197512
197512 197512
User Manual: 197512
Open the PDF directly: View PDF ![]() .
.
Page Count: 28
computers
and
people
The
Computer
Glass Box (Part 2)
The
Universal Product Code
Software Should
Be
Patentable
Computer-Assisted Tutorials in College Mathematics
Computers and Society: A Course
at
York University
I
SCIENCE
AND
BUS~NESS
'
December,
1975
Vol.
24, No. 12
formerly Computers
and
Automation
UB~y
USE
ONt y
-
H.
A.
Peelle
-Thomas
V.
Sobczak
-ADAPSO
225
CHRISTMAS
FLOWERS
by
William
Kolomyjec
-
J.
L.
Caldwell
and
Doug/as Polley
-
Larry
J.
Murphy
7 3

"RIDE
THE
EAST
WIND:
Parables
of
Yesterday
and
Today"
by
Edmund
C.
Berkeley,
Author
and Anthologist
The Fly, the Spider, and the Hornet
Once a Fly, a Spider, and a Hornet were trapped inside a
window
.screen
in
an attic. For several hours
they
walked up
and
down, left
and right, here
and
there, all over
the
screen.
They
could
look
through
the
screen
at
the
summer woods, feel
the
summer breezes,
and
smell
the
summer smells;
but
they
could
not
find
any
hole
to
pass through
the
screen
to
the
woods
and
fields so tantalizingly close,
yet
so far
away.
Finally
they
decided
to
hold a conference
on
the
problem of
get-
ting through
the
screen. The Fly spoke first, and said,
"My
Col-
leagues,
....
The Fox
of
Mt. Etna and the Grapes
Once
there
was a Fox
who
lived
on
the
lower slopes of Mt. Etna,
the
great volcano in Sicily. These slopes are extremely fertile;
the
grapes
that
grow
there
may
well be
the
most delicious
in
the
world;
and
of all
the
farmers there, Farmer Mario was probably
the
best.
And this Fox longed and longed for some of Farmer Mario's grapes.
But
they
grew very high on arbors, and all
the
arbors were inside a
vineyard with high walls, and
the
Fox
had a problem. Of course,
the
Fox of Mt. Etna had utterly
no
use for his famous ancestor,
who
leaping for grapes
that
he could not reach, called
them
sour,
and
went
away.
The
Fox decided
that
what
he needed was Engineering
Techno-
logy. So he
went
to
a retired Engineer who lived
on
the
slopes of
Mt.
Etna, because he liked
the
balmy climate and
the
view of
the
Mediterranean Sea
and
the
excitement
of
watching his instruments
that
measured
the
degree of sleeping or waking of
Mt.
Etna.
The
Fox
put
his problem before
the
Engineer
....
The Fire
Squ
irrels
Scene: Two squirrels, a
young
one
named
Quo,
and
an
older
one
named
era-era,
are
sitting
by
a
small
campfire
in
a
field
at
the
edge
of
a wood.
Behind
them
hung
on
a
low
branch
of
a tree are
two
squirrel-size hammocks. Over each
of
the
hammocks
is a
small
can-
opy
that
can be
lowered
to
keep
out
biting
insects.
It
is a pleasant
summer
evening,' the sun
has
just
recently
set,
and
the stars
are
com-
ing
out:--
Quo:
Cra-Cra, you know I
don't
believe
the
old
myths
any
more.
Tell me again how it really happened.
era-era:
Just
this:
we
received
our
chance because
they
dropped
theirs. It
is
as simple as
that.
Quo:
In
other
words,
they
were
the
first animals
to
use tools,
and
we
are
the
second?
era-era:
Yes. There
is
a mode of surviving
in
the
world
....
2
Published
by
Quadrangle/The New
York
Times
Book Co., 1974, 224 pp, $6.95
Missile Alarm
from
Grunelandt
Once upon a time
there
were
two
very large
and
strong
coun-
tries called Bazunia
and
Vossnia. There were
many
great,
impor-
tant,
and powerful leaders
of
Bazunia who carefully cultivated
an
enormous
fear of Vossnia. Over
and
over again these
important
and
powerful leaders of Bazunia would say
to
their fellow
coun-
trymen,
"You
can't
trust
the
Vossnians." And
in
Vossnia
there
was a group of great, important, and powerful leaders
who
pointed
out
what
dangerous military activities
the
Bazunians were carrvinQ
on,
and
how
Vossnia had
to
be militarily strong
to
counteract
them.
The
Bazunian leaders persuaded their
countrymen
to
vote
to
give
them
enormous
sums
of
money
to
construct
something
called
the
Ballistic Missile Early Warning System, and
one
of its
stations was installed
in
a land called Grunelandt far
to
the
north
of Bazunia.
Now of course ballistic missiles with nuclear explosives can fly
any
kind of a path all
around
a spherical world,
and
they
do
not
have
to
fly over
northern
regions. But this kind of reasoning had
no influence
on
the
leaders
of
Bazunia
who
wanted
the
money
for building
BMEWS.
Nor did it have influence
on
their
country-
men,
who
were always busy, trying
to
make
money
-in fact
often
too
busy
to
think
clearly
....
52 parables (including fables, anecdotes, allegories)
23 never published before
27
authors
18 full-page illustrations
330 quotations and maxims
7 Parts: The Condition
of
Man /
On
Flattery and
Persuasion /
On
Perseverance
and
Resourcefulness /
Behavior -Moral and Otherwise / The Problem
of
Truth
/
On
Common
Sense
/ Problem Solving
THE
VALUE
OF
THIS
BOOK TO YOU
CAN
BE
VERY
GREAT
JUDGE
FOR
YOURSELF
AT
NO COST
RETURNABLE IN 10
DAYS
FOR
FULL
REFUND
IF NOT SATISFACTORY
You
can
read
it
all in 10 days -
and
keep
it
only
if
you
think
it
is
worth
keeping.
HOW
CAN YOU LOSE?
- - - - (may be copied
on
any piece
of
paper) - - - - - - -
I
I To: Berkeley Enterprises, Inc.
815
Washington St., S9, Newtonville,
MA
02160
Please send me copy(jes) of Ride the East
Wind:
I enclose
$7.00
per
copy
(includes handling).
Total enclosed
____
_ (Prepayment is necessary)
My
name
and
address are attached.
COMPUTERS and PEOPLE for December,
1975
....
The
6th
cumulative
edition
of
ttWHO'S
WHO
IN
COMPUTERS
AND
DATA
PROCESSING"
is due to
be
published in 1976
•
Send
us
your
order at the special prepublication price
of
$34.50
(Price after publication
will
be
$40.00)
The most essential components in computers and
data processing are PEOPLE -who are they?
what
do
they do? where do they do it?
"Who's Who in Computers and Data Processing" is par-
ticularly useful for:
Personnel managers
Libraries
Conference planners
Directors
of
computer
installations
Suppliers to the
computer
industry
Executive search organizations
Prospective authors
Prospective speakers
...
anyone who needs
to
keep up with the important people
in
the field.
Each computer professional has a capsule biography
detailing: last name; first name and middle initial
(if
any); occupation; year
of
birth; university education
and degrees; year entered the computer field; main
interests; job title; organization and its address; pub·
lications, honors and memberships; home address.
We
are confident
that
you
will find
the
subscription will
repay you
many
times over.
In
fact, one day when this
wealth
of
material gives
you
the
inside track
with
some-
one
important
to
you, you'll find
the
information
PRICELESS: the most essential component in EDP
is
CAPABLE PEOPLE.
COMPUTERS
and PEOPLE
for
December,
1975
"Who's Who in Computers and Data Processing"
is
jointly
published
by
Quadrangle/The New York Times
Book Co. and
"Computers
and People" (Berkeley
Enter-
prises Inc.)
This publication
is
based
on
"never ceasing" data gath-
ering
about
computer professionals carried
out
for more
than 10 years
by
"Computers
and People" (formerly
"Computers
and
Automation").
Our files contain inform-
ation
on
more than 17,000 computer professionals.
r -------(may
be
copied on any piece
of
paper)-
---
'-
- - - - - - -
I WHO'S
WHO
IN
COMPUTERS AND DATA PROCESSING
815
Washington St., Newtonville,
Mass.
02160
YES, please enroll me as a subscriber
to
Who's Who
in
Computers
and
Data Processing as follows:
I enclose $34.50 prepublication price for
the
1976
cumulative "Who's Who" when published.
I
can't
wait for a number of months. Please send
me
the
last cumulative edition, and 3 updating
supplements. I enclose $34.50.
Both. I enclose $69.00.
RETURNABLE
IN
10
DAYS
FOR
FULL
REFUND
IF
NOT
SATISFACTORY
Name
______________________________________
_
Tit
I e
______________________________________
_
Organization
_______________________________
_
Address,
___________________________________
_
City
_______________
State &
Zip
________
_
Your
Signature P.O.
No.
__
_
(if
company
order)
3

4
Vol.
24, No.
12
December, 1975
Editor and Edmund C. Berkeley
Publisher
Assistant to
Judith
P.
Callahan
the Publisher
Assistant
Editors
Art
Editor
Software
Editor
Contributing
Editors
London
Correspondent
Barbara
L.
Chaffee
Neil Macdonald
Grace
C.
Hertlein
Stewart
B. Nelson
John
Bennett
John
W.
Carr III
Grace
C.
Hertlein
Linda Ladd Lovett
Ted
Schoeters
Richard
E.
Sprague
Edward A. Tomeski
Thomas
Land
Advisory
Ed
Burnett
Committee
James
J.
Cryan
Editorial
Offices
Advertising
Contact
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
617-332-5453
The
Publisher
Berkeley Enterprises, Inc.
815
Washington St.
Newtonville,
MA
02160
617-332-5453
"Computers
and
People,"
formerly
"Computers
and
Automation,"
is
published
monthly,
12
issues
per
year,
at
815
Washing-
ton
St.,
Newtonville,
MA
02160,
by
Berkeley
Enterprises,
I
nco
Printed
in
U.S.A.
Second
Class
Postage
paid
at
Boston,
MA,
and
addi-
tional
mailing
points.
Subscription
rates:
United
States,
$11.50
for
one
year,
$22.00
for
two
years.
Canada:
add
$1
a
year;
elsewhere,
add
$6
a
year.
NOTE:
The
above
rates
do
not
include
our
publication
"The
Computer
Directory
and
Buyers'
Guide".
If
you
elect
to
re-
ceive
"The
Computer
Directory
and
Buyers'
Guide,"
please
add
$12.00
per
year
to
yo~r
subscription
rate
in
U.S.
and
Canada.
and
$15.00
elsewhere.
Please
address
mall
to:
Berkeley
Enter-
prises,
Inc.,
815
Washington
St.,
Newton-
ville,
MA
02160.
.
Postmaster:
Please
send
all
forms
3579
to
Berkeley
Enterprises,
Inc.,
815
Washing-
ton
St.,
Newtonville,
MA
02160.
©
Copyright
1975,
by
Berkeley
Enter-
prises,
Inc.
Change
of
address:
If
your
address
changes,
please
send
us
both
your
new
address
and
your
old
address
(as
it
ap-
pears
on
the
magazine
address
imprint),
and
allow
three
weeks
for
the
change
to
be
made.
computers
and
people
formerly Computers
and
Automation
Computer-Readable Marking and Consumers
7
The
Universal
Product
Code:
An
Introduction
to
What
[A]
It Means
for
Consumers
by
Thomas
V.
Sobczak,
Ph.D., Long Island City,
NY
11101
What
the
new
code
marking
on
grocery
store
pro-
ducts
means
and
how
it
is
likely
to
affect
customers,
who
will no longer have readable prices
marked
on
the
products.
The Computer Industry
14
Software
Should
Be
Patentable
by
ADAPSO (Association
of
Data Processing Services/
Software
Industry
Association), Philadelphia,
PA
A vigorous
argument
full
of
cogent
reasons
why
computer
programs
should
be
patentable.
10
Images
and
Reality
in
the
Computer
Field - A
Discussion
by
the
Editor
and
Jack
Biddle, President,
Computer
Industry
Association, Rosslyn, Va.
Some
of
the
things
that
I
BM
appears
to
do
and
actually
does -in advertising,
standards
setting,
entry
into
the
computer
peripherals
market,
and
so
on.
Computers and Education
22
Computer-Assisted
Tutorials
in College Mathematics
by
J.
L.
Caldwell, Dept.
of
Mathematics, University
of
Wisconsin- River Falls, River Falls, WI,
and
Douglas
Polley, Dept.
of
Mathematics, University
of
Minnesota,
Minneapolis,
MN
How
to
apply
a
computer
in
a
way
that
spots
the
plausible mistakes
that
students
make,
and
then
pro-
vides specific
instruction
that
removes
that
class
of
mistake.
[A]
[F]
[A]
17
The
Computer
"Glass
Box":
Teaching
with
APL
[A]
(Iverson's
"A
Programming Language") -
Part
II
by
Howard.A. Peelle, Director, Instructional Applica-
tions
of
Computers,
University
of
Massachusetts,
Amherst,
Mass.
A black
box
that
you
can see
into
and
can see
how
it
works
becomes
a "glass
box";
and
this
article
describes
how
a
true
innovator
in
computer
education
is
making
algorithms
and
programming
transparent
to
his
students.
26
Promoting
the
Use
of
a
Computer
in
Teaching
[N]
by
News Service,
The
University
of
Iowa, Iowa City,
IA
COMPUTERS
and
PEOPLE
for
December,
1975
"',

. "
The magazine
of
the
design, applications, and implications
of
information processing systems -and the pursuit
of
truth in
input,
output,
and processing, for
the
benefit
of
people.
Computer Graphics and
Art
10
"Computer
Graphics
and
Art"
-
Open
Letter
by
Grace
C.
Hertlein,
Editor
The
first issue of
this
new
quarterly
is
expected
to
be published in February,
1976;
and
who
are
the
contributing
editors
and
advisory board.
28
"Computer
Graphics
and
Art"
Announcement
Computer Applications
24
Computer
"Scenarios"
for
the
Application
of
Pesticides
Before
They
Are
Applied
by
Robert
Silber, Michigan
State
University, East
Lansing,
MI
24
Computer
Monitors Prescriptions
and
Helps Prevent
Adverse Drug
Reactions
by
Ken F leming,
Group
Health Cooperative
of
Puget
Sound,
Seattle,
WA
25
Minicomputer
Helps
Cut
University's Electric Bills
by
John
Kane,
Hewlett
Packard, Palo Alto, CA
Computers
and
Human Reiatiol1s
21
Computers
and
People: Case 1 -
"Stuart
University"
by
Dr. Edward A.
Tomeski,
Contributing
Editor,
"Computers
and
People",
Fordham
University,
Bronx,
NY
How
should
"Stuart
University",
with
given condi-
tions
and
data,
solve a set
of
problems
about
the
use
and
applications
of
its
computer?
Computers and Society
[F]
[F]
[N]
[N]
[N]
[A]
11
Computers
and
Society:
A Course
at
York
University [A]
by
Larry J. Murphy,
Atkinson
College,
York
University,
Downsview,
Ontario,
Canada
The
philosophy,
the
course
outlines,
and
the
referen-
ces
for
a successful
course
in
computers
and
society
taught
for
seven years
in
a Canadian university.
Computers and the Understanding
of
Ordinary Language
6
The
Potential
Understanding
of
Words
by
a
Computer
by
Edmund
C.
Berkeley, Editor
How
computers
may
and
do
understand
words,
and
where
such
understanding
may
lead
in
the
future.
Computers, Puzzles, and Games
[E]
27
Games
and
Puzzles
for
Nimble Minds -
and
Computers
[C]
by
Neil Macdonald, Assistant
Editor
NAYMANDIJ - A
systematic
pattern
among
randomness?
NUMBLES -Deciphering
unknown
digits
from
arithmetical
relations.
MAXIMDIJ -Guessing a
maxim
expressed
in
digits.
COMPUTERS
and
PEOPLE
for
December,
1975
Front Cover Picture
"225
Christmas
Flowers"
is
by
William Kolomyjec,
Instructor
in
the
College
of
Engineering, Michigan
State
University, East Lansing, Michi-
gan. It was drawn
on
a
Ca
IComp
plotter
driven
by
an
IBM
1800,
at
the
computer
research facility
of
the
College
of
Engineering.
Announcements
"Who's
Who
in
Computers
and
Data Processing":
3 Notice
13
Entry
Form
"Ride
the
East Wind:
Parables
of
Yesterday
and
Today":
2 Notice
Statement
of
Circulation
and
Ownership:
26
Notice
"The
Computer
Directory
and
Buyers'
Guide",
21
st
annual
edition,
1975:
Should be
off
press
in
December,
1975
-
the
delay
is
regretted.
Key
[A] Article
[C]
Monthly
Column
[E] Editorial
[F]
Forum
[N] Newsletter
[R] Reference
NOTICE
*0
ON
YOUR
ADDRESS
IMPRINT
MEANS
THAT
YOUR
SUBSCRIP-
TION
INCLUDES
THE COMPUTER
DIRECTORY.
*N
MEANS
THAT
YOUR
PRESENT SUBSCRIPTION
DOES
NOT
INCLUDE
THE COM-
PUTER
DIRECTORY.
5

