Billion Electric BIL-7404VGOX (3G)/VoIP/802.11g ADSL2+(VPN) Firewall Router User Manual 2
Billion Electric Co., Ltd. (3G)/VoIP/802.11g ADSL2+(VPN) Firewall Router Users Manual 2
Contents
- 1. Users Manual 1
- 2. Users Manual 2
Users Manual 2
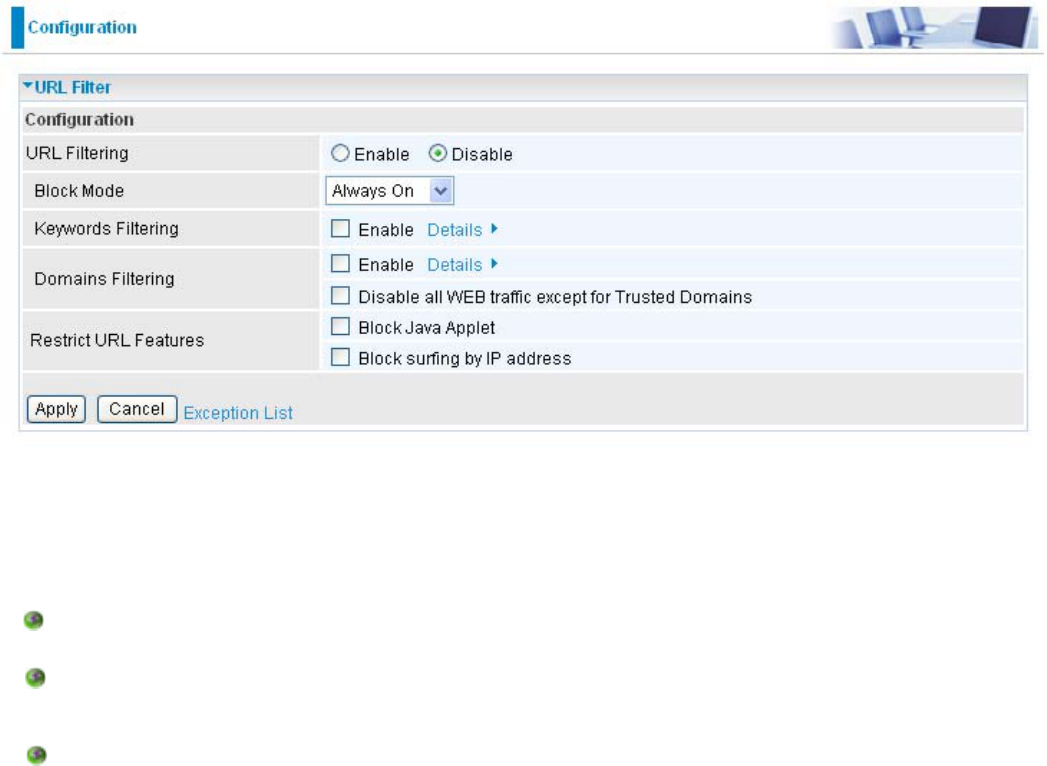
URL Filter
85/8QLIRUP5HVRXUFH/RFDWRU±HJDQDGGUHVVLQWKHIRUPRIKWWSZZZDEFGHFRPRUKWWS
ZZZH[DPSOHFRP¿OWHUUXOHVDOORZ\RXWRSUHYHQWXVHUVRQ\RXUQHWZRUNIURPDFFHVVLQJSDUWLFXODU
ZHEVLWHVE\WKHLU85/7KHUHDUHQRSUHGH¿QHG85/¿OWHUUXOHV\RXFDQDGG¿OWHUUXOHVWRPHHW
\RXUUHTXLUHPHQWV
Enable/Disable: To enable or disable URL Filter feature.
Block Mode: $OLVWRIWKHPRGHVWKDW\RXFDQFKRRVHWRFKHFNWKH85/¿OWHUUXOHV The default is
set to Always On.
Disabled: 1RDFWLRQZLOOEHSHUIRUPHGE\WKH%ORFN0RGH
Always On:$FWLRQLVHQDEOHG85/¿OWHUUXOHVZLOOEHPRQLWRULQJDQGFKHFNLQJDWDOOKRXUVRI
the day.
TimeSlot1 ~ TimeSlot16: ,WLVVHOIGH¿QHG WLPH SHULRG <RXPD\VSHFLI\WKHWLPHSHULRG
WRFKHFNWKH85/¿OWHUUXOHVLHGXULQJZRUNLQJKRXUV)RUVHWXSDQGGHWDLOUHIHUWRTime
Schedule section.
.H\ZRUGV)LOWHULQJ$OORZVEORFNLQJE\VSHFL¿FNH\ZRUGVZLWKLQDSDUWLFXODU85/UDWKHUWKDQKDYLQJ
WRVSHFLI\DFRPSOHWH85/HJWREORFNDQ\LPDJHFDOOHG³DGYHUWLVHPHQWJLI´:KHQHQDEOHG\RXU
VSHFL¿HGNH\ZRUGVOLVWZLOOEHFKHFNHGWRVHHLIDQ\NH\ZRUGVDUHSUHVHQWLQ85/VDFFHVVHGWR
GHWHUPLQHLIWKHFRQQHFWLRQDWWHPSWVKRXOGEHEORFNHG3OHDVHQRWHWKDWWKH85/¿OWHUEORFNVZHE
browser (HTTP) connection attempts using port 80 only.
For example, if the URL is http://www.abc.com/abcde.html, it will be dropped as the keyword
³DEFGH´RFFXUVLQWKH85/
81
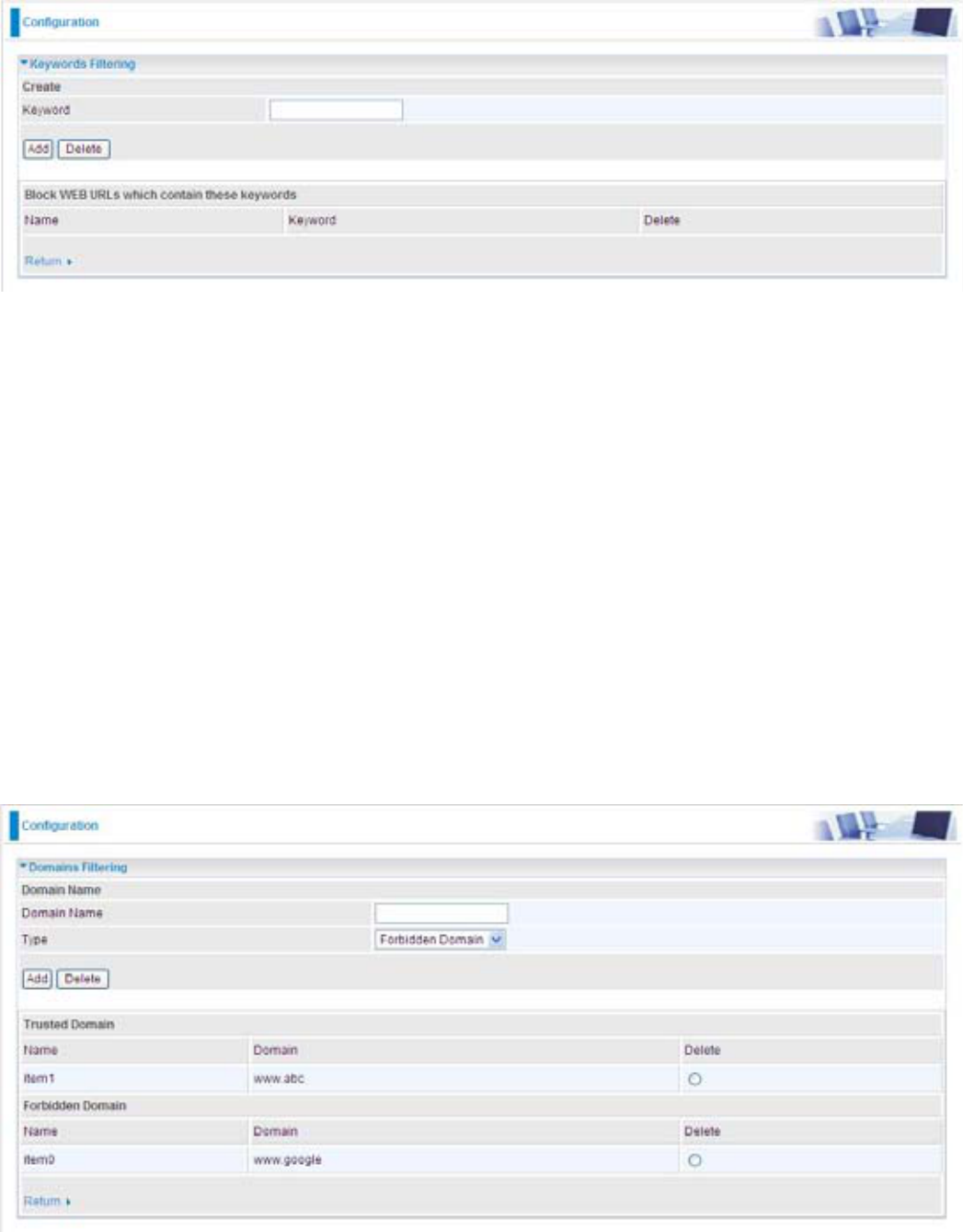
Domains Filtering: This function checks the whole URL not the IP address, in URLs accessed
DJDLQVW\RXUOLVWRIGRPDLQVWREORFNRUDOORZ,ILWLVPDWFKHGWKH85/UHTXHVWZLOOEHVHQW7UXVWHG
or dropped (Forbidden). For this function to be activated, both check-boxes must be checked. Here
is the checking procedure:
Check the domain in the URL to determine if it is in the trusted list. If yes, the connection attempt 1.
is sent to the remote web server.
If not, check if it is listed in the forbidden list. If yes, then the connection attempt will be 2.
dropped.
If the packet does not match either of the above two items, it is sent to the remote web server.3.
3OHDVHEHQRWHWKDWWKHFRPSOHWHG85/³ZZZ´GRPDLQQDPHVKDOOEHVSHFL¿HG)RUH[DPSOH4.
WREORFNWUDI¿FWRwww.google.com.auHQWHU³www.google´RU³www.google.com´
,QWKHH[DPSOHEHORZWKH85/UHTXHVWIRUwww.abc.com will be sent to the remote web server
EHFDXVHLWLVOLVWHGLQWKHWUXVWHGOLVWZKLOVWWKH85/UHTXHVWIRUwww.google or www.google.com
will be dropped, because www.google is in the forbidden list.
82

Example:
$QG\ZLVKHVWRGLVDEOHDOO:(%WUDI¿FH[FHSWIRURQHVOLVWHGLQWKHWUXVWHGGRPDLQZKLFKZRXOG
SUHYHQW%REE\IURPDFFHVVLQJRWKHUZHEVLWHV$QG\VHOHFWVERWKIXQFWLRQVLQWKH'RPDLQ)LOWHULQJ
DQGWKLQNVWKDWLWZLOOVWRS%REE\%XW%REE\NQRZVWKLVIXQFWLRQ'RPDLQ)LOWHULQJ21/<GLVDEOHV
DOO:(%WUDI¿FH[FHSW IRU7UXVWHG'RPDLQ %87QRWLWV,3DGGUHVV,IWKLVLV WKH VLWXDWLRQ%ORFN
VXU¿QJE\,3DGGUHVVIXQFWLRQFDQEHKDQG\DQGKHOSIXOWR$QG\1RZ$QG\FDQSUHYHQW%REE\
from accessing other sites.
Restrict URL Features: This function enhances the restriction to your URL rules.
Block Java Applet:7KLVIXQFWLRQFDQEORFN:HEFRQWHQWWKDWLQFOXGHVWKH-DYD$SSOHW,WLV
to prevent someone who wants to damage your system via standard HTTP protocol.
%ORFNVXU¿QJE\,3DGGUHVV Preventing someone who uses the IP address as URL for skip-
ping Domains Filtering function. Activates only and if Domain Filtering enabled.
83
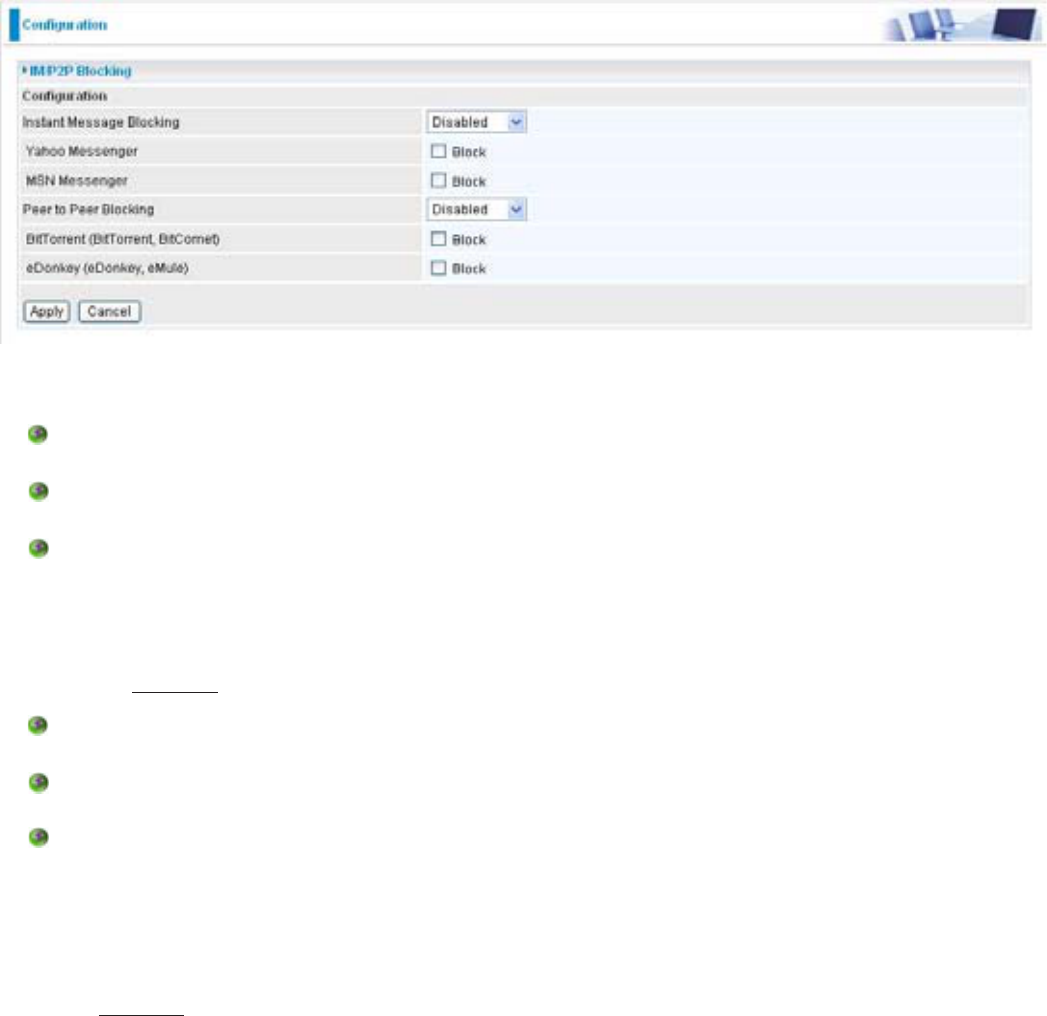
IM / P2P Blocking
,0 VKRUW IRU ,QVWDQW 0HVVDJH LV UHTXLUHG WR XVH client program software that allows users to
communicate LQ H[FKDQJLQJ WH[W PHVVDJH ZLWK RWKHU ,0 XVHUV LQ UHDO WLPH RYHU WKH ,QWHUQHW$
33 DSSOLFDWLRQ NQRZQ DV 3HHUWRSHHU LV JURXS RI FRPSXWHU XVHUV ZKR VKDUH ¿OH WR VSHFL¿F
JURXSVRISHRSOHDFURVVWKH,QWHUQHW%RWK,QVWDQW 0HVVDJH DQG 3HHUWRSHHU applications make
communication faster and easier but your network can become increasingly insecure at the same
WLPH%LOOLRQ¶V,0DQG33EORFNLQJKHOSVXVHUVWRUHVWULFW/$13&VWRDFFHVVWRWKHFRPPRQO\XVHG
,0<DKRRDQG061DQG33%LW7RUUHQWDQGH'RQNH\DSSOLFDWLRQVRYHUWKH,QWHUQHW
Instant Message Blocking: The default is set to Disabled.
Disabled: ,QVWDQW0HVVDJHEORFNLQJLVQRWWULJJHUHG1RDFWLRQZLOOEHSHUIRUPHG
Always On: Action is enabled.
TimeSlot1 ~ TimeSlot16: 7KLVLVWKHVHOIGH¿QHG WLPHSHULRG<RXPD\VSHFLI\WKHWLPH
period to trigger the blocking, i.e. during working hours. For setup and detail, refer to Time
Schedule section.
Yahoo/MSN Messenger: Check the box to blockHLWKHURUERWK<DKRRRUDQG0610HVVHQJHU7R
be sure you enabled the Instant Message Blocking¿UVW
Peer to Peer Blocking: The default is set to Disabled.
Disabled: ,QVWDQW0HVVDJHEORFNLQJLVQRWWULJJHUHG1RDFWLRQZLOOEHSHUIRUPHG
Always On: Action is enabled.
TimeSlot1 ~ TimeSlot16: This is theVHOIGH¿QHGWLPHSHULRG<RXPD\VSHFLI\WKHWLPHSHULRGWR
trigger the blocking, i.e. during working hours. For setup and detail, refer to Time Schedule section.
BitTorrent / eDonkey: Check the box to blockHLWKHURUERWK%LW7RUUHQWRUDQGH'RQNH\7REH
sure you enabledWKH3HHUWR3HHU%ORFNLQJ¿UVW
84
Firewall Log
)LUHZDOO/RJGLVSOD\ORJLQIRUPDWLRQRIDQ\XQH[SHFWHGDFWLRQZLWK\RXU¿UHZDOOVHWWLQJV
Check the Enable box to activate the logs.
Log information can be seen in the Status – Event Log after enabling.
85
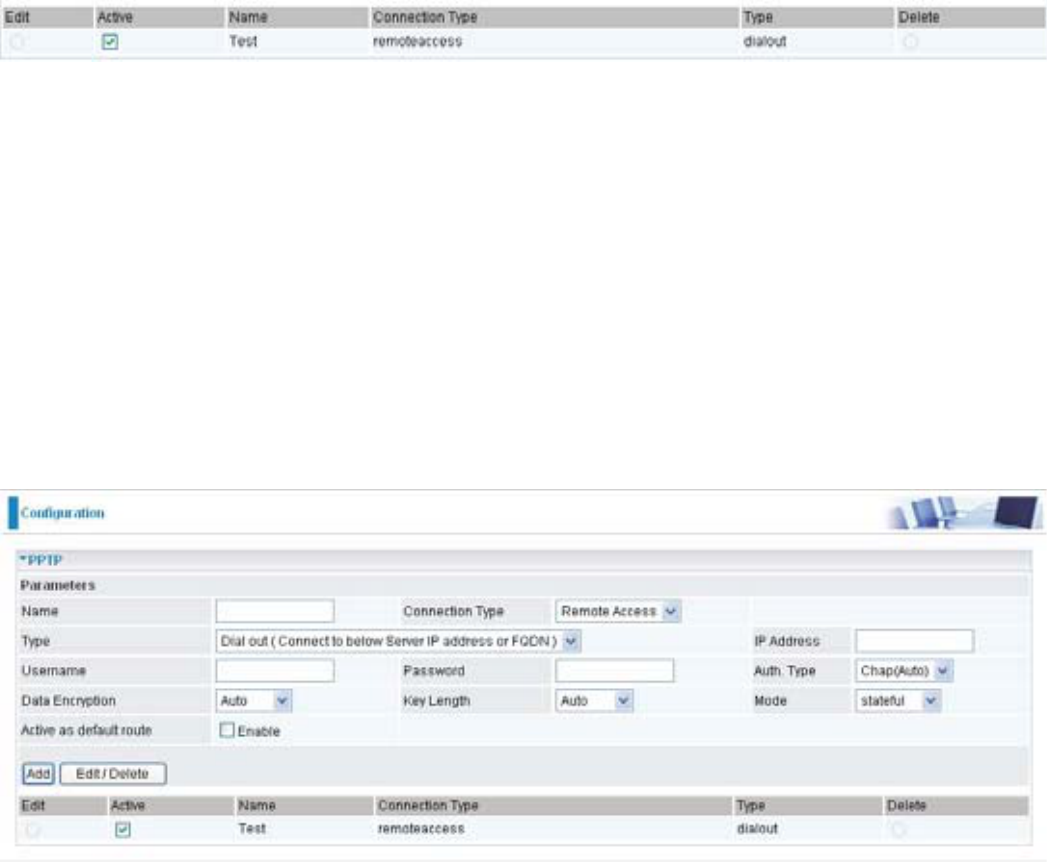
VPN - Virtual Private Networks (Only available for BiPAC 7404V(G)OX)
9LUWXDO3ULYDWH1HWZRUNVLVZD\VWRHVWDEOLVKVHFXUHGFRPPXQLFDWLRQWXQQHOVWRDQRUJDQL]DWLRQ¶V
network via the Internet. Your router supports three main types of VPN (Virtual Private Network):
PPTP, IPSec and L2TP.
PPTP (Point-to-Point Tunneling Protocol)
There are two types of PPTP VPN supported; Remote Access and LAN-to-LAN (please refer
EHORZIRUPRUHLQIRUPDWLRQ&OLFN&RQ¿JXUDWLRQ9313373
Name: A given name for the connection.
Active: This function activates or deactivates the PPTP connection. Check Active checkbox if you
want the protocol of tunnel to be activated and vice versa.
Note: When the Active checkbox is checked, the function of Edit and Delete will not be
available.
Connection Type: It informs your PPTP tunnel connection condition.
Type: This refers to your router operates as a client or a server, Dialout or Dialin respectively.
PPTP Connection - Remote Access
Name: $JLYHQQDPHIRUWKHFRQQHFWLRQHJ³FRQQHFWLRQWRRI¿FH´
Connection Type: Remote Access or LAN to LAN.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote
931VHUYHUHJ\RXURI¿FHVHUYHUFKHFN'LDO,QRSHUDWHVDVD931VHUYHU
:KHQFRQ¿JXULQJ\RXUURXWHUDVD&OLHQWHQWHUWKHUHPRWH6HUYHU,3$GGUHVVRU'RPDLQ1DPH
you wish to connect to.
:KHQFRQ¿JXULQJ\RXUURXWHUDVDVHUYHUHQWHUWKH3ULYDWH,3$GGUHVVDVVLJQHGWRWKH'LDOLQ
User.
86
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by your Host. If you are
a Dial-In user (server), enter your own password.
Authentication Type: Default is Auto if you want the router to determine the authentication type
to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or PAP
(Password Authentication Protocol) if you know which type the server is using (when acting as a
client), or else the authentication type you want clients connecting to you to use (when acting as a
VHUYHU:KHQXVLQJ3$3WKHSDVVZRUGLVVHQWXQHQFU\SWHGZKLOVW&+$3HQFU\SWVWKHSDVVZRUG
before sending, and also allows for challenges at different periods to ensure that an intruder has
not replaced the client.
Data Encryption: 'DWDVHQWRYHUWKH931FRQQHFWLRQFDQEHHQFU\SWHGE\DQ033(DOJRULWKP
Default is Auto, so that this setting is negotiated when establishing a connection, or else you can
manually Enable or Disable encryption.
Key Length: 7KHGDWDFDQEHHQFU\SWHGE\033(DOJRULWKPZLWKELWVRUELWV'HIDXOWLV
Auto, it is negotiated when establishing a connection. 128 bit keys provide stronger encryption
than 40 bit keys.
Mode: You may select Stateful or Stateless mode. The key will be changed every 256 packets
when you select Stateful mode. If you select Stateless mode, the key will be changed in each
packet.
Active as default route: Commonly used by the Dial-out connection which all packets will route
through the VPN tunnel to the Internet; therefore, active the function may degrade the Internet
performance.
Active: This function activates or deactivates the PPTP connection. Check Active checkbox if you
want the protocol of tunnel to be activated and vice versa.
Note: When the Active checkbox is checked, the function of Edit and Delete will not be
available.
&OLFN(GLW'HOHWHEXWWRQWRVDYH\RXUFKDQJHV
87
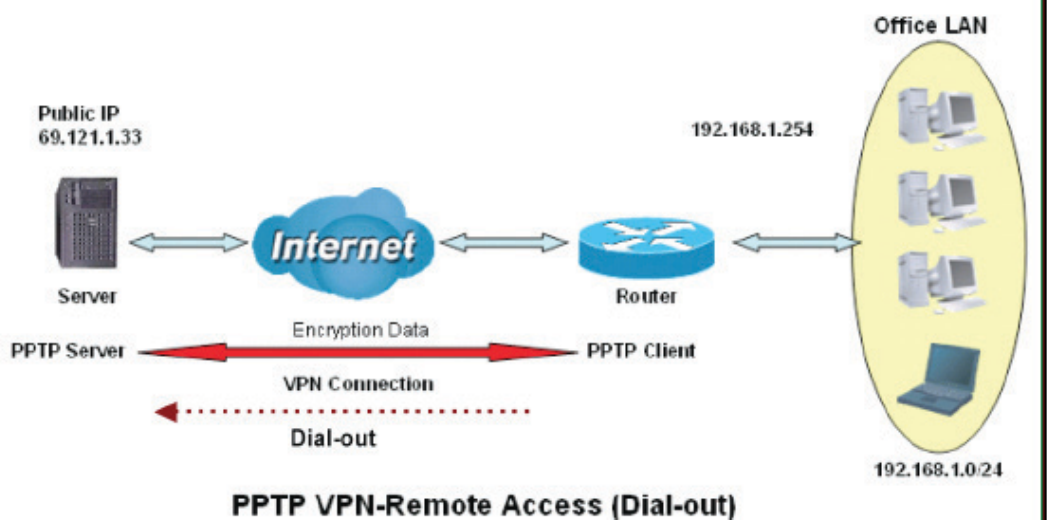
([DPSOH&RQ¿JXULQJD5HPRWH$FFHVV3373931'LDORXW&RQQHFWLRQ
$FRPSDQ\¶VRI¿FHHVWDEOLVKHVD3373931FRQQHFWLRQZLWKD¿OHVHUYHUORFDWHGDWDVHSDUDWH
ORFDWLRQ7KHURXWHULVLQVWDOOHGLQWKHRI¿FHFRQQHFWHGWRDFRXSOHRI3&VDQG6HUYHUV
88
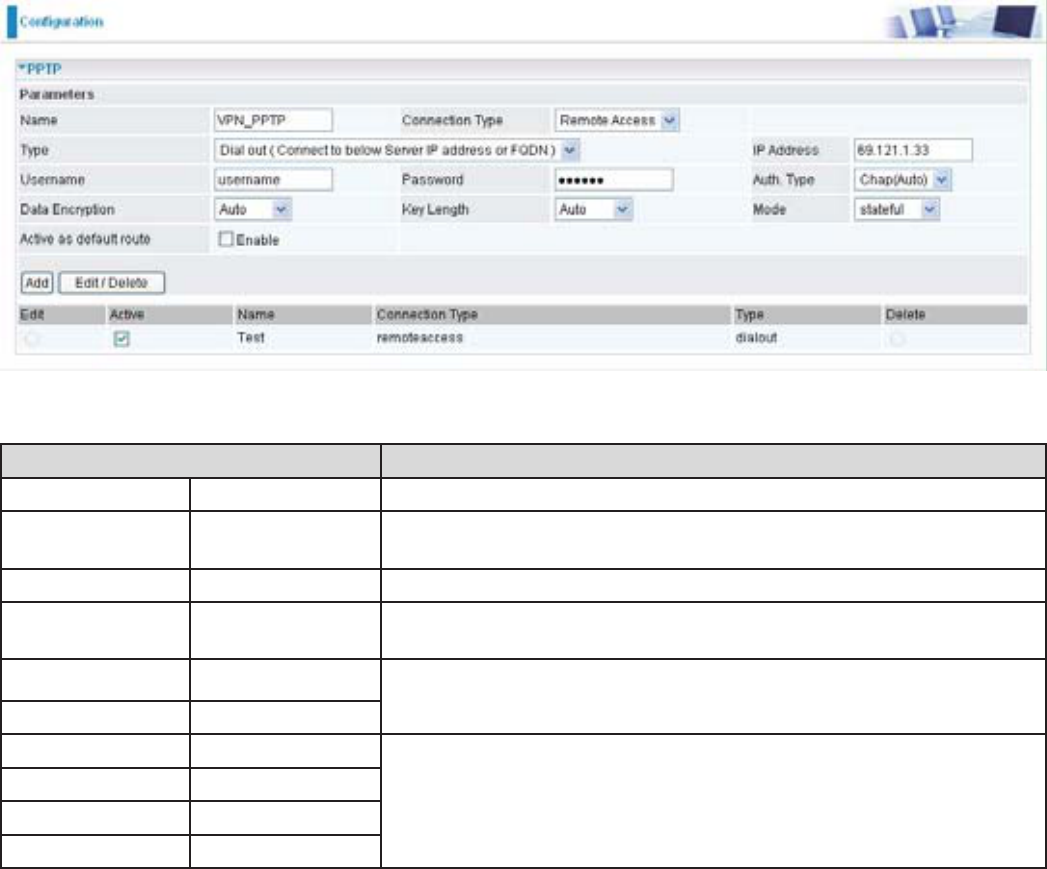
&RQ¿JXULQJWKH3373931LQWKH2I¿FH
&OLFN&RQ¿JXUDWLRQ9313373&KRRVH5HPRWH$FFHVVIURP&RQQHFW7\SHGURSGRZQPHQX<RX
can either input the IP address (69.1.121.33 in this case) or hostname to reach the server.
Function Description
Name VPN_PPTP Given name of PPTP connection
Connection
Type
Remote Access Select Remote Access from the Connection Type drop-down
menu
Type Dial out Select Dial out from the Type drop-down menu
IP Address (or
Domain name)
69.121.1.33 An Dialed server IP
Username Username A given username & password
Password 123456
Auth.Type Chap(Auto) .HHSDVGHIDXOWYDOXHLQPRVWRIWKHFDVHV3373VHUYHU
client will determine the value automatically. Refer to manual
for details if you want to change the setting.
Data Encryption Auto
.H\/HQJWK Auto
0RGH stateful
89
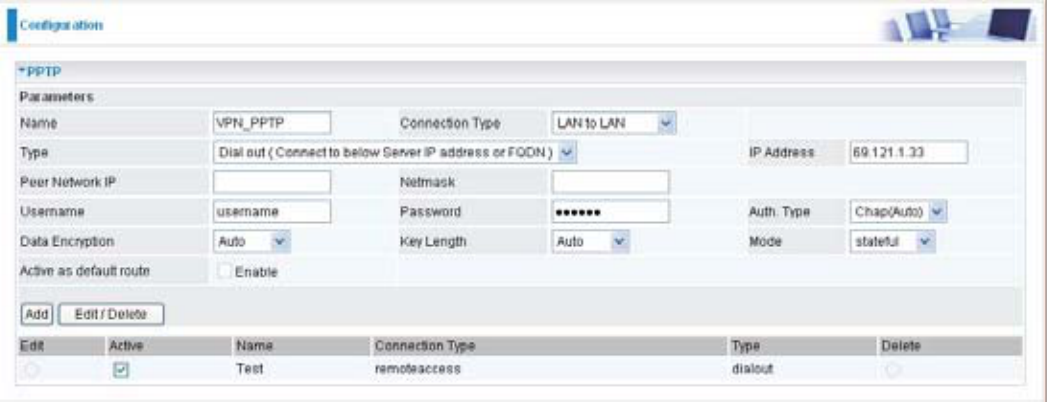
PPTP Connection - LAN to LAN
&OLFN&RQ¿JXUDWLRQ9313373&KRRVH/$1WR/$1IURP&RQQHFW7\SHGURSGRZQPHQX
Name: $JLYHQQDPHIRUWKHFRQQHFWLRQHJ³FRQQHFWLRQWRRI¿FH´
Connection Type: Remote Access or LAN to LAN.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote
931VHUYHUHJ\RXURI¿FHVHUYHUFKHFN'LDO,QRSHUDWHVDVD931VHUYHU
:KHQFRQ¿JXULQJ\RXUURXWHUDVD&OLHQWHQWHUWKHUHPRWH6HUYHU,3$GGUHVVRU'RPDLQ1DPH
you wish to connect to.
