Parallels Remote Application Server 16.0 Solutions Guide RAS V16 SG EN
User Manual: parallels Remote Application Server - 16.0 - Solutions Guide Free User Guide for Parallels Remote Application Server Software, Manual
Open the PDF directly: View PDF ![]() .
.
Page Count: 47
- What is Parallels Remote Application Server
- Advantages of Parallels Remote Application Server Based Computing
- Parallels Remote Application Server Components
- Understanding Deployment Scenario Diagrams
- Parallels RAS Basic Concepts
- Deployment Scenarios
- General Considerations
- Parallels RAS Deployment Scenarios
- Single Farm with One RD Session Host Server
- Single Farm with Two RD Session Host Servers
- Single Farm with Mixed Desktops
- Single Farm with Public & Private RAS Secure Client Gateways
- Single Farm with Dual RAS Secure Client Gateways
- High Availability with Multiple Gateways
- High Availability with Single or Dual F/W DMZ
- Mixed Scenarios
- Deploying Parallels RAS Reporting Service
- Port Reference and SSL Certificates
- Index

Parallels Remote
Application Server
Solutions Guide
v16
Parallels International GmbH
Vordergasse 59
8200 Schaffhausen
Switzerland
Tel: + 41 52 672 20 30
www.parallels.com
Copyright © 1999-2017 Parallels International GmbH. All rights reserved.
This product is protected by United States and international copyright laws. The product’s underlying technology,
patents, and trademarks are listed at http://www.parallels.com/about/legal/.
Microsoft, Windows, Windows Server, Windows Vista are registered trademarks of Microsoft Corporation.
Apple, Mac, the Mac logo, OS X, macOS, iPad, iPhone, iPod touch are trademarks of Apple Inc., registered in the US
and other countries.
Linux is a registered trademark of Linus Torvalds.
All other marks and names mentioned herein may be trademarks of their respective owners.
Contents
What is Parallels Remote Application Server ...................................................................... 4
Advantages of Parallels Remote Application Server Based Computing .............................. 4
Parallels Remote Application Server Components ............................................................. 5
Understanding Deployment Scenario Diagrams ................................................................ 7
Parallels RAS Basic Concepts ......................................................................................... 10
Parallels Client Connection Flow ............................................................................................ 13
Client Connection Modes ...................................................................................................... 14
Deployment Scenarios ............................................................................................ 16
General Considerations ................................................................................................... 16
Parallels RAS Deployment Scenarios............................................................................... 16
Single Farm with One RD Session Host Server ...................................................................... 16
Single Farm with Two RD Session Host Servers .................................................................... 18
Single Farm with Mixed Desktops .......................................................................................... 19
Single Farm with Public & Private RAS Secure Client Gateways ............................................ 20
Single Farm with Dual RAS Secure Client Gateways.............................................................. 21
High Availability with Multiple Gateways ................................................................................. 22
High Availability with Single or Dual F/W DMZ ........................................................................ 24
Mixed Scenarios .................................................................................................................... 27
Deploying Parallels RAS Reporting Service ........................................................... 34
One Site with Multiple RD Session Host Servers ............................................................. 35
Multiple Sites with Multiple RD Session Host Servers ...................................................... 36
Port Reference and SSL Certificates ...................................................................... 39
Port Reference ................................................................................................................ 39
SSL Certificates .............................................................................................................. 44
Index ........................................................................................................................ 47
This guide is intended for system administrators deploying and managing Parallels Remote
Application Server (Parallels RAS) in their organizations. It begins with the introduction to Parallels
RAS and its key components and then outlines the basic principles of how these components
operate. The main topics of this guide describe various Parallels RAS deployment scenarios,
complete with diagrams and other information. The guide concludes with the information about
communication ports used by Parallels Remote Application Server and the information about using
SSL certificates.
In This Chapter
What is Parallels Remote Application Server ............................................................. 4
Advantages of Parallels Remote Application Server Based Computing ..................... 4
Parallels Remote Application Server Components .................................................... 5
Understanding Deployment Scenario Diagrams ........................................................ 7
Parallels RAS Basic Concepts .................................................................................. 10
What is Parallels Remote Application Server
Parallels Remote Application Server is a market leader for Windows application publishing on any
device, anywhere. It works with major hypervisors and Microsoft Remote Desktop Services,
providing PC, Mac, and mobile users with a seamless experience while increasing security and
reducing IT costs. It’s simple and empowers users with the freedom and flexibility to work how they
want.
With Parallels RAS, remote desktops and applications can be accessed from any device running
virtually any operating system, including Windows, Linux, OS X, iOS, Windows Phone, Android,
Chrome. Additionally, web access is available via Parallels Web Portal, as well as clientless access
via HTML5.
For an in-depth information about the rich Parallels RAS features, please read the Parallels Remote
Application Server Administrator's Guide, which can be downloaded from the Parallels website.
Advantages of Parallels Remote Application
Server Based Computing
Server-based computing
Less administration, higher availability, reduced TCO.
CHAPTER 1

5
Deployment Scenarios
Simplified administration
Central management of users, server-based OS patch management, application updates, virus
definition updates, and backups.
Higher security
All data is kept on a server side with centralized security and backup management. Only mouse
clicks, keyboard keystrokes, and desktop/application screenshots are transmitted to and from the
client device, thus preventing data leakages, viruses, Trojans, and other vulnerabilities on clients.
Hardware independence
Support for virtually all platforms on client devices, including Windows, Linux, macOS, iOS,
Windows Phone, Android, Chrome, and HTML5, all with minimum hardware requirements.
Easy access
Employees, customers, and partners telecommute/roam more easily with follow-me apps and
desktops on any device from anywhere.
Extended Windows PC Lifecycle
Achieve cost savings in hardware replacement by converting Windows PCs into pseudo thin
clients. Continue using Windows legacy operating systems to securely run virtual applications while
also restricting access to native OS features. What’s more, the administrator can choose which
applications a user runs locally and remotely on a PC.
Proactive monitoring
Parallels RAS Reporting helps IT administrators to proactively tackle any potential issue before it
occurs, providing reports and statistics on resources and services shown under one roof in the
Parallels RAS console.
End user support
Windows Client Management enables client device shadowing (user session control) and power
management for help desks, making routine end user assistance easier.
Parallels Remote Application Server Components
Farm is a collection of Parallels RAS components maintained as a logical entity with a unique
database and licensing.

6
Deployment Scenarios
Site is a managing entity usually based on a physical location. Each site consists of at least a RAS
Publishing Agent, RAS Secure Client Gateway, and agents installed on RD Session Host servers,
virtualization servers, and Windows PCs. There can be multiple sites in a given farm.
Parallels RAS Console is the primary graphical user interface to use to configure and access
Parallels Remote Application Server features.
RAS Publishing Agent is a service that provides access to published applications and desktops
and load balances application traffic. High availability can be achieved by adding a secondary RAS
Publishing Agent to a site.
RAS RD Session Host Agent is a service installed on an RD Session Host Server that enables
publishing of the server resources (applications and desktop). RAS Publishing Agent also collects
the necessary information from the server on which it's running and sends it to the RAS Publishing
Agent, which uses it for load balancing and some other purposes.
RAS Remote PC Agent is a service installed on a physical Windows computer or a Windows
virtual machine. It enables publishing of the computer resources (applications and desktop). RAS
Remote PC Agent also collects the necessary information from the computer on which it's running
and sends it to the RAS Publishing Agent, which uses it for load balancing and some other
purposes.
RAS Guest Agent is a service installed in the guest operating system of a virtual machine, which is
used as a VDI template on a hypervisor. The guest agent enables resource publishing from the VDI
desktops and collects information required by the Publishing Agent. You can find a detailed
information about VDI templates in the Parallels Remote Application Server Administrator's Guide.
RAS VDI Agent is a service application on Hyper-V and a virtual appliance on VMware and
XenServer. RAS VDI Agent provides an interface for managing a hypervisor through its native API
and also collects and sends information to the RAS Publishing Agent.
RAS Secure Client Gateway is a service that acts as a proxy between the Parallels Client software
running on client devices and Parallels Remote Application Server. The gateway encrypts the
communications using SSL. Multiple RAS Secure Client Gateways can work in high availability
mode with Parallels HALB.
High Availability Load Balancing (HALB) is an appliance that provides load balancing for RAS
Secure Client Gateways. Parallels HALB virtual appliance is available for the following hypervisors:
Hyper-V, VMware, XenServer. HALB deployment is per site, which means that a site must have at
least one Parallels HALB appliance deployed. Multiple HALB deployments can run simultaneously,
one acting as the master and others as slaves. The more HALB deployments a site has, the lower
the probability that end users will experience downtime. Master and slave HALB deployments share
a common or virtual IP address (VIP). Should the master HALB deployment fail, a slave is promoted
to master and takes its place.
Parallels RAS Web Portal is a web page that provides access to published resources via a web
browser.
7
Deployment Scenarios
Parallels Device Manager is a Parallels RAS feature that allows the administrator to manage
Windows computers. Windows XP up to Windows 10 are supported.
Parallels Desktop Replacement is a sub-feature of Parallels Device Manager (see above). It
allows the administrator to convert a standard desktop into a limited device similar to a thin client
without replacing the operating system on it.
Understanding Deployment Scenario Diagrams
Terms and Abbreviations
Deployment scenario diagrams include terms and abbreviations, which are explained in the
following table.
PA RAS Publishing Agent.
SCG RAS Secure Client Gateway (including HTML5 gateway).
Private SGW Private RAS Secure Client Gateway (used for direct client connections).
RDSH, RDS
host
RDSH Agent
RD Session Host server (formerly Terminal Server).
RAS RD Session Host Agent installed on an RD Session Host server.
Remote PC A remote Windows computer with RAS Remote PC Agent installed.
VDI
Virtual Desktop Infrastructure (a VDI host server with a hypervisor running virtual machines). The VDI
host server must have RAS VDI Agent installed. Each virtual machine must have RAS Guest Agent
installed.
HALB High Availability Load Balancing. An appliance that provides load balancing for RAS Secure Client
Gateways.
Converted PC A PC with Windows converted to a thin-client-like OS.
Icons
The following table describes the icons used in deployment scenario diagrams.
Parallels RAS Server Components
A server hosting RAS Publishing Agent. May also host other Parallels RAS components depending
on a deployment.
RAS Secure Client Gateway (including HTML5 gateway) used for secure (SSL) client connections.
Private RAS Secure Client Gateway, used for direct client connections.
8
Deployment Scenarios
RD Session Host server with RAS RD Session Host Agent installed.
A remote Windows computer with RAS Remote PC Agent installed. Not to be confused with
Converted PC described below (a similar icon in red color).
Virtual Desktop Infrastructure (a VDI host server with a hypervisor running virtual machines). The VDI
host server must have RAS VDI Agent installed. Each virtual machine must have RAS Guest Agent
installed.
High Availability Load Balancing. An appliance that provides load balancing for RAS Secure Client
Gateways.
Parallels RAS Client Devices
A desktop computer (Windows, Linux, Mac) with Parallels Client installed.
A PC with Windows converted to a thin-client-like OS. Not to be confused with a remote PC
described above (a similar icon in orange color).
A converted PC (same as above) with Kiosk mode enabled.
HTML5 enabled web browser.
Mobile device (iOS, Android, Windows Phone).
Other Components
Active Directory, DNS, and DHCP server(s).
RAS Reporting Server (uses Microsoft SQL Server).
RADIUS server (used for second-level authentication).
File server for storing user profiles and redirected folders.
Firewall (ports 80 and 443 are open).
9
Deployment Scenarios
Diagram Layout
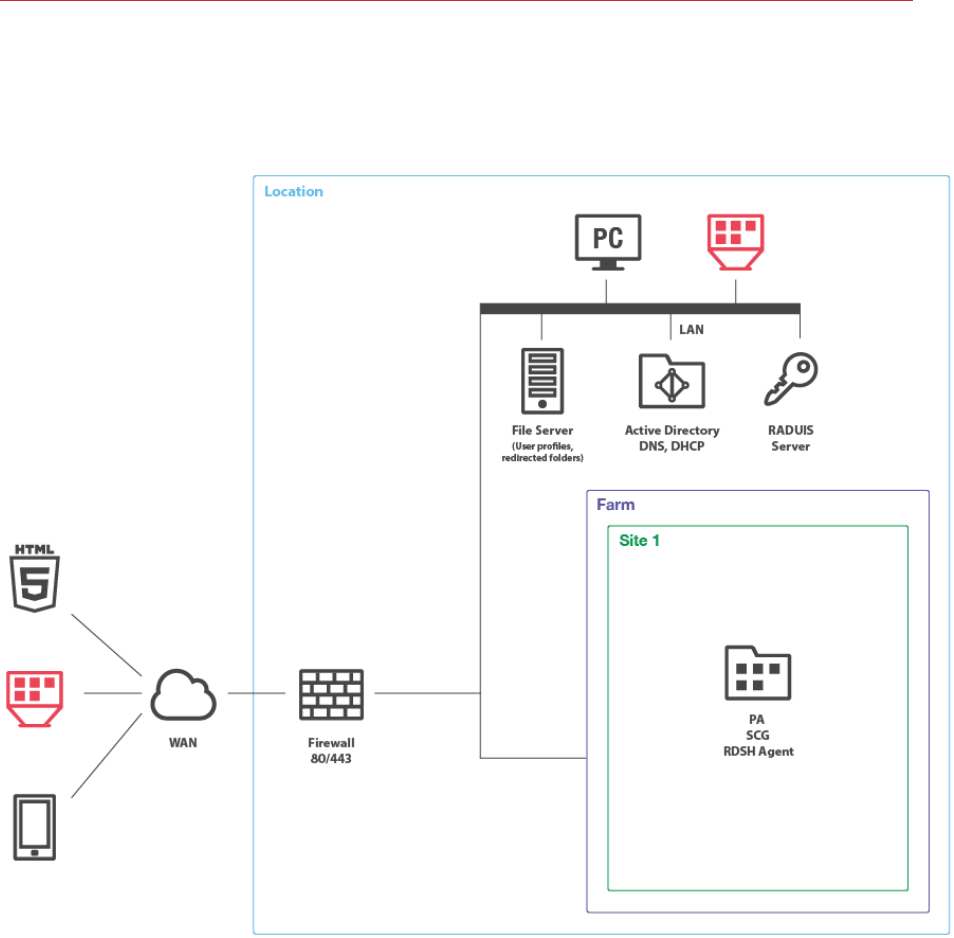
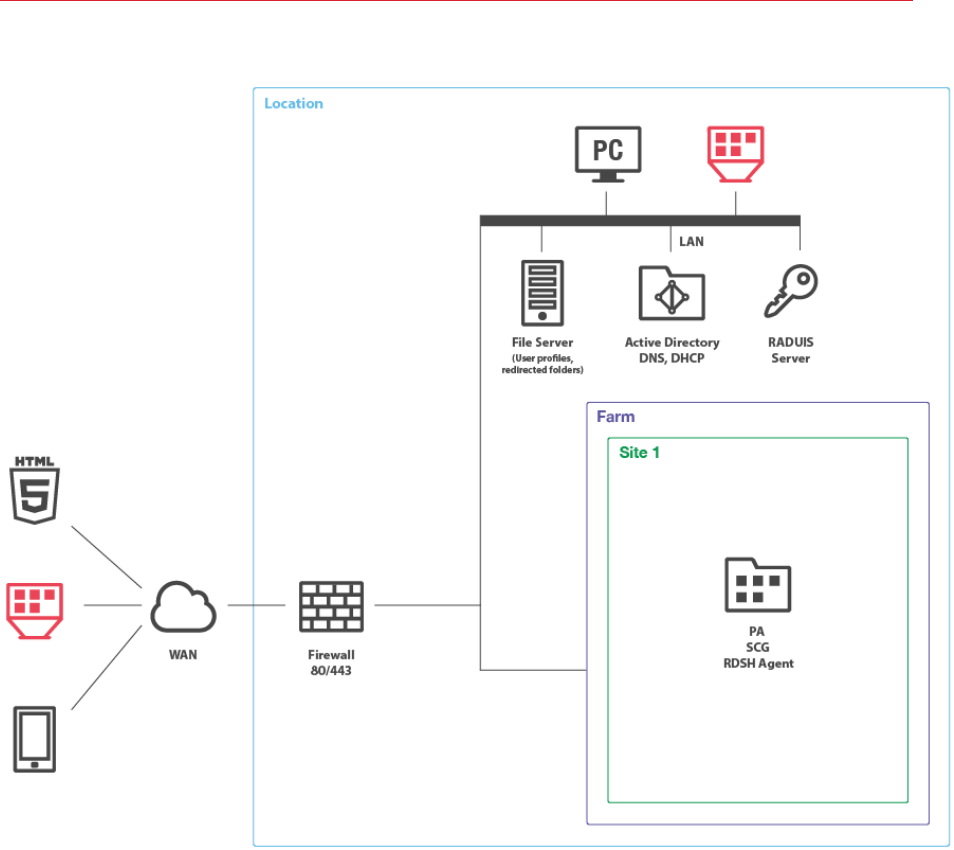
To understand the diagram layout, consider the following sample diagram:
The left side of the diagram displays client devices that can connect to Parallels Remote Application
Server. In the example above, the clients are (from top to bottom):
• HTML5 enabled web browser
• A converted Windows PC running in Kiosk mode
• A mobile device (iOS, Android, Windows Phone)
The Location rectangle denotes a physical location, such as an office.
The Farm rectangle represents a Parallels RAS farm, which is comprised of one or more sites.

