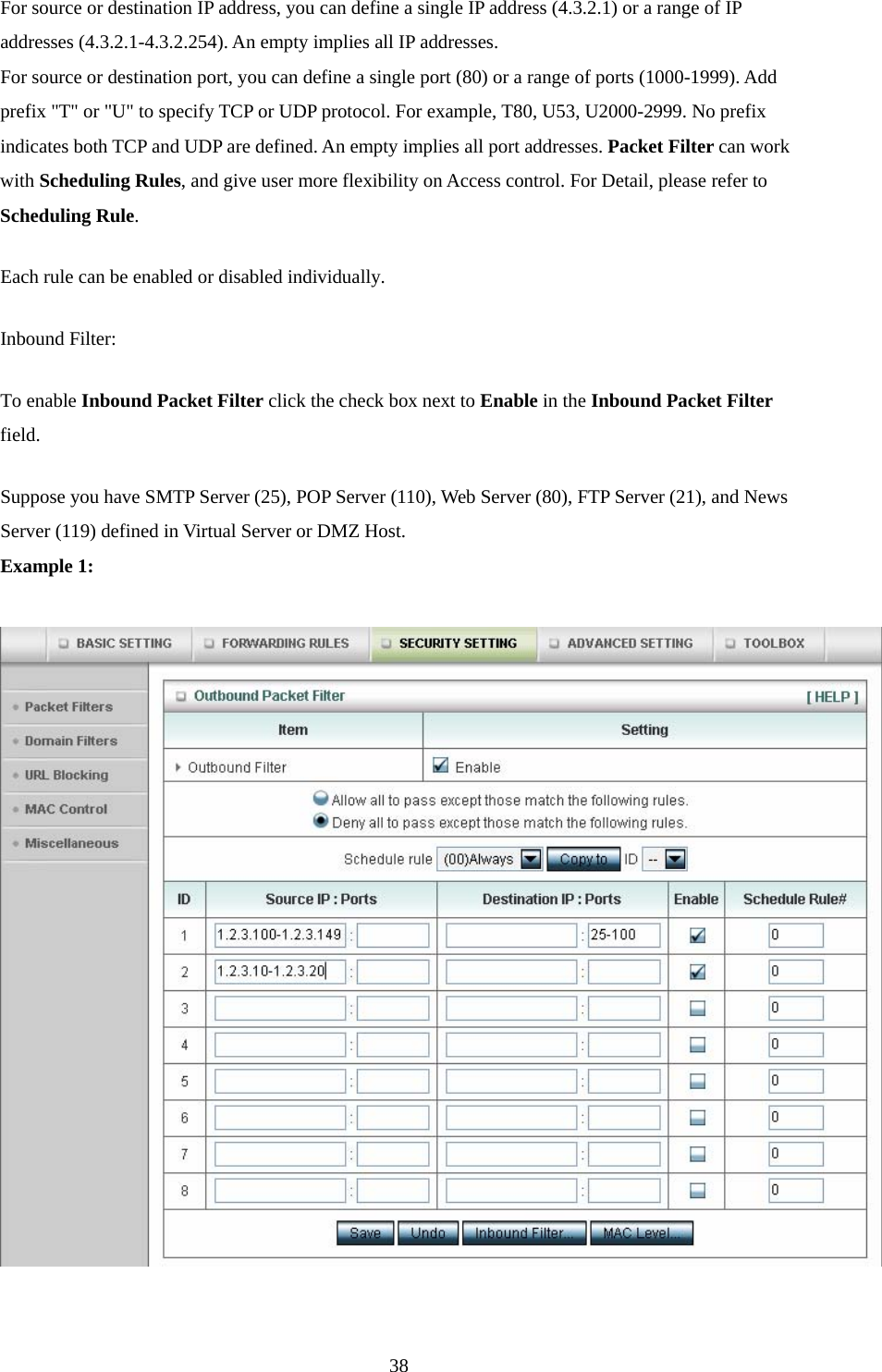
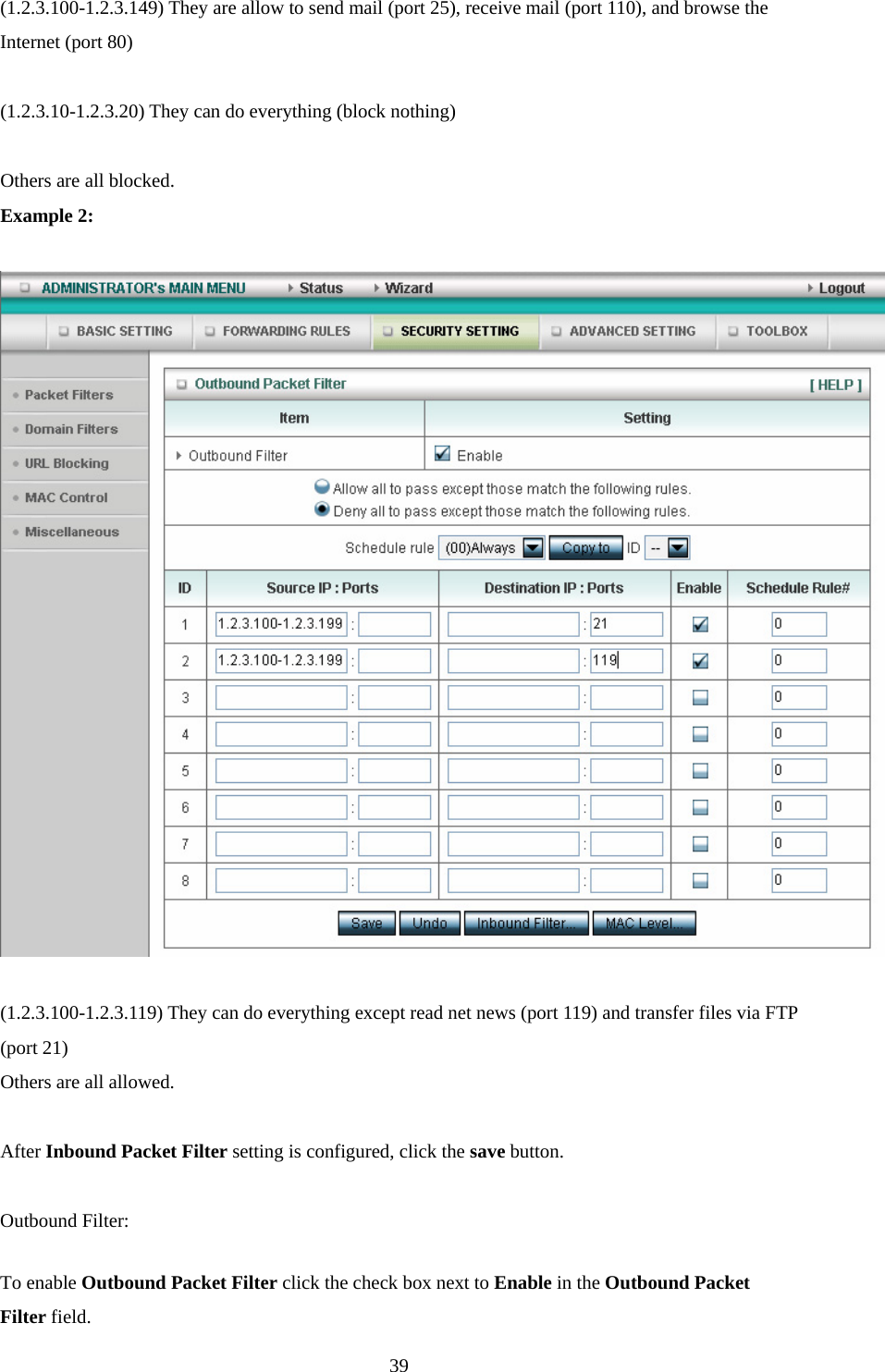
