Wistron NeWeb DRUZ USB WLAN Dongle User Manual DRUZ 81 G Manual Eng fcc
Wistron NeWeb Corporation USB WLAN Dongle DRUZ 81 G Manual Eng fcc
Manual revised

Wireless 802.11g
USB 2.0 Adapter
User’s Manual
Wistron NeWeb Corporation
Version 1.0__August, 2004

1
Copyright Statement
No part of this publication may be reproduced, stored in a retrieval system,
or transmitted in any form or by any means, whether electronic, mechanical,
photocopying, recording or otherwise without the prior writing of the
publisher.
Windows TM 98SE/Me/2000/XP are trademarks of Microsoft® Corp.
Pentium is a trademark of Intel.
All copyright reserved.

2
Regulatory Information
Federal Communication commission interference Statement
This equipment has been tested and found to comply with the limits for a Class
B digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and can radiate radio
frequency energy and, if not installed and used in accordance with the
instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and
on, the use is encouraged to try to correct the interference by one of the
following measures:
Ø Reorient or relocate the receiving antenna.
Ø Increase the separation between the equipment and receiver.
Ø Connect the equipment into an outlet on a circuit different form that to
which the receiver is connected.
Ø Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: To assure continued compliance, (example-use only shielded
interface cables when connecting to computer or peripheral devices) any
changes or modifications not expressly approved by the party responsible for
compliance could void the user’s authority to operate this equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions:
(1) This device many not cause harmful interference, and
(2) This device may accept any interference received, including interference
that may cause undesired operation.
Important Notice:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set
forth for an uncontrolled environment.
End users must follow the specific operation instruction for
satisfying RF exposure compliance.
This transmitter must not be co-located or operating in conjunction
with any other antenna or transmitter.

3
Table of Contents
1 Introduction ____________________________________________4
1.1 Package Contents __________________________________________4
1.2 Main Features of 802.11g USB 2.0 Adapter____________________5
1.3 Wireless Networking Scenarios ______________________________5
1.4 Advantages for Using Wireless Network_______________________7
2 Quick Start Guidance_____________________________________8
2.1 Installation _______________________________________________8
2.2 Connecting to an Existing Network__________________________10
2.3 Connecting to an Access Point (AP) _________________________14
3 Step-by-Step Installation _________________________________15
3.1 Installing WLAN 802.11g USB2.0 Adapter_____________________15
3.1.1 Additional Setup Processes_________________________________19
3.2 Setting Your 802.11g USB 2.0 Adapter _______________________20
3.3 Removing Your 802.11g USB 2.0 Adapter _____________________21
3.4 Uninstalling Your 802.11g USB 2.0 Adapter ___________________21
4 Creating an Ad-Hoc Network ______________________________23
5 Acting as an Access Point (AP)_____________________________25
6 Using the Utility (Client) _________________________________29
6.1 Link Status Tab ___________________________________________29
6.2 Configure Profile Tab______________________________________30
6.3 Site Survey Tab ___________________________________________31
7 Using the Utility (AP) ____________________________________32
7.1 AP Information Tab________________________________________32
7.2 Access Point Setting_______________________________________33
8 Network Application_____________________________________34
8.1 Surveying the Network Neighborhood _______________________34
8.2 File Sharing ______________________________________________35
9 Product Specification____________________________________37
10 Glossary_______________________________________________38

4
1 Introduction
Thank you for purchasing our 802.11g USB 2.0 Adapter, and welcome to
Wireless LAN- the easiest way to wireless networking!
This user’s manual introduces our 802.11g USB 2.0 Adapter and describes the
most common configurations, which will help you connect to your network
easily. Please read this guide to get familiar with the IEEE 802.11g Wireless
LAN. This manual contains detailed instructions in operation of this product.
Please keep this user’s manual for future reference.
As this product is designed especially to run under Microsoft Windows’ system,
it is recommended that to be installed by people who are familiar with the
installation procedures for network operating systems under Microsoft
Windows.
1.1 Package Contents
Your 802.11g USB 2.0 Adapter kit includes following items:
u 1 x 802.11g USB 2.0 Adapter;
u 1 x CD (Utility and Driver Installation Software);
u 1 x User’s Manual.
Note! If any of the items mentioned are missing or mismatched, please
contact your distributor.

5
1.2 Main Features of 802.11g USB 2.0 Adapter
ü Compact Size for Easy Wireless Enjoyment.
ü High-speed Wireless Connection, up to 54Mbps.
ü IEEE 802.11g (DSSS) Standard for 2.4GHz Wireless LAN.
ü Plug-and-Play Installation.
ü Full Mobility and Seamless Cell-to-Cell Roaming.
ü Worldwide Radio Support.
ü Five Times Faster than 802.11b Wireless LANs.
ü Backward Complaint with 802.11b.
ü Support of the standard Access Point mode for connection to wireless
clients.
ü Supports up to 128-bit WEP.
ü Includes Ad Hoc Mode and Infrastructure Mode Access.
ü Longer Range Support than 802.11a-based WLAN.
1.3 Wireless Networking Scenarios
As our 802.11g USB 2.0 Adapter is interoperable and compatible with other
IEEE 802.11g compliant products from other manufacturers, it offers you the
most freedom to establish your ideal wireless network. Therefore, after
installing 802.11g USB 2.0 Adapter, you can connect your computer to:
1. A Peer-to-Peer Workgroup of 802.11g compliant wireless devices.
2. A LAN (Local Area Networking) constructed by Access Point(s) or other
802.11g compliant systems.
3. Share your Internet access by using just one connection, share printers
and other peripheral devices, share data and image files between
networked PCs, play multi-player games, and use other network enabled
sharing resources.

6
Ad Hoc Mode
A group of wireless stations can form a wireless network without a centralized
Access Point involved. This is called an Independent Basic Service Set (IBSS
or Ad Hoc).
An Ad Hoc Network could be easily set up with this 802.11g USB 2.0 Adapter,
PCs or other WLAN devices. Therefore, it is very convenient to build a network
for temporary use, such as for demonstration in exhibition, for new sales
point/branch use and alike.
Cooperate LAN (Local Area Networking)
With some 802.11g USB 2.0 Adapters and Access Points, it will be easy to
construct a LAN with access to Internet for enterprise use.
The construction is quite easy that 802.11g USB 2.0 Adapter and Access Point
will automatically work at the most suitable frequency when Access Point is set
within the proper range.
In addition, commonly manufactures will bundle the Site-Survey tool for users
to check the communication quality.

