197412
197412 197412
User Manual: 197412
Open the PDF directly: View PDF ![]() .
.
Page Count: 36

computers
and
people
formerly
Computers and Automation
..
(:-
December,
1974
scrE~e{AND'
sUs.
NDESERT ROSEN
Engineering Computer Pro-
grams:
How
They
Grow
-A. Marcos
and
S.
L.
Chu
Changing Technology and
Medical Specialization
-
Ray
M.
Antley
and
Mary
Ann
Antley
The Computer
Industry
and Unionization
-A. A. I mberman
The Radiation
from
Com-
puters I
nto
Everywhere
-
Neil
Macdonald
Watergate South
-Nancy A.
Miller
The Assassination
of
the
Reverend Martin Luther
King, Jr., Conclusion
-Wayne Chastain,
Jr
.

INVENTORY
OF
THE
36
ISSUES
OF -
TITLES
AND
SUMMARIES
THE
NOTEBOOK
ON
COMMON
SENSE,
FIRST
YEAR
VOLUME 1
1. Right Answers - A
Short
Guide
to
Obtaining
Them
A collection
of
82
principles
and
maxims. Example:
"The
moment
you have
worked
out
an answer,
start
checking it -it
probably
isn't
right."
2.
The
Empty
Column
A parable
about
a symbol
for
zero,
and
the
failure
to
recognize
the
value
of
a good idea.
3.
The
Golden
Trumpets
of
Yap Yap
4.
Strategy
in
Chess
5.
The
Barrels
and
the
Elephant
A discussion
of
truth
vs. believability.
6.
The
Argument
of
the
Beard
The
accumulation
of
many
small differences
may
make a huge difference.
7.
The
Elephant
and
the
Grassy Hillside
The
concepts
of
the
ordinary everyday
world
vs.
the
pointer
readings
of
exact
science.
8.
Ground
Rules
for
Arguments
9. False Premises, Valid Reasoning,
and
True
Conclusions
The
fallacy
of
asserting
that
the
prem ises
must
first
be
correct
in
order
that
correct
conclusions be
derived.
10.
The
I nvestigation
of
Common
Sense
11. Principles
of
General Science
and
Proverbs
8 principles
and
42
proverbs.
12.
Common
Sense -Questions
for
Consideration
13. Falling
1800
Feet
Down a Mountain
The
story
of
a skimobiler
who
fell
1/3
of
a mile
down
Mt. Washington, N.H.,
and
was rescued
the
next
day;
and
how
he used his
common
sense
and
survived.
14.
The
Cult
of
the
Expert
15. Preventing Mistakes from Failure
to
Understand
Even
though
you do
not
understand
the
cause
of
some
trouble,
you may still be able
to
deal with
it.
The
famous
example
of
a
cure
for
malaria.
16.
The
Stage
of
Maturity
and
Judgement
17. Doomsday
in
St.
Pierre, Martinique -
Common
Sense
vs.
Catastrophe
How
30,000
people refusing
to
apply
their
common
sense died
from
a volcanic
eruption.
18.
The
History
of
the
Doasyoulikes
19. Individuality
in
Human Beings
Their chemical natures are as widely varied as
their
external features.
20. How
to
be Silly
71
recipes
for
being silly. Example:
"Use
twenty
words
to
say something when
two
will
do."
21.
The
Three
Earthworms
A parable
about
curiosity;
and
the
importance
of
making observations for oneself.
22.
The
Cochrans
vs.
Catastrophe
The history
of
Samuel Cochran,
Jr.,
who
ate
some
vichyssoise soup.
23. Preventing Mistakes from Forgetting
24. What
is
Common
Sense? -
An Operational Definition
A
proposed
definition of
common
sense
not
using
synonyms
but
using behavior
that
is
observable.
25.
The
Subject
of
What
is
Generally True
and
Important
-
Common
Sense, Elementary and Advanced
26. Natural History,
Patterns,
and
Common
Sense
Some
important
techniques
for observing.
27. Rationalizing
and
Common
Sense
28.
Opposition
to
New Ideas
Some
of
the
common
but
foolish reasons
for
opposing new ideas.
29. A Classification
and
Review
of
the
Issues
of
Vol.
30.
Index
to
Volume 1
2
VOLUME 2
31.
Adding Years
to
your
Life
Through
Common
Sense
A person
who
desires
to
live long
and
stay
well needs
to
understand
some
20
principles, including
how
to
test
all
the
health advice he receives
for
its
common
sense,
and
how
to
develop habits
of
health practices
which
fit
him.
32.
The
Number
of
Answers
to
a Problem
Problems may have
many
answers,
one
answer,
or
no
answer
...
and
answers
that
are
good
at
one
time
may
be bad
at
another.
33.
"Stupidity
has a Knack
of
Getting Its
Way"
"
...
as
we
should
see
if
we were
not
always so
much
wrapped
up
in
ourselves."
-
Albert
Camus
34. Time, Sense,
and
Wisdom -
Some
Notes
The
supply
of
time,
the
quantity
of
time,
the
kinds
of
time,
and
the
conversion
of
time.
.
..
A great deal
of
the
time
in
a
man's
life
is
regularly, systematically,
and
irretrievably wasted. This
is
a serious mistake.
35.
Time,
Sense,
and
Wisdom -
Some
Proverbs
and
Maxims
56
quotations
and
remarks
by
dozens
of
great men.
36.
Wisdom -
An
Operational Definition
"A
wise person
takes
things as
they
are
and,
knowing
the
conditions,
proceeds
to
deal with
them
in
such a
manner as
to
achieve
the
desired
result."
-Somerset Maugham
EXCITING: Q:
Is
the
Notebook
exciting?
A:
Some
of
the
issues, like
"Falling
1800
Feet
Down a
Mountain"
and
"Doomsday
in
St.
Pierre,
Martinique",
are among
the
most
exciting
true
stories
we
know.
USEFUL: Q:
Is
the
Notebook
useful?
A: It
ought
to
be
useful
to
anybody
-as useful
as
common
sense.
There
exists no
textbook
on
common
sense;
the
Notebook
tries
to
be a good beginning
to
common
sense, science, and wisdom.
PAST ISSUES: As a
new
subscriber,
you
do
not
miss past is-
sues. Every subscriber's subscription
starts
at
Vol. 1, no.
1,
and
he eventually receives all issues.
The
past
issues
are
sent
to
him usually
four
at
a
time,
every week
or
two,
until he has
caught
up,
and
thus
he
does
not
miss
important
and interesting issues
that
never go
out
of
date.
GUARANTEE:
(1) You
may
return
(in 7 days)
the
first batch
of
issues we send
you,
for
FULL
REFUND,
if
not
satis-
factory.
(2)
Thereafter,
you
may
cancel
at
any
time,
and
you will receive a
refund
for
the
unmailed
portion
of
your
subscription. -
WE
WANT ONLY HAPPY AND
SATISFIED
SUBSCRIBERS.
I - - - - - - - - - - (may be
copied
on
any
piece
of
paper) - - - - - - - - - - - - -
~
To:
Berkeley Enterprises, Inc.
815
Washington
St.,
Newtonville,
MA
02160
) YES, I
would
like
to
try
the
"Notebook
on
Common
Sense,
Elementary
and
Advanced".
Please
enter
my
subscription
at
$12
a year,
24
issues, newsletter style,
and
extras.
Please send
me
issues 1
to
6 as
FREE
PREMI UMS
for
subscribing.
I enclose
_____
_
) Please bill
my
organization.
Name Title
_________
_
Organization
__________________
_
Address
___________________________________
___
Signature
_________
Purch.
Order
No.
____
__
COMPUTERS
and
PEOPLE
for
December,
1974

9
1
The
Notebook
on
COMMON
SENSE,
ELEMENTARY
AND
ADVANCED
is
devoted
to
development,
exposition,
and
illustration
of
what
may
be
the
most
important
of
all fields
of
knowledge:
WHAT
IS
GENERAllY
TRUE
AND IMPORTANT
+ WISDOM +
+ +
PURPOSES:
to
help
you
avoid pitfalls
to
prevent
mistakes
before
they
happen
to
display new
paths
around
old
obstacles
to
point
out
new
solutions
to
old
problems
to
stimulate
your
resourcefulness
to
increase
your
accomplishments
to
improve
your
capacities
to
help
you
solve
problems
to
give
you
more
tools
to
think
with
8REASONS
TO
BE
INTERESTED IN THE
FIELD
OF
COMMON
SENSE,
WISDOM, AND
GENERAL
SCIENCE
COMPUTERS
are
important
-
But
the
computer
field
is
over
25
years old. Here
is
a
new
field
where
you
can
get
in
on
the
ground
floor
to
make
your
mark.
MATHEMATICS
is
important
-
But
this field
is
more
important
than
mathematics,
because
+
+
Topic:
AVOIDANCE
OF
LOGICAL
FALLACIES
THE
SYSTEMATIC
PREVENTION
OF
MISTAKES
Already Published
Preventing Mistakes
from:
Failure
to
Understand
Forgetting
Unforeseen Hazards
Placidity
Camouflage
To
Come
Preventing Mistakes
from:
Bias
Interpretation
Distraction
Gullibility
Failure
to
Observe
Failure
to
Inspect
Prejudice
+
Topic:
SYSTEMATIC EXAMINATION
OF
GENERAL
CONCEPTS
Already Published
The
Concept
of:
Expert
Rationalizing
Feedback
Model
Black Box
Evolution
Niche
Understanding
To
Come
Strategy
Teachable
Moment
Indeterminacy
System
Operational
Definition
+
common
sense,
wisdom,
and
general science have
more
applications.
LOGIC
is
important
-.- - - - - - - - - - - - - - - -
(may
be
copied
on
any
piece
of
paper) - - - - - - - - - - . - - . - - - - - - - - - .
~
o
To:
Berkeley Enterprises, Inc.
But
this
field
is
more
important
than
logic, because
common:
815
Washington
St.,
Newtonville,
MA
02160
sense plus
wisdom
plus science in general
is
much
broader
than
logic.
WISDOM
is
important
-
This field
can
be
reasonably called
"the
engineering
of
wisdom".
) Yes, please
enter
my
subscription
to
The
Notebook on Common
Sense,
Elementary
and
Advanced
at
$12
a year
(24
issues), plus
extras.
I
understand
that
you
always begin
at
the
beginning
and
so I shall
not
miss
any
issues.
COMMON
SENSE
is
important
-0 ( ) Please send
me
as
free
premiums
for
subscribing:
This field includes
the
systematic
study
and
development
of:
1.
Right
Answers
- A
Short
Guide
to
Obtaining
Them
4.
Strategy
in
Chess
2.
The
Empty
Column
5.
The
Barrels
and
the
Elephant
common
sense.
SCI ENCE is
important
-o
3.
The
Golden
Trumpets
of
Yap Yap
6.
The
Argument
of
the
Beard
This field includes
what
is
common
to
all
the
sciences,
what:
is
generally
true
and
important
in
the
sciences.
MISTAKES
are
costly
and
to
be AVOIDED -
This field includes
the
systematic
study
of
the
prevention
of
:
mistakes.
MON
EY
is
important
-
The
systematic
prevention
of
mistakes in
your
organization
0
might save
10
to
20%
of
its expenses
per
year.
COMPUTERS
and
PEOPLE
for
December,
1974
( ) I enclose $ ) Please bill
my
organization
RETURNABLE IN 7 DAYS
FOR
FULL
REFUND IF NOT SATISFACTORY
HOW
CAN YOU LOSE?
Name
_____________
Title
_______
_
Organization
____________________
_
Address
(including
zip)
_________________
_
Signature
__________
_
Purchase
Order
No.
___
_
3

Vol.
23, No. 12
December,
1974
Editor and
Edmund
C.
Berkeley
Publisher
Assistant
Editors
Art
Editor
Software
Editor
Contributing
Editors
Barbara
L.
Chaffee
Linda Ladd Lovett
Neil D. Macdonald
Grace C. Hertlein
Stewart
B.
Nelson
George
N.
Arnovick
John
Bennett
Moses
M.
Berlin
Andrew
D.
Booth
John
W.
Carr
III
Ted
Schoeters
Richard
E.
Sprague
London
Thomas
Land
Correspondent
Advisory
Ed
Burnett
Committee James
J.
Cryan
Editorial
Offices
Advertising
Contact
Bernard
Quint
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
617-332-5453
The
Publisher
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
617-332-5453
"Computers
and
People,"
formerly
"Computers
and
Automation,"
is
published
monthly,
12
issues
per
year,
at
815
Washing-
ton
St.,
Newtonville,
MA
02160,
by
Berkeley
Enterprises,
I
nco
Printed
in
U.S.A.
Second
Class
Postage
paid
at
Boston,
MA,
and
addi-
tional
mailing
points.
Subscription
rates:
United
States,
$11.50
for
one
year,
$22.00
for
two
years.
Canada:
add
$1
a
year;
Mexico,
add
$6
a
year.
Else-
where:
one
year,
Swiss
francs
60;
order
through
Reliable
Information
Publishing
Company,
P.O.
Box
52,
6354
Vitznau,
Switzerland.
NOTE:
The
above
rates
do
not
include
our
publication
"The
Computer
Directory
and
Buyers'
Guide".
If
you
elect
to
re-
ceive
"The
Computer
Directory
and
Buyers'
Guide,"
please
add
$12.00
per
year
to
your
subscription
rate
in
U.S.
and
Canada,
and
$15.00
in
Mexico;
elsewhere,
the
price
of
the
Directory
is
Swiss
francs
90,
not
includ-
ing
postage
and
handling;
please
order
through
Reliable
I
nformation
Publishing
Company,
P.O.
Box
52,
6354
Vitznau,
Switzerland.
Please
address
mall
to:
Berkeley
Enter-
prises,
Inc.,
815
Washington
St.,
Newton-
ville,
MA
02160,
or
to
Berkeley
Enterprises,
Inc.,
c/o
Reliable
I
nformation
Publishing
Co.,
P.O.
Box
52,
6354
Vitznau,
Switzerland.
Postmaster:
Please
send
all
forms
3579
to
Berkeley
Enterprises,
Inc.,
815
Washing-
ton
St.,
Newtonville,
MA
02160.
©
Copyright
1974,
by
Berkeley
Enter-
prises,
Inc.
Change
of
address:
If
your
address
changes,
please
send
us
both
your
new
address
and
your
old
address
(as
it
ap-
pears
on
the
magazine
address
imprint),
and
allow
three
weeks
for
the
change
to
be
made.
4
computers
and
people
formerly Computers
and
Automation
Computers
and
Engineering
8 Engineering
Computer
Programs:
How
They
Grow
by
A. Morcos
and
S. L.
Chu,
Sargent
and
Lundy,
Chicago,
III.
How
computer
programs
for
engineering
situations
actually
develop
and
evolve.
Computers
and
Medicine
15
Changing
Technology
and
Medical Specialization
by
Ray
M.
Antley
and
Mary
Ann
Antley,
Indianapolis, Ind.
How
25
years
of
applying
computer
systems
in
medicine
are
leading
to
integrated
control
of
the
environment
for
the
benefit
of
patients.
The Computer
Industry
[A]
[A]
12
The
Computer
Industry
and
Unionization
[A]
by
A. A. I
mberman,
I
mberman
and
DeForest,
Chicago,
III.
How
to
really listen
to
employee
grievances
while
they
are
still
minor,
and
respond
quickly
to
them,
to
the
advantage
of
nearly
everybody
concerned.
11
The
Radiation
from
Computers
Into
Everywhere [A]
by
Neil
Macdonald,
Survey
Editor,
Computers
and
People
Some
of
the
ever-widening influences
of
computers
upon
many
different
areas.
7
Contact
with
Holders
of
the
Certificate
of
Data Processing
[F)
by
John
K.
Swearingen, Pres., I
nstitute
for
Certification
of
Computer
Professionals, Chicago,
III.
An
effort
to
reach all COP holders.
7
Annual
Computer
Programming
Contest
[F)
by
Dr.
Gary
G.
Bitter,
Arizona
State
Univ.
For
students
in
grades 7
to
12:
the
annual
contest
of
the
Association
for
Educational
Data
Systems.
Applications
of
Computers
32
Computing
and
Data
Processing
Newsletter
[C)
Computer
Gives New Mexico Museum Full Access
to
its
Mineral
Collection
Computer
System
for
a Racing
Yacht
that
Won
Cameras
and
Computers
Combine
to
Analyze
Rocket
Flights
1
"Desert
Rose"
[Front
Cover]
A
"desert
rose"
of
crystal
gypsum,
at
the
New Mexico
Mineralogical Museum
of
the
New Mexico
Bureau
of
Mines. A
computer
uses X-ray results
to
analyze
each
specimen,
and
catalogs
it.
See page
32.
COMPUTERS
and
PEOPLE
for
December,
1974
..
,

The magazine
of
the
design, applications,
and
implications
of
information processing
systems
-
and
the
pursuit
of
truth
in
input,
output,
and
processing,
for
the
benefit
of
people.
6
"1
Am
Interested
To
Know
What a
Computer
Can Do [E]
For
Me"
by
Edmund
C. Berkeley,
Editor
What
sorts
of
questions
a
computer
can
answer,
and
how
it answers
them.
7
"Computer
Art
for
the
Artist"
-
Comment
[F]
by
James
C.
Ver Hague,
Jr.,
State
University
of
New
York
at
Buffalo
Additional
information
wanted
for
teaching
computer
art.
7
"Can
Tigger
Think?
Can Peder
Think?"
-
Comment
[F]
by
Bryce
M.
Mitchell, Universidade Federal
de
Sao
Carlos, Sao Carlos, Brazil
The Profession
of
Information
Engineer
and
the
Pursuit
of
Truth
18
Watergate
South
[A]
by
Nancy A. Miller,
Princeton,
N.J.
How a
third
effort
was
made
by
many
Watergate-
connected
figures
to
provoke
violence
and
riots,
and
prepare
the
groundwork
for
a
cancelation
of
the
1972 elections.
26
The
Assassination
of
the
Reverend Martin
Luther
King,
Jr.,
and
Possible Links
with
the
Kennedy
Murders -Part
11
(Conclusion)
[A]
by
Wayne Chastain,
Jr.,
Attorney,
Memphis,
Tenn.
The
final
instalment
of
a
report
of
a
diligent
study
into
the
details
and
circumstances
of
the
assassination
of
the
Reverend Martin
Luther
King,
Jr.,
on
April
4,
1968,
and
related events,
and
the
considerable
evidence
of
a conspiracy.
Computers, Puzzles,
and
Games
30
Games
and
Puzzles
for
Nimble Minds -
and
Computers
[C]
Key
[A]
[C]
[E]
[F]
by
Neil Macdonald, Assistant
Editor
GIZZMO -
Some
computational
Jabberwocky.
MAXIMDIJ -Guessing a
maxim
expressed
in
digits.
NA YMANDIJ - A
systematic
pattern
among
randomness?
NUMBLES -Deciphering
unknown
digits
from
arithmet-
ical relations.
SIXWORDO -Paraphrasing a passage
into
sentences
of
not
more
than
six
words
each.
Article
Monthly
Column
Editorial
Forum
NOTICE
*0
ON
YOUR
ADDRESS
IMPRINT
MEANS
THAT
YOUR
SUBSCRIP-
TION
INCLUDES
THE
COMPUTER
DIRECTORY.
*N
MEANS
THAT
YOUR
PRESENT SUBSCRIPTION
DOES
NOT
INCLUDE
THE
COM-
PUTER
DIRECTORY.
COMPUTERS
and
PEOPLE
for
December,
1974,
ANNOUNCEMENT
THE COMPUTER CENSUS
which
Computers
and
People has pub-
lished
in
the
past will
now
be
published
separately
and
more
completely
as a
quarterly
service, regular
subscription
price
$33.00
per year. Until
January:
10, 1975,
any
subscriber
to
Computers
and People
may
subscribe
at
half price.
Outside
U.S., Canada,
and
Mexico,
please
add
$5.00
per year
for
addi-
tional costs.
NEW
CONTRACTS
AND
NEW
INSTALLATIONS
which
Computers
and
People has
pub-
lished
in
the
past will
now
be
published
separately
and
more
completely
as a
bimonthly
service, regular
subscription
price
$30.00
per year. Until
January
10, 1975,
any
subscriber
to
Computers
and
People may subscribe
at
half price.
Outside
U.S., Canada,
and
Mexico,
please
add
$5.00
per year
for
addi-
tional costs.
------
-(may
be
copied
on-
------
--
I
any
piece
of
paper)
TO:
Computers
and
People
Berkeley Enterprises, Inc.
815
Washington Street
Newtonville,
MA
02160, U.S.A.
( ) YES, please send me
( )
THE
COMPUTER CENSUS,
quarterly,
at
$33.00 a year
NEW
CONTRACTS
AND
NEW
INSTALLATIONS,
bimonthly,
at
$30.00 a year
( ) I claim 50% discount
as
a subscriber
to
Computers
and
People
Total
payment
_____
_
I enclose check
Please
bill
my
organization;
the
pur-
chase
order no.
is
_____
_
My
name and address are attached.
5

EDITORIAL
ttl
Am
Interested
To
Know
What
a
Computer
Can
Do
For
Me"
The
man
who
said
that
to
me
was
an
old
friend.
He
was
no
mathematician,
but
a former dean
of
a
dental
school;
he
had
specialized
in
dental
public
health;
he
had had
an
excellent
education.
In
spite
of
be-
ing
no
mathematician
he
had
navigated
a small
ship
out
of
sight
of
land;
and he had computed means,
stan-
dard
deviations,
chi-squared
tests,
and
other
statis-
tical
measures.
How
could I answer
this
useful
question?
The
first
step
was
to
send
him
a
list
of
many
ap-
plications
of
computers.
In
1973
we
published
a
list
of
over 2400
applications
of
computers. That
list
contained
179
applications
in
medicine;
here
is
a
small
excerpt:
Coronary
artery
disease
prediction
Cystic
fibrosis:
detection
in
new-born
babies
Cytology
diagnosis
Cytophotometric
analysis
Dermatoglyphic
analysis
But what
is
the
second
step?
What
ideas
do
you
give
to
an
ordinary
person
(nontechnical
but
educa-
ted)
so
that
he
can conceive
of
how
a computer can
be
of
help
to
him?
In
the
case
of
a motor
car,
there
is
no
great
problem
in
"knowing what a motor
car
can
do
for
me."
A
car
can
take
you
somewhere where
you
want
to
go.
And
you
are
already
full
of
ideas
of
places
where
you
want
to
go.
However,
for
any
particular
trip
in
a motor
car
you
have
to
make
a
decision
about where
you
want
to
go. Also,
if
you
do
not
know
the
way
there,
you
have
to
get
hold
of
a
map
and choose
the
way: which roads
you
will
travel
on,
how
far
on
each
you
will
go, what
turnings
you
will
take,
what
signs
you
will
be
guided
by.
Much
the
same
situation
applies
when
you
want
to
find
some
information
that
has probably been
publish-
ed.
Recently
at
a
birthday
party
somebody
showed
me
an
old book:
Volume
2
of
"The
Life
of
George
Wash-
ington"
by
Washington
Irving,
published
in
1900.
My
curiosity
was
stirred
about George Washington.
The
next
day I looked
up
in
an
encyclopedia
the
entry
"George Washington,"
and
sati
sfied
much
of
my
curios-
ity.
I used
the
standard
travel-map
rules
applying
to
reference
books: begin with
an
encyclopedia,
and
look
for
the
topic
name
in
alphabetical
sequence.
A computer,
like
a motor
car
and
a
reference
book,
can
take
you
where
you
want
to
go.
First
you
have
to
want
to
know
something, and second
you
have
to
ob-
tain
knowledge
of
how
to
figure
it
out.
6
A computer can
figure
out
averages,
standard
de-
viations,
chi-squared
tests,
and
other
statistical
measures
--
if
you
want
to
know
them.
You
can
usu-
ally
buy
a
map
for
this
purpose, which
will
be
call-
ed a "computer program." A computer can even
tell
you
the
answer
(if
you
want
to
know
it)
to
such a
question
as,
"What
is
the
minimum
number
of
cubes
whi
ch
when
added
wi
11
equal a gi
ven
number?"
and
which cubes they
are.
For example, suppose
the
giv-
en number
is
229.
Then
the
ariswer
is
that
the
mini-
mum
number
of
cubes
is
7;
and
there
are
exactly
three
solutions,
and here they
are:
3 x
64
+ 1 x
27
+ 1 x 8 + 2 x 1
1 x 125 + 1 x
64
+ 5 x 8
1 x
216
+ 1 x 8 + 5 x 1
In
this
case,
the
map,
the
way
to
produce
the
answers
desired,
will
probably
require
some
clever
program-
mer
to
spend
several
hours producing a sequence
of
some
300
instructions
in
machine language
that
the
computer needs
for
a
map.
The
situation
of
computer
maps
is
much
like
driv-
ing
your
car
in
a
strange
land where
there
is
no
light,
only
thick
black
darkness
--
and
all
the
signs
are
written
in
a language
that
you
do
not
understand.
So
before
you
start
out
driving,
you
have
to
get
from
somebody
a complete and
accurate
set
of
instructions;
and
the
instructions
must
include
the
names
of
the
signposts
at
the
intersections;
and
when
you
come
to
an
intersection,
you
turn
on
your
flashlight,
read
all
the
signs
carefully,
compare them with
the
ap-
propriate
notes
in
your
set
of
instructions,
and
then
try
your
best
to
choose
the
right
turning.
Fortunately,
in
this
dark
land
where computer
maps
are
used, whenever
you
travel
a second time
from
place
A
to
place
B,
if
your road
map
worked
OK
the
first
time,
then
it
will
work
OK
over
and over
again.
And
each
later
time
it
will
work
lightning
fast.
So
whenever
you
want
to
travel
again,
you
have
practically
no
problem
at
all.
The
inefficien-
cy
of
the
first
trip
is
replaced
by
utmost
efficien-
cy
for
all
later
trips.
But
you
still
need a
place
you
want
to
go
to
(a
question
you
want answered) and a
map
of
how
to
get
there
(a complete
set
of
instructions
for
figuring
out
the
answer).
E"~d...c.
..
~
Edmund
C.
Berkeley
Editor
COMPUTERS
and
PEOPLE
for
December.
1974

THE
PURPOSE
OF FORUM
•
To
give
you, our readers,
an
opportunity to discuss
ideas that
seem
to you important.
•
To
express criticism or comments on what you
find
published in our
magazine.
•
To
help computer people and other people discuss
significant problems related to computers, 9ata
processing, and their applications
and
implications,
including information engineering, professional be-
havior, and the pursuit
of
truth in input, output,
and
pro
cessing.
Your participation
is
cordially invited.
ANNUAL
COMPUTER PROGRAMMING CONTEST
AEDS
Programming Contest
Association
for
Educational Data Systems
Dr. Gary
G.
Bitter
College
of
Education
Arizona State Univ.
Tempe,
AZ
85281
This
12th annual
contest
is
for
students
in
Grades
7 through 12. Seven
first
prizes
of
$25
(in
bonds)
will
be awarded
in
the
categories:
business,
bio-
logical
science;
computer
science;
games;
humanities;
mathematics;
physical
science.
