Acronis Backup Command Line Reference 11.7 Cmdlineref En
User Manual: acronis Backup 11.7 - Command-Line Reference Free User Guide for Acronis Backup Software, Manual
Open the PDF directly: View PDF ![]() .
.
Page Count: 149 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- 1 Command-line utility overview
- 2 Commands
- 2.1 Commands by services
- 2.2 help
- 2.3 Backup and recovery
- 2.4 Operations with archives and backups
- 2.5 Operations with Acronis Secure Zone
- 2.6 Operations with Acronis Startup Recovery Manager
- 2.7 Operations with tapes
- 2.8 Operations with vaults
- 2.9 Operations with disks
- 2.10 Operations with machines
- 2.11 Administration operations
- 3 Parameters
- 3.1 Access to a physical machine
- 3.2 Virtual machines
- 3.3 Access to applications
- 3.4 Location
- 3.5 Disks and volumes
- 3.6 Backup parameters
- 3.6.1 application_aware
- 3.6.2 backuptype
- 3.6.3 cleanup
- 3.6.4 Comments
- 3.6.5 copy_only
- 3.6.6 exclude
- 3.6.7 express
- 3.6.8 fixed_drive
- 3.6.9 ignore_app_errors
- 3.6.10 include
- 3.6.11 mssql_truncate_logs
- 3.6.12 plain_archive
- 3.6.13 raw
- 3.6.14 Backup options
- 3.6.14.1 cataloging
- 3.6.14.2 cbt_mode
- 3.6.14.3 compression
- 3.6.14.4 encryption
- 3.6.14.5 fast
- 3.6.14.6 hdd_speed
- 3.6.14.7 ignore_bad_sectors
- 3.6.14.8 metadata_level
- 3.6.14.9 multi_volume_snapshot
- 3.6.14.10 network_speed
- 3.6.14.11 Pre and post commands
- 3.6.14.12 snapshot
- 3.6.14.13 split
- 3.6.14.14 Tape management
- 3.6.14.15 use_vss
- 3.7 Recovery parameters
- 3.7.1 autorename
- 3.7.2 database
- 3.7.3 database_location
- 3.7.4 database_state
- 3.7.5 destination_database
- 3.7.6 destination_instance
- 3.7.7 disk_location
- 3.7.8 exclude
- 3.7.9 ext2_3
- 3.7.10 fat16_32
- 3.7.11 file
- 3.7.12 log_location
- 3.7.13 original_date
- 3.7.14 outlookmachine
- 3.7.15 overwrite
- 3.7.16 pit
- 3.7.17 power_on
- 3.7.18 preserve_mbr
- 3.7.19 recover_absolute_path
- 3.7.20 recovery_point
- 3.7.21 target_disk
- 3.7.22 target_volume
- 3.7.23 type
- 3.7.24 use_all_space
- 3.8 Mounting parameters
- 3.9 Acronis Secure Zone parameters
- 3.10 Filtering
- 3.10.1 content_path
- 3.10.2 content_type
- 3.10.3 filter_available_for_backup
- 3.10.4 filter_date
- 3.10.5 filter_edition
- 3.10.6 filter_guid
- 3.10.7 filter_host
- 3.10.8 filter_library
- 3.10.9 filter_machines
- 3.10.10 filter_name
- 3.10.11 filter_resource
- 3.10.12 filter_state
- 3.10.13 filter_status
- 3.10.14 filter_type
- 3.10.15 filter_user
- 3.10.16 filter_version
- 3.11 Tape management parameters
- 3.12 General parameters
- 3.12.1 credentials
- 3.12.2 Error handling
- 3.12.3 file_params
- 3.12.4 force_yes
- 3.12.5 id
- 3.12.6 log
- 3.12.7 log_format
- 3.12.8 oss_numbers
- 3.12.9 output
- 3.12.10 password
- 3.12.11 process_priority
- 3.12.12 progress
- 3.12.13 read_speed
- 3.12.14 reboot
- 3.12.15 recreate_archive_meta
- 3.12.16 report_format
- 3.12.17 silent_mode
- 3.12.18 use_registry_defaults
- 3.12.19 utc
- 4 Usage examples
- 4.1 Backup and recovery
- 4.2 Operations with archives and backups
- 4.3 Operations with Acronis Secure Zone
- 4.4 Operations with Acronis Startup Recovery Manager
- 4.5 Operations with tapes
- 4.6 Operations with vaults
- 4.7 Operations with disks
- 4.8 Operations with machines
- 4.9 Administration operations
- 4.10 Selecting logical volumes and MD devices for backup
- 4.11 Scheduling backups under Linux using the cron service
- 5 Comparison of the old and new command-line syntax
- 6 acronis_encrypt utility

Acronis Backup
Version 11.7
COMMAND-LINE REFERENCE
APPLIES TO THE FOLLOWING PRODUCTS
All products of the Acronis Backup family and the Acronis Backup Advanced suite
2 Copyright © Acronis International GmbH, 2002-2016
Copyright Statement
Copyright © Acronis International GmbH, 2002-2016. All rights reserved.
“Acronis” and “Acronis Secure Zone” are registered trademarks of Acronis International GmbH.
"Acronis Compute with Confidence", “Acronis Startup Recovery Manager”, “Acronis Active Restore”,
“Acronis Instant Restore” and the Acronis logo are trademarks of Acronis International GmbH.
Linux is a registered trademark of Linus Torvalds.
VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the
United States and/or other jurisdictions.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit
permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial
purposes is prohibited unless prior permission is obtained from the copyright holder.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS,
REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE
EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
Third party code may be provided with the Software and/or Service. The license terms for such
third-parties are detailed in the license.txt file located in the root installation directory. You can
always find the latest up-to-date list of the third party code and the associated license terms used
with the Software and/or Service at http://kb.acronis.com/content/7696
Acronis patented technologies
Technologies, used in this product, are covered and protected by one or more U.S. Patent Numbers:
7,047,380; 7,275,139; 7,281,104; 7,318,135; 7,353,355; 7,366,859; 7,475,282; 7,603,533; 7,636,824;
7,650,473; 7,721,138; 7,779,221; 7,831,789; 7,886,120; 7,895,403; 7,934,064; 7,937,612; 7,949,635;
7,953,948; 7,979,690; 8,005,797; 8,051,044; 8,069,320; 8,073,815; 8,074,035; 8,145,607; 8,180,984;
8,225,133; 8,261,035; 8,296,264; 8,312,259; 8,347,137; 8,484,427; 8,645,748; 8,732,121 and patent
pending applications.
3 Copyright © Acronis International GmbH, 2002-2016
Table of contents
1 Command-line utility overview ........................................................................................7
1.1 Installation ................................................................................................................................. 7
1.2 Backward compatibility and upgrade ........................................................................................ 8
1.3 Syntax ......................................................................................................................................... 8
1.4 Local, remote, and centralized management ............................................................................ 9
1.5 Uninstallation ...........................................................................................................................11
1.6 List of abbreviated names........................................................................................................12
2 Commands .................................................................................................................... 13
2.1 Commands by services ............................................................................................................13
2.1.1 Disk, file, virtual machine backup................................................................................................................. 13
2.1.2 Application backup ........................................................................................................................................ 15
2.2 help ..........................................................................................................................................18
2.3 Backup and recovery ...............................................................................................................18
2.3.1 Disks and volumes ......................................................................................................................................... 18
2.3.2 Files ................................................................................................................................................................. 24
2.3.3 Virtual machines ............................................................................................................................................ 27
2.3.4 Microsoft Exchange ....................................................................................................................................... 33
2.3.5 Microsoft SQL ................................................................................................................................................ 38
2.3.6 Microsoft Active Directory............................................................................................................................ 41
2.4 Operations with archives and backups ....................................................................................42
2.4.1 Archives .......................................................................................................................................................... 42
2.4.2 Backups .......................................................................................................................................................... 46
2.4.3 Mounting volumes ........................................................................................................................................ 53
2.4.4 Mounting SQL databases .............................................................................................................................. 54
2.5 Operations with Acronis Secure Zone .....................................................................................56
2.5.1 create asz ....................................................................................................................................................... 56
2.5.2 resize asz ........................................................................................................................................................ 57
2.5.3 cleanup asz..................................................................................................................................................... 58
2.5.4 delete asz_files .............................................................................................................................................. 58
2.5.5 delete asz ....................................................................................................................................................... 59
2.6 Operations with Acronis Startup Recovery Manager ..............................................................59
2.6.1 activate asrm ................................................................................................................................................. 59
2.6.2 deactivate asrm ............................................................................................................................................. 60
2.7 Operations with tapes .............................................................................................................60
2.7.1 list tape_libraries ........................................................................................................................................... 60
2.7.2 list tape_slots ................................................................................................................................................. 61
2.7.3 inventory tape ............................................................................................................................................... 61
2.8 Operations with vaults .............................................................................................................62
2.8.1 list vaults ........................................................................................................................................................ 62
2.8.2 validate vault ................................................................................................................................................. 63
2.8.3 catalog vault................................................................................................................................................... 63
2.9 Operations with disks ..............................................................................................................64
2.9.1 clone disk ....................................................................................................................................................... 64
2.10 Operations with machines .......................................................................................................65
2.10.1 add machine .................................................................................................................................................. 65
4 Copyright © Acronis International GmbH, 2002-2016
2.11 Administration operations .......................................................................................................66
2.11.1 Collecting information .................................................................................................................................. 66
2.11.2 Activities ......................................................................................................................................................... 67
2.11.3 Plans ............................................................................................................................................................... 68
2.11.4 Tasks ............................................................................................................................................................... 72
2.11.5 Licenses .......................................................................................................................................................... 74
2.11.6 Reports ........................................................................................................................................................... 74
3 Parameters .................................................................................................................... 76
3.1 Access to a physical machine ...................................................................................................76
3.1.1 host ................................................................................................................................................................. 76
3.1.2 service ............................................................................................................................................................ 76
3.1.3 address ........................................................................................................................................................... 76
3.2 Virtual machines ......................................................................................................................77
3.2.1 Access to a virtual machine .......................................................................................................................... 77
3.2.2 New virtual machine ..................................................................................................................................... 78
3.3 Access to applications ..............................................................................................................80
3.3.1 exchange_credentials ................................................................................................................................... 80
3.3.2 instance .......................................................................................................................................................... 81
3.3.3 items ............................................................................................................................................................... 81
3.3.4 Specifying Exchange data ............................................................................................................................. 82
3.3.5 Specifying SQL data ....................................................................................................................................... 83
3.3.6 Access to SQL Server instance ...................................................................................................................... 83
3.4 Location ...................................................................................................................................84
3.4.1 loc ................................................................................................................................................................... 84
3.4.2 arc ................................................................................................................................................................... 84
3.4.3 backup ............................................................................................................................................................ 85
3.4.4 target .............................................................................................................................................................. 86
3.4.5 target_arc....................................................................................................................................................... 88
3.4.6 mailbox_location ........................................................................................................................................... 88
3.5 Disks and volumes ...................................................................................................................88
3.5.1 disk ................................................................................................................................................................. 88
3.5.2 nt_signature ................................................................................................................................................... 89
3.5.3 volume ........................................................................................................................................................... 89
3.5.4 start ................................................................................................................................................................ 91
3.5.5 size .................................................................................................................................................................. 91
3.5.6 mbr_disk ........................................................................................................................................................ 91
3.5.7 target_mbr_disk ............................................................................................................................................ 92
3.6 Backup parameters ..................................................................................................................92
3.6.1 application_aware ......................................................................................................................................... 92
3.6.2 backuptype .................................................................................................................................................... 92
3.6.3 cleanup ........................................................................................................................................................... 92
3.6.4 Comments...................................................................................................................................................... 93
3.6.5 copy_only ....................................................................................................................................................... 93
3.6.6 exclude ........................................................................................................................................................... 93
3.6.7 express ........................................................................................................................................................... 95
3.6.8 fixed_drive ..................................................................................................................................................... 95
3.6.9 ignore_app_errors ........................................................................................................................................ 96
3.6.10 include ............................................................................................................................................................ 96
3.6.11 mssql_truncate_logs ..................................................................................................................................... 96
3.6.12 plain_archive ................................................................................................................................................. 97
3.6.13 raw .................................................................................................................................................................. 97
3.6.14 Backup options .............................................................................................................................................. 98
3.7 Recovery parameters .............................................................................................................103
5 Copyright © Acronis International GmbH, 2002-2016
3.7.1 autorename ................................................................................................................................................. 103
3.7.2 database ....................................................................................................................................................... 104
3.7.3 database_location ....................................................................................................................................... 104
3.7.4 database_state ............................................................................................................................................ 105
3.7.5 destination_database ................................................................................................................................. 105
3.7.6 destination_instance ................................................................................................................................... 106
3.7.7 disk_location ................................................................................................................................................ 106
3.7.8 exclude ......................................................................................................................................................... 106
3.7.9 ext2_3 .......................................................................................................................................................... 107
3.7.10 fat16_32 ....................................................................................................................................................... 107
3.7.11 file ................................................................................................................................................................. 107
3.7.12 log_location ................................................................................................................................................. 107
3.7.13 original_date ................................................................................................................................................ 108
3.7.14 outlookmachine .......................................................................................................................................... 108
3.7.15 overwrite ...................................................................................................................................................... 108
3.7.16 pit .................................................................................................................................................................. 109
3.7.17 power_on ..................................................................................................................................................... 109
3.7.18 preserve_mbr .............................................................................................................................................. 109
3.7.19 recover_absolute_path .............................................................................................................................. 109
3.7.20 recovery_point ............................................................................................................................................ 110
3.7.21 target_disk ................................................................................................................................................... 111
3.7.22 target_volume ............................................................................................................................................. 111
3.7.23 type ............................................................................................................................................................... 112
3.7.24 use_all_space .............................................................................................................................................. 112
3.8 Mounting parameters ............................................................................................................112
3.8.1 for_all_users ................................................................................................................................................ 112
3.8.2 letter ............................................................................................................................................................. 113
3.8.3 mount_point ................................................................................................................................................ 113
3.8.4 rw .................................................................................................................................................................. 113
3.9 Acronis Secure Zone parameters ...........................................................................................114
3.9.1 asz_size ........................................................................................................................................................ 114
3.10 Filtering ..................................................................................................................................114
3.10.1 content_path ............................................................................................................................................... 114
3.10.2 content_type ............................................................................................................................................... 115
3.10.3 filter_available_for_backup ........................................................................................................................ 115
3.10.4 filter_date .................................................................................................................................................... 116
3.10.5 filter_edition ................................................................................................................................................ 116
3.10.6 filter_guid ..................................................................................................................................................... 116
3.10.7 filter_host ..................................................................................................................................................... 116
3.10.8 filter_library ................................................................................................................................................. 117
3.10.9 filter_machines ............................................................................................................................................ 117
3.10.10 filter_name .................................................................................................................................................. 117
3.10.11 filter_resource ............................................................................................................................................. 117
3.10.12 filter_state.................................................................................................................................................... 118
3.10.13 filter_status .................................................................................................................................................. 118
3.10.14 filter_type .................................................................................................................................................... 118
3.10.15 filter_user ..................................................................................................................................................... 118
3.10.16 filter_version ................................................................................................................................................ 119
3.11 Tape management parameters .............................................................................................119
3.11.1 assign2free ................................................................................................................................................... 119
3.11.2 libraries ......................................................................................................................................................... 119
3.11.3 mode ............................................................................................................................................................ 119
3.11.4 slots .............................................................................................................................................................. 120
3.12 General parameters ...............................................................................................................120
3.12.1 credentials ................................................................................................................................................... 120
6 Copyright © Acronis International GmbH, 2002-2016
3.12.2 Error handling .............................................................................................................................................. 120
3.12.3 file_params .................................................................................................................................................. 121
3.12.4 force_yes ...................................................................................................................................................... 121
3.12.5 id ................................................................................................................................................................... 122
3.12.6 log ................................................................................................................................................................. 122
3.12.7 log_format ................................................................................................................................................... 122
3.12.8 oss_numbers ............................................................................................................................................... 122
3.12.9 output........................................................................................................................................................... 123
3.12.10 password ...................................................................................................................................................... 123
3.12.11 process_priority ........................................................................................................................................... 123
3.12.12 progress........................................................................................................................................................ 124
3.12.13 read_speed .................................................................................................................................................. 124
3.12.14 reboot ........................................................................................................................................................... 125
3.12.15 recreate_archive_meta .............................................................................................................................. 125
3.12.16 report_format.............................................................................................................................................. 125
3.12.17 silent_mode ................................................................................................................................................. 126
3.12.18 use_registry_defaults.................................................................................................................................. 126
3.12.19 utc ................................................................................................................................................................. 126
4 Usage examples ........................................................................................................... 127
4.1 Backup and recovery .............................................................................................................127
4.1.1 Disks and volumes ....................................................................................................................................... 127
4.1.2 Files ............................................................................................................................................................... 130
4.1.3 Virtual machines .......................................................................................................................................... 131
4.1.4 Microsoft Exchange ..................................................................................................................................... 132
4.1.5 Microsoft SQL .............................................................................................................................................. 134
4.1.6 Microsoft Active Directory.......................................................................................................................... 135
4.2 Operations with archives and backups ..................................................................................136
4.2.1 Archives ........................................................................................................................................................ 136
4.2.2 Backups ........................................................................................................................................................ 137
4.2.3 Mounting volumes ...................................................................................................................................... 139
4.2.4 Mounting SQL databases ............................................................................................................................ 139
4.3 Operations with Acronis Secure Zone ...................................................................................140
4.4 Operations with Acronis Startup Recovery Manager ............................................................141
4.5 Operations with tapes ...........................................................................................................141
4.6 Operations with vaults ...........................................................................................................142
4.7 Operations with disks ............................................................................................................143
4.8 Operations with machines .....................................................................................................143
4.9 Administration operations .....................................................................................................143
4.9.1 Collecting information ................................................................................................................................ 143
4.9.2 Activities ....................................................................................................................................................... 143
4.9.3 Plans ............................................................................................................................................................. 144
4.9.4 Tasks ............................................................................................................................................................. 145
4.9.5 Licenses ........................................................................................................................................................ 145
4.9.6 Reports ......................................................................................................................................................... 145
4.10 Selecting logical volumes and MD devices for backup ..........................................................145
4.11 Scheduling backups under Linux using the cron service .......................................................146
5 Comparison of the old and new command-line syntax .................................................. 148
6 acronis_encrypt utility ................................................................................................. 149
7 Copyright © Acronis International GmbH, 2002-2016
1 Command-line utility overview
Acronis Backup supports the command-line interface with the acrocmd utility.
Unlike the trueimagecmd utility used in the older Acronis products, acrocmd does not contain any
tools that physically execute the commands. It merely provides the command-line interface to
Acronis Backup components—agents, storage nodes and the management server.
Once installed on a Windows or Linux machine, the acrocmd utility can be run from any folder or
directory. This utility is also available in 64-bit Linux-based bootable media and in PE-based bootable
media.
1.1 Installation
Products with local management only (Acronis Backup)
If you have installed Acronis Backup, the command-line utility is already on your machine. Only local
management of this machine is available. This means that any command or script for this machine
can be run only locally.
Products with centralized management (Acronis Backup Advanced)
Acronis Backup Advanced enables you to perform local, remote and centralized management (p. 9)
of any machine where an Acronis Backup agent is installed.
As with Management Console, you install the command-line utility on the machine from which you
prefer to operate (run commands or scripts). The machine may run Windows or Linux. Using the
command-line utility, you can manage a Windows machine from a machine running Linux or vice
versa.
Installation steps
In Linux, the command-line utility is installed by default with Management Console or Agent for
Linux.
In Windows, you install the utility from the setup file as a separate component. To access this
component in the installer, select the I want to manually select the Acronis components and
customize the installation process check box. Or, you can extract and run the corresponding .msi
file.
To install the command-line utility from the .msi file:
1. Run the Acronis Backup setup program.
2. Click Extract installation files.
3. Select the check box corresponding to the AcronisCommandLineTool.msi file.
4. Specify the folder where to extract the file.
5. Click Extract.
6. After the file is successfully extracted, click Finish.
7. Go to the folder where the AcronisCommandLineTool.msi file is extracted, and launch the file.
8. Follow the Install Wizard instructions on the screen.
8 Copyright © Acronis International GmbH, 2002-2016
Installation paths
The default installation paths are:
%ProgramFiles%\Acronis\CommandLineTool (in 32-bit Windows)
%ProgramFiles(x86)%\Acronis\CommandLineTool (in 64-bit Windows)
/usr/lib/Acronis/CommandLineTool (in Linux)
1.2 Backward compatibility and upgrade
Upgrading the command-line utility from Acronis Backup & Recovery 10
When you upgrade a stand-alone edition of Acronis Backup & Recovery 10 to Acronis Backup, no
additional actions are needed to upgrade the command-line utility.
When you upgrade an edition with centralized management, the software installs the command-line
utility on every machine where an agent is installed. No additional actions are needed.
Backward compatibility
The Acronis Backup command-line utility is backward compatible with the Acronis Backup &
Recovery 10 command-line utility. You can continue using the old syntax. Just type acrocmd instead
of trueimagecmd.
To continue using your existing scripts, edit the scripts so that trueimagecmd is replaced with
acrocmd. If your scripts contain the path to the trueimagecmd utility, replace it with the path to
the acrocmd utility. Retain all other parameters and values.
Before switching to acrocmd, make sure that all the product components are upgraded. Acronis Backup &
Recovery 10 does not support acrocmd.
Combination of the old and new syntaxes is acceptable within a script, but is not acceptable within a
command string. When you create new scripts, we recommend that you use the new syntax.
Even when using the old syntax, logs and commands' output will appear in the new format.
Extensions of backup file names
The behavior of the /filename parameter with the backup commands is slightly different in Acronis
Backup & Recovery 10 and Acronis Backup. Unlike Acronis Backup & Recovery 10, where the
extension of a backup file is exactly the same as you specify in the parameter value, Acronis Backup
adds the *.tib extension to this value.
For example:
In Acronis Backup & Recovery 10, if you specify /filename:<path>my_backup.bak, the
backup file name will be my_backup.bak
In Acronis Backup, if you specify /filename:<path>my_backup.bak, the backup file name
will be my_backup.bak.tib. However, if you specify /filename:<path>my_backup.tib,
the backup file name will also be my_backup.tib.
1.3 Syntax
acrocmd has the following format:
acrocmd <command> --<parameter 1>=<value list 1> … --<parameter N>=<value list N>

9 Copyright © Acronis International GmbH, 2002-2016
Typographic conventions
Descriptions of commands and parameters use the following specific typographic conventions.
Between angle brackets (<>) – information that the user must supply. Example: <IP address or
hostname>
Between braces ({}); choices separated by pipe (|) – a set of choices from which the user must
choose only one. Example: {on|off}.
Parameter values
For some parameters, you should specify only one value. The description of such value is written in
the singular. For example, if you see --arc=<archive name>, specify only one archive name in this
parameter.
For some parameters, you can enter one or more values. The description of such values is written in
the plural. For example, if you see --volume=<volume numbers>, you can specify a list of volume
numbers in this parameter.
Separators
An equal sign separates a parameter name and a value list. A comma separates values in a value list.
Example:
acrocmd backup disk --disk=1,2
Enclosing parameter values that contain commas and space characters
General view
Example
"<value with space character>"
--include="C:\my documents"
\"<value with comma>\"
--include=\"E:\Employees(A,B)\"
"\"<value with space character and
comma>\""
--include="\"D:\my photos\my wife, my kids
and me\""
Files with input parameters
acrocmd supports files with input parameters. The contents of an input parameter file are
concatenated with the parameters in the command line.
For example, the command
acrocmd backup disk -f=params.txt
where the content of the file params.txt is
--disk=1 --loc=e:\my_backups --arc=archive123
equals to
acrocmd backup disk --disk=1 --loc=e:\my_backups --arc=archive123
1.4 Local, remote, and centralized management
Acronis Backup Advanced enables you to perform local, remote, and centralized management of any
machine where an Acronis Backup agent is installed.

10 Copyright © Acronis International GmbH, 2002-2016
Local management
For local management, you install the command-line utility on the same machine where the Acronis
Backup agent is installed. The operations are performed under the user account you are logged on
with.
Example
To view all disks of the local machine, run the following command:
acrocmd list disks
Remote management
For remote management, you install the command-line utility on the machine from which you prefer
to operate (run commands or scripts).
Along with the command, you specify:
the IP address or host name of the remote machine that has an Acronis Backup agent (--host)
credentials (a pair of user name and password) for access to that machine
The user whose credentials you specify must be a member of the Acronis Remote Users security
group on that machine. The operations are performed under this user account.
Example
To view all disks of a remote machine, run the following command:
acrocmd list disks --host=<IP address or hostname> --credentials=<user name>,<password>
Centralized management
Commands on a machine
Through Acronis Backup Management Server, you can manage any registered machine using the
credentials of the management server's administrator. Credentials for each remote machine are not
required.
For a number of commands, you can specify comma-separated addresses of multiple machines. The
operation will be executed on all the specified machines one after another.
Along with the command, you specify:
the IP address or host name of the machine that has an Acronis Backup agent (--address)
the IP address or host name of the management server (--host)
the name of the management server service (--service=ams)
credentials for access to the management server
The user whose credentials you specify must be a member of the Acronis Centralized Admins security
group on the management server. If you are running the command-line utility on a different machine,
the user must also be a member of the Acronis Remote Users security group on the management
server.
The operations on the machine are performed under the account of the agent service running on
that machine (Acronis Agent User account).
Example

11 Copyright © Acronis International GmbH, 2002-2016
To view all disks of a machine through the management server, run the following command:
acrocmd list disks --host=<ams hostname> --credentials=<user name>,<password>
--service=ams --address=<IP address or hostname>
Commands on the management server
There are commands that can be executed by the management server itself.
Example
To view the current activities of the management server, run the following command:
acrocmd list activities --host=<ams hostname> --credentials=<user name>,<password>
--service=ams
The below diagram shows options of access to a managed machine directly or via Acronis Backup
Management Server.
Options of access to a managed machine
1.5 Uninstallation
Uninstallation in Linux
In Linux, run the following commands to uninstall the command-line utility:
# cd /usr/lib/Acronis/CommandLineTool/uninstall
# ./uninstall
To uninstall the command-line utility in the unattended mode, run the ./uninstall commands
with the -a parameter.

12 Copyright © Acronis International GmbH, 2002-2016
Uninstallation in Windows
When you uninstall Acronis Backup by clicking Start -> All Programs -> Acronis -> Uninstall Acronis
Backup, the command-line utility is uninstalled along with all product components.
To uninstall the command-line utility separately from the product
1. Run the Acronis Backup setup program.
2. Click Extract installation files.
3. Select the check box corresponding to the AcronisCommandLineTool.msi file.
4. Specify the folder where to extract the file.
5. Click Extract.
6. After the file is successfully extracted, click Close.
7. Run the following command:
msiexec /uninstall <path>\AcronisCommandLineTool.msi /qb
where <path> is the folder where the file is extracted.
If you have Acronis Backup Advanced, you can also uninstall the command-line utility as follows. Run
the Acronis Backup setup program, click Install Acronis Backup, then click Modify, and then clear the
check box next to the name of the command-line utility.
1.6 List of abbreviated names
This document uses the following abbreviated names.
AMS – Acronis Backup Management Server and this component's service.
MMS – Acronis Managed Machine Service, the service running on a machine where an Acronis agent
is installed.
ASN – Acronis Backup Storage Node and this component's service.