7
1.4 Advantages for Using Wireless Network
802.11g USB 2.0 Adapter can wirelessly transmit and receive data, minimizing
the need for wired connections, at a speed of up to eleven megabits per
second. With the 802.11g USB 2.0 Adapter you can locate your PC wherever
you want without wires or cables.
The 802.11g USB 2.0 Adapter provides LAN users with an access to real-time
information anywhere in their organization. The mobility provides effectiveness
and efficiency, which are not available under wired networks.
The 802.11g USB 2.0 Adapter configuration is easy to switch between
peer-to-peer networks, suitable for a small number of users, and full
infrastructure networks of thousands of users that allow roaming around a
broad area.
Therefore, you may see many advantages for adopting Wireless Networking
as follows:
- Less Space Limits: The 802.11g USB 2.0 Adapter provides access to
network services without wires; therefore, it gives you more freedom to
allocate and style your living and working space. In addition, in some
areas where is hard or expensive to connect to wired networks, such as
historic buildings, classrooms or mobile connectivity, then you can count
on wireless networking.
- Flexible Workgroups and Lower Cost: For workspaces that are
frequently reconfigured for temporarily use such as demo in exhibitions,
wireless networking is easy to set up of lower total cost—and all
equipments are recyclable. You do not have to remove the old wires and
then build up the new ones again and again.
- Networked Conference Rooms: Users can access the network as they
move from a meeting to another, getting the access to information/data
and the ability to communicate decisions while “on the go”.
- Ad Hoc Networking: On site consulting and small workgroups may
increase productivity with quick network setup and collaboration software.
- Branch Office Networking: With an Access Point to bridge between the
LAN and Internet, wireless networking provides an easy to install, use and
maintain network for a remote or sales office.
- Campus-Wide Network Mobility: The roaming capabilities allow
enterprise to set up easy to use wireless networks that cover the entire
campus transparently.
8
2 Quick Start Guidance
2.1 Installation
1. Insert the Installation CD. It automatically starts the setup program for
software installation.
9
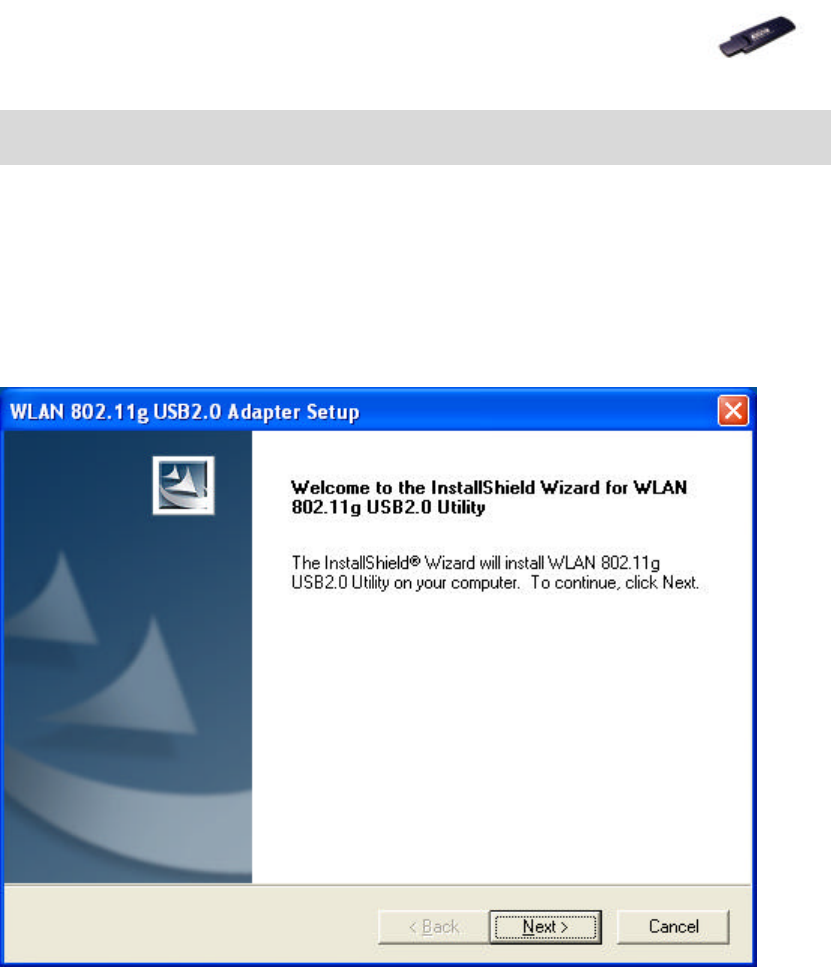
2. Follow the Installation Wizard to complete the software installation
process and restart your computer if necessary.
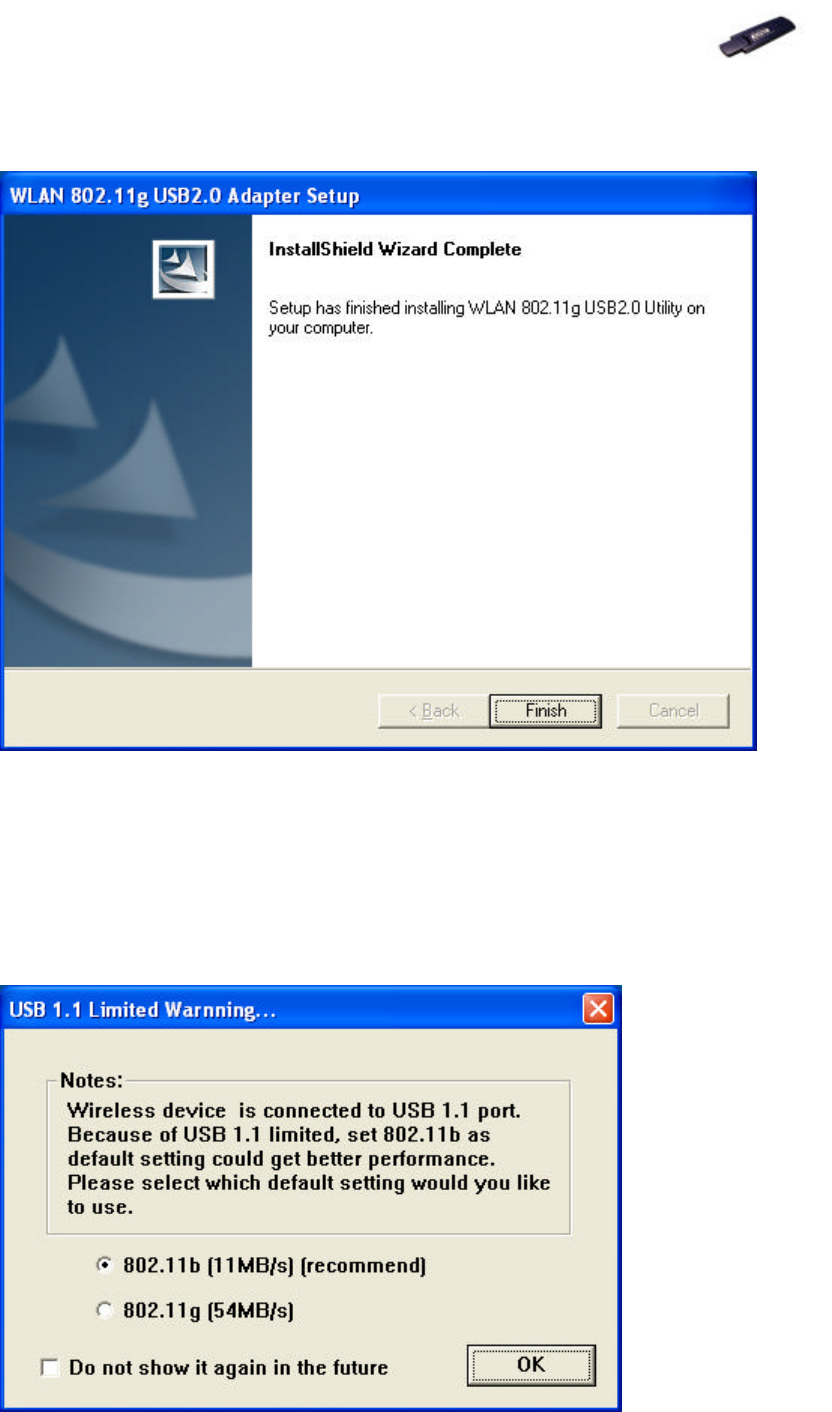
3. Connect your 802.11g USB 2.0 Adapter to your laptop PC or desktop PC.
Note! If your device is connected to an USB 1.1 port, a pop-up message
indicates on your screen, reminding you to set 802.11b as the
default setting to get a better connection quality.
10
4. Operation System will detect new device and verify the driver
automatically.
2.2 Connecting to an Existing Network
1. Go to Windows Start > Programs > WLAN 802.11g USB2.0 Utility >
WLAN 802.11g USB2.0 Utility to open the utility. The 802.11g USB2.0
Adapter Utility window appears. You can see the wireless configuration
icon in Windows System Tray. Double click the shortcut icon or the
wireless configuration icon to open the utility.
2. 802.11g USB2.0 Adapter automatically searches and connects to an
available network (network with security disabled) if there is any. And then
the red wireless configuration icon changes to Green . Follow the next
step to connect to a designated network.
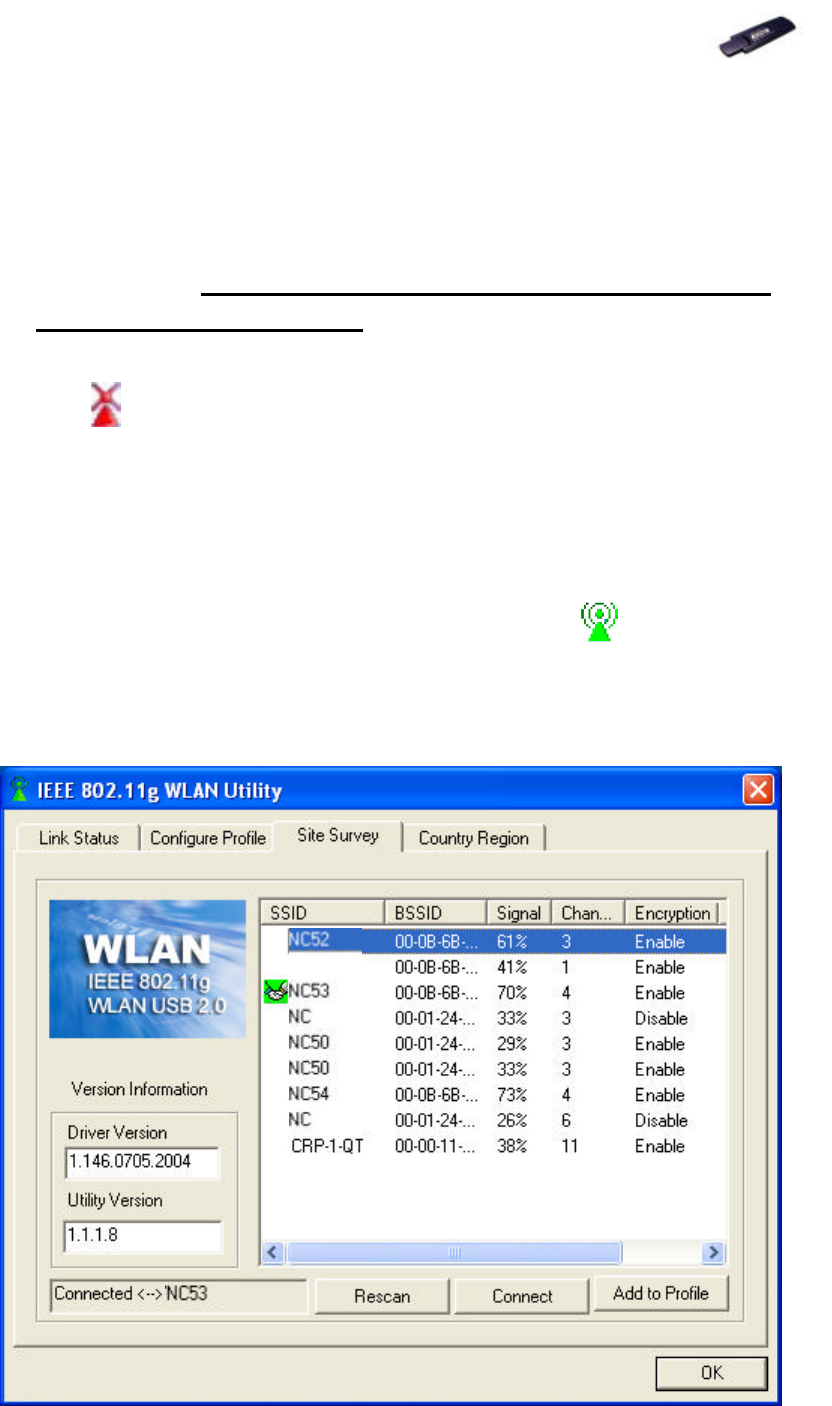
3. In Site Survey tab, choose (click) one network from the listed available
networks list, and click OK button.
11
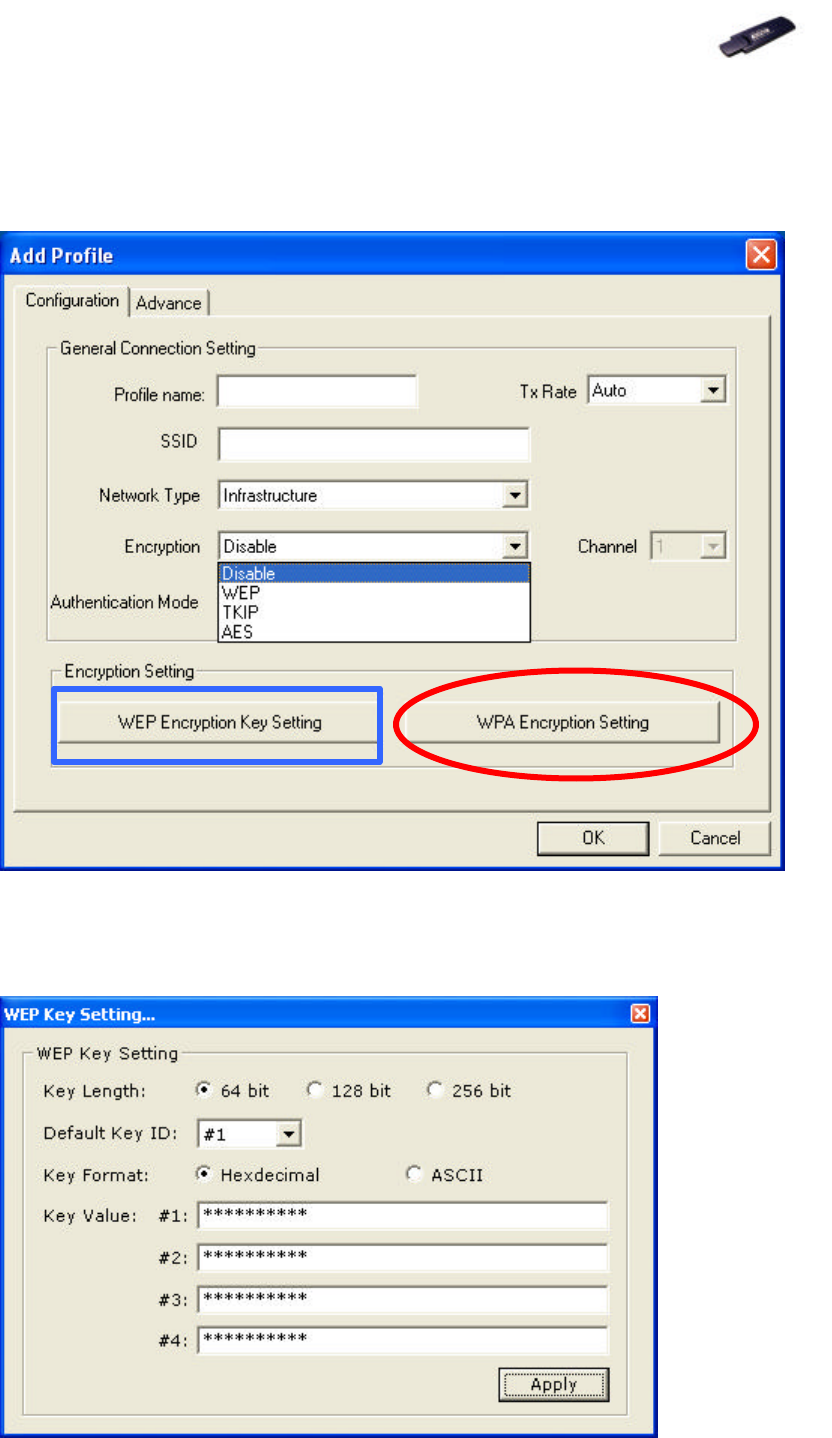
4. If the chosen network is security enabled, in Configure Profile tab click
Add and Add Profile window pops up. In Configuration tab, you can
either click WEP Encryption Key Setting or WPA Encryption Setting for
the Encryption Setting.
Ø In WEP Encryption Key Setting’s menu, click Change button and create
WEP keys manually. Insert the network key for Key Value, click Apply to
confirm the setting.
12
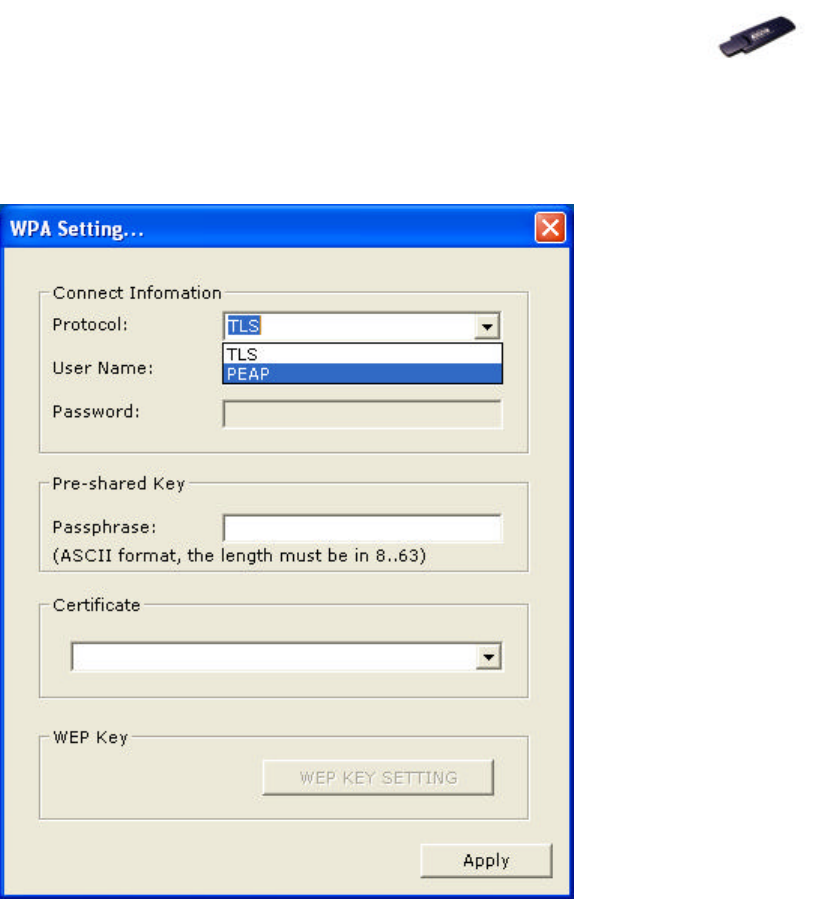
Ø In WPA Encryption Setting’s menu, select specific Protocol, key in User
Name and Password for authentication, then click Apply button. (Further
details contact your network provider).
13
5. Once connected, the wireless configuration icon appears green and the
icon shown in selected networks appears connected. You can click
Link Status tab to check the connection status.
6. For details of each tab in WLAN 802.11g USB2.0 Utility, please read
Chapter 6.