EDITORIAL
The
Potential
Understanding
of
Words
by
a
Computer
There
is
no
doubt
that
a computer can
understand
words
--
especially
if
we
stipulate
as
conditions
"some words" and "some
contexts".
If
I
type
into
a computer
with
an
appropriate
program
the
five-
lettered
word
"three",
the
computer can
translate
that
both
into
the
more customary "3" and
the
ma-
chine
language
for
3, and
it
can respond
appropriately,
as
for
example, by doing something
three
times,
thus
demonstrating
at
least
some
understanding.
Evidence
of
successful
communication
js
evidence
of
under-
standi
ng.
When
a computer program
displays
on
a
screen
"Do
you want
to
make
any
correction?
(Yes, No)" and you
then
type
in
"No",
the
computer
understands:
it
now
accepts
data
previously
labeled
"Tentative",
the
item
of
knowledge
that
you do
not
want
to
make
any
correction;
and
the
computer
proceeds
with
the
next
step
of
its
operations.
There
is
no
doubt
that
you can
play
the
game
of
Twenty
Questions
with
a computer
if
it
has an
ap-
propriate
program
inside
of
it,
to
respond
to
the
"Yes"
or
"No" answers
that
you
give
it.
For
example,
you can say
to
a computer
that
is
appropriately
pro-
grammed,
"I
am
thinking
of
a number
--
can you
guess
it?"
The
computer can
then
say,
"Is
it
less
than
a
million?";
and
as
soon
as
you
are
committed
to
ans-
wering "Yes"
or
"No"
to
appropriate
questions
that
will
pin
the
number down,
the
computer has
won
the
game.
If
you
tell
a computer "3
BUZZ
2
BANG
6" and "4
BUZZ
8
BANG
32", a computer
with
an
appropriate
pro-
gram can
promptly
guess
that
BUZZ
stands
for
TIMES
and
BANG
stands
for
EQUALS.
Suppose
you
want
to
edit
a computer program
using
a
certain
common
type
of
on-line
editor,
and
14
is
the
line
number
of
the
line
that
needs
correction.
You
can
type
14L,
for
example,
standing
for
"line
14,
display",
and
line
14
is
displayed
in
front
of
you. Then
you
type
14C.
standing
for
"line
14,
change";
the
computer
shifts
from
command
mode
into
text
mode;
you
retype
the
line
with
corrections:
and
when
you
press
the
appropriate
keys.
the
compu-
ter
returns
from
text
mode
to
command
mode. Then
if
you
type
14L
once more,
the
line
will
be
display-
ed
again
in
front
of
you. and you can
satisfy
your-
self
that
the
line
as
retyped
is
correct.
(If
not
correct,
repeat
the
process
once
more.)
More
and
more
and more,
the
computer
appropriately
programmed
will
understand
words
in
contexts;
and
eventually
active.
purposeful.
and broad
conversa-
tion
with
the
computer
will
take
place.
In
several
6
contexts
this
facility
is
already
arriving:
Diagnosis
of
disease,
by
conversational
inter-
action
between a
doctor
and
the
computer
Taking
of
the
medical
history
of
a
patient,
by
conversational
interaction
between a
pa-
tient
and
the
computer;
Learning
of
a
subject,
by
conversational
in-
teraction
between a
student
and a computer
program, as
in
computer-assisted
instruction
or
computer-m~naged
instruction.
In
this
issue,
we
publish
one
more
article
along
this
road
to
a
land
of
riches:
"Computer-Assisted
Tutorials
in
College
Mathematics"
by
J.
L. Caldwell
and Douglas
Polley.
The
authors
explore
typical
student
mistakes
in
solving
mathematical
problems,
diagnose
the
mistake.
and
then
help
the
student
correct
precisely
the
mistake
which
he
has made.
We
can even imagine a time
when
one
of
the
most
interesting
and
congenial
persons
you
can
talk
to
is
~n
appropriately
programmed computer.
It
will
know
what you want
to
know.
It
will
never
be
boring.
It
likes
questions.
It
is
unfailingly
polite,
pa-
tient,
sympathetic.
courteous,
friendly,
and
tact·
ful;
it
is
programmed
to
be
gently
encouraging.
If
the
computer
is
not
quite
sure
what
you
mean,
it
will
ask
questions
until
it
"knows" what
you
mean.
If
you
say
"Don't
overload
my
mind
by
telling
me
more
than
I can remember,"
then
its
replies
to
you
will
be condensed, and convey
only
the
most impor-
tant
facts.
It
might even
say
"If
you
know
these
5
things
about
the
Bering Sea,
then
you
know
enough
to
begin
with,"
or
"If
you
know
these
8
things
about
the
Russian
conquest
of
the
Caucasus
in
the
1800's,
then
you
know
more
than
10,000
people
taken
at
ran-
dom
know."
The
computer
technology
and
the
programming
technology
all
exist.
The
selection
of
knowledge to
be
stored
in
the
computer
memory
is
a
vast
field
for
research
and development
--
and
this
field
will
it
is
hoped be
cultivated
well
in
the
next twenty
years.
Edmund
C.
Berkeley
Editor
COMPUTERS and PEOPLE
for
December, 1975
..
.,

g
The
Universal
Product
Code:
An
Introduction
to
What
It
Means
for
Consumers
Thomas
V.
Sobczak, Ph.D.
Long Island City,
NY
11101
The
Universal
Product
Code
is
the
group
of
lines
or
bars
which have
appeared
on
almost
all
items
in
the
supermarket.
The
code
is
a planned system,
de-
veloped
by
the
Uniform Grocery
Product
Code
Council,
assigning
an
identification
number
to
every
manufac-
turer
in
the
United
States
and
to
each
of
the
manu-
facturer&'
products.
When
fully
operative
the
sys-
tem
will
enable
every
package
to
carry
a unique
UPC
which
will
enable
the
product
to
be checked
out
at
the
retail
store
counter
by
a combination
of
accur-
ate
scanning
and computer memory.
Why Develop
UPC
The
Supermarket
Industry
had
many
good
reasons,
but
they
can be
summed
up
in
one word, "PROFIT."
1. Labor
rates
in
the
supermarket
industry
are
expected
to
double
by
1980.
UPC
can
cut
the
store
staff
in
half.
2.
Industry
profits,
after
taxes,
are
less
than
1%.
UPC
studies
indicate
a
possible
35%
re-
turn
on
investment
after
taxes.
3.
Misrings
(an
error
made
by
the
checkout
clerk)
are
25%
of
sales.
UPC
eliminates
misrings
and
allows
price
changes
on
the
computer
faster
than
the
time
it
takes
you
to
walk from
the
shelf
to
the
checkout
stand.
How
Widespread
is
UPC
The
concept
of
UPC
is
being
marketed
by
Distribu-
tion
Codes
Inc.
DCI
is
owned
jointly
by
the
Uniform
Grocery Product
Code
Council
and
the
National
Asso-
ciation
of
Wholesalers/Distributors.
NAW/D
is
an
association
of
associations.
Each
association
mem-
ber
is
coordinating
its
activities
through
Distribu-
tion
Codes
Incorporated.
At
present,
UPC
exists
under
several
names.
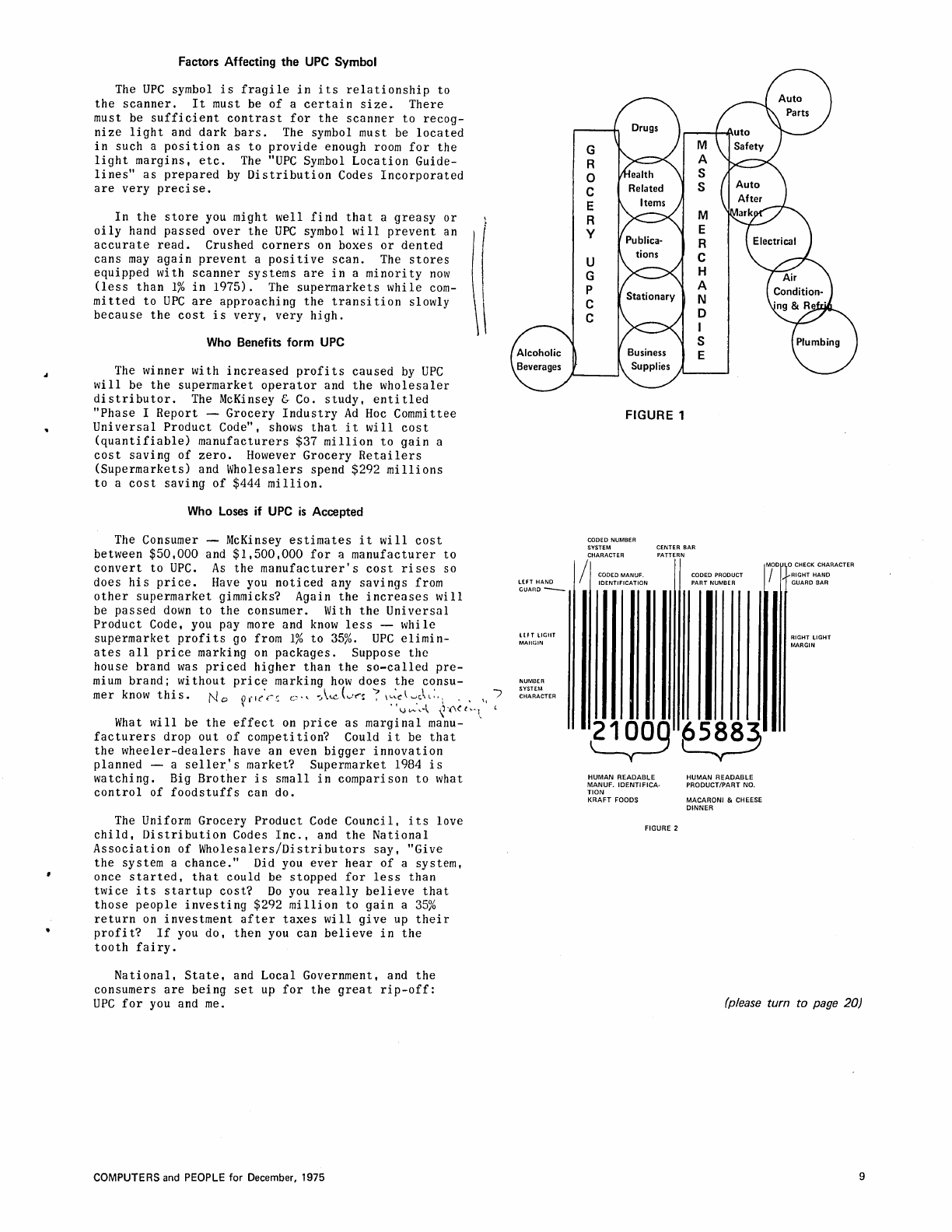
SPONSORING
DISTRIBUTOR
NAME
ABBREV.
ASSOCIATION
National
Drug
(NDC)
National
Wholesale
Code
Druggists
Health
Related
(HRI)
National
Wholesale
Items
Druggists
Publication
Code
CUPC)
Council
of
Publication
Distributors
Alcoholic
Bever-
CUPC)
Wine
and
Spirits
ages
Wholesalers
COMPUTERS and PEOPLE
for
December, 1975
"With the Universal Product
Code,
you pay more and
know
less
-
while supermarket
profits
change
from
1%
to
35%."
Stationary
& Bus-
(DC)
Business
Records Assoc.
iness
Supplies
Nat. Assoc.
Writing
Code
Instrument
Distribu-
tors
Nat.
Office
Products
Assn.
Nat. School Supply &
Equip. Assn.
Paper,
Stationary
&
Tablet
Manuf. Assn.
Wholesale
Stationers
Assn.
Electrical
Sup- (
DC)
Nat. Assn.
of
Electri-
plies
cal
Dist.
Air
Conditioning
(DC)
A/C-Refrigeration
Wholesalers
Plumbing
(DC)
Nat. Assn. Plumbing
Wholesalers
Distribution
(DC)
NIDA/SIDA
(Na
t.
&
Industries
Southern
Industrial
Distributions
UPC
is
growing
continually,
under
its
many
differ-
ent
names;
therefore
most
people
tend
to
underesti-
mate
its
power.
In
the
Grocery
Industry
the
middle-
men
and
supermarkets,
who
are
staunch
proponents
of
the
UPC,
want
to
eliminate
price
marking
on
the
shelf
items.
Their
lobby
is
so
strong
that:
A Maryland
bill
requiring
price
marking
died
in
a
State
Senate
Committee.
A
price
marking
bill
passed
the
Illinois
House
and
Senate
Committee only
to
lose
on
the
Senate
floor
by
seven
votes.
Virginia
Legislators
killed
a
price
marking
bill
because
they
didn't
feel
Automated Check-
out
Systems had been
given
a
fair
chance.
New
York
State's
price
marking measure
got
sidetracked
until
1976.
The
President's
Consumer
Affairs
advisor
is
favorable
to
UPC,
so
favorable
she
suggested
that
Congress
leave
the
UPC
alone.
Figure
I shows
the
domino
effect
on
industry
as
UPC
moves
from
place
to
place.
It
started
at
Grocery
(UPCC)
but
since
Drugs and
Health
related
items
are
sold
in
supermarkets,
the
Food
and Drug
Administra-
tion
were convinced
(lobbied?)
to
change
the
National
Drug
Code
and
the
Health
related
item code
to
the
7

UPC
format.
Books
are
sold
in
supermarkets,
as
are
magazines.
The
Publishers
were
the
next
to
give
in.
Look
at
the
UPC
on
the
cover
of
"Family
Circle".
Recently
the
Alcoholic
Beverage Commission
was
con-
vinced
to
specify
a
UPC
code.
Remember,
outside
of
New
York
State,
alcoholic
beverages
are
sold
in
su-
permarkets.
The
trend
continues
with
stationery
and
business
supplies.
The
logic
is
the
same.
In
time
everything
must
be
scanned
mechanically.
The
mass
merchandising
(Discount)
stores
are
ac-
cepting
UPC
because
it
exists
on
products
they
buy.
The
Federal
Department
of
Transportatiun
is
proposing
to
modify 49CFR577,
the
law
controlling
manufacturer
marking
of
auto
parts.
This
opens
the
door
to
UPC.
It
exists
in
wholesale
electrical,
air
conditioning,
refrigeration,
and plumbing.
UPC
goes
on
and
on
and
on
without
anyone
realizing
how
quickly
it
grows
or
how
much
it
affects
their
daily
lives.
What
Does
the
UPC
Symbol
Mean
The
symbol
is
the
means
by
which a machine
read-
able
identification
mark can be
placed
on
a package.
The
code
is
actually
eleven
digits
which
are
machine
readable.
The
first
digit
for
Grocery
Products
is
the
"0"
centered
before
the
first
Printed
Bar.
It
is
called
the
Number
System
Character.
It
was
added
to
allow
integration
of
other
industries
into
the
Grocery
field.
As
an example, Books, Drugs, and
Health
Related
items
are
sold
in
Supermarkets
as
are
Stationery
items.
A look
at
the
components
of
the
symbol
will
help
you
to
understand
how
it
works
in
the
scanning
pro-
cess.
Figure
2 should be looked
at
after
reading
each
paragraph
to
get
full
meaning. Let us
read
from
left
to
right.
The
first
area,
at
the
left,
is
a
white
space,
identified
as
the
"Left
Light
Margin."
This
space
separates
the
symbol from
other
printed
matter
on
the
package.
It
tells
the
scanner
that
a
UPC
symbol
is
coming.
Next
we
have a
double
vertical
dark
bar
separated
by
a
light
bar.
Thi
sis
called
the
"Left
Hand
Guard
Bar."
This
pattern
alerts
the
scanner
to
the
start
of
data
transmission.
The
first
character
scanned
is
the
"Number System
Character"
previously
mentioned.
The
example
(Fig-
ure
2) shows
the
bar
pattern
for
a
"zero"
which means
it
is
a
grocery
product.
The
"0"
in
the
left
light
margin
provides
a
human
readable
character
if
needed.
Random
weight
items
have a
Number
System
Character
of
2; Drugs and
Health
Related
items
use
3; Coupons
use
5;
Alcoholic
Beverages
will
use
8.
The
remainder
of
the
left
hand
half
of
the
symbol
is
occupied
by
the
five
characters
making
up
the
"Manufacturers
Identification
Number."
As
an exam-
ple,
Kraft
foods code
is
21000.
In
the
middle
of
the
symbol
is
the
"Center
Bar
Pattern".
Its
function
is
to
separate
left
coded
information
from
right
coded
information.
The
right
five
characters
are
the
Product/Part
Code
Number.
This
number
is
assigned
by
the
manufac-
turer
to
uniquely
identify
each item he
produces.
As
a
point
of
interest
the
left
side
is
constructed
of
a
different
combination
of
light
and
dark
bars
than
is
the
right.
This
construction
will
be
ex-
plained
later.
8
Following
the
Product/Part
Code
Number
is
the
Modulo Check
Character.
This
provides
the
method
by
which
the
computer
determines
that
what
the
scanning
machine has
read
is
accurate.
Finally,
the
scanner
sees
the
Right
Hand
Guard Bar
which
tells
the
computer
that
the
data
collection
cycle
for
this
symbol
is
at
an end.
A Right
Light
Margin
again
separates
the
symbol
from any
other
printed
matter.
What's
in
a
Bar
The
symbol
is
designed
so
that
the
computer
will
know
whether a
particular
character
is
on
the
left
or
on
the
right
hand
side
of
the
Center
Bar
Pattern.
A
Bar,
or
more
technically
a
Character,
is
com-
posed
of
7 modulos which
are
series
of
light
and
dark
bars.
Each number from 0
to
9 has a
different
ar-
rangement
of
the
7
light
and
dark
bars
which
make
up
the
character
on
either
the
left
or
right
side
of
Center
Bar
Pattern.
Figure
3 shows a
left
hand "0"
consisting
of
7
modules 2
barsj2
spaces
which
is
Binary
encoded
0001101 where
"0"
equals
light
and 1
equals
dark.
How
Does
the Computer
Check
for Accuracy
From
time
to
time
the
scanner
will
not be
able
to
read
the
UPC
symbol.
This
is
because
th~
Modulo
Check
Character
printed
on
the
symbol does not match
the
computer-calculated
check
character
based
on
what
the
scanner
read.
The
Modulo
Check
Character
is
a
mathematical
tech-
nique
through
which
the
scanner-computer
combination
verifies
each
product
to
make
sure
the
UPC
will
be
rejected
if
it
is
read
incorrectly.
It
works
as
shown
in
Figure
4:
The
complete coded symbol
is
shown
at
the
top
021000 65883.
The
middle
line
of
boxes shows
alternative
odd
numbers
beginning
with
box 1 - 010683. This group
of
numbers
is
added
equaling
18.
Multiply
the
total
by
3.
The
middle
line
total
is
54.
The
bottom
line
of
boxes shows
alternating
even
numbers
beginning
with
box 2 - 20058.
Added
the
to-
tal
is
15.
The
combined
total
of
the
middle and bottom
line
is
69.
This
is
subtracted
from
the
next
highest
mul-
tiple
of
10.
In
our
example
that
number
is
70.
The
result
is
a
Modulo
Check
Character
of
1,
enab-
ling
the
computer
to
instantaneously
verify
the
ac-
curacy
of
the
scanner
reading.
Mr.
Alan Haberman,
President
of
First
National
Stores,
suggested
that
if
consumers were
really
in-
terested
in
having
prices
on
merchandise,
the
super-
markets
would
be
glad
to
supply
grease
pencils
so
the
consumers could
do
the
marking
themselves.
An
acti-
vist
consumer group
with
grease
pencils
could
cause
havoc
by
making
vertical
lines
in
the
UPC
symbol.
The
computer
will
not
accept
the
scan (machine
read-
ing).
Even more
confusing
is
the
potential
of
con-
sumer
activists
to
break
the
code and modify
certain
items
of
both
the
UPC
and
its
resultant
modulo check
character.
The
computer would
go
berserk,
leaving
the
checkout
clerk
and
the
store
manager
in
chaos.
COMPUTERS
and
PEOPLE
for
December. 1975
•
Factors Affecting the
UPC
Symbol
The
UPC
symbol
is
fragile
in
its
relationship
to
the
scanner.
It
must be
of
a
certain
size.
There
must be
sufficient
contrast
for
the
scanner
to
recog-
nize
light
and
dark
bars.
The
symbol must be
located
in
such a
position
as
to
provide
enough
room
for
the
light
margins,
etc.
The
"UPC
Symbol
Location
Guide-
lines"
as
prepared
by
Distribution
Codes
Incorporated
are
very
precise.
In
the
store
you might
well
find
that
a
greasy
or
oily
hand
passed
over
the
UPC
symbol
will
prevent
an
accurate
read.
Crushed
corners
on
boxes
or
dented
cans
may
again
prevent
a
positive
scan.
The
stores
equipped
with
scanner
systems
are
in
a
minority
now
(less
than
1%
in
1975).
The
supermarkets
while
com-
mitted
to
UPC
are
approaching
the
transition
slowly
because
the
cost
is
very,
very
high.
I
\
Who Benefits
form
UPC
The
winner
with
increased
profits
caused
by
UPC
will
be
the
supermarket
operator
and
the
wholesaler
distributor.
The
McKinsey & Co.
study,
entitled
"Phase
I Report
--
Grocery
Industry
Ad
Hoc
Committee
Universal
Product
Code", shows
that
it
will
cost
(quantifiable)
manufacturers
$37
million
to
gain
a
cost
saving
of
zero.
However Grocery
Retailers
(Supermarkets)
and
Wholesalers
spend $292
millions
to
a
cost
saving
of
$444
million.
Who
Loses
if
UPC
is
Accepted
The
Consumer
--
McKinsey
estimates
it
will
cost
between $50,000 and
$1,500,000
for
a
manufacturer
to
convert
to
UPC.
As
the
manufacturer's
cost
rises
so
does
his
price.
Have
you
noticed
any
savings
from
other
supermarket
gimmicks? Again
the
increases
will
be
passed
down
to
the
consumer. With
the
Universal
Product
Code, you pay more and
know
less
--
while
supermarket
profits
go
from
1%
to
35%.
UPC
elimin-
ates
all
price
marking
on
packages.
Suppose
the
house brand
was
priced
higher
than
the
so-called
pre-
mium
brand;
without
price
marking
how
does
the
consu-
mer
know
this.
No
(Jllt'r,:
0"
~).<.Cc..
..
t"'s
-;
\\.~C~W(~L:.,
"
,."')
'·v",,',"\.
~'(\U"l
What
will
be
the
effect
on
price
as
marginal
manu- '
facturers
drop
out
of
competition?
Could
it
be
that
the
wheeler-dealers
have an even
bigger
innovation
planned
--
a
seller's
market? Supermarket 1984
is
watching.
Big
Brother
is
small
in
comparison
to
what
control
of
foodstuffs
can do.
The
Uniform Grocery
Product
Code
Council,
its
love
child,
Distribution
Codes
Inc.,
and
the
National
Association
of
Wholesalers/Distributors
say,
"Give
the
system a
chance."
Did you
ever
hear
of
a system,
once
started,
that
could be stopped
for
less
than
twice
its
startup
cost?
Do
you
really
believe
that
those
people
investing
$292
million
to
gain
a
35%
return
on
investment
after
taxes
will
give
up
their
profit?
If
you do,
then
you can
believe
in
the
tooth
fairy.
National,
State,
and Local Government, and
the
consumers
are
being
set
up
for
the
great
rip-off:
UPC
for
you and
me.
COMPUTERS and PEOPLE
for
December, 1975
LEFT
HAND
GUAno
___
llfT
LIGHT
NUMBER
SYSTEM
G
R
o
C
E
R
Y
FIGURE 1
CODED
NUMBER
SYSTEM
CHARACTER
PATTERN
/ CODED
MANUF.
IDENTIFICATION
HUMAN READABLE
MANUF. IDENTIFICA·
TION
KRAFT
FOODS
FIGURE 2
CODED PRODUCT
PART
NUMBER
HUMAN READABLE
PRODUCT/PART
NO.
MACARONI
8<
CHEESE
DINNER
7
0
°R~:=~KH~:~RACTER
GUARD
BAR
RIGHT
LIGHT
MARGIN
(please
turn
to
page
20)
9