:KHQFRQ¿JXULQJ\RXUURXWHUDVDVHUYHUHQWHUWKH3ULYDWH,3$GGUHVVDVVLJQHGWRWKH'LDOLQ
User.
Peer Network IP: Enter Peer network IP address.
Netmask: Enter the subnet mask of peer network based on the Peer Network IP setting.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by your Host. If you are
a Dial-In user (server), enter your own password.
Authentication Type: Default is Auto if you want the router to determine the authentication type
to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or PAP
(Password Authentication Protocol) if you know which type the server is using (when acting as a
client), or else the authentication type you want clients connecting to you to use (when acting as a
VHUYHU:KHQXVLQJ3$3WKHSDVVZRUGLVVHQWXQHQFU\SWHGZKLOVW&+$3HQFU\SWVWKHSDVVZRUG
before sending, and also allows for challenges at different periods to ensure that an intruder has
not replaced the client.
Data Encryption: 'DWDVHQWRYHUWKH931FRQQHFWLRQFDQEHHQFU\SWHGE\DQ033(DOJRULWKP
Default is Auto, so that this setting is negotiated when establishing a connection, or else you can
manually Enable or Disable encryption.
Key Length: 7KHGDWDFDQEHHQFU\SWHGE\033(DOJRULWKPZLWKELWVRUELWV'HIDXOWLV
Auto, it is negotiated when establishing a connection. 128 bit keys provide stronger encryption
90
than 40 bit keys.
Mode: You may select Stateful or Stateless mode. The key will be changed every 256 packets
when you select Stateful mode. If you select Stateless mode, the key will be changed in each
packet.
Active as default route: Commonly used by the Dial-out connection which all packets will route
through the VPN tunnel to the Internet; therefore, active the function may degrade the Internet
performance.
Active: This function activates or deactivates the PPTP connection. Check Active checkbox if you
want the protocol of tunnel to be activated and vice versa.
Note: When the Active checkbox is checked, the function of Edit and Delete will not be
available.
&OLFN(GLW'HOHWHEXWWRQWRVDYH\RXUFKDQJHV
91
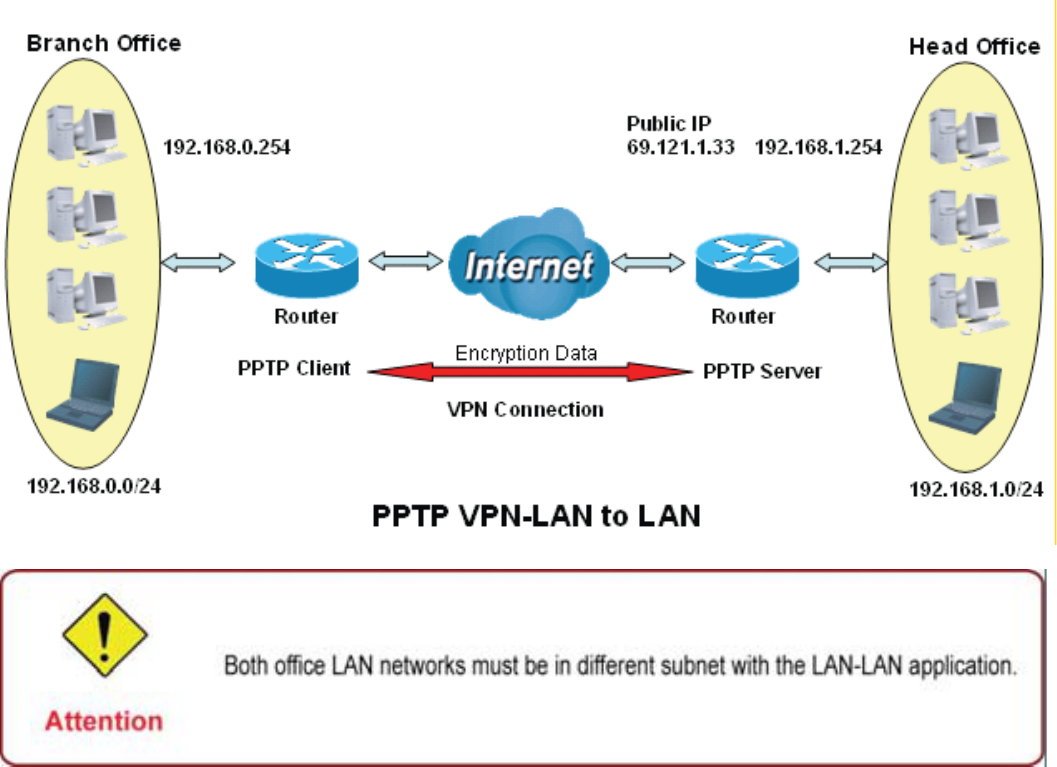
([DPSOH&RQ¿JXULQJD5HPRWH$FFHVV3373931'LDORXW&RQQHFWLRQ
7KHEUDQFKRI¿FHHVWDEOLVKHVD3373931WXQQHOZLWKKHDGRI¿FHWRFRQQHFWWZRSULYDWHQHWZRUNV
RYHUWKH,QWHUQHW7KHURXWHUVDUHLQVWDOOHGLQWKHKHDGRI¿FHDQGEUDQFKRI¿FHVDFFRUGLQJO\
92
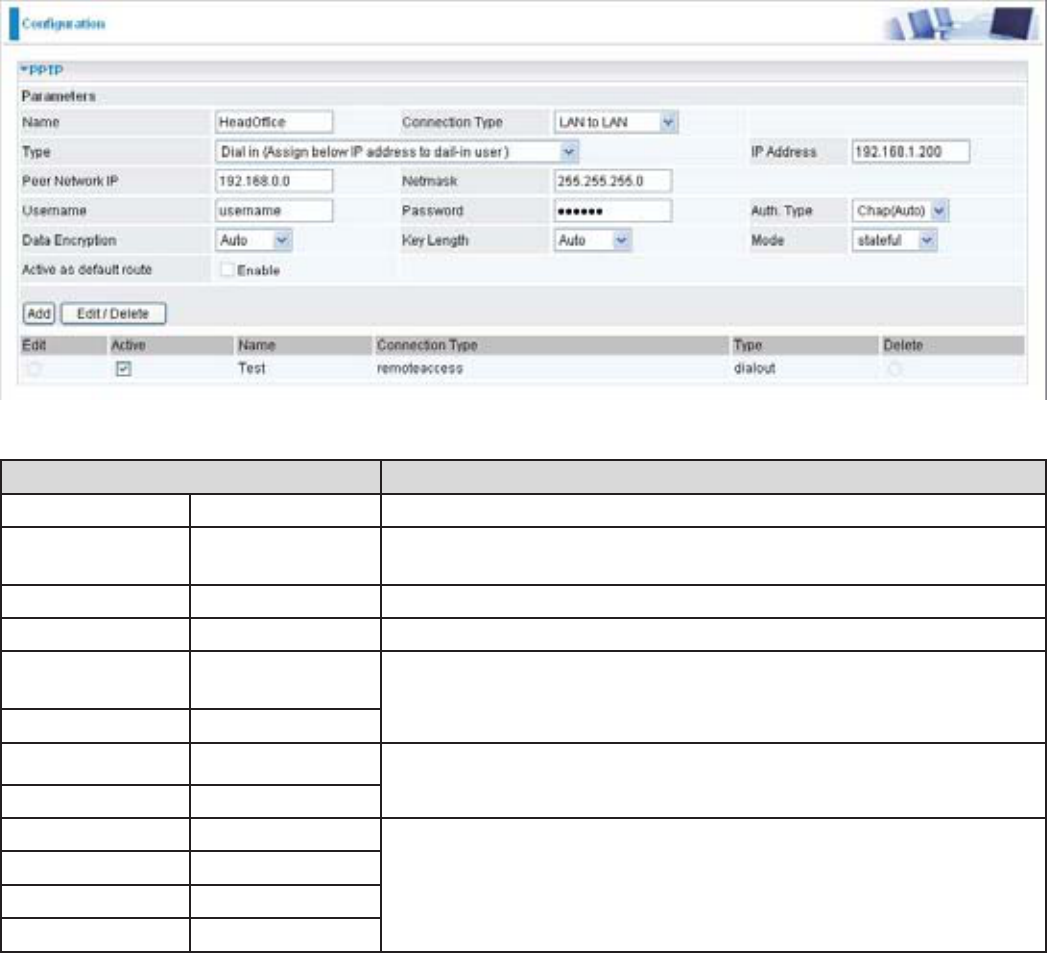
&RQ¿JXULQJWKH3373931LQWKH+HDG2I¿FH
7KH,3DGGUHVVZLOOEHDVVLJQHGWRWKHURXWHUORFDWHGLQWKHEUDQFKRI¿FH3OHDVH
PDNHVXUHWKLV,3LVQRWXVHGLQWKHKHDGRI¿FH/$1
Function Description
Name +HDG2I¿FH Given name of PPTP connection
Connection
Type
LAN to LAN Select LAN to LAN from the Connection Type drop-down
menu
Type Dial in Select Dial in from the Type drop-down menu
IP Address 192.168.1.200 ,3DGGUHVVDVVLJQHGWREUDQFKRI¿FHQHWZRUN
Peer Network
IP
192.168.0.0 %UDQFKRI¿FHQHWZRUN
Netmask 255.255.255.0
Username Username $JLYHQXVHUQDPHSDVVZRUGWRDXWKHQWLFDWHEUDQFKRI¿FH
network.
Password 123456
Auth.Type Chap(Auto) .HHSDVGHIDXOWYDOXHLQPRVWRIWKHFDVHV3373VHUYHU
client will determine the value automatically. Refer to manual
for details if you want to change the setting.
Data Encryption Auto
.H\/HQJWK Auto
0RGH stateful
93
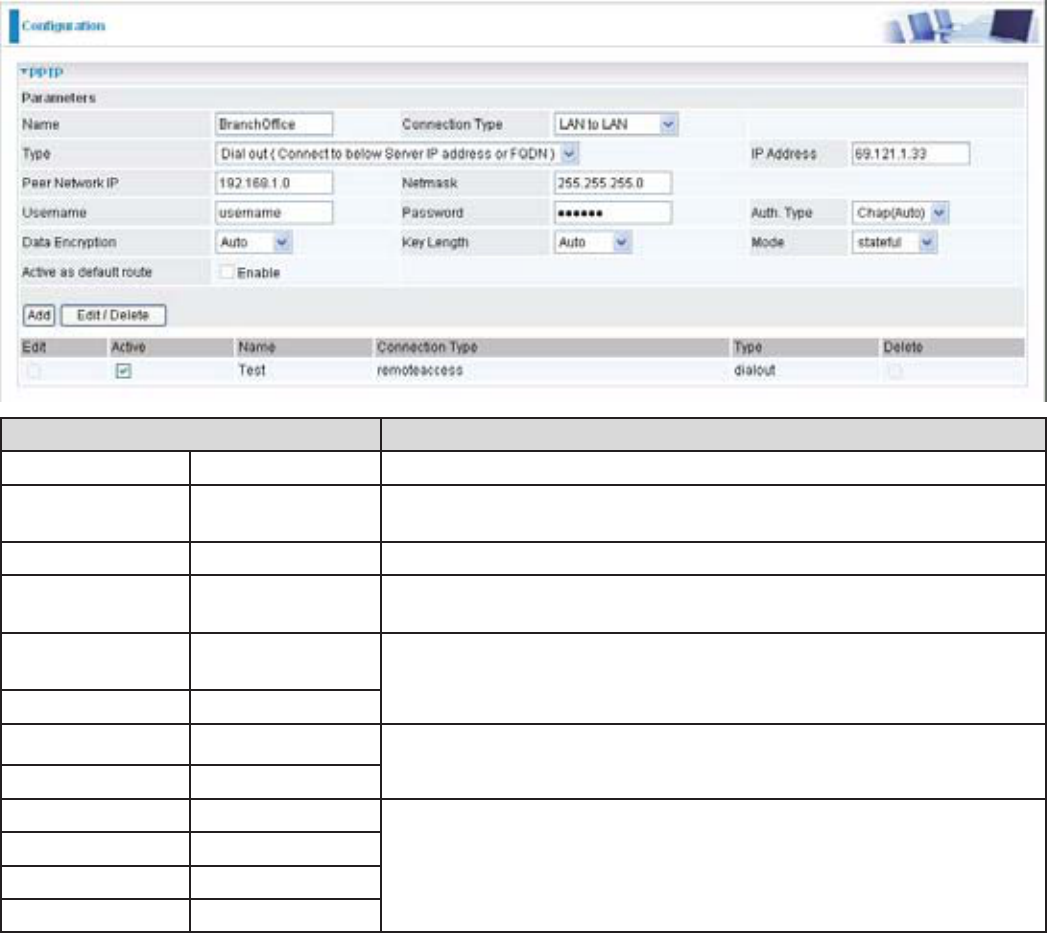
&RQ¿JXULQJWKH3373931LQWKH+HDG2I¿FH
7KH,3DGGUHVVLVWKH3XEOLF,3DGGUHVVRIWKHURXWHUORFDWHGLQKHDGRI¿FH,I\RX
registered the DDNS (please refer to the DDNS section of this manual), you can also use the
domain name instead of the IP address to reach the router.
Function Description
Name +HDG2I¿FH Given name of PPTP connection
Connection
Type
LAN to LAN Select LAN to LAN from the Connection Type drop-down
menu
Type Dial out Select Dial out from the Type drop-down menu
IP Address (or
Domain Name)
69.121.1.33 ,3DGGUHVVDVVLJQHGWREUDQFKRI¿FHQHWZRUN
Peer Network
IP
192.168.1.0 +HDGRI¿FHQHWZRUN
Netmask 255.255.255.0
Username Username $JLYHQXVHUQDPHSDVVZRUGWRDXWKHQWLFDWHEUDQFKRI¿FH
network.
Password 123456
Auth.Type Chap(Auto) .HHSDVGHIDXOWYDOXHLQPRVWRIWKHFDVHV3373VHUYHU
client will determine the value automatically. Refer to manual
for details if you want to change the setting.
Data Encryption Auto
.H\/HQJWK Auto
0RGH stateful
94
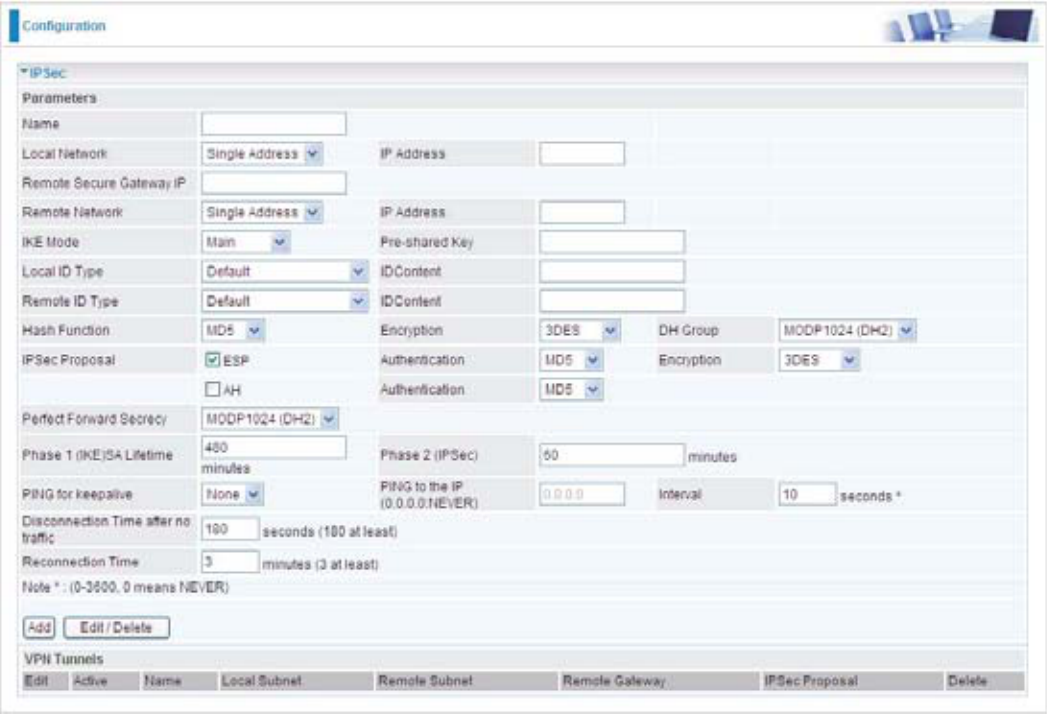
IPSec (IP Security Protocol)
Active: This function activates or deactivates the IPSec connection. Check Active checkbox if you
want the protocol of tunnel to be activated and vice versa.
Note: When the Active checkbox is checked, the function of Edit and Delete will not be
available.
Name: This is a given name of the connection.
Local Subnet: Displays IP address and subnet of the local network.
Remote Subnet: Displays IP address and subnet of the remote network.
Remote Gateway: This is the IP address or Domain Name of the remote VPN device that is
connected and established a VPN tunnel.
IPSec Proposal: This is selected IPSec security method.
95
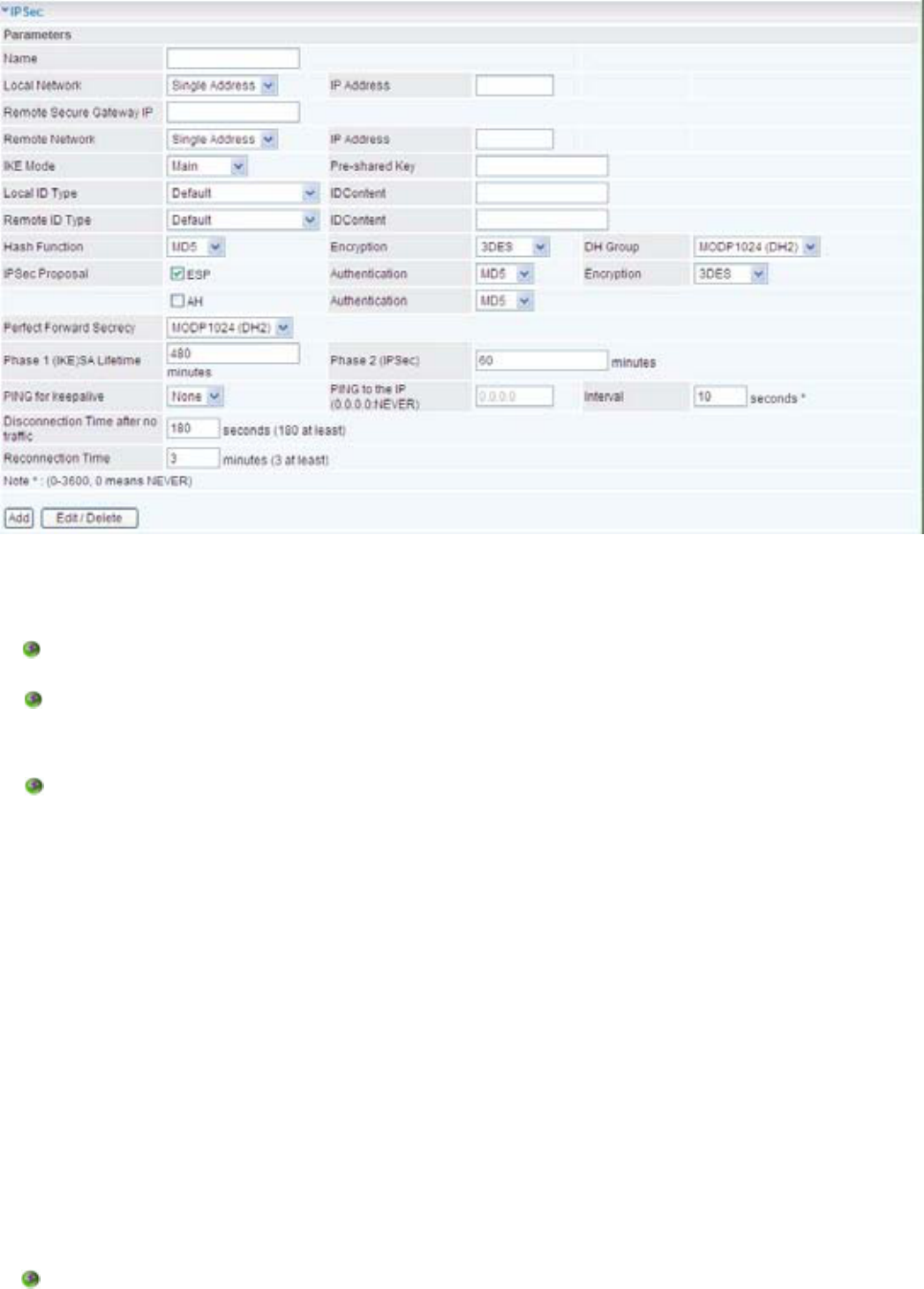
IPSec VPN Connection
Name:$JLYHQQDPHIRUWKHFRQQHFWLRQHJ³FRQQHFWLRQWRRI¿FH´
Local Network: Set the IP address, subnet or address range of the local network.
Single Address: The IP address of the local host.
Subnet: The subnet of the local network. For example, IP: 192.168.1.0 with netmask
VSHFL¿HVRQHFODVV&VXEQHWVWDUWLQJIURPLHWKURXJK
to 192.168.1.254).
IP Range: The IP address range of the local network. For example, IP: 192.168.1.1, end IP:
192.168.1.10.
Remote Secure Gateway Address (or Domain Name): The IP address or hostname of the
remote VPN device that is connected and establishes a VPN tunnel.
Remote Network: Set the IP address, subnet or address range of the remote network.
IKE (Internet key Exchange) Mode:6HOHFW,.(PRGHWR0DLQPRGHRU$JJUHVVLYHPRGH7KLV
,.(SURYLGHVVHFXUHGNH\JHQHUDWLRQDQGNH\PDQDJHPHQW
Pre-shared Key:7KLVLVIRUWKH,QWHUQHW.H\([FKDQJH,.(SURWRFRODVWULQJIURPWR
FKDUDFWHUV%RWKVLGHVVKRXOGXVHWKHVDPHNH\,.(LVXVHGWRHVWDEOLVKDVKDUHGVHFXULW\SROLF\
DQGDXWKHQWLFDWHGNH\VIRUVHUYLFHVVXFKDV,36HFWKDWUHTXLUHDNH\%HIRUHDQ\,36HFWUDI¿F
can be passed, each router must be able to verify the identity of its peer. This can be done by
manually entering the pre-shared key into both sides (router or hosts).
Local ID:
Content: Input ,'¶VLQIRUPDWLRQOLNHGRPDLQQDPHwww.ipsectest.com.
96

Remote ID:
,GHQWL¿HU,QSXWUHPRWH,'¶VLQIRUPDWLRQOLNHGRPDLQQDPHZZZLSVHFWHVWFRP
Hash Function: ,WLVD0HVVDJH'LJHVWDOJRULWKPZKLFKFRYHUWVDQ\OHQJWKRIDPHVVDJHLQWRD
XQLTXHVHWRIELWV,WLVZLGHO\XVHG0'0HVVDJH'LJHVWDQG6+$6HFXUH+DVK$OJRULWKP
DOJRULWKPV6+$LVPRUHUHVLVWDQWWREUXWHIRUFHDWWDFNVWKDQ0'KRZHYHULWLVVORZHU
MD5: $RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
SHA1:$RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
Encryption: Select the encryption method from the pull-down menu. There are several options,
DES, 3DES and AES (128, 192 and 256). 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as en-
cryption method.
'LI¿H+HOOPDQ*URXSIt is a public-key cryptography protocol that allows two parties to establish
a shared secret over an unsecured communication channel (i.e. over the Internet). There are
WKUHHPRGHV02'3ELW02'3ELWDQG02'3ELW02'3VWDQGVIRU0RGXODU
Exponentiation Groups.
IPSec Proposal: Select the IPSec security method. There are two methods of checking the
authentication information, AH (authentication header) and ESP (Encapsulating Security Payload).
Use ESP for greater security so that data will be encrypted and authenticated. Using AH data will
be authenticated but not encrypted.
Authentication: Authentication establishes the integrity of the datagram and ensures it is not
WDPSHUHGZLWKLQWUDQVPLW7KHUHDUHWKUHHRSWLRQV0HVVDJH'LJHVW0'6HFXUH+DVK
$OJRULWKP6+$RU121(6+$LVPRUHUHVLVWDQWWREUXWHIRUFHDWWDFNVWKDQ0'KRZHYHULWLV
slower.
MD5: $RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
SHA1:$RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
Encryption: Select the encryption method from the pull-down menu. There are several options,
DES, 3DES, AES (128, 192 and 256) and NULL. NULL means it is a tunnel only with no
encryption. 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as en-
cryption method.
Perfect Forward Secrecy: &KRRVHZKHWKHUWRHQDEOH3)6XVLQJ'LI¿H+HOOPDQSXEOLFNH\
cryptography to change encryption keys during the second phase of VPN negotiation. This
function cryptography protocol that allows two parties to establish a shared secret over an
97
XQVHFXUHGFRPPXQLFDWLRQFKDQQHOLHRYHUWKH,QWHUQHW7KHUHDUHWKUHHPRGHV02'3ELW
02'3ELWDQG02'3ELW02'3VWDQGVIRU0RGXODU([SRQHQWLDWLRQ*URXSV
SA Lifetime: Specify the number of minutes that a Security Association (SA) will stay active
EHIRUHQHZHQFU\SWLRQDQGDXWKHQWLFDWLRQNH\ZLOOEHH[FKDQJHG7KHUHDUHWZRNLQGVRI6$V,.(
DQG,36HF,.(QHJRWLDWHVDQGHVWDEOLVKHV6$RQEHKDOIRI,36HFDQ,.(6$LVXVHGE\,.(
Phase 1 (IKE):7RLVVXHDQLQLWLDOFRQQHFWLRQUHTXHVWIRUDQHZ931WXQQHO7KHUDQJHFDQ
be from 5 to 15,000 minutes, and the default is 480 minutes.
Phase 2 (IPSec): To negotiate and establish secure authentication. The range can be from 5
to 15,000 minutes, and the default is 60 minutes.
A short SA time increases security by forcing the two parties to update the keys. However, every
time the VPN tunnel re-negotiates, access through the tunnel will be temporarily disconnected.
PING for Keep Alive:
None: The default setting is None. To this mode, it will not detect the remote IPSec peer has
EHHQORVWRUQRW,WRQO\IROORZVWKHSROLF\RI'LVFRQQHFWLRQWLPHDIWHUQRWUDI¿FZKLFKWKHUH-
mote IPSec will be disconnected afther the time you set in this function.
PING: This mode will detect the remote IPSec peer has lost or not by pinging specify IP ad-
dress.
DPD: Dead peer detection (DPD) is a keeping alive mechanism that enables the router to be
detected lively when the connection between the router and a remote IPSec peer has lost.
Please be noted, it must be enabled on the both sites.
PING to the IP:,WLVDEOHWR,33LQJWKHUHPRWH3&ZLWKWKHVSHFL¿HG,3DGGUHVVDQGDOHUWZKHQ
the connection fails. Once alter message is received, Router will drop this tunnel connection.
5HHVWDEOLVKRIWKLVFRQQHFWLRQLVUHTXLUHG'HIDXOWVHWWLQJLVZKLFKGLVDEOHVWKHIXQFWLRQ
Interval: This sets the time interval between Pings to the IP function to monitor the connection
status. Default interval setting is 10 seconds. Time interval can be set from 0 to 3600 second, 0
second disables the function.
Ping to the IP Interval (sec) Ping to the IP Action
0.0.0.0 0 No
0.0.0.0 2000 No
xxx.xxx.xxx.xxx (A valid IP Address) 0 No
xxx.xxx.xxx.xxx(A valid IP Address) 2000 Yes, activate it in every 2000
second.
'LVFRQQHFWLRQ7LPHDIWHUQRWUDI¿F,WLVWKH125HVSRQVHWLPHFORFN:KHQQRWUDI¿FVWDJH
time is beyond the Disconnection time set, Router will automatically halt the tunnel connection and
re-establish it base on the Reconnection Time set. 180 seconds is minimum time interval for this
function.
Reconnection Time: It is the reconnecting time interval after NO TRAFFIC is initiated. 3 minutes
is minimum time interval for this function.