14
2.3 Connecting to an Access Point (AP)
Your 802.11g USB 2.0 Adapter also enables a group of wireless stations to
communicate with each other through it. Such a network is called an
Infrastructure BSS.
When the 802.11g USB 2.0 Adapter used as an ACCESS POINT(AP) , it can
be configured to operate as the following network configuration:
Your 802.11g USB 2.0 Adapter functioned as the ACCESS POINT (AP) further
provides bridging functions between the wireless network and the wired LAN
network.

15
3 Step-by-Step Installation
This section will lead you through the installation of 802.11g USB 2.0 Adapter
(both software and hardware) in detail. People who are familiar with the
installation and settings of wireless device may refer to Quick Start Guidance
to establish a network in a snap.
To establish your wireless network connection, the following steps should be
executed:
1. Install the software by using the installation CD.
2. Install the 802.11g USB 2.0 Adapter.
3. Install the required network protocols to communicate with your network.
Mostly, you will need to set the TCP / IP protocol.
The product is designed to operate under Windows 98SE, Me, 2000 and XP.
The installation procedure is about the same. Please follow the installation
wizard to install the software.
3.1 Installing WLAN 802.11g USB2.0 Adapter
Note! Please install the software before inserting the 802.11g USB 2.0
Adapter.
1. Insert the Installation CD. Insert the installation CD into your CD-ROM
drive. The Setup program automatically starts.
16
2. Click Next>.
3. Click Yes.
17
4. Read the Destination Folder and click Next>. The default destination
folder is displayed in the setup dialog box. You may change the default
folder by clicking “Browse” and select the destination folder you prefer.
Click Next> to go to the next screen.
18
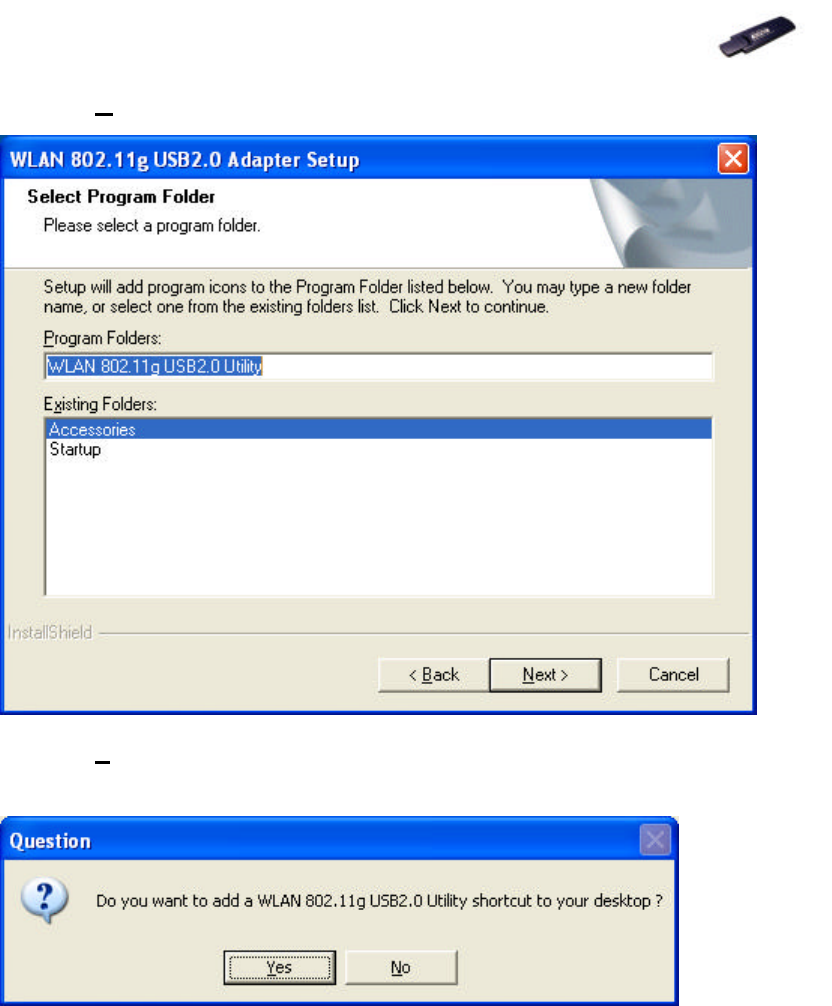
5. Click Next>.
6. Click Yes to create a shortcut. Installation is completed. Restart your
computer if necessary.
7. Connect the 802.11g USB 2.0 Adapter to your laptop PC/desktop PC.

