Zyxel Nsa325 Users Manual Book
2014-12-11
: Zyxel Zyxel-Nsa325-Users-Manual-121987 zyxel-nsa325-users-manual-121987 zyxel pdf
Open the PDF directly: View PDF ![]() .
.
Page Count: 535 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- Media Server
- User’s Guide
- Getting to Know Your NSA
- zMedia App
- NAS Starter Utility
- Web Configurator Basics
- Tutorials
- 5.1 Overview
- 5.2 Windows 7 Network
- 5.3 Windows 7 Network Map
- 5.4 Playing Media Files in Windows 7
- 5.5 Windows 7 Devices and Printers
- 5.6 Creating a Volume in a 2-Bay NSA
- 5.7 Creating a Volume in a 1-Bay NSA
- 5.8 Deleting a Volume
- 5.9 File Sharing Tutorials
- 5.10 Download Service Tutorial
- 5.11 Broadcatching Tutorial
- 5.12 Printer Server Tutorial
- 5.13 Copy and Flickr Auto Upload Tutorial
- 5.14 FTP Uploadr Tutorial
- 5.15 Web Configurator’s Security Sessions
- 5.16 Using FTPES to Connect to the NSA
- 5.17 Using a Mac to Access the NSA
- 5.18 How to Use the BackupPlanner
- Technical Reference
- Status Screen
- System Setting
- Storage
- Network
- Applications
- 10.1 Overview
- 10.2 What You Can Do
- 10.3 What You Need to Know
- 10.4 FTP Server
- 10.5 The Media Server Screens
- 10.6 The Download Service Screen
- 10.7 The Web Publishing Screen
- 10.8 The Broadcatching Screen
- 10.9 The Print Server Screen
- 10.10 The Copy/Sync Button Screen
- 10.11 Technical Reference
- 10.11.1 Sharing Media Files on Your Network
- 10.11.2 Download Service
- 10.11.3 Link Capture Browser Plugin
- 10.11.4 Download Service Notification
- 10.11.5 BitTorrent Security
- 10.11.6 Web Publishing Example
- 10.11.7 Web Publishing
- 10.11.8 Channel Guides for Broadcatching
- 10.11.9 Printer Sharing
- 10.11.10 Copying Files
- 10.11.11 Synchronizing Files
- Package Management
- 11.1 Overview
- 11.2 What You Can Do
- 11.3 What You Need to Know
- 11.4 Package Management Screen
- 11.5 DyDNS Screen
- 11.6 NFS Screen
- 11.7 SMART Screen
- 11.8 Protect Screens
- 11.9 Backup Screens
- 11.10 Restore Screen
- 11.11 Syslog Server Screen
- 11.12 TFTP Server Screen
- 11.13 eMule Screens
- 11.14 pyLoad Screen
- 11.15 Technical Reference
- Auto Upload
- Dropbox
- Users
- Groups
- Shares
- Maintenance Screens
- Protecting Your Data
- Using Time Machine with the NSA
- Troubleshooting
- 20.1 Troubleshooting Overview
- 20.2 Power, Hardware, Connections, and LEDs
- 20.3 NAS Starter Utility
- 20.4 NSA Login and Access
- 20.5 I Cannot Access The NSA
- 20.6 Users Cannot Access the NSA
- 20.7 External USB Drives
- 20.8 Firmware
- 20.9 File Transfer
- 20.10 Networking
- 20.11 Some Features’ Screens Do Not Display
- 20.12 Media Server Functions
- 20.13 Download Service and Broadcatching Functions
- 20.14 Web Publishing
- 20.15 Auto Upload
- 20.16 Package Management
- 20.17 Backups
- Product Specifications
- Setting Up Your Computer’s IP Address
- Pop-up Windows, JavaScripts and Java Permissions
- Common Services
- Importing Certificates
- Legal Information
- Index
- Open Source Licences

www.zyxel.com
www.zyxel.com
Media Server
NSA325
Copyright © 2011
ZyXEL Communications Corporation
Firmware Version 4.3
Edition 1, 08/2011
Default Login Details
Web Address nsa325
User Name admin
Password 1234

About This User's Guide
Media Server User’s Guide 3
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the NSA using the Web Configurator.
Note: This guide is a reference for a series of products. Therefore some features or
options in this guide may not be available in your product.
Tips for Reading User’s Guides On-Screen
When reading a ZyXEL User’s Guide On-Screen, keep the following in mind:
• If you don’t already have the latest version of Adobe Reader, you can download it from http://
www.adobe.com.
• Use the PDF’s bookmarks to quickly navigate to the areas that interest you. Adobe Reader’s
bookmarks pane opens by default in all ZyXEL User’s Guide PDFs.
• If you know the page number or know vaguely which page-range you want to view, you can
enter a number in the toolbar in Reader, then press [ENTER] to jump directly to that page.
• Type [CTRL]+[F] to open the Adobe Reader search utility and enter a word or phrase. This can
help you quickly pinpoint the information you require. You can also enter text directly into the
toolbar in Reader.
• To quickly move around within a page, press the [SPACE] bar. This turns your cursor into a
“hand” with which you can grab the page and move it around freely on your screen.
• Embedded hyperlinks are actually cross-references to related text. Click them to jump to the
corresponding section of the User’s Guide PDF.
Related Documentation
•Quick Start Guide
The Quick Start Guide is designed to help you get your NSA up and running right away. It
contains information on setting up your network and configuring for Internet access.
• Web Configurator Online Help
The embedded Web Help contains descriptions of individual screens and supplementary
information.
Note: It is recommended you use the web configurator to configure the NSA.
•Support Disc
Refer to the included CD for support documents.

Document Conventions
Media Server User’s Guide
4
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
Warnings tell you about things that could harm you or your device.
Note: Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The NSA may be referred to as the “NSA”, the “device” or the “system” in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
• A key stroke is denoted by square brackets and uppercase text, for example, [ENTER] means the
“enter” or “return” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the [ENTER] key. “Select”
or “choose” means for you to use one of the predefined choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For example,
Maintenance > Log > Log Setting means you first click Maintenance in the navigation panel,
then the Log sub menu and finally the Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value. For example, “k”
for kilo may denote “1000” or “1024”, “M” for mega may denote “1000000” or “1048576” and so
on.
• “e.g.,” is a shorthand for “for instance”, and “i.e.,” means “that is” or “in other words”.
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons. The NSA icon is not an exact
representation of your device.
Document Conventions
Media Server User’s Guide 5
Graphics in this book may differ slightly from the product due to differences in operating systems,
operating system versions, or if you installed updated firmware/software for your device. Every
effort has been made to ensure that the information in this manual is accurate.
NSA Computer Notebook computer
Server Television Firewall
Router Switch Wireless Access Point
Internet

Safety Warnings
Media Server User’s Guide
6
Safety Warnings
• Do NOT use this product near water, for example, in a wet basement or near a swimming pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk of electric shock
from lightning.
• Connect ONLY suitable accessories to the device.
• Do NOT open the device or unit. Opening or removing covers can expose you to dangerous high voltage
points or other risks. ONLY qualified service personnel should service or disassemble this device. Please
contact your vendor for further information.
• ONLY qualified service personnel should service or disassemble this device.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device.
• Connect the power adaptor or cord to the right supply voltage (for example, 110V AC in North America or
230V AC in Europe).
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the product where anyone can
walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause electrocution.
• If the power adaptor or cord is damaged, remove it from the power outlet.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order a new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a remote risk of
electric shock from lightning.
• CAUTION: RISK OF EXPLOSION IF BATTERY (on the motherboard) IS REPLACED BY AN INCORRECT TYPE.
DISPOSE OF USED BATTERIES ACCORDING TO THE INSTRUCTIONS. Dispose them at the applicable
collection point for the recycling of electrical and electronic equipment. For detailed information about
recycling of this product, please contact your local city office, your household waste disposal service or the
store where you purchased the product.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your device.
Your product is marked with this symbol, which is known as the WEEE mark. WEEE stands for Waste
Electronics and Electrical Equipment. It means that used electrical and electronic products should not be
mixed with general waste. Used electrical and electronic equipment should be treated separately.

Contents Overview
Media Server User’s Guide 7
Contents Overview
User’s Guide ...........................................................................................................................19
Getting to Know Your NSA .........................................................................................................21
zMedia App ................................................................................................................................25
NAS Starter Utility ......................................................................................................................35
Web Configurator Basics ...........................................................................................................43
Tutorials .....................................................................................................................................63
Technical Reference ............................................................................................................147
Status Screen ...........................................................................................................................149
System Setting .........................................................................................................................153
Storage .....................................................................................................................................157
Network ...................................................................................................................................171
Applications ..............................................................................................................................181
Package Management .............................................................................................................225
Auto Upload .............................................................................................................................275
Dropbox ....................................................................................................................................289
Users ........................................................................................................................................293
Groups .....................................................................................................................................299
Shares ......................................................................................................................................303
Maintenance Screens ..............................................................................................................311
Protecting Your Data ................................................................................................................331
Using Time Machine with the NSA ...........................................................................................337
Troubleshooting .......................................................................................................................347
Product Specifications ..............................................................................................................365
Open Source Licences ........................................................................................................447

Contents Overview
Media Server User’s Guide
8

Table of Contents
Media Server User’s Guide 9
Table of Contents
About This User's Guide..........................................................................................................3
Document Conventions ...........................................................................................................4
Safety Warnings........................................................................................................................6
Contents Overview .................................................................................................................. 7
Table of Contents .....................................................................................................................9
Part I: User’s Guide ................................................................................19
Chapter 1
Getting to Know Your NSA.....................................................................................................21
1.1 Overview ..............................................................................................................................21
1.1.1 Smartphone App .........................................................................................................22
1.1.2 Hard Disks for 2-Bay Models ......................................................................................22
1.1.3 Hard Disks for 1-Bay Models ......................................................................................22
1.1.4 COPY/SYNC Button ...................................................................................................23
1.1.5 RESET Button ............................................................................................................23
1.1.6 Removing a Hard Disk ................................................................................................23
Chapter 2
zMedia App..............................................................................................................................25
2.1 Overview ..............................................................................................................................25
2.2 Log into zMedia ....................................................................................................................25
2.3 File Browser .........................................................................................................................26
2.4 System .................................................................................................................................29
2.4.1 Settings .......................................................................................................................29
2.4.2 Status ..........................................................................................................................29
2.4.3 Shutdown ....................................................................................................................32
2.4.4 Applications ................................................................................................................33
2.4.5 Power .........................................................................................................................34
Chapter 3
NAS Starter Utility................................................................................................................... 35
3.1 Overview ..............................................................................................................................35
3.2 Starting the NAS Starter Utility .............................................................................................35
3.3 NAS Seeker Screen .............................................................................................................35

Table of Contents
Media Server User’s Guide
10
3.4 Main NAS Starter Utility Screen ...........................................................................................37
3.4.1 Directory of the NAS ...................................................................................................38
3.5 Import Files or Folders with zPilot ........................................................................................39
3.6 Network Drive .......................................................................................................................40
3.7 Manage the Device ..............................................................................................................41
3.8 Configure System Settings ...................................................................................................41
Chapter 4
Web Configurator Basics.......................................................................................................43
4.1 Overview ..............................................................................................................................43
4.2 Accessing the NSA Web Configurator .................................................................................43
4.2.1 Access the NSA Via NAS Starter Utility ......................................................................44
4.2.2 Web Browser Access ..................................................................................................44
4.3 Login ....................................................................................................................................45
4.4 Home Screens ....................................................................................................................46
4.4.1 Now Playing (Music) ...................................................................................................49
4.4.2 Exif and Google Maps (Photos) ..................................................................................50
4.4.3 Slideshow and CoolIris (Photos) ................................................................................50
4.4.4 Favorite .......................................................................................................................51
4.4.5 File Browser ...............................................................................................................52
4.4.6 Share and Folder Names ...........................................................................................55
4.4.7 Application Zone .........................................................................................................56
4.4.8 System Settings .........................................................................................................57
4.5 Administration Screens .......................................................................................................58
4.5.1 Global Administration Icons .......................................................................................59
4.5.2 Navigation Panel .......................................................................................................60
4.5.3 Main Window .............................................................................................................61
4.5.4 Status Messages .......................................................................................................61
4.5.5 Common Screen Icons ..............................................................................................61
4.5.6 Session Example (Windows) ......................................................................................62
Chapter 5
Tutorials................................................................................................................................... 63
5.1 Overview ..............................................................................................................................63
5.2 Windows 7 Network .............................................................................................................63
5.2.1 If the NSA Icon Does Not Display ...............................................................................65
5.2.2 NSA Icon Right-click Options .....................................................................................66
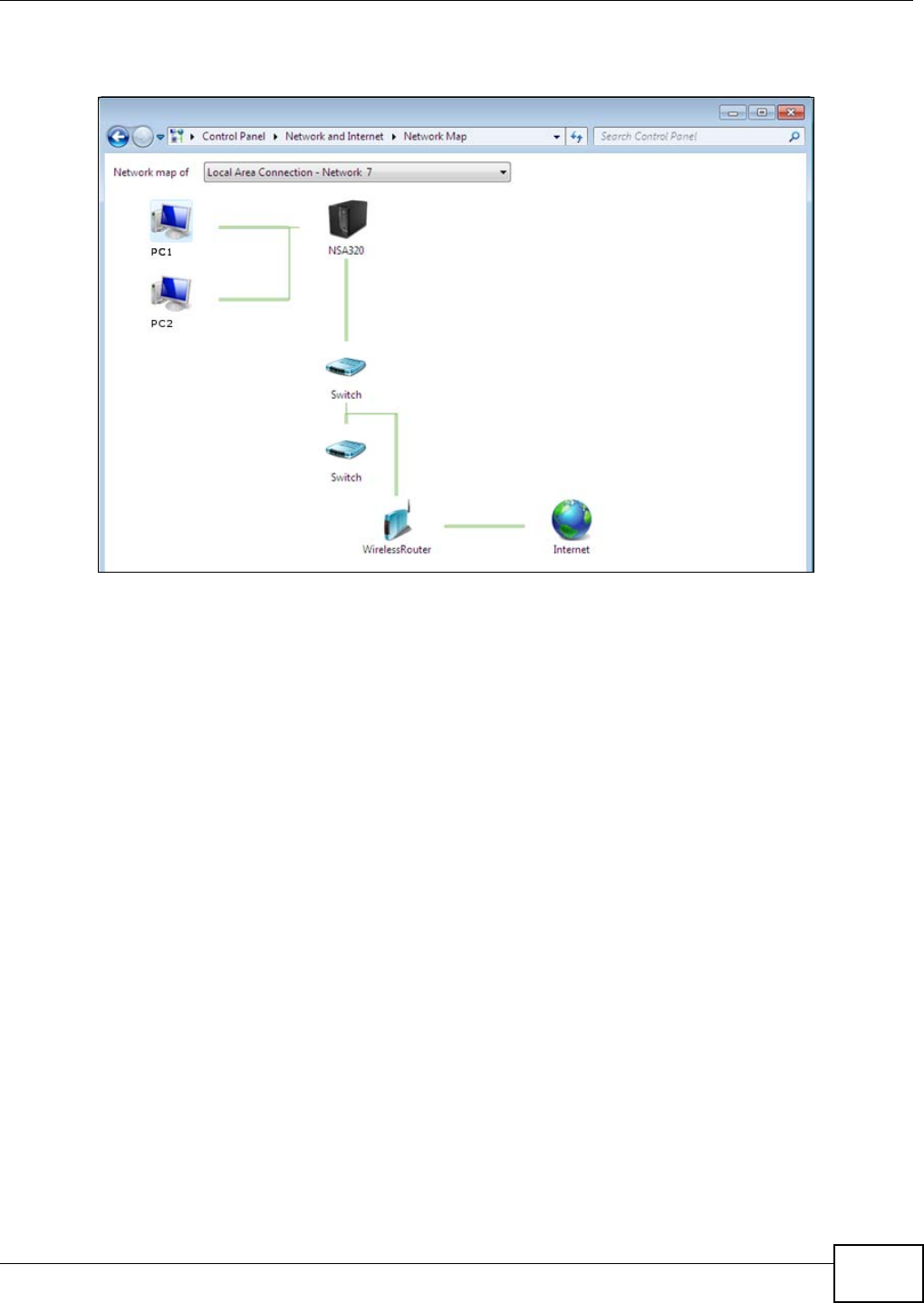
5.3 Windows 7 Network Map .....................................................................................................67
5.4 Playing Media Files in Windows 7 ........................................................................................70
5.5 Windows 7 Devices and Printers .........................................................................................70
5.5.1 Windows 7 Desktop Shortcut .....................................................................................72
5.6 Creating a Volume in a 2-Bay NSA ......................................................................................73
5.6.1 Creating a RAID 1 Volume .........................................................................................73

Table of Contents
Media Server User’s Guide 11
5.6.2 Migrate Button ............................................................................................................74
5.6.3 Create an Internal Volume Button ..............................................................................74
5.7 Creating a Volume in a 1-Bay NSA ......................................................................................75
5.7.1 Creating a RAID 1 Volume .........................................................................................76
5.7.2 Migrate Button ............................................................................................................76
5.7.3 Create a SATA Volume Button ....................................................................................77
5.7.4 Creating a PC Compatible Volume .............................................................................79
5.8 Deleting a Volume ................................................................................................................82
5.9 File Sharing Tutorials ...........................................................................................................83
5.9.1 Creating a User Account ............................................................................................83
5.9.2 Creating a Share ........................................................................................................85
5.9.3 Creating a Group ........................................................................................................87
5.9.4 Accessing a Share From Windows Explorer ..............................................................88
5.9.5 Accessing a Share Using FTP ....................................................................................90
5.9.6 Accessing a Share Through the Web Configurator ....................................................91
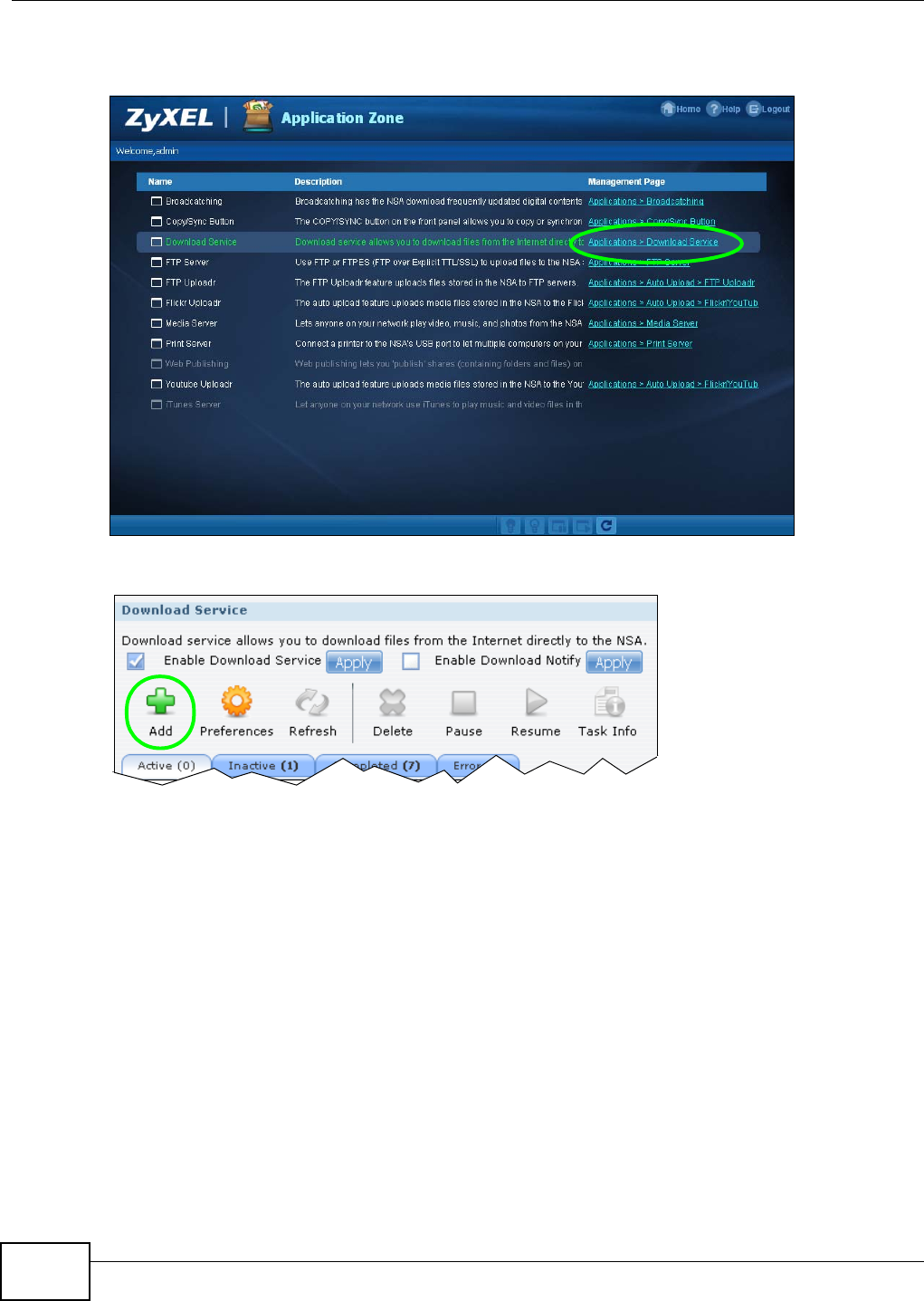
5.10 Download Service Tutorial .................................................................................................92
5.10.1 Copying/Pasting a Download Link ............................................................................92
5.10.2 Installing the Link Capture Browser Plugin ...............................................................95
5.10.3 Using the Link Capture Browser Plugin ..................................................................100
5.10.4 Configuring the Download Service Preferences .....................................................102
5.10.5 Using Download Service Notification ......................................................................104
5.11 Broadcatching Tutorial ......................................................................................................107
5.12 Printer Server Tutorial ...................................................................................................... 111
5.13 Copy and Flickr Auto Upload Tutorial .............................................................................. 113
5.14 FTP Uploadr Tutorial ........................................................................................................114
5.15 Web Configurator’s Security Sessions ............................................................................. 117
5.15.1 Customizing the NSA’s Certificate .......................................................................... 118
5.15.2 Downloading and Installing Customized Certificate ................................................ 119
5.15.3 Turn on the NSA’s Web Security ............................................................................123
5.16 Using FTPES to Connect to the NSA ...............................................................................130
5.17 Using a Mac to Access the NSA ......................................................................................131
5.17.1 Finder .....................................................................................................................132
5.17.2 Go Menu .................................................................................................................133
5.18 How to Use the BackupPlanner .......................................................................................134
5.18.1 Creating an Archive Backup ...................................................................................134
5.18.2 Creating a Synchronization Backup .......................................................................137
5.18.3 Restoring Archived Files by Backup Job ................................................................140
5.18.4 Restoring by Backup Files ......................................................................................143
Part II: Technical Reference.................................................................147

Table of Contents
Media Server User’s Guide
12
Chapter 6
Status Screen........................................................................................................................149
6.1 Overview ............................................................................................................................149
6.2 The Status Screen .............................................................................................................149
Chapter 7
System Setting...................................................................................................................... 153
7.1 Overview ............................................................................................................................153
7.2 What You Can Do ..............................................................................................................153
7.3 What You Need to Know ....................................................................................................153
7.4 The Server Name Screen .................................................................................................154
7.5 The Date/Time Screen .......................................................................................................154
Chapter 8
Storage ..................................................................................................................................157
8.1 Overview ............................................................................................................................157
8.1.1 What You Need to Know About Storage ...................................................................157
8.2 The Storage Screen ...........................................................................................................158
8.2.1 Disk Replacement Restrictions .................................................................................158
8.2.2 Storage Screen .........................................................................................................159
8.2.3 Volume Status ...........................................................................................................160
8.3 Creating an Internal (SATA) Volume ..................................................................................161
8.4 Editing a Volume ................................................................................................................163
8.4.1 Scanning a Volume ...................................................................................................164
8.5 Creating an External (USB) Volume ...................................................................................164
8.5.1 External Disks ...........................................................................................................165
8.6 Storage Technical Reference .............................................................................................166
8.6.1 Volumes and RAID ...................................................................................................166
8.6.2 Choosing a Storage Method for a Volume ................................................................166
8.6.3 Storage Methods ......................................................................................................167
Chapter 9
Network .................................................................................................................................171
9.1 Overview ............................................................................................................................171
9.2 What You Can Do ..............................................................................................................171
9.3 What You Need to Know ....................................................................................................171
9.4 The TCP/IP Screen ............................................................................................................173
9.5 UPnP Port Mapping Screen ...............................................................................................175
9.5.1 UPnP and the NSA’s IP Address ..............................................................................176
9.5.2 UPnP and Security ...................................................................................................176
9.5.3 The NSA’s Services and UPnP .................................................................................177
9.5.4 Configuring UPnP Port Mapping ..............................................................................177
9.6 The PPPoE Screen ...........................................................................................................179

Table of Contents
Media Server User’s Guide 13
Chapter 10
Applications ..........................................................................................................................181
10.1 Overview ..........................................................................................................................181
10.2 What You Can Do ............................................................................................................181
10.3 What You Need to Know ..................................................................................................181
10.4 FTP Server .......................................................................................................................184
10.5 The Media Server Screens ............................................................................................185
10.5.1 The Media Server Share Publish Screen .............................................................187
10.5.2 The Media Server ID3 Tag Decoding Screen .......................................................188
10.5.3 The Media Server iTunes Server Screen .............................................................189
10.5.4 The Media Server SqueezeCenter Screen ...........................................................189
10.6 The Download Service Screen .........................................................................................190
10.6.1 Adding a Download Task ........................................................................................193
10.6.2 Configuring General Settings .................................................................................195
10.6.3 Configuring the BitTorrent Settings .........................................................................197
10.6.4 Edit IP Filter ...........................................................................................................199
10.6.5 Selecting Files to Download ...................................................................................200
10.6.6 Displaying the Task Information .............................................................................201
10.7 The Web Publishing Screen .............................................................................................202
10.8 The Broadcatching Screen ...............................................................................................203
10.8.1 Adding a Broadcatching Channel ...........................................................................205
10.8.2 Editing a Broadcatching Channel ..........................................................................208
10.9 The Print Server Screen ..................................................................................................209
10.9.1 Print Server Rename .............................................................................................210
10.10 The Copy/Sync Button Screen ....................................................................................... 211
10.11 Technical Reference .......................................................................................................212
10.11.1 Sharing Media Files on Your Network ...................................................................212
10.11.2 Download Service .................................................................................................213
10.11.3 Link Capture Browser Plugin ................................................................................214
10.11.4 Download Service Notification ..............................................................................214
10.11.5 BitTorrent Security .................................................................................................215
10.11.6 Web Publishing Example ......................................................................................217
10.11.7 Web Publishing .....................................................................................................218
10.11.8 Channel Guides for Broadcatching .......................................................................219
10.11.9 Printer Sharing ......................................................................................................220
10.11.10 Copying Files ......................................................................................................220
10.11.11 Synchronizing Files .............................................................................................221
Chapter 11
Package Management ..........................................................................................................225
11.1 Overview ..........................................................................................................................225
11.2 What You Can Do .............................................................................................................225
11.3 What You Need to Know ..................................................................................................225

Table of Contents
Media Server User’s Guide
14
11.4 Package Management Screen ........................................................................................226
11.4.1 Displaying the Package Information ......................................................................229
11.5 DyDNS Screen ...............................................................................................................229
11.6 NFS Screen ....................................................................................................................230
11.6.1 Add/Edit NFS Share ...............................................................................................232
11.6.2 NFS Session ..........................................................................................................233
11.7 SMART Screen ..............................................................................................................233
11.7.1 SMART Brief Summary ..........................................................................................235
11.7.2 SMART Full Summary ...........................................................................................236
11.8 Protect Screens ..............................................................................................................237
11.9 Backup Screens ..............................................................................................................237
11.9.1 Backup: Step 1 .......................................................................................................238
11.9.2 Backup: Step 2 .......................................................................................................240
11.9.3 Backup: Step 3 .......................................................................................................242
11.9.4 Backup: Step 4 .......................................................................................................243
11.9.5 Edit Job Screen .......................................................................................................244
11.9.6 Edit Job: Step 1 ......................................................................................................245
11.9.7 Edit Job: Step 2 ......................................................................................................246
11.9.8 Restore Archive Screen ..........................................................................................247
11.9.9 Restore Archive: Step 1 .....................................................................................247
11.9.10 Restore Archive: Step 2 .......................................................................................248
11.9.11 Restore Archive: Step 3 .......................................................................................249
11.10 Restore Screen .............................................................................................................249
11.10.1 Restore: Step 1 ....................................................................................................250
11.10.2 Restore: Step 2 ....................................................................................................251
11.10.3 Restore: Step 3 ....................................................................................................252
11.10.4 Restore: Step 4 ....................................................................................................253
11.11 Syslog Server Screen ...................................................................................................253
11.12 TFTP Server Screen ....................................................................................................255
11.13 eMule Screens ............................................................................................................256
11.13.1 eMule Server Screen ...........................................................................................256
11.13.2 Add Server ...........................................................................................................258
11.13.3 Edit Server ...........................................................................................................258
11.13.4 My Info .................................................................................................................259
11.13.5 eMule Task Screen .............................................................................................260
11.13.6 Add Task ..............................................................................................................262
11.13.7 Preferences ..........................................................................................................263
11.13.8 Edit IP Filter .........................................................................................................266
11.13.9 Share Browsing ....................................................................................................266
11.13.10 Task Info .............................................................................................................268
11.13.11 eMule Search Screen ........................................................................................269
11.14 pyLoad Screen ...............................................................................................................271
11.15 Technical Reference .......................................................................................................271

Table of Contents
Media Server User’s Guide 15
11.15.1 S.M.A.R.T Attributes .............................................................................................272
Chapter 12
Auto Upload ..........................................................................................................................275
12.1 Overview ..........................................................................................................................275
12.2 What You Can Do ............................................................................................................275
12.3 What You Need to Know ..................................................................................................275
12.4 The Flickr/YouTube Screen .............................................................................................275
12.4.1 Configuring the Flickr Settings ...............................................................................276
12.4.2 Configuring the YouTube Settings .........................................................................281
12.5 The FTP Uploadr Screen ................................................................................................284
12.5.1 Adding or Editing an FTP Server Entry .................................................................285
12.5.2 The FTP Uploadr Preferences Screen ..................................................................286
Chapter 13
Dropbox.................................................................................................................................289
13.1 Overview ..........................................................................................................................289
13.2 Dropbox Screen ...............................................................................................................289
13.3 How to Use Dropbox with the NSA ..................................................................................291
Chapter 14
Users...................................................................................................................................... 293
14.1 Overview ..........................................................................................................................293
14.2 What You Can Do ............................................................................................................293
14.3 The Users Screen ...........................................................................................................293
14.3.1 User Icons ..............................................................................................................295
14.3.2 Adding or Editing an Account ................................................................................295
14.3.3 Usernames .............................................................................................................297
14.4 Displaying User Info .........................................................................................................297
Chapter 15
Groups ...................................................................................................................................299
15.1 Overview ..........................................................................................................................299
15.2 What You Can Do ............................................................................................................299
15.3 The Groups Screen .........................................................................................................299
15.3.1 Adding or Editing a Group ......................................................................................300
15.3.2 Group Names .........................................................................................................301
Chapter 16
Shares.................................................................................................................................... 303
16.1 Overview ..........................................................................................................................303
16.2 What You Can Do ............................................................................................................303
16.3 The Shares Screen .........................................................................................................303

Table of Contents
Media Server User’s Guide
16
16.3.1 Adding or Editing Share .........................................................................................305
16.3.2 Configuring Advanced Share Access ....................................................................306
16.3.3 Public and ANONYMOUS Share Access Rights ....................................................307
16.4 The Recycle Bin Configuration Screen ...........................................................................307
16.4.1 Recycle Bins ...........................................................................................................307
16.4.2 Configuring Recycle Bins .......................................................................................308
16.5 The Share Browser Screen .............................................................................................308
16.5.1 Moving or Copying Files ........................................................................................310
Chapter 17
Maintenance Screens........................................................................................................... 311
17.1 Overview .......................................................................................................................... 311
17.2 What You Can Do ............................................................................................................ 311
17.3 The Power Screen .......................................................................................................... 311
17.3.1 Editing the Power Control Schedule Screen .........................................................313
17.4 The Log Screen ...............................................................................................................315
17.4.1 Report Config Screen .............................................................................................315
17.4.2 Email Setting .........................................................................................................316
17.4.3 Report Setting ........................................................................................................317
17.4.4 Syslog Server Setting ............................................................................................317
17.5 The Configuration Screen ...............................................................................................318
17.6 SSL Certification .............................................................................................................319
17.6.1 Modifying or Creating a Certificate ........................................................................320
17.7 The Firmware Upgrade Screen ........................................................................................321
17.8 The Shutdown Screen .....................................................................................................322
17.9 Technical Reference .........................................................................................................323
17.9.1 Log Classes ............................................................................................................323
17.9.2 Log Severity Levels ................................................................................................324
17.9.3 Log Messages ........................................................................................................324
Chapter 18
Protecting Your Data ............................................................................................................331
18.1 Overview ..........................................................................................................................331
18.2 Protection Methods ..........................................................................................................331
18.3 Configuration File Backup and Restoration ......................................................................331
18.4 Memeo Autobackup .........................................................................................................332
18.4.1 Memeo Autobackup Installation and Setup ............................................................332
18.4.2 Using Memeo Autobackup After the Initial Setup ...................................................334
Chapter 19
Using Time Machine with the NSA......................................................................................337
19.1 Overview ..........................................................................................................................337
19.2 Create an Account and a Share on the NSA ...................................................................337

Table of Contents
Media Server User’s Guide 17
19.3 Set Time Machine to Support Network Volume ...............................................................339
19.4 Mounting the NSA on the Mac .........................................................................................340
19.5 Creating a Sparse Bundle File for the NSA ......................................................................341
19.5.1 Finding out Computer Name and MAC Address ....................................................341
19.5.2 Creating a Sparse Bundle File ................................................................................342
19.5.3 Mounting the Sparse Bundle to the NSA ................................................................344
19.6 Using Time Machine ........................................................................................................345
Chapter 20
Troubleshooting....................................................................................................................347
20.1 Troubleshooting Overview ...............................................................................................347
20.2 Power, Hardware, Connections, and LEDs ......................................................................347
20.3 NAS Starter Utility ............................................................................................................349
20.4 NSA Login and Access ....................................................................................................350
20.4.1 Enabling Scripting of Safe ActiveX Controls ...........................................................352
20.5 I Cannot Access The NSA ...............................................................................................354
20.6 Users Cannot Access the NSA ........................................................................................354
20.7 External USB Drives ........................................................................................................356
20.8 Firmware ..........................................................................................................................356
20.9 File Transfer .....................................................................................................................356
20.10 Networking .....................................................................................................................357
20.11 Some Features’ Screens Do Not Display .......................................................................357
20.12 Media Server Functions .................................................................................................358
20.13 Download Service and Broadcatching Functions ...........................................................360
20.14 Web Publishing ..............................................................................................................361
20.15 Auto Upload ...................................................................................................................362
20.16 Package Management ...................................................................................................362
20.17 Backups .........................................................................................................................363
Chapter 21
Product Specifications.........................................................................................................365
21.1 LEDs ................................................................................................................................365
21.2 Supported Media Server Content Formats ......................................................................366
21.3 Supported iTunes Server Content Formats ......................................................................367
Appendix A Setting Up Your Computer’s IP Address ..........................................................369
Appendix B Pop-up Windows, JavaScripts and Java Permissions...................................... 397
Appendix C Common Services............................................................................................407
Appendix D Importing Certificates ....................................................................................... 411
Appendix E Legal Information..............................................................................................437

19
PART I
User’s Guide

20
Media Server User’s Guide 21
CHAPTER 1
Getting to Know Your NSA
1.1 Overview
This chapter covers the main features and applications of the NSA. Use the NSA to do the following.
• Back up and share files on your network.
•Use the COPY/SYNC button to copy or synchronize files between the NSA and USB devices like
card readers, MP3 players, mass storage devices, and digital cameras without using a computer.
• Have the NSA handle large file downloads.
• Automatically download files from website feeds for convenient viewing.
• Use the included media client software or a media client device like the DMA-2501 to play the
video, music and photo files on the NSA.
• Use the NSA’s website to share files with remote users.
• Use iTunes on your computer to play video and music files stored on the NSA.
• Share printers.
• Automatically upload photo and video files to your FTP server, Flickr, and YouTube accounts.
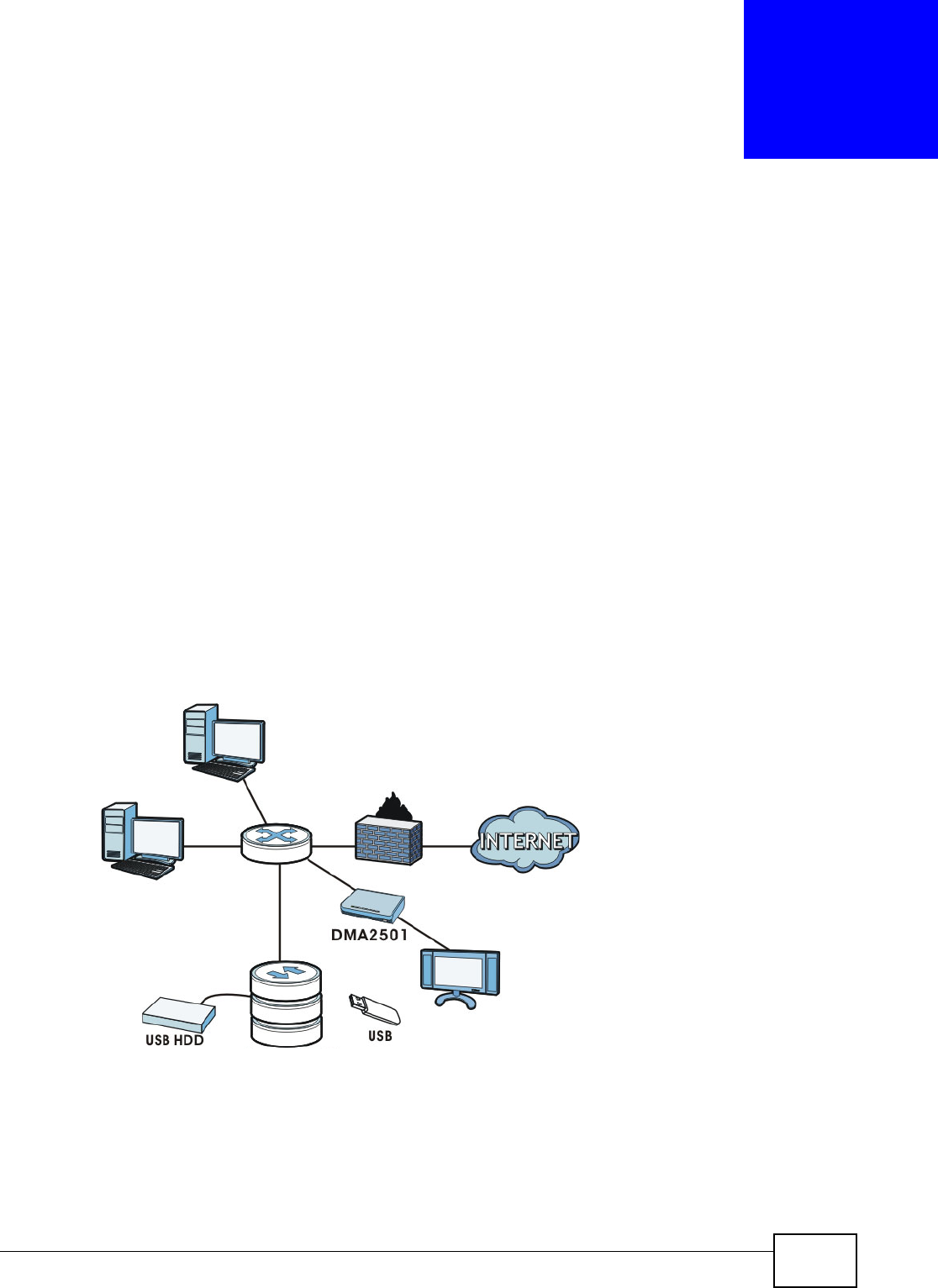
Figure 1 Example of the NSA in a Home Network
Above is the NSA in a home network. Users back up and share data on the NSA. The DMA-2501
plays the NSA’s media files on the TV. A USB hard drive provides extra storage space and files are
copied directly from the USB mass storage device to the NSA.
NSA

Chapter 1 Getting to Know Your NSA
Media Server User’s Guide
22
Place the NSA behind a firewall and/or IDP (Intrusion Detection and Prevention) device to protect it
from attacks from the Internet.
Note: See Chapter 21 on page 365 for a more detailed list of NSA features.
Refer to the Quick Start Guide for hardware connections and how to install hard drives.
Note: Turn off and disconnect the NSA before you install or remove the internal hard disk
or disks.
• The NSA325 is a 2-bay model.
• At the time of writing no 1-bay models support the firmware version documented in this User’s
Guide.
1.1.1 Smartphone App
Use ZyXEL’s zMedia app to play files and manage the NSA from your iOS version 3 or later device or
Android version 2.1 or later smartphone.
1.1.2 Hard Disks for 2-Bay Models
The 2-bay NSA models have two internal hard disk bays. Install one or two SATA (Serial Advanced
Technology Attachment) hard disks. Note that both SATA hard disks are treated as internal or SATA
volumes in the Storage > Volume screen (Section 8.3 on page 161). Any hard disk connected to
the USB port(s) is considered an external or USB volume.
1.1.3 Hard Disks for 1-Bay Models
The 1-bay NSA models have one internal hard disk bay and one external SATA (eSATA) port. This
allows you to connect one internal SATA (Serial Advanced Technology Attachment) hard disk and
one eSATA hard disk (optional).
Initializing the internal hard disk configures it as a JBOD volume by default. JBOD stands for Just a
Bunch Of Disk and in this storage method, all disk space is used for your data - none is used for
backup. If you are not using an eSATA hard disk, JBOD is the only storage method you can use.
If you attach an eSATA (external SATA) hard disk, you can create a RAID 1 volume. RAID 1 allows
data recovery in case your hard disk fails. To create a RAID 1 volume on the NSA, you must delete
the JBOD volume created by the firmware. Refer to Section 8.3 on page 161 for the Storage screen
where you can create the RAID 1 volume.
The eSATA hard disk can also be configured as a JBOD or a PC Compatible Volume. See Section
8.1.1 on page 157 for more information on these storage methods.
Note that both SATA and eSATA hard disks are treated as internal or SATA volumes in the Storage
screen (Section 8.3 on page 161). Any hard disk connected to the USB port(s) is considered an
external or USB volume.
Chapter 1 Getting to Know Your NSA
Media Server User’s Guide 23
1.1.4 COPY/SYNC Button
Use the COPY/SYNC button on the front panel to copy or synchronize files between a connected
USB device and the NSA. See Section 10.10 on page 211 for more details on how to configure the
copy/sync settings.
1.1.5 RESET Button
Use the RESET button on the rear panel to restore the NSA’s default settings.
Figure 2 The RESET Button
• Press the RESET button until you hear one beep (after about two seconds), then release it. You
will hear one more beep after you release the button.
This resets the NSA’s IP address and password to the default values.
• Press the RESET button until you hear two beeps. After the second beep, continue pressing the
button for five more seconds, then release it. You will hear three quick beeps after you release
the button.
This resets the NSA to the factory default configuration. All settings you have configured on the
NSA, including IP address, password, user accounts, groups, and so on will be reset to the
factory defaults.
The reset process does NOT affect the volume settings, nor data stored on the NSA.
You should periodically back up your configuration file to your computer (see Section 17.5 on page
318 for details about managing the NSA’s configuration file). You could then restore your
configuration in the event that you or someone else reset the NSA to the factory defaults.
Note: You should keep the NSA in a secure location in order to prevent unauthorized reset
of the device.
You may need to close and re-open the NAS Starter Utility to discover the NSA. This is because the
NSA automatically re-acquires IP address information, so its IP address may change. If no IP
address information is assigned, the NSA uses Auto-IP to assign itself an IP address and subnet
mask. For example, you could connect the NSA directly to your computer. If the computer is also
set to get an IP address automatically, the computer and the NSA will choose addresses for
themselves and be able to communicate.
1.1.6 Removing a Hard Disk
Turn off and disconnect the NSA before you remove an internal hard
disk.
Press 1 Beep 2 Beeps
IP Address
Password Clear All Settings
5 more seconds
Release to
Release to Reset

Chapter 1 Getting to Know Your NSA
Media Server User’s Guide
24
If you need to remove a hard drive, use the hard disk removal handle included inside the front lid.
Figure 3 Removing a Hard Disk
Media Server User’s Guide 25
CHAPTER 2
zMedia App
2.1 Overview
Install ZyXEL’s zMedia app from the Apple App Store, Android Market, or www.zyxel.com to play
files and manage the NSA from your iOS device or Android smartphone.
2.2 Log into zMedia
1Tap the zMedia icon to open the app and automatically search for NSAs on your network.
Figure 4 zMedia App Icon
2Select an NSA if you have more than one.
Figure 5 zMedia Automatic Discovery
Chapter 2 zMedia App
Media Server User’s Guide
26
3Use the admin user name and password to log in.
Figure 6 zMedia Login
2.3 File Browser
Tap File Browser to look through and play files on the NSA.
Figure 7 zMedia File Browser
Chapter 2 zMedia App
Media Server User’s Guide 27
Tap a share to view its contents.
Figure 8 zMedia Shares
Chapter 2 zMedia App
Media Server User’s Guide
28
Tap a file to play or open it using your device’s browser. Here are some examples.
Figure 9 zMedia File Playback
Music
Video
Photo
Document
Chapter 2 zMedia App
Media Server User’s Guide 29
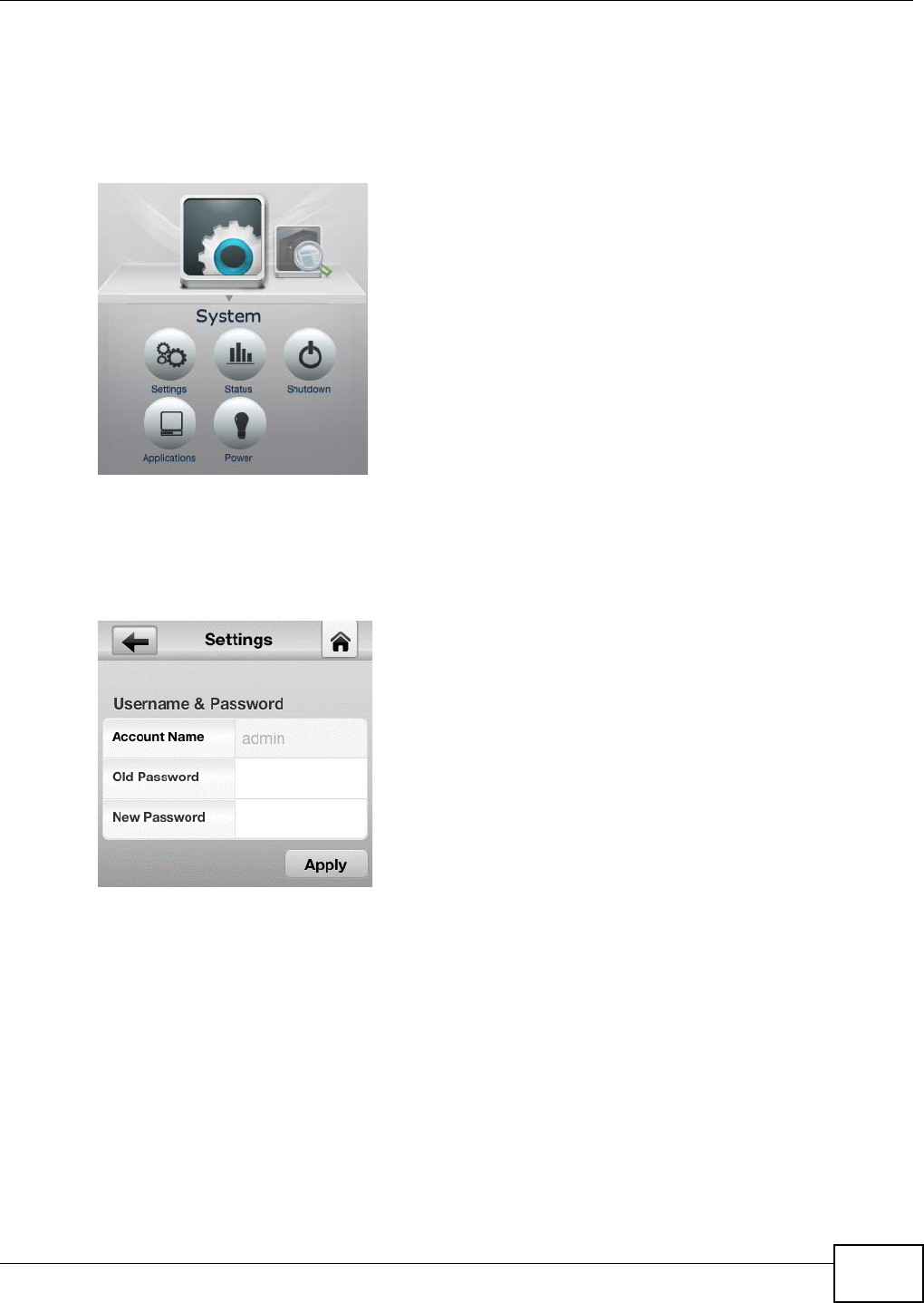
2.4 System
Tap System to view configure the admin account password, view system status, shutdown (or
restart), manage applications, or configure power schedule and management settings.
Figure 10 zMedia System
2.4.1 Settings
Set the admin account password.
Figure 11 zMedia Settings
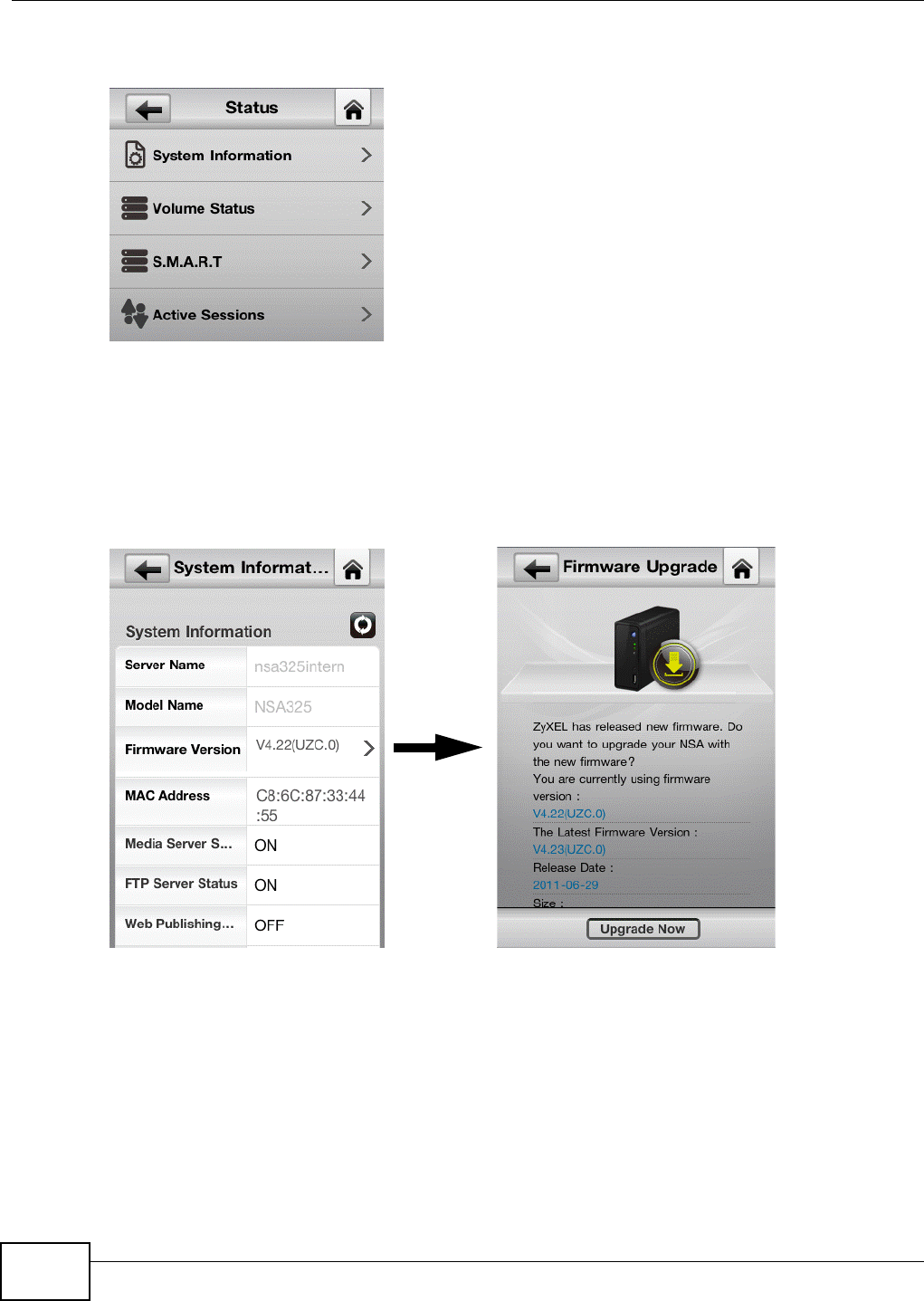
2.4.2 Status
•Tap System Information to see general NSA system information.
•Tap Volume Status to view information about the internal and external volumes.
•Tap S.M.A.R.T (this appears if the SMART package is installed) for hard disk health and
performance details.
Chapter 2 zMedia App
Media Server User’s Guide
30
•Tap Active Sessions to see which users are connected to the NSA.
Figure 12 zMedia Status
2.4.2.1 System Information
An arrow indicates a newer firmware version is available. Tap the arrow to upgrade the firmware.
Do not turn off the NSA while it is upgrading the firmware or you may
render it unusable.
Figure 13 zMedia System Information and Firmware Upgrade
Chapter 2 zMedia App
Media Server User’s Guide 31
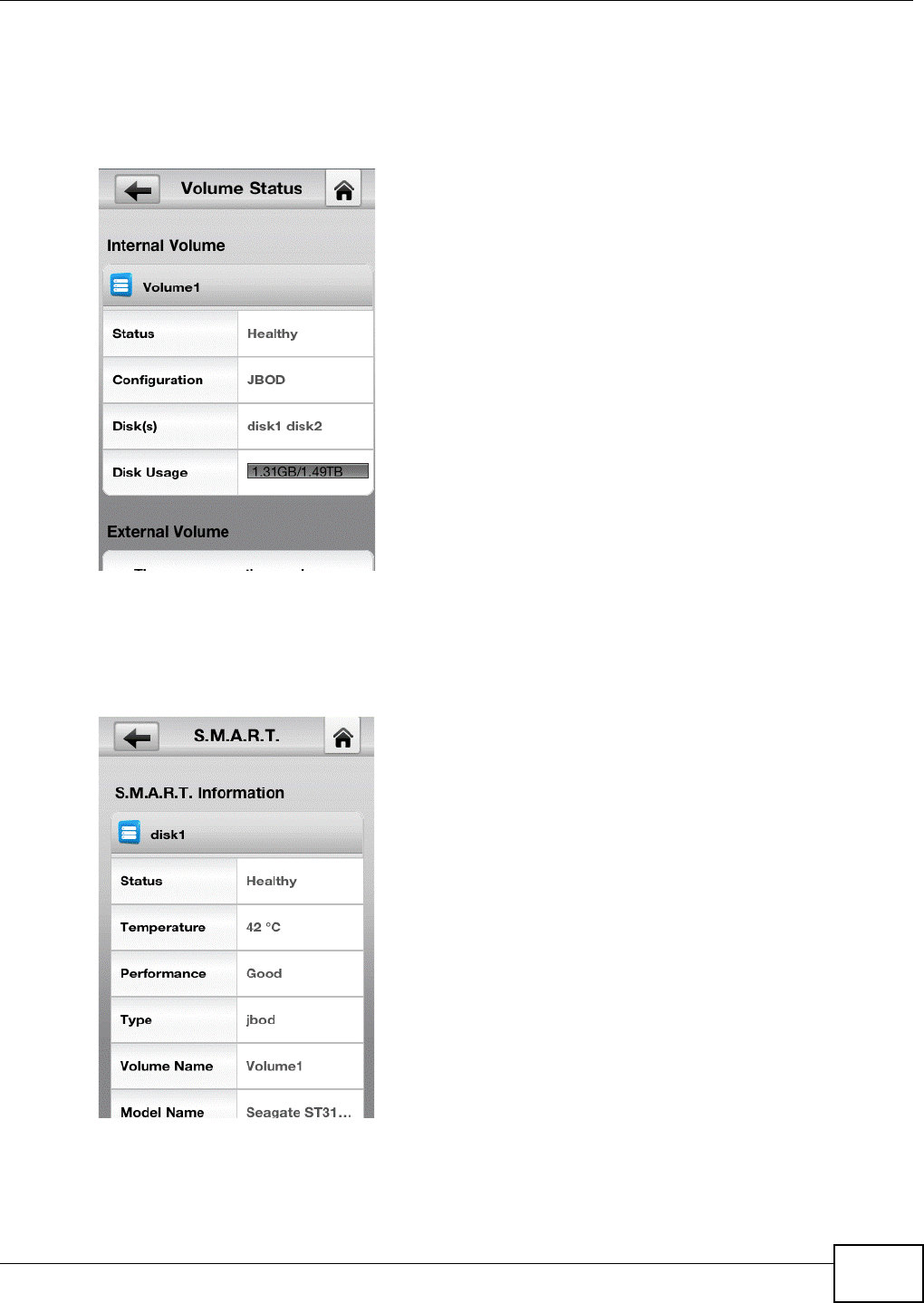
2.4.2.2 Volume Status
See Section 8.2.1 on page 158 for details on replacing a disk in a degraded or down RAID volume
and resynchronizing or recovering a RAID 1 Volume.
Figure 14 zMedia Volume Status
2.4.2.3 S.M.A.R.T.
Self Monitoring, Analysis, and Reporting Technology (S.M.A.R.T) detects and reports the reliability
of hard disks to help you anticipate possible disk failures.
Figure 15 zMedia S.M.A.R.T.
Chapter 2 zMedia App
Media Server User’s Guide
32
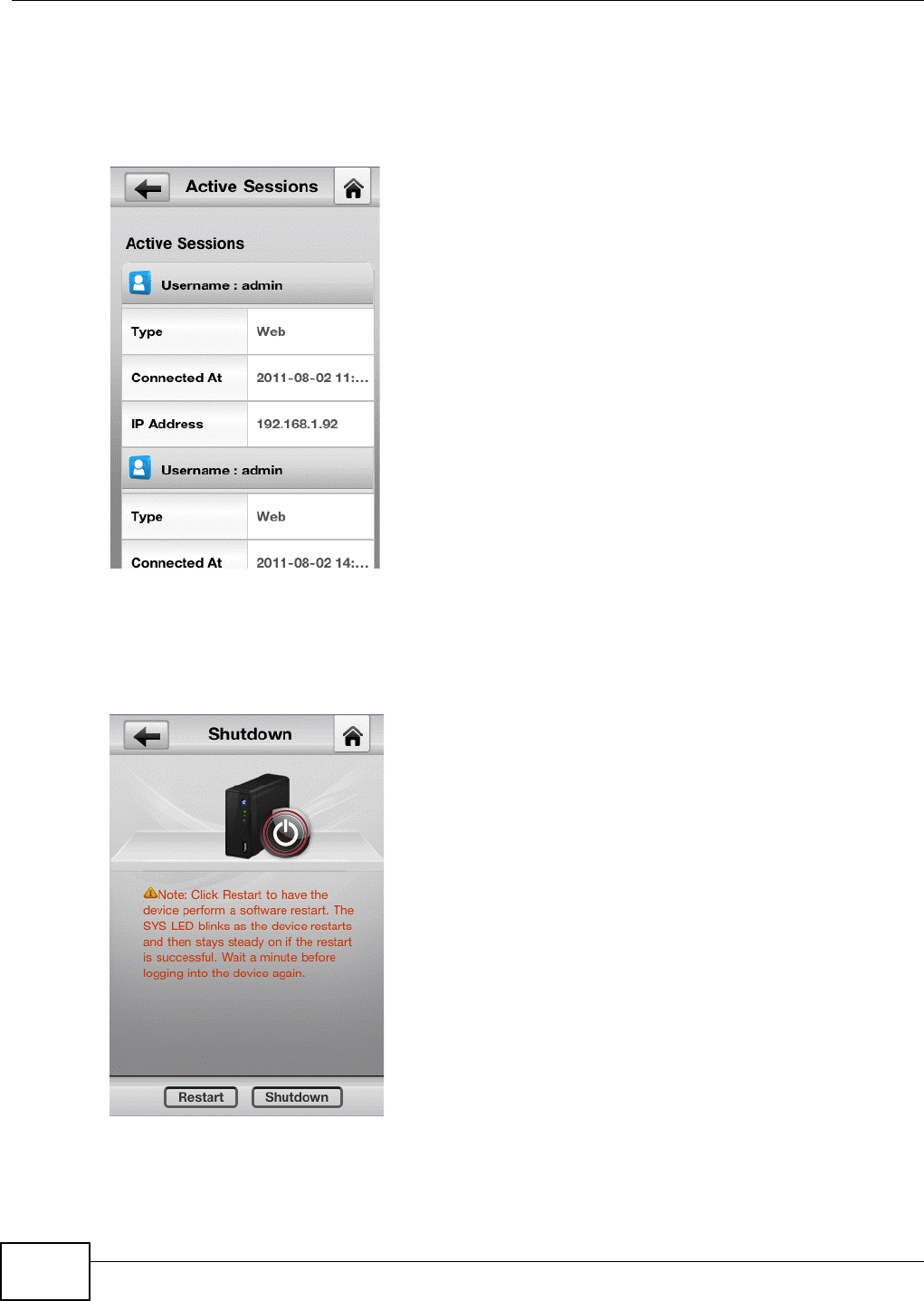
2.4.2.4 Active Sessions
This shows the users connected to the NSA, whether it’s a Windows/CIFS, web (web configurator),
or FTP connection, when they last connected, and the IP address of the user’s computer or device.
Figure 16 zMedia Active Sessions
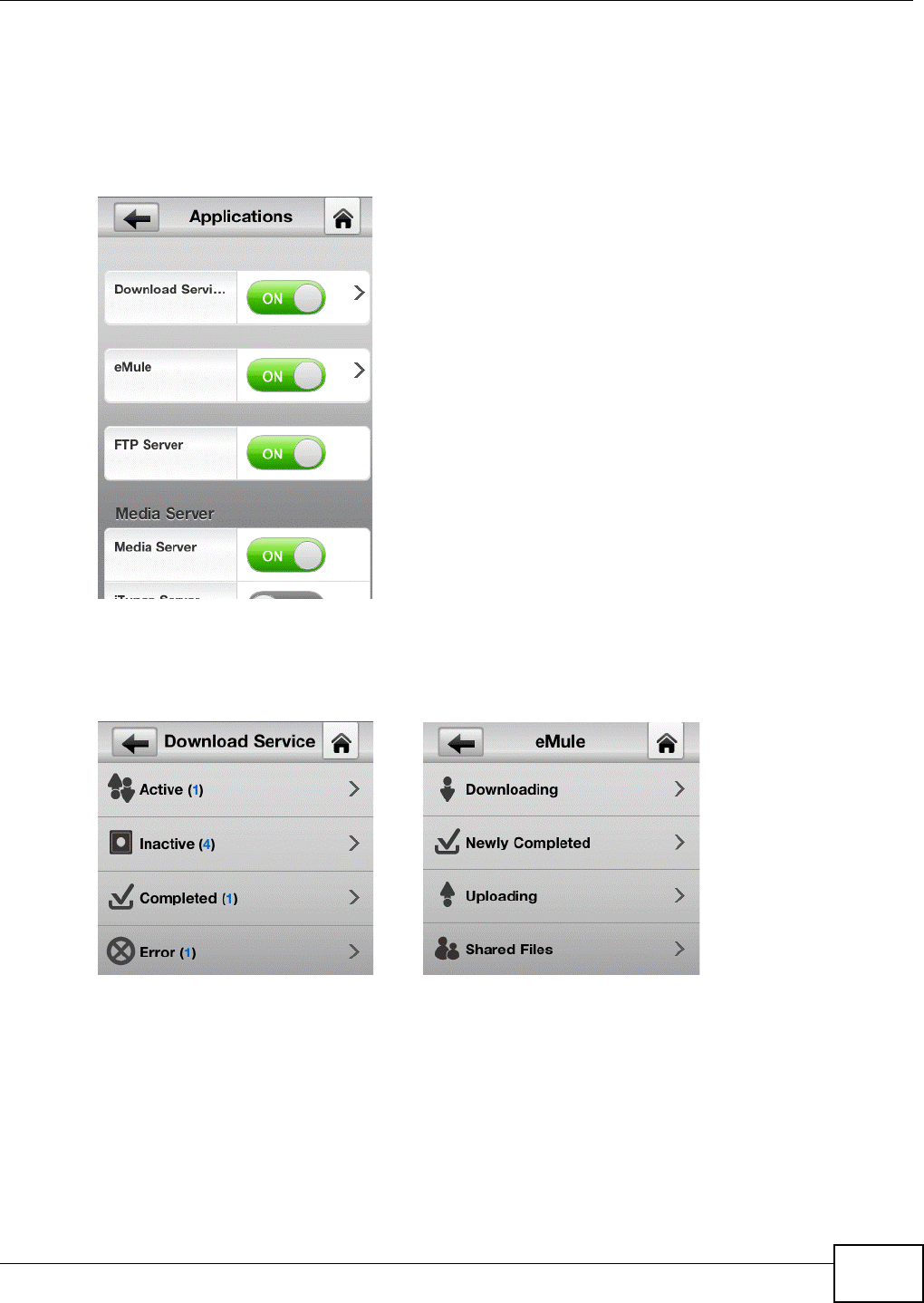
2.4.3 Shutdown
Tap the Restart button to reboot the NSA or the Shutdown button to turn it off.
Figure 17 zMedia Shutdown
Chapter 2 zMedia App
Media Server User’s Guide 33
2.4.4 Applications
Enable or disable individual applications. Some applications only appear if the corresponding
package is installed (see Chapter 11 on page 225). Tap the arrow next to Download Service or
eMule to see task status details.
Figure 18 zMedia Applications
2.4.4.1 Download Service and eMule
Tap the arrow next to a category of download tasks to see the related tasks.
Figure 19 zMedia Download Service and eMule
Chapter 2 zMedia App
Media Server User’s Guide
34
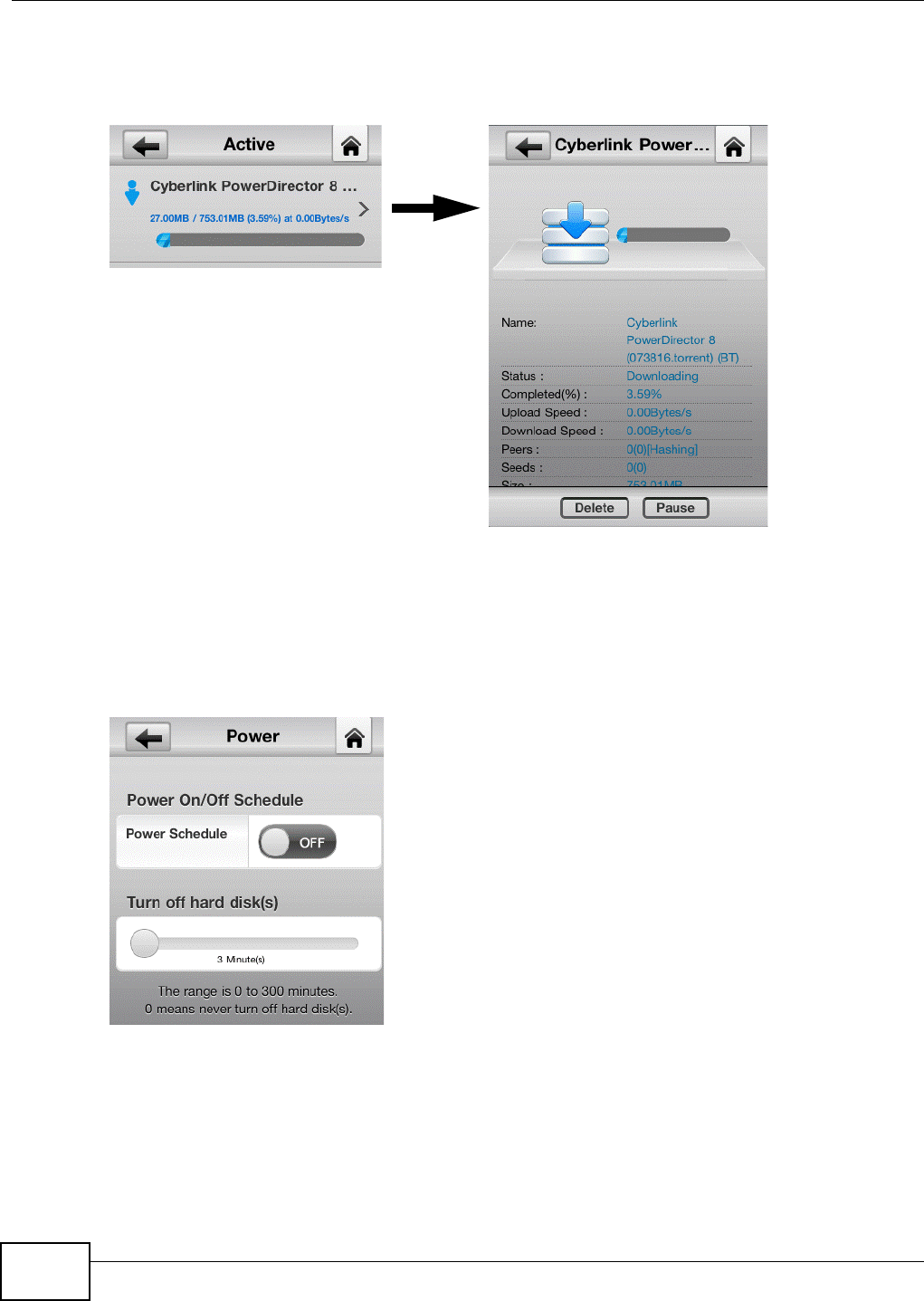
Tap the arrow next to a download task for details. Tap a button to remove, pause, or resume the
task. Download Service screens are shown here as an example. eMule screens are similar.
Figure 20 zMedia Download Service Active
2.4.5 Power
Turn the power control schedule on or off and set how long to let the hard disks remain idle before
putting them to sleep. Use the Web Configurator to configure the power control schedule (Section
17.3 on page 311).
Figure 21 zMedia Shutdown

Media Server User’s Guide 35
CHAPTER 3
NAS Starter Utility
3.1 Overview
This chapter describes the NAS Starter Utility. Use the NAS Starter Utility to find, set up, and
manage the NSA as well as copy files to it and access the files on it.
Make sure you have a backup of any existing data in the hard disk before
installing it in the NSA. Using the initialization wizard formats the hard
disk and deletes all data in the process.
There is a NAS Starter Utility available for Windows XP, Windows Vista, or Windows 7. Click Help to
open a web help page about the NAS Starter Utility screens. NAS Starter Utility screens are shown
here as they display with the Windows platform.
Note: Refer to the Quick Start Guide for your NSA’s hardware connections and the steps
for installing the NAS Starter Utility.
3.2 Starting the NAS Starter Utility
• The NAS Starter Utility broadcasts a request packet when you first run it. Each NSA has an NAS
Starter Utility Agent that always listens and responds to requests from the NAS Starter Utility.
The NAS Starter Utility receives the response packet that contains information, such as host
name, IP, and so on.
• If you plan to use more than one NSA in your network, configure them with unique server
names. This enables you to identify each NSA in the NAS Starter Utility screens.
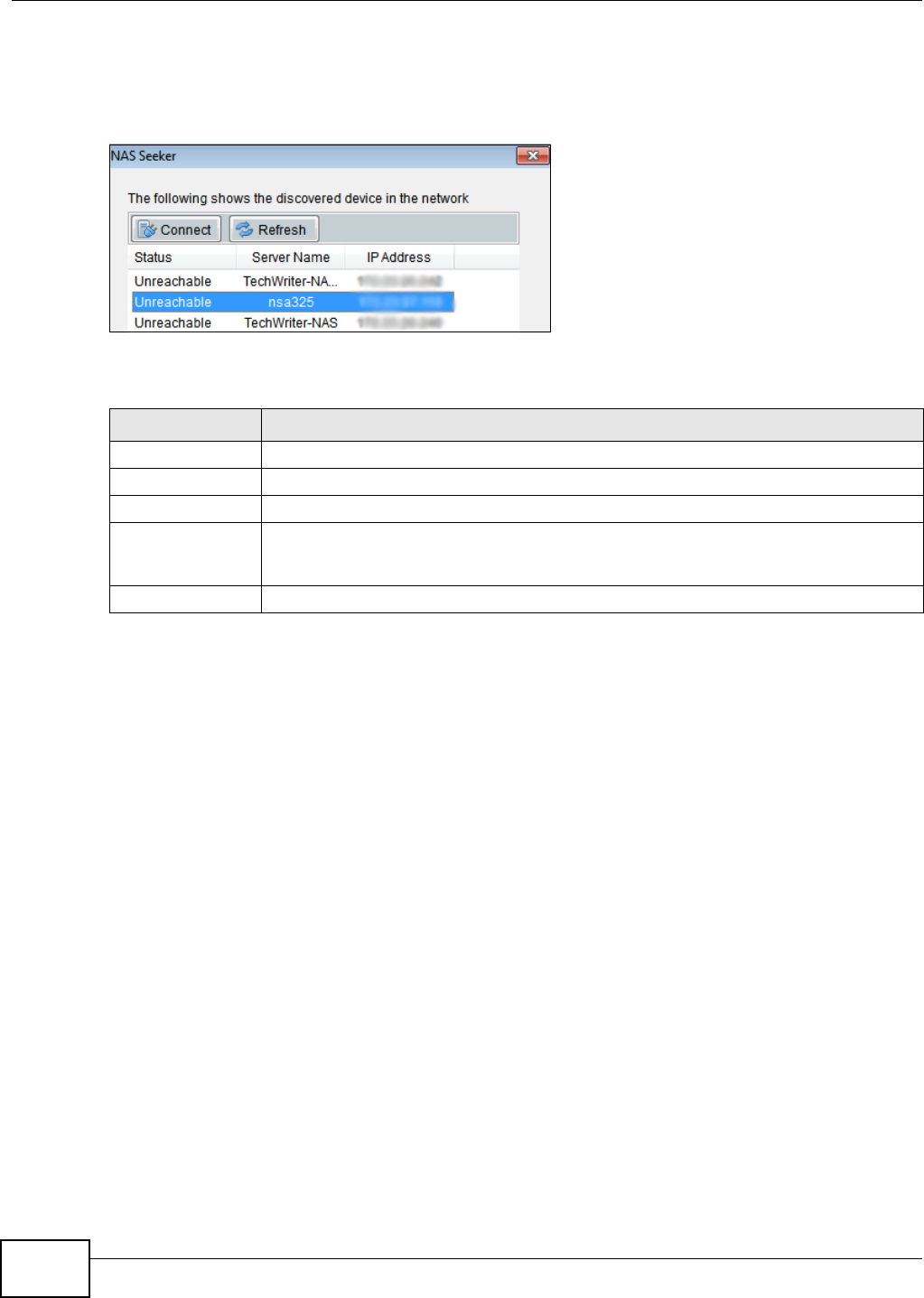
3.3 NAS Seeker Screen
Use this screen to view the NSAs in your network. The NSA’s Server Name. The default is ‘nsa’
followed by the number of your model (‘nsa325’ for example). See Section 3.8 on page 41 for how
to change it to a more recognizable one in your network.
Chapter 3 NAS Starter Utility
Media Server User’s Guide
36
Start the NAS Starter Utility (click the icon in your Desktop or in Start > Programs > ZyXEL >
NAS Starter Utility). The first time you open the NAS Starter Utility the discovery screen appears
as follows.
Figure 22 NAS Seeker
The following table describes the labels in this screen.
Table 1 NAS Seeker
LABEL DESCRIPTION
Connect Select a NSA and click this to connect to it.
Refresh Click this to refresh the screen. The NAS Starter Utility does not automatically refresh.
Status This shows whether the NSA is Online, Unreachable, Configuring, or Config Failed.
Server Name This is the server name you configured for the NSA. If you have more than one NSA in
your network, it is recommended that you give each one a unique name for identification
purposes.
IP Address This is the current IP address of the NSA.
Chapter 3 NAS Starter Utility
Media Server User’s Guide 37
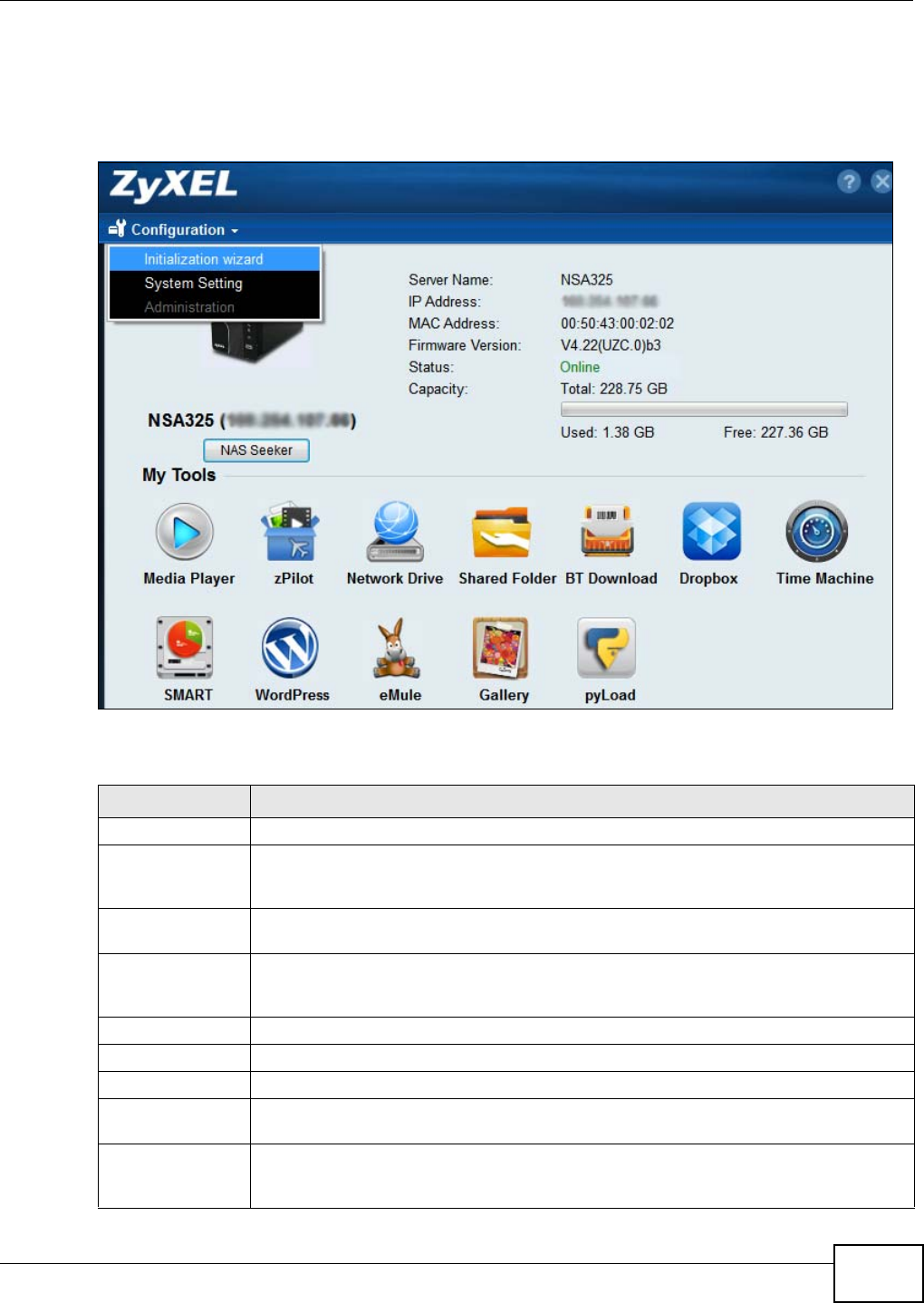
3.4 Main NAS Starter Utility Screen
The main NAS Starter Utility screen displays after you select an NSA in the NSA Seeker screen.
Figure 23 NAS Starter Utility Main Screen
The following table describes the labels in this screen.
Table 2 NAS Starter Utility Main Screen
LABEL DESCRIPTION
? Click this to display the utility help.
Configuration Click this to run the initialization wizard (see the utility help for details), configure system
settings (see Section 3.8 on page 41), or go to the NSA’s Web Configurator login screen
(see Section 4.3 on page 45).
NAS Seeker Click this to use the NSA Seeker screen (Section 3.3 on page 35) to find and connect to a
different NSA on your network.
Server Name This is the server name you configured for the NSA. If you have more than one NSA in
your network, it is recommended that you give each one a unique name for identification
purposes.
IP Address This is the current IP address of the NSA.
MAC Address This is the NSA’s unique physical hardware address (MAC).
Firmware Version This shows the version of firmware the NSA is currently using.
Status This shows whether the NSA is Online, Uninitialized, Unreachable, Configuring, or
Config Failed.
Run Initialization
Wizard This button displays if the NSA detects an installed hard disk that the NSA has not yet
configured. Click the button to run the initialization wizard (see the utility help for
details).
Chapter 3 NAS Starter Utility
Media Server User’s Guide
38
3.4.1 Directory of the NAS
Click Shared Folder to log into the NSA’s file directory in Windows Explorer. Enter the
administrator user name and password and click Login.
Figure 24 Login
Capacity This shows the NSA’s total, in-use, and remaining storage capacity.
Media Player Click this to go to the Home screens where you can play media files. See Section 4.4 on
page 46 for details on the Home screen.
zPilot Click this to launch the zPilot to drag and drop files onto the NSA.
Network Drive Click this to add the NSA as a network drive in your computer’s Windows Explorer.
Shared Folder Click this to log into the NSA’s file directory in Windows Explorer.
BT Download Click this to use the NSA to manage file downloads, including BitTorrent downloads.
Dropbox Click this to use your Dropbox account to move files to the NSA and have the NSA
download *.torrent files.
SMART This displays when the NSA has the SMART package installed. Click this to view hard disk
health and performance details.
WordPress This displays when the NSA has the WordPress package installed. Click this to create and
manage a blog or website. Use the NSA administrator credentials to log in. The
administrator can then create accounts for other users.
eMule This displays when the NSA has the eMule package installed. Click this to use the NSA’s
eMule peer-to-peer (P2P) file-sharing console to download and share files from the
Internet. See Section 11.13 on page 256 for details.
Gallery This displays when the NSA has the Gallery package installed. Click this to use your NSA
to host pictures. You can upload images in your local computer or shares to this
application. Use the NSA administrator account to log in to the Gallery console.
pyLoad This displays when the NSA has the pyLoad package installed. Click this to use pyLoad to
have the NSA manage your downloads, including those from one-click hosting sites. See
Section 11.14 on page 271 for details.
Table 2 NAS Starter Utility Main Screen
LABEL DESCRIPTION
Chapter 3 NAS Starter Utility
Media Server User’s Guide 39
The utility opens the NSA’s directory in Windows Explorer.
Figure 25 Directory
3.5 Import Files or Folders with zPilot
In the main NAS Starter Utility screen click zPilot to be able to drag and drop files from your
computer to the NSA.
Enter the administrator user name and password and click Login.
Figure 26 Login
The zPilot icon displays.
Figure 27 zPilot
Drag files onto the zPilot icon to move them to the NSA. zPilot automatically sorts music, photo, and
video files into the Music, Photo, and Video folders. zPilot automatically sorts the types of media
files listed in Table 125 on page 366 (except for the subtitles). Other types of files go to the Public
Chapter 3 NAS Starter Utility
Media Server User’s Guide
40
folder. For folders of files you are prompted to choose the target destination. The zPilot icon shows
the transfer rate.
Figure 28 zPilot Showing Transfer Rate
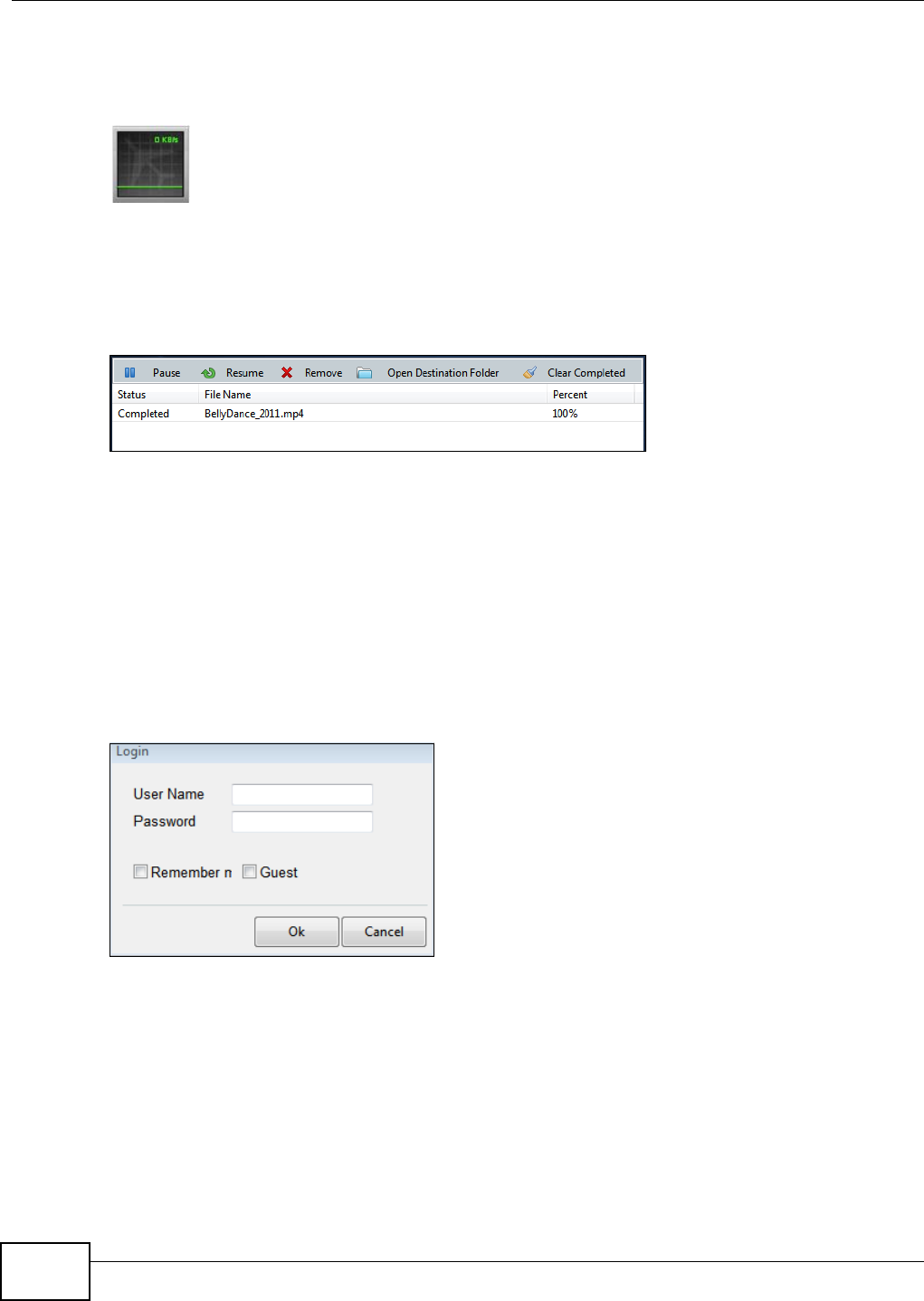
Double-click the zPilot icon to display status details about the file transfers. Select an entry and
click Pause, Resume, or Remove to control the transfer. After the transfer finishes you can select
the entry and click Open Destination Folder to see the file on the NSA. Click Clear Completed to
clear completed transfers from the list.
Figure 29 zPilot Transfer Details
3.6 Network Drive
In the main NAS Starter Utility screen click Network Drive to add the NSA as a network drive in
your computer’s Windows Explorer.
Enter your user name and password and click Login to be able to add the NSA’s shares to which
you have access as network drives. Otherwise select Guest and click Login to be able to add the
NSA’s public shares as network drives.
Figure 30 Login
Select a share on the NSA and the drive letter on your computer to which you want to map it. The
shares that each user can select to map depends on the user’s permissions. For example, if share1
is private to user1, then only user1 is allowed to map share1. The table displays the NSA shares
that are already mapped to drive letters on your computer. After you click Apply you can see the
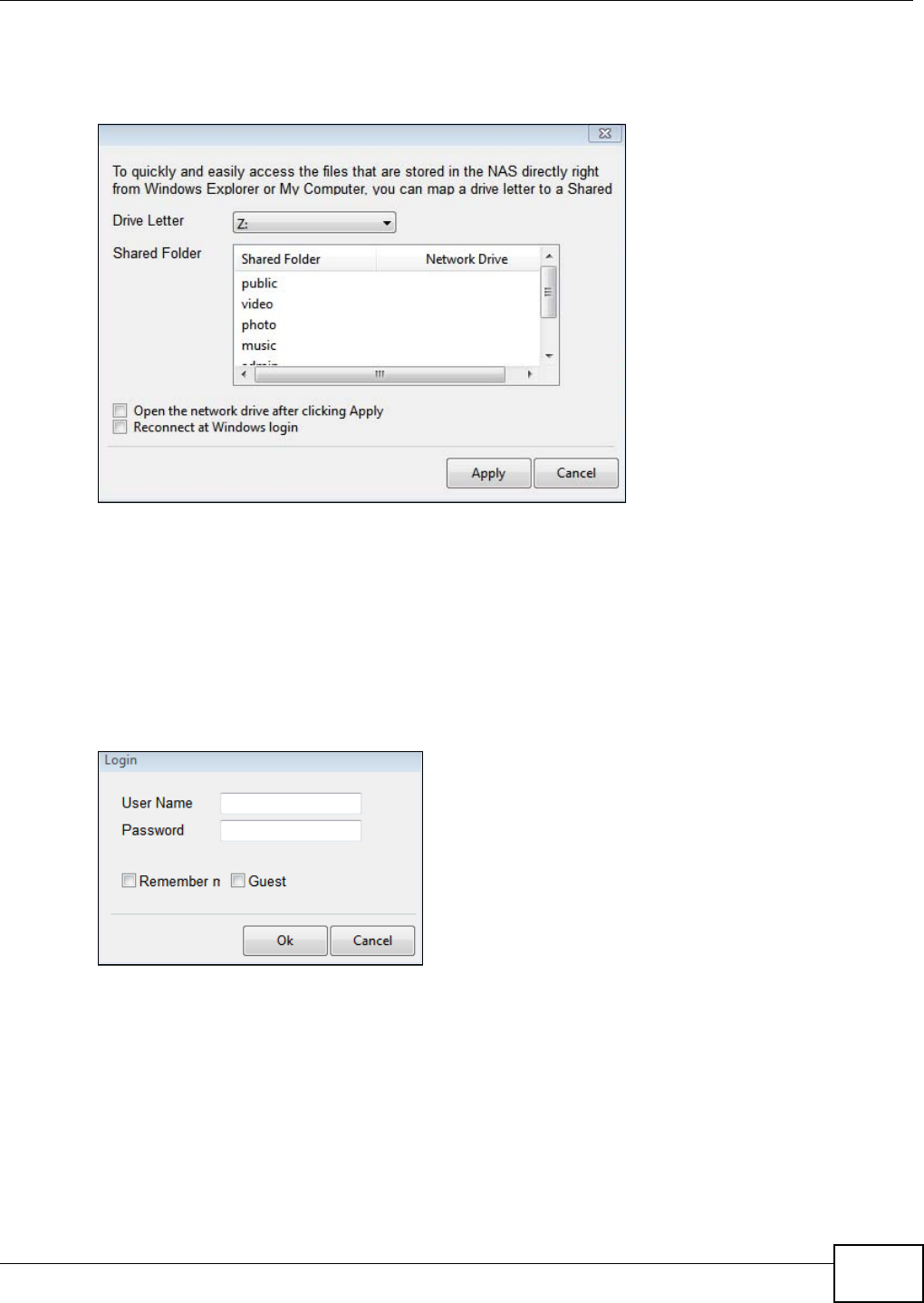
Chapter 3 NAS Starter Utility
Media Server User’s Guide 41
new drive in Windows Explorer (My Computer) where you can access and use it like your
computer’s other drives.
Figure 31 Network Drive
3.7 Manage the Device
In the main NAS Starter Utility screen click Configuration > Manage the Device to log into the
NSA’s administration screens where you can manage the NSA.
Enter the administrator user name and password and click Login.
Figure 32 Login
See Section 4.5 on page 58 for more on the administration screens.
3.8 Configure System Settings
Use these screens to be able to change the NSA’s server name, time zone, PPPoE, IP address,
subnet mask, default gateway, or DNS settings.
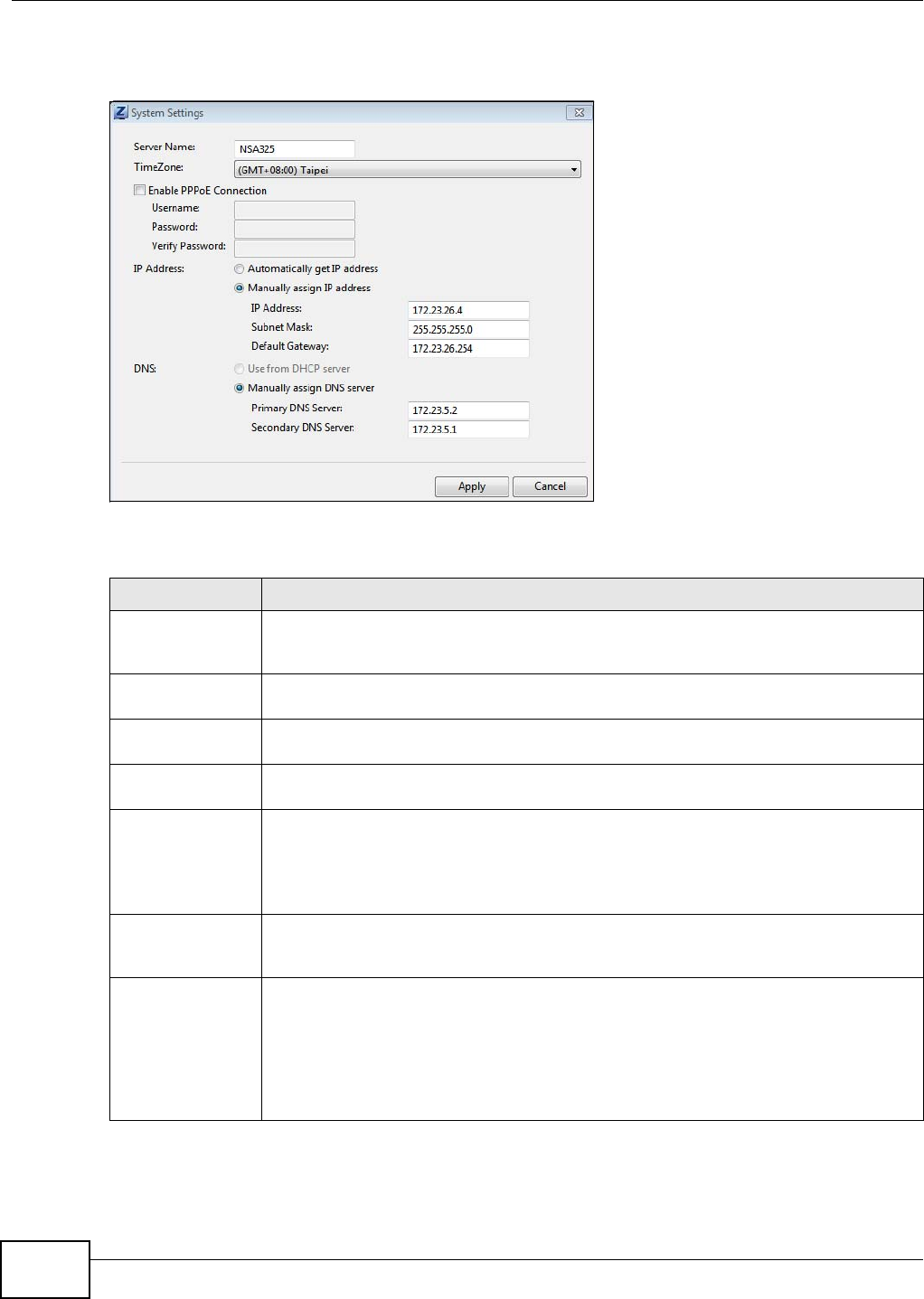
Chapter 3 NAS Starter Utility
Media Server User’s Guide
42
Click Configuration > System Setting in the main utility screen to display the following screen.
Figure 33 NAS Starter Utility > Configuration > System Setting
The following table describes the labels in this screen.
Table 3 NAS Starter Utility > Config
LABEL DESCRIPTION
Server Name Specify a name to uniquely identify the NSA on your network. You can enter up to 15
alphanumeric characters with minus signs allowed but not as the last character. The
name must begin with an alphabetic character (a-z) and is case sensitive.
Time Zone Choose the time zone of your location. This will set the time difference between your
time zone and Greenwich Mean Time (GMT).
Enable PPPoE
Connection Click this if your Internet connection requires you to enter a user name and password to
connect to the Internet. Enter your user name and password
Automatically get
IP address Select this if the NSA is automatically assigned an IP address from the ISP or a DHCP
server in your network.
Manually assign IP
address Select this if you want to assign the NSA a fixed IP address, subnet mask and default
gateway.
Note: Do not configure an IP address that is already in use in your network. This results to
a network IP address conflict and makes the NSA inaccessible.
Use from DHCP
server Domain Name System (DNS) is for mapping a domain name to its corresponding IP
address and vice versa. Select this if the NSA is automatically given DNS information
from the ISP or a DHCP server in your network.
DNS Domain Name System (DNS) is for mapping a domain name to its corresponding IP
address and vice versa.
Select Use from DHCP server if the NSA is automatically given DNS information from
the ISP or a DHCP server in your network.
Select Manually assign DNS server if you were given specific IP address(es) of the
DNS server(s). Enter the primary and secondary DNS in the corresponding fields.

Media Server User’s Guide 43
CHAPTER 4
Web Configurator Basics
4.1 Overview
This chapter describes how to access the NSA web configurator and provides an overview of its
screens.
The web configurator is an HTML-based management interface that allows easy NSA setup and
management using an Internet browser.
Use Internet Explorer 7.0, Mozilla Firefox 3.6, Safari 5, Google Chrome 10, or later versions of
these browsers. The recommended screen resolution is 1024 by 768 pixels or higher.
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by default in
Windows XP SP (Service Pack) 2.
• JavaScript (enabled by default).
4.2 Accessing the NSA Web Configurator
Make sure your NSA is properly connected and that your computer is in the same subnet as the
NSA (refer to the Quick Start Guide or the appendices).
Chapter 4 Web Configurator Basics
Media Server User’s Guide
44
4.2.1 Access the NSA Via NAS Starter Utility
If you don’t know the IP address of the NSA, use the NAS Starter Utility to find it. Refer to the Quick
Start Guide for how to install and run the NAS Starter Utility. See Chapter 3 on page 35 for more
information on the NAS Starter Utility.
Figure 34 NAS Starter Utility Main Screen
4.2.2 Web Browser Access
Configure the server name of your NSA using the Network Configuration screen (Section 3.8 on
page 41) of the NAS Starter Utility. Open your browser and type in the server name of the NSA. The
default is ‘nsa’ followed by the number of your model (‘nsa325’ for example).
Figure 35 NSA URL
nsa325
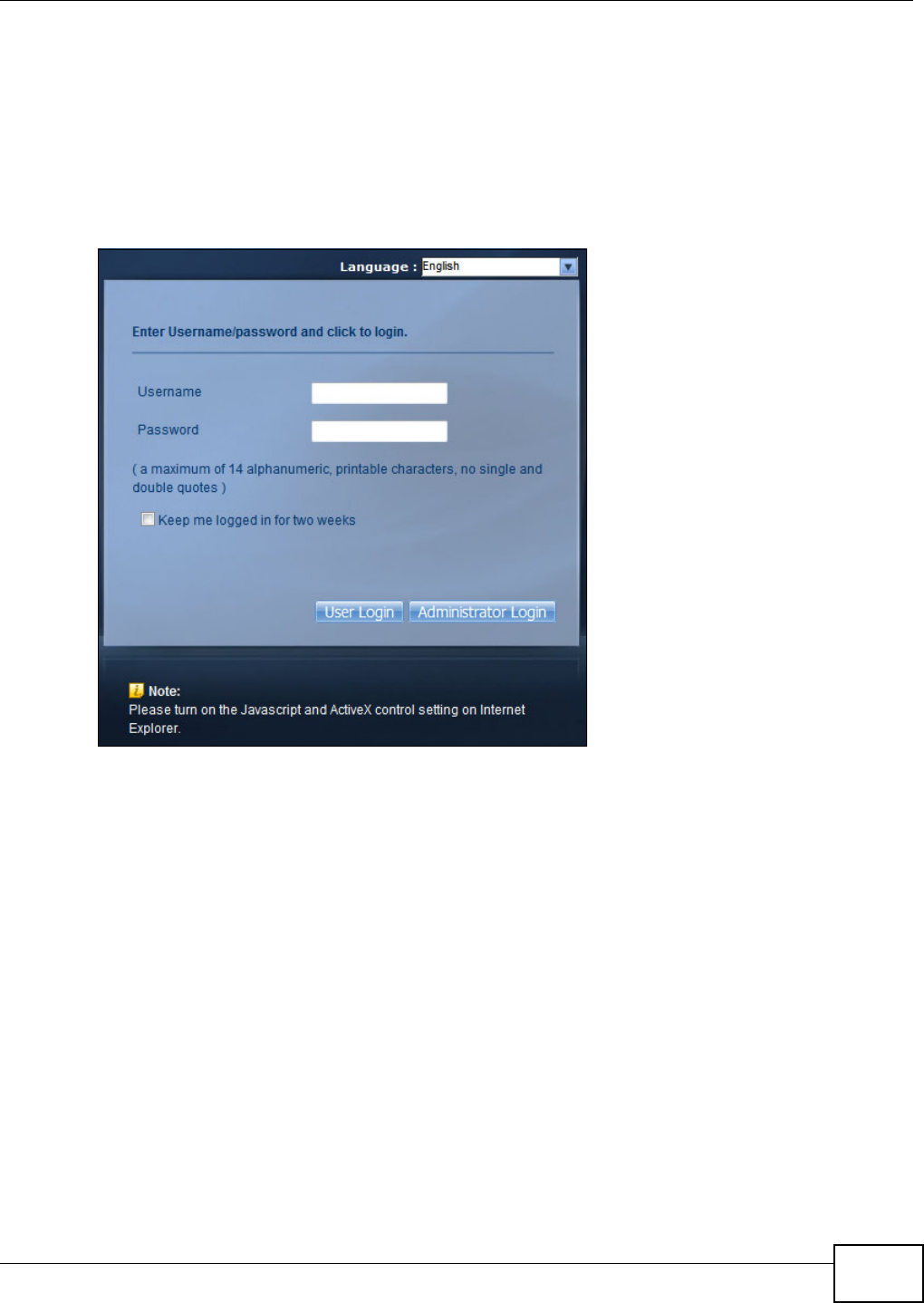
Chapter 4 Web Configurator Basics
Media Server User’s Guide 45
4.3 Login
The default username and password are ‘admin’ and ‘1234’ respectively. Enter your username and
password. See Chapter 14 on page 293 for how to create other user accounts. If you use the option
to stay logged in for two weeks (assuming you do not log out), make sure you keep your computer
secure from unauthorized access. Click User Login to go to the Home screens where you can play
media files. Click Administrator Login to go to the advanced administration screens.
Figure 36 NSA Login Screen
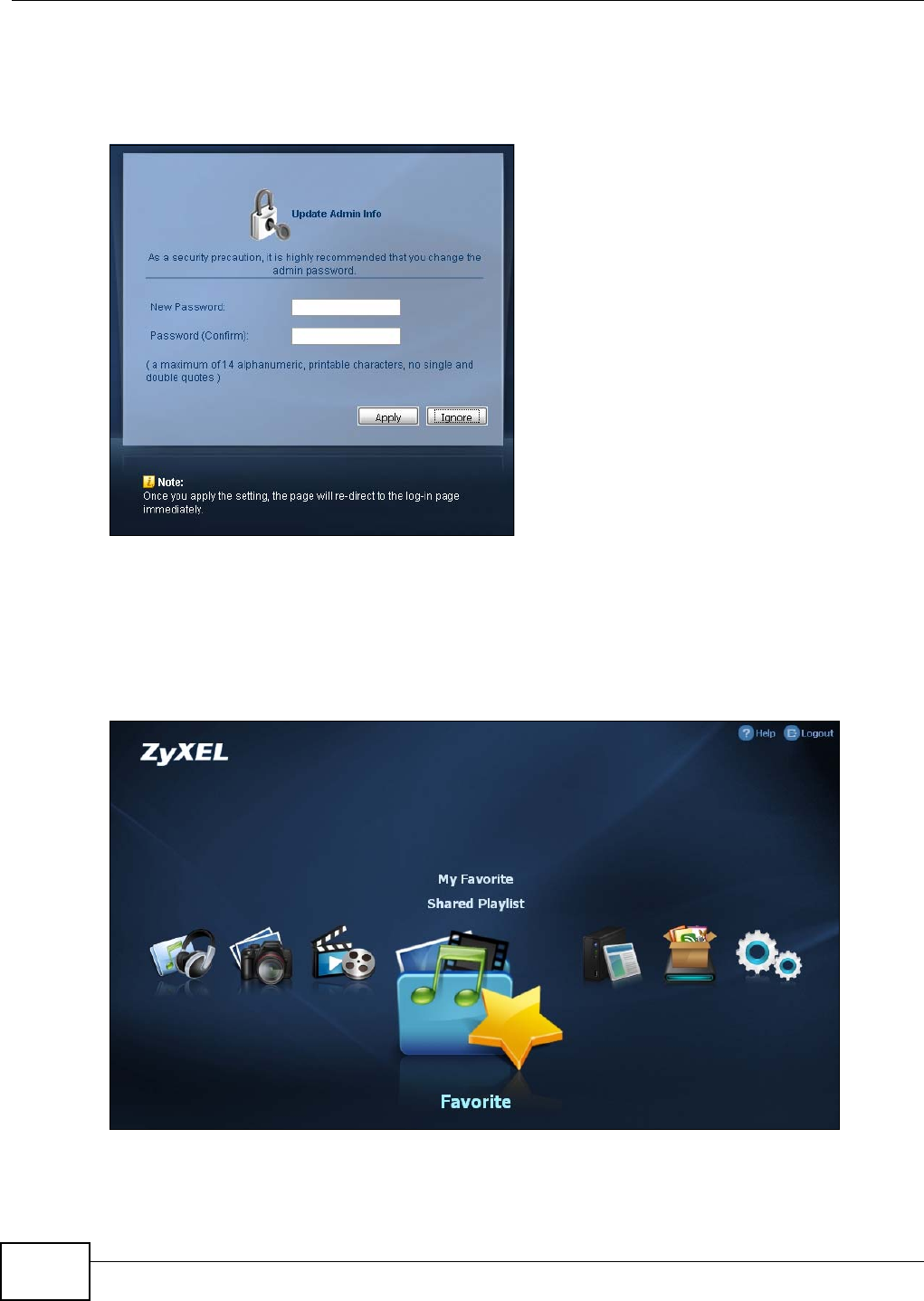
Chapter 4 Web Configurator Basics
Media Server User’s Guide
46
If you have not done so yet, you should see a screen asking you to change your password (highly
recommended) as shown next. Type a new password (and retype it to confirm) and click Apply or
click Ignore.
Figure 37 Change Password Screen
4.4 Home Screens
The Home screen after you log in using User Login.
Figure 38 Home
Note: If you did not select the option to stay logged in for two weeks when you logged in,
the web configurator management session automatically times out if it is left idle
for 15 minutes. Simply log back into the NSA if this happens to you.
Chapter 4 Web Configurator Basics
Media Server User’s Guide 47
The main Home screen displays icons for the various features you can access.
Note: Your browser may need Windows Media Player and VLC plugins installed to play
music and video files. To get the VLC plugins, you have to download and install VLC
(use the .exe file). To install a VLC plugin for Firefox, when you install VLC, you
have to select the Mozilla plugin option. To display your photos as a 3-D wall for
quick browsing, install the CoolIris plugin.
Current VLC plugins may not support srt file format subtitles when playing videos.
The icons at the top-right of the screen are visible from most screens. Use them to navigate
between the screens and menus. The following table describes the icons.
Table 4 Main Home Screen Icons
ICON DESCRIPTION
Use Music, Photo, and Video to play and organize your music, picture, and video files.
Use Favorite to create and edit playlists.
Use File Browser to see your files in a tree-folder structure.
Administrators can use Application Zone to install, access, and manage the NSA’s
applications.
Use System to edit general system settings or log into the administrator advanced
configuration screens.
Table 5 Global Home Labels and Icons
LABEL/ICON DESCRIPTION
Home Click this to return to the Home screen.
Help Click this to open a web help page specific to the screen you are currently configuring.
Logout Click this at any time to exit the web configurator.
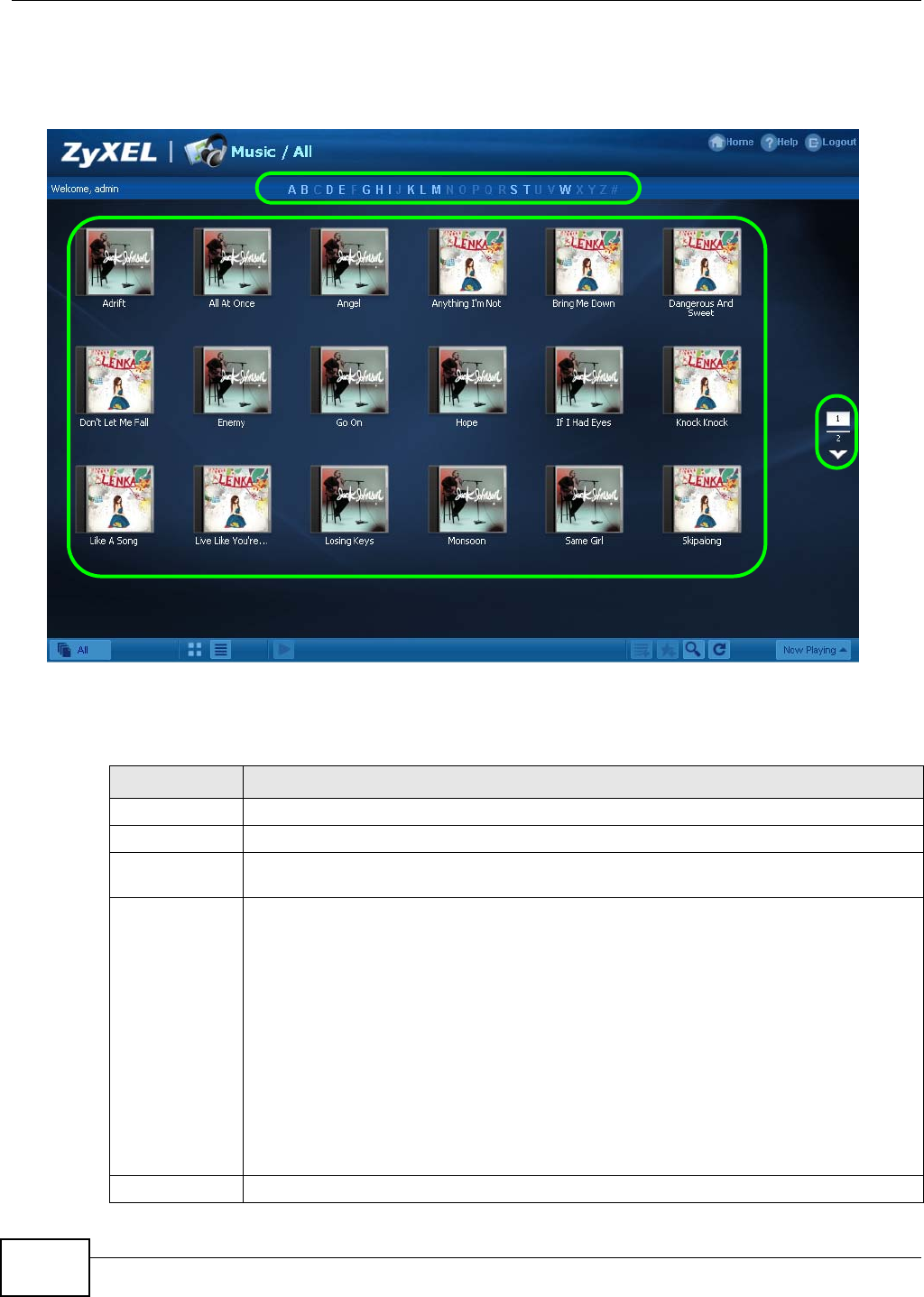
Chapter 4 Web Configurator Basics
Media Server User’s Guide
48
Here are some Home screen descriptions. A music screen is shown here as an example. Other
screens work in a similar way.
Figure 39 Music Screen
This table describes common labels in the Home media screens. Not every item displays in every
screen.
A
B
D
C
Table 6 Home Media Screens
LABEL DESCRIPTION
A Click a letter to go to the first item starting with that letter.
B View files. Double-click an item to play it.
C Shows which page is displaying and the total number of pages of entries. Click an arrow or
type a number to go to another page of entries.
D Select the sorting criteria:
Artist - Sort music by artist.
All - All of the menu’s files display here.
Genre - Sort music by category.
Folder - List the folders containing music files.
Album - List the identified music albums.
Current Playlist - Show the playing and queued songs.
The NSA categorizes files into genres and albums according to the information stored in
your files. Files may not appear in the proper folders if they have missing, incorrect or
incomplete information.
Thumbnail Click this to view the files as thumbnails.
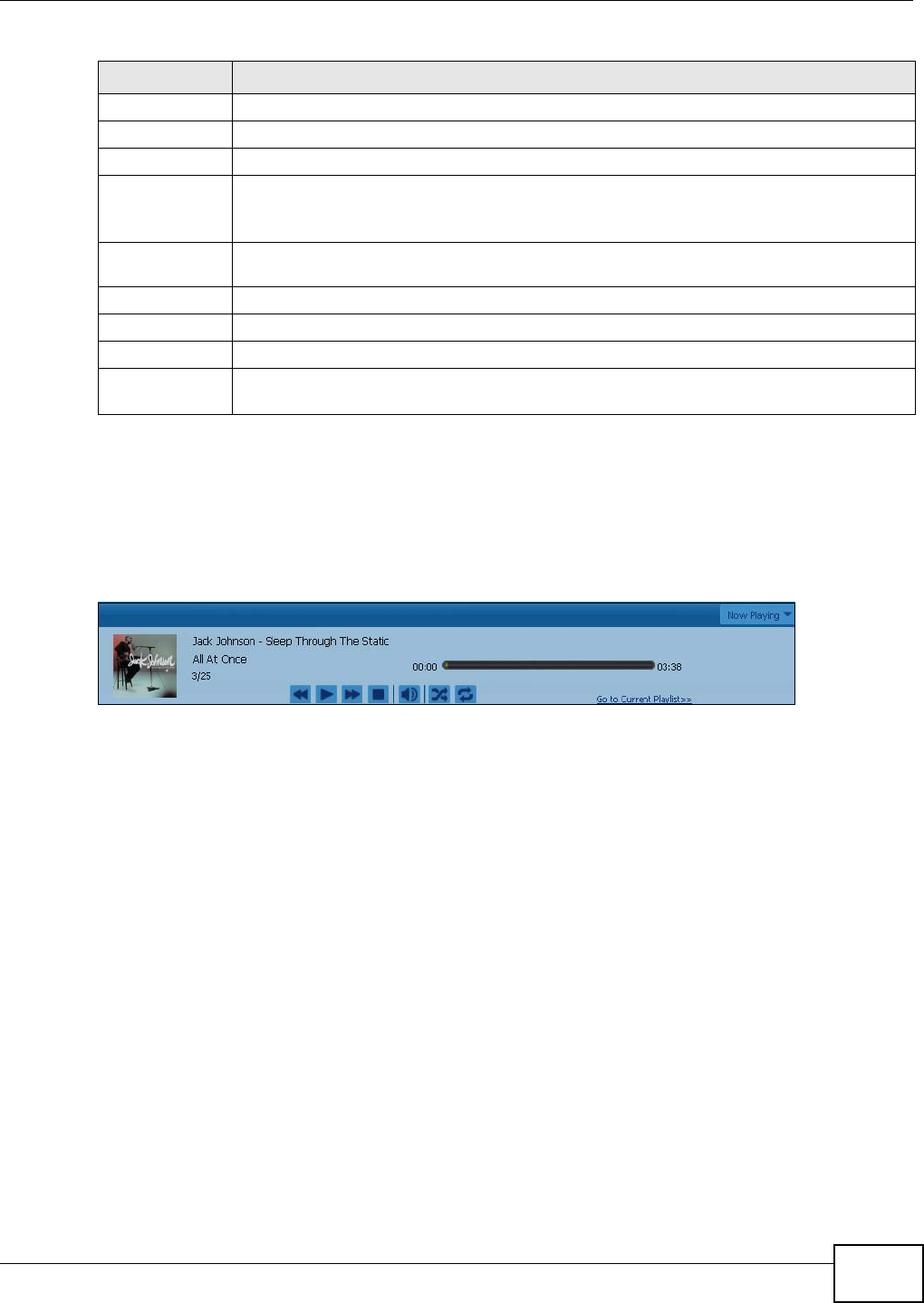
Chapter 4 Web Configurator Basics
Media Server User’s Guide 49
4.4.1 Now Playing (Music)
A Now Playing link displays when a song is playing. Click it to display a panel like the following.
This screen displays the name of the current song and it’s play progress and lets you control the
playback.
Figure 40 Now Playing
List Click this to view the files as a list.
Play Click this to play the currently selected file. You can also double-click a file to play it.
Delete Select an item and click Delete to remove it.
Rename Select an item and click Rename to change its name.
Note: When you change a file name, make sure you keep the file extension unchanged.
Add to Current
Playlist Click this to add the selected music file to the currently playing playlist.
Add to Playlist Click this to add the selected music file to a playlist.
Search Click this to look for a file or folder by name.
Refresh Click this to update the display in the screen.
Now Playing This link is available when a song is playing. Click it to see details about the song that is
currently playing.
Table 6 Home Media Screens
LABEL DESCRIPTION
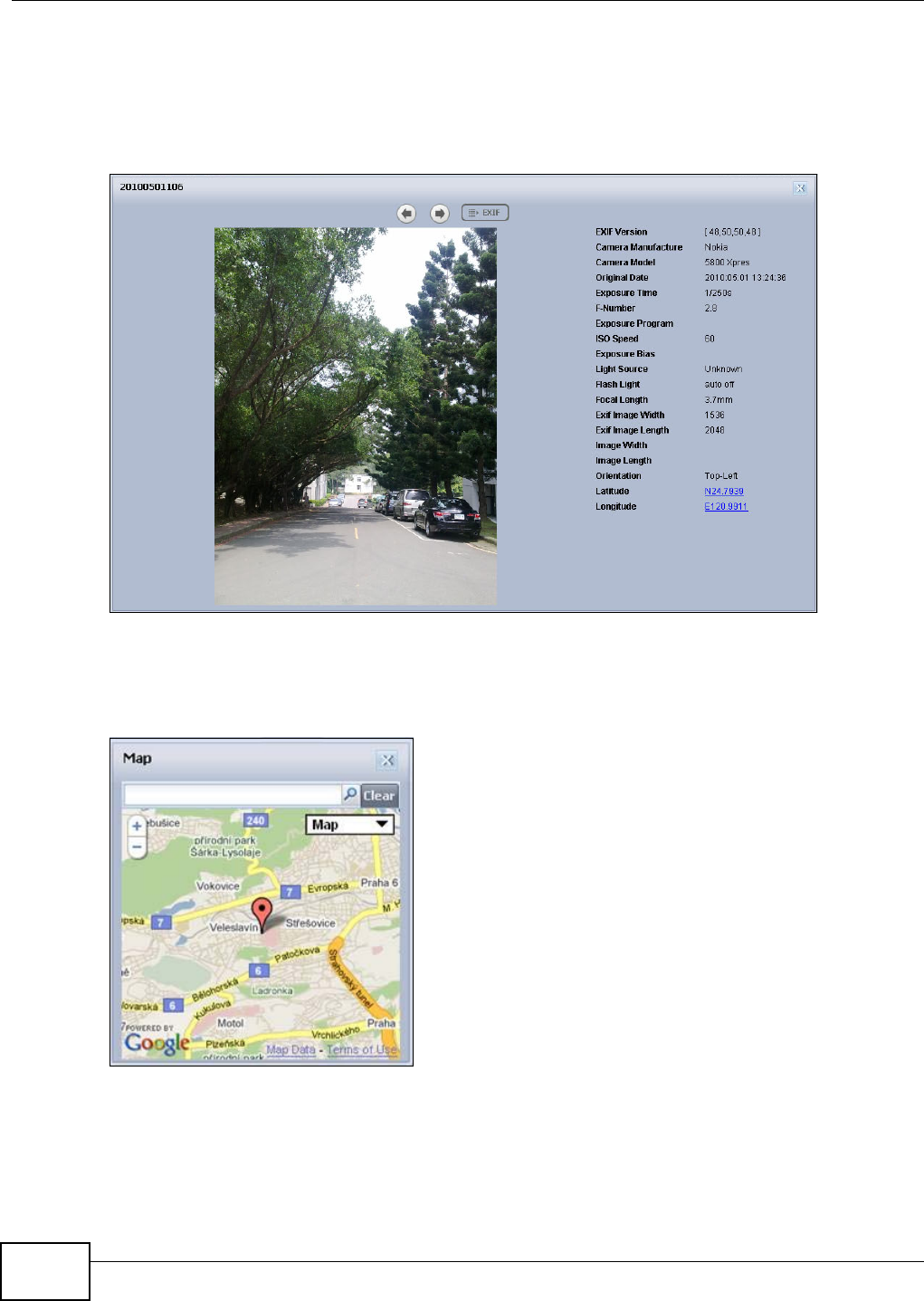
Chapter 4 Web Configurator Basics
Media Server User’s Guide
50
4.4.2 Exif and Google Maps (Photos)
Click a photo’s EXIF button to display or hide the photo’s Exchangeable image file format (Exif)
data.
Figure 41 Exif Information
If a photo’s Exif data includes GPS location data, click the latitude or longitude link to display the
location in Google Maps. Click Clear to delete the markers of other photos and only display the
current photo’s marker.
Figure 42 Google Maps
4.4.3 Slideshow and CoolIris (Photos)
In a Photo menu click the SlideShow button to display the menu’s files as a slideshow. Move your
cursor over the slideshow’s screen to display full screen, previous, pause, and next buttons for
controlling the slideshow.

Chapter 4 Web Configurator Basics
Media Server User’s Guide 51
Note: Your browser must have the Flash Player plug-in installed to view slideshows.
Figure 43 Slideshow
When the CoolIris plugin is installed in your browser, click the Launch CoolIris button to display
your photos as a 3-D wall for quick browsing.
4.4.4 Favorite
Use the Favorite menu to manage your playlists.
4.4.4.1 Shared Playlist
Use Favorite > Shared Playlist to view and play playlists that you created externally (in iTunes,
Windows Media Player, VLC media player, or Winamp for example) and saved to the NSA. When
using zPilot to move files to the NSA, playlists are automatically put into the music share.
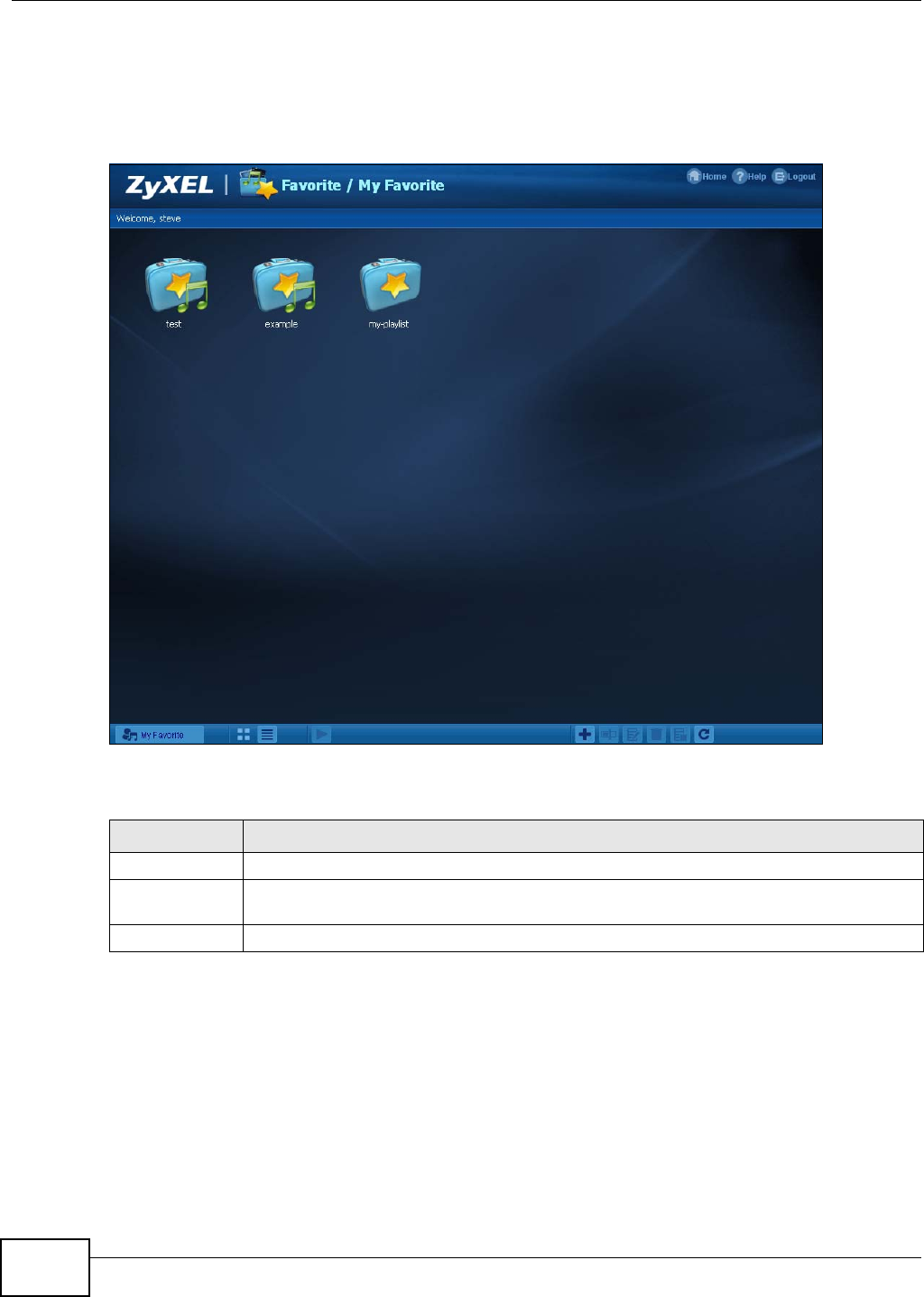
Chapter 4 Web Configurator Basics
Media Server User’s Guide
52
4.4.4.2 My Favorite
Use Favorite > My Favorite to create, edit, and play playlists. These playlists are specific to the
NSA and cannot be used in external music players.
Figure 44 Favorite > My Favorite
This table describes labels in this menu.
4.4.5 File Browser
Click File Browser to open the following screen. Use the file browsing screens to play, open,
upload, and download files. A share is a set of user access permissions for a specific folder on a
volume (gives someone access to a folder). It is equivalent to the Windows concept of a shared
folder, but the access rights are independent of the folder (you configure the share and the folder
separately). You can map a share to a network drive for easy and familiar file transfer for Windows
users.
• A folder icon with a hand indicates a share.
Table 7 Favorite > My Favorite
LABEL DESCRIPTION
New Click this to create a new playlist.
Edit Double-click a playlist or select it and click Edit to go to a screen where you can remove
songs from the playlist.
Delete All Within a playlist click Delete All to remove all of the playlist’s songs.
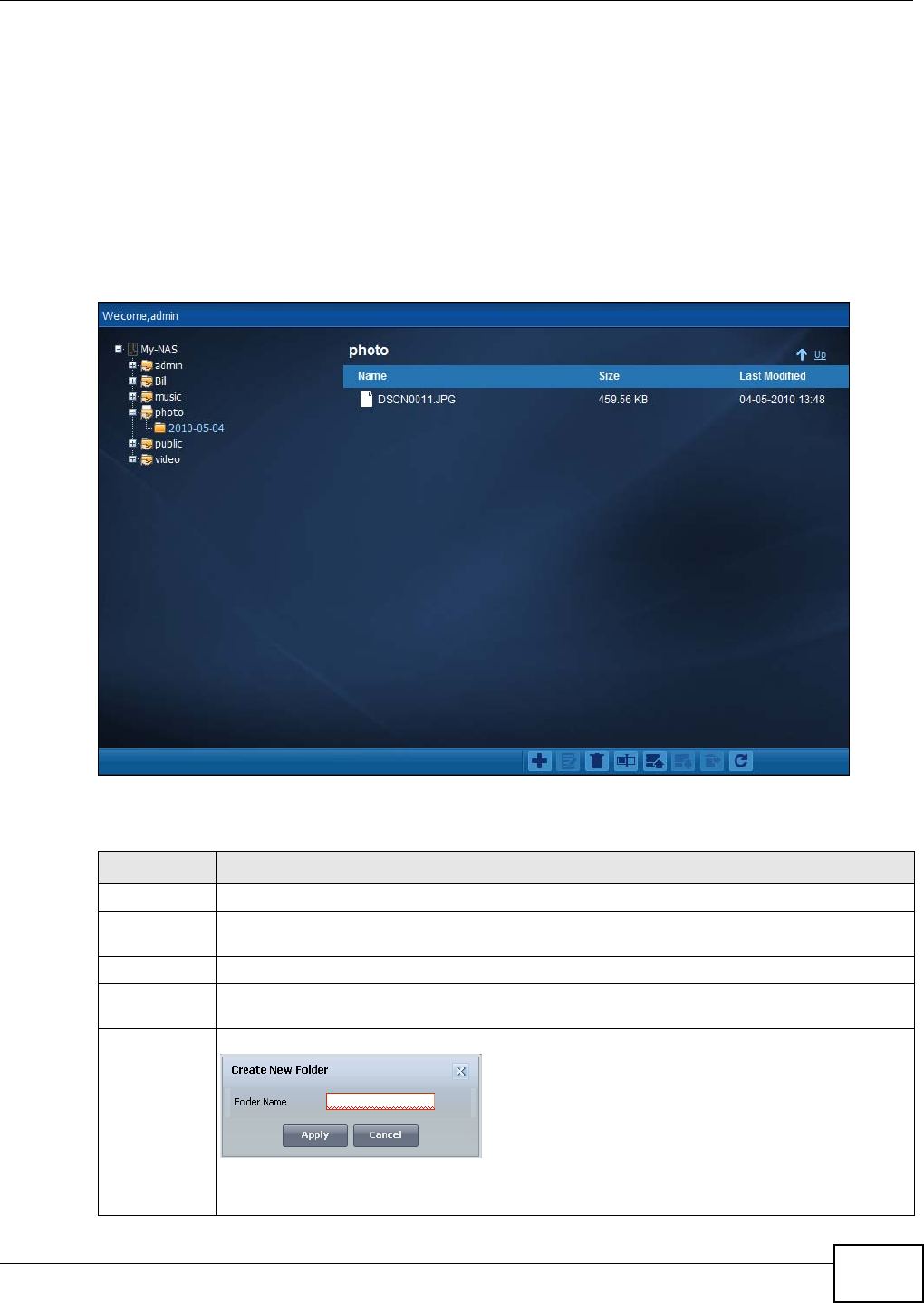
Chapter 4 Web Configurator Basics
Media Server User’s Guide 53
• The administrator owns and manages the public shares.
• Double-click a media file to open it. Double-click other types of files to be able to save them.
• Click to the right of a file or folder name to select it.
• Use the [SHIFT] key to select a range of entries. Hold down the [CTRL] key to select multiple
individual entries.
• Drag and drop files to open a screen that lets you choose whether to copy or move them.
• You can upload files of up to 2 GB in size.
• You can download individual files of up to 4 GB in size with Mozilla Firefox and Internet Explorer 7
and later or up to 2 GB in size with Internet Explorer 6.
Figure 45 File Browser
The following table describes the labels in this screen.
Table 8 File Browser
LABEL DESCRIPTION
Up Click this to go to the next higher layer in the share’s folder tree.
Name This column identifies the names of folders and files in the share. Click a file’s file name to
open the file or save it to your computer. Click a folder’s name to display the folder’s contents.
Size This column displays a file’s size in bytes.
Last Modified This column displays the last time the file or folder was changed (in year-month-day
hour:minute:second format).
Create New
Folder Click this to open a screen where you can create a new folder within the share.
Specify a name to identify the folder. See Section 4.4.6 on page 55 for more information on
folder names. Click Apply to create a folder or click Cancel to exit this screen.
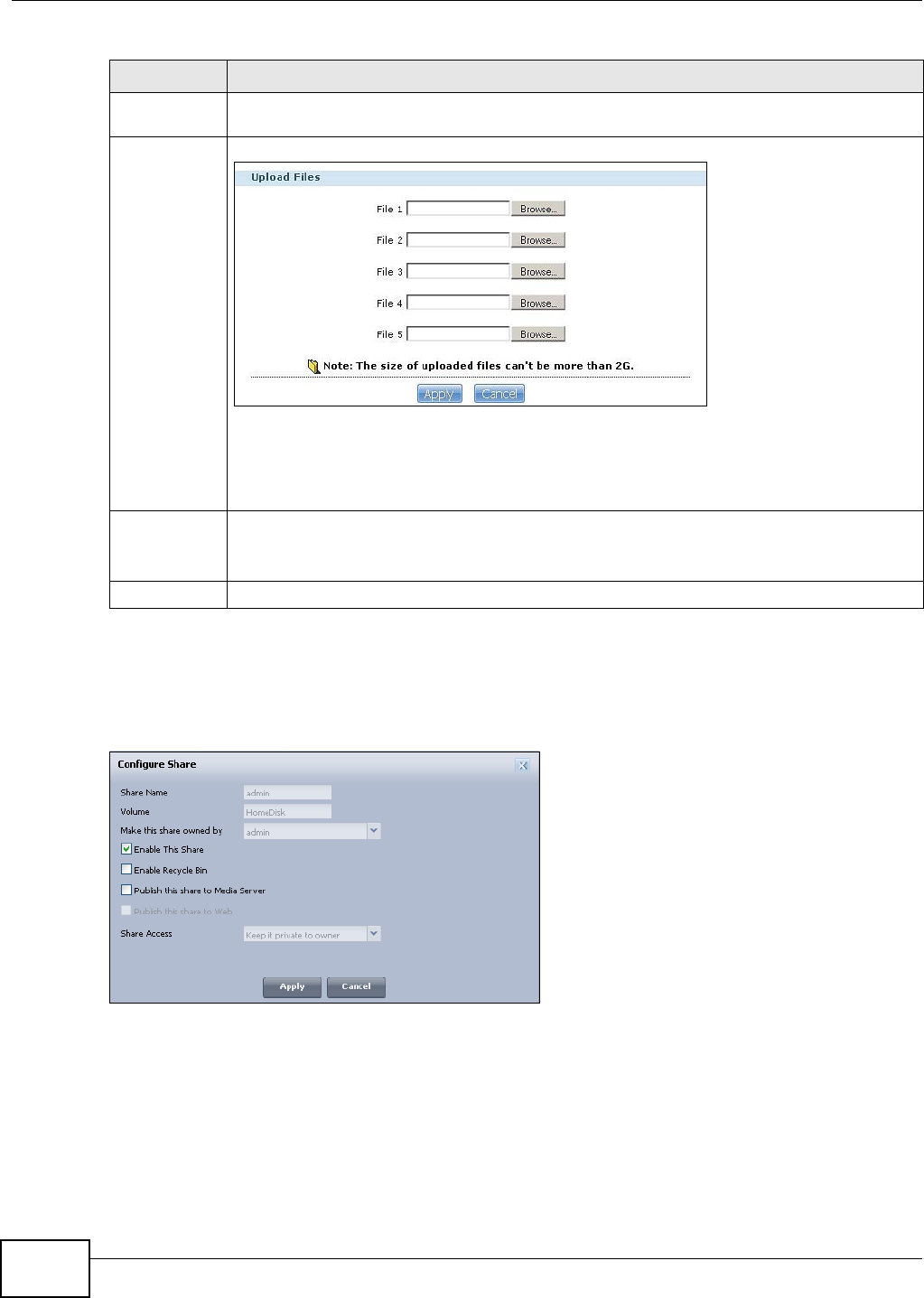
Chapter 4 Web Configurator Basics
Media Server User’s Guide
54
4.4.5.1 Configure Share Screen
In the File Browser screen, select a share and click Configure Share to open the following screen
where you can see and configure share management details.
Figure 46 File Browser > Configure Share
Configure
Share Select a share and click this link to open a screen where you can see and configure share
management details.
Upload Click this to open the following screen where you can add files to the share.
Use the Browse button to locate your file/s and click Apply to upload the file. Click Cancel to
close this screen.
Note: Do not refresh the screen while an upload is going on.
Download Select a file and click this to save the file to your computer.
Note: Do not refresh the screen while a download is going on.
Restore When you are in a recycle bin folder, select a folder or file and click this to restore it.
Table 8 File Browser (continued)
LABEL DESCRIPTION
Chapter 4 Web Configurator Basics
Media Server User’s Guide 55
The following table describes the labels in the this screen.
4.4.6 Share and Folder Names
The name can only contain the following characters:
• Alphanumeric (A-z, 0-9) and Unicode.
The NSA allows FTP access to shares, folders or files with names encoded in the UTF-8 (8-bit
UCS/Unicode Transformation Format) format. So your FTP client must support UTF-8 in order to
access shares, folders or files on the NSA with Unicode names.
•Spaces
• _ [underscores]
•. [periods]
•- [dashes]
Other limitations include:
• All leading and trailing spaces are removed automatically.
Table 9 File Browser > Configure Share
LABEL DESCRIPTION
Share Name Configure a name to identify this share. Type a share name from 1 to 239 single-byte (no
Chinese characters allowed for example) ASCII characters. The name cannot be the
same as another existing local share. See Section 4.4.6 on page 55 for more information
on share names. This is not configurable for the NSA’s default admin, music, photo,
public, and video shares.
Volume This shows the volume the share is on. It is read-only.
Make this share
owned by Select the administrator or user account that is to own (manage) this share. The share
owner controls access rights to the share. This is not configurable for the NSA’s default
admin and public shares.
Enable This Share Select this option to allow users to access this share. When this option is not selected,
you cannot see and access this share.
Enable Recycle Bin Select this option to keep deleted items in a recycle bin. When you delete an item, a
recycle folder is created within the share, and the deleted item is stored in the recycle
bin. Later if you want to retrieve a deleted item, you can select the item from the recycle
folder and move/copy the item to another share.
Publish this share
to Media Server Select this option to make the share’s files available to media clients.
Publish this share
to Web Select this option to let people use a web browser to access this share’s files without
logging into the Home screens.
Share Access Select who can access the files in the share and how much access they are to be given. If
you publish the share to the media server or the web, all users will have at least read-
only access to the share, regardless of what you configure here.
Select Keep it private to owner to allow only the share owner to read files in the share,
delete files in the share and save files to the share.
Select Make it public to allow anyone (with or without a user account on the NSA) to
read files in the share, delete files in the share and save files to the share.
Select Advanced to select which individual users can read the share’s files, which users
can delete the share’s files, and which users are blocked from doing either.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
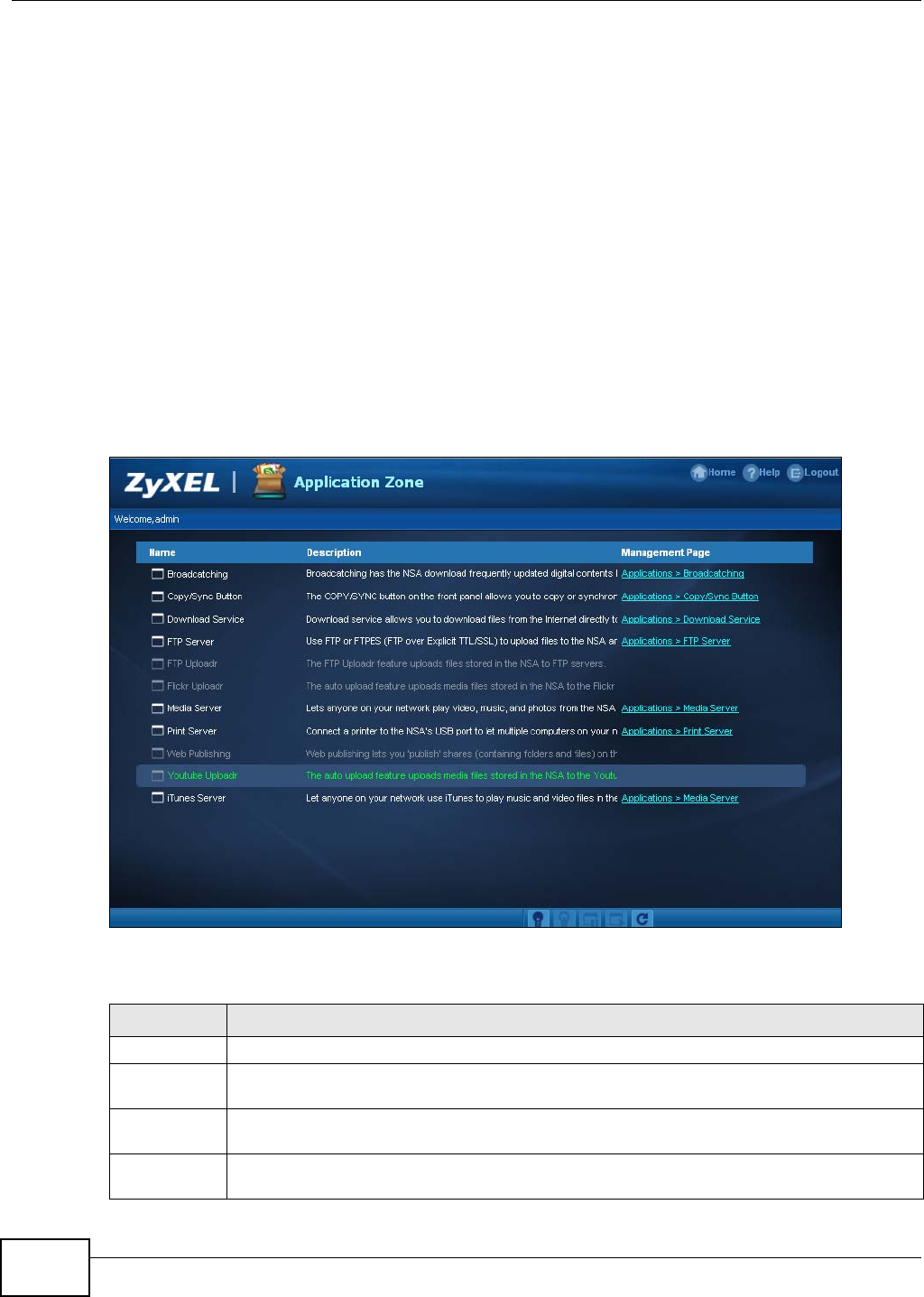
Chapter 4 Web Configurator Basics
Media Server User’s Guide
56
• Multiple spaces within names are converted to a single space.
• Share names must be unique (they cannot be the same as other share names).
• The NSA creates automatic volume names for external (USB) disk volumes. These are a type of
share, so the share name you configure cannot conflict with the external (USB) disk volume
names. “ExtVol1” or “ExtVol2” are examples of external (USB) disk volume names.
• Folder names must be unique (they cannot be the same as other folder names).
• The minimum character length of a name is one character, that is a name cannot be blank.
• The maximum character length of share name is 239 characters.
• Unicode is supported for share names, although your FTP client must support UTF-8. Full support
should be available in all Windows versions after Windows 2000.
4.4.7 Application Zone
Administrators can click Application Zone to go to a screen where you can enable or disable
various applications for file sharing and downloading.
Figure 47 Application Zone
The following table describes the labels in the this screen.
Table 10 Application Zone
LABEL DESCRIPTION
Name This is the name of the application.
Description This is a brief description of the application. See Chapter 10 on page 181 for more
information.
Management
Page Click this link to go the application’s management page where you can configure settings for
it. See Chapter 10 on page 181 for more information.
Enable Select a disabled application and click this to turn on the application. Some applications are
always enabled and cannot be disabled.
Chapter 4 Web Configurator Basics
Media Server User’s Guide 57
4.4.8 System Settings
Click System > Settings to open the following screen. Use this screen to change general settings
and an account password.
Figure 48 System > Settings
The following table describes the labels in this screen.
Disable Select an enabled application and click this to turn off the application. Select the Flickr or
Youtube Uploadr entry and click this to cancel all uploading. Some applications are always
enabled and cannot be disabled.
Pause Select the Flickr or Youtube Uploadr entry and click this to pause current uploading. Resume
will resume current uploading.
Resume Select the Flickr or Youtube Uploadr entry and click this to resume current uploading.
Table 10 Application Zone (continued)
LABEL DESCRIPTION
Table 11 System > Settings
LABEL DESCRIPTION
Double Click Behavior
Setting Select Replace current playlist and start to play to have double clicking a song
cause the NSA to immediately stop any currently playing song and start playing the
double-clicked song.
Select Append to current playlist to have double clicking a song add a song to the
end of the current playlist.
Slide Effect Enable the Ken Burns effect to have the NSA automatically pan and zoom photos in
slideshows. Disable it to display photos in slideshows normally.

Chapter 4 Web Configurator Basics
Media Server User’s Guide
58
4.5 Administration Screens
The System > Administration link displays when you log in as the administrator. Click System >
Administration in the Home screen to open the advanced administration screens.
Slide Interval Select how long to display each image in a slideshow before changing to the next.
Video Playback Select Play Next to play the rest of the video files in a folder. So for example, a folder
has video files 1~10 and you play video 3. When video 3 finishes the device continues
playing the rest of the videos in the folder (4~10). It does not loop back and play
videos 1 and 2.
Account Name Type the user name of the account for which you want to change the password.
Old Password Type the user’s current password.
New Password Create a new password for the user. You can type from one to 14 single-byte (no
Chinese characters allowed for example) ASCII characters.
Password (Confirm) You must type the exact same password that you just typed in the above field.
Language Select the web configurator language from the drop-down list box.
Go to system
administration page This link appears when you are logged in as the administrator. Click it to open the
advanced administration screens. See Section 4.5 on page 58 for more on the
advanced administration screens.
Apply Click this to save your changes.
Reset Click this to refresh the screen.
Cancel Click this to exit the screen without saving your changes.
Table 11 System > Settings (continued)
LABEL DESCRIPTION
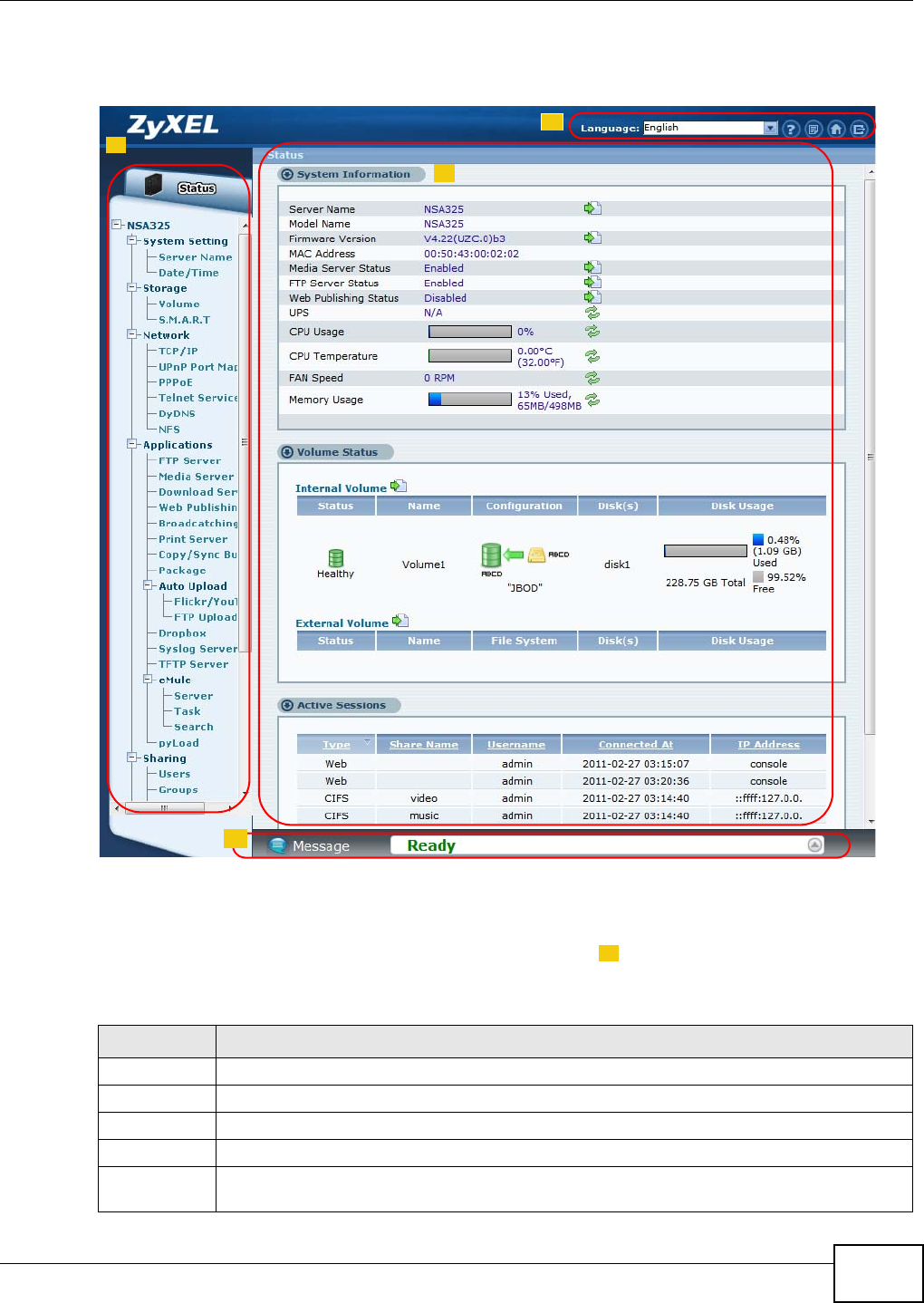
Chapter 4 Web Configurator Basics
Media Server User’s Guide 59
The Status screen is the first advanced administration screen that displays.
Figure 49 Status
4.5.1 Global Administration Icons
The icons and language label at the top-right of the screen ( ) are visible from most of the
administration screens. The following table describes the ‘global’ icons and labels.
3
4
1
2
Table 12 Global Labels and Icons
LABEL/ICON DESCRIPTION
Language Select the web configurator language from the drop-down list box.
Help Click this to open web help specific to the screen you are in.
About Click this to view the model name, firmware version and copyright.
Home Click this to return to the Home screens.
Logout Click this at any time to exit the web configurator. This is the same as clicking the Logout link
at the bottom of the navigation panel.
1

Chapter 4 Web Configurator Basics
Media Server User’s Guide
60
4.5.2 Navigation Panel
The navigation panel on the left of the Web Configurator screen ( ) contains screen links. Click a
link to display sub-links. There are no sub-links for the Status screen. Certain screens also contain
hyper links that allow you to jump to another screen.
The following table describes the navigation panel screens.
Table 13 Screens Summary
LINK SCREEN FUNCTION
Status This screen shows system information, the status of the volumes, and the
users who are currently using the NSA.
System
Setting Server Name Specify the NSA’s server name and workgroup name.
Date & Time Chose a time zone and/or allow the NSA to synchronize with a time server.
Storage Volume View volume and disk information and create and edit volumes. A volume is a
storage area that can span one or more internal disks or a single external
(USB) disk.
Network TCP/IP Assign the NSA a dynamic or static IP address and DNS information.
UPnP Port
Mapping Configure your Internet gateway to allow access from the WAN (Internet) to
services on the NSA.
PPPoE Configure PPPoE settings for a direct Internet connection.
Applications FTP Server Enable FTP file transfer to/from the NSA, set the number of FTP connections
allowed, an FTP idle timeout, and the character set.
Media Server Enable or disable the sharing of media files and select which shares to share.
Download
Service Have the NSA handle large file downloads.
Web
Publishing Let people use a web browser to access files in shares without logging into the
Home screens.
Broadcatching Subscribe the NSA to feeds to download frequently updated digital content like
TV programs, radio talk shows, Podcasts (audio files), YouTube videos, or even
BitTorrents.
Print Server View and manage the NSA’s list of printers and print jobs.
Copy/Sync
Button Copy or synchronize files between a USB device and the NSA.
Package Set up more useful applications in your NSA. The NSA can download multiple
packages/files at once and automatically goes through all the installation
steps.
Auto Upload -
Flickr/YouTube Upload files in selected shares to your Flickr and/or YouTube accounts.
Auto Upload -
FTP Uploadr Upload files in selected shares to FTP servers.
Dropbox Use your Dropbox account to move files to the NSA and have the NSA
download *.torrent files.
Syslog Server Use this to configure the NSA to accept syslog logs from syslog clients.
TFTP Server Use this to configure the NSA to accept log files from TFTP clients.
eMule Use this to use the NSA’s eMule peer-to-peer (P2P) file-sharing console to
download and share files from the Internet.
2
Chapter 4 Web Configurator Basics
Media Server User’s Guide 61
4.5.3 Main Window
The main window () shows the screen you select in the navigation panel. It is discussed in the
rest of this document.
The Status screen is the first administration screen to display. See Chapter 6 on page 149 for more
information about the Status screen.
4.5.4 Status Messages
The message text box at the bottom of the screen () displays status messages as you configure
the NSA.
4.5.5 Common Screen Icons
The following table explains some icons that appear in several configuration screens.
Sharing Users View, create and edit administrator and user accounts to let people use the
NSA.
Groups View, create and edit groups. Groups allow you to organize users into specific
groups. You can create shares accessible only by the group members.
Shares View, create and edit shares. Shares are shared folders to which you can allow
specific users read/write access rights.
Maintenance Power Configure power saving settings for the NSA and have the NSA turn itself off
and on or reboot according to the schedules you configure.
Log View the NSA’s logs and configure how you want to receive the log reports.
Configuration Back up and/or restore the NSA configuration file.
SSL Configure HTTPS and the NSA’s SSL certificate.
FW Upgrade Upload/upgrade new firmware to your NSA.
Shutdown Restart the NSA or shut it down.
Logout Click this to exit the web configurator. This is recommended to prevent
unauthorized administrator access to the NSA.
Table 13 Screens Summary (continued)
LINK SCREEN FUNCTION
3
4
Table 14 Common Configuration Screen Icons
ICON DESCRIPTION
Edit
Click this to go to a screen where you can change the configuration settings of an entry.
Delete
Click this to delete an entry from the list.
Edit
Click this to jump to related item’s configuration screen.
Refresh
Click this to refresh the data for the field or value with which it is associated.
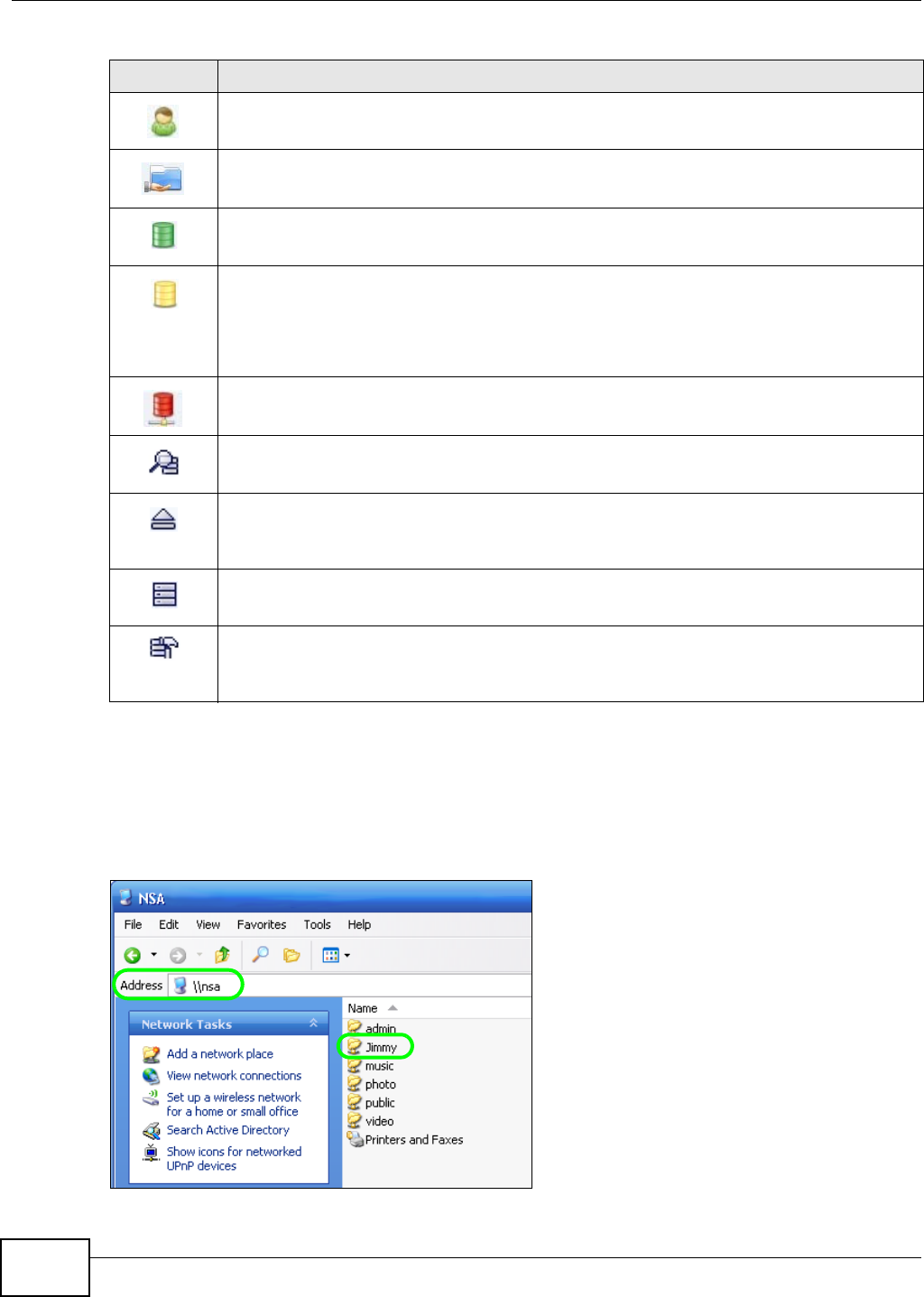
Chapter 4 Web Configurator Basics
Media Server User’s Guide
62
4.5.6 Session Example (Windows)
Open Windows Explorer and type two back slashes followed by the NSA name or IP address.
Initially you can only read and write to the Public, Video, Music, and Photo folders until you
create other shares on the NSA. This session is then displayed as shown in the following figure.
Session Example (Windows)
User
See the chapter on user accounts for detailed information on variants of this icon.
Share
See the chapter on shares for detailed information on variants of this icon.
Healthy
This represents a healthy volume.
Degraded
This represents a degraded RAID 1 volume. Replace the faulty disk. If the replacement disk
does not contain any partition, the NSA automatically restores the volume. If the replacement
disk already contains a volume, you need to delete the volume and then click the Repair icon
to fix the degraded RAID volume.
Down
This represents a down volume.
Scan Disk
Click this to scan a hard disk for file system errors.
Eject
Click this before you remove an external hard drive so that you do not lose data that is being
transferred to or from that hard drive.
Locate
Click this to cause the LED on the external storage device to blink.
Repair
If you replace a faulty disk with a disk that contains a volume, you need to delete the volume
and then click this to fix the degraded RAID volume.
Table 14 Common Configuration Screen Icons (continued)
ICON DESCRIPTION

