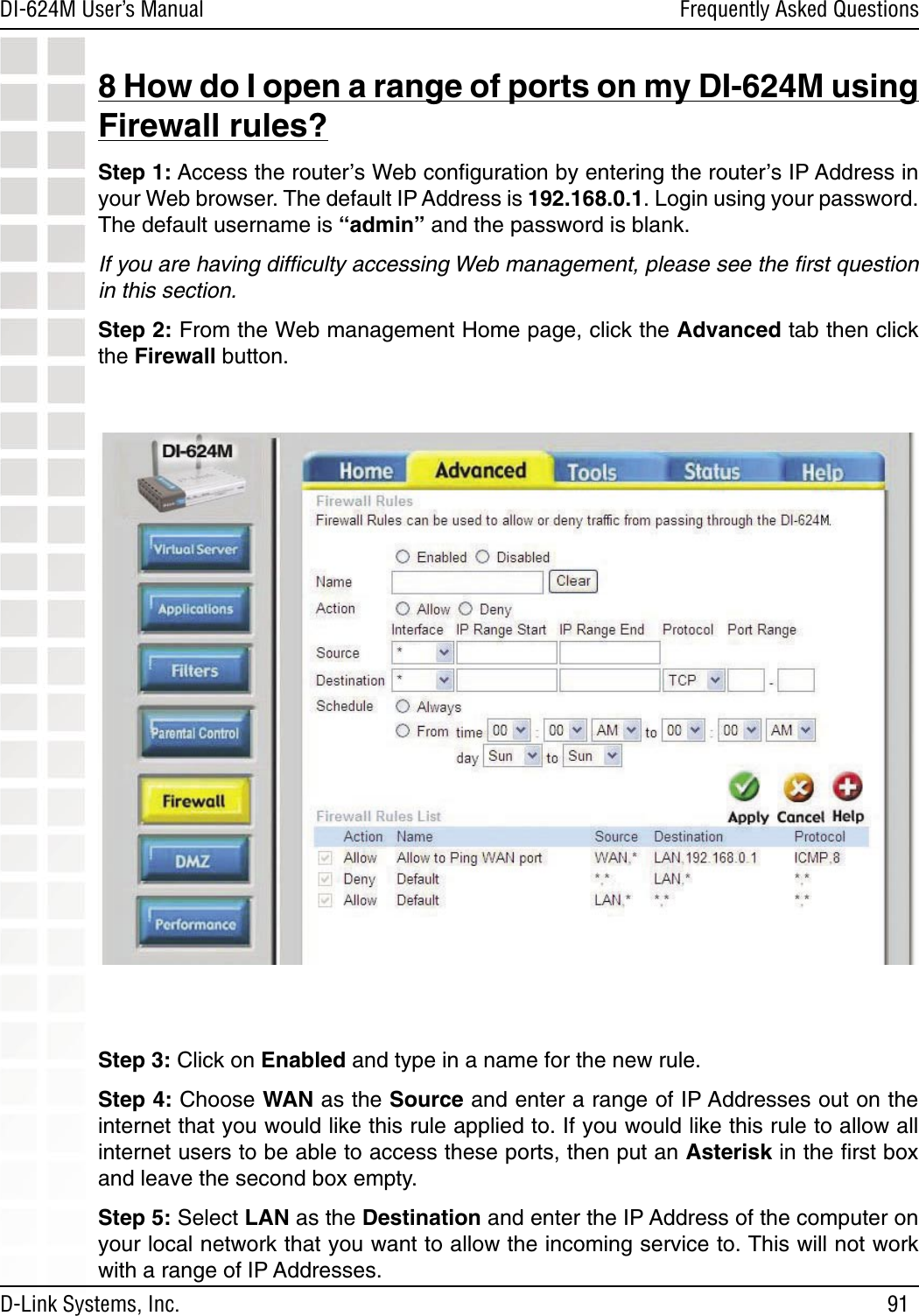
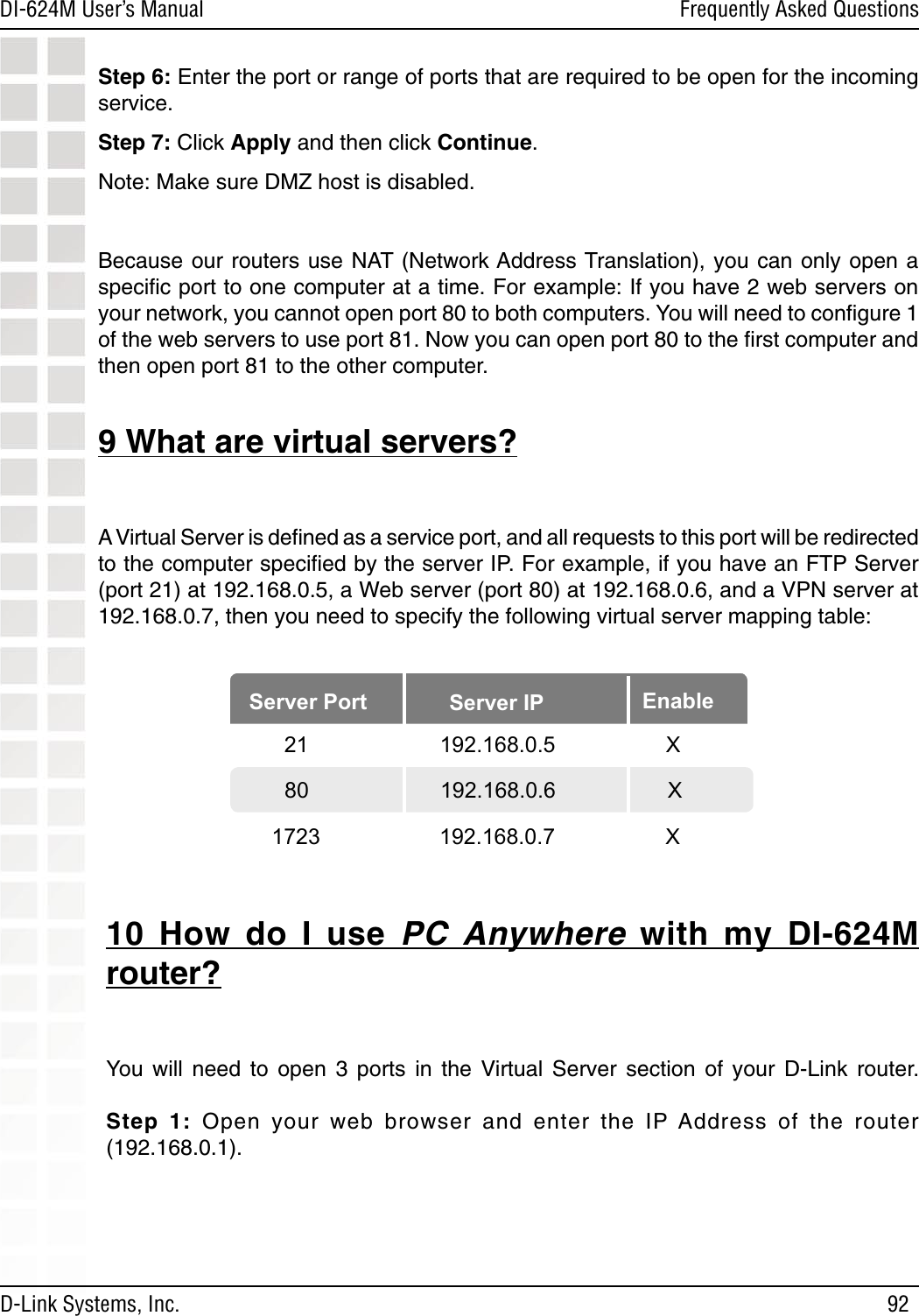
