Information Systems CPA F2.3 Study Manual
User Manual:
Open the PDF directly: View PDF ![]() .
.
Page Count: 198 [warning: Documents this large are best viewed by clicking the View PDF Link!]
- INTRODUCTION TO THE COURSE
- Introduction to Information Systems
- Contents
- Introduction to Information Systems
- A. THE ROLE OF INFORMATION SYSTEMS IN BUSINESS TODAY
- B. DIFFERENT PERSPECTIVES ON INFORMATION SYSTEMS
- C. DIFFERENT VIEWS OF INFORMATION SYSTEMS
- D. MANAGEMENT CHALLENGES
- 2
- Study Unit 2
- Types and Functions of Information Systems Used in Business
- A. BUSINESS PROCESSES AND INFORMATION SYSTEMS
- B. TYPES OF BUSINESS INFORMATION SYSTEMS
- C. SYSTEMS THAT SPAN THE ENTERPRISE
- D. THE INFORMATION SYSTEMS FUNCTION
- E. Using Information Systems to Achieve Competitive Advantage
- 3
- Study Unit 3
- Ethics Social and Political Issues of Information Systems
- A. ETHICAL AND SOCIAL ISSUES RELATED TO SYSTEMS
- B. ETHICAL DILEMMAS IN THE INFORMATION SOCIETY
- C. THE MORAL DIMENSIONS OF INFORMATION SYSTEMS
- Study Unit 4
- Computer Hardware and Software
- A. INFRASTRUCTURE
- B. KEY INFRASTRUCTURE COMPONENTS
- C. HARDWARE PLATFORMS
- D. HARDWARE PLATFORM TRENDS
- E. COMPUTER SOFTWARE PLATFORMS
- F. SOFTWARE PLATFORM TRENDS
- G. MANAGEMENT CHALLENGES POSED BY IT INFRASTRUCTURE
- Telecommunications, Networks, the Internet and Wireless
- A. NETWORKS AND COMMUNICATIONS
- B. COMMUNICATION NETWORKS
- C. THE INTERNET
- D. WIRELESS TECHNOLOGY
- E. MANAGEMENT OPPORTUNITIES AND CHALLENGES
- Study Unit 6
- Managing Data and Information Resources
- A. THE IMPORTANCE OF DATA
- B. FILE ORGANISATION
- C. THE DATABASE APPROACH TO DATA MANAGEMENT
- Database Structure
- Database Software
- A Database Management System (DBMS)
- Database Management Systems (DBMS) Versus File Organisation Methods
- Principal Types of Databases and Advantages and Disadvantages of Each
- Database Terms
- End User Involvement in selection and of a database management system
- The Role of the Database Administrator (DBA)
- Database Design
- D. USING DATABASES TO IMPROVE BUSINESS PERFORMANCE & DECISION MAKING
- E. MANAGING DATA RESOURCES
- F. MANAGEMENT CHALLENGES AND SOLUTIONS
- Study Unit 7
- E-Commerce
- Study Unit 8
- Management Decision Support Systems
- Study Unit 9
- Enterprise Systems
- A. ENTERPRISE RESOURCES PLANNING (ERP) SYSTEMS
- B. CUSTOMER RELATIONSHIP MANAGEMENT SYSTEMS
- C. SUPPLY CHAIN MANAGEMENT SYSTEMS
- D. ENTERPRISE INTEGRATION TRENDS
- E. CHALLENGES
- Study Unit 10
- Knowledge Management
- Study Unit 11
- Information Systems Security and Control
- Study Unit 12
- Information Systems Development and Acquisition
- A. BUILDING SYSTEMS AND PLANNED ORGANISATIONAL CHANGE
- B. SYSTEM DEVELOPMENT
- C. ALTERNATIVE APPROACHES TO DEVELOPING AND ACQUIRING SYSTEMS
- D. CONTEMPORARY APPROACHES TO APPLICATION DEVELOPMENT
- E. MANAGEMENT CHALLENGES
- Study Unit 13
- Business Value of Systems and Managing Change
- A. IMPORTANCE OF PROJECT MANAGEMENT
- B. SELECTING PROJECTS
- C. ESTABLISHING THE BUSINESS VALUE OF INFORMATION SYSTEMS
- D. CHANGE MANAGEMENT
- E. INFORMATION SYSTEMS PROBLEM AREAS
- F. MANAGEMENT CHALLENGES
- Appendix 1

LOSSARY
INSIDE COVER - BLANK

2
© iCPAR
All rights reserved.
