TRENDNET TEW684UB 450 MBPS WIRELESS N DUAL BAND USB ADAPTER User Manual
TRENDNET, Inc. 450 MBPS WIRELESS N DUAL BAND USB ADAPTER
TRENDNET >
USERS MANUAL

1
2
Contents
Introduction ........................................................................................................................... 4
Features......................................................................................................................... 4
Package Content............................................................................................................ 4
System Requirement...................................................................................................... 4
Wireless Performance Considerations............................................................................ 5
Installation............................................................................................................................. 6
Using the Utility ..................................................................................................................... 8
Profile............................................................................................................................. 9
Advanced ......................................................................................................................12
Wi-Fi Direct ...................................................................................................................14
Link Information.............................................................................................................20
Link Status ....................................................................................................................20
Throughput....................................................................................................................20
Statistics........................................................................................................................21
About.............................................................................................................................21
WPS.....................................................................................................................................22
PIN Method ...................................................................................................................22
PBC Method..................................................................................................................24
Security ................................................................................................................................25
WEP..............................................................................................................................25
WPA-PSK .....................................................................................................................27
WPA..............................................................................................................................28
Appendix ..............................................................................................................................32
Glossary........................................................................................................................32
Specification..................................................................................................................33
Limited Warranty ...........................................................................................................34

3
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital
device, pursuant to Part 15 of the FCC Rules. These limits are designed to
provide reasonable protection against harmful interference in a residential installation. This
equipment generates uses and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful interference
to radio communications. However, there is no guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference to radio or television
reception, which can be determined by turning the equipment off and on, the user is
encouraged to try to correct the interference by one of the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that to which the receiver
is connected.
- Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: Any changes or modifications not expressly approved by the party responsible
for compliance could void the user's authority to operate this equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions: (1) This device may not cause harmful interference, and (2) this device must
accept any interference received, including interference that may cause undesired operation.
IMPORTANT NOTE:
Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled
environment. End users must follow the specific operating instructions for satisfying RF
exposure compliance. To maintain compliance with FCC RF exposure compliance
requirements, please follow operation instruction as documented in this manual.
This transmitter must not be co-located or operating in conjunction with any other antenna or
transmitter.
SAR compliance has been established in typical laptop computer(s) with USB slot, and
product could be used in typical laptop computer with USB slot. Other application like
handheld PC or similar device has not been verified and may not compliance with related RF
exposure rule and such use shall be prohibited.
The availability of some specific channels and/or operational frequency bands are country
dependent and are firmware programmed at the factory to match the intended destination.
The firmware setting is not accessible by the end user.
CE Mark Warning
This is a Class B product. In a domestic environment, this product may cause radio
interference, in which case the user may be required to take adequate measures.
This transmitter must not be co-located or operation in conjunction with any other antenna or
transmitter.
The antenna(s) used for this transmitter must be installed to provide a separation distance of
at least 20 cm from all persons and must not be co-located or operated in conjunction with
any other antenna or transmitter
4
Introduction
TRENDnet’s compact 450Mbps Dual Band Wireless N USB Adapter, model TEW-684UB,
connects a laptop or desktop computer to an ultra-high performance 450Mbps dual band
wireless network.
Quickly connect to a 450Mbps 2.4GHz or 5GHz wireless network at the touch of a button
with the convenience of one-touch Wi-Fi Protected Setup (WPS). Seamlessly stream HD
video over the less congested 5GHz band.
Place the adapter in the most ergonomic location with the included USB extension cable.
Advanced Multiple Input Multiple Output (MIMO) antenna technology with three spatial
streams per antenna generates a maximum theoretical wireless throughput of 450Mbps.
WMM® Quality of Service (QoS) technology prioritizes gaming, Internet calls, and video
streams. LEDs on the front of the adapter convey device status. Upgrade your computer’s
wireless connection to experience the speed of a 450Mbps network.
Features
x1 x USB 2.0 connector
xWi-Fi compliant with IEEE 802.11n/g/b/a standards
xOne-touch wireless connection with external Wi-Fi Protected Setup (WPS) button
xMultiple Input Multiple Output (MIMO) technology
xMaximum reliability, throughput, and connectivity with automatic data rate switching
xSupports 64/128-bit WEP, WPA/WPA2-RADIUS, and WPA-PSK/WPA2-PSK
xWi-Fi Multimedia (WMM) Quality of Service (QoS) data prioritization
xEasy user setup and intuitive diagnostic utility
xCoverage of up to 50 meters indoor (164 feet) and 100 meters outdoor (320 feet)*
x3-year limited warranty
Package Content
xTEW-684UB
xCD-ROM (Utility and Driver)
xMulti-Language Quick Installation Guide
xUSB cable 100cm (39.3 in)
System Requirement
xPentium class notebook computers with at least one available USB slot
xMicrosoft Windows 7, Vista, XP and 2K
xCD-ROM drive
5
Wireless Performance Considerations
There are a number of factors that can impact the range of wireless devices.
1. Adjust your wireless devices so that the signal is traveling in a straight path, rather than
at an angle. The more material the signal has to pass through the more signal you will
lose.
2. Keep the number of obstructions to a minimum. Each obstruction can reduce the range of
a wireless device. Position the wireless devices in a manner that will minimize the
amount of obstructions between them.
3. Building materials can have a large impact on your wireless signal. In an indoor
environment, try to position the wireless devices so that the signal passes through less
dense material such as dry wall. Dense materials like metal, solid wood, glass or even
furniture may block or degrade the signal.
4. Antenna orientation can also have a large impact on your wireless signal. Use the
wireless adapter’s site survey tool to determine the best antenna orientation for your
wireless devices.
5. Interference from devices that produce RF (radio frequency) noise can also impact your
signal. Position your wireless devices away from anything that generates RF noise, such
as microwaves, radios and baby monitors.
6. Any device operating on the 2.4GHz frequency will cause interference. Devices such as
2.4GHz cordless phones or other wireless remotes operating on the 2.4GHz frequency
can potentially drop the wireless signal. Although the phone may not be in use, the base
can still transmit wireless signal. Move the phone’s base station as far away as possible
from your wireless devices.
If you are still experiencing low or no signal consider repositioning the wireless
devices or installing additional access points. The use of higher gain antennas may
also provide the necessary coverage depending on the environment.
6
Installation
Important! DO NOT install the TEW-684UB in the computer until instructed to do so.
Follow the instructions below to install the USB Adapter and Utility.
STEP 1
Insert the Driver and Utility CD into CD drive
STEP 2
Click “Install Utility” button. If your CD Autorun is enabled, the installation procedures will
be started. (Otherwise open your CD folder and double-click on the “setup.exe” file)
STEP 3
Select I accept the terms and of the license agreement and click Next.
STEP 4
Select Install driver and TRENDnet WLAN utility and click Next.
7
STEP 5
Select TRENDnet Configuration Tool and click Next.
STEP 6
Click Install on it.
STEP 7
Click Finish to complete the client utility installation.
8
Using the Utility
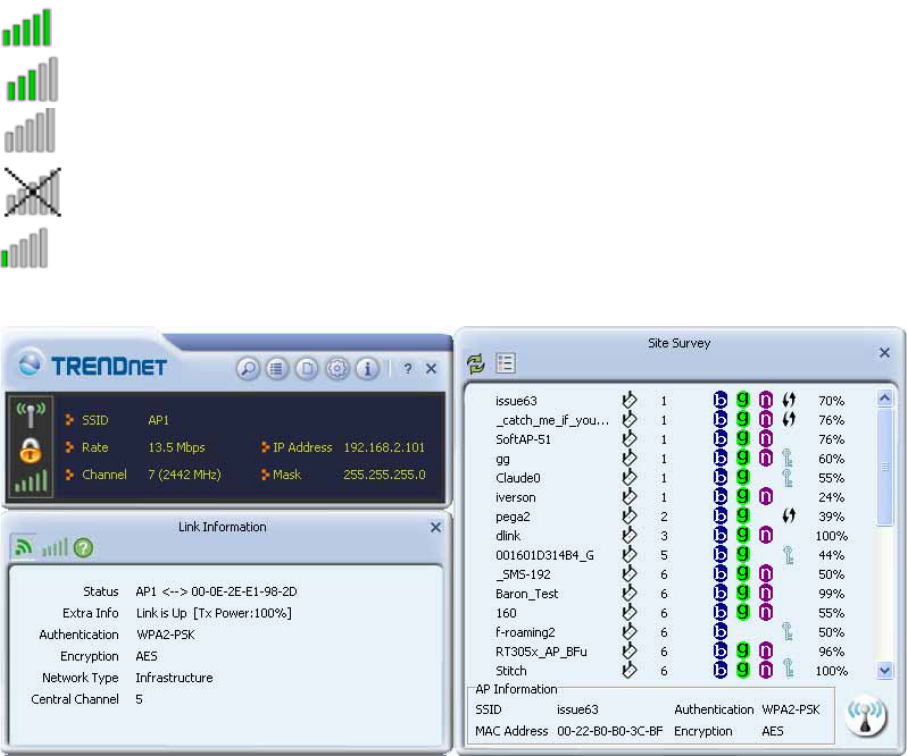
When starting the utility, a small TRENDnet wireless icon appears in the notifications area of
the taskbar. You can double click it to maximize the dialog box if you selected to close it
earlier. You may also use the mouse's right button to close the utility.
Additionally, the small icon will change color to reflect current wireless network connection
status. The status is shown as follows:
: Indicates the connected and signal strength is good.
: Indicates the connected and signal strength is normal.
: Indicates that it is not yet connected.
: Indicates that a wireless NIC can not be detected.
: Indicates that the connection and signal strength is weak.