10
Deployment Scenarios
The Site 1 rectangle represents a site with individual servers and components. In the example
above, the site has a single server with RAS Publishing Agent (PA), RAS Secure Client Gateway
(SCG), and RAS RD Session Host Agent installed.
The LAN bar represents a local area network with the following computers and servers connected
to it:
• Desktop computer
• Converted Windows PC running in Kiosk mode.
• File server
• Active Directory, DNS, and DHCP server(s)
• RADIUS server
The lines between icons denote the communication channels between individual components.
The Installation Notes section describes how a component (or components) must be installed on
a corresponding server. The following installation methods are used to install Parallels RAS server
components:
• Parallels RAS Installer (standard installation). This is a standard MSI installer package that
you run in Windows to install an application.
• Windows Installer (custom installation). This is the same type of installer as described above,
but you must choose the Custom installation type, which allows you to select which
component(s) you want to install.
• Push Installation. A component is installed remotely from the RAS console by pushing the MSI
installer packages to a remote server and then performing an unattended installation on it.
• Virtual appliance. A preconfigured virtual appliance for VMware or XenServer. You can
download a virtual appliance for the hypervisor you are using from the Parallels website by
visiting the following URL: http://www.parallels.com/products/ras/download/server/links/
Parallels RAS Basic Concepts
When a user connects to Parallels Remote Application Server from Parallels Client, they are
presented with published resources (applications, desktops, documents, or published URLs). The
user selects a resource and launches it. The system load-balances user requests automatically and
launches the requested resource from a least-loaded host. The user is then presented with their
requested resource seamlessly via RDP protocol, given that the resource is actually running on a
remote server rather than locally on the user’s device.
The Parallels Remote Application Server building blocks are (see the previous section for a detailed
explanation):
• Farm
• Site
11
Deployment Scenarios
• Agents
The first server added to a farm creates a new site and becomes the master RAS Publishing Agent
in that site. The server also becomes the farm’s Licensing Server handling device connection
licenses. Every Publishing Agent in the farm (when more than one exists) keeps a synchronized
copy of the Parallels RAS configuration database. When the administrator makes any changes to
the Parallels RAS configuration in the Parallels RAS console, the changes are replicated to all other
Publishing Agents.
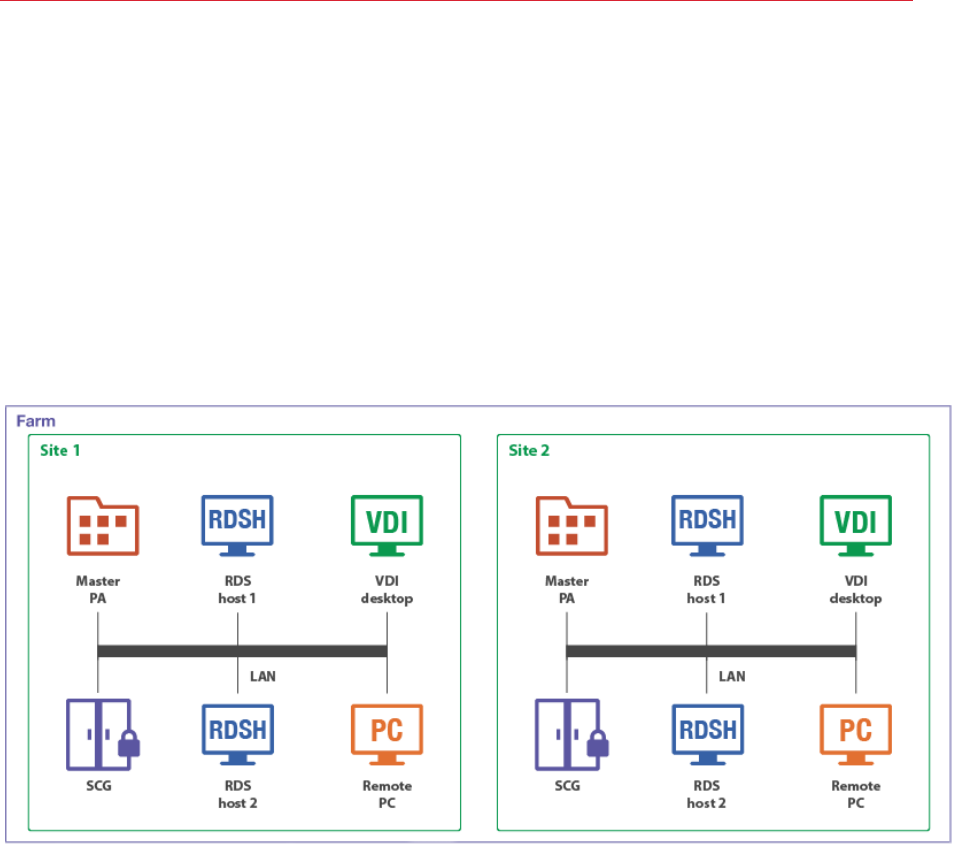
The following diagram illustrates a Parallels RAS installation with two sites (Site 1 and Site 2), each
consisting of a master Publishing Agent (Master PA), RAS Secure Client Gateway (SCG), RD
Session Host server (RDS host 1), a second RD Session Host server (RDS host 2), VDI (Virtual
Desktop Infrastructure) server, and a Windows PC.
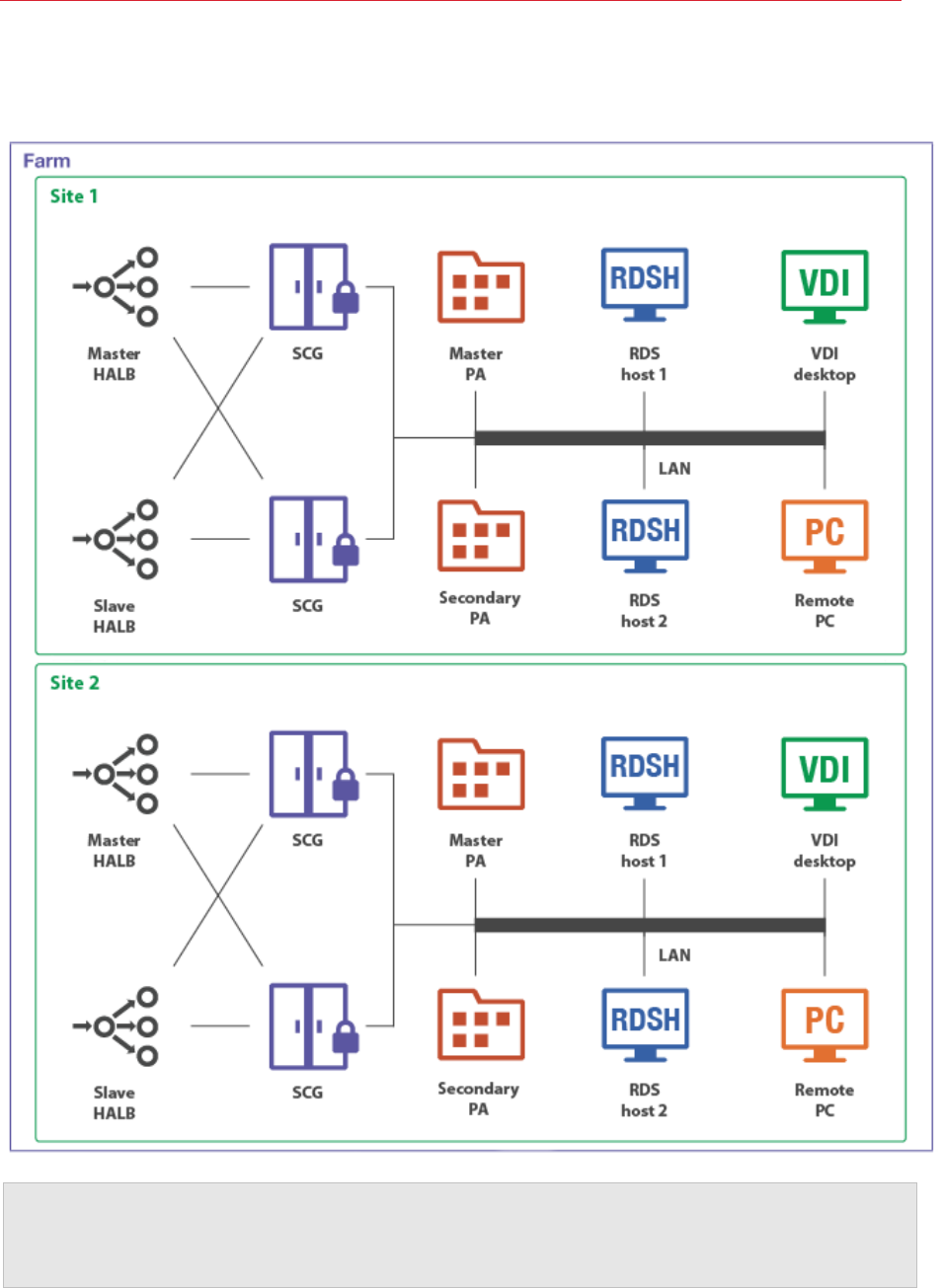
12
Deployment Scenarios
Adding more RAS Publishing Agents and RAS Secure Client Gateways adds redundancy to the
system. HALB is an optional component, which can be added to load balance application traffic.
Note: Resources (RD Session Host servers, Remote PCs, VDI desktops) that are members of one site
cannot be shared with other sites. For example, the RDS host 1 server is a member of Site 1, which
means that it cannot be accessed by users who are connecting through a Secure Client Gateway and a
Publishing Agent located in Site 2.

