Technicolor Delivery Technologies Belgium TG590 Broadband Home Router User Manual Setup and User Guide
Technicolor Delivery Technologies Belgium Broadband Home Router Setup and User Guide
Contents
- 1. User Manual 1
- 2. User Manual 2
User Manual 1

Banister, Valerie
[Type the abstract of the document here. The abstract is typically a short summary of the contents of
the document.]
Setup and User Guide
TG590

1
Copyright
Copyright © 2010-2011 Technicolor. All rights reserved.
Distribution and copying of this document, use and communication of its contents is not permitted without written authorization from
Technicolor. The content of this document is furnished for informational use only, may be subject to change without notice, and should
not be construed as a commitment by Technicolor. Technicolor assumes no responsibility or liability for any errors or inaccuracies that
may appear in this document.
Technicolor, 101 W.103rd Street, Indianapolis, IN 46290
http://www.technicolor.com
Trademarks
• The following trademarks may be used in this document:
• DECTM is a trademark of ETSI.
• MoCA® is an internationally registered trademark.
• Bluetooth® word mark and logos are owned by the Bluetooth SIG, Inc.
• EthernetM is a trademark of Xerox Corporation.
• Wi-Fi®, WMM® and the Wi-Fi logo are registered trademarks of the Wi-Fi Alliance®. Wi-Fi CERTIFIED, Wi-Fi ZONE, Wi-Fi
Protected Access, Wi-Fi Multimedia, Wi-Fi Protected Setup, WPA, WPA2 and their respective logos are trademarks of the Wi-Fi
Alliance®.
• UPnP AV is a certification mark of the UPnP AV Implementers Corporation.
• DLNA® is a registered trademark, DLNA disc logo is a service mark, and DLNA Certified is a trademark of the Digital Living
• Network Alliance. Digital Living Network Alliance is a service mark of the Digital Living Network Alliance.
• Microsoft®, MS-DOS®, Windows®, Windows NT® and Windows Vista® are either registered trademarks or trademarks of
Microsoft Corporation in the United States and/or other countries.
• Apple® and Mac OS® are registered trademarks of Apple Computer, Incorporated, registered in the United States and other
countries.
• UNIX® is a registered trademark of UNIX System Laboratories, Incorporated.
• Adobe®, the Adobe logo, Acrobat and Acrobat Reader are trademarks or registered trademarks of Adobe Systems, Incorporated
registered in the United States and/or other countries.
• Other brands and product names may be trademarks or registered trademarks of their respective holders. All other logos, trade-
marks and service marks are the property of their respective owners, where marked or not.
Document Information
Status: v0.4 DRAFT (November 2010)
Reference: E-DOC-CTC-20101117-0001
Short Title: Setup & User Guide TG590-BHR for Verizon (en)

2
Product Overview
Innovation at its Best
The TG590 is a MoCA Gigabit Ethernet home/office router and features 4 LAN Gigabit Ethernet ports and
Wi-Fi b/g/n wireless LAN interface.
It also features a dual Multimedia over Coax Alliance (MoCA®) port for LAN/WAN traffic: as WAN traffic on
MoCA® operates on a different frequency than LAN traffic, the single coax connection is split via a band pass
filter to differentiate the two types of traffic.
The TG590 uses Auto-Sensing to automatically determine the current WAN connection. This makes the
TG590 the ideal solution for home and Small Office/Home Office (SOHO) users who not only want speed, but
also the flexibility to handle their complex networking needs.
Features at a Glance
• 1 Gigabit Ethernet WAN port
• 1 MoCA port (LAN/WAN)
• WAN Port Auto-Sensing
• 4 Gigabit Ethernet LAN ports
• Wireless networking Wi-Fi b/g/n
• Wi-Fi Protected Setup
• UPnP A/V and DLNA (Future Release)
• 2 USB 2.0 host ports
• Remotely manageable
Hardware Specifications
Interfaces WAN 1 MoCA WAN
1 Ethernet WAN 10/100/1000 Base-T port
Interfaces LAN 1 LAN coax port
4-port autosensing 10/100/1000 Base-T auto-MDI/MDI-X Ethernet LAN switch
Wi-Fi IEEE 802.11b/g/n 2x2 on board
2 USB 2.0 host ports
Dimensions 47 x 128 x 215 mm (1.8 x 5 x 8.5 in.)
AC voltage 100-240 VAC (switched mode power supply)
Temperature 0° - 40° C (32° - 104° F)
Humidity 5% to 100%
Documentation and software updates
Technicolor continuously develops new solutions, but is also committed to improving its existing products. For more
information on Technicolor’s latest technological innovations, documents and software releases, visit us at
www.technicolor.com.

3
TABLE OF CONTENTS
1 Introduction
1.0 Contents / Accessories
1.1 Minimum System Requirements
1.2 Features
1.3 Getting to Know the TG590
2 TG590 Setup
2.0 Introduction
2.1 Setting Up the TG590
2.2 Network Configuration
2.3 Configuring the TG590
2.4 Features
2.5 Main Screen
3 Setting Up a Wireless Network
3.0 Introduction
3.1 Overview
3.2 Connecting a Wireless Device
3.3 Wireless Status
3.4 Basic Security Settings
3.5 Advanced Security Settings
3.6 Setting Up a Wireless Device
4 Configuring My Network Settings
4.0 Introduction
4.1 Accessing My Network Settings
4.2 Using My Network Settings

4
5 Using Network Connections
5.0 Introduction
5.1 Accessing Network Connections
5.2 Network (Home/Office) Connection
5.3 Ethernet Connection
5.4 Wireless Access Point Connection
5.5 Coax Connection
5.6 Broadband Ethernet Connection
5.7 Broadband Coax Connection
6 Configuring Security
6.0 Introduction
6.1 Overview
6.2 Firewall
6.3 Access Control
6.4 Port Forwarding
6.5 DMZ Host
6.6 Port Triggering
6.7 Remote Administration
6.8 Static NAT
6.9 Advanced Filtering
6.10 Security Log
7 Parental Controls
7.0 Introduction
7.1 Activating Parental Controls
7.2 Rule Summary

5
8 Configuring Advanced Settings
8.0 Introduction
8.1 Using Advanced Settings
8.2 Utilities
8.3 DNS Settings
8.4 Network Settings
8.5 Configuration Settings
8.6 Time Settings
8.7 Firmware Upgrade (Future Release)
8.8 Routing Settings
9 Monitoring the TG590
9.0 Introduction
9.1 Router Status
9.2 Advanced Status
10 Troubleshooting
10.0 Introduction
10.1 Troubleshooting Tips
10.2 Frequently Asked Questions
6
1 INTRODUCTION
In this chapter
In a few minutes, you will establish an Internet connection and create a network (home/office) for data and
media sharing between multiple devices using the Universal Plug-and-Play support built-in to the TG590.
In this chapter, we will take a closer look at following features:
Topic
Page
1.0 Contents / Accessories
1.1 System Requirements
1.2 Features
1.3 Getting to Know the TG590
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.

7
1 Getting Started
1.0 Contents / Accessories
Your box should contain the following items:
Item
Description
Quantity
1
TG590
1
2
LAN Ethernet Cable
Yellow (RJ-45;3 meters)
1
3
Power Supply
1
4
Quick Installation Guide
1
5
Wall Mount Drill Template / Safety Guide
1
6
WAN Ethernet Cable
White (RJ-45; 2 meters)
1
If one of these items is missing, please call the Help Desk at 800-837-4966.
Safety Instruction
Please read “Safety Instructions and Regulatory Notices” before you start with the installation of the TG590.
1.1 Minimum System Requirements
Applicability
The TG590 must be used with the following systems and software:
• Computer with Ethernet or Wi-Fi capability
• Internet Explorer 5.0 or higher; Netscape Navigator 7.0 or higher
• Microsoft Windows 98SE, 2000, XP, Vista, and Windows 7; Mac OS 9 or greater; Unix
• TCP/IP network protocol installed on each computer
8
1.2 Features
Once the installation of your TG590 is completed you will be able to benefit from all the services offered.
This Setup and User Guide will focus on the following features:
Multiple networking standards support, including:
• MoCA 1.1 for WAN and LAN
• Ethernet IEEE 802.3 for WAN and LAN
• Wi-Fi 802.11n for LAN
Integrated wired networking with 4-port 10/100/1000 Mbps Ethernet switch and MoCA
Integrated wireless networking with 802.11n access point featuring:
• 802.11n enabled to support speeds up to 130 Mbps
Enterprise-level security, including:
• Fully modifiable firewall with Stateful Packet Inspection
• Content filtering with URL-keyword based filtering, parental control, customizable filtering policies per
computer, and E-mail notification
Denial of service protection against IP spoofing attacks, intrusion and scanning attacks, IP fragment overlap,
ping of death, and fragmentation attacks
Event logging
Intrusion detection
MAC address filtering
DMZ hosting
Access control
Advanced wireless protection featuring WPA, WPA2, WEP 64/128 bit encryption, 802.1x authentication, and
MAC address filtering

9
Other options, including:
• DHCP server option
• DHCP server/PPPoE server auto-detection
• DNS server
• LAN IP and WAN IP address selection
• MAC address cloning
• Port forwarding
• PPPoE support
• QoS support (end to end layer 2/3) featuring Diffserv, 802.1p/q prioritization, configurable
upstream/downstream traffic shaping, random early detection and pass-through of WAN-side DSCPs,
PHBs, and queuing to LAN-side devices
• Static routing
• Time zone support
• VLAN Multicast support
• VPN IPSec (VPN pass-through only)

10
1.3 Getting to Know the TG590
This section introduces you to the different components of the TG590.
On the top panel of your TG590, you can find a number of status LEDs, indicating the state of the device.
The LEDs that are supported on the top panel are:
• Power
• WAN Ethernet
• WAN Coax
• Internet
• Four (4) LAN Ethernet LED, One (1) LED per Ethernet LAN port
• LAN Coax
• USB
• Wireless
Note: The top panel where the LEDs are located also features an integral WPS button.
11
LED
Color
State
Description
Power
Green
Solid
Powered on.
Blinking
Upgrade ongoing.
Do not remove any cables or switch of the
TG590 when the TG590 is upgrading.
Orange
Blinking
Starting upgrade mode.
Off
Not powered.
Ethernet WAN
Green
Solid
Ethernet connection to the Verizon Optical Network
Terminal (ONT) operational, no activity.
Blinking
Ethernet connection to the Verizon Optical Network
Terminal (ONT) operational, activity.
Off
No Ethernet connection to the Verizon
Optical Network Terminal (ONT).
Coax WAN
Green
Solid/Blinking
Connected to the Verizon Optical Network
Terminal (ONT) using the Coax port.
Off
Not connected to the ONT using the Coax port.
Internet
Green
Solid
Connected to the Internet, no activity detected.
Blinking
Connected to the Internet, activity.
Amber
Solid
Failed to connect to the Internet.
Off
The TG590 is either powered off or starting up.
USB
Green
Solid
Failed to connect to the Internet.
Off
The TG590 is either powered off or starting up.
Wireless
Green
Solid
Wireless is enabled on your TG590, no traffic ongoing.
Blinking
Wireless is enabled on your TG590, traffic ongoing.
Off
Wireless is disabled on your TG590.

1
Power
P
o
r
t:
T
h
e
Power port connects the
TG590
R
ou
t
e
r
to an electrical wall outlet via
t
h
e
Power c
o
r
d
.
Power
S
w
i
t
c
h:
T
h
e
Power switch powers the
TG590
R
ou
t
e
r
on and
o
ff
.
R
e
s
e
t
B
u
tt
o
n:
To
restore the
TG590
R
ou
t
e
r
’
s factory default s
e
tt
i
ng
s
,
press and hold the
R
e
s
e
t
button for approximately five
s
e
c
o
nd
s
.
T
h
e
reset process will start about
t
e
n
seconds after releasing the
b
u
tt
o
n
.
When the
TG590
R
ou
t
e
r
r
e
s
e
t
s
,
all the
li
gh
t
s
on
the front panel turn
o
ff
,
and then some of the lights start
f
l
a
s
h
i
ng
.
T
h
e
TG590
R
ou
t
e
r
has c
o
m
p
l
e
t
e
d
its reset process when the Power light glows s
t
e
a
d
il
y
g
r
ee
n
.
Caution! Do not unplug the Power cord from the
TG590
during
t
h
e
reset
p
r
o
c
e
ss
.
Doing so may result
in the loss of the
TG590
’
s c
o
n
f
i
g
u
r
a
t
i
o
n
i
n
f
o
r
ma
t
i
o
n
.
If
this
o
cc
u
r
s
,
reset the
TG590
R
ou
t
e
r
a
g
a
i
n
.
LAN
E
t
h
e
r
n
e
t
Ports (4):
T
h
e
LAN
E
t
h
e
r
n
e
t
ports connect devices to the
TG590
R
ou
t
e
r
via
E
t
h
e
r
n
e
t
c
a
b
l
e
s to create a local area network
(
L
A
N
)
.
T
h
e
LAN
E
t
h
e
r
n
e
t
ports are 10/100 Mbps auto-sensing
p
o
r
t
s
,
and either a s
t
r
a
i
gh
t
-
t
h
r
ou
gh
or crossover
E
t
h
e
r
n
e
t
c
a
b
l
e
can be used when connecting devices to the
p
o
r
t
s
.
WAN
E
t
h
e
r
n
e
t
P
o
r
t:
T
h
e
WAN
E
t
h
e
r
n
e
t
port connects the
TG590
R
ou
t
e
r
to the
ISP
using an
E
t
h
e
r
n
e
t
c
a
b
l
e
.
USB
P
o
r
t:
T
h
e
USB
port provides up to 5
VDC
for
attached
devices (to charge a cell
p
h
o
n
e
,
for
e
x
am
p
l
e
)
.
I
n
the
f
u
t
u
r
e
,
with a firmware release
u
p
g
r
a
de
,
the
USB
h
o
s
t
functionality will be available for devices such as
external storage and c
a
m
e
r
a
s
.
Wireless
A
n
t
e
nn
a:
The TG590’s wireless antenna is used to transmit a wireless signal to other wireless devices on its wireless
network. It is built-in.

2
2 TG590 SETUP
In this chapter
In this chapter, we will take a closer look at following features:
Topic
Page
2.0 Connecting the TG590
2.1 Configuring the Network
2.2 Configuring the TG590
2.3 Features
2.4 Main Screen
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.

3
2.0 Connecting the TG590
Please refer to Quick Installation Guide.

4
2.1 TG590 Setup
There are three major steps to consider when setting up the TG590:
1) Connecting the Cables
2) Configuring the TG590, and
3) Connecting Other Devices
Note: If a different router was being used previously, disconnect it. Remove all components, including power
supplies and cables; they will not work with the TG590.
2.1a Connecting the Cables
1. Unpack the TG590 and black Power cord from the box. Make sure the power button is off.
2. Plug the black power cord in the black port on the back of the TG590; and then, into a power outlet.
3. Turn the TG590 on.
4. Make sure the power light on the front of the TG590 glows steadily green. Plug the yellow Ethernet cable
from the box into one of the four yellow Ethernet ports on the back of the TG590.
5. Make sure the computer is powered on, and then plug the other end of the yellow Ethernet cable into an
Ethernet port on the computer.
6. Make sure at least one of the Ethernet LAN lights on the front of the TG590 glows steadily green.
This may take a few moments.
7. The phone company previously installed a high-speed wall jack somewhere in the house.
Locate it and note its type (Ethernet or coaxial).
8. If Ethernet, follow steps 8a and 8b. Then, continue to step 10.
a) If connecting via Ethernet, get the white Ethernet cable from the box plug one end into the white port
on the back of the TG590.
b) Plug the other end of the white Ethernet cable into the high-speed Ethernet jack.
9. If coaxial, follow steps 9a and 9b. Then, continue to step 10.
a) If connecting via coaxial cable, get a coaxial cable and connect one end to the red Coax port on the
back of the TG590.
b) Connect the other end of the coaxial cable to a coax jack.
10. Make sure the Ethernet WAN light (if connecting via Ethernet) or Coax WAN light (if connecting via
coaxial cable) on the front of the TG590 glows steadily green. If connecting via coaxial cable, this may
take a few minutes.
Note: If the Ethernet WAN light or Coax WAN light does not illuminate, make sure the cable (Ethernet or coaxial)
is connected properly at both ends.

5
2.1b Rear Panel
The rear panel of the TG590 has seven ports (Reset, Power, LAN Ethernet [4], COAX, and WAN Ethernet), a
Power switch, a Reset button, and a wireless antenna.
(Listed in order from left to right)
Reset Button
To restore the TG590’s factory default settings, press and hold the Reset button for approximately five
seconds. The reset process will start about ten seconds after releasing the button. When the TG590 resets, all
the lights on the front panel turn off, and then some of the lights start flashing. The TG590 has completed its
reset process when the Power light glows steadily green.
Caution! Do not unplug the Power cord from the TG590 during the reset process. Doing so may result
in the loss of the TG590’s configuration information. If this occurs, reset the TG590 again.
Coax
The Coax port connects the TG590 to the ISP or other devices using a coaxial cable.
Power
The Power port connects the TG590 to an electrical wall outlet via the Power cord.
Power Switch
The Power switch powers the TG590 on and off.
LAN Ethernet Ports (4)
The LAN Ethernet ports connect devices to the TG590 via Ethernet cables to create a local area network
(LAN). The LAN Ethernet ports are 10/100 Mbps auto-sensing ports, and either a straight through or
crossover Ethernet cable can be used when connecting devices to the ports.
WAN Ethernet Port
The WAN Ethernet port connects the TG590 to the ISP using an Ethernet cable.

6
2.1c Side Panel
USB Port
The USB port provides up to 5 VDC for attached devices (to charge a cell phone, for example). In the future,
with a firmware release upgrade, the USB host functionality will be available for devices such as external
storage and cameras.
Wireless Antenna (Built-in)
The TG590’s wireless antenna is built-in and used to transmit a wireless signal to other wireless devices on
its wireless network.

7
2.2 Computer Network Configuration
Each network interface on the computer should either be configured with a statically defined IP address and DNS address,
or instructed to automatically obtain an IP address using the DHCP server. The TG590 is set up, by default, with an active
DHCP server, and we recommend leaving this setting as is.
2.2a Configuring Dynamic IP Addressing
To set up a computer to use dynamic IP addressing:
Windows Vista
1. Select Network and Sharing in the Control Panel.
2. Click View Status, then click Properties.
3. Click Continue in the “User Account Control” window.
4. In the “General” tab of the “Local Area Connection Properties” window select Internet Protocol Version 4
(TCP/IPv4), then click Properties.
5. The “Internet Protocol Version 4 (TCP/IPv4) Properties” window appears.
6. Click the “Obtain an IP address automatically” radio button.
7. Click the “Obtain DNS server address automatically” radio button.
8. Click OK in the Internet Protocol Version 4(TCP/IPv4) Properties window, then click OK in the “Local
Area Connection Properties” screen to save the settings.
Windows XP
1. Select Network Connections in the Control Panel.
2. Right-click Ethernet Local Area Connection, then click Properties.
3. In the “General” tab, select Internet Protocol (TCP/IP), then click Properties.
4. The “Internet Protocol (TCP/IP) Properties” window appears.
5. Click the “Obtain an IP address automatically” radio button.
6. Click the “Obtain DNS server address automatically” radio button.
7. Click OK in the “Internet Protocol (TCP/IP) Properties” screen, then click OK in the “Local Area
Connection Properties” screen to save the settings.
Windows 98
1. Select Network in the Control Panel.
2. Select the TCP/IP settings for the network card, then click Properties.
3. Click the “Obtain an IP address automatically” radio button in the “IP Address” tab.
4. Click Disable DNS in the DNS configuration tab.
5. Click OK in the “TCP/IP Properties” screen.
6. Click OK in the “Network” screen to reboot and save the settings.

8
Windows NT
1. Click Network in the Control Panel. The “Network” window appears.
2. In the “Protocol” tab, select Internet Protocol (TCP/IP), then click Properties.
3. In the “IP Address” tab, click the “Obtain an IP address automatically” radio button.
4. In the “DNS” tab, verify no DNS server is defined in the “DNS Service Search Order” text box and no suffix
is defined in the “Domain Suffix Search Order” text box.
Macintosh OS X
1. Click on the Apple icon in the top left corner of the desktop.
2. From the menu that appears, select System Preferences.
3. The “System Preferences” window appears. Click Network.
4. From the “Network” window, make sure “Ethernet” in the list on the left is highlighted and displays
“Connected.”
5. Click Assist me.
6. From the tab that appears, click Diagnostics.
7. Follow the instructions in the “Network Diagnostics” assistant.
9
2.3 Configuring the TG590
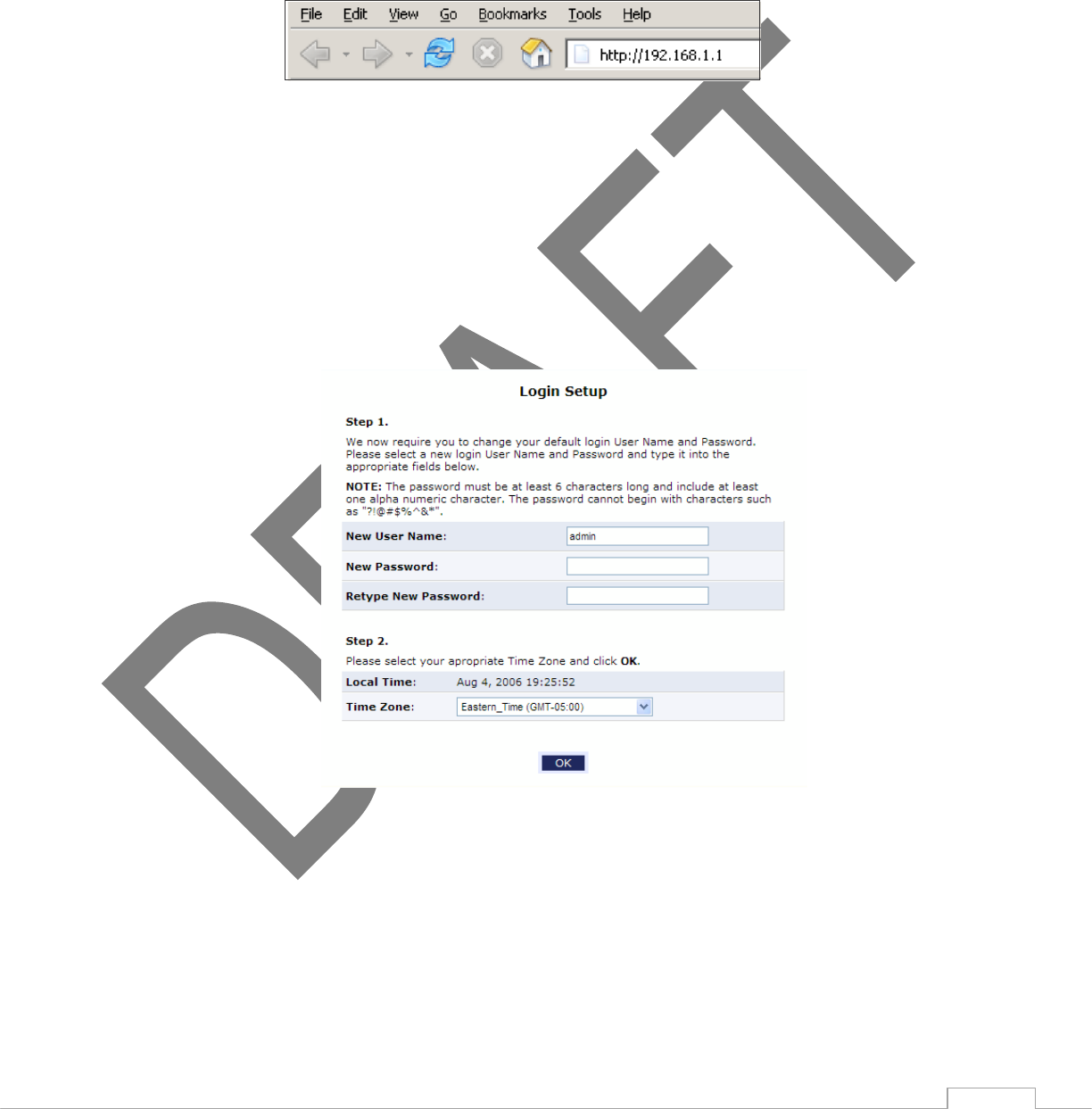
1. Open a web browser on the computer connected to the TG590. In the “Address” text box, type:
http://192.168.1.1, then press Enter on the keyboard.
2. The “Login Setup” screen appears. Select a new password and enter it in the appropriate text boxes (the
password must be entered twice, for validation purposes). Write the password down on a piece of paper
and keep it in a safe place, since it will be needed to access the TG590 ’s GUI (Graphical User Interface) in
the future.
3. In the bottom part of the screen, select the correct time zone from the “Time Zone” drop-down list. Then,
click OK at the bottom of the screen.
The TG590 is now configured.
10
2.3a Connecting Other Computers/Set Top Boxes
The TG590 can connect to other computers/set tops in three ways: 1) Ethernet, 2) wireless connection, or 3)
coaxial cable.
Ethernet
Get an Ethernet cable and plug one end into one of the open yellow Ethernet ports on the back of the
TG590.
Plug the other end of the Ethernet cable into an Ethernet port on the computer.
Make sure the corresponding Ethernet LAN light on the front of the TG590 glows steadily green.
Repeat these steps for each computer to be connected to the TG590 via Ethernet.
Wireless
Make sure each computer to be connected wirelessly has built-in wireless or an attached wireless
adapter.
Make sure the computer uses the same SSID and WPA2 key as the TG590 by launching the computer’s
wireless application
Enter the SSID and WPA2 key found on the sticker on the bottom of the TG590 in the computer’s
wireless settings and click Save. Make sure to configure the computer to use WPA2 encryption.
Make sure the changes were implemented by opening a web browser from the computer.
Repeat these steps for every other computer to be connected to the TG590 wirelessly.
Coaxial
Make sure all set top boxes are turned off.
Connect the coax to the set top
Power up the set top box.
Make sure the Coax LAN light on the front of the TG590 glows steadily green. This may take a few
minutes. When it does, the set top box is connected to the TG590
Note: The LED may be green from another set top. If so, check the set top instead.
11
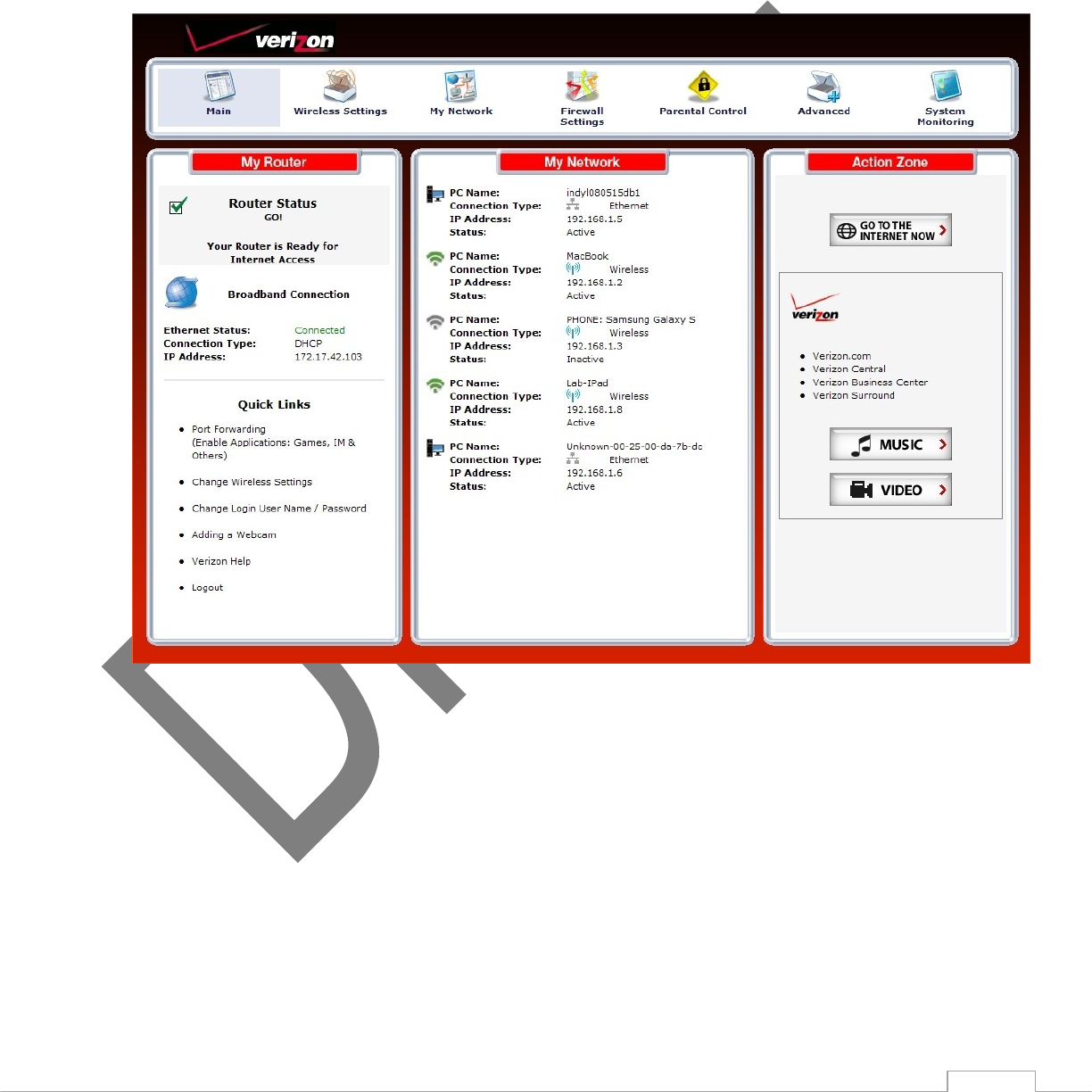
2.4 Main Screen
After logging into the TG590’s GUI (see “Configuring the TG590” at the beginning of this chapter), the “Main”
screen appears.
The Main screen has a menu occupying the top of the screen with the following: Wireless Settings, My
Network, Firewall Settings, Parental Control, Advanced, and System Monitoring. Below that, the screen
is divided into three columns: “My Router”, “My Network,” and “Action Zone.”