Media Server User’s Guide 63
CHAPTER 5
Tutorials
5.1 Overview
This chapter provides tutorials that show how to use the NSA.
•Windows 7 Network, see page 63
•Windows 7 Network Map, see page 67
•Playing Media Files in Windows 7, see page 70
•Windows 7 Devices and Printers, see page 70
•Creating a Volume in a 2-Bay NSA, see page 73
•Creating a Volume in a 1-Bay NSA, see page 75
•Deleting a Volume, see page 82
•File Sharing Tutorials, see page 83
•Download Service Tutorial, see page 92
•Broadcatching Tutorial, see page 107
•Copy and Flickr Auto Upload Tutorial, see page 113
•FTP Uploadr Tutorial, see page 114
•Web Configurator’s Security Sessions, see page 117
•Using FTPES to Connect to the NSA, see page 130
•Using a Mac to Access the NSA, see page 131
•How to Use the BackupPlanner, see page 134
5.2 Windows 7 Network
To see your NSA in a Windows 7 home or work network:
Chapter 5 Tutorials
Media Server User’s Guide
64
1Click Start > Control Panel. Set View by to Category and click Network and Internet.
2Click View network computers and devices.
Chapter 5 Tutorials
Media Server User’s Guide 65
3The NSA icon displays twice because the NSA is both a media server and a storage device. Double-
click either NSA icon to open the Web Configurator login screen.
5.2.1 If the NSA Icon Does Not Display
The network containing the NSA must be set as a home or work network in order for the NSA icons
to display. If the network containing the NSA displays as “Public”:
1Click Network and Sharing Center and then the network’s link (circled in the figure).
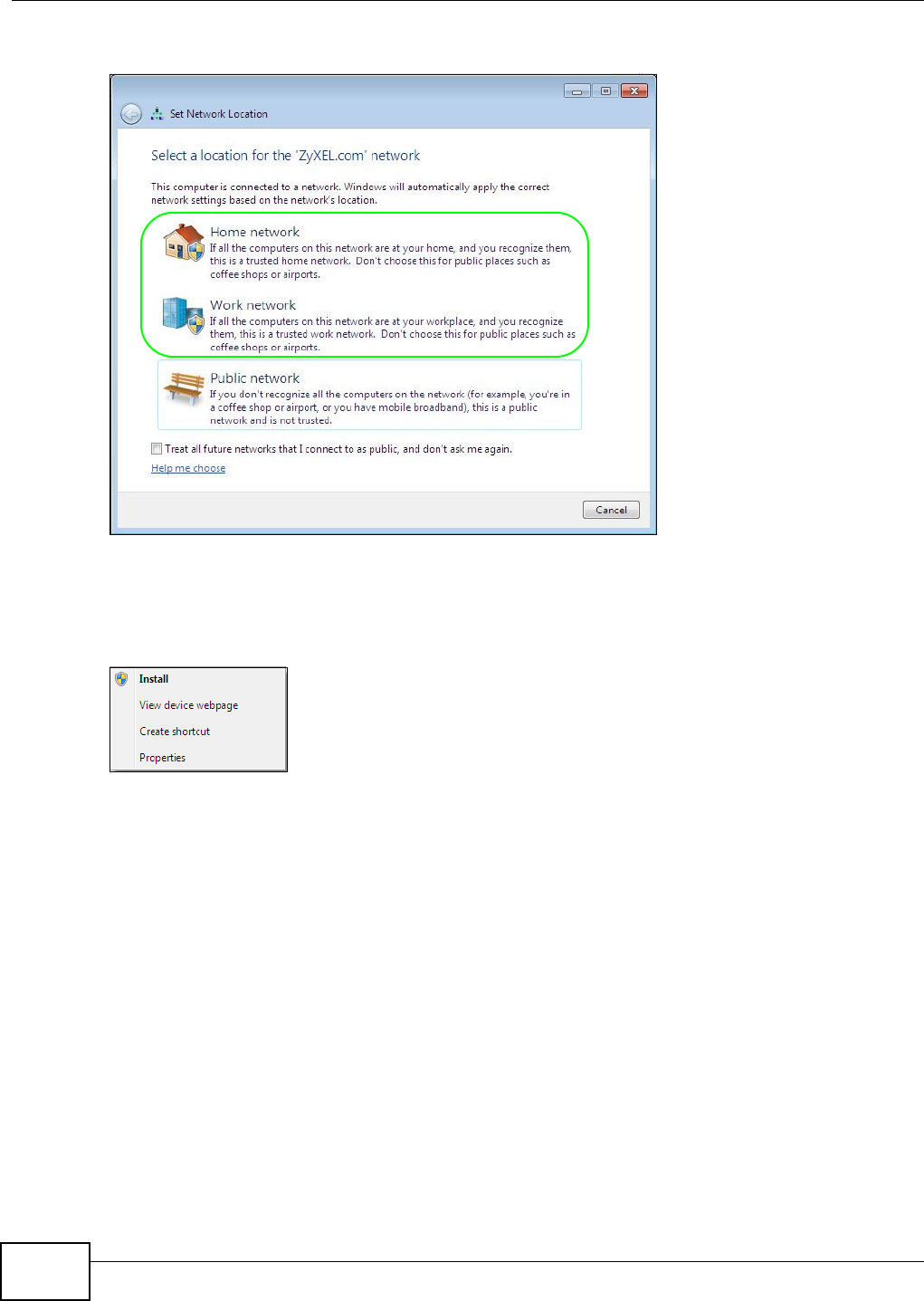
Chapter 5 Tutorials
Media Server User’s Guide
66
2Use the Set Network Location screen to set the network’s location to home or work.
5.2.2 NSA Icon Right-click Options
Right-click the NSA’s icon to see these options:
•Install/Uninstall: Click Install to add the NSA as a device in your computer. After you install
the NSA you can see it in the computer’s list of devices (see Section 5.5 on page 70. Click
Uninstall to remove the NSA from the list of devices installed in your computer.
•View device web page opens the Web Configurator login screen.
•Create shortcut adds a desktop shortcut to the Web Configurator login screen.
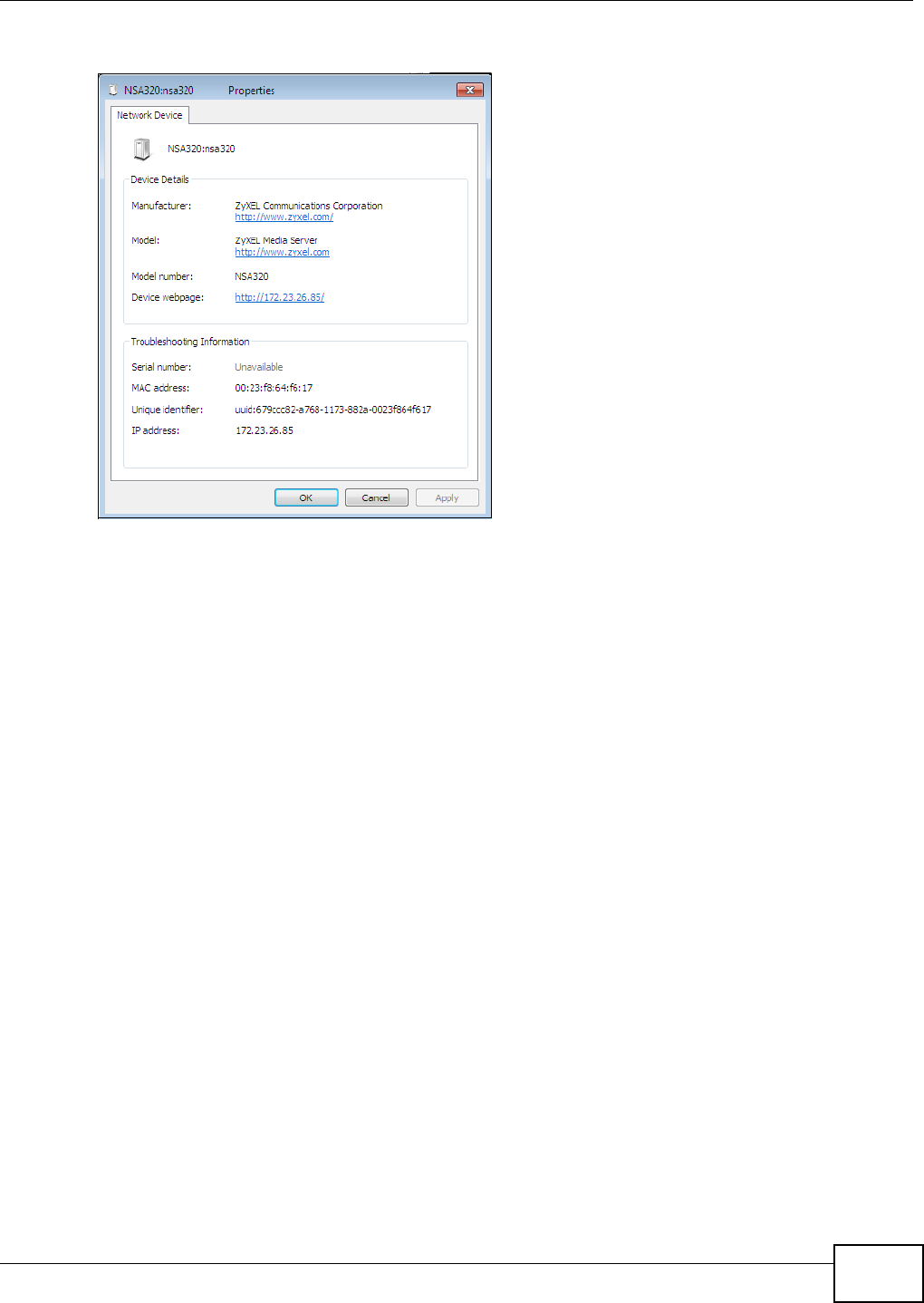
Chapter 5 Tutorials
Media Server User’s Guide 67
•Properties opens a window of NSA details and troubleshooting information.
•Manufacturer identifies the company that produced the NSA.
•Model identifies the NSA model.
•Model number identifies the NSA model number.
•Device webpage shows the IP address for accessing the Web Configurator.
•Serial number is unavailable because the NSA does not have one.
•MAC address is the NSA’s unique physical hardware address (MAC). You need the MAC
address to register the product at myZyXEL.com. Customer support may also request it for
troubleshooting purposes.
•Unique identifier is a unique UPnP ID that the NSA generated.
•IP address is the NSA’s IP address. It is also the IP address for accessing the Web
Configurator.
5.3 Windows 7 Network Map
To see your NSA in a Windows 7 home or work network map:
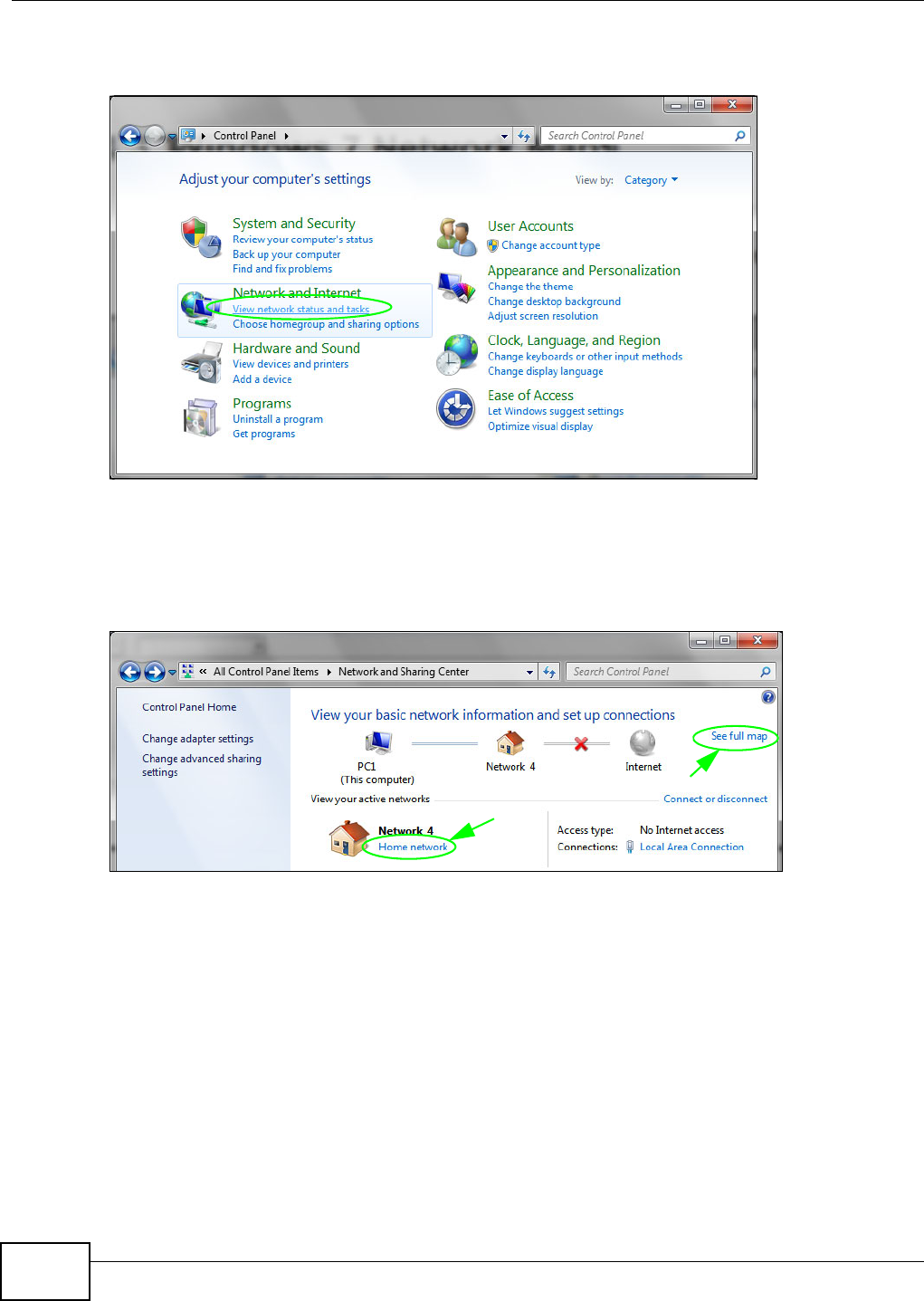
Chapter 5 Tutorials
Media Server User’s Guide
68
1Click Start > Control Panel > View network status and tasks (or Network and Sharing
Center if you view the Control Panel by icons).
2Click See full map (1 in the figure).
The network containing the NSA must be set as a home or work network in order to use the full
map feature. If the network containing the NSA displays as “Public”, click the network’s link (2 in
the figure, although it is already set to home here) and use the Set Network Location screen to
set the network’s location to home or work (see page 66).
2
1
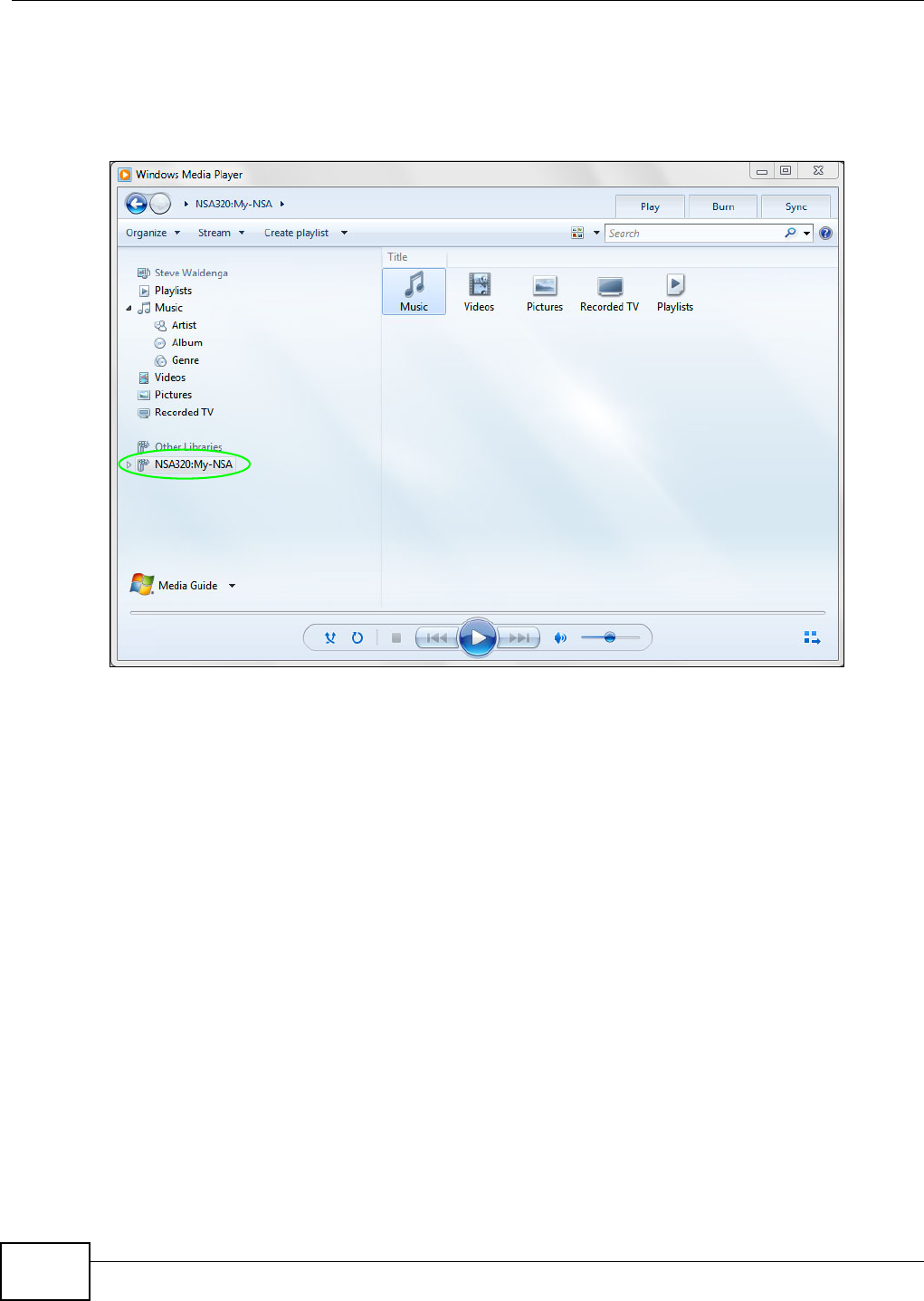
Chapter 5 Tutorials
Media Server User’s Guide
70
5.4 Playing Media Files in Windows 7
In Windows 7, the NSA automatically displays as a library in Windows Media Player.
Figure 50 NSA in Windows Media Player
5.5 Windows 7 Devices and Printers
After you use the NSA’s network icon’s install option you can manage the NSA from the Windows 7
Devices and Printers folder.
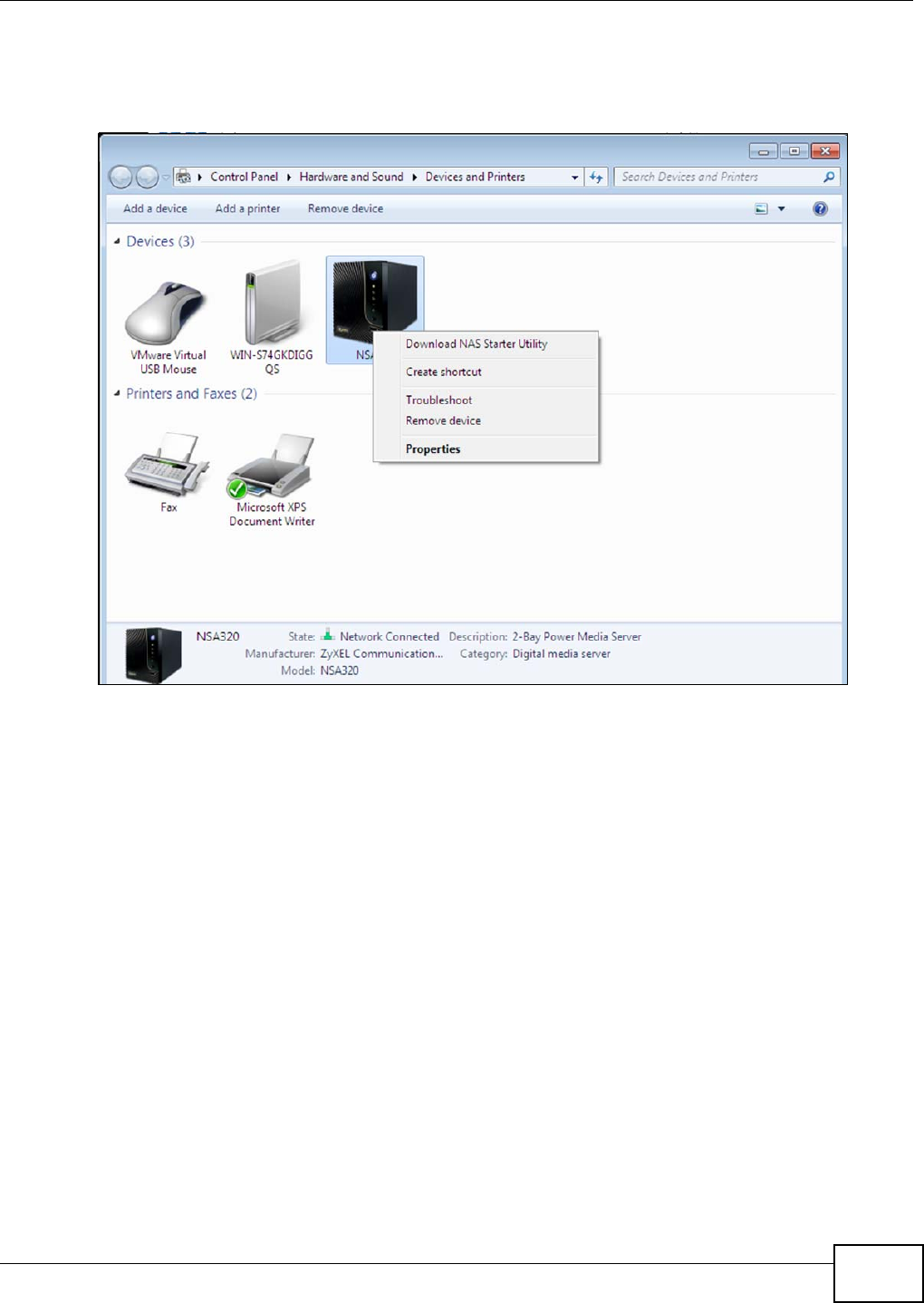
Chapter 5 Tutorials
Media Server User’s Guide 71
Click Start > Control Panel > Hardware and Sound > Devices and Printers. Select the NSA
icon to display information about the NSA. Double-click the NSA icon to open a properties window
(see page 67). Right-click the icon to display these options:
•Download NAS Starter Utility downloads the NSA’s Starter Utility. It lets you find, set up, and
manage the NSA as well as copy files to it and access the files on it. See Chapter 3 on page 35 for
details.
•Create shortcut has Windows make a desktop shortcut to this screen.
•Troubleshoot opens Windows’ device troubleshooting wizard.
•Remove device removes the NSA from the Windows 7 Devices and Printers folder.
•Properties opens a window of NSA details and troubleshooting information (see page 67).
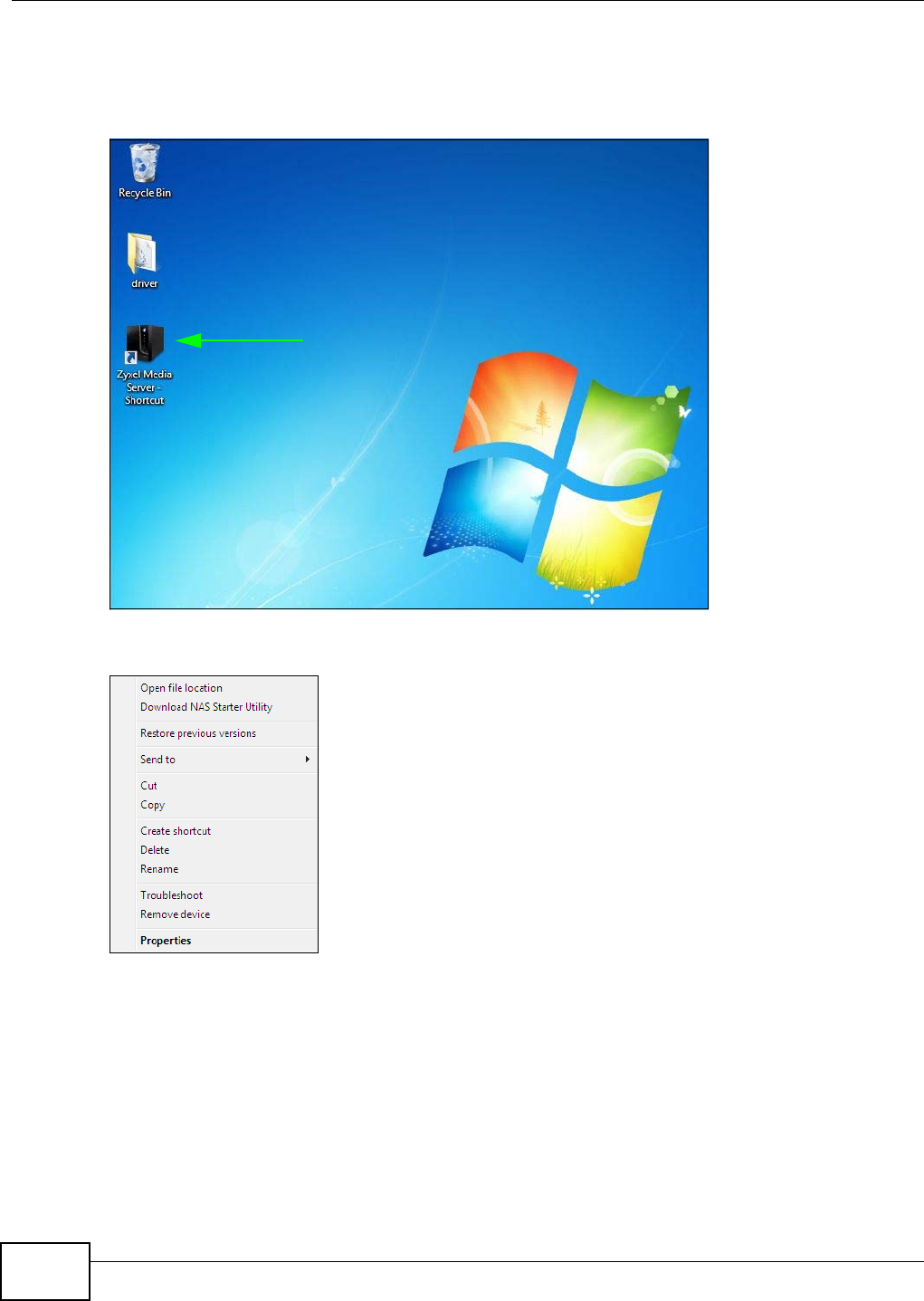
Chapter 5 Tutorials
Media Server User’s Guide
72
5.5.1 Windows 7 Desktop Shortcut
This is the NSA’s desktop shortcut. Double-click it to open a properties window (see page 67).
1Right-click the NSA’s desktop shortcut icon to see these options:
•Open file location takes you to the Windows 7 Devices and Printers folder.
•Download NAS Starter Utility downloads the NSA’s Starter Utility. It lets you find, set up, and
manage the NSA as well as copy files to it and access the files on it. See Chapter 3 on page 35 for
details.
•Restore previous versions is the Windows 7 option for restoring a file or folder. It does not
apply to this shortcut.
•Send to give you options for copying the shortcut to another location.
•Cut removes this shortcut so you can paste it somewhere else.
•Copy copies the shortcut so you can paste it somewhere else.
•Create shortcut has Windows make a desktop shortcut to this icon.
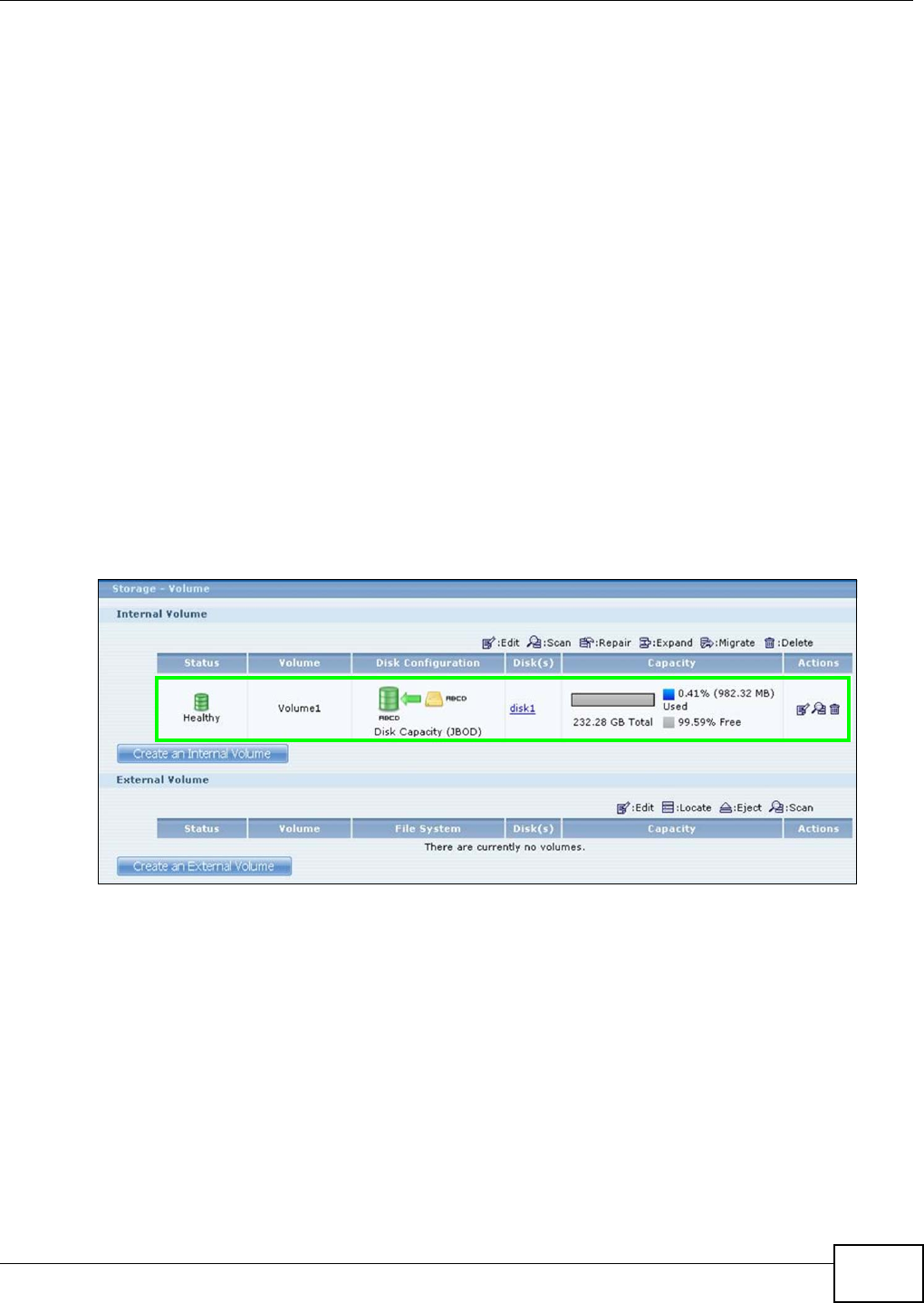
Chapter 5 Tutorials
Media Server User’s Guide 73
•Delete sends the shortcut to the recycle bin.
•Rename lets you change the name of the shortcut.
•Troubleshoot opens Windows’ device troubleshooting wizard.
•Remove device removes the NSA from the Windows 7 Devices and Printers folder.
•Properties opens a window of details about the shortcut.
5.6 Creating a Volume in a 2-Bay NSA
This section shows you how to create a volume in your 2-bay NSA.
Creating a volume deletes all existing data in the hard disk. Make sure
you have a backup of your existing data before following the steps in this
section.
Your NSA has two bays for Serial Advanced Technology Attachment (SATA) hard disks. The JBOD
storage method is used if you are using a single hard disk for your NSA.
This JBOD volume shows up in the Storage > Volume screen (Section 8.3 on page 161) as
follows.
5.6.1 Creating a RAID 1 Volume
This storage method allows recovery of data if your hard disk fails. To create a RAID 1 volume, you
must install two SATA hard disks in your NSA. There are two ways to create a RAID 1 volume:
• Click the Migrate button - If you already have a SATA hard disk with a volume and you later
install a second SATA hard disk in your NSA, use the Migrate button to convert the existing JBOD
volume to a RAID 1 volume.
• Click the Create an internal volume button - Use this if there are no existing volumes in your
NSA.
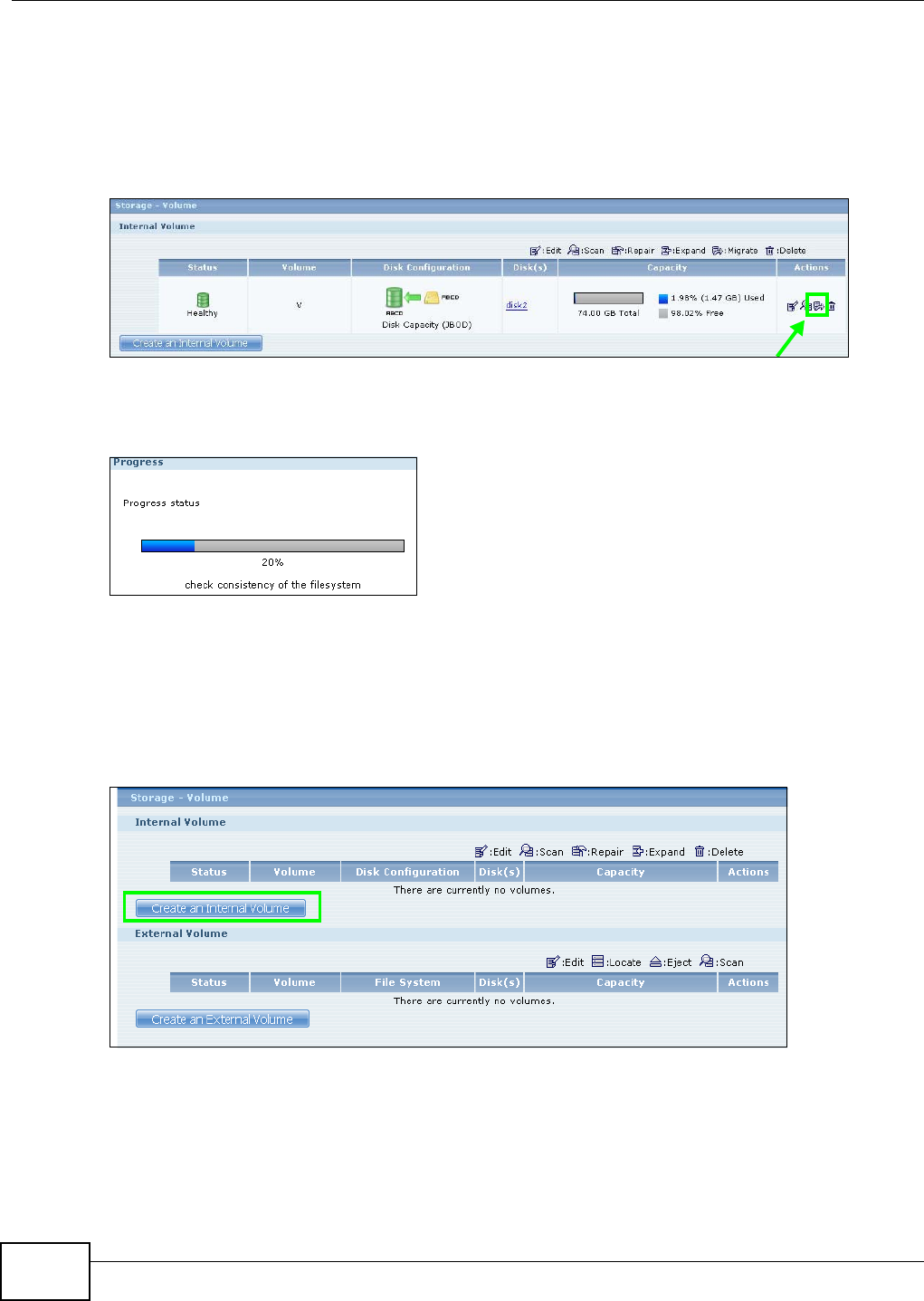
Chapter 5 Tutorials
Media Server User’s Guide
74
5.6.2 Migrate Button
Do the following steps to create a RAID 1 volume.
1Once you install a second SATA hard disk in the NSA, the Storage > Volume screen shows the
Migrate button.
2Click the Migrate button and you can see the following progress bar. Wait for the RAID 1 volume to
be created. This may take quite a while depending on how much data you have in the original
volume.
5.6.3 Create an Internal Volume Button
If you do not have an existing volume in the Storage > Volume screen, do the following steps to
create a RAID 1 volume.
1In the Storage > Volume screen, click Create an Internal Volume.
2In the Disk Configuration screen, you can select the storage method.
•Type in the Volume Name for your RAID 1 volume. The volume name can be 1 to 31 characters
(a-z, 0-9, " " [spaces], "_", and ".").
• Choose RAID 1 and click Apply.
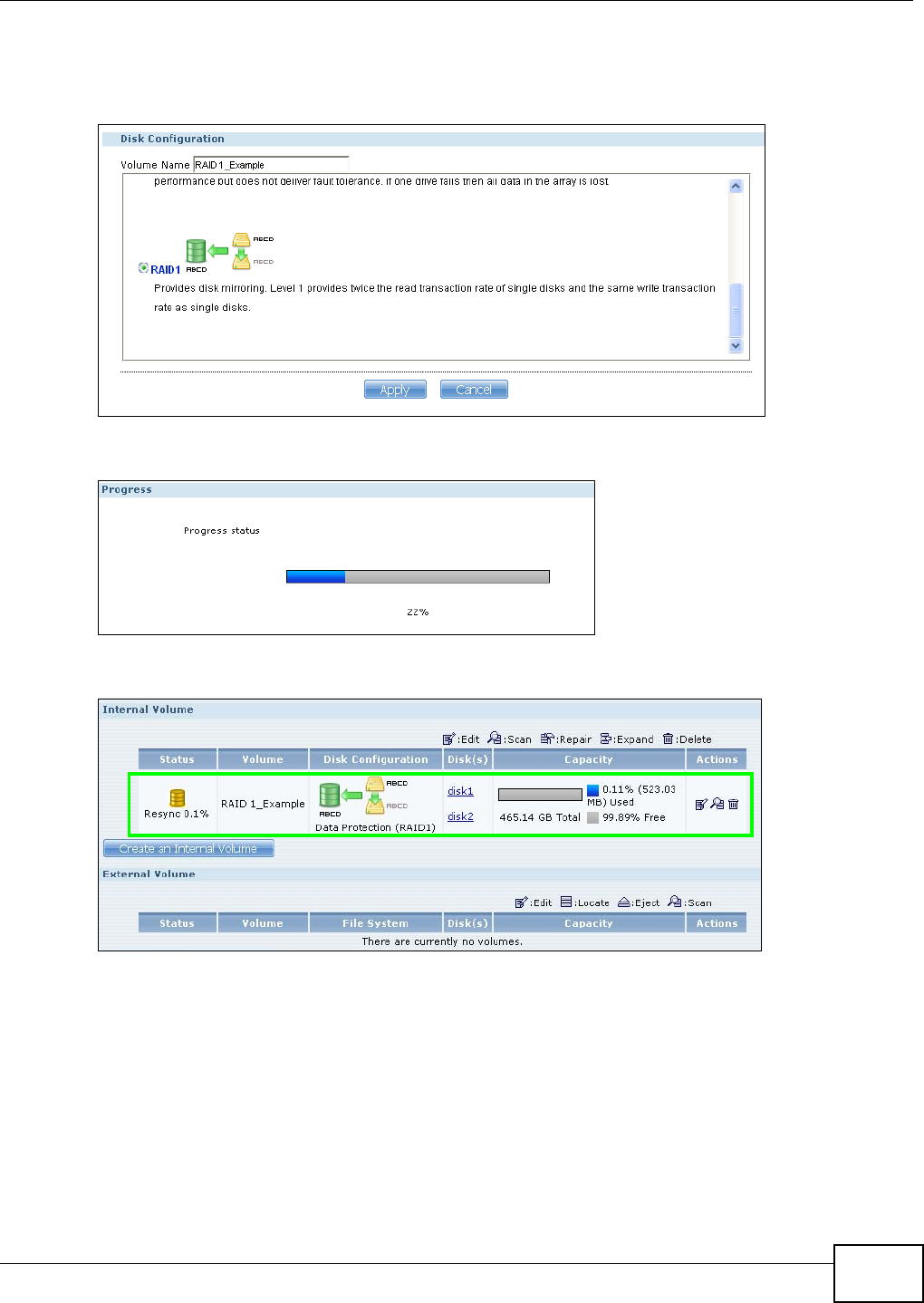
Chapter 5 Tutorials
Media Server User’s Guide 75
This deletes all existing data in the SATA hard disk. Make sure you have
a backup of any existing data in the hard disk.
The NSA starts creating the volume and you can see the following progress bar. Wait for the RAID 1
volume to be created.
3The Storage > Volume screen displays with your RAID 1 volume.
5.7 Creating a Volume in a 1-Bay NSA
This section shows you how to create a volume on your 1-bay NSA.
Creating a volume deletes all existing data in the SATA or eSATA hard
disk. Make sure you have a backup of your existing data before following
the steps in this section.
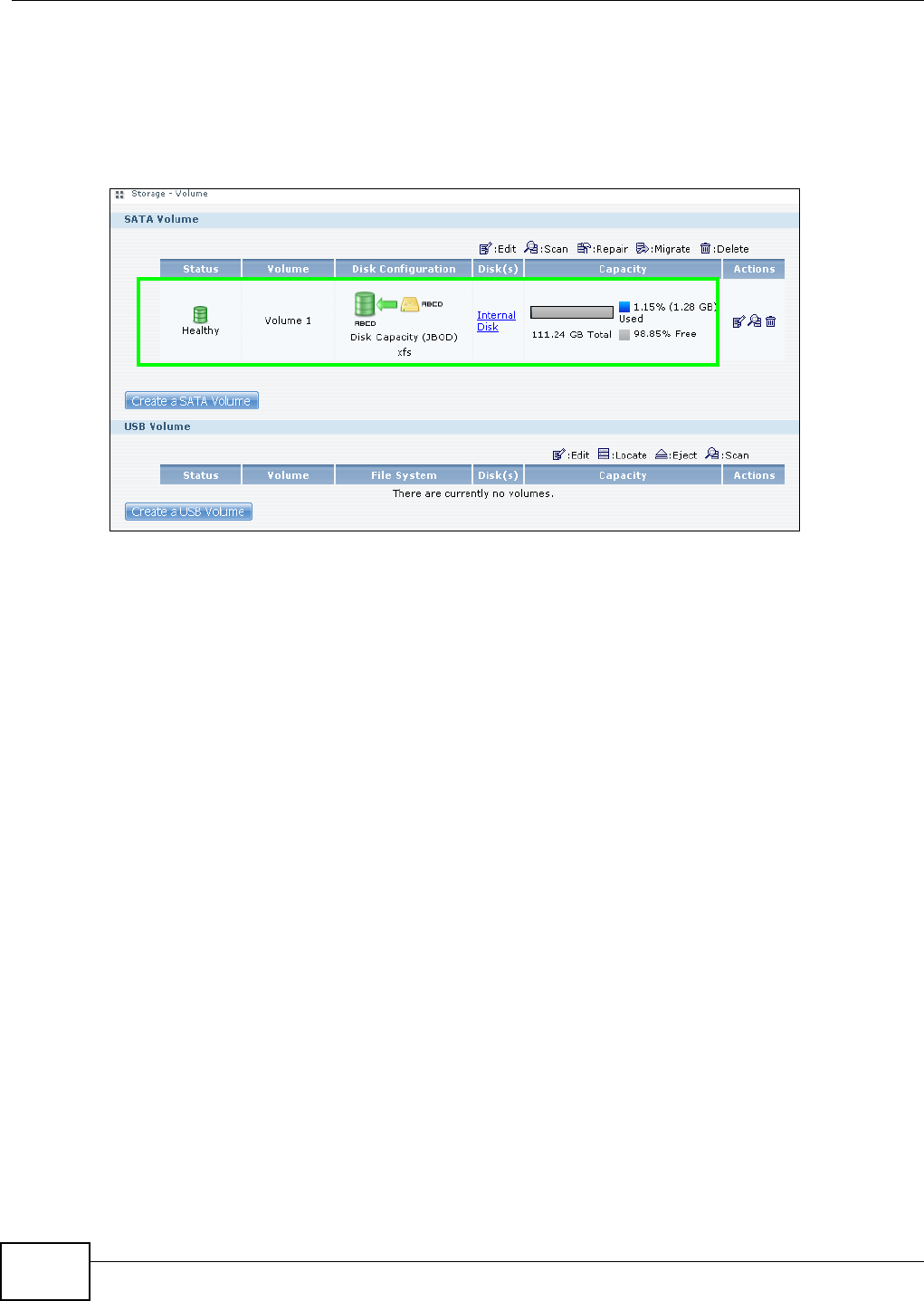
Chapter 5 Tutorials
Media Server User’s Guide
76
Your NSA has a single bay for a SATA (Serial Advanced Technology Attachment) hard disk. The
firmware installed during hard disk initialization (Chapter 3 on page 35) automatically creates a
JBOD volume on your SATA hard disk. JBOD is the default storage method if you are using a single
hard disk for your NSA.
This JBOD volume shows up in the Storage > Volume screen (Section 8.2 on page 158) as
follows.
When you attach an eSATA hard disk to your NSA, you can configure this volume as: 1) a backup to
your SATA hard disk (RAID 1); or 2) as a separate storage drive (either another JBOD or a PC
Compatible Volume).
5.7.1 Creating a RAID 1 Volume
This storage method allows recovery of data if your hard disk fails. To create a RAID 1 volume, you
must connect an eSATA hard disk to your NSA. There are two ways to create a RAID 1 volume:
• Click the Migrate button - This is a quick way to create a RAID 1 volume. Use this to
automatically synchronize data in the internal hard disk to the eSATA hard disk.
• Click the Create a SATA volume button - Use this if there are no existing volumes in your NSA.
5.7.2 Migrate Button
Do the following steps to create a RAID 1 volume.
1Once you attach the eSATA hard disk to the NSA, the Storage > Volume screen shows the
Migrate button.
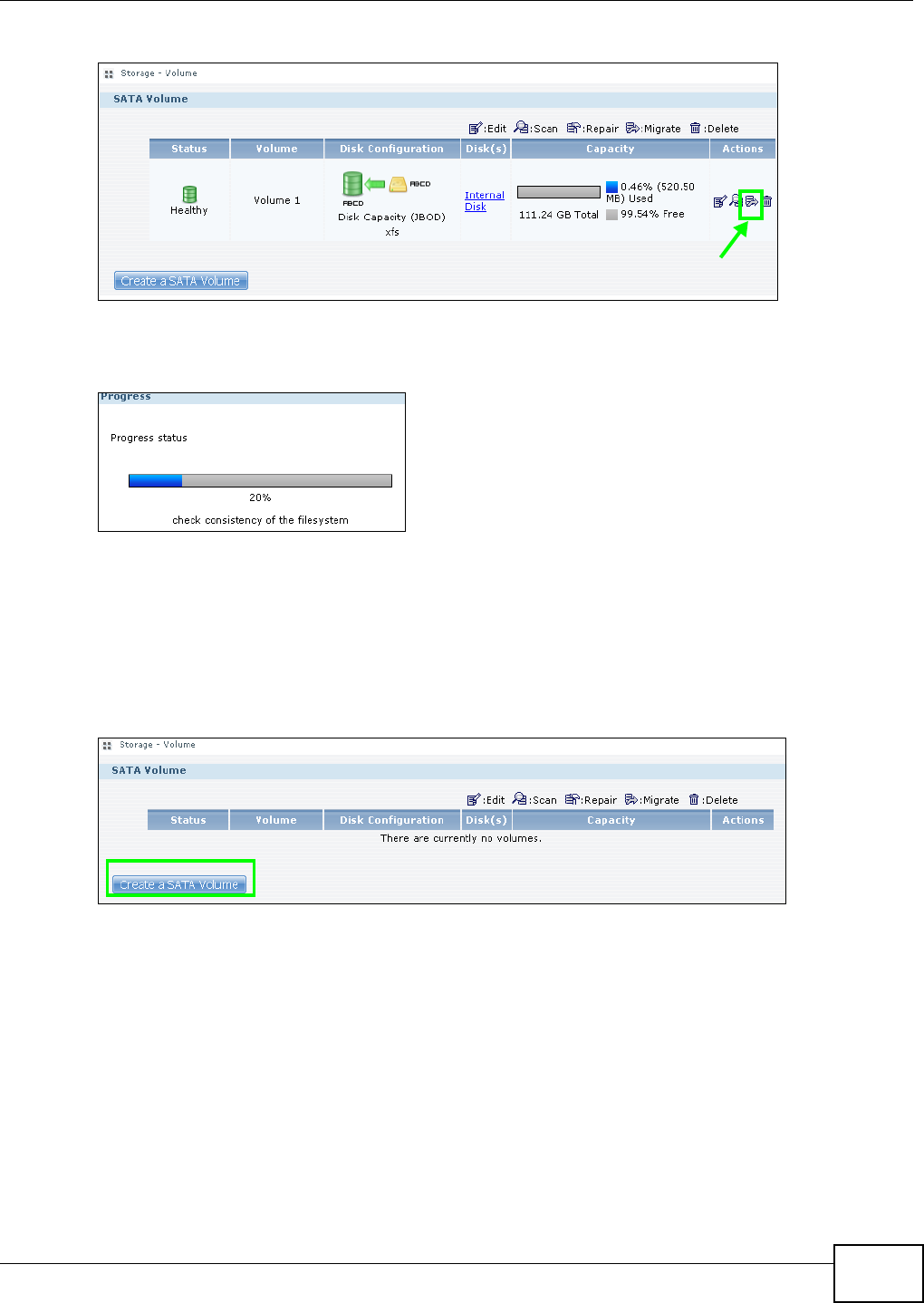
Chapter 5 Tutorials
Media Server User’s Guide 77
2Click the Migrate button and you can see the following progress bar. Wait for up to 10 minutes for
the RAID 1 volume to be created.
5.7.3 Create a SATA Volume Button
If you do not have an existing volume in the Storage > Volume screen, do the following steps to
create a RAID 1 volume.
1In the Storage > Volume screen, click Create a SATA Volume.
2In the Disk Configuration screen, you can select the storage method.
•Type in the Volume Name for your RAID 1 volume. The volume name can be 1 to 31 characters
(a-z, 0-9, " " [spaces], "_", and ".").
• Choose RAID 1 and click Apply.
This deletes all existing data in the eSATA hard disk. Make sure you have
a backup of any existing data in the hard disk.
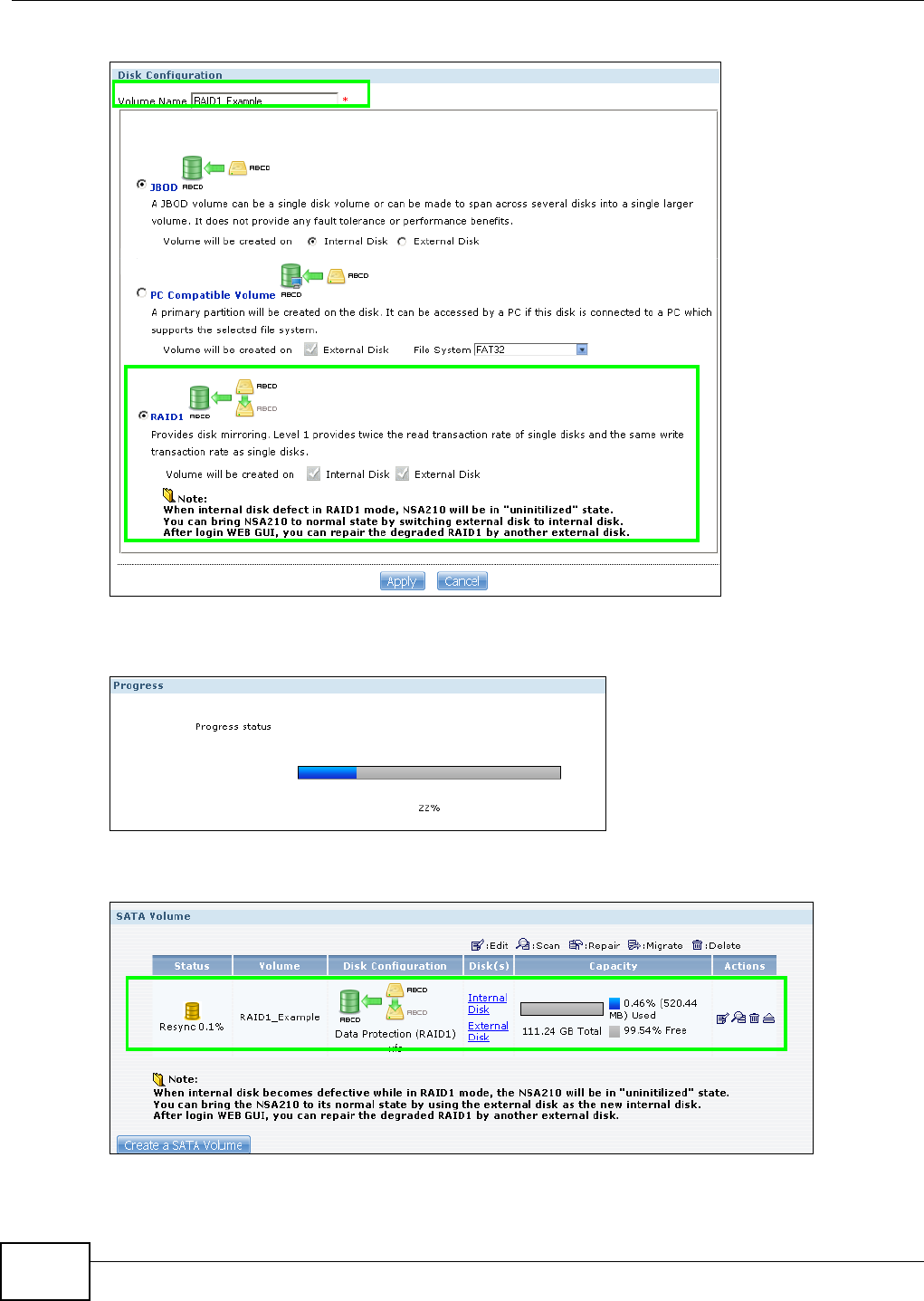
Chapter 5 Tutorials
Media Server User’s Guide
78
The NSA starts creating the volume and you can see the following progress bar. Wait for 2 minutes
for the RAID 1 volume to be created.
3The Storage > Volume screen displays with your RAID 1 volume.
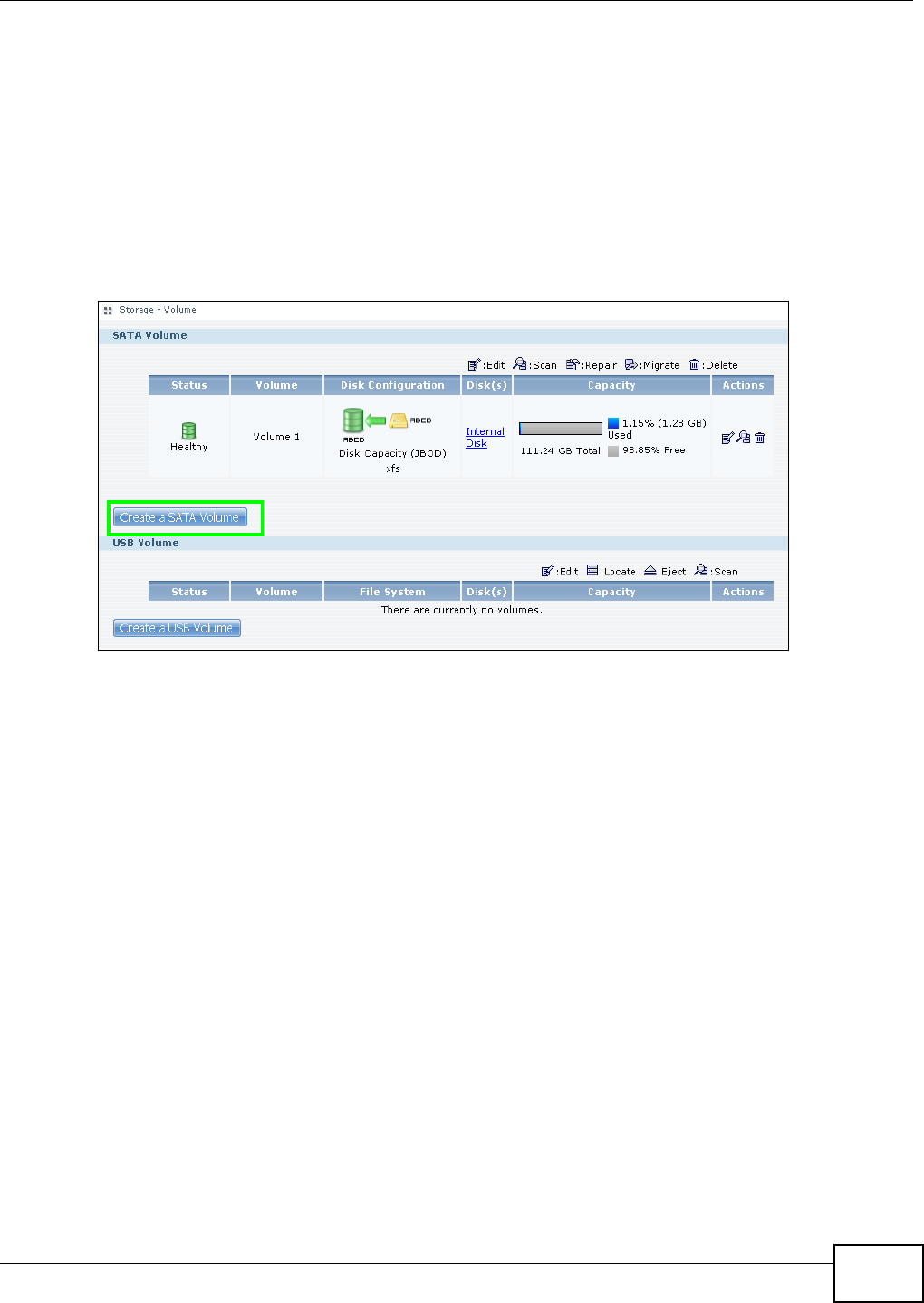
Chapter 5 Tutorials
Media Server User’s Guide 79
5.7.4 Creating a PC Compatible Volume
You can use your eSATA hard disk as a separate storage volume. The following section shows you
how to create a PC Compatible Volume. Use this storage method if you have an eSATA hard disk
that will be connected to a Windows computer when it is not connected to the NSA. However, the
computer’s platform (for example, Windows XP SP2) should support the file system you selected for
the eSATA hard disk.
1Connect the eSATA hard disk to your NSA and go to the Storage > Volume screen. Click Create a
SATA Volume.
2In the Disk Configuration screen, you can select the storage method.
•Type in the Volume Name for your PC Compatible volume. The volume name can be 1 to 31
characters (a-z, 0-9, " " [spaces], "_", and ".").
• Choose PC Compatible Volume.
• Select the File System you want to use (NTFS in this example). Make sure this file system is
supported by the Windows platform you are using in your computer. Refer to Table 23 on page
165 for file systems supported by your NSA. Click Apply.
This deletes all existing data in the eSATA hard disk. Make sure you have
a backup of any existing data in the hard disk.
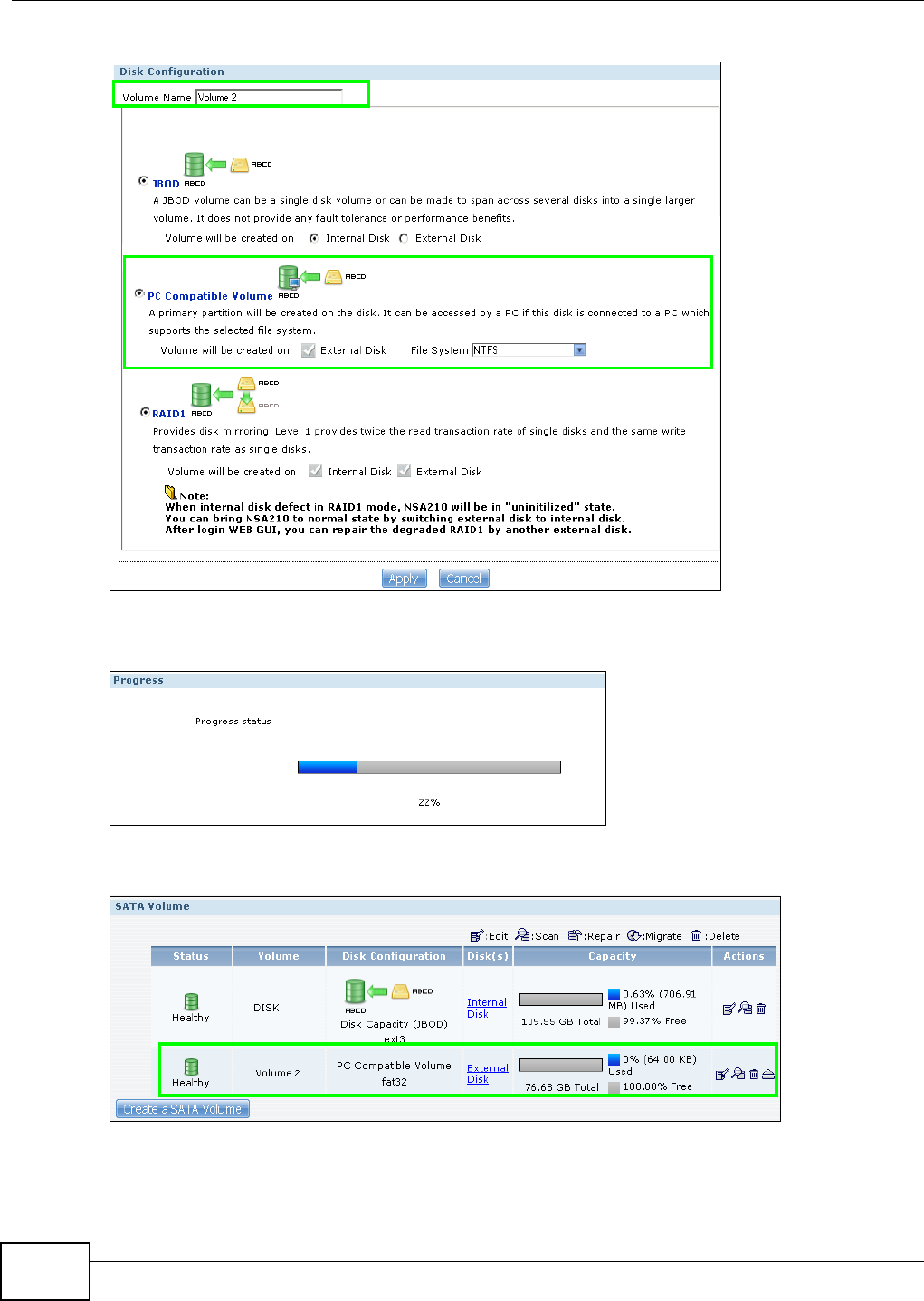
Chapter 5 Tutorials
Media Server User’s Guide
80
The NSA starts creating the volume and you can see the following progress bar. Wait for 2 minutes
for the volume to be created.
3The Storage > Volume screen displays with your PC Compatible Volume.
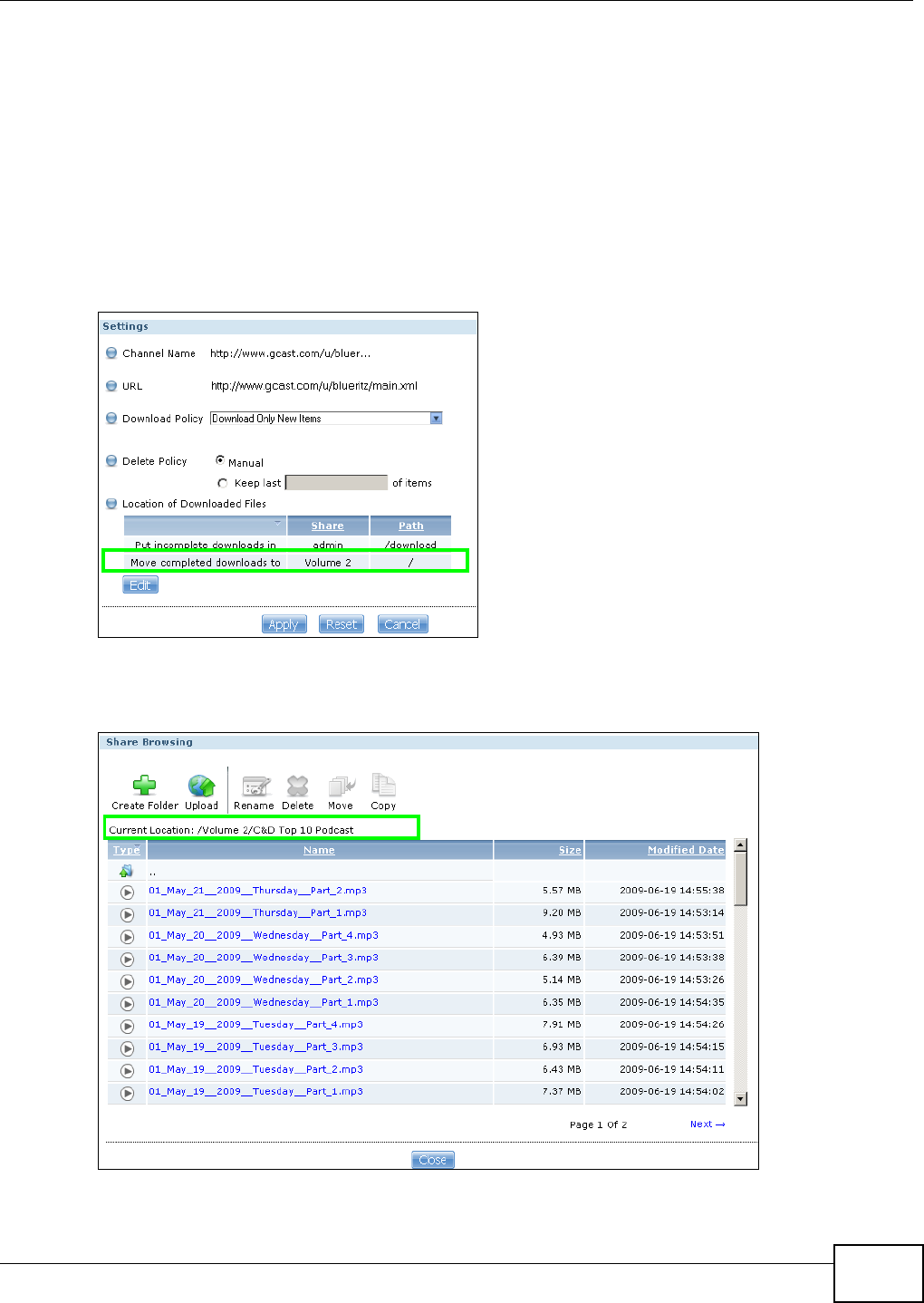
Chapter 5 Tutorials
Media Server User’s Guide 81
5.7.4.1 Checking Your PC Compatible Volume
The files in the eSATA hard disk that you configured as a PC Compatible Volume should be
accessible when you connect the eSATA hard disk to your computer.
You can configure the features of your NSA to save files to your eSATA hard disk. For example, you
can refer to Section 5.11 on page 107 to use the Broadcatching feature of your NSA to download
files to your eSATA disk.
1When asked for the Location of Downloaded Files, make sure you save the completed files to
the eSATA hard disk (Volume 2 in this example).
2The files downloaded by the NSA should be in the Volume 2 folder. You can check this when you
access the Volume 2 folder from My NSA > Share Browser screen as follows.
Chapter 5 Tutorials
Media Server User’s Guide
82
3Disconnect the eSATA hard disk from the NSA. Connect the eSATA hard disk to your computer. On
some systems, you can see the following notification.
4The computer assigns a letter to the eSATA hard disk (drive F in this example) that is accessible
from the My Computer screen. Double click the eSATA drive and check your files. They should be
the same files that are in the My NSA > Share Browser screen.
5.8 Deleting a Volume
Delete an existing volume in your NSA by doing the following steps.
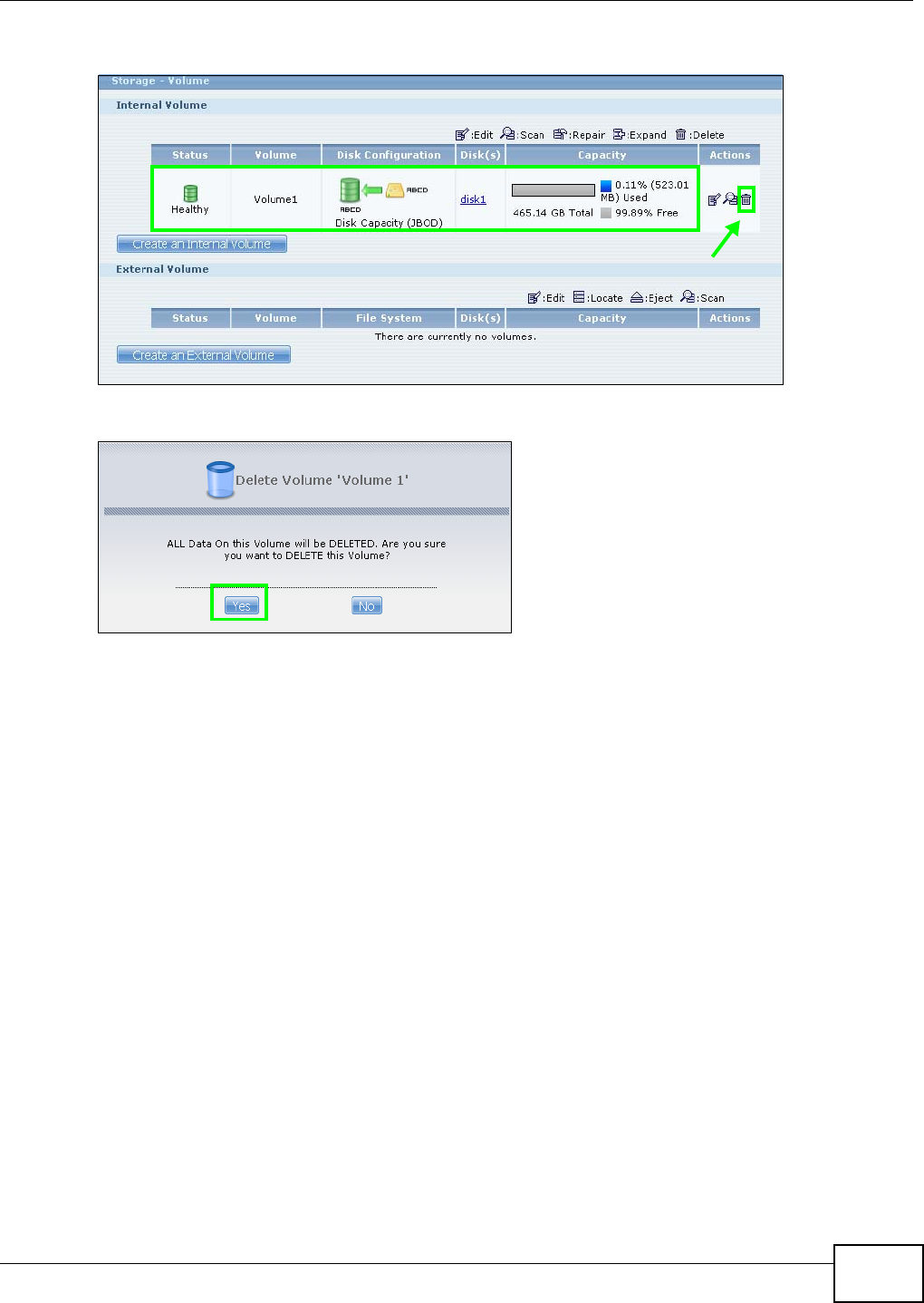
Chapter 5 Tutorials
Media Server User’s Guide 83
1 In the Storage > Volume screen, select the volume you want to delete and click the delete icon.
2A confirmation window appears as follows. Click Yes.
This deletes all existing data in the volume. Make sure you have a
backup of any existing data in the hard disk.
5.9 File Sharing Tutorials
The following sections cover using the NSA for file sharing. This chapter assumes you have already
followed the Quick Start Guide instructions to perform initial setup and configuration (so you have a
working volume). See the rest of this User’s Guide for details on configuring the NSA’s various
screens.
5.9.1 Creating a User Account
Bob wants to create accounts for his sons Jimmy and Kevin. This is how he would do it.
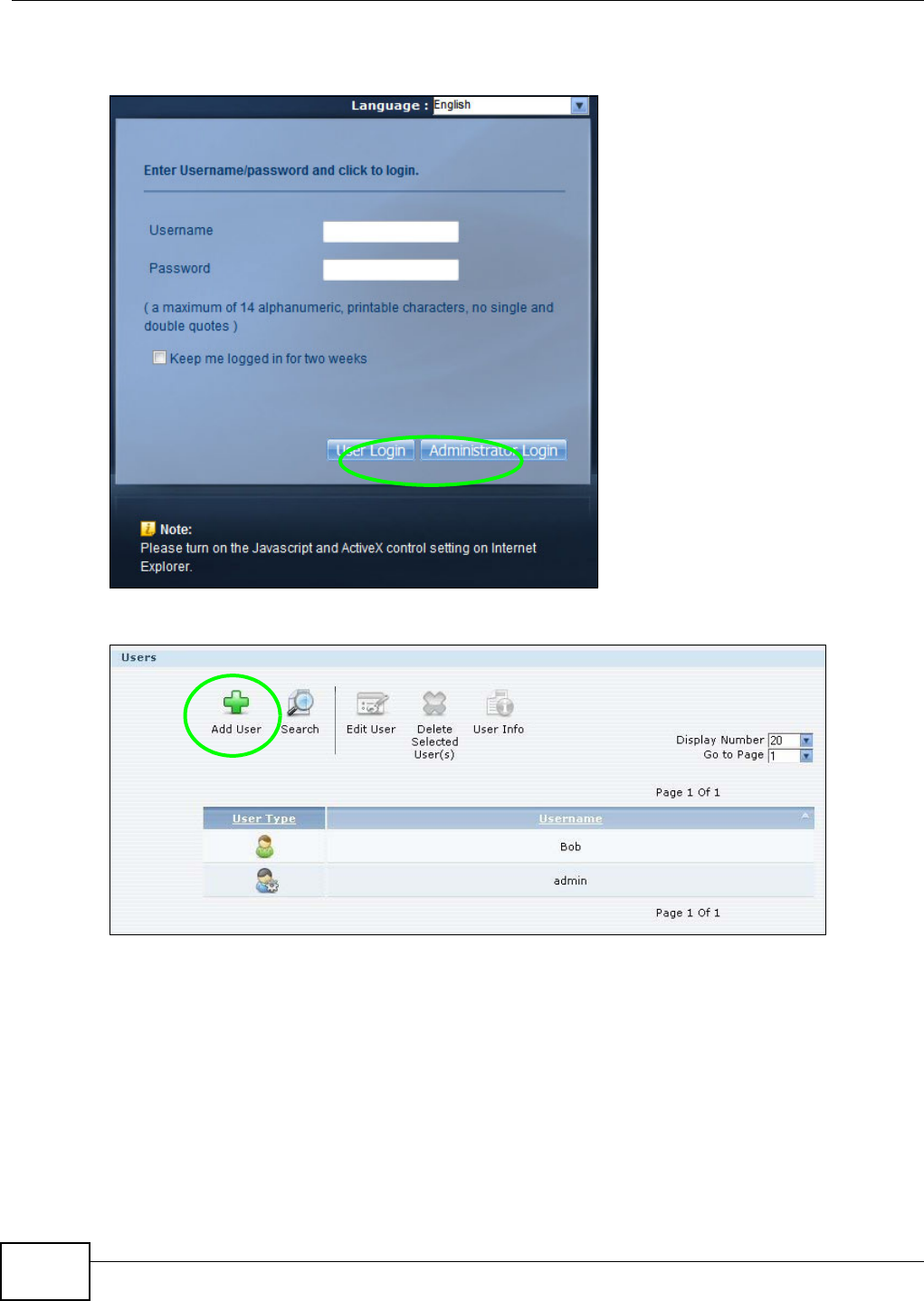
Chapter 5 Tutorials
Media Server User’s Guide
84
1At the NSA web configurator login screen enter the administrator account and password and click
Administrator Login to go to the advanced administration screens.
2Click Sharing > Users to open the Users screen. Then click Add User.
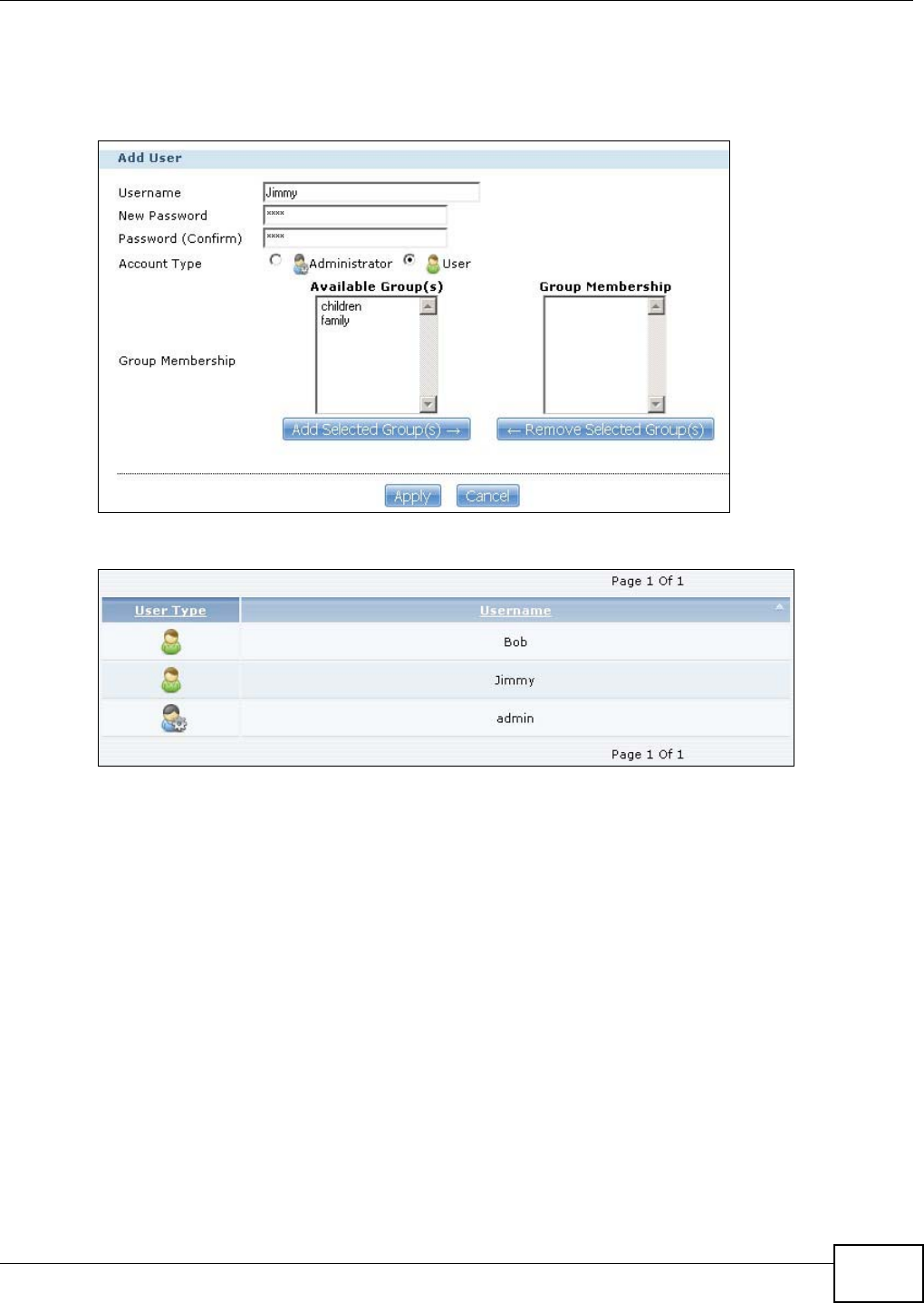
Chapter 5 Tutorials
Media Server User’s Guide 85
3Configure the screen as follows and write down the username and password to give to Jimmy. If the
username and password are the same as Jimmy’s Windows login, Jimmy will not need to enter a
username and password when he logs into his share from his computer. Set the Account Type to
User so Jimmy doesn’t get to configure the whole NSA. Click Apply to create the account.
4The account now displays in the Users screen.
Now that Bob has created Jimmy’s account, he can go through the steps again to create another
account for Kevin. After both accounts are created, he can go to Section 5.9.2 on page 85 to create
shares for Jimmy and Kevin.
5.9.2 Creating a Share
Suppose Bob has already created separate accounts for his sons Jimmy and Kevin. Now Bob wants
to create a share for each son. He also wants to make sure that each son can only access his own
share (to keep them from deleting each other’s files). This is how he would do it.
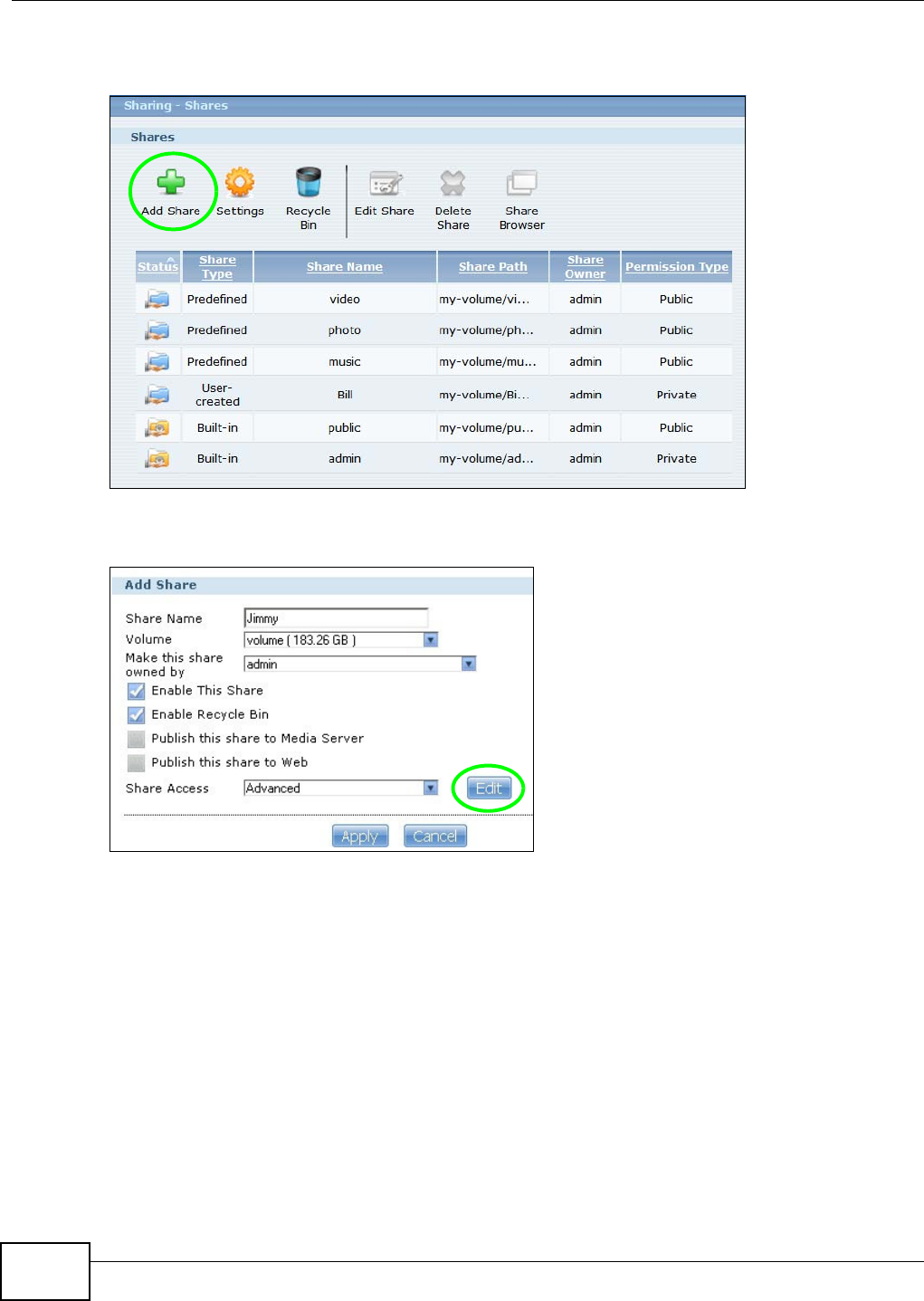
Chapter 5 Tutorials
Media Server User’s Guide
86
1In the NSA’s administration web configurator screens, click Shares > Add Share. Click Add Share
to create a new share.
2Specify a name for the share and select which volume it should be on. Configure the screen as
follows. Then click Edit.
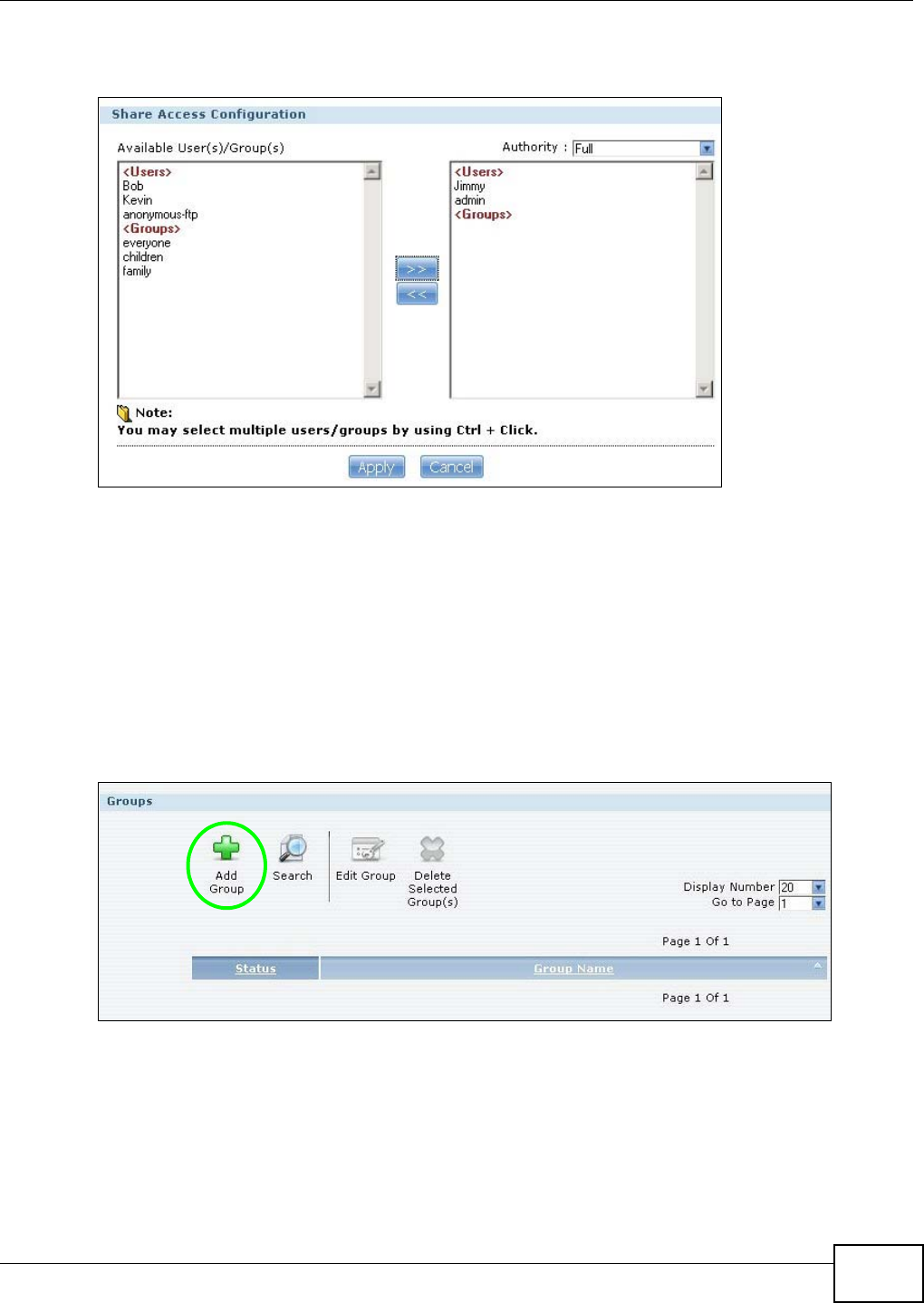
Chapter 5 Tutorials
Media Server User’s Guide 87
3Configure the screen as follows to give Jimmy full access right to the share. Then click Apply to
create the share.
Now that Bob has created Jimmy’s share, he can go through the steps again to create another
share for Kevin.
5.9.3 Creating a Group
After creating user accounts for Jimmy and Kevin, Bob wants to create a group for his sons and
another one for the parents. Bob can assign access rights to his sons’ group for certain shares such
as a cartoons share and allow only the parents’ group to access the scary movie share. This is how
he would create the group.
1In the NSA’s administration web configurator screen, click Groups > Add Group.
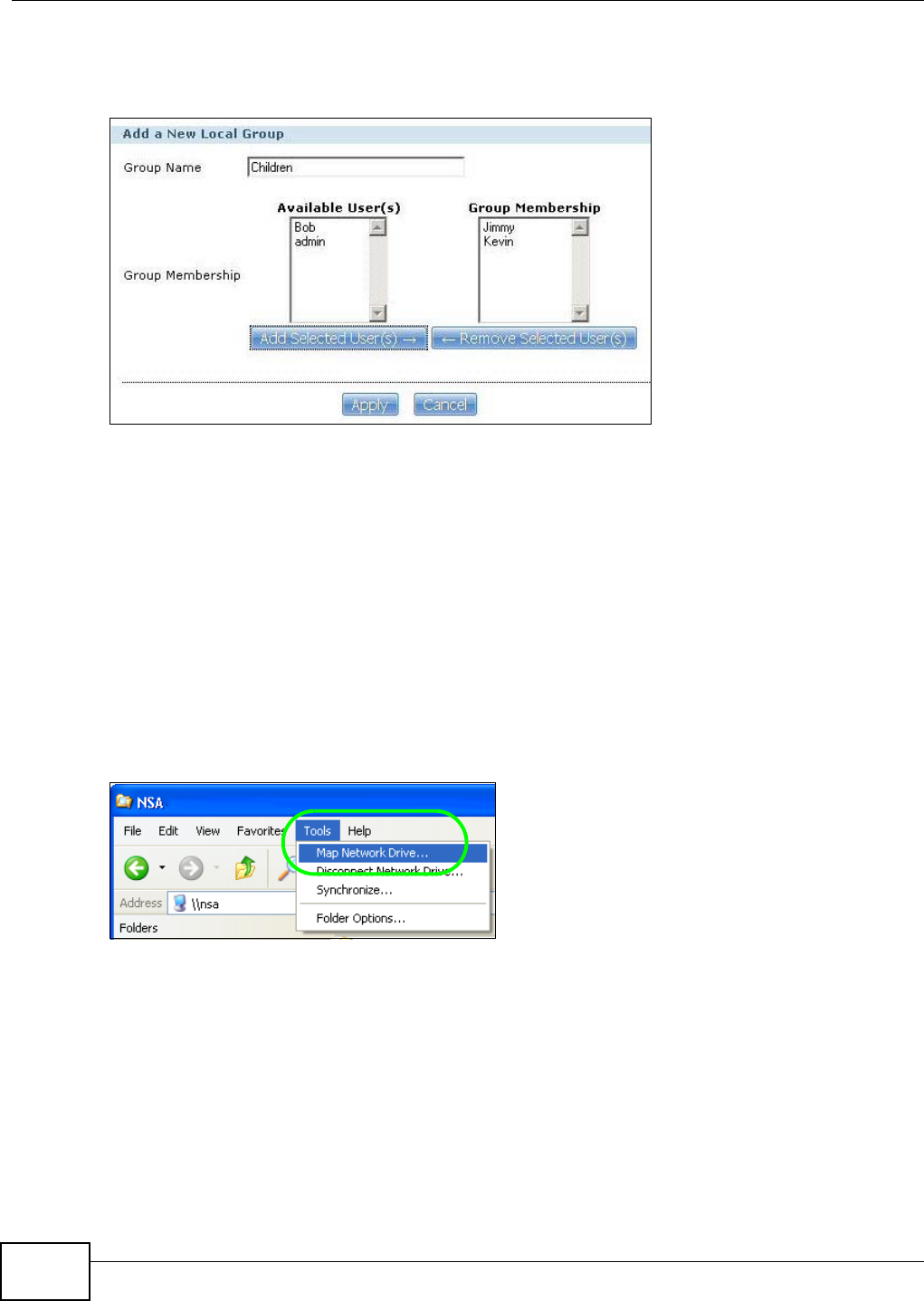
Chapter 5 Tutorials
Media Server User’s Guide
88
2Specify a name for the group. Select the user(s) you want to add to the group from the Available
User(s) list and click Add Selected User(s). Configure the screen as follows. Then click Apply to
create the group.
Now that Bob has created a group for Jimmy and Kevin, he can go through the steps again to
create another group for the parents. Then he can see the rest of the tutorials for how to use the
groups in assigning access rights to shares.
5.9.4 Accessing a Share From Windows Explorer
If you map a NSA share (where data is stored) to a Windows network drive, you can use Windows
Explorer to transfer files to and from the NSA as if it was another folder on your computer. Here he
maps Jimmy’s share to Jimmy’s computer.
1Start Windows Explorer and go to the NSA’s server name. The default is ‘nsa’ followed by the
number of your model (‘nsa325’ for example).
2Click Tools > Map Network Drive.
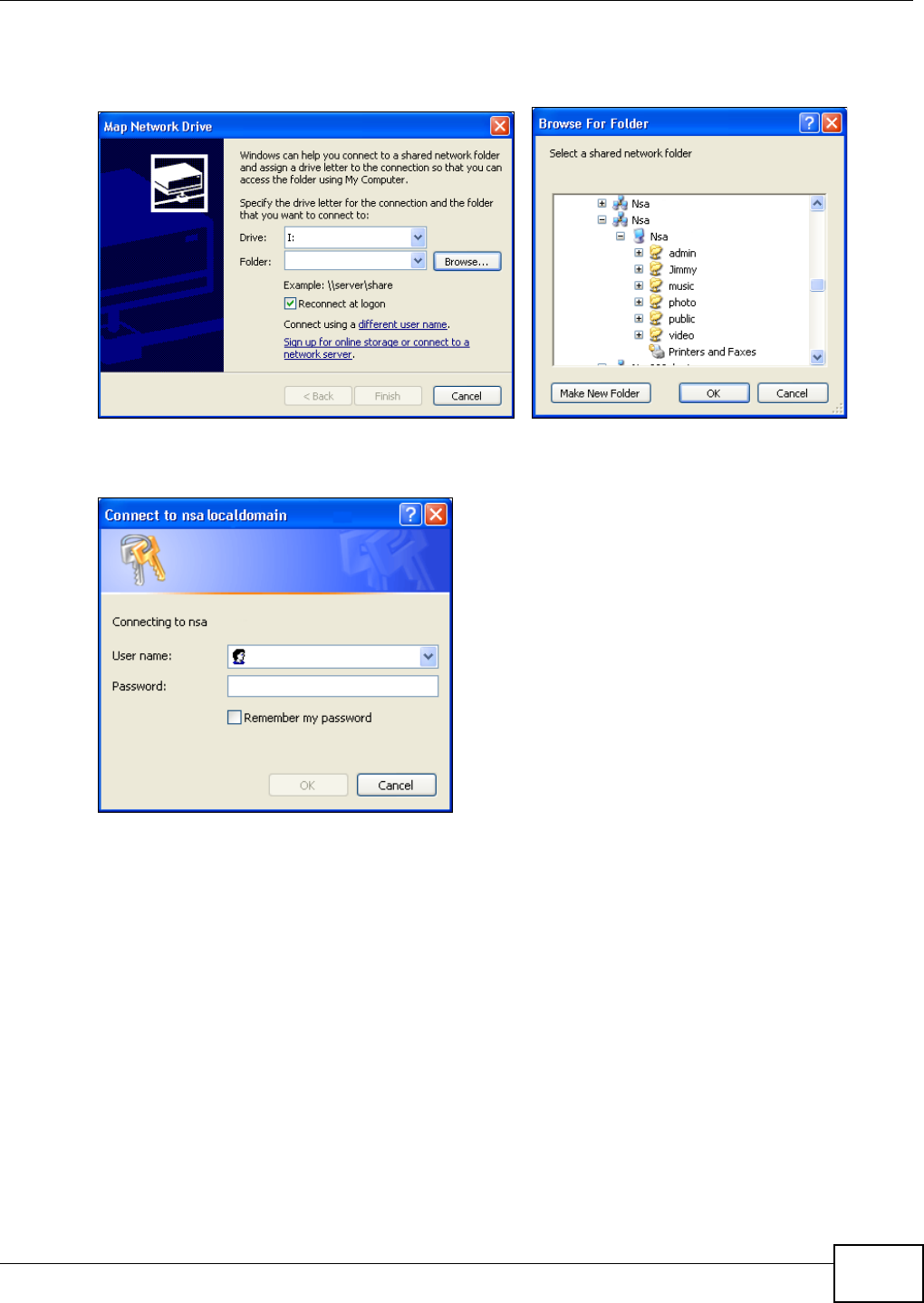
Chapter 5 Tutorials
Media Server User’s Guide 89
3Select the network drive that you want to map the NSA to from the Drive list box. This example
uses I. Then browse to and select the share on the NSA. Click Finish.
4Enter the username and password for Jimmy’s account and click OK. You do not need to do this if
the username and password are the same as Jimmy’s Windows login.
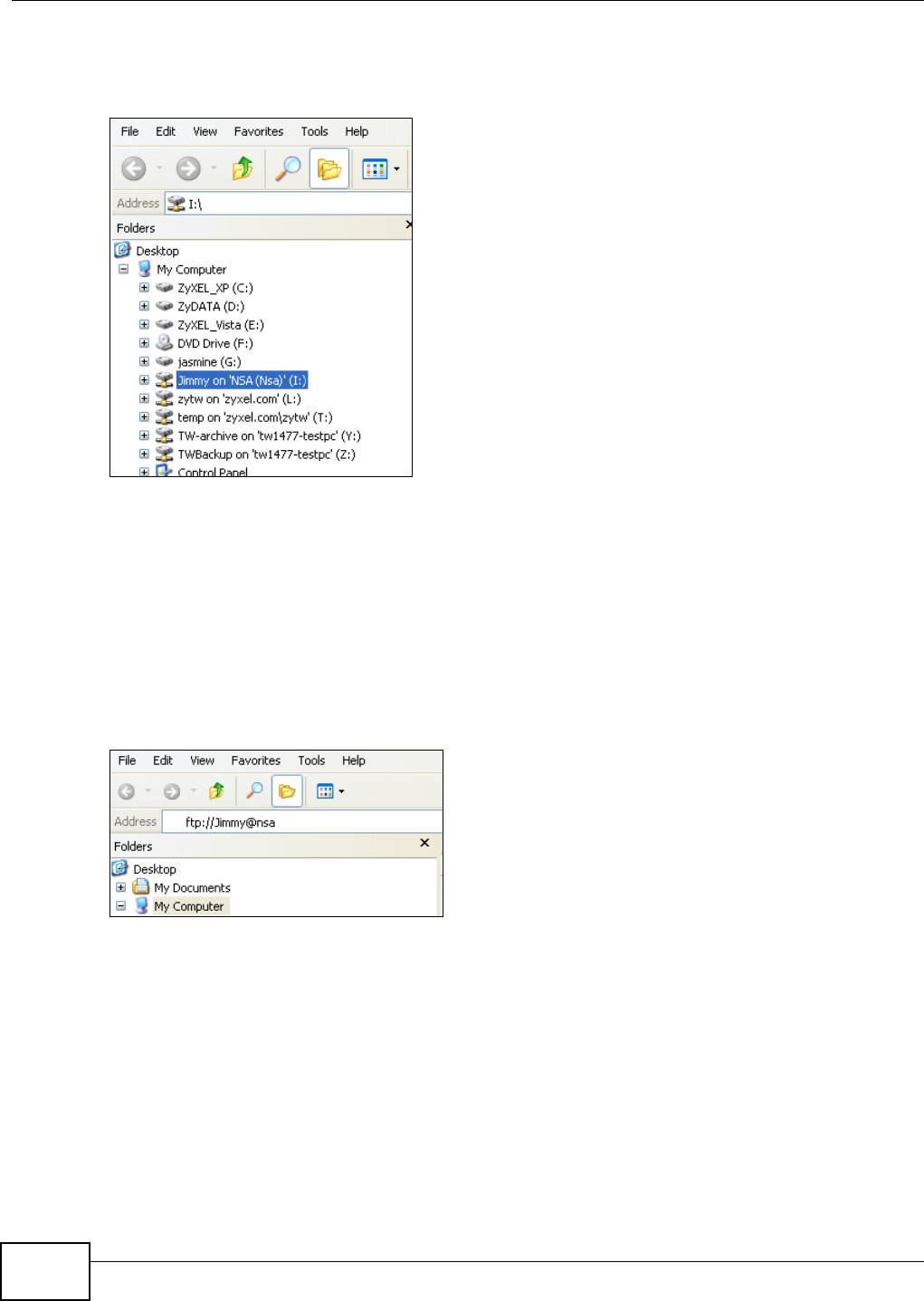
Chapter 5 Tutorials
Media Server User’s Guide
90
5After the mapping is done, you can then simply copy and paste or drag and drop files from/to your
local computer’s drives to or from this network folder. Just like the NSA’s share was another folder
on your computer.
Now that Bob has mapped Jimmy’s share to Jimmy’s computer, he can go through the steps again
to map Kevin’s share to Kevin’s computer.
5.9.5 Accessing a Share Using FTP
You can also use FTP to access the NSA. Suppose Jimmy is temporarily using a different computer
and wants to access his share without mapping it to the computer. This is how he would do it.
1Open the FTP client (Windows Explorer is used here) and type “ftp://username@server” where
“username” is the account’s username and “server” is the NSA’s IP address or server name.
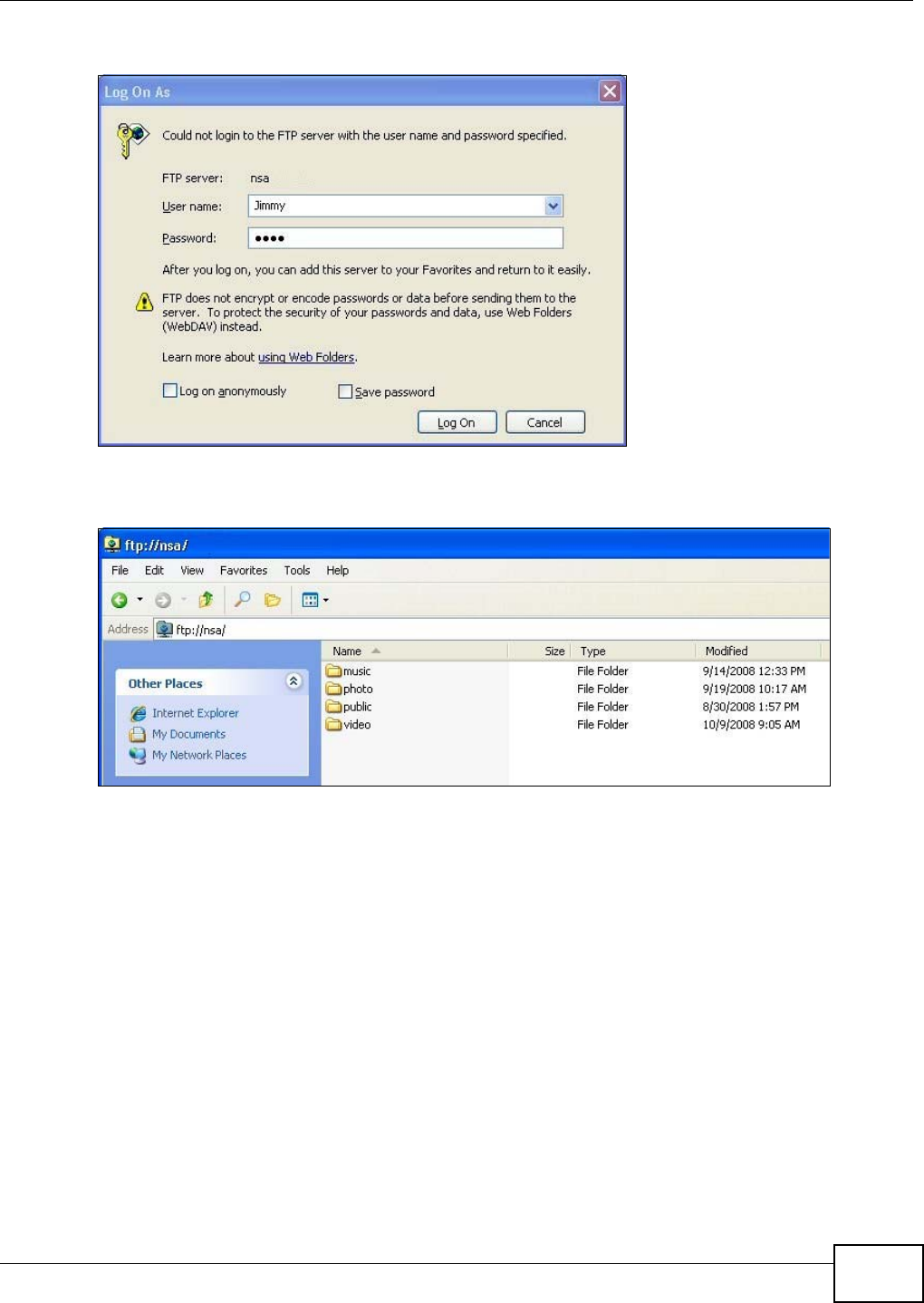
Chapter 5 Tutorials
Media Server User’s Guide 91
2Enter your password and click Login.
3Now you can access files and copy files from/to your local computer’s drives to or from this network
folder.
5.9.6 Accessing a Share Through the Web Configurator
You can browse and access files through the web configurator.
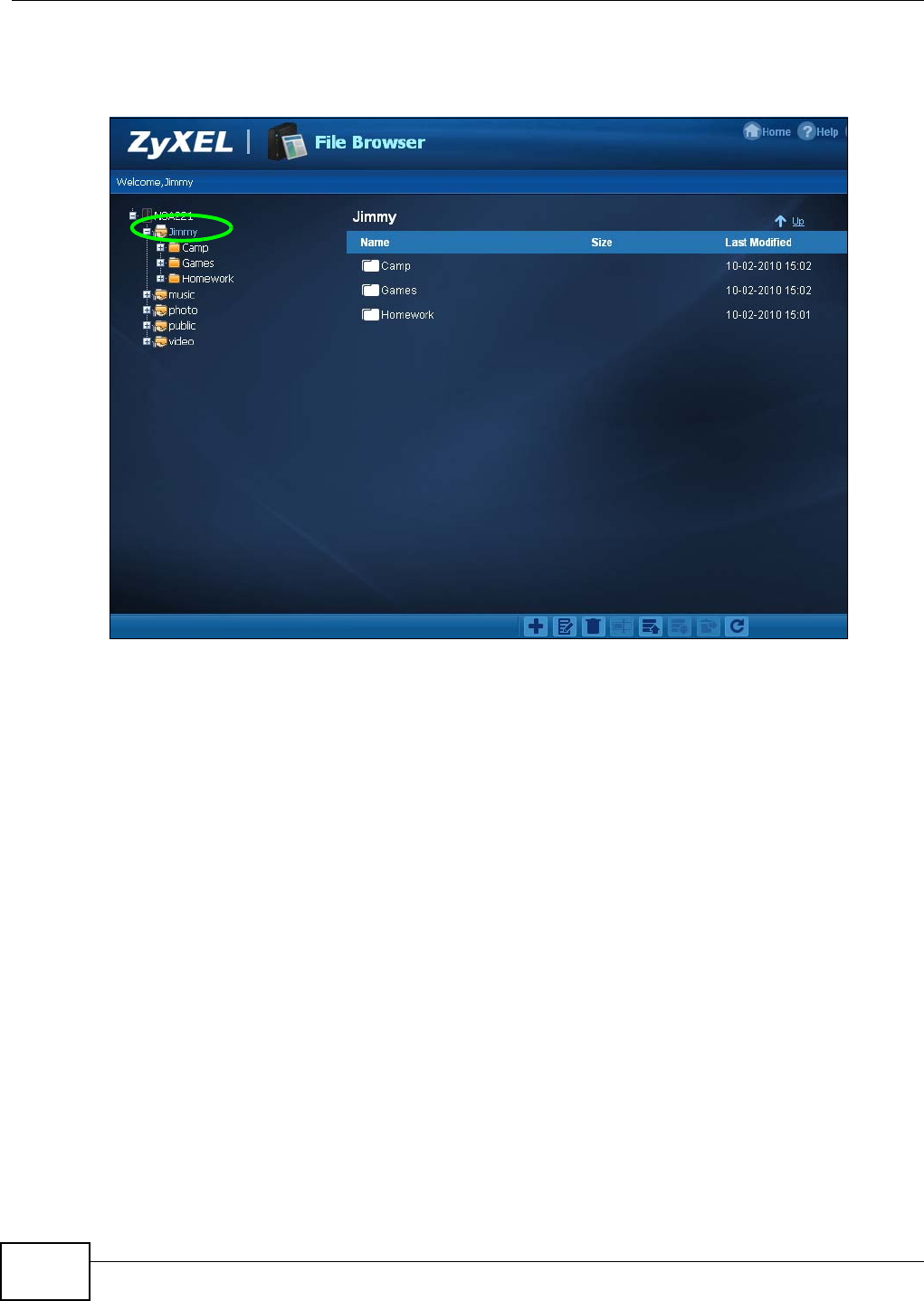
Chapter 5 Tutorials
Media Server User’s Guide
92
1Log into the NSA web configurator (see Section 4.3 on page 45) using the appropriate user name
and password (this example uses Jimmy’s) and click File Browser. Click a share (the Jimmy share
in this example) to see the top level of the share’s contents.
2Click a folder’s file name to browse the folder. You can open files or copy them to your computer.
You can also create new folders and upload additional files to the share.
3Click the logout icon when your are done.
5.10 Download Service Tutorial
This tutorial covers using the NSA to download a file from the Internet. Use this same procedure for
BitTorrent downloads as well as regular HTTP (web) and FTP downloads. See Section 10.11.2 on
page 213 for more on the download service.
5.10.1 Copying/Pasting a Download Link
1Open your Internet browser (this example uses Internet Explorer).
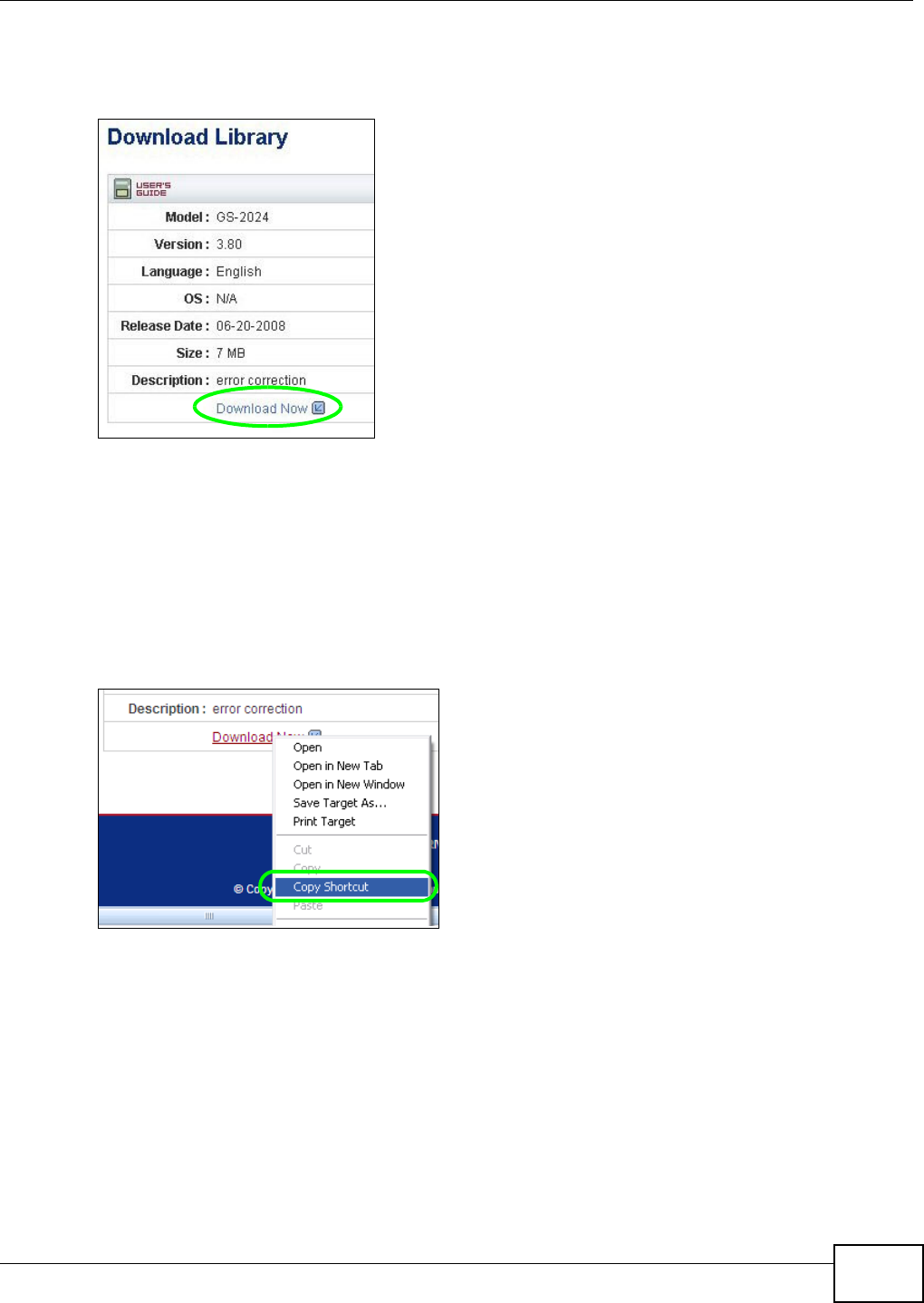
Chapter 5 Tutorials
Media Server User’s Guide 93
2Find a download link for the file you want. In this example, www.zyxel.com has a Download Now
link for downloading a datasheet for ZyXEL’s GS-2024 (a device for making phone calls over the
Internet).
Note: Make sure the link opens either the file you want or a pop-up window about how to
handle the file.
Note: It is also OK for the link to open a .torrent file. If you are redirected to a screen that
says the download should start in a few seconds, there may be a link to click if the
download does not start automatically. See if that link opens the file or the pop-up
window.
3Right-click the download link and select Copy Shortcut in Internet Explorer (or Copy Link
Location in Firefox).
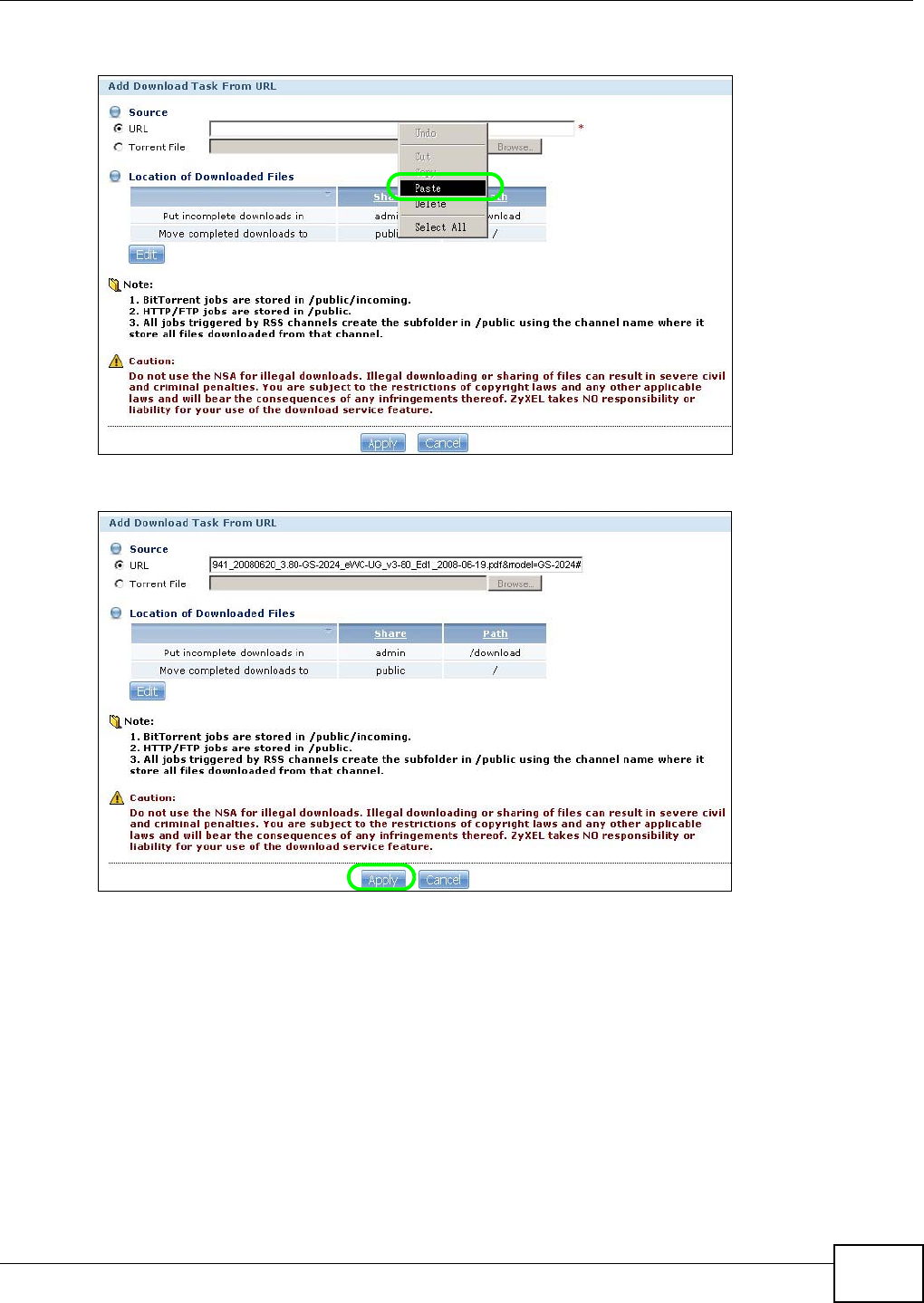
Chapter 5 Tutorials
Media Server User’s Guide 95
6Right-click the URL field and select Paste.
7The URL displays in the URL field. Click Apply.
8After a few moments, the download task appears in the Download Service screen’s Active tab.
The download appears in the Completed tab when it is done. By default the NSA stores all
downloads in the admin share’s download folder. See Section 5.9.4 on page 88, Section 5.9.5 on
page 90, or Section 5.9.6 on page 91 for how to access a share.
5.10.2 Installing the Link Capture Browser Plugin
In addition to copying and pasting a download link to the Download Service screen, you can also
install a link capture browser plugin in your web browser. Use the plugin to easily add a download
link to the NSA’s download service. See Section 10.11.3 on page 214 for more on the link capture
browser plugin.
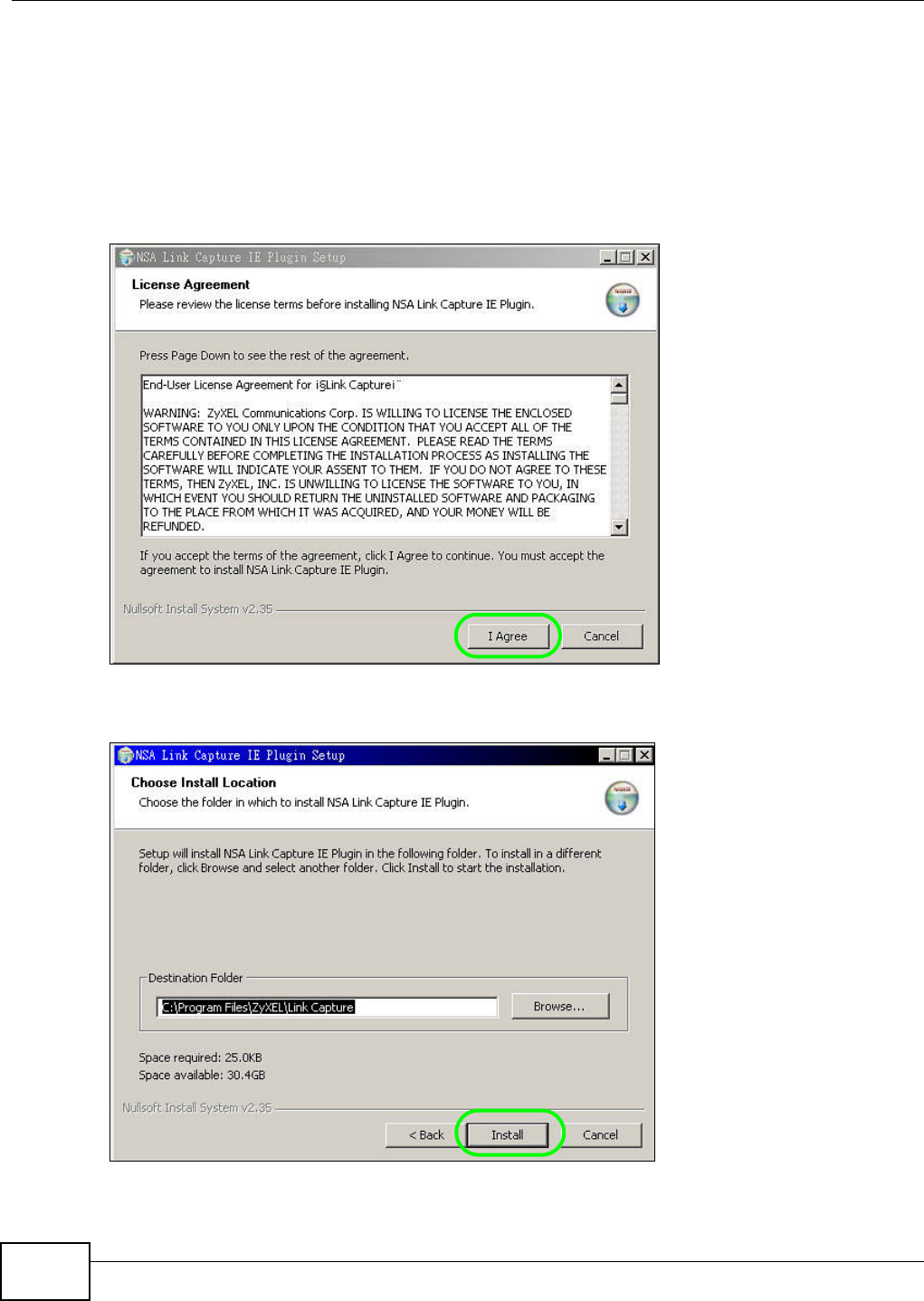
Chapter 5 Tutorials
Media Server User’s Guide
96
Note: At the time of writing the plugin supports Internet Explorer 6.0/7.0 and Mozilla
Firefox 2.0/3.0; it does not support Windows 7.
Internet Explorer
1Open the folder containing the link capture browser plugin.
2Double-click on the plugin to display the following screen. Click I Agree to begin installation.
3Select a location to save the plugin and click Install. Close the screen once the installation is
complete.
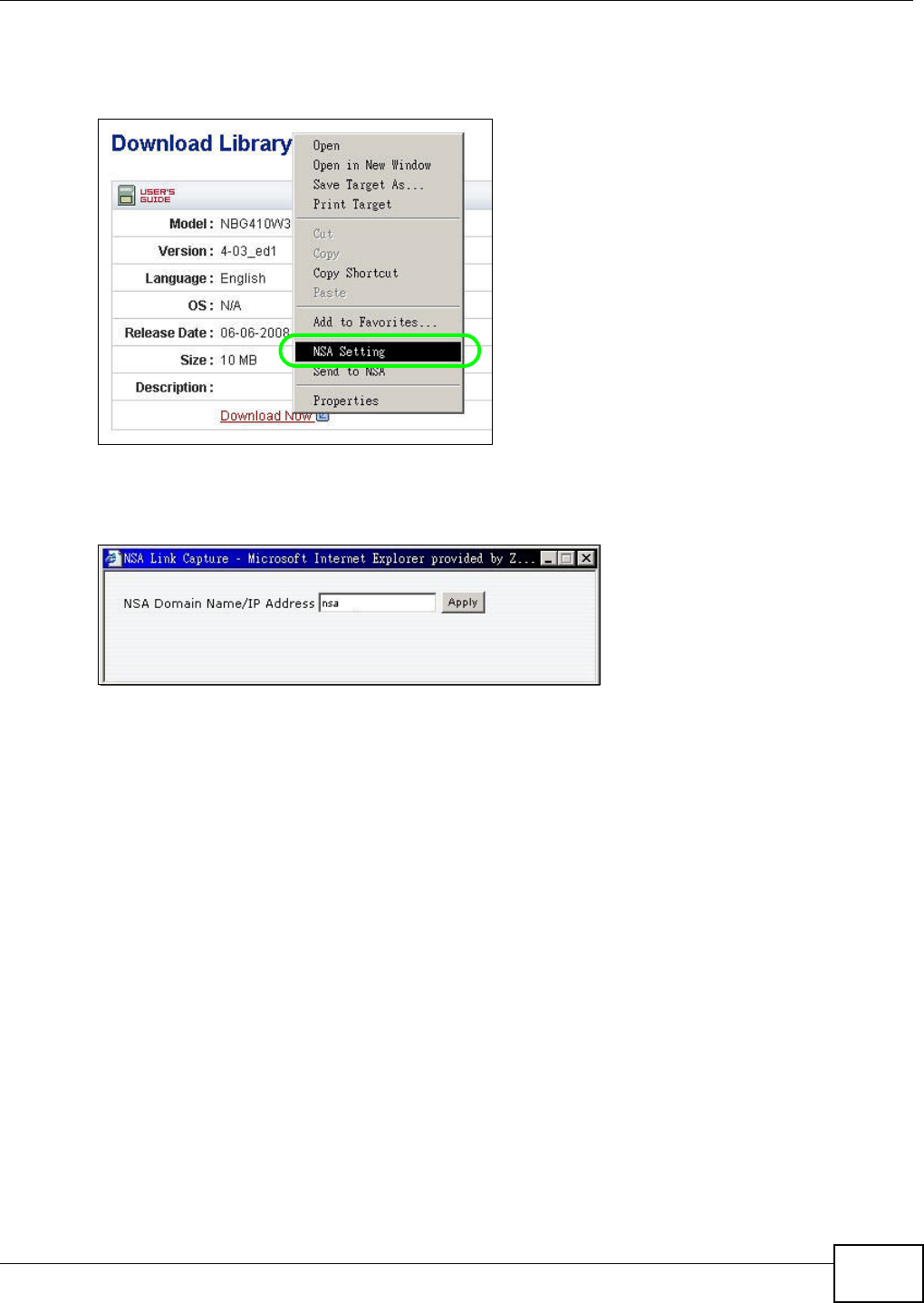
Chapter 5 Tutorials
Media Server User’s Guide 97
4Open Internet Explorer and locate a download link. In this example, www.zyxel.com has a
Download Now link for downloading a user’s guide for ZyXEL’s NBG410W3G (a 3G wireless
router). Right-click on the download link and select NSA Setting.
5Enter the NSA’s web address. The default is ‘nsa’ followed by the number of your model (‘nsa325’
for example). Then click Apply. A warning message displays asking for confirmation. Click OK to
apply the setting.
Firefox
1Open Firefox.
2Open the folder containing the link capture browser plugin.
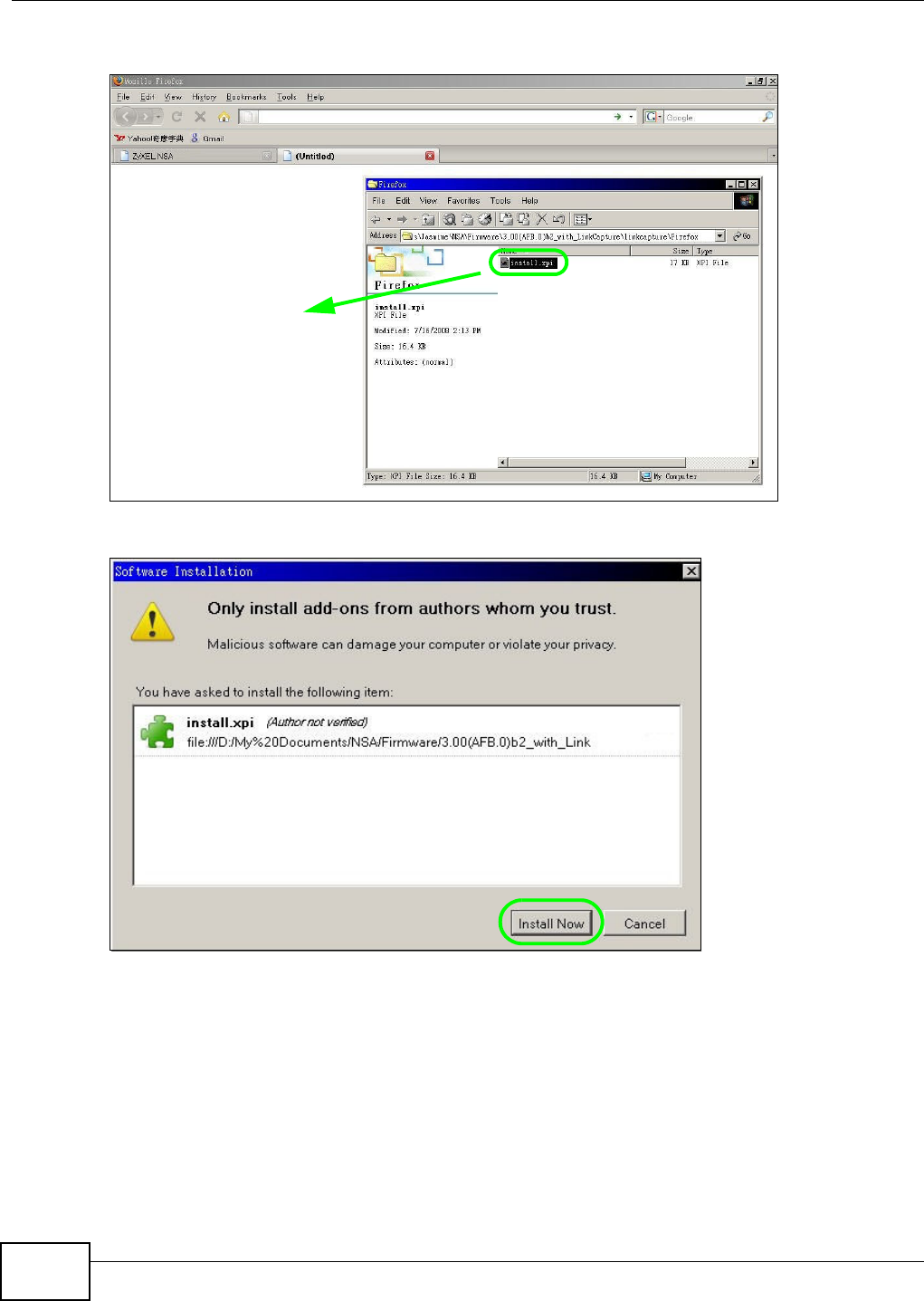
Chapter 5 Tutorials
Media Server User’s Guide
98
3To install the plugin, drag and drop the plugin to Firefox.
4The following screen displays. Click Install Now.
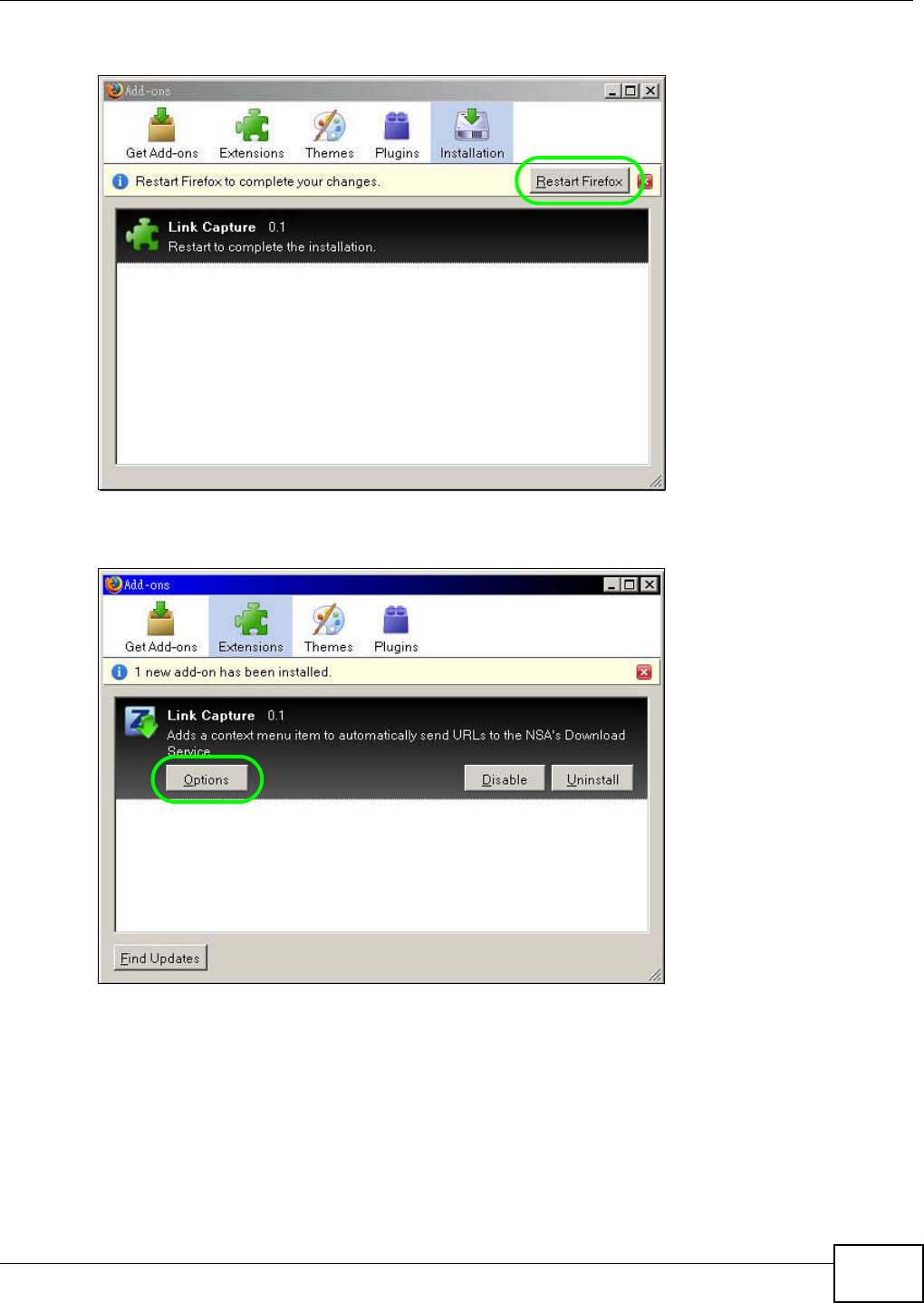
Chapter 5 Tutorials
Media Server User’s Guide 99
5You need to restart Firefox after the installation.
6When Firefox restarts, a message displays to show the installation succeeded. The plugin is
installed as an extension in Add-ons. Click Options to configure the NSA’s web address.
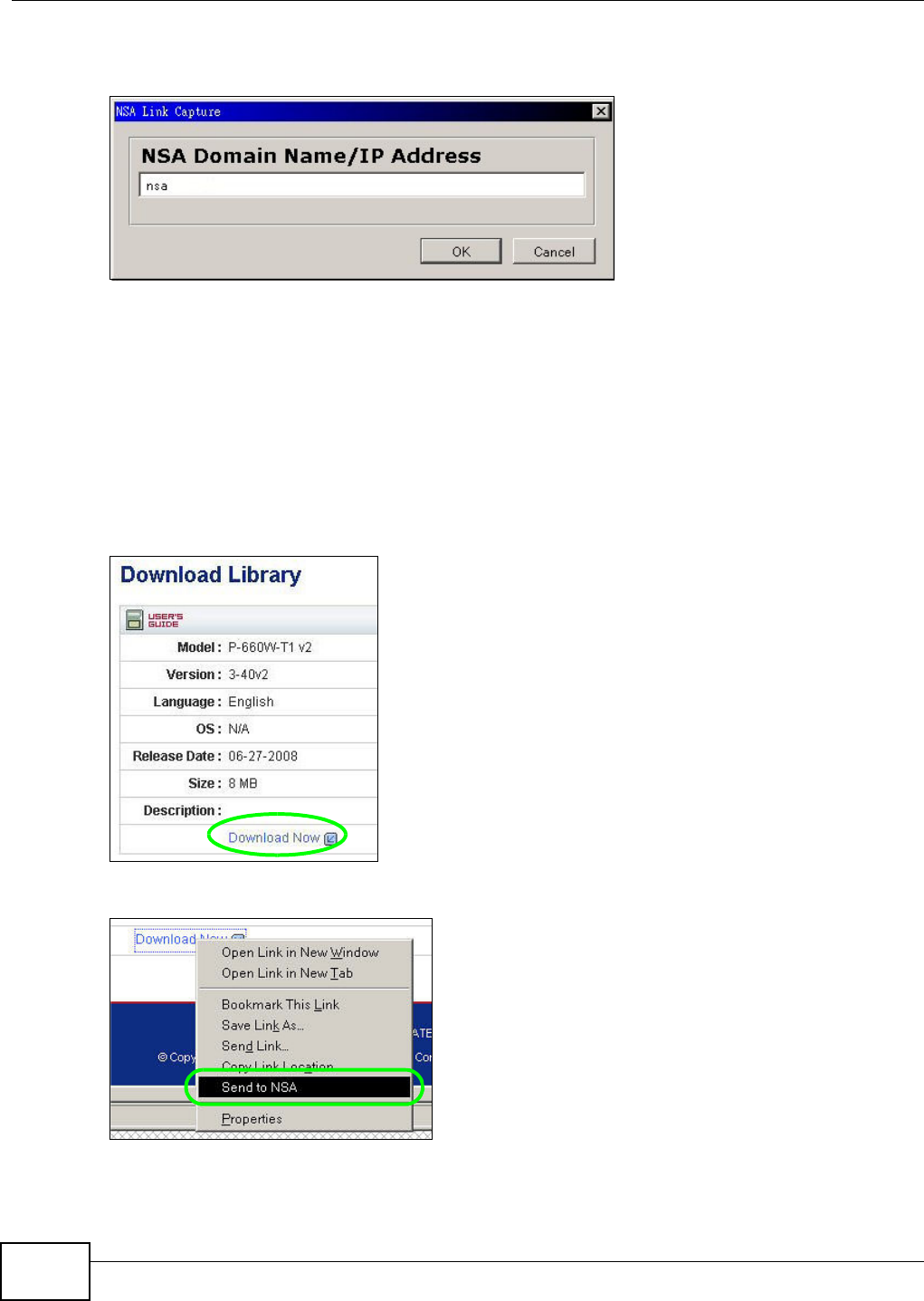
Chapter 5 Tutorials
Media Server User’s Guide
100
7Enter the NSA’s web address. The default is ‘nsa’ followed by the number of your model (‘nsa325’
for example). Then click OK.
5.10.3 Using the Link Capture Browser Plugin
Once you install the plugin, you may begin sending download links to the NSA from your web
browser. This example shows how to send a download link to the NSA’s download service using the
link capture browser plugin.
1Open your Internet browser (this example uses Firefox).
2Find a download link for the file you want. In this example, www.zyxel.com has a Download Now
link for downloading a user’s guide for ZyXEL’s P-660W-T1 (an ADSL router).
3Right-click on the download link and select Send to NSA.
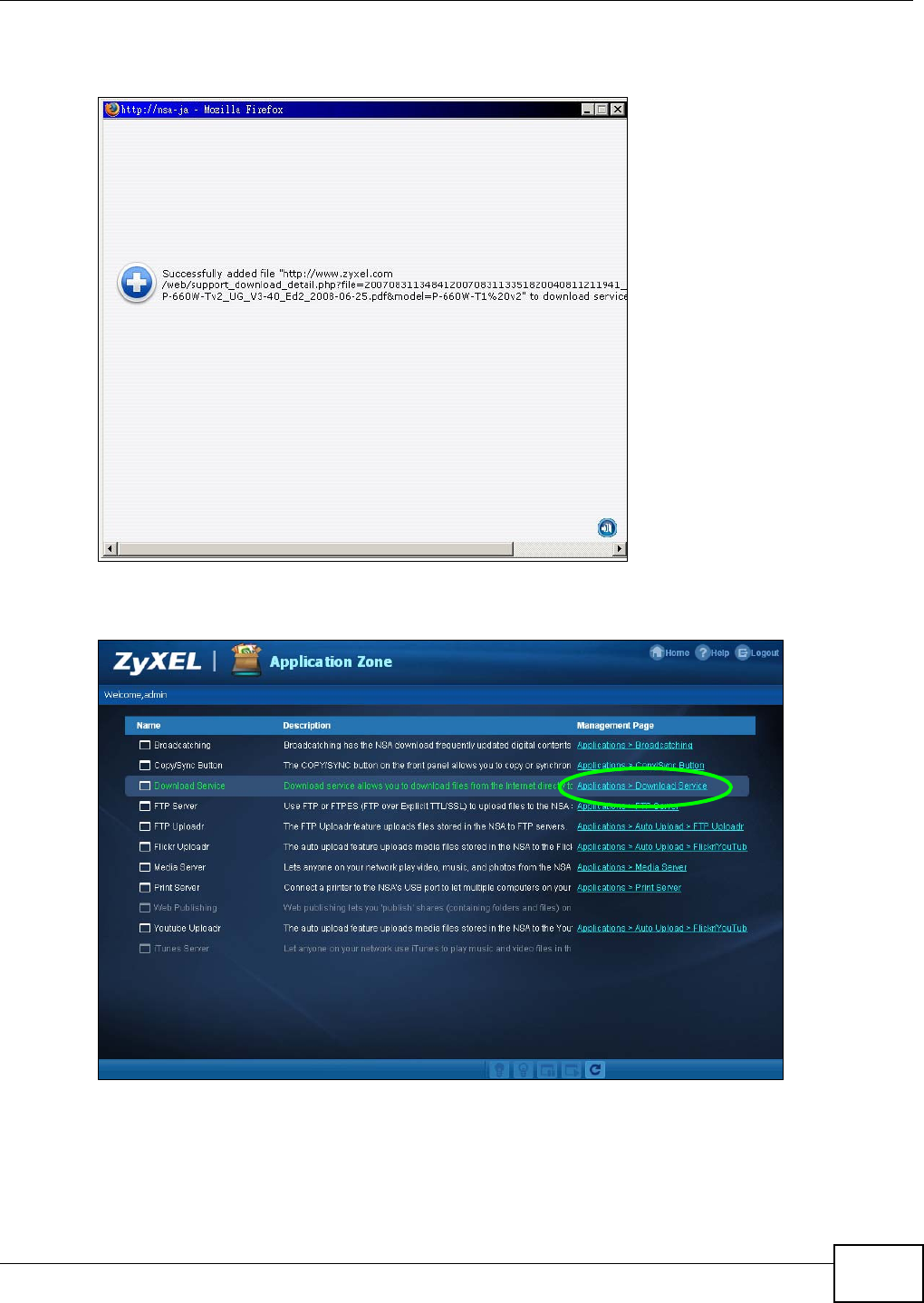
Chapter 5 Tutorials
Media Server User’s Guide 101
4The login screen shows up. Enter your NSA’s login information and click Login to send the link to
the download service. A confirmation message displays.
5Log into the NSA web configurator (see Section 4.3 on page 45) using the administrator account
and click Application Zone and the Application Zone > Download Service link.
6The download task appears in the Download Service screen’s Active or Queue tab. It may
appear in the Completed tab if the NSA already finished downloading the file or it may appear in
the Error tab if the NSA failed to download the file.
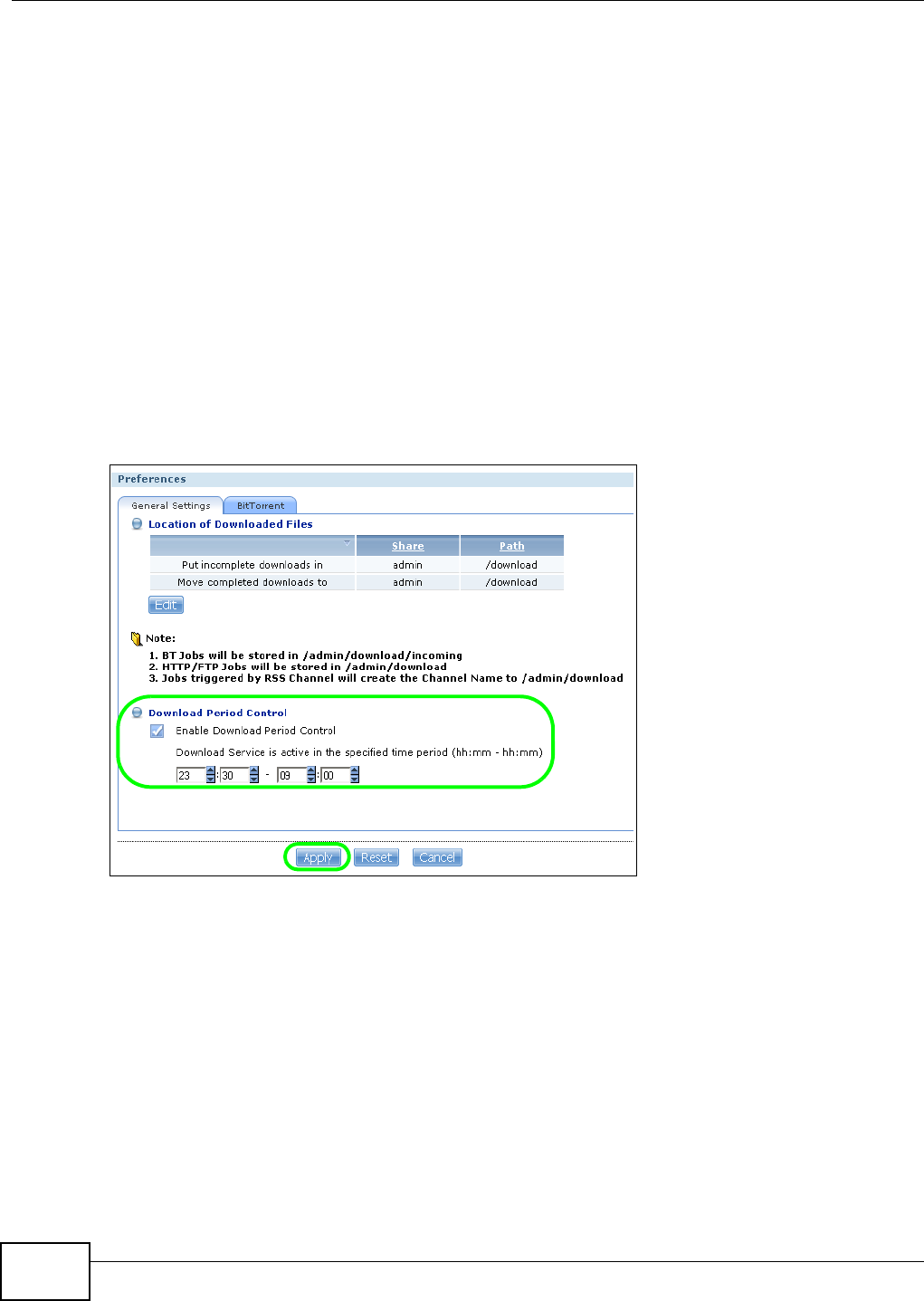
Chapter 5 Tutorials
Media Server User’s Guide
102
By default the NSA stores all downloads in the admin share’s download folder. See Section 5.9.4
on page 88, Section 5.9.5 on page 90, or Section 5.9.6 on page 91 for how to access a share.
5.10.4 Configuring the Download Service Preferences
Once you added a list of download tasks to the NSA (see Section 5.10.1 on page 92 and Section
5.10.3 on page 100), you can have the NSA download files during a specific time period of the day.
You can also configure the BitTorrent settings to control bandwidth and optimize download
efficiency.
Say you have the NSA turned on all the time, but you only want the NSA download files at night.
Here is how you use the download period control feature to set the time range.
1Click Applications > Download Service > Preferences to open the General Settings screen.
2Select Enable Download Period Control and use the arrows to adjust the time period from 23:30
to 09:00. Click Apply to save your changes. The NSA only downloads files within this 9.5-hour
period every day.
Note: If you configure the Power On/Off Schedule feature in the Power Management
screen, make sure your active download period does not conflict with the power-off
period.
Note: If power failure occurs during the active download period, the NSA will verify
whether the downloaded files were damaged. If a file is corrupted, the NSA will
download the file again. If the file is intact but not completely downloaded, the NSA
will resume the download task after it restarts.
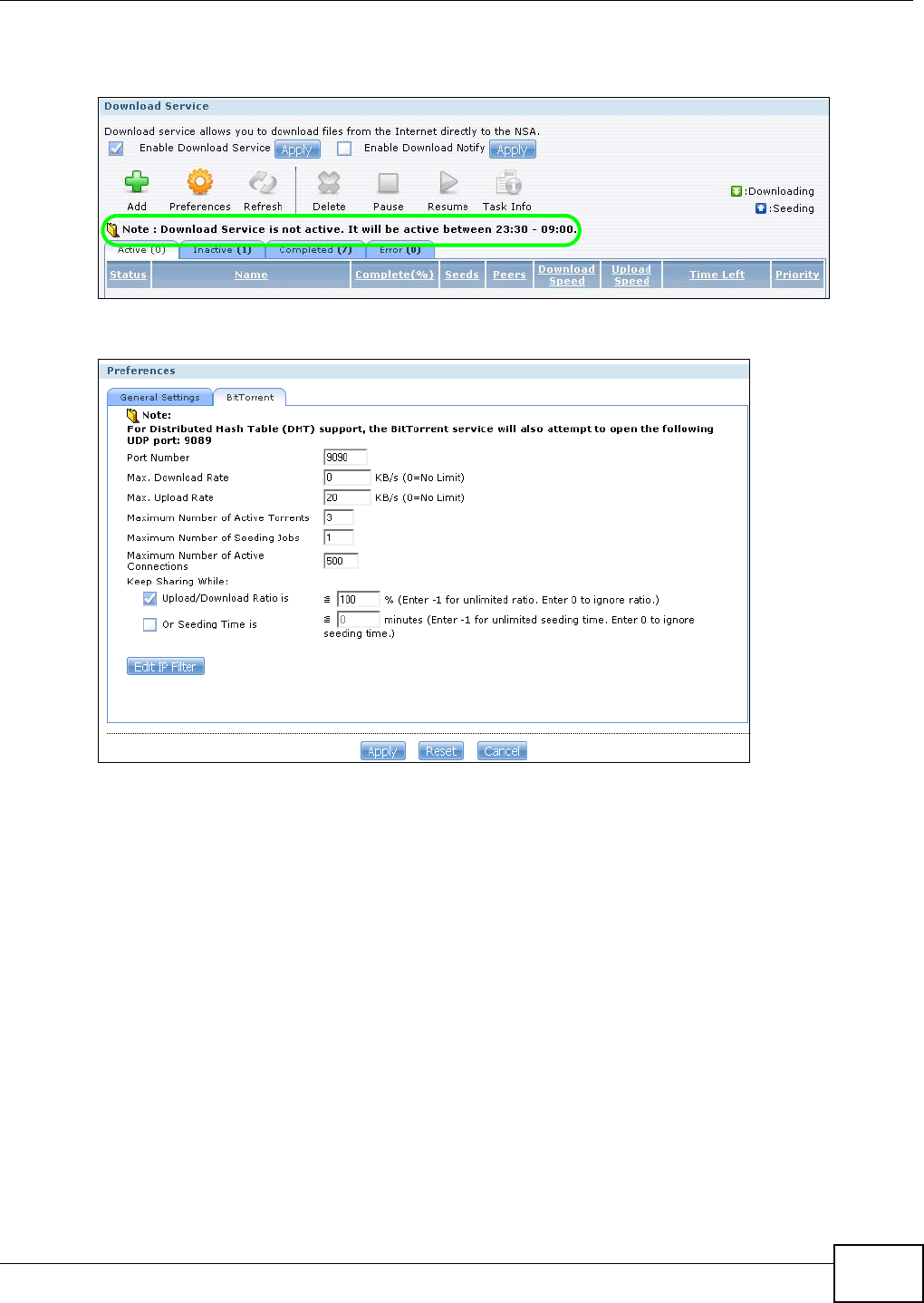
Chapter 5 Tutorials
Media Server User’s Guide 103
3When it is not the download time, you see a message in the Download Service screen, indicating
the active download period.
Click Applications > Download Service > Preferences > BitTorrent to open the following
screen. Enter the information below and then click Apply.
Here is a list of BitTorrent settings you want to configure for your NSA:
• Limit the maximum upload rate to 20 KB/s.
Enter this value in the Max. upload rate field.
• Actively download three torrent files but only upload one at a time.
Enter 3 in the Maximum Number of Active Torrents field and enter 1 in the Maximum
Number of Seeding Jobs field.
• Keep sharing until the NSA has shared equal or greater amount of the downloaded files.
Select the check box and enter 100 in the Upload/Download Ratio field.
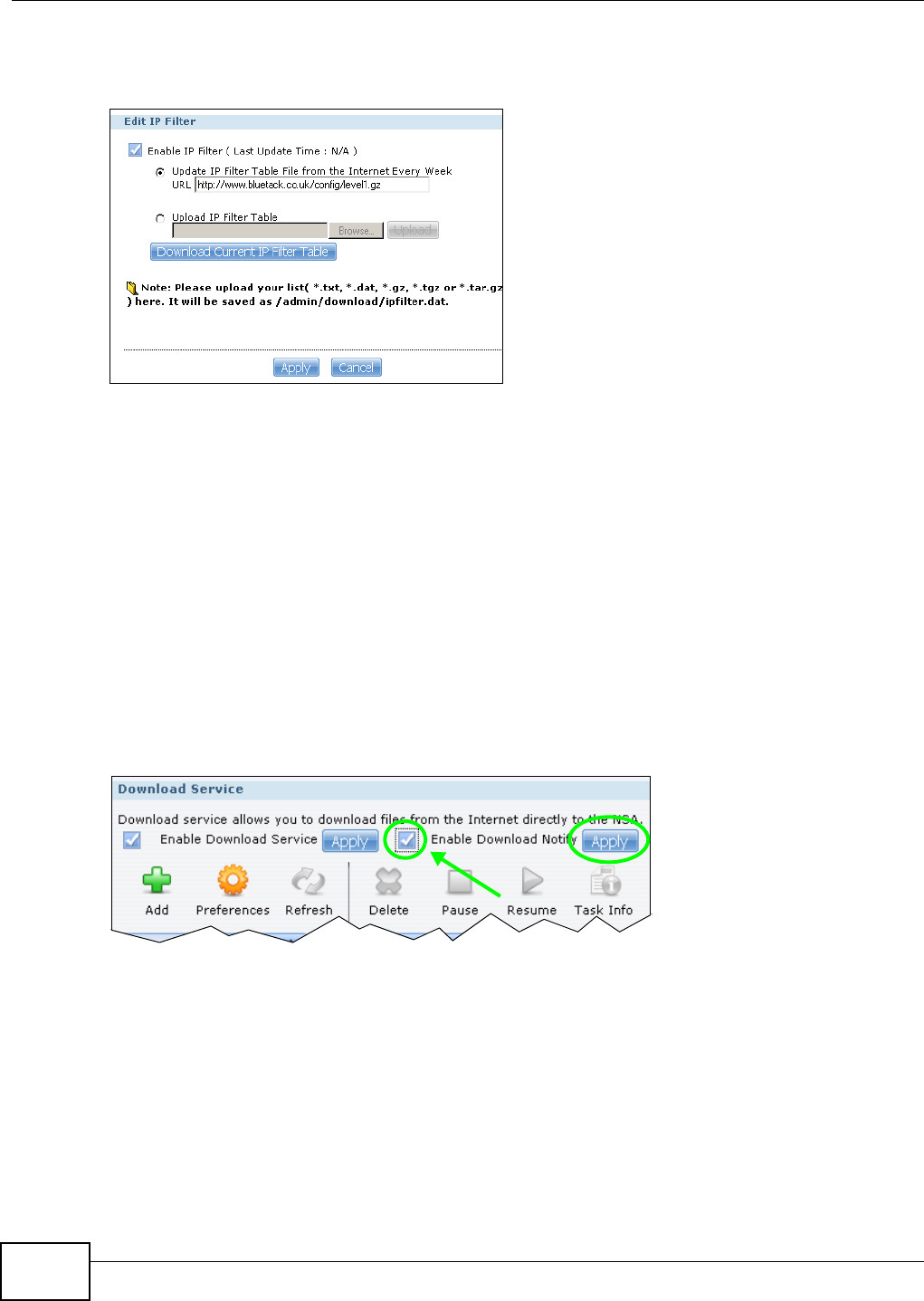
Chapter 5 Tutorials
Media Server User’s Guide
104
• Click Edit IP Filter. Use an online IP filter table from http://www.bluetack.co.uk/config/level1.gz
for example to protect BitTorrent downloads.
Enter the URL in the Update IP Filter from the Internet Every Week field.
5.10.5 Using Download Service Notification
Use an RSS feed reader on your computer to keep track of files the NSA has downloaded. The
following examples show how to subscribe to the NSA’s download service notifications. See Section
10.11.4 on page 214 for more on download service notifications.
Some RSS readers may not support the NSA’s download service notifications. For example, Google
Reader cannot support this feature if the NSA has a private IP address.
Note: It is recommended to subscribe to the download service notifications using the
built-in reader in Internet Explorer 7 or higher, or Firefox.
You have to activate this feature in the Download Service screen. Click Applications >
Download Service to open the following screen. Select Enable Download Notify and click
Apply.
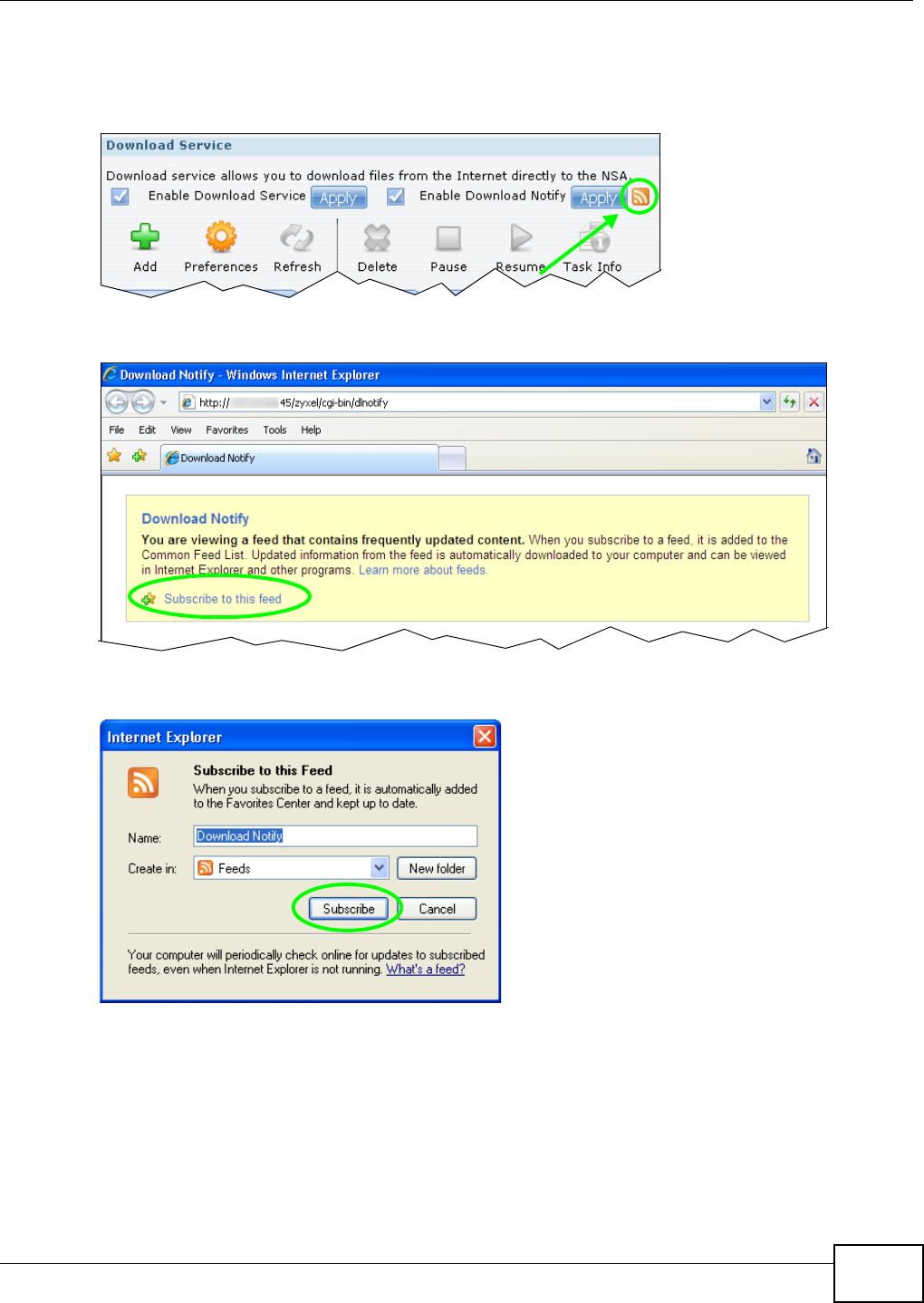
Chapter 5 Tutorials
Media Server User’s Guide 105
Internet Explorer 7 Example
1After you activate download service notification, click the RSS feed icon.
2The following screen displays. Select Subscribe to this feed.
3The following screen displays. Click Subscribe.
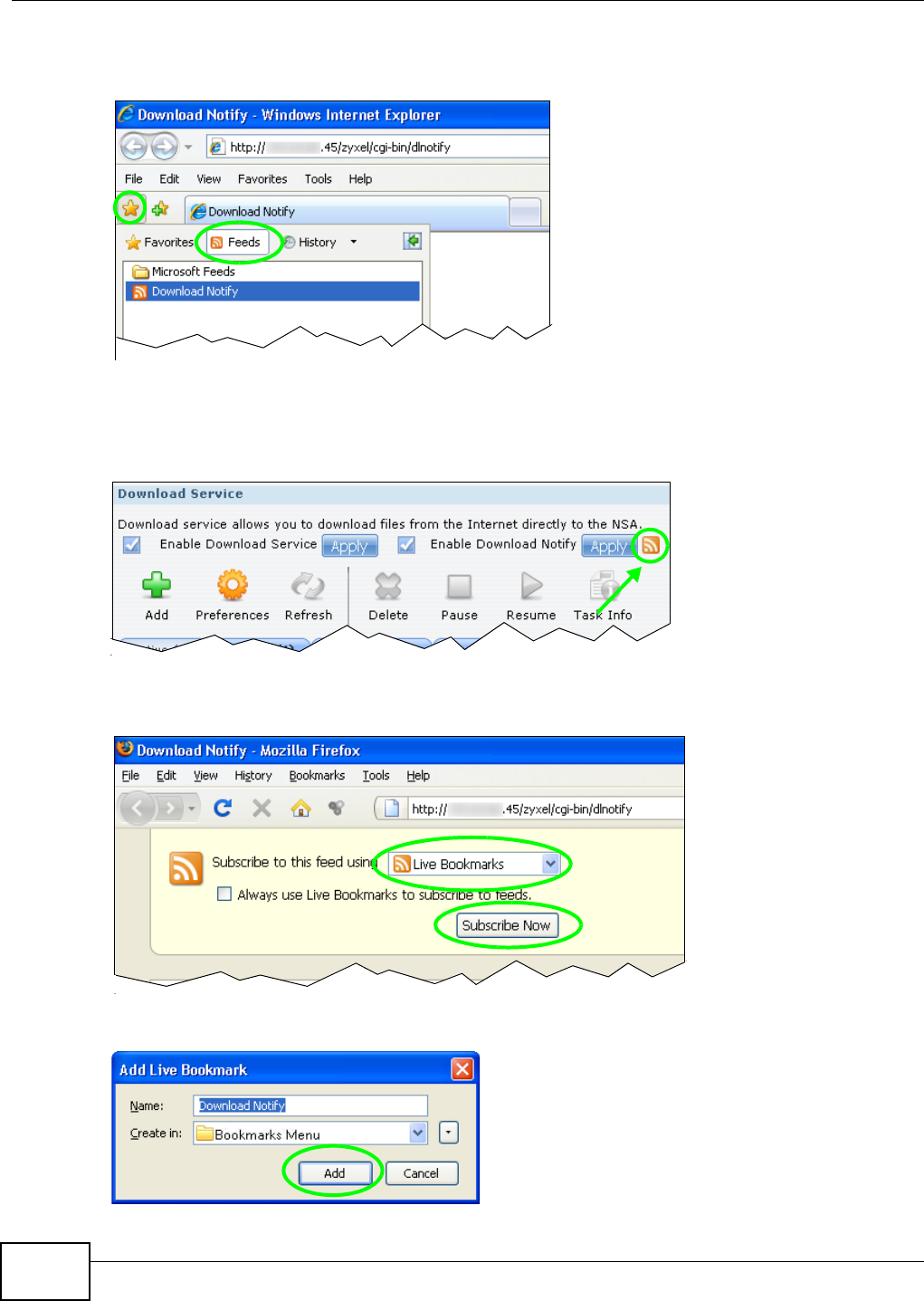
Chapter 5 Tutorials
Media Server User’s Guide
106
4Click the Favorite icon on your browser and select the Feeds tab to check the updates of your
NSA’s download list.
Firefox Example
1After you activate download service notification, click the RSS feed icon.
2The following screen displays. Select Live Bookmarks from the drop-down list and click
Subscribe Now.
3The following screen displays. Select Bookmarks Menu and click Add.
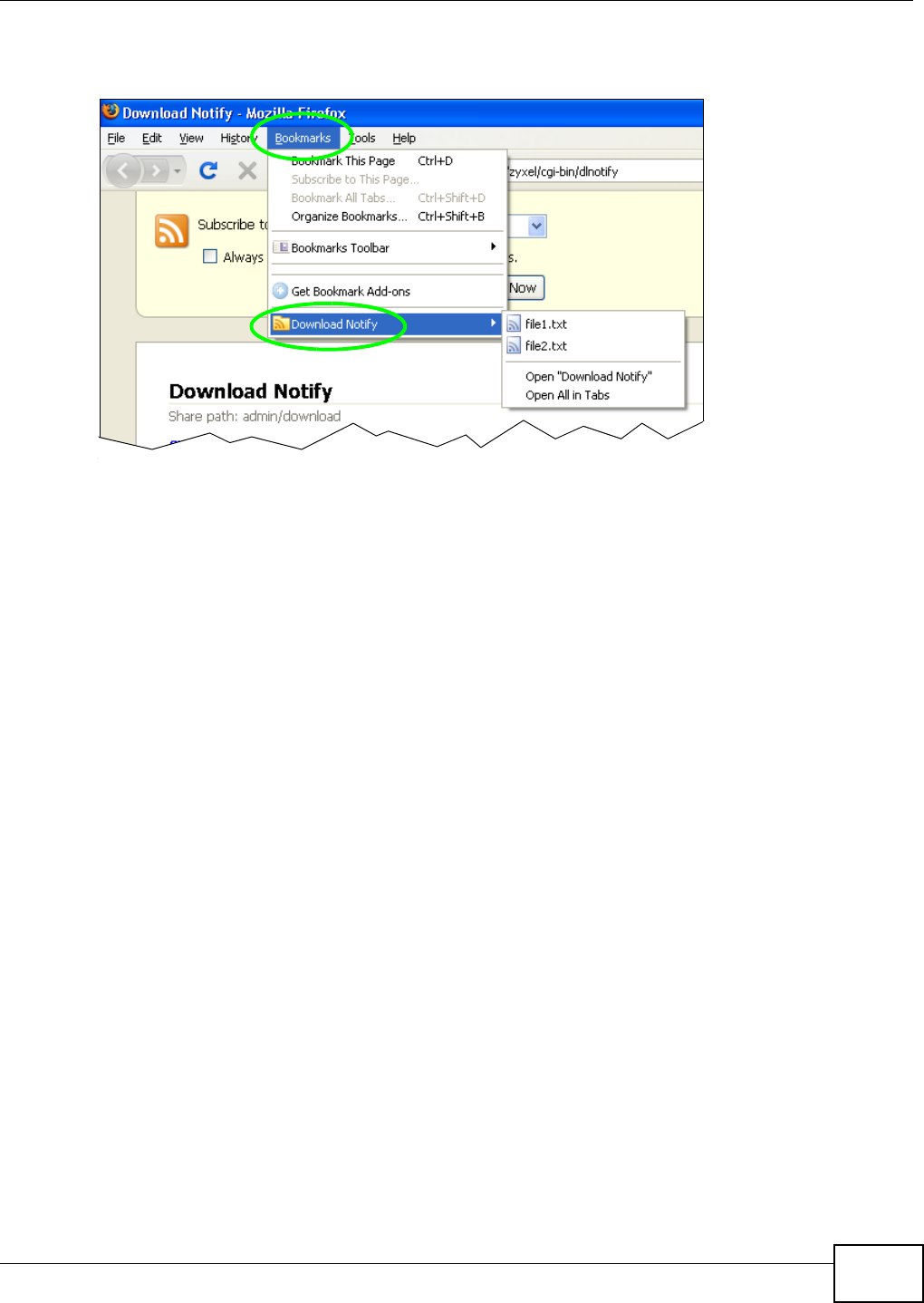
Chapter 5 Tutorials
Media Server User’s Guide 107
4From the Firefox’s Bookmarks Menu, select Download Notify to check the updates of your NSA’s
download list.
5.11 Broadcatching Tutorial
Use broadcatching to have the NSA download frequently updated digital content like TV programs,
radio talk shows, Podcasts (audio files), and blogs. This example shows how to subscribe the NSA
to the CNET TV Internet television channel. See Section 10.8 on page 203 for more on the
broadcatching service.
1Open your Internet browser (this example uses Firefox).
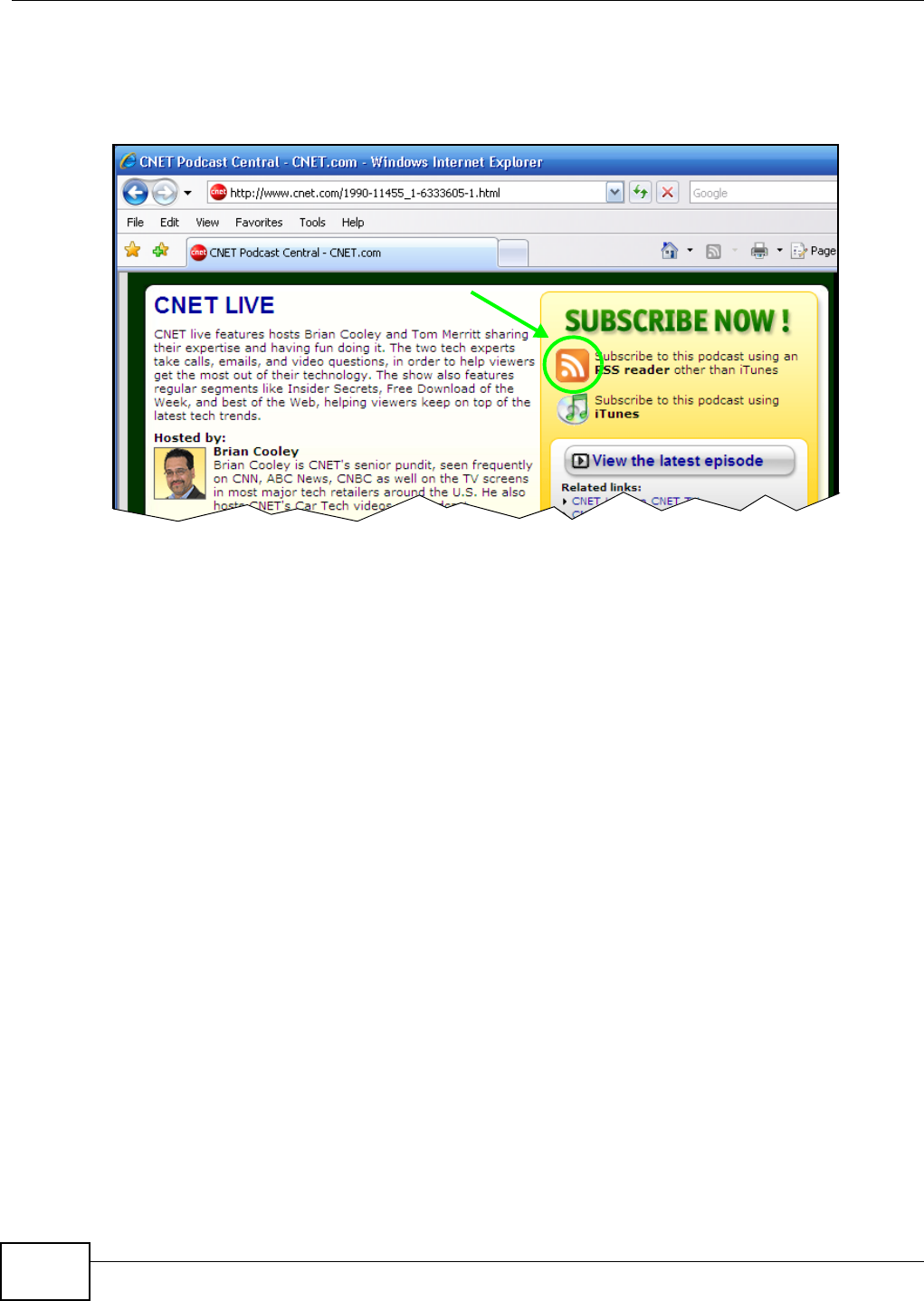
Chapter 5 Tutorials
Media Server User’s Guide
108
2Find the link for the RSS feed containing the channel you want to add. In this example, http://
reviews.cnet.com/4520-11455_7-6333605-1.html has an RSS link for subscribing to the CNET Live
podcast. However this is not the link for the actual RSS feed. Click the link to go to another screen
that has RSS feed links.
Note: Make sure the link goes to the actual RSS feed instead of to another list of links or
information about the channel.
One way to test this is by clicking the link. Clicking an actual RSS feed link opens a screen of XML
code (in browsers without an RSS feed aggregator) or a window where you can add the RSS feed
(in browsers with an RSS feed aggregator).
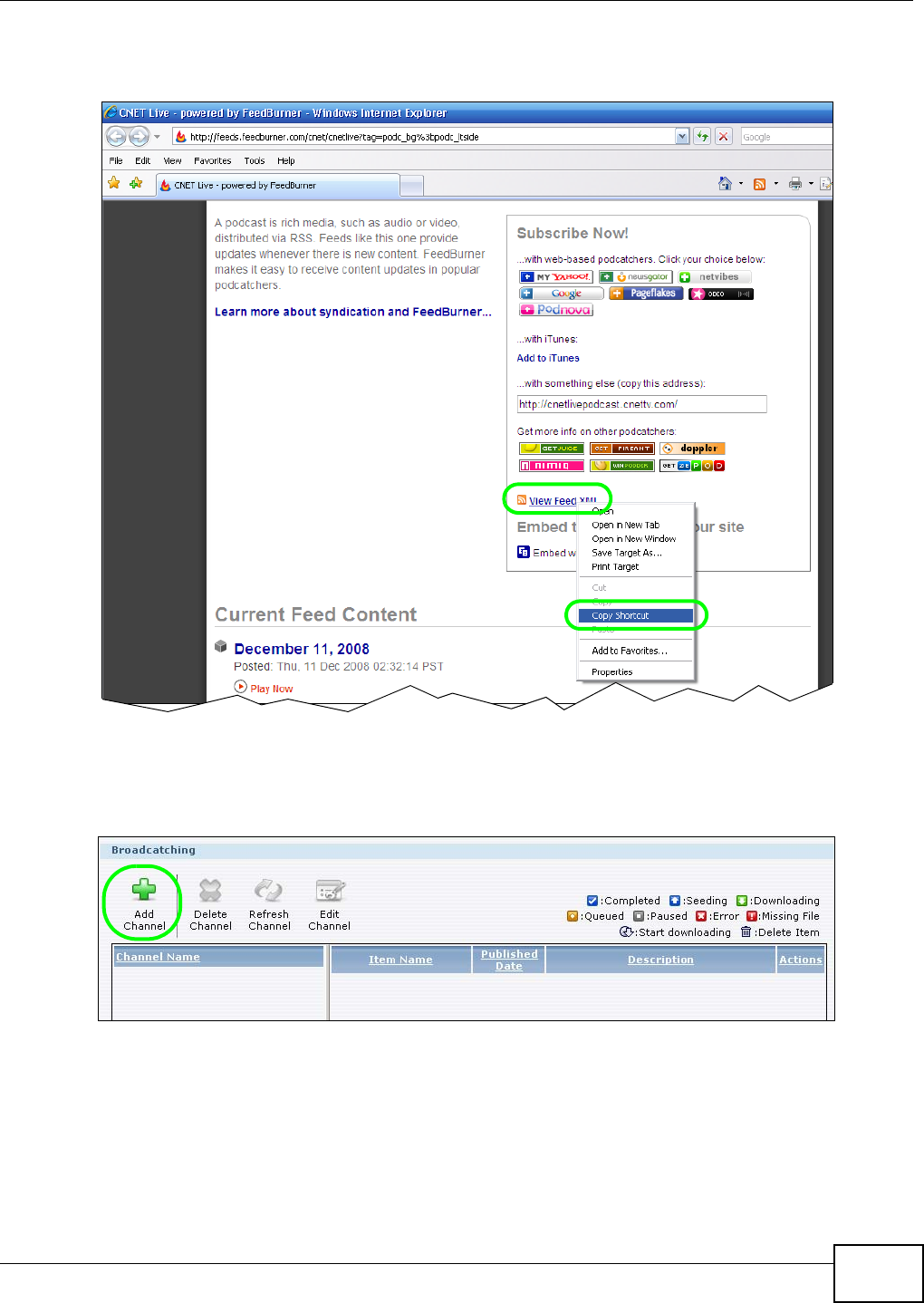
Chapter 5 Tutorials
Media Server User’s Guide 109
3Right-click the download link and select Copy Link Location in Firefox (or Copy Shortcut in
Internet Explorer).
4Log into the NSA web configurator (see Section 4.3 on page 45) using the administrator account
and click Administration > Applications > Broadcatching.
5Click Add Channel.
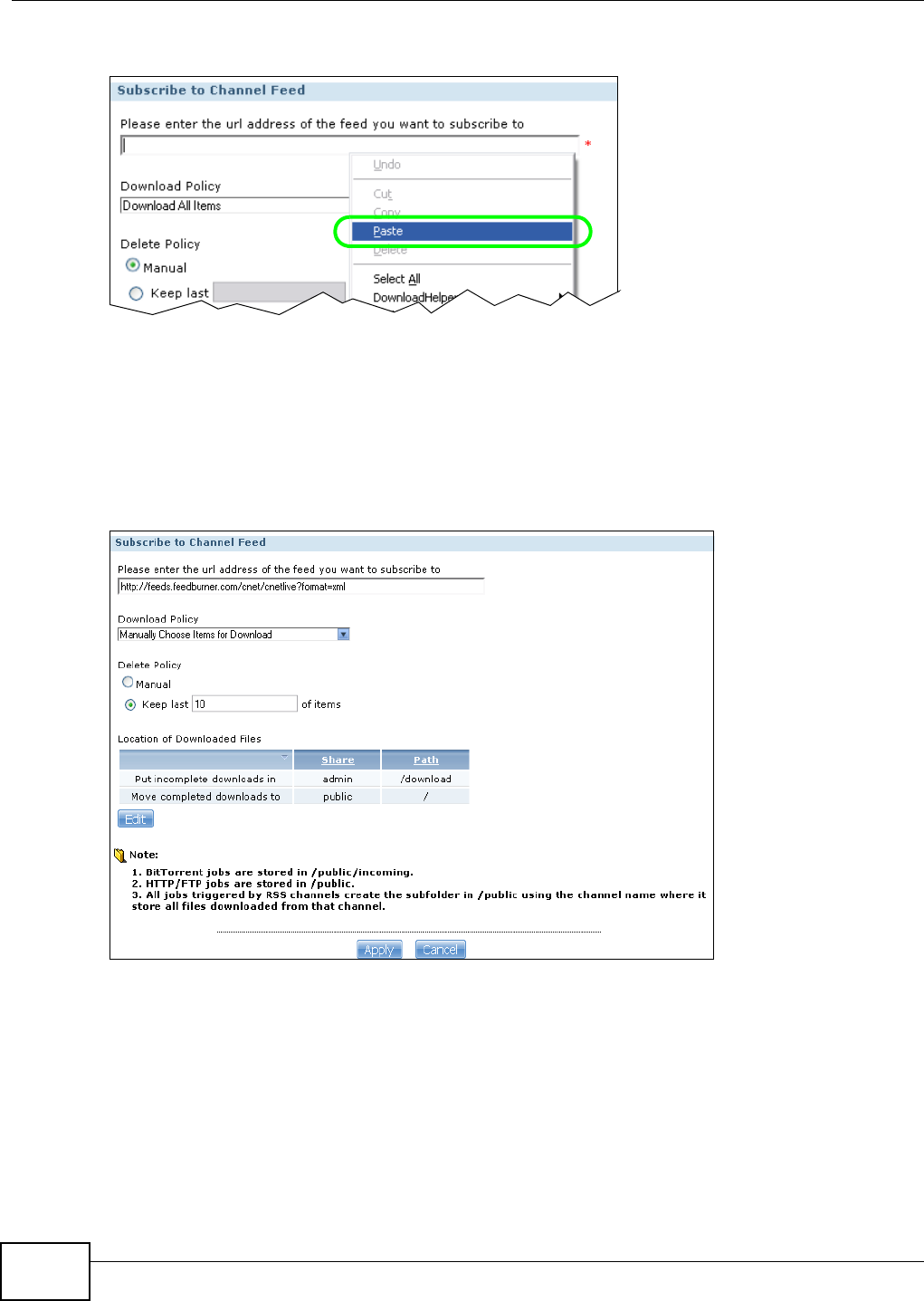
Chapter 5 Tutorials
Media Server User’s Guide
110
6Right-click the URL field and select Paste.
7The URL displays in the URL field.
8Select a policy for what items to download. This example uses Manually Choose Items for
Download so you will be able to select individual items to download later.
9Select a policy for what items to delete. This example keeps the most recent 10 items.
10 Click Apply.
11 After a few moments, the channel appears in the Broadcatching screen where you can select
items you want to download. The NSA saves the items you download in a folder named after the
channel. By default, the channel folders are created in the admin share’s download folder. The
NSA’s media server feature makes it easy for users on your network to play the broadcatching files
you download. See Section 10.11.1 on page 212 for more on the media server.
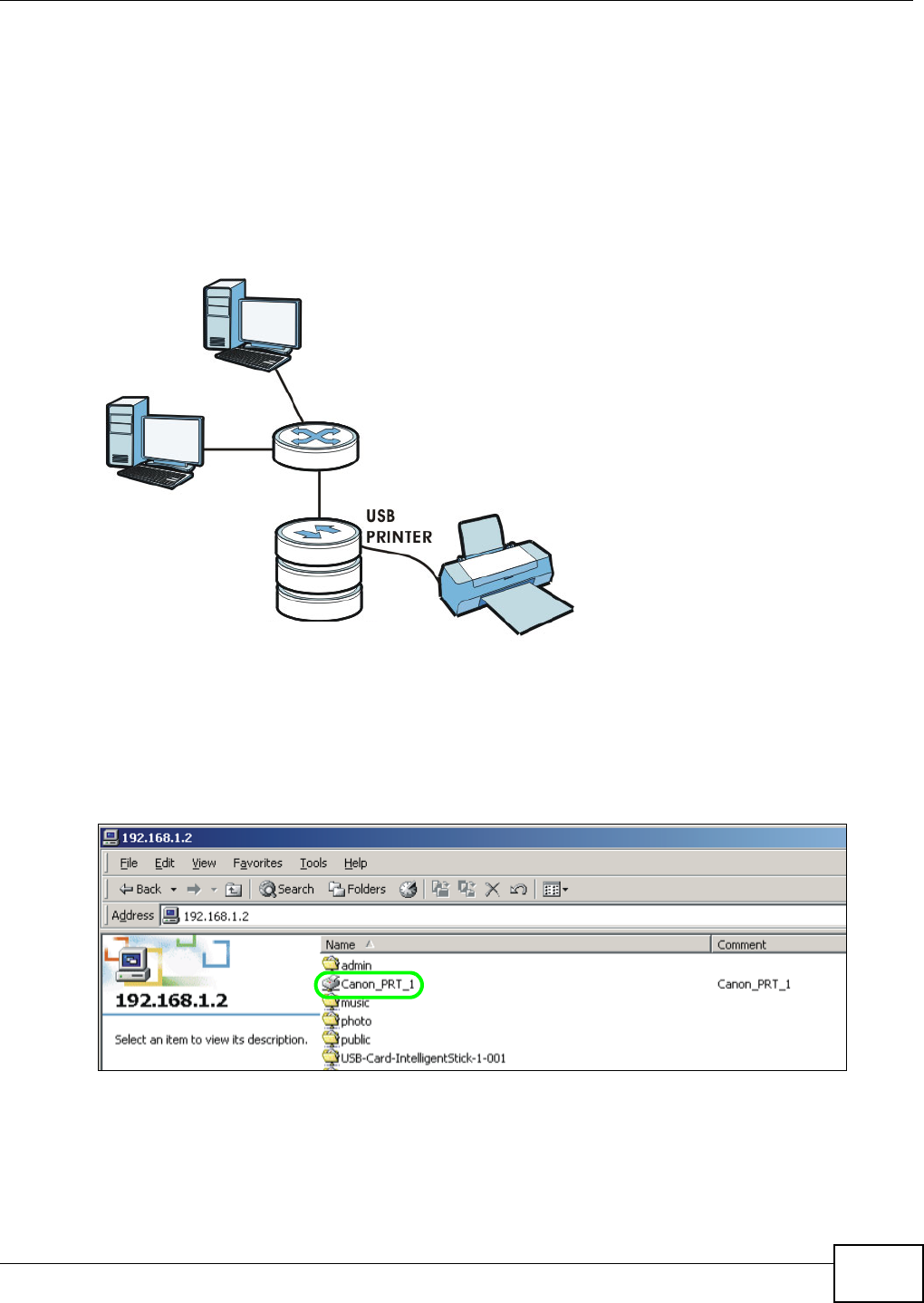
Chapter 5 Tutorials
Media Server User’s Guide 111
5.12 Printer Server Tutorial
Do the following to have the NSA let computers on your network share a printer. See
www.zyxel.com for a list of compatible printers.
1Make sure the NSA is on and the SYS light is on steady (not blinking).
2Use a USB cable to connect the printer’s USB port to one of the NSA’s USB ports. Make sure the
printer is also connected to an appropriate power source.
3Turn on the printer.
4The NSA detects the printer after a few moments.
5On your computer, open your CIFS file sharing program (Windows Explorer for example) and
browse to the NSA. Double-click the printer’s icon.
NSA
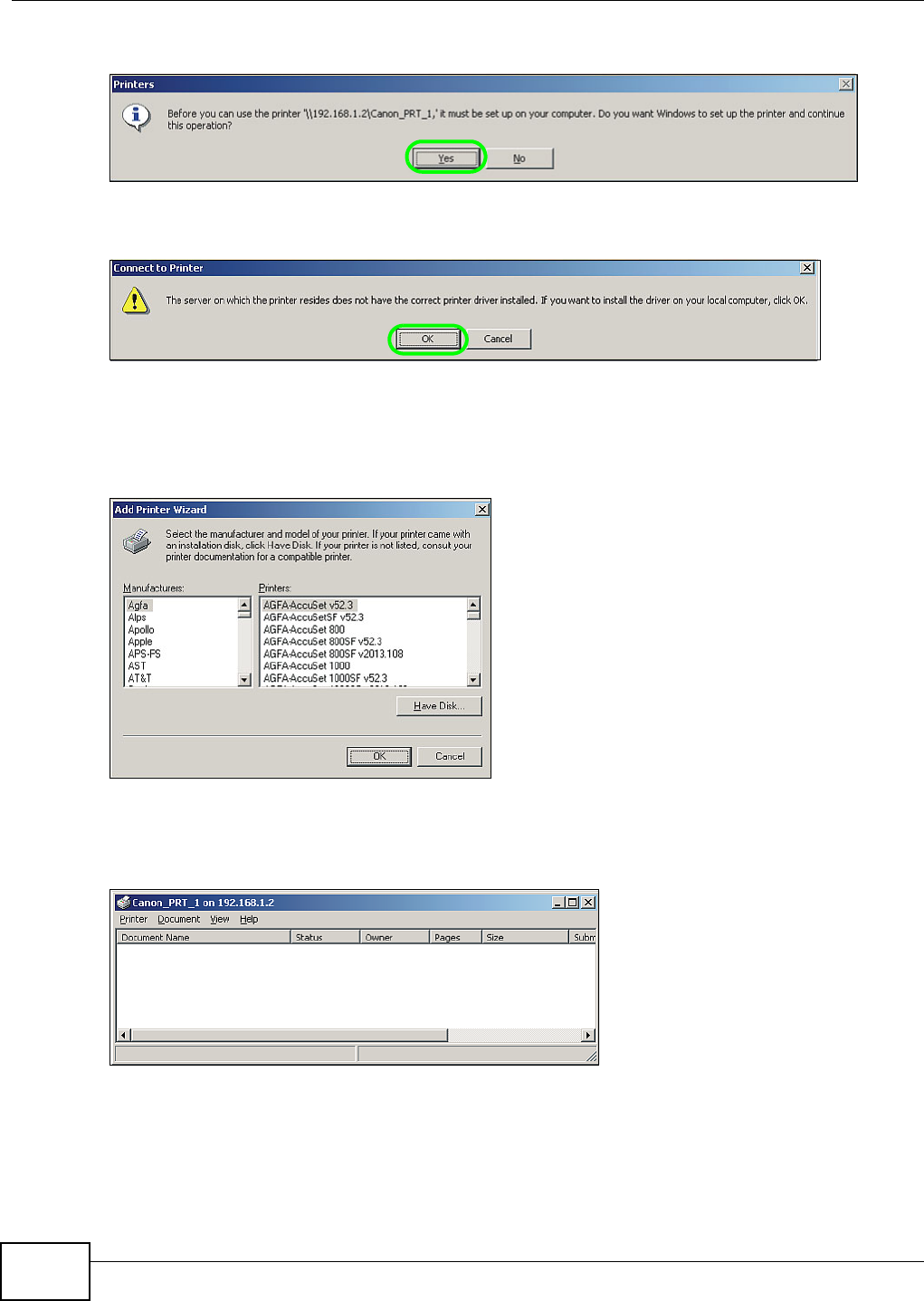
Chapter 5 Tutorials
Media Server User’s Guide
112
6If you get a warning screen, click the option that lets you continue (Yes in this example).
7If your computer does not already have the printer’s driver installed, you will need to install it. In
this example, click OK.
8Use the wizard screens to install the printer driver on the computer. You may need to get the file
from the printer’s CD or the printer manufacturer’s website (the driver is not installed on the NSA).
Note: You must install the printer driver on each computer that will use the printer.
After the driver installation finishes, the computer is ready to use the printer. Select the printer in
an application to use it to print. Browse to the NSA using a CIFS program (like Windows Explorer)
and double-click the printer’s icon to open the printer’s queue of print jobs.
Note: Repeat steps 5 to 8 on your other computers so they can also use the printer.
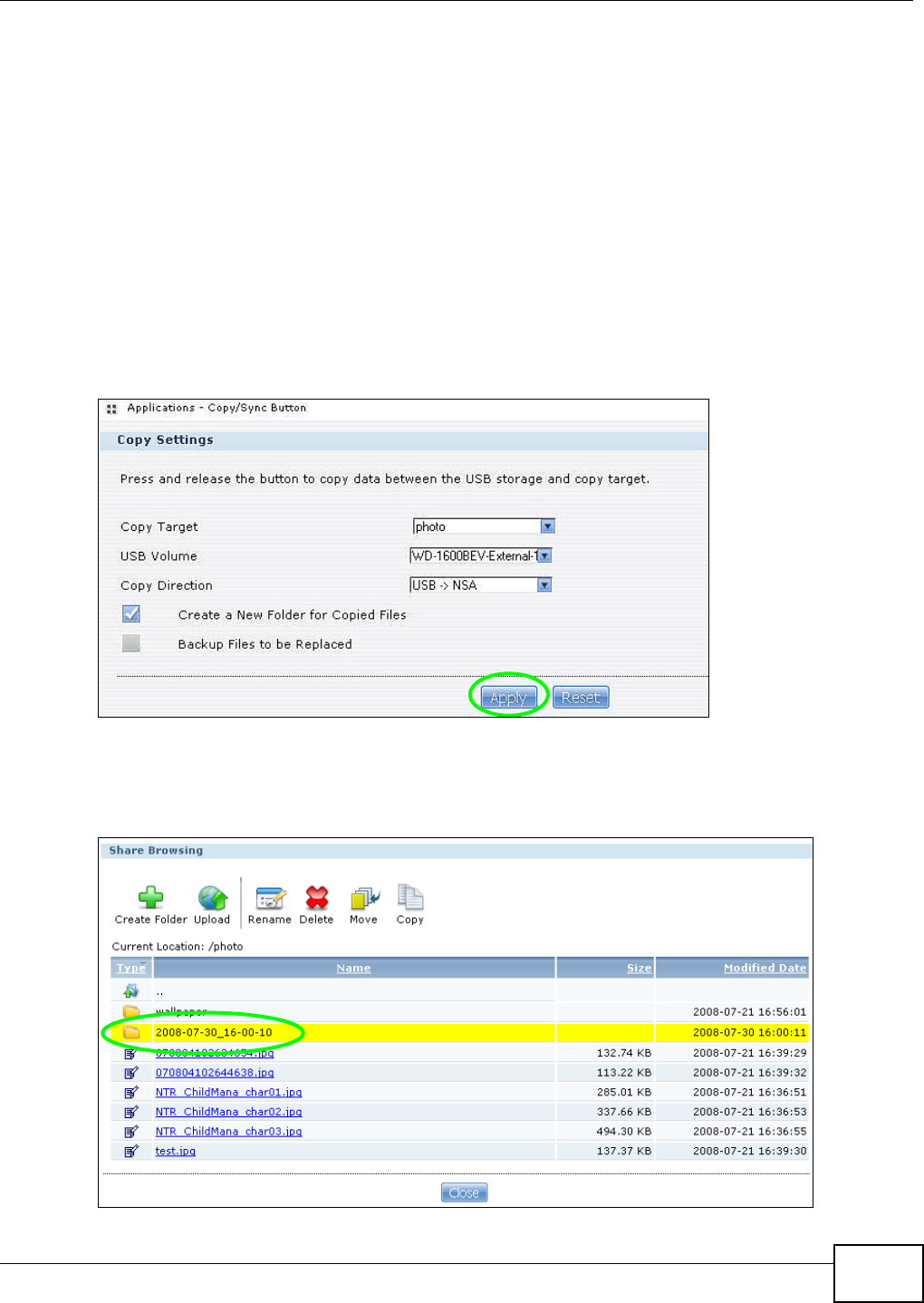
Chapter 5 Tutorials
Media Server User’s Guide 113
5.13 Copy and Flickr Auto Upload Tutorial
Amy received some photos taken during her best friend’s wedding and saved the files on a USB
disk. She wants to save a copy of the photos in the NSA and upload the photos to her Flickr
account.
Amy has to activate the NSA’s auto upload feature. See Section 12.4 on page 275 for more details
on setting up a Flickr account for auto upload. In this example Amy select the NSA’s photo share for
auto upload.
This is how Amy would transfer the files from her USB disk to the NSA.
1Click Applications > Copy/Sync Button in the navigation panel to open the screen.
2Configure the copy settings as shown and click Apply.
3Press and release the COPY/SYNC button on the NSA’s front panel to start copying files.
4The copied files can be found in a new folder in the photo share. The name of this folder is the date
(yyyy-mm-dd) and time (hh-mm-ss) when the folder is created.
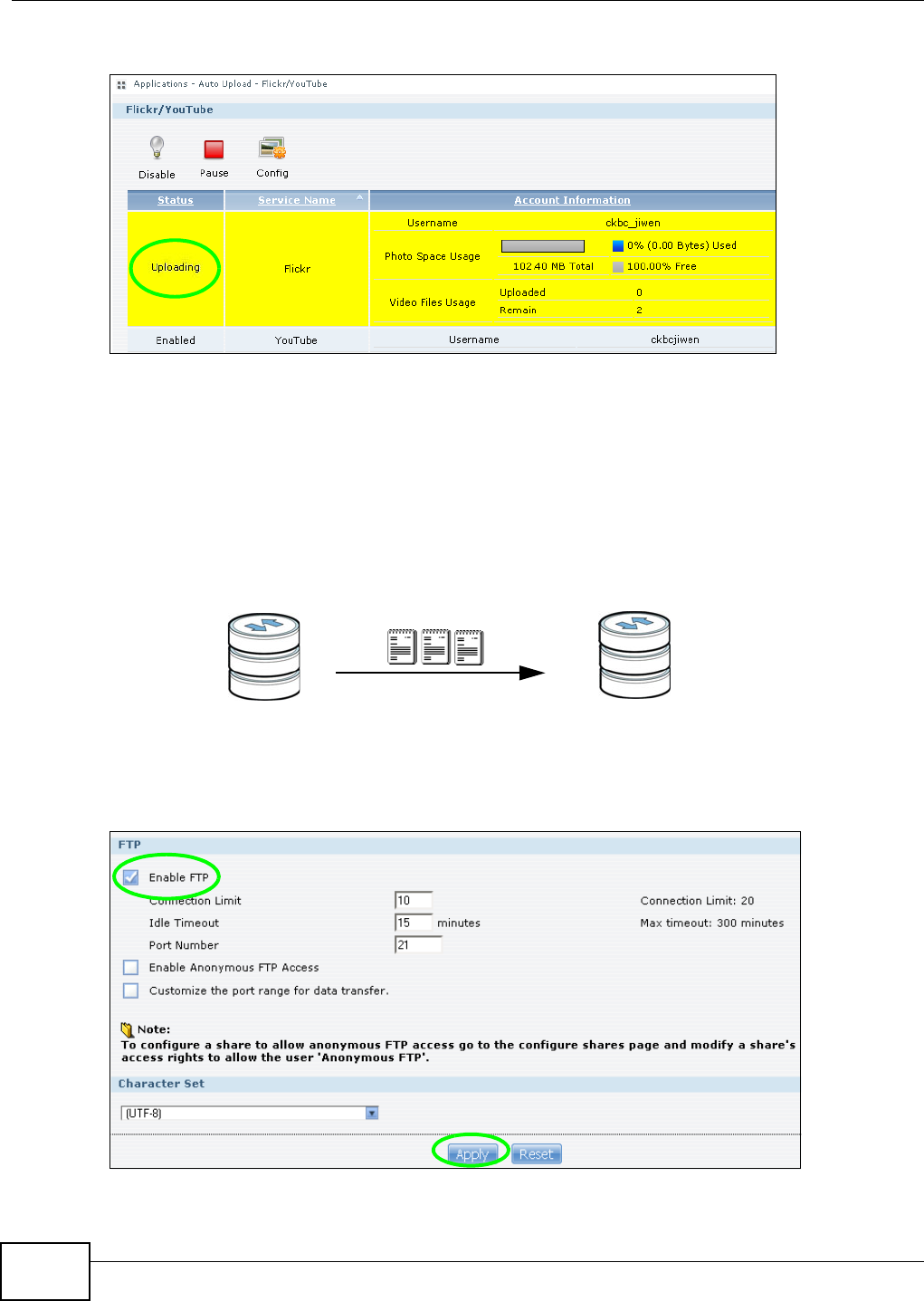
Chapter 5 Tutorials
Media Server User’s Guide
114
5The NSA also automatically uploads the copied files to Flickr.
r
5.14 FTP Uploadr Tutorial
FTP Uploadr can automatically upload files saved on the NSA to a remote FTP server. Amy wants to
share files on her NSA with Susan. They each have an NSA at home, so Susan has to set her NSA as
an FTP server for Amy to automatically send files using FTP Uploadr.
l
To set the NSA as an FTP server, click Applications > FTP to open the FTP screen. Select Enable
FTP and click Apply.
Amy’s NSA Susan’s NSA
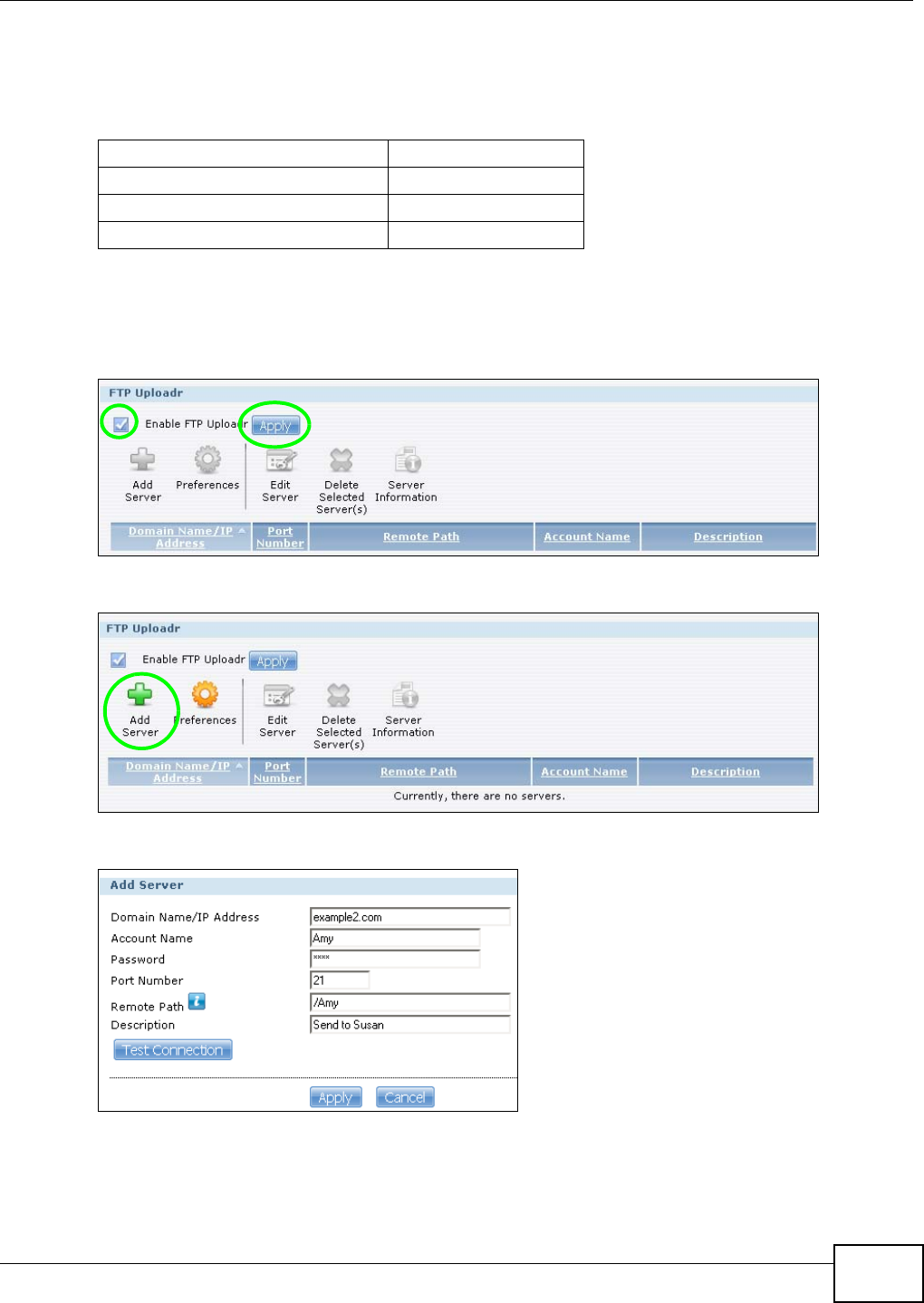
Chapter 5 Tutorials
Media Server User’s Guide 115
Susan also has to create a user account and share on her NSA for Amy to upload files. The share is
used for files uploaded from Amy’s NSA. Amy will then use the following information to configure
FTP Uploadr on her NSA.
This is how Amy would set up the NSA’s FTP Uploadr.
1Click Applications > Auto Upload > FTP Uploadr to open the FTP Uploadr screen. Select
Enable FTP Uploadr and click Apply to turn on FTP Uploadr.
2Click Add Server.
3Enter the information as describe in Table 15 on page 115. Click Apply to add the server.
Table 15 FTP Uploadr Tutorial: FTP Server Information
FTP Domain Name or IP Address example2.com
FTP User Name Amy
FTP Password xxxxx
Share (Remote Path) Amy
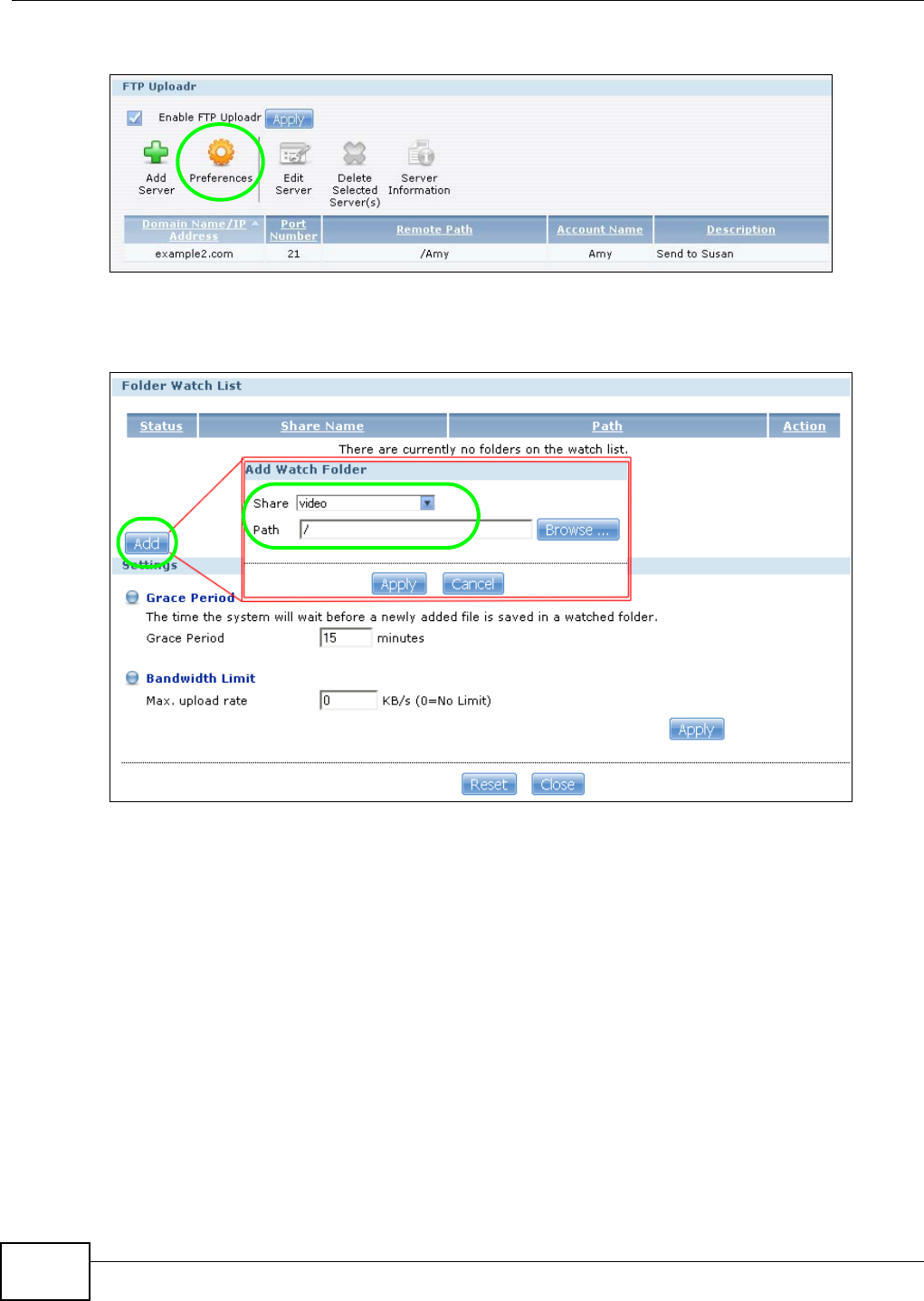
Chapter 5 Tutorials
Media Server User’s Guide
116
4In the FTP Uploadr screen, click Preferences to configure the auto upload settings.
5Amy wants to share video files with Susan. In the Preferences screen, click the Add button and
select video from the Shares drop-down list box, enter a forward slash in the Path field and click
Apply to add the share to the Folder Watch List.
t
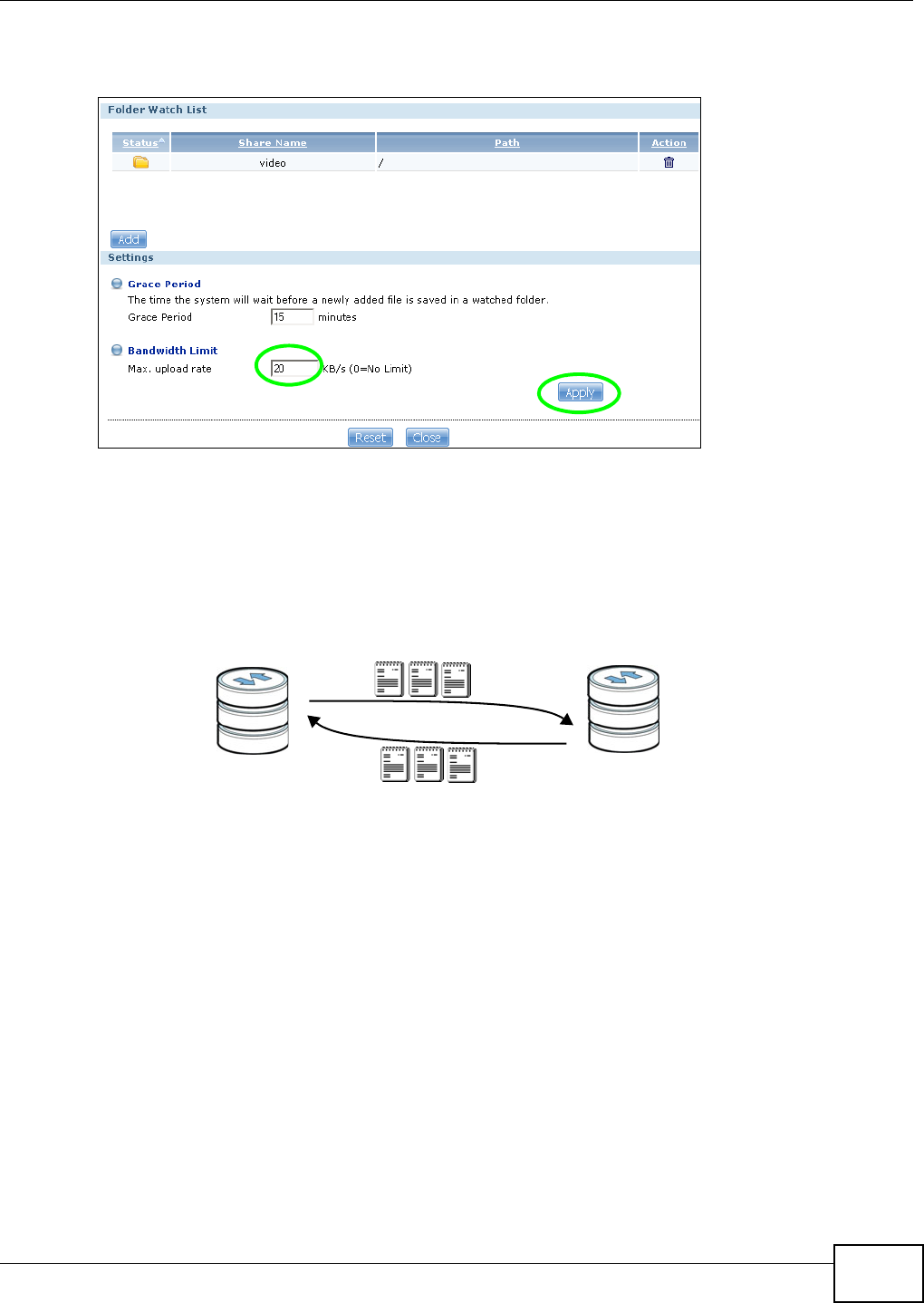
Chapter 5 Tutorials
Media Server User’s Guide 117
6Amy also set the Bandwidth Limit to 20KB/s so that the upload doesn’t slow down her Internet
connection.
Now Amy has set up FTP Uploadr to send files to Susan’s NSA. Every time Amy adds new files or
renames files in the video share, these new or modified files will be uploaded automatically to the
Amy share on Susan’s NSA.
Similarly, Susan can go through the steps described above to configure FTP Uploadr on her NSA.
Once Susan completes the setup, Amy can also receive files from Susan’s NSA.
5.15 Web Configurator’s Security Sessions
These tutorials show you how to configure security for the NSA’s Web Configurator sessions. You
will customize the NSA’s self-signed SSL certificate and distribute it to your users.
Amy’s NSA Susan’s NSA
Chapter 5 Tutorials
Media Server User’s Guide
118
5.15.1 Customizing the NSA’s Certificate
1Click Maintenance > SSL and then select Edit a self-signed CA certificate and click Edit.
2Next, let’s modify the certificate by changing the Common Name to this NSA’s host name of “nsa”,
the Organization to “ZyXEL” and the Key Length to 2048.
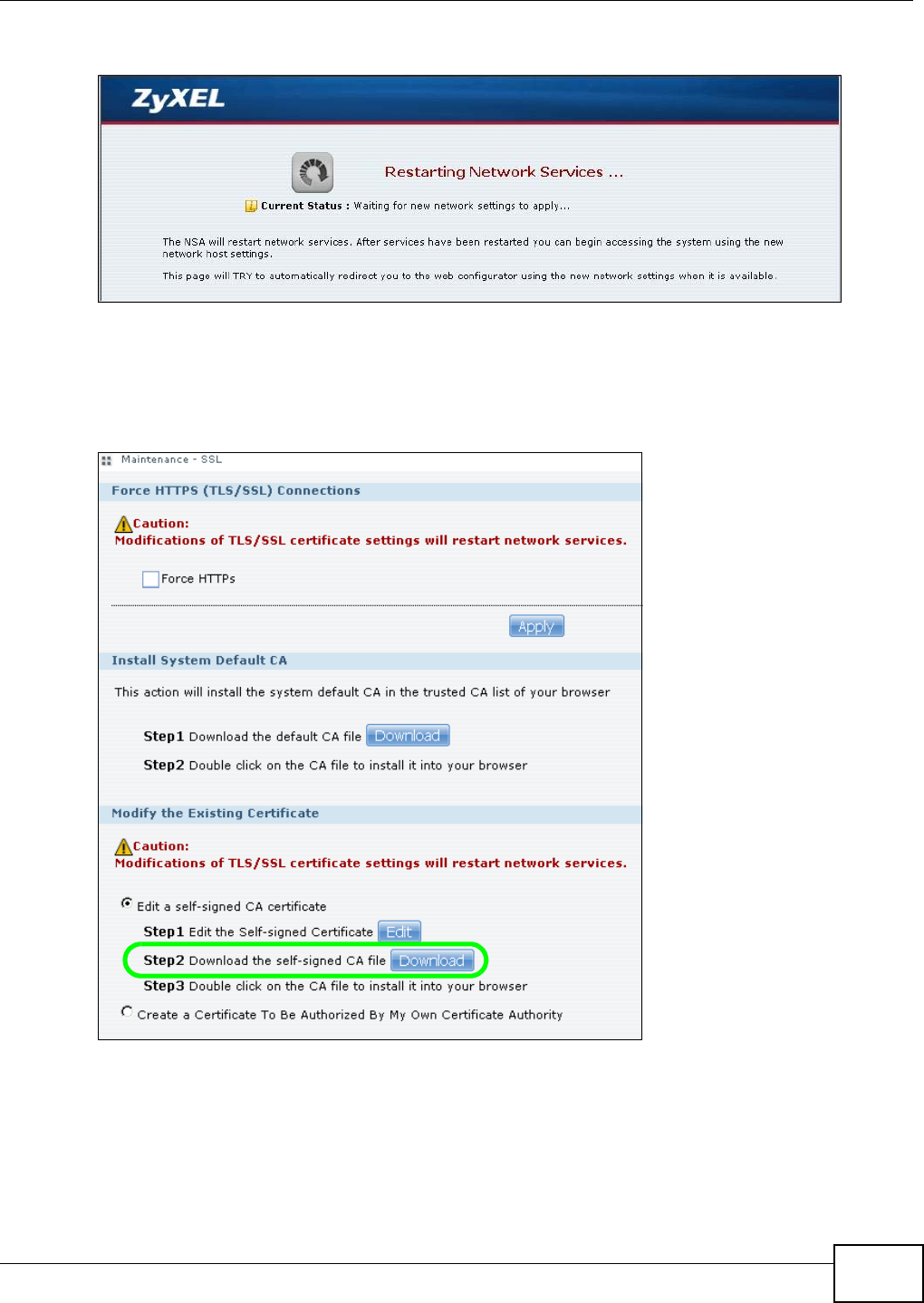
Chapter 5 Tutorials
Media Server User’s Guide 119
3The NSA restarts its network services and returns you to the login screen.
5.15.2 Downloading and Installing Customized Certificate
1Log in and return to Maintenance > SSL. Under Modify the Existing Certificate, click
Download.
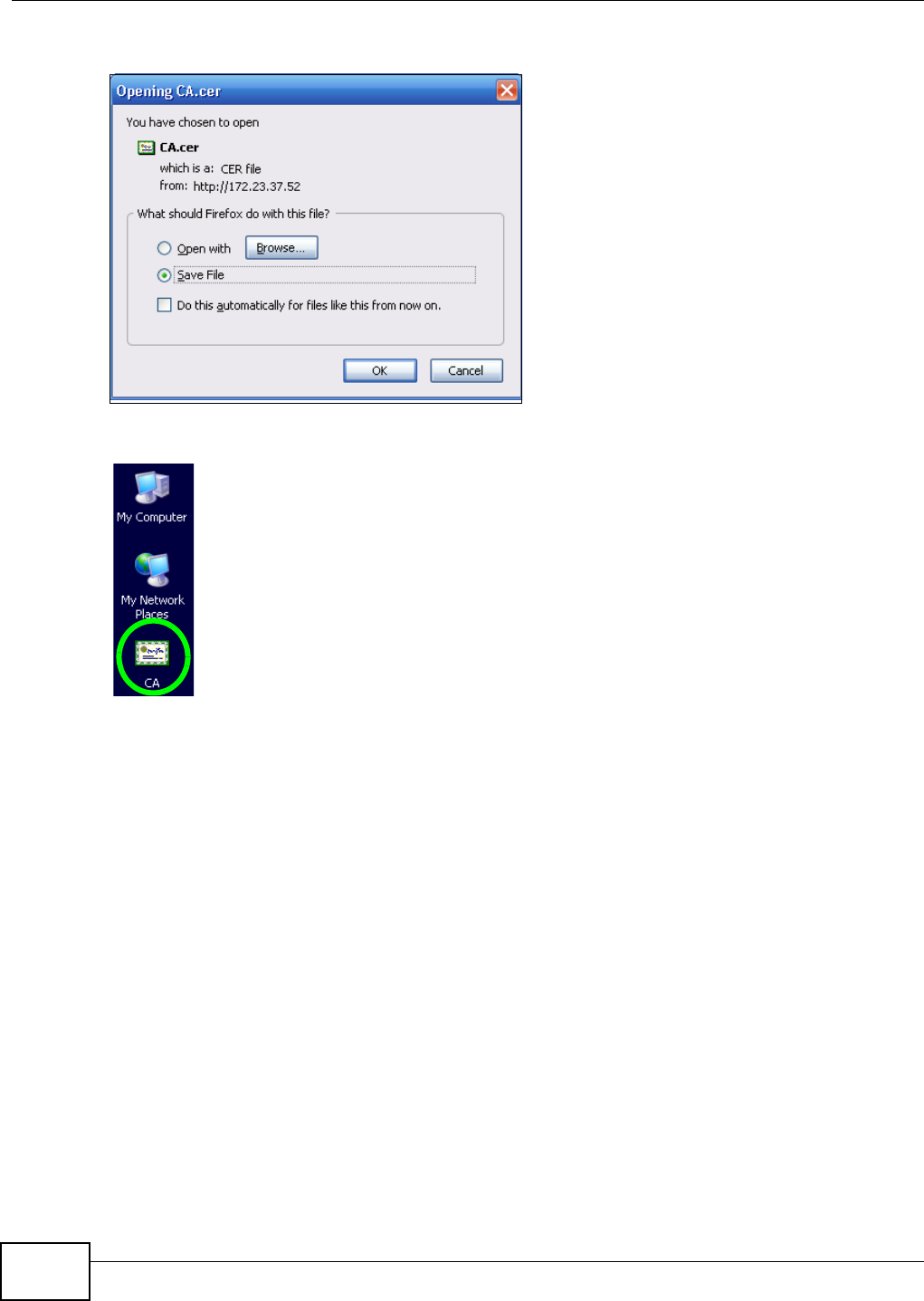
Chapter 5 Tutorials
Media Server User’s Guide
120
2Save the file to your computer.
3Find the certificate file on your computer and double-click it.
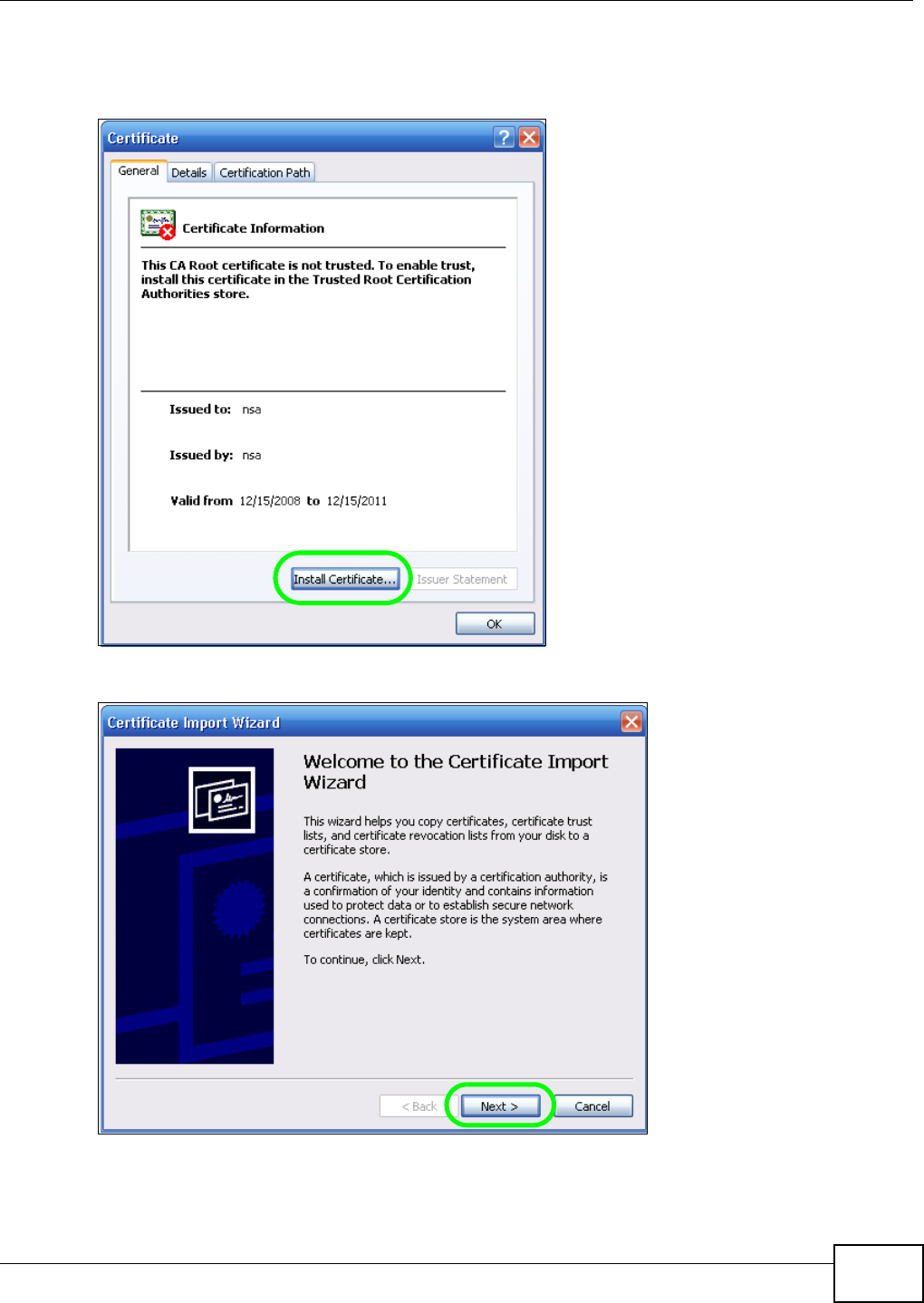
Chapter 5 Tutorials
Media Server User’s Guide 121
4Install the certificate. The rest of the steps in this section are an example of installing a certificate
in Windows. See Appendix D on page 411 for other examples. In the Certificate dialog box, click
Install Certificate.
5In the Certificate Import Wizard, click Next.
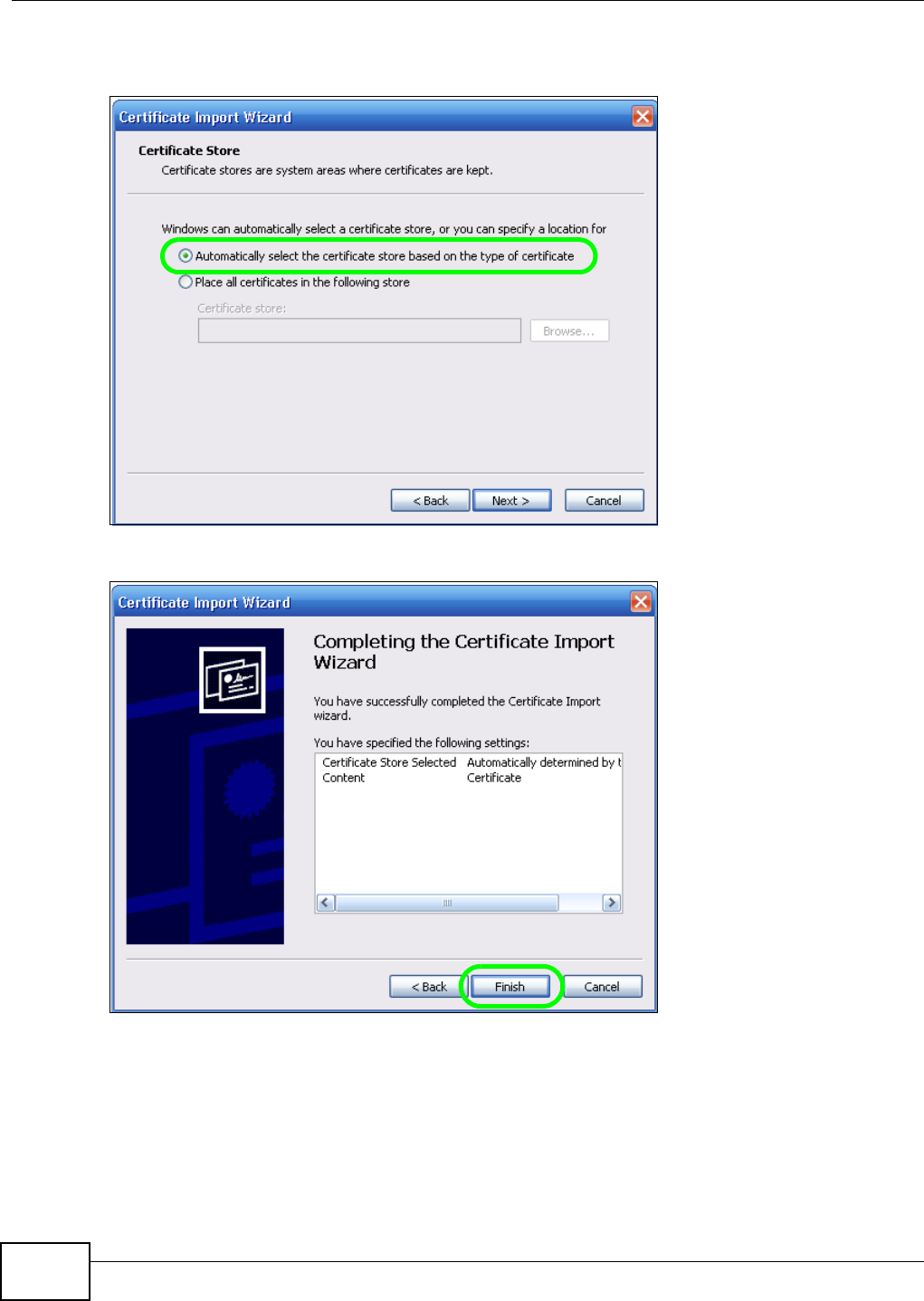
Chapter 5 Tutorials
Media Server User’s Guide
122
6Leave Automatically select certificate store based on the type of certificate selected and
click Next.
7In the Completing the Certificate Import Wizard screen, click Finish.
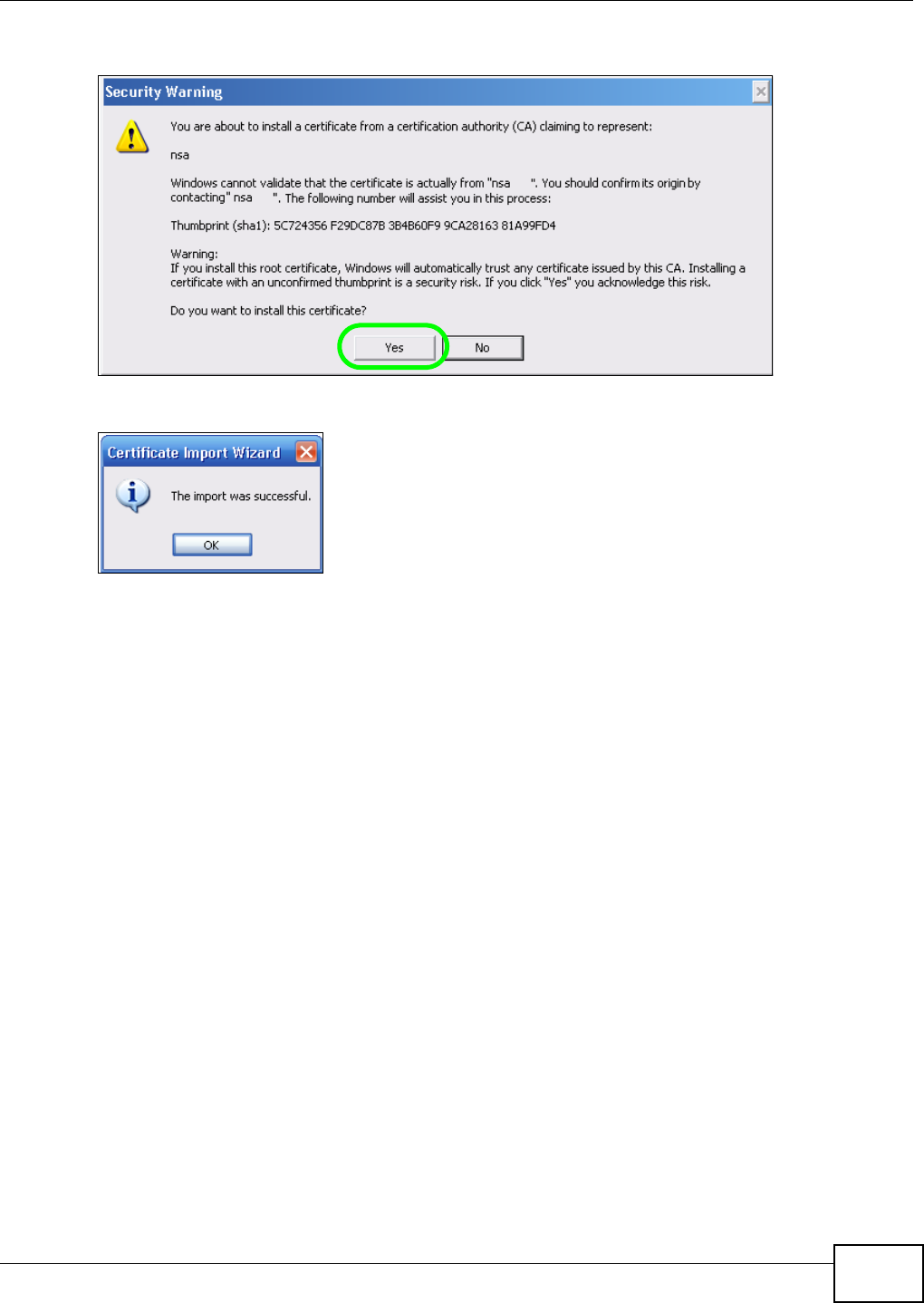
Chapter 5 Tutorials
Media Server User’s Guide 123
8If you are presented with another Security Warning, click Yes.
9Finally, click OK when presented with the successful certificate installation message.
5.15.3 Turn on the NSA’s Web Security
Now that you have customized the NSA’s certificate and installed it in your computer, you can turn
on security for your Web Configurator sessions. This example uses Firefox 3.0. See Appendix D on
page 411 for more information on browsers and certificates.
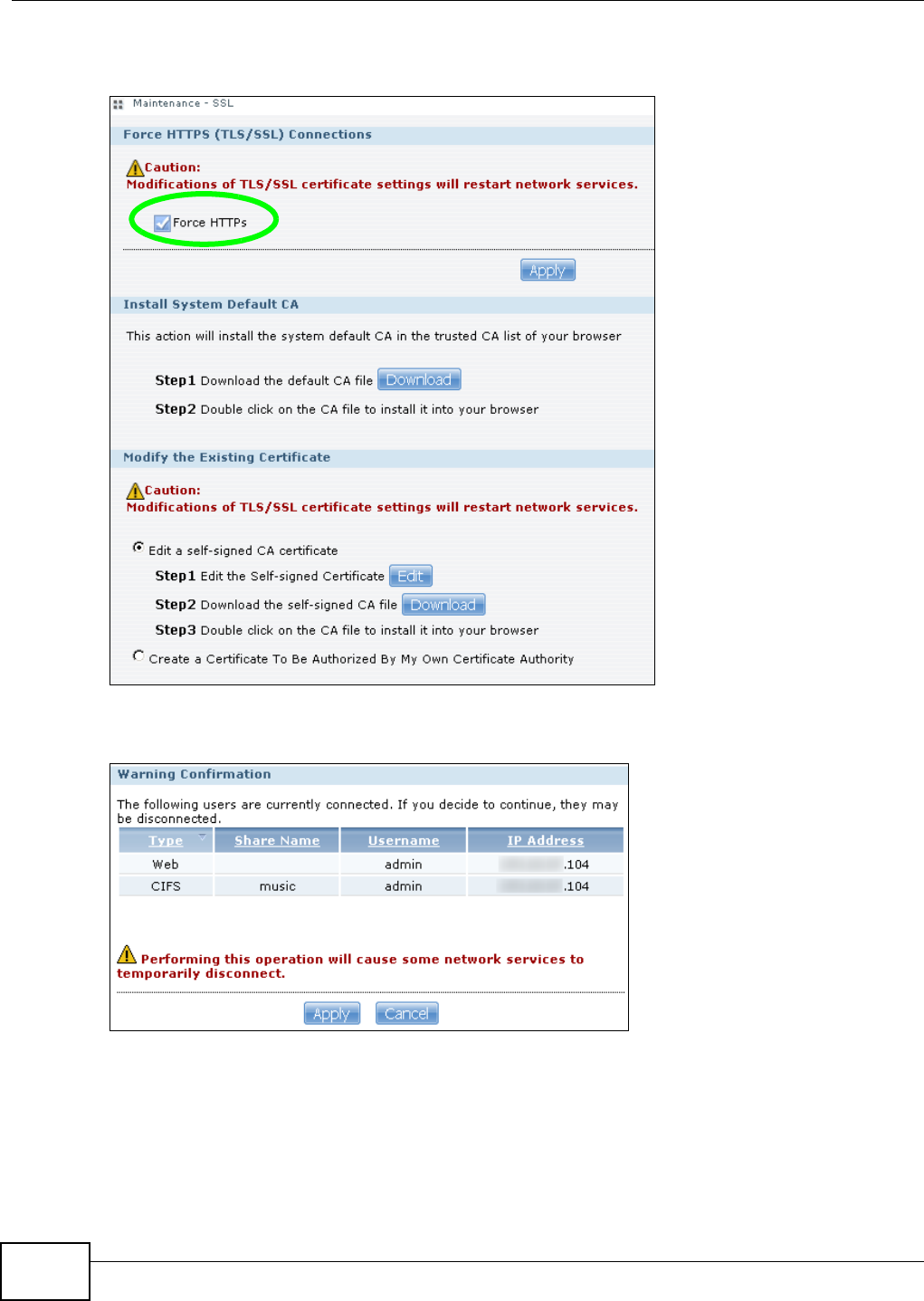
Chapter 5 Tutorials
Media Server User’s Guide
124
1Close your web browser and open it again to reset its session with the NSA. Log in and click
Maintenance > SSL. Select Force HTTPS and click Apply.
2A warning screen pops up if applying your change may disconnect some users. Click Apply to
continue.
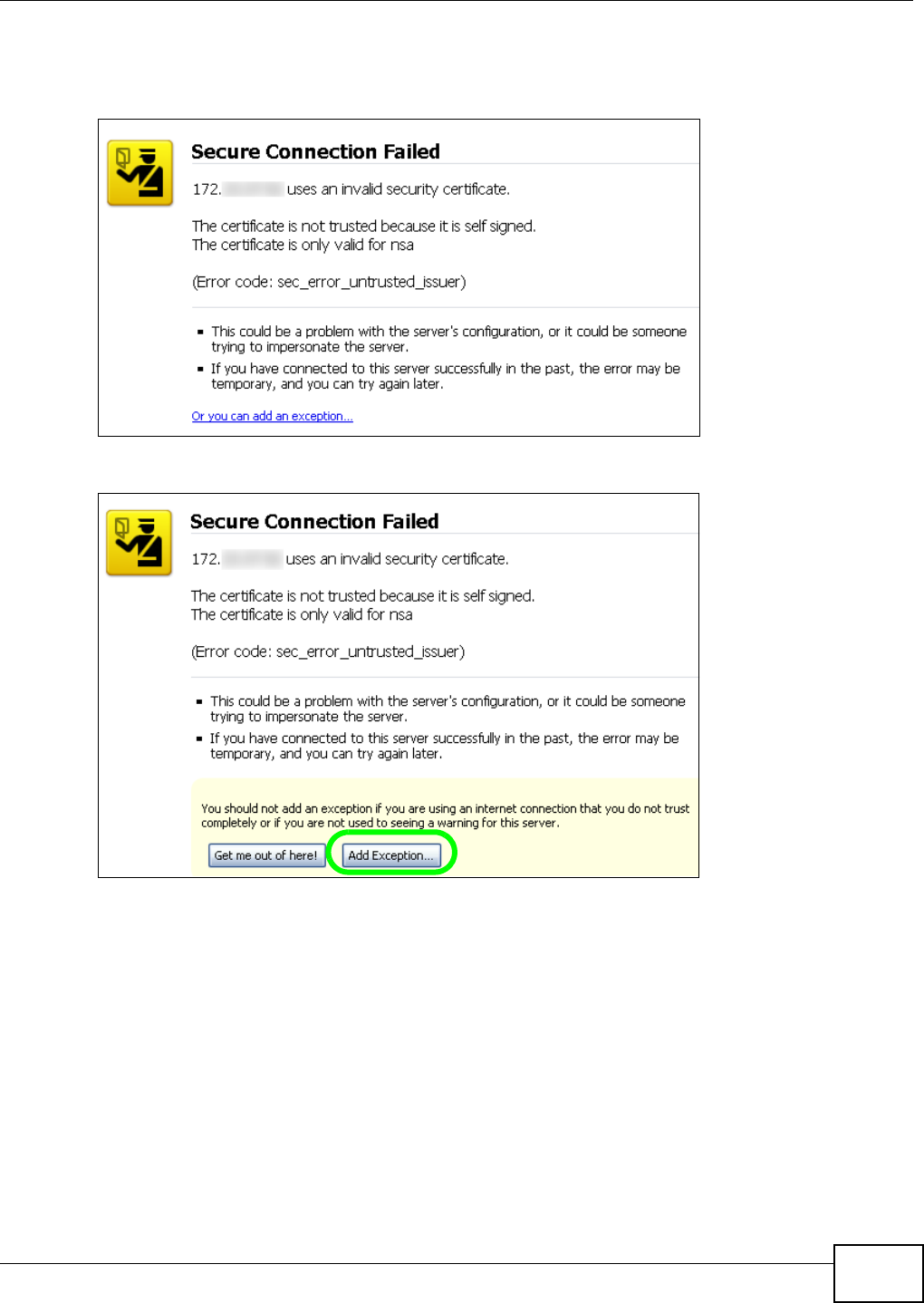
Chapter 5 Tutorials
Media Server User’s Guide 125
3The NSA logs you out and automatically redirects your formerly non-secure (HTTP) connection to a
secure (HTTPS) connection. Your browser may give you a warning about the device’s public key
certificate. Add an exception to allow your browser to bypass the warning.
4Click Add Exception.
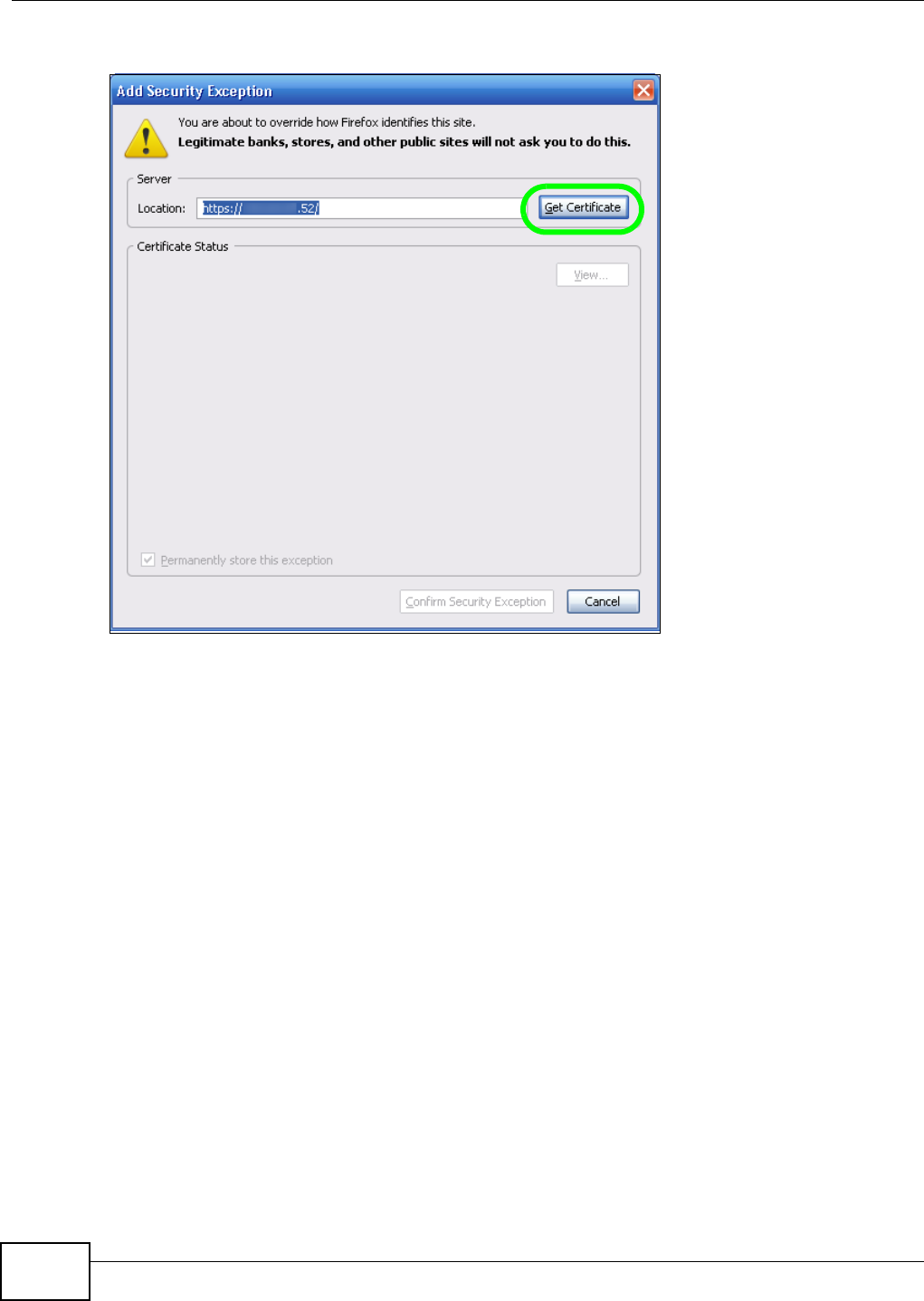
Chapter 5 Tutorials
Media Server User’s Guide
126
5Click Get Certificate.
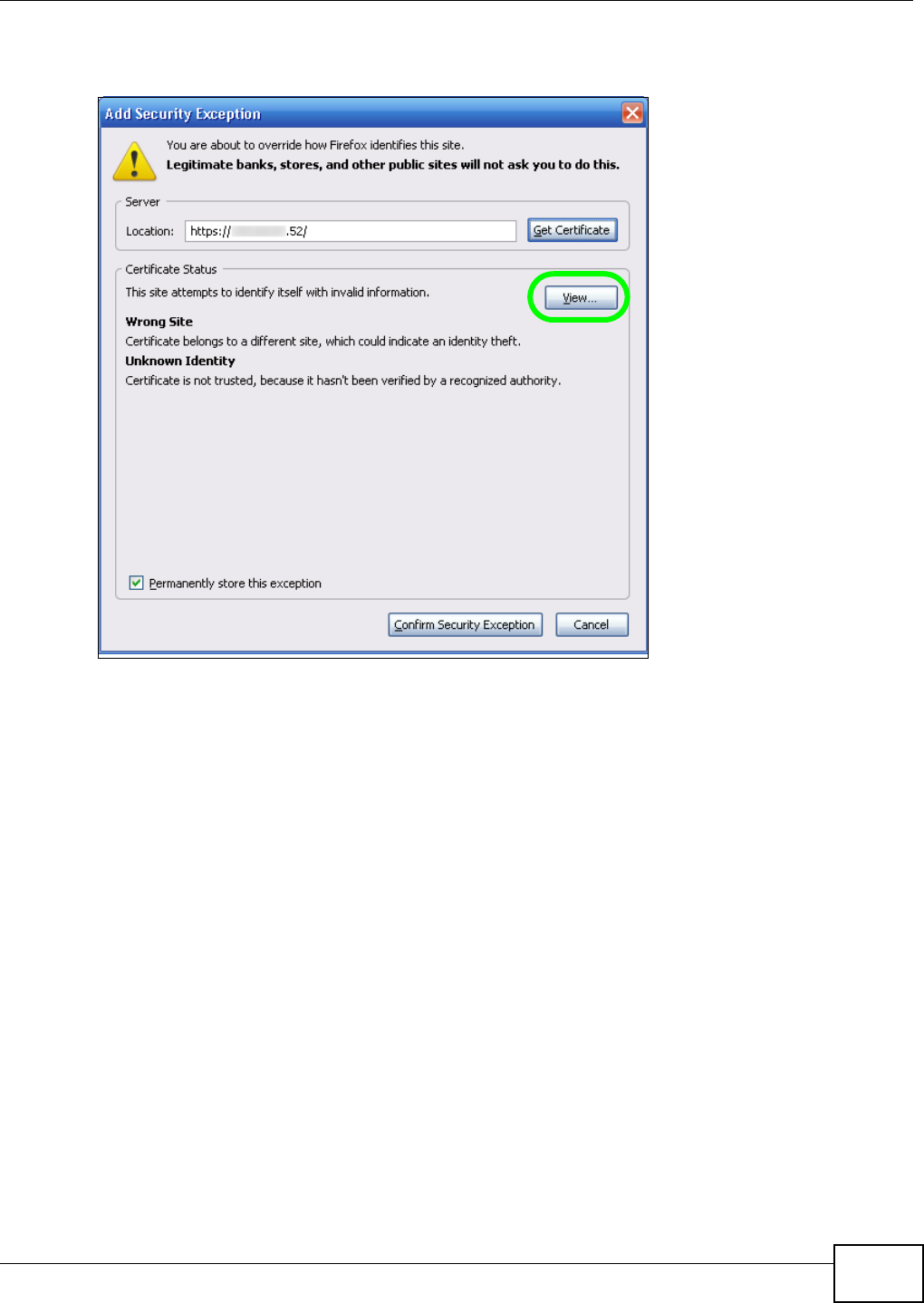
Chapter 5 Tutorials
Media Server User’s Guide 127
6Before you add an exception, verify that the device to which you are trying to connect is providing
the correct certificate. Click View.
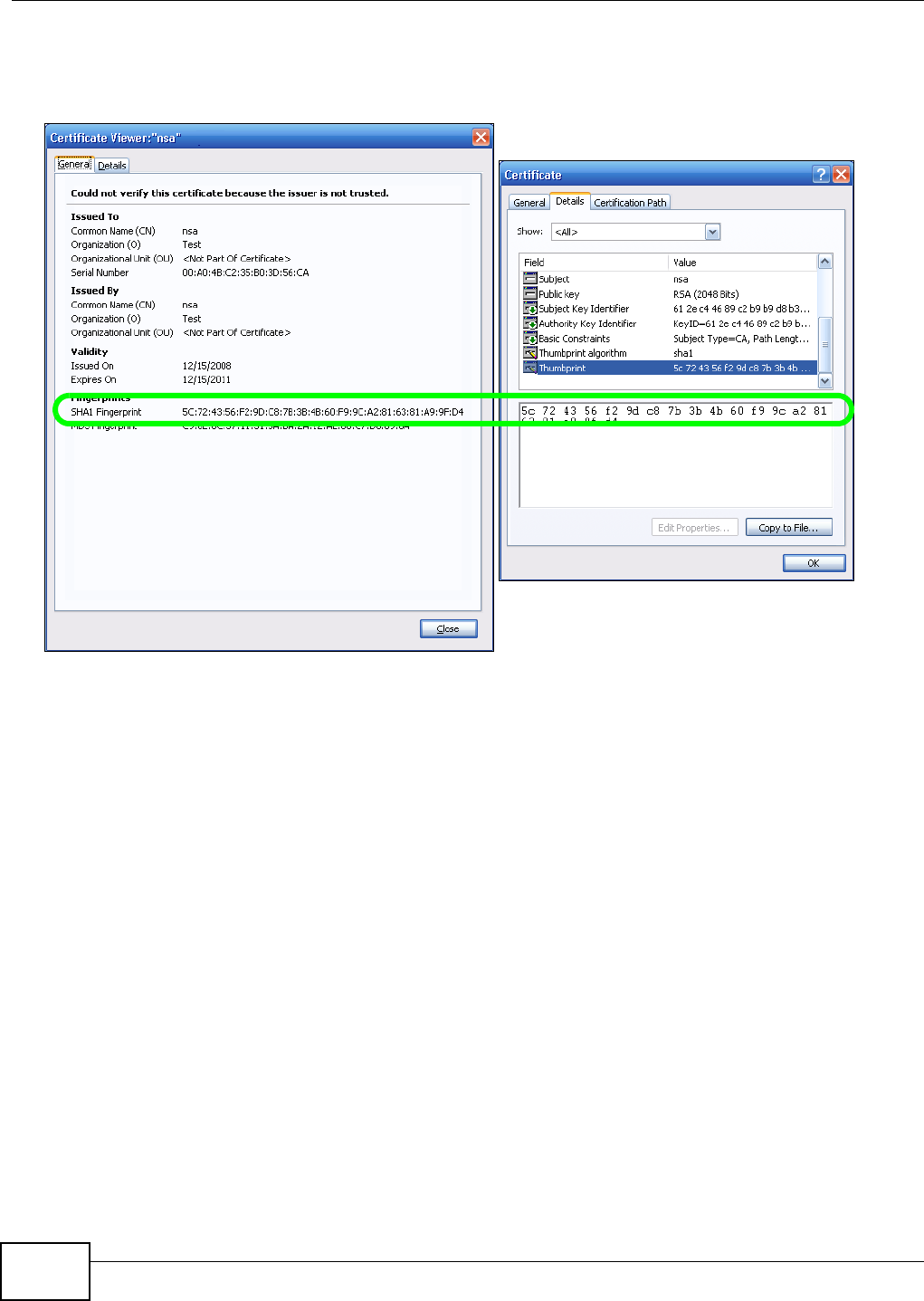
Chapter 5 Tutorials
Media Server User’s Guide
128
7The SHA1 fingerprint must match the NSA’s certificate you downloaded from the NSA to your
computer. (Double-click the NSA’s certificate file and then click Details and look at the
Thumbprint). Click Close.
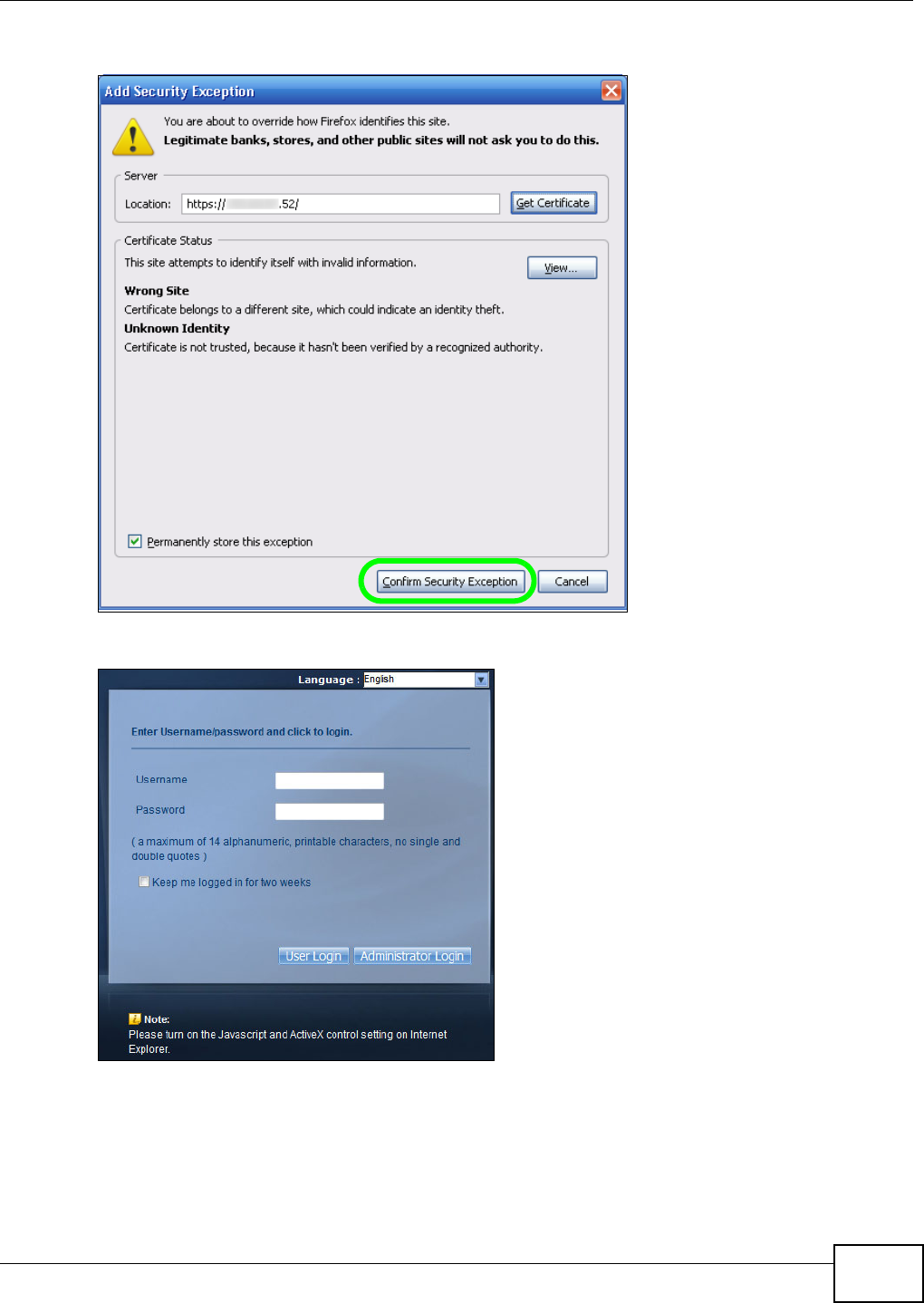
Chapter 5 Tutorials
Media Server User’s Guide 129
8If the certificate fingerprints match, click Confirm Security Exception, otherwise click Cancel.
9The login screen displays.
Now, anyone who connects to the NSA’s Web Configurator screens will automatically do so by
HTTPs. Use a secure method to let your users know the correct fingerprint for the NSA’s certificate
so they can check it before adding a security exception (as in steps 6 to 7 on pages 127 to 128).
See the next section for how to use FTPES with the NSA for secure FTP transfers.
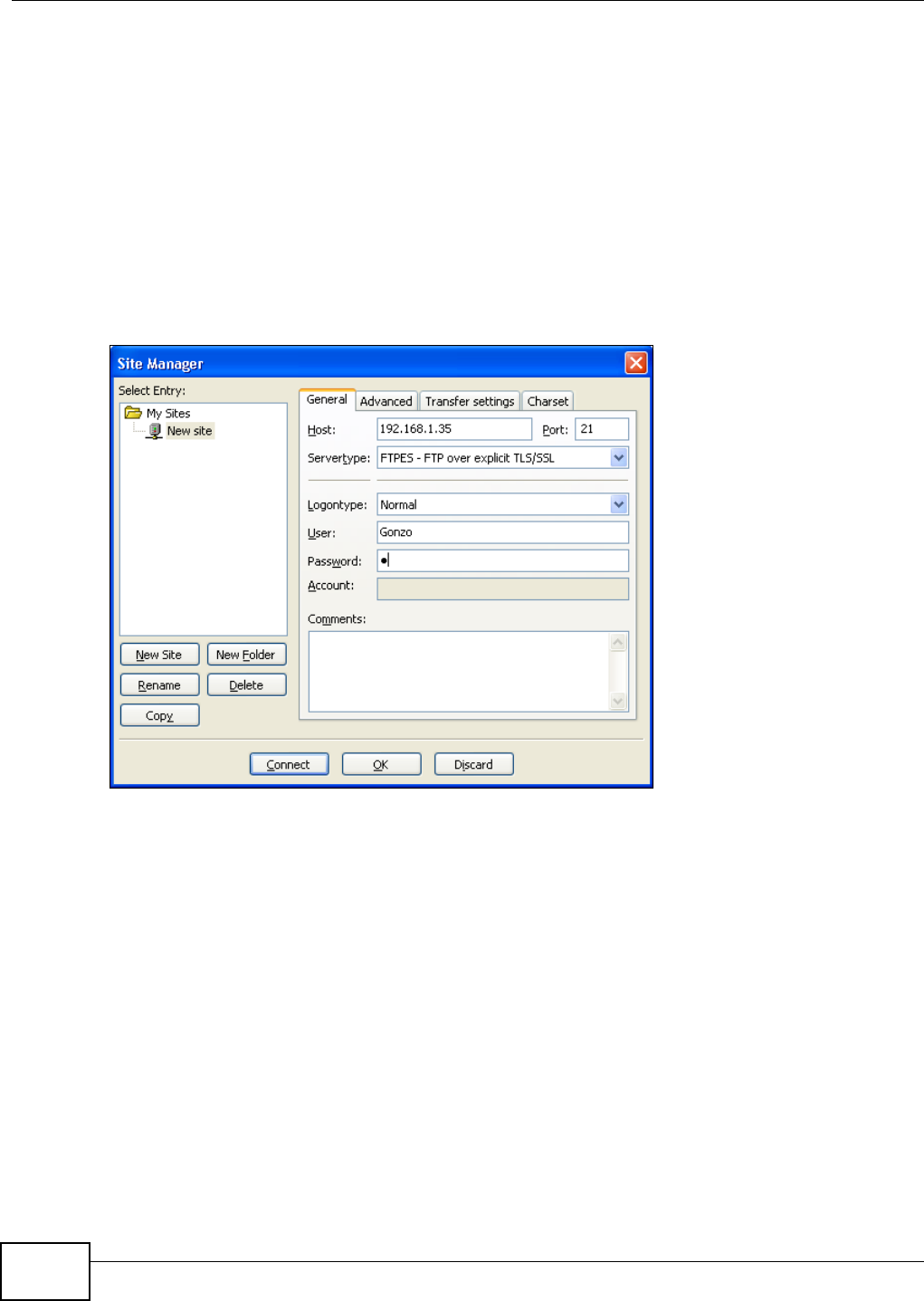
Chapter 5 Tutorials
Media Server User’s Guide
130
5.16 Using FTPES to Connect to the NSA
This section covers how to use FTP over Explicit TLS/SSL with the NSA for secure FTP transfers.
Before you go through this section, read Section 5.15 on page 117 to configure HTTPS. This
example uses FileZilla.
1Open FileZilla and click File > Site Manager > New Site.
• Configure the Host field with the NSA’s address.
•Set the Servertype to FTPES - FTP over explicit TLS/SSL.
• Configure the account name and password.
• Click Connect.
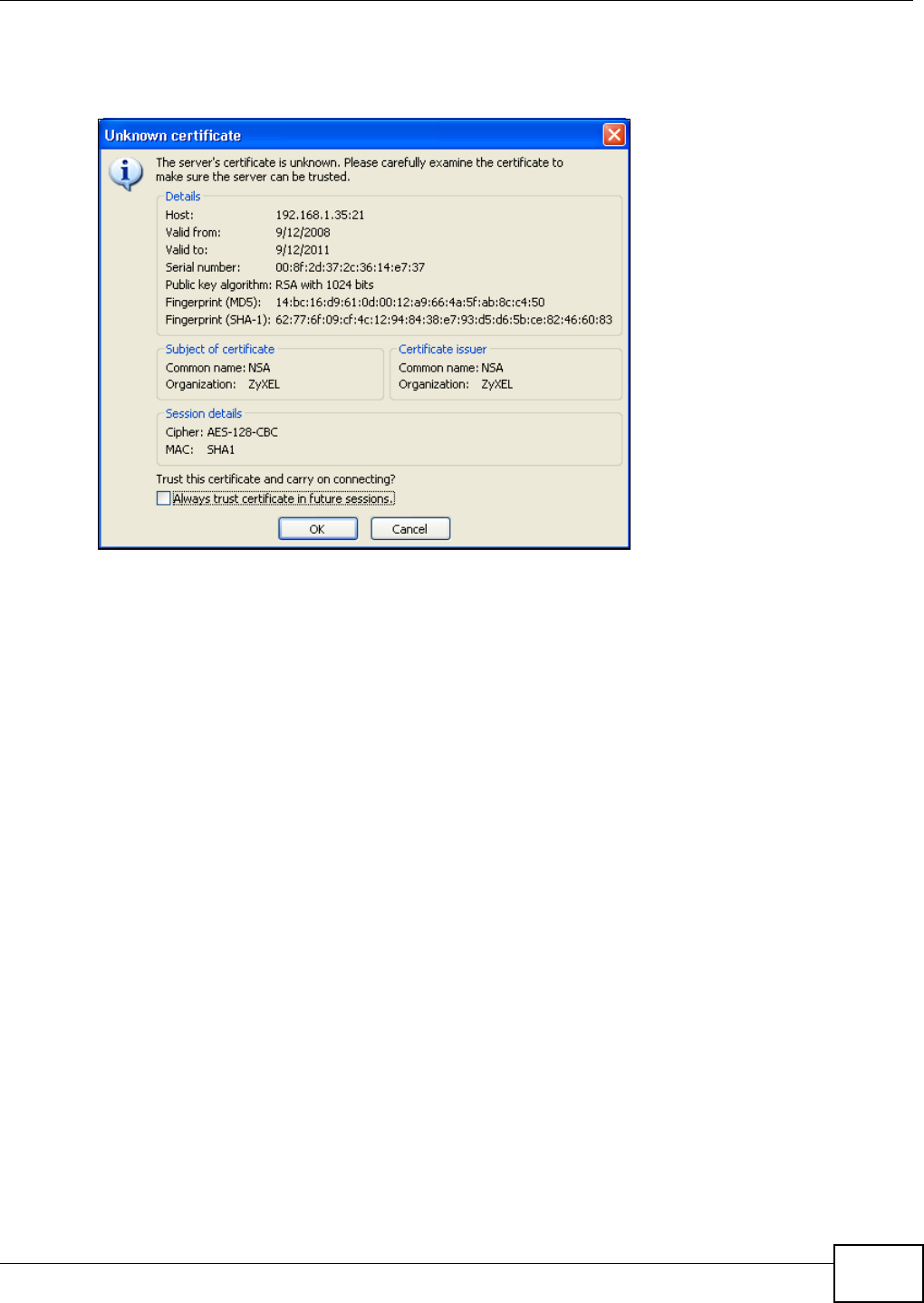
Chapter 5 Tutorials
Media Server User’s Guide 131
2A security warning screen displays. The SHA1 fingerprint must match the NSA’s certificate you
downloaded from the NSA to your computer. (Double-click the NSA’s certificate file and then click
Details and look at the Thumbprint). If they match, click OK.
The shares and folders to which Gonzo has access display. Now you can use FTP to securely transfer
files to or from the NSA. Use a secure method to let your users know the correct fingerprint for the
NSA’s certificate so they can check it before adding a security exception.
5.17 Using a Mac to Access the NSA
This tutorial shows you how to find the NSA on Mac OS X 10.5 (Leopard).
You can access the NSA in two ways:
•Use the Finder to browse for the NSA, or
•Use the Finder > Go option to connect to the NSA.
Chapter 5 Tutorials
Media Server User’s Guide
132
5.17.1 Finder
1Open a new Finder window.
2Select All under the SHARED sidebar. Look for the NSA from the Network list.
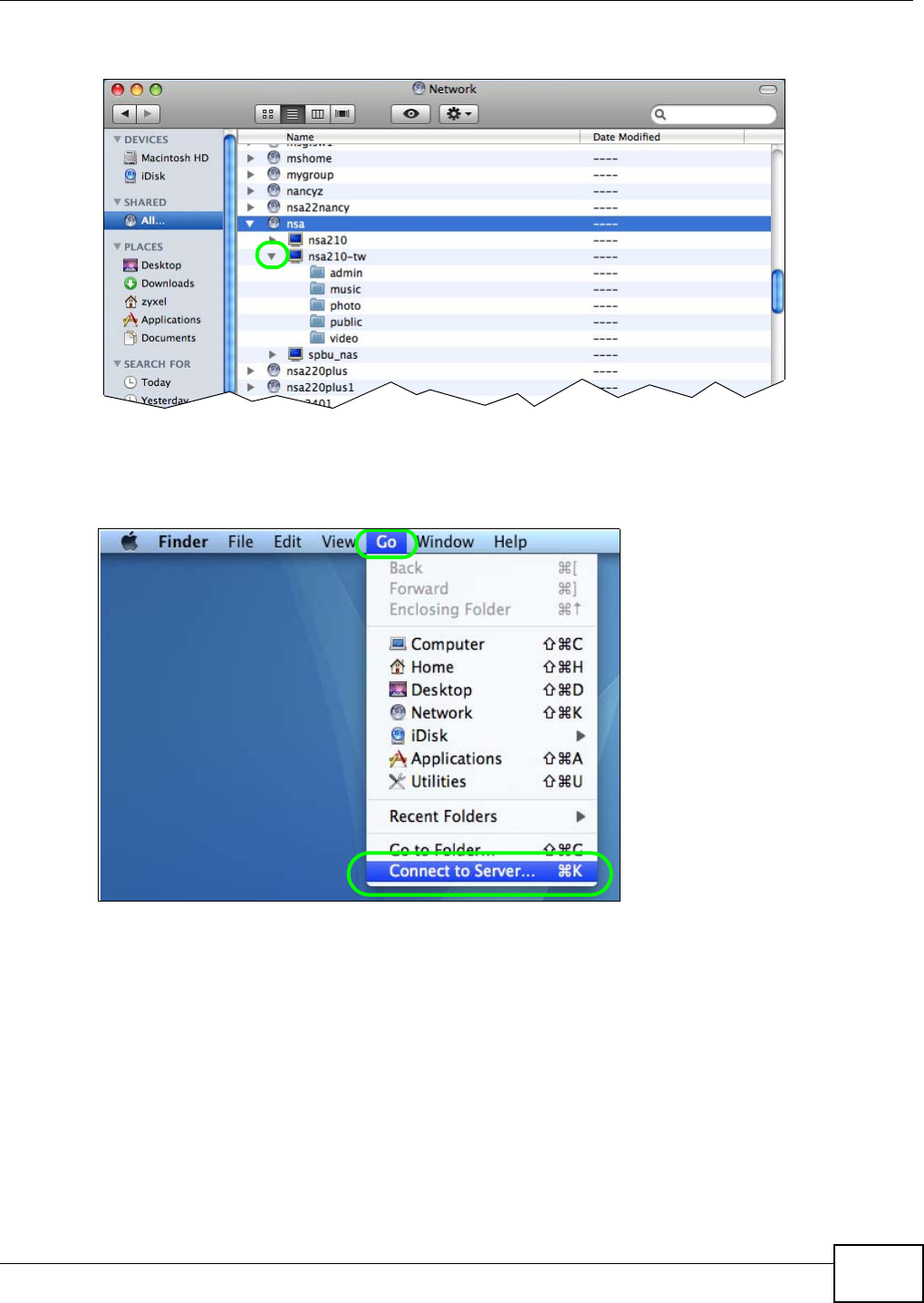
Chapter 5 Tutorials
Media Server User’s Guide 133
3Expand the NSA to display the shares you may access.
5.17.2 Go Menu
4In the Finder, click Go > Connect to Server.
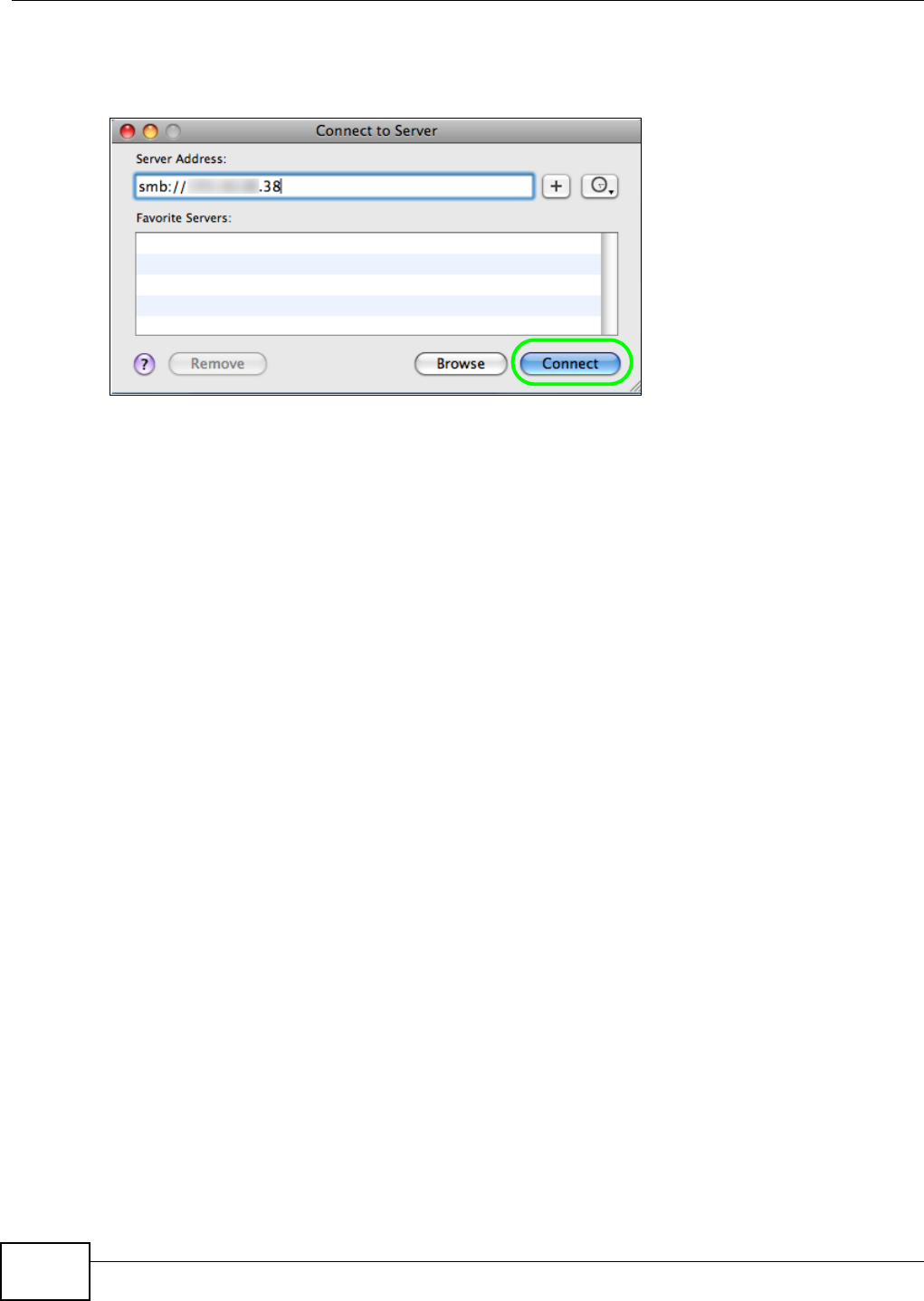
Chapter 5 Tutorials
Media Server User’s Guide
134
5When the Connect to Server dialog box opens, enter smb:// and the NSA’s IP address in the
Server Address field. You may also click Browse to have the Mac search for the NSA. Click
Connect.
6Once you establish the connection, you can access the NSA from the Finder or directly from the
desktop.
5.18 How to Use the BackupPlanner
Note: The screens and links in this section appear only after you have installed and
enabled BackupPlanner. BackupPlanner is an application that you can install using
Package Management (see Chapter 11 on page 225.)
Use the NSA’s BackupPlanner to have a backup of your files and folders.
Schedule backups for times when the network is not busy (like at night or on weekends). For
example, you might do daily backups of important individual files or folders and a weekly general
archive. You can save backups to another location so your files can survive even if the original RAID
or NSA fails.
5.18.1 Creating an Archive Backup
To backup the NSA every week to a remote NSA:
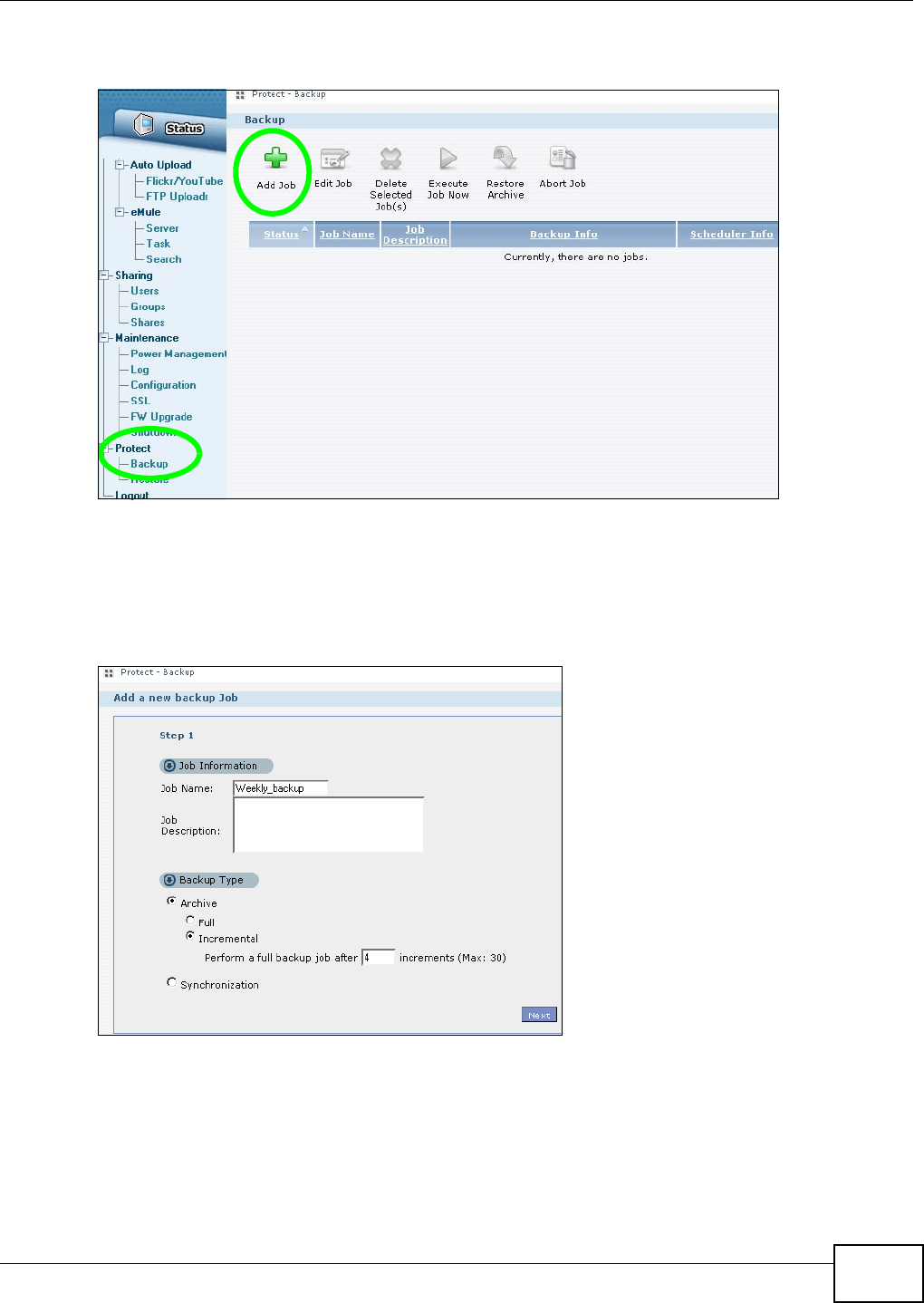
Chapter 5 Tutorials
Media Server User’s Guide 135
1Click Protect > Backup > Add Job.
Figure 51 Protect > Backup
2Identify the backup job and select Archive.
New files are often added to the shares that you need to back up and existing files are not
frequently changed so select Incremental. The NSA does a full backup first and later only copies
source files that are new and/or modified since the last backup. This example sets the NSA to do
another full backup after every four incremental backups.
Figure 52 Protect > Backup > Add Job: Step 1
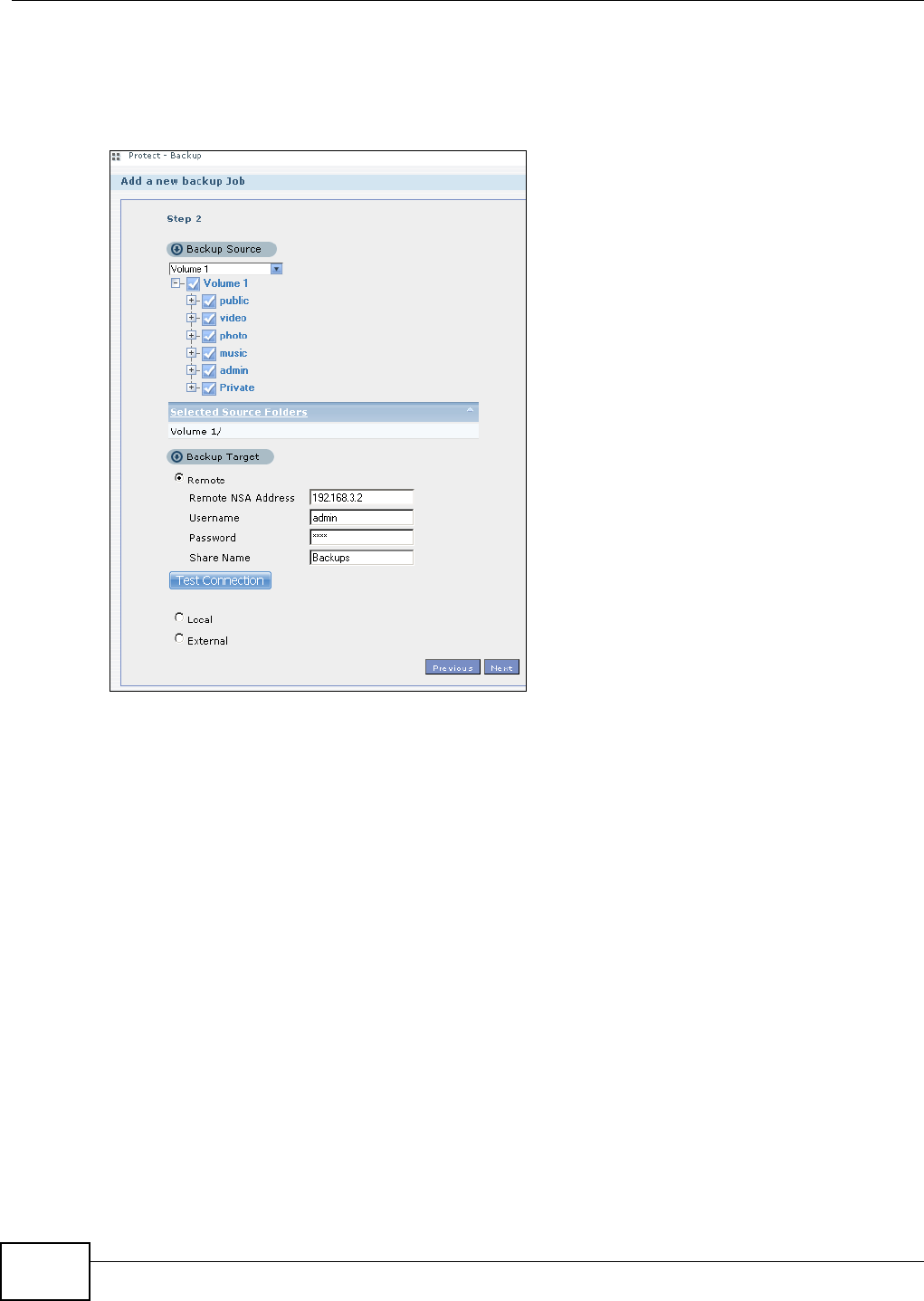
Chapter 5 Tutorials
Media Server User’s Guide
136
3Select the volume1 check box to select all the folders and files.
Select Remote and enter the other NSA’s address, username, password, and share name.
If you want to make sure the remote NSA is reachable, click Test Connection.
Figure 53 Protect > Backup > Add Job: Step 2
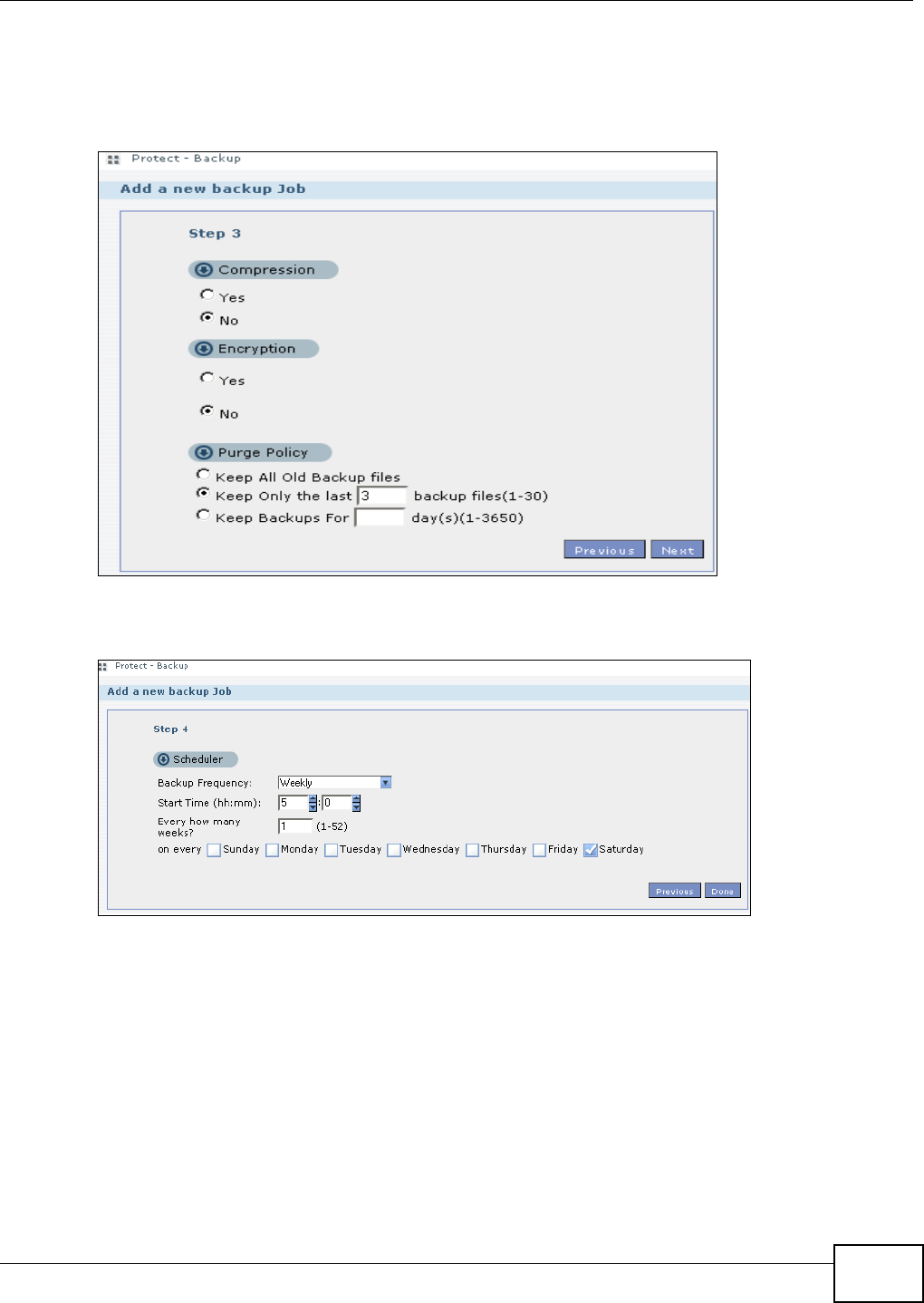
Chapter 5 Tutorials
Media Server User’s Guide 137
4In this example, the target NSA is on the LAN so leave the compression off.
Security is already configured on the target NSA so you can leave the encryption off, too.
Have the NSA keep 3 backups.
Figure 54 Protect > Backup > Add Job: Step 3
5Set the frequency to Weekly. Schedule the backup for 5:00 every Saturday morning.
Protect > Backup > Add Job: Step 4
5.18.2 Creating a Synchronization Backup
To create a synchronization backup:
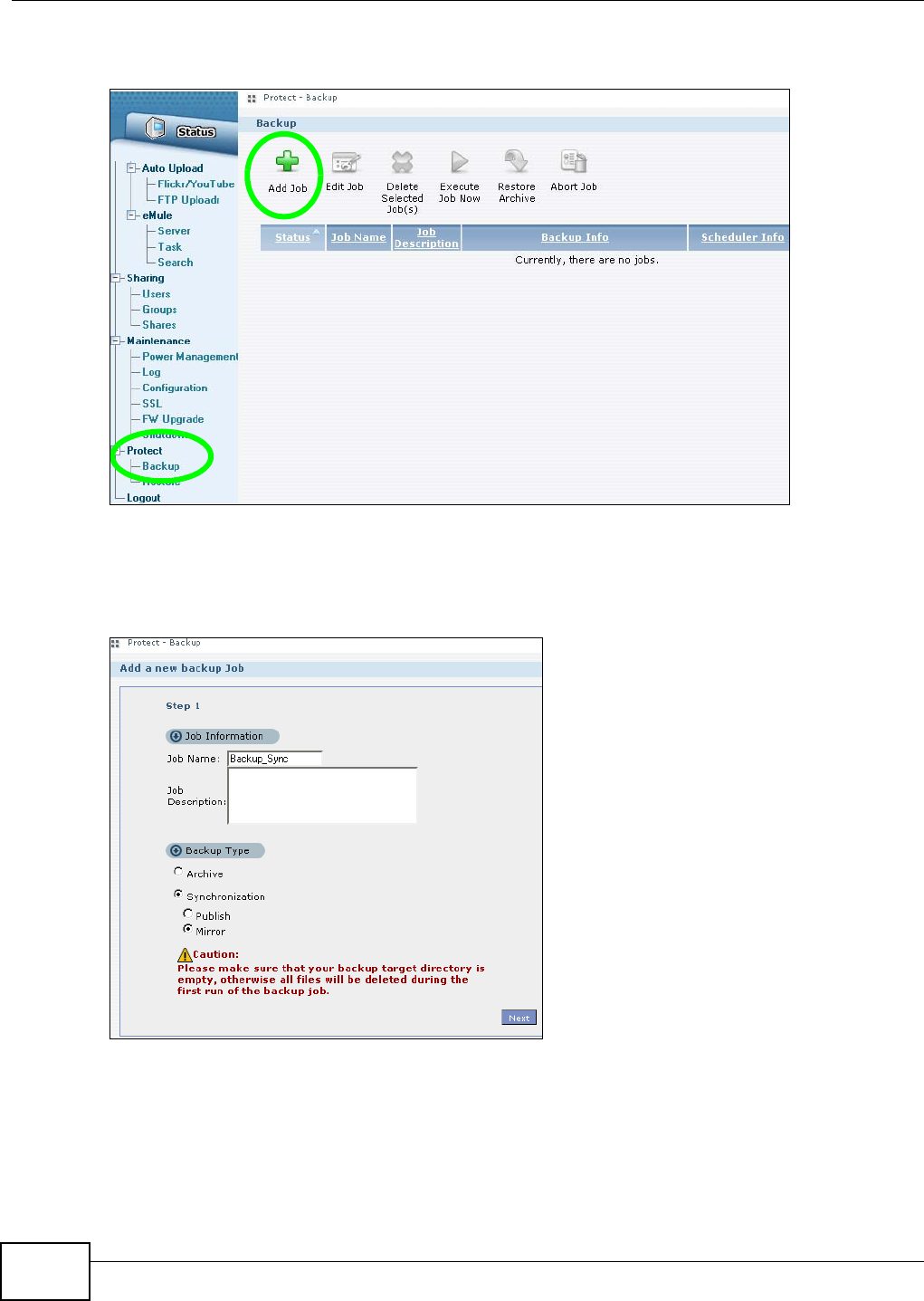
Chapter 5 Tutorials
Media Server User’s Guide
138
1Click Protect > Backup > Add Job.
Figure 55 Protect > Backup
Name the backup job and select Synchronization.
You want only your current set of files in the remote NSA’s folder, so you select Mirror to make the
target folder identical to the source folder. The NSA deletes any other files in the target folder.
Figure 56 Protect > Backup > Add Job: Step 1
2Select the folder that needs to be mirrored (your Private folder in this example) and Remote.
• Enter the other NSA’s address and administrator password.
• Click Show target content to display the remote NSA’s contents.
• Select the destination on the remote NSA (Backups in this example).
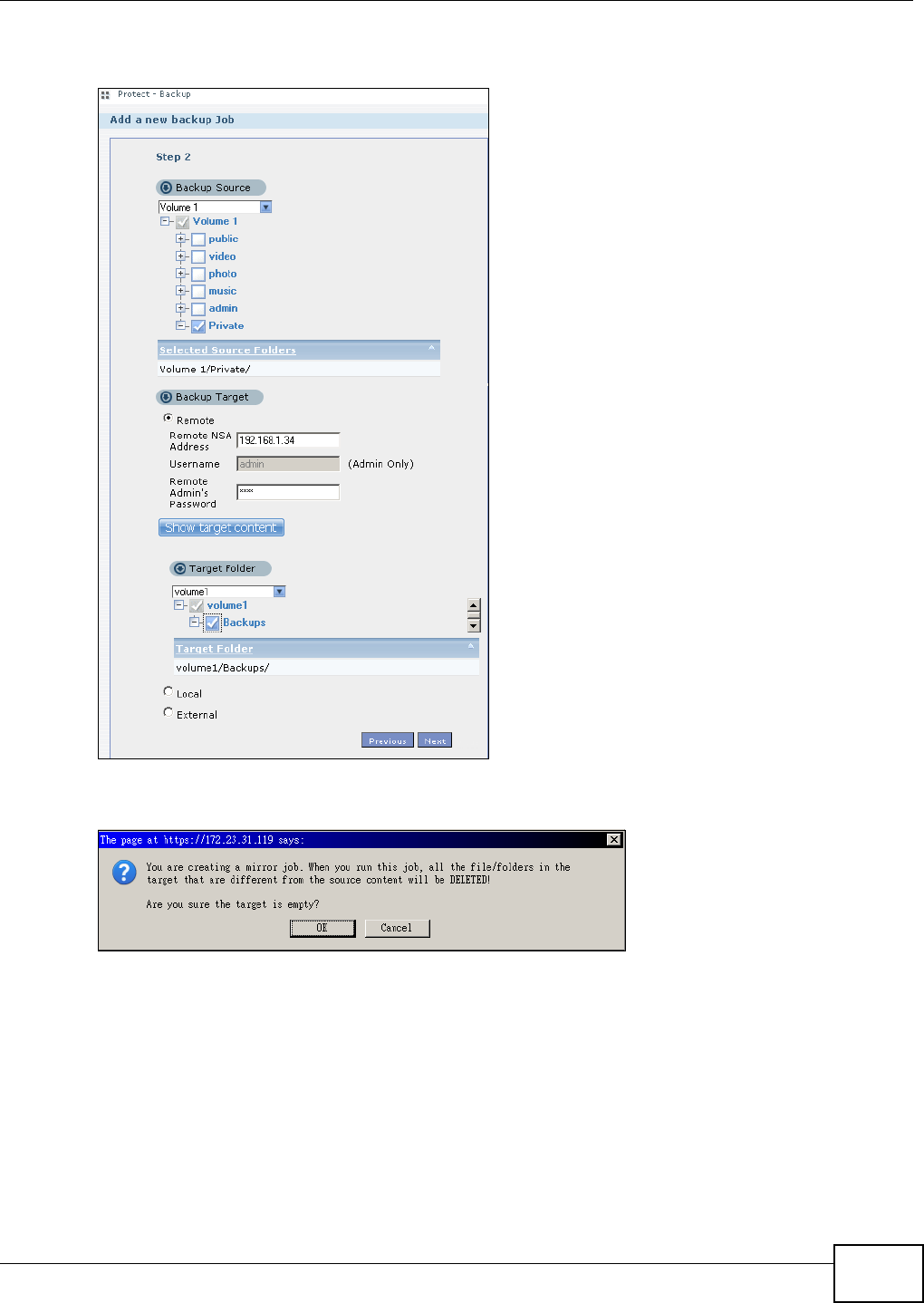
Chapter 5 Tutorials
Media Server User’s Guide 139
• Click Next.
Figure 57 Protect > Backup > Add Job: Step 2
3Click OK in the warning dialog box.
Figure 58 Protect > Backup > Add Job: Step 3
4For this example, assume the connection to the German branch office is a good one and not many
files need to be backed up so leave the compression off.
• Turn on the encryption to protect these sensitive files during the transfer. The final files stored
on the remote NSA will be unencrypted (usable).
• Restrict the bandwidth usage to 256 KB/s to stop the archives from using all of your network
connection’s available bandwidth.
• You don’t have to configure a purge policy for a synchronization backup.
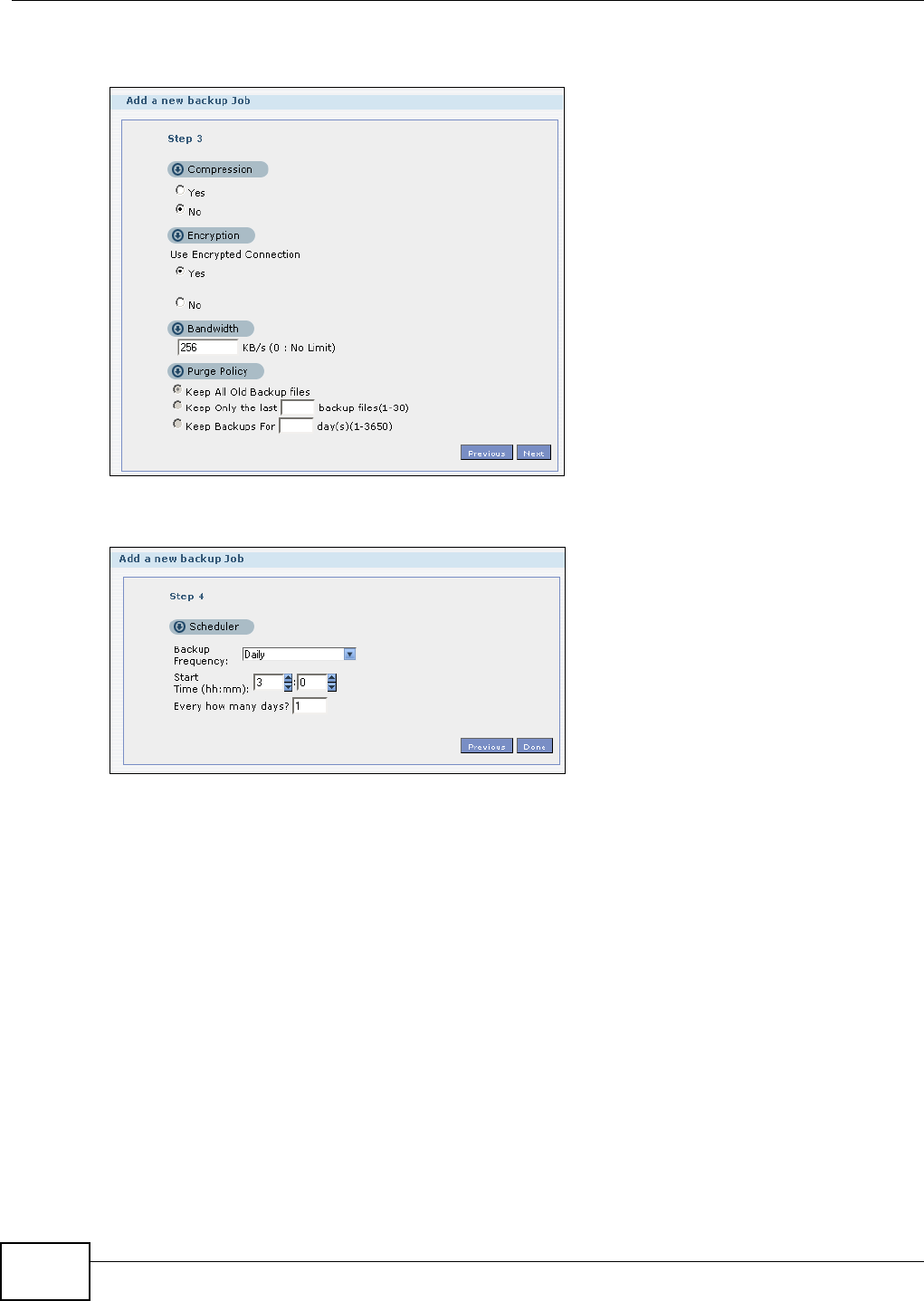
Chapter 5 Tutorials
Media Server User’s Guide
140
• Click Next.
Figure 59 Protect > Backup > Add Job: Step 3
5Schedule the backup to occur every morning at 3:00 and click Done.
Figure 60 Protect > Backup > Add Job: Step 4
You do not need to use a special restore process to use the files a synchronization backup creates.
The copy of files that the NSA creates on the other NSA’s Backups share can be used directly by
anyone with access to that share.
5.18.3 Restoring Archived Files by Backup Job
If you have backup jobs for which the NSA has already performed backups, you can restore the files
based on the backup job. Do the following:
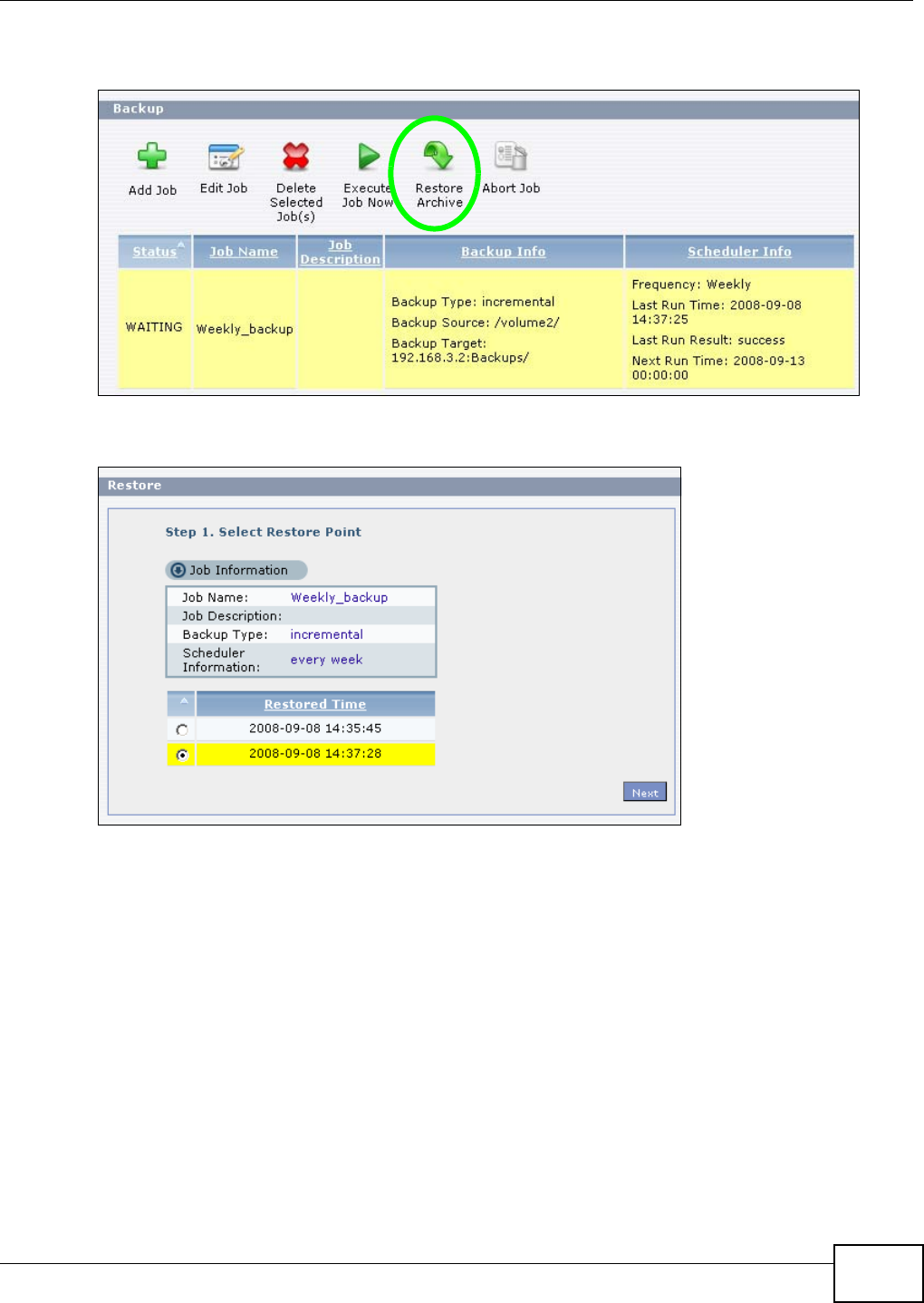
Chapter 5 Tutorials
Media Server User’s Guide 141
1Click Protect > Backup screen, select a backup job and click Restore Archive.
Figure 61 Protect > Backup
2Select which backup to use and click Next.
Figure 62 Protect > Backup > Restore Archive: Step 1
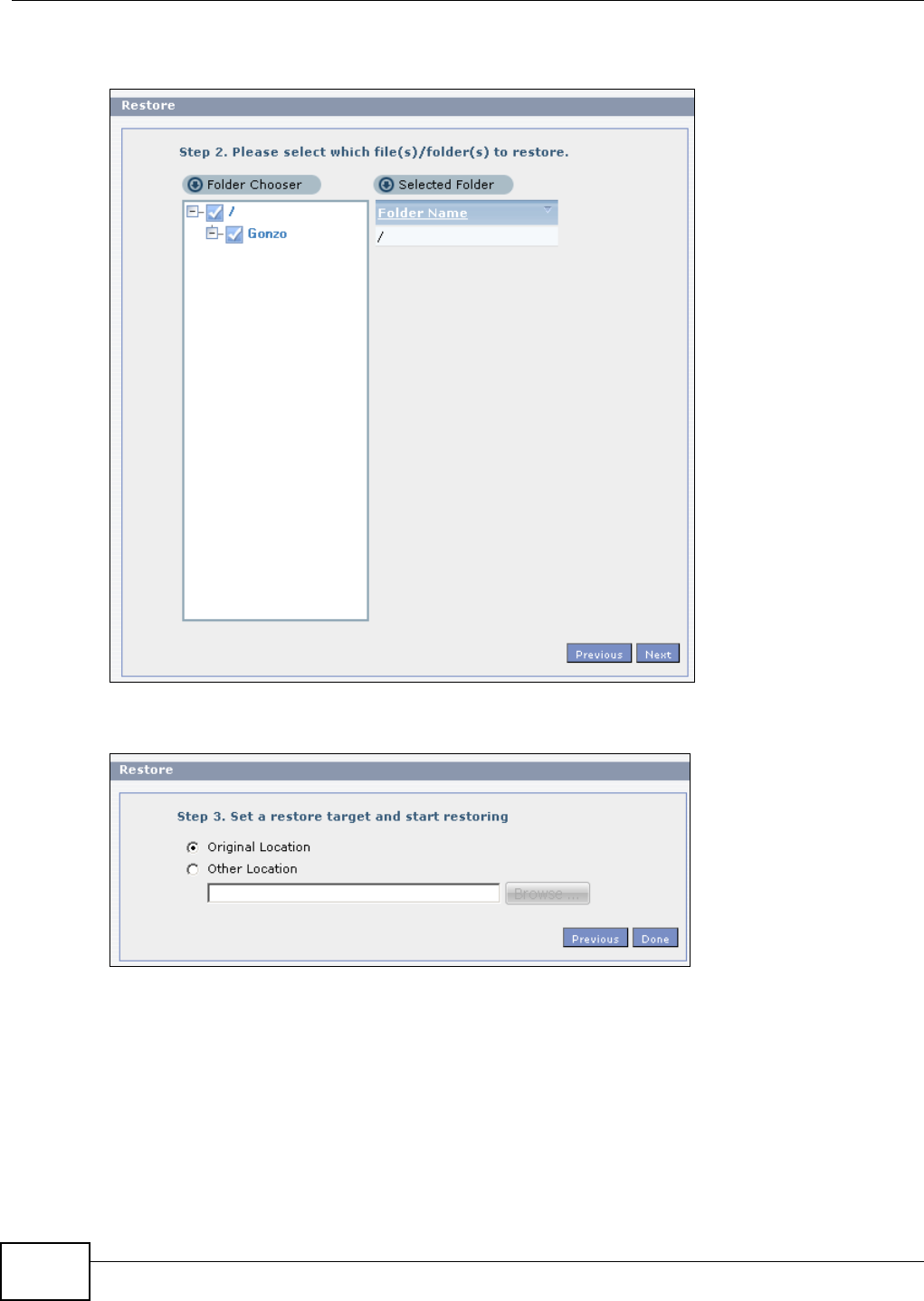
Chapter 5 Tutorials
Media Server User’s Guide
142
3Select the files and folders you want to restore and click Next.
Figure 63 Protect > Backup > Restore Archive: Step 2
4Select the original location and click Done.
Figure 64 Protect > Backup > Restore Archive: Step 3
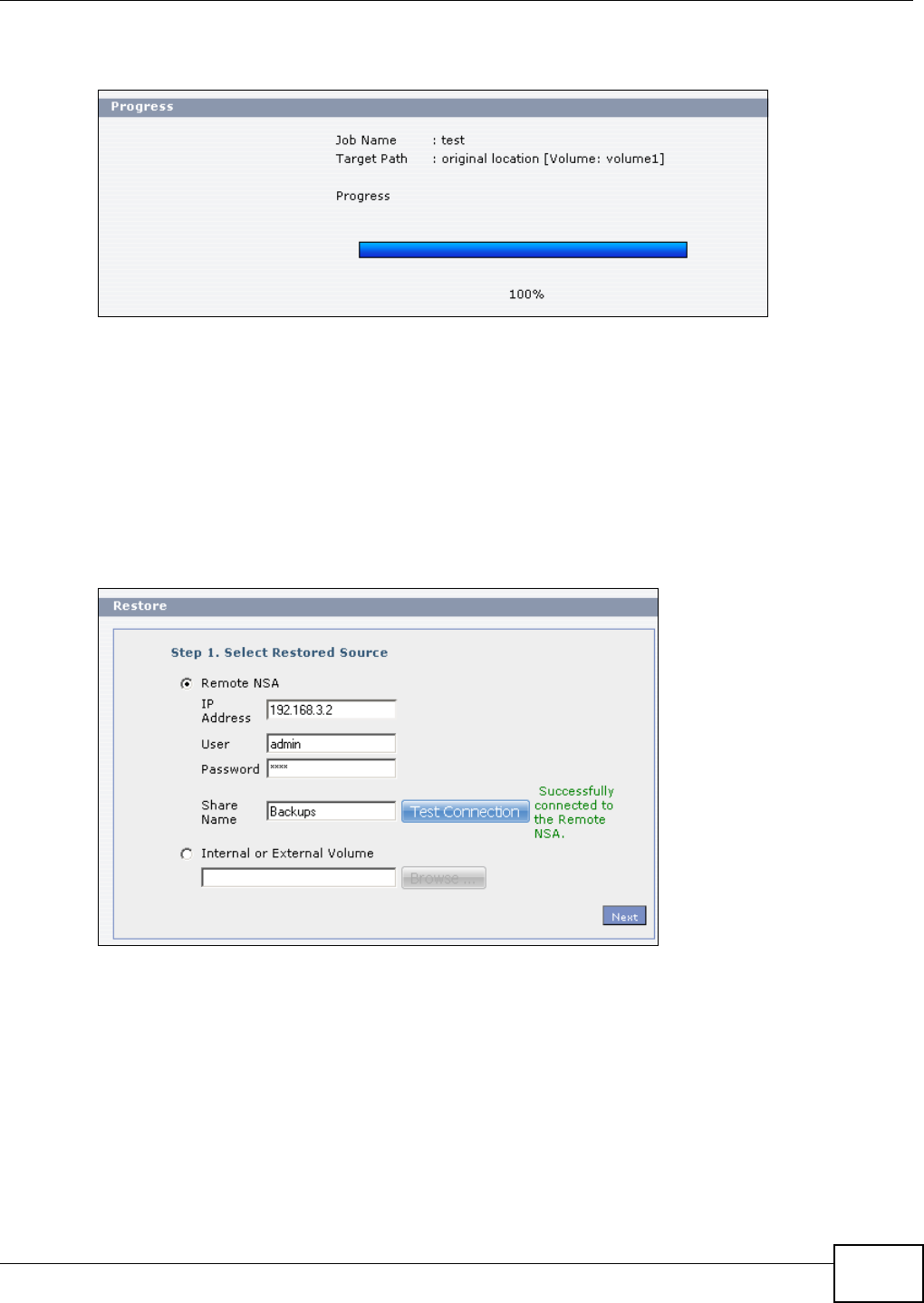
Chapter 5 Tutorials
Media Server User’s Guide 143
5The NSA restores the files into the share. When it finishes you can access the files.
Figure 65 Protect > Backup > Restore Archive: Progress
5.18.4 Restoring by Backup Files
If you deleted an archive backup job or the NSA or the RAID array containing the backup job failed
you cannot restore archived files by the backup job. In this example, the NSA’s RAID array failed.
You’ve replaced the hard drives and re-configured the RAID. To restore by backup files:
1Click Protect > Restore. Specify where the archive files are located. In this example, enter
“192.168.3.2” as the IP address, “admin” as the account name, “1234” as the password, and
“Backups” as the share name. Click Test Connection. Click Next.
Figure 66 Protect > Restore: Step 1
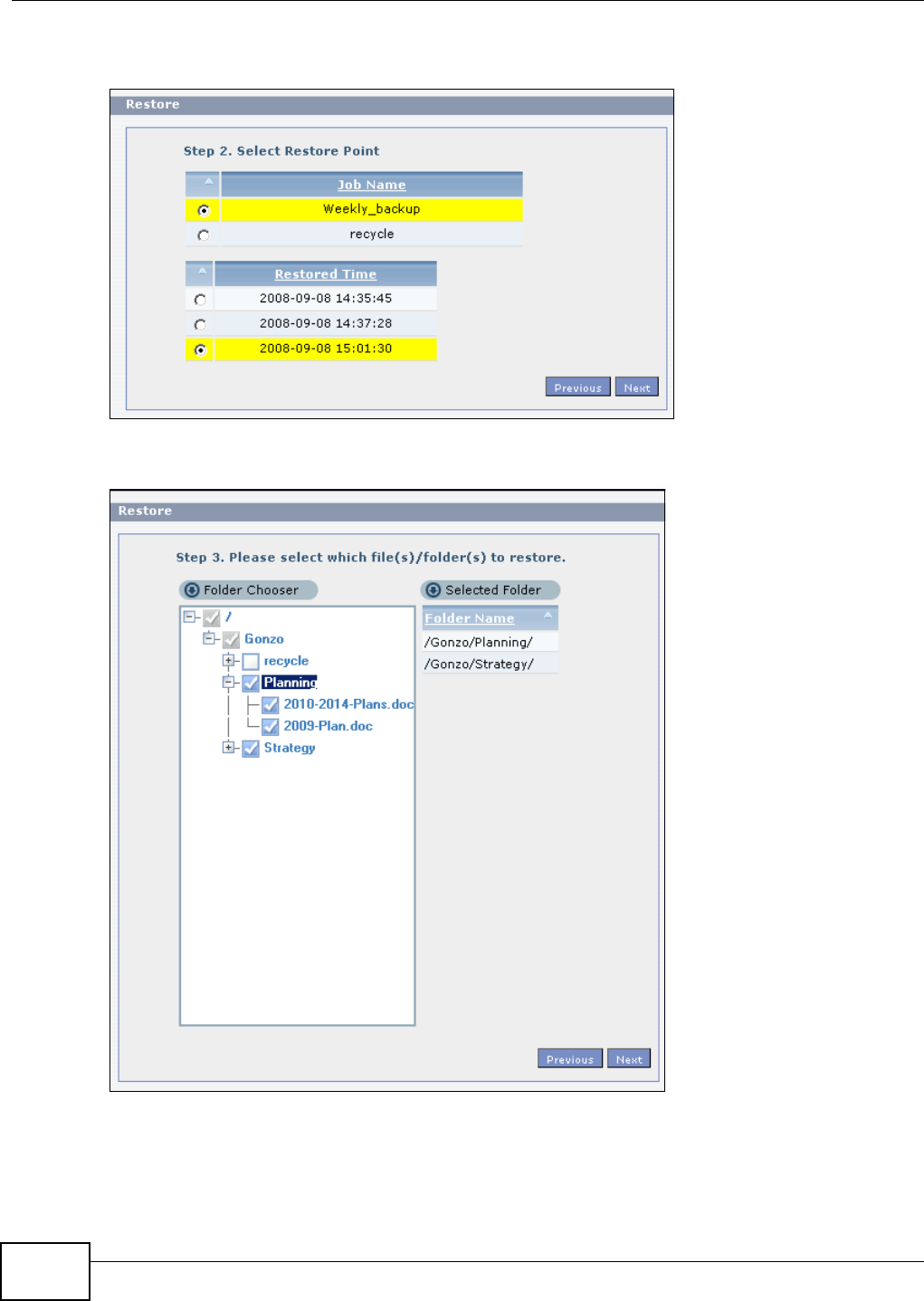
Chapter 5 Tutorials
Media Server User’s Guide
144
2Select the backup job and backup time and click Next.
Figure 67 Protect > Restore: Step 2
3Select everything in the share except the recycle folder. Click Next.
Figure 68 Protect > Restore: Step 3
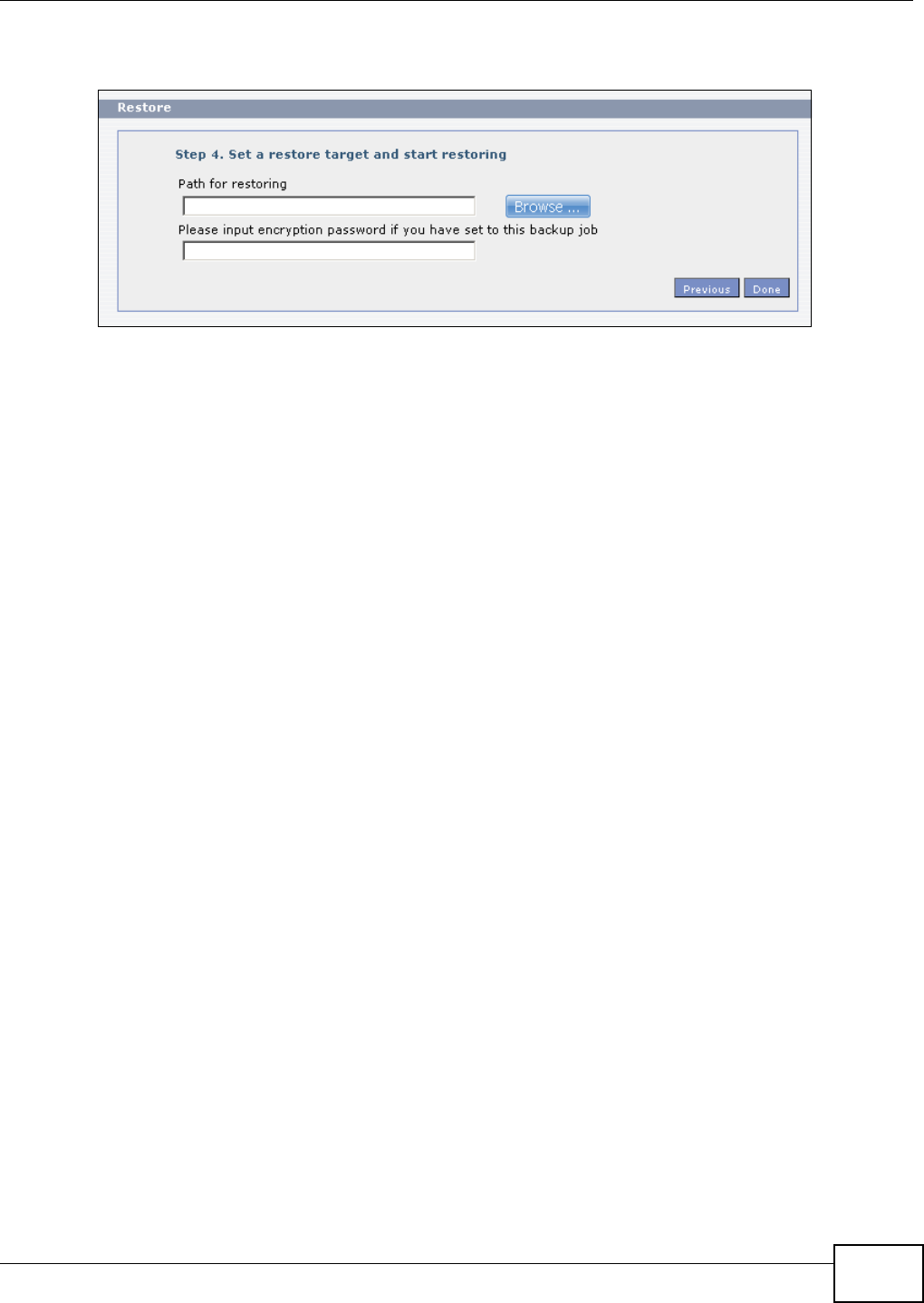
Chapter 5 Tutorials
Media Server User’s Guide 145
4Browse to the folder where you want to put the files. Click Done.
Figure 69 Protect > Restore: Step 4
5The NSA restores the files and you can use them again.