9
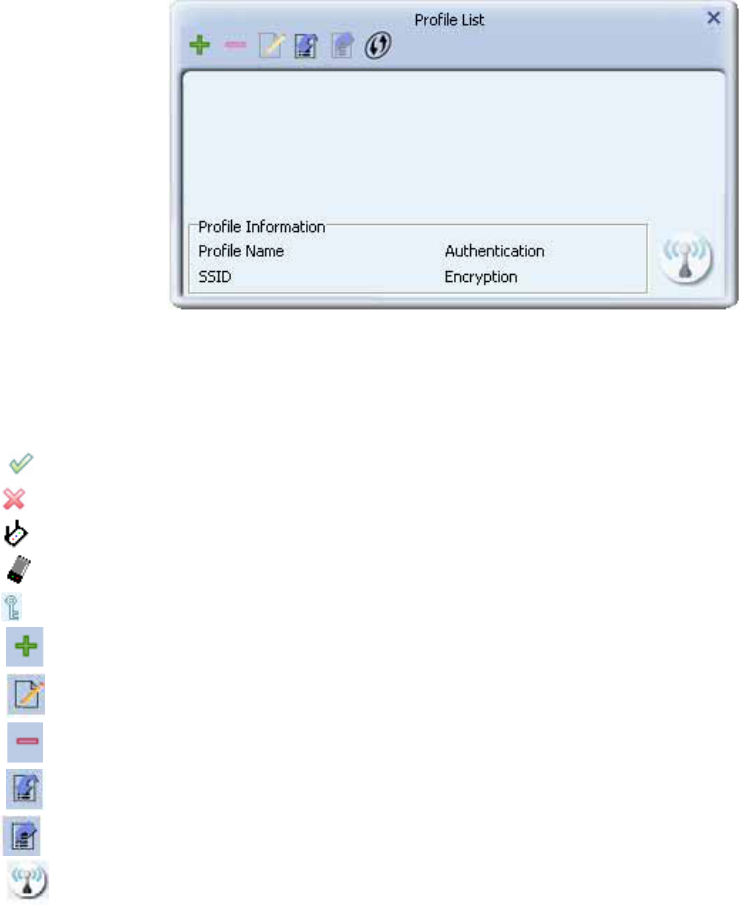
Profile
The Profile List keeps a record of your favorite wireless settings at home, office, and other
public hot-spots. You can save multiple profiles, and activate the correct one at your
preference.
Icons and buttons:
Indicates if a connection made from the currently activated profile.
Indicates if the connection has failed on a currently activated profile.
Indicates the network type is infrastructure mode.
Indicates the network type is in Ad-hoc mode.
Indicates if the network is security-enabled.
Click to add a new profile.
Click to edit an existing profile.
Deletes an existing profile.
Import an existing profile.
Export an existing profile.
Activates the selected profile.
Adding a Profile:
Click "Add" below the Profile List.
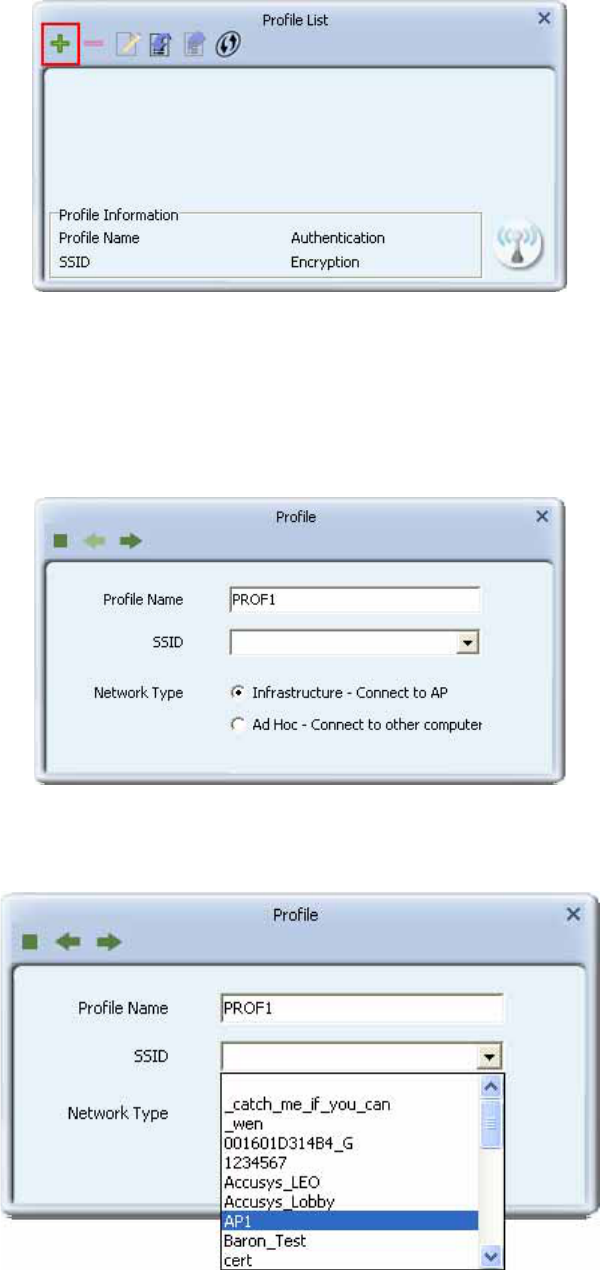
10
The "Add Profile" window will appear.
Enter or specify a profile name. Select an AP from the SSID drop-down list.
Now the profile which the user set appears in the profile list. Click "Activate" icon to
activate the connection.
11
Pre-logon Connect
Field definitions:
Pre-logon Connect: Use ID and Password in Profile.
** Recommend: You need to restart the computer when using/non-using Pre-logon connect
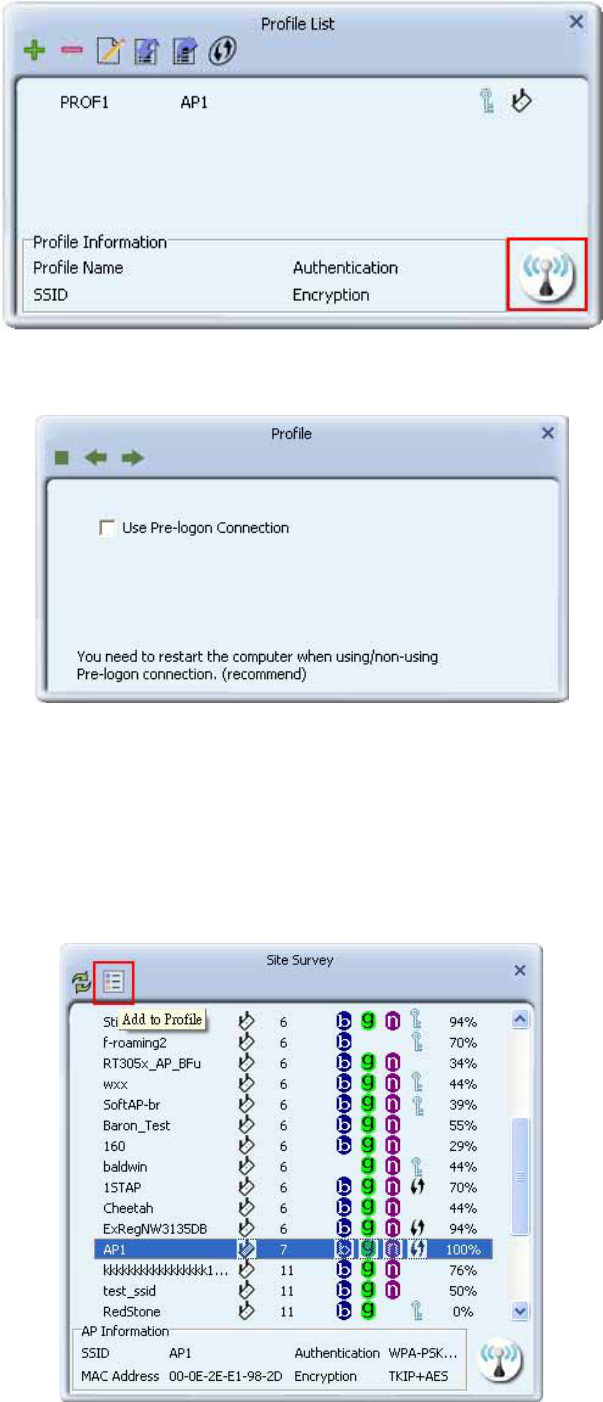
Adding a Profile to the Network using site survey
Select the AP from the list on the Network tab and click the “Add to Profile” button.
12
Verify the new profile in the profile list and click “Activate”.
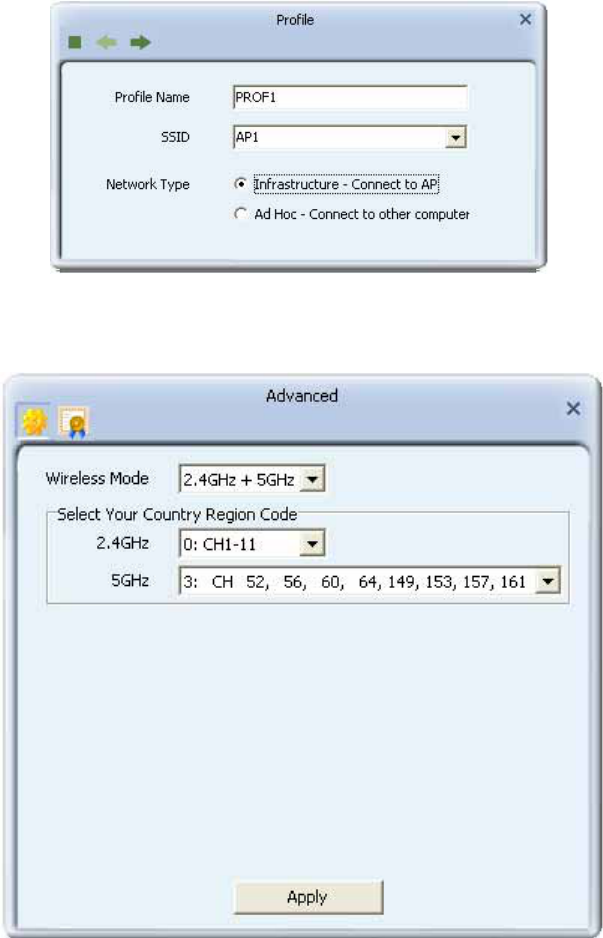
Advanced
1. Wireless mode: Select wireless mode. 2.4GHz, 5GHz and 2.4GHz+5GHz are supported.
2. Wireless Protection: Users can choose from Auto, On, and Off. (This is not supported by
802.11n adapters.)
zAuto: STA will dynamically change as AP announcement.
zOn: The frames are always sent with protection.
zOff: The frames are always sent without protection.