13
Deployment Scenarios
Parallels Client Connection Flow
The client connection flow consists of two stages: application enumeration and application
launching. The following describes each stage in detail. Please note that the steps described below
equally apply to all other types of published resources (not just applications), including remote
desktops, documents, Web applications, and network folders.
Application Enumeration
Application enumeration is the process of getting the list of published resources that a particular
user can use. During this stage, the following steps take place:
1 A user launches Parallels Client on their device and double-clicks a RAS connection (provided it
has been configured).
2 Parallels Client connects to the RAS Secure Client Gateway or the HALB appliance, if one is
installed.
3 If HALB is installed, the HALB appliance forwards the Parallels Client to the Secure Client
Gateway according to load balancing rules. If HALB is not engaged with SSL offload (HALB is
not installed or the pass-through mode is in place), an SSL session between the client and RAS
Secure Client Gateway is established.
4 RAS Secure Client Gateway builds a connection tunnel with a Publishing Agent to initiate client
authentication.
5 The Parallels Client transmits user credentials to the Publishing Agent.
6 If the user authentication is successful, the Publishing Agent returns the application list to the
Parallels Client via the Secure Client Gateway SSL tunnel.
7 The application list is displayed in the Parallels Client window on the user's device, so the user
can select an application to launch.
Application Launching
This stage comprises of the following steps:
1 The user launches an application.
2 The Parallels Client sends the request via the Secure Client Gateway tunnel to the Publishing
Agent.
3 The Publishing Agent selects the least loaded RD Session Host server and then sends its IP
address back to the Parallels Client via Secure Client Gateway.
4 Depending on the connection mode selected on the client side (see Client Connection Modes
below), the Parallels Client connects to the RD Session Host server directly or via RAS Secure
Client Gateway and passes the user credentials to it.
5 The RD Session Host server verifies the received credentials and, if they are valid, starts an
RDP session.

14
Deployment Scenarios
Client Connection Modes
Parallels Client can connect to Parallels Remote Application Server using one of the following
connections modes:
• Direct
• Direct SSL
• Gateway
• Gateway SSL
Direct
To use a direct connection, Parallels Client must be able to directly access an RD Session Host
server or a VDI host.
The connection is established as follows:
1 Parallels Client connects to a Secure Client Gateway through port 80 and negotiates a
connection to establish a session.
2 Parallels Client then initiates an RDP session directly with an RD Session Host server or a VDI
host through port 3389.
3 Client disconnects from the gateway and establishes a new session with the server.
The direct mode is the most efficient connection because the RAS Secure Client Gateway is used
only temporarily for a short period of time.
Direct SSL Mode
The direct SSL mode is the same as the direct mode but uses SSL encryption. To use a direct SSL
mode, Parallels Client must also be able to directly access an RD Session Host server or a VDI
host.
The connection is established as follows:
1 Parallels Client connects to a RAS Secure Client Gateway through port 443. Client and gateway
negotiate a connection to establish a session.
2 Parallels Client initiates an RDP session directly with an RD Session Host server or a VDI host
through port 3389.
3 Parallels Client disconnects from the gateway and establishes a new session with the server.

15
Deployment Scenarios
Gateway Mode
When Parallels Client cannot directly access an RD Session Host server or a VDI host, it must use
the gateway mode. The gateway mode is the simplest connection mode available. An administrator
need to open only a single port, which is usually port 80.
The connection is established as follows:
1 Parallels Client connects to the RAS Secure Client Gateway on port 80 and negotiates a
connection to establish a session.
2 Parallels Client requests the gateway to establish an RDP session through port 3389 with an
RD Session Host server or a VDI host using the same connection, thus forming a tunnel.
3 All communications between Parallels Client and the server then carried out using the
established tunnel.
Gateway SSL Mode
The gateway SSL mode is the same as the gateway mode but uses SSL encryption.
The connection is established as follows:
1 Parallels Client connects to the RAS Secure Client Gateway on port 443.
2 Once an SSL tunnel is established, the client and gateway negotiate to establish a secure
session.
3 Parallels Client requests the gateway to establish an RDP session through port 3389 with an
RD Session Host server or a VDI host using the same connection, thus forming a tunnel.
4 All communications between Parallels Client and the server then carried out using the
established tunnel.
Mixed Mode: Direct and Gateway SSL
Parallels Remote Application Server is able to handle multiple connection modes simultaneously.
For better utilization of RAS Secure Client Gateways, using the direct mode for LAN clients is
recommended whenever possible. For better security, using the gateway SSL mode is
recommended for WAN clients.
This chapter describes common Parallels Remote Application Server deployment scenarios.
In This Chapter
General Considerations ............................................................................................ 16
Parallels RAS Deployment Scenarios ........................................................................ 16
General Considerations
Regardless of the size of a Parallels RAS installation, redundancy among core components of your
setup is recommended to ensure the greatest possible uptime. For small deployments, all roles can
be installed on a single server, whereas role segregation is recommended for large setups.
The physical location of a Parallels Remote Application Server farm, including RD Session Host
servers and VDI desktops, must be selected based on the location of back-end resources, such as
databases and file servers. This means that if a front-end application connects to a database or
works with files on a file server, the RD Session Host server on which it will be installed should be
located close to the database (or the file server) on the intranet with fast, reliable, low latency LAN
connections. For example, let's say you have a client-server application that you want to make
available to your users. To do so, you will install the client part on an RD Session Host server and
publish it for your users. The database will continue to run on a dedicated server. To guarantee fast
and reliable database access, the RD Session Hosts server and the database server must be close
to each other on the local network.
Parallels RAS Deployment Scenarios
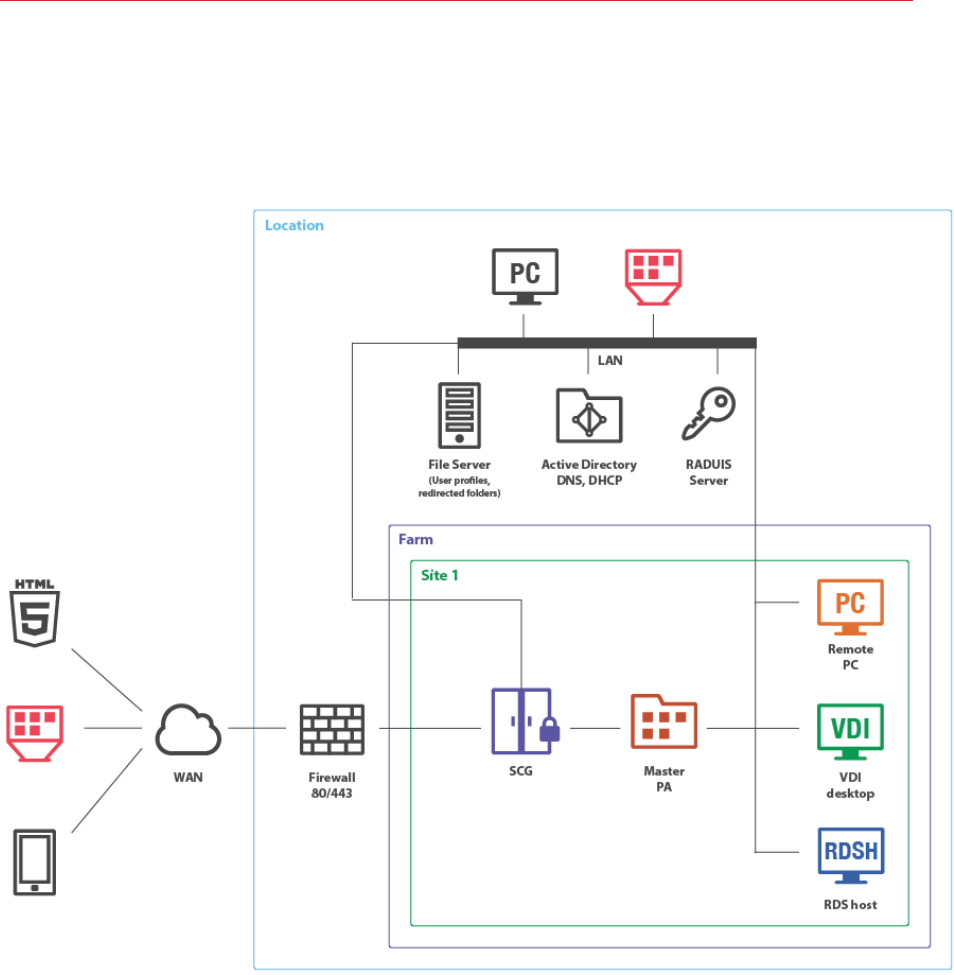
Single Farm with One RD Session Host Server
This scenario uses a single RD Session Host server for publishing applications and desktops. SSL
and HTML5 Gateway are enabled by default with a self-signed server certificate. The server
certificate should be deployed on client devices. Enterprise certificate or third-party trusted
Certificate Authority can be used for external access (for details, please see the SSL Certificates
section (p. 44)).
CHAPTER 2
Deployment Scenarios
17
Deployment Scenarios
Installation Notes
All server Parallels RAS components are installed using the Parallels RAS installer (standard
installation).
18
Deployment Scenarios
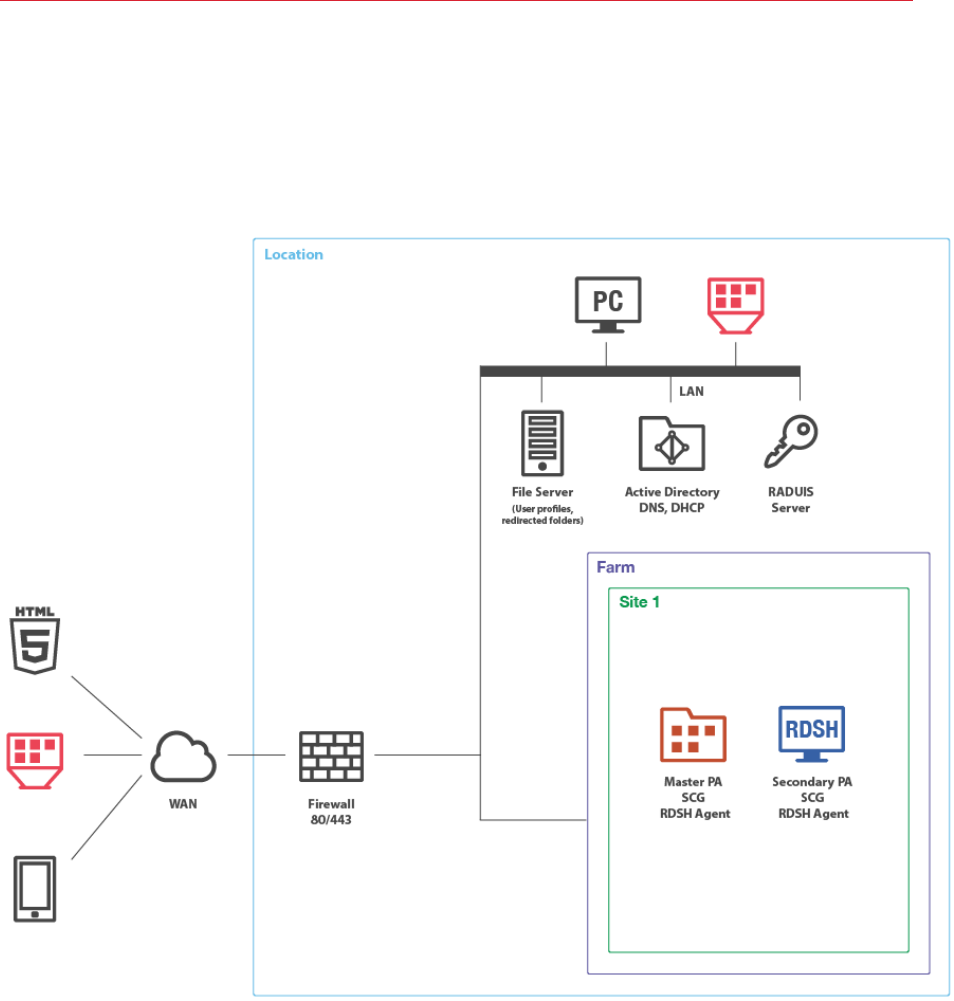
Single Farm with Two RD Session Host Servers
This scenario can be implemented by an organization that needs to load-balance published
applications and desktops between two RD Session Host servers. For high availability, a secondary
RAS Publishing Agent and RAS Secure Client Gateway should be installed on the second server.
Installation Notes
The components on the primary RD Session Host server (where the master RAS Publishing Agent
is installed) are installed using the Parallels RAS installer (standard installation).
The components on the secondary RD Session Host server are push-installed from the RAS
console.
19
Deployment Scenarios
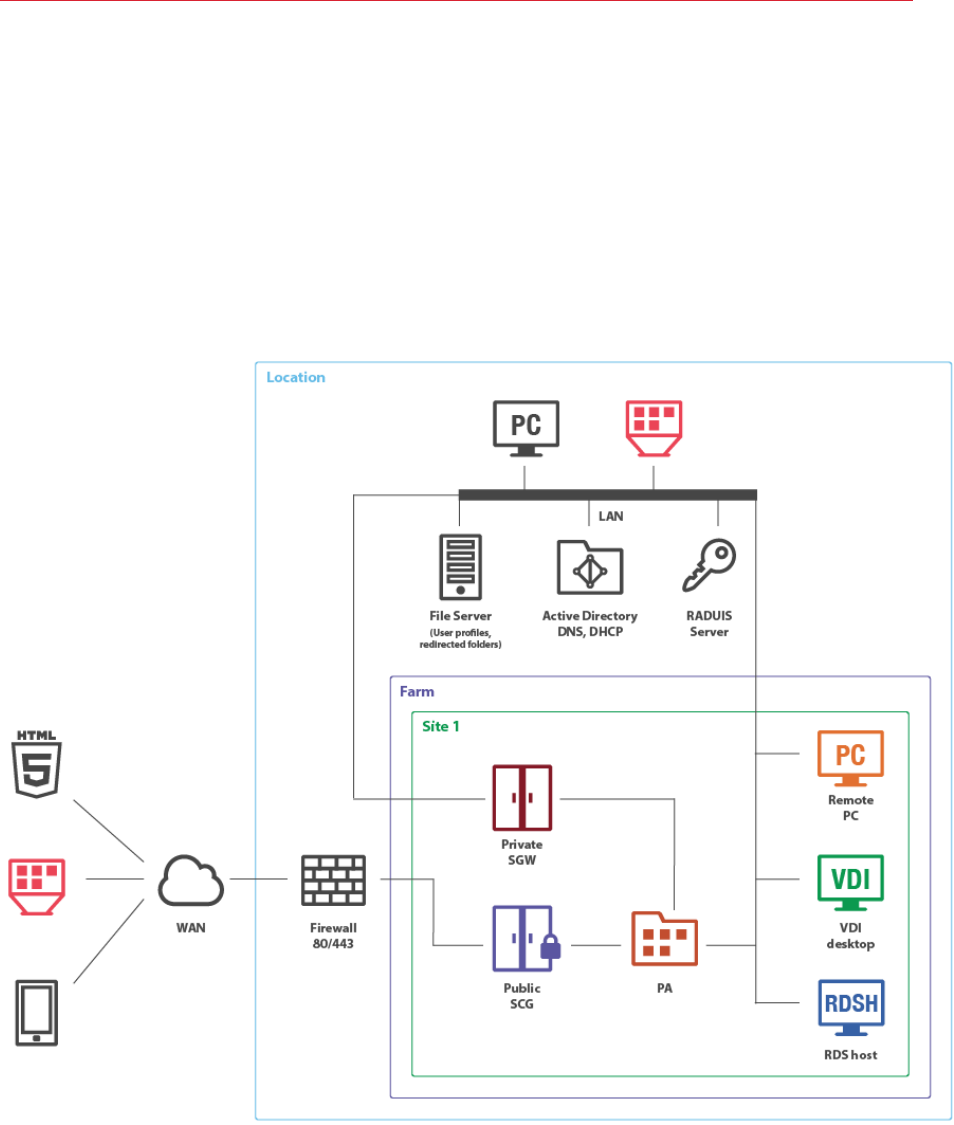
Single Farm with Mixed Desktops
By using this scenario you can publish applications and desktops from virtual machines, RD
Session Host servers, and Windows desktop computers located in your office.
Installation Notes
RAS Secure Client Gateway and master RAS Publishing Agent are installed using the Parallels RAS
installer (standard installation).
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
20
Deployment Scenarios
Single Farm with Public & Private RAS Secure Client Gateways
To handle more connections on Secure Client Gateways, using a designated RAS Secure Client
Gateway is recommended for intranet users (private) with direct client connection mode.
To apply stricter security settings to servers with Internet access, using a designated Secure Client
Gateway is recommended for Internet users (public) with Gateway SSL client connection mode.
The appropriate RAS connection settings can be applied either centrally via Client Policy in the
Parallels RAS Console or manually in the Parallels Client.
Installation Notes
Public RAS Secure Client Gateway and master RAS Publishing Agent are installed using the
Parallels RAS installer (standard installation).