12
2.4a Menu
The Main screen’s menu contains links to all of the configuration options of the TG590:
• Wireless Setup (chapter 3)
• My Network (chapter 4)
• Firewall Settings (chapter 6)
• Parental Controls (chapter 7)
• Advanced (chapter 8)
• System Monitoring (chapter ?)
2.4b My Router
This section displays the status of the TG590’s network and Internet connection. A green light signifies the
TG590 is connected; a yellow light means the TG590 is attempting to connect; and a red light signifies the
TG590 ’s connection is down.
Broadband Connection
The “Broadband Connection” section of the My column displays the state of the TG590 ’s broadband
connection (“Connected” or “Disconnected”) for the two connection options (“Coax Status” and “Ethernet
Status”), and the WAN IP address of the broadband connection.
Quick Links
The “Quick Links” section of the My column contains a list of frequently accessed settings, including “Change
Wireless Settings,”“Change Login User Name & Password,”“Enable Gaming,” and “Logout.”
2.4c My Network
The “My Network” column of the Main screen displays the connection type, name, and IP address of all
devices connected to the TG590’s network. The icon associated with the device will be displayed normally
(signifying an active device) or shaded (signifying the device has not been active for at least
60 seconds). The user can also configure the basic settings of each device by clicking on its icon. These
settings are described in more detail in chapter 3.
13
3 WIRELESS SETTINGS
In this chapter
With the built-in wireless access point you no longer need a cable connection between your computer and
your TG590. Wireless networking allows you to connect two or more devices without the wires, making your
devices more accessible and simple to use. This chapter explains how to create a wireless network using the
TG590, including accessing and configuring wireless security options.
In this chapter, we will take a closer look at following features:
Topic
Page
3.1 Overview
3.2 Connecting a Wireless Device
3.3 Wireless Status
3.4 Basic Security Settings
3.5 Advanced Security Settings
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.

14
3.1 Overview
The TG590 provides the user with wireless connectivity over the 802.11b, g, and n standards (the most
common wireless standards). 802.11b has a maximum data rate of 11 Mbps, while 802.11g has a maximum
data rate of 54 Mbps, and 802.11n has a maximum data rate of 130 Mbps. All operate in the 2.4 GHz range.
The TG590’s wireless feature is turned on, with wireless security activated, by default. The level of security is
WPA2 with a unique WPA2 key already entered. This information is displayed on a sticker located on the
bottom of the TG590.
The TG590 integrates multiple layers of security. These include the IEEE 802.1x port-based authentication
protocol, RADIUS client, EAP-MD5, EAP-TLS, EAP-TTLS, EAP-PEAP, Wired Equivalent Privacy (WEP), Wi-Fi
Protected Access (WPA) and firewall and VPN applications.
3.2 Connecting a Wireless Client
To connect a wireless client to the TG590:
Note: The following procedure assumes the TG590’s default wireless settings are intact. If they have been
changed, use the new SSID and wireless security settings. For more details, see the “Connecting a Wireless
Windows XP Client” section of this chapter.
1. In the wireless client’s configuration interface, enter the TG590’s SSID (found on a sticker on the bottom of
the TG590 ’s case) in the appropriate text box or field (this varies depending on the wireless client’s
manufacturer).
2. Enter the TG590’s WPA2 key (also found on the sticker on the bottom of the TG590’s case) in the wireless
client’s configuration interface.
3. Save the changes and exit the wireless client’s configuration interface. The client should now detect and
join the TG590’s wireless network. If not, check the wireless client’s documentation, or contact its
manufacturer.
15
3.3 Wireless Status
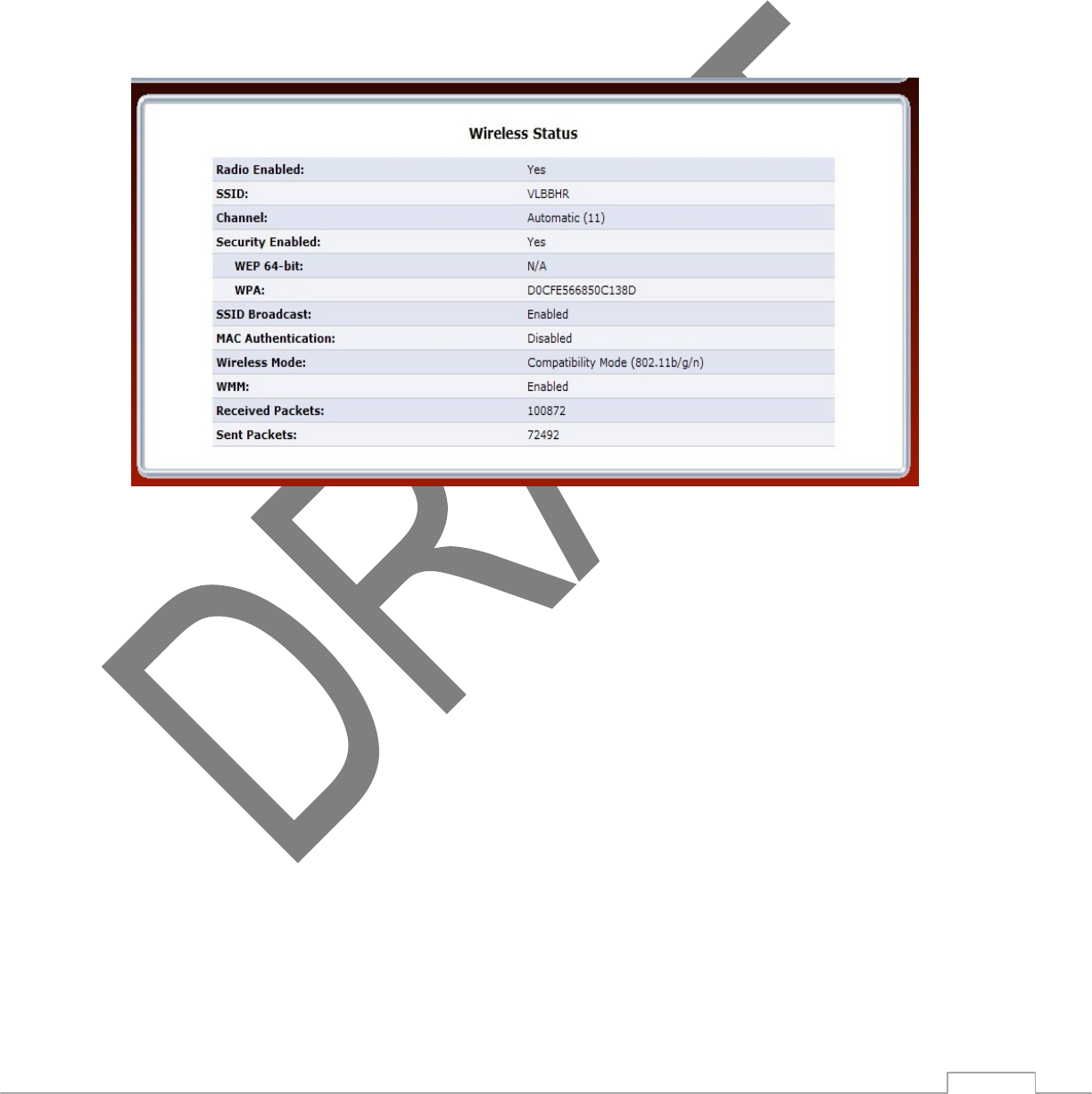
Clicking on the “Wireless Settings” icon from the Main screen’s menu generates the “Wireless Status” screen,
which displays the current status of the wireless connection.
3.3a Radio Enabled
Displays whether the TG590’s wireless radio is active.
3.3b SSID
The SSID (Service Set Identifier) is the network name shared among all devices on a particular wireless
network. The SSID must be identical for all devices on the wireless network. It is case-sensitive and cannot
exceed 32 characters. Make sure the SSID is the same for all devices to be connected to the wireless network.
The TG590 comes from the factory with an SSID already entered and displayed. The default SSID can also be
found on a sticker on the bottom of the TG590.
3.3c Channel
Displays the channel to which the wireless connection is currently set. All devices on the wireless network

16
must be on the same channel to function correctly.
3.3d Security Enabled
Displays what kind of security is active on the wireless connection, and the security encryption key.
3.3e SSID Broadcast
Displays whether the TG590 is broadcasting its SSID. If activated, the SSID of the TG590’s wireless network is
broadcast wirelessly.
3.3f MAC Authentication
Displays whether the TG590 is using MAC (Media Access Control) address authentication to allow wireless
devices to join the network.
3.3g Wireless Mode
Displays the types of wireless device that can join the network. Options include 802.11b, 802.11g, 802.11n or
Mixed (allows both 802.11b- 802.11g- and 802.11n- equipped wireless devices to join the network).
3.3h Packets Received/Sent
Displays the number of packets received and sent since the TG590’s wireless capability was activated.
17
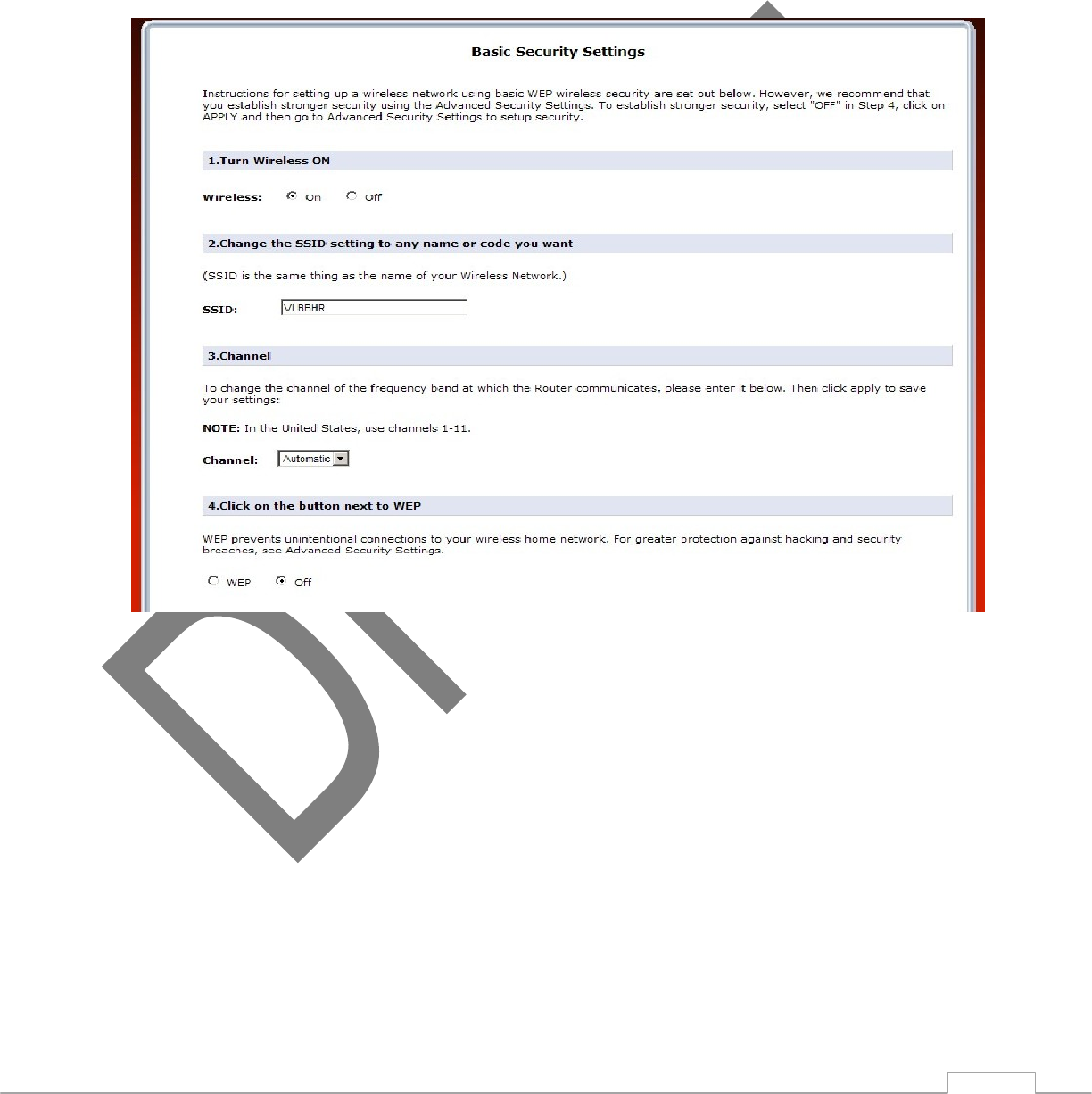
3.4 Basic Security Settings
To configure the TG590’s wireless network for basic security, select “Basic Security Settings” from the menu
on the left side of any Wireless Settings screen. The “Basic Security Settings” screen appears.
1) Click the “On” radio button to activate the TG590’s wireless radio.
2) Enter the name of the wireless network in the “SSID” text box (the SSID name in the figure above is an
example; enter a different name for the SSID).
3) The channel at which the TG590’s wireless radio communicates is automatically selected.
Note: If it needs to be changed, please select from the “Channel” drop-down list.
4) Click the “WEP” radio button to activate WEP (Wired Equivalent Privacy) security on the wireless network to
add devices unable to support WPA2 security.
5) Write down or print the screen displaying the wireless settings on the screen. Other wireless devices wishing
to join the TG590 ’s wireless network must use these same settings to access the TG590 network.
6) Click Apply to save the settings.

18
4 MY NETWORK CONFIGURATION
In this chapter
In this chapter, we will take a closer look at following features:
Topic
Page
4.0 Accessing My Network Settings
4.1 Network Status
4.2 Network Connections
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.

19

20
5 NETWORK CONNECTIONS
In this chapter
In this chapter, we will take a closer look at following features:
Topic
Page
5.1 Accessing Network Connections
5.2 Network (Home/Office) Connection
5.3 Ethernet Connection
5.4 Wireless Access Point Connection
5.5 Coax Connection
5.6 Broadband Ethernet Connection
5.7 Broadband Coax Connection
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.
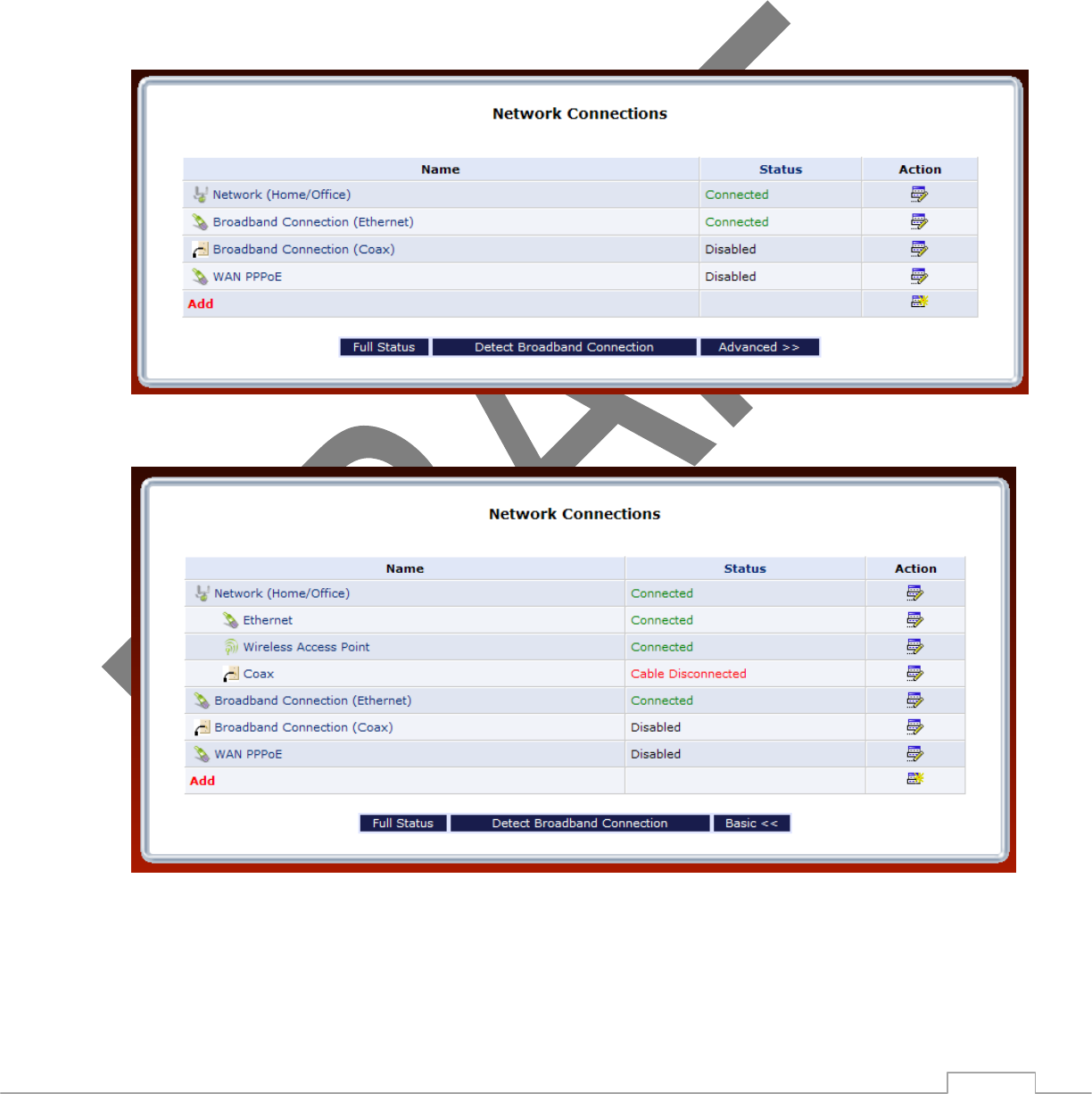
21
5.1 Accessing Network Connections
Caution: The settings covered in this chapter should be configured by experienced network technicians only.
To access the TG590’s network connections, in the “My Network” screen:
Click Network Connections from the menu on the left side. The “Network Connections” screen appears.
Click Advanced to expand the screen and display all connection entries.
Note: To return to the Basic view, click on Basic.
To select a connection, click on its name.
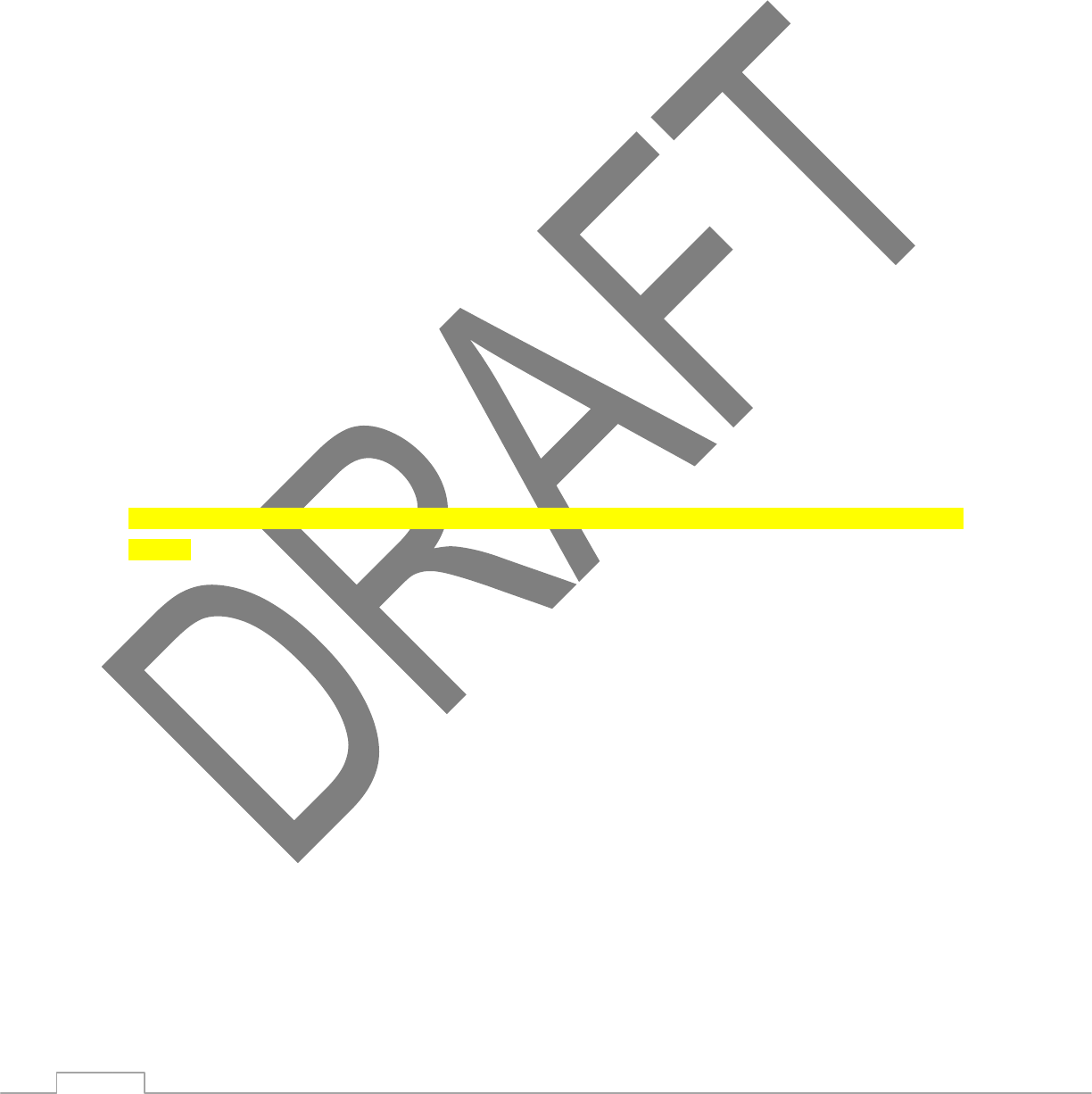
22
The remainder of this chapter describes the various network connections available on the TG590.
5.2 Network (Home/Office) Connection
Select Network (Home/Office) in the Network Connections screen to generate the “Network (Home/Office)
Properties” screen. This screen displays a list of the local network’s properties. The only modifications that
can be made from this screen are disabling the connection (by clicking Disable) or renaming the connection
(by entering a new name in the “Rule Name” text box). Note: When a network is disabled, its formerly
underlying devices will not be able to get the DHCP address from the network interface to which they were
connected.
Using Network Connections
The Network (Home/Office) connection is used to combine several network devices under one virtual
network. For example, a home/office network can be created for Ethernet and other network devices.
5.2a Configuring the Home/Office Network
Click Settings in the “Network (Home/Office) Properties” screen to generate the “Configure Network
(Home/Office)” screen.
General
The top part of the Configure Network (Home/Office) screen displays general communication parameters.
We recommend not changing the default values in this section unless familiar with networking concepts.
Status Displays the connection status of the network.
“When should this rule occur? Displays when the rule is active. To schedule rules, see the “Advanced Settings”
chapter.
Network Select the type of connection being configured from the drop-down list (options: Broadband
Connection, Network [Home/Office], or DMZ).
Connection Type Displays the type of connection.
Physical Address Displays the physical address of the network card used for the network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size permitted for Internet
transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the
MTU according to the DHCP connection, and “Manual,” which allows the MTU to be set manually.
Internet Protocol
This section has three options: No IP Address, Obtain an IP Address Automatically, and Use the Following IP
Address.
No IP Address Select this option if the connection will have no IP address. This is useful if the connection
operates under a bridge.