13 Copyright © Acronis International GmbH, 2002-2016
2 Commands
This section lists the supported commands and compatible parameters.
When using the command-line utility, you can view the information about the supported commands
by means of the help (p. 18) command.
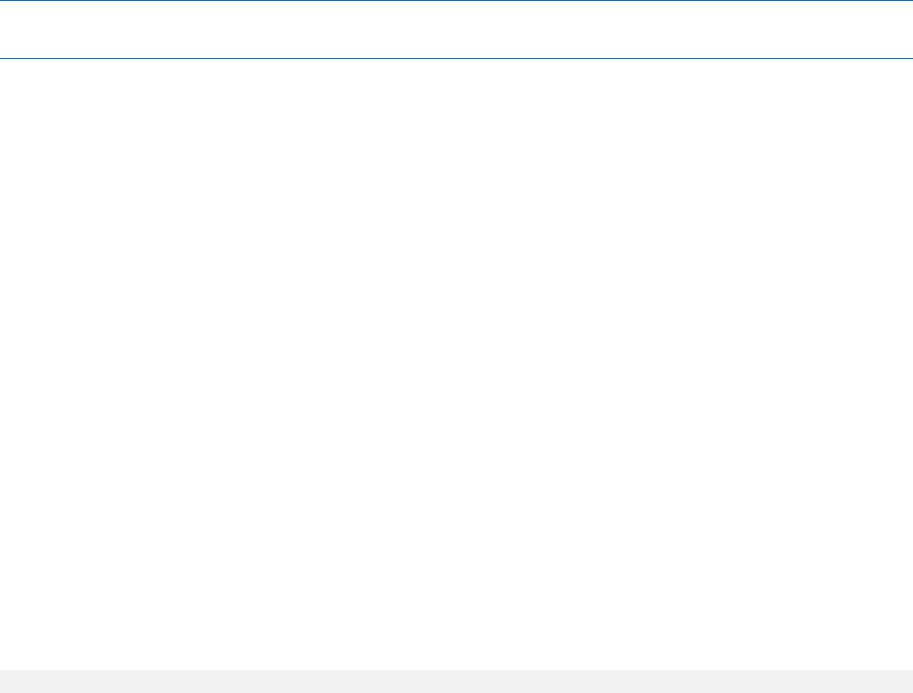
2.1 Commands by services
2.1.1 Disk, file, virtual machine backup
The following table summarizes the commands that can be executed by the Acronis services. For
questions on how to connect to an Acronis service, please see the --service (p. 76) command
description.
Command
AMS
MMS
ASN
Agent for
Windows
Agent for
Linux
Agent for
VMware or
Hyper-V
Bootable
media*
Backup and recovery
list disks (p. 18)
+
+
+
+
backup disk (p. 19)
+
+
+
recover disk (p. 20)
+
+
+
recover mbr (p. 22)
+
+
+
recover lvm_structure
(p. 23)
Linux-base
d
backup file (p. 24)
+
+
+
recover file (p. 25)
+
+
+
+
list vmservers (p. 27)
+
+
list vms (p. 27)
+
+
deploy vm_agent (p. 28)
+
backup vm (p. 29)
+**
+
recover vm (p. 31)
+**
+ (create
vm files)
+ (create
vm files)
+ (create vm
on a server)
Operations with archives and backups
list archives (p. 42)
+
+
+
+
+
+
export archive (p. 43)
+
+
+
+
+
+
validate archive (p. 44)
+
+
+
+
+
+
catalog archive (p. 44)
+
+
+
+ except Agent
for VMware
(VA)
+
delete archive (p. 45)
+
+
+
+
+
+
list backups (p. 46)
+
+
+
+
+
+

14 Copyright © Acronis International GmbH, 2002-2016
Command
AMS
MMS
ASN
Agent for
Windows
Agent for
Linux
Agent for
VMware or
Hyper-V
Bootable
media*
list content (p. 46)
+
+
+
+
+
+
validate backup (p. 47)
+
+
+
+
+
+
catalog backup (p. 48)
+
+
+
+ except Agent
for VMware
(VA)
+
export backup (p. 49)
+
+
+
+
+
+
replicate backup (p. 49)
+
+
+
+
+
+
convert full (p. 50)
+
+
+
+
+
+
consolidate backup (p.
51)
+
+
+
+
+
delete backup (p. 52)
+
+
+
+
+
+
list mounts (p. 53)
+
+
+
mount (p. 53)
+
+
+
umount (p. 54)
+
+
+
Operations with Acronis Secure Zone
create asz (p. 56)
+
+
+
resize asz (p. 57)
+
+
+
cleanup asz (p. 58)
+
+
+
delete asz_files (p. 58)
+
+
+
delete asz (p. 59)
+
+
+
Operations with Acronis Startup Recovery Manager
activate asrm (p. 59)
+
+
+
deactivate asrm (p. 60)
+
+
+
Operations with tapes
list tape_libraries (p.
60)
+
+
+
list tape_slots (p. 61)
+
+
+
inventory tape (p. 61)
+
+
+
Operations with vaults
list vaults (p. 62)
+
+
+
+
+
validate vault (p. 63)
+
+
+
+
+
+
catalog vault (p. 63)
+
+
+
+ except Agent
for VMware
(VA)
+
Operations with disks
clone disk (p. 64)
+
+
+
Operations with machines
add machine (p. 65)
+

15 Copyright © Acronis International GmbH, 2002-2016
Command
AMS
MMS
ASN
Agent for
Windows
Agent for
Linux
Agent for
VMware or
Hyper-V
Bootable
media*
Administration operations
get log (p. 66)
+
+
+
+
+
+
sysinfo (p. 66)
+
+
+
+
+
+
list activities (p. 67)
+
+
+
+
+
stop activity (p. 68)
+
+
+
+
+
list plans (p. 68)
+
+
+
+
delete plan (p. 71)
+
+
+
+
export plan (p. 69)
+
+
+
+
import plan (p. 70)
+
+
+
+
disable plan (p. 70)
+
+
+
+
enable plan (p. 71)
+
+
+
+
list tasks (p. 72)
+
+
+
+
run task (p. 72)
+
+
+
+
stop task (p. 73)
+
+
+
+
delete task (p. 73)
+
+
+
+
list licenses (p. 74)
+
+
+
+
generate report (p. 74)
+
* The command-line utility is not available in 32-bit Linux-based bootable media.
** The AMS service does not execute these commands by itself. It only defines which Agent for VMware or
Agent for Hyper-V can execute the command and transmits the command to the corresponding MMS.
2.1.2 Application backup
The following table summarizes the commands that can be executed by the Acronis services. For
questions on how to connect to an Acronis service, please see the --service (p. 76) command
description.
Command
AMS
MMS
ASN
Agent for
Exchange
Agent for
SQL*
Agent for
Active
Directory*
Reserved
Backup and recovery
list
exchange_databases (p.
33)
+
list
exchange_mailboxes (p.
33)
+
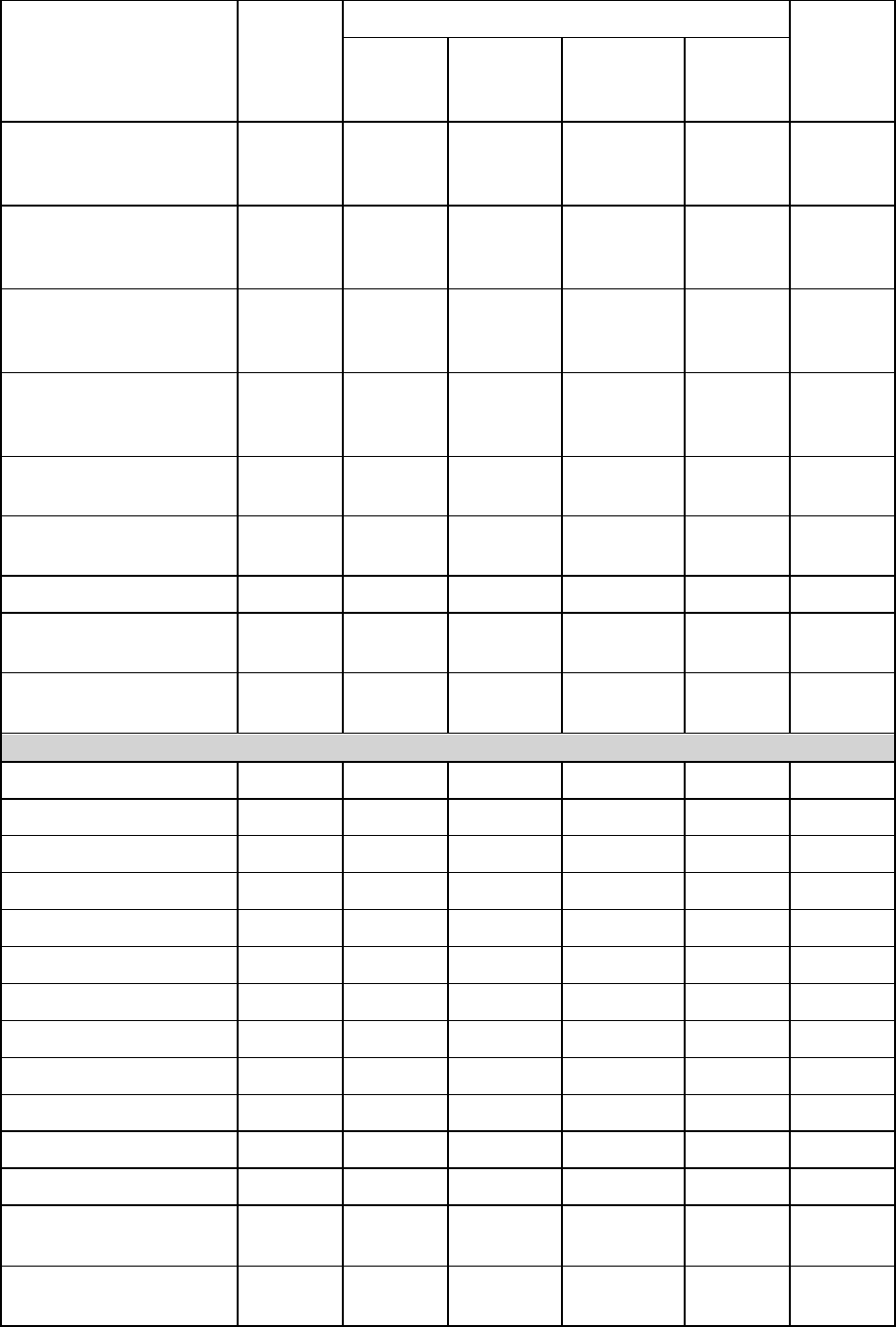
16 Copyright © Acronis International GmbH, 2002-2016
Command
AMS
MMS
ASN
Agent for
Exchange
Agent for
SQL*
Agent for
Active
Directory*
Reserved
backup
exchange_database (p.
34)
+
backup
exchange_mailbox (p.
35)
+
recover
exchange_database (p.
36)
+
recover
exchange_mailbox (p.
37)
+
list mssql_instances
(p. 39)
+
list mssql_databases
(p. 39)
+
backup disk (p. 19)
+
+
recover
mssql_database (p. 40)
+
recover ad_database (p.
41)
+
Operations with archives and backups
list archives (p. 42)
+
+
+
+
+
export archive (p. 43)
+
+
+
+
+
validate archive (p. 44)
+
+
+
+
+
catalog archive (p. 44)
+
+
+
+
+
delete archive (p. 45)
+
+
+
+
+
list backups (p. 46)
+
+
+
+
+
list content (p. 46)
+
+
+
+
+
validate backup (p. 47)
+
+
+
+
+
catalog backup (p. 48)
+
+
+
+
+
export backup (p. 49)
+
+**
+
+
+
replicate backup (p. 49)
+
+
+
+
+
delete backup (p. 52)
+
+***
+
+
+
list mssql_mounts (p.
55)
+
mount mssql_database
(p. 55)
+

17 Copyright © Acronis International GmbH, 2002-2016
Command
AMS
MMS
ASN
Agent for
Exchange
Agent for
SQL*
Agent for
Active
Directory*
Reserved
umount mssql_database
(p. 56)
+
Operations with tapes
list tape_libraries (p.
60)
+
+
+
+
list tape_slots (p. 61)
+
+
+
+
inventory tape (p. 61)
+
+
+
+
Operations with vaults
list vaults (p. 62)
+
+
+
+
+
validate vault (p. 63)
+
+
+
+
+
catalog vault (p. 63)
+
+
+
+
+
Operations with machines
add machine (p. 65)
+
Administration operations
get log (p. 66)
+
+
+
+
+
sysinfo (p. 66)
+
+
+
+
+
list activities (p. 67)
+
+
+
+
+
stop activity (p. 68)
+
+
+
+
+
list plans (p. 68)
+
+
+
+
delete plan (p. 71)
+
+
+
+
export plan (p. 69)
+
+
+
+
import plan (p. 70)
+
+
+
+
disable plan (p. 70)
+
+
+
+
enable plan (p. 71)
+
+
+
+
list tasks (p. 72)
+
+
+
+
run task (p. 72)
+
+
+
+
stop task (p. 73)
+
+
+
+
delete task (p. 73)
+
+
+
+
list licenses (p. 74)
+
+
+
generate report (p. 74)
+
18 Copyright © Acronis International GmbH, 2002-2016
* This agent can also execute all of the commands that can be executed by Agent for Windows (p. 13).
** When exporting a transaction log backup, the data from the entire backup chain (the full database backup
plus the set of subsequent transaction log backups including the selected one) is copied to a single backup.
Transaction log files will be applied to the database during recovery.
When exporting an incremental mailbox backup, the data from the backup chain (the full backup plus the set of
the subsequent incremental mailbox backups including the selected one) is consolidated into a single backup.
*** Backups that have no dependencies are deleted without any limitations. A backup that has dependencies
cannot be deleted separately from its dependent backups.
2.2 help
The command provides the information about the supported commands.
Type acrocmd help to get the list of all available commands.
Type acrocmd help <text fragment> to get the list of all commands that begin with the
fragment you specified.
For example, acrocmd help ba lists the following commands: backup disk, backup file, etc.
Type acrocmd help <complete command name> to view the information about this command.
For example, acrocmd help backup disk displays the information about the backup disk
command.
2.3 Backup and recovery
2.3.1 Disks and volumes
The commands listed in this section can be executed on a machine where Agent for Windows or
Agent for Linux is installed.
2.3.1.1 list disks
Lists available disk groups, disks, volumes and unallocated space.
Examples (p. 127)
Parameters
--oss_numbers={true|false} (p. 122)
Units of measurement
--size_measure={s|kb|mb|gb}
Measure of the size of disks and volumes. If not specified, the value is mb.
--start_measure={s|kb|mb|gb}
Measure of the offset of volumes. If not specified, the value is mb.
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
19 Copyright © Acronis International GmbH, 2002-2016
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
Access to a virtual machine (Acronis Backup Advanced for virtual environments only)
{--vmid=<virtual machine ID>|--vmname=<virtual machine
name>|--vmconfig=<path>} (p. 77)
2.3.1.2 backup disk
Creates a backup of the specified disks or volumes. If neither the --disk parameter nor the
--volume parameter is specified, the command backs up the entire machine.
Backing up the entire machine is highly recommended when you perform a single-pass disk and
application backup (i.e. specify the --application_aware parameter). Otherwise, application
data may be backed up incompletely.
Examples (p. 127)
Parameters
What to back up
--disk=<disk numbers> (p. 88)
--volume=<volume numbers> (p. 89)
--oss_numbers={true|false} (p. 122)
--exclude_hidden (p. 93)
--exclude_mask=<masks> (p. 93)
--exclude_names=<names> (p. 93)
--exclude_system (p. 93)
Where to save the backup
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
How to back up
--archive_comment=<comments> (p. 93)
--backup_comment=<comments> (p. 93)
--backuptype={full|incremental|differential} (p. 92)
--cleanup (p. 92)
--fixed_drive (p. 95)
--plain_archive (p. 97)
--raw (p. 97)
Single-pass backup
20 Copyright © Acronis International GmbH, 2002-2016
--application_aware (p. 92)
--ignore_app_errors (p. 96)
--mssql_truncate_logs (p. 96)
Backup options
--cataloging={full|fast} (p. 98)
--compression={none|normal|high|max} (p. 99)
--encryption={none|aes128|aes192|aes256} (p. 99)
--fast (p. 99)
--force_yes (p. 121)
--hdd_speed=<speed>{kb|p} (p. 99)
--ignore_bad_sectors (p. 100)
--multi_volume_snapshot={true|false} (p. 100)
--network_speed=<speed>{kb|p} (p. 101)
--post_cmd=<command> (p. 101)
--pre_cmd=<command> (p. 101)
--process_priority={low|normal|high} (p. 123)
--reboot_after (p. 125)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--split=<size> (p. 102)
--use_registry_defaults (p. 126)
--use_vss={none|auto|software_auto|software|hardware|acronis|native} (p. 103)
Tape management options
--tape_eject_successful (p. 102)
--tape_full_empty (p. 102)
--tape_overwrite (p. 102)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.1.3 recover disk
Recovers the specified disks or volumes.
21 Copyright © Acronis International GmbH, 2002-2016
A disk is always recovered along with its MBR. When you recover a volume, the MBR is not recovered
unless you use the --mbr_disk and --target_mbr_disk parameters.
Examples (p. 127)
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--disk=<disk numbers> (p. 88)
--nt_signature={auto|new|backup|existing} (p. 89)
--volume=<volume numbers> (p. 89)
--oss_numbers={true|false} (p. 122)
--mbr_disk=<disk number> (p. 91)
Where to recover
--target_disk=<disk numbers> (p. 111)
--target_volume=<volume numbers> (p. 111)
Recovering disks
If the --target_disk parameter is specified, the software will recover each disk specified in
the --disk parameter to the corresponding disk specified in the --target_disk parameter.
For example, if you type --disk=1,2 --target_disk=3,4, the software will recover disk 1 to
disk 3 and disk 2 to disk 4. If the number of values of the --disk and --target_disk
parameters differ, the command will fail.
If the --target_disk parameter is not specified, the software will automatically map the disks
specified in the --disk parameter to the target machine's disks. If the automatic mapping is not
successful, the command will fail.
Recovering volumes
If the --target_volume parameter is specified, the software will recover each volume
specified in the --volume parameter to the corresponding volume specified in the
--target_volume parameter. For example, if you type --volume=3-1,3-2
--target_volume=1-1,1-2, the software will recover volume 3-1 to volume 1-1 and volume
3-2 to volume 1-2. If the number of values of the --volume and --target_volume parameters
differ, the command will fail.
If the --target_volume parameter is not specified, and the --target_disk parameter is
specified, the software will try to recover all of the volumes specified in the --volume
parameter to the first unallocated space of a suitable size on the specified disk. If no unallocated
space of a suitable size is found, the command will fail. You can specify only one target disk, even
when recovering several volumes.
If neither the --target_volume parameter nor the --target_disk parameter is specified,
the software will automatically map the volumes specified in the --volume parameter to the
target machine's disks. If the automatic mapping is not successful, the command will fail.
--start=<offset>{s|kb|mb|gb} (p. 91)
--size=<volume size>{s|kb|mb|gb} (p. 91)
--target_mbr_disk=<disk number> (p. 92)
22 Copyright © Acronis International GmbH, 2002-2016
How to recover
--fat16_32 (p. 107)
--ext2_3 (p. 107)
--preserve_mbr (p. 109)
--type={active|primary|logical} (p. 112)
--use_all_space (p. 112)
--active_restore
If the parameter is specified, the Acronis Active Restore technology is enabled.
Recovery options
--force_yes (p. 121)
--reboot (p. 125)
--reboot_after (p. 125)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.1.4 recover mbr
Recovers the MBR from a disk or volume backup.
Use this command to repair an MBR on the same machine that was backed up. When migrating to
different hardware, use the recover disk (p. 20) command with either the --disk parameter (the
MBR will be recovered automatically) or the --volume, --mbr_disk, and --target_mbr_disk
parameters.
Examples (p. 127)
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)

23 Copyright © Acronis International GmbH, 2002-2016
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--disk=<disk number> (p. 88)
Where to recover
--target_disk=<disk number> (p. 111)
Recovery options
--force_yes (p. 121)
--reboot (p. 125)
--reboot_after (p. 125)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.1.5 recover lvm_structure
Creates the same logical volume structure on the specified machine as in the backed-up system. Use
this command if you need to recover a Linux system, along with its software RAID or LVM structure,
to a machine with different logical volume structure or without logical volumes.
The specified machine must be booted with 64-bit Linux-based bootable media. If you are using
32-bit media, either run the command on another machine with the acrocmd utility installed or
recover the LVM structure via the graphical user interface.
Before executing the command, ensure that the machine has enough disks that are as big or bigger
than the original disks. Execute the command prior to the recover disk (p. 20) command. Then,
recover each volume to the corresponding volume of the target machine.
Caution: As a result of this command execution, the current volume structure on the machine will be replaced
with the one stored in the backup. This will destroy the data that is currently stored on some or all of the
machine's hard disks.
Examples (p. 127)
Parameters
What to recover
24 Copyright © Acronis International GmbH, 2002-2016
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
Recovery options
--force_yes (p. 121)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
2.3.2 Files
The commands listed in this section can be executed on a machine where Agent for Windows or
Agent for Linux is installed.
2.3.2.1 backup file
Creates a backup of specified files and folders.
Examples (p. 130)
Parameters
What to back up
--include=<paths> (p. 96)
--exclude_hidden (p. 93)
--exclude_mask=<masks> (p. 93)
--exclude_names=<names> (p. 93)
--exclude_system (p. 93)
Where to save the backup
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
How to back up
--archive_comment=<comments> (p. 93)
--backup_comment=<comments> (p. 93)
--backuptype={full|incremental|differential} (p. 92)
--cleanup (p. 92)
25 Copyright © Acronis International GmbH, 2002-2016
--fixed_drive (p. 95)
--plain_archive (p. 97)
Backup options
--cataloging={full|fast} (p. 98)
--compression={none|normal|high|max} (p. 99)
--encryption={none|aes128|aes192|aes256} (p. 99)
--force_yes (p. 121)
--hdd_speed=<speed>{kb|p} (p. 99)
--ignore_bad_sectors (p. 100)
--multi_volume_snapshot={true|false} (p. 100)
--network_speed=<speed>{kb|p} (p. 101)
--post_cmd=<command> (p. 101)
--pre_cmd=<command> (p. 101)
--process_priority={low|normal|high} (p. 123)
--reboot_after (p. 125)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--snapshot={always|possible|none} (p. 102)
--split=<size> (p. 102)
--use_registry_defaults (p. 126)
--use_vss={none|auto|software_auto|software|hardware|acronis|native} (p. 103)
Tape management options
--tape_eject_successful (p. 102)
--tape_full_empty (p. 102)
--tape_overwrite (p. 102)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.2.2 recover file
Recovers files and folders from a file-level or disk-level backup.
Examples (p. 130)
26 Copyright © Acronis International GmbH, 2002-2016
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--file=<paths> (p. 107)
--exclude=<files, folders and masks> (p. 106)
Where to recover
--target=<path> (p. 86)
--credentials=<user name>,<password>,encrypted (p. 120)
How to recover
--overwrite={always|older|never} (p. 108)
--recover_absolute_path (p. 109)
--recover_security={true|false}
This parameter is effective only when recovering from a file-level backup of Windows files. If the
value is true or if the parameter is not specified, recover NTFS permissions for files along with
the files themselves. Otherwise, the files will inherit the NTFS permissions from the folder to
which they will be recovered.
--original_date (p. 108)
Recovery options
--force_yes (p. 121)
--reboot (p. 125)
--reboot_after (p. 125)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
27 Copyright © Acronis International GmbH, 2002-2016
2.3.3 Virtual machines
The commands listed in this section are available in Acronis Backup Advanced only if Agent for
VMware or Agent for Hyper-V is installed. (This does not apply to the recover vm (p. 31) command.)
2.3.3.1 list vmservers
Lists virtualization servers and server clusters that are present on the specified management server
or that are accessible to Agent for VMware.
Examples (p. 131)
Parameters
--filter_guid=<GUIDs> (p. 116)
--filter_name=<names> (p. 117)
--filter_machines=<quantities of machines> (p. 117)
--filter_type=<server types> (p. 118)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.3.2 list vms
Lists virtual machines that are present on the specified management server or that are managed by
Agent for VMware or Agent for Hyper-V, depending on the service that will execute the command.
Examples (p. 131)
Parameters
--filter_available_for_backup={true|false} (p. 115)
--filter_guid=<GUIDs> (p. 116)
--filter_host=<hostnames> (p. 116)
--filter_name=<names> (p. 117)
--filter_state=<states> (p. 118)
--filter_status=<statuses> (p. 118)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
28 Copyright © Acronis International GmbH, 2002-2016
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.3.3 deploy vm_agent
Deploys Agent for VMware (Virtual Appliance) to an ESX(i) host managed by a vCenter Server or to a
stand-alone ESX(i) host.
You can deploy only one agent at a time. The --service=ams parameter is mandatory because the
command is executed by the management server.
Examples (p. 131)
Parameters
--vsphere_address=<IP address or hostname>
vCenter Server that manages the vSphere to which you want to deploy the agent. If you need to
deploy the agent to a stand-alone ESX(i) host, specify this host.
If the parameter is not specified, the command will fail.
--credentials=<user name>,<password>,encrypted (p. 120)
Credentials for the vCenter Server or stand-alone ESX(i) host.
--vmconnection_credentials=<user name>,<password>,encrypted
Credentials that the agent will use to access the vCenter Server or the ESX(i) host. The account
must have the necessary privileges on the vCenter Server, as described in the "Privileges for VM
backup and recovery" section of the "Backing up virtual machines" document.
If the parameter is not specified, the agent will use the credentials specified after the
--vsphere_address parameter.
--vmhost=<IP address or hostname>
ESX(i) host to which you want to deploy the agent. If not specified, the host will be selected
automatically.
The parameter is used only if the --vsphere_address parameter points to a vCenter Server. If
it points to a stand-alone ESX(i) host, the --vmhost parameter is redundant.
--vmname=<virtual machine name>
Name of the virtual appliance. If not specified, the value is AcronisESXAppliance-[N] where
[N] is a sequence number of the appliance deployment attempt.
--vmstorage=<datastore name>
Location of the virtual appliance. If not specified, the software will automatically select one of
the datastores available to the host.
--vmnic={flexible|E1000|vmxnet|vmxnet2|vmxnet3}
29 Copyright © Acronis International GmbH, 2002-2016
Network interface card of the virtual appliance. If not specified, the value is vmxnet3.
--vmnetwork=<network label>
Network to which the virtual appliance's network interface card will be connected. For example,
--vmnetwork="VM Network". If not specified, the software will automatically select one of the
available networks.
--mac_address=<MAC address>
MAC address of the virtual appliance's network interface card. The format is
XX:XX:XX:XX:XX:XX. For example, --mac_address=00:50:56:8c:00:00. If not specified,
the software will generate the MAC address.
Network settings of the virtual appliance
If any of the parameters described in this section are not specified, the virtual appliance will obtain
the values from the DHCP server that is present on your network.
--ip_address=<IP address>
IP address. For example, --ip_address=10.200.200.10.
--subnet_mask=<subnet mask>
Subnet mask. For example, --subnet_mask=255.255.255.0.
--gateway=<default gateway>
Default gateway. For example, --gateway=10.200.200.1.
--dns=<DNS servers>
IP addresses of the DNS servers. For example, --dns=10.200.200.101,10.200.200.102.
--dns_suffix=<DNS suffix>
DNS suffix. For example, --dns_suffix=mydomain.com.
--wins=<WINS servers>
IP addresses of the WINS servers. For example, --wins=10.200.200.111,10.200.200.112.
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote management server
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
Access to the management server service
--service=ams (p. 76)
2.3.3.4 backup vm
Creates a backup of specified disks and volumes of the specified virtual machines. If neither --disk
nor --volume parameter is specified, the command backs up the entire machine.
30 Copyright © Acronis International GmbH, 2002-2016
Examples (p. 131)
Parameters
Access to a virtual machine
{--vmid=<virtual machine IDs>|--vmname=<virtual machine
names>|--vmconfig=<paths>} (p. 77)
You can specify one or more virtual machines to be backed up. The --vmname parameter is
case-sensitive.
--simultaneous_backup=<number>
Number of virtual machines to be backed up simultaneously by Agent for VMware or Agent for
Hyper-V. If not specified, each agent will back up virtual machines two at a time simultaneously.
To back up machines one at a time, set the parameter value to 1.
What to back up
--disk=<disk numbers> (p. 88)
--volume=<volume numbers> (p. 89)
--exclude_hidden (p. 93)
--exclude_mask=<masks> (p. 93)
--exclude_names=<names> (p. 93)
--exclude_system (p. 93)
Where to save the backup
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
How to back up
--archive_comment=<comments> (p. 93)
--backup_comment=<comments> (p. 93)
--backuptype={full|incremental|differential} (p. 92)
--cleanup (p. 92)
--raw (p. 97)
Backup options
--cataloging={full|fast} (p. 98)
--cbt_mode={on|off} (p. 98)
--compression={none|normal|high|max} (p. 99)
--encryption={none|aes128|aes192|aes256} (p. 99)
--fast (p. 99)
--force_yes (p. 121)
--hdd_speed=<speed>{kb|p} (p. 99)
--network_speed=<speed>{kb|p} (p. 101)
--process_priority={low|normal|high} (p. 123)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)