A Grand
Prize
of
$100
(in
bonds)
will
be awarded
to
one
of
the
win-
ners
in
the
individual
categories.
All
entries
must
be
received
by
March
1.
The
Association,
also
known
as
AEDS,
is
a
national
organization
comprised
of
administrators,
teachers,
systems
analysts,
and programmers
of
educational
data
processing
systems
in
vocational,
public,
and
pri-
vate
schools.
The
contest
is
on
the
approved
list
of
national
contests
and
activities
of
the
National
Association
of
Secondary School
Principals.
The
Programming
Contest
winner
will
receive
not
only
a U.S. Savings
Bond
but
also
an
expense-paid
trip
to
the
1975
AEDS
Convention
in
Virginia
Beach,
Virginia,
on
April
29-May
2.
The
winning
student's
teacher
also
will
receive
an
expense-paid
trip
to
the
convention.
"COMPUTER
ART
FOR THE
ARTIST"
-COMMENT
To:
The
Art
Editor:
From:
James
C.
Ver
Hague,
Jr.
Department
of
Art
State Univ.
of
New York
at
Buffalo
Buffalo,
NY
14214
Your
article,
"Computer Art
for
the
Artist,"
ap-
pearing
in
the
August 1974
issue
of
"Computers and
People,"
was
very
interesting
to
me.
The
Department
of
Art
here
is
initiating
a
course
in
computer
art
and
graphics
beginning
this
fall
semester.
As
the
instructor
for
the
course,
I found your
outline
to
be
very
well-conceived
and have
restructured
some
of
the
planned
course
material
as a
result.
I would
very
much
appreciate
your sending
to
me
a
more
de-
tailed
course
plan
including
your
bibliography
of
references
and/or
any
additional
material
that
you
feel
might
aid
in
getting
such a
course
successfully
off
the
ground.
Does
there
exist
the
possibility
of
an
exchange
of
computer programs
either
with
you
or
others
that
have
taught
a
similar
course?
COMPUTERS
and
PEOPLE
for
December,
1974
MULTI-ACCESS
FORUM
Like a number
of
people
interested
in
computer
art,
my
background
is
primarily
a
technological
one.
I have
an
M.S.
in
mathematics and worked
for
four
years
in
the
aerospace
developing
computer programs
for
structural
analysis
research.
While working
on
one
of
the
plot
programs, I
accidentally
began
gen-
erating
forms
that
suggested
sculptural
possibili-
ties
to
me.
Eventually,
I became
more
interested
in
the
potentialities
of
computer
art
than
in
the
work I
was
doing and
finally
quit
to
obtain
more
formal
training
in
the
field
of
art.
I
am
current-
ly
a Teaching
Assistant
completing
my
final
year
in
the
M.F.A. Program
at
Buffalo.
I
am
looking
forward
to
receiving
your
detailed
course
plan.
"CAN
TIGGER THINK? CAN PEDER
THINK?"
-COMMENT
Bryce
M.
Mitchell
universidade Federal
de
Sao
Carlos
Laboratorio
de
Idiomas
Sao
Carlos 13560, Brazil
We
would
like
to
request
permission
to
reprint
a
section
from "Computers and
People,"
Vol. 23,
No.
6,
page
6.
We
propose
to
use
this
editorial
by
Edmund
C.
Berkeley
as
a
reading
in
a
textbook
for
the
teaching
of
scientific
and
technical
English
to
speakers
of
other
languages.
We
will,
of
course,
give
full
credit
to
the
source.
Thank you very
much
for
your
consideration
in
this
matter.
EditD.rial Note:
Permission
granted.
CONTACT WITH HOLDERS OF THE CERTIFICATE OF
DATA
PROCESSING
John
K.
Swearingen, President
Institute
for
Certification
of
Computer Professionals
Box 1442
Chicago, III. 60690
The
Institute
of
the
Certification
of
Computer
Professionals
on
October
5,
1974
made
its
first
mail-
ing
to
approximately
15,000
holders
of
the
Certifi-
cate
of
Data
Processing
(COP).
In
order
to
contact
those
COP
holders
whose
up-
to-date
address
we
did
not
have, would
you
please
publish
this
notice,
addressed
to
holders
of
the
Certificate:
If
you
did
not
receive
our
mailing
of
October
5,
1974,
it
is
probably
because
we
do
not
have
your
correct
address.
We
have a message
of
in-
terest
and
importance
to
you.
Please
send us
your
correct
address,
class
year,
and
your
Cer-
tificate
Number
if
available.
7

Engineering Computer
Prlograms:
How
They
Grow
A.
Marcos
S.
L.
Chu
Structural Analytical Division
Sargent and Lundy, Engineers
55
East Monroe St.
Chicago,
IL
60603
"Although a program cannot
as
yet take over conceptual design, nevertheless, used
as
a
tool
for
analysis,
it
can
study complex models swiftly, and provide reliable and quick
estimates
of
the merits
of
various engineering solutions to a problem. "
Two Basic Functions
In
engineering
design
firms,
computer programs
perform
two
basic
functions:
carrying
out
calcula-
tions,
and
presenting
the
results
in
a
prescribed
format.
Yet
neither
the
programs nor
the
functions
they
perform
are
static.
Both change as
often
as
engineers
change
designs,
methods
of
analysis
or
even
personal
tastes
regarding
the
looks
of
computer
output.
This
is
especially
true
of
the
programs used
in
the
design
of
nuclear
power
plants,
an
area
which
is
a prime concern
with
us.
In
this
design
area,
there
is
a
continual
advance
in
technology.
Consequently,
it
naturally
follows
that
the
programs used must
con-
tinually
evolve
to
keep
pace.
Numerous Computer Programs
Although a program
cannot,
as
yet,
take
over
the
conceptual
design
function,
nevertheless,
used
as
a
tool
for
analysis,
it
can
study
complex models
swift-
ly,
and
provide
reliable
and quick
estimates
of
the
merits
of
various
engineering
solutions
to
a
given
problem. Because
of
this
increasing
importance,
it
is
not
unusual
to
find
numerous computer programs
being
conceived
daily
to
handle
the
ever-increasing
engineering
problems
confronting
engineering
design
firms.
Let's
follow
the
evolution
of
a
typical
en-
gineering
computer program.
Birth
of
a Program
The
conception
of
a
new
program and
its
subsequent
gestation
generally
take
place
in
engineering
research
groups;
at
Sargent
& Lundy
the
analytical
divisions
are
assigned
this
task.
These
divisions
may
inves-
tigate
and
recommend
modification
of
one
of
the
ex-
isting
programs
or
develop
a
new
one.
Validation
For our
purposes,
let's
consider
that
a
new
pro-
gram has been
initiated.
After
it
is
written
and
de-
bugged,
validation
begins.
By
this
process
the
pro-
gram
is
insured
of
doing what
the
programmer
intends
it
to;
or
in
other
words,
the
program
is
checked
for
internal
consistency.
Known
simple
calculations
may
be used
to
check
for
uniformity;
or
another
program
with
similar
capabilities
but
with
a
different
ap-
proach
may
be used
for
verification.
8
Continuing Growth
The
next
step
in
the
maturation
of
the
newly-born
program
is
qualification
for
the
problem
at
hand.
For
this,
a few examples
are
run
and
if
solved
satis-
factorily,
the
program
is
officially
issued.
The
qualification
process
does
not
stop
at
this
point
but
continues
indefinitely,
drawing
not
only from
experience
gained
through use
but
also
from
the
in-
teraction
between
the
writers
or
maintainers
of
the
program and
its
users.
The
interaction
between
user
and
writer
is
a
ma-
jor
factor
in
the
program's
growth.
Starting
with
a model
for
the
engineering
problem
at
hand,
the
user
and
writer
team examine
it.
They
decide
whether
the
program, as
written,
can
solve
the
problem.
This
process
of
user-writer
interaction
can
serve
to
qual-
ify
the
program
for
a
wider
set
of
problems,
or
dis-
qualify
it
for
certain
problems.
Continuing Qualification
The
program does
not
stop
evolving
after
the
qual-
ification
process
by
the
development team. A
con-
tinual
stream
of
techniques
for
refined
or
improved
analysis
calls
for
continual
reevaluation
of
the
com-
puter
programs
that
use
the
original
techniques.
This
process
of
selective
change and improvement
is
reminiscent
of
biological
evolution;
growth,
adjust-
ment,
atrophy,
specialization
and
breeding
are
all
present.
Biological Analogy
The
diagram
in
Figure
1
illustrates
this
biologi-
cal
analogy.
Let's
follow
the
evolution
of
this
particular
program. Version I
is
the
initial
stage
of a frame
analysis
program. Version
II
is
its
first
mutation
when
rigid
members
and end
releases
are
in-
troduced
and a
new
version
is
required.
With
the
ad-
vent
of
better
methodology, Version
III
is
developed.
This
negates
the
usefulness
of
Versions
I and
II.
New
requirements
imposed
by
the
Atomic Energy Commission
produce
yet
another
stage,
Version IV. However,
in
this
case
Version
III
may
still
be
functional
for
some
applications
and
therefore
is
not
discontinued.
In
time,
Version
IV
is
expanded upon
when
a
particu-
lar
group
in
the
company
requests
a
version
which
will
output
the
results
of
the
program
in
a format
to
suit
the
special
needs
of
that
group;
in
this
case,
a
specialized
version
is
written
for
that
group
while
the
original
Version
IV
is
kept
intact.
COMPUTERS
and
PEOPLE
for
December,
1974

Merger
with
Another
Program
Program Evolution
Figure 1
Then
again
another
group
may
request
that
two
types
of
analysis
be performed
in
one program, such
as
static
and dynamic
analyses.
To
accomplish
this,
it
may
be
necessary
to
combine
two
or
three
programs,
forming a
new
program.
If
the
company
leases
a
big-
ger
computer
that
allows
for
the
solving
of
more
joints
and members,
an
expanded
version
of
the
new
program
that
would
take
advantage
of
the
size
and
speed of
the
new
computer
is
written.
Thus,
the
computer program can
evolve
into
many
stages.
In
numerous
instances
issuing
the
first
version
of
a program
is
only
20
per
cent
of
the
to-
tal
work.
An
Example
of
Extensive Growth
A
typical
example
of
this
evolutionary
process
in
our
design
group
is
our
MASS
program
(~atrix
Analy-
sis
Seismic
Stresses).
First
written
in
1965,
it
performed dynamic
analysis
of
rigid
frames and
trus-
ses.
Since
that
time
MASS
II,
MASS
III,
MASS
IV,
and
MASS
V have been developed
to
incorporate
addi-
tional
features.
The
reactor
pressure
vessel
of
a
nuclear
plant
can be modeled
to
fit
into
the
MASS
program
(Figure
2).
A program
called
DYNAPIPE
evolved from
the
ongI-
nal
MASS
computer program as a
special
version
to
analyze
the
dynamic
behavior
of
the
piping
system.
For example,
when
a
pipe
break
is
postulated,
the
response
of
the
pipe
during
the
accident
can be
com-
COMPUTERS
and
PEOPLE
for
December,
1974
puted
by
this
program.
Just
as
the
first
~ffiSS
pro-
gram
was
continually
expanded, so
too
was
the
DYNA-
PIPE
program.
At
present
there
are
four
separate
versions.
A dynamic
analysis
program
created
independently
from
the
~ffiSS
family
(named
DSASS)
is
based
on
the
theory
that
slabs
and
walls
in
nuclear
plants
can
be modeled by a system
of
slabs
vibrating
in
their
own
plane
and
interconnected
by
translational
springs
representing
the
stiffness
of
the
walls.
Figure
3
shows
a
DSASS
model.
Guide
Tubes
Dynamic Model
of
Reactor
Pressure
Vessel
& Internals
Figure 2
Combining
the
MASS
IV
and
DSASS
programs produced
DYNAS,
which
is
used
to
perform
seismic
analysis
for
coupled
structures
in
a
nuclear
plant.
As
shown
in
Figure
4,
the
reactor
pressure
vessel
is
modeled
as
a system
of
discrete
masses and
weightless
members,
with
its
internals
connected
to
the
surrounding
slabs
and
walls.
SLSAP
is
a
modified
version
of
SAP
acquired
from
a
university;
it
is
a
general-purpose
finite-element
program.
It
is
used
to
investigate
framed
structures,
containment
structures
and
sacrificial
shields.
When
a
part
of
SLSAP
was
extracted
and combined
with
DYNA-
PIPE 4,
PIPSYS
was
born.
This program
was
instituted
to
perform
static
and dynamic
analysis
of
three
di-
mensional
piping
systems,
compute
the
combined
stress-
es,
and compare them
to
the
allowable
stresses
of
ap-
plicable
codes.
In
this
way
has
the
evolution
of
the
MASS
family
occurred
during
the
past
seven
years.
The
program
9

14
712-
12
642-
630
-
617
-
602-
2
592-
500
-
560
~~~~~m~~
Elevation
(Ft.)
DSASS
Model-Slabs and Shear
Walls
of
a Turbine-Auxiliary Building
Figure 3
4
3
has been expanded
many
times
from
its
original
size;
yet
it
still
possesses
the
capacity
to
grow
into
other
analysis
areas.
The Limitations
Although
expansion
is
an
important
step
in
achiev-
ing
a
versatile
computer program,
there
should
be a
limit
to
the
size
of
the
program
for
its
optimum
ef-
ficiency
at
an
engineering
design
office
(as
distinct
from a
software
development
firm).
Programs
develop-
ed
in
a
design
office
must remain
flexible
and
readi-
ly
modifiable.
Overly
large
programs which
involve
several
writers
tend
to
be
difficult
to
use,
diffi-
cult
to
maintain,
difficult
to
modify and
with
out-
puts,
difficult
to
interpret.
"Dinosaurs"
In
fact,
excessively
large
programs can run
the
risk
of
being
discarded
altogether
by
the
user
be-
cause
of
their
immense
size.
We
call
these
obese
algorithms
dinosaurs.
Nature,
like
some
programmers,
may
have
thought
the
bigger,
the
better,
when
dino-
saurs
were
produced.
But
when
flexibility
was
im-
portant,
dinosaurs
vanished
in
a
relatively
short
time.
Accept with Caution
More
important
than
the
limitation
of
computer
program
size
is
the
avoidance
of
blind
acceptance
of
the
computer's
output.
When
an
instructor
first
introduced
the
slide
rule
to
his
class
he
explained
that
the
simple
piece
of
wood
would
enable
them
to
divide,
multiply,
take
square
roots,
do
just
about
anything
except
add. But
he
then
cautioned
that
they
10
Slab
-
Shear
Wall
----------/'--------------
7
10
Space
Frame
~
6
19
18..----
....
5
17
24
9
8 4
16
23
3
Combined Building and
Reactor Pressure Vessel Dynamic Model
Figure 4
must
know
the
approximate
answer
since
the
slide
rule
does
not
give
the
decimal
point.
Although com-
puters
do
give
the
decimal
point,
the
instructor's
warning
is
still
true,
and
we
should
often
remind
ourselves
of
it.
Knowing
the
limitations
of
the
computer program
will
enhance
the
success
of
its
growth. 0
NOTICE
The plates for printing
TH
E
COM
PUTE
R D I RECTO
RY
AND
BUYERS' GUIDE, 1974, have been at
the
printer
and waiting
to
run on
his
presses since early September,
while
the
printer waits for the delivery of promised
pa-
per.
As
of
Nov.
13
the
printer was still waiting.
We
re-
gret very much this delay -which
is
outside
of
our pos-
sibilities of control.
To partially compensate for this delay, any purchaser
of
the
1974 directory may order a copy
of
the
1973 di-
rectory
at
half price ($9.25 instead of $18.50). Prepay-
ment
is
necessary.
Edmund
C.
Berkeley, Editor
COMPUTERS
and
PEOPLE
for
December.
1974

The
Radiation
from
Computers
Into
Everywhere
Neil
Macdonald, Survey
Editor
"Computers and People"
"Dear
#067-12-3948*:
You are in danger.
We
don't
know
who you are
but
the
government
does.
They've
got
your
number
and they're
not
the
only
ones.
"
1.
From
Society
of
Manufacturing Engineers
20501
Ford
Road
Dearborn,
MI
48128
How
industry
is
using
computer-aided
technology
to
obtain
good economic
results
will
be emphasized
at
the
third
Computer-Aided Design and Computer-Aided
Manufacturing Conference and
Exposition.
This
is
sponsored
by
the
Society
of
Manufacturing
Engineers
at
the
Hyatt
Regency O'Hare
Hotel
in
Chicago
Febru-
ary
10-13, 1975. Nine Conference
sessions
and dem-
onstrations
of computer-based equipment, systems, and
software
used
in
industrial
applications
will
com-
prise
CAD/CAM
III.
More
than
1,000
industrialists,
manufacturing
ex-
ecutives,
and
engineers
responsible
for
computer-
based
industrial
and
manufacturing
operations
are
expected
to
attend.
2.
From
Association
for
Computing Machinery
1133 Avenue
of
the Americas
New
York,
NY
10036
The
Association
for
Computing Machinery announces
a
new
quarterly,
ACM
TRANSACTIONS
ON
MATHEMATICAL
SOFTWARE
(TOMS).
The
first
issue
is
scheduled
for
March, 1975.
This
quarterly
will
publish
significant
research
and development
results
in
the
area
of
fundamental
mathematical
algorithms
and
associated
software
(com-
puter
programs).
Papers
and
other
items
will
have
natural
importance and
relevance
to
mathematical
soft-
ware and
they
will
support
significant
areas
of
com-
puter
application.
The
content
of
papers
in
those
areas
that
are
primarily
applications
will
be
rele-
vant
to
a
reasonably
wide
class
of
problems and
not
just
to
the
specific
considerations
that
motivated
the
paper.
There
will
be
increasing
emphasis
on
utilitarian
values
of
programs.
3.
From
David
L.
Emerick
Association
of
Computer Time-Sharing
Users
c/o Borg Warner Chemicals
Borg Warner Corporation
Parkersburg,
WV
26101
Computer
time-sharing
users
are
being
invited
to
join
a
new
non-profit
professional
association,
The
Association
of
Computer Time-Sharing
Users,
dubbed
"ACTSU."
The
stated
purpose
of
the
association
is
"the
evaluation,
comparison and improvement
of
the
COMPUTERS
and
PEOPLE
for
December,
1974
services
offered
by
the
time-sharing
industry."
The
Association
will
seek
to
help
time-sharing
users.
Comprehensive
industry
surveys
are
planned,
to
provide
members
with
comparisons and
evaluations
of
the
services
offered
by
time-sharing
companies.
Some
of
the
aspects
that
the
industry
surveys
will
cover
include:
processing
costs,
operating
charac-
teristics,
pre-programmed packages,
frequency
of
down-time,
quality
of
technical
support,
geographi-
cal
coverage,
liability
under
service
contracts,
and
quality
of
educational
materials.
Interested
persons
are
urged
to
write
ACTSU,
210
Fifth
Avenue,
New
York, N.Y. 10010
or
to
telephone
Hillel
Segal (212) 752-2000,
Ext.
8379,
for
addi-
tional
information
and membership
applications.
4.
From
Karen
A.
Duncan
Association
for
the Development
of
Computer-Based
Instructional Systems (ADCIS)
c/o
Office
of
Computer Resources
College
of
Dental Medicine
80
Barnes St.
Charleston,
SC
29401
The
1975
Winter
Conference
of
the
Association
for
the
Development
of
Computer-Based
Instructional
Sys-
tems
is
sponsored
by
this
college,
and
will
take
place
here
January
28-30, 1975.
Persons
interested
in
computer-assisted
instruc-
tion
or
computer-managed
instruction
are
invited.
This
conference
provides
a
professional
arena
for
the
sharing
of
research
findings,
operational
notes,
theories,
educational
strategies
and developments
regarding
CAl
and
CMI.
Commercial and noncommercial
groups
are
invited
to
discuss
their
release
policies
and
potential
ways
in
which courseware
may
be
shared.
5.
From
Civil Liberties Union
of
Massachusetts
3
Joy
St.
Boston, MA
02108
Dear u067-12-3948*:
You
are
in
danger.
We
don't
know
who
you
are,
but
the
government
does.
They've
got
your number and
they're
not
the
only
ones.
Your bank has
it,
and so does your
insurance
company,
your
credit
card
company, and even
the
Registry
of
(please
turn
to
page
29)
*This
is
a
fictitious
number.
11

The Computer Industry and Unionization
A.
A.
I mberman
I mberman and
De
Forest
Consultants to Management
209
South LaSalle St.
Chicago,
III.
60604
"The most painful way to
learn
about unionization
is
to lose
a National Labor Relations Board election. "
The
Computer
Field: Ripe for Unionization?
Can
the
computer
industry
grow and expand
in
pro-
duction
and
sales
without
experiencing
some
problems
with
labor?
The
rising
tide
of
strikes
(in
union-
ized
plants
producing
computer
hardware),
and
of
union
organizing
campaigns
in
the
non-union
plants,
is
some
indication
of
what
lies
ahead.
The
computer
industry
is
expected
to
chalk
up
new
performance
records
this
year,
with
shipments
ex-
ceeding
$10
billion.
A
10%
in~rease
is
forecast,
in
response
to
strong
demands
both
in
the
United
States
and
abroad.
Industry
revenues
are
currently
grow-
ing
even more
rapidly
than
shipments.
In
part,
this
differential
reflects
the
relatively
slow pace
of
trade-ins
of
third
generation
equipment
in
connec-
tion
with
the
purchase
of
new
computers.
Addition-
ally,
despite
stiff
borrowing
costs,
manufacturers
are
experiencing
a
higher
than
usual
percentage
of
outright
sales
and a
corresponding
decline
in
direct
leasing.
Helping
to
account
for
this
shift
are
gains
in
third-party
leasing
and
the
popularity
of
less
ex-
pensive
mini-computers.
The
computer
industry's
success
in
maintaining
impressive
growth
largely
reflects
an
impressive
ability
to
achieve
continuing
advances
in
hardware.
In
particular,
rapid
strides
in
semiconductor
tech-
nology have
led
to
significant
improvements
in
com-
puter
memory
capacities
and
operating
speeds
while,
at
the
same
time,
enabling
manufacturers
to
reduce
prices.
All
of
these
factors
indicate
eventual
la-
bor
union
activities.
212
Union Victories
In
the
last
four
years,
I have
analyzed
212 union
victories
in
representation
elections
in
a whole
va-
riety
of
industries.
Of
the
212 companies, 9 were
in
the
professional,
scientific
and
controlling
in-
struments
(manufacturing)
industry.
I found
that
timely
precautions
might have
prevented
most
of
these
union
victories.
How
the
trend
had gone
in
the
professional,
scientific
and
controlling
instru-
ments
industry
might be
judged
from
the
accompanying
table.
The
guideline
controls
have had
some
hamper-
ing
influence
on
union
activity.
As
a
result
of
our
comprehensive
study,
these
conclusions
became
evident:
1.
Most
elections
in
which wages and hours were
alleged
to
be
the
main
issue
(which
accounted
for
12
~.
A.
Imberman
did
his
undergraduate
work
at
New
York
Univ.,
and
his
graduate
work
at
Johns
Hopkins.
He
has
directed
the
Management Seminar
at
the
Univ.
of
Chicago and
Illinois
Institute
of
Technology
for
over
20
years.
He
has
written
widely,
and
is
an employee
relations
consultant
to
major companies,
including
Dupont, Avis,
Mc-
Graw
Edison,
Sears
Roebuck, and
many
others.
about
60
per
cent
of
the
elections),
were
won
by
the
unions
because
of
employee
ignorance
of
the
com-
petitive
situation
of
the
company. Employer
speeches
in
the
election
period
had
no
effect.
They were
too
late.
2.
Most
complaints
about working
conditions
(a
basic
cause
of
nearly
30
per
cent
of
the
elections)
were
well-founded
and
reflected
real
issues.
Elec-
tion
speeches
had
no
effect
here
either.
3.
Most
elections
in
which
arbitrary,
tyrannical
and
abusive
supervisors
were
specifically
named, were
truly
the
result
of
poor
supervisory
methods.
More
than
50
per
cent
of
the
elections
involved
his
is-
sue.
The
most
painful
way
to
learn
about
unionization
is
to
lose
a
National
Labor
Relations
Board
election.
Yet even
with
disputes
over money,
almost
all
labor
unrest
could
have been
quelled
before
unions took
control
of
the
work
force.
How?
By
setting
up
a
two-way communications system, and
training
super-
visors
in
modern management methods.
Failure
to
Listen
to
Employees
A
typical
example of
this
lack
of
two-way
commu-
nications
--
this
failure
to
listen
to
employees
--
taken
from
39
of
these
212
election
situations,
is
the
case
history
of
a
single
department
in
an
East
Coast
plant
in
this
industry
(professional,
scien-
tific
and
controlling
instruments
--
manufacturing).
The
department
had
developed
troubles
that
led
to
an
election.
This
was
a
basic
department
on
which
other
pro-
duction
departments
depended. Within
the
past
year
its
quality
of work had
deteriorated.
Production
schedules
seemed
too
often
to
be
out
of
gear
with
the
rest
of
the
plant.