Chapter 5 Tutorials
Media Server User’s Guide
146

147
PART II
Technical Reference

148
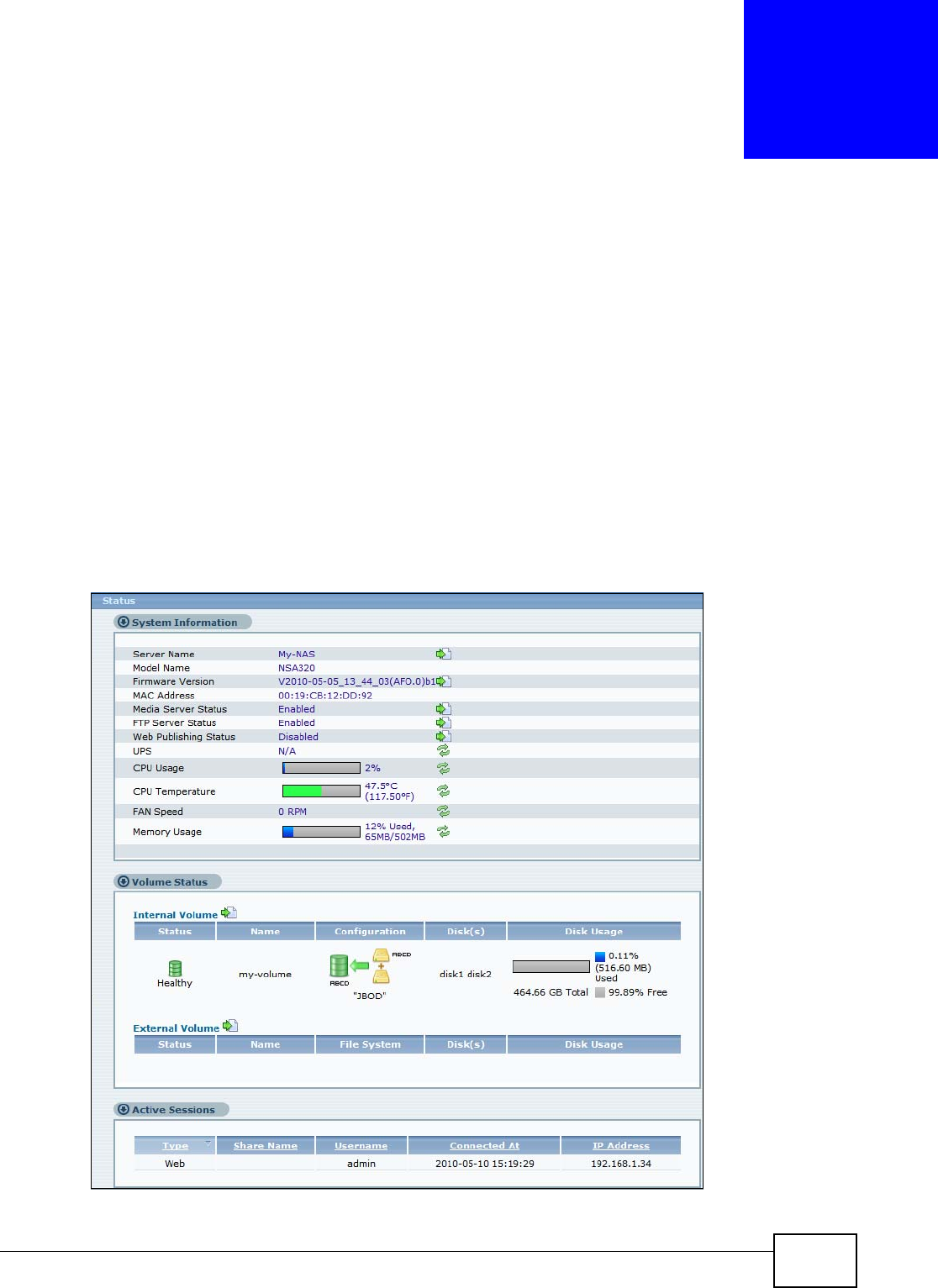
Media Server User’s Guide 149
CHAPTER 6
Status Screen
6.1 Overview
This chapter describes the Status screen, which is the first advanced administration screen that
displays.
6.2 The Status Screen
Click Administration in the Home screens (Section 4.5 on page 58) to open the Web Configurator.
You can also view the status screen, by clicking Status on the top-left of the navigation panel.
Figure 70 Status
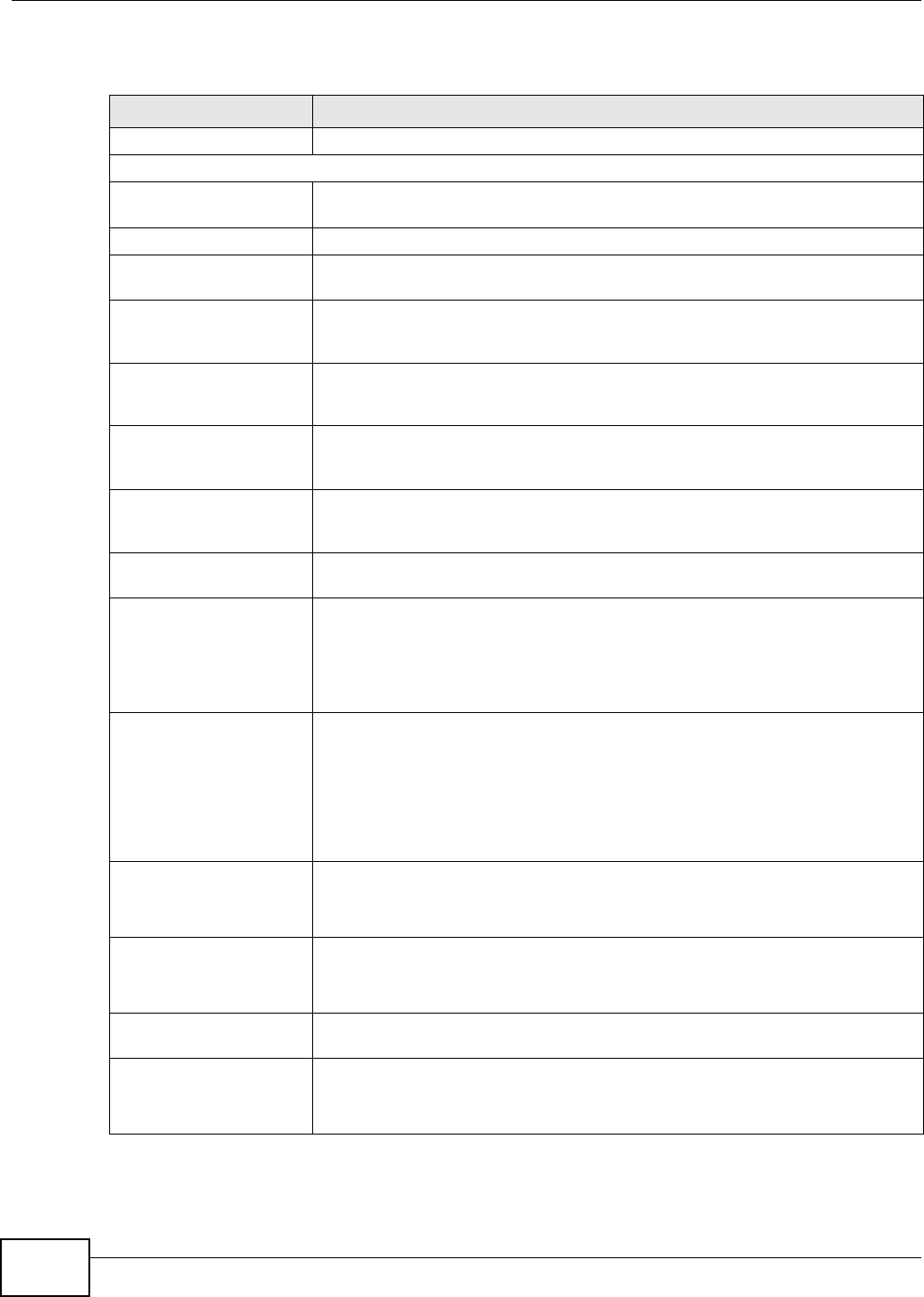
Chapter 6 Status Screen
Media Server User’s Guide
150
The following table describes the labels in this screen.
Table 16 Status
LABEL DESCRIPTION
Status Click this to refresh the status screen statistics.
System Information
Server Name This displays the name which helps you find the NSA on the network. Click the
Edit icon to go to the screen where you can configure this.
Model Name This displays which model this NSA device is.
Firmware Version This is the NSA firmware version. Click the Edit icon to go to the Maintenance >
FW Upgrade screen from which you can upload/upgrade new firmware.
MAC Address This displays the NSA’s unique physical hardware address (MAC). You need the
MAC address to register the product at myZyXEL.com. Customer support may also
request it for troubleshooting purposes.
Media Server Status This shows whether the media server function is enabled or disabled. It must be
enabled for media clients to play content files stored on the NSA. Click the Edit
icon to go to the screen where you can configure this.
FTP Server Status This shows whether the FTP server function is enabled or disabled. It must be
enabled to use FTP file transfer to/from the NSA. Click the edit icon to go to the
screen where you can configure this.
Web Publishing Status This shows whether the Web server function is enabled or disabled. It must be
enabled to use HTTP to access shares on the NSA. Click the Edit icon to go to the
screen where you can configure this.
UPS This shows the Uninterruptible Power Supply (UPS) capacity. Click the Edit icon to
go to the screen where you can configure this.
CPU Usage This displays a summary of CPU usage by all current processes.
Click the Refresh icon to update this display. It also automatically updates itself
every 10 seconds.
Note: If too many users are using the NSA then the NSA may appear sluggish.
CPU Temperature This displays the current temperature near the NSA’s CPU. The NSA generates an
emergency log if the temperature goes out of the normal operating range. If the
temperature goes even higher, the NSA shuts down automatically to avoid
damage from overheating. If the NSA overheats, make sure the fans are working
and it is in a well ventilated place.
Click the Refresh icon to update this display. It also automatically updates itself
every 60 seconds.
Fan Speed This is the RPM (Rotations Per Minute) of the NSA’s fans.
Click the Refresh icon to update this display. It also automatically updates itself
every 60 seconds.
Memory Usage This shows how much of the NSA's total memory is being used.
Click the Refresh icon to update this display. It also automatically updates itself
every 10 seconds.
Volume Status A volume is a storage area on a single disk or spread across a number of disks
within a single file system.
Internal Volume (or SATA
Volume) This displays the volumes created on the hard drives installed in the NSA.
Click the Edit icon to open the Storage screen. You can create and edit the NSA’s
internal volume. See Chapter 8 on page 157 for more details.

Chapter 6 Status Screen
Media Server User’s Guide 151
External Volume (or USB
Volume) This displays the volumes created on USB hard drives connected to the NSA. USB
disks are numbered in the order that you insert USB devices.
Click the Edit icon to open the Storage screen. You can create and edit the
external volume. See Chapter 8 on page 157 for more details.
Status This icon indicates whether the volume is healthy, degraded, or down.
Name This field shows the name for the volume.
Configuration This field (also known as Type) shows what type of data storage system (a RAID
type or JBOD) an internal volume is using.
File System This field shows what file system an external (USB) volume is using.
Disk(s) For internal drives, this shows which hard drive bays are included in the volume.
For external drives, this field shows front USB for the front USB port and rear
USB1 and rear USB2 for the rear USB ports.
Disk Usage This field shows total disk size, the percentage of the disk being used and the
percentage that is available.
Active Sessions This shows how many users are currently connected to the NSA.
Type This shows whether it’s a Windows/CIFS, web (web configurator), or FTP
connection to the NSA.
Share Name This displays the shared folder name on the NSA that the user is connected to for
CIFS sessions and is blank for FTP and web sessions.
Username This displays the name of the user connected to the NSA if one is defined.
ANONYMOUS FTP displays if a username is not defined for the user’s connection.
Connected At This displays the date and time the user last connected to the NSA in year, month,
day, hour, minute, second format.
IP Address This displays the IP address of the computer connected to the NSA.
Table 16 Status (continued)
LABEL DESCRIPTION

Chapter 6 Status Screen
Media Server User’s Guide
152

Media Server User’s Guide 153
CHAPTER 7
System Setting
7.1 Overview
This chapter gives an overview of the various features included in the system setting screens. You
can identify your NSA on the network and set the time that the NSA follows for its scheduled tasks/
logs.
7.2 What You Can Do
•Use the Server Name screen (Section 7.4 on page 154) to specify the NSA’s server and
workgroup names.
•Use the Date/Time screen (Section 7.5 on page 154) to set up date/time and choose a time
zone for the NSA.
7.3 What You Need to Know
Windows/CIFS
Common Internet File System (CIFS) is a standard protocol supported by most operating systems
in order to share files across the network.
• CIFS is included by default in Windows operating systems.
• You can use Samba with Linux to use CIFS.
• CIFS transfers use security.
Time Lag
Time lag occurs when the time on the NSA falls behind the time on the time server. This may
happen if:
• the time server is no longer reachable
• if the NSA is shut down often (the NSA internal battery keeps time when the NSA is shut down
and this may cause possible variance)
• power surges occur.
The NSA gives no warning if time lag occurs. You should resynchronize the time after a power surge
or after you have shut down the NSA several times.
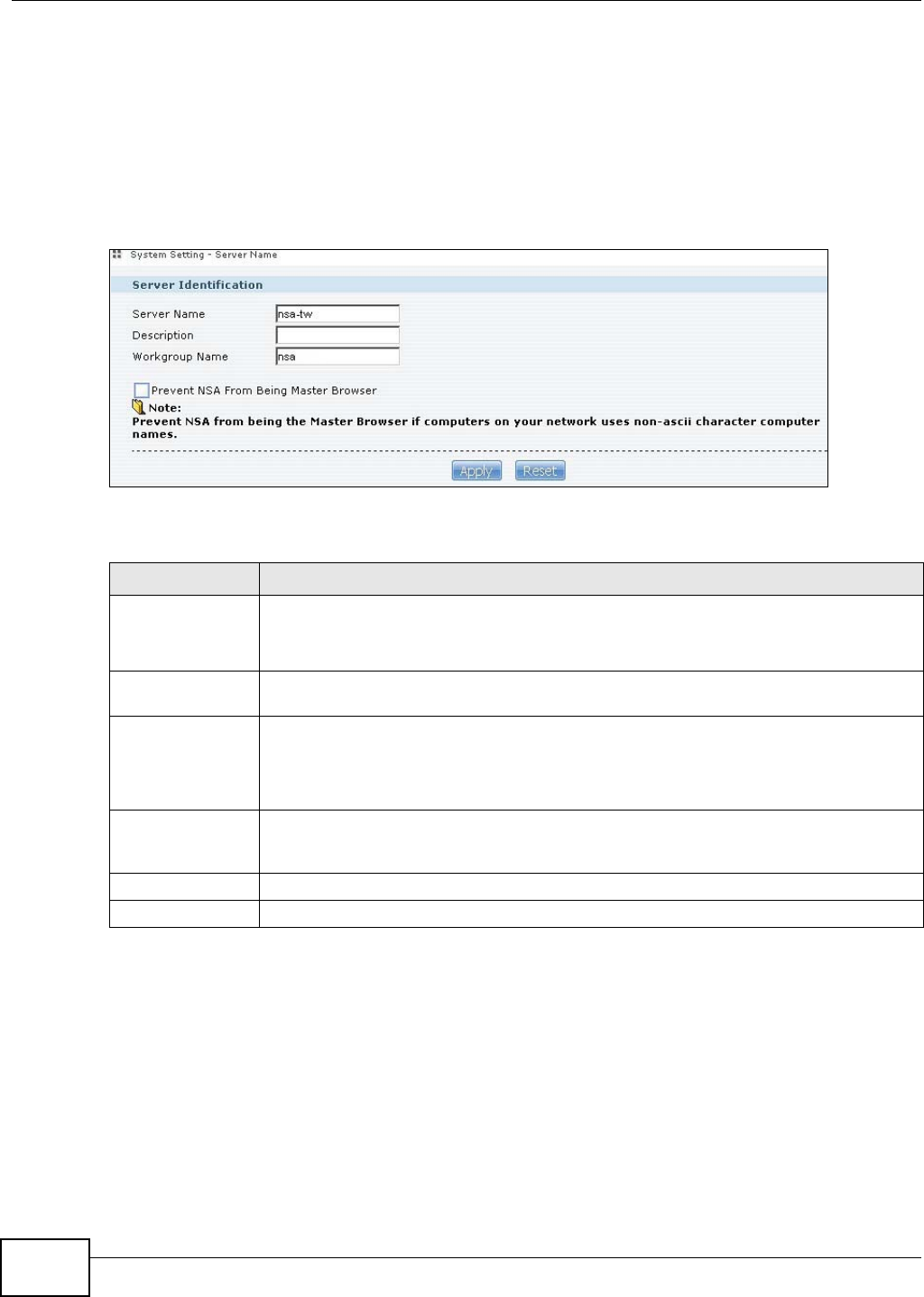
Chapter 7 System Setting
Media Server User’s Guide
154
7.4 The Server Name Screen
Click System Setting > Server Name to open the following screen. Use this screen to configure
your CIFS settings. In this screen you can set your server name and specify if your NSA is a part of
a workgroup.
Note: CIFS cannot be disabled on the NSA.
Figure 71 System Setting > Server Name
The following table describes the labels in these screens.
7.5 The Date/Time Screen
Use this screen to select a time zone and a time server from which your NSA can get the time and
date. This time is then used in NSA logs and alerts.
Table 17 System Setting > Server Name
LABEL DESCRIPTION
Server Name Enter a name to identify your NSA on the network in this field.
You can enter up to 15 alphanumeric characters with minus signs allowed but not as the
last character. The name must begin with an alphabet (a-z) and is NOT case sensitive.
Description Add text here to describe the NSA if the Server Name field is not enough. Use up to 61
characters. You can use all characters except the following: /\:|[]<>+;,?=*"~.
Workgroup Name Type your workgroup name in this field. A workgroup is a group of computers on a
network that can share files.These user accounts are maintained on the NSA.
You can enter up to 15 alphanumeric characters with minus signs allowed but not as the
last character. The name must begin with an alphabet (a-z) and is NOT case sensitive.
Prevent NSA From
Being Master
Browser
Select this option if computers in your workgroup are named with non-English characters
(such as Chinese and Russian). When you perform a search in the workgroup, this option
allows you to locate computers named with non-English characters.
Apply Click this to save your changes.
Reset Click this to restore previously saved settings.
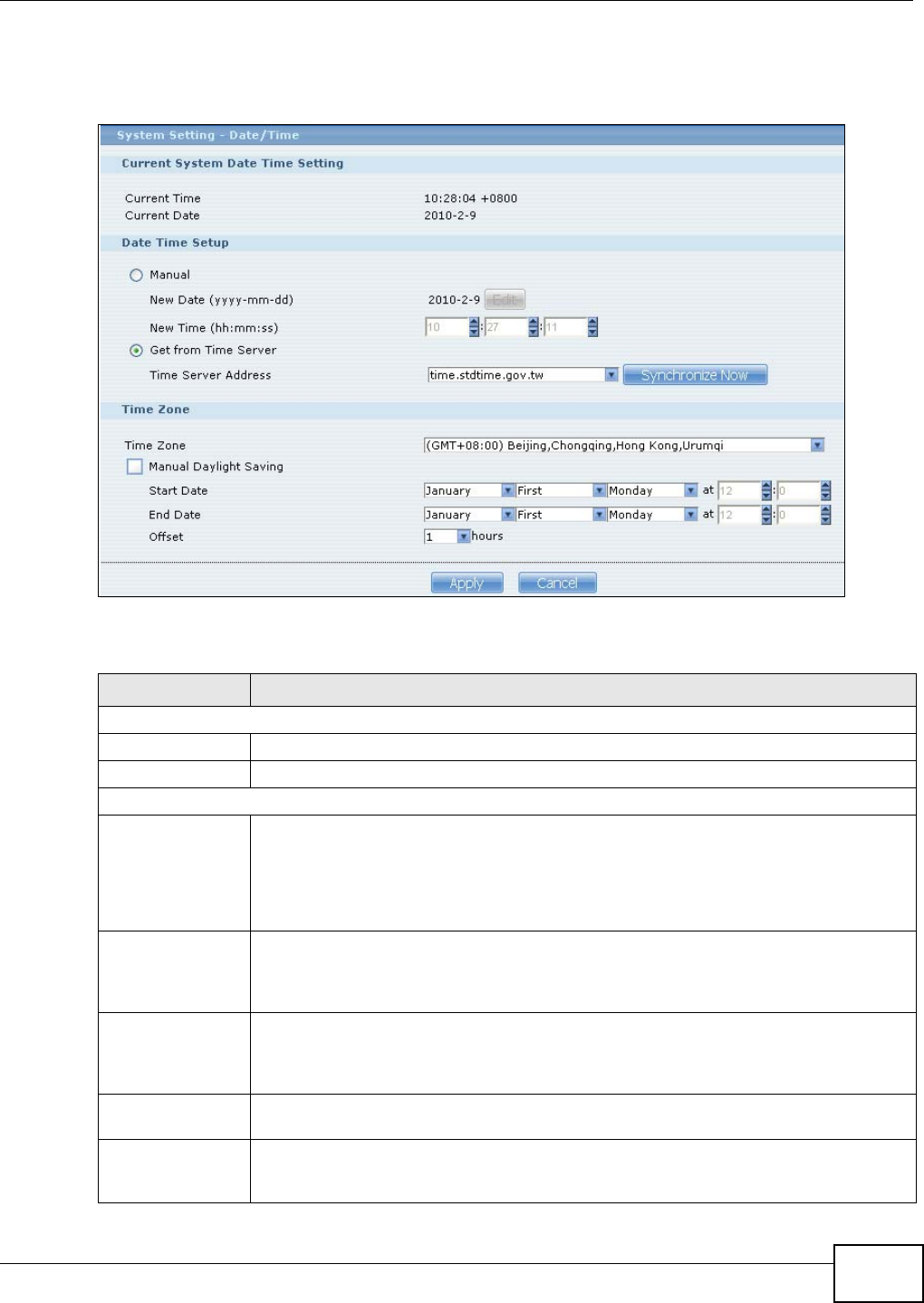
Chapter 7 System Setting
Media Server User’s Guide 155
Click the System Setting link in the navigation panel and then click the Date/Time link to access
the Date/Time screen.
Figure 72 System Setting > Date/Time
The following table describes the labels in this screen.
Table 18 System Setting > Date/Time
LABEL DESCRIPTION
Current System Date Time Setting
Current Time This field displays the time used by your NSA for its logs and alerts.
Current Date This field displays the date used by your NSA for its logs and alerts.
Date Time Setup
Manual Select this radio button to enter the time and date manually.
When you enter the time settings manually, the NSA uses the new setting once you click
Apply.
Note: If you enter time settings manually, they revert to their defaults when power is lost.
New Date
(yyyy-mm-dd) This field displays the last updated date from the time server or the last date configured
manually.
When you set Time and Date Setup to Manual, enter the new date in this field and
then click Apply.
New Time
(hh:mm:ss) This field displays the last updated time from the time server or the last time configured
manually.
When you set Time and Date Setup to Manual, enter the new time in this field and
then click Apply.
Get from Time
Server Select this check box to have the NSA get the time and date from the time server you
select in the Time Server Address field.
Time Server
Address Select a time server from the drop-down list box or select Specify my own time server
and enter the time server you wish to use in the field below. Check with your ISP/network
administrator if you are unsure of this information.
Chapter 7 System Setting
Media Server User’s Guide
156
Synchronize
Now Click this for the NSA to retrieve the correct time from the configured time server right
away.
Time Zone
Time Zone Choose the time zone of your location. This will set the time difference between your time
zone and Greenwich Mean Time (GMT).
Manual Daylight
Saving Daylight saving is a period from late spring to fall when many countries set their clocks
ahead of normal local time by one hour to give more daytime light in the evening.
Select this option to manually enter Daylight Saving Time settings. Clear this option to
have the NSA automatically retrieve Daylight Saving Time settings from the Internet. The
NSA will download a new daylight saving resource file from the Internet every month.
Start Date Configure the day and time when Daylight Saving Time starts if you selected Enable
Daylight Saving. The hour field uses the 24 hour format. Here are a couple of
examples:
Daylight Saving Time starts in most parts of the United States on the second Sunday of
March. Each time zone in the United States starts using Daylight Saving Time at 2 A.M.
local time. So in the United States you would use March, Second, Sunday, at 2:00.
Daylight Saving Time starts in the European Union on the last Sunday of March. All of the
time zones in the European Union start using Daylight Saving Time at the same moment
(1 A.M. GMT or UTC). So in the European Union you would select March, Last, Sunday.
The time you specify depends on your time zone. In Germany for instance, you would
type 2 because Germany's time zone is one hour ahead of GMT or UTC (GMT+1).
End Date Configure the day and time when Daylight Saving Time ends if you selected Enable
Daylight Saving. The o'clock field uses the 24 hour format. Here are a couple of
examples:
Daylight Saving Time ends in the United States on the first Sunday of November. Each
time zone in the United States stops using Daylight Saving Time at 2 A.M. local time. So
in the United States you would select November, First, Sunday, at 2:00.
Daylight Saving Time ends in the European Union on the last Sunday of October. All of the
time zones in the European Union stop using Daylight Saving Time at the same moment
(1 A.M. GMT or UTC). So in the European Union you would select October, Last,
Sunday. The time you specify depends on your time zone. In Germany for instance, you
would type 2 because Germany's time zone is one hour ahead of GMT or UTC (GMT+1).
Offset Specify by how many hours to change the time for Daylight Saving Time.
Apply Click this to save your changes. If you configured a new time and date, Time Zone and
Daylight Saving at the same time, all of the settings take affect.
Cancel Click this to restore your previously saved settings.
Table 18 System Setting > Date/Time (continued)
LABEL DESCRIPTION

Media Server User’s Guide 157
CHAPTER 8
Storage
8.1 Overview
Several NSA features require a valid internal volume. This chapter covers the management of
volumes and disks (both internal and external).
Use the Storage screen (Section 8.2 on page 158) to display information on all volumes, create
internal and external volumes, and configure the volume’s properties.
8.1.1 What You Need to Know About Storage
Disk
SATA or Serial ATA (Advanced Technology Attachment) is a computer bus technology that allows
high-speed data transfer to and from hard disks.
1-bay NSA models include an eSATA port. An eSATA (external SATA) hard disk has the same
specifications as a SATA hard disk but is attached to the NSA using a cable. It can be used either to
expand storage or backup data. The eSATA hard disk is optional. You can attach one SATA and one
eSATA to the NSA hard disk tray. Both SATA and eSATA hard disks are treated as internal disks/
volumes (refer to Section 8.3 on page 161).
USB-attached storage disks are treated as external disks/volumes.
Volume
A volume is a storage area on a disk or disks. You can create volumes on the internal disks and
external disks attached to the USB port(s). You can spread a volume across internal disks but not
between internal and external disks.
Storage Methods
The NSA uses the following storage methods:
• RAID (Redundant Array of Independent Disks)
• PC Compatible Volume (1-bay models)
• JBOD (Just a Bunch of Disks)
The storage method you use depends on how many disks you have and how many volumes you
want to create. It’s important that you consider this carefully as all data is deleted when you re-
create a volume. See Figure 8.6.2 on page 166 for details on choosing a storage method.

Chapter 8 Storage
Media Server User’s Guide
158
Note: 1-bay models configure the internal hard disk (SATA) as JBOD by default. You can
modify it if you attach a second internal hard disk (an eSATA hard disk).
Finding Out More
See Section 8.6 on page 166 for more technical background information on storage.
8.2 The Storage Screen
The Storage screen allows you to create and edit volumes in the NSA.
8.2.1 Disk Replacement Restrictions
See the Quick Start Guide for information on replacing disks in the NSA. When replacing a disk in a
degraded or down RAID volume, the new disk must be at least the same size or bigger than the
other disks that are already in the RAID volume, so as all data in the volume can be restored.
For example, if you have RAID with 250 GB disks, you must put in a 250 GB or bigger disk as a
replacement in order to restore all original data in that volume. If the replacement disk is of a
higher capacity, the extra space on the disk will not be used except if it is for a RAID 1 volume and
you follow the Expanding a RAID 1 Volume procedure.
Note: The NSA automatically repairs a degraded RAID volume if you insert an empty disk
without an existing file system. Otherwise, when you replace a disk you must go to
the Storage > Internal Volume > RAID screen, select the degraded array, and
click Repair.
Resynchronizing or Recovering a RAID 1 Volume
Resynchronizing or recovering a RAID 1 volume that was down is done block-by-block, so the time
it takes depends more on the size of your hard drive(s) than the amount of data you have on them.
Note: Do not restart the NSA while the NSA is resynchronizing or recovering a volume as
this will cause the synchronization to begin again after the NSA fully reboots.
Note: You can access data on a RAID volume while it is resynchronizing or recovering, but
it is not recommended.
Expanding a RAID 1 Volume
Replace a RAID 1 volume’s hard disks with higher capacity hard disks to be able to increase the
RAID 1 volume’s capacity. For example, you have two 500 GB hard disks. You replace one 500 GB
hard disk with a 1 TB hard disk and repair the volume. After the NSA finishes resynchronizing the
volume, you replace the second 500 GB hard disk with another 1 TB hard disk and repair the
volume again. After the NSA finishes the second repair, use the Expand icon to have the RAID1
volume use the rest of the hard disk capacity.
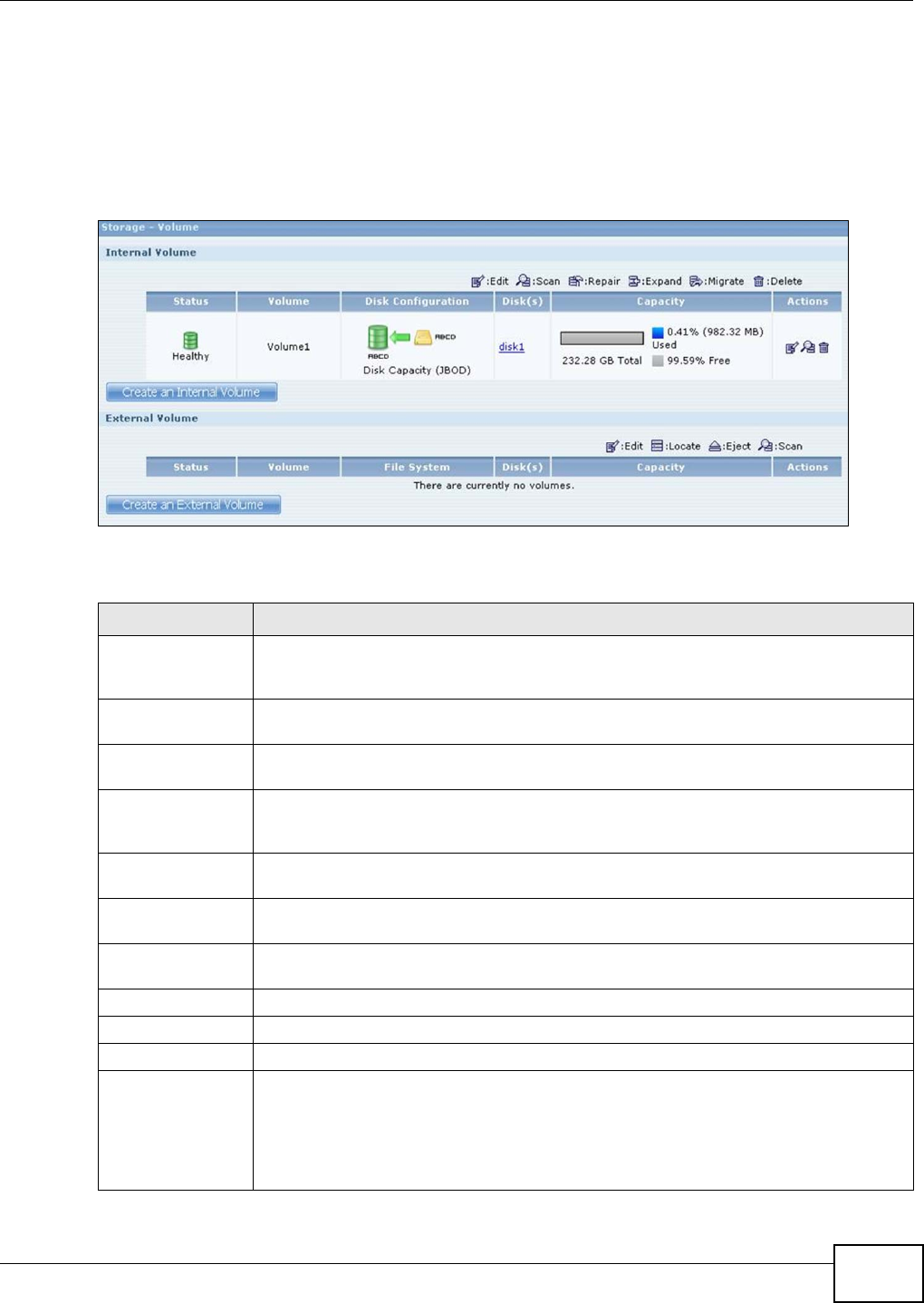
Chapter 8 Storage
Media Server User’s Guide 159
8.2.2 Storage Screen
Click Storage > Volume in the navigation panel to display the following screen. Use this screen to
display internal and external volumes on the NSA.
Note: It is recommended to scan the volume every three months or 32 reboots.
Figure 73 Storage > Volume
The following table describes the labels in this screen.
Table 19 Storage > Volume
LABEL DESCRIPTION
Internal/External
Volume (2-bay models) These tables display information on all internal volumes (created on NSA
internal disk drives) and external volumes (created on external disk drives attached to
the NSA USB ports).
Create an Internal
Volume (2-bay models) Click this to format internal hard drives and create a new volume. All
data on the disk(s) will be lost.
Create an External
Volume (2-bay models) Click this to format an external hard drive and create a new volume. All
data on the disk will be lost.
SATA/USB Volume (1-bay models) These tables display information on all internal SATA volumes (created
on NSA internal disk drives) and external volumes (created on external disk drives
attached to the NSA USB ports).
Create a SATA
Volume (1-bay models) Click this to format internal hard drives and create a new volume. All
data on the disk(s) will be lost.
Create a USB
Volume (1-bay models) Click this to format an external hard drive and create a new volume. All
data on the disk will be lost.
Status This field shows whether the volume is Healthy, Resync, Recovering, Degraded, or
Down.
Volume The NSA creates the volume name automatically. You can edit it.
Disk Configuration This field shows which disks and data storage system the volume is using.
File System This field displays the file system that an external (USB) volume is using.
Disk(s) Click or roll your mouse over a link in this column to display the following details about
the hard drive located in the corresponding hard drive bay.
Type: Whether it is an internal or external (USB) hard drive.
Model Name: This is the hard disk number that identifies the disk.
File System: The file system that an external volume is using
Capacity: The total storage space on the disk.
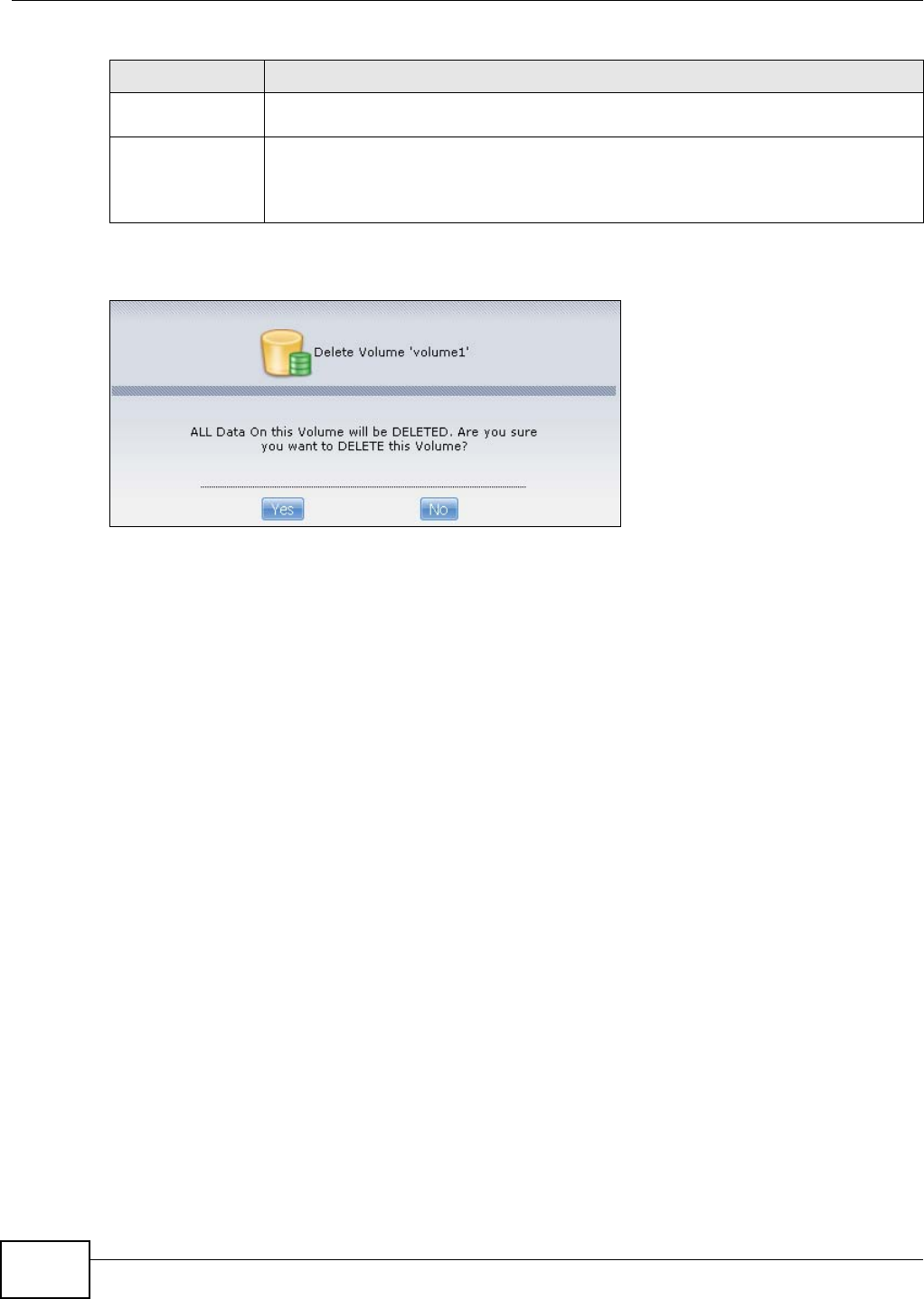
Chapter 8 Storage
Media Server User’s Guide
160
You see a warning screen before you delete a volume.
Figure 74 Delete a Volume Warning Screen
8.2.3 Volume Status
You (the administrator) can see the status of a volume in the Status or Storage screens.
The NSA has the following classifications for the status of a volume:
•Healthy if all disks in the volume are OK and the file system is functioning properly.
•OK means the USB connected device is functioning properly.
•Resync when you create a RAID volume.
•Recovering appears when repairing a RAID 1 volume. (A RAID1 volume was once degraded, but
you have installed a new disk and the NSA is restoring the RAID1 volume to a healthy state.)
•Degraded when a volume is currently down, but can be fixed. Data access may be slower from a
degraded volume, so it’s recommended that you replace the faulty disk and repair the volume as
soon as you can.
•Inactive when a disk is missing from a RAID 0 volume or a two-disk JBOD volume. The volume
is unusable. If you removed one of the disks you should be able to re-install it and use the
volume again (as long as you did not change anything on the disk). If a disk has failed, you need
to replace it and re-create the whole volume. All data will be lost. See page 348 for how to install
or replace a hard drive.
•Down when a volume is down and can not be fixed.
A down RAID volume cannot be used until you repair or replace the faulty disk(s) in the volume.
Degraded means one of the disks in the RAID volume is not available but the volume can still be
used. For a degraded volume, you should replace the faulty disk as soon as possible to obtain
previous performance. See your Quick Start Guide for more information on replacing a disk.
Capacity This field shows total disk size, the percentage of the volume being used and the
percentage that is available.
Actions This field displays icons allowing you to edit, scan, repair, expand, migrate, or delete a
volume. You can also locate or eject an external volume.
Note: If you delete a volume, all data in the volume disk(s) is erased.
Table 19 Storage > Volume (continued)
LABEL DESCRIPTION
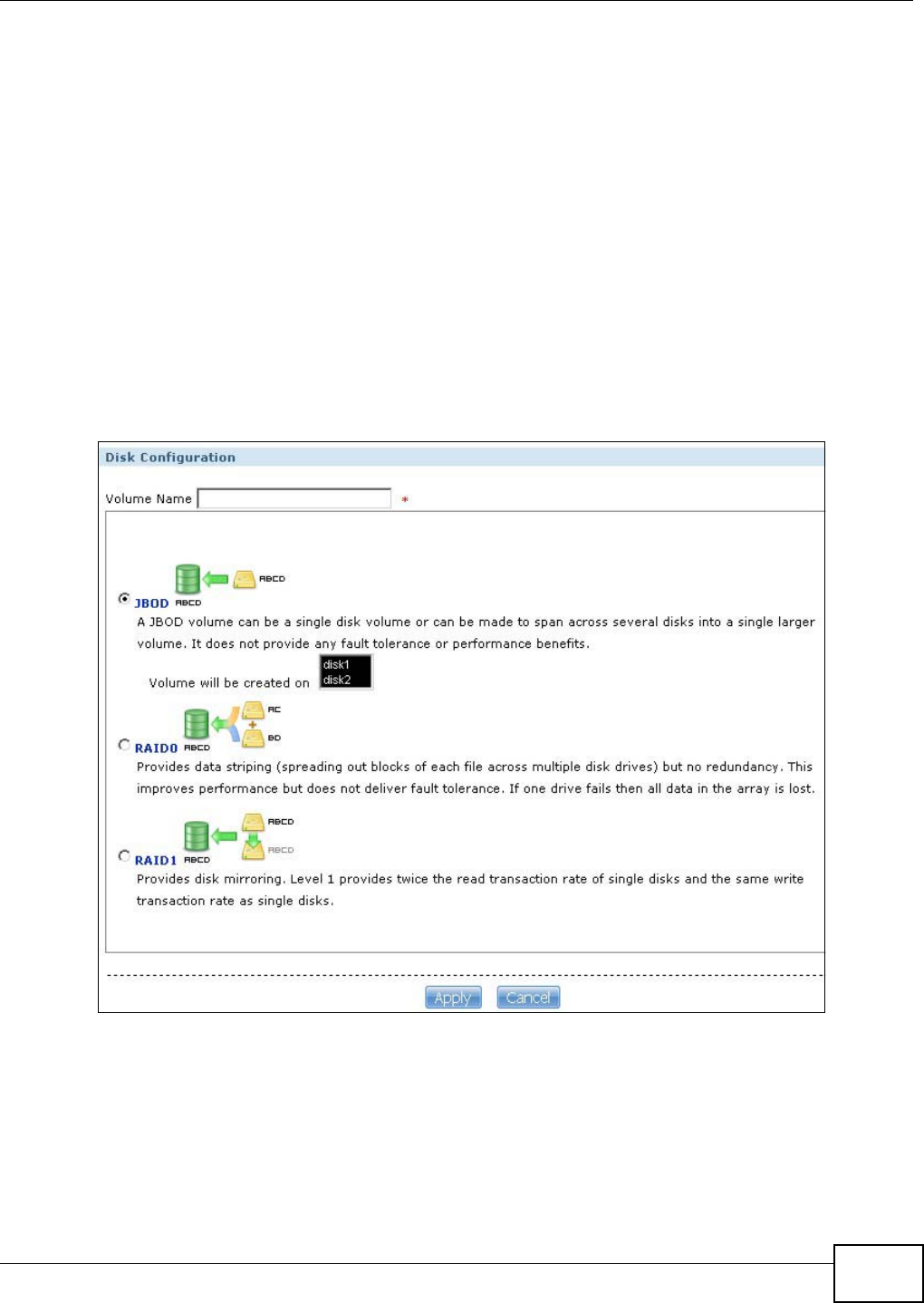
Chapter 8 Storage
Media Server User’s Guide 161
If it’s down, then the only indication is that you can no longer transfer files to/from the shares in
the down volume. If it’s degraded, then file transfer to/from the shares in the degraded volume will
be slower.
Note: There is no explicit message from CIFS that tells users their volume is degraded or
down.
8.3 Creating an Internal (SATA) Volume
In the Storage screen (Figure 73 on page 159), click the Create an Internal Volume or Create
a SATA Volume button (depending on your model) to open the following screen. Use this screen to
create a new NSA internal disk drive volume.
Note: Creating a volume formats the hard drive. All data on the disk will be lost.
Figure 75 Storage > Create an Internal Volume
Chapter 8 Storage
Media Server User’s Guide
162
The following table describes the labels in this screen.
Table 20 Storage > Create an Internal Volume
LABEL DESCRIPTION
Volume Name Type a volume name from 1 to 31 characters. To avoid confusion, it is highly recommended
that each volume use a unique name.
Acceptable characters are all alphanumeric characters, " " [spaces], "_" [underscores], and
"." [periods].
The first character must be alphanumeric (A-Z 0-9).
The last character cannot be a space " ".
For an external volume, type a volume name from 1 to 32 single-byte (no Chinese characters
allowed for example) ASCII characters. The name cannot be the same as another existing
external volume.
JBOD Use this if you want maximum storage capacity and/or you have other means of protecting
your data. JBOD is the only option if you only have one disk installed. With two disks, you can
choose to create a JBOD volume on one of the disks or both.
Select which disks should make up this volume. A disk can only belong to one volume. You do
not need to select anything if only one hard disk is installed.
•Internal Disk - Is the hard disk inside a 1-bay NSA.
•External Disk - Is the eSATA hard disk connected to a 1-bay NSA.
PC Compatible
Volume (1-bay models only)
This type is only available if you have attached an eSATA hard disk to your NSA.
A primary partition is created on the eSATA hard disk.
Use this to make your eSATA hard disk readable by other computer systems. However, the
computer’s platform (for example, Windows XP SP2) should support the file system you
selected for the eSATA hard disk.
•External Disk - This is checked automatically. It refers to the eSATA hard disk that you
can attach as a second drive to your NSA.
•File System - Select the file system you want the new volume to use.
Windows file systems include:
NTFS: Recommended for volumes greater than 40 GB.
FAT32: Newer, and more efficient than FAT16. Supports a volume size of up to 32 GB
(Giga Bytes) and individual file sizes of up to 4 GB.
FAT16: Compatible with older Windows operating systems. Supports volume and file
sizes of up to 2 GB.
Linux file systems include:
EXT2: Most commonly used on Linux platforms.
EXT3: The same as EXT2, but adds a journaled file system and is more robust.
ReiserFS: Offers better performance for small files.
XFS: Allows expansion for mounted volumes.
RAID 0 (2-bay models only)
Use this if you want maximum speed for your disks, and/or you have other means of
protecting your data. This is only available when you have two hard disks installed.
RAID 1 Use this if you want to mirror all data on one disk to the other disk. This is only available
when you have two hard disks installed.
Volume will be
created on This field lists all hard disks installed inside the NSA. Select which disks should make up this
volume. A disk can only belong to one volume. You do not need to select anything if only one
hard disk is installed.
Apply Click this to save your changes and create the volume.
Cancel Click this to exit this screen without saving your changes or creating a volume.
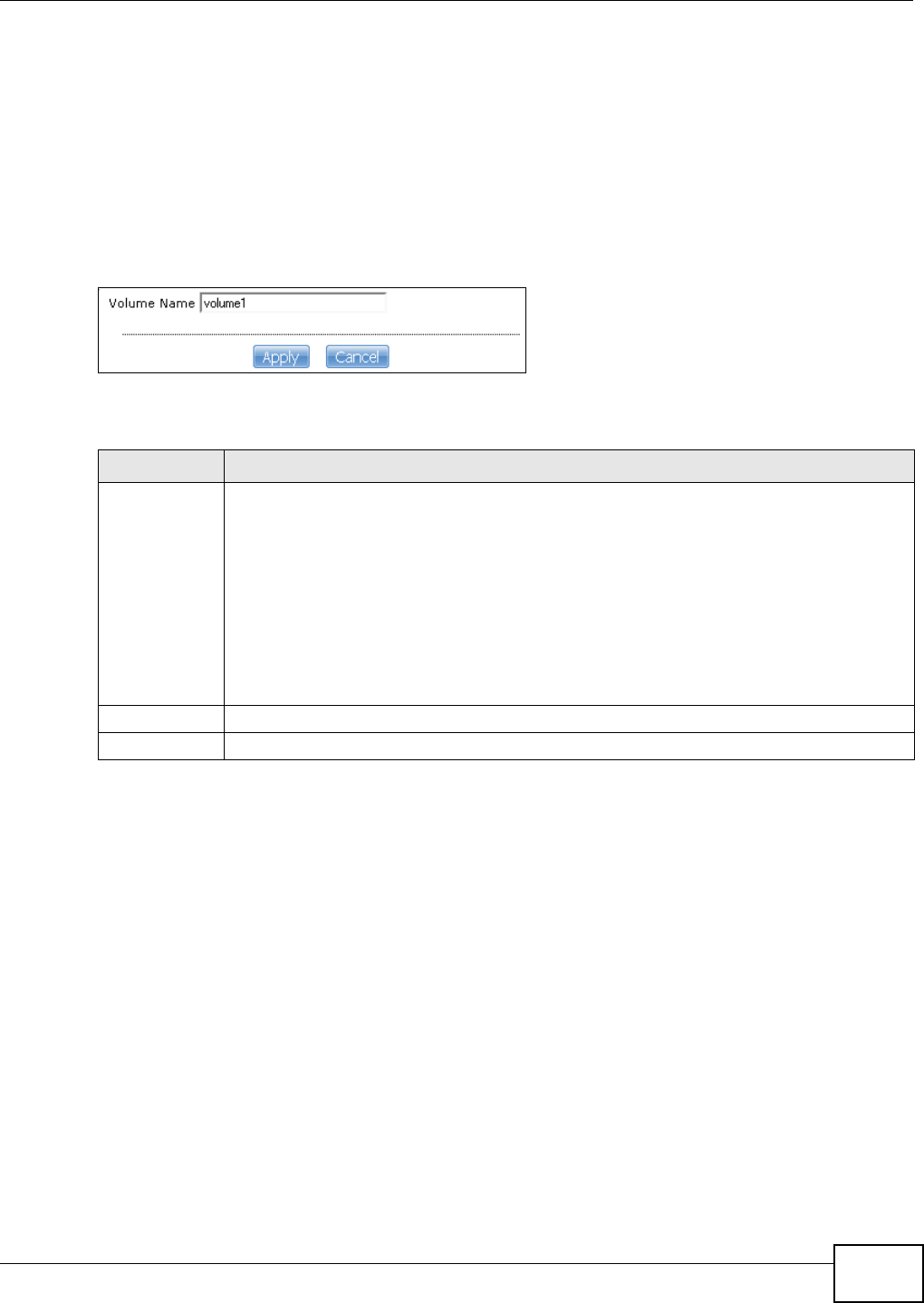
Chapter 8 Storage
Media Server User’s Guide 163
Note: Once you create the first volume on the NSA, it is recommended to restart the NSA
for better performance.
8.4 Editing a Volume
Click an internal volume’s Edit icon in the Storage screen as shown in Figure 73 on page 159 to
open the following screen. Use this screen to change the volume’s name.
Figure 76 Storage > Edit
The following table describes the labels in this screen.
Table 21 Storage > Edit
LABEL DESCRIPTION
Volume Name For an internal volume, type a volume name from 1 to 31 characters. To avoid confusion, it is
highly recommended that each volume use a unique name.
Acceptable characters are all alphanumeric characters and " " [spaces], "_" [underscores],
and "." [periods].
The first character must be alphanumeric (A-Z 0-9).
The last character cannot be a space " ".
For an external volume, type a volume name from 1 to 32 single-byte (no Chinese
characters allowed for example) ASCII characters. The name cannot be the same as another
existing external volume.
Apply Click this to save your changes and rename the volume.
Cancel Click this to close this screen without saving your changes.
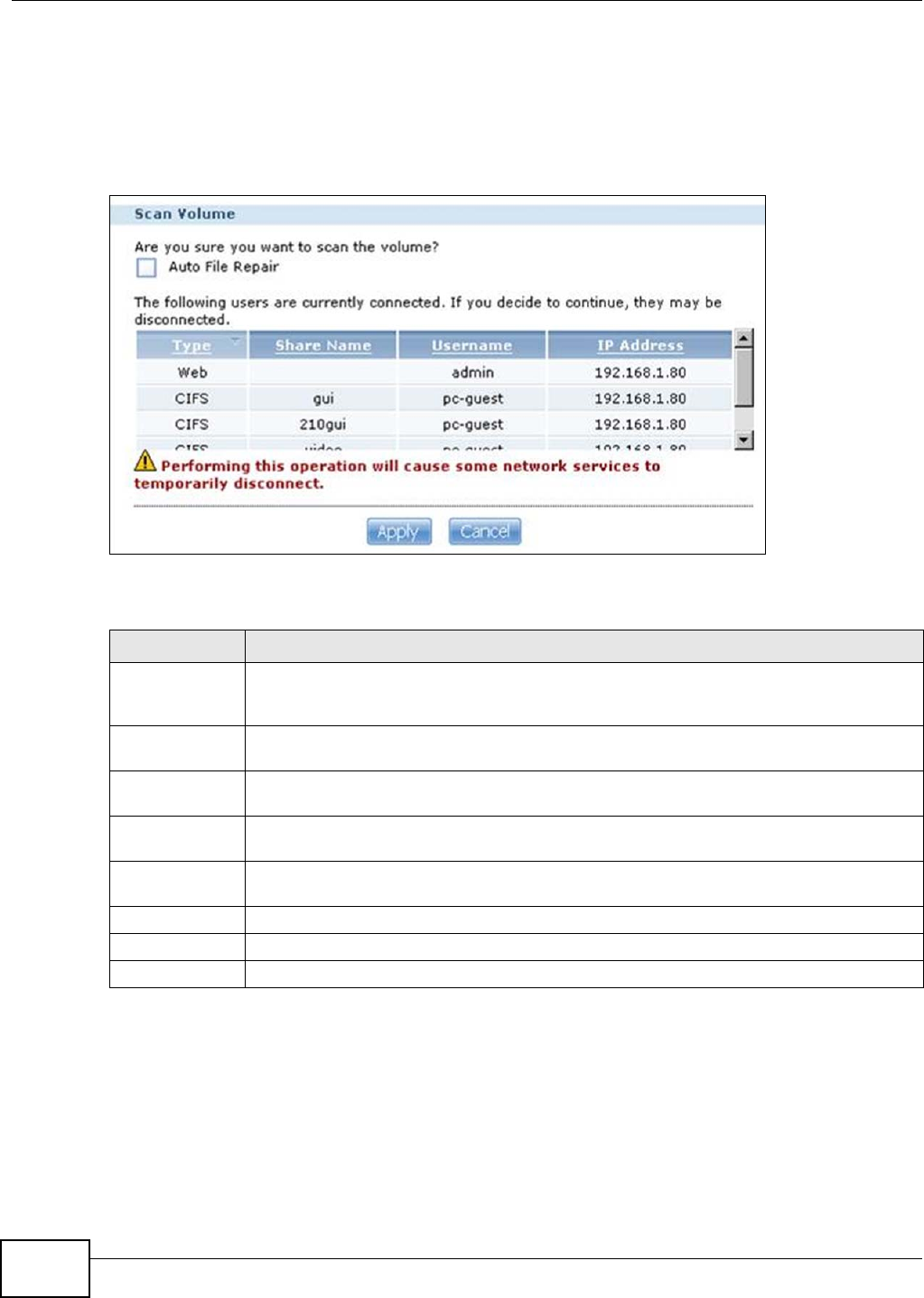
Chapter 8 Storage
Media Server User’s Guide
164
8.4.1 Scanning a Volume
Select a volume in the Storage > Volume screen (Section 8.2 on page 158) and click Scan to
open the following screen. Use this screen to scan the volume for errors and select whether or not
to have the NSA automatically repair them.
Figure 77 Storage > Volume > Scan
The following table describes the labels in this screen.
8.5 Creating an External (USB) Volume
Click the Create a New External Volume button (or the Create a USB Volume button
depending on your model) in the Storage screen as shown in Figure 73 on page 159 to open the
following screen. Use this screen to create a new NSA external disk drive volume.
Table 22 Storage > Volume > Scan
LABEL DESCRIPTION
Auto File Repair Select this to have the NSA automatically attempt to repair any errored files it detects
during the scan. This may also result in the NSA finding some files and placing them in the
Lost and Found share.
The rest of the screen shows which users are currently connected to the NSA. They will be
disconnected if you perform the scan.
Type This shows whether it’s a Windows/CIFS, web (Web Configurator), or FTP connection to the
NSA.
Share Name This displays the shared folder name on the NSA that the user is connected to for CIFS
sessions and is blank for FTP and web sessions.
Username This displays the name of the user connected to the NSA if one is defined. ANONYMOUS
FTP displays if a username is not defined for the user’s connection.
IP Address This displays the IP address of the computer connected to the NSA.
Apply Click this to have the NSA scan the volume.
Cancel Click this to close this screen without scanning the volume.
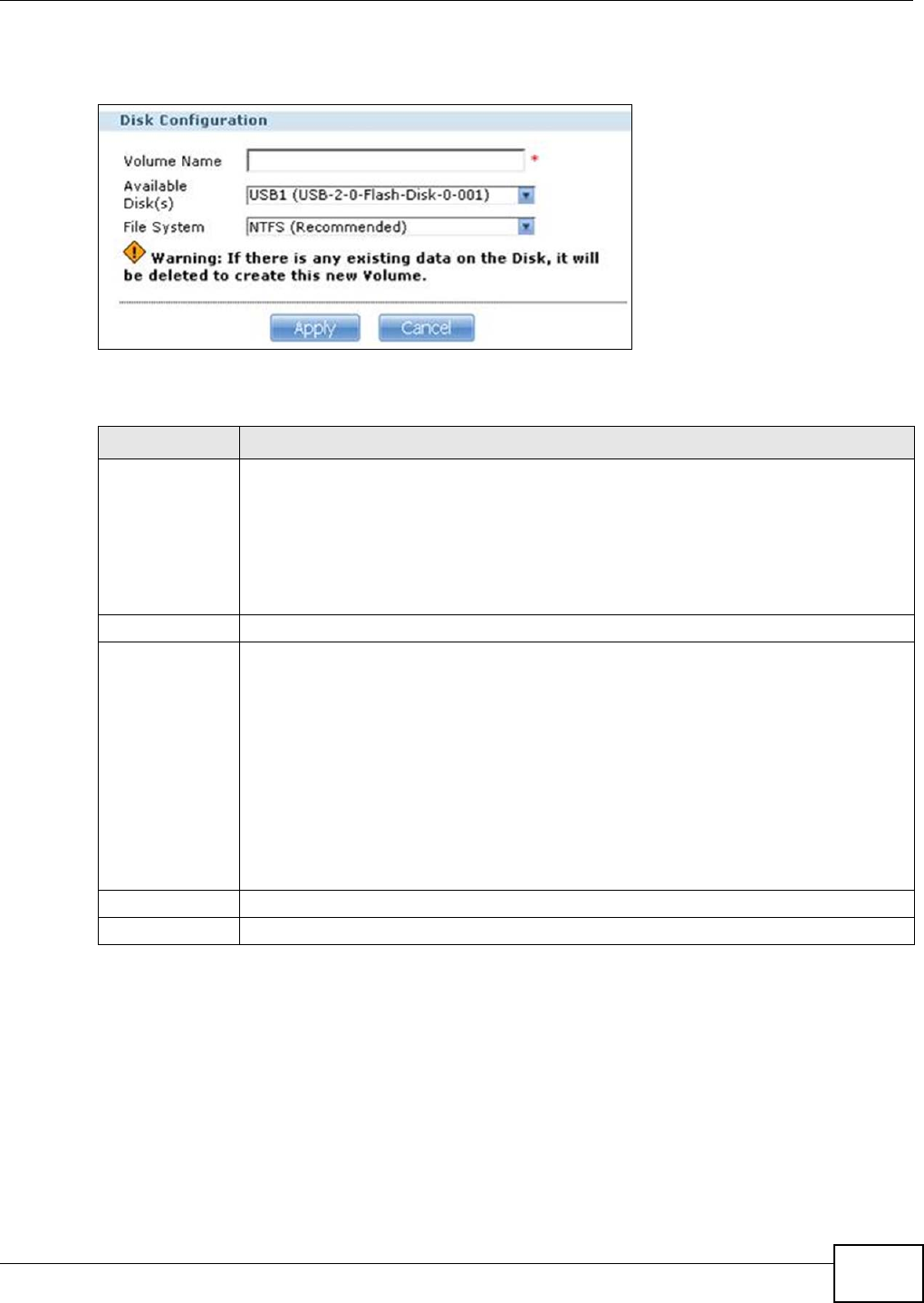
Chapter 8 Storage
Media Server User’s Guide 165
Note: Creating a volume formats the drive. All data on the disk will be lost.
Figure 78 Storage > Create an External Volume
The following table describes the labels in this screen.
8.5.1 External Disks
You may connect USB storage devices that support the following file systems to the NSA.
• Windows File Systems: NTFS, FAT32 and FAT16.
• Linux File Systems: ReiserFS, EXT2, EXT3, and XFS.
Table 23 Storage > Create an External Volume
LABEL DESCRIPTION
Volume Name Type a volume name from 1 to 31 characters. The name cannot be the same as another
existing external volume.
Acceptable characters are all alphanumeric characters and " " [spaces], "_" [underscores],
and "." [periods].
The first character must be alphanumeric (A-Z 0-9).
The last character cannot be a space " ".
Available Disk(s) Select the external (USB) device upon which you want to create the volume.
File System Select the file system you want the new volume to use.
Windows file systems
NTFS: Recommended.
FAT32: Newer, and more efficient than FAT16. Supports a volume size of up to 2 TB
(Tera Bytes) and individual file sizes of up to 4 GB.
FAT16: Compatible with older Windows operating systems. Supports volume and file
sizes of up to 2 GB.
Linux file systems
EXT2: Older file system.
EXT3: The same as EXT2, but adds a journaled file system and is more robust.
ReiserFS: Offers better performance for small files.
XFS: Allows expansion for mounted volumes.
Apply Click this to save your changes and create the volume.
Cancel Click this to exit this screen without saving changes.
Chapter 8 Storage
Media Server User’s Guide
166
8.6 Storage Technical Reference
This section provides some background information about the topics covered in this chapter.
8.6.1 Volumes and RAID
A volume is a storage area on a disk or disks. You can create volumes on the internal disks and
external disks attached to the USB port(s). You can spread a volume across internal disks but not
between internal and external disks.
RAID (Redundant Array of Independent Disks) or JBOD is the storage method that the NSA uses.
The storage method you use depends on how many disks you have and how many volumes you
want to create. It’s important that you consider this carefully as all data is deleted when you re-
create a volume.
Note: Back up your data before deleting or re-creating a volume!
For example if you originally have one disk configured as JBOD, and you then install another disk
and want to configure the two disks to use RAID 1, you should first back up all your data on the two
disks (see the Memeo Autobackup utility on the included CD) and then restore your data later after
you create the new volume type.
Below is a table that summarizes some attributes of the various RAID levels as supported on the
NSA. For capacity and storage efficiency, “S” is the size of the smallest drive in the array, and “N” is
the number of drives in the array.
Storage efficiency assumes all drives are of identical size.
Performance rankings are approximations.
8.6.2 Choosing a Storage Method for a Volume
The following is a guide to help you choose a storage method for the various number of disks
supported on the NSA. See Section 8.6.3 on page 167 for theoretical background on JBOD and the
RAID levels used on the NSA. Typical applications for each method are also shown there.
One Disk
If you only have one disk, you must use JBOD. All disk space is used for your data - none is used for
backup. If the disk fails, then you lose all the data on that volume (disk). You can add another disk
Table 24 RAID Quick Comparison
RAID Level 0 1
Number of Disks 2 2
Capacity S*N S*N/2
Storage Efficiency 100% 50%
Fault Tolerance None YYYY
Availability Y YYYY
Read Performance YYYY YYY
Write Performance YYYY YYY

Chapter 8 Storage
Media Server User’s Guide 167
to your one-disk JBOD volume later without having to re-create shares, access rights, and so on.
Alternatively, you could create a different JBOD volume if you install a second disk. (and create new
shares, access rights and so on).
Two Disks:
You may choose JBOD, RAID 0 or RAID 1. With two disks you could create:
• up to two JBOD volumes
• one RAID 0 or RAID 1 volume
• Choose JBOD for flexibility and maximum usage of disk space for data.
• If you have a 2-bay model, you can choose RAID 0 if performance matters more than data
security. RAID 0 has the fastest read and write performance but if one disk fails you lose all
your data on the volume. It has fast performance as it can read and write to two disks
simultaneously. Performance may matter more than data security to gamers for example. This
method may also be acceptable for data that is already backed up somewhere else.
• Choose RAID 1 if data security is more important than performance. Since RAID 1 mirrors data
onto a second disk, you can recover all data even if one disk fails, but the performance is slower
than RAID 0.
8.6.3 Storage Methods
This section contains theoretical background on JBOD and the RAID levels used on the NSA.
Redundant Array of Independent Disks (RAID) is a method of storing data on multiple disks to
provide a combination of greater capacity, reliability, and/or speed. JBOD (Just a Bunch Of Disks) is
not a RAID storage method but it is included in this discussion.
These are some terms that you need to know in order to understand storage systems.
• Mirroring
In a RAID system using mirroring, all data in the system is written simultaneously to two hard
disks instead of one. This provides 100% data redundancy as if one disk fails the other has the
duplicated data. Mirroring setups always require an even number of drives.
•Duplexing
Like in mirroring, all data is duplicated onto two distinct physical hard drives but in addition it
also duplicates the hardware that controls the two hard drives (one of the drives would be
connected to one adapter and the other to a second adapter).
• Striping
Striping is the breaking up of data and storing different data pieces on each of the drives in an
array. This allows faster reading and writing as it can be done simultaneously across disks.
Striping can be done at the byte level, or in blocks. Byte-level striping means that the first byte
of the file is sent to the first drive, then the second to the second drive, and so on. Block-level
striping means that each file is split into blocks of a certain size and those are distributed to the
various drives. The size of the blocks used is also called the stripe size (or block size).
•Parity
In mirroring 50% of the drives in the array are reserved for duplicate data. Parity is another way
to allow data recovery in the event of disk failure using calculations rather than duplicating the
data. If you have ‘n’ pieces of data, parity computes an extra piece of data. The’n+1’ pieces of
data are stored on ‘n+1’drives. If you lose any one of the ‘n+1’ pieces of data, you can recreate
Chapter 8 Storage
Media Server User’s Guide
168
it from the ‘n’ that remain, regardless of which piece is lost. Parity protection is used with
striping, and the “n” pieces of data are typically the blocks or bytes distributed across the drives
in the array. The parity information can either be stored on a separate, dedicated drive, or be
mixed with the data across all the drives in the array.
Note: In the following figures, A1, A2, A3 and so on are blocks of data from the A file.
Similarly, B1, B2, B3 and C1, C2, C3 ar blocks of data from the B and C files.
JBOD
JBOD allows you to combine multiple physical disk drives into a single virtual one, so they appear
as a single large disk. JBOD can be used to turn multiple different-sized drives into one big drive.
For example, JBOD could convert 80 GB and 100 GB drives into one large logical drive of 180 GB. If
you have two JBOD volumes (with one disk in each), a failure of one disk (volume) should not affect
the other volume (disk). JBOD read performance is not as good as RAID as only one disk can be
read at a time and they must be read sequentially. The following figure shows disks in a single
JBOD volume. Data is not written across disks but written sequentially to each disk until it’s full.
RAID 0
RAID 0 spreads data evenly across two or more disks (data striping) with no mirroring nor parity for
data redundancy, so if one disk fails the entire volume will be lost. The major benefit of RAID 0 is
performance. The following figure shows two disks in a single RAID 0 volume. Data can be written
and read across disks simultaneously for faster performance.
RAID 0 capacity is the size of the smallest disk multiplied by the number of disks you have
configured at RAID 0 on the NSA. For example, if you have two disks of sizes 100 GB and 200 GB
respectively in a RAID 0 volume, then the maximum capacity is 200 GB (2 * 100 GB, the smallest
disk size) and the remaining space (100 GB) is unused.
Table 25 JBOD
A1 B1
A2 B2
A3 B3
A4 B4
DISK 1 DISK 2
Table 26 RAID 0
A1 A2
A3 A4
A5 A6
A7 A8
DISK 1 DISK 2
Chapter 8 Storage
Media Server User’s Guide 169
Typical applications for RAID 0 are non-critical data (or data that changes infrequently and is
backed up regularly) requiring high write speed such as audio, video, graphics, games and so on.
RAID 1
RAID 1 creates an exact copy (or mirror) of a set of data on another disk. This is useful when data
backup is more important than data capacity. The following figure shows two disks in a single RAID
1 volume with mirrored data. Data is duplicated across two disks, so if one disk fails, there is still a
copy of the data.
As RAID 1 uses mirroring and duplexing, a RAID 1 volume needs an even number of disks (two or
four for the NSA).
RAID 1 capacity is limited to the size of the smallest disk in the RAID array. For example, if you
have two disks of sizes 150 GB and 200 GB respectively in one RAID 1 volume, then the maximum
capacity is 150 GB and the remaining space (50 GB) is unused.
Typical applications for RAID 1 are those requiring high fault tolerance without need of large
amounts of storage capacity or top performance, for example, accounting and financial data, small
database systems, and enterprise servers.
RAID and Data Protection
If a hard disk fails and you’re using a RAID 1 volume, then your data will still be available (but at
degraded speeds until you replace the hard disk that failed and resynchronize the volume).
However, RAID cannot protect against file corruption, virus attacks, files incorrectly deleted or
modified, or the NSA malfunctioning. Here are some suggestions for helping to protect your data.
• Place the NSA behind a hardware-based firewall. It should have stateful packet inspection, IDP
(Intrusion Detection and Prevention), and anti-virus (like ZyXEL’s ZyWALL UTM products for
example).
• Use anti-virus software on your computer to scan files from others before saving the files on the
NSA.
• Keep another copy of important files (preferably in another location).
Table 27 RAID 1
A1 A1
A2 A2
A3 A3
A4 A4
DISK 1 DISK 2

Chapter 8 Storage
Media Server User’s Guide
170

Media Server User’s Guide 171
CHAPTER 9
Network
9.1 Overview
This chapter discusses the network configuration screens. The Network screens allow you to
configure TCP/IP and PPPoE settings for the NSA.
9.2 What You Can Do
•Use the TCP/IP screen (Section 9.4 on page 173) to assign the NSA a dynamic or static IP
address and DNS information.
• Use UPnP port mapping (Section 9.5 on page 175) to automatically configure your Internet
gateway’s firewall and Network Address Translation (NAT) to allow access to the NSA from the
Internet.
•Use the PPPoE screen (Section 9.6 on page 179) to configure PPPoE settings for a direct Internet
connection.
9.3 What You Need to Know
IP Address
The NSA needs an IP address to communicate with other devices on your network. The NSA can get
an IP address automatically if you have a device on your network that gives them out. Or you can
assign the NSA a static (fixed) IP address.
IPv6
IPv6 (Internet Protocol version 6), is designed to increase IP address space and enhance features.
You can connect the NSA to both IPv4 and IPv6 networks.
DNS Server Address
A DNS (Domain Name System) server maps domain names (like www.zyxel.com) to their
corresponding numerical IP addresses. This lets you use domain names to access web sites without
having to know their IP addresses. The NSA can receive the IP address of a DNS server
automatically (along with the NSA’s own IP address). You can also manually enter a DNS server IP
address in the NSA.
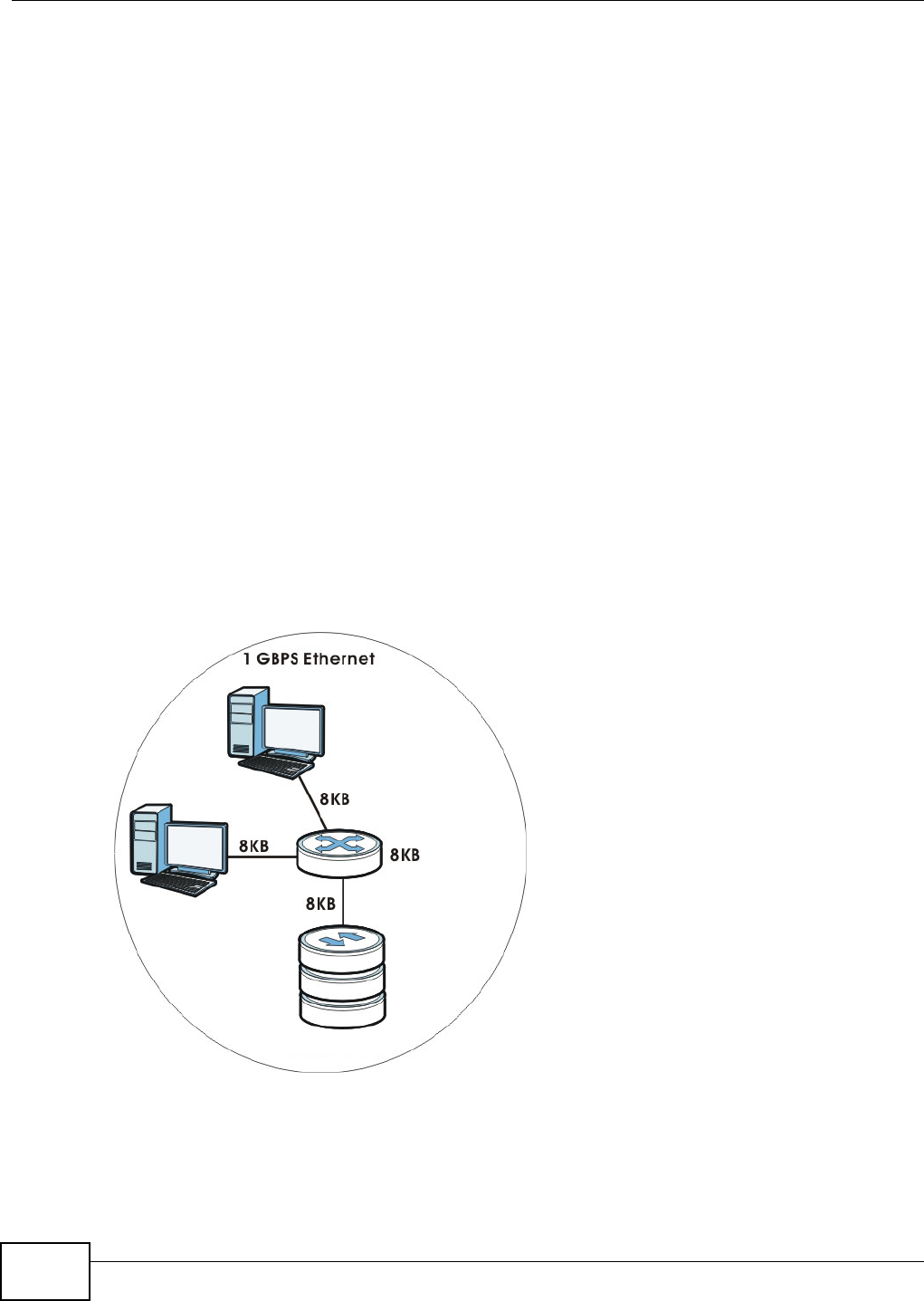
Chapter 9 Network
Media Server User’s Guide
172
PPPoE
Point-to-Point Protocol over Ethernet (PPPoE) allows the NSA to establish a direct Internet
connection if you do not have a router. PPPoE is a dial-up connection. You need a username and
password from your Internet Service Provider (ISP) to set up the connection.
Jumbo Frames
Jumbo frames are Ethernet frames larger than 1500 bytes. They enable data transfer with less
overhead. The bigger the frame, the better the network performance. Your network equipment
such as computers, switches and routers must be capable of supporting jumbo frames. You also
need to enable jumbo frames in all related network devices.
To use jumbo frames, your LAN must support 1 Gbps transmissions (Gigabit Ethernet). All of your
network devices (computer Ethernet cards and switches, hubs, or routers) must also support the
same size of jumbo frames that you specify in the NSA.
Note: If you enable jumbo frames on the NSA in a network that does not support them,
you will lose access to the NSA. If this occurs, you will have to restore the factory
default configuration. Push the RESET button on the NSA’s rear panel and release it
after you hear a beep.
In the following example, the NSA has jumbo frames enabled and set to 8KB frames. This means
the computer, notebook computer, and switch must also have jumbo frames enabled and be
capable of supporting 8KB frames.
Figure 79 Jumbo Frames
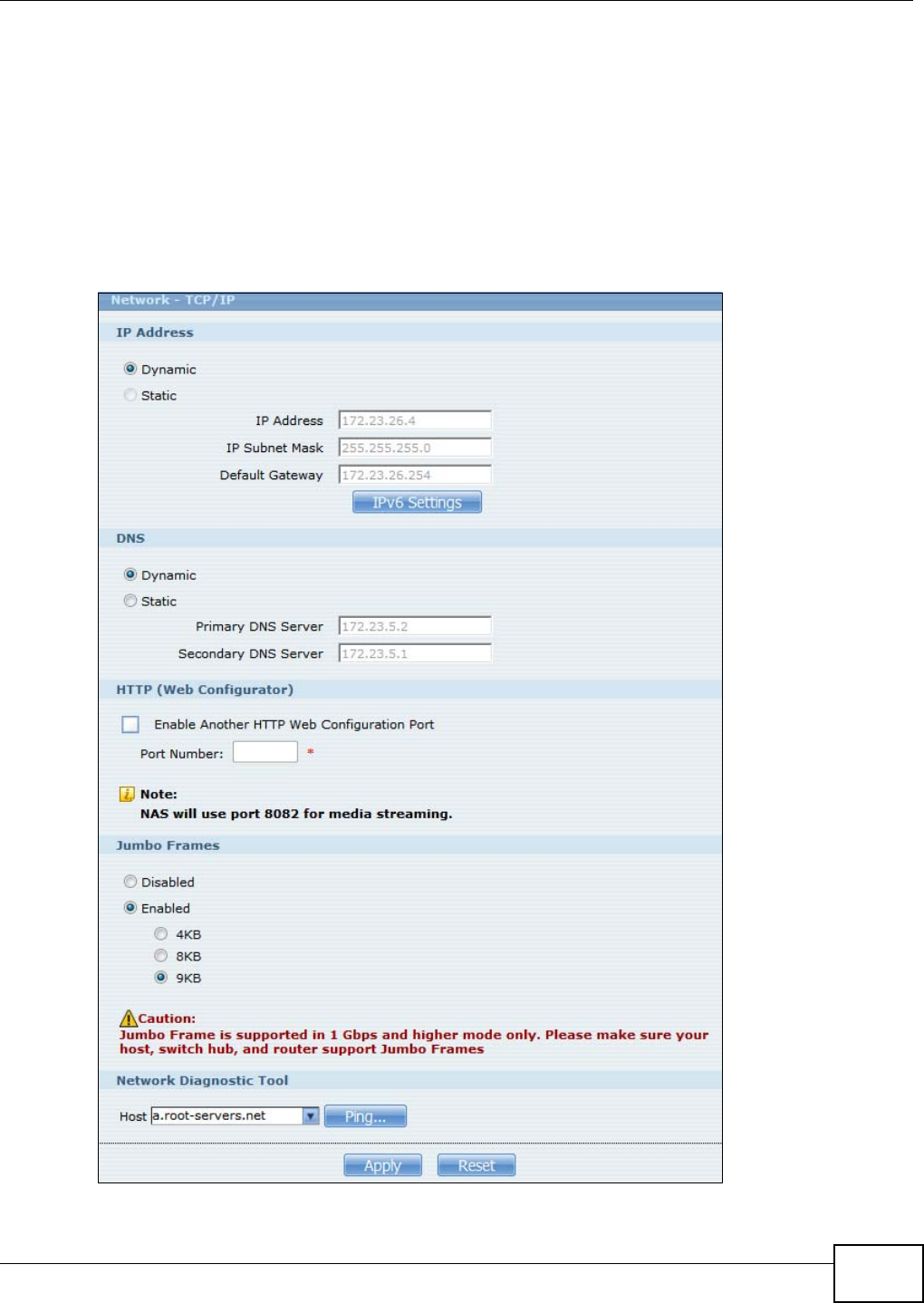
Chapter 9 Network
Media Server User’s Guide 173
9.4 The TCP/IP Screen
Use the TCP/IP screen to have the NSA use a dynamic or static IP address, subnet mask, default
gateway and DNS servers.
Click Network > TCP/IP in the navigation panel to open the following screen.
Note: If you change the NSA’s IP address, you need to log in again after you apply
changes.
Figure 80 Network > TCP/IP
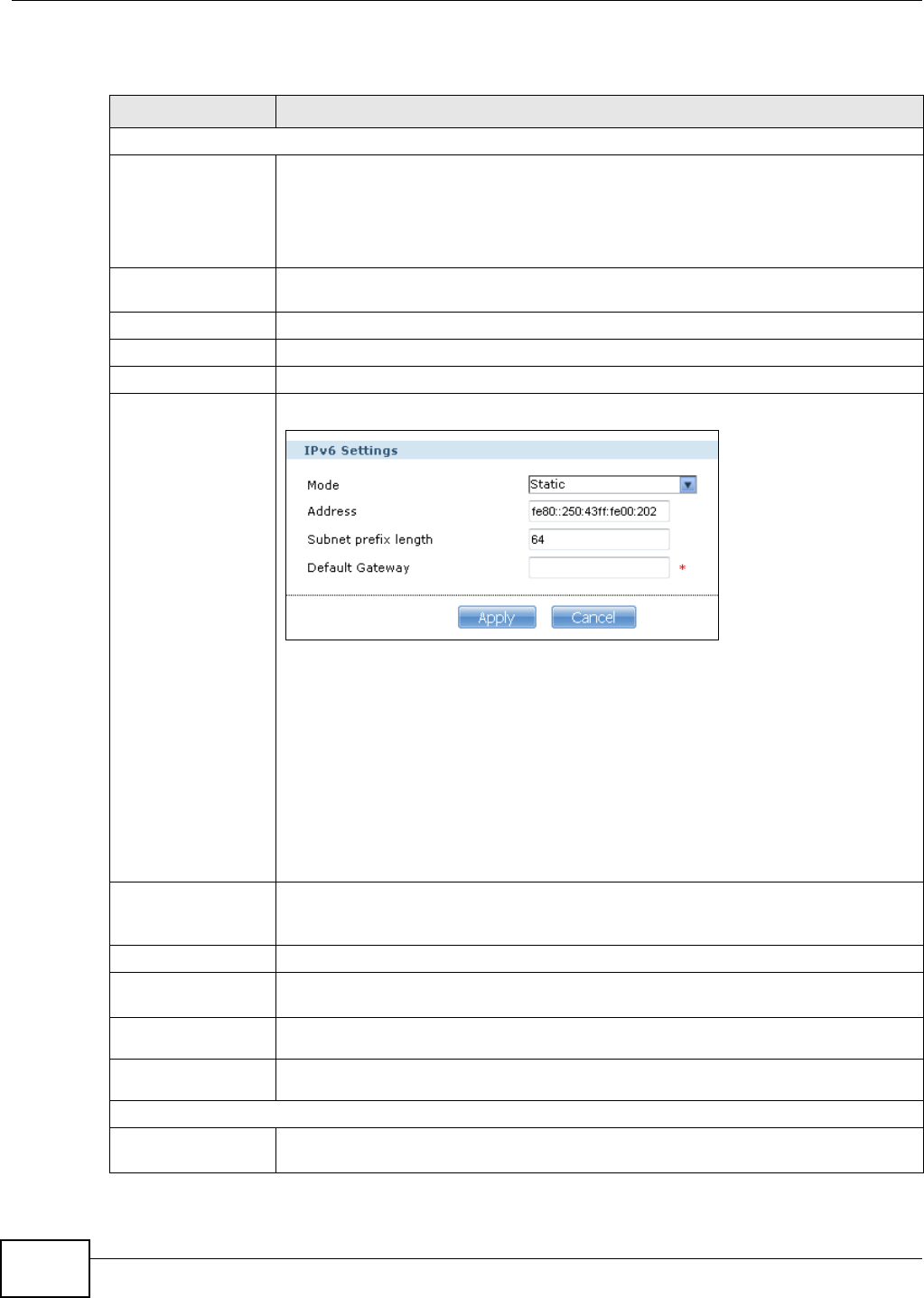
Chapter 9 Network
Media Server User’s Guide
174
The following table describes the labels in this screen.
Table 28 Network > TCP/IP
LABEL DESCRIPTION
IP Address
Dynamic Select this option to have the NSA get IP address information automatically.
If no IP address information is assigned, the NSA uses Auto-IP to assign itself an IP
address and subnet mask. For example, you could connect the NSA directly to your
computer. If the computer is also set to get an IP address automatically, the computer
and the NSA will choose addresses for themselves and be able to communicate.
Static Select this option for the NSA to use fixed TCP/IP information. You must fill in the
following fields.
IP Address Type an IP address in this field.
IP Subnet Mask Type an IP subnet mask in this field.
Default Gateway Type a default gateway address in this field.
IPv6 Settings Click this to open a screen where you can configure IPv6 address settings.
Mode: Select Auto to have the NSA use the IPv6 prefix from the connected router’s
Router Advertisement (RA) to generate an IPv6 address. Select Static to manually
enter a fixed IPv6 address. Select Disable to have the NSA not use IPv6.
Address: For static mode, enter the fixed IPv6 address here.
Subnet prefix length: For static mode, enter the IPv6 prefix length here.
Default Gateway: For static mode, enter the IPv6 address of the default gateway
here.
Click Apply to save and apply your settings or click Cancel to close this screen without
saving changes.
DNS DNS (Domain Name System) is for mapping a domain name to its corresponding IP
address and vice versa. If you have the IP address(es) of the DNS server(s), enter
them.
Dynamic Select the option to have the NSA get a DNS server address automatically.
Static Select this option to choose a static DNS server address. Type the DNS server IP
address(es) into the fields below.
Primary DNS
Server Type a primary DNS server IP address.
Secondary DNS
Server Type a secondary DNS server IP address.
HTTP (Web Configurator)
Enable Another Web
Configuration Port Select this to configure an additional HTTP port for accessing the web configurator.
Specify a number in the Port Number field.
Chapter 9 Network
Media Server User’s Guide 175
9.5 UPnP Port Mapping Screen
Use UPnP (Universal Plug and Play) port mapping to allow access from the WAN to services you
select on the NSA. It is recommended that you place the NSA behind an Internet gateway firewall
device to protect the NSA from attacks from the Internet (see RAID and Data Protection on page
169 for firewall type suggestions). Many such Internet gateways use UPnP to simplify peer-to-peer
network connectivity between devices. UPnP can automatically configure the Internet gateway’s
firewall and Network Address Translation (NAT) to allow access to the NSA from the Internet.
Figure 81 UPnP for FTP Access
In the above example, UPnP creates a firewall rule and NAT port forwarding mapping to send FTP
traffic (using TCP port number 21) from the public IP address a.b.c.d to the NSA’s private IP
address of 192.168.1.20.
Use the NSA’s UPnP Port Mapping screen to configure the UPnP settings your Internet gateway
uses to allow access from the WAN (Internet) to services you select on the NSA. You can also set
which port Internet users need to use in order to access a specific service on the NSA.
Note: To use UPnP port mapping, your Internet gateway must have UPnP enabled.
Jumbo Frames Jumbo frames improve network performance. You must have a 1 Gbps (Gigabit
Ethernet) network that supports jumbo frames. Select the largest size of frame that all
of your network devices (including computer Ethernet cards and switches, hubs, or
routers) support.
When enabled, you can choose between 4 KB, 8 KB, and 9 KB frame sizes.
Note: If you enable jumbo frames on the NSA in a network that does not support them,
you will lose access to the NSA. If this occurs, you will have to restore the factory
default configuration. Push the RESET button on the NSA’s rear panel and
release it after you hear a beep.
Network Diagnostic
Tool Use this section to test the network connection to a particular IP address or domain
name. Select an address or type it into the field. Then click Ping to have the NSA send
a packet to test the network connection.
•Successfully pinged host - The NSA is able to “ping” the host, the network
connection is OK.
•Unable to ping host - The NSA is able to “ping” the selected host.
Apply Click this to save your TCP/IP configurations. After you click Apply, the NSA restarts.
Wait until you see the Login screen or until the NSA fully boots and then use the NAS
Starter Utility to rediscover it.
Reset Click this to restore your previously saved settings.
Table 28 Network > TCP/IP (continued)
LABEL DESCRIPTION
TCP: 21
TCP: 21
192.168.1.20
a.b.c.d
Chapter 9 Network
Media Server User’s Guide
176
If your Internet gateway supports Port Address Translation (PAT is sometimes included with a port
forwarding feature), you can have the Internet users use a different TCP port number from the one
the NSA uses for the service.
Figure 82 UPnP Port Address Translation for FTP Example
In the above example, the Internet gateway uses PAT to accept Internet user FTP sessions on port
2100, translate them to port 21, and forward them to the NSA.
9.5.1 UPnP and the NSA’s IP Address
It is recommended that the NSA use a static IP address (or a static DHCP IP address) if you will
allow access to the NSA from the Internet. The UPnP-created NAT mappings keep the IP address
the NSA had when you applied your settings in the UPnP Port Mapping screen. They do not
automatically update if the NSA’s IP address changes.
Note: WAN access stops working if the NSA’s IP address changes.
For example, if the NSA’s IP address was 192.168.1.33 when you applied the UPnP Port Mapping
screen’s settings and the NSA later gets a new IP address of 192.168.1.34 through DHCP, WAN
access stops working because the Internet gateway still tries to forward traffic to IP address
192.168.1.33. Since you can no longer access the NSA from the WAN, you would have to access
the NSA from the LAN and re-apply your UPnP Port Mapping screen settings to update the
Internet gateway’s UPnP port mappings.
Figure 83 UPnP Using the Wrong IP Address
9.5.2 UPnP and Security
UPnP’s automated nature makes it easier to use than manually configuring firewall and NAT rules,
but it is also less secure. Using UPnP may make your network more susceptible to snooping and
hacking attacks.
TCP: 2100
TCP: 21
192.168.1.20
a.b.c.d
192.168.1.34
a.b.c.d
192.168.1.33

Chapter 9 Network
Media Server User’s Guide 177
9.5.3 The NSA’s Services and UPnP
This section introduces the NSA’s services which an Internet gateway can use UPnP to allow access
to from the Internet.
BitTorrent
BitTorrent is a distributed peer-to-peer file-sharing protocol that the NSA’s download service can
use. Using UPnP port mapping for BitTorrent lets BitTorrent work faster.
CIFS (Windows File Sharing)
Common Internet File System (CIFS) is a standard protocol supported by most operating systems
in order to share files across the network. Using UPnP port mapping for CIFS allows users to
connect from the Internet and use programs like Windows Explorer to access the NSA’s shares to
copy files from the NSA, delete files on the NSA, or upload files to the NSA from the Internet.
If you configure UPnP port mapping to allow CIFS access from the WAN but cannot get it to work,
you may also have to configure the Internet gateway to also allow NetBIOS traffic. See Section 7.3
on page 153 for more on CIFS.
FTP
File Transfer Protocol is a standard file transfer service used on the Internet. Using UPnP port
mapping for FTP allows remote users to use FTP from the Internet to access the NSA’s shares. A
user with read and write access to a share can copy files from the share, delete files from the share,
or upload files to the share. See Section 10.4 on page 184 for more on FTP. If you use UPnP to allow
FTP access from the WAN, you may want to use a different WAN port number (instead of the default
of port 21) to make it more secure. Remember to tell the remote users to use the custom port
number when using FTP to access the NSA.
HTTP (Web Configurator)
You can use UPnP port mapping to allow access to the NSA’s management screens. If you use UPnP
to allow web configurator access from the WAN, you may want to use a different WAN port number
(instead of the default of port 80) to make it more secure. Remember to use the custom port
number when accessing the NSA’s web configurator from the Internet.
HTTP (Web Published Shares)
This is the NSA’s web publishing feature that lets people access files using a web browser without
having to log into the Home screens. Use UPnP port mapping to allow access to these files from the
Internet without having to enter a user name or password. See Section 10.7 on page 202 for more
on web publishing.
9.5.4 Configuring UPnP Port Mapping
Click Network > UPnP > Port Mapping to display the UPnP Port Mapping screen.
Use this screen to set how the Internet gateway’s UPnP feature configure’s the Internet gateway’s
NAT IP address mapping and port mapping settings. These settings allow Internet users connected
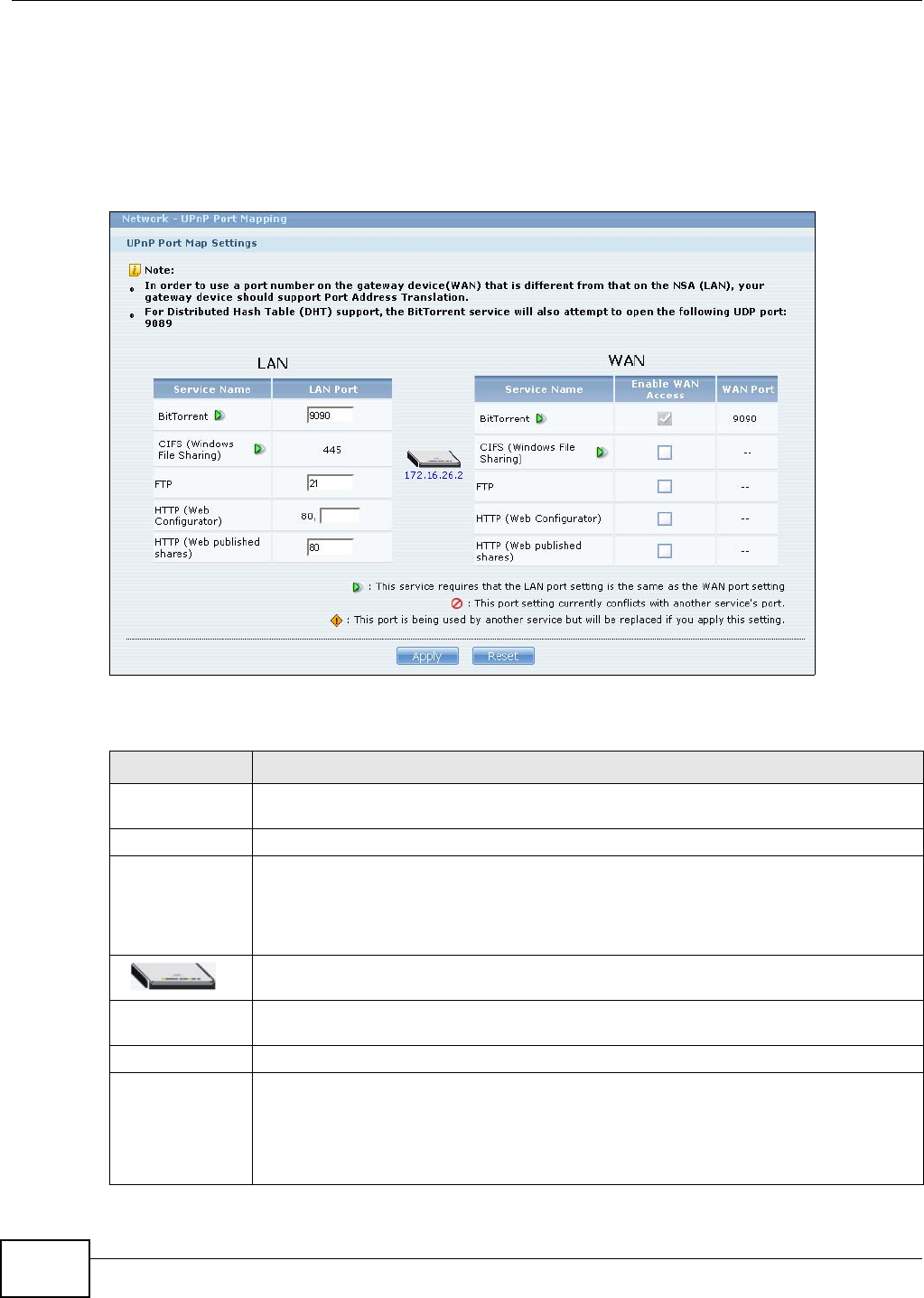
Chapter 9 Network
Media Server User’s Guide
178
to the Internet gateway’s WAN interface to access services on the NSA. You can set which port
Internet users need to use to access a specific service on the NSA.
Note: Some Internet gateways will delete all UPnP mappings after reboot. So if the
Internet gateway reboots, you may need to use this screen again to re-apply the
UPnP port mapping.
Figure 84 Network > UPnP > Port Mapping
The following table describes the labels in this screen.
Table 29 Network > UPnP > Port Mapping
LABEL DESCRIPTION
LAN Use these fields to specify what port the Internet gateway uses to connect from its LAN
port to the service on the NSA.
Service Name This read-only field identifies a service on the NSA.
LAN Port Specify the port number (1~65,536) the Internet gateway needs to use to connect from
its LAN port to the service on the NSA. This is the NSA’s internal port number for the
service. Changing a service’s port number in this screen also changes it in other NSA
screens that display it. Similarly, changing a service’s port number in another NSA screen
also changes it here.
The number below this icon is your Internet gateway’s WAN IP address (the IP address
your Internet gateway uses for connecting to the Internet).
WAN Use these fields to specify what port Internet users must use to connect to the Internet
gateway’s WAN port in order to connect to the service on the NSA.
Service Name This read-only field identifies a service on the NSA.
Enable WAN
Access Select this check box to have UPnP configure your Internet gateway to allow access from
the Internet to the NSA’s service.
If you clear this check box, people will not be able to access the NSA’s service from the
Internet unless you manually configure the Internet gateway’s firewall and NAT rules to
allow access.
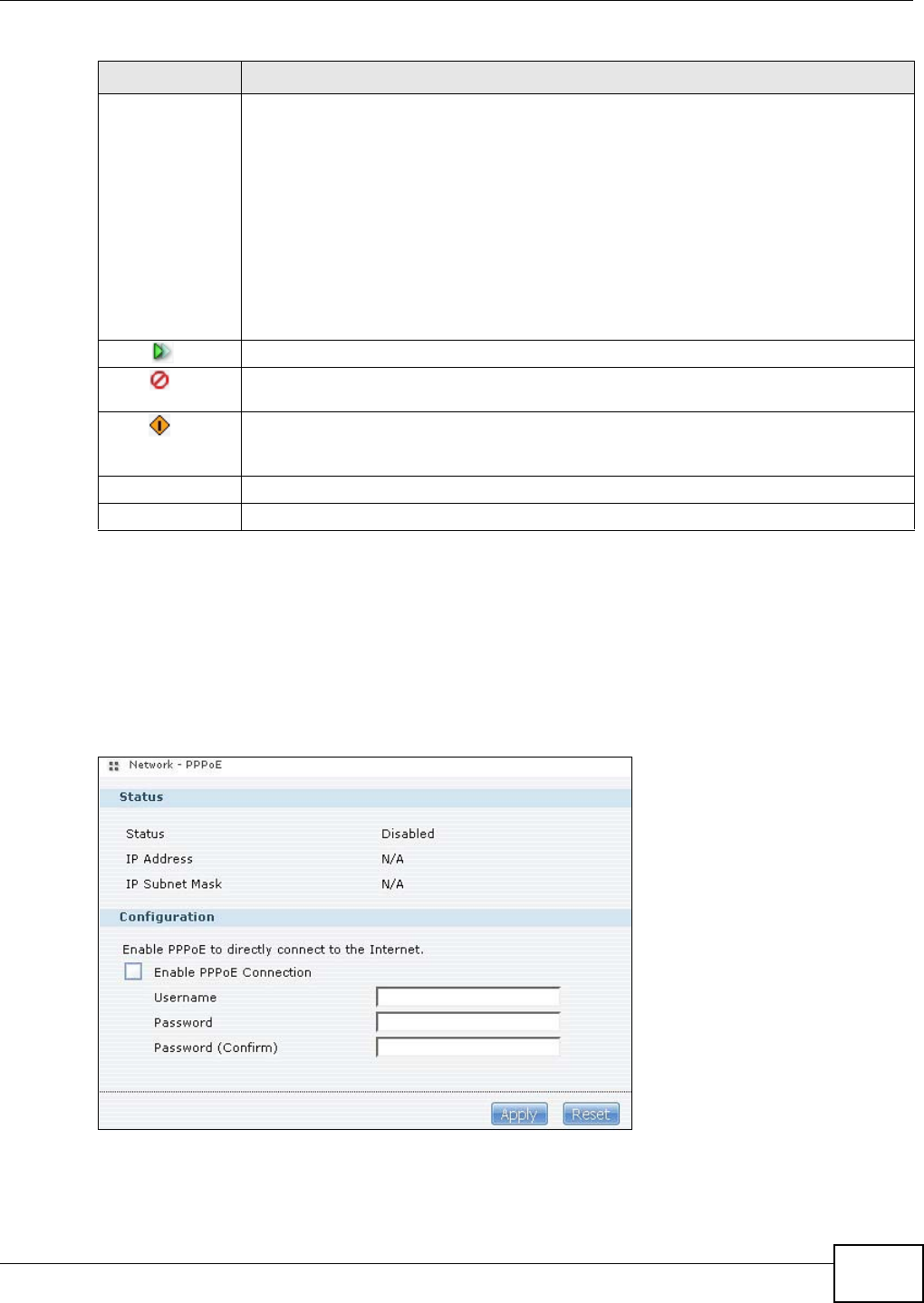
Chapter 9 Network
Media Server User’s Guide 179
9.6 The PPPoE Screen
Use this screen to configure PPPoE settings for a direct Internet connection.
Click Network > PPPoE in the navigation panel to open the following screen.
Figure 85 Network > PPPoE
WAN Port When you enable WAN access for one of the NSA’s services, specify the port number
(1~65,536) Internet uses need to use to connect to the Internet gateway’s WAN port in
order to access the service on the NSA. Whoever wants to access a service on the NSA
from the Internet must use this port number.
BitTorrent’s WAN port must be the same as the LAN port.
Make sure there is not another service using TCP protocol with the same port number. See
Appendix C on page 407 for a list of common services and their associated protocols and
port numbers.
If another device is using the same port (the Internet gateway has the same port number
mapped to another LAN IP address), the NSA overwrites it when you apply the setting and
WAN users can no longer access the other device.
This icon means the service’s LAN and WAN port numbers must be the same.
This icon means another service is using the same port number as this service. Change
the port number of one of the services so they use different port numbers.
This icon means another service is using the listed port, but the port the other service is
using will be replaced if you apply the setting. The other service will no longer be
accessible from the listed port.
Apply Click Apply to save your changes back to the NSA.
Reset Click Reset to begin configuring this screen afresh.
Table 29 Network > UPnP > Port Mapping (continued)
LABEL DESCRIPTION
Chapter 9 Network
Media Server User’s Guide
180
The following table describes the labels in this screen.
Table 30 Network > PPPoE
LABEL DESCRIPTION
Status
Status This field displays the status of PPPoE connection.
IP Address This field displays the IP address of your PPPoE connection.
IP Subnet Mask This field displays the IP subnet mask of your PPPoE connection.
Configuration
Enable PPPoE
Connection Select this option to establish a direct Internet connection for the NSA. You need to enter
the username and password as given by your ISP.
Username Enter the username exactly as your ISP assigned. If assigned a name in the form
user@domain where domain identifies a service name, then enter both components
exactly as given.
Password Enter the password associated with the username above.
Password
(Confirm) Retype the password for confirmation.
Apply Click this to save your changes.
Reset Click this to restore previously saved settings.

Media Server User’s Guide 181
CHAPTER 10
Applications
10.1 Overview
This chapter discusses the features in the Application screens. The NSA contains various
applications for file sharing and downloading.
10.2 What You Can Do
•Use the FTP Server screen (Section 10.4 on page 184) to configure settings for FTP file transfers
to/from the NSA.
•Use the Media Server screen (Section 10.5 on page 185) to share files with media clients.
•Use the Download Service screen (Section 10.6 on page 190) to download files from the
Internet.
•Use the Web Publishing screen (Section 10.7 on page 202) to publish shares for people to
access files using a web browser.
•Use the Broadcatching screen (Section 10.8 on page 203) to download frequently updated
digital content like TV programs, radio talk shows, Podcasts (audio files), and blogs.
•Use the Print Server screen (Section 10.9 on page 209) to share a printer.
•Use the Copy/Sync Button screen (Section 10.10 on page 211) to transfer files between a USB
device and the NSA.
•Use the Package screen (Chapter 11 on page 225) to set up additional applications in your NSA.
The NSA can download multiple packages/files at once and automatically goes through all the
installation steps.
•Use the Auto Upload screens (Chapter 12 on page 275) to upload files in selected shares to
your Flickr and/or YouTube accounts.
•Use the Dropbox screen (Chapter 13 on page 289) to synchronize and back up your Dropbox
account.
10.3 What You Need to Know
FTP
File Transfer Protocol (FTP) is a file transfer service that operates on the Internet. A system running
the FTP server accepts commands from a system running an FTP client. FTP is not a secure
protocol. Your file transfers could be subject to snooping.
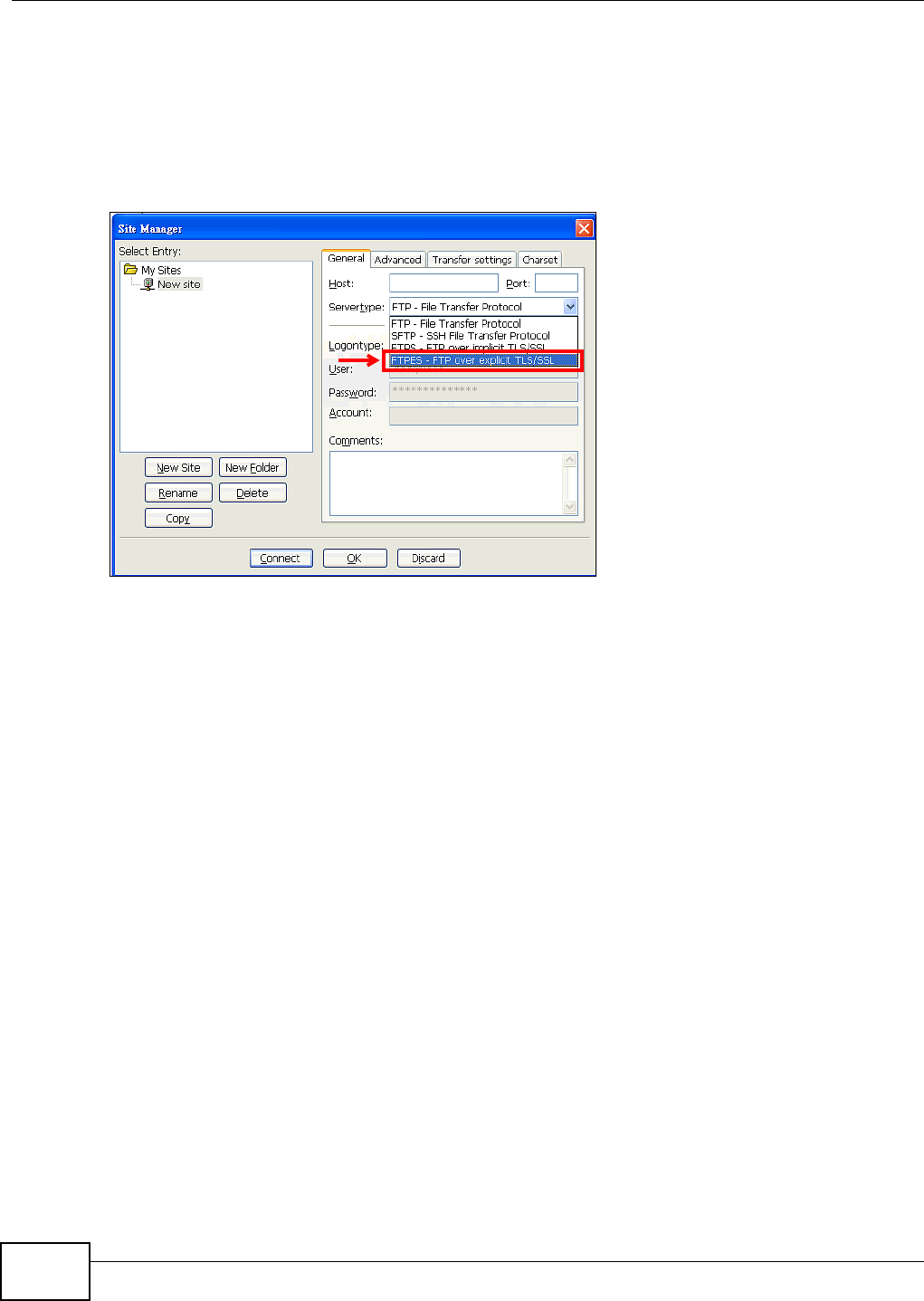
Chapter 10 Applications
Media Server User’s Guide
182
FTPES (File Transfer Protocol over Explicit TLS/SSL)
File Transfer Protocol over Explicit TLS/SSL (FTPES) is a file transfer service that uses either TLS
(Transport Layer Security) or SSL (Secure Sockets Layer) for secure transfers across the Internet.
It requests for a mutual method of encryption from the FTP server for its file transfer sessions. Your
FTP client must be set to use FTPES as in the following example.
Figure 86 FTP Client Example
DLNA Media Server
The media server feature lets anyone on your network play video, music, and photos from the NSA
(without having to copy them to another computer). The NSA can function as a DLNA-compliant
media server. The NSA streams files to DLNA-compliant media clients such as gaming consoles,
networked TVs, DVD players, stereos, home theaters, satellite boxes, set-top-boxes, mobile
phones, portable music players, and multimedia tablets. The Digital Living Network Alliance (DLNA)
is a group of personal computer and electronics companies that works to make products compatible
in a home network.
iTunes Server
The NSA iTunes server feature lets you use Apple’s iTunes software on a computer to play music
and video files stored on the NSA. You can download iTunes from www.apple.com.
Download Service
The NSA’s download service downloads files from the Internet directly to the NSA. You do not have
to download to your computer and then copy to the NSA. This can free up your computer’s system
resources.
The NSA can download using these protocols.
• HTTP: The standard protocol for web pages.
• FTP: A standard Internet file transfer service.
• BitTorrent: A popular distributed peer-to-peer files sharing protocol.

Chapter 10 Applications
Media Server User’s Guide 183
BitTorrent
The NSA includes a BitTorrent client for fast downloading and sharing of large files (such as
educational public domain videos). With BitTorrent, you share while you’re downloading the file.
BitTorrent breaks up the file and distributes it in hundreds of chunks. You start sharing the file as
soon as you have downloaded a single chunk.
Web Publishing
Web publishing lets you “publish” shares (containing folders and files) on the NSA so people can
access the files using a web browser without having to log into the Home screens. This way you can
share files with others without them having to know and enter a username and password.
For example, if you want to share photos in a FamilyPhotos share, you could “web publish” it and
others could use a web browser to access the photos at http://my-NSA’s-IP-Address/MyWeb/
FamilyPhotos.
Broadcatching
Broadcatching is the downloading of digital content from Internet feeds. Use broadcatching to have
the NSA download frequently updated digital content like TV programs, radio shows, podcasts
(audio files), and blogs.
RSS
RSS (Really Simple Syndication) is a format for delivering frequently updated digital content. A
channel uses a feed to deliver its contents (items). Subscribe the NSA to a feed to be able to
download the contents.
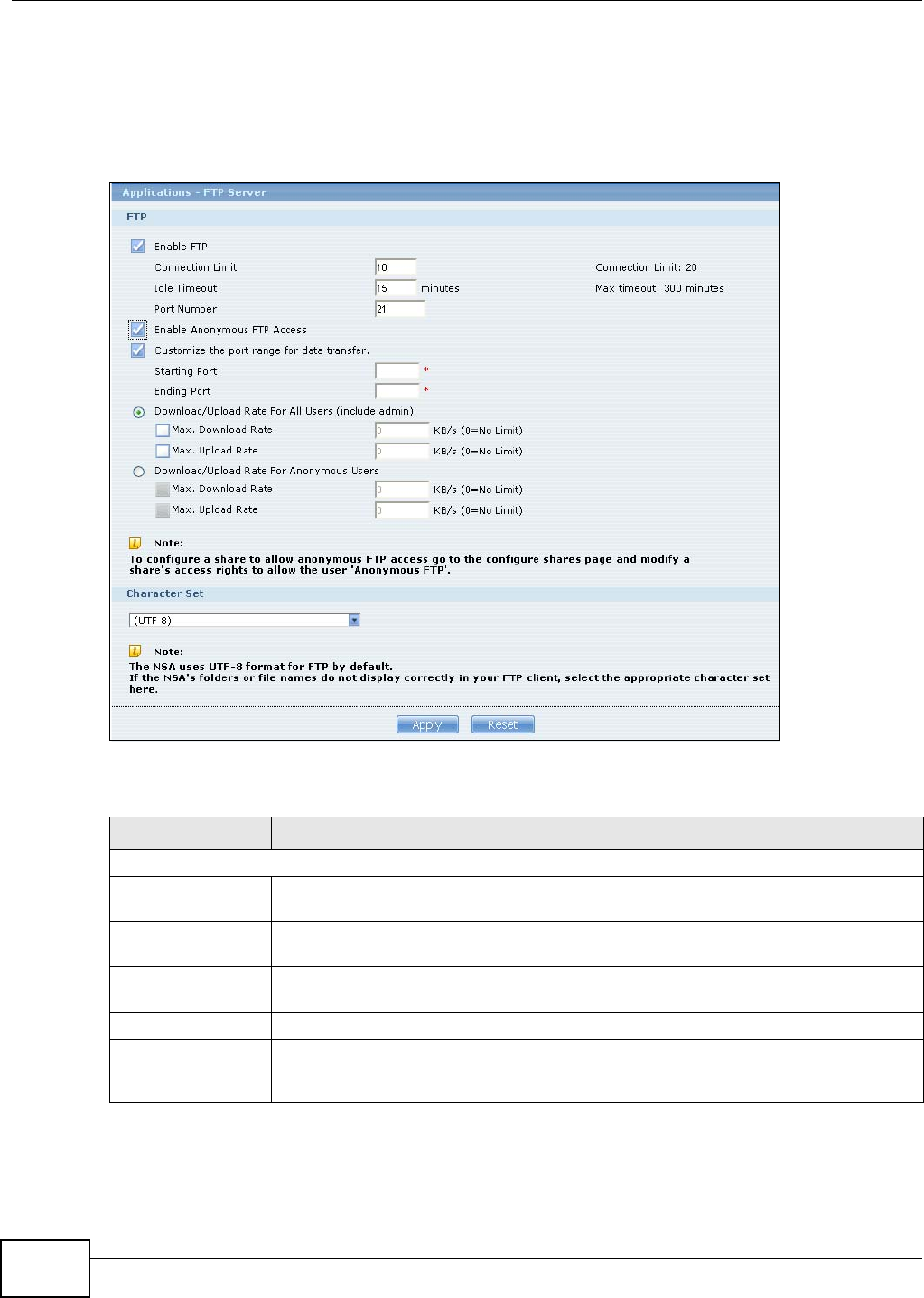
Chapter 10 Applications
Media Server User’s Guide
184
10.4 FTP Server
Use FTP or FTPES (FTP over Explicit TTL/SSL) to upload files to the NSA and download files from the
NSA. Click Applications > FTP to open the following screen.
Figure 87 Applications > FTP
The following table describes the labels in this screen.
Table 31 Applications > FTP
LABEL DESCRIPTION
FTP
Enable FTP You can use FTP to send files to the NSA or get files from the NSA. Select this check box
to allow users to connect to the NSA via FTP; otherwise clear the check box.
Connection Limit Enter the maximum number of concurrent FTP connections allowed on the NSA in this
field. See your screen for your model’s connection limit.
Idle Timeout Enter the length of time that an FTP connection can be idle before timing out. The
timeout limit is 300 minutes.
Port Number This is the port number used by the NSA for FTP traffic.
Enable Anonymous
FTP Access Select this check box to allow any user to log into the NSA using ‘FTP’ or ‘anonymous’
as a username and no password. Any other name is considered a username, so must be
valid and have a corresponding correct password.

Chapter 10 Applications
Media Server User’s Guide 185
10.5 The Media Server Screens
The media server application allows you to share media files with media clients.
Customize the port
range for data
transfer
Select this check box to assign a port range for FTP clients to use when downloading
files from the NSA using passive mode.
The connection limit is restricted to half of the port numbers within the range if this
value is smaller than the one configured in the Connection Limit field. For example,
you specified a port range from 1024 to 1029 and configured 10 in the Connection
Limit field. The FTP connection limit will only be 3 (6 ports in the range divided by 2)
because it is the smaller value.
Starting Port Enter the first port number in the range. Choose from 1024 to 65535.
Ending Port Enter the last port number in the range. Choose from 1024 to 65535.
Download/Upload
Rate For All Users
(include admin)
Select this if you want to limit the download/upload bandwidth for all users who are
logged into the NSA, including the administrator.
•Max. Download Rate - Enter the download speed (in kilobytes/s) that the NSA
allows for users who are logged into the NSA.
•Max. Upload Rate - Enter the upload speed (in kilobytes/s) that the NSA allows for
users who are logged into the NSA.
Download/Upload
Rate For
Anonymous Users
Select this if you want to limit the download/upload bandwidth for users who log into
the NSA using ‘FTP’ or ‘anonymous’ as a username and no password.
•Max. Download Rate - Enter the download speed (in kilobytes/s) that the NSA
allows for users who are logged into the NSA.
•Max. Upload Rate - Enter the upload speed (in kilobytes/s) that the NSA allows for
users who are logged into the NSA.
Character Set The NSA uses UTF-8 (8-bit UCS/Unicode Transformation Format) format for FTP by
default. If the NSA’s folders, or file names do not display correctly in your FTP client,
select the appropriate language encoding here.
This setting applies to all FTP client connections to the NSA. It does not affect your
Windows/CIFS connections (it will not correct the character display in Windows
Explorer).
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Table 31 Applications > FTP
LABEL DESCRIPTION
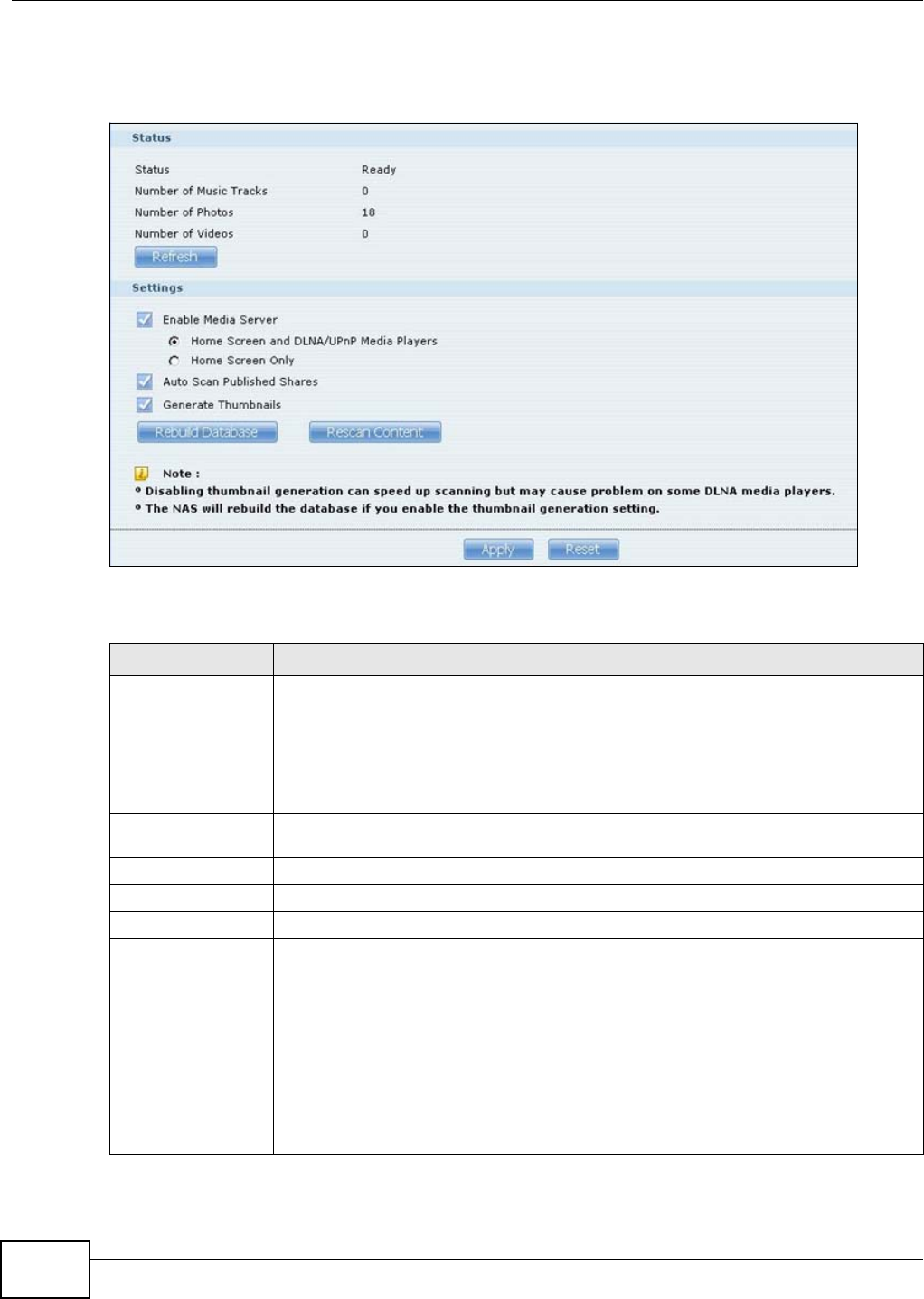
Chapter 10 Applications
Media Server User’s Guide
186
Click Applications > Media Server to open the following screen. Use this screen to view the
media server’s status and rebuild the media server database.
Figure 88 Applications > Media Server > Media Server
The following table describes the labels in this screen.
Table 32 Applications > Media Server > Media Server
LABEL DESCRIPTION
Status This shows the media server’s current state of activity.
Synchronizing displays while the NSA is building the media database.
Ready means the NSA has finished building the database.
Stopped displays when the media server is dead and for a short time while the media
server is restarted before rebuilding the database.
Number of Music
Tracks This is how many music files the media server has to share out to media clients.
Number of Photos This is how many photo files the media server has to share out to media clients.
Number of Videos This is how many video files the media server has to share out to media clients.
Refresh Click this to update the information in the Status field.
Enable Media Server Select this to have the NSA share the media files in the shares selected in the Share
Publish tab. Clear it to stop the NSA from sharing media files through the Home
screens or media players.
Select Home Screen and DLNA/UPnP Media Players to let users use the NSA’s
Home screens and media players to play the published media files. Users can play the
published media files by logging into the NSA or by using a media player connected to
the network without logging in.
Select Home Screen Only to require users to use the NSA’s Home screens play the
published media files. This lets you require users to log in to play the published media
files.
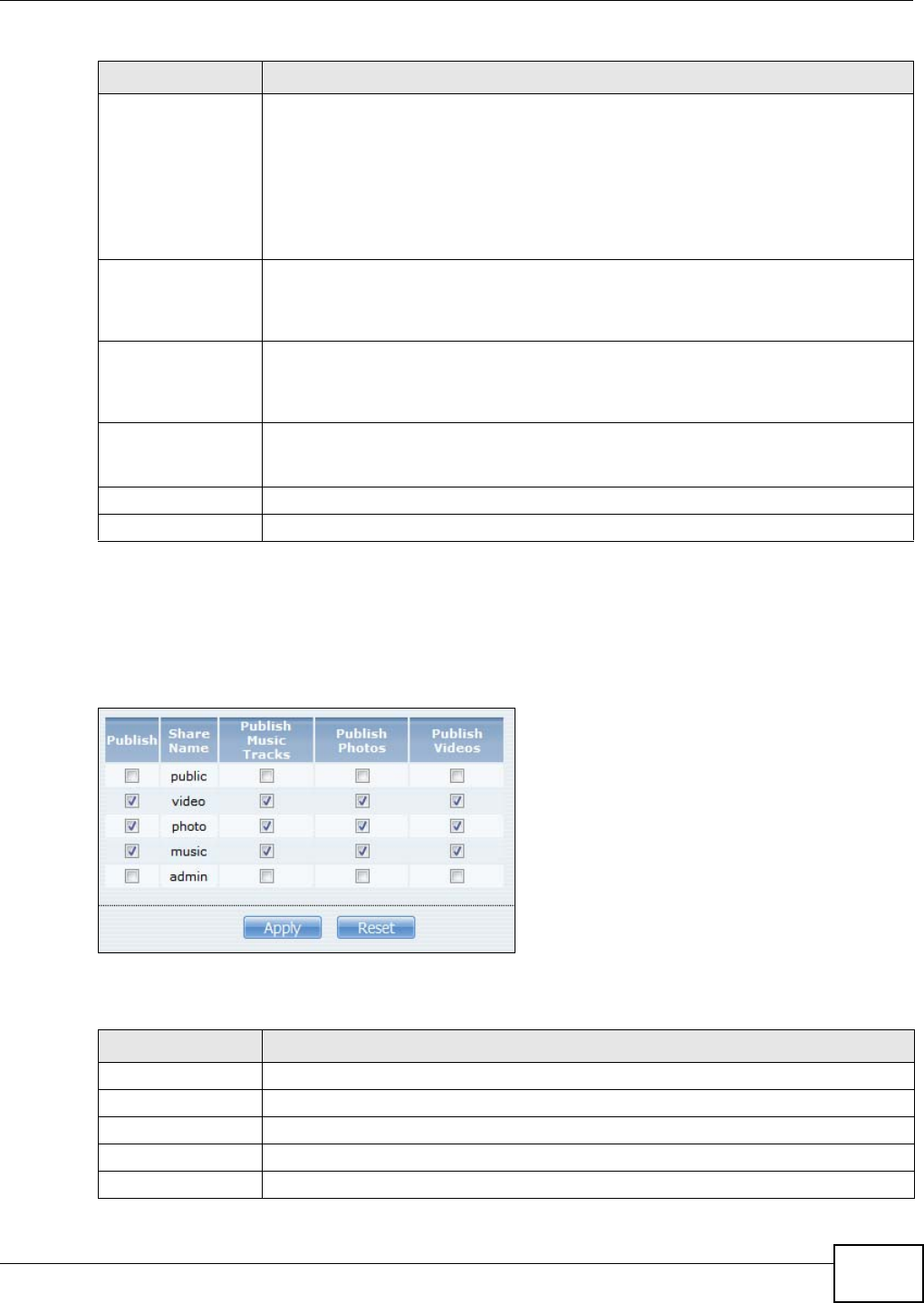
Chapter 10 Applications
Media Server User’s Guide 187
10.5.1 The Media Server Share Publish Screen
Click Applications > Media Server > Share Publish to open the following screen. Use this
screen to select shares to publish (share with media clients like the DMA-2501 and iTunes).
Figure 89 Applications > Media Server > Share Publish
The following table describes the labels in this screen.
Auto Scan Published
Shares The NSA has to scan the published shares and find the media files before the media
server can share them. Select this to automatically scan the published shares for media
files.
The auto-scan after adding a large number of files to your published shares could take
up enough of the NSA’s resources to slow other functions like file downloads or sharing.
Clear this option to stop the NSA from automatically scanning the published shares for
media files. With the auto-scan disabled, you can still click the Rescan Content button
to have the NSA scan for newly added media files.
Generate
Thumbnails Select this to have the NSA create thumbnails for media files. Clear it to stop the NSA
from creating thumbnails for media files. If you enable this and click Apply, the NSA
rebuilds the media server database. This can take a long time if the published shares
contain many files.
Rebuild Database Click this to have the NSA completely rebuild the media server database and scan all of
the published share contents for media files. This can take a long time if the published
shares contain many files. You may need to use this if the media clients cannot see the
files in the media server.
Rescan Content Click this to have the NSA scan for newly added media files. This only checks the files
added to the published shares since the last scan and is faster than rebuilding the
database.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Table 32 Applications > Media Server > Media Server
LABEL DESCRIPTION
Table 33 Applications > Media Server > Share Publish
LABEL DESCRIPTION
Publish Select this to have the media server share a share’s media files with media clients.
Share Name This column lists names of shares on the NSA.
Publish Music Tracks Select this to give media clients access to the share’s music files.
Publish Photos Select this to give media clients access to the share’s photo files.
Publish Videos Select this to give media clients access to the share’s video files.
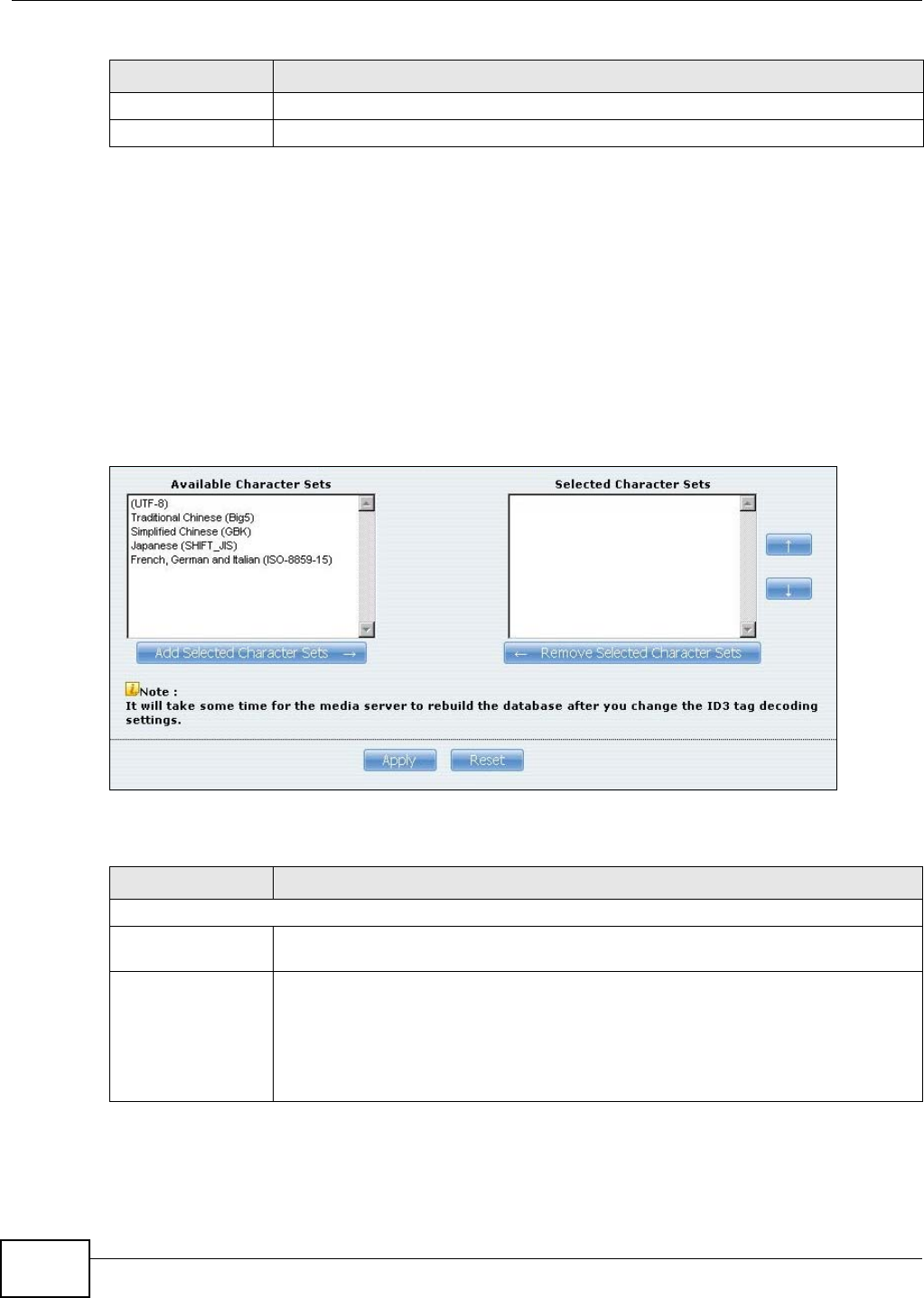
Chapter 10 Applications
Media Server User’s Guide
188
10.5.2 The Media Server ID3 Tag Decoding Screen
Click Applications > Media Server > ID3 Tag Decoding to open the following screen. ID3 tags
store information about a media file such as the title, artist, album, and genre in the file itself. To
help the NSA find the correct character set to decode these tags, use this screen to select which
character sets the NSA attempts to use and the order the NSA tries them in.
Note: It may take some time for the media server to rebuild the database after you
change the ID3 tag character set settings. How long it takes depends on how many
media files you have. Some of the media files may not appear in the Home screens
until the rebuilding finishes.
Figure 90 Applications > Media Server > ID3 Tag Decoding
The following table describes the labels in this screen.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Table 33 Applications > Media Server > Share Publish
LABEL DESCRIPTION
Table 34 Applications > Media Server > ID3 Tag Decoding
LABEL DESCRIPTION
Media Server
Available Character
Sets This list box displays the language character sets the NSA can perform.
Add Selected
Character Sets Select types of character set in the Available Character Sets box and click this to add
them to the list of character sets that the NSA should attempt to use to decode ID3
tags in your media files. Use the [SHIFT] key to select a range of entries. Hold down
the [CTRL] key to select multiple individual entries.
If the NSA is not able to decode a file’s ID3 tags using the selected character sets, it
attempts to auto-detect their encoding type.
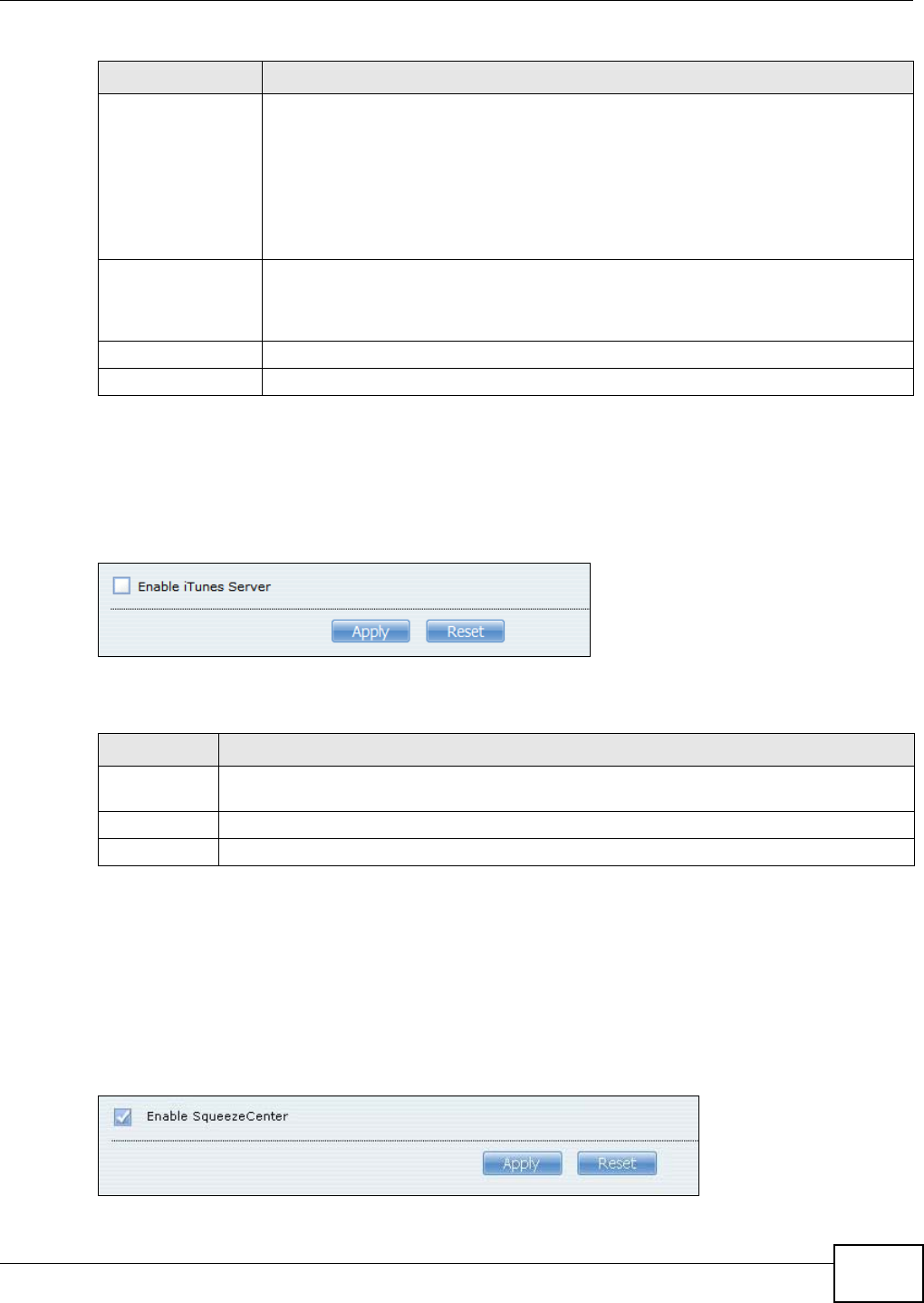
Chapter 10 Applications
Media Server User’s Guide 189
10.5.3 The Media Server iTunes Server Screen
Click Applications > Media Server > iTunes Server to open the following screen. Use this
screen to turn the iTunes server on or off.
Figure 91 Applications > Media Server > iTunes Server
The following table describes the labels in this screen.
10.5.4 The Media Server SqueezeCenter Screen
SqueezeCenter enables you to manage a Logitech's Squeezebox device connected to the NSA.
Click Applications > Media Server > SqueezeCenter to open the following screen. This screen
is available when the SqueezeCenter application is installed using Package Management (see
Section 11.4 on page 226). Use this screen to turn the SqueezeCenter application on or off.
Figure 92 Applications > Media Server > SqueezeCenter
Selected Character
Sets This list box displays the character sets the NSA can use to decode ID3 tags in your
media files. The NSA attempts to use them in the order listed so select character sets
and use the up or down arrow to change their order to match the types of files you
have. So if most of your files are German, move the French, German and Italian
(ISO-8859-15) selection to the top of the list.
If the NSA cannot find a match among your selected character sets (or you have not
selected any character sets) it tries to auto-detect which character set the tags are
encoded with.
Remove Selected
Character Sets Select character sets in the Selected Character Sets box and click this to have the
NSA not attempt to use them to decode ID3 tags in your media files. Use the [SHIFT]
key to select a range of entries. Hold down the [CTRL] key to select multiple individual
entries.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Table 34 Applications > Media Server > ID3 Tag Decoding
LABEL DESCRIPTION
Table 35 Applications > Media Server > iTunes Server
LABEL DESCRIPTION
Enable iTunes
Server Check this to let anyone on your network use iTunes to play music files in the published
shares.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
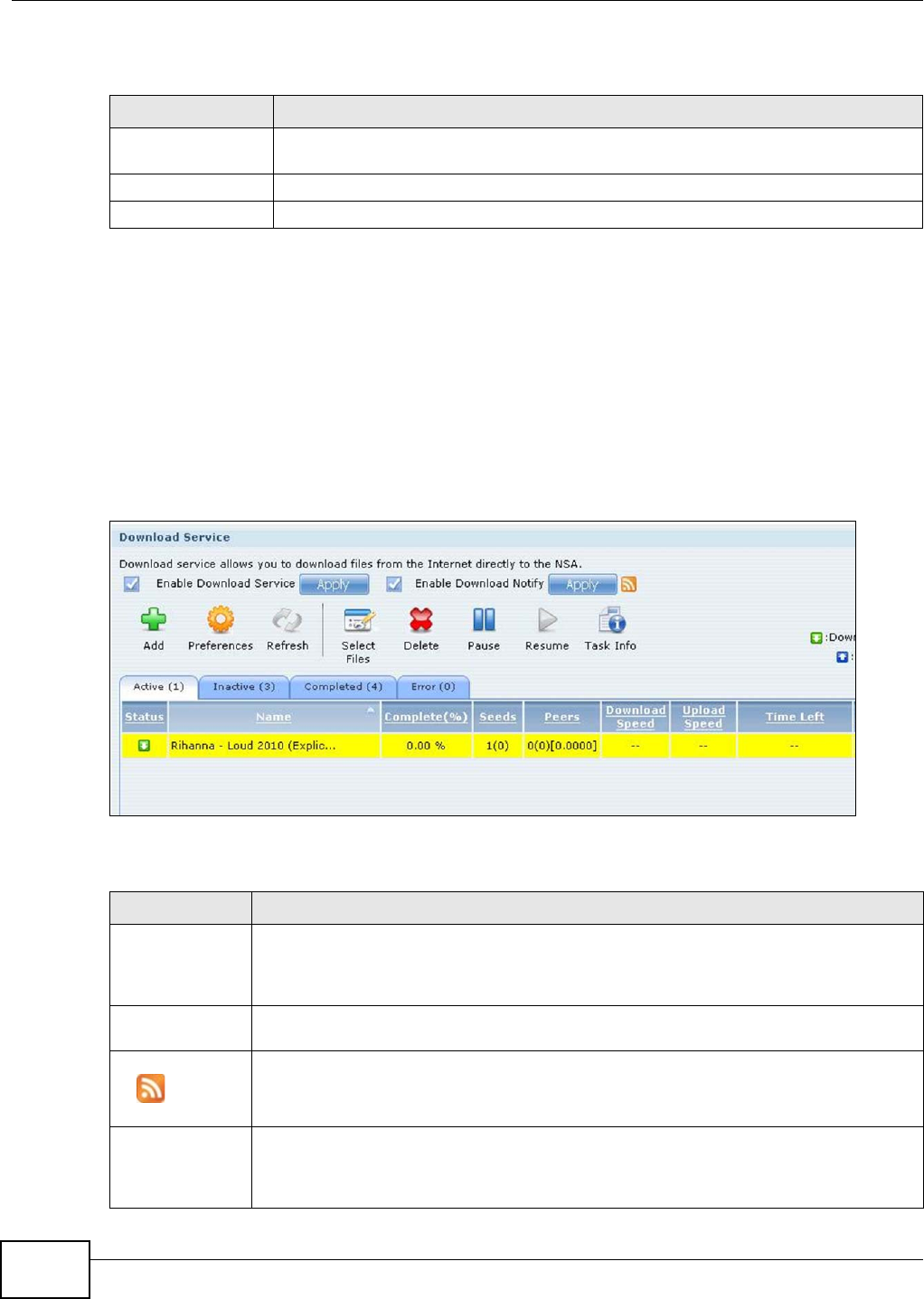
Chapter 10 Applications
Media Server User’s Guide
190
The following table describes the labels in this screen.
10.6 The Download Service Screen
The Download Service screen allows you to download files from the Internet.
Click Applications > Download Service to open the following screen. Use this screen to manage
the NSA’s file downloads.
Note: By default, the NSA saves downloads in the admin share’s download folder.
Figure 93 Applications > Download Service
The following table describes the labels in this screen.
Table 36 Applications > Media Server > SqueezeCenter
LABEL DESCRIPTION
Enable
SqueezeCenter Check this to enable SqueezeCenter.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Table 37 Applications > Download Service
LABEL DESCRIPTION
Enable Download
Service Use this option (and click the Apply button) to turn the download service off or on. If you
turn off the service, all downloads are paused. Files currently downloading are queued.
Turning on the download service resumes downloads (or restarts them if they are not able
to resume).
Enable Download
Notify Use this option (and click the Apply button) to turn the download service notification off
or on. See Section 10.11.4 on page 214 for more details about this feature.
At the time of writing, the NSA supports RSS 2.0 feeds.
Click this to get and subscribe to the NSA channel feed. This enables you to keep track and
download the NSA’s new contents (items).
Add After you find a file to download, copy the file’s URL. Then log into the NSA web
configurator and go to the Applications > Download Server screen and click this
button. A screen opens where you create a new download task. You can paste the file’s
URL or use a BitTorrent file.
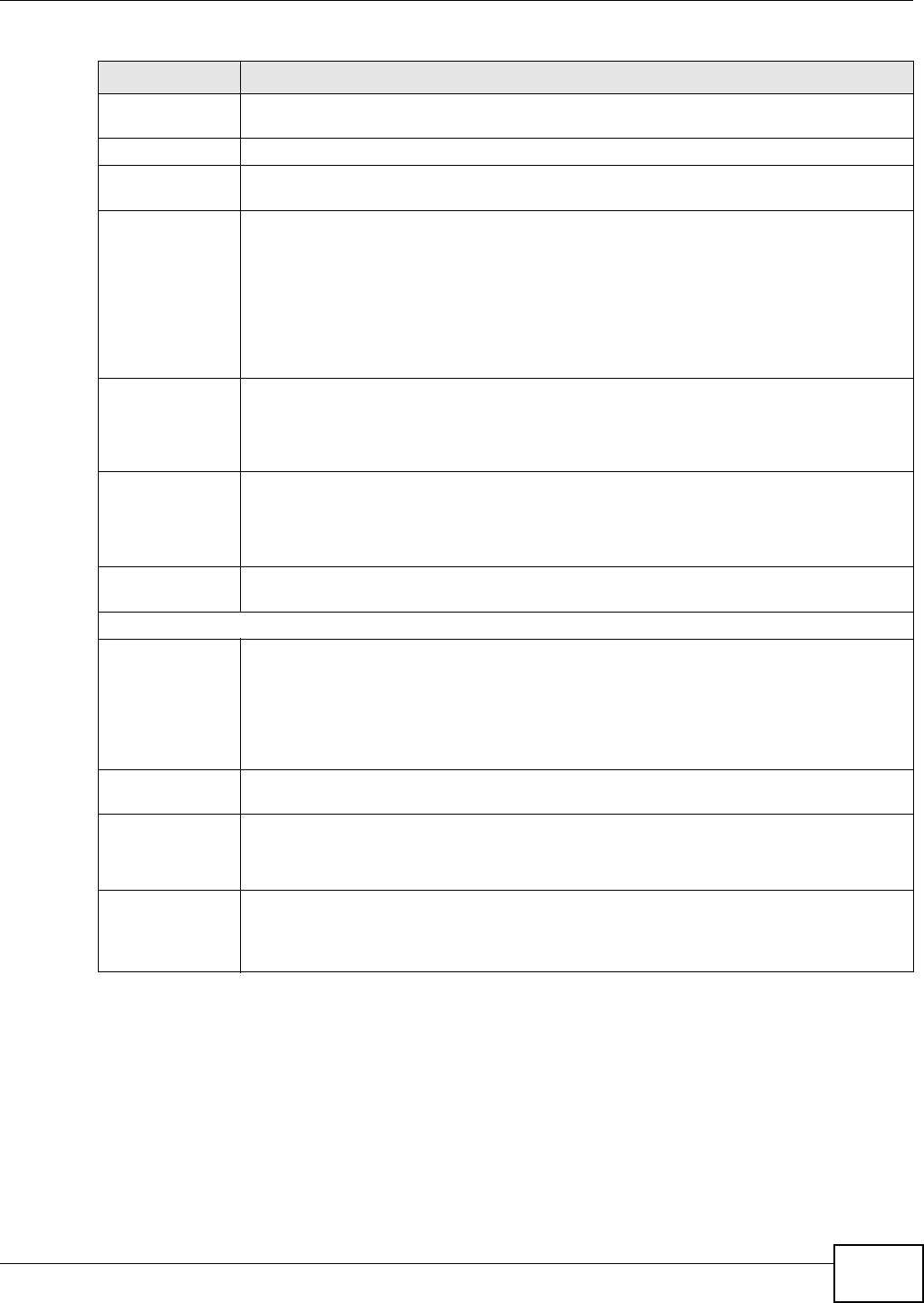
Chapter 10 Applications
Media Server User’s Guide 191
Preferences Click this to open a screen where you can set the default location for saving downloads
and configure your BitTorrent settings.
Refresh Click this to update the information displayed on the screen.
Select Files A single BitTorrent torrent file is often for multiple files. If you do not need all of the files
the torrent file specifies, click this to select which files to download.
Delete To delete download tasks (or manually clear out completed download tasks), select a
download task and click this to remove it from the list. A pop-up screen asks you to
confirm. Click Apply to delete or Cancel to quit. When you delete a download task, you
are given the option to delete the associated files. Selecting this option deletes a
downloaded file and in the case of a BitTorrent download task, also deletes the related
.torrent file.
Use your keyboard’s [SHIFT] key to select a range of download tasks. Use the [CTRL] key
and click individual download tasks to select multiple individual download tasks.
Pause Select a downloading item and click this to temporarily stop the download. Paused
downloads appear in the Download Service screen’s Inactive tab.
Use your keyboard’s [SHIFT] key to select a range of download tasks. Use the [CTRL] key
and click individual download tasks to select multiple individual download tasks.
Resume Select a paused item and click this to continue downloading the file.
Select a completed item and click this to re-seed a torrent file or download a file again. If
you want to re-seed a BitTorrent task, keep the torrent file and the completed file in their
original locations.
Task Info Select an item on the list and click this to display information about the download task.
See Section 10.6.6 on page 201 for more details.
The table lists your downloads. Click a column’s heading to sort the entries by that criteria.
Active Click this to see the list of files the NSA is currently downloading or sharing with other
BitTorrent users. The NSA handles a maximum of 10 active tasks at a time (or fewer
depending on how much of the NSA’s system memory is available). If you add more, they
appear in the Inactive tab.
BitTorrent downloads may appear in the Inactive tab for a while before showing in the
Downloading tab. The NSA automatically moves completed tasks to the Completed tab.
Inactive Click this to see the list of files that are queued (waiting in line) for the NSA to download or
the downloads that have been manually paused.
Completed Click this to see the list of files that the NSA has finished downloading.
The Location column shows where a downloaded file is saved on the NSA. Click on the
location link to open the share browser and access the file.
Error Click this to see the list of files that the NSA was not able to download. The NSA
automatically retries unsuccessful download attempts. The download displays in the error
tab when the re-attempts are also unsuccessful and the NSA stops trying to download the
file. To try the download again, use the Add button to create a new download task.
Table 37 Applications > Download Service (continued)
LABEL DESCRIPTION
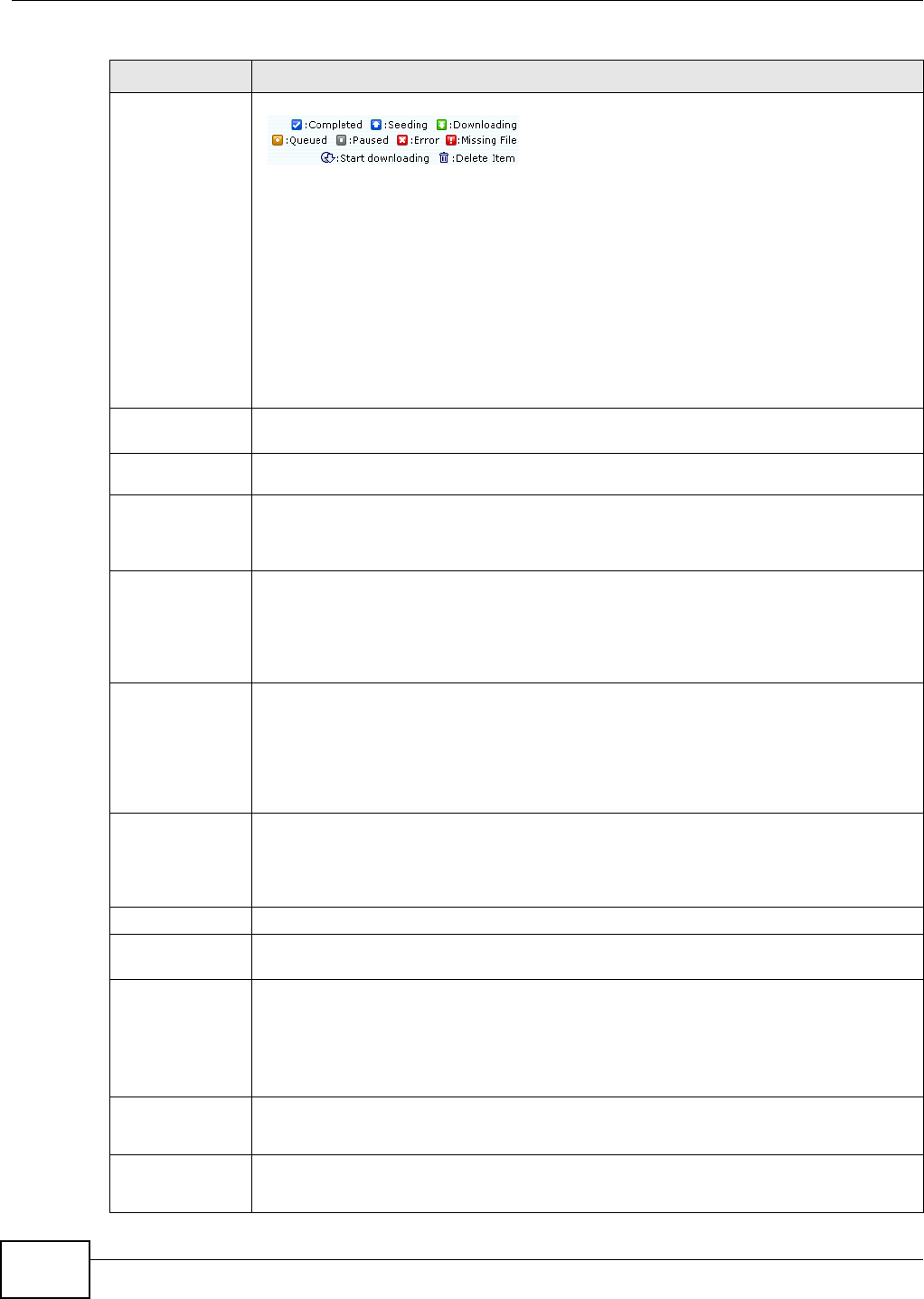
Chapter 10 Applications
Media Server User’s Guide
192
Status The following icons show the download’s status.
Completed: The NSA has downloaded the whole file.
Seeding: The download is finished and the NSA is allowing other BitTorrent users to
download it.
Downloading: The NSA is getting the file.
Queued: The download is waiting in line for the NSA to download it.
Pause: The download has been manually stopped. Select it and click Resume to continue
it.
Error: The NSA was not able to complete the download. Select it and click Resume to
reattempt the download.
Name This identifies the download file. A “...” indicates an abbreviated name. Hold your cursor
over the name to display the full name.
Complete
(%) This is the percentage of the file that the NSA has downloaded.
Location This appears in the Completed tab.
It displays the path for where the file is saved. Click on the location link to open the share
browser and access the file.
Seeds Seeds apply to BitTorrent downloads. This is the number of computers that are sharing the
complete file that you are downloading.
This value is in the format “Leeches(Seeds)” where Leeches refer to peers that do not
have a complete copy of the file yet and are still downloading; Seeds refer to peers that
have the complete file.
Peers Peers apply to BitTorrent downloads. This is the number of other computers that are also
downloading (and sharing) the file you are downloading.
This value is in the format “ConnectedPeers(AllPeers)[Health]” where Connected Peers is
the number of computers to which the NSA is connected in order to download the file;
AllPeers refer to the total number of computers to which the NSA can connect in order to
download the file; Health indicates the availability of the file.
Download
Speed This is how fast the NSA is getting the file.
It is normal for a BitTorrent download to start out with a slow download speed since it has
to set up numerous connections. The speed should increase as the download progresses
and decrease near the end of the download.
Upload Speed This is how fast the NSA is sending the file to other BitTorrent users.
Time Left This is how much longer (in hours, minutes, and seconds) it should take to finish the
download at the current download speed.
Priority This is the download’s priority on the NSA. You can set a currently downloading or queued
download to high or automatic priority. You can set a download to high priority to have the
NSA try to download it before the other files. However the actual download speed depends
more on factors like the speed of you Internet connection, the speed of the download
source’s Internet connection, how many others are trying to download at the same time,
the peers and seeds available and general network conditions.
Error Code This appears in the Error tab.
This shows the tag for the error that occurred.
Error
Message This appears in the Error tab.
This message states what went wrong with the download.
Table 37 Applications > Download Service (continued)
LABEL DESCRIPTION
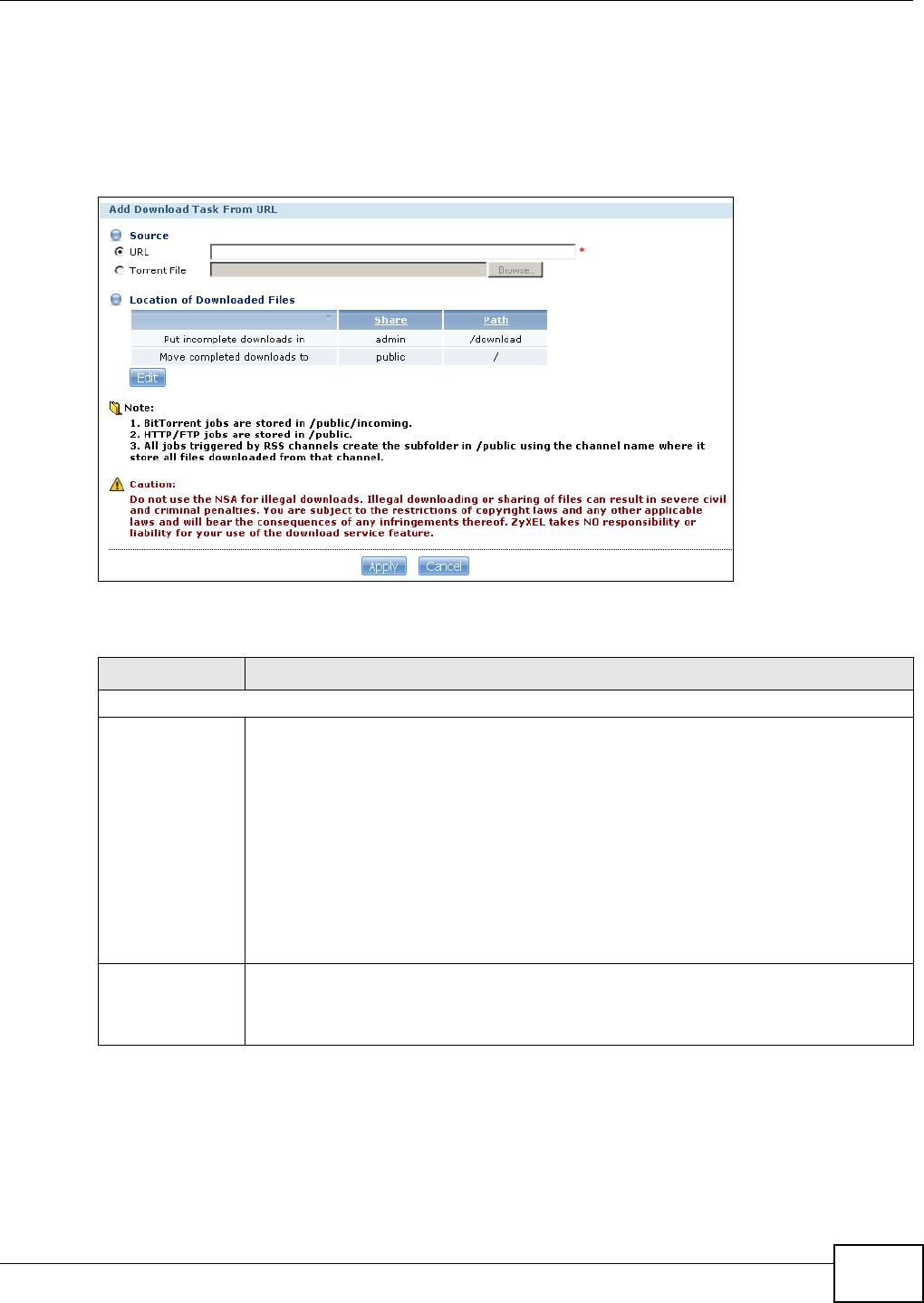
Chapter 10 Applications
Media Server User’s Guide 193
10.6.1 Adding a Download Task
Click Applications > Download Service > Add to open the following screen. Use this screen to
specify a file for the NSA to download. Section 5.10 on page 92 provides a tutorial on adding a
download task.
Figure 94 Applications > Download Service > Add
The following table describes the labels in this screen.
Table 38 Applications > Download Service > Add
LABEL DESCRIPTION
Source
URL Paste the URL of the file you want to download into this field. The URL can be for an HTTP,
FTP, or BitTorrent download.
For a BitTorrent download, you can copy and paste the URL of the .torrent file. The NSA
will automatically download the .torrent file and use it. You do not have to manually
download the .torrent file or save it to your computer.
Note: Make sure the link opens either the file you want or a pop-up window about how to
handle the file.
It is also OK for the link to open a .torrent file. If you are redirected to a screen that says
the download should start in a few seconds, there may be a link to click if the download
does not start automatically. See if that link opens the file or the pop-up window.
Torrent File A “torrent” file has information the NSA uses to do a BitTorrent download. A torrent file
uses a .torrent extension. If you already have a torrent file saved on your computer,
select the Torrent File option and specify its path or click Browse and look for its
location.
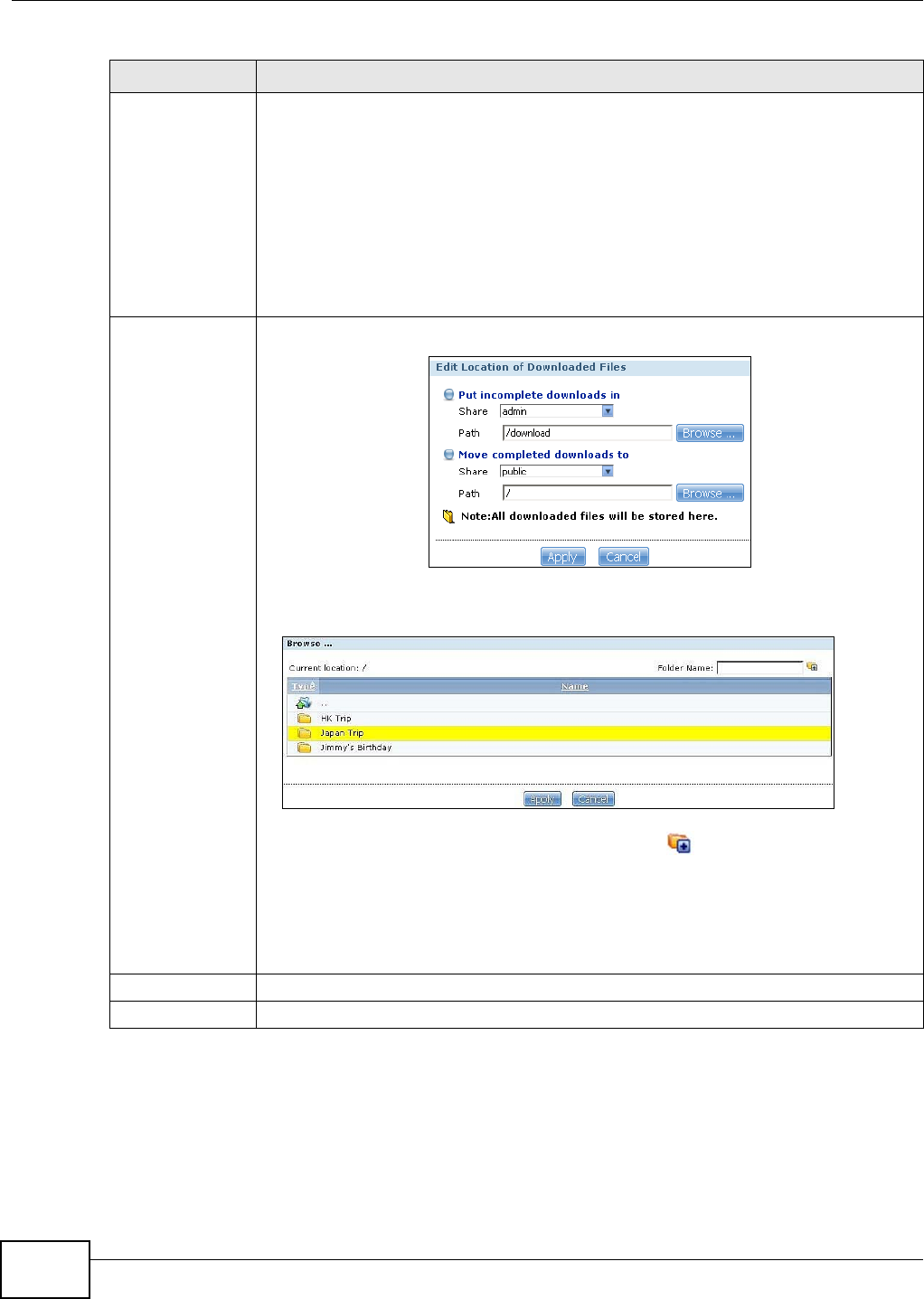
Chapter 10 Applications
Media Server User’s Guide
194
Location of
Downloaded Files This shows where the NSA stores new downloads (Put incomplete downloads in) and
where the NSA moves completed downloads (Move completed downloads to).
The Share column shows the name of the share where the file is downloaded.
The Path column points to the location in the share where the NSA will save the
downloaded files.
• BitTorrent jobs are stored in /*/incoming (where ‘*’ is a folder that you have set.)
• HTTP/FTP jobs are stored in /* (where ‘*’ is a folder that you have set.)
• All jobs triggered by RSS channels create the subfolder in /* using the channel name
where it store all files downloaded from that channel (where ‘*’ is a folder that you
have set.)
Edit Click this to open the following screen where you can set the default folder location where
you “Put incomplete downloads in” and “Move complete downloads to”:.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the file’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a folder or file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field.
All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 38 Applications > Download Service > Add
LABEL DESCRIPTION
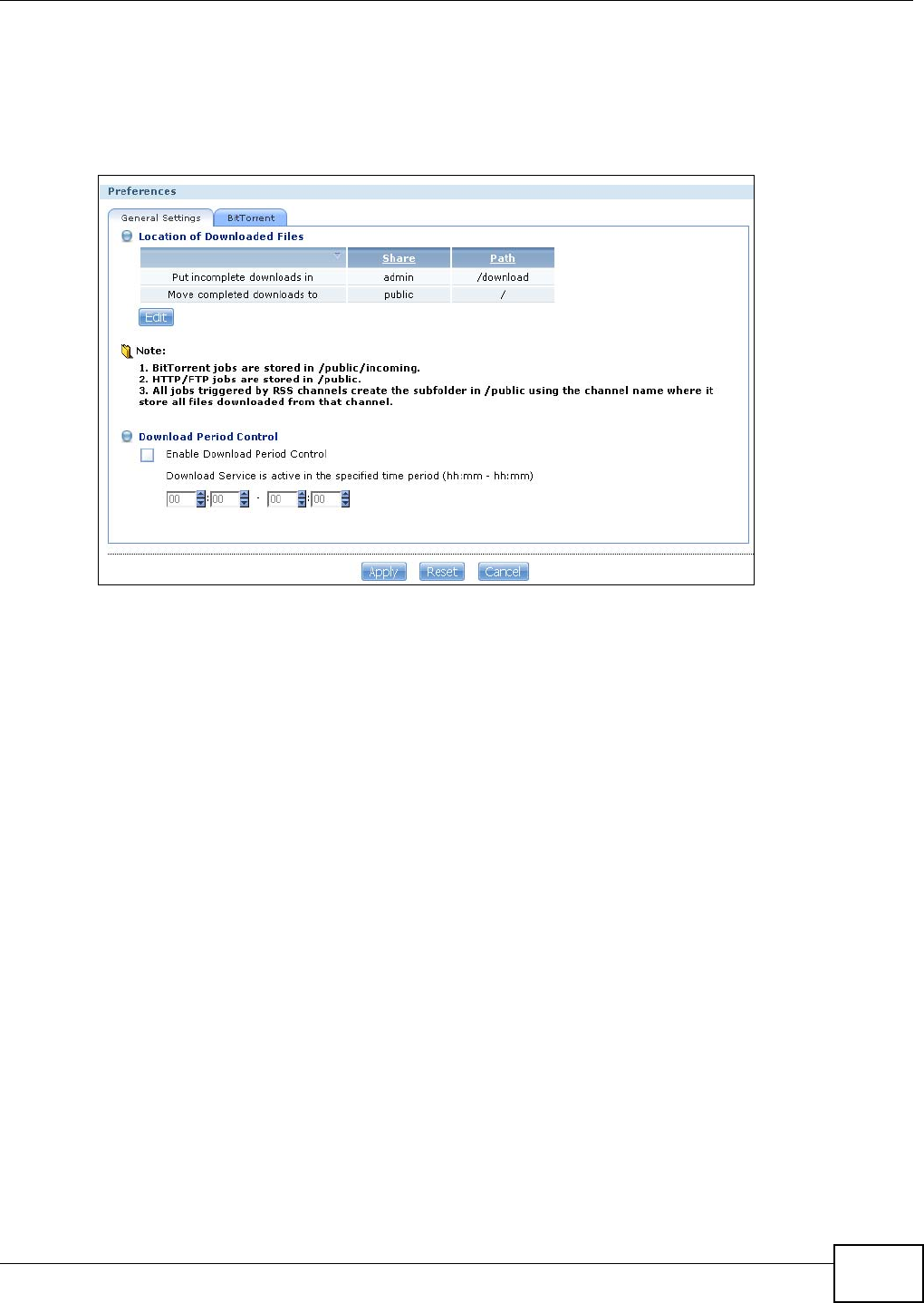
Chapter 10 Applications
Media Server User’s Guide 195
10.6.2 Configuring General Settings
Click Applications > Download Service > Preferences to open the following screen. Use this
screen to set the default location for saving downloads and configure the download period.
Figure 95 Applications > Download Service > Preferences > General Settings
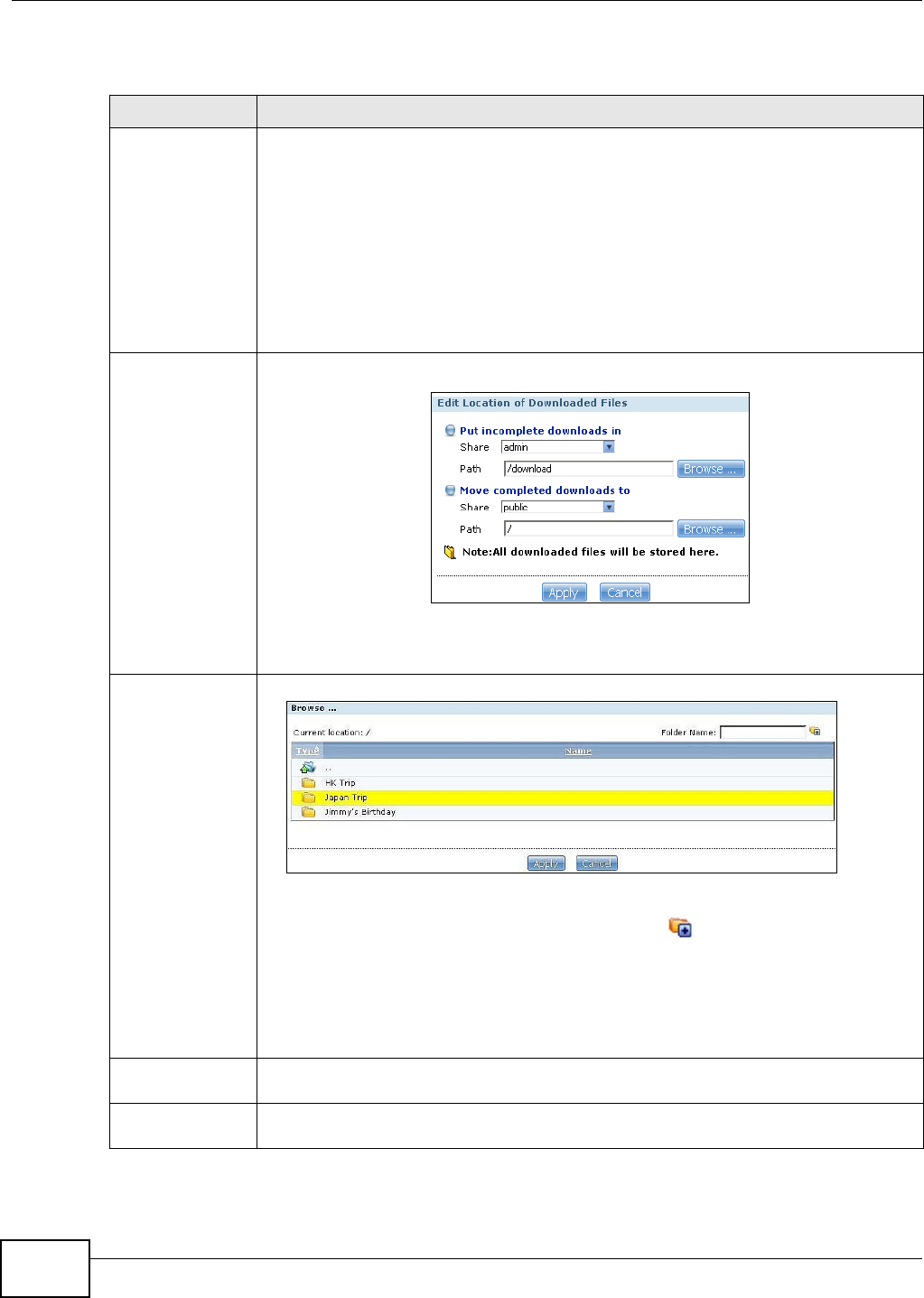
Chapter 10 Applications
Media Server User’s Guide
196
The following table describes the labels in this screen.
Table 39 Applications > Download Service > Preferences > General Settings
LABEL DESCRIPTION
Location of
Downloaded Files This shows where the NSA stores new downloads (Put incomplete downloads in) and
where the NSA moves completed downloads (Move completed downloads to).
The Share column shows the name of the share where the file is downloaded.
The Path column points to the location in the share where the NSA will save the
downloaded files.
• BitTorrent jobs are stored in /*/incoming (where ‘*’ is a folder that you have set.)
• HTTP/FTP jobs are stored in /* (where ‘*’ is a folder that you have set.)
• All jobs triggered by RSS channels create the subfolder in /* using the channel name
where it store all files downloaded from that channel (where ‘*’ is a folder that you
have set.)
Edit Click this to open the following screen where you can set the default folder location where
you “Put incomplete downloads in” and “Move complete downloads to”:.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the file’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a file or folder.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field.
All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Download Period
Control This feature sets the NSA to download files only within a specified time period.
Enable Download
Period Control Use the check box to turn the download period control on or off.
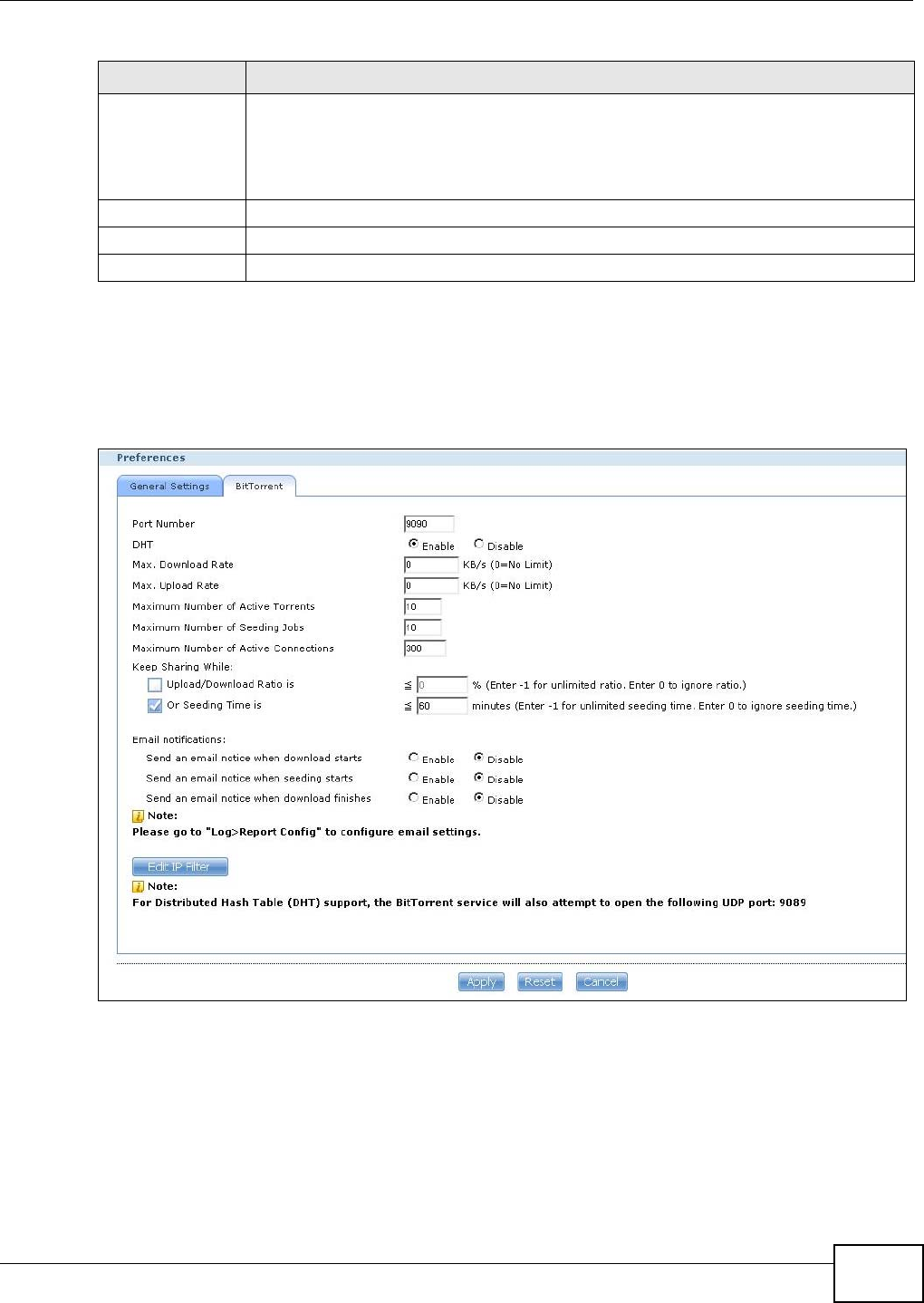
Chapter 10 Applications
Media Server User’s Guide 197
10.6.3 Configuring the BitTorrent Settings
Click Applications > Download Service > Preferences > BitTorrent to open the following
screen. Use this screen to configure BitTorrent settings.
Figure 96 Applications > Download Service > Preferences > BitTorrent
Download Service
is active in the
time period
(hh:mm -
hh:mm)
Specify the time period for the NSA to download files.
Note: If you also configured the Power On/Off Schedule feature in the Power
Management screen, make sure your active download period does not conflict with
the power-off period.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Cancel Click this to return to the previous screen without saving.
Table 39 Applications > Download Service > Preferences > General Settings
LABEL DESCRIPTION
Chapter 10 Applications
Media Server User’s Guide
198
The following table describes the labels in this screen.
Table 40 Applications > Download Service > Preferences > BitTorrent
LABEL DESCRIPTION
Port Number Assign a port number for BitTorrent downloads. You can select a number from 2 to
65536. It is recommended to use a port number greater than 1025.
DHT Select Enable or Disable to use Distributed Hash Table (DHT) or not.
Note: When you use DHT, the NSA will also attempt to open a UDP port one number
smaller than the BitTorrent port number. So if the BitTorrent port number is 9090,
the NSA uses UDP port 9089.
Max. download rate You may need to limit the bandwidth the NSA uses for BitTorrent downloads if your
network’s other Internet applications are not getting enough downstream bandwidth. 0
has the NSA impose no restriction.
Max. upload rate You may need to limit the bandwidth the NSA uses to share files through BitTorrent if
your network’s other Internet applications are not getting enough upstream bandwidth.
0 has the NSA impose no restriction.
If you do not allow any uploads, (for example, you set a limit of 1 KB/s) you will not
have a good standing in the BitTorrent community.
Note: The settings for maximum download/upload rates would not affect peers accessing
the NSA from the same LAN.
Maximum Number
of Active Torrents Specify how many simultaneous BitTorrent downloads are allowed on the NSA. You can
enter a number from 1 to 10.
Maximum Number
of Seeding Jobs Specify how many simultaneous seeds are allowed on the NSA. Enter a number from 1
to 10. This value cannot exceed the one you configured in the Maximum Number of
Active Torrents field.
Maximum Number
of Active
Connections
Specify how many active connections are allowed on the NSA. Enter a number from 1 to
500. This specifies the number of computers that can connect to the NSA to download
files being shared by the NSA.
Keep Sharing While With BitTorrent, the NSA starts sharing a file while you are downloading it. Set how long
to continue sharing a file after the NSA finishes the download.
Select Upload/Download Ratio to keep sharing a file until the NSA has uploaded a
specific percent compared to the download.
Select Seeding Time to keep sharing a file for a specific number of minutes after the
download finishes.
Continuing to share a file helps other BitTorrent users finish downloading it. Sharing out
at least as much as you download helps keep you in good standing in the BitTorrent
community.
Enter -1 to share a file indefinitely. Leave both check boxes blank to have the NSA stop
sharing the file as soon as the download finishes.
If you select both options, the NSA keeps sharing a file until both conditions exceed the
values you configure. For example, you entered 150% in the Upload/Download Ratio
field and 120 minutes in the Seeding Time field. The NSA keeps sharing a file until it
has shared 1.5 times the size of the file and has passed 120 minutes.
Email notifications Select whether or not to send emails to the email address configured for emailing log
reports (see Section 17.4.2 on page 316) when the NSA starts downloading the file,
seeding the file, and/or finishes downloading the file.
Edit IP Filter Click this to enable or disable IP filtering for BitTorrent downloads.
Refer to Section 10.6.4 on page 199 for information about the fields in this screen.
Apply Click this to save your changes.
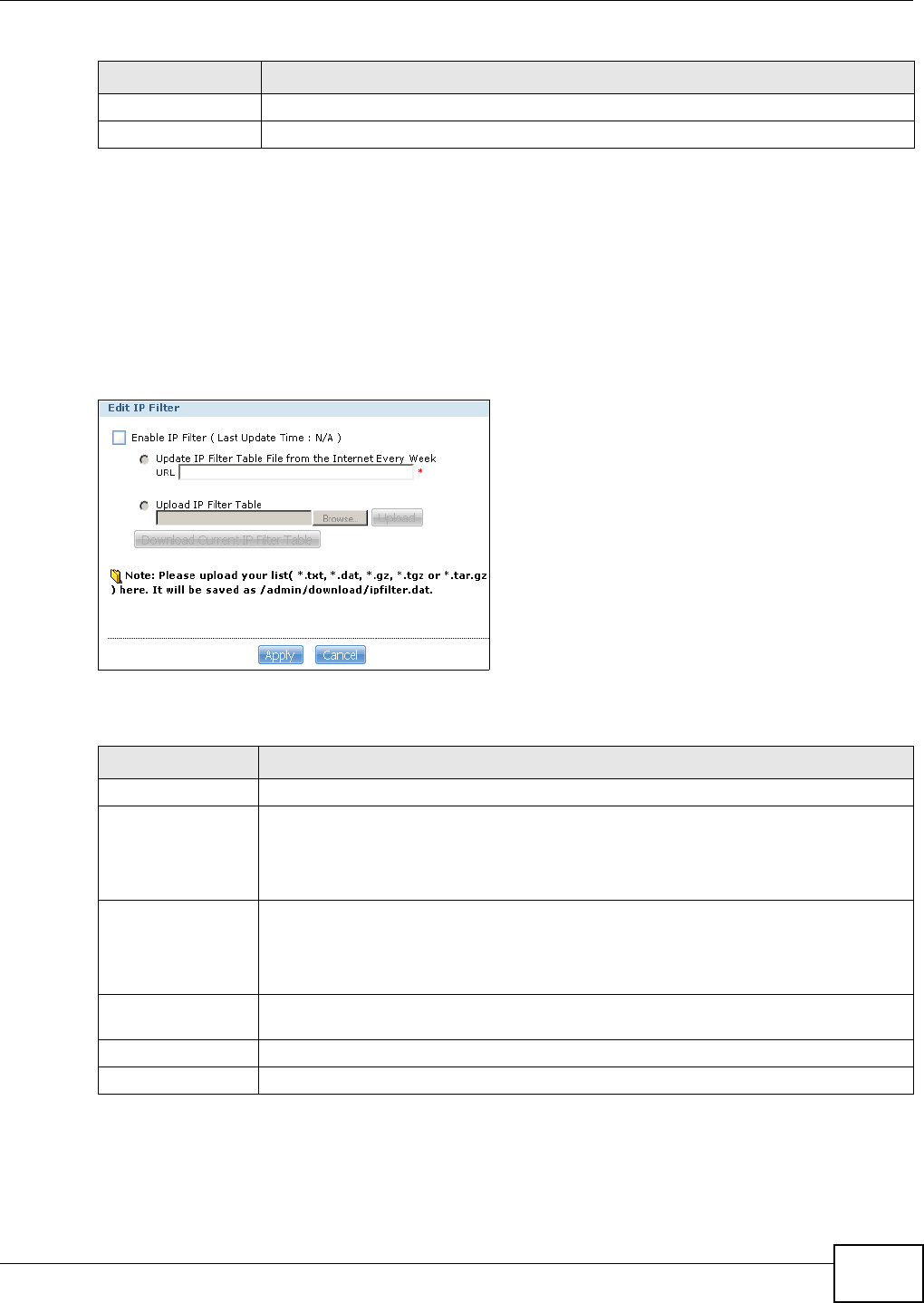
Chapter 10 Applications
Media Server User’s Guide 199
10.6.4 Edit IP Filter
Use this screen to enable or disable IP filtering for BitTorrent downloads. IP filtering blocks IP
addresses known to share fake files. You can either get an IP filter table from a website or use your
own table.
Click Edit IP Filter in the Applications > Download Service > Preferences > BitTorrent
screen.
Figure 97 Applications > Download Service > Preferences > BitTorrent > Edit IP Filter
The following table describes the labels in this screen.
Reset Click this to restore your previously saved settings.
Cancel Click this to return to the previous screen without saving.
Table 40 Applications > Download Service > Preferences > BitTorrent
LABEL DESCRIPTION
Table 41 Applications > Download Service > Preferences > BitTorrent > Edit IP Filter
LABEL DESCRIPTION
Enable IP Filter Click this to enable or disable IP filtering for BitTorrent downloads.
Update IP Filter
Table File from
the Internet
Every Week
Select this option and enter a URL to use an online IP filter table. You can find an online
IP filter table in websites such as http://www.bluetack.co.uk/config/level1.gz.
When you change the URL of the online IP filter table, the NSA also performs an update
after you click Apply.
Upload IP Filter
Table Select this option to upload your own IP filter table. Use the Browse button to locate
the file and click Upload to save it on the NSA.
The NSA supports .txt, .dat, .gz, .tgz, and .tar.gz file extensions. The NSA saves the IP
filter table as /admin/download/ipfilter.dat.
Download Current
IP Filter Table Click this to save a copy of the IP filter table on your computer.
Apply Click Apply to update the IP filter table from the specified URL.
Cancel Click this to return to the previous screen without saving.
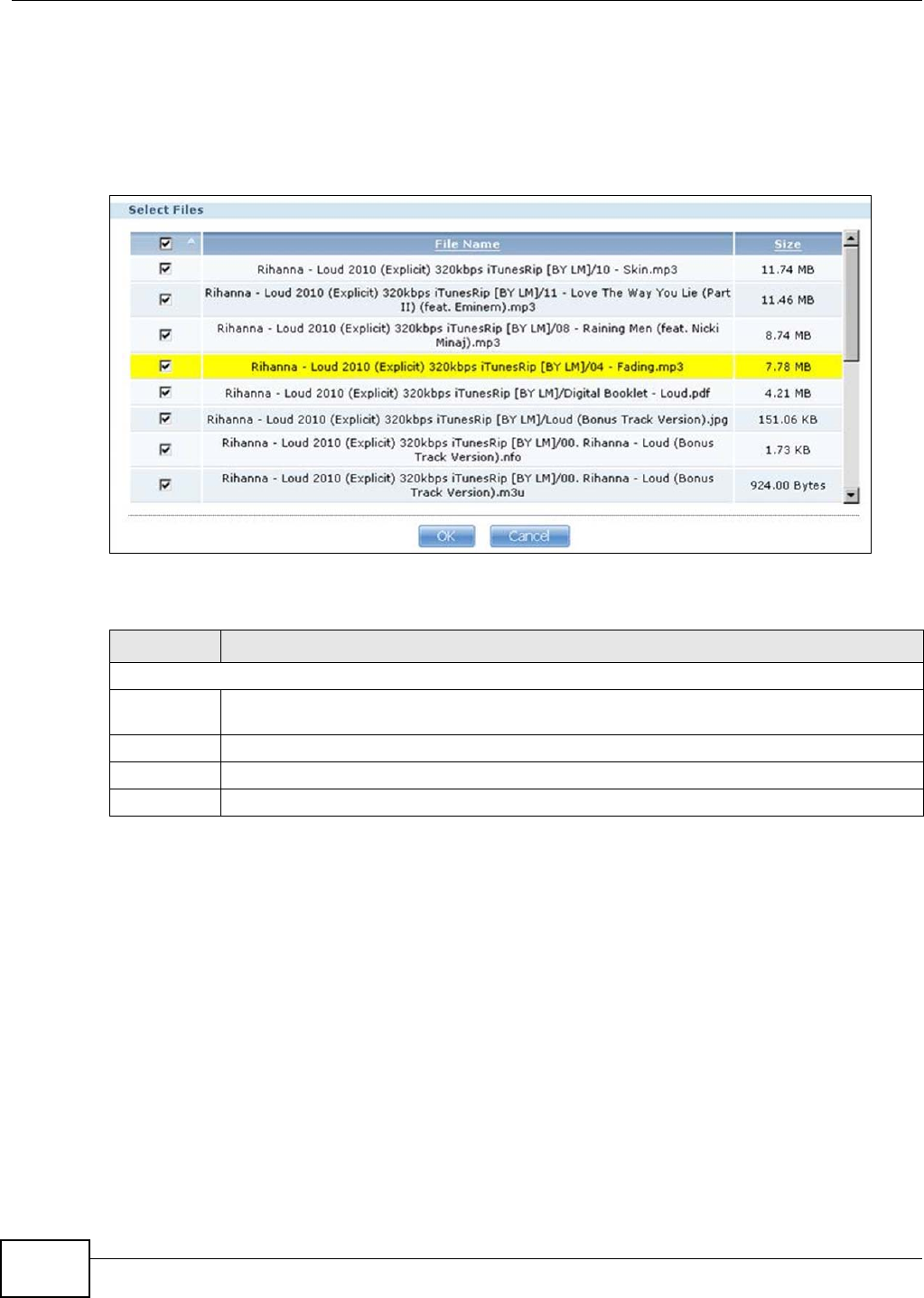
Chapter 10 Applications
Media Server User’s Guide
200
10.6.5 Selecting Files to Download
Select an item in the Applications > Download Service screen’s list and click Select Files to
open the following screen. Use this screen to select which of the torrent’s files to download. Section
5.10 on page 92 provides a tutorial on adding a download task.
Figure 98 Applications > Download Service > Select Files
The following table describes the labels in this screen.
Table 42 Applications > Download Service > Select Files
LABEL DESCRIPTION
Select Files
File Name This is the name of a file specified in the torrent file. Select the check boxes of the files you
want to download.
Size This is the size of the file to be downloaded.
OK Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
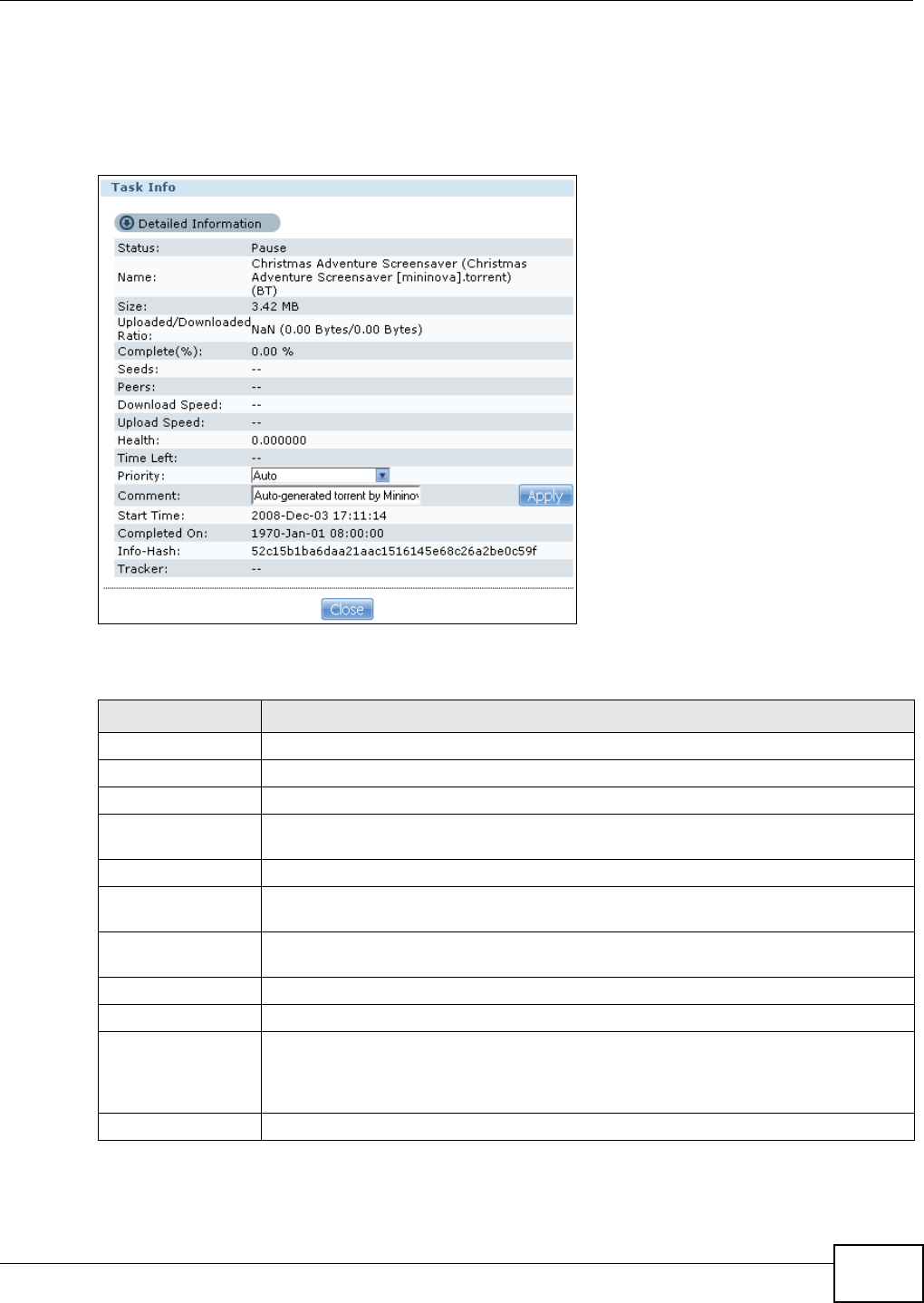
Chapter 10 Applications
Media Server User’s Guide 201
10.6.6 Displaying the Task Information
Select an item on the list and click Task Info. Use this screen to check detailed information about
the task.
Figure 99 Applications > Download Service > Task Info
The following table describes the labels in this screen.
Table 43 Applications > Download Service > Task Info
LABEL DESCRIPTION
Status This is the current status of the task.
Name This is the name of the task.
Size This is the size of the file to be downloaded.
Uploaded/
Downloaded Ratio This is the ratio of total uploaded data to downloaded data.
Complete(%) This field displays how much has been downloaded to the NSA.
Seeds This is the number of computers that are sharing the complete file that you are
downloading.
Peers This is the number of other computers that are also downloading (and sharing) the file
you are downloading.
Download Speed This field displays how fast the NSA downloads the file.
Upload Speed This field displays how fast the NSA uploads the file.
Health This field displays how many full copies of the file are available for this task. The NSA
can download a file with a higher health value more efficiently. If the health value is less
than 1 (0.65 for example), there is no full copy of the file, and the NSA may not be able
to complete downloading the file.
Time Left This is the time remaining to complete the task.
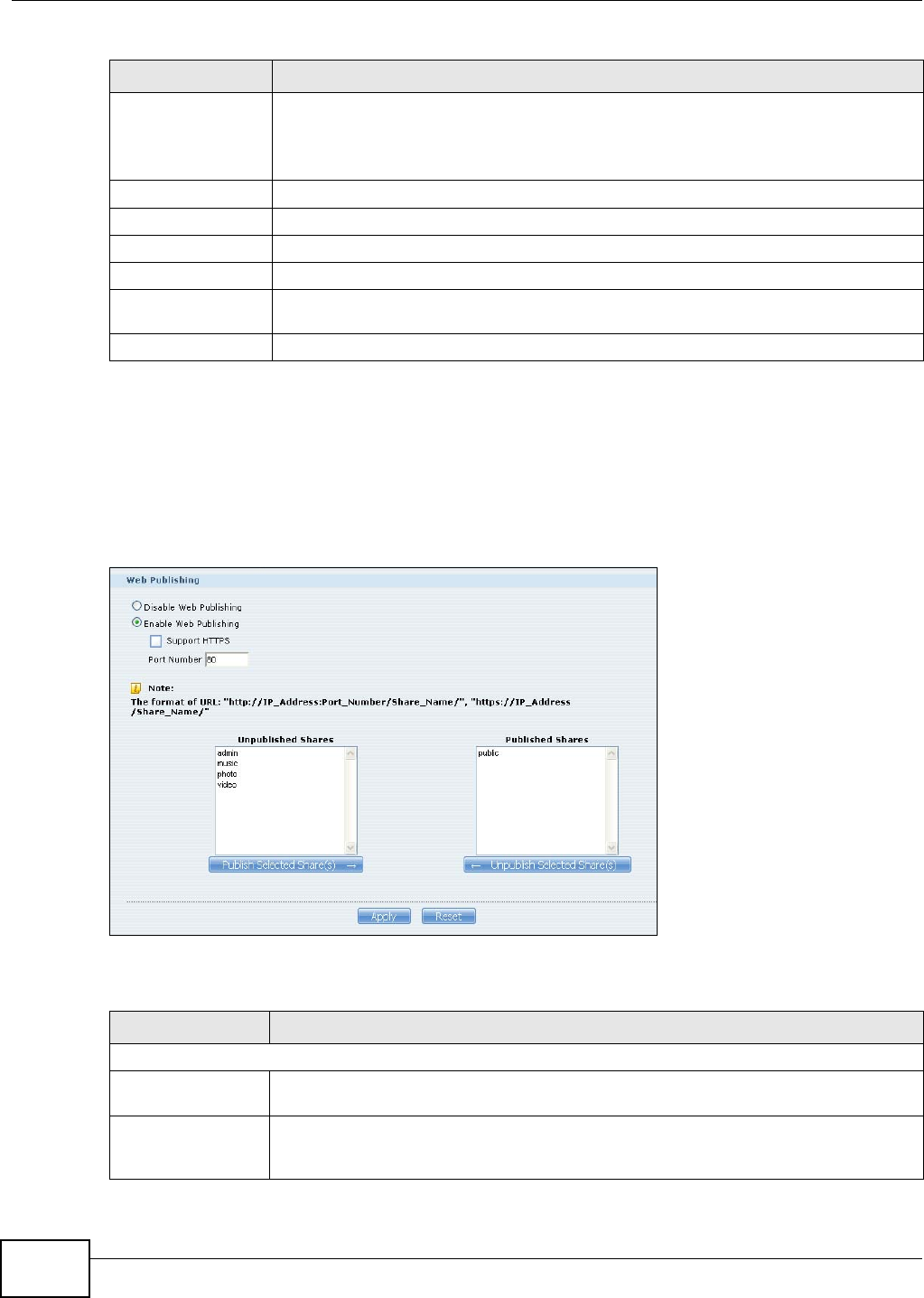
Chapter 10 Applications
Media Server User’s Guide
202
10.7 The Web Publishing Screen
Use this screen to turn web publishing on or off and select shares to publish. Click Applications >
Web Publishing to open the following screen.
Figure 100 Applications > Web Publishing
The following table describes the labels in this screen.
Priority Use this field to set the priority for downloading the task.
Select Auto to have the NSA automatically determine the task’s priority.
Select High to have the NSA download this file before the other files.
Comment Enter a description for this task. Click Apply to save the description.
Start Time This field displays when the NSA started to download files.
Completed on This field displays when the file was successfully downloaded to the NSA.
Info-Hash This information is used to verify the torrent file.
Tracker This field displays the tracker that NSA is currently connected to. A tracker is a server
used for finding peers sharing the file.
Close Click this to close the screen.
Table 43 Applications > Download Service > Task Info
LABEL DESCRIPTION
Table 44 Applications > Web Publishing
LABEL DESCRIPTION
Web Publishing
Disable / Enable
Web Publishing Turn on web publishing to let people access files in the published shares using a web
browser, without having to log into the Home screens.
Support HTTPS Select this to allow users to use web browser security for connections to the web-
published shares. In order to use secured connections users must use “https://” in the
NSA’s web address and install the NSA’s public key certificate.