&OLFN(GLW'HOHWHWRVDYH\RXUFKDQJHV
98
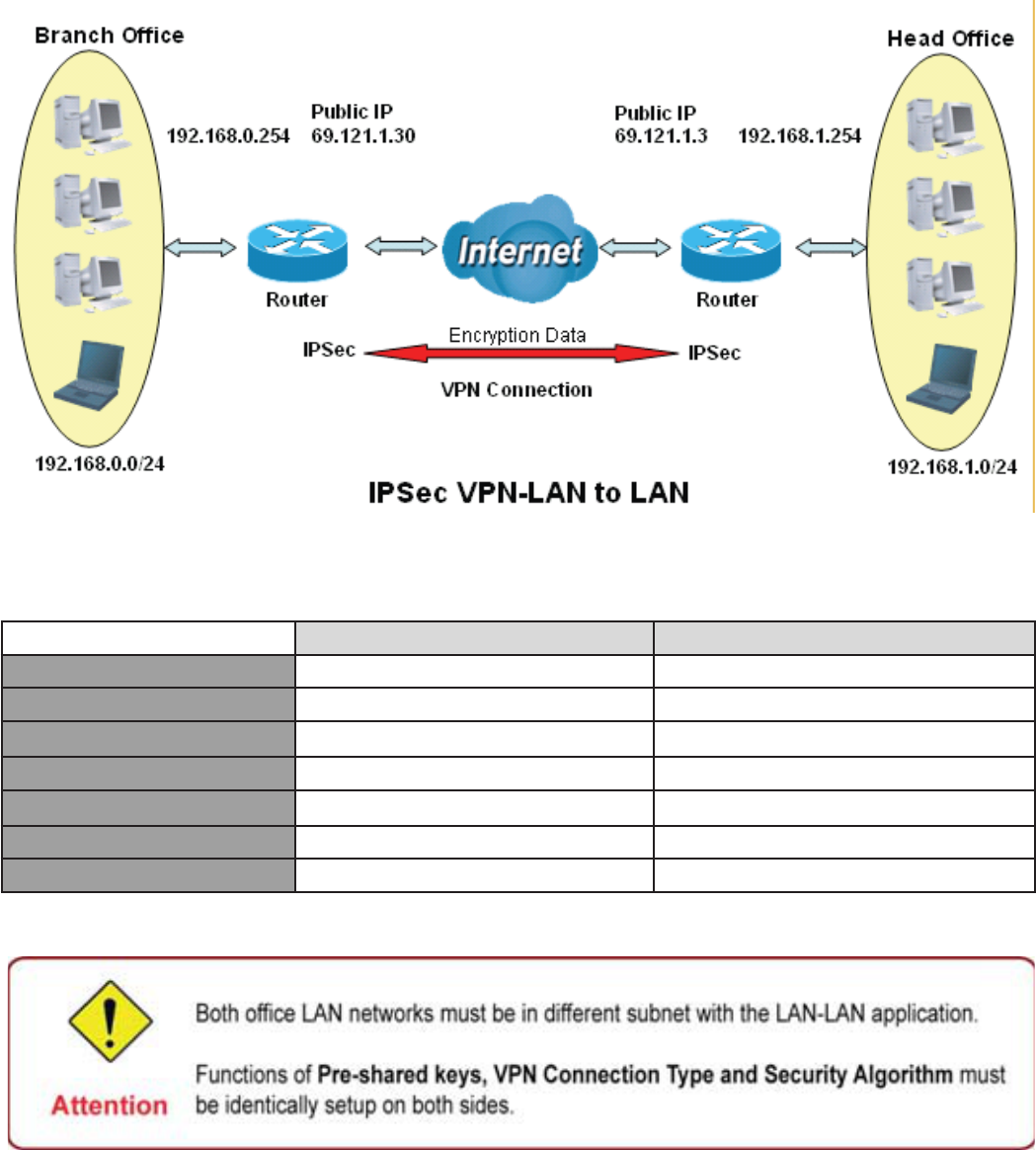
([DPSOH&RQ¿JXULQJDQ,36HF/$1WR/$1931&RQQHFWLRQ
7DEOH1HWZRUN&RQ¿JXUDWLRQDQG6HFXULW\3ODQ
%UDQFK2I¿FH +HDG2I¿FH
Local Network ID
Local Router IP 69.1.121.30 69.1.121.3
Remote Network ID
Remote Router IP 69.1.121.3 69.1.121.30
IKE Pre-shared Key 12345678 12345678
VPN Connection Type Tunnel mode Tunnel mode
Security Algorithm (630'ZLWK$(6 (630'ZLWK$(6
99
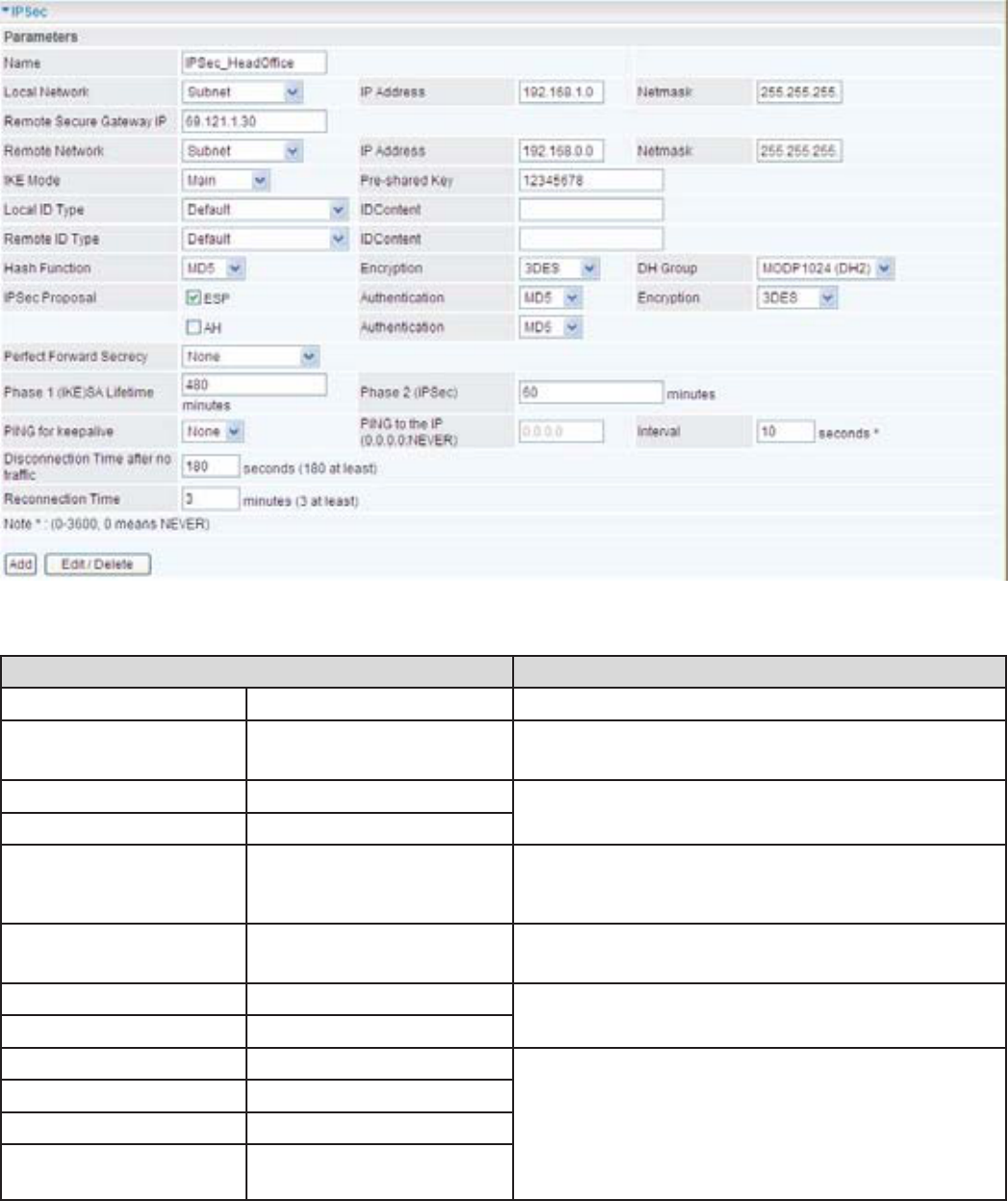
&RQ¿JXULQJ,36HF931LQWKH+HDG2I¿FH
Function Description
Name ,36HFB+HDG2I¿FH Give a name of IPSec Connection
Local Network Subnet Select Subnet from Local Network drop-down
menu.
IP Address 192.168.1.0 +HDGRI¿FHQHWZRUN
Netmask 255.255.255.0
Remote Secure
Gateway IP (or
Hostname)
69.121.1.30 ,3DGGUHVVRIWKHKHDGRI¿FHURXWHULQ:$1
side)
Remote Network Subnet Select Subnet from Remote Network drop-
down menu
IP Address 192.168.0.0 %UDQFKRI¿FHQHWZRUN
Netmask 255.255.255.0
3UHVKDUHG.H\ 12345678 Security plan
Authentication 0'
Encryption 3DES
Prefer Forward
Security
None
100
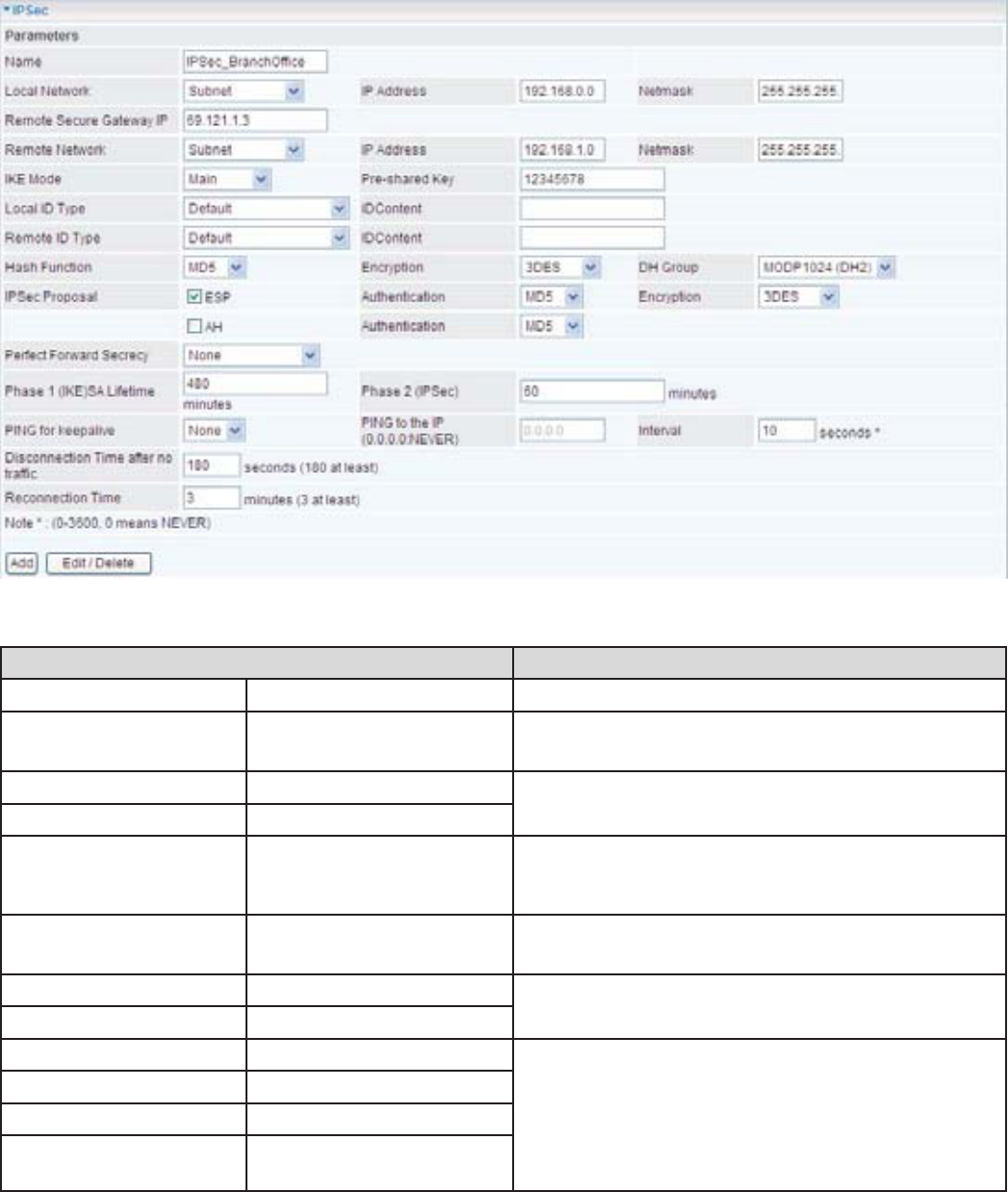
&RQ¿JXULQJ,36HF931LQWKH%UDQFK2I¿FH
Function Description
Name ,36HFB%UDQFK2I¿FH Give a name of IPSec Connection
Local Network Subnet Select Subnet from Local Network drop-down
menu.
IP Address 192.168.0.0 %UDQFKRI¿FHQHWZRUN
Netmask 255.255.255.0
Remote Secure
Gateway IP (or
Hostname)
69.121.1.3 ,3DGGUHVVRIWKHKHDGRI¿FHURXWHULQ:$1
side)
Remote Network Subnet Select Subnet from Remote Network drop-
down menu
IP Address 192.168.1.0 +HDGRI¿FHQHWZRUN
Netmask 255.255.255.0
3UHVKDUHG.H\ 12345678 Security plan
Authentication 0'
Encryption 3DES
Prefer Forward
Security
None
101
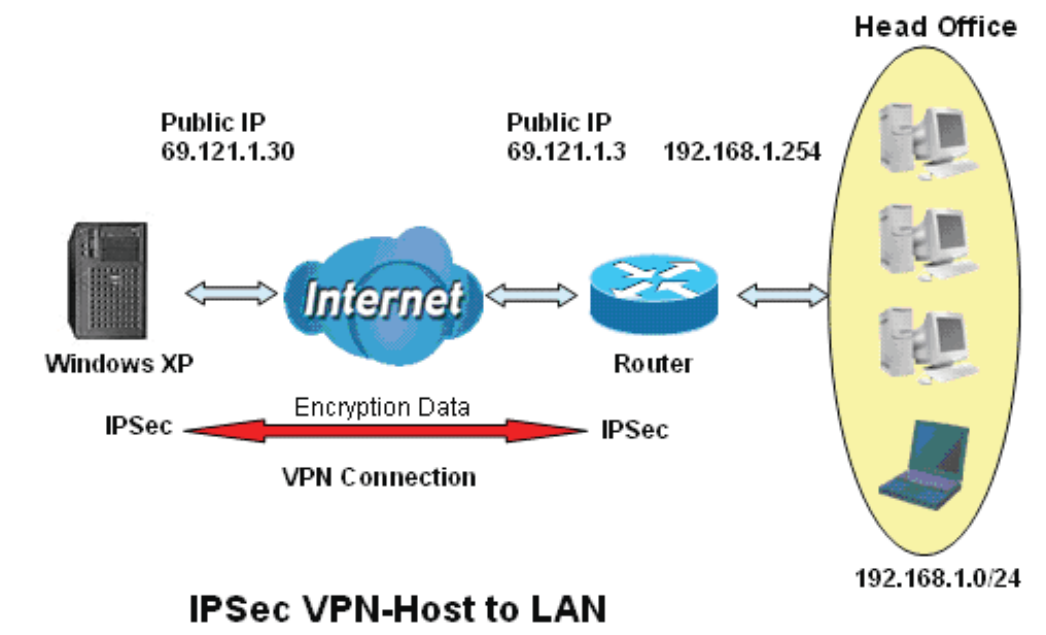
([DPSOH&RQ¿JXULQJDQ,36HF+RVWWR/$1931&RQQHFWLRQ
102
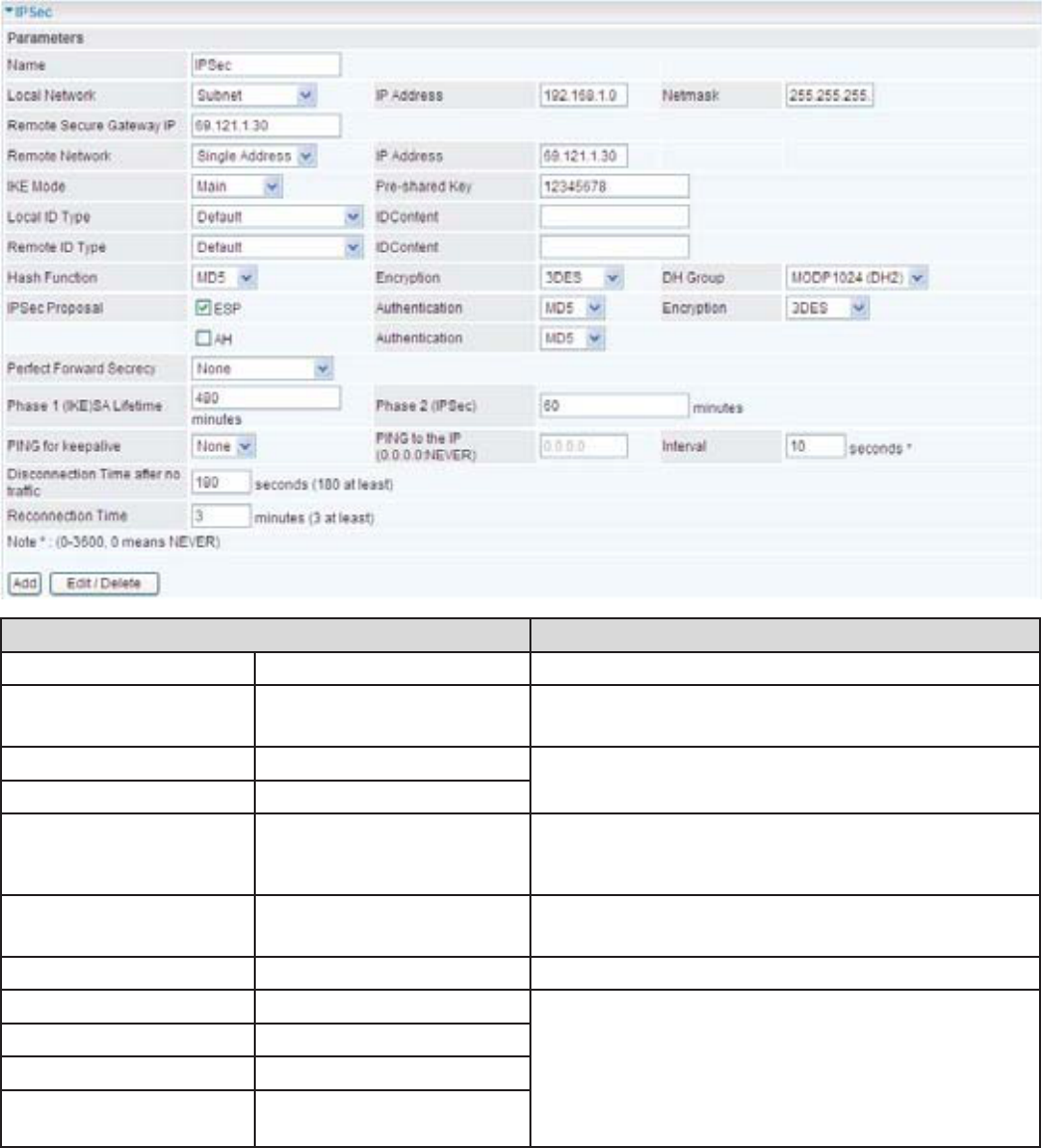
&RQ¿JXULQJ,36HF931LQWKH2I¿FH
Function Description
Name IPSec Give a name of IPSec Connection
Local Network Subnet Select Subnet from Local Network drop-down
menu.
IP Address 192.168.1.0 +HDGRI¿FHQHWZRUN
Netmask 255.255.255.0
Remote Secure
Gateway IP (or
Hostname)
69.121.1.30 ,3DGGUHVVRIWKHKHDGRI¿FHURXWHULQ:$1
side)
Remote Network Single Address Select Single Address from Remote Network
drop-down menu
IP Address 69.121.1.30 Remote worker's IP address
3UHVKDUHG.H\ 12345678 Security plan
Authentication 0'
Encryption 3DES
Prefer Forward
Security
None
103
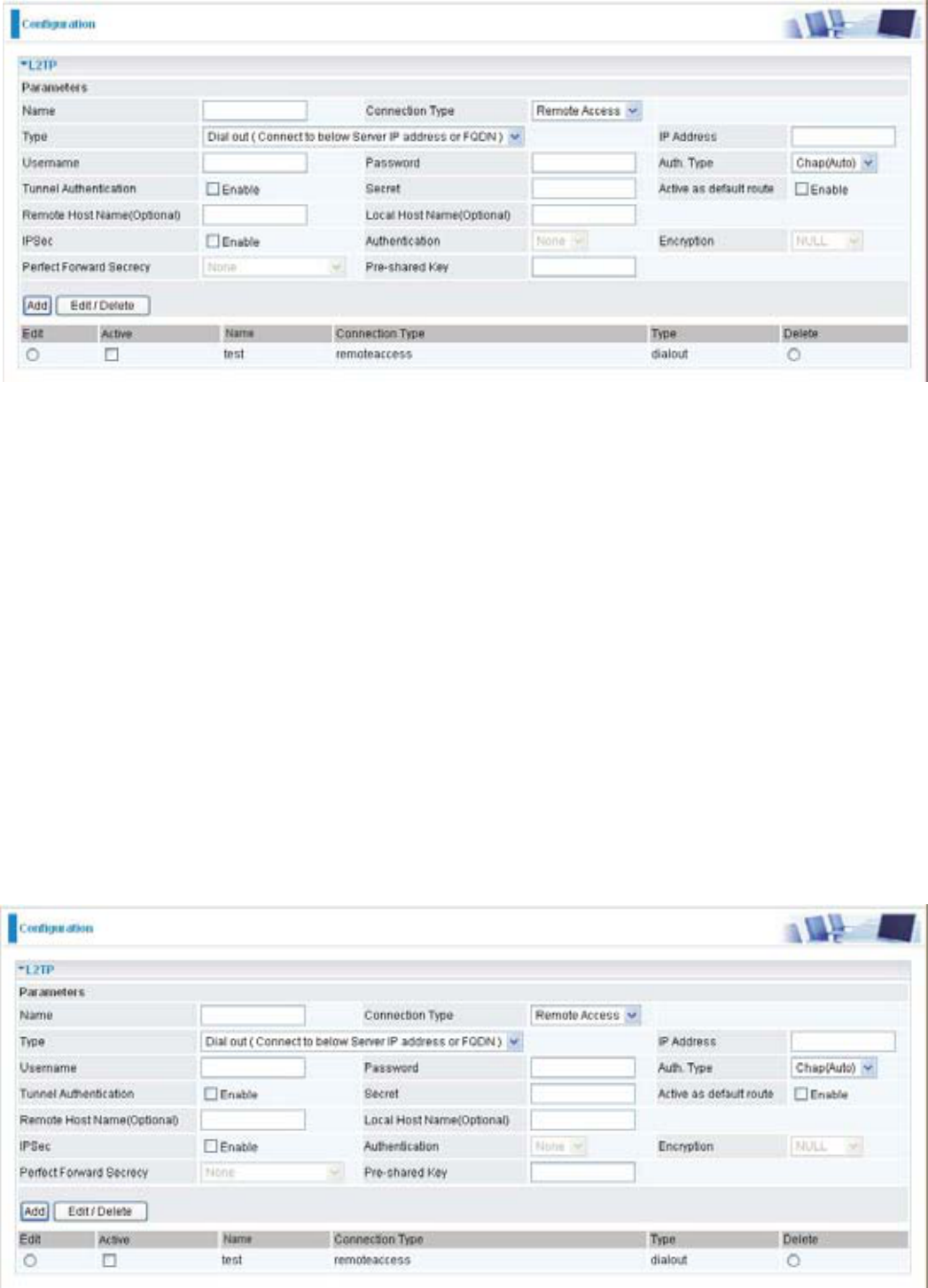
L2TP (Layer Two Tunneling Protocol)
Two types of L2TP VPN are supported Remote Access and LAN-to-LAN (please refer below for
more information.). Fill in the blank with information you need and click Add to create a new VPN
connection account.
Active: This function activates or deactivates the PPTP connection. Check Active checkbox if you
want the protocol of tunnel to be activated and vice versa.
Note: When the Active checkbox is checked, the function of Edit and Delete will not be
available.
Name: This is a given name of the connection.
Connection Type: Displays the condition of your L2TP tunneling connection.
Type: This refers to your router whether it operates as a client or a server, Dial-out or Dial-in
respectively.
L2TP Connection-Remote Access
104

Connection Type: Remote Access or LAN to LAN
Name:$JLYHQQDPHIRUWKHFRQQHFWLRQHJ³FRQQHFWLRQWRRI¿FH´
Connection Type: Remote Access or LAN to LAN.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote VPN
VHUYHUHJ\RXURI¿FHVHUYHUFKHFN'LDO,QRSHUDWHVDVD931VHUYHU
:KHQFRQ¿JXULQJ\RXUURXWHUDVD&OLHQWHQWHUWKHUHPRWH6HUYHU,3$GGUHVVRU+RVWQDPH\RX
wish to connect to.
:KHQFRQ¿JXULQJ\RXUURXWHUDVDVHUYHUHQWHUWKH3ULYDWH,3$GGUHVV$VVLJQHGWRWKH'LDOLQ
User.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by your Host. If you are
a Dial-In user (server), enter your own password.
Authentication Type: Default is Auto if you want the router to determine the authentication type
to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or PAP
(Password Authentication Protocol) if you know which type the server is using (when acting as a
client), or else the authentication type you want clients connecting to you to use (when acting as a
VHUYHU:KHQXVLQJ3$3WKHSDVVZRUGLVVHQWXQHQFU\SWHGZKLOVW&+$3HQFU\SWVWKHSDVVZRUG
before sending, and also allows for challenges at different periods to ensure that an intruder has
not replaced the client.
Tunnel Authentication: This enables router to authenticate both the L2TP remote and L2TP host.
This is only valid when L2TP remote supports this feature.
Secret: The secure password length should be 16 characters which may include numbers and
characters.
Active as default route: Commonly used by the Dial-out connection which all packets will route
through the VPN tunnel to the Internet; therefore, active the function may degrade the Internet
performance.
Remote Host Name (Optional):(QWHUKRVWQDPHRIUHPRWH931GHYLFH,WLVDWXQQHOLGHQWL¿HU
from the Remote VPN device matches with the Remote hostname provided. If remote hostname
matches, tunnel will be connected; otherwise, it will be dropped.
Cautious: This is only when the router performs as a VPN server. This option should be
used by advanced users only.
Local Host 1DPH2SWLRQDO(QWHUKRVWQDPHRI/RFDO931GHYLFHWKDWLVFRQQHFWHGHVWDEOLVKHV
D931WXQQHO$VGHIDXOW5RXWHU¶VGHIDXOW+RVWQDPHLVhome.gateway.
IPSec: Enable for enhancing your L2TP VPN security.
Authentication: Authentication establishes the integrity of the datagram and ensures it is not
WDPSHUHGZLWKLQWUDQVPLW7KHUHDUHWKUHHRSWLRQV0HVVDJH'LJHVW0'6HFXUH+DVK
$OJRULWKP6+$RU121(6+$LVPRUHUHVLVWDQWWREUXWHIRUFHDWWDFNVWKDQ0'KRZHYHULWLV
slower.
MD5:$RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
105

SHA1: $RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
Encryption: Select the encryption method from the pull-down menu. There are four options, DES,
3DES, AES and NULL. NULL means it is a tunnel only with no encryption. 3DES and AES are
more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES: Stands for Advanced Encryption Standards, it uses 128 bits as an encryption method.
Perfect Forward Secrecy: &KRRVHZKHWKHUWRHQDEOH3)6XVLQJ'LI¿H+HOOPDQSXEOLFNH\
cryptography to change encryption keys during the second phase of VPN negotiation. This
IXQFWLRQZLOOSURYLGHEHWWHUVHFXULW\EXWH[WHQGVWKH931QHJRWLDWLRQWLPH'LI¿H+HOOPDQLVD
public-key cryptography protocol that allows two parties to establish a shared secret over an
XQVHFXUHGFRPPXQLFDWLRQFKDQQHOLHRYHUWKH,QWHUQHW7KHUHDUHWKUHHPRGHV02'3ELW
02'3ELWDQG02'3ELW02'3VWDQGVIRU0RGXODU([SRQHQWLDWLRQ*URXSV
Pre-shared Key:7KLVLVIRUWKH,QWHUQHW.H\([FKDQJH,.(SURWRFRODVWULQJIURPWR
FKDUDFWHUV%RWKVLGHVVKRXOGXVHWKHVDPHNH\,.(LVXVHGWRHVWDEOLVKDVKDUHGVHFXULW\SROLF\
DQGDXWKHQWLFDWHGNH\VIRUVHUYLFHVVXFKDV,36HFWKDWUHTXLUHDNH\%HIRUHDQ\,36HFWUDI¿F
can be passed, each router must be able to verify the identity of its peer. This can be done by
manually entering the pre-shared key into both sides (router or hosts).
&OLFN(GLW'HOHWHWRVDYH\RXUFKDQJHV
106
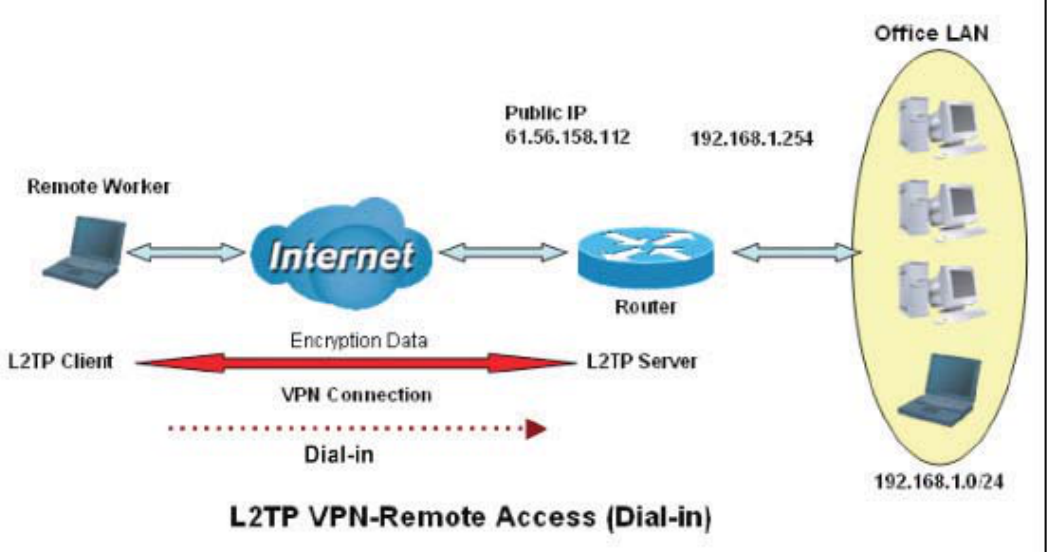
([DPSOH&RQ¿JXULQJD/739315HPRWH$FFHVV'LDOLQ&RQQHFWLRQ
$UHPRWHZRUNHUHVWDEOLVKHVD/73931FRQQHFWLRQZLWKWKHKHDGRI¿FHXVLQJ0LFURVRIWV931
$GDSWHULQFOXGHGZLWK:LQGRZV;30(HWF7KHURXWHULVLQVWDOOHGLQWKHKHDGRI¿FH
connected to a couple of PCs and Servers.