The text of this publication, or any part thereof, may not be reproduced or transmitted in any
form or by any means, electronic or mechanical, including photocopying, recording, storage
in an information retrieval system, or otherwise, without prior permission of the publisher.
Whilst every effort has been made to ensure that the contents of this book are accurate, no
responsibility for loss occasioned to any person acting or refraining from action as a result of
any material in this publication can be accepted by the publisher or authors. In addition to
this, the authors and publishers accept no legal responsibility or liability for any errors or
omissions in relation to the contents of this book.
INSTITUTE OF
CERTIFIED PUBLIC ACCOUNTANTS
OF
RWANDA
Foundation F2
F2.3 INFORMATION SYSTEMS
First Edition 2012
This study manual has been fully revised and updated
in accordance with the current syllabus.
It has been developed in consultation with experienced lecturers.
3
4
CONTENTS
Study
Unit
Title Page
Introduction to the Course 7
1
Introduction to Information Systems
12
The Role of Information Systems in Business Today
12
Different Perspectives on Information Systems
14
Different Views of Information Systems
18
Management Challenges 19
2
Types and Functions of Information Systems Used in Business
21
Business Processes and Information Systems
22
Types of Business Information Systems
23
Systems that Span the Enterprise
28
The Information Systems Function
30
Using Information Systems to Achieve Competitive Advantage 31
3
Ethics Social and Political Issues of Information Systems
34
Ethical and Social Issues Related To Systems
35
Ethical Dilemmas in the Information Society
37
The Moral Dimensions of Information Systems 38
4
Computer Hardware and Software
44
Infrastructure
45
Key Infrastructure Components
46
Hardware Platforms
46
Hardware Platform Trends
47
Computer Software Platforms
50
Software Platform Trends
52
Management challenges posed by IT infrastructure 57
5
Study
Unit
Title
Page
5
Telecommunications, Networks, the Internet and Wireless
59
Networks and Communications
60
Communication Networks
63
The Internet
67
Wireless Technology
74
Management Opportunities and Challenges 79
6
Managing Data and Information Resources
81
The Importance of Data
82
File Organisation
83
The Database Approach to Data Management
85
Using Databases to Improve Business Performance & Decision Making
93
Managing Data Resources
97
Management Challenges and Solutions 97
7
E-Commerce
98
Introduction to Electronic Commerce
99
Electronic Commerce
102
Mobile E-Commerce (M-Commerce)
105
E-Commerce Payment Systems
107
Management Challenge 109
8
Management Decision Support Systems
110
Decision Making
111
Business Intelligence
115
Systems to Support Decision Making
116
Executive Support Systems (ESS)
118
Group Decision Support Systems (GDSS)
119
Challenges 120
6
Study
Unit Title Page
9
Enterprise Systems
121
Enterprise Resources Planning (ERP) Systems
122
Customer Relationship Management Systems
123
Supply Chain Management Systems
125
Enterprise Integration Trends
128
Challenges 128
10
Knowledge Management
129
Introduction
130
Description of Knowledge
130
Enterprise knowledge management systems:
132
Knowledge Work Systems
134
Intelligent Systems and Techniques
136
Management Challenges and Solutions 140
11
Information Systems Security and Control
141
System Vulnerability and Threats
142
Security and Controls
145
Organisational and Managerial Framework for Security and Control
147
Tools and Technologies for Protecting Information Resources
151
Management Challenges 155
12
Information Systems Development and Acquisition
156
Building Systems and Planned Organisational Change
157
System Development
161
Alternative Approaches to Developing and Acquiring Systems
168
Contemporary Approaches to Application Development
174
Management Challenges 175
7
Study
Unit Title Page
13
Business Value of Systems and Managing Change
177
Importance of Project management
178
Selecting Projects
180
Establishing the Business Value of Information Systems
183
Change Management
186
Management Challenges
187
Information Systems Problem Areas 189
Appendix 1
190
Fair Information Practice Principles
191
Finance and IT - a special relationship?
194
8
INTRODUCTION TO THE COURSE
Stage: Foundation Level 2
Subject Title: F2.3 Information Systems
Aim
The aim of this subject is for students to develop an understanding of the role and application
of Information Systems (IS) and Information Technology (IT) in the management and control
of organisations. It provides the basis for the further development of students for the roles of
manager, advisor, assurance provider and designer of IS and IT.
Information Systems as an Integral Part of the Syllabus.
This is an essential subject for the later study of Auditing, Audit Practice & Assurance
Services and Strategy & Leadership. Students will develop their understanding of selecting
and advising on the implementation of appropriate systems, processes, controls and solutions
in a business environment.