MULTI-ACCESS
FORUM
COMPUTER GRAPHICS AND
ART
-
OPEN
LETTER
To: Subscribers and Intended Subscribers
of
COMPUTER GRAPHICS
AND
ART
Dear
Colleagues
in
Graphics,
In
our
announcements
we
said
we
hoped
to
publish
the
first
issue
of
COMPUTER
GRAPHICS
AND
ART
in
January,
1976.
We
now
have
to
delay
our
original
plan,
due
to
a temporary
illness
and
hospitalization
of
the
editor.
The
first
issue
of
COMPUTER
GRAPHICS
AND
ART
is
now
scheduled
for
February,
1976.
Our
advisory
board
members
and
contributing
edi-
tors
to
date
include:
Dr.
Al
Bork,
University
of'
California,
Irvine
Dr.
Charles
Csuri,
Ohio
State
University,
Cleveland,
Ohio
Dr.
Herbert
W.
Franke,
Munich,
Germany
Dr.
Ken
Knowlton,
Bell
Telephone
Laboratories,
Murray
Hill,
New
Jersey
Dr. Frank Malina, Edi
tor,
"Leonardo",
Paris,
France
Dr.
Abraham
Moles,
Stuttgart,
Germany
Dr.
Frieder
Nake, Bremen,
Germany
Prof.
Nicholas
Negroponte,
MIT,
Cambridge,
Mass.
Ms.
Jackie
Potts,
Social
Security
Administra-
tion,
Washington, D.C.
Dr. Joseph Raben, Edi
tor,
"Computers &
the
Humanities",
Flushing,
New
York
Prof.
Erich
Teicholz,
Harvard
Spatial
Analysis
Group, Cambridge, Mass.
The
first
issue
is
now
being
prepared.
If
you
are
interested
in
sending
materials
for
this
first
issue,
please
do
so
immediatelyl
If
you
wish
to
participate
in
other
issues
of
this
quarterly,
we
ask
that
you send
your
materials
as
early
as
pos-
sible
for
consideration.
We
look
forward
to
working
with
you,
to
make
this
a
significant
and
useful
periodical
for
people
in
computer
graphics
and
art.
We
need
your
help
and your
subscriptions.
If
you
have
not
yet
paid
for
your
subscription
to
COMPUTER
GRAPHICS
AND
ART,
please
do
so
now.
Or
you
may
wish
to
enter
a
Library
Subscription,
whereby you and your
colleagues
may
share
this
new
quarterly.
10
May
we
hear
from
you
soon?
Yours most
cordially,
Grace
C.
Hertlein
Editor,
COMPUTER
GRAPHICS
&
ART
Berkeley
Enterprises
Inc.
-
Chico Branch
555 Vallombrosa, #35
Chico,
Calif.
95926
IMAGES
AND
REALITY
IN THE COMPUTER
FIELD
-
A DISCUSSION
1.
From the Editor:
It
seems
to
me
that
IBM,
like
the
U.S.
govern-
ment and
the
advertising
people
on
Madison Ave.,
has
given
us
lessons
in
image making
--
the
pic-
turing
of
reality
as something
different
from what
it
is.
For example, I have
never
seen
an
IBM
ad
or
publicity
release
which
admitted
in
any
way
the
existence
of
any
other
computer companies
than
IBM
or
any
other
computer
products
except
those
pro-
duced
by
IBM.
So
if
you
read
only
IBM
advertising
and
publicity,
you
would
never
realize
that
other
companies
besides
IBM
are
in
the
computer
field.
2.
From Jack Biddle
President
Computer Industry Association
1911
N.
Fort Meyer
Dr.,
Suite 801
Rosslyn,
VA
22209
Why
should
IBM
mention
other
companies
in
its
ads?
That's
what an
ad
is
for
--
advertising
one
company
and
its
products.
I
think
it
would be
better
to
show:
(1)
How
IBM
argues
that
it
has
38%
of
the
market
when
their
own
studies
and docu-
ments
show
their
share
to
be 60
to
7~/o;
or
(2)
How
they
participate
in
voluntary
stand-
ards
meeting
to
develop
a communications
protocol
(SDLC)
while
simultaneously
de-
veloping
a
different
standard
internally
and
spring
their
de
facto
standard
on
the
world;
or
(3)
Their
contention
before
the
courts
that
"the
peripherals
market
is
one
big
market
because
of
the
ease
of
developing
inter-
faces,"
when
their
own
internal
studies
showed
that
they
couldn't
enter
the
PCM
market because
of
the
difficulty
and
ex-
pense
of
the
interface.
THE
PURPOSE
OF FORUM
To
give
you,
our
readers,
an
opportunity
to
discuss
ideas,
problems, and
issues
that
seem
to
you
important.
To
express
comments,
suggestions,
and
criticisms
on
what you
find
in
this
magazine.
COMPUTERS and PEOPLE
for
December, 1975
..

tJ
Computers and Society: A Course at
York
University
Larry
J.
Murphy
A tkinson College
York University
4700 Keele
St.
Donwnsview, Ontario M3J
2R7
Canada
"1
believe there
is
an
urgent need to 'humanize' the computer science major, in
fulfillment
of
C.
P.
Snow's efforts
for
a 'bridge between the two
cultures~"
The
Natural
Science
Department
of
Atkinson
Col-
lege,
York
University,
Toronto,
Ontario
has
offered
a
"general
education"
course
entitled
"Computers and
Society"
(N.
S. 178)
for
at
least
seven
years.
When
I began
to
conduct
the
course
five
years
ago,
it
had
already
been
offered
for
at
least
two
years
by
a
mathematician
who
treated
it
much
like
a programming
course.
But
since
the
original
course
outline
des-
cribed
an
~ssentially
humanities'
approach
course
on
computers,
there
was
little
problem doing what I
felt
should have been done
originally:
offer
a
gen-
eral
education
course
on
computers
for
both
non-com-
puter
and computer
majors.
I
believe
there
is
an
urgent
need
to
"humanize"
the
computer
science
major,
in
fulfillment
of
C.
P.
Snow's
efforts
for
a
"bridge
between
the
two
cul-
tures".
I
believe
no
instructors
should keep
him
back from
the
general
history,
the
history
of
the
theory,
the
literature
(both
fiction
and
non-fiction),
and
especially
the
ethics
of
his
chosen
field.
Over
the
past
five
years
N.
S.
178
has been
of-
fered
seven
times
(including
three
summers); a
total
of
about
400
students
have completed
the
course
(five
classes
of
about
50
students,
two
of
about
75).
The
course
is
a
full
year
course
as
is
customary
in
Canadian
universities;
it
meets
for
three
hours
a
week
from September
to
May,
for
a
total
of
about
70
class
hours.
The
summer
sessions
cover
the
same
material
over
the
same
number
of
class
hours,
but
in
half
the
number
of
months
(May
to
August).
Of
the
400
students
who
h~ve
completed
the
course,
approxi-
mately
8%
were Computer
Science
majors.
My
experi-
ence has been
that
they
were,
overall,
the
most
ap-
preciative
single
group
since
when
they
began
they
had
no
idea
there
was
a
"history
of
computers,"
let
alone
such an
extensive
one.
They
also
entered
the
class
with
a
total
lack
of
knowledge
of:
the
"history
of
the
theory
of
computers";
the
literature
on
com-
puters
(except
programming
manuals);
and most
shock-
ingly
of
all,
any
appreciation
for
ethical
questions
regarding
computers and
their
applications!
I
be-
lieve
this
experience
alone
is
enough
to
recommend
courses
in
"Computers and
Society"
to
all
computer
science
majors
and
minors.
The
readings
books used
in
N.
S. 178
are:
Pylyshyn,
Zenon
W.
(ed.):
"Perspecti
ves
on
the
Computer
Revolutio~',
Englewood
Cliffs,
N.
J.:
Prentice-Hall,
1970.
COMPUTERS and PEOPLE
for
December, 1975
Lewis,
Arthur
0.,
Jr.
(ed.):
"Of
Men
and Machines",
New
York: E.P.
Dutton
&
Co.,
1963.
Bowles,
Edmund
A.
(ed.):
"Computers
in
Humanistic
Research",
Englewood
Cliffs,
N.
J.:
Prentice
Hall,
1967.
and
either:
or:
Cress/Dirksen/Graham:
"Fortran
IV
with
Watfor and
Watfi
v",
Englewood
Cliffs,
N.
J.:
Prentice
Hall,
1970.
Smyth,
J.
Morgan: "York
APL",
Toronto:
Ryerson
Poly
technical
Institute,
1972.
For
those
who
feel
they
need
extra
support
in
the
basic
areas:
IBM:
"More About Computers,"
Armonk,
N.
Y.:
IBM,
1971.
Scientific
American:
"Information",
San
Francisco:
W.H.
Freeman &
Co.,
1966.
For
those
who
wish
to
specialize
in
applications
of
computers:
Kanter,
Jerome: "The Computer and
The
Executive",
Englewood
Cliffs,
N.J.:
Prentice
Hall,
Inc.,
1967.
Sanders,
Donald H.: "Computers
in
Business,
An
Introduction",
(2nd
Ed.),
New
York: McGraw-Hill,
1972.
Shorter,
Edward: "The
Historian
and
the
Computer",
Englewood
Cliffs,
N.J.:
Prentice
Hall,
1971.
The
course
is
divided
into
"lecture"
sessions
and
"tutorial/seminar"
sessions;
the
lecture
session
is
used
for
guest
lectures,
films,
and
the
general
dissemination
of
information.
Since
I've
come
to
computers
through
the
history
of
technology
--
Hol-
lerith
and
his
electric
data
tabulating
system
--
and most
research
in
what might be
called
the
"pre-
history
of
computers"
or
"prerequisites
of
the
com-
puter"
is
in
a
very
scattered
primary
literature,
if
even
that,
I can
see
no
better
alternative
to
the
traditional
lecture
as the
best
method
of
sharing
such background
with
the
class.
Certainly
no
ade-
quate
text
or
even
readings
book
has
yet
appeared.
In
the
"tutorial/seminar"
sessions
the
issues
brought
up
by
the
lectures,
the
readings,
and
the
students'
research
are
discussed.
11

In
addition
to
the
"lectures"
and
the
"tutorial/
seminars",
the
student
is
required
to
do
work
out-
side
of
class
which
includes
a minor programming
project
(relying
on
the
York
Computing
Centre
re-
source
personnel),
and
two
bibliographic
projects
(relying
on
the
York
Library
resource
personnel).
These
projects
require
the
student
to
actually
pro-
pose,
flow-chart,
programme, debug, and
successfully
run
a programme
on
the
computer, one
that
is
useful
in
their
area
of
interest.
They
may
use
either
FORTRAN
IV
with
WATFIV,
(or
COBOL
if
more
relevant
to
their
interest),
or
York
APL
(Iverson's
A
Pro-
gramming Language).
This
is
an
interactive-language
developed-at
York
as
an
alternative
to
the
batch-
mode
FORTRAN
IV
with
WATFIV.
The
projects
also
re-
quire
the
student
to
become
familiar
with
the
lit-
erature
of
and
on
computers;
they
require
the
stu-
dent
to
perform (manually
and/or
on-line),
two
bib-
liographic
searches
at
different
levels
on
computer
topics,
to
evaluate
the
retrieved
articles,
and
ultimately
to
abstract
selected
articles.
Systems
of
three
major
computer
manufacturers
are
visited
by
the
students:
IBM
at
York; Univac
at
the
Metro Toronto
Computer-Controlled
Traffic
Light
Centre;
and
CDC
at
the
Control
Data
Institute
in
Toronto.
Obviously,
the
structure
of
NS
178
is
different
from
other
proposed
courses,
but
the
content
is
very
similar,
as
can
be
seen
by
comparing
the
out-
line
below
with
that
of
other
courses
in
Computers
and
Society.
I
am
much
pleased
that
the
U.S. computer
commun-
ity
has been promoting
courses
in
Computers and So-
ciety,
since
I
feel
NS
178 has been very
valuable
to
most
of
the
students
who
have completed
it.
In
closing,
I wish
to
stress
how
important
I
believe
it
is
not
to
restrict
the
courses
in
Compu-
ters
and
Society
to
non-computer majors
or
minors.
In
fact
I
strongly
advocate
that,
if
a
university
has any
required
courses,
a
course
in
Computers and
Society
be
required
of
all
computer majors and
minors
--
and perhaps
not
just
of
the
students,
but
of
faculty
and
practitioners
of
Computer
Science
as
well.
Perhaps even a
national
or
international
so-
ciety
of
computer
scientists
could
(or
should)
offer
and promote such a
course
for
all
their
members.
Course Outline:
First Half Year:
Period 1: Lectures
Brief
history
of
western
civilization
as
the
history
of
science
and
technology.
Define
"field."
"Computer
Science":
is
it
a
science,
or
part
of
"In-
formation
Science"?
Computers
allow
"control"
of
information
for
the
first
time.
"Computer
Revolution"?
the
2nd
Industrial
Revolution.
Period 1: Tutorial/Seminars
Discussion/criticism
of:
Pylyshyn's
"Perspectives
on
the
Computer
Revolution."
12
Period 1: Outside
of
Class
FORTRAN
IV
with
WATFIV
or
York
APL
Visit
to
York
Computer
Centre
Series
of
12
1/2
hour video
tapes
on
Fortran
IV
with
WATFIV
Period 2: Lectures
Survey
of
"Pre-history"
or
"Prerequisi
tes
of
the
computer":
Information
Storage
and/or
Retrieval
Methods/
Devices: Language
(words);
writing,
(clay,
papyrus);
books
(scrolls
and
codices,
tape
and
cards);
Hero(n) odometer;
Vitruvius
odom-
eter;
Danzig
ribbon
weaving loom;
Wren
and
Hooke
(1660s);
Horse
way-wisers;
Falcon;
Bouchon; Vancanson;
Jacquard;
Babbage;
the
Scheutzs;
Ritty
Brothers;
Hollerith;
Powers;
Comrie; Aiken.
Mathematics,
mathematical
regularity:
Language
(numbers);
counting;
one-to-one
correspondence;
bases;
arithmetic
calculating
or
computing;
place
holder;
zero;
Leonardo
da
Pisa;
number
analysis
(concerned
with
calculation);
Stevin;
Napier
(logarithms);
method
of
differences;
Descartes;
Leibniz
(binary
arithmetic);
Boole;
Babbage; Maxwell
(formalization
of
the
gover-
nor);
number
theory.
Period
2:
Tutorial/Seminars
History
(integration
of
lectures
with
Pylyshyn and
general
history
of
western
civilization).
Period 2,
3:
Outside
of
Class
Minor Programming
Project
Period
3:
Lectures
Logic,
logic
devices:
Analysis
of
language
(both
words
and
numbers);
Aristotle's
logic
(syllogism);
Ramon
Lull;
Swift;
Hobbes;
Leibniz;
Charles,
the
Third
Earl
of
Stanhope; Boole;
Venn;
Jevons;
Peirce;
Marquand;
Turing
(Post),
Shannon.
Period
3:
Tutorial/Seminars
Theory:
Algorithms,
automata
(mathematical),
Cyber-
netics
(Wiener, von
Neumann)
Period
4:
Lectures
Digital
devices
(counting
devices:
Fingers
(toes);
one-to-one
representation;
abacus; computing
jetons;
digital
clocks;
Napiers'
bones/rods;
Schickard;
Pascal;
Leibniz;
Morland;
Stern;
De
Colmar; Babbage; the
Scheutzs;
additional
adding
machines
and
the
comptometer;
Ritty
Brothers;
Bollee;
Ludgate;
Richardson
(weather
"forecast
factory");
Shannon; Aiken
(A.S.C.C.);
Manchly
&
Eckert
(ENIAC).
Analog
devices
(measuring
devices):
Stonehenge;
ruler;
"tape
measure";
ancient
Greek computer;
Planetaria;
analog
clocks;
astrolabs;
Arab
plane-
tary
computers;
slide
rules
(circular
and
linear);
Orreries;
Big Horn Medicine Wheel; Amsler
plani-
meter;
Kelvin
(tide
predictor);
Kelvin
(differen-
tial
equation
solver);
Michelson &
Stratton
(harmonic
analyzer);
Bush
(differntial
analyzer).
Period
4:
Tutorial/Seminars
History
of
the
theory,
way
it
came
together.
COMPUTERS and PEOPLE
for
December, 1975
..