3.TX Rate: Manually select the transfer rate. The default setting is auto. (802.11n wireless
cards do not allow the user to select the TX Rate.)
4.Select Your Country Region Code: There are eight countries to choose from in the country
channel list. (11A ListBox only shows for 5G adapter.)
13
5. Apply the above changes.
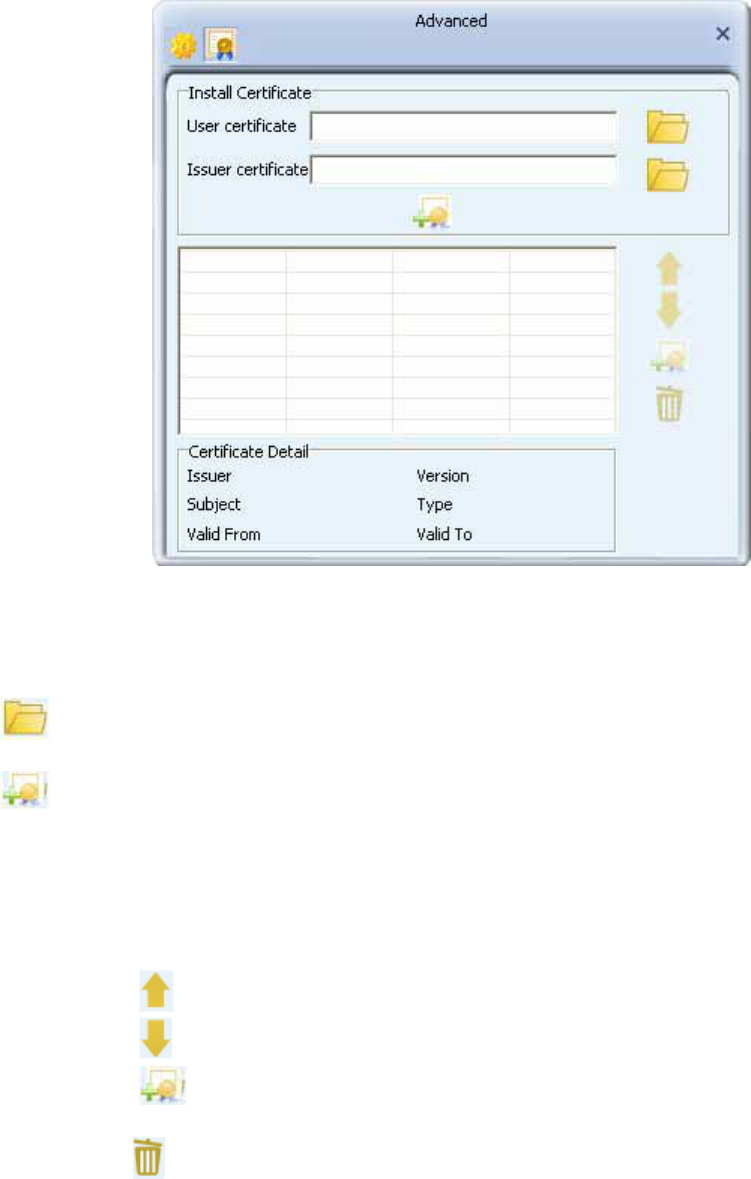
Certificate Management
Install Certificate :
1. Need to install user certificate and issuer certificate for the authentication.
2. Icons and buttons :
Indicates to browser the file.
Indicates to install the certificate.
Certificate List :
1. Show all installed certificates. There are ordered property.
2. Icons and buttons :
Move up the selected certificate.
Move down the selected certificate.
Install AS certificate for the selected certificate.
Delete the selected certificate.
14
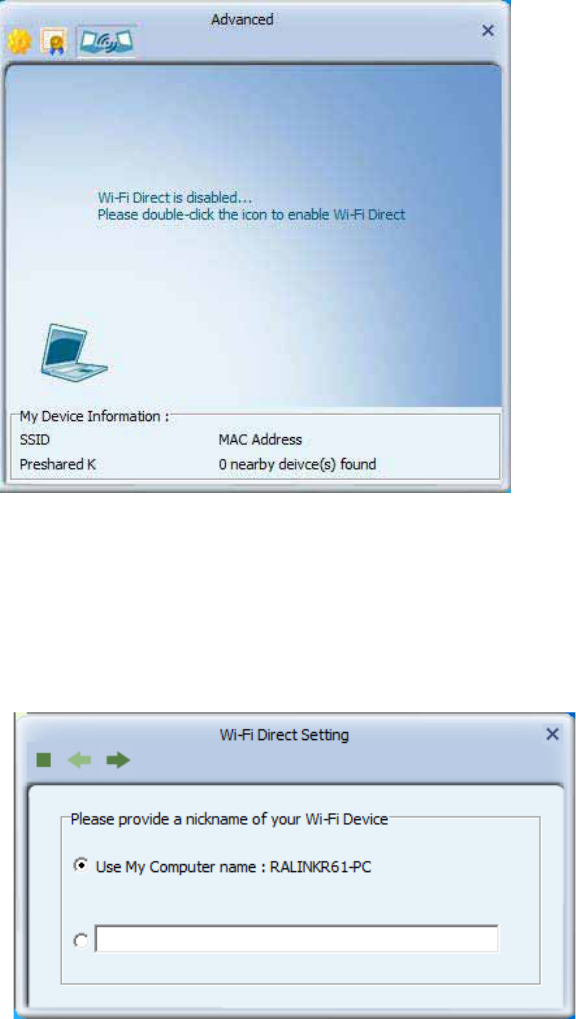
Wi-Fi Direct
Enable Wi-Fi Direct :
1. Need to double-click the notebook icon.
2. Specify the name of Wi-Fi Direct Device :
TRENDnet utility is able to discover other WiFi Direct topologies nearby
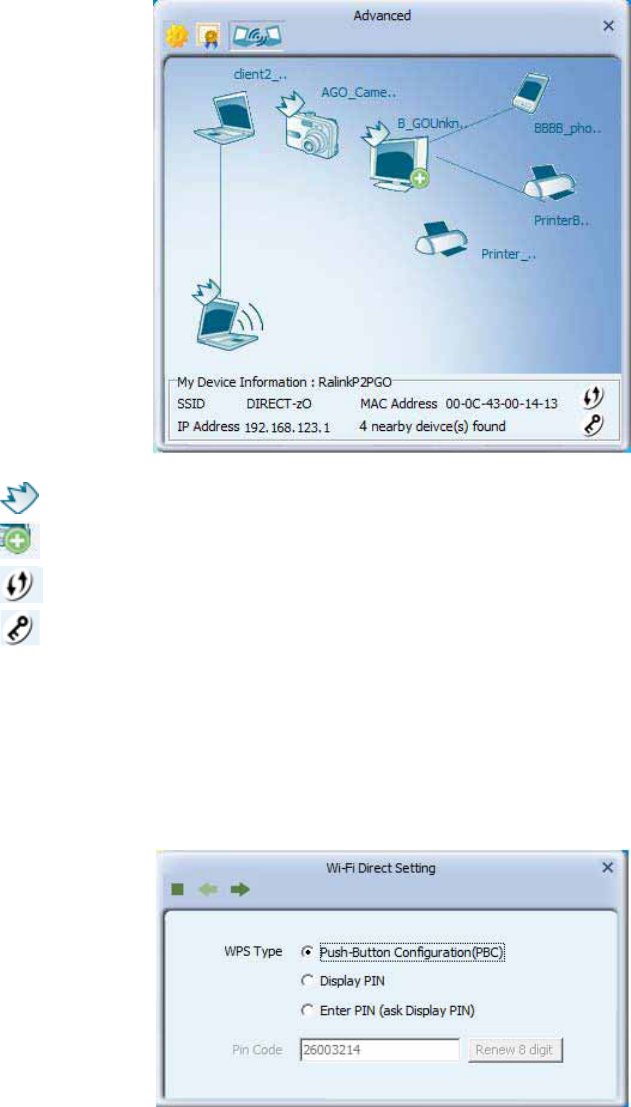
15
: GO : AP- like.
: GO with clients in the same group.
: configure WPS for GO
: Set WPA2PSK AES key
Connect to P2P device :
1. Double click the device icon to specify the connection.
2. Select the WPS connection type :
zPBC: Start the WPS progress using PBC configuration method.
zDisplay PIN : Start the WPS progress using display configuration method.
zEnter PIN : Start to WPS progres using keypad configuration method. Remember that
enter PIN Code shown from the P2P device.
zPIN Code: The user is required to enter an 8-digit PIN Code into Registrar in the pop-up
windows with Enter PIN.