Chapter 10 Applications
Media Server User’s Guide 203
Note: If you installed php-MySQL-phpMyAdmin through the Package Management
screen (Section 11.4 on page 226) and enable it, you can use PHP and MySQL in
your published web page.
10.8 The Broadcatching Screen
This screen displays the NSA’s subscribed channels and the associated contents.
• The NSA saves a channel’s downloaded items in a folder named after the channel.
• The NSA creates the channel folders in the same destination as the download service. See
Section 10.6.2 on page 195 to change the destination for saving downloads.
• The NSA’s media server feature makes it easy for users on your network to play the
broadcatching files you download. See Section 10.11.1 on page 212 for more on the media
server.
• If you add a channel that contains a torrent file, the NSA downloads the torrent file (.torrent) and
transfers it to Download Service (Section 10.6 on page 190) and start the BitTorrent download
task accordingly.
Port Number Specify a port number for accessing the published share websites hosted on the NSA. If
you enter a number other than 80, make sure you include it when telling others how to
access the web-published share. For example, say you specified port 8080, the NSA’s IP
address is 192.168.1.23, and the name of the web-published share is FamilyPhotos. You
would have to enter “http://192.168.1.23:8080/MyWeb/FamilyPhotos/” in your
browser’s address bar to access the share’s web page.
Unpublished Shares This list box displays the shares that the NSA does not publish for web browser access.
Publish Selected
Share(s) Select shares in the Unpublished Shares box and click this to let people access files in
the published shares using a web browser, without logging into the Home screens. Use
the [SHIFT] key to select a range of entries. Hold down the [CTRL] key to select
multiple individual entries.
Published Shares This list box displays the shares people can access using a web browser, without logging
into the Home screens.
Unpublish Selected
Share(s) Select shares in the Published Shares box and click this to not let people access using
a web browser without logging into the Home screens. Use the [SHIFT] key to select a
range of entries. Hold down the [CTRL] key to select multiple individual entries.
Apply Click this to save your changes.
Reset Click this to restore your previously saved settings.
Table 44 Applications > Web Publishing
LABEL DESCRIPTION
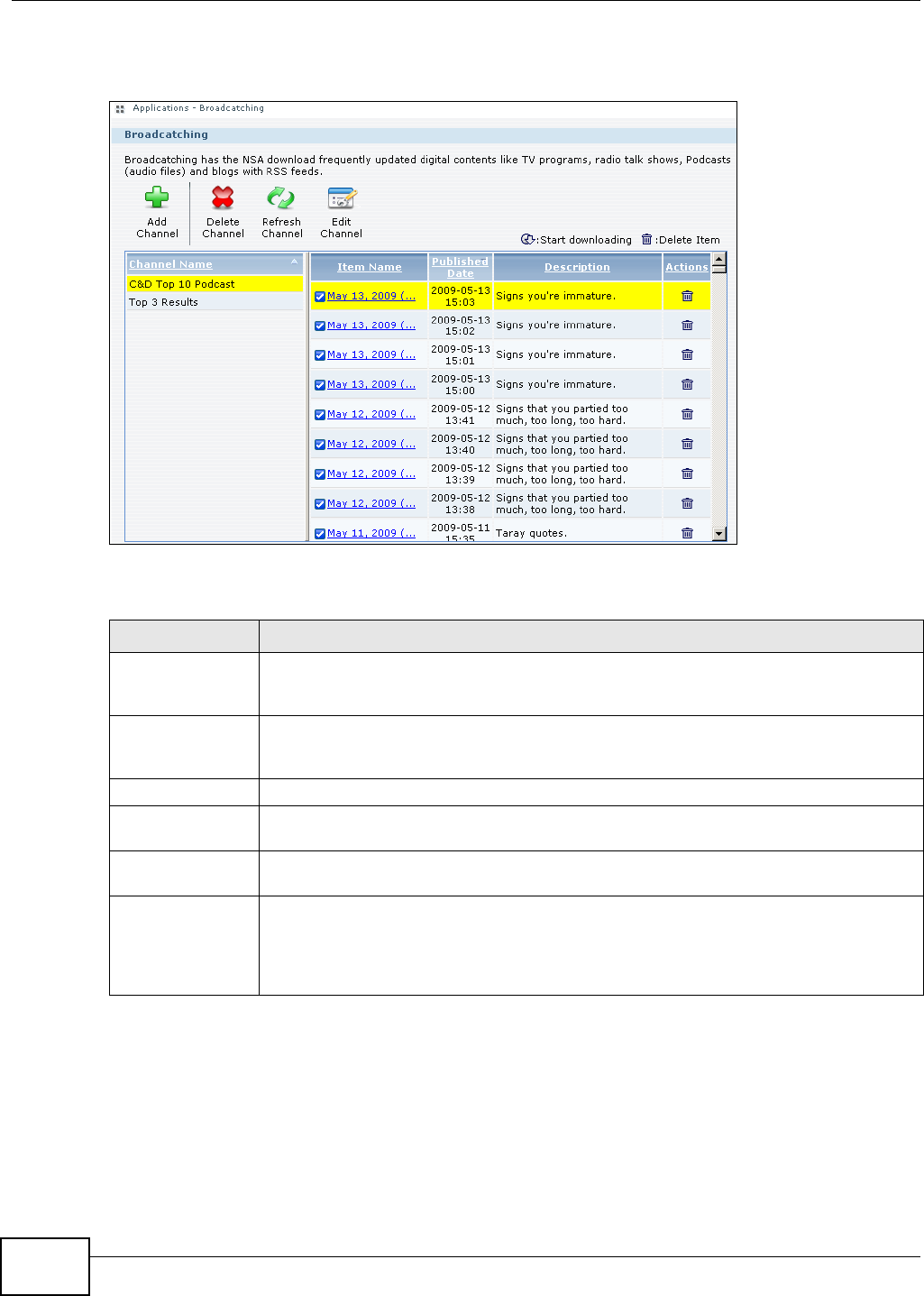
Chapter 10 Applications
Media Server User’s Guide
204
Click Applications > Broadcatching to open the following screen.
Figure 101 Applications > Broadcatching
The following table describes the labels in this screen.
Table 45 Applications > Broadcatching
LABEL DESCRIPTION
Add Channel When you find a channel to subscribe to, copy the URL of the channel’s feed and click this
button. A screen opens for you to subscribe to the feed. When you are done, the feed’s
channel and contents display in the Applications > Broadcatching screen.
Delete Channel Select a channel and click Delete Channel to remove the channel from the NSA. Any of
the channel’s items that you have already downloaded stay in the channel’s folder (in the
admin share’s download folder).
Refresh Channel Select a channel and click Refresh Channel to check for new files.
Edit Channel Select a channel and click Edit Channel to open a screen where you can set the
channel’s download and delete policies.
The table lists channels and their files. Click a column’s heading to sort the entries by that
criteria.
Channel Name This identifies the channel. A channel displays in red if there was an error the last time
the NSA attempted to connect to it. When this happens, you can select the channel and
click Refresh Channel to have the NSA reattempt to connect to it. Select a channel to
see its available files. A “...” indicates an abbreviated name. Hold your cursor over the
name to display the full name.

Chapter 10 Applications
Media Server User’s Guide 205
10.8.1 Adding a Broadcatching Channel
At the time of writing, the NSA supports RSS 2.0 feeds. Websites with a feed usually display a feed
icon (shown next). Copy and paste the feed’s URL into the Applications > Broadcatching > Add
Channel screen and you can download new files as they are added.
Figure 102 Feed Icon
A channel uses a feed to deliver its contents (items). Subscribe the NSA to a feed to be able to
download the contents.
Click Applications > Broadcatching > Add Channel to open the following screen. Use the Add
Channel screen to subscribe the NSA to a channel’s feed so you can view the channel. You also
Item Name These are the downloadable files. The following icons show the file’s status in the NSA.
Completed: The NSA has downloaded the whole file. Double-click the item to go to the
Download Service screen where you can see the file’s name and location.
Seeding: The NSA downloaded the complete file and NSA is sharing it with other
BitTorrent users. Double-click the item to go to the Download Service screen.
Downloading: The NSA is downloading the file. Double-click the item to go to the
Download Service screen.
Queued: The file is waiting in line for the NSA to download it. Double-click the item to go
to the Download Service screen.
Pause: The download has been manually stopped. Double-click the item to go to the
Download Service screen.
Missing File: The NSA could not find the file.
Error: The NSA automatically retries unsuccessful download attempts. The status
displays as error when the re-attempts are also unsuccessful and the NSA stops trying to
download the file. To try the download again, use the Add button to create a new task.
Note: A ... indicates an abbreviated file name. Hold your cursor over the name to display
the full name.
Published Date This is when the file was made available for download.
Description This is the publishers introduction for the file.
Actions Start Downloading: Click this to add the file to the NSA’s download queue or check the
file’s status in the NSA’s download service.
Click the Delete icon to remove the file from the channel’s list.
Table 45 Applications > Broadcatching
LABEL DESCRIPTION
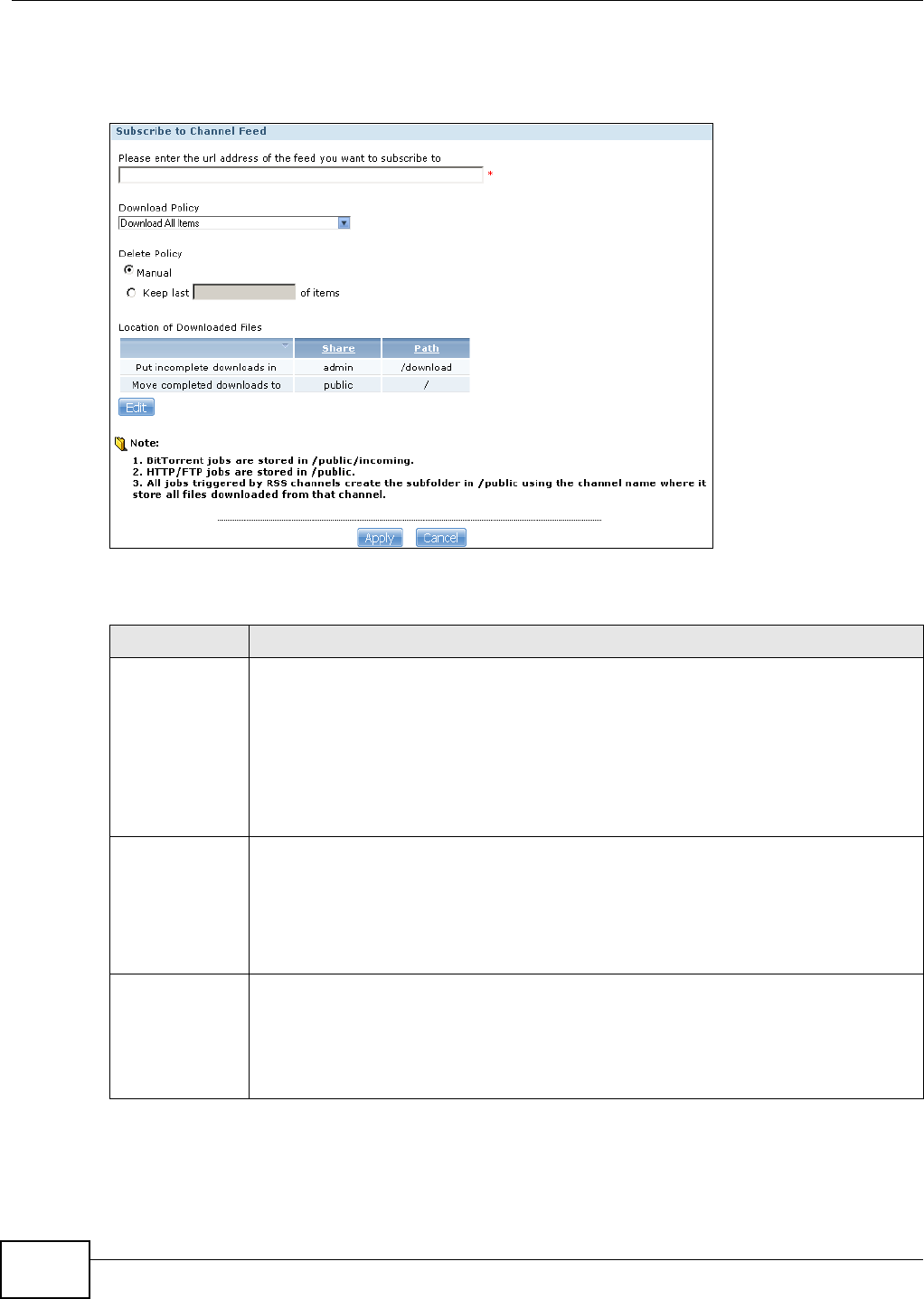
Chapter 10 Applications
Media Server User’s Guide
206
select policies for downloading and deleting the channel’s items. Section 5.11 on page 107 provides
a tutorial on adding a broadcatching channel.
Figure 103 Applications > Broadcatching > Add Channel
The following table describes the labels in this screen.
Table 46 Applications > Broadcatching > Add Channel
LABEL DESCRIPTION
Subscribe to
Channel Feed Paste (or type) the URL of the feed for the channel to which you want to subscribe into this
field. This is read-only in the Preferences screen.
Note: Make sure the link goes to the actual RSS feed instead of to another list of links or
information about the channel.
One way to test this is by clicking the link. Clicking an actual RSS feed link opens a screen
of XML code (in browsers without an RSS feed aggregator) or a window where you can add
the RSS feed (in browsers with an RSS feed aggregator).
Download Policy Set which of the channel’s items the NSA downloads.
Download All Items: Download every file in the feed.
Download Only New Items: Download new files from today on.
Manually Choose Items for Download: Only download individual files you select later
in the Broadcatching screen.
Delete Policy Set how the NSA handles deleting the items downloaded from the channel.
Manual: Only delete individual files you select later in the Broadcatching screen.
Keep last N of items: Select this to set the NSA to only keep a number of the channel’s
most recent files. When this number has been reached, if the NSA downloads another file
from the channel, it deletes the oldest file from the NSA.
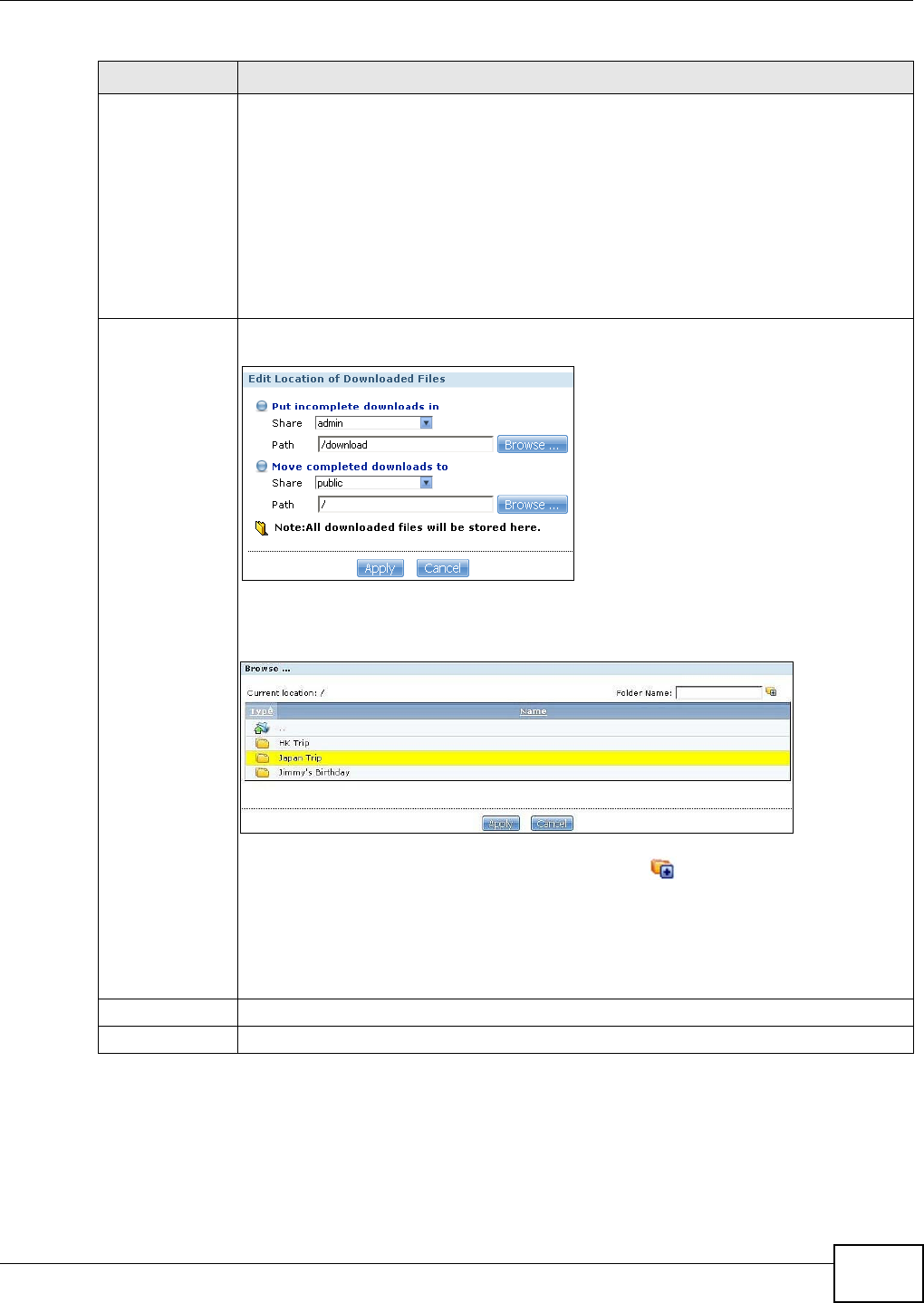
Chapter 10 Applications
Media Server User’s Guide 207
Location of
Downloaded
Files
This shows where the NSA stores new downloads (Put incomplete downloads in) and
where the NSA moves completed downloads (Move completed downloads to).
The Share column shows the name of the share where the file is downloaded.
The Path column points to the location in the share where the NSA will save the
downloaded files.
• BitTorrent jobs are stored in /*/incoming (where ‘*’ is a folder that you have set.)
• HTTP/FTP jobs are stored in /* (where ‘*’ is a folder that you have set.)
• All jobs triggered by RSS channels create the subfolder in /* using the channel name
where it store all files downloaded from that channel (where ‘*’ is a folder that you
have set.)
Edit Click this to open the following screen where you can set the default folder location where
you “Put incomplete downloads in” and “Move complete downloads to”:.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the file’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a file or folder.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field. All
contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 46 Applications > Broadcatching > Add Channel
LABEL DESCRIPTION
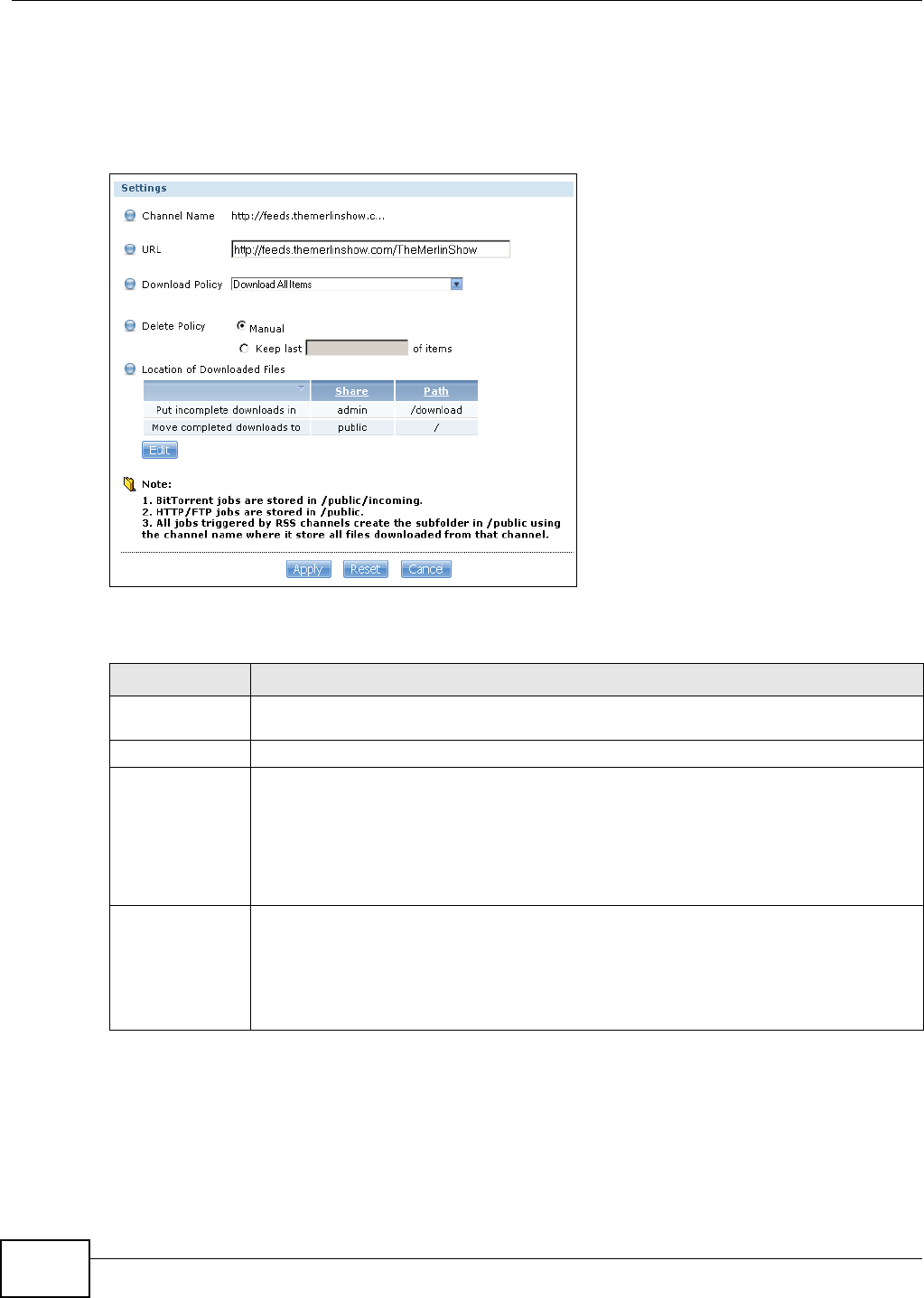
Chapter 10 Applications
Media Server User’s Guide
208
10.8.2 Editing a Broadcatching Channel
Click Applications > Broadcatching, then select a channel and click Edit Channel to open a
similar Edit screen. Use the Edit Channel screen to change the download or delete policies.
Figure 104 Applications > Broadcatching > Edit Channel
The following table describes the labels in this screen.
Table 47 Applications > Broadcatching > Edit Channel
LABEL DESCRIPTION
Channel Name This is the name of the feed for the channel to which you want to subscribe into this field.
This is read-only.
URL This is the address of the channel.
Download Policy Set which of the channel’s items the NSA downloads.
Download All Items: Download every file in the feed.
Download Only New Items: Download new files from today on.
Manually Choose Items for Download: Only download individual files you select later
in the Broadcatching screen.
Delete Policy Set how the NSA handles deleting the items downloaded from the channel.
Manual: Only delete individual files you select later in the Broadcatching screen.
Keep last N of items: Select this to set the NSA to only keep a number of the channel’s
most recent files. When this number has been reached, if the NSA downloads another file
from the channel, it deletes the oldest file from the NSA.
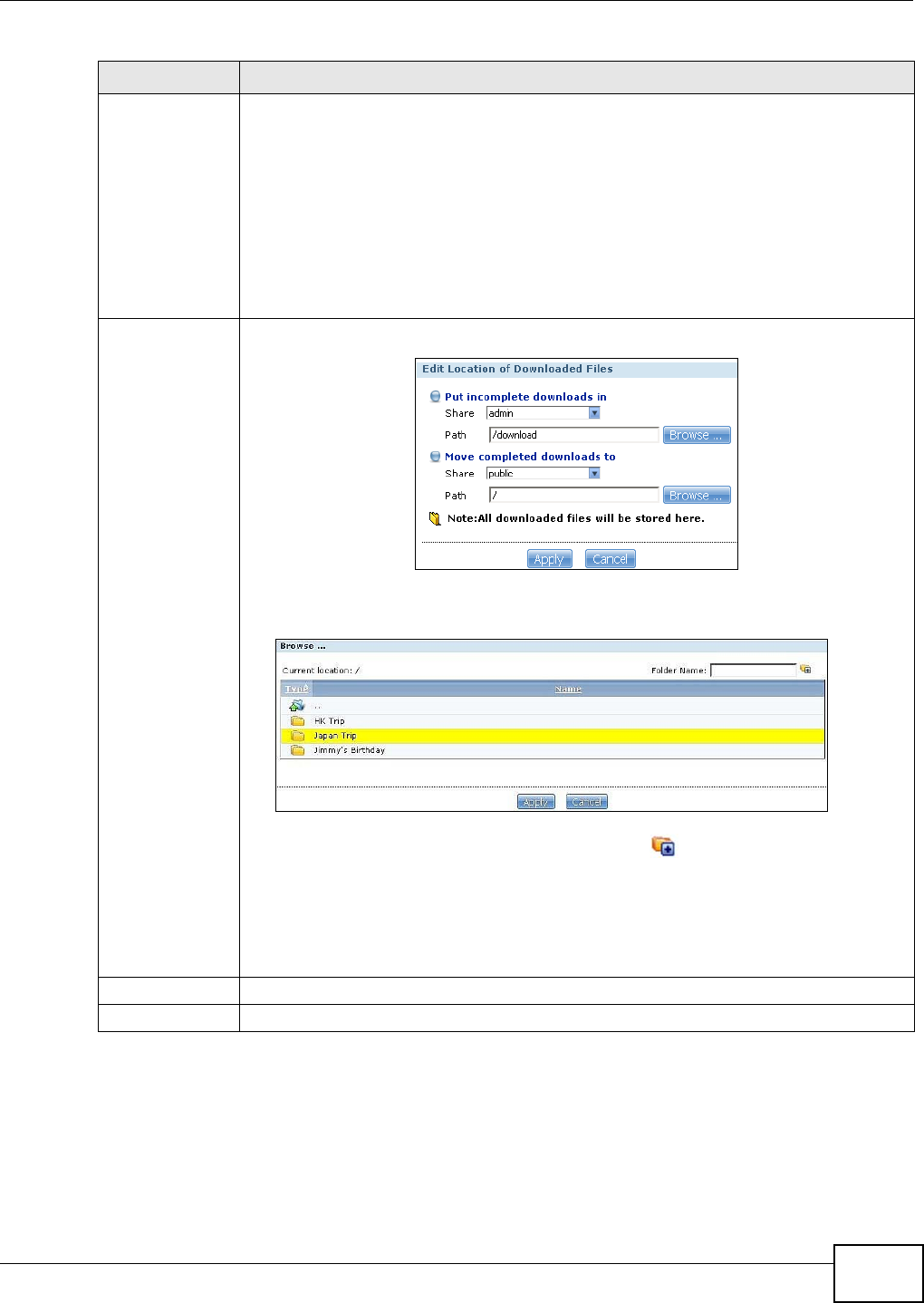
Chapter 10 Applications
Media Server User’s Guide 209
10.9 The Print Server Screen
Use the Print Server screen to view and manage the NSA’s list of printers and print jobs.
Location of
Downloaded Files This shows where the NSA stores new downloads (Put incomplete downloads in) and
where the NSA moves completed downloads (Move completed downloads to).
The Share column shows the name of the share where the file is downloaded.
The Path column points to the location in the share where the NSA will save the
downloaded files.
• BitTorrent jobs are stored in /*/incoming (where ‘*’ is a folder that you have set.)
• HTTP/FTP jobs are stored in /* (where ‘*’ is a folder that you have set.)
• All jobs triggered by RSS channels create the subfolder in /* using the channel name
where it store all files downloaded from that channel (where ‘*’ is a folder that you
have set.)
Edit Click this to open the following screen where you can set the default folder location where
you “Put incomplete downloads in” and “Move complete downloads to”:.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the file’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a file or folder.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field. All
contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 47 Applications > Broadcatching > Edit Channel
LABEL DESCRIPTION
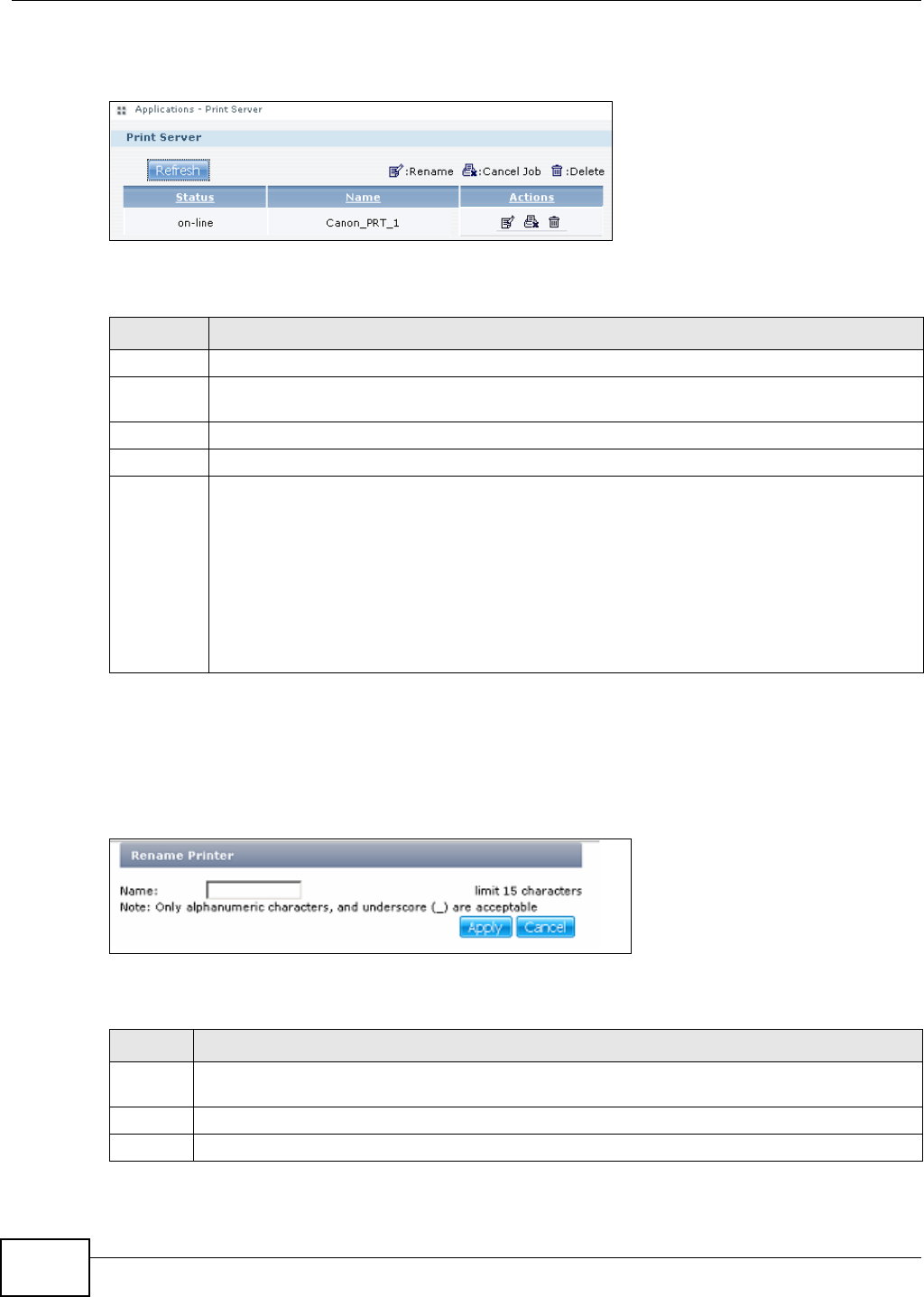
Chapter 10 Applications
Media Server User’s Guide
210
Click Applications > Print Server to open the following screen.
Figure 105 Applications > Print Server
The following table describes the labels in this screen.
10.9.1 Print Server Rename
Click Applications > Print Server and a printer’s Rename icon to open the following screen. Use
this screen to change the name the NSA uses for the printer.
Figure 106 Applications > Print Server > Rename
The following table describes the labels in this screen.
Table 48 Applications > Print Server
LABEL DESCRIPTION
Refresh Click this to update the list of printers and print jobs.
The table lists printers and their queued print jobs. Click a column’s heading to sort the entries
by that criteria.
Status This fields shows whether the printer is connected and turned on (on-line) or not (off-line).
Name This identifies the printer. Each printer connected to the NSA must use a unique name.
Actions Rename: Click this to change the name the NSA uses for the printer.
Cancel Job: Click this to remove all print jobs from the NSA queue for a particular printer.
However, since the NSA sends print jobs to the printer as soon as it can, this button may only
have an effect if there are very large or many print jobs in the queue. To stop a print job that
has already started, you may have to turn off the printer.
Delete: Click this to remove a printer from the NSA’s printer list. To add the printer back into
the list, disconnect the printer from the NSA’s USB port and reconnect it. If that does not work,
disconnect the USB port and turn off the printer’s power. Then reconnect the printer and turn it
back on.
Table 49 Applications > Print Server > Rename
LABEL DESCRIPTION
Name Type a new name to identify the printer. The name must be unique from all the other names of
printers connected to the NSA.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
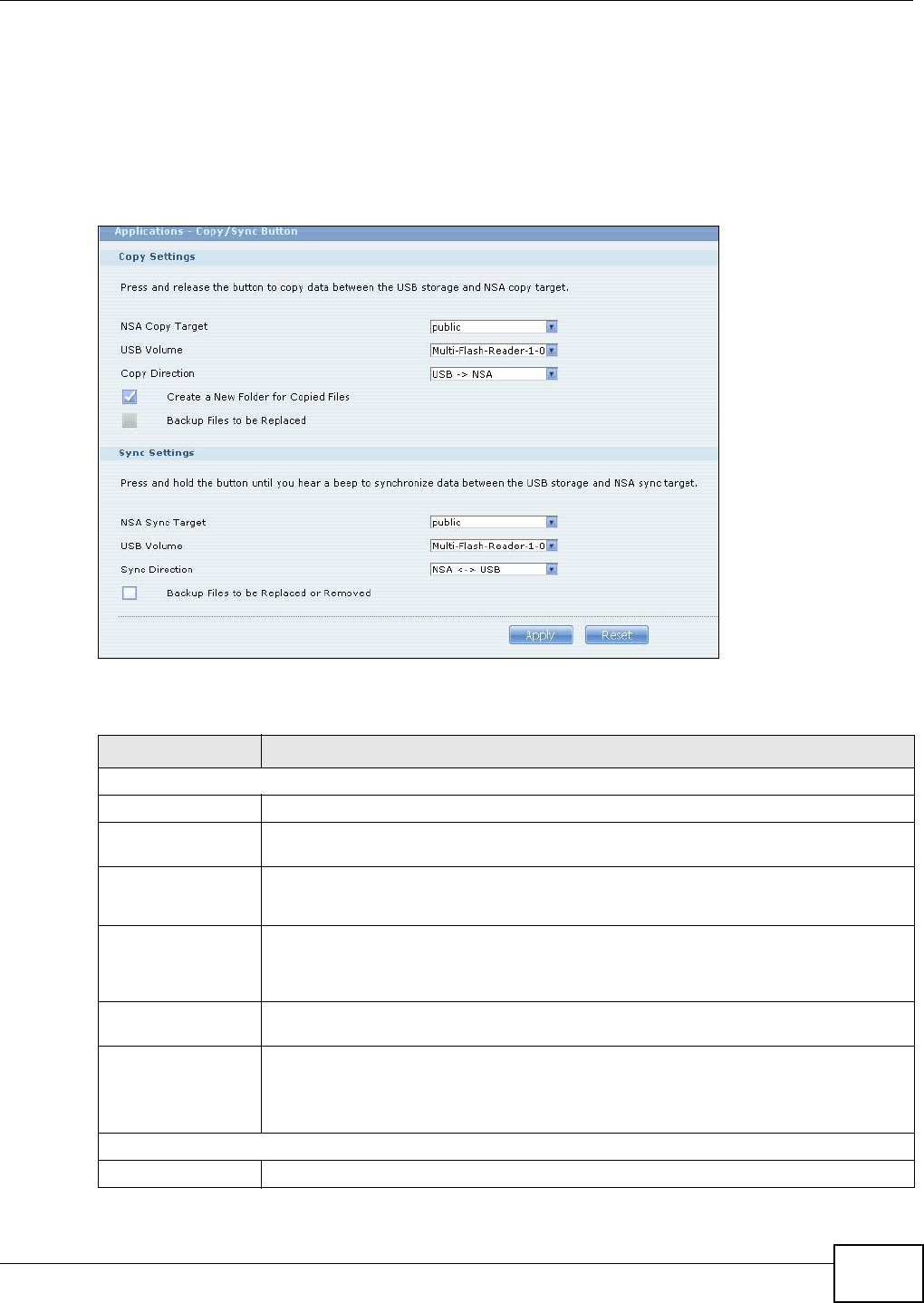
Chapter 10 Applications
Media Server User’s Guide 211
10.10 The Copy/Sync Button Screen
The Copy/Sync button on the front panel allows you to copy or synchronize files between a
connected USB device and the NSA.
Click Applications > Copy/Sync Button to open the following screen.
Figure 107 Applications > Copy/Sync Button
The following table describes the labels in this screen.
Table 50 Applications > Copy/Sync Button
LABEL DESCRIPTION
Copy Settings
NSA Copy Target Select the NSA share to use with the copy function.
USB Volume If your USB device has multiple partitions, select which partition to use with the copy
function.
Copy Direction Select USB -> NSA to copy files from your USB device to the NSA.
Select NSA -> USB to copy files from the NSA to your USB device.
Create a New Folder
for Copied Files Select this option to place the copied files in a new folder.
The name of the folder created for the copied files consists of the date and time of the
copy in year_month_day_hour_minute_second format.
Backup Files to be
Replaced This option is only available if you do not select Create a New Folder for Copied
Files. Select this option to save the files that will be replaced by the source files.
Backup Target Select a share in which to save the backup files.
Note: The NSA will not create a new folder to store the backup files. It is recommended to
create a specific share (such as “backup”) for backup purposes.
Sync Settings
NSA Sync Target Select the NSA share to use with the synchronization function.
Chapter 10 Applications
Media Server User’s Guide
212
10.11 Technical Reference
This section provides technical background information on the topics discussed in this chapter.
10.11.1 Sharing Media Files on Your Network
The media server feature lets anyone on your network play video, music, and photos from the NSA
(without having to copy them to another computer). The NSA can function as a DLNA-compliant
media server and/or an iTunes server. The NSA streams files to DLNA-compliant media clients or
computers using iTunes. The Digital Living Network Alliance (DLNA) is a group of personal computer
and electronics companies that works to make products compatible in a home network.
• Publish shares to let others play the contained media files.
• The media server is a convenient way to share files you download using the broadcatching
service (see Section 10.8 on page 203).
• Hardware-based media clients like the DMA-2501 can also play the files. See Section 21.2 on
page 366 for the supported multimedia file formats.
Note: Anyone on your network can play the media files in the published shares. No user
name and password or other form of security is used. The media server is enabled
by default with the video, photo, and music shares published.
Songs from the iTunes Store
After using iTunes on your computer to download songs from Apple’s iTunes Store, you can copy
them to the NSA. Many of these songs have DRM (Digital Rights Management). At the time of
writing, you can use your Apple account ID and password to authorize up to a total of five
computers to play the files. To authorize a computer, open iTunes and click Store > Authorize
Computer.
USB Volume If your USB device has multiple partitions, select which partition to use with the
synchronization function.
Sync Direction Select USB -> NSA to synchronize files from your USB device to the NSA.
Select NSA -> USB to synchronize files from the NSA to your USB device.
Select NSA <-> USB to synchronize files in both directions simultaneously.
Backup Files to be
Replaced or
Removed
Select this option to save the files that will be replaced by the source files.
Backup Target Select a share in which to save the backup files.
Note: The NSA will not create a new folder to store the backup files. It is recommended to
create a specific share (such as “backup”) for backup purposes.
Apply Click this to save your changes.
The configuration file is saved on the USB device.
Reset Click this to restore your previously saved settings.
Table 50 Applications > Copy/Sync Button
LABEL DESCRIPTION
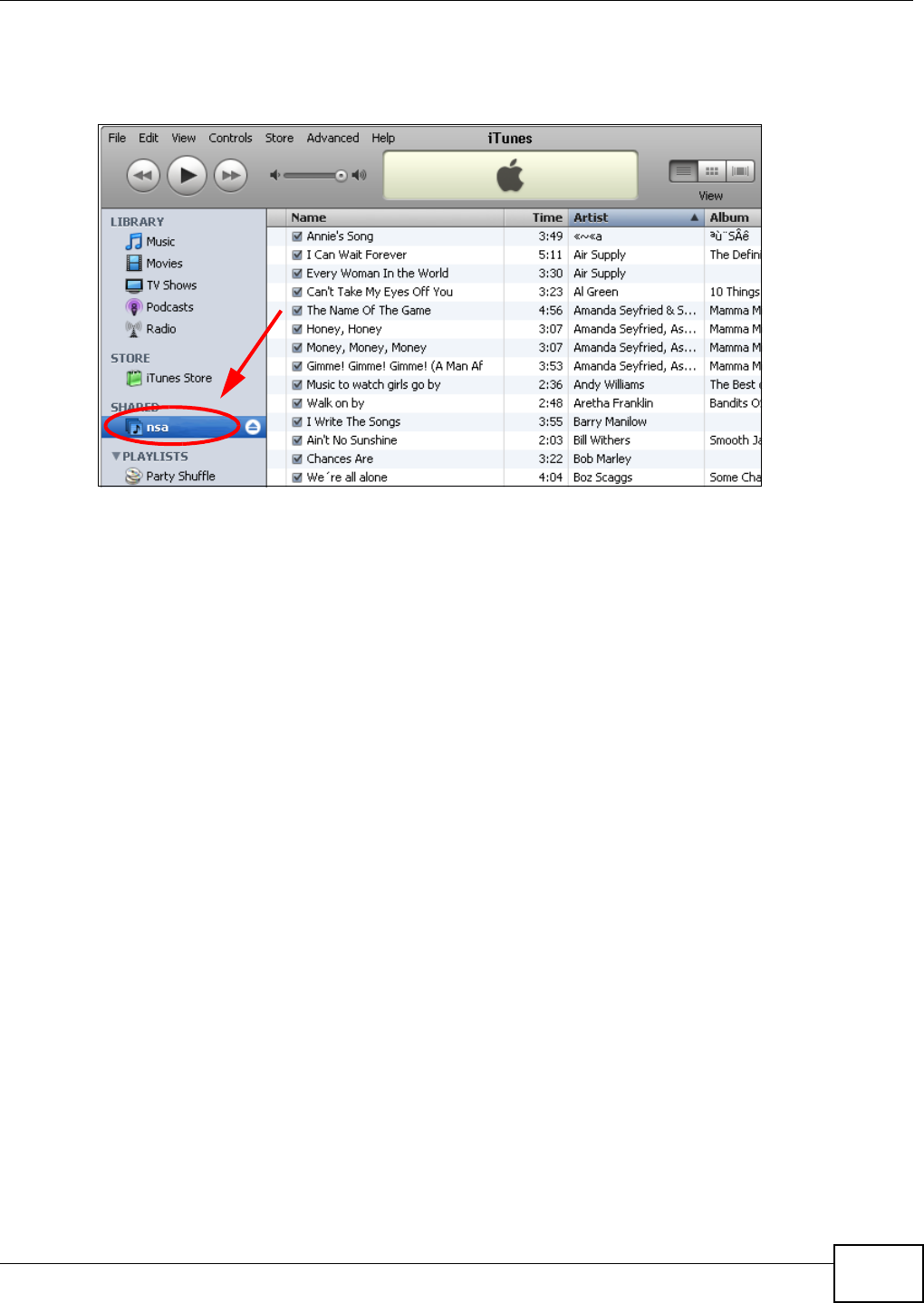
Chapter 10 Applications
Media Server User’s Guide 213
A link for the NSA in iTunes under SHARED. Click it to display the NSA’s published media files as
shown next.
Figure 108 NSA link in iTunes
10.11.2 Download Service
The NSA’s download service downloads files from the Internet directly to the NSA. You do not have
to download to your computer and then copy to the NSA. This can free up your computer’s system
resources. The download service also handles your broadcatching downloads. See Section 10.8 on
page 203 for information on broadcatching.
The NSA can download using these protocols.
• HTTP: The standard protocol for web pages.
• FTP: A standard Internet file transfer service.
• BitTorrent: A popular distributed peer-to-peer files sharing protocol.
Note: Do not use the NSA for illegal purposes. Illegal downloading or sharing of files can
result in severe civil and criminal penalties. You are subject to the restrictions of
copyright laws and any other applicable laws and will bear the consequences of any
infringements thereof. ZyXEL bears NO responsibility or liability for your use of the
download service feature.
Torrent Files
The NSA needs a “.torrent” file for BitTorrent to download a file. The torrent file gives the NSA
information about the file to be downloaded (and shared) and the tracker(s) (computers) that
coordinates the distribution of the file.
When you add a BitTorrent download task in the NSA’s web configurator screens, you can copy and
paste the URL of the torrent file. The NSA automatically downloads the torrent file and saves it in a
torrent folder within the folder where the NSA stores downloaded files (the admin share’s
download folder by default).
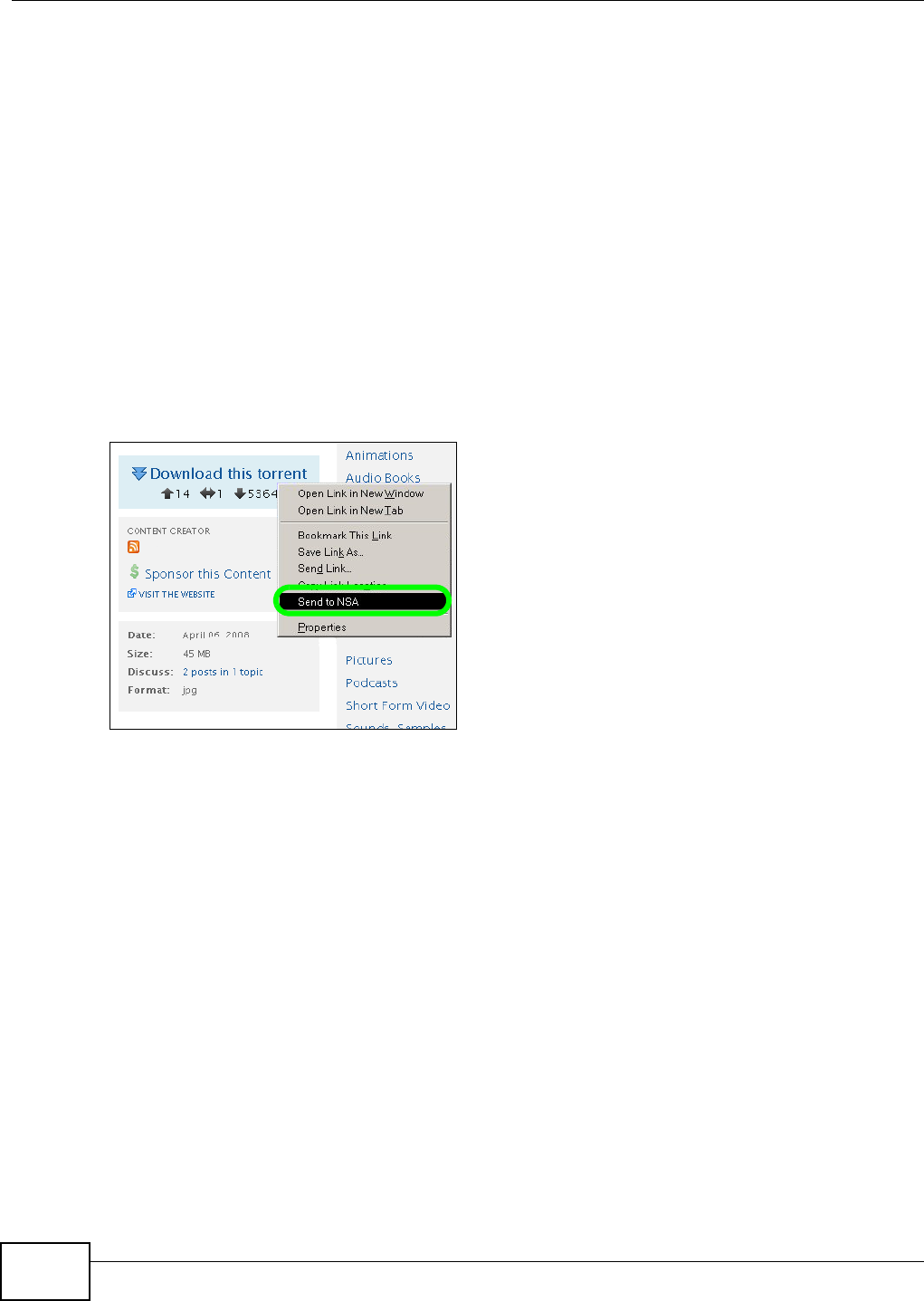
Chapter 10 Applications
Media Server User’s Guide
214
If you already have the torrent file saved on your computer, you can just specify its location when
adding a download task through the web configurator. Another method is to use FTP or a CIFS
program (Windows Explorer for example) to copy the torrent file into the torrent folder. The NSA
automatically uses the torrent file.
After your BitTorrent download and sharing are finished, you can go to the incoming folder within
the destination share or folder and delete the .torrent file if you need to free up hard disk space.
10.11.3 Link Capture Browser Plugin
The link capture browser plugin is an add-on feature for your web browser. Use the plugin to
directly add a file’s URL to the NSA’s download service.
Note: The link capture browser plugin is located in the included CD.
The following screen displays how the plugin works.
Figure 109 Link Capture Browser Plugin
Instead of copying and pasting a file’s URL to the NSA’s download service, you can right-click on the
URL in the web browser and select Send to NSA. The URL is then added to the NSA’s download
service list.
See Section 5.10.2 on page 95 and Section 5.10.3 on page 100 for tutorials about installing and
using the link capture browser plugin.
Note: At the time of writing the plugin supports Internet Explorer 6.0/7.0/8.0 and Mozilla
Firefox 2.0/3.0.
10.11.4 Download Service Notification
Use the download service notification to keep track of downloaded files on the NSA. You can
subscribe to the NSA’s download list on your computer. When the NSA finishes downloading new
files, your RSS reader displays the information and links for the files. You can also download the
files from the RSS reader to your computer.
See Section 5.10.5 on page 104 for a tutorial about using the download service notification.
In the Download Service screen, select Enable Download Notify and click Apply. An RSS feed
icon appears. Click the icon to subscribe to the NSA’s download list.
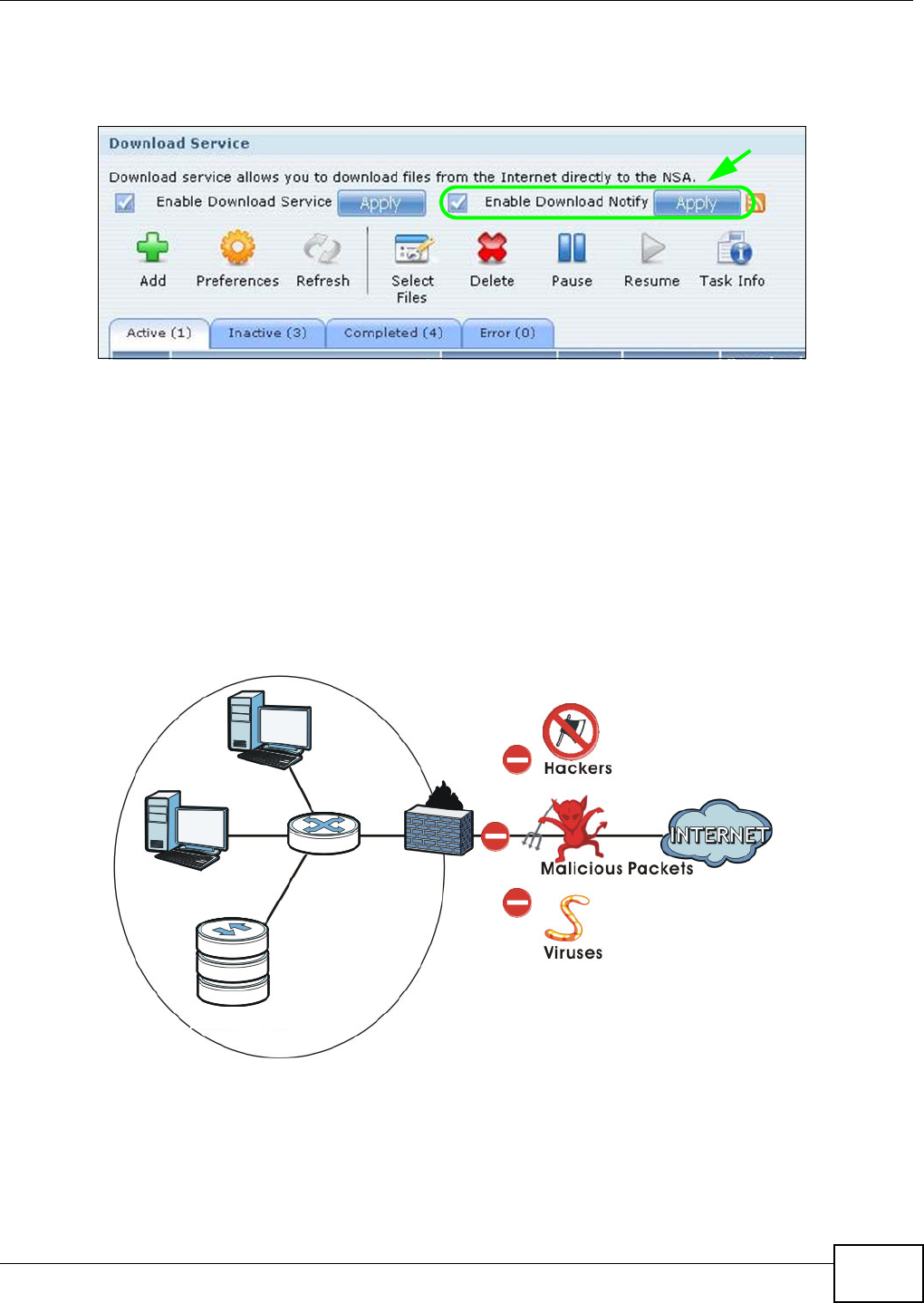
Chapter 10 Applications
Media Server User’s Guide 215
Note: The download service notification only keeps track of files downloaded via
BitTorrent.
Figure 110 Download Service Notification
10.11.5 BitTorrent Security
When you download using BitTorrent, you reveal your IP address. This increases the risk of hacking
attacks, which can be protected against by a good firewall.
Use a Hardware-based Firewall
Place a hardware-based firewall between your network and the Internet (a software-based firewall
on your computer would just protect the computer itself, not the NSA since your computer is not
between your NSA and the Internet).
Figure 111 Firewall
Ideally your firewall should have the following:
• Stateful packet inspection to control access between the Internet and your network and protect
your NSA (and computers) from hacking attacks.
• IDP (Intrusion Detection and Prevention) to detect malicious packets within normal network
traffic and take immediate action against them.
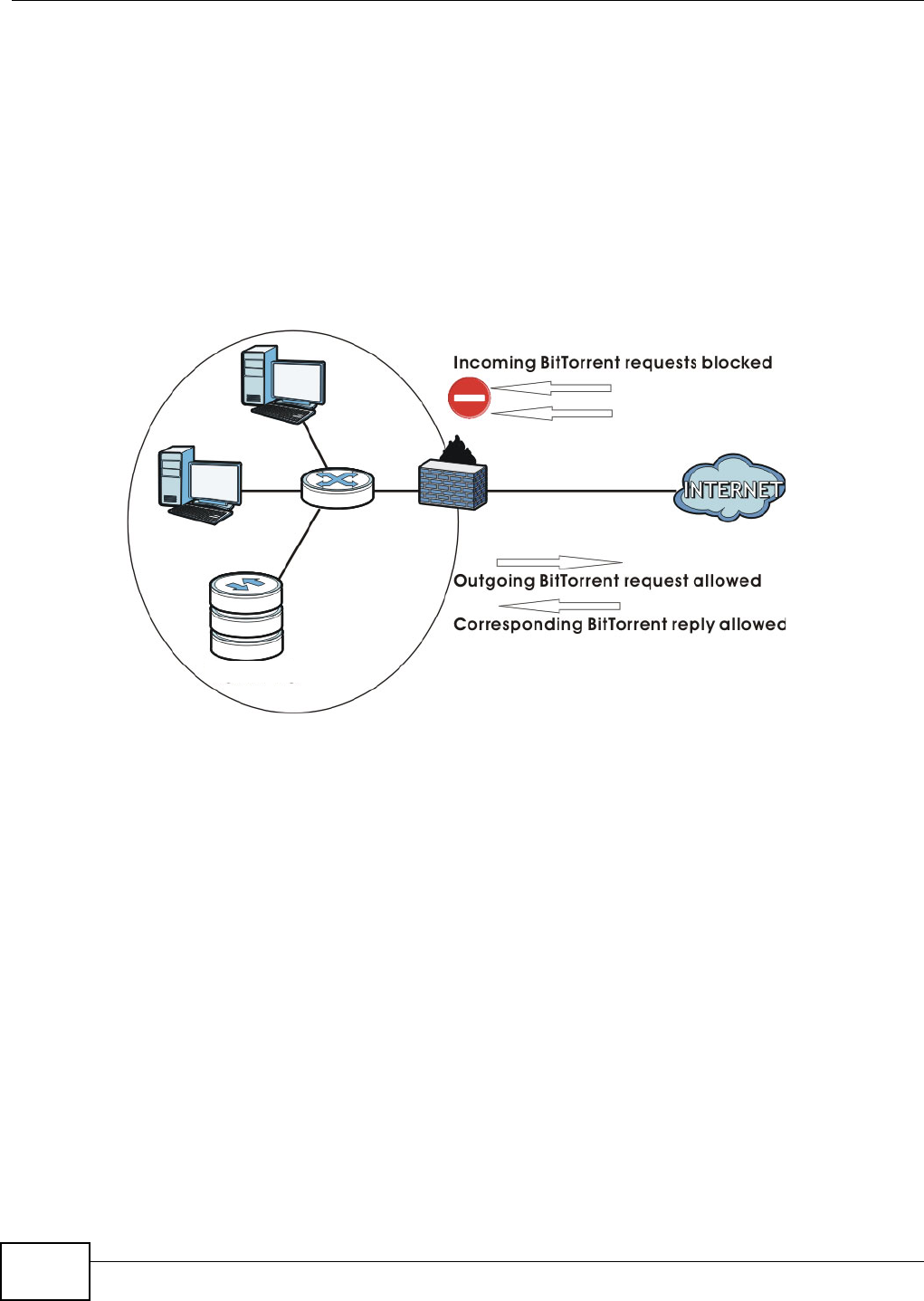
Chapter 10 Applications
Media Server User’s Guide
216
• Anti-virus to check files you download for computer viruses.
BitTorrent and Your Firewall
The anti-virus feature on a firewall probably cannot check BitTorrent downloads for viruses, so use
anti-virus software on your computer to scan the NSA for viruses.
When you download using BitTorrent, many other BitTorrent users are also trying to download the
file from you. The firewall slows this down because by default, it only allows traffic from the
Internet in response to a request that originated on the LAN (it lets you get files from the Internet
and blocks those on the Internet from getting files from you).
Figure 112 Firewall Blocking Incoming BitTorrent Requests
To speed up BitTorrent file transfers, configure your firewall’s port forwarding to send incoming TCP
port 9090 and UDP port 9089 connections to the NSA. You probably need to use your firewall’s
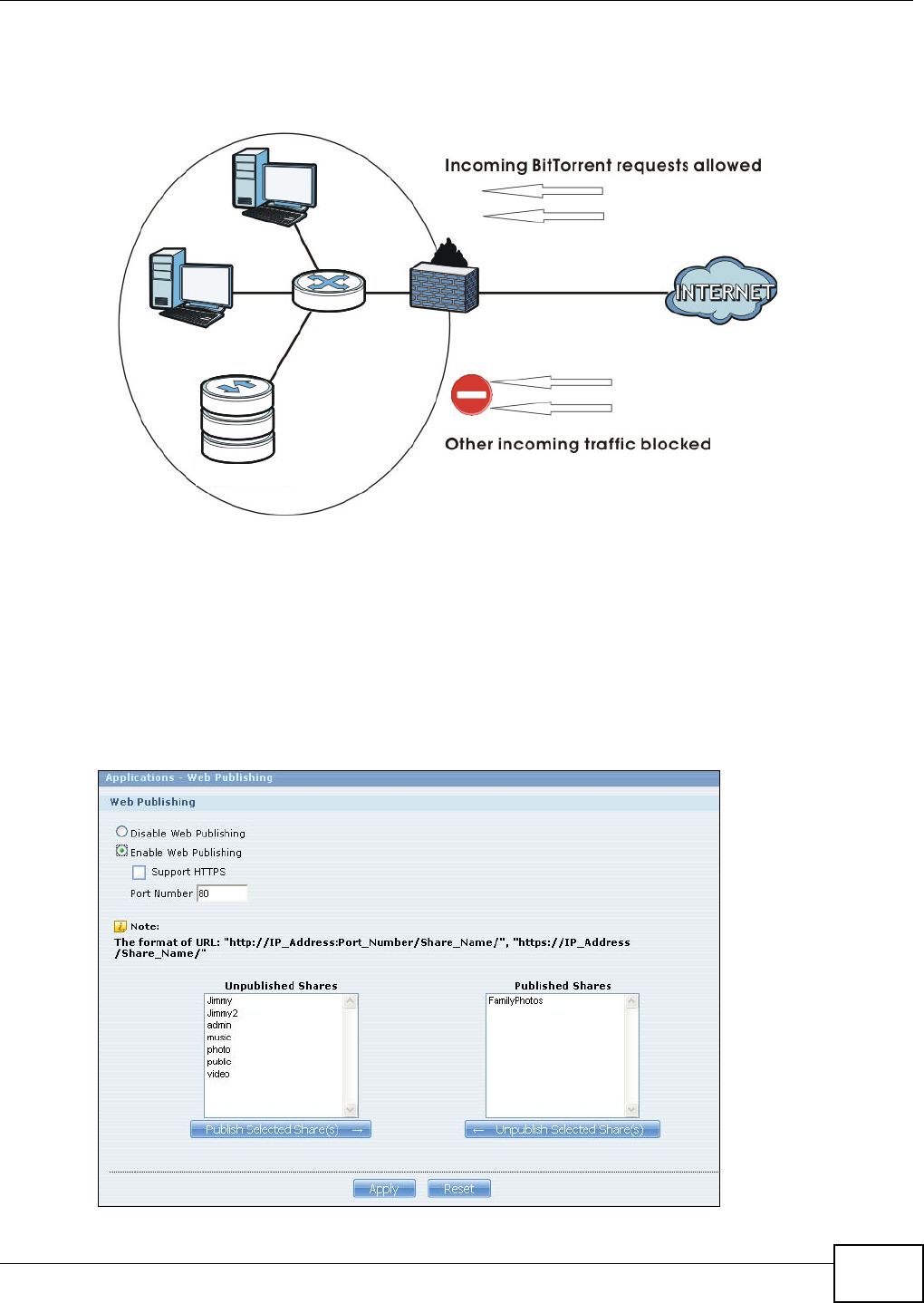
Chapter 10 Applications
Media Server User’s Guide 217
HTML (web-based) configuration interface to set this up (see the firewall’s manual for details). You
may also have to configure a corresponding firewall rule.
Figure 113 Firewall Configured to Allow Incoming BitTorrent Requests
10.11.6 Web Publishing Example
This example covers how to configure the Web Publishing screen to let people use a web browser
to access a share named FamilyPhotos without logging into the Home screens and shows how to
access the share through the Internet.
1Click Applications > Web Publishing and configure the screen as shown (enable the web
publishing and move FamilyPhotos over to Published Shares) and click Apply.
Figure 114 Applications > Web Publishing (Example)
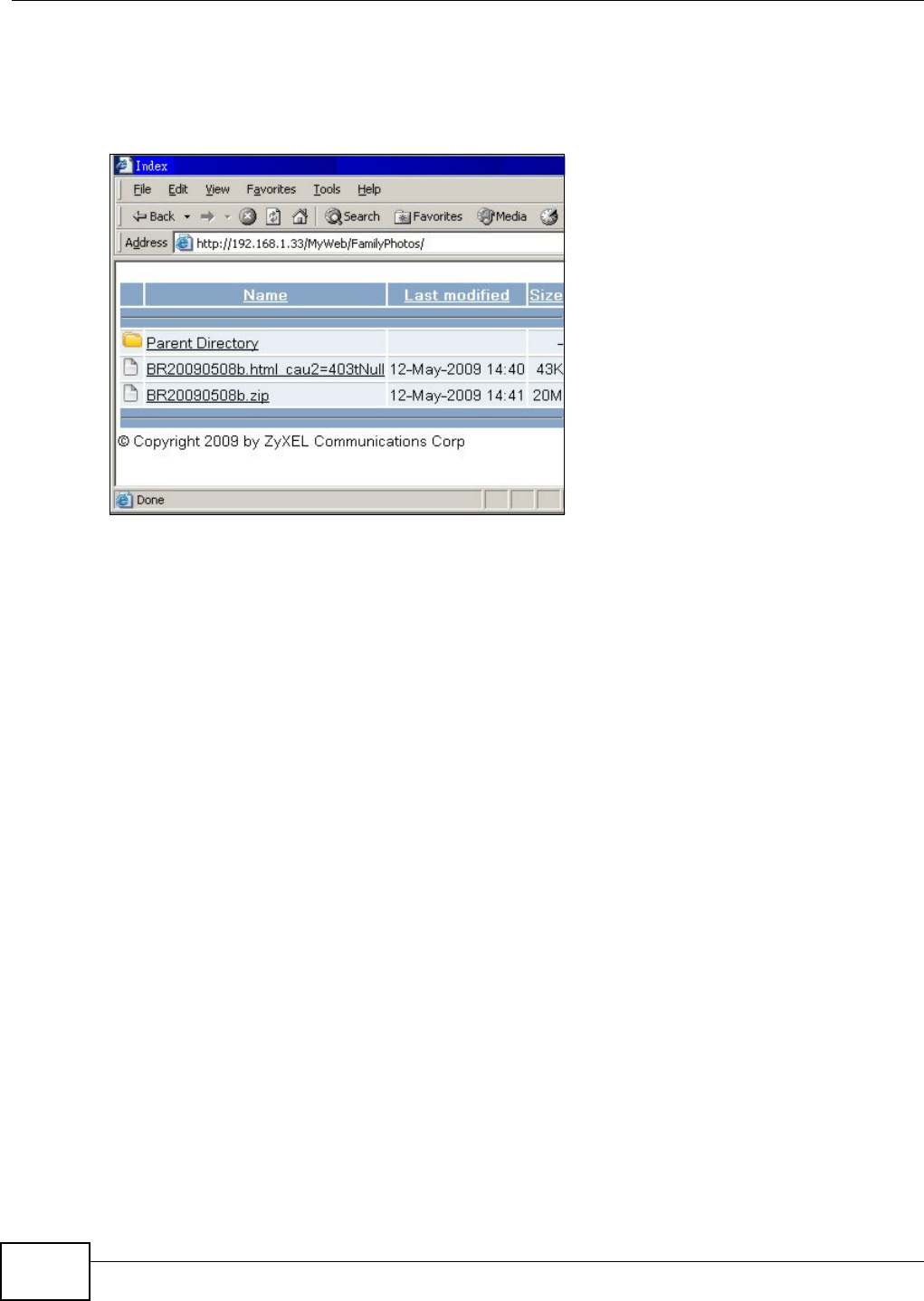
Chapter 10 Applications
Media Server User’s Guide
218
2Now open your web browser and type in the address of the NSA’s FamilyPhotos web page. In this
example, the NSA’s IP address is 192.168.1.33, and the name of the web-published share is
FamilyPhotos. So you would enter “http://192.168.1.33/MyWeb/FamilyPhotos/” in your browser’s
address bar. Then press [ENTER] or click Go. A screen displays listing the share’s files.
Figure 115 Browsing to an NSA Share Example
• Click a file’s link to open the file.
• Right-click a file’s link and select Save Target As.. (in Internet Explorer) to save a copy of the
file.
• Click a label in the heading row to sort the files by that criteria.
• To customize how the page looks and works, create an index.html or index.htm file and store it in
the share.
10.11.7 Web Publishing
Web publishing lets you “publish” shares (containing folders and files) on the NSA so people can
access the files using a web browser without having to log into the Home screens. This way you
can share files with others without them having to know and enter a user name and password.
For example, if you want to share photos in a FamilyPhotos share, you could “web publish” it and
others could use a web browser to access the photos at http://my-NSA’s-IP-Address/MyWeb/
FamilyPhotos.
Note: The NSA does not use any security for the files in the published folders. It is not
recommended to publish shares if you do not have the NSA behind a good
hardware-based firewall. See page 215 for more on firewalls.
Additionally, you can use HTML editing software (not included) to create an index.html or index.htm
file to define and customize how your website works and looks.
Accessing Web-published Shares from the Internet
You need to use a public address to access the NSA’s web-published shares from the Internet. If
your NSA uses a private IP address, you may need to use the public IP address of your Internet
gateway and configure NAT or port forwarding on your Internet gateway and possibly firewall rules
in order to let people access the NSA’s web-published shares from the Internet.
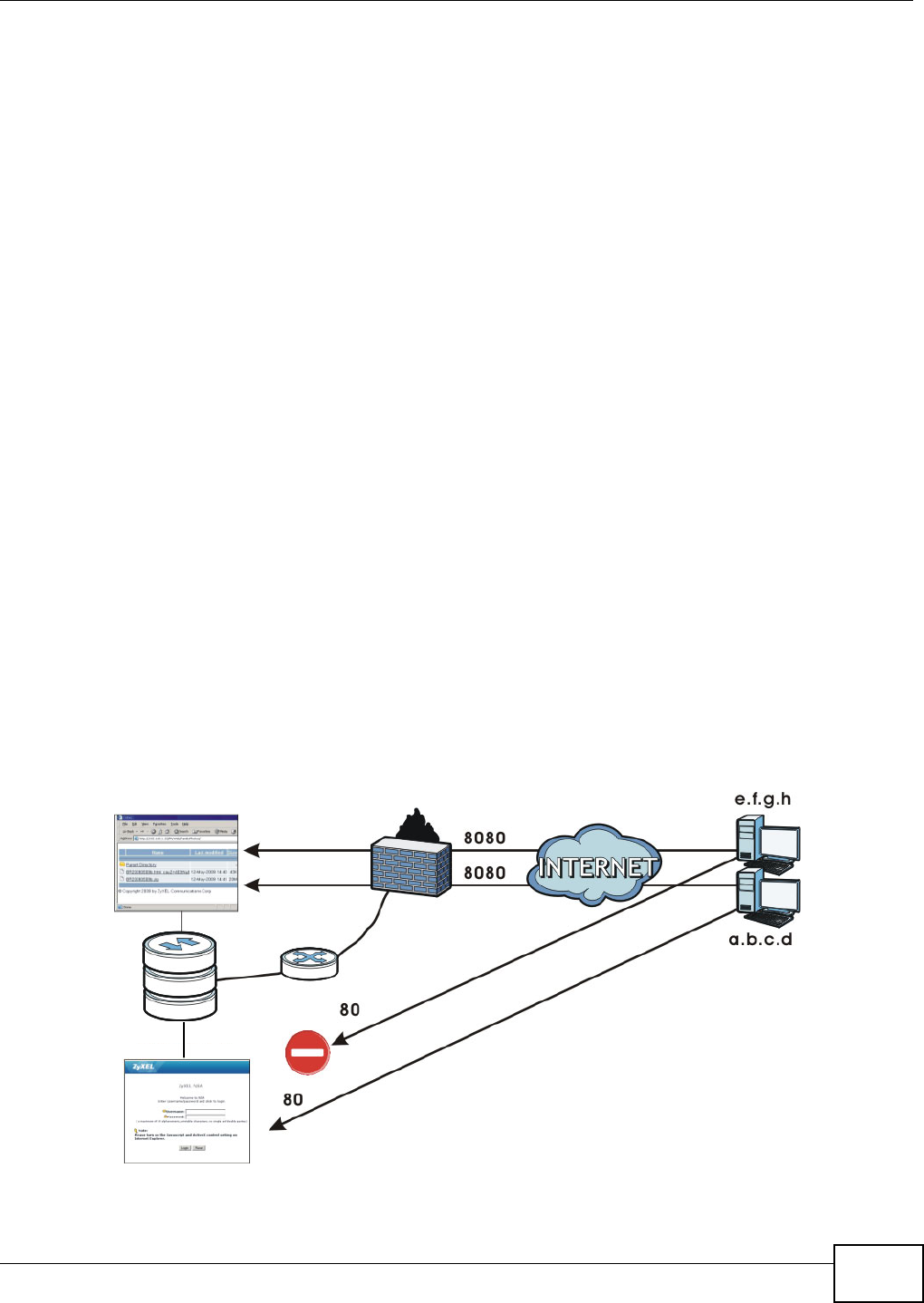
Chapter 10 Applications
Media Server User’s Guide 219
Web Publishing Port Number
If the web-published shares use a port number other than 80 (the normal port for web traffic),
users must include it after the NSA’s IP address in order to access the NSA’s web-published shares.
For example, say you specified port 8080, the NSA’s IP address is 192.168.1.23, and the name of
the web-published share is FamilyPhotos. You would have to enter “http://192.168.1.23:8080/
MyWeb/FamilyPhotos/” in your browser’s address bar to access the share’s web page.
The NSA’s web configurator uses port 80. To make the web configurator more secure, you can have
the web-published shares use another port number. Then you can configure one set of firewall rules
and NAT or port forwarding settings on your Internet gateway specifically for allowing access to the
web-published shares and another separate set of rules for accessing the NSA’s web configurator.
10.11.8 Channel Guides for Broadcatching
Here are some popular broadcatching channel guide web sites.
Note: ZyXEL does not endorse these web sites and is not responsible for any of their
contents. Use these or any other web sites at your own risk and discretion.
• http://www.zencast.com/
• http://www.miroguide.com/
• http://www.vuze.com/
• http://www.mefeedia.com/
• http://www.vodstock.com/
• http://www.mininova.org
In the following example, the Internet gateway’s firewall is configured to allow anyone to access the
NSA’s web-published screens using port 8080. Web configurator access (port 80) however, is only
allowed from IP address a.b.c.d.
Figure 116 Web Publishing Port Number Example
Chapter 10 Applications
Media Server User’s Guide
220
10.11.9 Printer Sharing
The NSA can act as a print server. A print server lets multiple computers share a printer. Connect a
printer to the NSA’s USB port to let multiple computers on your network use it. See www.zyxel.com
for a list of compatible printers.
Figure 117 Printer Sharing
10.11.10 Copying Files
You can copy files from a USB device to the NSA or from the NSA to a USB device. Simply press and
release the COPY/SYNC button to start copying files. See Section 10.10 on page 211 for details
about configuring the copy settings.
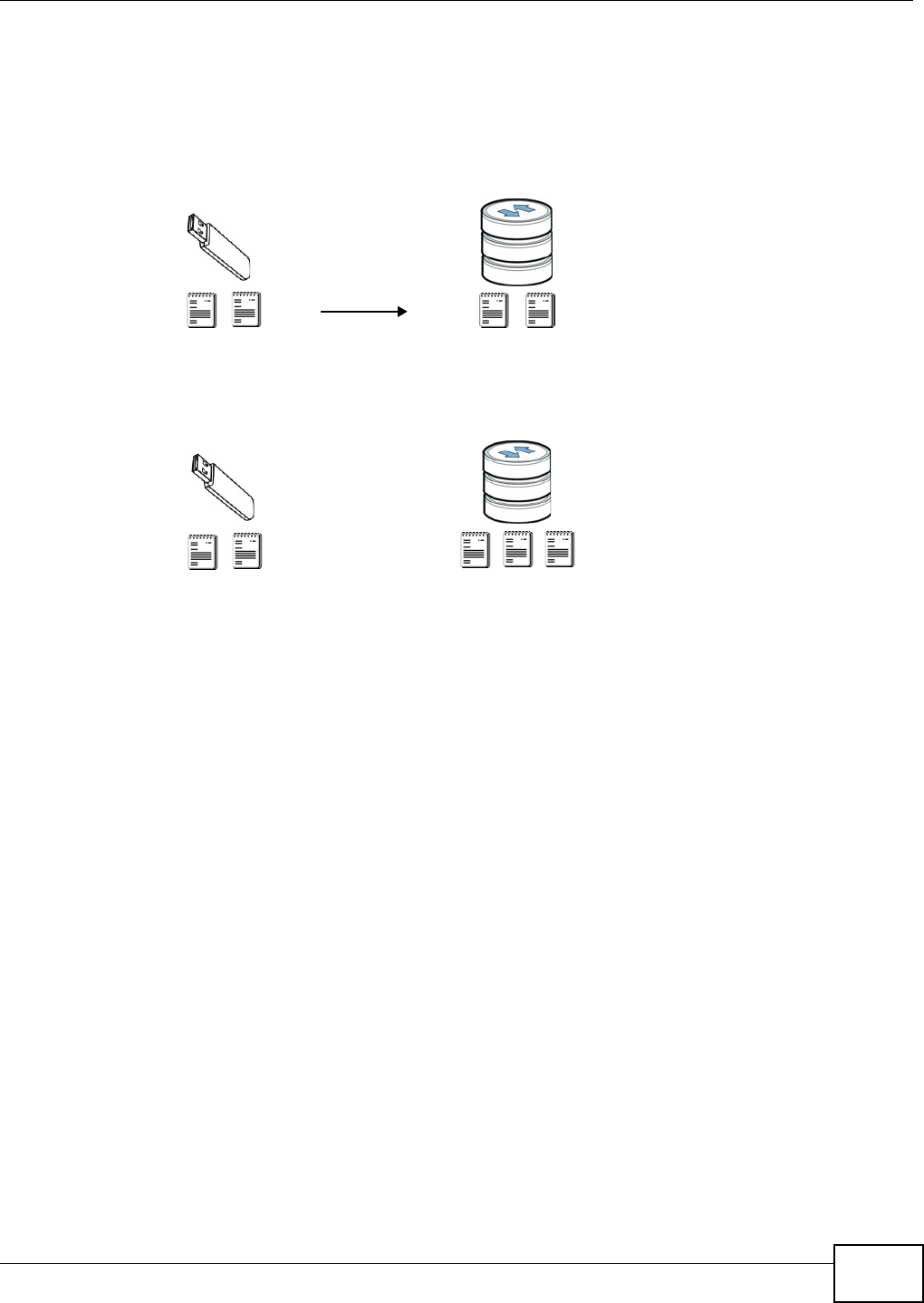
Chapter 10 Applications
Media Server User’s Guide 221
The following figure illustrates how copying files works when you copy files from a USB device to
the NSA. The same concept applies when you copy files from the NSA to a USB device.
Figure 118 Copying Files Example
Both storage devices contain file A.
• A copy of files A and B from the USB device is transferred to the NSA.
• File A from the USB device replaces file A on the NSA.
10.11.11 Synchronizing Files
Synchronization makes the contents on the target device identical to the ones on the source device.
You can synchronize files from a USB device to the NSA or from the NSA to a USB device. In
addition, you may also synchronize files in both directions simultaneously.
Press and hold the COPY/SYNC button until you hear a beep to synchronize files. See Section
10.10 on page 211 for details about configuring the synchronization settings.
USB -> NSA or USB <- NSA
When you synchronize files in one direction, contents on the source device replace the files on the
target device.
AC
Before Copy
After Copy
USB NSA
AB
C
USB NSA
AB AB
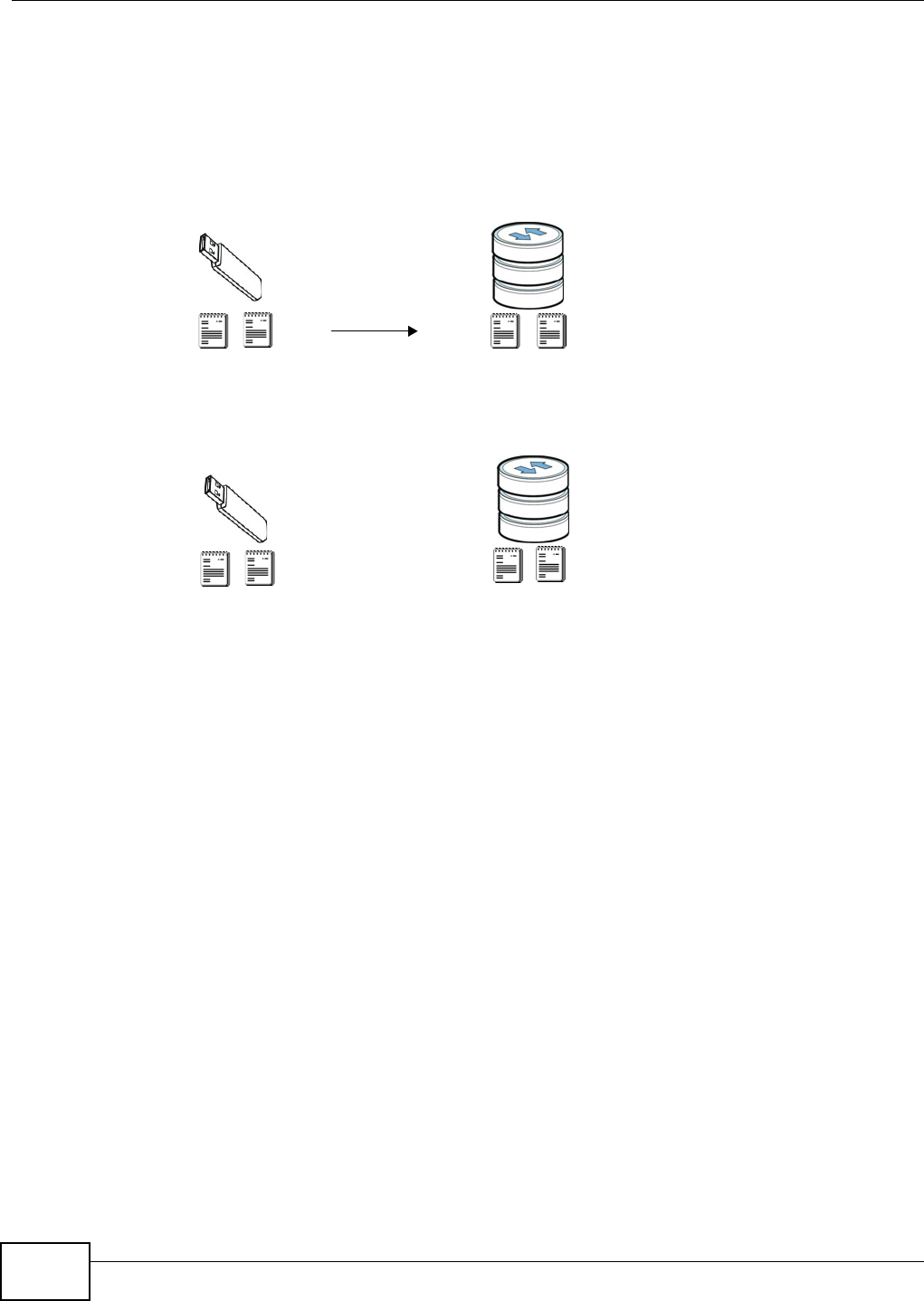
Chapter 10 Applications
Media Server User’s Guide
222
The following figure illustrates how synchronization works when you synchronize files from a USB
device to the NSA. The same concept applies when you synchronize files from the NSA to a USB
device.
Figure 119 Synchronizing Files Example 1
Both storage devices contain A.
• A copy of files A and B from the USB device is transferred to the NSA.
• File A from the USB device replaces file A on the NSA.
• File C on the NSA is deleted.
USB <-> NSA
When you synchronize files in both directions simultaneously, both storage devices transfer unique
files to one another. Files with the same file name are synchronized according to their modification
date/time. The difference in modification time between the two files has to be greater than five
minutes. More recently modified files overwrite the older ones during synchronization.
AC
Before Sync
After Sync
USB NSA
AB
USB NSA
AB AB
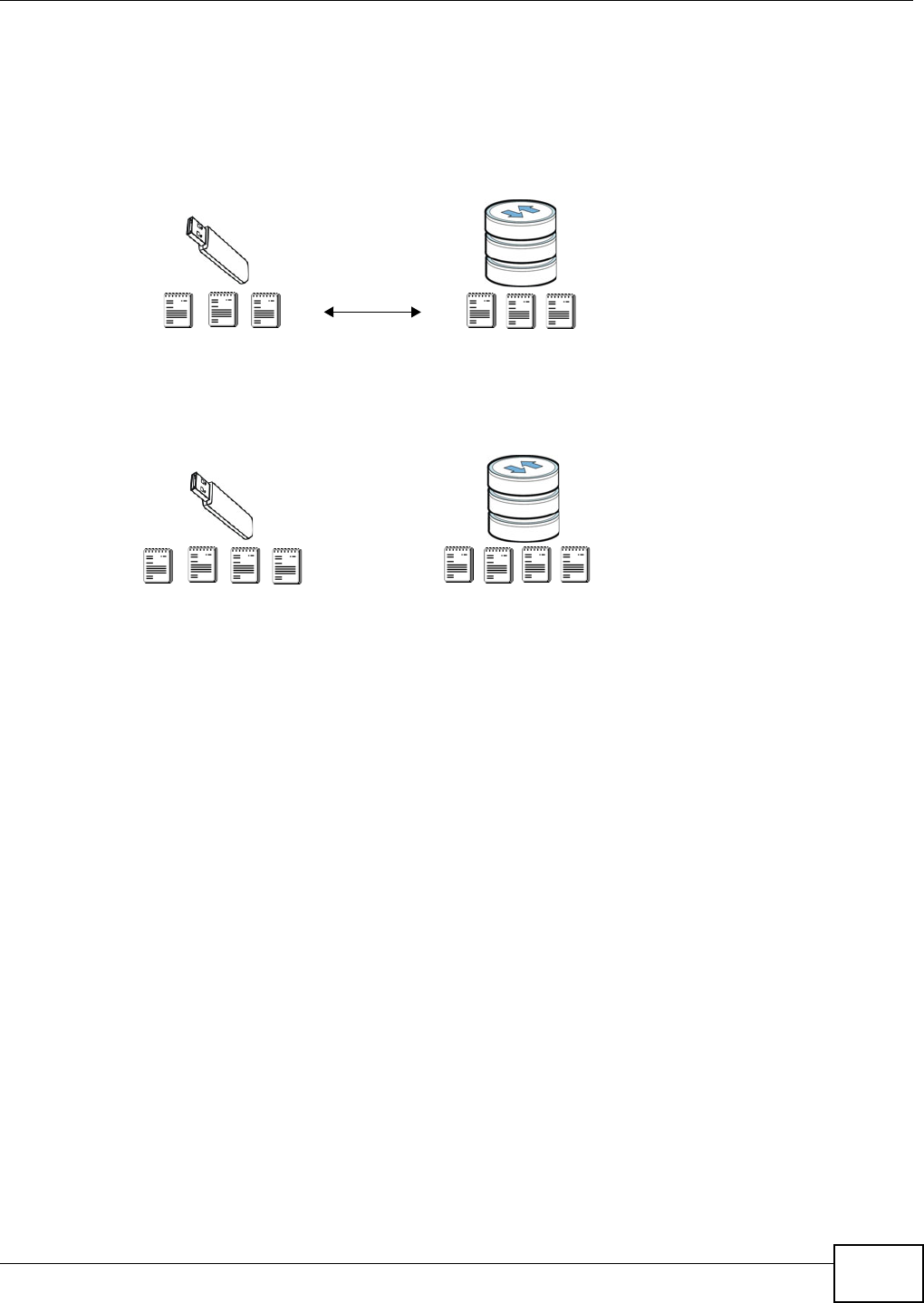
Chapter 10 Applications
Media Server User’s Guide 223
The following figure illustrates how synchronization works when you synchronize files in both
directions simultaneously.
Figure 120 Synchronizing Files Example 2
A on the USB device and B on the NSA are modified more recently.
• File A from the USB device replaces file A on the NSA.
• File B from the NSA replaces file B on the USB device.
• A copy of file C from the USB device is transferred to the NSA.
• A copy of file D from the NSA is transferred to the USB device.
AB
Before Sync
After Sync
USB NSA
AB
USB NSA
CD
B
ABCD
DC
(new)
A
(new)
(new)
(new)
(new) (new)

Chapter 10 Applications
Media Server User’s Guide
224

Media Server User’s Guide 225
CHAPTER 11
Package Management
11.1 Overview
Package Management can be used to set up more useful applications in your NSA. The NSA can
download multiple packages/files at once and automatically goes through all the installation steps.
11.2 What You Can Do
•Use the Package Management screen (Section 11.4 on page 226) to download and install
applications from the web.
•Use the DyDNS screen (Section 11.5 on page 229) to configure the domain name settings of
your NSA.
•Use the NFS screen (Section 11.6 on page 230) to configure the Network File System (NFS)
settings of your NSA.
•Use the SMART screens (Section 11.7 on page 233) to view your NSA hard disk(s) statistics and
monitor their performance.
•Use the Protect screens (Section 11.8 on page 237) to configure and schedule the back up and
restore jobs of your NSA.
•Use the Syslog Server screen (Section 11.11 on page 253) to configure the NSA to accept
syslog logs from syslog clients.
•Use the TFTP Server screen (Section 11.12 on page 255) to configure the NSA to accept log files
from TFTP clients.
•Use the eMule screens (Section 11.13 on page 256) to configure the server, task and search
settings for the eMule application.
•Use the pyLoad screen (Section 11.14 on page 271) to configure the NAS so you can have it
manage your downloads including those from one-click hosting sites.
11.3 What You Need to Know
This feature enables you to use the following applications:
•BackupPlanner - Use this to schedule and run backup jobs for files stored in your NSA to an
internal drive, external storage device or to another NSA in the network.
•DyDNS - This gives your NSA a domain name with a dynamic IP address. At the time of writing,
this package supports accounts from the following service providers: DynDNS, NoIP, 3322,
ZoneEdit, and DHS.

Chapter 11 Package Management
Media Server User’s Guide
226
•Gallery - This web-based application allows your NSA to host pictures. You can upload images in
your local computer or shares to this application. Use the administrator account of your NSA to
log in to the Gallery console. The administrator can then create accounts for other users.
•NFS - NFS (Network File System) is a file-sharing protocol most commonly implemented on
Unix-like systems.
•PHP-MySQL-phpMyAdmin - This tool can be used to manage MySQL through the web. Enter
'root' as the username and '1234' as the password to log in. This includes MySQL 5.1.30, PHP
5.2.8 and phpMyAdmin 3.1.1.
•SMART - Use S.M.A.R.T. (Self Monitoring, Analysis, and Reporting Technology) to monitor hard
disks. It detects and reports the reliability of hard disks using standard indicators, enabling
administrators to anticipate possible disk failures.
•SqueezeCenter - This enables you to manage a Logitech's Squeezebox device connected to the
NSA.
•Syslog - Use this to configure the NSA to accept syslog logs from syslog clients.
•TFTP - Use this to configure the NSA to accept log files from TFTP clients.
•Wordpress - This allows you to create and manage a blog or website. Use the NSA administrator
credentials to log in. The administrator can then create accounts for other users.
•eMule - eMule is an open-source peer-to-peer (P2P) file-sharing application similar to eDonkey,
which can be used to download files from the Internet. It uses the Kad protocol.
•pyLoad - Use this to have the NAS manage your downloads including those from one-click
hosting sites. One-click hosting sites allow Internet users to easily upload files to the one-click
host's server so others can download them.
The following applications come with their own web configurator and documentation:
• Gallery
• PHP-MySQL-phpMyAdmin
•SqueezeCenter
• WordPress
11.4 Package Management Screen
Use this screen to download and install applications from the web.
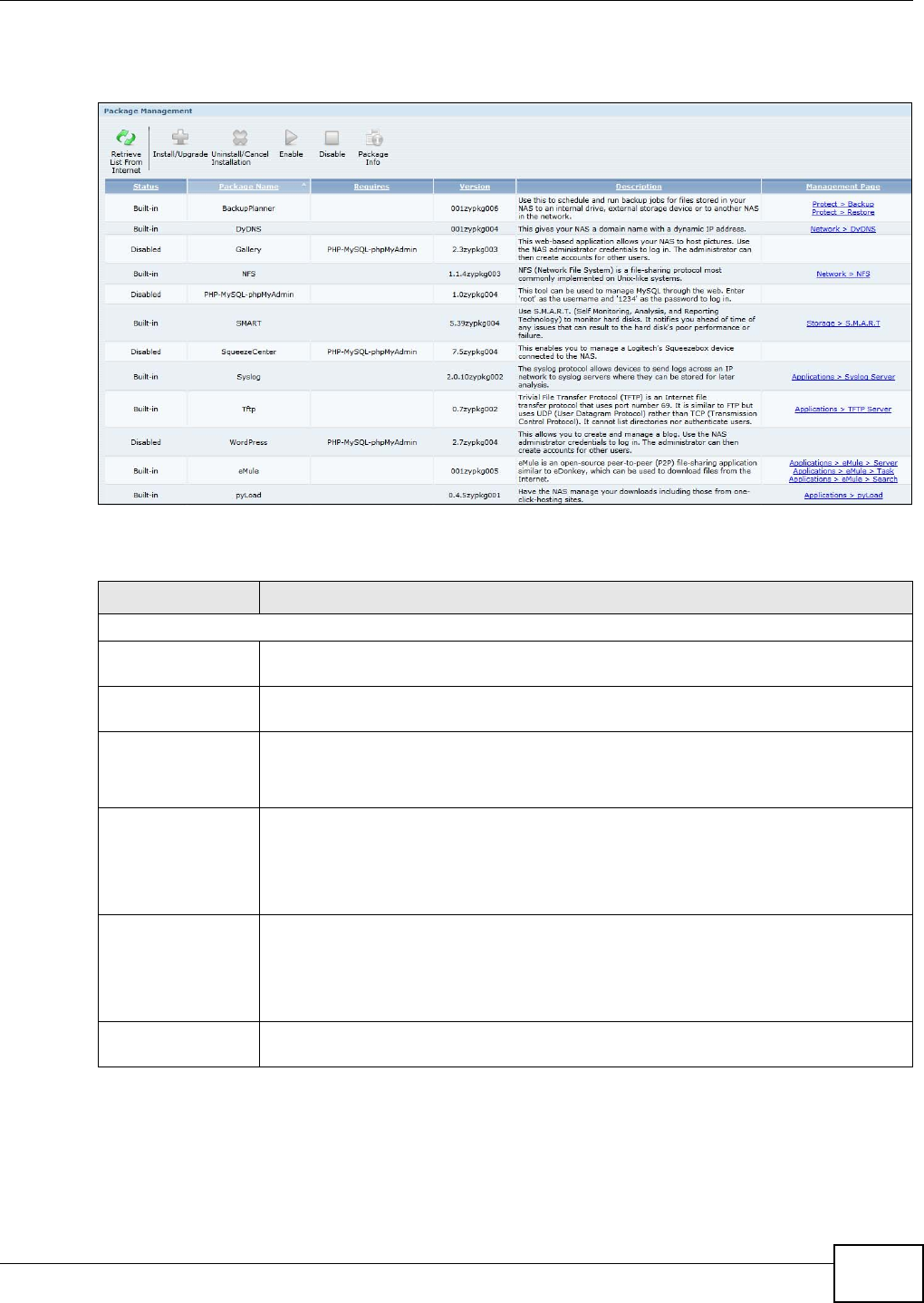
Chapter 11 Package Management
Media Server User’s Guide 227
Click Applications > Package to open the following screen.
Figure 121 Applications > Package
The following table describes the labels in this screen.
Table 51 Applications > Package
LABEL DESCRIPTION
Package Management
Retrieve List From
Internet Click this to retrieve a list of available packages from the ZyXEL website.
Install/Upgrade Choose the item(s) on the list and click this to install the selected application(s) on your
system or upgrade to the latest version if you have previously installed the application.
Uninstall/Cancel
Installation Choose the item(s) on the list and click this to uninstall the selected application(s) from
your system or cancel their active download(s) or install process/es.
This is only available if you have previously installed the package.
Enable This option is only for non built-in packages.
Choose the item(s) on the list and click this to enable the application(s) on your
system.
This is only available if you have previously installed the package.
Disable This option is only for non built-in packages.
Choose the item(s) on the list and click this to disable the application on your system.
You have to enable the application again in order to use it.
This is only available if you have previously installed the package.
Package Info Select an item on the list and click this to display information about the package. See
Section 11.4.1 on page 229 for more details.
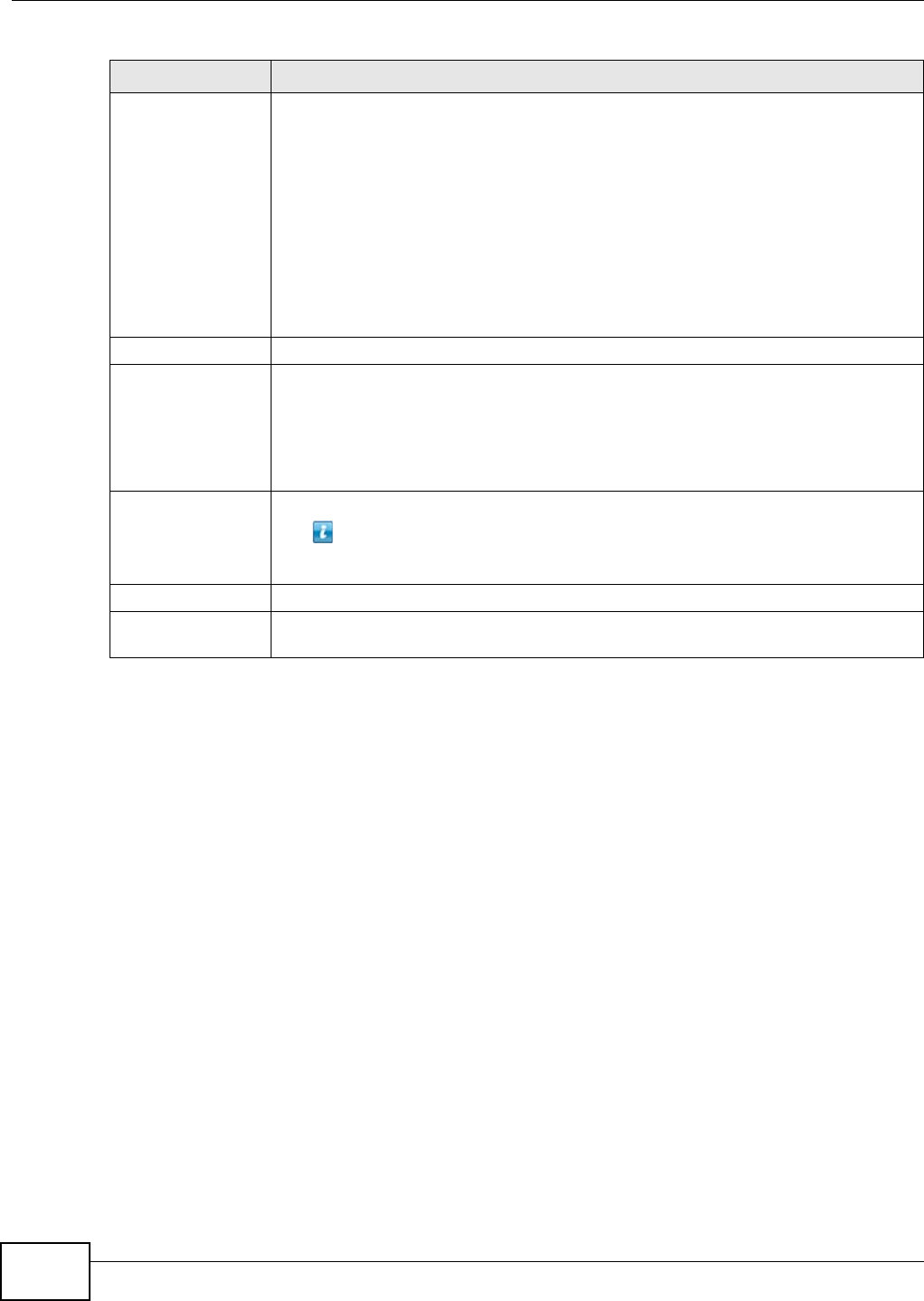
Chapter 11 Package Management
Media Server User’s Guide
228
Note: A navigation panel link displays after you install and enable eMule, DyDNS, NFS,
SMART, BackupPlanner, Syslog Server, or TFTP Server. Use the Package
Management screen’s links to access the Gallery, PHP-MySQL-phpMyAdmin,
SqueezeCenter, and WordPress screens. Use the Applications > pyLoad
screen’s link (or address and port number) to access the pyLoad screens.
Status This is the current status of the application. It shows:
•Not Installed - This displays for applications that have not been installed by the
NSA.
•Installing (%) - This displays when the application is being installed. It also shows
the percent of the package already installed.
•Built-in - This displays for applications installed by the NSA that you can configure
in the NSA Web Configurator.
•Enabled - This displays for applications installed and enabled by the NSA that have
their own web configurators.
•Disabled - This displays for applications installed and disabled by the NSA that
have their own web configurators.
•Unknown - It is possible to get this status if the web location for the application is
unavailable.
Package Name This is the name of the application.
Requires This shows the other packages required in order to run this application.
Note: A package would be disabled/enabled simultaneously if its prerequisite package(s)
has been disabled/enabled. For example, when you enable WordPress, this also
enables PHP-MySQL-phpMyAdmin automatically. However when you enable
PHP-MySQL-phpMyAdmin, this does not automatically enable WordPress.
Version This is the version number of the item.
The icon indicates that the application has a newer version available. Move your
mouse over this icon to see the latest version number. Choose this item and click
Install/Upgrade.
Description This shows a brief description of the application.
Management
Page This shows the location of the screens or web configurator where you can manage the
application (after the package has been installed on the system).
Table 51 Applications > Package (continued)
LABEL DESCRIPTION
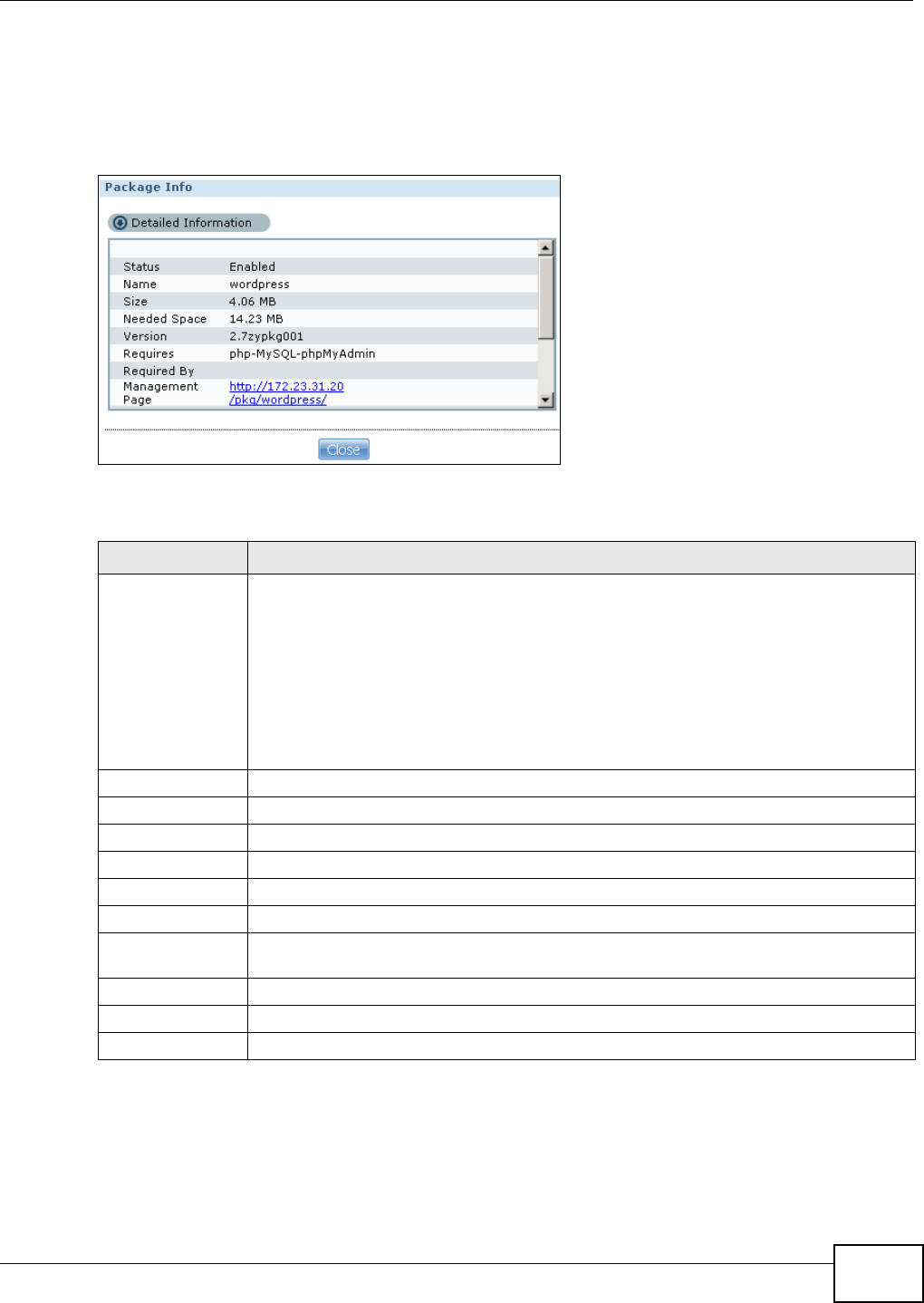
Chapter 11 Package Management
Media Server User’s Guide 229
11.4.1 Displaying the Package Information
Select an item on the list and click Package Info. Use this screen to check detailed information
about the task.
Figure 122 Applications > Package Management > Package Info
The following table describes the labels in this screen.
11.5 DyDNS Screen
Use this to enable and configure DyDNS.
Table 52 Applications > Package Management > Package Info
LABEL DESCRIPTION
Status This is the current status of the application. It shows:
•Not Installed - This displays for applications that have not been installed by the NSA.
•Installing (%) - This displays when the application is being installed. It also shows
the percent of the package already installed.
•Built-in - This displays for applications installed by the NSA that you can configure in
the NSA Web Configurator.
•Enabled - This displays for applications installed and enabled by the NSA that have
their own web configurators.
•Disabled - This displays for applications installed and disabled by the NSA that have
their own web configurators.
Name This is the name of the application.
Size This is the size of the application at initial download.
Needed Space This is the needed space to complete the installation of the application.
Version This is the version number of the application.
Requires This shows other package/s required to run this application.
Required By This shows which other packages require this application in order to be usable.
Management Page This shows the location of the screens, console or web configurator where you can
manage the application (after the package has been installed on the system).
Source This shows the location of the installed files of the application.
Description This shows a brief description of the item.
Close Click this to close the screen.
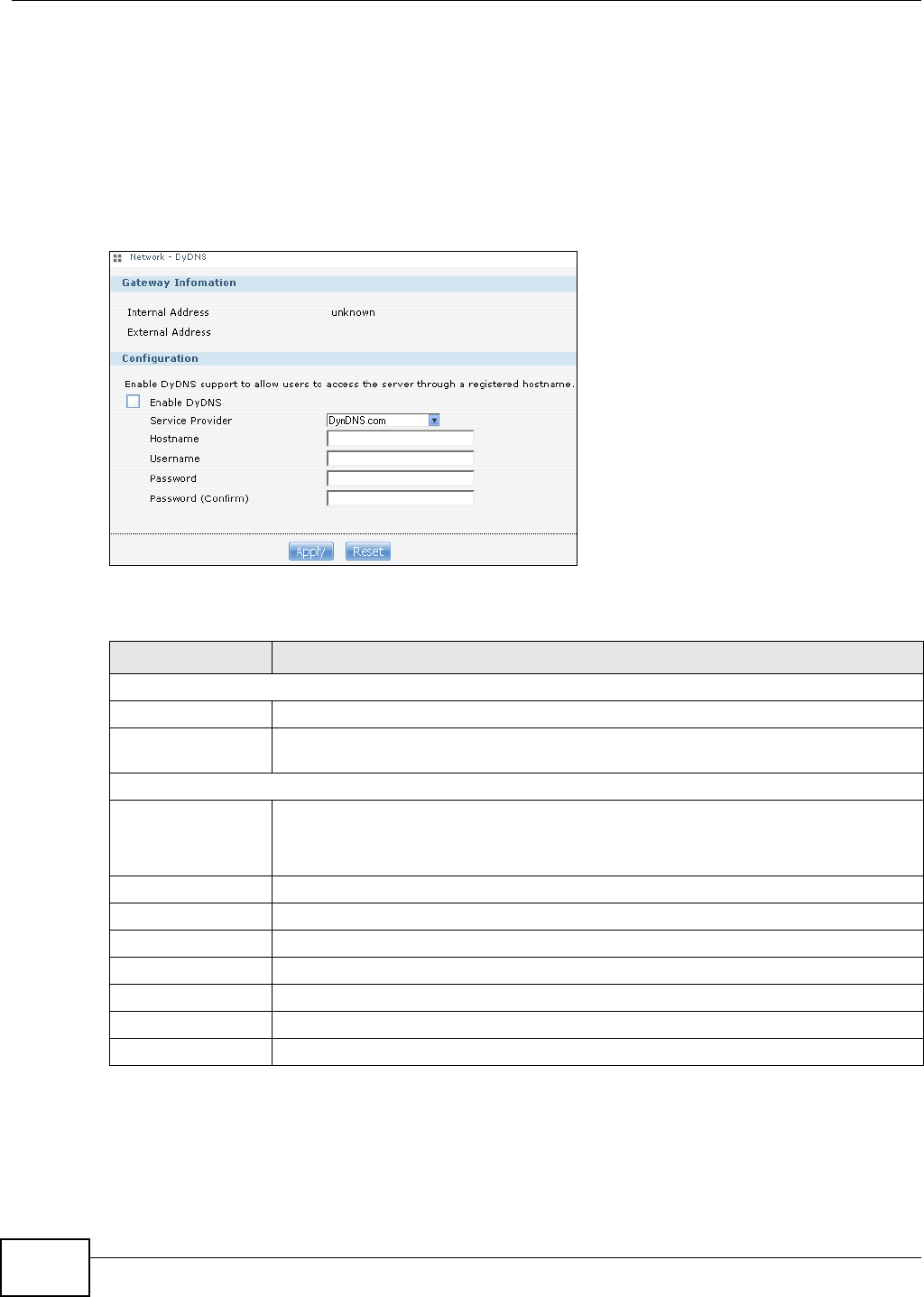
Chapter 11 Package Management
Media Server User’s Guide
230
Dynamic DNS allows you to update your current dynamic IP address with a dynamic DNS service so
that anyone can contact you (such as through NetMeeting or CUSeeMe). You can also access your
FTP server or Web site on your own computer using a domain name (for instance myhost.dhs.org,
where myhost is a name of your choice) that will never change instead of using an IP address that
changes each time you reconnect. Your friends or relatives will always be able to call you even if
they don't know your IP address.
Click Network > DyDNS to open the following screen.
Figure 123 Network > DyDNS
The following table describes the labels in this screen.
11.6 NFS Screen
Use this screen to enable and configure Network File System (NFS) settings on your NSA.
Table 53 Network > DyDNS
LABEL DESCRIPTION
Gateway Information
Internal Address This shows the IP address assigned to the NSA by the gateway in your local network.
External Address This shows the IP address of the NSA that can be accessed in the Wide Area Network
(WAN). Note that this is not assigned by the DyDNS server.
Configuration
Enable DyDNS Select this to use dynamic DNS.
You need to have registered a dynamic DNS account with a service provider such as
www.dyndns.org. The Dynamic DNS service provider will give you a password or key.
Service Provider Select your Dynamic DNS service provider.
Hostname Enter your host name provided by the Dynamic DNS service.
Username Enter your user name for your DNS account.
Password Enter the password assigned to your DNS account.
Password (Confirm) Confirm the password you entered.
Apply Click this to save your changes.
Reset Click this to clear the fields.
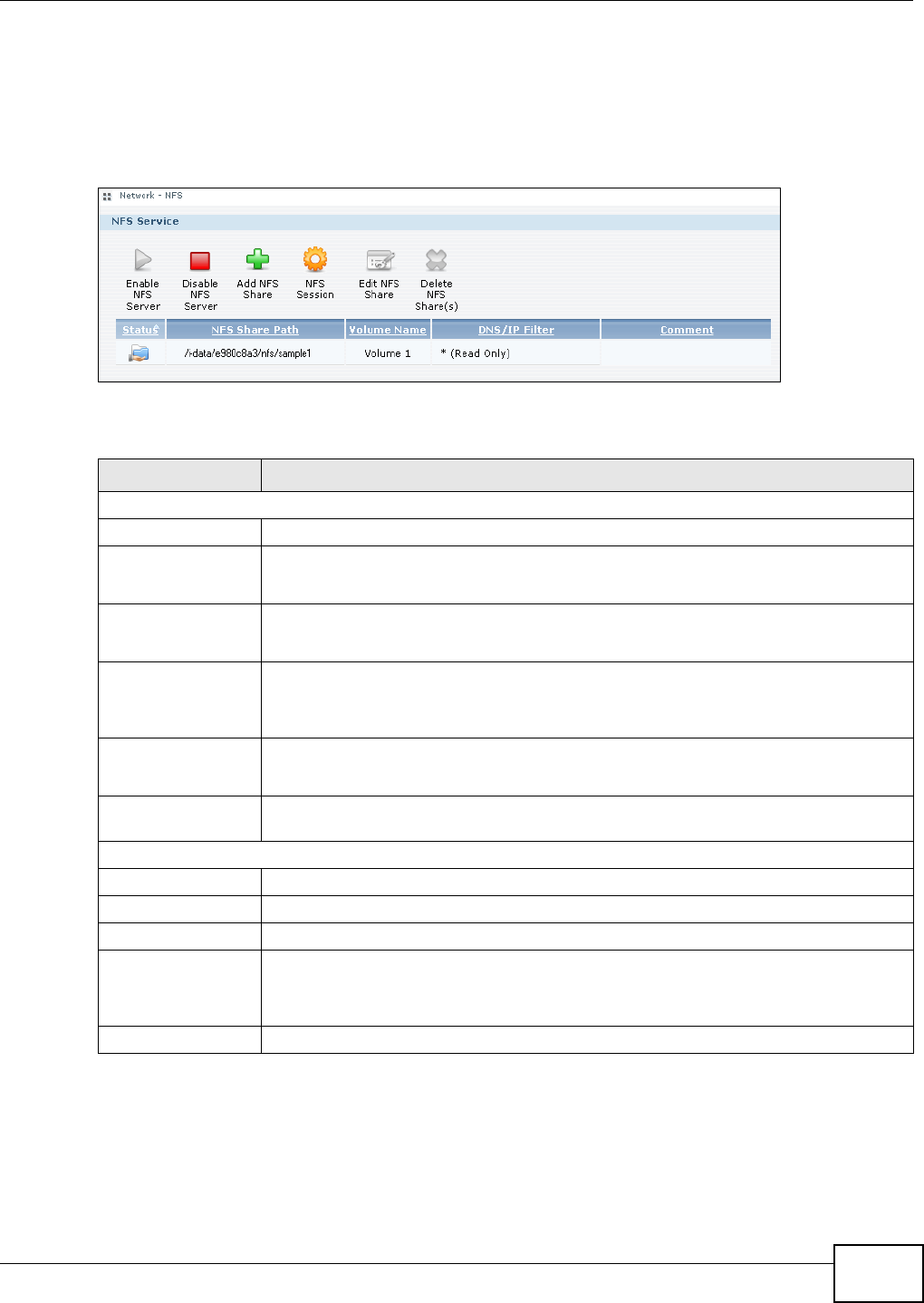
Chapter 11 Package Management
Media Server User’s Guide 231
NFS is a client/server distributed file service that provides transparent file sharing for network
environments. This allows shared folders in your NSA to be accessible like a local folder in a user’s
computer.
Click Network > NFS to open the following screen.
Figure 124 Network > NFS
The following table describes the labels in this screen.
Table 54 Network > NFS
LABEL DESCRIPTION
NFS Service
Enable NFS Server Click this to employ NFS in your NSA.
Disable NFS Server Click this to stop using NFS.
This makes all NFS shares unavailable.
Add NFS Share Click this to add an NFS share.
Refer to Section 11.6.1 on page 232 for the Add NFS Share screen.
NFS Session Click this to view active NFS sessions. You can see the list of users who have access to
the NFS shares.
Refer to Section 11.6.2 on page 233 for the NFS Session screen.
Edit NFS Share Select an NFS share from the list and click this to edit it.
Refer to Section 11.6.1 on page 232 for the Edit NFS Share screen.
Delete NFS Share
(s) Select an NFS share from the list and click this to delete it.
The table lists your NFS shares. Click a column’s heading to sort the entries by that criteria.
Status This shows whether the share is active or not.
NFS Share Path This shows the location of the share in the NSA.
Volume Name This shows the volume where the NFS share is located.
DN/IP Filter This shows which domain name(s) or IP address(es) have read/write access to the NFS
shares.
Refer to Section 11.6.1 on page 232 for the screen where you can configure this.
Comment This shows a short description of the share.
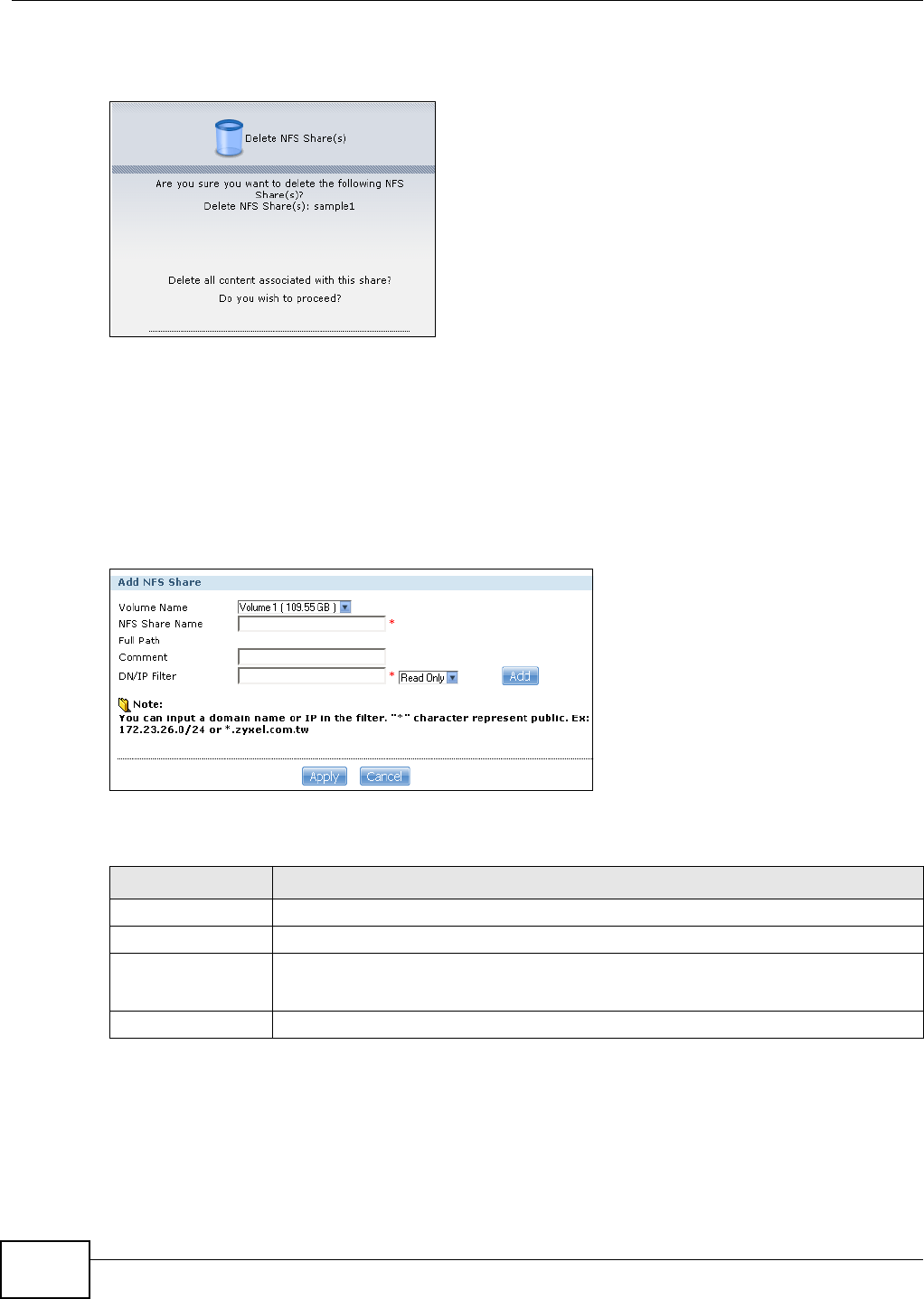
Chapter 11 Package Management
Media Server User’s Guide
232
You see a warning screen before you delete a volume.
Figure 125 Delete an NFS Share
11.6.1 Add/Edit NFS Share
Use this screen to add or edit an NFS share.
Note: Some attributes of the NFS share cannot be edited.
Click Add or Edit in the Network > NFS screen to open the following:
Figure 126 Network > NFS: Add/Edit
The following table describes the labels in this screen.
Table 55 Network > NFS: Add/Edit
LABEL DESCRIPTION
Volume Name Select the volume where the folder you want to add as an NFS share is located.
NFS Share Name Enter the name you want to give to the NFS share.
Full Path This shows the location of the NFS share in the NSA.
The NFS server assigns this path to the share folder you input.
Comment Enter a short description for the share.
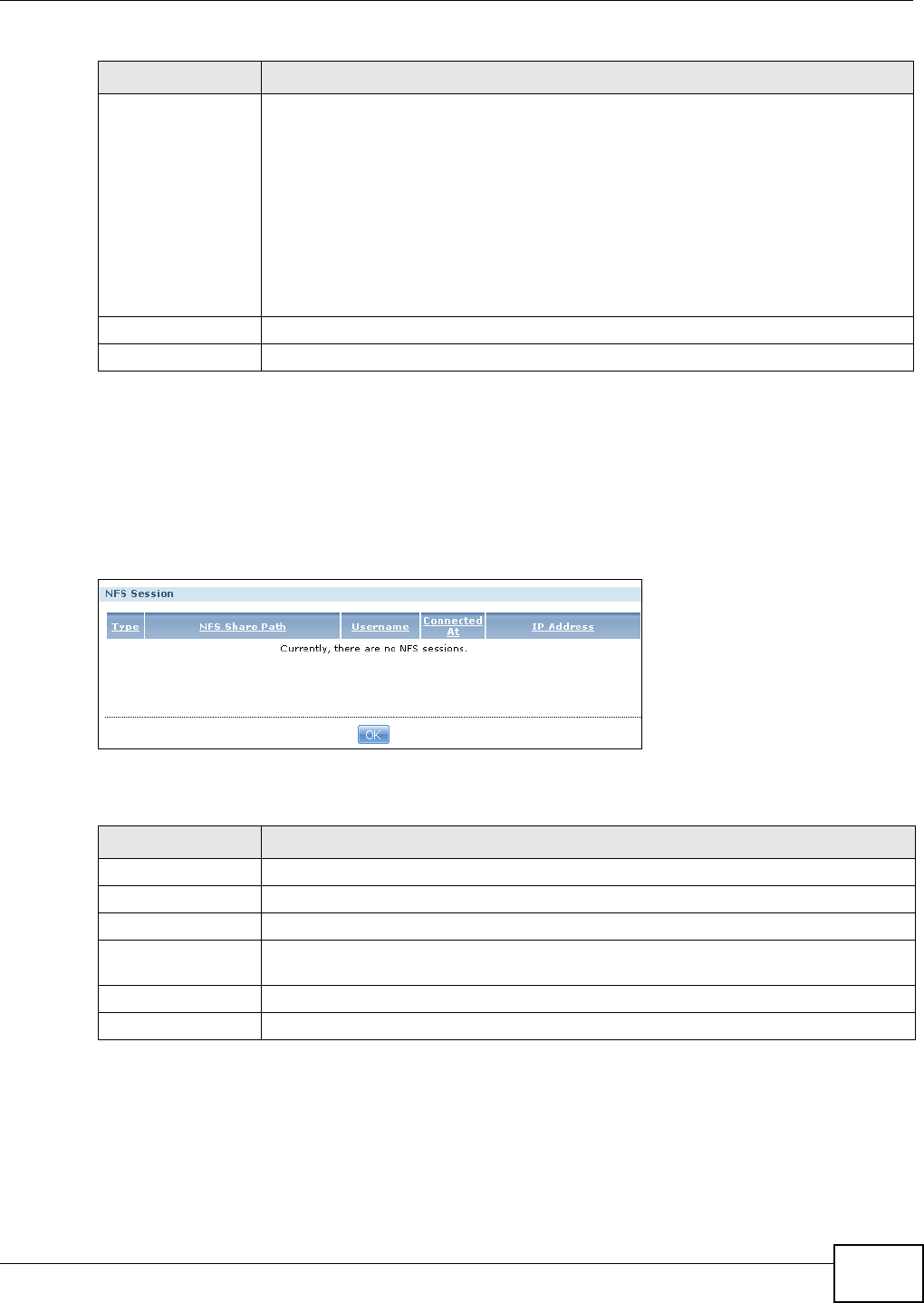
Chapter 11 Package Management
Media Server User’s Guide 233
11.6.2 NFS Session
Use this screen to view a list of active NFS sessions. You can see which users are connected the NFS
shares.
Click NFS Session in the Network > NFS screen to open the following.
Figure 127 Network > NFS: NFS Session
The following table describes the labels in this screen.
11.7 SMART Screen
Use this screen to view indicators of your NSA’s hard disk(s) health.
DN/IP Filter Enter the domain name(s) or IP address(es) that can have access to the NFS share.
Enter ‘*’ to make the share available to all users in the network. You can also enter a
wildcard, such as ‘*.domain.com’ to indicate that all users within that network have
access to the share.
Select the access rights you want to grant to each domain name or IP address you
enter and click Add.
•Read Only - Users with this access right can only view and copy files in the NFS
share but cannot modify or delete them.
•Read/Write - Users with this access right can view, edit or delete files in the NFS
share.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 55 Network > NFS: Add/Edit
LABEL DESCRIPTION
Table 56 Network > NFS: NFS Session
LABEL DESCRIPTION
Type This shows if the NFS share is active or not.
NFS Share Path This shows the location of the share in the NSA.
Username This shows the username of the active user connected to the NFS share.
Connected At This displays the date and time the user last connected to the NSA in year, month, day,
hour, minute, second format.
IP Address This shows the IP address of the user accessing the NFS share.
OK Click this to close the window.
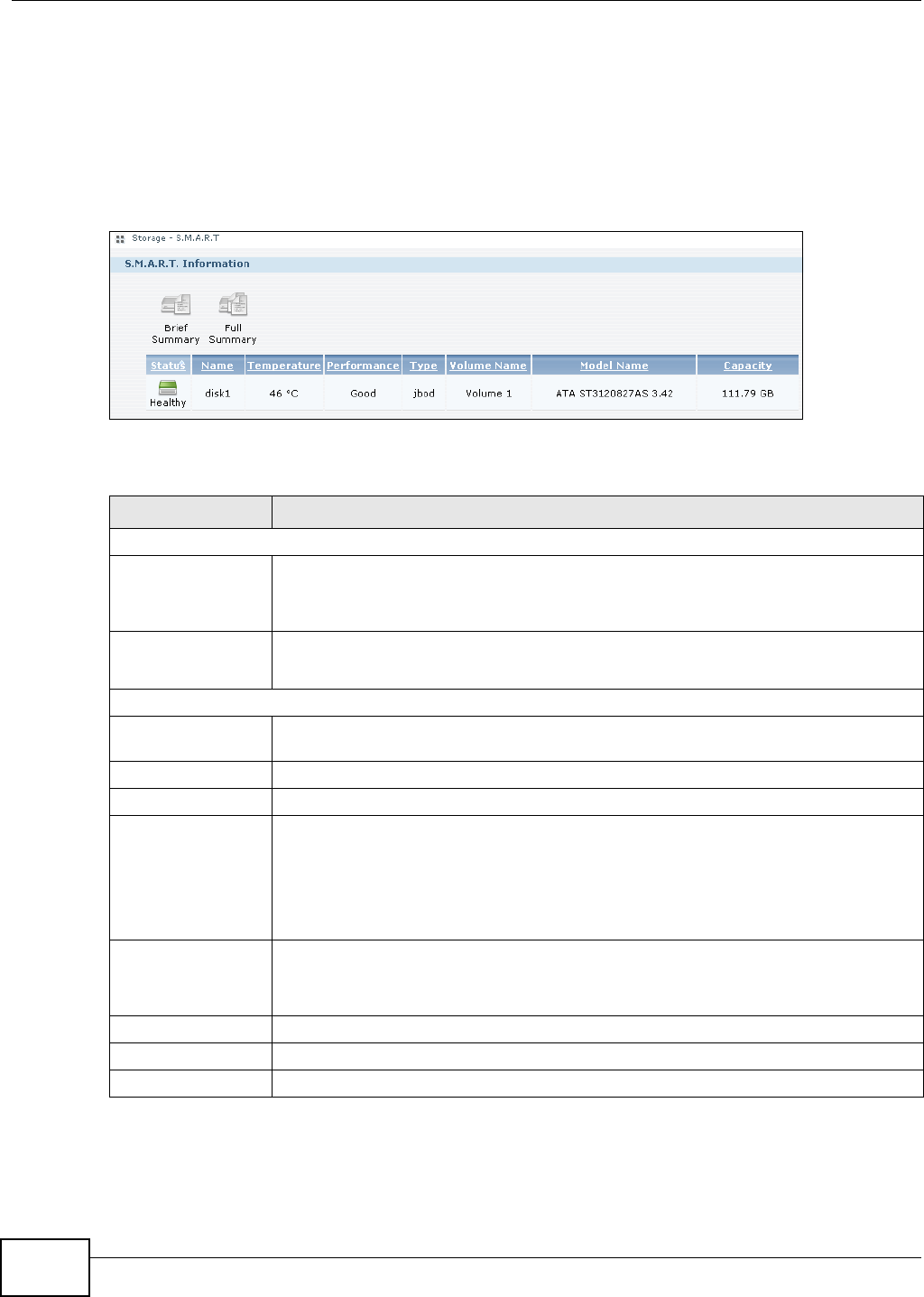
Chapter 11 Package Management
Media Server User’s Guide
234
Self Monitoring, Analysis, and Reporting Technology (S.M.A.R.T) detects and reports the reliability
of hard disks using standard indicators (called “attributes”), to help you anticipate possible disk
failures.
Note: The fields included the screens may vary depending on the hard disk that you use.
Click Storage > S.M.A.R.T to open the following screen.
Figure 128 Storage > S.M.A.R.T
The following table describes the labels in this screen.
Table 57 Storage > S.M.A.R.T
LABEL DESCRIPTION
S.M.A.R.T. Information
Brief Summary Select a hard disk volume from the list and click this to display information about the
volume, such as the hard disk vendor, specific model, hard disk capacity and so on.
See Section 11.7.1 on page 235 to view the Brief Summary screen.
Full Summary Select a volume and click this to display more detailed information about the volume.
See Section 11.7.1 on page 235 to view the Full Summary screen.
The table lists your hard disks. Click a column’s heading to sort the entries by that criteria.
Status This shows the condition of the hard disk volume. Go to Section 8.4 on page 163 for
more information.
Name This shows the name assigned to the hard disk.
Temperature This shows the temperature of the hard disk in degrees celsius.
Performance This shows your hard disk’s performance. Refer to Section 11.7.2 on page 236 for more
information on how S.M.A.R.T determines your hard disk’s condition. This displays:
•Good - This shows when you compare each Value with the Threshold Value and
all the Value is greater than the Threshold Value.
•Bad - This shows when you compare each Value with the Threshold Value and at
least one Value is less than or equal to the Threshold Value.
Type This shows volume type or file system that the hard disk is using, such as JBOD, PC
Compatible Volume and RAID or FAT32, FAT16 and NTFS.
See Section 8.6.3 on page 167 for descriptions of the volume types.
Volume Name This shows the name of the hard disk volume.
Model Name This shows the factory model of the hard disk.
Capacity This shows the total hard disk space of the hard disk volume.
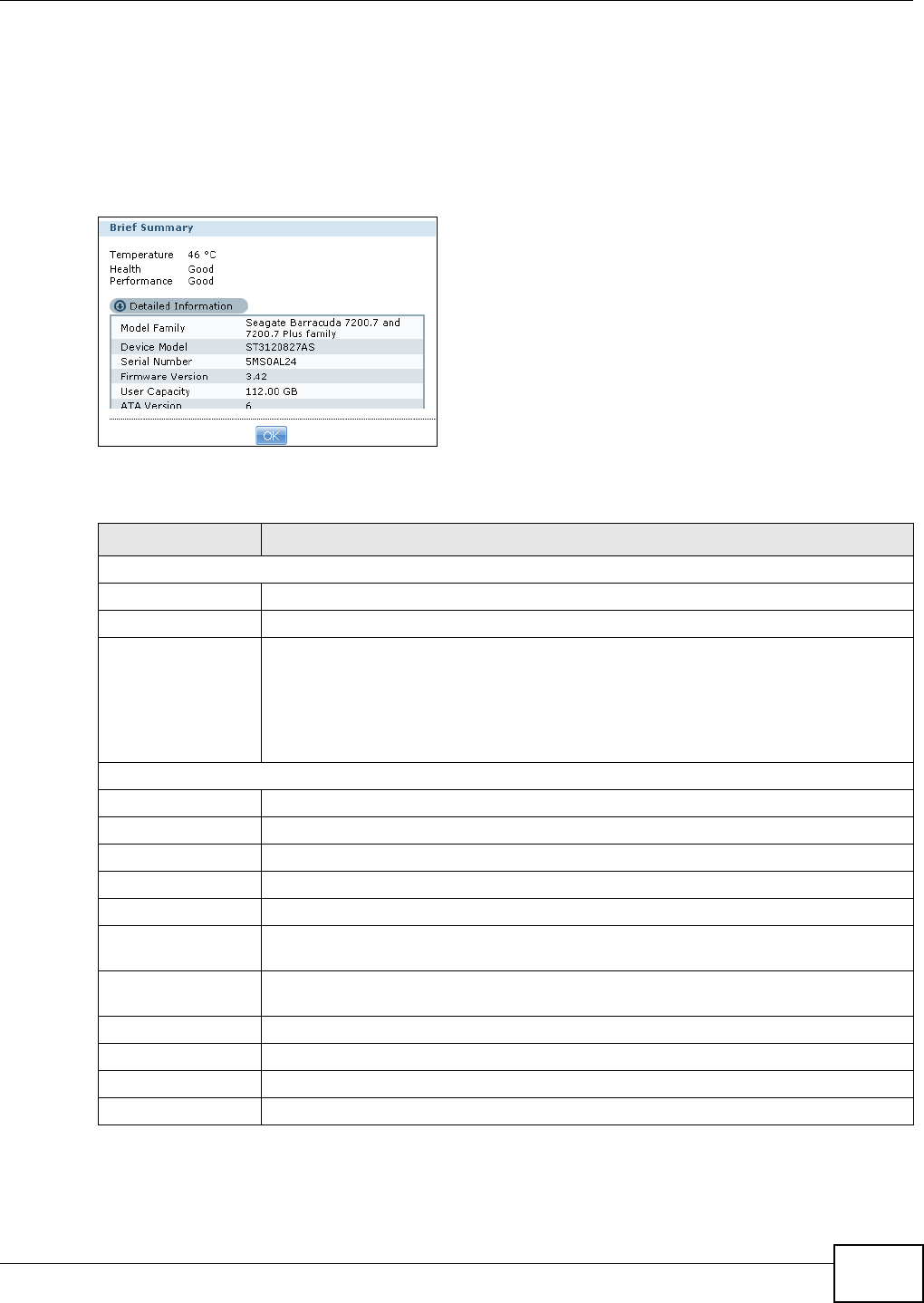
Chapter 11 Package Management
Media Server User’s Guide 235
11.7.1 SMART Brief Summary
Use this screen to display information about the volume, such as the hard disk vendor, specific
model, hard disk capacity and so on.
Click Brief Summary in the Storage > S.M.A.R.T screen to display the following.
Figure 129 Storage > S.M.A.R.T: Brief Summary
The following table describes the labels in this screen.
Table 58 Storage > S.M.A.R.T: Brief Summary
LABEL DESCRIPTION
Brief Summary
Temperature This shows the current temperature of the hard disk in degrees celsius.
Health This describes the overall health of the volume based on S.M.A.R.T diagnostics.
Performance This shows your hard disk’s performance. Refer to Section 11.7.2 on page 236 for more
information on how S.M.A.R.T determines your hard disk’s condition. This displays:
•Good - This shows when you compare each Value with the Threshold Value and
all the Value is greater than the Threshold Value.
•Bad - This shows when you compare each Value with the Threshold Value and at
least one Value is less than or equal to the Threshold Value.
Detailed Information
Model Family This shows the vendor and product family of the hard disk.
Device Model This shows the factory model of the hard disk.
Serial Number This shows the serial number of the hard disk.
Firmware Version This shows the firmware version installed in the hard disk.
User Capacity This shows the total hard disk space of the hard disk volume.
ATA Version This shows the ATA version of the hard disk, which refers to an industry standard
category for storage devices and connectors used.
ATA Standard This field displays the Advanced Technology Attachment standard the hard drive
supports.
Local Time This field displays the local time that the hard drive is using.
SMART support This field displays whether or not the hard drive is SMART-capable.
SMART support This field displays whether or not the hard drive has SMART monitoring turned on.
OK Click this to close the window.
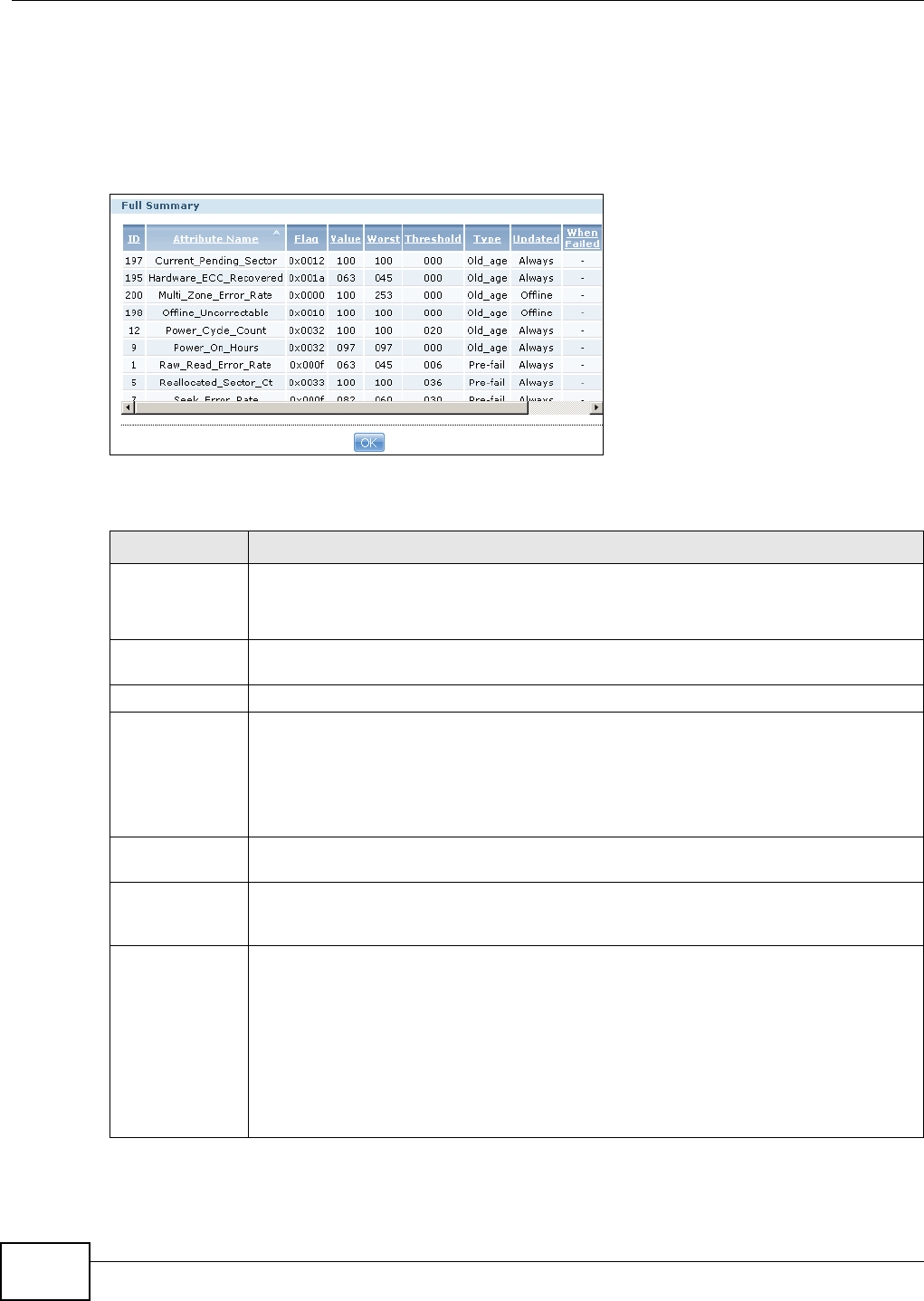
Chapter 11 Package Management
Media Server User’s Guide
236
11.7.2 SMART Full Summary
Use this screen to display more details information about the volume.
Click Full Summary in the Storage > S.M.A.R.T screen to display the following.
Figure 130 Storage > S.M.A.R.T: Full Summary
The following table describes the labels in this screen.
Table 59 Storage > S.M.A.R.T: Full Summary
LABEL DESCRIPTION
ID This is the identification number used to tag a hard disk attribute.
This is standard across all S.M.A.R.T-enabled storage devices. However it depends on the
storage vendor which attributes it will allow S.M.A.R.T to diagnose.
Attribute Name This refers to an attribute of the hard disk that S.M.A.R.T can assess. Attributes describe
the hard disk’s physical state, performance, wear-and-tear, and so on.
Flag This shows a code that S.M.A.R.T uses to determine the current state of the hard disk.
Value This is a value that corresponds to the Raw Value. Compare this with the Threshold
Value.
S.M.A.R.T compresses the raw value(s) into a digit from 1 to 253, where 1 indicates the
worst scenario while 253 indicates the best scenario.
The values 100 or 200 usually represent the mean or normal value.
Worst This is the lowest value attained by the hard disk since S.M.A.R.T started its assessment of
the hard disk.
Threshold This is the attribute’s threshold value. If the attribute’s current normalized value is less
than or equal to the threshold, the attribute has failed. An attribute value close to or below
the threshold indicates the hard drive is no longer reliable.
Type This shows S.M.A.R.T’s assessment of the hard disk.
Old_age indicates end-of-product life from old-age (normal wearing out) if the attribute
value is less than or equal to the threshold.
Pre-fail indicate imminent hard drive failure if the attribute value is less than or equal to
the threshold.
Note that just because an attribute is of the Pre-fail type does not mean your hard drive is
ready to fail. It only means this if the current normalized value of the attribute is less than
or equal to the threshold.
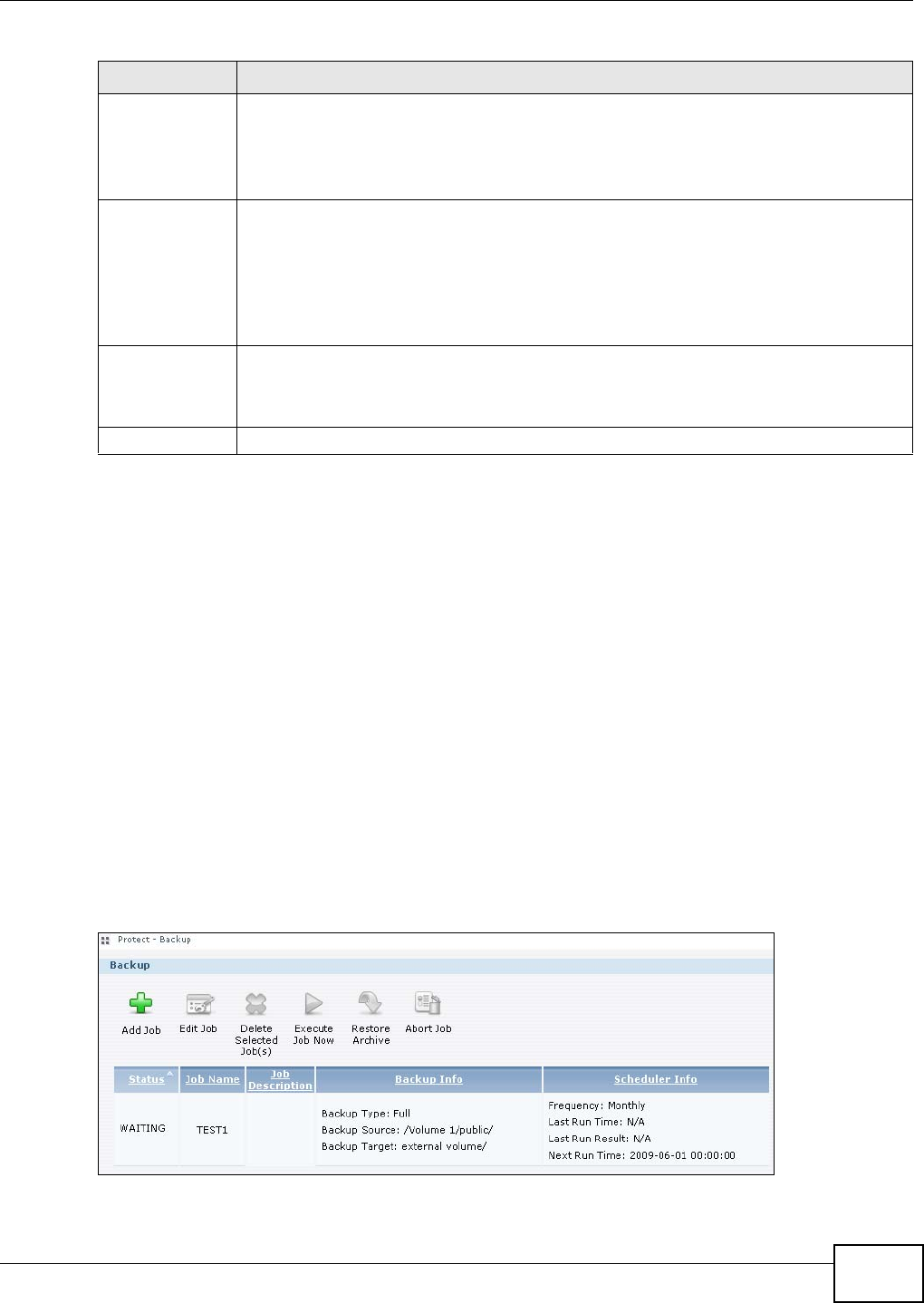
Chapter 11 Package Management
Media Server User’s Guide 237
11.8 Protect Screens
The Protect screens include:
•Backup screens - These include steps to create and customize backup jobs.
•Restore screens - These include steps to restore previous backups made with the NSA.
11.9 Backup Screens
Use this screen to create and customize scheduled backup jobs for your files.
You can have several backup jobs for specific folders and time periods.
Click Protect > Backup to open the following screen.
Figure 131 Protect > Backup
Updated This indicates when the hard drive updates the value for this attribute.
•Always means the hard drive updates this attribute during normal operation and
during offline activities.
•Offline means the hard drive only updates this attribute when no one is accessing the
hard drive.
When Failed This column indicates when (if ever) the attribute failed. An attribute has failed if the
normalized value is less than or equal to the threshold.
•-: This displays if the attribute is not failing now and has never failed in the past.
•FAILING_NOW: This displays if the attribute’s current normalized value is less than or
equal to the threshold.
•In_the_past: This displays if the attribute’s current normalized value is greater than
the threshold but the worst recorded value is less than or equal to the threshold.
Raw Value This is the attribute’s unprocessed raw data. These values show exact amounts of time or
numbers of attempts or errors. The meaning to the raw values is specific to the hard drive
manufacturer. Table 42 on page 156 has some information about whether a higher or lower
individual raw S.M.A.R.T. attribute value is better.
OK Click this to close this window.
Table 59 Storage > S.M.A.R.T: Full Summary
LABEL DESCRIPTION
Chapter 11 Package Management
Media Server User’s Guide
238
The following table describes the labels in this screen.
11.9.1 Backup: Step 1
Use this screen to specify the job information and back up type.
Table 60 Protect > Backup
LABEL DESCRIPTION
Backup
Add Job Click this to create and customize a backup job.
Edit Job Select a backup job in the list and click this to make some changes to it.
Delete Selected
Job(s) Select a backup job in the list and click this to delete it.
Execute Job Now Select a backup job in the list and click this to run the backup job immediately.
Restore Archive Select a backup job in the list and click this to restore the file(s) included in that backup
job to the NSA.
This applies to Archive backups only. Refer to Section 11.9.8 on page 247 to see the
screens.
Abort Job Select a backup job in the list and click this to stop the process if the backup job is
currently active.
Status This shows the current state of the backup job.
•Waiting means the backup job is not active but is scheduled to run at some time.
•Running indicates that the NSA is currently doing the backup job. When the backup
job is running, you can also see a progress bar.
Job Name This identifies the backup job.
Job Description This is a short description of the backup job.
Backup Info This lists down the backup job details: type, source and target. Refer to Section 11.9.1
on page 238 and Section 11.9.2 on page 240.
Scheduler Info This shows the backup schedule, including the frequency, the time it was last run in
(and whether or not it succeeded), and when it is scheduled to run again. The times use
yyyy-mm-dd hh:mm:ss format.
Refer to Section 11.9.4 on page 243.
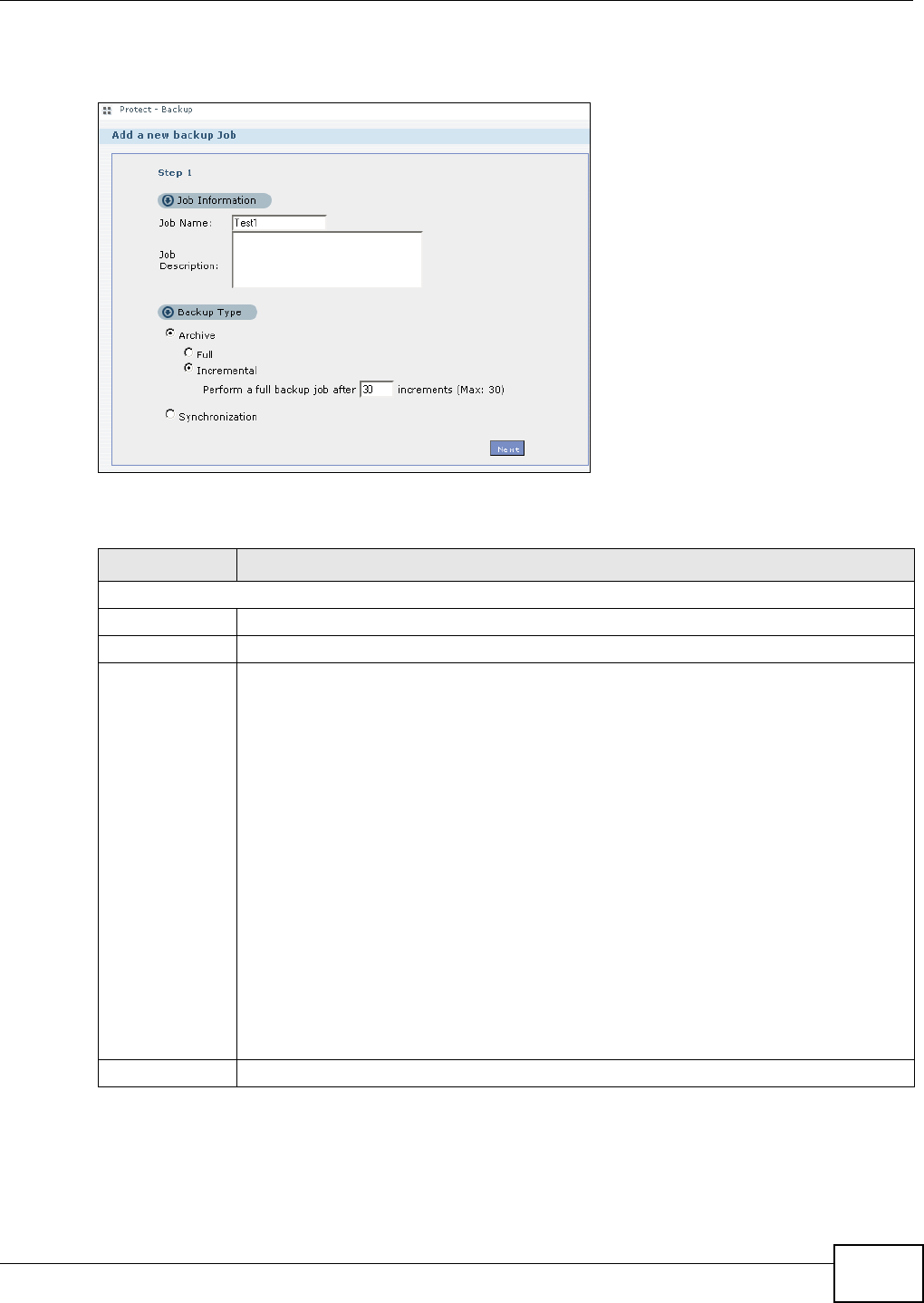
Chapter 11 Package Management
Media Server User’s Guide 239
Click Add Job in the Protect > Backup screen to open the following:
Figure 132 Protect > Backup: Step 1
The following table describes the labels in this screen.
Table 61 Protect > Backup: Step 1
LABEL DESCRIPTION
Job Information
Job Name Enter a name to identify the backup job.
Job Description Enter a short description (up to 100 keyboard characters) for the backup job.
Backup Type Choose the backup type that you want the NSA to implement for the backup job.
Archive - This is a backup of the source folder in an archive format. Once you backup your
files in the target folder, you cannot access the files individually unless you have the
extracting tool used by the NSA. If there are existing files in the target folder prior to the
NSA’s backup job, the files remain undisturbed. You can also choose between the following
types of archive:
•Full - The NSA does a fresh backup each time. This provides the most protection but
also requires the most storage space.
•Incremental - The NSA backs up new or modified files from the source folder since the
last backup. The first backup is a full backup. You can also do a full backup after several
incremental backups. Enter how many incremental backups the NSA runs before it
performs a full backup of the source folder. You must keep the latest full backup to be
able to restore the files later.
Synchronization - This does a backup of individual files. If you use this type, you cannot
use the Restore feature of the NSA. You can also choose between the following types of
synchronization:
•Mirror - The NSA deletes all data in the target folder before running the backup. It
makes the target folder identical to the source folder.
•Publish- The NSA does a backup of individual files to the target folder without
overwriting existing files in that folder. It makes a copy of the source files.
Next Click this to go to the next step.
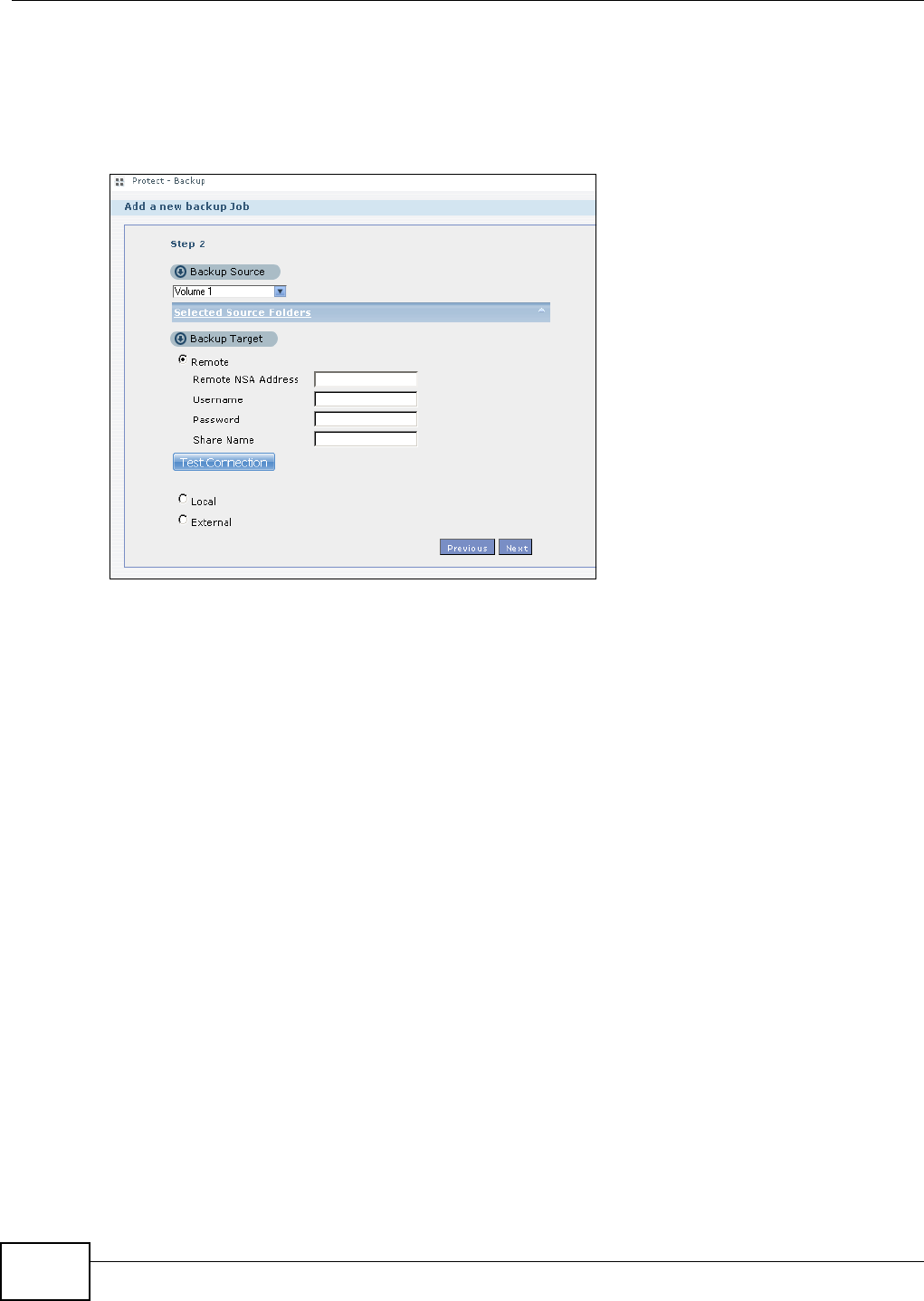
Chapter 11 Package Management
Media Server User’s Guide
240
11.9.2 Backup: Step 2
Use this screen to specify where the files you want to backup are located and set where you want
the backup to be stored.
Figure 133 Protect > Backup: Step 2