Union
organization
in
the
COMPUTERS
and
PEOPLE
for
December,
1974
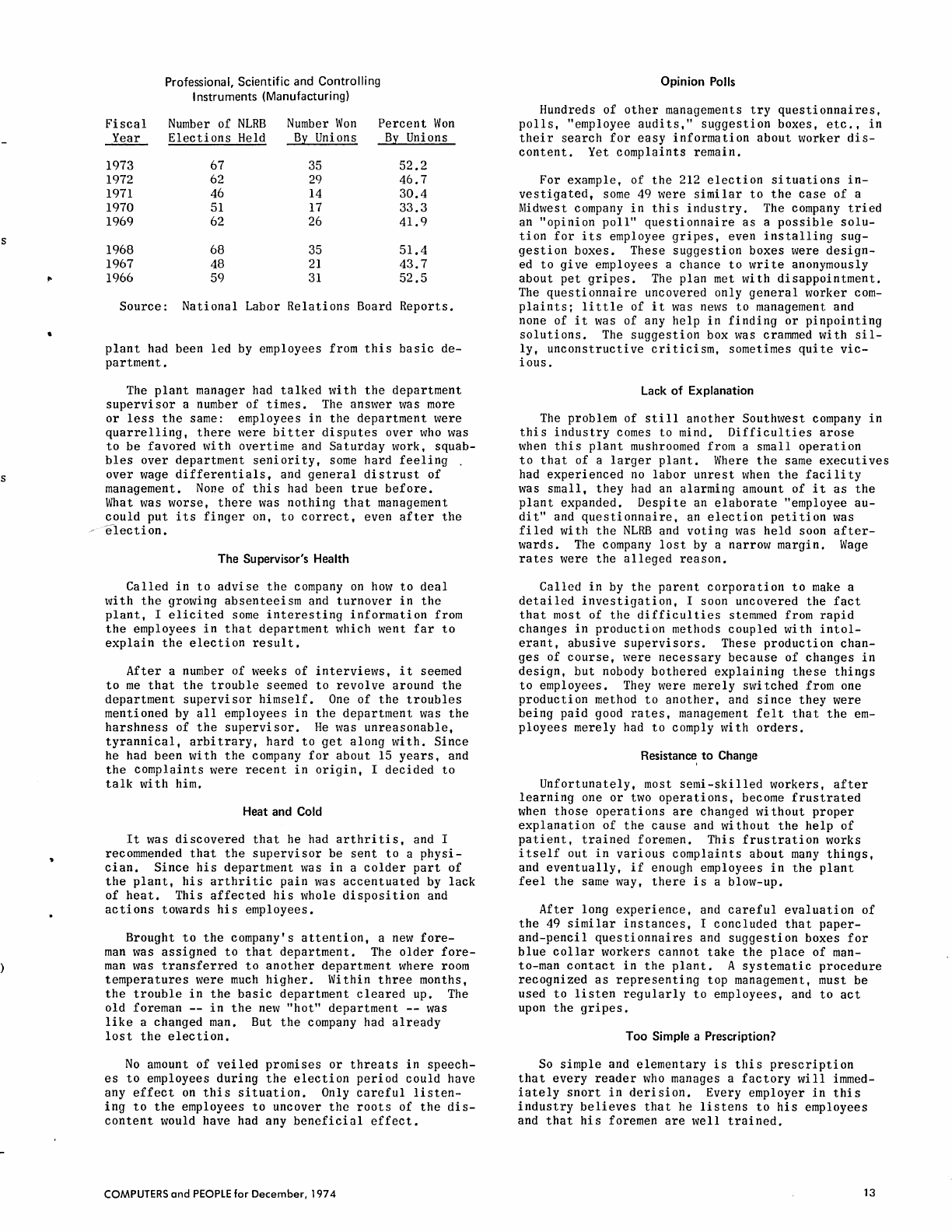
s
s
Professional, Scientific and Controlling
I nstruments (Manufacturing)
Fiscal
Number
of
NLRB
Number
Won
Percent
Won
Year
Elections
Held
By
Unions
By
Unions
1973 67
35
52.2
1972 62
29
46.7
1971
46
14
30.4
1970
51
17
33.3
1969 62
26
41.9
1968 68
35
51.4
1967 48
21
43.7
1966 59
31
52.5
Source:
National
Labor
Relations
Board
Reports.
plant
had been
led
by employees from
this
basic
de-
partment.
The
plant
manager had
talked
with
the
department
supervisor
a number of
times.
The
answer
was
more
or
less
the
same: employees
in
the
department
were
quarrelling,
there
were
bitter
disputes
over
who
was
to
be
favored
with
overtime
and
Saturday
work, squab-
bles
over
department
seniority,
some
hard
feeling
over
wage
differentials,
and
general
distrust
of
management.
None
of
this
had been
true
before.
What
was
worse,
there
was
nothing
that
management
could
put
its
finger
on,
to
correct,
even
after
the
~
election.
The Supervisor's Health
Called
in
to
advise
the
company
on
how
to
deal
with
the
growing
absenteeism
and
turnover
in
the
plant,
I
elicited
some
interesting
information
from
the
employees
in
that
department
which went
far
to
explain
the
election
result.
After
a number
of
weeks
of
interviews,
it
seemed
to
me
that
the
trouble
seemed
to
revolve
around
the
department
supervisor
himself.
One
of
the
troubles
mentioned by
all
employees
in
the
department
was
the
harshness
of
the
supervisor.
He
was
unreasonable,
tyrannical,
arbitrary,
hard
to
get
along
with.
Since
he had been
with
the
company
for
about
15
years,
and
the
complaints
were
recent
in
origin,
I
decided
to
talk
with
him.
Heat
and
Cold
It
was
discovered
that
he had
arthritis,
and I
recommended
that
the
supervisor
be
sent
to
a
physi-
cian.
Since
his
department
was
in
a
colder
part
of
the
plant,
his
arthritic
pain
was
accentuated
by
lack
of
heat.
This
affected
his
whole
disposition
and
actions
towards
his
employees.
Brought
to
the
company's
attention,
a
new
fore-
man
was
assigned
to
that
department.
The
older
fore-
man
was
transferred
to
another
department
where
room
temperatures
were
much
higher.
Within
three
months,
the
trouble
in
the
basic
department
cleared
up. The
old
foreman
--
in
the
new
"hot"
department
--
was
like
a changed man. But
the
company had
already
lost
the
election.
No
amount
of
veiled
promises
or
threats
in
speech-
es
to
employees
during
the
election
period
could
have
any
effect
on
this
situation.
Only
careful
listen-
ing
to
the
employees
to
uncover
the
roots
of
the
dis-
content
would have had any
beneficial
effect.
COMPUTERS
and
PEOPLE
for
December,
1974
Opinion
Polls
Hundreds
of
other
managements
try
questionnaires,
polls,
"employee
audits,"
suggestion
boxes,
etc.,
in
their
search
for
easy
information
about
worker
dis-
content.
Yet
complaints
remain.
For example,
of
the
212
election
situations
in-
vestigated,
some
49
were
similar
to
the
case
of
a
Midwest company
in
this
industry.
The company
tried
an
"opinion
poll"
questionnaire
as
a
possible
solu-
tion
for
its
employee
gripes,
even
installing
sug-
gestion
boxes.
These
suggestion
boxes were
design-
ed
to
give
employees a chance
to
write
anonymously
about
pet
gripes.
The
plan
met
with
disappointment.
The
questionnaire
uncovered
only
general
worker
com-
plaints;
little
of
it
was
news
to
management and
none of
it
was
of
any
help
in
finding
or
pinpointing
solutions.
The
suggestion
box
was
crammed
with
sil-
ly,
unconstructive
criticism,
sometimes
quite
vic-
ious.
Lack
of Explanation
The
problem
of
still
another
Southwest company
in
this
industry
comes
to
mind.
Difficulties
arose
when
this
plant
mushroomed from a
small
operation
to
that
of
a
larger
plant.
Where
the
same
executives
had
experienced
no
labor
unrest
when
the
facility
was
small,
they
had an
alarming
amount of
it
as
the
plant
expanded.
Despite
an
elaborate
"employee
au-
dit"
and
questionnaire,
an
election
petition
was
filed
with
the
NLRB
and
voting
was
held
soon
after-
wards.
The
company
lost
by a narrow margin.
Wage
rates
were
the
alleged
reason.
Called
in
by
the
parent
corporation
to
make
a
detailed
investigation,
I soon uncovered
the
fact
that
most of
the
difficulties
stemmed from
rapid
changes
in
production
methods
coupled
with
intol-
erant,
abusive
supervisors.
These
production
chan-
ges of
course,
were
necessary
because
of
changes
in
design,
but
nobody
bothered
explaining
these
things
to
employees. They were merely
switched
from one
production
method
to
another,
and
since
they
were
being
paid
good
rates,
management
felt
that
the
em-
ployees
merely had
to
comply
with
orders.
Resistance,
to
Change
Unfortunately,
most
semi-skilled
workers,
after
learning
one
or
two
operations,
become
frustrated
when
those
operations
are
changed
without
proper
explanation
of
the
cause
and
without
the
help
of
patient,
trained
foremen.
This
frustration
works
itself
out
in
various
complaints
about
many
things,
and
eventually,
if
enough employees
in
the
plant
feel
the
same
way,
there
is
a blow-up.
After
long
experience,
and
careful
evaluation
of
the
49
similar
instances,
I
concluded
that
paper-
and-pencil
questionnaires
and
suggestion
boxes
for
blue
collar
workers
cannot
take
the
place
of
man-
to-man
contact
in
the
plant.
A
systematic
procedure
recognized
as
representing
top
management, must be
used
to
listen
regularly
to
employees, and
to
act
upon
the
gripes.
Too Simple a Prescription?
So
simple
and
elementary
is
this
prescription
that
every
reader
who
manages a
factory
will
immed-
iately
snort
in
derision.
Every employer
in
this
industry
believes
that
he
listens
to
his
employees
and
that
his
foremen
are
well
trained.
13

Unfortunately,
most
employers,
with
the
utmost
good
will
in
the
world,
do
not
have
the
patience
to
listen,
or
the
time,
or
the
systematic
machinery.
They
therefore
depend upon
personnel
department
peo-
ple
and more
particularly,
on
foremen and
line
super-
visors
to
listen.
Very few
of
these
people
know
how
to
listen
"with
the
third
ear,"
a
talent
which can
be
developed
by
training.
Moreover,
very
few
of
these
management
people
can
be depended upon
to
give
management a
straightfor-
ward
report
on
what employees
are
saying
--
not
that
personnel
department
people,
foremen,
line
supervi-
sors,
et
al.
wish
to
deceive
the
front
office.
On
the
contrary,
most
often
they
are
wholeheartedly
on
management's
side.
But most
of
these
people
(consciously
or
uncon-
sciously)
report
only
what
they
LIKE
to
report,
or
report
only
what
THEY
think
is
important.
Often
this
is
not
the
whole
story,
even
if
employees gave them
the
whole
story,
which
they
rarely
do.
Listening
to
employees
is
also
a
way
for
employ-
ers
to
forestall
union
organizers
who
roam
smaller
communities of
every
state,
seeking
plants
to
organ-
ize.
Once
organized,
union
officials
believe,
the
employees
are
locked
into
the
union
for
years
and
years.
How
often
does a
decertification
election
succeed?
Not
too
often.
Union Tactics
One
common
attack
by
union
organizers
is
to
visit
employees
in
their
homes
and promise them
all
sorts
of
pie
in
the
sky.
The
organizers
don't
have
to
deliver
anything.
Under
the
law
they
can promise
anything
they
like.
If
their
promises
don't
work
out,
it's
the
selfish
employer's
fault.
And
the
trouble
continues.
What
can employers do?
For
this
sort
of
common
tactic,
there
is
only
one weapon:
LISTEN
TO
THE
EMPLOYEE
and
train
your
supervisors.
There
is
no
other
way
that
an employer can
find
out
just
what
is
troubling
his
employees,
or
what he must
do
to
overcome
the
difficulties
on
which union
organizers
build.
Center
of
Trouble on 3rd
or
4th
Floor
Another example, from
about
21
similar
cases
cov-
ered
in
this
study,
might be
of
interest
here.
It
was
a
California
company
in
this
industry.
The
hot-
bed
of
union
sentiment
seemed
to
be
centered
on
the
third
of
the
four
floors
of
the
plant.
There seemed
no
obvious
reason,
yet
judicious
and
cautious
inter-
viewing
of
employees
throughout
the
plant
led
a
skil-
led
consultant
interviewer
to
uncover
some
interest-
ing
facts.
No
Refrigerator
The
first,
second, and
fourth
floors
had
small
refrigerators
in
the
employee's
restrooms.
The
wo-
men
brought
their
lunches
and
deposited
the
bags
in
the
refrigerators.
But
the
women
on
the
third
floor
had
no
refrigerator.
Theirs
had broken
down
a
year
ago, and had
never
been
repaired.
They used
the
second
or
fourth
floor
refrigerators.
By
so
doing,
their
lunch bags were
often
pushed
aside
by
the
em-
ployees
of
the
other
floors;
sometimes,
if
there
wasn't
enough room,
the
third
floor
lunch bags were
removed from
the
refrigerators
entirely.
They had
complained
to
their
foremen over and
over,
but
the
foremen were
too
busy
to
raise
the
question
with
the
plant
manager.
14
Now
it
is
difficult
to
believe
that
anything
so
trivial
would
heat
up
a group of
about
80 employees,
yet
such
was
the
fact.
From
this
small
beginning,
festering
for
about
a
year,
80 employees became
dis-
satisfied
with
everything
--
the
ventilation
in
the
plant,
the
location
of
the
overhead
lights,
the
treatment
they
received
from
supervisors,
wage
rates,
etc.
Everything
the
company
did,
was bad, bad, bad.
From
this
humble
beginning,
employee
dissatisfaction
spread
through
the
plant.
Not a
single
foreman had
tried
to
deal
with
the
situation,
or
reported
it
higher
up.
It
took seven weeks
of
careful
interviewing,
care-
ful
listening,
and
running
down
of
all
clues,
to
un-
cover
this
basic
trivial
cause.
Installation
of a
$80
renovated
refrigerator
in
the
third
floor
rest-
room
cleared
up
most
of
the
difficulty.
Could
the
company have uncovered
clues
indicat-
ing
that
lack
of
a
refrigerator
to
hold
employee
lunch bags
on
the
third
floor
was
causing
a
severe
shift
in
employee
sentiment?
Without foremen
train-
ed
to
listen
and
report,
the
only
other
alternative
would be
to
talk
to
every
employee
in
the
plant.
Troublesome
as
that
might have been,
it
doesn't
com-
pare
with
the
subsequent
trouble
(and
expense)
of
dealing
with
a
union.
"Trained Ear" Gets Results
It
takes
special
training
and
special
techniques
to
invite
and
enjoy
the
confidence
of
employees.
(Here and
there
throughout
the
country
are
some
skilled
consultants,
who
specialize
in
such
labor-
management
techniques.
Usually,
these
men
are
con-
nected
with
a
college
or
university.
Interested
company
executives
might
secure
a
list
of
recommen-
ded names
by
writing
to
the
University
Research Cen-
ter,
121
West
Adams,
Chicago,
Illinois
60603.)
Sudden Labor Trouble
Here
is
another
case
from our
study
which some-
what
parallels
32
others.
About 300
men
were
in-
volved.
A
70-year-old
company
in
this
industry,
with
no
labor
or
union
trouble
history,
suddenly
found
itself
facing
an
organization
drive.
The
com-
pany
wage
scale
was
in
line
with
that
of
the
com-
munity
--
yet
suddenly
men
in
the
plant
seemed
to
be swallowing
all
sorts
of union
organizer
promises
--
something
they
had
never
done
before.
Why
the
sudden
labor
trouble?
In
this
small
town,
no
other
company had a
union,
yet
somehow
the
union seemed
to
have
gathered
streng-
th
in
this
plant.
The
company
won
the
election
by
a
very
slim
majority,
and
then
as
a
result
of
unfair
labor
charges,
another
election
was
ordered.
How-
ever,
in
the
interim,
the
company had used
an
out-
side
consultant
who
did
nothing
but
interview
and
listen
to
employees, and
provide
training
for
super-
visors.
Hearing Loss?
The
basis
of
his
findings
was
the
noise
in
one
department
that
caused a number
of
employees
to
fear
hearing
loss.
This
was
mainly
a
reaction
to
the
current
publicity
about
OSHA
legislation,
on
which
the
union
organizer
capitalized.
Those
em-
ployees
who
complained had
merely
been
given
uncom-
fortable
ear
plugs
without
explanation
--
a
sort
of
impersonal
treatment
which
many
resented.
This
re-
sentment cropped
up
in
complaints
about
many
other
working
conditions
--
formerly
accepted
as
a
matter
(please
turn
to
page
25)
COMPUTERS
and
PEOPLE
for
December,
1974

i
r
i-
r.
I,
..
·10
Changing Technology and
Medical
Speciali,zation
Ray
M.
Antley,
M.D.
Department
of
Medical Genetics
Indiana
Univ.
School
of
Medicine
Indianapolis,
Ind.
46202
and
Mary
Ann
Antley, M.A.
Department
of
English
Indiana Univ.-Purdue
Univ.
at
Indianapolis
Indianapolis,
Ind.
46202
"The process
of
data collecting
by
computers will cause interaction
between the technology and the illness which
it
is
designed to
diag-
nose and treat, and these changes will result in computers perform-
ing
not
old jobs better
but
completely
new
jobs. "
Twenty-Five Years
of
Computers
in Medicine
Twenty-five
years
of
computers,
and computers
in
medicine,
bring
us
to
the
threshold
of
their
acceler-
ated
introduction
into
clinical
medicine.
To
date,
there
has been an
opportunistic
application
of
com-
puters
to
medicine.
This
unstructured
approach
is
about
to
change, however,
(1)
because
of
the
techno-
logical
advances which have been
achieved
through
computer
research
and
are
ready
for
utilization,
and
(2)
because
of
the
developments
in
concepts
of
com-
prehensive
health
care
and
its
delivery.
People
who
have had
little
or
no
care,
people
who
have had
par-
tial
care
through
some
form
of
insurance,
and
people
who
have been
able
to
afford
total
care,
are
collec-
tively,
either
through
insurance,
through
unions,
or
through
government
health
programs, demanding compre-
hensive
health
care
at
moderate
cost
to
modest
cost.
The
dual
problems
of
obtaining
manpower
to
staff
such
a
health
service
and
of
keeping
the
total
cost
of
that
service
as
low
as
possible,
lend
themselves
to
solutions
through
technology.
Evolution
of
Technology
The
developments
in
technology
act
in
concert
with
the
recognition
of
the
need
for
expanded
medical
care.
They
are
compounded
by
the
existing
doctor
shortage.
These powerful
interacting
forces
will
structure
the
future
application
and development
of
automation
in
medicine.
These
forces
have
thus
far
tended
to
chan-
nel
technological
application
towards
assisting
the
primary
physician
in
the
delivery
of
health
care.
Furthermore,
the
evolution
of
technology
is
such
that
this
assisting
phase
will
be
transient,
for
pro-
grams
are
already
being
developed
which
will
do
much
of what
the
physician
does
now.
Finally,
the
process
of
data
collecting
by computers
will
cause
interac-
tions
between
the
technology
and
the
substrate
of
ill-
ness
which
it
is
designed
to
diagnose
and
treat,
an V
these
changes
will
result
in
computers
performing
no
old
jobs
better,
but
completely
new
jobs
•
_____
This
article
seeks
to
explore
the
evolution
of
machines
in
medicine
and
to
discuss
some
of
the
prob-
lems
inherent
in
change.
We
have
divided
the
evolu-
tion
in
medical
technology
into
three
phases
based
upon
inferences
about
the
role
of
the
physician
in
relationship
to
his
machines and
his
patients.
Phase
I
is
called
the
assisting
phase;
Phase
II,
the
auto-
mated
phase;
and Phase
III,
the
environmental
control
phase.
After
each
phase
we
have
attempted
to
indi-
COMPUTERS
and
PEOPLE
for
December,
1974
cate
some
of
the
consequences
of
the
different
stages.
It
should
be
apparent
that
different
lev-
els
of
the
progression
are
occurring
simultaneously
and
that
there
is
no
sharp
demarkation
between
phas-
es.
What
might
not
be
apparent
is
that
Phase
II
should
be a
reality
in
the
next
decade
and
that
Phase
III
will
probably
be
the
dominant form
of
medical
practice
within
the
career
of
present
day
medical
students.
Phase I -
The
Assisting Phase
The
introduction
of
technology
into
medicine
has
been
at
such a
rate
that
each
new
machine has been
seen as an
individual
innovation
which
helps
with
a
particular
diagnostic
or
treatment
function.
When
a
new
machine
appears,
it
is
tested
and
incorpora-
ted
into
the
doctor's
routine
on
the
basis
of
its
utility
and
efficiency.
This
random
incorporation
of
such
innovations
as
the
electrocardiogram
(ECG),
the
electroencephalogram
(EEG),
the
fiber
gastro-
scope,
the
heart-lung
machine and
patient
monitor-
ing
equipment
throughout
all
fields
of
medicine
has
obscured
the
collective
impact
on
medical
practice
of
machines,
i.e.,
the
channelling
of
medical
prac-
tice
toward
technological
specialties.
The
phenom-
ena
of
medical
specialization
has been
largely
at-
tributed
to
an
increased
work load and
to
the
in-
formation
explosion.
This
hypothesis,
however,
misses
the
important
relationship
between
the
de-
velopment
of
a machine and
the
development
of
in-
formation
and a
specialty
as
a
direct
result
of
that
machine.
The
Electrocardiogram and
the
Cardiologist
For
example,
the
introduction
of
the
electrocar-
diogram
did
much
to
strengthen
the
cardiologist
--
who
was
previously
solely
organ
based.
The
ECG
established
scientific
credibility
to
the
diagnosis
and
treatment
of
myocardial
infarction
syndrome.
Second, a
literature
developed
about
the
technical
aspects
of
the
ECG
machine
itself,
followed
by
a
literal
explosion
of
information
about
ECG
diagnosis.
Each
diagnosis
has
usually
been enhanced
by
reports
related
to
prognosis
and
treatment
to
such an
extent
that
it
becomes a
full
time
job
keeping
abreast
of
the
publications
in
this
field
alone.
Although more has gone
into
the
development
of
cardiology
than
the
ECG,
it
is
hard
to
conceive
of
that
specialty
without
it.
From
this
beginning
there
has been a
proliferation
of
other
innovations:
15

the
intensive
care
units,
specialists
in
intensive
care,
respiration
therapists,
second
generation
ma-
chines
like
pace makers and
cardiac
monitors.
As
technology
provides
equipment
to
investigate
a
par-
ticular
organ system
in
depth,
a
new
information
ex-
plosion
and
subsequent
specialty
frequently
develops.
Thus,
the
new
technology's
effects
have been
to
im-
prove medicine
through
specialization,
to
increase
its
complexity,
and
to
heighten
its
intellectual
stimulation
related
to
content.
New Innovations
in
Machines
Relatively
recent
innovated
machines
are
in
the
laboratory,
the
nursery,
the
intensive
care
unit,
the
emergency
room
and
the
operating
room. They
pervade
the
care
of
the
critically
ill
inpatient.
They
structure
the
clinic's
business
procedures
if
not
influencing
the
individual
doctor's
practice
pro-
cedures.
It
is
significant
that,
in
addition
to
helping
the
doctor
do
what he
did
before,
these
machines
do
jobs
which
really
cannot
be
equaled
by
the
physician
alone.
Increasingly,
machines
are
molding
the
way
in
which medicine
is
practiced,
even
to
the
extent
of
having
influence
over
the
formulation
of
medical
ethics
in
regard
to
the
definition
of
death.
This
same
technology,
by
its
very
existence,
raises
ex-
tremely
perplexing
questions
about
who
will
die.
Dependence
of
the
Doctor
on Machines
The
introduction
of
technology
into
medicine has
several
effects
upon
the
doctor.
One
is
that
in
routine
practice,
the
doctor
has
unconsciously
be-
come
dependent
on
the
laboratory,
x-ray,
drugs
pack-
aged
by
automated systems and
various
electronic
in-
struments
to
such
an
extent
that
the
practice
of
medicine would be
starkly
different
if
they
were
suddenly removed.
By
examining
the
prospects
of
their
removal, one
is
able
to
develop
some
feel
for
the
amount of
evolution
they
have
induced.
Also, a
forward
anticipation
of
comparable change
in
the
next
ten
years
to
what
we
have had
in
the
past
25
years
is
helpful
in
grasping
the
magnitude and
rates
of
change
we
will
experience.
Changes in Medical Practice
Thus,
these
machines, which have been
readily
ac-
quired
and used
by
the
medical
profession
to
help
them perform
tasks
and
detect
disease
more
quickly
and
accurately,
have
subtly
effected
a change
in
the
environment
of
medical
practice
in
the
twentieth
cen-
tury.
A change
in
the
environment
is
rarely
only
additive
or
linear.
You
seldom,
if
ever,
have an
old
environment
PLUS
a
new
element,
such as a
printing
press
or
an
ele~tric
plug;
what you have
is
a
totally
new
envIronment. l
From
the
individual
family
doctor
of
the
early
1900's
who
treated
a
patient
for
all
his
illnesses,
practice
has evolved
in
a
predictable
technological
form
into
a system
in
which
many
specialists
treat
specific
diseases
that
manifest
themselves
in
the
same
patient.
This
evolution
from
patient-centered
to
disease-centered
treatment
has
taken
place
grad-
ually
over
the
past
70
years.
The
rate
of
change
has been slow enough
to
allow
for
the
training
of
new
physicians
in
the
new
specialties
created
by an
expanding medical
technology.
The
very
real
changes
in
the
role
of
the
physician
and
the
system
of
health
delivery
that
have
occurred
have been
effected
with
relatively
little
trauma
to
the
earlier
physicians
16
who
have been
able
to
continue
their
roles
as
gen-
eralists
in
an
increasingly
specialized
world.
Med-
icine
has
adjusted
to
the
presence
of
technology
and
now
reflects
its
qualities
so smoothly and so
com-
pletely
that
it
requires
a
detached
view
to
even
rec-
ognize
the
great
change
in
orientation
that
has oc-
curred.
Phase II -
The
Automated
Phase
Now,
into
this
seemingly
stabilized
system of
health
delivery
care
based
on
scientific,
technolo-
gical
specialization,
a
different
sort
of
machine
is
being
introduced.
Its
long term
effects
will
re-
sult
in
another
major change
in
the
environment
of
medical
practice.
These
are
automated machines
that
are
capable
of
replacing
those
functions
which have
so
far
been performed only
by
the
physician
himself.
Because
the
physician
has
become
conditioned
to
ac-
cepting
technology
in
medicine,
these
more
sophisti-
cated
instruments
have been
introduced
without
arous-
ing
questions
about
their
long-term
implications,
or,
more
often,
without
even a
recognition
of
what
these
implications
are.
A
computer-acquired
history
and a programmed phy-
sical
examination
are
today almost
existing
reali-
ties.
2
,3,4,5
Machines which
will
perform
a
physical
examination
by
analyzing
data
coming
directly
from
self-propelled
sensing
devices
are
projected
at
this
time.
Once
the
software
has been
developed,
the
retrieval
of
data
from medical
records,
along
with
results
from automated
clinical
laboratories,
and
the
integration
of
these
data
for
processing
by
a computer
will
be
simple
procedures.
The
import
from
the
capabilities
of
these
existing
and
realis-
tically
projected
machines
is
that
they
are,
and
will
be,
able
to
do
what
the
physician
now
does.
Here
again,
as
in
1900,
the
role
of
the
physician-
will
be
affected
and
the
present
system
of
health
delivery
will
restructure
itself
around a
new
con-
cept
in
patient
care.
But
this
change
will
be un-
like
the
gradual
readjustment
that
accrued
when
medi-
cine
entered
the
technological
era.
Because
of
the
productive
capacity
of
our
electronics
industry,
the
lead
time between
the
development
of
an automated
process
in
health
delivery
care
and
the
moment
when
widespread change
occurs
will
be
short,
that
is
years,
not
decades.
The
resulting
effect
on
the
physician
will
be one
of
frequent
and
significant
change
in
his
role.
Trained
as
a
specialist
in
disease
detection
he
will
be
confronted
with
ma-
chines
that
are
equally
specialized,
that
can
also
differentiate
diseases,
and
that
will
bring
to
this
process
a
degree
of
efficiency
and a
capability
for
information
storage
far
beyond
human
abilities.
"Future
Shock"
for
the
Physician
Thus, as
in
so
many
other
fields
that
have
be-
come
automated,
the
physician
will
experience
not
.the
introduction
of
new
techniques
which can
co-
exist
with
his
present
job,
but
the
actual
replac~
ment
of
much
of
his
present
function
by
a machine.