107
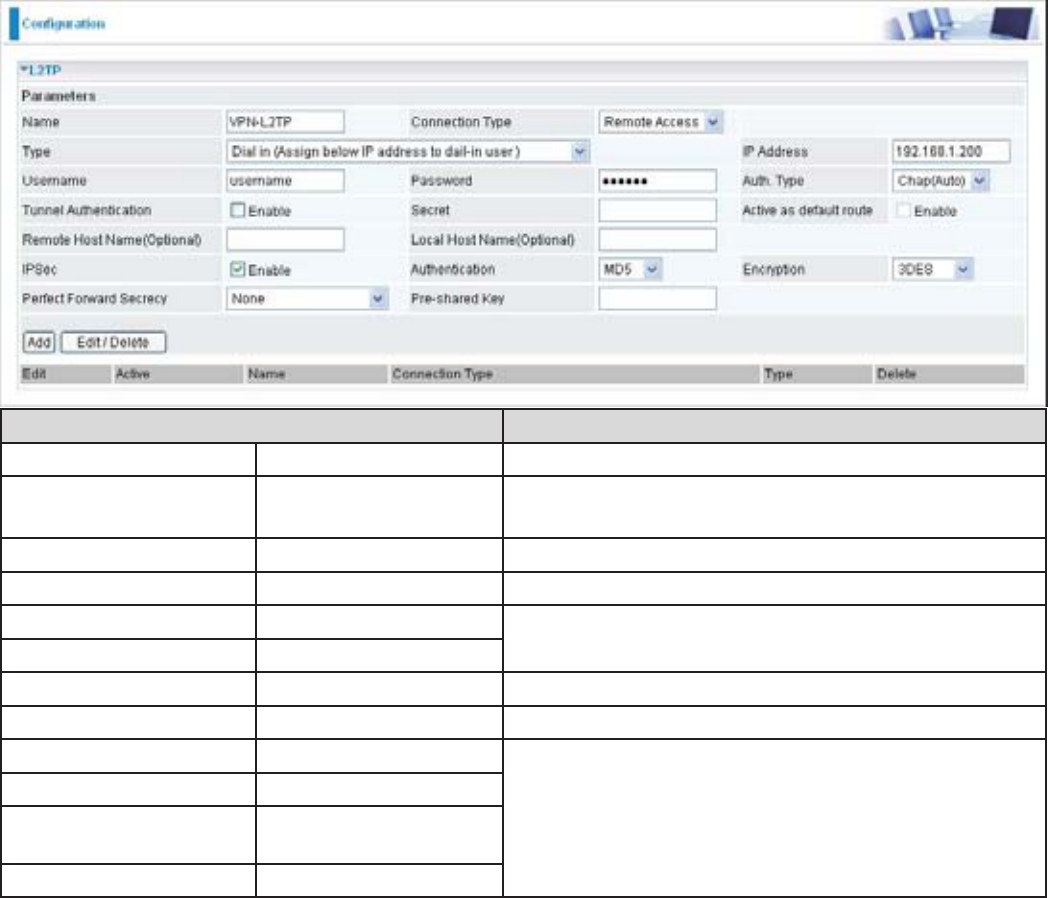
&RQ¿JXULQJ/73931LQWKH2I¿FH
The input IP address 192.168.1.200 will be assigned to the remote worker. Please make sure this
,3LVQRWXVHGLQWKH2I¿FH/$1
Function Description
Name VPN_L2TP Give a name of L2TP Connection
Connection Type Remote Access Select Remote Access from the Connection Type
drop-down menu
Type Dial in Select Dial in from the Type drop down menu
IP Address 192.168.1.200 An IP assigned to the remote client
Username username Enter the username and password to
authenticate a remote client
Password 123456
Auth. Type Chap (Auto) .HHSWKLVDVWKHGHIDXOWYDOXHIRUPRVWFDVHV
IPSec Enable Enable this to enhance your L2TP VPN security
Authentication 0' %RWKVLGHVVKRXOGXVHWKHVDPHYDOXH
Encryption 3DES
Perfect Forward
Secrecy
None
3UH6KDUHG.H\ 12345678
108
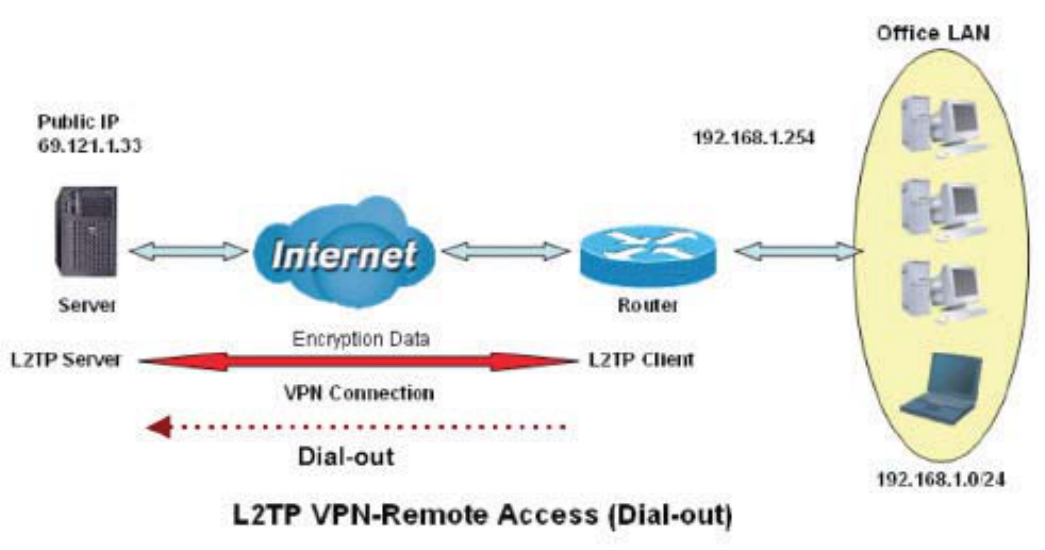
([DPSOH&RQ¿JXULQJD5HPRWH$FFHVV/73931'LDORXW&RQQHFWLRQ
$FRPSDQ\¶VRI¿FHHVWDEOLVKHVD/73931FRQQHFWLRQZLWKD¿OHVHUYHUORFDWHGDWDVHSDUDWH
ORFDWLRQ7KHURXWHULVLQVWDOOHGLQWKHRI¿FHFRQQHFWHGWRDFRXSOHRI3&VDQG6HUYHUV
109
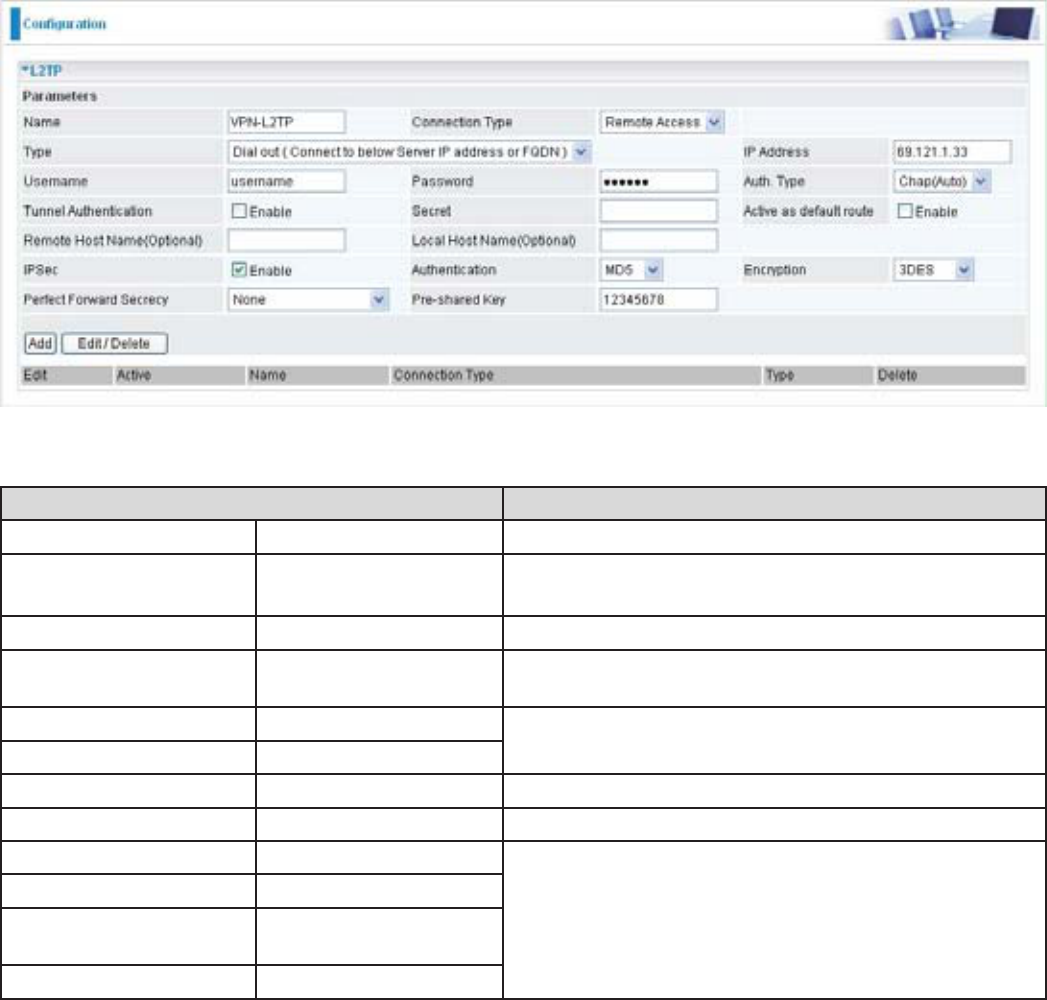
&RQ¿JXULQJ/73931LQWKH2I¿FH
The input IP address 192.168.1.200 will be assigned to the remote worker. Please make sure this
,3LVQRWXVHGLQWKH2I¿FH/$1
Function Description
Name VPN_L2TP Give a name of L2TP Connection
Connection Type Remote Access Select Remote Access from the Connection Type
drop-down menu
Type Dial out Select Dial out from the Type drop down menu
IP Address (or
Hostname)
69.121.1.33 A Dialed Server IP
Username username An assigned username and password
Password 123456
Auth. Type Chap (Auto) .HHSWKLVDVWKHGHIDXOWYDOXHIRUPRVWFDVHV
IPSec Enable Enable this to enhance your L2TP VPN security
Authentication 0' %RWKVLGHVVKRXOGXVHWKHVDPHYDOXH
Encryption 3DES
Perfect Forward
Secrecy
None
3UH6KDUHG.H\ 12345678
([DPSOH&RQ¿JXULQJ\RXU5RXWHUWR'LDOLQWRWKH6HUYHU
&XUUHQWO\0LFURVRIW:LQGRZVRSHUDWLRQV\VWHPGRHVQRWVXSSRUW/73LQFRPLQJVHUYLFH
$GGLWLRQDOVRIWZDUHPD\EHUHTXLUHGWRVHWXS\RXU/73LQFRPLQJVHUYLFH
110
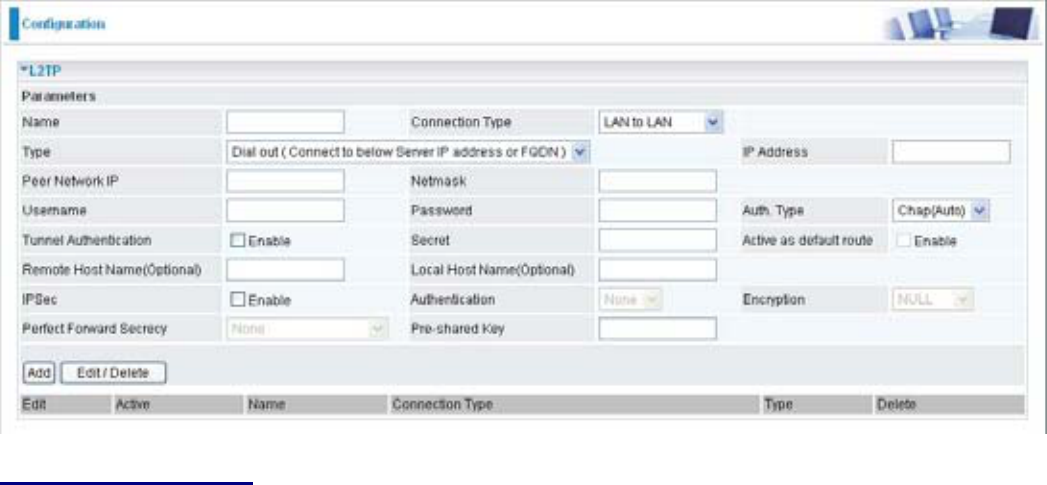
L2TP Connection - LAN to LAN
L2TP VPN Connection
Name: A given name for the connection
Connection Type: Remote Access or LAN to LAN.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote VPN
VHUYHUHJ\RXURI¿FHVHUYHUFKHFN'LDO,QWRKDYHLWRSHUDWHDVD931VHUYHU
:KHQFRQ¿JXULQJ\RXUURXWHUWRHVWDEOLVKDFRQQHFWLRQWRDUHPRWH/$1HQWHUWKHUHPRWH6HUYHU
IP Address (or Hostname) you wish to connect to.
:KHQFRQ¿JXULQJ\RXUURXWHUDVDVHUYHUWRDFFHSWLQFRPLQJFRQQHFWLRQVHQWHUWKH3ULYDWH,3
Address assigned to the Dial in User.
Peer Network IP: Enter Peer network IP address.
Netmask: Enter the subnet mask of peer network based on the Peer Network IP setting.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by your Host. If you are
a Dial-In user (server), enter your own password.
Authentication Type: Default is Auto if you want the router to determine the authentication type
to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or PAP
(Password Authentication Protocol) if you know which type the server is using (when acting as a
client), or else the authentication type you want clients connecting to you to use (when acting as a
VHUYHU:KHQXVLQJ3$3WKHSDVVZRUGLVVHQWXQHQFU\SWHGZKLOVW&+$3HQFU\SWVWKHSDVVZRUG
before sending, and also allows for challenges at different periods to ensure that the client has not
been replaced by an intruder.
Tunnel Authentication: This enables router to authenticate both the L2TP remote and L2TP host.
This is only valid when L2TP remote supports this feature.
Secret: The secure password length should be 16 characters which may include numbers and
characters.
111

Active as default route: Commonly used by the Dial-out connection which all packets will route
through the VPN tunnel to the Internet; therefore, active the function may degrade the Internet
performance.
Remote Host Name (Optional):(QWHUKRVWQDPHRIUHPRWH931GHYLFH,WLVDWXQQHOLGHQWL¿HU
from the Remote VPN device matches with the Remote hostname provided. If remote hostname
matches, tunnel will be connected; otherwise, it will be dropped.
Cautious: This is only when the router performs as a VPN server. This option should be
used by advanced users only.
Local Host 1DPH2SWLRQDO(QWHUKRVWQDPHRI/RFDO931GHYLFHWKDWLVFRQQHFWHGHVWDEOLVKHV
D931WXQQHO$VGHIDXOW5RXWHU¶VGHIDXOW+RVWQDPHLVhome.gateway.
IPSec: Enable for enhancing your L2TP VPN security.
Authentication: Authentication establishes the integrity of the datagram and ensures it is not
WDPSHUHGZLWKLQWUDQVPLW7KHUHDUHWKUHHRSWLRQV0HVVDJH'LJHVW0'6HFXUH+DVK
$OJRULWKP6+$RU121(6+$LVPRUHUHVLVWDQWWREUXWHIRUFHDWWDFNVWKDQ0'KRZHYHULWLV
slower.
MD5:$RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
SHA1: $RQHZD\KDVKLQJDOJRULWKPWKDWSURGXFHVDíELWKDVK
Encryption: Select the encryption method from the pull-down menu. There are four options, DES,
3DES, AES and NULL. NULL means it is a tunnel only with no encryption. 3DES and AES are
more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES: Stands for Advanced Encryption Standards, it uses 128 bits as an encryption method.
Perfect Forward Secrecy: &KRRVHZKHWKHUWRHQDEOH3)6XVLQJ'LI¿H+HOOPDQSXEOLFNH\
cryptography to change encryption keys during the second phase of VPN negotiation. This
IXQFWLRQZLOOSURYLGHEHWWHUVHFXULW\EXWH[WHQGVWKH931QHJRWLDWLRQWLPH'LI¿H+HOOPDQLVD
public-key cryptography protocol that allows two parties to establish a shared secret over an
XQVHFXUHGFRPPXQLFDWLRQFKDQQHOLHRYHUWKH,QWHUQHW7KHUHDUHWKUHHPRGHV02'3ELW
02'3ELWDQG02'3ELW02'3VWDQGVIRU0RGXODU([SRQHQWLDWLRQ*URXSV
Pre-shared Key:7KLVLVIRUWKH,QWHUQHW.H\([FKDQJH,.(SURWRFRODVWULQJIURPWR
FKDUDFWHUV%RWKVLGHVVKRXOGXVHWKHVDPHNH\,.(LVXVHGWRHVWDEOLVKDVKDUHGVHFXULW\SROLF\
DQGDXWKHQWLFDWHGNH\VIRUVHUYLFHVVXFKDV,36HFWKDWUHTXLUHDNH\%HIRUHDQ\,36HFWUDI¿F
can be passed, each router must be able to verify the identity of its peer. This can be done by
manually entering the pre-shared key into both sides (router or hosts).
&OLFN(GLW'HOHWHWRVDYH\RXUFKDQJHV
112
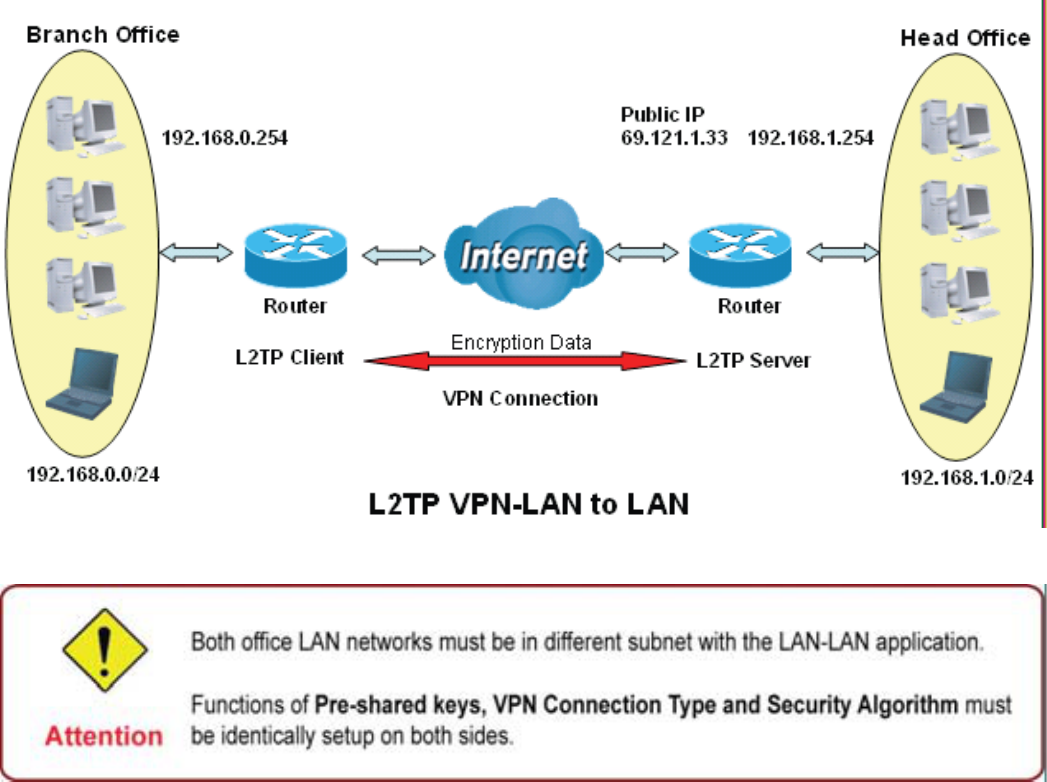
([DPSOH&RQ¿JXULQJ/73/$1WR/$1931&RQQHFWLRQ
7KHEUDQFKRI¿FHHVWDEOLVKHVD/73931WXQQHOZLWKKHDGRI¿FHWRFRQQHFWWZRSULYDWHQHWZRUNV
RYHUWKH,QWHUQHW7KHURXWHUVDUHLQVWDOOHGLQWKHKHDGRI¿FHDQGEUDQFKRI¿FHDFFRUGLQJO\
113
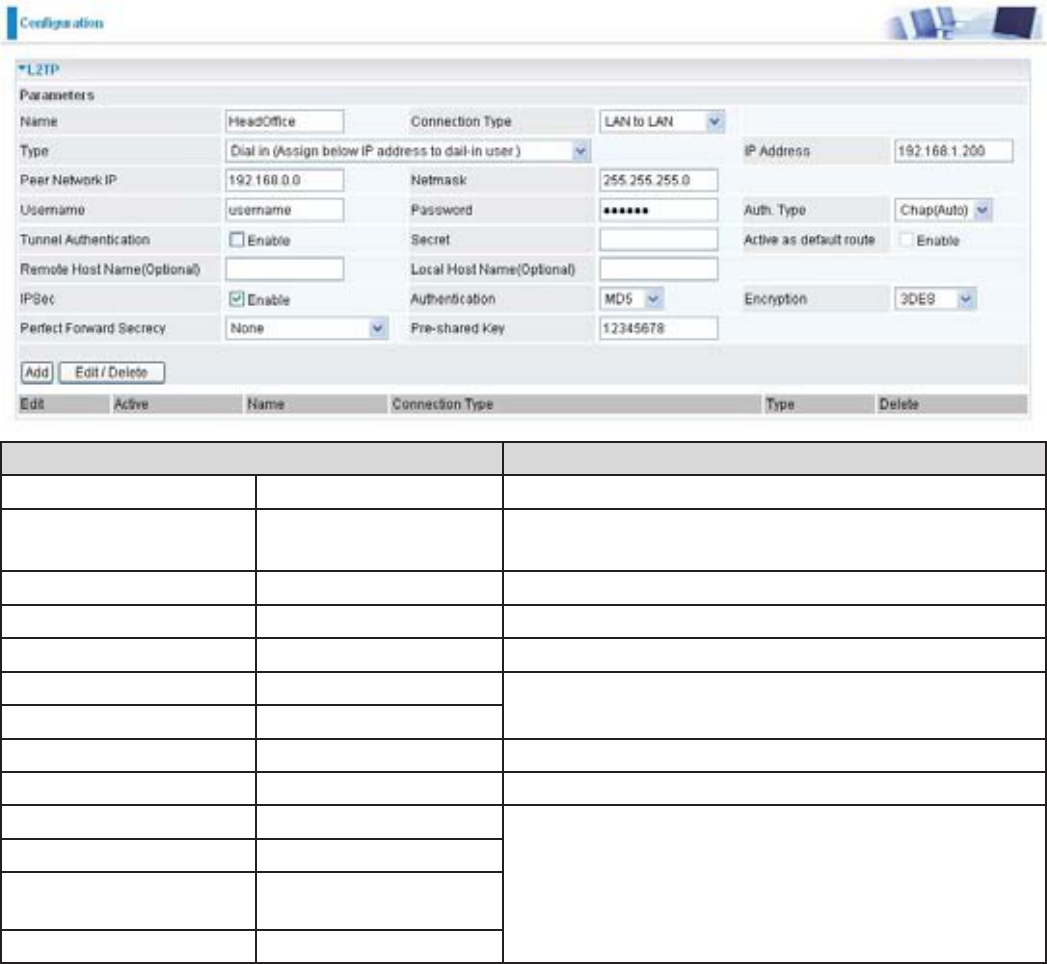
&RQ¿JXULQJ/73931LQWKH+HDG2I¿FH
7KH,3DGGUHVVZLOOEHDVVLJQHGWRWKHURXWHUORFDWHGLQWKHEUDQFKRI¿FH3OHDVH
PDNHVXUHWKLV,3LVQRWXVHGLQWKHKHDGRI¿FH/$1
Function Description
Name +HDG2I¿FH Give a name of L2TP Connection
Connection Type LAN to LAN Select LAN to LAN from the Connection Type
drop-down menu
Type Dial in Select Dial in from the Type drop down menu
IP Address 192.168.1.200 ,3DGGUHVVDVVLJQHGWREUDQFKRI¿FHQHWZRUN
Peer Network IP 192.168.0.0 %UDQFKRI¿FHQHWZRUN
Username username An assigned username and password to
DXWKHQWLFDWHEUDQFKRI¿FHQHWZRUN
Password 123456
Auth. Type Chap (Auto) .HHSWKLVDVWKHGHIDXOWYDOXHIRUPRVWFDVHV
IPSec Enable Enable this to enhance your L2TP VPN security
Authentication 0' %RWKVLGHVVKRXOGXVHWKHVDPHYDOXH
Encryption 3DES
Perfect Forward
Secrecy
None
3UH6KDUHG.H\ 12345678
114
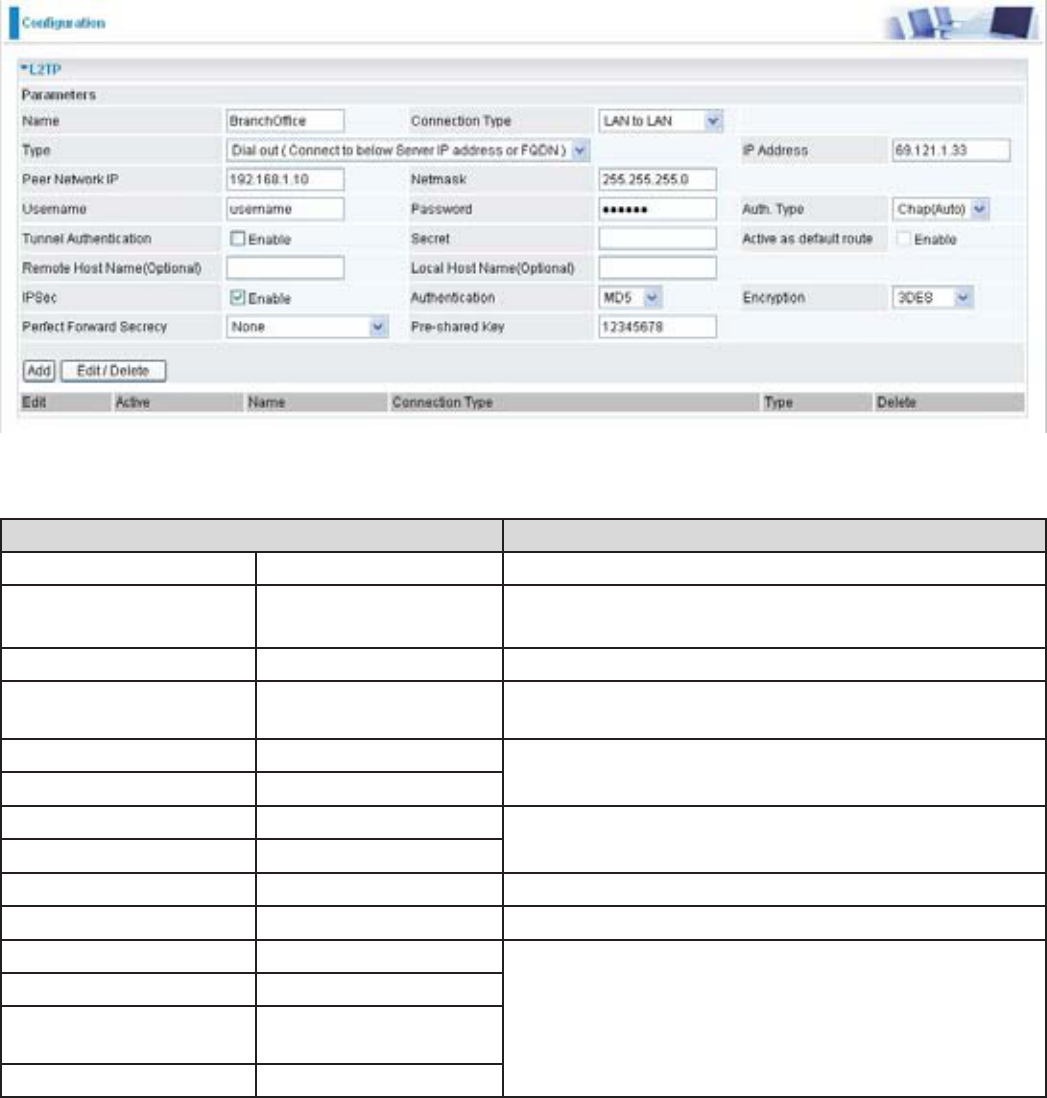
&RQ¿JXULQJ/73931LQWKH%UDQFK2I¿FH
7KH,3DGGUHVVLVWKH3XEOLF,3DGGUHVVRIWKHURXWHUORFDWHGLQKHDGRI¿FH,I\RX
registered the DDNS (please refer to the DDNS section of this manual), you can also use the
domain name instead of the IP address to reach the router.
Function Description
Name %UDQFK2I¿FH Give a name of L2TP Connection
Connection Type LAN to LAN Select LAN to LAN from the Connection Type
drop-down menu
Type Dial out Select Dial out from the Type drop down menu
IP Address (or
Hostname)
69.121.1.33 ,3DGGUHVVDVVLJQHGWREUDQFKRI¿FHQHWZRUN
Peer Network IP 192.168.1.0 +HDGRI¿FHQHWZRUN
Netmask 255.255.255.0
Username username An assigned username and password to
DXWKHQWLFDWHEUDQFKRI¿FHQHWZRUN
Password 123456
Auth. Type Chap (Auto) .HHSWKLVDVWKHGHIDXOWYDOXHIRUPRVWFDVHV
IPSec Enable Enable this to enhance your L2TP VPN security
Authentication 0' %RWKVLGHVVKRXOGXVHWKHVDPHYDOXH
Encryption 3DES
Perfect Forward
Secrecy
None
3UH6KDUHG.H\ 12345678
115

116
VoIP - Voice over Internet Protocol
VoIP enables telephone calls through existing Internet connection instead of going through the
PSTN (Public Switched Telephone Network). It is not only cost-effective, especially for a long
GLVWDQFHWHOHSKRQHFKDUJHVEXWDOVRWROOTXDOLW\YRLFHFDOOVRYHUWKH,QWHUQHW
Here are the items within the VoIP section: SIP Device Parameters, SIP Accounts, Phone Port,
PSTN Dial Plan, VoIP Dial Plan, Call Features, Speed Dial and Ring &Tone.
117
SIP Device Parameters
This section provides easy setup for your VoIP service. Phone port 1 and 2 can be registered to
different SIP Service Provider.
SIP Device Parameters
SIP: To use VoIP SIP as VoIP call signaling protocol. Default is set to Disable.
Silence Suppression (VAD): Voice Activation Detection (VAD) prevents transmitting the nature
silence to consume the bandwidth. It is also known as Silence Suppression which is a software
application that ensures the bandwidth is reserved only when voice activity is activated. Default is
set to Enable.
Echo Cancellation: G.168 echo canceller is an ITU-T standard. It is used for isolating the echo
ZKLOH\RXDUHRQWKHSKRQH7KLVKHOSV\RXQRWWRKHDUPXFKRI\RXURZQYRLFHUHÀHFWLQJRQWKH
phone while you talk. Default is set to Enable.
RTP Port: Provide the based value from the media (RTP) ports that are assigned for various
endpoints and the different call sessions that may exist within an end-point. (Range from 5100 to
65535, default value is 5100)
Region: This selection is a drop-down box, which allows user to select the country for which the
9R,3GHYLFHPXVWZRUN:KHQDFRXQWU\LVVHOHFWHGWKHFRXQWU\SDUDPHWHUVDUHDXWRPDWLFDOO\
loaded.
Voice QoS, DSCP Marking: 'LIIHUHQWLDWHG6HUYLFHV&RGH3RLQW'6&3LWLVWKH¿UVWELWVLQ
WKH7R6E\WH'6&30DUNLQJDOORZVXVHUVWRDVVLJQVSHFL¿Fapplication WUDI¿Fto be executed in
priority by the next Router based on the DSCP value. See Table 4. TKH'6&30DSSLQJ7DEOH
Note: To be sure the router(s) in the backbones network have the capability in executing and
checking the DSCP through-out the QoS network.
118
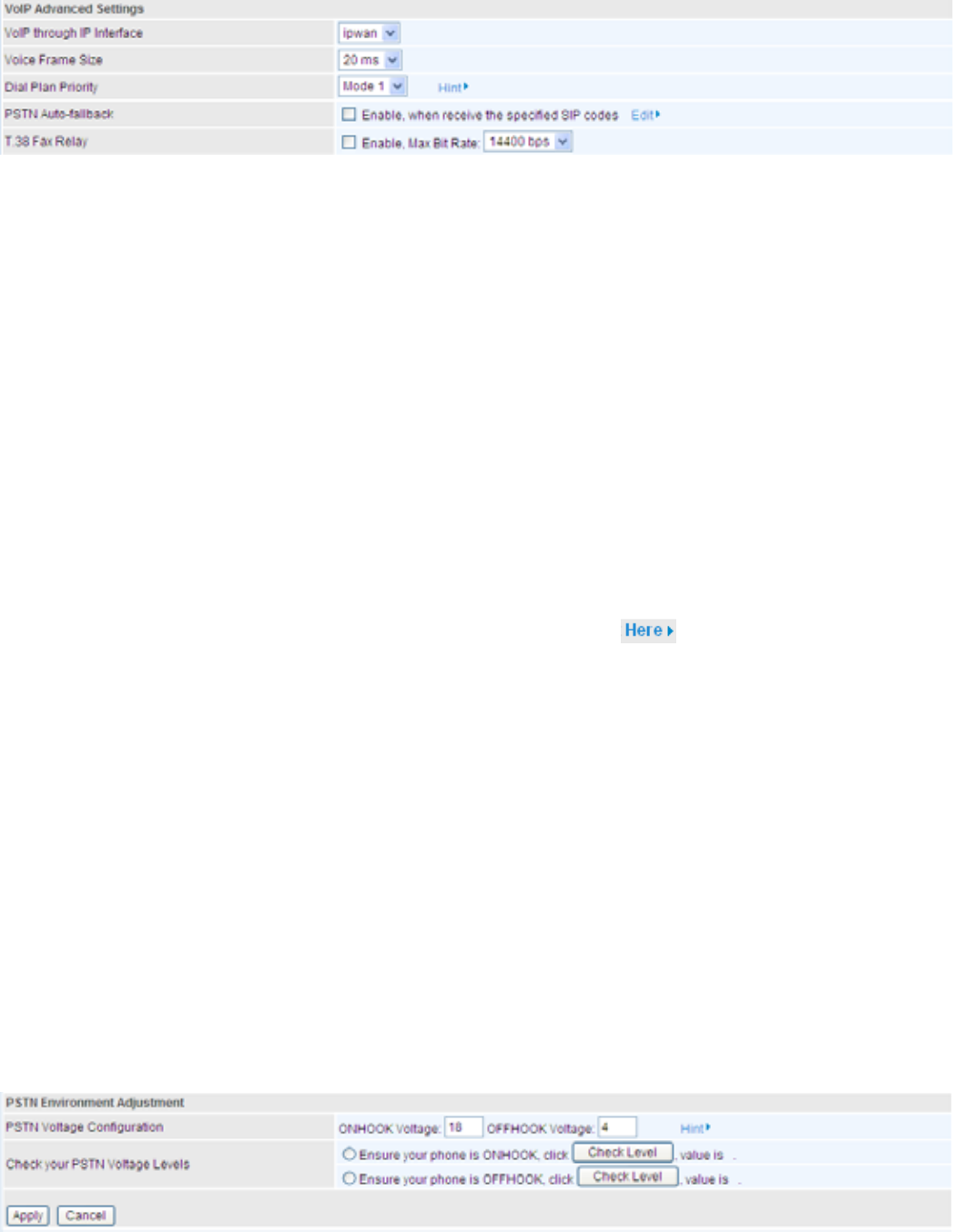
Advanced – Parameters
VoIP through IP Interface: ,3,QWHUIDFHGHFLGHVZKHUHWRVHQGUHFHLYHWKHYRLSWUDI¿FLWLQFOXGHV
ipwan and iplan. Easy way to select the interface is to check the location of the SIP server. If
it locates some where in the Internet then select ipwan. If the VoIP SIP server is on the local
Network then select iplan.
Voice Frame Size: Frame size is available from 10ms to 60ms. Frame size meaning how many
PLOOLVHFRQGVWKH9RLFHSDFNHWVZLOOEHTXHXHGDQGVHQWRXW,WLVLGHDOWRKDYHWKHVDPHIUDPH
size in both of Caller and Receiver.