31 Copyright © Acronis International GmbH, 2002-2016
--split=<size> (p. 102)
--use_registry_defaults (p. 126)
Tape management options
--tape_eject_successful (p. 102)
--tape_full_empty (p. 102)
--tape_overwrite (p. 102)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote physical machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.3.5 recover vm
Recovers a disk or volume backup onto a new or existing virtual machine. The recover vm command
replaces and enhances the convert command which was available in earlier versions of the Acronis
software.
The recover vm command can be executed by the following agents:
Agent for VMware recovers a disk (volume) backup to a new or existing ESX(i) virtual machine.
Agent for Hyper-V recovers a disk (volume) backup to a new or existing Hyper-V virtual machine.
Agent for Windows and Agent for Linux recover a disk (volume) backup to a new virtual machine
of any of the following types: VMware Workstation, Microsoft Virtual PC, Red Hat Enterprise
Virtualization, or Citrix XenServer Open Virtual Appliance (OVA).
Files of the fully configured and operational machine will be placed in the folder you select. You
can start the machine using the corresponding virtualization software or prepare the machine
files for further usage. The OVA virtual appliance can be imported to XenServer. Disks of a Virtual
PC can be attached to a Hyper-V virtual machine.
A virtual machine must be powered off during the recovery to this machine. The target machine located on an
ESX(i) or Hyper-V host will be powered off without a prompt. Please be sure to specify the correct machine.
Examples (p. 131)
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
32 Copyright © Acronis International GmbH, 2002-2016
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--disk=<disk numbers> (p. 88)
--volume=<volume number> (p. 89)
Where to recover
If you want to recover to an existing virtual machine:
{--vmid=<virtual machine ID>|--vmname=<virtual machine
name>|--vmconfig=<path>} (p. 77)
If you want to create a new virtual machine on an ESX(i) or Hyper-V host:
--vmname=<virtual machine name> (p. 78)
--vmstorage=<path> (p. 78)
{--vmserver_name=<server name>|--vmserver_id=<server GUID>} (p. 78)
--vmram=<memory size> (p. 78)
--vmcpu=<number of CPUs> (p. 78)
--vmdisk_size=<disk sizes> (p. 78)
--vmdisk_type=<disk types> (p. 78)
--vmdisk_provisioning=<disk provisioning types> (p. 78)
If you want to create a new virtual machine in a local or network folder:
--vmname=<virtual machine name> (p. 80)
--vmtype={vmware|virtualpc|redhat|xen} (p. 80)
--vmstorage=<path> (p. 80)
--credentials=<user name>,<password>,encrypted (p. 120)
Credentials for a network folder where the virtual machine is to be created.
--target_disk=<disk number> (p. 111)
--target_volume=<volume number> (p. 111)
--start=<offset>{s|kb|mb|gb} (p. 91)
--size=<volume size>{s|kb|mb|gb} (p. 91)
How to recover
--ext2_3 (p. 107)
--fat16_32 (p. 107)
--preserve_mbr (p. 109)
--type={active|primary|logical} (p. 112)
--use_all_space (p. 112)
Recovery options
--force_yes (p. 121)
--power_on (p. 109)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
33 Copyright © Acronis International GmbH, 2002-2016
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.4 Microsoft Exchange
The commands listed in this section can be executed on a machine where Agent for Exchange is
installed.
2.3.4.1 list exchange_databases
Lists storage groups (for Exchange 2003/2007) and databases.
Examples (p. 132)
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
--exchange_credentials=<domain user name>,<password>,encrypted (p. 80)
Access to a remote machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine
--service={mms|ams} (p. 76)
2.3.4.2 list exchange_mailboxes
Lists mailboxes and public folders in the specified Exchange database.
Examples (p. 132)
Parameters
--mailbox_location=<path> (p. 88)
--filter_name=<names> (p. 117)
General parameters
34 Copyright © Acronis International GmbH, 2002-2016
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
--exchange_credentials=<domain user name>,<password>,encrypted (p. 80)
Access to a remote machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine
--service={mms|ams} (p. 76)
2.3.4.3 backup exchange_database
Creates a backup of the specified storage groups (for Exchange 2003/2007) or databases (for
Exchange 2010 or later).
Examples (p. 132)
Parameters
What to back up
--items=<items> (p. 81)
Where to save the backup
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
How to back up
--archive_comment=<comments> (p. 93)
--backup_comment=<comments> (p. 93)
--backuptype={full|transaction_log} (p. 92)
--cleanup (p. 92)
--copy_only (p. 93)
--express (p. 95)
Backup options
--cataloging={full|fast} (p. 98)
--compression={none|normal|high|max} (p. 99)
--encryption={none|aes128|aes192|aes256} (p. 99)
--force_yes (p. 121)
--metadata_level={{mailboxes_only|1}|{folders_and_mailboxes|2}|{all|3}} (p.
100)
--post_cmd=<command> (p. 101)
--pre_cmd=<command> (p. 101)
--retry_count=<number of attempts> (p. 120)
35 Copyright © Acronis International GmbH, 2002-2016
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--split=<size> (p. 102)
--use_registry_defaults (p. 126)
Tape management options
--tape_eject_successful (p. 102)
--tape_full_empty (p. 102)
--tape_overwrite (p. 102)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
--exchange_credentials=<domain user name>,<password>,encrypted (p. 80)
Access to a remote machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine
--service={mms|ams} (p. 76)
2.3.4.4 backup exchange_mailbox
Creates a backup of the specified mailboxes and public folders. The command cannot be used to back
up data of Microsoft Exchange 2013 or later.
Examples (p. 132)
Parameters
What to back up
--items=<items> (p. 81)
--exclude_age=<date> (p. 93)
--exclude_attach=<files and masks> (p. 93)
--exclude_size=<size>{kb|mb|gb} (p. 93)
--exclude_types=<types> (p. 93)
Where to save the backup
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
How to back up
36 Copyright © Acronis International GmbH, 2002-2016
--archive_comment=<comments> (p. 93)
--backup_comment=<comments> (p. 93)
--backuptype={full|incremental} (p. 92)
--cleanup (p. 92)
Backup options
--cataloging={full|fast} (p. 98)
--compression={none|normal|high|max} (p. 99)
--encryption={none|aes128|aes192|aes256} (p. 99)
--force_yes (p. 121)
--post_cmd=<command> (p. 101)
--pre_cmd=<command> (p. 101)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--split=<size> (p. 102)
--use_registry_defaults (p. 126)
Tape management options
--tape_eject_successful (p. 102)
--tape_full_empty (p. 102)
--tape_overwrite (p. 102)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
--exchange_credentials=<domain user name>,<password>,encrypted (p. 80)
Access to a remote machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine
--service={mms|ams} (p. 76)
2.3.4.5 recover exchange_database
Recovers the specified storage groups (for Exchange 2003/2007) or databases (for Exchange 2010 or
later).
Examples (p. 132)
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
37 Copyright © Acronis International GmbH, 2002-2016
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--recovery_point={point_of_failure|latest_backup|point_in_time|selected_ba
ckup} (p. 110)
--pit=<date and time> (p. 109)
--backup=<backup ID> (p. 85)
--items=<items> (p. 81)
Where to recover
--target={original|disk|another_database|recovery_database} (p. 86)
--disk_location=<path> (p. 106)
--credentials=<user name>,<password>,encrypted (p. 120)
--destination_database=<db> (p. 105)
--database=<db_name> (p. 104)
--database_location=<local path> (p. 104)
--log_location=<local path> (p. 107)
How to recover
--overwrite (p. 108)
--active_restore
If the parameter is specified, the Acronis Active Restore technology is enabled.
Recovery options
--force_yes (p. 121)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
--exchange_credentials=<domain user name>,<password>,encrypted (p. 80)
Access to a remote machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine
--service={mms|ams} (p. 76)
2.3.4.6 recover exchange_mailbox
Recovers the specified mailboxes and public folders from a database-level or mailbox-level backup.
Examples (p. 132)
38 Copyright © Acronis International GmbH, 2002-2016
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--recovery_point={latest_backup|point_in_time|selected_backup} (p. 110)
--pit=<date and time> (p. 109)
--backup=<backup ID> (p. 85)
--items=<items> (p. 81)
Where to recover
--target={original|pst} (p. 86)
--disk_location=<local path> (p. 106)
--outlookmachine=<IP address or hostname> (p. 108)
--credentials=<user name>,<password>,encrypted (p. 120)
How to recover
--overwrite (p. 108)
Recovery options
--force_yes (p. 121)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
--exchange_credentials=<domain user name>,<password>,encrypted (p. 80)
Access to a remote machine
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine
--service={mms|ams} (p. 76)
2.3.5 Microsoft SQL
The commands listed in this section can be executed on a machine where Agent for SQL is installed.
39 Copyright © Acronis International GmbH, 2002-2016
2.3.5.1 list mssql_instances
Lists Microsoft SQL Server instances.
Examples (p. 134)
Parameters
--filter_edition=<editions> (p. 116)
--filter_name=<names> (p. 117)
--filter_version=<versions> (p. 119)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.5.2 list mssql_databases
Lists Microsoft SQL databases of the specified instance. Only the databases whose files are stored in
local folders of the SQL server are displayed.
Examples (p. 134)
Parameters
--filter_name=<names> (p. 117)
--instance=<instance name> (p. 81)
--credentials=<user name>,<password>,encrypted
For information about specifying access credentials for Microsoft SQL Server, see "Access to SQL
Server instance" (p. 83).
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
40 Copyright © Acronis International GmbH, 2002-2016
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.5.3 recover mssql_database
Recovers the specified Microsoft SQL databases.
Examples (p. 134)
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--items=<items> (p. 81)
Where to recover
--target={original|disk|another_instance} (p. 86)
--disk_location=<path> (p. 106)
--credentials=<user name>,<password>,encrypted (p. 120)
--destination_instance=<instance name> (p. 106)
--credentials=<user name>,<password>,encrypted
For information about specifying access credentials for Microsoft SQL Server, see "Access to SQL
Server instance" (p. 83).
--database_location=<local path> (p. 104)
How to recover
--overwrite (p. 108)
--autorename (p. 103)
--database_state={recovery|norecovery|standby} (p. 105)
--active_restore
If the parameter is specified, the Acronis Active Restore technology is enabled.
Recovery options
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
41 Copyright © Acronis International GmbH, 2002-2016
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.3.6 Microsoft Active Directory
The command described in this section can be executed on a machine where Agent for Active
Directory is installed.
2.3.6.1 recover ad_database
Extracts Microsoft Active Directory database files and the SYSVOL folder from a single-pass backup to
a local or network folder. Full paths of the files are recreated.
For information about what to do with the extracted files, refer to the "Recovering the Active
Directory data from a single-pass backup" section of the product Help or the User Guide.
Examples (p. 135)
Parameters
What to recover
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
Where to recover
--target=<path> (p. 86)
--credentials=<user name>,<password>,encrypted (p. 120)
How to recover
--overwrite={always|older|never} (p. 108)
--original_date (p. 108)
Recovery options
--force_yes (p. 121)
--retry_count=<number of attempts> (p. 120)
--retry_delay=<delay> (p. 120)
--silent_mode={on|off} (p. 126)
--use_registry_defaults (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
42 Copyright © Acronis International GmbH, 2002-2016
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4 Operations with archives and backups
2.4.1 Archives
2.4.1.1 list archives
Lists the information about archives in the specific location. The displayed records are sorted by date
in descending order.
Examples (p. 136)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--filter_type=<types> (p. 118)
{-a|--all}
If the parameter is specified, the following properties will be displayed for each archive: name,
type, creation date, machine whose data is contained in the archive, owner (the user who saved
the archive to the destination), occupied space in bytes, comments on the archive, whether the
archive is encrypted (password-protected) or not, and size of the backed-up data. If not specified,
only name, type, and creation date will be displayed for each archive.
--recreate_archive_meta={true|false} (p. 125)
--utc (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)

43 Copyright © Acronis International GmbH, 2002-2016
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.1.2 export archive
Copies the archive specified by the --arc parameter from the location specified by the --loc
parameter to the location specified by the --target parameter.
To export individual backups, use the export backup (p. 49) command.
If the --arc parameter is not specified, the command will export all the archives stored in the
source location.
The command always creates a new archive in the target location. You cannot specify an existing
archive in the --target_arc parameter.
Using this command, you can, for example, import an archive to a centralized managed vault or
export the entire vault to a different location. See the examples for more details.
Examples (p. 136)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--target=<path> (p. 86)
--credentials=<user name>,<password>,encrypted (p. 120)
--target_arc=<archive name> (p. 88)
--cataloging={full|fast} (p. 98)
--silent_mode={on|off} (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
Exporting archives from a managed vault (--loc=bsp://<storage node>/<vault name>) is
always executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
44 Copyright © Acronis International GmbH, 2002-2016
2.4.1.3 validate archive
Validates the archive data integrity.
Examples (p. 136)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--process_priority={low|normal|high} (p. 123)
--read_speed=<speed>{kb|p} (p. 124)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.1.4 catalog archive
Performs a full cataloging of all the backups in the specified archive.
Usage tip. To speed up backups, you can prohibit full cataloging by adding the --cataloging=fast
parameter to the backup command. Use the catalog backup (p. 48), catalog archive (p. 44), or
catalog vault (p. 63) command to perform the full cataloging at a later time.
Examples (p. 136)
Parameters
--loc=<path> (p. 84)
The command does not support the following locations: Acronis Cloud Storage, encrypted
managed vaults, and removable media such as CD, DVD, BD, Iomega REV, RDX or USB devices.
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
45 Copyright © Acronis International GmbH, 2002-2016
The command does not support encrypted and password-protected archives, archives created by
using Acronis True Image Echo or earlier product versions, and archives that use the simplified
backup naming (p. 97).
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.1.5 delete archive
Deletes an archive.
Examples (p. 136)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
46 Copyright © Acronis International GmbH, 2002-2016
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.2 Backups
2.4.2.1 list backups
Lists backups in the specified archive. The displayed records are sorted by date in descending order.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--filter_date=<dates and times> (p. 116)
--filter_type=<types> (p. 118)
--recreate_archive_meta={true|false} (p. 125)
--utc (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.2.2 list content
Lists the contents of a backup (backed-up disks, volumes, files, virtual machines, databases, etc.).
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
47 Copyright © Acronis International GmbH, 2002-2016
--backup=<backup ID> (p. 85)
--content_type={volume|file|exchange_database|exchange_mailbox|mssql_datab
ase|ad_database} (p. 115)
--content_path=<path> (p. 114)
--oss_numbers={true|false} (p. 122)
--utc (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.2.3 validate backup
Validates the backup data integrity.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--process_priority={low|normal|high} (p. 123)
--read_speed=<speed>{kb|p} (p. 124)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
48 Copyright © Acronis International GmbH, 2002-2016
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.2.4 catalog backup
Performs a full cataloging of the specified backup.
Usage tip. To speed up backups, you can prohibit full cataloging by adding the --cataloging=fast
parameter to the backup command. Use the catalog backup (p. 48), catalog archive (p. 44), or
catalog vault (p. 63) command to perform the full cataloging at a later time.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
The command does not support the following locations: Acronis Cloud Storage, encrypted
managed vaults, and removable media such as CD, DVD, BD, Iomega REV, RDX or USB devices.
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
The command does not support encrypted and password-protected archives, archives created by
using Acronis True Image Echo or earlier product versions, and archives that use the simplified
backup naming (p. 97).
--backup=<backup ID> (p. 85)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.

49 Copyright © Acronis International GmbH, 2002-2016
2.4.2.5 export backup
Copies the archive specified by the --arc parameter from the location specified by the --loc
parameter to the location specified by the --target parameter. The copy will contain only the
backups specified by the --backup parameter.
To export an entire archive or all the archives stored in a location, use the export archive (p. 43) command.
The command always creates a new archive in the target location. You cannot specify an existing
archive in the --target_arc parameter. Both the --target and the --target_arc parameters
are mandatory.
If the --backup parameter is not specified, the command will export only the latest backup.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup IDs> (p. 85)
--target=<path> (p. 86)
--credentials=<user name>,<password>,encrypted (p. 120)
--target_arc=<archive name> (p. 88)
--cataloging={full|fast} (p. 98)
--silent_mode={on|off} (p. 126)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
Exporting backups from a managed vault (--loc=bsp://<storage node>/<vault name>) is
always executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.2.6 replicate backup
Replicates the latest backup of the specified archive to a different location. If the --backup
parameter is specified, the specified backups will be replicated. If the target location is the same as
the source one, the command will fail.
50 Copyright © Acronis International GmbH, 2002-2016
If the target archive exists, the command will append the specified backups to it. This means that a
backup will not be replicated if the target archive already contains a backup with the same GUID.
Using this command, you can replicate each backup of your archive to a second location immediately
after backing up or on a schedule. This helps you make your archive more reliable by maintaining its
copy in a different location.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
The command does not support archives that use the simplified backup naming (p. 97).
--password=<password>,encrypted (p. 123)
--target=<path> (p. 86)
--credentials=<user name>,<password>,encrypted (p. 120)
--target_arc=<archive name> (p. 88)
--backup={<backup IDs>|all} (p. 85)
If the value is all, all backups of the specified archive will be selected for replication.
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
Replicating backups from a managed vault (--loc=bsp://<storage node>/<vault name>)
is always executed by the storage node service. If you specify a different service, it will transmit
the command to asn.
2.4.2.7 convert full
Converts an incremental or differential backup into a full one. The backup time stamp remains
unchanged. The dependent incremental and differential backups are also updated. However, the old
backup versions are deleted only after the new ones have been created. Therefore, the location must
have enough space to temporarily store both the old and the new versions.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
51 Copyright © Acronis International GmbH, 2002-2016
The command does not support the following locations: Acronis Cloud Storage, tape and
CD/DVD.
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
The command does not support archives that use the simplified backup naming (p. 97) and
archives of Microsoft Exchange Server data (p. 33).
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.4.2.8 consolidate backup
Modifies an archive so that only the backups specified in the --backup parameter are kept. All
other backups of the archive are deleted.
If the --backup parameter is not specified, only the latest backup of the archive is kept. As a result,
the archive will contain only one backup.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
The command does not support the following location: Acronis Backup Storage Node.
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup IDs> (p. 85)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
52 Copyright © Acronis International GmbH, 2002-2016
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4.2.9 delete backup
Deletes the selected backup from an archive. If incremental or differential backups depend on the
backup being deleted, a consolidation will be performed. This consolidation may be time and
resource consuming.
A backup stored on a tape (--loc=atis:///tape) is not physically deleted until the tape is
overwritten. Therefore, the backup will be present in the output of the list backups (p. 46)
command.
Examples (p. 137)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.

53 Copyright © Acronis International GmbH, 2002-2016
2.4.3 Mounting volumes
Mounting volumes from a disk-level backup lets you access the volumes as though they were
physical disks.
2.4.3.1 list mounts
Lists the volumes mounted from backups.
Examples (p. 139)
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4.3.2 mount
Mounts the specified volumes from the backup to the system where Agent for Windows or Agent for
Linux is installed.
Limitation: You can only mount backups stored in a local or shared folder or in Acronis Secure Zone.
Examples (p. 139)
Parameters
What to mount
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--volume=<volume numbers> (p. 89)
How to mount (Agent for Windows only)
--rw (p. 113)
--letter=<letters> (p. 113)
--for_all_users={true|false} (p. 112)
How to mount (Agent for Linux only)
54 Copyright © Acronis International GmbH, 2002-2016
--rw (p. 113)
--mount_point=<mount points> (p. 113)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4.3.3 umount
Unmounts the volume with the specified letter (Agent for Windows only).
Unmounts the device mounted at the mount point, destroys the kernel space block device and stops
the user space daemon (Agent for Linux only).
Examples (p. 139)
Parameters
--letter={<letter>|all} (p. 113) (Agent for Windows only)
--mount_point=<mount point> (p. 113) (Agent for Linux only)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4.4 Mounting SQL databases
The commands listed in this section can be executed on a machine where Agent for SQL is installed.

55 Copyright © Acronis International GmbH, 2002-2016
2.4.4.1 list mssql_mounts
Lists the Microsoft SQL databases mounted from single-pass backups.
Examples (p. 139)
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4.4.2 mount mssql_database
Mounts the specified Microsoft SQL databases from the backup to the specified Microsoft SQL Server
instance.
Limitation: You can only mount backups stored in a local or shared folder or in Acronis Secure Zone.
Examples (p. 139)
Parameters
What to mount
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
--backup=<backup ID> (p. 85)
--items=<items> (p. 81)
Where to mount
--destination_instance=<instance name> (p. 106)
--credentials=<user name>,<password>,encrypted
For information about specifying access credentials for Microsoft SQL Server, see "Access to SQL
Server instance" (p. 83).
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
56 Copyright © Acronis International GmbH, 2002-2016
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.4.4.3 umount mssql_database
Unmounts the specified Microsoft SQL databases.
Examples (p. 139)
Parameters
--items=<items> (p. 81)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.5 Operations with Acronis Secure Zone
Acronis Secure Zone is a secure volume for storing backup archives within a managed machine.
2.5.1 create asz
Creates Acronis Secure Zone on the selected disk. The command first uses the unallocated space on
that disk and then, if the unallocated space is insufficient, takes free space from the selected
volumes.
Examples (p. 140)
Parameters
--disk=<disk number> (p. 88)
--volume={<volume numbers>|all} (p. 89)
--oss_numbers={true|false} (p. 122)
57 Copyright © Acronis International GmbH, 2002-2016
--asz_size={<size>{s|kb|mb|gb}|unallocated} (p. 114)
--password=<password>,encrypted (p. 123)
--reboot (p. 125)
--later (p. 125)
--silent_mode={on|off} (p. 126)
--force_yes (p. 121)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.5.2 resize asz
Changes the Acronis Secure Zone size and displays the resulting size and free space. Without the
--asz_size parameter, displays the current Acronis Secure Zone size and free space.
Examples (p. 140)
Parameters
--asz_size={<size>{s|kb|mb|gb}|unallocated} (p. 114)
--volume={<volume numbers>|all} (p. 89)
--oss_numbers={true|false} (p. 122)
--size_measure={s|kb|mb|gb}
Measure of the Acronis Secure Zone size and free space in the command output. If not specified,
the value is mb.
--reboot (p. 125)
--later (p. 125)
--silent_mode={on|off} (p. 126)
--force_yes (p. 121)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
58 Copyright © Acronis International GmbH, 2002-2016
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.5.3 cleanup asz
Deletes the backups corrupted due to a power loss or another reason, from Acronis Secure Zone.
Examples (p. 140)
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.5.4 delete asz_files
Deletes the latest backup of an archive located in Acronis Secure Zone. If the specified archive
contains only one backup, such backup will not be deleted.
Examples (p. 140)
Parameters
--credentials=<password>,encrypted (p. 120)
Password for Acronis Secure Zone.
--arc=<archive name> (p. 84)
--password=<password>,encrypted (p. 123)
Password for the archive.
--force_yes (p. 121)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
59 Copyright © Acronis International GmbH, 2002-2016
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.5.5 delete asz
Deletes Acronis Secure Zone.
Examples (p. 140)
Parameters
--volume=<volume numbers> (p. 89)
--oss_numbers={true|false} (p. 122)
--silent_mode={on|off} (p. 126)
--force_yes (p. 121)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.6 Operations with Acronis Startup Recovery Manager
Acronis Startup Recovery Manager is the bootable rescue utility that can be started at boot time by
pressing F11.
2.6.1 activate asrm
Activates the Acronis Startup Recovery Manager.
Examples (p. 141)
60 Copyright © Acronis International GmbH, 2002-2016
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.6.2 deactivate asrm
Deactivates the Acronis Startup Recovery Manager.
Examples (p. 141)
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP addresses or hostnames> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.7 Operations with tapes
2.7.1 list tape_libraries
Lists tape libraries and/or stand-alone tape drives attached to a machine where an Acronis Backup
agent or Acronis Backup Storage Node is running.
Examples (p. 141)
Parameters
--filter_guid=<GUIDs> (p. 116)
--filter_name=<names> (p. 117)
61 Copyright © Acronis International GmbH, 2002-2016
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
2.7.2 list tape_slots
Lists slots of the tape libraries attached to a machine where an Acronis Backup agent or Acronis
Backup Storage Node is running. The following information will be displayed for each slot: name;
GUID; type (mail for mail slots, drive for drives, storage for other slots); barcode and label of the
tape that occupies the slot (if any); GUID of the tape library.
Examples (p. 141)
Parameters
--filter_library=<GUID> (p. 117)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
2.7.3 inventory tape
Detects tapes loaded into a tape device and assigns names to those that have none. Run this
command every time you load tapes into the tape device slots.
Examples (p. 141)
62 Copyright © Acronis International GmbH, 2002-2016
Parameters
--mode={full|fast} (p. 119)
--libraries=<GUIDs> (p. 119)
--slots=<GUIDs> (p. 120)
--assign2free (p. 119)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
2.8 Operations with vaults
2.8.1 list vaults
Lists the vaults available to a managed machine or to the management server or attached to a
storage node (depending on the --service parameter value).
Examples (p. 142)
Parameters
--filter_type={central|personal}
To output either centralized or personal vaults.
--filter_managed
To output only managed vaults.
--filter_unmanaged
To output only personal and centralized unmanaged vaults.
--filter_dedup
To output only deduplicating vaults.
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
63 Copyright © Acronis International GmbH, 2002-2016
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
2.8.2 validate vault
Validates data integrity of all archives in the specified location except for password-protected ones.
To validate a password-protected archive, use the validate archive (p. 44) command.
Examples (p. 142)
Parameters
--loc=<path> (p. 84)
--credentials=<user name>,<password>,encrypted (p. 120)
--process_priority={low|normal|high} (p. 123)
--read_speed=<speed>{kb|p} (p. 124)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.8.3 catalog vault
Performs a full cataloging of the backups stored in the specified location.
The following backups will be skipped because they are not supported by the data catalog:
Backups contained in encrypted and password-protected archives.
Backups created by using Acronis True Image Echo or earlier product versions.
Backups that have simplified names (p. 97).
Usage tip. To speed up backups, you can prohibit full cataloging by adding the --cataloging=fast
parameter to the backup command. Use the catalog backup (p. 48), catalog archive (p. 44), or
catalog vault (p. 63) command to perform the full cataloging at a later time.
64 Copyright © Acronis International GmbH, 2002-2016
Examples (p. 142)
Parameters
--loc=<path> (p. 84)
The command does not support the following locations: Acronis Cloud Storage, encrypted
managed vaults, and removable media such as CD, DVD, BD, Iomega REV, RDX or USB devices.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
In a managed vault (--loc=bsp://<storage node>/<vault name>), the operation is always
executed by the storage node service. If you specify a different service, it will transmit the
command to asn.
2.9 Operations with disks
2.9.1 clone disk
Clones a hard disk. Use this operation if you need to transfer all the source disk data to a target disk.
The software does not resize the volumes of the source disk. Therefore, the target disk should have a
greater capacity than the source disk. Otherwise, the command will fail.
Examples (p. 143)
Parameters
--source=<source disk number>
The number of the source disk.
--target=<target disk number>
The number of the target disk.
--reboot (p. 125)
--reboot_after (p. 125)
General parameters
65 Copyright © Acronis International GmbH, 2002-2016
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
--progress (p. 124)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.10 Operations with machines
The command described in this section is available only in Acronis Backup Advanced.
2.10.1 add machine
Adds a machine with an agent to the management server. The --service=ams parameter is
mandatory because the command is executed by the management server.
Examples (p. 143)
Parameters
--machine_address=<IP address or hostname>
Machine to be added.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote management server
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
Access to the management server service
--service=ams (p. 76)
66 Copyright © Acronis International GmbH, 2002-2016
2.11 Administration operations
2.11.1 Collecting information
2.11.1.1 get log
Exports the log of the activity with the specified GUID in the Acronis XML format. To learn GUIDs of
activities, use the list activities (p. 67) command.
Examples (p. 143)
Parameters
--id=<GUID> (p. 122)
--loc=<full path> (p. 84)
The file to export the log to. The following locations are supported: local path, SMB, NFS, FTP and
SFTP. The software exports logs in the Acronis xml format regardless of the extension of the file.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
When getting the log of a storage node activity, you can specify only ams or asn as a parameter
value.
2.11.1.2 sysinfo
Collects the system information of a machine and saves the information in the .zip file format.
Examples (p. 143)
Parameters
--loc=<full path> (p. 84)
Full path to the file where the system information will be saved. The following locations are
supported: local path, SMB, and NFS.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
67 Copyright © Acronis International GmbH, 2002-2016
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
When getting the system information of a machine with several services, you can select any of
these services.
2.11.2 Activities
2.11.2.1 list activities
Lists the current and past activities of the specified service (Acronis Managed Machine Service,
Acronis Backup Management Server, Acronis Backup Storage Node).
The command displays no more than the latest 5000 records. The displayed records are sorted by
date in descending order.
If the --service (p. 76) parameter is not specified, the activities of Acronis Managed Machine
Service are listed.
For Acronis Backup Management Server, only its own activities are listed. The activities of the
Managed Machine Services that run on the registered machines are not included in the list.
If a machine performs too slowly, you might want to use the command to find out the activity that
has been running for an unexpectedly long time. Thus, you will be able to detect and stop (p. 68)
hung-up processes.
Examples (p. 143)
Parameters
--filter_guid=<GUIDs> (p. 116)
--filter_resource=<resource name> (p. 117)
--filter_state=<states> (p. 118)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
68 Copyright © Acronis International GmbH, 2002-2016
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
When listing activities of a storage node, you can specify only ams or asn as a parameter value.
2.11.2.2 stop activity
Stops the activity with the specified GUID. To learn GUIDs of activities, use the list activities (p.
67) command.
Examples (p. 143)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
2.11.3 Plans
2.11.3.1 list plans
Lists the backup plans existing on a managed machine or on the management server. The displayed
records are sorted by date in descending order.
Examples (p. 144)
Parameters
--filter_state=<states> (p. 118)
--filter_status=<statuses> (p. 118)
--filter_user=<user names> (p. 118)
--utc (p. 126)
General parameters
69 Copyright © Acronis International GmbH, 2002-2016
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.3.2 export plan
Exports the specified backup plan to an .xml file. The operation creates a file with complete
configuration of the backup plan. You can import the file (p. 70) to reuse the exported backup plan
on another machine.
The export files of backup plans can be edited with text editors. Passwords are encrypted in the
export files.
Centralized backup plans can be exported from a management server and imported to a
management server only.
Examples (p. 144)
Parameters
--id=<GUID> (p. 122)
--loc=<full path>
Full path to the file to which the backup plan will be exported.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
70 Copyright © Acronis International GmbH, 2002-2016
2.11.3.3 import plan
Imports a backup plan from an *.xml file. An XML file with complete configuration of a backup plan
can be created by means of the export plan (p. 69) command.
Centralized backup plans can be exported from a management server and imported to a
management server only.
Examples (p. 144)
Parameters
--loc=<full path>
Full path to the file from which the backup plan will be imported.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.3.4 disable plan
Disables the specified backup plan. As a result, the backup plan will not run according to its schedule.
Examples (p. 144)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
71 Copyright © Acronis International GmbH, 2002-2016
--service={mms|ams} (p. 76)
2.11.3.5 enable plan
Enables a previously disabled (p. 70) backup plan. As a result, the specified backup plan will run again
according to its schedule.
Examples (p. 144)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.3.6 delete plan
Deletes the specified backup plan.
Examples (p. 144)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
72 Copyright © Acronis International GmbH, 2002-2016
2.11.4 Tasks
2.11.4.1 list tasks
Lists the tasks existing on a managed machine or on the management server. The displayed records
are sorted by date in descending order.
Examples (p. 145)
Parameters
--filter_state=<states> (p. 118)
--filter_user=<user names> (p. 118)
--filter_last_result=<last_results>
To display only tasks with specific last execution results, specify one or more of the following
values: not_run_yet, succeeded, succeeded_with_warnings, failed, or stopped.
--filter_plan_guid=<GUIDs>
GUIDs of backup plans whose tasks are to be output. If not specified, tasks belonging to any
backup plan will be listed.
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams|asn} (p. 76)
2.11.4.2 run task
Starts execution of the specified task.
Examples (p. 145)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)