Chapter 11 Package Management
Media Server User’s Guide 241
The following table describes the labels in this screen.
Table 62 Protect > Backup: Step 2
LABEL DESCRIPTION
Backup Source Select an (internal) volume and the folders and files to back up using this tree interface.
Click to browse through folders, sub-folders and files.
Click to close a folder in the tree. This is useful if there are many folders or files that
you wish to hide from view.
Click to select a folder or file to back up. This also selects all sub-folders and files.
Click to deselect the folder or file. This also deselects all sub-folders and files.
and appear when there are too many folders/files to display. Click the
arrows to scroll up or down through the folders/files.
for a folder means all sub-folders and files and new folders/files added later will be
backed up.
for a file means the file will be backed up.
(a grayed out check box) for a folder means that only some sub-folders and files under
the folder will be backed up. Newly added folders/files will NOT be backed up.
means the file structure is still loading. Please wait for the folders/files to display.
Note: If you select to back up an entire folder and then de-select a sub-folder or file within
that folder, the main folder icon will turn and any new sub-folders and files added
to this main folder after the initial backup configuration will NOT be backed up.
A list of your select folders and files displays below the selection fields.
Selected Source
Folders This shows the path of the backup source folder you selected.
Backup Target Select the target folder where you want to place your backup.
Remote Select this to back up to another device.
For Archives:
The remote device can be another NSA in the network. Fill in the following fields in order
to be able to access it.
• Remote NSA Address
•Username
•Password
• Share Name
Click Test Connection to see if your NSA can communicate with the remote device.
For Synchronization:
The remote device must be another NSA compatible with the NSA’s synchronization
feature. Fill in the following fields in order to be able to access it.
• Remote NSA Address
• Username (always “admin”)
• Remote Admin’s Password
Click Show target content to connect to the remote NSA so you can select the target
share for the backup.
Local Select this if you want to place your backup in another volume in the NSA. Select the
folder where you want to place the backup.
External Select this if you have a USB hard disk connected to the NSA that you want to use for
your backup. Select the folder where you want to place the backup.
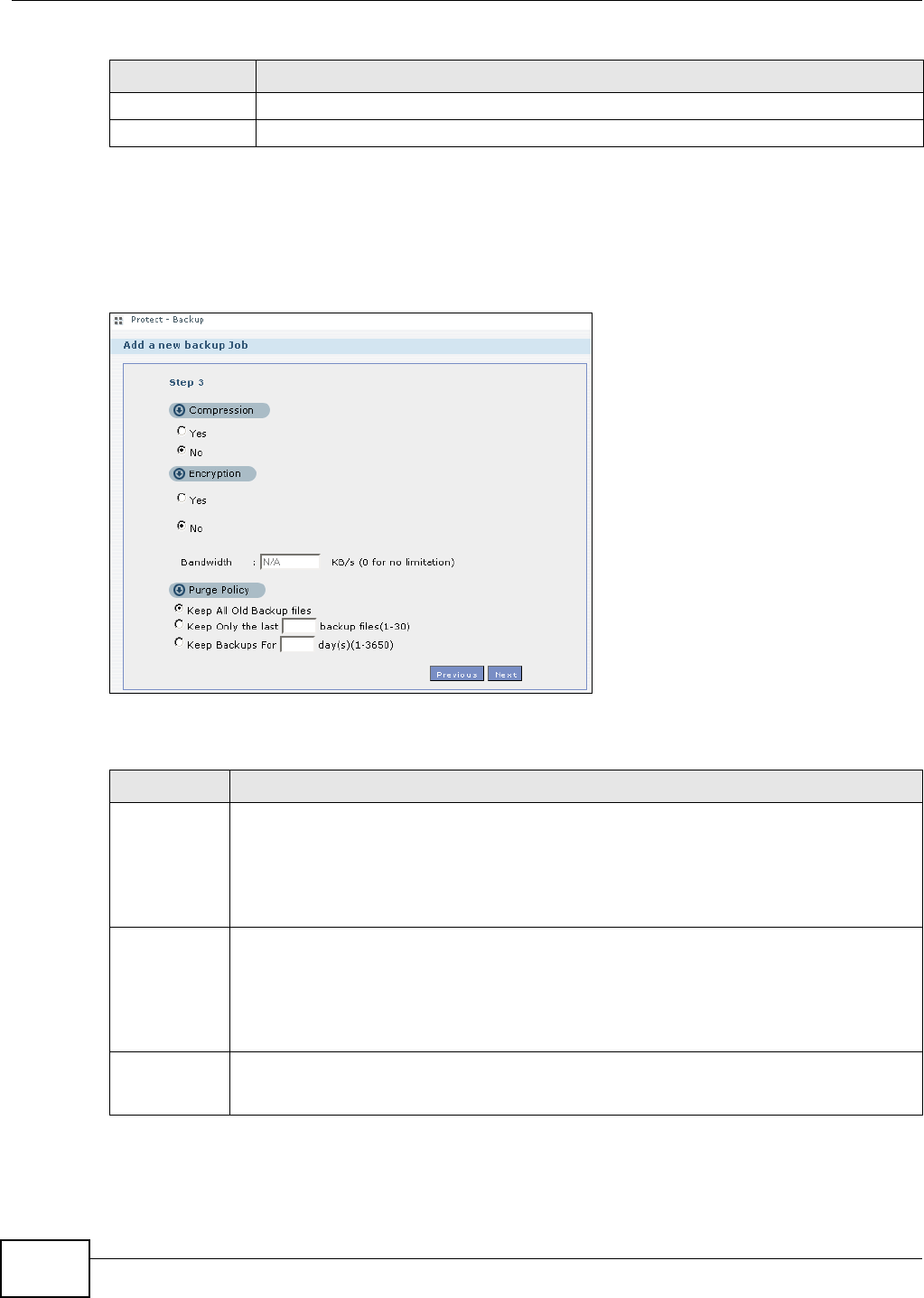
Chapter 11 Package Management
Media Server User’s Guide
242
11.9.3 Backup: Step 3
Use this screen to specify compression, encryption and purge policies for the backup job. This step
is only available if you are doing an archive backup or a synchronization backup to a remote target.
Figure 134 Protect > Backup: Step 3
The following table describes the labels in this screen.
Previous Click this to go back to the previous screen.
Next Click this to go to the next screen.
Table 62 Protect > Backup: Step 2
LABEL DESCRIPTION
Table 63 Protect > Backup: Step 3
LABEL DESCRIPTION
Compression Select Yes if you want NSA to compress the files for your backup. Otherwise, choose No.
In an Archive backup, compression is a method of packing computing files in a way that
saves hard disk space.
For a Synchronization backup (to a remote target), the source data will be compressed
before the transmission to reduce the transmission time. It is used in slow networks only.
Encryption Select Yes if you want NSA to encrypt the files for your backup. Otherwise, choose No.
In an Archive backup, this means using a password to secure files.
For a Synchronization backup (to a remote target), this means securing the file transfer
session. However the final file stored on the remote NSA is unencrypted. This takes a long
time. Make sure you really need this feature before enabling it.
Bandwidth Restrict the bandwidth of synchronization backups to help stop them from using all of your
network connection’s available bandwidth. This is more important when backing up to a
remote NSA or computer through the Internet.
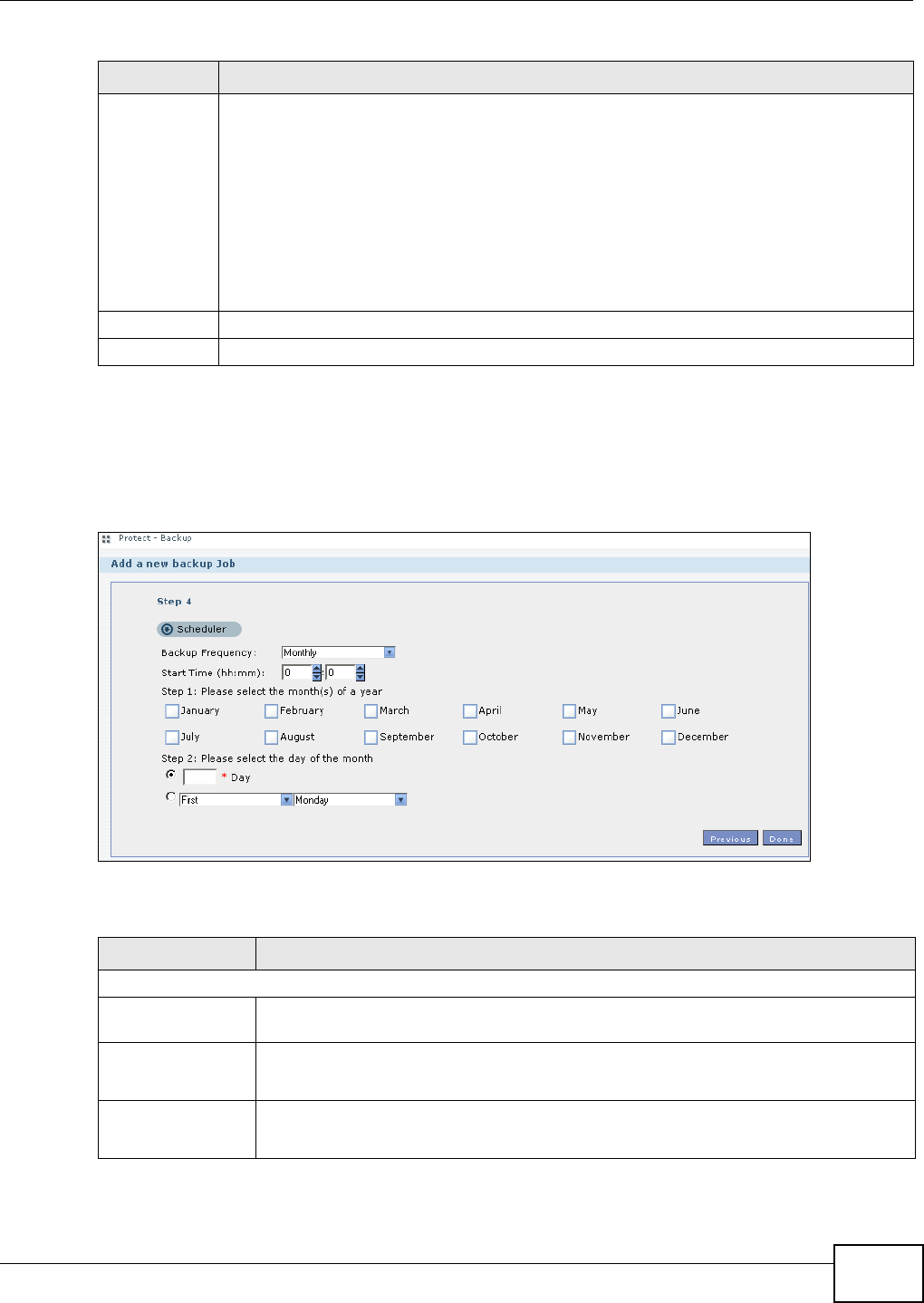
Chapter 11 Package Management
Media Server User’s Guide 243
11.9.4 Backup: Step 4
Click this to specify the schedule for the backup job. The backup job automatically runs according
to the schedule that you set in this screen.
Figure 135 Protect > Backup: Step 4
The following table describes the labels in this screen.
Purge Policy The NSA maintains the files that have been included in your backups. However to save hard
disk space, you can choose to delete files that have been included in previous backups.
• Select Keep All Old Backup files to store all files that have been included in previous
backups.
• If you want to store a certain number of backup files, select Keep Only the last n
backup files (1-30). Enter a value (n) from 1 to 30 to specify how many backups the
NSA stores. All backup files older than the last one are deleted. You will not be able to
recover files that existed (only) in those previous backups. Select this if backup space is
limited and recovery of old files is not important.
• If you want to store all backups for a certain time period, select Keep Backups for n
day(s)(1-3650). Enter a value (n) from 1 to 3650 to specify how many days the NSA
stores all backup files. After this day has expired, all backup files will be deleted.
Previous Click this to go back to the previous screen.
Next Click this to go to the next screen.
Table 63 Protect > Backup: Step 3
LABEL DESCRIPTION
Table 64 Protect > Backup: Step 4
LABEL DESCRIPTION
Scheduler
Backup Frequency Select from Hourly, Daily, Weekly and Monthly backup intervals. The screen changes
depending on the item you select.
Every how many
hours? This is only available if you selected Hourly as your backup frequency.
Select every how many hours the NSA performs the backup job.
On which minute of
the hour? This is only available if you selected Hourly as your backup frequency.
Select the minute (from 0 to 59) in an hour when the NSA performs the backup job.
Chapter 11 Package Management
Media Server User’s Guide
244
11.9.5 Edit Job Screen
Use this screen to edit an existing backup job. Some attributes of the backup job cannot be
changed, such as the name, backup type, source folder and so on.
Start Time
(hh:mm) This is available if you selected Daily, Weekly or Monthly as your backup frequency.
Select the time in hour:minute format when you want the NSA to perform the backup
job.
Every how many
days? This is only available if you selected Daily as your backup frequency.
Enter the interval between days when the NSA performs the backup job.
Every how many
weeks? This is only available if you selected Weekly as your backup frequency.
Enter the interval between weeks when NSA performs the backup job.
Step 1: Please
select the month(s)
of a year
This is only available if you selected Monthly as your backup frequency.
Select the month(s) when you want the NSA to perform the backup job.
Step 2: Please
select the day of
the month
This is only available if you selected Monthly as your backup frequency.
Select the day in a month when you want the NSA to perform the backup job.
Previous Click this to go back to the previous screen.
Done Click this to close the screen.
Table 64 Protect > Backup: Step 4
LABEL DESCRIPTION
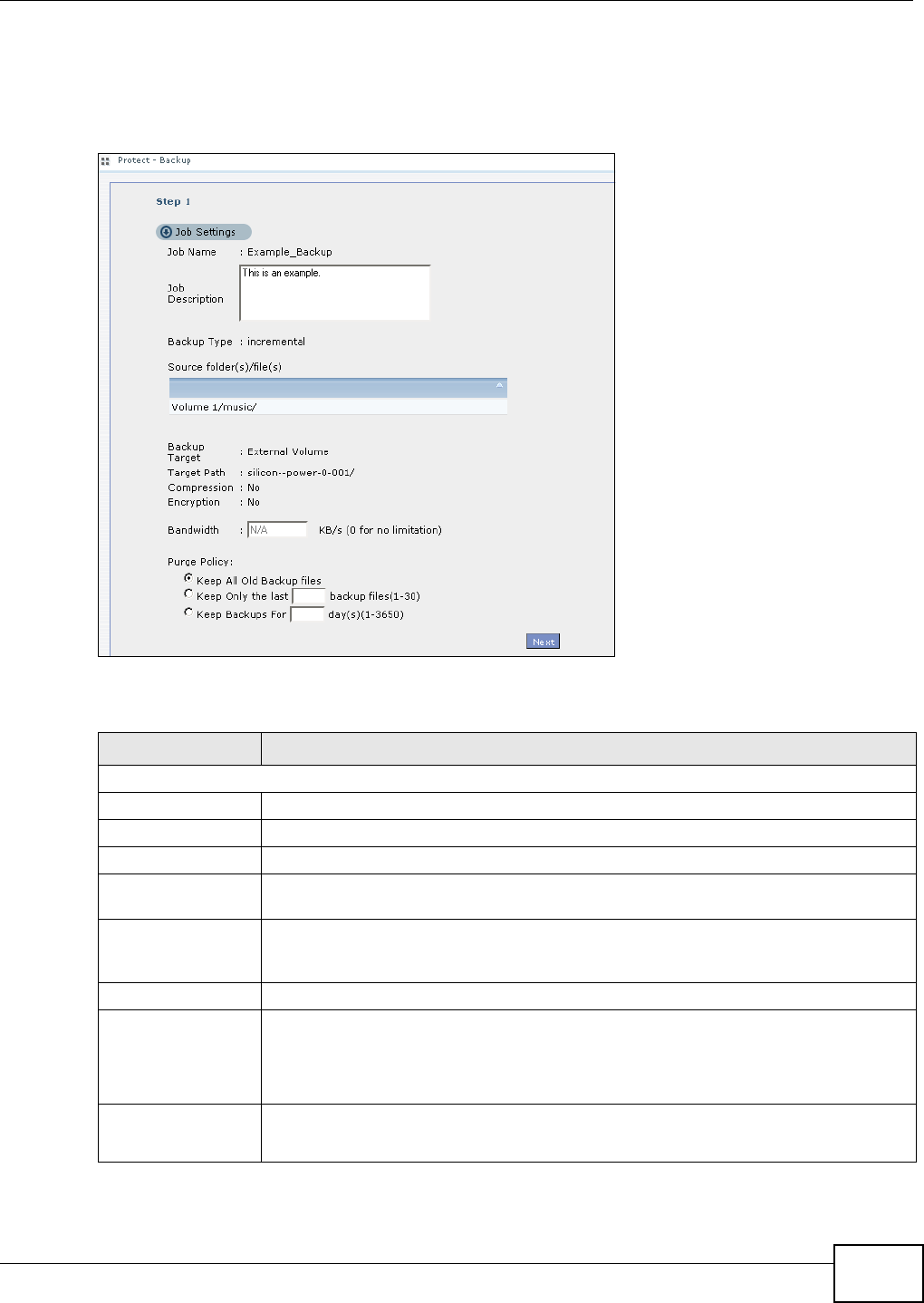
Chapter 11 Package Management
Media Server User’s Guide 245
11.9.6 Edit Job: Step 1
Click Protect > Backup. Select a backup job from the list and click Edit Job to open the following.
Figure 136 Protect > Backup > Edit: Step 1
The following table describes the labels in this screen.
Table 65 Protect > Backup > Edit: Step 1
LABEL DESCRIPTION
Job Settings
Job Name This field is read-only and shows the name of the backup job.
Job Description Enter a short description for the backup job.
Backup Type This field is read-only and shows the backup type.
Source folder(s)/
file(s) This is read-only and shows the path of the source folder for backup.
Backup Target This field is read-only and shows on which volume (whether internal or external) the
backup files are stored. If the target location is a remote NSA, this shows the remote IP
address.
Target Path This field is read-only and shows the target folder for the backup files.
Compression This field is read-only and shows whether the backup employs compression.
Compression reduces the size of the file that you want to back up. Backup is then faster,
but restoring may be slower, so if backup space is not a concern and recovery speed is,
then turn off compression.
Encryption This field is read-only and shows whether the backup employs encryption.
You can have the NSA use a password to encrypt the backup files.
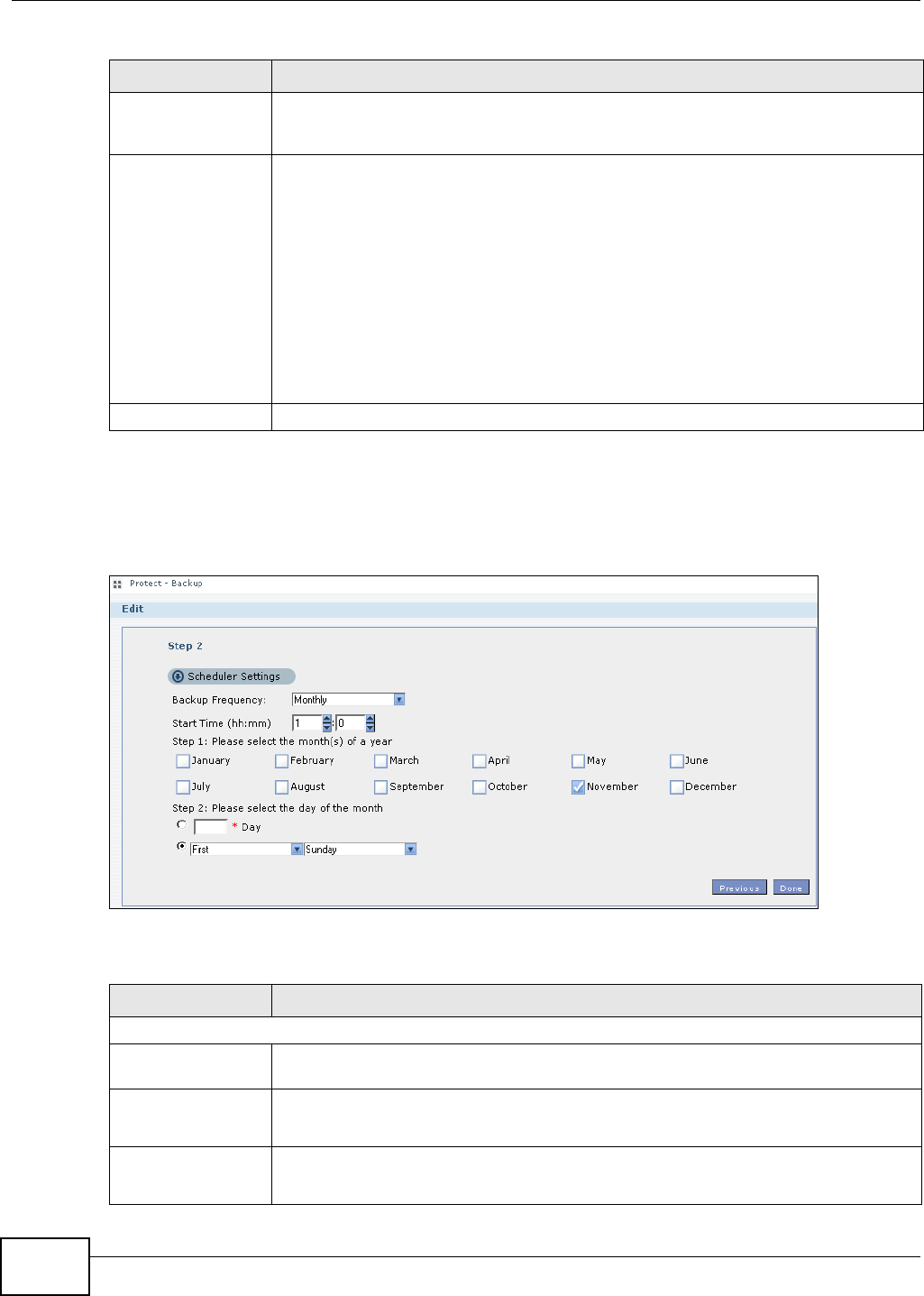
Chapter 11 Package Management
Media Server User’s Guide
246
11.9.7 Edit Job: Step 2
Use this screen to edit the schedule for the backup job.
Figure 137 Protect > Backup > Edit: Step 2
The following table describes the labels in this screen.
Bandwidth For backups to a remote NSA, you can restrict the bandwidth to help prevent the
backups from using all of your network connection’s available bandwidth. This is more
important when backing up to a remote NSA or computer through the Internet.
Purge Policy The NSA maintains the files that have been included in your backups. However to save
hard disk space, you can choose to delete files that have been included in previous
backups.
• Select Keep All Old Backup files to store all files that have been included in
previous backups.
• If you want to store a certain number of backup files, select Keep Only the last n
backup files (1-30). Enter a value (n) from 1 to 30 to specify how many backups
the NSA stores. All backup files older than the last one are deleted. You will not be
able to recover files that existed (only) in those previous backups. Select this if
backup space is limited and recovery of old files is not important.
• If you want to store all backups for a certain time period, select Keep Backups for
n day(s)(1-3650). Enter a value (n) from 1 to 3650 to specify how many days the
NSA stores all backup files. After this day has expired, all backup files will be
deleted.
Next Click this to go to the next screen.
Table 65 Protect > Backup > Edit: Step 1
LABEL DESCRIPTION
Table 66 Protect > Backup > Edit: Step 2
LABEL DESCRIPTION
Scheduler Settings
Backup Frequency Edit this by selecting from Hourly, Daily, Weekly and Monthly backup intervals. The
screen changes depending on the item you select.
Every how many
hours? This is only available if you selected Hourly as your backup frequency.
Select every how many hours the NSA performs the backup job.
On which minute of
the hour? This is only available if you selected Hourly as your backup frequency.
Select the minute (from 0 to 59) in an hour when the NSA performs the backup job.
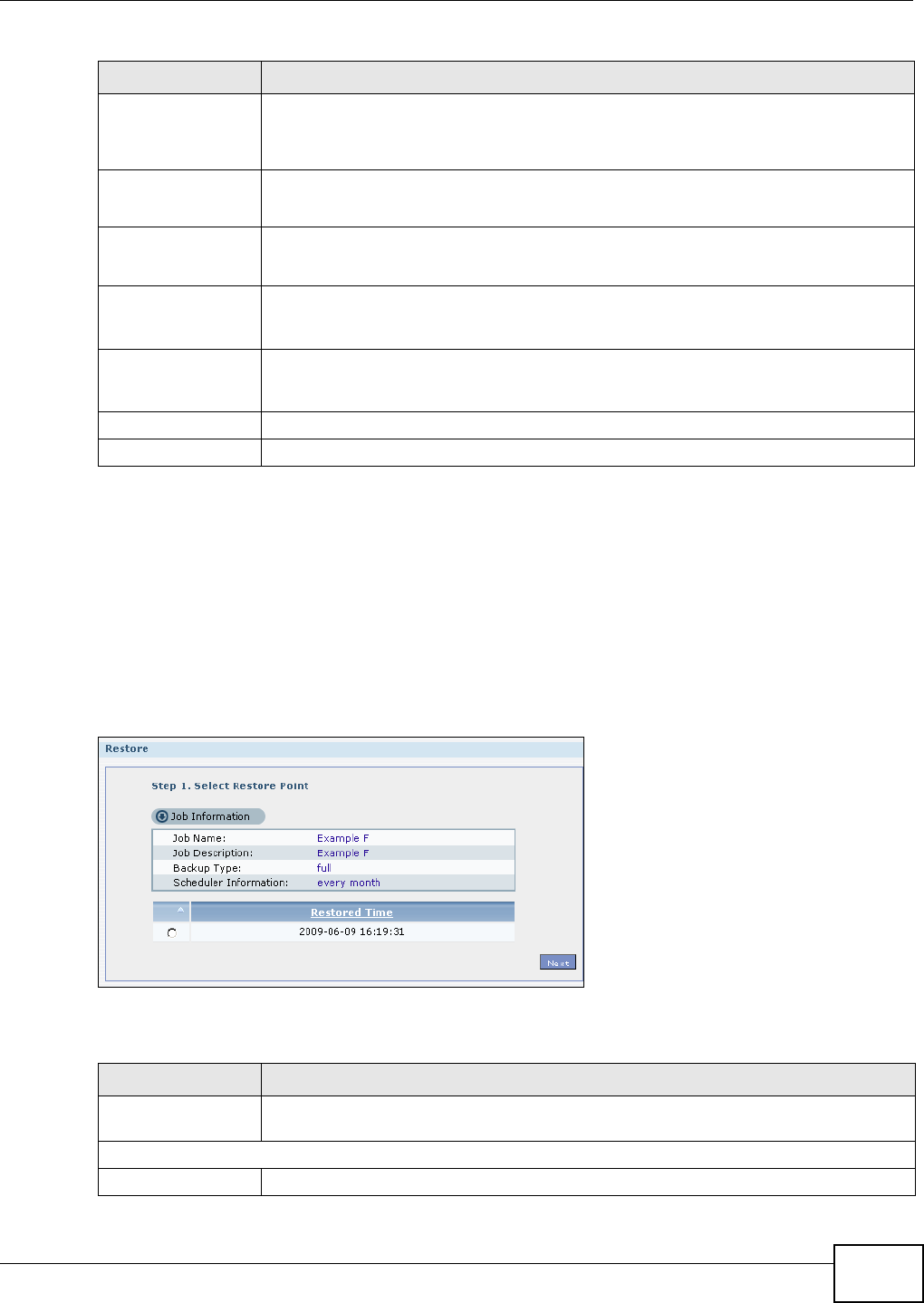
Chapter 11 Package Management
Media Server User’s Guide 247
11.9.8 Restore Archive Screen
Use this screen to restore previous backups made with the NSA.
11.9.9 Restore Archive: Step 1
Click Protect > Backup screen (Section 11.9 on page 237). You can restore a previous backup job
by selecting a backup job from the list and clicking Restore Archive.
Figure 138 Protect > Backup > Restore Archive: Step 1
The following table describes the labels in this screen.
Start Time (hh:mm) This is available if you selected Daily, Weekly or Monthly as your backup frequency.
Select the time in hour:minute format when you want the NSA to perform the backup
job.
Every how many
days? This is only available if you selected Daily as your backup frequency.
Enter the interval between days when the NSA performs the backup job.
Every how many
weeks? This is only available if you selected Weekly as your backup frequency.
Enter the interval between weeks when NSA performs the backup job.
Step 1: Please
select the month(s)
of a year
This is only available if you selected Monthly as your backup frequency.
Select the month(s) when you want the NSA to perform the backup job.
Step 2: Please
select the day of the
month
This is only available if you selected Monthly as your backup frequency.
Select the day in a month when you want the NSA to perform the backup job.
Previous Click this to go back to the previous screen.
Done Click this to close the screen.
Table 66 Protect > Backup > Edit: Step 2
LABEL DESCRIPTION
Table 67 Protect > Backup > Restore Archive: Step 1
LABEL DESCRIPTION
Step 1. Select
Restore Source Select a previous archive backup that you want to restore to the NSA.
Job Information
Job Name This is the name to identify the backup job.
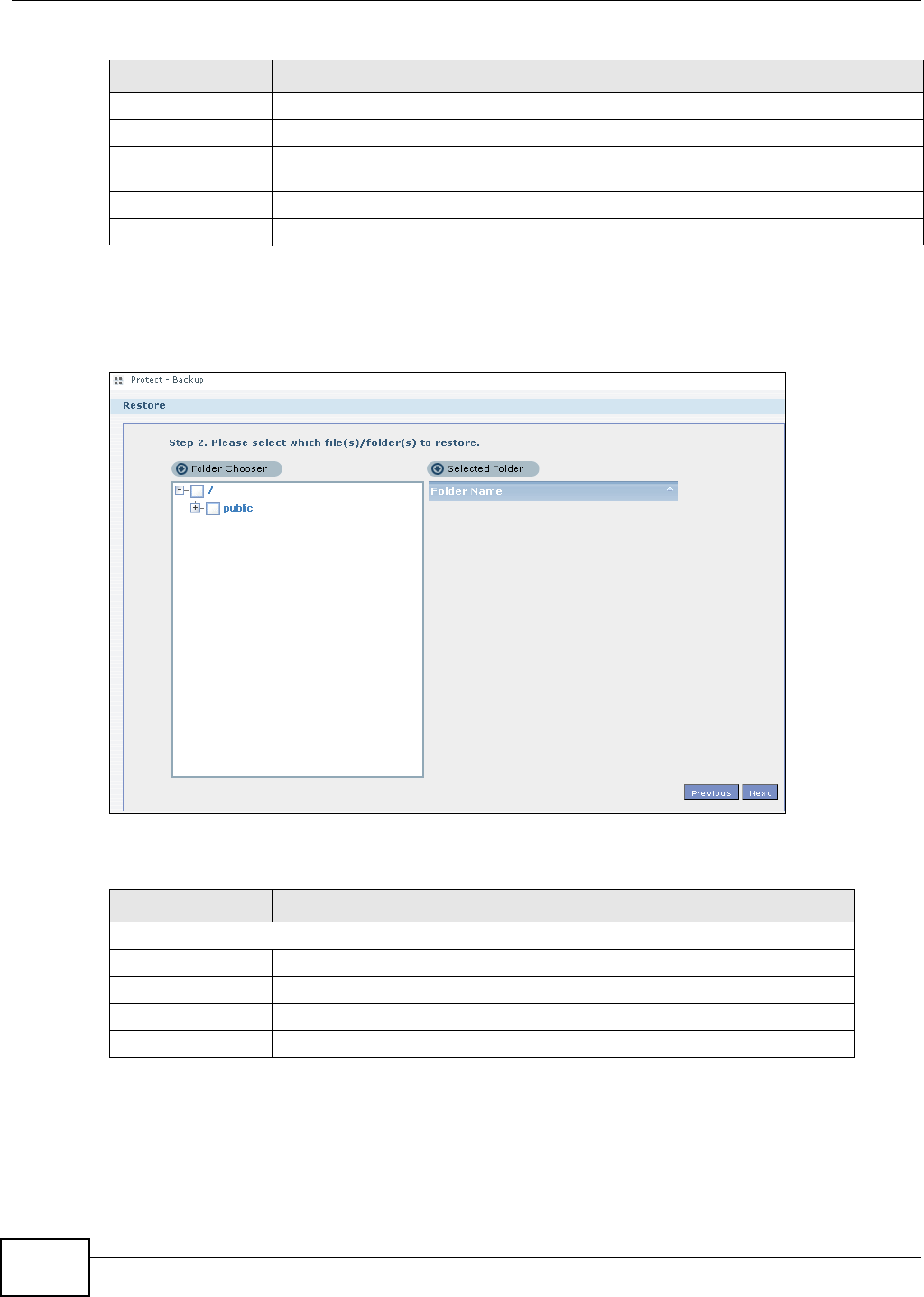
Chapter 11 Package Management
Media Server User’s Guide
248
11.9.10 Restore Archive: Step 2
Use this screen to select the folder where the archive you want to restore is located.
Figure 139 Protect > Backup > Restore Archive: Step 2
The following table describes the labels in this screen.
Job Description This is a short description (up to 100 keyboard characters) for the backup job.
Backup Type This is the type of backup implemented for the backup job.
Scheduler
Information This field displays the backup’s frequency.
Restored Time Select a previous backup in the list that you want to restore to your NSA.
Next Click this to go to the next screen.
Table 67 Protect > Backup > Restore Archive: Step 1
LABEL DESCRIPTION
Table 68 Protect > Backup > Restore Archive: Step 2
LABEL DESCRIPTION
Step 2. Please select which file(s)/folder(s) to restore.
Folder Chooser Select the folder where the backup you want to restore is located.
Selected Folder This shows the path of the folder you selected.
Previous Click this to go back to the previous screen.
Next Click this to go to the next screen.
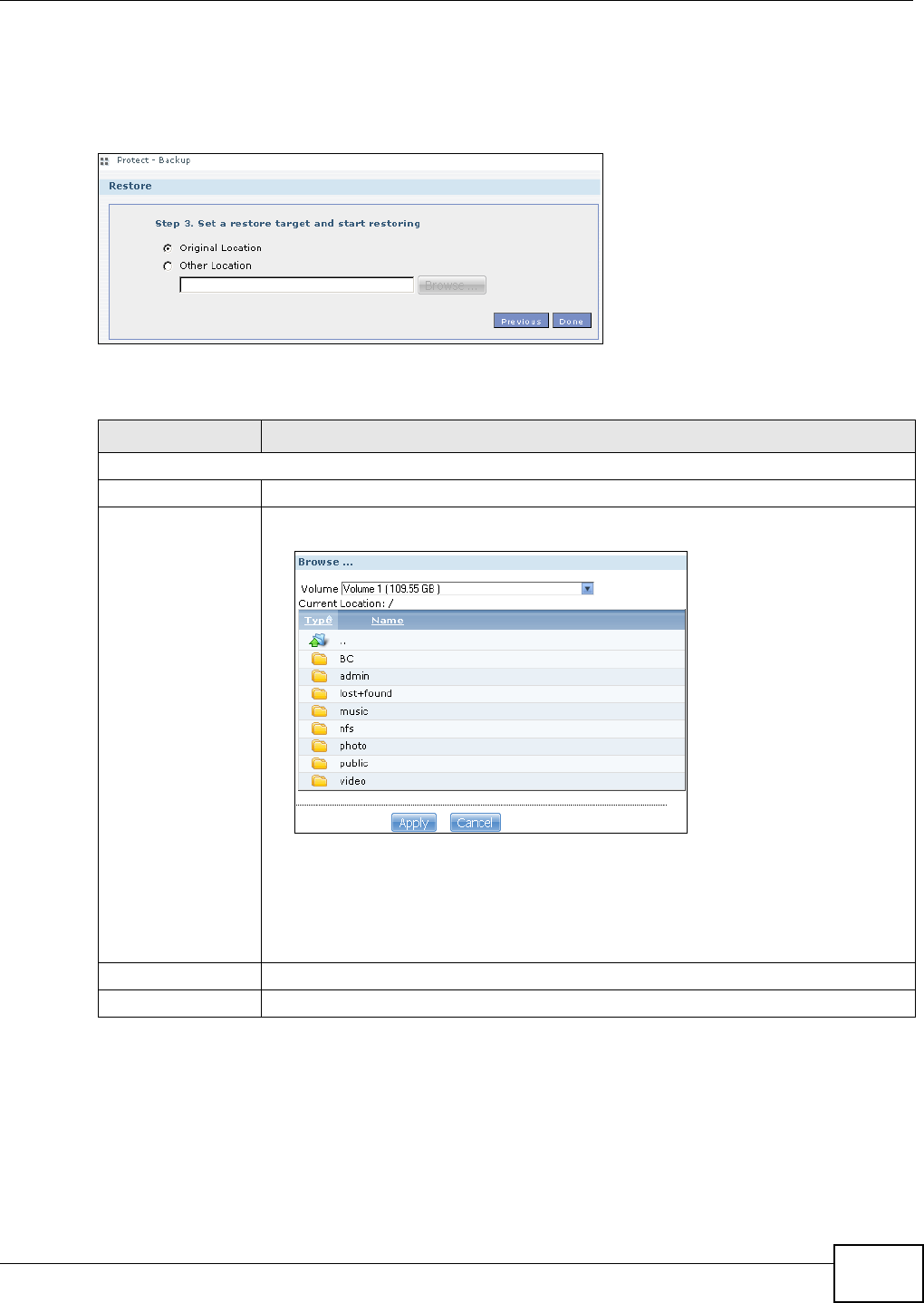
Chapter 11 Package Management
Media Server User’s Guide 249
11.9.11 Restore Archive: Step 3
Use this screen to select the location in the NSA where you want to restore your backup.
Figure 140 Protect > Backup > Restore Archive: Step 3
The following table describes the labels in this screen.
11.10 Restore Screen
Use this screen to restore previous backups made with the NSA, including archives and folders from
internal, external or remote NSAs to the NSA.
Table 69 Protect > Backup > Restore Archive: Step 3
LABEL DESCRIPTION
Step 3. Set a restore target and start restoring
Original Location Select this to restore the files to their original location in the NSA.
Other Location Click this to select a folder where you want to place the restored files. Click Browse to
open the following screen.
•Volume - Select a volume from the list.
•Current Location - This is the location of the selected folder.
•Type - This identifies the item as a file or folder.
•Name - This is the name of the folder/file.
Click Apply to save your settings and Cancel to close the screen.
Previous Click this to go back to the previous screen.
Done Click this to run the restore process and go back to the Backup screen.
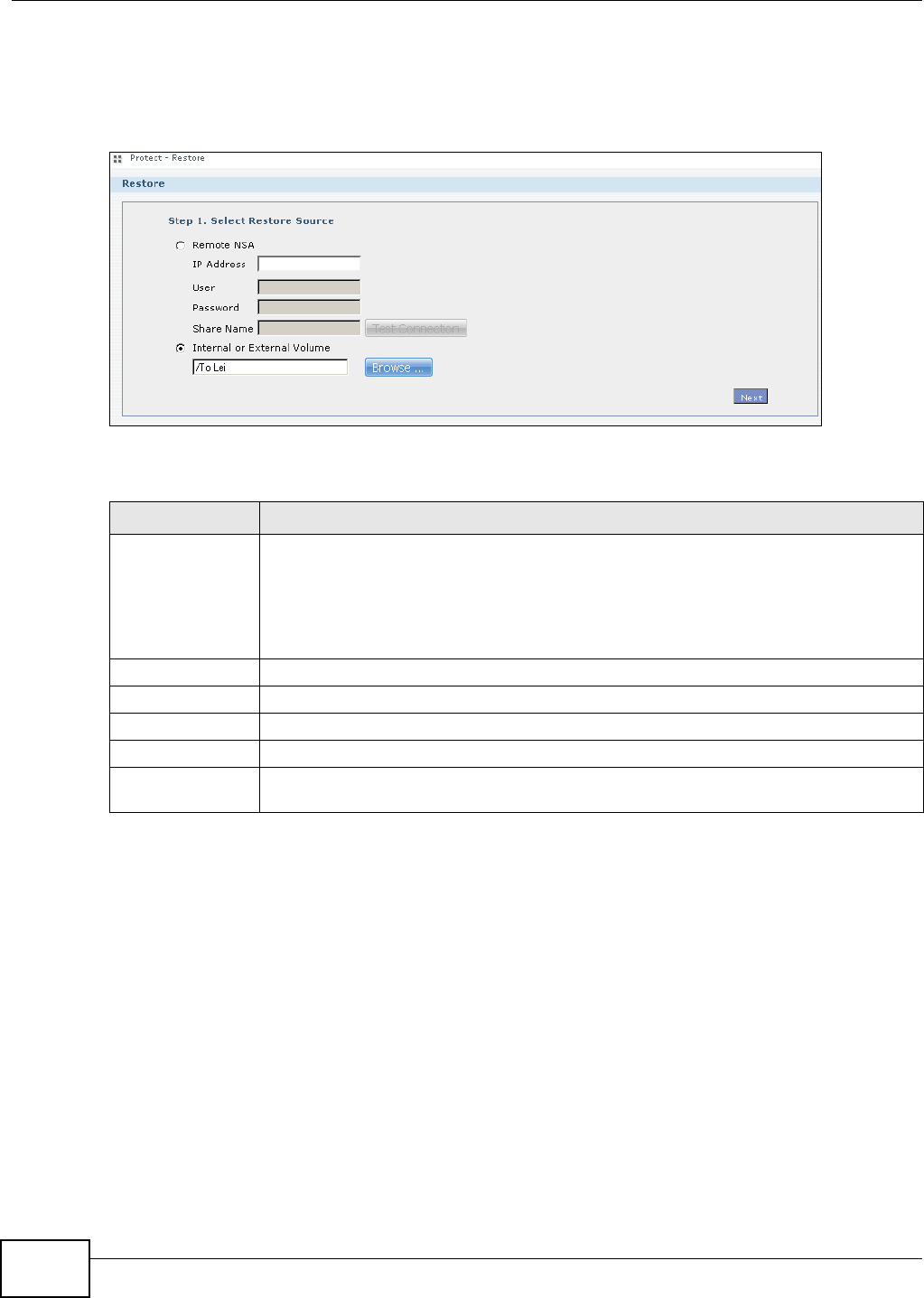
Chapter 11 Package Management
Media Server User’s Guide
250
11.10.1 Restore: Step 1
You can access this screen by clicking Protect > Restore.
Figure 141 Protect > Restore: Step 1
The following table describes the labels in this screen.
Table 70 Protect > Restore: Step 1
LABEL DESCRIPTION
Step 1. Select
Restore Source Select a previous archive backup that you want to restore to the NSA.
Select Remote NSA if the file is in another NSA in the network that you used for your
backup. Fill in the fields below when you choose this option.
Select Internal or External Volume if you want to use another volume in the NSA or an
attached USB hard disk for your backup. Click Browse to select the backup file.
IP Address Enter the address of the NSA you want to use.
User Enter the username you use to access the NSA.
Password Enter the password of your NSA account.
Share Name Enter the name of the share you want to use.
Test Connection Click this to test your connection to the remote NSA that you have specified in the fields
above.
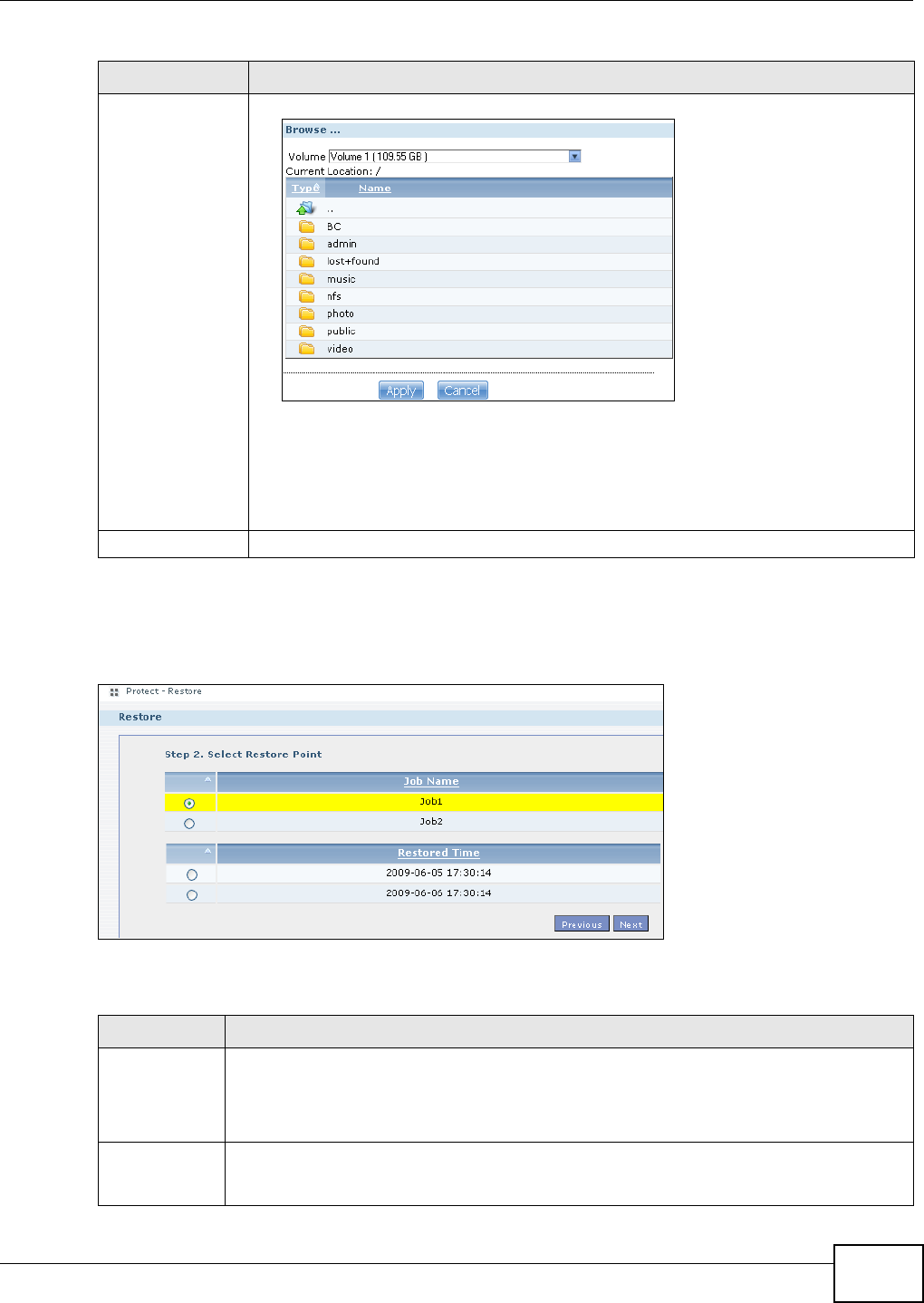
Chapter 11 Package Management
Media Server User’s Guide 251
11.10.2 Restore: Step 2
Select a previous archive backup that you want to restore to the NSA.
Figure 142 Protect > Restore: Step 2
The following table describes the labels in this screen.
Browse Click this to select where the previous backup that you want to restore is located.
•Volume - Select a volume from the list.
•Current Location - This is the location of the selected folder.
•Type - This identifies the item as a file or folder.
•Name - This is the name of the folder/file.
Click Apply to save your settings and Cancel to close the screen.
Next Click this to go to the next screen.
Table 70 Protect > Restore: Step 1
LABEL DESCRIPTION
Table 71 Protect > Restore: Step 2
LABEL DESCRIPTION
Step 2. Select
Restore Point If you selected Remote NSA for the backup you want to restore, you can see a list of all the
backups you performed in the Job Name table.
If you selected Internal or External Volume for the backup you want to restore, you can
see a list of restore times for the backups you performed in the Restored Time table.
Job Name Select a previous backup job in the list that you want to restore to your NSA. Once you
choose a job name, all available restore times for that backup job shows in the Restored
Time table.
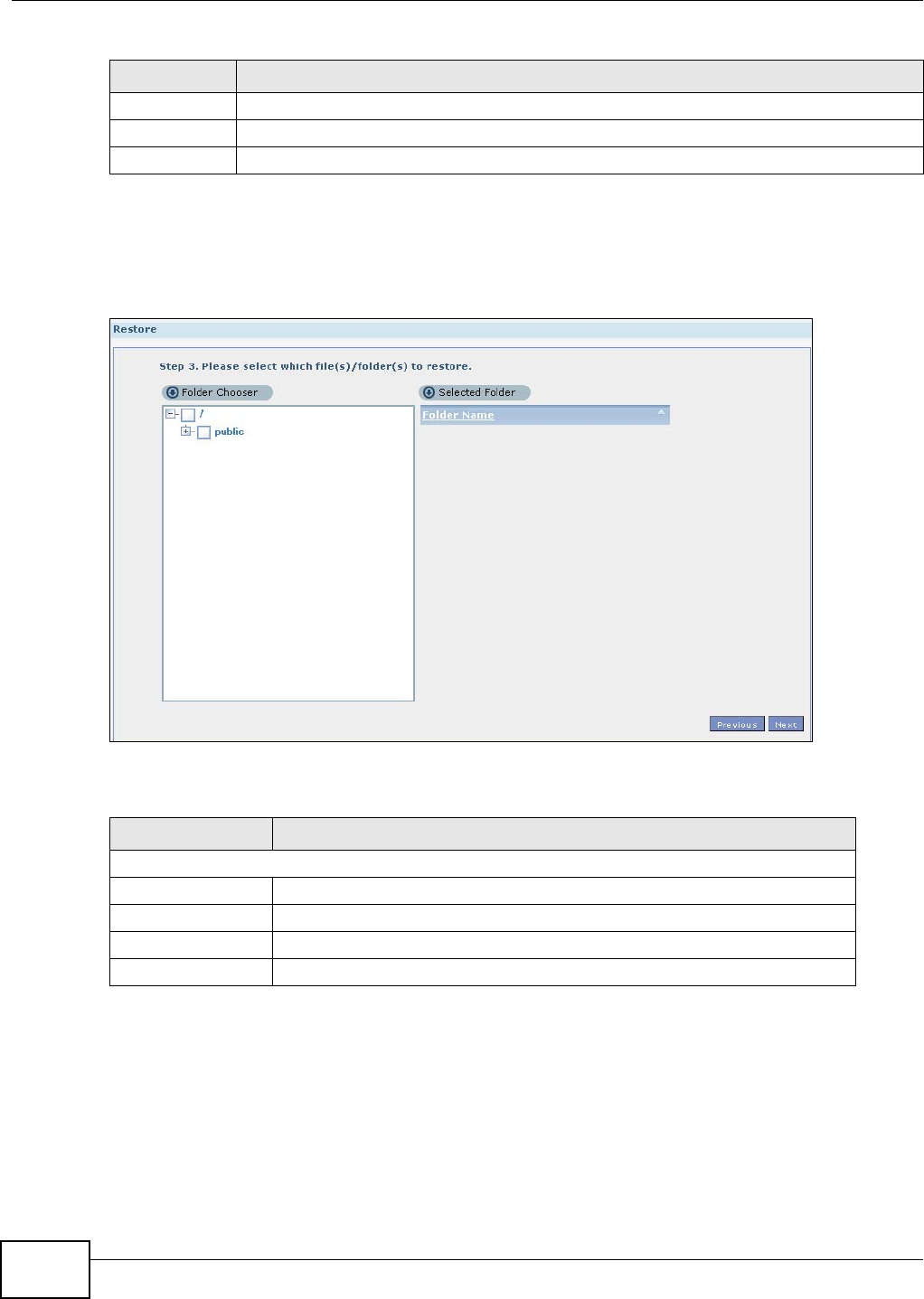
Chapter 11 Package Management
Media Server User’s Guide
252
11.10.3 Restore: Step 3
Use this screen to select the folder where the archive you want to restore is located.
Figure 143 Protect > Restore: Step 3
The following table describes the labels in this screen.
Restored Time Select a previous backup job in the list that you want to restore to your NSA.
Previous Click this to go back to the previous screen.
Next Click this to go to the next screen.
Table 71 Protect > Restore: Step 2
LABEL DESCRIPTION
Table 72 Protect > Restore: Step 3
LABEL DESCRIPTION
Step 3. Please select which file(s)/folder(s) to restore.
Folder Chooser Select the folder where the backup you want to restore is located.
Selected Folder This shows the path of the folder you selected.
Previous Click this to go back to the previous screen.
Next Click this to go to the next screen.
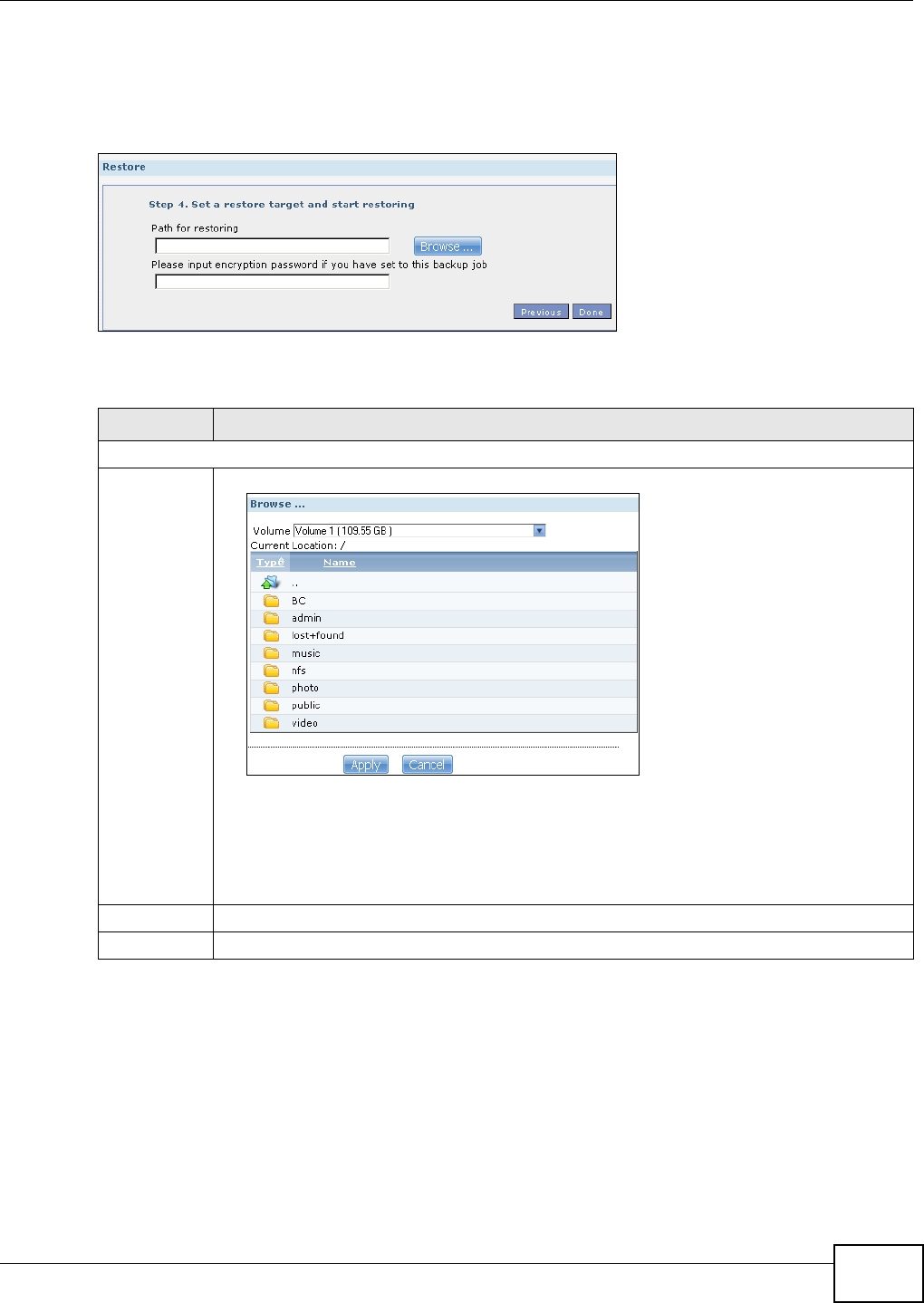
Chapter 11 Package Management
Media Server User’s Guide 253
11.10.4 Restore: Step 4
Use this screen to select the location in the NSA where you want to restore your backup.
Figure 144 Protect > Restore: Step 4
The following table describes the labels in this screen.
11.11 Syslog Server Screen
Use this screen to configure the NSA to accept syslog logs from syslog clients such as ZyXEL’s G-
4100 v2.
Note: You may need to configure any firewalls between the NSA and the syslog clients in
order to let the syslog traffic go to the NSA.
Table 73 Protect > Restore: Step 4
LABEL DESCRIPTION
Step 3. Set a restore target and start restoring
Browse Click this to select a folder where you want to place the restored files.
•Volume - Select a volume from the list.
•Current Location - This is the location of the selected folder.
•Type - This identifies the item as a file or folder.
•Name - This is the name of the folder/file.
Click Apply to save your settings and Cancel to close the screen.
Previous Click this to go back to the previous screen.
Done Click this to run the restore process and go back to the Backup screen.
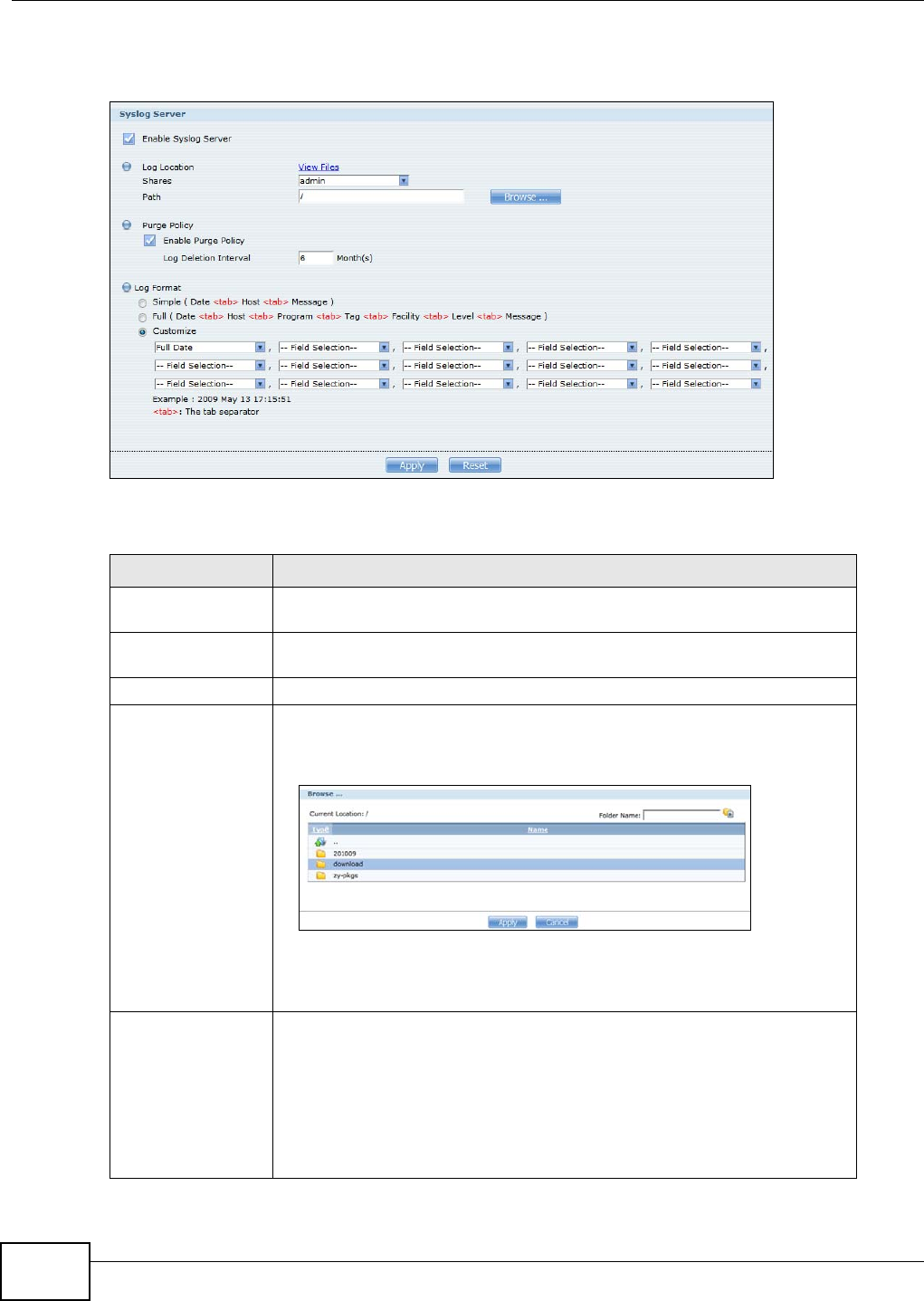
Chapter 11 Package Management
Media Server User’s Guide
254
Click Applications > Syslog Server to open the following screen.
Figure 145 Applications > Syslog Server
The following table describes the labels in this screen.
Table 74 Applications > Syslog Server
LABEL DESCRIPTION
Enable Syslog
Server Select this to have the NSA accept syslog logs from syslog clients. Clear it to
stop the NSA from accepting syslog logs from syslog clients.
Log Location Click View Files to browse to where you want to store the syslog logs on the
NSA.
Shares Select the share in which to store the syslog logs.
Path Use this if you want to further specify a folder within the share. This field
displays the share folder’s path. Type the location of the folder using forward
slashes as branch separators or use Browse to find or create a folder on the
NSA.
After you click Apply in the Syslog Server screen the NSA creates a folder
for the current month’s logs. The folder’s name uses the year and month in
YYYYMM format.
Purge Policy Select Enable Purge Policy and set a number of months in the Log
Deletion Interval field that displays to have the NSA delete the syslog
messages after keeping them for the specified period of time.
Regardless of how you set the purge policy, to save hard disk space the NSA
archives the syslog logs in a .tgz file on the second day of each month and
deletes the original folder and syslog files. The NSA creates a new folder for
the syslog logs it receives after that. You can use a zip program such as 7-zip
to open the archives.
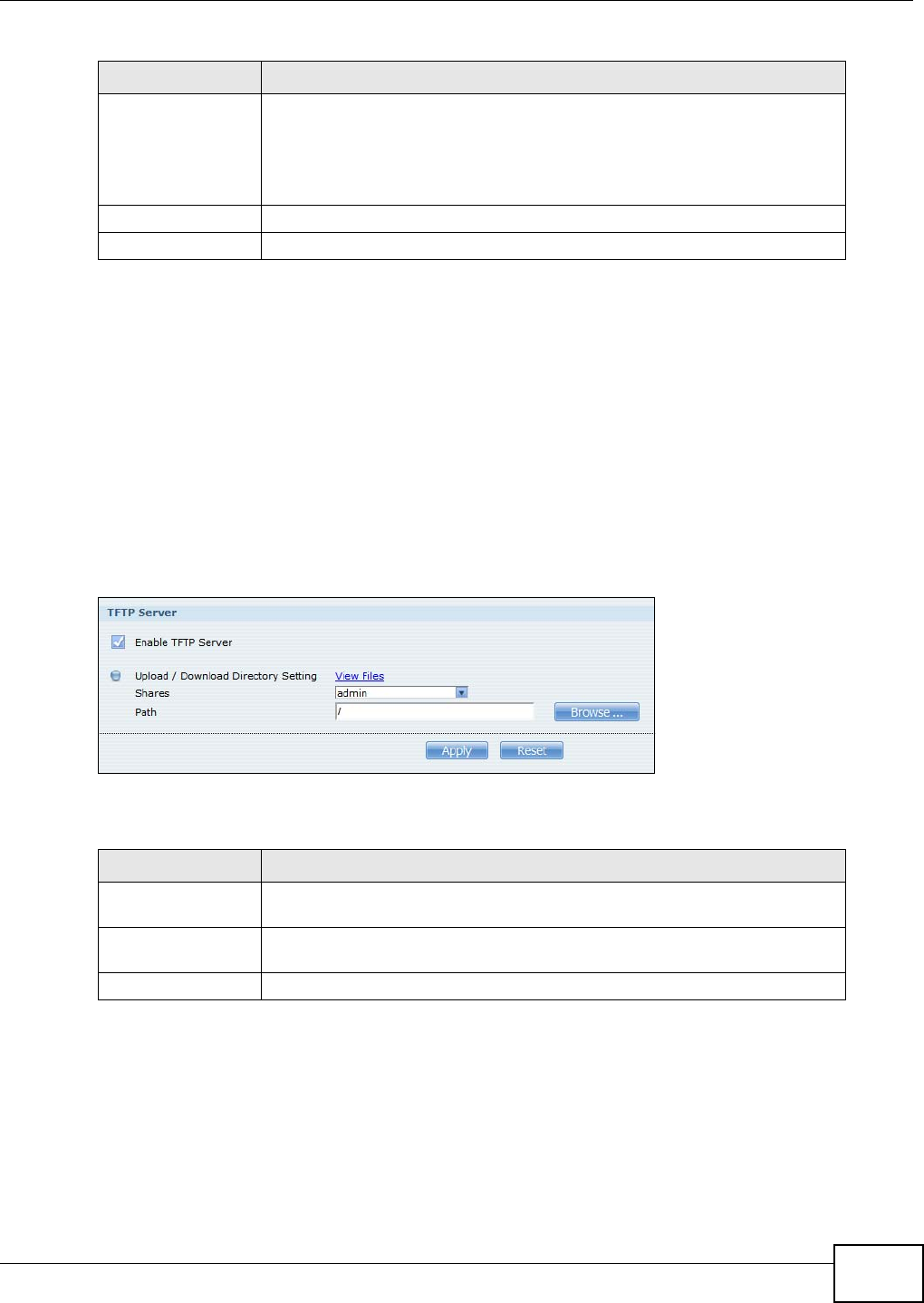
Chapter 11 Package Management
Media Server User’s Guide 255
11.12 TFTP Server Screen
Trivial File Transfer Protocol (TFTP) is an Internet file transfer protocol similar to FTP and often used
for transmitting large numbers of small files. Use this screen to configure the NSA to accept log files
from TFTP clients such as ZyXEL’s G-4100 v2.
Note: You may need to configure any firewalls between the NSA and the TFTP clients in
order to let the log files go to the NSA.
Click Applications > TFTP Server to open the following screen.
Figure 146 Applications > TFTP Server
The following table describes the labels in this screen.
Log Format Select the format you want to use for recording the received logs.
The Example item below the drop-down list boxes displays how the selected
custom format looks. For example, if you select Full Date, the individual log
entries would display with something like 2009 May 13 17:15:51 in front of
them.
Apply Click this to save your changes.
Reset Click this to restore the screen’s last-saved settings.
Table 74 Applications > Syslog Server
LABEL DESCRIPTION
Table 75 Applications > TFTP Server
LABEL DESCRIPTION
Enable TFTP Server Select this to have the NSA accept log files from TFTP clients. Clear it to stop
the NSA from accepting log files from TFTP clients.
Upload / Download
Directory Setting Click View Files to browse to where you want to store the log files on the
NSA.
Shares Select the share in which to store the log files.
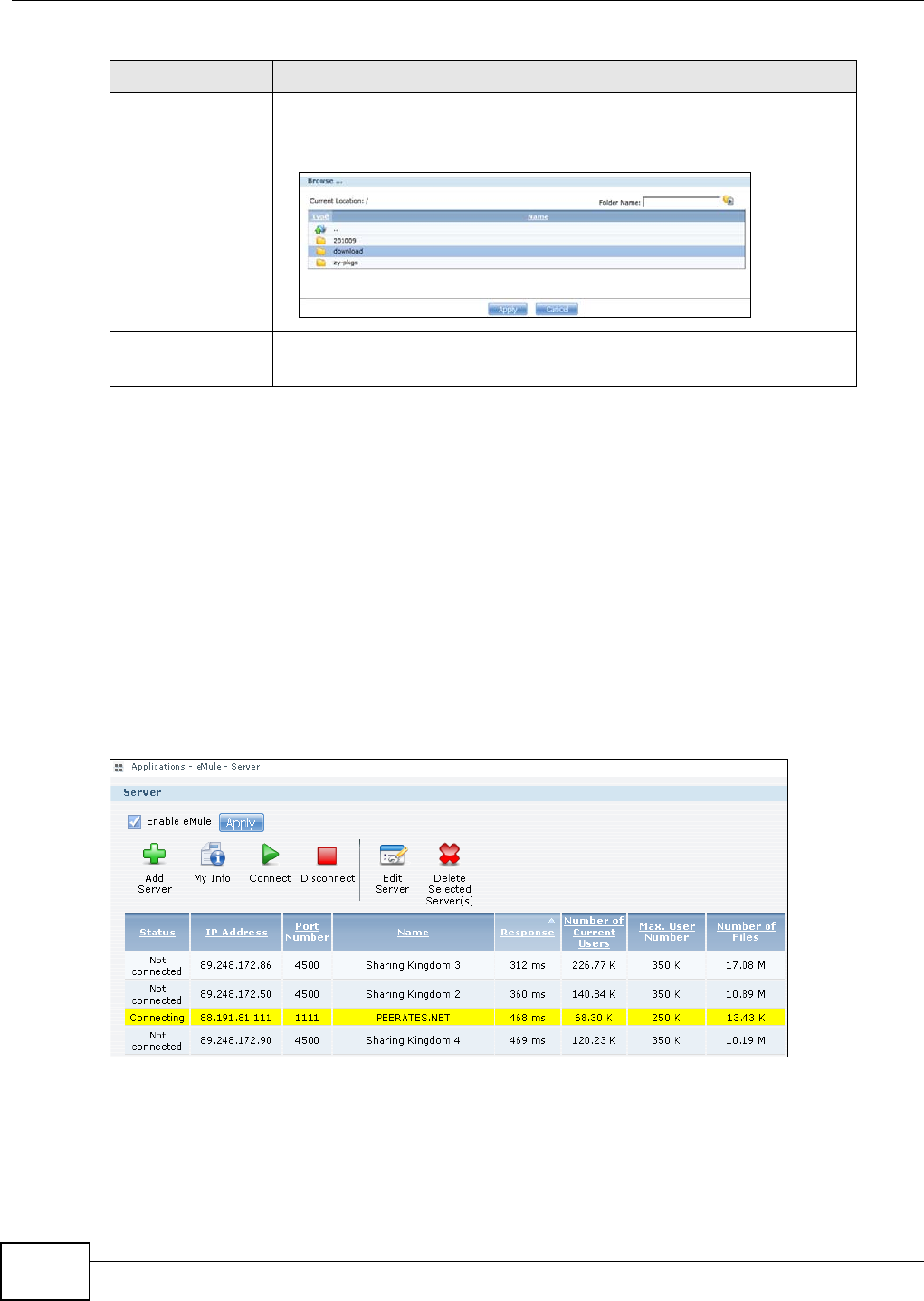
Chapter 11 Package Management
Media Server User’s Guide
256
11.13 eMule Screens
Use these screens to manage the eMule application in your NSA. eMule is a peer-to-peer (P2P) file-
sharing console that lets you download files from the Internet. It works with eDonkey and Kad
networks.
11.13.1 eMule Server Screen
Use this screen to configure the eMule server.
Click Applications > eMule > Server to open the following screen.
Figure 147 Applications > eMule > Server
Path Use this if you want to further specify a folder within the share This field
displays the share folder’s path. Type the location of the folder using forward
slashes as branch separators or use Browse to find or create a folder on the
NSA.
Apply Click this to save your changes.
Reset Click this to restore the screen’s last-saved settings.
Table 75 Applications > TFTP Server
LABEL DESCRIPTION
Chapter 11 Package Management
Media Server User’s Guide 257
The following table describes the labels in this screen.
You see a warning screen before you delete a server.
Figure 148 Delete a Server
Table 76 Applications > eMule > Server
LABEL DESCRIPTION
Server - You can add multiple servers in this screen. However, the NSA can only connect to one eMule server
at a time.
Enable eMule Check this and click Apply to enable the eMule application.
Add Server Click this to add an eMule server. A server provides a list of available files for download,
users sharing them and other information.
Refer to Section 11.13.2 on page 258 for the Add Server screen.
My Info Select a server from the list and click this to view the details and connection status of the
server.
Refer to Section 11.13.4 on page 259 for the My Info screen.
Connect Click this to connect to the selected server or a random server if no server is selected.
Disconnect Select a server from the list and click this to disconnect from the server.
Edit Server Select a server from the list and click this to edit the server’s information, including the
server name and IP address.
Refer to Section 11.13.3 on page 258 for the Edit Server screen.
Delete Selected
Server(s) Select the server(s) from the list and click this to delete the server(s) from the list.
The table lists your servers. Click a column’s heading to sort the entries by that criteria.
Status This shows the status of the NSA’s connection to the server: Connected, Connecting or
Not Connected.
IP Address This shows the IP address of the server.
Port Number This shows the port number used by the server for file-sharing.
Name This shows the name of the server.
Response This shows the length of time (in milliseconds) that the server took to reply to the NSA.
Number of
Current Users This shows the number of users currently connected to the server.
Max. User
Number This shows the total number of users that can connect to the server at the same time.
Number of Files This shows the number of files available for download in the server.
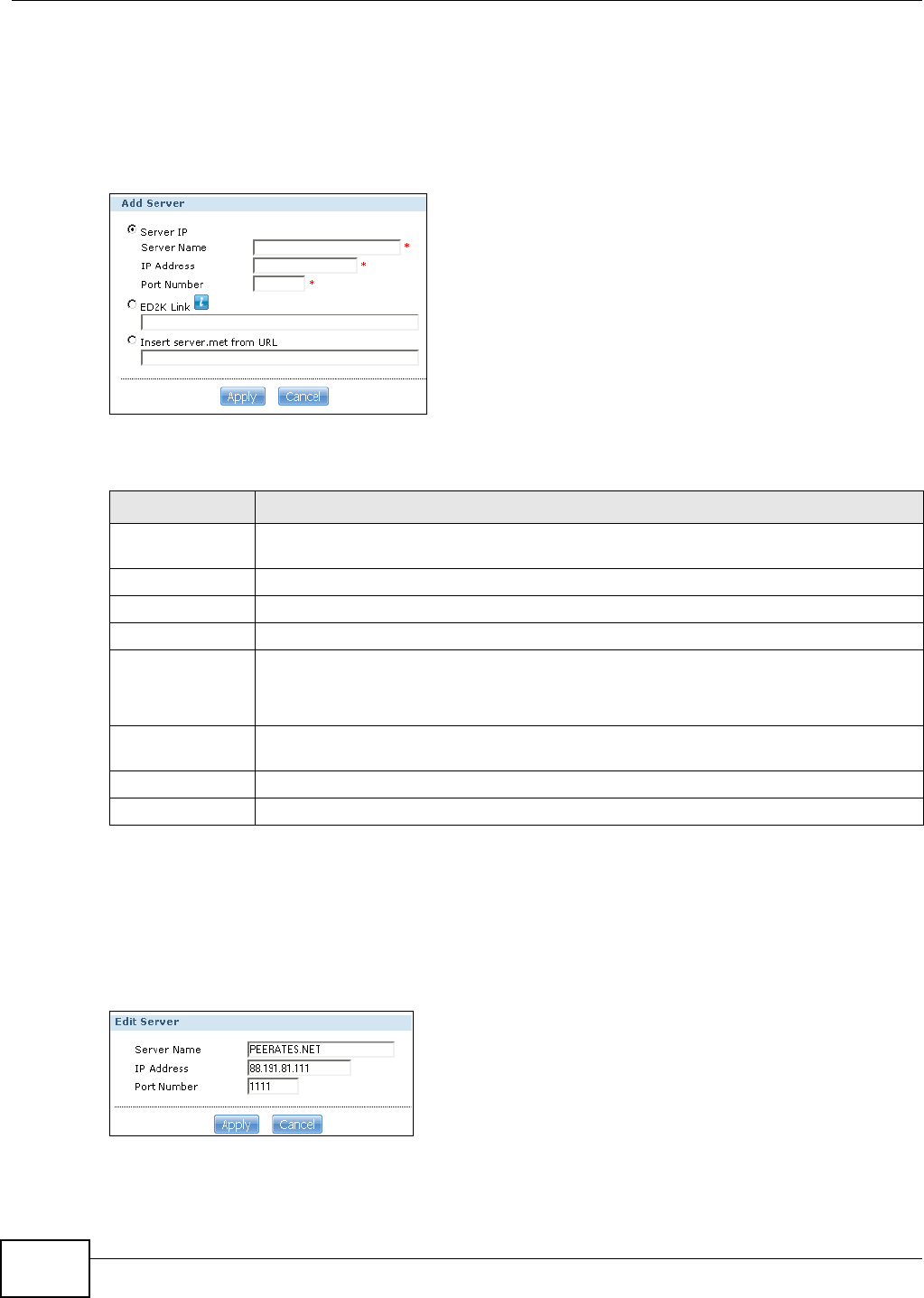
Chapter 11 Package Management
Media Server User’s Guide
258
11.13.2 Add Server
Use this screen to add a server for the eMule application.
Click Add in the Applications > eMule > Server screen to add a server.
Figure 149 Applications > eMule > Server: Add
The following table describes the labels in this screen.
11.13.3 Edit Server
Use this screen to edit a server for the eMule application.
Click Edit in the Applications > eMule > Server screen to edit a server.
Figure 150 Applications > eMule > Server: Edit
Table 77 Applications > eMule > Server: Add
LABEL DESCRIPTION
Server IP Select this if you know the server name, IP address and port number of the eMule server
you want to add.
Server Name Enter the server name.
IP Address Enter the IP address of the server.
Port Number Enter the port number used by the server for file-sharing.
ED2K Link Select this and enter the ED2K link for the eMule server you want to add.
The ED2K link is used within the eMule network and contains information about the
server.
Insert server.met
from URL Select this and enter the URL from which you want to download the server list that you
want the NSA to use.
Apply Click this to apply your changes.
Cancel Click this to return to the previous screen without saving.
Chapter 11 Package Management
Media Server User’s Guide 259
The following table describes the labels in this screen.
11.13.4 My Info
Use this screen to view the server details, including the status, IP address and download/upload
speeds.
Click MyInfo in the Applications > eMule > Server screen to view the server details.
Figure 151 Applications > eMule > Server: MyInfo
The following table describes the labels in this screen.
Table 78 Applications > eMule > Server: Edit
LABEL DESCRIPTION
Server Name Enter the server name.
IP Address Enter the IP address of the server.
Port Number Enter the port number of the server.
Apply Click this to apply your changes.
Cancel Click this to return to the previous screen without saving.
Table 79 Applications > eMule > Server: MyInfo
LABEL DESCRIPTION
ED2k Status This shows the status of the NSA’s connection to the server: Connected, Connecting
or Not Connected.
ED2k ID This is the identification given to the NSA by the eMule server. The ID comes in two
types:
•High ID - The NSA connects to the server directly.
•Low ID - The NSA connects to the server from behind a firewall.
ED2k IP This is the IP address of the eMule server to which the NSA is connected.
ED2k Port This is the port number of the eMule server to which the NSA is connected.
Kad This shows the status of the NSA’s connection to the Kad network: Connected or Not
Connected.
Kad is a shortcut for Kademlia network, which does not use servers to store files or user
information in order to run a peer-to-peer network. Instead it employs peers/clients as
small “servers” and runs queries through these peers.
Download Speed This shows the current download speed of the eMule client.
Upload Speed This shows the current upload speed of the eMule client.
Client in Queue This shows the number of peers waiting to connect to the NSA to download its file (s).
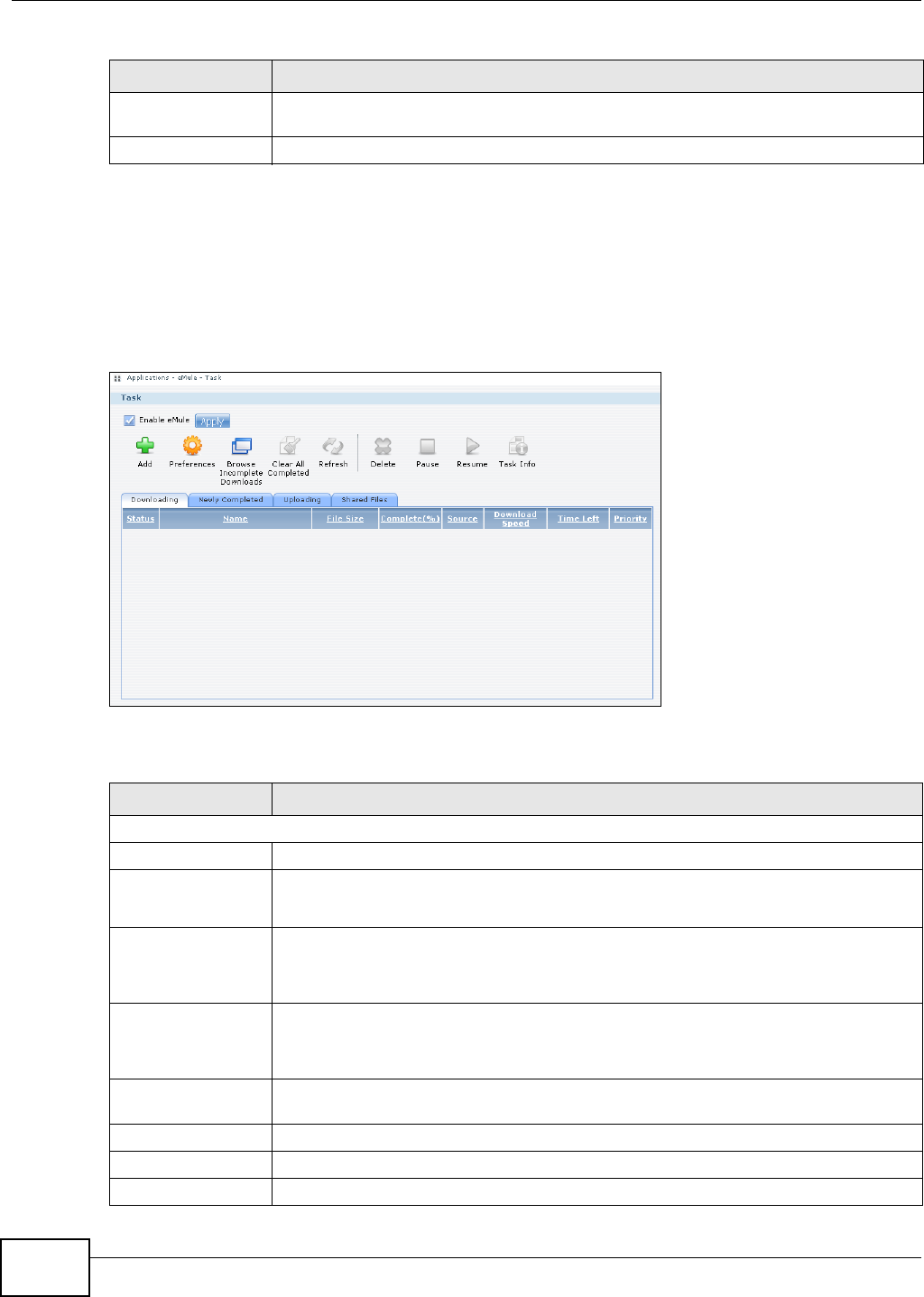
Chapter 11 Package Management
Media Server User’s Guide
260
11.13.5 eMule Task Screen
Use this screen to view tasks, including completed, downloading, uploading and shared tasks, that
are being handled by the NSA.
Click Applications > eMule > Task screen to view the task details.
Figure 152 Applications > eMule > Task
The following table describes the labels in this screen.
Sources This shows the total number of peers that can share the required files to the NSA eMule
client.
Close Click this to exit the screen.
Table 79 Applications > eMule > Server: MyInfo
LABEL DESCRIPTION
Table 80 Applications > eMule > Task
LABEL DESCRIPTION
Task
Enable eMule Check this and click Apply to enable the eMule application.
Add Click this to add a download task (ED2K link) to the list.
Refer to Section 11.13.6 on page 262 for the Add Task screen.
Preferences Click this to open a screen where you can set the default location for saving downloaded
files. You can also configure your eMule download settings.
Refer to Section 11.13.7 on page 263 for the Preferences screen.
Browse Incomplete
Downloads Click this to open a screen where you can see a list of *.part.met files that the NSA is
still in the process of downloading.
Refer to Section 11.13.9 on page 266 for the Share Browsing screen.
Clear All Completed Click this to remove all completed downloads from the task list. This only removes the
newly completed task(s) in this session.
Refresh Click this to refresh the task screen.
Delete Select an item from the list and click this to delete the task.
Pause Select an item from the list and click this to pause the task.
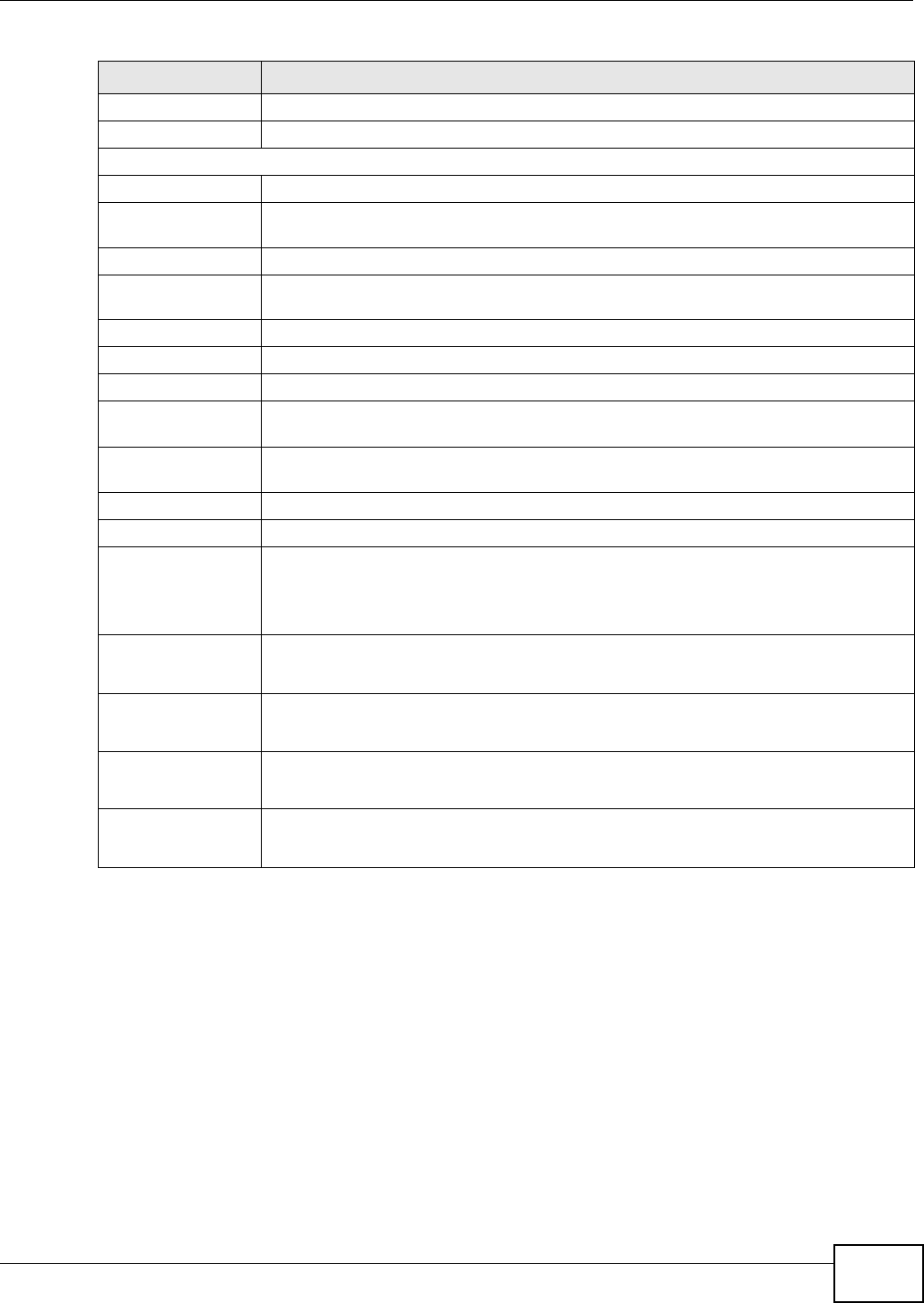
Chapter 11 Package Management
Media Server User’s Guide 261
Note: Download tasks initially appear in the Downloading tab of the eMule Task screen.
Depending on its status, it can eventually show up in the other tabs (Newly
Completed, Uploading or Shared Files tabs).
Resume Select a paused item from the list and click this to resume the task.
Task Info Select an item from the list and click this to view the details and status of the task.
The table lists your tasks. Click a column’s heading to sort the entries by that criteria.
Downloading This table shows a list of download tasks that are still in progress.
Newly Completed This table shows a list of tasks that have been completed but have not been cleared
from the list.
Uploading This table shows a list of upload tasks that are still in progress.
Shared Files This table shows a list of files on the NSA that are available for download by other peers
in the network.
Status This shows the current status of the task: Waiting or Downloading.
Name/File Name This shows the name of the file(s) associated to the task.
File Size/Size This shows the size of the file(s) associated in the task.
Complete (%) This shows the percentage of the file that has been downloaded by the NSA. It also
indicates what percent of the file still needs to be downloaded.
Source This shows the total number of peers that can share the required files to the NSA eMule
client.
Download Speed This shows the download speed of the NSA for the task.
Time Left This shows how much more time the NSA needs to complete the file’s download.
Priority Use this field to set the priority for the task. Choose from Auto, Low, Normal or High.
Select Auto to have the NSA automatically determine the task’s priority.
Select High to have the NSA complete this task before the others.
Transferred This shows what percent of the file the NSA has uploaded to other peers.
This column is available in the Uploading tab.
Upload Speed This shows the upload speed of the NSA.
This column is available in the Uploading tab.
Requests This shows the number of requests for a shared file.
This column is available in the Shared Files tab.
Accepted Requests This shows the number of file requests granted by the NSA.
This column is available in the Shared Files tab.
Table 80 Applications > eMule > Task
LABEL DESCRIPTION
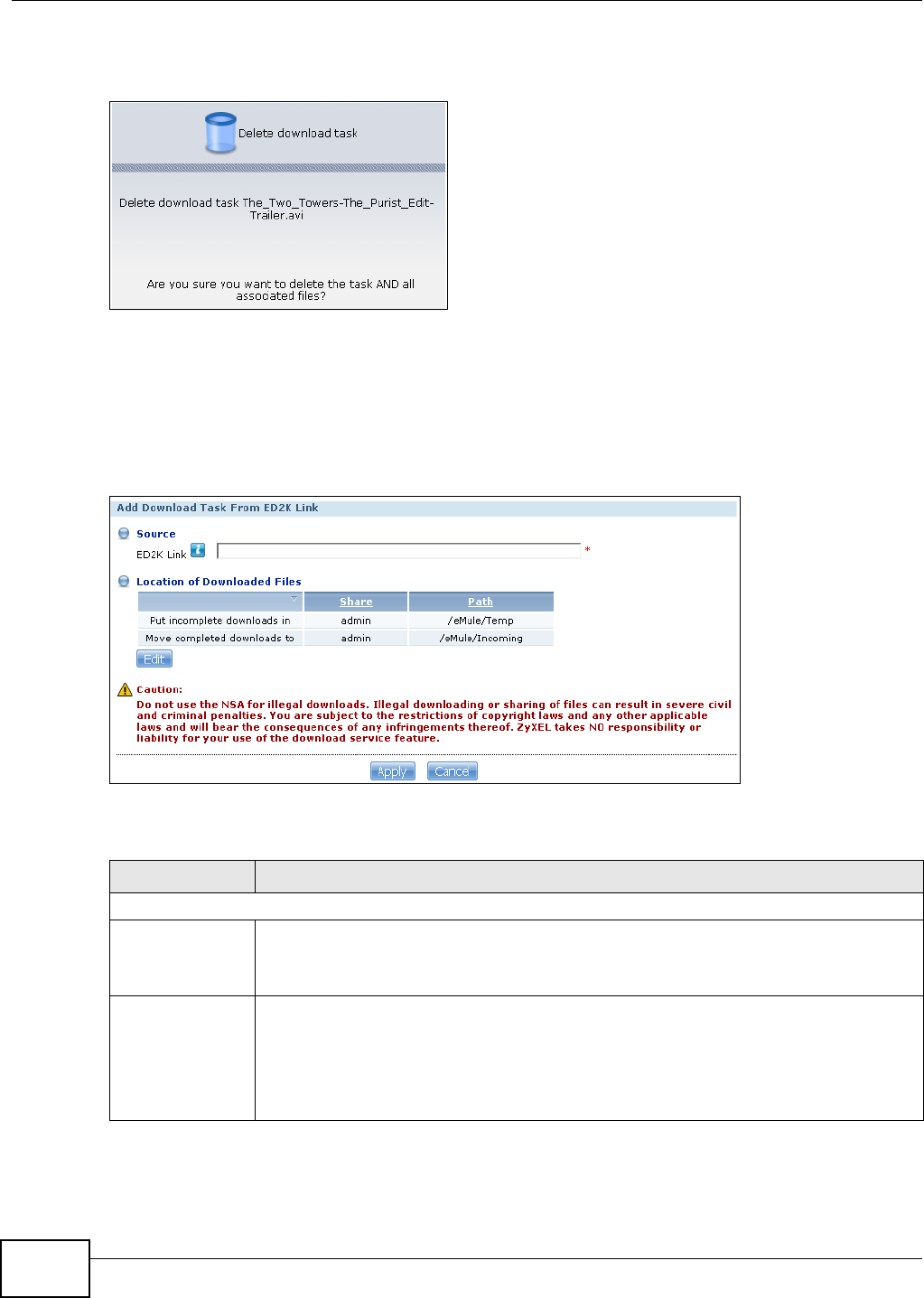
Chapter 11 Package Management
Media Server User’s Guide
262
You see a warning screen before you delete a task.
Figure 153 Delete a Task
11.13.6 Add Task
Use this to add a download task to the NSA.
Click Add in the Applications > eMule > Task screen to add a task.
Figure 154 Applications > eMule > Task: Add
The following table describes the labels in this screen.
Table 81 Applications > eMule > Task: Add
LABEL DESCRIPTION
Source
ED2K Link Paste the ED2K link of the file you want to download into this field.
The ED2K link identifies files in the eMule network. It starts with ed2k:// and may contain
the name and size of the file you want to download.
Location of
Downloaded Files This shows where the NSA stores new downloads (Put incomplete downloads in) and
where the NSA moves completed downloads (Move completed downloads to).
The Share column shows the name of the share where the file is downloaded.
The Path column points to the location in the share where the NSA will save the
downloaded files.
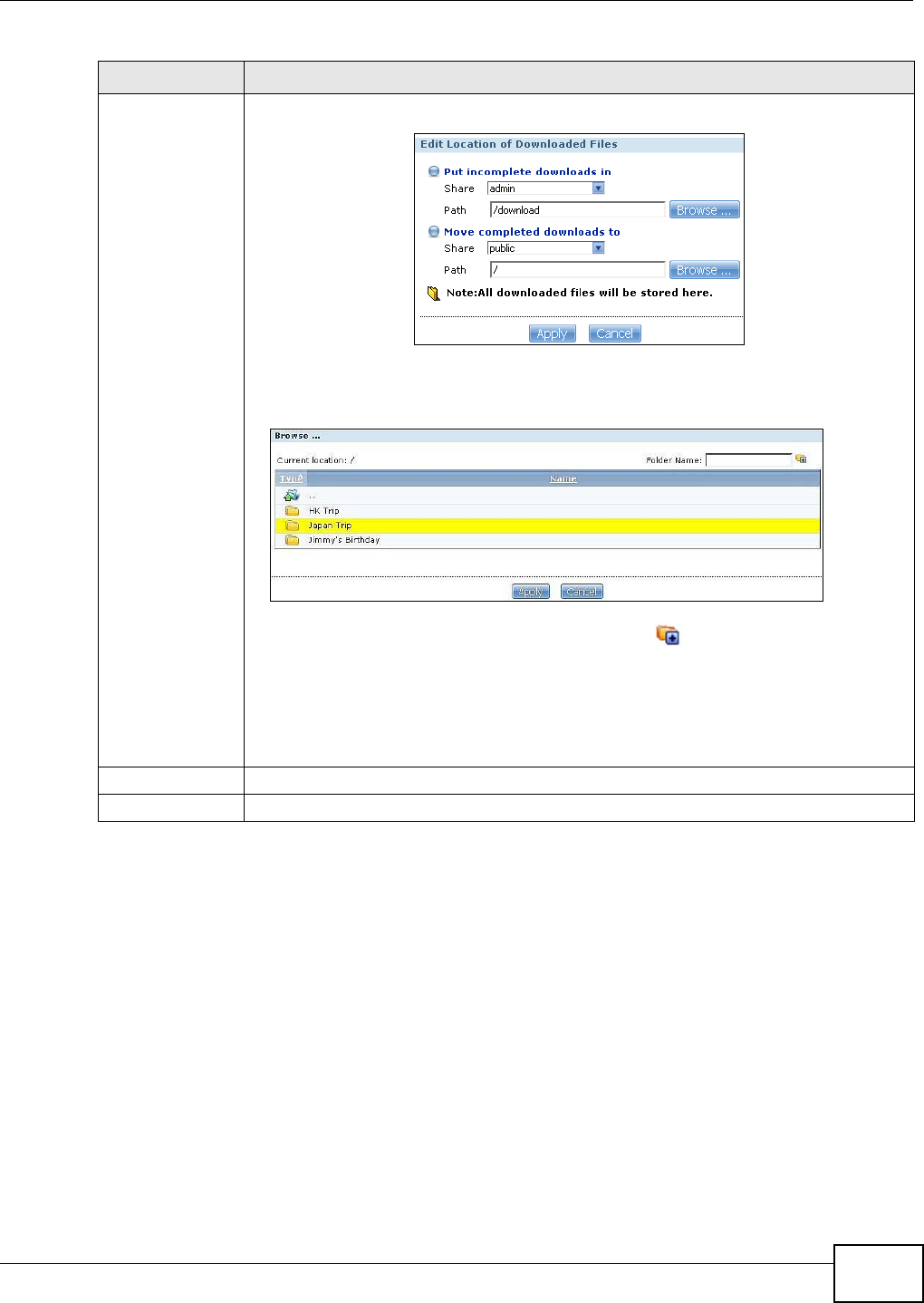
Chapter 11 Package Management
Media Server User’s Guide 263
11.13.7 Preferences
Use this screen to configure your eMule settings, such as port numbers to use, its download/upload
rates and the maximum number of peers allowed to connect to the NSA.
Edit Click this to open the following screen where you can set the default folder location where
you “Put incomplete downloads in” and “Move complete downloads to”:.
•Share - Select the destination share from the drop-down list.
•Path - This field displays the share folder’s path. You can use Browse to find or create
a folder on the NSA or type the location of the folder using forward slashes as branch
separators.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a folder or file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field.
All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 81 Applications > eMule > Task: Add
LABEL DESCRIPTION
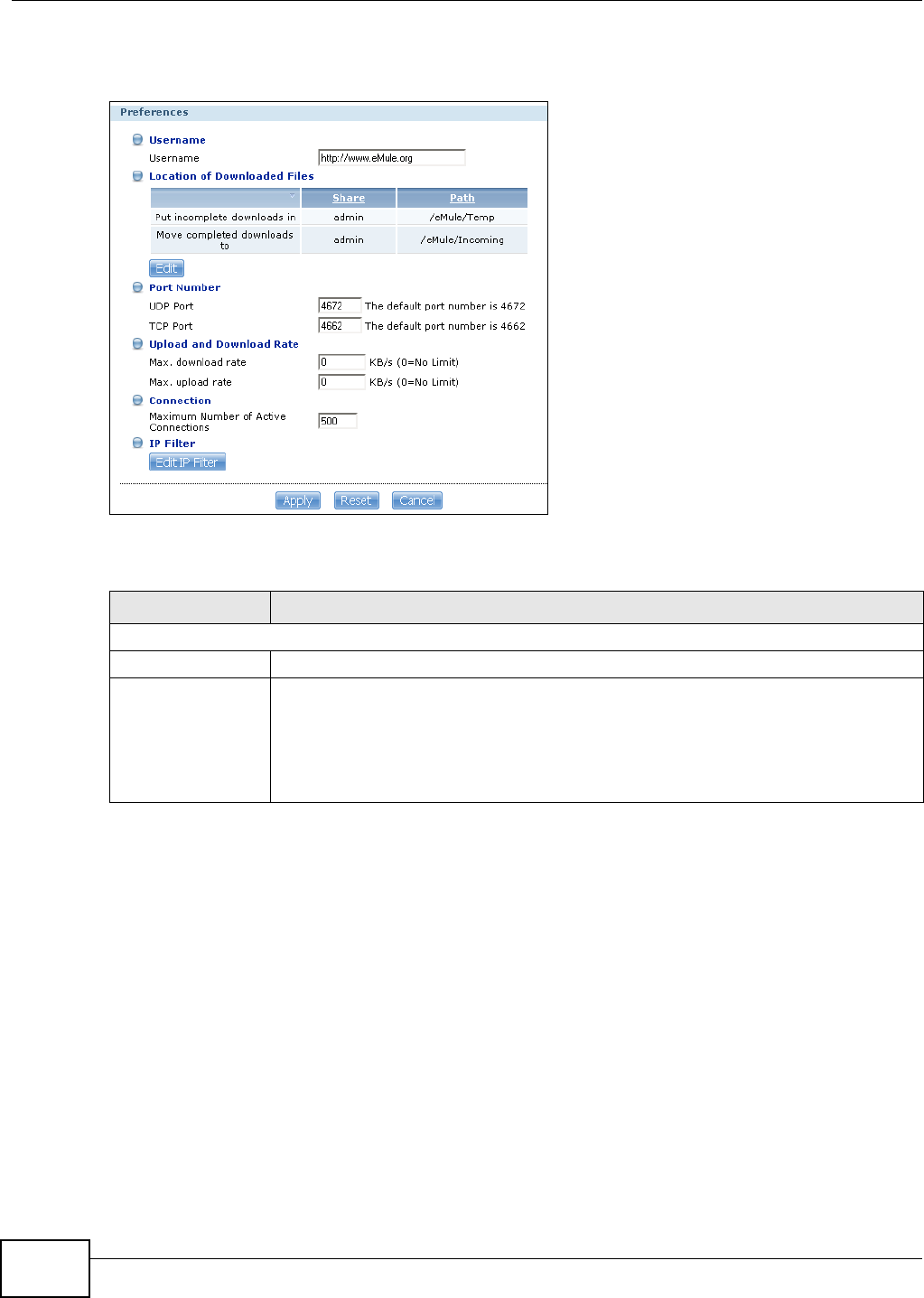
Chapter 11 Package Management
Media Server User’s Guide
264
Click Applications > eMule > Task > Preferences to open the following screen.
Figure 155 Applications > eMule > Task > Preferences
The following table describes the labels in this screen.
Table 82 Applications > eMule > Task > Preferences
LABEL DESCRIPTION
Username
Username Enter your user name that identifies the NSA in the eMule network.
Location of
Downloaded Files This shows where the NSA stores new downloads (Put incomplete downloads in) and
where the NSA moves completed downloads (Move completed downloads to).
The Share column shows the name of the share where the file is downloaded.
The Path column points to the location in the share where the NSA will save the
downloaded files.
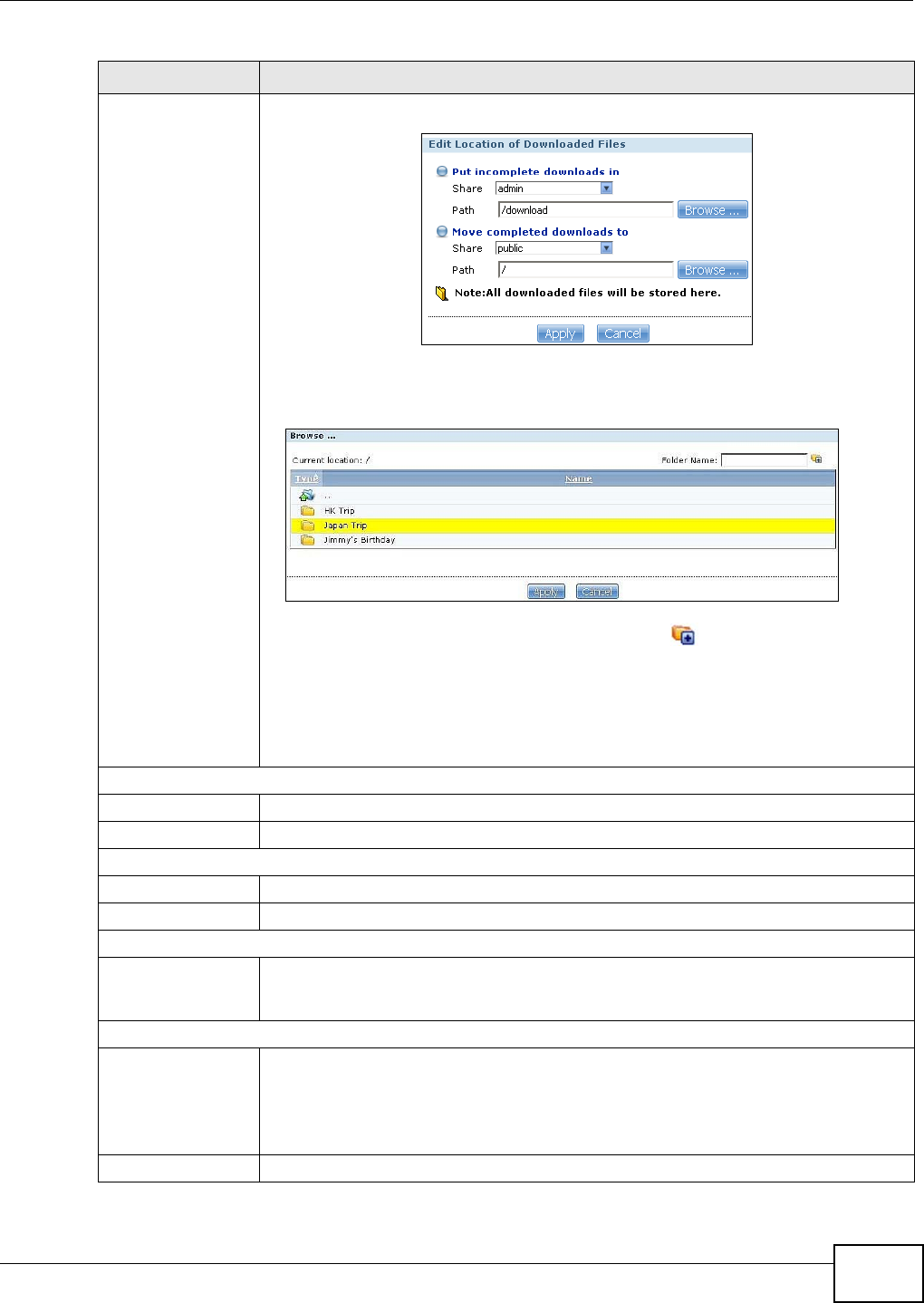
Chapter 11 Package Management
Media Server User’s Guide 265
Edit Click this to open the following screen where you can set the default folder location
where you “Put incomplete downloads in” and “Move complete downloads to”:.
•Share - Select the destination share from the drop-down list.
•Path - This field displays the share folder’s path. You can use Browse to find or
create a folder on the NSA or type the location of the folder using forward slashes as
branch separators.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a folder or file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field.
All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Port Number
UDP Port Enter the UDP port number you want to use for file transfers.
TCP Port Enter the TCP port number you want to use for file transfers.
Upload and Download Rate
Max. download rate Enter the maximum download rate for download tasks.
Max. upload rate Enter the maximum upload rate for upload tasks.
Connection
Maximum Number
of Active
Connections
Enter the maximum number of eMule peer-to-peer connections.
IP Filter
Edit IP Filter Click this to edit the IP Filter.
IP filtering prevents your NSA from accessing certain networks and IP addresses that
may be hosting malicious programs.
Refer to Section 11.13.8 on page 266 to view and configure the Edit IP Filter screen.
Apply Click this to save your changes.
Table 82 Applications > eMule > Task > Preferences
LABEL DESCRIPTION
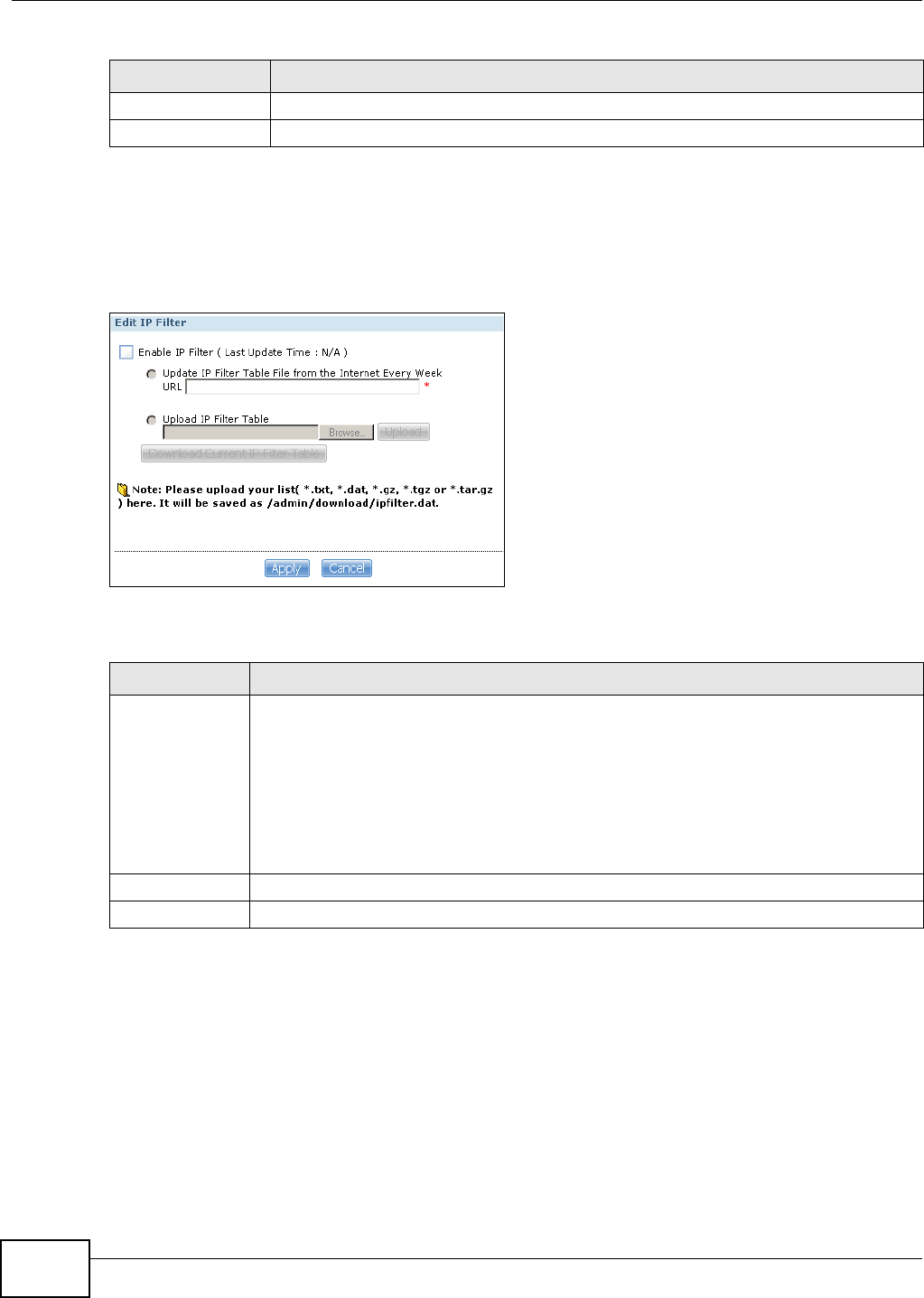
Chapter 11 Package Management
Media Server User’s Guide
266
11.13.8 Edit IP Filter
Use this screen to enable IP filtering which prevents your NSA from accessing certain networks and
IP addresses that may be hosting malicious programs.
Figure 156 Applications > eMule > Task > Preferences: Edit IP Filter
The following table describes the labels in this screen.
11.13.9 Share Browsing
Use this screen to view a list of files that are still being downloaded by the NSA. The files are
located in the eMule\Temp folder in the Admin share by default.
Reset Click this to clear the fields.
Cancel Click this to return to the previous screen without saving.
Table 82 Applications > eMule > Task > Preferences
LABEL DESCRIPTION
Table 83 Applications > eMule > Task > Preferences: Edit IP Filter
LABEL DESCRIPTION
Enable IP Filter Click this to enable IP filtering. This prevents your NSA from accessing certain networks
and IP addresses that may be hosting malicious programs.
Select Update IP Filter Table File from the Internet Every Week if you know the web
location of the IP filter table you want to use. Enter the link where your NSA can acquire
the list of networks and IP addresses. The NSA checks this link every week and uses the
latest IP filter table available.
Select Upload IP Filter Table if you want to use an IP filter table from your local
computer.
Apply Click this to save your changes.
Reset Click this to return to the previous screen without saving.
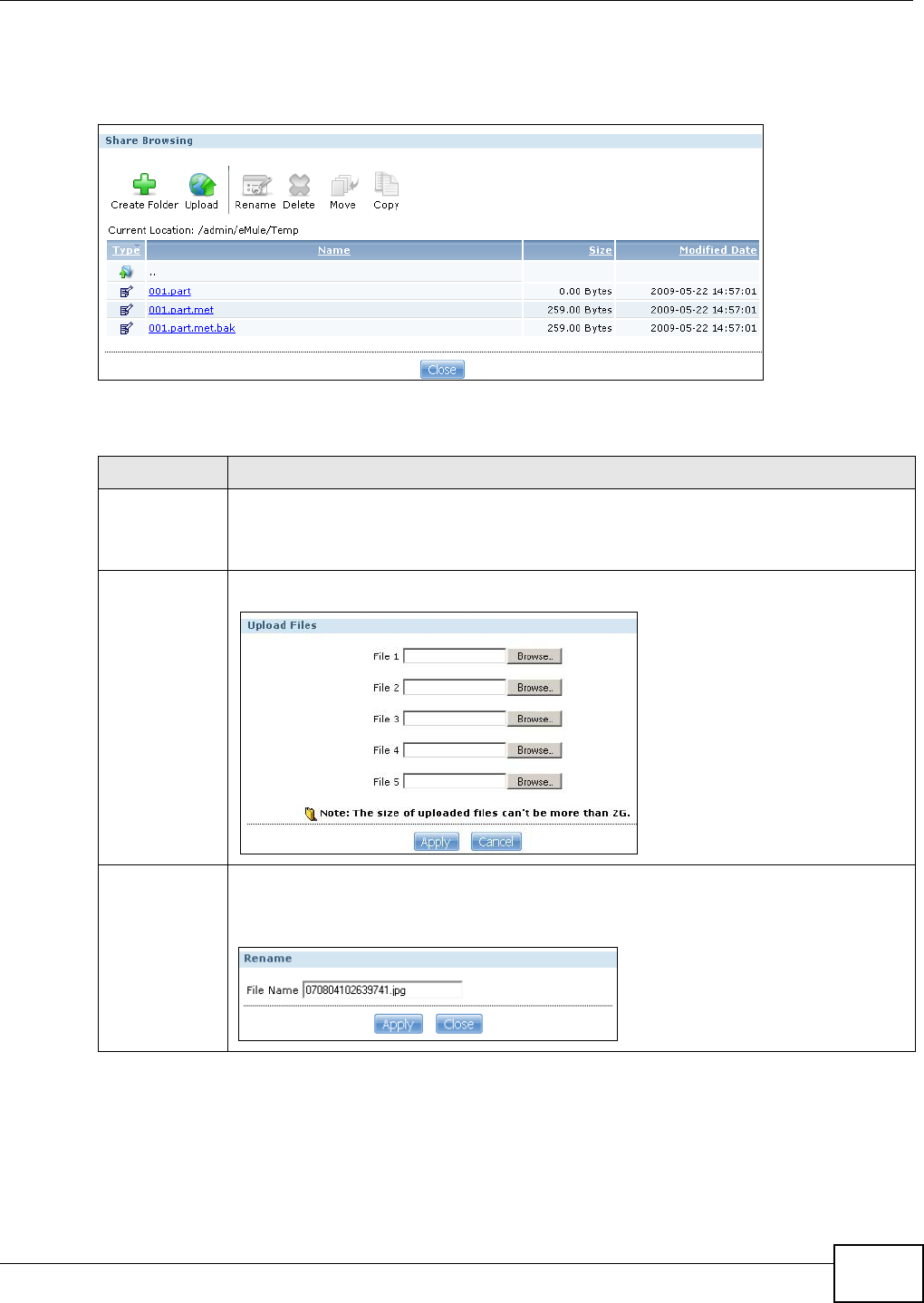
Chapter 11 Package Management
Media Server User’s Guide 267
Click Applications > eMule > Task > Browse Incomplete Downloads to open the following
screen.
Figure 157 Applications > eMule > Task > Browse Incomplete Downloads
The following table describes the labels in this screen.
Table 84 Sharing > Shares > Share Browser
LABEL DESCRIPTION
Create Folder Type a folder name and click Apply to make a new folder. The name can be 1 to 239 single-
byte (no Chinese characters allowed for example) ASCII characters. The name cannot be the
same as another existing folder in the same path. See Section 4.4.6 on page 55 for more
information on folder names.
Upload Click this to add files to the share. Use Browse to locate a file and click Apply to upload the
file. Note that the size of each file should be less than 2 GB.
Rename Select a folder or file and click this to open a screen. Enter the name you want and click OK
to make the changes.
Note: When you change a file name, make sure you keep the file extension
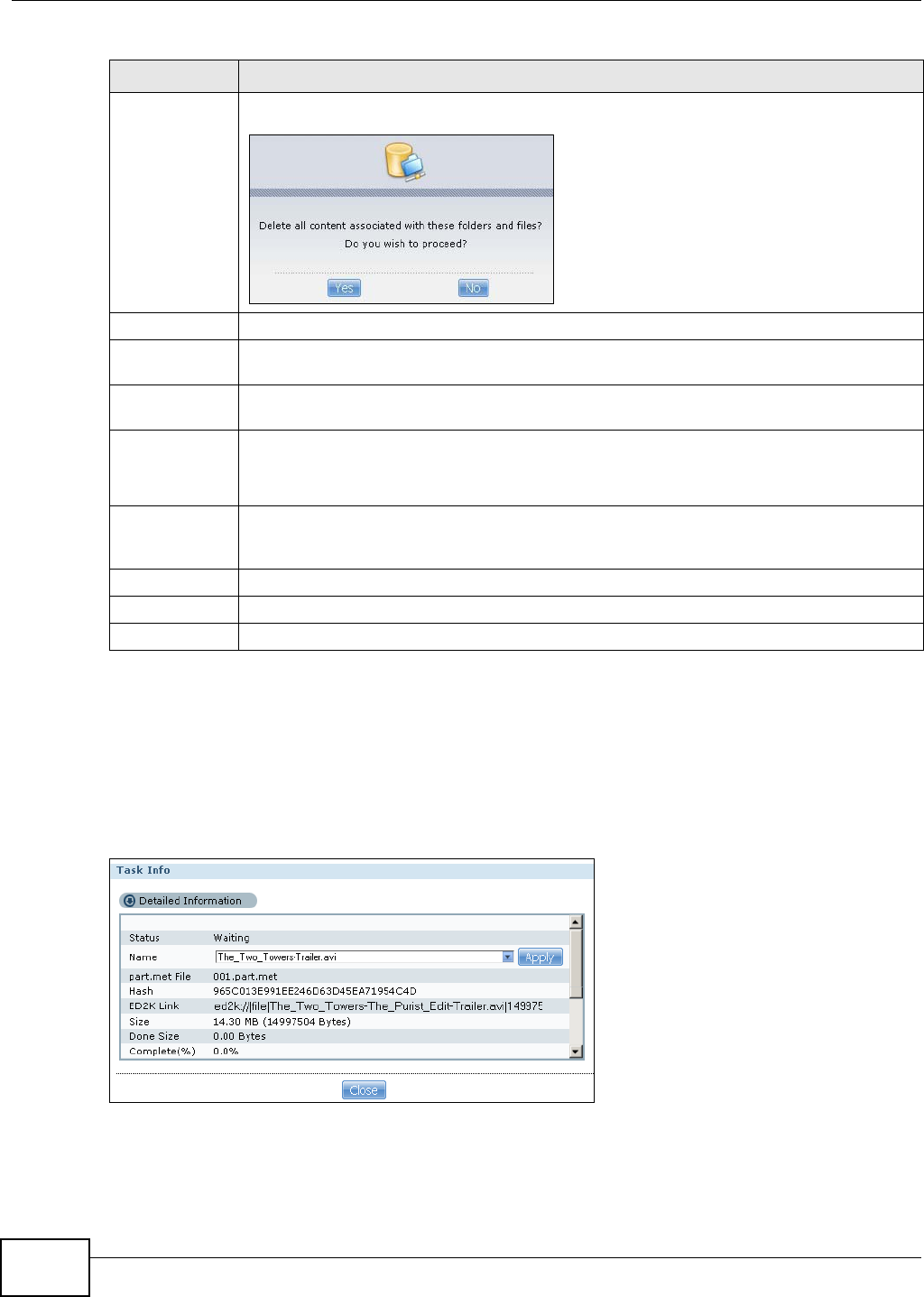
Chapter 11 Package Management
Media Server User’s Guide
268
11.13.10 Task Info
Use this screen to view eMule task details, such as status, file name, file size and its download
progress.
Click Task Info in Applications > eMule > Task screen to open the following.
Figure 158 Applications > eMule > Task: Task Info
Delete Select a file/folder from the list and click this to open a warning screen. Click Yes to delete
the file/folder, or click No to close the screen.
Move Select a file/folder from the list and click this to relocate the file/folder to another share.
Copy Select a file/folder from the list and click this to make a duplicate of the file/folder to another
share.
Current
location This is the name of the share and folder path that you are in.
Type The icon in this column identifies the entry as a folder or a file.
The folder with an arrow pointing up is for the link that takes you to the next higher layer in
the share’s folder tree.
Name This section lists the share’s existing folders or files. Click to the right of the file/folder name
to select the file/folder. You can also click the folder’s name to navigate to a sub-folder
within the folder.
Size This field displays size of the file.
Modified Date This field displays a file’s latest modification date.
Close Click this to close the screen.
Table 84 Sharing > Shares > Share Browser (continued)
LABEL DESCRIPTION
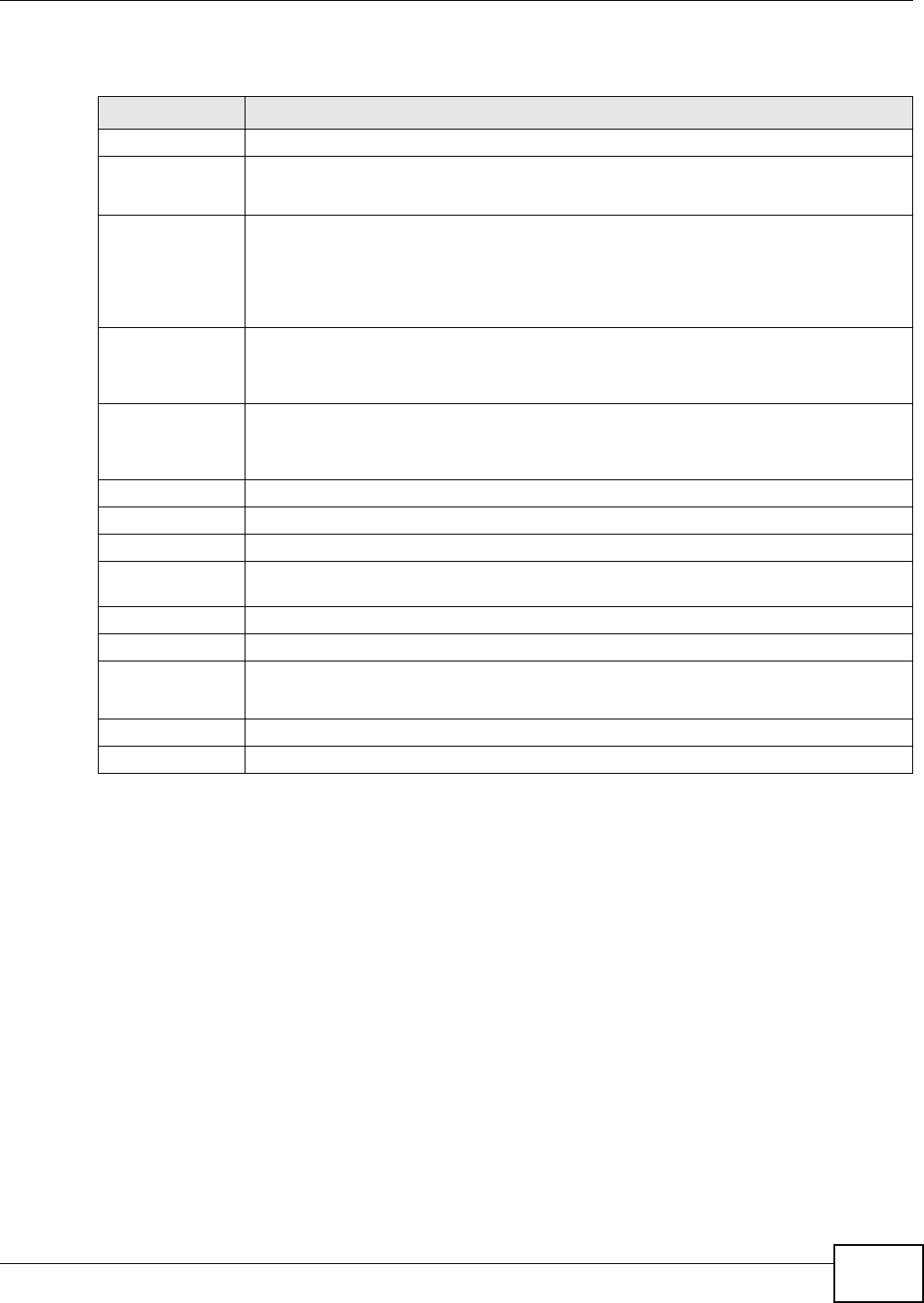
Chapter 11 Package Management
Media Server User’s Guide 269
The following table describes the labels in this screen.
11.13.11 eMule Search Screen
Use this screen to search for files available in an eMule server using keywords and other
parameters, such as file type, file size and extension names.
Table 85 Applications > eMule > Task: Task Info
LABEL DESCRIPTION
Status This shows the current status of the task - Waiting or Downloading.
Name This shows the file name of the file associated with the task.
You can change this file name by entering the new name and clicking Apply.
part.met File This shows the temporary file name for an incomplete file.
Files in peer-to-peer networks can be divided into several parts for easier download. Once
all the parts have been downloaded, you can run one part and the file automatically
rebuilds itself. If the download of the file(s) is not completed, the file parts cannot open
on their own.
Hash This shows the hash value of the download file.
This is a text string that can be interpreted by eMule to check the downloaded file’s
integrity.
ED2K Link This shows the ED2K link for this file.
The ED2K link identifies files in the eMule network. It starts with ed2k:// and may contain
the name and size of the file you want to download.
Size This shows the size of the file associated with the task.
Done Size This shows the size of the file that has been downloaded so far.
Complete (%) This shows what percent of the file has been downloaded so far.
Source This shows the total number of peers that can share the required files to the NSA eMule
client.
Download Speed This shows the download speed for the task.
Time Left This shows how much time is needed to complete the task.
Priority This shows the priority of this task.
You can set this in Section 11.13.5 on page 260.
Seen Complete This shows the last time a source with the complete file was online.
Close Click this to exit the screen.
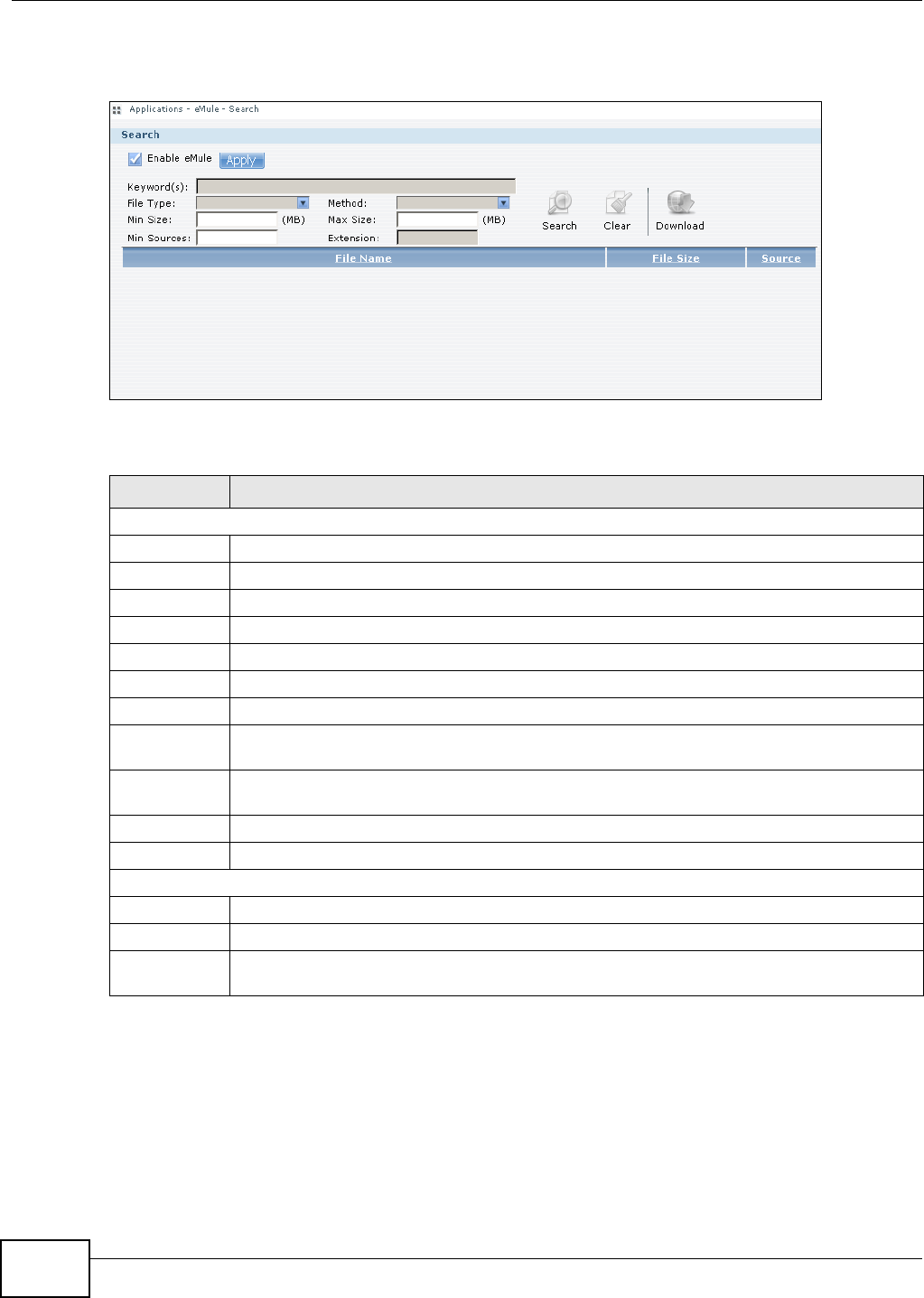
Chapter 11 Package Management
Media Server User’s Guide
270
Click Applications > eMule > Search to open the following screen.
Figure 159 Applications > eMule > Search
The following table describes the labels in this screen.
Table 86 Applications > eMule > Search
LABEL DESCRIPTION
Search
Enable eMule Check this and click Apply to enable the eMule application.
Keyword(s) Enter words that are related to the file you want to download.
File Type Select the file type that you want to download.
Method Select the search method you want eMule to employ.
Min Size Enter the minimum file size you want included in the search results.
Max Size Enter the maximum file size you want included in the search results.
Min Sources Enter the minimum number of peers sharing the file you want to download.
Extension Enter the file extensions separated by commas of files you want included in the search
results.
Search Click this to have the NSA search the eMule network for files that match the criteria you have
set.
Clear Click this to clear the fields.
Download Select a file from the results and click this to start downloading the file.
This table shows the results of the search.
File Name This shows the name of the file(s) that match the criteria you have set.
File Size This shows the size of the file(s) that match the criteria you have set.
Source This shows how many peers are currently available to share this file so that the NSA can
download it.
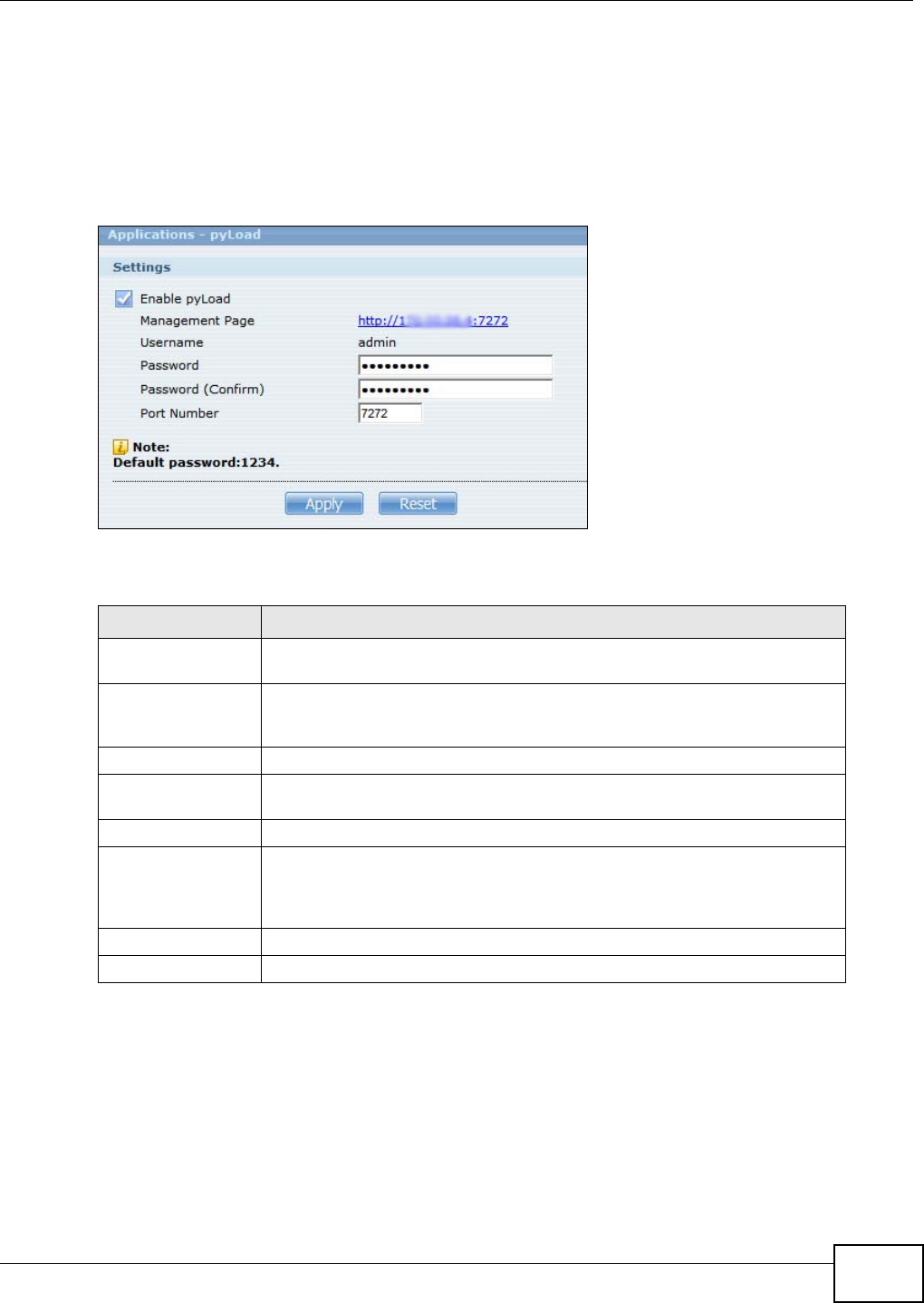
Chapter 11 Package Management
Media Server User’s Guide 271
11.14 pyLoad Screen
Use this screen to configure the NAS so you can use pyLoad to manage your downloads, including
those from one-click hosting sites.
Click Applications > pyLoad to open the following screen.
Figure 160 Applications > pyLoad
The following table describes the labels in this screen.
11.15 Technical Reference
This section provides technical background information on the topics discussed in this chapter.
Table 87 Applications > pyLoad
LABEL DESCRIPTION
Enable pyLoad Select this to have the NSA manage your downloads. Clear it to turn the
feature off.
Management Page This is the IP address and port number of the NSA’s pyLoad management
login screen. The pyLoad management login screen uses the NSA’s IPv4
address and the port number you configure. Click this link to go to it.
Username Only the admin account can log into the pyLoad management screen.
Password You can configure a separate password for using the admin account to access
the NSA’s pyLoad management screen.
Password (Confirm) Type the same password again to make sure you entered it correctly.
Port Number Set the pyLoad management page’s port number. The range of valid port
numbers is 1024~65536. Include this port number after the IP address when
manually entering the pyLoad management login page’s address in your
browser’s address bar. For example, 192.168.1.2:7272.
Apply Click this to save your changes.
Reset Click this to restore the screen’s last-saved settings.
Chapter 11 Package Management
Media Server User’s Guide
272
11.15.1 S.M.A.R.T Attributes
The following table describes some common S.M.A.R.T. attributes. If a higher or lower raw attribute
value is better, it is indicated in the BETTER column. Since S.M.A.R.T. attributes and their
definitions vary by manufacturer, refer to the hard drive manufacturer for details about the
attributes your hard drive supports.
Table 88 S.M.A.R.T. Attributes
ID ATTRIBUTE
NAME BETTER DESCRIPTION
01 Read Error Rate Low Shows the rate of hardware read errors. If this is not zero, there is a
problem with the disk surface or the read/write heads.
02 Throughput
Performance High This is the hard drive’s general (overall) throughput performance. A
decreasing value indicates a problem.
03 Spin-Up Time Low This is the average number of milliseconds the hard drive took for spindle
spin up (from zero RPM to fully operational).
04 Start/Stop Count The total number of spindle start and stop cycles.
05 Reallocated
Sectors Count Low Total number of reallocated sectors on the hard drive. When the hard
drive detects a read/write/verification error, it marks the sector as
“reallocated” and transfers the data to a specially reserved (spare) area.
The process is also known as remapping with “reallocated” sectors known
as remaps. The more sectors the hard drive has to reallocate, the slower
read and write speeds become.
06 Read Channel
Margin This is the margin of a channel when it reads data.
07 Seek Error Rate Low This is the rate of the magnetic heads’ seek errors. A failure in the
mechanical positioning system, such as servo damage or a thermal
widening of the disk, results in seek errors. An increasing number of seek
errors indicate the condition of the disk surface and the mechanical
subsystem are worsening.
08 Seek Time
Performance High This is an average performance indicator for the seek operations of the
magnetic heads. Mechanical subsystem problems cause this value to
decrease.
09 Power-On Hours
(POH) Low This is how many hours the hard drive has been in a power-on state. The
raw value lists the total number of hours (or minutes, or seconds
depending on the manufacturer).
10 Spin Retry Count Low This is the total number of spin start retry attempts. This is the number of
attempts to spin up to fully operational speed the hard drive has made
when the first attempt did not succeed. An increase in this value is an
indicator of hard disk mechanical subsystem problems.
11 Recalibration
Retries High This is the number of times recalibration was requested when the first
attempt did not succeed. A decrease in this value is an indicator of hard
disk mechanical subsystem problems.
12 Device Power
Cycle Count This is the number of times the hard drive has gone through a full power
on and power off.
13 Soft Read Error
Rate Low This is the number of uncorrected read errors the hard drive has
reported. If this is not zero, back up your data.
190 Airflow
Temperature Low This indicates the temperature of the airflow measured by a Western
Digital hard drive.
190 Temperature
Difference from
100
High This indicates the value of 100 - the temperature in degrees Celsius.
Manufacturers can set a minimum threshold that corresponds to a
maximum temperature.
191 G-sense error
rate Low This is the number of mistakes caused by impact loads.
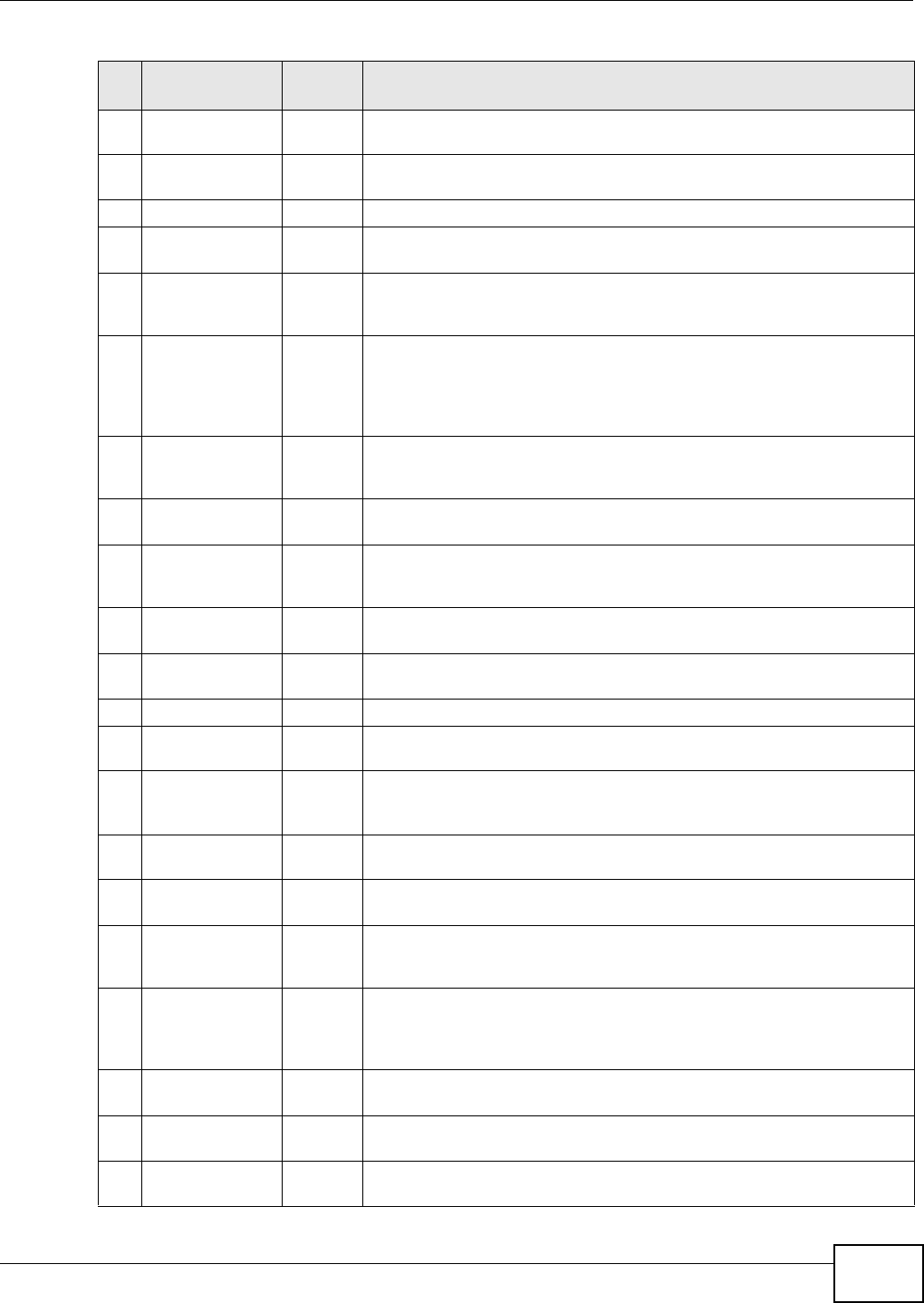
Chapter 11 Package Management
Media Server User’s Guide 273
192 Power-off Retract
Count Low This is how many times the heads are loaded off the media.
193 Load/Unload
Cycle Low This is the number of load and unload cycles into head landing zone
position.
194 Temperature Low This is the hard drive’s internal temperature.
195 Hardware ECC
Recovered High This is the time between ECC (Error Correction Code)-corrected errors.
196 Reallocation
Event Count Low This is the total number of reallocation (remap) operations. The raw value
is the total attempts to move data from reallocated sectors to a spare
area. Successful and unsuccessful attempts are both included.
197 Current Pending
Sector Count Low This is the number of unstable sectors awaiting reallocation. If the sector
is later successfully written or read, this value decreases and reallocation
is not performed. Only failed write attempts cause a reallocation, not read
errors. This can be difficult to test since only direct I/O writes to the disk
cause reallocations, not cached writes.
198 Uncorrectable
Sector Count Low This is the number of errors reading or writing a sector that were not
correctable. An increase in this value is an indicator of disk surface
defects or mechanical subsystem problems.
199 UltraDMA CRC
Error Count Low This is the number of data transfer errors through the interface cable
according to the ICRC (Interface Cyclic Redundancy Check).
200 Write Error Rate
/ Multi-Zone
Error Rate
Low This is the total number of errors in writing sectors.
201 Soft Read Error
Rate Low This is the number of read/write head off-track errors. If the value is not
zero, make a backup.
202 Data Address
Mark Errors Low This is the number of data address mark errors. This could also be a
different, manufacturer-specific attribute.
203 Run Out Cancel Low This is the number of ECC (Error Correction Code) errors.
204 Soft ECC
Correction Low This is the number of errors corrected by software ECC (Error Correction
Code).
205 Thermal Asperity
Rate (TAR) Low This is the number of thermal asperity errors. Thermal asperity is a read
signal spike caused by sensor temperature rise due to touching the disk
surface or contaminant particles.
206 Flying Height This is the height of the hard drive’s read/write heads above the disk
surface.
207 Spin High
Current This is the quantity of high current used to spin up the drive.
208 Spin Buzz This is the number of buzz routines to spin up the drive. When the arm
holding the read/write heads is stuck, the motor driving it tries to oscillate
the arm to free it. This causes an audible vibration.
209 Offline Seek
Performance This is the hard drive’s seek performance during offline operations. Offline
operations are tests the drive does itself as opposed to those that an
external diagnostic tool has it do. Seek performance is how quickly the
drive moves from track to track.
220 Disk Shift Low This is how far the disk has moved relative to the spindle (this kind of
shift is usually due to shock).
221 G-Sense Error
Rate Low This is the number of errors that have resulted from external vibration
and shock.
222 Loaded Hours This is how long the hard drive has operated under data load (this
requires movement of the magnetic head armature).
Table 88 S.M.A.R.T. Attributes (continued)
ID ATTRIBUTE
NAME BETTER DESCRIPTION
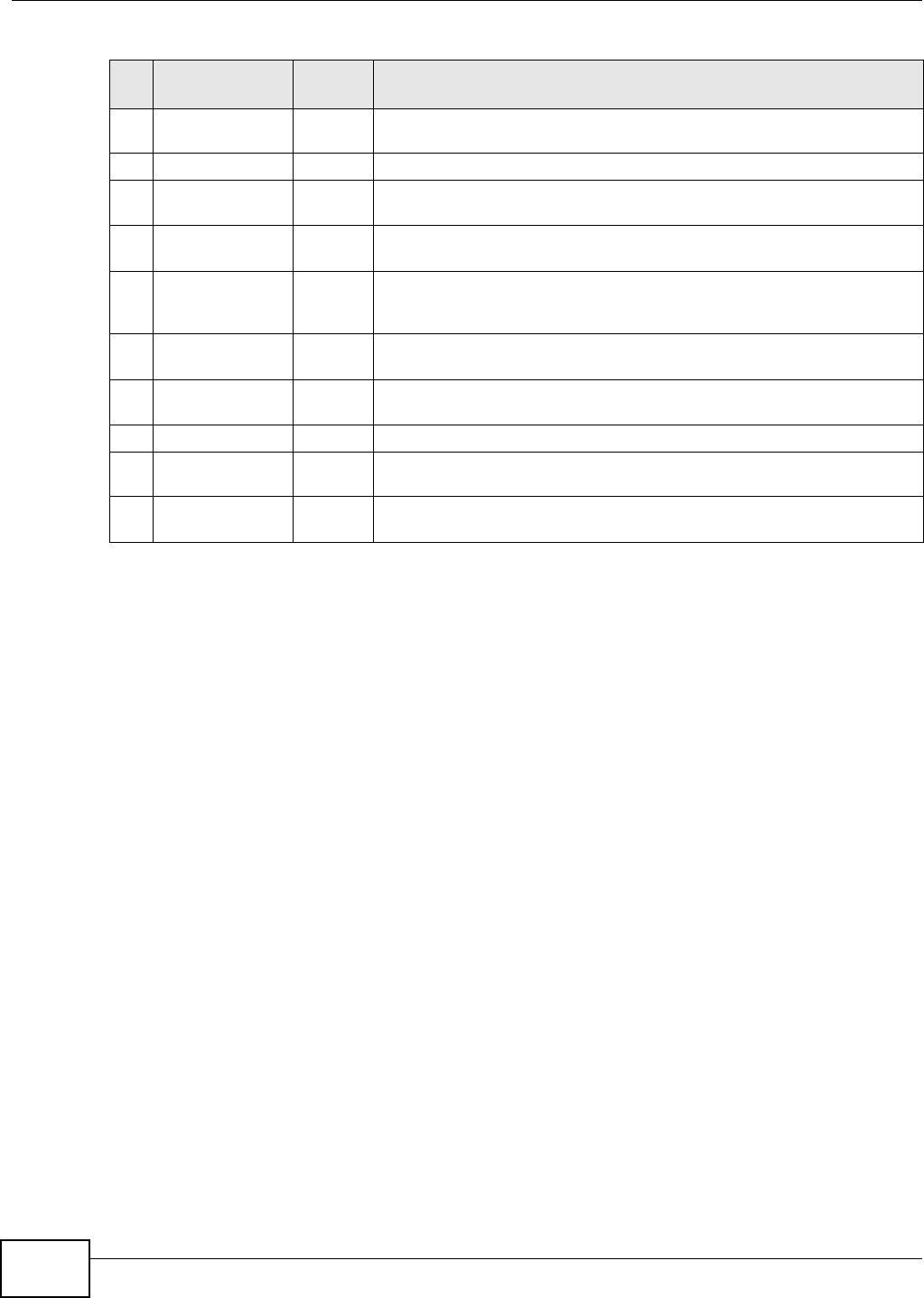
Chapter 11 Package Management
Media Server User’s Guide
274
223 Load/Unload
Retry Count This is how many time the magnetic head has changed position.
224 Load Friction Low This is resistance caused by friction in mechanical parts during operation.
225 Load/Unload
Cycle Count Low This is the total number of load cycles.
226 Load 'In'-time This is the total time that the magnetic heads actuator has had a load
(not been in the parking area).
227 Torque
Amplification
Count
Low This is the number of attempts to compensate for variations in platter
speed.
228 Power-Off
Retract Cycle Low This is how many times the magnetic armature was automatically
retracted because the power was cut.
230 GMR Head
Amplitude This is the amplitude of thrashing (or the distance of repetitive forward
and reverse head motion).
231 Temperature Low This is the hard drive’s temperature.
240 Head Flying
Hours This is the total time that the head has been positioning.
250 Read Error Retry
Rate Low This is the number of errors in reading from the disk.
Table 88 S.M.A.R.T. Attributes (continued)
ID ATTRIBUTE
NAME BETTER DESCRIPTION

Media Server User’s Guide 275
CHAPTER 12
Auto Upload
12.1 Overview
This chapter discusses the features in the Auto Upload screens.
The auto upload feature uploads media files stored in the NSA to the Flickr and/or YouTube sharing
websites. Besides web publishing and media server, auto upload is another convenient way to share
media files with your friends and family. You can link the NSA to your Flickr and/or YouTube account
and select shares for the NSA to upload. The NSA uploads the media files stored in the specified
shares to your Flickr and/or YouTube account. When you add new files to the specified shares, the
NSA also automatically uploads the new files to your Flickr and/or YouTube account.
12.2 What You Can Do
•Use the Flickr/YouTube screen (Section 12.4 on page 275) to upload photos and videos to your
Flickr and YouTube accounts.
•Use the FTP Uploadr screen (Section 12.5 on page 284) to upload files to FTP servers.
12.3 What You Need to Know
FTP
File Transfer Protocol (FTP) is a file transfer service that operates on the Internet. A system running
the FTP server accepts commands from a system running an FTP client. FTP is not a secure
protocol. Your file transfers could be subject to snooping.
FTPES (File Transfer Protocol over Explicit TLS/SSL)
File Transfer Protocol over Explicit TLS/SSL (FTPES) is a file transfer service that uses TLS
(Transport Layer Security) or Secure Socket Layer (SSL) for secure transfers across the Internet.
12.4 The Flickr/YouTube Screen
Use this screen to upload photos and videos to your Flickr and YouTube accounts.
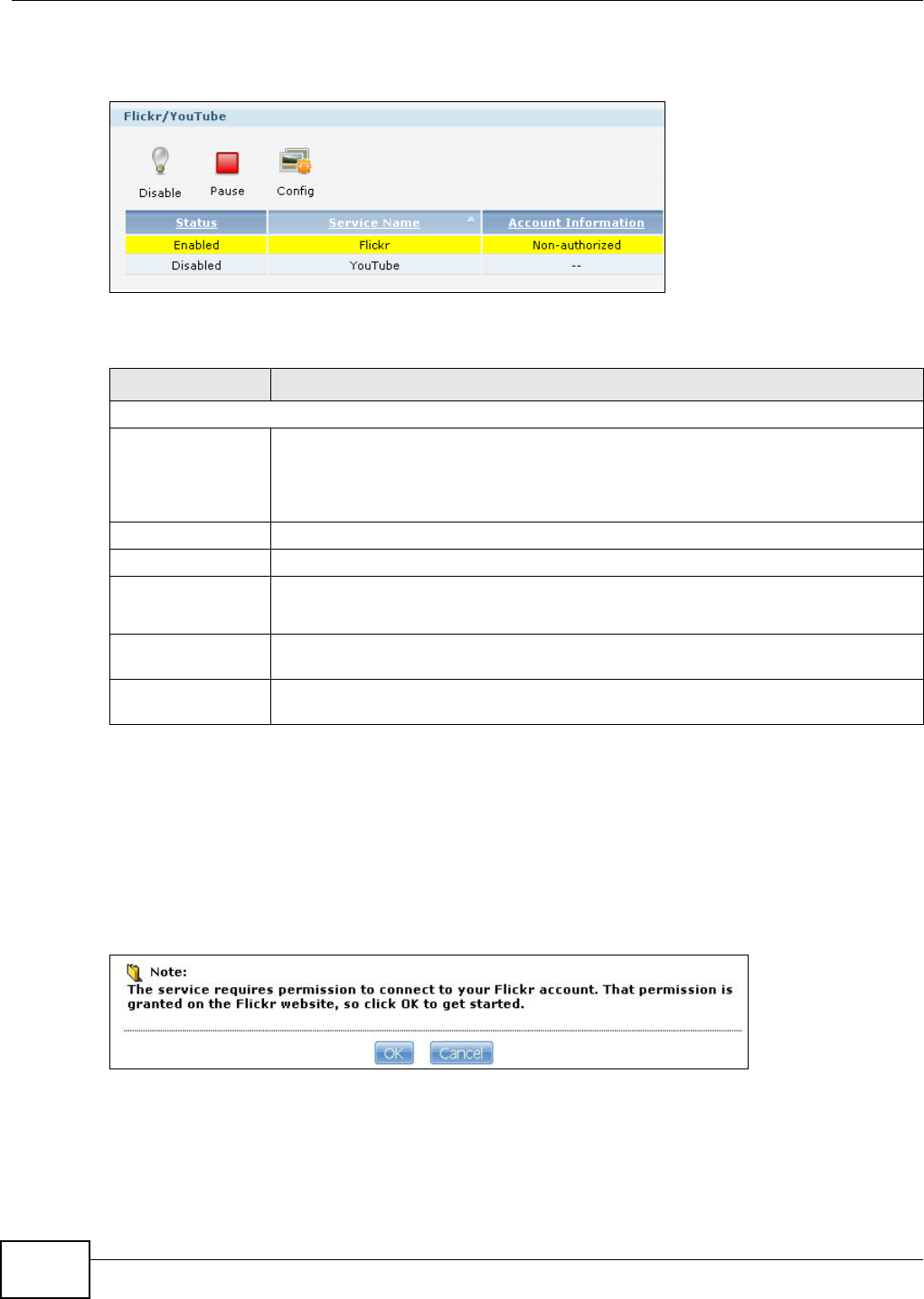
Chapter 12 Auto Upload
Media Server User’s Guide
276
Click Applications > Auto Upload > Flickr/YouTube to open the following screen.
Figure 161 Applications > Auto Upload > Flickr/YouTube
The following table describes the labels in this screen.
12.4.1 Configuring the Flickr Settings
In the Applications > Auto Upload > Flickr/YouTube screen, select Flickr from the list and then click
the Config button.
The following screen displays if you have not authorized the NSA to use a Flickr account. Click OK
to continue the authorization process.
Figure 162 Linking NSA to Flickr
Table 89 Applications > Auto Upload > Flickr/YouTube
LABEL DESCRIPTION
Flickr/YouTube
Disable/Enable Select a service from the list and click this to turn the service on or off.
If you disable the service and add more files to the watch folder(s), the NSA will not
auto upload these files. However, the NSA still uploads any files added before you
turned off the service.
Pause/Resume Select a service from the list and click this to pause or resume the auto upload feature.
Config Select a service from the list and click this to manage the service’s settings.
Status This field displays the service’s status.
The service may be Enabled, Disabled, Uploading or Paused.
Service Name This field displays the name of a sharing website to which the NSA can automatically
upload files.
Account
Information This field displays the username and related information of the account to use with the
auto upload feature.
Chapter 12 Auto Upload
Media Server User’s Guide 277
The web browser opens the Yahoo! Flickr login page. Enter your Yahoo account’s information and
click Sign In.
Figure 163 Yahoo! Flickr Login Page
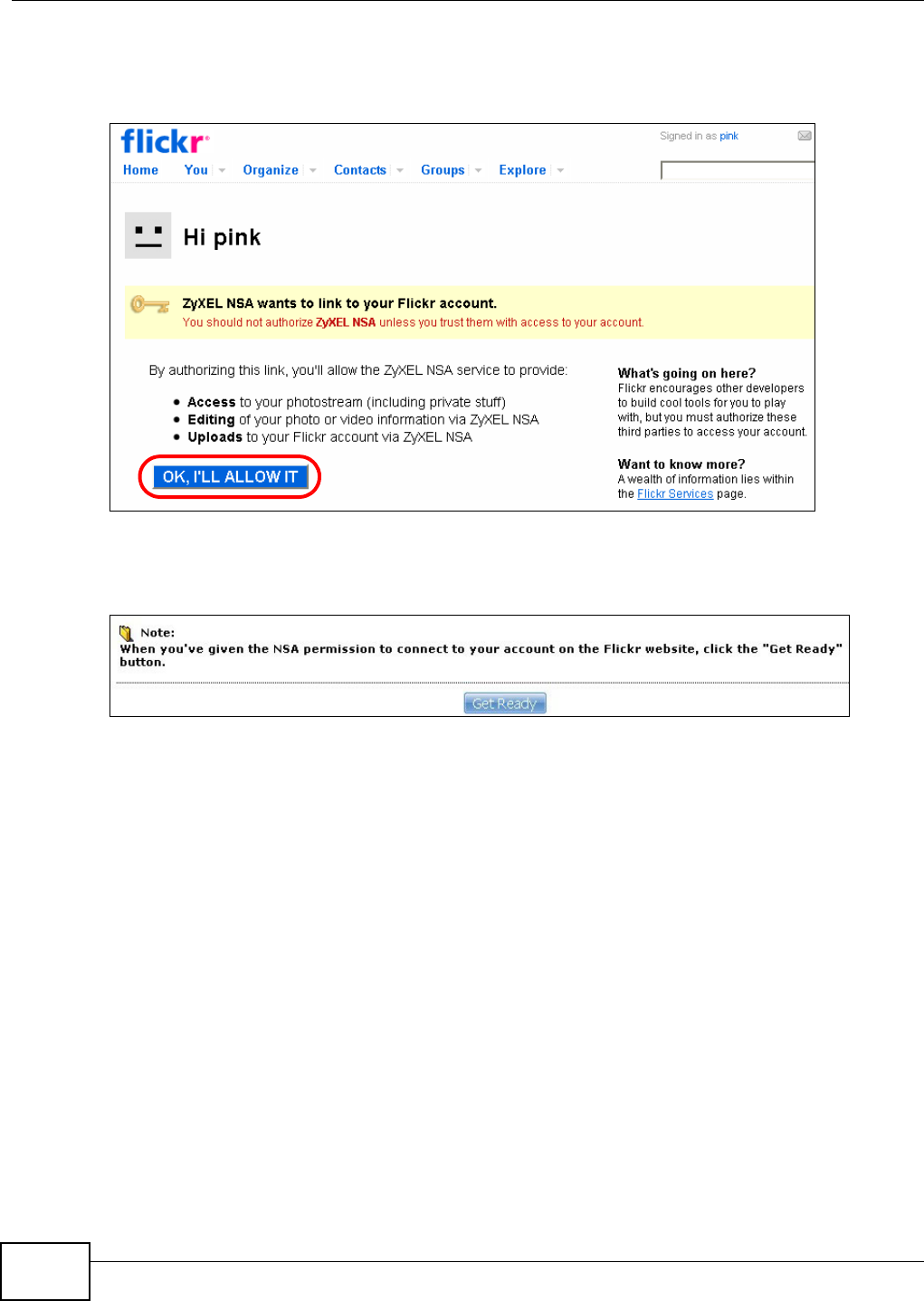
Chapter 12 Auto Upload
Media Server User’s Guide
278
The following page displays asking for your authorization. Click OK, I’LL ALLOW IT to establish a
link between the NSA and your Flickr account.
Figure 164 Flickr Authorization
A confirmation page displays indicating successful authorization. Return to the NSA web
configurator. Click Get Ready in the following screen to complete the authorization process.
Figure 165 Confirming Flickr Authorization
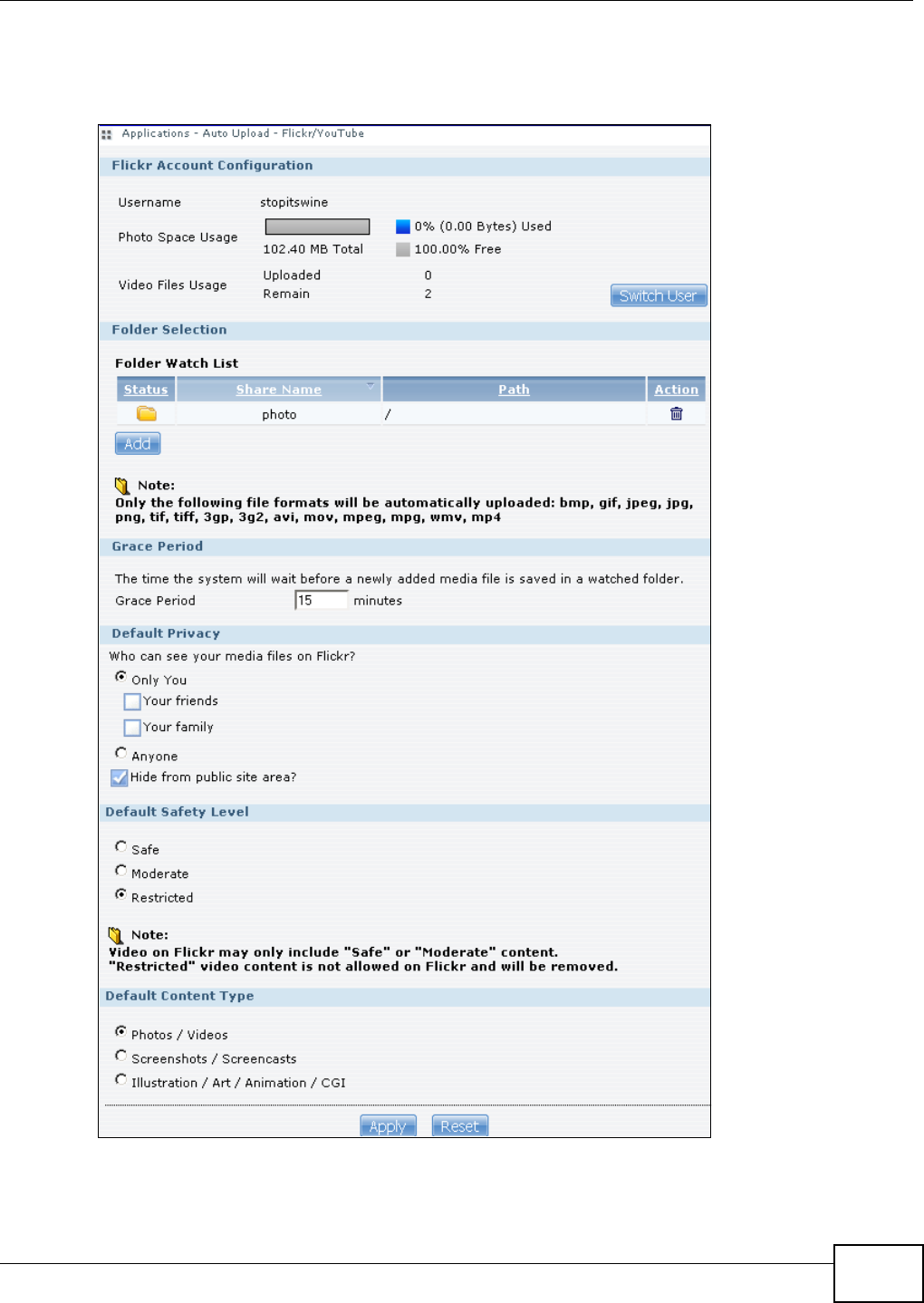
Chapter 12 Auto Upload
Media Server User’s Guide 279
Once the NSA is associated with your Flickr account, you can configure auto upload settings in the
following screen.
Figure 166 Applications > Auto Upload > Flickr/YouTube > Config (Flickr)
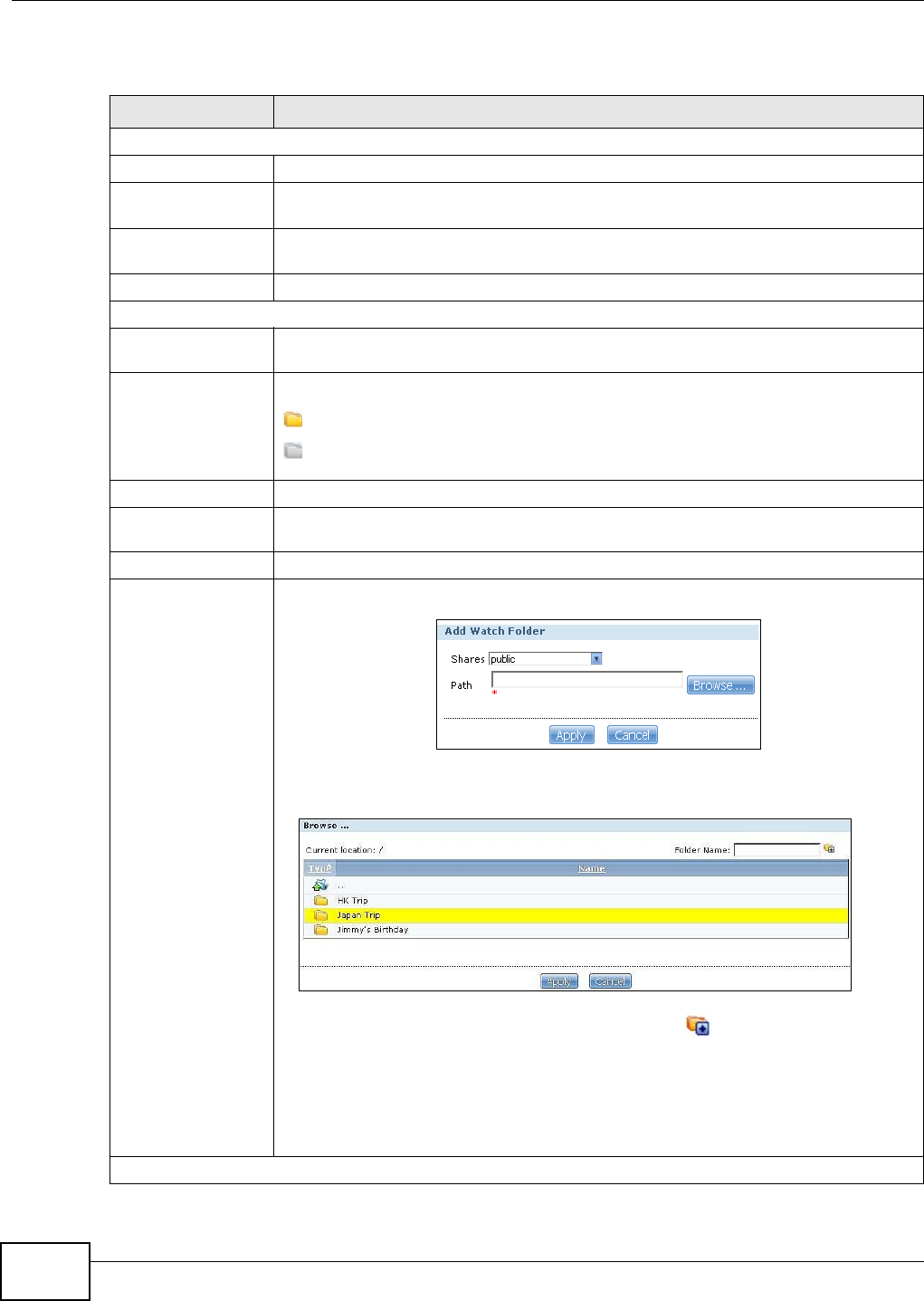
Chapter 12 Auto Upload
Media Server User’s Guide
280
The following table describes the labels in this screen.
Table 90 Applications > Auto Upload > Flickr/YouTube > Config (Flickr)
LABEL DESCRIPTION
Flickr Account Configuration
Username This field displays the Flickr account authorized for the auto upload feature.
Photo Space Usage This shows how much storage space for photos (in size and percentage) you have
used and how much space is still available on your Flickr account.
Video Files Usage This shows how many videos you have uploaded and how many videos you can still
upload to your Flickr account.
Switch User Click this to use a different Flickr account for the auto upload feature.
Folder Selection
Folder Watch List This table displays a list of shares and folders selected for auto upload. Files stored in
these locations are uploaded to your Flickr account.
Status This indicates whether the folder or share is available.
represents a valid folder. The folder is available for auto upload.
represents a missing folder. The share may be deleted from the NSA, or the hard
disk was removed from the NSA.
Share Name This is the share selected for auto upload.
Path This is the path of a folder selected for auto upload. The NSA only uploads files stored
in the specified share or folder to your Flickr account.
Action Use the Remove icon to remove a folder from the Folder Watch List.
Add Click this to open the following screen where you can set a folder that contains files you
want the NSA to automatically upload.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the folder’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This is the type of the folder/file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field.
All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Grace Period
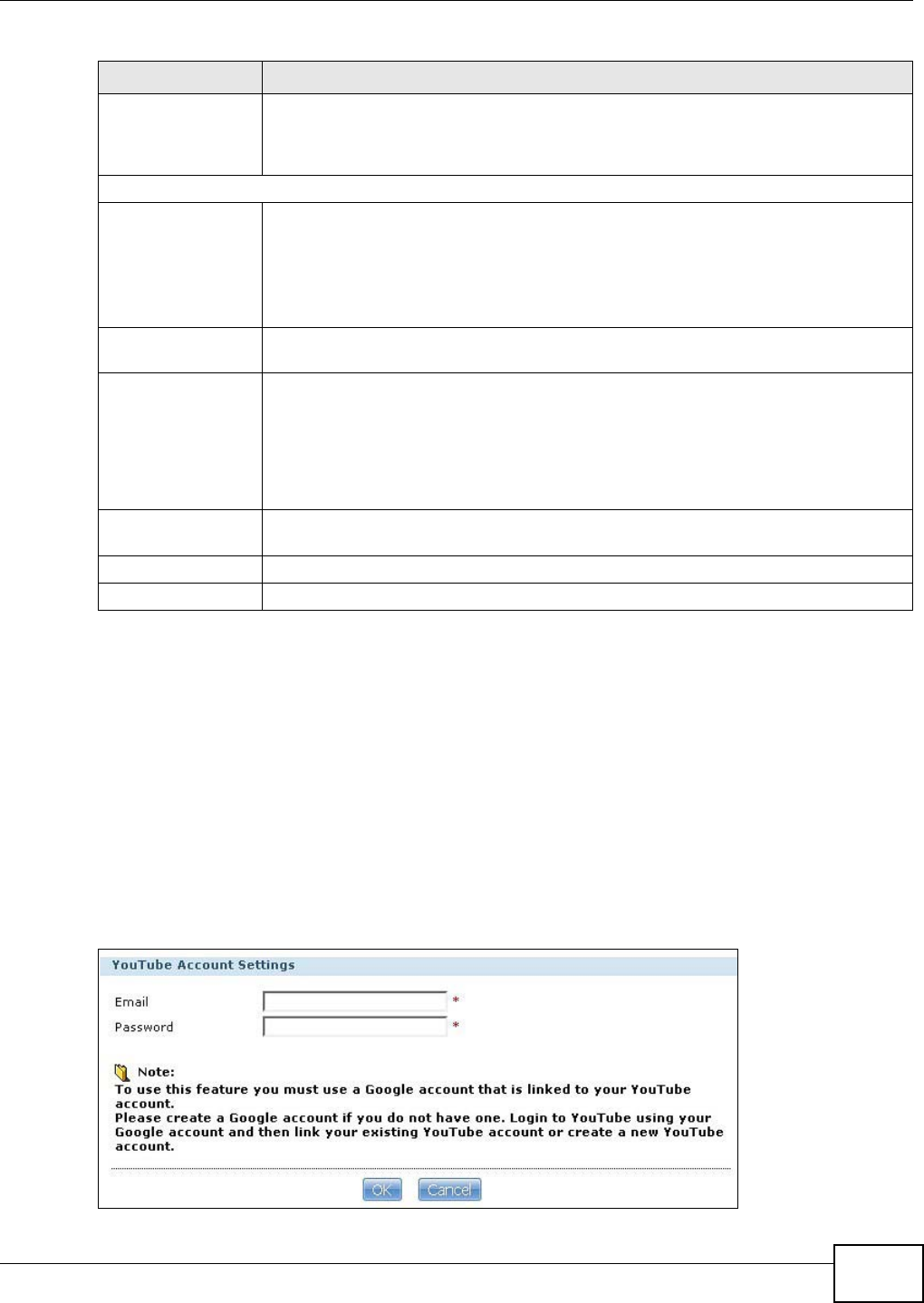
Chapter 12 Auto Upload
Media Server User’s Guide 281
12.4.2 Configuring the YouTube Settings
In the Applications > Auto Upload > Flickr/YouTube screen, select YouTube from the list and
then click the Config button.
Note: Your YouTube account must be associated with a Google account.
Get a Google account and use it to log into YouTube. You can then merge the existing YouTube
account to your Google account.
If you have not authorized a YouTube account on the NSA, the following screen displays. Enter your
Google account’s e-mail address and password in the fields and click OK to authorize the service.
Figure 167 YouTube Account Settings
Grace Period N
minutes Specify how long the NSA should wait when you add a new file for auto upload. For
example, if you set the grace period to 5 minutes, the NSA uploads a new file after it
has been in a watched folder for 5 minutes. You can choose from a range of 1 to 10080
minutes (up to one week).
Default Privacy
Who can see your
media files on
Flickr?
Determine who has the right to see files uploaded to your Flickr account.
Select Only You if you do not want anyone else to see your files. You may also restrict
the access to Your friends and/or Your family. You can set up a friend/family list in
your Flickr account.
Select Anyone to allow everyone to see your files.
Hide from public site
area Check this option to prevent others from finding your files when they perform a search
in the Flickr website.
Default Safety Level Assign a safety level to your files.
Select Safe if the contents of your files are suitable for the general public.
Select Moderate if the contents of your files may be offensive to some people.
Select Restricted if the contents of your files are not suitable for certain people, such
as children or your colleagues.
Default Content
Type Select a content type for your files. You can choose Photo/Video, Screenshots/
Screencasts, or Illustration/Art/Animation/CGI.
Apply Click this to save your changes.
Reset Click this to restore previously saved settings.
Table 90 Applications > Auto Upload > Flickr/YouTube > Config (Flickr) (continued)
LABEL DESCRIPTION
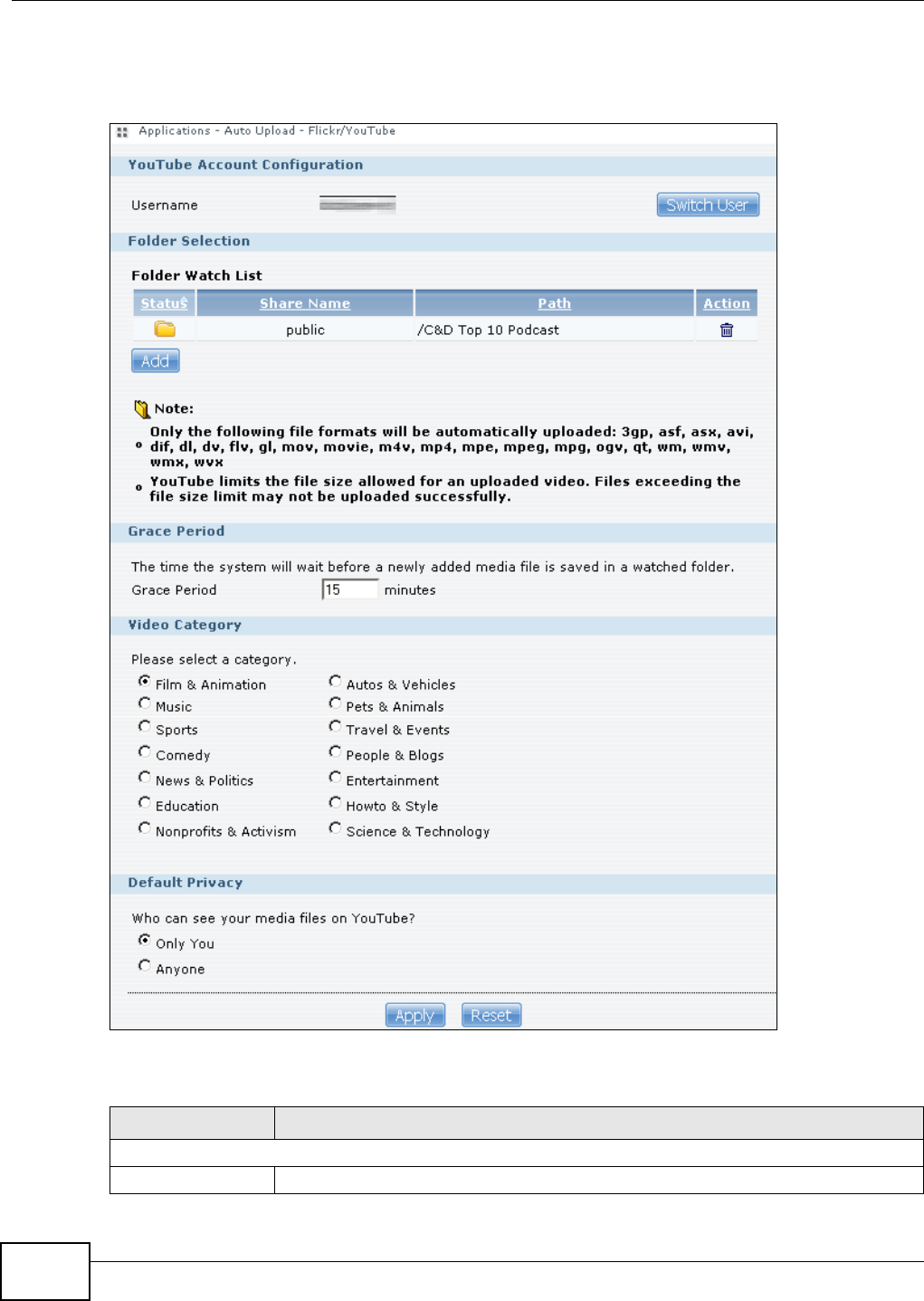
Chapter 12 Auto Upload
Media Server User’s Guide
282
Once the NSA is associated with your YouTube account, you can configure auto upload settings in
the following screen.
Figure 168 Applications > Auto Upload > Flickr/YouTube > Config (YouTube)
The following table describes the labels in this screen.
Table 91 Applications > Auto Upload > Config (YouTube)
LABEL DESCRIPTION
Youtube Account Configuration
Username This field displays the Youtube account authorized for the auto upload feature.
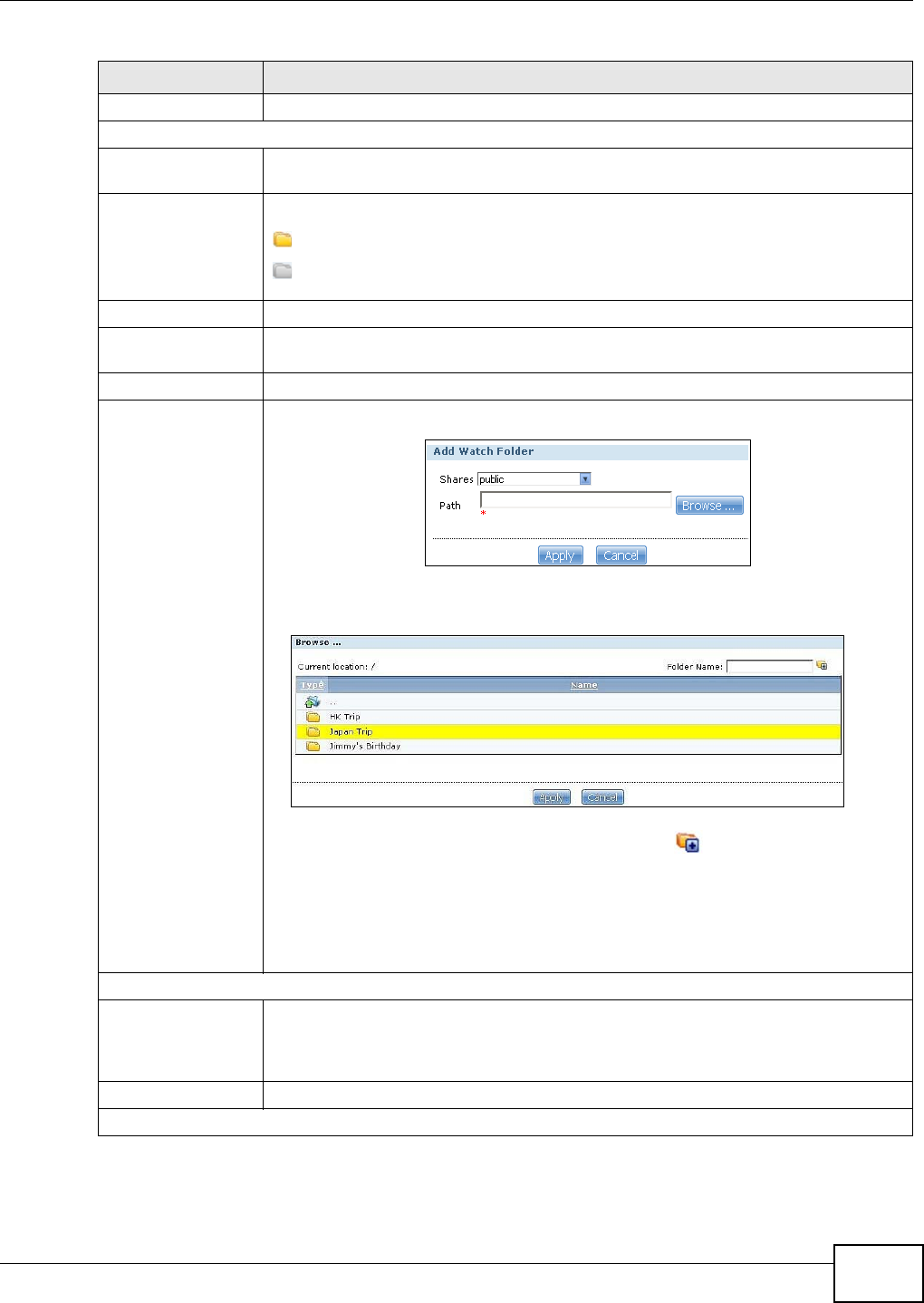
Chapter 12 Auto Upload
Media Server User’s Guide 283
Switch User Click this to use a different YouTube account for the auto upload feature.
Folder Selection
Folder Watch List This table displays a list of shares and folders selected for auto upload. Files stored in
these locations are uploaded to your YouTube account.
Status This field indicates whether the share or folder is available.
represents a valid folder. The folder is available for auto upload.
represents a missing folder. The share may be deleted from the NSA, or the hard
disk was removed from the NSA.
Share Name This field displays the share selected for auto upload.
Path This field displays the path of a folder selected for auto upload. The NSA only uploads
the files stored in the specified share or folder to your YouTube account.
Action Use the Remove icon to delete a folder from the Folder Watch List.
Add Click this to open the following screen where you can set a folder that contains files you
want the NSA to automatically upload.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the folder’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This is the type of the folder/file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path
field. All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Grace Period
Grace Period N
minutes Specify how long the NSA should wait when you add a new file for auto upload. For
example, if you set the grace period to 5 minutes, the NSA uploads a new file after it
has been in a watched folder for 5 minutes. You can choose from a range of 1 to 10080
minutes (up to one week).
Video Category Select the category that best describes the media files you want to upload.
Default Privacy
Table 91 Applications > Auto Upload > Config (YouTube) (continued)
LABEL DESCRIPTION
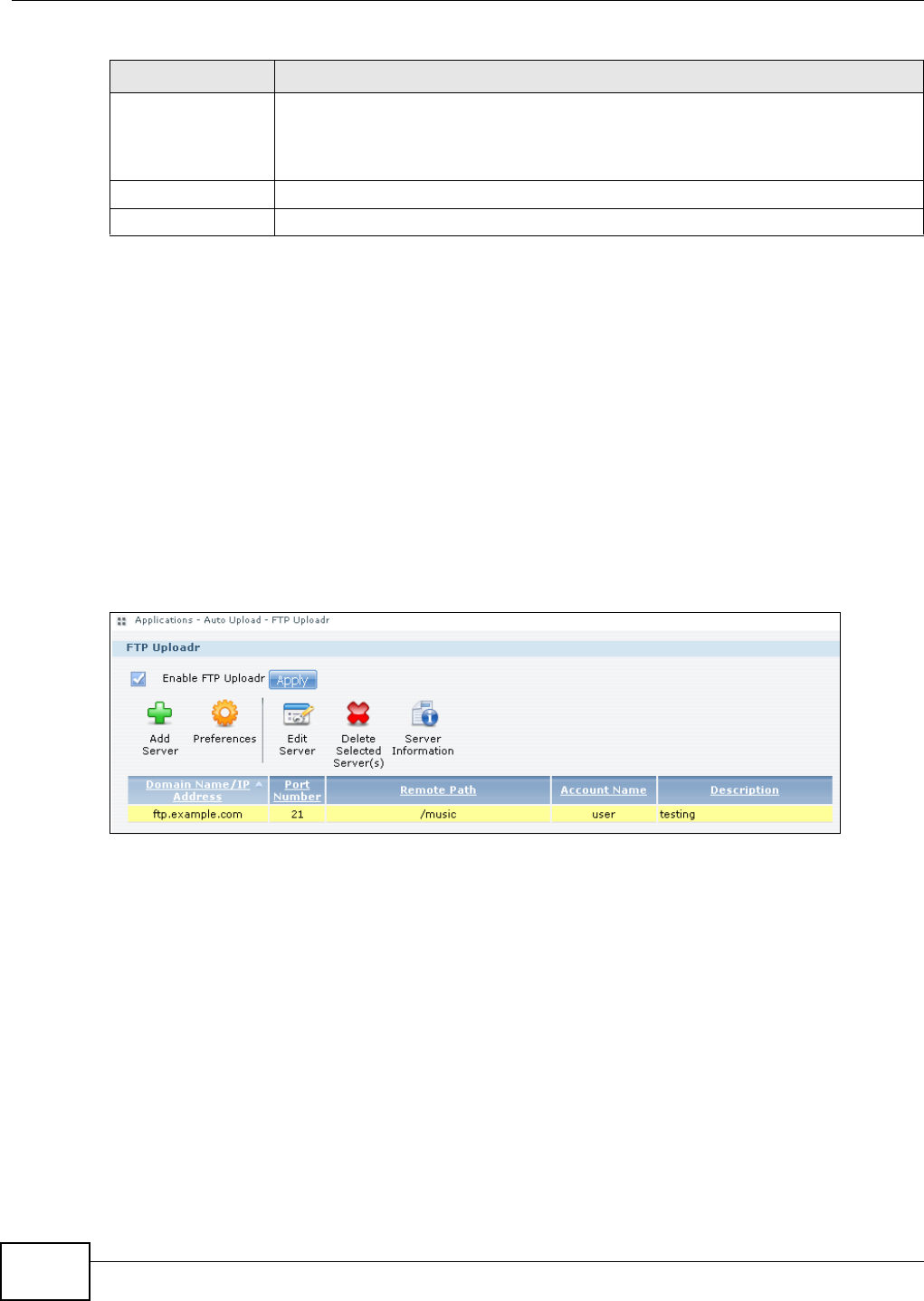
Chapter 12 Auto Upload
Media Server User’s Guide
284
12.5 The FTP Uploadr Screen
The FTP Uploadr feature uploads files stored in the NSA to FTP servers. Besides web publishing and
media server, auto upload is another convenient way to share media files with your friends and
family. You can link the NSA to the FTP server or the FTP server on another NSA and select shares
or folders for the NSA to upload. The NSA uploads the files stored in the specified shares to the FTP
server. When you add new files to the specified shares, the NSA also automatically uploads the new
files to the FTP server.
Use this screen to configure the FTP Uploadr.
Click Applications > Auto Upload > FTP Uploadr to open the screen shown next.
Figure 169 Applications > Auto Upload > FTP Uploadr
Who can see your
media files on
YouTube?
Determine who has the right to see files uploaded to your YouTube account.
Select Only You if you do not want anyone else to see your files.
Select Anyone to allow everyone to see your files.
Apply Click this to save your changes.
Reset Click this to restore your previously stored settings.
Table 91 Applications > Auto Upload > Config (YouTube) (continued)
LABEL DESCRIPTION
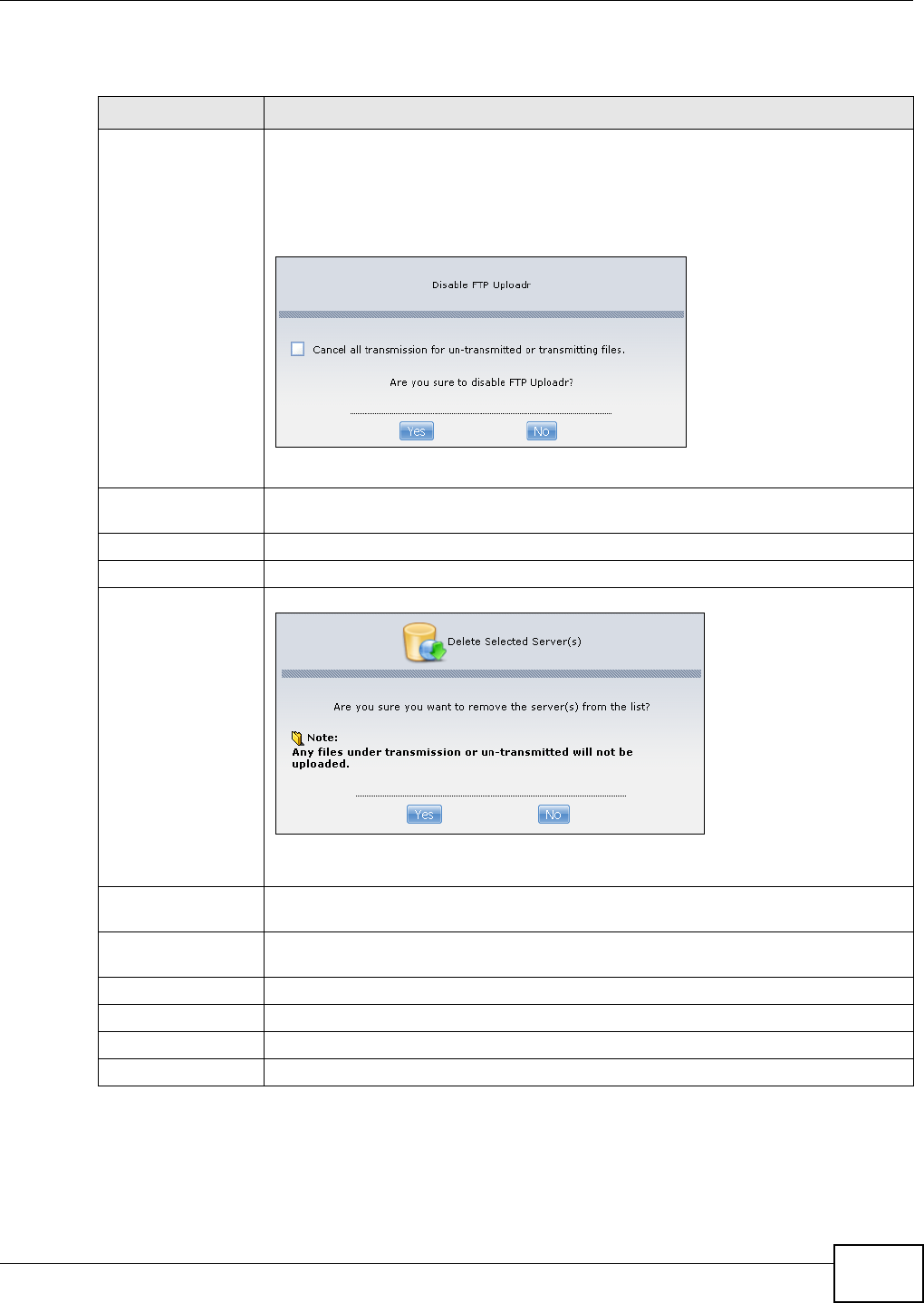
Chapter 12 Auto Upload
Media Server User’s Guide 285
The following table describes the labels in this screen.
12.5.1 Adding or Editing an FTP Server Entry
Use this screen to add or edit an FTP server entry for auto upload.
Table 92 Applications > Auto Upload > FTP Uploadr
LABEL DESCRIPTION
Enable FTP Uploadr Use the check box to enable or disable the FTP Uploadr. Click Apply to save your
changes.
When you disable the FTP Uploadr, a screen opens requesting confirmation. Select the
check box to stop any current or queued uploads. If you do not select the check box,
the FTP Uploadr will finish uploading the files that are already in the queue list. Clicking
Yes will disable the FTP Uploadr.
Add Server Click this to add a target FTP server entry. See Section 12.5.1 on page 285 for more
details.
Preferences Click this to manage the settings of the FTP Uploadr.
Edit Server Select a server from the list and click this to edit the FTP server entry.
Delete Selected
Server(s) Select a server from the list and click this to remove the FTP server entry.
Server Information Select a server from the list and click this to display the status and settings about the
FTP server.
Domain Name/IP
Address This is the domain name or IP address of the FTP server.
Port Number This is the port number used by the FTP server.
Remote Path The NSA automatically uploads files to this location of the FTP server.
Account Name This is the login account for the FTP server.
Description This is the information related to the FTP server.
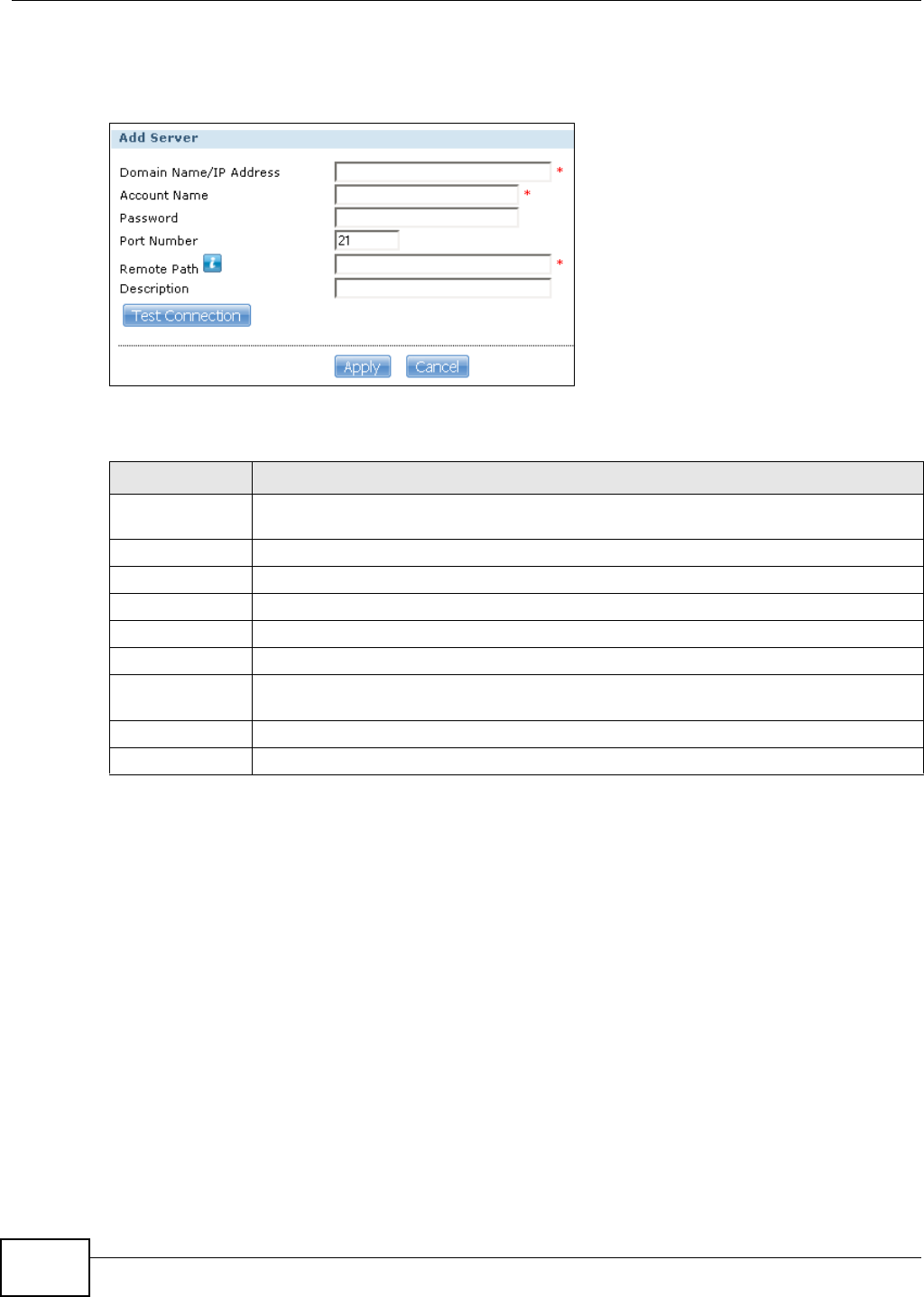
Chapter 12 Auto Upload
Media Server User’s Guide
286
In the FTP Uploadr screen, click the Add Server or Edit Server button to open the following
screen.
Figure 170 Applications > Auto Upload > FTP Uploadr > Add or Edit a Server
The following table describes the labels in this screen.
12.5.2 The FTP Uploadr Preferences Screen
Use this screen to configure the general settings for the FTP Uploadr.
Table 93 Applications > Auto Upload > FTP Uploadr > Add or Edit a Server
LABEL DESCRIPTION
Domain Name/IP
Address Enter the domain name or IP address of the FTP server.
Account Name Enter the account name used to access the FTP server.
Password Enter the password associated with the account name.
Port Number Enter the port number for the FTP server.
Remote Path Enter the path of the FTP server where the NSA automatically uploads files.
Description Enter additional information about this FTP server.
Test Connection Click this to test your settings and check whether you can use the settings to connect to
the FTP server.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
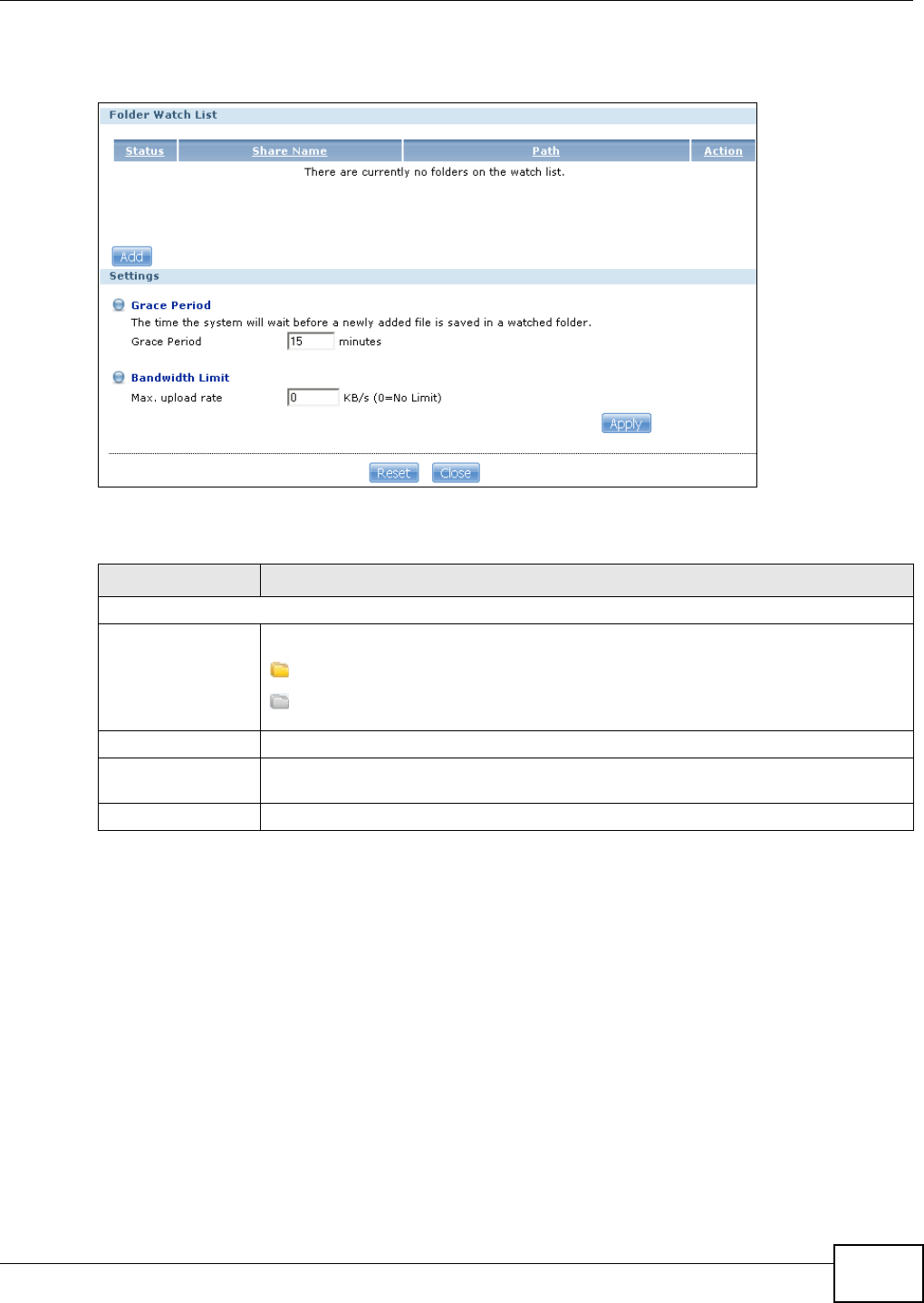
Chapter 12 Auto Upload
Media Server User’s Guide 287
In the FTP Uploadr screen, click the Preferences icon to open the following screen.
Figure 171 Applications > Auto Upload > FTP Uploadr > Preferences
The following table describes the labels in this screen.
Table 94 Applications > Auto Upload > FTP Uploadr > Preferences
LABEL DESCRIPTION
Folder Watch List
Status This field indicates whether the share or folder is available.
represents a valid folder. The folder is available for auto upload.
represents a missing folder. The share may be deleted from the NSA, or the hard
disk was removed from the NSA.
Share Name This is the share selected for auto upload.
Path This is the path of a folder selected for auto upload. The NSA only uploads files stored in
the specified share or folder to your FTP server.
Action Use the Remove icon to delete a folder from the Folder Watch List.
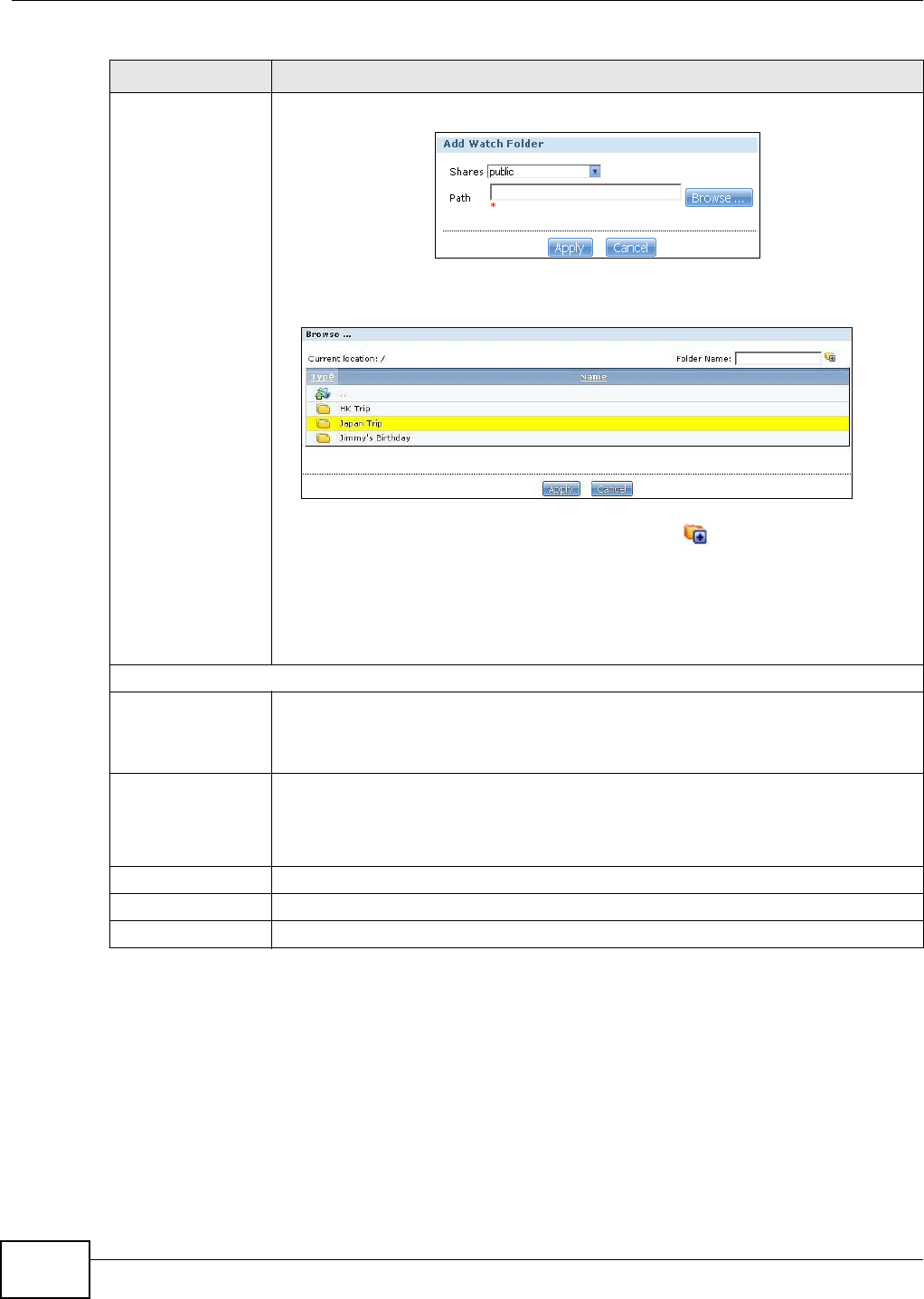
Chapter 12 Auto Upload
Media Server User’s Guide
288
Add Click this to open the following screen where you can set a folder that contains files you
want the NSA to automatically upload.
•Share - Select the share from the list.
•Path - Type the folder location in the share directly or click Browse to open the
following screen and navigate to the folder’s location.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This is the type of the folder/file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field.
All contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Settings
Grace Period Specify how long the NSA should wait when you add a new file for auto upload. For
example, if you set the grace period to 5 minutes, the NSA uploads a new file after it
has been in a watched folder for 5 minutes. You can choose from a range of 1 to 10080
minutes (up to one week).
Bandwidth Limit Enter the maximum upload rate for auto upload. You can choose from a range of 0 to
100,000 KB/s. Enter 0 if you do not want to set any limit.
Use this to leave bandwidth on your network connection for other traffic, especially if
your Internet connection has restricted upload speed.
Apply Click this to save your changes in this section.
Reset Click this to restore previously saved settings.
Close Click this to return to the previous screen without saving.
Table 94 Applications > Auto Upload > FTP Uploadr > Preferences (continued)
LABEL DESCRIPTION
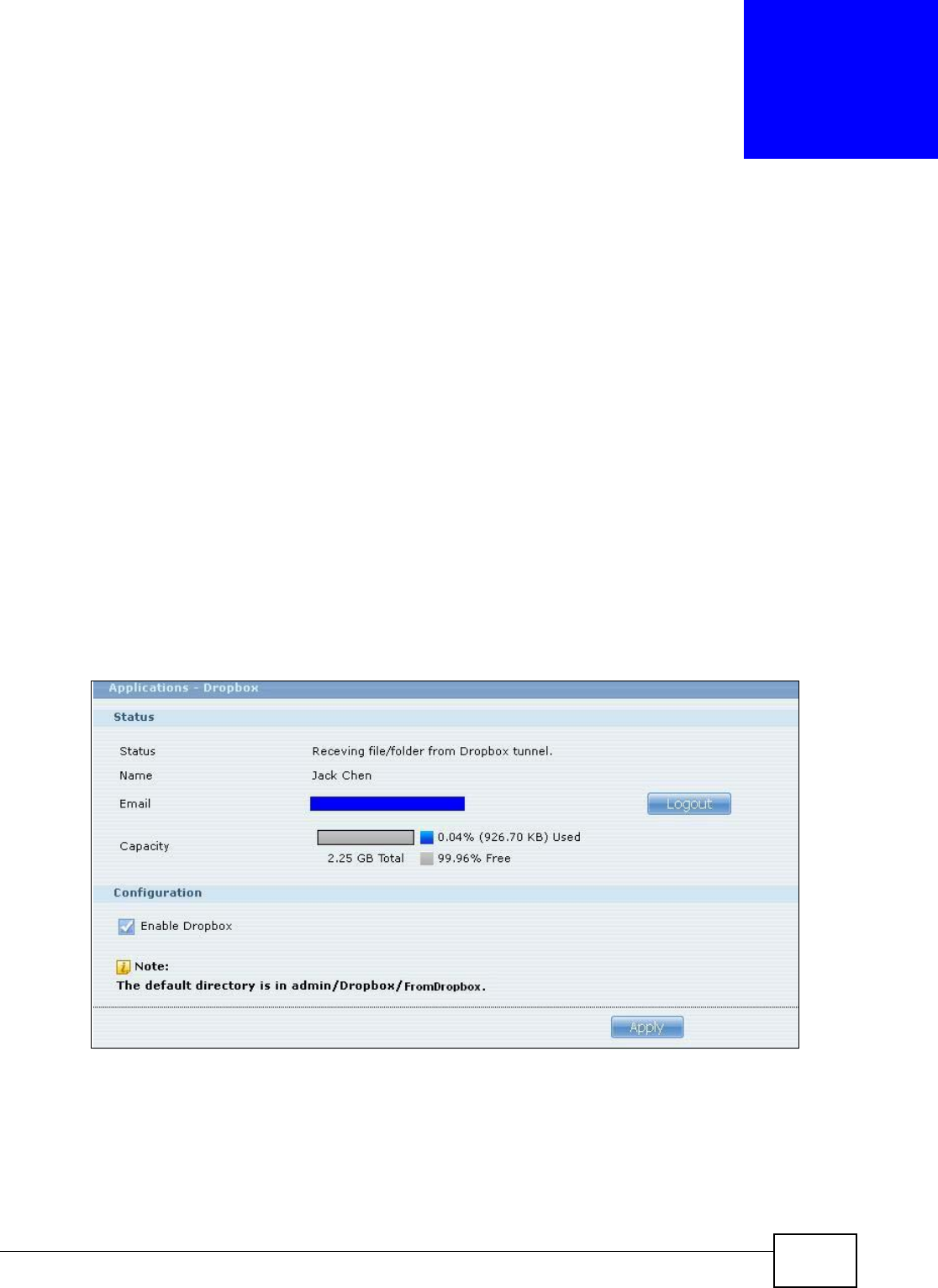
Media Server User’s Guide 289
CHAPTER 13
Dropbox
13.1 Overview
The Dropbox Web-based file hosting service uses cloud computing to let you use file
synchronization to store and share files and folders with others across the Internet. Use your
Dropbox account to easily move files to your NSA and have the NSA download *.torrent files.
13.2 Dropbox Screen
Use the Dropbox screen to log the NSA into your Dropbox account. This creates Drop2NAS and
zDownload folders in your Dropbox account. See Section 13.3 on page 291 for how to use the
folders to move files to your NSA and have the NSA download *.torrent files. The NSA checks the
Dropbox account’s Drop2NAS and zDownload folders every three minutes.
Click Applications > Dropbox to open the following screen.
Figure 172 Applications > Dropbox

Chapter 13 Dropbox
Media Server User’s Guide
290
The following table describes the labels in this screen.
Table 95 Applications > Dropbox
LABEL DESCRIPTION
Status This shows the status of the NSA Dropbox application’s interaction with the Dropbox
server.
Disable: The NSA Dropbox application is turned off.
Ready: The NSA Dropbox application has authenticated with the Dropbox server and is
ready to use.
Authenticating with Dropbox. Please wait.: The NSA Dropbox application is logging
into the Dropbox server.
Failed to negotiate link with Dropbox. Please contact your vendor.: The NSA
cannot find the Dropbox server at the normal address.
Receiving file/folder from Dropbox tunnel.: The NSA is getting a file from your
Dropbox account.
Dropbox account has been already used on other NAS.: One Dropbox account can
only work with one NSA at a time. Log the other NSA out of your Dropbox account to be
able to use the account with this NSA.
Name This is the owner of the Dropbox account the NSA is configured to use.
Email This is the e-mail address of the owner of the Dropbox account the NSA is configured to
use.
Logout This displays after the NSA connects to Dropbox. Click Logout to stop syncing your
files with Dropbox and have the NSA log out from your Dropbox account. Use this to be
able to use the NSA with another Dropbox account. If you only want to stop syncing
your files with Dropbox, you can just clear the Enable Dropbox option and click
Apply.
Capacity This shows how much total storage space is available on the NSA to use for Dropbox as
well as the amounts already in use and still available.
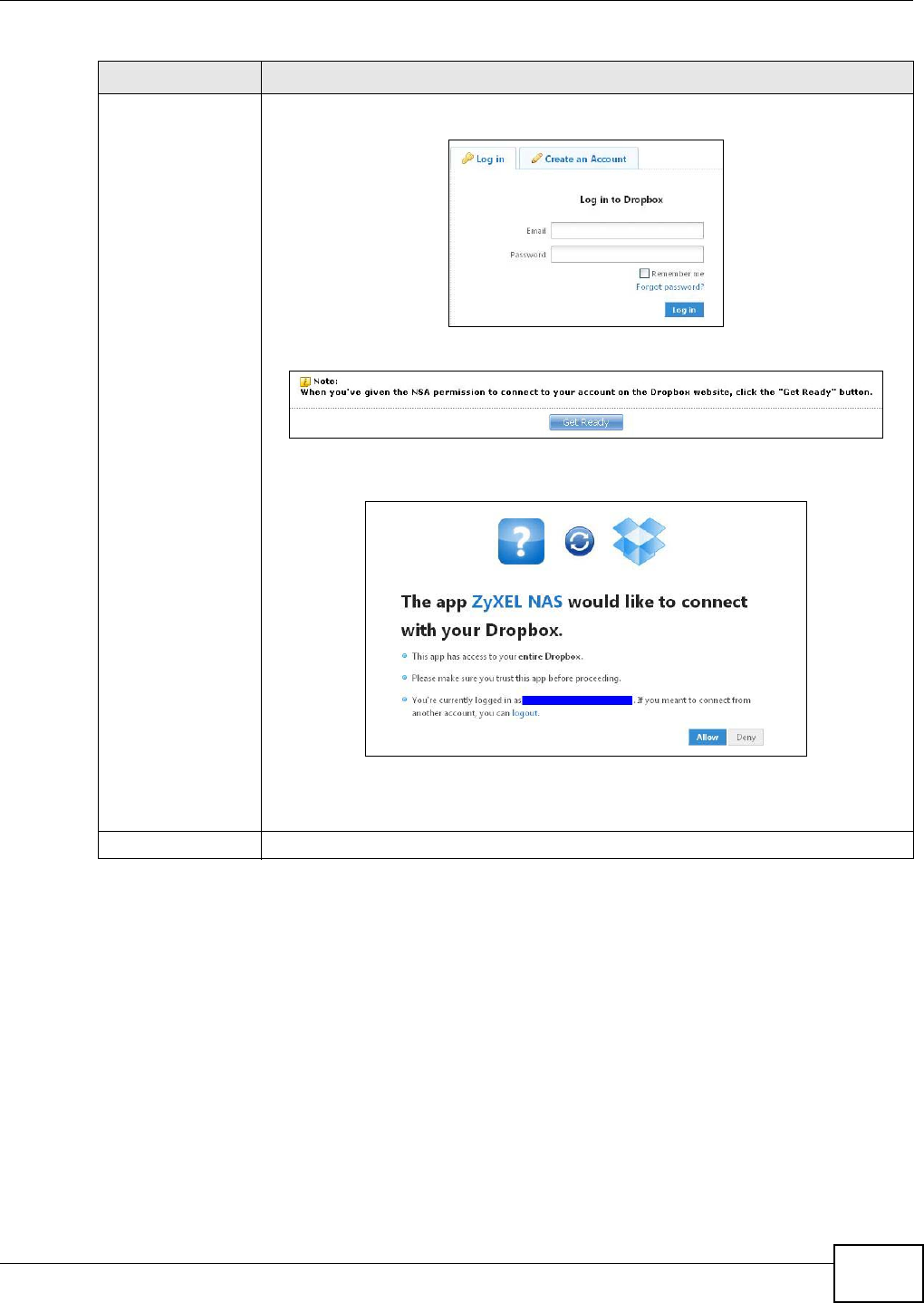
Chapter 13 Dropbox
Media Server User’s Guide 291
13.3 How to Use Dropbox with the NSA
Here is how to use the Drop2NAS and zDownload folders the NSA creates in your Dropbox account.
Using the Drop2NAS Folder
The NSA connects to Dropbox and copies files in the Drop2NAS folder to the NSA’s
admin\Dropbox\FromDropbox folder and empties the Drop2NAS folder. The NSA initiates
connections to the Dropbox server so you do not need to configure rules on a firewall in front of the
NSA to allow access to the NSA. Dropbox is not connecting to the NSA. When you upload files of the
same name to the Drop2NAS folder, the NSA adds a number to the names of the files in the NSA’s
Enable Dropbox Select this to synchronize and back up your Dropbox account. The first time you do this
a Dropbox screen prompts you to log into your Dropbox account.
Then a NSA pop-up opens. Click Get Ready.
Click Allow when the Dropbox screen notifies you of the NSA’s DropNAS application
trying to connect to your Dropbox account.
After the NSA connects to Dropbox, clear the Enable Dropbox option and click Apply
to stop syncing your files with Dropbox without logging out from your Dropbox account.
Click Logout instead to be able to use the NSA with another Dropbox account.
Apply Click this to save your changes.
Table 95 Applications > Dropbox (continued)
LABEL DESCRIPTION
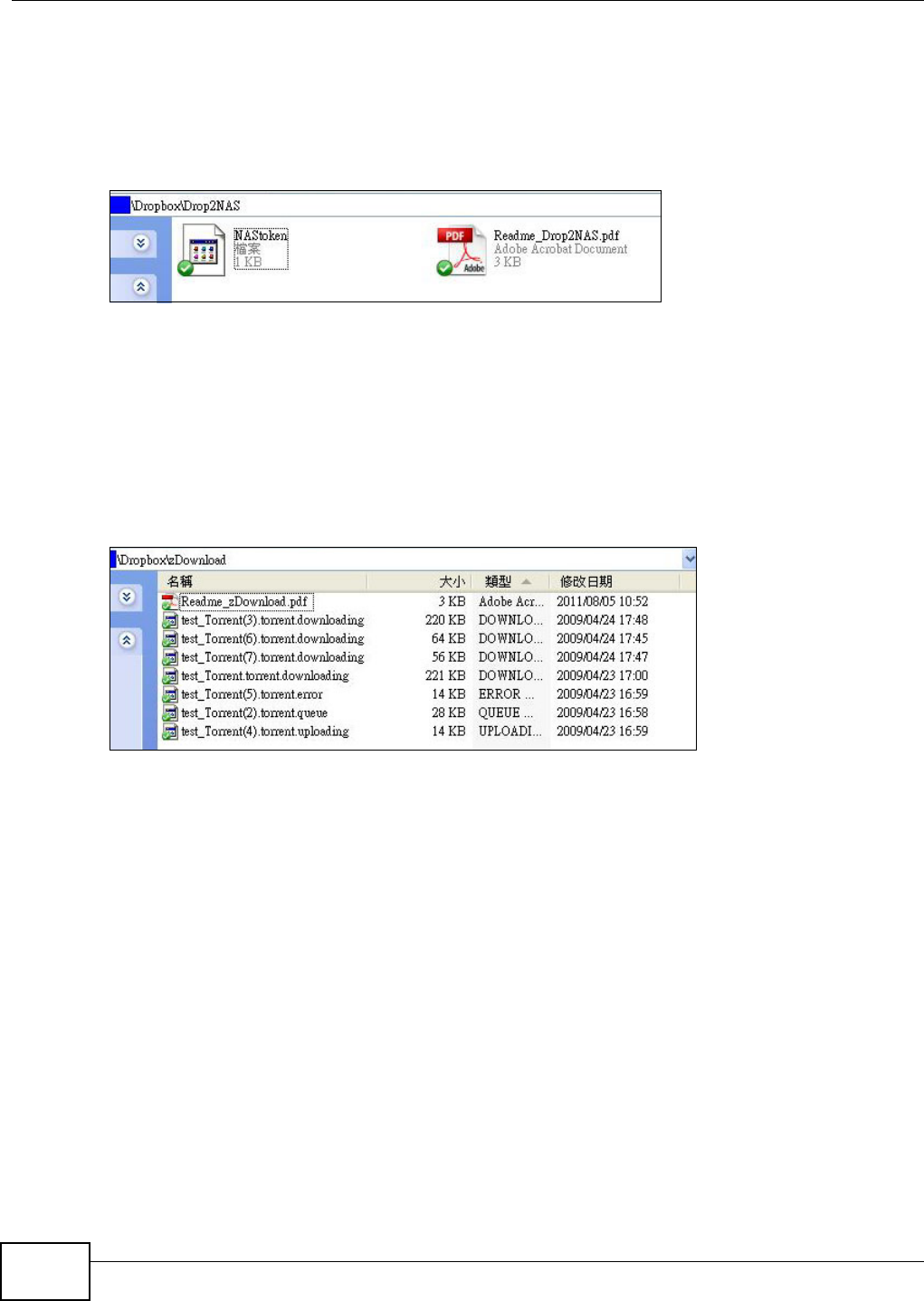
Chapter 13 Dropbox
Media Server User’s Guide
292
admin\Dropbox\FromDropbox folder in the format of “filename(n).extension”. Here is an example
of the Drop2NAS folder.
Note: Do not delete the NAStoken file as it is needed for your NSA to work with the
Dropbox account.
Figure 173 Dropbox\Drop2NAS
Using the zDownload Folder
The NSA copies *.torrent files in the zDownload folder to the NSA’s admin\download\torrents folder
and automatically starts downloading them. The NSA adds a suffix to the name of each torrent file
in the Dropbox account’s zDownload folder and keeps updating it to show the job’s state
(downloading, queued, paused, canceled, uploading, finished, error, or retrying). The NSA does not
take any action for folders nor other types of files in the zDownload folder. Here is an example of
torrent files in the zDownload folder.
Figure 174 Dropbox\zDownload

Media Server User’s Guide 293
CHAPTER 14
Users
14.1 Overview
This chapter introduces the Users screens of the NSA. Use the Users screens to create and
manage administrator and user accounts.
Administrators can:
• Configure and manage the NSA.
• Create volumes, shares, and user accounts.
• Assign individual users specific access rights for specific shares.
Users are people who have access rights to the NSA and can store files there for later retrieval. A
user can:
• Manage shares that he owns.
• Change his own password.
• Access the contents of other shares to which he is given access rights.
14.2 What You Can Do
•Use the main Users screen (Section 14.3 on page 293) to display a list of user accounts created
on the NSA.
•Use the Add User screen (Section 14.3.2 on page 295) to create new user accounts.
•Use the Edit User screen (Section 14.3.2 on page 295) to edit the properties of an existing
account.
•Use the User Info screen (Section 14.4 on page 297) to display the amount of volume space
used by a selected account and the account’s membership in any groups.
14.3 The Users Screen
Click Sharing > Users to display the screen shown next.
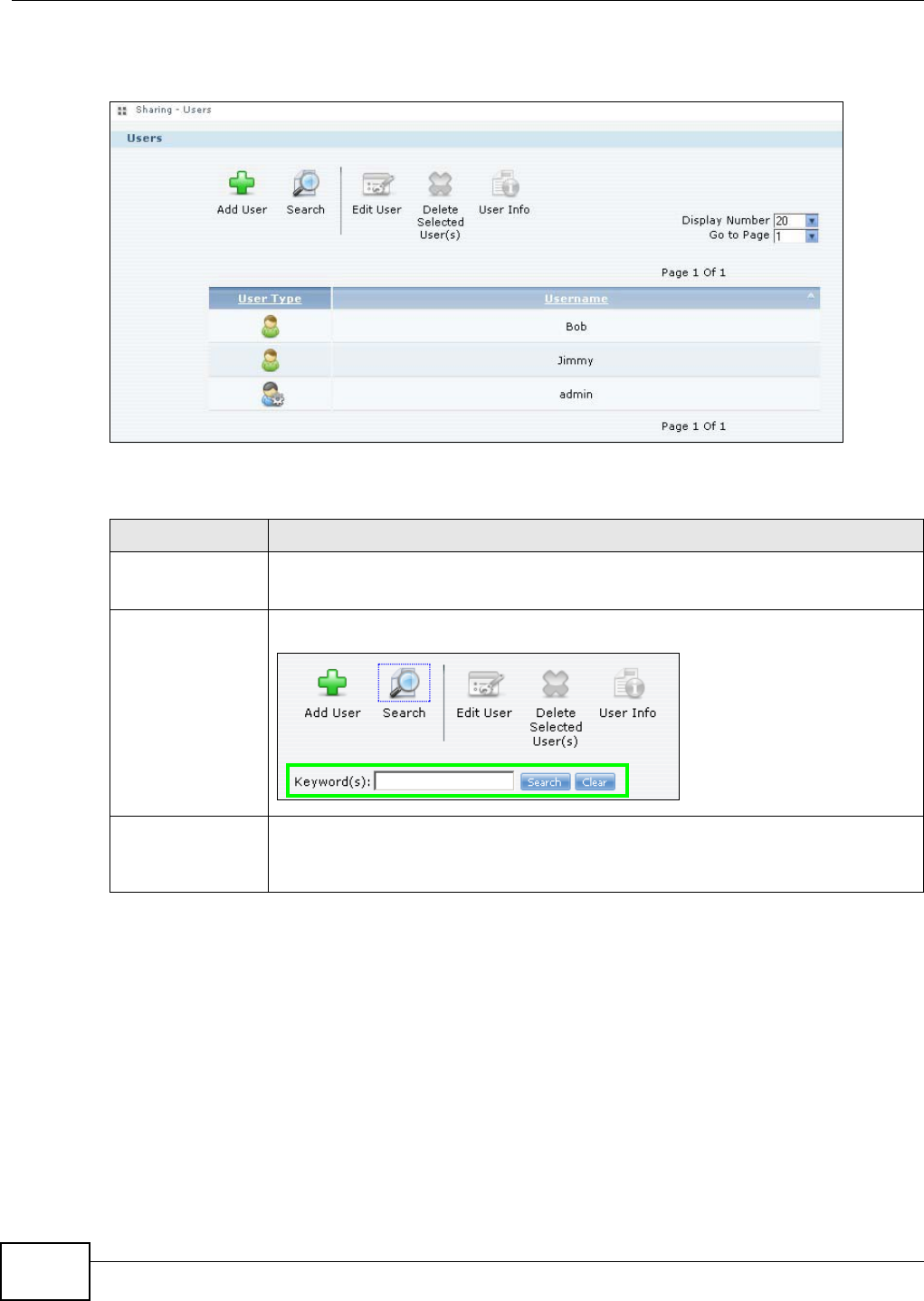
Chapter 14 Users
Media Server User’s Guide
294
Use this screen to create and manage accounts for users who can store files on the NSA.
Figure 175 Sharing > Users
The following table describes the labels in this screen.
Table 96 Sharing > Users
LABEL DESCRIPTION
Add User Click this to open a screen where you can configure a new user account.
Refer to Section 14.3.2 on page 295 to see the screen.
Search Click this to display a search field. Type in the name of an account and then click
Search to look up the account you specified. Click Clear to close the search function.
Edit User Select an account and click this to open a screen where you can edit the properties of
the account.
Refer to Section 14.3.2 on page 295 to see the screen.
Chapter 14 Users
Media Server User’s Guide 295
14.3.1 User Icons
The following table describes the user icons.
14.3.2 Adding or Editing an Account
Use this screen to create or edit a NSA user account with NSA access password.
Delete Selected
Users Select an account and click this to open a screen where you can delete the user
account.
User Info Select an account and click this to open a screen displaying the amount of storage space
used by the account. You can also check the account’s membership in any groups.
Refer to Section 14.4 on page 297 to see the screen.
Display Number Click the drop-down menu to set how many accounts you want to display in one screen.
Go to Page Click the drop-down menu to display and access more user accounts.
User Type This field displays whether the account is an administrator account or a user account.
Username This field displays the username of each account.
Table 96 Sharing > Users (continued)
LABEL DESCRIPTION
Table 97 User Icons
ICON DESCRIPTION
The blue icon is for an administrator account.
The green icon is for a user account.
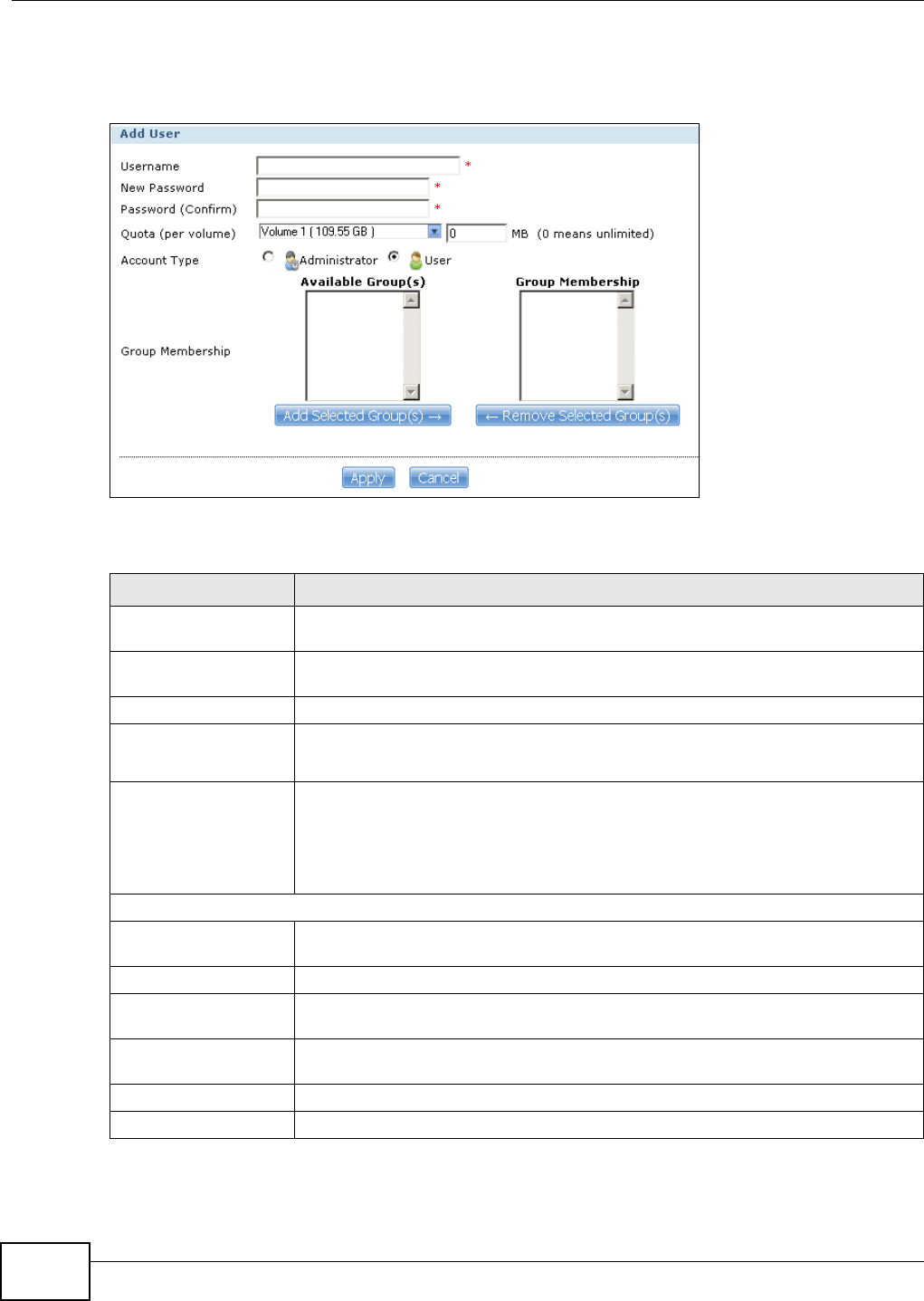
Chapter 14 Users
Media Server User’s Guide
296
Click the Add User button in the Users screen to open the following screen. Click the Edit User
button in the screen shown previously to edit an existing account.
Figure 176 Sharing > Users > Add or Edit a User
The following table describes the labels in this screen.
Table 98 Users > Add or Edit a User
LABEL DESCRIPTION
Username Type a name from 1 to 32 single-byte (no Chinese characters allowed for example)
ASCII characters. See Section 14.3.3 on page 297 for more details on usernames.
New Password Create a password associated with this user. You can type from one to 14 single-
byte (no Chinese characters allowed for example) ASCII characters.
Password (Confirm) You must type the exact same password that you just typed in the above field.
Quota (per volume) Select the volume in which you want the user’s files to be stored.
Enter how much space (in megabytes) you want to allow for the user to store files.
Account Type Select Administrator to give the account full configuration and management
access to the NSA.
Select User to give the account basic access rights to the NSA and allow the user to
manage his own shares, change his own password, and access the contents of other
shares to which he is given access rights.
Group Membership
Available Group(s) This field lists the groups created on the NSA to which the selected account does not
belong.
Group Membership This field lists the groups that the selected account belongs to.
Add Selected
Group(s) Select a group from the Available Groups list and click this to add the account to
that group.
Remove Selected
Group(s) Select a group from the Group Membership list and click this to remove the
account from that group.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.

Chapter 14 Users
Media Server User’s Guide 297
14.3.3 Usernames
Enter a username from one to 32 characters. The first character must be alphabetical (case
insensitive, [A-Z a-z]); numeric characters are not allowed as the first character.
The username can only contain the following characters:
• Alphanumeric A-z 0-9. Unicode usernames are supported with CIFS logins, but not FTP or web
configurator logins.
•Spaces
• _ [underscores]
•. [periods]
•- [dashes]
Other limitations on usernames are:
• All leading and trailing spaces are removed automatically.
• Multiple spaces within names are converted to a single space.
• Usernames are case insensitive. The username cannot be the same (no matter the letter case) as
an existing user. For example, if a user exists with the name 'BOB', you cannot create a user
named 'bob'. If you enter a user 'bob' but use 'BOB' when connecting via CIFS or FTP, it will use
the account settings used for 'bob'.
• The username cannot be the same as a system username such as ANONYMOUS-FTP nor be the
same as an existing user. Other reserved usernames that are not allowed are:
•bin
•daemon
•ftp
• anonymous-ftp
• anonymous
• nobody
• root
•pc-guest
•admin
• password
14.4 Displaying User Info
Use this screen to display a user’s information.
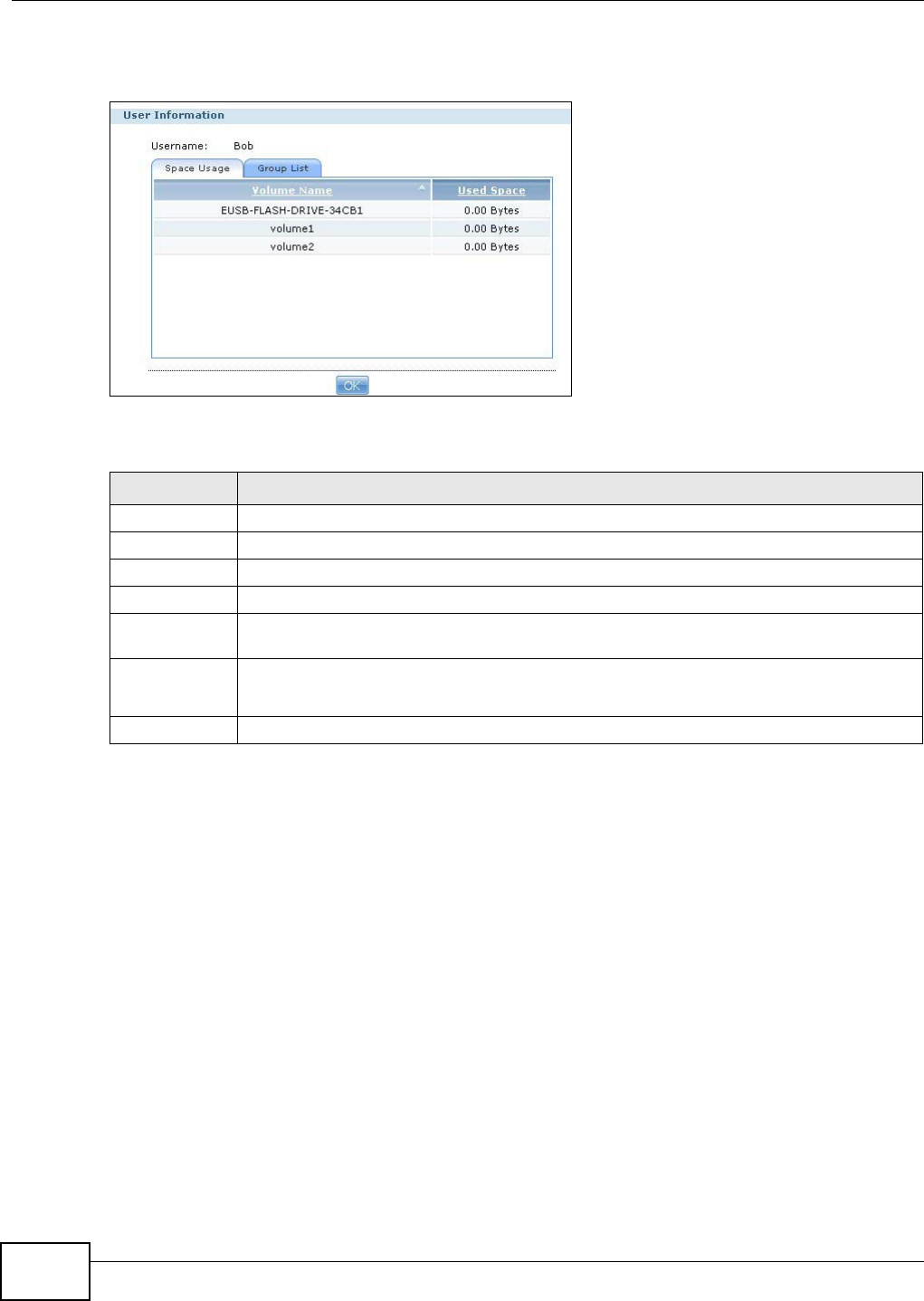
Chapter 14 Users
Media Server User’s Guide
298
In the Users screen, select an account and click User Info to open the following screen.
Figure 177 Sharing > Users > User Info
The following table describes the labels in this screen.
Table 99 Sharing > Users > User Info
LABEL DESCRIPTION
Username This field displays the selected username.
Space Usage Click this to display the amount of volume space used by the selected account.
Group List Click this to display the selected user’s group membership.
Volume Name This field displays the volume(s) created on the NSA.
Used Space This field displays how much storage space the selected account is currently using. This only
applies for files that the user saved onto the NSA while logged in with that username.
Group Name This shows when you click the Group List tab.
This displays the list of groups to which the selected user belongs.
OK Click this to close the current screen.
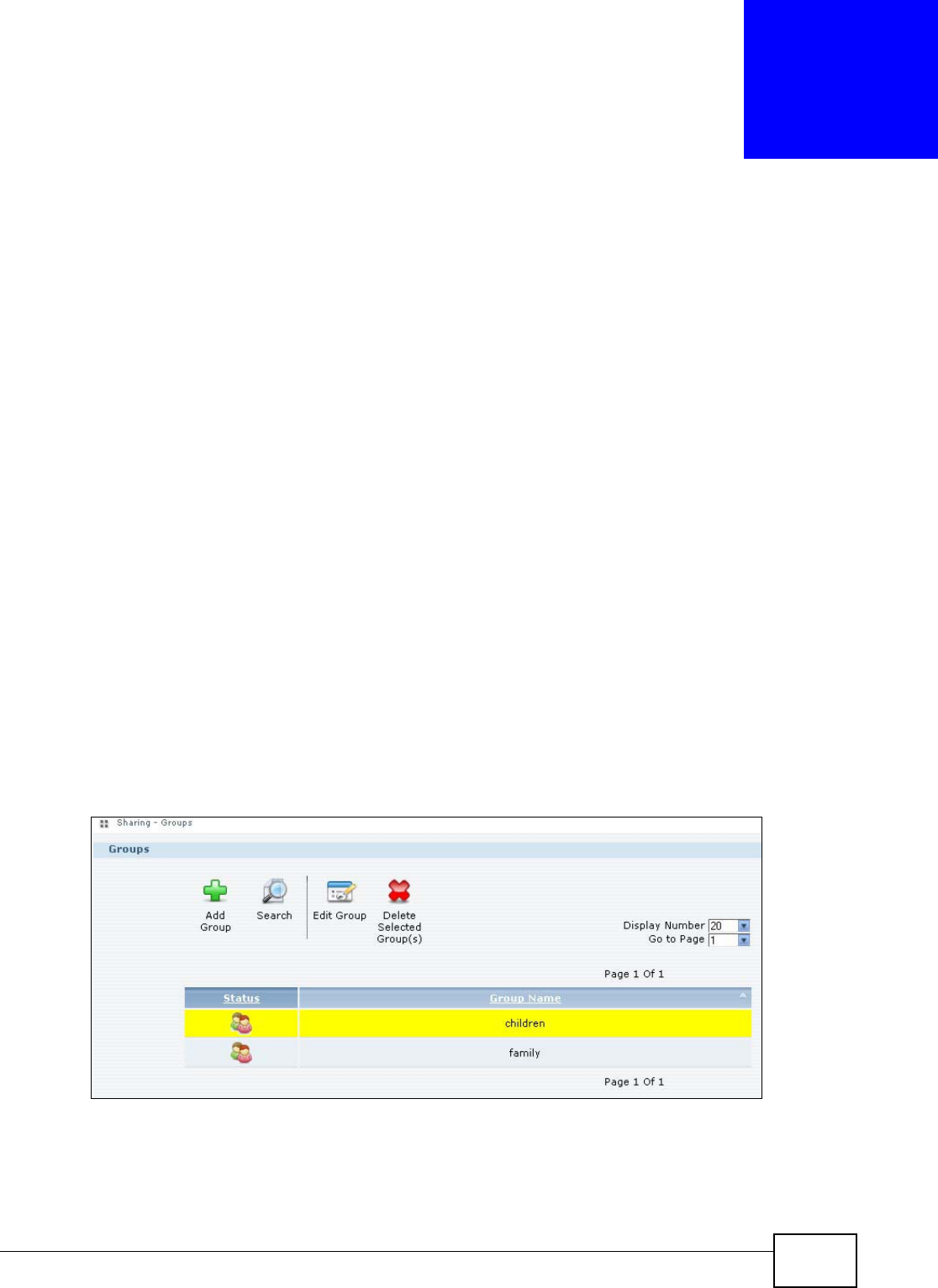
Media Server User’s Guide 299
CHAPTER 15
Groups
15.1 Overview
This chapter introduces the Groups screens. Use the Groups screens to create and manage
groups. You can assign users to groups and grant individual groups access rights to specific shares.
15.2 What You Can Do
•Use the main Groups screen (Section 15.3 on page 299) to display and manage a list of groups
created on the NSA.
•Use the Add Group screen (Section 15.3.1 on page 300) to create new groups.
•Use the Edit Group screen (Section 15.3.1 on page 300) to edit the properties of an existing
group.
15.3 The Groups Screen
Use this screen to create and manage groups.
Click Sharing > Groups to display the screen shown next.
Figure 178 Sharing > Groups
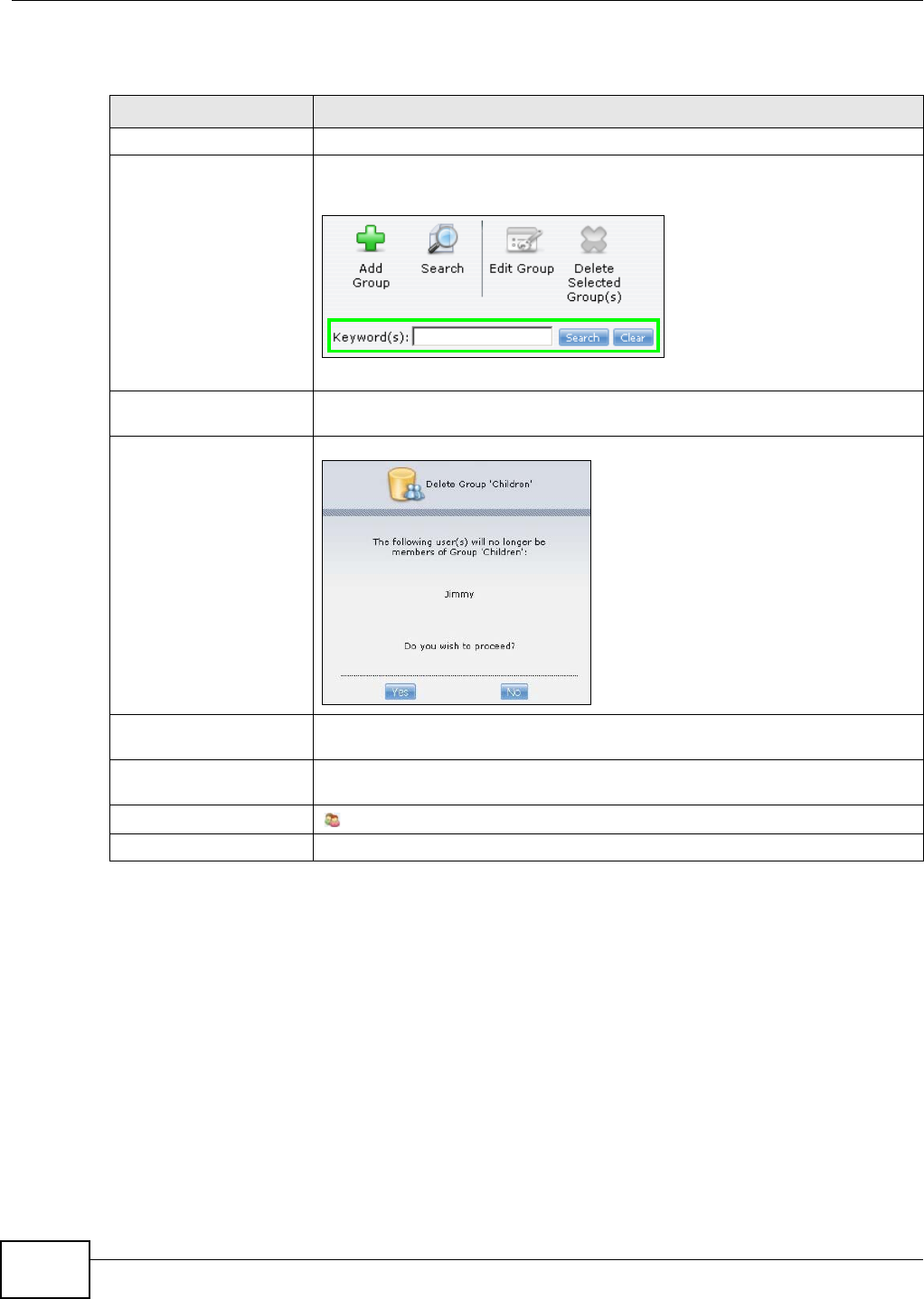
Chapter 15 Groups
Media Server User’s Guide
300
The following table describes the labels in this screen.
15.3.1 Adding or Editing a Group
Use this screen to create or edit a NSA group.
Table 100 Sharing > Groups
LABEL DESCRIPTION
Add Group Click this to open a screen where you can configure a new group.
Search Click this to display a search field. Type the name of a group and then click
Search to look up the group you specified. Click Clear to close the search
function.
Edit Group Select a group and click this to open a screen where you can edit the properties of
the selected group.
Delete Selected Group(s) Select a group and click this to open a screen where you can delete the group.
Display Number Click the drop-down menu to set how many groups you want to display in one
screen.
Go to Page Click the drop-down menu to select a page number. Jump to a different page to
display and access more groups.
Status This field displays the group icon.
Group Name This field displays the group names created on the NSA.
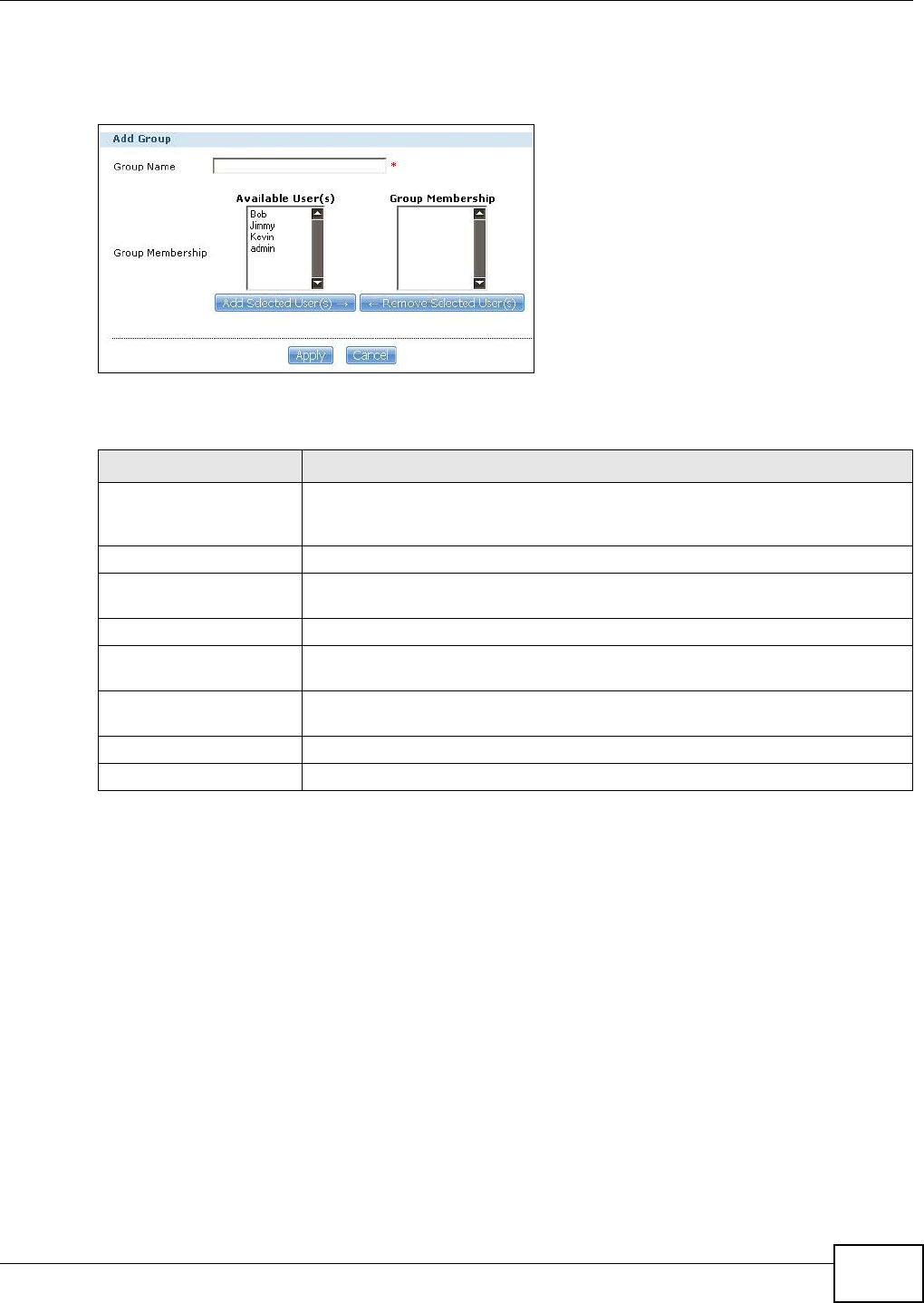
Chapter 15 Groups
Media Server User’s Guide 301
Click the Add Group button in the Groups screen to open the following screen. Click the Edit
Group button in the screen shown previously to edit an existing group.
Figure 179 Sharing > Groups > Add or Edit a Group
The following table describes the labels in this screen.
15.3.2 Group Names
Enter a group name from 1 to 32 characters. The first character must be alphabetical (case
insensitive, [A-Z a-z]); numeric characters are not allowed as the first character.
The group name can only contain the following characters:
• Alphanumeric A-z 0-9. Unicode usernames are supported with CIFS logins, but not FTP or web
configurator logins.
•Spaces
• _ [underscores]
•. [periods]
•- [dashes]
Other limitations on group names are:
• All leading and trailing spaces are removed automatically.
Table 101 Sharing > Groups > Add or Edit a Group
LABEL DESCRIPTION
Group Name Type a name from 1 to 32 single-byte (no Chinese characters allowed for
example) ASCII characters. See Section 15.3.2 on page 301 for more details on
group names.
Group Membership Use this field to assign group membership to individual users.
Available User(s) This field lists the user accounts created on the NSA that are not members of the
current group.
Group Membership This field lists the user accounts added to the group.
Add Selected User(s) Select a user account from the Available Users list and click this to add the
account to the group.
Remove Selected
User(s) Select a user account from the Group Membership list and click this to remove
the account from the group.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.