Dial Plan Priority:'H¿QHWKHSULRULW\EHWZHHQ9R,3DQG3671GLDOSODQ
PSTN Auto-fallback: :KHQHYHU9R,36IP responses error and error code matching with the
codes in the Edit section, the VoiP calls will automatically fallback to PSTN. In the other word, the
call will be called via the PSTN when VoIP SIP returns an error code.
Click the Edit to add or remove the responses code. To be sure the code is separated by a
comma (,).
For more information about SIP responses codes, please check to link to http://voip-info.
org/wiki/view/sip+response+codes where you can get to know the meaning of each error code.
T.38 Fax Relay: It allows the transfer of facsimile documents in real-time between two standard
Group 3 facsimile terminals over the Internet or other networks using IP protocols. It will only
function when both sites are support this feature and enabled.
Advanced – PSTN Environment Adjustment
PSTN Environment Adjustment options will help you to adjust the onhook and offhook voltage
detection values for your environment. You should use these if the default values are incorrect
and result in PSTN calls not being detected properly, e.g. calls being terminated within 5 seconds
of being answered. The actual levels are determined by your environment including the number
and type of telephones used.
Note: ONHOOK means hung up.
119
7RWDNH\RXUSKRQH2))+22.OLIWWKHUHFHLYHUWKHQSUHVV+RRN)ODVKXQWLO\RXKHDU\RXUQRUPDO
3671GLDOWRQHQRW\RXU9R,3GLDOWRQH:DLWVHYHUDOVHFRQGVDQGWKHQSUHVV&KHFN/HYHO
<RXVKRXOGFKHFNWKH2))+22.YDOXHIRUHDFKWHOHSKRQH\RXKDYHFRQQHFWHGWRWKLVGHYLFH
6HWWKH2))+22.YROWDJHWRWKHORZHVWVHWWLQJUHJLVWHUHGIRUDOO\RXUWHOHSKRQHVHJLI\RXU
WHOHSKRQHVUHWXUQYDOXHVRIDQGWKHQ\RXVKRXOGVHW\RXU2))+22.YROWDJHWR
Note: The detected values will not automatically be set by the Check Level function; you
must enter the lowest level detected after testing all your telephones.
120
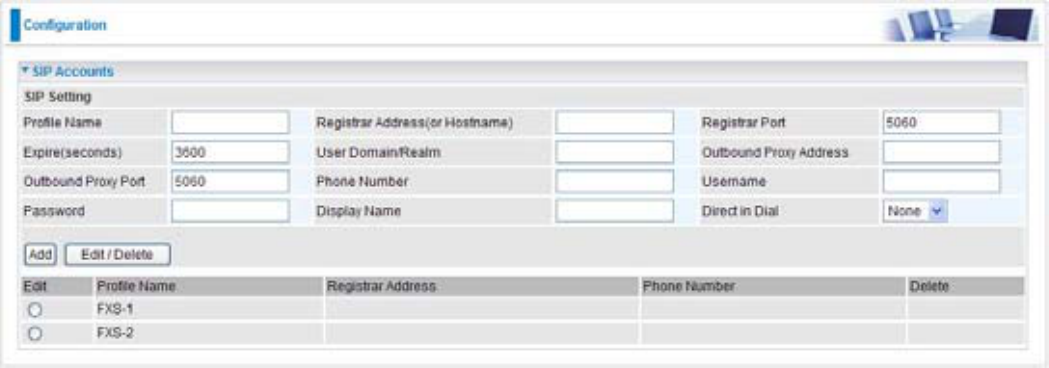
SIP Accounts
7KLVVHFWLRQUHÀHFWVDQGFRQWDLQVEDVLFVHWWLQJVIRUWKH9R,3PRGXOHIURPVHOHFWHGSURYLGHULQWKH
:L]DUGVHFWLRQ)DLOWRSURYLGHFRUUHFWLQIRUPDWLRQZLOOKDOWPDNLQJFDOOVRXWWRWKH,QWHUQHW
3UR¿OH1DPHUVHUGH¿QHGQDPHLVIRULGHQWLI\LQJWKH3UR¿OH
Registrar Address (or Hostname): Indicate the VoIP SIP registrar IP address.
Registrar Port: Specify the port of the VoIP SIP registrar on which it will listen for register
UHTXHVWVIURP9R,3GHYLFH
Expire: Expire time for the registration message sending.
User Domain/Realm: Set different domain name for the VoIP SIP proxy server.
Outbound Proxy Address: Indicate the VoIP SIP outbound proxy server IP address. This
parameter is very useful when VoIP device is behind a NAT.
Outbound Proxy Port: Specify the port of the VoIP SIP outbound proxy on which it will listen for
messages.
Phone Number: This parameter holds the registration ID of the user within the VoIP SIP registrar.
Username: Same as Phone Number.
Password: This parameter holds the password used for authentication within VoIP SIP registrar.
Display Name: This parameter will be appeared on the Caller ID.
Direct in Dial: Select the ringing port when getting an incoming VoIP call.
121
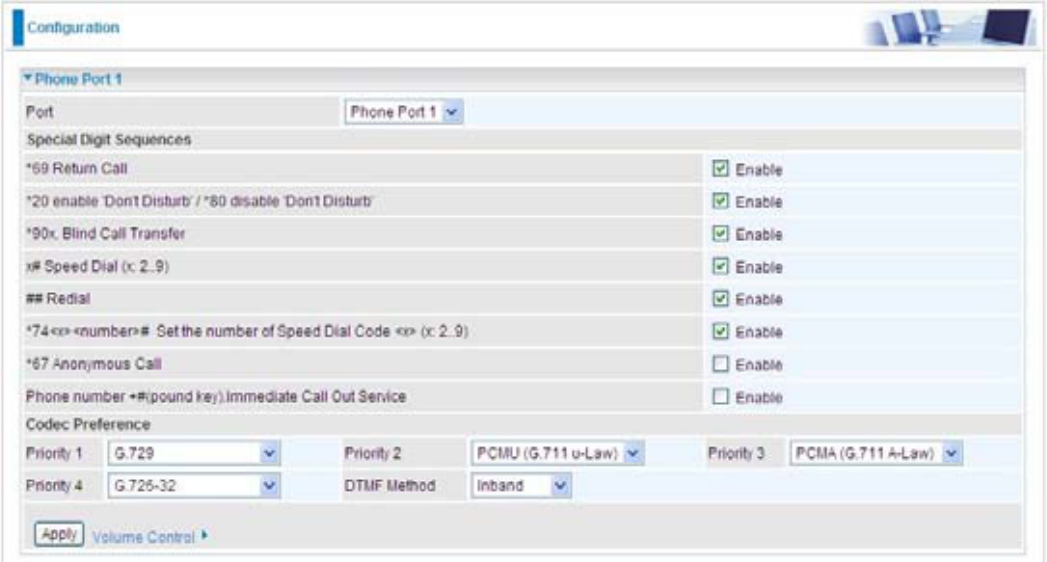
Phone Port
This section displays status and allows you to edit the account information of your Phones. Click
Edit to update your phone information.
Port: ,WDOORZV\RXWRFKDQJHWKHSKRQHSRUWVHWWLQJIRUVSHFLI\);6SRUW
*69 (Return Call): Dial *69 to return the last missed call. It is only available for VoIP call(s).
*20 (Do not Disturb ON): Dial *20 to set the No Disturb on. Your phone will not ring if someone
calls.
*80 (Do not Disturb OFF): Dial *80 to set the No Disturb off. Your will be able to hear ring tone
when someone calls.
*90x (Blind Call Transfer): 'LDOSKRQHQXPEHUWRWUDQVODWHDFDOOWRDWKLUGSDUW\7KLV
feature is enabled by default.
x# Speed Dial (x:2..9): 5HIHUWR3KRQH3RUWVHFWLRQLQWKH:HE*8,6HWXS\RXU6SHHG'LDO
SKRQHERRN¿UVWEHIRUHDFFHVVLQJWKH6SHHG'LDOIHDWXUH,WLVHQDEOHGE\GHIDXOW
## Redial: Press ## to redial the latest number you dialed. This feature is enabled by default.
*74<x><number>#: Use your phone key pad to insert a phone number to the Speed Dial phone
book. Or you can update your Speed Dial phone number manually. Refer to the Phone Port
section in the:HE*8,IRUGHWDLOV
*67 Anonymous Call: Hide the own phone number for each call and it will not be displayed on the
remote site. It is only applied to the next call when you enter this control character. The detailed
operation procedure is ³Off Hook -> *67 -> On Hook -> Off Hook -> Dial´. This feature is disabled
by default.
Phone Number + #: This is the fast dial which you can dial out a phone number immediately
122
without waiting.
Note: Refer to Special Dial Code section in this Manual for more details.
Codec Preference
Codec is known as Coder-Decoder used for data signal conversion. Set the priority of voice
compression; Priority 1 owns the top priority.
G.729: It is used to encoder and decoder voice information into a single packet which reduces the
bandwidth consumption.
*ȝ/$:,WLVDEDVLFQRQFRPSUHVVHGHQFRGHUDQGGHFRGHUWHFKQLTXHȝ/$:XVHVSXOVH
FRGHPRGXODWLRQ3&0HQFRGHUDQGGHFRGHUWRFRQYHUWELWOLQHDUVDPSOH
G.711A-LAW:,WLVDEDVLFQRQFRPSUHVVHGHQFRGHUDQGGHFRGHUWHFKQLTXHA/$:XVHVSXOVH
FRGHPRGXODWLRQ3&0HQFRGHUDQGGHFRGHUWRFRQYHUWELWOLQHDUVDPSOH
G.726-32: It is used to encoder and decoder voice information into a single packet which reduces
the bandwidth consumption.&XUUHQWO\RQO\VXSSRUWVELWUDWHZLWK.ESV
DTMF Method: The Inband, RFC 2833 and SIP INFO (RFC 2976) are supported.
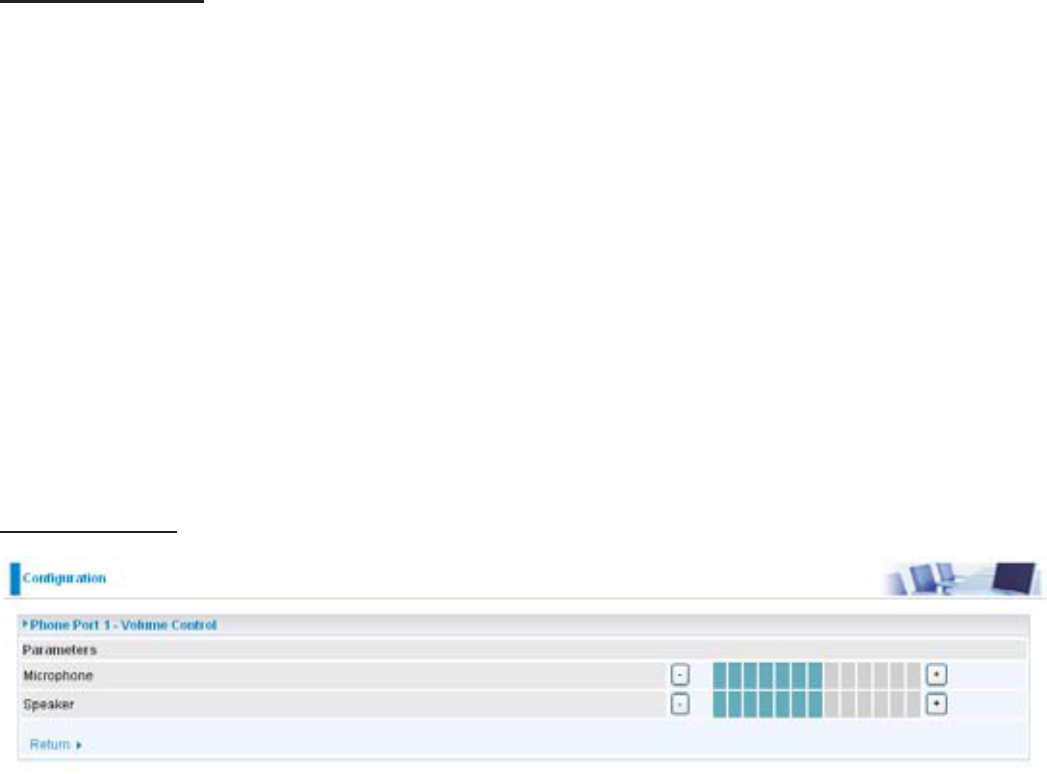
Volume Control
9ROXPHFRQWUROKHOSV\RXWRDGMXVWWKHYRLFHTXDOLW\RIWHOHSKRQHWRWKHEHVWFRPIRUWDEOHOLVWHQLQJ
level.
3UHVV³³WKHPLQXVVLJQWRUHGXFHHLWKHUPLFURSKRQHRUERWKVSHDNHU¶VOHYHORI\RXUWHOHSKRQH
3UHVV³³WKHSOXVVLJQWRLQFUHDVHHLWKHUPLFURSKRQHRUERWKVSHDNHU¶VOHYHORI\RXUWHOHSKRQH
123
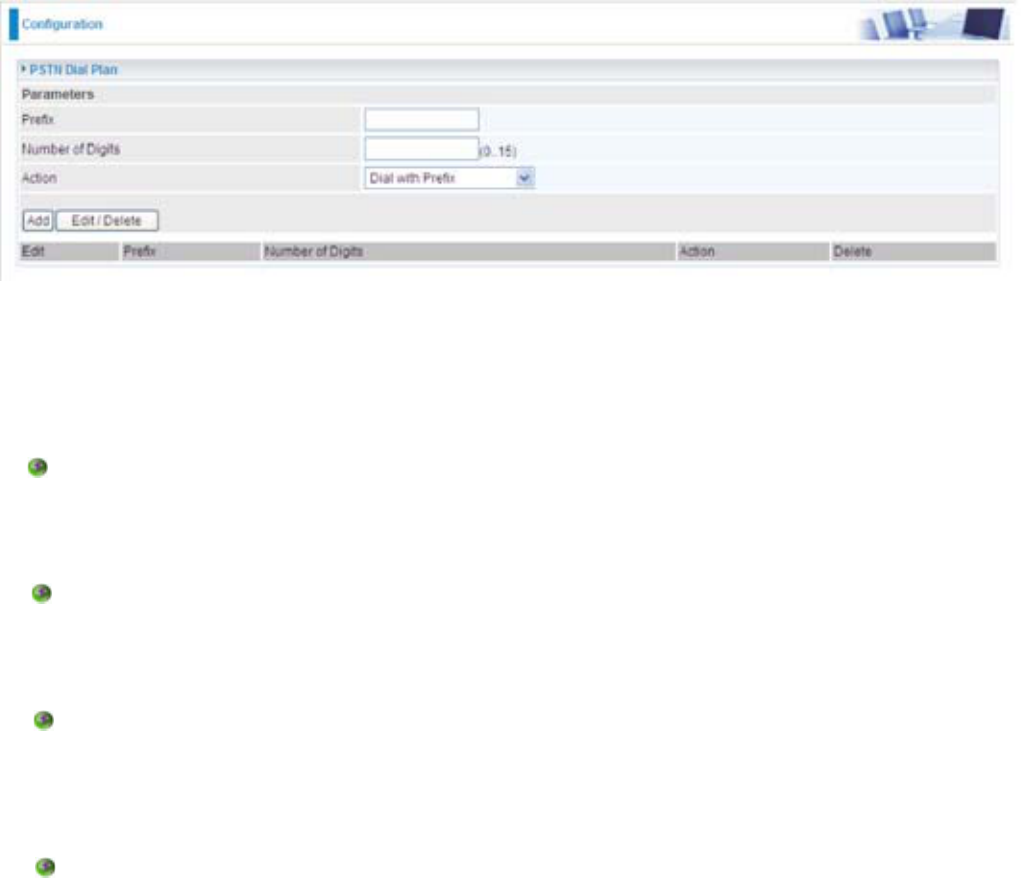
PSTN Dial Plan (Router with LINE port only)
7KLVVHFWLRQHQDEOHV\RXWRFRQ¿JXUH³9R,3ZLWK3671VZLWFKLQJ´RQ\RXUV\VWHP<RXFDQGH¿QH
DUDQJHRIGLDOSODQVWRPDNHUHJXODUFDOOIURP9R,3VZLWFKLQJWR3671OLQH3UH¿[QXPEHUVLV
essential key to make a distinguishing between VoIP and Regular phone call. If actual numbers
GLDOHGPDWFKHVZLWKSUH¿[QXPEHUGH¿QHGLQWKLVGLDOSODQWKHGLDOHGQXPEHUZLOOEHURXWHGWRWKH
PSTN to make a regular call. Otherwise, the number will be routed to the VoIP networks.
Reminder! In order to utilize this feature, you must have registered and connected to your
SIP Server first.
3UH¿[Specify number(s) for switching to a PSTN call.
Number of Digits: 6SHFLI\WKHWRWDOQXPEHURIGLJLWVZLVKWRGLDORXW0D[LPXPGLJLWQXPEHULV
Action: Specify a dialing method you wish to make PSTN call(s).
'LDOZLWK3UH¿[ The dialed number with SUH¿[ZLOOEHVHQWFDOOWKURXJKWKH3671
Note: The actual dialed number of valid digits length requires matching in the Number of
'LJLWV¿OHG
'LDOZLWKRXW3UH¿[ The dialed number will be sent call through the PSTN without SUH¿[
Note: The actual dialed number of valid digits length requires matching in the Number of
'LJLWV¿OHG
Dial at Timeout: The dialed number will be sent call through the PSTN with WKHSUH¿[ZKHQ
WLPHRXWVWDUWV7KLVWLPHRXWDFWLYDWHVZKHQQRPRUHGLJLWVDUHGLDOHGLQDVSHFL¿FGXUDWLRQ
Note: The actual dialed number of valid digits length MUST NOT exceed in the Number of
'LJLWV¿OHG
'LDODW7LPHRXWQR3UH¿[The dialed number will be sent call through the PSTN without
SUH¿[ZKHQWLPHRXWVWDUWV7KLVWLPHRXWDFWLYDWHVZKHQQRPRUHGLJLWVDUHGLDOHGLQDVSHFL¿F
duration.
Note: The actual dialed number of valid digits length MUST NOT exceed in the Number of
'LJLWV¿OHG
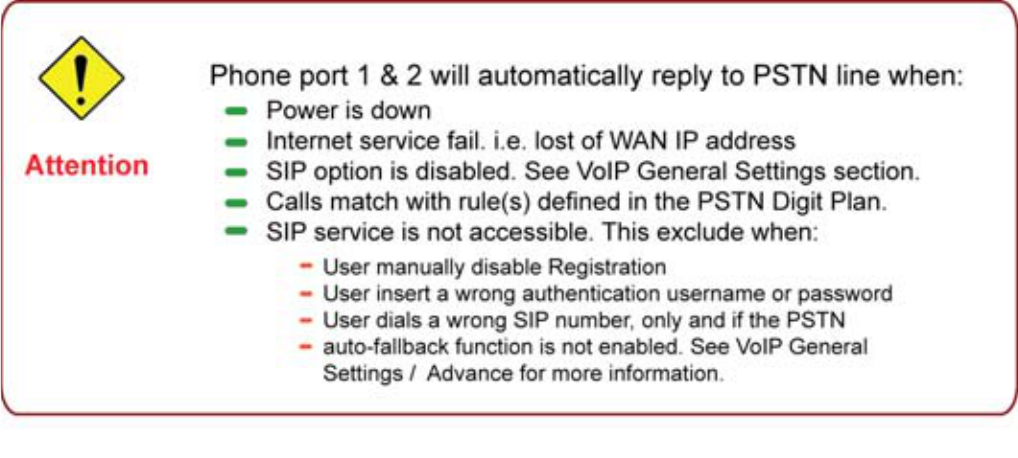
124
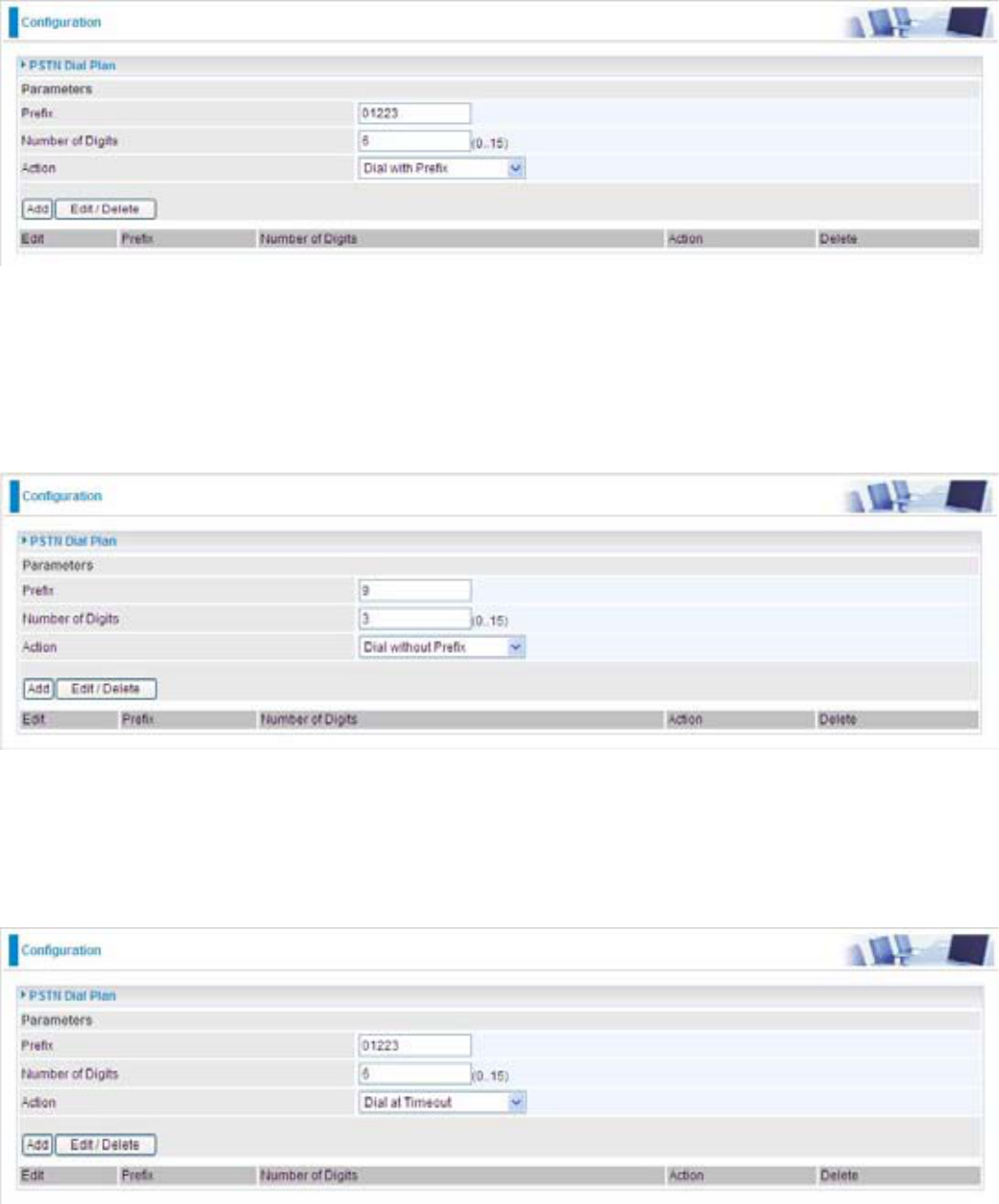
125
PSTN Dial Plan Examples:
'LDOZLWK3UH¿[1.
,I\RXGLDOQXPEHUZLOOEHGLDOHGRXWYLD);2WRPDNHDUHJXODUSKRQH
call.
'LDOZLWKRXW3UH¿[2.
,I\RXGLDOWKHQXPEHUZLOORQO\EHGLDOHGRXWYLD);2SRUWWRPDNHDUHJXODUSKRQHFDOO
Dial at Timeout3.
If you only dial 01223 7070 and no more numbers, after the timeout activates, 012237070 will be
GLDOHGWRPDNHDUHJXODUFDOOYLD);2SRUW
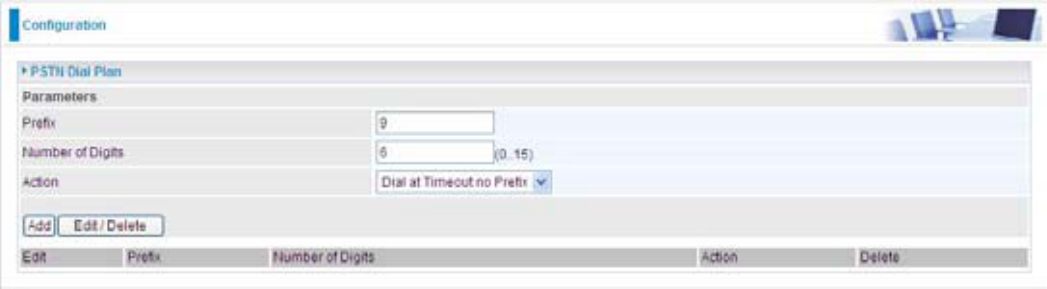
126
(YHQWKRXJKRQO\GLJLWVGRHVQRWPDWFKZLWKQXPEHURIGLJLWVGH¿QHGLQWKH¿OHG
is still a valid phone number since it has not exceeded 6 digits.
'LDODW7LPHRXWQR3UH¿[4.
If you only dial 97070 and no more numbers, after the timeout activates, 7070 will be dialed
ZLWKRXWSUH¿[WRPDNHDUHJXODUFDOOYLD);2SRUW
(YHQWKRXJKRQO\GLJLWVGRHVQRWPDWFKZLWKQXPEHURIGLJLWVGH¿QHGLQWKH¿OHG
is still a valid phone number since it has not exceed 6 digits.
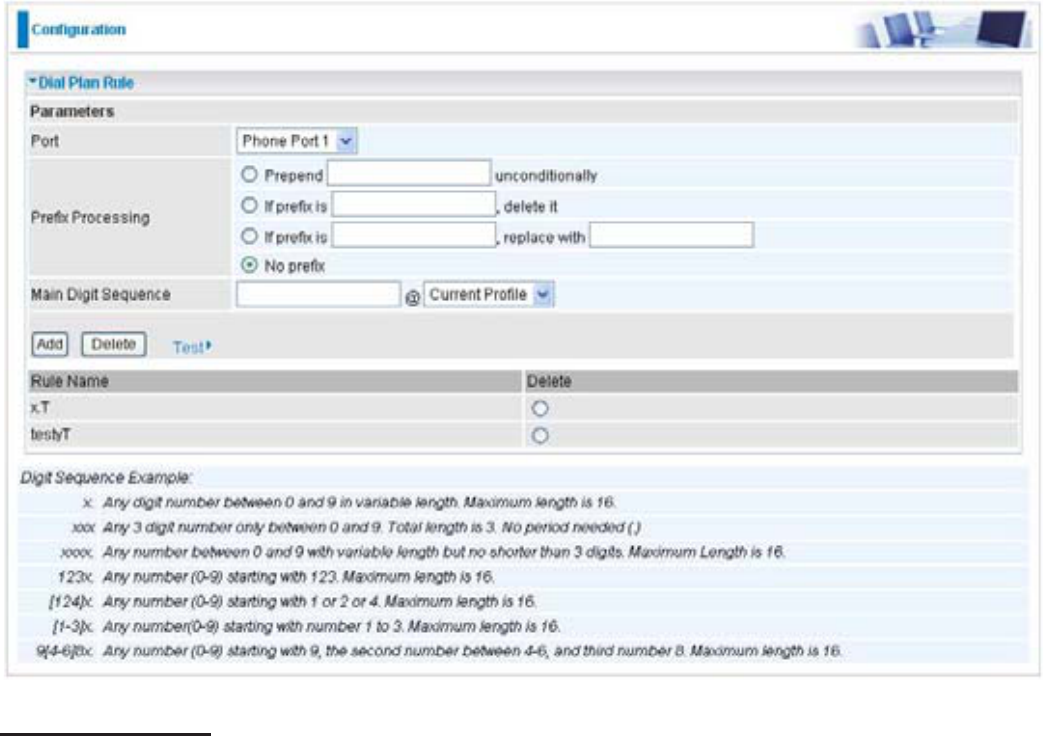
127
VoIP Dial Plan
This section helps you to make a telephony number dialed as making a regular call via VoIP.
You no longer need to memorize a long dial string of number for making a VoIP call. Go to
&RQ¿JXUDWLRQ > VoIP > VoIP Dial Plan.
Dial Plan Rules
&OLFNWKH$GGEXWWRQWRFUHDWHDQGGH¿QHD9R,3GLDOSODQUXOHV
3UH¿[3URFHVVLQJ
Prepend xxx unconditionally: xxx number is appended unconditionally to the front of the dialing
number when making a call. 3UH¿[FDQDOVREHLQFOXGHGZLWKDQ\QXPEHUDQGRUcharacter such as
+,*, #.
Note: For special service with +, *, #, you may need to check with your VoIP or Local Telephone
Service Provider for information.
,I3UH¿[LV[[[GHOHWHLW3UH¿[[[[LVUHPRYHG from the dialing numbers before making a call.
,I3UH¿[LV[[[UHSODFHZLWK3UH¿[[[[LVDSSHQGHGWRWKHIURQWRIWKHGLDOLQJQXPEHUVZKHQ
making a call.
1RSUH¿[1RSUH¿[LVDSSHQGHGWRWKHIURQWRIWKHGLDOLQJQXPEHUV,WLVVHWDVLQGHIDXOWVHWWLQJV
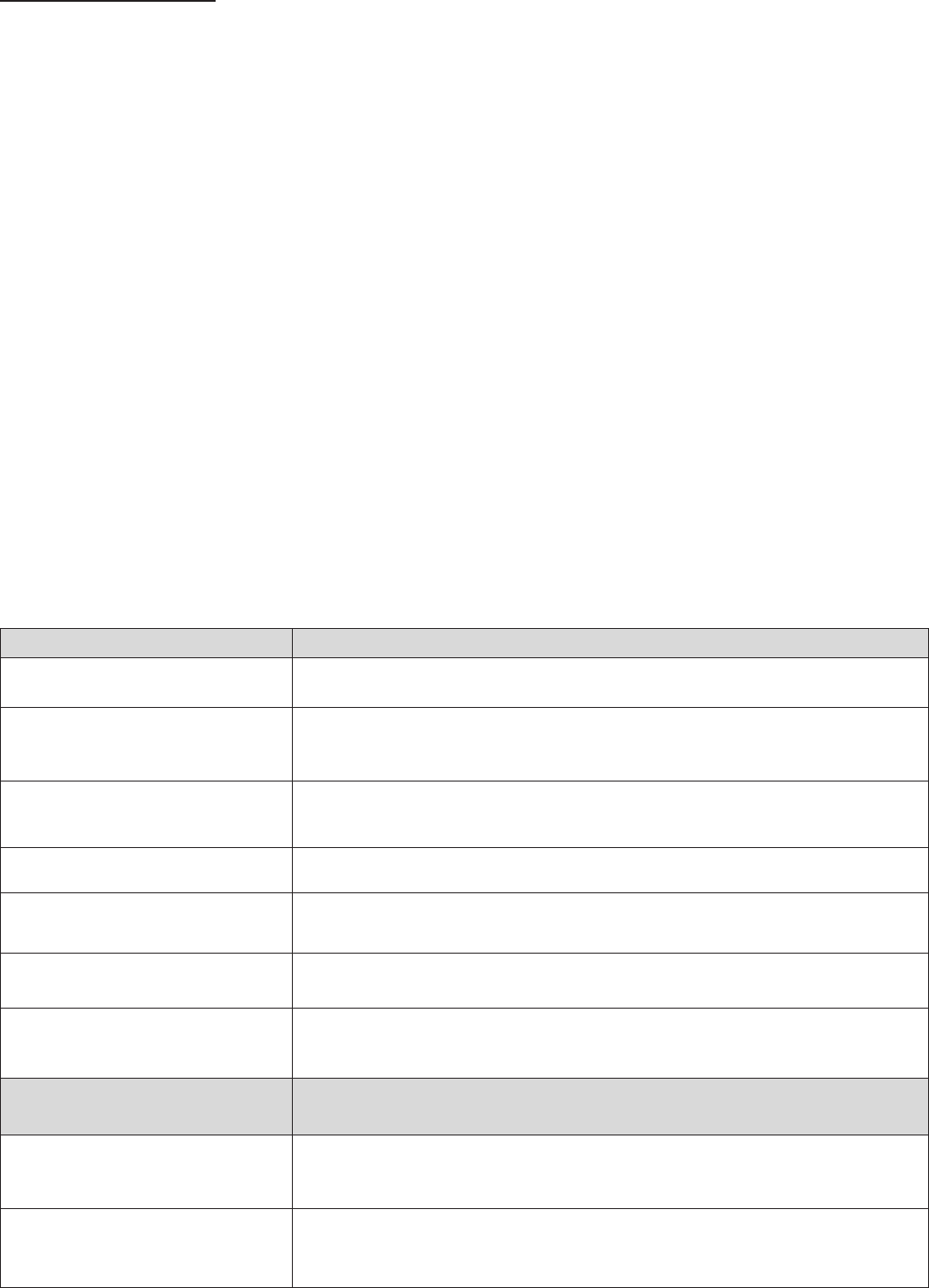
128
Main Digit Sequence: The call(s) can be called out via SIP or PSTN or ENUM.
x: Any numeric number between 0 and 9.