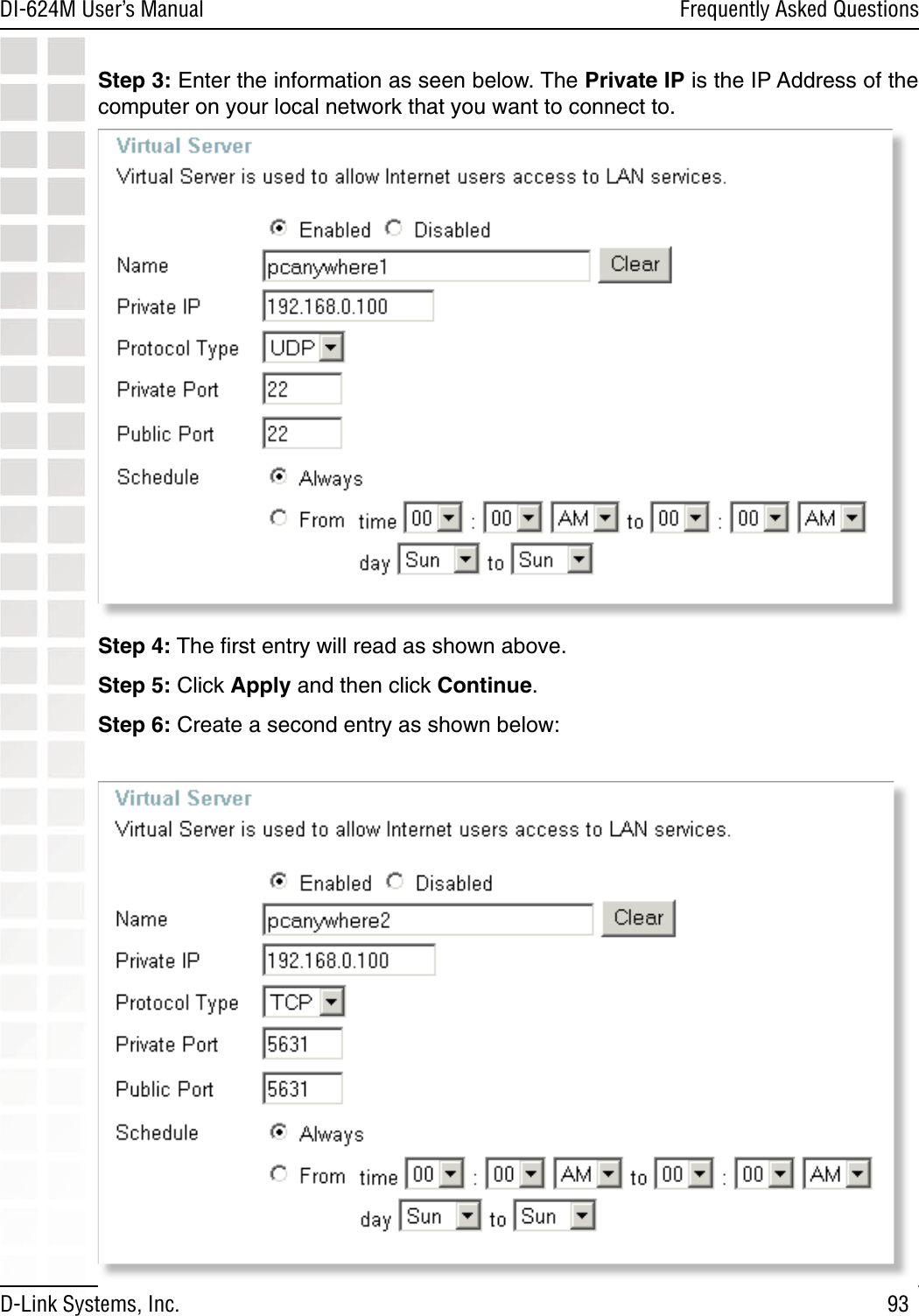
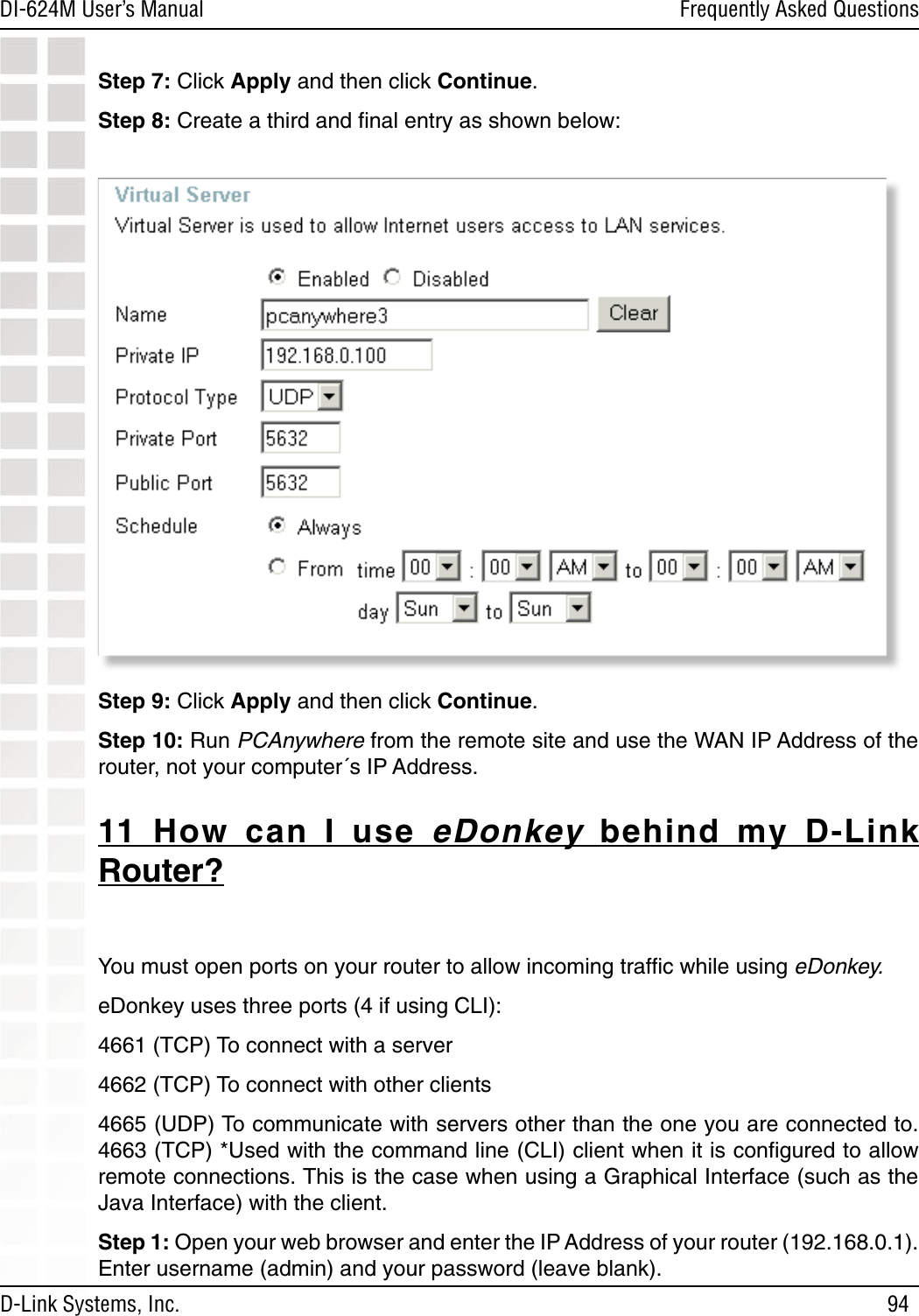
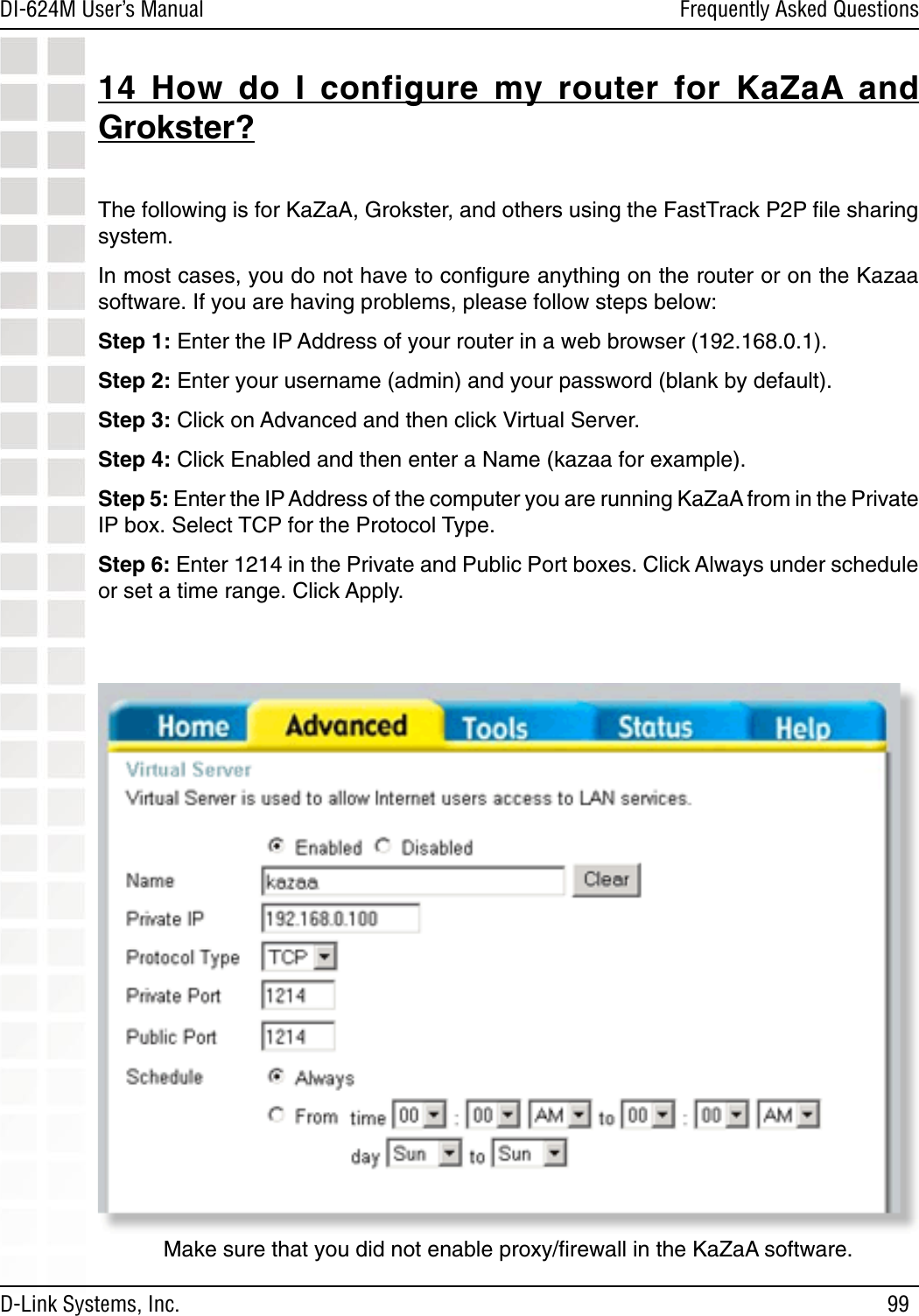