73 Copyright © Acronis International GmbH, 2002-2016
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.4.3 stop task
Stops execution of the specified task.
Examples (p. 145)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.4.4 delete task
Deletes the specified task.
A task belonging to a backup plan cannot be deleted separately from the plan.
Examples (p. 145)
Parameters
--id=<GUID> (p. 122)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
74 Copyright © Acronis International GmbH, 2002-2016
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.5 Licenses
2.11.5.1 list licenses
Lists Acronis Backup licenses assigned to a machine. If the licenses are registered on the license
server, the agent also checks the status of the licenses on the license server.
Examples (p. 145)
Parameters
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
--output={formatted|raw} (p. 123)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote machine (Acronis Backup Advanced only)
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
--address=<IP address or hostname> (p. 76)
Access to a specific service within a machine (Acronis Backup Advanced only)
--service={mms|ams} (p. 76)
2.11.6 Reports
2.11.6.1 generate report
Generates a management server report and saves it in the XML or HTML format. The
--service=ams parameter is mandatory because the command is executed by the management
server.
Examples (p. 145)
Parameters
--id={machines_by_status|vms_by_status|archives_by_managed_vaults|plans_by
_status|managed_vaults_statistics_for_last_month|tasks_by_last_result|acti
vities_for_last_month} (p. 122)
--report_format={xml|html} (p. 125)
--loc=<path>
The report location. If the parameter is not specified, the command will fail.
If --report_format=xml, the parameter value is a full path to the report file.
75 Copyright © Acronis International GmbH, 2002-2016
If --report_format=html, the parameter value is a local or network folder.
--credentials=<user name>,<password>,encrypted (p. 120)
General parameters
--log=<full path> (p. 122)
--log_format={structured|unstructured} (p. 122)
{-f|--file_params}=<full local path> (p. 121)
Access to a remote management server
--host=<IP address or hostname> (p. 76)
--credentials=<user name>,<password>,encrypted (p. 120)
Access to the management server service
--service=ams (p. 76)

76 Copyright © Acronis International GmbH, 2002-2016
3 Parameters
3.1 Access to a physical machine
3.1.1 host
--host=<IP address or hostname>
Specifies the machine running an Acronis service to connect to. If not specified, the command-line
utility connects to the local host.
Examples:
--host=server1
--host=192.168.1.2
3.1.2 service
--service={mms|ams|asn}
Specifies the Acronis service to connect to.
If not specified, the command-line utility connects to the agent service (Acronis Managed Machine
Service, MMS). To connect to a storage node or the management server, you must explicitly specify
the asn or the ams service using the --service parameter. This parameter is required even if an
agent is not installed on that server or is unable to execute the command by design.
Example
acrocmd validate archive --loc=bsp://<storage node>/<vault name> --arc=<archive name>
You can run this command on a machine where an agent and the command-line utility are
installed. The command-line utility connects to the local agent. The agent addresses a storage
node.
acrocmd validate archive --loc=bsp://<storage node>/<vault name> --arc=<archive name>
--host=<storage node> --credentials=<user name>,<password> --service=asn
You can run this command on a machine where only the command-line utility is installed. In this
case, the command-line utility connects directly to a storage node.
In both cases validation will be performed by a storage node, using that node's CPU resource.
3.1.3 address
--address=<IP address or hostname>
Specifies a machine registered on the management server.
Some commands can be applied to multiple machines. This is done by separating the machine
addresses with commas. Such commands include backup disk (p. 19), backup file (p. 24),
recover disk (p. 20), recover mbr (p. 22), recover file (p. 25), create asz (p. 56), delete
asz (p. 59), activate asrm (p. 59), and deactivate asrm (p. 60). The operation will be executed
on the specified machines one after another. The parameter for the above commands has been
specified in the following way: --address=<IP addresses or hostnames>.

77 Copyright © Acronis International GmbH, 2002-2016
The management server must also be specified when using this parameter. Credentials for the
machine are not required. Only the management server credentials are needed.
Example
To view all machine disks through the management server, run the following command:
acrocmd list disks --host=<ams hostname> --credentials=<user name>,<password>
--service=ams --address=<IP address or hostname>
3.2 Virtual machines
3.2.1 Access to a virtual machine
{--vmid=<virtual machine ID>|--vmname=<virtual machine name>|--vmconfig=<path>}
The methods of access to a virtual machine
If Agent for VMware or Agent for Hyper-V is registered on the management server, you can access a
virtual machine directly from the management server without specifying the virtualization host:
--host=<ams hostname> --credentials=<user name>,<password> --service=ams
--vmname=<virtual machine name>
If Agent for VMware or Agent for Hyper-V is not registered on the management server, specify the
virtual appliance or the Windows host running the agent:
--host=<agent hostname> --credentials=<user name>,<password> --vmname=<virtual
machine name>
When operating within the virtual appliance or the Windows host running the agent, you do not
need to specify access parameters other than --vmname or --vmid.
vmid
--vmid=<virtual machine ID>
Virtual machine unique identifier, assigned by the virtualization software. Use the list vms (p. 27)
command to obtain identifiers of virtual machines.
With the backup vm (p. 29) command, you can specify several values of this parameter.
vmname
--vmname=<virtual machine name>
Virtual machine name. This parameter is case-sensitive. If the Acronis agent finds more than one
virtual machine with the same name, an error occurs (this does not apply to clustered Hyper-V virtual
machines). In this case, use the --vmid or --vmconfig parameter.
With the backup vm (p. 29) command, you can specify several values of this parameter.
vmconfig
--vmconfig=<path>
Path to the virtual machine configuration file on the ESX(i) server (to the .vmx file). The parameter
cannot be used for Hyper-V servers. The format is as follows:
[<storage>] <folder>/…/<folder N>/<VMX file name>

78 Copyright © Acronis International GmbH, 2002-2016
Example
--vmconfig="[Local_storage_2] Windows 2008 R2 Dev/Windows 2008 R2 Dev.vmx"
With the backup vm (p. 29) command, you can specify several values of this parameter.
3.2.2 New virtual machine
3.2.2.1 New virtual machine on an ESX(i) or Hyper-V host
vmname
--vmname=<virtual machine name>
Name of a new virtual machine.
vmstorage
--vmstorage=<path>
Location of the new virtual machine.
When creating a virtual machine on an ESX(i) server, specify the name of the datastore.
Example:
--vmstorage=Storage_1
When creating a virtual machine on a Hyper-V server, specify the path to the server's local folder.
Example:
--vmstorage=C:\ProgramData\Microsoft\Windows\Hyper-V\Virtual Machines
vmserver_name
--vmserver_name=<server name>
Name of the ESX(i) or Hyper-V server or cluster where a virtual machine will be created. To learn
names of virtualization servers or clusters, use the list vmservers (p. 27) command. The
--vmserver_name and --vmserver_id parameters are mutually exclusive.
vmserver_id
--vmserver_id=<server GUID>
Identifier of the ESX(i) or Hyper-V server or cluster where a virtual machine will be created. To learn
identifiers of virtualization servers or clusters, use the list vmservers (p. 27) command. The
--vmserver_id and --vmserver_name parameters are mutually exclusive.
Virtual machine configuration (p. 78)
3.2.2.2 Virtual machine configuration
Use the parameters described in this section with the recover vm (p. 31) command when creating a
new virtual machine on an ESX(i) or Hyper-V host.
vmram
--vmram=<memory size>{mb|gb}
Memory sizeof the new virtual machine. If the parameter is not specified, the value is as follows:

79 Copyright © Acronis International GmbH, 2002-2016
If a virtual machine was backed up, the memory size of the backed-up machine.
If a physical machine was backed up, the default setting of the virtualization server.
Examples:
--vmram=512mb
--vmram=1gb
vmcpu
--vmcpu=<number of CPUs>
Number of virtual processorsof the new virtual machine. If the parameter is not specified, the value
is 1.
Virtual disk parameters
If you specify one of the --vmdisk_size, --vmdisk_type, and --vmdisk_provisioning
parameters, you must specify all of them.
vmdisk_size
--vmdisk_size=<disk sizes>
Sizes of the virtual disks to be created. The software assigns each value specified in the
--vmdisk_size parameter to the corresponding disk specified in the --disk (p. 88) parameter. If
the number of values of the --diskand --vmdisk_size parameters differ, the command will fail.
You can specify values in megabytes and gigabytes.
Example:
--vmdisk_size=100gb,512mb,120gb
If the parameter is not specified, the software will reproduce the sizes of the original machine's disks.
vmdisk_type
--vmdisk_type=<disk types>
Interface types of the virtual disks to be created. The available values are ide and scsi. The
software assigns each value specified in the --vmdisk_type parameter to the corresponding disk
specified in the --disk (p. 88) parameter. If the number of values of the --disk and
--vmdisk_type parameters differ, the command will fail.
Example:
--vmdisk_type=ide,scsi,scsi
If the parameter is not specified, the software assigns the following values.
On an ESX(i) host:
If the backed-up machine has no IDE disks, the system disk is assigned the scsi value.
If the backed-up machine has at least one IDE disk, the system disk is assigned the ide value.
On a Hyper-V host, the system disk is assigned the ide value.
A non-system disk is assigned the type of the corresponding disk of the original machine.
vmdisk_provisioning
--vmdisk_provisioning=<disk provisioning types>
80 Copyright © Acronis International GmbH, 2002-2016
Provisioning types of the virtual disks to be created. The available values are thick and thin. The
software assigns each value specified in the --vmdisk_provisioning parameter to the
corresponding disk specified in the --disk (p. 88) parameter. If the number of values of the --disk
and --vmdisk_provisioning parameters differ, the command will fail.
Example:
--vmdisk_provisioning=thin,thin,thick
If the parameter is not specified, the software assigns the following values.
If a physical machine was backed up, all disks have the thick provisioning type.
If a virtual machine was backed up, the software reproduces the provisioning types of the
original machine's disks.
3.2.2.3 New virtual machine in a local or network folder
vmname
--vmname=<virtual machine name>
Name of a new virtual machine.
vmtype
--vmtype={vmware|virtualpc|redhat|xen}
Type of the new virtual machine.
vmstorage
--vmstorage=<path>
Location of the new virtual machine. Specify a local or network folder path.
Examples:
--vmstorage=c:\vms
--vmstorage=\\srv1\folder1
3.3 Access to applications
3.3.1 exchange_credentials
--exchange_credentials=<domain user name>,<password>,encrypted
Credentials to access an Exchange server. In this parameter, you must specify credentials of a domain
user. The user name has the following format: <DOMAIN>\<user name> or <user
name>@<domain>. The user must be granted the permissions sufficient for the required operation.
For detailed information about the permissions, see the "Permissions for Exchange backup and
recovery" section of the "Backing up Microsoft Exchange Server data" document.
If the third parameter value (encrypted) is specified, it means that the preceding password was
encrypted by the acronis_encrypt utility (p. 149).
In Windows Server 2008 and later, the user specified in the --exchange_credentials parameter
must differ from the user specified in the --credentials (p. 120) parameter that follows the
--host parameter.
81 Copyright © Acronis International GmbH, 2002-2016
Example
--host=exch_srv --credentials=user,pass1
--exchange_credentials=domain1\exch_user1,12345
3.3.2 instance
--instance=<instance name>
The parameter is used with the list mssql_databases (p. 39) command. The parameter defines
the instance whose databases will be listed. If not specified, the command will fail.
3.3.3 items
--items=<items>
Microsoft Exchange Server data items
For Microsoft Exchange Server data backups, this parameter specifies Exchange items to back up or
recover. For detailed information about the value format, see "Specifying Exchange data" (p. 82).
Command: backup exchange_database
In the backup exchange_database (p. 34) command, each item in the parameter value is a name
of a storage group or database.
If the parameter is not specified, the software will back up all the databases on an Exchange server.
Command: recover exchange_database
In the recover exchange_database (p. 36) command, each item in the parameter value is a name
of a storage group or database.
If the --target (p. 86) parameter value is another_database or recovery_database, the
--items parameter must contain only one database or storage group. If the --target parameter
value is original or disk, you can specify several databases and storage groups in the --items
parameter.
If the parameter is not specified, the software will recover all the databases in a backup.
To learn the names of the backed-up storage groups or databases, use the list content (p. 46)
command.
Command: backup exchange_mailbox
In the backup exchange_mailbox (p. 35) command, each item in the parameter value is a path to
a mailbox or to a public folder. If the path ends with a database name, the software will back up all
the mailboxes or public folders of the specified database.
If the parameter is not specified, the software will back up all the mailboxes and public folders on an
Exchange server.
Command: recover exchange_mailbox
In the recover exchange_mailbox (p. 37) command, each item in the parameter value is a path
within a backup to a mailbox, to a public folder, or to a subfolder. If the path ends with a database
name, the software will recover all the mailboxes or public folders of the specified database.
82 Copyright © Acronis International GmbH, 2002-2016
If the parameter is not specified, the software will recover all the mailboxes and public folders
contained in a backup.
To learn the exact paths in the backup, use the list content (p. 46) command.
Microsoft SQL Server data items
For single-pass backups of Microsoft SQL Server, this parameter specifies databases or instances to
recover or mount. For detailed information about the value format, see "Specifying SQL data" (p. 83).
Commands: recover mssql_database, mount mssql_database
In the recover mssql_database (p. 40) and mount mssql_database (p. 55) commands, each
item in the parameter value is a path within a backup to a database or to an instance. If the
parameter is not specified, the command will fail.
To learn the names of the backed-up databases, use the list content (p. 46) command.
Command: umount mssql_database
In the umount mssql_database (p. 56) command, each item in the parameter value is a path to a
mounted database or to an instance. If the parameter is not specified, the software will unmount all
the mounted databases on an SQL server.
3.3.4 Specifying Exchange data
Use the following notation to access Microsoft Exchange Server databases, mailboxes and folders
when backing them up or when recovering them from a backup.
Database (for Exchange 2010 or later)
<database>
Example:
"Mailbox Database"
Storage group (for Exchange 2003 and 2007)
<storage group>
Example:
"First Storage Group"
Mailbox or public folder
For Exchange 2013 or later:
<database>/<mailbox>
Example:
"Mailbox database/John P. Smith"
For Exchange 2010:
<database>/<mailbox>
<database>/<public folder>
Examples:
"Mailbox database/John P. Smith"
"Mailbox database/Folder for accountants"

83 Copyright © Acronis International GmbH, 2002-2016
For Exchange 2003 and 2007:
<storage group>/<database>/<mailbox>
<storage group>/<database>/<public folder>
Examples:
"Storage group 1/Mailbox database/John P. Smith"
"Storage group 1/Mailbox database/Folder for accountants"
Mailbox folder
For Exchange 2010 or later: <database>/<mailbox>/<folder 1>/…/<folder N>
Example:
"Mailbox database/John P. Smith/Inbox/Mails from Boss"
For Exchange 2003 and 2007: <storage group>/<database>/<mailbox>/<folder
1>/…/<folder N>
Example:
"Storage group 1/Mailbox database/John P. Smith/Inbox/Mails from Boss"
3.3.5 Specifying SQL data
Use the following notation to access Microsoft SQL Server databases.
<instance>
All databases of the specified instance.
<instance>/<database>
The specified database of the specified instance.
<database>
If the backup contains databases of only one instance, you can specify only the database name.
Examples:
"My Instance"
"My Instance/Accountants"
Accountants
3.3.6 Access to SQL Server instance
Acronis Backup can use either SQL Server Authentication or Windows Authentication to connect to a
Microsoft SQL Server instance.
By default, Windows Authentication is used. This means that the software applies the credentials
with which you are logged on to Windows, or the credentials you specify after the --host (p. 76)
parameter in order to access a remote machine.
SQL Server Authentication is possible only if it is enabled in the instance properties. To connect to the
instance by using SQL Server Authentication, specify the --credentials parameter after the
--instance or --destination_instance parameter.

84 Copyright © Acronis International GmbH, 2002-2016
3.4 Location
3.4.1 loc
--loc=<path>
When backing up, the path to the location where the backup is to be created. For other operations,
the path to the location where the backups are stored.
The path can be specified in the following formats:
Type of storage
Format
Local path (in Windows)
<drive>:\<folder>
Local path (in Linux)
/<directory 1>/.../<directory N>
SMB
\\<server>\<folder>
NFS
nfs://<server>/<share>:/<folder>
FTP, SFTP
ftp://<server>/<folder>/*
sftp://<server>/<folder>/
Acronis Backup Storage Node
bsp://<storage node>/<vault name>
Acronis Cloud Storage
online://
Acronis Secure Zone
atis:///asz
Tape
atis:///tape?<GUID of attached library>**
* To establish an active mode FTP connection, use the following notation: aftp://<server>/<folder>/
**Using this format, you can access a tape library or drive only if it is directly attached to the managed machine.
You can determine the GUID of this library or drive by using the list tape_libraries (p. 60) command.
For a tape library or drive attached to a storage node, a centralized vault should be created on that storage
node. To access such tape library or drive, use the bsp://<storage node>/<vault name> format.
3.4.2 arc
--arc=<archive name>
Name of the archive. Parameter values are case-sensitive.
The parameters that provide access to an archive must be specified in the following order: --loc (p.
84), --credentials (p. 120) (if required to access the location), --arc, --password (p. 123) (if
the archive is or will be password-protected).
Example:
--loc=\\bkpsrv\backups --credentials=bkpuser,pass --arc=disk_archive
--password=123
Restrictions on archive names
When using the --plain_archive (p. 97) parameter or when backing up Microsoft Exchange
Server data (commands backup exchange_database (p. 34) and backup
exchange_mailbox (p. 35)), the archive name cannot end with a number.
When using the --plain_archive (p. 97) parameter, the FAT16, FAT32, and NTFS file systems
do not allow the following characters in the file name: backslash (\), slash (/), colon (:),

85 Copyright © Acronis International GmbH, 2002-2016
asterisk (*), question mark (?), quotation mark ("), less than sign (<), greater than sign (>), and
pipe (|).
Using variables in archive names
When you back up more than one machine with a single backup command, data from all of the
machines is saved to the same location. Each machine backs up to a separate archive. Archive names
must be unique within the location. Otherwise, the backup operation will fail.
Add variables to the archive names to make them unique within the location. For the backup vm (p.
29) command, the archive name must contain the [Virtualization Server Type] and
[Virtual Machine Name] variables. For other backup commands, use the [MachineName]
variable.
You can also use these variables when backing up a single machine if this is practical or efficient for
you.
Examples:
--arc="[Virtualization Server Type]_[Virtual Machine Name]_archive1" – for the
backup vm command
--arc=[MachineName]_archive1 – for the backup disk and backup file commands
Specifying archives by backup file names
In this parameter, you can specify an archive by the file name of a backup that belongs to the
archive; for example: --arc=my_backup2.tib.
This syntax is the only way to access an archive in command line if the archive's metadata has been
lost. If the metadata is intact, the --arc parameter refers to the entire archive. If the metadata is
lost, the --arc parameter refers to the backup chain that contains the specified backup. (A backup
chain is a full backup and all of its dependent incremental and differential backups.)
When using this syntax in a command operating with backups, you still need to specify the
--backup (p. 85) parameter.
Example:
--arc=my_backup2.tib --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
If the --backup parameter is not specified and if the archive's metadata is intact, the command will
apply to the latest backup of the archive. If the metadata is lost, the command will apply to the latest
backup of the backup chain that contains the specified backup.
Restriction: You cannot specify file names of backups stored on Acronis Storage Node, Acronis Cloud
Storage, Acronis Secure Zone or tape.
3.4.3 backup
--backup=<backup ID>
Identifier of the backup with which the operation is to be performed (for example, the backup from
which the data is to be recovered).
With the export backup (p. 49), consolidate backup (p. 51) and replicate backup (p. 49)
commands, you can specify several backups.
If the parameter is not specified, the operation will be applied to the latest backup. However, you
must specify this parameter with the recover exchange_database (p. 36) and recover

86 Copyright © Acronis International GmbH, 2002-2016
exchange_mailbox (p. 37) commands, if the --recovery_point (p. 110) parameter value is
selected_backup.
3.4.4 target
Commands: export archive, export backup, recover file, recover
ad_database, replicate backup
--target=<path>
In the recover file (p. 25) command, the parameter specifies a local or network folder where
folders/files will be recovered (a target folder). The formats of the parameter value are the same as
in the --loc (p. 84) parameter. If the --target parameter is not specified, the original path will be
re-created from the backup.
In the recover ad_database (p. 41) command, the parameter specifies a local or network folder
where the Microsoft Active Directory database and the SYSVOL folder will be extracted (a target
folder). The formats of the parameter value are the same as in the --loc (p. 84) parameter. If the
--target parameter is not specified, the command will fail.
In the export archive (p. 43), export backup (p. 49), or replicate backup (p. 49) command,
the parameter specifies the location where the archive or backup will be exported or replicated. The
formats of the parameter value are the same as in the --loc (p. 84) parameter, except for
online:// which is not supported by the export archive and export backup commands. If the
--target parameter is not specified, the command will fail.
Command: recover exchange_database
--target={original|disk|another_database|recovery_database}
In the recover exchange_database (p. 36) command, available values of the parameter are as
follows:
original
The software will recover the selected databases or storage groups to their original paths. The
paths are taken from the backup.
disk
The software will save the selected databases or storage groups, along with transaction log files,
to a local or network folder. If this value is used, you need to specify the --disk_location (p.
106) parameter. If necessary, add the --credentials (p. 120) parameter.
another_database
The software will recover the selected database or storage group to a new or existing database
or storage group. Only one database or storage group can be recovered at a time.
If this value is used, you need to specify the --destination_database (p. 105) parameter. If
the destination database does not exist, also specify the --database_location (p. 104) and
--log_location (p. 107) parameters. If the destination storage group does not exist, specify
the --log_location (p. 107) parameter and pairs of the --database (p. 104) and
--database_location (p. 104) parameters for each database of the storage group being
recovered.
recovery_database
The software will recover the selected database or storage group to a recovery database or
storage group. Only one database or storage group can be recovered at a time.

87 Copyright © Acronis International GmbH, 2002-2016
When recovering a database, you need to specify the --database_location (p. 104) and
--log_location (p. 107) parameters.
When recovering a storage group, you need to specify pairs of the --database (p. 104) and
--database_location (p. 104) parameters for each database of this storage group. If the
destination recovery storage group does not exist, specify also the --log_location (p. 107)
parameter.
If the parameter is not specified, the command will fail.
Command: recover exchange_mailbox
--target={original|pst}
In the recover exchange_mailbox (p. 37) command, available values of the parameter are as
follows:
original
The software will recover the selected mailboxes, public folders, and their contents to the
Exchange server where the command will be executed.
Mailboxes that have no matching user accounts, enabled in the Active Directory, are skipped
during recovery.
If the original mailbox does not exist, it will not be recreated automatically. If you need to
recover a non-existing mailbox, create a new mailbox for the same account in advance.
If all of the selected mailboxes are skipped, the command will fail.
pst
The software will save the selected mailboxes, public folders or mailbox folders to a Personal
Storage Table (.pst) file. If this value is used, you need to specify the --disk_location (p. 106)
parameter. If necessary, add the --credentials (p. 120) and --outlookmachine (p. 108)
parameters.
If the parameter is not specified, the command will fail.
Command: recover mssql_database
--target={original|disk|another_instance}
In the recover mssql_database (p. 40) command, available values of the parameter are as
follows:
original (by default)
The software will recover the selected databases to their original paths. The paths are taken from
the backup.
In this case, you cannot specify the credentials to access the SQL Server instance where the
databases will be recovered. So, the software will use Windows Authentication to connect to the
instance. If you need to use SQL Server Authentication, specify the another_instance value
along with the original instance name, original database file path and the --credentials
parameter.
disk
The software will save the selected databases, along with the transaction log files, to a local or
network folder. If this value is used, you need to specify the --disk_location (p. 106)
parameter. If necessary, add the --credentials (p. 120) parameter.
another_instance
The software will recover the selected databases to the specified instance.