Learning Outcomes
On successful completion of this subject students should be able to:
• Explain the role of information systems in today’s competitive business environment.
• Appraise and discuss the major management challenges to building and using
information systems in organisations.
• Recognise and discuss ethical, social, and legal issues in the design and use of
information systems.
• Analyse how information systems support various business strategies for competitive
advantage.
• Analyse and discuss the challenges posed by strategic information systems and
management solutions.
• Examine the role of Internet technology in facilitating management and coordination
of internal and inter-organisational business processes.
• Assess the challenges posed and opportunities offered by electronic business and
electronic commerce and management solutions.
• Identify the challenges posed and opportunities offered by data resource management
and management solutions.
• Evaluate the challenges of managing IT infrastructure and management solutions.
• Discuss alternative methods for building information systems and alternative
methodologies for modelling systems.
• Explain what ‘eXtensible Business Reporting Language’ (XBRL) is and describe how
it improves the reliability and ease of communicating complex financial information
among internal and external users.
• Critically analyse Information Technology based case studies, thus incorporating their
strategic and practical knowledge of Information Systems to real life business
situations.
9
Syllabus:
1. The Digital Firm
• Describe and discuss why information systems should be employed.
• Approaches to Information Systems.
• The role of information systems.
• The role of information systems in business strategy.
• Information systems support in the decision making process.
• Information systems and management issues.
• Ethical, social, and political issues of information systems.
• The impact of contemporary information systems and the Internet on the protection
of individual privacy and intellectual property.
• The role of information systems in today’s competitive business environment.
• The impact of the Internet and Internet Technology on business and government.
• Defining an information system from both a technical and business perspective and
distinguishing between computer literacy and information systems literacy.
• The major management challenges to building and using information
systems in organisation
2. Types of Information Systems in Business
• Information systems supporting the major business functions: sales and marketing,
manufacturing and production, finance and accounting, and human resources.
• The relationship between organisations, information systems, and business
processes.
• Transaction Processing Systems.
• Office Information Systems.
3. Functions of Information Systems
• The functions of Information Systems.
• Relationships between different information systems and where information
systems are used within the firm.
• Information systems support for business strategies for competitive advantage.
• The challenges posed by strategic information systems and management solutions.
4. Electronic Business & Mobile Commerce
• The Internet: new information technology infrastructure for the Digital Firm.
• Internet platforms.
• The use of electronic business and electronic commerce.
• Technologies used for electronic business and electronic business models.
• Internal and external applications of electronic business and electronic commerce.
• Management issues associated with electronic business.
• The impact of Internet Technology on value propositions and business models.
• The impact of electronic commerce on consumer retailing and business-to-business
transactions.
• Payment systems for electronic commerce.
• The role of Internet Technology in facilitating management and coordination of
internal and inter-organisational business processes.
10
• The challenges posed by electronic business and electronic commerce and
management solutions.
• Wireless transmission media and devices, cellular network standards and generations,
and standards for mobile Web access.
• M-commerce in business and m-commerce applications.
• Wireless applications in business.
• Cloud computing
5. Information Technology
5.1 Computer Hardware
• The stages of IT infrastructure evolution.
• The technology drivers of IT infrastructure evolution.
• Contemporary computer hardware platform trends.
• The components of a computer system.
• Computer processing, storage, input and output technology.
• Types and classifications of computer systems.
• Managing hardware assets.
• Managing IT infrastructure and management solutions.
5.2 Computer Software
• Operating systems.
• Application software packages.
• Programming languages.
• Managing software assets.
• Contemporary software platform trends.
• Extensible Business Reporting Language (XBRL).
5.3 Telecommunications and Networks
• Components and functions of telecommunications systems.
• Communication networks.
• eBusiness and eCommerce technologies.
• Networking/telecommunications platforms.
• Consulting and system integration services.
5.4 Database And File Organisation
• The file organisation approach.
• The database management systems (DBMS) approach.
• Database management systems (DBMS) vs. file organisation methods.
• Types of databases.
• Database purchase issues.
• Database design & maintenance issues.
• Database design principles.
• Database trends.
• Managing data resources and management solutions.
11
6. Organisational Support Systems
6.1 Knowledge Based Systems
• Knowledge Based Systems.
• The flow of Knowledge Management.
• The control of Knowledge Management.
6.2 Management Decision Support Tools
• Decision Support Systems.
• Group Decision Support Systems.
• Executive Support Systems.
• Knowledge Working
7. Information System Development
• The System Development Life Cycle (SDLC).
• Alternatives to SDLC e.g. Prototyping, RADE, etc.
• System development and management considerations.