19
3.1.1 Additional Setup Processes
During software installation procedure, each operating system may prompt
different specific options. Mostly, you will be asked to add some necessary
protocols and to edit some networking settings.
1. Windows 98SE: The system may request the original Windows CD during
the installation process. Please check with the network administrator for the
values of the settings. When the installation is finished, you’ll have to
restart your computer.
2. Windows Me: Please check with the network administrator for the values
of the settings. Please restart your computer when the installation is
finished.
3. Windows 2000: When ”Welcome to the InstallShield Wizard for WLAN
802.11g USB2.0 Utility” appears on the screen, click “Next” to continue
installation.
4. Windows XP: When ”Welcome to the InstallShield Wizard for WLAN
802.11g USB2.0 Utility” appears on the screen, click “Next” to continue
installation.

20
3.2 Setting Your 802.11g USB 2.0 Adapter
Your 802.11g USB 2.0 Adapter has its own management software, named
IEEE 802.11g WLAN Utility. You can control all provided functions from it. The
wireless configuration icon is displayed on the Windows System Tray.
The IEEE 802.11g WLAN Utility contains three major tabs: Link Status,
Configure Profile, Site Survey.
Wireless Configuration Icons:
ü Connected (Green)
ü Disconnected (Red)
To communicate in a Peer-to-Peer network, every station must have the same
channel number and Network Name, and all connected computers should
have the same net ID and subnet ID.
Note! To open IEEE 802.11g WLAN Utility, you may double click the
wireless configuration icon in the Windows System Tray.