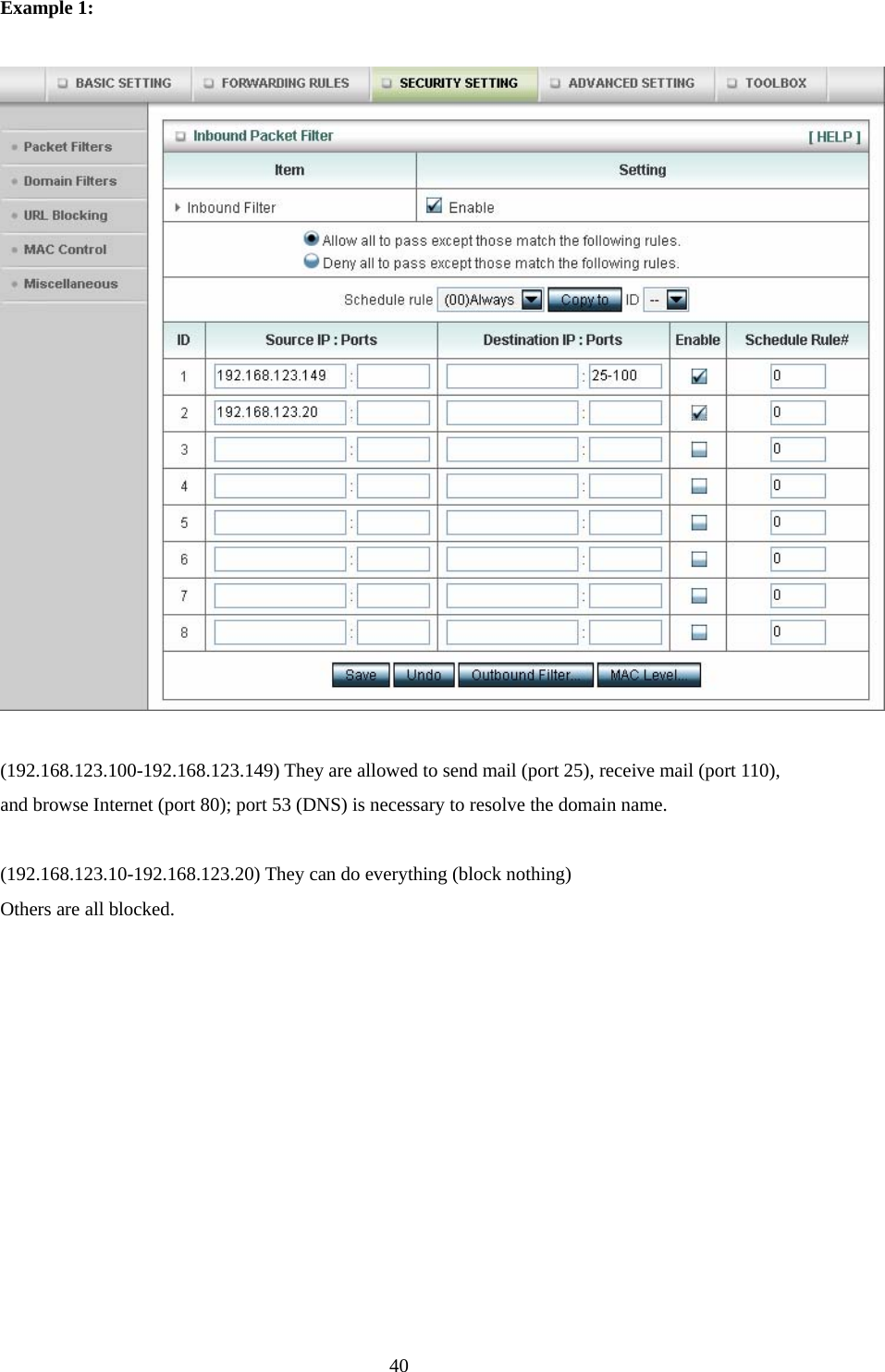
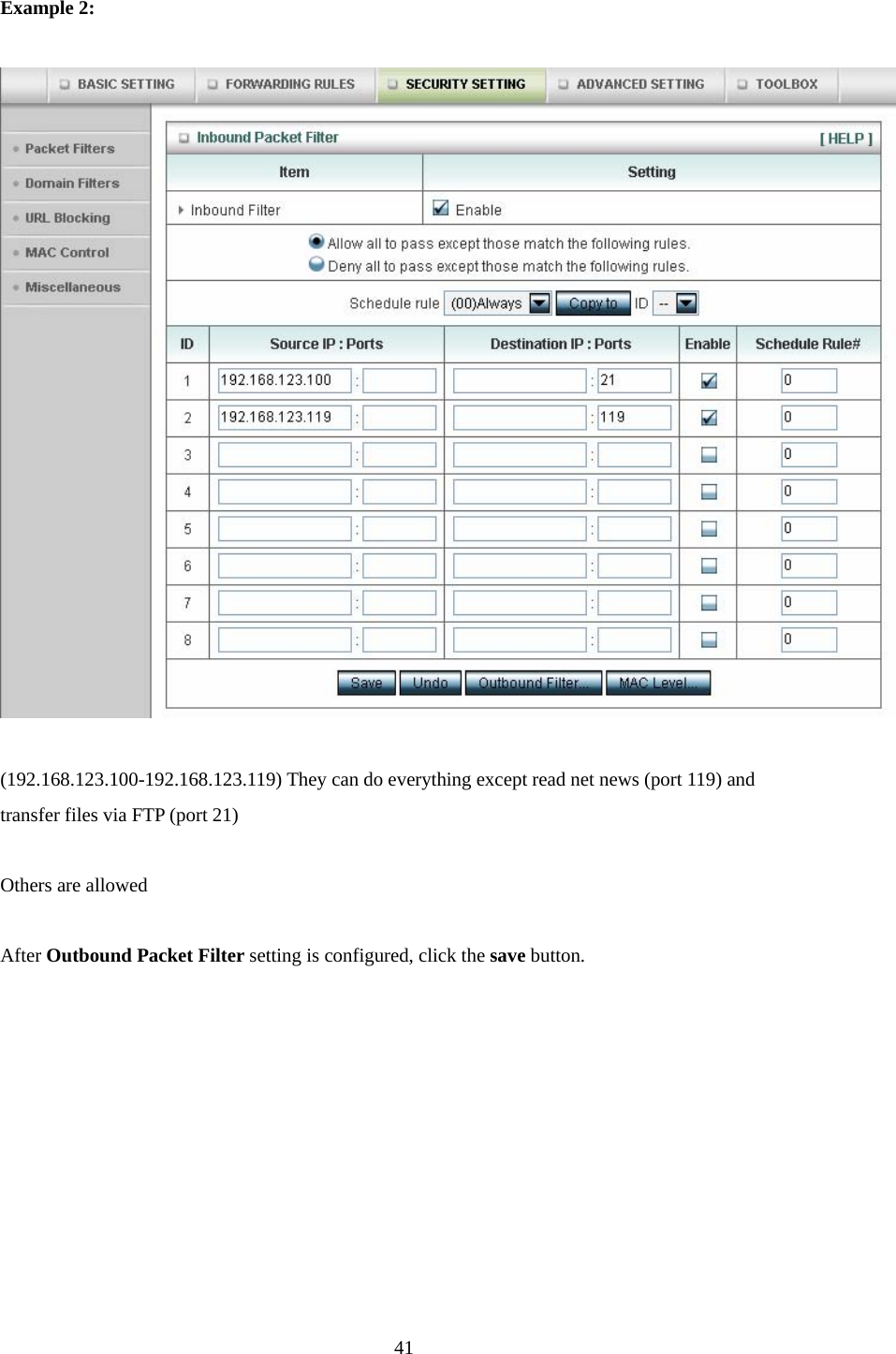