• The impact of building new systems on organisational change.
• Developing information systems that support an organisation’s business plan.
• The core activities in the systems development process.
• Alternative methods for building information systems and alternative methodologies
for modelling systems.
• The challenges of building information systems and management solutions.
8. Feasibility Study & Business Value of Systems
• Aims, objectives, problem identification, responsibilities, planning, management and
lifecycle.
• Cost benefit analysis and final outputs.
• Models for understanding the business value of information systems.
• Change management requirements for building successful systems.
9. System Security and Control
• The need for special protection from destruction, error, and abuse of information
systems.
• The business value of security and control.
• Organisational and managerial frameworks for security and control.
• System vulnerability and abuse.
• Preventative maintenance techniques and security controls.
• Disaster recovery planning.
• Quality control and quality assurance.
• Tools and technologies for safeguarding information resources.
• Identify the challenges posed by information systems security and control and
management solutions.
12
Study Unit 1
Introduction to Information Systems
Contents
A.
The Role of Information Systems in Business Today
B.
Different Perspectives on Information Systems
C.
Different Views of Information Systems
D.
Management Challenges
13
Introduction to Information Systems
This purpose of this chapter is to introduce the role played by information systems and
technology in business firms. The topics introduced in this chapter will be covered in detail in
the remainder of the manual.
The objectives of this chapter are to:
• Explain why information systems are so essential in business today.
• Describe the digital economy and the digital firm
• Identify the business objectives for investing in information systems
• Define an information system from both a technical and a business perspective.
• Identify and describe the three dimensions of information systems
– Organisation, management and information technology.
• Assess the other assets required for information technology to provide value to a
business
• Describe the different approaches to the study of information systems:
– Technical approach - Behavioural approach - Sociotechnical systems
A. THE ROLE OF INFORMATION SYSTEMS IN BUSINESS TODAY
How Information Technology and Systems Are Transforming Business
Information systems are transforming business in a number of different ways. Information
systems and the internet have dramatically cut the cost of acquiring and distributing
information. The availability of information has increased the decision power of operational
staff. The use of information systems has also made it easier for managers to monitor
performance of staff. These two changes have contributed to a reduction in the number of
middle managers and have lead to a general flattening of organisational structures.
Information technology and systems have enabled organisations to be more flexible. For
example organisations such as the computer manufacturer, Dell, can support mass
customisation of products without increasing costs. Companies are also linked electronically
to suppliers enabling automatic triggering of orders, purchasing and payment thus reducing
order times and also reducing stock holding costs.
Organisations are using real-time business intelligence and predictive analysis to enable
faster decision-making and to cope with an ever changing market place where there are both
threats and great opportunities.
Through its ease of use and countless advantages for enhancing business, the Internet has had
a major impact on the globalisation of businesses.
Globalisation Opportunities
The Internet is now a global communications network that has dramatically reduced the cost
of operating on a global scale. Customers can now shop in a global marketplace 24 hours a
day, 7 days a week. Global business is no longer the preserve of large multinational
14
enterprises. Even small businesses can use the internet to sell their products and services in
other countries and even in other continents. Companies can use the Internet to reduce
production expenses by sourcing low cost supplies and managing factories in other countries.
Companies such as Facebook, Amazon and Google can use the Internet to duplicate their
business models and services in many different countries.
The Digital Economy and the Digital Firm
In a 2011 research paper by Oxford Economics (supported by AT&T, Cisco, Citi, PwC and
SAP) titled the “The Digital Economy”, it argues that the recent recession and financial crisis
has speeded up the adoption of key technologies such as mobility, cloud computing, business
intelligence and social media that are transforming businesses. Driven by the phenomenal
growth of the internet we are now in a global digital economy. Over the next five years, many
sectors, including technology, telecommunications, entertainment, media, banking, retail and
healthcare, will continue to be reshaped through the application of information technology
and systems. To survive and flourish in the digital economy, organisations will need to utilise
technology to the fullest extent possible.
The digital firm is a term used to describe a company that has enabled its key business
relationships with customers, suppliers, employees and business partners using digital
networks and information systems. Information technology is also used widely throughout
the organisation to support key functions and to manage internal processes. These
information systems include Enterprise Resource Planning (ERP) Systems, Supply Chain
Management (SCM) Systems, Customer Relationship Management (CRM) Systems and
Knowledge Management Systems. The aim of the digital firm is to integrate functions and
systems to enable the seamless exchange of information between internal employees and
externally with suppliers, business partners and customers.
The term “The Digital Firm” was first used by Laudon, K. in his book Management
Information Systems.