The
years
of
training
in
scientific
disease
detec-
'
tion
and
the
old
methods of
specialist-based
health
care
delivery
will
have been made,
in
large
measure,
obsolete.
He
will,
in
fact,
experience
"future
shock".
Future
shock
occurs
when
you
are
confronted
by
the
fact
that
the
world you were
educated
to
believe
in
doesn't
exist.
Your images
of
re-
ality
are
apparitions
that
disappear
on
con-
tact.
There
are
several
ways
of
responding
to
such a
condition,
one
of
which
is
to
with-
COMPUTERS
and
PEOPLE
for
December,
1974

.
v
draw and
allow
oneself
to
be overcome by a
sense
of
impotence.
More
commonly, one con-
tinues
to
act
as
if
his
apparitions
were
sub-
stantial,
relentlessly
pursuing
a
course
of
action
that
he
knows
will
fail
him.l
A
third
reaction
to
being
suddenly exposed
to
a
new
environment
is
to
rationally
evaluate
your
situ-
ation
and
adjust
to
the
demands
of
the
new
milieu.
In
order
to
make
this
reorientation,
the
physician
will
first
need
to
recognize
that
there
is
a
new
environment.
Then
he
will
need
to
have
the
flexi-
bility
necessary
to
adapt
to
the
new
roles
which
the
doctor
will
fulfill
in
a world
of
automated
medicine.
Some
of
these
roles
will
be
in
the
new
specialties,
created
by
the
machines once more;
others
will
be
in
computer
administration
and programming;
many
more
will
be
connected
with
counseling
patients
and
re-
sponding
to
their
illnesses
with
empathy. There
are
many
variations
within
these
categories.
The
important
thing
is
for
the
physician
today
to
recog-
nize
the
change which
is
going
on
in
medicine
and
automation
so
that
he
will
be
prepared
for
the
new
demands which
will
follow.
Phase
III
-
The
Environmental
Control
Phase
The
development
of
machines which
are
able
to
replace
hitherto
unique
diagnostic
functions
of
the
physician
is
only
the
intermediary
phase
in
the
evo-
lution
of
machines
in
medicine.
Rapidly
following
this
era
will
come
the
stage
in
which
heuristic
com-
puters
interact
to
develop
strategies
for
medical
care
which
are
peculiarly
suitable
to
the
abilities
of
technology
rather
than
to
human
organization.
Changes
in
information
about
the
illness
and
the
alterations
in
disease
caused
by
the
automation
\~ill
result
in
changes
not
only
in
functions
related
to
diagnosis
and
treatment,
but
also
in
the
goals
of
medical
care.
Perhaps
the
first
goal
of
automated
medical
care
should
be
to
treat
a
sick
person,
and
this
would
shift
to
prevention
of
illness,
and
in
time
this
might change
to
maintaining
an
equilibrium
between
birth
and
death
rates.
These
goals
will
undoubtedly
be
altered
from
time
to
time
by
the
needs
of
society.
At
this
point,
the
computer
may
be
assigned
a
task
and
the
assigner
not
know
how
the
computer
arrived
at
an answer,
but
only
that
it
arrived
at
a
carefully
planned
answer,
perhaps
making
calculations
and
tri-
als
that
it
would
take
an
individual
100
or
more
years
to
duplicate.
This
later
phase
of
automation
will
be
characterized
by
two
new
facets
as
described
by John
Diebold:
(1)
Technological
advances
are
self-gener-
ating.
"No
longer
must
technological
progress
wait
on
the
next
individual
scientific
discovery:
tech-
nology
itself
is
pushing
research
into
new
discov-
eries
and
new
dimensions."
This
process
will
produce
whole
new
sets
of
com-
puters
which
will
acquire,
store,
and
process
infor-
mation which
only
the
machine
through
its
own
pro-
cesses
evaluated
as
being
relevant
to
treatment
and
health
to
begin
wi
th
--
wholly
a machine
idea.
(2)
Computers
rather
than
being
given
a
defined
task
to
perform,
can be
assigned
a
goal,
the
computer
at
this
highest
point
of
machine
intelligence
will
pursue
a
goal
with
minimum
instruction,
devising
its
own
stra-
tegy
in
pursuit
of
that
goal.
6 _
Direction Determined
by
the
Machine
In
this
final
stage,
machines
will
again
be
re-
sponsible
for
a changed environment
in
medicine,
but
this
time
the
change
will
occur
not
through
the
re-
structuring
of
the
present
system around a newly
in-
COMPUTERS
and
PEOPLE
for
December,
1974
troduced
mechanism,
but
under
the
external
direction
of
the
machine
itself.
For example,
in
a world whose
goals
are
a
healthy
population,
the
emphasis
of
medi-
cine
in
the
future
may
well
be
on
prevention
rather
than
diagnosis
and
treatment.
With
the
precedent
for
using
machines
in
problem
solving
situations
firmly
established,
and
with
the
concurrent
develop-
ment
of
machines
that
can
devise
strategy
in
the
pursuit
of
goals,6
it
is
predictable
that
these
com-
puters
will
be used
in
problem
solving
situations
in
health
delivery.
We
predict
that
their
recommended
approaches
to
health
delivery
problems
will
influ-
ence
the
direction
that
medicine
takes
in
the
next
decade.
Thus
far,
the
three
phases
of
the
evolution
of
machines
in
medicine
have been
delineated.
It
may
be seen
that
the
first
phase,
in
which machines
as~
sist
the
physician,
is
evolving
into
Phase
II,
in
which machines
are
designed
to
replace
functions
which
heretofore
had been unique
to
the
role
of
the
physician.
It
may
also
be seen
that
this
second
phase
is
only
intermediary
in
a
progression
that
will
result
in
machines
themselves
being
used
to
devise
new
approaches
to
health
care.
Thus,
tech-
nology
continues
to
shape
the
direction
of
medical
practice
through
its
increasing
incorporation
into
diagnosis
and
treatment.
The
development
of
new
skills
by
physicians
in
response
to
technical
ad-
vancement
will
be
necessary,
while
appropriate
edu-
cation
in
medical
school
should
facilitate
this
a-
daptive
development.
Culture
Influencing
the
Physician
The
preceding
discussion
has
demonstrated
that
the
physician
is
influenced
both
subtly
and
overtly
by
the
culture
in
which he
lives.
At
the
present
time
that
culture
is
technological,
and
both
the
practice
of
medicine
and
the
job
of
the
physician
are
inseparably
chained
to
that
technology.
Tech-
nological
advances,
such
as
the
ECG,
which have
cre-
ated
new
jobs
and
new
fields
of
medicine
are
exam-
ples
of
this
interdependency
upon
technology
in
medi-
cine
today.
In
like
manner,
it
may
be assumed
that
new
machines
will
continue
to
structure
new
special-
ties
and
define
new
jobs
in
the
future.
Therefore,
because
of
what has happened
in
the
past
twenty
years
and
is
continuing,
predictions
can be
made
about
the
effect
of
technological
ad-
vances
on
the
role
of
the
physician
in
the
future.
Finally,
with
these
changes
in
mind
it
is
possible
to
suggest
some
changes
in
the
present
medical
edu-
cation
system
that
will
be
necessary
in
order
to
prepare
physicians
to
practice
medicine
in
an
in-
creasingly
automated
environment.
Changes in Medical
Education
Among
the
possibilities
that
cluster
around
the
role
of
the
physician
in
the
late
twentieth
century,
two
large
areas
may
be emphasized.
Some
doctors
will
need
to
become advanced
technologists
in
order
to
conceive,
design,
operate,
and
understand
the
new
generations
of
machines.
Secondly,
with
the
increased
use
of
machines
for
technical
functions,
many
physicians
will
be
called
upon
to
help
the
pa-
tient
understand
the
technical
findings
of
his
exami-
nation
and
to
facilitate
the
constructive
use
of
this
information
in
the
patient's
life.
The
genetic
counselor
already
serves
this
function
today,
helping
the
counselee
to
incorporate
the
information
that
he
has
acquired
in
the
counseling
session
for
construc-
tive
planning;
while
the
thanoto!ogist
works
with
terminally
ill
patients
as
they
deal
with
the
know-
ledge
of
thei
r
approachi
ng
dea
tli·
r I 25)
p
case
turn to
page
17

WATERGATE
SOUTH
Nancy
A.
Miller
16 Ober Road
Princeton, NJ 08540
"In Fayetteville, Arkansas, I
was
working with Vietnam Veterans Against the
War.
One
of
the veterans there, William
W.
Lemmer, turned
out
to be an FBI informer .
...
We
broke
his cover and exposed him.
He
immediately suggested he become a double agent on the FBI."
Introduction
Investigations
by
the
press,
Congressional
com-
mittees,
and
the
courts
have
slowly
revealed
the
nature
of
"Watergate
East"
and
"Watergate
West."
The
first
refers
to
efforts
to
undermine Democratic
Party
presidential
candidates
and
the
subsequent
cover-up;
the
second,
Watergate
West,
to
the
viola-
tion
of
the
rights
of
Dr. Lewis
Fielding
in
an
at-
tempt
to
seal
off
leaks.
The
inter-relationship
be-
tween
Watergates
East
and
West
is
rather
ambiguous
without
an
examination
of
"Watergate
South,"
which
has been
almost
totally
overlooked.
The
evidence
supporting
the
hypothesis
that
there
was
a
southern
extension
is
scattered
through
Ervin
Committee
tes-
timony,
press
statements,
affidavits
and
depositions
filed
in
several
courts,
and
other
statements
by
some
of
those
involved.
Many
clues
or
references
may
still
lie
undetected,
but
a
consistent
picture
has
emerged, from
those
that
have been found,
of
an
attempt
to
keep
Richard
M.
Nixon
in
the
White House
at
almost
any
cost.
I
first
stumbled
into
Watergate
South
in
a most
unlikely
place,
Fayetteville,
Arkansas. I
was
liv-
ing
there
in
the
spring
of
1972 and working
with
the
Vietnam
Veterans
Against
the
War
(VVAW).
One
of
the
veterans
there,
William
W.
Lemmer,
turned
out
to
be
an
FBI
informer.
It
was
through
him
that
several
of
us began
to
learn
of
what was
being
planned
for
that
presidential
election
year.
In
late
May,
1972,
we
broke
Lemmer's
cover
and exposed him
as
an
informer.
He
immediately
suggested
that
he become a
double
agent,
spying
on
the
FBI.
To
prove
the
good
faith
of
his
offer,
he
voluntarily
agreed
to
be
interview-
ed,
on
tape,
by
two
other
Fayetteville
veterans.
The
interview
was
conducted
on
June 3 and
4,
two
weeks
before
the
discovery
of
the
Watergate
break-ins.
I
was
present
during
the
second
day's
session,
when
Lemmer
made
his
most ominous
statements.
Assertions
that
Violence
Was
Planned
for
the
1972
Political Conventions
Watergates
East
and West
reveal
an
hysterical
at-
tempt
to
seal
the
White House
off
from
the
rest
of
the
country.
But
why
the
hysteria?
Why
the
frantic
cover-up?
Much
of
the
answer
lies
in
Watergate
South.
Even
the
most
cooperative
witnesses
have
shied
away
from
this
area
of
the
total
puzzle,
probably
because
its
implications
are
so
staggering.
James
W.
McCord,
Jr.,
came
close
to
it
when
he
was
testifying
before
the
Ervin
Committee
in
May
of
1973.
He
stated
that
18
he
believed
he had
acted
in
the
nation's
best
inter-
est
because
of
plans
allegedly
being
made
by
groups,
working
with
the
Democrats,
to
violently
disrupt
the
conventions.
Therefore,
telephone
taps
of
Democra-
tic
committee members were
necessary
to
learn
of
plans
in
time
to
head
off
the
trouble
makers.
Mc-
Cord
testified
to
receiving
"almost
daily"
reports
from
the
Internal
Security
Division
of
the
Justice
Department,
some
of
which
linked
the
Democratic
Par-
ty
to
VVAW.
One
of
those
reports
came
concurrently
with
some
other
information
that that
same
group
(VVAW)
was
planning
vio-
lence
at
the
Republican
National
Convention
involving
danger
to,
threats
to
life
of
indi-
viduals.
• • •
The
Vietnam
Veterans
Against
the
War
was
one
violence-oriented
group
that
was
already
saying
in
the
spring
of
1972
that
they
were
going
to
cause
destruction
to
life
and
property
at
the
August
Republican
conven-
tion,
using
in
their
own
words,
their
own
bod-
ies
and weapons
as
the
spearhead
of
the
attack
there
--
these
are
their
exact
words, and
some
of
them
(the
Gainesville
8)
have
since
been
indicted
in
Tallahassee,
Florida,
with
addi-
tional
plans
to
damage
the
life
and
property
of
the
convention.
l
Earlier,
during
the
trial
of
the
Watergate
burg-
lars
in
January,
1973, one
of
McCord's
attorneys,
Gerald Alch,
explained
the
rationale
of
this
de-
fense.
If
one
is
under a
reasonable
apprehension
--
regardless
of
whether
that
apprehension
is
in
fact
correct
--
he
is
justified
in
breaking
a
law
to
avoid
the
greater
harm, which
in
this
case
would be
violence
directed
to
Republican
officials,
including
but
not
limited
to,
the
President.
2
The
first
question
that
needs
to
be asked
is:
did
McCord
have
cause
for
a
"reasonable
apprehen-
sion"
that
violence
was
planned
for
the
1972 conven-
tions?
The
answer
to
this
question
seems
to
be:
yes,
violence
was
planned.
The
proof
of
this
answer
is
found
in
the
tangled
web
of
a second
question:
who
was
planning
to
initiate
and
direct
the
violence?
Questionable Nature
of
Internal
Security
Division
Information
Supporting
Charges Against VVAW
The
government
alleged
that
VVAW
members
conspired
to
be
the
instigators
of
the
violence.
The
source
COMPUTERS
and
PEOPLE
for
December,
1974
f
i-
I'
1,/

d
and
veracity
of
these
allegations,
however,
is
high-
ly
questionable.
The
"New
York
Times" spoke
with
a
highly
placed
Florida
law
enforcement
official
who
participated
in
the
security
planning
and
operation
for
both
conventions
and saw
the
top-
level
intelligence
reports
(who)
said
in
an
interview
last
August (1972)
that
there
was
no
mention
in
the
intelligence
reports
of
the
plot
described
by
the
Government
in
its
indict-
ment
(of
the
Gainesville
8).
After
checking
the
intelligence
reports
for
the
security
operation
again
to
refresh
his
memory,
the
source
repeated
that
the
strongest
warning
about
any
potential
activities
of
the
V.V.A.W.
was
a
report
that
it
had bought
"be-
tween
five
and one-hundred
slingshots."
And
a check
of
the
secret
intelligence
and
op-
eration
logs
of
the
Dade
County
Public
Safety
Department,
made
available
to
the
New
York
Times,
also
shows
no
signs
of
Federal,
state
and
local
reports
of
the
alleged
plot.
3
At
least
two
undercover
officers
with
the
Dade
County
Public
Safety
Department,
Gerald
Rudoff and
Harrison
Crenshaw, had
infiltrated
VVAW
as
informers
and had
attended
VVAW
meetings
in
the
Miami
area
prior
to
the
conventions.
Had
they
heard
of
any
plans
that
could
be
construed
as
potentially
dis-
ruptive,
surely
Rudoff and Crenshaw would have
re-
ported
them. These
reports
should have been
among
the
materials
available
to
the
Florida
law
enforce-
ment
official
if
he and
his
co-workers
were
to
be
able
to
maintain
order
and
to
protect
the
lives
of
those
present
in
and around
the
conventions.
The
use
of
informants
is
based
upon
the
need
to
fulfill
such
responsibilities.
In
view
of
the
absence
of
such
reports,
it
is
reasonable
to
assume
that
there
had been
no
indications
that
VVAW,
or
any
other
movement
group,
was
planning
to
incite
violence.
Facts
tend
to
support
this
contention.
Convention Disruptions
Started
by
People
Apparently
Not
in
the
Peace Movement
VVAW
was
the
only
movement
organization
whose
members were
indicted
for
conspiring
to
violently
disrupt
either
convention.
It
was
also
the
only
group mentioned by
McCord
in
his
testimony
as
being
a
source
of
concern
to
security
personnel
at
the
conventions.
Aside from
sporadic
trashing
and a
disorganized
skirmish
the
last
night
of
the
Republican
Convention,
there
was
no
violence
at
either.
That
incident
the
final
night
involved
little
more
than
blocking
traf-
fic,
which
is
far
from
the
blowing
up
of
the
Cause-
way
to
Miami
Beach,
of
police
stations,
and
of
com-
munications
installations
that
the
Gainesville
8
were charged
with
planning.
Of
the
1,200
demonstra-
tors
arrested
that
night,
only
a few
--
some
reports
say
no
--
VVAW
members were
arrested.
Several
times
people
in
Miami
Beach
noticed
that
groups
of
younger
demonstrators
were
roused
to
start
trashing
by
agitators
who
quickly
faded from view
when
the
trouble
started.
Some
of
these
instigators
may
have been
irrational
hotheads
from
the
ranks
of
the
movement,
but
not
all
of
them
were.
A
reporter
for
the
"Miami
Herald"
saw
two
pro-Nixon
youths
physically
disrupt
a
\~omen's
anti-war
demonstration
outside
conven-
tion
hall.
One
of
the
young
men
identified
himself
as
Stephen McNellis, Minnesota
coordi-
COMPUTERS
and
PEOPLE
for
December,
1974
nator
for
VVJP
(Vietnam
Veterans
for
a
Just
Peace)
.•••
Since
then,
as
part
of
the
Watergate
disclo-
sures,
the
White House has
admitted
that
the
pro-Nixon
veterans
group
(VVJP)
was
in
fact
financed
with
GOP
campaign funds and
directed
by
Charles
Colson.4
No
Government Case
to
Support
Indictment
of
the
Gainesville 8
Sizable
contingents
of
VVAW
members were
present
at
both
conventions,
yet
the
expected
violence
did
not
occur.
It
is
conceivable,
if
the
charges
against
the
Gainesville
8 were
true,
that
VVAW
abandoned
its
plans
for
the
August
convention
after
some
of
its
members were
indicted
in
July.
However,
the
jury
found
the
eight
defendants
innocent
of
all
charges
after
hearing
a month
of
prosecution
witnesses,
only
one
defense
witness,
and
after
deliberating
for
only
four
hours.
Obviously,
the
government had
no
case
to
support
its
charges,
despite
the
fact
that
VVAW
was
heavily
infiltrated.
Two
FBI
inform-
ers,
Lemmer
and Karl Becker, were
present
during
the
meetings
from which
the
indictment
was
derived.
An-
other
FBI
informer,
Emerson
L.
Poe,
was
working
close-
ly
with
the
Florida
VVAW
coordinator,
Scott
Camil,
who
was
later
indicted
as
one
of
the
Gainesville
8.
Rudoff and Crenshaw were working
on
the
local level
in
Miami
with
Camil and Alton
C.
Foss,
another
de-
fendant.
All
but
Rudoff
testified
at
the
trial
and
still
the
government had
no
case.
The
only
assump-
tion
that
can
possibly
be drawn
is
that
there
was
no
conspiracy
by
VVAW
members
to
initiate
violence
at
the
conventions.
If
violence
was
planned,
but
it
was
not
planned
by
the
VVAW,
then
others
must have done
so.
If
other
movement groups had,
then
the
indictment
of
the
Gainesville
8 would
not
have
inhibited
them.
They might even have assumed
that
they
were
not
un-
der
heavy
surveillance
and,
therefore,
were
free
to
do
as
they
wished,
with
a
fair
degree
of
assurance
that
they
would
escape
blame
since
others
had
al-
ready
been
charged
with
what
they
planned
to
do.
The
absence
of
any
serious
outbursts
is
indicative
of
the
peaceful
intentions
of
the
demonstrators.
This
fact,
together
with
the
questionable
activities
of
members
of
such groups
as
the
pro-Nixon
VVJP,
sup-
port
the
belief
that
the
conspirators
were
not
among
the
sincere
protestors.
The
Case Against
the
Government
The
Gainesville Meeting
Adding
still
further
credence
to
this
possibility
are
two
examples
of
government
involvement
through
the
FBI.
First,
the
so
called
Gainesville
meeting,
from which most
of
the
indictment
against
the
8
was
derived,
was
set
up
by
Becker.
Donald
C.
Donner, a
veteran
from
Fayetteville,
Arkansas,
who
had
under-
taken
the
responsibility
of
arranging
for
the
meet-
ing,
got
so
far
as
sending
out a
letter
asking
for
suggestions
on
a
date
and
place
to
meet
before
Beck-
er
took
over.
As
Donner
said:
The
meeting
was
apparently
set
up
by Karl
(Becker)
•••.
Karl
told
me
that
he went
on
with
my
idea,
informed everybody,
tried
to
inform
me
and
was
unable
to
do
so.
I
shouldn't
have been
that
hard
to
find
•.••
He
said
he
went ahead
with
a
date
on
the
letter
and
there
is
not
a
date
on
the
letter.
All
in
all,
the
way
the
meeting
got
set
up
is
very
question-
able.
S
19

Second,
Lemmer
was
instructed
to
go
to
the
meeting
by
his
control,
Special
Agent Richard
J.
O'Connell,
who
made
it
known
to
me
prior
to
my
leaving
.••
that
the
Jacksonville
office,
Jacksonville,
Florida,
office
of
the
FBI, had
requested
my
presence
in
Gainesville
and I
was
told
that
it
would be
up
to
them
to
finance
my
trip
down
there
--
that
if
and
when
it
came
time
to
move,
I
was
to
contact
John
Maher
and
pick
up
money
for
that
trip
down
there
• • • •
They
gave
me
$210
to
make
the
round
trip
from
New
York
to
Gainesville
and back
to
New
York. 6
Squad
19
It
looks
as though
members
of
the
government were
the
actual
conspirators
and
that
they
were
attempt-
ing
to
set
VVAW
up
as
a
scapegoat
for
their
actions.
A September, 1971,
statement
by
Louis Tackwood, a
former Los Angeles
Police
Department
agent
provoca-
teur,
suggests
a
disturbing
basis
for
this
conten-
tion.
Tackwood,
in
a
press
conference,
described
a
plot
involving
a
special
group, Squad 19, which
was
created
by
the
Criminal
Conspiracy
Section
of
the
Los
Angeles
Police
Department and
the
FBI.
This
plan
entailed
planting
a number
of
agent
provocateurs
both
inside
and
outside
the
Con-
vention.
Agents were
to
infiltrate
the
groups
planning
demonstrations
against
the
war and
poverty.
At
the
time
of
the
demonstrations,
the
agents
were
to
provoke
street
battles
with
police
surrounding
the
convention
hall.
Mean-
while,
agents
inside
the
convention
hall
were
to
plant
explosives
timed
to
blow
up
coinci-
dental
with
riots
in
the
streets.
The
purpose
was
to
kill
a number
of
delegates.
The
result
would be
to
create
a
nationwide
hysteria
that
would
then
provide
President
Nixon
with
the
popular
support
necessary
to
declare
a
state
of
national
emergency. Orders
for
Squad
19
came
directly
from
the
California
State
Depart-
ment
of
Justice,
and
State
Attorney
General
Evelle
Younger. Richard Nixon would
then
ar-
rest
all
militants
and
left-wing
revolutiona-
ries
and
cancel
the
1972
elections.
He
could
invoke
special
emergency powers
leading
to
the
detention
of
political
activists.
7
Agent Provocateurs Active in VVAW Planning
for
the
Convention
Demonstrations
William Lemmer
Tackwood's
charges
are
too
serious
to
be
accepted
without
an
examination
of
available
facts.
First,
he claimed
that
"agent
provocateurs
• • • were
to
infiltrate
the
groups
planning
demonstrations."
VVAW,
which
was
planning
demonstrations,
was
infiltrated
and
at
least
one
of
the
infiltrators
was
a
provoca-
teur:
Lemmer,
the
"star"
witness
in
the
Gainesville
8
trial.
While he
was
stationed
at
Fort
Benning,
Georgia,
he encouraged
others
to
telephone
bomb
threats
and
tried
to
get
them
to
blow
up
a
water
tower.
After
he
got
out
of
the
Army,
in
July,
1971,
he
moved
to
Fayetteville,
Arkansas, where he
instruc-
ted
a high school
student
in
the
manufacture
of
a
fire
bomb
and
then
accompanied
the
boy
to
the
site
of
the
attempted
fire
bombing.
Lemmer
described
the
incident
to
the
three
of
us
in
Fayetteville.
20
He
asked
me
if
ether
would be a
better
fuel
than
gasoline
and I
told
him,
by
all
means,
ether
would
definitely
be
better
than
gaso-
line.
The
night
that
he
got
busted
(arrested)
we
went over
to
his
house,
picked
up
the
material,
and I went
out
to
watch. 8
Lemmer
also
talked
a
Fayetteville
veteran
into
send-
ing
a
bomb
threat.
And
in
another
incident,
he
helped
talk
demonstrators
at
an
Air
Force
base
in
Oklahoma
into
going
on
the
base
despite
police
and
military
orders
not
to
do
so.
In
the
last
three
in-
stances
people,
other
than
Lemmer,
served
time.
Lemmer
also
tried
to
project
a
violent
image
of
VVAW,
contradictory
to
the
organization's
history
of
only
staging
peaceful
protests.
During a
local
Arkansas march,
Lemmer
insisted,
in
vain,
that
the
VVAW
members
be armed and
defy
police
orders.
In
May
of
1972, he
stepped
up
his
campaign.
At
a dem-
onstration
in
Washington
Lemmer
tried
to
get
fire-
works and
explosives
to
set
off
in
trashcans,
which
would sound
like
gun
fire,
in
order
to
divert
police
attention
away
from
the
main body
of
demonstrators
and
on
to
VVAW.
Again
he
was
unsuccessful.
About
a
week
later,
on
a
trip
to
Florida,
while
easily
identifiable
as a
VVAW
member
since
he
was
wearing
military
fatigues
and a
VVAW
button,
he
talked
loud-
ly
in
public
places
about bombing and
killing.
Pablo
Fernandez
Another
agent
provocateur,
Pablo
M.
Fernandez,
while
not
actually
infiltrating
VVAW,
did
befriend
Camil and
other
Florida
veterans.
As
an
FBI
and
Miami
Police
Department
informer,
Fernandez
tried
to
sell
weapons, from guns
to
hand
grenades
and
mines,
to
Camil and
Foss.
Major
Adam
Klimkowski,
Commander
of
the
Miami
Police
Department's
Special
Investigations
Section,
stated:
We
were hoping
for
the
overt
act
necessary
to
produce a
charge
of
conspiracy
..••
We
did
not
want Camil
to
actually
acquire
wea-
pons,
•••
we
wanted
to
find
out
what
was
in
the
back
of
his
mind. 9
Government
witnesses
have
consistently
contended
that
Camil and Foss asked
for
weapons,
while
the
two
defendants
have
insisted
they
were
offered
them.