21
Deployment Scenarios
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
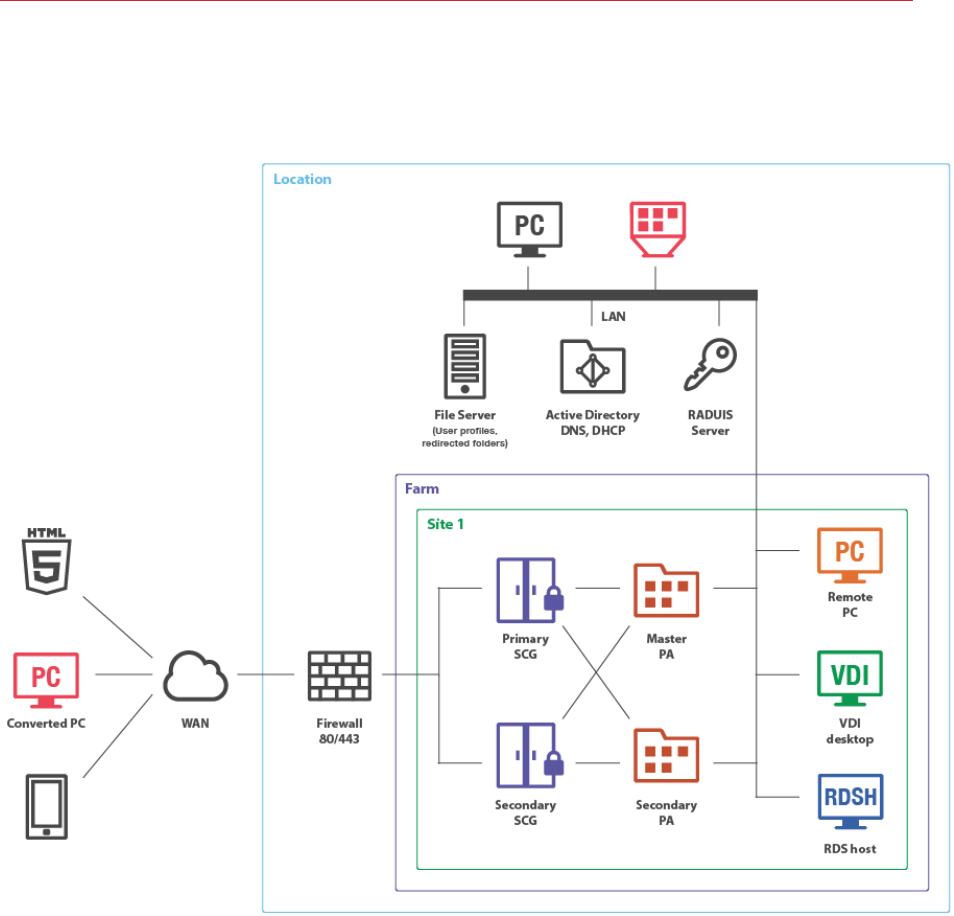
Single Farm with Dual RAS Secure Client Gateways
This scenario enables high availability for client connections using RAS connection settings on
either the Parallels Client side or round-robin DNS.
To enable high availability for client connections using RAS connection settings, the Parallels Client
should be configured to connect to primary and secondary Secure Client Gateways using the
primary and secondary connection settings in the RAS connection properties. In this case, primary
and secondary RAS Secure Client Gateways must be configured to connect to the same RAS
Publishing Agents (using the Advanced Client Gateway Settings). When the Primary RAS Secure
Client Gateway is not available, Parallels Clients can connect to the farm using the Secondary RAS
Secure Client Gateway. The client settings can be applied either centrally (via Client Policy in the
Parallels Application Server Console) or manually.
22
Deployment Scenarios
To enable high availability for client connections using round-robin DNS, two new host records
must be created in the DNS forward lookup zone with the same name (e.g. myhost.example.com)
but with two different IP addresses of primary and secondary RAS Secure Client Gateways.
Installation Notes
RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
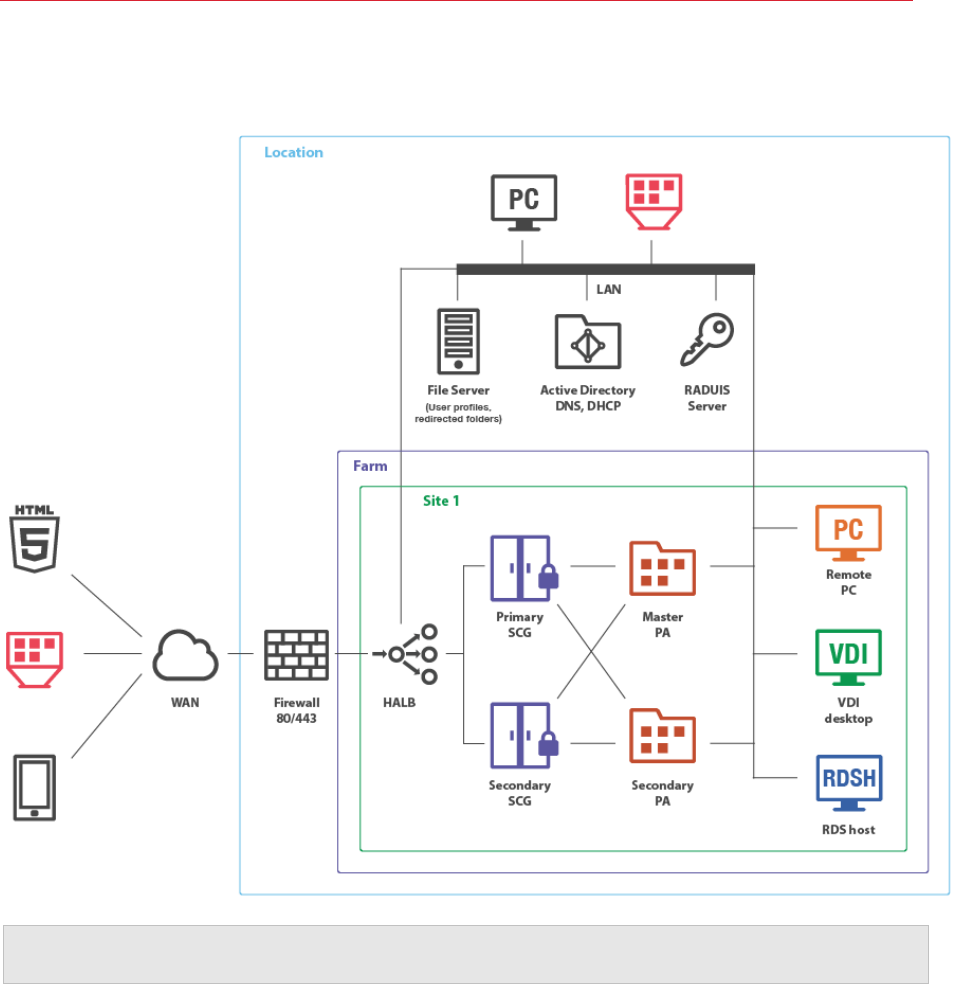
High Availability with Multiple Gateways
This scenario is ideal for high availability environments with more than 300 concurrent users
connected in SSL mode. Each client gateway should optimally handle 300 to 500 concurrent user
connections* (see the note below). This can be scaled horizontally accordingly.
23
Deployment Scenarios
Both LAN and WAN users connect to the virtual address of a high availability and load balancing
virtual appliance in an internal network.
*300 users through SSL tunneled gateway mode or 500 standard gateway connections, assuming the
gateway machine is only acting as such (with no other demanding services using these machines).
All RAS Secure Client Gateways must be configured to connect to the same RAS Publishing
Agents (using the Advanced Client Gateway Settings—see above).
Installation Notes
RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
HALB is installed as a ready-to-use virtual appliance.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
24
Deployment Scenarios
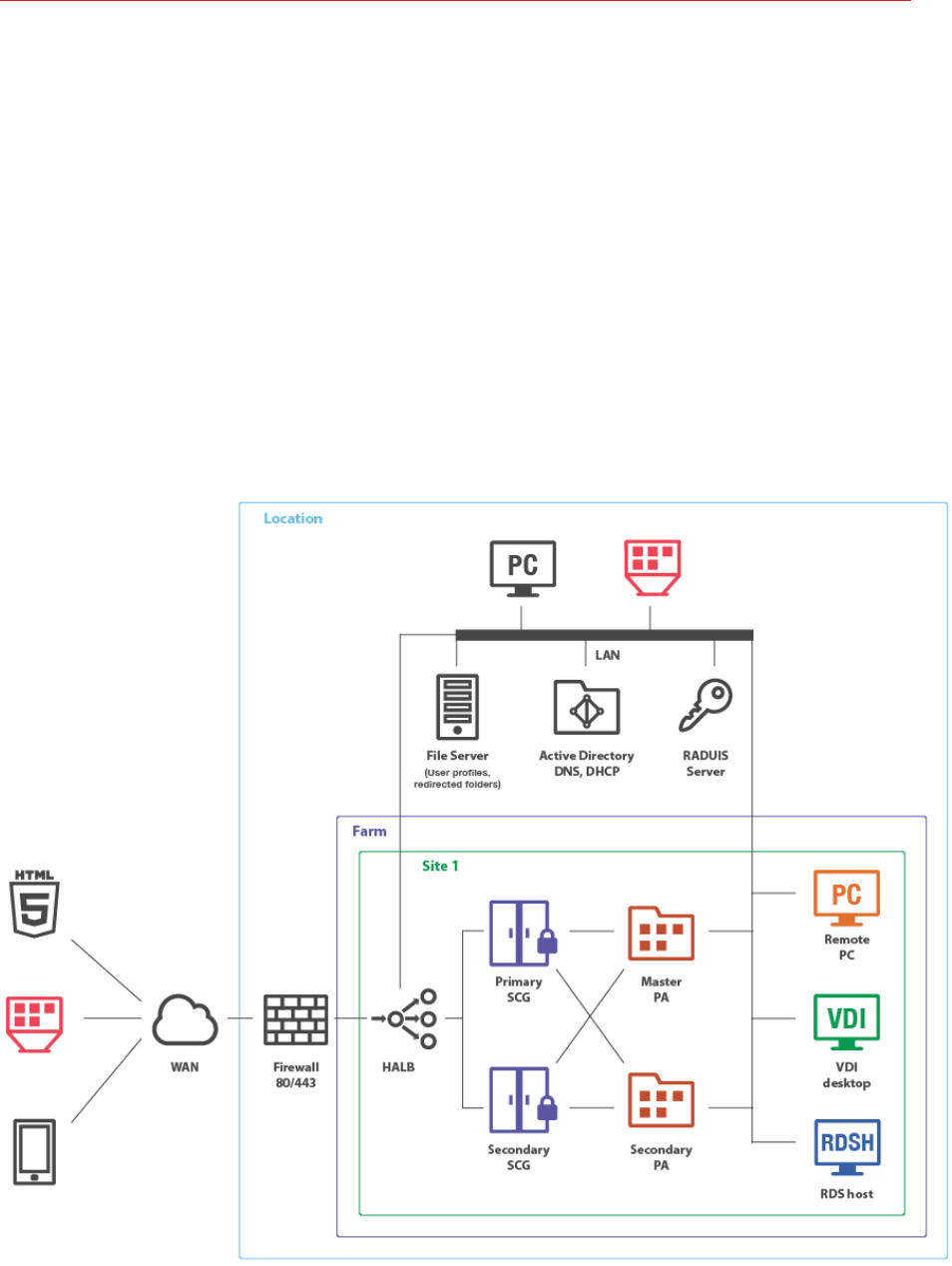
High Availability with Single or Dual F/W DMZ
Many companies use the DMZ layout to separate servers that handle exposed services from those
that handle internal services. There are two types of DMZ: single and dual-firewall, with the latter
being more expensive but more secure (with the dual firewall approach, using two different firewall
technologies allows you to avoid one weakness or one type of attack breaking both firewalls). A
firewall between RAS Secure Client Gateways and the intranet must allow gateways and systems
to connect to a Publishing Agent using the standard port.
Single Firewall DMZ
In a single firewall DMZ scenario, the firewall system must be capable of routing connections
properly from RAS Secure Client Gateways to RAS Publishing Agents. The firewall system is also
responsible for connections from the Internet to the virtual IP address presented by a HALB virtual
appliance or other generic protocol load balancing scenarios.