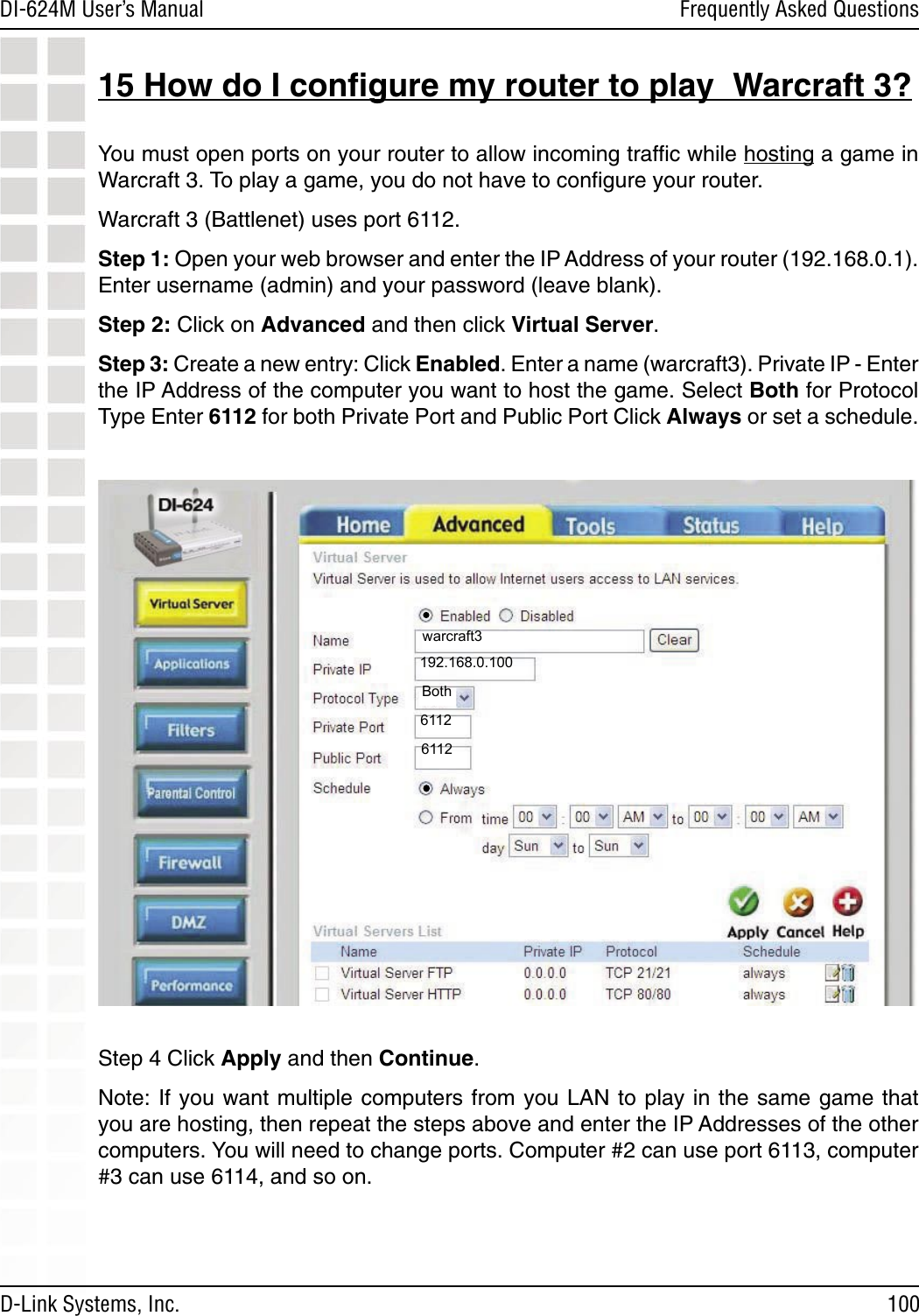
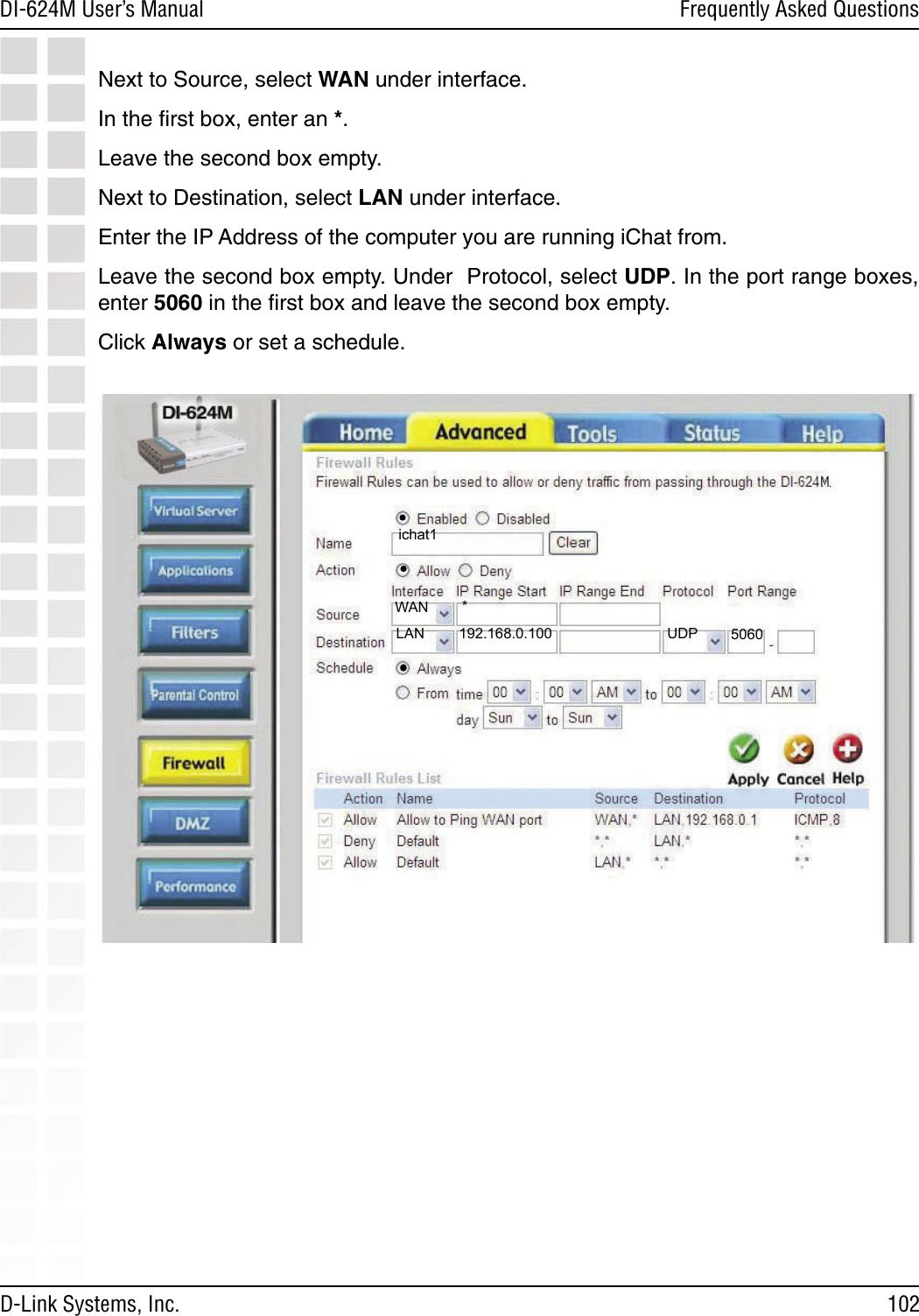
