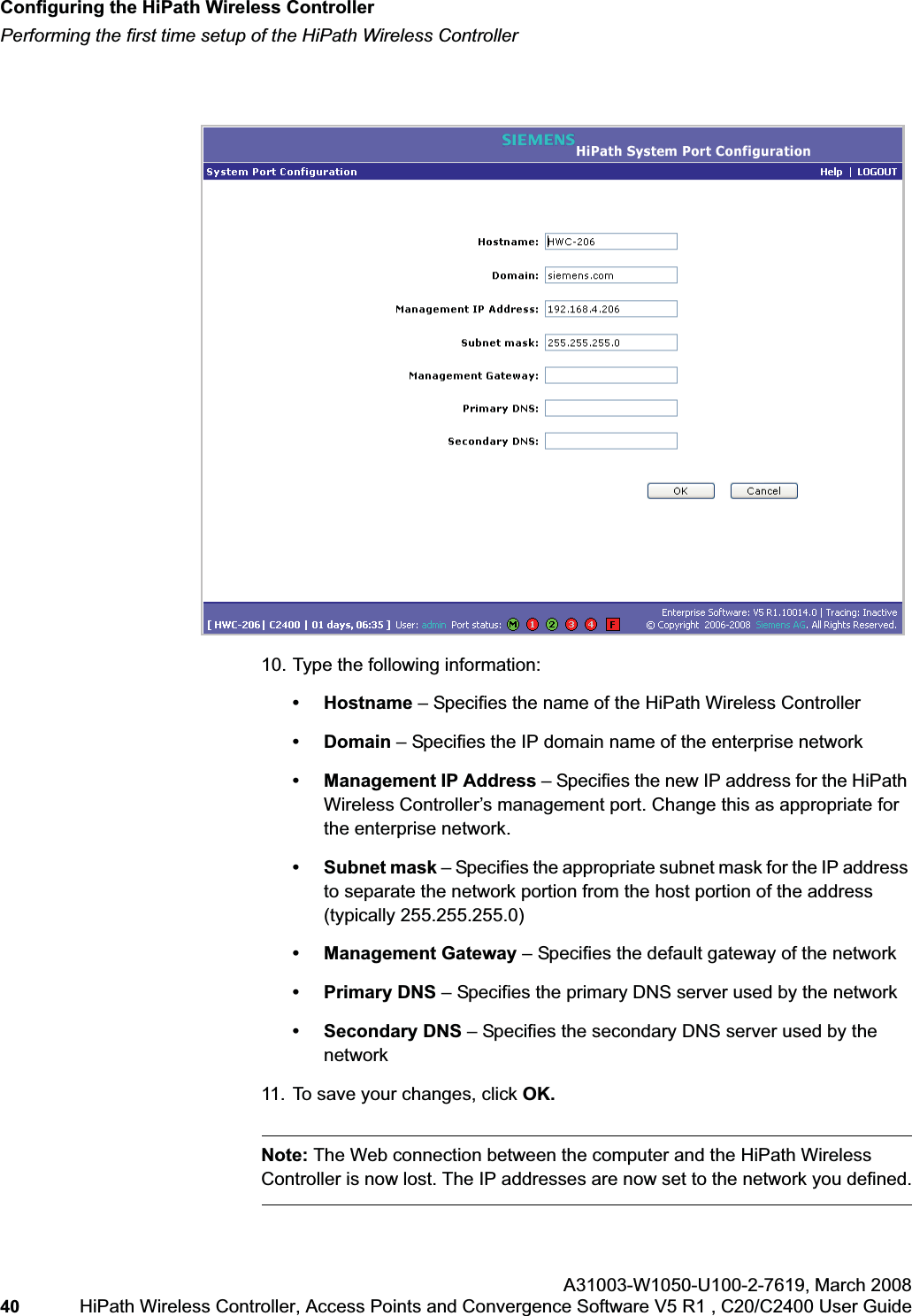
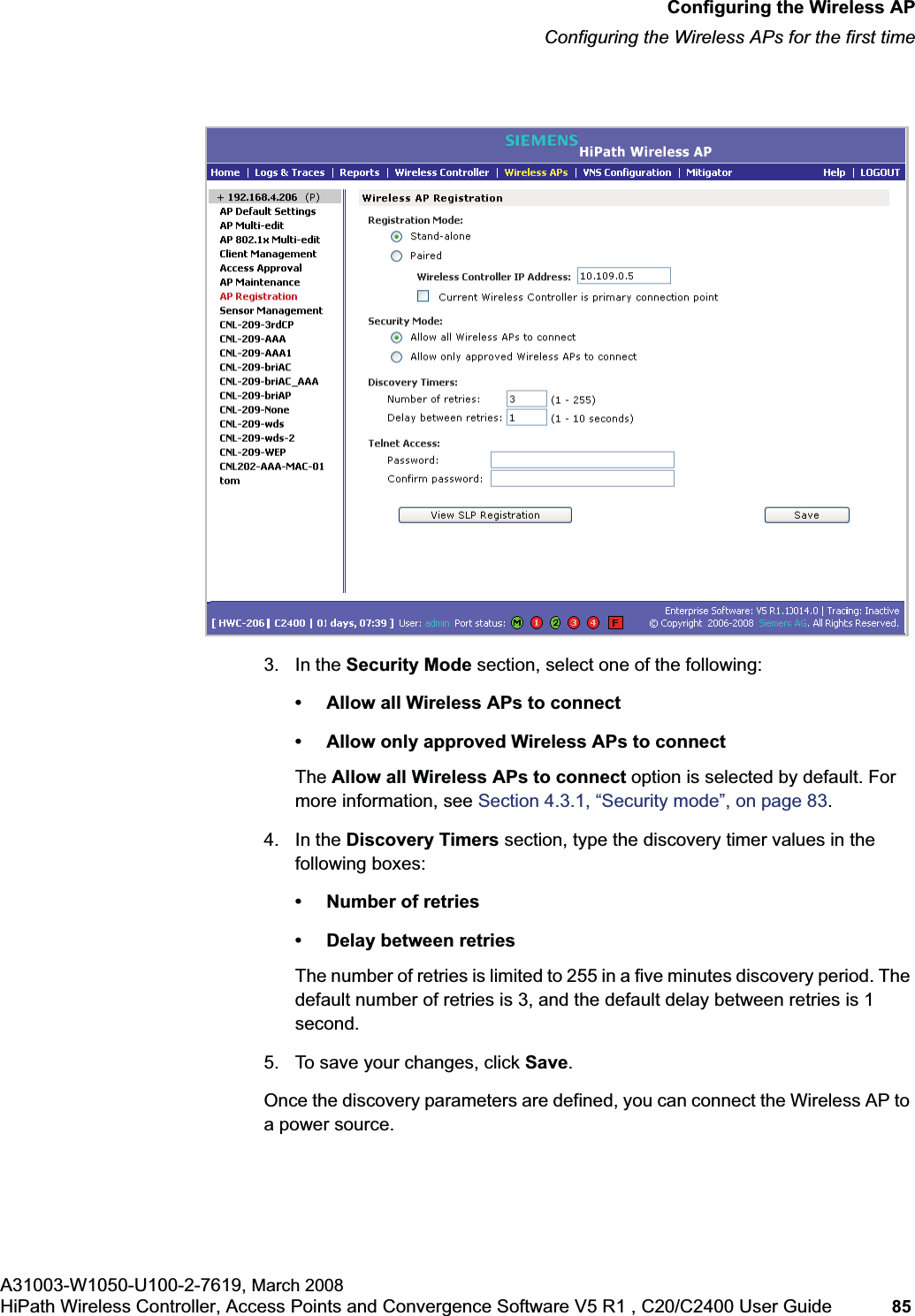
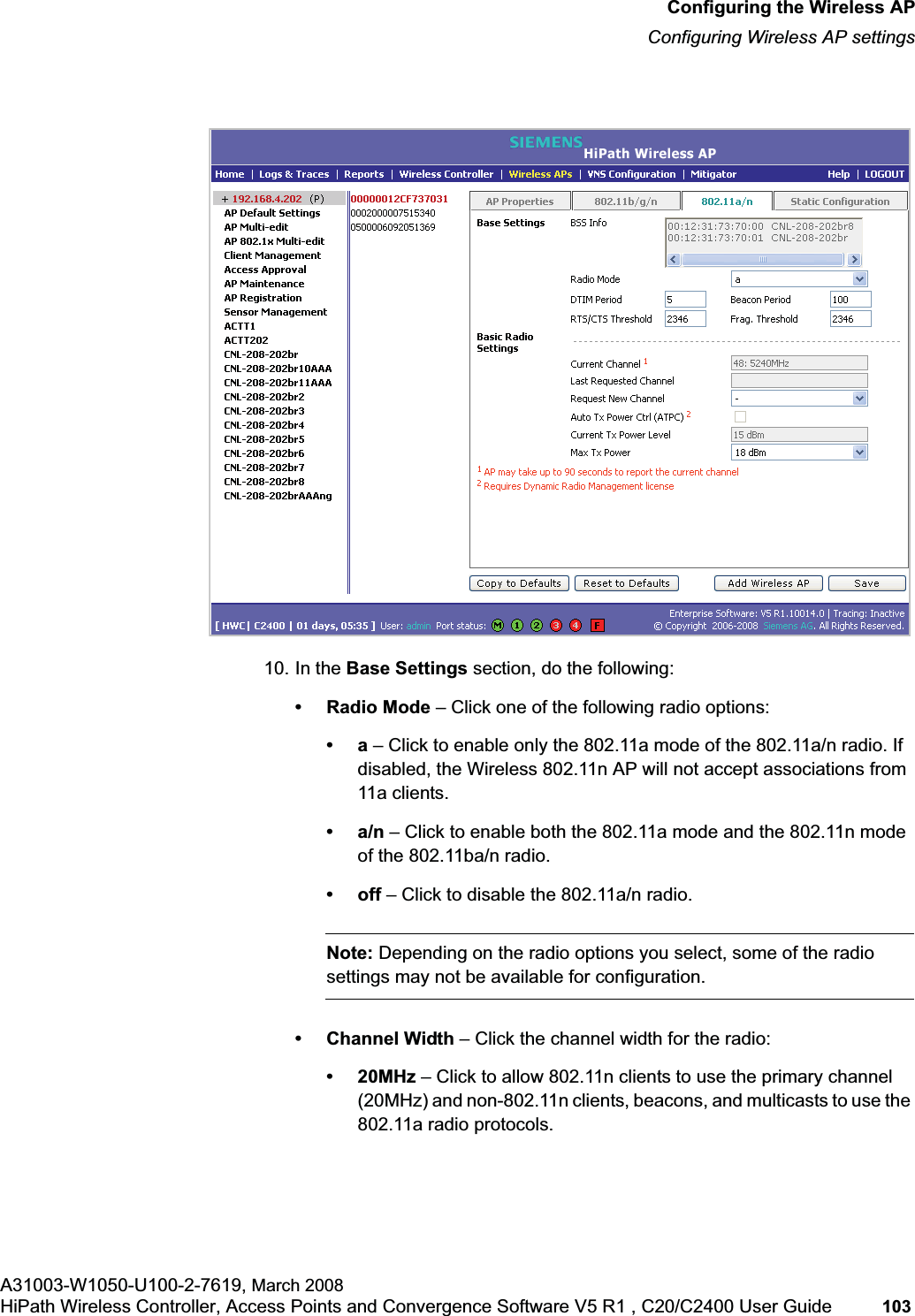
![hwc_startup.fmConfiguring the HiPath Wireless ControllerPerforming the first time setup of the HiPath Wireless ControllerA31003-W1050-U100-2-7619, March 2008HiPath Wireless Controller, Access Points and Convergence Software V5 R1 , C20/C2400 User Guide 39 Note: All images of the HiPath Wireless Assistant in this User Guide represent the HiPath Wireless Controller C2400. In the footer of the HiPath Wireless Assistant, the following is displayed:• [host name | product name | up time]For example, [HWC-206 | C2400 | 01 days, 06:29]. If your HiPath Wireless Assistant is running the C2400 license, the footer will display C2400.• If there is no key (unlicensed), the product name will not be displayed.• User is the user id you used to login in. For example, admin.• Port Status is the connectivity state of the port. M represents the Management interface, which is on eth0 and the numbered lights reflect the esa ports on the system. Green indicates the interface is up and running. Red indicates the interface is down. The F icon represents the flash drive status: green if the flash drive is mounted, and red if the flash drive is not mounted.7. From the main menu, click Wireless Controller Configuration. The HiPathWireless Controller Configuration