Chapter 15 Groups
Media Server User’s Guide
302
• Multiple spaces within names are converted to a single space.
• Group names are case insensitive. The group name cannot be the same (no matter the letter
case) as an existing group. For example, if a group exists with the name 'FAMILY', you cannot
create a group named 'family'.
• The group name cannot be the same as a system group name such as EVERYONE nor be the
same as an existing group. Other reserved groups names that are not allowed are:
• nobody
• root
•everyone
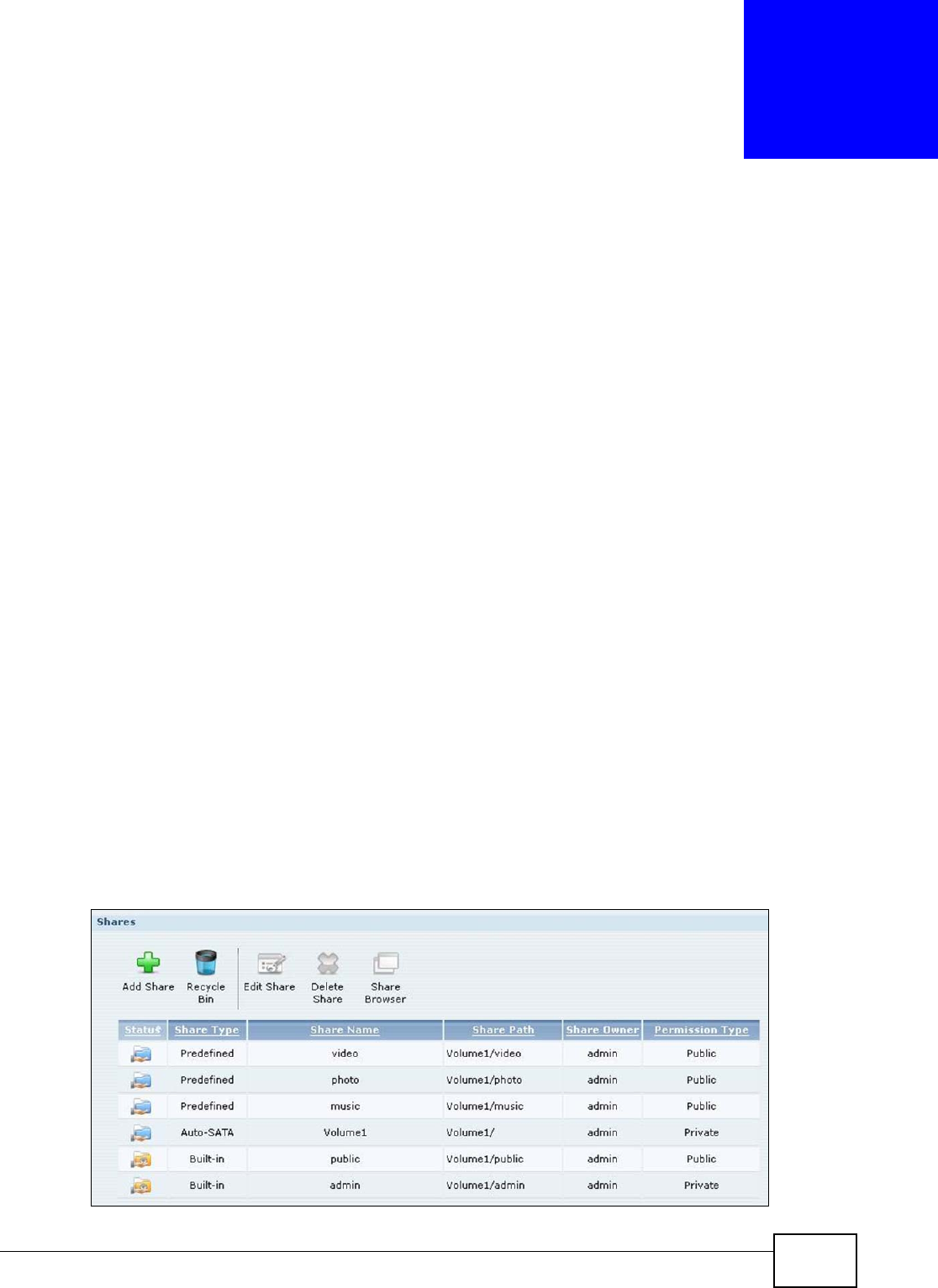
Media Server User’s Guide 303
CHAPTER 16
Shares
16.1 Overview
A share is a set of access permissions mapped to a specific folder on a volume. It is equivalent to
the Windows concept of a shared folder. You can map a share to a network drive for easy and
familiar file transfer for Windows users.
16.2 What You Can Do
•Use the Shares screen (Section 16.3 on page 303) to navigate a list of shares created on the
NSA.
•Use the Add Shares screen (Section 16.3.1 on page 305) to create additional shares on the
NSA.
•Use the Recycle Bin screen (Section 16.4 on page 307) to configure and clean up the recycle
bins.
•Use the Edit Share screen (Section 16.3.1 on page 305) to edit a share’s properties.
•Use the Share Browser screen (Section 16.5 on page 308) to navigate, add and edit the
contents in a share.
16.3 The Shares Screen
Click Sharing > Shares in the navigation panel to open the following screen. This screen lists all
shares created on the NSA.
Figure 180 Sharing > Shares
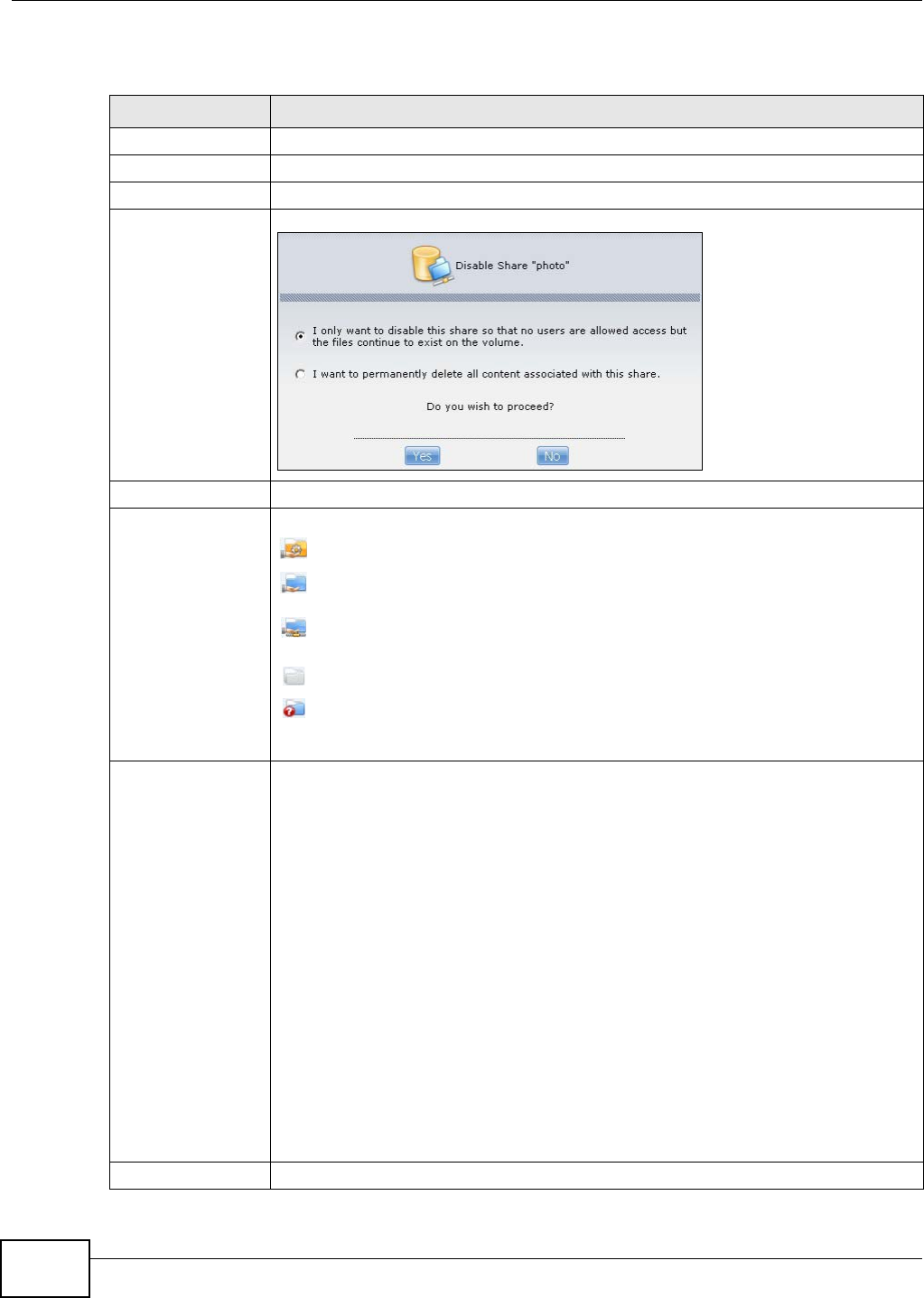
Chapter 16 Shares
Media Server User’s Guide
304
The following table describes the labels in this screen.
Table 102 Sharing > Shares
LABEL DESCRIPTION
Add Share Click this to create a new share.
Recycle Bin Click this to configure recycle bins.
Edit Share Select a share and click this to edit the share.
Delete Share Select a share and click this to remove or restrict access to the share.
Share Browser Select a share and click this to browse the share’s contents.
Status This field displays the share icons.
represents a Built-in share on a volume on the internal hard drives.
represents an Auto-SATA, Predefined, or User-Created share on a volume on
the internal hard drives.
represents an Auto or User-Created share on a volume on the external (USB)
devices.
represents a disabled share that no user can access.
represents a missing share. The NSA cannot find the hard disk associated with the
share (the disk may be removed from the NSA for example). You may install the disk
back to the NSA to recover the share, or you may delete the share from the NSA.
Share Type The NSA automatically creates an Auto-SATA share for each internal SATA volume. The
auto-SATA share has the same name as the volume and is the volume’s root (or
“master”) share. It contains all of the volume’s shares. All new shares you create on the
volume are also automatically included in the auto-SATA share. You cannot delete, edit,
or use the share browser with the auto-SATA share.
Note: Use the admin account to map the auto SATA share to a Windows network drive.
This gives the administrator convenient access to all of the volume’s shares
through a single Windows network drive. External disk (volume) shares must still
be mapped individually.
This field displays Built-in for system shares. You cannot delete these shares. These
are the public and admin shares.
This field displays Predefined for default shares. You cannot delete these shares. These
are the video, music, and photo shares.
This field displays User-created for shares that an administrator has created. You can
delete these shares.
This field displays Auto for shares that are automatically created on an external (USB)
device when a user plugs in the device.
Share Name This field displays the share’s names.
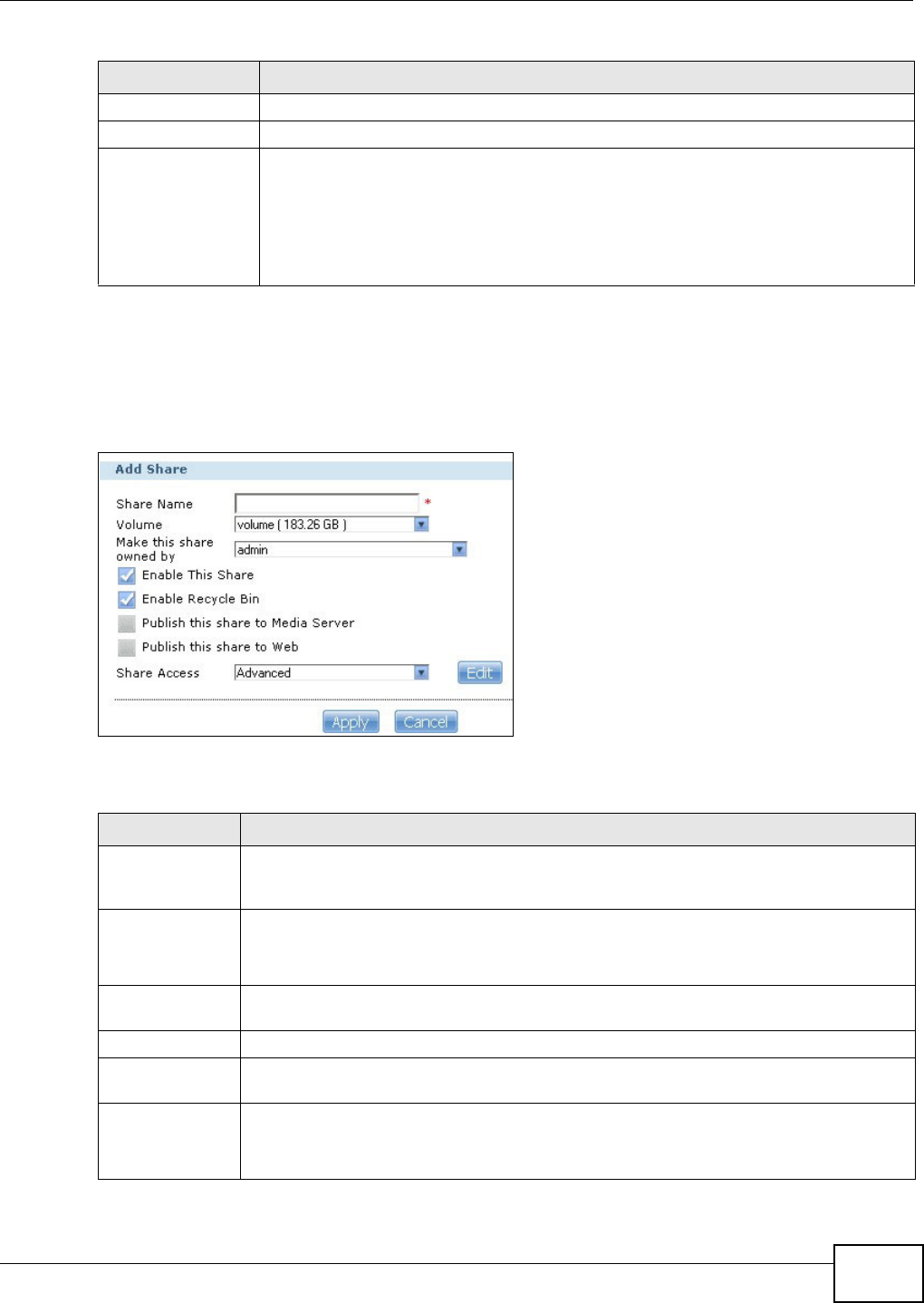
Chapter 16 Shares
Media Server User’s Guide 305
16.3.1 Adding or Editing Share
Click Add Share to create a new share. In the Shares screen, select a share and click Edit Share
to open the following screen. Use this screen to create or edit a share.
Figure 181 Shares > Add Share (or Edit Share)
The following table describes the labels in this screen.
Share Path This field displays the share’s file path, for example, volume1/music.
Share Owner This is the name of the user account to which this share belongs.
Permission Type This field displays the access permission of a share.
Everyone on the network can access a Public share.
Only the share owner can access a Private share.
An Advanced share allows you to assign specific access rights (read-only for example)
to individual users/groups.
Table 102 Sharing > Shares (continued)
LABEL DESCRIPTION
Table 103 Shares > Add Share (or Edit Share)
LABEL DESCRIPTION
Share Name Type a share name from 1 to 239 single-byte (no Chinese characters allowed for example)
ASCII characters. The name cannot be the same as another existing share. See Section
4.4.6 on page 55 for more information on share names.
Volume You should have already created volumes (a single accessible storage area with a single
file system) on the NSA. Select the one that contains the folder that you want to share out.
You cannot modify this when editing a share.
Make this share
owned by Select the administrator or user account that can own (manage) this share. The share
owner controls access rights to the share.
Enable this share Click this to allow access to this share.
Enable Recycle
Bin Click this to activate the recycle bin. When you delete a file from this share, a recycle
folder is created to store the deleted item.
Publish this share
to Media Server This shows only when you enable the Media Server (Section 10.5 on page 185).
Select this option to have the NSA share files in this folder with media clients. The media
clients do not have to use a password to play the shares you publish.
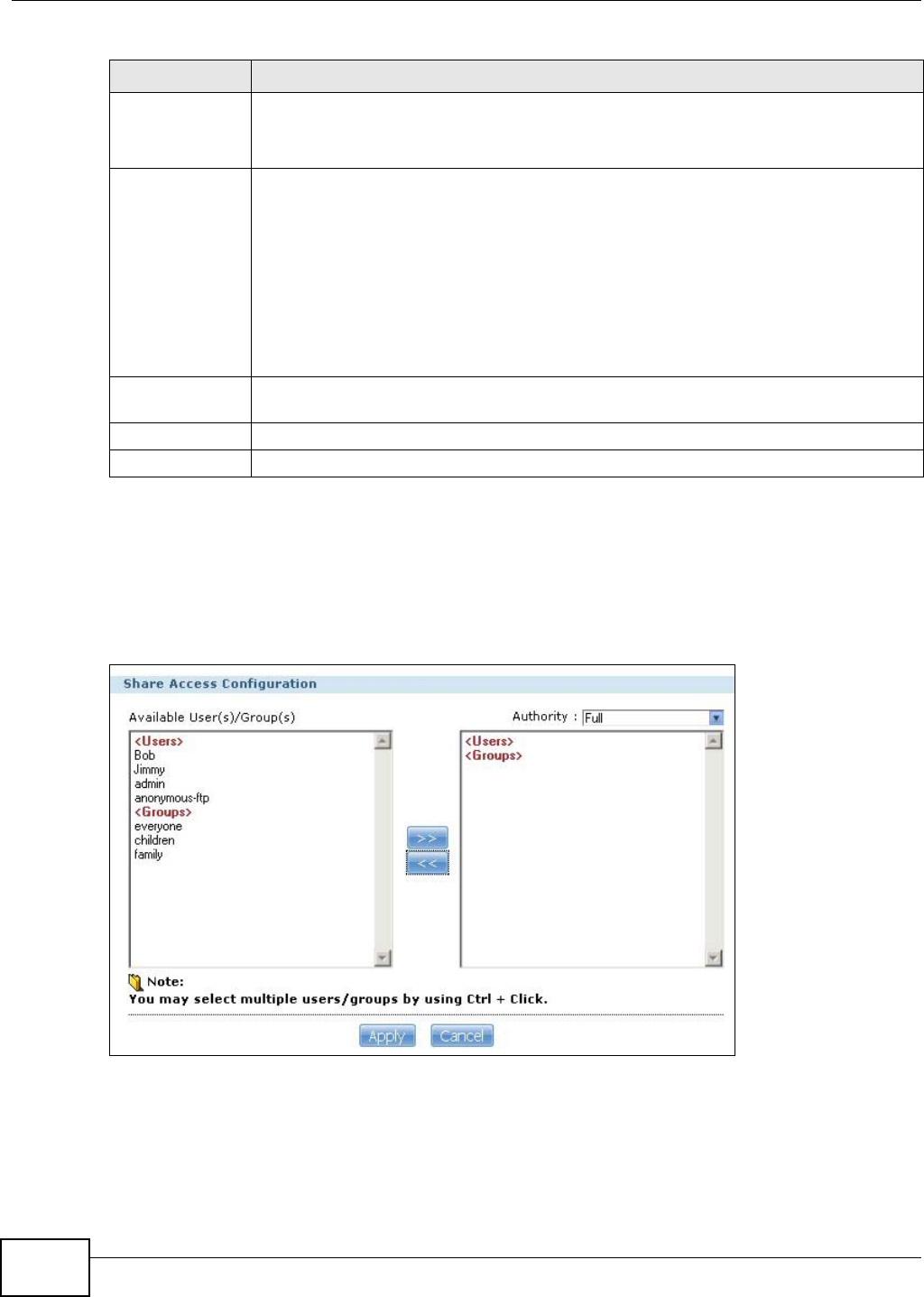
Chapter 16 Shares
Media Server User’s Guide
306
16.3.2 Configuring Advanced Share Access
In the Sharing > Shares > Add Share or Edit Share screen, select Advanced from the Share
Access drop-down list. Click Edit to open the following screen. Use this screen to configure share
access rights for individual users and groups.
Figure 182 Sharing > Shares > Add Share (or Edit Share) > Advanced
Publish this share
to Web This shows only when you enable the Web Publish (Section 10.7 on page 202).
Select this option to let people use a web browser to access this share’s files without
logging into the Home screens.
Share Access Assign access rights (full, read only or deny) to users or groups. If you publish the share
to the media server or the web, all users will have at least read-only access to the share,
regardless of what you configure here.
Keep it private to owner means only the share owner (selected above) can access the
share.
Make it Public means every user (including people who do not have accounts on the
NSA) can access the share.
Advanced allows you to assign specific access rights (full, read only or deny) to individual
users/groups.
Edit This button is available only when you select Advanced share access. Click this to
configure advanced share access rights.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 103 Shares > Add Share (or Edit Share) (continued)
LABEL DESCRIPTION

Chapter 16 Shares
Media Server User’s Guide 307
The following table describes the labels in this screen.
16.3.3 Public and ANONYMOUS Share Access Rights
If you make a share public, users do not need to log in.
With ANONYMOUS FTP, you must enter either 'anonymous' or 'ftp' as the username. Any other
name is considered a username, so must be valid and have a corresponding correct password.
16.4 The Recycle Bin Configuration Screen
Use this screen to periodically clean up items in all recycle bins.
16.4.1 Recycle Bins
Recycle bins in the NSA help users recover accidentally deleted files or folders in the shares. When
you delete an item, a recycle folder is created within the share to hold the deleted item.
Every share can have its own recycle folder. You must enable the recycle-bin function to recycle
deleted items. You can configure this setting when you add or edit a share. See Section 16.3.1 on
page 305 for details on activating the recycle bin in a share.
Later if you want to retrieve a deleted item, you can locate the item in the recycle folder. You may
move or copy the deleted item to another share.
Table 104 Sharing > Shares > Add Share (or Edit Share) > Advanced
LABEL DESCRIPTION
Available Users/Groups This field lists the users/groups to which you can assign access rights.
Authority Use this field to assign access rights to users/groups.
Full Control gives users/groups full access (read, write and execute) to all files
contained within this share.
Read-Only gives users/groups read-only access (they cannot modify nor
execute) to all files contained within this share.
Deny blocks access (users/groups cannot read, modify, nor execute) to all files
contained within this share.
Among all access rights, Deny has the highest priority. For example, User A
belongs to Group 1. You assign User A full access rights to the Music share but
deny access rights to Group 1. Then User A cannot access the Music share.
Note: If you deny access to all users, no-one can use the share, not even the
administrator.
Click an arrow button to move users/groups between the left and right fields. Use
the arrow buttons to assign access rights to users/groups.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
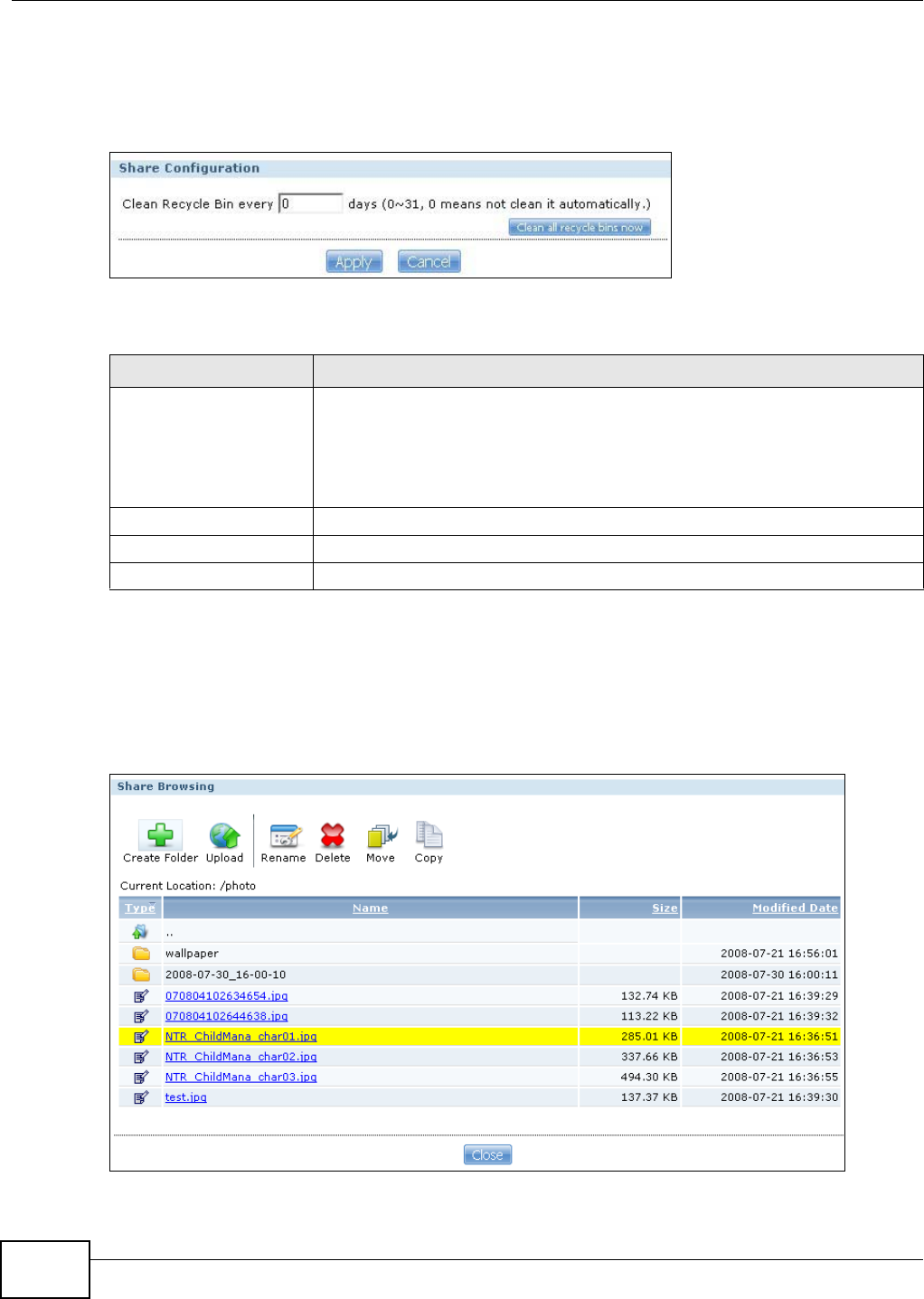
Chapter 16 Shares
Media Server User’s Guide
308
16.4.2 Configuring Recycle Bins
In the Sharing > Shares screen, click Recycle Bin to open the following screen.
Figure 183 Sharing > Shares > Recycle Bin
The following table describes the labels in this screen.
16.5 The Share Browser Screen
Use this screen to create folders, upload files, and edit files within the share.
Figure 184 Sharing > Shares > Share Browser
Table 105 Sharing > Shares > Recycle Bin
LABEL DESCRIPTION
Clean Recycle Bin every N
days Specify how often you want to clear the contents in all recycle bins. The specified
days correspond to how long a file has been stored in a recycle bin. For example,
if you set the interval to be 3 days, recycle bins will clean up items deleted or not
accessed for 3 days.
Note: Cleaning up recycle bins permanently removes the files from the NSA.
Clean all recycle bins now Click this to immediately remove contents from all recycle bins.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
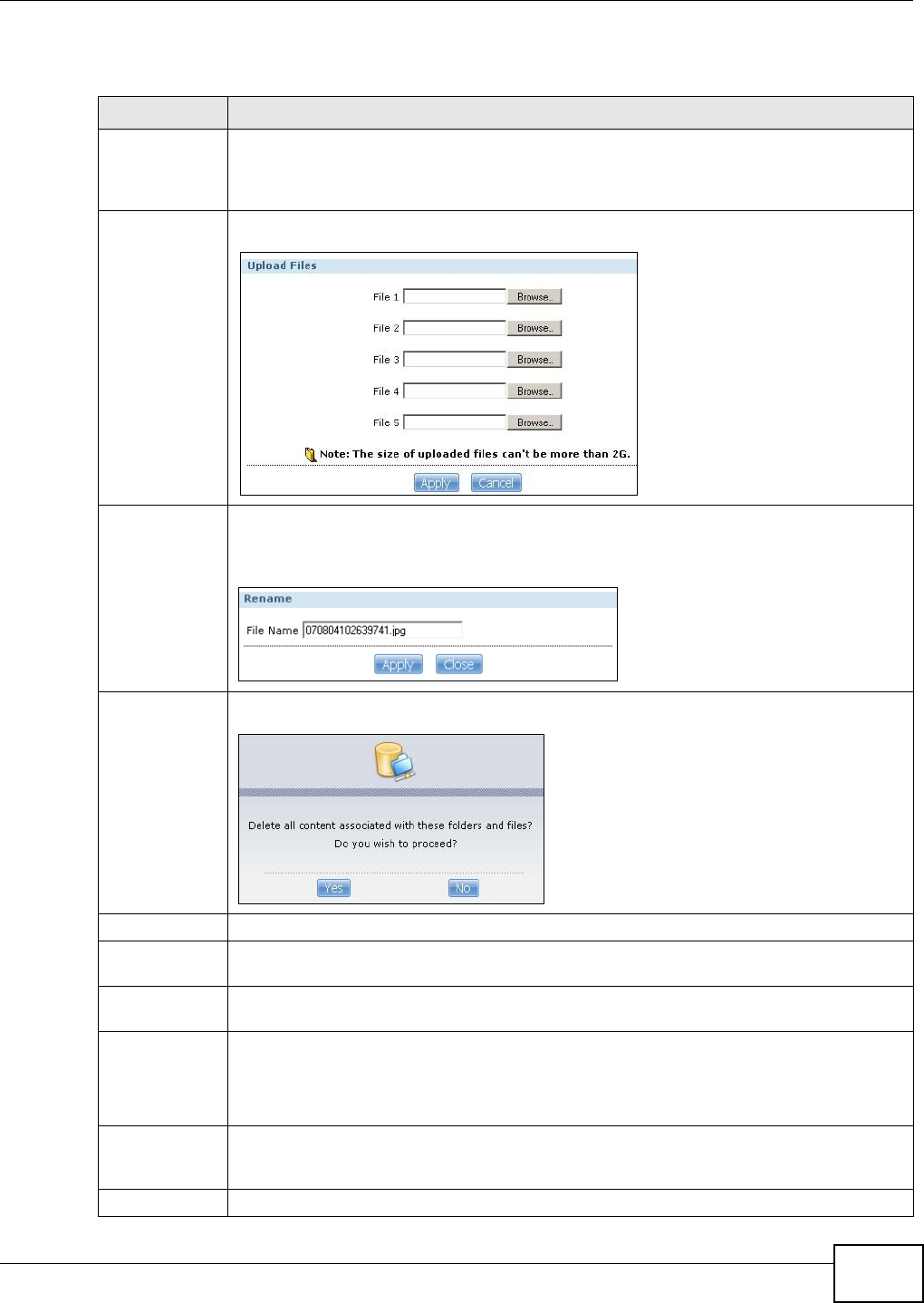
Chapter 16 Shares
Media Server User’s Guide 309
The following table describes the labels in this screen.
Table 106 Sharing > Shares > Share Browser
LABEL DESCRIPTION
Create Folder Type a folder name and click Apply to make a new folder. The name can be 1 to 239 single-
byte (no Chinese characters allowed for example) ASCII characters. The name cannot be
the same as another existing folder in the same path. See Section 4.4.6 on page 55 for
more information on folder names.
Upload Click this to add files to the share. Use Browse to locate a file and click Apply to upload the
file. Note that the size of each file should be less than 2 GB.
Rename Select a folder or file and click this to open a screen. Enter the name you want and click OK
to make the changes.
Note: When you change a file name, make sure you keep the file extension
Delete Select a file/folder from the list and click this to open a warning screen. Click Yes to delete
the file/folder, or click No to close the screen.
Move Select a file/folder from the list and click this to relocate the file/folder to another share.
Copy Select a file/folder from the list and click this to make a duplicate of the file/folder to
another share.
Current
location This is the name of the share and folder path that you are in.
Type The icon in this column identifies the entry as a folder or a file. Click a music or video file’s
play icon to play the file.
The folder with an arrow pointing up is for the link that takes you to the next higher layer in
the share’s folder tree.
Name This section lists the share’s existing folders or files. Click to the right of the file/folder name
to select the file/folder. You can also click the folder’s name to navigate to a sub-folder
within the folder.
Size This field displays size of the file.
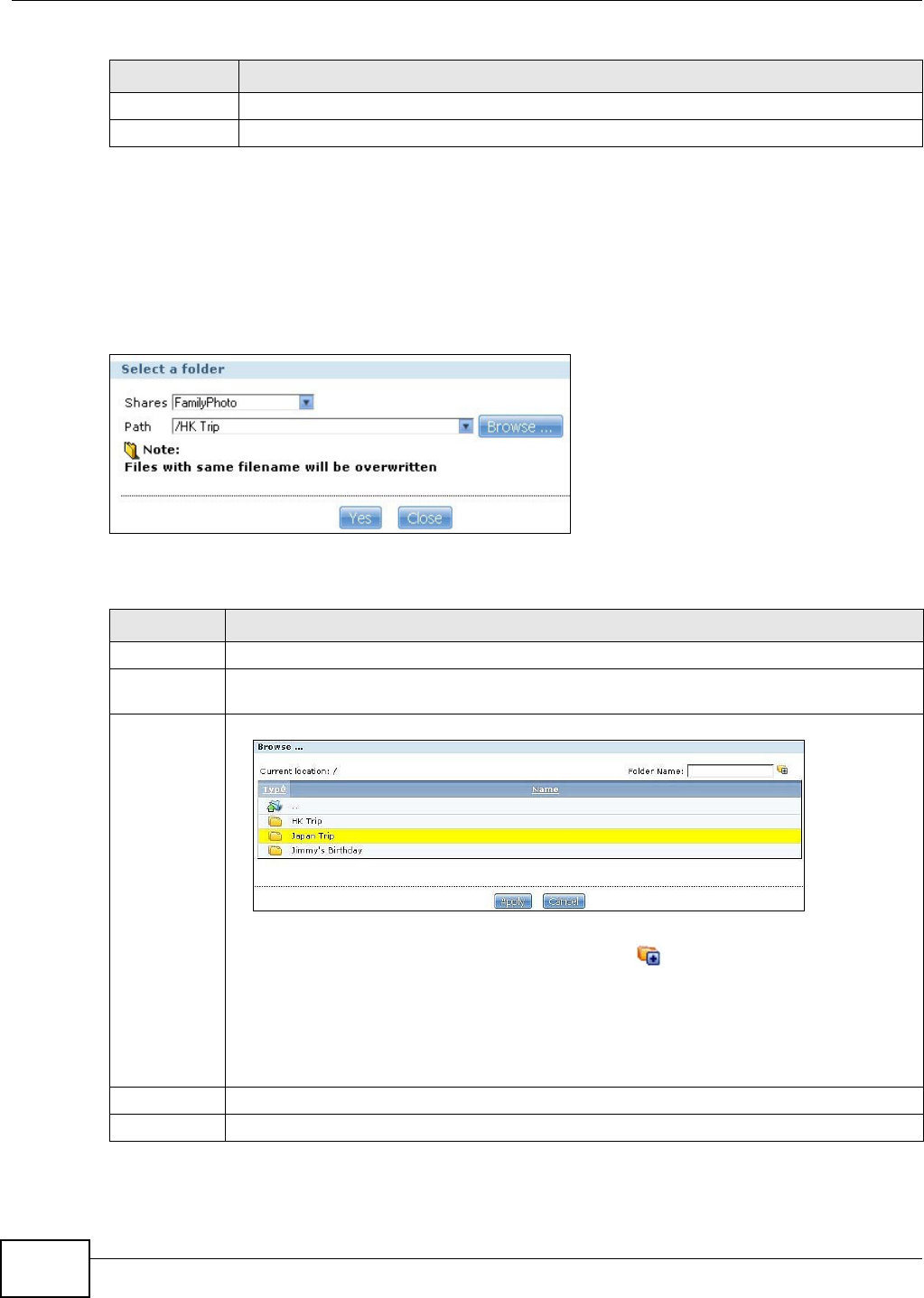
Chapter 16 Shares
Media Server User’s Guide
310
16.5.1 Moving or Copying Files
Use this screen to move or copy files to another share.
In the Share Browser screen, select a file or folder and click Move or Copy to open the following
screen.
Figure 185 Sharing > Shares > Share Browser > Move (or Copy)
The following table describes the labels in this screen.
Modified Date This field displays a file’s latest modification date.
Close Click this to close the screen.
Table 106 Sharing > Shares > Share Browser (continued)
LABEL DESCRIPTION
Table 107 Sharing > Shares > Share Browser > Move (or Copy)
LABEL DESCRIPTION
Shares Select the destination share from the drop-down list.
Path This field displays the share folder’s path. You can use Browse to find or create a folder on
the NSA or type the location of the folder using forward slashes as branch separators.
Browse Click this to open the following screen and navigate to the location of the file/folder.
•Current Location - This is the location of the selected folder.
•Folder Name - Enter a new folder name and click to create it.
•Type - This identifies the item as a folder or file.
•Name - This is the name of the folder/file.
Select a folder. If you don’t select a folder, a forward slash (/) displays in the Path field. All
contents within the specified share are automatically selected.
Click Apply to save your settings and Cancel to close the screen.
Yes Click this to move or copy the file/folder to the designated share.
Close Click this to return to the Share Browser screen.

Media Server User’s Guide 311
CHAPTER 17
Maintenance Screens
17.1 Overview
This chapter discusses the Maintenance screens. The Maintenance screens allow you to manage
system configurations.
17.2 What You Can Do
•Use the Power screen (Section 17.3 on page 311) to configure power settings for the NSA,
including power saving, UPS, power on/off after power failure, power on/off schedule, and Wake
on LAN.
•Use the Log screen (Section 17.4 on page 315) to check the system’s logs.
•Use the Configuration screen (Section 17.5 on page 318) to backup or restore the NSA
configuration file.
•Use the SSL screen (Section 17.6 on page 319) to configure HTTPS and the NSA’s SSL certificate.
•Use the Firmware Upgrade screen (Section 17.7 on page 321) to upload new firmware.
•Use the Shutdown screen (Section 17.8 on page 322) to restart or shut down your NSA.
17.3 The Power Screen
Use this screen to manage power settings for the NSA.
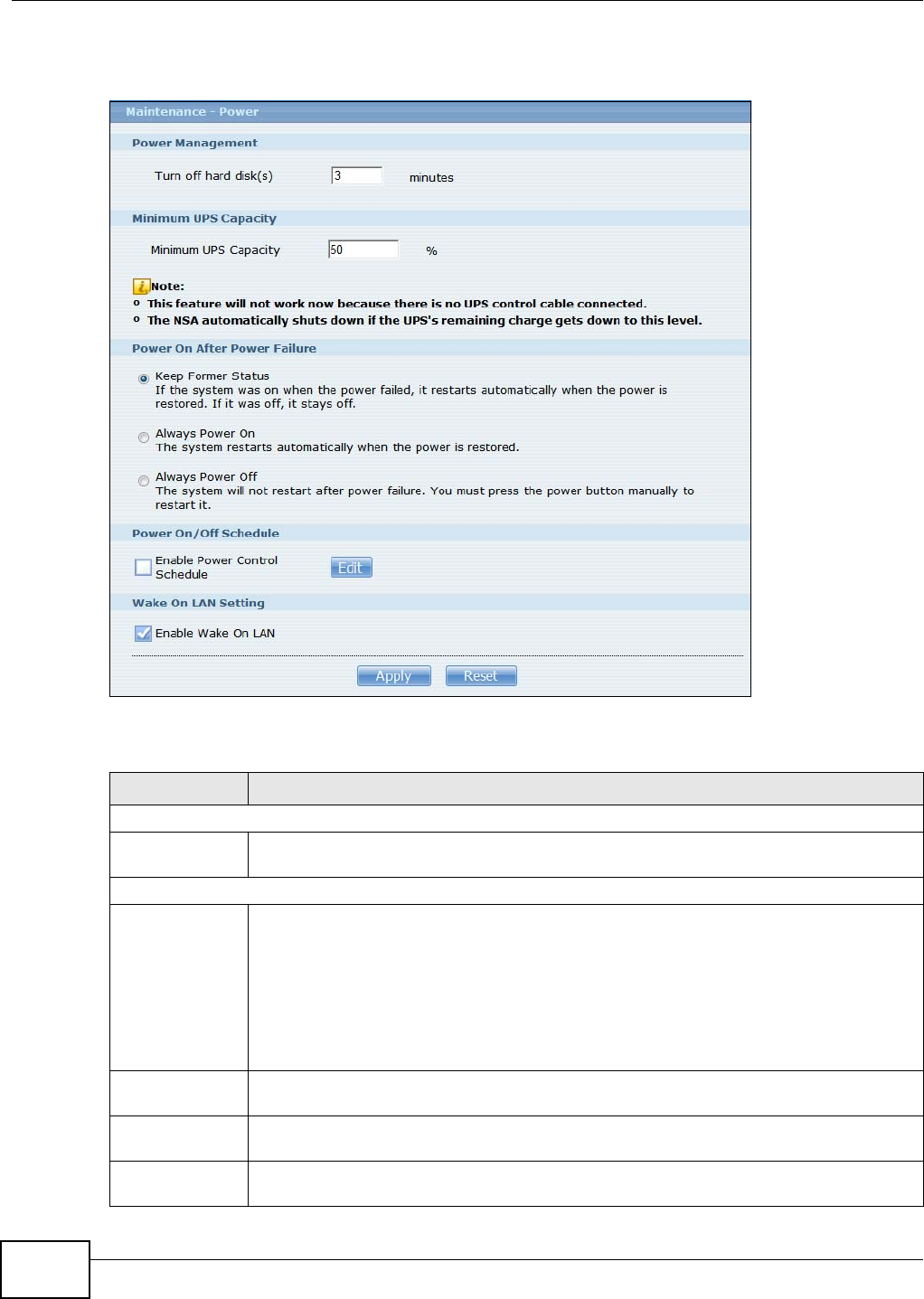
Chapter 17 Maintenance Screens
Media Server User’s Guide
312
Click Maintenance > Power to display the following screen.
Figure 186 Maintenance > Power
The following table describes the labels in this screen.
Table 108 Maintenance > Power
LABEL DESCRIPTION
Power Management
Turn off hard
disk(s) Enter the number of minutes the NSA will sit idle before spinning the hard disks down to
sleep. The default power-off time is 15 minutes.
Minimum UPS Capacity
Minimum UPS
Capacity When you use an APC Uninterruptible Power Supply (UPS) with a USB connection to the
NSA, the NSA shuts itself down if the APC UPS’s battery charge gets down to the
percentage you specify in this field. This allows the NSA to shut down properly and avoid
data loss caused by a power failure when the UPS stops supplying power.
A setting around 50% is recommended. A setting close to 100% is not recommended since
it would cause the NSA to shut down whenever the UPS is charging. A setting close to 0 is
also not recommended since the UPS would not have enough power to allow the NSA to
shutdown properly.
Power On After
Power Failure Select an option to set whether or not the NSA restarts when the power is restored after a
power failure.
Keep Former
Status Select this option to have the NSA automatically restart only if it was operating when the
power failed. The NSA remains off if it was already off when the power failed.
Always Power On Select this option to keep the NSA operating as much of the time as possible. The NSA
restarts automatically even if it was turned off when the power failed.
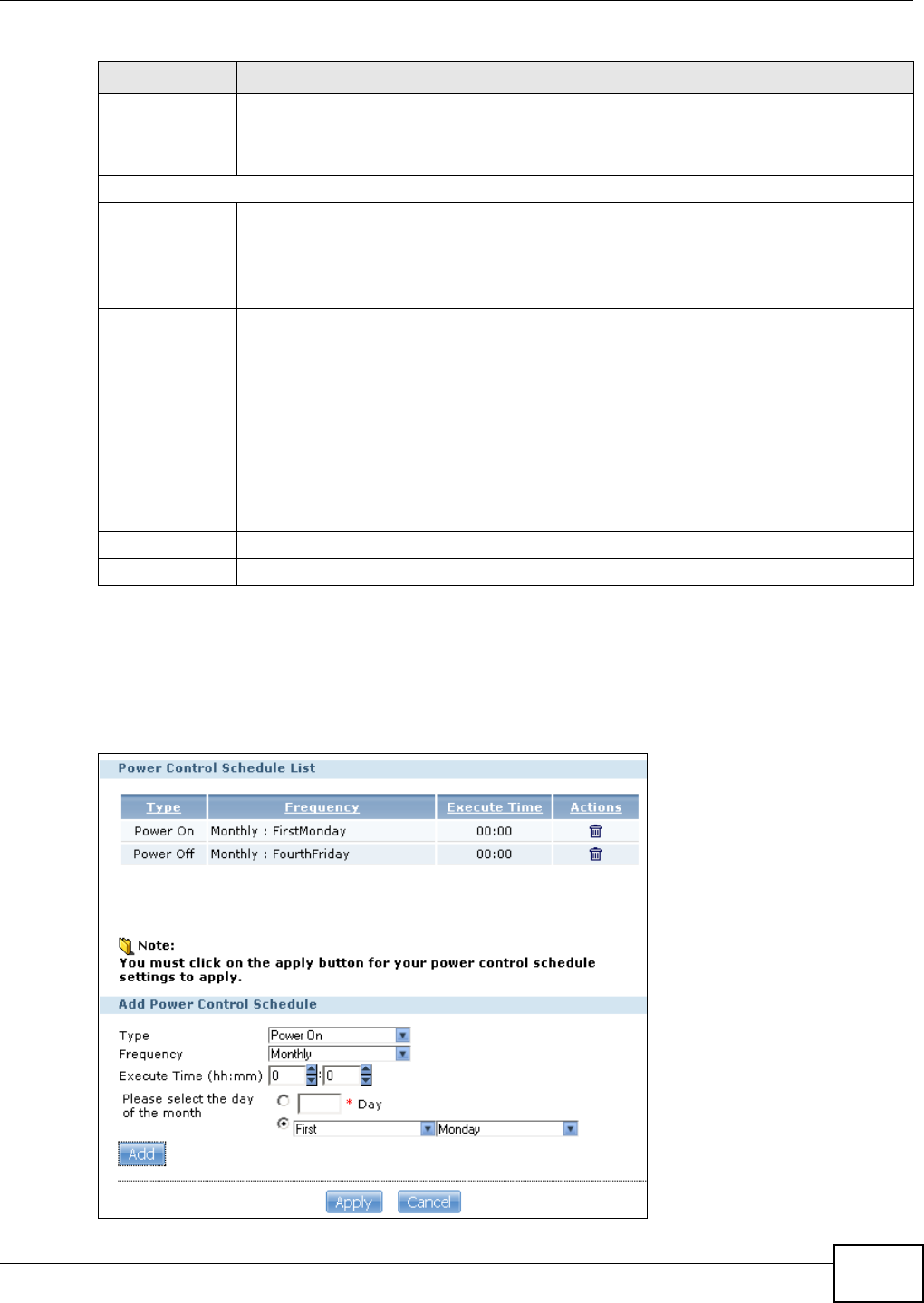
Chapter 17 Maintenance Screens
Media Server User’s Guide 313
17.3.1 Editing the Power Control Schedule Screen
Click Maintenance > Power Management > Edit to open this screen. Use this screen to
configure power control schedules to have the NSA turn on, turn off, or reboot at specified times.
Figure 187 Maintenance > Power Management > Edit
Always Power
Off Select this option to keep the NSA from automatically restarting when the power is
restored after a power failure. This is a computer’s “traditional” behavior. Select this if you
have other servers such as a domain controller or DNS server that you want to start or
check after a power failure before the NSA turns on.
Power On/Off Schedule
Enable Power
Control Schedule Select this option to have the NSA turn itself off and on or reboot according to the
schedules you configured.
Click Edit to go to the screen where you can configure the power control schedules.
Refer to Section 17.3.1 on page 313 for this screen.
Enable Wake On
LAN Enable Wake On LAN to be able to turn on the NSA through its wired Ethernet connection.
You must have a computer or router on your LAN that supports sending Wake On LAN
“magic packets” to turn on the NSA.
To use Wake On LAN from a computer on your LAN, install a program such as Wake On LAN
EX or another Wake On LAN program that supports sending magic packets.
You can use Wake On LAN from a remote location if the router in front of the NSA supports
sending magic packets.
Use the NSA’s power button or the Web Configurator’s Maintenance > Shutdown menu
to turn off the NSA.
Apply Click this to save your changes.
Reset Click this to restore previously saved settings.
Table 108 Maintenance > Power (continued)
LABEL DESCRIPTION
Chapter 17 Maintenance Screens
Media Server User’s Guide
314
The following table describes the labels in this screen.
Table 109 Maintenance > Power Management > Edit
LABEL DESCRIPTION
Power Control
Schedule List This table lists the power on, power off, and reboot schedules. For example, you could
have one schedule to turn the NSA on every morning, at 8:00, another schedule to turn it
off every evening at 18:00, and a third schedule to have it reboot every Friday at 14:00.
Click a column’s heading cell to sort the schedules by that column’s criteria. Click the
heading cell again to reverse the sort order.
Type This field displays whether the power control schedule has the NSA turn on, turn off, or
reboot.
Frequency This field shows how often (monthly, weekly, or daily) the NSA is to apply this power
control schedule.
Execute Time This field shows when the NSA is to use this power control schedule (when the NSA is to
turn on, turn off, or reboot).
Actions Click the Delete icon to remove a power control schedule from the list.
Add Power
Control Schedule Use this part of the screen to configure power on, power off, and reboot times.
Type Select whether this power control schedule has the NSA turn on, turn off, or reboot.
Frequency Select whether the NSA is to apply this power control schedule entry on a monthly, weekly,
or daily basis.
Execute Time
(hh:mm) Enter the time, day, and/or day of the month as appropriate for this power control
schedule entry. Leave more than 10 minutes between the execution times of the entries.
If the NSA turns off or restarts while a user is transferring files to or from the NSA, the
transfer fails. The user will need to restart the transfer.
The NSA skips a scheduled restart or power off if the execution time comes while the NSA
is doing any of the following:
• Resynchronizing a RAID
• Upgrading firmware
• Replacing the configuration file
If the NSA is turned off at the time when a restart or power off is scheduled, the NSA does
not perform the restart or power off.
If the NSA is turned on at the time when a power on is scheduled, the NSA does not
perform the power on.
Use this part of the screen to configure power on, power off, and reboot times.
Please select the
day of the month This is only available if you set the Frequency to Monthly.
Choose the day of each month for the power control schedule entry.
Every how many
weeks? This is only available if you set the Frequency to Weekly.
Enter the interval between weeks and choose the day of the week for the power control
schedule entry.
Every how many
days? This is only available if you set the Frequency to Daily.
Enter the interval between days for the power control schedule entry.
Add Click this to add the power control schedule to the list.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
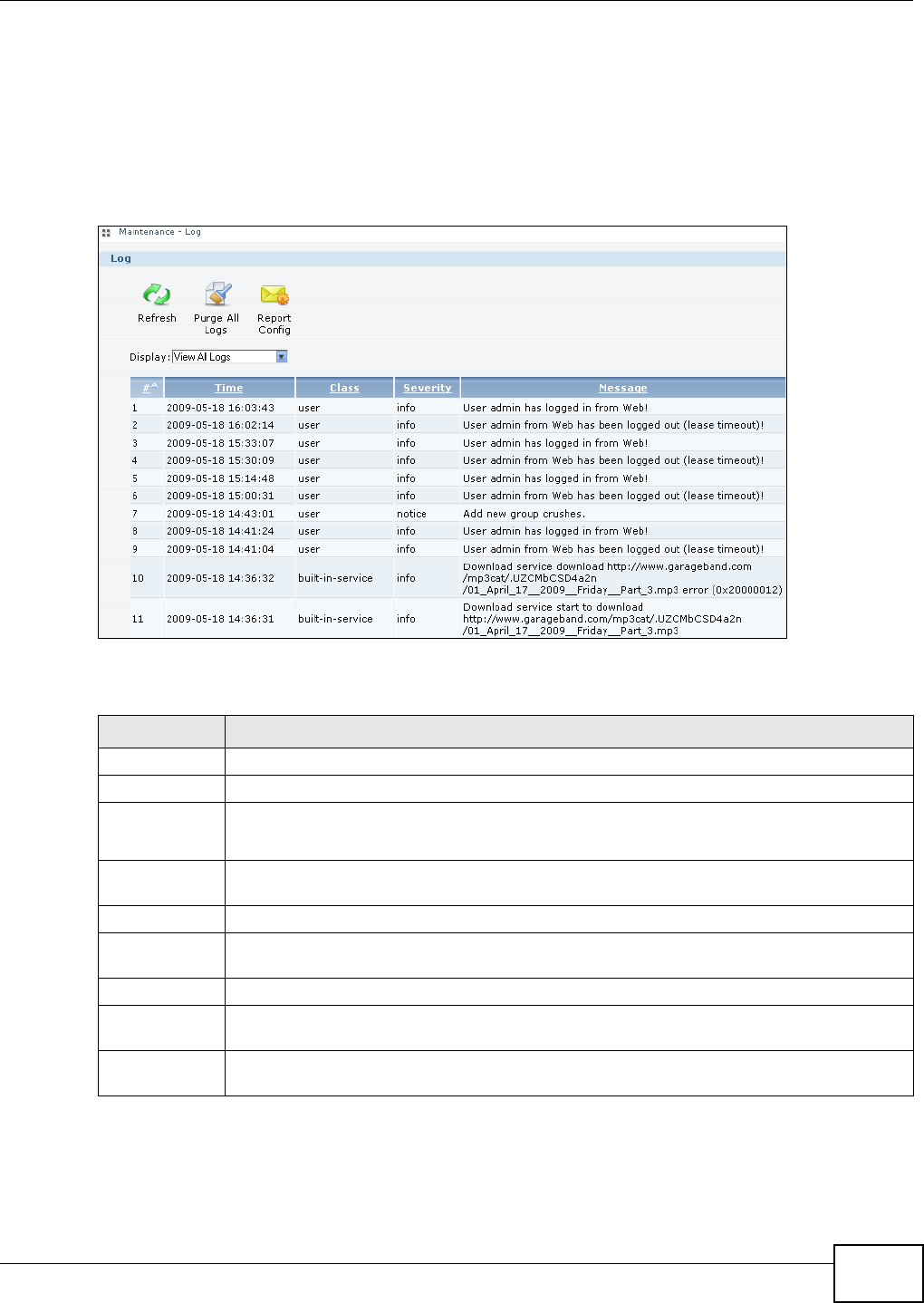
Chapter 17 Maintenance Screens
Media Server User’s Guide 315
17.4 The Log Screen
Click Maintenance > Log to open the following screen.
Use this screen to display all NSA logs. There are at most 512 entries in the log. Older logs are
removed by the system. You cannot download the log file via FTP or CIFS.
Figure 188 Maintenance > Log
The following table describes the labels in this screen.
17.4.1 Report Config Screen
In the Log screen, click Report Config to do the following:
Table 110 Maintenance > Log
LABEL DESCRIPTION
Refresh Click this to update the log display.
Purge all Logs Click this to erase all logs from the NSA.
Report Config Click this to open a screen where you can configure email alerts for logs.
Refer to Section 17.4.1 on page 315 to see the screens for this.
Display The screen always shows all logs by default. Choose a specific log category to view logs for
just that category.
# This is the log entry’s number in the list according to the currently selected sort order.
Time This shows the date and time the log was created. Click the top of the column to sort by
oldest or newest.
Class This displays the log category; see Table 119 on page 323for details.
Severity This displays how serious the log is rated by the NSA. See Table 120 on page 324for more
information.
Message This displays a description of the log. Click the top of the column to sort by alphabetical or
reverse alphabetical order.
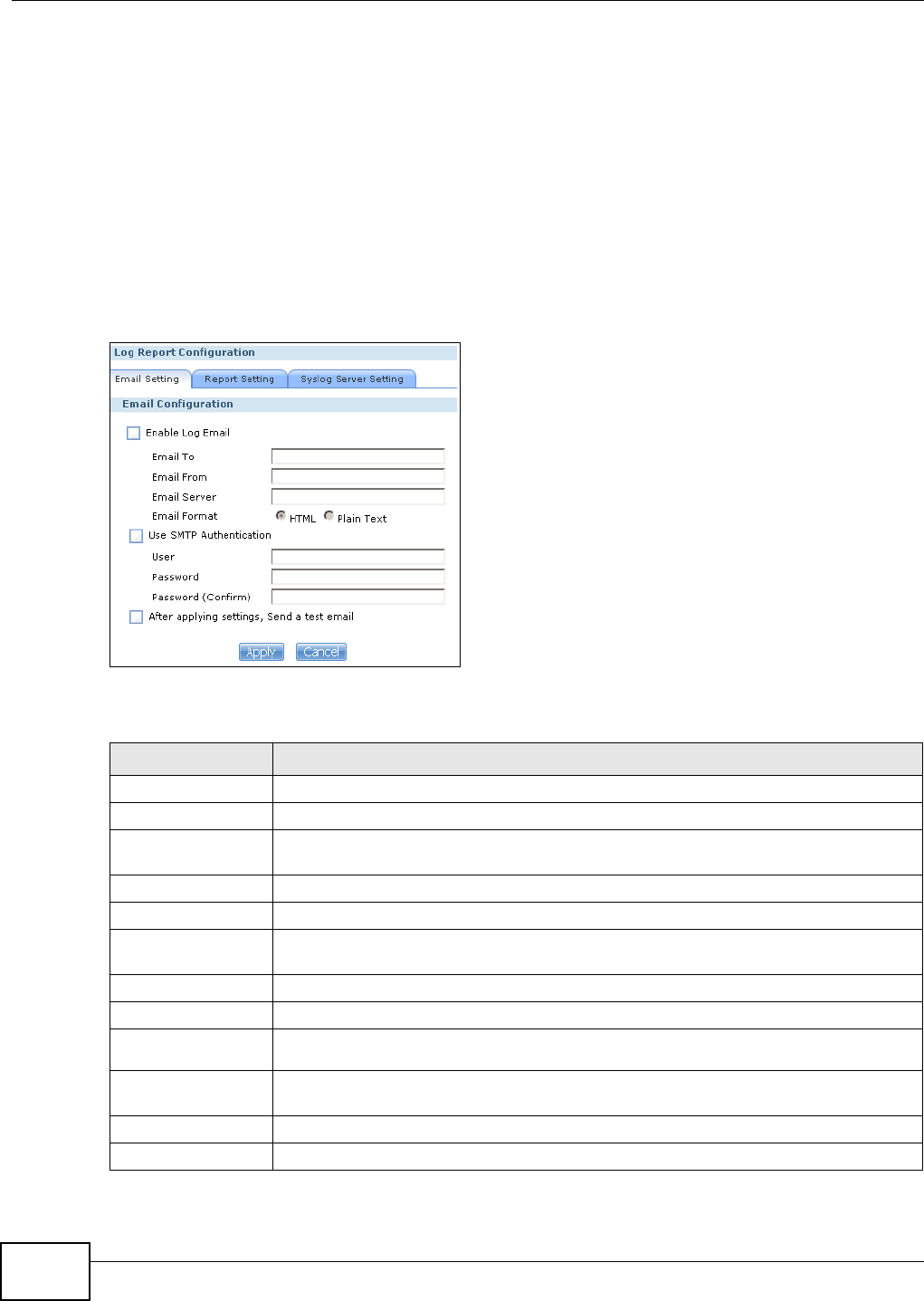
Chapter 17 Maintenance Screens
Media Server User’s Guide
316
•Use the Email Setting screen (Section 17.4.2 on page 316) to enable and configure e-mail
alerts from the NSA.
•Use the Report Setting screen (Section 17.4.3 on page 317) to select the type of alerts you
want to receive through e-mail and schedule when the NSA e-mails the alerts.
•Use the Syslog Server Setting screen (Section 17.4.4 on page 317) to enable the syslog server
and select the categories to include in the log report.
17.4.2 Email Setting
You can enable and configure e-mail alerts from the NSA. In the Report Config screen, click the
Email Setting tab to open the following screen.
Figure 189 Maintenance > Log > Report Config: Email Setting
The following table describes the labels in this screen.
Table 111 Maintenance > Log > Report Config: Email Setting
LABEL DESCRIPTION
Enable Log Email Click this to have the NSA e-mail log alerts to your e-mail account.
Email To Enter the e-mail address where you want to receive the log alerts.
Email From Enter the e-mail address the NSA uses in the From field of the e-mail header for its log
alerts.
Email Server Enter the e-mail server address the NSA uses to send e-mail alerts,
Email Format Select the e-mail format you want the NSA to use in its e-mail alerts.
Use SMTP
Authentication Click this if the e-mail server you want the NSA to use for its e-mail alerts requires a
username and password.
User Enter the username for the e-mail server.
Password Enter the password for the e-mail server.
Password
(Confirm) Re-enter the password to confirm it.
After apply settings,
send a test email Click this to have the NSA send a test e-mail to the settings you have entered.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
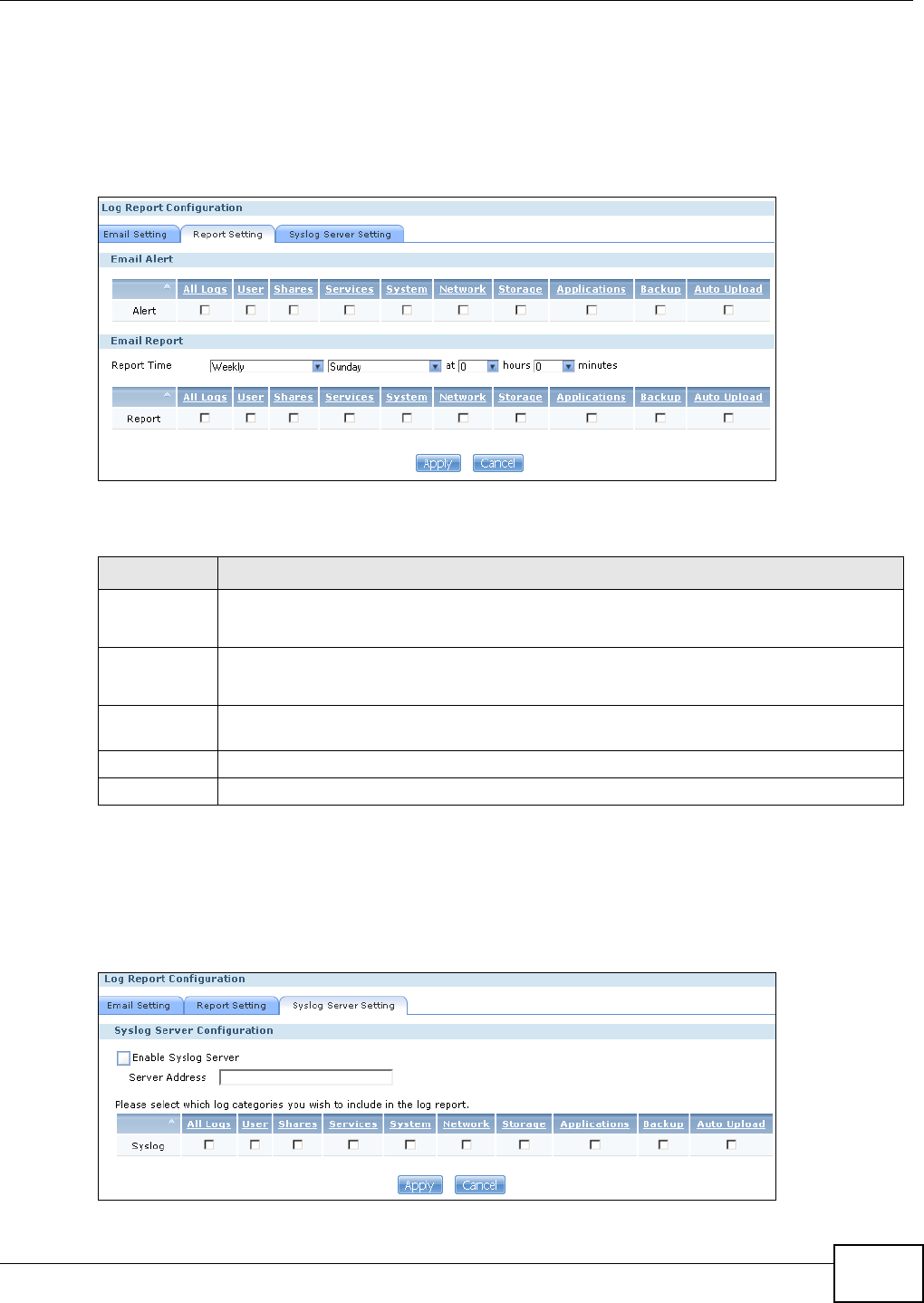
Chapter 17 Maintenance Screens
Media Server User’s Guide 317
17.4.3 Report Setting
You can select the type of alerts you want to receive through e-mail and schedule when the NSA e-
mails the alerts. In the Report Config screen, click the Report Setting tab to open the following
screen.
Figure 190 Maintenance > Log > Report Config: Report Setting
The following table describes the labels in this screen.
17.4.4 Syslog Server Setting
You can enable the syslog server and select the categories to include in the log report. In the
Report Config screen, click the Syslog Server Setting tab to open the following screen.
Figure 191 Maintenance > Log > Report Config: Syslog Server Setting
Table 112 Maintenance > Log > Report Config: Report Setting
LABEL DESCRIPTION
Email Alert Check the type of log alerts you want to receive in your e-mail.
Select All Log to include all types of log alerts.
Email Report Check the type of log alerts you want to receive in your e-mail.
Select All Log to include all types of log alerts.
Report Time Select how often (Weekly, Daily or Hourly), what day in the week (Monday to Sunday)
and which time (hour:minutes) the NSA delivers its e-mail alerts.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
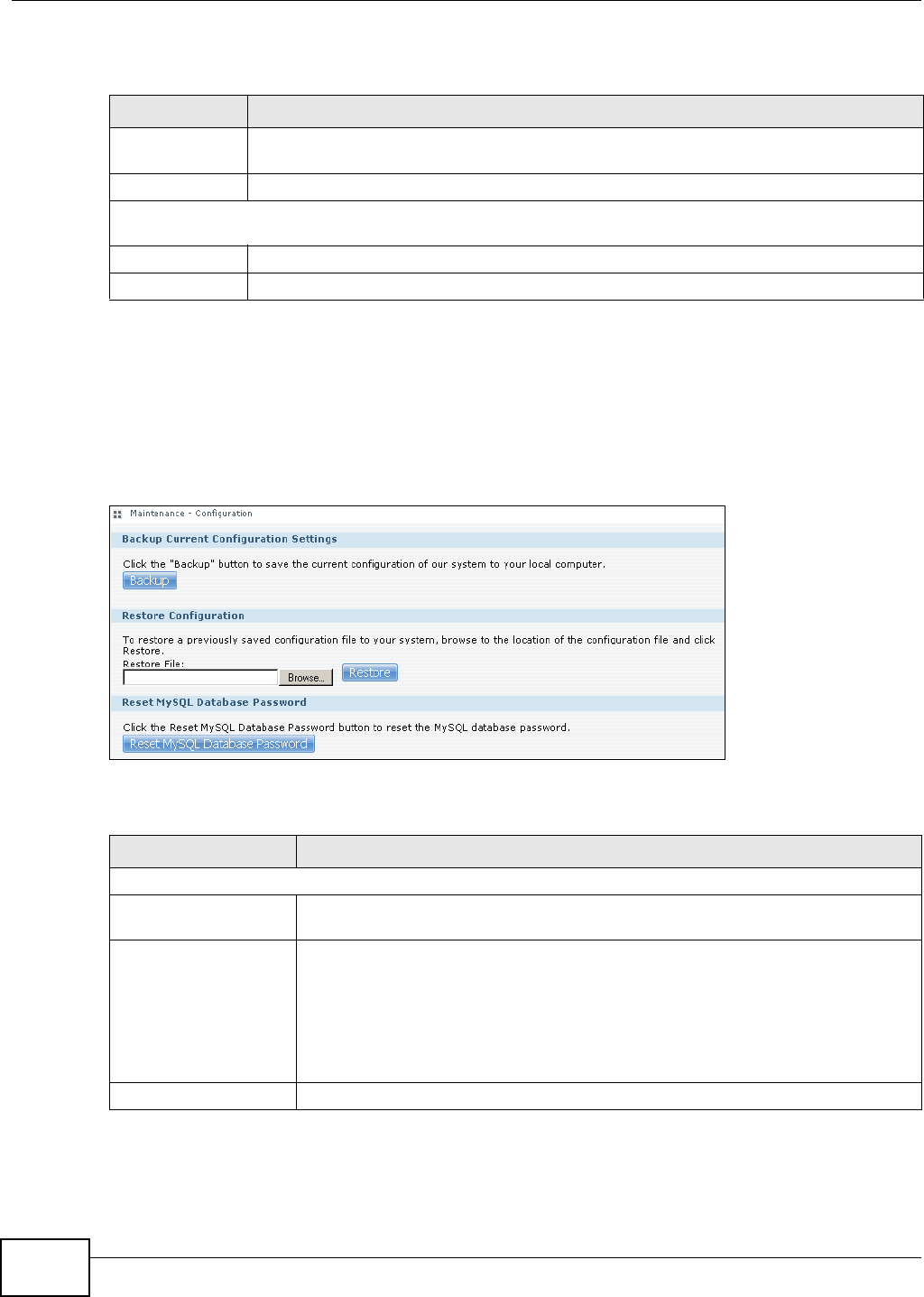
Chapter 17 Maintenance Screens
Media Server User’s Guide
318
The following table describes the labels in this screen.
17.5 The Configuration Screen
Click Maintenance > Configuration to open the following screen. Use this screen to backup or
restore the NSA configuration settings.
Figure 192 Maintenance > Configuration
The following table describes the labels in this screen.
Table 113 Maintenance > Log > Report Config: Syslog Server Setting
LABEL DESCRIPTION
Enable Syslog
Server Check this to enable syslog server.
Server Address Enter the syslog server address you want the NSA to use for its log alerts.
In the table below, check the type of log alerts you want to receive in your e-mail. Select All Log to include all
types of log alerts.
Apply Click this to save your changes.
Cancel Click this to return to the previous screen without saving.
Table 114 Maintenance > Configuration
LABEL DESCRIPTION
Backup Current Configuration Settings
Backup Click this to save the current configuration of the NSA to your computer. A pop-up
screen appears asking you to confirm. Click OK to continue or Cancel to quit.
Restore Configuration When you restore a file configuration, the NSA checks the volumes/share paths on
the NSA and the configuration file.
If the volume exists but the share path is missing in the NSA, the NSA automatically
creates this share path.
If the volume does not exist on the NSA, the Status of the share will show “missing
share icon” in Shares screen (see Table 102 on page 304).
Browse Click this to locate a previously-saved configuration file.
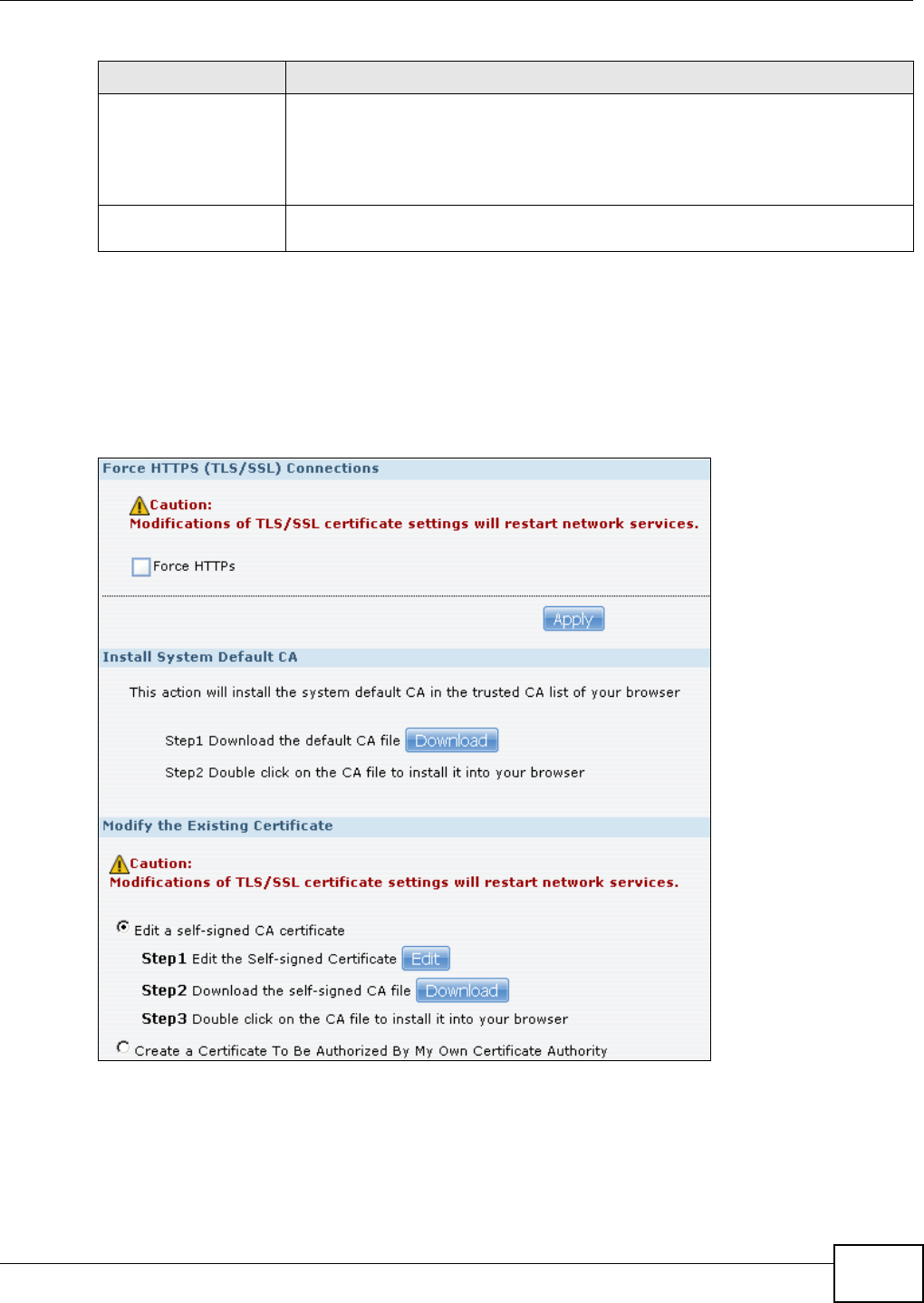
Chapter 17 Maintenance Screens
Media Server User’s Guide 319
17.6 SSL Certification
Click Maintenance > SSL to open this screen, where you can turn on HTTPS, create a public key
certificate, or upload a public key certificate that was issued by a known certificate authority.
Figure 193 Maintenance > SSL
Restore Click this to load the previously-saved configuration file to the NSA. This replaces
your current NSA configuration settings with the settings in the previously-saved
configuration file.
A pop-up screen appears asking you to confirm. Click OK to continue or Cancel to
quit.
Reset MySQL Database
Password Click this to reset the password for your MySQL database.
Table 114 Maintenance > Configuration
LABEL DESCRIPTION
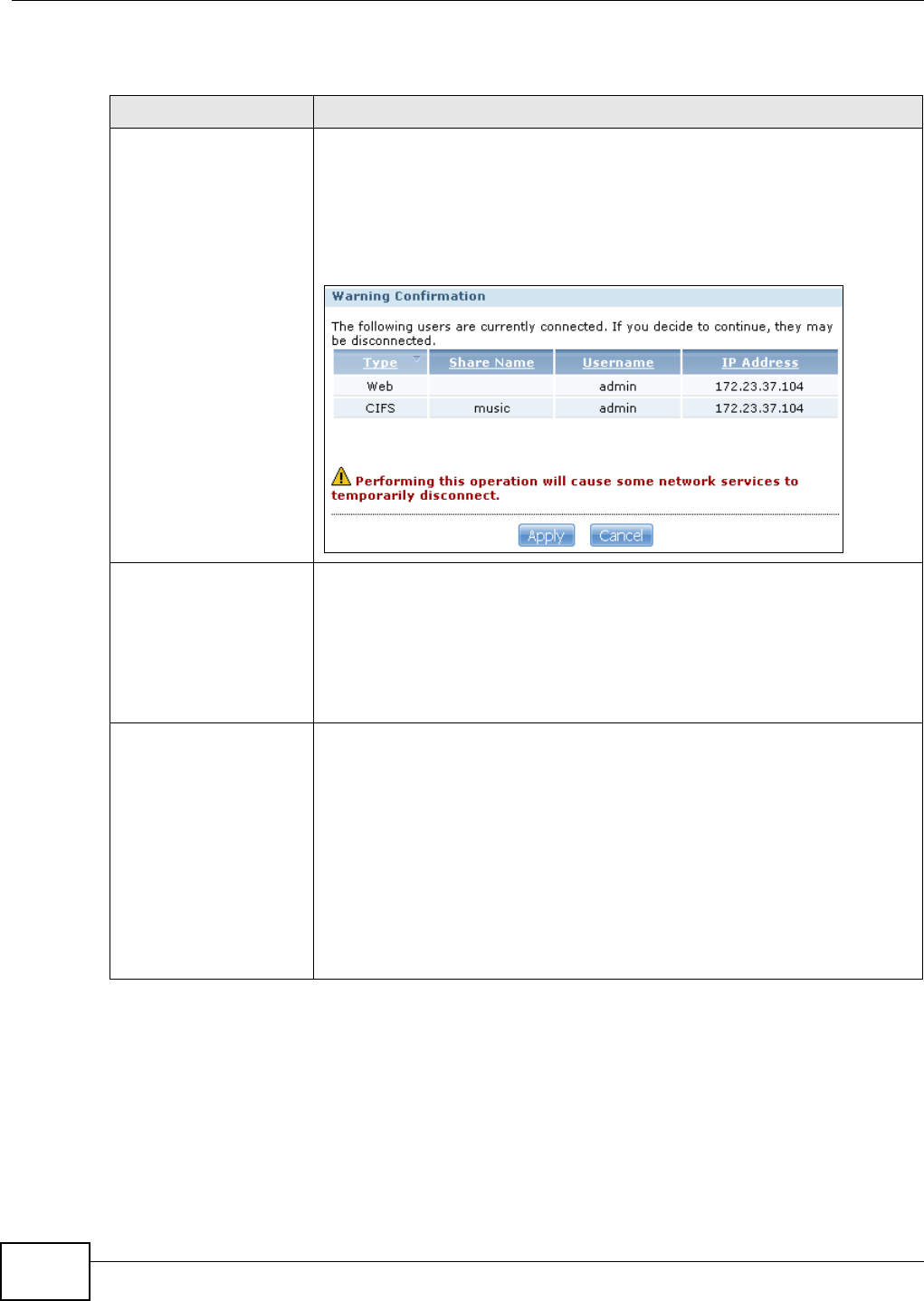
Chapter 17 Maintenance Screens
Media Server User’s Guide
320
The following table describes the labels in this screen.
17.6.1 Modifying or Creating a Certificate
When you select the Edit a self-signed CA certificate option, then click the Edit button, a screen
opens to allow you to make adjustments to the NSA’s public key certificate.
Table 115 Maintenance > SSL
LABEL DESCRIPTION
Force HTTPs Select the Force HTTPs option to turn on the NSA’s web browser security.
Anyone who connects via HTTPS to the NSA must install the public key certificate
associated with it.
Note: The NSA will restart the web configurator after you click Apply.
The NSA displays a warning screen if applying your change may disconnect some
users. Click Apply if you want to continue.
Install System Default CA Click Download button to save a copy of the NSA’s public key certificate to your
local computer. This is useful for installing the certificate without having to
connect to the NSA, or for sending by email to other users for them to install prior
to logging into the NSA for the first time. After saving the certificate to your
computer, double-click it to install it.
Note: Each web browser handles certificate installation differently. See Appendix D
on page 411 for more information.
Modify the Existing
Certificate Select Edit a self-signed CA certificate, then follow the on-screen instructions
for creating a public key certificate signed by the NSA as the local certificate
authority.
Note: Use certificates created and signed by the NSA if the device is not open to
external access.
Select Create a certificate authorized by other CA, then follow the on-screen
instructions to install a certificate that has been authorized by a third-party
certificate authority.
Note: Use this method if the device is open to external access, such as allowing
users to connect through the Internet using FTP over TLS or HTTPs.
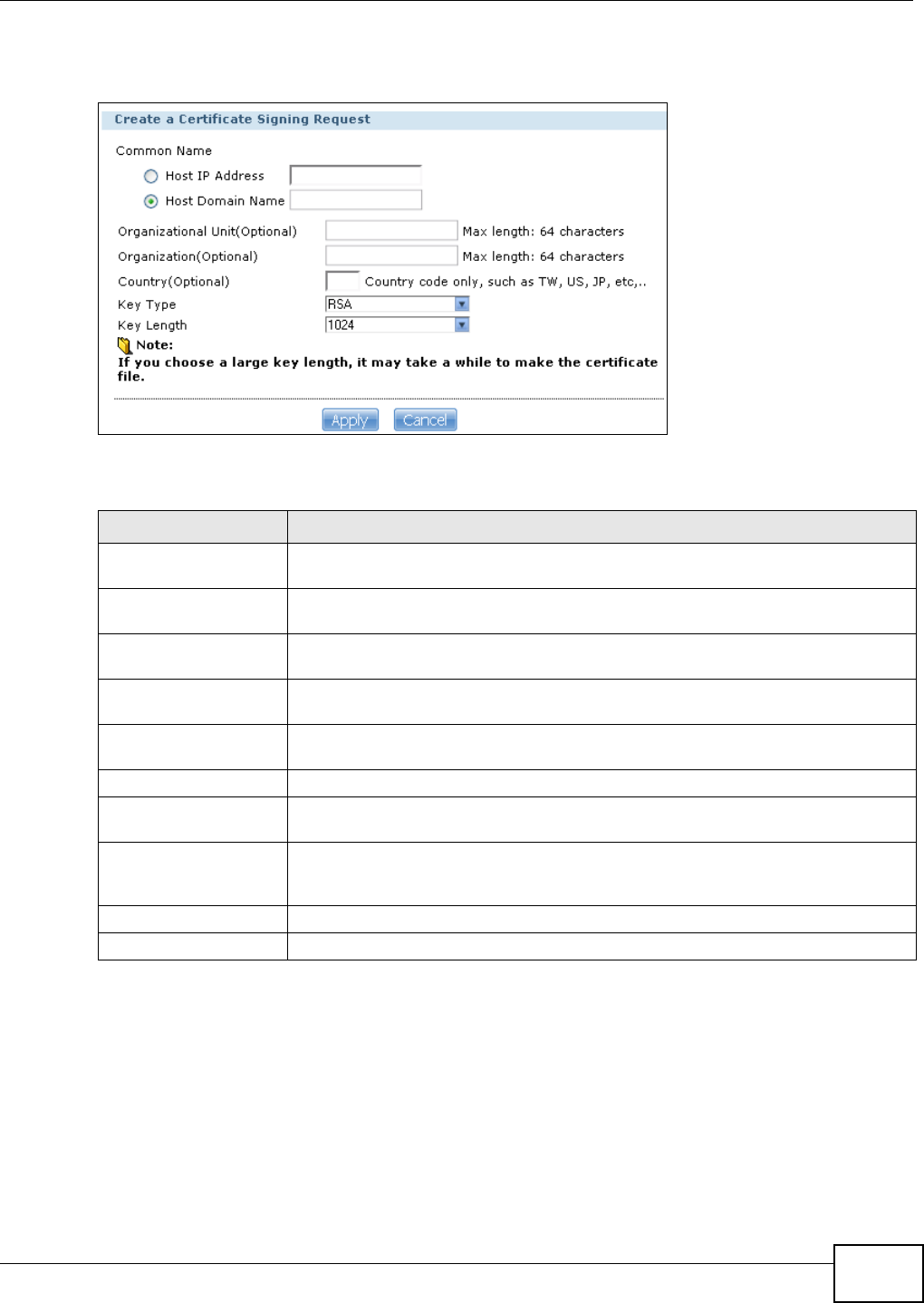
Chapter 17 Maintenance Screens
Media Server User’s Guide 321
The screen is also the same for the Create a certificate authorized by other CA option.
Figure 194 Maintenance > SSL > Create or Edit a Certificate
The following table describes the labels in this screen.
17.7 The Firmware Upgrade Screen
Use this screen to upgrade the NSA firmware. You should first have downloaded the latest firmware
files from the ZyXEL website.
Do not turn off the NSA while it is upgrading the firmware or you may
render it unusable.
Table 116 Maintenance > SSL > Create or Edit a Certificate
LABEL DESCRIPTION
Common Name This name describes the certificate’s origin, either in the form of an IP address or a
domain name.
Host IP Address Select this option and enter the NSA’s IP address if you want to use this for the
common name.
Host Domain Name Select this option and enter the NSA’s domain name if you want to use this for the
common name
Organizational Unit
(Optional) Enter this name of the organizational unit which owns or maintains the NSA. This is
an optional field.
Organization (Optional) Enter this name of the organization or company which owns or maintains the NSA.
This is an optional field.
Country (Optional) Enter this name of the country in which the NSA is located. This is an optional field.
Key Type Select the certificate’s key type, either RSA or DSA. RSA is a public-key encryption
and digital signature algorithm, while DSA is only a digital signature algorithm.
Key Length Select the encryption key length. The longer the key, the better the encryption
security. The only drawback to having a long key is that the file encrypted with it
swells in size as well.
Apply Click this to save your changes.
Cancel Click this to discard changes and close the window.
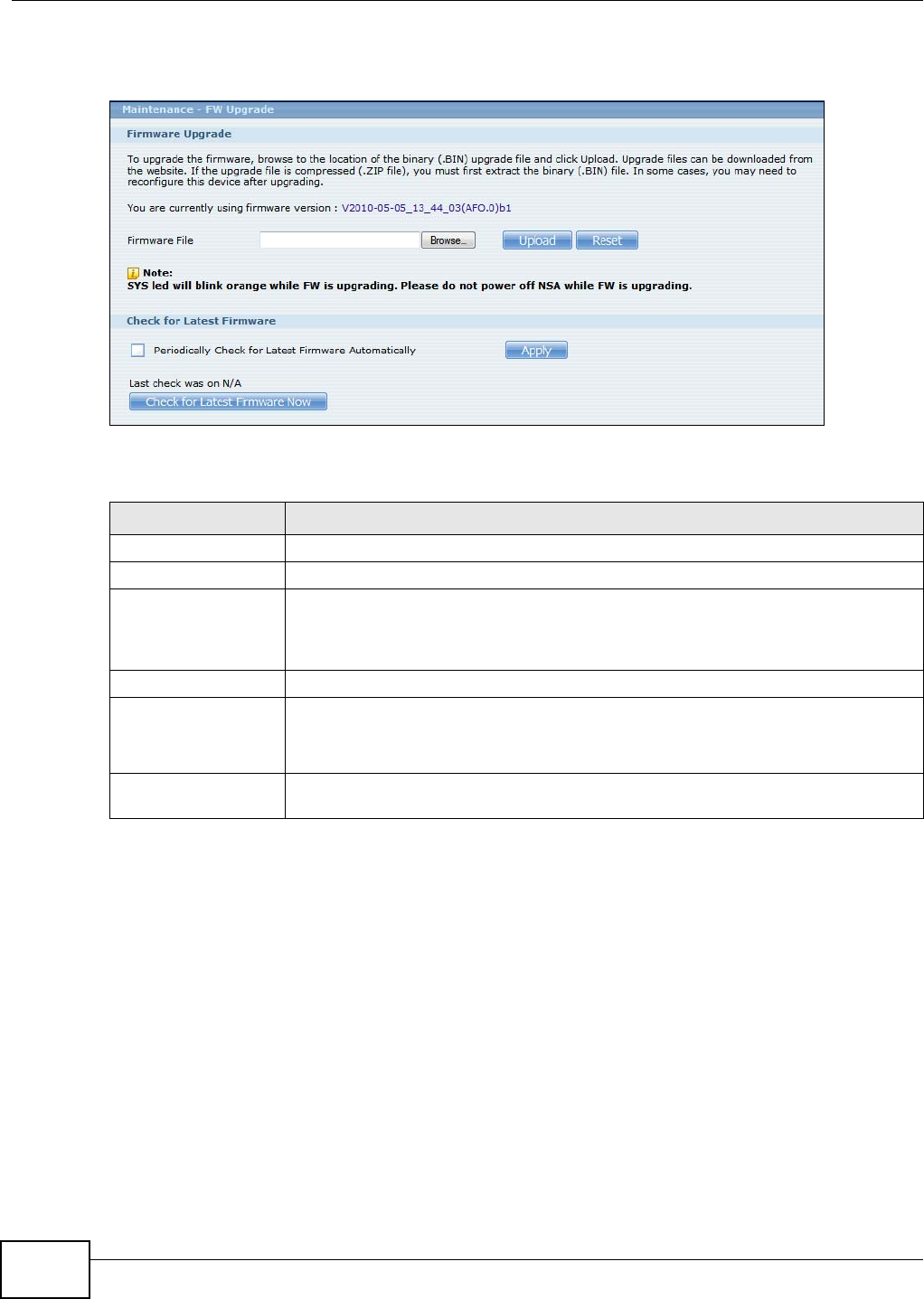
Chapter 17 Maintenance Screens
Media Server User’s Guide
322
Click Maintenance > FW Upgrade to open the following screen.
Figure 195 Maintenance > FW Upgrade
The following table describes the labels in this screen.
17.8 The Shutdown Screen
Use this screen to turn off the NSA or perform a software restart. A software restart is faster than
turning the NSA off and then turning it on again. Before shutting down or restarting, check the
System Status > Active Sessions screen to make sure that no one is logged into the NSA or
transferring files to or from the NSA.
Table 117 Maintenance > FW Upgrade
LABEL DESCRIPTION
Firmware File Type the location of the firmware file you want to upload
Browse Click this to find the file on your computer
Upload Click this to upload the new firmware. The NSA automatically restarts after you
upgrade. Wait until the restart completes before accessing the NSA again. If you
interrupt the upgrade, then the NSA may become unusable. See Section 21.1 on page
365 for your model’s LED behavior during firmware upgrade.
Reset Click this to refresh the screen.
Periodically Check for
Latest Firmware
Automatically
Select this to have the NSA regularly check ZyXEL’s server for updated firmware. The
NSA notifies you at login if a new firmware is available.
Click Apply to save this field’s setting.
Check for Latest
Firmware Now Click this to check ZyXEL’s server for updated firmware.
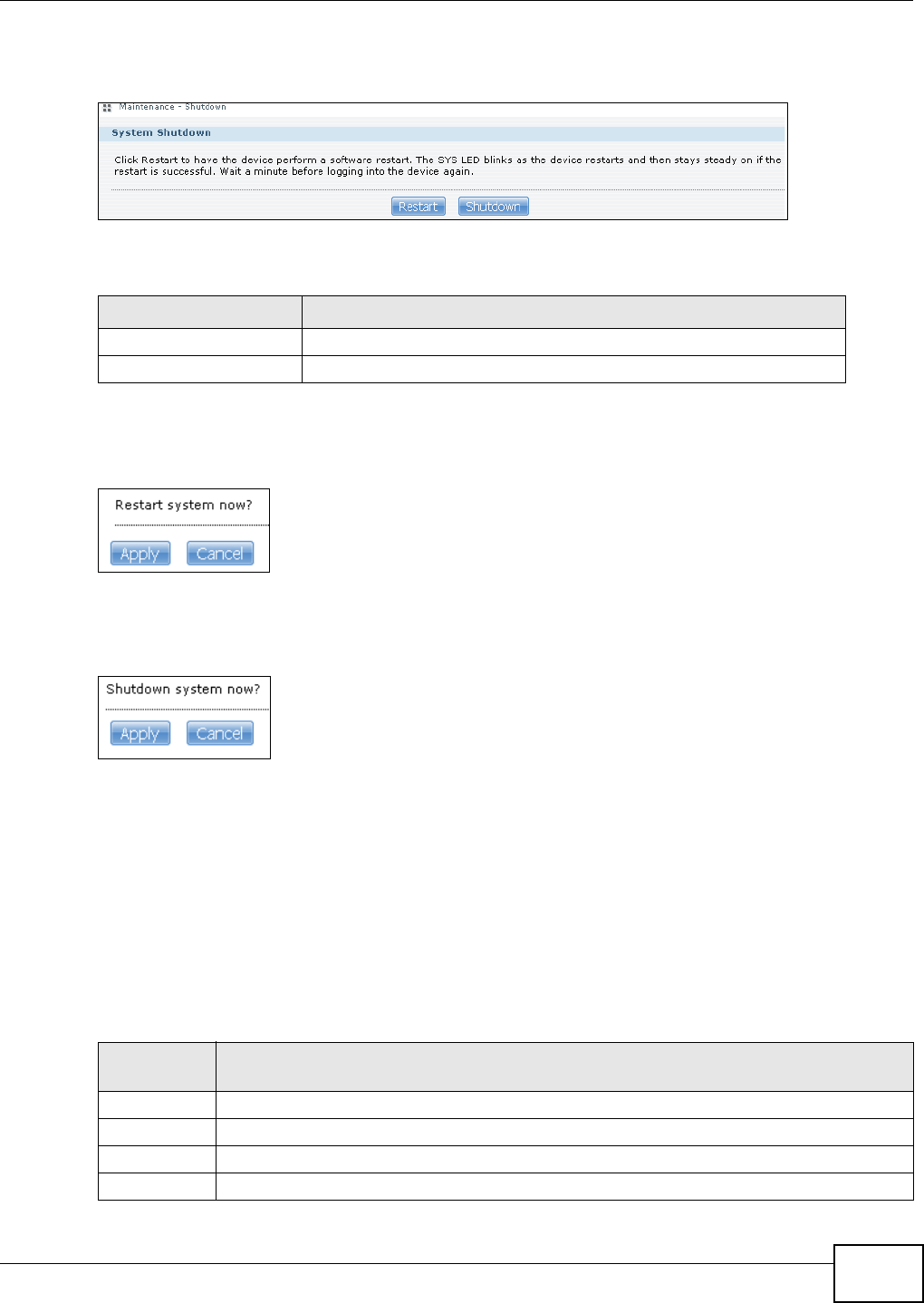
Chapter 17 Maintenance Screens
Media Server User’s Guide 323
Click Maintenance > Shutdown to open the following screen.
Figure 196 Maintenance > Shutdown
The following table describes the labels in this screen.
When you click the Restart button a pop-up screen will appear asking you to confirm. Click OK to
continue or Cancel to quit the restart.
Figure 197 Maintenance > Shutdown > Confirm Restart
When you click the Shutdown button a pop-up screen will appear asking you to confirm. Click OK
to continue or Cancel to quit the shutdown.
Figure 198 Maintenance > Shutdown > Confirm Shutdown
17.9 Technical Reference
This section provides technical background information on the topics discussed in this chapter.
17.9.1 Log Classes
The following table shows information on log classes.
Table 118 Maintenance > Shutdown
LABEL DESCRIPTION
Restart Click this to have the device perform a software restart.
Shutdown Click this to shut down the system and restart it again later.
Table 119 Log Classes
LOG
CATEGORY DESCRIPTION
Users This log class shows information on user access to the NSA.
Shares This log class shows information on shares being created or deleted.
Services This log class shows information on the operation of the NSA’s built-in services.
System This log class shows all other system related messages.
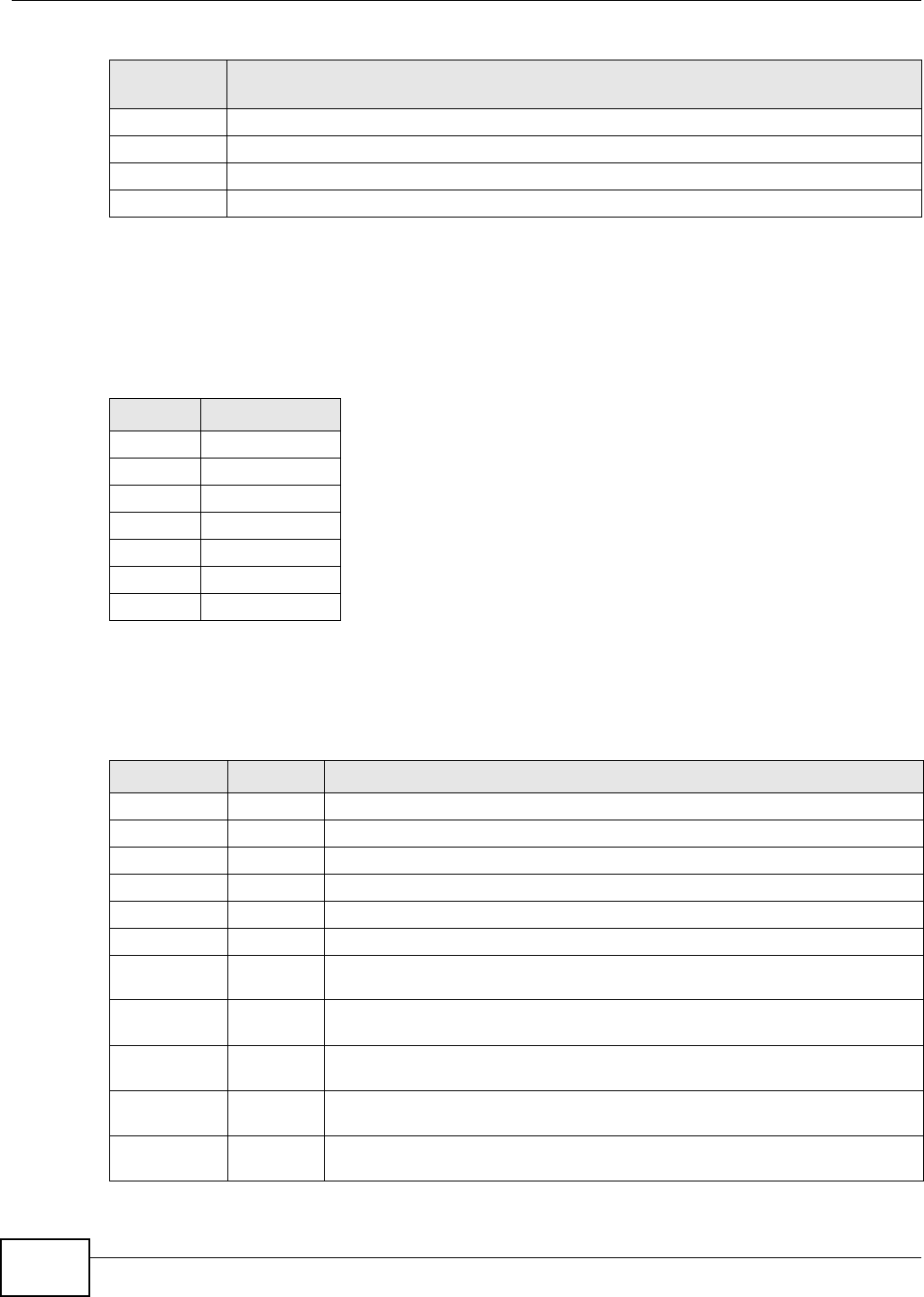
Chapter 17 Maintenance Screens
Media Server User’s Guide
324
17.9.2 Log Severity Levels
The following table shows information on log severity levels. Levels range from 0 to 6 with 0 being
the most severe level log and 6 being an informational log only. Log levels are not displayed in the
logs and are for your reference only.
17.9.3 Log Messages
Here are some example log messages.
Network This log class shows information on network configuration, setting changes and so on.
Storage This log class shows information on the NSA’s internal and external storage activities.
Backup This log class shows information on all backup-related activities.
Auto Upload This log class shows information on automatic uploads done by the NSA.
Table 119 Log Classes (continued)
LOG
CATEGORY DESCRIPTION
Table 120 Log Severity Levels
LEVEL DESCRIPTION
0Emergency
1Alert
2Critical
3 Error
4 Warning
5Notice
6Info
Table 121 Log Messages
CLASS SEVERITY MESSAGE
Auto upload INFO %s is queued.
Auto upload INFO %s uploaded (Flickr or YouTube Upload).
Auto upload WARNING error uploading "%s" (%s): %s
Auto upload INFO %s will not be uploaded to %s for there is already a duplicate file.
Auto upload INFO Failed to upload %s to %s (FTP Upload) : %s
Auto upload INFO Successfully upload %s to %s (FTP Upload)
Copy/Sync
Button ERROR [USB %s] Backup Folder Does Not Exist.
Copy/Sync
Button ERROR [USB %s] Target Folder Does Not Exist.
Copy/Sync
Button ERROR [USB Sync] Failed at %s: It is a Folder in Internal Volume. But It is not a Folder
in USB.
Copy/Sync
Button ERROR [USB Sync] Failed at %s: It is a Folder in USB. But It is not a Folder in Internal
Volume.
Copy/Sync
Button ERROR [USB Sync] Failed at File %s.
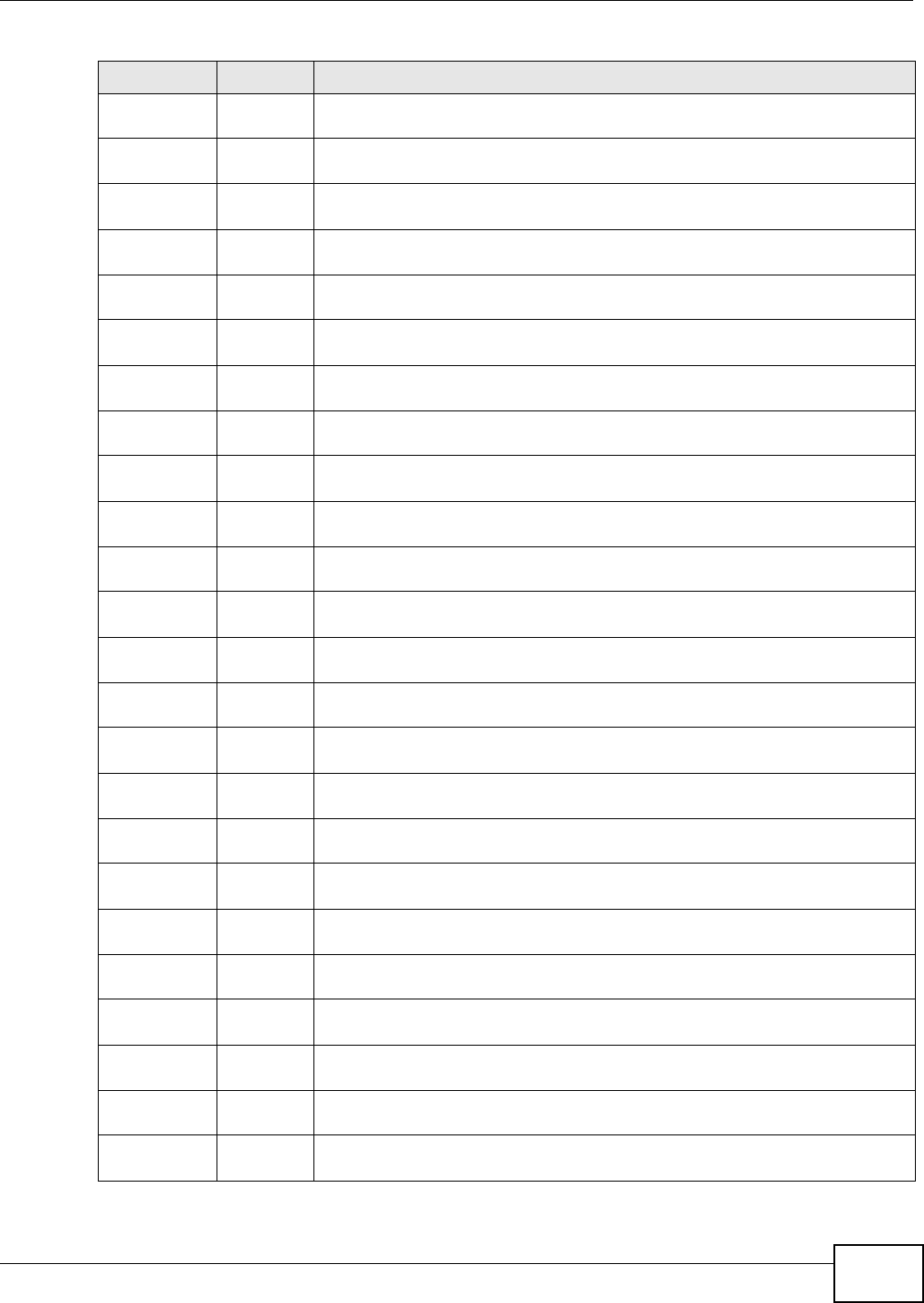
Chapter 17 Maintenance Screens
Media Server User’s Guide 325
Copy/Sync
Button ERROR [USB Sync] Sync Failed at Folder %s.
Copy/Sync
Button ERROR Modify COPY/SYNC Button Configuration: %s
Copy/Sync
Button ERROR Please Change Your Folder Name. Invalid Path: %s
Copy/Sync
Button INFO [USB Sync] Copying %s from Internal Volume to Backup Folder.
Copy/Sync
Button INFO [USB Sync] Copying %s from Internal Volume to USB.
Copy/Sync
Button INFO [USB Sync] Copying %s from USB to Backup Folder.
Copy/Sync
Button INFO [USB Sync] Copying %s from USB to Internal Volume.
Copy/Sync
Button INFO [USB Sync] Deleting %s from Internal Volume.
Copy/Sync
Button INFO [USB Sync] Deleting %s from USB.
Copy/Sync
Button INFO [USB Sync] Deleting %s from USB Recursively.
Copy/Sync
Button INFO [USB Sync] Finished. Elapsed Time %s Seconds.
Copy/Sync
Button INFO [USB Sync] Moving %s from Internal Volume to Backup Folder.
Copy/Sync
Button INFO [USB Sync] Moving %s from USB to Backup Folder
Copy/Sync
Button INFO [USB Sync] Skip %s: File not Exist
Copy/Sync
Button INFO [USB Sync] Skip %s: Not a Regular File.
Copy/Sync
Button INFO [USB Sync] Start Pre-Processing: Generating File Lists.
Copy/Sync
Button NOTICE [USB Sync] Start Copying Files.
Download
Service ERROR Download service cannot find a volume
Download
Service ERROR Download service failed to find ipfilter.dat
Download
Service INFO Download service add a URL download job %s
Download
Service INFO Download service delete %s by user
Download
Service INFO Download service download %s error (0x%08x)
Download
Service INFO Download service download %s finished in %s
Download
Service INFO Download service found a new torrent file %s
Table 121 Log Messages (continued)
CLASS SEVERITY MESSAGE

Chapter 17 Maintenance Screens
Media Server User’s Guide
326
Download
Service INFO Download service initialized
Download
Service INFO Download service pause %s by user
Download
Service INFO Download service set %s to %s priority by user
Download
Service INFO Download service set default download location to %s
Download
Service INFO Download service set max BT download rate to %d KB/s by user
Download
Service INFO Download service set max BT upload rate to %d KB/s by user
Download
Service INFO Download service set max download slot to %d
Download
Service INFO Download service set seeding time to %d minutues
Download
Service INFO Download service set TCP port to %d and UDP port to %d
Download
Service INFO Download service set torrent monitor location to %s
Download
Service INFO Download service start to download %s
Download
Service INFO Download service stopped
Download
Service INFO Download service suspend %s because of no data income detected or to limit
max download slot
Download
Service INFO Download service add comment %s to %s by user
Download
Service INFO Download service set min upload/download ratio to %d%
Download
Service INFO Download service set max seed slot to %d
Download
Service INFO Download service start loading ipfilter.dat
Download
Service INFO Download service clear all ipfilter rules
Download
Service INFO Download service blocked peer removed from peer list
Download
Service INFO Download service disconnected blocked peer
Download
Service INFO Download service incoming connection blocked by IP filter
Download
Service INFO Download service peer from tracker blocked by IP filter
Download
Service INFO Download service abort loading ipfilter.dat
Download
Service INFO Download service will update ipfilter.dat from %s after %d day(s)
Table 121 Log Messages (continued)
CLASS SEVERITY MESSAGE
Chapter 17 Maintenance Screens
Media Server User’s Guide 327
Download
Service INFO Download service added %d rules from ipfilter.dat
Download
Service INFO Download service detected invalid ip range %s in ipfilter.dat
Download
Service WARNING Download service default location does not exist. Load default
Download
Service WARNING Download service default torrent location does not exist. Load default
Groups NOTICE Add new group %s.
Groups NOTICE Delete group %s.
Network NOTICE %s is active because of changing Port Group. Enable DHCP client.
Network NOTICE %s is inactive because of changing Port Group. Disable DHCP client.
Network NOTICE %s MTU > (%s MTU - 8), %s may not work correctly.
Network NOTICE (%s MTU - 8) < %s MTU, %s may not work correctly.
Network NOTICE Add interface %s.
Network NOTICE Because %s link down. Default route will not apply until %s link up.
Network NOTICE Because base interface %s will be disabled.Interface %s is disabled now.,
base_ud_iface
Network NOTICE Network Config setting is changed
Network NOTICE Interface %s was disabled.
Network NOTICE Interface %s was enabled.
Network NOTICE Port Group on %s is changed. Renew DHCP client.
Network NOTICE Account pppoe was changed
Network NOTICE Add account pppoe
Network NOTICE ADD interface ppp0
Network NOTICE Interface ppp0 will reapply because Device-Ha become active status.
Network NOTICE Interface ppp0 will reapply because Device-Ha is not running.
Network NOTICE Network port is disabled
Network NOTICE Network port is enabled
Services INFO HTTP management port has changed to %s
Services INFO Clock timezone is set to GMT%s
Services INFO Clock timezone is set to default
Services INFO Clock daylight saving is enabled
Services INFO Clock daylight saving is disabled
Services INFO Clock has disable daylight saving
Services INFO MyClock has enable daylight saving
Services INFO MyClock has set timezone to %s
Services INFO MyClock has set timezone to default
Services INFO The date and time are updated from NTP server.
Services INFO The date and time are updated manually.
Services INFO The time is updated manually.
Services NOTICE FTP server stops
Services NOTICE FTP server starts
Table 121 Log Messages (continued)
CLASS SEVERITY MESSAGE

Chapter 17 Maintenance Screens
Media Server User’s Guide
328
Services NOTICE MyClock has changed daylight saving interval
Services NOTICE MyClock has disabled daylight saving interval
Services NOTICE NTP server has set to '%s'
Services NOTICE NTP server has set to null
Services NOTICE The NTP service is disabled.
Services NOTICE The NTP service is enabled.
Services WARNING Reaching Maximum Allowed Rules
Services WARNING Rule is empty
Services WARNING The Rule Does Not Exist
Shares INFO Expire recycle-bin finish for share %s, process time: %s seconds, remove %s
file (%s bytes)
Shares NOTICE Add new disabled share %s for unshared folder: %s in volume: %s.
Shares NOTICE Add new share %s.
Shares NOTICE Delete share %s.
Shares NOTICE Purge all files in recycle-bin folder in share: %s.
Shares NOTICE Recycle-bin disabled. Remove recycle-bin folder in share: %s.
Storage ERROR Eject External Disk (%s): FAILED
Storage INFO Eject External Disk (%s): SUCCESS
Storage ERROR Relabel Raid to [%s]: FAILED
Storage ERROR Start Repairing Degraded Raid by disk%s: FAILED
Storage INFO Relabel Raid to [%s]: SUCCESS
Storage INFO Start Repairing Degraded Raid by disk%s: SUCCESS
Storage NOTICE Auto Repair Degraded RAID by disk%s.
Storage NOTICE There is a RAID Degraded.
Storage ERROR Cancel External Volume Scan: FAILED
Storage ERROR Cancel Internal Volume Scan: FAILED
Storage ERROR Cannot Unmount Volume and RAID. System Busy Using Volume and RAID:
Please Reboot and Try Again
Storage ERROR Create External Normal Volume [%s] (%s): FAILED
Storage ERROR Create Internal Volume [%s] (%s): FAILED
Storage ERROR Rename External Volume to [%s]: FAILED
Storage ERROR Scan External Volume: FAILED
Storage ERROR Scan Internal Volume (%s operation): FAILED
Storage INFO Cancel External Volume Scan: SUCCESS
Storage INFO Cancel Internal Volume Scan: SUCCESS
Storage INFO Create External Normal Volume [%s] (%s): SUCCESS
Storage INFO Create Internal Volume [%s] (%s): SUCCESS
Storage INFO Rename External Volume to [%s]: SUCCESS
Storage INFO Scan External Volume: SUCCESS
Storage INFO Scan Internal Volume (%s operation): SUCCESS
System INFO NTP update failed
System INFO NTP updates successfully from %s
Table 121 Log Messages (continued)
CLASS SEVERITY MESSAGE
Chapter 17 Maintenance Screens
Media Server User’s Guide 329
System INFO NTP fails to update from %s
System INFO Device is rebooted by administrator!
System INFO Device is shutdown by administrator!
System NOTICE DNS server is changed.
System NOTICE Hostname is cleared.
System NOTICE Hostname is set to '%s'.
System NOTICE System description is changed.
System NOTICE System description is empty now.
System NOTICE DNS server setting is changed
System NOTICE DNS server address is changed to be given from DHCP server
System NOTICE DNS server address is changed to be assigned by user
System NOTICE Name server is changed.
USB NOTICE An external APC UPS device is plugged/unplugged.
USB NOTICE An external Mass Storage device is plugged/unplugged.
USB NOTICE An external Printer device is plugged/unplugged.
USB NOTICE An external USB hub device is plugged/unplugged.
Users ALERT Failed %s login attempt (incorrect password or inexistent username)
Users ALERT Failed %s login attempt (incorrect password or inexistent username)
Users INFO User %s has logged in from %s!
Users INFO User %s has logged out from %s!
Users INFO User %s from %s has been logged out (re-auth timeout)!
Users INFO User %s from %s has been logged out (lease timeout)!
Users NOTICE Add new user %s by %s from %s.
Users NOTICE User %s password has been changed.
Users NOTICE Delete user %s by %s from %s.
Users NOTICE The user %s from %s has attempted to change the user %s password but old
password verification fail.
Users NOTICE User %s on %u.%u.%u.%u has been denied access from %s
Users NOTICE User %s password has been changed by %s from %s.
Backup/
Restore ERROR When query remote target [%s]: %s
Backup/
Restore INFO Backup job [%s] successfully
Backup/
Restore ERROR When backup [%s]: %s
Backup/
Restore ERROR When backup [%s], error happens: %s
Backup/
Restore INFO Start to restore backup job [%s].
Backup/
Restore INFO Restore backup job [%s] successfully.
Backup/
Restore ERROR Restore backup job [%s] failed: %s
Table 121 Log Messages (continued)
CLASS SEVERITY MESSAGE
Chapter 17 Maintenance Screens
Media Server User’s Guide
330
Backup/
Restore INFO Start to restore backup job [%s] from [%s].
Backup/
Restore INFO Restore from [%s] successfully.
Backup/
Restore ERROR Restore from [%s] failed: %s
Backup/
Restore ERROR When restore [%s]: %s
Backup/
Restore ERROR When restore job [%s], error happens: %s
Power
Management INFO Job [%s] is triggered by schedule
Power
Management INFO Job [%s] is triggered by user
Power
Management ERROR Job [%s] is resulted as failed
Power
Management INFO Job [%s] is finished successfully
Power
Management INFO Job [%s] is pending because other job is running
Power
Management INFO Job [%s] is canceled by user
Power
Management INFO Restore job [%s] is triggered by user
Power
Management INFO [Power On] schedule is triggered.
Power
Management INFO [Power Off] schedule is triggered.
Power
Management INFO [Reboot] schedule is triggered.
Table 121 Log Messages (continued)
CLASS SEVERITY MESSAGE
Media Server User’s Guide 331
CHAPTER 18
Protecting Your Data
18.1 Overview
This chapter compares the different ways of protecting data on the NSA and explains how to use
backup management software included on the CD.
18.2 Protection Methods
There are a variety of ways to protect your data on the NSA. Below is a summary table of what can
be done in each situation.
The following sections describe these methods in more detail. See Section 8.6.3 on page 167 for
more information on RAID.
18.3 Configuration File Backup and Restoration
Use the Maintenance > Configuration menus to create a file of your NSA configurations such as
passwords, shares and volumes created, network settings and so on. If you’re going to do some
major configuration changes, then it is advisable to create a configuration backup file. If things go
wrong after you make the configuration changes, you can always go back to the previous
configuration by restoring an earlier configuration file.
Table 122 Overview of Protection Methods
SITUATION ACTION
Unexpected NSA behavior after configuration
changes Back up the NSA configuration file before you make
major configuration changes.
Need to transfer data from your computer to the
NSA after volume(s) have been created Use the Memeo Autobackup program.
Data infected by virus Use anti-virus software on your computer to scan files
before saving them onto the NSA. Although this may be
slow so you may want to schedule it to occur while no
one is using the NSA.
Use a firewall with anti-virus capability on your network.
Hard drive malfunction. Use RAID.
NSA malfunction
Network down
Natural disaster such as a fire or earthquake occurs
where your NSA is located
Back up data to another NSA or external USB hard
drive.

Chapter 18 Protecting Your Data
Media Server User’s Guide
332
If you forgot the NSA password, then use the RESET button (see Section 1.1.5 on page 23) to
return the NSA to the factory default configuration.
Note: Configuration File Backup and Restoration does not affect data (your files and
folders), volumes on the NSA.
18.4 Memeo Autobackup
Use the Memeo Autobackup software (included on the CD) on your computer to schedule and
manage backups. You can backup from your computer to the NSA. You can also backup from one
NSA on your network to another. You can set the Memeo Autobackup software to automatically
back up files from your computer to the NSA whenever you modify the files.
Install the included DLNA-compliant Memeo Autobackup software on your Windows XP or later
computers to let them browse and play files stored on the NSA.
Note: The Memeo Autobackup program uses the same network port as the NAS Starter
Utility to discover the NSA. To avoid a port conflict, do not run the Memeo
Autobackup program at the same time as the NAS Starter Utility.
Use the Memeo Autobackup software included on the CD to automatically back up selected files
from your computer to the NSA whenever you modify the files.
Memeo Autobackup works with Windows XP, Windows Vista, and both the 32 bit and 64 bit versions
of Windows 7.
18.4.1 Memeo Autobackup Installation and Setup
Note: The Memeo Autobackup program uses the same network port as the discovery
utility to discover the NSA. To avoid a port conflict, turn off the discovery utility
before using Memeo Autobackup.
1Since a computer restart is required, close your other files and programs before installing the
Memeo Autobackup software.
2Insert the included CD into your CD-ROM drive. Click the Tools icon in the screen that displays.
Then click Memeo Instant Backup Software.
Note: If this screen does not display, use Windows Explorer (My Computer) to go to the
CD-ROM (commonly drive D). Double-click setup.exe.
3Follow the instructions to install the software.
Note: Memeo Autobackup requires Microsoft.NET version 2.0. The wizard installs it for
you if it is not already on your computer.
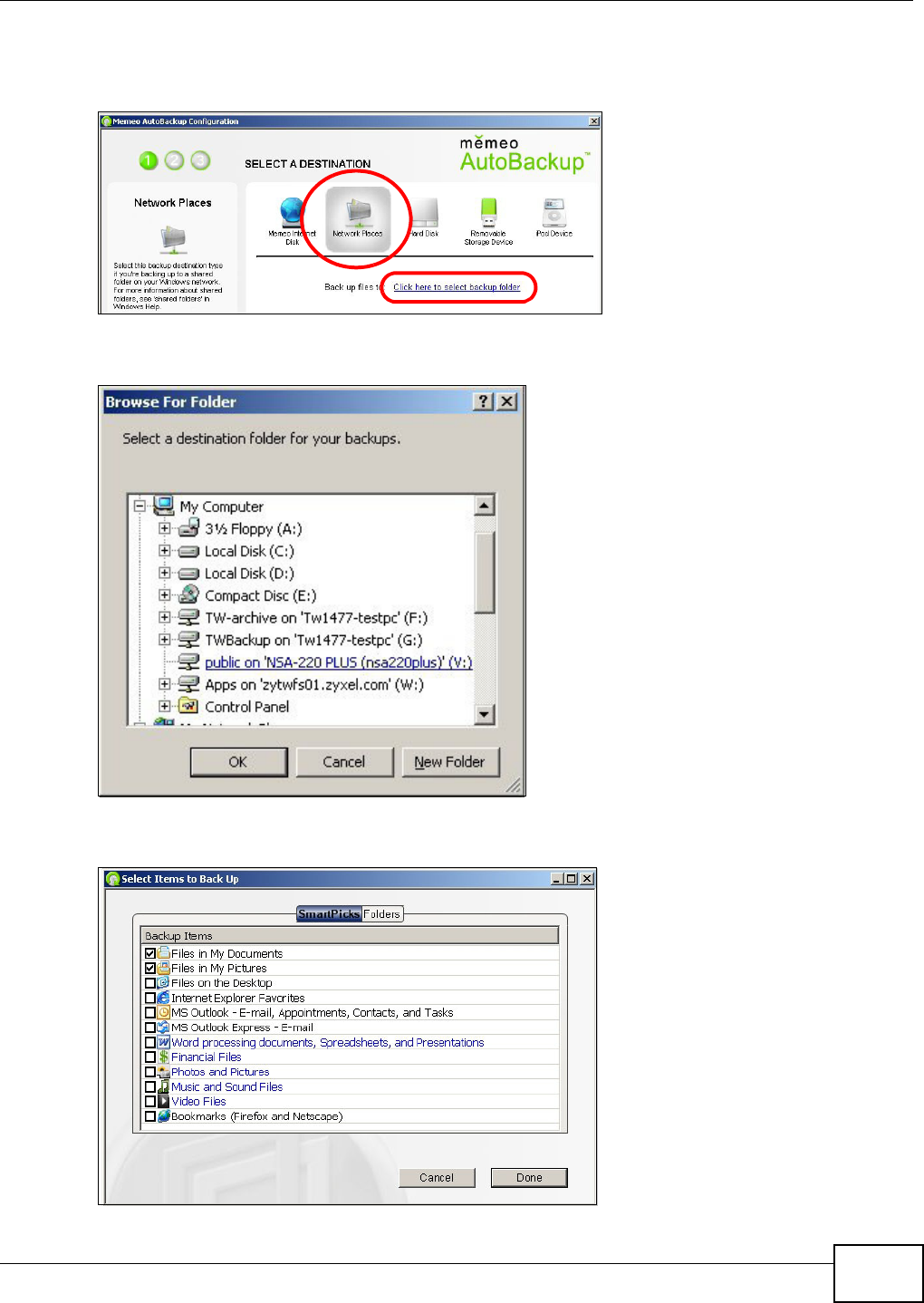
Chapter 18 Protecting Your Data
Media Server User’s Guide 333
4When you see the following screen, select Network Places and click the link to select your backup
folder.
Figure 199 Memeo Autobackup Configuration
5Select the NSA’s mapped drive and click OK.
Figure 200 Mapped Drive
6In this screen, select the items that you want to back up.
Figure 201 Backup Items
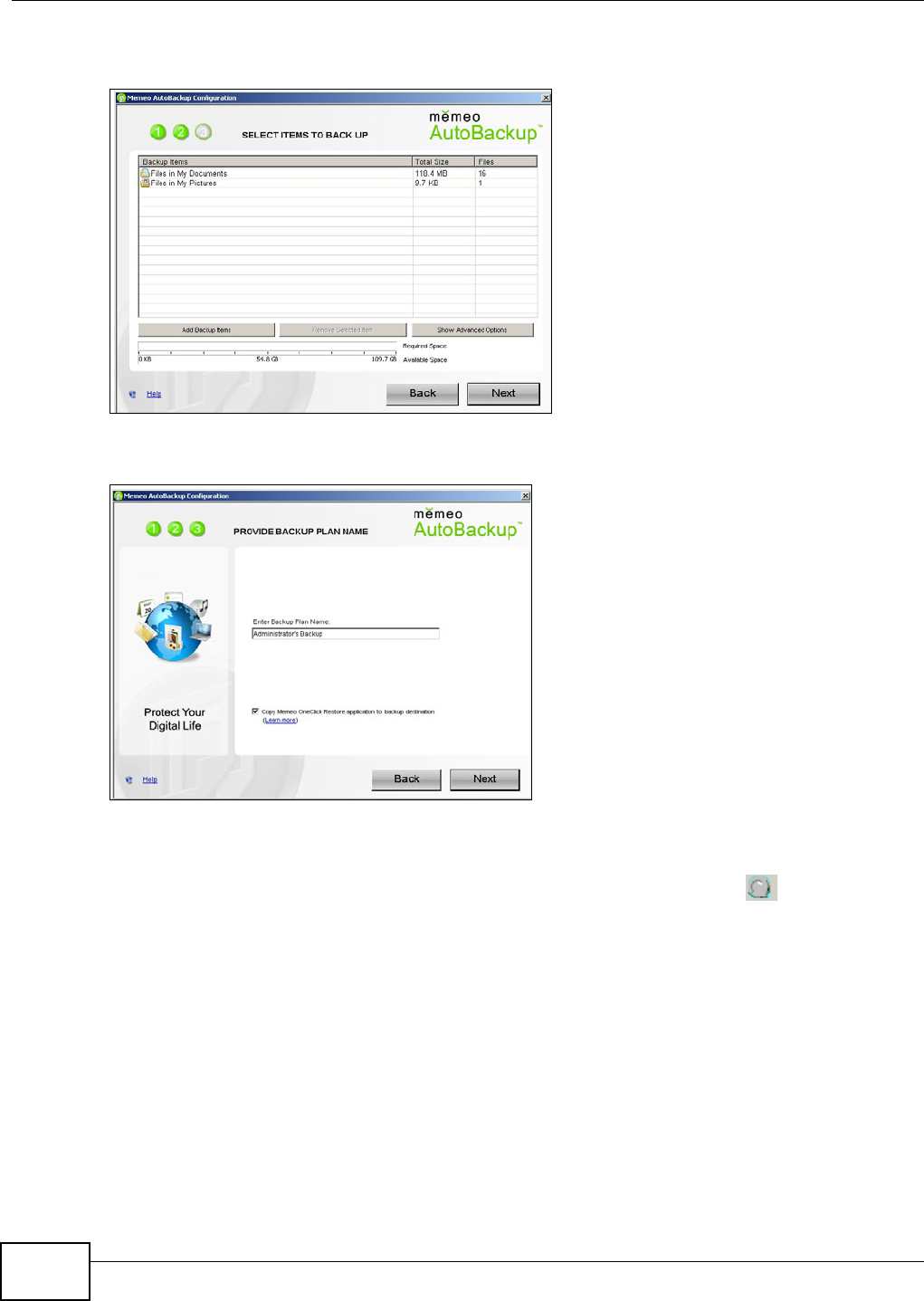
Chapter 18 Protecting Your Data
Media Server User’s Guide
334
7This screen lists the items you selected for backup. Confirm your selections and click Next.
Figure 202 Confirm Backup Items
8Specify a name for your backup plan (or just use the default). Click Next and then Done.
Figure 203 Backup Plan Name
18.4.2 Using Memeo Autobackup After the Initial Setup
After you have installed and configured Memeo Autobackup, double-click the icon in the
system tray to open the program’s start screen.
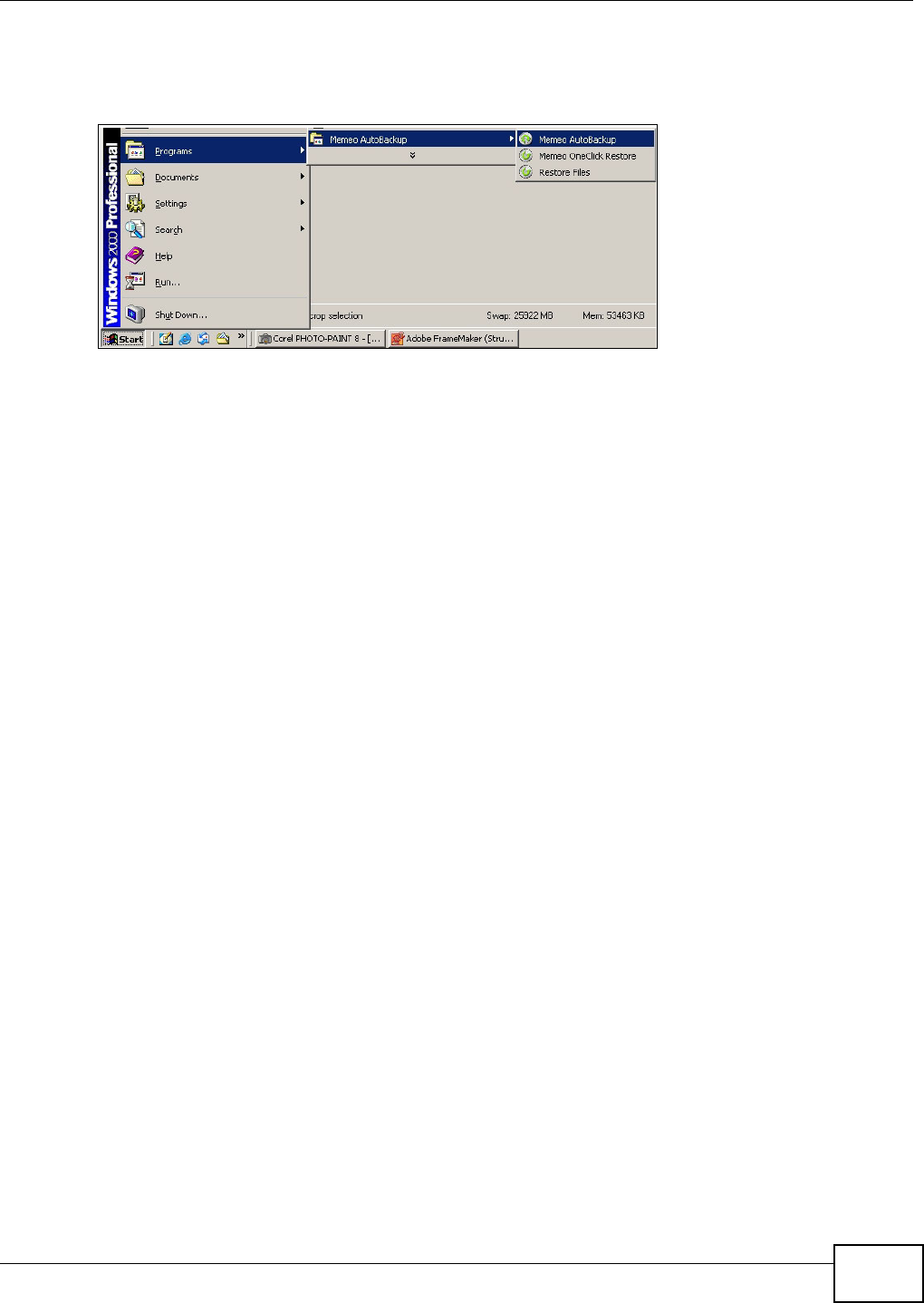
Chapter 18 Protecting Your Data
Media Server User’s Guide 335
If the icon is not displayed, you can click Start > Programs > Memeo Autobackup > Memeo
Autobackup to start it.
Figure 204 Memeo Autobackup

Chapter 18 Protecting Your Data
Media Server User’s Guide
336
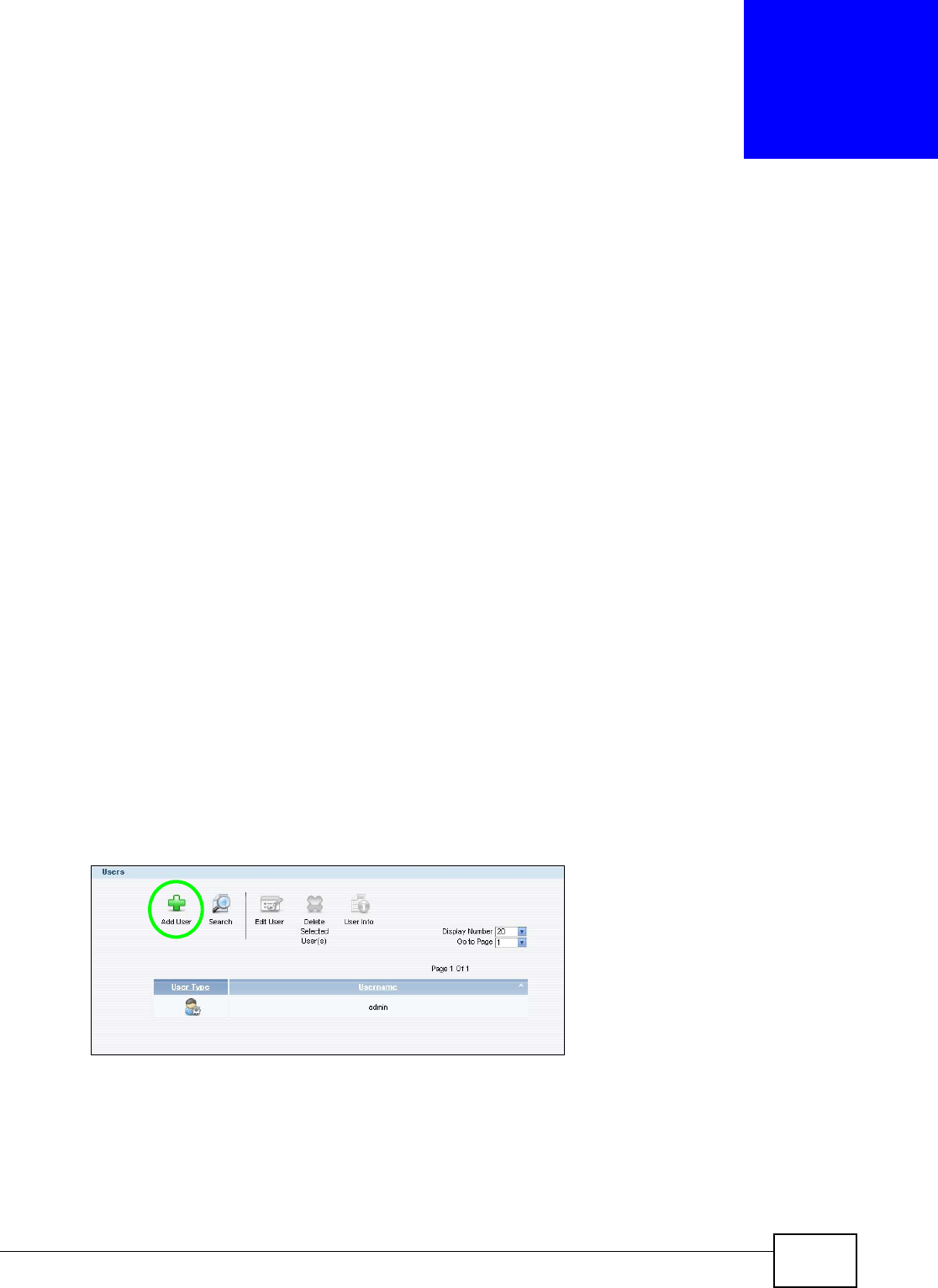
Media Server User’s Guide 337
CHAPTER 19
Using Time Machine with the NSA
19.1 Overview
Time Machine is a backup system provided by Mac OS X. It automatically backs up everything on
your Mac, including pictures, music, videos, documents, applications, and settings. This chapter
helps you to enable Time Machine in OS X to allow and use your NSA as a backup volume.
Follow the steps below to set up Time Machine on your Mac so your NSA can be used for backup.
1Create an Account and a Share on the NSA
2Set Time Machine to Support Network Volume
3Mounting the NSA on the Mac
4Creating a Sparse Bundle File for the NSA
5Using Time Machine
19.2 Create an Account and a Share on the NSA
Before configuring Time Machine on your Mac, you need to create an account and a share on the
NSA through Web GUI using a Web browser.
1Login to your NSA. Click Sharing > Users to display the Users screen. Click Add User.
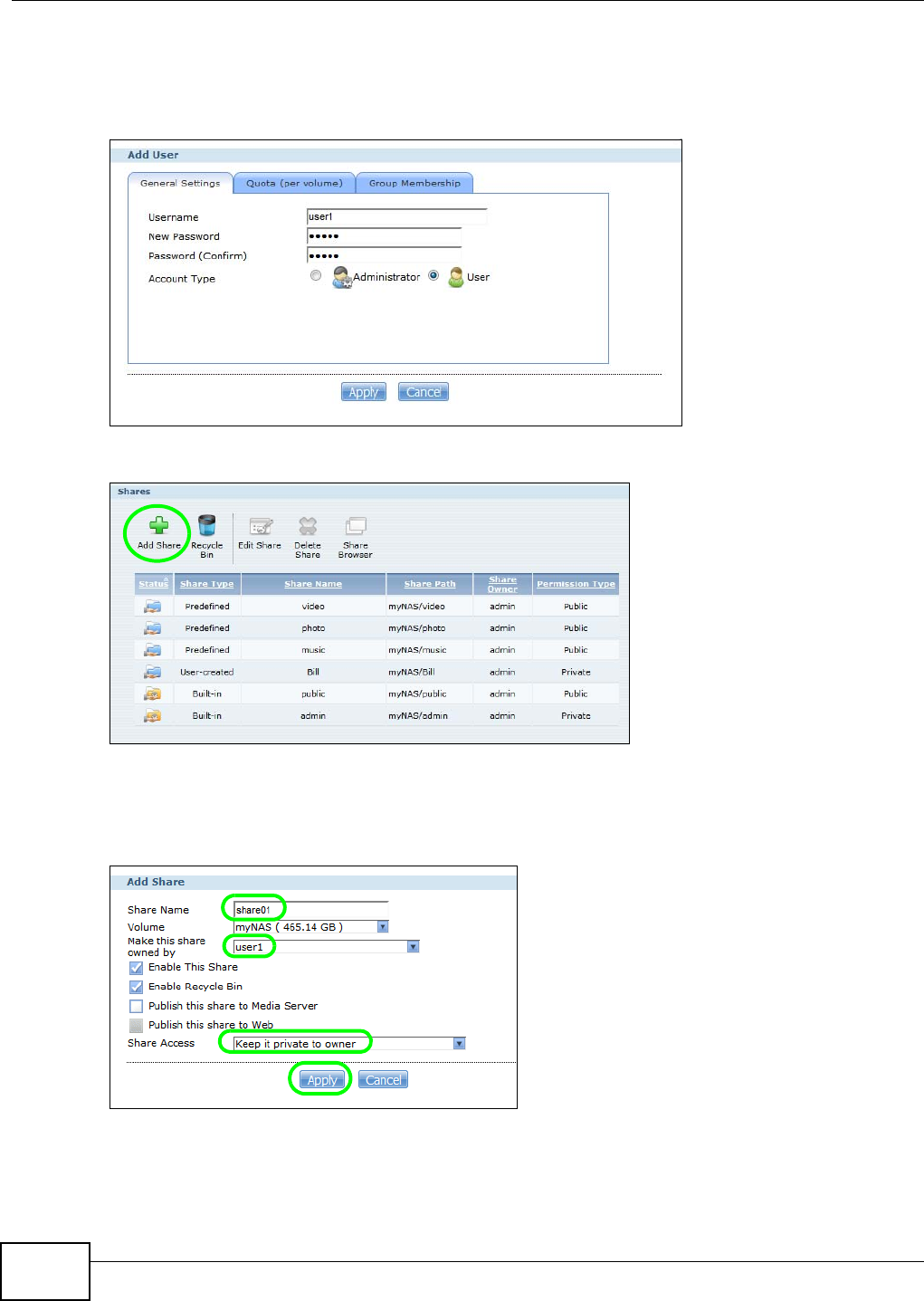
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide
338
2Enter user1 as the Username and 12345 as the New Password. Retype the password to
confirm. Then click Apply to finish adding the new user account. User1 will be added to the list on
the Users screen. (If you need more information about adding user account, please refer to
Section 14.3.2 on page 295.)
3Click Sharing > Shares to display the Shares screen. Click Add Share.
4Enter share01 as the Share Name. In the Make this share owned by list, select user1. Then in
the Share Access list, select Keep it private to owner. Click Apply to save the settings.
Share01 is added to the list on the Shares screen. (If you need more information about adding
share, refer to Section 16.3.1 on page 305.)
5Now the account user1 and share share1 have been created on your NSA. You may begin with
configurations on your computer.
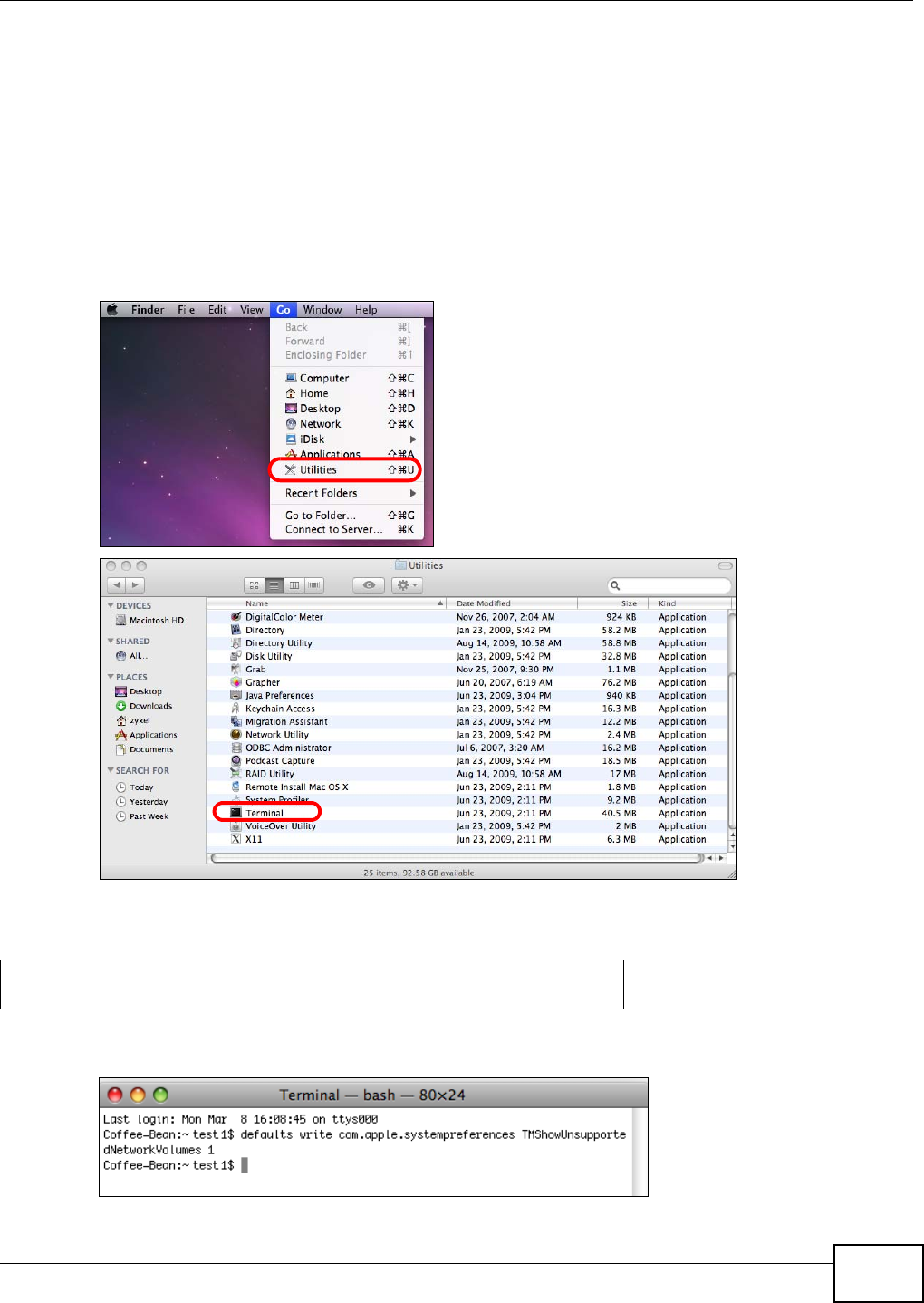
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide 339
Note: It is suggested to set a static IP address for the NSA so you do not need to update
the IP each time your computer connects to the NSA. Refer to Section 9.4 on page
173 for more information on how to set your NSA to a static IP address.
19.3 Set Time Machine to Support Network Volume
Follow the steps below to set Time Machine function so it can support the network volume NSA.
1Click Finder > Go > Utilities to open the Utilities window. Open the Terminal application.
2Enter the following in Terminal:
then press [Enter].
defaults write com.apple.systempreferences
TMShowUnsupportedNetworkVolumes 1
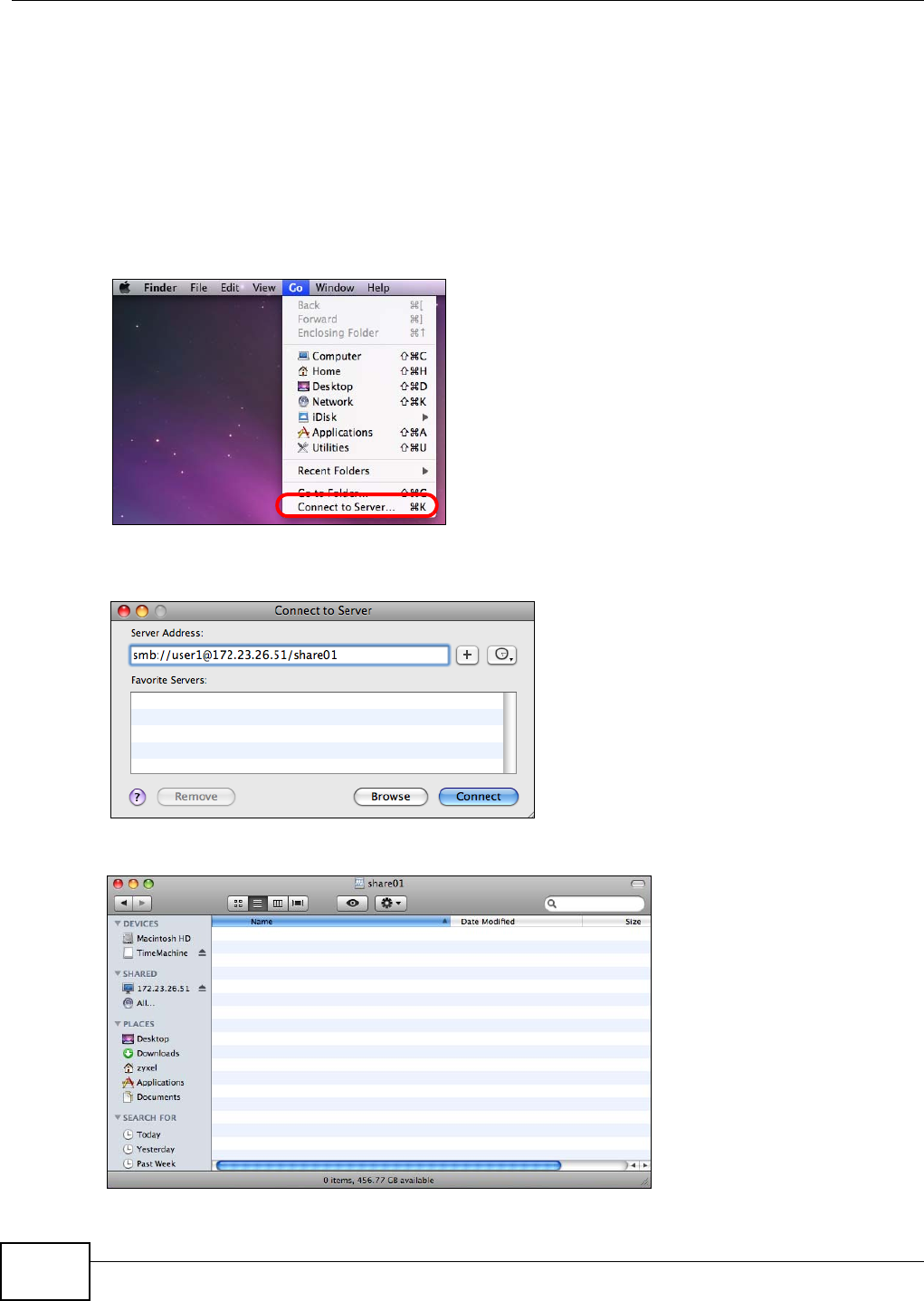
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide
340
3This allows Time Machine to support a network volume. Reboot your computer.
19.4 Mounting the NSA on the Mac
Now you need to mount share01 on the NSA to your computer. This is the place where you will
backup your files.
1Click Finder > Go > Connect to Server. The Connect to Server window opens.
2In the Sever Address box, enter: smb://username@ip-address-of-nas/backup-folder. For this
example, enter: smb://user1@172.23.26.51/share01. Then click Connect.
3When share01 is successfully mounted to the Mac, the screen looks like this:
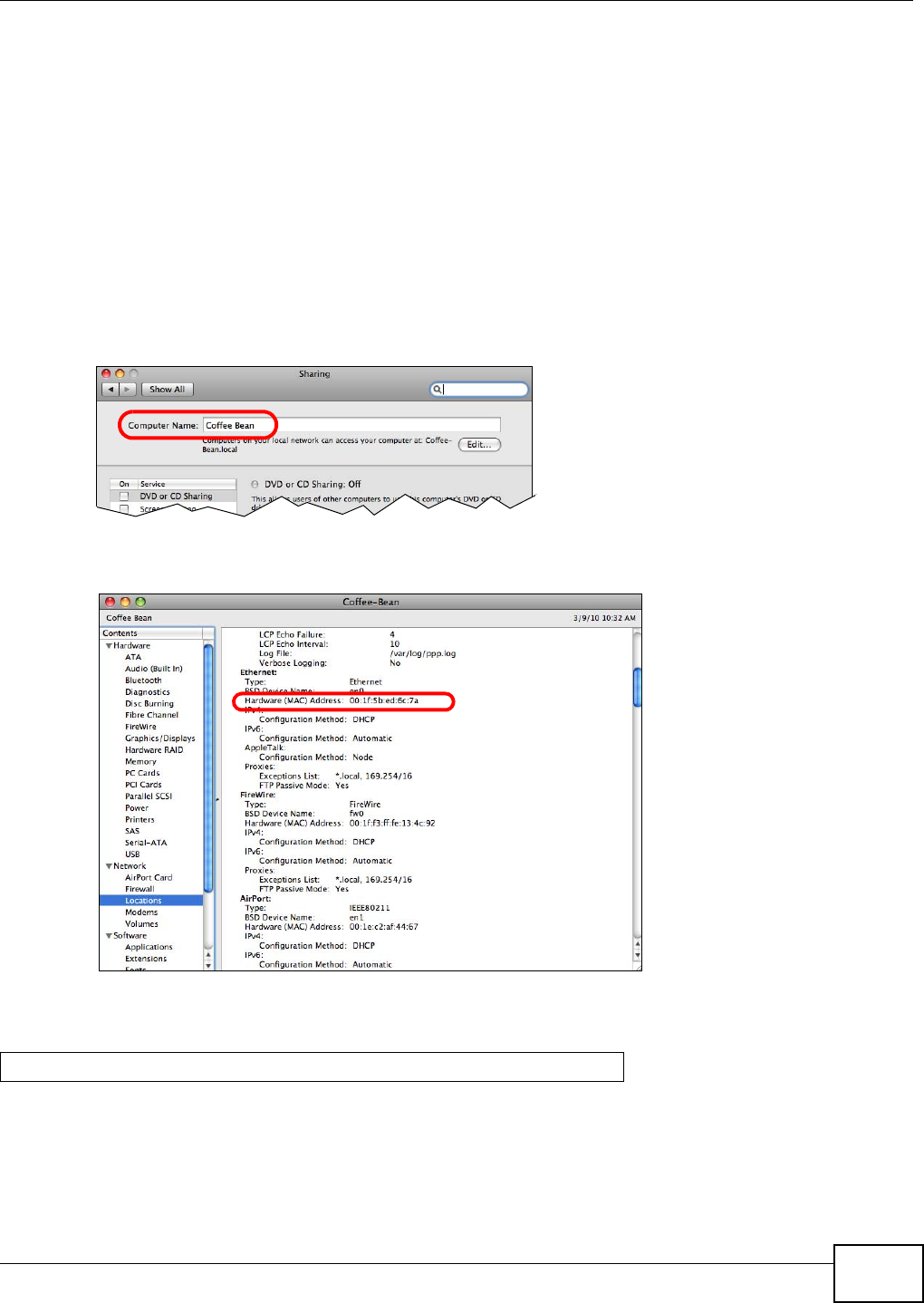
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide 341
19.5 Creating a Sparse Bundle File for the NSA
Now you need to create a sparse bundle disk image file, which is a virtual file system image that
Time Machine can backup your files. It should be created locally on the Mac and then mounted to
share01 of the NSA.
19.5.1 Finding out Computer Name and MAC Address
Before creating a spare bundle, you need to know the computer name and MAC address of your
computer.
1To find out your computer name, go to the Apple menu > System Preferences > Sharing. The
computer name is at the top of the screen.
2To find out the MAC address of your computer, click Apple > About This MAC > More Info >
Network > Locations. The MAC address is under Ethernet.
3Another way to find out the MAC address is to enter the following in Terminal:
ifconfig en0 | grep ether | sed s/://g | sed s/ether//
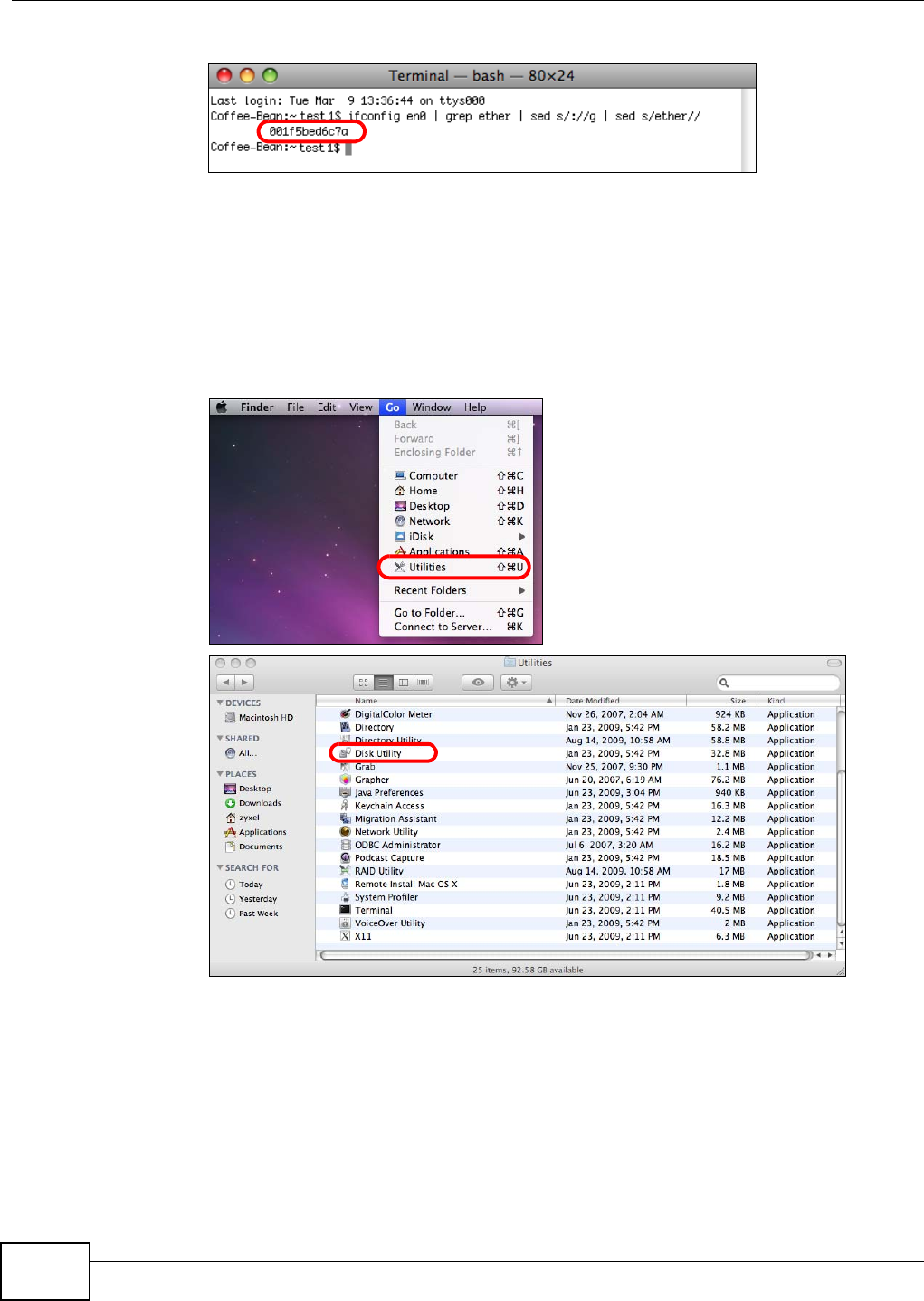
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide
342
Press [Enter] to display the MAC address.
19.5.2 Creating a Sparse Bundle File
There are two ways to create a sparse bundle disk image file. You can use Disk Utility or
Terminal.
19.5.2.1 Disk Utility
Click Finder > Go > Utilities. Open the Disk Utility application.
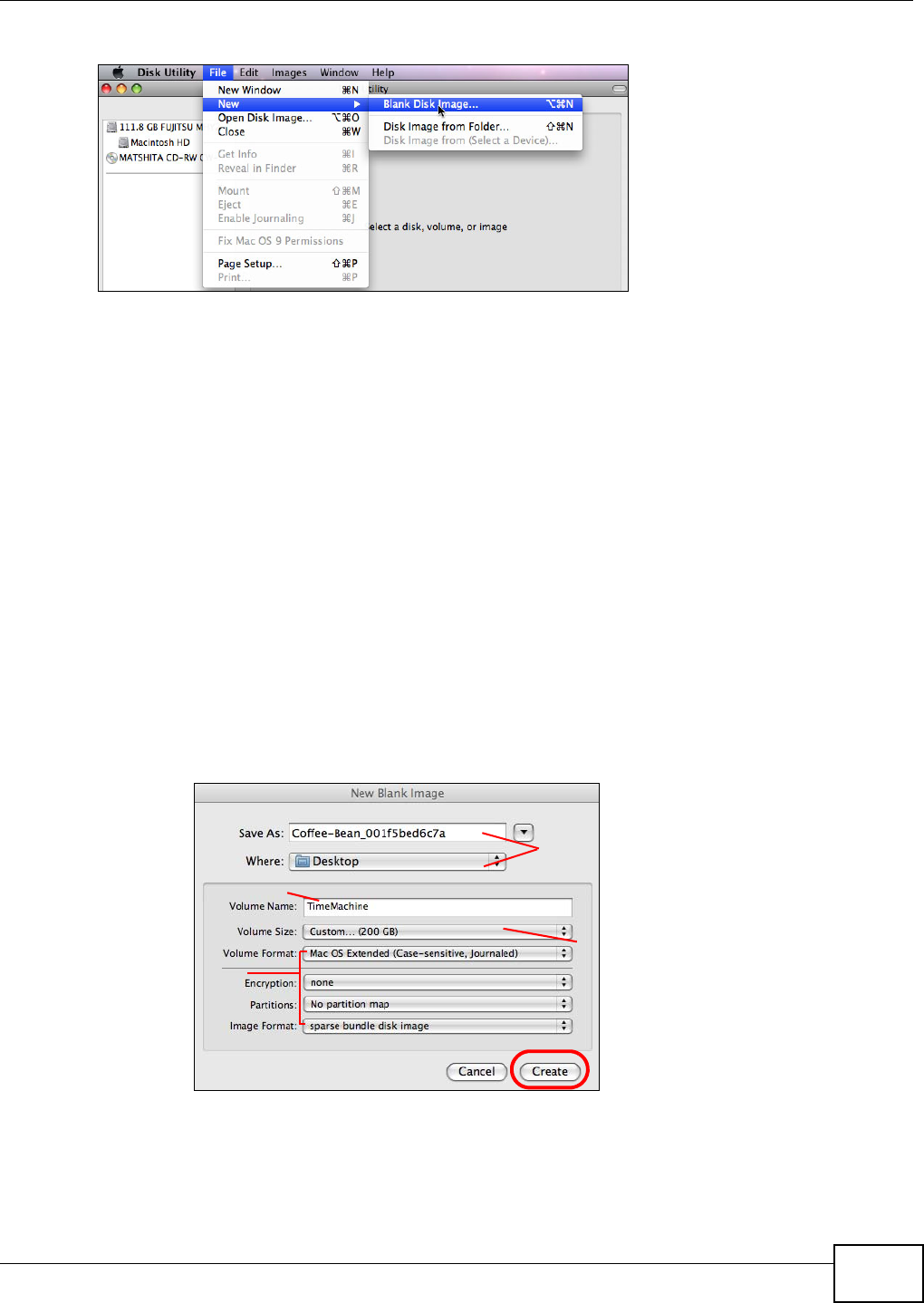
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide 343
4Click File > New > Blank Disk Image.
5In the New Blank Image screen, do the following:
5a Enter the name of the sparse bundle in Save As. The format of the name is
“ComputerName_MacAddress”. Use “-” for spaces in the computer name and remove all colons
in the MAC address. In this example, the sparse bundle name is Coffee-
Bean_001f5bed6c7a. Then select the place that you want to save the file in Where.
5b Enter a name for the volume. Here, we use TimeMachine.
5c Setup the Volume Format, Encryption, Partitions, and Image Format as step c shows in
the screen below.
5d After finishing steps a - c, setup the Volume Size of the sparse bundle. This is the virtual
volume size for you to save your files. Select Custom if you want to manually enter the volume
size. It is suggested to set the size larger than that of your physical hard drive so all files on
your hard drive can be backed up. to Click Create to start creating the sparse bundle.
Note: Set the Volume Size after you’ve set Image Format to sparse bundle disk
image. The size of a sparse bundle file is smaller than the full physical size because
it only takes up as much actual disk space as the data contained within (without
unused space). You might not be able to set the Volume Size if your image format
is not correct.
a
b
cd
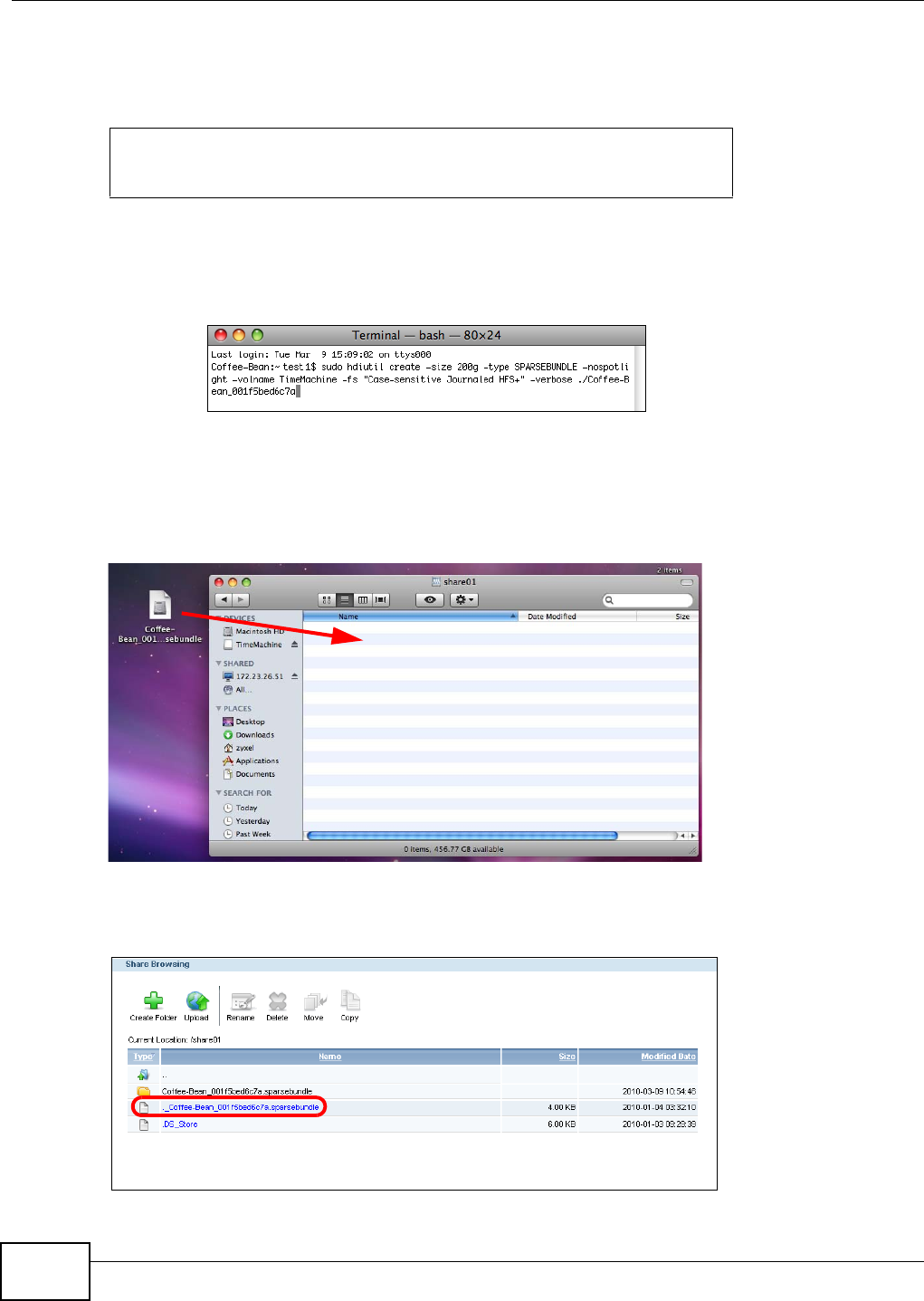
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide
344
19.5.2.2 Terminal
You can also create a sparse bundle file by using Terminal. Enter the following:
In $SPECSIZE, enter the volume size for the sparse bundle. Here, the size is set to 200g. In
$VOLUMENAME, enter the volume name TimeMachine. For $COMPUTERNAME_MACADDRESS, enter the
computer name and MAC address: Coffee-Bean_001f5bed6c7a. Click [Enter] to start creating.
The sparse bundle file will be in your Home folder.
19.5.3 Mounting the Sparse Bundle to the NSA
1After the sparse bundle file is created on the desktop or Home folder, copy the file to share01 of
the NSA.
2Open share01 on your NSA. There should be a sparse bundle folder. This is the place where all
your backup files from Time Machine will be. Remove the local sparse bundle file on your computer
and the hidden file ._Coffee-Bean_001f5bed6c7a.sparsebundle in share01.
sudo hdiutil create -size $SPECSIZE -type SPARSEBUNDLE -
nospotlight -volname $VOLUMENAME -fs "Case-sensitive Journaled
HFS+" -verbose ./$COMPUTERNAME_MACADDRESS
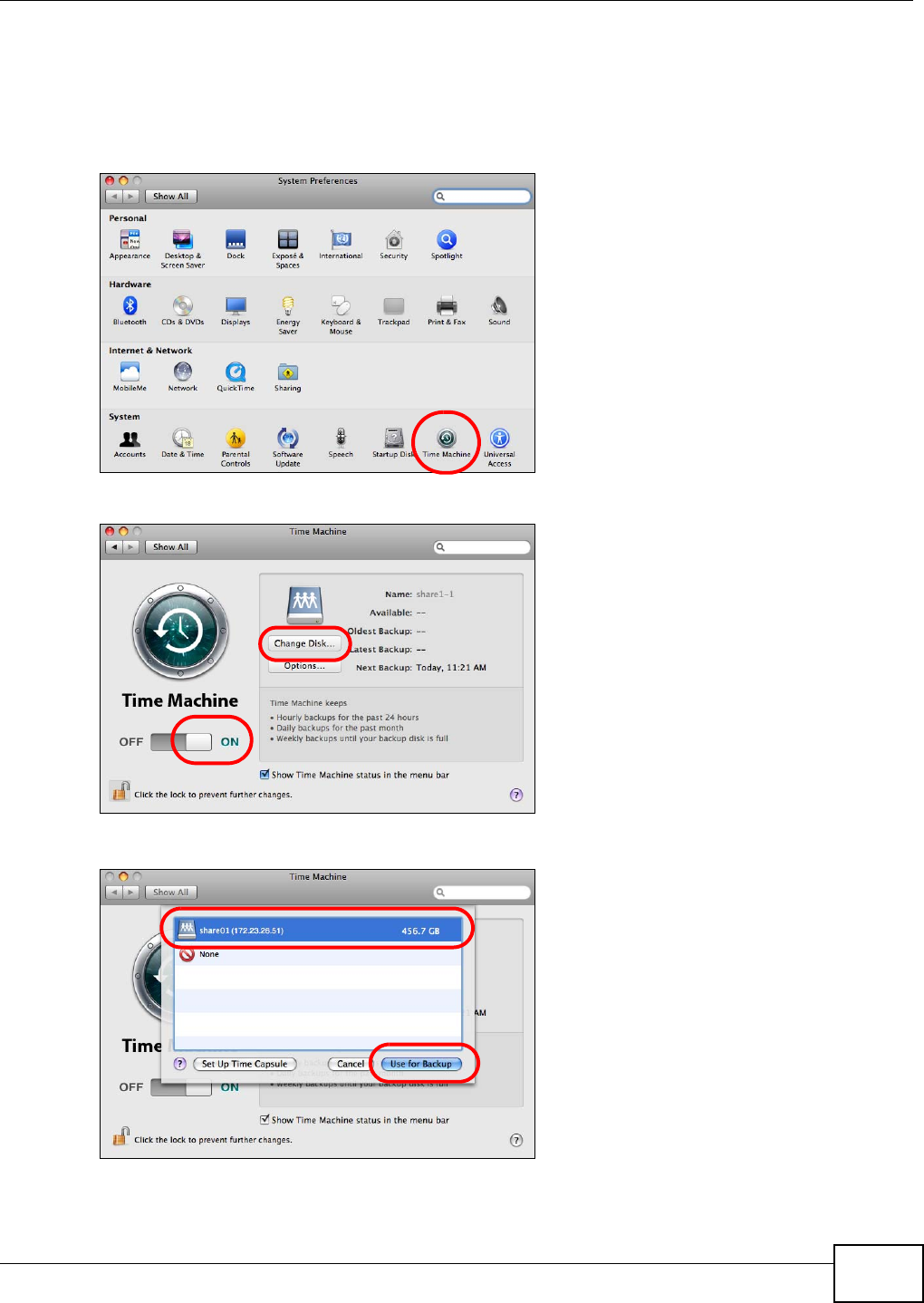
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide 345
19.6 Using Time Machine
Now the NSA is ready to be used as a backup volume for your computer.
1Click Apple > System Preferences. Then go to System and select Time Machine.
2Turn Time Machine ON. Then click Change Disk.
3Select share01 as the backup disk. Then click Use for Backup.
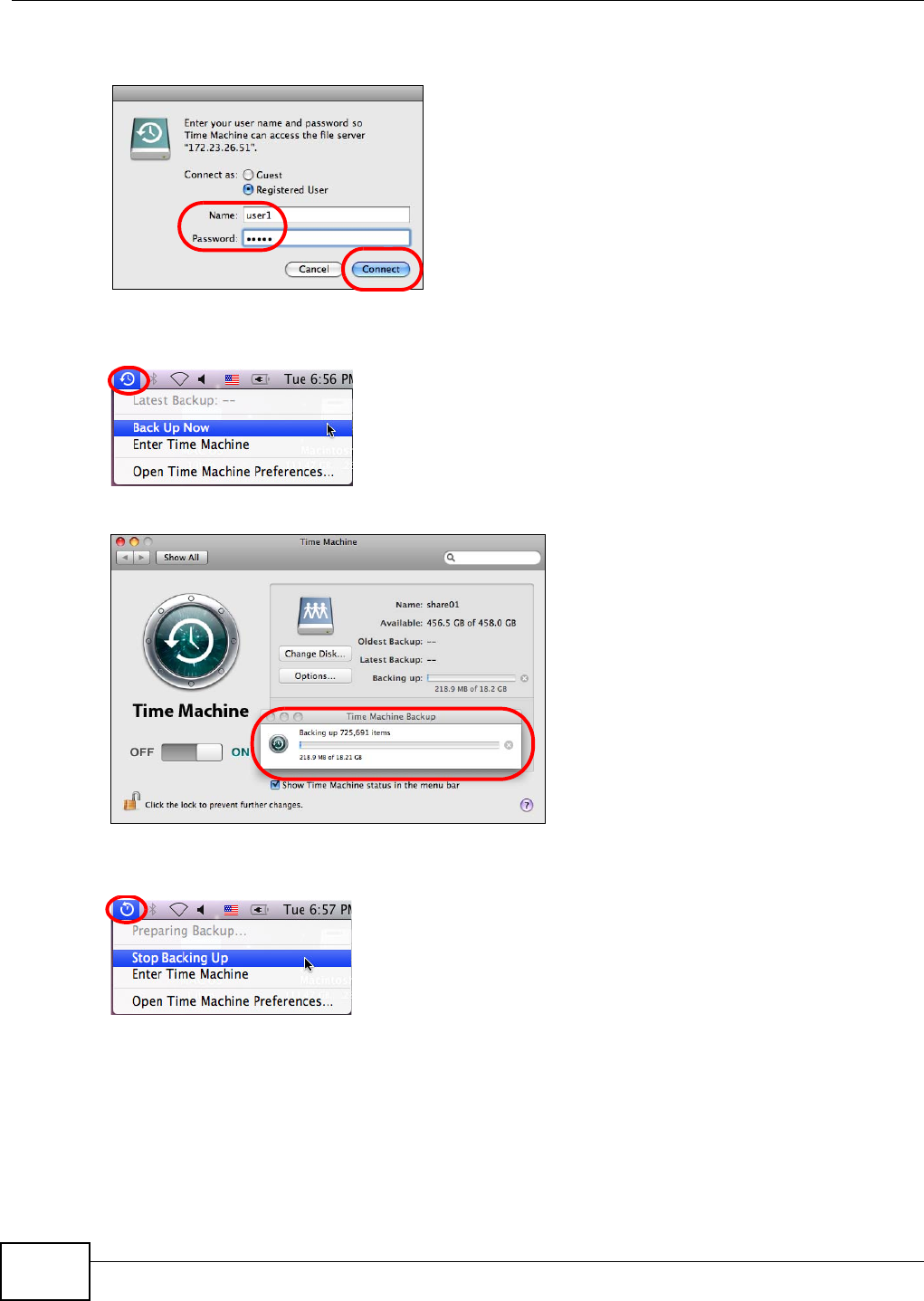
Chapter 19 Using Time Machine with the NSA
Media Server User’s Guide
346
4When prompted, the username and password of share01, enter user1/12345. Then click
Connect.
5Time Machine starts backing up files to share01 after 120 seconds. If you want to backup
immediately, click Time Machine icon and select Backup Now.
6The screen shows the status of the backup once the process begins.
7If you want to stop the backup process, click Time Machine icon and select Stop Backing Up. Then
turn Time Machine OFF.

Media Server User’s Guide 347
CHAPTER 20
Troubleshooting
20.1 Troubleshooting Overview
This chapter offers some suggestions to solve problems you might encounter. The potential
problems are divided into the following categories.
•Power, Hardware, Connections, and LEDs
•NAS Starter Utility
•NSA Login and Access
•I Cannot Access The NSA
•Users Cannot Access the NSA
•External USB Drives
•Firmware
•File Transfer
•Networking
•Some Features’ Screens Do Not Display
•Media Server Functions
•Download Service and Broadcatching Functions
•Web Publishing
•Auto Upload
•Package Management
•Backups
20.2 Power, Hardware, Connections, and LEDs
The NSA PWR LED does not turn on (no LEDs are on).
• Make sure the NSA is turned on.
• Make sure you are using the power adaptor or cord included with the NSA.
• Make sure the power adaptor or cord is connected to the NSA and plugged in to an appropriate
power source. Make sure the power source is turned on.
• Turn the NSA off and on.
• If the problem continues, contact the vendor.
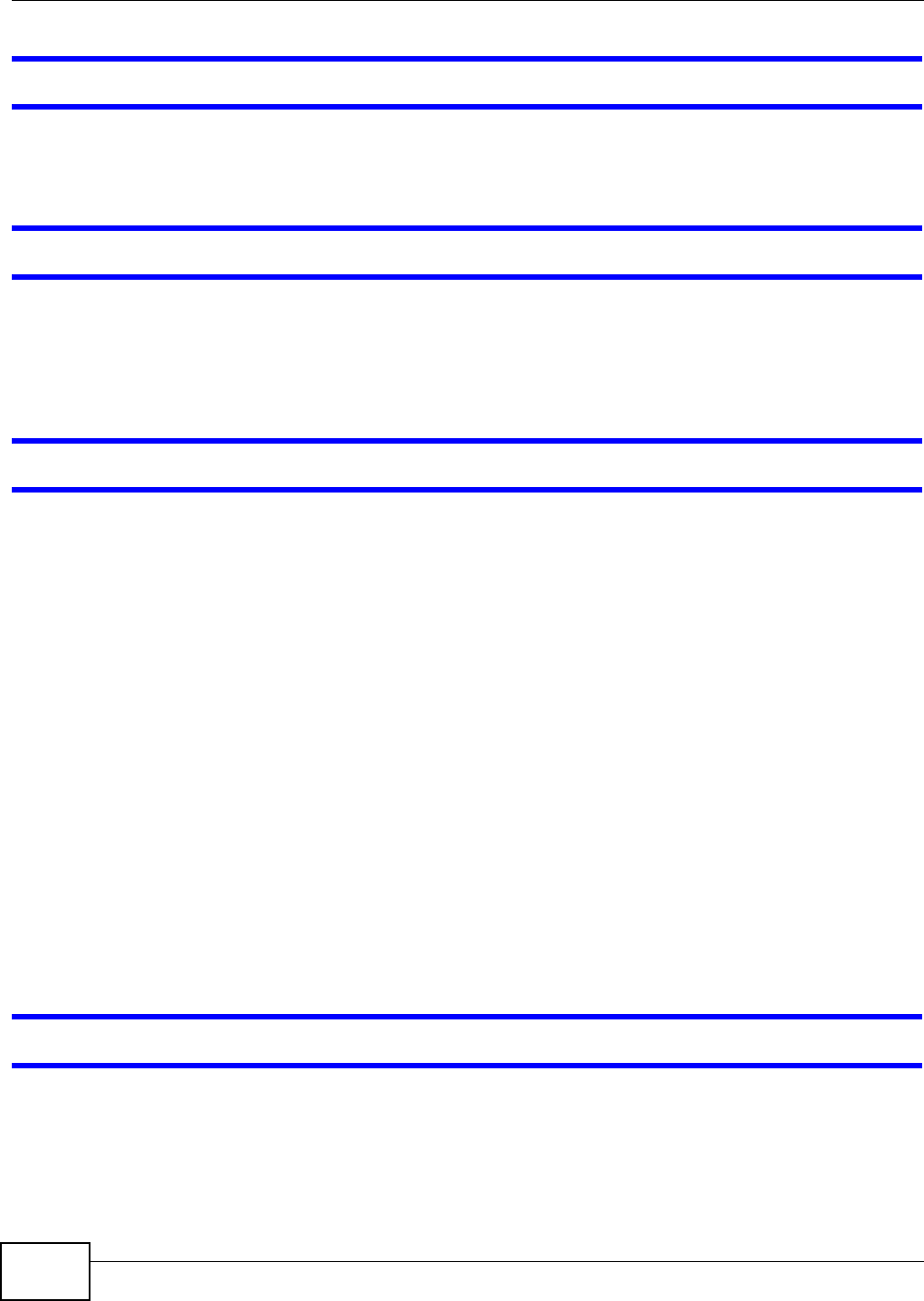
Chapter 20 Troubleshooting
Media Server User’s Guide
348
An HDD LED is off.
The HDD LED is off when the NSA cannot detect a hard drive in the drive bay. Replace or install a
hard drive. See Installing or replacing a hard disk.
An HDD LED is red.
Red means that the NSA detected an error on the hard drive (like a bad sector for example). The
NSA automatically tries to recover a bad sector, but the LED stays red until the NSA restarts. Even
if the hard drive still functions, it is recommended that you replace it since errors are a sign that the
hard drive may fail soon. See Installing or replacing a hard disk.
Installing or replacing a hard disk.
Do not remove or install a hard disk while the NSA is turned on. The NSA
must be turned off before you remove or install the hard disk.
1Turn the NSA off, remove the front panel and make sure:
• there is a SATA I or SATA II (3.0 Gbit/s) compatible hard disk installed.
• the hard disk is installed correctly in the disk bay. Push the disk back into the NSA disk bay
until the hard disk is fitted snugly inside the NSA (see the NSA Quick Start Guide and Section
8.2.1 on page 158).
• the hard disk could be faulty. Try a different hard drive or test the original hard disk in a
different NSA or computer.
2If you had to replace the drive, turn on the NSA and go to the Storage screen.
• If you have a RAID I volume click the Repair icon next to the new drive.
• If you are using RAID 0 you will need to recreate the whole volume. All of your data is lost.
• If you are using a single-disk JBOD volume, you need to create a new volume on the new
drive.
• If you are using a two-disk JBOD volume, you need to create a whole new volume on both
drives.
The LAN LED (by the LAN port) is off.
• Make sure the Ethernet cable is connected properly to the NSA and connected to another
(Ethernet) device. Make sure the other device is turned on. If it’s connected directly to a
computer, make sure that the computer network card is working (ping 127.0.0.1 on the
computer).

Chapter 20 Troubleshooting
Media Server User’s Guide 349
• Use another Ethernet cable. If you’re connecting to a Gigabit Ethernet, make sure you’re using
an 8-wire Ethernet cable.
• If the problem continues, contact the vendor.
See Section 21.1 on page 365 for a description of NSA LEDs.
The NSA turns off or reboots by itself.
Check the Power Management screen. This is where you configure power settings for the NSA,
including power saving, UPS, power on/off during power failure and power on/off schedule. The
NSA may be set to turn off under certain conditions.
A power failure occurred while the NSA is downloading files.
• If power failure occurs during the active download period, the NSA will verify whether the
downloaded files were damaged.
• If a file is corrupted, the NSA will download the file again.
• If the file is intact but not completely downloaded, the NSA will resume the download task after
it restarts.
20.3 NAS Starter Utility
The NAS Starter Utility cannot discover my NSA.
• Close the NAS Starter Utility and reopen it.
• Check your hardware connections and make sure they are set up correctly.
• Only one instance of the NAS Starter Utility can run on your computer. Make sure you close any
duplicate windows for this application.
• Wait for the SYS LED to stop blinking before clicking Discover.
• Confirm that the computer running the NAS Starter Utility has a network connection. See the
section on the NSA’s LAN connection for related information.
• The computer running the NAS Starter Utility can only discover NSAs in the same subnet. NSAs
connected to the same switch or router as your NAS Starter Utility computer are usually in the
same subnet unless the router is doing subnetting or the switch is implementing VLAN.
• The Memeo Autobackup program uses the same network port as the NAS Starter Utility to
discover the NSA. To avoid a port conflict, do not run the Memeo Autobackup program at the
same time as the NAS Starter Utility.
Chapter 20 Troubleshooting
Media Server User’s Guide
350
The NAS Starter Utility discovered my NSA but the status is always unreachable, even though
I can access it.
You may need to add the NAS Starter Utility to your software firewall’s allow list or lower your
software firewall or anti-virus scanner’s security level. Alternatively you may have to configure your
software firewall or other security software to allow UDP port 50127 traffic from the NSA. If there is
a hardware firewall between you and the NSA, configure it to allow UDP port 50127 traffic from the
NSA.
I was able to access the NSA on a previous attempt but I cannot access the NSA anymore.
If you enable jumbo frames on the NSA in a network that does not support them, you will lose
access to the NSA. If this occurs, you will have to restore the factory default configuration. The
reset process does NOT affect the volume settings, nor data stored on the NSA. Press the RESET
button until you hear two beeps. After the second beep, continue pressing the button for five more
seconds, then release it. You will hear three quick beeps after you release the button.
I have at least two NSAs in my network, how do I identify which one I want to configure in
the NAS Starter Utility screens.
If you have several NSAs connected to your computer/network, give each a unique name. You may
have to disconnect all but one and use the NAS Starter Utility to rename it. Then connect another
NSA and rename it and continue to connect and rename the NSAs one-by-one until they are all
connected and each has a unique name.
Alternatively, if you have a DHCP server on your network and you can access it’s list of assigned IP
addresses, you could see which IP address belongs to which NSA. You can check the MAC address
of your NSA by checking the attached sticker in the device housing.
20.4 NSA Login and Access
I forgot the server name of the NSA.
• The default server name is ‘nsa’ followed by the number of your model (‘nsa325’ for example).
• Use the NAS Starter Utility to discover your NSA. If you have admin privileges, you can directly
change the IP address of the NSA using the NAS Starter Utility.
• If the server name has changed and you don’t have the NAS Starter Utility, see Section 1.1.5 on
page 23 to use the RESET button to return to the default setting.
Chapter 20 Troubleshooting
Media Server User’s Guide 351
I cannot get to the NSA login screen.
• Use the NAS Starter Utility to discover your NSA. If you have admin privileges, you can directly
change the IP address of the NSA using the NAS Starter Utility.
• Make sure you have used the NAS Starter Utility to initialize your NSA.
• If you used the RESET button, the NSA may have a new IP address. Close and reopen the NAS
Starter Utility to discover the NSA.
• Make sure the NSA is turned on.
• If you are trying to login directly by typing the server name into your web browser’s address
field, make sure you are using the correct server name as the web site address.
• The default server name is ‘nsa’ followed by the number of your model (‘nsa325’ for
example). If you have changed the server name, use the new one.
• If the server name has been changed and you do not know the new server name, see the
troubleshooting suggestions for I forgot the server name of the NSA.
• If it still doesn’t work, try using the NAS Starter Utility.
• Check the hardware connections, and make sure the LEDs are behaving as expected. See the
Quick Start Guide and Section 21.1 on page 365.
• By default, the NSA gets an IP address automatically. The NSA assigns itself an IP address if no
device assigns one. If your computer is also set to get an IP address automatically, the computer
and the NSA can both assign themselves IP addresses and communicate. See Section 9.4 on
page 173 if you need to configure the NSA with a static IP address.
• If you are connecting to the NSA by its IP address, make sure you use the correct one. If the NSA
has a wired Ethernet connection and a wireless connection through an attached USB wireless
dongle, the NSA has a different IP address for each connection. To connect through the wired
Ethernet connection, use the wired Ethernet connection’s IP address. To connect through the
wireless connection, use the wireless connection’s IP address.
• Make sure your computer’s IP address is in the same subnet as the NSA’s IP address. You can use
the NAS Starter Utility to find the NSA’s IP address. See Appendix A on page 369 for how to
change your computer’s IP address. Skip this if you know that there are routers between your
computer and the NSA.
• Ping the NSA from your computer. Make sure your computer’s Ethernet adapter is installed and
functioning properly. In a (Windows) computer, click Start, (All) Programs, Accessories and
then Command Prompt. In the Command Prompt window, type “ping” followed by the NSA’s
IP address (use the NAS Starter Utility to find the NSA’s IP address if you don’t know it) and then
press [ENTER].
• Make sure you are using Internet Explorer 6.0 (and later) or Firefox 1.07 (and later).
• Make sure your Internet browser does not block pop-up windows and has JavaScript and Java
enabled. See Appendix B on page 397. With Internet Explorer 6, you may also have to enable
scripting of safe ActiveX controls. See Section 20.4.1 on page 352.
I forgot the password.
• The default password is 1234.
• If you have changed the password and forgotten it, you will have to reset the NSA.
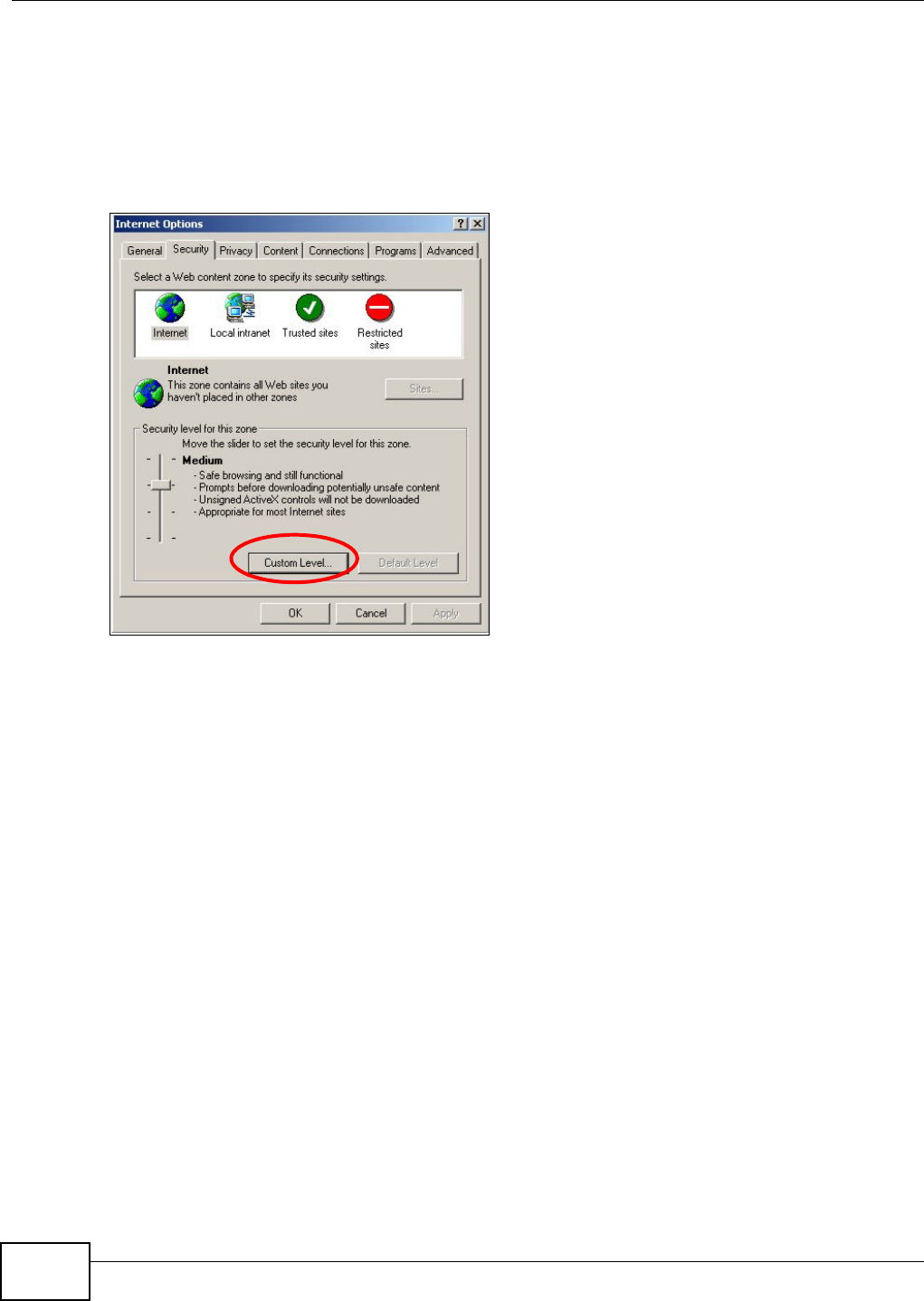
Chapter 20 Troubleshooting
Media Server User’s Guide
352
20.4.1 Enabling Scripting of Safe ActiveX Controls
If pages of the web configurator do not display properly in Internet Explorer, check that scripting of
safe ActiveX controls is enabled.
1In Internet Explorer, click Tools, Internet Options and then the Security tab.
Figure 205 Internet Options: Security
2Click the Custom Level... button.
3Under Script ActiveX controls marked safe for scripting, make sure that Enable is selected
(the default).
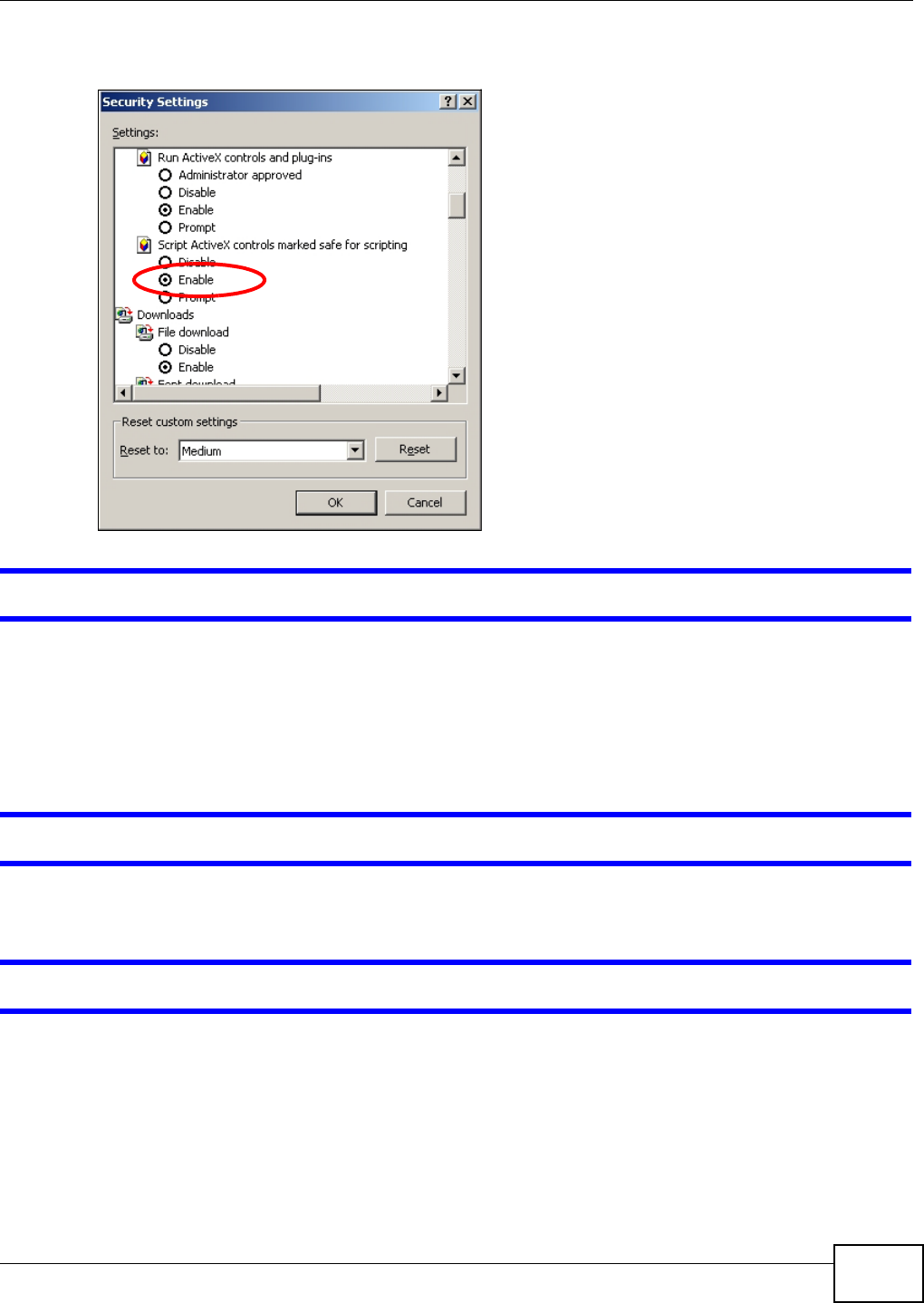
Chapter 20 Troubleshooting
Media Server User’s Guide 353
4Click OK to close the window.
Figure 206 Security Settings - Script Safe ActiveX Controls
I can see the login screen, but I cannot log in to the NSA.
• Make sure you have entered the username and password correctly. The default username is
admin, and the default password is 1234. These fields are case-sensitive, so make sure [Caps
Lock] is not on.
• Turn the NSA off and on.
• If this does not work, see Section 1.1.5 on page 23 to reset the device.
I cannot see the multi-language web configurator screens while using Internet Explorer.
Use Section 20.4.1 on page 352 to enable the scripting of safe ActiveX controls.
The Web Configurator logs out by itself.
The web configurator management session automatically times out if it is left idle for 15 minutes.
Simply log back into the NSA if this happens to you.
Chapter 20 Troubleshooting
Media Server User’s Guide
354
20.5 I Cannot Access The NSA
I cannot access a share.
• Check that the NSA is turned on and connected to the network. Try to ping the NSA or use the
NAS Starter Utility to discover it.
• Make sure you have used the NAS Starter Utility to initialize your NSA. See Chapter 3 on page 35
for more information.
• Check that you entered your login name and password correctly.
• Check that the share exists and check its access settings.
• Check if the shared folder is a subfolder of another (parent) share. Check that the parent share’s
access rights do not conflict with the subfolder share. It is recommended that you do not create
subfolder shares.
• Check if there are any existing mapped network drives to the NSA. You may need to disconnect
existing mapped network drives as a new mapped network drive connection may use (different)
previously-saved login information. To do this, open Windows Explorer and click Tools >
Disconnect Mapped Network Drives.
• Check that the volume in which the share resides, exists and is not down or degraded. If it is
down or degraded, see Section 20.2 on page 347.
• Make sure you have the client for Microsoft networks installed and enabled in your network
connection’s properties.
• In Windows XP or 2000, click Start > Settings > Control Panel > Network Connections
(Network and Dial-up Connections in Windows 2000/NT) > Local Area Connection >
Properties.
•Check that Client for Microsoft Networks is in the list of components and has its check box
selected.
20.6 Users Cannot Access the NSA
A local user cannot access a share
• Check that the NSA is turned on and connected to the network. The local user should try to ping
the NSA or use the NAS Starter Utility to discover it.
• The local user should check that he entered his login name and password correctly.
• Check if the share exists and has the correct access settings for this user.
• Check the Access Control List (ACL) of read/write permissions associated with specific files and/
or folders. Account names added to the list are linked to the files and folders that they are
allowed to access, along with what kinds of actions they are allowed to perform with those files
and folders (delete, move, rename, and so on).
Chapter 20 Troubleshooting
Media Server User’s Guide 355
• The user’s computer may already be connected to another of the NSA’s shares using a different
user name and/or password. This can happen without the user realizing it if the user’s computer
automatically connects to a share at logon. Right-click any other connected shares and click
Disconnect. Then re-attempt to connect to the desired share.
• Check if the share has an ANONYMOUS or EVERYONE access right. If the user is already logged
into a share using her username and password, she will NOT be able to access a share that has
ANONYMOUS FTP only access rights (as these require ‘no login’). In this case she should log out
and try to access the share again without logging in. See Section 10.4 on page 184 for more
details.
• Check if the shared folder is a subfolder of another (parent) share. Check that the parent share’s
access rights do not conflict with the subfolder share. It is recommended that you do not create
subfolder shares.
• Check if the user belongs to a group with conflicting access rights. DENY always takes
precedence. If you allow a user FULL access to a share but set his group to DENY, then he will
NOT be able to access the share.
• The local user should check if there are any existing mapped network drives to the NSA. He may
need to disconnect existing CIFS connections as new CIFS connection may use previously-saved
login information that may be different to NSA login.
• Check that the array in which the share resides, exists and is not down or degraded. If the array
is down or degraded, see Section 20.2 on page 347.
• If the user is using DFS links, then he can only access the NSA using CIFS and not FTP.
• Check that the share has not been disabled.
I cannot import domain user or user group information even though testing of the connection
to the domain controller is OK.
• Check the NSA’s DNS setting. The DNS server the NSA is using must be able to resolve the
domain controller’s address. If the domain controller uses a private IP address, the NSA needs to
use a private DNS server. If the domain controller uses a public IP address, the NSA needs to use
a public DNS server.
• Leave the domain and re-join it.
A domain user can’t access a share.
In addition to the checks listed previously for local users, check that the domain controller is turned
on and connected to the network.
A user can access a share but cannot access individual folders or files within the share.
• Check the Access Control List (ACL) of read/write permissions associated with the share’s
specific files and/or folders. Account names added to the list are linked to the files and folders
that they are allowed to access, along with what kinds of actions they are allowed to perform
with those files and folders (delete, move, rename, and so on).

Chapter 20 Troubleshooting
Media Server User’s Guide
356
20.7 External USB Drives
The COPY LED is red.
Copying files from a USB device failed. The USB device may not be compatible with the NSA. Try to
save the files onto a computer and then from the computer to the NSA (through the network
connection).
20.8 Firmware
I want to know the firmware version on the NSA.
Go to the Status screen. The Firmware field shows you the current firmware version running.
20.9 File Transfer
I want to transfer my file(s) from my local computer or storage device to the NSA.
• After you initialize your hard disk, you can directly access the folders in your NSA and transfer
files in the same way you transfer files in your local computer:
1On your Windows computer, click Start > Run or open a web browser.
2Enter \\nsa followed by the number of your model (320 for example) or the Server Name you
assigned the NSA. This shows you the folders in the NSA.
3Use drag-and-drop or copy-and-paste to transfer files over to your NSA.
•Use the COPY/SYNC button to transfer files from an external (USB) storage device to the NSA.
• If the file you want to transfer is less than or equal to 2GB, you can use the NSA Starter Utility’s
zPilot screen (see Section 3.5 on page 39).
I want to transfer my file(s) from the NSA to my local computer or storage device.
• After you initialize your hard disk, you can directly access the folders in your NSA and transfer
files in the same way you transfer files in your local computer:
Chapter 20 Troubleshooting
Media Server User’s Guide 357
1On your Windows computer, click Start > Run or open a web browser.
2Enter \\nsa followed by the number of your model (320 for example) or the Server Name you
assigned the NSA. This shows you the folders in the NSA.
3Use drag-and-drop or copy-and-paste to transfer files from your NSA to your local computer’s folder
or your storage device.
• You can download the files from your NSA. Just click on the file(s) in the Share Browsing screen
(Section 4.4.5 on page 52). Your computer will prompt you for the location where you want to
save the file.
20.10 Networking
I want to control who can access my folder(s)/file(s).
• If you are an administrator, you can configure a user’s access rights. Use the Shares screen
(Section 16.3 on page 303) to do this.
•If you enabled Web Publishing for a folder, anyone on your network can play the media files in
the published shares. No user name and password or other form of security is used. The media
server is enabled by default with the video, photo, and music shares published.
One of the computers in my network cannot use the printer I connected to the NSA.
• You must install the printer driver on each computer that will use the printer.
•Check Section 20.4 on page 350 and check for related connectivity issues.
20.11 Some Features’ Screens Do Not Display
Many NSA features require a valid internal volume.
Features like the print server, download service, broadcatching, FTP and Windows/CIFS access will
not work without a valid internal volume. Make sure you have a volume on an internal disk and that
the volume is in the healthy state.
• Install an internal disk if one is not installed yet or has failed. See the Quick Start Guide for how
to install an internal disk.
• Create a new volume if you do not have one on the internal disk yet.
• Make sure the volume on the installed internal disk is in a healthy state.
Chapter 20 Troubleshooting
Media Server User’s Guide
358
I cannot use some applications in the Web Configurator.
• The firmware installed in your NSA includes the features mentioned in Section 4.5.2 on page 60.
This does not include the applications you can install using the Package Management screen.
• You can use the Package Management screen (Chapter 11 on page 225) to install more
applications from a web location (specified in the firmware) to your NSA.
• If you have installed the application and can see the application’s configuration screen but still
cannot use it, check that you have Enabled the application.
20.12 Media Server Functions
I set the media server function to publish a folder, but some of the files in the folder do not
display in the list on the media client.
Files with formats that are not supported on the media server may not display in the list. See
Section 21.2 on page 366 for the file formats that the media server supports.
I published a folder with the media server function, but the media client does not play some
of the files (or does not play them properly).
1Files with formats that are not supported on the media server may not display in the list. See
Section 21.2 on page 366 for the file formats that the media server supports.
2If you are using media client software, you may need to install codecs on your computer. Since the
media client software uses your computer’s installed codecs, files do not play if the required codec
is not installed on your computer.
3The media client may not support the file’s format.
iTunes does not display the names of all the music files I just put on the NSA.
1Make sure the files are a format supported by iTunes. See Section 21.3 on page 367.
2Go to Applications > Media Server. Make sure the share containing the music files is published
and the iTunes server option is enabled.
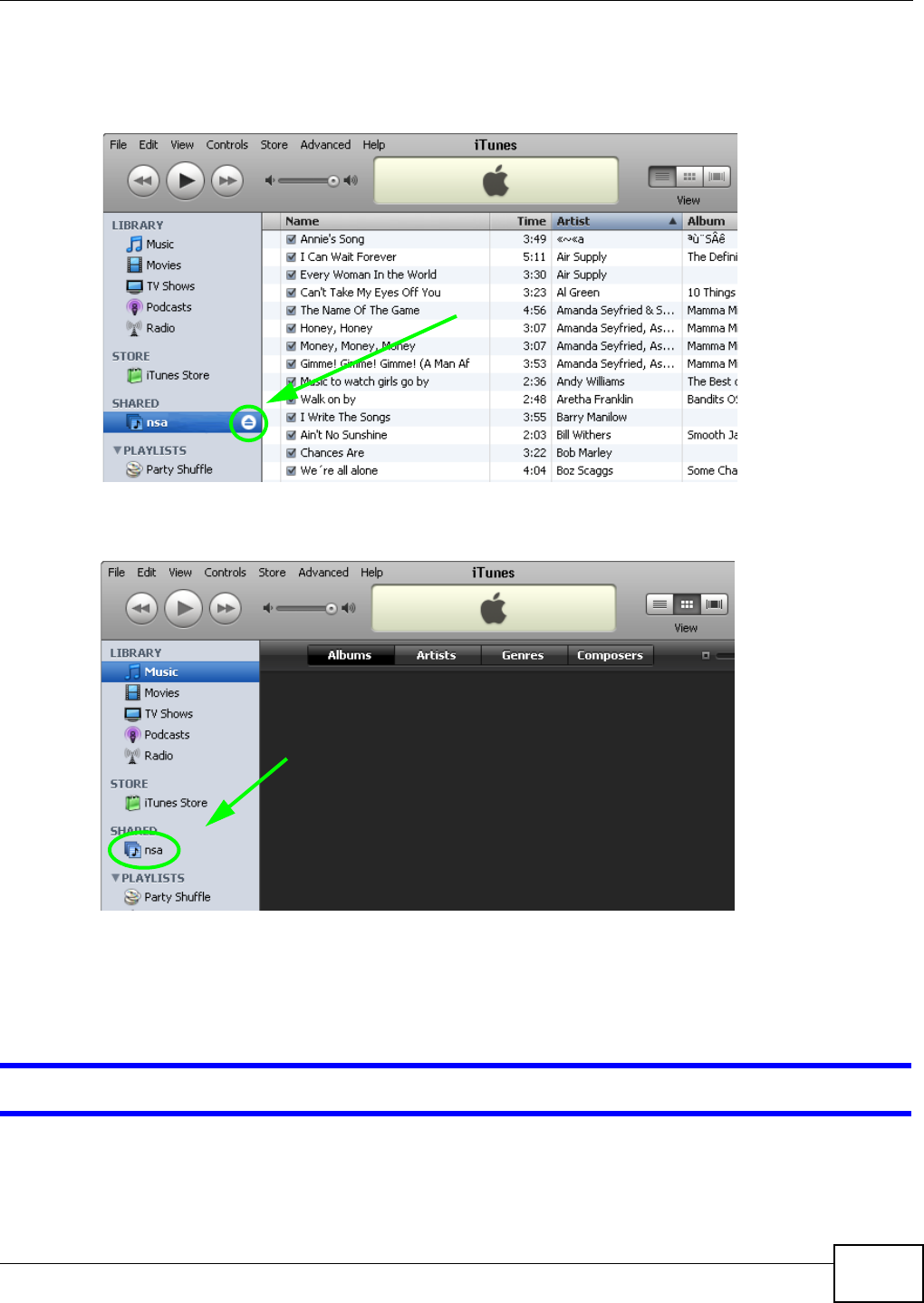
Chapter 20 Troubleshooting
Media Server User’s Guide 359
3If an iTunes client is connected, the NSA’s iTunes server function scans the published media server
folders for files every three minutes. Leave iTunes connected to the NSA for three minutes. Then
use the NSA’s eject button (as shown next) to disconnect.
Figure 207 iTunes Eject Button
4Then click the NSA’s link to reconnect.
Figure 208 iTunes Reconnected
5Another way to get the NSA’s iTunes server function to scan the published media server folders for
files is to go to Applications > Media Server and disable and re-enable the iTunes server option.
If you uploaded many files, it may take awhile for the NSA to find and list all of them. Then try
reconnecting your iTunes client.
I cannot use iTunes to play files located on my NSA.
1Make sure the files are a format supported by iTunes. See Section 21.3 on page 367.
Chapter 20 Troubleshooting
Media Server User’s Guide
360
2If you have files from the iTunes Store that use DRM, you need to use your Apple account ID and
password to authorize other computers to play the files. Apple permits you to authorize up to five
computers at a time. To authorize a computer, open iTunes and click Store > Authorize
Computer.
3If you are connecting through a NAT router, make sure that TCP port 3689 and UDP port 5353 are
open for traffic on both the server and the client and all points in between (especially the NAT
router). If your router includes a firewall, make sure it also allows TCP port 3689 and UDP port
5353 traffic.
20.13 Download Service and Broadcatching Functions
The download list or broadcatching items are missing after I removed a hard drive.
The NSA’s download and broadcatching lists are stored on the system volume. If you have two
JBOD volumes, it is possible to remove one and still use the other. However if you remove the
system volume, you may lose the download and broadcasting lists. With two JBOD volumes, the
hard disk that was installed first is usually the system volume.
The channel I added in the Broadcatching screen is active but no files are downloaded to
the NSA.
Check the Download Policy for that channel (see Section 10.8.1 on page 205). It may be set to
manual download. You can configure your NSA to download all items or only new items
automatically once the channel is updated.
I cannot find the download files.
By default, the Download Service and Broadcatching features store downloaded files as follows:
• BitTorrent jobs are stored in /*/incoming (where ‘*’ is a folder that you have set.)
• HTTP/FTP jobs are stored in /* (where ‘*’ is a folder that you have set.)
• All jobs triggered by RSS channels create the subfolder in /* using the channel name where it
store all files downloaded from that channel (where ‘*’ is a folder that you have set.)
Check your Preferences in the Download Service (Section 10.6 on page 190) and
Broadcatching (Section 10.8 on page 203) screens to know or configure where downloaded files
are stored.
Chapter 20 Troubleshooting
Media Server User’s Guide 361
20.14 Web Publishing
A web-published share cannot be accessed by web browser from the Internet.
• Make sure the person trying to access the share is using the correct web address (and port
number if the NSA’s web publishing feature is not using port 80). See page 219 for details.
• Make sure the publishing feature is turned on and the share is in the list of published shares.
• Make sure the person trying to access the share is using Internet Explorer 6.0 (and later) or
Firefox 1.07 (and later).
• You need to use a public address to access the NSA’s web-published shares from the Internet. If
your NSA uses a private IP address, use the public IP address of your Internet gateway (firewall)
and configure NAT or port forwarding on your Internet gateway and possibly firewall rules in
order to let people access the NSA’s web-published shares from the Internet.
• Make sure the firewall’s public IP address is static or that the firewall uses a Dynamic Domain
Name (DDNS).
• Web publishing uses TCP protocol and the port number you specify. Make sure there is not
another service using TCP protocol with the same port number. See Appendix C on page 407 for
a list of common services and their associated protocols and port numbers.
• If Firefox access to the share does not work, check that you did not set the Web publishing
feature to use one of the following ports. (Firefox blocks these ports by default.)
Table 123 Ports Blocked By Default in Firefox
PORT SERVICE PORT SERVICE PORT SERVICE
1 tcpmux 95 supdup 513 login
7 echo 101 hostriame 514 shell
9 discard 102 iso-tsap 515 printer
11 systat 103 gppitnp 526 tempo
13 daytime 104 acr-nema 530 courier
15 netstat 109 POP2 531 chat
17 qotd 110 POP3 532 netnews
19 chargen 111 sunrpc 540 uucp
20 ftp data 113 auth 556 remotefs
21 ftp control 115 sftp 563 NNTP+SSL
22 ssh 117 uucp-path 587 submission
23 telnet 119 NNTP 601 syslog
25 smtp 123 NTP 636 LDAP+SSL
37 time 135 loc-srv epmap 993 IMAP+SSL
42 name 139 netbios 995 POP3+SSL
43 nicname 143 IMAP2 2049 nfs
53 domain 179 BGP 4045 lockd
77 priv-rjs 389 LDAP 6000 X11
79 finger 465 SMTP+SSL
87 ttylink 512 print exec
Chapter 20 Troubleshooting
Media Server User’s Guide
362
• Make sure your ISP allows you to run a server and is not blocking the port number of the NSA’s
web publishing feature.
20.15 Auto Upload
The NSA does not automatically upload files to Flickr or YouTube.
1Make sure the NSA is connected to the Internet. See Section 9.4 on page 173 for details about
testing network connections.
2Click Maintenance > Log to check the NSA’s log for a message about the file.
2a If the log message displays “no such file or directory”, the file may have been removed from
the NSA. Make sure the file still exists in the watch folder.
2b If the log message displays “filename is queued”, the file may still be waiting for auto upload.
Check the grace period setting in the service’s Configuration screen. You can set a smaller
grace period to shorten the queue time.
2c If you cannot find any log messages about the file:
•Make sure the Folder Watch List includes the folder containing the file. You can upload the
file to the watch folder again.
• Make sure the file’s format is supported by Flickr or YouTube. You can find the supported file
extensions in the Folder Watch List.
2d If the log message displays “not authorized yet”, check if you can enter the NSA’s
Configuration screen for the service. If you changed the password of your Flickr or YouTube
account, you cannot access the service’s Configuration screen, and the NSA cannot auto
upload files. Make sure you also update the account information in the NSA.
3Make sure the file size does not exceed the limit imposed by the service. At the time of writing,
Flickr restricts the file size to 10 MB, and YouTube restricts the file size to 100 MB.
4Make sure you did not exceed the service’s upload quota. Flickr and YouTube have different policies
about how much you can upload within a certain period, for example, 100 MB/week.
5The NSA may have temporarily failed to connect to the service. You can upload the file to the watch
folder again.
20.16 Package Management
The NSA won’t install the package(s) I selected in the Package Management screen.

Chapter 20 Troubleshooting
Media Server User’s Guide 363
• The web location of the package may be undergoing maintenance. Try again at a later time.
Upgrade the firmware of the NSA.
• If a new firmware is available, do an upgrade and try installing the package(s) again.
The eMule Search screen does not work.
You need to be connected to an eMule server before you can use the Search screen. Wait for the
NSA to connect to a server before configuring the Search screen.
I want to know how my hard disk is performing.
Use S.M.A.R.T. (Self Monitoring, Analysis, and Reporting Technology) to monitor hard disks. It
detects and reports the reliability of hard disks using standard indicators, enabling administrators to
anticipate possible disk failures. Go to the Package Management screen to install the S.M.A.R.T.
application.
20.17 Backups
I cannot make a backup.
• Check that enough space is available on the external disk. If there isn’t you may need to purge
older backups or delete other files on the backup USB disk or NSA (see Section 11.8 on page
237).
•If you are using BackupPlanner (Section 11.9 on page 237):
• You can look at the Backup screen’s Last Run Result display.
• If you’re backing up to another NSA, another NSA, or a computer, check that it allows the NSA
to write files to it. For a synchronization backup, the target must be another NSA or another
compatible model.
• Check that the NSA is not performing another backup job. Scheduler queues backups when a
different backup is already going on at the time a backup is scheduled.
The backup does not run at the time configured.
• Check that the correct time is configured on the NSA.
• Check that the NSA is able to access the time server from which it gets the time; see Section 7.5
on page 154.

Chapter 20 Troubleshooting
Media Server User’s Guide
364

Media Server User’s Guide 365
CHAPTER 21
Product Specifications
See also Chapter 1 on page 21 for a general overview of the key features.
21.1 LEDs
This table describes the NSA’s LEDs.
Table 124 LEDs
LED NAME COLOR STATUS DESCRIPTION
POWER Blue On The NSA is turned on and receiving power.
Off The NSA is turned off.
SYSTEM Green On The NSA has fully started and is operating normally.
Blinking The NSA is starting up.
Note: Do not turn off the NSA while it is upgrading the firmware or
you may render it unusable.
Orange Blinking The NSA is upgrading the firmware.
Note: Do not turn off the NSA while it is upgrading the firmware or
you may render it unusable.
HDD Green On The hard disk drive is connected properly to the NSA.
Blinking The NSA is saving data to the hard disk drive.
Red On The NSA detected an error on the hard disk drive (like a bad sector
for example). The NSA automatically tries to recover a bad sector,
but the LED stays red until the NSA restarts.
Amber Blinking
(slowly) The hard disk is in hibernation mode.
Off The NSA cannot detect a hard disk in the disk bay.
USB Green On The USB device is connected properly to the NSA.
Blinking The NSA is saving data to the USB device.
Red On The USB device has failed and the NSA can no longer detect it.
Off No USB device connected to the USB port.
LAN Green On The NSA has a successful 10/100 Mbps Ethernet connection.
Blinking The 100M LAN is sending or receiving packets.
Off The NSA does not have a 10/100 Mbps Ethernet connection.
Amber On The NSA has a successful 1000 Mbps Ethernet connection.
Blinking The 1000 M LAN is sending or receiving packets.
Off The NSA does not have a 1000 Mbps Ethernet connection.