Klimkowski's
statement,
while
ambiguous,
tends
to
support
Camil and
Foss.
Whatever
the
truth
may
be,
one
fact
is
irrefutable:
no
member
of
VVAW
followed
up
and bought any
of
the
weapons.
Fernandez
was
part
of
a group
of
agitators
paid
to
go
to
J.
Edgar Hoover's
funeral,
May
5,
1972,
to
harrass
demonstrators.
The
group
included
Watergate
burglars
Bernard L.'
Barker,
Frank
Fiorini
(alias
Frank
A.
Sturgis),
Virgilio
R.
Gonzales, and
per-
haps Eugenio Rolando
Martinez,
under
the
name
of
Rolando
Martinez.
One
of
the
Fielding
burglars,
Felipe
de Diego,
was
also
in
the
party
as were
Reinaldo
Pico,
Angel
Ferrer,
and Humberto Lopez.
In
a
"Miami
Herald"
article,
Fernandez
is
quoted
as
saying:
I
kicked
a
hippie.
. • . I
knew
someone
big
was
protecting
us
because
the
Capitol
police
did
not
try
to
arrest
me.
lO
Fernandez went
into
more
detail
when
he
discussed
this,
and
other
activities,
with
another
Miamian,
Angelica Rohan. She
appears
to
be
nearly
the
only
informant
involved
in
convention
intelligence
who
was
sincerely
working
for
peaceful
demonstrations,
"so
the
name
of
the
Cubans would be
clean
and
every-
thing
would be good
for
the
Cubans."ll
On
May
23,
1973,
Rohan
gave sworn
testimony
to
U.
S.
District
Judge
W.
O.
Merhtens
in
which she
read
and
interpre-
ted
her
notes
of
what Fernandez had
told
her.
Many
COMPUTERS
and
PEOPLE
for
December.
1974
to,
t
/t<.,
-,!J
\1
~

;-
I
i'
'It"
of
the
points
she mentioned
are
supported
by
other
reports
of
the
incident.
I
am
going
to
quote whatever Pablo (Fernandez)
told
me,
which I took
down
as he
was
giving
it
to
me.
I
read
it
back
to
him, and
when
some-
thing
was
not
clear
I went back and
redid
it
Briefed
by
Mr.
Bernard
Barker
and
Mr.
Martinez
at
the
hotel
before
the
2-hour
break
upon
ar-
rival
in
Washington.
When
we
had
to
go
to
the
funeral,
the
instructions
were
that
one
of
the
group
that
spoke
English
had
to
insult
Mr.
Dan-
iel
Ellsberg
or
Doctor
Daniel
Ellsberg.
One
group would
destroy
Ellsberg's
loud
speakers
and
all
his
equipment
••••
They were
given
pictures
of
Mr.
Ellsberg
and he
told
them
to
aim
at
him
••••
(Sturgis)*
started
insulting
Ellsberg,
then
Pablo,
then
Barker.
Pico
threw
a punch
at
a
hippie
and
that
is
when
everything
started.
Rolando Martinez and
Virgilio
Gon-
zales
had whoever appeared
to
be
Ellsberg's
security
man,
held
him
while
Pablo punched
him.
(Sturgis)
and
Ferrer
were
taken
by
the
police,
the
Riot
Control,
to
a
car
and
then
released.
Capitol
police
were
five
feet
away
and were
like
protecting
the
Cubans, you
know,
like
"Well
done,"
by
a
sergeant
of
the
police
at
the
Capitol
told
Pablo
after
punching
Ells-
berg's
security
man.
The
police
protected
Pablo and he
left
the
site.
12
Barker
paid
all
the
expenses
and gave $100
in
cash
to
each
participant,
according
to
Rohan's
statement.
Sometime
after
that
trip,
Eugenio Martinez
tried
to
enlist
Fernandez's
services
to
create
trouble
at
the
Democratic
convention.
Watergate
burglar
Eugenio
R.
Martinez
offered
(Fernandez) $700 a
week
to
infiltrate
protest
groups
at
last
summer's Democratic
convention
and embarrass George
McGovern
"for
the
Repub-
lican
Party."
Pablo Manuel Fernandez, 28, a
burly,
heavy
equipment
parts
clerk
who
left
Cuba
as
a
teen-
ager,
said
he
was
told
by
Martinez:
"You
get
10
people
and
get
inside
McGovern
headquarters
in
the
hotel."
••
Fernandez
said
Martinez
came
to
him
with
the
long-range
offer
in
which he
was
told
he
could
make
$700 a
week
from
last
June (1972)
until
"after
the
President
took
office
early
this
year",
presumably meaning
the
inauguration
of
Nixon's
second
term.
13
According
to
Rohan,
at
least
two
other
Cubans were
to
head
other
teams, which sound
very
similar
to
the
fireteams
the
Gainesville
8 were accused
of
forming.
Others
Asked
to
Infiltrate
VVAW
Vincent
Hannard
Frank
Sturgis
approached
another
Floridian
with
a
similar
offer.
Vincent
J.
Hannard gave sworn
testi-
mony
in
private
and
then
spoke
to
reporters.
'*
Rohan
used
Fiorini,
but
I have
substituted
Sturgis
since
this
is
the
name
by
which most
people
know
him.
COMPUTERS
and
PEOPLE
for
December,
1974
Vincent
J.
Hannard
of
Miramar, a
private
in-
vestigator
• • •
said
he
was
offered
work
in
"intelligence
and
instigation"
during
the
con-
ventions
at
Miami
Beach.
Hannard
claimed
he
received
separate
calls
from
Sturgis,
and
maybe
Barker,
and
two
others
and
they
asked
him
to
help
disrupt
activities
of
the
Vietnam
Veterans
Against
the
War
--
an
organization
thoroughly
infiltrated
by
police
and
federal
informers
before
and
during
the
conventions.
According
to
Hannard, each
call
came
from a
different
person,
and each
caller
tried
to
persuade
him
that
it
was
his
patriotic
duty
to
help
undermine
the
VVAW.
Hannard
said
he
was
sure
it
was
Sturgis,
be-
cause
he
has
known
him
for
more
than
13
years
and
recognized
his
voice.
Hannard
said
another
caller
identified
himself
as
Barker.
However, Hannard
said
he
never
has
met
Barker
and
could
not
be
certain
who
act-
ually
called
him. . • •
Hannard
said
he
told
an
FBI
agent,
Jack
Acker-
ly,
about
the
calls
shortly
after
he
received
them. Ackerly
said
he
knows
Hannard,
but
re-
fused
to
talk
about
conversations
he
may
have
had
with
him.
According
to
Hannard, none
of
the
four
callers
told
him
what would be
expected
of
him
if
he
agreed
to
do
the
proposed
undercover
work.
But he
said
each mentioned
the
VVAW
and
de-
scribed
the
task
as
covert
intelligence
and
instigation.
"It
was
clear
from what
they
said
that
I
was
supposed
to
incite
trouble
or
riots
from
the
anti-war
groups,"
he
said.
"I
was
told
it
would be
activity
pertaining
to
the
convention
and
an
opportunity
to
travel.
"And
there
would be
great
rewards
when
the
President
was
re-elected."
Hannard
said
he
was
offered
$1,000
a
week
for
that
work
but
that
in
the
fourth
call
the
of-
fer
was
raised
to
$1,500.
14
John
Kifner,
for
"The
New
York
Times,"
filled
in
some
details
in
Hannard's
story.
In
a long
deposition
taken
by
the
Broward
County
State's
Attorney's
Office,
a
man
with
Cuban
and
Central
Intelligence
Agency
ties,
Vincent
J.
Hannard
said
that
he had been
of-
fered
$1,500
a
week
in
a
telephone
call
from
a
man
calling
himself
"Eduardo"
--
(E. Howard)
Hunt's
code
name
--
to
infiltrate
the
VVAWand
cause
trouble.
"Basically
we
had
to
expose
the
V.V.A.W.
be-
ing
pink
and Communist and
all
this
stuff,"
he
said,
adding
that
he
was
wanted
"because
of
my
reputation
as
an
instigator
rather
than
an
investigator."
He
said
that
he had
refused
because
the
amount
of
money
being
offered
made
the
job
seem
too
dangerous.
Mr.
Hannard has worked
as
an
In-
former
for
the
C.I.A.,
the
F.B.I.
and
local
police
forces
.15
21

Alfred Baldwin and John
Eck
Alfred
C.
Baldwin,
3rd,
the
ex-FBI
agent
who
mon-
itored
the
illegally
placed
telephone
taps
at
the
Democratic
National
Headquarters,
was
also
asked
to
infiltrate
VVAW.
A
Miami
gun
dealer,
John Eck, ad-
mitted
that
he
too
had been
contacted
but
would not
say
by
whom
other
than
by
someone
named
in
connec-
tion
with
the
Watergate
case.
Government Support
of
Plans
to
Kill
Convention Delegates
Returning
to
Tackwood's
statement,
to
examine
another
of
his
contentions,
he
said
that
"the
pur-
pose"
of
the
riots
and
explosions
"was
to
kill
a
number
of
delegates."
Fernandez
claimed
to
be
able
to
get
the
weapons
necessary
to
produce
the
explo-
sions.
Lemmer
proposed a
variation.
In
January
or
February,
1972
--
just
four
or
five
months
after
Tackwood's
press
conference
and
six
months
before
the
first
national
political
convention
--
Lemmer
suggested
to
several
VVAW
members
that
they
should
break
down
automatic
weapons,
strap
them
to
their
bodies
under
their
clothes,
smuggle them
into
the
convention
hall,
and
"rip
people
off"
--
in
other
words,
kill
them.
Just
as
no
one bought weapons
from Fernandez,
no
one
accepted
Lemmer's
suggestion.
Lemmer,
like
Fernandez,
confided
in
a
woman,
Bar-
bara
Stocking.
On
May
25
and 26,
during
a
drive
to
Florida,
he
told
Stocking
of
plans
that
she found
so
disturbing
she
filed
an
affidavit,
in
which she
said
Lemmer
said
that
I
should
not
go
to
the
Miami
con-
ventions
because,
he
said,
all
of
the
VVAW
leaders
were
going
to
be picked
up
and
taken
out of
circulation,
and he and
some
other
people
were going
to
shoot
leaders
of
the
New
Left,
and
start
a
riot,
and
there
would be a
lot
of
fighting
and
shooting,
and everyone
would be
arrested.
He
also
spoke
of
shooting
the
"Trots"
(Trotskyites)
and
Progressive
Labor
movement
people
and
pretending
that
VVAW
had done
it,
and
this
would
discredit
the
VVAW
and
split
the
peace movement.
He
said
he had a
source
of
unlimited
funds
to
carry
this
out.
16
Stocking's
statement
that
Lemmer
told
her
"there
would be a
lot
of
fighting
and
shooting
and everyone
would be
arrested,"
supports
Tackwood's
contention
that
"the
result
would be
to
create
a
nationwide
hysteria
that
would
then
provide
President
Nixon
with
the
popular
support
necessary
to
•••
invoke
special
emergency powers
leading
to
the
detention
of
political
activists."
Proposed
Mass
Kidnappings
of
Movement Activists
FBI
Participation
There
is
a good
bit
of
evidence
that
preparations
were
being
made
for
the
"detention
of
political
ac-
tivists."
When
describing
his
activities
with
the
FBI,
Lemmer
told
us a
little
about a
plan
the
FBI
had
to
round
up
movement
leaders.
22
LE~mIER:
I
was
told
to
prepare
a
Ii
st
of
move-
ment
people
around
me,
around
Fayetteville,
a
list
of
movement
people
who
I
could
count
on
should I have
to
go underground.
The
fact
that
they
said,
"I
have
to
go
underground"
told
me
something, more
than
in
the
back
of
my
mind.
Q:
The
resident
agent
here
requested
it?
A:
Right.
Well, I
guess
you
could
say
re-
quested.
I
was
told
to
prepare
a
list.
The
list
of
people
was
made
up. I have
discussed
with
him,
not
the
list
specifically,
but
the
possibilities
of
certain
developments
in
Miami
and
across
the
country
making
it
necessary
for
a round-up,
similar
to
the
ones
we
saw
of
the
Japanese-Americans
in
World
War
II.
He
has
confirmed
that
possibility
openly
at
one
of
our
meetings,
in
fact,
the
last
of
our meet-
ings.
Q:
Did he
give
you any
sort
of a
•••
proba-
bility
reading
on
it?
A:
An
extremely
good
possibility,
to
the
point
that
we
discussed
alternate
identifica-
tion
for
myself
so
that
I would have
the
abili-
ty
to
move
about
the
country,
have freedom
of
movement,
during
any
type
of
round-up, any
type
of
situation
during
which
the
movement
would have
to
go
clearly
underground.
17
There was,
indeed,
a
list
of
local
movement
people
in
the
files
of
the
Fayetteville,
Arkansas,
FBI
of-
fice.
White House and CRP Participation
Both John
W.
Dean,
3rd,
and
Jeb
Stuart
Magruder,
in
their
testimony
to
the
Ervin
Committee,
stated
that
mass
kidnappings
of
radicals
had
at
least
been
considered
by
them and John
Mitchell
as
a
part
of
the
so
called
Liddy
plan,
devised
by
G.
Gordon Liddy.
MAGRUDER:
There were
projects
relating
to
the
abduction
of
individuals,
particularly
members
of
radical
groups
that
we
were
con-
cerned
about
on
the
convention
at
San
Diego.*
Mr.
Liddy had a
plan
where
the
leaders
would
be abducted and
detained
in
a
place
like
Mexi-
co and
that
they
would
then
be
returned
to
this
country
at
the
end of
the
convention.
18
DEAN:
Plans
called
for
mugging squads,
kid-
napping teams,
prostitutes
to
compromise
the
opposition,
and
electronic
surveillance.
He
(Liddy)
explained
that
the
mugging squad
could,
for
example, rough
up
demonstrators
that
were
causing
problems.
The
kidnapping
teams
could
remove
demonstration
leaders
and
take
them
below
the
Mexican
border
and
thereby
diminish
the
ability
of
the
demonstrators
to
cause
trouble
at
the
San
Diego
convention.
19
Lemmer
told
us
that
the
detained
activists
would be
held
in
the
old
concentration
camps, where
the
Jap-
anese-Americans were
held,
which he claimed were
being
renovated,
but
he
told
Stocking
that
the
radi-
cals
would be
taken
to
Mexico
City.
Both Magruder and
Dean
referred
to
the
kidnapping
and mugging teams only
in
reference
to
the
first
of
Liddy's
proposals,
which
was
rejected,
leaving
the
implication
that
they
were
among
the
more
"bizarre"
elements
that
had
to
be removed
before
the
plan
could
be approved, as
it
was
on
March
30, 1972. But
Magruder,
in
his
book
"An
American
Life:
One
Man's
Road
to
Watergate",
mentions
that
he
told
his
wife
in
the
spring
of
1972
that
the
government might have
to
round
up
radicals
and
take
them
to
Mexico, adding
that
they
might
not
come
back.
Since
the
first
two
*At
the
time
that
the
Liddy
plan
was
under
consider-
ation,
the
Republican Convention
was
still
scheduled
to
be
held
in
San
Diego.
COMPUTERS
and
PEOPLE
for
December.
1974
..

;,
J-
versions
of
Liddy's
plan
were
considered
on
January
27
and
February
4, which
are
unquestionably
in
the
winter,
Magruder's
statement
suggests
that
the
idea
of
the
kidnappings
was
still
under
consideration,
at
least,
when
the
plan
was
finally
approved
in
late
March.
Putting
a few
events
into
chronological
order
shows
that
such
bizarre
acts
as
kidnapping
and
mug-
ging
at
government
direction
may
not
have been
among
those
aspects
of
the
Liddy
plan
that
were removed.
The
plan
was
approved
on
March
30, 1972. Fernandez
admitted
to
being
part
of
a mugging team
(although
without
using
those
exact
words)
at
Hoover's
funeral
on
May
5.
Lemmer's
descriptions,
in
late
May
and
early
June,
of
a
kidnapping
plot
is
almost
an
exact
duplicate
of
the
one
described
by
both
Dean
and
Ma-
gruder
a
year
later.
Detention
of
VVAW
Members
Mass
kidnappings
did
not
occur,
probably
because
the
June
17
discovery
of
the
Watergate
break-ins
forced
a change
in
plans.
More
than
twenty
VVAW
members were
detained,
however,
during
the
Democrat-
ic
National
Convention.
In
a
coordinated
two-day
sweep,
covering
at
least
five
states,
FBI
agents
issued
subpoenas
to
approximately
twenty-three
VVAW
members
ordering
them
to
appear
before
a
federal
grand
jury
in
Tallahassee
the
morning
of
July
10,
the
day
the
Democratic Convention opened. Never
be-
fore
had so
many
people
been subpoenaed by a
federal
grand
jury
to
appear
on
a
single
day.
This
raised
at
least
three
questions.
The
first
involved
the
possibility
that
the
government
was
deliberately
denying
these
people's
rights
to
present
their
case
to
political
delegates
by
detaining
them.
The
sec-
ond,
the
probability
that
the
government used
the
grand
jury
to
further
embarrass
the
Democratic
Party
by
calling
an
unusual
evening
session
from which an
indictment
was
issued
against
some
of
the
veterans
about
two
hours
after
the
Democrats approved a
reso-
lution
in
support
of
the
subpoenaed
VVAW
people.
But
the
third
question
raises
the
most
disturbing
suspicions.
Was
the
government hoping
to
turn
those
VVAW
demonstrators
who
were
in
Miami
Beach
into
an
unruly
mob?
These members were
furious
about
the
subpoenas.
The
government
may
well
have assumed
that
the
veterans
were
without
leaders,
since
most
of
the
men
responsible
for
VVAW's
demonstrations
were
being
held
in
Tallahassee.
Angry
leaderless
groups
of
people
can be
roused
to
violence
and
several
agi-
tators
were found
in
their
midst.
At
least
one,
after
being
evicted
from
the
campsite
by
veterans
because
he
was
causing
trouble,
is
reported
to
have
returned
with
the
police
and
identified
himself
as
an
undercover
agent.
The
veterans,
however,
did
manage
to
maintain
discipline,
directing
their
an-
ger
into
explanations
of
the
situation
to
the
dele-
gates.
Riots as Excuse
to
Cancel
1972
Elections
Finally,
Tackwood
stated
that
"a
nationwide
hys-
teria
•••
would
then
provide
President
Nixon
with
the
popular
support
necessary
to
declare
a
state
of
national
emergency • • . and
cancel
the
1972
elec-
ti
ons.
" There
is
evidence
that
members
of
the
gov-
ernment had
given
serious
consideration
to
such a
cance
lla
ti
on.
In
the
spring
of
1970, William Howard, a Wash-
ington,
D.C.
reporter
for
the
conservative
Newhouse
chain,
published
a
story
about
a
"contingency
plan
to
cancel
the
1972
elec-
tions,"
which he
claimed
he
learned
about
COMPUTERS
and
PEOPLE
for
December.
1974
from
the
wife
of
a
Rand
Corporation
executive.
There
was
a
virtual
news
blackout
on
the
sub-
j
ect.
According
to
Howard,
the
President
(Nixon) had
ordered
the
Rand
Corporation
think
tank
in
Santa
Monica,
California,
to
do
a
"feasibili
ty
study"
of
the
cancellati
on
possibi
li
ty
in
1972,
because
of
Nixon's
concern
about
possible
"dis-
ruption
by
the
left."
The
"Los Angeles
Free
Press"
picked
up
the
story
and
was
told
privately
by
persons
at
Rand
that
it
"had
for
once done a good and
right
thing
in
publishing
the
story."20
This
study
may
have been
ordered
originally
as
a
precaution
against
pOlitically
oriented
violence,
which
did
seem
to
be
escalating
in
1969 and 1970.
This
would be a
perfectly
valid
reason
for
doing
such a
study.
But
it
assumes
sinister
implications
when
seen from
the
perspective
of
1972.
By
this
time,
incidences
of
violence
from
the
left
had dwin-
dled
drastically,
as had
talk
of
it
within
movement
groups.
But
while
interest
in
violence
had been
languishing,
provocateurs
had been
proliferating.
Aside from
those
known
to
be
involed
with
VVAW,
there
was
Robert Hardy,
without
whose
help,
and
the
money
he
received
from
the
FBI,
the
Camden
28
would
not
have
destroyed
draft
files.
There
is
good
reason
to
believe
that
some
of
the
Weathermen
might
not
have done so
much
damage
if
FBI
provoca-
teur
Larry
Grantwohl had
not
been so
insistent.
These
are
just
two
of
many
such
cases.
It
is
rea-
sonable
to
assume,
therefore,
that
members
of
the
Nixon
administration,
and
others
working
in
concert
with
them, were hoping
for
the
disturbances
that
would
justify
the
invocation
of
martial
law and
the
cancellation
of
the
elections
as a means
to
circum-
vent
the
balancing
controls
contained
in
the
con-
stitution.
This
would
give
them an
indefinite
ten-
ure
in
a
position
of
power beyond
reach
of
either
Congress
or
the
courts.
Thus,
the
existence
of
such
a
study
in
a
climate
so
infected
with
provocateurs
indicates
that
members
of
the
government were
at-
tempting
to
ensure
that
the
havoc
they
needed would
occur.
Conclusion
Watergate
South
appears
to
go
far
beyond what
has
thus
far
been
revealed
in
Watergates
East
and
West,
into
a scheme
to
subvert
the
United
States'
constitutional
system
of
government.
The
evidence,
while
not
being
conclusive,
is
consistent.
It
in-
dicates'
that
a
plan
may
have been implemented
in
which
provocateurs
would
instigate
riots
at
one
or
both
1972
political
conventions.
Leaders
of
the
movement would be
arrested
and
taken
from
the
coun-
try.
This would be done
either
before
the
conven-
tions
to
prevent
them from
controlling
their
people,
so
that
the
provocateurs
could
be more
effective,
or
in
response
to
the
instigated
rioting,
thus
provok-
ing
still
more
violent
reactions
from
those
remain-
ing.
The
American
people,
terrified
by
such
dis-
turbances,
would
then
be amenable
to
the
imposition
of
martial
law, and
perhaps
even
the
cancellation
of
the
elections.
This
is
a
disturbing
hypothesis,
but
events
do
tend
to
support
it.
Far
more
inten-
sive
investigations
must be conducted
either
to
prove
or
to
disprove
this
theory.
The
implications
of
Watergate South
are
too
serious
to
remain an ob-
scure
question
of
which
only
a few
people
are
aware.
(more)
23

Biographical Information
Jack
ACKERLY
-
Florida
FBI
agent
to
whom
Vincent Han-
nard
allegedly
reported
the
offer
from Frank
Stur-
gis
to
infiltrate
VVAW
Gerald
ALCH
-Attorney
for
James
McCord
during
his
trial
for
the
Watergate
break-in
Alfred
C.
BALDWIN,
3rd -Former
FBI
agent
who
moni-
tored
taps
on
telephones
at
the
DNC,
asked
to
in-
filtrate
VVAW
Bernard
L.
BARKER
-Convicted
member
of
the
"plumbers"
unit
who
directed
Cuban
agitators
at
J.
Edgar
Hoover's
funeral
Karl
BECKER
-
Charles
Henry Becker,
3rd,
FBI
inform-
er
from
New
Orleans
who
testified
against
the
Gainesvi
lle
8
Scott
CAMIL
- A
Gainesville
8 defendant and formerly
Florida
regional
coordinator
for
VVAW
Charles
W.
COLSON
-Former
special
counsel
to
then
President
Richard Nixon, pleaded
guilty
to
ob-
structing
justice
Harrison
CRENSHAW
-
Dade
County
(Florida)
Public
Safety
Department
officer
who
infiltrated
VVAW,
now
deceased
John
W.
DEAN,
3rd -Former counsel
to
then
President
Richard Nixon, pleaded
guilty
to
conspiracy
to
obstruct
justice
Felipe
de
DIEGO
-
Cuban
exile
and
member
of
the
"plumbers"
unit
who
has admitted
breaking
into
Dr. Lewis
Fielding's
office
Donald
C.
DONNER
-
The
VVAW
member
from
Fayetteville,
Arkansas,
who
conducted
the
June, 1972,
interview
with William
Lemmer
John
ECK
-
Miami
gun
dealer
asked
to
infiltrate
VVAW
"EDUARDO"
-See
E.
Howard
Hunt,
Jr.
Daniel
J.
ELLSBERG
-Former
Rand
Corporation
employ-
ee
who
turned over
the
Pentagon Papers
to
"The
New
York
Times"
Pablo
M.
FERNANDEZ
-
Cuban
exile,
FBI
and
police
in-
former
in
Miami,
and
paid
agitator
at
J.
Edgar
Hoover's
funeral
Angel
FERRER
-
Cuban
exile
and
paid
agitator
at
J.
Edgar Hoover's
funeral
Lewis
FIELDING
-Daniel
Ellsberg's
psychiatrist
whose
office
was
broken
into
by
members
of
the
"plumbers"
unit
Frank
FIORINI
- A
soldier
of
fortune,
convicted
mem-
ber
of
the
"plumbers"
unit,
better
known
as Frank
Sturgis
Alton
C.
FOSS
- A
Gainesville
8
defendant
and
for-
merly
Dade
County
coordinator
for
VVAW
Virgilio
R.
GONZALEZ
-
Cuban
exile
and
convicted
member
of
the
"plumbers"
unit
Larry
GRANTWOHL
-
An
FBI
informer and
provocateur,
in
late
1969
and
early
1970,
who
trained
and
en-
couraged Weathermen
in
Ohio
Vincent
J.
HANNARD
-
Private
investigator
from Mira-
mar,
Florida,
who
was
active
in
Cuba
when
Castro
took over, asked
to
infiltrate
VVAW
Robert
HARDY
-
An
FBI
informant whose admissions
in
court
led
to
the
dismissal
of
the
Camden
28
char-
ges
on
grounds
of
entrapment
J.
Edgar
HOOVER
-Former
FBI
Director
who
died
May
2,
1972
William
HOWARD
-
The
reporter
who
broke
the
story
of
the
Rand
Corporation
study
on
the
cancella-
tion
of
the
1972
elections
E.
Howard
HUNT,
Jr.
-Former
CIA
agent,
White
House
consultant,
and
convicted
of
conspiracy,
bribery,
and
wiretapping,
known
to
Cuban
exiles
as Eduardo
John
Kifner
-
Reporter
for
"The
New
York
Times"
who
covered
the
Gainesville
8
case
Major
Adam
KLIMKOWSKI
-
Commander
of
the
Special
In-
vestigations
Section
of
the
Miami
Police
Depart-
ment
William
W.
LEMMER
-Former
FBI
informer
from Arkan-
sas
and
principal
witness
against
the
Gainesville
8
24
G.
Gordon
LIDDY
-Former White House
aide,
counsel
to
CRP,
convicted
of
bribery
and
wiretapping
Humberto
LOPEZ
-
Cuban
exile
and paid
agitator
at
J.
