D Link WL2600APA1 802.11n Single-band Unified Access Point User Manual Part 1
D Link Corporation 802.11n Single-band Unified Access Point Part 1
D Link >
Contents
- 1. User Manual Part 1
- 2. User Manual Part 2
- 3. User Manual Part 3
User Manual Part 1







![Page 9March 2012Section 1 - About This DocumentSection 1 - About This DocumentPoint (UAP) on a wireless network.Document OrganizationThe contains the following sections:“Section 1 - About This Document” on page 9“Section 3 - Viewing Access Point Status” on page 22“Section 4 - Managing the Access Point” on page 35“Section 7 - Maintaining the Access Point” on page 79“Section 9 - Clustering Multiple APs” on page 104“Appendix A - Default AP Settings” on page 113Additional DocumentationThe describes the commands available from the command-line The multiple UAPs. software packages, including issues and workarounds.This section describes the conventions this document uses.A note provides more information about a feature or technology and cross-references to related topics.Caution! settings, events, or procedures that can adversely affect network connectivity, security, and so on.The following table describes the typographical conventions used in this guide. DescriptionBold Click Apply to save your settings. Menu titles, page names, and button names.Blue Text See “Document Conventions” on page 9Hyperlink text.Courier Font WLAN-AP# show network command-line entries.Courier Font ItalicsValue Command parameter, which might be a variable or Square Brackets [ ] [Value] ](https://usermanual.wiki/D-Link/WL2600APA1.User-Manual-Part-1/User-Guide-1742598-Page-9.png)
![Page 10March 2012Section 1 - About This Document DescriptionCurly Braces {} {Choice1 | Choice2} Indicates that you must select a parameter from the list of choices.Vertical Bars | Choice1 | Choice2 Separates the mutually exclusive choices.Braces within square brackets [{}][{Choice1 | Choice2}] Indicate a choice within an optional element.Table 1 - Online Help, Supported Browsers, and Limitationsthe user interface (UI). The information in the online help is a subset of the information available in the .Online help information corresponds to each page on the UAP Administration UI. Figure 1 - Administrator UI Online Help](https://usermanual.wiki/D-Link/WL2600APA1.User-Manual-Part-1/User-Guide-1742598-Page-10.png)
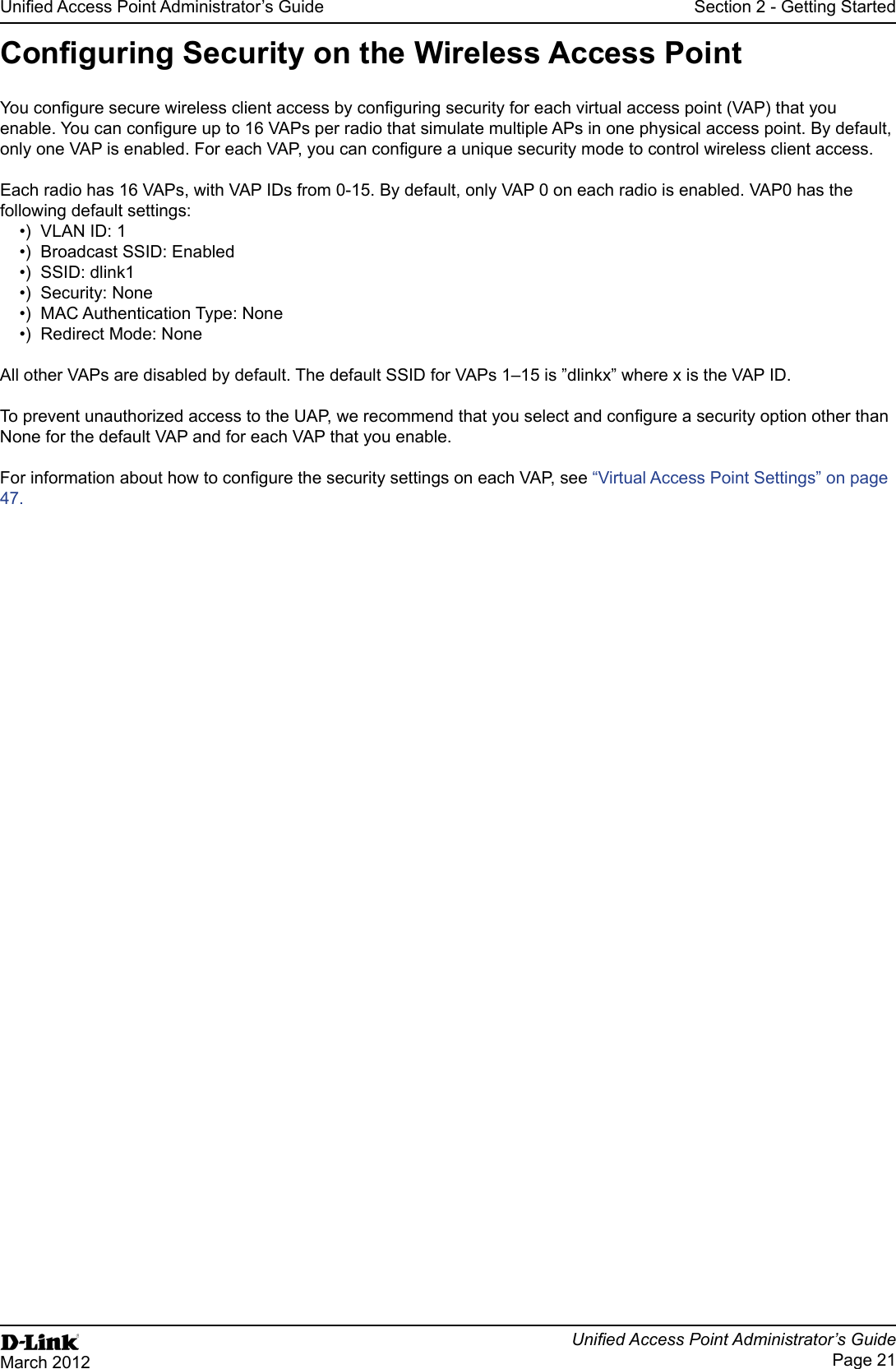
![Page 17March 2012Field Description issues related to the AP. Table 4 - Basic Settings PageTo connect to the AP by using the IPv6 global address or IPv6 link local address, you must enter the AP address into your browser in a special format.might not work with other browsers.[2520::230:abff:fe00:2420].To connect to the iPv6 link local address, replace the colons (:) with hyphens (-), add the interface number preceded 2420s6.ipv6-literal.net.Using the CLI to View the IP AddressThe DHCP client on the UAP is enabled by default. If you connect the UAP to a network with a DHCP server, the AP automatically acquires an IP address. To manage the UAP by using the Administrator UI, you must enter the IP address of the access point into a Web browser. If a DHCP server on your network assigns an IP address to the UAP, and you do not know the IP address, use the following steps to view the IP address of the UAP:1.) Using a null-modem cable, connect a VT100/ANSI terminal or a workstation to the console (serial) port.TeraTerm.2.) Baud rate: 115200 bpsData bits: 8Parity: noneStop bit: 13.) Press the return key, and a login prompt should appear.The login name is admin. The default password is admin. After a successful login, the screen shows the ()# prompt. 4.) At the login prompt, enter get management.Information similar to the following prints to the screen.](https://usermanual.wiki/D-Link/WL2600APA1.User-Manual-Part-1/User-Guide-1742598-Page-17.png)