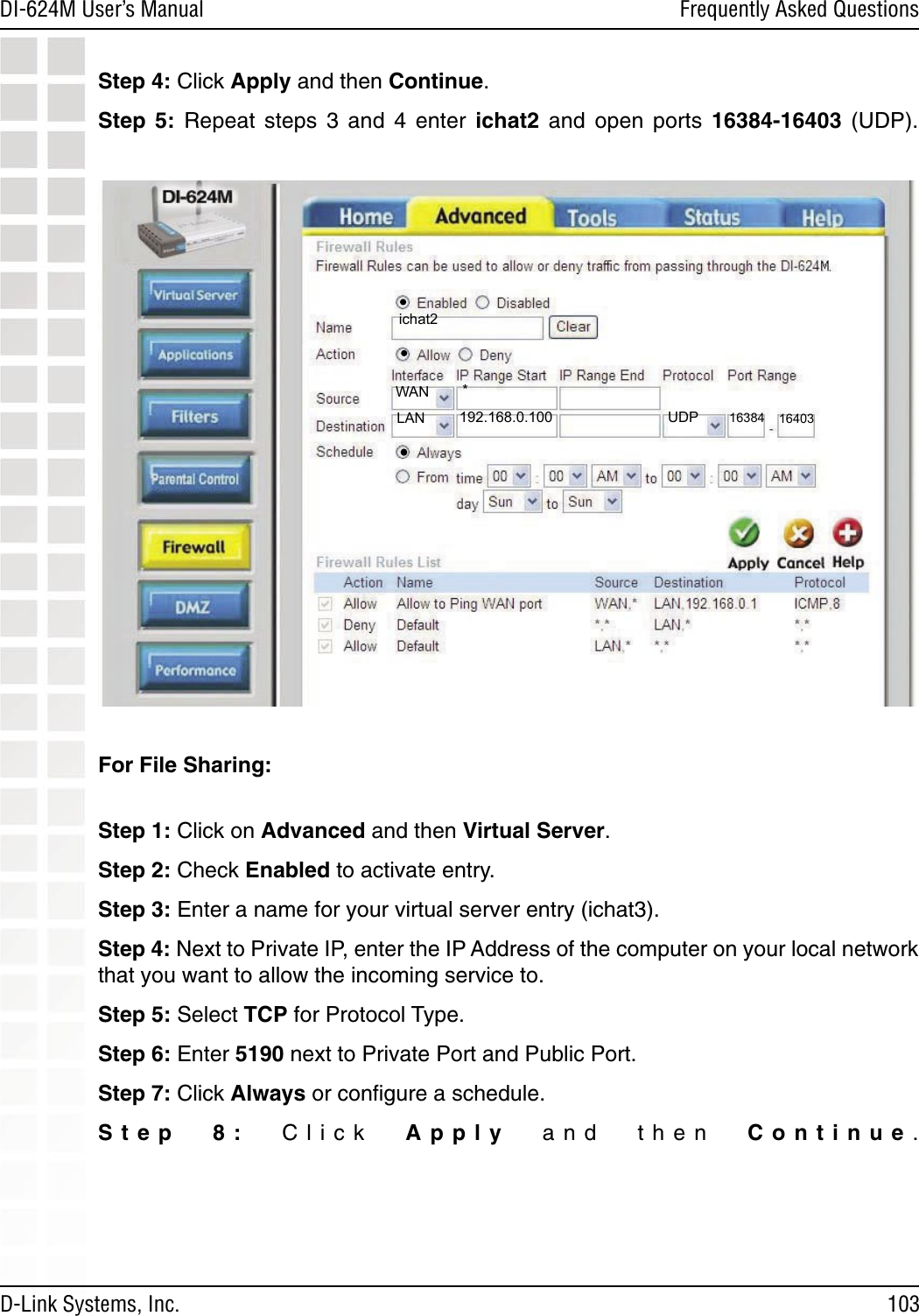
D Link DI624MA1 802.11g WLAN Mini-PCI