Edgar Hoover's
funeral
Jeb
Stuart
MAGRUDER
-Former White
House
aide,
chief-
of-staff
for
CRP,
pleaded
guilty
to
conspiring
to
obstruct
justice
John F.
MAHER
-
FBI
agent working out of
the
New
York
City
office
Eugenio
R.
MARTINEZ
-
Cuban
exile
and
convicted
mem-
ber
of
the
"plumbers"
unit
Rolando
MARTINEZ
-Paid
agitator
at
J.
Edgar Hoover's
funeral
who
may
be
convicted
"plumber" Eugenio
R.
Martinez
James
W.
McCORD,
Jr.
-Former
CIA
agent,
security
coordinator
for
CRP,
and
convicted
of
burglary
and
wiretapping
George
McGOVERN
-
The
1972
Democratic
presidential
candidate
Stephen
McNELLIS
-Minnesota
coordinator
of
the
Vietnam Veterans
for
a
Just
Peace
W.
O.
WEHRTENS
-U.S.
District
Judge
in
Miami
John
N.
MITCHELL
-Former U.S.
Attorney
General,
director
of
CRP,
and
under
indictment
for
con-
spiracy,
obstruction
of
justice,
and
perjury
Richard
M.
NIXON
-Former
President
of
the
United
States,
unindicted
co-conspirator
for
obstruction
of
justice,
since
pardoned
Richard
J.
O'CONNELL
-
FBI
agent
and William Lemmer's
resident
control
in
Fayetteville,
Arkansas
Reinaldo
PICO
-
Cuban
exile
and
paid
agitator
at
J.
Edgar Hoover's
funeral
Emerson
L.
POE
-
FBI
informer
from
Florida
who
tes-
tified
against
the
Gainesville
8
Angelica
ROHAN
-
Cuban
exile
and
police
informant
in
1972
to
whom
Pablo Fernandez
confided
Gerald
RUDOFF
-
Dade
County
(Florida)
Public
Safety
Department
officer
who
infiltrated
VVAW
Barbara
STOCKING
-Former Teaching Fellow
in
Philo-
sophy
at
Boston
University
to
whom
William
Lemmer
confided
Frank
A.
STURGIS
-See Frank
Fiorini
Louis
TACKWOOD
-
Los
Angeles
agent
provocateur
for
ten
years
who
broke
his
cover and
talked
in
1971
Evelle
YOUNGER
-
California
State
Attorney
General
allegedly
directing
Squad
19
Bibliography
1. James
W.
McCord,
Jr.,
May
18
and 22, 1973, Hear-
ings
before
the
Select
Committee
on
Presidential
Campaign
Activities
of
the
United
States
Senate,
Phase
I:
Watergate
Investigation,
Book
1, pp.
180 and
200
2. Gerald Alch, as quoted
by
Walter Rugaber, "The
New
York
Times," January 17, 1973
3.
John
Kifner,
"The
New
York
Times," August 9, 1973
4.
Rob
Elder,
"Miami
Herald,"
June 13, 1973
5.
Unpublished commentary
by
Donald
C.
Donner
on
the
June, 1972,
interview
of WHliam
Lemmer
6.
Transcript
of unpublished
interview
with William
Lemmer
conducted June 3 and 4,
1972
7. Richard
E.
Sprague, "The June 1972 Raid
on
Demo-
cratic
Party
Headquarters (The Watergate
Incident)
--
Part
2,
"Computers and Automation," October,
1972, pp. 24-25
8.
Interview
with William
Lemmer
9.
Rob
Elder,
"Miami
Herald,"
May
26,
1973
10.
Rob
Elder,
"Miami
Herald,"
May
23, 1973
11. Unpublished
statement
given
by
Angelica
Rohan
to
U.S.
District
Judge
W.O.
Mehrtens
on
May
23,
1973
12. Statement
of
Angelica
Rohan
13.
Rob
Elder,
"Miami
Herald,"
May
23,
1973
14. Dennis Holder,
"Miami
Herald,"
June 8,
1973
15. John
Kifner,
"The
New
York
Times:' August 8,
1973
16. Unpublished
affidavit
submitted
by
Barbara
Stock-
ing
on
July
9, 1972
COMPUTERS
and
PEOPLE
for
December.
1974

e
17.
Interview
of William
Lemmer
10.
Jeb
Stuart
Magruder,
June
14, 1973,
Hearings
be-
fore
the
Select
Committee, Phase
I,
Book
2, pp.
707-788
19. John
W.
Dean,
3rd,
June 25, 1973,
Hearings
be-
fore
the
Select
Committee, Phase
I,
Book
3,
p.
929
20.
Citizens
Research and
Investigation
Committee
and Loui s
E.
Tackwood, "The
Glass
House
Tapes,"
Avon,
New
York, 1973,
p.
171
0
Imberman
-Continued
from
page
14
of
course
--
and
was
responsible
for
the
union
ac-
tivity.
The
consultant
recommended a system
of
baffles
~e
installed
to
cut
the
noise
in
the
department,
ahd
In
the
nearby
area.
In
addition,
he
suggested
piped-
in
music which (by
contrast)
seemed
to
diminish
the
racket.
Having music
in
the
plant
was
so novel
that
it
went
far
to
eliminate
the
basic
complaint.
In
ad-
dition,
improvements were
made
in
the
physical
work-
ing
condi
tions
that
had been mentioned
by
many
employ-
ees.
The company
won
the
second
election
2-to-l.
Most
often,
our
research
indicates,
worker
dis-
satisfaction
does
not
seek
outlet
along
union
lines.
Such
dissatisfaction
is
simply
channelled
in
that
direction
by
organizers
who
know
how
to
take
advan-
tage
of
discontent.
Recognize
Discontent
It
is
therefore
vital
for
management
to
discover
what
is
breeding
worker
discontent.
Some
trivial
things
such as
inadequate
lighting,
poor
circula-
tion
of
heat
in
a
department,
wet
or
dirty
floors,
leaky
restrooms,
or
begrimed windows
may
be
the
cause
and
very
often
is
the
cause
--
if
employers
had a good upward communications system
to
bring
those
matters
to
the
surface
quickly.
A more im-
portant
matter
such
as
heavy-handed foremen
may
cause
worker
revolt
despite
the
fact
that
they
have
borne
that
burden
for
years.
This
latter
is
common
but
most
executives
never
recognize
it.
Or
finally:
the
demand
for
cost-of-living
increases
--
far
ex-
ceeding
guidelines
--
crops
up,
with
employees
ig-
norant
of
what such
cost
increases
might
do
to
the
company's
competitive
position
AND
EMPLOYEE
JOBS.
Understanding Employees
It
takes
a
great
deal
of
time,
effort
and
skill
to
listen
to
employees and
to
understand
them.
This
important
chore
is
part
of
sophisticated
foremen
training,
and
is
not
too
common.
In
this
connec-
tion,
I have been
through
288
NLRB
elections
win-
ning
9~.4
~er
cent
just
by
inaugurating
a
tw~-way
commUnICatIons system and foremen
training.
Most
of
the
losses
were
the
result
of
being
called
in
when
the
fire
was
already
up
to
the
attic.
Given
time,
techniques
employed
by
such
experts
can be
learned
by company
personnel.
Employee Goodwill
Such
techniques
work
splendidly,
not
to
under-
mine union
sentiment
particularly,
but
more impor-
tantly
to
win employee
goodwill
for
management
--
even where
unions
exist.
Then
production
and
sales
may
go
on
uninterruptedly,
enabling
both
management
and
labor
to
earn
larger
returns.
For management and
labor
each
to
earn
its
fair
share,
it
becomes
important
to
listen
with
a
trained
"third
ear"
and
to
train
supervisors
and
top
manage-
ment
how
to
do
so
--
if
the
number
of
NLRB
elections
in
this
industry
is
to
be
reduced
and
not
extended.
0
COMPUTERS
and
PEOPLE
for
December,
1974
Antley
-Continued
from
page 17
We
can
predict
the
need
for
physicians
who
can
di-
r~c~
the
advancing
technology
of
medicine,
and phy-
SICIans
who
can
interpret
the
knowledge
made
possible
through
technology
to
the
patients.
But
because
of
~he.rapid
chan~es
in
medicine
which
are
occurring,
It
IS
not
possIble
to
foresee
all
of
the
specific
a7e~s
that
w~ll
demand
new
skills.
A
formal
recog-
nItIon
of
thIS
state
of
rapid
change
should
be
ac-
knowledged, however.
It
should
be
taken
into
con-
sideration
in
a
reorganization
of
medical
education,
so
that
new
physicians
will
be
educated
with
the
skill
to
recognize
and
adapt
to
new
situations.
The
Super-Technologist
Indeed,
perhaps
the
greatest
significance
to
be
gained
from
predicting
the
role
of
the
physician
in
the
near
future
is
in
the
adaptation
of
medical
edu-
cation
today.
Obviously
two
different
areas
need
to
receive
serious
consideration
in
an
evolving
cur-
riculum.
The
first
would be
concerned
with
training
the
super-technologist.
The
emphasis
on
this
train-
ing
should
be towards
proficiency
in
theoretical
mathematics,
statistics,
physics,
computers and
electronics.
However,
the
fact
that
it
may
be
nec-
essary
for
a
man
to
retrain
himself
several
times
in
his
career
should
be
stressed,
and
adaptive
skills
for
this
should
be
developed.
This
is
not
a
simple
task.
Its
requirements
infer
that
the
trainee
needs
to
have
the
most
current
technical
information
either
~ithout
having
his
identity
strongly
associated
with
Its
content
or
that
he have
the
capacity
to
take
a
new
identity
with
each
retraining.
The
Really Effective Counselor
A second
area
of
emphasis
in
medical
education
should be
on
helping
the
physician
to
become an
ef-
fective
counselor.
There
are
several
approaches
to
this
problem.
Educational
programs
for
clinical
psychologists
and
psychiatrists
have
already
devel-
oped methods
of
training
aspirants
in
communicative
and
facilitory
skills.
These
techniques
are
avail-
able
to
the
aspiring
physician-counselor
and
should
be
uti
Ii
zed.
Techniques,
however.
are
not
in
themselves
solu-
tions
to
educating
counselors.
The
ability
to
em-
pathize
with
patients,
to
accept
each
one
as
an
in-
dividual.
and
to
respect
his
value
system and
life-
style
is
not
~cquired
through
skill
courses.
It
may
be
developed
In
part
through
the
study
of
sociology
and
anthropology,
but
philosophical
knowledge does
not
equal
compassion and
sensitivity.
To
develop
these
paramount
qualities
of
a
counselor
some
work
in
personal
growth,
either
in
group
or
i~dividual
therapy
is
probably
required.
Group
work
described
by Cadden
et
a1
7 and Kubler-Ross8
with
severely
ill
pati~n~s.suggests
effective
methods
for
developing
sensItIVIty.
Thus.
technology
continues
to
shape
the
direction
of
medical
practice
through
its
increasing
incorpora-
tion
into
diagnosis
and
treatment.
The
development
of
new
skills
by
physicians
in
response
to
technical
adv~nce~ent
w~
11
be
necessary;
while
appropriate
edu-
catIon
In
medIcal
school
should
facilitate
this
adap-
tive
development.
References
1.
Postman N ••
Weingartner
C.:
Teaching
as
a
sub-
versive
activity.
Dell
Publishing
Co.,
Inc.,
1969
(please
turn
to
page
34)
25

The
Assassination of the Reverend
Martin
Luther
King,
Jr.,
and
Possible
Links
With the Kennedy Murders
Wayne Chastain, Jr.
810
Washington Ave.,
Apt.
408
Memphis, Tenn.
38105
Was
the
murder
of
the Reverend
Martin
Luther
King, Jr.,
the result
of
a conspiracy? Previous installments
of
this
series described the "eggs
and
sausage" man, later given the
code name
of
Jack Armstrong, who appeared
on
the scene
the
day
of
the murder.
Also
appearing on the scene were
Tony'Benavides
and
J.
Christ Bonnevecche who claimed
to
have
information
and
understanding
of
Dr. King's
and
John
F.
Kennedy's assassinations.
Are
these
two
men
to
be believed?
Are
they
one
and
the
same
person -possibly
aliases
for
Jack Armstrong?
Is
there a relationship between these assassinations? a
con-
spiracy
at
work
by
an organization
or
several individuals?
or
are these murders more
simply
vendettas? Mr. Chastain
con-
tinues
to
seek the answer to these questions
and
to
the
mur-
ders
of
Dr.
King
and
the Kennedys.
Charlie
Q.
Stephens
Neither
Atty.
Gen.
Phil
Canale
nor
his
team
of
prosecutors
ever
summoned
Jones
or
myself
to
testify.
No
doubt,
Jones'
credibility
would have been
attacked
by
prosecutors
if
the
defense
had
attempted
to
put
Jones
on
the
stand.
Jones
has a
criminal
record
because
of
felony
convictions
for
theft
by
check.
On
the
other
hand,
Canale
and
his
prosecutors
had
no
qualms
about
constructing
their
entire
case
on
the
testimony
of
Charlie
Q.
Stephens,
a
man
with
155
arrests
on
his
record,
including
an
assault
to
mur-
der
with
firearms.
Why
would
Stephens
be deemed by
the
prosecution
as
a more
reliable
witness
than
Jones,
despite
154
more
arrests
than
Jones?
Jones
is
black
and
Stephens
is
white.
As
stated
in
Part
9,
Stevens
said
he
saw
the
man
who
ran
out
of
the
bathroom and
that
he was
"nig-
ger".
Stephens
made
this
statement
to
this
reporter,
both
on
the
night
of
the
slaying
and
the
next
day.
On
the
night
of
the
slaying,
Mrs. Brewer and Mrs.
Walden,
who
were
both
sober,
told
me
to
ignore
Ste-
phens
because
he was
"falling
down
drunk"
at
the
time
of
King's
slaying.
A
third
witness,
Charles
McGraw,
the
cab
driver,
would
later
inform
me
also
that
Ste-
phens
was
intoxicated
at
the
time.
Police
and
FBI
agents
ignored
Stephens'
state-
ments
for
several
weeks
after
King's
death.
Then,
Stephens
changed
his
story
and
his
credibility
is
seemingly enhanced.
Stephens
came
forth
and
said
he
saw
a
white
man
come
out
of
the
bathroom and
that
Ray
was
the
man.
26
-
Part
11
(Conclusion)
The metamorphosis
of
memory
evolved
along
a
tor-
tuous
route,
climaxed
with
the
transformation
of
a
drunken
derelict
into
a
reliable
witness,
and
the
degredation
of
a
reliable
witness
--
Mrs. Walden
--
into
a supposed
psychotic.
Could
the
discrediting
of
Mrs. Walden have been
the
result
of
her
earlier
state-
ment
that
she had
heard
the
shot
fired
from
outside
the
rooming house
--
a
statement
that
confirms
Jones'
contention
that
he
saw
the
man
outside
the
rooming
house and
in
the
bushes
--
and
that
the
man
she
saw
coming
out
of
the
bedroom
was
neither
Ray
nor
the
man
described
by Mrs. Brewer
as
John
Willard?
Stephens'
belated
recall
came
after
a
drinking
session
with
a
British
newspaper man.
Ray
had
just
been apprehended
in
London.
The
British
newspaper
man
gratuitously
provided
Stephens
with
a
fifth
of
whisky and
at
least
$30
in
cash.
Wayne
Chastain
of
Memphis,
Tenn.,
is
a
veteran
newspaper
reporter
and
Southern
j
ournali
st
wi
th
experience
on
several
metropoli
tan
dailies
in
Texas,
including
EI Paso, Houston,
Dallas
and San
Antonio, as
well
as
on
the
St.
Louis Globe-Demo-
crat
and a
Memphis
daily.
He
had
traveled
with
Dr.
King's
entourage
on
and
off
for
two
years
prior
to
the
assassination.
He
had
spent
the
last
two
days
of
King's
life
covering
hi
s
speeches
in
Memphi
s
pri
or
to
the
shooting.
He
was
on
the
mur-
der
scene
wi
thin
10
minutes
after
Dr. King
was
shot.
He
interviewed
eyewitnesses
for
one
of
the
fi
rst
comprehensive
news
accounts
to
the
nati
on
of
Dr.
King's
death.
A
native
Texan and a
graduate
of
the
Uni
versi
ty
of
Texas
wi
th
a
bachelor's
de-
gree
in
hi
story
and
poli
tical
science.
Mr.
Chas-
tain
also
spent
several
months
in
early
1964
in-
vestigating
and
researching
the
assassination
of
President
Kennedy,
Jack
Ruby's
link
with
Lee
Har-
vey Oswald and a group
of
pro-Cuban arms
runners,
and
other
activities
related
to
Kennedy's
death.
Months
before
The
Warren Commission's
report,
which
was
published
in
the
fall
of
1964,
Mr.
Chas-
tain
--
after
exhaustive
interviews
with
hundreds
of
witnesses
--
had
reached
the
conclusion
that
President
Kennedy's
death
was
the
result
of
a
plot
involving
paramilitary
professionals
financed
by
a group
of
weal
thy,
right-wing
Texans
wi
th
strong
connections
wi
th
former
high
officials
with
the
Central
Intelligence
Agency
as
well
as lower
echelon
CIA
personnel
still
assigned
to
the
bu-
reau.
The
present
installment
is
an
excerpt
from
a
forthcoming
book
enti
tIed:
Who
Really
Ki
lIed
Dr. King
--
And
the
Kennedys? A
Disturbing
View
of
Political
Assassinations
In America.
COMPUTERS
and
PEOPLE
for
December,
1974

...
,
The
next
day, under
the
newspaperman's
byline,
Stephens
is
quoted
as
saying
he
recognized
Ray
from
newspaper
photographs
as
the
man
whom
he had seen
running
out
of
the
bathroom.
FBI
and
Police Disbelieve
Stephens
FBI
and
Memphis
police
assiduously
avoided
Ste-
phens
--
especially
after
his
previous
drunken
as-
serti
ons
that
it
was
a
"nigger"
--
as
early
as
the
morning
after
the
slaying,
after
Mrs. Brewer and
Mrs. Walden had
described
his
condition
of
the
night
before
to
them.
Suddenly,
Stephens'
recuperative
recall
powers
re-awakened
the
interest
of
the
FBI.
Inspector
N.
E. Zachary,
although
a
fervent
believer
in
the
lone
assassin
theory,
never
did
attach
any
credence
to
Stephens'
statements
--
even
after
the
elaborate
rehabilitation
of
Stephens
by
the
FBI.
Zachary
accounts
for
the
transformation
of
Ste-
phens
into
a
credible
witness
as
a
"bureacratic
blun-
der."
An
FBI
agent
in
Washington, D.C., happened
to
read
the
story
by
the
British
newspaper
writer
quoting
Ste-
phens.
There
was
nothing
in
the
investigative
reports
coming
to
Washington
about
a
witness
named
Stephens.
(He
was
deemed so
lacking
in
credibility
that
the
field
agents
did
not
even mention him
in
their
reports.)
So,
the
Washington
agent
clipped
the
British
article
and
sent
an immediate
bulletin
to
the
~lemphis
office
of
the
FBI
to
pick
up
Stephens.
The
FBI
notified
the
police
dispatcher
to
have
Stephens
picked
up.
Stephens
was
a well-known
police
character,
and
his
early
morning
hang-outs
were
well
known
to
the
police
dispatcher,
who
immediately
sent
a
patrol
car
to
a downtown park
to
have
Ste-
phens
picked
up.
After
Stephens
was
picked
up,
the
patroman
called
the
dispatcher
back and asked where
to
take
him.
The
dispatcher,
knowing Zachary
as
the
inspector
in
charge
of
the
Memphis
police
department
investigation
of
the
King
slaying,
told
the
patrolman
to
take
Stephens
to
Zachary's
office,
temporarily
forgetting
that
the
request
came
from
the
FBI.
The
patrolman
delivered
Stephens
to
Zachary's
office.
Zachary
was
on
the
phone, so
the
patrolman
left
Stephens
with
another
officer
outside
Zachary's
office.
When
Zachary's
call
was
finished,
the
offi-
cer
outside
said
Stephens
was
there.
Zachary,
familiar
with
the
statements
by Mrs.
Brewer, Mrs. Walden, and
others
in
the
rooming house,
said:
"What do I want
with
him
.•.
let
him
go."
Later
in
the
day
when
the
FBI
called
again
and
asked
if
Stephens
had been
picked
up,
the
search
for
Stephens
was
launched
again
and he
was
located.
"lie
was
strictly
an FBI
witness
•••
not
ours,"
Zachary
later
said.
Iluring
the
extradition
hearings,
FBI
agents
took
Stephens
into
protective
custody,
kept
him
in
posh
motels,
and
provided
him
with
money
and
liquor
--
and
away
from
the
press.
Mrs. Walden Disappears
Meanwhile, Mrs. Walden
mysteriously
disappeared.
Tlli s
reporter
spent
three
days
looking
for
Mrs. Wal-
COMPUTERS
and
PEOPLE
for
December,
1974
den
after
the
State
Department
said
Stephens'
state-
ment
identifying
Ray
as
the
man
Stephens
saw
come
out
of
the
bathroom
was
introduced
into
evidence
during
the
extradition
hearing
in
London.
Later,
I
learned
she had been committed
to
the
West Tennessee
Psychiatric
Hospital
in
Bolivar,
about
60
miles
from Memphis,
on
the
same
day
that
the
FBI
finally
got
custody
of
Stephens
as
a
material
witness.
The
procedures
used
to
commit Mrs. Walden were
not
only
unorthodox,
but
illegal,
as
a
subsequent
hearing
three
years
later
confirmed.
Staff
physicians
at
the
institution
said
Mrs. Walden
should
never
have
been committed,
but
with
her
common-law husband
in
protective
custody
by
the
FBI,
there
were
no
family
members
that
could
obtain
her
release
or
protest
the
commi
ttment.
In
January
1969, a month
before
the
trial
of James
Earl
Ray, a
staff
psychiatrist
at
the
hospital
recom-
mended Mrs. Walden be
immediately
discharged
and
noted
in
his
record
that
her
committment had
violated
the
procedures
set
forth
in
the
Tennessee
mental
health
committment
statute
--
a modern law
based
on
model codes
prescribed
by
both
legal
and
medical
associations.
In
his
report,
the
psychiatrist
said
Mrs. Walden
had
never
had a
psychiatric
history;
at
the
time
of
her
committment, she
did
not
exhibit
any symptoms
of
psychosis
serious
enough
to
warrant
her
committment
to
Western
State.
This
institution
usually
becomes
the
repository
of
mental
patients
who
have
failed
to
respond
to
rehabilitative
therapy
at
the
Tennessee
Psychiatric
Hospital
in
Memphis.
Someone
in
the
City
of
Memphis
government
first
had Mrs. Walden committed
in
the
City
of
Memphis
Hospital's
psychiatric
ward which
is
under
the
con-
trol
of
the
Memphis
police
department.
At
that
facility,
patients
undergo
only
brief
therapy,
and
are
either
discharged
or
committed
for
short
'range
therapy
--
sometimes
lasting
less
than
a
week
and
sometimes
lasting
three
months
--
at
the
Tennessee
Psychiatric
Hospital
three
blocks
away
in
Memphis.
Charles
Murphy, a
Memphis
attorney
who
later
was
retained
to
represent
Mrs. Walden, was
eventually
successful
in
gaining
an
adjudication
that
Mrs. Wal-
den
was
illegally
committed.
Murphy
said
when
Mrs. Walden
was
rushed
from
the
rooming house
to
the
City
of
Memphis
Hospital's
psychiatric
ward,
she
had been
recovering
from an
operation
for
a
rare
skin
disease.
She
had been an
alcoholic
and had been
rehabilitated
under an
AA
program
that
met
at
the
Tennessee
Psychiatric
Hos-
pital.
"She had been
sober
for
a month
before
King's
death,
and
she
had been
sober
for
a month
after-
wards,
right
up
until
the
time
of
her
committment,"
Murphy
said.
The
normal
procedure
would have been
to
have
turned
Mrs. Walden
over
to
a
clinical
psychiatrist
at
the
Tennessee
Psychiatric
Ilospital
for
an
evalu-
ation
and
for
a
short-range
commitment
at
the
Mem-
phis
institution
before
she would be
sent
to
West-
ern
State.
"They
bypassed
the
entire
procedure,"
Murphy
said.
"She
was
in
the
City
psychiatric
ward
less
than
a
day
before
she
was
transferred
to
Western
State,
60
miles
away."
(more)
27

Murphy
cites
Mrs. Walden
as
the
source
of
the
report
that
Stephens,
her
common-law husband,
was
induced
to
change
his
story
by
the
blandishments
of
the
British
newspaper
man.
"They had
to
get
rid
of
me
to
make
Charlie's
story
stand
up
in
court,"
Murphy
quoted Mrs.
Walden
as
say-
ing.
Meanwhile,
while
Charlie
Stephens
was
in
the
pro-
tective
custody
of
the
FBI,
another
frequent
female
companion
of
Stephens met an
unfortunate
fate
--
one
more
fatal
than
Mrs. Walden.
Mrs. Walden Illegally
Committed
"She
was
found
beaten
to
death
in
a
vacant
lot,"
Murphy
said.
Murphy,
in
a
brief
filed
in
the
Circuit
Court
in
Hardeman County,
Tenn.,
where Western
State
Hospi-
tal
is
located,
charged
that
members
of
the
Shelby
County
Attorney
General's
office,
the
FBI, and
the
Memphis
police
department
illegally
conspired
to
commit Mrs. Walden
to
a
psychiatric
institution
for
two
reasons:
First,
to
destroy
her
credibility
as
a
witness
in
case
she gave
testimony
that
conflicted
with
Stephens
at
Ray's
trial;
and,
Second,
to
get
her
out
of
Memphis
and
away
from
newsmen
who
might
tell
her
version
of
the
events
that
occurred
in
the
~ooming
house
on
the
night
Dr.
King
was
slain.
Aftermath
of
King's Assassination
Dr. Martin
Luther
King
Jr.,
Nobel Peace
Prize
recipient,
preached
non-violence,
but
on
April
4,
1968, Dr. King became a
victim
of
the
very
virulence
he preached
against.
A
sniper
killed
him
with
a
rifle
as
he
stood
on
a
Memphis
motel
balcony.
Less
than
two
hours
later,
the
shot
had echoed
around
the
world.
Guerilla
warfare
erupted
in
the
largest
cities
of
the
nation
--
a
pattern
of
vio-
lence
unfolded
in
a manner
not
entirely
unlike
the
hi
t and run
tactics
of
the
Viet
Cong
in
South Vietnam.
Less
than
a
week
before,
President
Lyndon Johnson
had
virtually
abdicated
by
announcing he would
not
run
for
a second
elected
term, and
that
he
was
going
to
wind
down
the
Vietnam
War
--
a
sharp
and
surpris-
ing
reversal
of
the
escalation
policies
he had
forced
on
the
nation
for
the
past
three
years.
The
more
despairing
right-wing
columnists
seethed.
They lamented
that
President
Johnson
--
once
the
hawk's
hawk
--
had
capitulated
to
the
subversive
forces
both
domestically
and
abroad.