21
3.3 Removing Your 802.11g USB 2.0 Adapter
You can remove the device after you finished the action with the device.
However, in Windows XP, Me and 2000, please follow the safe removal
procedure. You can figure out a safe removal icon in your computer’s
notification area.
1. Double click the safe removal icon.
2. The “Unplug” or “Eject Hardware” window will pop up. You can select the
device you want to remove.
3. Then click the “Stop” button.
Note! When removing the 802.11g USB 2.0 Adapter, you will lose your
connection to the network. Make sure you have closed all files and
network applications (such as e-mail) prior to removing the 802.11g
USB 2.0 Adapter.
3.4 Uninstalling Your 802.11g USB 2.0 Adapter
1. Make sure the Utility is closed.
2. Go to windows Start > Programs_>WLAN 802.11g USB2.0 Utilily >
UnInstall WLAN 802.11g USB2.0 Adapter.
3. Follow the Uninstall Wizard to complete the uninstallation.
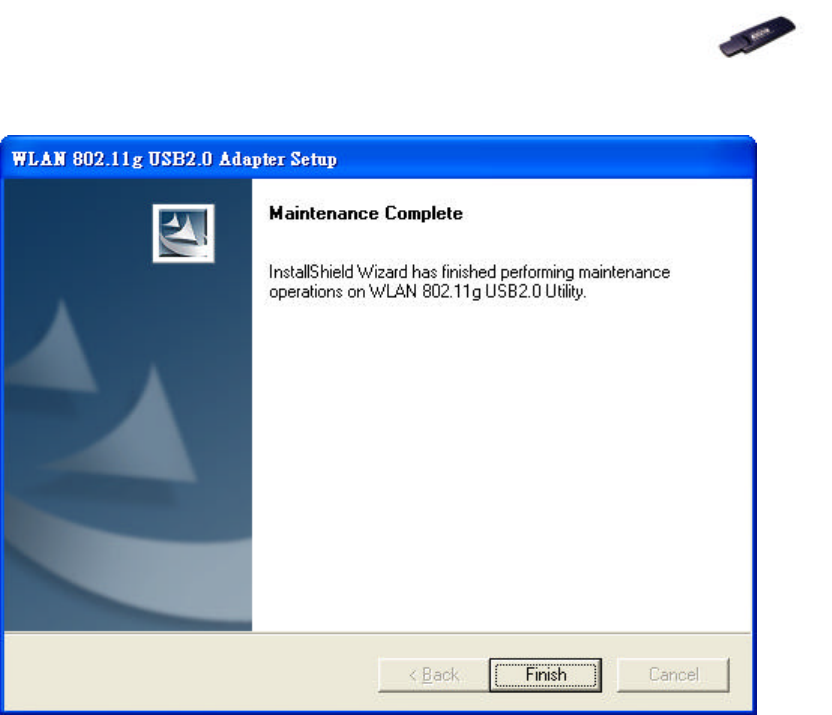
22
4. When the process is completed, click Finish to close the wizard.
23
4 Creating an Ad-Hoc Network
n If you have more computers and only want to place them in a local area
network, or you want to communicate directly without using an Access
Point or any connection to a wired network, you can create a new Ad-Hoc
Network.
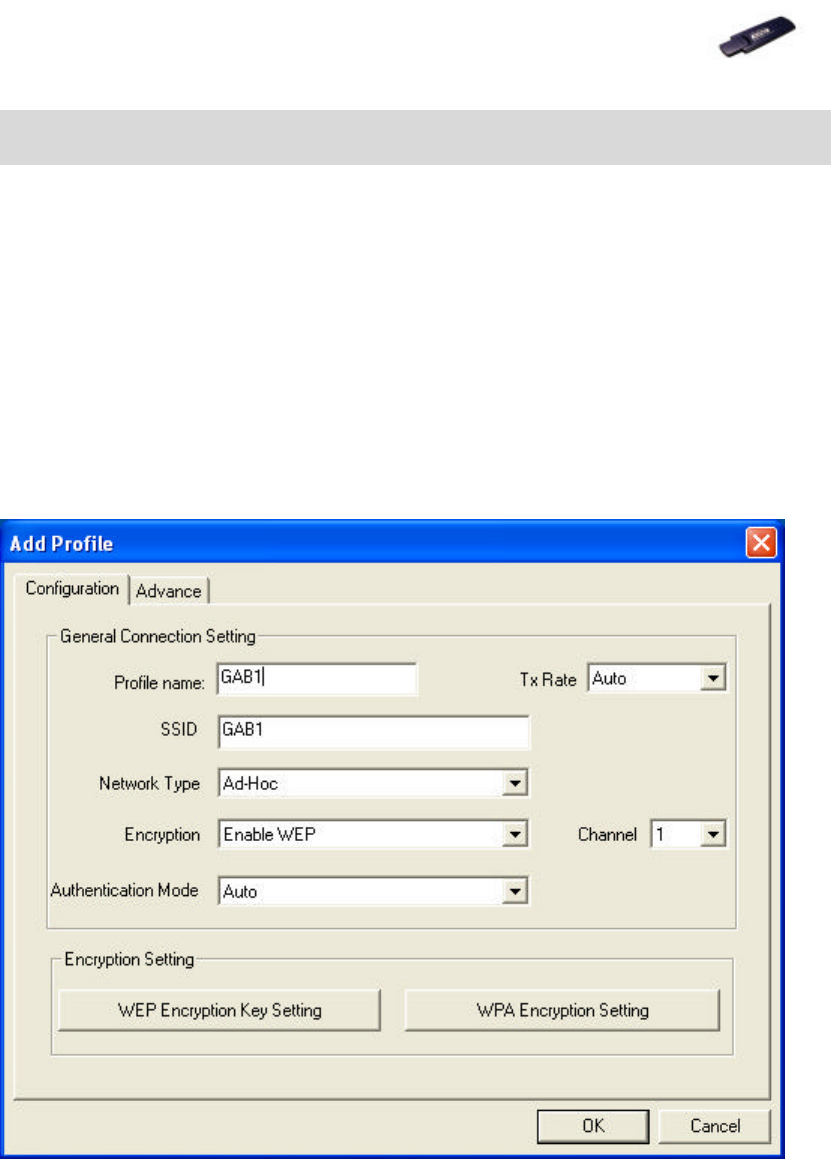
1. In Configure Profile tab, click Add button. Add Profile window pops up.
2. Select Network Type to Ad-Hoc.
3. Set Encryption if necessary.
4. Input Profile name and SSID.
5. The default value for Authentication Mode is set as Auto.
6. Click OK button.
24
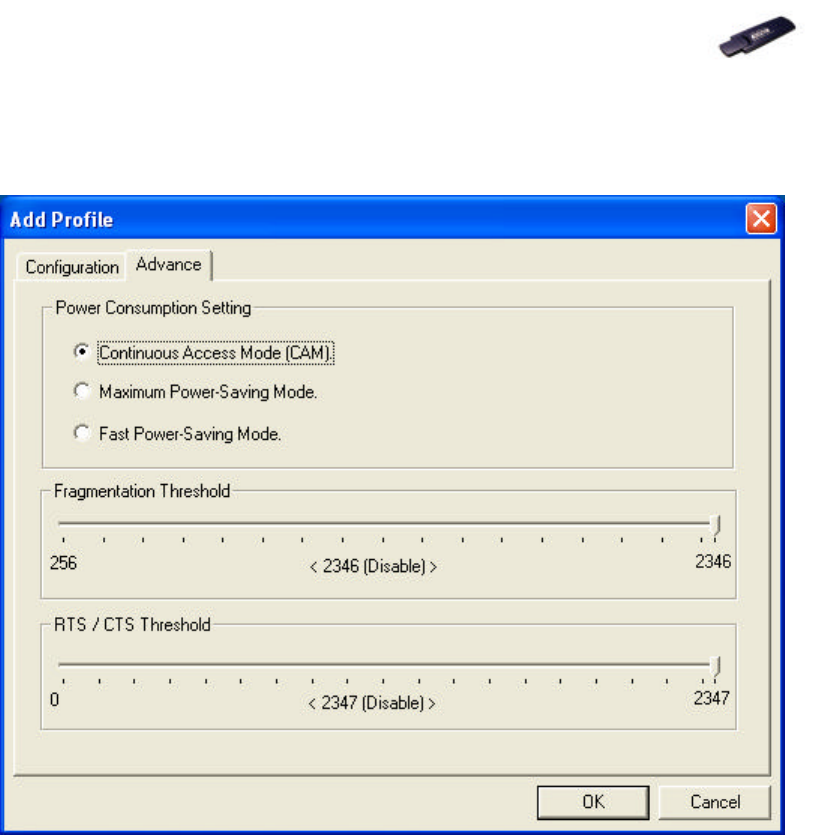
7. In Advance tab (Ad-Hoc Mode), there are alternatives for Power
Consumption Setting, Fragmentation Threshold and RTS/CTS
Threshold.
25
5 Acting as an Access Point (AP)
n The 802.11g USB 2.0 Adapter can function as a simple Access Point (AP),
and act as the center point of a wireless network supporting a data rate of
up to 11 Mbps. It can also connect these wireless devices to wired
network through the LAN interface.
n Radio ON indicates to connect the network ; if you want to disconnect the
network, then click Radio OFF.
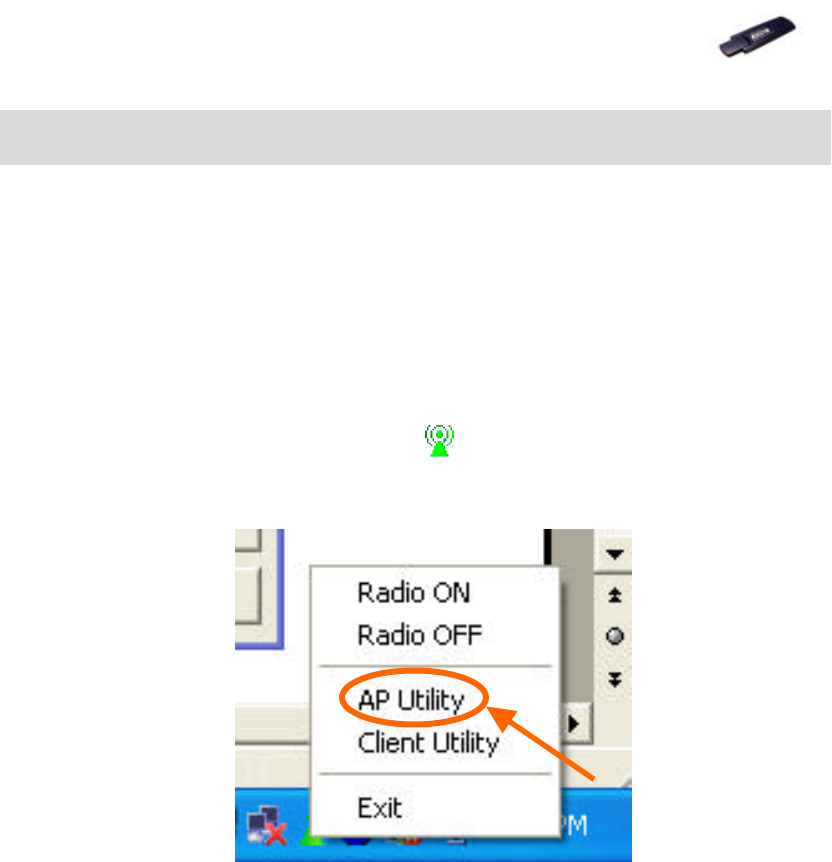
1. Go to the wireless configuration icon in Windows System Tray, press
the right key, an option list pops up and click AP Utility.
26
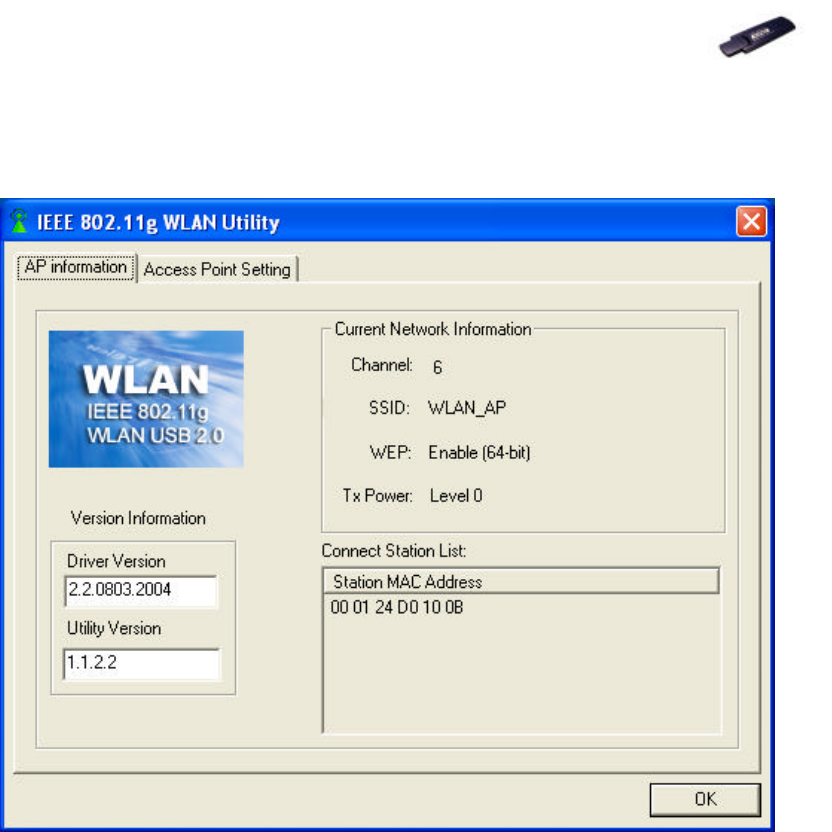
2. In AP information tab, all information related to the Current Network is
listed. The Connect Station List allows you to grant/deny access to/from
specified wireless stations.
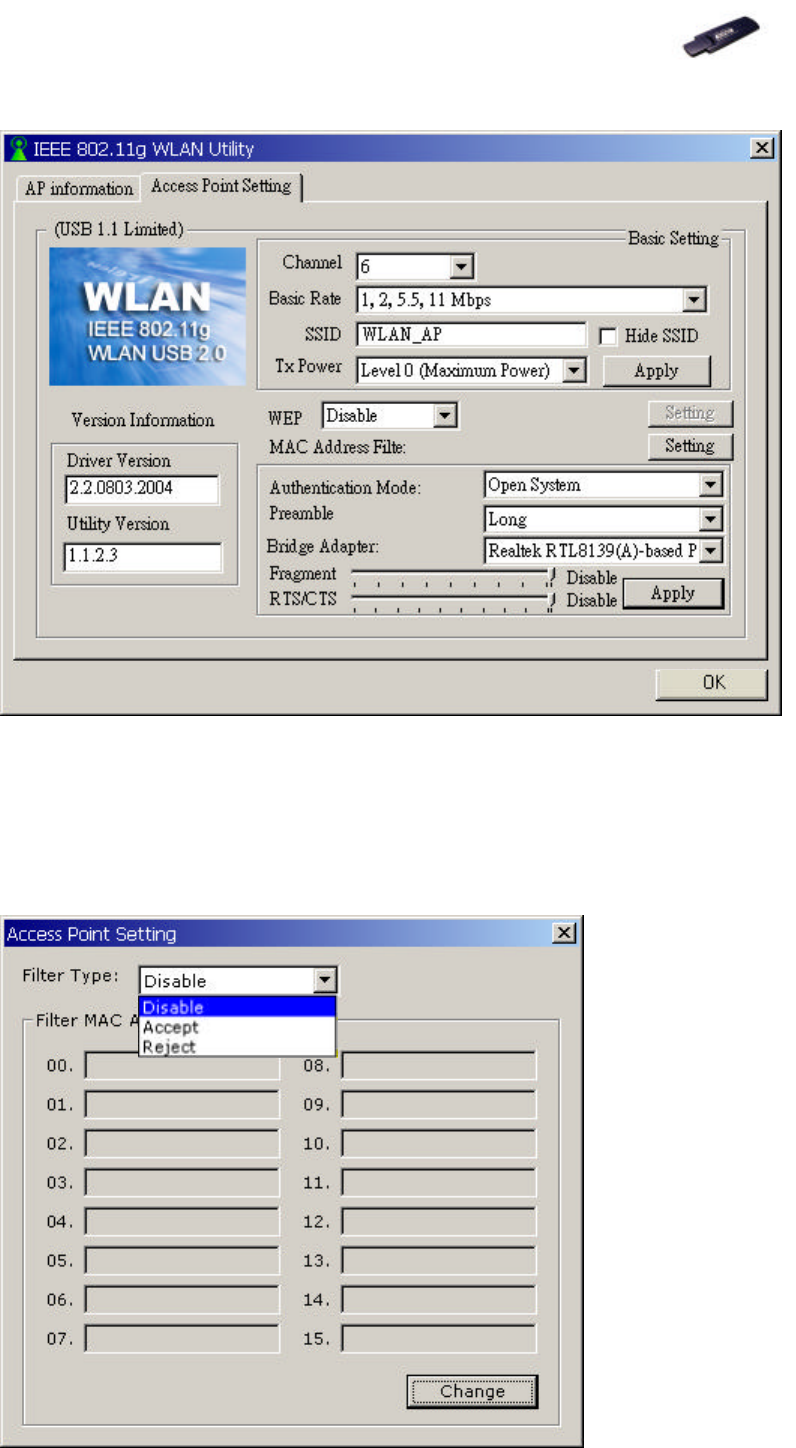
3. In Access Point Setting tab, you can set Channel (1 to 6), Basic Rate
(usually remain as default value), SSID and Tx Power. Your setting will be
consistent as indicated in Current Network information.
27
4. After the Basic Setting is done, click Apply to renew the values.
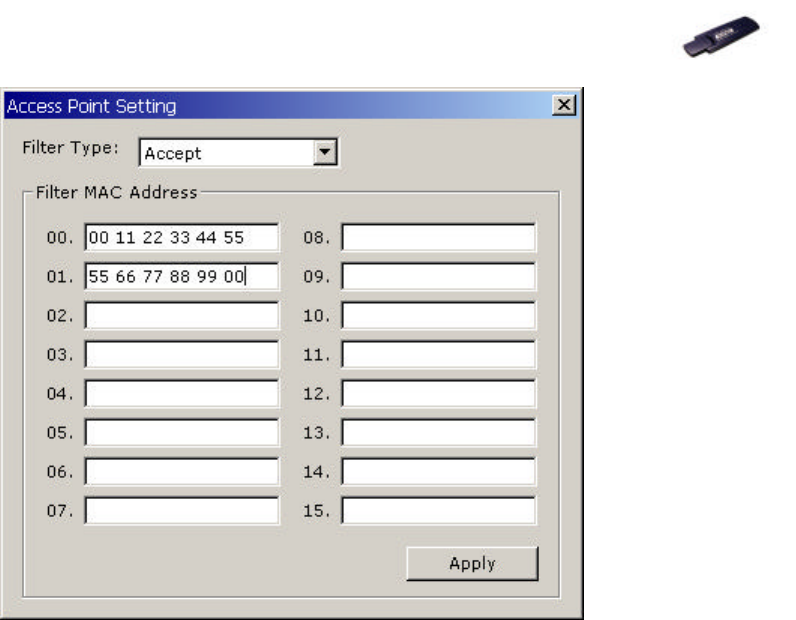
5. For MAC Address Filter setting, you may set Filter Type and add Filter
Mac Address.
ü Filter Type Disable: Not activate Filter Type.
ü Filter Type Accept: Accept networks added in Filter Mac Address.
ü Filter Type Reject: Reject networks noted in Filter Mac Address.
28
6. After setting Filter Type and Filter MAC Address, click Apply to renew the
values.
7. For details of each tab in WLAN 802.11g USB2.0 Utility (for AP Setting),
please read Chapter 7.
29
6 Using the Utility (Client)
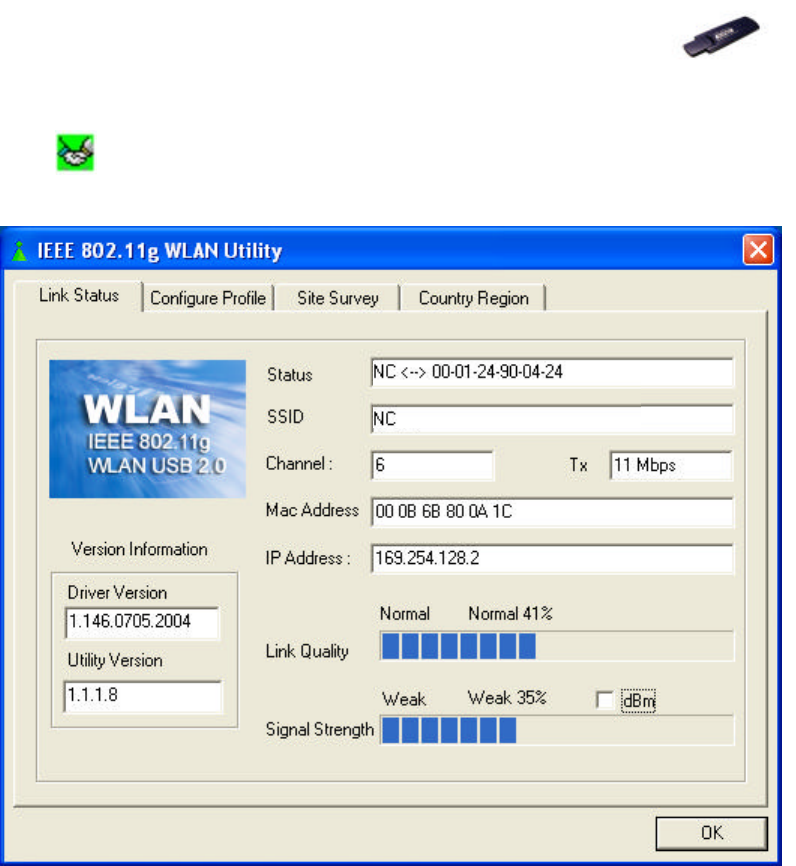
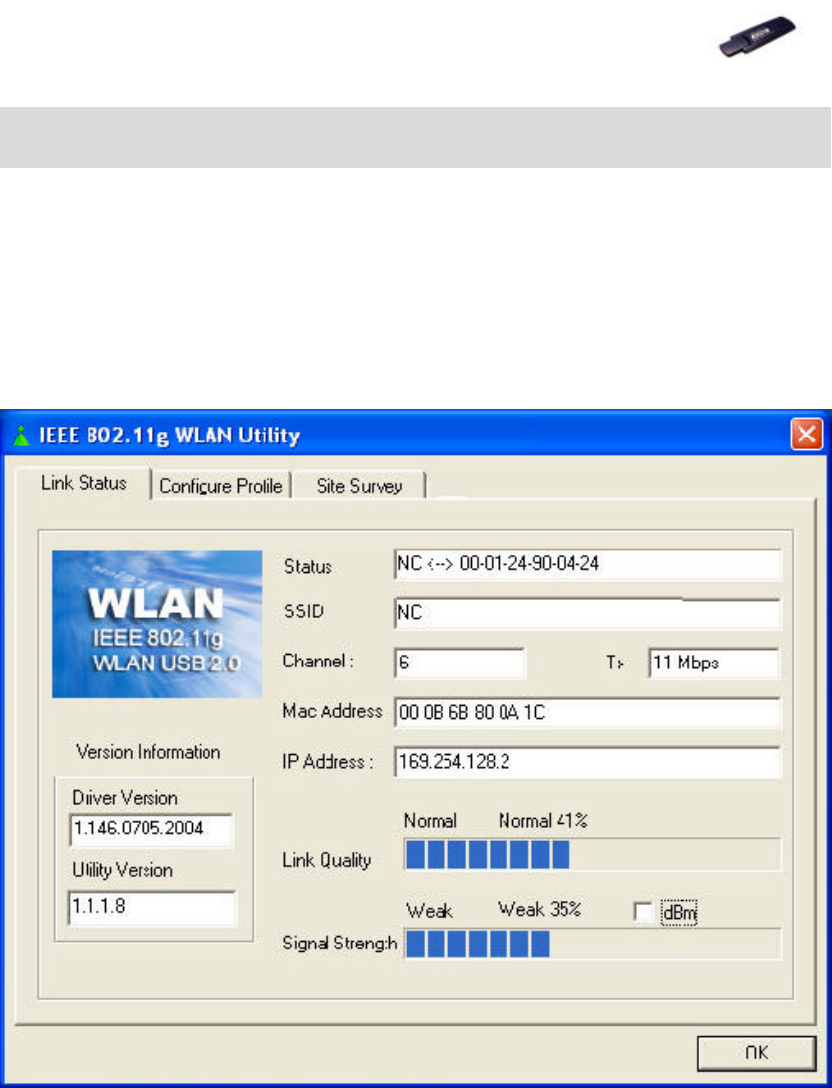
6.1 Link Status Tab
This tab indicates Connection information such as the Status, Link Quality,
Signal Strength, SSID, etc.
30
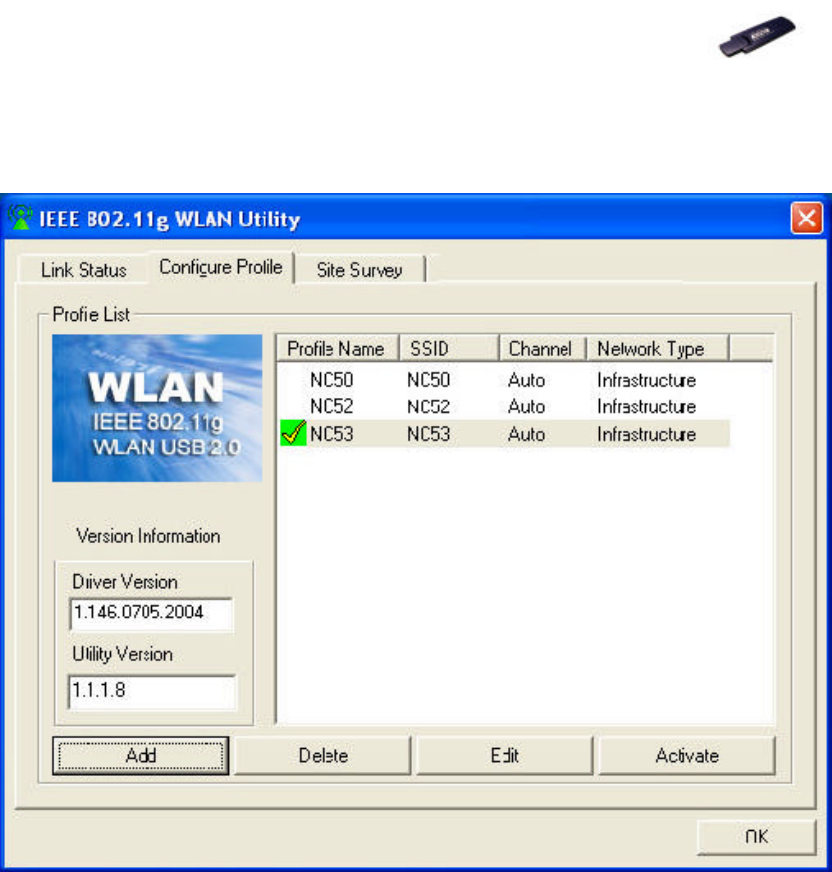
6.2 Configure Profile Tab
1. Profile Name: You may create several profiles to save different sets of
network settings.
2. SSID: The name of the wireless network.
3. Channel: Every station in the network should set the same number of
channel.
4. Network Type: Ad hoc mode or Infrastructure mode.
5. Add button: Click to create a new network.
6. Delete button: Click to remove a selected network.
7. Edit button: Click to modify the network.
8. Activate button: Activate the highlighted profile.
9. Driver Version: Help to recognize the current driver version.
10. Utility Version: Help to recognize the current utility version.
31
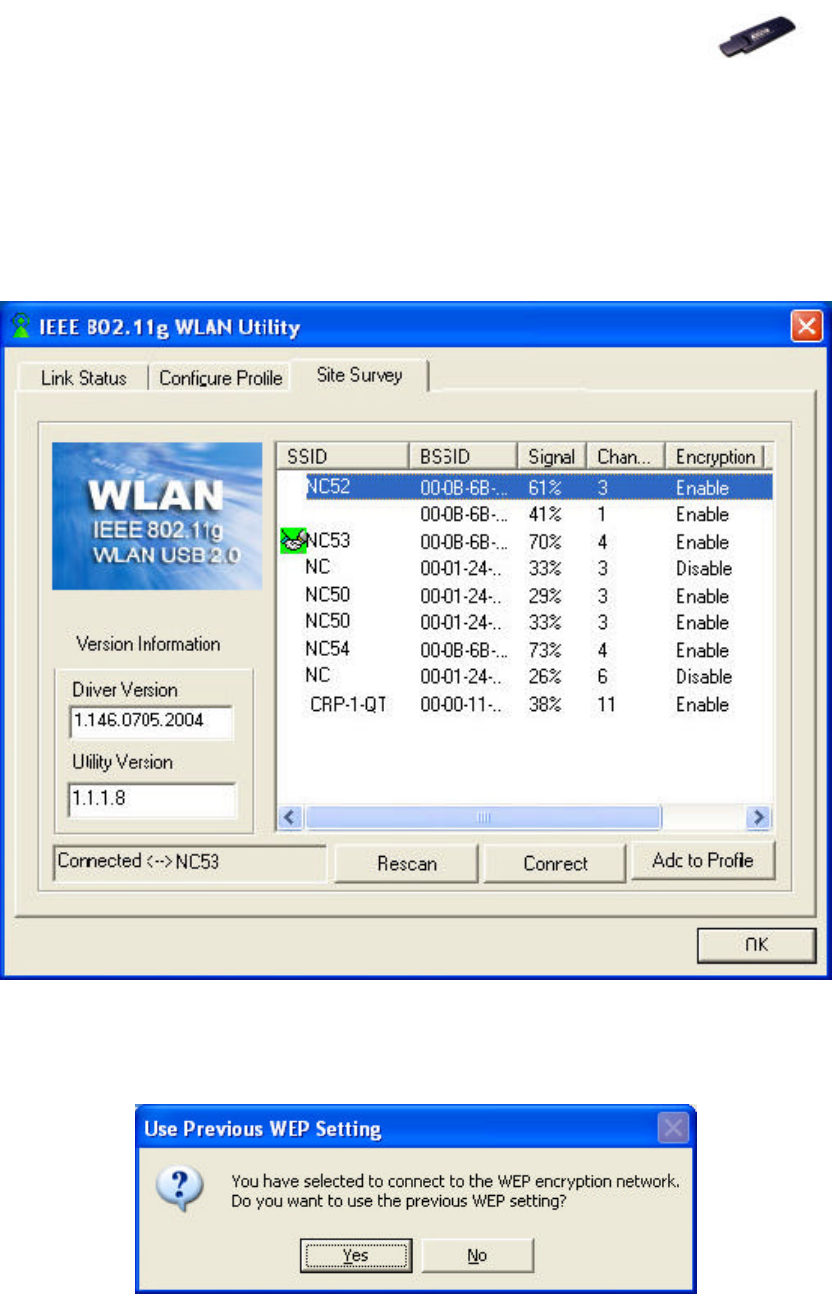
6.3 Site Survey Tab
This tab lists all available networks and indicates each network’s information
such as SSID, BSSID, Signal, Channel and Encryption.
Note! Before changing to another network, a message will pop up asking
you whether to use the previous WEP setting or not.
32
7 Using the Utility (AP)
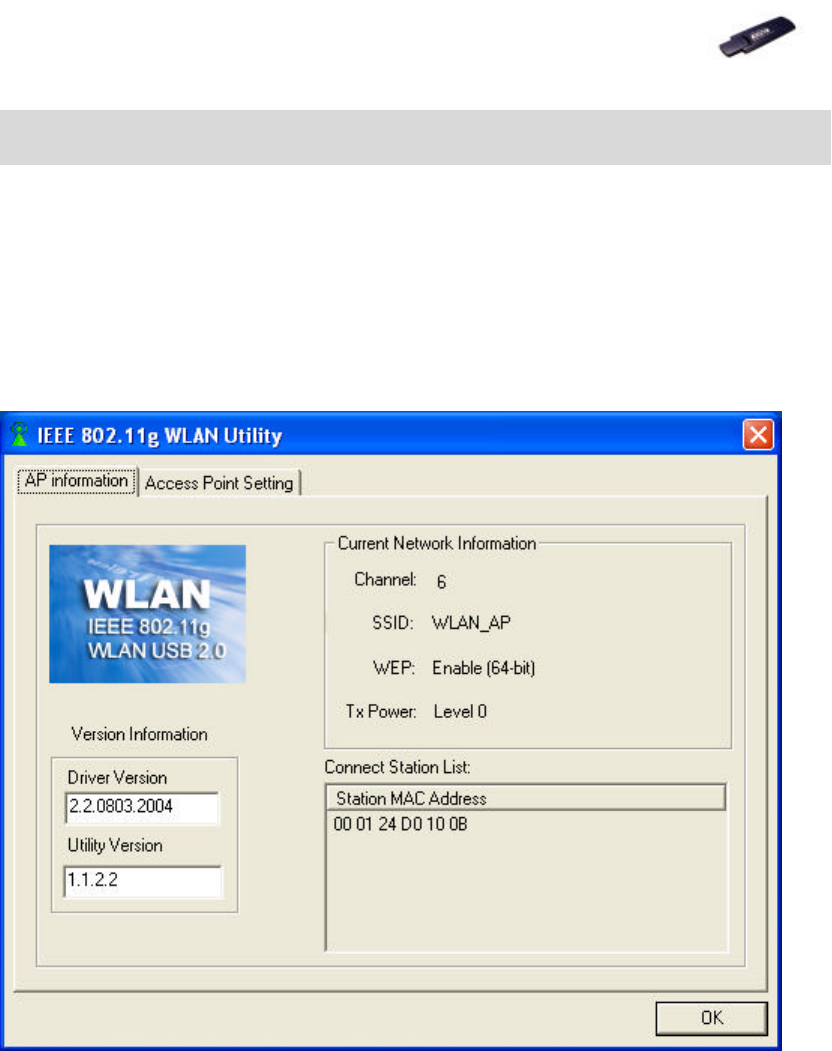
7.1 AP Information Tab
This tab indicates the Current Network Information such as SSID, WEP and
Power Transmission Rate (Tx Power). All Client MAC Addresses will also list in
the Connect Station List.
33
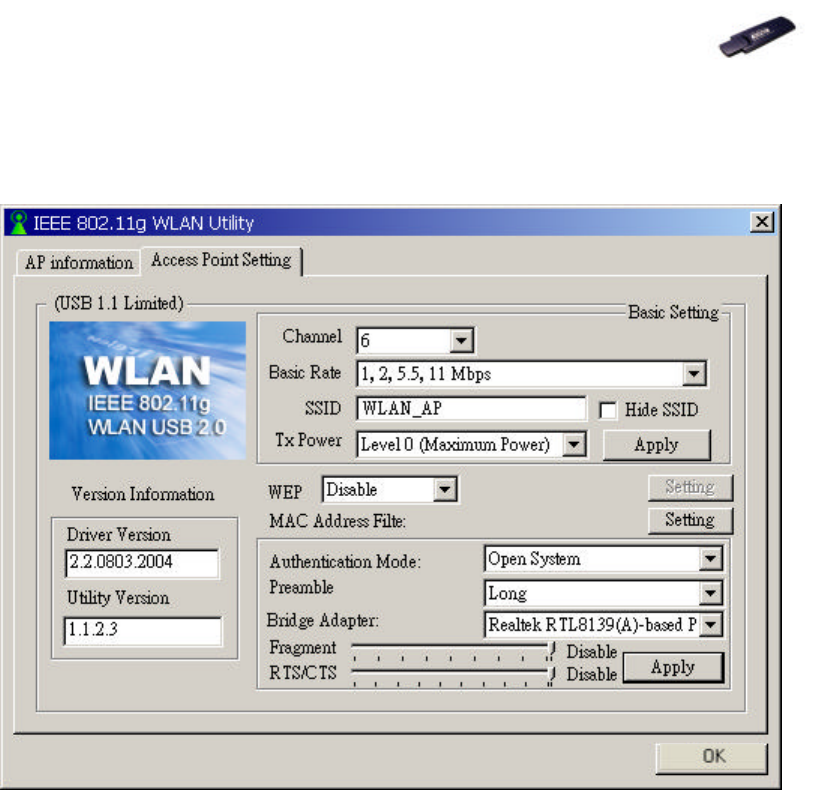
7.2 Access Point Setting
Channel: Six categories (1 to 6).
Basic Rate: Four categories (1, 2, 5.5 or 11 Mbps) of network connecting rate.
SSID: The name of the wireless network.
Hide SSID: Conceal the name of the wireless network while site surveying.
Tx Power: Different power transmission rate can save power cost.
WEP: Two options (Enable/Disable).
Authentication Mode: Two options (Open System/Shared Key).
Preamble: Two options offered (Long/Short).
Bridge Adapter: Activate or not activate bridge adapter.
Fragment: Sending data by batches.
RTS/CTS: RTS: Request To Send; CTS: Clear To Send.