3. Select the preferred operating channel and whether save profile :
16
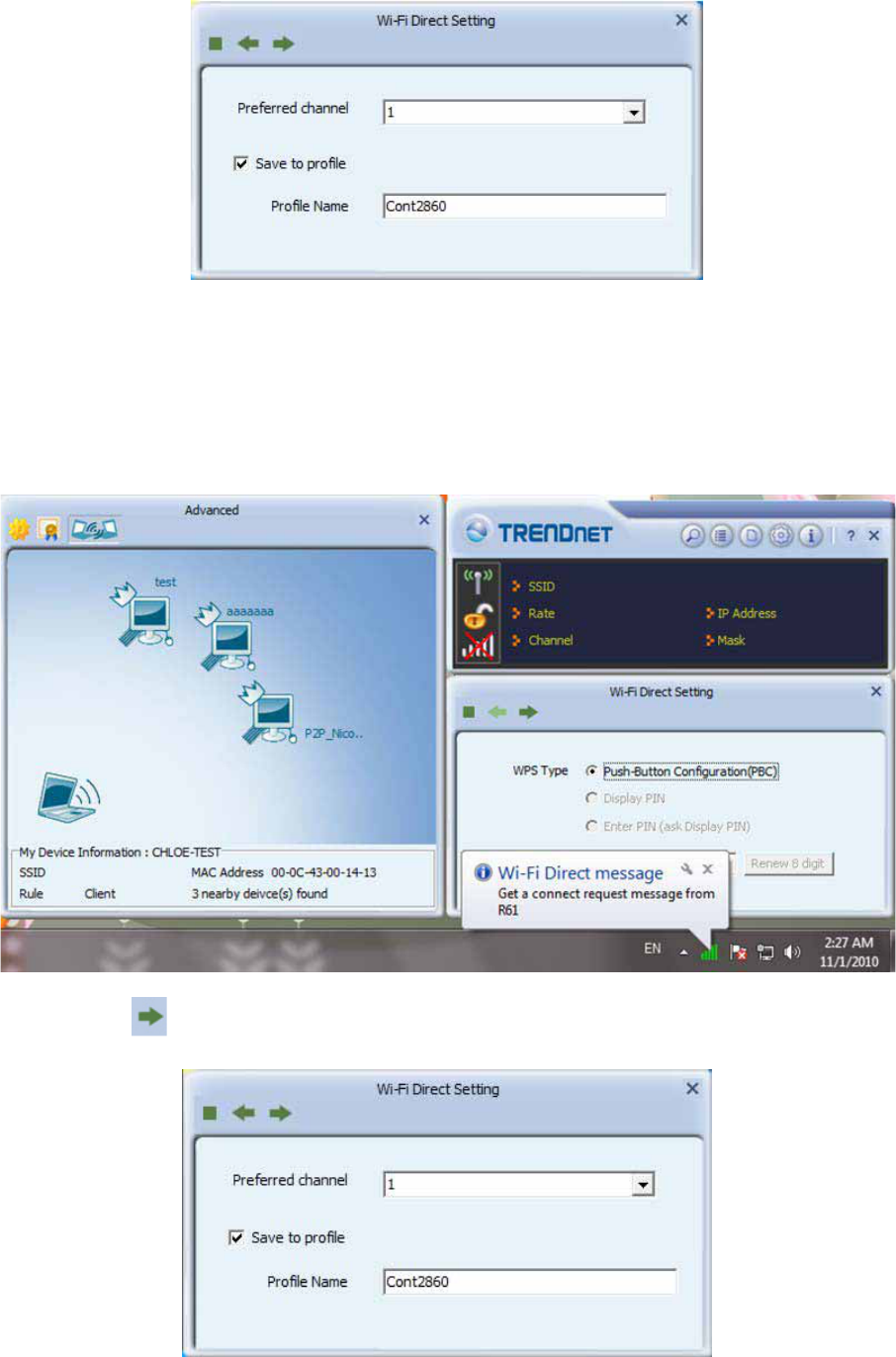
Accept one P2P device's connection request :
1. Once someone wants to connect to me, TRENDnet Utility would show a bubble
message and pop up the corresponding setting page as follows
2. Press to select the preferred operating channel and whether save profile :
17
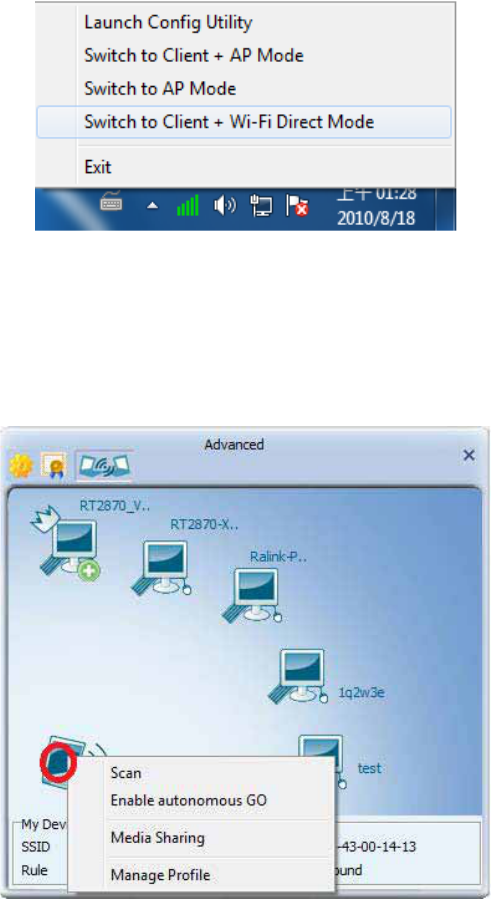
Switch to Wi-Fi Direct concurrent mode:
Switch to Concurrent mode ( legacy Client + WiFi Direct GO ) by right-click TRENDnet utility
tray icon
Wi-Fi Direct function:
Click mouse right button on My Device.
1. Scan : Choose "Scan" to update discovery topology.
2. Enable autonomous GO : Autonomous GO allow user to start a GO manually
2.1 Choose "Enable autonomous GO" to open Wi-Fi Direct setting page for
autonomous GO.
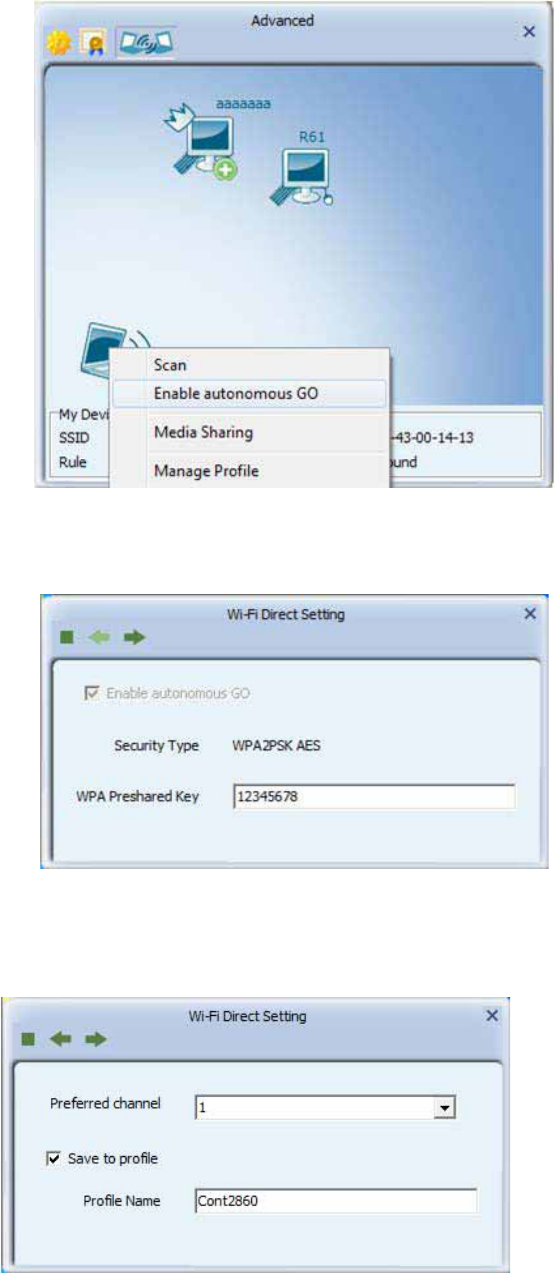
18
2.2 Enter the WPA2-PSK key for GO
2.3 Select the preferred operating channel and whether save profile : the GO will send
beacon on the channel.
19
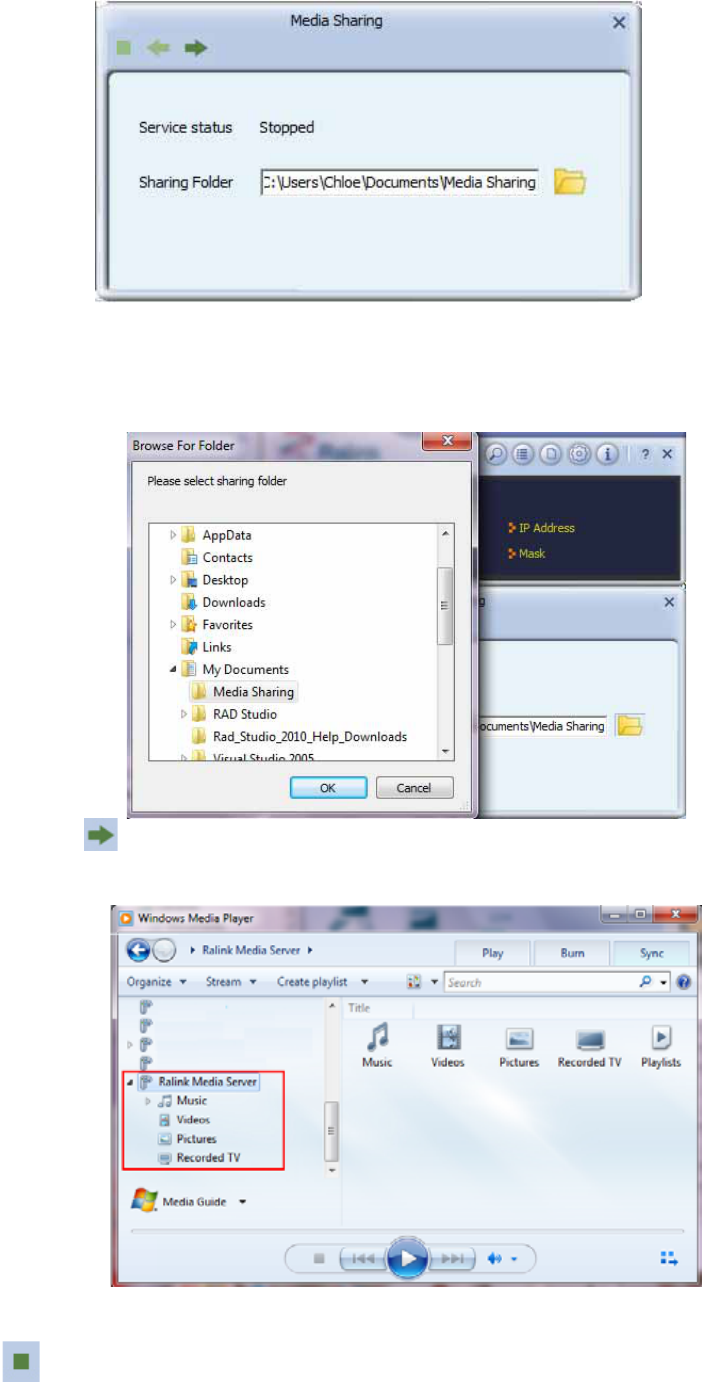
3. Media sharing: Media Sharing is disabled as default.
3.1 Select sharing folder. (utility would create ”r;Media Sharing” in C:\User\xxx\Document as
default)
Press to start sharing. After device connected, user can search the media
server and play music/video by media player.