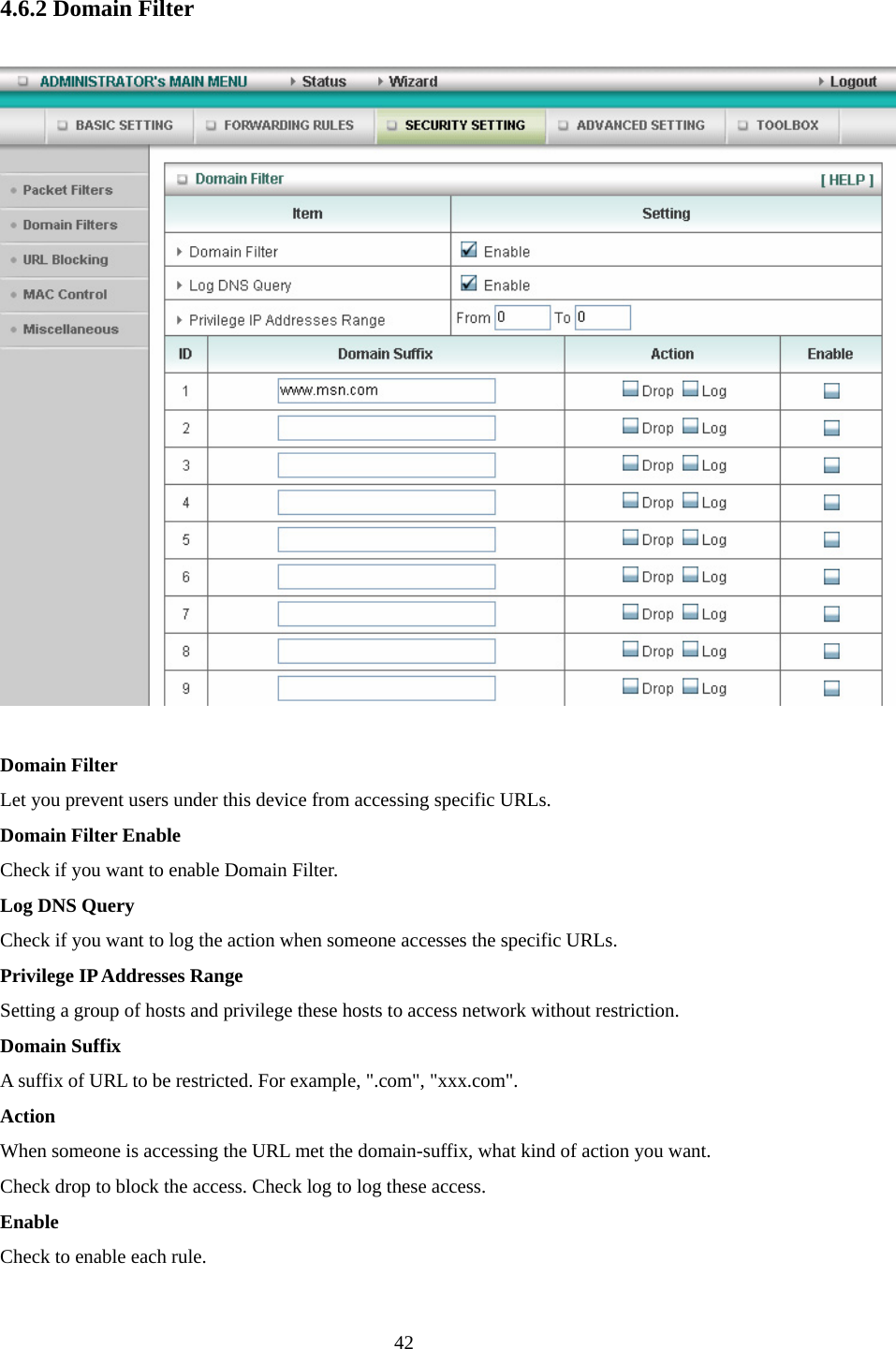