. ( period ): Repeat numeric number(s) between 0 and 9.
* (asterisk sign): It is normal character ‘*¶ on phone key pad. Please check if special service(s) is
provided by your VoIP Service Provider or your Local Telephone Service Provider.
# (pound sign): It is normal character ‘#¶ on phone key pad. Please check if it is provided by your
VoIP Service Provider or Local Telephone Service Provider for special service(s).
#&XUUHQW3UR¿OH!Referring to the VoIP account registered on the VoIP WizardIRU3RUW
<@ PSTN>: 0HDQLQJPDNLQJFDOOVYLDWKH3671OLQH
<@ENUM>: 0HDQLQJPDNLQJD9R,36,3GLUHFWFDOOYLD(QXPEHU³(180´WRDQ(180
callee.
Electronic1XPEHU(180XVHVWKH'16'RPDLQNetwork System) based technology to map
between a traditional phone number3671WRDQ,QWHUQHWDGGUHVVHV6,385/7KH(180
QXPEHUPXVWEHUHJLVWHUHGYLDDSXEOLF(180VLWHRU\RXU9R,36HUYLFH3URYLGHU
<@ SIPgateway>: It is used for the Intelligent Call Routing feature where you need to set up
\RXU6,3DFFRXQWRQWKH9R,38VHUGH¿QHG3UR¿OHVOLQNRQWKH9R,3:L]DUGSDJH*RWRWKH9R,3
:L]DUGLQWKLVPDQXDOIRUPRUHinformation.
Dial-Plan Examples: Description
x. $Q\GLJLWQXPEHUEHWZHHQDQGLQYDULDEOHOHQJWK0D[LPXP
length is 16.
xxx Any 3 digit number only between 0 and 9. Total length is 3.
Note: No period is needed (.)
xxxx. Any number between 0 and 9 with variable length but no shorter
than 3GLJLWV0D[LPXPOHQJWKLV
123x. $Q\QXPEHUVWDUWLQJZLWK0D[LPXPOHQJWKLV
[x…x]x.
For example: [124]x.
$Q\QXPEHUVWDUWLQJZLWKRURU0D[LPXPOHQJWKLV
16.
[x-x]x.
For example: [1-3]x.
$Q\QXPEHUVWDUWLQJZLWKQXPEHUWR0D[LPXPOHQJWKLV
16.
x[x-x]x.
For example: 9[4-6]8x.
Any number (0-9) starting with 9, the second number between
DQGWKLUGQXPEHU0D[LPXPOHQJWKLV
Special Dial Plan
Examples: Description
*xx*x. Starting with ‘* sign¶Dny two digit numbers DQ\QXPEHU
LQYDULDEOHOHQJWK0D[LPXPOHQJWKLV
*xx
Starting with ‘* sign¶Dny 2 digit numbers between 0 and 9. Total
length including the * is 3.
Note: No period is needed (.)
129
**xx*x. Starting with ‘** sign¶Dny two digit numbers between 0 DQ\
number (0-9) LQYDULDEOHOHQJWK0D[LPXPOHQJWKLV
#xx. Starting with ‘# sign¶Dny digit number (0-9) in variable length
but no shorter than 1 digits0D[LPXPOHQJWKLV
##xx*x. Starting with ‘## sign¶Dny two digit numbers ‘* sign¶DQ\
number (0-9) LQYDULDEOHOHQJWK0D[LPXPOHQJWKLV
130
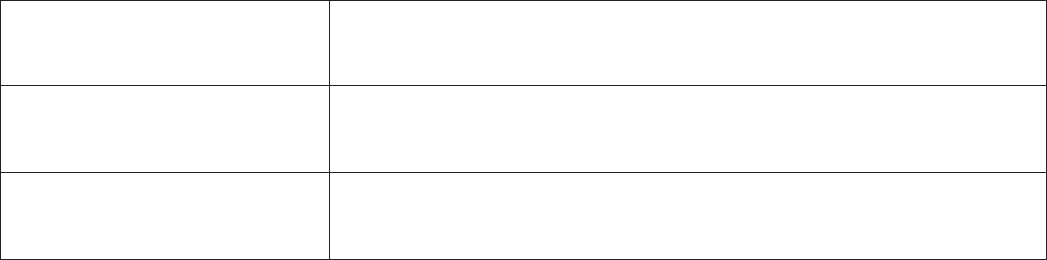
Call Feature
9R,3KDVDOOWKHEDVLFIHDWXUHVRIDWUDGLWLRQDOSKRQH%HVLGHVWKHSURYLGHGEDVLFIHDWXUHV9R,3
also comes with several enhanced features that allows you to further customize their settings to
suit your personal needs such as call forwarding setting, call waiting time length, conference call
feature, anonymous call feature and incoming no answer timer.
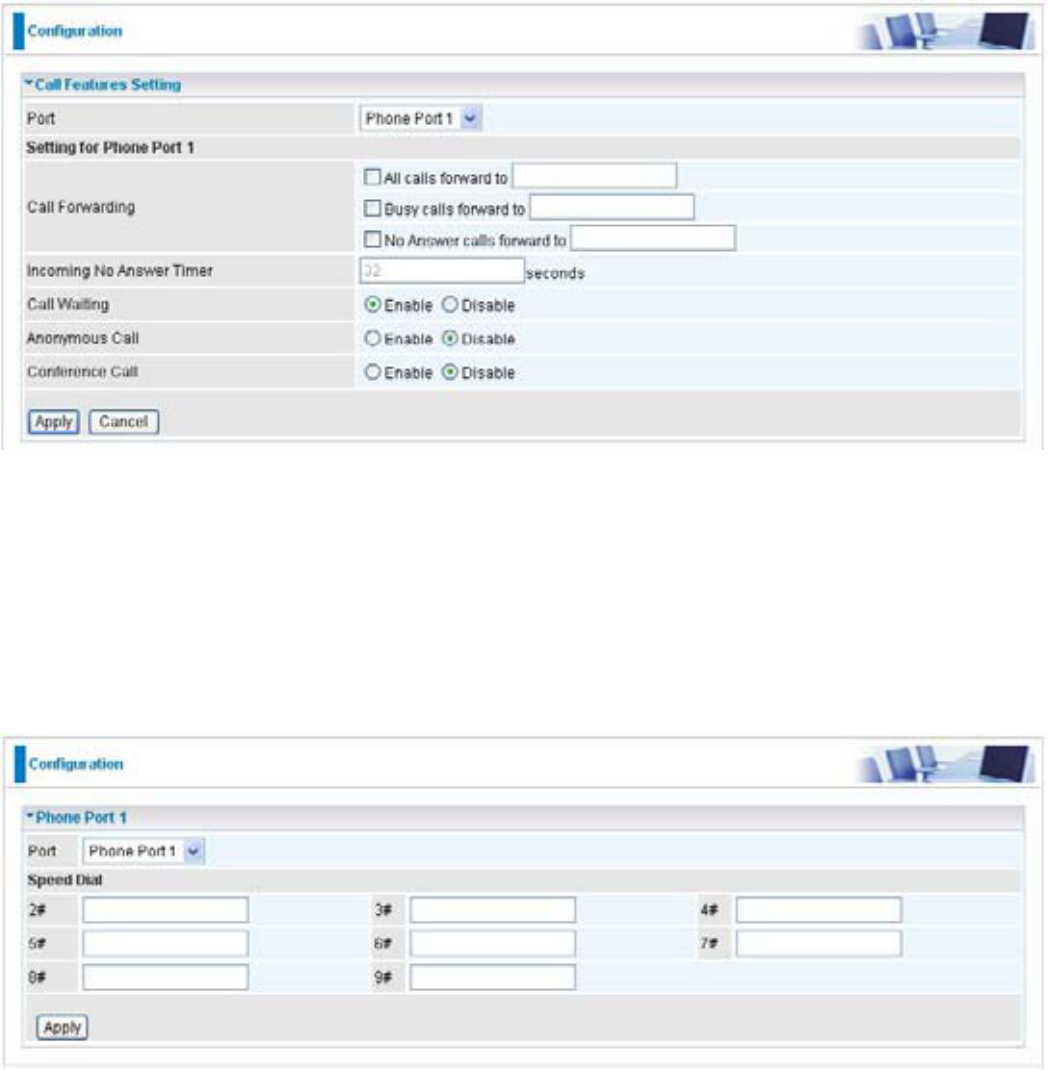
Speed Dial
6SHHG'LDOFRPHVLQKDQG\WRVWRUHIUHTXHQWO\XVHGWHOHSKRQHQXPEHUVZKLFK\RXFDQSUHVV
number from 0 to 9 and the pound sign (#) on the phone keypad to activate the function. For
example, speed dial to phone number lists on 9, just press keypad 9 then #. Your router will
automatically call out to number listed on entry 9.
131
Ring & Tone
7KLVVHFWLRQDOORZVDGYDQFHGXVHUWRFKDQJHWKHH[LVWLQJRUQHZO\GH¿QHGSDUDPHWHUVIRUWKH
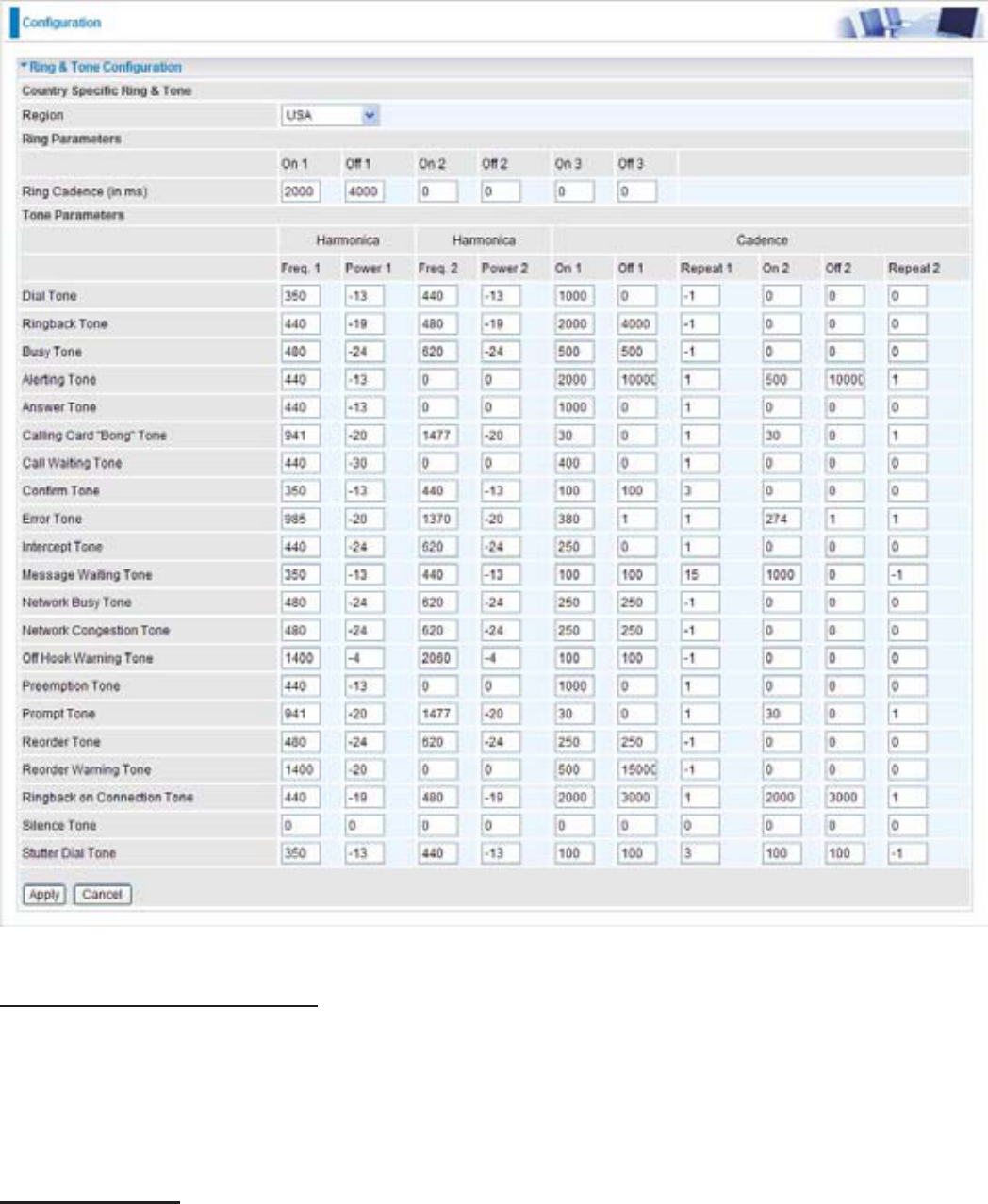
various ring tones (dial tone, busy tone, answer tone and etc.)
&RXQWU\6SHFL¿F5LQJ7RQH
Region: Select a country ring-tone, from the drop-down list, where you are located. This VoIP
router provides default parameter of ring tones according to different countries. The ring-tone
SDUDPHWHUVDUHDXWRPDWLFDOO\GLVSOD\HGDIWHUHQWHULQJDVSHFL¿FFRXQWU\,I\RXUFRXQWU\LVQRWLQ
the list, you may manually create ring-tone parameters.
Ring Parameters
Ring Cadence (in ms): 5LQJFDGHQFHLVGH¿QHGE\WKUHH¿HOGV)UHTXHQF\2Q7LPH2II7LPH
2Q7LPH2II7LPHDQG2Q7LPH2II7LPH)UHTXHQF\LVVSHFL¿HGLQ+HUW]7LPHLVJLYHQLQ
milliseconds.

132
Tone Parameters
You may need to check with your local telephone service provider for such information. Also, it is
UHFRPPHQGHGWKDWWKLVRSWLRQEHFRQ¿JXUHGE\DGYDQFHd user unless you are instructed to do so.
Click Apply to apply the settings.
133
QoS - Quality of Service
4R6IXQFWLRQKHOSV\RXWRFRQWURO\RXUQHWZRUNWUDI¿FIRUHDFKDSSOLFDWLRQIURP/$1(WKHUQHW
DQGRU:LUHOHVVWR:$1,QWHUQHW,WIDFLOLWDWHV\RXWRFRQWUROWKHGLIIHUHQWTXDOLW\DQGVSHHGRI
through put for each application when the system is running with full loading of upstream.
Here are the items within the QoS section: Prioritization, Outbound IP Throttling & Inbound IP
Throttling (bandwidth management).
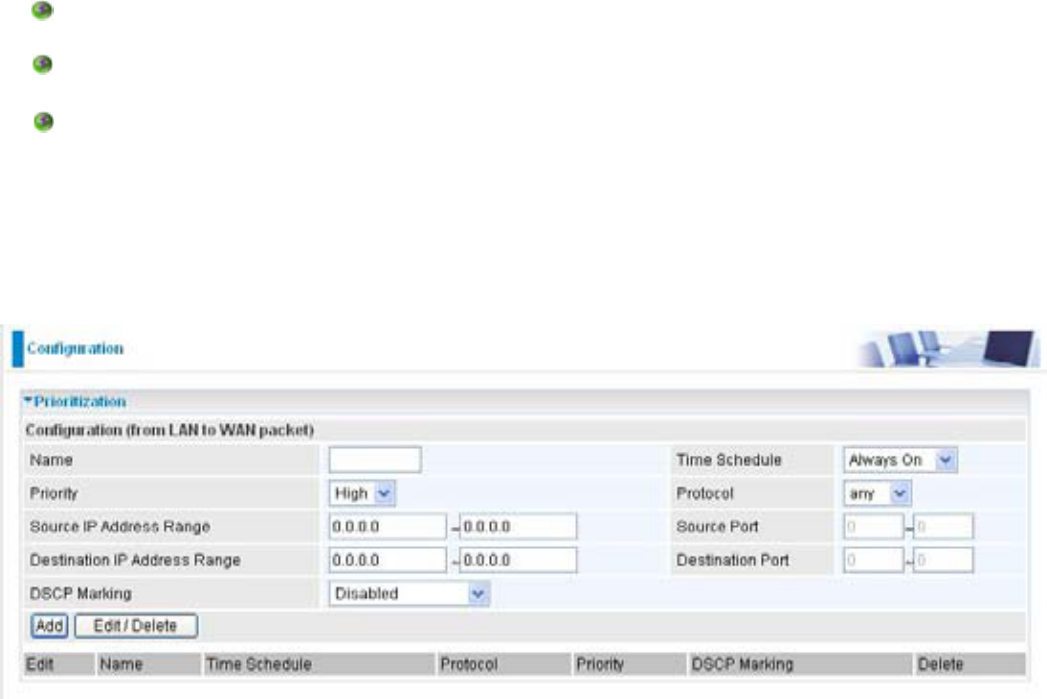
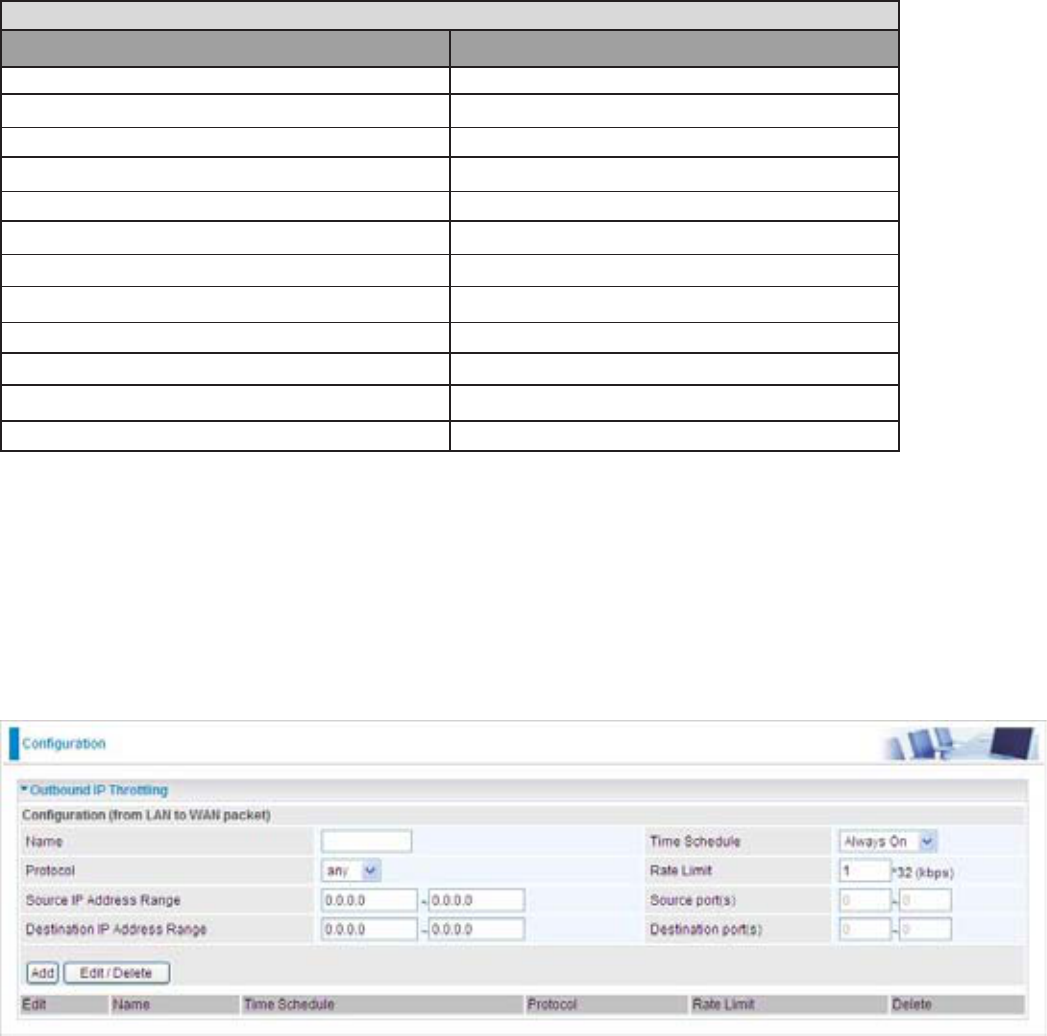
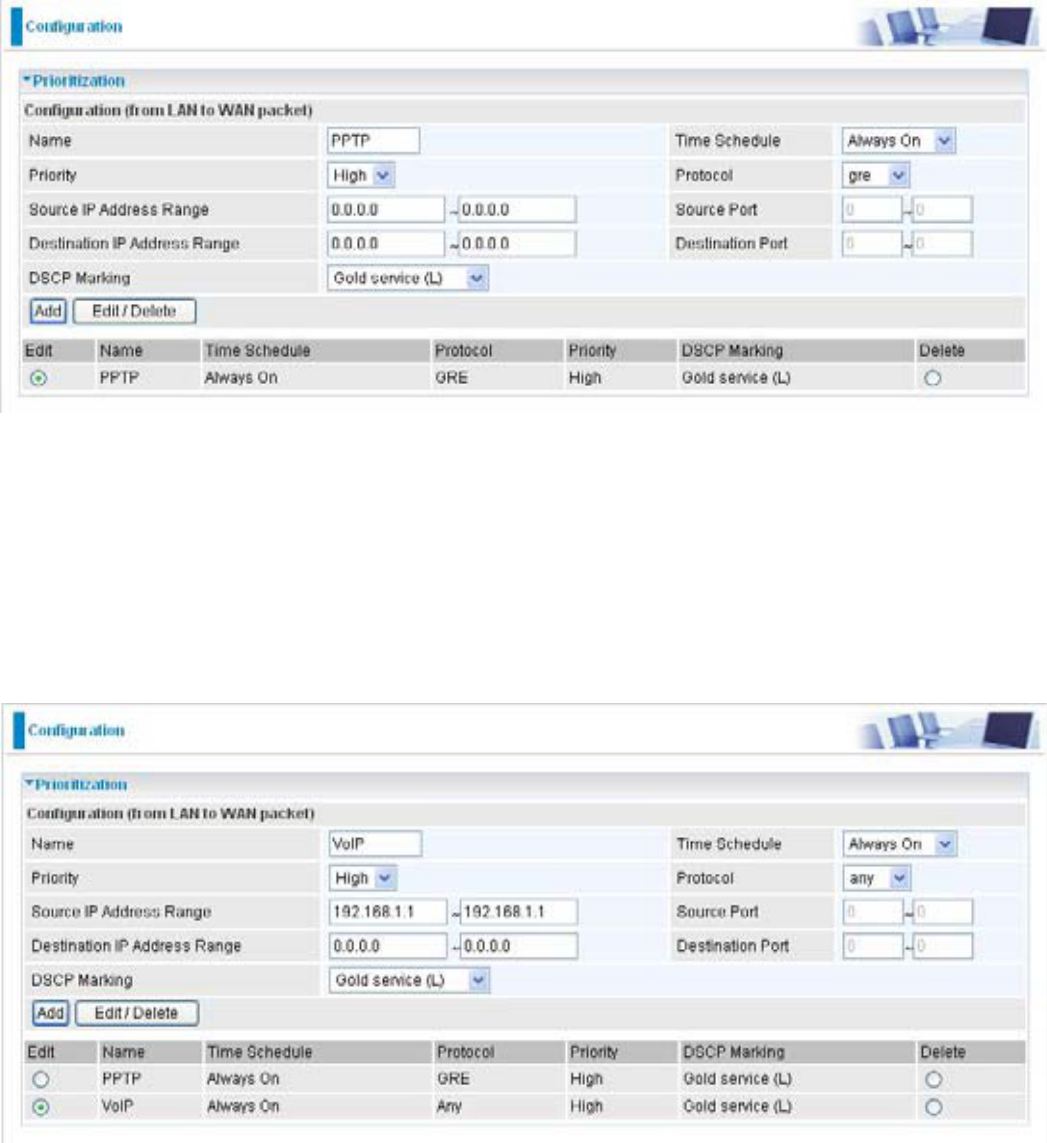
Prioritization
There are three priority settings to be provided in the Router:
High
Normal7KHGHIDXOWLVQRUPDOSULRULW\IRUDOORIWUDI¿FZLWKRXWVHWWLQJ
Low
And the balances of utilization for each priority are High (60%), Normal (30%) and Low (10%).
7RGHOHWHWKHDSSOLFDWLRQ\RXFDQFKRRVH'HOHWHRSWLRQDQGWKHQFOLFN(GLW'HOHWH
Name:UVHUGH¿QHGHVFULSWLRQWRLGHQWLI\WKLVQHZSROLF\DSSOLFDWLRQ
Time Schedule: Scheduling your prioritization policy.
Priority7KHSULRULW\JLYHQWRHDFKSROLF\DSSOLFDWLRQ,WVGHIDXOWVHWWLQJLVVHWWR+LJK\RXPD\
adjust this VHWWLQJWR¿W\RXUSROLF\DSSOLFDWLRQ
Protocol: The name of supported protocol.
Source IP Address Range: The source IP address or range of packets to be monitored.
Source Port: The source port of packets to be monitored.
134
Destination IP address Range: The destination IP address or range of packets to be monitored.
Destination Port: The destination port of packets to be monitored.
DSCP Marking'LIIHUHQWLDWHG6HUYLFHV&RGH3RLQW'6&3LWLVWKH¿UVWELWVLQWKH7R6E\WH
'6&30DUNLQJDOORZVXVHUVWRDVVLJQVSHFL¿Fapplication WUDI¿Fto be executed in priority by the
next Router based on the DSCP value. See Table 4 for DSCP Mapping Table.
Note: To be sure the router(s) in the backbones network have the capability in executing and
checking the DSCP through-out the QoS network.
Table 4: DSCP Mapping Table
DSCP Mapping Table
:LUHOHVV$'6/5RXWHU Standard DSCP
Disabled None
%HVW(IIRUW %HVW(IIRUW
Premium Express Forwarding (101110)
Gold service (L) Class 1, Gold (001010)
*ROGVHUYLFH0 Class 1, Silver (001100)
Gold service (H) &ODVV%URQ]H
Silver service (L) Class 2, Gold (010010)
6LOYHUVHUYLFH0 Class 2, Silver (010100)
Silver service (H) &ODVV%URQ]H
%URQ]HVHUYLFH/ Class 3, Gold (011010)
%URQ]HVHUYLFH0 Class 3, Silver (011100)
%URQ]HVHUYLFH+ &ODVV%URQ]H
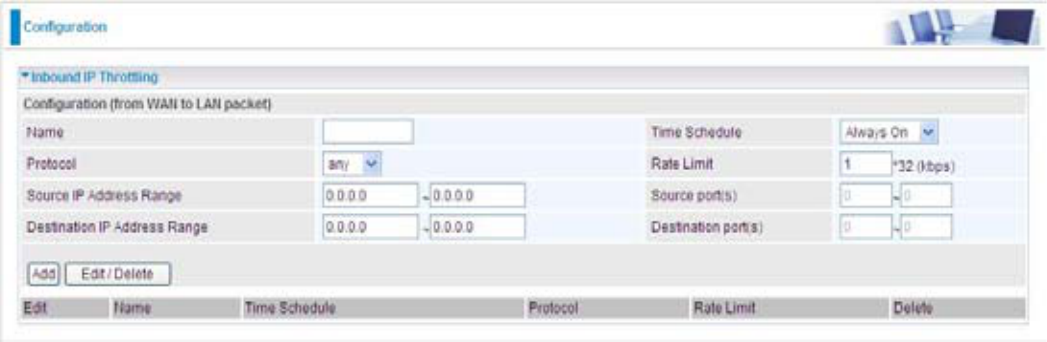
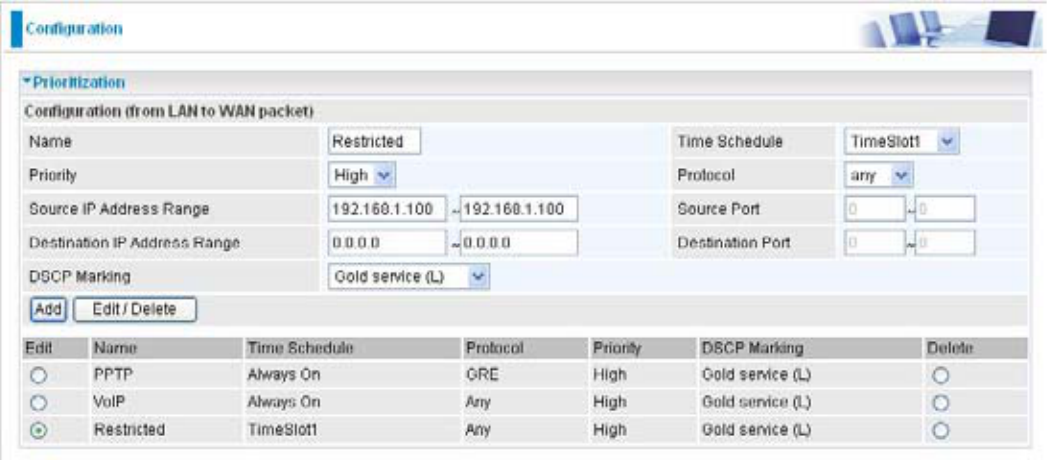
Outbound IP Throttling (LAN to WAN)
,37KURWWOLQJDOORZV\RXWROLPLWWKHVSHHGRI,3WUDI¿F7KHYDOXHHQWHUHGZLOOOLPLWWKHVSHHGRIWKH
DSSOLFDWLRQWKDW\RXVHWWRWKHVSHFL¿HGYDOXH¶VPXOWLSOHRINESV
Name:UVHUGH¿QHGHVFULSWLRQWRLGHQWLI\WKLVQHZSROLF\name.
Time Schedule: Scheduling your prioritization policy. Refer to Time Schedule for more
135
information.
Protocol: The name of supported protocol.
Rate Limit7ROLPLWWKHVSHHGRIRXWERXQGWUDI¿F
Source IP Address Range: The source IP address or range of packets to be monitored.
Source Port(s): The source port of packets to be monitored.
Destination IP Address Range: The destination IP address or range of packets to be monitored.
Destination Port(s): The destination port of packets to be monitored.