23
Obtain an IP Address Automatically Select this option if the network connection is required by the ISP to
obtain an IP address automatically. The server assigning the IP address also assigns a subnet mask address,
which can be overridden by entering another subnet mask address.
Use the Following IP Address Select this option if the network connection uses a permanent (static) IP
address, then the IP address and subnet mask address.
Bridge
The “Bridge” section of the Configure Network (Home/Office) screen is used to specify which networks can
join the network bridge. Verizon does not support using the TG590 Router in Bridge mode. Using Bridge
mode may cause problems with the TG590 Router, including the complete disabling of all video services used
with the TG590 Router.
Status The “Status” column displays the connection status of a particular device.
STP Click in the device’s “STP” check box to enable Spanning Tree Protocol
on the device. This protocol provides path redundancy while preventing undesirable loops in the network.
Action The “Action” column contains an icon that, when clicked, generates the configuration screen of the
particular device.
DNS Server
Domain Name System (DNS) is the method by which website or domain names are translated into IP
addresses. Specify such an address manually, according to the information provided by the ISP.
To manually configure DNS server addresses, select Use the Following DNS Server Addresses. Specify up to
two different DNS server addresses, one primary, the other secondary.
IP Address Distribution
The “IP Address Distribution” section of the Configure Network (Home/Office) screen is used to configure the
TG590 Router’s Dynamic Host Configuration Protocol (DHCP) server parameters. DHCP automatically assigns
IP addresses to network devices. If enabled, make sure to configure the network devices as “DHCP Clients.”
There are three options in this section: Disabled, DHCP Server, and DHCP Relay.
Disabled Select this option if statically assigning IP addresses to the network devices.
DHCP Server To set up the network bridge to function as a DHCP server:
1. Select DHCP Server.
2. Enter the IP address at which the TG590 Router starts issuing addresses in the “Start IP Address” text
boxes. Since the TG590 Router’s default IP address is 192.168.1.1, the Start IP Address should be 192.168.1.2.
3. Enter the end of the IP address range used to automatically issue IP addresses in the “End IP Address” text
boxes. The “maximum” IP address that can be entered here is 192.168.1.254.
4. Enter the subnet mask address in the “Subnet Mask” text boxes. The subnet mask determines which
portion of a destination LAN IP address is the network portion, and which portion is the host portion.
If Windows Internet Naming Service (WINS) is being used, 5. enter the WINS server address in the “WINS

24
Server” text boxes.
6. Enter the amount of time a network device will be allowed to connect to the TG590 Router with its
currently issued dynamic IP address in the “Lease Time in Minutes” text box.
7. Click in the “Provide Host Name If Not Specified by Client” check box to have the TG590 Router
automatically assign network devices with a host name, in case a host name is not provided by the user.
DHCP Relay Select this option to have the TG590 Router function as a DHCP relay, and enter the IP address in
the screen that appears.
Routing
The TG590 Router can be configured to use static or dynamic routing. Dynamic routing automatically adjusts
how packets travel on the network, while static routing specifies a fixed routing path to neighboring
destinations.
There are two options in the “Routing” section of the Configure Network (Home/Office) screen: Basic or
Advanced.
Basic Select this option for basic routing operation.
Advanced To set up the TG590 Router’s network bridge for advanced routing:
1. Select Advanced from the “Routing” drop-down menu.
2. Enter a device metric in the “Device Metric” text box. The device metric is a
value used by the TG590 Router to determine whether one route is superior to
another, considering parameters such as bandwidth and delay time.
3. Click in the “Default Route” check box to define this device as a default route.
4. Click in the “Multicast - IGMP Proxy Internal” check box to activate multicasting.
Routing Table
Clicking New Route generates the “New Route” window, where a new route can
be configured.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen,
where additional IP addresses can be created to access the TG590 Router via the
Network (Home/Office) connection.
5.3 Ethernet Connection
An Ethernet connection connects computers to the TG590 Router using Ethernet cables, either directly or via
network hubs and switches. Click Ethernet in the Network Connections screen (if needed, click Advanced at
the bottom of the screen to reveal the “Ethernet” link below “Network [Home/Office]”) to generate the
“Ethernet Properties” screen. This screen displays a list of the connection’s properties. The only modifications
that can be made from this screen are disabling the connection (by clicking Disable) or renaming the
connection (by entering a new name in the “Rule Name” text box).

25
Note: If disabling the connection, the TG590 Router must be rebooted for the change to take effect.
5.3a Configuring the Ethernet Connection
Click Settings at the bottom-right of the Ethernet Properties screen to generate the “Configure Ethernet”
screen.
General
The top part of the Configure Ethernet screen displays general communication parameters. We recommend
not changing the default values in this section unless familiar with networking concepts.
Status Displays the connection status of the Ethernet switch.
When should this rule occur? Displays when the rule is active. To schedule rules, see the “Advanced Settings”
chapter.
Network Select the type of connection being configured from the drop-down list (Network [Home/Office],
Broadband Connection, or DMZ).
Connection Type Displays the type of connection.
Physical Address Displays the physical address of the network card used for the network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size permitted for Internet
transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the
MTU according to the DHCP connection, and “Manual,” which allows the MTU to be set manually.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen, where additional IP addresses
can be created to access the TG590 Router via the Ethernet connection.
HW Switch Ports
This section displays the connection status of the TG590 Router’s four Ethernet ports.
Clicking on a connection’s “Action” icon (in the column on the right) generates
the “Port VLANs” screen, where ingress and egress policies can be edited.

26
5.4 Coax Connection
A Coax connection connects devices (such as set-top boxes) to the TG590 Router
using a coaxial cable. Click Coax in the Network Connections screen (if needed, click Advanced at the bottom
of the screen to reveal the “Coax” link below “Network [Home/Office]”) to generate the “Coax Properties”
screen. This screen displays a list of the connection’s properties. The only modifications that can be made
from this screen are disabling the connection (by clicking Disable) or renaming the connection (by entering a
new name in the “Name” text box).
Note: If disabling the connection, the TG590 Router must be rebooted for the change to take effect.
5.4a Configure Coax
Click Settings at the bottom-right of the Coax Properties screen generates the “Configure Coax” screen.
General
The top part of the Configure Coax screen displays general communication
parameters. We recommend not changing the default values in this section
unless familiar with networking concepts.
Status Displays the status of the coax connection.
When should this rule occur? Displays when the rule is active. To schedule rules, see the “Advanced Settings”
chapter
Network Displays the type of network.
Connection Type Displays the type of connection.
Physical Address Displays the physical address of the network card used for the network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size permitted for Internet
transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the
MTU according to the DHCP connection, and “Manual,” which allows the MTU to be set manually.
Coax Link
Set up the coax link options in this section of the Configure Coax screen. Options
include Channel, Privacy, and Password.
Channel Select the Channel from the drop-down list (select from 1-6, or
“Automatic”).
Privacy Toggle “Privacy” by clicking in the “Enabled” check box. If Privacy is
activated, all devices connected via coaxial cable must use the same password.
We recommend leaving the Privacy option deactivated.
Password Enter the Coax Link password in this text box.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen,
where additional IP addresses can be created to access the TG590 Router via the

27
Coax Link Ethernet connection.
Coax Connection Status
Click Go to LAN Coax Stats to generate the “Coax Connection Status” screen,
which gives an overview of all the devices connected to the TG590 Router via
coaxial cable.
5.5 Broadband Ethernet Connection
A Broadband Ethernet connection connects the TG590 Router to the Internet
using an Ethernet cable. Click Broadband Connection (Ethernet) from the
Network Connections screen to generate the “Broadband Connection (Ethernet)
Properties” screen. This screen displays a list of the connection’s properties.
The only modifications that can be made from this screen are disabling the
connection (by clicking Disable) or renaming the connection (by entering a
new name in the “Rule Name” text box).
Note: If disabling the connection, the TG590 Router must be rebooted for the
change to take effect.
5.5a Configuring the Broadband Ethernet Connection
Click Settings at the bottom-right of the Broadband Connection (Ethernet)
Properties window to generate the “Configure Broadband Connection
(Ethernet)” screen.
General
The top part of the screen displays general communication parameters. We
recommend not changing the default values in this section unless you are
familiar with networking concepts.
Status Displays the status of the Ethernet connection (“Down,” “Connected,” etc.)
Schedule Displays when the rule is active. To configure rules, see the “Advanced
Settings” chapter.
Network Select the type of connection being configured from the drop-down
list (options: Network [Home/Office], Broadband Connection, or DMZ).
Connection Type Displays the type of connection. Since this is an Ethernet
Connection, “Ethernet” is displayed.
Physical Address Displays the physical address of the network card used for
the network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size
permitted for Internet transmission. “Automatic, sets the MTU at 1500. Other
choices include “Automatic by DHCP,” which sets the MTU according to the

28
DHCP connection, and “Manual,” which allows the MTU to be set manually.
Internet Protocol
This section includes three options: No IP Address, Obtain an IP Address Automatically, and Use the
Following IP Address.
No IP Address Select this option if the connection has no IP address. This is useful if the connection is
operating under a bridge.
Obtain an IP Address Automatically Select this option if the ISP requires the connection to obtain an IP
address automatically. The server assigning the IP address also assigns a subnet mask address, which can be
overridden by clicking in the “Override Subnet Mask” check box and entering another subnet mask address.
Additionally, the DHCP lease can be renewed and/or released by clicking on the appropriate “DHCP Lease”
button. The “Expires In” value displays how long until the DHCP lease expires.
Use the Following IP Address Select this option if the connection uses a permanent (static) IP address. The ISP
should provide this address, along with a subnet mask address, default gateway address, and, optionally,
primary and secondary DNS server addresses.
DNS Server
The Domain Name System (DNS) is the method by which website or domain names are translated into IP
addresses. This connection can be configured to automatically obtain a DNS server address, or an address can
be specified manually, according to the information provided by the ISP.
To configure the connection to automatically obtain a DNS server address, select Obtain DNS Server Address
Automatically from the “DNS Server” drop-down list. To manually configure DNS server addresses, select Use
the Following DNS Server Addresses. Specify up to two different DNS server addresses, one primary, the
other secondary.
IP Address Distribution
The “IP Address Distribution” section of the Configure Broadband Connection (Ethernet) screen is used to
configure the TG590 Router’s Dynamic Host Configuration Protocol (DHCP) server parameters. DHCP
automatically assigns IP addresses to network devices. If enabled, make sure to configure the network
devices as “DHCP Clients.” There are three options in this section: Disabled, DHCP Server, and DHCP Relay.
Caution! We strongly recommend leaving this setting at “Disabled.”
Disabled Select this option if statically assigning IP addresses to the network devices.

29
DHCP Server To set up the TG590 Router to function as a DHCP server:
1) Select DHCP Server.
2) Enter the IP address at which the TG590 Router starts issuing addresses in the “Start IP Address” text
boxes. Since the TG590 Router’s default IP address is 192.168.1.1, the Start IP Address must be
192.168.1.2 or higher.
3) Enter the end of the IP address range used to automatically issue IP addresses in the “End IP Address”
text boxes.
4) Enter the subnet mask address in the “Subnet Mask” text boxes. The subnet mask determines which
portion of a destination LAN IP address is the network portion, and which portion is the host portion.
5) If a Windows Internet Naming Service (WINS) is being used, enter the WINS server address in the “WINS
Server” text boxes.
6) Enter the amount of time a network device will be allowed to connect to the TG590 Router with its
currently issued dynamic IP address in the “Lease Time in Minutes” text box. Just before the time is up,
the device’s user will need to make a request to extend the lease or get a new IP address.
7) Click in the “Provide Host Name If Not Specified by Client” check box to have the TG590 Router
automatically assign network devices with a host name, in case a host name is not provided by the user.
Additionally, to add a new product or product family, click New IP Range in the “Vendor Class ID” column
below “IP Address Distribution According to DHCP Option 60 (Vendor Class Identifier).” This generates the
“DHCP Server Pool Settings” screen. Set the device name, IP range, and priority level in the appropriate text
boxes, then click Apply.
DHCP Relay Select this option to have the TG590 Router function as a DHCP relay. To enter a new IP address
for the relay, click New IP Address. The “DHCP Relay Server Address” screen appears. Enter the new IP
address in the appropriate text boxes, then click Apply.
Routing
The TG590 Router can be configured to use static or dynamic routing. Dynamic
routing automatically adjusts how packets travel on the network, while static
routing specifies a fixed routing path to neighboring destinations.
There are two options in the “Routing” section of the “Configure Broadband
Connection (Ethernet)” screen: Basic or Advanced.

30
Basic Select this option for basic routing operation.
Advanced To set up the TG590 Router’s Broadband Ethernet connection for advanced routing:
1) Select Advanced from the Routing drop-down menu.
2) Enter a device metric in the “Device Metric” text box. The device metric is a value used by the TG590
Router to determine whether one route is superior to another, considering parameters such as
bandwidth and delay time.
3) Click in the “Default Route” check box to define this device as a the default route.
4) Click in the “Multicast - IGMP Proxy Internal” check box to activate multicasting. Multicasting enables the
TG590 Router to issue IGMP (Internet Group Management Protocol) host messages on behalf of hosts the
TG590 Router discovers through standard IGMP interfaces. IGMP proxy enables the routing of multicast
packets according to the IGMP requests of local network devices asking to join multicast groups.
Routing Table
Clicking New Route generates the “New Route” window, where a new route can be configured.
Internet Connection Firewall
Click in the “Enabled” check box to activate the TG590 Router’s firewall on the connection.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen, where additional IP addresses
can be created to access the TG590 Router via the connection.

31
5.6 Coax Broadband Connection
A Coax Broadband connection connects the TG590 Router to the Internet using a coaxial cable. Click
Broadband Connection (Coax) in the Network Connections screen to generate the “Broadband Connection
(Coax) Properties” screen. This screen displays a list of the connection’s properties. The only modifications
that can be made from this screen are disabling the connection (by clicking Disable) or renaming the
connection (by entering a new name in the “Name” text box).
Note: If disabling the connection, the TG590 Router must be rebooted for the change to take effect.
5.6a Configuring the Coax Broadband Connection
Click Settings at the bottom of the Broadband Connection (Coax) Properties screen to generate the “Configure
Broadband Connection (Coax)” screen.
General
The top part of the screen displays general communication parameters. We recommend not changing the
default values in this section unless you are familiar with networking concepts.
Status Displays the status of the connection (“Down,” “Connected,” etc.).
When should this rule occur? Displays when the rule is active. To schedule rules, see the “Advanced Settings”
chapter.
Network Displays the type of network to which the link is connected. Since this is a broadband connection
(connected to the Internet), “Broadband Connection” is displayed.
Connection Type Displays the type of connection. Since this is a coaxial connection, “Coax” is displayed.
Physical Address Displays the physical address of the network card used for the network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size permitted for Internet
transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the
MTU according to the DHCP connection, and “Manual,” which allows the MTU to be set manually.
Coax Link
Check and configure the coax link connection in this section of the screen.
Channel Displays the channel frequency range of the coaxial connection. This setting is not user configurable;
it is for information only.
Privacy Toggle “Privacy” by clicking in the “Enabled” check box. If Privacy is activated, all devices connected
via coaxial cable must use the same password.
We recommend leaving the Privacy option deactivated.
Auto Detection Select whether you want the TG590 to automatically detect a coaxial link here.
Password Enter the Coax Link password here.

32
CM Ratio Select the CM Ratio from the drop-down menu here.
WAN Coax Connection Speeds
This section displays the TG590 Router’s Tx and Rx speeds (in Mbps).
Internet Protocol
This section includes three options: No IP Address, Obtain an IP Address Automatically, and Use the
Following IP Address.
No IP Address Select this option if the connection has no IP address. This is useful when the connection is
operating under a bridge.
Obtain an IP Address Automatically Select this option if the ISP requires the connection to obtain an IP
address automatically. The server assigning the IP address also assigns a subnet mask address, which can be
overridden by clicking in the “Override Subnet Mask” check box and entering another subnet mask address.
Additionally, the DHCP lease can be renewed and/or released by clicking on the appropriate “DHCP Lease”
button. The “Expires In” value displays how long until the DHCP lease expires.
Use the Following IP Address Select if the WAN connection is configured using a permanent (static) IP
address. The ISP should provide this address, along with a subnet mask address, default gateway address,
and, optionally, primary and secondary DNS server addresses.
DHCP Lease
Renew or release the current DHCP lease by clicking on the appropriate button.
DNS Server
The Domain Name System (DNS) is the method by which website or domain names are translated into IP
addresses. The connection can be set to automatically obtain a DNS server address, or an address can be set
manually, according to information provided by the ISP.
To configure the connection to automatically obtain a DNS server address, select Obtain DNS Server Address
Automatically from the “DNS Server” drop-down list. To manually configure DNS server addresses, select Use
the Following DNS Server Addresses. Specify up to two different DNS server addresses, one primary, the
other secondary.
33
IP Address Distribution
The “IP Address Distribution” section of the Configure Broadband Connection (Coax) screen allows the user
to configure the TG590 Router’s Dynamic Host Configuration Protocol (DHCP) server parameters. The DHCP
automatically assigns IP addresses to network devices. If enabled, make sure to configure the network
devices as “DHCP Clients.” There are three options in this section:
Disabled,
DHCP Server, and
DHCP Relay.
Caution! We strongly recommend leaving this setting at “Disabled”.
Disabled
Select this option if statically assigning IP addresses to the network devices.
DHCP Server To set up the Broadband Connection (Coax) to function as a DHCP server:
1. Select DHCP Server.
2. Enter the IP address at which the TG590 Router starts issuing addresses in the “Start IP Address” text
boxes. Since the TG590 Router’s default IP address is 192.168.1.1, the Start IP Address must be 192.168.1.2.
3. Enter the end of the IP address range used to automatically issue IP addresses in the “End IP Address” text
boxes.
4. Enter the subnet mask address in the “Subnet Mask” text boxes. The subnet mask determines which
portion of a destination LAN IP address is the network portion, and which portion is the host portion.
5. If a Windows Internet Naming Service (WINS) is being used, enter the WINS server address in the “WINS
Server” text boxes.
6. Enter the amount of time a network device will be allowed to connect to the TG590 Router with its
currently issued dynamic IP address in the “Lease Time in Minutes” text box. Just before the time is up, the
device’s user will need to
make a request to extend the lease or get a new IP address.
7. Click in the “Provide Host Name If Not Specified by Client” check box to have the TG590 Router
automatically assign network devices with a host name, in case a host name is not provided by the user.
DHCP Relay Select this option to have the TG590 Router function as a DHCP relay, and enter the IP address in
the screen that appears.

34

35
Routing
The TG590 can be configured to use dynamic routing. Dynamic routing automatically adjusts how packets
travel on the network. There are two options in the “Routing” section of the Configure Broadband Connection
(Coax) screen:

36
Basic or Advanced.
WARNING! Do not use static routing unless instructed to do so by your ISP.
Basic Select this option for basic routing operation.
Advanced
To set up the TG590 Router’s Coax broadband connection for advanced routing:
1. Select Advanced from the Routing drop-down list.
2. Enter a device metric in the “Device Metric” text box. The device metric is a value used by the TG590 Router
to determine whether one route is superior to another, considering parameters such as bandwidth and delay
time.
3. Click in the “Default Route” check box to define this device as the default route.
4. Click in the “Multicast - IGMP Proxy Internal” check box to activate multicasting. Multicasting enables the
TG590 Router to issue IGMP (Internet Group Management Protocol) host messages on behalf of hosts the
TG590 Router discovers through standard IGMP interfaces. IGMP proxy enables the routing of multicast
packets according to the IGMP requests of local network devices asking to join multicast groups.
Internet Connection Firewall
Enable or disable the firewall for this interface. It is recommended to keep the
firewall enabled for all of the TG590 Router’s connection interfaces.
Additional IP Addresses
Click New IP Address to generate the “Additional IP Address Settings” screen, where additional IP addresses
can be created to access the TG590 Router via the connection.

37
5.7 WAN PPPoE Connection
WAN Point-to-Point Protocol over Ethernet (PPPoE) relies on two widely accepted standards: Point-to-Point
Protocol and Ethernet. PPPoE enables Ethernet networked computers to exchange information with
computers on the Internet. PPPoE supports the protocol layers and authentication widely used in PPP and
enables a point-to-point connection to be established in the normally multipoint architecture of Ethernet. A
discovery process in PPPoE determines the Ethernet MAC address of the remote device in order to establish a
session.
Click WAN PPPoE in the Network Connections screen to generate the “WAN PPPoE Properties” screen. This
screen displays a list of the connection’s properties. The only modifications that can be made from this screen
are disabling the connection (by clicking Disable) or renaming the connection (by entering a new name in the
“Name” text box).

38
5.7a Configuring the WAN PPPoE Connection
Click Settings in the WAN PPPoE Properties screen to generate the “Configure WAN PPPoE” screen.
General
The top part of the Configure WAN PPPoE screen displays general communication parameters. We
recommend not changing the default values in this section unless familiar with networking concepts.
Status Displays the connection status of the WAN PPPoE connection. (“Down,” “Disabled,” “Connected,” etc.)
When should this rule occur? Displays when the rule is active. To schedule rules, see “Advanced Settings”
chapter.
Network Select the type of connection being configured from the drop-down list (Broadband Connection,
Network (Home/Office), or DMZ).
Connection Type Displays the type of connection. Since this is PPPoE connection, “PPPoE” is displayed.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size permitted for Internet
transmission. “Automatic, sets the MTU at 1492. Other choices include “Automatic,” which sets the MTU
according to the connection to the ISP, and “Manual,” which allows the MTU to be set manually.
Underlying Connection Specify the underlying connection above which the protocol initiates from the drop-
down list, which displays all possible underlying devices.
PPP Configuration
Point-to-Point Protocol (PPP) is the most popular method for transporting packets between the user and the
ISP.
Service Name Specify the networking peer’s service name, if provided by the ISP, in this text box.
On-Demand To use PPP on demand to initiate the point-to-point protocol session only when packets are
actually sent over the Internet, click in this check box. This option should be active on a limited basis Idle
Time Before Hanging Up Enter the amount of idle time, in minutes, before the PPP session automatically ends.
Time Between Reconnect Attempts In this text box, specify the duration between PPP reconnect attempts, as
provided by the ISP.
PPP Authentication
Point-to-Point Protocol (PPP) currently supports four authentication protocols: Password Authentication
Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), and Microsoft CHAP versions 1 and 2.
Select the authentication protocols the TG590 Router may use when negotiating with a PPTP server in this
section. Select all the protocols if no information is available about the server’s authentication methods. Note
that encryption is performed only if Microsoft CHAP, Microsoft CHAP version 2, or both are selected.
Warning! The PPP Authentication settings should not be changed unless instructed to do so by your ISP.

39
Login User Name Enter the user name (provided by the ISP) in this text box.
Login Password Enter the password (provided by the ISP) in this text box.
Support Unencrypted Password (PAP) Password Authentication Protocol (PAP) is a simple, plain-text
authentication scheme. The user name and password are requested by the networking peer in plain-text. PAP,
however, is not a secure authentication protocol. Man-in-the-middle attacks can easily determine the remote
access client’s password. PAP offers no protection against replay attacks, remote client impersonation, or
remote server impersonation.
Support Challenge Handshake Authentication (CHAP) Click in this check box to activate CHAP, a challenge-
response authentication protocol that uses MD5 to hash the response to a challenge. CHAP protects against
replay attacks by using an arbitrary challenge string per authentication attempt.
Support Microsoft CHAP Click in this check box if communicating with a peer that uses Microsoft CHAP
authentication protocol.
Support Microsoft CHAP Version 2 Select this check box if communicating with a peer that uses Microsoft
CHAP Version 2 authentication protocol.
PPP Compression
The PPP Compression Control Protocol (CCP) is responsible for configuring, enabling, and disabling data
compression algorithms on both ends of the point-to-point link. It is also used to signal a failure of the
compression/decompression mechanism in a reliable manner.
For each compression algorithm (BSD and Deflate), select one of the following from the drop-down list:
Reject Selecting this option rejects PPP connections with peers that use the compression algorithm. If Reject
is activated, throughput may diminish.
Allow Selecting this option allows PPP connections with peers that use the compression algorithm.
Require Selecting this option insures a connection with a peer using the compression algorithm.
Internet Protocol
Select one of the following Internet Protocol options from the “Internet Protocol” drop-down list:
Obtain an IP Address Automatically This option is selected by default. Change only if required by the ISP. The
server that assigns the TG590 Router with an IP address also assigns a subnet mask. Override the
dynamically assigned subnet mask by selecting the “Override Subnet Mask” and entering a different subnet
mask.
Use the Following IP Address Select this option to configure the TG590 to use a permanent (static) IP address.
The ISP should provide this address.
DNS Server
The Domain Name System (DNS) is the method by which website or domain names are translated into IP
addresses. The TG590 Router can be configured to automatically obtain a DNS server address, or the address

40
can be entered manually, according to the information provided by the ISP.
To configure the connection to automatically obtain a DNS server address, select Obtain DNS Server Address
Automatically from the “DNS Server” drop-down list. To manually configure DNS server addresses, select Use
the Following DNS Server Addresses from the “DNS Server” drop-down list. Up to two different DNS server
addresses can be entered (Primary and Secondary).
Routing
Select Advanced or Basic from the “Routing” drop-down list. If Advanced is selected, additional options
appear, as listed below.
Routing Mode Select one of the following three Routing modes:
• Route - This option causes the TG590 Router to act as a router between two networks.
• NAT - This option activates Network Address Translation (NAT), which translates IP addresses to a valid,
public address on the Internet. NAT adds security, since the IP addresses of the devices on the
network are not transmitted publicly. In addition, NAT allows many addresses to exist behind a
single valid address. Use the NAT routing mode only if the local network consists of a single device,
or collisions may occur if more than one device attempts to communicate using the same port.
NAPT -This option activates NAPT (Network Address and Port Translation),
which refers to network address translation involving the mapping of port
numbers and allows multiple machines to share a single IP address. Use NAPT
if the local network contains multiple devices, a topology that necessitates
port translation in addition to address translation.
Device Metric The device metric is a value used by the TG590 Router to
determine whether one route is superior to another, considering parameters
such as bandwidth, delay, and more.
Default Route Click in this check box to make the connection the default route.
Multicast - IGMP Proxy Default Click in this check box to enable the TG590 to issue IGMP (Internet Group
Management Protocol) host messages on behalf of hosts the TG590 Router discovers through standard IGMP
interfaces.
IGMP proxy enables the routing of multicast packets according to the IGMP requests of local network devices
asking to join multicast groups.