Press to stop sharing
20
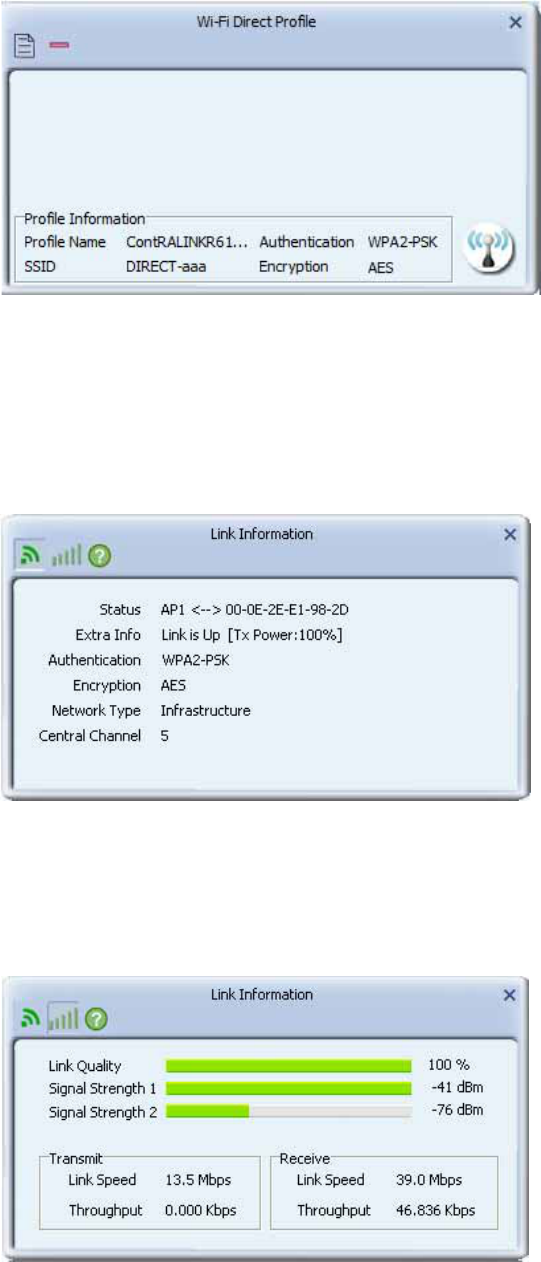
4. Manage profile : Choose "manage profile" to open profile page
.
Link Information
Link Status
The link status page displays detailed information about the current connection as shown in.
Throughput
The throughput page displays detailed information about the current connection as shown in.
21
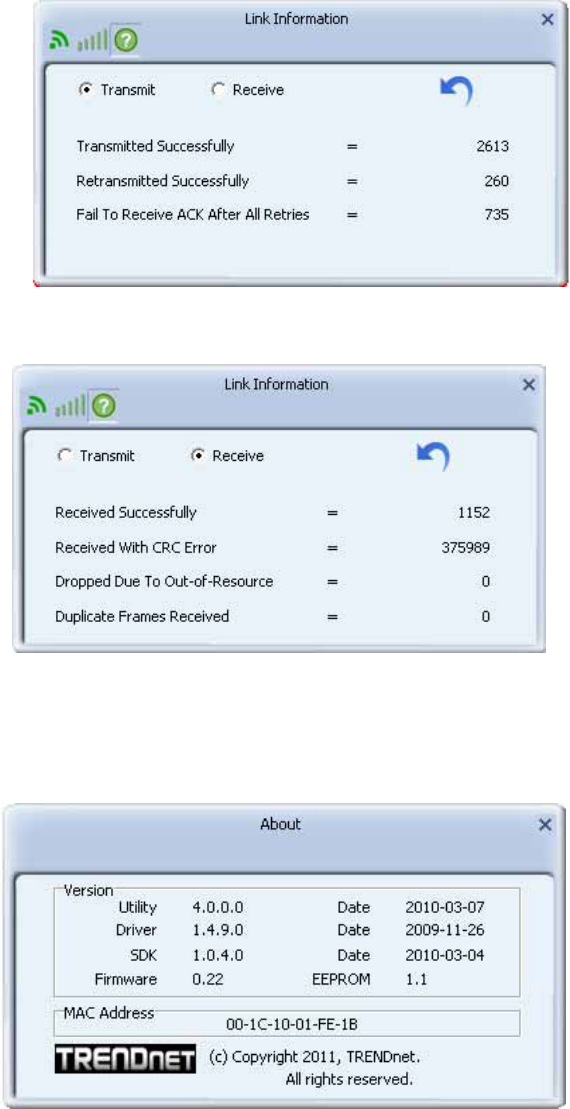
Statistics
The Statistics page displays detailed counter information based on 802.11 MIB counters.
This page translates that MIB counters into a format easier for the user to understand.
Transmit Statistics:
Receive Statistics:
About
Click "About" to display the wireless card and driver version information.
22
WPS
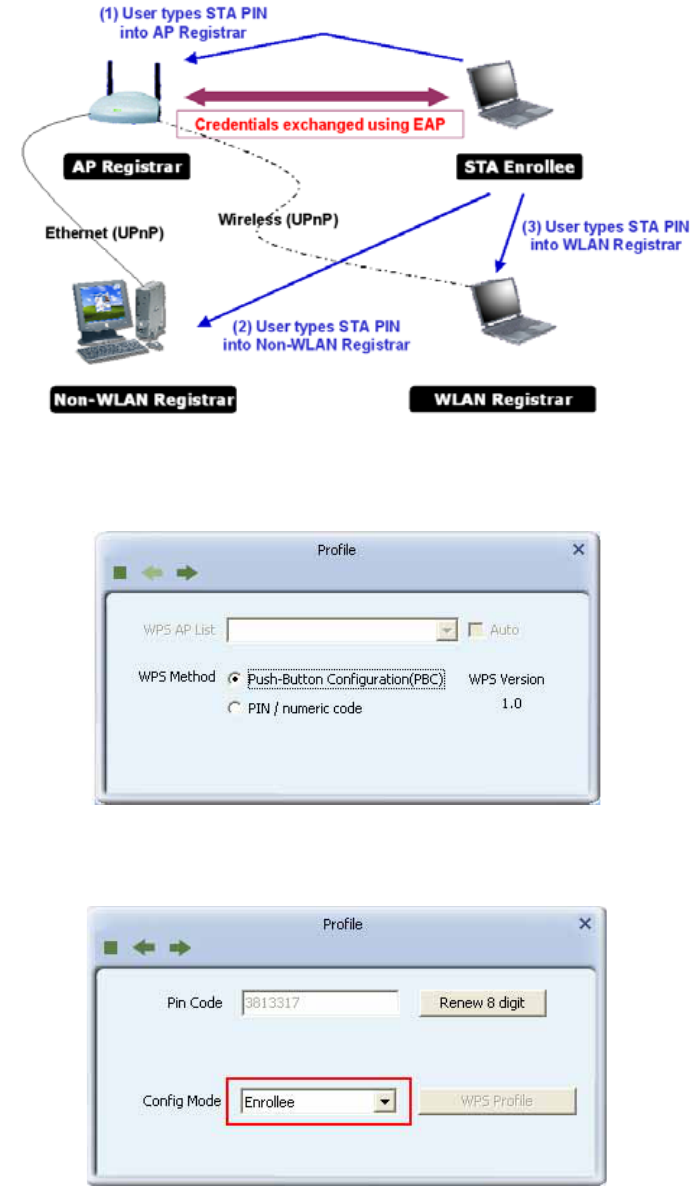
PIN Method
The user obtains a device password (PIN Code) from the STA and enters the password into
the Registrar. Both the Enrollee and the Registrar use PIN Config method for the
configuration setup. The following image outlines the process.
1. Select an AP (SSID/BSSID) that STA will join to and Select the "PIN/ numeric code"
method.
2. Select "Enrollee" from the Config Mode drop-down list.
3. Enter the PIN Code of the STA into the Registrar when prompted by the Registrar.
23
If you use Microsoft Window Connection Now as an External Registrar, you must start PIN
connection at STA first. After that, search out your WPS Device name and MAC address at
Microsoft Registrar. Add a new device and enter PIN Code of STA at Microsoft Registrar
when prompted.