136
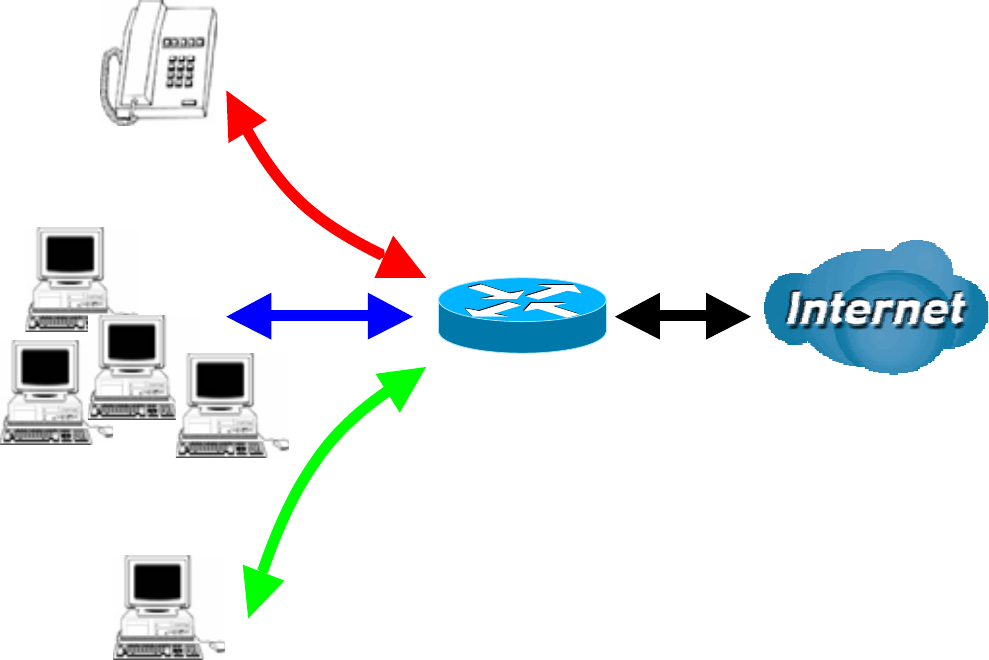
Inbound IP Throttling (WAN to LAN)
,37KURWWOLQJDOORZV\RXWROLPLWWKHVSHHGRI,3WUDI¿F7KHYDOXHHQWHUHGZLOOOLPLWWKHVSHHGRIWKH
DSSOLFDWLRQWKDW\RXVHWWRWKHVSHFL¿HGYDOXH¶VPXOWLSOHRINESV
Name:UVHUGH¿QHGHVFULSWLRQWRLGHQWLI\WKLVQHZSROLF\DSSOLFDWLRQ
Time Schedule: Scheduling your prioritization policy. Refer to Time Schedule for more
information.
Protocol: The name of supported protocol.
Rate Limit7ROLPLWWKHVSHHGRIIRULQERXQGWUDI¿F
Source IP Address Range: The source IP address or range of packets to be monitored.
Source Port(s): The source port of packets to be monitored.
Destination IP Address Range: The destination IP address or range of packets to be monitored.
Destination Port(s): The destination port of packets to be monitored.
137
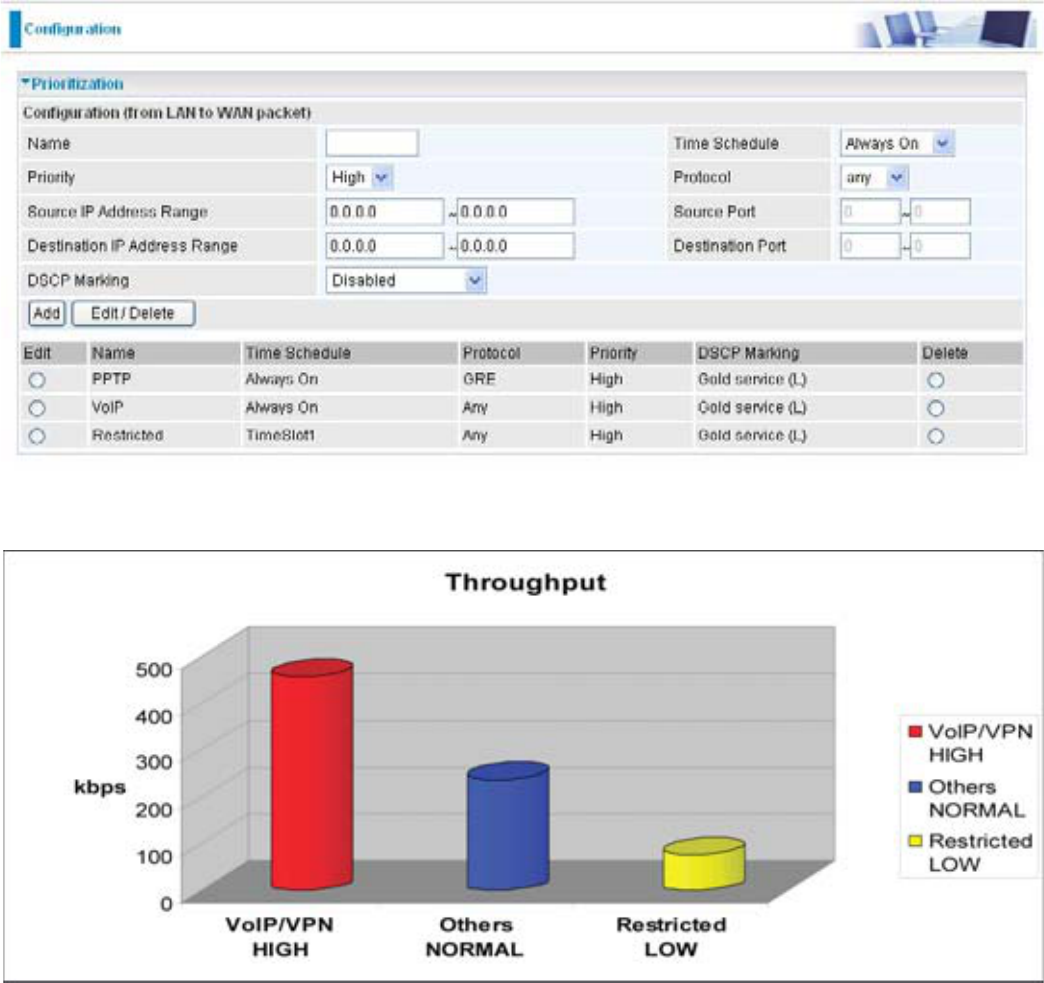
Example: QoS for your Network
Connection Diagram
Restricted PC
Normal PCs
VoIP
138
Information and Settings
Upstream: 928 kbps
'RZQVWUHDP0ESV
VoIP User : 192.168.1.1
Normal Users : 192.168.1.2~192.168.1.5
Restricted User: 192.168.1.100
139
Mission-critical application
0RVWO\WKH931FRQQHFWLRQLVPLVVLRQFULWLFDODSSOLFDWLRQIRUGRLQJGDWDH[FKDQJHEHWZHHQKHDG
DQGEUDQFKRI¿FH
The mission-critical application must be sent out smoothly without any dropping. Set priority as
high level for preventing any other applications to saturate the bandwidth.
Voice application
9RLFHLVODWHQF\VHQVLWLYHDSSOLFDWLRQ0RVW9R,3GHYLFHVDUHXVH6,3SURWRFRODQGWKHSRUWQXPEHU
ZLOOEHDVVLJQHGE\6,3PRGXOHDXWRPDWLFDOO\%HWWHUWRXVH¿[HG,3DGGUHVVIRUFDWFKLQJ9R,3
packets as high priority.
$ERYHVHWWLQJVZLOOKHOSWRLPSURYHTXDOLW\RI\RXU9R,3VHUYLFHZKHQWUDI¿FLVIXOOORDGLQJ
Restricted Application
Some of companies will setup FTP server for customer downloading or home user sharing their
¿OHVE\XVLQJ)73
140
:LWKDERYHVHWWLQJVWKDWKHOSWROLPLWXWLOL]DWLRQRIXSVWUHDPRI)737LPHVFKHGXOHDOVRKHOS\RXWR
only limit utilization at daytime.
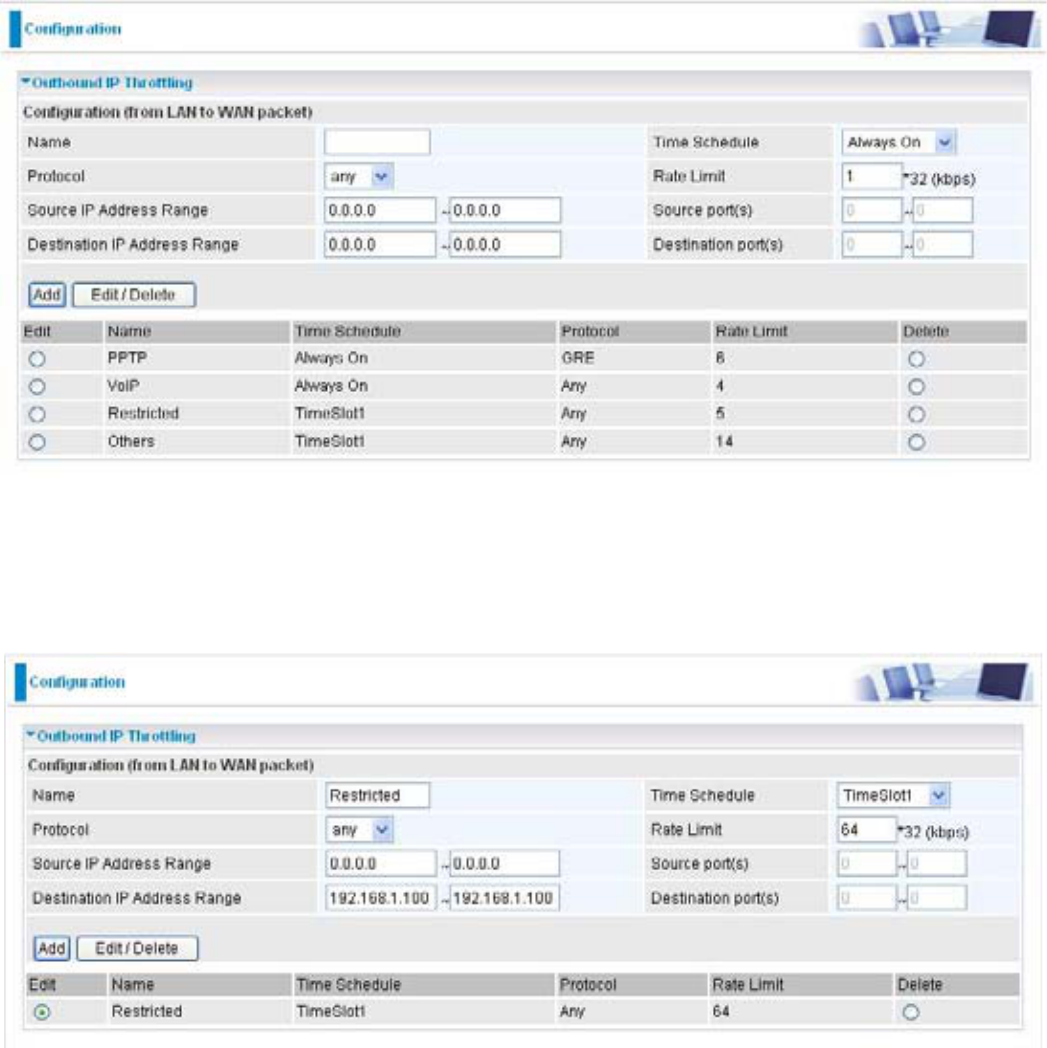
Advanced setting by using IP throttling
:LWK,3WKURWWOLQJ\RXFDQVSHFLI\PRUHGHWDLOIRUDOORFDWLQJEDQGZLGWKHYHQWKHDSSOLFDWLRQVDUH
located in the same level.
Upstream: 928kbps (29*32kbps)
0LVVLRQFULWLFDO$SSOLFDWLRQNESVNESV
Voice Application: 128kbps (4*32kbps)
Restricted Application: 160kbps (5*32kbps)
Other Applications: 448kbps (14*32kbps)
NESV NESV
141
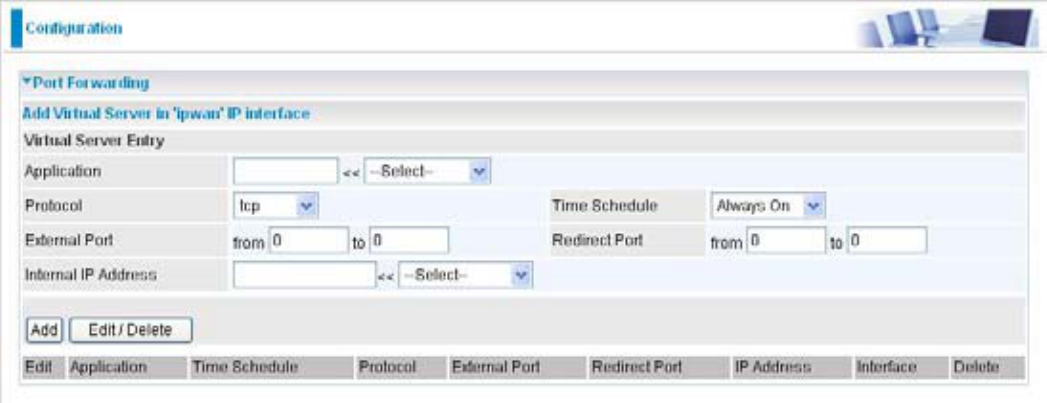
6RPHWLPH\RXUFXVWRPHUVRUIULHQGVPD\XSORDGWKHLU¿OHVWR\RXU)73VHUYHUDQGWKDWZLOO
saturate your downstream bandwidth. The settings below help you to limit bandwidth for the
restricted application.
142
Virtual Server (known as Port Forwarding)
,Q7&3,3DQG8'3QHWZRUNVDSRUWLVDELWQXPEHUXVHGWRLGHQWLI\ZKLFKDSSOLFDWLRQSURJUDP
(usually a server) incoming connections should be delivered to. Some ports have numbers that
are pre-assigned to them by the IANA (the Internet Assigned Numbers Authority), and these are
UHIHUUHGWRDV³ZHOONQRZQSRUWV´6HUYHUVIROORZWKHZHOONQRZQSRUWDVVLJQPHQWVVRFOLHQWVFDQ
locate them.
,I\RXZLVKWRUXQDVHUYHURQ\RXUQHWZRUNWKDWFDQEHDFFHVVHGIURPWKH:$1LHIURPRWKHU
machines on the Internet that are outside your local network), or any application that can accept
LQFRPLQJFRQQHFWLRQVHJ3HHUWRSHHU33VRIWZDUHVXFKDVLQVWDQWPHVVDJLQJDSSOLFDWLRQV
DQG33¿OHVKDULQJDSSOLFDWLRQVDQGDUHXVLQJ1$71HWZRUN$GGUHVV7UDQVODWLRQWKHQ\RXZLOO
XVXDOO\QHHGWRFRQ¿JXUH\RXUURXWHUWRIRUZDUGWKHVHLQFRPLQJFRQQHFWLRQDWWHPSWVXVLQJVSHFL¿F
ports to the PC on your network running the application. You will also need to use port forwarding
if you want to host an online game server.
The reason for this is that when using NAT, your publicly accessible IP address will be used by and
SRLQWWR\RXUURXWHUZKLFKWKHQQHHGVWRGHOLYHUDOOWUDI¿FWRWKHSULYDWH,3DGGUHVVHVXVHGE\\RXU
3&V3OHDVHVHHWKH:$1FRQ¿JXUDWLRQVHFWLRQRIWKLVPDQXDOIRUPRUHLQIRUPDWLRQRQ1$7
7KHGHYLFHFDQEHFRQ¿JXUHGDVDYLUWXDOVHUYHUVRWKDWUHPRWHXVHUVDFFHVVLQJVHUYLFHVVXFK
DV:HERU)73VHUYLFHVYLDWKHSXEOLF:$1,3DGGUHVVFDQEHDXWRPDWLFDOO\UHGLUHFWHGWRORFDO
VHUYHUVLQWKH/$1QHWZRUN'HSHQGLQJRQWKHUHTXHVWHGVHUYLFH7&38'3SRUWQXPEHUWKH
GHYLFHUHGLUHFWVWKHH[WHUQDOVHUYLFHUHTXHVWWRWKHDSSURSULDWHVHUYHUZLWKLQWKH/$1QHWZRUN
143
Add Virtual Server
%HFDXVH1$7FDQDFWDVD³QDWXUDO´,QWHUQHW¿UHZDOO\RXUURXWHUSURWHFWV\RXUQHWZRUNIURPEHLQJ
accessed by outside users when using NAT, as all incoming connection attempts will point to your
URXWHUXQOHVV\RXVSHFL¿FDOO\FUHDWH9LUWXDO6HUYHUHQWULHVWRIRUZDUGWKRVHSRUWVWRD3&RQ\RXU
network.
:KHQ\RXUURXWHUQHHGVWRDOORZRXWVLGHXVHUVWRDFFHVVLQWHUQDOVHUYHUVHJDZHEVHUYHU)73
VHUYHU(PDLOVHUYHURUJDPHVHUYHUWKHURXWHUFDQDFWDVD³YLUWXDOVHUYHU´<RXFDQVHWXSDORFDO
VHUYHUZLWKDVSHFL¿FSRUWQXPEHUIRUWKHVHUYLFHWRXVHHJZHE+773SRUW)73SRUW
7HOQHWSRUW6073SRUWRU323SRUW:KHQDQLQFRPLQJDFFHVVUHTXHVWWRWKH
URXWHUIRUDVSHFL¿HGSRUWLVUHFHLYHGLWZLOOEHIRUZDUGHGWRWKHFRUUHVSRQGLQJLQWHUQDOVHUYHU
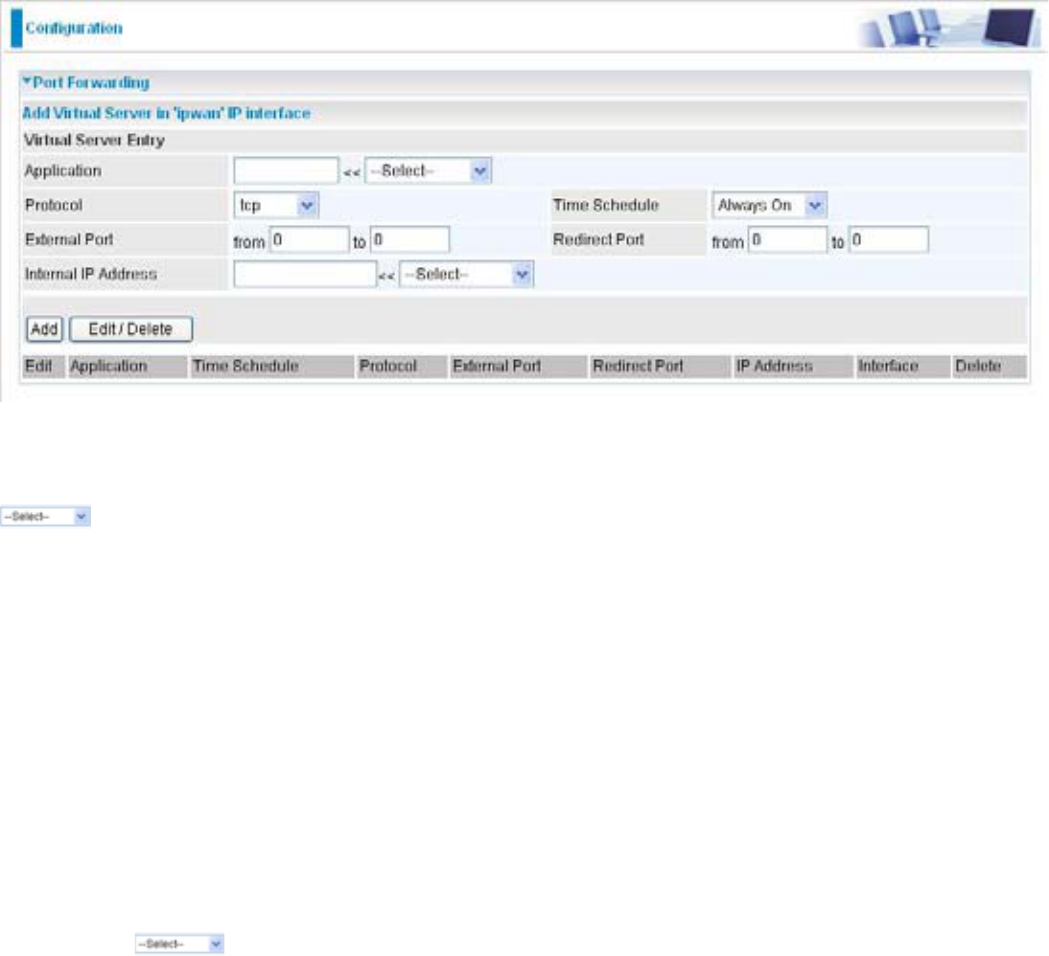
Application8VHUVGH¿QHGHVFULSWLRQWRLGHQWLI\WKLVHQWU\RUFOLFNWKH$SSOLFDWLRQ drop-down menu
WRVHOHFWDQH[LVWLQJSUHGH¿QHGUXOHV
:SUHGH¿QHGUXOHVDUHDYDLODEOH$SSOLFDWLRQ3URWRFRODQG([WHUQDO5HGLUHFW3RUWVZLOO
EH¿OOHGDIWHUWKHVHOHFWLRQ
Protocol: It is the supported protocol for the virtual server. In addition to specifying the port
number to be used, you will also need to specify the protocol used. The protocol used is
GHWHUPLQHGE\WKHSDUWLFXODUDSSOLFDWLRQ0RVWDSSOLFDWLRQVZLOOXVH7&3RU8'3
Time Schedule: UserGH¿QHGWLPHSHULRGWRHQDEOH\RXUYLUWXDOVHUYHU<RXPD\VSHFLI\DWLPH
schedule or Always on for the usage of this Virtual Server Entry. For setup and detail, refer to
Time Schedule section
External Port: 7KH3RUWQXPEHURQWKH5HPRWH:$1VLGHXVHGZKHQDFFHVVLQJWKHYLUWXDOVHUYHU
Redirect Port: The Port number used by the Local server in the LAN network.
Internal IP Address: The private IP in the LAN network, which will be providing the virtual server
application. List all existing PCs connecting to the network. You may assign a PC with IP
DGGUHVVDQG0$&IURPWKLVOLVW
Example:
II\RXOLNHWRUHPRWHDFFHVVLQJ\RXU5RXWHUWKURXJKWKH:HE+773DWDOOWLPH\RXZRXOGQHHGWR
144
HQDEOHSRUWQXPEHU:HE+773DQGPDSWR5RXWHU¶V,3$GGUHVV7KHQDOOLQFRPLQJ+773
UHTXHVWVIURP\RX5HPRWHVLGHZLOOEHIRUZDUGHGWRWKH5RXWHUZLWK,3DGGUHVVRI
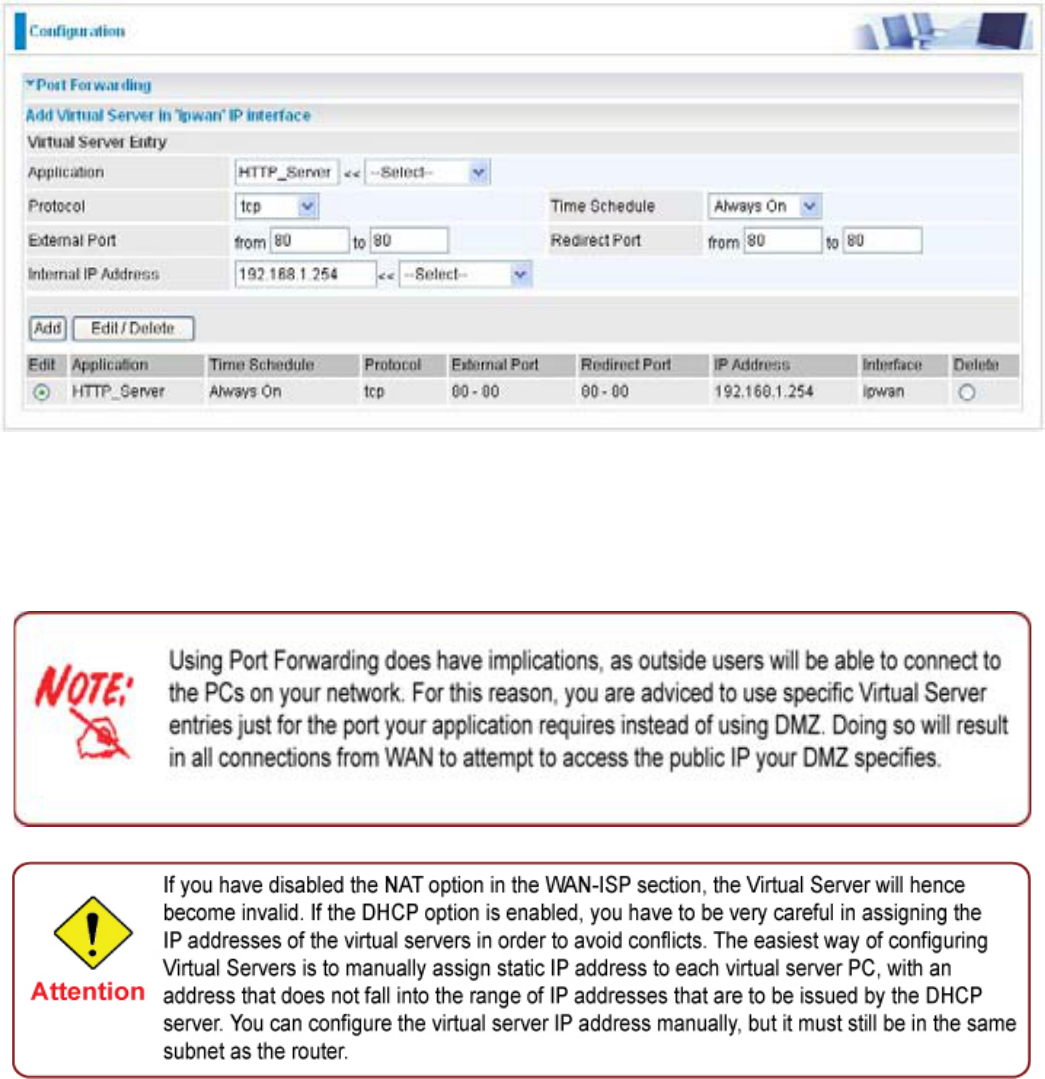
6LQFHSRUWQXPEHUKDVDOUHDG\EHHQSUHGH¿QHGQH[WWRWKH$SSOLFDWLRQFOLFN+HOSHU$OLVWRI
SUHGH¿QHGUXOHVZLQGRZZLOOSRSDQGVHOHFW+773B6HYHU
Application: HTTP_Sever
Time Schedule: Always On
Protocol: tcp
External Port: 80-80
Redirect Port: 80-80
IP Address: 192.168.1.254
Add: Click it to apply your settings.
Edit/Delete: Click it to edit or delete this virtual server application.
145
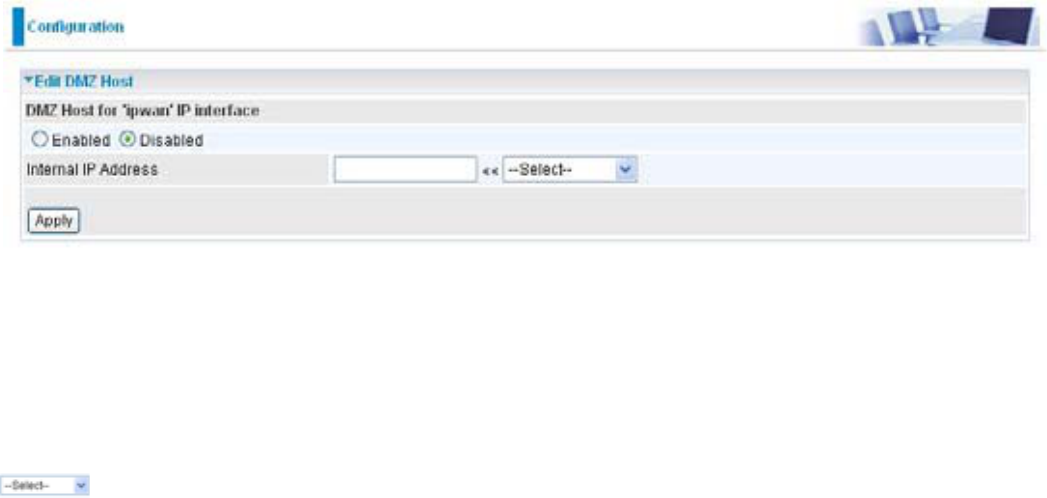
Edit DMZ Host
7KH'0=+RVWLVDORFDOFRPSXWHUH[SRVHGWRWKH,QWHUQHW:KHQVHWWLQJDSDUWLFXODULQWHUQDO
,3DGGUHVVDVWKH'0=+RVWDOOLQFRPLQJSDFNHWVZLOOEHFKHFNHGE\WKH)LUHZDOODQG1$7
DOJRULWKPVWKHQSDVVHGWRWKH'0=KRVWZKHQDSDFNHWUHFHLYHGGRHVQRWXVHDSRUWQXPEHU
used by any other Virtual Server entries.
Cautious: This Local computer exposing to the Internet may face varies of security risks.
*RWR&RQ¿JXUDWLRQ > Virtual Server > (GLW'0=+RVW
Enabled: ,WDFWLYDWHV\RXU'0=IXQFWLRQ
Disabled: $VVHWLQGHIDXOWVHWWLQJLWGLVDEOHVWKH'0=IXQFWLRQ
Internal IP Address: *LYHDVWDWLF,3DGGUHVVWRWKH'0=+RVWZKHQEnabled radio button is
FKHFNHG%HDZDUHWKDWWKLV,3ZLOOEHH[SRVHGWRWKH:$1,QWHUQHW
List all existing PCs connecting to the network. You may assign a PC with IP address from
this list.
Select the Apply button to apply your changes.
146
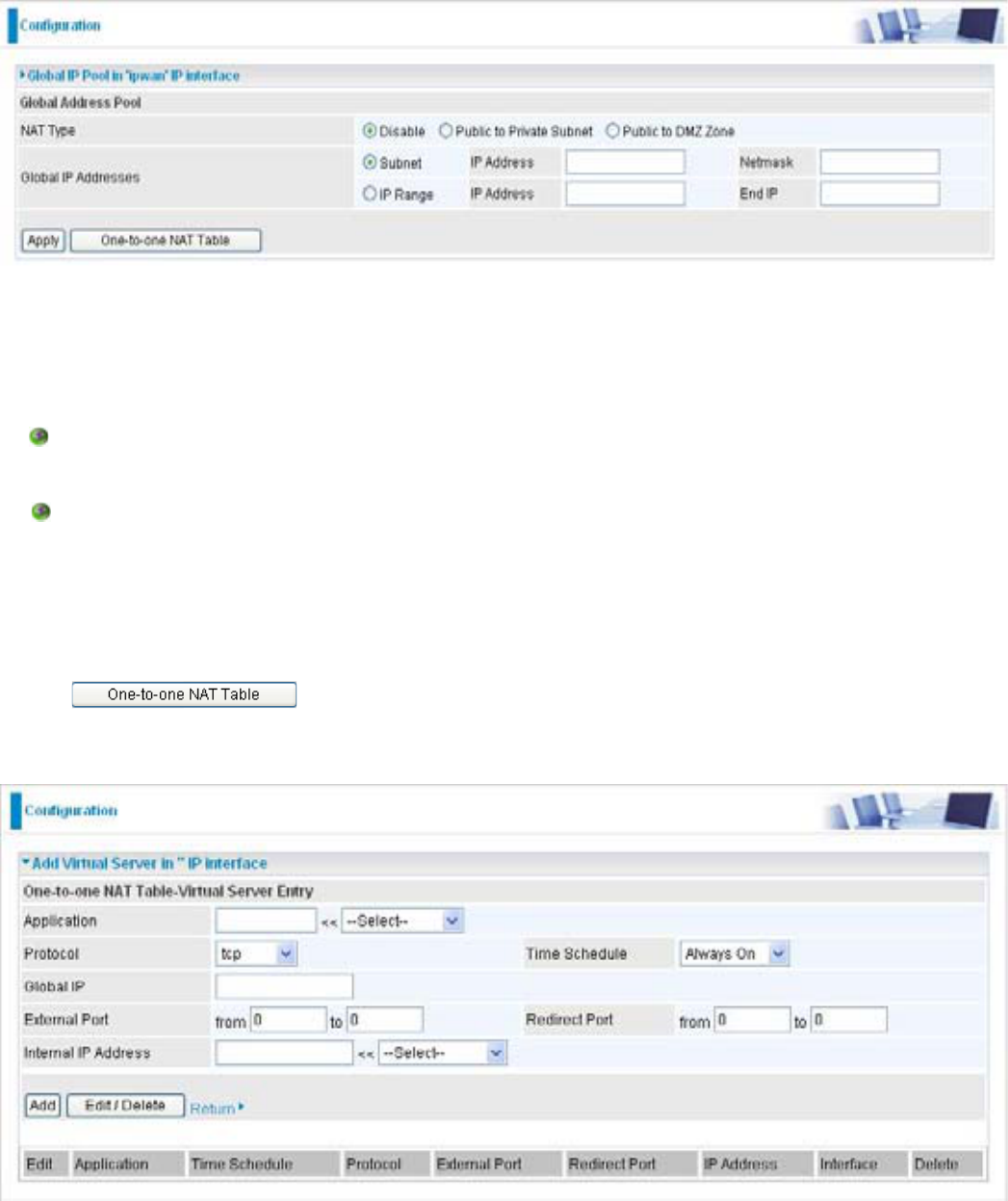
Edit One-to-One NAT (Network Address Translation)
2QHWR2QH1$7PDSVDVSHFL¿FSULYDWHORFDO,3DGGUHVVWRDJOREDOSXEOLF,3DGGUHVV
,I\RXKDYHPXOWLSOHSXEOLF:$1,3DGGUHVVHVIURP\RX,63\RXDUHHOLJLEOHIRU2QHWR2QH1$7
to utilize these IP addresses.