•
rJ
e
Period
4:
Outside
of
Class
Visit
to
outside
computer
facility.
Period
5:
Lectures
Feedback
devices;
(C)
or
Ktesibus
(waterclock);
Hero(n) (wine
dispenser);
thermostats;
windmill
control
mechanisms;
Harrison's
chronometer;
Watt's
steam engine
governor;
Babbage's
bell;
Claude
Bernard;
L.J.
Henderson; Walter
B.
Cannon; Wiener
(cybernetics);
von
Neumann.
Automata: Mechanical
regularity;
Hero(n);
Albertus
Magnus;
clocks-clockwork
mechanisms;
Orreries;
Descartes;
Newton
(clockwork
universe);
Borelli;
Vaucanson; Droz;
La
Mettrie;
Industrial
Revolu-
tion
(automatic
actions
sophisticated);
Babbage;
"Turing
Machine."
Period
5:
Tutorial/Seminars
Artificial
Intelligence
Period
5:
Outside
of
Class
First
Bibliographic
Project
(on computer
literature
in
general)
Period
6:
Lectures
Electricity,
communications: Lodestone; atomic
theories
(Democritus &
Lucretius);
compass;
Gil-
bert;
2
fluid
theories
of
electricity;
Franklin;
electrical
games;
electrical
medicine/psychology;
Volta;
Ampere;
Faraday;
Ohm;
Henry; Morse
(tele-
graph);
Bell
(telephone);
Edison
(Pearl
Street
station);
AC/DC
battle;
Niagara
Hydro; Marconi;
Kettering;
relays;
vacuum
tube
(diode/triode);
Shannon & Weaver;
Bell
labs;
transistor.
General
integration
of
the
8
"strands"
which
come
together
to
form
the
modern
digital
computer.
Examples
of
combinations
of
"threads"
prior
to
total
combination.
Arrival
of
modern
digital
computer: U.S. (A.S.C.Co,
ENIAC,
UNIVAC);
England
(National
Lab, Cambridge,
Manchester);
Canada (Saskatchewan);
Rest
of
World (Zuse,
etc.)
Software/Hardware.
Structure
of
a computer
Changing Technology,
futures
re:
technological
limits.
Example
of
subtraction
unit.
Computer
languages
(according
to
Jean Sammet, over
1500
languages),
futures
Period
6:
Tutorial/Seminars
Artificial
Intelligence
Period 6: Outside
of
Class
First
Bibliographic
Project
(on
computer
literature
in
general)
Second Half
of
Course
Lectures
Applications:
Business/Commerce:
Bookkeeping/accounting,
etc.;
Inventory
control
(guest
lecturer
from
local
bank)
Industrial:
Hybrid computers;
Control
of
mfg.
process;
Examples
Physical
sciences:
History
of
use;
Exceptional
use;
Examples
Social
Sciences:
History
of
use;
Exceptional
use;
Examples (Guest
lecturer
from
Traffic
Planning
Department
of
Toronto)
COMPUTERS and PEOPLE
for
December, 1975
Humanities:
Control
of
literature
(umbrella);
Art-graphics
(film,
examples); Music
(listen
to
tapes,
examples);
Poetry
(examples);
Future.
"Where's
it
all
leading?":
Leisure
Ethic
over-
taking
the
Work
Ethic.
T utoria I/Seminars
Discussion/criticism
of
Lewis, "Of
Men
and Machines"
and
latter
part
of
Pylyshyn,
especially
questions/
problems
of
ethics/privacy
(Canada,
Great
Britain,
U.S.
hearings/legislation
on
data
bank,
etc.)
Guarantee
of
privacy
re:
data
banks
Computer Crime
"Computer
as
Friend"
"Computer as
Enemy"
Futures
Discussion/Criticism
of
Bowles "Computers
in
Human-
istic
Research": Comparison
of
humanistic
appli-
cations
with
non-humanistic
applications;
Com-
parison
of
EDP
and computer
applications
in
scholarly
research
•
Outside
of
Class
Second
Bibliographic
Project
(on
the
literature
of
computer
applications,
theory,
history,
in
all
8
choices).
Visit
to
UNIVAC
Computer
facility.
Optional
major
research
project
(historical,
theoret-
ical
or
applied)
in
respect
of
interest
of
stu-
dent
(about
1/3
of
the
class).
0
WHO'S WHO I N COMPUTERS
AND DATA PROCESSING
THE
SIXTH
CUMULATIVE
EDITION
WHO'S WHO
ENTRY
FORM
(may
be
copied and
expanded
on
any
piece of paper)
1.
Name
(please
print)
____________
_
2.
Home Address
(with
Zip)
__________
_
3.
Organization
______________
_
4.
Its Address
(with
Zip)
___________
_
5.
Your
Title
_______________
_
6.
Your
Main Interests:
Applications (
logic
Sales ( )
Business ( Management ( Systems ( )
Construction
( Mathematics (
Other
( )
Design Programming ( please specify:
7.
Year
of
Birth
______________
_
8. Education and
Degrees
___________
_
9. Year Entered Computer Field
________
_
10.
Your
Present Occupation
__________
_
11. Publications, Honors, Memberships, and
other
Distinctions:
______________
_
12. Do you
have
access
to
a computer? ( ) Yes ( ) No
a.
If
yes,
what
kind:
Manufacturer?
_____
_
______
ModeI ?
_________
_
b. Where
is
it
installed: Organization?
___
_
Address?
_________
--::--
____
_
c.
Is
your
access:
Batch ( )
Time-Sh~red
( )
Other ( )
Please
explain
________
_
13. Do you subscribe: -
to
Computers and People (formerly
Computers and Automation):
()
Yes
( ) No
-
to
The
New York Times: ( ) Yes ( ) No
14. Associates
or
colleagues who should
be
sent Who's Who
entry
forms (name and address)
(attach
paper
if needed)
When
completed,
please send
promptly
to:
Who',
Who Editor, Who's
Who in Computers and
Data
Processing. RFD, Box
177,
Hampton,
CT
06247
13

Software
Should
Be
Patentable
ADAPSO
[Association
of
Data
Processing Services/
Software Industry Association]
1420 Walnut St.
Philadelphia,
Pa.
19102
"Making clear that patents
may
be available
for
inventions in software
would unleash enormous innovative talent."
Association
of
Data
Processing
Service
Organiza-
tions,
Software
Industry
Association
(hereinafter
ADAPSO/SIA)
is
a
nonprofit
trade
association
of
62
companies
in
the
computer
field/l/,
approximately
7~/o
of
whom
concentrate
their
attention
in
the
soft-
ware
products
industry,
and
the
remainder
largely
~~
the
furnishing
of
varied
software
services
to
computer
users
and
to
hardware
manufacturers.
ADAPSO/SIA
presents
its
views
to
the
Court
be-
cause
an
inaccurate
description
of
software
tech-
nology and
the
software
products
industry
has been
set
forth
by
Petitioner's
Brief
and
the
supporting
brief
of
the
hardware
manufacturers'
association,
CBEMA.
ADAPSO/SIA
companies
are
not
"idea
or
think
tanks."
They
are
companies engaged
in
building
and
marketing machines
for
which
profit-conscious
companies
will
and
do
expend
money.
ADAPSO/SIA's
members
believe
they
are
entitled
to
the
same
patent
protection
for
their
innovative
products
as
that
granted
the
hardware
manufacturers.
Nature
of
the
Industry
A.
The Absence
of
Competition in Software
Whereas
ADAPSO/SIA
is
an
organization
of
rela-
tively
small companies, with
no
one
company
exert-
ing
dominance
over
all
the
others,
CBEMA
is
an
or-
ganization
of
relatively
large
companies,
operating
in
a computer hardware
industry
"shaped and domina-
ted
by
IBM."/2/ IBM's dominance
is
such
that
its
70%
or
better
share
of
the
computer hardware market
is
nearly
ten
times
that
of
its
nearest
competitor,
Sperry-Rand./3/
Other
giant
companies such as
Honeywell, Burroughs, Control Data and
National
Cash
Register
are
compelled
to
share
the
remaining
portion
of
the
market; General
Electric
and
RCA
found themselves
forced
to
withdraw
entirely
from
competition.
Thus,
it
is
IBM's voice
and
actions
which have
and
which
do
dominate
the
computer
in-
dustry.
In
this
case
the
Government remains
silent
while
CBEMA
distorts
the
history
of
the
computer
industry
to
assert
that
"the
computer
industry
has developed
in
an
atmosphere
of
free
interchange
of
computer
Based
on
a
portion
of
the
Brief
Amicus
Curiae
No.
74-1033
for
ADAPSO/SIA
filed
with
the
U.S. Supreme
Court
on
October 16, 1975.
14
programs
••••
"/4/
How
"free"
the
atmosphere has
been
in
the
computer
industry
is
best
shown
by
the
Government's
pretrial
brief
in
"United
States
of
America v.
International
Business Machines Corpora-
tion./5/
The
Government
in
its
antitrust
action
against
IBM
notes
the
development
of
the
computer
industry
and
fi
nds
that
in
"the
earliest
days
of
the
develop-
ment
of
the
computer
industry,
there
was
nothing
that
could
be
identified
as a
software
industry."/6/
This
was
in
part
because
users
design
some
of
their
own
software
and
because
the
"computer systems manu-
facturers,
following
IBM's
lead,
provided
[free]
much
of
the
software
[that]
users
required."/7/
It
was
not
until
the
late
1960' s
that
"the
in-
dependent
software
products
market emerged,
pioneer-
ed
by
the
fi
rm
Applied Data Research,
Inc.,"
/8/
one
of
the
amici
herein.
As
the
Government
notes,
"in
light
of
the
fact
that
IBM
provided
its
cus-
tomers with
their
software
requirements as
part
of
the
IBM
'total
systems
solution,'
independent
soft-
ware product firms had
to
market
their
offerings
against
products
for
which
there
was
no
identifiable
price.
As
a
result,
only
those
companies which
could
offer
products
not
available
'free'
from
IBM
or
which could demonstrate
the
technological
super-
iority
of
their
products
in
comparison
to
IBM's
had any chance
of
survival."/9/
The
result
was
that
the
independent
software
product firms lacked
"a
realistic
opportunity
to
compete."/lO/
That
this
was
not
an
innocent
case
of
cause and
effect
was
shown
by
IBM
internal
memoranda
which
revealed
that
"the
value
of
this
exclusionary
effect
derived
from bundled
pricing
[so-called
free
software]/ll/
was
fully
appreciated
by
IBM
••••
The
effect
of
IBM's
ability
to
wield such
exclusionary
power has been
felt
most
acutely
•••
by
those
firms seeking
to
market
software
products."/12/
The
Government has
also
noted
that
"IBM
internal
memoranda
.••
reflect
that
from as
early
as 1965,
IBM
was
aware
of
the
marketing
benefits
derived
from
bundled
pricing
and
the
anticompetitive
effect
it
had
on
software
companies."/13/
The
net
effect
was
that
"bundled
pricing
enabled
IBM
to
exclude
com-
petition
from independent
software
vendors."/14/
The
Government concludes
that
its
study
of
IBM
documents
"i
llustrate
wi
thout
ambigui
ty
that.
its
bundled
pricing
marketing approach
was
a
practice
known
by
IBM
to
be,
legally
indefensible.
Neverthe-
COMPUTERS and PEOPLE
for
December, 1975
t
~
.,
C~

s
less,
IBM
consciously
continued
bundled
prIcIng
because
of
the
competitive
leverage
it
afforded
IBM
in
maintaining
its
monopoly
position."/lS/
Software
monopolies
are
also
maintained
by
other
hardware
manufacturers
through
the
use
of
bundling.
A small
software
company
has sued Sperry Rand,
charg-
ing
it
with
refusing
to
place
a
price
on
its
bundled
software
and
thereby
making
it
impossible
for
the
small
company
to
sell
its
software
in
competition.
/16/
Honeywell
in
bundling
its
software
and
hard-
ware
asserts
that
the
software
is
"free."
But
when
the
hardware
buyer
attempts
to
transfer
that
soft-
ware along
with
the
hardware
to
another
company,
Honeywell
claims
that
it
owns
the
software
and
will
control
who
can have
possession./17/
B.
The
Resulting Poor-Quality Software
The
CBEMA
brief
also
boats
of
"the
tremendous
growth
of
the
computer
software
industry
and
the
vast
number
of
breakthroughs
in
the
field
of
pro-
gramming, which have
occurred
in
the
last
two
de-
cades"
(CBEMA
Br.
12).
How
different
the
facts
really
are
in
the
computer
software
field
is
made
clear
by
the
testimony
of
Dr.
Ruty
M.
Davis,
Direc-
tor
of
the
Center
for
Computer
Services
and Tech-
nology
of
the
National
Bureau
of
Standards/18/
char-
acterizing
the
present
condition
of
software
as
"poor-quali
ty
software,"
a condi
ti
on
whi
ch
she
described
as
the
"crucial
computer problem"
con-
fronting
the
nation
today.
Speaking
on
the
"serious-
ness
of
the
problems
besetting
both
the
consumers
of
computer
products
and
services
and
the
suppliers
of
these
products
and
services"
Dr. Davis
stated:
The
crippling
problems
are
lining
up
in
the
software
rather
than
in
the
hardware
field.
In
particular,
they
fall
under what
we
call
the
application-independent
problem
category
..•
these
are
the
software
problems which
are
common
to
many
applications.
That
the
condition
described
by
Dr. Davis
in
1972
still
holds
true
is
seen
by
her
warning
at
the
CBEMA
Spring
meeting,
May
29, 1974
that
"the
difficulty
and
cost
of
developing
and
maintaining
quality
software
have become
the
single
largest
consideration
in
computer
utilization
and composes
a
serious
limitation
on
the
cost-effective
use
of
computers."
Even
IBM
acknowledges
that
"the
biggest
problem
facing
programming today
is
the
extreme
difficulty
and
cost
encountered
in
creating
and
maintaining
large
programming
systems."/19/
At
the
National
Computer Conference
held
early
this
year
it
was
ad-
mitted
by
a
leading
hardware
manufacturer
that
the
"software
dinosaur"
has
not
"kept
pace
with
the
technical
needs
of
the
industry."/20/
As
a
result
of
the
software
users
being
at
the
mercy
of
the
hardware
manufacturers,
the
users
are
forced
to
make
do
with
the
"free,"
poor and
technically
in-
ferior
software./2l/
The
reason
for
the
poor
state
of
the
development
of
software
lies
in
the
shackles
IBM
has
placed
upon
free
competition.
History
shows
that
it
has
been
small
technological
companies and
independent
inventors,
and
not
the
vast
financial
combines such
as
IBM,
which have been
responsible
for
much
of
the
innovation
of
this
age.
A
recent
government
report
has found
that
"studies
of
the
sources
of
invention
and
innovation
have
shown
that
independent
inven-
tors
and
small
technologically
based companies
are
responsible
for
a remarkably high
percentage
of
the
important
inventions
and
innovation
of
this
century.
/22/
COMPUTERS
and
PEOPLE
for
December, 1975
C.
The
Small Company Potential for Competition
The
small,
mostly "young and
struggling",
com-
panies
who
"surely
possess
excellent
technical
in-
novative
capabilities"
and
"the
principal
technical
capability
•••
to
work
.••
on
our
critical
computer
problems"
/23/
have been
wrongfully
denied
the
in-
centive
of
the
patent
system, which has been
as-
sured
to
the
hardware
manufacturers
for
products
they
sell.
The
patent
incentive
is
both a form
of
recognition
and a major
aid
in
obtaining
the
nec-
essary
financing
without
which
these
companies
face
the
prospect
of
shriveling
and
dying.
It
is
no
ac-
cident
that
the
monopolistic
and
exclusionary
prac-
tices
of
IBM
have
permitted
only a small number
of
companies
in
the
software
products
field
to
achieve
a
relative
degree
of
success.
As
the
Government
states
in
its
pretrial
brief
"operating
systems
continue
to
be
part
of
IBM's bundled
price
struc-
ture.
Thes
continue
to
be bundled
for
the
marketing
leverage
they
afford
IBM
in
terms
of
increasing
the
sale
of
IBM
computer equipment and
forestalling
the
growth
of
independent
software
companies."/24/
D.
The Importance
of
Patent Incentives
A
patent
on
a
software
program
creates
an
econ-
omic
toehold
in
the
monopoly-dominated computer
field.
The
software
products
company
characterized
by
the
Government
as
the
pioneer
in
the
independent
software
products
market, Applied Data Research,
Inc.,/2S/
stands
as
proof
of
the
importance
of
soft-
ware
patents./26/
To
a
large
financial
giant,
the
economic
value
of
a
patent
may
not
loom
large;
to
the
small
soft-
ware companies upon which
the
future
of
the
develop-
ment
of
quality
software
depends,
the
financial
value
of
the
patent
may
spell
the
difference
be-
tween
life
and
death.
To
banks
and
financial
in-
stitutions
the
existence
of
apatent
or
even
the
potentiality
of
obtaining
one
may
well
be a
decisive
factor
in
determining
whether
a
loan
should
be
grant-
ed.
To
prospective
investors
a
patent
or
the
pos-
sibility
of
obtaining
one
may
be
the
principal
ele-
ment
in
the
decision
whether
to
invest.
Making
clear
that
patents
may
be
available
for
inventions
in
software
would
unleash
enormous
in-
novative
talent.
It
would have
the
direct
opposite
effect
forecast
by
IBM
and
the
other
hardware manu-
facturers
--
it
would
enable
competition
with
those
companies and
provide
the
needed
incentive
to
stimu-
late
innovation.
Patent
protection
would encourage
the
free
dis-
semination
of
program
innovations
which
is
so
ne-
cessary
to·
stimulate
technological
progress.
Dis-
closure
is
the
statutory
price
paid
by
the
inventor
for
patent
protection.
Without such
protection
inventors
principally
have
to
rely
on
the
law
of
trade
secrets
in
order
to
secure
the
economic
value
of
their
inventions,
thereby
excluding
from
the
world-at-large
disclosure
of
the
invention.
When
the
Patent
Office
for
its
own
convenience/27/
urges
that
inventors
rely
on
trade
secrets
in
lieu
of
patents,
it
is
ignoring
the
mandate
of
the
Patent
Laws, and
when
it
urges
copyrights
as
another
po-
tential
alternative,
it
is
denying
the
inventive-
ness
of
an
entire
technology,
thus
abdicating
its
responsibility
under
the
Patent
Laws
to
grant
pa-
tents
for
machines
that
"advance
the
Progress
of
the
useful
Arts."
Such computer programs as
are
freely
disclosed
in
the
trade
literature
of
the
computer
industry
15