Business Objectives and Information Systems
Information systems are critical to supporting the day-to-day business in most organisations
in the developed world. Some firms, such as Amazon, eBay and Facebook couldn’t exist
without information systems. Some service industries such as finance, insurance and airlines
could not operate without information systems. The ability of a firm to use Information
technology and systems is closely linked with the firm's ability to implement its business
strategy.
There is a growing interdependence between a firm’s information systems and its business
capabilities. Changes in strategy, rules and business processes increasingly require changes in
hardware, software, databases and telecommunications. Often, what the organisation would
like to do depends on what its systems will allow it to do.
Business firms invest in information systems to accomplish six primary strategic business
objectives:
1. Operational excellence: Efficiency, productivity and improved changes in business
practices and management behaviour
15
2. New products, services and business models: A business model describes how a
company produces, delivers and sells a product or service to generate profit.
Information systems and technologies create opportunities for products, services and
new ways to engage in business.
3. Customer and supplier intimacy: Improved communication and enhanced services
to customers will help raise revenues. Closer relationships with suppliers will lead to
lower costs of supplies.
4. Improved decision making: Accurate and timely information is essential if business
managers are to make the best possible decisions.
5. Competitive advantage: Implementing effective and efficient information systems
can allow a company to charge less than competitors for quality products, leading to
higher sales and profits.
6. Survival: Information systems can also be a necessity of doing business. A necessity
may be driven by industry-level changes, such as the widespread adoption by many
airlines of online booking of flights and check-in. A necessity may also be driven by
governmental regulations, such as one requiring a business to retain data and report
specific information for a period of time.
B. DIFFERENT PERSPECTIVES ON INFORMATION SYSTEMS
What is an Information System?
An information system is a set of interrelated parts that collect, process, store and distribute
information to support decision making and control in an organisation. Information systems
can also be used to analyse problems and to create new products and services.
Data and Information
Data is raw facts and figures, while information is data that has been processed or shaped
into some useful forms for human use.
Raw data from a supermarket checkout counter point of sales system (POS) can be processed
and organised to produce meaningful information, such as the total number of litres of milk
sold in a particular shop during a particular period.
Attributes of Quality Information
For information to be useful to organisations it should possess certain attributes or qualities
which include:
• Completeness: Information should be complete – in other words all information
which is relevant to a decision should be provided.
• Accuracy: Information should be free of errors and bias. The degree of accuracy
required is relative to the intended use of the information. For example an invoice
must be accurate to the nearest RWF whereas a sales forecast might be rounded to the
nearest RWF1000.
• Relevant for purpose: Information should be relevant to its purpose.
• Timely: Information needs to be up to date; information has little value if it is out of
date.
16
• Reputable source: For information to be used effectively, the managers or users of
the information must have confidence in the source of the information.
• Value: The value of the information should be greater than the cost of producing it.
Information has value if it leads to decisions that reduce costs, eliminate losses,
increase sales and allows for better utilisation of resources etc.
It is one of the challenges for Information System designers to produce information that is
relevant, accurate and timely.
Input Processing and Output
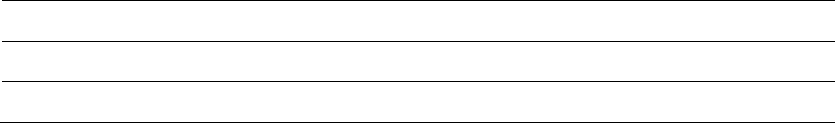
Input, processing, and output are the three main activities in an information system. Input
captures or collects raw data. Processing converts this raw input into a meaningful form.
Output transfers the processed information to the people who will use it. Information
systems also require feedback, which is output that is returned to help evaluate or refine the
input stage. Feedback enables the system to control itself; this may involve modifying
processing and/or input. See Figure 1.1.
For example, an Automatic Teller Machine (ATM) uses a number of input, processing and
output cycles to perform its function. The initial input is the customer card details; this is
processed by the ATM system. A message is output to the screen which asks the customer to
input their Pin code after which the system processes this to check if it is correct. Another
output to the screen asks the customer to input the services and amounts of money they want.
After input and processing, the amount of money is output from the machine and a receipt
may also be printed out.
Figure 1.1: A basic model of an information system
The different people who interact with an organisation’s information systems include
customers, suppliers, business partners and regulatory agencies.
Dimensions of Information Systems
It is possible to distinguish information systems, which are designed to produce information
and solve organisational problems, from the computer technology and software that is
typically used to create and manage information systems.