88 Copyright © Acronis International GmbH, 2002-2016
If this value is used, you need to specify the destination_instance (p. 106) and
database_location (p. 104) parameters. For information about specifying access credentials
for Microsoft SQL Server, see "Access to SQL Server instance" (p. 83).
3.4.5 target_arc
--target_arc=<archive name>
The name of the target archive in the export archive (p. 43), export backup (p. 49), and
replicate backup (p. 49) commands.
If the parameter is used with the export archive or export backup command, the name has to
be unique within the target location. If there is an archive with the same name or if the parameter is
not specified, the command will fail.
If the parameter is used with the replicate backup command and if the target archive exists, the
command will append the backup to it. Otherwise, it will create a new archive.
3.4.6 mailbox_location
--mailbox_location=<path>
The path to the database whose mailboxes are to be displayed. The parameter is used with the list
exchange_mailboxes (p. 33) command.
For detailed information about the value format, see "Specifying Exchange data" (p. 82).
If the parameter is not specified, the software will display all the mailboxes on an Exchange server.
3.5 Disks and volumes
3.5.1 disk
Commands: backup disk and backup vm
--disk=<disk numbers>
The parameter is used with the backup disk (p. 19) and backup vm (p. 29) commands to specify
disks to be backed up.
Use the list disks (p. 18) command to obtain numbers of available disks and volumes.
You can use the --disk and --volume (p. 89) parameters within one command line, for example:
--disk=1 --volume=E
If neither the --disk parameter nor the --volume parameter is specified, the software will back up
all of the machine's disks.
Commands: recover disk, recover mbr, recover vm, create asz
--disk=<disk number>

89 Copyright © Acronis International GmbH, 2002-2016
Command with which
the parameter is used
What does the parameter mean?
What if the parameter is not specified?
recover disk (p. 20)
recover vm (p. 31)
Numbers of the disks to be
recovered from a backup
If the --volume (p. 89) parameter is
specified, this volume will be recovered.
Otherwise, the command will recover all of
the backed-up disks.
recover mbr (p. 22)
The number of the disk whose MBR
is to be recovered from a backup
The command will fail.
create asz (p. 56)
The number of the disk on which
Acronis Secure Zone is to be created
The command will fail.
3.5.2 nt_signature
--nt_signature={auto|new|backup|existing}
The NT signature is a record that is kept in the hard disk's MBR. It uniquely identifies the hard disk for
the operating system.
When recovering a disk (p. 20) containing a system volume, you can choose what to do with the NT
signature of the target disk. Specify any of the following parameters:
auto (default)
The software will keep the NT signature of the target disk if it is the same NT signature as the one
stored in the backup. (In other words, if you recover the disk to the same disk that was backed
up.) Otherwise, the software will generate a new NT signature for the target disk.
new
The software will generate a new NT signature for the target disk.
backup
The software will replace the NT signature of the target disk with the one from the backup.
existing
The software will leave the NT signature of the target disk untouched.
3.5.3 volume
Commands: backup disk and backup vm
--volume=<volume numbers>
The parameter is used with the backup disk (p. 19) and backup vm (p. 29) commands to specify
volumes to be backed up.
Volume numbers are specified as <disk number>-<volume number>. For example:
--volume=1-1,1-2
Dynamic volumes (in Windows) or logical volumes (in Linux) are specified with the DYN prefix or by
their GUIDs. For example:
--volume=DYN1
--volume=e6ee6edc-d1ba-11d8-813e-806e6f6e6963
To back up all dynamic volumes or all logical volumes, specify:
--volume=DYN

90 Copyright © Acronis International GmbH, 2002-2016
Both basic and dynamic volumes can be specified by their letters. For example:
--volume=C
Mixed notation is also acceptable. For example:
--volume=1-1,E,e6ee6edc-d1ba-11d8-813e-806e6f6e6963
To view disk and volume numbers, volume letters and GUIDs, use the list disks (p. 18) command.
To display the full length of GUIDs, add the --output=raw parameter.
You can use the --disk (p. 88) and --volume parameters in one command. For example:
--disk=1 --volume=E
If neither the --disk parameter nor the --volume parameter is specified, the software will back up
all of the machine's disks.
Commands: recover disk, recover vm, mount
--volume=<volume number>
Command with which
the parameter is used
What does the parameter mean?
What if the parameter is not specified?
recover disk (p. 20)
recover vm (p. 31)
The volume whose data is to be recovered from a
backup.
With the recover disk command, you can specify
several volumes.
If the --disk (p. 88) parameter is
specified, this disk will be recovered.
Otherwise, the command will recover
all of the backed-up disks.
mount (p. 53)
The volume to be mounted from a backup. You can
specify several volumes.
The command will fail.
Volume numbers are specified as <disk number>-<volume number>. For example:
--volume=1-1,1-2
Dynamic volumes (in Windows) or logical volumes (in Linux) are specified with the DYN prefix. For
example:
--volume=DYN1
To recover all dynamic volumes or all logical volumes, specify:
--volume=DYN
Both basic and dynamic volumes can be specified by their letters. For example:
--volume=C
Mixed notation is also acceptable. For example:
--volume=1-1,E,DYN1
To view disks and volumes contained in a backup, use the list content (p. 46) command.
Command: create asz
--volume={<volume numbers>|all}
In the create asz (p. 56) command, the parameter specifies volumes from which the free space for
Acronis Secure Zone will be taken if the unallocated space on the specified disk is not enough. The
91 Copyright © Acronis International GmbH, 2002-2016
free space will be taken in proportion to each volume's size. If --volume=all is specified, the free
space will be taken from all volumes of the specified disk.
Without this parameter, Acronis Secure Zone will use the unallocated space only.
Command: resize asz
--volume={<volume numbers>|all}
If you use the resize asz (p. 57) command to increase Acronis Secure Zone, the software will
behave in the same way as described earlier for the create asz command.
If you use the command to decrease Acronis Secure Zone, the parameter specifies volumes where
the free space will be added. The space will be distributed to each volume equally. If --volume=all
is specified, the free space will be added to all volumes of the disk where the zone is located.
Without the --volume parameter, the freed space becomes unallocated.
Command: delete asz
--volume=<volume numbers>
In the delete asz (p. 59) command, the parameter specifies volumes where the free space will be
added after the Acronis Secure Zone deletion. The space will be distributed to each volume equally.
Without this parameter, the freed space becomes unallocated.
3.5.4 start
--start=<offset>{s|kb|mb|gb}
This parameter specifies the start position of the volume being recovered. If no measurement unit is
specified, the offset is measured in megabytes (mb).
Use this parameter with the recover disk (p. 20) and recover vm (p. 31) commands when
recovering a volume to unallocated space of a hard disk.
The --start parameter and the --target_volume (p. 111) parameter are mutually exclusive. If
you specify both, an error will occur.
3.5.5 size
--size=<volume size>{s|kb|mb|gb}
The parameter specifies the new size of the volume being recovered. If no measurement unit is
specified, the size is measured in megabytes (mb).
Use this parameter with the recover disk (p. 20) and recover vm (p. 31) commands if you need
to resize the volume during recovery.
3.5.6 mbr_disk
--mbr_disk=<disk number>
Number of the disk whose master boot record (MBR) is to be recovered from a backup. The
parameter is used with the recover disk (p. 20) command to recover an MBR in addition to
recovering a volume.
You will usually recover an MBR in the following cases:

92 Copyright © Acronis International GmbH, 2002-2016
When migrating a machine to different hardware.
When recovering custom or non-Windows boot loaders. Acronis Backup automatically updates
Windows loaders after the volume recovery, so there is no need to recover the MBR unless it is
damaged.
3.5.7 target_mbr_disk
--target_mbr_disk=<disk number>
The disk where the master boot record specified in the --mbr_disk (p. 91) parameter will be
recovered. The parameter is used with the recover disk (p. 20) command to recover an MBR in
addition to recovering a volume. If the parameter is not specified, the command will fail.
3.6 Backup parameters
3.6.1 application_aware
--application_aware
The parameter is used with the backup disk (p. 19) command. If specified, the software will create
a single-pass backup of the specified disks and volumes.
The --application_aware parameter and the --raw (p. 97) parameter are mutually exclusive. If
you specify both, an error will occur.
3.6.2 backuptype
The type of the backup. If not specified, the value is full.
Commands: backup disk, backup file, backup vm
If the parameter is used with the backup disk (p. 19), backup file (p. 24), and backup vm (p. 29)
commands, its format is as follows:
--backuptype={full|incremental|differential}
Command: backup exchange_database
If the parameter is used with the backup exchange_database (p. 34) command, its format is as
follows:
--backuptype={full|transaction_log}
Command: backup exchange_mailbox
If the parameter is used with the backup exchange_mailbox (p. 35) command, its format is as
follows:
--backuptype={full|incremental}
3.6.3 cleanup
--cleanup

93 Copyright © Acronis International GmbH, 2002-2016
With this parameter, the software will clear space for the backup being created by deleting old
backups. If the parameter is not specified and the destination is out of space, the software prompts
you to manually free up disk space.
The parameter is not effective when you back up to an RDX drive or USB flash drive in the removable
media mode (p. 95).
Cleanup algorithm
The archive will be cleaned up only during backup and only if there is not enough space to complete
the operation. The software will act as follows:
Delete the oldest full backup with all dependent incremental/differential backups
If there is only one full backup left and a full backup is in progress, then delete the last full
backup with all dependent incremental/differential backups
If there is only one full backup left, and an incremental or differential backup is in progress, an
error occurs saying there is a lack of available space
3.6.4 Comments
archive_comment
--archive_comment=<comments>
Comments on the archive that is specified in the --arc (p. 84) parameter. To view comments on
archives, use the list archives (p. 42) command with the -a parameter.
backup_comment
--backup_comment=<comments>
Comments on the backup that is specified in the --backup (p. 85) parameter. To view comments on
backups, use the list backups (p. 42) command.
3.6.5 copy_only
--copy_only
The parameter is used with the backup exchange_database (p. 34) command only if the
--backuptype (p. 92) parameter value is full.
The copy-only backup method allows creating full backups without truncating the transaction log
files. The method can be used to obtain a full backup without interrupting other ongoing backups.
The copy-only backups can be easily stored off-site for testing, analysis or other purposes.
The parameter cannot be used together with the --express (p. 95) parameter.
3.6.6 exclude
Disk-level and file-level backups
The following four parameters are used with the backup disk (p. 19), backup file (p. 24), and
backup vm (p. 29) commands.
exclude_names
--exclude_names=<names>

94 Copyright © Acronis International GmbH, 2002-2016
Files and folders to be excluded from the backup. For example,
c:\pagefile.sys,c:\hiberfil.sys.
exclude_mask
--exclude_mask=<masks>
Masks to select files to be excluded from the backup. For more details, see the description of the
exclude (p. 106) parameter used in the recover file command.
exclude_system
--exclude_system
In file systems that are supported by Windows, type this parameter to skip files and folders with the
System attribute. If a folder has the System attribute, all of its contents (including files that do not
have the System attribute) will be excluded.
exclude_hidden
--exclude_hidden
Type this parameter to skip files and folders that have the Hidden attribute (for file systems that are
supported by Windows) or that start with a period (.) (for file systems in Linux such as Ext2 and Ext3).
If a folder is hidden, all of its contents (including files that are not hidden) will be excluded.
Microsoft Exchange Server data backups
The following four parameters are used with the backup exchange_mailbox (p. 35) command.
exclude_age
--exclude_age=<date>
If the parameter is set, the software will exclude all items created before the specified date and time.
The value format is "DD.MM.YYYY HH24:MM". You cannot omit any part of the date.
Without this parameter, items with any creation date and time will be backed up.
exclude_attach
--exclude_attach=<files and masks>
If the parameter is set, the software will exclude all attachments whose names match the specified
values. You can use one or more wildcard characters * and ? in a file mask.
Example:
--exclude_attach=Vid*.avi,App?.exe,*.mp3
Without this parameter, all attachments will be backed up.
exclude_size
--exclude_size=<size>{kb|mb|gb}
If the parameter is set, the software will exclude all attachments larger than the specified value. If no
measurement unit is specified, the size is measured in megabytes (mb).
Without this parameter, items with any size will be backed up.

95 Copyright © Acronis International GmbH, 2002-2016
exclude_types
--exclude_types=<types>
If the parameter is set, the software will exclude all items of the specified type. You can specify one
or more of the following values: deleted ("Deleted Items" folders will be excluded), sent ("Sent
Items" folders will be excluded), or junk ("Junk E-mail" folders will be excluded).
Example:
--exclude_types=deleted,junk
Without this parameter, items of any type will be backed up.
3.6.7 express
--express
The parameter is used with the backup exchange_database (p. 34) command. If specified, the
backup will be created by using the express full backup method. Compared to regular full database
backups, the express full backups are created much faster and occupy less space.
The parameter can be used only if all of the following conditions are met.
The --backuptype (p. 92) parameter value is full.
The --loc (p. 84) parameter value is bsp://<storage node>/<vault name> and this vault is
deduplicating.
The --express and --copy_only (p. 93) parameters are mutually exclusive.
3.6.8 fixed_drive
--fixed_drive
The parameter is used with the backup commands only if the backup destination (the --loc (p. 84)
parameter value) is an RDX drive or USB flash drive.
If the parameter is specified, the device will be used as a fixed drive. Otherwise, the device will be
used as removable media.
The following table summarizes the difference between the two modes.
Functionality
Fixed drive
Removable media
If there is insufficient space to continue backing up, the
software will prompt you to...
...manually free up disk
space.
...insert new media.
Simplified naming (p. 97) of backup files...
...is unavailable even if
you specify the
--plain_archive
parameter.
...is always used even if
you do not specify the
--plain_archive
parameter.
An archive with several full backups can be created.
Yes
No. Before creating a
new full backup, the
software will delete the
entire archive and start
a new one.
96 Copyright © Acronis International GmbH, 2002-2016
Functionality
Fixed drive
Removable media
The --cleanup (p. 92) parameter is effective.
Yes
No. An archive contains
only one full backup
which cannot be
deleted.
You can delete (p. 52) any backup of any archive.
Yes
No. You can delete only
a backup that does not
have dependent
backups.
In Linux, the parameter is effective if the device is specified by its name (for example, sdf:/). If a
device is specified by its mount point (for example, /mnt/backup), it behaves as a fixed drive.
With the backup vm (p. 29), backup exchange_database (p. 34), or backup
exchange_mailbox (p. 35) commands, the device is always used in the fixed drive mode, so, this
parameter is ignored.
3.6.9 ignore_app_errors
--ignore_app_errors
The parameter is used with the backup disk (p. 19) command if the --application_aware (p.
92) parameter is specified.
The parameter determines the software behavior when it fails to collect application metadata during
a backup. For example, this happens if a database is corrupted or the application service is stopped.
If the parameter is not specified, the backup will fail.
If the parameter is specified, the backup will continue but the application metadata will be ignored.
Hence, you will not be able to recover individual SQL databases (p. 40) or Active Directory data (p.
41). However, recovery of disks, volumes and files will still be possible.
The parameter must follow the --application_aware parameter.
3.6.10 include
--include=<paths>
Files or folders to be included into the backup. The parameter is used with the backup file (p. 24)
command.
3.6.11 mssql_truncate_logs
--mssql_truncate_logs
The parameter is used with the backup disk (p. 19) command only if the --application_aware
(p. 92) parameter is specified.
If the parameter is specified, the Microsoft SQL Server log will be truncated after each full,
incremental or differential backup. The truncation occurs only if the SQL Server metadata has been
successfully collected during the backup.
Do not specify this parameter if you use a third-party application, such as the SQL Server backup and
restore component, for backing up the SQL Server data.

97 Copyright © Acronis International GmbH, 2002-2016
3.6.12 plain_archive
--plain_archive
Enables simplified naming of backup files.
With this parameter, full backups are named using the archive name (the --arc parameter value);
for example: MyData.tib. Names of incremental or differential backups have an index; for example:
MyData2.tib, MyData3.tib. Before creating a new full backup, the software will delete the entire
archive and start a new one.
This parameter is useful in the following cases:
If you want to create a portable image of a machine on a detachable media
If you are planning to move the backups to a different location by using a script
If you want to rotate USB hard drives so that each drive keeps a single full backup or all backups
created during a week
Without this parameter, each backup will have a unique file name with the exact time stamp and the
backup type; for example: MyData_2010_03_26_17_01_38_960D.tib. This standard file naming
allows for a wider range of backup destinations and backup schemes.
When you back up to a removable device (p. 95), the --plain_archive parameter is not needed.
Instead, the --fixed_drive parameter determines whether the standard or simplified naming
scheme will be used.
Restrictions
Do not specify the --plain_archive parameter in the following commands:
backup vm (p. 29)
backup exchange_database (p. 34) and backup exchange_mailbox (p. 35)
Any command that backs up to Acronis Storage Node, Acronis Cloud Storage, Acronis Secure
Zone, or tape
Do not apply the following commands to backups that have simplified names:
replicate backup (p. 49)
convert full (p. 50)
Restrictions on archive names
The archive name cannot end with a number.
The FAT16, FAT32, and NTFS file systems do not allow the following characters in the file name:
backslash (\), slash (/), colon (:), asterisk (*), question mark (?), quotation mark ("), less than
sign (<), greater than sign (>), and pipe (|).
3.6.13 raw
--raw
The parameter is used with the backup disk (p. 19) and backup vm (p. 29) commands. Use this
parameter to create a backup of a disk (volume) with unrecognized or unsupported file system. This
will copy all disk/volume contents sector-by-sector. Without this parameter only the sectors
containing data are backed up.

98 Copyright © Acronis International GmbH, 2002-2016
3.6.14 Backup options
3.6.14.1 cataloging
--cataloging={full|fast}
Cataloging a backup adds the contents of the backup to the data catalog. The data catalog enables
you to easily find the required data version using the GUI and to select it for recovery.
Cataloging is always performed as soon as a backup is created or exported to another vault. The
--cataloging parameter enables you to choose between full and fast cataloging.
Full cataloging
If the parameter value is full or is not specified, the backup contents are cataloged to the highest
possible level of detail. This means that the following data will be displayed in the catalog:
For a disk-level backup - disks, volumes, files, and folders.
For a file-level backup - files and folders.
For an Exchange database-level backup - databases or storage groups and mailboxes (always);
folders and e-mails (depends on the --metadata_level (p. 100) parameter value).
For an Exchange mailbox-level backup - mailboxes, folders, and e-mails.
Fast cataloging
You may want to set the parameter to fast if the full cataloging tends to affect the performance of
the managed machine or if your backup window is too narrow. The following data will be displayed in
the catalog:
For a disk-level backup - only disks and volumes.
For a file-level backup - nothing.
For an Exchange database-level backup - only databases or storage groups and mailboxes.
For an Exchange mailbox-level backup - only mailboxes.
To add the full contents of already existing backups to the catalog, you can start the full cataloging
manually when appropriate.
Note for users of Acronis Backup Advanced for virtual environments: When backing up to an unmanaged vault
(except for a locally-attached storage), Agent for VMware (Virtual Appliance) always performs fast cataloging.
Data catalog limitations
Encrypted or password-protected data cannot be included in the catalog. Also, cataloging is not
supported for certain types of storage. Do not specify the --cataloging parameter:
When using the --encryption (p. 99), --password (p. 123), or --plain_archive (p. 97)
parameters.
When backing up to removable media, such as CD, DVD, BD, Iomega REV, RDX or USB devices.
When backing up to Acronis Cloud Storage (--loc=online:// (p. 84)).
3.6.14.2 cbt_mode
--cbt_mode={on|off}
This parameter determines whether to use Changed Block Tracking (CBT) when performing an
incremental or differential backup of an ESX(i) virtual machine.

99 Copyright © Acronis International GmbH, 2002-2016
The Changed Block Tracking mechanism tracks changes to the contents of virtual disks. This leads to
faster backups and reduces the load on the storage during a backup.
Available parameter values
on (by default)
Acronis Backup uses CBT for each virtual machine that is backed up.
off
Acronis Backup does not use CBT.
3.6.14.3 compression
--compression={none|normal|high|max}
Data compression level. If not specified, the value is normal.
3.6.14.4 encryption
--encryption={none|aes128|aes192|aes256}
The algorithm to encrypt the archive. If not specified, the value is none.
This parameter cannot be used without the --password (p. 123) parameter.
3.6.14.5 fast
--fast
Defines whether a file change is detected using the file size and time stamp or by comparing the file
contents to those stored in the archive. Use this parameter to speed up incremental and differential
disk-level backup.
If specified, the software determines whether a file has changed or not by the file size and the
date/time when the file was last modified.
If not specified, the software will compare the entire file contents to those stored in the archive.
3.6.14.6 hdd_speed
--hdd_speed=<speed>{kb|p}
The speed of writing the data being backed up to a hard disk.
This parameter is used if the backup destination (the --loc (p. 84) parameter value) is an internal
(fixed) hard disk of the machine being backed up. For other locations, the parameter is ignored.
<speed> should be a positive number. If the measurement unit is kb, the speed is measured in
kilobytes per second. If the measurement unit is p or is not specified, the speed is measured in the
percentage of the maximum I/O speed of the destination hard disk.
If the parameter is not specified, the hard disk usage is not limited (as if you typed
--hdd_speed=100p).
Examples:

100 Copyright © Acronis International GmbH, 2002-2016
--hdd_speed=500kb – the data writing speed will be 500 kilobytes per second
--hdd_speed=50p or --hdd_speed=50 – the data writing speed will be 50% of the maximum
speed.
3.6.14.7 ignore_bad_sectors
--ignore_bad_sectors
Use this parameter to back up a rapidly dying disk without user interaction. Without this parameter,
the software asks for user interaction each time it comes across a bad sector during backup. This
behavior does not change even if the silent mode (p. 126) is enabled.
3.6.14.8 metadata_level
--metadata_level={{mailboxes_only|1}|{folders_and_mailboxes|2}|{all|3}}
The parameter is used with the backup exchange_database (p. 34) command. The parameter
defines the amount of metadata collected during a backup. The more detailed the metadata is, the
longer the backup creation takes. However, the browsing and recovery of individual e-mails and
other items contained in the mailboxes will be faster.
If a database was backed up with the default parameter value then, in order to access folders or
individual e-mails, the software has to open the database directly from the backup and apply
transaction logs to the database. This process may take considerable time depending on the number
of transaction logs contained in the backup.
Note that individual e-mails can be browsed and recovered only by using graphical user interface. If
you use command-line interface only, collecting metadata to the e-mail level does not make sense. If
you need to recover entire mailboxes only, you can safely use the default value in order to speed up
backups.
Available values of the parameter are as follows:
mailboxes_only or 1 (by default)
The metadata will be the least detailed and the backup will be the fastest. Only mailboxes and
public folders can be accessed without opening a database.
folders_and_mailboxes or 2
Individual folders within mailboxes and public folders can be accessed without opening a
database.
all or 3
The metadata will be the most detailed and the backup will take the longest time to complete.
Individual e-mails and other items within mailboxes and public folders can be accessed without
opening a database.
3.6.14.9 multi_volume_snapshot
--multi_volume_snapshot={true|false}
This parameter is effective only for Windows operating systems.
This parameter is used with the backup disk (p. 19) command. This parameter is also used with the
backup file (p. 24) command when the --snapshot (p. 102) parameter is specified.

101 Copyright © Acronis International GmbH, 2002-2016
The parameter determines whether to take snapshots of multiple volumes at the same time or one
by one.
If the value is true or if the parameter is not specified, snapshots of all volumes being backed up will
be created simultaneously. Use this parameter to create a time-consistent backup of data spanned
across multiple volumes, for instance for an Oracle database.
If the parameter value is false, the volumes' snapshots will be taken one after the other. As a result,
if the data spans across several volumes, the resulting backup may be not consistent.
3.6.14.10 network_speed
--network_speed=<speed>{kb|p}
The speed of transferring the data being backed up through network.
This parameter is used if the backup destination (the --loc (p. 84) parameter value) is a location on
the network, i.e., a network share, a managed vault, an FTP/SFTP server, or Acronis Cloud Storage.
For other location types, this parameter is ignored.
The parameter defines the amount of the network connection bandwidth allocated for transferring
the backup data. If the parameter is not specified, the software uses all the network bandwidth it can
get when transferring the backup data. You can reserve a part of the network bandwidth for other
network activities.
<speed> should be a positive number. If the measurement unit is kb, the speed is measured in
kilobytes per second. If the measurement unit is p or is not specified, the speed is measured in the
percentage of the estimated maximum speed of the network connection. For the cloud storage, only
the kb measurement unit is effective.
Examples:
--network_speed=500kb – the data transferring speed will be 500 kilobytes per second
--network_speed=50p or --network_speed=50 – the data transferring speed will be 50% of the
estimated maximum speed.
3.6.14.11 Pre and post commands
pre_cmd
--pre_cmd=<command>
Pre data capture command. The parameter value should be the path to a batch file containing the
required command along with its parameters.
Use this parameter to suspend operation of a database or application for a short period of time in
order to take a snapshot of the data being backed up. While suspending the database, all running
transactions are completed to prevent loss of data consistency. If this parameter is specified, you
must specify the --post_cmd parameter.
Example:
--pre_cmd=c:\temp\pre_cmd.bat
where the contents of the batch file is
"net stop MSSQLSERVER"

102 Copyright © Acronis International GmbH, 2002-2016
post_cmd
--post_cmd=<command>
Post data capture command. The parameter value should be the path to a batch file containing the
required command along with its parameters.
Use this parameter to resume operation of the database or application after the data capture is
complete.
Example:
--post_cmd=c:\temp\post_cmd.bat
where the contents of the batch file is
"net start MSSQLSERVER"
3.6.14.12 snapshot
--snapshot={always|possible|none}
Defines whether to back up files (p. 24) directly (one by one) or by taking an instant data snapshot.
Available values of the parameter are as follows:
possible (by default)
Create a snapshot if it is possible. Back up files directly if taking a snapshot is not possible.
none
Do not create a snapshot. Always back up files directly. Trying to back up files that are opened for
exclusive access will result in a read error. Also, files in the backup may not be time-consistent.
always
Always create a snapshot. Using a snapshot enables the backing up of all local files. This includes
files opened for exclusive access. The files will be backed up at the same point in time. If a
snapshot cannot be taken, the backup will fail.
3.6.14.13 split
--split=<size>
If specified, the backup will be split into multiple files of the specified size (in MB). If not specified,
the software will split the backup when necessary. Such might be the case when the backup is placed
on removable media or on FAT16 and FAT32 file systems that have a file size limit of 2GB and 4GB,
respectively.
3.6.14.14 Tape management
tape_eject_successful
--tape_eject_successful
If the parameter is specified, the software will eject tapes after each successful backup. Otherwise,
tapes will not be ejected automatically.
tape_full_empty
--tape_full_empty

103 Copyright © Acronis International GmbH, 2002-2016
If the parameter is specified, each full backup will be written onto a free tape. Otherwise, the
software will try to write a backup onto a tape containing backups of the same backup chain or
archive. If not found, the software will try to use a free tape.
tape_overwrite
--tape_overwrite
The parameter applies only to stand-alone tape drives. If the parameter is specified, a tape inserted
into a drive will be overwritten every time a full backup is created.
3.6.14.15 use_vss
--use_vss={auto|software_auto|acronis|native|software|hardware|none}
Volume Shadow Copy Service (VSS) notifies VSS-aware applications that the backup is about to start.
This ensures the consistent state of all data being used by such applications. Then, VSS tells a
snapshot provider to create the snapshot. You can select the snapshot provider that VSS will use for
taking snapshots.
Available values of the parameter are described below. If a snapshot cannot be taken by using any of
the specified providers, Acronis Backup will not use VSS. Instead, it will take a snapshot by using its
own Snapshot Manager driver (snapman.sys).
auto
VSS will use the hardware-based provider that supports the source volume. If one is not found,
VSS will try to use a software-based provider, the Microsoft Software Shadow Copy provider, and
Acronis VSS Provider in turn.
software_auto
VSS will use any available software-based provider. If one is not found, VSS will try to use the
Microsoft Software Shadow Copy provider, and Acronis VSS Provider in turn.
acronis
VSS will use Acronis VSS Provider.
native (by default)
VSS will use the Microsoft Software Shadow Copy provider.
software
VSS will use any available software-based provider that supports the source volume.
hardware
VSS will use the hardware-based provider that supports the source volume.
none
Choose this value if your database is incompatible with VSS. Acronis Backup will take a snapshot
by using its own Snapshot Manager driver (snapman.sys). Snapshots are taken faster but data
consistency of the applications whose transactions are not completed cannot be guaranteed.
3.7 Recovery parameters
3.7.1 autorename
--autorename

104 Copyright © Acronis International GmbH, 2002-2016
The parameter is used with the recover mssql_database (p. 40) command. The parameter
enables the renaming of databases that have the same names as those in the destination instance. A
recovered database will have the following name: <original database name>-Recovered. If a
database with this name already exists, the recovered database will be named as follows:
<original database name>-Recovered (<sequence number>).
Examples: MyDatabase-Recovered, MyDatabase-Recovered (2).
If the --autorename parameter is not specified, the command execution result depends on the
--overwrite (p. 108) parameter. If the --overwrite parameter is present, the command will
overwrite the existing database. Otherwise, the database will be skipped during the recovery.
If you specify both the --autorename and the --overwrite parameters, an error will occur.
3.7.2 database
--database=<db_name>
The name of a database to be recovered.
The parameter is used with the recover exchange_database (p. 36) command only when
recovering a storage group.
The parameter is needed in the following cases:
If the --target (p. 86) parameter value is another_database and the destination storage
group does not exist.
If the --target parameter value is recovery_database.
You need to specify pairs of the --database and --database_location (p. 104) parameters for
each database of the storage group being recovered. Otherwise, the operation will fail.
To learn the names of the backed-up databases, use the list content (p. 46) command.
Example:
--database=DB1 --database_location=C:\databases\DB1 --database=DB4
--database_location=D:\my_documents\DB4
3.7.3 database_location
--database_location=<local path>
Command: recover exchange_database
A folder on the Exchange server to which a database will be recovered.
The parameter is used with the recover exchange_database (p. 36) command in the following
cases:
If the --target (p. 86) parameter value is another_database and the destination database
or storage group does not exist.
If the --target parameter value is recovery_database.
When recovering a storage group, you need to specify pairs of the --database (p. 104) and
--database_location parameters for each database of this storage group. Otherwise, the
operation will fail.

105 Copyright © Acronis International GmbH, 2002-2016
Example:
--database=DB1 --database_location=C:\databases\DB1 --database=DB4
--database_location=D:\my_documents\DB4
When recovering a database, the --database (p. 104) parameter is not needed.
Command: recover mssql_database
A folder on the SQL server to which files of the recovered databases will be written.
The parameter is used with the recover mssql_database (p. 40) command if the --target (p.
86) parameter value is another_instance.
If the parameter is not specified, the command will fail.
3.7.4 database_state
--database_state={recovery|norecovery|standby}
The state of the recovered database. The parameter is used with the recover mssql_database (p.
40) command.
Available values of the parameter are as follows:
recovery (by default)
After the recovery completes, the database will be ready for use. Users will have full access to it.
The software will roll back all uncommitted transactions of the recovered database that are
stored in the transaction logs. You will not be able to recover additional transaction logs from the
native Microsoft SQL backups.
norecovery
After the recovery completes, the database will be non-operational. Users will have no access to
it. The software will keep all uncommitted transactions of the recovered database. You will be
able to recover additional transaction logs from the native Microsoft SQL backups and thus reach
the necessary recovery point.
standby
After the recovery completes, users will have read-only access to the database. The software will
undo any uncommitted transactions. However, it will save the undo actions in a temporary
standby file so that the recovery effects can be reverted.
The standby value is primarily used to detect the point in time when a SQL Server error
occurred.
When recovering a system database, this parameter is ignored. System databases are always
recovered in the recovery state.
3.7.5 destination_database
--destination_database=<db>
The parameter is used with the recover exchange_database (p. 36) command if the --target
(p. 86) parameter value is another_database.
The parameter specifies the database or storage group to which the database or storage group
specified in the --items (p. 81) parameter will be recovered. An existing database or storage group

106 Copyright © Acronis International GmbH, 2002-2016
can be overwritten only if you add the --overwrite (p. 108) parameter. If the specified database or
storage group does not exist, it will be created.
For detailed information about the value format, see "Specifying Exchange data" (p. 82).
If the parameter is not specified, the command will fail.
3.7.6 destination_instance
--destination_instance=<instance name>
The parameter is used:
With the recover mssql_database (p. 40) command only if the --target (p. 86) parameter
value is another_instance.
With the mount mssql_database (p. 55) command.
The parameter specifies the instance where the databases specified in the --items (p. 81)
parameter will be recovered or mounted.
If the parameter is not specified or if you type a non-existing instance name, the command will fail.
3.7.7 disk_location
--disk_location=<path>
The local or network folder to which the recovered data items will be saved. The parameter is used:
With the recover exchange_database (p. 36) and recover mssql_database (p. 40)
commands only if the --target (p. 86) parameter value is disk.
With the recover exchange_mailbox (p. 37) command only if the --target (p. 86)
parameter value is pst.
If the parameter is not specified, the commands will fail.
3.7.8 exclude
--exclude=<files, folders and masks>
Files and folders to be excluded from the recovery. You can either specify files and folders explicitly
or use wildcard characters.
Note: Exclusions override selection of data items to recover. For example, if you select to recover file MyFile.tmp
and to exclude all .tmp files, file MyFile.tmp will not be recovered.
Specify the name of the file or folder, such as Document.txt.
The names are not case-sensitive, both in Windows and Linux. For example, if you choose to exclude
all .tmp files and the Temp folders, also excluded will be all .Tmp files, all .TMP files, and the TEMP
folders.
You can use one or more wildcard characters * and ?:
The asterisk (*) substitutes for zero or more characters. For example, Doc*.txt covers files such
as Doc.txt and Document.txt.
The question mark (?) substitutes for exactly one character. For example, Doc?.txt covers files
such as Doc1.txt and Docs.txt, but not the files Doc.txt or Doc11.txt.