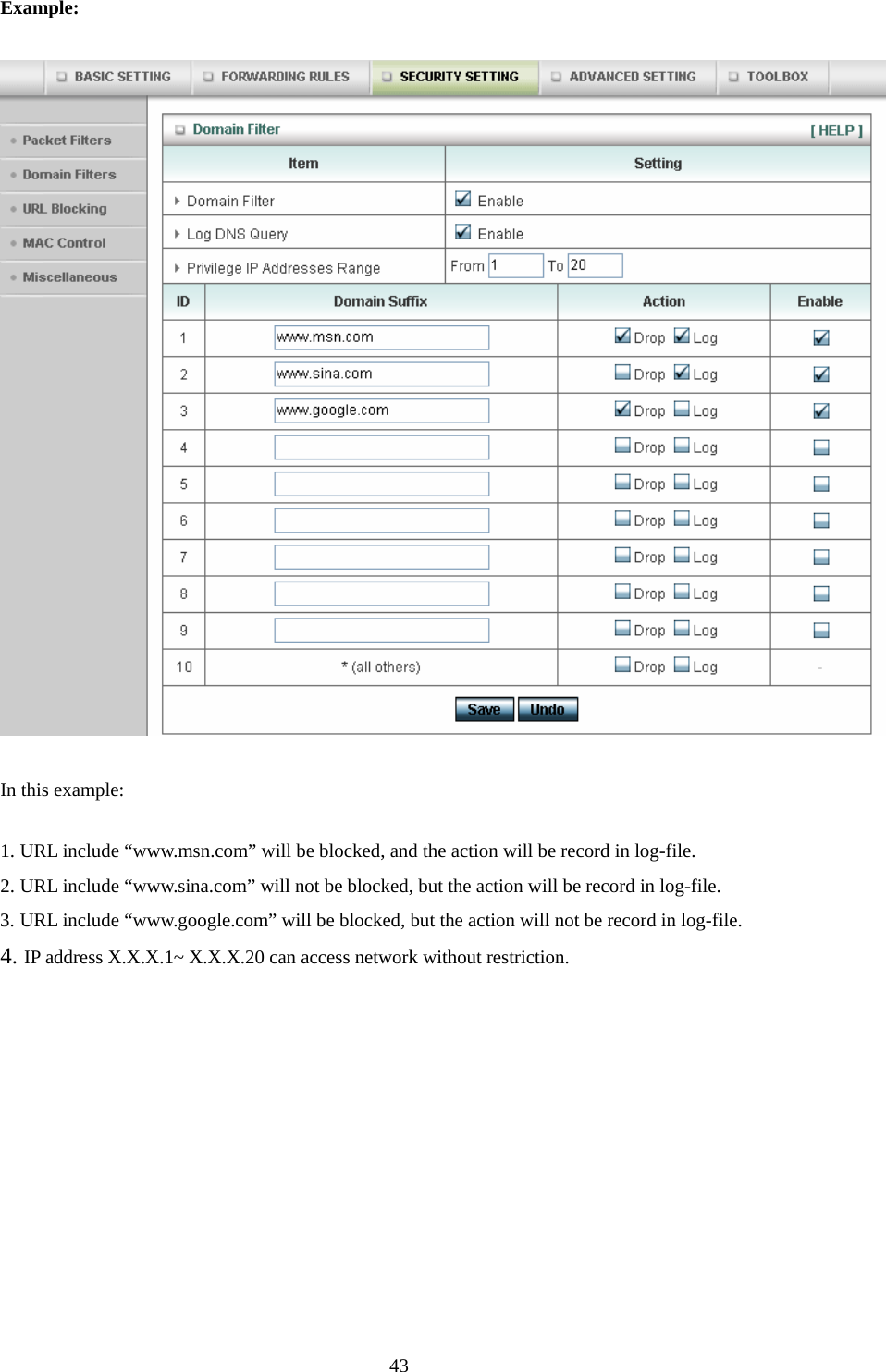
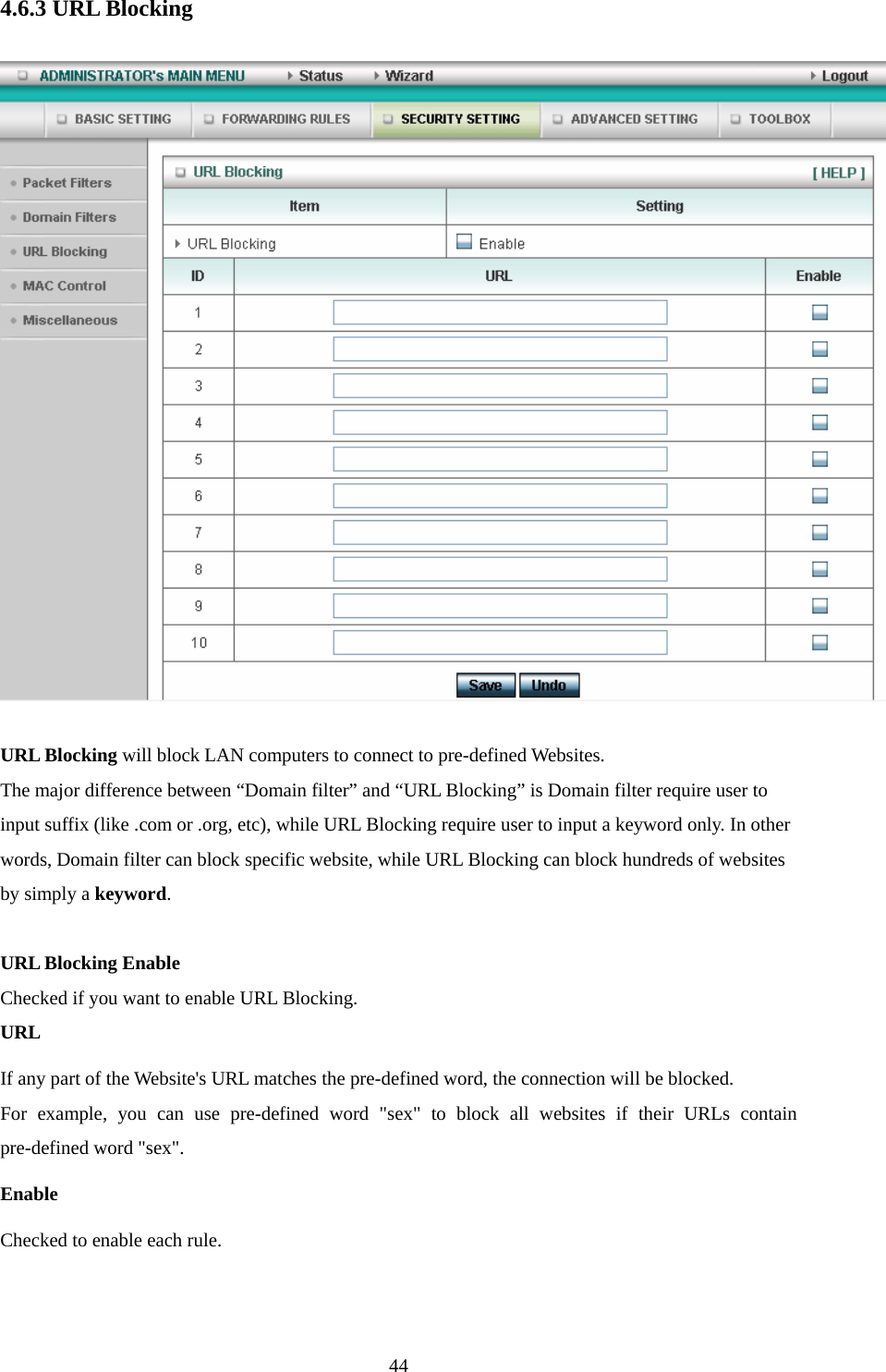