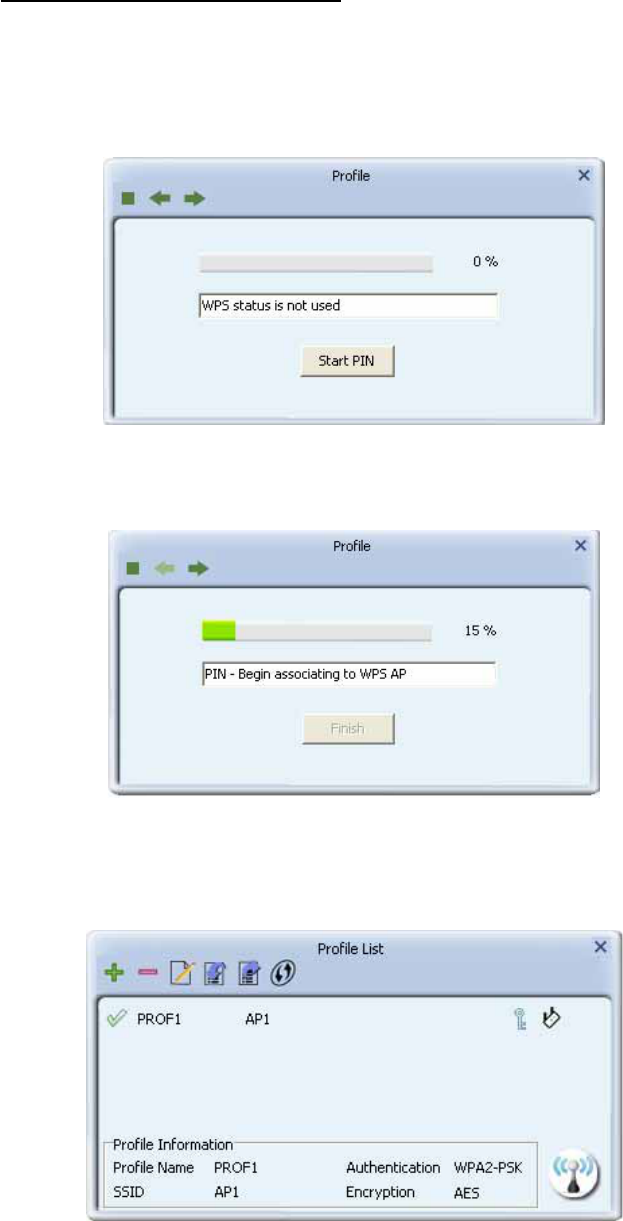
4. Click "PIN" to enter the PIN
5. The result should appear as the image below.
7. Configure one or more credentials
24
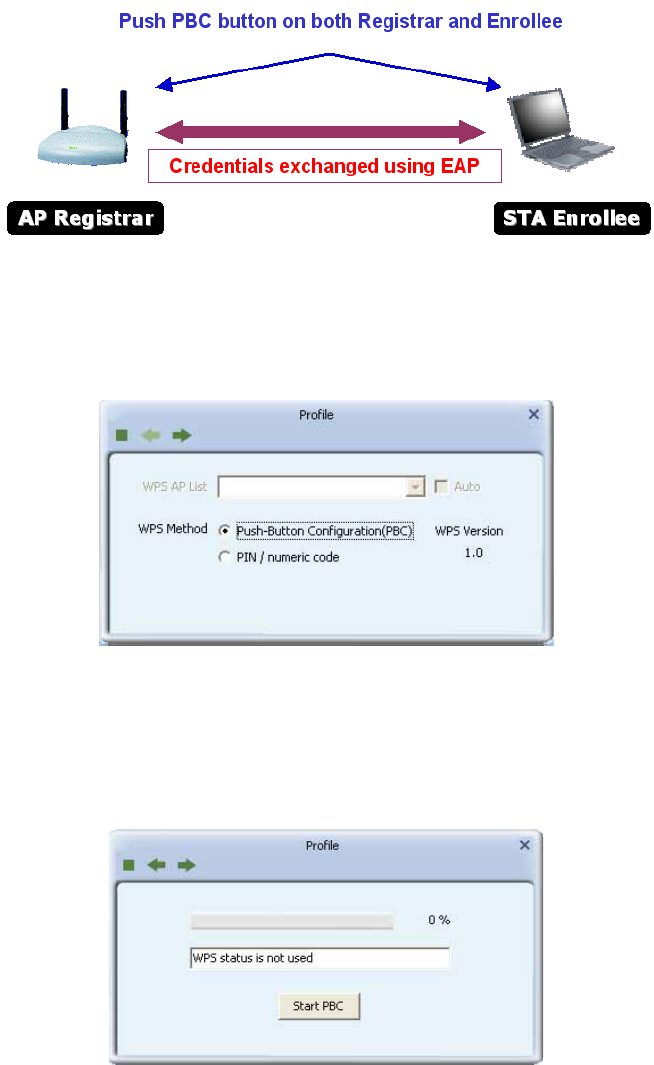
PBC Method
The PBC method requires the user to press a PBC button on both the Enrollee and the
Registrar within a two-minute interval called the Walk Time. If there is only one Registrar in
PBC mode, the PBC mode selected is obtained from ID 0x0004, and is found after a
complete scan. The Enrollee can then immediately begin running the Registration Protocol.
If the Enrollee discovers more than one Registrar in PBC mode, it MUST abort its connection
attempt at this scan and continue searching until the two-minute timeout.
*Before you press PBC on STA and candidate AP. Make sure all APs aren't PBC mode or
APs using PBC mode have left their Walk Time.
1. Select an AP (SSID/BSSID) that STA will join to and Select the "Push-button
Configuration" method.
2. Click PBC to start the PBC connection.
3. Push the PBC on AP.
25
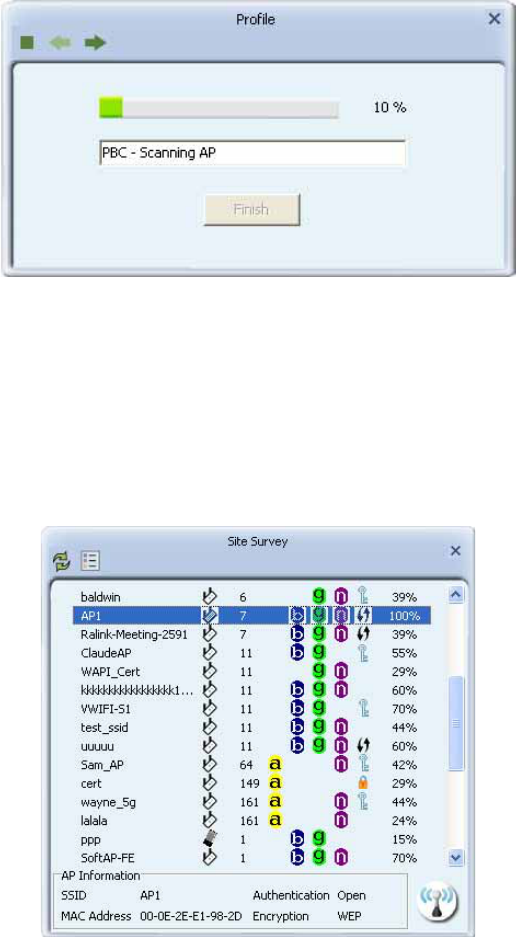
4. The progress bar as shown in the figure below indicates that scanning progress.
Security
WEP
1. Select an AP with WEP encryption and click "Connect".
2. The Authentication \ Encryption function will appear as below;
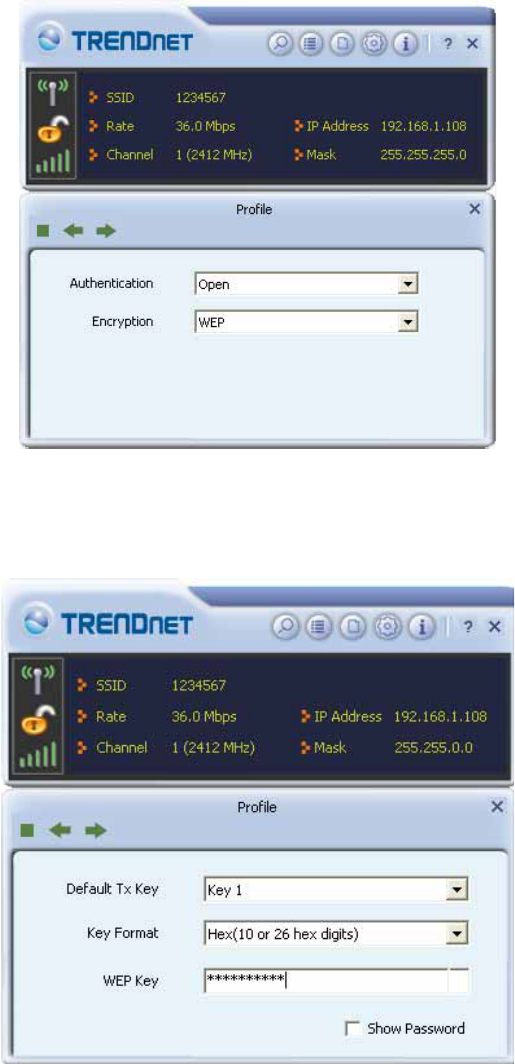
26
3. Enter in the assigned WEP key in the field. This value is same as our intended AP's
setting.
27
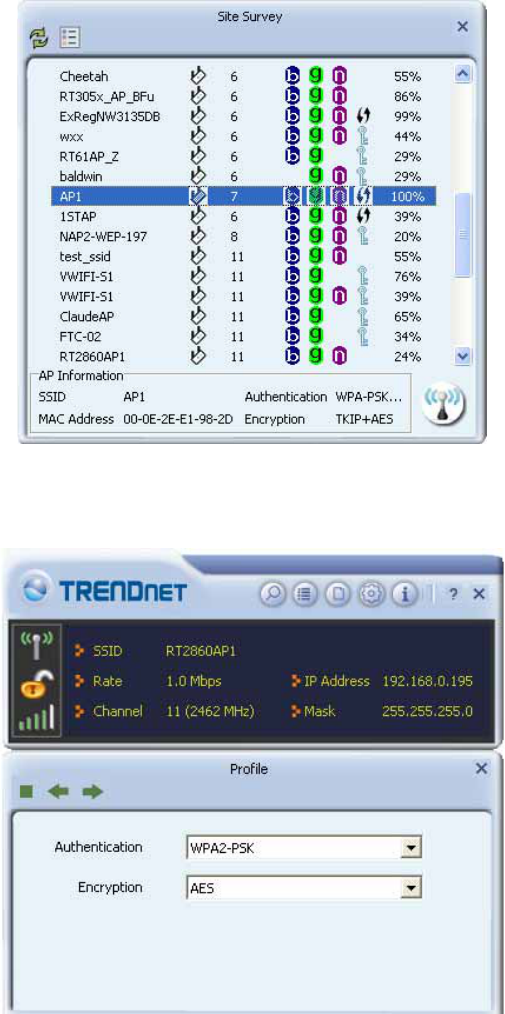
WPA-PSK
1. Select the AP with a WPA-PSK authentication mode and click "Connect".
2. Authentication \ Encryption function appears.
3. Select WPA-PSK as the Authentication Type. Select TKIP or AES encryption. Enter the
WPA Pre-Shared Key as "12345678".
28
4. Click "OK". Be careful, if the WPA Pre-Shared Key entered is not correct, you won’t be
able to exchange any data frames, even though the AP can be connected.