25
Deployment Scenarios
In a configuration of this type, HALB is installed in front of RAS Secure Client Gateways in the
internal network. The WAN users connect to HALB VIP address, whereas LAN users use primary
and secondary gateways configured in the primary and secondary connections settings of the RAS
connection properties. The Parallels Client settings can be configured either centrally (via Client
Policy in the Parallels RAS console), or locally on a device where Parallels Client is running. To add
high availability for HALB, a second appliance can be deployed.
Installation Notes
RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
HALB is installed as a ready-to-use virtual appliance.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
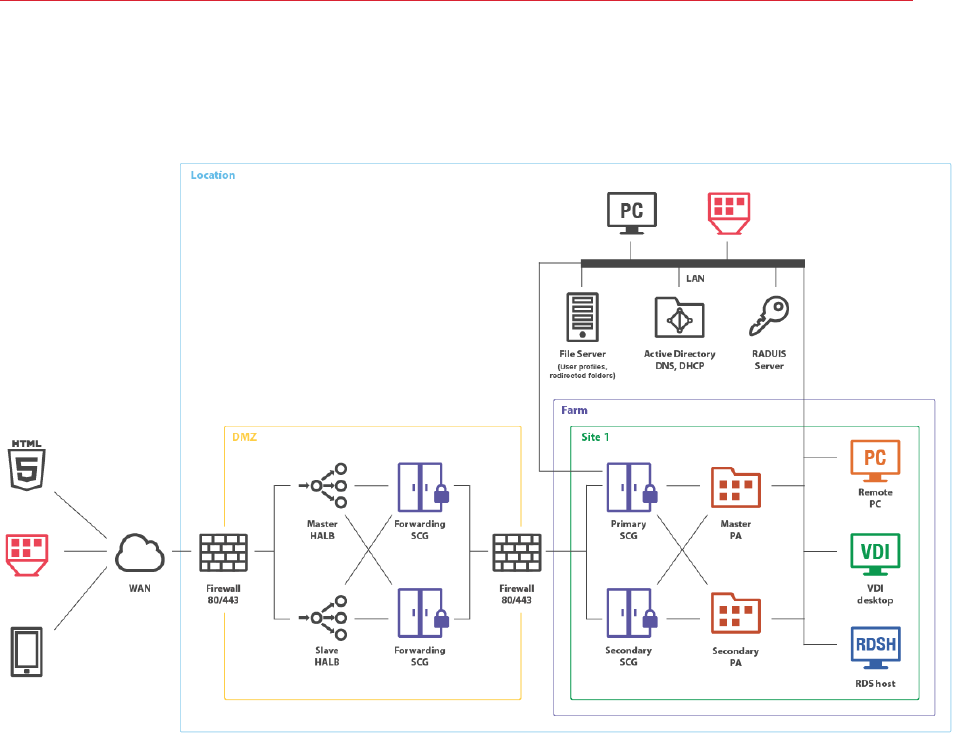
Dual Firewall DMZ
In a dual firewall scenario, settings are simpler and the protection from external malicious agents is
higher. Dual Firewall DMZ requires Forwarding RAS Secure Client Gateway installed in the
perimeter network to pass client connections to the RAS Secure Client Gateway residing in the
internal network.
In such a configuration, a HALB pair (master and slave) is installed in front of Forwarding RAS
Secure Client Gateways in DMZ. WAN users connect to Parallels RAS using the HALB's VIP
address, whereas LAN users connects to Primary and Secondary Gateways (set up as primary and
secondary connection options of a RAS connection on the client side). Parallels RAS connection
properties can be configured either centrally (using Client Policy in the RAS Console) or manually in
Parallels Client.
26
Deployment Scenarios
Forwarding RAS Secure Client Gateways forward network traffic using the Forward requests to
next RAS Secure Client Gateway in chain option in the Advanced tab of the Forwarding RAS
Secure Client Gateway properties.
Installation Notes
RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
HALB is installed as a ready-to-use virtual appliance.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
If the Forwarding RAS Secure Client Gateway cannot be push-installed for any reason, you can run
the Parallels RAS installer on the target server. When doing so, select Custom installation type and
then choose the RAS Secure Client Gateway component.