Input Output
Processing
Feedback
17
Computer Literacy and Information Systems Literacy
Computer literacy focuses primarily on knowledge of information technology; i.e. on
computer hardware and software. It involves understanding how computer technology works
and operates; how technology is built and how it is programmed.
Information systems literacy focuses on an understanding of information systems; i.e. how
the systems operate, their capabilities, how these systems can provide solutions to business
problems and create information that is useful to the business and its employees. The field of
management information systems (MIS) tries to achieve this broader information systems
literacy.
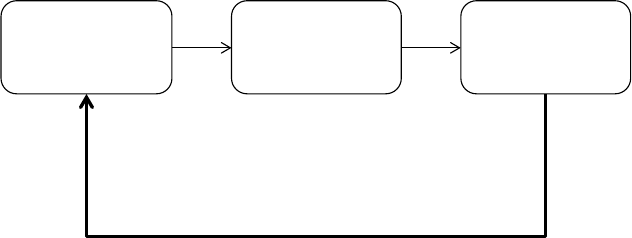
Three Dimensions of Information Systems
Information systems are more than just technology; there are also management and
organisational dimensions to information systems (see Figure 1.2). To be able to fully
understand information systems and utilise them effectively requires an understanding of how
systems impact and are impacted on by operational and management issues.
Figure 1.2 Three Dimensions of Information Systems
Organisation
Information systems are part of organisations, and in some cases (such as Internet
companies), they are the organisation itself. Information systems will have the procedures
and processes and the culture of an organisation imbedded within them.
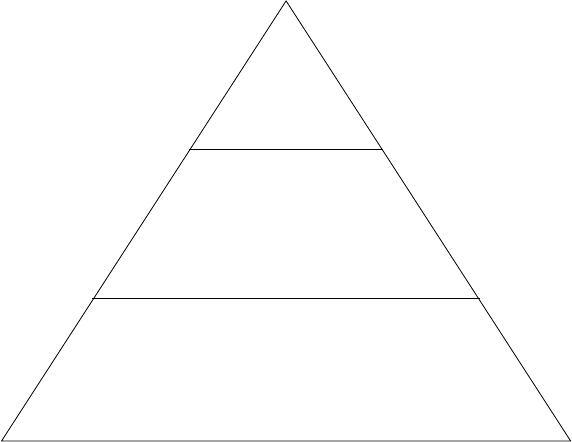
The organisation structure consists of three main levels; each performing different duties and
each using information systems for different purposes (See figure 1.3).
Management
Technology
Organisation
Information
Systems
18
Senior management makes long-range strategic decisions and ensures the firm's financial
performance. Middle management carries out the plans of senior management and
operational management monitors the firm's daily activities. All these activities are enabled
through information systems.
Specialists are employed in the major business functional areas such as sales and marketing,
manufacturing and production, finance and accounting, and human resources. Work within
each business function and between business functions is coordinated and enabled by detailed
business processes. These processes are increasingly made possible by information systems.
Figure 1.3: Organisational Structure.
Management
Information systems supply tools and information needed by managers to manage their work
and make decisions, in the case of both short and long term decisions. Information systems
enable managers to monitor operations, analyse data, identify changes in the market place
and help create new products and services.
Technology
Management uses technology (hardware, software, storage and telecommunications) to carry
out their functions. Information technology is one of the many tools used by management to
cope with change.
A firm's information technology (IT) infrastructure is the platform on which an organisation
can build its information systems. IT infrastructure consists of:
• Computer hardware: The physical equipment and computing devices used for input,
storage, processing, output and telecommunications. For example; keyboards,
monitors, processors, hard disks, modems etc.
• Computer software: The programs that control and coordinate the computer
hardware components. Computer software would include operating systems such
Windows and Unix.
Senior
Management
Middle
Management
Operational
Management
19
• Data management software: This software controls the organisation of data on
physical storage media.
• Networking and telecommunications technology: This is the hardware and software
used to link various devices and transfer data from one location to another to enable
the sharing of data such as files, images, sounds, video, or to share resources such as a
printer.
Each of these topics listed above are discussed in detail later in this manual.
A Business Perspective on Information Systems
Information systems enable the firm to increase its revenue or decrease its costs by providing
information that helps managers make better decisions or that improves the efficiency of
business processes.
The value of an information system to a business is determined by how the use of the system
will lead to better management decision making, more efficient business processes and
ultimately to higher profits.
This business view of information systems highlights the link between the organisation
(business process), management and information systems.
Information Technology Investments
Some organisations achieve better returns from their information systems investments than
others. Studies of returns from information technology investments show that those firms that
get lower return on investment are those that fail to adopt a new business model that better
suits the new technology.