107 Copyright © Acronis International GmbH, 2002-2016
Exclusion examples
Criterion
Example
Description
By name
F.log
F
Excludes all files named "F.log"
Excludes all folders named "F"
By mask (*)
*.log
F*
Excludes all files with the .log extension
Excludes all files and folders with names starting with "F"
(such as folders F, F1 and files F.log, F1.log)
By mask (?)
F???.log
Excludes all .log files with names consisting of four
symbols and starting with "F"
3.7.9 ext2_3
--ext2_3
If the parameter is specified, the file system will be converted from Ext2 to Ext3. The parameter is
used with the recover disk (p. 20) and recover vm (p. 31) commands. Without this parameter,
the recovered volume will inherit the file system from the backup.
3.7.10 fat16_32
--fat16_32
If the parameter is specified, the file system will be converted from FAT16 to FAT32. The parameter is
used with the recover disk (p. 20) and recover vm (p. 31) commands. Without this parameter,
the recovered volume will inherit the file system from the backup.
It is recommended to use the parameter if the volume size after recovery is likely to exceed 2 GB.
3.7.11 file
--file=<paths>
Files and folders to recover from the file-level backup. If not specified, all contents of the backup are
recovered.
You can disable recovery of certain files and folders by using the --exclude (p. 106) parameter.
A file or folder specified in both the --file and --exclude parameters will be recovered.
3.7.12 log_location
--log_location=<local path>
A folder on the Exchange server where the transaction log files will be recovered.
The parameter is used with the recover exchange_database (p. 36) command in the following
cases:
If the --target (p. 86) parameter value is another_database and the destination database
or storage group does not exist.
If the --target parameter value is recovery_database, and the destination recovery
storage group does not exist.

108 Copyright © Acronis International GmbH, 2002-2016
If the parameter is not specified, the operation will fail.
3.7.13 original_date
--original_date
The parameter is used with the recover file (p. 25) and recover ad_database (p. 41)
commands. Recover the original date and time of the files from the backup. If not specified, the
current date and time are assigned.
3.7.14 outlookmachine
--outlookmachine=<IP address or hostname>
The name or IP address of the machine where Microsoft Outlook 2003 or later is installed. The
parameter is used with the recover exchange_mailbox (p. 37) command only if the --target (p.
86) parameter value is pst.
If specified, the created .pst file will be of the new format, and you will be able to open such a file by
using Microsoft Outlook 2003 or later. If not specified, the created .pst file will be of the old format,
and you will be able to open such a file by using Microsoft Outlook 97-2002.
After this parameter, you need to specify the valid user account in the --credentials (p. 120)
parameter. When entering the name of an Active Directory user account, be sure to also specify the
domain name (DOMAIN\Username or Username@domain). The user account has to be a member of
the Administrators group on the machine.
3.7.15 overwrite
Commands: recover file, recover ad_database
--overwrite={always|older|never}
In the recover file (p. 25) or recover ad_database (p. 41) command, the parameter specifies
what to do if the program finds in the target folder a file that has the same name as in the backup.
Available values of the parameter are as follows:
always (by default) - this will give the file in the backup priority over the file on the hard disk.
older - this will give priority to the most recent file modification, whether it be in the backup or
on the disk.
never - this will give the file on the hard disk priority over the file in the backup.
In the recover file (p. 25) command, if you allow files to be overwritten, you still have an option
to prevent overwriting of specific files by excluding (p. 106) them from the recovery operation.
Commands: recover exchange_database, recover exchange_mailbox,
recover mssql_database
--overwrite
In the recover exchange_database (p. 36) command, the parameter allows the overwriting of
the existing database or storage group (if the overwriting is allowed in the properties of the selected
databases). If the parameter is not specified and the destination database or storage group exists,
the operation will fail.

109 Copyright © Acronis International GmbH, 2002-2016
In the recover exchange_mailbox (p. 36) command, the parameter allows the overwriting of
items (e-mails, calendar events, contacts, tasks, etc.) that have the same IDs as those in the backup.
If the parameter is not specified, such items in the target mailbox will be skipped.
Note: If you recover the same items more than once, each subsequent recovery will duplicate the items because
original item IDs change after the overwriting.
In the recover mssql_database (p. 40) command, the parameter allows the overwriting of
databases that have the same names as those in the backup. If the parameter is not specified, the
command execution result depends on the --autorename (p. 103) parameter. If the
--autorename parameter is present, the command will rename the recovered database. Otherwise,
the database will be skipped during the recovery. If you specify both the --autorename and the
--overwrite parameters, an error will occur.
3.7.16 pit
--pit=<date and time>
The date and time to which the data will be recovered. The parameter value is specified in the
following format: "DD.MM.YYYY HH24:MM" (for example, "27.02.2012 13:00").
The parameter is used with the recover exchange_database (p. 36) and recover
exchange_mailbox (p. 37) commands only if the --recovery_point (p. 110) parameter value is
point_in_time.
The software automatically finds (in the transaction log backup) the transaction log file which
includes the specified point in time. After that, the data is recovered to the time of this transaction
log file creation. If there are no log files that include the specified time, the software will use the
nearest point from the transaction log file backed up previously.
If the point in time is not specified, the operation will fail.
3.7.17 power_on
--power_on
Power on the target virtual machine when the recovery is complete.
3.7.18 preserve_mbr
--preserve_mbr
When recovering a volume over an existing one, the target volume is deleted from the disk along
with its entry in the target disk MBR. Then, with this parameter, the recovered volume's entry will
occupy the upper empty position in the target disk MBR. Thus, the target disk MBR is preserved. If
the parameter is not specified, the recovered volume's entry will occupy the same position as in the
source disk MBR saved in the backup. If the position is not empty, the existing entry will be moved to
another position.
3.7.19 recover_absolute_path
--recover_absolute_path
The parameter is used with the recover file (p. 25) command. Recover with full paths to files and
folders. If not specified, full paths are not used.

110 Copyright © Acronis International GmbH, 2002-2016
Example
You backed up folder My folder located at C:\My data\Dir1, and now you recover it from the latest
backup to D:\Sample\Dir2.
recover file --loc=E:\my_backups --arc=my_archive --file="My folder"
--target=D:\Sample\Dir2
The --recover_absolute_path parameter is not specified. The recovered folder will be located
at D:\Sample\Dir2\My folder.
recover file --loc=E:\my_backups --arc=my_archive --file="My folder"
--target=D:\Sample\Dir2 --recover_absolute_path
The --recover_absolute_path parameter is specified. The recovered folder will be located at
D:\Sample\Dir2\Drive(C)\My data\Dir1\My folder.
3.7.20 recovery_point
The state to which the data will be recovered.
Command: recover exchange_database
--recovery_point={point_of_failure|latest_backup|point_in_time|selected_backup}
In the recover exchange_database (p. 36) command, available values of the parameter are as
follows:
point_of_failure (by default)
The data will be recovered to the state of the most recent transaction log file existing in
Exchange. If transaction logs are not available (lost, deleted or corrupted), the data will be
recovered to the moment of backup creation.
latest_backup
The data will be recovered from the latest backup of an archive.
point_in_time
The data will be recovered to a certain date and time. The software will first recover data to the
time of the last created full backup before the specified time, and then apply the transaction log
files from the transaction log backups.
If this value is used, you need to specify the --pit (p. 109) parameter.
selected_backup
The data will be recovered from the backup that you specify with the --backup (p. 85)
parameter.
Command: recover exchange_mailbox
--recovery_point={latest_backup|point_in_time|selected_backup}
In the recover exchange_mailbox (p. 37) command, available values of the parameter are as
follows:
latest_backup (by default)
The data will be recovered from the latest backup of an archive.
point_in_time
The data will be recovered to a certain date and time. This value can be used only if you recover
a mailbox, a public folder or a mailbox folder from a database-level backup.

111 Copyright © Acronis International GmbH, 2002-2016
If this value is used, you need to specify the --pit (p. 109) parameter.
selected_backup
The data will be recovered from the backup that you specify with the --backup (p. 85)
parameter.
3.7.21 target_disk
--target_disk=<disk number>
The parameter is used with the recover disk (p. 20), recover vm (p. 31), and recover mbr (p.
22) commands.
When recovering volumes, use this parameter to place the volumes to unallocated space of the
specified basic disk. You can specify only one target disk.
When recovering disks, use this parameter to specify the target disks.
By using the recover vm command, you can recover only one disk at a time. So, only one target
disk can be specified.
With the recover disk command, you can specify several disks. The number of disks specified
in the --target_disk parameter must be the same as the number of disks specified in the
--disk parameter.
When recovering a master boot record by using the recover mbr command, use this parameter
to specify the target disk.
3.7.22 target_volume
--target_volume=<volume number>
Volume where you will recover data which has been selected in the --volume (p. 89) parameter.
The parameter is used with the recover disk (p. 20) and recover vm (p. 31) commands.
With the recover disk (p. 20) command, you can specify several volumes. The number of volumes
specified in the --target_volume parameter must be the same as the number of volumes
specified in the --volume parameter.
If you need to recover a volume to the unallocated space of a basic disk, use one of the following
methods:
Type --target_volume=UNALLOCATED-<disk number>-<unallocated space sequence
number> to specify unallocated space on a specific disk.
Specify the --target_disk (p. 111) parameter instead of the --target_volume parameter.
In this case, the software will try to recover the volume to the first unallocated space of a
suitable size on the specified disk.
Specify the --target_disk (p. 111) and --start (p. 91) parameters instead of the
--target_volume parameter. In this case, the software will recover the volume to the
unallocated space on the specified disk starting from the specified start position.
Examples
--target_volume=C – to recover to a basic volume
--target_volume=DYN1 – to recover to a dynamic volume (Windows) or to a logical volume
(Linux)
--target_volume=UNALLOCATED-1-1 – to recover to the first unallocated space of the first basic
disk

112 Copyright © Acronis International GmbH, 2002-2016
--target_volume=UNALLOCATED-DYN – to recover to the unallocated space of the disk group (for
Windows only)
3.7.23 type
--type={active|primary|logical}
Sets the recovered volume as active, primary or logical. However, this may not be possible (for
example, because there cannot be more than four primary volumes on a disk). Setting a volume
active sets it as primary. On the other hand, a volume set primary may remain inactive.
If the type is not specified, the software will try to keep the target volume type. If the target volume
is active, the recovered volume is set active. If the target volume is primary and there are other
primary volumes on the disk, one of them will be set active while the recovered volume becomes
primary. If no other primary volumes remain on the disk, the recovered volume is set active.
When recovering a volume on unallocated space, the software extracts the volume type from the
backup. For the primary volume, the type will be set as follows:
if the target disk is the 1st according to BIOS and it has no other primary volumes, the recovered
volume will be set active
if the target disk is the 1st according to BIOS and there are other primary volumes on it, the
recovered volume will be set logical
if the target disk is not the 1st, the recovered volume will be set logical.
3.7.24 use_all_space
--use_all_space
This parameter is used with the recover disk (p. 20) and recover vm (p. 31) commands in the
following cases:
You recover a disk to a larger disk.
If the parameter is specified, the recovered disk's volumes will be resized so they occupy the
whole target disk.
You recover a volume to unallocated space.
If the parameter is specified, the recovered volume will occupy all the unallocated space.
If the parameter is not specified, the recovered disk or volume size will be equal to the original disk
or volume size.
3.8 Mounting parameters
3.8.1 for_all_users
--for_all_users={true|false}
The parameter is used with the mount (p. 53) command when mounting volumes in Windows.
If the value is true, the backed-up volumes will be available to all users.
If the value is false or if the parameter is not specified, the backed-up volumes will be available to
the current user only.

113 Copyright © Acronis International GmbH, 2002-2016
3.8.2 letter
Command: mount
--letter=<letters>
Letters to be assigned to the mounted volumes. The parameter is used with the mount (p. 53)
command when mounting volumes in Windows.
The letters you specify are assigned to the volumes according to the volume order in the --volume
(p. 89) parameter.
Example
--volume=2-1,1-3,1-1 --letter=K,L,M
The letters will be assigned as follows: 2-1=K; 1-3=L; 1-1=M.
If no letter is specified for one or several volumes, the software will assign the first available letters.
In this case, use the list disks (p. 18) command to get the letters assigned to the volumes. If you
specify more letters than volumes, the operation will fail.
Command: umount
--letter={<letter>|all}
The letter of the volume to be disconnected. The parameter is used with the umount (p. 54)
command when unmounting a volume in Windows. If the value is all, all volumes will be
disconnected. If the parameter is not specified, the operation will fail.
3.8.3 mount_point
Command: mount
--mount_point=<mount points>
Directories to mount the volumes to. The parameter is used with the mount (p. 53) command in
Linux. If the parameter is not specified or if the number of mount points differs from the number of
volumes, the operation will fail.
Command: umount
--mount_point=<mount point>
The directory to unmount the volume from. The parameter is used with the umount (p. 54)
command in Linux. If the parameter is not specified, the operation will fail.
3.8.4 rw
--rw
If specified, the backed-up volume will be mounted in the read/write mode. You will be able to
modify its contents (save, move, create, delete files or folders) and run executables consisting of one
file.
If not specified, the volume will be mounted in the read-only mode.

114 Copyright © Acronis International GmbH, 2002-2016
3.9 Acronis Secure Zone parameters
3.9.1 asz_size
--asz_size={<size>{s|kb|mb|gb}|unallocated}
If no measurement unit is specified, the size is measured in megabytes (mb).
Command: create asz
In the create asz (p. 56) command, the parameter specifies the size of Acronis Secure Zone.
If the parameter is not specified, the size is set as the average between the maximal (unallocated
space plus free space on the volumes selected with the --volume (p. 89) parameter) and minimal
(about 50 MB) values.
Either way, the software will first use the unallocated space. If there is not enough unallocated space,
the selected volumes will be decreased. Resizing of locked volumes requires a reboot (p. 125).
With the unallocated value, the zone will use all unallocated space on the disk. Volumes will be
moved, if necessary, but will not be resized. Moving of locked volumes requires a reboot. The
--volume (p. 89) parameter is ignored.
Command: resize asz
In the resize asz (p. 57) command, the parameter specifies the new size of Acronis Secure Zone.
If you increase Acronis Secure Zone, the software will behave in the same way as described earlier
for the create asz command.
If you decrease Acronis Secure Zone, the freed space will be added to the volumes specified in the
--volume (p. 89) parameter. Resizing of locked volumes requires a reboot (p. 125). Without the
--volume parameter or if the --asz_size parameter is set to unallocated, the freed space
becomes unallocated.
If the parameter is not specified, the software just displays the current Acronis Secure Zone size and
free space.
3.10 Filtering
The filtering parameters are used to filter the data retrieved by the listing commands (list
activities (p. 67), list archives (p. 42) and others).
3.10.1 content_path
The path to the contents inside the backup. The parameter is used with the list content (p. 46)
command unless the --content_type (p. 115) parameter value is volume or ad_database. If not
specified, the first 5000 root elements will be shown.
Disk-level and file-level backups
For disk-level and file-level backups, this parameter is a file system path. In Windows, specify
volumes in the path by their letters (not numbers, like 1-1). In Linux, specify the volume's mount
point.
Examples:

115 Copyright © Acronis International GmbH, 2002-2016
--content_path=C:\Windows\system32
--content_path=/home/user1/work
Microsoft Exchange Server data backups
For detailed information about the value format, see "Specifying Exchange data" (p. 82).
Single-pass backups
For single-pass backups, the value format depends on the data type you want to view. This data type
is determined by the --content_type parameter value.
If --content_type=mssql_database, this parameter is an instance name.
Example:
--content_path=NEWSERVER
If --content_type=file, this parameter is a file system path. Specify volumes in the path by
their letters (not numbers, like 1-1).
Example:
--content_path=D:\databases
3.10.2 content_type
--content_type={volume|file|exchange_database|exchange_mailbox|mssql_database|ad_d
atabase}
The type of content to display. The parameter is used with the list content (p. 46) command
when viewing the contents of a disk-level or database-level backup.
Disk-level backups
When viewing the contents of a disk-level backup, the applicable values of the parameter are
volume and file. If the value is volume or if the parameter is not specified, the command will list
disks and volumes contained in the backup. Otherwise, the list of backed up files and folders will be
shown.
Microsoft Exchange Server data backups
When viewing the contents of a database-level backup, the applicable values of the parameter are
_exchange_database and exchange_mailbox. If the value is exchange_database or if the
parameter is not specified, the command will list storage groups and databases contained in the
backup. Otherwise, the list of backed up mailboxes and public folders will be shown.
Single-pass backups
When viewing the contents of a single-pass backup of Microsoft SQL Server, the applicable values of
the parameter are mssql_database, volume, and file. When viewing the contents of a
single-pass backup of Microsoft Active Directory data, the applicable values of the parameter are
ad_database, volume, and file.
If the value is volume or if the parameter is not specified, the command will list disks and volumes
contained in the backup.
3.10.3 filter_available_for_backup
--filter_available_for_backup={true|false}

116 Copyright © Acronis International GmbH, 2002-2016
If the parameter value is true, the software lists only virtual machines that are being managed by an
agent. If the value is false, only unmanageable virtual machines are displayed. A virtual machine is
unmanageable if the agent is absent, stopped or corrupted. This makes it unavailable for the
management server. The parameter is used with the list vms (p. 27) command. If the parameter is
not specified, the command shows both manageable and unmanageable virtual machines.
3.10.4 filter_date
--filter_date=<dates and times>
The parameter is used with the list backups (p. 46) command. If specified, the command will
retrieve only backups that were created on certain dates and at certain time. If not specified,
backups with any creation date and time will be displayed.
Specify a list of exact dates and times in the following format: "DD.MM.YYYY HH24:MM:SS". You can
omit seconds, minutes and hours. This will mean "any second", "any second and any minute" or "any
second, any minute and any hour", respectively.
Examples:
--filter_date="15.02.2011 12:00" shows backups created between 15.02.2011 12:00:00
and 15.02.2011 12:00:59.
--filter_date="15.02.2011 12" shows backups created between 15.02.2011 12:00:00 and
15.02.2011 12:59:59.
--filter_date=15.02.2011 shows backups created between 15.02.2011 00:00:00 and
15.02.2011 23:59:59.
3.10.5 filter_edition
--filter_edition=<editions>
The parameter is used with the list mssql_instances (p. 39) command. If specified, the
software will list only instances of those Microsoft SQL Server editions that contain the values you
have specified.
Without this parameter, instances of any Microsoft SQL Server edition will be displayed.
Example:
If you specify --filter_edition=Enterprise, the software will display instances of the
following Microsoft SQL Server editions: Microsoft SQL Server 2005 Enterprise Edition, Microsoft SQL
Server 2008 R2 Enterprise Edition, and Microsoft SQL Server 2012 Enterprise Edition.
3.10.6 filter_guid
--filter_guid=<GUIDs>
GUIDs for selecting objects to be output. The parameter is used with the list tape_libraries (p.
60), list vms (p. 27), and list activities (p. 67) commands. If not specified, objects with any
GUID will be displayed.
3.10.7 filter_host
--filter_host=<hostnames>
117 Copyright © Acronis International GmbH, 2002-2016
The parameter is used with the list vms (p. 27) command. If specified, the software will display
only virtual machines residing on the listed hosts. If not specified, virtual machines residing on all
registered hosts will be displayed.
3.10.8 filter_library
--filter_library=<GUID>
The GUID of the tape library whose slots you want to list with the list tape_slots (p. 61)
command. If not specified, the command will list slots of all the tape libraries attached to the
machine.
To learn the GUID of a tape library, use the list tape_libraries (p. 60) command.
3.10.9 filter_machines
--filter_machines=<quantities of machines>
The parameter is used with the list vmservers (p. 27) command. If specified, the software will list
only those virtualization servers or server clusters that contain the specified quantities of machines.
If not specified, servers or clusters with any quantity of machines will be displayed.
3.10.10 filter_name
--filter_name=<names>
Object names for selecting objects to be output.
If the parameter is used with the list tape_libraries (p. 60), list vms (p. 27) or list
vmservers (p. 27) command, the software will display objects whose names coincide with the
values you have specified.
If the parameter is used with the list exchange_mailboxes (p. 33), list mssql_instances (p.
39), or list mssql_databases (p. 39) command, the software will display objects whose names
contain the values you have specified.
Without this parameter, objects with any name will be displayed.
3.10.11 filter_resource
--filter_resource=<resource names>
The parameter is used with the list activities (p. 67) command. If specified, the command will
output only those activities that back up the resources whose names contain the values you have
specified.
Specify a disk by a number; a volume by a label; a file, folder, or virtual machine by its name.
Examples:
--filter_resource="Disk 2"
--filter_resource="System (C:)"
--filter_resource="My Folder","my_thesis.doc"
--filter_resource=my_vm_1
Without this parameter, activities will be displayed regardless of the related resources.
118 Copyright © Acronis International GmbH, 2002-2016
3.10.12 filter_state
--filter_state=<states>
States for selecting objects to be output. The parameter is used with the list activities (p. 67),
list tasks (p. 72), list plans (p. 68), and list vms (p. 27) commands. If the parameter is not
specified, objects with any state will be listed.
For the list activities command, you can specify one or more of the following states: running,
paused, waiting, waiting_for_children, or completed.
For the list tasks and list plans commands, you can specify one or more of the following
states: idle, waiting, running, or need_interaction.
For the list vms command, you can specify one or more of the following states: running,
stopped, suspended, wait_input, or unknown.
3.10.13 filter_status
--filter_status=<statuses>
Statuses for selecting objects to be output. The parameter is used with the list vms (p. 27) and
list plans (p. 68) commands. If not specified, objects with any status will be displayed.
A virtual machine status shows how successful the machine is backed up. It depends on the statuses
of all backup plans related to this virtual machine.
You can specify one or more of the following statuses: ok, warning, error, or unknown.
3.10.14 filter_type
Types for selecting objects to be output.
Commands: list archives, list backups
--filter_type=<types>
In the list archives (p. 42) command, you can specify one or more of the following types: disk,
file, exchange_db, and exchange_doc.
In the list backups (p. 46) command, you can specify one or more of the following types: full,
incremental, differential, and transaction_log.
Command: list vmservers
--filter_type=<server types>
In the list vmservers (p. 27) command, you can specify one or more of the following types:
standalone and cluster.
3.10.15 filter_user
--filter_user=<user names>
The parameter is used with the list tasks (p. 72) and list plans (p. 68) commands. If specified,
the software will list only tasks that run (or only plans whose tasks run) under the specified user
accounts. If not specified, tasks run under any user account will be displayed.
119 Copyright © Acronis International GmbH, 2002-2016
3.10.16 filter_version
--filter_version=<versions>
The parameter is used with the list mssql_instances (p. 39) command. If specified, the
software will list only instances of those Microsoft SQL Server versions that contain the values you
have specified.
Without this parameter, instances of any Microsoft SQL Server version will be displayed.
Example:
If you specify --filter_version=500, the software will display instances of the following
Microsoft SQL Server versions: 9.00.5000.00 and 10.00.5500.00.
3.11 Tape management parameters
3.11.1 assign2free
--assign2free
The parameter is used with the inventory tape (p. 61) command. If specified, the detected tapes
will be moved from the Unrecognized tapes or Imported tapes pools to the Free tapes pool.
Warning. Only use this parameter if you are absolutely sure that the data stored on your tapes can be
overwritten.
3.11.2 libraries
--libraries=<GUIDs>
GUIDs of tape libraries or stand-alone tape drives to be inventoried. The parameter is used with the
inventory tape (p. 61) command.
If not specified, the command will fail. To learn GUIDs of tape libraries or stand-alone tape drives, use
the list tape_libraries (p. 60) command.
3.11.3 mode
--mode={full|fast}
The method of inventorying tapes (p. 61).
Fast inventorying
If the parameter value is fast or is not specified, Acronis Backup scans tapes for barcodes. Using
barcodes, the software can quickly return a tape to the pool where it was before.
Select this method to recognize tapes used by the same tape device attached to the same machine.
Other tapes will be sent to the Unrecognized tapes pool.
If your tape library contains no barcode reader, all tapes will be sent to the Unrecognized tapes pool.
To recognize your tapes, perform full inventorying or combine fast and full inventorying as described
later in this section.

120 Copyright © Acronis International GmbH, 2002-2016
Full inventorying
If the parameter value is full, Acronis Backup reads tags written by Acronis software and analyzes
other information about the contents of the loaded tapes. Select this method to recognize empty
tapes and tapes written by Acronis software on any tape device and any machine.
Combination of fast and full inventorying
Full inventorying of an entire tape device may take a long time. If you need to inventory only a few
tapes, combine fast and full inventorying. Step-by-step instructions are provided in "Operations with
tapes" (p. 141).
3.11.4 slots
--slots=<GUIDs>
GUIDs of tape library slots to be inventoried. The parameter is used with the inventory tape (p.
61) command only if the --libraries (p. 119) parameter contains the GUID of one library.
If the parameter is not specified, all of the tape library slots will be inventoried. To learn GUIDs of
tape library slots, use the list tape_slots (p. 61) command.
3.12 General parameters
3.12.1 credentials
--credentials=<user name>,<password>,encrypted
Credentials to access a machine, a backup location, or a folder. The parameter must directly follow
the object for which credentials are required (for example, --host, --loc, --target).
To access Acronis Secure Zone, specify only the password in this parameter.
To access a network share that does not require credentials, specify --credentials=anonymous.
If the third parameter value (encrypted) is specified, it means that the preceding password was
encrypted by the acronis_encrypt utility (p. 149).
A command can contain several --credentials parameters.
Example
acrocmd export archive --loc=bsp://ASN/my_vault --credentials="ASN user",pass1
--arc=my_archive --password=123 --target=\\bkpsrv\backups
--credentials=netuser,pass2
This command exports a password-protected archive from a managed vault to a network share. The
first credentials are required to access the vault my_vault managed by the storage node ASN. The
--password parameter specifies the password for the archive my_archive. The second credentials
enable writing to the shared folder \\bkpsrv\backups.
3.12.2 Error handling
--retry_count=<number of attempts>
--retry_delay=<delay>

121 Copyright © Acronis International GmbH, 2002-2016
These parameters are used with the backup and recovery commands only.
When a recoverable error occurs, the software re-attempts to perform the unsuccessful operation.
You can set the number of attempts and the time interval between attempts. The attempts will be
stopped as soon as the operation succeeds OR the specified number of attempts is performed,
depending on which comes first.
You need to specify both parameters. The --retry_delay parameter must directly follow the
--retry_count parameter.
Example: --retry_count=10 --retry_delay=20s
If the parameters are not specified, the number of attempts is 5 and the time interval between
attempts is 30 seconds (as if you typed --retry_count=5 --retry_delay=30s). To completely
disable re-attempts, specify --retry_count=0.
The interval may be set in seconds (s, by default), minutes (m) or hours (h).
Examples:
10-second interval: --retry_delay=10 or --retry_delay=10s
1-minute interval: --retry_delay=1m
1-hour interval: --retry_delay=1h
3.12.3 file_params
{-f|--file_params}=<full local path>
Specifies the full path to an input parameter file. The path must be local (for example,
c:\temp\1.txt or /home/user1/1.txt). For more detailed information, see Syntax (p. 8).
3.12.4 force_yes
--force_yes
If the parameter is specified, the software will automatically handle situations requiring user
interaction as if the user answers Yes or OK to the interaction request. If the interaction request
does not imply these answers (for example, the possible answers to a reboot prompt are Reboot
and Cancel), the software will ignore this request. If an operation cannot continue without user
interaction, it will fail.
If the parameter is not specified, the command allows interaction with the user.
The parameter is mainly intended for the recover lvm_structure (p. 23) command. It automates
the recovery of a Linux system, along with its software RAID/LVM structure, to a machine with
different logical volume structure or without logical volumes. This command always prompts the user
to confirm the replacement of the machine's logical volume structure.
Please be aware that by using the --force_yes parameter you may unintentionally confirm
deletion of useful data. If you want the software to simply ignore interaction requests, use the
--silent_mode (p. 126) parameter rather than the --force_yes parameter. These parameters
are mutually exclusive.