have
little
economic value
or
technological
worth.
All
that
this
kind
of
"free
exchange" has produced
for
the
computer
industry
has been
"crippling
prob-
lems" and
"poor
quali
ty
software."
The
real
strides
forward
in
computer development occurred
in
hard-
ware,
an
area
fully
protected
by
the
patent
laws.
In a
competitive
economy,
that
which
is
given
away
for
nothing
tends
to
have
the
same
value.
Non-profit
companies
are
non-existent
in
the
computer
industry.
CBEMA
favors
its
version
of
"free
interchange
of
programs" because
that
has been
one
of
its
major
techniques
in
excluding
competition
and
in
monopoliz-
ing
the
computer
industry.
It
is
profits
and
not
"free
interchange
of
programs"
or
"innovative
soft-
ware
that
CBEMA
seeks."
The
economic
forces
opposed
to
patent
protection
were
clearly
identified
by
Judge Rich
in
his
dis-
senting
opinion
below.
As
he
stated
it:
On
the
one
side
•••
against
patenting
programs
or
software
[were]
collective
forces
of
major
hardware
(i.e.,
computer) manufacturers and
their
representative
associations
who,
for
economic
reasons,
did
not
want
patents
granted
on
programs
for
their
machines. (Emphasis
in
the
ori
gi
nal.
)
This
portion
of
Judge
Rich's
"dissent"
(a
dis-
sent
whose purpose
was
to
provoke
this
Supreme
Court review
to
obtain
a
ruling
providing
for
soft-
ware
patents)/28/
is
ignored
by
the
Government as
is
the
fact
that
Judge Rich
reaffirmed
his
view as
to
the
soundness
of
his
previous
opinions
on
com-
puter
technology.
When
one
knows
that
every
action
taken
by
IBM
has been motivated
by
its
monopolistic
and
exclus-
ionary
desires,
one
understands
why
IBM
has
led
the
legal
fight
against
patents
for
software.
It
is
not
to
strengthen
the
computer
industry
but
only
to
strengthen
IBM's
stranglehold
upon
it
that
IBM
postulates
its
legal
theories
in
opposition
to
patents.
Strange
indeed
is
it
that
the
Government
despite
its
firsthand
knowledge
of
IBM's
efforts
aimed
at
"forestalling
the
growth
of
independent
software
companies"/29/
joins
hands
herein
with
IBM
in
furtherance
of
IBM's
monopolistic
endeavors.
To
arbitrarily
deny
patent
coverage as urged
herein
by
the
Patent
Office
is
to
denigrate
soft-
ware technology and
to
cast
a
chilling
effect
upon
inventi
veness.
Summary
of
Argument
The
writ
of
certiorari
should
be
dismissed as
improvidently
granted.
because
of
the
inadequate
record,
the
jurisdictional
barrier
to
the
recon-
sideration
of
a
central
factual
issue,
and
the
in-
appropriateness
of
the
principal
question
for
which
certiorari
was
granted.
To
consider
what
the
Patent
Commissioner
presents
as
the
key
issues
in
this
case would
require
this
Court
to
undertake a
thor-
ough
inquiry
into
the
complex
technological
issues
of
special-purpose
computer
construction,
but
the
record
does not provide
the
factual
basis
which
would
enable
the
Court
to
do
so.
The
Supreme Court
is
not
the
appropriate
forum
for
initial
fact
find-
ing.
The
most
basic
technological
issue
--
the
Board
of
Appeals'
finding
that
programming a
general-pur-
pose computer
restructures
the
computer
into
a
dif-
ferent
machine
--
is
not
jurisdictionally
subject
to
review because 35 U.S.C. 141,
et.
seq. bind
the
Commissioner
of
Patents
by
Board
determinations.
16
Since
the
Board
is
the
alter
ego
of
the
commission-
er,
his
attempt
to
appeal
its
finding
is
in
essence
a
nonjusticiable
intra-agency
dispute.
Moreover,
the
C.C.P.A.
and
the
Board have
considered
the
basic
technological
fact
issue,
each has
special
creden-
tials
of
technological
expertise
and
both have
found
in
favor
of
the
restructuring
principle.
The
broad
question
for
which
certiorari
was
granted
--
whether
innovative
machines which can be
embodied
in
computer programs
are
patentable
sub-
ject
matter
--
is
inappropriate
for
judicial
reso-
lution
in
this
case because
patentability
depends
on
the
structural
nature
of
the
specific
invention
not
which
of
alternative
types
of
construction
was
employed.
The
petitioner
has conceded
that
the
Court cannot formulate a
rule
of
general
applica-
bility
in
its
decision
of
this
case
and
that
the
only
other
question
presented
--
obviousness under
35
U.S.C. 103
--
is
not
worthy
of
this
Court's
at~
tention.
The
petitioner's
main
legal
arguments depend
on
a
mischaracterization
of
computer program technology.
An
accurate
picture
of
this
technology
reveals
that
a programmed
general
purpose computer
is
a
differ-
ent
machine than
the
unprogrammed machine.
The
de-
signer
of
software,
like
any
engineer,
builds
ma-
chine
structures.
not
methods
of
doing
business;
he
develops machine
solutions
for
machine problems.
Computer
innovations
embodied with
stored
computer
programs
are
legally
entitled
to
the
same
patent
protection
as
innovations
embodied
in
wire-connected
electronic
circuits,
for
technologically
"hardware"
and
"software"
are
equivalent.
The
facts
that
a programmed computer (what
re-
spondent
defines
as
his
invention)
is
a machine and
the
innovative
aspect
of
it
is
a machine
structure
cannot
be
overcome
by
petitioner's
legal
arguments.
A machine
is
not
a method
of
doing
business.
An
innovative
machine
structure
is
not
the
mere embodi-
ment
of
an
abstract
idea.
Machines
are
patentable
subject
matter
and
respondent's
only argument
again-
st
software
being
patentable
subject
matter
is
the
unsupported
statement
--
appealing
perhaps
to
a
layman
but
universally
rejected
by
the
experts
--
that
a program
is
not
a machine
but
merely
an
idea,
"new
use,"
or
"method
of
doing
business."
Patent
protection
for
software
is
vital
to
the
health
of
the
data
processing
industry.
In
a
field
dominated
by
IBM,
the
growth
of
the
small
indepen-
dent
software
company
has been
stifled
by
the
bund-
ling
practices
of
the
hardware
manufacturers
which
continue
to
this
day
in
the
systems programs
area.
Only through
the
availabi
li
ty
of
protecti
on
for
their
products
can
the
software
producers hope
to
bring
competition
to
an
industry
that
sorely
needs
it.
The
absence
of
patent
protection
has
forced
reliance
on
trade
secrecy
and has had
the
negative
effect
of
deterring
disclosure
of
innovations.
The
availability
of
patents,
with
their
public
disclos-
ure
requirement,
would "promote
the
progress
of
the
useful
Arts,"
in
this
most
sophisticated.
pervasive
and
vital
area
of
technology.
Copyright
protection
is
inadequate
and
inappro-
priate
to
protect
innovative
machine
structures.
Copyright
of
a
particular
set
of
computer language
statements
does
not
protect
the
novel machine
struc-
ture
that
is
the
core
of
any
software
invention.
The
Constitution
establishes
innovation
as
the
pre-
requisite
for
a
grant
of
exclusive
rights
to
machine
structures;
attempts
to
protect
them
via
copyright
(please
turn
to
page
20)
COMPUTERS
and
PEOPLE
for December, 1975
,
·r
•

Je
:e;
,
l'
I
,.
'I
I)
;
) ;
It
...
The
Computer
"Glass
Box":
Teaching
with
APL
-Iverson's
"A
Programming
Language"
-
Part
12
Howard A.
Peel/e,
Director
Instructional Applications
of
Computers
University
of
Massachusetts
Amherst,
Mass.
01002
'This
approach utilizes a
computer
program more
as
a
glass
box
than a
black
box,
and
seeks
to
make
key
computer concepts become transparent
to
the
student."
(Continued
from
the November
issue
of
"Computers
and
People", page 26)
The
enterprising
student
might
elect
to
automate
Soon
it
should
become
clear
that
these
two
SCENES
the
production
of
MICROSCENEs:
cannot be
distinguished
on
the
basis
of
random
micro-
scenes
alone.
(Of
course,
if
one
could
trace
se-
[lJ
[2J
[3J
[4J
V
AUTOPEEK
quentially
through a
scene,
its
"connectedness"
or
"non-connectedness"
could
be determined
easily.)
I I
PEEK
MYSTERY
I'
-+1
AUTOPEEK
***
*
***
*
*
*
*
*
****
**
*
*
*
**
Computer Art
The
world of computer
art
can be opened
to
stu-
dents
through a few simple
APL
programs. Beginning
with
an
excursion
into
automated
design,
the
student
can proceed
to
encounter
questions
of
aesthetic
judgement and
artistic
technique.
For example,
consider
the
following
DESIGN
pro-
gram.
V PICTURE +
SIZE
DESIGN
COLORS
[1
J
llOWMANY
+ P
COLORS
[2J
PICTURE + COLORS[?SIZEpliOWMANYJ
V
DESIGN
uses
some
COLORS
(symbols
on
the
keyboard)
and
some
SIZE
(two dimensions of a
matrix)
to
pro-
duce a
PICTURE.
A simple program
like
DESIGN
goes a long
way
with
children.
They
seem
never
to
tire
of
it,
for
it
can produce
quite
a
variety
of
designs:
10
20
DESIGN
'--11-_
I
1-1_-11
1--
-I
--
_I-
--_ - - - - _ -
-I
I
- - I - - I -
--
-
1__
-- I 1- I L - I -
- I I
__
I
1_
I I - - I
_-
- I I
I -_ I I I I 1- -1_ - - I
11--_--1-
11_--_
I-I
_
-1
__
1
---
--
-
- -
--11----1------
COMPUTERS and PEOPLE
for
December, 1975 17

10
20
DESIGN
'//6~V\\'
6\6V\\6V/V/V/V//*\//
V/8VV6V/V\/~\///6/\V
\VV///V~/\~\\/\\8\V\
V/V~/\6//V\//\//V~VV
6V\\*V6\V\/V/~v/\\\\
/88//~V8///\6/8/V~8~
//6\V/\v/V\/\~8il/V\\
VVV\\~\~V/\6Vil~6666/
\/*\VVV~\8V\//\~\V~\
V~b\\\VV\68V\~\\\6\il
0
00
0 0
,0
0
0
• 0
10
20
DESIGN
,-,
10
20
DESIGN
'0
0 0
00
0
00,0
0 0
00
0
0
00
0
0000
0
0
0 0
00
00
0
00,
0 0
0
00
00
0
000
0
0000
000
,0
0 0
0 a
o .
10
20
DESIGN
'00*
*00'
*
*UD
*UOOOO*ODD**D
UOOO
0 0000* **00*
*OODUO
*OUO*O*
00*00
*0
00000*0
OOO*UO
OO***OOO**UO
00*0000
***0**00**00*
00*000
* *****00*
**00*00*0
*0*00*00*0*0*0
0*0*
*0
*000*
00*0
*0000
000000000*0*
00*0000
These
black
and
white
"Computer
hieroglyphics"
may
have dubious
aesthetic
appeal.
But one can
imagine
--
instead
of
these
typed symbols
--
randomly
generated
swatches
of
color,
perhaps
displayed
on
a
television-like
screen.
Extensions
of
this
approach
to
computer
art
in-
clude:
(a)
automating
DESIGN,
(b)
weighting
the
selection
of
COLORS,
(c)
asking
for
human
judgement
(Do
you
like
it
or
not?)
in
order
to
adjust
weights
on
COLORS
or
other
aesthetic
factors,
and
(c)
piec-
ing
together
several
computer-generated
PICTUREs
into
a montage.
18
Another approach
to
computer
art
involves
viewing
programs which
simulate
an
artistic
technique.
For
example,
consider
the
program
MONDRIAN
below
(named
after
the
Dutch
abstract
painter).
V
MONDRIAN
[ 1 J t: A
l{
VAS
+ 3 0 5 0
p'
,
[2J
DAB:
COLOR
+
'00*'[?3J
[3J
SIZE
+ 3 5
?6
10
[4]
PICK:
PLACE
+ ?30
50-3I2E
[5]
OVERLAP
+
+/+/CANVAS[PLACE[l]+lSIZE[l];
PLACE[2]+13IZE[2]]~'
,
[6]
+PICK
IF
OVERLAP> 2
[7]
CANVAS[PLACE[1]+lSIZE[1],PLACE[2]+
lSIZE[2]]
+
COLOR
[8]
+DAB
IF
(PERCENT ' ,
ON
CANVAS) >
67
[9]
CANVAS
MONDRIAN
begins
with
a blank canvas
(arbitrarily
set
at.30
by
50).
Then
the
program chooses a random
COLOR,
SIZE
and
PLACE
to
DAB.
OVERLAP
measures
the
extent
of
overlap
with
DABs
already
on
the
CANVAS.
IF
OVERLAP
is
greater
than
2, then
it
will
PICK
another
PLACE.
(This
is
tantamount
to
finding
re-
latively
open space
on
the
CANVAS).
IF,
however,
OVERLAP
is
not too
large,
the
COLOR
is
put
on
the
CANVAS
at
the
PLACE
and
in
the
SIZE
se-
lected.
The
program
continues
to
DAB
IF
the
PERCENT
of
blank
spaces
ON
the
CANVAS
is
greater
than 67. In
other
words, as soon as
it
is
1/3
filled
up,
CANVAS
is
displayed.
Note:
MONDRIAN
uses
two
simple sub-programs (mostly
for
readability).
They
are
PERCENT
and
ON:
V
HUNDREDTHS
+
PBRCBNT
N
[1]
HUNDREDTHS
+LO.5+100
xN
V DBNSITY +
SYMBOL
ON
PICTURE
[1]
DBNSITY + (+/+/SYNBOL=PICTURE) T
( X/pPICTURE)
COMPUTERS and PEOPLE
for
December, 1975
"