page is displayed.8. In the left pane, click IP Addresses. The factory default settings for the HiPath Wireless Controller are displayed.9. In the Management Port Settings section, click Modify. The System Port Configuration page is displayed.](https://usermanual.wiki/Siemens-Communications/AP36V1B.User-Manual-Part-1/User-Guide-936679-Page-39.png)


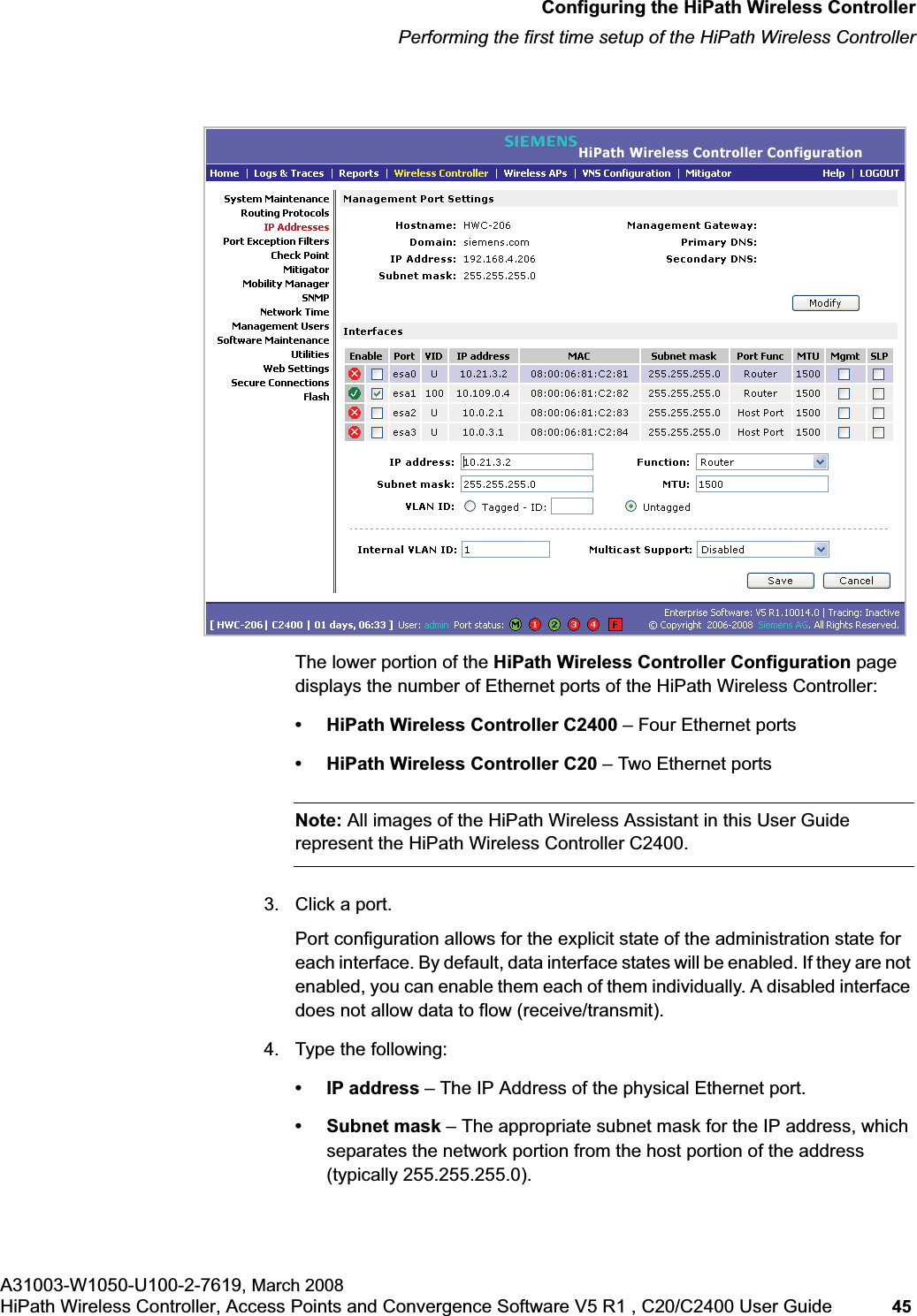


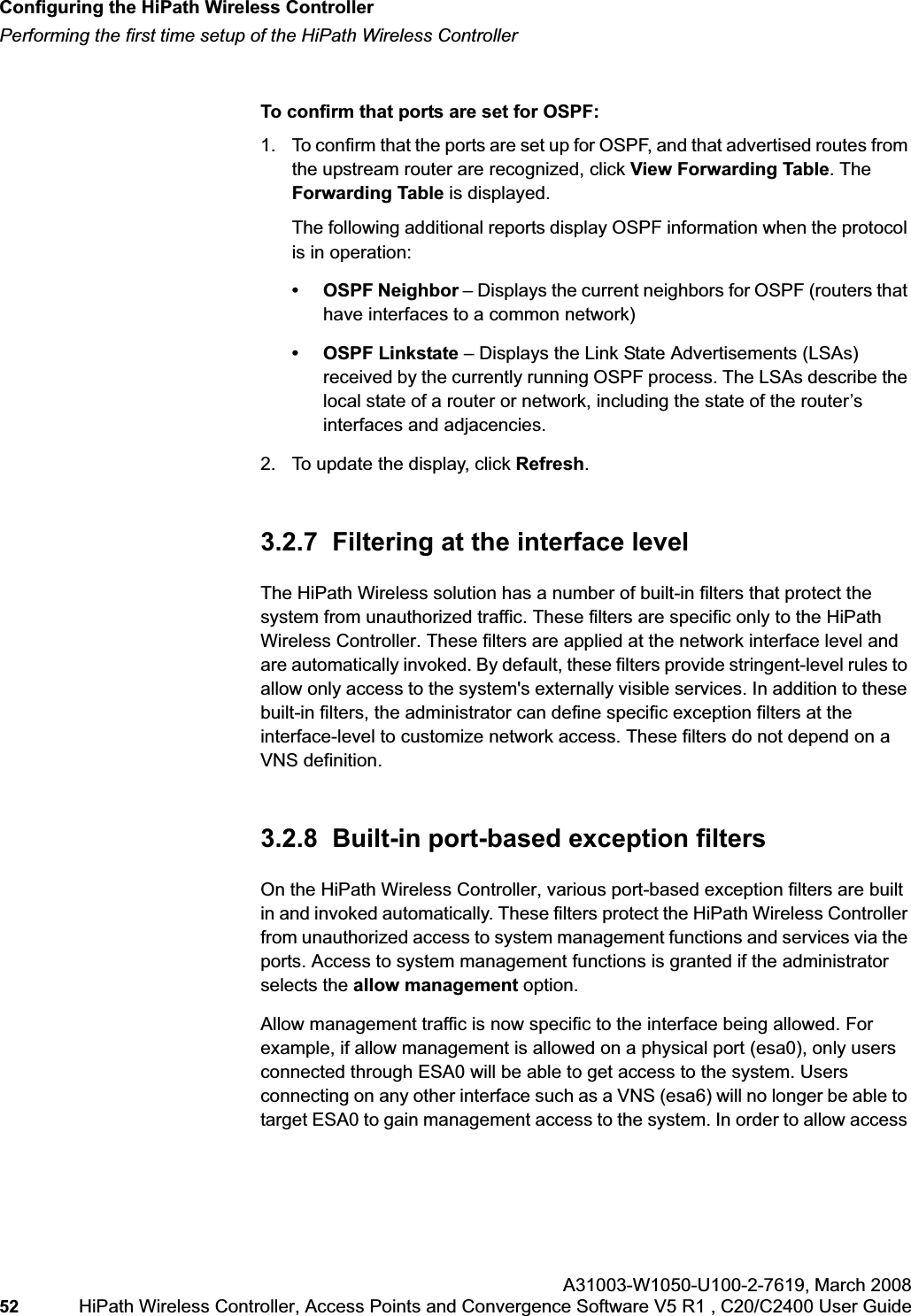
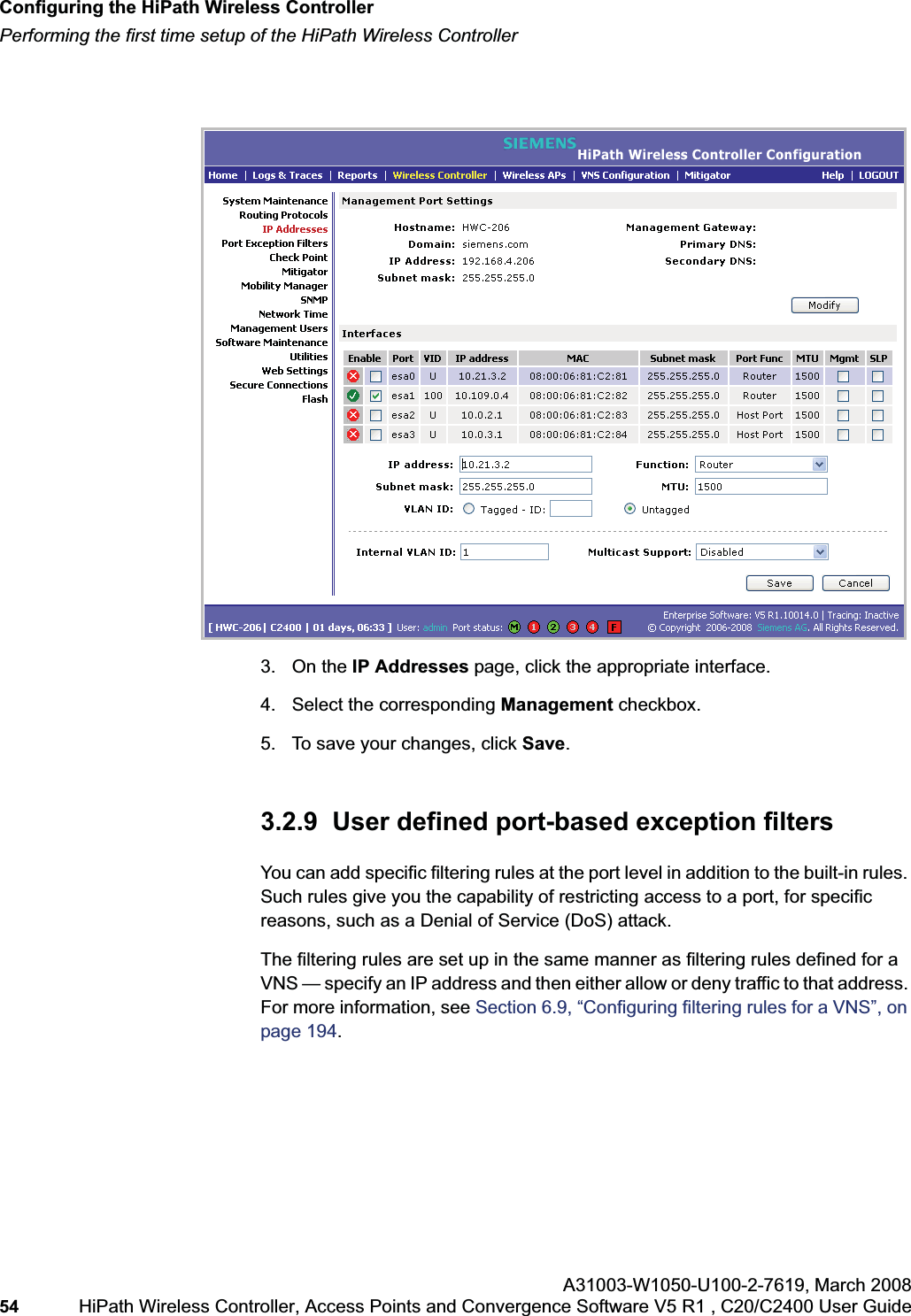
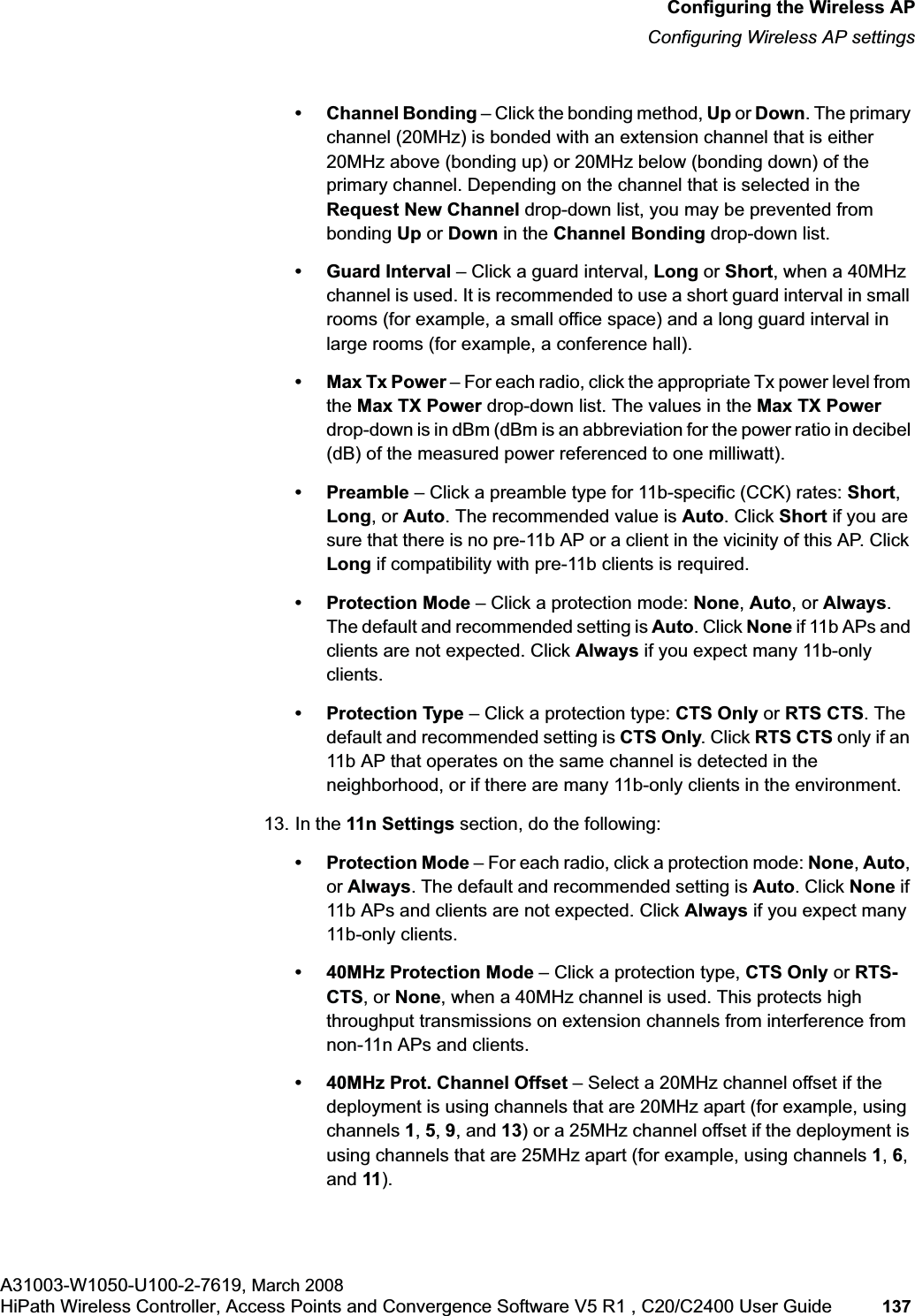
![hwc_startup.fmConfiguring the HiPath Wireless ControllerPerforming the first time setup of the HiPath Wireless ControllerA31003-W1050-U100-2-7619, March 2008HiPath Wireless Controller, Access Points and Convergence Software V5 R1 , C20/C2400 User Guide 53 for users connected on a VNS, the VNS configuration itself must have allow management enabled and users will only be able to target the VNS interface specifically.Note: You can also enable management traffic in the VNS definition.For example, on the HiPath Wireless Controller’s data interfaces (both physical interfaces and VNS virtual interfaces), the built-in exception filter prohibits invoking SSH, HTTPS, or SNMP. However, such traffic is allowed, by default, on the management port.If management traffic is explicitly enabled for any interface (physical port or VNS), access is implicitly