41
Routing Table
Clicking New Route generates the “New Route” screen, where a new route can be configured.
Internet Connection Firewall
Click in the “Enabled” check box to activate the TG590 Router’s firewall on the WAN PPPoE connection.
42
6 SECURITY SETTINGS
In this chapter
In this chapter, we will take a closer look at following features:
Topic
Page
6.0 Firewall
6.1 Access Control
6.2 Port Forwarding
6.3 DMZ Host
6.4 Port Triggering
6.5 Static NAT (Future Release)
6.6 Advanced Filtering
6.7 Security Log
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.
43
6.0 Firewall
T
h
e
firewall is the
foundation
of the
TG590 ’s
security s
u
i
t
e, and it
has been tailor-made to meet the need of
the residential/office network user and is
configured
to give the best p
r
o
t
e
c
t
ion and flexibility to users using
interactive applications, such as Internet gaming and video conferencing.
T
h
e
firewall controls the flow of data between the local network and
t
h
e
I
n
t
e
r
n
e
t
.
B
o
t
h
incoming and
outgoing data are inspected and then
e
i
t
h
e
r
accepted (allowed
)
or rejected (barred)
f
r
o
m
passing through
the
TG590
according
to a set
o
f
r
u
l
e
s
.
T
h
e
rules are calculated to stop
unwanted
intrusions from the
ou
t
s
i
d
e
,
while allowing local network users access to required
I
n
t
e
r
n
e
t
s
e
r
v
i
c
e
s
.
T
h
e
TG590
features three pre-defined firewall security
l
e
v
e
l
s
:
M
aximum
,
T
ypic
al
,
and
M
inimum
.
T
h
e
table
below summarizes the behavior of the TG590 for each of the three security
l
e
v
e
l
s
.
Security
L
e
vel
I
n
t
e
r
n
e
t
r
eq
u
e
s
t
s
(incoming
t
r
a
ff
i
c
)
L
o
c
a
l
network
r
eq
u
e
s
t
s
(
o
u
t
g
o
i
ng
t
r
a
ff
i
c
)
Maximum
S
ecurit
y
Blocked - No access
t
o
local network
f
r
o
m
I
n
t
e
r
n
e
t
,
except
a
s configured
in the
P
o
r
t
F
o
r
w
a
r
d
i
ng
,
DMZ
h
o
s
t
,
a
nd
R
e
m
o
t
e
Access sc
r
ee
n
s
.
Limited -
Only
c
o
mm
o
n
l
y
used
s
e
r
v
i
c
e
s
,
such
a
s
web browsing and
e
ma
il
,
are
pe
r
m
i
tt
e
d
.
Typical
S
ecurit
y
Blocked - No access
t
o
local network
f
r
o
m
I
n
t
e
r
n
e
t
,
except
a
s configured
in the
P
o
r
t
F
o
r
w
a
r
d
i
ng
,
DMZ
h
o
s
t
,
a
nd
R
e
m
o
t
e
Access sc
r
ee
n
s
.
Unrestricted
-
All
s
e
r
v
i
c
e
s are
pe
r
m
i
tt
e
d
,
except
a
s
configured in the Access
Control sc
r
ee
n
.
M
inimum
S
ecurit
y
Unrestricted
-
P
e
r
m
i
t
s full access
from
I
n
t
e
r
n
e
t
to local
n
e
t
w
o
r
k
;
all
connection
a
tt
e
m
p
t
s
pe
r
m
i
tt
e
d
.
Unrestricted
-
All
s
e
r
v
i
c
e
s are
pe
r
m
i
tt
e
d
,
except
a
s
configured in the Access
Control sc
r
ee
n
.
T
h
e
s
e
services include
T
e
l
n
e
t
,
F
T
P
,
HTTP, HTTPS,
D
N
S
,
I
M
A
P
,
POP3 and
S
M
T
P
.
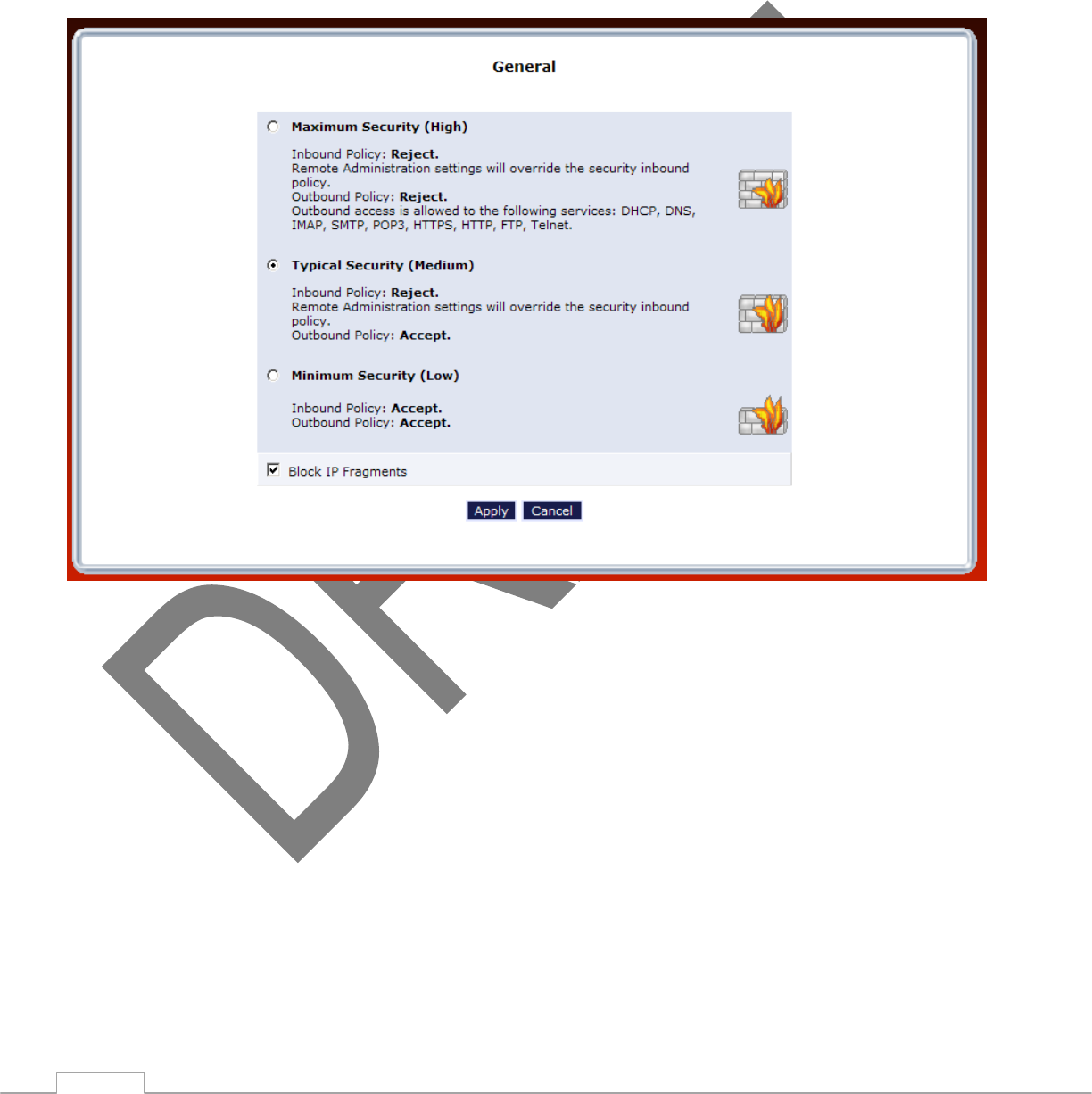
44
To
configure the
TG590
’
s firewall security s
e
tt
i
ng
s
:
1. From the General sc
r
ee
n
,
select a security level by
clicking
the
a
pp
r
o
p
r
i
a
t
e
radio
b
u
tt
o
n
.
Using
the
Minimum Security setting may expose the local network to significant security
r
i
s
k
s
,
and thus should only be
used for s
h
o
r
t
periods of
t
i
m
e
.
2. Check the
“Block
IP
F
r
a
g
m
e
n
t
s
”
box to protect the local network
f
r
o
m
a common type of hacker attack that
uses
f
r
a
g
m
e
n
t
e
d
data packets
t
o sabotage
the
n
e
t
w
o
r
k
.
Note that
VPN
over
I
P
S
e
c and some
U
D
P
-
b
a
s
e
d
services make legitimate use of
IP
f
r
a
g
m
e
n
t
s
.
IP
fragments must be
a
ll
o
w
e
d
to pass into the local network to
use these s
e
r
v
i
c
e
s
.
3.
Click
Apply to save c
h
a
ng
e
s
.

45
6.1 Access
C
on
tr
ol
Access control is used to block specific
computers
within the local network (or even the whole network) from
accessing certain services on the
I
n
t
e
r
n
e
t
.
For
e
x
am
p
l
e
,
one
computer
can be
p
r
o
h
i
b
i
t
e
d
from surfing the
I
n
t
e
r
n
e
t
,
a
n
o
t
h
e
r
computer
from transferring files using
F
T
P
,
and the whole network
f
r
o
m
receiving incoming
e
ma
il
.
Access control defines restrictions on the types of requests that can pass
f
r
o
m
the local network out to the
I
n
t
e
r
n
e
t
,
and thus may block traffic flowing in
b
o
t
h d
i
r
e
c
t
i
o
n
s
.
I
n
the email example given
a
b
o
v
e
,
computers
in the local
n
e
t
w
o
r
k
can be
prevented
from receiving email by blocking their outgoing requests
t
o
POP3
servers on the
I
n
t
e
r
n
e
t
.
Access control also
i
n
c
o
r
p
o
r
a
t
e
s a list of preset services in the form
o
f
applications and common port
s
e
tt
i
ng
s
.
6.1a Allow or Restrict Services
To view and allow/restrict these services:
1. Select Access Control from the left side of any Security screen. The “Access
Control” screen appears.
Note: The “Allowed” section is only visible when the firewall is set to “Maximum.”
2. Click Add. The “Add Access Control Rule” screen appears.
Note: To block a service, click Add in the “Blocked” section of the Access Control screen. To allow outgoing
traffic, click Add in the “Allowed” section of the screen.

46
3. If this access control rule applies to all networked devices, select Any from the “Networked
Computer/Device” list box. If this rule applies to certain devices only, select User Defined and click Add. Then,
create and add a network object (for more details about adding network objects, see the “Advanced
Connection” chapter of this manual).
4. Select the Internet protocol to be allowed or blocked from the “Protocol” drop-down list.
5. If the rule will be active all the time, select Always from the “When should this rule occur?” drop-down list.
If the rule will only be active at certain times, select User Defined and click Add. Then, add a schedule rule (for
more details about schedule rules, see the “Advanced Connection” chapter of this manual).
6. Click Apply to save the changes. The Access Control screen will display a summary of the new access
control rule.
Note: To block a service not included in the list, select User Defined from the Protocol drop-down menu. The
“Edit Service” screen appears. Define the service, then click OK. The service will then be automatically added
to the top section of the “Add Access Control Rule” screen, and will be selectable.
An access control can be disabled and the service made available without having to remove the service from
the Access Control table. This may be useful to make the service available temporarily, with the expectation
that the restriction will be reinstated later.
To temporarily disable an access control, clear the check box next to the service name.
To reinstate the restriction at a later time, select the check box next to the service name.
To remove an access restriction from the Access Control table, click Remove for the service. The service
will be removed from the Access Control table.

47
6.2 Port Forwarding
In its default state, the TG590 blocks all external users from connecting to or communicating with the
network, making it safe from hackers who may try to intrude on the network and damage it. However, the
network can be exposed to the Internet in certain limited and controlled ways to enable some applications to
work from the local network (game, voice, and chat applications, for example) and to enable Internet access
to servers in the network. Port forwarding (sometimes referred to as local servers) supports both of these
functions.
To grant Internet users access to servers inside the local network, each service provided, as well as the
computer providing it, must be identified. To do this:
1) Select Port Forwarding from the left side of any Security screen. The “Port Forwarding” screen appears.
2) Click Add. The “Add Port Forwarding Rule” screen appears.
3) Enter the host name (from the drop-down list) or local IP address of the computer providing the service
in the “Local Host” text box. Note that only one local network computer can be assigned to provide a
specific service or application.
4) Select the Internet protocol to be provided from the “Protocol” drop-down list. Depending on the protocol
selected, additional options appear in the screen.
5) Select the connection with which this port forwarding rule will be active from the “WAN Connection
Type” drop-down list.
6) To select a port to forward communications to (this is optional), select “Specify” from the “Forward to
Port” drop-down list, then, in the text box that appears, enter the port number. If no port is identified,
select “Same as Incoming Port.”
If this port will be active all the time, select “Always” from the “When should this rule occur?” drop-down list.
If the rule will only be active at certain times, select “Specify Schedule” and click Add. Then, add a schedule
rule (for more details about schedule rules, see the “Advanced Connection” chapter of this manual).
8. Click Apply to save the changes.
How many computers can use a service or play a game simultaneously? The answer may be a bit confusing.
All the computers on the network can behave as clients and use a specific service simultaneously. Being a
client means the computer within the network initiates the connection; for example, a computer on the
network can open an FTP connection with an FTP server on the Internet. But only one computer on the
network can operate as a server and respond to requests from computers on the Internet (outside the local
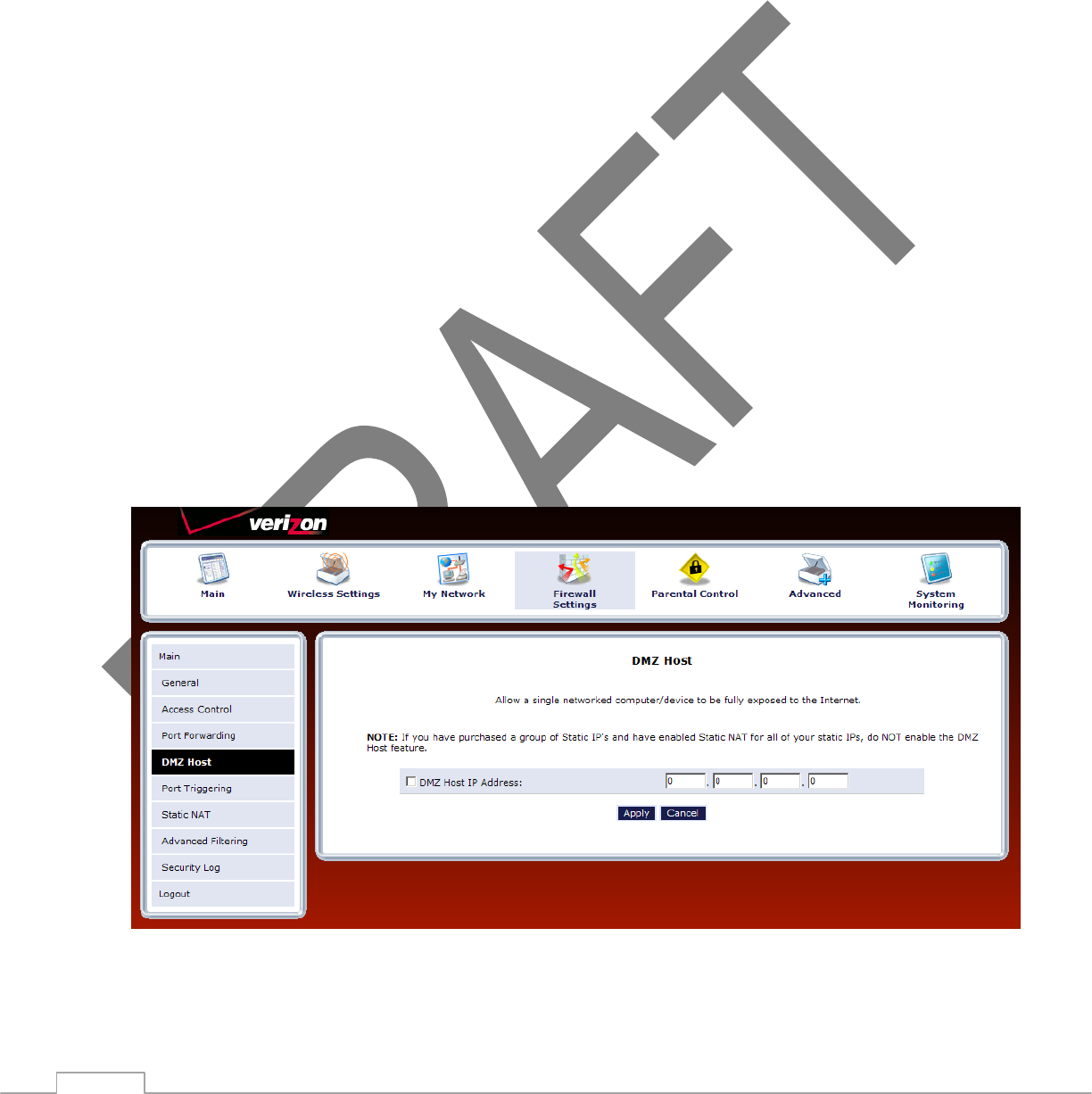
48
network).
6.3 DMZ Host
The DMZ (De-Militarized Zone) host feature allows one device on the network to operate outside the firewall.
Designate a DMZ host:
• To use an Internet service, such as an online game or video-conferencing program, not present in the
Port Forwarding list and for which no port range information is available.
• To expose one computer to all services without restriction or security.
Warning: A DMZ host is not protected by the firewall and may be vulnerable to attack. Designating a DMZ host
may also put other computers in the local network at risk. When designating a DMZ host, consider the security
implications and protect it if necessary.
To designate a local computer as a DMZ host:
1. Select DMZ Host from the left side of the Firewall Settings screen . The “DMZ Host” screen appears.

49
2. Click in the “DMZ Host IP Address” check box, then enter the IP address of the computer to be designated
as a DMZ host.
Note: Only one network computer can be a DMZ host at any time.
3. Click Apply.
Note: to disable the DMZ Host, Click in the “DMZ Host IP Address” check box.

50
6.4 Port Triggering
Port triggering can be used for dynamic port forwarding configuration. By setting port triggering rules,
inbound traffic is allowed to arrive at a specific network host using ports different than those used for the
outbound traffic. The outbound traffic triggers which ports inbound traffic is directed.
For example, a gaming server is accessed using UDP protocol on port 2222. The gaming server responds by
connecting the user using UDP on port 3333 when starting gaming sessions. In this case, port triggering must
be used, since it conflicts with the following default firewall settings:
• The firewall blocks inbound traffic by default.
• The server replies to the TG590’s IP, and the connection is not sent back to the host, since it is not
part of a session.
To resolve the conflict, a port triggering entry must be defined, which allows inbound traffic on UDP port
3333, only after a network host generated traffic
to UDP port 2222. This results in accepting the inbound traffic from the gaming server, and sending it back to
the network host which originated the outgoing traffic to UDP port 2222.
To use port triggering:
1. Select Port Triggering from the left side of any Security screen. The “Port Triggering” screen appears.
2. Select either “User Defined” or “Show All Services” from the drop-down list next to “Add.”
3. If Show All Services is selected in step 2, select a Service from the list. The service is added to the Port

51
Triggering screen as an active protocol.
4. If User Defined is selected in step 2, the “Edit Port Triggering Rule” screen appears. Enter a service name
in the appropriate text box, then configure its inbound and outbound trigger ports by clicking the
appropriate links..
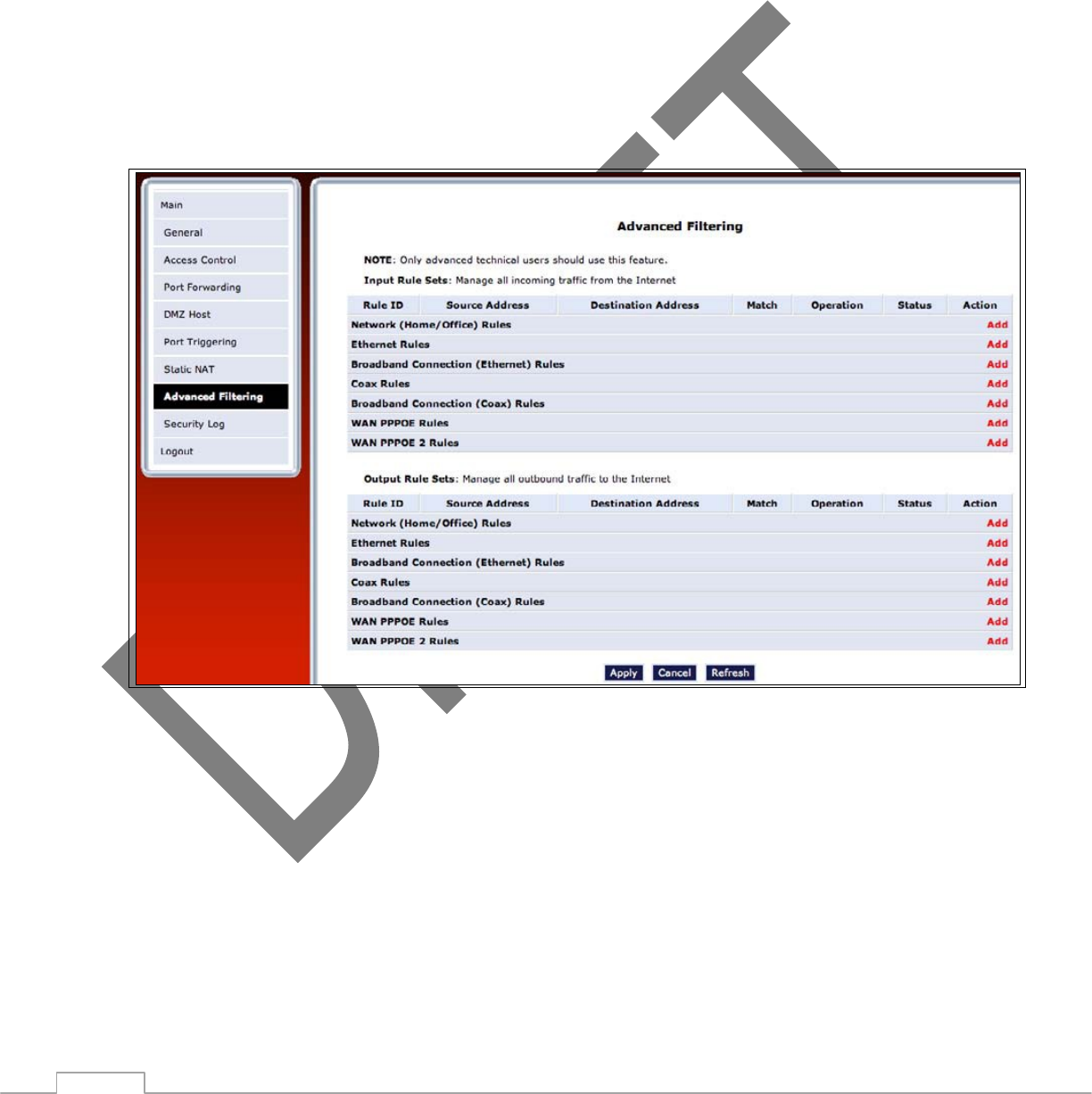
52
6.5 Advanced Filtering
Advanced filtering is designed to allow comprehensive control over the firewall’s behavior. Specific input and
output rules can be defined, the order of logically similar sets of rules controlled, and distinctions made
between rules that apply
to Internet and rules that apply to local network devices.
To access, select Advanced Filtering from any Security screen. The “Advanced Filtering” screen appears.
Two sets of rules can be configured: input rules and output rules. Following is a description of the set
ordering for inbound and outbound packets.
53
6.6 Security Log
The security log displays a list of firewall-related events, including attempts to establish inbound and
outbound connections, attempts to authenticate at an administrative interface (MegaControl Panel or Telnet
terminal), firewall configuration, and system start-up.
To access the security log, select Security Log from any Security screen. The “Security Log” screen appears.
6.6a Time
The time (based on the TG590’s date and time settings) the event occurred.
6.6b Event
There are three kinds of events listed in the system log: Firewall Info, Firewall Setup, and System Log.
6.6c Event-Type
The “Details” column displays more information about the packet or the event, such as protocol, IP addresses,
ports, etc.
6.6d Details
Displays a textual description of the event

54
6.6e Security Log Settings
To view or change the security log settings:
1. Click Settings in the Security Log screen. The “Security Log Settings” screen appears.
2. Select the type of activities that will generate a log message:
Accepted Incoming Connections - activating this check box generates a log message for each successful
attempt to establish an inbound connection to the local network.
Accepted Outgoing Connections - activating this check box generates a log message for each successful
attempt to establish an outgoing connection to the public network.
3. Select the type of blocked events to be listed in the log:
All Blocked Connection Attempts - activating this check box generates log messages for all blocked events.
Other Blocked Events - if “All Blocked Connection Attempts” is un-checked, select specific blocked events
from this list to generate log messages.
4. Click in the “Remote Administration Attempts” check box to write a log message for each remote-
administration connection attempt, whether successful or not.
5. Click in the “Connection States” check box to track connection handling by the firewall and Application
Level Gateways (ALGs).
6. Click Apply to save changes.

55
6.6a Inbound/Outbound Packets - Rule Sets
There are numerous rules automatically inserted by the firewall to provide improved security and block
harmful attacks. These pre-populated rules displayed are required for operation on the Verizon Network.
To configure advanced filtering rules, click Add next to the rule title. The “Add Advanced Filter” screen
appears.
To add an advanced filtering rule, define the following rule parameters:
6.9c Matching
To apply a firewall rule, a match must be made between IP addresses or ranges and ports. Use the “Source
Address” and “Destination Address” drop-down lists to define the coupling of source and destination traffic.
Port matching will be defined when selecting protocols. For example, if the FTP protocol is selected, port 21
will be checked for matching traffic flow between the defined source and destination IPs.
6.9d Operation
This is where the action the rule will take is defined. Select one of the following radio buttons:
Drop - Deny access to packets that match the source and destination IP addresses and vCP reset to the
origination peer.
Accept - Allow access to packets that match the source and destination IP addresses and protocol ports
defined in upper section of the screen. The data transfer session will be handled using Stateful Packet
Inspection (SPI).

56
Accept Packet - Allow access to packets that match the source and destination IP addresses and protocol
ports defined in upper section of the screen. The data transfer session will not be handled using Stateful
Packet Inspection (SPI), so other packets that match this rule will not be automatically allowed access.
This setting is useful when creating rules that allow broadcasting.
6.9e Logging
Click in this check box to add entries relating to this rule to the security log.
6.9f Scheduler (When should this rule occur?)
If advanced filtering needs to be active all the time, select Always from the “When should this rule occur?”
drop-down list. If the rule will only be active at certain times select User Defined and click Add. Then, add a
schedule rule (for more details about schedule rules, see the “Advanced Connection” chapter of this manual)

57
7 PARENTAL CONTROL
In this chapter
In this chapter, we will take a closer look at following features:
Topic
Page
7.1 Setting the Parental Controls
7.2 Rule Summary
7.3 Parental Control Log
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.
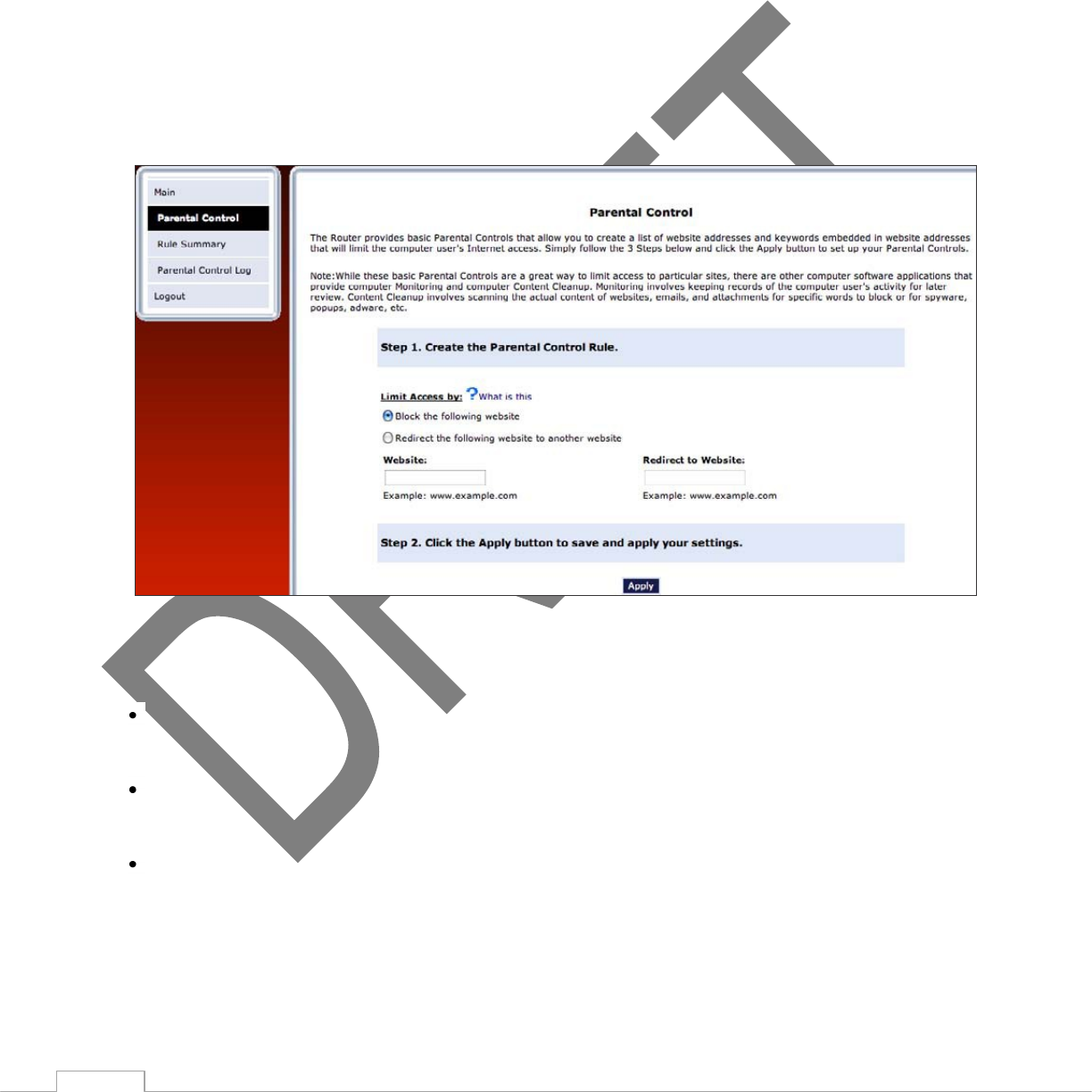
58
7.1 Setting the Parental Controls
To create a basic access policy for a computer on the TG590’s network, click Parental Control from the top of
the Home screen and follow these instructions:
1. The “Parental Control” screen appears. From the “Networked Computer/Device” list box, select a
computer/device, and then click Add. The computer/ device appears in the “Selected Devices” list box.
2. In the “Limit Access by” section, select one of the following options:
Block the following Websites - blocks all websites entered in step 4 from being accessed on the
computers/devices selected in step 2.
Allow the following Websites - allows access only to the websites entered in step 4 on the
computers/devices selected in step 2.
Blocking ALL Internet Access - blocks all Internet access on the computers/devices selected in step 2.
3. Enter the URL address of a website and, if applicable, the embedded keyword within the website. Click
Add. The websites and/or keywords selected will appear in the textbox to the right. If you make a mistake, or
wish to delete a previously entered website/keyword, select it, then click Remove.