e
t
I1S
5
Now,
MONDRIAN
at
work:
UOOOOO
OOOUOO
000000
*****
MONDRIAN
0000000000
0000000000
0000000000
**********
**********
**********
**********00000
0000000
0000000
0000000
00000
00000
OUOOOOUOO
00000
000000000
OUOOOOUOO
00000
00000
0000000
0000000
0000000
OOOOOuU
0000000
UOOOOOO
*****
*****
*****
00000
00000
00000
OOOOOOOLJ
00000000
00000000
00000000
00000000
OUOOUUOO
*****
***** ******
*****000000
*****OOOLJOO
*****000000
********
********
********
********
********
*****
*****
*****
0000000000
************
0000000000
0000000000
*****
*****
******
******
******
******
**********
******
******
******
******
******
Possible
extensions
of
this
kind of program
in-
clude:
(a)
simulating
and combining
additional
artis-
tic
techniques
(those
that
can be
operationalized),
(b)
computing
abstract
measures of
difference
be-
tween random
"painting"
produced
by
the
computer,
(c)
converging
to
minimal
differences
from a
pre-
viously
specified
"ideal"
painting,
and (d)
develop-
ing
a model
for
aesthetic
judgement
--
perhaps one
which
"evolves."
Computer-Assisted Instruction
In
order
to
emphasize
the
contrast
with
conven-
tional
uses of computers
for
teaching,
the
last
glass
box program
here
illustrated
is
from
the
area
of
computer-assisted
instruction.
Instead
of con-
cealing
the
CAl
program
--
usually
designed
to
con-
trol
the
child's
behavior
--
we
show
him
the
mechan-
ism
itself
so
that
he
may
see
how
it
works and
ul-
timately
see
how
to
control
the
computer and
control
it.
Consider
the
APL
program below which exposes
the
essence
of
drill-and-practice
in
multiplication
skills.
ry
DRILL
[lJ
NEWPROBLEM:
[2J
'lviULT
IPLY'
[3J
o +
FIRST
+
?20
[4J
o +
SECOND
+
?20
[5J
ENTER:
ANSW8R
+ 0
[6J
~NEWPROBLEM
IF
ANSWER
FIRSTxSECOND
[7J
'NOPE. TRY AGAIN. ,
[8J
~ENTER
COMPUTERS and PEOPLE
for
December, 1975
The
DRILL
program beings with a
NEWPROBLEM
and
prints
'MULTIPLY',
a
simplified
message
telling
the
student
what
to
do
with
the
two
numbers
that
will
follow.
The
FIRST
number
is
an
integer
randomly chosen between 1 and 20, and
the
SEC-
OND
number
likewise.
The
student
may
ENTER
his
ANSWER
which
is
then
judged
for
correctness
by
the
program.
IF
the
ANSWER
equals
the
FIRST
number times
the
SECOND
number, a
NEWPROI3LEM
is
gi
ven; otherwi se
(if
ANSWER
is
wrong)
'NOPE.
TRY
AGAIN.'
is
printed,
and
the
student
may
ENTER
his
answer
again.
In
order
to
use
the
DRILL
program,
its
name
is
typed, as
shown
below:
DRILL
MULTIPLY
19
2
0:
38
MULTIPLY
16
18
0:
248
NOPE.
TRY
AGAIN.
0:
288
MULTIPLY
8
12
0:
96
MULTIPLY
14
18
0:
Students
notice
immediately
that
this
program
has a
flaw.
It
does
not
stopl
Scrutinizing
the
program's
definition
reveals
that
after
getting
a
multiplication
problem
correct,
one always
gets
a
new
problem
--
ad
infinitum.
Also,
after
getting
a problem wrong,
the
student
must answer
that
same
problem
again
--
another
potentially
endless
loop.
The
student's
first
task,
then,
might be
to
build
in
an
option
to
stop
the
program
at
will.
DRILL
is,
of
course,
only a
prototype
program.
With
other
modifications
of
one's
choosing,
DRILL
19
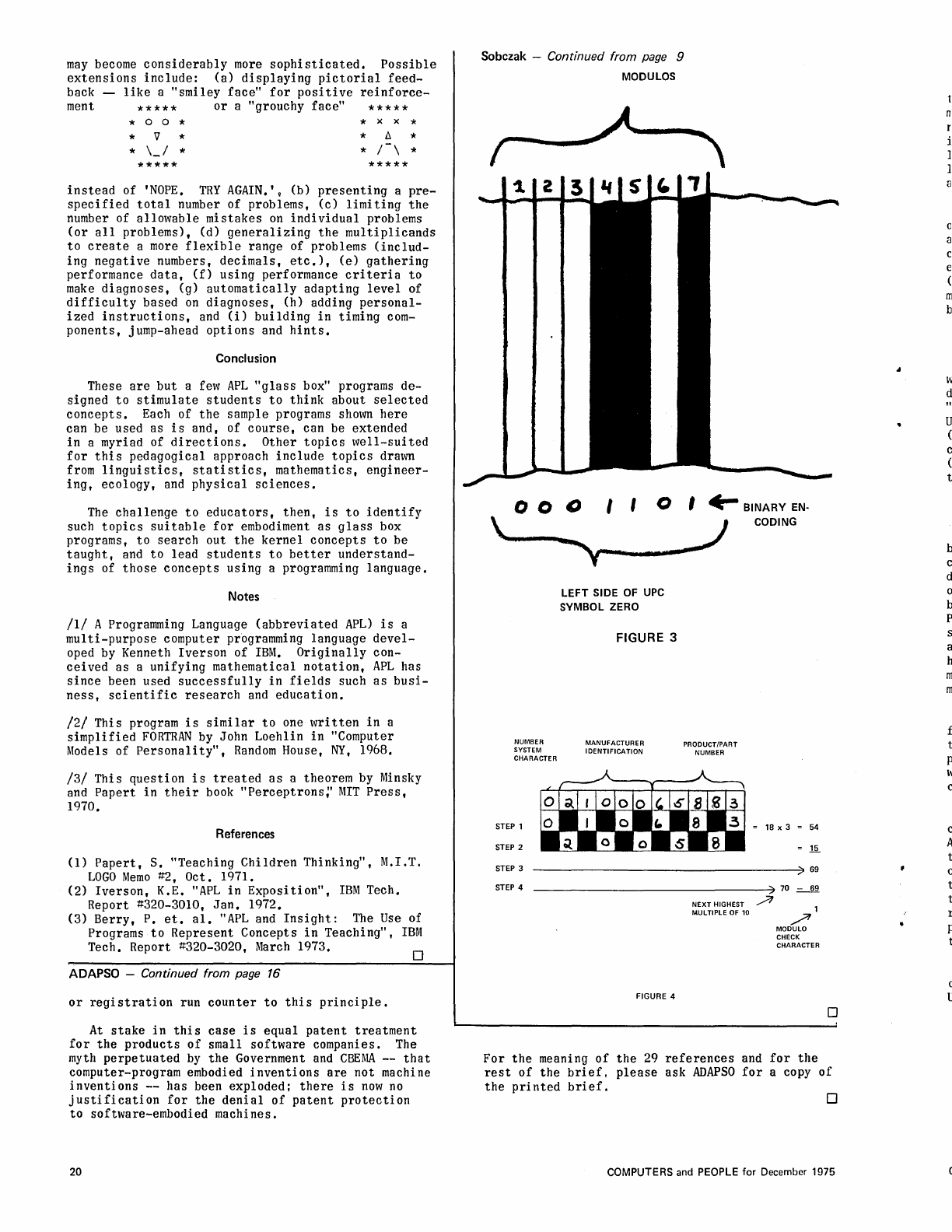
may
become
considerably
more
sophisticated.
Possible
extensions
include:
(a)
displaying
pictorial
feed-
back
like
a
"smiley
face"
for
positive
reinforce-
ment
*****
or
a "grouchy face"
*****
*
00*
* V *
*
\_1
*
* x x *
* A *
*
1-\
*
*****
*****
instead
of
'NOPE.
TRY
AGAIN.'
v (b)
presenting
a
pre-
specified
total
number of problems,
(c)
limiting
the
number of
allowable
mistakes
on
individual
problems
(or
all
problems), (d)
generalizing
the
multiplicands
to
create
a
more
flexible
range of problems
(includ-
ing
negative
numbers,
decimals,
etc.),
(e)
gathering
performance
data,
(f)
using
performance
criteria
to
make
diagnoses,
(g)
automatically
adapting
level
of
difficulty
based
on
diagnoses,
(h) adding
personal-
ized
instructions,
and
(i)
building
in
timing
com-
ponents,
jump-ahead
options
and
hints.
Conclusion
These
are
but
a
few
APL
"glass
box" programs
de-
signed
to
stimulate
students
to
think
about
selected
concepts.
Each of
the
sample programs
shown
here
can be used as
is
and, of
course,
can be extended
in
a myriad of
directions.
Other
topics
well-suited
for
this
pedagogical approach
include
topics
drawn
from
linguistics,
statistics,
mathematics,
engineer-
ing,
ecology,
and
physical
sciences.
The
challenge
to
educators,
then,
is
to
identify
such
topics
suitable
for
embodiment as
glass
box
programs,
to
search
out
the
kernel
concepts
to
be
taught,
and
to
lead
students
to
better
understand-
ings
of
those
concepts
using
a programming language.
Notes
/1/
A Programming Language
(abbreviated
APL)
is
a
mUlti-purpose computer programming language
devel-
oped
by
Kenneth
Iverson
of
IBM.
Originally
con-
ceived
as a
unifying
mathematical
notation,
APL
has
since
been used
successfully
in
fields
such as
busi-
ness,
scientific
research
and
education.
/2/
This program
is
similar
to
one
written
in
a
simplified
FORTRAN
by
John Loehlin
in
"Computer
Models
of
Personality",
Random
House,
NY,
1968.
/3/
This
question
is
treated
as
a theorem
by
Minsky
and
Papert
in
their
book
"Perceptrons;'
MIT
Press,
1970.
References
(1)
Papert,
S. "Teaching
Children
Thinking", M.LT.
LOGO
Memo
#2, Oct. 1971.
(2)
Iverson,
K.E.
"APL
in
Exposition",
IBM
Tech.
Report #320-3010,
Jan.
1972.
(3)
Berry,
p.
et.
al.
"APL
and
Insight:
The
Use
of
Programs
to
Represent Concepts
in
Teaching",
IBM
Tech. Report #320-3020,
March
1973. o
ADAPSO
-Continued
from
page
16
or
registration
run
counter
to
this
principle.
At
stake
in
this
case
is
equal
patent
treatment
for
the
products
of
small
software
companies.
The
myth
perpetuated
by
the
Government
and
CBEI\IA
--
that
computer-program embodied
inventions
are
not machine
inventions
--
has been exploded;
there
is
now
no
justification
for
the
denial
of
patent
protection
to
software-embodied machines.
20
Sobczak -Continued
from
page
9
MODULOS
1.
2 3
000
I I o , +-
BINARY
EN·
NUMBER
SYSTEM
CHARACTER
STEP 1
STEP
2
LEFT
SIDE
OF
UPC
SYMBOL ZERO
FIGURE 3
MANUFACTURER
IDENTIFICATION PRODUCT/PART
NUMBER
CODING
18 x 3
54
STEP
3
------------------
__________________
~)
69
STEP
4
--------------------------------7)
70
~
FIGURE 4
NEXT HIGHEST
MULTIPLE
OF
10 ? 1
?
MODULO
CHECK
CHARACTER
o
For
the
meaning
of
the
29
references
and
for
the
rest
of
the
brief,
please
ask
ADAPSO
for
a copy
of
the
printed
brief.
o
COMPUTERS
and
PEOPLE
for
December 1975
a
e
(
m
b
v.
d
u
(
c
(
t
b
c
d
o
b
P
s
a
h
m
m
f
t
P
w
c
c
A
t
o
t
t
r
p
t
c
U
C

r
k
t
f
c
Computers
and
People: Case 1
IIStuart Universityll
Dr.
Edward A. Tomeski
Contributing Editor, "Computers and People"
Fordham University
Bronx,
NY
10458
Stuart
University·
was
founded
in
the
1890s and
has
an
enrollment
of
more
than 10,000
full-time
equivalent
students
and
about 500
faculty
members.
Administratively,
the
university
consists
of
the
board
of
trustees,
the
president,
and
vice
pres-
idents
of
academic
affairs,
research,
financial
affairs,
student
affairs,
public
relations,
and
planning.
The
various
academic
units
are
adminis-
tered
by
deans
and
their
assistants.
Administra-
tion
of
Stuart,
a
private
institution,
has
histori-
cally
been
relatively
centralized
and
informal.
Recently,
there
has been a
gradual
movement
toward
some
decentralized
decision-making
as
well
as
for-
malizing
of
policy
and
procedures.
Long-range
planning,
budgeting,
and
institutional
research
are
all
receiving
increased
attention
at
Stuart.
Overall,
student
enrollment
has had
some
modest
growth. but
some
specific
educational
programs
have had
serious
declines
in
enrollment.
The
data
processing
center
began
operating
in
the
late
1950s. mostly
for
academic uses
in
the
areas
of
mathematics and
science.
At
that
time,
the
center
was
administered
on
a
part-time
basis
by
a
faculty
member.
In
the
1960s,
the
data
pro-
cessing
center
was
placed
under
the
supervision
of
a
full-time
computer
specialist
who
reported
to
the
Vice
President
of
planning.
Several
full-time
computer programmers were
hired.
In
a
few
years
the
major use
of
the
computer
was
for
administra-
tive
applications
(e.g.,
payroll,
accounting,
stu-
dents'
grades,
registration
records)
rather
than
for
academic work.
In
the
early
1970s, a
univer-
sity
computer committee
was
established;
the
com-
mittee
contained
representatives
from
administra-
tion
and academic
departments.
The
committee recom-
mended
the
establishment
of
an
integrated
informa-
tion
system
for
the
university.
A systems
task
force
was
designated
to
design
and develop such a
system.
The
head
of
the
task
force,
a
fUll-time
systems
analyst,
also
reported
directly
to
the
vice
president
of
planning.
Two
goals
were
set
for
the
task
force:
1.
The
design
and development
of
two
data
bases;
a
student
file
and a
faculty
file.
These would
constitute
the
beginning
of
an
inte-
grated
information
system. 2.
An
attempt
to
de-
velop a
university
simulation
model
to
be
used as
an
aid
in
predictive
planning
for
the
university.
';'Whilc
based
on
an
actual
si
tunti
on,
the
case
ma-
terial
has been
slightly
modified
to
conceal
the
identity
of
the
institution.
COMPUTERS and PEOPLE
for
December, 1975
From
time
to
time "Computers and People"
presents
a
capsule
case which
illustrates
practical
prob-
lems and
issues
related
to
computer technology
and
its
use
in
organizations.
A
case
includes
questions.
Readers
are
invited
to
compose
their
answers
to
the
questions
and,
if
they wish, mail
them
to
Dr.
Tomeski
before
the
10th
of
the
month
following
the
month
of
publication.
In
a
sub-
sequent
issue
each
case
will
be
discussed
and
selected
responses
by
readers
will
be
printed,
along
with
a proposed
solution
by
Dr. Tomeski.
Recently,
the
use
of
the
computer has been
in-
creasing
in
the
academic
areas
for
educational
and
research
purposes.
The
data
processing
center,
how-
ever,
has a mandate
to
concentrate
most
of
its
time
on
administrative
areas
and
the
integrated
infor-
mation system. Consequently,
there
have been
in-
creasing
complaints from
faculty
that
educational
technology
is
being
neglected,
and
that
such
ne-
glect
harms
the
quality
of
the
university
education
and
research
effort.
Some
professors
use
outside
computers, because
the
university's
computer
is
either
inadequate
for
larger
problems
or
the
response
time
is
poor. Because
of
the
increase
in
operating
costs
(e.g.,
faculty
salaries,
fuel
bills)
and
eco-
nomic
uncertainty,
the
university
is
operating
under
a very
tight
budget.
Questions:
1.
From
the
information
available,
do
you
think
the
faculty
complaints appear
justified?
What
can
the
faculty
do
to
alleviate
the
problem?
2.
What
are
the
dangers,
to
the
university,
if
more
computer power
is
not
made
available
to
academic and
research
users?
3.
What
is
your assessment
of
the
university
com-
puter
committee and
its
role
related
to
the
data
processing
center?
Can
you
reconcile
the
re-
sponsibilities
of
the
vice
president
of
planning,
director
of
the
data
processing
center,
and
the
systems
analyst
who
heads
the
systems
task
force?
4.
What
is
the
best
way
of
balancing
the
center's
service
between
the
administrative
and academic
users
of
the
university?
5.
What
actions
would
you
take
if
you
were
the
vice
president
of
planning?
0
21

Computer-Assisted
Tutorials
J.
L.
Caldwell
Dept.
of
Mathematics
University
of
Wisconsin-River Falls
River Falls,
WI
54022
Douglas Polley
Dept.
of
Mathematics
University
of
Minnesota
Minneapolis,
MN
55455
.
In
College
Mathematics
"While operating the programs, the students showed a most unusual enthusiasm
for
quadratic formula and line
problems."
Many
uses
of
computers
in
mathematics
education
are
well
known.
We
believe
that
our approach
dif.·
fers
in
important
aspects
from most
standard
uses.
It
is
hoped
that
this
note
will
encourage
others
to
experiment
with
techniques
similar
to
the
one
pre-
sented.
Analyzing Student Answers
The
programs which
the
authors
have
designed
and
written
were
specifically
intended
to
analyze
the
students'
answers
to
computational
problems.
We
call
this
approach
tutorial
(although
this
terminol-
ogy
is
nonstandard)
because
the
programs mimic
the
role
of
a
tutor
in
the
traditional
sense.
No
new
material
is
presented
via
the
computer.
We
assume
that
the
student
has
received
instruction
in
basic
formulae
before
using
the
programs.
If
the
student
responds
incorrectly
to
problems
generated
by
the
program,
the
program
analyzes
the
student's
answers
in
an
attempt
to
identify
common
errors.
The
first
programs
deal
with
quadratic
equations
and
equations
of
straight
lines.
A program
dealing
with
sums
of
rational
functions
is
under
construc-
tion.
Problems with Randomly
Chosen
Parameters
The
format
of
all
the
programs
is
the
same.
The
student,
seated
at
a
teletype,
receives
a problem
with
randomly chosen
parameters.
The
student
then
solves
the
problem and
enters
his
solution.
If
his
solution
agrees
with
the
computer's
solution,
then
another
problem
is
presented.
If
the
student's
sol-
ution
is
incorrect,
the
computer
then
works
the
pro-
blem
incorrectly
in
several
different
ways,
each
time
checking
its
answer
against
the
student's.
If
a match
is
obtained,
then
the
computer
suggests
that
the
student
has
made
a
certain
error
and
asks
him
to
try
again.
If
none
of
the
incorrect
answers match
the
student's
answer,
then
the
computer
will
check
the
student's
work
step
by
step.
For example,
in
the
case
of
the
quadratic
equation
program,
the
stu-
dent
is
first
asked "What
did
you
get
for
A,
B,
C?"
and
then
later
"What
did
you
get
for
B
-4AC?"
Fi n-
ally,
if
the
student
does not
enter
the
correct
an-
swer,
he
receives
a
detailed
solution.
(For
over
90%
of
the
problems
we
have checked
thus
far,
the
student
has
eventually
entered
the
correct
answer.)
If
a
student
requires
detailed
solutions
to
several
problems,
he
is
asked
to
contact
the
instructor.
Reprinted
with
permission from
the"
American Mathematical
Monthly",
October,
1975
22
Programming
Languages
The
programs were
written
in
FORTRAN
and
imple-
mented
on
a
CDC
6400 computer,
but
other
choices
would
serve
well
also.
In
particular,
the
size
of
the
CDC
6400
is
unnecessary
because
such programs
are
easily
divided
into
subprograms.
FORTRAN
could
be
replaced,
and
in
fact
the
programs
are
currently
being
translated
into
BASIC
to
premit
their
use
on
other
time
sharing
systems.
The
use
of
an
instruc-
tional
dialogue
language (IOL) would
greatly
facili-
tate
the
writing;
but
unfortunately
the
authors
know
of
no
IOL
which has
the
capability
of
generating
problems
at
random.
Hopefully
this
void
will
soon
be
fi
lled.
The
principal
use
of
the
programs has been
by
precalculus
and
linear
algebra
students
at
the
Uni-
versity
of
Wisconsin-River
Falls
and
the
Minneapolis
and Morris campuses
of
the
University
of
Minnesota.
In
addition,
several
other
members
of
the
Minnesota
Educational
Regional
Interactive
Time-Sharing System
(MERITSS)
have been
involved.
Those
readers
desiring
additional
information
about
the
programs
are
invited
to
write
UWRF.
Discovering the Source
of
a Student's Error
It
was
our
intention
to
identify
the
source
of
a
student's
error
as
soon as
possible
with
minimal
interrogation
of
the
student.
This
presents
some
interesting
theoretical,
as
well
as
practical,
ques-
tions.
On
the
theoretical
side,
we
may
ask
just
how
much
can
we
tell
about
the
source
of
the
error
based
on
our knowledge
of
the
incorrect
response,
the
cor-
rect
response,
and a knowledge
of
the
technique
being
used.
On
the
practical
side,
we
have
the
considera-
tions
motivated
by
the
following
example
of
two
in-
correct
solutions
to
the
problem:
"Find
the
equation
of
the
line
through
the
point
(2,
-3)
wi
th
slope
2."
I
II
y 3
2(x
-2) y + 3 =
2(x
-
2)
y 3 2x 4 y + 3 = 2x -4
y 2x y = 2x -
COMPUTERS and PEOPLE for December,
1975