Research also found that information technology investments cannot make organisations and
managers more effective unless they are accompanied by investments in complementary
assets which include:
• Organisational assets: These include a supportive business culture that values
efficiency and effectiveness, an appropriate business model, efficient business
processes, decentralisation of authority and decision rights.
• Managerial assets: These include strong senior management support for change,
incentive systems that monitor and reward individual innovation, an emphasis on
teamwork and collaboration, training programs and a management culture that values
flexibility and knowledge.
• Social assets: These are generally investments by governments, and other bodies in
such areas as the Internet, educational system and regulations and laws.
Research indicates that firms that support their technology investments with investments in
complementary assets, such as new business processes or training, receive higher returns.
C. DIFFERENT VIEWS OF INFORMATION SYSTEMS
Information systems are referred to as socio-technical systems. Although they are made up of
technology, they require substantial input from people to make them work properly. Since
20
problems with information systems and their solutions, are seldom either technical or
behavioural, a multidisciplinary approach is needed.
Technical Approach
A technical approach to information systems emphasises the use of mathematical models to
study information systems, the physical technology used to construct the systems and the
capabilities of information systems. The areas of study that contribute to the technical
approach are computer science, management science and operational research.
Behavioural Approach
The behavioural approach does not ignore technology, but tends to focus on non-technical
areas. A behavioural approach to information systems focuses on questions such as strategic
business integration, behavioural problems related to systems use, logical system design and
implementation, social and organisational impacts of information systems, political impacts
of information systems and individual responses to information systems. Solutions to
problems created by information technology are primarily changes in attitudes, management,
organisational policy and behaviour. The disciplines that contribute to the behavioural
approach are psychology, sociology and economics.
A Socio-technical Systems Approach
The study of Management Information Systems (MIS) combines the work of computer
science, management science and operations research with a practical focus towards
developing system solutions to business problems. It is also concerned with behavioural
issues surrounding the development, use and impact of information systems, which are
typically discussed in the fields of sociology, economics and psychology.
In the sociotechnical view of systems, the best possible organisational performance is
achieved by optimising both the social and technical systems used in production. Technology
must be changed and designed to fit organisational and individual needs. Organisations and
individuals must also be adapted through training, learning and planned organisational
change to utilise the new technology as much as possible.
In a sociotechnical perspective, the performance of a system is optimised when both the
technology and the organisation adjust to one another until a satisfactory fit is obtained.
D. MANAGEMENT CHALLENGES
Laudon & Laudon (2010) identifies five key management challenges involved in building,
operating and maintaining information systems, which include the following:
• The strategic business challenge is how information technology can be used to design
organisations so that are competitive, effective and digitally enabled.
• The globalisation challenge facing organisations is how organisations understand the
system requirements of a global economic environment.
• The information architecture and infrastructure challenge is that organisations must
be able to develop an information architecture that is able to support the company goals
when both the business conditions and the technologies are changing so rapidly.
21
• The information systems investment challenge is how organisations determine the
business value of systems.
• The responsibility and control challenge is how organisations can ensure that their
information systems are used in an ethical and socially responsible way.
The topics discussed throughout this manual should provide the knowledge required to deal
with these challenges.

22
Study Unit 2
Types and Functions of Information Systems Used in Business
Contents
A.
Business Processes and Information Systems
B.
Types of Business Information Systems
C.
Systems that Span the Enterprise
D.
The Information Systems Function
E.
Using Information Systems to Achieve Competitive Advantage
23
Introduction
This chapter provides an overview of the role of information systems in business.
The objectives of this chapter are to:
• Define and describe business processes and their relationship to information systems.
• Describe the information systems supporting the major business functions.
• Describe the role played by systems serving the various levels of management in a
business and their relationship to each other.
• Explain how enterprise applications and intranets promote business process
integration and improve organisational performance.
• Assess the role of the information systems function in a business.
A. BUSINESS PROCESSES AND INFORMATION SYSTEMS
As previously discussed in Chapter 1, the “digital firm” means connecting each functional
area and each management level to one another so they can share information. Data input to
the system in manufacturing must be made available to sales, accounting and logistics.
Managers in the human resources department must have access to a range of information
related to employees. Integrating information from different sources is important for the
digital firm.
As we go through this chapter, we’ll look at the types of information systems organisations
use at each management level.
Business Processes
Business processes refer to work that is organised, coordinated and focused to produce a
product or service. Business processes also refer to the ways in which organisations co-
ordinate and organise activities, information and knowledge to produce their products or
services. Every firm has its own set of business processes.