59
4. If needed, you can create a schedule for when you want the rule to be active, or inactive. In the “Create
Schedule” section, select the affected days.
5. Select whether the rule will be active or inactive during the schedule you created by clicking the radio
button next to the appropriate option.
6. If you want more precise control over the schedule, set up an hourly schedule by entering the start and end
times in the appropriate text boxes. Make sure to specify AM or PM.
Note: The hourly schedule only affects the days selected in step 5. For example, if you select Saturday and Sunday,
a start time of 10 a.m., and an end time of 3 p.m., the scheduled time will be Saturday/Sunday, 10 a.m. to 3 p.m.
7. In the “Create Rule Name” section, enter a rule name and description in the appropriate text boxes.
8. Click Apply to save and apply the new rule.
60
7.2 Rule Summary
Clicking Rule Summary from the menu on the left side generates the “Rule Summary” screen.
The Rule Summary screen displays a list of all rules created for the TG590. Additionally, the rule can be
viewed by clicking the magnifying glass in the “View Rule” column, or edited by clicking on the icon in the
“Edit Rule” column.
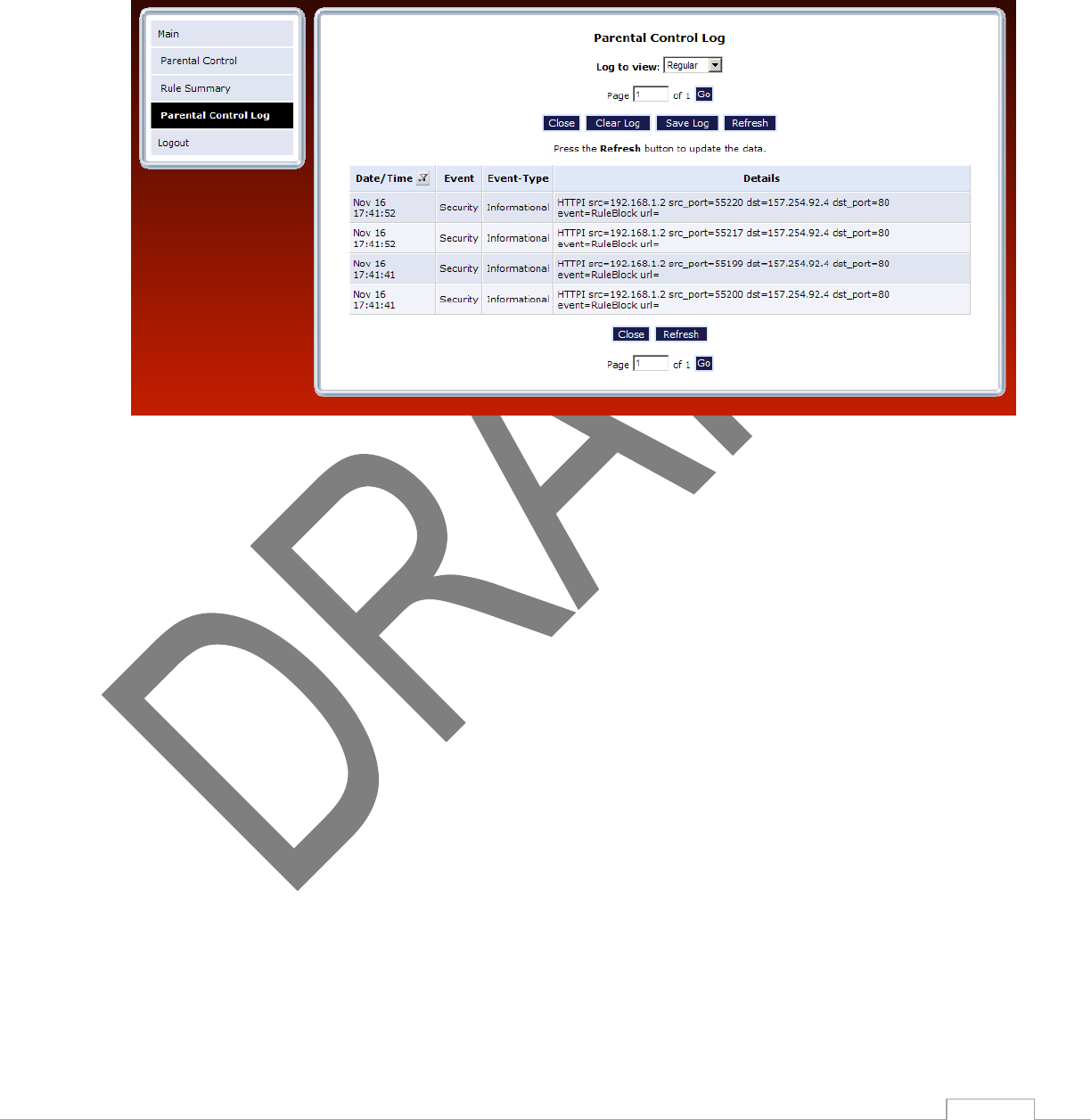
61
7.3 Parental Control Log
Clicking Parental Control Log from the menu on the left side generates the “Parental Control Log” screen.
The Parental Control Log screen displays a list of all events/sites visited or attempted.
Additionally, the log can be filtered by the “Date/Time”. A log can also be saved, refreshed to view recent
activity, or cleared.

62
8 ADVANCED SETTINGS
In this chapter
In this chapter, we will take a closer look at following features:
Topic
Page
8.1 Using Advanced Settings
8.2 Utilities
8.3 DNS Settings
8.4 Network Settings
8.5 Configuration Settings
8.6 Time Settings
8.7 Firmware Upgrade
8.8 Routing Settings
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.
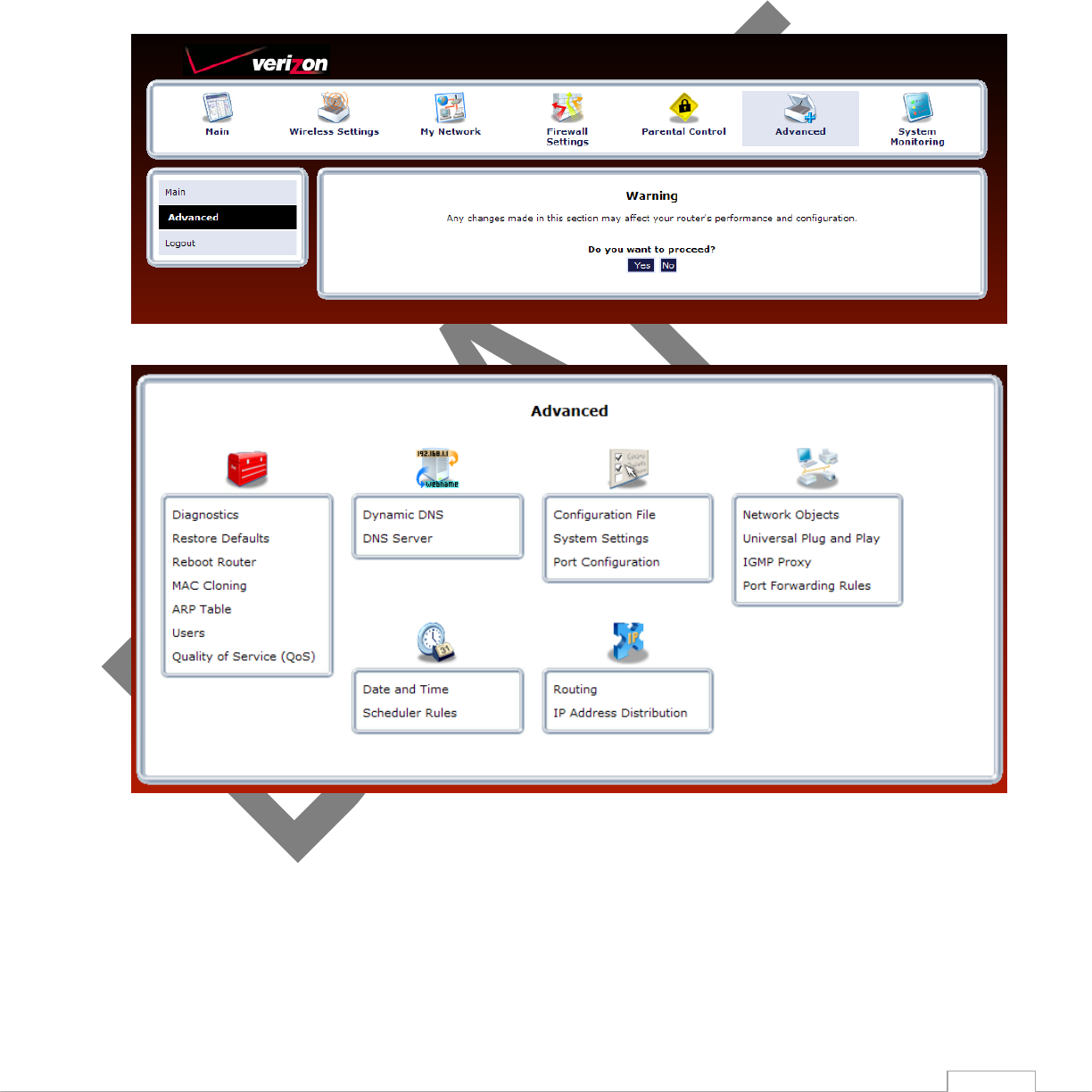
63
8.1 Using Advanced Settings
To access the TG590’s Advanced Settings, click Advanced at the top of the Home screen.
Click “Yes” in the “Warning” screen, and the “Advanced” screen appears.
64
The following settings are explained in this chapter:
• Diagnostics - perform diagnostic tests on the TG590
• Restore Defaults - reset the TG590 to its default settings
• Reboot Router - restart the TG590
• MAC Cloning - clone MAC addresses
• ARP Table - display active devices and their IP and MAC addresses, etc.
• Users - create and manage remote users
• Quality of Service (QoS) - explained in Appendix A of this manual
• Dynamic DNS - configure Dynamic DNS settings
• DNS Server - manage the local (LAN) network for host name and IP address
65
• Network Objects - create and manage network objects (discrete LAN subsets)
• Universal Plug & Play - ?
• IGMP Proxy - ?
• Port Forwarding Rules - configure the TG590’s ports
• Date and Time - configure the TG590 ’s clock and calendar
• Scheduler Rules - schedule firewall activation
• Routing - manage routing policies
• IP Address Distribution - manage the IP addresses of devices on the network
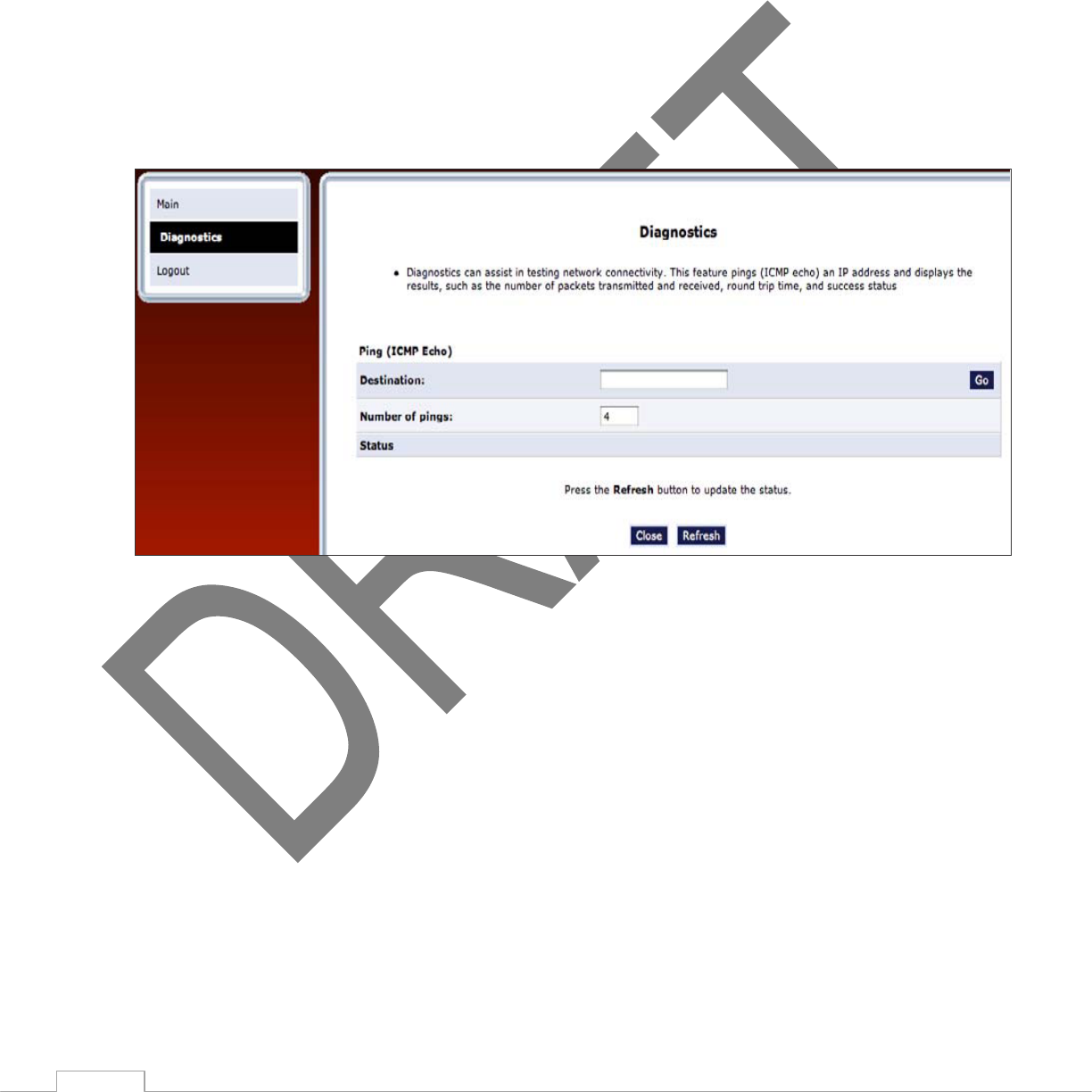
66
8.2 Utilities
The first collection of Advanced Connection (beneath the Toolbox icon) is the Utilities.
8.2a Diagnostics
The Diagnostics screen can assist in testing network connectivity. This feature pings (ICMP echo) an IP
address and displays the results, such as the number of packets transmitted and received, round trip time,
and success status. To diagnose network connectivity:
1. Click Diagnostics from the Advanced screen. The “Diagnostics” screen appears.
2. Enter the IP address or domain name to be tested in the “Destination” field.
3. Click Go.
4. In a few seconds, diagnostics statistics will be displayed. If no new information is displayed, click
Refresh.
67
8.2b Restore Defaults
If the TG590’s factory default settings need to be restored (to build a new network from the beginning, for
example), use the following procedure:
1. Click Restore Defaults in the Advanced screen. The “Attention” screen appears.
2. If needed, click Save Configuration File to save the TG590’s current configuration to a file. The
TG590’s current settings can then be reapplied after restoring default settings (see “Configuration
File” in this chapter for more information).
3. Click Restore Defaults. The TG590 will restart, and factory default settings will be applied.
Note: All of the TG590’s settings and parameters will be restored to their default values after performing the
Restore Default procedure. This includes the administrator password; a user-specified password will no
longer be valid.
68
8.2c Reboot the TG590
To reboot the TG590:
1. Click Reboot Router under the red tool box icon on the Advanced screen.
2. The “Reboot Router” screen appears.
2. Click OK to restart the TG590. This may take up to two minutes.
Note: To access the TG590’s GUI after restarting the TG590, click the web browser’s “Refresh” button, then log in
using the
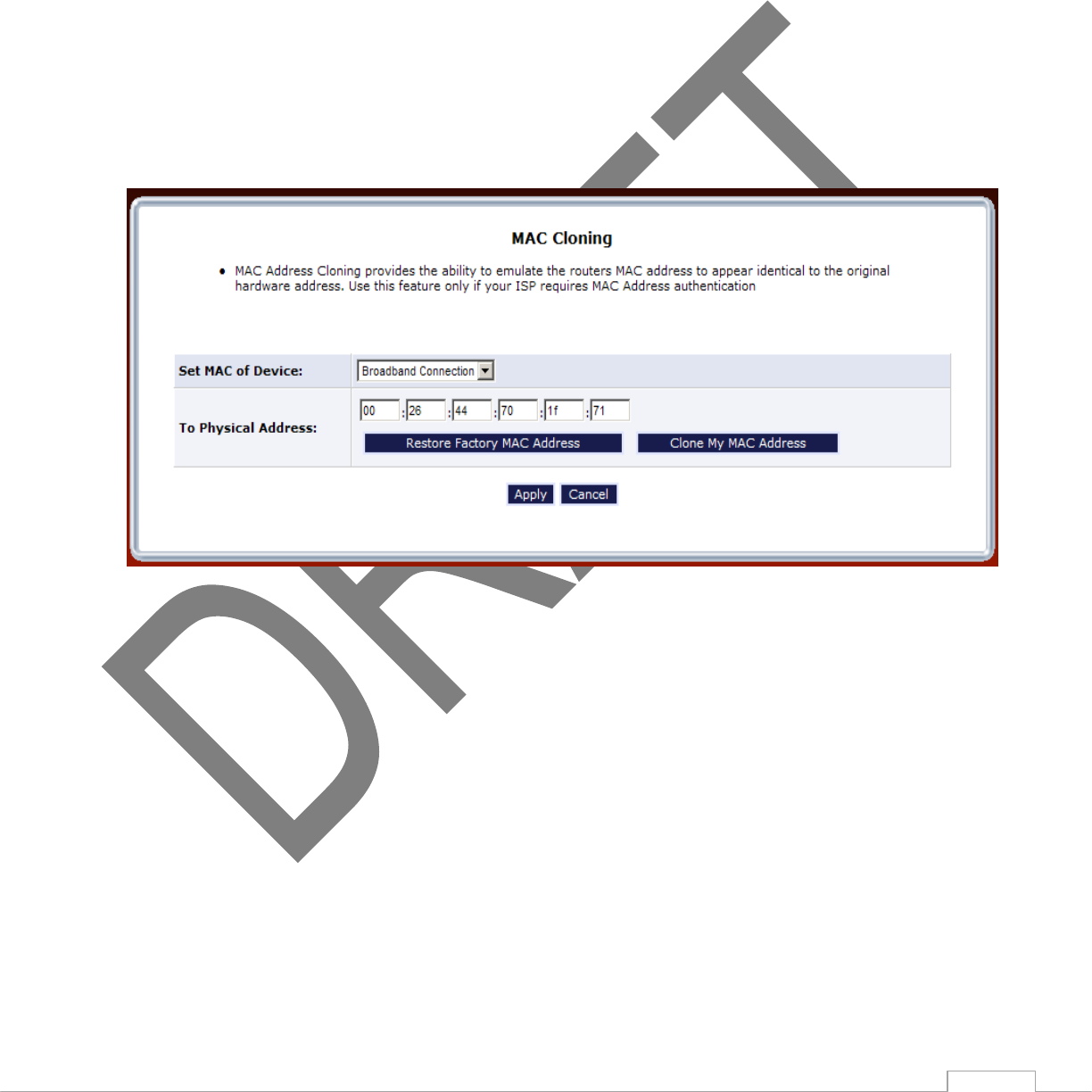
69
8.2d MAC Cloning
A MAC (Media Access Control) address is a unique hexadecimal code that identifies a device on a network. All
networkable devices have a MAC address. When replacing another network device with the TG590, the
installation process can be simplified by copying the MAC address of the existing networking device to the
TG590. To do this:
1. Click MAC Cloning under the red toolbox icon on the Advanced screen.
2. The “MAC Cloning” screen appears.
3. Enter the MAC address to be cloned in the “To Physical Address” text boxes.
4. Click Clone My MAC Address to capture the MAC address of the computer currently accessing the TG590’s
GUI. The TG590 will now have the new MAC address.
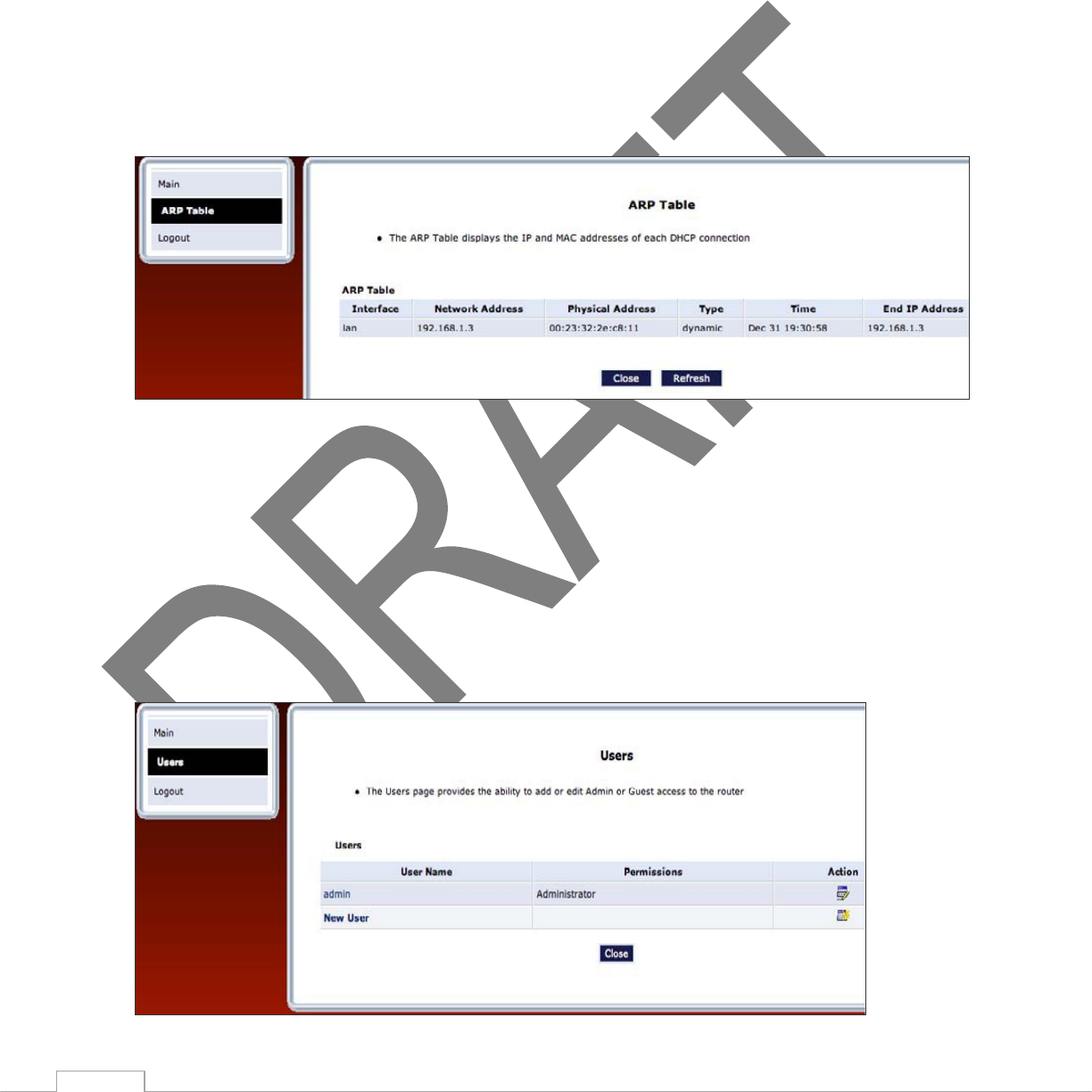
70
8.2e ARP (Address Resolution Protocol) Table
Clicking ARP Table in the Advanced screen generates the “ARP Table” screen. This screen displays the IP and
MAC addresses of each DHCP connection.
8.2f Users
To manage individual users:
1. Click Users in the Advanced screen, which generates the “Users” screen.
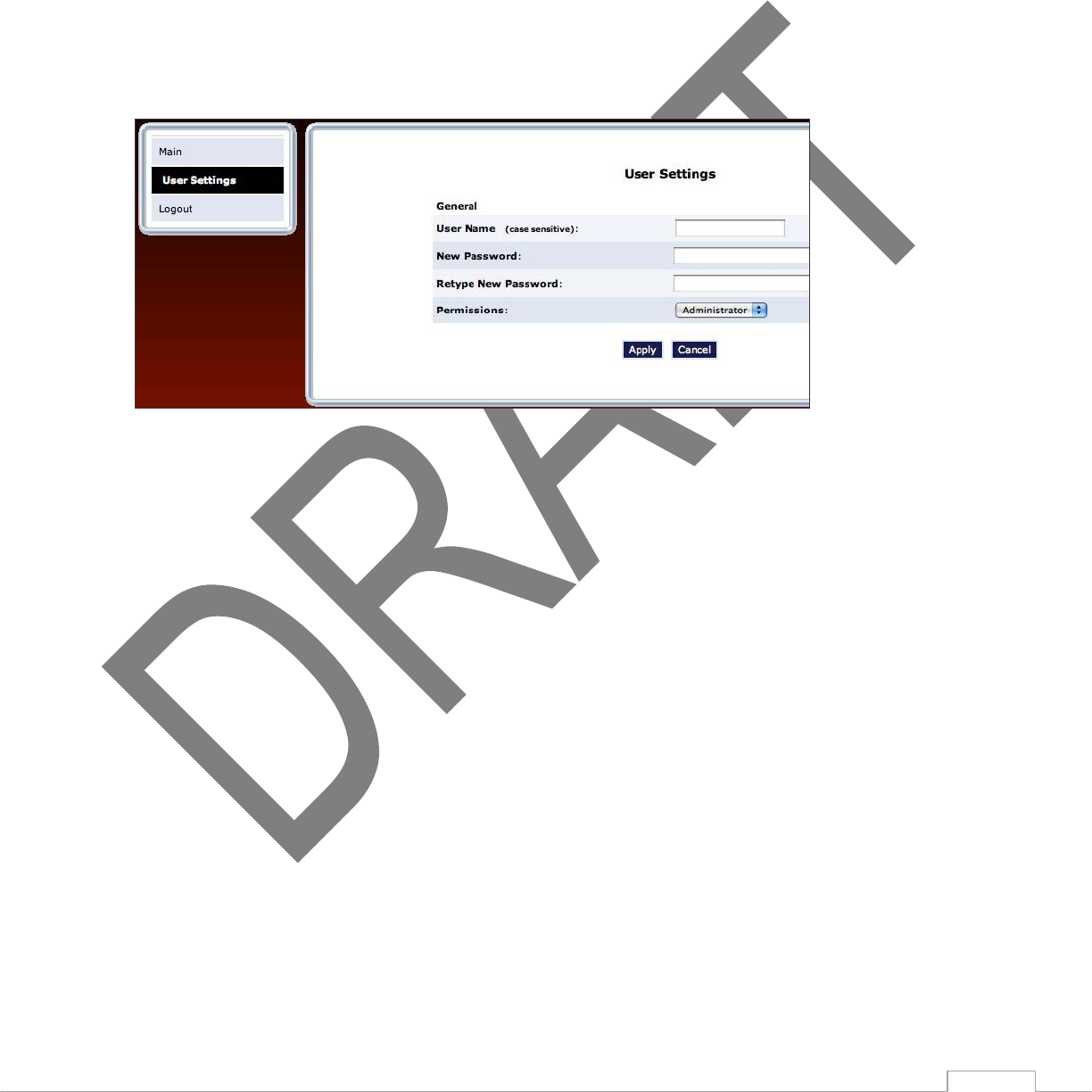
71
2. Click New User, which generates the “User Settings” screen.
3. When adding a user, specify the following parameters:
• User Name - The name a remote user will use to access the home or office network. This entry is case-
sensitive.
• New Password/Retype New Password - The password for the user (and enter again to confirm).
• Permissions - The level of access the user is allowed. Options include: Administrator or User.
• E-mail Notification - Email notification can be used to receive indications of system events for a
predefined severity classification. The available types of events are “System” or “Security” events. The
available severity of events are Error, Warning, and Information. To configure Email notification for a
specific user:
1) Make sure an outgoing mail server has been configured in “System Settings”.
If not, click “Click Here" to Configure Notification Mail Server to configure the outgoing mail server.
2) Enter the user’s Email address in the “Notification Address” text box.
3) Select the “System” and “Security” notification levels in the “System Notify Level” and “Security Notify
Level” drop-down lists.