27
Deployment Scenarios
Mixed Scenarios
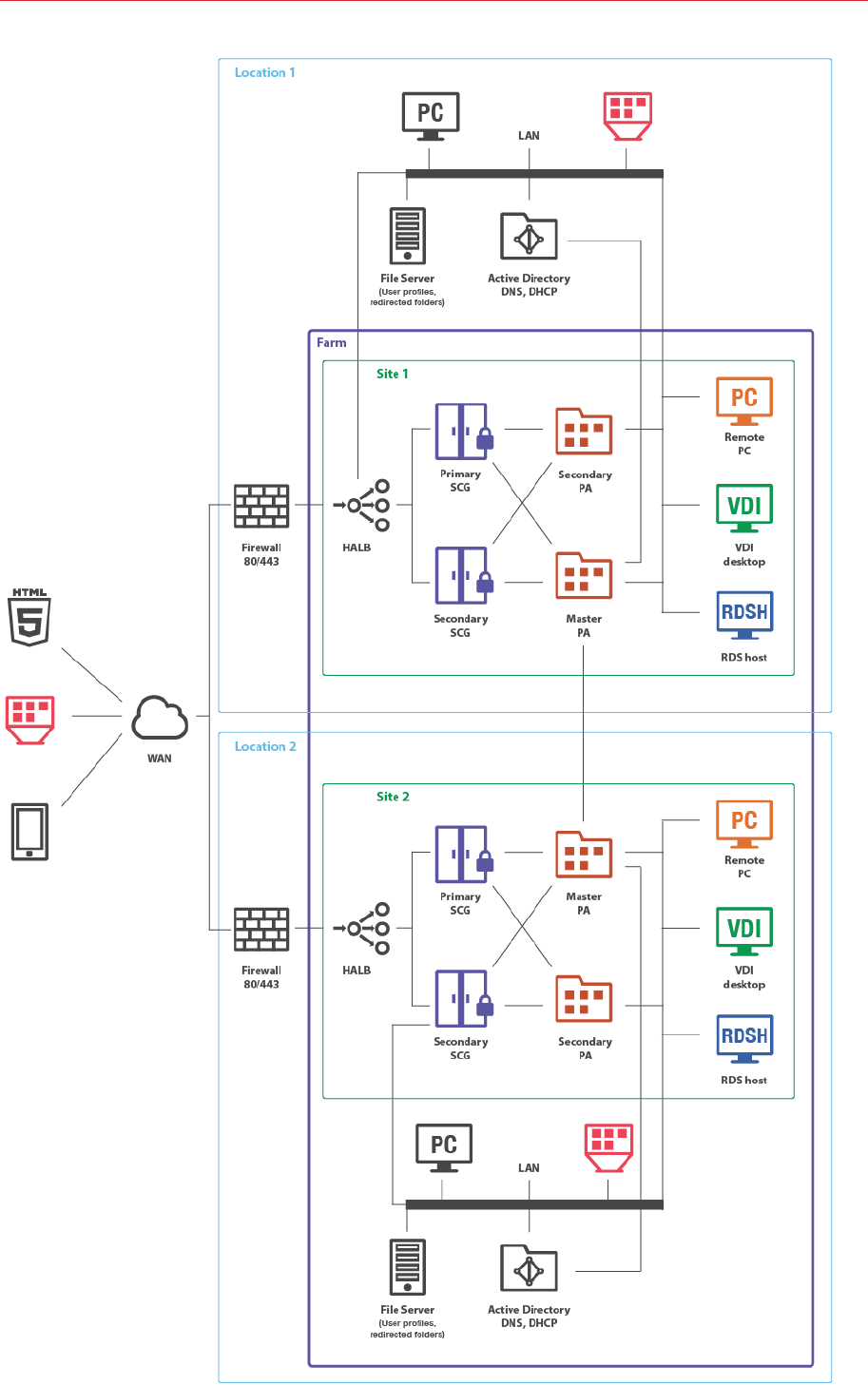
Multi-Site Scenario
This scenario is suited for environments where published resources are distributed between two or
more physical locations. Different administrators can administer a Parallels RAS farm containing
multiple sites.
28
Deployment Scenarios
29
Deployment Scenarios
Each site consists of at least a RAS Publishing Agent, RAS Secure Client Gateway (or multiple
gateways), and agents installed on RD Session Host or VDI servers, or Windows PCs.
Note: To add high availability for HALB, a second appliance can be deployed in each site.
If the resource set is similar, end users can use both sites via a single RAS connection. The
following settings should be used as RAS connection properties in Parallels Client:
LAN users of Site1
• Primary connection: local Primary Secure Client Gateway.
• Secondary connections:
• Local Secondary Secure Client Gateway.
• HALB VIP address of Site2.
LAN users of Site2
• Primary connection – local Primary Secure Client Gateway
• Secondary connections:
• Local Secondary Secure Client Gateway
• HALB VIP address of Site1
WAN users
• Primary connection - HALB VIP address of Site1
• Secondary connections - HALB VIP address of Site2
RAS connection settings can be configured either centrally (via Client Policy in the Parallels Remote
Application Server Console) or manually.
Installation Notes
RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
HALB is installed as a ready-to-use virtual appliance.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
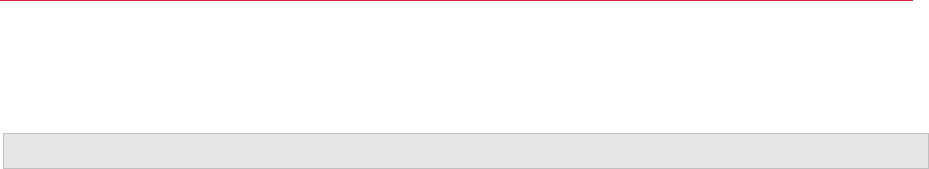
Business Continuity and Disaster Recovery
A Parallels Remote Application server farm placement depends on the location of a back-end
resource. Therefore, it is possible to continue operations by adding an additional remote location
where the back-end resources are replicated (the appropriate software and hardware solutions are
out of the scope of this document) and placing one more Parallels Remote Application Server site
in this location.
30
Deployment Scenarios
Setting up a disaster recovery site, and then configuring the Parallels Client to use the closest site
as the primary connection and the disaster recovery site as the secondary connection, allows users
to always be connected to the primary site and to continue working using the disaster recovery site
in case of failure.
WAN users can be invited to use both sites and setup HALB VIP address of the first site as Server
Address and HALB VIP address of the second site as Secondary Server IP in the RAS connection
settings on the Parallels Client side. The RAS connection settings can be configured either centrally
(via Client Policy in the Parallels Remote Application Server Console) or manually.
Installation Notes
Master RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
Secondary RAS Publishing Agent is push-installed from the RAS Console.
HALB is installed as a ready-to-use virtual appliance.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.
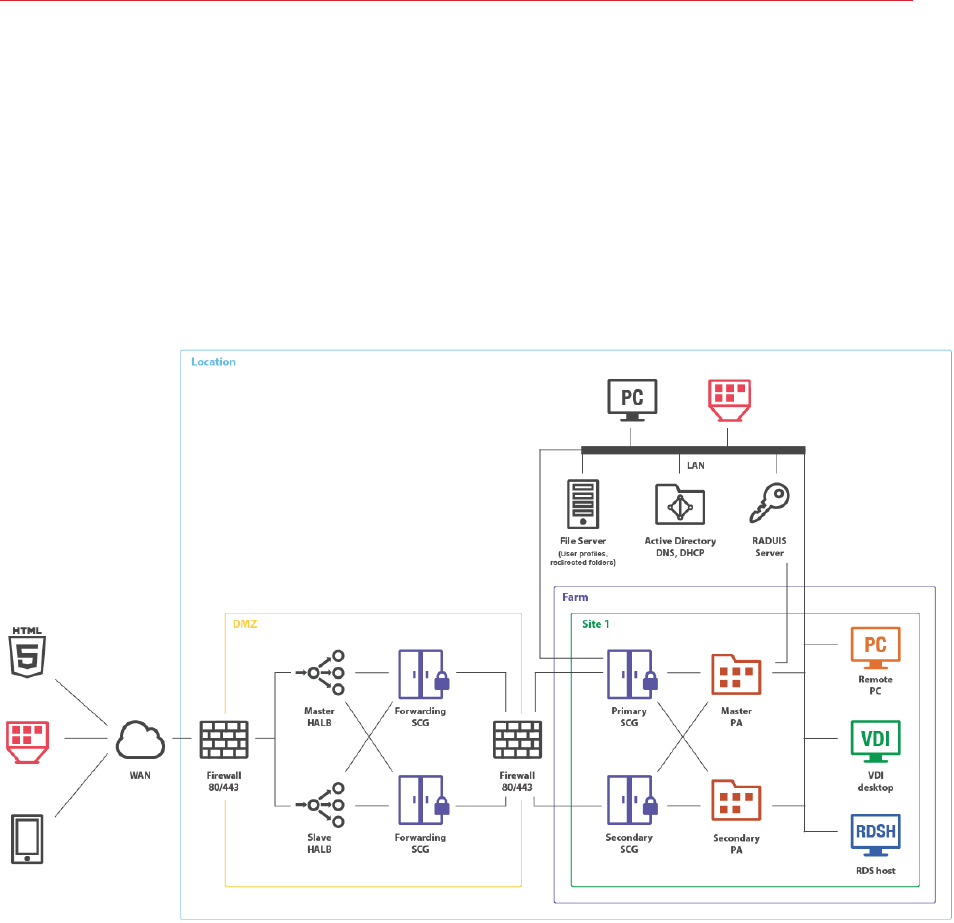
31
Deployment Scenarios
Secure Setup with Dual Firewall DMZ and Second-Level Authentication
Second-level authentication provides a high level of protection via different types of security tokens
for two-factor authentication. Users have to authenticate through two successive stages to get the
remote application list. In addition to a standard user name and password, or a smart card
authentication, second-level authentication uses a one-time password generated by a token. The
second level of authentication can be provided by DualShield, Safenet, or a RADIUS server.
A RADIUS server is recommended to be placed in the Intranet together with the RAS Publishing
Agent and Active Directory domain controller to speed up application enumeration.
In a configuration of this type the second-level authentication via a RADIUS server is performed
first. If the authentication procedure is successful, the next authentication takes place at the Active
Directory level using either a user name and password or a smart card.
Installation Notes
Master RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
Secondary RAS Publishing Agent is push-installed from the RAS Console.
Master and slave HALB are installed as ready-to-use virtual appliances.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.

32
Deployment Scenarios
Client Manager and Desktop Replacement
The Client Manager feature allows the administrator to convert Windows devices running Windows
XP up to Windows 10 into a thin-client-like OS. After the Windows Device Enrollment has been
performed, features like Desktop Replacement, Kiosk Mode, Power Off, Reboot, and Shadow
become available.
Shadowing
Shadowing provides access to the full Windows client device desktop and allows controlling
applications running locally on the system, as well as any remote applications published from
Parallels Remote Application Server. Shadowing requires a direct connection between the machine
on which the Parallels RAS console is running and the device itself.
Desktop Replacement
The Replace Desktop option limits users from changing system settings or installing new
applications. Replacing the Windows Desktop with Parallels Client transforms the Windows
operating system into a thin-client-like OS without replacing the operating system itself. This way,
users can only deploy applications from the client, thus providing the administrator with a higher
level of control over connected devices.
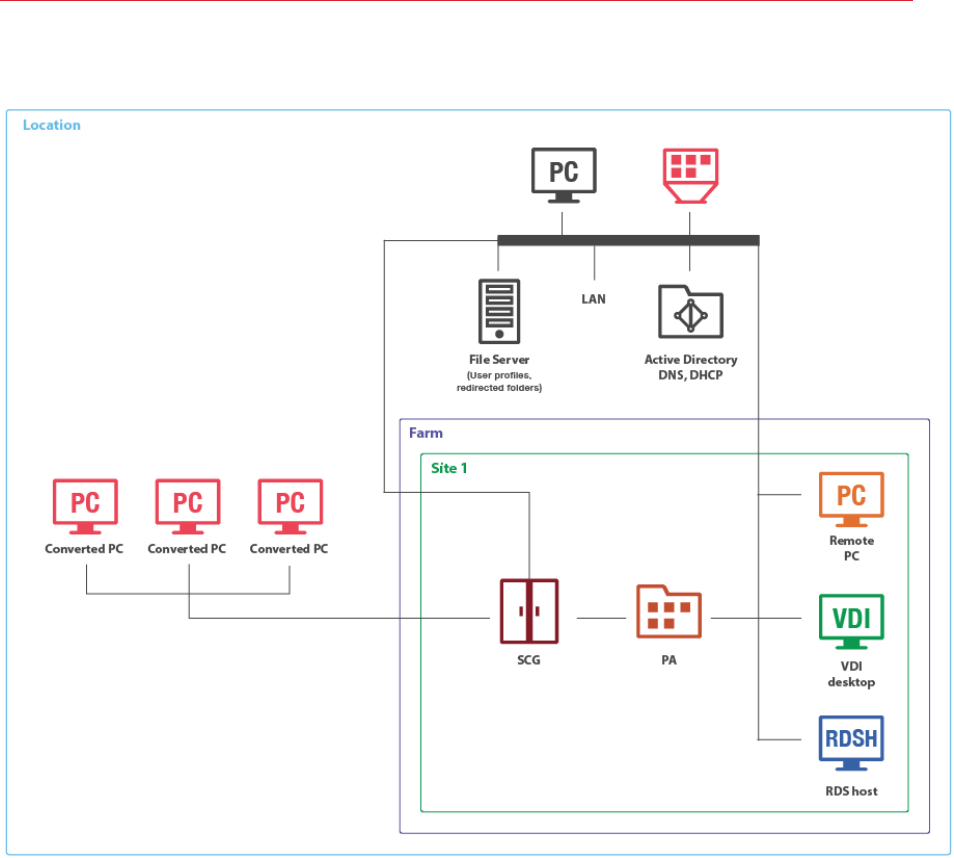
33
Deployment Scenarios
Additionally, Kiosk mode prevents users from shutting down or rebooting their computers.
Installation Notes
RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
All other server-side components are push-installed from the RAS console (RAS VDI Agent can be
optionally installed as a virtual appliance).
Parallels Client is installed on client desktop computers and converted Windows PCs using the
Parallels Client installer.
This chapter describes common scenarios for deploying the Parallels Remote Application Server
Reporting Service.
In This Chapter
One Site with Multiple RD Session Host Servers ....................................................... 35
Multiple Sites with Multiple RD Session Host Servers ................................................ 36
CHAPTER 3
Deploying Parallels RAS Reporting Service
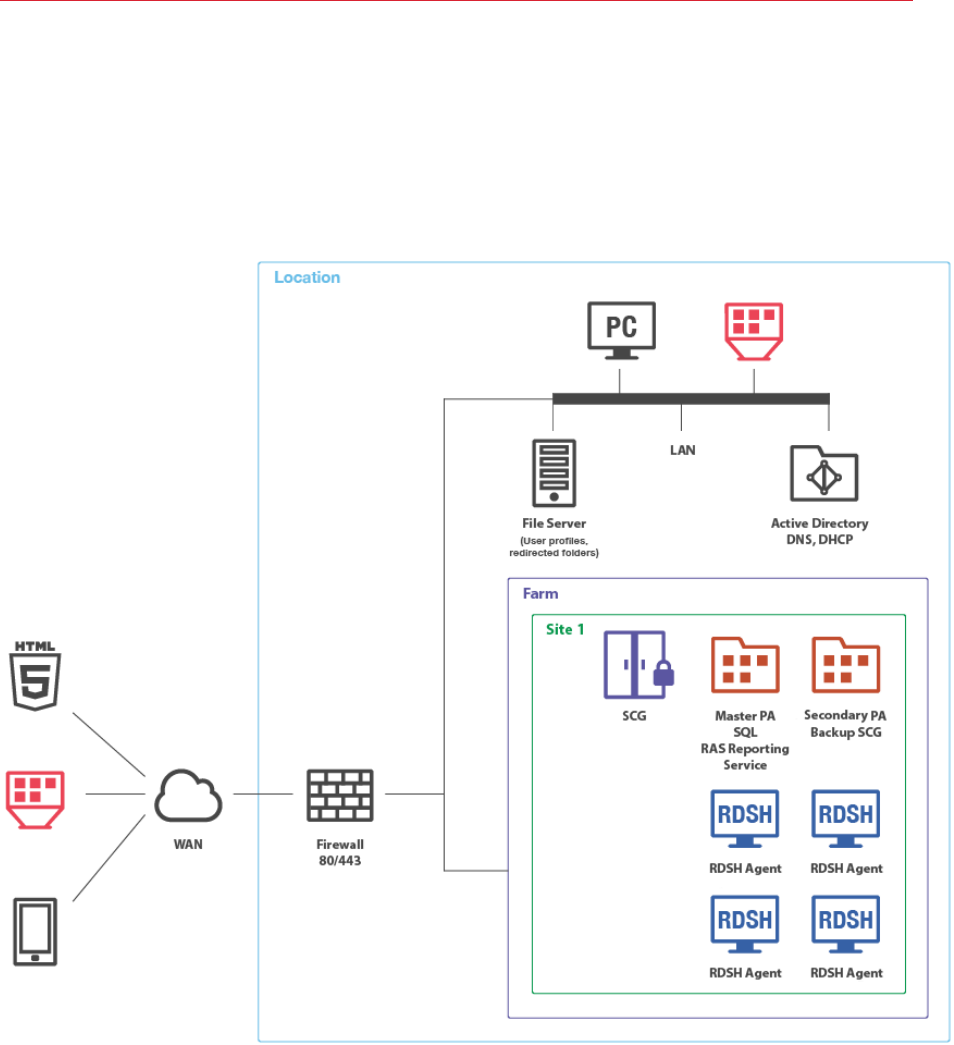
35
Deploying Parallels RAS Reporting Service
One Site with Multiple RD Session Host Servers
RAS Reporting Service relies on Microsoft SQL Server and Reporting Services. In small
environments, a database instance and RAS Reporting Service can be installed on the same
machine where Parallels Remote Application Server is running.
Installation Notes
Primary RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
Secondary RAS Publishing Agent is push-installed from the RAS console.
All other components are push-installed from the RAS console.