Module User Manual 1
D Link Corporation 802.11g WLAN Mini-PCI Module 1
D Link >
Contents
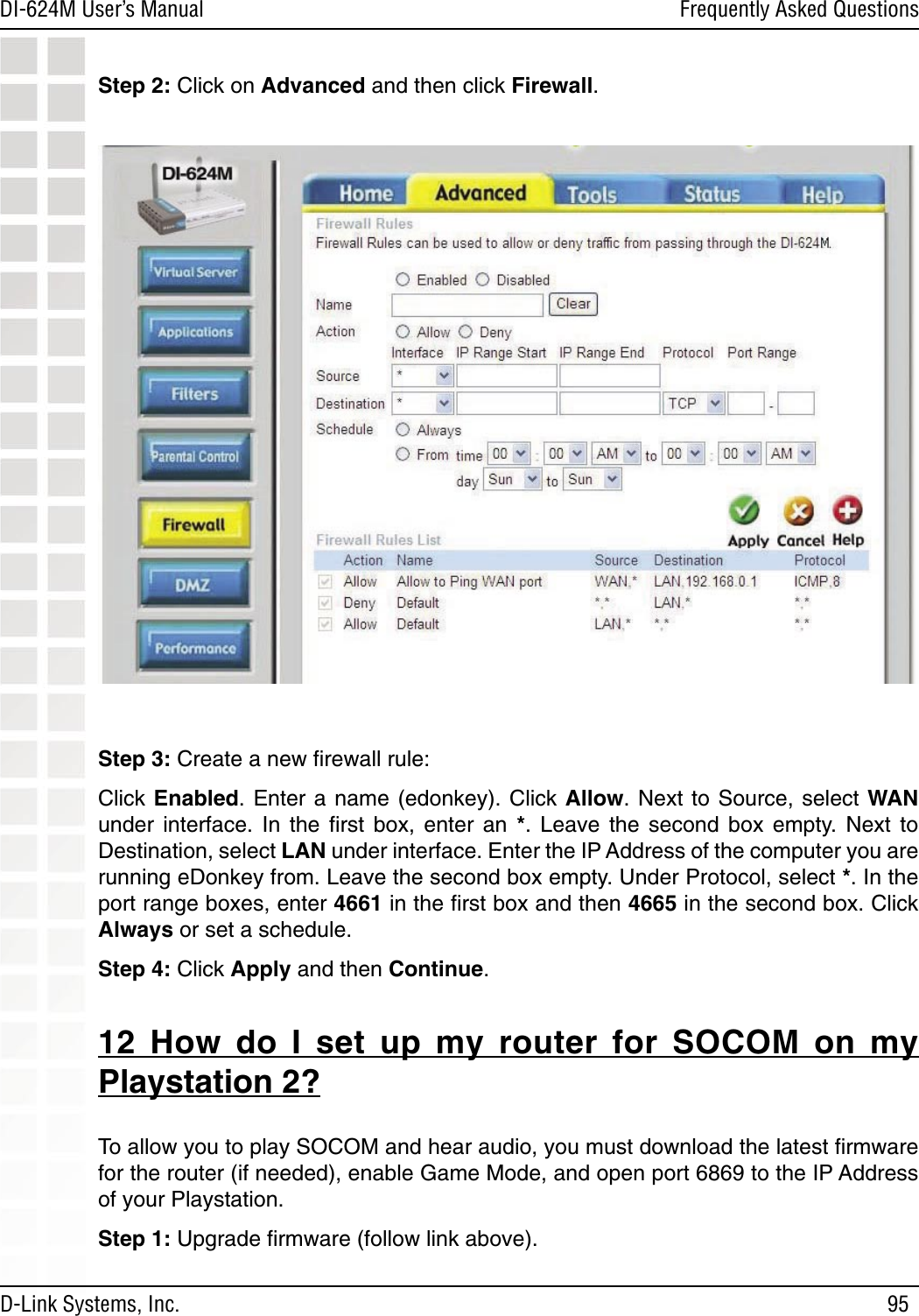
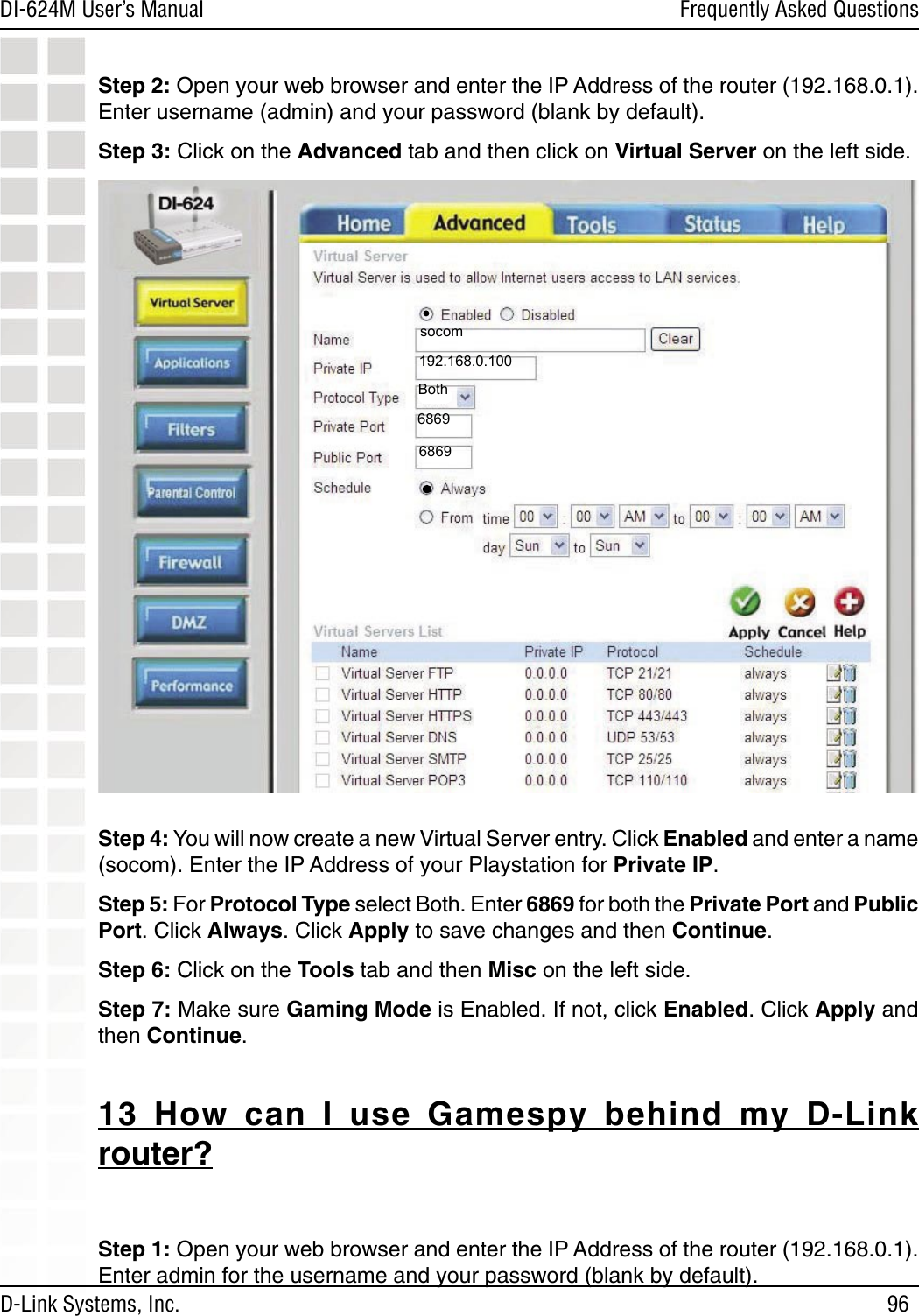