72
Note: Changing any of the user parameters will prompt the connection associated with the user to terminate.
For changes to take effect, activate the connection manually after modifying user parameters.

73
8.2g Quality of Service
The TG590’s QoS (Quality of Service) capabilities are covered in detail in appendix A of this manual.
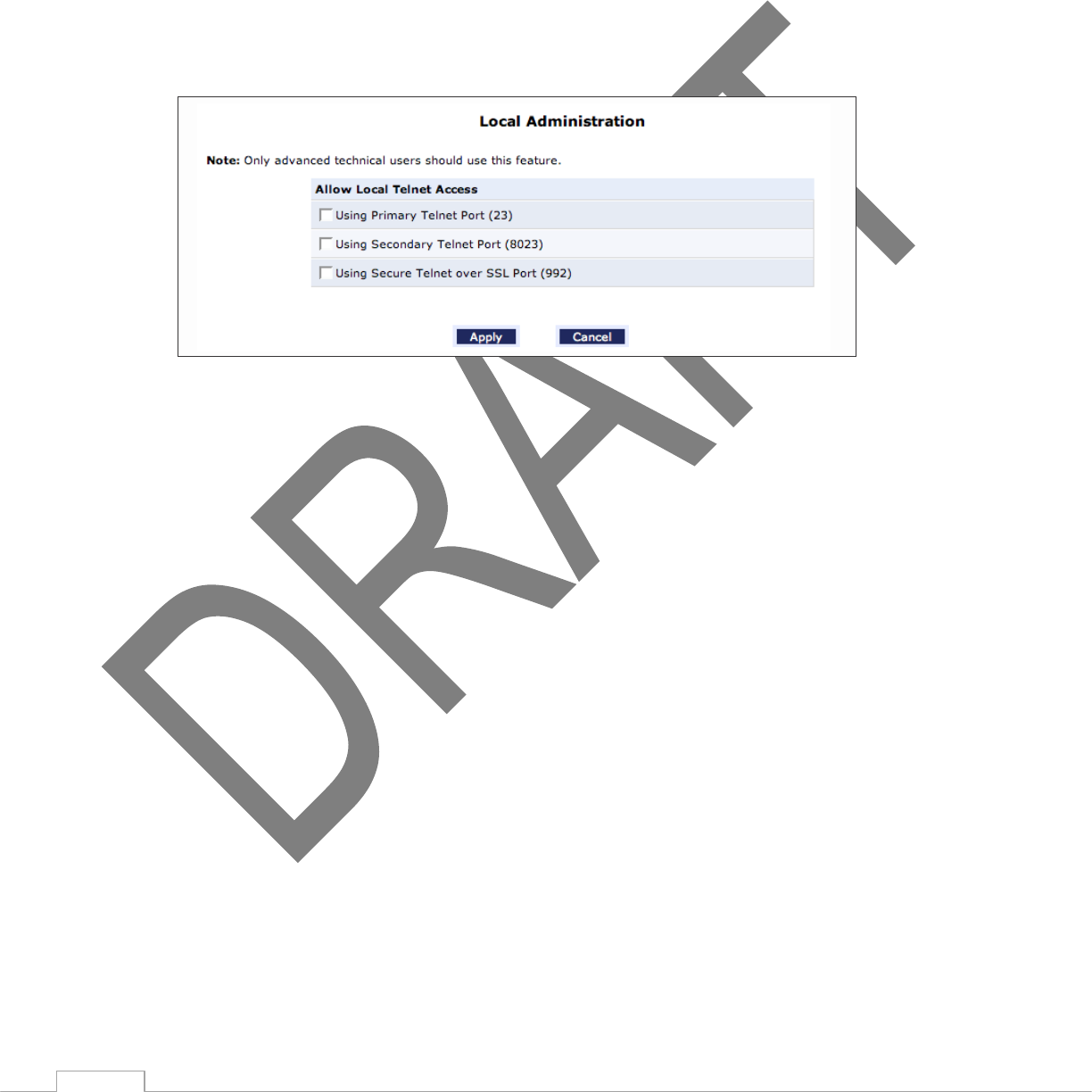
74
8.2h Local Administration
Clicking Local Administration in the Advanced screen generates the “Local Administration” screen. This
screen allows the user to grant local Telnet access using a particular Telnet port.
To use, select a Telnet port by clicking in the appropriate check box, then click Apply.

75
8.3 DNS Settings
The second section of the Advanced window is the DNS (Domain Name System) settings section, which
includes “Dynamic DNS” and “DNS Server.”
8.3a Dynamic DNS
Dynamic DNS creates a dynamic IP address to be aliased to a static hostname, allowing a computer on the
network to be more easily accessible from the Internet. Typically, when connecting to the Internet, the service
provider assigns an unused IP address from a pool of IP addresses, and this address is used only for the
duration of a specific connection. Dynamically assigning addresses extends the usable pool of available IP
addresses, while maintaining a constant domain name. This allows the user to access a device (portable hard
drive, for example) from a remote location, since the device will always have the same IP address.
When using Dynamic DNS, the IP address changes based upon the service provider’s changes, the DNS
database changes accordingly to reflect the change. In this way, even though the IP address of the computer
changes often, its domain name remains constant and accessible.
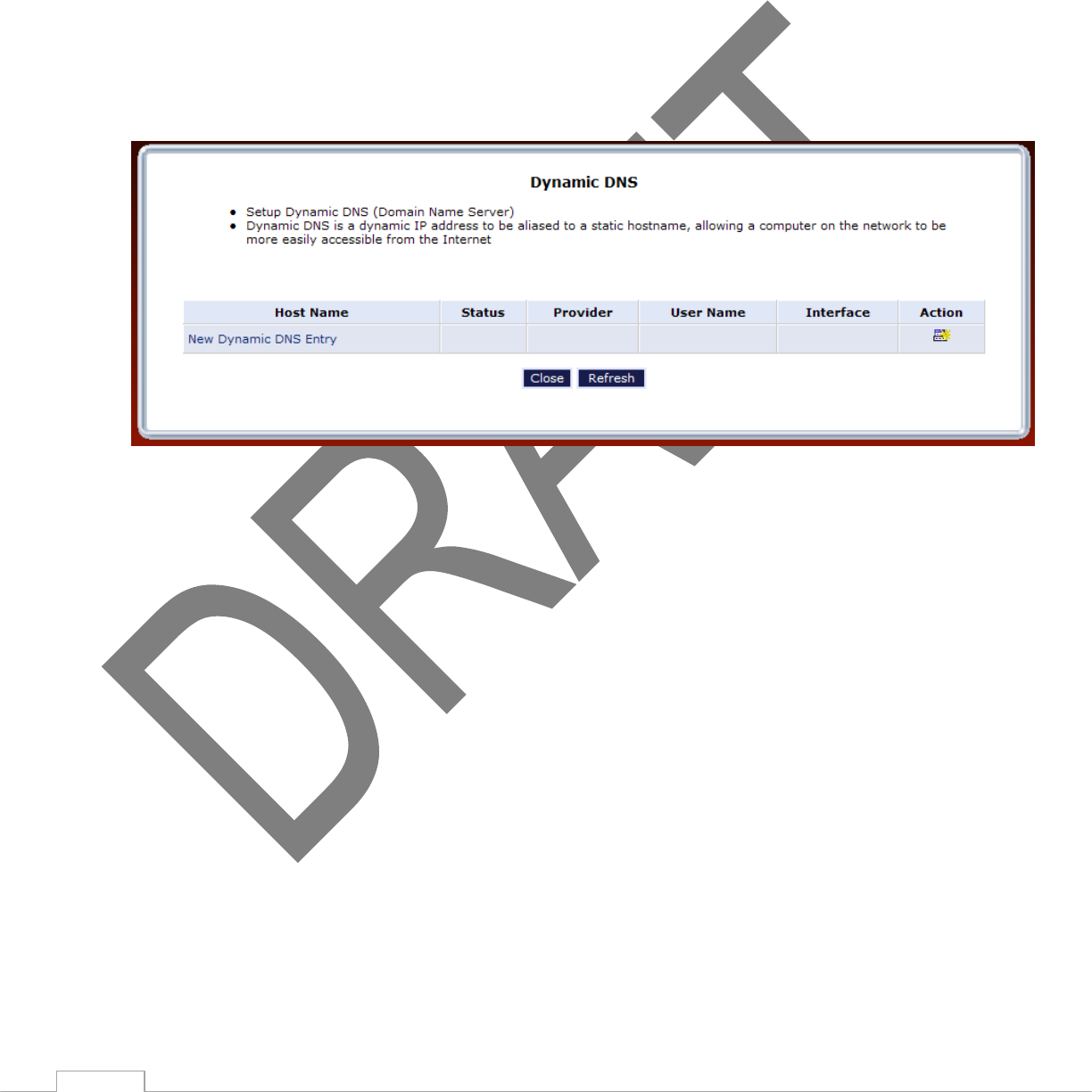
76
Setting up Dynamic DNS
To set up Dynamic DNS on the TG590, click Dynamic DNS in the Advanced screen. When the “Dynamic DNS”
screen appears, click New Dynamic DNS Entry.
Another Dynamic DNS screen appears.
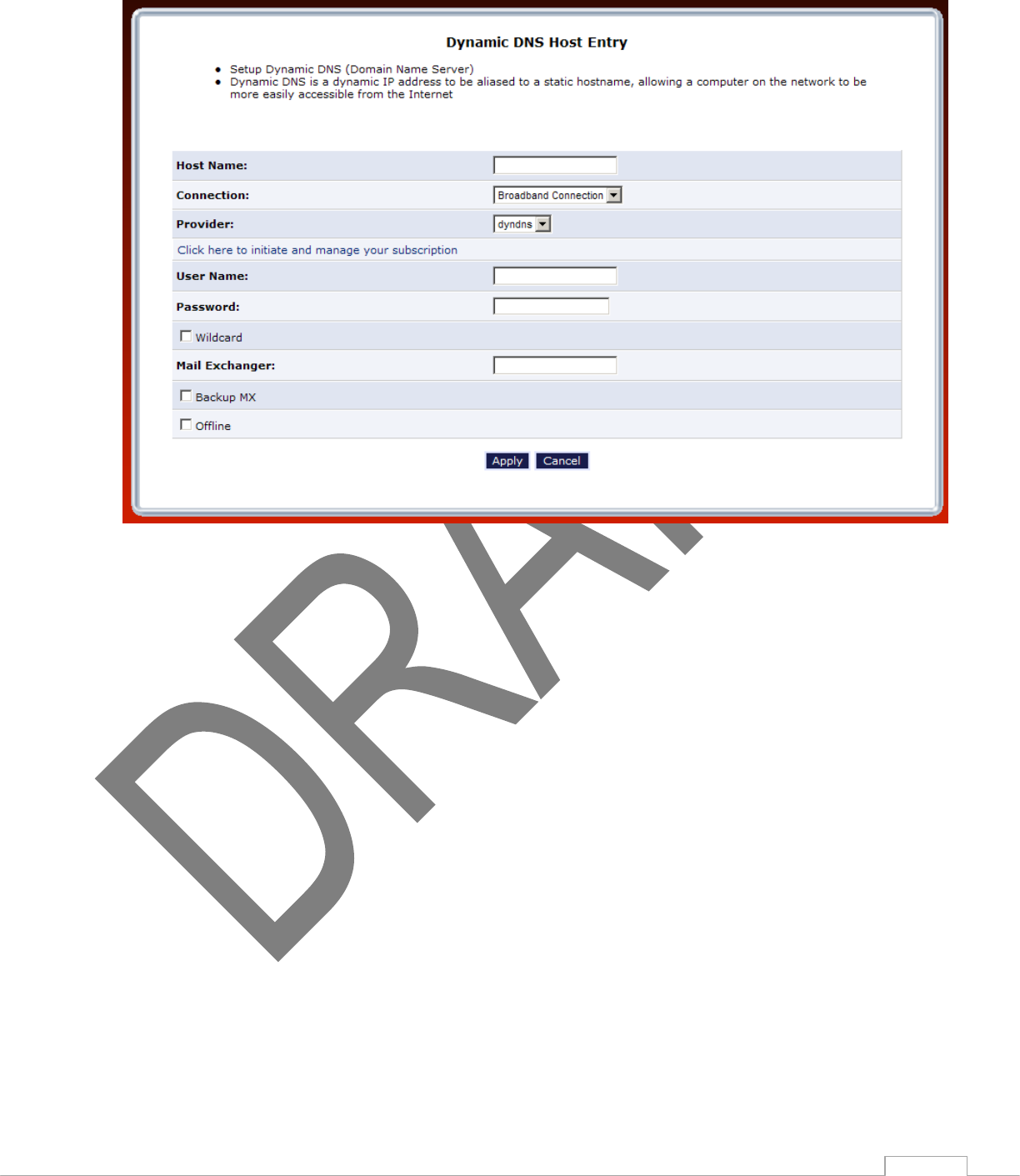
77
Configure the following parameters:
• Host Name: Enter the full Dynamic DNS domain in this text box.
• Connection: Select the connection with which to couple the Dynamic DNS service. Options include Broadband
Connection (Ethernet), Broadband Connection (Coax)
• Provider: Select the TG590’s Dynamic DNS account provider from the drop-down list.
• User Name: Enter the Dynamic DNS user name in this text box.
• Password: Enter the Dynamic DNS password in this text box.
• Wildcard: Select the “Wildcard” check box to allow any URL that includes the domain name
(here.yourhost.vztch.com, for example) to connect.
• Mail Exchanger: Enter the mail exchange server address. This will redirect all Emails arriving at the Dynamic DNS
address to the mail server.
• Backup MX: Select this check box to designate the mail exchange server to be a backup server.