Chapter 21 Product Specifications
Media Server User’s Guide
366
21.2 Supported Media Server Content Formats
The following describes the details about the files that the NSA media server can publish.
COPY/
SYNC Green On A USB device is connected to the NSA.
Blinking The NSA is copying or synchronizing files to or from the USB device.
Red On Copying or synchronizing files to or from the USB device failed.
Off No USB device is connected.
Table 124 LEDs (continued)
LED NAME COLOR STATUS DESCRIPTION
Table 125 Supported Media Server Content Formats
CATEGORY FILE TYPE EXTENSION
Video MPEG-1/MPEG-2 dat, dvr-ms, iso, m1v, m2p, m2t, m2v, mp2, mpe, mpeg, mpeg2,
mpg, mpg2, ts, vob, m2ts, tts
MPEG-4 m4v, mp4
AVI avi
DivX divx, avi
Motion JPEG mjpeg, mjpg
Quick Time Video mov, qt
RealMedia rmvb, rm
Ogg ogm
Matroska mkv
ASF asf
Windows Media Video asf, wmv
ISO iso
Flash Video flv
Subtitle srtA, ssa, idx, sub
Chapter 21 Product Specifications
Media Server User’s Guide 367
Note: Not all published file types can be viewed by all client applications.
21.3 Supported iTunes Server Content Formats
At the time of writing, the NSA supports iTunes publishing audio files of the following formats: mp3,
m4a, m4p, wav, and mp4.
Music MP3 mp3, mpa
Ogg Vorbis ogg
RealMedia ra, ram
WAVE wav
Windows Media Audio wma
Matroska mka
Monkeys Audio ape
MP1 mp1
MP4 mp4, m4a, m4p
PCM pcm
LPCM lpcm
DTS dts
AC3 ac3
Free Lossless Audio
Codec flac
Au au
AAC aac
3GPP 3gp, 3g2
AIFF aif, aiff
RIFF-based MIDI rmi
Playlist wpl, pls, asx, wax, m3u
Photo Bitmap bmp
JPEG jpe, jpeg, jpg
PNG png
A. Current VLC plugins may not support srt file format subtitles when playing videos.
Table 125 Supported Media Server Content Formats (continued)
CATEGORY FILE TYPE EXTENSION

Chapter 21 Product Specifications
Media Server User’s Guide
368

Media Server User’s Guide 369
APPENDIX A
Setting Up Your Computer’s IP Address
Note: Your specific NSA may not support all of the operating systems described in this
appendix. See the product specifications for more information about which
operating systems are supported.
This appendix shows you how to configure the IP settings on your computer in order for it to be
able to communicate with the other devices on your network. Windows Vista/XP/2000, Mac OS 9/
OS X, and all versions of UNIX/LINUX include the software components you need to use TCP/IP on
your computer.
If you manually assign IP information instead of using a dynamic IP, make sure that your network’s
computers have IP addresses that place them in the same subnet.
In this appendix, you can set up an IP address for:
•Windows XP/NT/2000 on page 369
•Windows Vista on page 373
•Windows 7 on page 377
•Mac OS X: 10.3 and 10.4 on page 381
•Mac OS X: 10.5 and 10.6 on page 384
•Linux: Ubuntu 8 (GNOME) on page 387
•Linux: openSUSE 10.3 (KDE) on page 391
Windows XP/NT/2000
The following example uses the default Windows XP display theme but can also apply to Windows
2000 and Windows NT.
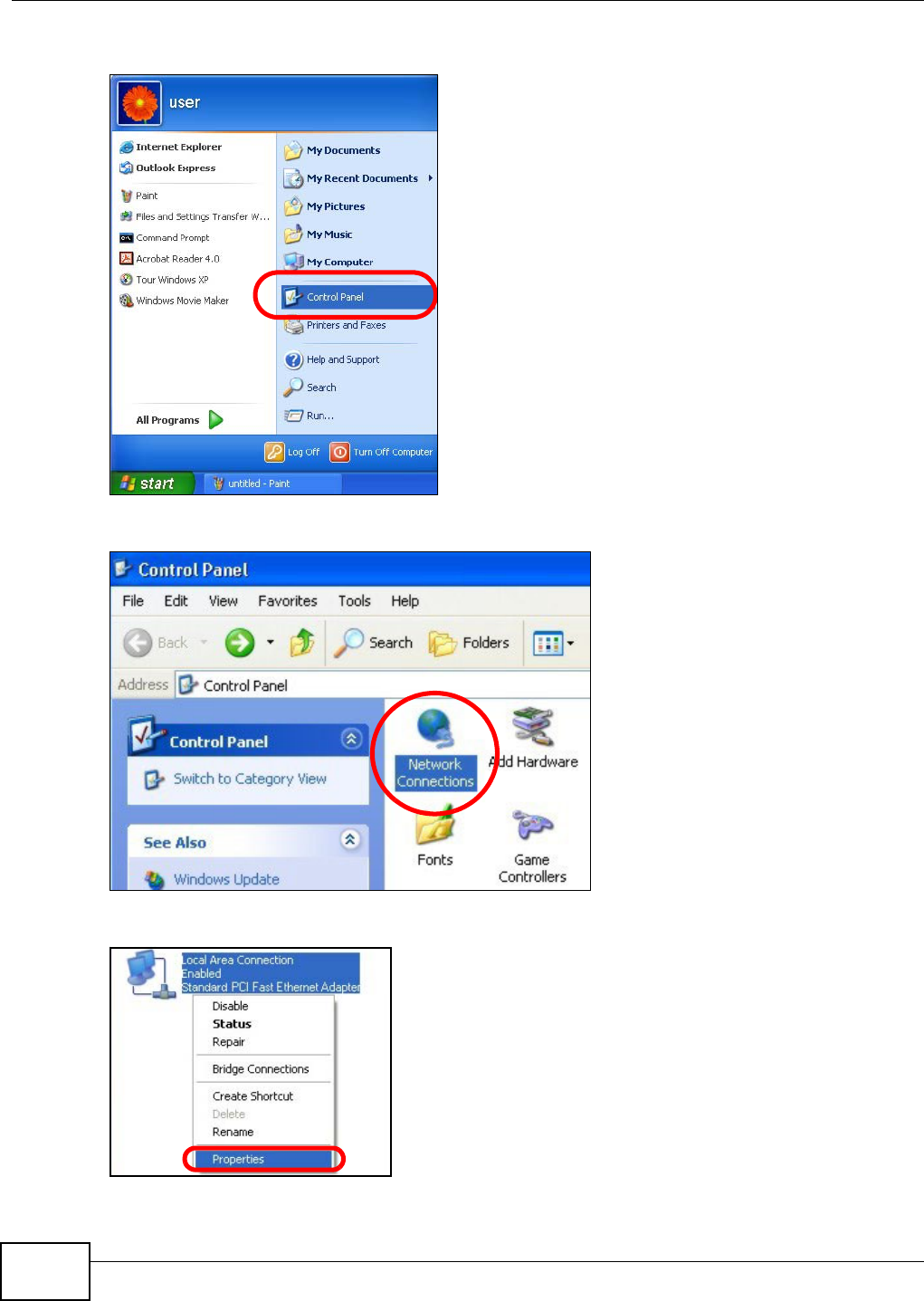
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
370
1Click Start > Control Panel.
2In the Control Panel, click the Network Connections icon.
3Right-click Local Area Connection and then select Properties.
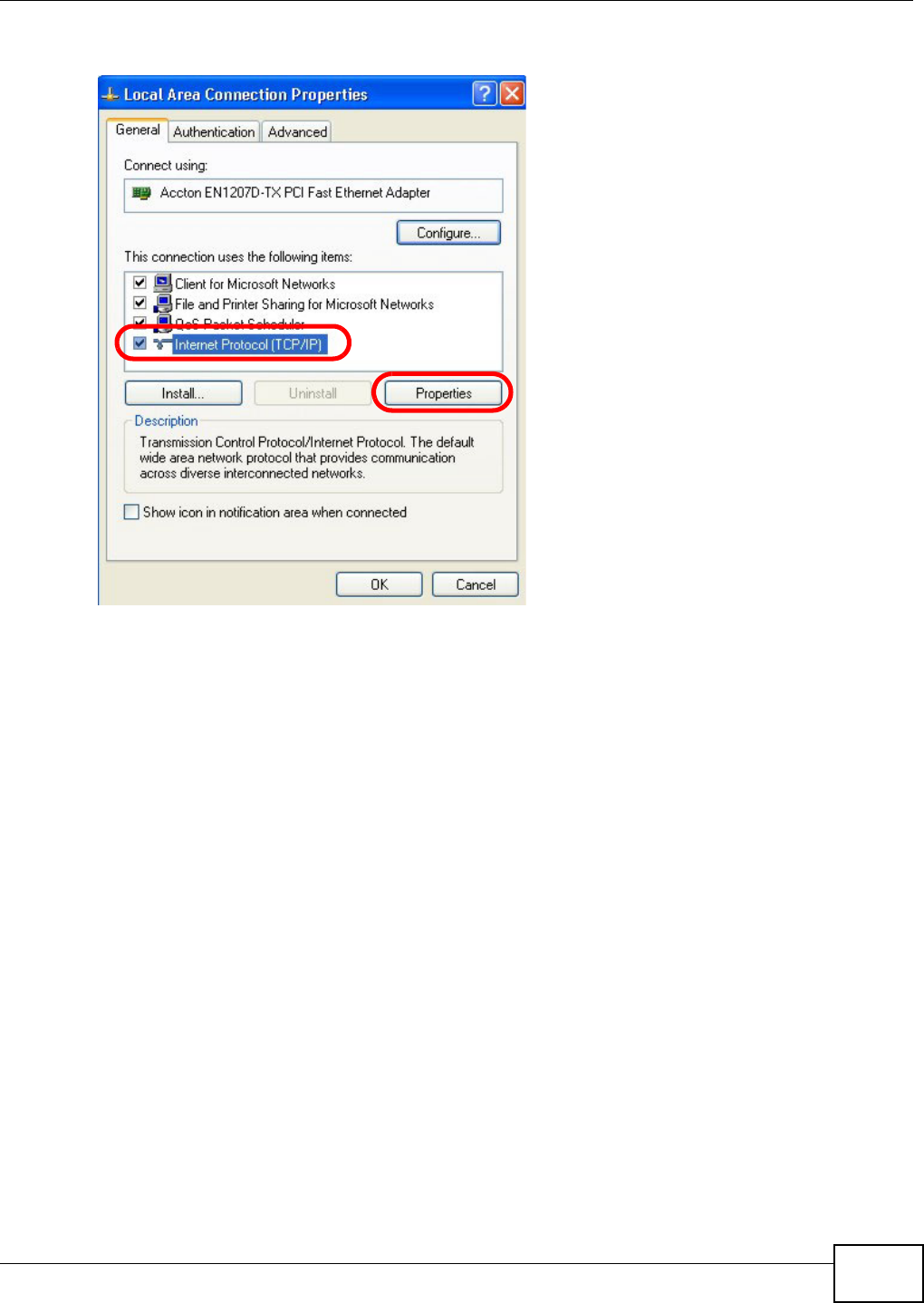
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 371
4On the General tab, select Internet Protocol (TCP/IP) and then click Properties.
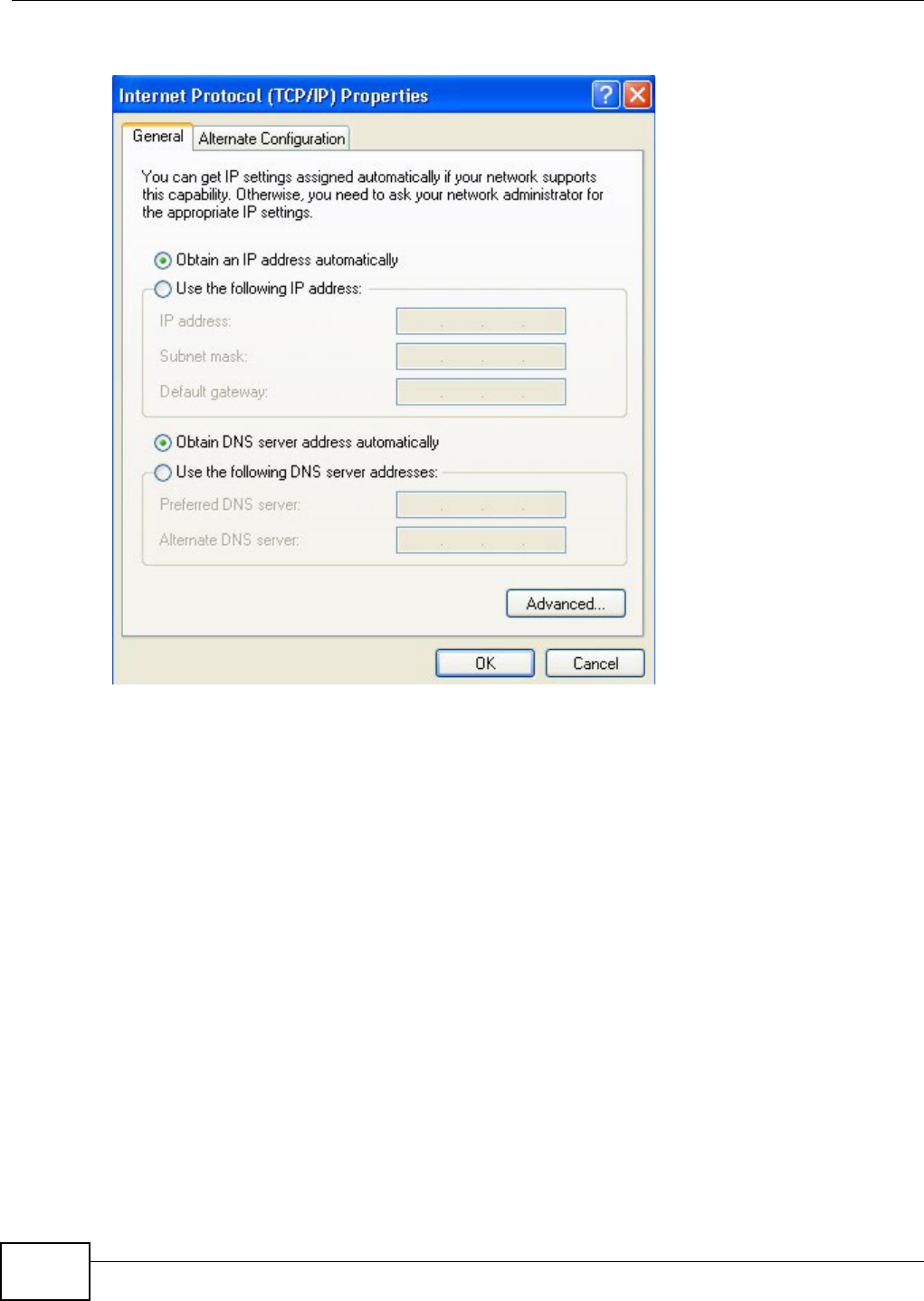
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
372
5The Internet Protocol TCP/IP Properties window opens.
6Select Obtain an IP address automatically if your network administrator or ISP assigns your IP
address dynamically.
Select Use the following IP Address and fill in the IP address, Subnet mask, and Default
gateway fields if you have a static IP address that was assigned to you by your network
administrator or ISP. You may also have to enter a Preferred DNS server and an Alternate DNS
server, if that information was provided.
7Click OK to close the Internet Protocol (TCP/IP) Properties window.
8Click OK to close the Local Area Connection Properties window.
Verifying Settings
1Click Start > All Programs > Accessories > Command Prompt.
2In the Command Prompt window, type "ipconfig" and then press [ENTER].
You can also go to Start > Control Panel > Network Connections, right-click a network
connection, click Status and then click the Support tab to view your IP address and connection
information.
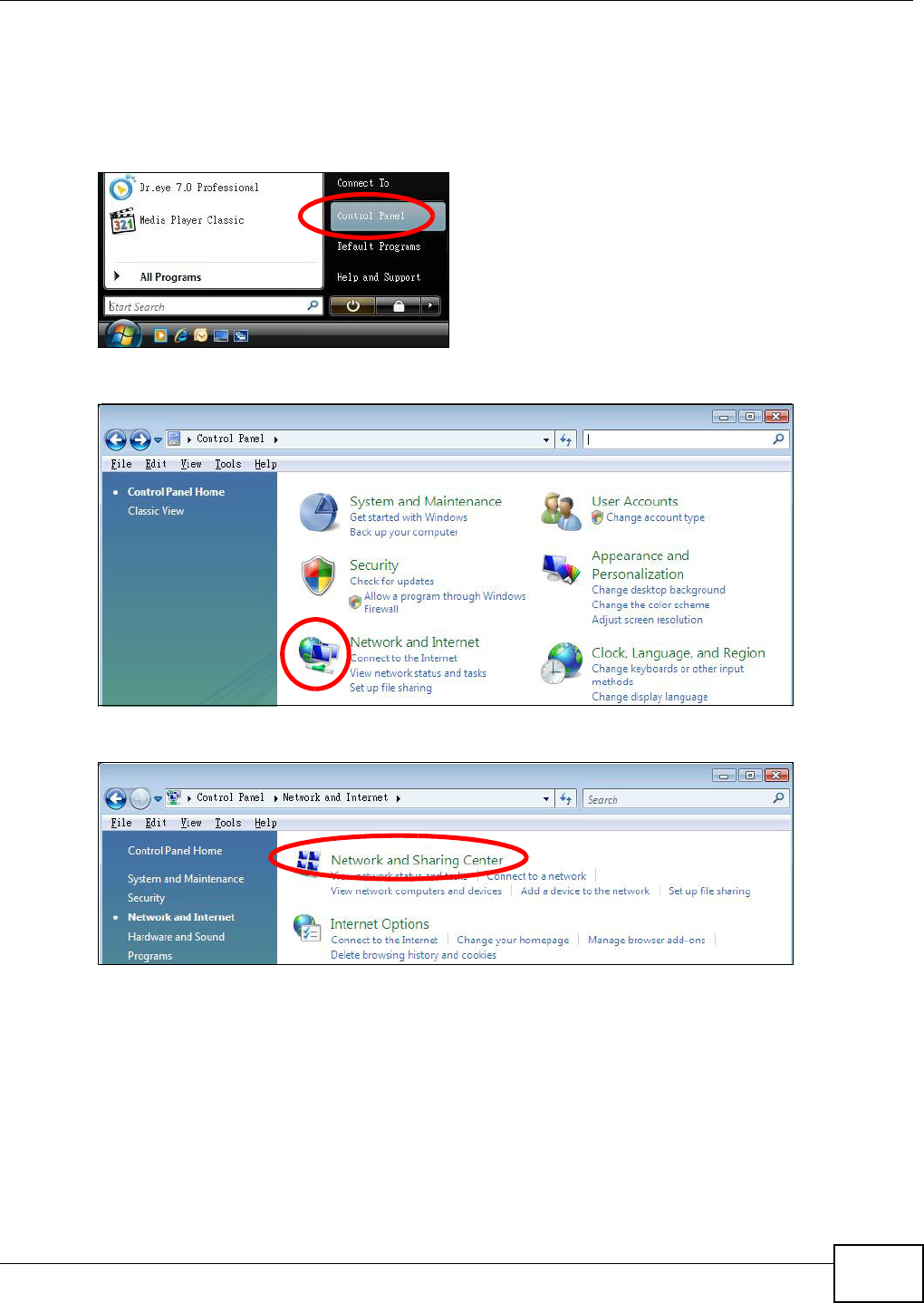
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 373
Windows Vista
This section shows screens from Windows Vista Professional.
1Click Start > Control Panel.
2In the Control Panel, click the Network and Internet icon.
3Click the Network and Sharing Center icon.
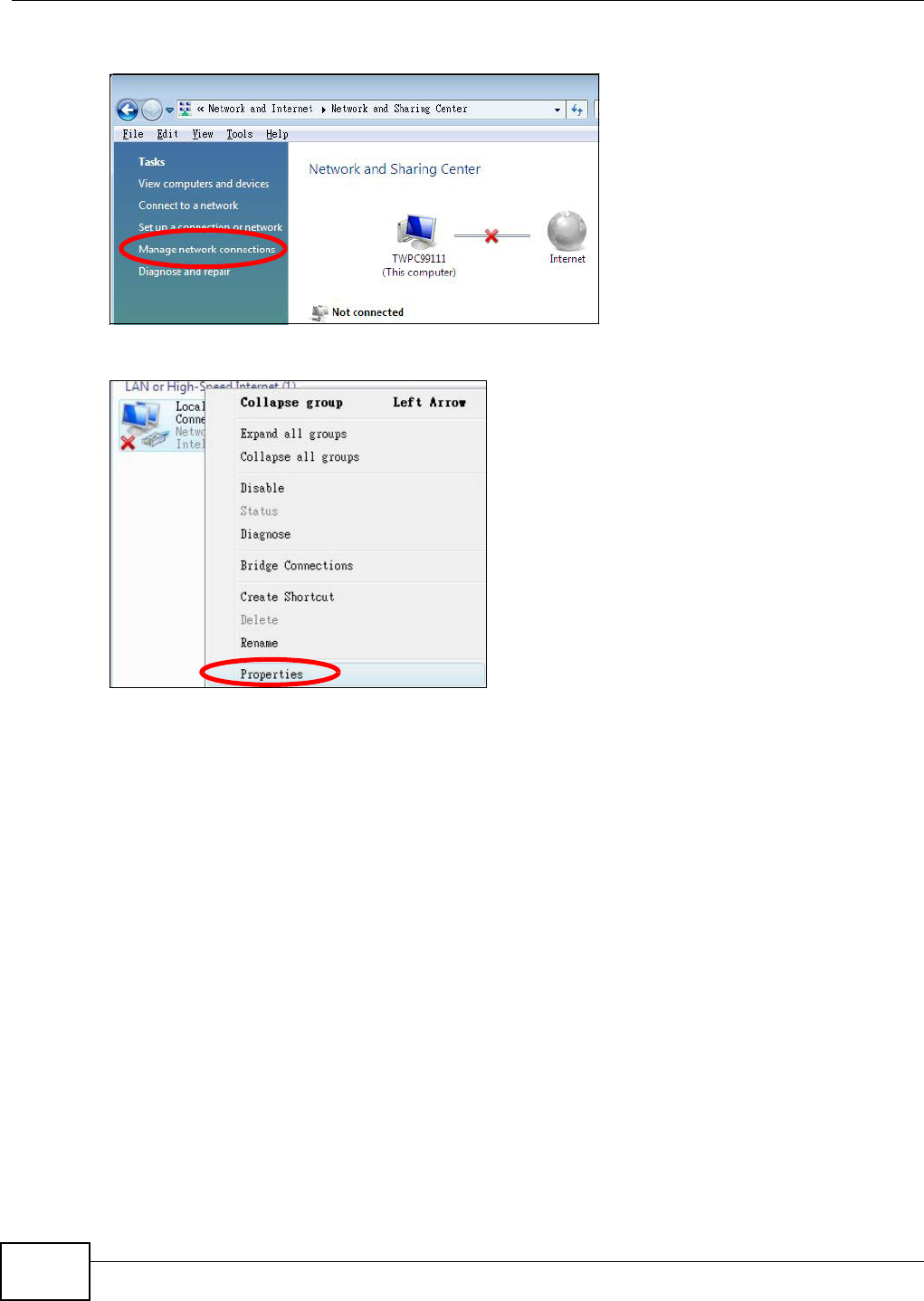
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
374
4Click Manage network connections.
5Right-click Local Area Connection and then select Properties.
Note: During this procedure, click Continue whenever Windows displays a screen saying
that it needs your permission to continue.
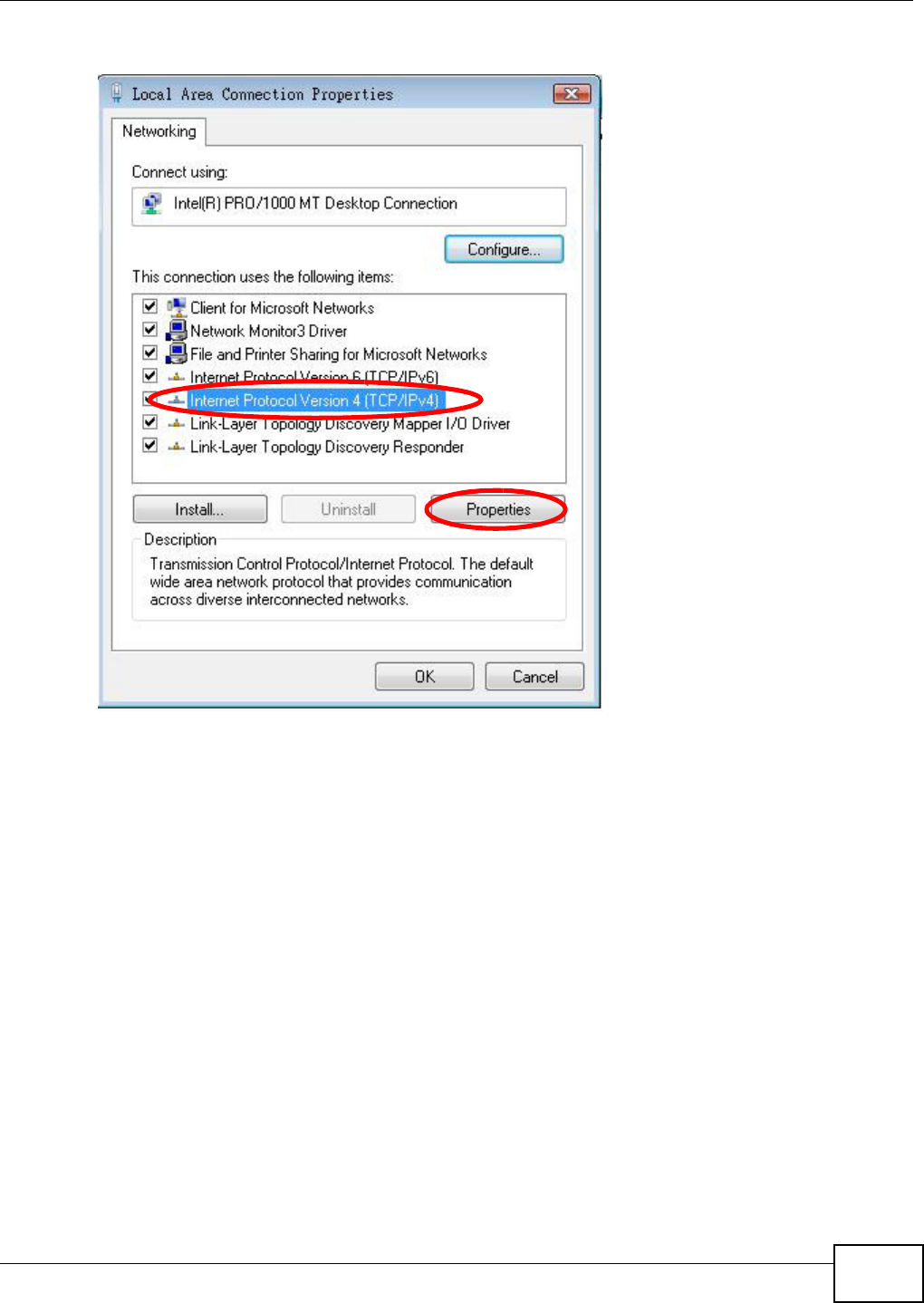
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 375
6Select Internet Protocol Version 4 (TCP/IPv4) and then select Properties.
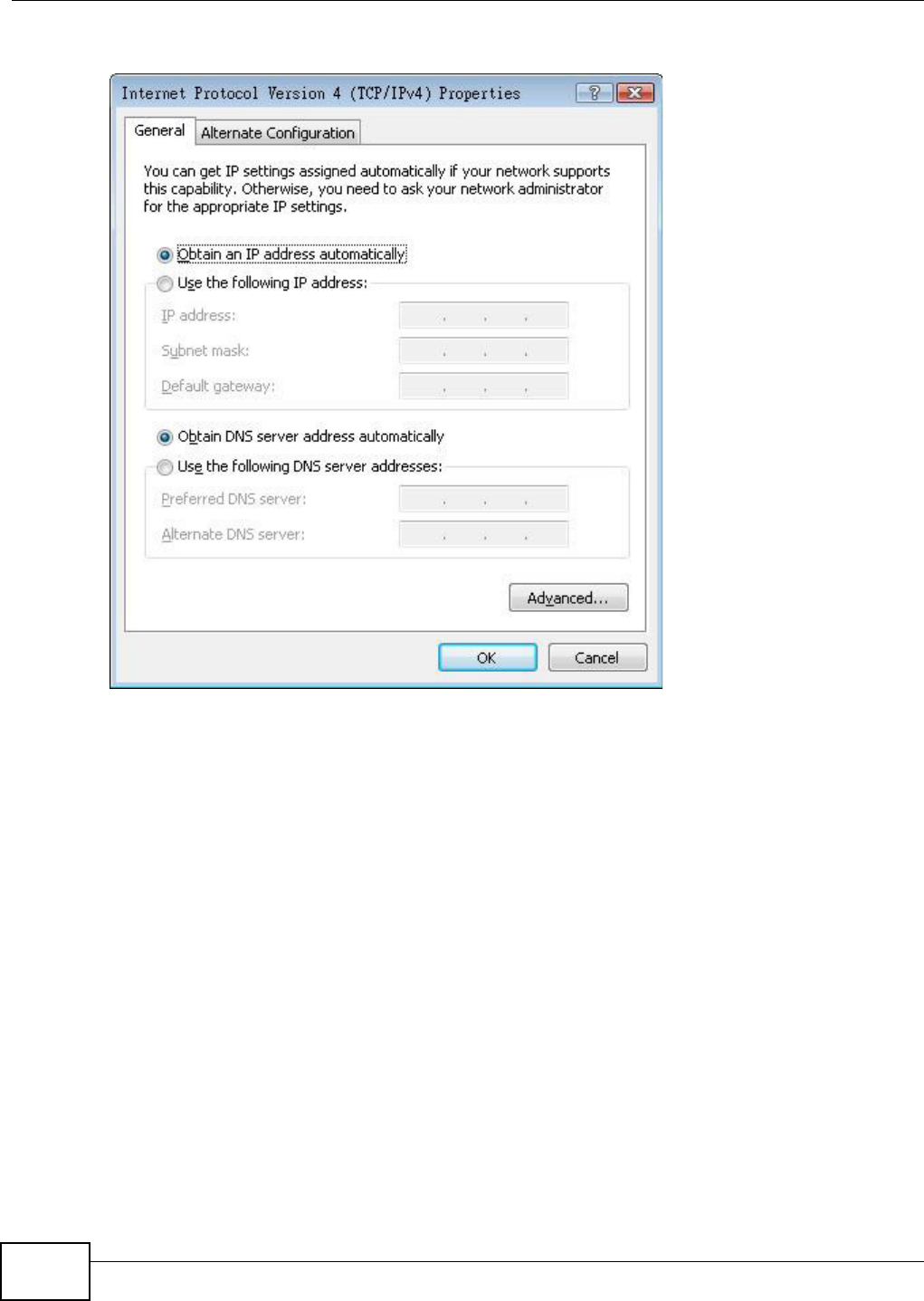
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
376
7The Internet Protocol Version 4 (TCP/IPv4) Properties window opens.
8Select Obtain an IP address automatically if your network administrator or ISP assigns your IP
address dynamically.
Select Use the following IP Address and fill in the IP address, Subnet mask, and Default
gateway fields if you have a static IP address that was assigned to you by your network
administrator or ISP. You may also have to enter a Preferred DNS server and an Alternate DNS
server, if that information was provided.Click Advanced.
9Click OK to close the Internet Protocol (TCP/IP) Properties window.
10 Click OK to close the Local Area Connection Properties window.
Verifying Settings
1Click Start > All Programs > Accessories > Command Prompt.
2In the Command Prompt window, type "ipconfig" and then press [ENTER].
You can also go to Start > Control Panel > Network Connections, right-click a network
connection, click Status and then click the Support tab to view your IP address and connection
information.
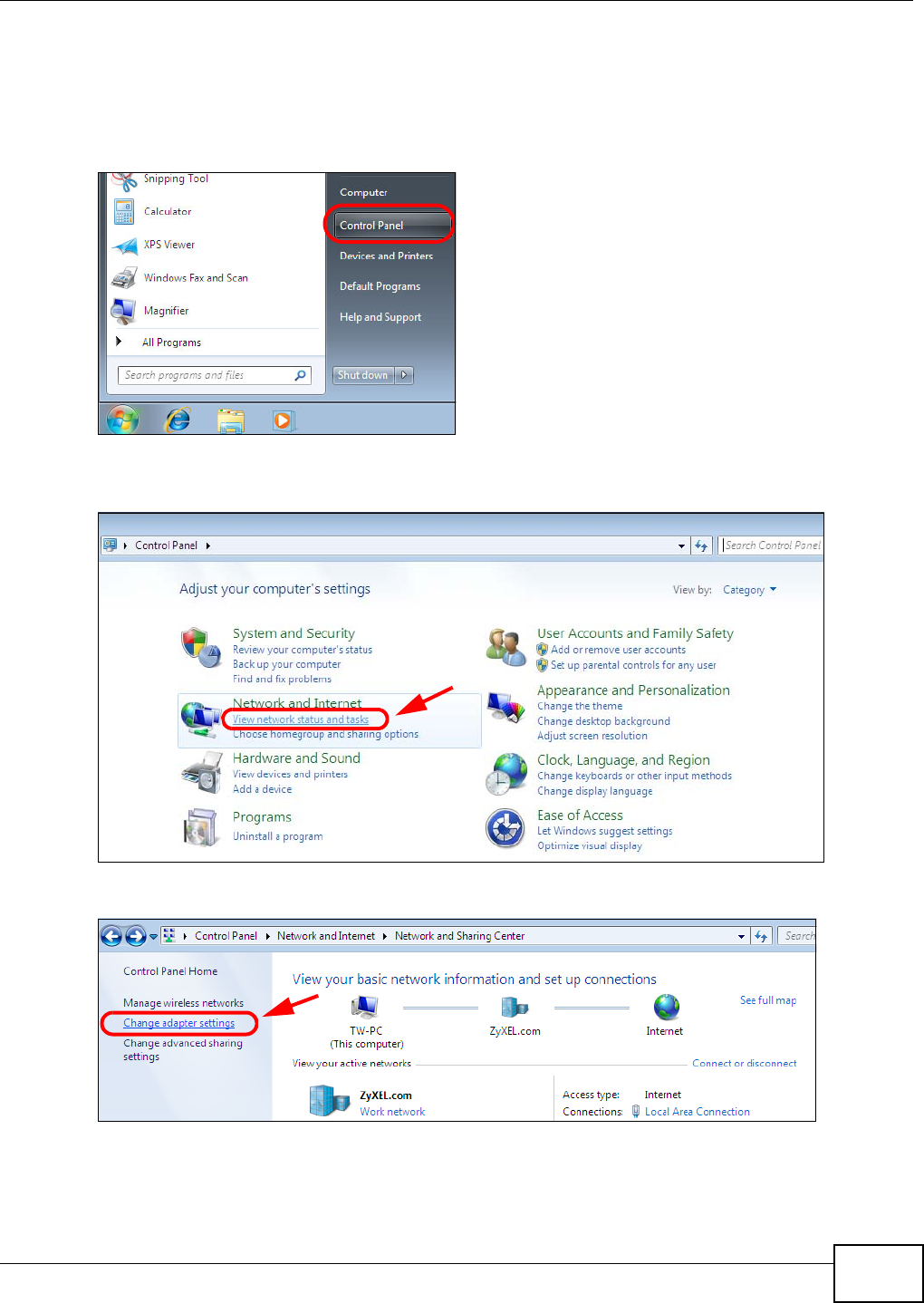
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 377
Windows 7
This section shows screens from Windows 7 Enterprise.
1Click Start > Control Panel.
2In the Control Panel, click View network status and tasks under the Network and Internet
category.
3Click Change adapter settings.
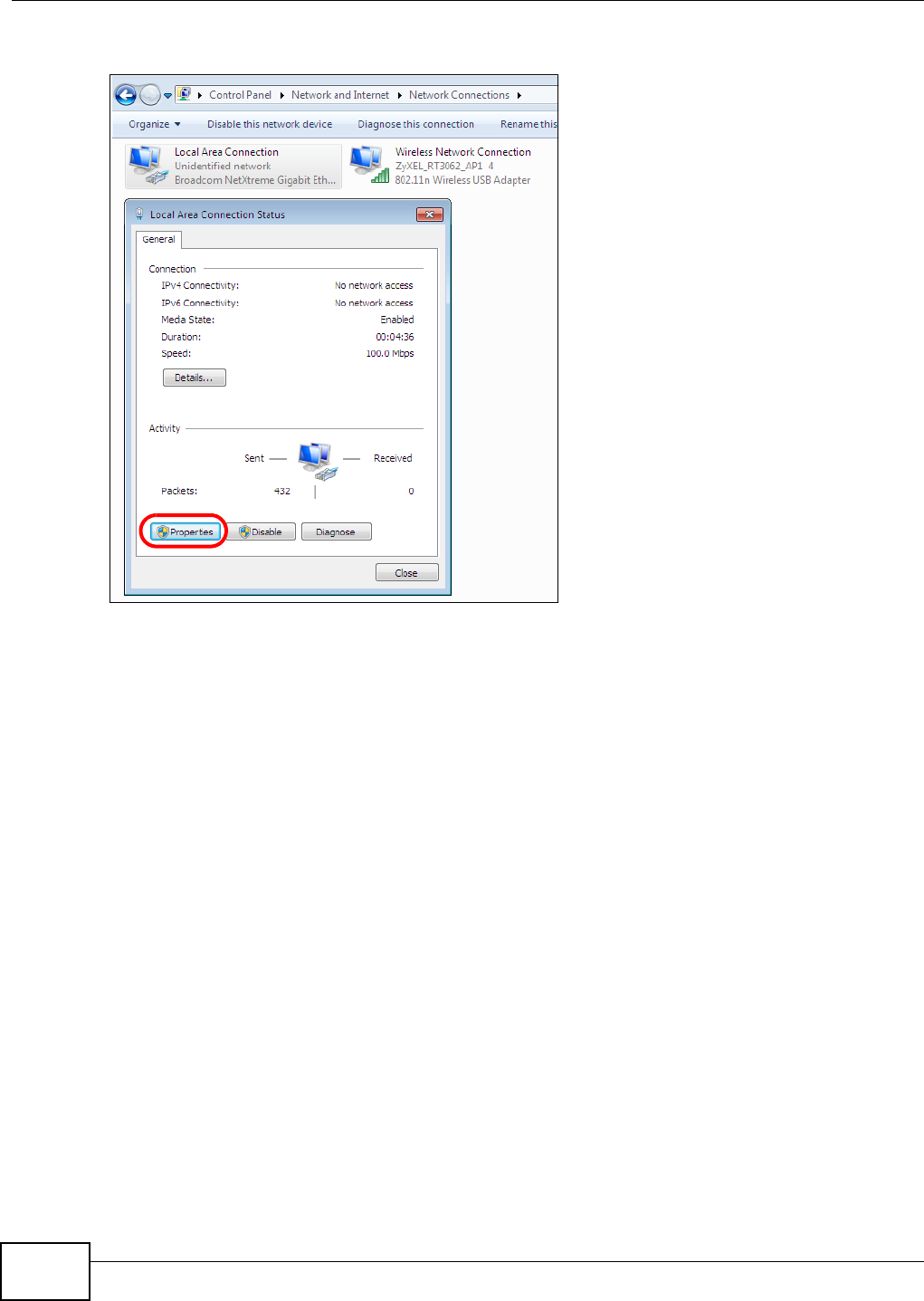
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
378
4Double click Local Area Connection and then select Properties.
Note: During this procedure, click Continue whenever Windows displays a screen saying
that it needs your permission to continue.
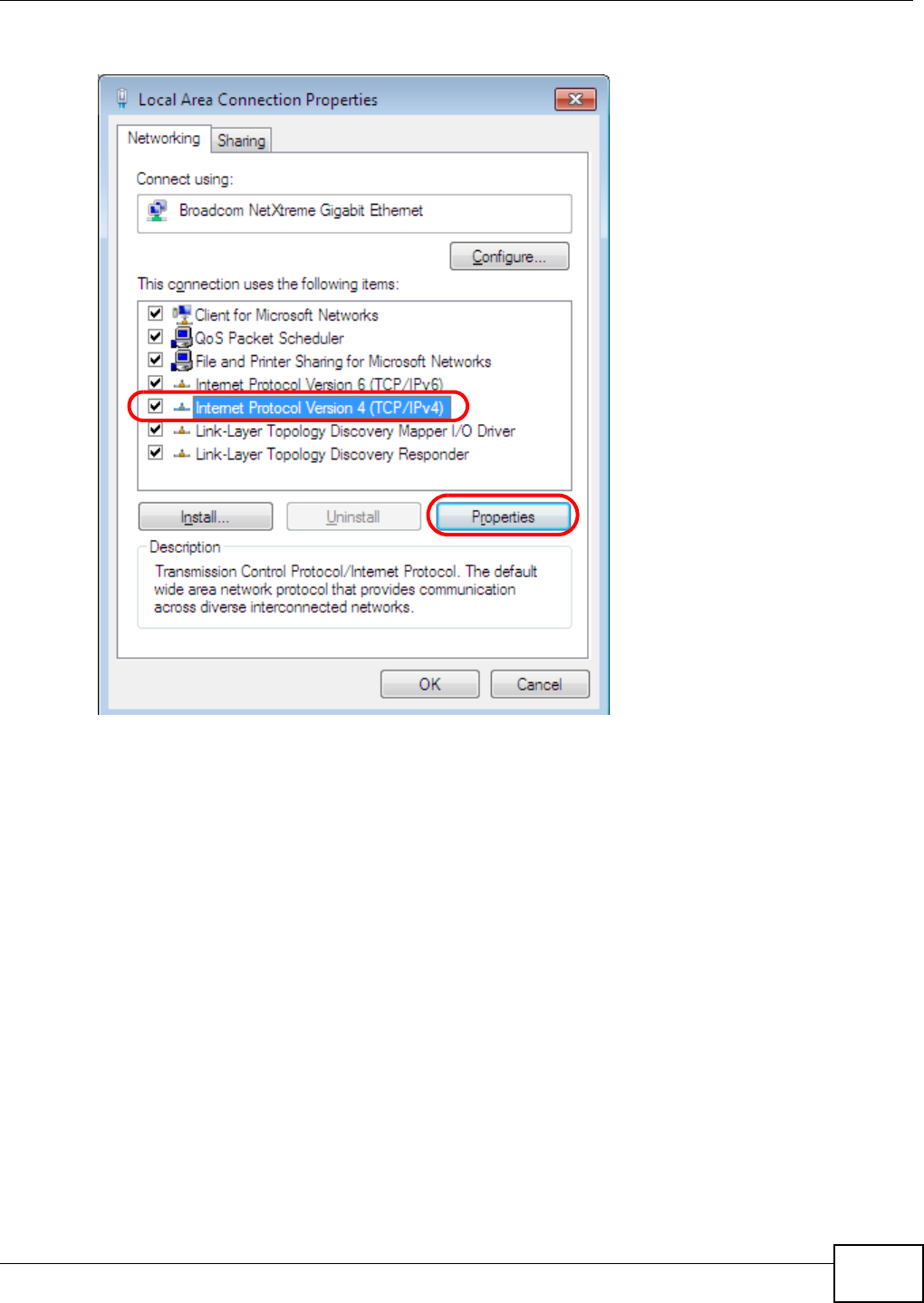
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 379
5Select Internet Protocol Version 4 (TCP/IPv4) and then select Properties.
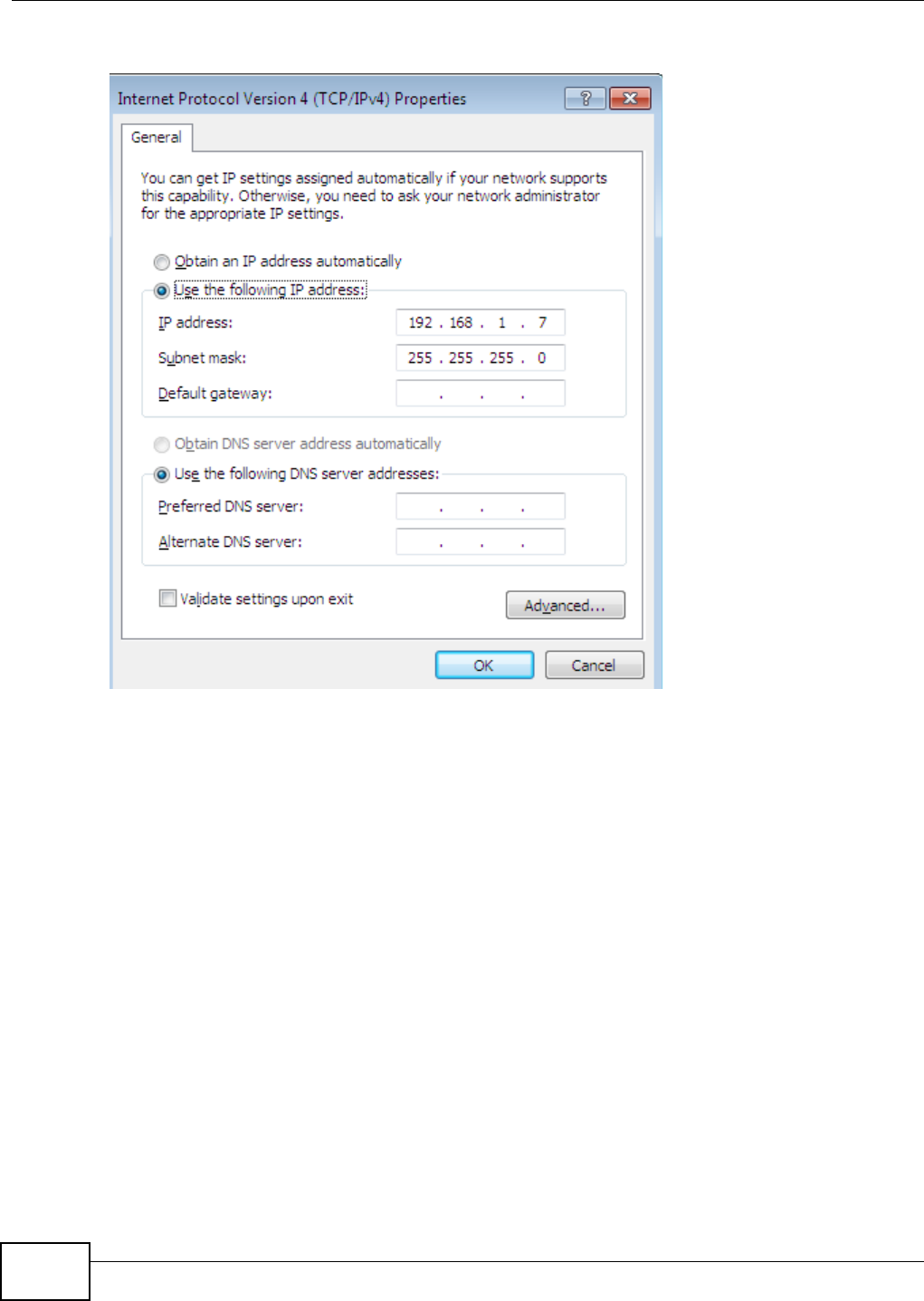
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
380
6The Internet Protocol Version 4 (TCP/IPv4) Properties window opens.
7Select Obtain an IP address automatically if your network administrator or ISP assigns your IP
address dynamically.
Select Use the following IP Address and fill in the IP address, Subnet mask, and Default
gateway fields if you have a static IP address that was assigned to you by your network
administrator or ISP. You may also have to enter a Preferred DNS server and an Alternate DNS
server, if that information was provided. Click Advanced if you want to configure advanced
settings for IP, DNS and WINS.
8Click OK to close the Internet Protocol (TCP/IP) Properties window.
9Click OK to close the Local Area Connection Properties window.
Verifying Settings
1Click Start > All Programs > Accessories > Command Prompt.
2In the Command Prompt window, type "ipconfig" and then press [ENTER].
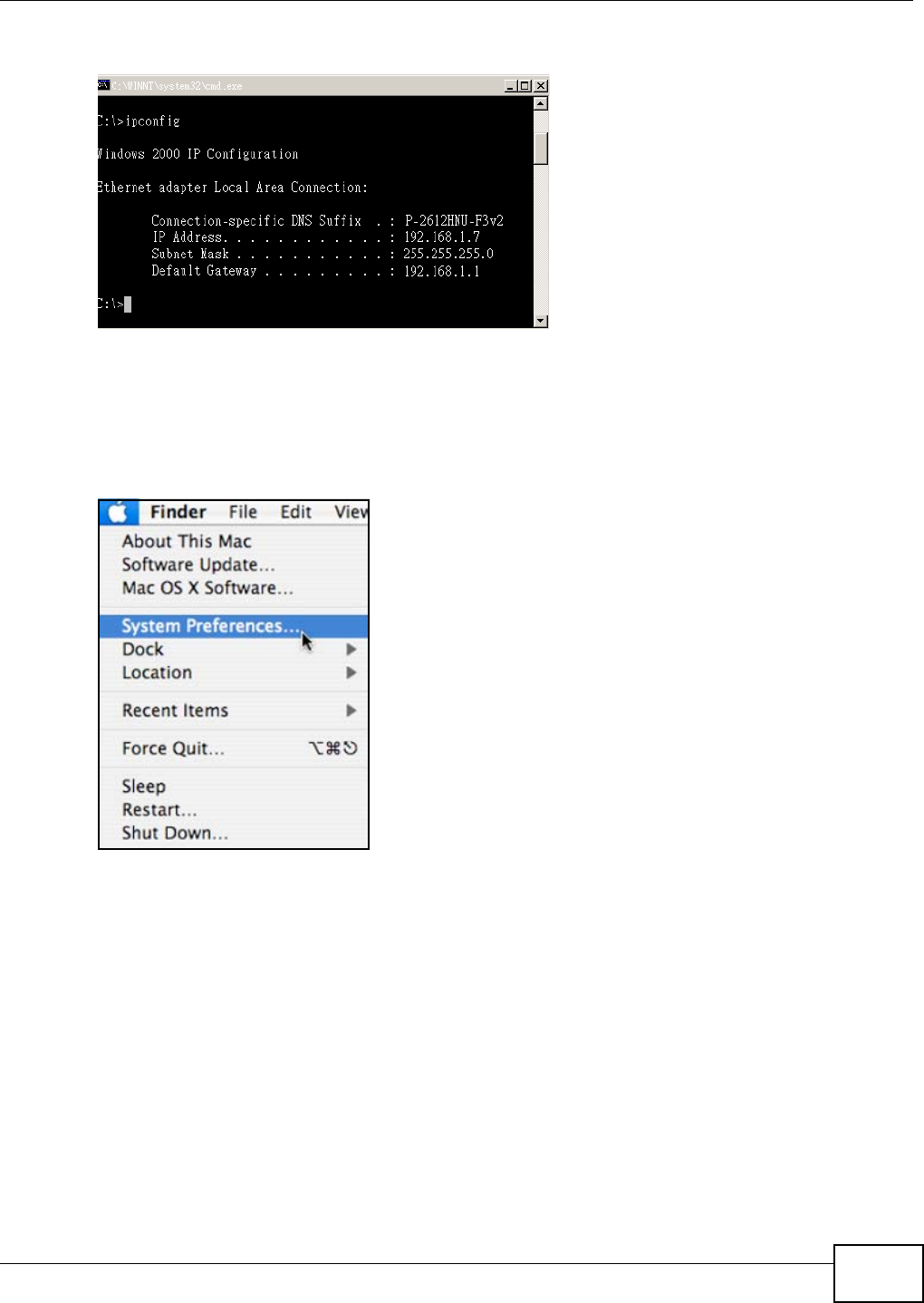
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 381
3The IP settings are displayed as follows.
Mac OS X: 10.3 and 10.4
The screens in this section are from Mac OS X 10.4 but can also apply to 10.3.
1Click Apple > System Preferences.
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
382
2In the System Preferences window, click the Network icon.
3When the Network preferences pane opens, select Built-in Ethernet from the network
connection type list, and then click Configure.
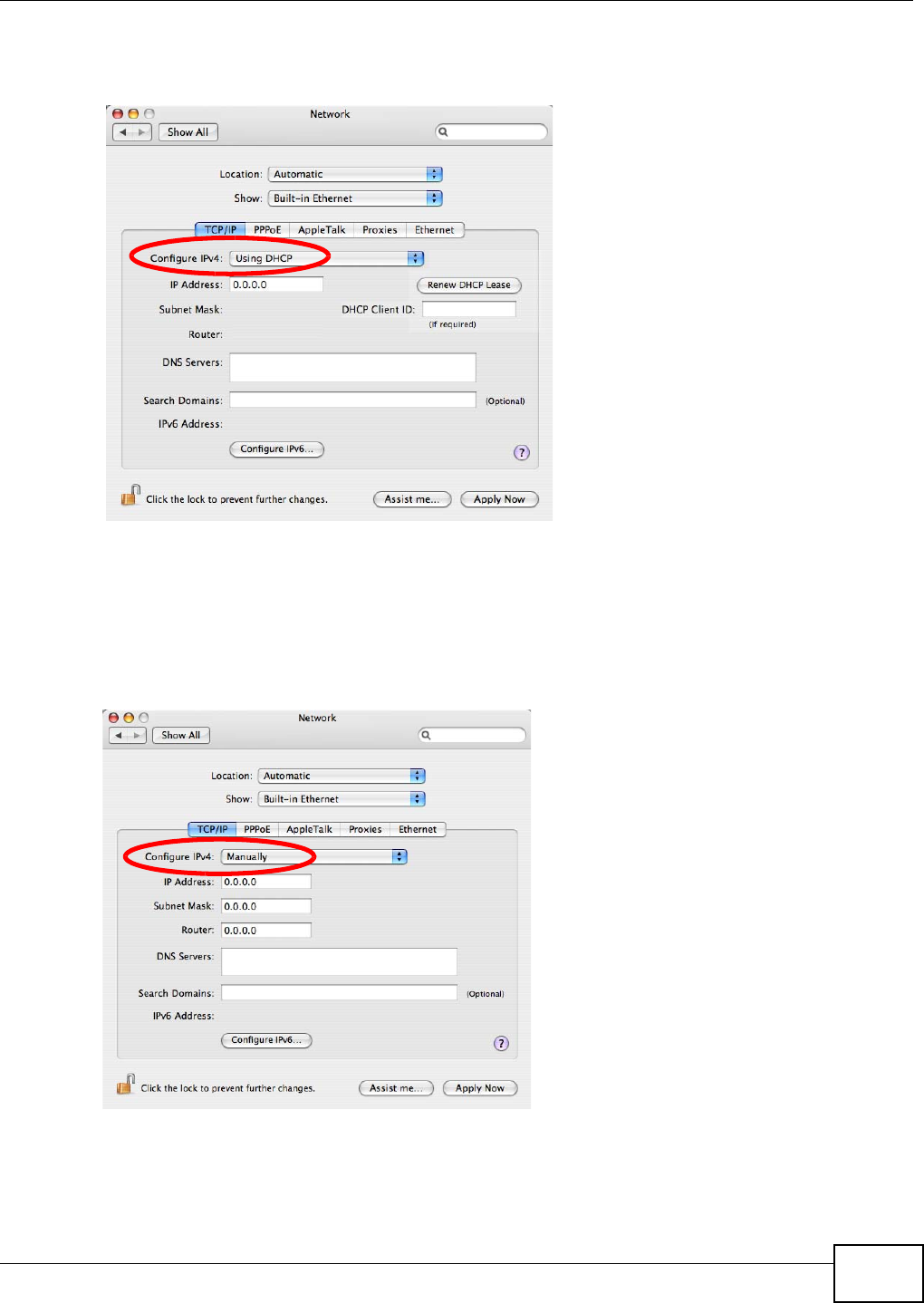
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 383
4For dynamically assigned settings, select Using DHCP from the Configure IPv4 list in the TCP/IP
tab.
5For statically assigned settings, do the following:
•From the Configure IPv4 list, select Manually.
•In the IP Address field, type your IP address.
•In the Subnet Mask field, type your subnet mask.
•In the Router field, type the IP address of your device.
6Click Apply Now and close the window.
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
384
Verifying Settings
Check your TCP/IP properties by clicking Applications > Utilities > Network Utilities, and then
selecting the appropriate Network Interface from the Info tab.
Figure 209 Mac OS X 10.4: Network Utility
Mac OS X: 10.5 and 10.6
The screens in this section are from Mac OS X 10.5 but can also apply to 10.6.
1Click Apple > System Preferences.
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 385
2In System Preferences, click the Network icon.
3When the Network preferences pane opens, select Ethernet from the list of available connection
types.
4From the Configure list, select Using DHCP for dynamically assigned settings.
5For statically assigned settings, do the following:
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
386
•From the Configure list, select Manually.
•In the IP Address field, enter your IP address.
•In the Subnet Mask field, enter your subnet mask.
•In the Router field, enter the IP address of your NSA.
6Click Apply and close the window.
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 387
Verifying Settings
Check your TCP/IP properties by clicking Applications > Utilities > Network Utilities, and then
selecting the appropriate Network interface from the Info tab.
Figure 210 Mac OS X 10.5: Network Utility
Linux: Ubuntu 8 (GNOME)
This section shows you how to configure your computer’s TCP/IP settings in the GNU Object Model
Environment (GNOME) using the Ubuntu 8 Linux distribution. The procedure, screens and file
locations may vary depending on your specific distribution, release version, and individual
configuration. The following screens use the default Ubuntu 8 installation.
Note: Make sure you are logged in as the root administrator.
Follow the steps below to configure your computer IP address in GNOME:
1Click System > Administration > Network.
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
388
2When the Network Settings window opens, click Unlock to open the Authenticate window. (By
default, the Unlock button is greyed out until clicked.) You cannot make changes to your
configuration unless you first enter your admin password.
3In the Authenticate window, enter your admin account name and password then click the
Authenticate button.
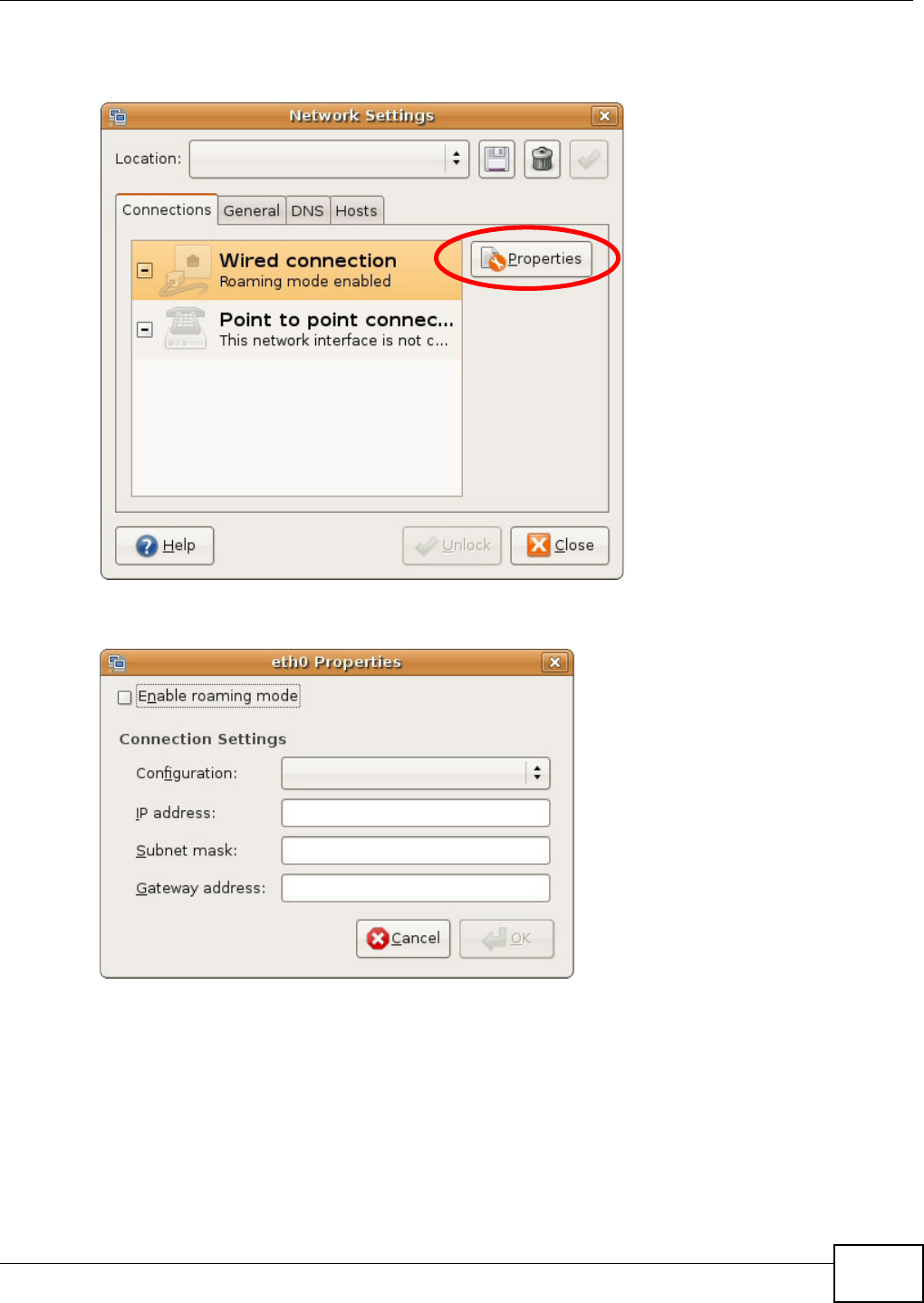
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 389
4In the Network Settings window, select the connection that you want to configure, then click
Properties.
5The Properties dialog box opens.
•In the Configuration list, select Automatic Configuration (DHCP) if you have a dynamic IP
address.
•In the Configuration list, select Static IP address if you have a static IP address. Fill in the
IP address, Subnet mask, and Gateway address fields.
6Click OK to save the changes and close the Properties dialog box and return to the Network
Settings screen.
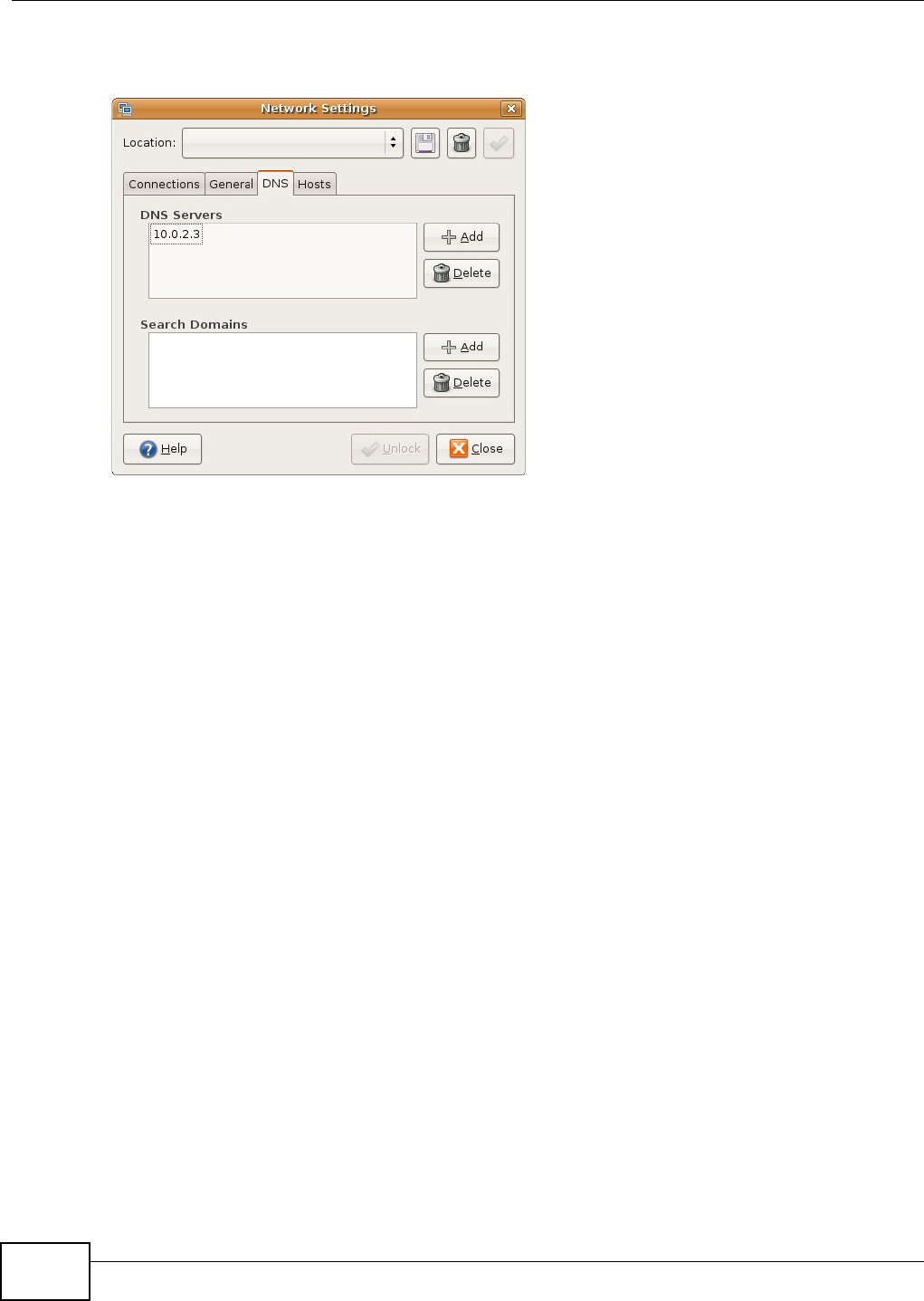
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
390
7If you know your DNS server IP address(es), click the DNS tab in the Network Settings window
and then enter the DNS server information in the fields provided.
8Click the Close button to apply the changes.
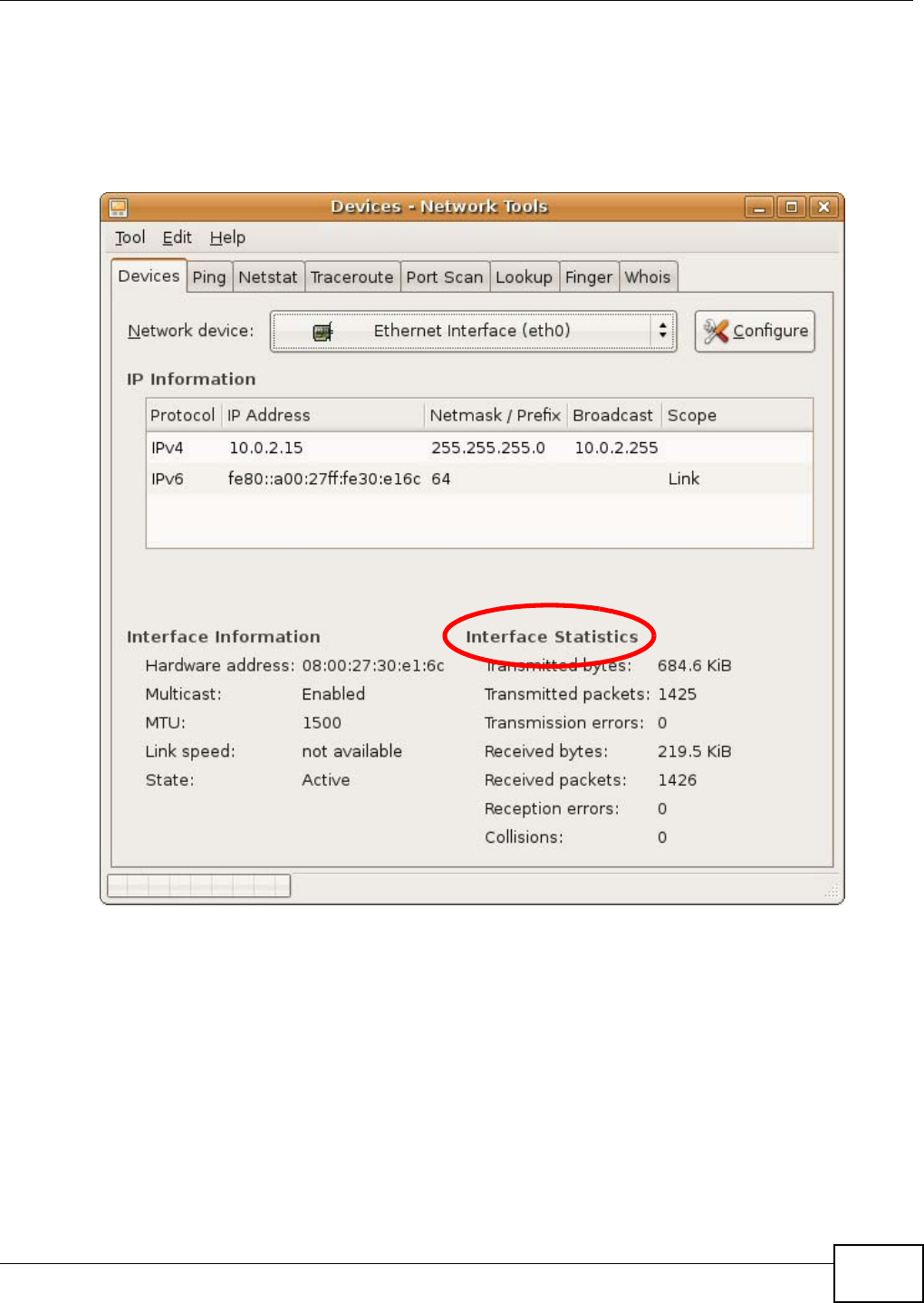
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 391
Verifying Settings
Check your TCP/IP properties by clicking System > Administration > Network Tools, and then
selecting the appropriate Network device from the Devices tab. The Interface Statistics
column shows data if your connection is working properly.
Figure 211 Ubuntu 8: Network Tools
Linux: openSUSE 10.3 (KDE)
This section shows you how to configure your computer’s TCP/IP settings in the K Desktop
Environment (KDE) using the openSUSE 10.3 Linux distribution. The procedure, screens and file
locations may vary depending on your specific distribution, release version, and individual
configuration. The following screens use the default openSUSE 10.3 installation.
Note: Make sure you are logged in as the root administrator.
Follow the steps below to configure your computer IP address in the KDE:
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
392
1Click K Menu > Computer > Administrator Settings (YaST).
2When the Run as Root - KDE su dialog opens, enter the admin password and click OK.
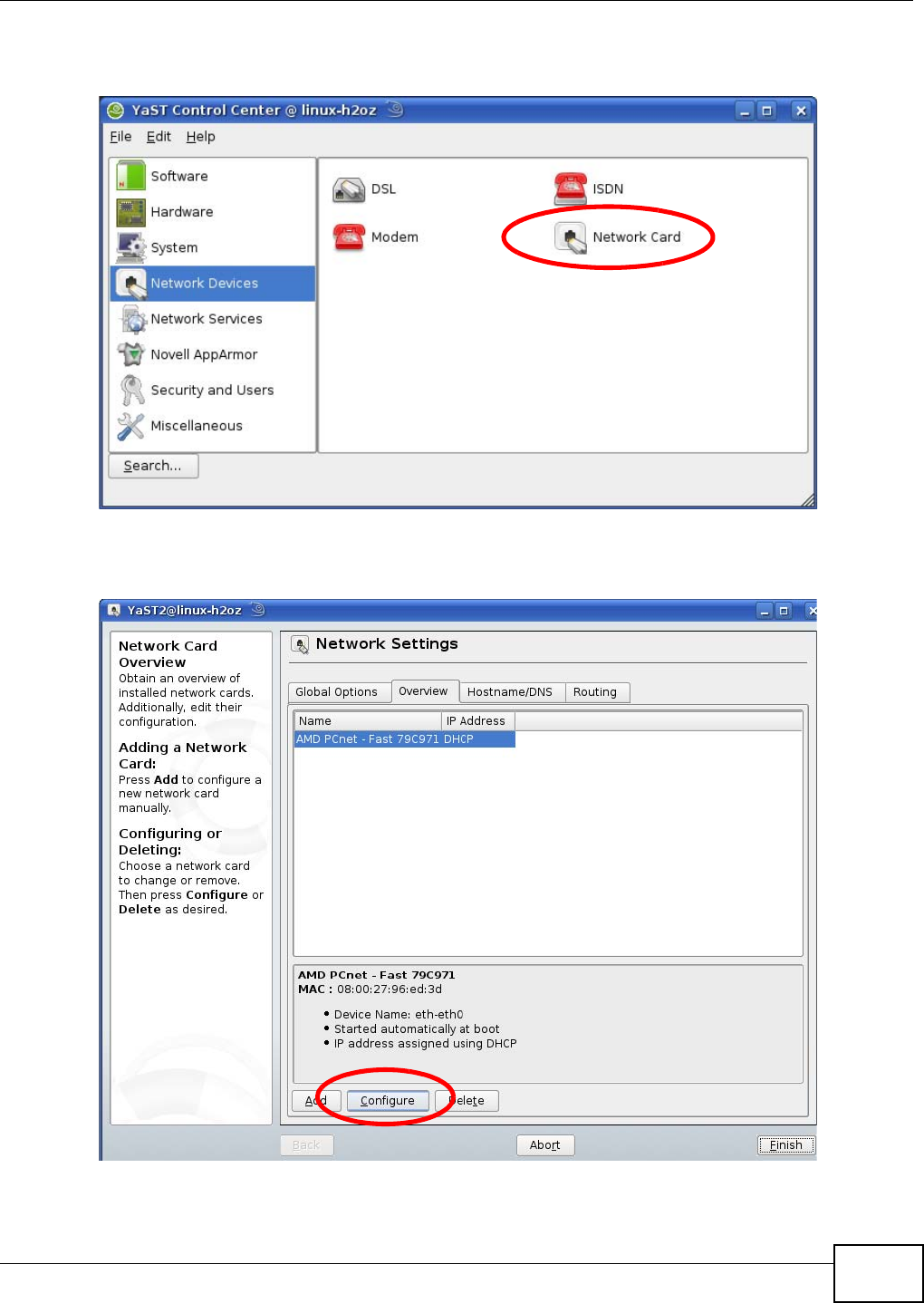
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 393
3When the YaST Control Center window opens, select Network Devices and then click the
Network Card icon.
4When the Network Settings window opens, click the Overview tab, select the appropriate
connection Name from the list, and then click the Configure button.
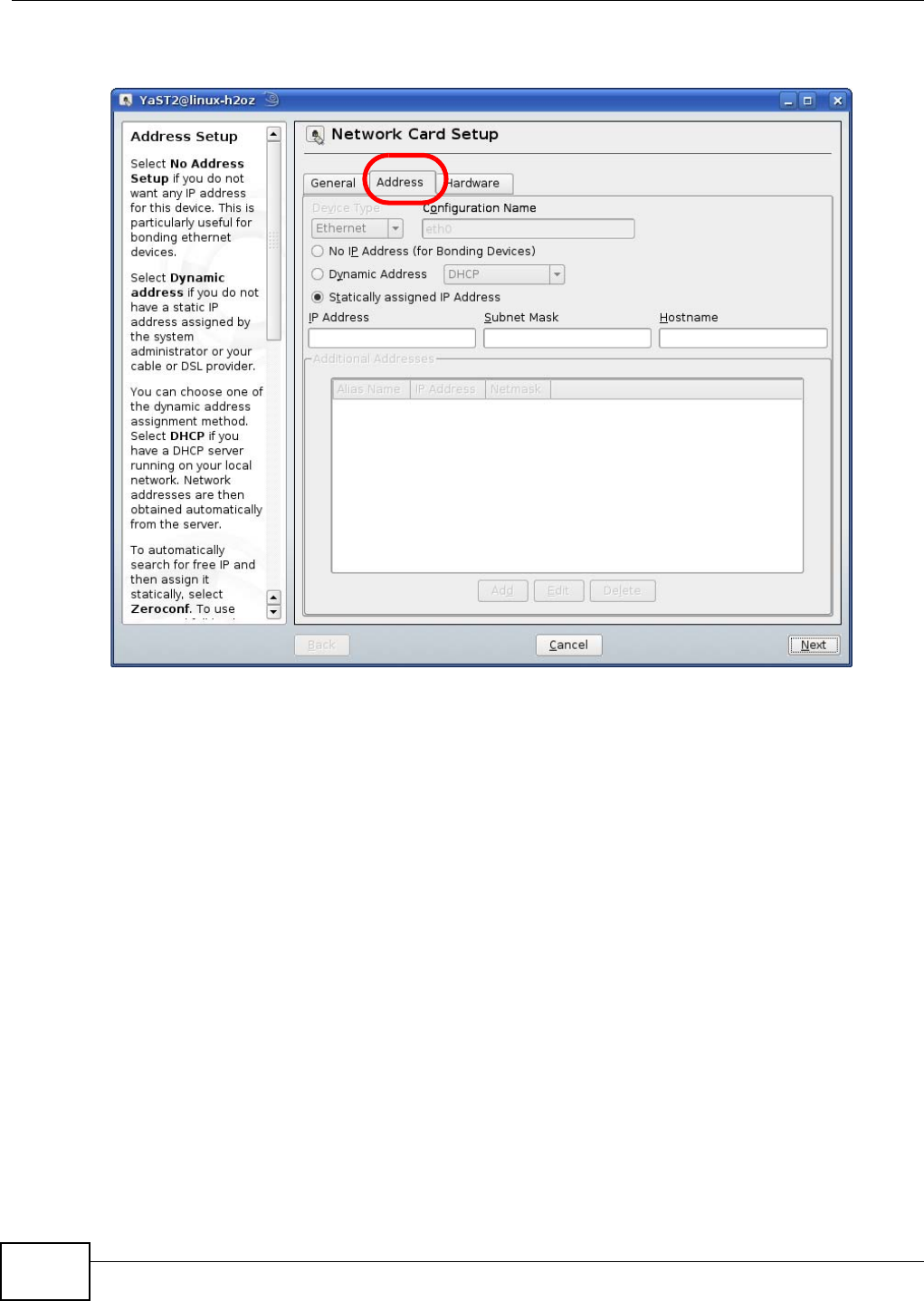
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
394
5When the Network Card Setup window opens, click the Address tab
Figure 212 openSUSE 10.3: Network Card Setup
6Select Dynamic Address (DHCP) if you have a dynamic IP address.
Select Statically assigned IP Address if you have a static IP address. Fill in the IP address,
Subnet mask, and Hostname fields.
7Click Next to save the changes and close the Network Card Setup window.
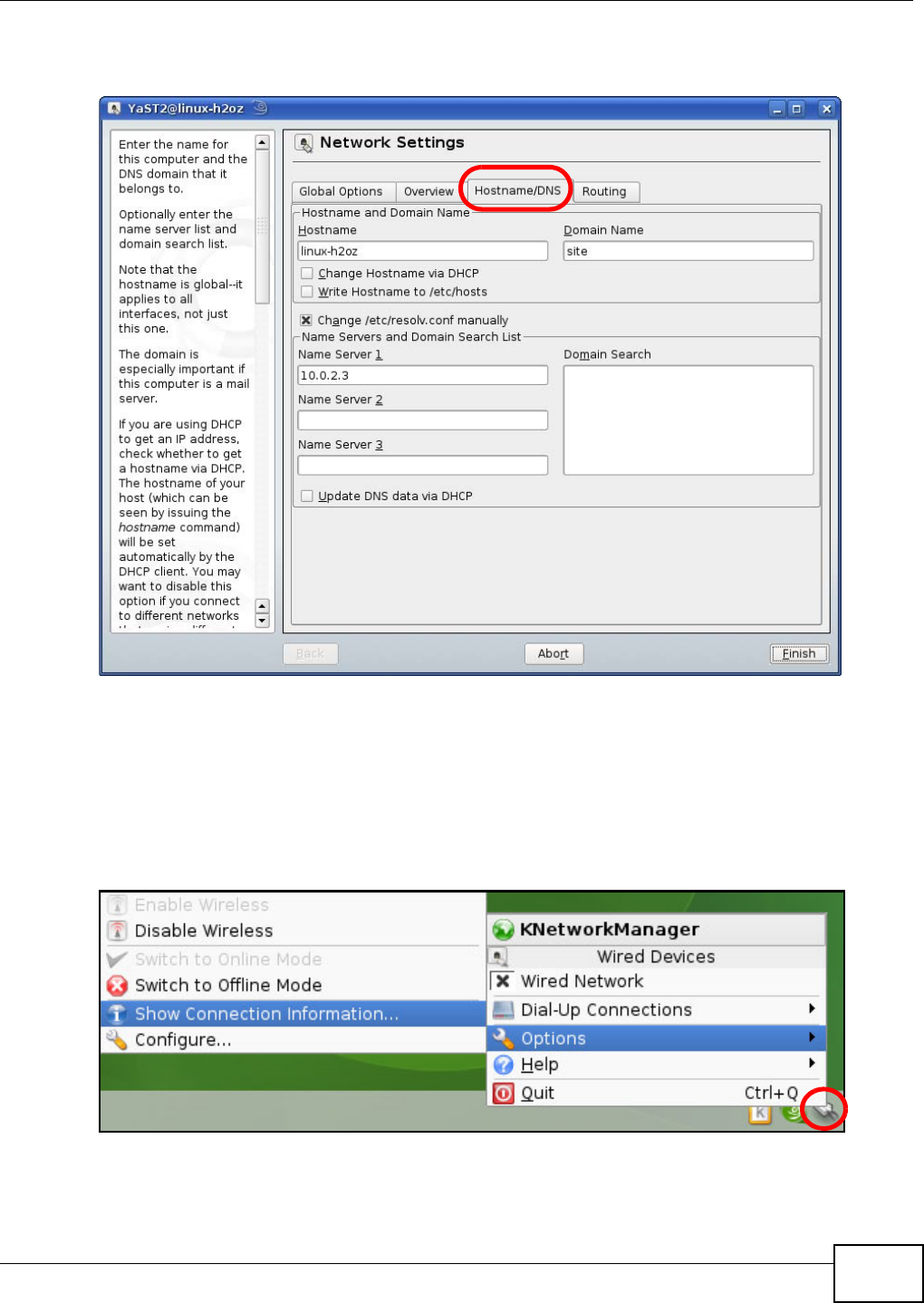
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide 395
8If you know your DNS server IP address(es), click the Hostname/DNS tab in Network Settings
and then enter the DNS server information in the fields provided.
9Click Finish to save your settings and close the window.
Verifying Settings
Click the KNetwork Manager icon on the Task bar to check your TCP/IP properties. From the
Options sub-menu, select Show Connection Information.
Figure 213 openSUSE 10.3: KNetwork Manager
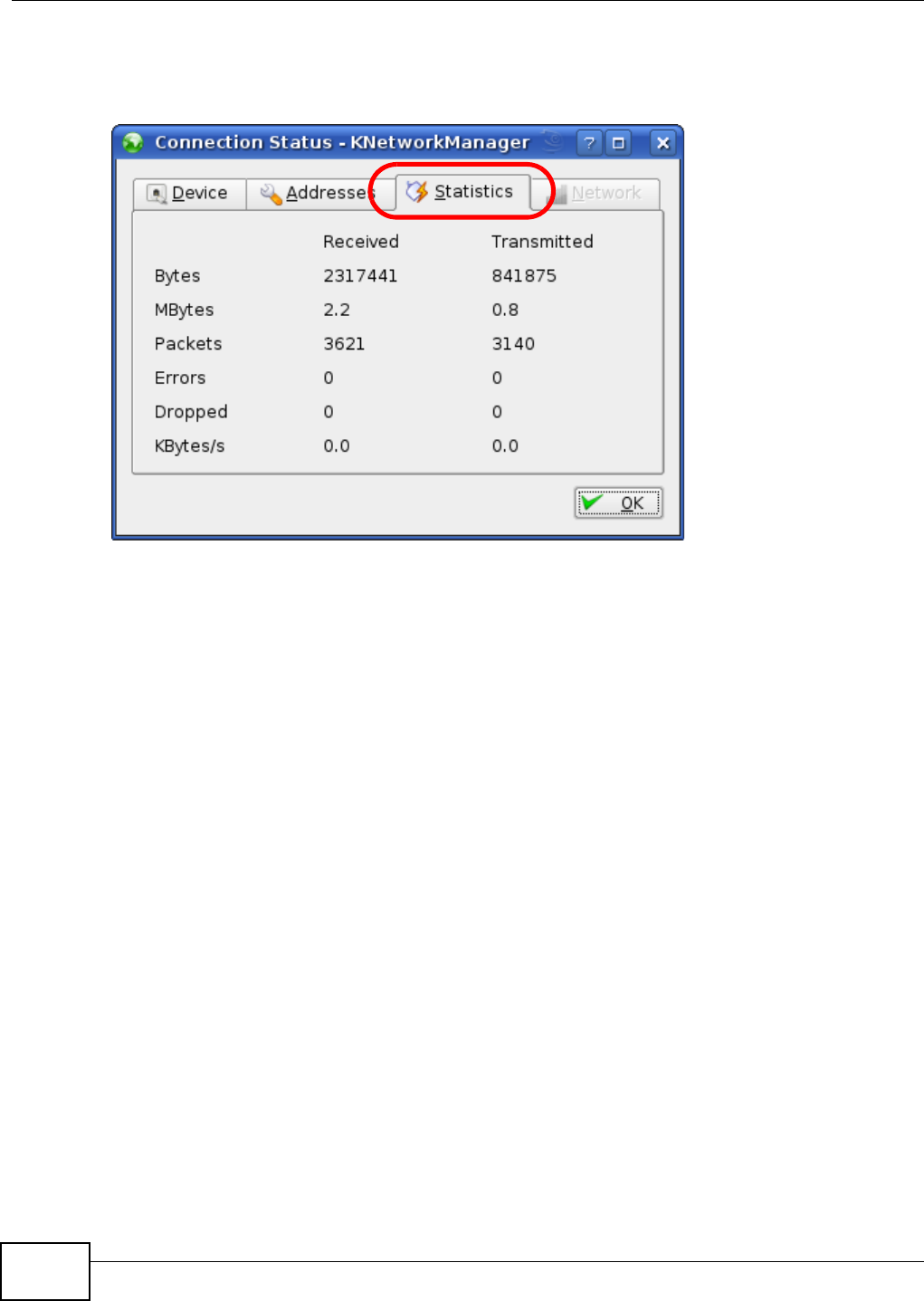
Appendix A Setting Up Your Computer’s IP Address
Media Server User’s Guide
396
When the Connection Status - KNetwork Manager window opens, click the Statistics tab to
see if your connection is working properly.
Figure 214 openSUSE: Connection Status - KNetwork Manager

Media Server User’s Guide 397
APPENDIX B
Pop-up Windows, JavaScripts and Java
Permissions
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device.
• JavaScripts (enabled by default).
• Java permissions (enabled by default).
Note: Internet Explorer 6 screens are used here. Screens for other Internet Explorer
versions may vary.
Internet Explorer Pop-up Blockers
You may have to disable pop-up blocking to log into your device.
Either disable pop-up blocking (enabled by default in Windows XP SP (Service Pack) 2) or allow
pop-up blocking and create an exception for your device’s IP address.
Disable Pop-up Blockers
1In Internet Explorer, select Tools, Pop-up Blocker and then select Turn Off Pop-up Blocker.
Figure 215 Pop-up Blocker
You can also check if pop-up blocking is disabled in the Pop-up Blocker section in the Privacy tab.
1In Internet Explorer, select Tools, Internet Options, Privacy.
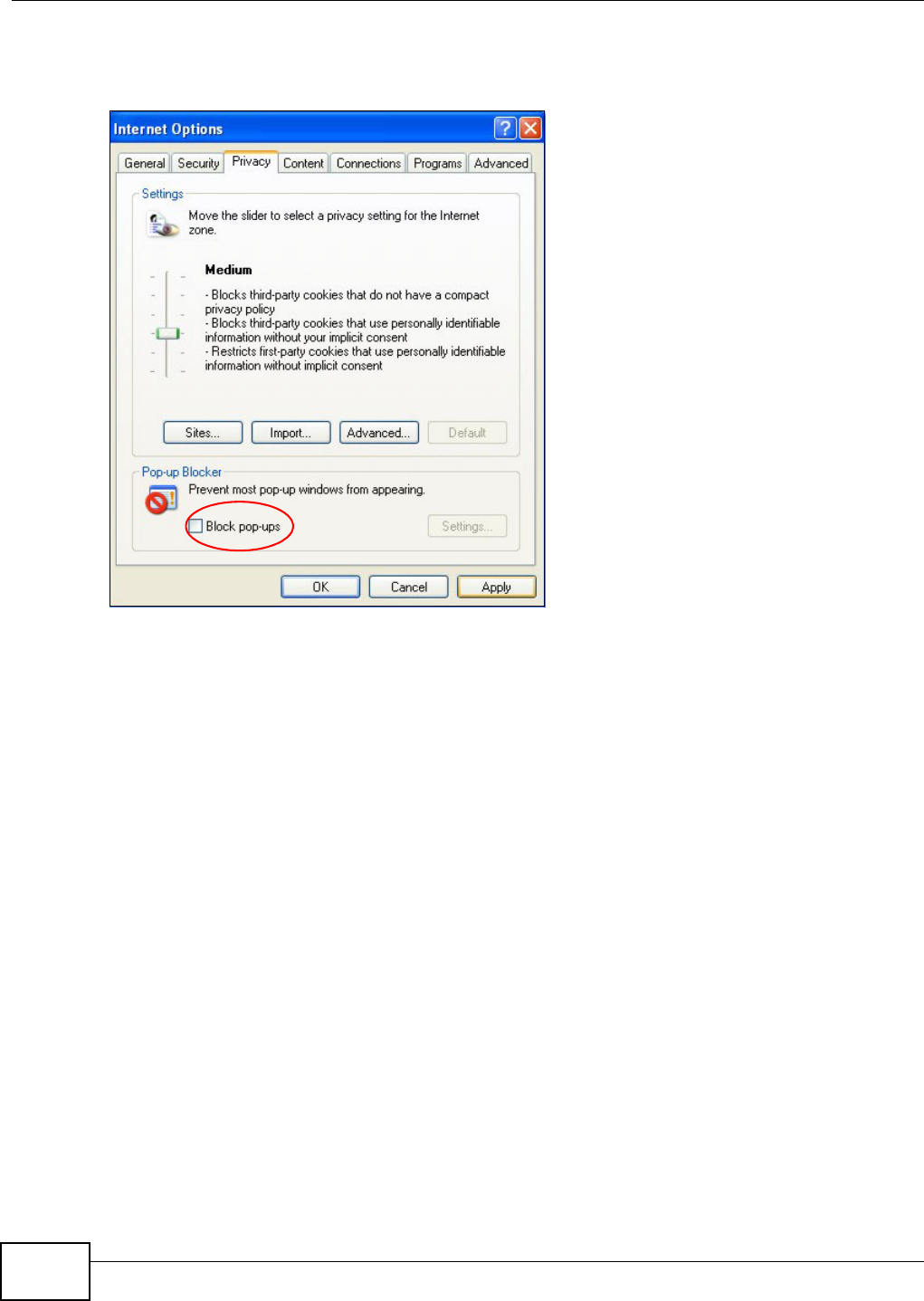
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide
398
2Clear the Block pop-ups check box in the Pop-up Blocker section of the screen. This disables any
web pop-up blockers you may have enabled.
Figure 216 Internet Options: Privacy
3Click Apply to save this setting.
Enable Pop-up Blockers with Exceptions
Alternatively, if you only want to allow pop-up windows from your device, see the following steps.
1In Internet Explorer, select Tools, Internet Options and then the Privacy tab.
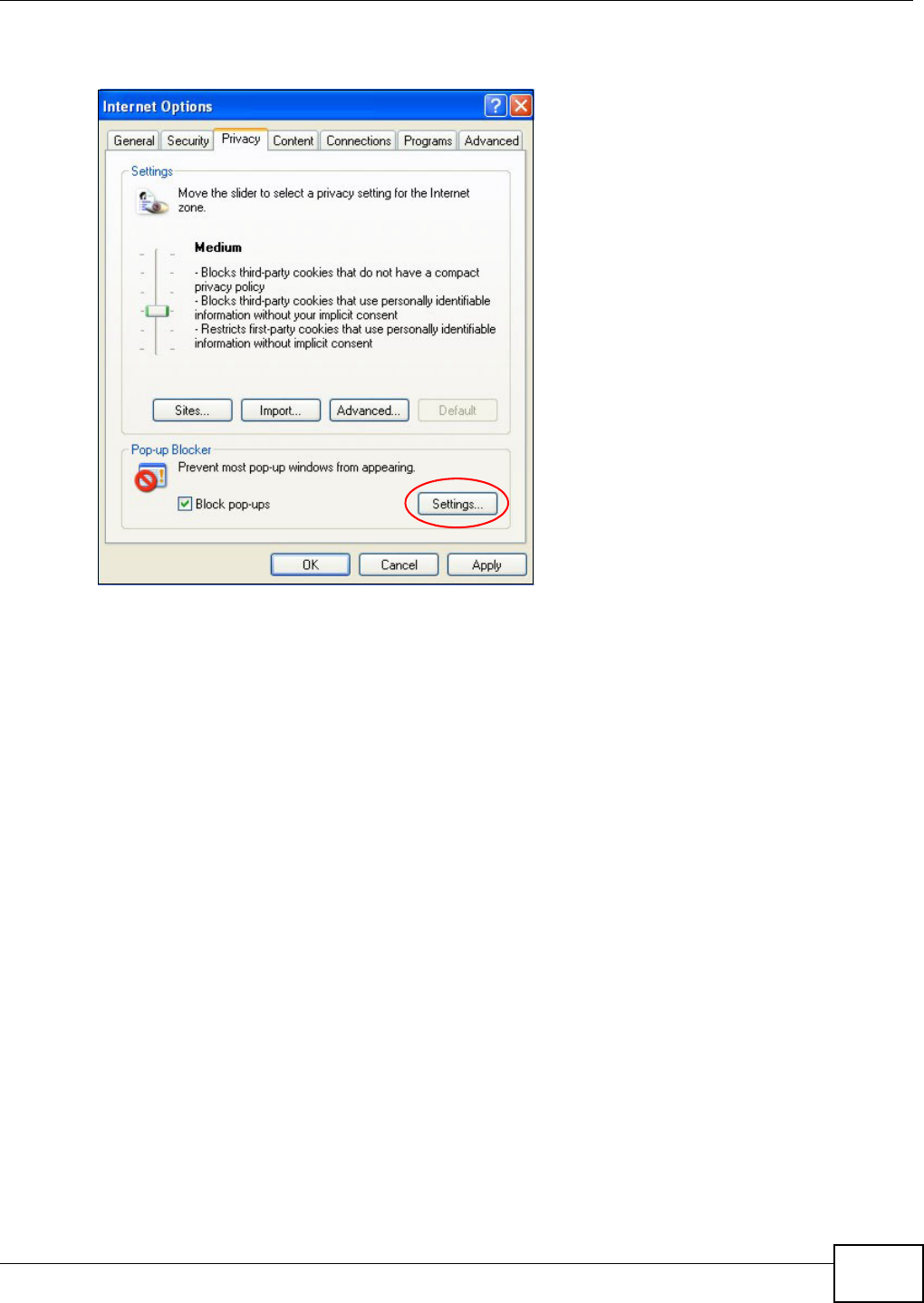
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide 399
2Select Settings…to open the Pop-up Blocker Settings screen.
Figure 217 Internet Options: Privacy
3Type the IP address of your device (the web page that you do not want to have blocked) with the
prefix “http://”. For example, http://192.168.167.1.
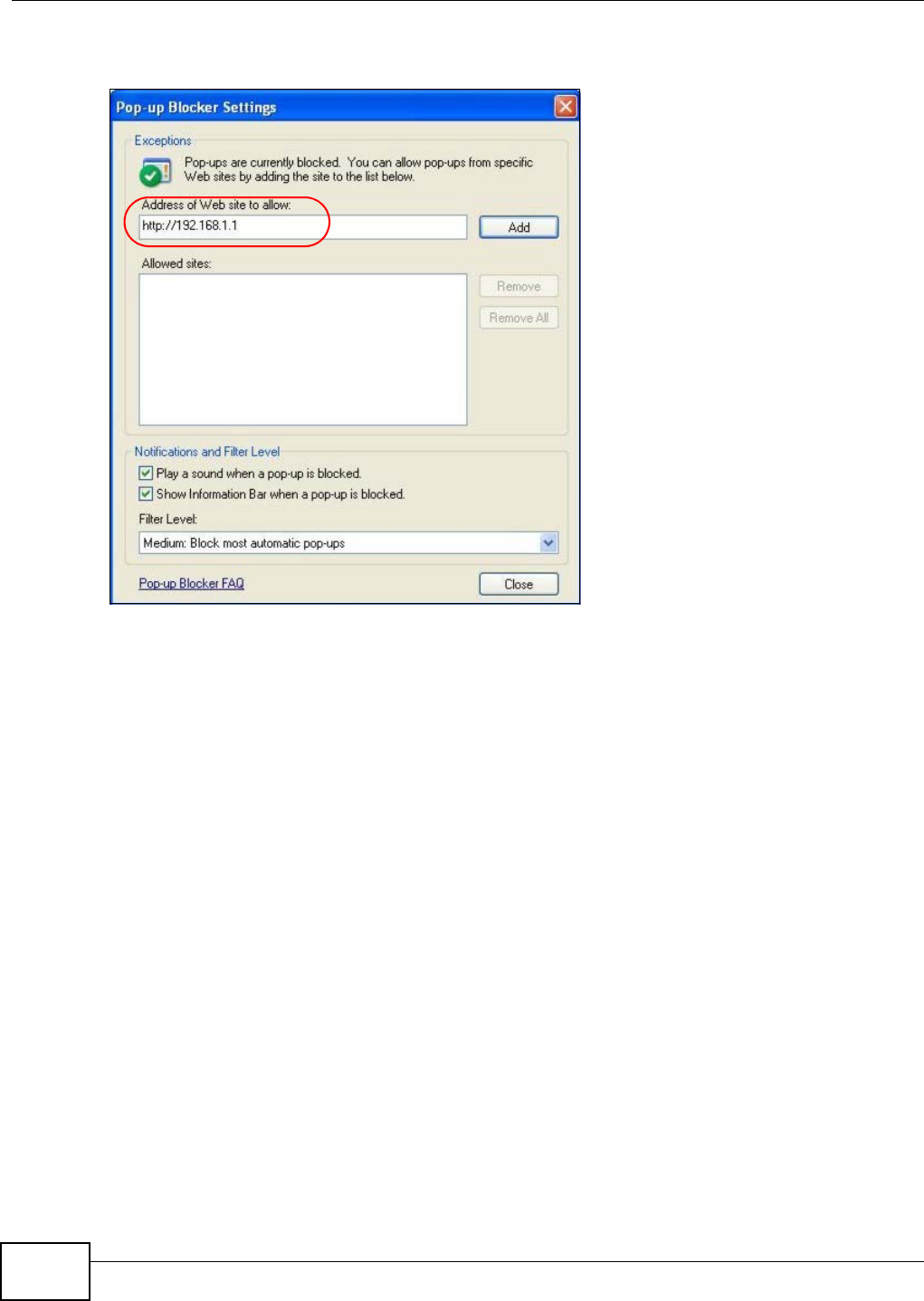
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide
400
4Click Add to move the IP address to the list of Allowed sites.
Figure 218 Pop-up Blocker Settings
5Click Close to return to the Privacy screen.
6Click Apply to save this setting.
JavaScripts
If pages of the web configurator do not display properly in Internet Explorer, check that JavaScripts
are allowed.
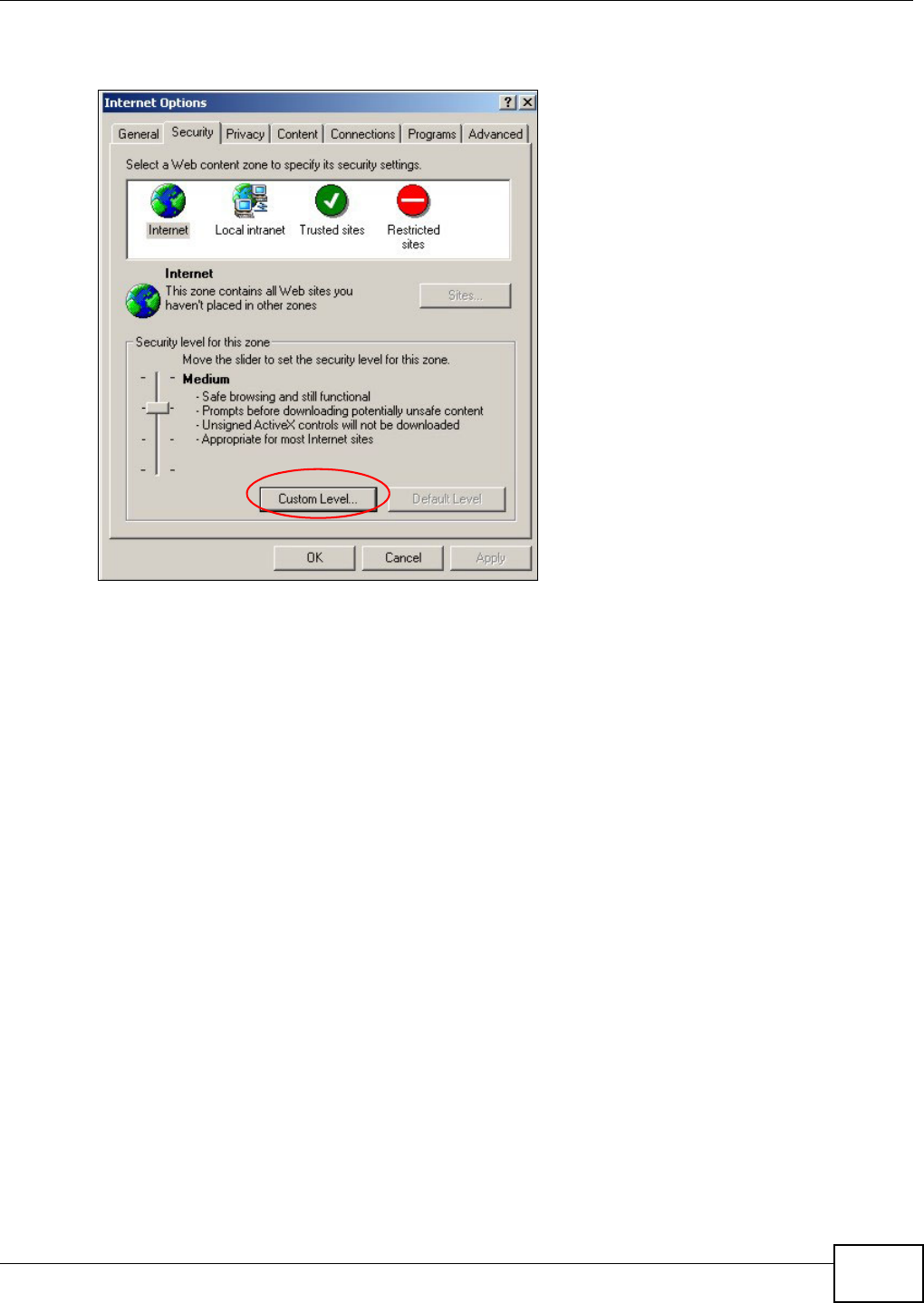
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide 401
1In Internet Explorer, click Tools, Internet Options and then the Security tab.
Figure 219 Internet Options: Security
2Click the Custom Level... button.
3Scroll down to Scripting.
4Under Active scripting make sure that Enable is selected (the default).
5Under Scripting of Java applets make sure that Enable is selected (the default).
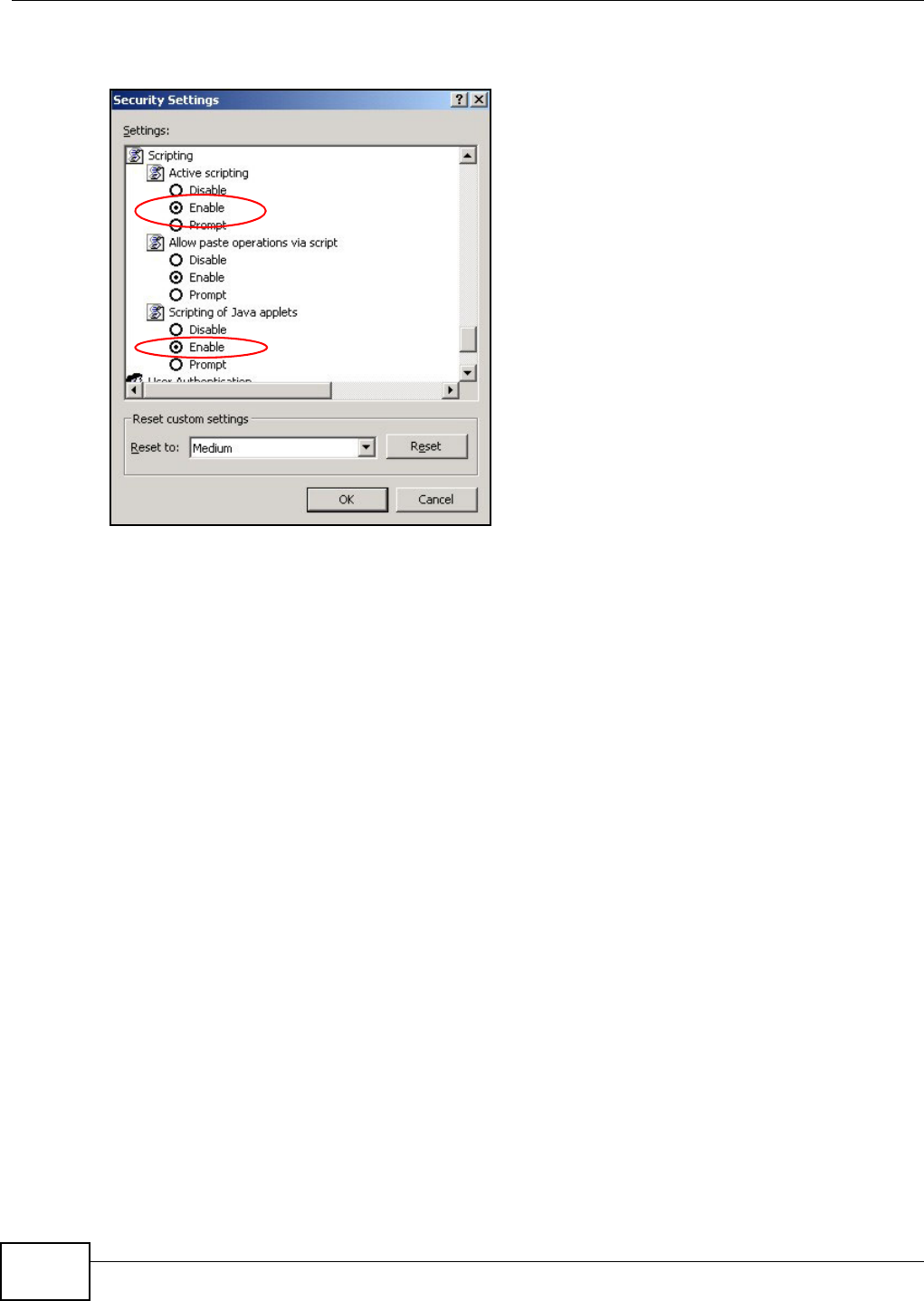
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide
402
6Click OK to close the window.
Figure 220 Security Settings - Java Scripting
Java Permissions
1From Internet Explorer, click Tools, Internet Options and then the Security tab.
2Click the Custom Level... button.
3Scroll down to Microsoft VM.
4Under Java permissions make sure that a safety level is selected.
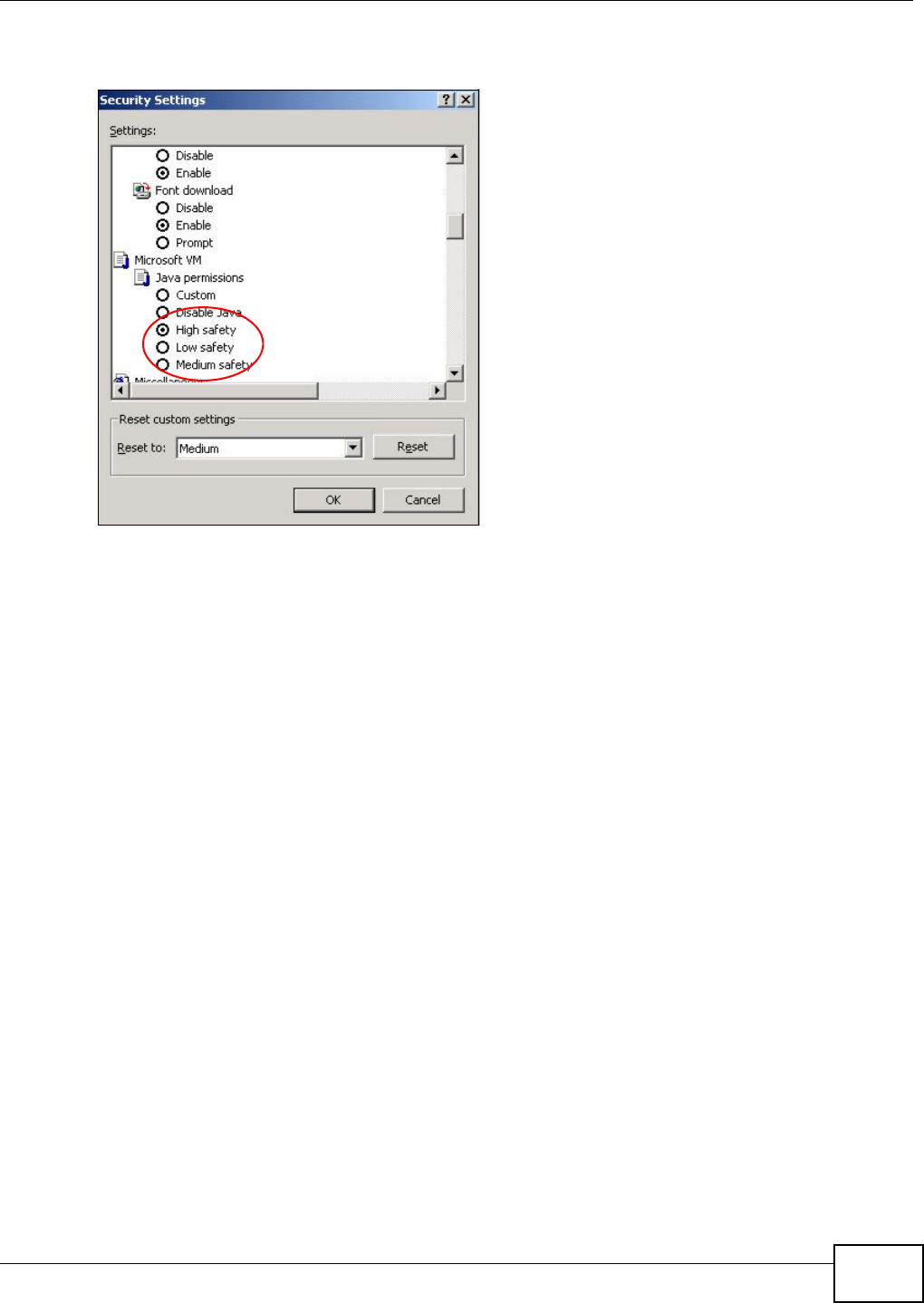
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide 403
5Click OK to close the window.
Figure 221 Security Settings - Java
JAVA (Sun)
1From Internet Explorer, click Tools, Internet Options and then the Advanced tab.
2Make sure that Use Java 2 for <applet> under Java (Sun) is selected.
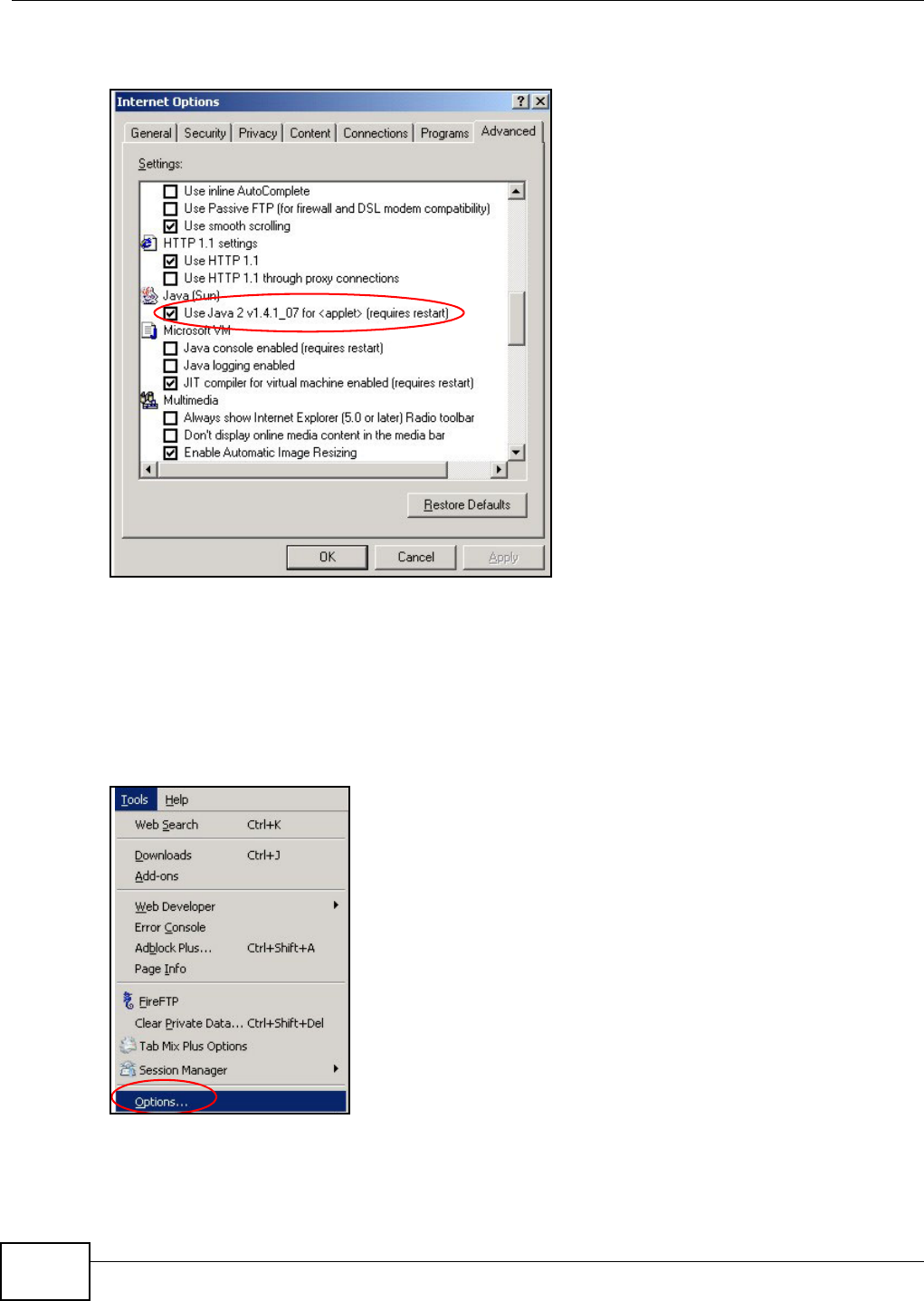
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide
404
3Click OK to close the window.
Figure 222 Java (Sun)
Mozilla Firefox
Mozilla Firefox 2.0 screens are used here. Screens for other versions may vary.
You can enable Java, Javascripts and pop-ups in one screen. Click Tools, then click Options in the
screen that appears.
Figure 223 Mozilla Firefox: Tools > Options
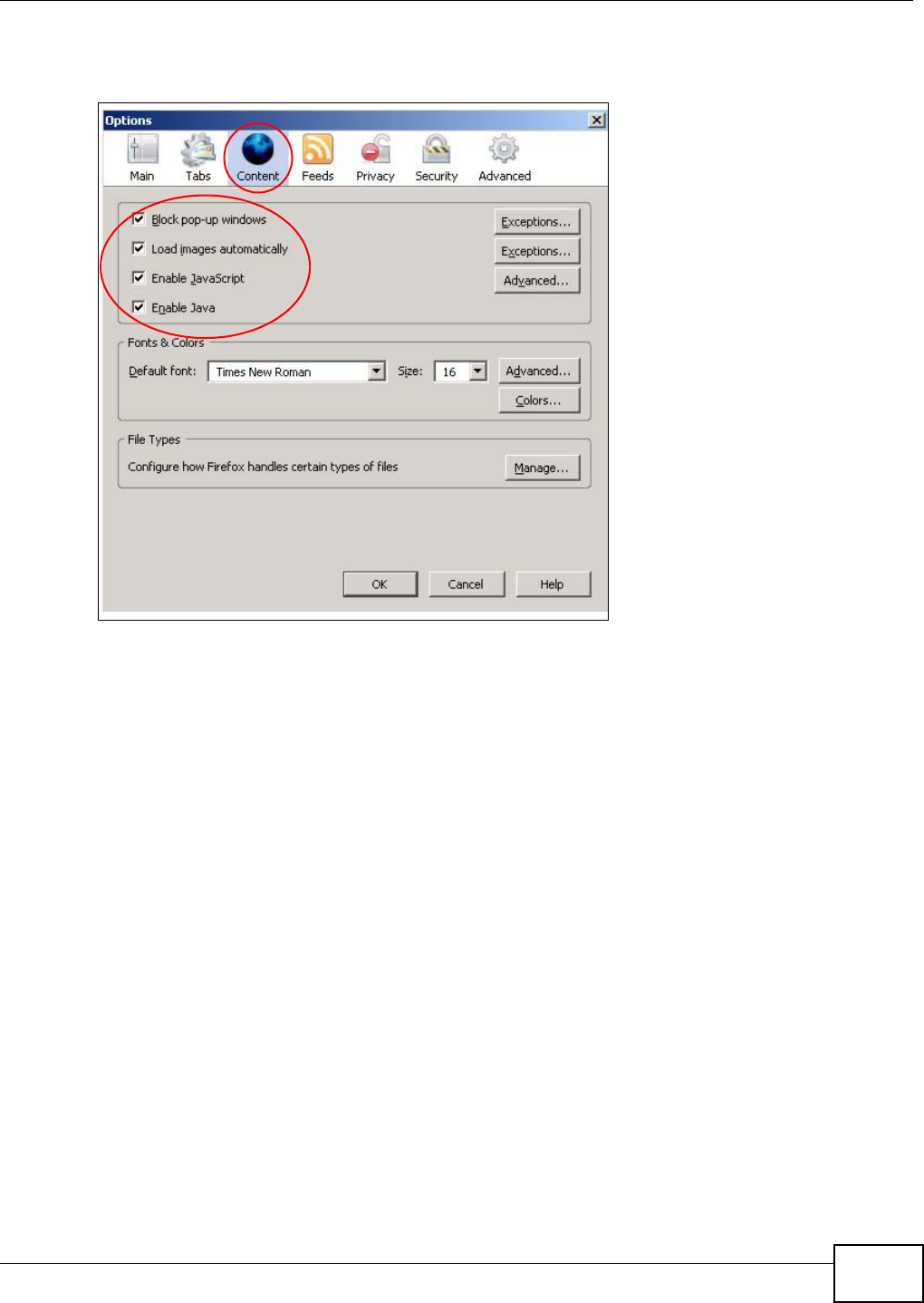
Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide 405
Click Content.to show the screen below. Select the check boxes as shown in the following screen.
Figure 224 Mozilla Firefox Content Security

Appendix B Pop-up Windows, JavaScripts and Java Permissions
Media Server User’s Guide
406
Media Server User’s Guide 407
APPENDIX C
Common Services
The following table lists some commonly-used services and their associated protocols and port
numbers. For a comprehensive list of port numbers, ICMP type/code numbers and services, visit
the IANA (Internet Assigned Number Authority) web site.
•Name: This is a short, descriptive name for the service. You can use this one or create a
different one, if you like.
•Protocol: This is the type of IP protocol used by the service. If this is TCP/UDP, then the service
uses the same port number with TCP and UDP. If this is USER-DEFINED, the Port(s) is the IP
protocol number, not the port number.
•Port(s): This value depends on the Protocol. Please refer to RFC 1700 for further information
about port numbers.
•If the Protocol is TCP, UDP, or TCP/UDP, this is the IP port number.
•If the Protocol is USER, this is the IP protocol number.
•Description: This is a brief explanation of the applications that use this service or the situations
in which this service is used.
Table 126 Commonly Used Services
NAME PROTOCOL PORT(S) DESCRIPTION
AH
(IPSEC_TUNNEL) User-Defined 51 The IPSEC AH (Authentication Header) tunneling
protocol uses this service.
AIM/New-ICQ TCP 5190 AOL’s Internet Messenger service. It is also used as a
listening port by ICQ.
AUTH TCP 113 Authentication protocol used by some servers.
BGP TCP 179 Border Gateway Protocol.
BOOTP_CLIENT UDP 68 DHCP Client.
BOOTP_SERVER UDP 67 DHCP Server.
CU-SEEME TCP
UDP
7648
24032
A popular videoconferencing solution from White Pines
Software.
DNS TCP/UDP 53 Domain Name Server, a service that matches web
names (for example www.zyxel.com) to IP numbers.
ESP
(IPSEC_TUNNEL) User-Defined 50 The IPSEC ESP (Encapsulation Security Protocol)
tunneling protocol uses this service.
FINGER TCP 79 Finger is a UNIX or Internet related command that can
be used to find out if a user is logged on.
FTP TCP
TCP
20
21
File Transfer Program, a program to enable fast
transfer of files, including large files that may not be
possible by e-mail.
H.323 TCP 1720 NetMeeting uses this protocol.
HTTP TCP 80 Hyper Text Transfer Protocol - a client/server protocol
for the world wide web.
HTTPS TCP 443 HTTPS is a secured http session often used in e-
commerce.
Appendix C Common Services
Media Server User’s Guide
408
ICMP User-Defined 1Internet Control Message Protocol is often used for
diagnostic or routing purposes.
ICQ UDP 4000 This is a popular Internet chat program.
IGMP (MULTICAST) User-Defined 2Internet Group Management Protocol is used when
sending packets to a specific group of hosts.
IKE UDP 500 The Internet Key Exchange algorithm is used for key
distribution and management.
IRC TCP/UDP 6667 This is another popular Internet chat program.
MSN Messenger TCP 1863 Microsoft Networks’ messenger service uses this
protocol.
NEW-ICQ TCP 5190 An Internet chat program.
NEWS TCP 144 A protocol for news groups.
NFS UDP 2049 Network File System - NFS is a client/server
distributed file service that provides transparent file
sharing for network environments.
NNTP TCP 119 Network News Transport Protocol is the delivery
mechanism for the USENET newsgroup service.
PING User-Defined 1Packet INternet Groper is a protocol that sends out
ICMP echo requests to test whether or not a remote
host is reachable.
POP3 TCP 110 Post Office Protocol version 3 lets a client computer
get e-mail from a POP3 server through a temporary
connection (TCP/IP or other).
PPTP TCP 1723 Point-to-Point Tunneling Protocol enables secure
transfer of data over public networks. This is the
control channel.
PPTP_TUNNEL
(GRE) User-Defined 47 PPTP (Point-to-Point Tunneling Protocol) enables
secure transfer of data over public networks. This is
the data channel.
RCMD TCP 512 Remote Command Service.
REAL_AUDIO TCP 7070 A streaming audio service that enables real time
sound over the web.
REXEC TCP 514 Remote Execution Daemon.
RLOGIN TCP 513 Remote Login.
RTELNET TCP 107 Remote Telnet.
RTSP TCP/UDP 554 The Real Time Streaming (media control) Protocol
(RTSP) is a remote control for multimedia on the
Internet.
SFTP TCP 115 Simple File Transfer Protocol.
SMTP TCP 25 Simple Mail Transfer Protocol is the message-
exchange standard for the Internet. SMTP enables you
to move messages from one e-mail server to another.
SNMP TCP/UDP 161 Simple Network Management Protocol.
SNMP-TRAPS TCP/UDP 162 Traps for use with the SNMP (RFC:1215).
SQL-NET TCP 1521 Structured Query Language is an interface to access
data on many different types of database systems,
including mainframes, midrange systems, UNIX
systems and network servers.
SSH TCP/UDP 22 Secure Shell Remote Login Program.
Table 126 Commonly Used Services (continued)
NAME PROTOCOL PORT(S) DESCRIPTION
Appendix C Common Services
Media Server User’s Guide 409
STRM WORKS UDP 1558 Stream Works Protocol.
SYSLOG UDP 514 Syslog allows you to send system logs to a UNIX
server.
TACACS UDP 49 Login Host Protocol used for (Terminal Access
Controller Access Control System).
TELNET TCP 23 Telnet is the login and terminal emulation protocol
common on the Internet and in UNIX environments. It
operates over TCP/IP networks. Its primary function is
to allow users to log into remote host systems.
TFTP UDP 69 Trivial File Transfer Protocol is an Internet file transfer
protocol similar to FTP, but uses the UDP (User
Datagram Protocol) rather than TCP (Transmission
Control Protocol).
VDOLIVE TCP 7000 Another videoconferencing solution.
Table 126 Commonly Used Services (continued)
NAME PROTOCOL PORT(S) DESCRIPTION

Appendix C Common Services
Media Server User’s Guide
410
Media Server User’s Guide 411
APPENDIX D
Importing Certificates
This appendix shows you how to import public key certificates into your web browser.
Public key certificates are used by web browsers to ensure that a secure web site is legitimate.
When a certificate authority such as VeriSign, Comodo, or Network Solutions, to name a few,
receives a certificate request from a website operator, they confirm that the web domain and
contact information in the request match those on public record with a domain name registrar. If
they match, then the certificate is issued to the website operator, who then places it on the site to
be issued to all visiting web browsers to let them know that the site is legitimate.
Many ZyXEL products, such as the NSA-2401, issue their own public key certificates. These can be
used by web browsers on a LAN or WAN to verify that they are in fact connecting to the legitimate
device and not one masquerading as it. However, because the certificates were not issued by one of
the several organizations officially recognized by the most common web browsers, you will need to
import the ZyXEL-created certificate into your web browser and flag that certificate as a trusted
authority.
Note: You can see if you are browsing on a secure website if the URL in your web
browser’s address bar begins with https:// or there is a sealed padlock icon
( ) somewhere in the main browser window (not all browsers show the padlock
in the same location.)
In this appendix, you can import a public key certificate for:
• Internet Explorer on page 412
•Firefox on page 420
•Opera on page 425
• Konqueror on page 432
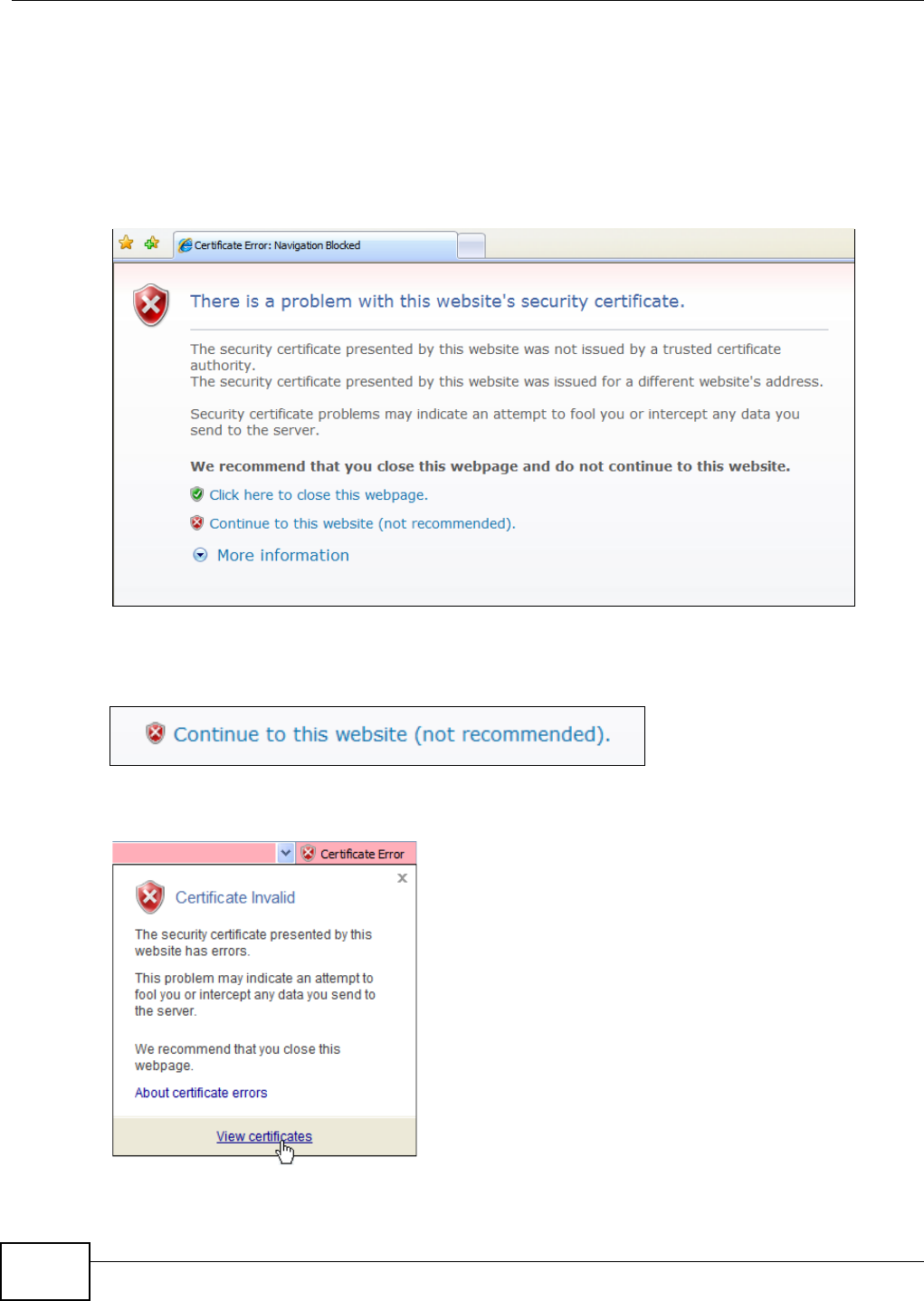
Appendix D Importing Certificates
Media Server User’s Guide
412
Internet Explorer
The following example uses Microsoft Internet Explorer 7 on Windows XP Professional; however,
they can also apply to Internet Explorer on Windows Vista.
1If your device’s Web Configurator is set to use SSL certification, then the first time you browse to it
you are presented with a certification error.
Figure 225 Internet Explorer 7: Certification Error
2Click Continue to this website (not recommended).
Figure 226 Internet Explorer 7: Certification Error
3In the Address Bar, click Certificate Error > View certificates.
Figure 227 Internet Explorer 7: Certificate Error
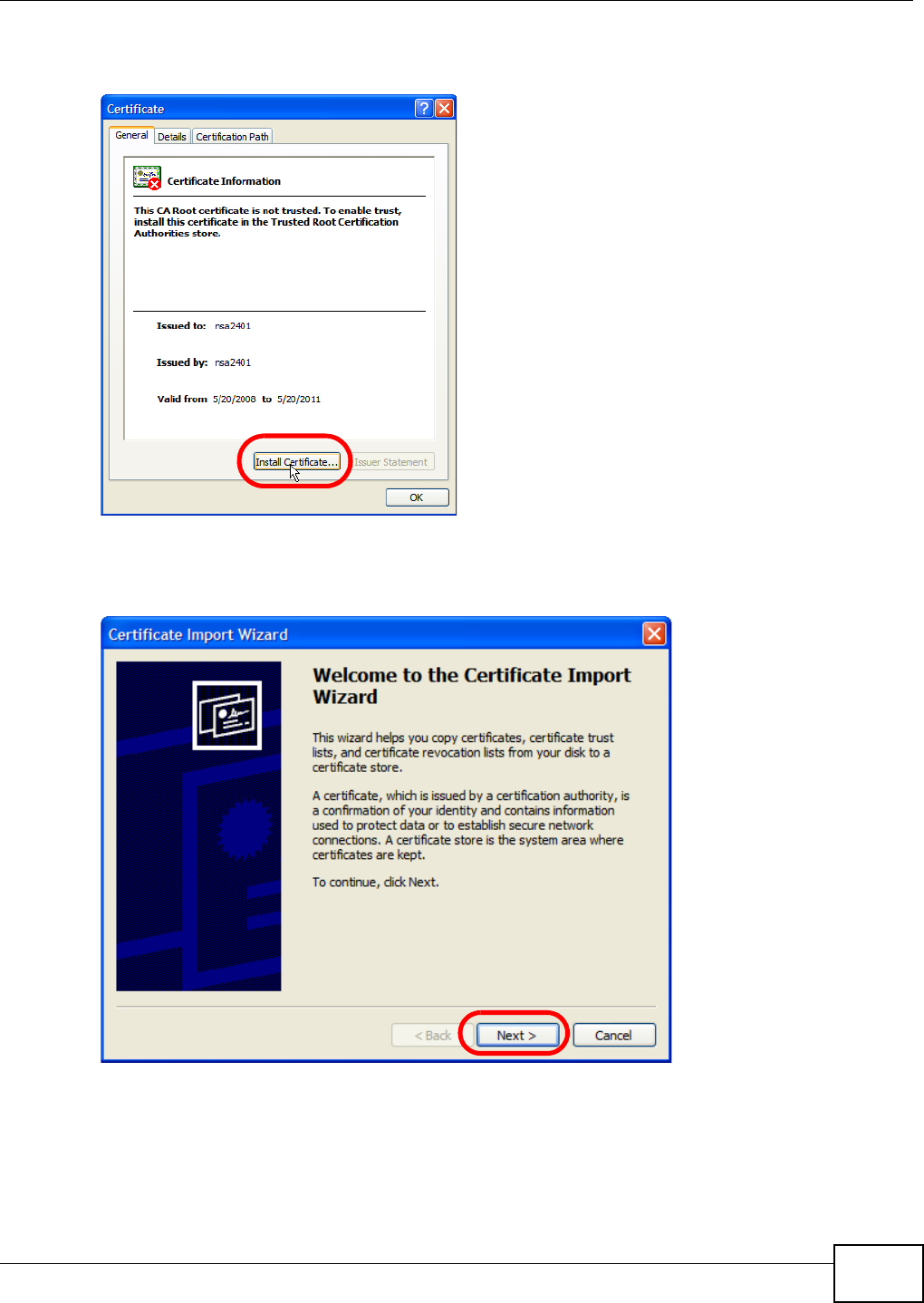
Appendix D Importing Certificates
Media Server User’s Guide 413
4In the Certificate dialog box, click Install Certificate.
Figure 228 Internet Explorer 7: Certificate
5In the Certificate Import Wizard, click Next.
Figure 229 Internet Explorer 7: Certificate Import Wizard
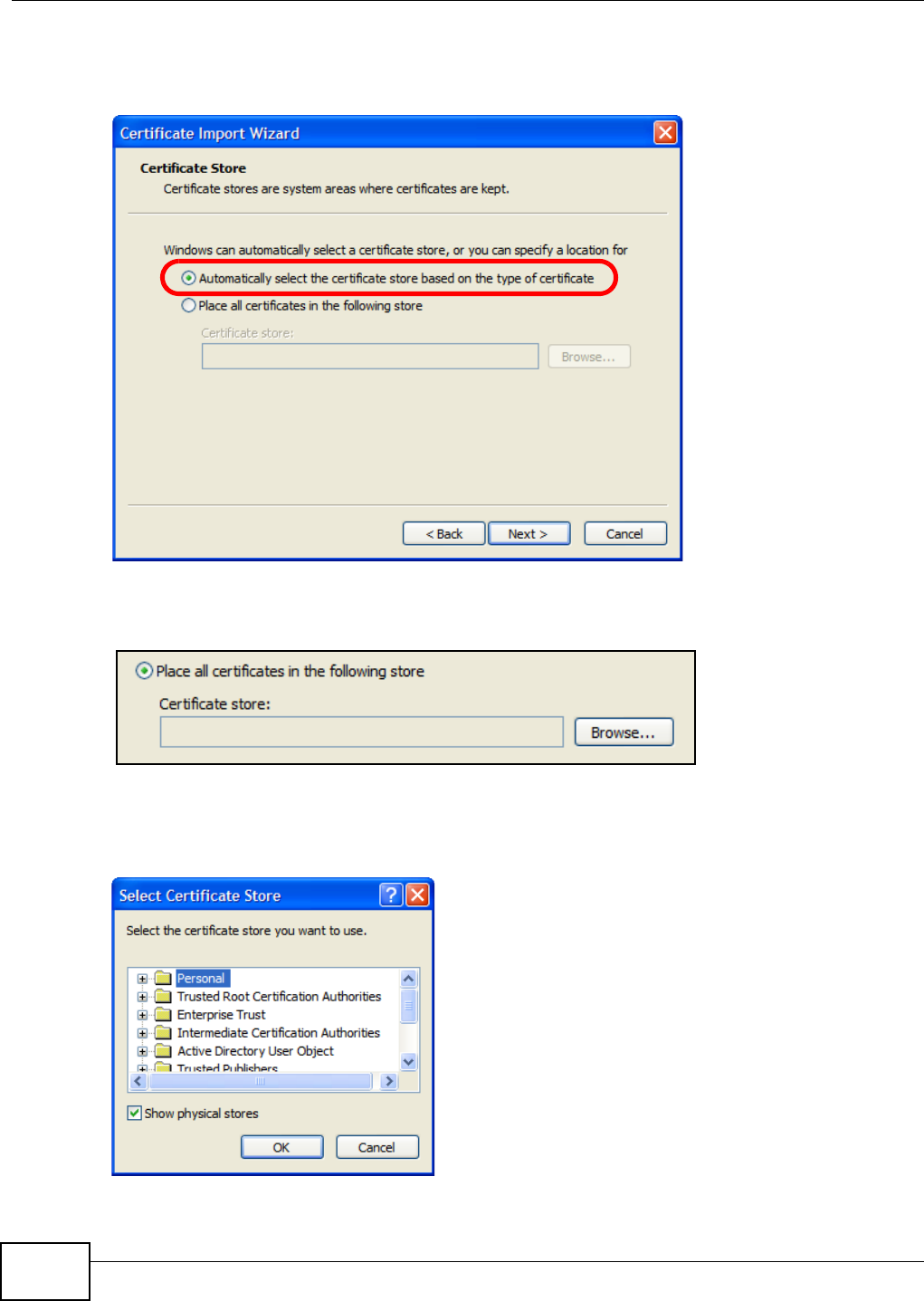
Appendix D Importing Certificates
Media Server User’s Guide
414
6If you want Internet Explorer to Automatically select certificate store based on the type of
certificate, click Next again and then go to step 9.
Figure 230 Internet Explorer 7: Certificate Import Wizard
7Otherwise, select Place all certificates in the following store and then click Browse.
Figure 231 Internet Explorer 7: Certificate Import Wizard
8In the Select Certificate Store dialog box, choose a location in which to save the certificate and
then click OK.
Figure 232 Internet Explorer 7: Select Certificate Store
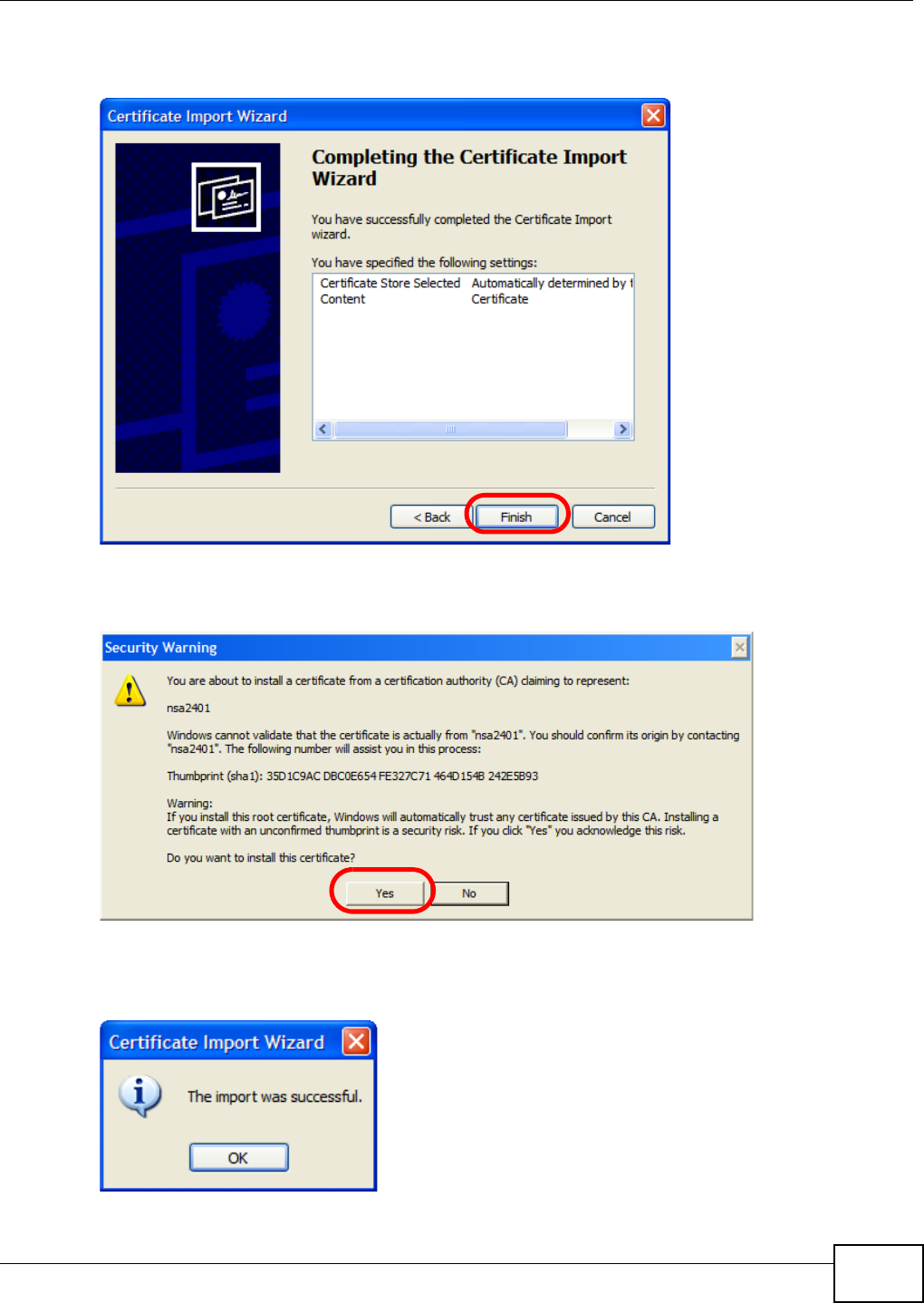
Appendix D Importing Certificates
Media Server User’s Guide 415
9In the Completing the Certificate Import Wizard screen, click Finish.
Figure 233 Internet Explorer 7: Certificate Import Wizard
10 If you are presented with another Security Warning, click Yes.
Figure 234 Internet Explorer 7: Security Warning
11 Finally, click OK when presented with the successful certificate installation message.
Figure 235 Internet Explorer 7: Certificate Import Wizard
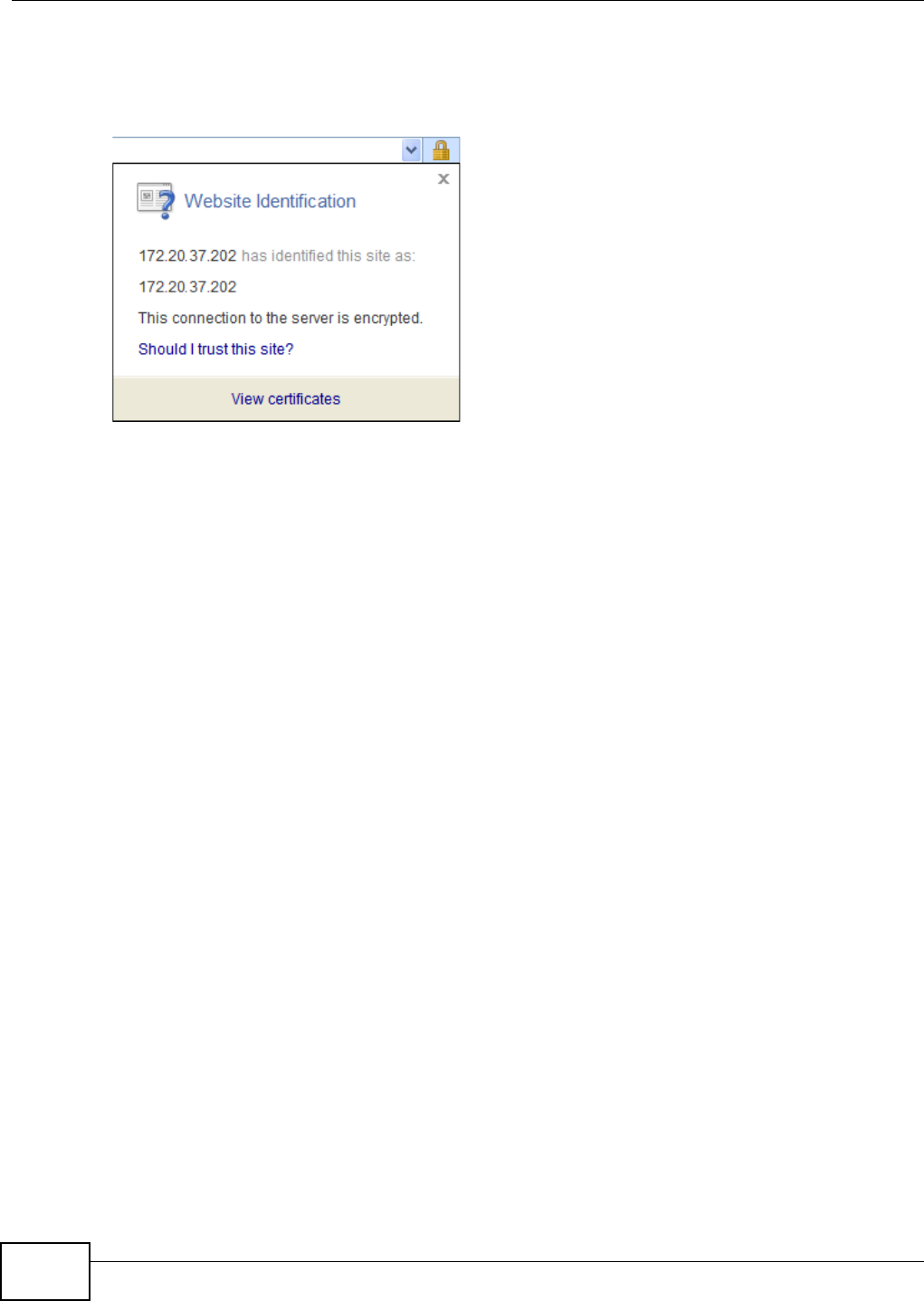
Appendix D Importing Certificates
Media Server User’s Guide
416
12 The next time you start Internet Explorer and go to a ZyXEL Web Configurator page, a sealed
padlock icon appears in the address bar. Click it to view the page’s Website Identification
information.
Figure 236 Internet Explorer 7: Website Identification
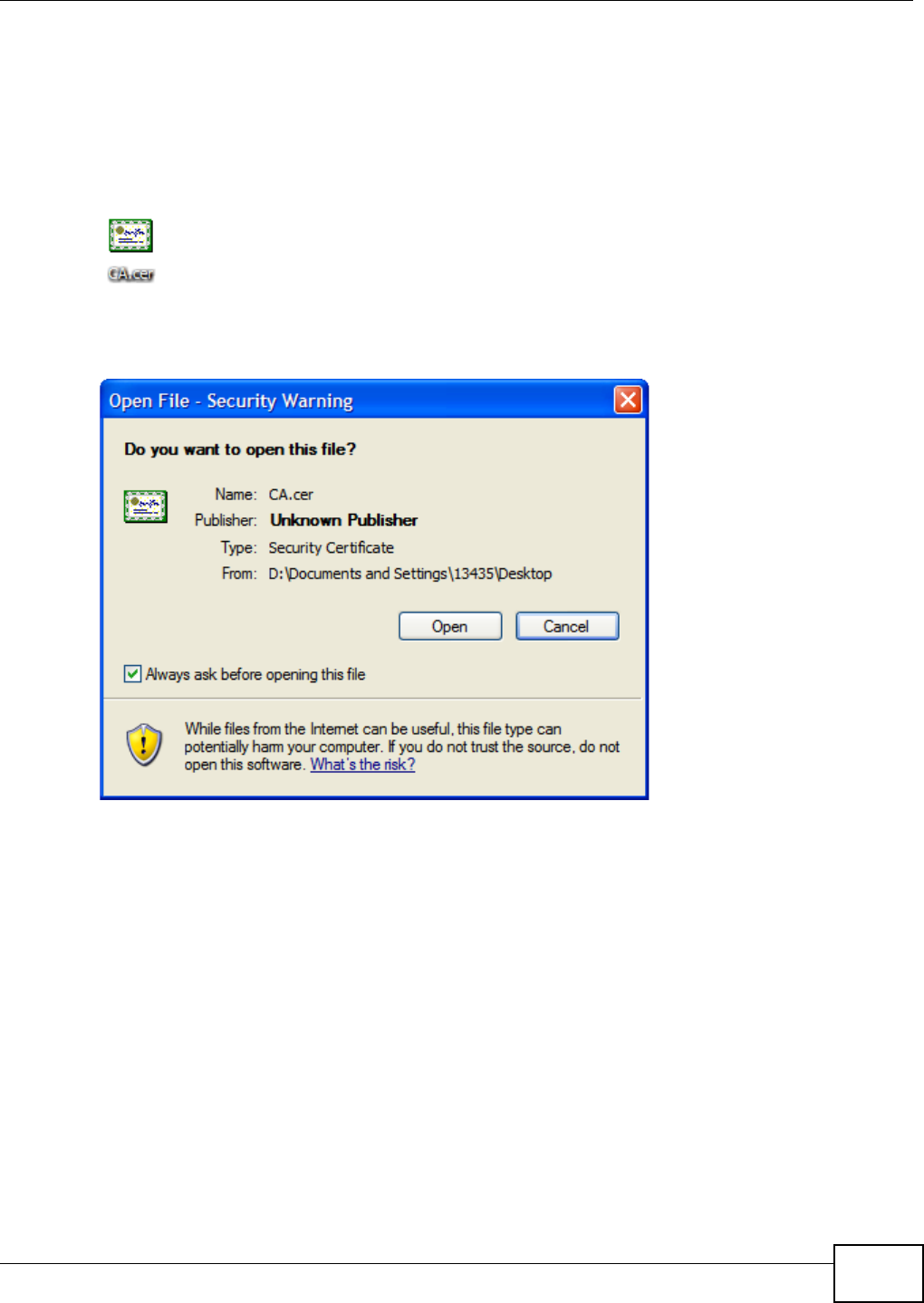
Appendix D Importing Certificates
Media Server User’s Guide 417
Installing a Stand-Alone Certificate File in Internet Explorer
Rather than browsing to a ZyXEL Web Configurator and installing a public key certificate when
prompted, you can install a stand-alone certificate file if one has been issued to you.
1Double-click the public key certificate file.
Figure 237 Internet Explorer 7: Public Key Certificate File
2In the security warning dialog box, click Open.
Figure 238 Internet Explorer 7: Open File - Security Warning
3Refer to steps 4-12 in the Internet Explorer procedure beginning on page 412 to complete the
installation process.
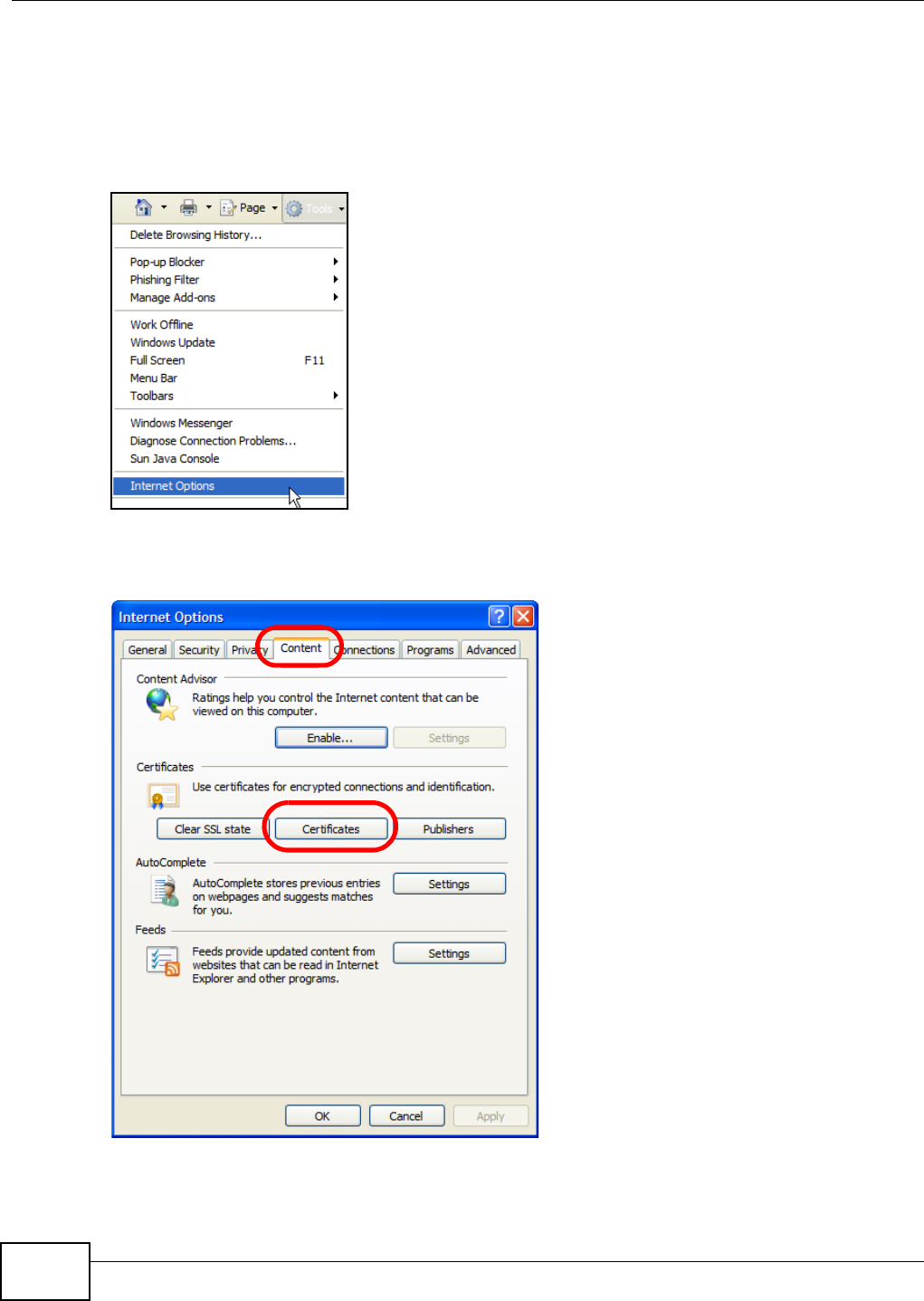
Appendix D Importing Certificates
Media Server User’s Guide
418
Removing a Certificate in Internet Explorer
This section shows you how to remove a public key certificate in Internet Explorer 7.
1Open Internet Explorer and click Tools > Internet Options.
Figure 239 Internet Explorer 7: Tools Menu
2In the Internet Options dialog box, click Content > Certificates.
Figure 240 Internet Explorer 7: Internet Options
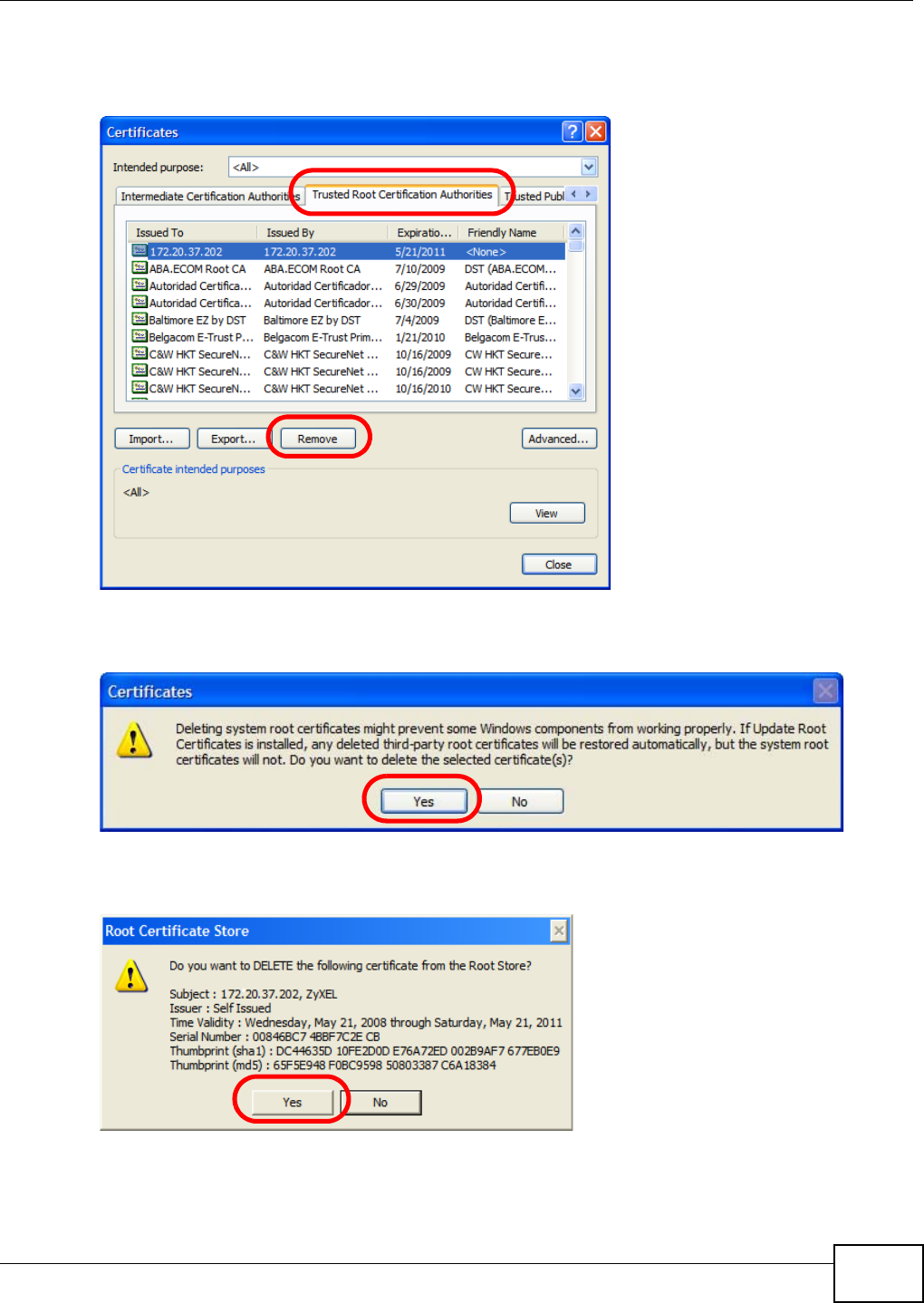
Appendix D Importing Certificates
Media Server User’s Guide 419
3In the Certificates dialog box, click the Trusted Root Certificates Authorities tab, select the
certificate that you want to delete, and then click Remove.
Figure 241 Internet Explorer 7: Certificates
4In the Certificates confirmation, click Yes.
Figure 242 Internet Explorer 7: Certificates
5In the Root Certificate Store dialog box, click Yes.
Figure 243 Internet Explorer 7: Root Certificate Store
6The next time you go to the web site that issued the public key certificate you just removed, a
certification error appears.
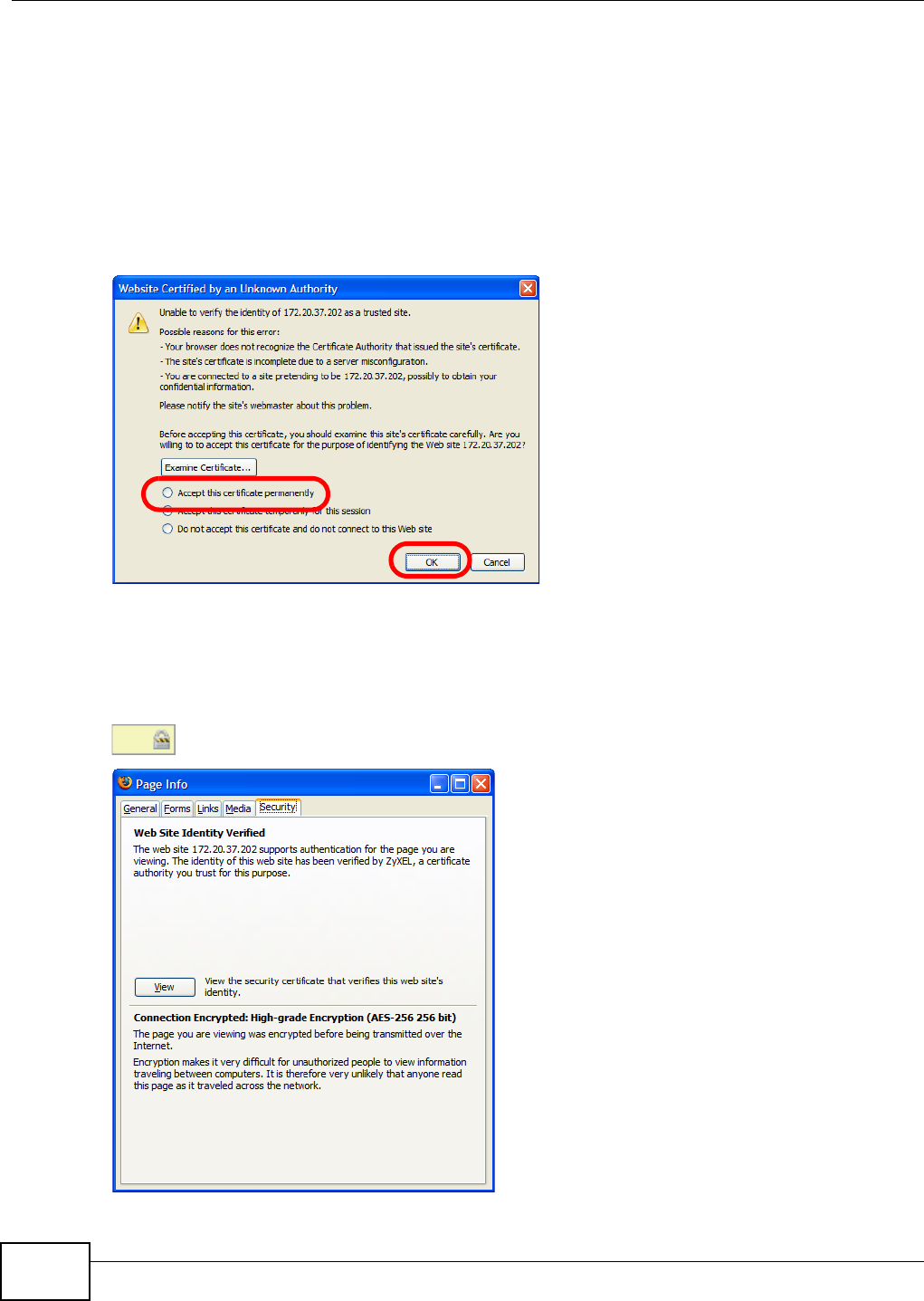
Appendix D Importing Certificates
Media Server User’s Guide
420
Firefox
The following example uses Mozilla Firefox 2 on Windows XP Professional; however, the screens can
also apply to Firefox 2 on all platforms.
1If your device’s Web Configurator is set to use SSL certification, then the first time you browse to it
you are presented with a certification error.
2Select Accept this certificate permanently and click OK.
Figure 244 Firefox 2: Website Certified by an Unknown Authority
3The certificate is stored and you can now connect securely to the Web Configurator. A sealed
padlock appears in the address bar, which you can click to open the Page Info > Security window
to view the web page’s security information.
Figure 245 Firefox 2: Page Info
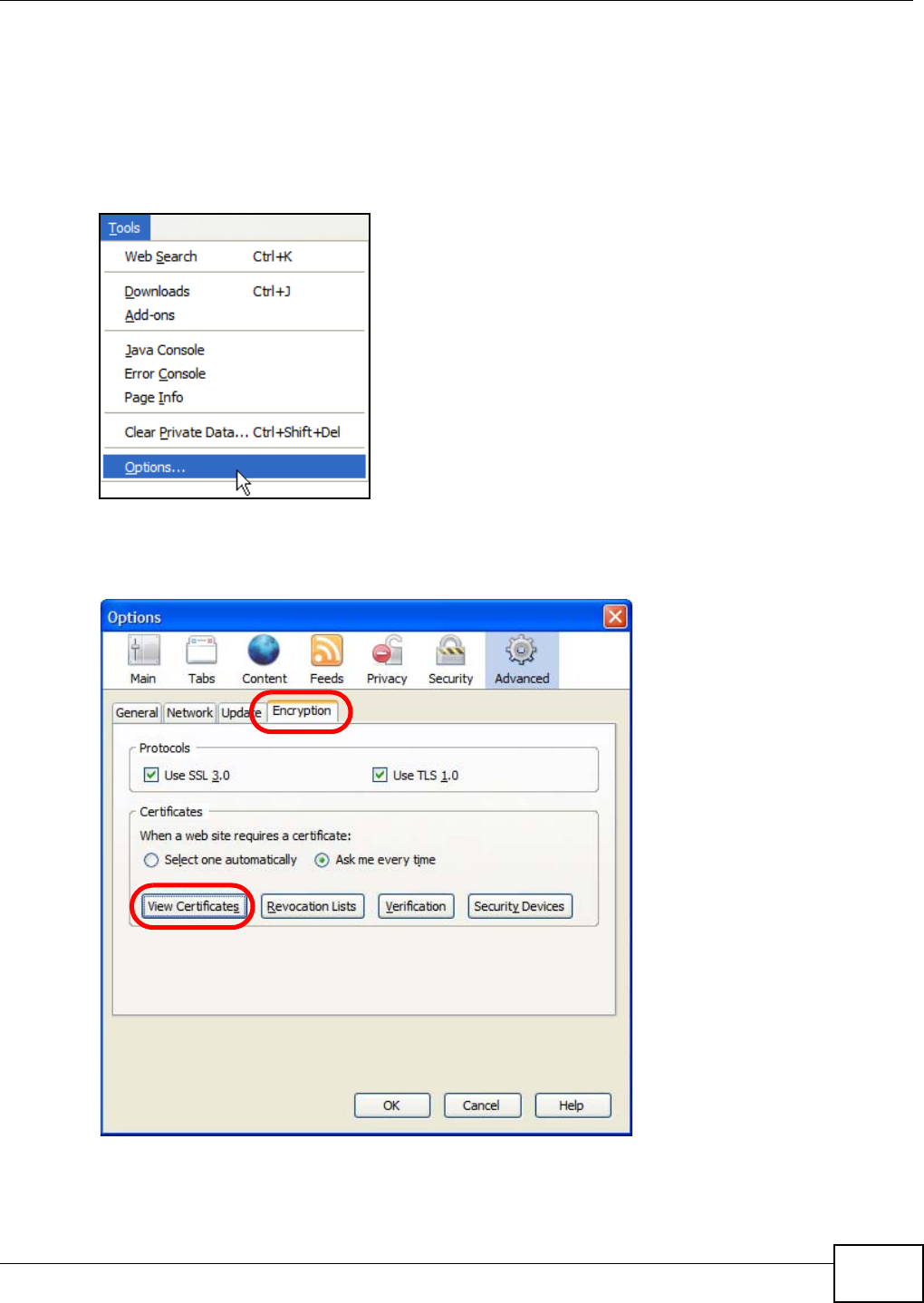
Appendix D Importing Certificates
Media Server User’s Guide 421
Installing a Stand-Alone Certificate File in Firefox
Rather than browsing to a ZyXEL Web Configurator and installing a public key certificate when
prompted, you can install a stand-alone certificate file if one has been issued to you.
1Open Firefox and click Tools > Options.
Figure 246 Firefox 2: Tools Menu
2In the Options dialog box, click Advanced > Encryption > View Certificates.
Figure 247 Firefox 2: Options
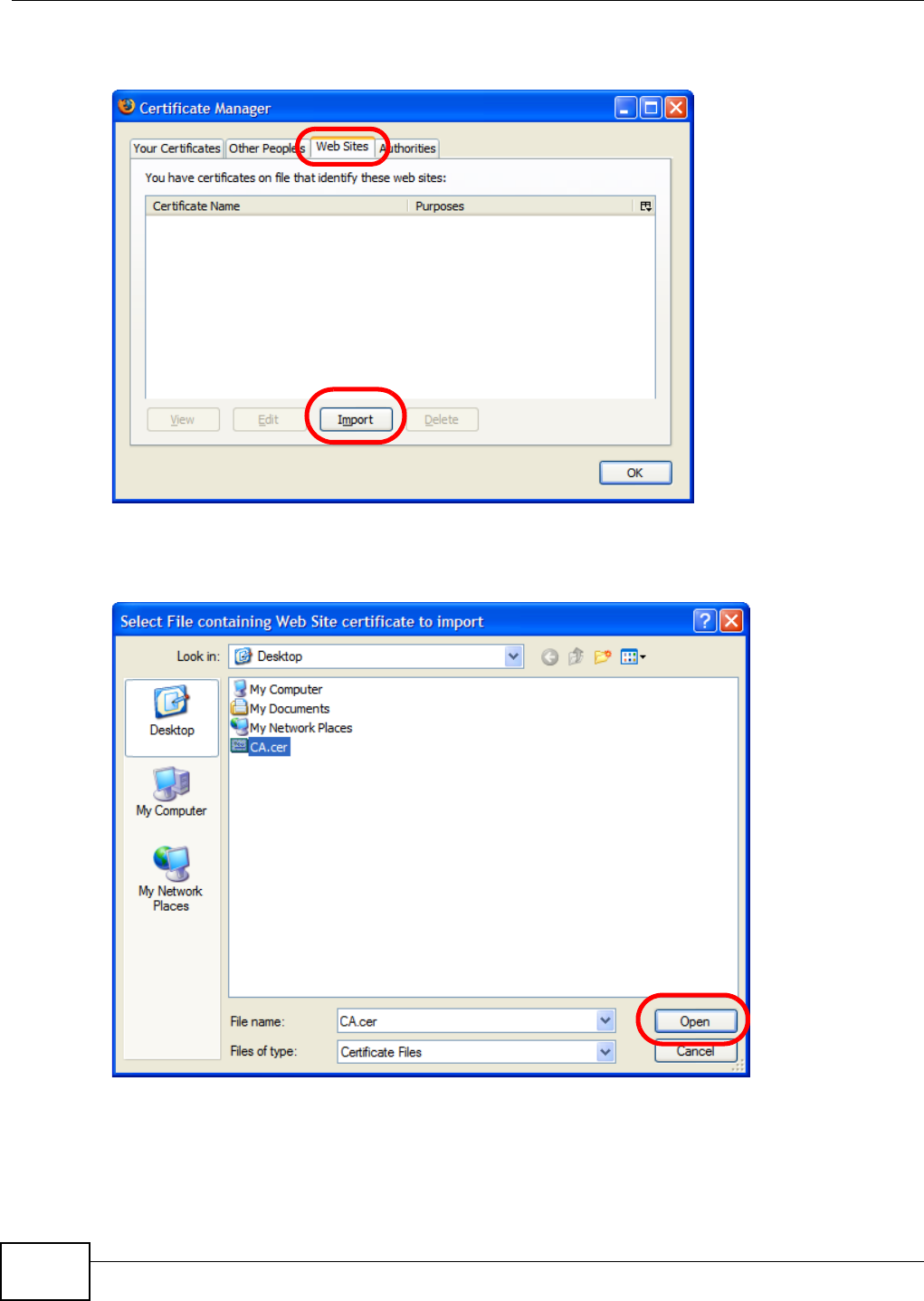
Appendix D Importing Certificates
Media Server User’s Guide
422
3In the Certificate Manager dialog box, click Web Sites > Import.
Figure 248 Firefox 2: Certificate Manager
4Use the Select File dialog box to locate the certificate and then click Open.
Figure 249 Firefox 2: Select File
5The next time you visit the web site, click the padlock in the address bar to open the Page Info >
Security window to see the web page’s security information.
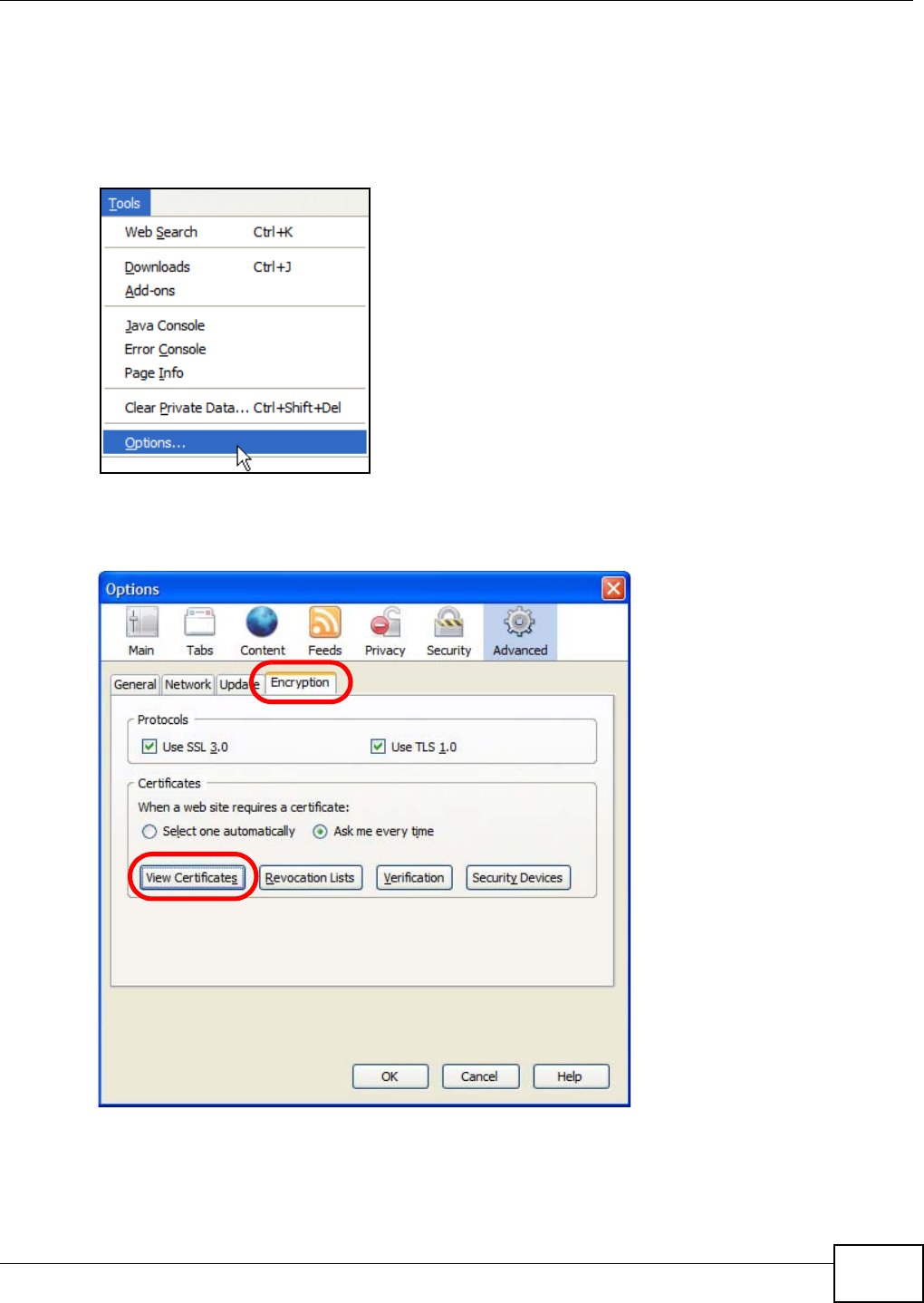
Appendix D Importing Certificates
Media Server User’s Guide 423
Removing a Certificate in Firefox
This section shows you how to remove a public key certificate in Firefox 2.
1Open Firefox and click Tools > Options.
Figure 250 Firefox 2: Tools Menu
2In the Options dialog box, click Advanced > Encryption > View Certificates.
Figure 251 Firefox 2: Options
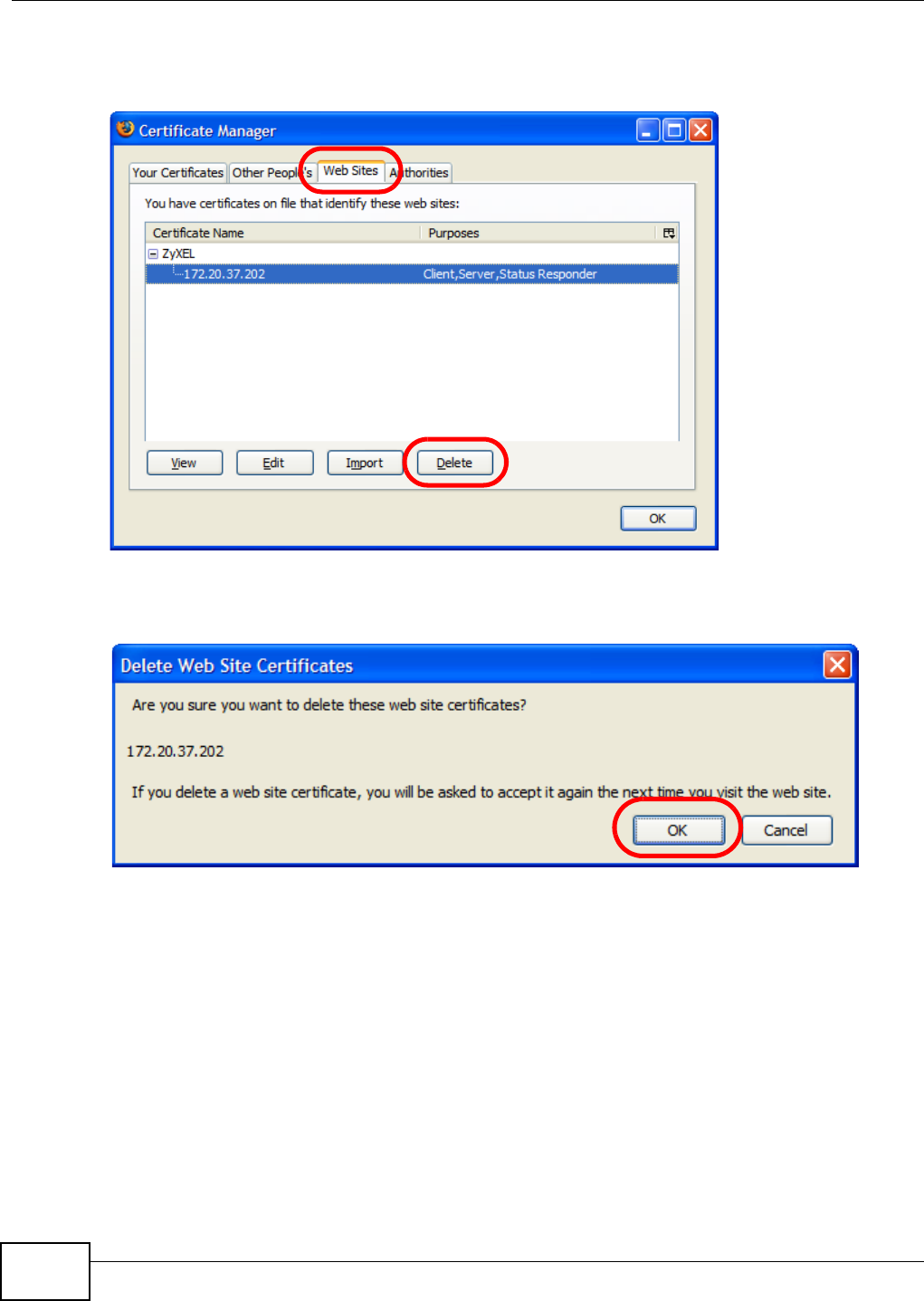
Appendix D Importing Certificates
Media Server User’s Guide
424
3In the Certificate Manager dialog box, select the Web Sites tab, select the certificate that you
want to remove, and then click Delete.
Figure 252 Firefox 2: Certificate Manager
4In the Delete Web Site Certificates dialog box, click OK.
Figure 253 Firefox 2: Delete Web Site Certificates
5The next time you go to the web site that issued the public key certificate you just removed, a
certification error appears.
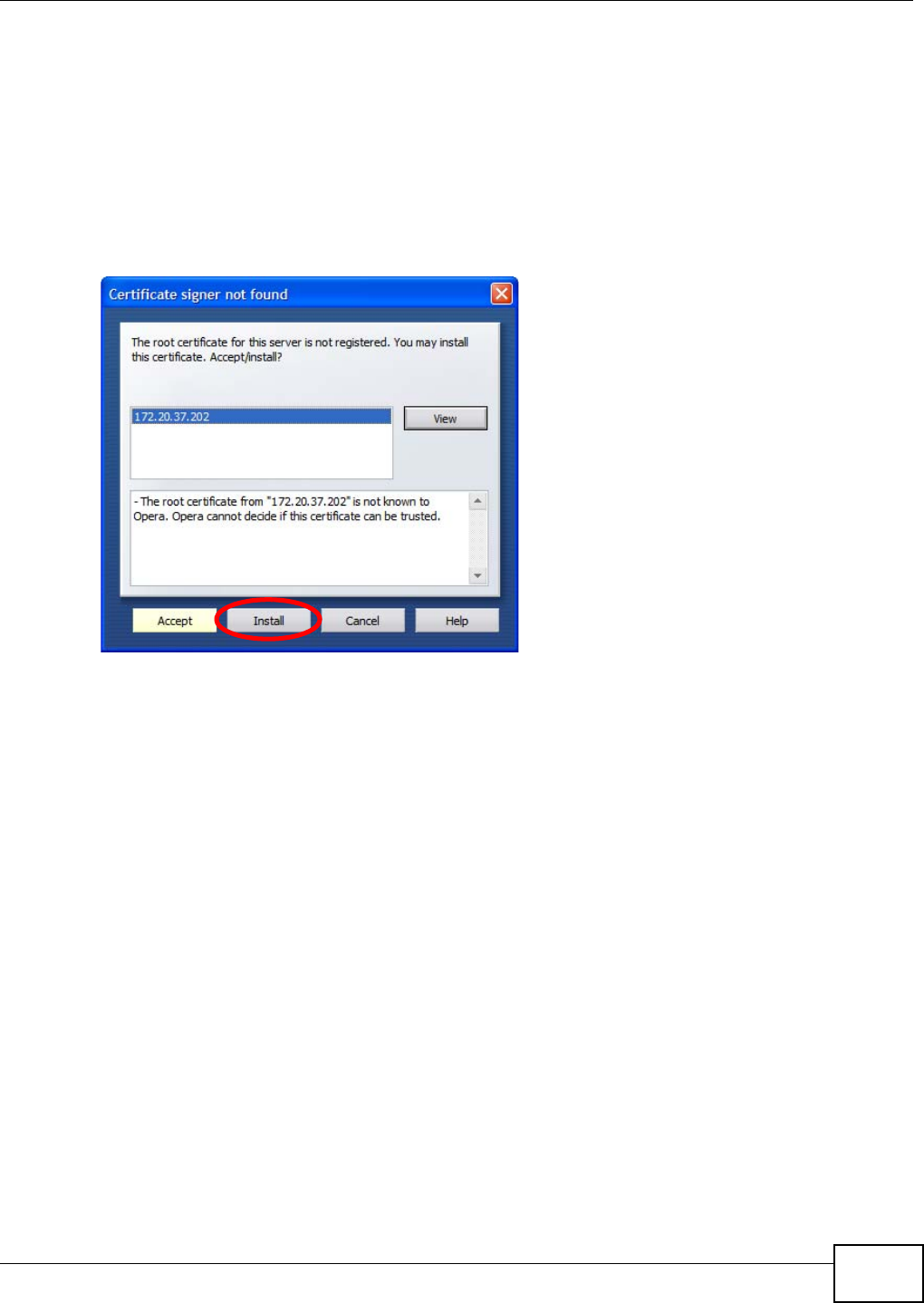
Appendix D Importing Certificates
Media Server User’s Guide 425
Opera
The following example uses Opera 9 on Windows XP Professional; however, the screens can apply
to Opera 9 on all platforms.
1If your device’s Web Configurator is set to use SSL certification, then the first time you browse to it
you are presented with a certification error.
2Click Install to accept the certificate.
Figure 254 Opera 9: Certificate signer not found
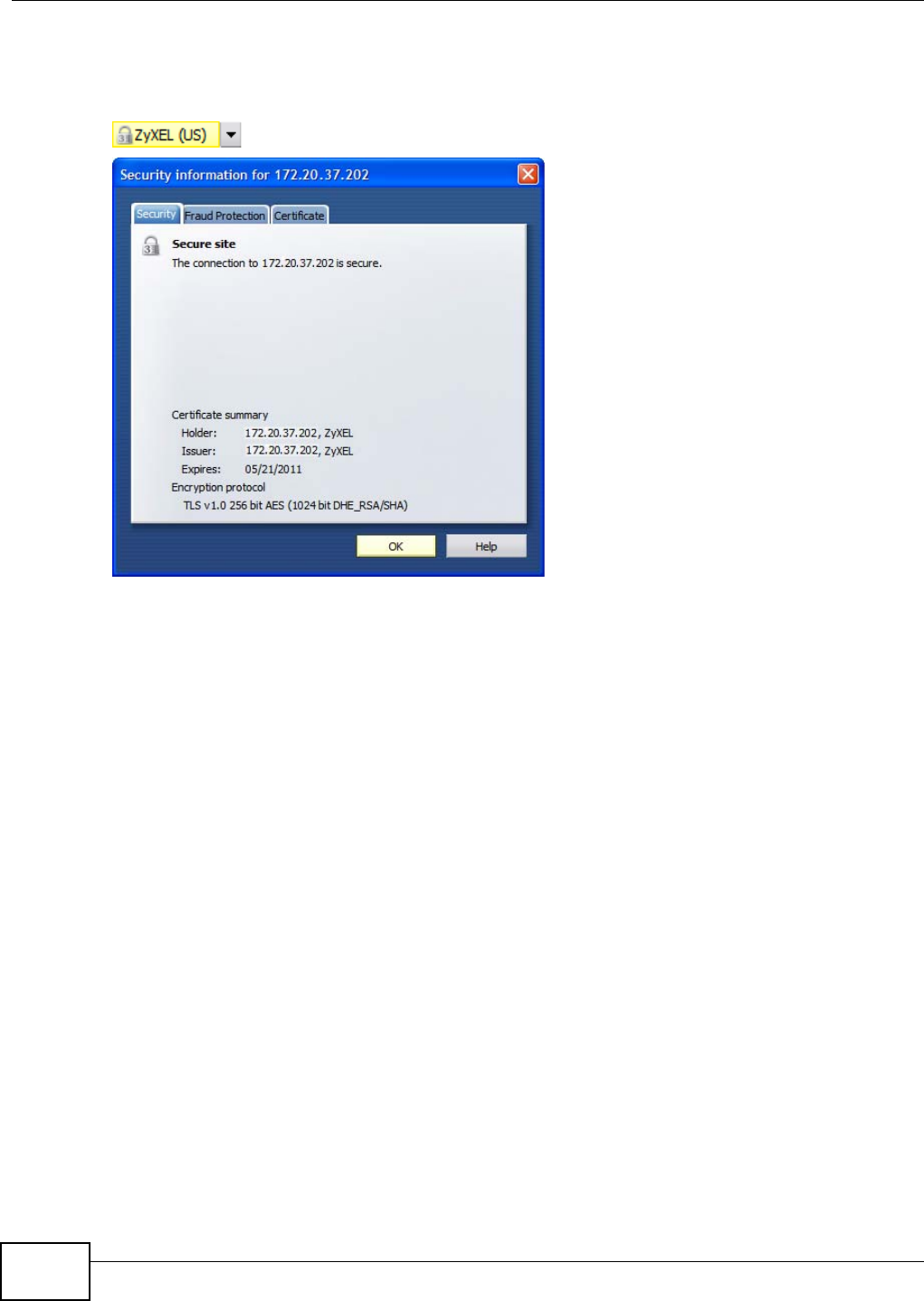
Appendix D Importing Certificates
Media Server User’s Guide
426
3The next time you visit the web site, click the padlock in the address bar to open the Security
information window to view the web page’s security details.
Figure 255 Opera 9: Security information
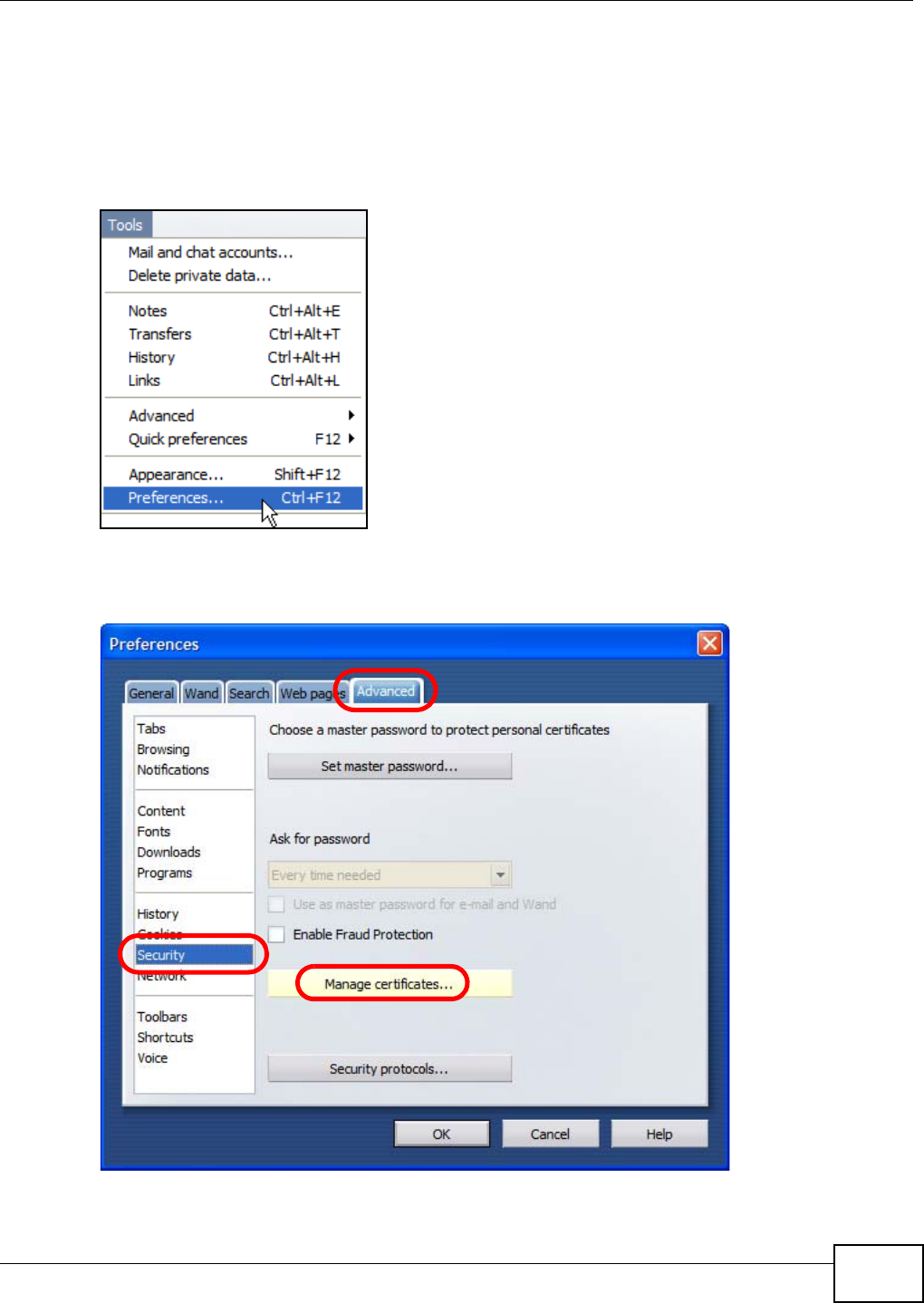
Appendix D Importing Certificates
Media Server User’s Guide 427
Installing a Stand-Alone Certificate File in Opera
Rather than browsing to a ZyXEL Web Configurator and installing a public key certificate when
prompted, you can install a stand-alone certificate file if one has been issued to you.
1Open Opera and click Tools > Preferences.
Figure 256 Opera 9: Tools Menu
2In Preferences, click Advanced > Security > Manage certificates.
Figure 257 Opera 9: Preferences
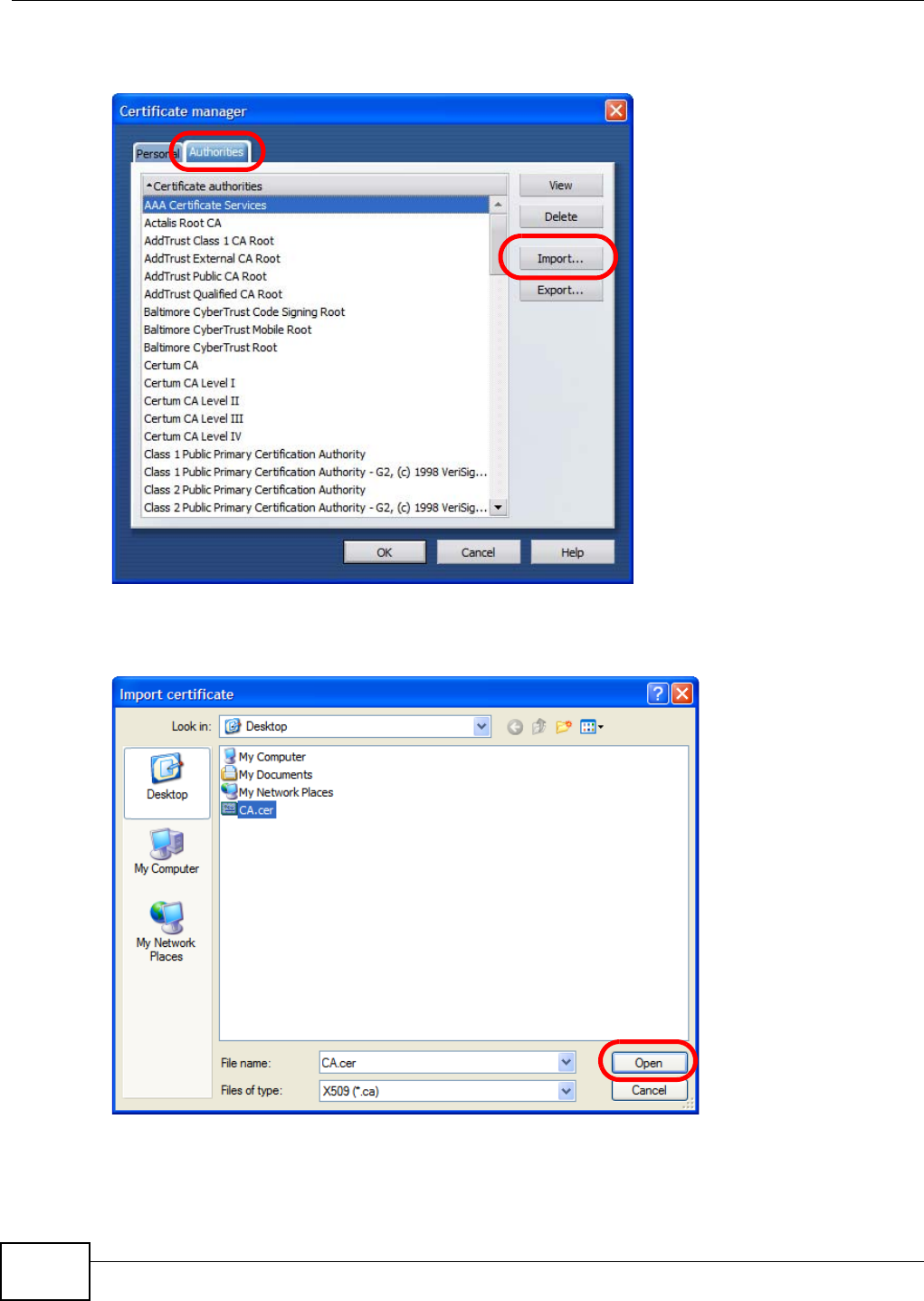
Appendix D Importing Certificates
Media Server User’s Guide
428
3In the Certificates Manager, click Authorities > Import.
Figure 258 Opera 9: Certificate manager
4Use the Import certificate dialog box to locate the certificate and then click Open.
Figure 259 Opera 9: Import certificate
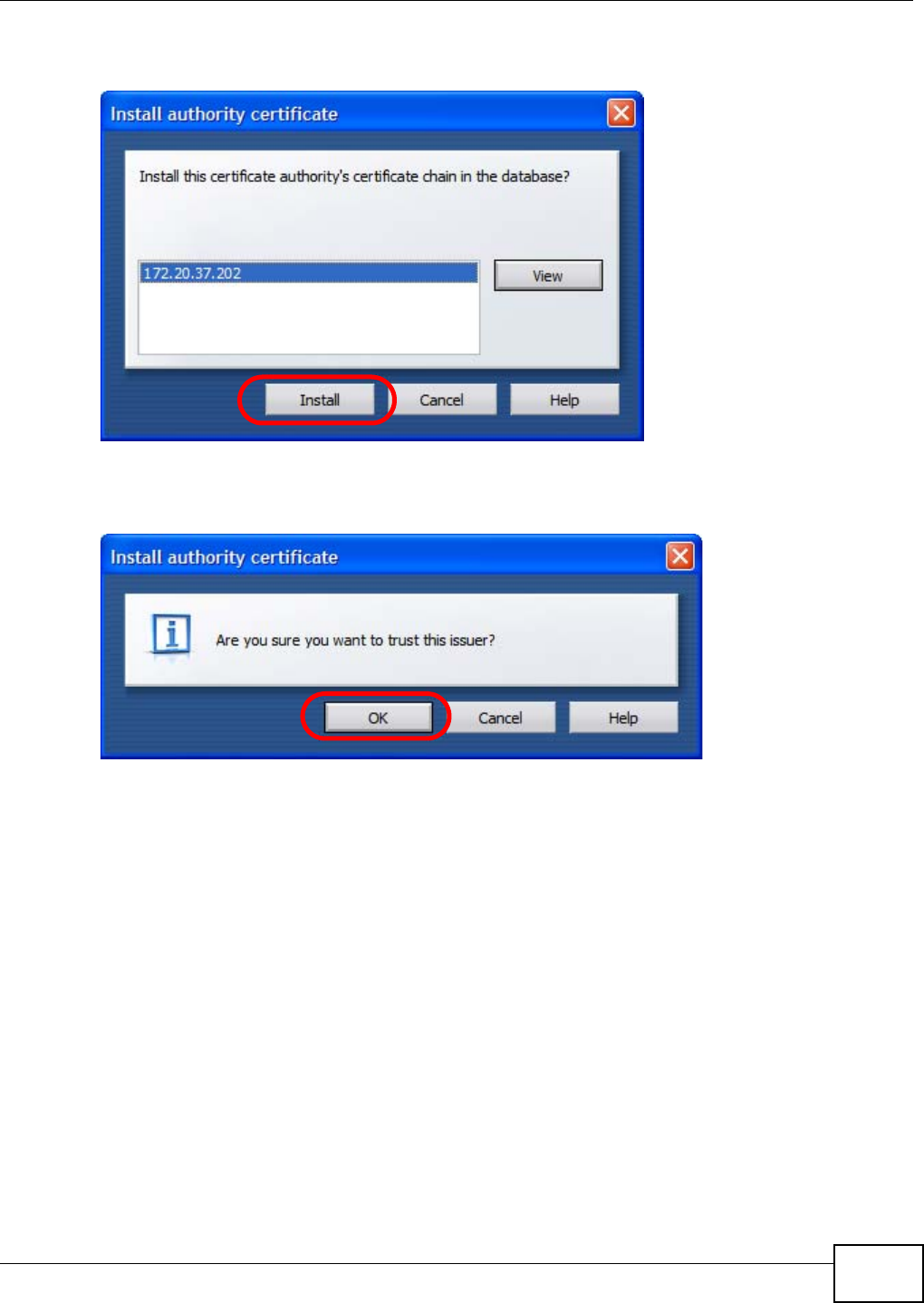
Appendix D Importing Certificates
Media Server User’s Guide 429
5In the Install authority certificate dialog box, click Install.
Figure 260 Opera 9: Install authority certificate
6Next, click OK.
Figure 261 Opera 9: Install authority certificate
7The next time you visit the web site, click the padlock in the address bar to open the Security
information window to view the web page’s security details.
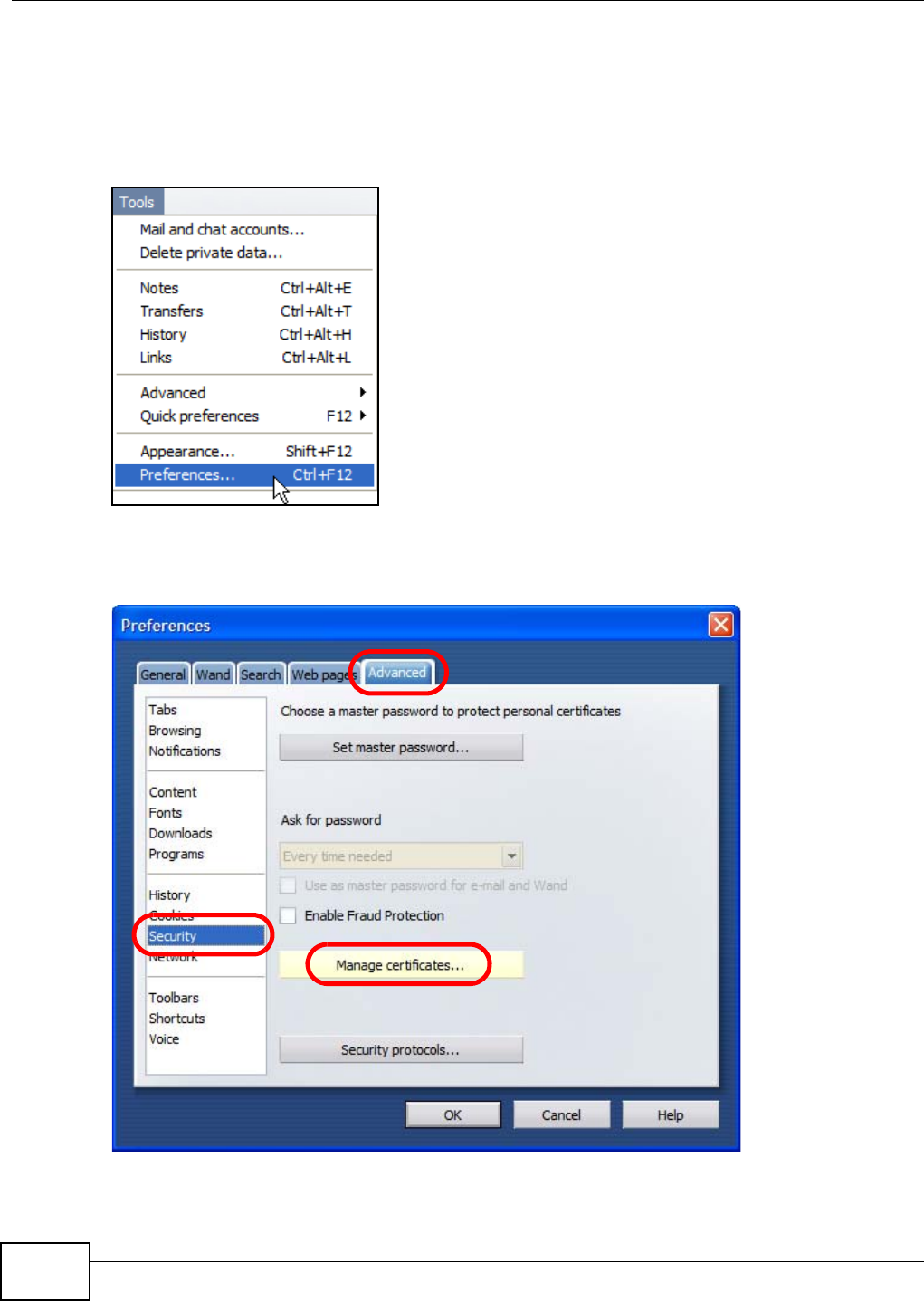
Appendix D Importing Certificates
Media Server User’s Guide
430
Removing a Certificate in Opera
This section shows you how to remove a public key certificate in Opera 9.
1Open Opera and click Tools > Preferences.
Figure 262 Opera 9: Tools Menu
2In Preferences, Advanced > Security > Manage certificates.
Figure 263 Opera 9: Preferences
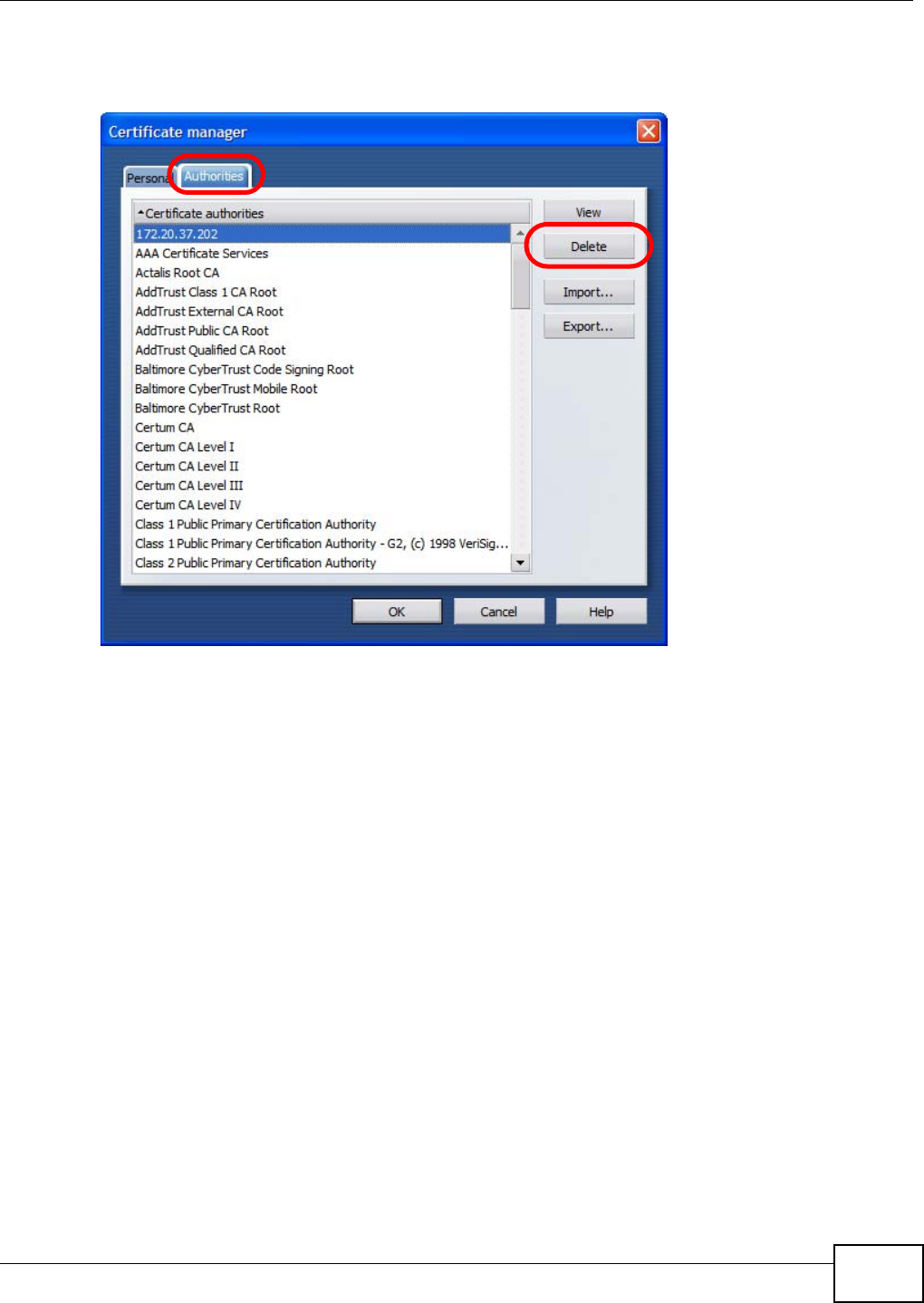
Appendix D Importing Certificates
Media Server User’s Guide 431
3In the Certificates manager, select the Authorities tab, select the certificate that you want to
remove, and then click Delete.
Figure 264 Opera 9: Certificate manager
4The next time you go to the web site that issued the public key certificate you just removed, a
certification error appears.
Note: There is no confirmation when you delete a certificate authority, so be absolutely
certain that you want to go through with it before clicking the button.
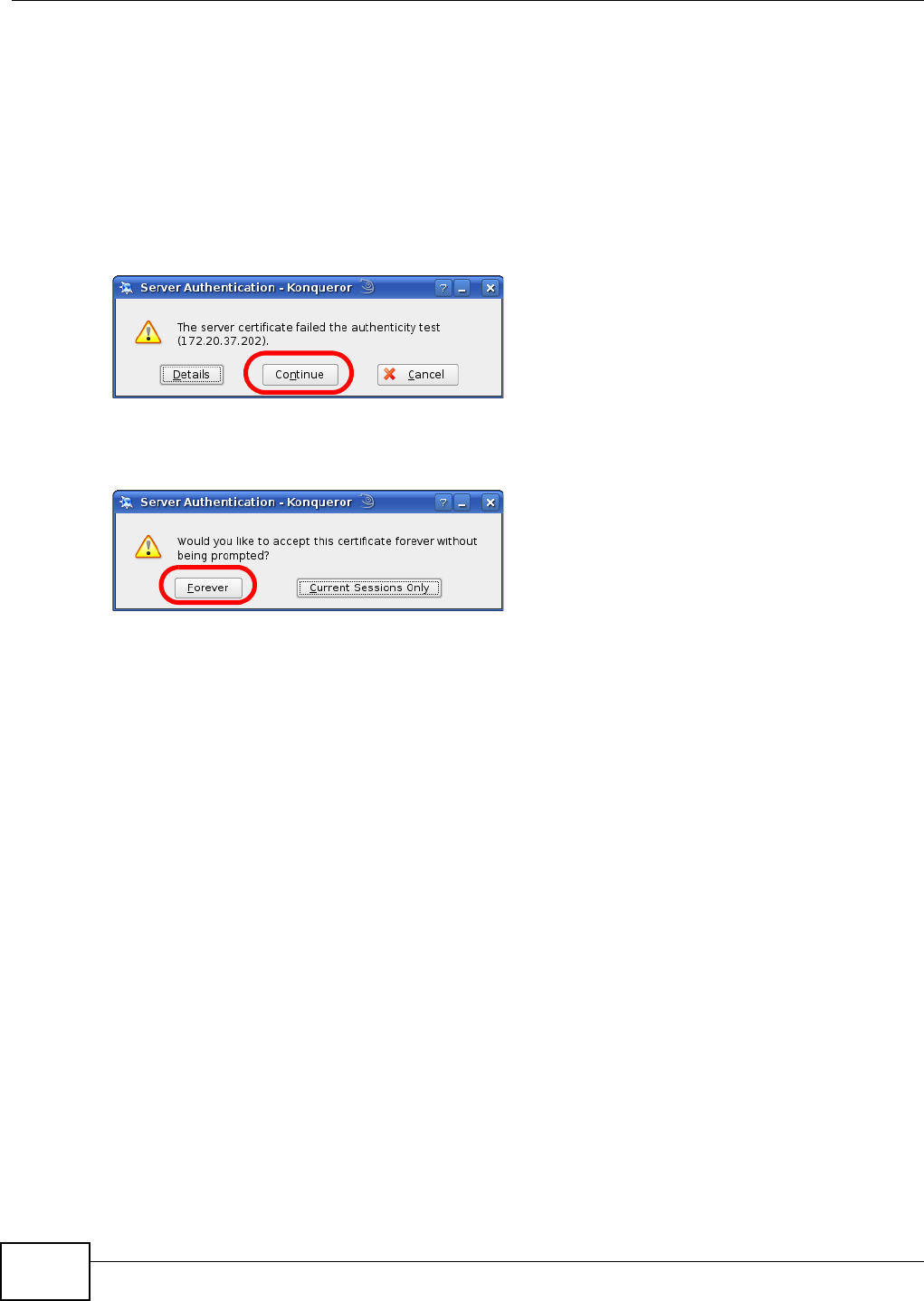
Appendix D Importing Certificates
Media Server User’s Guide
432
Konqueror
The following example uses Konqueror 3.5 on openSUSE 10.3, however the screens apply to
Konqueror 3.5 on all Linux KDE distributions.
1If your device’s Web Configurator is set to use SSL certification, then the first time you browse to it
you are presented with a certification error.
2Click Continue.
Figure 265 Konqueror 3.5: Server Authentication
3Click Forever when prompted to accept the certificate.
Figure 266 Konqueror 3.5: Server Authentication
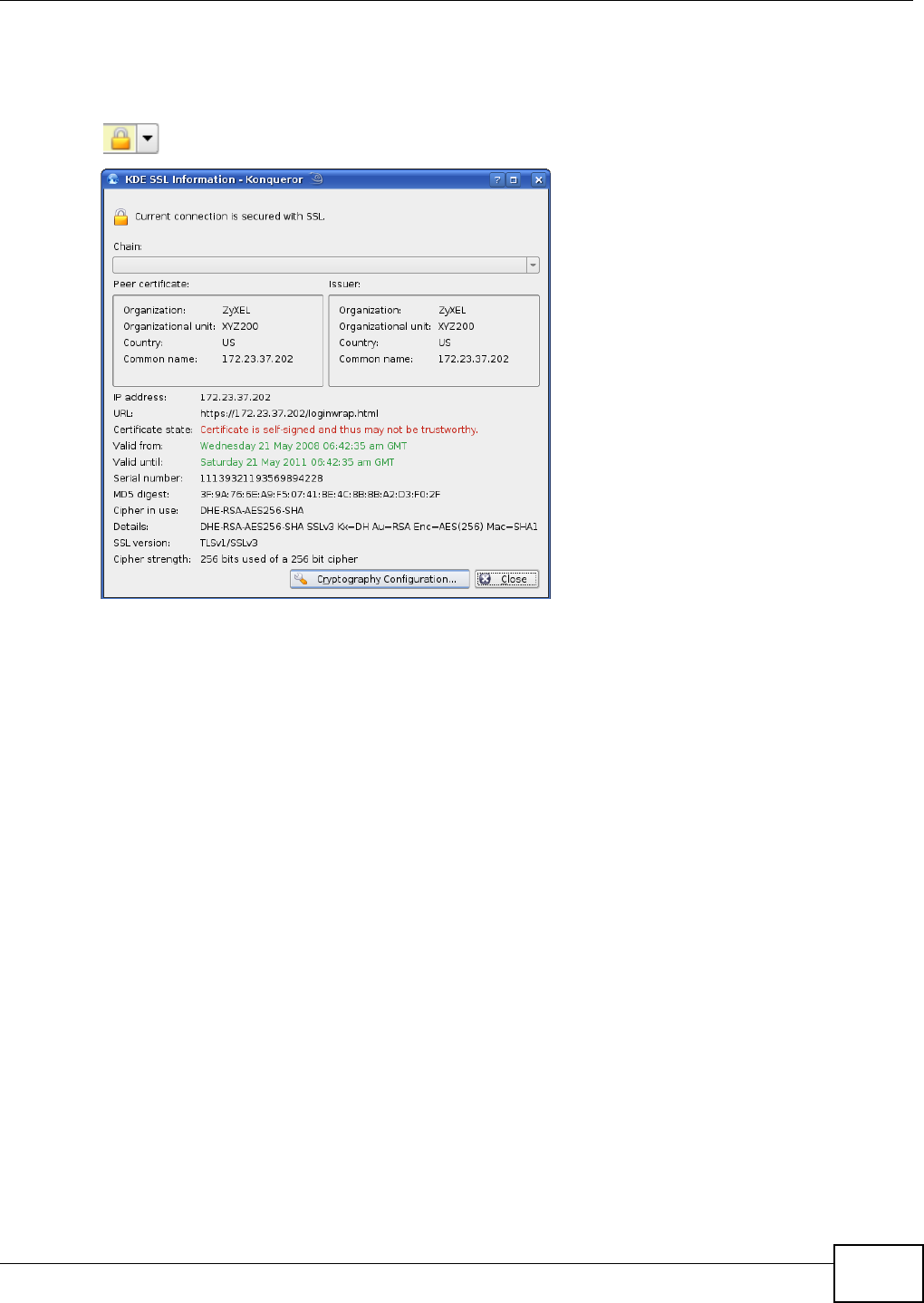
Appendix D Importing Certificates
Media Server User’s Guide 433
4Click the padlock in the address bar to open the KDE SSL Information window and view the web
page’s security details.
Figure 267 Konqueror 3.5: KDE SSL Information
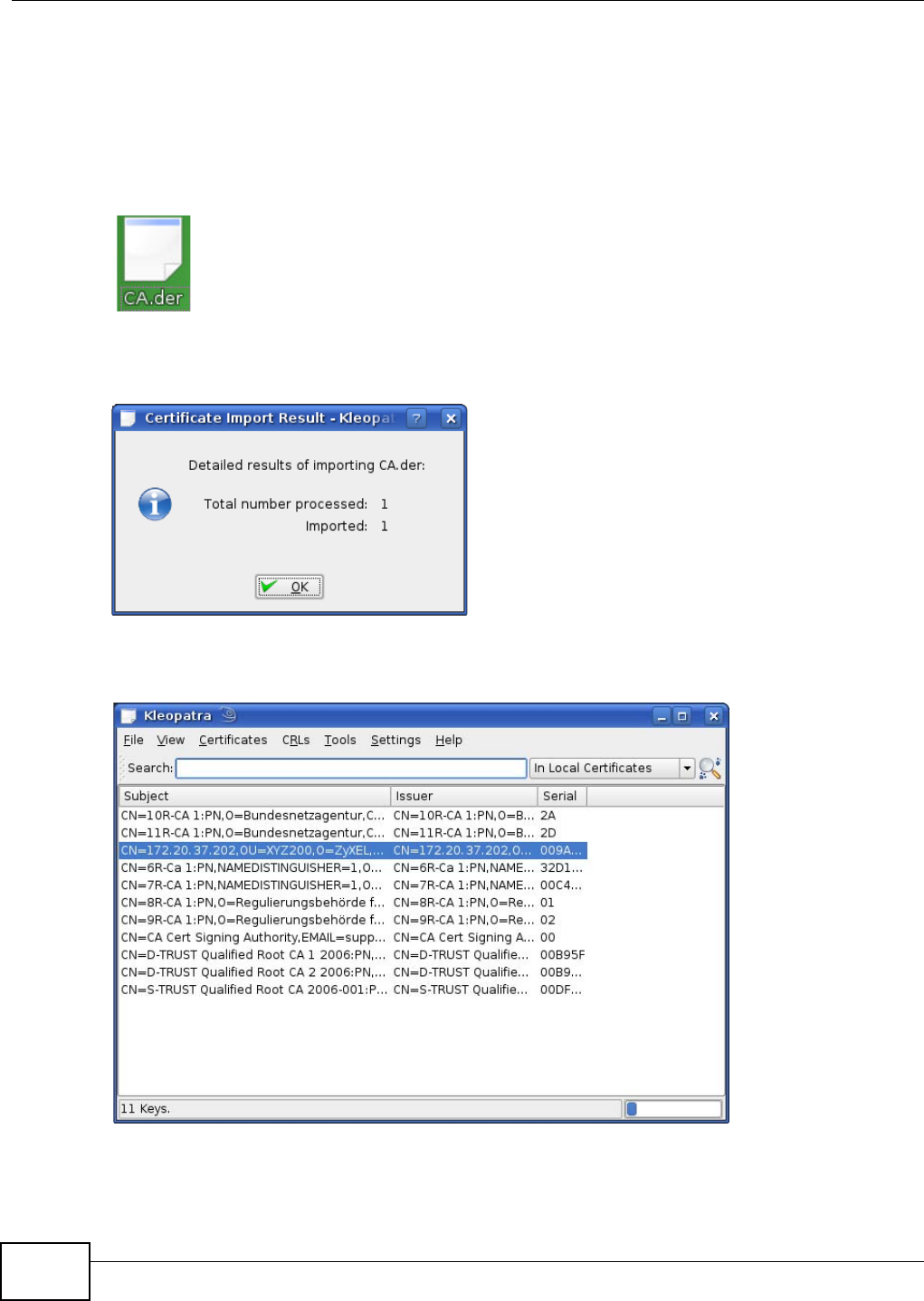
Appendix D Importing Certificates
Media Server User’s Guide
434
Installing a Stand-Alone Certificate File in Konqueror
Rather than browsing to a ZyXEL Web Configurator and installing a public key certificate when
prompted, you can install a stand-alone certificate file if one has been issued to you.
1Double-click the public key certificate file.
Figure 268 Konqueror 3.5: Public Key Certificate File
2In the Certificate Import Result - Kleopatra dialog box, click OK.
Figure 269 Konqueror 3.5: Certificate Import Result
The public key certificate appears in the KDE certificate manager, Kleopatra.
Figure 270 Konqueror 3.5: Kleopatra
3The next time you visit the web site, click the padlock in the address bar to open the KDE SSL
Information window to view the web page’s security details.
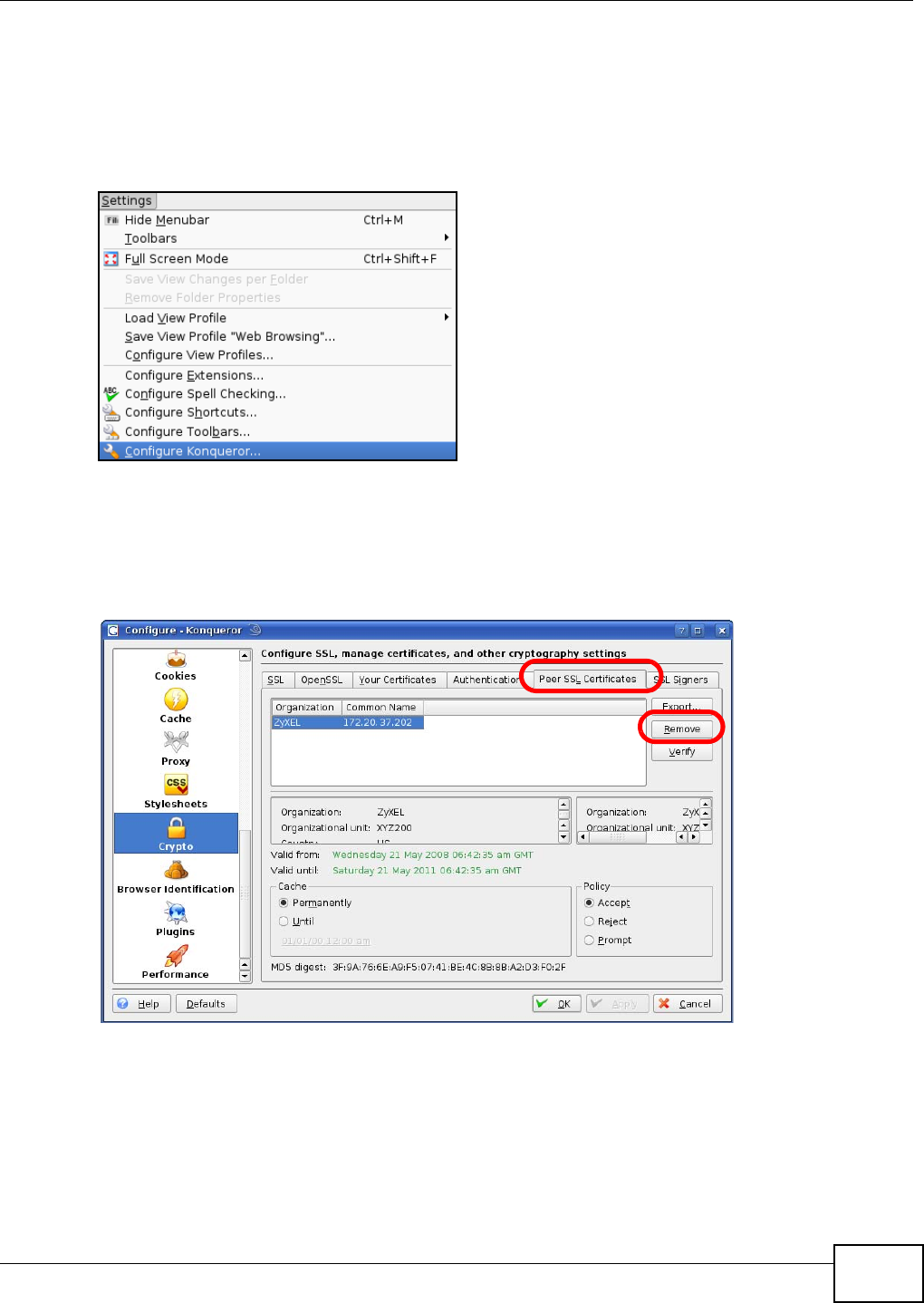
Appendix D Importing Certificates
Media Server User’s Guide 435
Removing a Certificate in Konqueror
This section shows you how to remove a public key certificate in Konqueror 3.5.
1Open Konqueror and click Settings > Configure Konqueror.
Figure 271 Konqueror 3.5: Settings Menu
2In the Configure dialog box, select Crypto.
3On the Peer SSL Certificates tab, select the certificate you want to delete and then click
Remove.
Figure 272 Konqueror 3.5: Configure
4The next time you go to the web site that issued the public key certificate you just removed, a
certification error appears.
Note: There is no confirmation when you remove a certificate authority, so be absolutely
certain you want to go through with it before clicking the button.