36
Deploying Parallels RAS Reporting Service
Multiple Sites with Multiple RD Session Host
Servers
For installations running in a multiserver farm environment, installing MS SQL Server on a dedicated
machine is recommended.
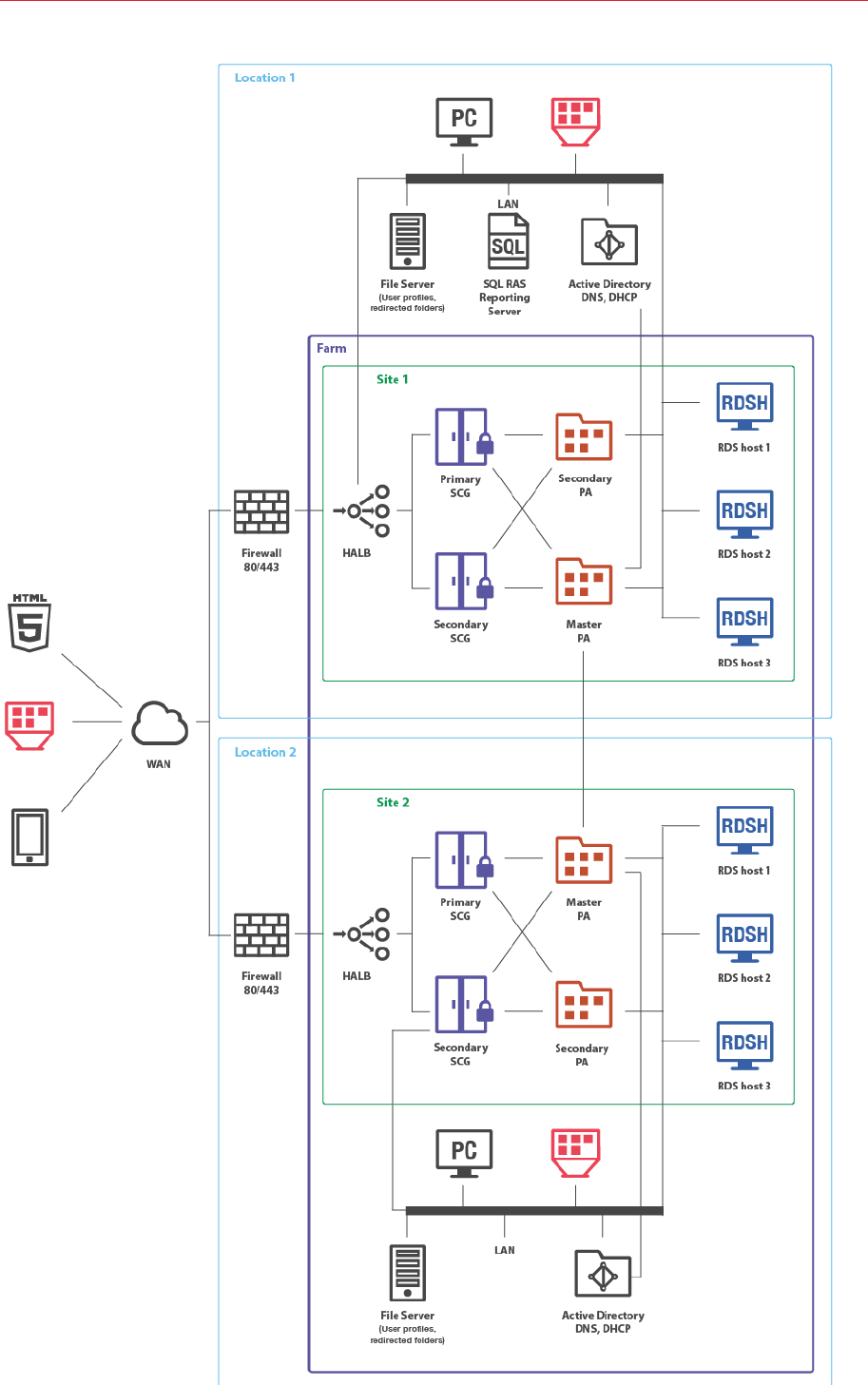
37
Deploying Parallels RAS Reporting Service

38
Deploying Parallels RAS Reporting Service
Installation Notes
Master RAS Publishing Agent is installed using the Parallels RAS installer (standard installation).
Secondary RAS Publishing Agent is push-installed from the RAS Console.
HALB is installed as a ready-to-use virtual appliance.
SQL RAS Reporting Server is installed using the Windows installer.
All other components are push-installed from the RAS console. Additionally, RAS VDI Agent can be
optionally installed as a virtual appliance.

This chapter provides reference information about ports used by Parallels Remote Application
Server and describes how SSL certificates are used in Parallels RAS.
In This Chapter
Port Reference ......................................................................................................... 39
SSL Certificates ........................................................................................................ 44
Port Reference
Parallels Remote Application Server v16
Table 1: Parallels Client
Source Destination Protocol/s Port/s Description
Parallels Client
HALB
TCP
UDP
TCP, UDP
80, 443, 3389
80, 443
20009
• TCP 3389 if RDP Load Balancing is
enabled.
• If RDP-UDP is used.
•
Client Manager, shadowing via FW.
Secure Gateway
(Normal and
Forwarding modes)
TCP
UDP
TCP, UDP
80, 443, 3389
80, 443
20009
• TCP 3389 if RDP Load Balancing is
enabled.
• If RDP-UDP is used.
• Client Manager, shadowing via FW.
Parallels Guest Agent
Terminal Server Agent
Parallels Remote PC
Agent
TCP, UDP
TCP
TCP
3389
443
30005
• Connections in Direct Mode.
• Connections in Direct SSL Mode.
• TCP 30005 Parallels Remote PC
Agent Communication Port (server
for internal commands - memshell,
printer redirector).
Table 2: Web Browsers
Source Destination Protocol/s Port/s Description
HTML5 web
browser Secure Gateway TCP 20020 • HTML5 (in Normal mode only).
CHAPTER 4
Port Reference and SSL Certificates

40
Port Reference and SSL Certificates
Web browser
Web Portal TCP
TCP
81
443
• Web portal UI. Actual session uses
the Parallels client information.
•
If SSL enabled.
Table 3: Secure Client Gateway
Source Destination Protocol/s Port/s Description
Secure Gateway
in Forwarding
Mode
Secure Gateway in
Normal Mode)
TCP
UDP
TCP, UDP
80, 443, 3389
80, 443
20009
• TCP 3389 if RDP Load Balancing is
enabled.
• If RDP-UDP is used.
•
Client Manager, shadowing via FW.
Parallels Client
TCP
UDP
TCP, UDP
80, 443, 3389
80, 443
20009
• TCP 3389 if RDP Load Balancing is
enabled.
• If RDP-UDP is used.
•
Client Manager, shadowing via FW.
Secure Gateway
in Normal Mode
Parallels Guest Agent
Terminal Server Agent
Parallels Remote PC
Agent
TCP, UDP 3389 • RDP Connections.
Publishing Agent TCP 20002, 20030
• TCP 20002 Publishing Agent Service
Port - communications with RAS
Secure Client Gateways and the RAS
Console (in Normal mode only).
Parallels Client TCP, UDP 3389 • Standard RDP Connections.
Table 4: Publishing Agent
Source Destination Protocol/s Port/s Description
Publishing Agent
Secure Gateway UDP 20000, 20009
• UDP 20009 (if Client Manager is
enabled).
•
UDP 20000 (Gateway Lookup).
Publishing Agent TCP 20001, 20010,
20030
• TCP 20001 Redundancy Service.
• TCP 20010.
• TCP 20030 Communication between
Publishing Agents running in the
same site.
Parallels Licensing
Server TCP 443
• Outbound TCP 443- Publishing
Agent (Master PA in Licensing Site)
communicates with Parallels
Licensing Server
(https://ras.parallels.com).

41
Port Reference and SSL Certificates
Terminal Server Agent TCP, UDP
TCP, UDP
20003
30004
• TCP, UDP 20003 Terminal Server
Agent Port - communications with
Terminal Server agents.
• TCP, UDP 30004 Server for PA
requests.
Parallels VDI Agents UDP
TCP, UDP
30004
30006
• UDP 30004 Used when the VDI
Agent is verified.
• TCP, UDP 30006 VDI Agent
Communication Port.
Parallels Guest Agent TCP, UDP
TCP
30004
30005
• TCP, UDP 30004 Parallels Guest
Agent Communication Port (agent
state, counters and session
information).
• TCP 30005 Parallels Remote PC
Agent Communication Port (server
for internal commands - memshell,
printer redirector).
Parallels Remote PC
Agent
TCP, UDP
TCP
30004
30005
• TCP, UDP 30004 Remote PC Agent
Communication Port (agent state,
counters and session information).
• TCP 30005 Parallels Remote PC
Agent Communication Port (server
for internal commands - memshell,
printer redirector).
Table 5: RAS Console
Source Destination Protocol/s Port/s Description
RAS Console
SQL host with SSRS
and Reporting
component
TCP 30008 • Publishing Agent (RAS Console and
Reporting).
HALB TCP, UDP 31006
•
TCP, UDP 31006 configuration.
Parallels Client TCP
TCP, UDP
50005
20009
• Shadowing from RAS Console in
case of direct network connection.
•
Client Manager, shadowing via FW.
Parallels Guest Agent
Terminal Server Agent
Parallels Remote PC
Agent
Publishing Agent
Secure Gateway
TCP 135, 445, 49179 • Remote Install Push/Takeover of
Software.
2FA Server/s TCP,UDP 8080, 80, 1812,
1813 • Deepnet / Safenet / Radius.