34
8 Network Application
This section consists of the network applications of 802.11g USB 2.0 Adapter,
including:
Ø To survey the network neighborhood
Ø To share your folder with your network member(s)
Ø To share your printer with your network member(s)
Ø To access the shared folder(s)/file(s) of your network members(s)
Ø To use the shared printer(s) of your network member(s)
In fact, the network applications of 802.11g USB 2.0 Adapter are the same as
they are in a wired network environment. You may refer to the following 3
examples of Surveying the Network Neighborhood, File Sharing and Using the
Shared Folder.
8.1 Surveying the Network Neighborhood
When multiple base stations are up and running in your wireless network, you
can use the procedure described below to display the other computers:
Double-click My Network Places to display all stations in your Microsoft
Windows Network Group.
To display other workgroups in the network environment, double-click Entire
Network.
If there is a second network operating system running in your network
environment (for example a Novell NetWare network), the “Entire Network”
window will also display available servers running under the second network
operating system. If you click on these servers, you may be asked to enter
your user name and password that applies to the other network operating
system. If you cannot find it, verify whether the other wireless computers are:
Powered up and logged on to the network.
Configured to operate with identical Microsoft Network settings concerning:
ü Networking Protocol.
ü Wireless Network Name.
To enable the sharing of Internet access, you should set your WLAN mode as
“Infrastructure” and connect to the access point.
35
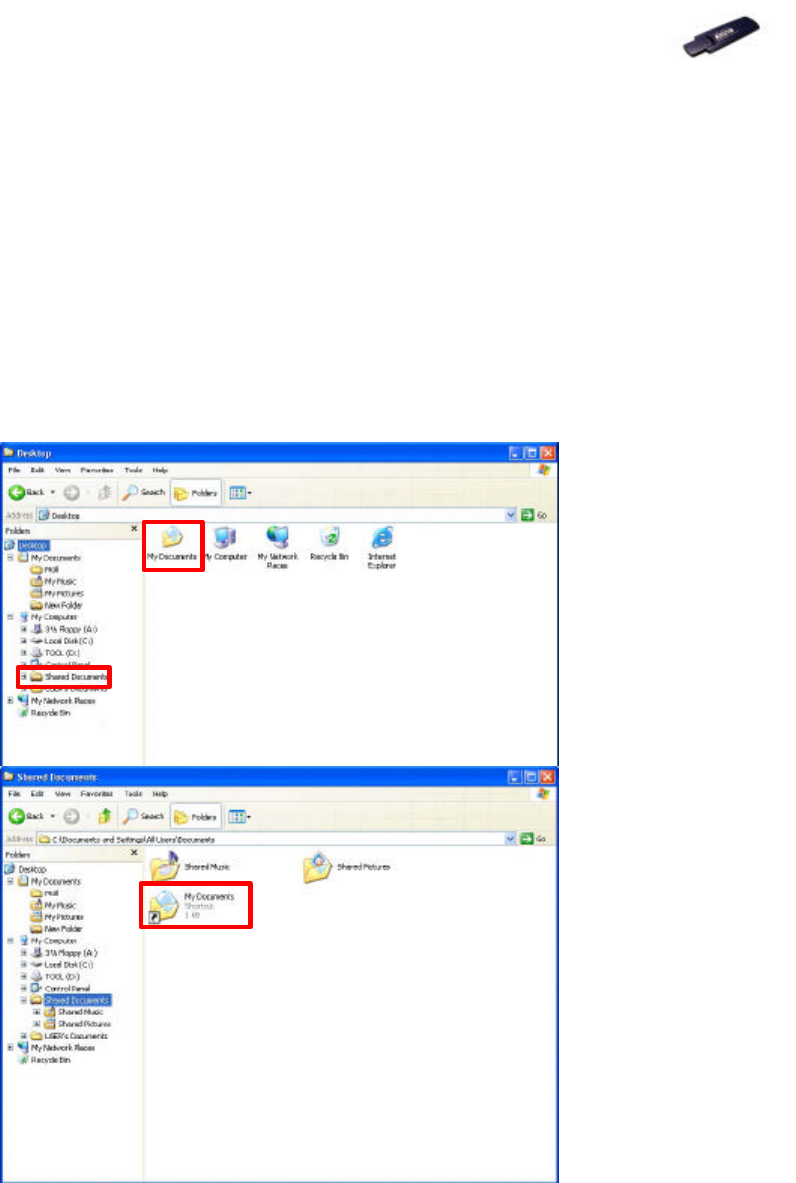
8.2 File Sharing
802.11g USB 2.0 Adapter allows the sharing of files between computers that
are logged onto the same wireless network. If you want to share your folder
“My Documents” with other computers of the wireless network, please
highlight the folder “My Documents” and drag it to Shared Documents
folder.
Sharing files in the IEEE802.11g wireless network will be like sharing files on a
wired LAN.