Appendix D Importing Certificates
Media Server User’s Guide
436

Media Server User’s Guide 437
APPENDIX E
Legal Information
Copyright
Copyright © 2011 by ZyXEL Communications Corporation.
The contents of this publication may not be reproduced in any part or as a whole, transcribed,
stored in a retrieval system, translated into any language, or transmitted in any form or by any
means, electronic, mechanical, magnetic, optical, chemical, photocopying, manual, or otherwise,
without the prior written permission of ZyXEL Communications Corporation.
Published by ZyXEL Communications Corporation. All rights reserved.
Disclaimers
ZyXEL does not assume any liability arising out of the application or use of any products, or
software described herein. Neither does it convey any license under its patent rights nor the patent
rights of others. ZyXEL further reserves the right to make changes in any products described herein
without notice. This publication is subject to change without notice.
Do not use the NSA for illegal purposes. Illegal downloading or sharing of files can result in severe
civil and criminal penalties. You are subject to the restrictions of copyright laws and any other
applicable laws and will bear the consequences of any infringements thereof. ZyXEL bears NO
responsibility or liability for your use of the download service feature.
Make sure all data and programs on the NSA are also stored elsewhere. ZyXEL is not responsible for
any loss of or damage to any data, programs, or storage media resulting from the use, misuse, or
disuse of this or any other ZyXEL product.
Certifications
Federal Communications Commission (FCC) Interference Statement
The device complies with Part 15 of FCC rules. Operation is subject to the following two conditions:
• This device may not cause harmful interference.
• This device must accept any interference received, including interference that may cause
undesired operations.
This device has been tested and found to comply with the limits for a Class B digital device pursuant
to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against
harmful interference in a residential installation. This device generates, uses, and can radiate radio
frequency energy, and if not installed and used in accordance with the instructions, may cause
harmful interference to radio communications. However, there is no guarantee that interference will
not occur in a particular installation.

Appendix E Legal Information
Media Server User’s Guide
438
Notices
Changes or modifications not expressly approved by the party responsible for compliance could
void the user's authority to operate the equipment.
This Class B digital apparatus complies with Canadian ICES-003.
Cet appareil numérique de la classe B est conforme à la norme NMB-003 du Canada.
Viewing Certifications
1Go to http://www.zyxel.com.
2Select your product on the ZyXEL home page to go to that product's page.
3Select the certification you wish to view from this page.
ZyXEL warrants to the original end user (purchaser) that this product is free from any defects in
materials or workmanship for a period of up to two years from the date of purchase. During the
warranty period, and upon proof of purchase, should the product have indications of failure due to
faulty workmanship and/or materials, ZyXEL will, at its discretion, repair or replace the defective
products or components without charge for either parts or labor, and to whatever extent it shall
deem necessary to restore the product or components to proper operating condition. Any
replacement will consist of a new or re-manufactured functionally equivalent product of equal or
higher value, and will be solely at the discretion of ZyXEL. This warranty shall not apply if the
product has been modified, misused, tampered with, damaged by an act of God, or subjected to
abnormal working conditions.
Note
Repair or replacement, as provided under this warranty, is the exclusive remedy of the purchaser.
This warranty is in lieu of all other warranties, express or implied, including any implied warranty of
merchantability or fitness for a particular use or purpose. ZyXEL shall in no event be held liable for
indirect or consequential damages of any kind to the purchaser.
To obtain the services of this warranty, contact your vendor. You may also refer to the warranty
policy for the region in which you bought the device at http://www.zyxel.com/web/
support_warranty_info.php.
Registration
Register your product online to receive e-mail notices of firmware upgrades and information at
www.zyxel.com for global products, or at www.us.zyxel.com for North American products.

Index
Media Server User’s Guide 439
Index
Numbers
1-bay 22
2-bay 22
3-D photo wall 51
A
access rights 55
Flickr 281
shares 306, 307
YouTube 284
activation
download service 190
Flickr/YouTube 276
FTP 184
FTP Uploadr 285
recycle bins 55, 305
web publishing 202
ANONYMOUS FTP 355
anonymous FTP access 184
application zone 56
applications 181, 275
auto upload
Flickr/YouTube 275
FTP Uploadr 284
broadcatching 183, 203
adding channels 190, 204, 205
channel guides 219
RSS 183
COPY/SYNC button 211
configuration 211
example 221
synchronization 221
download service 182, 213
activation 190
adding a task 193, 200
BitTorrent 183, 193, 213
configuration 190
link capture browser plugin 214
notifications 214
preferences 195
protection 215, 216
status 192
URL 193, 262
FTP 181, 184, 275
activation 184
anonymous access 184
passive mode transfer 185
media server 182, 185
configuration 186
iTunes server 182, 212, 213
print server 220
configuration 210
name 210
web publishing 183, 202, 218
activation 202
example 217
port number 219
archive 134
authorization
Flickr 276, 278
YouTube 281
auto upload
Flickr/YouTube 275
activation 276
authorization 276, 281
configuration 280, 281
FTP Uploadr 284
activation 285
bandwidth limit 288
configuration 286
server entry 285
grace period 281, 283, 288
B
backup 134
archive 134
synchronization tutorial 137
tutorial 137
backup files
restoring files by 143

Index
Media Server User’s Guide440
backup job
restoring files by 140
backup settings 318
bandwidth limit 288
BitTorrent 183
IP filtering 198, 199
protection 215, 216
re-seeding 191
settings 197
torrent files 193, 213
health 201
info-hash 202
trackers 202
broadcatching 183, 203
adding channels 190, 204, 205
channel guides 219
RSS 183
browser plugin, capturing link 214
browsing shares 52
C
capturing download links 214
certificate 320
editing 320
tutorial 118
verifying 128
changing password 46
channel guides 219
CIFS 153
configuration
COPY/SYNC button 211
download service 190
Flickr 280
FTP Uploadr 286
print server 210
recycle bins 308
YouTube 281, 282
CoolIris 51
COPY/SYNC button 23, 211
configuration 211
example 221
synchronization 221
copying contents 310
CPU
temperature 150
usage 150
creating
groups 300, 301
shares 304, 305
users 294, 295
volumes 161, 164
D
data protection 169
date 154
diagnostic tool 175
diagnostic tools 175
discovery 35
disk
S.M.A.R.T. attributes 272
disk replacement 158
displaying user information 297
DLNA 182, 212
DNS 171, 174
Domain Name System, see DNS
domain user
troubleshooting 355
troubleshooting share access 355
download period control 196
download service 182, 213
activation 190
adding a task 193, 200
BitTorrent 183
IP filtering 198, 199
protection 215, 216
re-seeding 191
settings 197
torrent files 193, 213
configuration 190
download period control 196
link capture browser plugin 214
notifications 214
activation 190
preferences 195
status 192
URL, download service 193, 262
downloading files 54
duplexing 167

Index
Media Server User’s Guide 441
E
Exchangeable image file format, see Exif
Exif 50
explicit TLS/SSL 130
external volumes 164
F
fan speed 150
file
troubleshooting access 355
file browser
configure share 54
share browser 52
File Transfer Protocol over Explicit TLS, see FTPES
File Transfer Protocol over TLS, see FTPS
files
downloading 54
uploading 54
FileZilla 130
fingerprint 128
firmware, upgrading 322
Flickr 275
access rights 281
activation 276
authorization 276, 278
grace period 281
safety level 281
folder
troubleshooting access 355
folder creation 53
FTP 130, 181, 184, 275
activation 184
anonymous access 184
over TLS 130
passive mode transfer 185
FTP Uploadr 284
activation 285
bandwidth limit 288
configuration 286
grace period 288
server entry 285
FTPES 182
FTPES - FTP over explicit TLS/SSL 130
FTPS 130, 275
G
global icons 47, 59
GMT 42, 156
Google Maps 50
GPS 50
grace period 281, 283, 288
groups 299
adding 300, 301
editing 301
membership 296, 301
names 301
searching 300
H
Home
icons 47
HTTP port 174
HTTPS 123, 319
I
icons 47, 59, 61
global 47, 59
users 295
ID3 tags 188
IP address 171
IP filtering 198, 199
iTunes server 182, 189, 212, 213
J
JBOD 162, 166, 168
jumbo frames 172, 175

Index
Media Server User’s Guide442
K
Ken Burns 57
L
lag, time 153
language 58
latitude 50
link capture browser plugin 214
login 45
Logitech SqueezeCenter 189
logs 315
longitude 50
M
maintenance 311
backup settings 318
logs 315
power management 311
failure 312
resume 312
schedule 313
UPS 312
reset 318
restoring settings 318
shutdown 323
upgrading firmware 322
master browser 154
media server 182, 185
configuration 186
ID3 tags 188
iTunes server 182, 189, 213
rebuild database 185
share publish 187
SqueezeCenter 189
status 185
membership 296
groups 296, 301
mirroring 167
moving contents 310
N
naming
server 154
shares 55
volumes 163
workgroup 154
NAS Starter Utility 35, 44
navigation panel 60
network 171
diagnostic tools 175
DNS 171, 174
HTTP port 174
IP address 171
jumbo frames 172, 175
PPPoE 172, 179
activation 180
TCP/IP 173
network connection test 175
notifications
download service
activation 190
notifications, download service 214
P
parity 167
passive mode transfer 185
password 46, 57
photo wall 51
ping 175
Play Next 58
port mapping 175
port, HTTP 174
power management 311
failure 312
resume 312
schedule 313
UPS 312
PPPoE 172, 179
activation 180
preferences, download service 195
print server 220
configuration 210
name 210

Index
Media Server User’s Guide 443
protect 134
backup 134
backup tutorial 137
protection, download service 215, 216
public key certificate 320
editing 320
publishing shares 187
R
RAID 162, 166
degraded 160
RAID 0 167, 168
RAID 1 167, 169
recovering 158
replacing disks 158
resynchronization 158
rebuild media server database 185
recycle bins 307
activation 55, 305
configuration 304, 308
related documentation 3
replacing disks 158
reset 23, 318
restoring
by backup files tutorial 143
by backup job tutorial 140
files 140
restoring settings 318
RSS 183
download service notifications 214
S
S.M.A.R.T.
attributes 272
safety level, Flickr 281
scanning volumes 164
schedule, power management 313
scheduling, download service 196
secure connections 123
server
Syslog 253
TFTP 255
server entry, FTP Uploadr 285
server name 154
setup
BitTorrent 197
COPY/SYNC button 211
download service 190
Flickr 280
FTP Uploadr 286
media server 186
print server 210
YouTube 281, 282
share
configuration 54
troubleshooting local user access 354
share publishing 187
shares 52, 303
access rights 55, 306, 307
adding 304, 305
browser 52
copying contents 310
downloading files 54
editing 305
folder creation 53
moving contents 310
names 55
recycle bins 304, 307
activation 305
configuration 308
share browser 304, 308
status 304
types 304
uploading files 54, 267, 309
shutdown 323
SqueezeCenter 189
SSL130, 319
certificate 320
editing 320
tutorial 118
status 59, 150
download service 192
shares 304
volume 159, 160
storage 157
creating volumes 161
disk replacement 158
JBOD 157, 162, 166, 168
methods 166

Index
Media Server User’s Guide444
duplexing 167
mirroring 167
parity 167
striping 167
naming volumes 163
RAID 157, 162, 166
degraded 160
RAID 0 167, 168
RAID 1 167, 169
recovering 158
resynchronization 158
status 159, 160
USB devices 164, 165
volumes 157, 166
striping 167
synchronization 211, 221
configuration 211
directions 212
single direction 221
tutorial 137
two directions 222
Syslog server 253
system
date/time 154
login 45
master browser 154
password 46
reset 23
server name 154
settings 153
status 150
time lag 153
workgroup name 154
system settings 57
T
TCP/IP 173
temperature
CPU 150
TFTP server 255
thumbprint 128
time 154
lag 153
server 155
zone 42, 156
Time Machine 337
TLS 130, 182, 275
torrent files 193, 213
health 201
info-hash 202
trackers 202
Transport Layer Security, see TLS
troubleshooting
domain user 355
domain user share access 355
file access 355
files not in proper folders 48
folder access 355
forgot password 350, 351
LED indicators 347
LAN 348
local user share access 354
login 353
media files 358
NAS Starter Utility 349
overview 347
user share access 354
web configurator access 351
U
Universal Plug and Play. See UPnP.
upgrading firmware 322
uploading files 54, 267, 309
UPnP 175
port mapping 175
UPS 312
URL 193, 262
USB devices 164, 165
User Name 230
usernames 297
users 293
adding an account 294, 295
displaying information 295, 297
editing an account 295
group membership 296, 301
icons 295
search 294
usernames 297

Index
Media Server User’s Guide 445
V
video category, YouTube 283
video playback 58
volumes 157, 166
creation 161, 164
JBOD 157, 162, 166, 168
names 163
RAID 157, 162, 166
degraded 160
RAID 0 167, 168
RAID 1 167, 169
recovering 158
resynchronization 158
scanning 164
status 159, 160
storage methods 166
duplexing 167
mirroring 167
parity 167
striping 167
W
web configurator 43
icons 47
login 45
navigation panel 60
password 46, 57
status 59
web publishing 183, 202, 218
activation 202
example 217
port number 219
troubleshooting 361
web security 123
workgroup name 154
Y
YouTube 275
access rights 284
activation 276
authorization 281
configuration 281, 282
grace period 283
video category 283
Z
zPilot 39

Index
Media Server User’s Guide446

447
PART III
Open Source
Licences

448
End-User License Agreement for “NSA325”
WARNING: ZyXEL Communications Corp. IS WILLING TO LICENSE THE SOFTWARE TO YOU ONLY UPON THE
CONDITION THAT YOU ACCEPT ALL OF THE TERMS CONTAINED IN THIS LICENSE AGREEMENT. PLEASE
READ THE TERMS CAREFULLY BEFORE COMPLETING THE INSTALLATION PROCESS AS INSTALLING THE
SOFTWARE WILL INDICATE YOUR ASSENT TO THEM. IF YOU DO NOT AGREE TO THESE TERMS, THEN ZyXEL
IS UNWILLING TO LICENSE THE SOFTWARE TO YOU, IN WHICH EVENT YOU SHOULD RETURN THE
UNINSTALLED SOFTWARE AND PACKAGING TO THE PLACE FROM WHICH IT WAS ACQUIRED OR ZyXEL, AND
YOUR MONEY WILL BE REFUNDED. HOWEVER, CERTAIN ZYXEL’S PRODUCTS MAY CONTAIN–IN
PART-SOME THIRD PARTY’S FREE AND OPEN SOFTWARE PROGRAMS WHICH ALLOW YOU TO FREELY COPY,
RUN, DISTRIBUTE, MODIFY AND IMPROVE THE SOFTWARE UNDER THE APPLICABLE TERMS OF SUCH THRID
PARTY’S LICENSES (“OPEN-SOURCED COMPONENTS”). THE OPEN-SOURCED COMPONENTS ARE LISTED IN
THE NOTICE OR APPENDIX BELOW. ZYXEL MAY HAVE DISTRIBUTED TO YOU HARDWARE AND/OR
SOFTWARE, OR MADE AVAILABLE FOR ELECTRONIC DOWNLOADS THESE FREE SOFTWARE PROGRAMS OF
THRID PARTIES AND YOU ARE LICENSED TO FREELY COPY, MODIFY AND REDISTIBUTE THAT SOFTWARE
UNDER THE APPLICABLE LICENSE TERMS OF SUCH THIRD PARTY. NONE OF THE STATEMENTS OR
DOCUMENTATION FROM ZYXEL INCLUDING ANY RESTRICTIONS OR CONDITIONS STATED IN THIS END USER
LICENSE AGREEMENT SHALL RESTRICT ANY RIGHTS AND LICENSES YOU MAY HAVE WITH RESPECT TO THE
OPEN-SOURCED COMPONENTS UNDER THE APPLICABLE LICENSE TERMS OF SUCH THIRD PARTY.
1. Grant of License for Personal Use
ZyXEL Communications Corp. ("ZyXEL") grants you a non-exclusive, non-sublicense, non-transferable license to use the
program with which this license is distributed (the "Software"), including any documentation files accompanying the Software
("Documentation"), for internal business use only, for up to the number of users specified in sales order and invoice. You have
the right to make one backup copy of the Software and Documentation solely for archival, back-up or disaster recovery purposes.
You shall not exceed the scope of the license granted hereunder. Any rights not expressly granted by ZyXEL to you are reserved
by ZyXEL, and all implied licenses are disclaimed.
2. Ownership
You have no ownership rights in the Software. Rather, you have a license to use the Software as long as this License Agreement
remains in full force and effect. Ownership of the Software, Documentation and all intellectual property rights therein shall
remain at all times with ZyXEL. Any other use of the Software by any other entity is strictly forbidden and is a violation of this
License Agreement.
3. Copyright
The Software and Documentation contain material that is protected by international copyright law, trade secret law, international
treaty provisions, and the applicable national laws of each respective country. All rights not granted to you herein are expressly
reserved by ZyXEL. You may not remove any proprietary notice of ZyXEL or any of its licensors from any copy of the
Software or Documentation.
4. Restrictions
You may not publish, display, disclose, sell, rent, lease, modify, store, loan, distribute, or create derivative works of the Software,
or any part thereof. You may not assign, sublicense, convey or otherwise transfer, pledge as security or otherwise encumber the
rights and licenses granted hereunder with respect to the Software. ZyXEL is not obligated to provide any maintenance, technical
or other support for the resultant modified Software. You may not copy, reverse engineer, decompile, reverse compile, translate,
adapt, or disassemble the Software, or any part thereof, nor shall you attempt to create the source code from the object code for
the Software. Except as and only to the extent expressly permitted in this License, you may not market, co-brand, and private
label or otherwise permit third parties to link to the Software, or any part thereof. You may not use the Software, or any part
thereof, in the operation of a service bureau or for the benefit of any other person or entity. You may not cause, assist or permit
any third party to do any of the foregoing. Portions of the Software utilize or include third party software and other copyright
material. Acknowledgements, licensing terms and disclaimers for such material are contained in the License Notice as below for
the third party software, and your use of such material is exclusively governed by their respective terms. ZyXEL has provided, as
part of the Software package, access to certain third party software as a convenience. To the extent that the Software contains
third party software, ZyXEL has no express or implied obligation to provide any technical or other support for such software
other than compliance with the applicable license terms of such third party, and makes no warranty (express, implied or statutory)
whatsoever with respect thereto. Please contact the appropriate software vendor or manufacturer directly for technical support
and customer service related to its software and products.
5. Confidentiality
You acknowledge that the Software contains proprietary trade secrets of ZyXEL and you hereby agree to maintain the
confidentiality of the Software using at least as great a degree of care as you use to maintain the confidentiality of your own most
confidential information. You agree to reasonably communicate the terms and conditions of this License Agreement to those

persons employed by you who come into contact with the Software, and to use reasonable best efforts to ensure their compliance
with such terms and conditions, including, without limitation, not knowingly permitting such persons to use any portion of the
Software for the purpose of deriving the source code of the Software.
6. No Warranty
THE SOFTWARE IS PROVIDED "AS IS." TO THE MAXIMUM EXTENT PERMITTED BY LAW, ZyXEL DISCLAIMS
ALL WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION,
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE, AND
NON-INFRINGEMENT. ZyXEL DOES NOT WARRANT THAT THE FUNCTIONS CONTAINED IN THE SOFTWARE
WILL MEET ANY REQUIREMENTS OR NEEDS YOU MAY HAVE, OR THAT THE SOFTWARE WILL OPERATE ERROR
FREE, OR IN AN UNINTERUPTED FASHION, OR THAT ANY DEFECTS OR ERRORS IN THE SOFTWARE WILL BE
CORRECTED, OR THAT THE SOFTWARE IS COMPATIBLE WITH ANY PARTICULAR PLATFORM. SOME
JURISDICTIONS DO NOT ALLOW THE WAIVER OR EXCLUSION OF IMPLIED WARRANTIES SO THEY MAY NOT
APPLY TO YOU. IF THIS EXCLUSION IS HELD TO BE UNENFORCEABLE BY A COURT OF COMPETENT
JURISDICTION, THEN ALL EXPRESS AND IMPLIED WARRANTIES SHALL BE LIMITED IN DURATION TO A
PERIOD OF THIRTY (30) DAYS FROM THE DATE OF PURCHASE OF THE SOFTWARE, AND NO WARRANTIES
SHALL APPLY AFTER THAT PERIOD.
7. Limitation of Liability
IN NO EVENT WILL ZyXEL BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY INCIDENTAL OR
CONSEQUENTIAL DAMAGES (INCLUDING, WITHOUT LIMITATION, INDIRECT, SPECIAL, PUNITIVE, OR
EXEMPLARY DAMAGES FOR LOSS OF BUSINESS, LOSS OF PROFITS, BUSINESS INTERRUPTION, OR LOSS OF
BUSINESS INFORMATION) ARISING OUT OF THE USE OF OR INABILITY TO USE THE SOFTWARE OR PROGRAM,
OR FOR ANY CLAIM BY ANY OTHER PARTY, EVEN IF ZyXEL HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES. ZyXEL's TOTAL AGGREGATE LIABILITY WITH RESPECT TO ITS OBLIGATIONS UNDER THIS
AGREEMENT OR OTHERWISE WITH RESPECT TO THE SOFTWARE AND DOCUMENTATION OR OTHERWISE
SHALL BE EQUAL TO THE PURCHASE PRICE, BUT SHALL IN NO EVENT EXCEED THE PRODUCT’S PRICE.
BECAUSE SOME STATES/COUNTRIES DO NOT ALLOW THE EXCLUSION OR LIMITATION OF LIABILITY FOR
CONSEQUENTIAL OR INCIDENTAL DAMAGES, THE ABOVE LIMITATION MAY NOT APPLY TO YOU.
8. Export Restrictions
THIS LICENSE AGREEMENT IS EXPRESSLY MADE SUBJECT TO ANY APPLICABLE LAWS, REGULATIONS,
ORDERS, OR OTHER RESTRICTIONS ON THE EXPORT OF THE SOFTWARE OR INFORMATION ABOUT SUCH
SOFTWARE WHICH MAY BE IMPOSED FROM TIME TO TIME. YOU SHALL NOT EXPORT THE SOFTWARE,
DOCUMENTATION OR INFORMATION ABOUT THE SOFTWARE AND DOCUMENTATION WITHOUT COMPLYING
WITH SUCH LAWS, REGULATIONS, ORDERS, OR OTHER RESTRICTIONS. YOU AGREE TO INDEMNIFY ZyXEL
AGAINST ALL CLAIMS, LOSSES, DAMAGES, LIABILITIES, COSTS AND EXPENSES, INCLUDING REASONABLE
ATTORNEYS' FEES, TO THE EXTENT SUCH CLAIMS ARISE OUT OF ANY BREACH OF THIS SECTION 8.
9. Audit Rights
ZyXEL SHALL HAVE THE RIGHT, AT ITS OWN EXPENSE, UPON REASONABLE PRIOR NOTICE, TO PERIODICALLY
INSPECT AND AUDIT YOUR RECORDS TO ENSURE YOUR COMPLIANCE WITH THE TERMS AND CONDITIONS OF
THIS LICENSE AGREEMENT.
10. Termination
This License Agreement is effective until it is terminated. You may terminate this License Agreement at any time by destroying
or returning to ZyXEL all copies of the Software and Documentation in your possession or under your control. ZyXEL may
terminate this License Agreement for any reason, including, but not limited to, if ZyXEL finds that you have violated any of the
terms of this License Agreement. Upon notification of termination, you agree to destroy or return to ZyXEL all copies of the
Software and Documentation and to certify in writing that all known copies, including backup copies, have been destroyed. All
provisions relating to confidentiality, proprietary rights, and non-disclosure shall survive the termination of this Software License
Agreement.
11. General
This License Agreement shall be construed, interpreted and governed by the laws of Republic of China without regard to
conflicts of laws provisions thereof. The exclusive forum for any disputes arising out of or relating to this License Agreement
shall be an appropriate court or Commercial Arbitration Association sitting in ROC, Taiwan if the parties agree to a binding
arbitration. This License Agreement shall constitute the entire Agreement between the parties hereto. This License Agreement,
the rights granted hereunder, the Software and Documentation shall not be assigned by you without the prior written consent of
ZyXEL. Any waiver or modification of this License Agreement shall only be effective if it is in writing and signed by both
parties hereto. If any part of this License Agreement is found invalid or unenforceable by a court of competent jurisdiction, the
remainder of this License Agreement shall be interpreted so as to reasonably effect the intention of the parties.
NOTE: Some components of this product incorporate free software programs covered under the
open source code licenses which allows you to freely copy, modify and redistribute the software.
For at least three (3) years from the date of distribution of the applicable product or software, we
will give to anyone who contacts us at the ZyXEL Technical Support (support@zyxel.com.tw), for
a charge of no more than our cost of physically performing source code distribution, a complete
machine-readable copy of the complete corresponding source code for the version of the
Programs that we distributed to you if we are in possession of such.

Notice
Information herein is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
otherwise noted. No part may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose,
except the express written permission of ZyXEL Communications Corporation.
This Product includes Linux Kernel, uboot, cups, busybox, dhcpcd, fuse, gphoto2, gphotofs, ipkg, libeeprog, libid3tag, libol,
lm-sensors, mdadm, mt-daapd, mtd-utils, ntfs-3g, pciutils, quotatool, reiserfsprogs, samba, sg3_utils, syslog-ng, upnpigdctrl,
squeezecenter, netatalk, dar, ez-ipupdate, inadyn, aMule, pkg-config, gallery, nfs-utils, mysql, phpMyAdmin, smartmontools,
squeezeboxserver, WordPress, Audio-Scan, DBD-mysql, DBI, flac, PERL, AutoXS-Header, Class-C3-XS, Class-XSAccessor,
Class-XSAccessor-Array, Compress-Raw-Zlib, Digest-SHA1, EV, ExtUtils-Cbuilder, GD, HTML-Parser, JSON-XS, Module-Build,
Sub-Name, Template-Toolkit and XML-Parser software under GPL 2.0 license.
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
59 Temple Place - Suite 330, Boston, MA 02111-1307, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU General Public
License is intended to guarantee your freedom to share and change free software--to make sure the software is free for all its users.
This General Public License applies to most of the Free Software Foundation's software and to any other program whose authors
commit to using it. (Some other Free Software Foundation software is covered by the GNU Library General Public License instead.)
You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge for this service if you wish), that you receive source code or
can get it if you want it, that you can change the software or use pieces of it in new free programs; and that you know you can do
these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if you distribute copies of the software, or if you modify it. For
example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients all the rights that you
have. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know
their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license which gives you legal permission to
copy, distribute and/or modify the software. Also, for each author's protection and ours, we want to make certain that everyone
understands that there is no warranty for this free software. If the software is modified by someone else and passed on, we want its
recipients to know that what they have is not the original, so that any problems introduced by others will not reflect on the original
authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger that redistributors of a free
program will individually obtain patent licenses, in effect making the program proprietary. To prevent this, we have made it clear
that any patent must be licensed for everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the copyright holder saying it may be
distributed under the terms of this General Public License. The "Program", below, refers to any such program or work, and a "work
based on the Program" means either the Program or any derivative work under copyright law: that is to say, a work containing the
Program or a portion of it, either verbatim or with modifications and/or translated into another language. (Hereinafter, translation is
included without limitation in the term "modification".) Each licensee is addressed as "you". Activities other than copying,
distribution and modification are not covered by this License; they are outside its scope. The act of running the Program is not
restricted, and the output from the Program is covered only if its contents constitute a work based on the Program (independent of
having been made by running the Program). Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in any medium, provided that you
conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty; and give any other recipients of the Program a copy of this
License along with the Program. You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work based on the Program, and copy
and distribute such modifications or work under the terms of Section 1 above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is derived from the Program or any
part thereof, to be licensed as a whole at no charge to all third parties under the terms of this License.
c) If the modified program normally reads commands interactively when run, you must cause it, when started running for such
interactive use in the most ordinary way, to print or display an announcement including an appropriate copyright notice and a notice
that there is no warranty (or else, saying that you provide a warranty) and that users may redistribute the program under these
conditions, and telling the user how to view a copy of this License. (Exception: if the Program itself is interactive but does not
normally print such an announcement, your work based on the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the Program,
and can be reasonably considered independent and separate works in themselves, then this License, and its terms, do not apply to
those sections when you distribute them as separate works. But when you distribute the same sections as part of a whole which is a
work based on the Program, the distribution of the whole must be on the terms of this License, whose permissions for other
licensees extend to the entire whole, and thus to each and every part regardless of who wrote it. Thus, it is not the intent of this
section to claim rights or contest your rights to work written entirely by you; rather, the intent is to exercise the right to control the
distribution of derivative or collective works based on the Program. In addition, mere aggregation of another work not based on the
Program with the Program (or with a work based on the Program) on a volume of a storage or distribution medium does not bring
the other work under the scope of this License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code or executable form under the
terms of Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code, which must be distributed under the terms of
Sections 1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a charge no more than your cost of
physically performing source distribution, a complete machine-readable copy of the corresponding source code, to be distributed
under the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or, c) Accompany it with the
information you received as to the offer to distribute corresponding source code. (This alternative is allowed only for
noncommercial distribution and only if you received the program in object code or executable form with such an offer, in accord
with Subsection b above.) The source code for a work means the preferred form of the work for making modifications to it. For an
executable work, complete source code means all the source code for all modules it contains, plus any associated interface definition
files, plus the
scripts used to control compilation and installation of the executable. However, as a special exception, the source code distributed
need not include anything that is normally distributed (in either source or binary form) with the major components (compiler, kernel,
and so on) of the operating system on which the executable runs, unless that component itself accompanies the executable. If
distribution of executable or object code is made by offering access to copy from a designated place, then offering equivalent access
to copy the source code from the same place counts as distribution of the source code, even though third parties are not compelled to
copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided under this License. Any attempt
otherwise to copy, modify, sublicense or distribute the Program is void, and will automatically terminate your rights under this
License. However, parties who have received copies, or rights, from you under this License will not have their licenses terminated
so long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else grants you permission to modify
or distribute the Program or its derivative works. These actions are prohibited by law if you do not accept this License. Therefore,
by modifying or distributing the Program (or any work based on the Program), you indicate your acceptance of this License to do so,
and all its terms and conditions for copying, distributing or modifying the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient automatically receives a license from
the original licensor to copy, distribute or modify the Program subject to these terms and conditions. You may not impose any
further restrictions on the recipients' exercise of the rights granted herein. You are not responsible for enforcing compliance by third
parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License, they
do not excuse you from the conditions of this License. If you cannot distribute so as to satisfy simultaneously your obligations under

this License and any other pertinent obligations, then as a consequence you may not distribute the Program at all. For example, if a
patent license would not permit royalty-free redistribution of the Program by all those who receive copies directly or indirectly
through you, then the only way you could satisfy both it and this License would be to refrain entirely from distribution of the
Program. If any portion of this section is held invalid or unenforceable under any particular circumstance, the balance of the section
is intended to apply and the section as a whole is intended to apply in other circumstances. It is not the purpose of this section to
induce you to infringe any patents or other property right claims or to contest validity of any such claims; this section has the sole
purpose of protecting the integrity of the free software distribution system, which is implemented by public license practices. Many
people have made generous contributions to the wide range of software distributed through that system in reliance on consistent
application of that system; it is up to the author/donor to decide if he or she is willing to distribute software through any other
system and a licensee cannot impose that choice. This section is intended to make thoroughly clear what is believed to be a
consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Program under this License may add an explicit geographical distribution limitation
excluding those countries, so that distribution is permitted only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the General Public License from time to time. Such
new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns. Each
version is given a distinguishing version number. If the Program specifies a version number of this License which applies to it and
"any later version", you have the option of following the terms and conditions either of that version or of any later version published
by the Free Software Foundation. If the Program does not specify a version number of this License, you may choose any version
ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution conditions are different, write to the
author to ask for permission. For software which is copyrighted by the Free Software Foundation, write to the Free Software
Foundation; we sometimes make exceptions for this. Our decision will be guided by the two goals of preserving the free status of all
derivatives of our free software and of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE PROGRAM, TO
THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE
COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND
PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE
COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT
HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED
ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT
NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR
THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH
HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
All other trademarks or trade names mentioned herein, if any, are the property of their respective owners.
This Product includes cups, libgcgi, libgphoto2, libraw1394, pam_mount, upnpigdctrl, wxWidgets, libdaemon, avahi and flac
software under LGPL 2.1 license.
GNU LESSER GENERAL PUBLIC LICENSE
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. [This is the
first released version of the Lesser GPL. It also counts
as the successor of the GNU Library Public License, version 2, hence the version number 2.1.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU General Public
Licenses are intended to guarantee your freedom to share and change free software--to make sure the software is free for all its
users.
This license, the Lesser General Public License, applies to some specially designated software packages--typically libraries--of the
Free Software Foundation and other authors who decide to use it. You can use it too, but we suggest you first think carefully about
whether this license or the ordinary General Public License is the better strategy to use in any particular case, based on the
explanations below.
When we speak of free software, we are referring to freedom of use, not price. Our General Public Licenses are designed to make
sure that you have the freedom to distribute copies of free software (and charge for this service if you wish); that you receive source
code or can get
it if you want it; that you can change the software and use pieces of it in new free programs; and that you are informed that you can
do these things.
To protect your rights, we need to make restrictions that forbid distributors to deny you these rights or to ask you to surrender these
rights. These restrictions translate to certain responsibilities for you if you distribute copies of the library or if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you must give the recipients all the rights that we
gave you. You must make sure that they, too, receive or can get the source code. If you link other code with the library, you must
provide complete object files to the recipients, so that they can relink them with the library after making changes to the library and
recompiling it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the library, and (2) we offer you this license, which gives you legal
permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that there is no warranty for the free library. Also, if the library is
modified by someone else and passed on, the recipients should know that what they have is not the original version, so that the
original author's reputation will not be affected by problems that might be introduced by others.
Finally, software patents pose a constant threat to the existence of any free program. We wish to make sure that a company cannot
effectively restrict the users of a free program by obtaining a restrictive license from a patent holder. Therefore, we insist that any
patent license obtained for a version of the library must be consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the ordinary GNU General Public License. This license, the GNU
Lesser General Public License, applies to certain designated libraries, and is quite different from the ordinary General Public
License. We use this license for certain libraries in order to permit linking those libraries into non-free programs.
When a program is linked with a library, whether statically or using a shared library, the combination of the two is legally speaking
a combined work, a derivative of the original library. The ordinary General Public License therefore permits such linking only if the
entire combination fits its criteria of freedom. The Lesser General Public License permits more lax criteria for linking other code
with the library.
We call this license the "Lesser" General Public License because it does Less to protect the user's freedom than the ordinary General
Public License. It also provides other free software developers Less of an advantage over competing non-free programs. These
disadvantages are the reason we use the ordinary General Public License for many libraries. However, the Lesser license provides
advantages in certain special circumstances.
For example, on rare occasions, there may be a special need to encourage the widest possible use of a certain library, so that it
becomes a de-facto standard. To achieve this, non-free programs must be allowed to use the library. A more frequent case is that a
free library does the same job as widely used non-free libraries. In this case, there is little to gain by limiting the free library to free
software only, so we use the Lesser General Public License. In other cases, permission to use a particular library in non-free
programs enables a greater number of people to use a large body of free software. For example, permission to use the GNU C
Library in non-free programs enables many more people to use the whole GNU operating system, as well as its variant, the
GNU/Linux operating system.
Although the Lesser General Public License is Less protective of the users' freedom, it does ensure that the user of a program that is
linked with the Library has the freedom and the wherewithal to run that program using a modified version of the Library.
The precise terms and conditions for copying, distribution and modification follow. Pay close attention to the difference between a
"work based on the library" and a "work that uses the library". The former contains code derived from the library, whereas the latter
must be combined with the library in order to run.
GNU LESSER GENERAL PUBLIC LICENSE TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND
MODIFICATION
0. This License Agreement applies to any software library or other program which contains a notice placed by the copyright holder
or other authorized party saying it may be distributed under the terms of this Lesser General Public License (also called "this
License").
Each licensee is addressed as "you".
A "library" means a collection of software functions and/or data prepared so as to be conveniently linked with application programs
(which use some of those functions and data) to form executables. The "Library", below, refers to any such software library or work
which has been distributed under these terms. A "work based on the Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a portion of it, either verbatim or with modifications and/or translated
straightforwardly into another language. (Hereinafter, translation is included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for making modifications to it. For a library, complete source code
means all the source code for all modules it contains, plus any associated interface definition files, plus the scripts used to control
compilation and installation of the library. Activities other than copying, distribution and modification are not covered by this
License; they are outside its scope. The act of running a program using the Library is not restricted, and output from such a program
is covered only if its contents constitute a work based on the Library (independent of the use of the Library in a tool for writing it).
Whether that is true depends on what the Library does and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library's complete source code as you receive it, in any medium, provided
that you conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of warranty; keep
intact all the notices that refer to this License and to the absence of any warranty; and distribute a copy of this License along with
the Library. You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty protection
in exchange for a fee.
2. You may modify your copy or copies of the Library or any portion of it, thus forming a work based on the Library, and copy and
distribute such modifications or work under the terms of Section 1 above, provided that you also meet all of these conditions: a) The
modified work must itself be a software library. b) You must cause the files modified to carry prominent notices stating that you
changed the files and the date of any change. c) You must cause the whole of the work to be licensed at no charge to all third parties
under the terms of this License. d) If a facility in the modified Library refers to a function or a table of data to be supplied by an
application program that uses the facility, other than as an argument passed when the facility is invoked, then you must make a good
faith effort to ensure that, in the event an application does not supply such function or table, the facility still operates, and performs
whatever part of its purpose remains meaningful. (For example, a function in a library to compute square roots has a purpose that is
entirely well-defined independent of the application. Therefore, Subsection 2d requires that any application-supplied function or
table used by this function must be optional: if the application does not supply it, the square root function must still compute square
roots.) These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the
Library, and can be reasonably considered independent and separate works in themselves, then this License, and its terms, do not
apply to those sections when you distribute them as separate works. But when you distribute the same sections as part of a whole
which is a work based on the Library, the distribution of the whole must be on the terms of this License, whose permissions for
other licensees extend to the entire whole, and thus to each and every part regardless of who wrote
it. Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or collective works based on the Library. In addition, mere aggregation of
another work not based on the Library with the Library (or with a work based on the Library) on a volume of a storage or
distribution medium does not bring the other work under the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public License instead of this License to a given copy of the
Library. To do this, you must alter all the notices that refer to this License, so that they refer to the ordinary GNU General Public
License, version 2, instead of to this License. (If a newer version than version 2 of the ordinary GNU General Public License has
appeared, then you can specify that version instead if you wish.) Do not make any other change in these notices. Once this change is
made in a given copy, it is irreversible for that copy, so the ordinary GNU General Public License applies to all subsequent copies
and derivative works made from that copy. This option is useful when you wish to copy part of the code of the Library into a
program that is not a library.
4. You may copy and distribute the Library (or a portion or derivative of it, under Section 2) in object code or executable form under
the terms of Sections 1 and 2 above provided that you accompany it with the complete corresponding machine-readable source code,
which must be distributed under the terms of Sections 1 and 2 above on a medium customarily used for software interchange. If
distribution of object code is made by offering access to copy from a designated place, then offering equivalent access to copy the
source code from the same place satisfies the requirement to distribute the source code, even though third parties are not
compelled to copy the source along with the object code.
5. A program that contains no derivative of any portion of the Library, but is designed to work with the Library by being compiled
or linked with it, is called a "work that uses the Library". Such a work, in isolation, is not a derivative work of the Library, and
therefore falls outside the scope of this License.
However, linking a "work that uses the Library" with the Library creates an executable that is a derivative of the Library (because it
contains portions of the Library), rather than a "work that uses the library". The executable is therefore covered by this License.
Section 6 states terms for distribution of such executables. When a "work that uses the Library" uses material from a header file that
is part of the Library, the object code for the work may be a derivative work of the Library even though the source code is not.
Whether this is true is especially significant if the work can be linked without the Library, or if the work is itself a library. The
threshold for this to be true is not precisely defined by law. If such an object file uses only numerical parameters, data structure
layouts and accessors, and small macros and small inline functions (ten lines or less in length), then the use of the object file is
unrestricted, regardless of whether it is legally a derivative work. (Executables containing this object code plus portions of the
Library will still fall under Section 6.) Otherwise, if the work is a derivative of the Library, you may distribute the object code for
the work under the terms of Section 6. Any executables containing that work also fall under Section 6, whether or not they are
linked directly with the Library itself.
6. As an exception to the Sections above, you may also combine or link a "work that uses the Library" with the Library to produce a
work containing portions of the Library, and distribute that work under terms of your choice, provided that the terms permit
modification of the work for the customer's own use and reverse engineering for debugging such modifications. You must give
prominent notice with each copy of the work that the Library is used in it and that the Library and its use are covered by this License.
You must supply a copy of this License. If the work during execution displays copyright notices, you must include the copyright
notice for the Library among them, as well as a reference directing the user to the copy of this License. Also, you must do one of
these things: a) Accompany the work with the complete corresponding
machine-readable source code for the Library including whatever changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked with the Library, with the complete machine-readable "work that
uses the Library", as object code and/or source code, so that the user can modify the Library and then relink to produce a modified
executable containing the modified Library. (It is understood that the user who changes the contents of definitions files in the
Library will not necessarily be able to recompile the application to use the modified definitions.) b) Use a suitable shared library
mechanism for linking with the Library. A suitable mechanism is one that (1) uses at run time a
copy of the library already present on the user's computer system, rather than copying library functions into the executable, and (2)
will operate properly with a modified version of the library, if the user installs one, as long as the modified version is
interface-compatible with the version that the work was made with. c) Accompany the work with a written offer, valid for at least
three years, to give the same user the materials specified in Subsection 6a, above, for a charge no more than the cost of performing
this distribution. d) If distribution of the work is made by offering access to copy from a designated place, offer equivalent access to
copy the above specified materials from the same place. e) Verify that the user has already received a copy of these materials or that
you have already sent this user a copy. For an executable, the required form of the "work that uses the Library" must include any
data and utility programs needed for reproducing the executable from it. However, as a special exception, the materials to be
distributed need not include anything that is normally distributed (in either source or binary form) with the major components
(compiler, kernel, and so on) of the operating system on which the executable runs, unless that component itself accompanies the
executable.
It may happen that this requirement contradicts the license restrictions of other proprietary libraries that do not normally accompany
the operating system. Such a contradiction means you cannot use both them and the Library together in an executable that you
distribute.
7. You may place library facilities that are a work based on the Library side-by-side in a single library together with other library
facilities not covered by this License, and distribute such a combined library, provided that the separate distribution of the work
based on the Library and of the other library facilities is otherwise permitted, and provided that you do these two things: a)
Accompany the combined library with a copy of the same work based on the Library, uncombined with any other library facilities.
This must be distributed under the terms of the Sections above. b) Give prominent notice with the combined library of the fact that
part of it is a work based on the Library, and explaining where to find the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute the Library except as expressly provided under this License. Any
attempt otherwise to copy, modify, sublicense, link with, or distribute the Library is void, and will automatically terminate your
rights under this License. However, parties who have received copies, or rights, from you under this License will not have their
licenses terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not signed it. However, nothing else grants you permission to modify
or distribute the Library or its derivative works. These actions are prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Library (or any work based on the Library), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying the Library or works based on it.
10. Each time you redistribute the Library (or any work based on the Library), the recipient automatically receives a license from the
original licensor to copy, distribute, link with or modify the Library subject to these terms and conditions. You may not impose any
further restrictions on the recipients' exercise of the rights granted herein. You are not responsible for enforcing compliance by third
parties with this License.
11. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License, they
do not excuse you from the conditions of this License. If you cannot distribute so as to satisfy simultaneously your obligations under

this License and any other pertinent obligations, then as a consequence you may not distribute the Library at all. For example, if a
patent license would not permit royalty-free redistribution of the Library by all those who receive copies directly or indirectly
through you, then the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Library. If any portion of this section is held invalid or unenforceable under any particular
circumstance, the balance of the section is intended to apply, and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the integrity of the free software distribution system which is
implemented by public license practices. Many people have made generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot impose that choice. This section is intended to make
thoroughly clear what is believed to be a consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Library under this License may add an explicit geographical distribution limitation
excluding those countries, so that distribution is permitted only in or among countries not thus excluded. In such case, this License
incorporates the limitation as if written in the body of this License.
13. The Free Software Foundation may publish revised and/or new versions of the Lesser General Public License from time to time.
Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns. Each
version is given a distinguishing version number. If the Library specifies a version number of this License which applies to it and
"any later version", you have the option of following the terms and conditions either of that version or of any later version published
by the Free Software Foundation. If the Library does not specify a license version number, you may choose any version ever
published by the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free programs whose distribution conditions are incompatible with
these, write to the author to ask for permission. For software which is copyrighted by the Free Software Foundation, write to the
Free Software Foundation; we sometimes make exceptions for this. Our decision will be guided by the two goals of preserving the
free status of all derivatives of our free software and of promoting the sharing
and reuse of software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE LIBRARY, TO
THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE
COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND
PERFORMANCE OF THE LIBRARY IS WITH YOU. SHOULD THE LIBRARY PROVE DEFECTIVE, YOU ASSUME THE
COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT
HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED
ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE LIBRARY (INCLUDING BUT
NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR
THIRD PARTIES OR A FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER SOFTWARE), EVEN IF SUCH
HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCHDAMAGES.
END OF TERMS AND CONDITIONS.
This Product includes libiconv, Glib, pango software under LGPL 2.0 license
GNU LIBRARY GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1991 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
[This is the first released version of the library GPL. It is
numbered 2 because it goes with version 2 of the ordinary GPL.]
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
Licenses are intended to guarantee your freedom to share and change
free software--to make sure the software is free for all its users.
This license, the Library General Public License, applies to some
specially designated Free Software Foundation software, and to any
other libraries whose authors decide to use it. You can use it for
your libraries, too.
When we speak of free software, we are referring to freedom, not
price. Our General Public Licenses are designed to make sure that you
have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it
if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid
anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if
you distribute copies of the library, or if you modify it.
For example, if you distribute copies of the library, whether gratis
or for a fee, you must give the recipients all the rights that we gave
you. You must make sure that they, too, receive or can get the source
code. If you link a program with the library, you must provide
complete object files to the recipients so that they can relink them
with the library, after making changes to the library and recompiling
it. And you must show them these terms so they know their rights.
Our method of protecting your rights has two steps: (1) copyright
the library, and (2) offer you this license which gives you legal
permission to copy, distribute and/or modify the library.
Also, for each distributor's protection, we want to make certain
that everyone understands that there is no warranty for this free
library. If the library is modified by someone else and passed on, we
want its recipients to know that what they have is not the original
version, so that any problems introduced by others will not reflect on
the original authors' reputations.
Finally, any free program is threatened constantly by software
patents. We wish to avoid the danger that companies distributing free
software will individually obtain patent licenses, thus in effect
transforming the program into proprietary software. To prevent this,
we have made it clear that any patent must be licensed for everyone's
free use or not licensed at all.
Most GNU software, including some libraries, is covered by the ordinary
GNU General Public License, which was designed for utility programs. This
license, the GNU Library General Public License, applies to certain
designated libraries. This license is quite different from the ordinary
one; be sure to read it in full, and don't assume that anything in it is
the same as in the ordinary license.
The reason we have a separate public license for some libraries is that
they blur the distinction we usually make between modifying or adding to a
program and simply using it. Linking a program with a library, without
changing the library, is in some sense simply using the library, and is
analogous to running a utility program or application program. However, in
a textual and legal sense, the linked executable is a combined work, a
derivative of the original library, and the ordinary General Public License
treats it as such.
Because of this blurred distinction, using the ordinary General
Public License for libraries did not effectively promote software
sharing, because most developers did not use the libraries. We
concluded that weaker conditions might promote sharing better.
However, unrestricted linking of non-free programs would deprive the
users of those programs of all benefit from the free status of the
libraries themselves. This Library General Public License is intended to
permit developers of non-free programs to use free libraries, while
preserving your freedom as a user of such programs to change the free
libraries that are incorporated in them. (We have not seen how to achieve
this as regards changes in header files, but we have achieved it as regards
changes in the actual functions of the Library.) The hope is that this
will lead to faster development of free libraries.
The precise terms and conditions for copying, distribution and
modification follow. Pay close attention to the difference between a
"work based on the library" and a "work that uses the library". The
former contains code derived from the library, while the latter only
works together with the library.
Note that it is possible for a library to be covered by the ordinary
General Public License rather than by this special one.
GNU LIBRARY GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License Agreement applies to any software library which
contains a notice placed by the copyright holder or other authorized
party saying it may be distributed under the terms of this Library
General Public License (also called "this License"). Each licensee is
addressed as "you".
A "library" means a collection of software functions and/or data
prepared so as to be conveniently linked with application programs
(which use some of those functions and data) to form executables.
The "Library", below, refers to any such software library or work
which has been distributed under these terms. A "work based on the
Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a
portion of it, either verbatim or with modifications and/or translated
straightforwardly into another language. (Hereinafter, translation is
included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for
making modifications to it. For a library, complete source code means
all the source code for all modules it contains, plus any associated
interface definition files, plus the scripts used to control compilation
and installation of the library.
Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of
running a program using the Library is not restricted, and output from
such a program is covered only if its contents constitute a work based
on the Library (independent of the use of the Library in a tool for
writing it). Whether that is true depends on what the Library does
and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library's
complete source code as you receive it, in any medium, provided that
you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact
all the notices that refer to this License and to the absence of any
warranty; and distribute a copy of this License along with the
Library.
You may charge a fee for the physical act of transferring a copy,
and you may at your option offer warranty protection in exchange for a
fee.
2. You may modify your copy or copies of the Library or any portion
of it, thus forming a work based on the Library, and copy and
distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) The modified work must itself be a software library.
b) You must cause the files modified to carry prominent notices
stating that you changed the files and the date of any change.
c) You must cause the whole of the work to be licensed at no
charge to all third parties under the terms of this License.
d) If a facility in the modified Library refers to a function or a
table of data to be supplied by an application program that uses
the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that,
in the event an application does not supply such function or
table, the facility still operates, and performs whatever part of
its purpose remains meaningful.
(For example, a function in a library to compute square roots has
a purpose that is entirely well-defined independent of the
application. Therefore, Subsection 2d requires that any
application-supplied function or table used by this function must
be optional: if the application does not supply it, the square
root function must still compute square roots.)
These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Library,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Library, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote
it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library
with the Library (or with a work based on the Library) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public
License instead of this License to a given copy of the Library. To do
this, you must alter all the notices that refer to this License, so
that they refer to the ordinary GNU General Public License, version 2,
instead of to this License. (If a newer version than version 2 of the
ordinary GNU General Public License has appeared, then you can specify
that version instead if you wish.) Do not make any other change in
these notices.
Once this change is made in a given copy, it is irreversible for
that copy, so the ordinary GNU General Public License applies to all
subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of
the Library into a program that is not a library.
4. You may copy and distribute the Library (or a portion or
derivative of it, under Section 2) in object code or executable form
under the terms of Sections 1 and 2 above provided that you accompany
it with the complete corresponding machine-readable source code, which
must be distributed under the terms of Sections 1 and 2 above on a
medium customarily used for software interchange.
If distribution of object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the
source code from the same place satisfies the requirement to
distribute the source code, even though third parties are not
compelled to copy the source along with the object code.
5. A program that contains no derivative of any portion of the
Library, but is designed to work with the Library by being compiled or
linked with it, is called a "work that uses the Library". Such a
work, in isolation, is not a derivative work of the Library, and
therefore falls outside the scope of this License.
However, linking a "work that uses the Library" with the Library
creates an executable that is a derivative of the Library (because it
contains portions of the Library), rather than a "work that uses the
library". The executable is therefore covered by this License.
Section 6 states terms for distribution of such executables.
When a "work that uses the Library" uses material from a header file
that is part of the Library, the object code for the work may be a
derivative work of the Library even though the source code is not.
Whether this is true is especially significant if the work can be
linked without the Library, or if the work is itself a library. The
threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data
structure layouts and accessors, and small macros and small inline
functions (ten lines or less in length), then the use of the object
file is unrestricted, regardless of whether it is legally a derivative
work. (Executables containing this object code plus portions of the
Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may
distribute the object code for the work under the terms of Section 6.
Any executables containing that work also fall under Section 6,
whether or not they are linked directly with the Library itself.
6. As an exception to the Sections above, you may also compile or
link a "work that uses the Library" with the Library to produce a
work containing portions of the Library, and distribute that work
under terms of your choice, provided that the terms permit
modification of the work for the customer's own use and reverse
engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the
Library is used in it and that the Library and its use are covered by
this License. You must supply a copy of this License. If the work
during execution displays copyright notices, you must include the
copyright notice for the Library among them, as well as a reference
directing the user to the copy of this License. Also, you must do one
of these things:
a) Accompany the work with the complete corresponding
machine-readable source code for the Library including whatever
changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked
with the Library, with the complete machine-readable "work that
uses the Library", as object code and/or source code, so that the
user can modify the Library and then relink to produce a modified
executable containing the modified Library. (It is understood
that the user who changes the contents of definitions files in the
Library will not necessarily be able to recompile the application
to use the modified definitions.)
b) Accompany the work with a written offer, valid for at
least three years, to give the same user the materials
specified in Subsection 6a, above, for a charge no more
than the cost of performing this distribution.
c) If distribution of the work is made by offering access to copy
from a designated place, offer equivalent access to copy the above
specified materials from the same place.
d) Verify that the user has already received a copy of these
materials or that you have already sent this user a copy.
For an executable, the required form of the "work that uses the
Library" must include any data and utility programs needed for
reproducing the executable from it. However, as a special exception,
the source code distributed need not include anything that is normally
distributed (in either source or binary form) with the major
components (compiler, kernel, and so on) of the operating system on
which the executable runs, unless that component itself accompanies
the executable.
It may happen that this requirement contradicts the license
restrictions of other proprietary libraries that do not normally
accompany the operating system. Such a contradiction means you cannot
use both them and the Library together in an executable that you
distribute.
7. You may place library facilities that are a work based on the
Library side-by-side in a single library together with other library
facilities not covered by this License, and distribute such a combined
library, provided that the separate distribution of the work based on
the Library and of the other library facilities is otherwise
permitted, and provided that you do these two things:
a) Accompany the combined library with a copy of the same work
based on the Library, uncombined with any other library
facilities. This must be distributed under the terms of the
Sections above.
b) Give prominent notice with the combined library of the fact
that part of it is a work based on the Library, and explaining
where to find the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute
the Library except as expressly provided under this License. Any
attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your
rights under this License. However, parties who have received copies,
or rights, from you under this License will not have their licenses
terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Library or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Library (or any work based on the
Library), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Library or works based on it.
10. Each time you redistribute the Library (or any work based on the
Library), the recipient automatically receives a license from the
original licensor to copy, distribute, link with or modify the Library
subject to these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties to
this License.
11. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Library at all. For example, if a patent
license would not permit royalty-free redistribution of the Library by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Library.
If any portion of this section is held invalid or unenforceable under any
particular circumstance, the balance of the section is intended to apply,
and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Library under this License may add
an explicit geographical distribution limitation excluding those countries,
so that distribution is permitted only in or among countries not thus
excluded. In such case, this License incorporates the limitation as if
written in the body of this License.
13. The Free Software Foundation may publish revised and/or new
versions of the Library General Public License from time to time.
Such new versions will be similar in spirit to the present version,
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library
specifies a version number of this License which applies to it and
"any later version", you have the option of following the terms and
conditions either of that version or of any later version published by
the Free Software Foundation. If the Library does not specify a
license version number, you may choose any version ever published by
the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free
programs whose distribution conditions are incompatible with these,
write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free
Software Foundation; we sometimes make exceptions for this. Our
decision will be guided by the two goals of preserving the free status
of all derivatives of our free software and of promoting the sharing
and reuse of software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO
WARRANTY FOR THE LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE LAW.
EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR
OTHER PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE
LIBRARY IS WITH YOU. SHOULD THE LIBRARY PROVE DEFECTIVE, YOU ASSUME
THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY
AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU
FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE
LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A
FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER SOFTWARE), EVEN IF
SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES.
END OF TERMS AND CONDITIONS

Appendix: How to Apply These Terms to Your New Libraries
If you develop a new library, and you want it to be of the greatest
possible use to the public, we recommend making it free software that
everyone can redistribute and change. You can do so by permitting
redistribution under these terms (or, alternatively, under the terms of the
ordinary General Public License).
To apply these terms, attach the following notices to the library. It is
safest to attach them to the start of each source file to most effectively
convey the exclusion of warranty; and each file should have at least the
"copyright" line and a pointer to where the full notice is found.
<one line to give the library's name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This library is free software; you can redistribute it and/or
modify it under the terms of the GNU Library General Public
License as published by the Free Software Foundation; either
version 2 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
Library General Public License for more details.
You should have received a copy of the GNU Library General Public
License along with this library; if not, write to the Free
Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston,
MA 02110-1301, USA
Also add information on how to contact you by electronic and paper mail.
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a "copyright disclaimer" for the library, if
necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the
library `Frob' (a library for tweaking knobs) written by James Random Hacker.
<signature of Ty Coon>, 1 April 1990
Ty Coon, President of Vice
That's all there is to it!
This Product includes upnpigdctrl software under below license
/***************************************************************************
* COPYING -- Describes the terms under which libigdctrl is distributed. *
* - Files libigdctrl.c and libigdctrl.h are under LGPL *
* - Files main.c, upnpigdctrl.c and upnpc.c are under GPL *
* Copies of GPL and LGPL are available in ./GPL and ./LGPL *
* - Translations of these licences are available at: *
* http://www.gnu.org/licenses/translations.html *

***************************************************************************/
This Product includes mediainfo software under below license
MediaInfo(Lib) License
Version 1.1, 3 January 2010
Copyright 2002-2010 MediaArea.net SARL. All rights reserved.
Redistribution and use in source and binary forms, without modification, are permitted provided that the following conditions are
met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
Redistribution and use in source and binary forms, with modification, are permitted provided that the GNU Lesser General Public
License as published by the Free Software Foundation, either version 3 of the License, or any later version is met.
Dynamic or static linking to this software are not deemed a modification.
THIS SOFTWARE IS PROVIDED BY MEDIAAREA.NET SARL ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL MEDIAAREA.NET OR CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER
IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
GNU LESSER GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright (C) 2007 Free Software Foundation, Inc. <http://fsf.org/>
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
This version of the GNU Lesser General Public License incorporates the terms and conditions of version 3 of the GNU General
Public License, supplemented by the additional permissions listed below.
0. Additional Definitions.
As used herein, “this License” refers to version 3 of the GNU Lesser General Public License, and the “GNU GPL” refers to version
3 of the GNU General Public License.
“The Library” refers to a covered work governed by this License, other than an Application or a Combined Work as defined below.
An “Application” is any work that makes use of an interface provided by the Library, but which is not otherwise based on the
Library. Defining a subclass of a class defined by the Library is deemed a mode of using an interface provided by the Library.
A “Combined Work” is a work produced by combining or linking an Application with the Library. The particular version of the
Library with which the Combined Work was made is also called the “Linked Version”.
The “Minimal Corresponding Source” for a Combined Work means the Corresponding Source for the Combined Work, excluding
any source code for portions of the Combined Work that, considered in isolation, are based on the Application, and not on the
Linked Version.
The “Corresponding Application Code” for a Combined Work means the object code and/or source code for the Application,
including any data and utility programs needed for reproducing the Combined Work from the Application, but excluding the System
Libraries of the Combined Work.
1. Exception to Section 3 of the GNU GPL.
You may convey a covered work under sections 3 and 4 of this License without being bound by section 3 of the GNU GPL.
2. Conveying Modified Versions.
If you modify a copy of the Library, and, in your modifications, a facility refers to a function or data to be supplied by an
Application that uses the facility (other than as an argument passed when the facility is invoked), then you may convey a copy of the
modified version:
a) under this License, provided that you make a good faith effort to ensure that, in the event an Application does not
supply the function or data, the facility still operates, and performs whatever part of its purpose remains meaningful, or
b) under the GNU GPL, with none of the additional permissions of this License applicable to that copy.
3. Object Code Incorporating Material from Library Header Files.
The object code form of an Application may incorporate material from a header file that is part of the Library. You may convey
such object code under terms of your choice, provided that, if the incorporated material is not limited to numerical parameters, data
structure layouts and accessors, or small macros, inline functions and templates (ten or fewer lines in length), you do both of the
following:

a) Give prominent notice with each copy of the object code that the Library is used in it and that the Library and its use
are covered by this License.
b) Accompany the object code with a copy of the GNU GPL and this license document.
4. Combined Works.
You may convey a Combined Work under terms of your choice that, taken together, effectively do not restrict modification of the
portions of the Library contained in the Combined Work and reverse engineering for debugging such modifications, if you also do
each of the following:
a) Give prominent notice with each copy of the Combined Work that the Library is used in it and that the Library and its
use are covered by this License.
b) Accompany the Combined Work with a copy of the GNU GPL and this license document.
c) For a Combined Work that displays copyright notices during execution, include the copyright notice for the Library
among these notices, as well as a reference directing the user to the copies of the GNU GPL and this license document.
d) Do one of the following:
o 0) Convey the Minimal Corresponding Source under the terms of this License, and the Corresponding
Application Code in a form suitable for, and under terms that permit, the user to recombine or relink the
Application with a modified version of the Linked Version to produce a modified Combined Work, in the
manner specified by section 6 of the GNU GPL for conveying Corresponding Source.
o 1) Use a suitable shared library mechanism for linking with the Library. A suitable mechanism is one that (a)
uses at run time a copy of the Library already present on the user's computer system, and (b) will operate
properly with a modified version of the Library that is interface-compatible with the Linked Version.
e) Provide Installation Information, but only if you would otherwise be required to provide such information under
section 6 of the GNU GPL, and only to the extent that such information is necessary to install and execute a modified
version of the Combined Work produced by recombining or relinking the Application with a modified version of the
Linked Version. (If you use option 4d0, the Installation Information must accompany the Minimal Corresponding Source
and Corresponding Application Code. If you use option 4d1, you must provide the Installation Information in the manner
specified by section 6 of the GNU GPL for conveying Corresponding Source.)
5. Combined Libraries.
You may place library facilities that are a work based on the Library side by side in a single library together with other library
facilities that are not Applications and are not covered by this License, and convey such a combined library under terms of your
choice, if you do both of the following:
a) Accompany the combined library with a copy of the same work based on the Library, uncombined with any other
library facilities, conveyed under the terms of this License.
b) Give prominent notice with the combined library that part of it is a work based on the Library, and explaining where to
find the accompanying uncombined form of the same work.
6. Revised Versions of the GNU Lesser General Public License.
The Free Software Foundation may publish revised and/or new versions of the GNU Lesser General Public License from time to
time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library as you received it specifies that a certain numbered version of
the GNU Lesser General Public License “or any later version” applies to it, you have the option of following the terms and
conditions either of that published version or of any later version published by the Free Software Foundation. If the Library as you
received it does not specify a version number of the GNU Lesser General Public License, you may choose any version of the GNU
Lesser General Public License ever published by the Free Software Foundation.
If the Library as you received it specifies that a proxy can decide whether future versions of the GNU Lesser General Public License
shall apply, that proxy's public statement of acceptance of any version is permanent authorization for you to choose that version for
the Library.
GNU GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright (C) 2007 Free Software Foundation, Inc. <http://fsf.org/>
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
Preamble
The GNU General Public License is a free, copyleft license for software and other kinds of works.
The licenses for most software and other practical works are designed to take away your freedom to share and change the works. By
contrast, the GNU General Public License is intended to guarantee your freedom to share and change all versions of a program--to
make sure it remains free software for all its users. We, the Free Software Foundation, use the GNU General Public License for
most of our software; it applies also to any other work released this way by its authors. You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge for them if you wish), that you receive source code or can get
it if you want it, that you can change the software or use pieces of it in new free programs, and that you know you can do these
things.
To protect your rights, we need to prevent others from denying you these rights or asking you to surrender the rights. Therefore, you
have certain responsibilities if you distribute copies of the software, or if you modify it: responsibilities to respect the freedom of
others.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must pass on to the recipients the same
freedoms that you received. You must make sure that they, too, receive or can get the source code. And you must show them these
terms so they know their rights.
Developers that use the GNU GPL protect your rights with two steps: (1) assert copyright on the software, and (2) offer you this
License giving you legal permission to copy, distribute and/or modify it.
For the developers' and authors' protection, the GPL clearly explains that there is no warranty for this free software. For both users'
and authors' sake, the GPL requires that modified versions be marked as changed, so that their problems will not be attributed
erroneously to authors of previous versions.
Some devices are designed to deny users access to install or run modified versions of the software inside them, although the
manufacturer can do so. This is fundamentally incompatible with the aim of protecting users' freedom to change the software. The
systematic pattern of such abuse occurs in the area of products for individuals to use, which is precisely where it is most
unacceptable. Therefore, we have designed this version of the GPL to prohibit the practice for those products. If such problems arise
substantially in other domains, we stand ready to extend this provision to those domains in future versions of the GPL, as needed to
protect the freedom of users.
Finally, every program is threatened constantly by software patents. States should not allow patents to restrict development and use
of software on general-purpose computers, but in those that do, we wish to avoid the special danger that patents applied to a free
program could make it effectively proprietary. To prevent this, the GPL assures that patents cannot be used to render the program
non-free.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS
0. Definitions.
“This License” refers to version 3 of the GNU General Public License.
“Copyright” also means copyright-like laws that apply to other kinds of works, such as semiconductor masks.
“The Program” refers to any copyrightable work licensed under this License. Each licensee is addressed as “you”. “Licensees” and
“recipients” may be individuals or organizations.
To “modify” a work means to copy from or adapt all or part of the work in a fashion requiring copyright permission, other than the
making of an exact copy. The resulting work is called a “modified version” of the earlier work or a work “based on” the earlier
work.
A “covered work” means either the unmodified Program or a work based on the Program.
To “propagate” a work means to do anything with it that, without permission, would make you directly or secondarily liable for
infringement under applicable copyright law, except executing it on a computer or modifying a private copy. Propagation includes
copying, distribution (with or without modification), making available to the public, and in some countries other activities as well.
To “convey” a work means any kind of propagation that enables other parties to make or receive copies. Mere interaction with a
user through a computer network, with no transfer of a copy, is not conveying.
An interactive user interface displays “Appropriate Legal Notices” to the extent that it includes a convenient and prominently visible
feature that (1) displays an appropriate copyright notice, and (2) tells the user that there is no warranty for the work (except to the
extent that warranties are provided), that licensees may convey the work under this License, and how to view a copy of this License.
If the interface presents a list of user commands or options, such as a menu, a prominent item in the list meets this criterion.
1. Source Code.
The “source code” for a work means the preferred form of the work for making modifications to it. “Object code” means any
non-source form of a work.
A “Standard Interface” means an interface that either is an official standard defined by a recognized standards body, or, in the case
of interfaces specified for a particular programming language, one that is widely used among developers working in that language.
The “System Libraries” of an executable work include anything, other than the work as a whole, that (a) is included in the normal
form of packaging a Major Component, but which is not part of that Major Component, and (b) serves only to enable use of the
work with that Major Component, or to implement a Standard Interface for which an implementation is available to the public in
source code form. A “Major Component”, in this context, means a major essential component (kernel, window system, and so on) of
the specific operating system (if any) on which the executable work runs, or a compiler used to produce the work, or an object code
interpreter used to run it.
The “Corresponding Source” for a work in object code form means all the source code needed to generate, install, and (for an
executable work) run the object code and to modify the work, including scripts to control those activities. However, it does not
include the work's System Libraries, or general-purpose tools or generally available free programs which are used unmodified in
performing those activities but which are not part of the work. For example, Corresponding Source includes interface definition files
associated with source files for the work, and the source code for shared libraries and dynamically linked subprograms that the work
is specifically designed to require, such as by intimate data communication or control flow between those subprograms and other
parts of the work.
The Corresponding Source need not include anything that users can regenerate automatically from other parts of the Corresponding
Source.
The Corresponding Source for a work in source code form is that same work.
2. Basic Permissions.
All rights granted under this License are granted for the term of copyright on the Program, and are irrevocable provided the stated
conditions are met. This License explicitly affirms your unlimited permission to run the unmodified Program. The output from
running a covered work is covered by this License only if the output, given its content, constitutes a covered work. This License
acknowledges your rights of fair use or other equivalent, as provided by copyright law.
You may make, run and propagate covered works that you do not convey, without conditions so long as your license otherwise
remains in force. You may convey covered works to others for the sole purpose of having them make modifications exclusively for
you, or provide you with facilities for running those works, provided that you comply with the terms of this License in conveying all
material for which you do not control copyright. Those thus making or running the covered works for you must do so exclusively on
your behalf, under your direction and control, on terms that prohibit them from making any copies of your copyrighted material
outside their relationship with you.
Conveying under any other circumstances is permitted solely under the conditions stated below. Sublicensing is not allowed; section
10 makes it unnecessary.
3. Protecting Users' Legal Rights From Anti-Circumvention Law.
No covered work shall be deemed part of an effective technological measure under any applicable law fulfilling obligations under
article 11 of the WIPO copyright treaty adopted on 20 December 1996, or similar laws prohibiting or restricting circumvention of
such measures.
When you convey a covered work, you waive any legal power to forbid circumvention of technological measures to the extent such
circumvention is effected by exercising rights under this License with respect to the covered work, and you disclaim any intention to
limit operation or modification of the work as a means of enforcing, against the work's users, your or third parties' legal rights to
forbid circumvention of technological measures.
4. Conveying Verbatim Copies.
You may convey verbatim copies of the Program's source code as you receive it, in any medium, provided that you conspicuously
and appropriately publish on each copy an appropriate copyright notice; keep intact all notices stating that this License and any
non-permissive terms added in accord with section 7 apply to the code; keep intact all notices of the absence of any warranty; and
give all recipients a copy of this License along with the Program.
You may charge any price or no price for each copy that you convey, and you may offer support or warranty protection for a fee.
5. Conveying Modified Source Versions.
You may convey a work based on the Program, or the modifications to produce it from the Program, in the form of source code
under the terms of section 4, provided that you also meet all of these conditions:
a) The work must carry prominent notices stating that you modified it, and giving a relevant date.
b) The work must carry prominent notices stating that it is released under this License and any conditions added under
section 7. This requirement modifies the requirement in section 4 to “keep intact all notices”.
c) You must license the entire work, as a whole, under this License to anyone who comes into possession of a copy. This
License will therefore apply, along with any applicable section 7 additional terms, to the whole of the work, and all its
parts, regardless of how they are packaged. This License gives no permission to license the work in any other way, but it
does not invalidate such permission if you have separately received it.
d) If the work has interactive user interfaces, each must display Appropriate Legal Notices; however, if the Program has
interactive interfaces that do not display Appropriate Legal Notices, your work need not make them do so.
A compilation of a covered work with other separate and independent works, which are not by their nature extensions of the covered
work, and which are not combined with it such as to form a larger program, in or on a volume of a storage or distribution medium, is
called an “aggregate” if the compilation and its resulting copyright are not used to limit the access or legal rights of the
compilation's users beyond what the individual works permit. Inclusion of a covered work in an aggregate does not cause this
License to apply to the other parts of the aggregate.
6. Conveying Non-Source Forms.
You may convey a covered work in object code form under the terms of sections 4 and 5, provided that you also convey the
machine-readable Corresponding Source under the terms of this License, in one of these ways:
a) Convey the object code in, or embodied in, a physical product (including a physical distribution medium),
accompanied by the Corresponding Source fixed on a durable physical medium customarily used for software
interchange.
b) Convey the object code in, or embodied in, a physical product (including a physical distribution medium),
accompanied by a written offer, valid for at least three years and valid for as long as you offer spare parts or customer
support for that product model, to give anyone who possesses the object code either (1) a copy of the Corresponding
Source for all the software in the product that is covered by this License, on a durable physical medium customarily used
for software interchange, for a price no more than your reasonable cost of physically performing this conveying of source,
or (2) access to copy the Corresponding Source from a network server at no charge.
c) Convey individual copies of the object code with a copy of the written offer to provide the Corresponding Source. This
alternative is allowed only occasionally and noncommercially, and only if you received the object code with such an
offer, in accord with subsection 6b.
d) Convey the object code by offering access from a designated place (gratis or for a charge), and offer equivalent access
to the Corresponding Source in the same way through the same place at no further charge. You need not require
recipients to copy the Corresponding Source along with the object code. If the place to copy the object code is a network
server, the Corresponding Source may be on a different server (operated by you or a third party) that supports equivalent
copying facilities, provided you maintain clear directions next to the object code saying where to find the Corresponding
Source. Regardless of what server hosts the Corresponding Source, you remain obligated to ensure that it is available for
as long as needed to satisfy these requirements.
e) Convey the object code using peer-to-peer transmission, provided you inform other peers where the object code and
Corresponding Source of the work are being offered to the general public at no charge under subsection 6d.
A separable portion of the object code, whose source code is excluded from the Corresponding Source as a System Library, need not
be included in conveying the object code work.
A “User Product” is either (1) a “consumer product”, which means any tangible personal property which is normally used for
personal, family, or household purposes, or (2) anything designed or sold for incorporation into a dwelling. In determining whether
a product is a consumer product, doubtful cases shall be resolved in favor of coverage. For a particular product received by a
particular user, “normally used” refers to a typical or common use of that class of product, regardless of the status of the particular
user or of the way in which the particular user actually uses, or expects or is expected to use, the product. A product is a consumer
product regardless of whether the product has substantial commercial, industrial or non-consumer uses, unless such uses represent
the only significant mode of use of the product.
“Installation Information” for a User Product means any methods, procedures, authorization keys, or other information required to
install and execute modified versions of a covered work in that User Product from a modified version of its Corresponding Source.
The information must suffice to ensure that the continued functioning of the modified object code is in no case prevented or
interfered with solely because modification has been made.
If you convey an object code work under this section in, or with, or specifically for use in, a User Product, and the conveying occurs
as part of a transaction in which the right of possession and use of the User Product is transferred to the recipient in perpetuity or for
a fixed term (regardless of how the transaction is characterized), the Corresponding Source conveyed under this section must be
accompanied by the Installation Information. But this requirement does not apply if neither you nor any third party retains the ability
to install modified object code on the User Product (for example, the work has been installed in ROM).
The requirement to provide Installation Information does not include a requirement to continue to provide support service, warranty,
or updates for a work that has been modified or installed by the recipient, or for the User Product in which it has been modified or
installed. Access to a network may be denied when the modification itself materially and adversely affects the operation of the
network or violates the rules and protocols for communication across the network.
Corresponding Source conveyed, and Installation Information provided, in accord with this section must be in a format that is
publicly documented (and with an implementation available to the public in source code form), and must require no special
password or key for unpacking, reading or copying.
7. Additional Terms.
“Additional permissions” are terms that supplement the terms of this License by making exceptions from one or more of its
conditions. Additional permissions that are applicable to the entire Program shall be treated as though they were included in this
License, to the extent that they are valid under applicable law. If additional permissions apply only to part of the Program, that part
may be used separately under those permissions, but the entire Program remains governed by this License without regard to the
additional permissions.
When you convey a copy of a covered work, you may at your option remove any additional permissions from that copy, or from any
part of it. (Additional permissions may be written to require their own removal in certain cases when you modify the work.) You
may place additional permissions on material, added by you to a covered work, for which you have or can give appropriate
copyright permission.
Notwithstanding any other provision of this License, for material you add to a covered work, you may (if authorized by the
copyright holders of that material) supplement the terms of this License with terms:
a) Disclaiming warranty or limiting liability differently from the terms of sections 15 and 16 of this License; or
b) Requiring preservation of specified reasonable legal notices or author attributions in that material or in the Appropriate
Legal Notices displayed by works containing it; or
c) Prohibiting misrepresentation of the origin of that material, or requiring that modified versions of such material be
marked in reasonable ways as different from the original version; or
d) Limiting the use for publicity purposes of names of licensors or authors of the material; or
e) Declining to grant rights under trademark law for use of some trade names, trademarks, or service marks; or
f) Requiring indemnification of licensors and authors of that material by anyone who conveys the material (or modified
versions of it) with contractual assumptions of liability to the recipient, for any liability that these contractual
assumptions directly impose on those licensors and authors.
All other non-permissive additional terms are considered “further restrictions” within the meaning of section 10. If the Program as
you received it, or any part of it, contains a notice stating that it is governed by this License along with a term that is a further
restriction, you may remove that term. If a license document contains a further restriction but permits relicensing or conveying
under this License, you may add to a covered work material governed by the terms of that license document, provided that the
further restriction does not survive such relicensing or conveying.
If you add terms to a covered work in accord with this section, you must place, in the relevant source files, a statement of the
additional terms that apply to those files, or a notice indicating where to find the applicable terms.
Additional terms, permissive or non-permissive, may be stated in the form of a separately written license, or stated as exceptions;
the above requirements apply either way.
8. Termination.
You may not propagate or modify a covered work except as expressly provided under this License. Any attempt otherwise to
propagate or modify it is void, and will automatically terminate your rights under this License (including any patent licenses granted
under the third paragraph of section 11).
However, if you cease all violation of this License, then your license from a particular copyright holder is reinstated (a)
provisionally, unless and until the copyright holder explicitly and finally terminates your license, and (b) permanently, if the
copyright holder fails to notify you of the violation by some reasonable means prior to 60 days after the cessation.
Moreover, your license from a particular copyright holder is reinstated permanently if the copyright holder notifies you of the
violation by some reasonable means, this is the first time you have received notice of violation of this License (for any work) from
that copyright holder, and you cure the violation prior to 30 days after your receipt of the notice.
Termination of your rights under this section does not terminate the licenses of parties who have received copies or rights from you
under this License. If your rights have been terminated and not permanently reinstated, you do not qualify to receive new licenses
for the same material under section 10.
9. Acceptance Not Required for Having Copies.
You are not required to accept this License in order to receive or run a copy of the Program. Ancillary propagation of a covered
work occurring solely as a consequence of using peer-to-peer transmission to receive a copy likewise does not require acceptance.
However, nothing other than this License grants you permission to propagate or modify any covered work. These actions infringe
copyright if you do not accept this License. Therefore, by modifying or propagating a covered work, you indicate your acceptance
of this License to do so.
10. Automatic Licensing of Downstream Recipients.
Each time you convey a covered work, the recipient automatically receives a license from the original licensors, to run, modify and
propagate that work, subject to this License. You are not responsible for enforcing compliance by third parties with this License.
An “entity transaction” is a transaction transferring control of an organization, or substantially all assets of one, or subdividing an
organization, or merging organizations. If propagation of a covered work results from an entity transaction, each party to that
transaction who receives a copy of the work also receives whatever licenses to the work the party's predecessor in interest had or
could give under the previous paragraph, plus a right to possession of the Corresponding Source of the work from the predecessor in
interest, if the predecessor has it or can get it with reasonable efforts.
You may not impose any further restrictions on the exercise of the rights granted or affirmed under this License. For example, you
may not impose a license fee, royalty, or other charge for exercise of rights granted under this License, and you may not initiate
litigation (including a cross-claim or counterclaim in a lawsuit) alleging that any patent claim is infringed by making, using, selling,
offering for sale, or importing the Program or any portion of it.
11. Patents.
A “contributor” is a copyright holder who authorizes use under this License of the Program or a work on which the Program is
based. The work thus licensed is called the contributor's “contributor version”.
A contributor's “essential patent claims” are all patent claims owned or controlled by the contributor, whether already acquired or
hereafter acquired, that would be infringed by some manner, permitted by this License, of making, using, or selling its contributor
version, but do not include claims that would be infringed only as a consequence of further modification of the contributor version.
For purposes of this definition, “control” includes the right to grant patent sublicenses in a manner consistent with the requirements
of this License.
Each contributor grants you a non-exclusive, worldwide, royalty-free patent license under the contributor's essential patent claims,
to make, use, sell, offer for sale, import and otherwise run, modify and propagate the contents of its contributor version.
In the following three paragraphs, a “patent license” is any express agreement or commitment, however denominated, not to enforce
a patent (such as an express permission to practice a patent or covenant not to sue for patent infringement). To “grant” such a patent
license to a party means to make such an agreement or commitment not to enforce a patent against the party.
If you convey a covered work, knowingly relying on a patent license, and the Corresponding Source of the work is not available for
anyone to copy, free of charge and under the terms of this License, through a publicly available network server or other readily
accessible means, then you must either (1) cause the Corresponding Source to be so available, or (2) arrange to deprive yourself of
the benefit of the patent license for this particular work, or (3) arrange, in a manner consistent with the requirements of this License,
to extend the patent license to downstream recipients. “Knowingly relying” means you have actual knowledge that, but for the
patent license, your conveying the covered work in a country, or your recipient's use of the covered work in a country, would
infringe one or more identifiable patents in that country that you have reason to believe are valid.

If, pursuant to or in connection with a single transaction or arrangement, you convey, or propagate by procuring conveyance of, a
covered work, and grant a patent license to some of the parties receiving the covered work authorizing them to use, propagate,
modify or convey a specific copy of the covered work, then the patent license you grant is automatically extended to all recipients of
the covered work and works based on it.
A patent license is “discriminatory” if it does not include within the scope of its coverage, prohibits the exercise of, or is conditioned
on the non-exercise of one or more of the rights that are specifically granted under this License. You may not convey a covered
work if you are a party to an arrangement with a third party that is in the business of distributing software, under which you make
payment to the third party based on the extent of your activity of conveying the work, and under which the third party grants, to any
of the parties who would receive the covered work from you, a discriminatory patent license (a) in connection with copies of the
covered work conveyed by you (or copies made from those copies), or (b) primarily for and in connection with specific products or
compilations that contain the covered work, unless you entered into that arrangement, or that patent license was granted, prior to 28
March 2007.
Nothing in this License shall be construed as excluding or limiting any implied license or other defenses to infringement that may
otherwise be available to you under applicable patent law.
12. No Surrender of Others' Freedom.
If conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License,
they do not excuse you from the conditions of this License. If you cannot convey a covered work so as to satisfy simultaneously
your obligations under this License and any other pertinent obligations, then as a consequence you may not convey it at all. For
example, if you agree to terms that obligate you to collect a royalty for further conveying from those to whom you convey the
Program, the only way you could satisfy both those terms and this License would be to refrain entirely from conveying the Program.
13. Use with the GNU Affero General Public License.
Notwithstanding any other provision of this License, you have permission to link or combine any covered work with a work
licensed under version 3 of the GNU Affero General Public License into a single combined work, and to convey the resulting work.
The terms of this License will continue to apply to the part which is the covered work, but the special requirements of the GNU
Affero General Public License, section 13, concerning interaction through a network will apply to the combination as such.
14. Revised Versions of this License.
The Free Software Foundation may publish revised and/or new versions of the GNU General Public License from time to time.
Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies that a certain numbered version of the GNU General
Public License “or any later version” applies to it, you have the option of following the terms and conditions either of that numbered
version or of any later version published by the Free Software Foundation. If the Program does not specify a version number of the
GNU General Public License, you may choose any version ever published by the Free Software Foundation.
If the Program specifies that a proxy can decide which future versions of the GNU General Public License can be used, that proxy's
public statement of acceptance of a version permanently authorizes you to choose that version for the Program.
Later license versions may give you additional or different permissions. However, no additional obligations are imposed on any
author or copyright holder as a result of your choosing to follow a later version.
15. Disclaimer of Warranty.
THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT
WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE
PROGRAM “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR
CORRECTION.
16. Limitation of Liability.
IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT
HOLDER, OR ANY OTHER PARTY WHO MODIFIES AND/OR CONVEYS THE PROGRAM AS PERMITTED ABOVE, BE
LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL
DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO
LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES
OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR
OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
17. Interpretation of Sections 15 and 16.
If the disclaimer of warranty and limitation of liability provided above cannot be given local legal effect according to their terms,
reviewing courts shall apply local law that most closely approximates an absolute waiver of all civil liability in connection with the
Program, unless a warranty or assumption of liability accompanies a copy of the Program in return for a fee.
This Product includes rsync software under GPL 3.0 license

GNU GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright © 2007 Free Software Foundation, Inc. <http://fsf.org/>
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
Preamble
The GNU General Public License is a free, copyleft license for software and other kinds of works.
The licenses for most software and other practical works are designed to take away your freedom to share and change the works. By
contrast, the GNU General Public License is intended to guarantee your freedom to share and change all versions of a program--to
make sure it remains free software for all its users. We, the Free Software Foundation, use the GNU General Public License for most
of our software; it applies also to any other work released this way by its authors. You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge for them if you wish), that you receive source code or can get
it if you want it, that you can change the software or use pieces of it in new free programs, and that you know you can do these
things.
To protect your rights, we need to prevent others from denying you these rights or asking you to surrender the rights. Therefore, you
have certain responsibilities if you distribute copies of the software, or if you modify it: responsibilities to respect the freedom of
others.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must pass on to the recipients the same
freedoms that you received. You must make sure that they, too, receive or can get the source code. And you must show them these
terms so they know their rights.
Developers that use the GNU GPL protect your rights with two steps: (1) assert copyright on the software, and (2) offer you this
License giving you legal permission to copy, distribute and/or modify it.
For the developers' and authors' protection, the GPL clearly explains that there is no warranty for this free software. For both users'
and authors' sake, the GPL requires that modified versions be marked as changed, so that their problems will not be attributed
erroneously to authors of previous versions.
Some devices are designed to deny users access to install or run modified versions of the software inside them, although the
manufacturer can do so. This is fundamentally incompatible with the aim of protecting users' freedom to change the software. The
systematic pattern of such abuse occurs in the area of products for individuals to use, which is precisely where it is most
unacceptable. Therefore, we have designed this version of the GPL to prohibit the practice for those products. If such problems arise
substantially in other domains, we stand ready to extend this provision to those domains in future versions of the GPL, as needed to
protect the freedom of users.
Finally, every program is threatened constantly by software patents. States should not allow patents to restrict development and use
of software on general-purpose computers, but in those that do, we wish to avoid the special danger that patents applied to a free
program could make it effectively proprietary. To prevent this, the GPL assures that patents cannot be used to render the program
non-free.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS
0. Definitions.
“This License” refers to version 3 of the GNU General Public License.
“Copyright” also means copyright-like laws that apply to other kinds of works, such as semiconductor masks.
“The Program” refers to any copyrightable work licensed under this License. Each licensee is addressed as “you”. “Licensees” and
“recipients” may be individuals or organizations.
To “modify” a work means to copy from or adapt all or part of the work in a fashion requiring copyright permission, other than the
making of an exact copy. The resulting work is called a “modified version” of the earlier work or a work “based on” the earlier
work.
A “covered work” means either the unmodified Program or a work based on the Program.
To “propagate” a work means to do anything with it that, without permission, would make you directly or secondarily liable for
infringement under applicable copyright law, except executing it on a computer or modifying a private copy. Propagation includes
copying, distribution (with or without modification), making available to the public, and in some countries other activities as well.
To “convey” a work means any kind of propagation that enables other parties to make or receive copies. Mere interaction with a
user through a computer network, with no transfer of a copy, is not conveying.
An interactive user interface displays “Appropriate Legal Notices” to the extent that it includes a convenient and prominently visible
feature that (1) displays an appropriate copyright notice, and (2) tells the user that there is no warranty for the work (except to the
extent that warranties are provided), that licensees may convey the work under this License, and how to view a copy of this License.
If the interface presents a list of user commands or options, such as a menu, a prominent item in the list meets this criterion.
1. Source Code.
The “source code” for a work means the preferred form of the work for making modifications to it. “Object code” means any
non-source form of a work.
A “Standard Interface” means an interface that either is an official standard defined by a recognized standards body, or, in the case
of interfaces specified for a particular programming language, one that is widely used among developers working in that language.
The “System Libraries” of an executable work include anything, other than the work as a whole, that (a) is included in the normal
form of packaging a Major Component, but which is not part of that Major Component, and (b) serves only to enable use of the
work with that Major Component, or to implement a Standard Interface for which an implementation is available to the public in
source code form. A “Major Component”, in this context, means a major essential component (kernel, window system, and so on) of
the specific operating system (if any) on which the executable work runs, or a compiler used to produce the work, or an object code
interpreter used to run it.
The “Corresponding Source” for a work in object code form means all the source code needed to generate, install, and (for an
executable work) run the object code and to modify the work, including scripts to control those activities. However, it does not
include the work's System Libraries, or general-purpose tools or generally available free programs which are used unmodified in
performing those activities but which are not part of the work. For example, Corresponding Source includes interface definition files
associated with source files for the work, and the source code for shared libraries and dynamically linked subprograms that the work
is specifically designed to require, such as by intimate data communication or control flow between those subprograms and other
parts of the work.
The Corresponding Source need not include anything that users can regenerate automatically from other parts of the Corresponding
Source.
The Corresponding Source for a work in source code form is that same work.
2. Basic Permissions.
All rights granted under this License are granted for the term of copyright on the Program, and are irrevocable provided the stated
conditions are met. This License explicitly affirms your unlimited permission to run the unmodified Program. The output from
running a covered work is covered by this License only if the output, given its content, constitutes a covered work. This License
acknowledges your rights of fair use or other equivalent, as provided by copyright law.
You may make, run and propagate covered works that you do not convey, without conditions so long as your license otherwise
remains in force. You may convey covered works to others for the sole purpose of having them make modifications exclusively for
you, or provide you with facilities for running those works, provided that you comply with the terms of this License in conveying all
material for which you do not control copyright. Those thus making or running the covered works for you must do so exclusively on
your behalf, under your direction and control, on terms that prohibit them from making any copies of your copyrighted material
outside their relationship with you.
Conveying under any other circumstances is permitted solely under the conditions stated below. Sublicensing is not allowed; section
10 makes it unnecessary.
3. Protecting Users' Legal Rights From Anti-Circumvention Law.
No covered work shall be deemed part of an effective technological measure under any applicable law fulfilling obligations under
article 11 of the WIPO copyright treaty adopted on 20 December 1996, or similar laws prohibiting or restricting circumvention of
such measures.
When you convey a covered work, you waive any legal power to forbid circumvention of technological measures to the extent such
circumvention is effected by exercising rights under this License with respect to the covered work, and you disclaim any intention to
limit operation or modification of the work as a means of enforcing, against the work's users, your or third parties' legal rights to
forbid circumvention of technological measures.
4. Conveying Verbatim Copies.
You may convey verbatim copies of the Program's source code as you receive it, in any medium, provided that you conspicuously
and appropriately publish on each copy an appropriate copyright notice; keep intact all notices stating that this License and any
non-permissive terms added in accord with section 7 apply to the code; keep intact all notices of the absence of any warranty; and
give all recipients a copy of this License along with the Program.
You may charge any price or no price for each copy that you convey, and you may offer support or warranty protection for a fee.
5. Conveying Modified Source Versions.
You may convey a work based on the Program, or the modifications to produce it from the Program, in the form of source code
under the terms of section 4, provided that you also meet all of these conditions:
a) The work must carry prominent notices stating that you modified it, and giving a relevant date.
b) The work must carry prominent notices stating that it is released under this License and any conditions added under
section 7. This requirement modifies the requirement in section 4 to “keep intact all notices”.
c) You must license the entire work, as a whole, under this License to anyone who comes into possession of a copy. This
License will therefore apply, along with any applicable section 7 additional terms, to the whole of the work, and all its
parts, regardless of how they are packaged. This License gives no permission to license the work in any other way, but it
does not invalidate such permission if you have separately received it.
d) If the work has interactive user interfaces, each must display Appropriate Legal Notices; however, if the Program has
interactive interfaces that do not display Appropriate Legal Notices, your work need not make them do so.
A compilation of a covered work with other separate and independent works, which are not by their nature extensions of the covered
work, and which are not combined with it such as to form a larger program, in or on a volume of a storage or distribution medium, is
called an “aggregate” if the compilation and its resulting copyright are not used to limit the access or legal rights of the
compilation's users beyond what the individual works permit. Inclusion of a covered work in an aggregate does not cause this
License to apply to the other parts of the aggregate.
6. Conveying Non-Source Forms.
You may convey a covered work in object code form under the terms of sections 4 and 5, provided that you also convey the
machine-readable Corresponding Source under the terms of this License, in one of these ways:
a) Convey the object code in, or embodied in, a physical product (including a physical distribution medium),
accompanied by the Corresponding Source fixed on a durable physical medium customarily used for software
interchange.
b) Convey the object code in, or embodied in, a physical product (including a physical distribution medium),
accompanied by a written offer, valid for at least three years and valid for as long as you offer spare parts or customer
support for that product model, to give anyone who possesses the object code either (1) a copy of the Corresponding
Source for all the software in the product that is covered by this License, on a durable physical medium customarily used
for software interchange, for a price no more than your reasonable cost of physically performing this conveying of source,
or (2) access to copy the Corresponding Source from a network server at no charge.
c) Convey individual copies of the object code with a copy of the written offer to provide the Corresponding Source. This
alternative is allowed only occasionally and noncommercially, and only if you received the object code with such an
offer, in accord with subsection 6b.
d) Convey the object code by offering access from a designated place (gratis or for a charge), and offer equivalent access
to the Corresponding Source in the same way through the same place at no further charge. You need not require
recipients to copy the Corresponding Source along with the object code. If the place to copy the object code is a network
server, the Corresponding Source may be on a different server (operated by you or a third party) that supports equivalent
copying facilities, provided you maintain clear directions next to the object code saying where to find the Corresponding
Source. Regardless of what server hosts the Corresponding Source, you remain obligated to ensure that it is available for
as long as needed to satisfy these requirements.
e) Convey the object code using peer-to-peer transmission, provided you inform other peers where the object code and
Corresponding Source of the work are being offered to the general public at no charge under subsection 6d.
A separable portion of the object code, whose source code is excluded from the Corresponding Source as a System Library, need not
be included in conveying the object code work.
A “User Product” is either (1) a “consumer product”, which means any tangible personal property which is normally used for
personal, family, or household purposes, or (2) anything designed or sold for incorporation into a dwelling. In determining whether a
product is a consumer product, doubtful cases shall be resolved in favor of coverage. For a particular product received by a
particular user, “normally used” refers to a typical or common use of that class of product, regardless of the status of the particular
user or of the way in which the particular user actually uses, or expects or is expected to use, the product. A product is a consumer
product regardless of whether the product has substantial commercial, industrial or non-consumer uses, unless such uses represent
the only significant mode of use of the product.
“Installation Information” for a User Product means any methods, procedures, authorization keys, or other information required to
install and execute modified versions of a covered work in that User Product from a modified version of its Corresponding Source.
The information must suffice to ensure that the continued functioning of the modified object code is in no case prevented or
interfered with solely because modification has been made.
If you convey an object code work under this section in, or with, or specifically for use in, a User Product, and the conveying occurs
as part of a transaction in which the right of possession and use of the User Product is transferred to the recipient in perpetuity or for
a fixed term (regardless of how the transaction is characterized), the Corresponding Source conveyed under this section must be
accompanied by the Installation Information. But this requirement does not apply if neither you nor any third party retains the ability
to install modified object code on the User Product (for example, the work has been installed in ROM).
The requirement to provide Installation Information does not include a requirement to continue to provide support service, warranty,
or updates for a work that has been modified or installed by the recipient, or for the User Product in which it has been modified or
installed. Access to a network may be denied when the modification itself materially and adversely affects the operation of the
network or violates the rules and protocols for communication across the network.
Corresponding Source conveyed, and Installation Information provided, in accord with this section must be in a format that is
publicly documented (and with an implementation available to the public in source code form), and must require no special
password or key for unpacking, reading or copying.
7. Additional Terms.
“Additional permissions” are terms that supplement the terms of this License by making exceptions from one or more of its
conditions. Additional permissions that are applicable to the entire Program shall be treated as though they were included in this
License, to the extent that they are valid under applicable law. If additional permissions apply only to part of the Program, that part
may be used separately under those permissions, but the entire Program remains governed by this License without regard to the
additional permissions.
When you convey a copy of a covered work, you may at your option remove any additional permissions from that copy, or from any
part of it. (Additional permissions may be written to require their own removal in certain cases when you modify the work.) You
may place additional permissions on material, added by you to a covered work, for which you have or can give appropriate
copyright permission.
Notwithstanding any other provision of this License, for material you add to a covered work, you may (if authorized by the
copyright holders of that material) supplement the terms of this License with terms:
a) Disclaiming warranty or limiting liability differently from the terms of sections 15 and 16 of this License; or
b) Requiring preservation of specified reasonable legal notices or author attributions in that material or in the Appropriate
Legal Notices displayed by works containing it; or
c) Prohibiting misrepresentation of the origin of that material, or requiring that modified versions of such material be
marked in reasonable ways as different from the original version; or
d) Limiting the use for publicity purposes of names of licensors or authors of the material; or
e) Declining to grant rights under trademark law for use of some trade names, trademarks, or service marks; or
f) Requiring indemnification of licensors and authors of that material by anyone who conveys the material (or modified
versions of it) with contractual assumptions of liability to the recipient, for any liability that these contractual
assumptions directly impose on those licensors and authors.
All other non-permissive additional terms are considered “further restrictions” within the meaning of section 10. If the Program as
you received it, or any part of it, contains a notice stating that it is governed by this License along with a term that is a further
restriction, you may remove that term. If a license document contains a further restriction but permits relicensing or conveying
under this License, you may add to a covered work material governed by the terms of that license document, provided that the
further restriction does not survive such relicensing or conveying.
If you add terms to a covered work in accord with this section, you must place, in the relevant source files, a statement of the
additional terms that apply to those files, or a notice indicating where to find the applicable terms.
Additional terms, permissive or non-permissive, may be stated in the form of a separately written license, or stated as exceptions;
the above requirements apply either way.
8. Termination.
You may not propagate or modify a covered work except as expressly provided under this License. Any attempt otherwise to
propagate or modify it is void, and will automatically terminate your rights under this License (including any patent licenses granted
under the third paragraph of section 11).
However, if you cease all violation of this License, then your license from a particular copyright holder is reinstated (a)
provisionally, unless and until the copyright holder explicitly and finally terminates your license, and (b) permanently, if the
copyright holder fails to notify you of the violation by some reasonable means prior to 60 days after the cessation.
Moreover, your license from a particular copyright holder is reinstated permanently if the copyright holder notifies you of the
violation by some reasonable means, this is the first time you have received notice of violation of this License (for any work) from
that copyright holder, and you cure the violation prior to 30 days after your receipt of the notice.
Termination of your rights under this section does not terminate the licenses of parties who have received copies or rights from you
under this License. If your rights have been terminated and not permanently reinstated, you do not qualify to receive new licenses
for the same material under section 10.
9. Acceptance Not Required for Having Copies.
You are not required to accept this License in order to receive or run a copy of the Program. Ancillary propagation of a covered
work occurring solely as a consequence of using peer-to-peer transmission to receive a copy likewise does not require acceptance.
However, nothing other than this License grants you permission to propagate or modify any covered work. These actions infringe
copyright if you do not accept this License. Therefore, by modifying or propagating a covered work, you indicate your acceptance
of this License to do so.
10. Automatic Licensing of Downstream Recipients.
Each time you convey a covered work, the recipient automatically receives a license from the original licensors, to run, modify and
propagate that work, subject to this License. You are not responsible for enforcing compliance by third parties with this License.
An “entity transaction” is a transaction transferring control of an organization, or substantially all assets of one, or subdividing an
organization, or merging organizations. If propagation of a covered work results from an entity transaction, each party to that
transaction who receives a copy of the work also receives whatever licenses to the work the party's predecessor in interest had or
could give under the previous paragraph, plus a right to possession of the Corresponding Source of the work from the predecessor in
interest, if the predecessor has it or can get it with reasonable efforts.
You may not impose any further restrictions on the exercise of the rights granted or affirmed under this License. For example, you
may not impose a license fee, royalty, or other charge for exercise of rights granted under this License, and you may not initiate
litigation (including a cross-claim or counterclaim in a lawsuit) alleging that any patent claim is infringed by making, using, selling,
offering for sale, or importing the Program or any portion of it.
11. Patents.
A “contributor” is a copyright holder who authorizes use under this License of the Program or a work on which the Program is based.
The work thus licensed is called the contributor's “contributor version”.
A contributor's “essential patent claims” are all patent claims owned or controlled by the contributor, whether already acquired or
hereafter acquired, that would be infringed by some manner, permitted by this License, of making, using, or selling its contributor
version, but do not include claims that would be infringed only as a consequence of further modification of the contributor version.
For purposes of this definition, “control” includes the right to grant patent sublicenses in a manner consistent with the requirements
of this License.
Each contributor grants you a non-exclusive, worldwide, royalty-free patent license under the contributor's essential patent claims,
to make, use, sell, offer for sale, import and otherwise run, modify and propagate the contents of its contributor version.
In the following three paragraphs, a “patent license” is any express agreement or commitment, however denominated, not to enforce
a patent (such as an express permission to practice a patent or covenant not to sue for patent infringement). To “grant” such a patent
license to a party means to make such an agreement or commitment not to enforce a patent against the party.
If you convey a covered work, knowingly relying on a patent license, and the Corresponding Source of the work is not available for
anyone to copy, free of charge and under the terms of this License, through a publicly available network server or other readily
accessible means, then you must either (1) cause the Corresponding Source to be so available, or (2) arrange to deprive yourself of
the benefit of the patent license for this particular work, or (3) arrange, in a manner consistent with the requirements of this License,
to extend the patent license to downstream recipients. “Knowingly relying” means you have actual knowledge that, but for the
patent license, your conveying the covered work in a country, or your recipient's use of the covered work in a country, would
infringe one or more identifiable patents in that country that you have reason to believe are valid.
If, pursuant to or in connection with a single transaction or arrangement, you convey, or propagate by procuring conveyance of, a
covered work, and grant a patent license to some of the parties receiving the covered work authorizing them to use, propagate,
modify or convey a specific copy of the covered work, then the patent license you grant is automatically extended to all recipients of
the covered work and works based on it.
A patent license is “discriminatory” if it does not include within the scope of its coverage, prohibits the exercise of, or is conditioned
on the non-exercise of one or more of the rights that are specifically granted under this License. You may not convey a covered work
if you are a party to an arrangement with a third party that is in the business of distributing software, under which you make
payment to the third party based on the extent of your activity of conveying the work, and under which the third party grants, to any
of the parties who would receive the covered work from you, a discriminatory patent license (a) in connection with copies of the
covered work conveyed by you (or copies made from those copies), or (b) primarily for and in connection with specific products or
compilations that contain the covered work, unless you entered into that arrangement, or that patent license was granted, prior to 28
March 2007.
Nothing in this License shall be construed as excluding or limiting any implied license or other defenses to infringement that may
otherwise be available to you under applicable patent law.
12. No Surrender of Others' Freedom.
If conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License,
they do not excuse you from the conditions of this License. If you cannot convey a covered work so as to satisfy simultaneously
your obligations under this License and any other pertinent obligations, then as a consequence you may not convey it at all. For
example, if you agree to terms that obligate you to collect a royalty for further conveying from those to whom you convey the
Program, the only way you could satisfy both those terms and this License would be to refrain entirely from conveying the Program.
13. Use with the GNU Affero General Public License.
Notwithstanding any other provision of this License, you have permission to link or combine any covered work with a work
licensed under version 3 of the GNU Affero General Public License into a single combined work, and to convey the resulting work.
The terms of this License will continue to apply to the part which is the covered work, but the special requirements of the GNU
Affero General Public License, section 13, concerning interaction through a network will apply to the combination as such.
14. Revised Versions of this License.
The Free Software Foundation may publish revised and/or new versions of the GNU General Public License from time to time.
Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies that a certain numbered version of the GNU General
Public License “or any later version” applies to it, you have the option of following the terms and conditions either of that numbered
version or of any later version published by the Free Software Foundation. If the Program does not specify a version number of the
GNU General Public License, you may choose any version ever published by the Free Software Foundation.
If the Program specifies that a proxy can decide which future versions of the GNU General Public License can be used, that proxy's
public statement of acceptance of a version permanently authorizes you to choose that version for the Program.
Later license versions may give you additional or different permissions. However, no additional obligations are imposed on any
author or copyright holder as a result of your choosing to follow a later version.
15. Disclaimer of Warranty.
THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM
“AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE
RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE PROGRAM PROVE
DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. Limitation of Liability.
IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT
HOLDER, OR ANY OTHER PARTY WHO MODIFIES AND/OR CONVEYS THE PROGRAM AS PERMITTED ABOVE, BE
LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL
DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO

LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR
A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER
PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
17. Interpretation of Sections 15 and 16.
If the disclaimer of warranty and limitation of liability provided above cannot be given local legal effect according to their terms,
reviewing courts shall apply local law that most closely approximates an absolute waiver of all civil liability in connection with the
Program, unless a warranty or assumption of liability accompanies a copy of the Program in return for a fee.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the public, the best way to achieve this is to
make it free software which everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest to attach them to the start of each source file to most effectively
state the exclusion of warranty; and each file should have at least the “copyright” line and a pointer to where the full notice is found.
<one line to give the program's name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
Also add information on how to contact you by electronic and paper mail.
If the program does terminal interaction, make it output a short notice like this when it starts in an interactive mode:
<program> Copyright (C) <year> <name of author>
This program comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
This is free software, and you are welcome to redistribute it
under certain conditions; type `show c' for details.
The hypothetical commands `show w' and `show c' should show the appropriate parts of the General Public License. Of course, your
program's commands might be different; for a GUI interface, you would use an “about box”.
You should also get your employer (if you work as a programmer) or school, if any, to sign a “copyright disclaimer” for the program,
if necessary. For more information on this, and how to apply and follow the GNU GPL, see <http://www.gnu.org/licenses/>.
The GNU General Public License does not permit incorporating your program into proprietary programs. If your program is a
subroutine library, you may consider it more useful to permit linking proprietary applications with the library. If this is what you
want to do, use the GNU Lesser General Public License instead of this License. But first, please read
<http://www.gnu.org/philosophy/why-not-lgpl.html>.
This Product includes dojo, libupnp, sg3_utils, cherrypy and YAML-Syck software under BSD license
BSD
Copyright (c) [dates as appropriate to package]
The Regents of the University of California. All rights reserved. Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
Neither the name of the University nor of the Laboratory may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOS E ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR

CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This Product includes openssl software under below license
LICENSE ISSUES
==============
The OpenSSL toolkit stays under a dual license, i.e. both the conditions of
the OpenSSL License and the original SSLeay license apply to the toolkit.
See below for the actual license texts. Actually both licenses are BSD-style
Open Source licenses. In case of any license issues related to OpenSSL
please contact openssl-core@openssl.org.
OpenSSL License
---------------
/* ====================================================================
* Copyright (c) 1998-2008 The OpenSSL Project. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
*
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
*
* 4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
*
* 5. Products derived from this software may not be called "OpenSSL"
* nor may "OpenSSL" appear in their names without prior written
* permission of the OpenSSL Project.
*
* 6. Redistributions of any form whatsoever must retain the following
* acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)"
*
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
* ====================================================================
*
* This product includes cryptographic software written by Eric Young
* (eay@cryptsoft.com). This product includes software written by Tim
* Hudson (tjh@cryptsoft.com).
*
*/
Original SSLeay License
-----------------------
/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
*
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions
* apply to all code found in this distribution, be it the RC4, RSA,
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
*
* Copyright remains Eric Young's, and as such any Copyright notices in
* the code are not to be removed.
* If this package is used in a product, Eric Young should be given attribution
* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* "This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)"
* The word 'cryptographic' can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specific code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)

* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence
* [including the GNU Public Licence.]
*/
This Product includes flac software under FDL license
GNU Free Documentation License
Version 1.2, November 2002
Copyright (C) 2000,2001,2002 Free Software Foundation, Inc.
51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
0. PREAMBLE
The purpose of this License is to make a manual, textbook, or other functional and useful document "free" in the sense of freedom:
to assure everyone the effective freedom to copy and redistribute it, with or without modifying it, either commercially or
noncommercially. Secondarily, this License preserves for the author and publisher a way
to get credit for their work, while not being considered responsible for modifications made by others. This License is a kind of
"copyleft", which means that derivative works of the document must themselves be free in the same sense. It complements the GNU
General Public License, which is a copyleft license designed for free software.
We have designed this License in order to use it for manuals for free software, because free software needs free documentation: a
free program should come with manuals providing the same freedoms that the software does. But this License is not limited to
software manuals; it can be used for any textual work, regardless of subject matter or whether it is published as a printed book. We
recommend this License principally for works whose purpose is instruction or reference.
1. APPLICABILITY AND DEFINITIONS
This License applies to any manual or other work, in any medium, that contains a notice placed by the copyright holder saying it can
be distributed under the terms of this License. Such a notice grants a world-wide, royalty-free license, unlimited in duration, to use
that work under the conditions stated herein. The "Document", below, refers to any such manual or work. Any member of the
public is a licensee, and is addressed as "you". You accept the license if you copy, modify or distribute the work in a way requiring
permission under copyright law.
A "Modified Version" of the Document means any work containing the Document or a portion of it, either copied verbatim, or with
modifications and/or translated into another language. A "Secondary Section" is a named appendix or a front-matter section of
the Document that deals exclusively with the relationship of the publishers or authors of the Document to the Document's overall
subject (or to related matters) and contains nothing that could fall directly within that overall subject. (Thus, if the Document is in
part a textbook of mathematics, a Secondary Section may not explain any mathematics.) The relationship could be a matter of
historical connection with the subject or with related matters, or of legal, commercial, philosophical, ethical or political position
regarding them.
The "Invariant Sections" are certain Secondary Sections whose titles are designated, as being those of Invariant Sections, in the
notice that says that the Document is released under this License. If a section does not fit the above definition of Secondary then it is
not allowed to be designated as Invariant. The Document may contain zero Invariant Sections. If the Document does not identify
any Invariant Sections then there are none. The "Cover Texts" are certain short passages of text that are listed, as Front-Cover Texts
or Back-Cover Texts, in the notice that says that the Document is released under this License. A Front-Cover Text may
be at most 5 words, and a Back-Cover Text may be at most 25 words.
A "Transparent" copy of the Document means a machine-readable copy, represented in a format whose specification is available to
the general public, that is suitable for revising the document straightforwardly with generic text editors or (for images composed of
pixels) generic paint programs or (for drawings) some widely available drawing editor, and that is suitable for input to text or
matters or for automatic translation to a variety of formats suitable for input to text formatters. A copy made in an otherwise
Transparent file format whose markup, or absence of markup, has been arranged to thwart or discourage subsequent modification by
readers is not Transparent. An image format is not Transparent if used for any substantial amount of text. A copy that is not
"Transparent" is called "Opaque".
Examples of suitable formats for Transparent copies include plain ASCII without markup, Texinfo input format, LaTeX input
format, SGML or XML using a publicly available DTD, and standard-conforming simple HTML, PostScript or PDF designed for
human modification. Examples of transparent image formats include PNG, XCF and JPG. Opaque formats include proprietary
ormats that can be read and edited only by proprietary word processors, SGML or XML for which the DTD and/or processing tools
are not generally available, and the machine-generated HTML, PostScript or PDF produced by some word processors for output
purposes only.
The "Title Page" means, for a printed book, the title page itself, plus such following pages as are needed to hold, legibly, the
material this License requires to appear in the title page. For works in formats which do not have any title page as such, "Title Page"
means the text near the most prominent appearance of the work's title, preceding the beginning of the body of the text. A section
"Entitled XYZ" means a named subunit of the Document whose title either is precisely XYZ or contains XYZ in parentheses
following text that translates XYZ in another language. (Here XYZ stands for a specific section name mentioned below, such as
"Acknowledgements", "Dedications", "Endorsements", or "History".) To "Preserve the Title" of such a section when you modify
the Document means that it remains a section "Entitled XYZ" according to this definition.
The Document may include Warranty Disclaimers next to the notice which states that this License applies to the Document. These
Warranty Disclaimers are considered to be included by reference in this License, but only as regards disclaiming warranties: any
other implication that these Warranty Disclaimers may have is void and has no effect on the meaning of this License.
2. VERBATIM COPYING
You may copy and distribute the Document in any medium, either commercially or noncommercially, provided that this License,
the copyright notices, and the license notice saying this License applies to the Document are reproduced in all copies, and that you
add no other conditions whatsoever to those of this License. You may not use technical measures to obstruct or control the reading
or further copying of the copies you make or distribute. However, you may accept compensation in exchange for copies. If you
distribute a large enough number of copies you must also follow the conditions in section 3.
You may also lend copies, under the same conditions stated above, and you may publicly display copies.
3. COPYING IN QUANTITY
If you publish printed copies (or copies in media that commonly have printed covers) of the Document, numbering more than 100,
and the Document's license notice requires Cover Texts, you must enclose the copies in covers that carry, clearly and legibly, all
these Cover Texts: Front-Cover Texts on the front cover, and Back-Cover Texts on the back cover. Both covers must also clearly
and legibly identify you as the publisher of these copies. The front cover must present the full title with all words of the title
equally prominent and visible. You may add other material on the covers in addition. Copying with changes limited to the covers,
as long as they preserve the title of the Document and satisfy these conditions, can be treated as verbatim copying in other respects.
If the required texts for either cover are too voluminous to fit legibly, you should put the first ones listed (as many as fit reasonably)
on the actual cover, and continue the rest onto adjacent pages.
If you publish or distribute Opaque copies of the Document numbering more than 100, you must either include a machine-readable
Transparent copy along with each Opaque copy, or state in or with each Opaque copy a computer-network location from which the
general network-using public has access to download using public-standard network protocols a complete Transparent copy of the
Document, free of added material. If you use the latter option, you must take reasonably prudent steps, when you begin distribution
of Opaque copies in quantity, to ensure that this Transparent copy will remain thus accessible at the stated location until at least one
year after the last time you distribute an Opaque copy (directly or through your agents or retailers) of that edition to the public.
It is requested, but not required, that you contact the authors of the Document well before redistributing any large number of copies,
to give them a chance to provide you with an updated version of the Document.
4. MODIFICATIONS
You may copy and distribute a Modified Version of the Document under the conditions of sections 2 and 3 above, provided that you
release the Modified Version under precisely this License, with the Modified Version filling the role of the Document, thus
licensing distribution and modification of the Modified Version to whoever possesses a copy of it. In addition, you must do these
things in the Modified Version:
A. Use in the Title Page (and on the covers, if any) a title distinct from that of the Document, and from those of previous versions
(which should, if there were any, be listed in the History section of the Document). You may use the same title as a previous
version if the original publisher of that version gives permission.
B. List on the Title Page, as authors, one or more persons or entities
responsible for authorship of the modifications in the Modified Version, together with at least five of the principal authors of the
Document (all of its principal authors, if it has fewer than five), unless they release you from this requirement.
C. State on the Title page the name of the publisher of the Modified Version, as the publisher.
D. Preserve all the copyright notices of the Document.
E. Add an appropriate copyright notice for your modifications adjacent to the other copyright notices.
F. Include, immediately after the copyright notices, a license notice giving the public permission to use the Modified Version under
the terms of this License, in the form shown in the Addendum below.
G. Preserve in that license notice the full lists of Invariant Sections and required Cover Texts given in the Document's license notice.
H. Include an unaltered copy of this License.
I. Preserve the section Entitled "History", Preserve its Title, and add to it an item stating at least the title, year, new authors, and
publisher of the Modified Version as given on the Title Page. If there is no section Entitled "History" in the Document, create
one stating the title, year, authors, and publisher of the Document as given on its Title Page, then add an item describing the
Modified Version as stated in the previous sentence.
J. Preserve the network location, if any, given in the Document for public access to a Transparent copy of the Document, and
likewise the network locations given in the Document for previous versions it was based on. These may be placed in the
"History" section. You may omit a network location for a work that was published at least four years before the Document itself,
or if the original publisher of the version it refers to gives permission.
K. For any section Entitled "Acknowledgements" or "Dedications", Preserve the Title of the section, and preserve in the section all
the substance and tone of each of the contributor acknowledgements and/or dedications given therein.
L. Preserve all the Invariant Sections of the Document, unaltered in their text and in their titles. Section numbers
or the equivalent are not considered part of the section titles.
M. Delete any section Entitled "Endorsements". Such a section may not be included in the Modified Version.
N. Do not retitle any existing section to be Entitled "Endorsements" or to conflict in title with any Invariant Section.
O. Preserve any Warranty Disclaimers.
If the Modified Version includes new front-matter sections or appendices that qualify as Secondary Sections and contain no material
copied from the Document, you may at your option designate some or all of these sections as invariant. To do this, add their titles
to the list of Invariant Sections in the Modified Version's license notice.These titles must be distinct from any other section titles.
You may add a section Entitled "Endorsements", provided it contains nothing but endorsements of your Modified Version by
various parties--for example, statements of peer review or that the text has been approved by an organization as the authoritative
definition of a standard.
You may add a passage of up to five words as a Front-Cover Text, and a passage of up to 25 words as a Back-Cover Text, to the end
of the list of Cover Texts in the Modified Version. Only one passage of Front-Cover Text and one of Back-Cover Text may be
added by (or through arrangements made by) any one entity. If the Document already includes a cover text for the same cover,
previously added by you or by arrangement made by the same entity you are acting on behalf of, you may not add another; but you
may replace the old one, on explicit permission from the previous publisher that added the old one.
The author(s) and publisher(s) of the Document do not by this License give permission to use their names for publicity for or to
assert or imply endorsement of any Modified Version.
5. COMBINING DOCUMENTS
You may combine the Document with other documents released under this License, under the terms defined in section 4 above for
modified versions, provided that you include in the combination all of the Invariant Sections of all of the original documents,
unmodified, and list them all as Invariant Sections of your combined work in its license notice, and that you preserve all their
Warranty Disclaimers.
The combined work need only contain one copy of this License, and multiple identical Invariant Sections may be replaced with a
single copy. If there are multiple Invariant Sections with the same name but different contents, make the title of each such section
unique by adding at the end of it, in parentheses, the name of the original author or publisher of that section if known, or else a
unique number. Make the same adjustment to the section titles in the list of Invariant Sections in the license notice of the combined
work.
In the combination, you must combine any sections Entitled "History" in the various original documents, forming one section
Entitled "History"; likewise combine any sections Entitled "Acknowledgements", and any sections Entitled "Dedications". You
must delete all sections Entitled "Endorsements".
6. COLLECTIONS OF DOCUMENTS
You may make a collection consisting of the Document and other documents released under this License, and replace the individual
copies of this License in the various documents with a single copy that is included in the collection, provided that you follow the
rules of this License for verbatim copying of each of the documents in all other respects.
You may extract a single document from such a collection, and distribute it individually under this License, provided you insert a
copy of this License into the extracted document, and follow this License in all other respects regarding verbatim copying of that
document.
7. AGGREGATION WITH INDEPENDENT WORKS
A compilation of the Document or its derivatives with other separate and independent documents or works, in or on a volume of a
storage or distribution medium, is called an "aggregate" if the copyright resulting from the compilation is not used to limit the legal
rights of the compilation's users beyond what the individual works permit. When the Document is included in an aggregate, this
License does not apply to the other works in the aggregate which are not themselves derivative works of the Document.
If the Cover Text requirement of section 3 is applicable to these copies of the Document, then if the Document is less than one half
of the entire aggregate, the Document's Cover Texts may be placed on covers that bracket the Document within the aggregate, or the
electronic equivalent of covers if the Document is in electronic form. Otherwise they must appear on printed covers that bracket the
whole aggregate.
8. TRANSLATION
Translation is considered a kind of modification, so you may distribute translations of the Document under the terms of section 4.
Replacing Invariant Sections with translations requires special permission from their copyright holders, but you may include
translations of some or all Invariant Sections in addition to the original versions of these Invariant Sections. You may include a
translation of this License, and all the license notices in the Document, and any Warranty Disclaimers, provided that you also
include the original English version of this License and the original versions of those notices and disclaimers. In case of a
disagreement between the translation and the original version of this License or a notice or disclaimer, the original version will
prevail.
If a section in the Document is Entitled "Acknowledgements", "Dedications", or "History", the requirement (section 4) to Preserve
its Title (section 1) will typically require changing the actual title.
9. TERMINATION
You may not copy, modify, sublicense, or distribute the Document except as expressly provided for under this License. Any other
attempt to copy, modify, sublicense or distribute the Document is void, and will automatically terminate your rights under this
License. However, parties who have received copies, or rights, from you under this License will not have their licenses terminated
so long as such parties remain in full compliance.
10. FUTURE REVISIONS OF THIS LICENSE
The Free Software Foundation may publish new, revised versions of the GNU Free Documentation License from time to time.
Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns.
See http://www.gnu.org/copyleft/.
Each version of the License is given a distinguishing version number. If the Document specifies that a particular numbered version
of this License "or any later version" applies to it, you have the option of following the terms and conditions either of that specified

version or of any later version that has been published (not as a draft) by the Free Software Foundation. If the Document does not
specify a version number of this License, you may choose any version ever published (not as a draft) by the Free Software
Foundation.
ADDENDUM: How to use this License for your documents
To use this License in a document you have written, include a copy of the License in the document and put the following copyright
and license notices just after the title page:
Copyright (c) YEAR YOUR NAME.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation
License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no
Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU
Free Documentation License".
If you have Invariant Sections, Front-Cover Texts and Back-Cover Texts, replace the "with...Texts." line with this:
with the Invariant Sections being LIST THEIR TITLES, with the Front-Cover Texts being LIST, and with the Back-Cover Texts
being LIST.
If you have Invariant Sections without Cover Texts, or some other combination of the three, merge those two alternatives to suit the
situation. If your document contains nontrivial examples of program code, we recommend releasing these examples in parallel under
your choice of free software license, such as the GNU General Public License, to permit their use in free software.
This Product includes Encode-Detect software under MPL 1.1 license
MOZILLA PUBLIC LICENSE
Version 1.1
1. Definitions.
1.0.1. "Commercial Use" means distribution or otherwise making the
Covered Code available to a third party.
1.1. "Contributor" means each entity that creates or contributes to
the creation of Modifications.
1.2. "Contributor Version" means the combination of the Original
Code, prior Modifications used by a Contributor, and the Modifications
made by that particular Contributor.
1.3. "Covered Code" means the Original Code or Modifications or the
combination of the Original Code and Modifications, in each case
including portions thereof.
1.4. "Electronic Distribution Mechanism" means a mechanism generally
accepted in the software development community for the electronic
transfer of data.
1.5. "Executable" means Covered Code in any form other than Source
Code.
1.6. "Initial Developer" means the individual or entity identified
as the Initial Developer in the Source Code notice required by Exhibit
A.
1.7. "Larger Work" means a work which combines Covered Code or
portions thereof with code not governed by the terms of this License.
1.8. "License" means this document.
1.8.1. "Licensable" means having the right to grant, to the maximum
extent possible, whether at the time of the initial grant or
subsequently acquired, any and all of the rights conveyed herein.
1.9. "Modifications" means any addition to or deletion from the
substance or structure of either the Original Code or any previous
Modifications. When Covered Code is released as a series of files, a
Modification is:
A. Any addition to or deletion from the contents of a file
containing Original Code or previous Modifications.
B. Any new file that contains any part of the Original Code or
previous Modifications.
1.10. "Original Code" means Source Code of computer software code
which is described in the Source Code notice required by Exhibit A as
Original Code, and which, at the time of its release under this
License is not already Covered Code governed by this License.
1.10.1. "Patent Claims" means any patent claim(s), now owned or
hereafter acquired, including without limitation, method, process,
and apparatus claims, in any patent Licensable by grantor.
1.11. "Source Code" means the preferred form of the Covered Code for
making modifications to it, including all modules it contains, plus
any associated interface definition files, scripts used to control
compilation and installation of an Executable, or source code
differential comparisons against either the Original Code or another
well known, available Covered Code of the Contributor's choice. The
Source Code can be in a compressed or archival form, provided the
appropriate decompression or de-archiving software is widely available
for no charge.
1.12. "You" (or "Your") means an individual or a legal entity
exercising rights under, and complying with all of the terms of, this
License or a future version of this License issued under Section 6.1.
For legal entities, "You" includes any entity which controls, is
controlled by, or is under common control with You. For purposes of
this definition, "control" means (a) the power, direct or indirect,
to cause the direction or management of such entity, whether by
contract or otherwise, or (b) ownership of more than fifty percent
(50%) of the outstanding shares or beneficial ownership of such
entity.
2. Source Code License.
2.1. The Initial Developer Grant.
The Initial Developer hereby grants You a world-wide, royalty-free,
non-exclusive license, subject to third party intellectual property
claims:
(a) under intellectual property rights (other than patent or
trademark) Licensable by Initial Developer to use, reproduce,
modify, display, perform, sublicense and distribute the Original
Code (or portions thereof) with or without Modifications, and/or
as part of a Larger Work; and
(b) under Patents Claims infringed by the making, using or
selling of Original Code, to make, have made, use, practice,
sell, and offer for sale, and/or otherwise dispose of the
Original Code (or portions thereof).
(c) the licenses granted in this Section 2.1(a) and (b) are
effective on the date Initial Developer first distributes
Original Code under the terms of this License.
(d) Notwithstanding Section 2.1(b) above, no patent license is
granted: 1) for code that You delete from the Original Code; 2)
separate from the Original Code; or 3) for infringements caused
by: i) the modification of the Original Code or ii) the
combination of the Original Code with other software or devices.
2.2. Contributor Grant.
Subject to third party intellectual property claims, each Contributor
hereby grants You a world-wide, royalty-free, non-exclusive license
(a) under intellectual property rights (other than patent or
trademark) Licensable by Contributor, to use, reproduce, modify,
display, perform, sublicense and distribute the Modifications
created by such Contributor (or portions thereof) either on an
unmodified basis, with other Modifications, as Covered Code
and/or as part of a Larger Work; and
(b) under Patent Claims infringed by the making, using, or
selling of Modifications made by that Contributor either alone
and/or in combination with its Contributor Version (or portions
of such combination), to make, use, sell, offer for sale, have
made, and/or otherwise dispose of: 1) Modifications made by that
Contributor (or portions thereof); and 2) the combination of
Modifications made by that Contributor with its Contributor
Version (or portions of such combination).
(c) the licenses granted in Sections 2.2(a) and 2.2(b) are
effective on the date Contributor first makes Commercial Use of
the Covered Code.
(d) Notwithstanding Section 2.2(b) above, no patent license is
granted: 1) for any code that Contributor has deleted from the
Contributor Version; 2) separate from the Contributor Version;
3) for infringements caused by: i) third party modifications of
Contributor Version or ii) the combination of Modifications made
by that Contributor with other software (except as part of the
Contributor Version) or other devices; or 4) under Patent Claims
infringed by Covered Code in the absence of Modifications made by
that Contributor.
3. Distribution Obligations.
3.1. Application of License.
The Modifications which You create or to which You contribute are
governed by the terms of this License, including without limitation
Section 2.2. The Source Code version of Covered Code may be
distributed only under the terms of this License or a future version
of this License released under Section 6.1, and You must include a
copy of this License with every copy of the Source Code You
distribute. You may not offer or impose any terms on any Source Code
version that alters or restricts the applicable version of this
License or the recipients' rights hereunder. However, You may include
an additional document offering the additional rights described in
Section 3.5.
3.2. Availability of Source Code.
Any Modification which You create or to which You contribute must be
made available in Source Code form under the terms of this License
either on the same media as an Executable version or via an accepted
Electronic Distribution Mechanism to anyone to whom you made an
Executable version available; and if made available via Electronic
Distribution Mechanism, must remain available for at least twelve (12)
months after the date it initially became available, or at least six
(6) months after a subsequent version of that particular Modification
has been made available to such recipients. You are responsible for
ensuring that the Source Code version remains available even if the
Electronic Distribution Mechanism is maintained by a third party.
3.3. Description of Modifications.
You must cause all Covered Code to which You contribute to contain a
file documenting the changes You made to create that Covered Code and
the date of any change. You must include a prominent statement that
the Modification is derived, directly or indirectly, from Original
Code provided by the Initial Developer and including the name of the
Initial Developer in (a) the Source Code, and (b) in any notice in an
Executable version or related documentation in which You describe the
origin or ownership of the Covered Code.
3.4. Intellectual Property Matters
(a) Third Party Claims.
If Contributor has knowledge that a license under a third party's
intellectual property rights is required to exercise the rights
granted by such Contributor under Sections 2.1 or 2.2,
Contributor must include a text file with the Source Code
distribution titled "LEGAL" which describes the claim and the
party making the claim in sufficient detail that a recipient will
know whom to contact. If Contributor obtains such knowledge after
the Modification is made available as described in Section 3.2,
Contributor shall promptly modify the LEGAL file in all copies
Contributor makes available thereafter and shall take other steps
(such as notifying appropriate mailing lists or newsgroups)
reasonably calculated to inform those who received the Covered
Code that new knowledge has been obtained.
(b) Contributor APIs.
If Contributor's Modifications include an application programming
interface and Contributor has knowledge of patent licenses which
are reasonably necessary to implement that API, Contributor must
also include this information in the LEGAL file.
(c) Representations.
Contributor represents that, except as disclosed pursuant to
Section 3.4(a) above, Contributor believes that Contributor's
Modifications are Contributor's original creation(s) and/or
Contributor has sufficient rights to grant the rights conveyed by
this License.
3.5. Required Notices.
You must duplicate the notice in Exhibit A in each file of the Source
Code. If it is not possible to put such notice in a particular Source
Code file due to its structure, then You must include such notice in a
location (such as a relevant directory) where a user would be likely
to look for such a notice. If You created one or more Modification(s)
You may add your name as a Contributor to the notice described in
Exhibit A. You must also duplicate this License in any documentation
for the Source Code where You describe recipients' rights or ownership
rights relating to Covered Code. You may choose to offer, and to
charge a fee for, warranty, support, indemnity or liability
obligations to one or more recipients of Covered Code. However, You
may do so only on Your own behalf, and not on behalf of the Initial
Developer or any Contributor. You must make it absolutely clear than
any such warranty, support, indemnity or liability obligation is
offered by You alone, and You hereby agree to indemnify the Initial
Developer and every Contributor for any liability incurred by the
Initial Developer or such Contributor as a result of warranty,
support, indemnity or liability terms You offer.
3.6. Distribution of Executable Versions.
You may distribute Covered Code in Executable form only if the
requirements of Section 3.1-3.5 have been met for that Covered Code,
and if You include a notice stating that the Source Code version of
the Covered Code is available under the terms of this License,
including a description of how and where You have fulfilled the
obligations of Section 3.2. The notice must be conspicuously included
in any notice in an Executable version, related documentation or
collateral in which You describe recipients' rights relating to the
Covered Code. You may distribute the Executable version of Covered
Code or ownership rights under a license of Your choice, which may
contain terms different from this License, provided that You are in
compliance with the terms of this License and that the license for the
Executable version does not attempt to limit or alter the recipient's
rights in the Source Code version from the rights set forth in this
License. If You distribute the Executable version under a different
license You must make it absolutely clear that any terms which differ
from this License are offered by You alone, not by the Initial
Developer or any Contributor. You hereby agree to indemnify the
Initial Developer and every Contributor for any liability incurred by
the Initial Developer or such Contributor as a result of any such
terms You offer.
3.7. Larger Works.
You may create a Larger Work by combining Covered Code with other code
not governed by the terms of this License and distribute the Larger
Work as a single product. In such a case, You must make sure the
requirements of this License are fulfilled for the Covered Code.
4. Inability to Comply Due to Statute or Regulation.
If it is impossible for You to comply with any of the terms of this
License with respect to some or all of the Covered Code due to
statute, judicial order, or regulation then You must: (a) comply with
the terms of this License to the maximum extent possible; and (b)
describe the limitations and the code they affect. Such description
must be included in the LEGAL file described in Section 3.4 and must
be included with all distributions of the Source Code. Except to the
extent prohibited by statute or regulation, such description must be
sufficiently detailed for a recipient of ordinary skill to be able to
understand it.
5. Application of this License.
This License applies to code to which the Initial Developer has
attached the notice in Exhibit A and to related Covered Code.
6. Versions of the License.
6.1. New Versions.
Netscape Communications Corporation ("Netscape") may publish revised
and/or new versions of the License from time to time. Each version
will be given a distinguishing version number.
6.2. Effect of New Versions.
Once Covered Code has been published under a particular version of the
License, You may always continue to use it under the terms of that
version. You may also choose to use such Covered Code under the terms
of any subsequent version of the License published by Netscape. No one
other than Netscape has the right to modify the terms applicable to
Covered Code created under this License.
6.3. Derivative Works.
If You create or use a modified version of this License (which you may
only do in order to apply it to code which is not already Covered Code
governed by this License), You must (a) rename Your license so that
the phrases "Mozilla", "MOZILLAPL", "MOZPL", "Netscape",
"MPL", "NPL" or any confusingly similar phrase do not appear in your
license (except to note that your license differs from this License)
and (b) otherwise make it clear that Your version of the license
contains terms which differ from the Mozilla Public License and
Netscape Public License. (Filling in the name of the Initial
Developer, Original Code or Contributor in the notice described in
Exhibit A shall not of themselves be deemed to be modifications of
this License.)
7. DISCLAIMER OF WARRANTY.
COVERED CODE IS PROVIDED UNDER THIS LICENSE ON AN "AS IS" BASIS,
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING,
WITHOUT LIMITATION, WARRANTIES THAT THE COVERED CODE IS FREE OF
DEFECTS, MERCHANTABLE, FIT FOR A PARTICULAR PURPOSE OR NON-INFRINGING.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE COVERED CODE
IS WITH YOU. SHOULD ANY COVERED CODE PROVE DEFECTIVE IN ANY RESPECT,
YOU (NOT THE INITIAL DEVELOPER OR ANY OTHER CONTRIBUTOR) ASSUME THE
COST OF ANY NECESSARY SERVICING, REPAIR OR CORRECTION. THIS DISCLAIMER
OF WARRANTY CONSTITUTES AN ESSENTIAL PART OF THIS LICENSE. NO USE OF
ANY COVERED CODE IS AUTHORIZED HEREUNDER EXCEPT UNDER THIS DISCLAIMER.
8. TERMINATION.
8.1. This License and the rights granted hereunder will terminate
automatically if You fail to comply with terms herein and fail to cure
such breach within 30 days of becoming aware of the breach. All
sublicenses to the Covered Code which are properly granted shall
survive any termination of this License. Provisions which, by their
nature, must remain in effect beyond the termination of this License
shall survive.
8.2. If You initiate litigation by asserting a patent infringement
claim (excluding declatory judgment actions) against Initial Developer
or a Contributor (the Initial Developer or Contributor against whom
You file such action is referred to as "Participant") alleging that:
(a) such Participant's Contributor Version directly or indirectly
infringes any patent, then any and all rights granted by such
Participant to You under Sections 2.1 and/or 2.2 of this License
shall, upon 60 days notice from Participant terminate prospectively,
unless if within 60 days after receipt of notice You either: (i)
agree in writing to pay Participant a mutually agreeable reasonable
royalty for Your past and future use of Modifications made by such
Participant, or (ii) withdraw Your litigation claim with respect to
the Contributor Version against such Participant. If within 60 days
of notice, a reasonable royalty and payment arrangement are not
mutually agreed upon in writing by the parties or the litigation claim
is not withdrawn, the rights granted by Participant to You under
Sections 2.1 and/or 2.2 automatically terminate at the expiration of
the 60 day notice period specified above.
(b) any software, hardware, or device, other than such Participant's
Contributor Version, directly or indirectly infringes any patent, then
any rights granted to You by such Participant under Sections 2.1(b)
and 2.2(b) are revoked effective as of the date You first made, used,
sold, distributed, or had made, Modifications made by that
Participant.
8.3. If You assert a patent infringement claim against Participant
alleging that such Participant's Contributor Version directly or
indirectly infringes any patent where such claim is resolved (such as
by license or settlement) prior to the initiation of patent
infringement litigation, then the reasonable value of the licenses
granted by such Participant under Sections 2.1 or 2.2 shall be taken
into account in determining the amount or value of any payment or
license.
8.4. In the event of termination under Sections 8.1 or 8.2 above,
all end user license agreements (excluding distributors and resellers)
which have been validly granted by You or any distributor hereunder
prior to termination shall survive termination.
9. LIMITATION OF LIABILITY.
UNDER NO CIRCUMSTANCES AND UNDER NO LEGAL THEORY, WHETHER TORT
(INCLUDING NEGLIGENCE), CONTRACT, OR OTHERWISE, SHALL YOU, THE INITIAL
DEVELOPER, ANY OTHER CONTRIBUTOR, OR ANY DISTRIBUTOR OF COVERED CODE,
OR ANY SUPPLIER OF ANY OF SUCH PARTIES, BE LIABLE TO ANY PERSON FOR
ANY INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY
CHARACTER INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF GOODWILL,
WORK STOPPAGE, COMPUTER FAILURE OR MALFUNCTION, OR ANY AND ALL OTHER
COMMERCIAL DAMAGES OR LOSSES, EVEN IF SUCH PARTY SHALL HAVE BEEN
INFORMED OF THE POSSIBILITY OF SUCH DAMAGES. THIS LIMITATION OF
LIABILITY SHALL NOT APPLY TO LIABILITY FOR DEATH OR PERSONAL INJURY
RESULTING FROM SUCH PARTY'S NEGLIGENCE TO THE EXTENT APPLICABLE LAW
PROHIBITS SUCH LIMITATION. SOME JURISDICTIONS DO NOT ALLOW THE
EXCLUSION OR LIMITATION OF INCIDENTAL OR CONSEQUENTIAL DAMAGES, SO
THIS EXCLUSION AND LIMITATION MAY NOT APPLY TO YOU.
10. U.S. GOVERNMENT END USERS.
The Covered Code is a "commercial item," as that term is defined in
48 C.F.R. 2.101 (Oct. 1995), consisting of "commercial computer
software" and "commercial computer software documentation," as such
terms are used in 48 C.F.R. 12.212 (Sept. 1995). Consistent with 48
C.F.R. 12.212 and 48 C.F.R. 227.7202-1 through 227.7202-4 (June 1995),
all U.S. Government End Users acquire Covered Code with only those
rights set forth herein.
11. MISCELLANEOUS.
This License represents the complete agreement concerning subject
matter hereof. If any provision of this License is held to be
unenforceable, such provision shall be reformed only to the extent
necessary to make it enforceable. This License shall be governed by
California law provisions (except to the extent applicable law, if
any, provides otherwise), excluding its conflict-of-law provisions.
With respect to disputes in which at least one party is a citizen of,
or an entity chartered or registered to do business in the United
States of America, any litigation relating to this License shall be
subject to the jurisdiction of the Federal Courts of the Northern
District of California, with venue lying in Santa Clara County,
California, with the losing party responsible for costs, including
without limitation, court costs and reasonable attorneys' fees and
expenses. The application of the United Nations Convention on
Contracts for the International Sale of Goods is expressly excluded.
Any law or regulation which provides that the language of a contract
shall be construed against the drafter shall not apply to this
License.
12. RESPONSIBILITY FOR CLAIMS.
As between Initial Developer and the Contributors, each party is
responsible for claims and damages arising, directly or indirectly,
out of its utilization of rights under this License and You agree to
work with Initial Developer and Contributors to distribute such
responsibility on an equitable basis. Nothing herein is intended or
shall be deemed to constitute any admission of liability.
13. MULTIPLE-LICENSED CODE.
Initial Developer may designate portions of the Covered Code as
"Multiple-Licensed". "Multiple-Licensed" means that the Initial
Developer permits you to utilize portions of the Covered Code under
Your choice of the NPL or the alternative licenses, if any, specified
by the Initial Developer in the file described in Exhibit A.
EXHIBIT A -Mozilla Public License.
``The contents of this file are subject to the Mozilla Public License
Version 1.1 (the "License"); you may not use this file except in
compliance with the License. You may obtain a copy of the License at
http://www.mozilla.org/MPL/
Software distributed under the License is distributed on an "AS IS"
basis, WITHOUT WARRANTY OF ANY KIND, either express or implied. See the
License for the specific language governing rights and limitations
under the License.
The Original Code is ______________________________________.
The Initial Developer of the Original Code is ________________________.
Portions created by ______________________ are Copyright (C) ______
_______________________. All Rights Reserved.
Contributor(s): ______________________________________.
Alternatively, the contents of this file may be used under the terms

of the _____ license (the "[___] License"), in which case the
provisions of [______] License are applicable instead of those
above. If you wish to allow use of your version of this file only
under the terms of the [____] License and not to allow others to use
your version of this file under the MPL, indicate your decision by
deleting the provisions above and replace them with the notice and
other provisions required by the [___] License. If you do not delete
the provisions above, a recipient may use your version of this file
under either the MPL or the [___] License."
[NOTE: The text of this Exhibit A may differ slightly from the text of
the notices in the Source Code files of the Original Code. You should
use the text of this Exhibit A rather than the text found in the
Original Code Source Code for Your Modifications.]
This Product includes DBD-mysql software under below license
Copyright (c) 2003 Rudolf Lippan
Copyright (c) 1997-2003 Jochen Wiedmann
You may distribute under the terms of either the GNU General Public
License or the Artistic License, as specified in the Perl README file.
This Product includes sg3_utils software under below license
Upstream Authors: Douglas Gilbert <dgilbert at interlog dot com>,
Bruce Allen <ballen at gravity dot phys dot uwm dot edu>,
Peter Allworth <linsol at zeta dot org dot au>,
James Bottomley <jejb at parisc-linux dot org>,
Lars Marowsky-Bree <lmb at suse dot de>,
Kurt Garloff <garloff at suse dot de>,
Grant Grundler <grundler at parisc-linux dot org>,
Christophe Varoqui <christophe dot varoqui at free dot fr>,
Michael Weller <eowmob at exp-math dot uni-essen dot de>,
Eric Youngdale <eric at andante dot org>
Copyright:
This software is copyright(c) 1994-2007 by the authors
You are free to distribute this software under the terms of
the GNU General Public License.
On Debian systems, the complete text of the GNU General Public
License can be found in /usr/share/common-licenses/GPL file.
many parts of this package are covered by the BSD license.
These include central error processing code (sg_lib.[hc]),
common command code (sg_cmds_basic.[hc] and sg_cmds_extra.[hc])
and later utilities. They are Copyright: Douglas Gilbert.
The author's intention is that the BSD licensed code can be used
freely by others. On Debian systems, the complete text of the
BSD License can be found in `/usr/share/common-licenses/BSD'.
This Product includes DBI software under below license
The DBI module is Copyright (c) 1994-2008 Tim Bunce. Ireland.
All rights reserved.

You may distribute under the terms of either the GNU General Public
License or the Artistic License, as specified in the Perl README file.
This Product includes flac software under below license
This is the Win32 binary release for the FLAC project.
All programs and plugins are released under the GPL (see COPYING.GPL)
except the Winamp 2 plugin which is LGPL (see COPYING.LGPL).
The documentation is released under the FDL (see COPYING.FDL).
This Product includes boost software under below license
BOOST SOFTWARE LICENSE
o License text
o Introduction
o History
o Rationale
o FAQ
o Transition
o Acknowledgements
INTRODUCTION
The Boost Software License specifies the terms and conditions of use for those Boost libraries that it covers.
Currently, some Boost libraries have their own licenses. The hope is that eventually all Boost libraries will be covered by the Boost
Software License. In the meantime, all libraries comply with the Boost License requirements.
HISTORY
As Boost grew, it became unmanageable for each Boost file to have its own license. Users complained that each license needed to be
reviewed, and that reviews were difficult or impossible if Boost libraries contained many different licenses. Boost moderators and
maintainers spent excessive time dealing with license issues. Boost developers often copied existing licenses without actually
knowing if the license wording met legal needs.
To clarify these licensing issues, the Boost moderators asked for help from the Berkman Center for Internet & Society at Harvard
Law School, Cambridge, Massachusetts, USA. It was requested that a single Boost license be developed that met the traditional
requirements that Boost licenses, particularly:
o Must be simple to read and understand.
o Must grant permission without fee to copy, use and modify the software for any use (commercial and non-commercial).
o Must require that the license appear with all copies [including redistributions] of the software source code.
o Must not require that the license appear with executables or other binary uses of the library.
o Must not require that the source code be available for execution or other binary uses of the library.
Additionally, other common open source licenses were studied to see what additional issues were being treated, and additions
representing good legal practice were also requested. The result is the Boost Software License:
Boost Software License - Version 1.0 - August 17th, 2003
Permission is hereby granted, free of charge, to any person or organization
obtaining a copy of the software and accompanying documentation covered by
this license (the "Software") to use, reproduce, display, distribute,
execute, and transmit the Software, and to prepare derivative works of the
Software, and to permit third-parties to whom the Software is furnished to
do so, all subject to the following:
The copyright notices in the Software and this entire statement, including
the above license grant, this restriction and the following disclaimer,
must be included in all copies of the Software, in whole or in part, and
all derivative works of the Software, unless such copies or derivative
works are solely in the form of machine-executable object code generated by
a source language processor.

THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NON-INFRINGEMENT. IN NO EVENT
SHALL THE COPYRIGHT HOLDERS OR ANYONE DISTRIBUTING THE SOFTWARE BE LIABLE
FOR ANY DAMAGES OR OTHER LIABILITY, WHETHER IN CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
RATIONALE
The following rationale was provided by Devin Smith, the lawyer who wrote the Boost Software License. It has been edited slightly
for brevity. Editorial additions are shown in square brackets.
BENEFIT OF COMMON SOFTWARE LICENSE
If one of Boost's goals is to ease use and adoption of the various libraries made available by Boost, it does make sense to try to
standardize the licenses under which the libraries are made available to users. (I make some recommendations about a possible
short-form license below.)
[Standardizing the license will not] necessarily address the issue of satisfying corporate licensees. Each corporation will have its
own concerns, based on their own experiences with software licensing and distribution and, if they're careful, will want to carefully
review each license, even if they've been told that they're all standard. I would expect that, unless we're remarkably brilliant (or
lucky) in drafting the standard Boost license, the standard license won't satisfy the legal departments of all corporations. I imagine
that some will, for instance, absolutely insist that licensors provide a warranty of title and provide indemnification for third-party
intellectual property infringement claims. Others may want functional warranties. (If I were advising the corporations, I would point
out that they're not paying anything for the code and getting such warranties from individual programmers, who probably do not
have deep pockets, is not that valuable anyway, but other lawyers may disagree.)
But this can be addressed, not by trying to craft the perfect standard license, but by informing the corporations that they can, if they
don't like the standard license, approach the authors to negotiate a different, perhaps even paid, license.
One other benefit of adopting a standard license is to help ensure that the license accomplishes, from a legal perspective, what the
authors intend. For instance, many of the [original] licenses for the libraries available on boost.org do not disclaim the warranty of
title, meaning that the authors could, arguably, be sued by a user if the code infringes the rights of a third party and the user is sued
by that third party. I think the authors probably want to disclaim this kind of liability.
SHORT-FORM LICENSE
Without in anyway detracting from the draft license that's been circulated [to Boost moderators], I'd like to propose an alternative
"short-form" license that Boost could have the library authors adopt. David [Abrahams] has expressed a desire to keep things as
simple as possible, and to try to move away from past practice as little as possible, and this is my attempt at a draft.
This license, which is very similar to the BSD license and the MIT license, should satisfy the Open Source Initiative's Open Source
Definition: (i) the license permits free redistribution, (ii) the distributed code includes source code, (iii) the license permits the
creation of derivative works, (iv) the license does not discriminate against persons or groups, (v) the license does not discriminate
against fields of endeavor, (vi) the rights apply to all to whom the program is redistributed, (vii) the license is not specific to a
product, and (viii) the license is technologically neutral (i.e., it does not [require] an explicit gesture of assent in order to establish a
contract between licensor and licensee).
This license grants all rights under the owner's copyrights (as well as an implied patent license), disclaims all liability for use of the
code (including intellectual property infringement liability), and requires that all subsequent copies of the code [except
machine-executable object code], including partial copies and derivative works, include the license.
FAQ
How should Boost programmers apply the license to source and header files? Add a comment based on the following template,
substituting appropriate text for the italicized portion:
// Copyright Joe Coder 2004 - 2006.
// Distributed under the Boost Software License, Version 1.0.
// (See accompanying file LICENSE_1_0.txt or copy at
// http://www.boost.org/LICENSE_1_0.txt)
Please leave an empty line before and after the above comment block. It is fine if the copyright and license messages are not on
different lines; in no case there should be other intervening text. Do not include "All rights reserved" anywhere.
Other ways of licensing source files have been considered, but some of them turned out to unintentionally nullify legal elements of
the license. Having fixed language for referring to the license helps corporate legal departments evaluate the boost distribution.
Creativity in license reference language is strongly discouraged, but judicious changes in the use of whitespace are fine.
How should the license be applied to documentation files, instead? Very similarly to the way it is applied to source files: the user
should see the very same text indicated in the template above, with the only difference that both the local and the web copy of
LICENSE_1_0.txt should be linked to. Refer to the HTML source code of this page in case of doubt.
Note that the location of the local LICENSE_1_0.txt needs to be indicated relatively to the position of your documentation file

(../LICENSE_1_0.txt, ../../LICENSE_1_0.txt etc.)
How is the Boost license different from the GNU General Public License (GPL)? The Boost license permits the creation of
derivative works for commercial or non-commercial use with no legal requirement to release your source code. Other differences
include Boost not requiring reproduction of copyright messages for object code redistribution, and the fact that the Boost license is
not "viral": if you distribute your own code along with some Boost code, the Boost license applies only to the Boost code (and
modified versions thereof); you are free to license your own code under any terms you like. The GPL is also much longer, and thus
may be harder to understand.
Why the phrase "machine-executable object code generated by a source language processor"? To distinguish cases where we
do not require reproduction of the copyrights and license, such as object libraries, shared libraries, and final program executables,
from cases where reproduction is still required, such as distribution of self-extracting archives of source code or precompiled header
files. More detailed wording was rejected as not being legally necessary, and reducing readability.
Why is the "disclaimer" paragraph of the license entirely in uppercase? Capitalization of these particular provisions is a US
legal mandate for consumer protection. (Diane Cabell)
Does the copyright and license cover interfaces too? The conceptual interface to a library isn't covered. The particular
representation expressed in the header is covered, as is the documentation, examples, test programs, and all the other material that
goes with the library. A different implementation is free to use the same logical interface, however. Interface issues have been
fought out in court several times; ask a lawyer for details.
Why doesn't the license prohibit the copyright holder from patenting the covered software? No one who distributes their code
under the terms of this license could turn around and sue a user for patent infringement. (Devin Smith)
Boost's lawyers were well aware of patent provisions in licenses like the GPL and CPL, and would have included such provisions in
the Boost license if they were believed to be legally useful.
Why doesn't the copyright message say "All rights reserved"? Devin Smith says "I don't think it belongs in the copyright notice
for anything (software, electronic documentation, etc.) that is being licensed. It belongs in books that are sold where, in fact, all
rights (e.g., to reproduce the book, etc.) are being reserved in the publisher or author. I think it shouldn't be in the BSD license."
Do I have to copyright/license trivial files? Even a test file that just contains an empty main() should have a copyright. Files
without copyrights make corporate lawyers nervous, and that's a barrier to adoption. The more of Boost is uniformly copyrighted
and licensed, the less problem people will have with mounting a Boost release CD on a corporate server.
Can I use the Boost license for my own projects outside Boost? Sure; there are no restrictions on the use of the license itself.
Is the Boost license "Open Source"? Yes. The Open Source Initiative certified the Boost Software License 1.0 in early 2008.
TRANSITION
To ease the transition of the code base towards the new common license, several people decided to give a blanket permission for all
their contributions to use the new license. This hopefully helps maintainers to switch to the new license once the list contains
enough names without asking over and over again for each change. Please consider adding your name to the list.
ACKNOWLEDGEMENTS
Dave Abrahams led the Boost effort to develop better licensing. The legal team was led by Diane Cabell, Director, Clinical
Programs, Berkman Center for Internet & Society, Harvard Law School. Devin Smith, attorney, Nixon Peabody LLP, wrote the
Boost License. Eva Chan, Harvard Law School, contributed analysis of Boost issues and drafts of various legal documents. Boost
members reviewed drafts of the license. Beman Dawes wrote this web page.
Revised $Date: 2009-06-07 07:14:52 -0400 (Sun, 07 Jun 2009) $
Copyright Beman Dawes, Daniel Frey, David Abrahams, 2003-2004.
Copyright Rene Rivera 2004-2005.
Distributed under the Boost Software License, Version 1.0.
This Product includes curl software under below license
COPYRIGHT AND PERMISSION NOTICE
Copyright (c) 1996 - 2009, Daniel Stenberg, <daniel@haxx.se>.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose
with or without fee is hereby granted, provided that the above copyright
notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY RIGHTS. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE
OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not
be used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization of the copyright holder.
License Issues
Curl and libcurl are released under a MIT/X derivate license. The license is
very liberal and should not impose a problem for your project. This section
is just a brief summary for the cases we get the most questions. (Parts of
this section was much enhanced by Bjorn Reese.)
We are not lawyers and this is not legal advice. You should probably consult
one if you want true and accurate legal insights without our prejudice.
6.1 I have a GPL program, can I use the libcurl library?
Yes!
Since libcurl may be distributed under the MIT/X derivate license, it can be
used together with GPL in any software.
6.2 I have a closed-source program, can I use the libcurl library?
Yes!
libcurl does not put any restrictions on the program that uses the library.
6.3 I have a BSD licensed program, can I use the libcurl library?
Yes!
libcurl does not put any restrictions on the program that uses the library.
6.4 I have a program that uses LGPL libraries, can I use libcurl?
Yes!
The LGPL license doesn't clash with other licenses.
6.5 Can I modify curl/libcurl for my program and keep the changes secret?
Yes!
The MIT/X derivate license practically allows you to do almost anything with
the sources, on the condition that the copyright texts in the sources are
left intact.
6.6 Can you please change the curl/libcurl license to XXXX?
No.
We have carefully picked this license after years of development and
discussions and a large amount of people have contributed with source code
knowing that this is the license we use. This license puts the restrictions
we want on curl/libcurl and it does not spread to other programs or
libraries that use it. It should be possible for everyone to use libcurl or
curl in their projects, no matter what license they already have in use.
6.7 What are my obligations when using libcurl in my commercial apps?
Next to none. All you need to adhere to is the MIT-style license (stated in
the COPYING file) which basically says you have to include the copyright
notice in "all copies" and that you may not use the copyright holder's name
when promoting your software.

You do not have to release any of your source code.
You do not have to reveal or make public any changes to the libcurl source
code.
You do not have to reveal or make public that you are using libcurl within
your app.
As can be seen here: http://curl.haxx.se/docs/companies.html and
elsewhere, more and more companies are discovering the power
of libcurl and take advantage of it even in commercial environments.
This Product includes httpd software under below license
Apache HTTP Server
Copyright 2008 The Apache Software Foundation.
This product includes software developed at
The Apache Software Foundation (http://www.apache.org/).
Portions of this software were developed at the National Center
for Supercomputing Applications (NCSA) at the University of
Illinois at Urbana-Champaign.
This software contains code derived from the RSA Data Security
Inc. MD5 Message-Digest Algorithm, including various
modifications by Spyglass Inc., Carnegie Mellon University, and
Bell Communications Research, Inc (Bellcore).
Regular expression support is provided by the PCRE library package,
which is open source software, written by Philip Hazel, and copyright
by the University of Cambridge, England. The original software is
available from
ftp://ftp.csx.cam.ac.uk/pub/software/programming/pcre/
Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1. Definitions.
"License" shall mean the terms and conditions for use, reproduction,
and distribution as defined by Sections 1 through 9 of this document.
"Licensor" shall mean the copyright owner or entity authorized by
the copyright owner that is granting the License.
"Legal Entity" shall mean the union of the acting entity and all
other entities that control, are controlled by, or are under common
control with that entity. For the purposes of this definition,
"control" means (i) the power, direct or indirect, to cause the
direction or management of such entity, whether by contract or
otherwise, or (ii) ownership of fifty percent (50%) or more of the
outstanding shares, or (iii) beneficial ownership of such entity.
"You" (or "Your") shall mean an individual or Legal Entity
exercising permissions granted by this License.
"Source" form shall mean the preferred form for making modifications,
including but not limited to software source code, documentation
source, and configuration files.
"Object" form shall mean any form resulting from mechanical
transformation or translation of a Source form, including but
not limited to compiled object code, generated documentation,
and conversions to other media types.
"Work" shall mean the work of authorship, whether in Source or
Object form, made available under the License, as indicated by a
copyright notice that is included in or attached to the work
(an example is provided in the Appendix below).
"Derivative Works" shall mean any work, whether in Source or Object
form, that is based on (or derived from) the Work and for which the
editorial revisions, annotations, elaborations, or other modifications
represent, as a whole, an original work of authorship. For the purposes
of this License, Derivative Works shall not include works that remain
separable from, or merely link (or bind by name) to the interfaces of,
the Work and Derivative Works thereof.
"Contribution" shall mean any work of authorship, including
the original version of the Work and any modifications or additions
to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner
or by an individual or Legal Entity authorized to submit on behalf of
the copyright owner. For the purposes of this definition, "submitted"
means any form of electronic, verbal, or written communication sent
to the Licensor or its representatives, including but not limited to
communication on electronic mailing lists, source code control systems,
and issue tracking systems that are managed by, or on behalf of, the
Licensor for the purpose of discussing and improving the Work, but
excluding communication that is conspicuously marked or otherwise
designated in writing by the copyright owner as "Not a Contribution."
"Contributor" shall mean Licensor and any individual or Legal Entity
on behalf of whom a Contribution has been received by Licensor and
subsequently incorporated within the Work.
2. Grant of Copyright License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
copyright license to reproduce, prepare Derivative Works of,
publicly display, publicly perform, sublicense, and distribute the
Work and such Derivative Works in Source or Object form.
3. Grant of Patent License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
(except as stated in this section) patent license to make, have made,
use, offer to sell, sell, import, and otherwise transfer the Work,
where such license applies only to those patent claims licensable
by such Contributor that are necessarily infringed by their
Contribution(s) alone or by combination of their Contribution(s)
with the Work to which such Contribution(s) was submitted. If You
institute patent litigation against any entity (including a
cross-claim or counterclaim in a lawsuit) alleging that the Work
or a Contribution incorporated within the Work constitutes direct
or contributory patent infringement, then any patent licenses
granted to You under this License for that Work shall terminate
as of the date such litigation is filed.
4. Redistribution. You may reproduce and distribute copies of the
Work or Derivative Works thereof in any medium, with or without
modifications, and in Source or Object form, provided that You
meet the following conditions:
(a) You must give any other recipients of the Work or
Derivative Works a copy of this License; and
(b) You must cause any modified files to carry prominent notices
stating that You changed the files; and
(c) You must retain, in the Source form of any Derivative Works
that You distribute, all copyright, patent, trademark, and
attribution notices from the Source form of the Work,
excluding those notices that do not pertain to any part of
the Derivative Works; and
(d) If the Work includes a "NOTICE" text file as part of its
distribution, then any Derivative Works that You distribute must
include a readable copy of the attribution notices contained
within such NOTICE file, excluding those notices that do not
pertain to any part of the Derivative Works, in at least one
of the following places: within a NOTICE text file distributed
as part of the Derivative Works; within the Source form or
documentation, if provided along with the Derivative Works; or,
within a display generated by the Derivative Works, if and
wherever such third-party notices normally appear. The contents
of the NOTICE file are for informational purposes only and
do not modify the License. You may add Your own attribution
notices within Derivative Works that You distribute, alongside
or as an addendum to the NOTICE text from the Work, provided
that such additional attribution notices cannot be construed
as modifying the License.
You may add Your own copyright statement to Your modifications and
may provide additional or different license terms and conditions
for use, reproduction, or distribution of Your modifications, or
for any such Derivative Works as a whole, provided Your use,
reproduction, and distribution of the Work otherwise complies with
the conditions stated in this License.
5. Submission of Contributions. Unless You explicitly state otherwise,
any Contribution intentionally submitted for inclusion in the Work
by You to the Licensor shall be under the terms and conditions of
this License, without any additional terms or conditions.
Notwithstanding the above, nothing herein shall supersede or modify
the terms of any separate license agreement you may have executed
with Licensor regarding such Contributions.
6. Trademarks. This License does not grant permission to use the trade
names, trademarks, service marks, or product names of the Licensor,
except as required for reasonable and customary use in describing the
origin of the Work and reproducing the content of the NOTICE file.
7. Disclaimer of Warranty. Unless required by applicable law or
agreed to in writing, Licensor provides the Work (and each
Contributor provides its Contributions) on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
implied, including, without limitation, any warranties or conditions
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
PARTICULAR PURPOSE. You are solely responsible for determining the
appropriateness of using or redistributing the Work and assume any
risks associated with Your exercise of permissions under this License.
8. Limitation of Liability. In no event and under no legal theory,
whether in tort (including negligence), contract, or otherwise,
unless required by applicable law (such as deliberate and grossly
negligent acts) or agreed to in writing, shall any Contributor be
liable to You for damages, including any direct, indirect, special,
incidental, or consequential damages of any character arising as a
result of this License or out of the use or inability to use the
Work (including but not limited to damages for loss of goodwill,
work stoppage, computer failure or malfunction, or any and all
other commercial damages or losses), even if such Contributor
has been advised of the possibility of such damages.
9. Accepting Warranty or Additional Liability. While redistributing
the Work or Derivative Works thereof, You may choose to offer,
and charge a fee for, acceptance of support, warranty, indemnity,
or other liability obligations and/or rights consistent with this
License. However, in accepting such obligations, You may act only
on Your own behalf and on Your sole responsibility, not on behalf
of any other Contributor, and only if You agree to indemnify,
defend, and hold each Contributor harmless for any liability
incurred by, or claims asserted against, such Contributor by reason
of your accepting any such warranty or additional liability.
END OF TERMS AND CONDITIONS
APPENDIX: How to apply the Apache License to your work.
To apply the Apache License to your work, attach the following
boilerplate notice, with the fields enclosed by brackets "[]"
replaced with your own identifying information. (Don't include
the brackets!) The text should be enclosed in the appropriate
comment syntax for the file format. We also recommend that a
file or class name and description of purpose be included on the
same "printed page" as the copyright notice for easier
identification within third-party archives.
Copyright [yyyy] [name of copyright owner]
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
APACHE HTTP SERVER SUBCOMPONENTS:
The Apache HTTP Server includes a number of subcomponents with
separate copyright notices and license terms. Your use of the source
code for the these subcomponents is subject to the terms and
conditions of the following licenses.
For the mod_mime_magic component:
/*
* mod_mime_magic: MIME type lookup via file magic numbers
* Copyright (c) 1996-1997 Cisco Systems, Inc.
*
* This software was submitted by Cisco Systems to the Apache Group in July
* 1997. Future revisions and derivatives of this source code must
* acknowledge Cisco Systems as the original contributor of this module.
* All other licensing and usage conditions are those of the Apache Group.
*
* Some of this code is derived from the free version of the file command
* originally posted to comp.sources.unix. Copyright info for that program
* is included below as required.
* ---------------------------------------------------------------------------
* - Copyright (c) Ian F. Darwin, 1987. Written by Ian F. Darwin.
*
* This software is not subject to any license of the American Telephone and
* Telegraph Company or of the Regents of the University of California.
*
* Permission is granted to anyone to use this software for any purpose on any
* computer system, and to alter it and redistribute it freely, subject to
* the following restrictions:
*
* 1. The author is not responsible for the consequences of use of this
* software, no matter how awful, even if they arise from flaws in it.
*
* 2. The origin of this software must not be misrepresented, either by
* explicit claim or by omission. Since few users ever read sources, credits
* must appear in the documentation.
*
* 3. Altered versions must be plainly marked as such, and must not be
* misrepresented as being the original software. Since few users ever read
* sources, credits must appear in the documentation.
*
* 4. This notice may not be removed or altered.
* -------------------------------------------------------------------------
*
*/
For the modules\mappers\mod_imagemap.c component:
"macmartinized" polygon code copyright 1992 by Eric Haines, erich@eye.com
For the server\util_md5.c component:
/************************************************************************
* NCSA HTTPd Server
* Software Development Group
* National Center for Supercomputing Applications
* University of Illinois at Urbana-Champaign
* 605 E. Springfield, Champaign, IL 61820
* httpd@ncsa.uiuc.edu
*
* Copyright (C) 1995, Board of Trustees of the University of Illinois
*
************************************************************************
*
* md5.c: NCSA HTTPd code which uses the md5c.c RSA Code
*
* Original Code Copyright (C) 1994, Jeff Hostetler, Spyglass, Inc.
* Portions of Content-MD5 code Copyright (C) 1993, 1994 by Carnegie Mellon
* University (see Copyright below).
* Portions of Content-MD5 code Copyright (C) 1991 Bell Communications
* Research, Inc. (Bellcore) (see Copyright below).
* Portions extracted from mpack, John G. Myers - jgm+@cmu.edu
* Content-MD5 Code contributed by Martin Hamilton (martin@net.lut.ac.uk)
*
*/
/* these portions extracted from mpack, John G. Myers - jgm+@cmu.edu */
/* (C) Copyright 1993,1994 by Carnegie Mellon University
* All Rights Reserved.
*
* Permission to use, copy, modify, distribute, and sell this software
* and its documentation for any purpose is hereby granted without
* fee, provided that the above copyright notice appear in all copies
* and that both that copyright notice and this permission notice
* appear in supporting documentation, and that the name of Carnegie
* Mellon University not be used in advertising or publicity
* pertaining to distribution of the software without specific,
* written prior permission. Carnegie Mellon University makes no
* representations about the suitability of this software for any
* purpose. It is provided "as is" without express or implied
* warranty.
*
* CARNEGIE MELLON UNIVERSITY DISCLAIMS ALL WARRANTIES WITH REGARD TO
* THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
* AND FITNESS, IN NO EVENT SHALL CARNEGIE MELLON UNIVERSITY BE LIABLE
* FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
* WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN
* AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING
* OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
* SOFTWARE.
*/
/*
* Copyright (c) 1991 Bell Communications Research, Inc. (Bellcore)
*
* Permission to use, copy, modify, and distribute this material
* for any purpose and without fee is hereby granted, provided
* that the above copyright notice and this permission notice
* appear in all copies, and that the name of Bellcore not be
* used in advertising or publicity pertaining to this
* material without the specific, prior written permission
* of an authorized representative of Bellcore. BELLCORE
* MAKES NO REPRESENTATIONS ABOUT THE ACCURACY OR SUITABILITY
* OF THIS MATERIAL FOR ANY PURPOSE. IT IS PROVIDED "AS IS",
* WITHOUT ANY EXPRESS OR IMPLIED WARRANTIES.
*/
For the srclib\apr\include\apr_md5.h component:
/*
* This is work is derived from material Copyright RSA Data Security, Inc.
*
* The RSA copyright statement and Licence for that original material is
* included below. This is followed by the Apache copyright statement and
* licence for the modifications made to that material.
*/
/* Copyright (C) 1991-2, RSA Data Security, Inc. Created 1991. All
rights reserved.
License to copy and use this software is granted provided that it
is identified as the "RSA Data Security, Inc. MD5 Message-Digest
Algorithm" in all material mentioning or referencing this software
or this function.
License is also granted to make and use derivative works provided
that such works are identified as "derived from the RSA Data
Security, Inc. MD5 Message-Digest Algorithm" in all material
mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either
the merchantability of this software or the suitability of this
software for any particular purpose. It is provided "as is"
without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this
documentation and/or software.
*/
For the srclib\apr\passwd\apr_md5.c component:
/*
* This is work is derived from material Copyright RSA Data Security, Inc.
*
* The RSA copyright statement and Licence for that original material is
* included below. This is followed by the Apache copyright statement and
* licence for the modifications made to that material.
*/
/* MD5C.C - RSA Data Security, Inc., MD5 message-digest algorithm
*/
/* Copyright (C) 1991-2, RSA Data Security, Inc. Created 1991. All
rights reserved.
License to copy and use this software is granted provided that it
is identified as the "RSA Data Security, Inc. MD5 Message-Digest
Algorithm" in all material mentioning or referencing this software
or this function.
License is also granted to make and use derivative works provided
that such works are identified as "derived from the RSA Data
Security, Inc. MD5 Message-Digest Algorithm" in all material
mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either
the merchantability of this software or the suitability of this
software for any particular purpose. It is provided "as is"
without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this
documentation and/or software.
*/
/*
* The apr_md5_encode() routine uses much code obtained from the FreeBSD 3.0
* MD5 crypt() function, which is licenced as follows:
* ----------------------------------------------------------------------------
* "THE BEER-WARE LICENSE" (Revision 42):
* <phk@login.dknet.dk> wrote this file. As long as you retain this notice you
* can do whatever you want with this stuff. If we meet some day, and you think
* this stuff is worth it, you can buy me a beer in return. Poul-Henning Kamp
* ----------------------------------------------------------------------------
*/
For the srclib\apr-util\crypto\apr_md4.c component:
* This is derived from material copyright RSA Data Security, Inc.
* Their notice is reproduced below in its entirety.
*
* Copyright (C) 1991-2, RSA Data Security, Inc. Created 1991. All
* rights reserved.
*
* License to copy and use this software is granted provided that it
* is identified as the "RSA Data Security, Inc. MD4 Message-Digest
* Algorithm" in all material mentioning or referencing this software
* or this function.
*
* License is also granted to make and use derivative works provided
* that such works are identified as "derived from the RSA Data
* Security, Inc. MD4 Message-Digest Algorithm" in all material
* mentioning or referencing the derived work.
*
* RSA Data Security, Inc. makes no representations concerning either
* the merchantability of this software or the suitability of this
* software for any particular purpose. It is provided "as is"
* without express or implied warranty of any kind.
*
* These notices must be retained in any copies of any part of this
* documentation and/or software.
*/
For the srclib\apr-util\include\apr_md4.h component:
*
* This is derived from material copyright RSA Data Security, Inc.
* Their notice is reproduced below in its entirety.
*
* Copyright (C) 1991-2, RSA Data Security, Inc. Created 1991. All
* rights reserved.
*
* License to copy and use this software is granted provided that it
* is identified as the "RSA Data Security, Inc. MD4 Message-Digest
* Algorithm" in all material mentioning or referencing this software
* or this function.
*
* License is also granted to make and use derivative works provided
* that such works are identified as "derived from the RSA Data
* Security, Inc. MD4 Message-Digest Algorithm" in all material
* mentioning or referencing the derived work.
*
* RSA Data Security, Inc. makes no representations concerning either
* the merchantability of this software or the suitability of this
* software for any particular purpose. It is provided "as is"
* without express or implied warranty of any kind.
*
* These notices must be retained in any copies of any part of this
* documentation and/or software.
*/
For the srclib\apr-util\test\testmd4.c component:
*
* This is derived from material copyright RSA Data Security, Inc.
* Their notice is reproduced below in its entirety.
*
* Copyright (C) 1990-2, RSA Data Security, Inc. Created 1990. All
* rights reserved.
*
* RSA Data Security, Inc. makes no representations concerning either
* the merchantability of this software or the suitability of this
* software for any particular purpose. It is provided "as is"
* without express or implied warranty of any kind.
*
* These notices must be retained in any copies of any part of this
* documentation and/or software.
*/
For the srclib\apr-util\xml\expat\conftools\install-sh component:
#
# install - install a program, script, or datafile
# This comes from X11R5 (mit/util/scripts/install.sh).
#
# Copyright 1991 by the Massachusetts Institute of Technology
#
# Permission to use, copy, modify, distribute, and sell this software and its
# documentation for any purpose is hereby granted without fee, provided that
# the above copyright notice appear in all copies and that both that
# copyright notice and this permission notice appear in supporting
# documentation, and that the name of M.I.T. not be used in advertising or
# publicity pertaining to distribution of the software without specific,
# written prior permission. M.I.T. makes no representations about the
# suitability of this software for any purpose. It is provided "as is"
# without express or implied warranty.
#
For the srclib\pcre\install-sh component:
#
# Copyright 1991 by the Massachusetts Institute of Technology
#
# Permission to use, copy, modify, distribute, and sell this software and its
# documentation for any purpose is hereby granted without fee, provided that
# the above copyright notice appear in all copies and that both that
# copyright notice and this permission notice appear in supporting
# documentation, and that the name of M.I.T. not be used in advertising or
# publicity pertaining to distribution of the software without specific,
# written prior permission. M.I.T. makes no representations about the
# suitability of this software for any purpose. It is provided "as is"
# without express or implied warranty.
For the pcre component:
PCRE LICENCE
------------
PCRE is a library of functions to support regular expressions whose syntax
and semantics are as close as possible to those of the Perl 5 language.
Release 5 of PCRE is distributed under the terms of the "BSD" licence, as
specified below. The documentation for PCRE, supplied in the "doc"
directory, is distributed under the same terms as the software itself.
Written by: Philip Hazel <ph10@cam.ac.uk>
University of Cambridge Computing Service,
Cambridge, England. Phone: +44 1223 334714.
Copyright (c) 1997-2004 University of Cambridge
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of the University of Cambridge nor the names of its
contributors may be used to endorse or promote products derived from
this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
End PCRE LICENCE
For the test\zb.c component:
/* ZeusBench V1.01
===============
This program is Copyright (C) Zeus Technology Limited 1996.

This program may be used and copied freely providing this copyright notice
is not removed.
This software is provided "as is" and any express or implied waranties,
including but not limited to, the implied warranties of merchantability and
fitness for a particular purpose are disclaimed. In no event shall
Zeus Technology Ltd. be liable for any direct, indirect, incidental, special,
exemplary, or consequential damaged (including, but not limited to,
procurement of substitute good or services; loss of use, data, or profits;
or business interruption) however caused and on theory of liability. Whether
in contract, strict liability or tort (including negligence or otherwise)
arising in any way out of the use of this software, even if advised of the
possibility of such damage.
Written by Adam Twiss (adam@zeus.co.uk). March 1996
Thanks to the following people for their input:
Mike Belshe (mbelshe@netscape.com)
Michael Campanella (campanella@stevms.enet.dec.com)
*/
For the expat xml parser component:
Copyright (c) 1998, 1999, 2000 Thai Open Source Software Center Ltd
and Clark Cooper
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY
CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT,
TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
====================================================================
This Product includes libtecla software under below license
Copyright (c) 2000, 2001, 2002, 2003, 2004 by Martin C. Shepherd.
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, and/or sell copies of the Software, and to permit persons

to whom the Software is furnished to do so, provided that the above
copyright notice(s) and this permission notice appear in all copies of
the Software and that both the above copyright notice(s) and this
permission notice appear in supporting documentation.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT
OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR
HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL
INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING
FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION
WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Except as contained in this notice, the name of a copyright holder
shall not be used in advertising or otherwise to promote the sale, use
or other dealings in this Software without prior written authorization
of the copyright holder.
This Product includes libtorrent-rasterbar software under below license
Copyright (c) 2003 - 2007, Arvid Norberg
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions
are met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in
the documentation and/or other materials provided with the distribution.
* Neither the name of Rasterbar Software nor the names of its
contributors may be used to endorse or promote products derived
from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This Product includes libupnp software under below license
Copyright (c) 2000-2003 Intel Corporation
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.

* Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
* Neither name of Intel Corporation nor the names of its contributors
may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL INTEL OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This Product includes cups software under below license
Common UNIX Printing System
License Agreement
Copyright 1997-2005 by Easy Software Products
44141 AIRPORT VIEW DR STE 204
HOLLYWOOD, MARYLAND 20636 USA
Voice: +1.301.373.9600
Email: cups-info@cups.org
WWW: http://www.cups.org
Introduction
The Common UNIX Printing SystemTM, ("CUPSTM"), is provided under the GNU General
Public License ("GPL") and GNU Library General Public License ("LGPL"), Version 2, with
exceptions for Apple operating systems and the OpenSSL toolkit. A copy of the exceptions
and licenses follow this introduction.
The GNU LGPL applies to the CUPS API library, located in the "cups" subdirectory of the
CUPS source distribution and in the "cups" include directory and library files in the binary
distributions. The GNU GPL applies to the remainder of the CUPS distribution, including the
"pdftops" filter which is based upon Xpdf and the CUPS imaging library.
For those not familiar with the GNU GPL, the license basically allows you to:
Use the CUPS software at no charge.
Distribute verbatim copies of the software in source or binary form.
Sell verbatim copies of the software for a media fee, or sell support for the
software.
Distribute or sell printer drivers and filters that use CUPS so long as source code
is made available under the GPL.
What this license does not allow you to do is make changes or add features to CUPS and
then sell a binary distribution without source code. You must provide source for any new
drivers, changes, or additions to the software, and all code must be provided under the GPL
or LGPL as appropriate. The only exceptions to this are the portions of the CUPS software
covered by the Apple operating system license exceptions outlined later in this license
agreement.
The GNU LGPL relaxes the "link-to" restriction, allowing you to develop applications that
use the CUPS API library under other licenses and/or conditions as appropriate for your
application.
License Exceptions
In addition, as the copyright holder of CUPS, Easy Software Products grants the following
special exceptions:
1. Apple Operating System Development License Exception;
a. Software that is developed by any person or entity for an Apple
Operating System ("Apple OS-Developed Software"), including but not
limited to Apple and third party printer drivers, filters, and backends for
an Apple Operating System, that is linked to the CUPS imaging library
or based on any sample filters or backends provided with CUPS shall not
be considered to be a derivative work or collective work based on the
CUPS program and is exempt from the mandatory source code release
clauses of the GNU GPL. You may therefore distribute linked
combinations of the CUPS imaging library with Apple OS-Developed
Software without releasing the source code of the Apple OS-Developed
Software. You may also use sample filters and backends provided with
CUPS to develop Apple OS-Developed Software without releasing the
source code of the Apple OS-Developed Software.
b. An Apple Operating System means any operating system software
developed and/or marketed by Apple Computer, Inc., including but not
limited to all existing releases and versions of Apple's Darwin, Mac OS
X, and Mac OS X Server products and all follow-on releases and future
versions thereof.
c. This exception is only available for Apple OS-Developed Software and
does not apply to software that is distributed for use on other operating
systems.
d. All CUPS software that falls under this license exception have the
following text at the top of each source file:
This file is subject to the Apple OS-Developed Software exception.
2. OpenSSL Toolkit License Exception;
a. Easy Software Products explicitly allows the compilation and
distribution of the CUPS software with the OpenSSL Toolkit.
No developer is required to provide these exceptions in a derived work.
Trademarks
Easy Software Products has trademarked the Common UNIX Printing System, CUPS, and
CUPS logo. You may use these names and logos in any direct port or binary distribution of
CUPS. Please contact Easy Software Products for written permission to use them in
derivative products. Our intention is to protect the value of these trademarks and ensure that
any derivative product meets the same high-quality standards as the original.
Binary Distribution Rights
Easy Software Products also sells rights to the CUPS source code under a binary distribution
license for vendors that are unable to release source code for their drivers, additions, and
modifications to CUPS under the GNU GPL and LGPL. For information please contact us at
the address shown above.
The Common UNIX Printing System provides a "pdftops" filter that is based on the Xpdf
software. For binary distribution licensing of this software, please contact:
Derek B. Noonburg
Email: derekn@foolabs.com
WWW: http://www.foolabs.com/xpdf/
Support
Easy Software Products sells software support for CUPS as well as a commercial printing
product based on CUPS called ESP Print Pro. You can find out more at our web site:
http://www.easysw.com/
This Product includes libxml2 software under below license
Except where otherwise noted in the source code (e.g. the files hash.c,
list.c and the trio files, which are covered by a similar licence but
with different Copyright notices) all the files are:
Copyright (C) 1998-2003 Daniel Veillard. All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is fur-
nished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FIT-
NESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
DANIEL VEILLARD BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CON-
NECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of Daniel Veillard shall not
be used in advertising or otherwise to promote the sale, use or other deal-
ings in this Software without prior written authorization from him.
This Product includes ntp software under below license
Copyright (c) University of Delaware 1992-2010
Permission to use, copy, modify, and distribute this software and its documentation for any purpose with or without fee is hereby
granted, provided that the above copyright notice appears in all copies and that both the copyright notice and this permission notice
appear in supporting documentation, and that the name University of Delaware not be used in advertising or publicity pertaining to
distribution of the software without specific, written prior permission. The University of Delaware makes no representations about
the suitability this software for any purpose. It is provided "as is" without express or implied warranty.
The following individuals contributed in part to the Network Time Protocol Distribution Version 4 and are acknowledged as authors
of this work.
1. Mark Andrews <mark_andrews@isc.org> Leitch atomic clock controller
2. Bernd Altmeier <altmeier@atlsoft.de> hopf Elektronik serial line and PCI-bus devices
3. Viraj Bais <vbais@mailman1.intel.com> and Clayton Kirkwood <kirkwood@striderfm.intel.com> port to WindowsNT
3.5

4. Michael Barone <michael,barone@lmco.com> GPSVME fixes
5. Jean-Francois Boudreault <Jean-Francois.Boudreault@viagenie.qc.ca>IPv6 support
6. Karl Berry <karl@owl.HQ.ileaf.com> syslog to file option
7. Greg Brackley <greg.brackley@bigfoot.com> Major rework of WINNT port. Clean up recvbuf and iosignal code into
separate modules.
8. Marc Brett <Marc.Brett@westgeo.com> Magnavox GPS clock driver
9. Piete Brooks <Piete.Brooks@cl.cam.ac.uk> MSF clock driver, Trimble PARSE support
10. Reg Clemens <reg@dwf.com> Oncore driver (Current maintainer)
11. Steve Clift <clift@ml.csiro.au> OMEGA clock driver
12. Casey Crellin <casey@csc.co.za> vxWorks (Tornado) port and help with target configuration
13. Sven Dietrich <sven_dietrich@trimble.com> Palisade reference clock driver, NT adj. residuals, integrated Greg's Winnt
port.
14. John A. Dundas III <dundas@salt.jpl.nasa.gov> Apple A/UX port
15. Torsten Duwe <duwe@immd4.informatik.uni-erlangen.de> Linux port
16. Dennis Ferguson <dennis@mrbill.canet.ca> foundation code for NTP Version 2 as specified in RFC-1119
17. John Hay <jhay@icomtek.csir.co.za> IPv6 support and testing
18. Dave Hart <davehart@davehart.com> General maintenance, Windows port interpolation rewrite.
19. Claas Hilbrecht <neoclock4x@linum.com> NeoClock4X clock driver
20. Glenn Hollinger <glenn@herald.usask.ca> GOES clock driver
21. Mike Iglesias <iglesias@uci.edu> DEC Alpha port
22. Jim Jagielski <jim@jagubox.gsfc.nasa.gov> A/UX port
23. Jeff Johnson <jbj@chatham.usdesign.com> massive prototyping overhaul
24. Hans Lambermont <Hans.Lambermont@nl.origin-it.com> or <H.Lambermont@chello.nl> ntpsweep
25. Poul-Henning Kamp <phk@FreeBSD.ORG> Oncore driver (Original author)
26. Frank Kardel <kardel (at) ntp (dot) org> PARSE <GENERIC> driver (>14 reference clocks), STREAMS modules for
PARSE, support scripts, syslog cleanup, dynamic interface handling
27. William L. Jones <jones@hermes.chpc.utexas.edu> RS/6000 AIX modifications, HPUX modifications
28. Dave Katz <dkatz@cisco.com> RS/6000 AIX port
29. Craig Leres <leres@ee.lbl.gov> 4.4BSD port, ppsclock, Magnavox GPS clock driver
30. George Lindholm <lindholm@ucs.ubc.ca> SunOS 5.1 port
31. Louis A. Mamakos <louie@ni.umd.edu> MD5-based authentication
32. Lars H. Mathiesen <thorinn@diku.dk> adaptation of foundation code for Version 3 as specified in RFC-1305
33. Danny Mayer <mayer@ntp.org>Network I/O, Windows Port, Code Maintenance
34. David L. Mills <mills@udel.edu> Version 4 foundation: clock discipline, authentication, precision kernel; clock drivers:
Spectracom, Austron, Arbiter, Heath, ATOM, ACTS, KSI/Odetics; audio clock drivers: CHU, WWV/H, IRIG
35. Wolfgang Moeller <moeller@gwdgv1.dnet.gwdg.de> VMS port
36. Jeffrey Mogul <mogul@pa.dec.com> ntptrace utility
37. Tom Moore <tmoore@fievel.daytonoh.ncr.com> i386 svr4 port
38. Kamal A Mostafa <kamal@whence.com> SCO OpenServer port
39. Derek Mulcahy <derek@toybox.demon.co.uk> and Damon Hart-Davis <d@hd.org> ARCRON MSF clock driver
40. Rob Neal <neal@ntp.org> Bancomm refclock and config/parse code maintenance
41. Rainer Pruy <Rainer.Pruy@informatik.uni-erlangen.de> monitoring/trap scripts, statistics file handling
42. Dirce Richards <dirce@zk3.dec.com> Digital UNIX V4.0 port
43. Wilfredo Sánchez <wsanchez@apple.com> added support for NetInfo
44. Nick Sayer <mrapple@quack.kfu.com> SunOS streams modules
45. Jack Sasportas <jack@innovativeinternet.com> Saved a Lot of space on the stuff in the html/pic/ subdirectory
46. Ray Schnitzler <schnitz@unipress.com> Unixware1 port
47. Michael Shields <shields@tembel.org> USNO clock driver
48. Jeff Steinman <jss@pebbles.jpl.nasa.gov> Datum PTS clock driver
49. Harlan Stenn <harlan@pfcs.com> GNU automake/autoconfigure makeover, various other bits (see the ChangeLog)
50. Kenneth Stone <ken@sdd.hp.com> HP-UX port
51. Ajit Thyagarajan <ajit@ee.udel.edu>IP multicast/anycast support
52. Tomoaki TSURUOKA <tsuruoka@nc.fukuoka-u.ac.jp>TRAK clock driver
53. Paul A Vixie <vixie@vix.com> TrueTime GPS driver, generic TrueTime clock driver
54. Ulrich Windl <Ulrich.Windl@rz.uni-regensburg.de> corrected and validated HTML documents according to the HTML
DTD
This Product includes pam software under below license
Unless otherwise *explicitly* stated the following text describes the licensed conditions under which the contents of this

Linux-PAM release may be distributed:
Redistribution and use in source and binary forms of Linux-PAM, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain any existing copyright notice, and this entire permission notice in its entirety, including
the disclaimer of warranties.
2. Redistributions in binary form must reproduce all prior and current copyright notices, this list of conditions, and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The name of any author may not be used to endorse or promote products derived from this software without their specific prior
written permission.
ALTERNATIVELY, this product may be distributed under the terms of the GNU General Public License, in which case the
provisions of the GNU GPL are required INSTEAD OF the above restrictions. (This clause is necessary due to a potential conflict
between the GNU GPL and the restrictions contained in a BSD-style copyright.)
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED.IN NO EVENT SHALL THE AUTHOR(S) BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS
OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
This Product includes pure-ftpd software under below license
Pure-FTPd is covered by the following license :
/*
* Copyright (c) 2001, 2002, 2003, 2004, 2005, 2006
* Frank Denis <j@pureftpd.org> with the help of all Pure-FTPd contributors.
*
* Permission to use, copy, modify, and distribute this software for any
* purpose with or without fee is hereby granted, provided that the above
* copyright notice and this permission notice appear in all copies.
*
* THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES
* WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
* MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR
* ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
* WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
* ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF
* OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
*/
------------------------------------------
The bsd-glob.c, bsd-glob.h, bsd-realpath.c, bsd-getopt_long.c and
bsd-getopt_long.h source codes are based upon the OpenBSD and NetBSD projects
and they are covered by the BSD license.
The original license is enclosed at the beginning of the related files.

This Product includes setsystz software under below license
/* setsystz: set the Linux kernel's idea of the time zone */
/* Copyright (c) 2007 David A. Madore, Public Domain */
This Product includes sqlite software under below license
SQLite Copyright
All of the deliverable code in SQLite has been dedicated to the public domain by the authors. All code authors, and representatives
of the companies they work for, have signed affidavits dedicating their contributions to the public domain and originals of those
signed affidavits are stored in a firesafe at the main offices of Hwaci. Anyone is free to copy, modify, publish, use, compile, sell, or
distribute the original SQLite code, either in source code form or as a compiled binary, for any purpose, commercial or
non-commercial, and by any means.
The previous paragraph applies to the deliverable code in SQLite - those parts of the SQLite library that you actually bundle and
ship with a larger application. Portions of the documentation and some code used as part of the build process might fall under other
licenses. The details here are unclear. We do not worry about the licensing of the documentation and build code so much because
none of these things are part of the core deliverable SQLite library.
All of the deliverable code in SQLite has been written from scratch. No code has been taken from other projects or from the open
internet. Every line of code can be traced back to its original author, and all of those authors have public domain dedications on file.
So the SQLite code base is clean and is uncontaminated with licensed code from other projects.
Obtaining An Explicit License To Use SQLite
Even though SQLite is in the public domain and does not require a license, some users want to obtain a license anyway. Some
reasons for obtaining a license include:
You are using SQLite in a jurisdiction that does not recognize the public domain.
You are using SQLite in a jurisdiction that does not recognize the right of an author to dedicate their work to the public
domain.
You want to hold a tangible legal document as evidence that you have the legal right to use and distribute SQLite.
Your legal department tells you that you have to purchase a license.
If you feel like you really have to purchase a license for SQLite, Hwaci, the company that employs the architect and principal
developers of SQLite, will sell you one.
Contributed Code
In order to keep SQLite completely free and unencumbered by copyright, all new contributors to the SQLite code base are asked to
dedicate their contributions to the public domain. If you want to send a patch or enhancement for possible inclusion in the SQLite
source tree, please accompany the patch with the following statement:
The author or authors of this code dedicate any and all copyright interest in this code to the public domain. We make this dedication
for the benefit of the public at large and to the detriment of our heirs and successors. We intend this dedication to be an overt act of
relinquishment in perpetuity of all present and future rights to this code under copyright law.
We are not able to accept patches or changes to SQLite that are not accompanied by a statement such as the above. In addition, if
you make changes or enhancements as an employee, then a simple statement such as the above is insufficient. You must also send
by surface mail a copyright release signed by a company officer. A signed original of the copyright release should be mailed to:
Hwaci
6200 Maple Cove Lane
Charlotte, NC 28269
USA
A template copyright release is available in PDF or HTML. You can use this release to make future changes
Copyright Release for
Contributions To SQLite
SQLite is software that implements an embeddable SQL database engine. SQLite is available for free download from
http://www.sqlite.org/. The principal author and maintainer of SQLite has disclaimed all copyright interest in his contributions to
SQLite and thus released his contributions into the public domain. In order to keep the SQLite software unencumbered by copyright
claims, the principal author asks others who may from time to time contribute changes and enhancements to likewise disclaim their
own individual copyright interest.
Because the SQLite software found at http://www.sqlite.org/ is in the public domain, anyone is free to download the SQLite
software from that website, make changes to the software, use, distribute, or sell the modified software, under either the original
name or under some new name, without any need to obtain permission, pay royalties, acknowledge the original source of the
software, or in any other way compensate, identify, or notify the original authors. Nobody is in any way compelled to contribute
their SQLite changes and enhancements back to the SQLite website. This document concerns only changes and enhancements to
SQLite that are intentionally and deliberately contributed back to the SQLite website.

For the purposes of this document, "SQLite software" shall mean any computer source code, documentation, makefiles, test scripts,
or other information that is published on the SQLite website, http://www.sqlite.org/. Precompiled binaries are excluded from the
definition of "SQLite software" in this document because the process of compiling the software may introduce information from
outside sources which is not properly a part of SQLite.
The header comments on the SQLite source files exhort the reader to share freely and to never take more than one gives. In the spirit
of that exhortation I make the following declarations:
1. I dedicate to the public domain any and all copyright interest in the SQLite software that was publicly available on the
SQLite website (http://www.sqlite.org/) prior to the date of the signature below and any changes or enhancements to the
SQLite software that I may cause to be published on that website in the future. I make this dedication for the benefit of
the public at large and to the detriment of my heirs and successors. I intend this dedication to be an overt act of
relinquishment in perpetuity of all present and future rights to the SQLite software under copyright law.
2. To the best of my knowledge and belief, the changes and enhancements that I have contributed to SQLite are either
originally written by me or are derived from prior works which I have verified are also in the public domain and are not
subject to claims of copyright by other parties.
3. To the best of my knowledge and belief, no individual, business, organization, government, or other entity has any
copyright interest in the SQLite software as it existed on the SQLite website as of the date on the signature line below.
4. I agree never to publish any additional information to the SQLite website (by CVS, email, scp, FTP, or any other means)
unless that information is an original work of authorship by me or is derived from prior published versions of SQLite. I
agree never to copy and paste code into the SQLite code base from other sources. I agree never to publish on the SQLite
website any information that would violate a law or breach a contract.
Signature:
Date:
N
ame (printed):
This Product includes tz32 software under below license
=== asctime.c==========
** This file is in the public domain, so clarified as of
** 1996-06-05 by Arthur David Olson.
=== asctime.c==========
=== date.c ==========
/*
* Copyright (c) 1985, 1987, 1988 The Regents of the University of California.
* All rights reserved.
*
* Redistribution and use in source and binary forms are permitted
* provided that the above copyright notice and this paragraph are
* duplicated in all such forms and that any documentation,
* advertising materials, and other materials related to such
* distribution and use acknowledge that the software was developed
* by the University of California, Berkeley. The name of the
* University may not be used to endorse or promote products derived
* from this software without specific prior written permission.
* THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR
* IMPLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED
* WARRANTIES OF MERCHANT[A]BILITY AND FITNESS FOR A PARTICULAR PURPOSE.
*/
=== difftime.c ==========
/*
** This file is in the public domain, so clarified as of
** 1996-06-05 by Arthur David Olson.
*/
=============
====== localtime.c =====
/*
** This file is in the public domain, so clarified as of

** 1996-06-05 by Arthur David Olson.
*/
==================
====== logwtmp.c =====
/*
* Copyright (c) 1988 The Regents of the University of California.
* All rights reserved.
*
* Redistribution and use in source and binary forms are permitted
* provided that the above copyright notice and this paragraph are
* duplicated in all such forms and that any documentation,
* advertising materials, and other materials related to such
* distribution and use acknowledge that the software was developed
* by the University of California, Berkeley. The name of the
* University may not be used to endorse or promote products derived
* from this software without specific prior written permission.
* THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR
* IMPLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED
* WARRANTIES OF MERCHANT[A]BILITY AND FITNESS FOR A PARTICULAR PURPOSE.
*/
===================
====== private.h =====
** This file is in the public domain, so clarified as of
** 1996-06-05 by Arthur David Olson.
====== private.h =====
======tzfile.h =====
** This file is in the public domain, so clarified as of
** 1996-06-05 by Arthur David Olson.
====== tzfile.h =====
This Product includes crypto++ software under below license
License
The License of Crypto++ is somewhat unusual amongst open source projects. A distinction is made between the library as a
compilation (i.e., collection), which is copyrighted by Wei Dai, and the individual files in it, which are public domain (with the
exception of mars.cpp which is subject to its own license, included in that file).
The library is copyrighted as a compilation in order to place certain disclaimers (regarding warranty, export, and patents) in the
license and to keep the attributions and public domain declarations intact when Crypto++ is distributed in source code form. The
fact that individual files are public domain means that legally you can place code segments, entire files, or small sets of files (up to
the limit set by fair use) into your own project and do anything you want with them without worrying about the copyright.
Because one purpose of the project is to act as a repository of public domain (not copyrighted) cryptographic source code, the code
in Crypto++ was either written specifically for this project by its contributors and placed in the public domain, or derived from other
sources that are public domain (again with the exception of mars.cpp).
Compilation Copyright (c) 1995-2009 by Wei Dai. All rights reserved.
This copyright applies only to this software distribution package
as a compilation, and does not imply a copyright on any particular
file in the package.
The following files are copyrighted by their respective original authors,
and their use is subject to additional licenses included in these files.
mars.cpp - Copyright 1998 Brian Gladman.
All other files in this compilation are placed in the public domain by
Wei Dai and other contributors.
I would like to thank the following authors for placing their works into

the public domain:
Joan Daemen - 3way.cpp
Leonard Janke - cast.cpp, seal.cpp
Steve Reid - cast.cpp
Phil Karn - des.cpp
Andrew M. Kuchling - md2.cpp, md4.cpp
Colin Plumb - md5.cpp
Seal Woods - rc6.cpp
Chris Morgan - rijndael.cpp
Paulo Baretto - rijndael.cpp, skipjack.cpp, square.cpp
Richard De Moliner - safer.cpp
Matthew Skala - twofish.cpp
Kevin Springle - camellia.cpp, shacal2.cpp, ttmac.cpp, whrlpool.cpp, ripemd.cpp
Permission to use, copy, modify, and distribute this compilation for
any purpose, including commercial applications, is hereby granted
without fee, subject to the following restrictions:
1. Any copy or modification of this compilation in any form, except
in object code form as part of an application software, must include
the above copyright notice and this license.
2. Users of this software agree that any modification or extension
they provide to Wei Dai will be considered public domain and not
copyrighted unless it includes an explicit copyright notice.
3. Wei Dai makes no warranty or representation that the operation of the
software in this compilation will be error-free, and Wei Dai is under no
obligation to provide any services, by way of maintenance, update, or
otherwise. THE SOFTWARE AND ANY DOCUMENTATION ARE PROVIDED "AS IS"
WITHOUT EXPRESS OR IMPLIED WARRANTY INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. IN NO EVENT WILL WEI DAI OR ANY OTHER CONTRIBUTOR BE LIABLE FOR
DIRECT, INCIDENTAL OR CONSEQUENTIAL DAMAGES, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
4. Users will not use Wei Dai or any other contributor's name in any
publicity or advertising, without prior written consent in each case.
5. Export of this software from the United States may require a
specific license from the United States Government. It is the
responsibility of any person or organization contemplating export
to obtain such a license before exporting.
6. Certain parts of this software may be protected by patents. It
is the users' responsibility to obtain the appropriate
licenses before using those parts.
If this compilation is used in object code form in an application
software, acknowledgement of the author is not required but would be
appreciated. The contribution of any useful modifications or extensions
to Wei Dai is not required but would also be appreciated.
This Product includes wxWidgets software under below license
Licence
Background
wxWidgets is currently licensed under the "wxWindows Licence" pending approval of the "wxWidgets Licence" which will be
identical apart from the name.

The wxWindows Licence is essentially the L-GPL (Library General Public Licence), with an exception stating that derived works in
binary form may be distributed on the user's own terms. This is a solution that satisfies those who wish to produce GPL'ed software
using wxWidgets, and also those producing proprietary software.
Participants in the discussion that led to this decision include the folk from Abisource, Robert Roebling, Julian Smart, Markus Fleck,
Karsten Ballueder, and some advice from Richard Stallman. Richard has confirmed that the new licence is compatible with GPL'ed
applications. However, there are no significant restrictions on proprietary applications.
The wxWindows Licence has been approved by the Open Source Initiative, and you can find the licence on their site here.
In August 2005, an ambiguity in Clause 2 was removed (replaced "the user's" with "your") and the version bumped to 3.1.
The wxWindows Library Licence
Copyright (c) 1998 Julian Smart, Robert Roebling [, ...]
Everyone is permitted to copy and distribute verbatim copies
of this licence document, but changing it is not allowed.
WXWINDOWS LIBRARY LICENCE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
This library is free software; you can redistribute it and/or modify it
under the terms of the GNU Library General Public Licence as published by
the Free Software Foundation; either version 2 of the Licence, or (at
your option) any later version.
This library is distributed in the hope that it will be useful, but
WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Library
General Public Licence for more details.
You should have received a copy of the GNU Library General Public Licence
along with this software, usually in a file named COPYING.LIB. If not,
write to the Free Software Foundation, Inc., 59 Temple Place, Suite 330,
Boston, MA 02111-1307 USA.
EXCEPTION NOTICE
1. As a special exception, the copyright holders of this library give
permission for additional uses of the text contained in this release of
the library as licenced under the wxWindows Library Licence, applying
either version 3 of the Licence, or (at your option) any later version of
the Licence as published by the copyright holders of version 3 of the
Licence document.
2. The exception is that you may use, copy, link, modify and distribute
under the user's own terms, binary object code versions of works based
on the Library.
3. If you copy code from files distributed under the terms of the GNU
General Public Licence or the GNU Library General Public Licence into a
copy of this library, as this licence permits, the exception does not
apply to the code that you add in this way. To avoid misleading anyone as
to the status of such modified files, you must delete this exception
notice from such code and/or adjust the licensing conditions notice
accordingly.
4. If you write modifications of your own for this library, it is your
choice whether to permit this exception to apply to your modifications.
If you do not wish that, you must delete the exception notice from such
code and/or adjust the licensing conditions notice accordingly.
This Product includes squeezecenter and squeezeboxserver software under below license
SLIM DEVICES LICENSE NOTICE
Please be aware that not all software distributed by Slim Devices
is licensed under the GPL. If you wish to redistribute any of our
software, please be sure to first read the GPL, and then make sure
that you are only distributing materials which we've explicity
licensed for such use. Feel free to contact us if you have any
questions, or would like permission to distribute our other non-GPL
programs. Also, be aware that standard copyright rules apply in any
case where no particular license is given.
Each of the software products we ship are licensed as follows:
- All of Squeezebox Server's perl code is licensed for redistribution
or inclusion in other software per version 2 of the GPL license,
included below for your convenience.
- SoftSqueeze is (c) Richard Titmuss and is licensed under GPL.
- The CODE2000 TrueType Font is (c) James Kass and is Shareware.
See Graphics/CODE2000.HTM for more information.
- Certain integral components of Slim Server, such as CPAN modules,
are (c) of their respective authors, and are included in Squeezebox Server
per their respective licenses.
- Certain ancillary programs included in the Squeezebox Server distribution
on our web site are licensed to us only for direct distribution to
end-users. These include the Windows installer and Activestate
binaries.
- Squeezebox firmare may not be redistributed under any
circumstances. It is (c) Slim Devices, and additonally contains
code which is (c) Ubicom. Ubicom's code is licenced to us only
for direct distribution in binary form. You may use the firmware
only on hardware manufactured by Slim Devices.
- SLIMP3 firmware is (c) Slim Devices, and source is available
under the Slim Devices Public Source Licence, for certain educational
and hobbyist uses. Please read the license carefully.
- Slim Devices logos, graphics, animations, and documentation are
(c) Slim Devices and are not licensed for redistribution. When in
doubt look for a GPL notice at the top of the file, or ask us for
written permission to redistribute, which we will grant for any
reasonable purpose.
- Squeezebox2 firmware additionally contains the following code:
- Kiss FFT, Copyright (c) 2003-2004, Mark Borgerding, licensed under
a modified BSD license (reproduced below).
- 16:16 fixed math routines, Copyright (c) 2001 Beartronics, licensed
under the "Artistic License"
(http://www.opensource.org/licenses/artistic-license.html). Copies of
modified source files can be found at
http://www.slimdevices.com/opensource/fixed_math.tar.gz.
- The following applies to Squeezebox2 distribution:
This product is protected by certain intellectual property rights of
Microsoft Corporation. Use or distribution of such technology outside
of this product is prohibited without a license from Microsoft or
authorized Microsoft subsidiary.
#------------------------------------------------------------------
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
License is intended to guarantee your freedom to share and change free
software--to make sure the software is free for all its users. This
General Public License applies to most of the Free Software
Foundation's software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by
the GNU Library General Public License instead.) You can apply it to
your programs, too.
When we speak of free software, we are referring to freedom, not
price. Our General Public Licenses are designed to make sure that you
have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it
if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid
anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether
gratis or for a fee, you must give the recipients all the rights that
you have. You must make sure that they, too, receive or can get the
source code. And you must show them these terms so they know their
rights.
We protect your rights with two steps: (1) copyright the software, and
(2) offer you this license which gives you legal permission to copy,
distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain
that everyone understands that there is no warranty for this free
software. If the software is modified by someone else and passed on, we
want its recipients to know that what they have is not the original, so
that any problems introduced by others will not reflect on the original
authors' reputations.
Finally, any free program is threatened constantly by software
patents. We wish to avoid the danger that redistributors of a free
program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any
patent must be licensed for everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and
modification follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains
a notice placed by the copyright holder saying it may be distributed
under the terms of this General Public License. The "Program", below,
refers to any such program or work, and a "work based on the Program"
means either the Program or any derivative work under copyright law:
that is to say, a work containing the Program or a portion of it,
either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in
the term "modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of
running the Program is not restricted, and the output from the Program
is covered only if its contents constitute a work based on the
Program (independent of having been made by running the Program).
Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's
source code as you receive it, in any medium, provided that you
conspicuously and appropriately publish on each copy an appropriate
copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty;
and give any other recipients of the Program a copy of this License
along with the Program.
You may charge a fee for the physical act of transferring a copy, and
you may at your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion
of it, thus forming a work based on the Program, and copy and
distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices
stating that you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in
whole or in part contains or is derived from the Program or any
part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License.
c) If the modified program normally reads commands interactively
when run, you must cause it, when started running for such
interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a
notice that there is no warranty (or else, saying that you provide
a warranty) and that users may redistribute the program under
these conditions, and telling the user how to view a copy of this
License. (Exception: if the Program itself is interactive but
does not normally print such an announcement, your work based on
the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Program,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Program, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program
with the Program (or with a work based on the Program) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may copy and distribute the Program (or a work based on it,
under Section 2) in object code or executable form under the terms of
Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable
source code, which must be distributed under the terms of Sections
1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three
years, to give any third party, for a charge no more than your
cost of physically performing source distribution, a complete
machine-readable copy of the corresponding source code, to be
distributed under the terms of Sections 1 and 2 above on a medium
customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer
to distribute corresponding source code. (This alternative is
allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such
an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for
making modifications to it. For an executable work, complete source
code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to
control compilation and installation of the executable. However, as a
special exception, the source code distributed need not include
anything that is normally distributed (in either source or binary
form) with the major components (compiler, kernel, and so on) of the
operating system on which the executable runs, unless that component
itself accompanies the executable.
If distribution of executable or object code is made by offering
access to copy from a designated place, then offering equivalent
access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not
compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program
except as expressly provided under this License. Any attempt
otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under
this License will not have their licenses terminated so long as such
parties remain in full compliance.
5. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the
Program), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the
Program), the recipient automatically receives a license from the
original licensor to copy, distribute or modify the Program subject to
these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties to
this License.
7. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent
license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under
any particular circumstance, the balance of the section is intended to
apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding
those countries, so that distribution is permitted only in or among
countries not thus excluded. In such case, this License incorporates
the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions
of the General Public License from time to time. Such new versions will
be similar in spirit to the present version, but may differ in detail to
address new problems or concerns.
Each version is given a distinguishing version number. If the Program
specifies a version number of this License which applies to it and "any
later version", you have the option of following the terms and conditions
either of that version or of any later version published by the Free
Software Foundation. If the Program does not specify a version number of
this License, you may choose any version ever published by the Free Software
Foundation.
10. If you wish to incorporate parts of the Program into other free
programs whose distribution conditions are different, write to the author
to ask for permission. For software which is copyrighted by the Free
Software Foundation, write to the Free Software Foundation; we sometimes
make exceptions for this. Our decision will be guided by the two goals
of preserving the free status of all derivatives of our free software and
of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
#------------------------------------------------------------------
Kiss FFT used under the following license:
Copyright (c) 2003-2004, Mark Borgerding
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:

* Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer
in the documentation and/or other materials provided with the distribution.
* Neither the author nor the names of any contributors may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS
OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE
COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN
IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#------------------------------------------------------------------
The Code2000 font is copyright James Kass, distributed by permission of the author.
Details about Code2000 may be found in Graphics/CODE2000.HTM
This Product includes php software under below license
PHP 4 and PHP 5 are distributed under the PHP License v3.01, copyright (c) the PHP Group.
This is an Open Source license, certified by the Open Source Initiative.
The PHP license is a BSD-style license which does not have the "copyleft" restrictions associated with GPL.
Some files have been contributed under other (compatible) licenses and carry additional requirements and copyright
information.
This is indicated in the license + copyright comment block at the top of the source file.
Practical Guidelines:
Distributing PHP
Contributing to PHP
--------------------------------------------------------------------
The PHP License, version 3.01
Copyright (c) 1999 - 2009 The PHP Group. All rights reserved.
--------------------------------------------------------------------
Redistribution and use in source and binary forms, with or without
modification, is permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in
the documentation and/or other materials provided with the
distribution.
3. The name "PHP" must not be used to endorse or promote products
derived from this software without prior written permission. For
written permission, please contact group@php.net.
4. Products derived from this software may not be called "PHP", nor
may "PHP" appear in their name, without prior written permission
from group@php.net. You may indicate that your software works in
conjunction with PHP by saying "Foo for PHP" instead of calling
it "PHP Foo" or "phpfoo"

5. The PHP Group may publish revised and/or new versions of the
license from time to time. Each version will be given a
distinguishing version number.
Once covered code has been published under a particular version
of the license, you may always continue to use it under the terms
of that version. You may also choose to use such covered code
under the terms of any subsequent version of the license
published by the PHP Group. No one other than the PHP Group has
the right to modify the terms applicable to covered code created
under this License.
6. Redistributions of any form whatsoever must retain the following
acknowledgment:
"This product includes PHP software, freely available from
<http://www.php.net/software/>".
THIS SOFTWARE IS PROVIDED BY THE PHP DEVELOPMENT TEAM ``AS IS'' AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE PHP
DEVELOPMENT TEAM OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE POSSIBILITY OF SUCH DAMAGE.
--------------------------------------------------------------------
This software consists of voluntary contributions made by many
individuals on behalf of the PHP Group.
The PHP Group can be contacted via Email at group@php.net.
For more information on the PHP Group and the PHP project,
please see <http://www.php.net>.
PHP includes the Zend Engine, freely available at
<http://www.zend.com>.
This Product includes AutoXS-Header, Class-C3-XS, Class-XSAccessor, Class-XSAccessor-Array, Compress-Raw-Zlib,
Digest-SHA1, EV, ExtUtils-Cbuilder, GD, HTML-Parser, JSON-XS, Module-Build, Sub-Name, Template-Toolkit and XML-Parser
software under the same terms as Perl ‘s license
Perl5 is Copyright (C) 1993-2005, by Larry Wall and others.
It is free software; you can redistribute it and/or modify it under the terms of either:
a) the GNU General Public License as published by the Free Software Foundation; either version 1, or (at your option) any later
version, or
b) the "Artistic License".
For those of you that choose to use the GNU General Public License, my interpretation of the GNU General Public License is that
no Perl script falls under the terms of the GPL unless you explicitly put said script under the terms of the GPL yourself.
Furthermore, any object code linked with perl does not automatically fall under the terms of the GPL, provided such object code
only adds definitions of subroutines and variables, and does not otherwise impair the resulting interpreter from executing any
standard Perl script. I consider linking in C subroutines in this manner to be the moral equivalent of defining subroutines in the Perl

language itself. You may sell such an object file as proprietary provided that you provide or offer to provide the Perl source, as
specified by the GNU General Public License. (This is merely an alternate way of specifying input to the program.) You may also
sell a binary produced by the dumping of a running Perl script that belongs to you, provided that you provide or offer to provide the
Perl source as specified by the GPL. (The fact that a Perl interpreter and your code are in the same binary file is, in this case, a form
of mere aggregation.)
This is my interpretation of the GPL. If you still have concerns or difficulties understanding my intent, feel free to contact me. Of
course, the Artistic License spells all this out for your protection, so you may prefer to use that.
-- Larry Wall
This Product includes gd software under below license
Portions copyright 1994, 1995, 1996, 1997, 1998, 1999, 2000, 2001,
2002 by Cold Spring Harbor Laboratory. Funded under Grant
P41-RR02188 by the National Institutes of Health.
Portions copyright 1996, 1997, 1998, 1999, 2000, 2001, 2002 by
Boutell.Com, Inc.
Portions relating to GD2 format copyright 1999, 2000, 2001, 2002
Philip Warner.
Portions relating to PNG copyright 1999, 2000, 2001, 2002 Greg
Roelofs.
Portions relating to gdttf.c copyright 1999, 2000, 2001, 2002 John
Ellson (ellson@lucent.com).
Portions relating to gdft.c copyright 2001, 2002 John Ellson
(ellson@lucent.com).
Portions copyright 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007
Pierre-Alain Joye (pierre@libgd.org).
Portions relating to JPEG and to color quantization copyright 2000,
2001, 2002, Doug Becker and copyright (C) 1994, 1995, 1996, 1997,
1998, 1999, 2000, 2001, 2002, Thomas G. Lane. This software is
based in part on the work of the Independent JPEG Group. See the
file README-JPEG.TXT for more information.
Portions relating to WBMP copyright 2000, 2001, 2002 Maurice
Szmurlo and Johan Van den Brande.
Permission has been granted to copy, distribute and modify gd in
any context without fee, including a commercial application,
provided that this notice is present in user-accessible supporting
documentation.
This does not affect your ownership of the derived work itself, and
the intent is to assure proper credit for the authors of gd, not to
interfere with your productive use of gd. If you have questions,
ask. "Derived works" includes all programs that utilize the
library. Credit must be given in user-accessible documentation.
This software is provided "AS IS." The copyright holders disclaim
all warranties, either express or implied, including but not
limited to implied warranties of merchantability and fitness for a
particular purpose, with respect to this code and accompanying
documentation.
Although their code does not appear in gd, the authors wish to thank
David Koblas, David Rowley, and Hutchison Avenue Software Corporation
for their prior contributions.