The
monolithic
forces
of
international
Communism
had
not
only
pene-
trated
the
perimeter
of
domestic U.S.
security,
but
had deployed
its
insurgent
forces
in
our
city
to
break
down
law and
order.
Only
with
this
background
in
mind, can one
effec-
tively
evaluate
the
meaning and
significance
of
Dr.
King's
death.
Also,
the
perspective
would
not
be complete
unless
one
recalls
that
Dr. King
at
this
point
of
his
career
had amassed a
formidable
coalition
of
blacks,
Chica-
nos,Indians
and poor
whites
for
his
Poor
People's
March
on
Washington, D.C.
It
would
begin
in
June
--
less
than
two
months away.
It
would
begin
its
long,
hard
trek
in
Memphis
and
points
in
North
Mississippi.
28
This
would be
during
the
first
hot
month
of
what
many
urbanologists
predicted
would be
another
vola-
tile
and
violent
summer. Shock
tremors
were
still
in
the
air
from
the
summer
before
when
racial
vio-
lence
rocked
Newark
and
Patterson,
N.J.,
and
Detroit,
Mich.
King's Killer a Racist
Dr. King had done more
than
any
other
man
to
break
down
the
barriers
of
governmentally
sanctioned
segregation
in
the
south.
He
had
just
then
began
to
expand
his
civil
rights
movement and
mobilize
the
strength
of
his
supporters
in
the
Southern
Christian
Leadership
Conference
to
uproot
other
social,
eco-
nomic and
international
injustices.
But
it
was
his
effectiveness
as a
civil
rights
leader
breaking
down
the
segregation
barriers
that
made
most
persons
--
including
intellectuals
on
the
right
and
the
left
--
assume
that
a
conspiracy,
if
it
did
exist,
must have been
rooted
in
racism.
Thus, Dr.
King's
killer
had
to
be a
racist.
l
After
all,
why
was
King
in
Memphis
at
the
time he
was
killed?
This
was
the
question
most
often
asked
by
those
who
suspected
that
racism
alone
provides
the
clues
to
explaining
King's
death.
These
people
would
argue
that
a
two
month
old
sanitation
strike
by
black
workers
against
the
City
of
Memphis
had
released
a
latent
racism
among
city
political
leaders
--
a
racism
that
had been assumed
by
more
enlightened
citizens
to
have been
sublimated,
if
not
extirpated
by
its
roots,
by
a
prior
liberal
city
administration
that
had
integrated
schools,
restaurants,
public
parks
and had
prevented
violence
in
the
tense
summer
of
the
year
before.
However,
those
who
suspect
racism
alone
provides
an
entire
explanation
as
to
why
King
was
killed
failed
to
perceive
the
more
variegated
social
back-
ground upon which
King's
assassination
had impinged.
By
early
1968, Dr. Martin
Luther
King had
evolved
into
something more
than
a
black
civil
rights
leader.
He
led
one
of
the
most dynamic
coalitions
in
the
nation
--
a
coalition
that
could
bring
its
influence
to
bear
on
international
as
well
as domestic
issues.
The
"paranoid
patriots,"
a term used
by
Rev.
James Lawson, had begun
to
think
of
King
as
a
"national
security
threat."
Yet
King's
organization
and
other
protest
groups had
just
succeeded
in
"turn-
ing
President
Johnson around
on
the
Vietnam War".
A Grave Domestic
Situation
If
those
who
espoused
the
hard-line,
cold
war men-
tality
could
regard
a
civil
war
in
an underdeveloped
Southeast
Asian
nation
less
than
20,000
miles
away
as
an
immediate and
direct
threat
to
America's
national
security,
imagine
how
these
cold
warriers
would
evaluate
the
gravity
of
a domestic
crisis.
They would
claim
it
was
caused
by
the
confrontation
of
protest
groups,
which had
just
turned
a hawkish
President
around
on
the
Vietnam
War,
marching
to
the
nation's
capital
and demanding
reform
legislation
from
Congress.
Assembled
in
the
nation's
capital
city,
could
not
such a
formidable
group
force
Con-
gress
into
shifting
its
priorities
from needs of
national
defense
to
domestic
reforms?
If
one
put
himself
in
the
mind of one of
the
"pnr-
anoid
patriots",
could
not
the
Poor
People's
March
in
June 1968 be viewed as
critical
as
the
urban
con-
COMPUTERS
and
PEOPLE
for
December,
1974

frontation
in
Moscow
in
1917?
If
the
domino
theory
haunted
these
so-called
paranoid
patriots,
think
what
terror
may
have
flashed
across
their
minds
when
they
pondered
the
domestic
effects
of
the
Poor
People's
March
and
their
demands
on
the
U.S. Govern-
ment
in
the
nation's
capital?
Could
not
this
be
deemed a
surgical
thrust
at
the
nation's
jugular
vein'?
As
Sen.
Ervin's
subcommittee would
reveal
two
years
later,
the
military
reflected
this
frenetic
fear
and
pathological
preoccupation
with
the
threat
of
domestic
subversion
when
it
launched
its
massive
surveillance
program
against
the
civilian
population
of
America.
Conducted
by
the
Army
military
intelligence,
the
program
assigned
military
counter-intelligence
agents
to
spy
on
civilians,
to
compile
exhaustive
dossiers
on
leading
liberal
leaders
in
Congress, prominent
judges,
and
active
civil
rights
workers.
The
purpose
of
these
investigations,
according
to
the
defenders
of
the
system,
was
to
produce
intelligence
needed
in
the
event
that
disruptive,
crippling,
urban
gue-
rilla
warfare
did
break
out
in
America.
This
cold
war atmosphere
characterized
by
the
"enemy
within"
syndrome -had
reached
its
apogee
in
the
months
shortly
before
King's
death.
Footnote
1. Huie and Frank
both
strongly
contend
that
Ray
killed
King because he
was
a
racist.
Relatives
and
acquaintenances
who
knew
Ray
when
he
was
grow-
ing
up
in
East
St.
Louis,
and
Alton,
Ill.,
said
they
never
heard
him
express
any
racial
animosity.
Dr.
McCarthy DeMere, a prominent
physician
who
is
also
a
licensed
attorney
and
professor
of
forensic
law
and
medicine,
spent
almost
six
months
with
Ray
at
the
Shelby County
jail.
DeMere
said
he
never
heard
Ray
express
any
hostility
toward
blacks.
An
Establish-
ment
figure,
DeMere
is
a
reserve
deputy
sheriff
and
a
friend
of
the
then
sheriff,
Bill
Morris,
who
asked
him
to
leave
his
medical
practice
and
take
on
an
assignment
of
protecting
Ray's
health
on
a
daily
basis,
up
to
the
time
of
the
trial.
Dr.
DeMere
and
Sheriff
Morris,
unlike
most
members
of
the
Memphis
establishment,
have
expressed
on
occasions
doubts
that
Ray
acted
alone
in
the
King
slaying.
Also,
probably
no
other
two
men
spent
as
much
time
with
Ray
as
DeMere
and
Morris.
D
Editorial
Note:
As
is
clear
from
the
articles
which
we
have
published,
the
"true"
story
of
the
assassination
of
Martin
Luther
King
and
any
conspiracy
behind
it,
is
not
complete.
.
So
these
articles should
be
looked
on
as a
preliminary
report.
For
information
in
regard
to
the
book
on
this
subject
by
Wayne Chastain, please
write
to
him.
Corrections:
On page 5
of
the
July,
August,
September,
October,
and
November issues
of
Computers
and
People, change
the
author's
name
"Wayne
C.
Chastain"
to
"Wayne
Chastain".
In Part
8,
page
27,
left
column,
line
10
from
the
top,
change
"definitely
the
man"
to
read
"definitely
not
the
man".
In Part 9, page
26,
left
column,
line 5
from
the
top,
and
same page, right
column,
line 7
from
the
bottom,
change
"Willie O.
Stephens"
to
"Charles
O.
Stephens".
In Part 10, first paragraph,.
delete
the
final
remark
in
parentheses.
COMPUTERS
and
PEOPLE
for
December,
1974
MACDONALD -Continued
from
page
11
Motor
Vehicles.
Take a look
at
your Blue Cross
card
•••
chances
are
you'll
find
the
same
number.
In
the
computer age,
the
details
of
your
personal
life
have become so
accessible
as
to
seriously
threa-
ten the
entire
idea
of
privacy.
AND
THERE
IS
NO
PO-
LITICAL
FREEDOM
WITHOUT
PRIVACY
I
Today,
the
"Social
Security"
number has been
transformed
into
a
Universal
Identifier.
Linked
by
computer
tape
from one
data
bank
to
another,
it
po-
tentially
allows
anyone
who
has
it
to
obtain
infor-
mation about you from anyone
else
who
has
it.
Consider
just
a few examples
of
how
your
life
is
recorded:
-
The
US
Treasury
Department
now
requires
banks
to
keep a
microfilm
record
of
every
sizable
check you
write.
Most
banks simply
record
all
your
checks.
Government
agencies
may
then
in-
spect
these
records
without
your knowledge
or
permission.
Your
banking
transactions
are
a
mirror
of
your
entire
life
••.
the
groups you
join,
the
doctors
you
consult,
the
causes
you
support.
-
Private
dossier
companies,
called
credit
bureaus,
maintain
secret
files
on
over 50
million
Ameri-
cans,
containing
information
not
only
on
your
finances,
but
personal
information
such
as
who
your
friends
are,
what your
habits
are,
what
your
neighbors
or
co-workers
think
of
you.
These
credit
bureaus
are
protected
by
federal
law from your
efforts
to
see
your
own
file
or
adequately
challenge
its
accuracy.
Next time
you
are
mysteriously
denied
insurance,
or
cre-
dit,
or
a
job,
the
chances
are
it's
because
of
what's
in
your
file.
-
In
Massachusetts,
whenever you
receive
in-pa-
tient
psychiatric
treatment,
your
name,
Social
Security
number,
diagnosis
and
course
of
treat-
ment
are
reported
to
the
Department
of
Mental
Health.
Among
the
recipients
of
this
informa-
tion
are
insurance
companies,
chiefs
of
police,
the
Registry
of
Motor
Vehicles,
and
all
other
licensing
authorities.
The
Department has
plans
for
extending
this
data
bank
to
people
getting
out-patient
services
as
well.
WHAT
CAN
YOU
DO?
By
yourself,
not
much. But you
can
join
forces
with
275,000
other
Americans
(9,000
in
Massachusetts)
who
are
defending
their
rights
through
membership
in
the
American
Civil
Liberties
Union. Right
now
the
ACLU
and
its
affiliate,
the
Civil
Liberties
Union
of
Massachusetts
are
pressing
for
urgently
needed
legislation
that
will
help
con-
trol
government
access
to
the
intimate
details
of
your
life.
Even
more
important,
the
ACLU
can be
counted
on
to
fight
back whenever
individual
rights
are
threat-
ened by abuses
of
government power.
If
these
rights
are
to
be
preserved,
and government
is
to
be
the
servant
rather
than
the
master
of
its
people,
a
strong
Civil
Liberties
presence
must be
maintained
from
the
smallest
hamlet,
through
state
government,
to
Washington, D.C.
Be
a
part
of
that
presence.
Join
the
one
organi-
zation
whose
sole
purpose
is
to
assure
that
our
government does
not
exceed
its
authority
in
the
ex-
ercise
of
its
power.
29
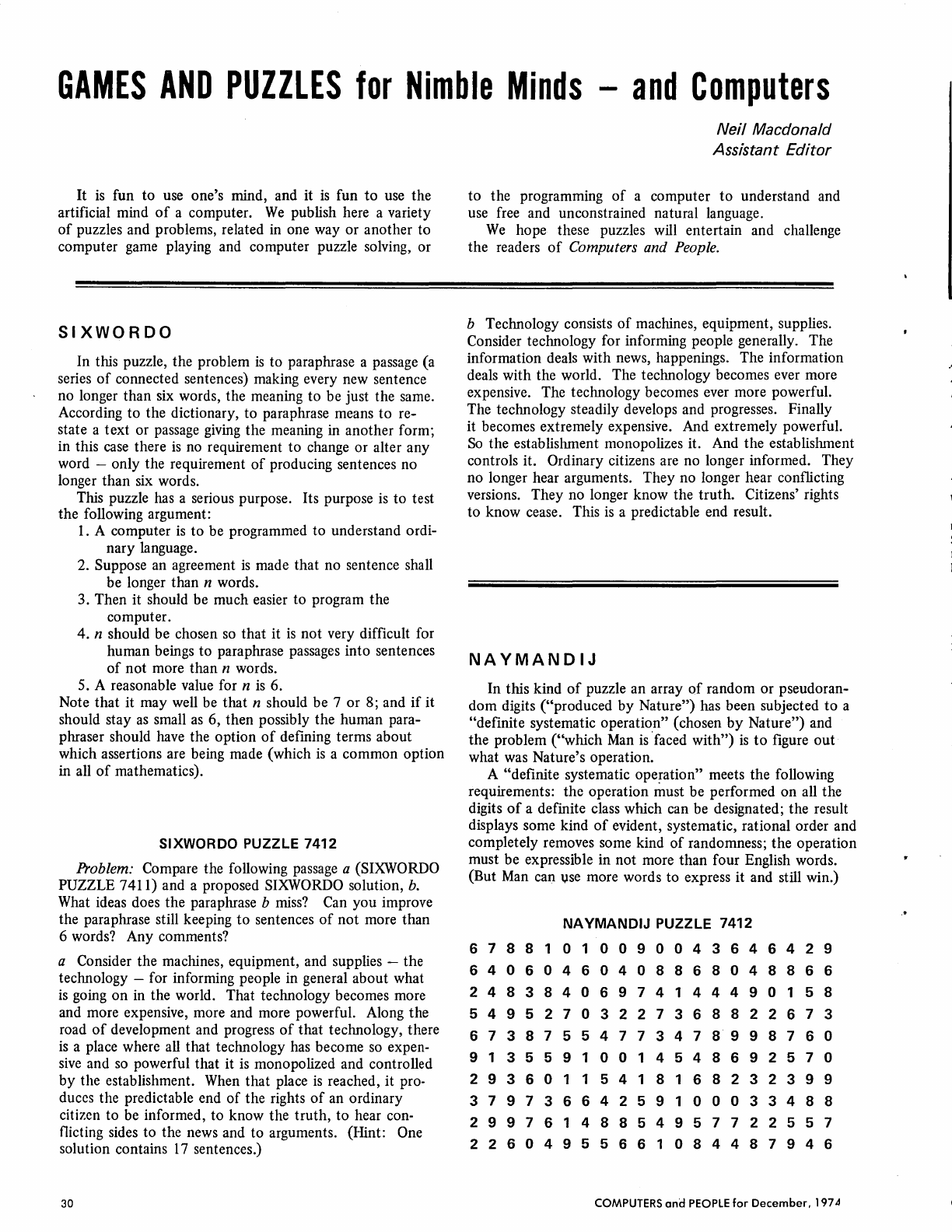
GAMES
AND
PUZZLES
for
Nimble
Minds
and
Computers
It
is
fun to use one's mind, and it
is
fun
to
use the
artificial mind
of
a computer.
We
publish here a variety
of
puzzles and problems, related in one way or another to
computer game playing and computer puzzle solving, or
SIXWORDO
In this puzzle, the problem
is
to paraphrase a passage (a
series
of
connected sentences) making every new sentence
no longer than six words, the meaning to be just the same.
According
to
the dictionary,
to
paraphrase means
to
re-
state a text or passage
giving
the meaning in another form;
in this case there
is
no requirement
to
change or alter any
word -only the requirement
of
producing sentences no
longer than six words.
This puzzle has a serious purpose. Its purpose
is
to
test
the following argument:
1.
A computer
is
to
be programmed
to
understand ordi-
nary language.
2. Suppose an agreement
is
made that no sentence shall
be longer than n words.
3. Then it should be much easier to program the
computer.
4.
n should be chosen
so
that it
is
not very difficult for
human beings
to
paraphrase passages into sentences
of
not more than n words.
5. A reasonable value for n
is
6.
Note that it may well be that n should be 7 or 8; and
if
it
should stay
as
small
as
6, then possibly the human para-
phraser should have the option
of
defining terms about
which assertions are being made (which
is
a common option
in all
of
mathematics).
SIXWORDO PUZZLE 7412
Problem: Compare the following passage a (SIXWORDO
PUZZLE 7411) and a proposed SIXWORDO solution,
b.
What ideas does the paraphrase b miss? Can you improve
the paraphrase still keeping
to
sentences
of
not
more than
6 words? Any comments?
a Consider the machines, equipment, and supplies -the
technology -for informing people in general about what
is
going
on
in the world. That technology becomes more
and more expensive, more and more powerful. Along the
road
of
development and progress
of
that technology, there
is
a place where all that technology has become
so
expen-
sive
and
so
powerful that it
is
monopolized and controlled
by the establishment. When that place
is
reached, it pro-
duces the predictable end
of
the rights
of
an ordinary
citizen to be informed,
to
know the truth,
to
hear con-
flicting sides to the news and to arguments. (Hint: One
solution contains
17
sentences.)
30
Neil Macdonald
Assistant Editor
to
the programming
of
a computer
to
understand and
use free and unconstrained natural language.
We
hope these puzzles will entertain and challenge
the readers
of
Computers and People.
b Technology consists
of
machines, equipment, supplies.
Consider technology for informing people generally. The
information deals with news, happenings. The information
deals with the world. The technology becomes ever more
expensive. The technology becomes ever more powerful.
The technology steadily develops and progresses. Finally
it becomes extremely expensive. And extremely powerful.
So
the establishment monopolizes it. And the establishment
controls it. Ordinary citizens are no longer informed. They
no longer hear arguments. They no longer hear conflicting
versions. They no longer know the truth. Citizens' rights
to know cease. This
is
a predictable end result.
NAYMANDIJ
In this kind
of
puzzle an array
of
random or pseudoran-
dom digits ("produced by Nature") has been subjected
to
a
"definite systematic operation" (chosen
by
Nature") and
the problem ("which
Man
is
'faced with")
is
to
figure
out
what was Nature's operation.
A "definite systematic operation" meets the following
requirements: the operation must be performed on all the
digits
of
a definite class which can be designated; the result
displays some kind
of
evident, systematic, rational order and
completely removes some kind
of
randomness; the operation
must be expressible in not more than four English words.
(But
Man
can
l,lse
more words to express it and still win.)
NAYMANDIJ PUZZLE 7412
6 7 8 8 1 0 1 0 0 9 0 0 4
364
6 4 2 9
640
604
604
0 8 8 6
804
886
6
2 4 8
384
0 6 9
741
444
901
5 8
5 4 9 5
270
3 2 2 7 3 6 8 8 2
267
3
6 7 3 8 7
554
7 7
347
899
8 7 6 0
9 1 3 5 5 9 1
001
454
869
2 5 7 0
2 9 3
601
154
1 8 1 6
823
2 3 9 9
3 7 9 7 3
664
259
1
000
334
8 8
2 9 9 7 6 1 4 8
854
9 5 7 7
225
5 7
2 2 6 0
495
566
1 0 8
448
794
6
COMPUTERS
and
PEOPLE
for
December,
1974
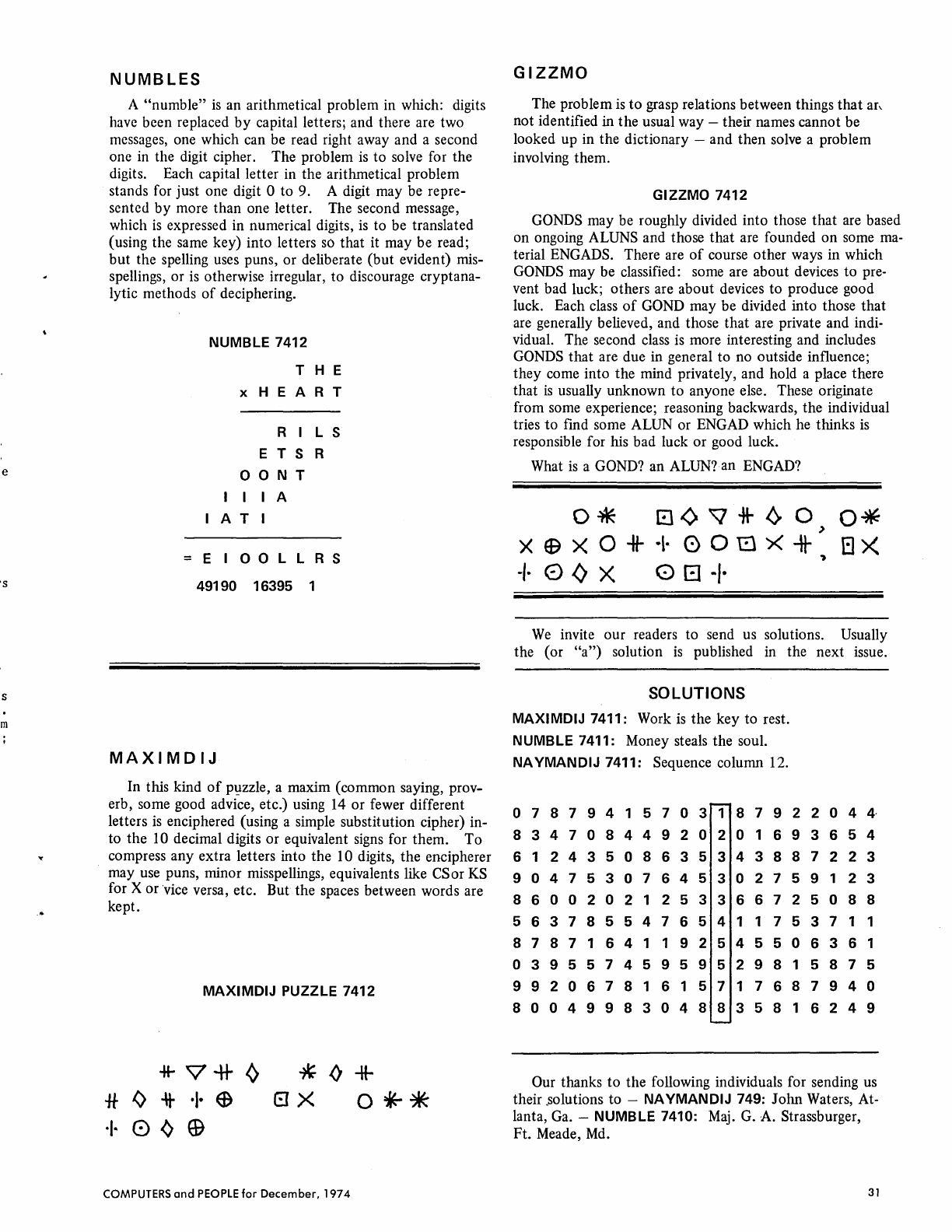
e
'S
.S
1m
:;
NUMBLES
A "numble"
is
an arithmetical problem in which: digits
have been replaced
by
capitallettersj and there are two
messages, one which can be read right away and a second
one
in
the digit cipher. The problem
is
to solve for the
digits. Each capital letter in the arithmetical problem
stands for just one digit 0 to 9. A digit may be repre-
sented by more than one letter. The second message,
which
is
expressed in numerical digits,
is
to be translated
(using the same key) into letters
sO
that it may be read;
but the spelling uses puns, or deliberate (but evident) mis-
spellings, or is otherwise irregular,
to
discourage cryptana-
lytic methods
of
deciphering.
NUMBLE 7412
T H E
x H E A R T
R I L S
E T S R
OONT
A
ATI
= E
100
L L R S
49190 16395 1
MAXIMDIJ
In this kind
of
p~zzle,
a maxim (common saying, prov-
erb, some good advice, etc.) using 14 or fewer different
letters
is
enciphered (using a simple substitution cipher) in-
to the 10 decimal digits or equivalent signs for them. To
compress any extra letters into the 10 digits, the encipherer
may
use
puns, minor misspellings, equivalents like CSor
KS
for X or
'vice
versa, etc.
But
the spaces between words are
kept.
MAXIMDIJ
PUZZLE 7412
*7*1:j
#1:)*+$
+0Q6)
~(j*
ax
o*'*
COMPUTERS
and
PEOPLE
for
December.
1974
GIZZMO
The problem
is
to
grasp relations between things
that
ar~
not identified in the usual way -their names cannot be
looked up in the dictionary -and then solve a problem
involving them.
GIZZMO 7412
GONDS may be roughly divided into those that are based
on ongoing ALUNS and those that are founded
on
some ma-
terial ENGADS. There are
of
course other ways in which
GONDS
may be classified: some are about devices
to
pre-
vent bad luck; others are about devices
to
produce good
luck. Each class
of
GOND may be divided into those that
are generally believed, and those that are private and indi-
vidual. The second class
is
more interesting and includes
GONDS
that are due in general to no outside influence;
they come into the mind privately, and hold a place there
that
is
usually unknown
to
anyone else. These originate
from some experience; reasoning backwards, the individual
tries
to
find some ALUN or ENGAD which he thinks
is
responsible for his bad luck or good luck.
What
is
a GOND? an ALUN?an ENGAD?
0* 8 <) ";] *
t.>
0 >
0*
X e X 0 if-
·l-
008)(*
EX
,
-,.
0¢X
<:)
EI
-I-
We
invite our readers to send us solutions. Usually
the (or
"a")
solution
is
published in the next issue.
SOLUTIONS
MAXIMDIJ
7411: Work
is
the key
to
rest.
NUMBLE 7411: Money steals the soul.
NAYMANDIJ 7411: Sequence column 12.
0 7 8 7 9 4 1 5 7 0 3 1 8 7 9 2 2 0 4
4·
8 3 4 7 0 8 4 4 9 2 0 2 0 1 6 9 3 6 5 4
6 1 2 4 3 5 0 8 6 3 5 3 4 3 8 8 7 2 2 3
9 0 4 7 5 3 0 7 6 4 5 3 0 2 7 5 9 1 2 3
8 6 0 0 2 0 2 1 2 5 3 3 6 6 7 2 5 0 8 8
5 6 3 7 8 5 5 4 7 6 5 4 1 1 7 5 3 7 1 1
8 7 8 7 1 6 4 1 1 9 2 5 4 5 5 0 6 3 6 1
0 3 9 5 5 7 4 5 9 5 9 5 2 9 8 1 5 8 7 5
9 9 2 0 6 7 8 1 6 1 5 7 1 7 6 8 7 9 4 0
8 0 0 4 9 9 8 3 0 4 8 8 3 5 8 1 6 2 4 9
Our thanks
to
the following individuals for sending
us
their .solutions to -NA YMANDIJ 749: John Waters, At-
lanta, Ga. -NUMBLE 7410: Maj.
G.
A. Strassburger,
Ft. Meade,
Md.
31

Computing
and
Data
Processing
Newsletter
COMPUTER GIVES NEW MEXICO MUSEUM
FULL
ACCESS TO ITS
MINERAL
COLLECTION
Jack
B.
Pearce
New Mexico Institute
of
Mining and Technology
Socorro,
NM
87801
The
prospector
of
years
past
learned
to
identify
rocks
and
minerals
by
sight
as
he probed
for
gold
and
silver
in
the
rocky
deserts
of
the
Southwest.