J.
In
I
the
mistake
occurs
in
the
first
line,
while
in
II
the
error
is
in
the
subtraction
of
the
last
line.
In
both
cases
the
answer
given
is
the
same.
Although
the
existence
of
the
error
can
be
readily
identified,
and
it
may
be
reasonable
to
assume
that
any
incorrect
answer of
the
form y =
2x
- 1
is
due
to
one
of
these
methods,
we
still
cannot
tell
which
is
the
case.
In
programming
the
response
to
this
situation
we
may
issue
a message
of
the
form
"I
think
you computed y -
y.
incorrectly,
or
perhaps
you
com-
bined terms
incorrectly."
Alternatively,
we
may
in-
quire
"What
did
you
get
for
y -
y,
?"
While
the
latter
choice
is
less
ambiguous,
it
is
more
diffi-
cult
to
program because
it
involves
additional
de-
cisions.
In
situations
where
the
error
is
not
among
those
errors
deemed most
likely
to
occur,
it
may
be
acceptable
to
respond
in
the
former manner.
System
Design
Considerations
For
those
who
want
to
develop a
series
of
inte-
grated
tutorial
programs
there
will
be
some
addi-
tional
system
design
considerations.
One
problem
is
how
to
allow
a
student
to
progress
through problems
of
varying
levels
of
difficulty.
One
possibility
is
to
have a
level
indicator
which
determines
the
dif-
ficulty
of
the
problem
generated
as
well
as
the
de-
tails
of
the
interrogation
of
the
student.
In
the
case
of a
student
who
has
made
several
mistakes
we
would
assign
a lower number and
ask
him
to
enter
his
work a
step
at
a
time.
For a
student
who
is
not
making
many
mistakes
we
would not ask
for
as
many
intermediate
steps
and
give
more
opportunities
to
correct
mistakes
before
we
present
the
solution.
Another item
of
some
import
will
be a
series
of
software
routines
for
such
things
as
reading
student
input
(e.g.,
polynomials)
and
extracting
relevant
data.
Other
such
routines
might
include
a means
for
comparing
algebraic
expressions
to
determine
if
they
are
equivalent
(see
Uttral
[6]).
Of
course,
once
such
routines
have been
written
they can
serve
a
large
number
of
tutorial
programs.
Immediate Individualized Help
We
believe
that
this
approach
is
a
valid
utiliza-
tion
of
computer
facilities
because
it
offers
imme-
diate,
individualized
help
to
students
in
a manner
that
can be
duplicated
only
by
actual
consultation
with
an
instructor.
The
advantage
to
the
student
is
a
source
of
immediate feedback which might not
be
available
if
he
had
to
compete
with
other
students
for
help
from
the
instructor.
The
advantage
to
the
instructor
is
more time
to
deal
with
conceptual
pro-
blems which
are
basically
computational
in
nature.
Reduction
in
Teletype Time
We
feel
that
this
approach has
advantages
over
the
setting
in
which
the
entire
course
is
presented
via
the
computer.
First
there
is
a
reduction
in
the
teletype
time
required
because
the
student
first
at-
tends
class
or
perhaps
studies
a programmed
text,
then
comes
to
the
computer
to
work
problems.
Even
more
teletype
time can
be
saved
if
our
system
is
modified
by
assigning
to
the
students
problems
that
are
stored
in
the
"computer. Then
the
student
would
come
to
the
computer only
with
problems he could not
work. (Minimizing
teletype
time
is
important
because
it
is
often
more
scarce
than
computer
time.)
A
sec-
ond
advantage
is
that
tutorial
programs
are
compat-
ible
with
different
presentations
of
the
course
ma-
terial,
thus
leaving
more
control
in
the
hands
of
the
individual
instructor.
COMPUTERS and PEOPLE for December, 1975
Experience
in
Developing the Programs
Another
benefit
of
a system
of
tutorial
programs
is
the
experience
gained
in
developing
them.
The
authors
are
currently
having
senior
mathematics
edu-
cation
students
create
additional
programs because
we
believe
that
they
will
thus
obtain
a
better
un-
derstanding
of
the
errors
a
student
may
make
and
also
develop
a
facility
in
explaining
the
material.
The
student
designer
will,
of
course,
learn
much
in
the
area
of
system programming.
Enthusiasm
Our
experience
with
programs developed so
far
has
indicated
that
there
is
considerable
potential
in
this
type
of
computer-assisted
instruction,
particu-
larly
at
the
college
algebra
level.
The
manipula-
tive
nature
of
many
of
the
topics
in
college
alge-
bra
(such
as
determinants,
systems
of
equations,
etc.)
makes
them
suitable
for
the
problem and answer
analysis
framework. Programs
in
this
area
would
also
provide
review
material
for
calculus
students
whose
problem-solving
techniques
need improvement.
In
response
to
a
questionnaire.
students
who
have used
existing
programs
indicated
they
considered
the
pro-
cess
most
helpful
and would
recommend
it
to
their
fellow
students.
They
also
expressed
a
willingness
to
try
new
programs
when
they become
available.
While
operating
the
programs.
the
students
showed
a
most
unusual
enthusiasm
for
quadratic
formula and
line
problems.
It
was
most
encouraging
to
see
the
students'
satisfaction
in
obtaining
the
correct
sol-
tions
with
the
assistance
of
the
computer. For
these
reasons
the
authors
hope
that
this
approach
will
be
expanded and improved.
References
I.
E.
D.
Koffman, A
generative
CAl
tutor
for
com-
puter
science
concepts,
AFIPS
Conference
Pro-
ceedings,
40, 1972.
Spring
Joint
Computer
Con., p. 379.
2.
H.
A.
Lekan, Index
to
Computer
Assisted
Instruc-
tion,
Harcourt.
Brace.
Jovanovich.
New
York.
1971.
3.
A.
W.
Luehrmann. Should
the
computer
teach
the
student,
or
vica
versa?,
AFIPS
Conference
Pro-
ceedings,
40, 1972.
Spring
Joint
Computer
Con.,
p.
407.
4.
W.
Stenberg,
Computing
in
the
high
school
--
past
present
and
future
--
and
its
unreasonable
effectiveness
in
the
teaching
of
mathematics,
AFIPS
Conference
Proceedings,
40. 1972.
Spring
Joint
Computer Con., p. 1051.
5.
P.
C.
Suppes.
M.
Jerman,
D.
Brian
et
al.,
Com-
puter
Assisted
Instruction:
Stanford's
1965-
1966
Arithmetic
Program. Academic
Press.
New
York, 1968.
6.
W.
R.
Uttral.
Reaction
paper.
Computer
Assisted
Instruction
and
the
Teaching
of
Mathematics,
National
Council
of
Teachers
of
Mathematics,
Inc.,
1969. o
23
Computing
and
Data
Processing
Newsletter
COMPUTER "SCENARIOS" FOR THE APPLICATION
OF PESTICIDES BEFORE THEY ARE APPLIED
Robert Silber
Dept.
of
Information
Services
Michigan State University
East Lansing, Mich.
48824
Biological
and computer
scientists
at
Michigan
State
University
are
going
to
attempt
to
head
off
ecological
and
environmental
crises
before
they
start.
They
will
develop
computer
"scenarios"
of
the
expec-
ted
future
effects
of
pesticide
applications.
They
are
funded
by
a
$360,000
grant
from
the
federal
Envi-
ronmental
Protection
Agency. Under
the
general
man-
agement
of
Pesticide
Research
Center
at
MSU,
a
re-
search
team
of
biologists,
a group
of
systems
scien-
tists
and
pesticide
experts
will
examine
the
environ-
mental
impact
of
12
of
the
most commonly used
"soft"
pesticides.
Dr.
Erik
Goodman,
assistant
professor
of
Electrical
Engineering
and Systems
Science
will
head
the
group.
.
Soft
pesticides
--
usually
organic
phosphorous and
carbamate
compounds
--
are
generally
considered
safer
by
environmentalists
because
of
their
relatively
ra-
pid
breakdown
to
nontoxic
compounds. But
in
nature,
things
are
rarely
simple
and
loss
of
toxicity
in
the
laboratory
doesn't
mean
that
a
chemical
will
behave
identically
in
the
field.
Even
transient
toxicity
can have
long-term
detrimental
effects
in
an
ecolo-
gical
system.
Temperature,
humidity,
or
the
activity
of
bacteria
and
fungi
can
drastically
alter
the
per-
sistance
of
a
pesticide.
To
forecast
the
effects
of
an
application,
these
and a number
of
other
variables
should
be,
but
rarely
are,
taken
into
account.
The
characteristics
of
an
ecosystem
--
its
geogra-
phic
location,
the
kinds
of
animals
and
plants
in
it,
its
physical
and
chemical
properties
--
all
can have
tremendous
i~fluence
on
the
effects
of
a
given
~esti
cide.
A
chemical
application
having
minimal
side
effects
in
a
northern
forest,
could
be
disasterous
to
shellfish
living
in
waters
adjacent
to
a
southern
farm
field.
Because
the
ecological
consequences
of
an
improper
chemical
application
can be
severe,
and
because
there
are
so
many
variables
to
consider,
we
need computer
simulations
to
handle
efficiently
all
the
information
relevant
to
rational
decisions.
With
many
scientist
contributing
information
from
many
places,
solving
such a problem
resembles
working
on
a
jigsaw
puzzle
without
being
sure
of
having
all
of
the
pieces.
Computer models
will
help
direct
future
research
by
putting
available
information
in
perspective,
allowing
scientists
to
identify
infor-
mation
gaps and
to
establish
relevant
research
goals.
24
COMPUTER MONITORS PRESCRIPTIONS
AND
HELPS PREVENT ADVERSE DRUG REACTIONS
Ken Fleming
Executive Assistant
for
Public
Affairs
Group Health Cooperative
of
Puget Sound
200
-15th Avenue East
Seattle,
WA
98112
Prescription
drugs
offer
remedies
for
almost
everything
from
circulatory
disease
to
headaches,
these
same
drugs
can pose
hazards
if
taken
in
the
wrong
combinations.
The
average
adult
today
consumes
thousands
of
doses
of
medication
a
year.
Tranquilizers,
antacids,
aspirin,
antibiotics,
cold
remedies
--
the
list
is
long
and
diverse.
We
know
of
at
least
17,000
documented drug
inter-
actions
with
other
drugs,
foods,
miscellaneous
sub-
stances,
conditions
and
circumstances.
Many
of
these
interactions
are
harmless;
others
can produce symp-
toms
requiring
treatment,
or
even
endanger
life.
It
costs
an
estimated
$2
billion
a
year
to
treat
people
in
the
United
States
suffering
adverse
drug
reactions.
Nearly
20
per
cent
of
all
hospital
days
in
the
nation
are
devoted
to
care
of
these
patients.
To
help
prevent
these
mishaps,
Group
Health
Coop-
erative
has
installed
a computer system
to
monitor
more
than
one
million
prescriptions
issued
yearly.
The
Co-Op
is
a
prepaid
health
care
provider.
and
has m6re
than
200,000
m~mbers
in
the
Puget Sound
area
and a
medical
staff
of
200.
It
operates
a
major
hos-
pital
and
ten
neighborhood
medical
centers,
each
with
its
own
pharmacy.
Patient
profiles,
listing
the
medication
history,
drug
allergies
and
chronic
illnesses
of
all
GHC
pati-
ents,
are
stored
in
a
central
computer.
Another
file
lists
all
pharmaceuticals
in
stock.
their
chemical
formulations,
side-effects
and
interaction
problems,
if
any.
This
information
is
instantly
accessible
by means
of
remote
TV-like
computer
terminals
in
the
outlying
pharmacies.
When
a
Co-Op
member
presents
a
new
prescription,
the
pharmacist
enters
the
patient's
name
and number
into
the
system,
which
then
scans
the
appropriate
medication
history.
If
the
drug
prescribed
will
re-
act
negatively
with
those
the
patient
already
is
tak-
ing
--
including
patent
medicines
--
the
computer .
automatically
stops
the
process
and
indicates
that
the
prescription
should
not
be
filled.
If
the
pati-
COMPUTERS and PEOPLE for December.
197G
."
TIl(
infc
inpi
COl
1(J
2S
Cal
2~
2!
COl
2'
Co,
l'
Co
Co
2