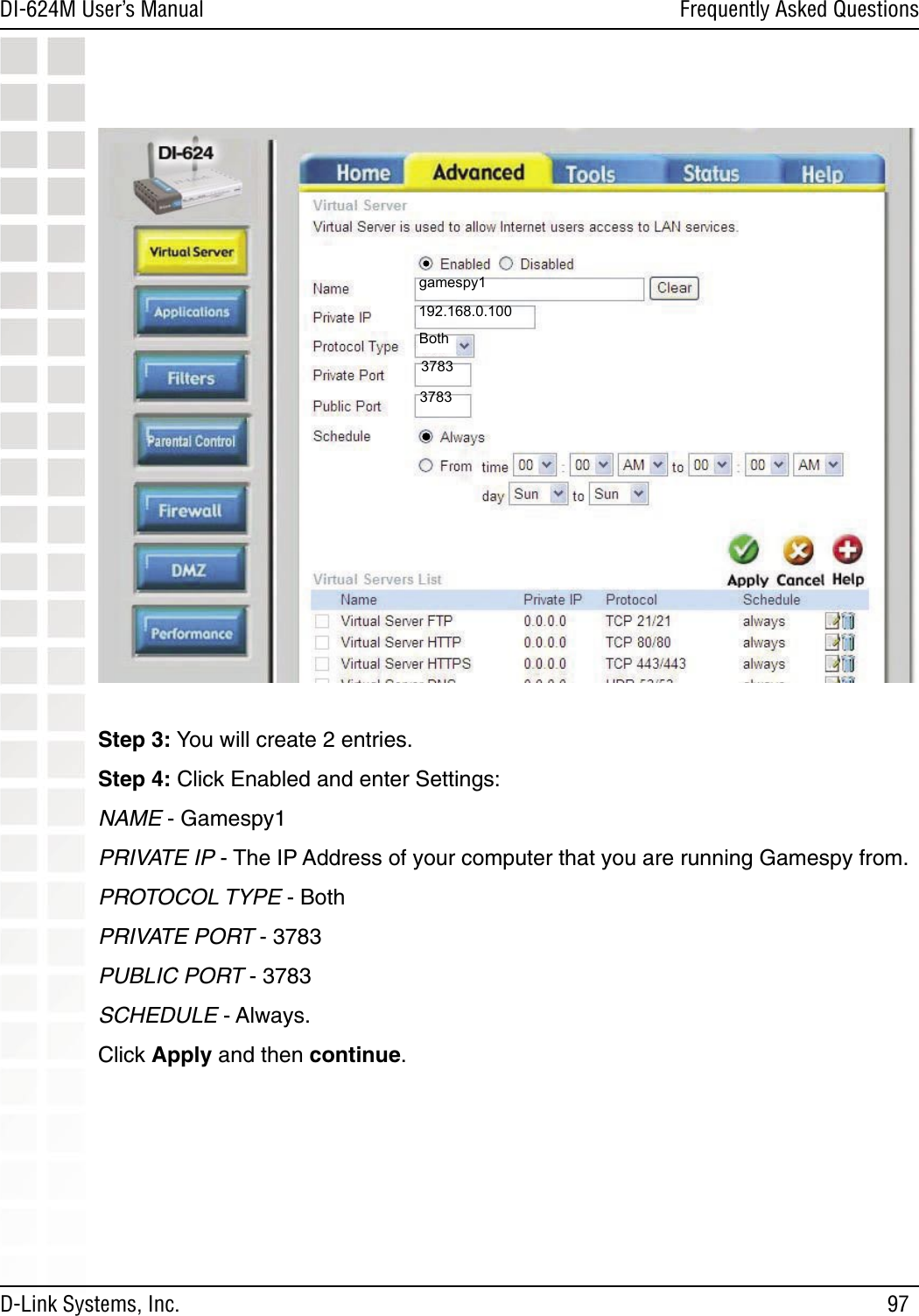
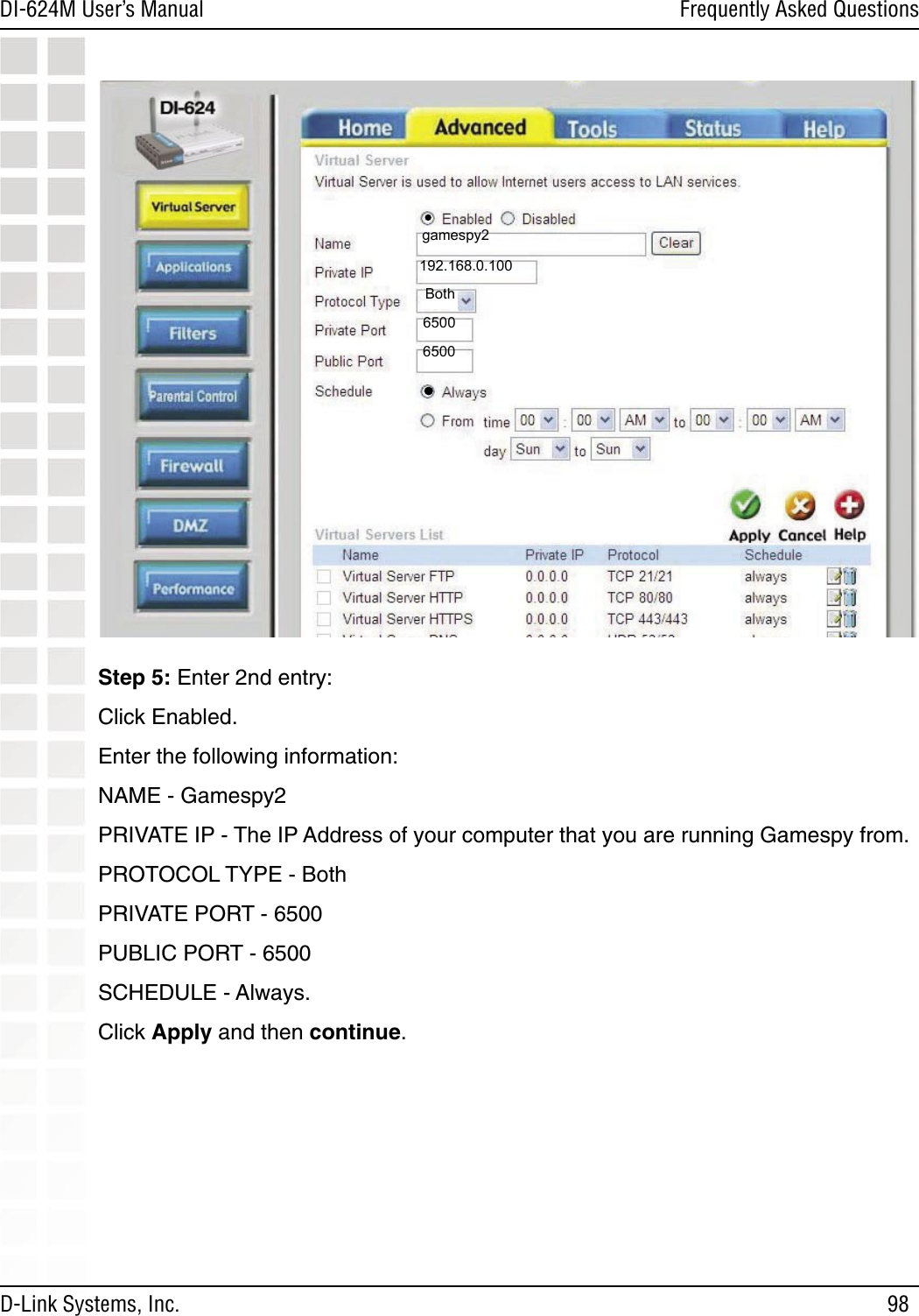
- 1. User Manual 1 of 2 for Access Poiint
- 2. User Manual 2 of 2 for Access Poiint
User Manual 2 of 2 for Access Poiint