36
8.3 Using the Shared Folder
If you would like to access a shared folder stored in other stations of same
network, please follow the process below:
Double-click the “My Network Places” icon, and then double-click the computer
where the shared folder is located.
Double-click the folder you want to connect to.
Now you may open the needed file(s).
Note! If a password is required, the Windows will prompt a password
column to you. Then you need to enter the password that had been
assigned to this shared folder.
37
9 Product Specification
Item Key Specifications
Frequency Range Ø DSSS: 2.4~2.483.5GHz
Modulation Technique Ø 802.11g: OFDM
Ø 802.11b: CCK (11Mbps), DQPSK (2Mbps),
DBPSK (1Mbps)
Host Interface Ø USB 2.0
Channels Support Ø US/Canada: 11(1~11)
Output Power Ø 11b:18 dBm
Ø 11g:19 dBm
Operation Voltage Ø 5.0V +/-10%
Power Consumption Ø Transmission Mode: 350mA@5V
Ø Receive Mode: 180mA@5V
Ø Power Saving Mode: 80mA@5V
Ø Suspend Mode: 1.7mA @ 5V
Operation System Supported Ø Windows® XP, 2000, ME
Dimension Ø 80mm (L) x 25mm (W) x 10mm (H)
Weight Ø Approx. 20g.
Security WEP Ø 64-bit/128-bit WEP
Ø AES
Ø WPA
Operation Mode Ø Infrastructure and Ad-Hoc Mode
Transfer Data Rate Ø 802.11g: 6, 9, 12, 18, 24, 36, 48, 54Mbps
Ø 802.11b:1,2, 5.5, 11Mbps
LED Indicator Ø Wireless LAN Activity Indicator
Operation Temperature Ø 00C~550C
Storage Temperature Ø -250C~700C
WHQL Ø Microsoft® XP, 2000 Complaint
EMC Certification Ø FCC part 15 (USA)