'tarnation
[A]
[F]
[A]
[A]
[N]
ent's
computer
record
shows an
allergy
to
the
medica-
tion,
or
one
of
its
ingredients,
the
system
displays
this
information
on
the
remote
terminal
screen.
In
either
case,
the
pharmacist
then
contacts
the
prescribing
physician
and
requests
alternative
ther-
apy.
For
example,
if
a
person
is
allergic
to
penicillin,
the
doctor
will
prescribe
a
different
type
of
anti-
biotic
drug.
But
if
this
substitute
should
contain
some
form
of
penicillin,
the
computer
will
halt
the
prescription-filling
process
and
alert
the
pharmacist.
The
effects
of
certain
antibiotics
can be
nulli-
fied
if
taken
in
combination
with
food
or
antacids.
If
a Group
Health
Cooperative
member
regularly
takes
antacids,
this
fact
will
be
noted
in
his
computer
record.
When
this
patient
presents
a
prescription
for
an
antibiotic,
the
computer
will
alert
the
phar-
macist
who.
then
advises
the
patient
how
to
avoid
the
interaction.
To
deal
with
another
situation,
the
computer
sys-
tem
will
reject
a
prescription
for
a
sugar-based
cough
syrup,
if
that
should
be
ordered
inadvertently
for
a
diabetic.
If
no
problems
appear
when
the
patient's
profile
is
scanned,
the
new
prescription
is
added
to
the
record
and a
label
is
automatically
printed.
The
system
does
not
replace
the
trained
pharmacist
or
physician,
but
it
serves
as
a
major
aid
in
dispen-
sing
the
most
effective
and
safe
medications.
At
the
same
time,
it
reduces
the
tedious
chores
which
phar-
macists
and
their
assistants
would have
to
perform
by
hand.
All
pharmacies
in
the
State
of
Washington soon
will
be
required
to
maintain
medication
profiles
on
regular
consumers.
The
Cooperative's
computer system
will
keep
these
records,
ensuring
compliance
with
the
new
ruling
and
conserving
thousands
of
hours
of
phar-
macists'
time
--
time
that
would have been
spent
on
maintaining
manual
records.
Another
benefit
of
the
system
is
that
the
computer
is
programmed
to
monitor
the
drug
inventory.
So
the
size
of
the
inventory
can be
reduced,
and
costs
cut,
without
fear
of
sudden
exhaustion
of
stock.
The
sys-
tem
will
generate
reorders
when
quantities
are
low.
The
newly-installed
computer
system
will
save
money
and,
in
addition,
provide
better
service
to
the
CO,Op
members, making a
larger
contribution
to
their
good
health.
The
computer used
is
an
IBM
System 370 Model 125.
MINICOMPUTER HELPS CUT
UNIVERSITY'S
ELECTRIC BILLS
John Kane
Hewlett Packard
1501
Page
Mill
Road
Palo
Alto,
CA
94304
Administrators
at
the
University
of
California
at
Berkeley
have
installed
a
minicomputer
system
to
mon-
itor
the
use
of
about
$125,000
per
month
worth
of
electrical
energy.
The
system
is
helping
facility
managers
here
discover
exactly
where and
how
power
is
consumed and
how
best
to
reduce
the
large
monthly
bi
11.
COMPUTERS and PEOPLE
for
December,
1975
While
itself
consuming
no
more
energy
than
a
room
air
conditioner,
the
system
monitors
more
than
20
megawatts
of
power used
in
75
buildings
on
this
cam-
pus.
The Lawrence
Berkeley
Laboratory
is
separate
electrically
and
accounts
for
another
20
megawatts.
The
system
includes
a
data
acquisition
and
pro-
cessing
system
containing
a
minicomputer
and
31
transducers
which
sense
voltage
and
current
flow
in
the
feeder
circuits
to
all
the
campus
buildings.
The
computer
scans
the
transducers
once
per
minute
to
take
a
new
set
of
readings.
l~ese
transducers
are
situated
in
the
central,
high
voltage
distribu-
tion
cubicles,
each
of
which
suppliesa
single
large
building
or
several
small
buildings.
Signals
from
the
transducers
are
conditioned
by
a
scaling
device.
Then
they
travel
over
both
campus
and
dedicated
telephone
company
lines
through
an
analog-to-digital
converter
and
finally
arrive
at
the
computer.
In
real
time,
the
computer
generates
displays
of
energy
use
in
each
of
the
25
cubicles.
The
displays
are
monitored
by
a
console
in
the
plant
engineer's
office,
and
displayed
data
is
also
stored
on one
of
two
disc
drives.
Later,
the
displays
are
plotted
offline
on
a
digital
plotter,
and
graphi-
cally
display
patterns
of
energy
use
over
periods
of
a
day,
a week,
or
a month. A
teletype
is
also
avail-
able
for
producing
data
tabulations
and
for
program
development
entries
and
output.
The
Berkeley
system
is
being
used
to
examine
the
two
main
factors
which
go
into
the
calculation
of
the
institution's
monthly
bill
--
energy
demand and
energy
usage.
Demand
represents
how
much
energy
the
campus
may
require
at
any
given
moment,
while
the
power
or
energy
used
is,
of
course,
the
summation
for
a
given
time
period.
High demand peaks
occur
at
the
university
when
several
experimental
apparatus
such
as
the
main
campus' wind
tunnel,
small
nuclear
reactors,
and
plasma
experiments
are
turned
on
simultaneously
and
superimposed
on
the
ordinary
"background"
loads
such
as
lighting,
heating,
cooling
and
continuously-run
experiments.
A
high
demand peak pays a heavy
penalty.
To
help
defray
the
costs
of
turbines,
generators
and
trans-
mission
lines
necessary
to
meet
the
highest
peaks
which
may
arise,
no
matter
how
short
their
duration,
the
Pacific
Gas
and
Electric
Company
(PG
&
E)
incor-
porates
peak demand
into
the
billing
equation
very
significantly.
In
charging
for
peaks
in
demand,
PG
& E employs
what
is
called
a
"ratchet
effect",
whereby
the
high-
est
peak
occurring
during
any
half-hour
period
for
the
month
is
carried
forward
in
calculating
the
next
II
monthly
bills,
or
until
a
new
half-hour
peak
is
registered
in
some
succeeding
month.
This
ratcheted
peak
is
averaged-in
with
each
month's
actual
peak.
As
an example,
suppose
a
three-megawatt
peak
over
and above
the
normal demand
for
a
half-hour
period
is
recorded
but
never
repeated
again.
At
present
demand
costs
--
about
$1800
per
megawatt
--
this
amounts
to
$5400
extra
for
the
first
month and $2700
for
the
next
11
months
for
a
total
cost
of
$35.100
for
the
year
for
that
one
peak.
Facility
managers
are
taking
aim
at
these
costly
peaks
in
demand. They
are
beginning
to
knock them
down
by
a
notch
or
two
through
using
the
minicomputer
system
to
observe
their
occurrence.
25
A
lamp
removal program
is
underway
to
eliminate
all
unnecessary
lamps
while
still
providing
illumin-
ation
required
for
a
practical
environment.
A
pro-
gram
designed
to
upgrade
lighting
fixtures
to
diffuse
light
more
efficiently
has begun.
Also,
a
scheduling
program
is
being
set
up
whereby
experiments
requiring
substantial
amounts
of
electricity
are
staggered,
avoiding
simultaneous
use
wherever
possible
and
util-
izing
evening and weekend time
periods
when
back-
ground
loads
are
lowest.
A look
at
the
pen
plots
generated
by
the
computer
for
Moffitt
Library
demonstrates
how
revealing
the
detailed
information
on
electrical
demand
can
be.
Analysis
showed
that
most
of
Moffitt's
load
was
the
result
of
lighting
rather
than
experimental
equip-
ments,
machinery,
or
HVAC
systems.
Examination of
the
plots
also
revealed
two
unaccounted
for
and
cost-
ly
afternoon
demand
peaks,
two
weeks
apart.
A check
of
weather
conditions
(the
weather
bureau
hai
a
sta-
tion
on
campus) showed
these
were
exceptionaily
warm
winter
days and
air
conditioning
units
were
turned
on.
The
100
kw
air
conditioning
units
operate
automa-
tically
for
Moffitt
from
sensors
located
outdoors.
The
building's
extensive
fluorescent
lighting
pro-
vides
all
the
heat
necessary
on
most
days.
Facili-
ties
managers concluded
that
by
turning
off
50
per-
cent
of
the
lights
on
warm
days,
the
air
conditioners
needn't
be
used as
often.
This
was
accomplished
without
impairing
normal
use
of
the
building.
The
monitoring
of
load
peaking
will
have
other
benefits
as
well.
The
system
functions
as a main-
tenance
tool
for
electricians.
On
the
console,
feed-
er
lines
can be
identified
and
instantaneous
readings
of
voltage
and
current
can
be
taken.
This
permits
electricians
to
find
overloaded
lines
and
switch
loads,
preventing
individual
transformers
and
cables
from
taking
the
brunt
of
the
load,
which
shortens
their
productive
lives.
The
system
installation
was
very
inexpensive.
The
transducers
cost
about
$30
each;
there
was
little
special
wiring
necessary.
Each
of
the
31
monitoring
points
cost
about $150
to
install
completely.
The
monitoring
system should pay
for
itself
in
two
years.
If
so,
the
saving
in
monthly
electric
bill
would
be
more
than
10
percent.
PROMOTING THE
USE
OF A COMPUTER IN TEACHING
News
Service
The
University
of
Iowa
700 Jefferson Building
Iowa City, IA 52242
The
University
of
Iowa has
received
a
National
Science
Foundation
grant
of
$375,000 so
that
it
can
serve
as
a
center
for
the
review,
testing
and
dissem-
ination
of
selected
computer-based
materials
for
col-
lege
science
courses.
The
project
is
being
carried
out
by
CONDUIT,
a
consortium
of
eight
educational
computer networks
directed
by
James
W.
Johnson
of
The
University
of
Iowa Computer
Center.
The
main
objective
of
CONDUIT
is
to
improve
edu-
cation
by
providing
for
instructors
and
students
alternative
ways
of
learning
concepts
and methods.
Because of
the
newness
of
the
use
of
computer
tech-
nology
in
education,
structures
to
effectively
dis-
seminate
innovations
do
not
now
exist.
The
IS-month
grant
will
provide
support
for
the
CONDUIT
central
office
on
the
U
of
I campus
to
re-
26
view,
test,
evaluate,
and
distribute
the
best
avail-
able
computer-based
materials
for
classroom
use
in
the
physical
and
social
sciences.
This
activity
will
require
establishing
quality
standards
for
mat-
erials;
it
also
requires
the
development
of
mechan-
isms
for
delivering
materials
to
instructors.
The
grant
is
from
the
Technological
Innovations
in
Education
Group
of
the
National
Science
Founda-
tion;
it
will
enable
CONDUIT
to
continue
work
on
the
development
of
procedures,
techniques,
standards
and
systems
for
disseminating
complex computer-based
instructional
packages.
In
addition,
CONDUIT
will
assemble
panels
of
ex-
perts
to
provide
state-of-the-art
reports
on
instruc-
tional
computing
in
the
fields
of
chemistry,
physics,
economics,
biology,
mathematics,
sociology,
geogra-
phy,
political
science,
business
and psychology.
CONDUIT
was
founded
in
1972
to
study
and promote
the
exchange
of
computer-based
instructional
materi-
als.
The
original
members
of
the
CONDUIT
consortium
were Dartmouth
College.
North
Carolina
Educational
Computing
Service,
Oregon
State
University,
The
Uni-
versity
of
Iowa. and
the
University
of
Texas,
Austin.
The
project
will
be expanded
this
year
with
the
in-
clusion
of
10
new
members
in
the
consortium.
The
use
of
the
computer
to
provide
new
and
excit-
ing
techniques
for
learning
has become
much
more
fea-
sible
because
of
dramatic
decreases
in
equipment
costs.
But
the
real
effectiveness
of
the
new
tech-
nology depends
on
the
dissemination
of
ideas
on
the
use
of
computers
in
education.
The
main
job
of
CONDUIT
is
to
assure
that
the
best
ideas,
some
of
which
currently
pass
unnoticed,
are
widely
dissem-
i
nated
and
adopted.
0
3.
FAEOUENCYM:n~:~~
!~~=SW;;::PA$~
.50
4.
LOCATION
OF
KNOWN
OFFtCEOf
PUBLICATION
(8"...1.
cit",
COlI"",.
"ar.
IPId
ZIP
cOlI"
IN.,
prin,.,..,j
Fore
go
615 Washington
St..
Newtonville.
Middlesex
County.
Mass. 02160
NAMES AND ADDRESSES OF PUBLISHER, EDITOR, AND MANAGING EDITOR
PUIILISHER
/N
........
"d..Jd
.....
}
Edmund
C.
Berkeley.
615 Washington
St
..
Newtonville.
Mass. 02160
EDITOR
(Na".
.....
ndaddn
..
,
Same
MA.NAGING
EDITOR
(Nam.gnd
addNU)
Same
7.
OWNER
(If
OUlII .. d
by
a
corpo""io
...
It.
IIG_
.1141
~
'"'"'
k
""ted
.tlef
""0
(mmecllat.ly
,h
..
Nund
..
,.
'hI'
"ll'Inl"
.,nd
addn
....
o(
"ocArhald
.....
ownin,
01'
holdln,
J
pl'rt:l'n'
or
mo",
of
fo'"
_au"f
of
doell.
"
"ot
owned
by
•
corporaHon,
fh.
"om
..
o"d
Gddre,H"
of
Ihe
Indi
...
lduol
owne",
",ud
be
'I
....... "
ownl/a
b)l
II
pcvtrwrMlp
or
0""."
Itllincorporatl/d
fl~m.
It.
110m.
AIId
oddreu
•
..
_II
..
th.d
of
.och
~~~~
of
New
Yor~~~LW.a.Sh'~ntnn~;,
N.
W:.'
M.
n?"n
James
J.
CrYan
33
Sandra
"ane. W.vn.
N.T
n747n
Ed
Burnett
40
Eas'
to
St
Npw
Ynrk.
NY
10003
8. KNOWN BONDHOLDERS, MORTGAGEES, ANO
OTHER
SECURITY HOLDERS OWNING OR
HOLDING
1 PERCENT OA MORE OF
TOTAL
AMOUNT
OF BONOS MORTGAGES OR
OTHER
SECURITIES I
the",
0"'
"anI!'
.odoll!'
9.
FOR
OPTIONAL
COMPLETION BY PUBLISHERS
MAILING
AT
THE
REGULAR
RATES
(Section
1:12.121,
Polloi
S.MJice Man!lal!
39
U.
S,
C.
3626
provid
••
In
pe,t,n.nt
pe":
"No
peraon
who
would
hMld
~n
ontltlOd
10 mart
mener
undor
former
"c1ion
4359
of
th
•• 1itle
:::~~I:I:~
·t~c':n:":;,.:n:;
;~·.ur:::e~,:~lded
undor
thl,
lIU~on
un
........
fil"
."n!llily
....
111'1
tho
Pottl'
Sorvlco
.....
ri1t11n'.qu.ufor
!;t=~~:::~:I:
:~~~;~:.:r~~I~;n~.o~,
~.i~:~~U10,
I
....
1"IIby
Nqueft
permlalon
10
meil
tho
pubilcetion
nemed
In
It.",
1
at
1ho
r.duced
po.11190
~
•
.;:~:~gh.,.,blt'ino
..
",an
......
or_"""J
j
10.
~~~u;?~~::~~~
BY NONPROFIT
OAGANIZATIONS
AUTHORllEOTO
MAIL
AT
SPECIAL
AATES
(Sl!'rtioli
132.122
PDfla!
Sl!'roiC"'1!'
B.
PAID
CIRCULATION
1.
SALES
THROUGH
OEALERS
ANO
CARRIERS,
STREET
VENOORS
ANO
COUNTER
SA
LES
O.
FREE
DISTRIBUTION
BY
MAIL,
CARRIER
OR
OTHER
MEANS
SAMPLES,COMPLIMENTARY,AND
OTHER
FREE
COPIES
AVERAGE
NO. COPIES
P~:gE~~DtY~~~~S
6350 5800
5326 4283
5326 4283
100 100
E.
TOTAL
OISTRIBUTION
(SUi'll
ofC.1Id
DJ
5428 4383
F.
COPIES
NOTOIliTRIBVTED
.-----1---..::..:.:"'-----+---------1
1.
~~~~CRE
..
":.~T~~~·OVER.
UNACCOUNTED,
SPOILED
922 1417
6350
5800
I
cerJ:ify
that
the statements made
by
me above are
correct
~
~I~~~J~~~E
OF
EOITO~
...
U:LI:EfII,
BU51,..F.SS
""A,..AO(;"'.
I
andcolnplete.
".
t:~
C'.~
~tr9;'s
3526
(Page 1)
(See
inJtructiollJ
on
f'n't.'neJ
I
.cOMPUTERS and PEOPLE
for
December, 1975
....
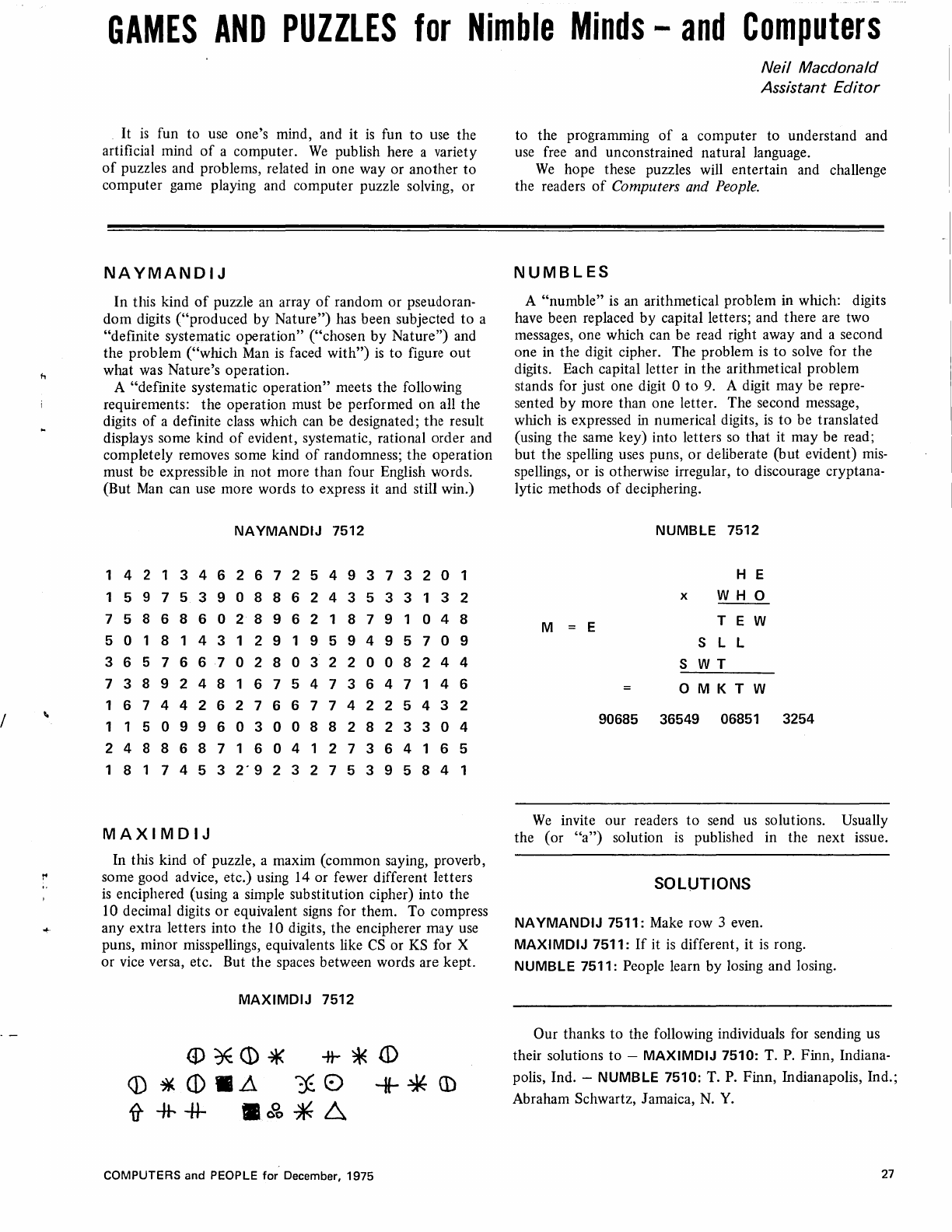
/
GAMES
AND
PUZZLES
for
Nimble
Minds
-
and
Computers
It
is
fun to use one's mind, and it
is
fun
to
use the
artificial mind
of
a computer.
We
publish here a variety
of
puzzles and problems, related
in
one way or another
to
computer game playing and computer puzzle solving, or
NAYMANDIJ
In
this kind
of
puzzle an array
of
random or pseudoran-
dom digits ("produced
by
Nature") has been subjected
to
a
"definite systematic operation" ("chosen
by
Nature") and
the problem ("which
Man
is
faced
with")
is
to figure
out
what was Nature's operation.
A "definite systematic operation" meets the following
requirements: the operation must be performed
on
all the
digits
of
a definite class which can be designated; the result
displays some kind
of
evident, systematic, rational order and
completely removes some kind
of
randomness; the operation
must be expressible
in
not more than four English words.
(But
Man
can use more words to express it and still win.)
NA
YMANDIJ
7512
142
1
346
2 6 7 2 5
493
7 3
201
1 5 9 7 5 3 9
088
6
243
5
331
3 2
7 5 8 6 8 6
028
962
1
879
1
048
5018143
1
291
9
594
9 5
709
3 6 5
766
7
028
032
2
008
244
738
9 2 4 8 6 7 5 4 7 3 6 4 7 4 6
1 6
744
2 6 2 7 6 6 7 7 4 2 2 5
432
1 1 5
099
6 0 3 0
088
2 8 2 3
304
2 4 8
868
7 1
604
2 7
364
6 5
1 8
745
3
2'9
2 3 2 7 5 3 9 5 8 4 1
MAXIMDIJ
In this kind
of
puzzle, a maxim (common saying, proverb,
some good advice, etc.) using 14 or fewer different letters
is
enciphered (using a simple substitution cipher) into the
10 decimal digits
or
equivalent signs for them. To compress
any extra letters into the 10 digits, the encipherer may use
puns, minor misspellings, equivalents like
CS
or
KS
for X
or vice versa, etc. But the spaces between words are kept.
MAXIMDIJ
7512
(D~CD*
<D
~
CD
•
.tl
1r**
.~
COMPUTERS and PEOPLE
for
December, 1975
Neil Macdonald
Assistant Editor
to the programming
of
a computer to understand and
use free and unconstrained natural language.
We
hope these puzzles will entertain and challenge
the readers
of
Computers and People.
NUMBLES
A
"numble"
is
an arithmetical problem in which: digits
have been replaced
by
capital letters; and there are two
messages, one which can be read right away and a second
one in the digit cipher. The problem
is
to
solve for the
digits. Each capital letter in the arithmetical problem
stands for just one digit 0 to 9. A digit may be repre-
sented
by
more than one letter. The second message,
which
is
expressed
in
numerical digits,
is
to
be translated
(using the same key) into letters
so
that it may be read;
but the spelling uses puns, or deliberate (but evident)
mis-
spellings, or
is
otherwise irregular,
to
discourage cryptana-
lytic methods
of
deciphering.
M E
90685
NUMBLE
7512
x
H E
WHO
T E W
S L L
S W T
OMKTW
36549 06851 3254
We
invite our readers
to
send us solutions. Usually
the (or
"a")
solution
is
published in the next issue.
SOLUTIONS
NA
YMANDIJ
7511: Make row 3 even.
MAXIMDIJ
7511:
If
it
is
different, it
is
rong.
NUMBLE
7511: People learn by losing and losing.
Our thanks to the following individuals for sending us
their solutions to -
MAXIMDIJ
7510: T.
P.
Finn, Indiana-
polis, Ind. -
NUMBLE
7510: T.
P.
Finn, Indianapolis, Ind.;
Abraham Schwartz, Jamaica,
N.
Y.
27
.
I
I
Announcing
plans for a
new
quarterly
magazin~:
COMPUT,ER
GRAPHICS
AND
ART
To
all
persons interested
in:
Applied Arts and Graphics
Architectural Graphics
Cartography Systems
Computer Aided Design
Computer Assisted Instruction
Computer Graphics
in
Physics,
Chemistry, Mathematics, and
Other Sciences
Computer Graphics
in
Business,
I ndustry, and Other Branches
of Knowledge
in
Computer Graphics
Computer Graphics
in
Literature,
Semantics, Fine Arts, Applied
Arts, and Other Fields
Interactive Graphics Languages
Courses
in
Computer Graphics
Dear
Colleague,
At
the
present
time
we
are
exploring
the
possibi-
lity
of
publishing
a
new
magazine
on
interdisciplin-
ary
computer
graphics
and computer
art
aimed
at
the
college
level.
We
need your
feedback
concerning
the
graphic
interests
that
you have and
that
you
know
of.
We
want
this
magazine
to
be
useful
to
you and
your
colleagues.
Accordingly,
this
is
your
invitation
to
submit
material
and
to
begin
subscribing
(or
indicate
your
intention
of
subscribing)
to
COMPUTER
GRAPHICS
AND
ART
a
new
quarterly
to
be
published
starting
probably
early
in
1976, and
for
which I have been asked
to
be
the
editor.
At
the
present
time
an
advisory
board
of
distin-
guished
people
and a group
of
contributing
editors
well
known
in
,graphic
fields
are
being
assembled.
Your
suggestions
and nominations
will
be welcome.
You
and your
colleagues
are
cordially
invited
to
submit
papers,
articles,
computer
graphics,
photo-
graphs,
reviews,
computer
art,
ideas,
etc.
--
no
holds
barred
--
for
us
to
consider
for
publication.
In
addition,
your
suggestions
about
authors
whom
you
would
like
to
have
papers
from
will
be most welcome.
One
of
our
goals
is
to
publish
materials
on
computer
graphics
early;
and
then
authors
can
more
quickly
establish
their
professional
claims
for
origination
of
good
ideas
and programs. Every
author
receives
permission
to
reprint
his
or
her
material
unlimited-
ly,
although
the
magazine
is
copyrighted
by
the
pub-
lisher.
We
look
on
subscribers
as
colleagues
in
a mutual
effort,
and
not
as
listeners
in
a
lecture
room.
Your
help
and
cooperation
in
this
mutual'under-
taking
is
warmly
invited
and
will
be most
appreciated.
May
we
hear
from you?
Cordially.
~c-.~~.-
~
~race
C.
Hertlein
Editor,
"Computer Graphics and
Art"
Associate
Professor
Department
of
Computer
Science
California
State
University,
Chico
Chico,
Calif.
95926
Here
is
your
chance
for
feedback to us:
-(may
be
copied
on
any
piece
of
paper)-
TO:
COMPUIER
GRAPHICS
AND
ART
Berkeley
Enterprises,
Inc.,
Chico Branch
555 Vallombrosa, #
35
Chico,
Calif.
95926
I.
Yes,
please
enter
my
annual
subscription
to
the
quarterly
COMPUTER
GRAPHICS
AND
ART:
( )
personal,
$10; ( )
library,
$15
( )
department,
, $15
and
bill
me.
2.
Yes,
please
record
my
intention
to
subscribe
annually:
( )
personal,
$10; ( )
library,
$15
( )
department,
, $15
and
notify
me
when
plans
are
firm.
3.
I hope
to
submit
for
consideration
for
pub-
lication,
material
on
the
following
topics:
~'A
4.
I would
be
particularly
interested
in
cove-
rage
of
the
following
subjects:
':'A
5.
I
am
interested
in
reading
material~
by
the
following
authors:
'~A
6.
Please
send
me
further
information
on
bonuses
for
subscribing:
( ) Computer Art
Reprints
( )
FORTRAN
IV
programs
for
computer
art
( ) Computer Graphics
Bibliography
7.
I
suggest
you
send
information
to
my
friends
and
associates
whose
names
and
addresses
follow:
'!<A
8.
Any
Remarks
or
Comments?
____________________
___
':'A
Name
Title
-----
Organization
__________________
__
Address _______________________________________ ___
*A
-
attach
paper
if
needed
c