78
• Offline: Disable the Dynamic DNS feature by clicking this check box. This feature is available only to users who
have purchased some type of upgrade credit from the Dynamic DNS provider.
Note: Changing the redirection URL can only be performed via the Dynamic DNS provider’s website.
SL Mode
If the Dynamic DNS service chosen supports SSL, select the SSL mode from the drop-down menu (options:
None, Chain, Direct).
To edit the host name or IP address of an entry:
1. Click the appropriate “Edit” icon in the Action column. The “DNS Entry” screen appears.
2. If the host was manually added to the DNS Table, its host name and/or IP address can be modified.
Otherwise, only modify its host name.
3. Click Apply to save the changes.
To remove a host from the DNS table, click the appropriate “Delete” icon in the Action column. The entry will
be removed from the table.
8.3b DNS Server
79
The Domain Name System (DNS) translates domain names into IP addresses and vice versa. The TG590 ’s
DNS server is an auto-learning DNS, which means that when a new computer is connected to the network, the
DNS server learns
its name and automatically adds it to the DNS table. Other network users can immediately communicate with
this computer using either its name or its IP address.
The TG590’s DNS also provides the following services:
Shares a common database of domain names and IP addresses with the DHCP server.
Supports multiple subnets within the local network simultaneously.
Automatically appends a domain name to unqualified names.
Allows new domain names to be added to the database using the TG590’s GUI.
Permits a computer to have multiple host names.
Permits a host name to have multiple IPs (needed if a host has multiple network cards).
The DNS Server does not require configuration. However, the list of computers known by the DNS can be
viewed or a new computer can be added to the list.
DNS Table
To view the list of computers stored in the DNS table:
1. Click DNS Server in the Advanced screen.
2. The “DNS Server” screen appears.
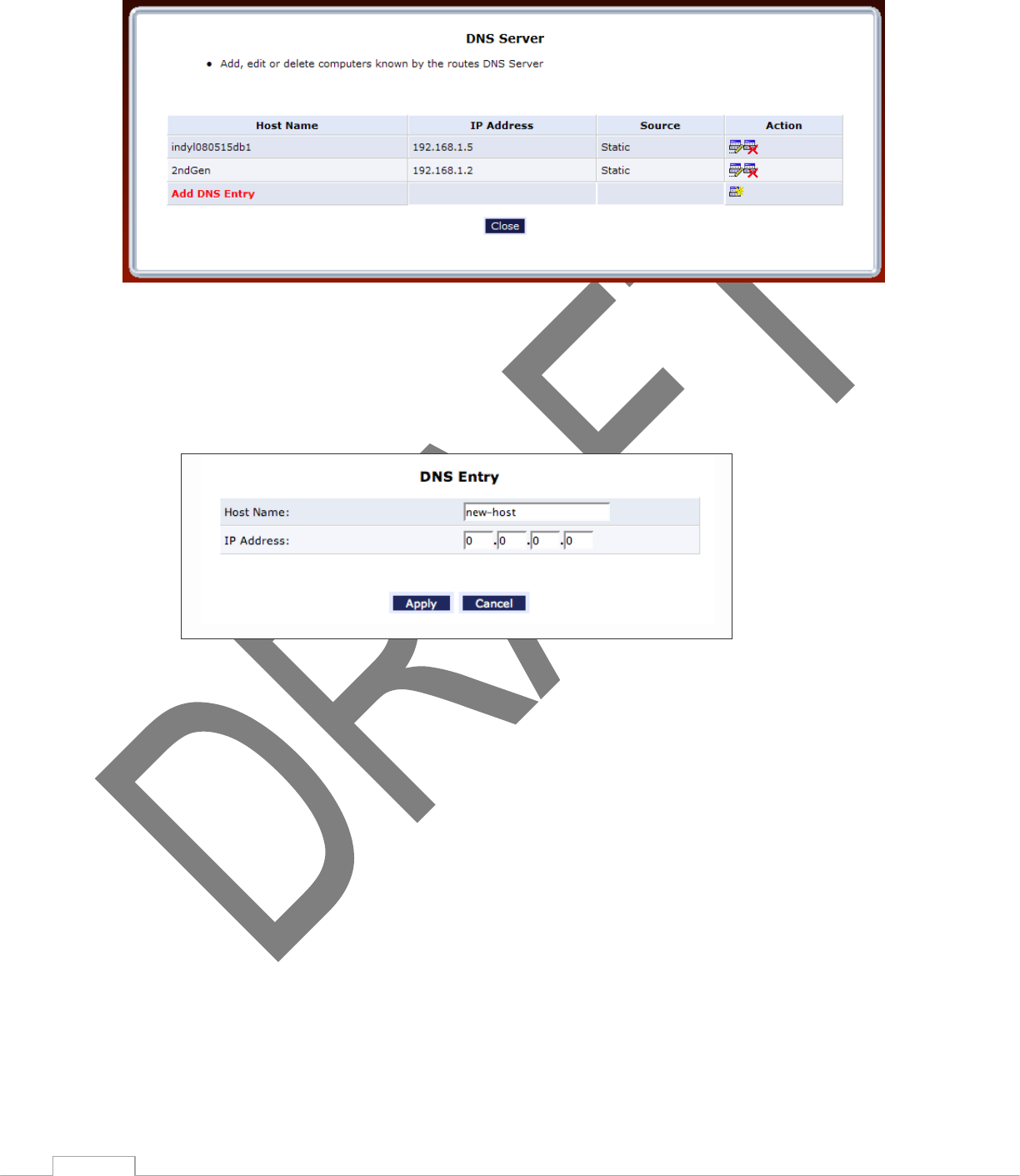
80
To add a new entry to the list:
Click Add DNS Entry in the DNS Server screen. The “DNS Entry” screen appears.
2. Enter the computer’s host name in the “Host Name” text box.
3. Enter the computer’s IP address in the “IP Address” text boxes.
4. Click Apply to save the changes.
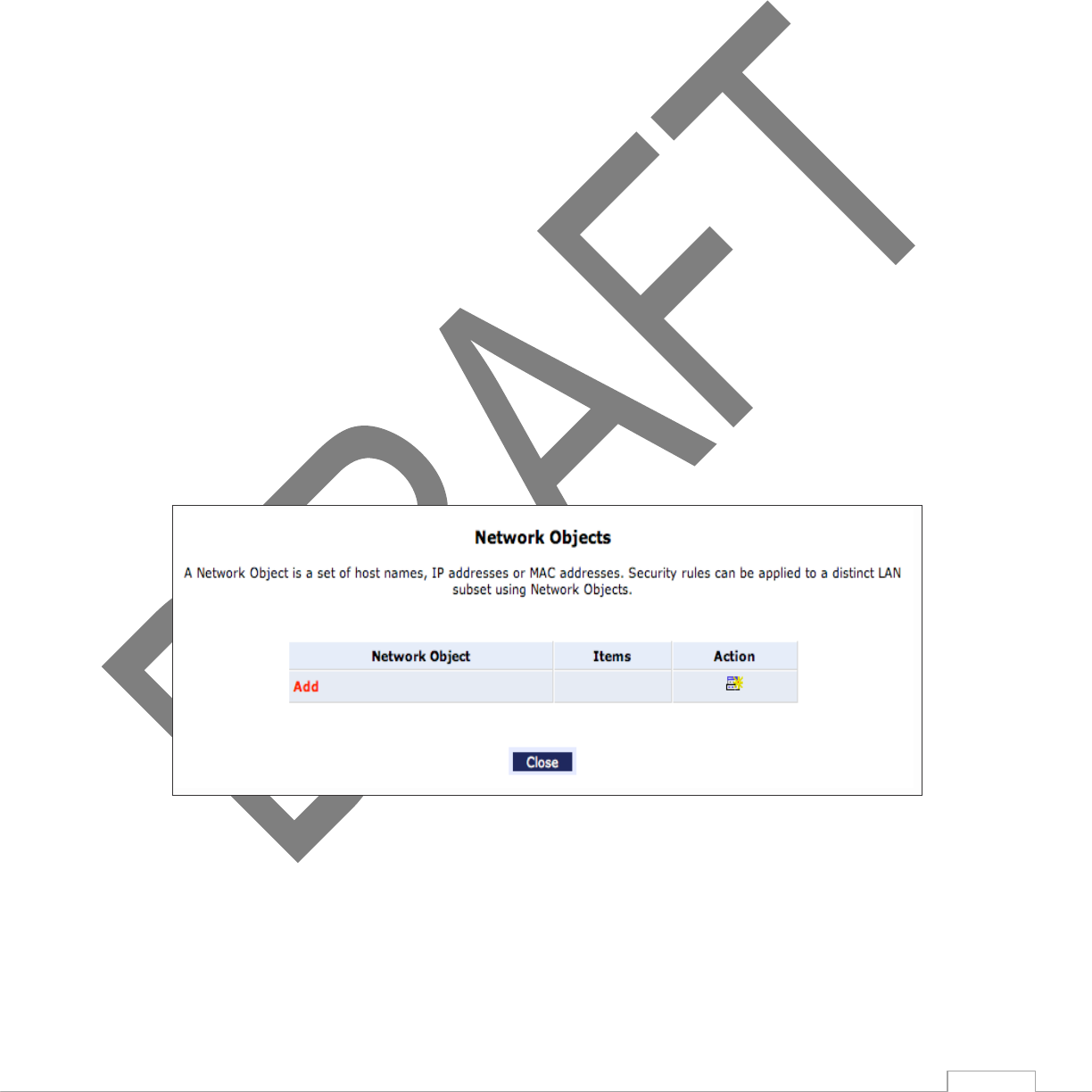
81
8.4 Network Settings
The Network Settings section of the Advanced screen includes settings that affect the TG590’s network.
8.4a Network Objects
A network object is used to define a part of the TG590’s network (a group of computers, for example) by MAC
addresses, IP addresses, and/or host names. The defined part becomes a “network object,” and settings, such
as configuring system rules, can be applied to all the devices defined as part of the network object at once. For
example, instead of setting the same website filtering configuration to five computers one at a time, the
computers can be defined as a network object, and website filtering configuration can then be applied to all
the computers simultaneously.
Network objects can be used to apply security rules based on host names instead of IP addresses. This may be
useful, since IP addresses change from time to time. Moreover, it is possible to define network objects
according to MAC addresses, making rule application more persistent against network configuration settings.
To define a network object:
Click Network Objects in the Advanced screen. The “Network Objects” screen appears.
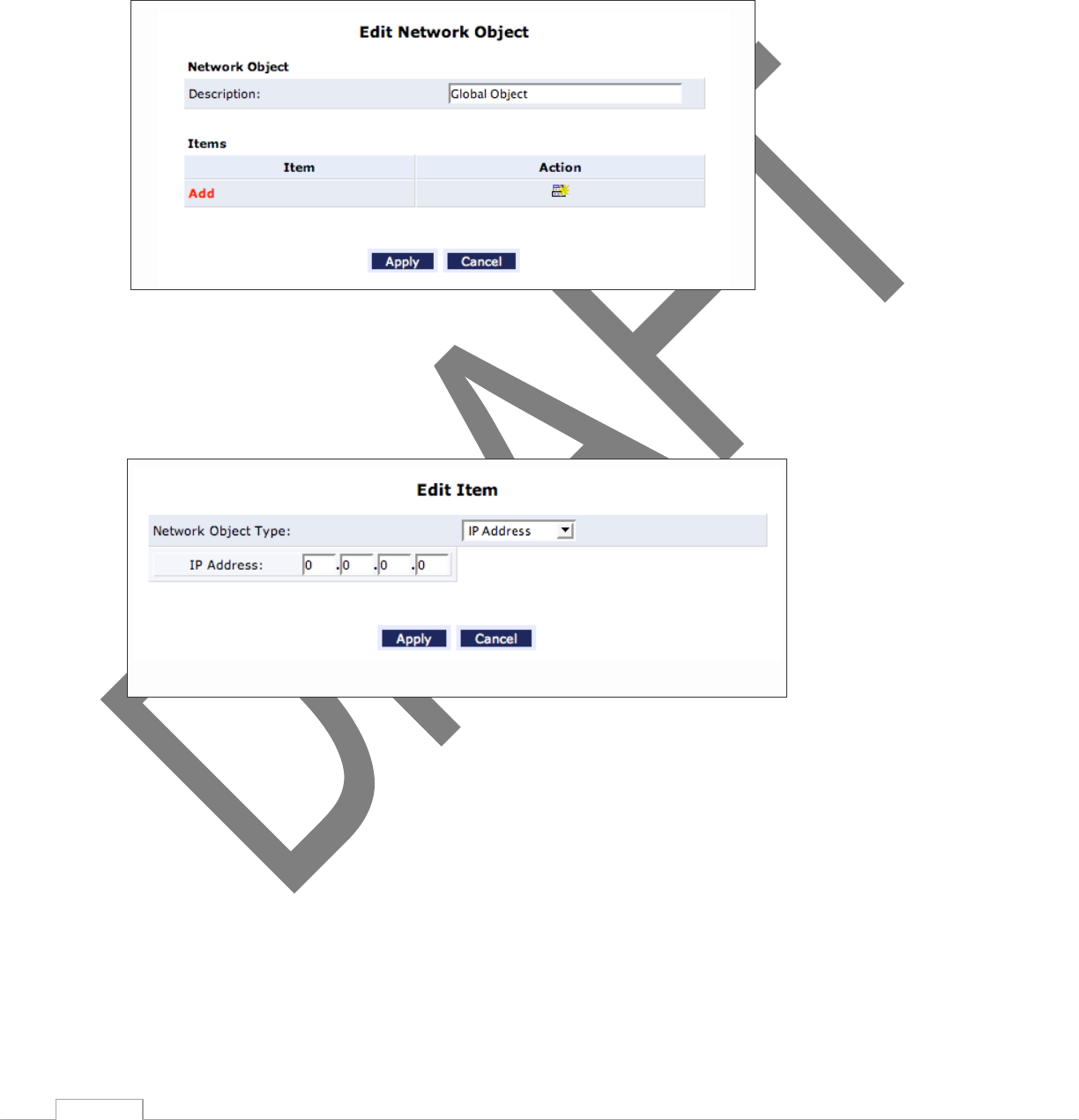
82
Click Add. The “Edit Network Object” screen appears.
Specify a name for the network object in the “Description” text box.
Click Add. The “Edit Item” screen appears.
Select the type of network object type from the “Network Object Type” list box. Options include IP address, IP
Subnet, IP Range, MAC Address, Host Name, and DHCP Option.
6. Repeat to create other network objects, if needed. When finished, click Apply
to save all created network objects.
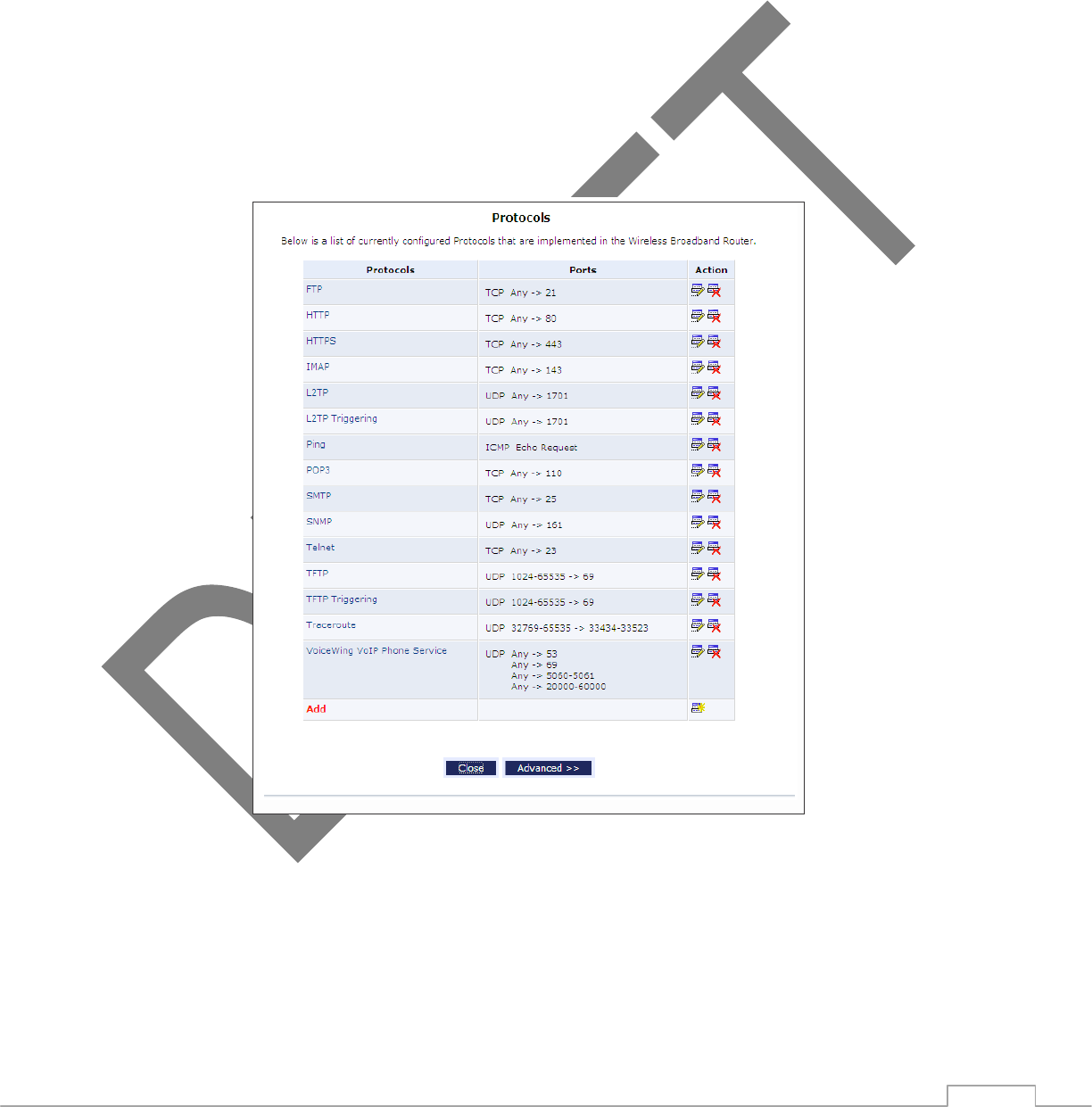
83
8.4c Protocols
Protocols feature a list of preset and user-defined applications and common port settings. Protocols can be
used in various security features, such as Access Control and Port Forwarding. New protocols can be added to
support new applications or existing ones can be edited when needed. To define a protocol:
1. Click Protocols in the Advanced screen. The “Protocols” screen appears.
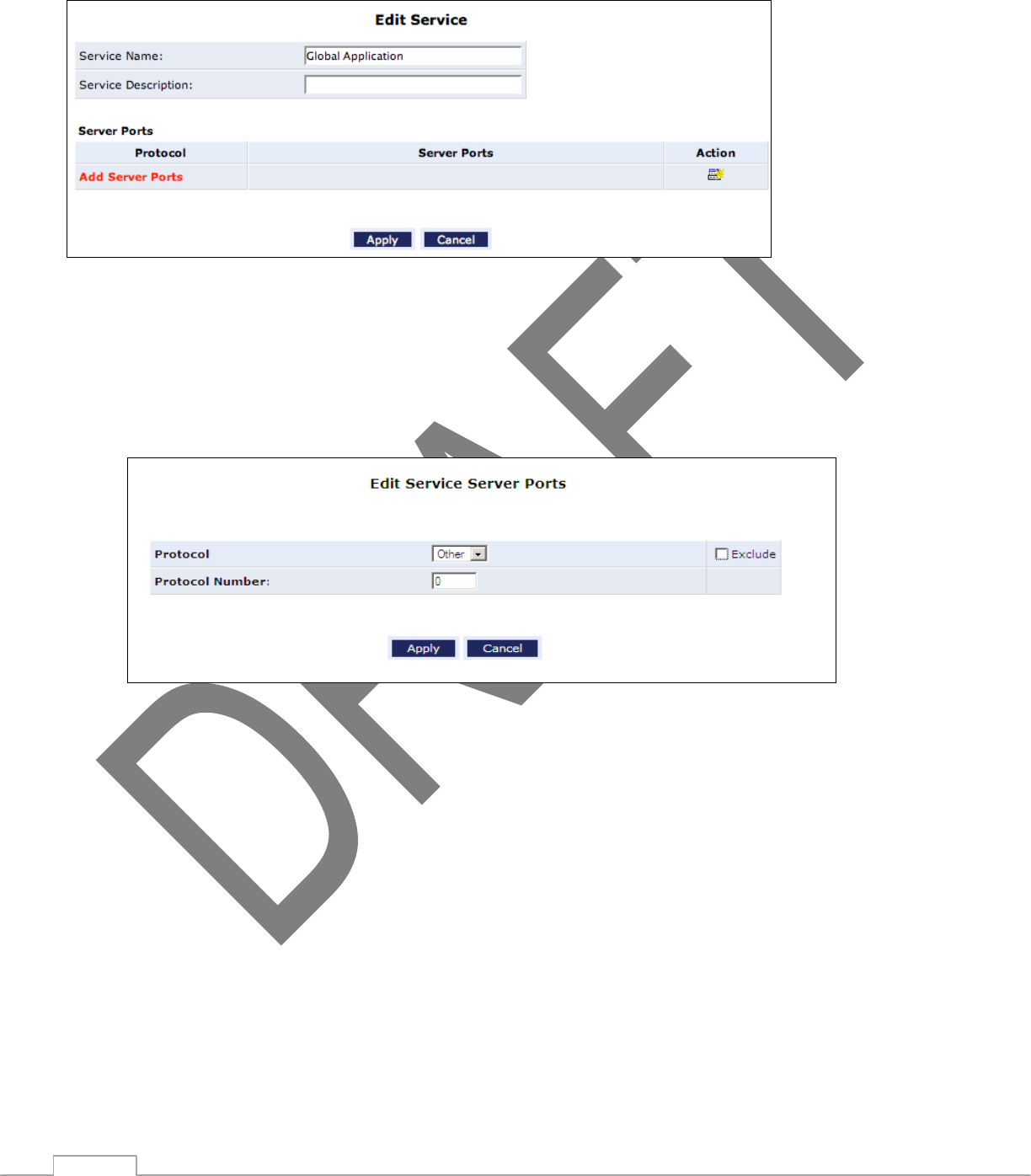
84
2. Click Add at the bottom of the screen. The “Edit Service” screen appears.
3. Name the service in the “Service Name” text box and, if needed, enter a description of the service in the
“Service Description” text box, then click Add Service Ports. The “Edit Service Server Ports” screen
appears.
Select a protocol from the “Protocol” drop-down list. To create a new protocol, select “Other.” After selecting a
protocol, the screen will refresh, displaying the relevant text boxes needed to edit the particular protocol.
5. Click Apply to save the changes.

85
8.5 Configuration Settings
This section includes settings that affect the TG590’s configuration.
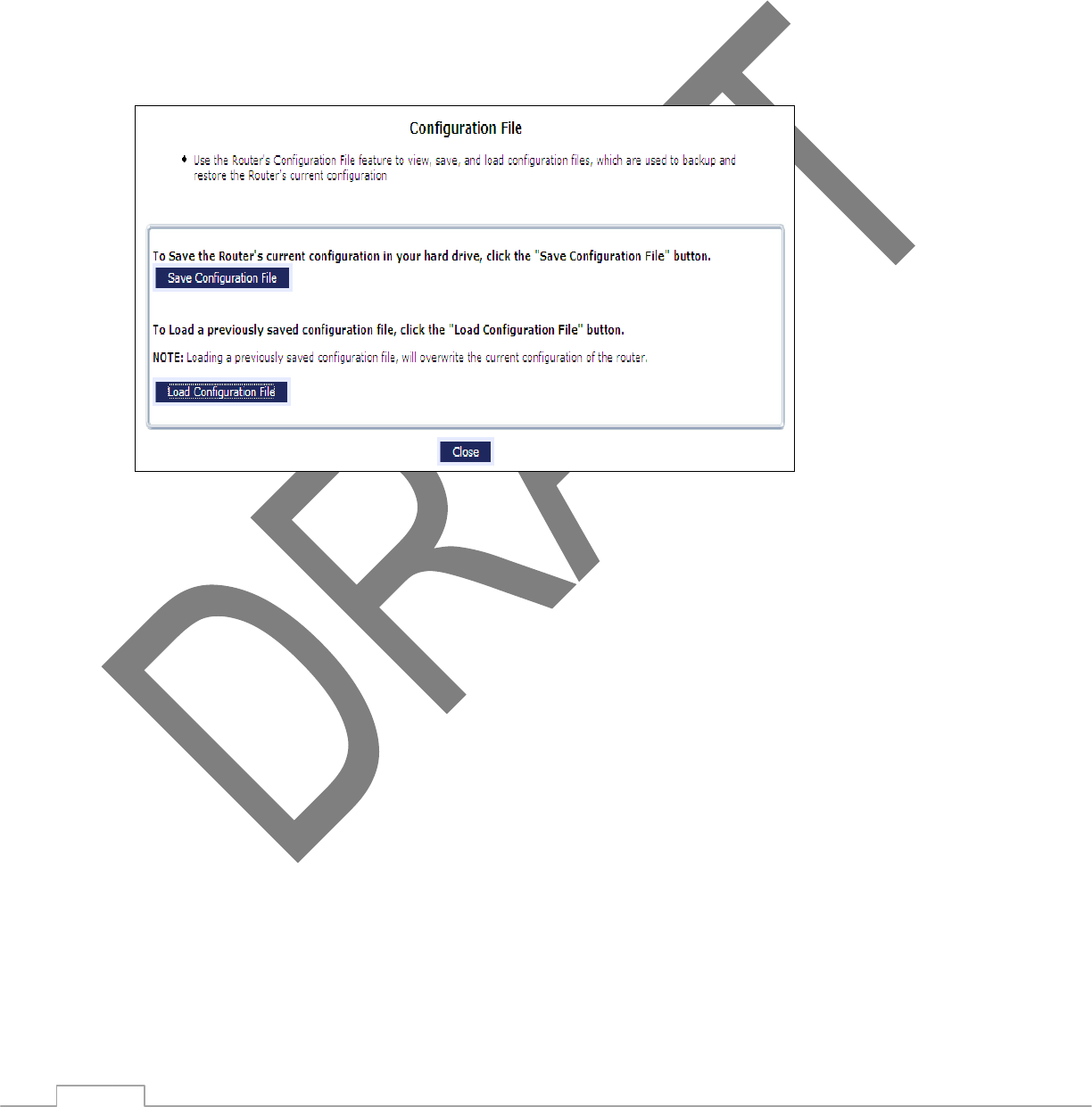
86
8.5a Configuration File
Use the TG590’s Configuration File feature to view, save, and load configuration files, which are used to
backup and restore the TG590 ’s current configuration. To do this:
1. Click Configuration File in the Advanced screen. The “Configuration File” screen appears.
Click Load Configuration File to load the previous configuration from a file and restart the TG590. Only
configuration files saved on a particular TG590 can be applied to the TG590; configuration files cannot be
transferred between TG590s.
1. Click Save Configuration File to backup the current configuration to a file.
Warning: Manually editing a configuration file can cause the TG590 to malfunction or become completely
inoperable.
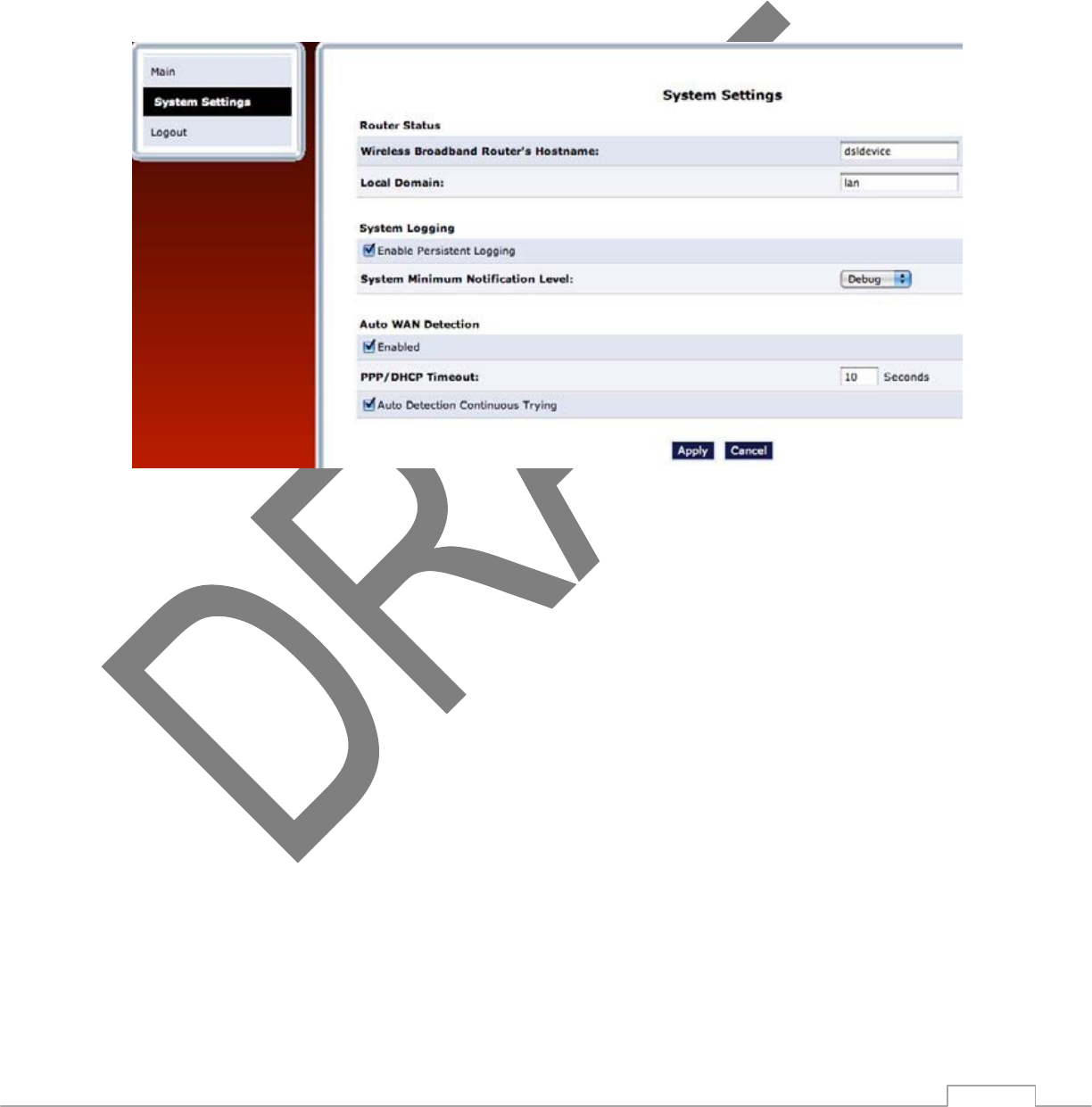
87
8.5b System Settings
Clicking System Settings in the Advanced screen generates the “System Settings” screen, where various
system and management parameters can be configured.
88
System
Use the “System” section of this screen to configure the following two options:
Wireless Broadband’s Hostname - Specify the TG590’s host name by entering it into the text box. The host
name is also the TG590’s URL address, so it can be entered here rather than 192.168.1.1.
Local Domain - Specify the network’s local domain by entering it into this text box.
Wireless Broadband
Use this section to configure the following:
Automatic Refresh of System Monitoring Web Page - Click in this check box to activate the automatic refresh
of system monitoring web pages.
Prompt for Password When Accessing via LAN - Click in this check box to cause the TG590 to ask for a
password when trying to connect to the network.
Warn User Before Network Configuration Changes - Click in this check box to activate user warnings before
network configuration changes take effect.
Session Lifetime - After the TG590 has been inactive for a period of time, the user must reenter a user name
and password to continue accessing the GUI. To change the length of this time period, enter the amount of
time (in seconds) in the “Session Lifetime” text box.
Configure a number of concurrent users… - Used to limit the number of users that can access the TG590 at the
same time. Select the number of users from the drop-down list.

89
Management Application Ports
This section allows the following management application ports to have their default port numbers to be
changed:
Primary/secondary HTTP ports
Primary/secondary HTTPS ports
Primary/secondary Telnet ports
Secure Telnet over SSL ports
Management Application SSL Authentication Options
This section allows the user to access the TG590’s GUI through a browser or Telnet as a secure socket layer
(SSL) session.
System Logging
Use this section to configure the following system log options.
Enable Logging - Click in this check box to activate system logging.
Low Capacity Notification Enabled - Click in this check box to activate low capacity notification (works in
tandem with “Allowed Capacity Before Email Notification” and “System Log Buffer Size” options).
Allowed Capacity Before Email Notification - Enter the percentage of system log buffer capacity reached to
trigger an email notification.
System Log Buffer Size - Enter the size of the system log buffer in this text box.
Remote System Notify Level - This feature is used to specify the type of information received for remote
system logging. Options include None, Error, Warning, and Information.
90
Security Logging
Use this section to configure the following security log options.
Low Capacity Notification Enabled - Click in this check box to activate low capacity notification (works in
tandem with “Allowed Capacity Before Email Notification” and “Security Log Buffer Size” options).
Allowed Capacity Before Email Notification - Enter the percentage of security log buffer capacity reached to
trigger an email notification.
Security Log Buffer Size - Enter the size of the security log buffer in this text box.
Remote Security Notify Level - This feature is used to specify the type of information received for security
logging. Options include None, Error, Warning, and Information.
Outgoing Mail Server
Use this section to configure the outgoing mail server options. This server is used to format and send system
and security log email notifications.
Server - Enter the host name of the outgoing (SMTP) server in this text box.
From Email Address - Email notifications require a “from” address. Enter a “from” email address in this text
box.
Port - Enter the port number of the email server in this text box.
Server Requires Authentication - If the email server requires authentication, click in this check box, then
enter a user name and password in the “User Name” and “Password” text boxes that appear.
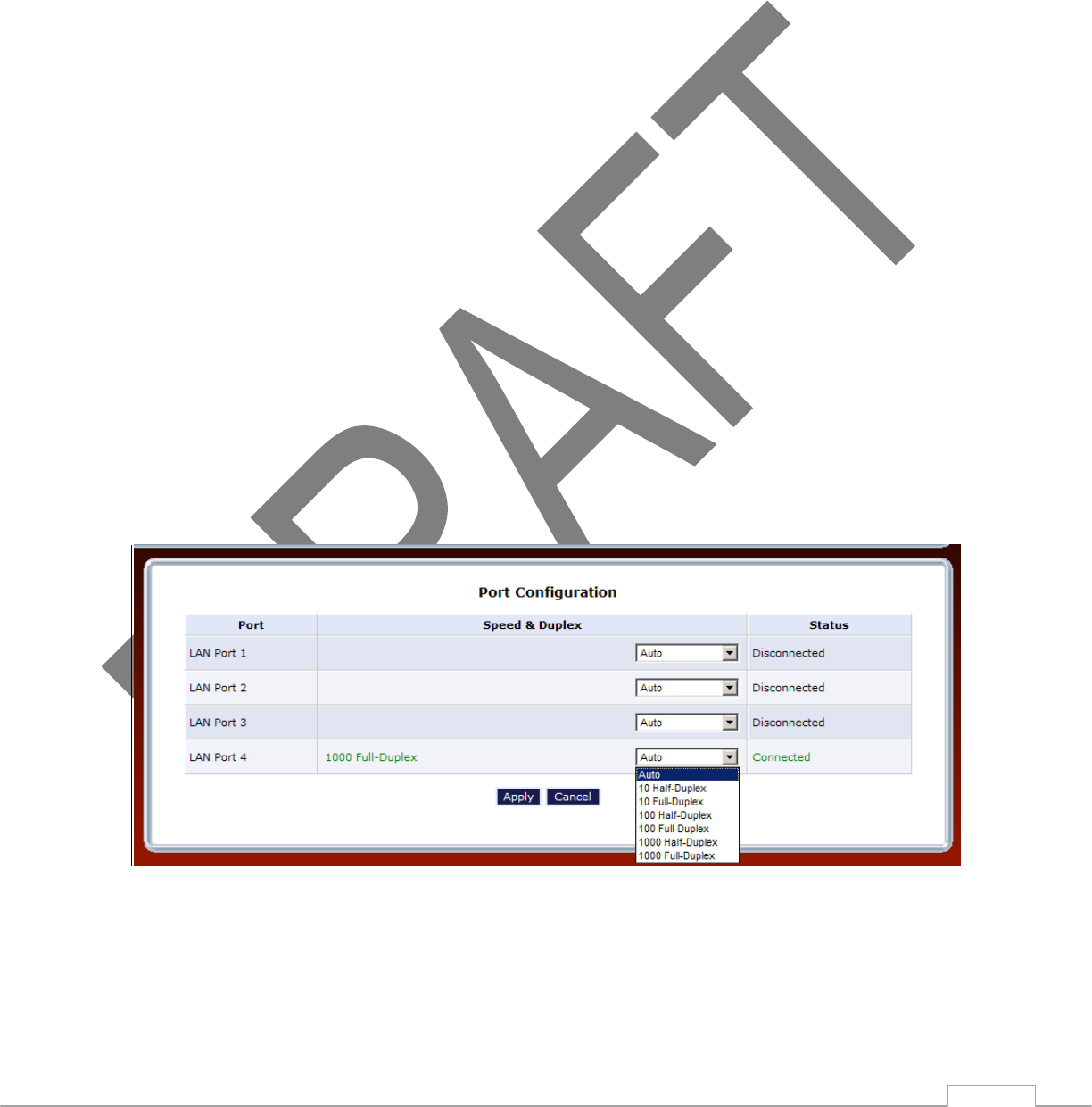
91
Auto WAN Detection
When activated, Auto WAN Detection causes the TG590 to automatically search for a WAN connection.
Enable Logging - Clicking in this check box activates automatic WAN detection.
PPP Timeout - Enter the amount of time (in seconds) before the TG590 stops attempting to establish a
broadband PPP connection.
DHCP Timeout - Enter the amount of time (in seconds) before the TG590 stops attempting to establish a
broadband DHCP connection.
Number of Cycles - Enter the number of times the TG590 attempts to detect a broadband PPP and DHCP
connection.
Auto Detection Continuous Trying - Click in this check box to cause the TG590 to indefinitely search for a
broadband connection.
8.5c Port Configuration
Port configuration allows the user to set up the TG590 ’s Ethernet ports as either full- or half-duplex ports, at
either 10 Mbps, 100 Mbps, or 1 Gbps. Selecting the “Auto” option causes the port to negotiate the speed and
duplex configuration of the port with which it is communicating.
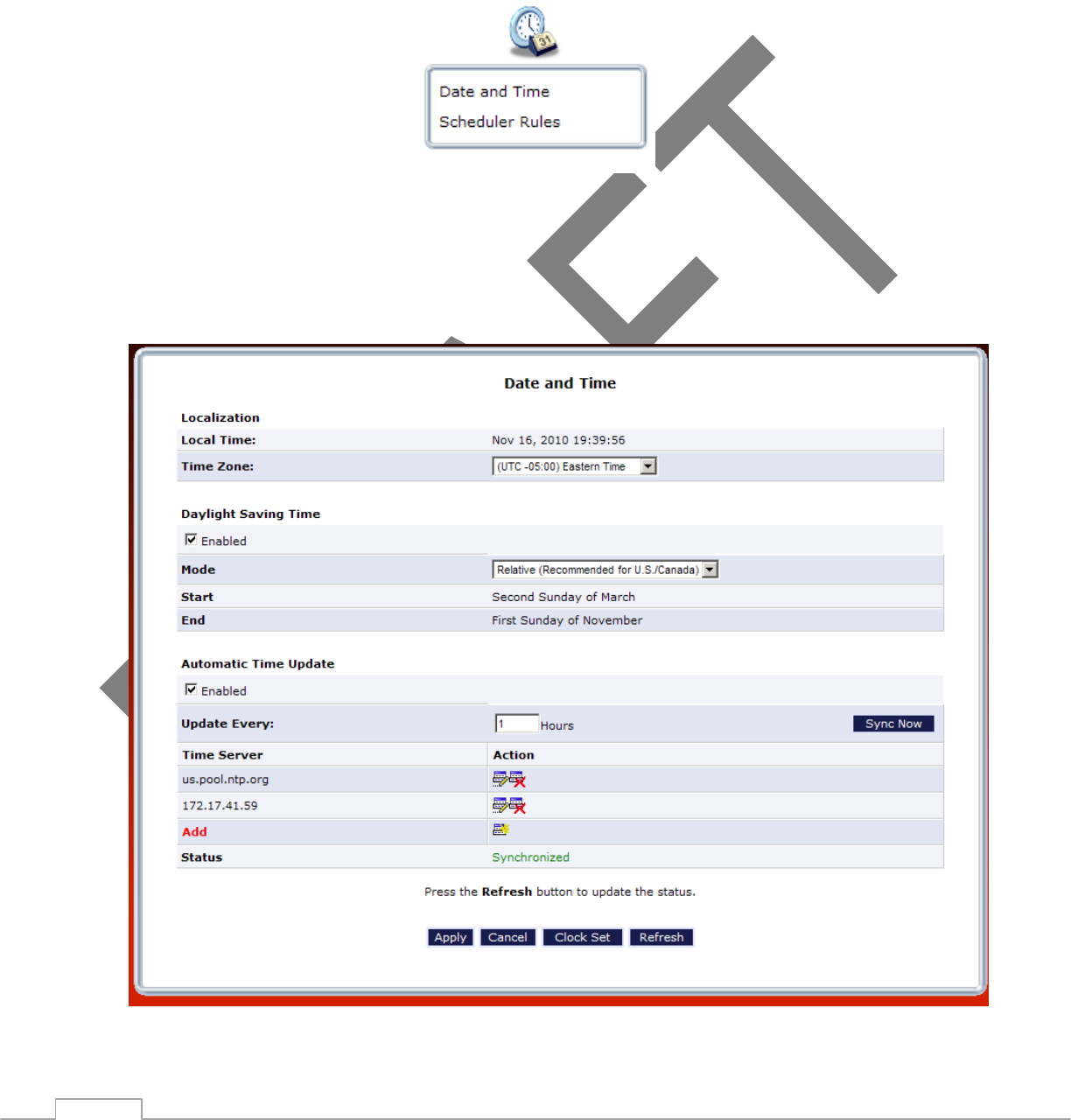
92
8.6 Time Settings
The Time settings section of the Advanced window features utilities that involve times, dates and schedules.
8.6a Date and Time
To configure date and time, do the following:
1) Click Date and Time on the Advanced screen. The “Date and Time” screen appears.