38
10 Glossary
CHAP: Challenge Handshake Authentication Protocol. Security feature
supported on lines using PPP encapsulation that prevents
unauthorized access. CHAP does not itself prevent unauthorized
access, but merely identifies the remote end. The router or access
server then determines whether that user is allowed access.
EAP: Extensible Authentication Protocol. Framework that supports multiple,
optional authentication mechanisms for PPP, including clear text
passwords, challenge-response, and arbitrary dialog sequences.
LEAP: Lightweight Extensible Authentication Protocol is a Cisco proprietary
EAP-Type. It is designed to overcome some basic wireless
authentication concerns through Mutual Authentication and the use
of dynamic WEP keys.
MD5: MD5 is an EAP-Type for authentication. It is analogous to the PPP
CHAP protocol. A challenge string is sent from the Authentication
Server to the Supplicant in the MD5-Challenge Request. The
challenge string with the user password is hashed using MD5 and the
hash is returned in the MD5-Challenge Response. The Authentication
Server performs the same hash and compares the result with that
returned by the Supplicant to determine whether the authentication is
a Success.
PAP: Password Authentication Protocol. Authentication protocol that allows
PPP peers to authenticate one another. The remote router attempting
to connect to the local router is required to send an authentication
request. Unlike CHAP, PAP passes the password and the host name
or username in the clear (unencrypted). PAP does not itself prevent
unauthorized access but merely identifies the remote end. The router
or access server then determines whether that user is allowed access.
PAP is supported only on PPP lines.

39
PEAP: Protected Extensible Authentication Protocol is a two-phase
authentication like TLS. In the first phase the Authentication Server is
authenticated to the Supplicant. Using TLS, a secure channel is
established through which any other EAP-Type can be used to
authenticate the Supplicant to the Authentication Server during the
second phase. A certificate is only required at the Authentication
Server. PEAP also supports identity hiding where the Authenticator
is only aware of the anonymous username used to establish the TLS
channel during the first phase but not the individual user authenticated
during the second phase.
SSID: Name of wireless network.
TLS: TLS is an EAP-Type for authentication based upon X.509 certificates.
Because it requires both the Supplicant and the Authentication
Server to have certificates, it provides explicit Mutual Authentication
and is resilient to man-in-the-middle attacks. After successful
authentication a secure TLS link is established to securely
communicate a unique session key from the Authentication Server
to the Authenticator.
TTLS: Tunneled TLS is an EAP-Type for authentication that employs a
two-phase authentication process. In the first phase the
Authentication Server is authenticated to the Supplicant. Using TLS,
a secure channel is established through which the Supplicant can be
authenticated to the Authentication Server using legacy PPP
authentication protocols such as PAP, CHAP, and MS-CHAP. TTLS
has the advantage over TLS that it only requires a certificate at the
Authentication Server. It also makes possible forwarding of
Supplicant requests to a legacy RADIUS server. TTLS also supports
identity hiding where the Authenticator is only aware of the
anonymous username used to establish the TLS channel during the
first phase but not the individual user authenticated during the second
phase.

40
WPA: Wi-Fi Protected Access is a replacement security standard for WEP. It
is a subset of the IEEE 802.11i standard being developed. WPA
makes use of TKIP to deliver security superior to WEP. 802.1X access
control is still employed. The Authentication Server provides the
material for creating the keys.