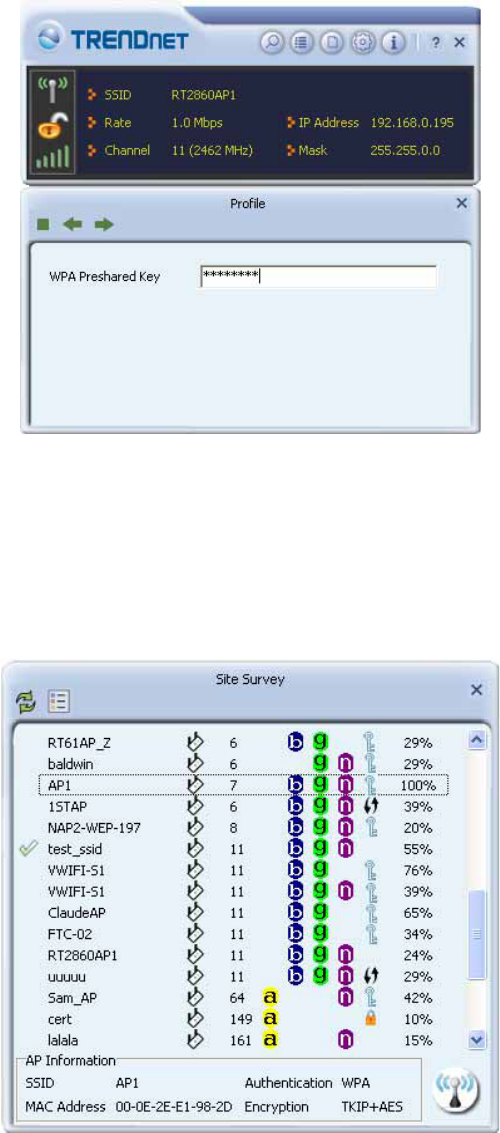
WPA
1. Select an AP with WPA authentication mode and click "Connect".
2. The Authentication \Encryption function window will pop up.
29
3. Click "8021X" and the setting page will appear.
4. Authentication type and setting method :
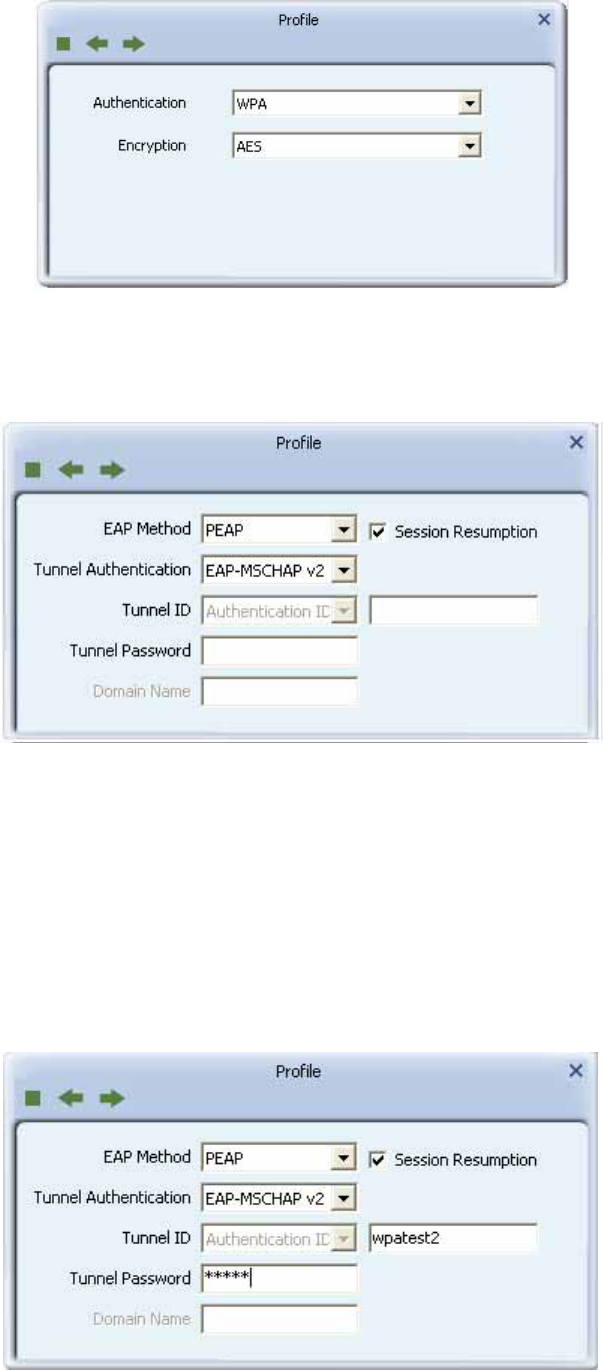
PEAP:
Select "PEAP" as the Authentication type from the drop-down list. Key-in "wpatest2" for the
identity. "Select "EAP-MSCHAP v2" from the drop-down list for tunnel authentication and
key-in the tunnel identity as "wpatest2" and the tunnel password as "test2". These settings
are the same as our intended AP's setting.
30
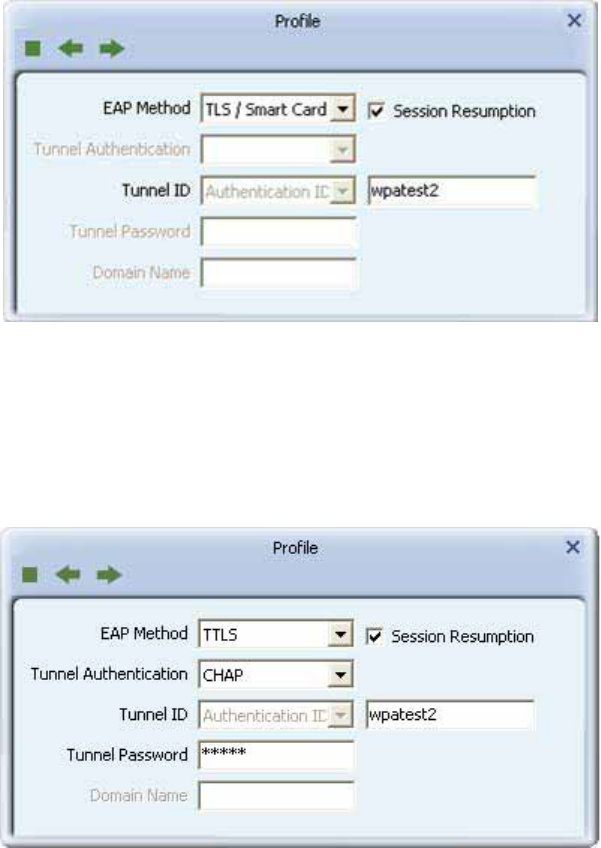
TLS / Smart Card :
"Select TLS / Smart Card" from the Authentication type drop-down list. TLS only requires the
identification to be set as "wpatest2" for server authentication. TLS must use client
certification. Click "Client Certification" and select a certification for server authentication.
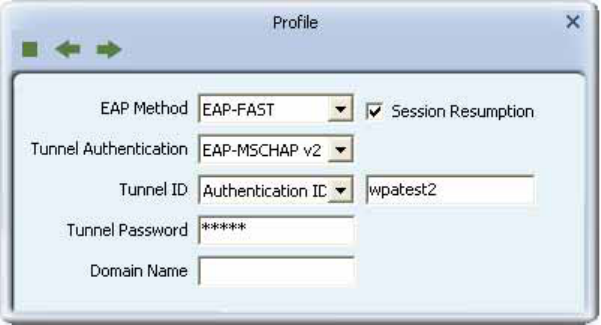
TTLS :
Select TTLS from the Authentication type drop-down list. Key-in the identity as "wpatest2".
Select CHAP for tunnel authentication, and key-in the identity as "wpatest2" and tunnel
password as "test2". These settings are the same as our intended AP's setting.
31
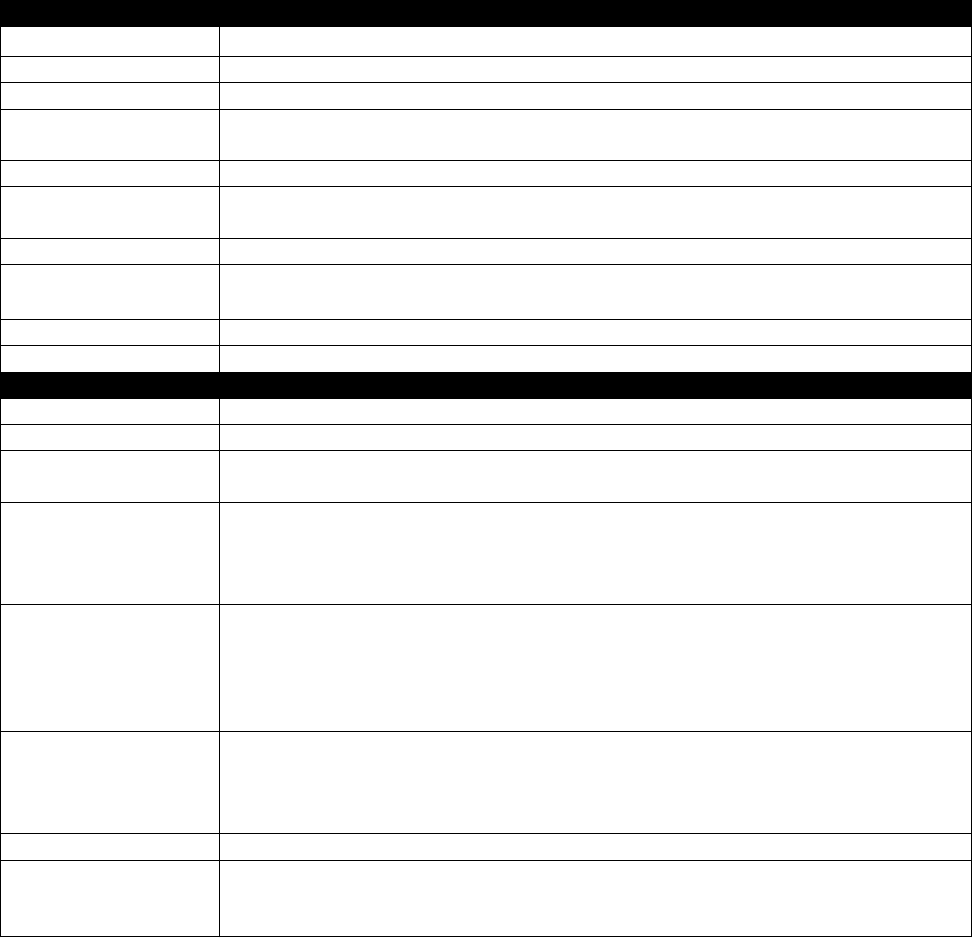
EAP-FAST:
Select EAP-FAST from the Authentication type drop-down list. Key-in the identity as
"wpatest2" and a domain name into the blank field. The tunnel identity is "wpatest2" and
password is "test2". These setting are the same as our intended AP's setting.