93
2) Select the local time zone from the drop-down list. The TG590 can automatically detect daylight saving
setting for selected time zones. If the Daylight Saving Time setting for a time zone is not automatically
detected, the following two fields will be displayed:
• Enabled - Select this check box to enable daylight saving time.
• Mode- Relative (Recommended for U.S./Canada) or Absolute.
To perform an automatic time update:
1) Click in the “Enabled” check box in the “Automatic Time Update” section.
2) Select the protocol to be used to perform the time update by selecting either the “Time of Day”
or “Network Time Protocol” radio button.
3) Specify how often to perform the update in the “Update Every” text box.
4) To synchronize the settings, click on “Sync Now”.
5) Define time server addresses by clicking Add on the bottom of the “Automatic Time Update” section and
entering the IP address or domain name of the time server in the “Time Server Settings” screen.
94
8.6b Scheduler Rules
Scheduler rules are used for limiting the activation of firewall rules to specific time periods, either for days of
the week, or for hours of each day. To define a rule:
Make sure the TG590’s date and time are set correctly. To do this, see the “Date and Time” section in this
chapter.
Click Scheduler Rules in the Advanced screen. The “Scheduler Rules” screen appears.
3. Click Add. The “Set Rule Schedule” screen appears.
4. Enter a name for the rule in the “Rule Name” text box.
5. Indicate if the rule will be “active” or “inactive” during the designated time period by clicking the
appropriate “Rule Settings” radio button.
6. Click Add Rule Schedule. The “Edit Rule Schedule” screen appears.
95
7. Select or active or inactive days of the week by clicking in the appropriate text boxes.
8. If applicable, click New Hours Range Entry to define an active/inactive hourly range. The “Edit Hour
Range” screen appears. Enter a start and end time in the appropriate text boxes.
Note: Make sure the TG590 ’s date and time settings are properly configured for the time zone.
9. Click Apply.
96
8.6c Clock Set
Click on this link from the Date and Time screen to set the TG590 ’s time and date. The Local Date can be set
by using the drop-down list; and the Local Time can be manually entered into the text boxes. Then, click on
Apply.
The final section of the Advanced screen is Routing settings, which includes Routing and IP Address
Distribution.
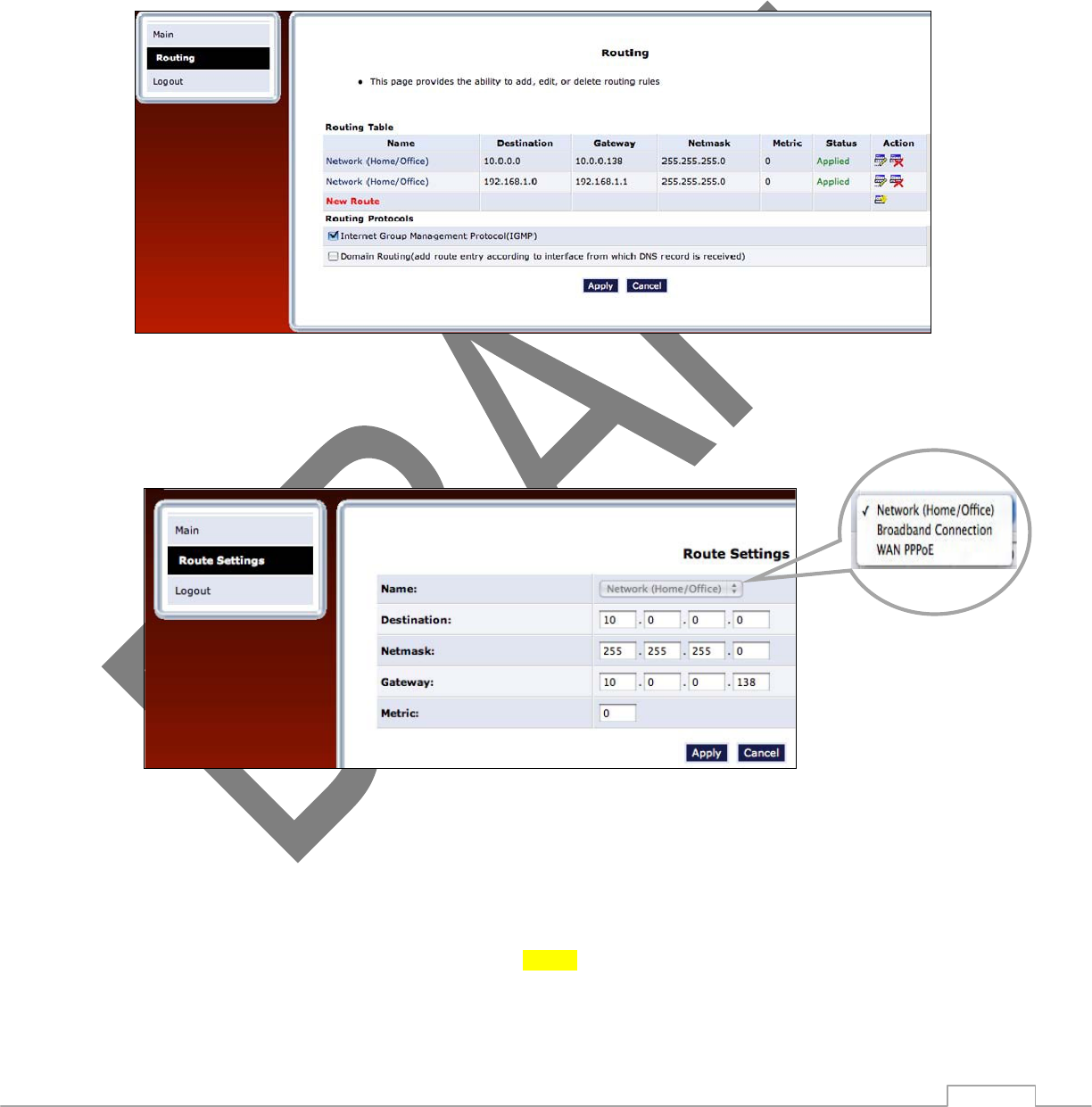
97
8.8a Routing
Access the routing table rules by clicking Routing in the Advanced screen. The “Routing” screen appears.
Routing rules can be added, edited, or deleted from the Routing screen. To add a , click New Route.
The “Route Settings” screen appears.
When adding a routing rule, the following parameters must be specified:
• Route Name - Select the type of network from the drop-down list.
• Destination - The destination is the destination host, subnet address, network address, or default
route. The destination for a default route is 0.0.0.0.
• Netmask - The network mask is used in conjunction with the destination to determine when a route
is used.
98
• Gateway - Enter the TG590’s IP address.
• Metric - A measurement of the preference of a route. Typically, the lowest metric is the most
preferred route. If multiple routes exist to a given destination network, the route with the lowest
metric is used.
IGMP (Internet Group Management Protocol) Multicasting
The TG590 provides support for IGMP multicasting, which allows hosts connected to a network to be updated
whenever an important change occurs in the network. A multicast is simply a message that is sent
simultaneously to a pre-defined group of recipients. When joining a multicast group, all messages addressed
to the group will be received by the user, much like when an email message is sent to a mailing list. To
activate IGMP multicasting
1) Select Routing in the Advanced screen.
2) Activate the “Internet Group Management Protocol” check-box.
3) Click Apply.
Domain Routing
Domain routing is used in multi- local network configurations. Normally, to access a device connected to one
from another on the network, its IP address must be used. Activating domain routing (by clicking in the
appropriate check box) allows the user to access the computer by name (as well as IP address).

99
8.8b IP Address Distribution
The TG590’s DHCP server makes it possible to easily add computers configured as DHCP clients to the
network. It provides a mechanism for allocating IP addresses to these hosts and for delivering network
configuration parameters to them.
For example, a client (host) sends out a broadcast message on the network requesting an IP address for itself.
The DHCP server then checks its list of available addresses and leases a local IP address to the host for a
specific period of time and simultaneously designates this IP address as “taken.” At this point, the host is
configured with an IP address for the duration of the lease.
The host can choose to renew an expiring lease or let it expire. If it chooses to renew a lease, it will also
receive current information about network services,
as it did with the original lease, allowing it to update its network configurations to reflect any changes that
occurred since it first connected to the network. If the host wishes to terminate a lease before its expiration, it
can send a release message to the DHCP server, which will then make the IP address available for use by
others.
The TG590’s DHCP server:
• Displays a list of all DHCP hosts devices connected to the TG590.
• Defines the range of IP addresses that can be allocated in the network.
• Defines the length of time for which dynamic IP addresses are allocated.
• Provides the above configurations for each network device and can be configured and
enabled/disabled separately for each network device.
• Can assign a static lease to a network computer so that it receives the same IP address each time it
connects to the network, even if this IP address is within the range of addresses that the DHCP server
may assign to other computers.
• Provides the DNS server with the host name and IP address of each computer connected to the
network.

100
To view a summary of the services currently being provided by the DHCP server, click IP Address Distribution
in the Advanced screen. The “IP Address Distribution” screen appears.
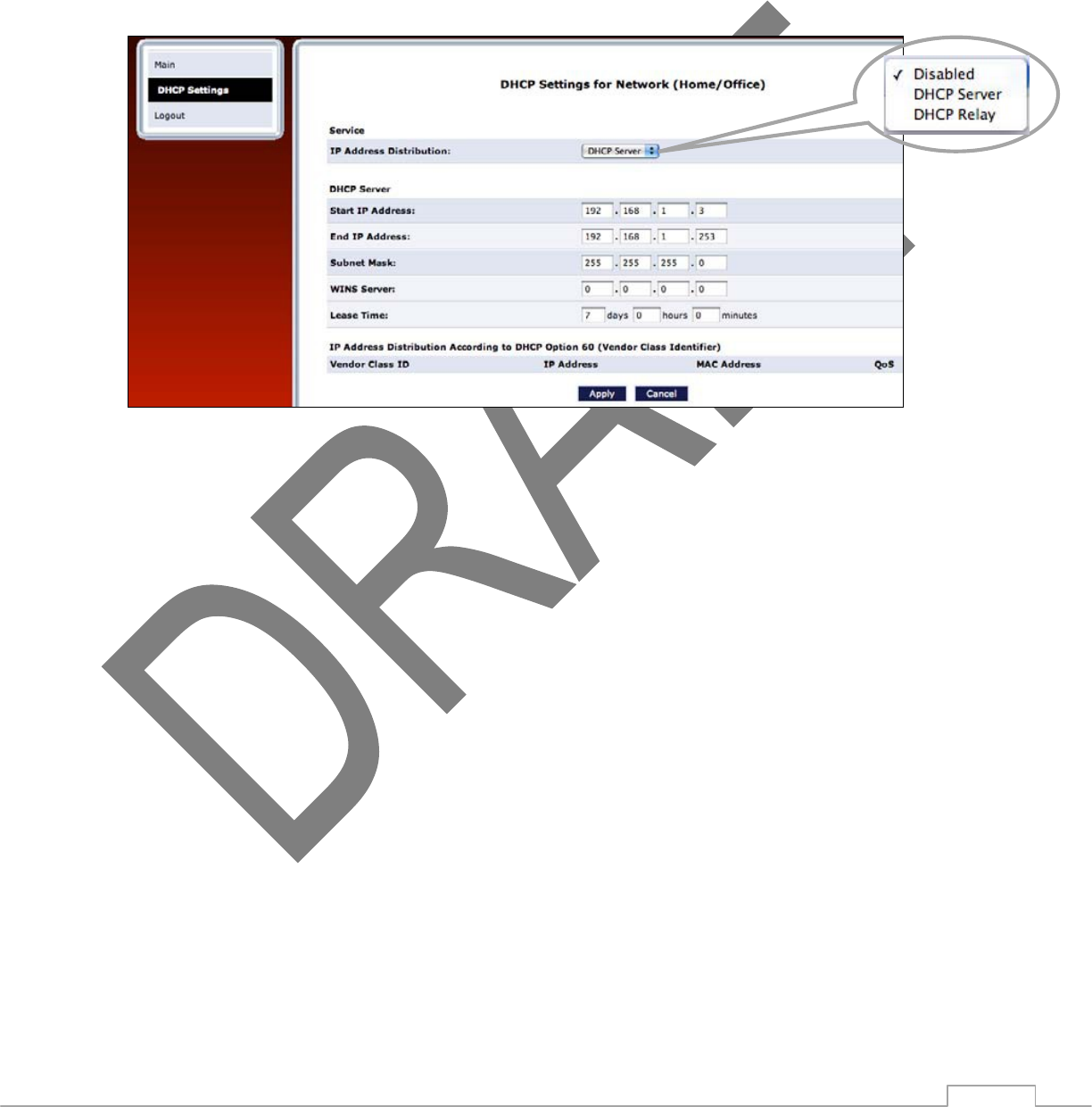
101
Editing DHCP Server Settings
To edit the DHCP server settings for a device:
1. Click the appropriate icon in the “Action” column. The “DHCP Settings” screen for the device appears.
2. Select the “IP Address Distribution” from the drop-down list. Options include DHCP Server, DHCP Relay,
or Disable.
3. Complete the following fields:
• Start IP Address Range, End IP Address Range - determines the number of hosts connected to the
network in this subnet.“Start” specifies the first IP address assigned in this subnet and “End” specifies
the last IP address in the range.
• Subnet Mask - used to determine to which subnet an IP address belongs. An example of a subnet
mask value is 255.255.0.0.
• WINS Server - The WINS (Windows Internet Naming Service) server determines the IP address
associated with a network device.
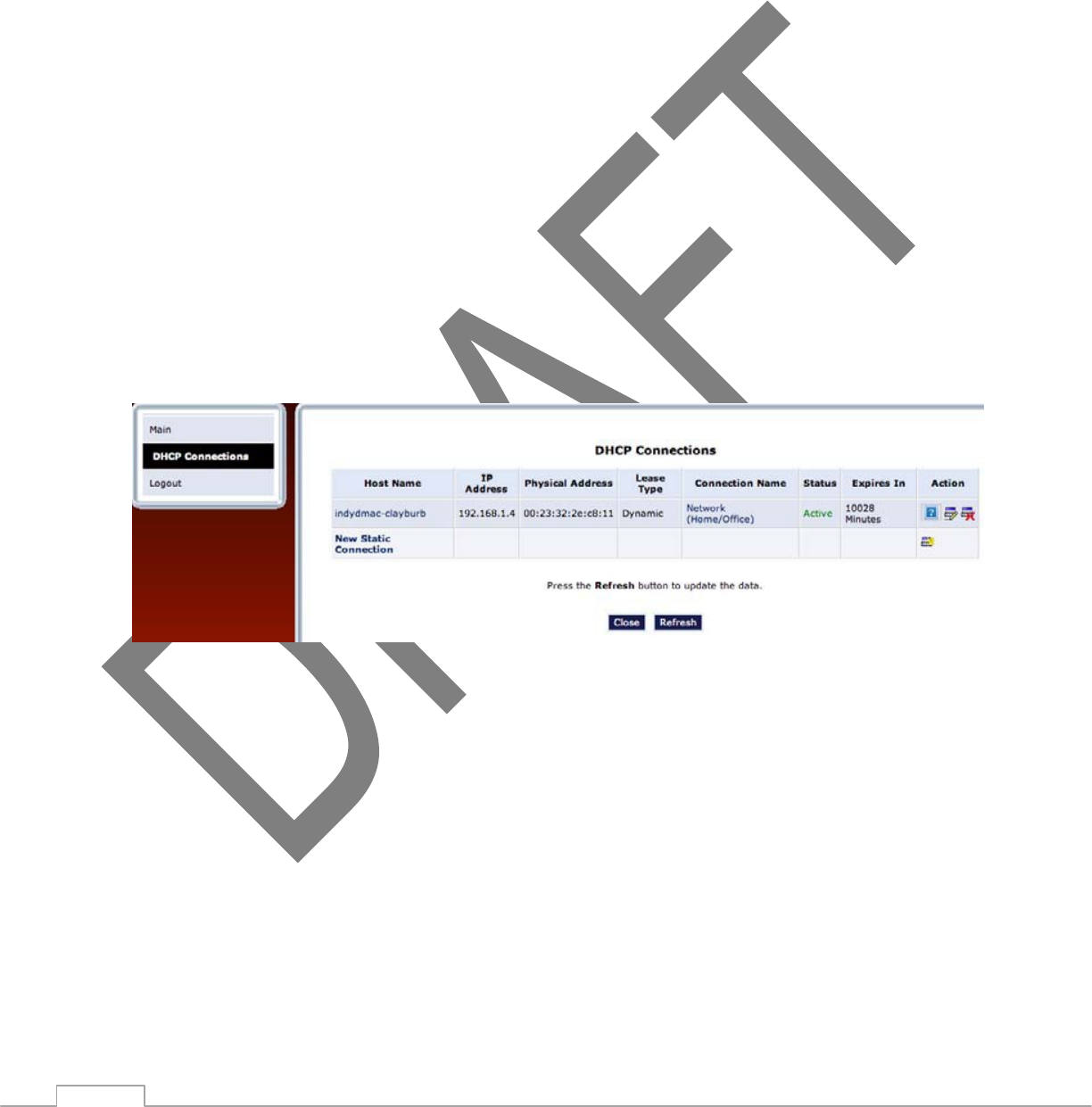
102
• Lease Time - each device will be assigned an IP address by the DHCP server for a limited time (“Lease
Time”) when it connects to the network. When the lease expires, the server will determine if the
computer has disconnected from the network. If it has, the server may reassign this IP address to a
newly- connected computer. This feature ensures that IP addresses not in use will become available
for other computers on the network.
• Provide host name if not specified by client - when activated, the TG590 assigns the client a default
name if the DHCP client has no host name.
4. Click Apply to save the changes.
DHCP Connections
To view a list of computers currently recognized by the DHCP server, click Connection List at the bottom of
the IP Address Distribution screen. The “DHCP Connections” screen appears.

103
To define a new connection with a fixed IP address:
1. Click New Static Connection in the DHCP Connections screen. The “DHCP Connection Settings” screen
appears.
2. Enter a host name for this connection.
3. Enter the fixed IP address to assign to the computer.
4. Enter the MAC address of the computer’s network card.
5. Click the Apply to save changes.
Note: A device’s fixed IP address is actually assigned to the specific network card’s MAC address
installed on the network computer. If this network card is replaced, the device’s entry in the
DHCP Connections list must be updated with the new network card’s MAC address.
To remove a host from the table, click the appropriate “Delete” icon in the Action column.
104
9 TROUBLESHOOTING
In this chapter
In this chapter, we will take a closer look at suggested solutions for problems you may encounter while installing,
configuring or using your TG590.
Topic
Page
9.1 Package Contents
9.2 System Requirements
9.3 ?
9.4 ?
Feature availability
Depending on the configuration offered by your service provider, some features may not be available on your
TG590. For more information, please contact your service provider.

105
9 Troubleshooting
The TG590’s System Monitoring screens display important system information, including basic settings, system log,
key network device parameters and network traffic statistics.
9.1 Status
Click System Monitoring at the top of the Home screen to display the “ Status” screen, which displays the TG590’s
basic settings.
9.2 Advanced Status
After selecting Advanced Status and clicking Yes in the Warning screen, the monitoring options appear: System
Logging, Full Status/System wide Monitoring of Connections, Traffic Monitoring, and Broadband Monitoring.
9.2a System Logging
Click System Logging in the Advanced Status screen to generate the “System Log” screen. The System Log displays a
list of the most recent activities of the TG590.
9.2b Full Status/System wide Monitoring of Connections
1. Click Full Status/System wide Monitoring of Connections in the Advanced Status screen (and click through the
Warning screen) to generate the “Full Status/System wide Monitoring of Connections” screen, which features a
table summarizing the monitored connection data.
2. Click Refresh to update the table, or click Automatic Refresh On to constantly update the displayed parameters.
9.2c Traffic Monitoring
The TG590 constantly monitors traffic within the local network and between the local network and the Internet. To
view up-to-the-second statistical information about data received from and transmitted to the Internet, and about
data received from and transmitted to computers in the local network, click Traffic Monitoring in the Advanced Status
screen. This generates the “Traffic Monitoring” screen.
9.2d Bandwidth Monitoring
To monitor the TG590’s bandwidth use, click Bandwidth Monitoring. The “Bandwidth Monitor” screen appears.

106
107
Check the LEDs
If the TG590 does not work as expected, the status LEDs on the front panel may provide you enough information to
locate the problem:
LED
Color
State
Description
Ethernet LAN
Green
Solid
Connected to the Ethernet device, no data traffic ongoing
Blinking
Connected to the Ethernet device, data traffic ongoing
Off
No device connected.
Coax LAN
Green
Solid/
Blinking
One or more devices (e.g. a Set-top-box) are connected to
the local coaxial network.
Off
No devices connected to the local coaxial network.
USB
Green
Solid
USB device connected to the USB port.
Off
No USB device connected to the USB port.
Wireless
Solid
Green
Wireless is enabled on your TG590, no traffic ongoing.
Blinking
Wireless is enabled on your TG590, traffic ongoing.
Off
Wireless is disabled on your TG590.
LED
Color
State
Description
Power
Green
Solid
Powered on.
Blinking
Upgrade ongoing.
Do not remove any cables or switch of the
TG590 when the TG590 is upgrading.
Orange
Blinking
Starting upgrade mode.
Off
Not powered.
Ethernet WAN
Green
Solid
Ethernet connection to the Verizon Optical Network
Terminal (ONT) operational, activity.
Blinking
Ethernet connection to the Verizon Optical Network
Terminal (ONT) operational, no activity.
108
Off
No Ethernet connection to the Verizon
Optical Network Terminal (ONT).
Coax WAN
Green
Solid/
Blinking
Connected to the Verizon Optical Network
Terminal (ONT) using the Coax port.
Off
Not connected to the ONT using the Coax port.
Internet
Green
Solid
Connected to the Internet, no activity detected.
Blinking
Connected to the Internet, activity.
Amber
Solid
Failed to connect to the Internet.
Off
The TG590 is either powered off or starting up.
Poor wireless connectivity
Try the following:
1) Change the wireless channel.
Note: The default setting automatically selects the best wireless channel.
2) Check the signal strength, indicated by the wireless client manager. If the signal is low, try to move the TG590 for
optimal performance.
3) Use WPA2-PSK as encryption.
Resetting your TG590
If at some point you can no longer connect to the TG590 or you want to make a fresh install, it may be useful to
perform a reset to factory defaults.
Warning: A reset to factory default settings deletes all configuration changes you made.
Proceed as follows:
1) Make sure the TG590 is turned on.
2) Push the Reset button on the back panel until the Power LED lights red - this will take about 5 seconds.
3) Release the Reset button.
4) The TG590 will restart.
Call the Help Desk
If you did not find a solution in the Troubleshooting section, please call the Help Desk at 800-837-4966.