extended to that interface through any of the other interfaces (VNS). Only traffic specifically allowed by the interface’s exception filter is allowed to reach the HiPath Wireless Controller itself. All other traffic is dropped. Exception filters are dynamically configured and regenerated whenever the system's interface topology changes (for example, a change of IP address for any interface). Enabling management traffic on an interface adds additional rules to the exception filter, which opens up the well-known IP(TCP/UDP) ports, corresponding to the HTTPS, SSH, and SNMP applications.The port-based built-in exception filtering rules, in the case of traffic from VNS users, are applicable to traffic targeted directly for the VNSs interface. For example, a VNS filter may be generic enough to allow traffic access to the HiPath Wireless Controller's management (for example, Allow All [*.*.*.*]). Exception filter rules are evaluated after the user's VNS assigned filter policy, as such, it is possible that the VNS policy allow the access to management functions that the exception filter denies. These packets are dropped. To enable SSH, HTTPS, or SNMP access through a data interface:1. From the main menu, click Wireless Controller Configuration. The HiPathWireless Controller Configuration page is displayed.2. In the left pane, click IP Addresses. The Management Port Settings page is displayed.](https://usermanual.wiki/Siemens-Communications/AP36V1B.User-Manual-Part-1/User-Guide-936679-Page-53.png)