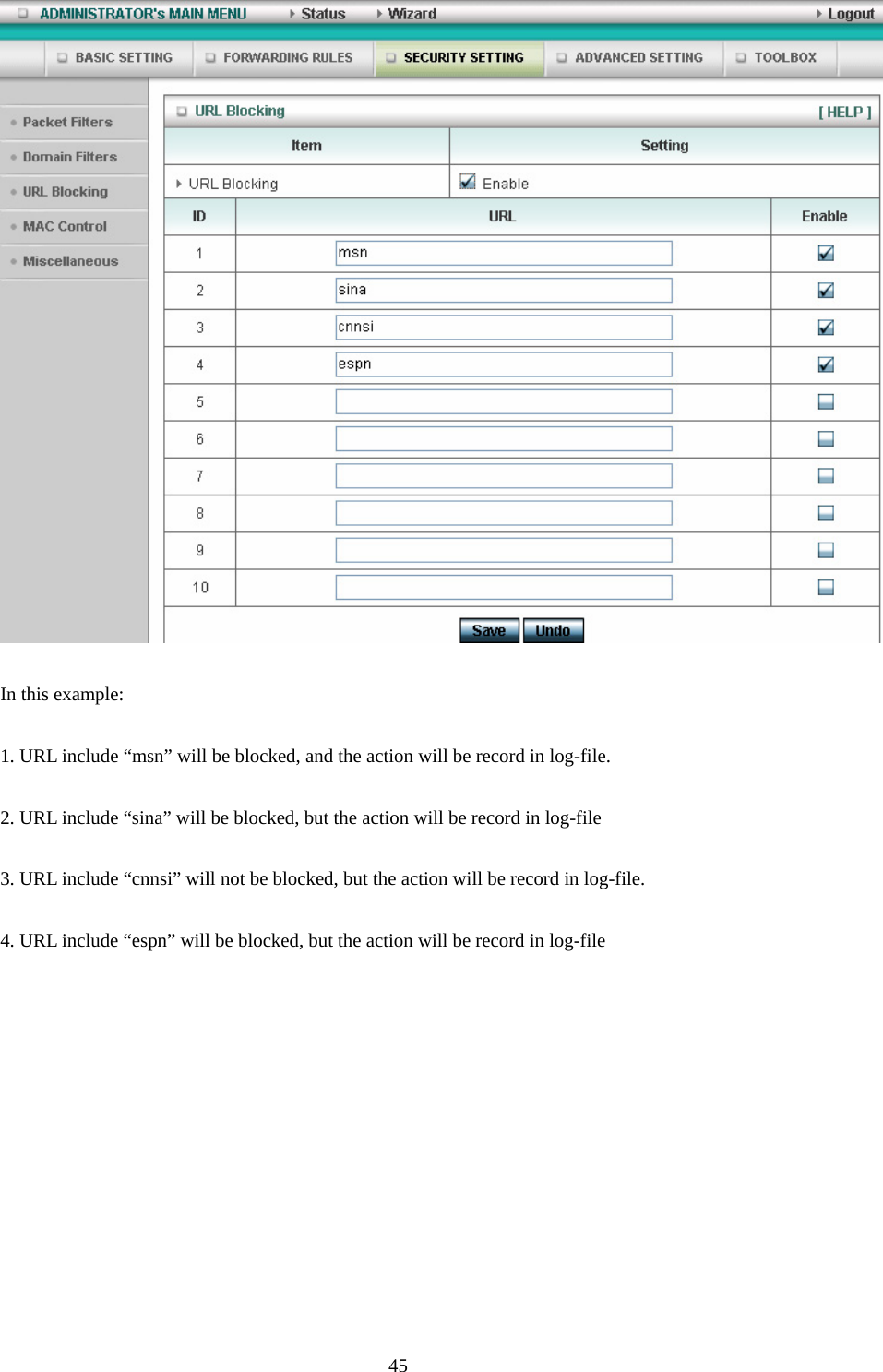
Advance Multimedia Internet Technology WIQ318 Wireless Broadband Router User Manual II
Advance Multimedia Internet Technology Inc. Wireless Broadband Router Users Manual II
Contents
- 1. Users Manual I
- 2. Users Manual II
- 3. Users Manual III
Users Manual II