*RWR&RQ¿JXUDWLRQ > Virtual Server > Edit One-to-one NAT
NAT Type: Select desired NAT type. As set in default setting, it disables the One-to-One NAT
function.
Global IP Address:
Subnet: 7KHVXEQHWRIWKHSXEOLF:$1,3DGGUHVVJLYHQE\\RXU,63,I\RXU,63KDVSUR-
vided this information, you may insert it here. Otherwise, use IP Range method.
IP Range: 7KH ,3 DGGUHVV UDQJH RI \RXU SXEOLF:$1 ,3 DGGUHVVHV )RU H[DPSOH ,3
192.168.1.1, end IP: 192.168.1.10
Select the Apply button to apply your changes.
Check to create a new One-to-One NAT rule:
147
Application8VHUVGH¿QHGGHVFULSWLRQWRLGHQWLI\WKLVHQWU\RUFOLFN drop-down menu to
VHOHFWH[LVWLQJSUHGH¿QHGUXOHV
:SUHGH¿QHGUXOHVDUHDYDLODEOH $SSOLFDWLRQ3URWRFRODQG([WHUQDO5HGLUHFW3RUWVZLOO
EH¿OOHGDIWHUWKHVHOHFWLRQ
Protocol: It is the supported protocol for the virtual server. In addition to specifying the port
number to be used, you will also need to specify the protocol used. The protocol used is
GHWHUPLQHGE\WKHSDUWLFXODUDSSOLFDWLRQ0RVWDSSOLFDWLRQVZLOOXVH7&3RU8'3
Time Schedule: UserGH¿QHGWLPHSHULRGWRHQDEOH\RXUYLUWXDOVHUYHU<RXPD\VSHFLI\DWLPH
schedule or Always on for the usage of this Virtual Server Entry. For setup and detail, refer to
Time Schedule section
Global IP: 'H¿QHDSXEOLF:$1,3DGGUHVVIRUWKLV$SSOLFDWLRQWRXVH7KLV*OREDO,3DGGUHVV
PXVWEHGH¿QHGLQWKH*OREDO,3$GGUHVV
External Port: 7KH3RUWQXPEHURQWKH5HPRWH:$1VLGHXVHGZKHQDFFHVVLQJWKHYLUWXDOVHUYHU
Redirect Port: The Port number used by the Local server in the LAN network.
Internal IP Address: The private IP in the LAN network, which will be providing the virtual server
application. List all existing PCs connecting to the network. You may assign a PC with IP
address from this list.
Select the Add button to apply your changes.
148
Example: List of some well-known and registered port numbers.
The Internet Assigned Numbers Authority (IANA) is the central coordinator for the assignment
RIXQLTXHSDUDPHWHUYDOXHVIRU,QWHUQHWSURWRFROV3RUWQXPEHUVUDQJHIURPWREXWRQO\
SRUWVQXPEHUVWRDUHUHVHUYHGIRUSULYLOHJHGVHUYLFHVDQGDUHGHVLJQDWHGDV³ZHOONQRZQ
SRUWV´3OHDVHUHIHUWR7DEOH7KHUHJLVWHUHGSRUWVDUHQXPEHUHGIURPWKURXJK
The remaining ports, referred to as dynamic or private ports, are numbered from 49152 through
65535.
)RUIXUWKHULQIRUPDWLRQSOHDVHVHH,$1$¶VZHEVLWHDWhttp://www.iana.org/assignments/port-
numbers
For help on determining which private port numbers are used by common applications on this list,
SOHDVHVHHWKH)$4V)UHTXHQWO\$VNHG4XHVWLRQVDWhttp://www.billion.com
Table 5: Well-known and registered Ports
Port Number Protocol Description
20 TCP FTP Data
21 TCP FTP Control
22 TCP & UDP SSH Remote Login Protocol
23 TCP Telnet
25 TCP 60736LPSOH0DLO7UDQVIHU3URWRFRO
53 TCP & UDP DNS (Domain Name Server)
69 UDP TFTP (Trivial File Transfer Protocol)
80 TCP :RUOG:LGH:HE+773
110 TCP 3233RVW2I¿FH3URWRFRO9HUVLRQ
119 TCP 1(:61HWZRUN1HZV7UDQVIHU3URWRFRO
123 UDP NTP (Network Time Protocol)61736LPSOH1HWZRUN
Time Protocol)
161 TCP 6103
443 TCP & UDP HTTPS
1503 TCP T.120
1720 TCP H.323
4000 TCP ICQ
7070 UDP RealAudio
149
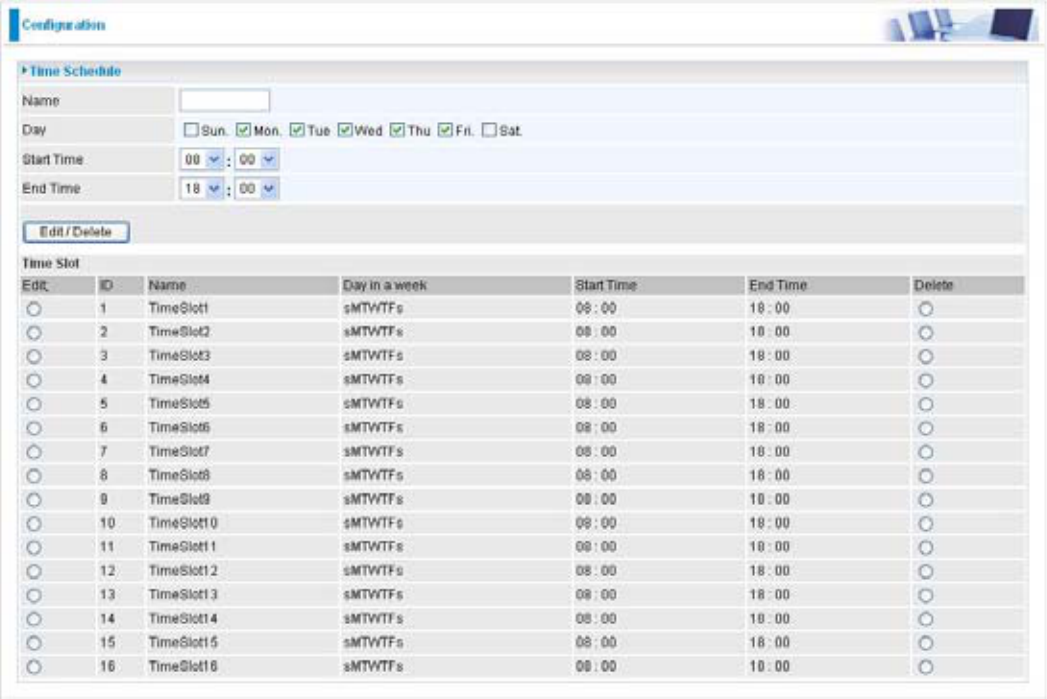
Time Schedule
The Time Schedule supports up to 16 time slots which helps you to manage your Internet
FRQQHFWLRQ,QHDFKWLPHSUR¿OH\RXPD\VFKHGXOHVSHFL¿FGD\VLH0RQGD\WKURXJK6XQGD\WR
restrict or allowing the usage of the Internet by users or applications.
7KLV7LPH6FKHGXOHFRUUHODWHVFORVHO\ZLWKURXWHU¶VWLPHVLQFHURXWHUGRHVQRWKDYHDUHDOWLPH
clock on board; it uses the Simple Network Time Protocol (SNTP) to get the current time from an
SNTP server from the Internet. Refer to Time Zone for details. You router time should correspond
with your local time. If the time is not set correctly, your Time Schedule will not function properly.
150
&RQ¿JXUDWLRQRI7LPH6FKHGXOH
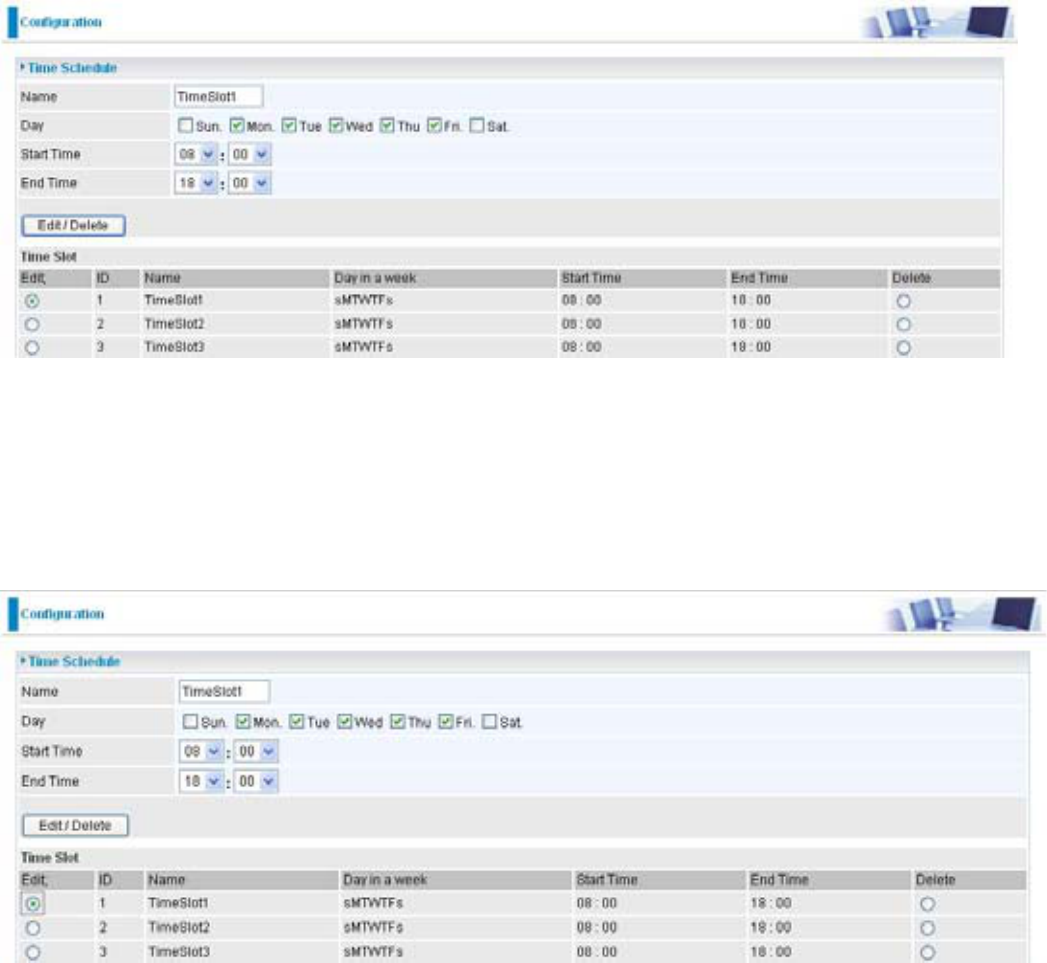
Edit a Time Slot
Choose any Time Slot (ID 1 to ID 16) to edit, click Edit radio button.1.
Note: Watch it carefully, the days you have selected will present in capital letter. Lower case
letter shows the day(s) is not selected, and no rule will apply on this day(s).
A detailed setting of this Time Slot will be shown.
2.
ID: This is the index of the time slot.
Name:$XVHUGH¿QHGHVFULSWLRQWRLGHQWLI\WKLVWLPHSRUWIROLR
Day in a week: 7KHGHIDXOWLVVHWIURP0RQGD\WKURXJK)ULGD\<RXPD\VSHFLI\WKHGD\VIRUWKH
schedule to be applied.
Start Time:7KHGHIDXOWLVVHWDW$0<RXPD\VSHFLI\WKHVWDUWWLPHRIWKHVFKHGXOH
End Time:7KHGHIDXOWLVVHWDW30<RXPD\VSHFLI\WKHHQGWLPHRIWKHVFKHGXOH
Choose Edit radio button and click (GLW'HOHWH button to apply your changes.
151
Delete a Time Slot
Select the Delete radio button of the selected Time Slot under the Time Slot section, and click the
(GLWDelete buttonWRFRQ¿UPWKHGHOHWLRQRIWKHVHOHFWHG7LPHSUR¿OHLHHUDVHWKH'D\DQGEDFNWR
GHIDXOWVHWWLQJRI6WDUW7LPH(QG7LPH
152
Advanced
&RQ¿JXUDWLRQRSWLRQVZLWKLQWKH$GYDQFHGVHFWLRQDUHIRUXVHUVZKRZLVKWRWDNHDGYDQWDJHRI
the more advanced features of the router. Users who do not understand the features should not
DWWHPSWWRUHFRQ¿JXUHWKHLUURXWHUXQOHVVDGYLVHGWRGRVRE\VXSSRUWVWDII
Here are the items within the Advanced section: Static Route, Dynamic DNS, Check Email,
Device Management, IGMP and VLAN Bridge.
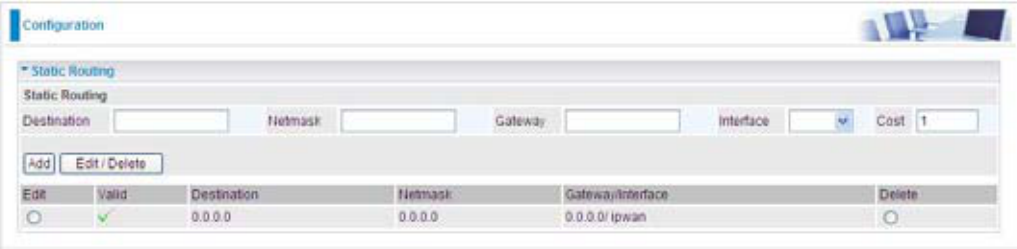
Static Route
*RWR&RQ¿JXUDWLRQ!$GYDQFHG!6WDWLF5RXWH
Destination: This is the destination subnet IP address.
Netmask: Subnet mask of the destination IP addresses based on above destination subnet IP.
Gateway: This is the gateway IP address to which packets are to be forwarded.
Interface: Select the interface through which packets are to be forwarded.
Cost: This is the same meaning as Hop. This should usually be left at 1.
153
Dynamic DNS
The Dynamic DNS function allows you to alias a dynamic IP address to a static hostname,
allowing users whose ISP does not assign them a static IP address to use a domain name. This is
especially useful for hosting servers via your ADSL connection, so that anyone wishing to connect
to you may use your domain name, rather than having to use your dynamic IP address, which
FKDQJHVIURPWLPHWRWLPH7KLVG\QDPLF,3DGGUHVVLVWKH:$1,3DGGUHVVRIWKHURXWHUZKLFKLV
assigned to you by your ISP.
<RXZLOO¿UVWQHHGWRUHJLVWHUDQGHVWDEOLVKDQDFFRXQWZLWKWKH'\QDPLF'16SURYLGHUXVLQJWKHLU
website, for example http://www.dyndns.org/
There are more than 5 DDNS services supported.
Dynamic DNS:
Disable: Check to disable the Dynamic DNS function.
Enable: &KHFNWRHQDEOHWKH'\QDPLF'16IXQFWLRQ7KHIROORZLQJ¿HOGVZLOOEHDFWLYDWHGDQG
UHTXLUHG
Dynamic DNS Server: Select the DDNS service you have established an account with.
Domain Name, Username and Password: Enter your registered domain name and your username
and password for this service.
Period: Set the time period between updates, for the Router to exchange information with the DDNS
server. In addition to updating periodically as per your settings, the router will perform an update
when your dynamic IP address changes.
154
Check Email
This function allows you to have the router check your POP3 mailbox for new Email messages.
7KH0DLO/('RQ\RXUURXWHUZLOOOLJKWZKHQLWGHWHFWVQHZPHVVDJHVZDLWLQJIRUGRZQORDG<RX
may also view the status of this function using the Status – Email Checking section of the web
interface, which also provides details on the number of new messages waiting. See the Status
section of this manual for more information.
Check Email:
Disable: &KHFNWRGLVDEOHWKHURXWHU¶V(PDLOFKHFNLQJIXQFWLRQ
Enable: &KHFNWRHQDEOHWKHURXWHUV(PDLOFKHFNLQJIXQFWLRQ7KHIROORZLQJ¿HOGVZLOOEHDF-
WLYDWHGDQGUHTXLUHG
Account Name: Enter the name (login) of the POP3 account you wish to check. Normally, it is the
WH[WLQ\RXUHPDLODGGUHVVEHIRUHWKH³#´V\PERO,I\RXKDYHWURXEOHZLWKLWSOHDVHFRQWDFW\RXU
ISP.
Password: (QWHUWKHDFFRXQW¶VSDVVZRUG
POP3 Mail Server: Enter your (POP) mail server name. You Internet Service Provider (ISP) or
network administrator will be able to supply you with this.
Period: Enter the value in minutes between periodic mail checks.
Dial-out for checking emails: :KHQWKHIXQFWLRQLVHQDEOHG\RXU$'6/URXWHUZLOOFRQQHFWWR
your ISP automatically to check emails if your Internet connection dropped. Please be careful
when using this feature if your ADSL service is charged by time online.
155
Device Management
7KH'HYLFH0DQDJHPHQWDGYDQFHGFRQ¿JXUDWLRQVHWWLQJVDOORZ\RXWRFRQWURO\RXUURXWHU¶V
security options and device monitoring features.
Device Host Name
Host Name: Assign it a name.
(The Host Name cannot be used with one word only. There are two words should be
connected with a ‘.’ at least.
Example:
Host Name: homegateway ==> Incorrect
Host Name: home.gateway or my.home.gateway ==> Correct)
Embedded Web Server ( 2 Management IP Accounts)
HTTP Port: 7KLVLVWKHSRUWQXPEHUWKHURXWHU¶VHPEHGGHGZHEVHUYHUIRUZHEEDVHG
FRQ¿JXUDWLRQZLOOXVH7KHGHIDXOWYDOXHLVWKHVWDQGDUG+773SRUW8VHUVPD\VSHFLI\DQ
alternative if, for example, they are running a web server on a PC within their LAN.
Management IP Address: You may specify an IP address allowed to logon and access the
URXWHU¶VZHEVHUYHU6HWWLQJWKH,3DGGUHVVWRZLOOGLVDEOH,3DGGUHVVUHVWULFWLRQVDOORZLQJ
users to login from any IP address.
Expire to auto-logout: 6SHFLI\DWLPHIUDPHIRUWKHV\VWHPWRDXWRORJRXWWKHXVHU¶VFRQ¿JXUDWLRQ
session.

156
For Example: User A changes HTTP port number to 100VSHFL¿HVWKHLURZQ,3DGGUHVV
of 192.168.1.55, and sets the logout time to be 100 seconds. The router will only allow
User A access from the IP address 192.168.1.55WRORJRQWRWKH:HE*8,E\W\SLQJ
http://192.168.1.254:100 in their web browser. After 100 seconds, the device will automatically
logout User A.
Universal Plug and Play (UPnP)
UPnP offers peer-to-peer network connectivity for PCs and other network devices, along with
control and data transfer between devices. UPnP offers many advantages for users running
NAT routers through UPnP NAT Traversal, and on supported systems makes tasks such as port
IRUZDUGLQJPXFKHDVLHUE\OHWWLQJWKHDSSOLFDWLRQFRQWUROWKHUHTXLUHGVHWWLQJVUHPRYLQJWKHQHHG
IRUWKHXVHUWRFRQWURODGYDQFHGFRQ¿JXUDWLRQRIWKHLUGHYLFH
%RWKWKHXVHU¶V2SHUDWLQJ6\VWHPDQGWKHUHOHYDQWDSSOLFDWLRQPXVWVXSSRUW83Q3LQDGGLWLRQ
WRWKHURXWHU:LQGRZV;3DQG:LQGRZV0HQDWLYHO\VXSSRUW83Q3ZKHQWKHFRPSRQHQWLV
LQVWDOOHGDQG:LQGRZVXVHUVPD\LQVWDOOWKH,QWHUQHW&RQQHFWLRQ6KDULQJFOLHQWIURP:LQGRZV
;3LQRUGHUWRVXSSRUW83Q3:LQGRZVGRHVQRWVXSSRUW83Q3
Disable: &KHFNWRGLVDEOHWKHURXWHU¶V83Q3IXQFWLRQDOLW\
Enable: &KHFNWRHQDEOHWKHURXWHU¶V83Q3IXQFWLRQDOLW\
UPnP Port: Its default setting is 2800. It is highly recommended for users to use this port value. If
WKLVYDOXHFRQÀLFWVZLWKRWKHUSRUWVDOUHDG\EHLQJXVHG\RXPD\ZLVKWRFKDQJHWKHSRUW
SNMP Access Control (Software on a PC within the LAN is required in order to utilize this
function) – Simple Network Management Protocol.
SNMP V1 and V2:
Read Community: 6SHFLI\DQDPHWREHLGHQWL¿HGDVWKH5HDG&RPPXQLW\DQGDQ,3DGGUHVV
7KLVFRPPXQLW\VWULQJZLOOEHFKHFNHGDJDLQVWWKHVWULQJHQWHUHGLQWKHFRQ¿JXUDWLRQ¿OH2QFHWKH
string name is matched, user obtains this IP address will be able to view the data.
Write Community: 6SHFLI\DQDPHWREHLGHQWL¿HGDVWKH:ULWH&RPPXQLW\DQGDQ,3DGGUHVV
7KLVFRPPXQLW\VWULQJZLOOEHFKHFNHGDJDLQVWWKHVWULQJHQWHUHGLQWKHFRQ¿JXUDWLRQ¿OH2QFHWKH
string name is matched, users from this IP address will be able to view and modify the data.
Trap Community: 6SHFLI\DQDPHWREHLGHQWL¿HGDVWKH7UDS&RPPXQLW\DQGDQ,3DGGUHVV
7KLVFRPPXQLW\VWULQJZLOOEHFKHFNHGDJDLQVWWKHVWULQJHQWHUHGLQWKHFRQ¿JXUDWLRQ¿OH2QFHWKH
VWULQJQDPHLVPDWFKHGXVHUVIURPWKLV,3DGGUHVVZLOOEHVHQW61037UDSV
SNMP V3:
6SHFLI\DQDPHDQGSDVVZRUGIRUDXWKHQWLFDWLRQ$QGGH¿QHWKHDFFHVVULJKWIURPLGHQWL¿HG,3
address. Once the authentication has succeeded, users from this IP address will be able to view
and modify the data.
SNMP Version: SNMPv2c and SNMPv3
6103YFLVWKHFRPELQDWLRQRIWKHHQKDQFHGSURWRFROIHDWXUHVRI6103YZLWKRXWWKH6103Y
VHFXULW\7KH³F´FRPHVIURPWKHIDFWWKDW6103YFXVHVWKH6103YFRPPXQLW\VWULQJSDUDGLJP
157
IRU³VHFXULW\´EXWLVZLGHO\DFFHSWHGDVWKH6103YVWDQGDUG
6103YLVDVWURQJDXWKHQWLFDWLRQPHFKDQLVPDXWKRUL]DWLRQZLWK¿QHJUDQXODULW\IRUUHPRWH
monitoring.
Traps supported: Cold Start, Authentication Failure.
7KHIROORZLQJ0,%VDUHVXSSRUWHG
From RFC 1213 (MIB-II)System group
System group
Interface group
Address Translation group
IP group
ICMP Group
TCP group
UDP group
EGP (not applicable)
Transmission
6103JURXS
From RFC 1650 (EtherLike-MIB)
dot3stats
From RFC 1493 (Bridge MIB)
GRWG%DVHJURXS
dot1 dTp group
GRW G6WS JURXS LI FRQ¿JXUHG DV VSDQ-
ning tree)
From RFC 1471 (PPP/LCP MIB)
pppLink group
pppLgr group (not applicable)
From RFC 1472 (PPP/Security MIB)
PPP security group
From RFC 1473 (PPP/IP MIB)
PPP IP group
From RFC 1474 (PPP/Bridge MIB)
333%ULGJHJURXS
From RFC 1573 (IfMIB)
LI0,%2EMHFWVJURXS
From RFC 1695 (atmMIB)
DWP0,%2EMHFWV
From RFC 1907 (SNMPv2)
only snmpSetSerialNo OID
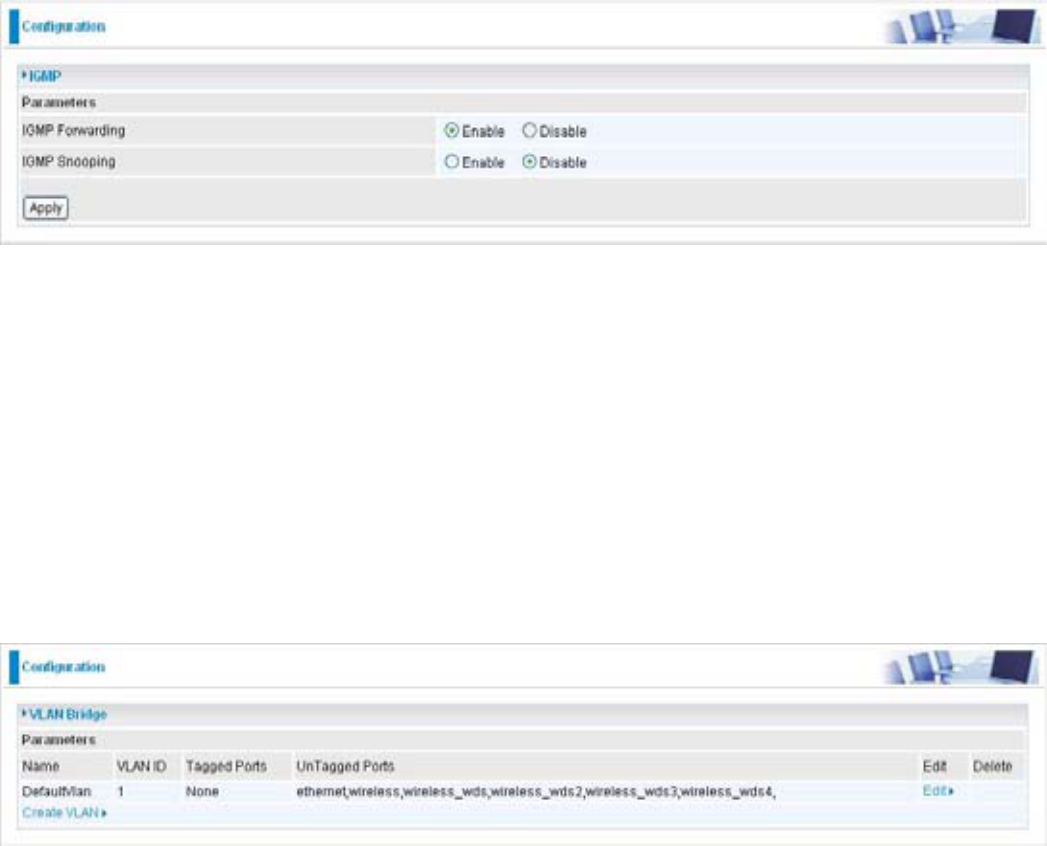
158
IGMP
,*03NQRZQDV,QWHUQHW*URXS0DQDJHPHQW3URWRFROLVXVHGWRPDQDJHPHQWKRVWVIURP
multicast group.
IGMP Forwarding: Accepting multicast packet. Default is set to Enable.
IGMP Snooping: Allowing switched Ethernet to check and make correct forwarding decisions.
Default is set to Disable.
VLAN Bridge
This section allows you to create VLAN group and specify the member.
Edit: Edit your member ports in selected VLAN group.
Create VLAN: To create another VLAN group.
159
Logout
7RH[LWWKHURXWHUZHELQWHUIDFHFKRRVH/RJRXW3OHDVHVDYH\RXUFRQ¿JXUDWLRQVHWWLQJEHIRUH
logging out of the system.
%HDZDUHWKDWWKHURXWHUFRQ¿JXUDWLRQLQWHUIDFHFDQRQO\EHDFFHVVHGE\RQH3&DWDWLPH
Therefore when a PC has logged into the system interface, the other users cannot access the
system interface until the current user has logged out of the system. If the previous user forgets to
ORJRXWWKHVHFRQG3&FDQRQO\DFFHVVWKHURXWHUZHELQWHUIDFHDIWHUDXVHUGH¿QHGDXWRORJRXW
period which is by default 3 minutes. You can however modify the value of the auto logout period
XVLQJWKH$GYDQFHG!'HYLFH0DQDJHPHQWVHFWLRQRIWKHURXWHUZHELQWHUIDFH3OHDVHVHHWKH
Advanced section of this manual for more information.
160
Chapter 5: Troubleshooting
If your router is not functioning properly, please refer to the suggested solutions provided in this
chapter. If your problems persist or the suggested solutions do not meet your needs, please kindly
FRQWDFW\RXUVHUYLFHSURYLGHURU%LOOLRQIRUVXSSRUW
Problems with the router
Problem Suggested Action
None of the LEDs lit when the router is
turned on.
Check the connection between the router and the
adapter. If the problem persists, most likely it is due
to the malfunction of your hardware. Please contact
\RXUVHUYLFHSURYLGHURU%LOOLRQIRUWHFKQLFDOVXSSRUW
You have forgotten your login username
or password
Try the default username & password (Please refer
to Chapter 3). If this fails, restore your router to its
default setting by pressing the reset button for more
than 6 seconds.
Problems with WAN interface
Problem Suggested Action
Initialization of PVC connection (line-
sync)fail
0DNHVXUHWKDWWKHWHOHSKRQHFDEOHLVSURSHUO\FRQ-
nected between the ADSL port and the wall jack. The
ADSL LED on the front panel should lit. Check that
your VPI, VCI, encapsulation type and type of multi-
plexing settings are the same as those provided by
your ISP. Reboot the router GE. If you still have prob-
lem, you may need to verify these settings with your
ISP.
Frequent loss of ADSL linesync
(disconnection)
0DNHVXUHWKDWDOOGHYLFHVHJWHOHSKRQHID[PD-
chine, analogue modems) that are connected to the
WHOHSKRQHOLQHDV\RXUURXWHUKDYHDOLQH¿OWHUFRQ-
nected between them and the wall outlet (unless your
are using a Central Splitter or Central Filter installed by
DTXDOL¿HGDQGOLFHQVHGHOHFWULFLDQ0DNHVXUHWKDWDOOO
OLQH¿OWHUVDUHFRUUHFWO\LQVWDOOHGDVPLVVLQJOLQH¿OWHUV
RULQFRUUHFWLQVWDOODWLRQRIOLQH¿OWHUVFDQFDXVH$'6/
FRQQHFWLRQSUREOHPLQFOXGLQJIUHTXHQWGLVFRQQHF-
tions.
161
Problem with LAN interface
Problem Suggested Action
Cannot PING any PC on LAN Check the Ethernet LEDs on the front panel. The LED
should be on for the port that has a PC connected. If it does
not lit, check to see if the cable between your router and the
3&LVSURSHUO\FRQQHFWHG0DNHVXUH\RXKDYH¿UVWXQLQ-
VWDOOHG\RXU¿UHZDOOSURJUDPEHIRUHWURXEOHVKRRWLQJ
Verify that the IP address and the subnet mask are consis-
tent for both the router and the workstations.

162
Appendix: Product Support & Contact
Following the suggestions listed in the Troubleshooting section of the user manual can help you
solve most of your problems. However if your problems persist or you come across other technical
issues that are not listed in the Troubleshooting section, please contact the dealer from where you
purchased your product.
Contact Billion
0$&26LVDUHJLVWHUHG7UDGHPDUNRI$SSOH&RPSXWHU,QF
:LQGRZV:LQGRZV17:LQGRZV:LQGRZV0H:LQGRZV;3DQG:LQGRZV9LVWDDUHUHJLVWHUHG
7UDGHPDUNVRI0LFURVRIW&RUSRUDWLRQ
Worldwide:
http://www.billion.com