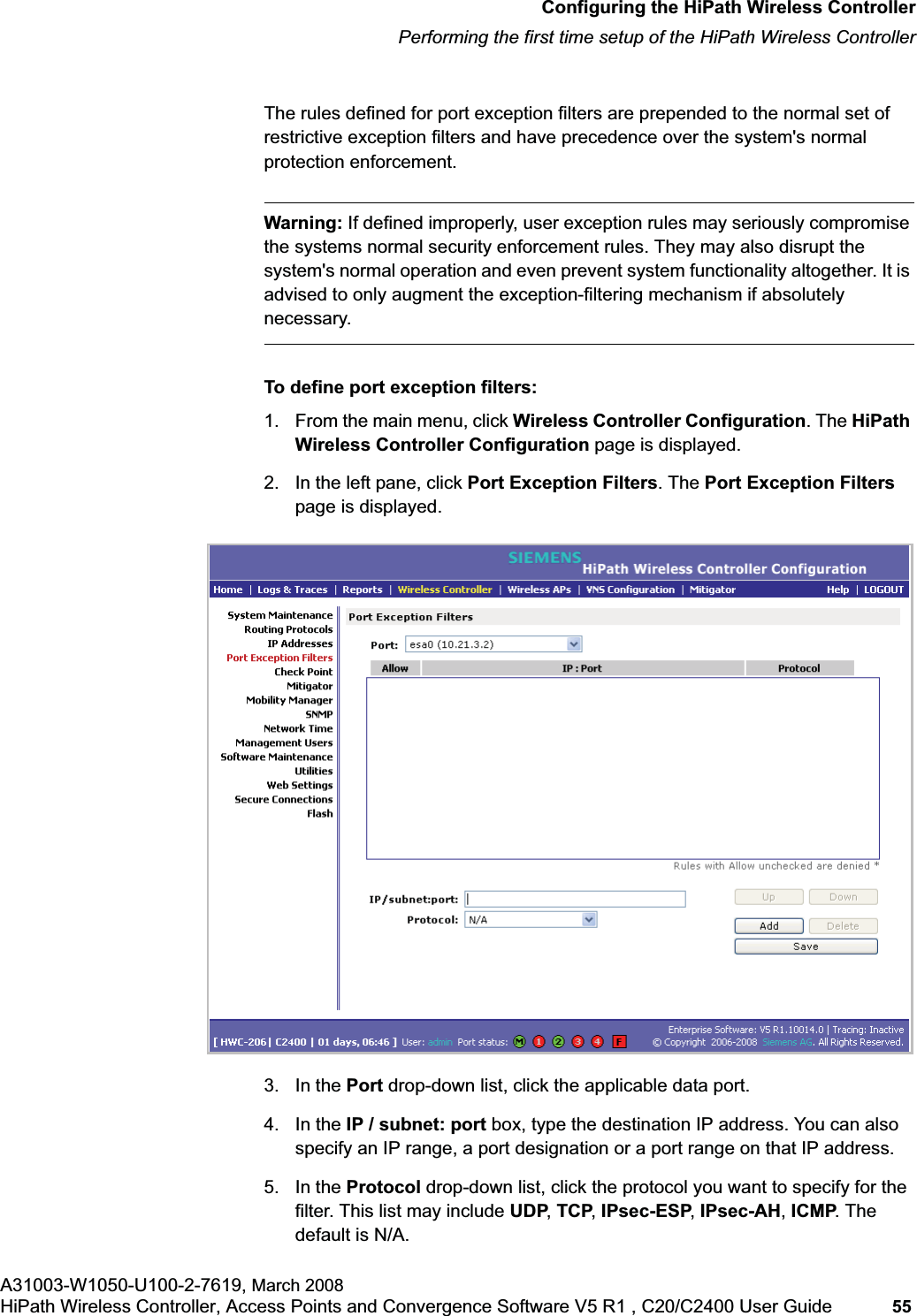








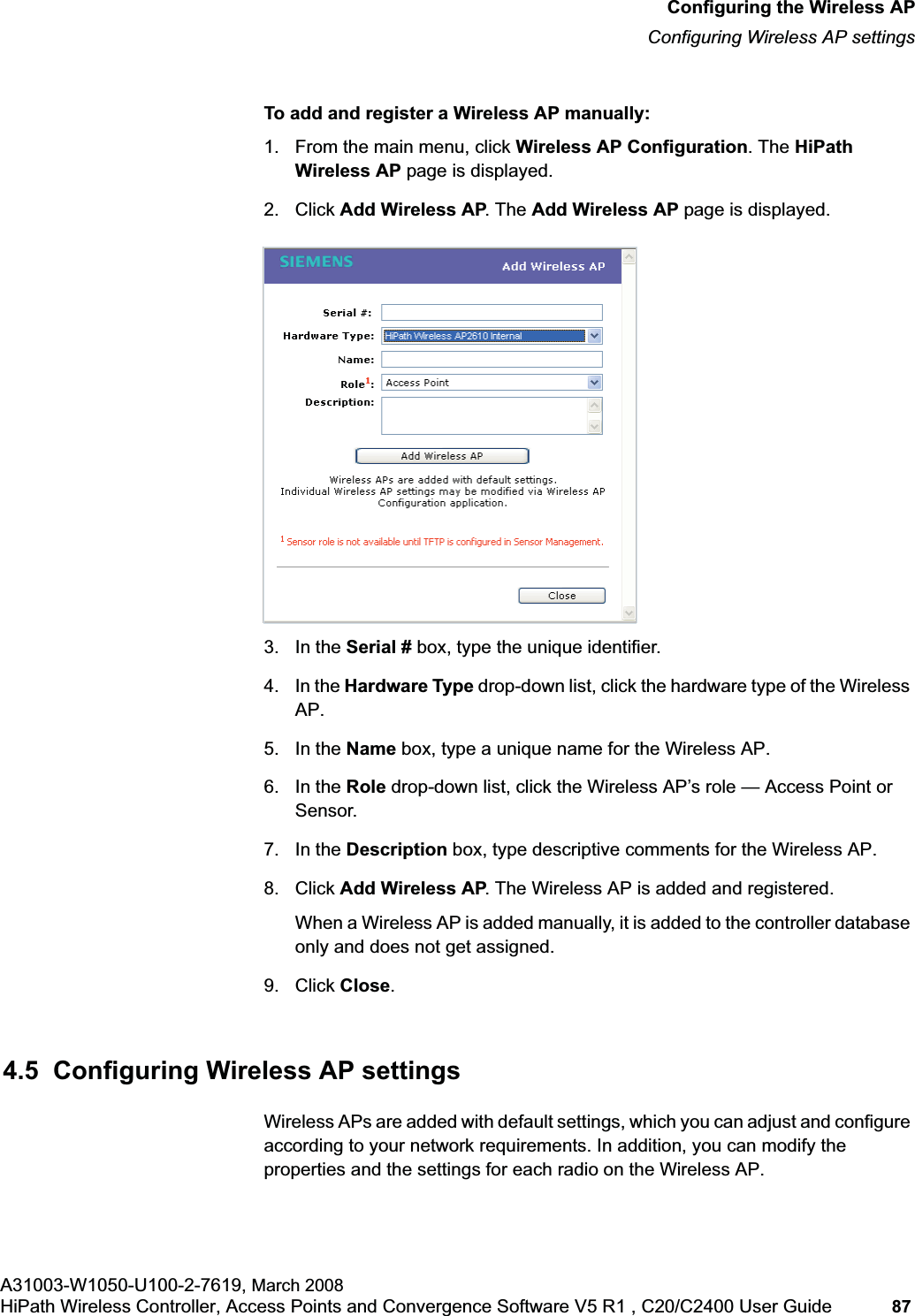
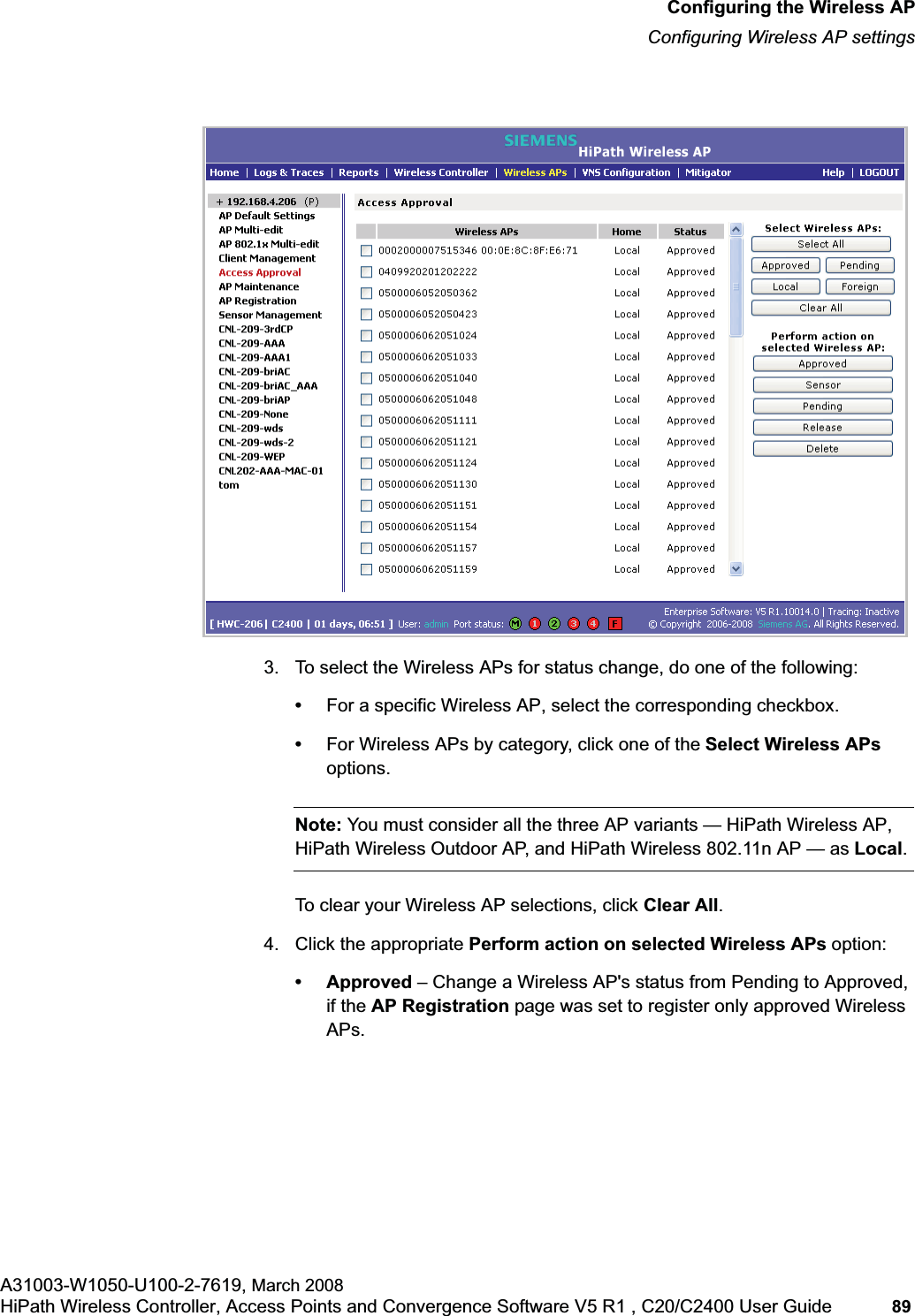








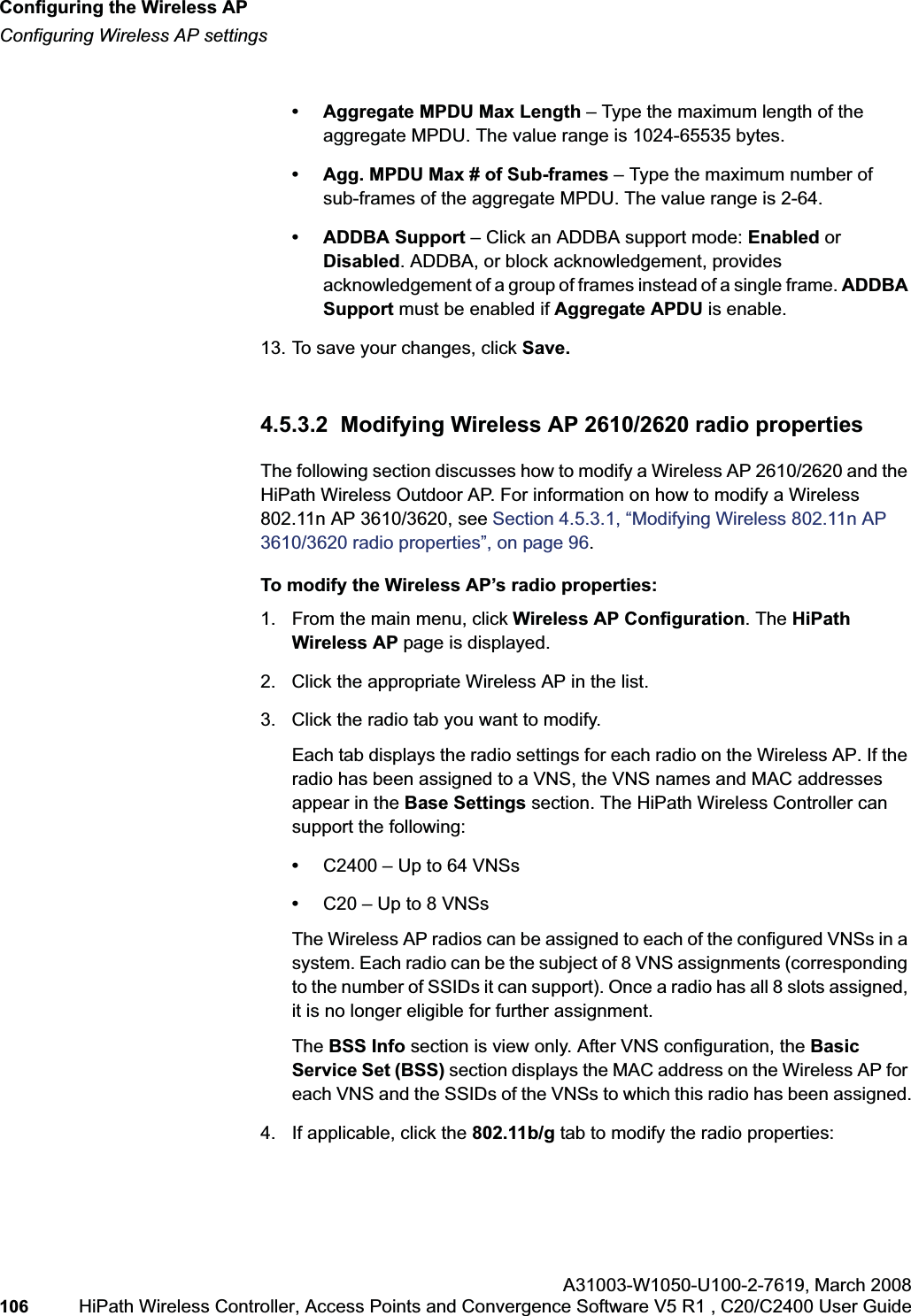
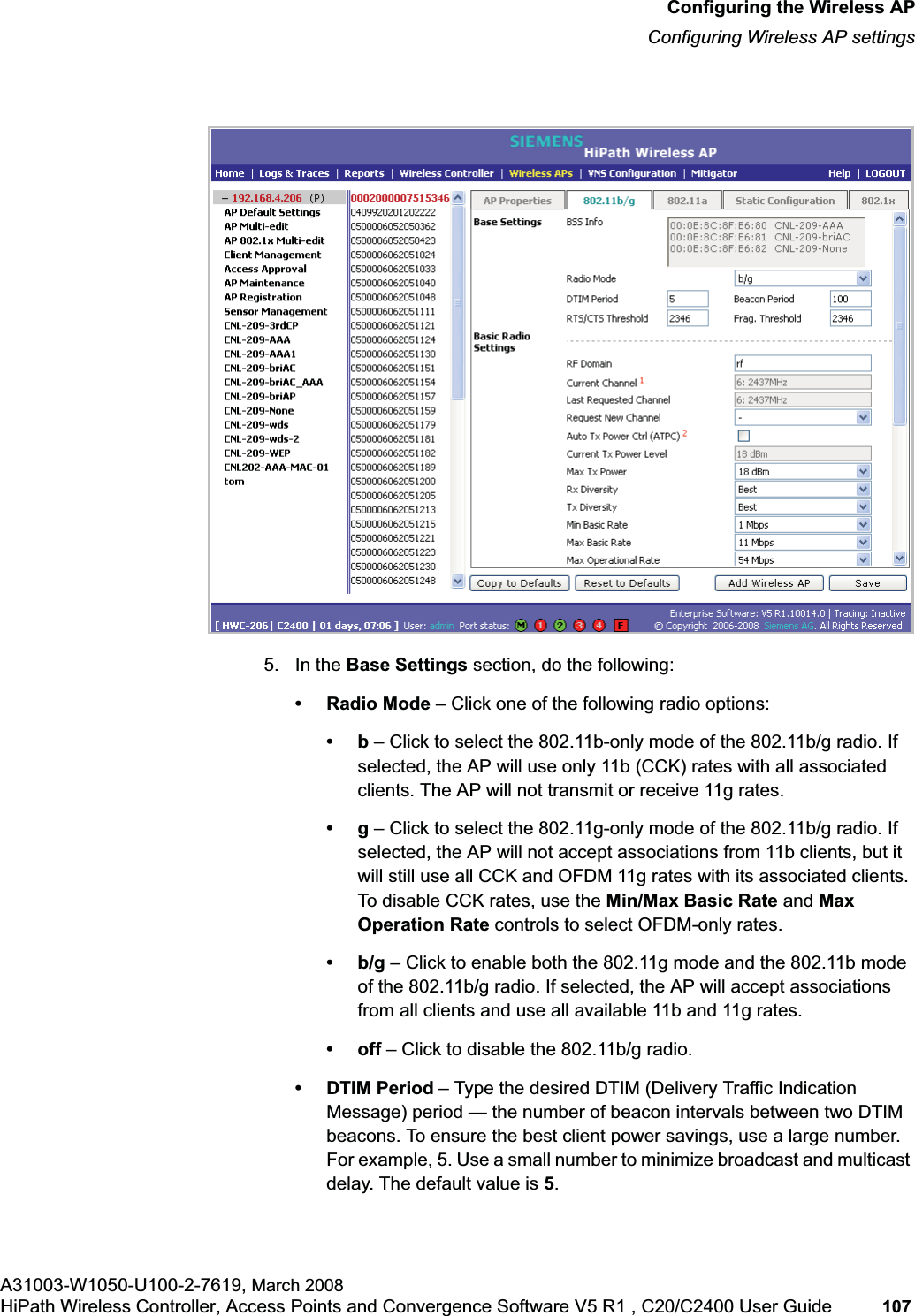



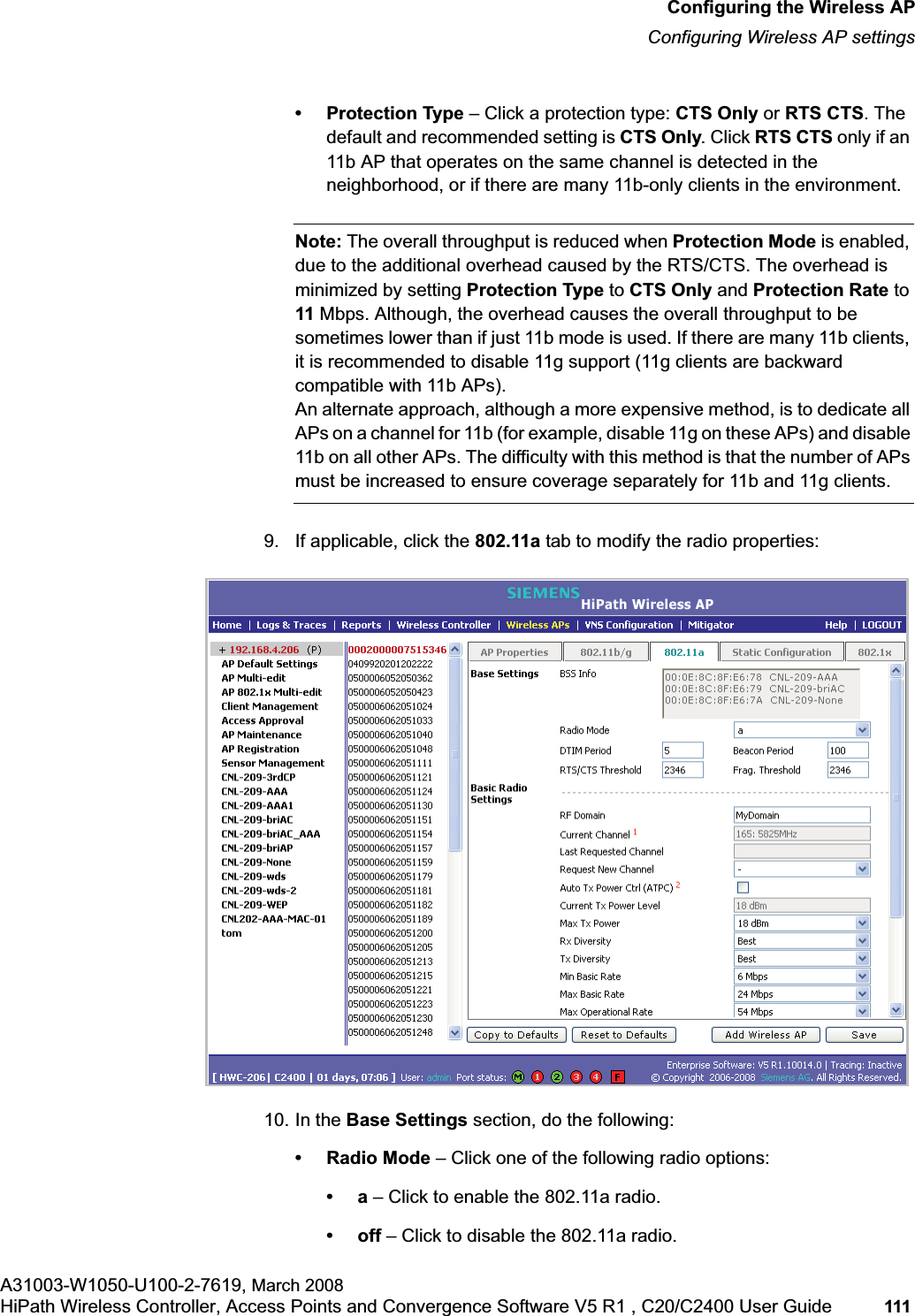



















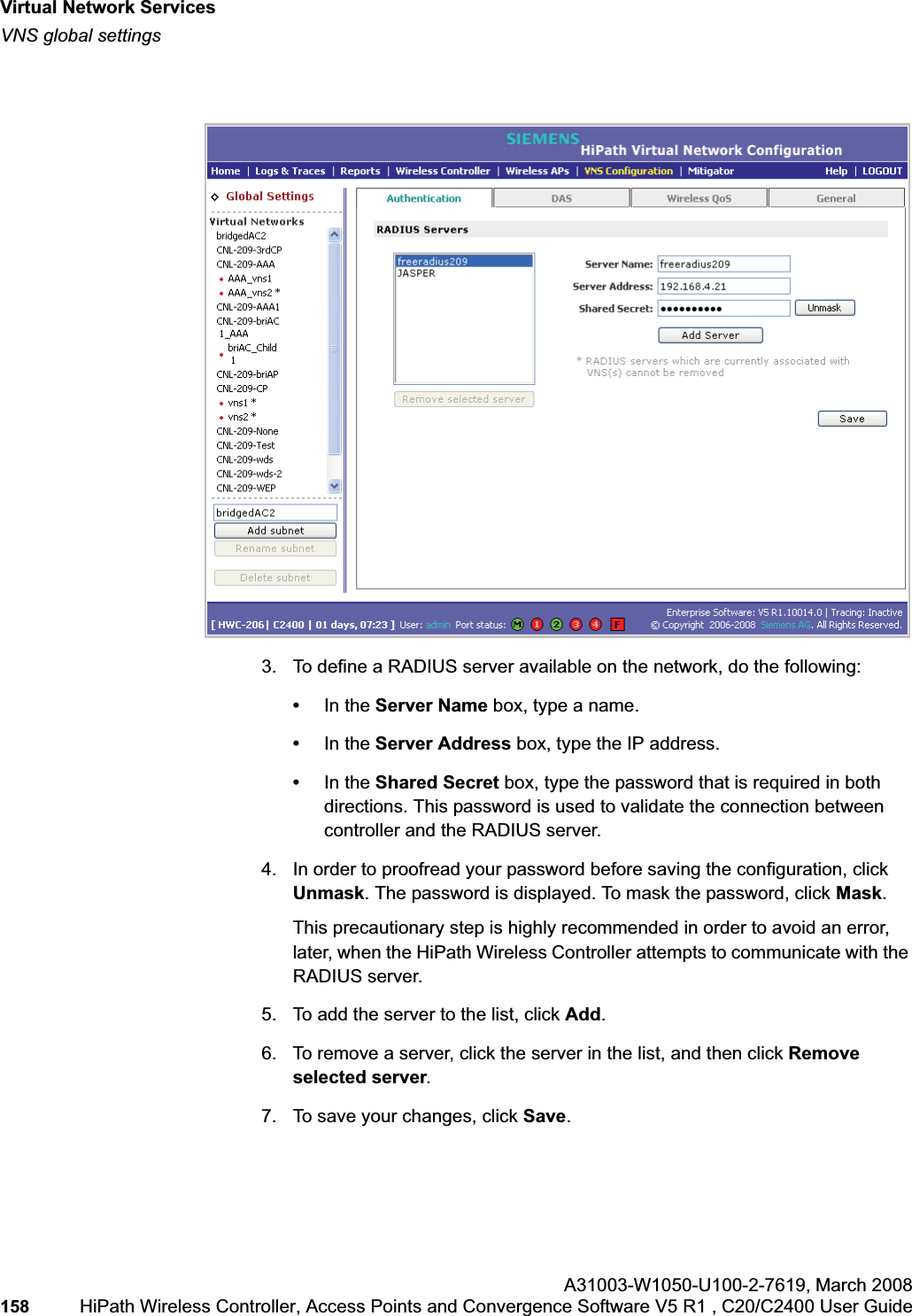













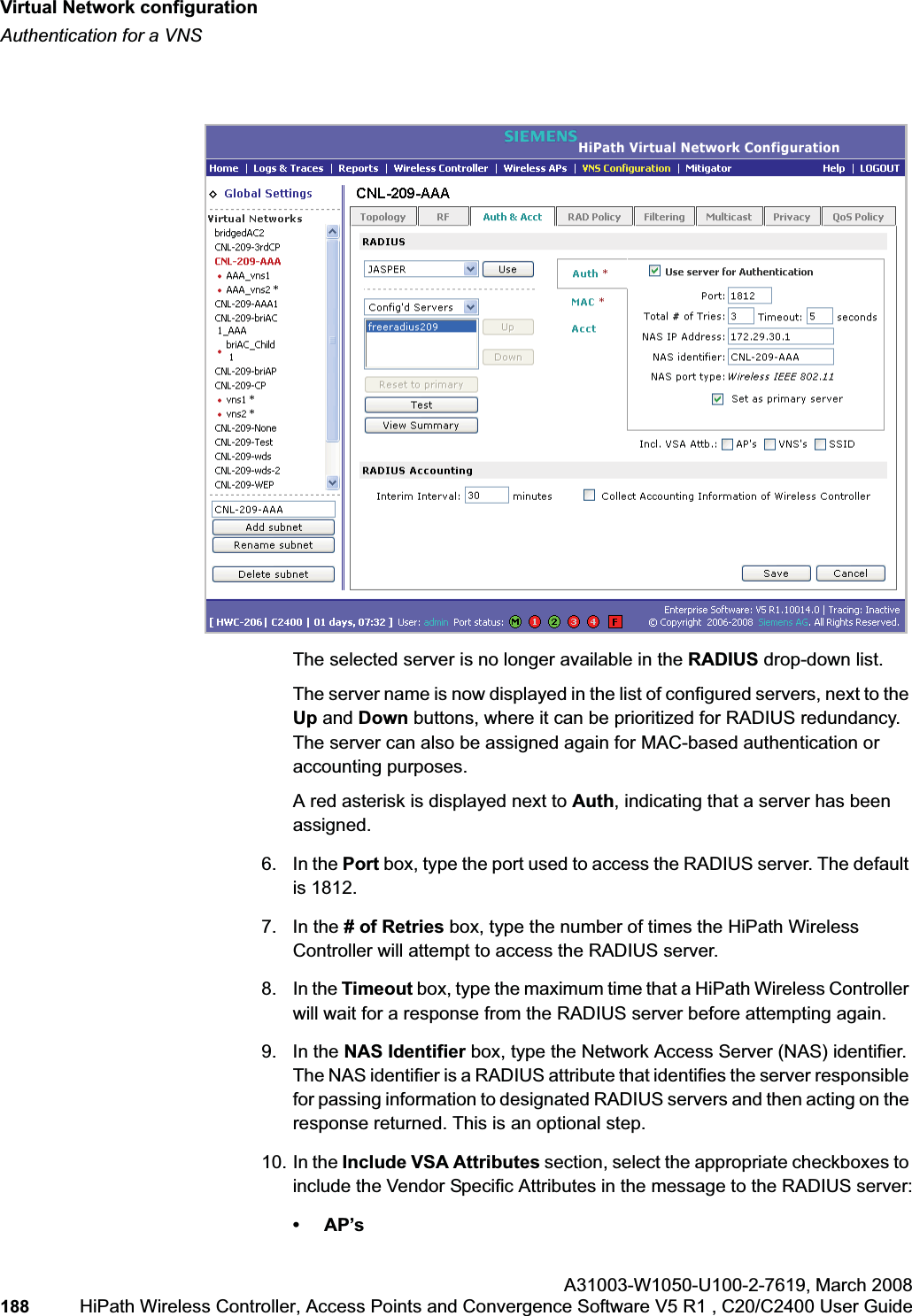


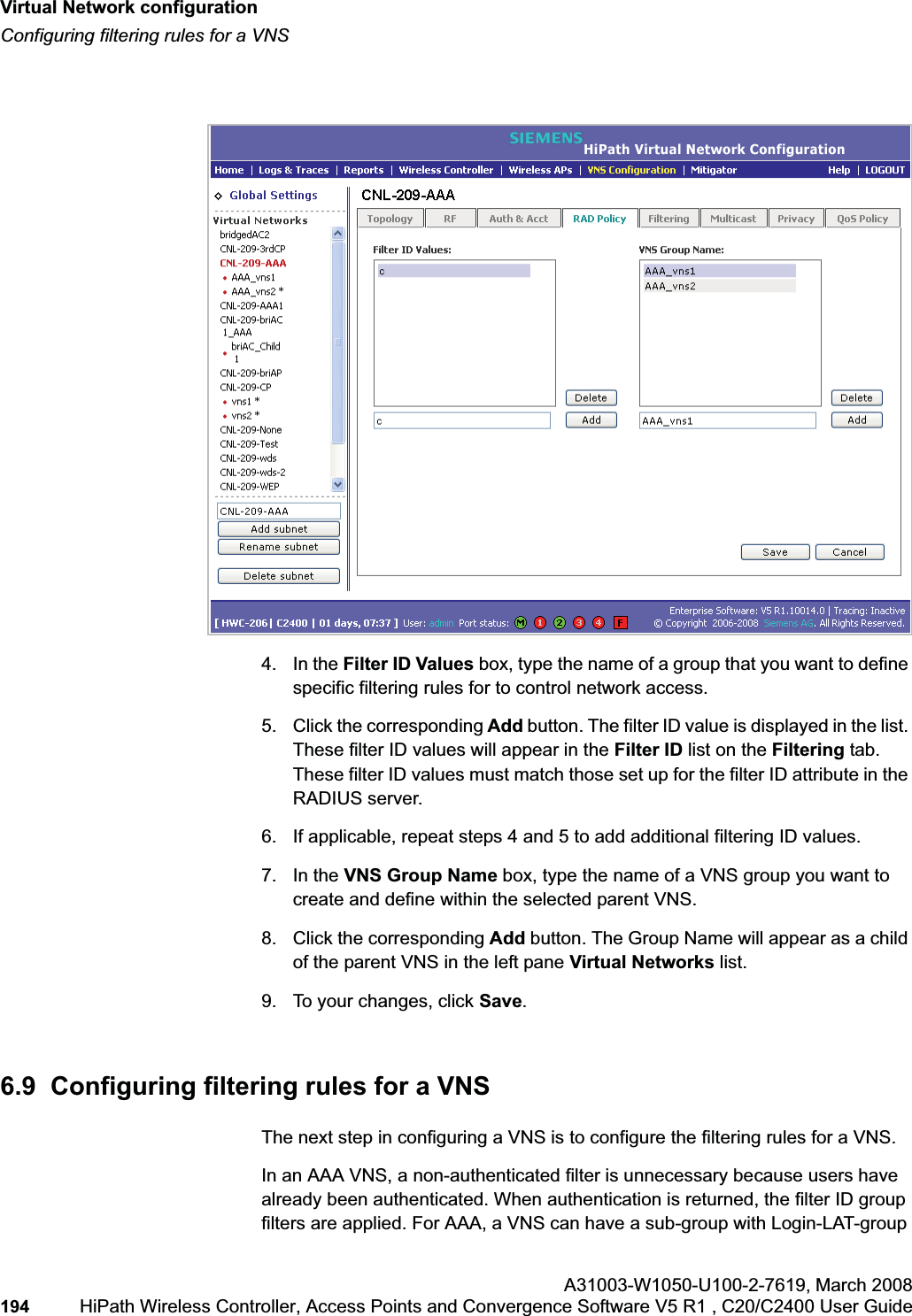

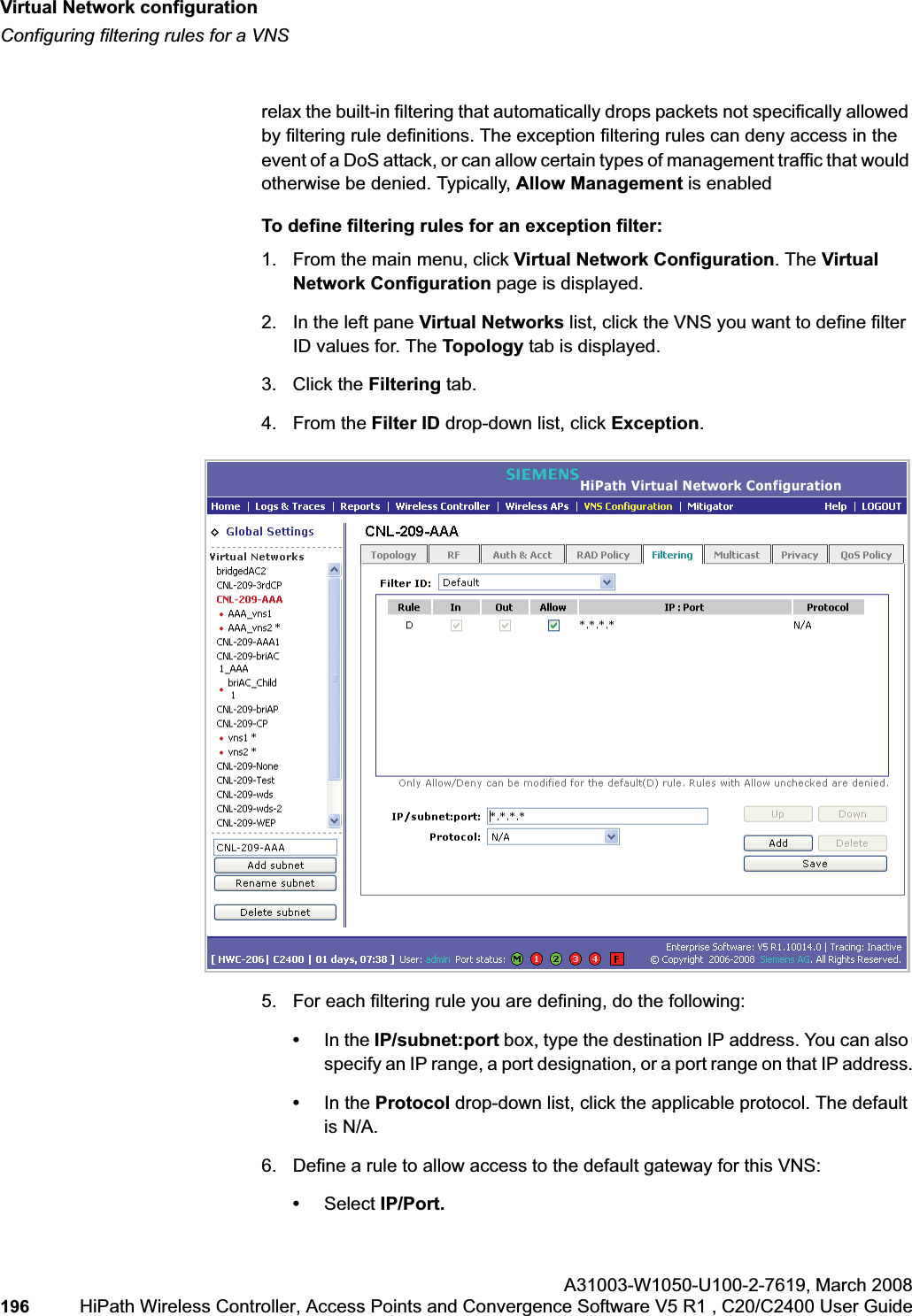


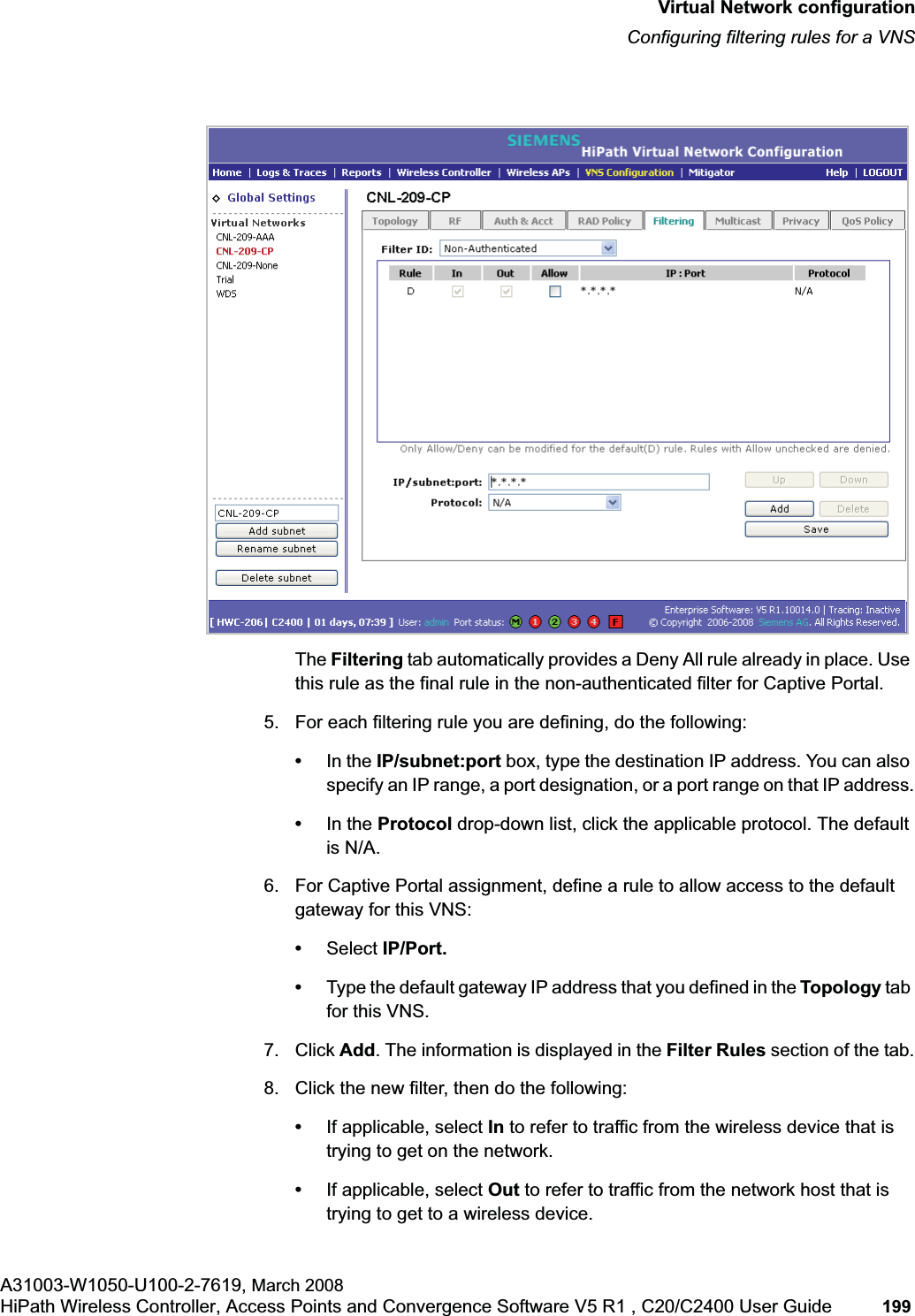
![hwc_vnsconfiguration.fmVirtual Network configurationConfiguring filtering rules for a VNSA31003-W1050-U100-2-7619, March 2008HiPath Wireless Controller, Access Points and Convergence Software V5 R1 , C20/C2400 User Guide 201 Once a wireless device user has logged in on the Captive Portal page, and has been authenticated by the RADIUS server, then the following filters will apply:• Filter ID – If a filter ID associated with this user was returned by the authentication server.• Default filter – If no matching filter ID was returned from the authentication server.6.9.3 Filtering rules for a filter ID groupWhen the wireless device user provides the identification credentials, identification is sent by the HiPath Wireless