32
Appendix
Glossary
For unfamiliar terms used below, look for entries elsewhere in the glossary.
AD-HOC (IBSS)
Ad-hoc mode does not require an AP or a wired network. A network that transmits wireless
from computer to computer without the use of a base station (access point).
Two or more wireless stations communicate directly to each other. An ad-hoc network
may sometimes be referred to as an Independent Basic Service Set (IBSS).
CHANNEL
A radio frequency used by a wireless device is called a channel.
EAP AUTHENTICATION
EAP (Extensible Authentication Protocol) is an authentication protocol that runs on top of
the IEEE802.1X transport mechanism in order to support multiple types of user
authentication. By using EAP to interact with an EAP-compatible RADIUS server, an
access point helps a wireless station and a RADIUS server perform authentication.
ENCRYPTION
The reversible transformation of data from the original to a difficult-to-interpret format.
Encryption is a mechanism for protecting confidentiality, integrity, and authenticity of data.
It uses an encryption algorithm and one or more encryption keys.
FRAGMENTATION THRESHOLD
This is the maximum data fragment size that can be sent before the packet is fragmented
into smaller packets.
IEEE 802.1X
The IEEE 802.1X standard outlines enhanced security methods for both the authentication
of wireless stations and encryption key management. Authentication can be done using an
external RADIUS server.
INFRASTRUCTURE (BSS)
When a number of wireless stations are connected using a single AP, you have a Basic
Service Set (BSS).
ROAMING
In an infrastructure network, wireless stations are able to switch from one BSS to another
as they move between the coverage areas. During this period, the wireless stations
maintain uninterrupted connection to the network. This is roaming. As the wireless station
moves from place to place, it is responsible for choosing the most appropriate AP
depending on the signal strength, network utilization among other factors.
SSID
The SSID (Service Set Identity) is a unique name shared among all wireless devices in a
wireless network. Wireless devices must have the same SSID to communicate with each
other.
TEMPORAL KEY INTEGRITY PROTOCOL (TKIP)
Temporal Key Integrity Protocol (TKIP) uses 128-bit keys that are dynamically generated and
distributed by the authentication server.
USER AUTHENTICATION
WPA applies IEEE 802.1X and Extensible Authentication Protocol (EAP) to authenticate
wireless clients using an external RADIUS database. If you do not have an external RADIUS
server, use WPA-PSK/WPA2-PSK (WPA -Pre-Shared Key) that only requires a single
(identical) password entered into each access point, wireless gateway and wireless client. As
long as the passwords match, clients will be granted access to a WLAN.
WEP
WEP (Wired Equivalent Privacy) encryption scrambles all data packets transmitted between
the WCB-321A and the AP or other wireless stations to keep network communications pri-
vate. Both the wireless stations and the access points must use the same WEP key for data
encryption and decryption.
33
Specification
Hardware
Interface
USB 2.0
Standards
IEEE 802.11a, IEEE 802.11b, IEEE 802.11g and IEEE 802.11n
Button
WPS button: enables quick wireless connection with WPS function
Power
Consumption
Receive mode: 406mA (max.)
Transmit mode : 428mA (max)
Supported OS
Windows 7 (32/64-bit), Vista (32/64-bit), XP and 2000
Dimensions
(LxWxH)
72 x 50 x 31 mm (2.8 x 2.0 x 1.2 in.)
Weight
40 g (1.41 oz)
Temperature Operating: 0q~ 40qC (32q~ 104qF)
Storage: -20
q
~ 60
q
C (-4
q
~ 140
q
F)
Humidity
Max. 85% (non-condensing)
Certifications
CE, FCC
Wireless
Modulation
CCK/ OFDM - BPSK, QPSK, 16-QAM, 64-QAM, DBPSK, DQPSK
Antenna
3 Built-in on board antenna
Frequency
802.11b/g/n: 2.412 ~ 2.484 GHz
802.11a/n: 5.15 ~ 5.825GHz (FCC), 5.470 ~ 5.725GHz (ETSI)
Data Rate (auto
fallback)
802.11a: up to 54Mbps
802.11b: up to 11Mbps
802.11g: up to 54Mbps
802.11n: up to 450Mbps
Output Power
802.11a: 13dBm (typical)
802.11b: 18dBm (typical)
802.11g: 15dBm (typical)
802.11n/g: 13dBm (typical)
802.11n/a: 11dBm (typical)
Receiving
Sensitivity
802.11b: -84dBm (typical) at 11mpbs
802.11g: -72dBm (typical) at 54Mbps
802.11n/g: -65dBm (typical) at 450Mbps
802.11n/a: -64dBm (typical) at 450Mbps
Encryption
64/128-bit WEP, WPA/WPA2-RADIUS, WPA-PSK/WPA2-PSK
Channels
802.11b/g/n: 1~11 (FCC), 1~13 (ETSI)
802.11a/n: 36, 40, 44, 48, 149, 153, 157, 161, 165 (FCC), 36, 40, 44, 48
(ETSI)
8
02.11a:13dBm(typical)
8
02.11b:18dBm(typical)
8
02.11g:15dBm(typical)
8
02.11n/g:14dBm(typical)
8
02.11n/a:12dBm(typical)
802.11g:15dBm(typical)
34
Limited Warranty
TRENDnet warrants its products against defects in material and workmanship, under normal
use and service, for the following lengths of time from the date of purchase.
TEW-684UB – 3 Years Warranty
AC/DC Power Adapter, Cooling Fan, and Power Supply carry 1 year warranty.
If a product does not operate as warranted during the applicable warranty period, TRENDnet
shall reserve the right, at its expense, to repair or replace the defective product or part and
deliver an equivalent product or part to the customer. The repair/replacement unit’s warranty
continues from the original date of purchase. All products that are replaced become the
property of TRENDnet. Replacement products may be new or reconditioned. TRENDnet
does not issue refunds or credit. Please contact the point-of-purchase for their return
policies.
TRENDnet shall not be responsible for any software, firmware, information, or memory data
of customer contained in, stored on, or integrated with any products returned to TRENDnet
pursuant to any warranty.
There are no user serviceable parts inside the product. Do not remove or attempt to service
the product by any unauthorized service center. This warranty is voided if (i) the product has
been modified or repaired by any unauthorized service center, (ii) the product was subject to
accident, abuse, or improper use (iii) the product was subject to conditions more severe than
those specified in the manual.
Warranty service may be obtained by contacting TRENDnet within the applicable warranty
period and providing a copy of the dated proof of the purchase. Upon proper submission of
required documentation a Return Material Authorization (RMA) number will be issued. An
RMA number is required in order to initiate warranty service support for all TRENDnet
products. Products that are sent to TRENDnet for RMA service must have the RMA number
marked on the outside of return packages and sent to TRENDnet prepaid, insured and
packaged appropriately for safe shipment. Customers shipping from outside of the USA and
Canada are responsible for return shipping fees. Customers shipping from outside of the
USA are responsible for custom charges, including but not limited to, duty, tax, and other
fees.
WARRANTIES EXCLUSIVE: IF THE TRENDNET PRODUCT DOES NOT OPERATE AS
WARRANTED ABOVE, THE CUSTOMER’S SOLE REMEDY SHALL BE, AT TRENDNET’S
OPTION, REPAIR OR REPLACE. THE FOREGOING WARRANTIES AND REMEDIES ARE
EXCLUSIVE AND ARE IN LIEU OF ALL OTHER WARRANTIES, EXPRESSED OR
IMPLIED, EITHER IN FACT OR BY OPERATION OF LAW, STATUTORY OR OTHERWISE,
INCLUDING WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. TRENDNET NEITHER ASSUMES NOR AUTHORIZES ANY OTHER PERSON
TO ASSUME FOR IT ANY OTHER LIABILITY IN CONNECTION WITH THE SALE,
INSTALLATION MAINTENANCE OR USE OF TRENDNET’S PRODUCTS.
TRENDNET SHALL NOT BE LIABLE UNDER THIS WARRANTY IF ITS TESTING AND
EXAMINATION DISCLOSE THAT THE ALLEGED DEFECT IN THE PRODUCT DOES NOT
EXIST OR WAS CAUSED BY CUSTOMER’S OR ANY THIRD PERSON’S MISUSE,
NEGLECT, IMPROPER INSTALLATION OR TESTING, UNAUTHORIZED ATTEMPTS TO
REPAIR OR MODIFY, OR ANY OTHER CAUSE BEYOND THE RANGE OF THE
INTENDED USE, OR BY ACCIDENT, FIRE, LIGHTNING, OR OTHER HAZARD.
LIMITATION OF LIABILITY: TO THE FULL EXTENT ALLOWED BY LAW TRENDNET ALSO
EXCLUDES FOR ITSELF AND ITS SUPPLIERS ANY LIABILITY, WHETHER BASED IN
35
CONTRACT OR TORT (INCLUDING NEGLIGENCE), FOR INCIDENTAL,
CONSEQUENTIAL, INDIRECT, SPECIAL, OR PUNITIVE DAMAGES OF ANY KIND, OR
FOR LOSS OF REVENUE OR PROFITS, LOSS OF BUSINESS, LOSS OF INFORMATION
OR DATE, OR OTHER FINANCIAL LOSS ARISING OUT OF OR IN CONNECTION WITH
THE SALE, INSTALLATION, MAINTENANCE, USE, PERFORMANCE, FAILURE, OR
INTERRUPTION OF THE POSSIBILITY OF SUCH DAMAGES, AND LIMITS ITS LIABILITY
TO REPAIR, REPLACEMENT, OR REFUND OF THE PURCHASE PRICE PAID, AT
TRENDNET’S OPTION. THIS DISCLAIMER OF LIABILITY FOR DAMAGES WILL NOT BE
AFFECTED IF ANY REMEDY PROVIDED HEREIN SHALL FAIL OF ITS ESSENTIAL
PURPOSE.
Governing Law: This Limited Warranty shall be governed by the laws of the state of
California.
36