Today
these
same
minerals
are
on
display
in
a
mu-
seum
in
Socorro,
New
Mexico -and a computer
iden-
tifies
each one
by
X-ray
analysis.
In
addition,
the
computer keeps a complete
record
of
each
of
the
9,200
sepcimens
at
the
New
Mexico
Bureau
of
Mines
Mineralogical
Museum.
The
collec-
tion,
while
emphasizing
southwestern
minerals,
also
displays
other
geological
and
mineral
specimens
from around
the
world.
--
Halite,
crystallized
on
this
bush from
Cal-
ifornia's
Salton
Sea,
gets
a
careful
dusting
from
Charles
Grigsby,
assistant
curator
of
the
New
Mexico Bureau
of
Mines
Mineralogical
Museum.
The
museum
was
begun
in
the
early
1900's.
It
was
maintained
by
the
Institute
of
Mining and Technology
until
1964,
when
it
was
turned
over
to
the
Bureau
of
Mines.
"Much
of
the
material
had
never
been
classi-
fied,"
explained
Dr.
Jacques
Renault,
a
geologist
who
also
teaches
at
the
New
Mexico
Institute
of
Min-
ing
and Technology.
"Some
of
it
was
in
cardboard
boxes and
desk
drawers.
Several
people
tackled
the
job,
but
it
was
an
immense
task.
"Finally
we
decided
a computer
could
handle
it
better
than
any team
of
individuals
possibly
could
because
of
the
tremendous amount
of
statistical
work
involved.
So
in
1969
we
began working
up
a computer
file
that
recorded
various
information
about each
specimen."
Mineralogists
punched computer
cards
that
cata-
logued
the
various
minerals
in
each
item,
other
ge-
ological
details,
its
donor
or
source,
when
acquired
and
its
location
in
the
museum.
Later
they
began
using
the
computer
to
analyze
the
mineral
content
of
each sample.
32
"X-ray
analysis
enables
us
to
identify
any un-
known
minerals
or
chemical
compositions
in
the
spe-
cimen, as
well
as any
crystalline
structure,"
Dr.
Renault
said.
"It's
very
much
like
a
fingerprint."
--
This
delicate
mineral
specimen
containing
goethite
and
psilomelane
was
found
in
Socorro,
N.M.
It
and
9,200
other
samples from around
the
world have been
catalogued
and X-ray
an-
alyzed
by
computer.
Every
mineral
diffracts
X-rays
in
a
characteris-
tic
pattern
because
of
the
atomic
spacing
in
the
crystal.
It
is
relatively
simple
to
determine
the
diffraction
patterns
for
all
minerals
commonly
found
in
the
Southwest and reduce
these
data
to
mathematical
tables.
Then,
by
comparing
the
results
of
any
diffraction
test
with
these
standard
tables,
experts
can
identify
the
minerals
present
in
the
sample.
"As
a
result
we
have
everything
at
our
finger-
tips,"
Dr. RenaUlt
said.
"When
we
want a
list
of
every
sample
of
--
for
instance
--
cerussite
in
the
museum,
we
can
get
it
back from
the
computer
in
just
COMPUTERS
and
PEOPLE
for
December,
1974

'ion
-
.,
a
few
seconds.
Equally
important,
we
can
find
it
immediately because
the
printout
gives
each
sample's
exact
location."
Similar
speedy computer
search
techniques
can
turn
up
all
minerals
from any
geographic
area
or
from
anyone
donor.
The
computer
is
an
IBM
Sys-
tem/360-44.
"Research
is
the
reason
for
our
existence,"
Dr.
Renault
said.
"The computer
helps
make
this
museum
a
living
research
facility."
COMPUTER SYSTEM FOR A RACING YACHT
THAT
WON
Bob Palmer
Data General Corporation
Southboro, MA 01772
In
September 1974,
the
winner
of
the
America Cup,
the
yacht
Courageous,
carried
a minicomputer aboard
for
navigational
and
tactical
calculations.
The
computer
was
the
heart
of
a
special
system
devel-
oped and
built
by
Dick McCurdy, a
consultant
to
the
Courageous
Syndicate.
Halsey
Herreshoff,
navigator,
used
the
system
during
the
trials
this
summer
and
during
the
final
four
victories
over
the
Australian
challenger,
Southern
Cross.
After
the
races,
McCurdy
stated:
"Overall,
the
computer system exceeded
my
expec-
tations.
In
spite
of
the
rough
conditions,
the
com-
puter
was
operational
over
eighty
percent
of
the
time.
It
did
everything
we
wanted
it
to,
and
more
it
was
a
great
success.
"The most
important
task
done
by
the
computer
was
to
predict
the
apparent
wind
in
the
next
leg
of
the
race.
This
information
allowed Courageous
to
select
the
right
spinnaker
every
single
time."
The
Navigator,
Herreshoff,
commented:
"The computer
was
a
big
help
to
us.
It
has added
a
new
dimension
to
sailing
by
giving
us
information
never
before
available,
like
the
predictions
of
ap-
parent
wind.
Especially
valuable
was
the
constant
and
rapid
updating
of
information
by
the
computer.
For
instance,
when
there
was
a wind change as
we
approached
the
weather
mark,
we
immediately
knew
what
our
revised
apparent
wind would be
on
the
next
leg.
We
were
able
to
change
our
choice
of
spinnaker
at
the
last
minute,
which
was
a
real
advantage."
The
computer supplements
the
expertise
of
the
skipper
and crew
by
doing
navigation
calculations
that
are
needed
to
obtain
the
best
speed from
the
craft.
There
is
not
time
available
in
a
race
to
do
all
of
the
calculations
manually.
Most
of
the
yacht's
instruments
are
connected
to
the
computer;
they
supply
signals
representing
apparent
wind speed
and
direction,
boat
speed,
heel
angle,
compass
course
and
other
variables.
At
any
time,
the
navigator
can
"ask"
the
computer
to
display
the
true
wind speed and
direction,
which
are
updated
four
times
a second. Because
true
wind
speed and
direction
cannot be measured
directly
on
a moving
vessel
--
they
can
only
be
calculated
from
instrument
readings
-
this
is
an
ideal
computer
task.
Knowing
true
wind speed and
direction
enables
the
navigator
and
tactician
to
make
decisions
on
how
to
race
the
course.
Among
the
other
tasks
of
the
computer
is
the
cal-
culation
of
a
quantity
called
"speed
made
good
to
windward."
This
indicates
actual
forward
progress
COMPUTERS
and
PEOPLE
for
December.
1974
in
a
tacking
situation.
Tacking
is
the
technique
of
sailing
into
the
wind
by
a back and
forth
course,
making
some
forward
progress
each
time.
The
comput-
er
can
calculate
this
forward
progress
from
the
in-
strument
inputs.
The
computer can
also
compare
tacking
patterns
and
help
establish
the
most
effi-
cient
system
of
tacking.
While
these
calculations
may
seem
routine,
the
computer's
location
certainly
is
not.
The
yacht's
cockpit
is
open
to
the
sea
and
air,
and
there
is
no
110-volt
power
available.
There
is
just
enough
room
for
the
11
crewmen
to
move
around.
The
computer
chosen
was
small and
light
and
the
power supply
per-
mitted
an
easy
conversion
to
36-volt
dc
operation.
Three automobile
batteries
would keep
the
system
running
for
10
to
12
hours,
and
they
could
be
re-
charged each
night.
The
computer
was
housed
in
a
suitcase-sized,
weatherproof
metal box
that
hung
beneath
the
cockpit
sole.
The
computer and
the
box weighed
less
than
70
pounds.
The
computer
was
cooled
by
a
battery-
powered
circulation
system, and
coolant
was
bilge
water.
The
computer
was
a
NOVA
1200 computer
sup-
plied
by
Data
General.
Communication between
the
navigator
and
the
com-
puter
system
was
handled
by
a compact
station
mount-
ed
at
the
chart
table
next
to
the
helm. A
32-channel
scheme produced a
four-digit-plus-sign
display.
Manual
inputs
and
commands
were
entered
with
a
touch-
pad;
the
desired
display
is
selected
with
a
series
of
switches.
All
this
takes
but
a
few
seconds,
and
the
calculation
result
appears
almost
immediately.
CAMERAS AND COMPUTERS COMBINE
TO
ANALYZE
ROCKET FLIGHTS
Kent Roberts
New Mexico State University
Box
3548
Las
Cruces,
NM
88001
Rockets
streaking
across
the
skies
at
more
than
four
times
the
speed
of
sound
are
being
studied
every
second
of
the
way
by
scientists
at
the
Physi-
cal
Science
Laboratory,
at
New
Mexico
State
Univ.
Using a computer and
high-speed
cameras,
the
scien-
tists
collect
and
analyze
information
on
rockets,
missiles,
and
other
aircraft
tested
at
White Sands
Missile
Range
near
here.
The
computer
is
used
in
many
areas
where
precise
measurements and
calculations
are
necessary
includ-
ing:
determining
where
to
put
cameras
to
obtain
the
best
filming
angles;
analyzing
measurements from
thousands
of
feet
of
film
taken
during
flights;
and
compiling
reports
on
flight
performance.
"The computer
reports
enable
engineers
to
deter-
mine
if
aircraft
performed
the
way
they
were
de-
signed
to,"
said
Keith
Hennigh,
data
processing
division
manager
of
the
laboratory.
"If
the
flight
didn't
conform
to
plans
or
if
a
malfunction
occurred,
the
computer
analysis
points
out
what went wrong.
Modifications
and
design
changes
are
made
accordingly."
Using
information
such
as
estimated
speed and
intended
path
of
the
aircraft,
the
computer
calcu-
lates
ideal
camera
locations.
As
many
as
20 cam-
eras,
some
capable
of
taking
5,000
frames a second,
can be used
during
tests.
Following
the
flight,
the
film
is
processed
and frames
not
related
to
measurement
data
are
edited
out.
33

Film
readers
connected
to
a
projector
measure
the
position
of
the
aircraft
on
each
film
frame.
Reference
points
such as surveyed
targets,
poles
or
stars
are
used
to
determine
camera
orientation
and
to
calibrate
the
camera
lens.
When
no
reference
points
are
in
the
field
of
view, cameras
with
pre-
calibrated
lenses
are
used.
As
each frame
is
measured,
information
enters
a
Serial
Encoded Data Exchange
(SENDEX),
a
device
de-
signed
and
developed
by
PSL
employees
to
convert
measurements
into
computer
readable
form.
A second computer
arranges
film
frames from each
camera
in
their
proper
sequence.
It
is
also
pro-
grammed
to
analyze
trends
in
the
measurement
read-
ings
before
it
transfers
the
information
to
the
first
computer.
The
computer combines
film
measurements
with
in-
formation
collected
by
electronic
equipment aboard
the
aircraft
to
provide
a
highly
detailed
analysis
of
a
flight.
--
Flight
patterns
of
rockets,
such
as
the
one
being
launched
above,
are
being
studied
by
sci-
entists
at
New
Mexico
State
University
using
cameras and a computer.
The
system
is
programmed
to
take
into
considera-
tion
any
factors
which
may
affect
the
flight
in-
cluding
wind and
atmospheric
conditions,
and
en-
ables
engineers
to
study
and
analyze
the
flight
from
the
instant
it
begins
to
completion.
The
com-
puter
report
provides
information
on
a
variety
of
34
flight
parameters
including
position,
velocity,
ac-
celeration,
object
attitude,
roll
rate,
and
other
requested
information.
An
entire
flight
mission
can be
analyzed
in
24
hours
using
the
computer.
"Before
the
computer system
was
installed,
many
of
our
calculations
would have
taken
weeks, "
Mr.
Hennigh
said.
The
laboratory
employs
almost
200
New
Mexico
State
students
in
its
various
~rojects.
Many
of
them
are
involved
in
a
variety
of
highly
skilled
jobs
as
film
readers,
computer
operators,
program-
mers, and keypunch
operators.
The
Physical
Science
Laboratory
is
a
non-profit
organization
providing
support
for
military
and
federal
agencies.
The
two
computers
are
an
IBM
System/370,
Model
135, and an
IBM
System
7.
Antley
-Continued
from
page
25
2.
Slack
W.V.,
VanCura L.
J.:
Computer-based
Patient
Interviewi
ng.
Post-graduate
Med
43
:68-76, 115-120,
1968
3.
Grossman
J.
M.,
Barnett
G.
0.,
McGuire
M.
T.,
et
al:
Evaluation
of
computer-acquired
patient
his-
tories.
JAMA
215:1286-1291, 1971
4.
Mayne
J.
G.,
Weksel
W.,
Shol
tz
P.
N.: Toward
automating
the
medi
cal
hi
story.
Mayo
Cli
n Proc 43:
1-25,
1968
5.
Kanner
I.F.:
The
programmed
physical
examination
wi
th
orwi
thout
a computer.
JAMA
215:1281-1291,1971
6.
Diebold
J.:
"Man
and
the
Computer,"
Avon
Books,
New
York
City,
p.
161-2,
1969
7. Cadden J.
J.,:
Flach
F.
F.,
Blakelee
S.
and
Carl
ton
R.:
Growth
in
medical
students
through
group
process.
Amer
J.
Psychiat
126:862-868, 1969
8.
Kubler-Ross
E.:
"On
Death and Dying," The
Mac-
Millan
Company,
New
York
City,
1969
U nsettl i ng, Disturbi ng, Critica I
Compu
ters
and
People
(formerly
Computers and
Automation),
establi
shed 1951 and
therefore
the
oldest
magazine
in
the
field
of
computers and
data
processing,
believes
that
the
profession.of
infor-
mation
engineer
includes
not
only
competence
in
handling
information
using
computers and
other
means,
but
also
a broad
responsibiiity,
in
a
pro-
fessional
and
engineering
sense,
for:
The
reliability
and
social
significance
of
pertinent
input
data;
The
social
value
and
truth
of
the
output
results.
In
the
same
way, a
bridge
engineer
takes
a
pro-
fessional
responsibi
li
ty
for
the
reliabi
li
ty
and
significance
of
the
data
he
uses,
and
the
safety
and
efficiency
of
the
bridge
he
builds,
for
human
beings
to
risk
their
lives
on.
Accordingly,
Computers and
People
publishes
from
time
to
time
articles
and
other
information
related
to
socially
useful
input
and
output
of
data
systems
in
a broad
sense.
To
this
end
we
seek
to
publish
what
is
unsettling,
disturbing,
critical
--
but
producti
ve
of
thought
and an improved and
safer
"house"
for
all
humanity, an
earth
in
which our
children
and
later
generations
may
have a
future,
instead
of
facing
extinction.
The
professional
information
engineer
needs
to
relate
his
engineering
to
the
most
important
and
most
serious
problems
in
the
world
today:
war,
nuclear
weapons,
pollution,
the
population
explo-
sion,
and
many
more.
COMPUTERS
and
PEOPLE
for
December,
1974

A fabulous
gift:
18
illustrations
in
pen
and
ink
"RIDE
THE
EAST
WIND:
Parables
of
Yesterday
and
Today"
by
Edmund
C.
Berkeley,
Author
and
Anthologist
Published
by
Quadrangle/The New
York
Times
Book Co., 1974, 224 pp, $6.95
Table of Contents
Part 1.
The
Condition
of
Man
Pandora and the Mysterious Box / H.
A.
Guerber
The Garden
of
Parad
ise
* / Hans Christian Andersen
*to
which
the
King's son was
transported
by
the
East Wind
The
History
of
the
Doasyoulikes / Charles Kingsley
The Locksmith and the Stranger / Edmund
C.
Berkeley (B)
The Elephant and
the
Donkey / James Reston
Where
that
Superhighway Runs, There
Used
to
be
a
Cornfield / Robert Redfield
The Fire Squirrels / B
Part 2.
On
Flattery
and
Persuasion
The
Crow
and the
Fox
/ Jean
de
La
Fontaine
The
Visitor
who
Got
a
Lot
for
Three Dollars /
George Ade
The Cuckoo and
the
Eagle / Ivan
A.
Kriloff
The Wind and
the
Sun / Aesop
The Lion in Love / Aesop
The
Crow
and
the
Mussel/Aesop,
B
The
Two
Raccoons and the
Button
/ B
Part
3.
On
Perseverance and Resourcefulness
The Crow and the Pitcher / Aesop
Robert Bruce and the Spider / Sir Walter Scott
Hannibal Mouse and
the
Other
End
of
the
World / B
The Fly, the Spider, and
the
Hornet / B
Part 4. Behavior -Moral and Otherwise
A Small Wharf
of
Stones / Benjamin Franklin
The Three Bricklayers / Anonymous, B
The Good Samaritan / St. Luke
Much Obliged, Dear Lord /
Fulton
Oursler
The Fisherman,
the
Farmer, and
the
Peddler / B
Part
5.
The
Problem
of
Truth
On Being a Reasonable Creature / Benjamin
Franklin
The
Monkey
and the Spectacles / Ivan
A.
Kriloff
The Golden Trumpets
of
Yap Yap / Mike Quin
The Barrels and
the
Pittsburgh Manufacturer / B
The
Empty
Column / William J. Wiswesser
The Differences in
Two
Strains
of
Corn / Edgar Anderson
The Six Blind Men
of
Nepal / B
The Sighting
of
a Whale / B
The Stars and the Young Rabbit / B
The Ocean
of
Truth
/ Sir Isaac Newton
Part 6. On Common
Sense
The Lark and her Young Ones / Aesop
The Bear and the Young Dog / B
COMPUTERS
and
PEOPLE
for
December,
1974
The
Fox
of
Mt.
Etna and
the
Grapes
Once
there
was a
Fox
who
lived
on
the
lower slopes
of
Mt.
Etna,
the
great volcano in Sicily. These slopes are ex-
tremely
fertile;
the
grapes
that
grow
there
may well
be
the
most delicious in
the
world; and
of
all
the
farmers
there,
Farmer Mario was
probably
the
best.
And
this
Fox
longed
and
longed
for
some
of
Farmer
Mario's grapes.
But
they
grew very high
on
arbors,
and
all
the
arbors
were
inside a
vineyard
with
high walls,
and
the
Fox
had a
problem.
Of
course,
the
Fox
of
Mt
Etna
had
utterly
no use
for
his fam-
ous
ancestor,
who
leaping
for
grapes
that
he
could
not
reach,
called
them
sour,
and
went
away.
The
Fox
decided
that
what
he needed was Engineering
Technology.
So
he
went
to
a retired Engineer
who
lived
on
the
slopes
of
Mt.
Etna,
because he liked
the
balmy
climate
and
the
view
of
the
Mediterranean
Sea
and
the
excitement
of
watching
his
instruments
that
measured
the
degree
of
sleep-
ing
or
waking
of
Mt.
Etna.
The
Fox
put
his
problem
be-
fore
the
Engineer.
The Bear and the Young Calf / B
The Bear and the Young Beaver / B
The
Wasps
and the Honey Pot / Sir Roger l'Estrange
The Six-Day
War
and
the
Gulf
of
Dong / B
The Deceived
Eagle
/ James Northcote
Missile
Alarm
from
Grunelandt / B
The National Security
of
Adularia / B
Doomsday in St. Pierre,
Martinique
/ B
Part 7. Problem Solving
The
Wolf
and the Dog
of
Sherwood / Aesop, B
The Three Earthworms / B
The Hippopotamus and
the
Bricks / B
The Cricket
that
Made Music / Jean de
La
Fontaine, B
The
Fox
of
Mt.
Etna and
the
Grapes / B
The Mice
of
Cambridge
in
Council/Aesop,
B
Brer Badger's Old
Motor
Car
that
Wouldn't
Go / B
The First Climbing
of
the
Highest Mountain in
the
World / Sir John
Hunt,
B
The Evening Star and the Princess / B
Notes
Some Collections
of
Parables and Fables
RETURNABLE
IN 10
DAYS
FOR
FULL
REFUND
IF
NOT
SATISFACTORY
(You
can
read
it
all in 10 days -and keep
it
only
if
you
think
it
is
worth
keeping.)
HOW CAN
YOU
LOSE?
- - - - - - -
(may
be
copied
on
any
piece
of
paper)
- - - - - - - - - - .
To:
Berkeley Enterprises, Inc.
815
Washington St., Dept. R
12,
Newtonville,
MA
02160
Please send
me
___
copy(ies)
of
Ride the East Wind:
I enclose
$7.00
per
copy
!includes handling).
Total enclosed
(Prepayment
is
necessary)
My
name
and
address are
attached.
35

II
Q;
~
~
WILL
YOU
HELP?
Yes, you.
It
may come
as
a surprise
that
you'd
be
asked
...
but
as
a reader
of
Computers
and
People
(formerly
Computers
and
Automation)
you are in a unique position
to
help
us.
NAMES
...
people,
institutions,
companies
who
should
be
interested in 1) the computer
industry
and/or
2) seek-
ing
truth
in
information
are very much needed
to
join
you
as
readers
of
Computers
and
People.
Will
you
tell
us who
they
are?
And
perhaps even more,
will
you let
us
use
your
name
in
writing
to
them?
But
with
or
without
your
name (we'll
only
use
it
if
you grant
permission) we need
to
know
those
you
think
might
be
interested in also read ing Computers
and
People.
*
*"
*
*"
reprint
from
cornJ:!,~a~!!n!:~
Science and
the
Advanced Society, by C. P. Snow, Ministry
of
Technology,
London,
England (April 1966)
The
Information
Revolution and the Bill
of
Rights, by
Dr. Jerome
B.
Wiesner, M.LT. (May
1971)
Employment,
Education, and the Industrial
S~stem,
by
Prof.
John
Kenneth
Galbraith, Harvard Umv. (Aug.
1965)
Computers and the Consumer, by Ralph Nader,
Washington, D.C. (Oct. 1970)
Please
give us
their
names and addresses on the
form
below
or
add another sheet
of
paper.
Trim
out
the
card
with
scissors and
drop
it
in
the
mail. We'll gladly
pay
the
postage
to
learn
of
possible new friends. And many
thanks
for
your
help! As a
token
of
our
appreciation
we'll
send
you
our
****Reprint.
P.S.
If
you
like
you
may mail
your
list separately
to:
R.
A.
Sykes, Circulation Mgr.
Computers
and
People
815 Washington Street
Newtonville,
MA
02160
cut
here and
tuck
in
flap
r--------------------------,
I
TO:
R.
A.
Sykes, Circulation Mgr. \
I
I Computers
and
People \
: I suggest
you
send
information
on
Computers
and
People \
\
:
to
...
(attach
list
if
you
like)
\
I \
I
(1)Name_________________________________
\
I \
I
Address______________________
\
I
\~
el
\~
tVl
City
_________
State
______
ZIP____
\~
~,
\~
:;
I
,.
u, \
I (2)
Name'_____________________________________
\
I \
I
Address___________________
\
I \
I
I
City
State
ZIP
____
__
\
I \
:
May
we
use
your
name? 0 YES 0 NO \
\
I Please give
us
your
name
and
address
on
the
form
belo.w
.so
we
can
: send
you
your
****Reprint.
Just
cross
out
the
subscription
request
\
\
\
I -unless
you
also
want
to
enter
your
new
or
renewal
order.
,
---
cut
here
__
_
__
_
____________
Fold
here -
do
not
cut
"""
M
en
Ln
M
e/)
~
M
~
~
~
ci
..J
z·
U Z
I-
0
l-
e/)
l-
e/)
a:
~
0
L1.
a:
III
U
w Z
a..
vi
VI w
e
~
~
a:
a..
en
a:
lJ
w
.~
I-
~
Z
c w
2
::J
>-
OJ OJ
W
:J
{:
...J
c;,
W
0 c
~
a:
OJ
lJ
W
Q.
OJ
en
III
co
>-
1;;
E
en
I
....
0
III
..J
~
>
~
....
a..
~
~
w
OJ
en
U
...J
>-
OJ
..J
C
...J
a..
c.
3:
w
a:
E w
~
<.:J
(/)
VI «
(/)
OJ
I-
w
Cl
en
Z
~
0
Ci.j
a..
c
0
'';:::;
co
w E
0
-I
+-'
::l
c..
c:x:
0
W
"0
0.. c +'"
co
Cl)
Q
Vl
Q,)
10...
~
OJ
+'"
Z
+-'
en
«
::l
Q.
c::
Cf.)
E 0
0 +'"
0:
u
C)
w
c::
l-
t
.J:
en
:::>
CO
0..
~
$:
~
-E
LO
0 -
U
CO
:::J
0
III
c.
0
Z
0
(0
-
N
0
«
~
!E."
.:;;
c::
0
+'"
:1:
Cl)
Z
''0
:]
''0
•
1;
·
~
4l
.~
''0
· c
:1l
YES,
start
my
subscription
to
COMPUTERS
AND
PEOPLE
according
to
the
instructions
checked
below.
One
Year
(including
the
Computer
Directory
and
Buyers'
Guide
--
13
issues)
U.S.
only.
0
$23.50·
One
Year
(excluding
the
Computer
Directory
and
Buyers'
Guide
--
12
issues)
U.S.
only.
0
$11.50
Name:~
_______
~
Title:
___
~_
._~
__
_
Organization:
_______
_
Add
ress:
__________________
.
City:
State:
_________
Zip
Country
if
not
U.S.:
_____
_
Signatu
re: ___
~_
o
Payment
enclosed
o
Renewal
o
Bill
me
o
New
subscription'
To
SPEED
the
processing
of
your
order,
please
check
the
one
best
desuiptor
in
eath
of
the
two
categories below.
(ThIs
InformatIon
\\ ill be used for statist
ita
I
purposes
only.)
BUSINESS
TYPE
Ol-Computer
Manufacturer
02-Aerospace ! Aircraft
Manufacturer
03-other
Manufacturing
04-Raw
Materials
Processing;
(chemical,
primary
metal,
petroleum,
food.
etc.)
OS-Mining
and
Construction
06-Computing &
Consulting
07-Finance,
Insurance,
Pub!',
and
Service
Organizations
OB-Transportation
Companies
09
-Public Utilities
, O-Research
"-Wholesale,
Retail,
Sales,
and
Marketing
Firms
, 2-Educational;
(College,
University,
or
School)
, 3-Government
and
Military
, 4-Libraries
JOB
FUNCTION
I-Technical
Management;
(computer
installation
management,
program
management,
or
engineering
mgmU
2-Computer
Center
Personnel;
(methods
&
procedure
analysts,
and
operators)
J-Programming
Personnel;
(systems,
application &
research
programmers)
4-Professional:
(systems
analysts,
mathematicians,
operations
researc~ers,
and
professors)
5-General
Management
Executives;
(corporate
o!l;cers,
owners,
and
partners)
6-E~gineering
Personnel;
(systems
.
engineers,
research
&
development
engineers)
7-Research
Personnel
a-Students
9-Library
Subscription
10-Subscription
in
Company
Name
Only
aJ I
B I
OJ
I
:J
c;,
I
~
0
0>
OJ
I~
Q.
::J
III
I u
1;;
I
~
I
\,
\'i
If
I,