Controller to the RADIUS server, or other authentication server, through a sequence of exchanges depending on the type of authentication protocol used. When the server allows this request for authentication—the server sends an access-accept message, the RADIUS server may also send back to the HiPath Wireless Controller a filter ID attribute value associated with the user. For an AAA VNS, a Login-LAT-Group identifier for the user may also be returned. VNS Policy is also applicable for Captive Portal and MAC-based authorization.If the filter ID attribute value (or Login-LAT-Group attribute value) from the RADIUS server matches a filter ID value that you have set up on the HiPath Wireless Controller, the HiPath Wireless Controller applies the filtering rules that you defined for that filter ID value to the wireless device user. If no filter ID is returned by the authentication server, or no match is found on the HiPath Wireless Controller, the filtering rules in the default filter will apply to the wireless device user.In Out Allow IP / Port Descriptionx x x IP address of the default gatewayAllow all incoming wireless devices access to the default gateway of the VNS.x x x IP address of the DNS ServerAllow all incoming wireless devices access to the DNS server of the VNS.x x [a specific IP address, or address plus range]Deny all traffic to a specific IP address, or to a specific IP address range (such as:0/24).x x x *.*.*.*:80 Allow all port 80 (HTTP) traffic.x x *.*.*.* Deny everything else. Table 16 Non-authenticated filter example B](https://usermanual.wiki/Siemens-Communications/AP36V1B.User-Manual-Part-1/User-Guide-936679-Page-201.png)
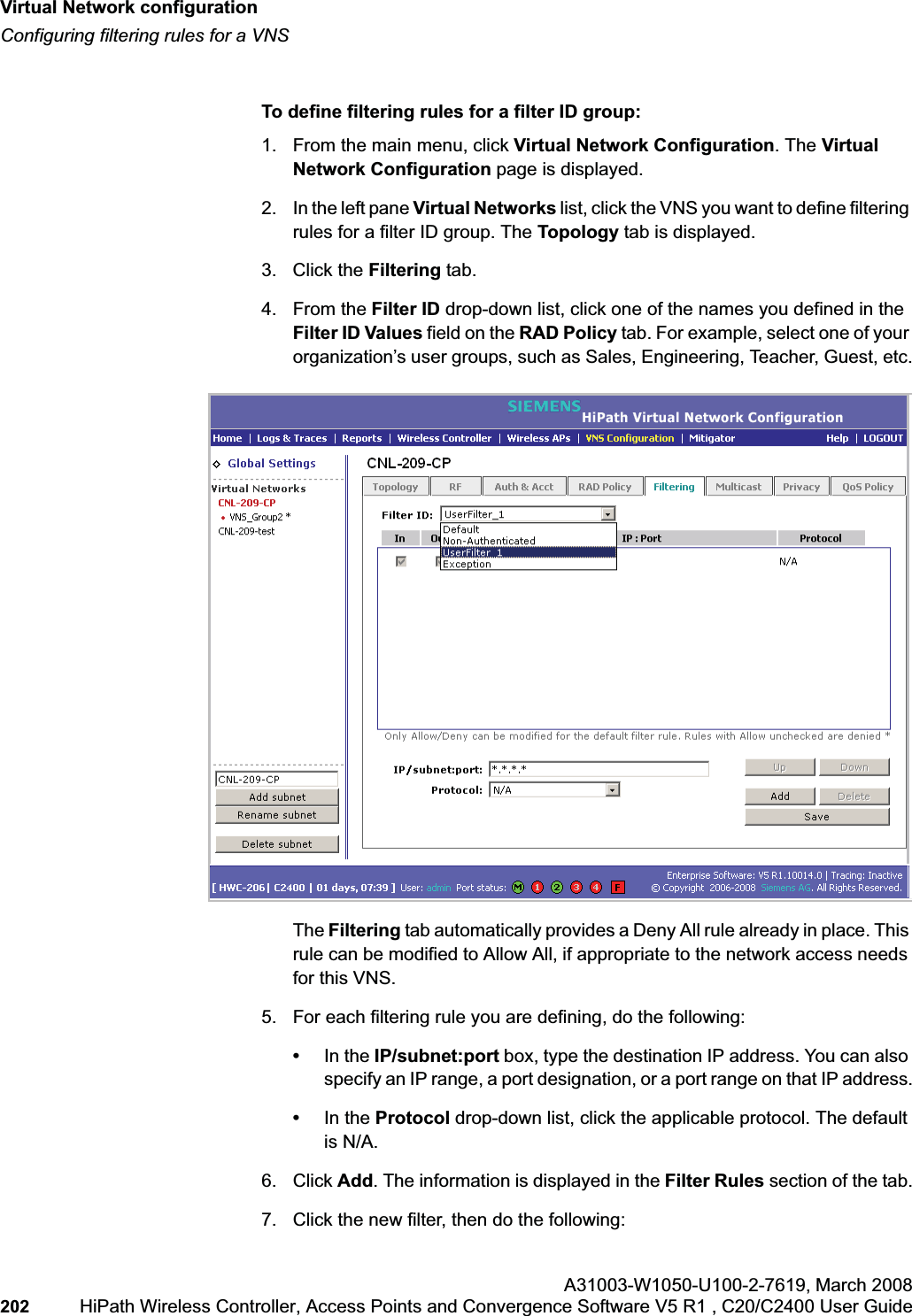
![hwc_vnsconfiguration.fmVirtual Network configurationConfiguring filtering rules for a VNSA31003-W1050-U100-2-7619, March 2008HiPath Wireless Controller, Access Points and Convergence Software V5 R1 , C20/C2400 User Guide 203 •If applicable, select In to refer to traffic from the wireless device that is trying to get on the network.•If applicable, select Out to refer to traffic from the network host that is trying to get to a wireless device. •Select the Allow checkbox applicable to the rule you defined.8. To edit the order of filters, click the filter, and then click the Up and Downbuttons. The filtering rules are executed in the order you define here.9. To save your changes, click Save.6.9.3.1 Filtering rules by filter ID examplesBelow are two examples of possible filtering rules for a filter ID. The first example disallows some specific access before allowing everything else.The second example does the opposite of the first example. It allows some specific access and denies everything else. 6.9.4 Filtering rules for a default filterAfter authentication of the wireless device user, the default filter will apply only after:•No match is found for the Exception filter rules.