42
Port Reference and SSL Certificates
www.turbo.net TCP 80, 443
• When Turbo containerized apps
publishing is enabled and used.
Used to obtain app categories and
available apps metadata for further
publishing.
Table 6: RD Session Host / VDI / Guest / Remote PC Agents
Source Destination Protocol/s Port/s Description
RD Session Host
Agent
Publishing Agent
TCP, UDP
TCP, UDP
TCP
30004
20003
30005
• TCP, UDP 30004 Terminal Server
Agent Communication Port.
• TCP, UDP 20003. Communications
with Publishing Agents.
• TCP 30005 Terminal Server Agent
Communication Port (server for
internal commands - memshell,
printer redirector).
Secure Gateway TCP, UDP 3389
•
RDP Connections.
Parallels Client TCP, UDP 3389 • TCP 3389 if RDP Load Balancing is
enabled.
www.turbo.net TCP 80, 443
• When Turbo containerized
application support is enabled and
used. Used for download Turbo
installation package. Used to
download and install / update
application containers.
Parallels VDI
Agents Publishing Agent UDP
TCP, UDP
30004
30006
• UDP 30004 Used when the VDI
Agent is verified.
• TCP, UDP 30006 VDI Agent
Communication Port.
Parallels Guest
Agent
Publishing Agent TCP, UDP
TCP
30004
30005
• TCP, UDP 30004 Parallels Guest
Agent Communication Port (agent
state, counters and session
information).
• TCP 30005 Parallels Remote PC
Agent Communication Port (server
for internal commands - memshell,
printer redirector).
Secure Gateway TCP, UDP 3389
•
RDP Connections.
Parallels Client TCP, UDP 80, 443, 3389
•
Standard RDP Connections.
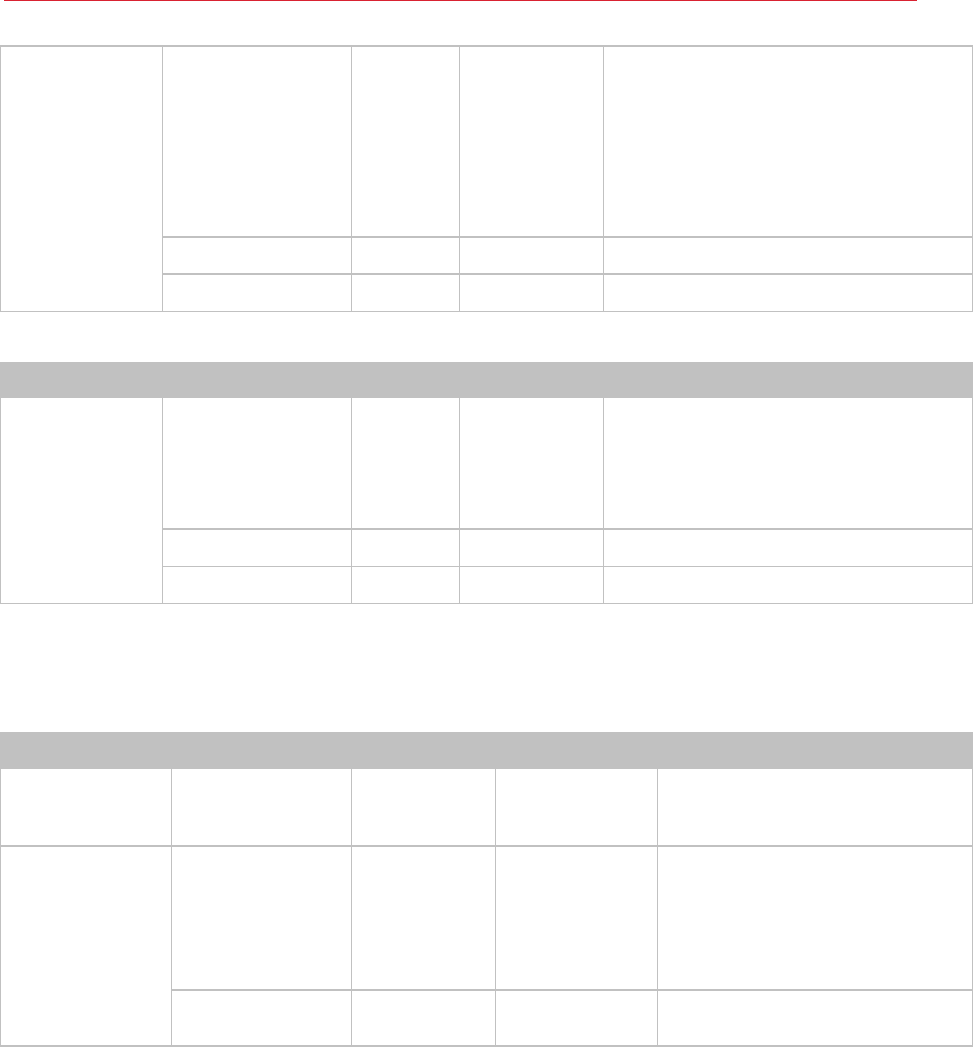
43
Port Reference and SSL Certificates
Parallels Remote
PC Agent
Publishing Agent TCP, UDP
TCP
30004
30005
• TCP, UDP 30004 Remote PC Agent
Communication Port (agent state,
counters and session information).
• TCP 30005 Parallels Remote PC
Agent Communication Port (server
for internal commands - memshell,
printer redirector).
Secure Gateway TCP, UDP 3389
•
RDP Connections.
Parallels Client TCP, UDP 3389
•
Standard RDP Connections.
Table 7: HALB
Source Destination Protocol/s Port/s Description
HALB
Parallels Client
TCP
UDP
TCP, UDP
80, 443, 3389
80, 443
20009
• TCP 3389 if RDP Load Balancing is
enabled.
• If RDP-UDP is used.
•
Client Manager, shadowing via FW.
HALB VRRP 112
•
RAW.
RAS Console TCP, UDP 31006
•
TCP, UDP 31006 configuration.
Common Communication Ports
Source Destination Protocol/s Port/s Description
RAS Console
Any host where to
which Agents are
pushed
TCP 135, 445, 49179 • Remote Install Push/Takeover
of Software.
Master PA
AD DS controllers
TCP
TCP
TCP
UDP
389, 3268
636, 3269
88
53
• LDAP
• LDAPS
• Kerberos
•
DNS
2FA Server/s TCP,UDP 8080, 80, 1812,
1813 • Deepnet / Safenet / Radius.
For Active Directory and Active Directory Domain Services port requirements, please see the
following article: https://technet.microsoft.com/en-us/library/dd772723%28v=ws.10%29.aspx

44
Port Reference and SSL Certificates
SSL Certificates
This section explains how to use SSL certificates in Parallels Application Server deployments. You
should read this section if you are setting up a RAS environment to test one or more of the
deployment scenarios described earlier in this guide.
By default, a self-signed certificate is installed on a RAS Secure Client Gateway. Each RAS Secure
Client Gateway has its own certificate, which should be added to Trusted Root Authorities on the
client side to avoid security warnings.
To simplify the Parallels Client configuration, using a certificate issued either by a third-party Trusted
Certificate Authority or Enterprise Certificate Authority (CA) is recommended.
If an Enterprise CA certificate is used, Windows clients receive a Root or Intermediate Enterprise
CA certificate from Active Directory. Client devices on other platforms require manual configuration.
If a third-party certificate issued by a well-known Trusted Certificate Authority (e.g. Verisign) is used,
the client device trusts using Trusted Certificate Authority updates for the platform.
Using Third-Party Trusted Certificate Authority
1 In the RAS Console, navigate to Farm > Gateway > Properties and click the SSL/TLS tab.
2 Select TLS 1.2 as the SSL settings option.
3 Choose CSR.
4 Fill in the data.
5 Copy and paste the CSR into a text editor and save the file for your records.
6 Paste the CSR into the party Vendors Website page or email it to the vendor.
7 Request a return certificate in the following format: Apache, with the private, public and
intermediate CA all in one file, with extension .pem.
8 When you receive the file, place it in a secure folder for backup retrieval.
9 Click Import Public Key and navigate to the folder (or navigate to a secondary location where
you have a copy of the single all-in-one cert) and insert the .pem file into the Certificate key
field.
10 Click Apply and Test.
Note: The private key should already be populated from your initial CSR request.

45
Port Reference and SSL Certificates
Using Enterprise Certificate Authority
Use IIS to receive a certificate from Enterprise CA. The certificate should be exported in the pfx
format and then converted into the PEM format using the OpenSSL tool, available at
http://gnuwin32.sourceforge.net/packages/openssl.htm
Note: The trusted.pem file on the Parallels Client side must include the intermediate certificate to be
able to verify the cert from the third-party vendor. If the intermediate certificate for the vendor is not in the
trusted.pem file, you will have to paste it in manually, or create a trusted.pem template file with the
proper Intermediate Certificates and then replace the old trusted.pem file with the newly updated one.
This file resides in Program Files\Parallels or Program Files(x86)\ Parallels on the client side.
To convert a PFX file to a PEM file, follow these steps on a Windows machine:
1 Run the OpenSSL tool.
2 Create the c:\certs folder and copy the cert.pfx file into it.
3 Open the command prompt and enter cd %ProgramFiles%\GnuWin32\bin
4 Type the following command to convert the PFX file to unencrypted PEM file:
OPENSSL pkcs12 -in c:\certs\cert.pfx -out c:\certs\scg.pem -nodes
5 When prompted for the import password, enter the password you used when you exported the
certificate to a PFX file. You should receive a message saying, "MAC verified OK".
Enable SSL on RAS Secure Client Gateway with cert.pem
1 On the Parallels Client Gateway page, enable secure sockets layer (SSL) and click […] to
browse for the pem file.
2 Place the single file generated in the Private Key and Public Key fields.
3 Click Apply to apply the new settings.
4 Your browser may not support displaying this image.
Parallels Clients Configuration
In case the certificate is self-signed, or the certificate issued by Enterprise CA, Parallels Clients
should be configured as described below.
1 Export the certificate in Base-64 encoded X.509 (.CER) format.
2 Open the exported certificate with a text editor, such as notepad or WordPad, and copy the
contents to the clipboard.
To add the certificate with the list of trusted authorities on the client side and enable Parallels Client
to connect over SSL with a certificate issued from an organization’s Certificate Authority.

46
Port Reference and SSL Certificates
1 On the client side in the directory "C:\Program Files\Parallels\Remote Application Server Client\"
there should be a file called trusted.pem. This file contains certificates of common trusted
authorities.
2 Paste the content of the exported certificate (attached to the list of the other certificates).

Index
A
Advantages of Parallels Remote Application
Server Based Computing - 4
B
Business Continuity and Disaster Recovery -
29
C
Client Connection Modes - 14
Client Manager and Desktop Replacement -
32
D
Deploying Parallels RAS Reporting Service -
34
Deployment Scenarios - 16
Dual Firewall DMZ - 25
G
General Considerations - 16
H
High Availability with Multiple Gateways - 22
High Availability with Single or Dual F/W DMZ
- 24
M
Mixed Scenarios - 27
Multiple Sites with Multiple RD Session Host
Servers - 36
Multi-Site Scenario - 27
O
One Site with Multiple RD Session Host
Servers - 35
P
Parallels Client Connection Flow - 13
Parallels RAS Basic Concepts - 10
Parallels RAS Deployment Scenarios - 16
Parallels Remote Application Server
Components - 5
Port Reference - 39
Port Reference and SSL Certificates - 39
S
Secure Setup with Dual Firewall DMZ and
Second-Level Authentication - 31
Single Farm with Dual RAS Secure Client
Gateways - 21
Single Farm with Mixed Desktops - 19
Single Farm with One RD Session Host
Server - 16
Single Farm with Public & Private RAS Secure
Client Gateways - 20
Single Farm with Two RD Session Host
Servers - 18
Single Firewall DMZ - 24
SSL Certificates - 44
U
Understanding Deployment Scenario
Diagrams - 7
W
What is Parallels Remote Application Server -
4
Index