122 Copyright © Acronis International GmbH, 2002-2016
3.12.5 id
Commands: get log; task, plan, and activity management commands
--id=<GUID>
GUID of the activity, task, or backup plan with which the operation is to be performed. The
parameter is used with the get log (p. 66) command and with the task (p. 72), plan (p. 68), and
activity (p. 67) management commands.
To learn the GUID, use the list activities (p. 67), list tasks (p. 72), or list plans (p. 68)
command.
Command: generate report
--id={machines_by_status|vms_by_status|archives_by_managed_vaults|plans_by_status|
managed_vaults_statistics_for_last_month|tasks_by_last_result|activities_for_last_
month}
Contents of the report that will be created by the generate report (p. 74) command. If the
parameter is not specified, the command will fail.
The parameter values correspond to the following predefined reports:
machines_by_status—the Machines with agents (by status) report
vms_by_status—the Virtual machines (by status) report
archives_by_managed_vaults—the Archives (by managed vaults) report
plans_by_status—the Backup plans (by status) report
managed_vaults_statistics_for_last_month—the Managed vaults' statistics for last
month report
tasks_by_last_result—the Tasks (by last result) report
activities_for_last_month—the Tasks' activity for last month report
3.12.6 log
--log=<full path>
Saves the log of the operation with which the parameter is used to the specified file. The format of
the log file depends on the --log_format (p. 122) parameter value.
3.12.7 log_format
--log_format={structured|unstructured}
The format of the log file specified in the --log (p. 122) parameter. If the value is structured or if
the parameter is not specified, the software will write logs in the structured xml format. The format
is described in the acrocmd.xsd file located in the folder where the command-line utility is installed.
The default installation paths of the utility are listed in the "Installation" (p. 7) section under
"Installation paths".
If the value is unstructured, the software will write logs in the Acronis xml format.
3.12.8 oss_numbers
--oss_numbers={true|false}

123 Copyright © Acronis International GmbH, 2002-2016
The parameter is used in the following cases:
With the backup disk (p. 19), recover disk (p. 20), create asz (p. 56), resize asz (p. 57),
and delete asz (p. 59) commands. With these commands, the parameter applies to the
volumes specified in the --volume (p. 89) parameter value.
With the list content (p. 46) command if the --content_type parameter value is volume
or with the list disks (p. 18) command. With these commands, the parameter applies to
numbers of the output volumes.
If the value is true or if the parameter is not specified, the volume numbers are adjusted for the
MBR partition table. This means that primary volumes have numbers 1-1, 1-2, 1-3, 1-4; logical
volume numbers start with 1-5.
If the parameter value is false, consecutive volume numbering must be used.
Example
If the disk has one primary and two logical partitions, their numbers can appear as follows:
--volume=1-1,1-5,1-6
or
--oss_numbers=false --volume=1-1,1-2,1-3
3.12.9 output
--output={formatted|raw}
Output mode. Applicable values are:
formatted (by default)
Outputs human-readable formatted table. The maximum width of a table column is 20
characters. The text is left aligned. Table headers and header separators are shown.
raw
This mode is intended for use as input for a third-party parser. Headers are not visible; column
header separator lines are not visible; the column separator is "\t" (tab character). Also, this
mode enables you to see the full length of a value that is longer than 20 characters (for example,
the GUID of a backup plan).
3.12.10 password
--password=<password>,encrypted
Password for the archive in the backup and recovery operations, archive and backup management
operations. The parameter must directly follow the --arc (p. 84) parameter.
Also, this parameter is used in the create asz (p. 56) command to specify a password for Acronis
Secure Zone.
If the second parameter value (encrypted) is specified, it means that the preceding password was
encrypted by the acronis_encrypt utility (p. 149).
3.12.11 process_priority
--process_priority={low|normal|high}

124 Copyright © Acronis International GmbH, 2002-2016
The priority of a backup or validation process running in a system. In the validation commands, this
parameter is ignored if the backup destination is a managed vault.
This parameter determines the amount of CPU and system resources allocated to that process.
Decreasing the priority will free more resources for other applications. Increasing the priority might
speed up the backup or validation process by requesting the operating system to allocate more
resources like the CPU to the backup application. However, the resulting effect will depend on the
overall CPU usage and other factors like disk in/out speed or network traffic.
Available values are as follows:
low (by default)
Use this value to minimize resources taken by the backup or validation process and leave more
resources to other processes running on the machine.
normal
Use this value to run the backup or validation process at the normal speed and allocate resources
on a par with other processes.
high
Use this value to maximize the backup or validation process speed by taking resources from
other processes.
3.12.12 progress
--progress
Enables displaying the operation progress information (percent completed, elapsed time, estimated
time) on the screen. The progress information is recorded in the log regardless of the --progress
parameter presence.
3.12.13 read_speed
--read_speed=<speed>{kb|p}
The speed of reading the backups being validated. The parameter is used with the validate
archive (p. 44), validate backup (p. 47), and validate vault (p. 63) commands.
The parameter is used if the backup location (the --loc (p. 84) parameter value) is one of the
following:
1. A network share, an FTP/SFTP server, or Acronis Cloud Storage.
The parameter defines the amount of the network connection bandwidth allocated for
transferring the data. If the parameter is not specified, the software uses all the network
bandwidth it can get when transferring the data.
2. A hard disk of the machine where the command is executed.
For other location types, this parameter is ignored.
<speed> should be a positive number.
If the measurement unit is kb, the speed is measured in kilobytes per second. For the cloud storage,
only the kb measurement unit is effective.
If the measurement unit is p or is not specified, the speed is measured in the percentage of the
estimated maximum speed of the network connection or of the maximum I/O speed of the hard disk.

125 Copyright © Acronis International GmbH, 2002-2016
Examples:
--read_speed=500kb – the data reading speed will be 500 kilobytes per second
--read_speed=50p or --read_speed=50 – the data reading speed will be 50% of the estimated
maximum speed.
3.12.14 reboot
reboot and reboot later
--reboot
--reboot --later
Reboot the machine before the operation (if required).
Use the --reboot parameter when performing the following operations that require a reboot:
recovering a volume that contains the currently active operating system, recovering locked files,
creating/deleting Acronis Secure Zone on a system disk, cloning a system disk. The machine will be
rebooted without a prompt.
If neither the --reboot parameter nor the --silent_mode=on (p. 126) parameter is specified, the
operation will request user interaction. If the --reboot parameter is not specified and the
--silent_mode=on parameter is specified, the operation will fail.
To postpone the operation until a user reboots the system manually, add the --later parameter.
With this parameter, the operation will be performed after the user initiates a reboot. This
parameter can only be used with the create asz (p. 56) and resize asz (p. 57) commands.
If you specify the --reboot parameter with operations that do not necessarily require a reboot, this
parameter will be ignored.
reboot after
--reboot_after
Reboot the server after the operation is completed.
3.12.15 recreate_archive_meta
--recreate_archive_meta={true|false}
The parameter is used with the list archives (p. 42) and list backups (p. 46) command.
If the value is true or if the parameter is not specified, the archive metadata will be recreated during
the command execution. This ensures that the command will not fail even if the metadata is missing
or corrupted.
If the value is false, the archive metadata will remain intact. This will accelerate the command
execution.
3.12.16 report_format
--report_format={xml|html}
Format of the report created by the generate report (p. 74) command.
Available values of the parameter are as follows:

126 Copyright © Acronis International GmbH, 2002-2016
html (by default)
The report will be saved as a set of files: htc, xml, xslt, gif, and png. To view the report, open the
report.xml file in a web browser.
xml
The report will be saved as an .xml file.
3.12.17 silent_mode
--silent_mode={on|off}
If the parameter value is on, the silent mode is enabled. It means that the software will automatically
handle situations requiring user interaction. If an operation cannot continue without user interaction,
it will fail. Details of the operation, including errors, if any, can be found in the operation log.
If the value is off or if the parameter is not specified, the command allows interaction with the user.
Set this value if the operation requires a user interaction, such as inserting removable media (CD,
DVD or tape).
To prohibit interaction when the software comes across a bad sector during backup, use the
--ignore_bad_sectors (p. 100) parameter. The --silent_mode parameter does not work in
this particular case.
The --silent_mode and --force_yes (p. 121) parameters are mutually exclusive.
3.12.18 use_registry_defaults
--use_registry_defaults
The parameter is used with the backup and recovery commands, except for recover mbr (p. 22). It
determines the values of backup and recovery options that are not explicitly specified in a command
string.
If the parameter is specified, the software will use the default values of backup and recovery options
set in the graphical user interface of Acronis Backup. These values are stored on the machine with
the agent that performs the command. On a machine running Windows, the values are stored in the
registry; on a machine running Linux, the values are stored in the Acronis Backup configuration files.
If the parameter is not specified, the software will use the default values described in this
Command-Line Reference. These values are contained in the command-line utility code.
3.12.19 utc
--utc
The parameter is used with the list archives (p. 42), list backups (p. 46), list content (p.
46), and list plans (p. 68) commands. If specified, the date and time values in the command
output will be shown in Coordinated Universal Time (UTC). Otherwise, the values will be shown in
the time zone of the machine where you run the command.

127 Copyright © Acronis International GmbH, 2002-2016
4 Usage examples
4.1 Backup and recovery
4.1.1 Disks and volumes
Listing disks (p. 18)
Listing all disks of the local machine.
acrocmd list disks
Listing disks of a remote machine.
acrocmd list disks --host=192.168.1.2 --credentials=user1,pass1
Listing disks of a virtual machine.
acrocmd list disks --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
--vmid=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Backing up disks and volumes (p. 19)
Backing up the first volume of the second disk and the third volume of the first disk. The backup
will be saved to a local folder and will be split into 4.5-GB parts to be later written on DVDs. To
get the volume numbers, use the list disks (p. 18) command.
acrocmd backup disk --volume=2-1,1-3 --split=4608 --loc="F:\my backups" --arc="my
archive"
Backing up the entire machine to a file with a simplified name. For more details, see the
--plain_archive (p. 97) parameter description. The operation log will be saved to a text file.
acrocmd backup disk --loc=F:\ --arc=my_machine --plain_archive
--log=D:\logs\log.txt
Backing up disks 1 and 2 excluding .bak files. The compression level will be set to maximum. The
backup will be saved to a network shared folder. To get the disk numbers, use the list disks
(p. 18) command.
acrocmd backup disk --disk=1,2 --compression=max --exclude_mask=*.bak
--loc=\\bkpsrv\backups --credentials=bkpuser,pass --arc=disk_archive
Creating an incremental backup of volume C:. The Volume Shadow Copy Service (VSS) will be
enabled and will automatically select between the available hardware-based and software-based
snapshot providers. The backup will be saved to a managed vault.
acrocmd backup disk --volume=C --backuptype=incremental --use_vss=auto
--loc=bsp://storage_node1/my_vault --credentials=bkpuser,pass --arc=c_archive
Backing up the first (according to the list disks (p. 18) command output) dynamic volume in
Windows or logical volume in Linux. The backup will be saved to a network shared folder.
acrocmd backup disk --volume=DYN1 --loc=\\srv1\backups
--credentials=netuser1,pass1 --arc=dyn1_arc
For more information about selecting logical volumes in Linux, see Selecting logical volumes and
MD devices for backup (p. 145)
Backing up all dynamic volumes in Windows or all logical volumes in Linux. The backup will be
saved to an FTP server.
acrocmd backup disk --volume=DYN --loc=ftp://srv1/backups
--credentials=ftpuser1,pass1 --arc=alldyn_arc
128 Copyright © Acronis International GmbH, 2002-2016
Single-pass disk and application backup
Creating a single-pass backup of the local machine. The backup will be saved to a network shared
folder. Since the --mssql_truncate_logs (p. 96) parameter is not specified, the Microsoft
SQL Server log will not be truncated. If the software fails to collect the application metadata, the
backup will continue.
acrocmd backup disk --application_aware --loc=\\srv1\backups
--credentials=netuser1,pass1 --arc=machine1_app --ignore_app_errors
The user who runs the command must be a member of the sysadmin role on each of the
instances installed on the machine.
Creating a single-pass backup of a remote machine. The backup will be saved to a vault on a
storage node. Microsoft SQL Server logs will be truncated after each backup. Logs of other
VSS-aware applications will not be truncated. If the software fails to collect the metadata of any
application, the backup will fail because the --ignore_app_errors (p. 96) parameter is not
specified.
acrocmd backup disk --host=192.168.1.2 --credentials=user1,pass1
--application_aware --loc=bsp://storage_node1/my_vault --arc=my_archive_app
--mssql_truncate_logs
The user whose credentials are specified after the --host parameter must be a member of the
sysadmin role on each of the instances installed on the machine. If there is no such user, you
may access the machine through the management server:
acrocmd backup disk --host=srv1 --credentials="srv1\AMS user",pass --service=ams
--address=192.168.1.2 --application_aware --loc=bsp://storage_node1/my_vault
--arc=my_archive_app --mssql_truncate_logs
In this case, the command will be executed under the account of the agent service running on
the machine.
Recovering disks and volumes (p. 20)
Recovering disks
Recovering a machine from the latest backup of an archive residing on a network share. Since
neither the --disk (p. 88) nor the --volume (p. 89) parameter is specified, the command will
recover all of the backed-up disks. Since neither the --target_disk (p. 111) nor the
--target_volume (p. 111) parameter is specified, the software will automatically map the
disks to the target machine's disks. If you run the command in the operating system, a reboot
prompt will be displayed.
acrocmd recover disk --loc=\\srv1\folder1 --credentials=user1,pass1
--arc=my_machine
Recovering hard disks 1 and 2 from the latest backup of an archive to hard disks 3 and 4.
acrocmd recover disk --loc=F:\backups --arc=my_archive --disk=1,2 --target_disk=3,4
Recovering hard disk 2 from a backup located in an NFS shared folder to hard disk 1.
acrocmd recover disk --loc=nfs://server/backups:/ --arc=my_archive
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --disk=2 --target_disk=1
Recovering two hard disks from the latest backup of an archive located on tapes. Since the
--target_disk (p. 111) parameter is not specified, the software will automatically map the
disks to the target machine's disks.
acrocmd recover disk --loc=atis:///tape?XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--arc=disk_archive --disk=2,3
Recovering hard disk 1 from the latest backup of an archive to hard disk 4.

129 Copyright © Acronis International GmbH, 2002-2016
The archive is specified by the file name of a backup that belongs to the archive
(my_machine2.tib). Please be aware that the command will apply to the latest backup rather
than to the one specified in the --arc parameter. If the archive metadata is lost, the command
will apply to the latest backup of the backup chain. (A backup chain is a full backup and all of its
dependent incremental and differential backups.)
acrocmd recover disk --loc=F:\backups --arc=my_machine2.tib --disk=1
--target_disk=4
Recovering volumes
Recovering the second volume of the first disk from the latest backup of an archive.
Since neither the --target_disk (p. 111) nor the --target_volume (p. 111) parameter is
specified, the software will automatically map the volume to the original one. If the original
volume is not found, the software will recover to the first unallocated space of a suitable size. If
no unallocated space of a suitable size is found, the command will fail.
acrocmd recover disk --loc=/home/user1/my_backups --arc=my_machine1 --volume=1-2
Recovering three volumes from a backup to the specified volumes.
acrocmd recover disk --loc=F:\ --arc=my_machine
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --volume=1-1,1-2,2-1
--target_volume=3-1,3-3,4-1
Recovering a volume from a backup residing in a managed vault to hard disk 2. A new volume will
be created starting from megabyte 8192. It will have the size of 6400 megabytes and the "active"
flag.
acrocmd recover disk --loc=bsp://storage_node1/my_vault --credentials=admin,pass
--arc=my_archive --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --volume=1-1
--target_disk=2 --start=8192 --size=6400 --type=active
Recovering a basic volume from the latest backup of an archive to the first dynamic volume (in
Windows) or logical volume (in Linux).
acrocmd recover disk --loc=\\srv1\backups --credentials=netuser1,pass1
--arc=machine1_dyn1 --volume=2-1 --target_volume=DYN1
Recovering a basic volume (2-2) and a dynamic (logical) volume (DYN4) onto a basic disk.
Since the --target_disk (p. 111) parameter is specified, the volumes will be recovered to the
unallocated space of that disk. The resulting volumes will be basic. If no unallocated space of a
suitable size is found, the command will fail.
acrocmd recover disk --loc=F:\ --arc=my_machine
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --volume=2-2,DYN4 --target_disk=3
Recovering a dynamic (logical) volume from a backup to a dynamic (logical) volume.
acrocmd recover disk --loc=ftp://srv1/backups --credentials=ftpuser1,pass1
--arc=alldyn_arc --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --volume=DYN3
--target_volume=DYN4
Recovering a volume to the unallocated space of a disk group. The resulting volume will be
dynamic.
In the following example, the type of the resulting volume will be simple because a basic volume
was backed up.
acrocmd recover disk --loc=F:\ --arc=my_machine --volume=2-3
--target_volume=UNALLOCATED-DYN
In the following example, the type of the resulting volume will be inherited from the backed-up
volume because a dynamic volume was backed up.

130 Copyright © Acronis International GmbH, 2002-2016
acrocmd recover disk --loc=ftp://srv1/backups --credentials=ftpuser1,pass1
--arc=alldyn_arc --volume=DYN3 --target_volume=UNALLOCATED-DYN
Recovering MBR (p. 22)
Recovering an MBR of hard disk 1 from the latest backup of an archive located in Acronis Secure
Zone to the same hard disk 1.
acrocmd recover mbr --loc=atis:///asz --arc=my_archive --disk=1 --target_disk=1
Recovering logical volume structure (p. 23)
Creating the same logical volume structure on the local machine as in the latest backup of an
archive. The machine must be booted with Linux-based bootable media.
acrocmd recover lvm_structure --loc=\\bkpsrv\backups --credentials=netuser1,pass1
--arc=my_archive
4.1.2 Files
Backing up files and folders (p. 24)
Backing up a file. The backup will be saved to a local folder.
acrocmd backup file --include=C:\documents\my_thesis.doc
--loc=E:\backups\my_thesis --arc=my_thesis
Creating a backup of network shared folders. The backup will be saved to a local folder. The
archive will be protected by a password and encrypted.
acrocmd backup file --include=\\srv1\folder1,\\srv2\folder2 --password=123
--encryption=aes256 --loc=D:\backups --arc=my_archive
Creating a backup of a local folder. The backup will be saved to a vault on a storage node. The
disk snapshot must be taken. If taking a snapshot is not possible, the backup will fail.
acrocmd backup file --include=D:\documents --snapshot=always
--loc=bsp://storage_node1/my_vault --arc=my_archive
Backing up the user home directory in Linux. The backup will be saved to a SAMBA share.
acrocmd backup file --include=/home/anna --loc=\\bkpsrv\backups\anna
--credentials=netuser1,pass1 --arc=home_dir
Creating a backup of a local folder. The backup will be placed to Acronis Cloud Storage, with
encryption enabled.
acrocmd backup file --include=c:\work --password=123 --encryption=aes256
--loc=online:// --credentials="user@mail.com",pass --arc=my_archive
Recovering files and folders (p. 25)
Recovering a file from a backup stored in a local folder to the original folder. Since the
--overwrite parameter is not specified, the existing file will be overwritten.
acrocmd recover file --loc=E:\backups\my_thesis --arc=my_thesis
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --file=C:\documents\my_thesis.doc
Recovering a folder and its contents from the latest backup of an archive residing in Acronis
Secure Zone to a local folder.
acrocmd recover file --loc=atis:///asz --arc=my_archive --file=C:\Documents
--target=D:\my_folder
Recovering a folder and its contents from a backup. The archive is specified by the file name of a
backup that belongs to the archive (my_machine3.tib). This syntax is useful for archives
created using the --plain_archive (p. 97) parameter.
131 Copyright © Acronis International GmbH, 2002-2016
Please be aware that the command will apply to the backup specified in the --backup
parameter rather than to the one specified in the --arc parameter.
acrocmd recover file --loc=E:\backups\my_machine --arc=my_machine3.tib
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --file=C:\Documents
--target=D:\my_folder
Recovering all contents of the latest backup of an archive residing on a network share to the
original folder. The existing files and folders will not be overwritten. The files' security settings
and original dates will be preserved.
acrocmd recover file --loc=nfs://server/backups:/ --arc=my_data --overwrite=never
--recover_security=true --original_date
Recovering the user home directory in Linux from a backup stored on a SAMBA share.
acrocmd recover file --loc=\\bkpsrv\backups\anna --credentials=netuser1,pass1
--arc=home_dir --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --file=/home/anna
Recovering the contents of the latest backup of an archive residing on a network share. The
software will recover all files and folders except for the *.tmp and *.bak files.
acrocmd recover file --loc=\\srv1\folder1 --credentials=user1,pass1 --arc=my_docs
--exclude=*.tmp,*.bak
4.1.3 Virtual machines
Listing virtualization servers (p. 27)
Listing virtualization servers and server clusters that are present on the specified management
server.
acrocmd list vmservers --host=srv1 --credentials="srv1\AMS user",pass1
--service=ams
Listing virtual machines (p. 27)
Listing virtual machines that are managed by the management server.
acrocmd list vms --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
Listing virtual machines that are managed by the management server and that have the "error"
status.
acrocmd list vms --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
--filter_status=error
Deploying Agent for VMware (Virtual Appliance) (p. 28)
Deploying Agent for VMware (Virtual Appliance) with default parameters. The agent name will
be AcronisESXAppliance-[N], where [N] is a sequence number of the appliance
deployment attempt.
acrocmd deploy vm_agent --vsphere_address=10.200.200.10 --credentials="vsphere
user",pass --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
Deploying Agent for VMware (Virtual Appliance) with non-default parameters.
acrocmd deploy vm_agent --vsphere_address=10.200.200.10 --credentials="vsphere
user",pass --vmhost=10.200.200.100 --vmname=John's_VA --vmstorage=datastore3
--mac_address=00:50:56:8c:00:00 --ip_address=10.200.200.150 --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
Backing up virtual machines (p. 29)
Backing up a virtual machine. The incremental backup will be saved to a managed vault. Changed
Block Tracking (CBT) will be used. Progress will be shown.
132 Copyright © Acronis International GmbH, 2002-2016
acrocmd backup vm --vmid=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--loc="bsp://storage_node1/my vm vault" --arc="my vm archive"
--backuptype=incremental --progress --cbt_mode=on --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
Backing up four virtual machines. A separate archive will be created for each machine. All
machines will be backed up in parallel.
acrocmd backup vm
--vmid=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX1,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX
2,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX3,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX4
--loc=\\srv1\folder1 --credentials=netuser1,pass1 --arc="[Virtualization Server
Type]_[Virtual Machine Name]_archive1" --simultaneous_backup=4 --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
Recovering virtual machines (p. 31)
Recovering all disks from the latest backup of the archive residing in a managed vault to an
existing virtual machine.
acrocmd recover vm --vmid=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--loc="bsp://storage_node1/my vm vault" --arc="my vm archive" --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
Recovering the first disk from the latest backup of an archive stored in the \\bkpsrv\vms shared
folder to a new VMware Workstation virtual machine. The virtual machine files will be saved to
the \\srv1\vms shared folder.
acrocmd recover vm --disk=1 --vmname=my_vm_1 --vmtype=vmware --vmstorage=\\srv1\vms
--credentials=netuser1,pass1 --loc=\\bkpsrv\vms --credentials=netuser2,pass2
--arc="my vm archive" --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
Recovering all disks from the specified backup to a new ESX(i) virtual machine. The virtual
machine will be created in Storage1 of the specified ESX(i) server (Server1).
acrocmd recover vm --vmname=my_vm_1 --vmserver_name=Server1 --vmstorage=Storage1
--loc=\\bkpsrv\vms --credentials=netuser1,pass1 --arc="my vm archive"
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
Recovering all disks from the latest backup of an archive to a new Hyper-V virtual machine. The
virtual machine will be created in a local folder of the specified Hyper-V server (Server1).
acrocmd recover vm --vmname=my_vm_1 --vmserver_name=Server1
--vmstorage="C:\ProgramData\Microsoft\Windows\Hyper-V\Virtual Machines"
--loc=\\bkpsrv\vms --credentials=netuser1,pass1 --arc="my vm archive" --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
4.1.4 Microsoft Exchange
Listing Exchange storage groups and databases (p. 33)
Listing Exchange storage groups and databases on the local Exchange server.
acrocmd list exchange_databases --exchange_credentials=domain1\exch_user1,12345
Listing Exchange storage groups and databases on an Exchange server. The Exchange server is
accessed via the management server.
acrocmd list exchange_databases --host=srv1 --credentials=user,pass1 --service=ams
--address=exch_srv --exchange_credentials=domain1\exch_user1,12345
Listing mailboxes and public folders (p. 33)
Listing mailboxes and public folders of all the databases on the local Exchange server.

133 Copyright © Acronis International GmbH, 2002-2016
acrocmd list exchange_mailboxes --exchange_credentials=domain1\exch_user1,12345
Listing mailboxes and public folders of a database on an Exchange server.
acrocmd list exchange_mailboxes --host=exch_srv --credentials=user,pass1
--exchange_credentials=domain1\exch_user1,12345 --mailbox_location=db1
Backing up Exchange storage groups and databases (p. 34)
Backing up two storage groups on the local Exchange server. The backup will be saved to a
managed vault. Since the --metadata_level (p. 100) parameter is not specified, the backup
will be the fastest as compared with other values of this parameter. However, access to
individual e-mails in the resulting backup (by using graphical user interface) may take
considerable time.
acrocmd backup exchange_database --exchange_credentials=domain1\exch_user1,12345
--items=storage_group_1,storage_group_2 --loc=bsp://storage_node1/my_vault
--credentials=bkpuser,pass --arc=exchg_db_arc(1)
Creating an express full backup of three databases on an Exchange 2010 server. The backup will
be saved to a network share. Since the --metadata_level (p. 100) parameter is set to all,
the backup will be the slowest as compared with other values of this parameter. However, access
to individual e-mails in the resulting backup (by using graphical user interface) will be the fastest.
acrocmd backup exchange_database --host=exch_srv --credentials=user,pass1
--exchange_credentials=domain1\exch_user1,12345 --items=db1,db2,db5
--loc=\\bkpsrv\exchg_backups --credentials=bkpuser,pass --arc=exchg_db_arc(2)
--express --metadata_level=all
Backing up mailboxes and public folders (p. 35)
Backing up two mailboxes on an Exchange server. The backup will be saved to a managed vault.
acrocmd backup exchange_mailbox --host=exch_srv --credentials=user,pass1
--exchange_credentials=domain1\exch_user1,12345 --items="storage group 1/mailbox
database/John P. Smith","storage group 1/mailbox database/Mary Ann Johnson"
--loc=bsp://storage_node1/my_vault --credentials=bkpuser,pass
--arc=exchg_mb_arc(1)
Backing up all mailboxes and public folders of a database on the local Exchange server. The
backup will be saved to a network share. "Deleted Items" and "Junk E-Mail" folders as well as
attachments larger than 1 MB will be excluded.
acrocmd backup exchange_mailbox --exchange_credentials=domain1\exch_user1,12345
--items="mailbox database" --loc=\\bkpsrv\exchg_backups
--credentials=bkpuser,pass --arc=exchg_mb_arc(2) --exclude_size=1mb
--exclude_types=deleted,junk
Recovering Exchange storage groups and databases (p. 36)
Recovering a storage group containing two databases from the latest backup of an archive. The
storage group will be recovered to a new storage group.
acrocmd recover exchange_database --host=exchange_srv
--credentials=user123,pass123 --exchange_credentials=domain1\exch_user1,12345
--loc=bsp://storage_node1/my_vault --credentials=bkpuser,pass
--arc=exchg_db_arc(1) --items=storage_group_1 --recovery_point=latest_backup
--target=another_database --destination_database=new_sg --database=db1
--database_location=d:\ExchData\db1 --database=db2
--database_location=d:\ExchData\db2 --log_location=e:\new_sg_logs
Recovering a database (Exchange 2010 or later) to the point of failure. (The --recovery_point
(p. 110) parameter is not specified, therefore its default value point_of_failure is used.) The
database will be recovered to its original location on the server.