•No filter ID attribute value is returned by the authentication server for this user.•No match is found on the HiPath Wireless Controller for a filter ID value.In Out Allow IP / Port Descriptionx x *.*.*.*:22-23 SSH and telnet sessionsx x [specific IP address, range]Deny all traffic to a specific IP address or address rangex x x *.*.*.*. Allow everything elseTable 17 Filtering rules by filter ID example AIn Out Allow IP / Port Descriptionx x x [specific IP address, range]Allow traffic to a specific IP address or address range.x x *.*.*.*. Deny everything else.Table 18 Filtering rules by filter ID example B](https://usermanual.wiki/Siemens-Communications/AP36V1B.User-Manual-Part-1/User-Guide-936679-Page-203.png)
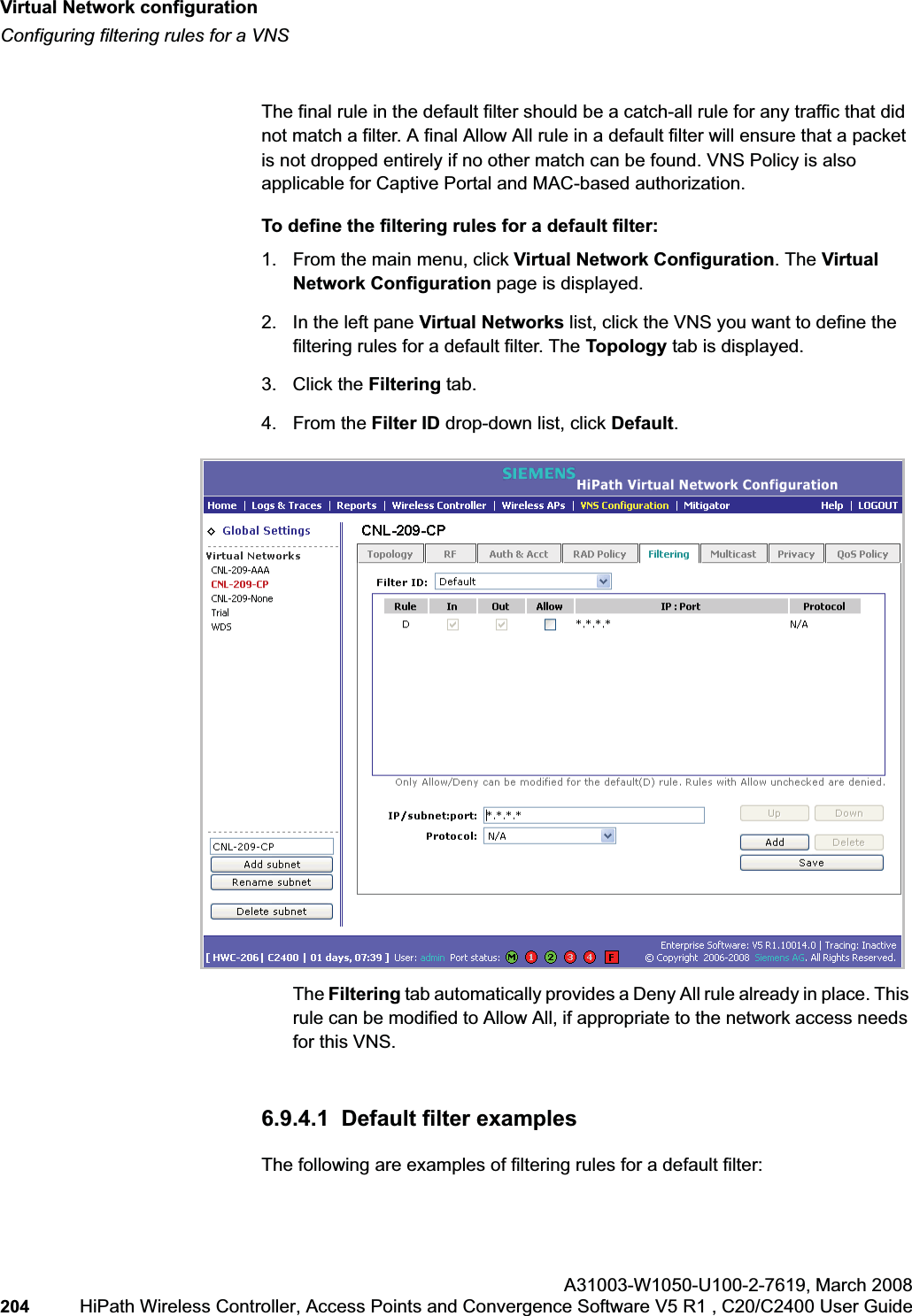
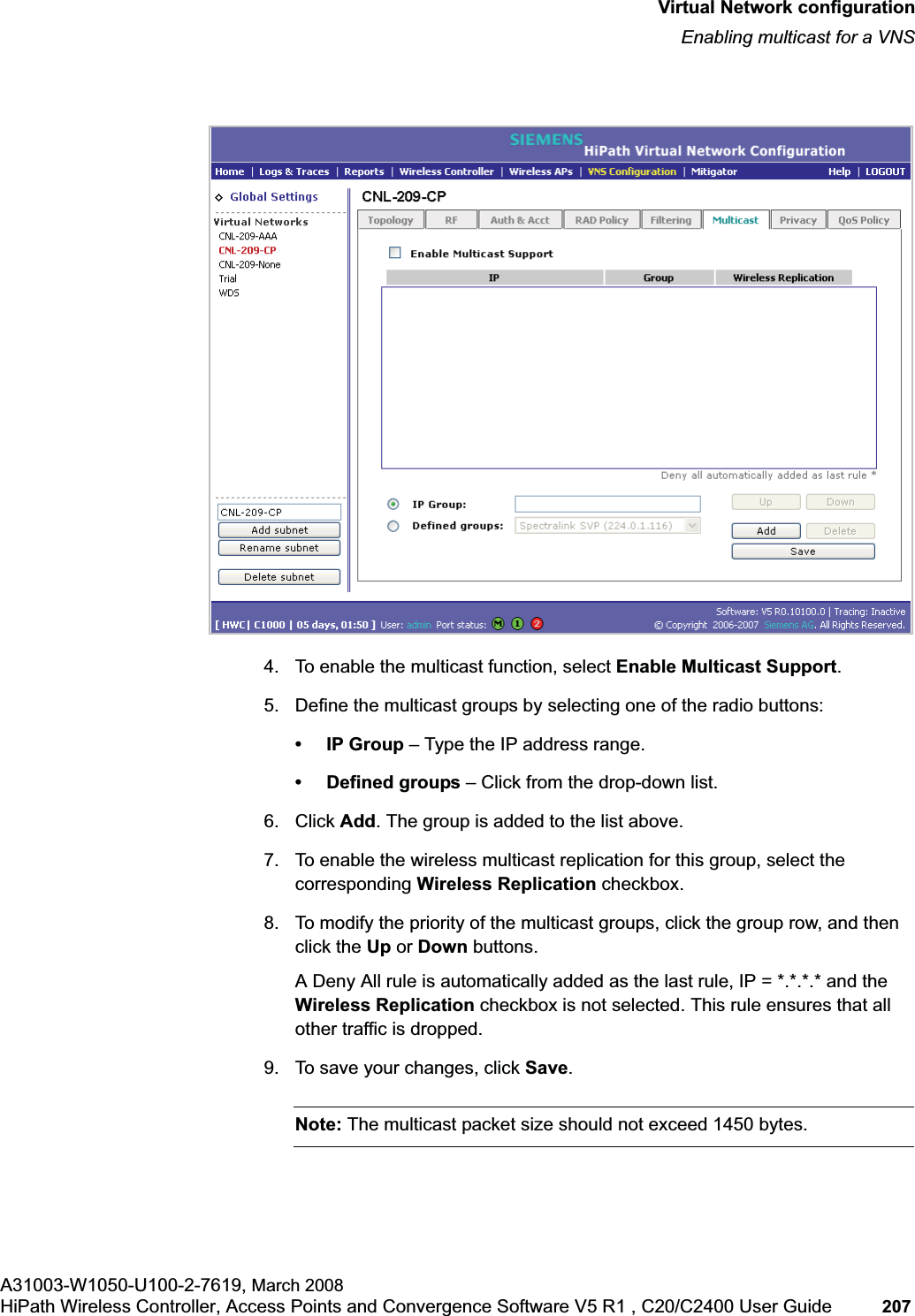
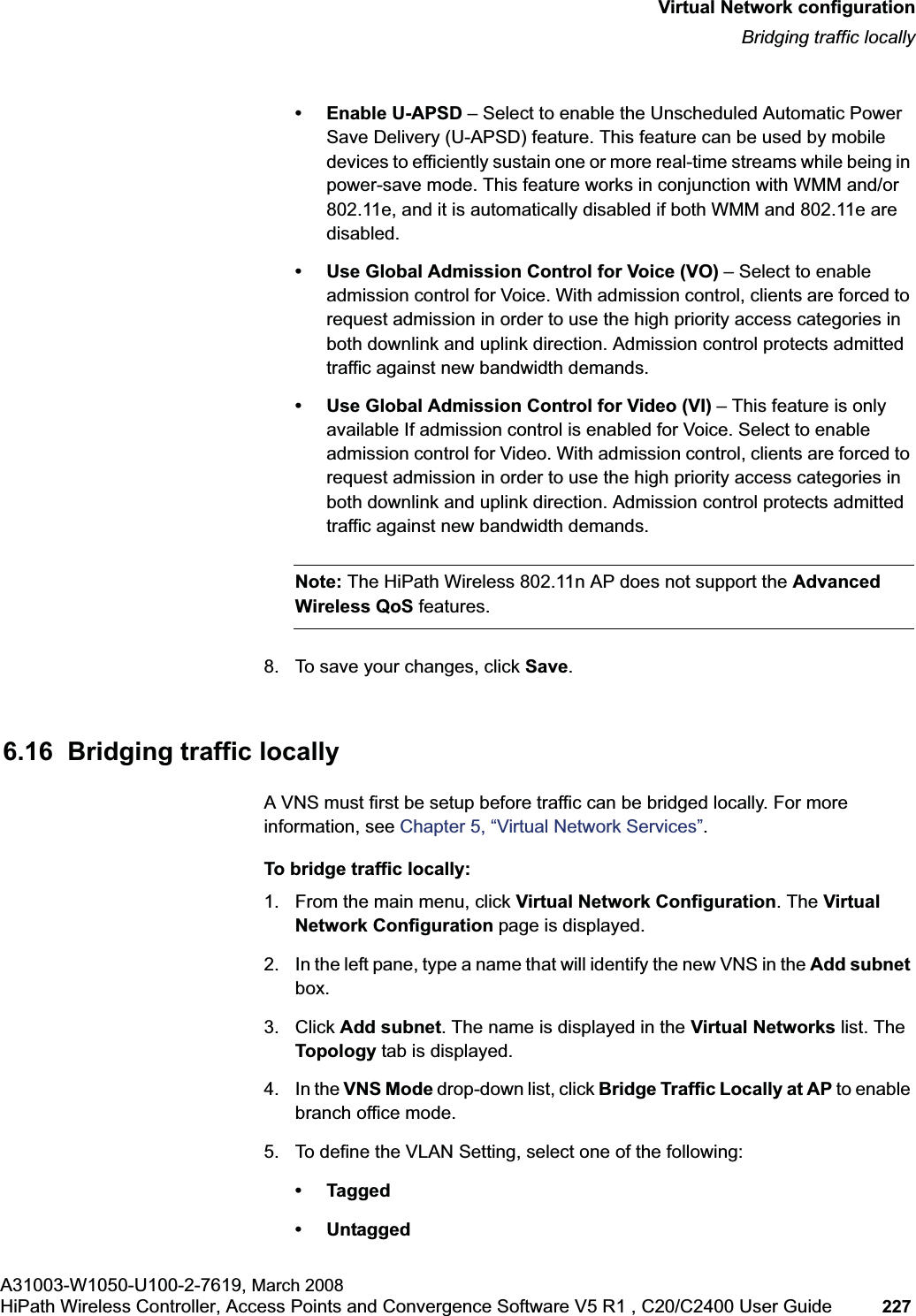
![Virtual Network configurationhwc_vnsconfiguration.fmEnabling multicast for a VNSA31003-W1050-U100-2-7619,March 2008206 HiPath Wireless Controller, Access Points and Convergence Software V5 R1 , C20/C2400 User Guide 6.10 Enabling multicast for a VNSA mechanism that supports multicast traffic can be enabled as part of a VNS definition. This mechanism is provided to support the demands of VoIP and IPTV network traffic, while still providing the network access control.Note: To use the mobility feature with this VNS, you must select the EnableMulticast Support checkbox for the data port.Define a list of multicast groups whose traffic is allowed to be forwarded to and from the VNS. The default behavior is to drop the packets. For each group defined, you can enable Multicast Replication by group.Note: Before enabling multicast filters and depending on the topology of the VNS, you may need to define which physical interface to use for multicast relay. Define the multicast port on the IP Addresses page. For more information, see Section3.2.4, “Setting up the data ports”, on page 42.To enable multicast for a VNS:1. From the main menu, click Virtual Network Configuration. The Virtual Network Configuration page is displayed.2. In the left pane Virtual Networks list, click the VNS you want to enable Multicast for. The Topology tab is displayed.3. Click the Multicast tab.In Out Allow IP / Port Descriptionx x x [Intranet IP] Allow access to the Gateway IP address of the VNS onlyx x [Intranet IP, range] Deny all access to the VNS subnet range (such as 0/24)x x x *.*.*.*. Allow everything elseTable 21 Rules between two wireless devices](https://usermanual.wiki/Siemens-Communications/AP36V1B.User-Manual-Part-1/User-Guide-936679-Page-206.png)