134 Copyright © Acronis International GmbH, 2002-2016
acrocmd recover exchange_database --host=exchange_srv
--credentials=user123,pass123 --exchange_credentials=domain1\exch_user1,12345
--loc=bsp://storage_node1/my_vault --credentials=bkpuser,pass
--arc=exchg_db_arc(2) --items=db1 --target=original
Recovering two databases (Exchange 2010 or later) to a point in time. The databases and
transaction log files will be saved to a network share.
acrocmd recover exchange_database --host=exchange_srv
--credentials=user123,pass123 --exchange_credentials=domain1\exch_user1,12345
--loc=\\bkpsrv\exchg_backups --credentials=bkpuser,pass --arc=exchg_db_arc(2)
--items=db1,db2 --recovery_point=point_in_time --pit="06.09.2011 17:00"
--target=disk --disk_location=\\host\share --credentials=netuser,pass
Recovering mailboxes and public folders (p. 37)
Recovering a mailbox from the latest backup of an archive. (The --recovery_point (p. 110)
parameter is not specified, therefore its default value latest_backup is used.) The mailbox will
be recovered to the specified Exchange server.
acrocmd recover exchange_mailbox --host=exchange_srv
--credentials=user123,pass123 --exchange_credentials=domain1\exch_user1,12345
--loc=bsp://storage_node1/my_vault --credentials=bkpuser,pass
--arc=exchg_mb_arc(1) --items="storage group 1/mailbox database/John P. Smith"
--target=original
Recovering a mailbox to a point in time. This method of recovery is available only from a
database-level backup. The mailbox will be recovered to the specified Exchange server.
acrocmd recover exchange_mailbox --host=exchange_srv
--credentials=user123,pass123 --exchange_credentials=domain1\exch_user1,12345
--loc=bsp://storage_node1/my_vault --credentials=bkpuser,pass
--arc=exchg_mb_arc(1) --items="storage group 1/mailbox database/Mary Ann Johnson"
--recovery_point=point_in_time --pit="06.09.2011 17:00" --target=original
Recovering a mailbox from the specified backup. The mailbox will be recovered to a .pst file.
The .pst file will be saved to a local folder.
acrocmd recover exchange_mailbox --exchange_credentials=domain1\exch_user1,12345
--loc=\\bkpsrv\exchg_backups --credentials=bkpuser,pass --arc=exchg_mb_arc(2)
--items="mailbox database/Peter D. Wayne" --recovery_point=selected_backup
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --target=pst
--disk_location="e:\pst files"
4.1.5 Microsoft SQL
Listing Microsoft SQL Server instances (p. 39)
Listing Microsoft SQL Server instances on the local machine.
acrocmd list mssql_instances
Listing instances of Microsoft SQL Server 2005 that are located on a remote machine and whose
names contain the fragment "WEB".
acrocmd list mssql_instances --host=192.168.1.2 --credentials=user1,pass1
--filter_edition=2005 --filter_name=WEB
Listing Microsoft SQL databases (p. 39)
Listing databases of a Microsoft SQL Server instance located on a remote machine. Since the
--credentials parameter is not specified after the --instance parameter, the software will
use Windows Authentication (the credentials specified after the --host parameter) to connect
to the specified instance.

135 Copyright © Acronis International GmbH, 2002-2016
acrocmd list mssql_databases --host=192.168.1.2 --credentials=user1,pass1
--instance=WEBSERVER
Listing only those databases of the "NEWSERVER" instance whose names contain the fragment
"account". Since the --credentials parameter is specified after the --instance parameter,
the software will use SQL Server Authentication to connect to the instance.
acrocmd list mssql_databases --instance=NEWSERVER --credentials="SQL user",pass
--filter_name=account
Backing up Microsoft SQL servers
This operation is performed by using the backup disk (p. 19) command. See the examples in the
"Disks and volumes" (p. 127) section under "Single-pass disk and application backup".
Recovering Microsoft SQL databases (p. 40)
Recovering a database from the latest backup of an archive. Since the --target (p. 86)
parameter is not specified, the database will be recovered to the original instance. The user who
runs the command must be a member of the sysadmin role on this instance. If a database with
the same name exists in this instance, it will be overwritten. The database will be recovered in
the norecovery state so that you can recover additional transaction logs from the native
Microsoft SQL backups.
acrocmd recover mssql_database --loc=\\srv1\backups --credentials=netuser1,pass1
--arc=machine1_app --items=WEBSERVER/Accountants --overwrite
--database_state=norecovery
Extracting all databases of an instance from the specified backup. The database files along with
the transaction log files will be saved to a network share.
acrocmd recover mssql_database --loc=\\srv1\backups --credentials=netuser1,pass1
--arc=machine1_app --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--items=NEWSERVER --target=disk --disk_location=\\host\share
--credentials=netuser,pass
Recovering two databases from the specified backup. The databases will be recovered to another
instance. If a database with the same name exists in the that instance, the recovered database
will be renamed. Since the --database_state parameter is not specified, the databases will
be recovered in the recovery state and will be ready for use.
acrocmd recover mssql_database --loc=bsp://storage_node1/my_vault
--arc=my_archive_app --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--items=WEBSERVER/Accountants,NEWSERVER/Anna --target=another_instance
--destination_instance=SUPERVISION --credentials="SQL user",pass2
--database_location=D:\databases --autorename
If the user who runs the command is a member of the sysadmin role on the destination instance,
the --credentials parameter is not needed after the --destination_instance
parameter. Otherwise, you need to specify the sysadmin credentials.
4.1.6 Microsoft Active Directory
Backing up a domain controller
This operation is performed by using the backup disk (p. 19) command. See the examples in the
"Disks and volumes" (p. 127) section under "Single-pass disk and application backup."
136 Copyright © Acronis International GmbH, 2002-2016
Recovering Microsoft Active Directory data (p. 41)
Extracting Microsoft Active Directory data as files from the latest backup of an archive residing
on a network share. The files will be saved to a local folder. Since the --overwrite (p. 108)
parameter is not specified, the existing files will be overwritten.
acrocmd recover ad_database --loc=\\srv1\backups --credentials=netuser1,pass1
--arc=machine1_app --target=E:\ad_db
Extracting Microsoft Active Directory data as files from a backup stored in a vault on a storage
node. The files will be saved to a network share. The existing files will not be overwritten. The
original dates of the files will be preserved.
acrocmd recover ad_database --loc=bsp://storage_node1/my_vault
--credentials=bkpuser,pass --arc=my_archive_app
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --target=\\share\active_dir\new
--credentials=netuser2,pass2 --overwrite=never --original_date
4.2 Operations with archives and backups
4.2.1 Archives
Listing archives (p. 42)
Listing archives in a managed vault. Since the --all parameter is specified, all fields will be
output for each archive: name; creation date; machine whose data is contained in the archive;
owner (the user who saved the archive to the destination); occupied space in bytes; and
comments on the archive.
acrocmd list archives --all --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass123
Exporting archives (p. 43)
Exporting a password-protected archive stored in a shared folder to a local folder.
acrocmd export archive --loc=\\bkpsrv\backups --credentials=netuser1,pass
--arc=my_archive --password=123 --target=E:\copies --target_arc=my_archive_copy
Exporting all archives from a managed vault to a shared folder.
acrocmd export archive --loc=bsp://storage_node/my_vault --credentials="ASN
user",pass --target=\\bkpsrv\backups --credentials=netuser,pass2
The first credentials must belong to an administrator of the specified vault, in order to enable
access to all archives stored there. The second credentials enable writing to the shared folder.
Exporting archives from a managed vault is always executed by the storage node service. In the
above example, the mms service running on the local machine will transmit the command to the
asn service. If you want to run the same command directly on the storage node (where no mms is
running), specify the "ASN user" credentials after the storage node host:
acrocmd export archive --host=storage_node --credentials="ASN user",pass
--service=asn --loc=bsp://storage_node/my_vault --target=\\bkpsrv\backups
--credentials=netuser,pass2
Importing an archive from a local folder of the storage node to a managed vault.
Usage scenario: create an archive with an initial full backup on a removable device, bring this
device to the remote location where a storage node is installed, and then import the archive to a
managed vault. After that, you can direct or replicate the subsequent incremental backups to the
managed vault over the network.
137 Copyright © Acronis International GmbH, 2002-2016
acrocmd export archive --host=storage_node --credentials="ASN user",pass
--service=asn --loc=E:\folder --arc=my_archive
--target=bsp://storage_node/my_vault --progress
In this example, the parameter value --service=asn is used because the archive is imported
from the local folder of the storage node. When importing an archive from a network share, you
can make any service (asn, mms or ams) execute the command. However, the asn service is the
most appropriate executor if you want to off-load the import from the agent installed on the
production server.
Validating an archive (p. 44)
Validating all backups of an archive.
acrocmd validate archive --loc=E:\backups\ --arc=my_archive
Cataloging an archive (p. 44)
Cataloging all the backups of an archive stored in a shared folder.
acrocmd catalog archive --loc=\\bkpsrv\backups --credentials=netuser,pass
--arc=my_archive
Deleting an archive (p. 45)
Deleting an archive.
acrocmd delete archive --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass123 --arc=my_archive
4.2.2 Backups
Listing backups (p. 46)
Listing backups of an archive stored in a local folder. The output will be displayed in the raw
format (p. 123). Therefore, you will be able to see and use complete GUIDs of backups.
acrocmd list backups --loc=E:\backups\ --arc=my_archive --output=raw
Listing backups of an archive stored in a managed vault and saving the complete output to a text
file. This allows you to use GUIDs of backups in scripts.
In the following example, the output in the raw format (p. 123) is redirected to a text file.
acrocmd list backups --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass123 --arc=my_archive --output=raw > c:\GUID.txt
In the following example, the operation log, including the output data, is written to a text file in
the structured xml format.
acrocmd list backups --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass123 --arc=my_archive --log=c:\log.txt
Listing backup content (p. 46)
Listing the content of a backup from an archive residing in Acronis Secure Zone.
acrocmd list content --loc=atis:///asz --credentials=aszpass --arc=my_archive
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Validating a backup (p. 47)
Validating a backup.
acrocmd validate backup --loc=E:\backups\ --arc=my_archive
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX

138 Copyright © Acronis International GmbH, 2002-2016
Cataloging a backup (p. 48)
Cataloging the latest backup of an archive stored in a network folder.
acrocmd catalog backup --loc=\\bkpsrv\backups --credentials=netuser,pass2
--arc=my_archive
Cataloging a backup stored in a managed vault. The cataloging is always executed by the storage
node, regardless of the machine where you run this command from. This example assumes that
you run the command on the storage node.
acrocmd catalog backup --loc=bsp://storage_node1/my_vault --arc=my_archive
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --service=asn
Exporting backups (p. 49)
Exporting the selected backups of an archive stored in a managed vault to a local folder.
acrocmd export backup --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass --arc=my_archive --password=123
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX1,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX
XX2 --target=E:\copies --target_arc=my_archive_copy
Importing the latest backup of an archive from a network folder to a managed vault.
acrocmd export backup --host=storage_node --credentials=user1,pass1 --service=asn
--loc=\\bkpsrv\backups --credentials=netuser,pass2 --arc=my_archive
--target=bsp://storage_node/my_vault --progress
Because the parameter value --service=asn is used, the command will be executed by the
storage node service. The first credentials must belong to a user of the specified vault. The
second credentials enable reading from the shared folder.
Replicating a backup (p. 49)
Replicating the latest backup of an archive stored in a local folder to a tape device directly
attached to the machine.
acrocmd replicate backup --loc=C:\Backups --arc=my_archive --password=123
--target=atis:///tape?XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Replicating the selected backup of an archive from a network share to Acronis Cloud Storage.
acrocmd replicate backup --loc=\\bkpsrv\backups --credentials=netuser,pass1
--arc=my_archive --backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--target=online:// --credentials=user@mail.com,pass2
--target_arc=my_archive_copy
Converting a backup to full (p. 50)
Converting the latest backup of the archive to a full backup. As a result of the operation, the
incremental or differential backup is substituted with a full one (for the same point in time).
acrocmd convert full --loc=C:\Backups --arc=my_archive
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Consolidating backups (p. 51)
Deleting all backups from an archive except for the specified ones.
acrocmd consolidate backup --loc=C:\Backups --arc=my_archive --password=123
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX1,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX
XX2
Deleting backups (p. 52)
Deleting the specified backups from an archive.

139 Copyright © Acronis International GmbH, 2002-2016
acrocmd delete backup --loc=C:\Backups --arc=my_archive --password=123
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX1,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX
XX2
4.2.3 Mounting volumes
Listing mounts (p. 53)
Listing the volumes mounted from backups.
acrocmd list mounts
Mounting (p. 53) (Agent for Windows only)
Mounting the first volume of the first disk from a backup in the read-only mode. The resulting
volume will be assigned letter "Z".
acrocmd mount --loc=E:\backups --arc=my_archive
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --volume=1-1 --letter=Z
Mounting (p. 53) (Agent for Linux only)
Mounting the first volume of the second disk from the latest backup of an archive located on the
srv1 node in the /backups directory exported by NFS.
acrocmd mount --mount_point=/mnt/md1 --loc=nfs://srv1/backups:/ --arc=my_archive
--volume=1-2
Mounting the first volume of the first disk from a backup in the read-write mode.
acrocmd mount --mount_point=/mnt/md2 --loc=/home/backups --arc=mybackup
--backup=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --volume=1-1 --rw
Unmounting (p. 54) (Agent for Windows only)
Unmounting a volume.
acrocmd umount --letter=Z
Unmounting (p. 54) (Agent for Linux only)
Unmounting a device mounted at the mount point.
acrocmd umount --mount_point=/mnt/md1
4.2.4 Mounting SQL databases
Listing mounts (p. 55)
Listing the Microsoft SQL databases mounted from backups.
acrocmd list mssql_mounts
Mounting SQL databases (p. 55)
Mounting two databases from the latest backup of an archive.
acrocmd mount mssql_database --loc=\\srv1\backups --credentials=netuser1,pass1
--arc=machine1_app --items=WEBSERVER/Accountants,NEWSERVER/Anna
--destination_instance=SUPERVISION --credentials="SQL user",pass2
Unmounting SQL databases (p. 56)
Unmounting all databases mounted to the "SUPERVISION" instance by using the mount
mssql_database command.
acrocmd umount mssql_database --items=SUPERVISION

140 Copyright © Acronis International GmbH, 2002-2016
4.3 Operations with Acronis Secure Zone
Creating Acronis Secure Zone (p. 56)
Creating Acronis Secure Zone on disk 2 of the local machine. Since the --asz_size (p. 114)
parameter is not specified, Acronis Secure Zone will be created with a default size which is the
average between the maximal (all the unallocated space) and minimal (about 50 MB) values.
acrocmd create asz --disk=2
Creating Acronis Secure Zone of size 500 MB on disk 1 of the local machine. If the unallocated
space is not enough, the space will be taken from the second volume of that disk.
acrocmd create asz --disk=1 --volume=1-2 --asz_size=500
Creating Acronis Secure Zone of size 20 GB on disk 1 of a remote machine.
acrocmd create asz --host=192.168.1.2 --credentials=john,pass1 --disk=1
--asz_size=20gb
Resizing Acronis Secure Zone (p. 57)
Displaying the Acronis Secure Zone size and free space in gigabytes.
acrocmd resize asz --size_measure=gb
Increasing Acronis Secure Zone on the local machine (we assume that the current size is less than
10 GB). Acronis Secure Zone is on disk 1. If the unallocated space on that disk is not enough, the
space will be taken from the second volume of that disk. The command output will contain the
resulting size and free space in gigabytes.
acrocmd resize asz --asz_size=10gb --volume=1-2 --size_measure=gb
Decreasing Acronis Secure Zone on a remote machine (we assume that the current size is more
than 10 GB). Since the --volume parameter is not specified, the freed space will become
unallocated. The command output will contain the resulting size and free space in megabytes
because the --size_measure parameter is not specified.
acrocmd resize asz --host=192.168.1.2 --credentials=john,pass1 --asz_size=10gb
Cleaning up Acronis Secure Zone (p. 58)
Cleaning up Acronis Secure Zone on the local machine. The cleanup operation deletes the
backups corrupted due to a power loss or another reason.
acrocmd cleanup asz
Cleaning up Acronis Secure Zone on a remote machine.
acrocmd cleanup asz --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
--address=192.168.1.2
Deleting a backup from Acronis Secure Zone (p. 58)
Deleting the latest backup of an archive stored in Acronis Secure Zone on the local machine.
acrocmd delete asz_files --credentials=asz_pass --arc=my_archive --password=123
Deleting Acronis Secure Zone (p. 59)
Deleting Acronis Secure Zone from the local machine. The freed space will be added to the 1st
volume of disk 1. (This is the disk where Acronis Secure Zone is located.)
acrocmd delete asz --volume=1-1
Deleting Acronis Secure Zone from a remote machine. The freed space will become unallocated.
acrocmd delete asz --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
--address=192.168.1.2

141 Copyright © Acronis International GmbH, 2002-2016
4.4 Operations with Acronis Startup Recovery Manager
Activating Acronis Startup Recovery Manager (p. 59)
Activating Acronis Startup Recovery Manager on the local machine.
acrocmd activate asrm
Activating Acronis Startup Recovery Manager on a remote machine.
acrocmd activate asrm --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
--address=192.168.1.2
Deactivating Acronis Startup Recovery Manager (p. 60)
Deactivating Acronis Startup Recovery Manager on the local machine.
acrocmd deactivate asrm
Deactivating Acronis Startup Recovery Manager on a remote machine.
acrocmd deactivate asrm --host=srv1 --credentials="srv1\AMS user",pass1
--service=ams --address=192.168.1.2
4.5 Operations with tapes
Listing tape libraries (p. 60)
Viewing the information about all tape libraries and stand-alone tape drives attached to the local
machine. The output will be displayed in the raw format (p. 123). Therefore, you will be able to
see and use complete GUIDs of tape libraries.
acrocmd list tape_libraries --output=raw
Viewing the information about a tape device attached to the local machine.
acrocmd list tape_libraries --filter_name="hp MSL6060"
Viewing the information about all tape devices attached to Acronis Backup Storage Node.
acrocmd list tape_libraries --host=storage_node --credentials="ASN user",pass
--service=asn
Listing tape slots (p. 61)
Viewing the information about slots of all tape libraries attached to the local machine.
acrocmd list tape_slots
Viewing the information about slots of a tape library attached to the local machine. The output
will be displayed in the raw format (p. 123). Therefore, you will be able to see and use complete
GUIDs of tape library slots.
acrocmd list tape_slots --filter_library=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--output=raw
Inventorying tapes (p. 61)
Inventorying the tapes loaded into two tape devices. Since the --mode (p. 119) parameter is not
specified, fast inventory will be performed.
acrocmd inventory tape
--libraries=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX1,XXXXXXXX-XXXX-XXXX-XXXX-XXXXXX
XXXXX2
Full inventory of the tapes loaded into a tape device. The detected tapes will be moved from the
Unrecognized tapes or Imported tapes pools to the Free tapes pool.

142 Copyright © Acronis International GmbH, 2002-2016
acrocmd inventory tape --libraries=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--mode=full --assign2free
Full inventory of the tapes loaded into three slots of a tape library.
acrocmd inventory tape --mode=full
--libraries=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--slots=YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYY1,YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYY
Y2,YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYY3
Combination of fast and full inventorying.
Full inventorying of an entire tape device may take a long time. If you need to inventory only a
few tapes, combine fast and full inventorying.
1. Perform fast inventorying of the tape device:
acrocmd inventory tape --libraries=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
2. List tape slots of the tape device. Specify the --output=raw parameter to see complete
GUIDs of tape slots.
acrocmd list tape_slots --filter_library=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--output=raw
3. In the command output, find the tapes you want to inventory and note which slots they
occupy.
4. Perform full inventorying of these slots:
acrocmd inventory tape --mode=full
--libraries=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--slots=YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYY1,YYYYYYYY-YYYY-YYYY-YYYY-YYYYYY
YYYYY2
4.6 Operations with vaults
Listing vaults (p. 62)
Listing all vaults available to the local machine. The output will be displayed in the raw format (p.
123).
acrocmd list vaults --output=raw
Listing all managed vaults available to the management server.
acrocmd list vaults --filter_managed --host=srv1 --credentials="srv1\AMS
user",pass1 --service=ams
Validating a vault (p. 63)
Validating all archives in a managed vault except for password-protected ones. To validate a
password-protected archive, use the validate archive (p. 44) command.
acrocmd validate vault --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass123
Validating all archives in a network shared folder except for password-protected ones.
acrocmd validate vault --loc=\\srv1\backups --credentials=netuser1,pass1
Cataloging a vault (p. 63)
Cataloging all the backups stored in a local folder (except for backups that are not supported by
the data catalog, see the command description).
acrocmd catalog vault --loc=E:\backups\

143 Copyright © Acronis International GmbH, 2002-2016
Cataloging all the backups stored in a managed vault (except for backups that are not supported
by the data catalog, see the command description). This operation is always executed by the
storage node service.
acrocmd catalog vault --loc=bsp://storage_node1/my_vault --credentials="ASN
user",pass123 --progress
Exporting a vault and importing archives to a vault
These operations are performed by means of the export archive (p. 43) command (see examples
(p. 136)).
4.7 Operations with disks
Cloning a disk (p. 64)
Cloning disk 2 of the local machine to disk 3 of the same machine.
acrocmd clone disk --source=2 --target=3
4.8 Operations with machines
Adding a machine (p. 65)
Adding a machine to the management server.
acrocmd add machine --machine_address=192.168.1.2 --credentials=user,pass
--host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
4.9 Administration operations
4.9.1 Collecting information
Getting log (p. 66)
Exporting the log of an activity with the specified GUID to a file.
acrocmd get log --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --loc=c:\logs\task.log
Getting system information (p. 66)
Saving the system information of the local machine to a file.
acrocmd sysinfo --loc=c:\logs\sysinfo.zip
4.9.2 Activities
Listing activities (p. 67)
Viewing all current activities of Acronis Managed Machine Service that runs on the local machine.
The output will be displayed in the raw format (p. 123). Therefore, you will be able to see and
use complete GUIDs of activities.
acrocmd list activities --output=raw
Viewing the running activities of Acronis Backup Management Server.
acrocmd list activities --host=srv1 --credentials="srv1\AMS user",pass1
--service=ams --filter_state=running
Viewing activities of Acronis Managed Machine Service that runs on a remote machine. The
software will show only completed activities.
144 Copyright © Acronis International GmbH, 2002-2016
acrocmd list activities --host=srv1 --credentials="srv1\AMS user",pass1
--service=ams --address=192.168.1.2 --filter_state=completed
Viewing the running activities of Acronis Backup Storage Node. By reviewing the command
output, which displays the time elapsed from an activity start, you can detect hung-up processes
on the storage node.
acrocmd list activities --host=srv1 --credentials="srv1\ASN user",pass1
--service=asn --filter_state=running
Stopping activities (p. 68)
Stopping an activity on the local machine.
acrocmd stop activity --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
4.9.3 Plans
Listing plans (p. 68)
Viewing all backup plans on the local machine. The output will be displayed in the raw format (p.
123). Therefore, you will be able to see and use complete GUIDs of plans.
acrocmd list plans --output=raw
Viewing all centralized backup plans existing on Acronis Backup Management Server.
acrocmd list plans --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
Viewing all backup plans with the warning status on the local machine.
acrocmd list plans --filter_status=warning
Deleting a plan (p. 71)
Deleting a backup plan on the local machine.
acrocmd delete plan --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Exporting a plan (p. 69)
Exporting a backup plan from the local machine to a file.
acrocmd export plan --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
--loc=c:\temp\plan.xml
Importing a plan (p. 70)
Importing a backup plan to the local machine.
acrocmd import plan --loc=c:\temp\plan.xml
Disabling a plan (p. 70)
Disabling a backup plan on the local machine.
acrocmd disable plan --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Enabling a plan (p. 71)
Enabling a previously disabled backup plan on the local machine.
acrocmd enable plan --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
145 Copyright © Acronis International GmbH, 2002-2016
4.9.4 Tasks
Listing tasks (p. 72)
Viewing all tasks on the local machine. The output will be displayed in the raw format (p. 123).
Therefore, you will be able to see and use complete GUIDs of tasks.
acrocmd list tasks --output=raw
Viewing all running tasks on a remote machine.
acrocmd list tasks --host=192.168.1.2 --credentials=user1,pass1
--filter_state=running
Running a task (p. 72)
Starting execution of a task on the local machine.
acrocmd run task --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Stopping a task (p. 73)
Stopping execution of a task on a remote machine.
acrocmd stop task --host=srv1 --credentials="srv1\AMS user",pass1 --service=ams
--address=192.168.1.2 --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Deleting a task (p. 73)
Deleting a task on the local machine.
acrocmd delete task --id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
4.9.5 Licenses
Listing licenses (p. 74)
Listing the Acronis Backup licenses assigned to a remote machine.
acrocmd list licenses --host=192.168.1.2 --credentials=user1,pass1
4.9.6 Reports
Generating a management server report (p. 74)
Generating the Machines with agents (by status) report. The report will be saved in the HTML
format to a local folder on the machine where the management server is installed.
acrocmd generate report --id=machines_by_status --loc=f:\reports\rep_machines
--service=ams
Generating the Backup plans (by status) report. The report will be saved in the XML format to a
network folder. The --host parameter points to the machine where the management server is
installed.
acrocmd generate report --id=plans_by_status --report_format=xml
--loc=\\srv\share\rep_plans --credentials=user,pass --host=srv1
--credentials="srv1\AMS user",pass1 --service=ams
4.10 Selecting logical volumes and MD devices for backup
Let's assume that the system has four physical disks: Disk 1, Disk 2, Disk 3 and Disk 4.
A RAID-1 volume is configured on two basic volumes: sdb1, sdd1
A logical volume is configured on two basic volumes: sdb2, sdd2

146 Copyright © Acronis International GmbH, 2002-2016
Disk 3 is empty.
A list of volumes can be obtained by using the following command:
acrocmd list disks
Num Partition Flags Start Size Type GUID
----------- ----------- -------- ---------- ---------- -------- -----------
Disk 1 16,384 MB PS_MBR
1-1 sda1 Pri,Act 0.031 MB 203.9 MB Ext 2
1-2 sda2 Pri 204 MB 12,002 MB Reiser
1-3 sda3 Pri 12,206 MB 1,028 MB Linux swap
Unallocated-1-1 Unallocated 13,233 MB 3,151 MB
Disk 2 8,192 MB PS_MBR
Unallocated-2-1 Unallocated 4,110 MB 4,082 MB
Disk 3 1,024 MB PS_NONE
Unallocated-3-1 Unallocated 0 MB 1,024 MB
Disk 4 8,192 MB PS_MBR
Unallocated-4-1 Unallocated 4,110 MB 4,082 MB
Dynamic volumes:
1 Dyn1 MyVG-MyLV 0 MB 4,096 MB Ext 3 A5C349F8...
1 Dyn2 md0 0 MB 2,055 MB Ext 2 FFF5E076...
The logical volume, DYN1, occupies basic volumes 2-2 and 4-2 (which are not shown by the above
command). The RAID-1 volume, DYN2, occupies basic volumes 2-1 and 4-1 (which are not shown by
the above command either).
To back up the logical DYN1 volume, run the following command (here, the name of the backup is
assumed to be my_archive and its location to be /home/user):
acrocmd backup disk --volume=DYN1 --loc=/home/user --arc=my_archive
To back up the RAID-1 volume DYN2, run the following command:
acrocmd backup disk --volume=DYN2 --loc=/home/user --arc=my_archive
To back up all three hard disks with volumes, select the volumes 1-1, 1-2, 1-3, DYN1 and DYN2:
acrocmd backup disk --volume=1-1,1-2,1-3,DYN1,DYN2 --loc=/home/user --arc=my_archive
If you select Disk 3 or volumes 2-1, 2-2, 4-1 or 4-2, the program will create a raw (sector-by-sector)
backup.
4.11 Scheduling backups under Linux using the cron
service
To automate backups, you can use the cron service familiar to many UNIX users.
Example
Let’s assume that you need to back up a volume regularly. A full backup has to be created weekly,
supported by incremental backups created daily.
Use the list disks (p. 18) command to obtain the necessary volume number. For example, the
volume number is 2-1.
Create two executable files for the daily and weekly backup (for example, abr.cron) and place them
into the /etc/cron.daily and /etc/cron.weekly directories, respectively.
To initiate weekly full backups of volume 2-1, add the following line to the
/etc/cron.weekly/abr.cron file:

147 Copyright © Acronis International GmbH, 2002-2016
#!/bin/bash
acrocmd backup disk --volume=2-1 --loc=/mnt/my_archives/my_host --arc=my_archive
where /mnt/my_archives/my_host is the path to the backup location.
The second abr.cron file is needed to initiate daily incremental backups.
#!/bin/bash
acrocmd backup disk --volume=2-1 --backuptype=incremental
--loc=/mnt/my_archives/my_host --arc=my_archive
For more information, see Help of the cron service.

148 Copyright © Acronis International GmbH, 2002-2016
5 Comparison of the old and new command-line
syntax
The following table lists commands that were used in the Acronis Backup & Recovery 10
command-line utility, and the corresponding commands of the Acronis Backup command-line utility.
This comparison can help you learn new commands faster and easier.
Old syntax
New syntax
asrm_activate
activate asrm
asrm_deactivate
deactivate asrm
asz_content
list archives
asz_create
create asz
asz_delete
delete asz
asz_delete_files
delete asz_files
asz_files
—
clone
clone disk
consolidate
export backup
convert
recover vm
create
backup disk
deploy
recover disk
deploy_mbr
recover mbr
explore
mount
export
export archive
export /include_pits:[pits numbers]
export backup
filebackup
backup file
filerestore
recover file
list
list disks
list /arc:[archive name] or
list /arc_id:[archive id]
list backups
list /filename:[file name]
list content
list /vault:[path]
list archives
ls_check
list licenses
pit_info
list backups
unplug
umount
verify
validate archive
149 Copyright © Acronis International GmbH, 2002-2016
6 acronis_encrypt utility
The acronis_encrypt utility allows you to encrypt a string of characters, for example, a password.
The utility is available on any machine where the acrocmd utility or Acronis Backup Management
Console is installed. The path to the utility is as follows:
In a 32-bit version of Windows: %CommonProgramFiles%\Acronis\Utils
In a 64-bit version of Windows: %CommonProgramFiles(x86)%\Acronis\Utils
In Linux: /usr/sbin
To use the utility, perform the following steps.
1. Type acronis_encrypt <string you want to encrypt>.
2. The utility outputs a string, for example "XXXYYYZZZ888".
3. Copy this string and paste it into the necessary command string or script.