The performance of a firm will to some extent depend on how well its business processes are
designed and coordinated. Many business processes are linked to a specific functional area,
such as sales and marketing, while others cross many different functional areas and will also
require coordination across departments.
Business processes for the manufacturing and production area include product assembling
and stock control. For the sales and marketing area, business processes include processing
orders. In finance and accounting, business processes involves paying creditors. In the case of
human resources, business processes involve evaluating employee performance.
How Information Technology Enhances Business Processes
Information systems enhance business processes in two main ways by:
1. Increasing the efficiency of existing processes
2. Enabling entirely new processes that have the potential to transform the business
24
Information systems can improve the efficiency of a business by removing many of the
manual activities. Some processes can be automated through the use of information systems.
Internet banking enables customers to pay bills, transfer money and check account balances
without any involvement of bank employees.
Information systems can transform the way the business operates and make completely new
business processes possible. Companies such as Amazon and Apple have employed entirely
new business processes based on new business models that would not be possible without
information technology. Ryanair’s business processes both for purchasing tickets, checking in
for flights and even checking in luggage would not be possible without information systems
and the Internet in particular.
B. TYPES OF BUSINESS INFORMATION SYSTEMS
No single system can provide all the information required by an organisation. Even small
firms have a collection of different systems, for example: e-mail systems, sales tracking
systems, etc. In this section we look at the types of systems used in business from two
different perspectives (summarised in Figure 2.1):
1. Functional perspective: identifying systems by their business function.
2. Constituency perspective: identifies systems in terms of the major organisational groups
that they serve.
Figure 2.1: The main types of business information systems (adapted from Laudon and
Laudon, 2010).
Transaction
Processing
Systems (TPS)
Management Information
Systems (MIS)
Decision-Support
Systems (DSS)
Executive Information
Systems (EIS)
Strategic Management
Tactical Management
Operation Level
Management
Sales and Marketing Manufacturing & Production Finance & Accounting Human Resources
Order Processing Production
planning
system
Accounts
Payable Employee
Performance
appraisal
Sales
Management Inventory
Control Skills
Analysis
Budgeting
5-year Sales Forecasting
5-Year Operating Plan
Profit Planning
Personnel Planning
25
Systems from a Functional Perspective
There are four primary types of information systems that serve different functional areas:
• Sales and marketing systems
• Manufacturing and production systems
• Finance and accounting systems
• Human resources systems
Sales and Marketing Systems
Sales and marketing information systems assist the firm in marketing and sale of products
and services to customers. An important operational system in this area is the sales order
processing system which is used to capture customer orders. At a strategic level, information
systems are used to forecast trends.
Manufacturing and Production Systems
Manufacturing and production information systems deal with the planning, development and
production of products. An important system in this area is an inventory system which is used
to provide information about the number of items held in inventory to support manufacturing
and production activities.
Finance and Accounting Systems
Finance and accounting information systems keep a record of the firm's financial assets and
the flow of funds. The finance function is responsible for managing the firm’s financial assets
such as cash, shares and other investments. To establish if the firm is getting the best return
on its investments, the finance function must obtain information from both external and
internal sources. The accounting function is responsible for maintaining and managing the
firm’s financial records. The accounting function attains information mainly from sources
internal to the firm.
An accounts receivable system is an example of a system used by the financial and
accounting functional area. It tracks and stores important customer data, such as payment
history, credit rating and billing history. Other systems used in this area include accounts
payable and budgeting systems.
Human Resources Systems
Human resources information systems maintain employee records, record employee skills,
job performance and training, and assist planning of employee compensation and career
development. An example of a system used in the human resources area would be a
performance appraisal tracking system which is used to track details of each employee’s
performance evaluations.
26
Systems from a Constituency Perspective
Taking a functional perspective on systems tell us how systems serve the various functions
but does not tell us much about how the systems help managers with managing the
organisation. We can also look at systems in terms of the various levels of management and
the type of decisions they support.
The four major types of systems from a contingency perspective are:
1. Transaction Processing Systems (TPS)
2. Management Information Systems (MIS
3. Decision Support Systems (DSS)
4. Executive Support Systems (ESS)
Transaction Processing Systems (TPS)
Transaction processing systems are generally found at the operational level of the
organisation. Examples of these systems include order processing, material movement
control, payroll, accounts payable and employee record keeping.
Transaction Processing Systems (TPS) support the day-to-day or week-to-week processing
and recording of routine business transactions such as Orders, Despatch Notes, Invoices,
Credit Notes, Payments etc. One example is a sales order processing system.
One of the most important applications of IT has been in making business operations more
efficient. Computer based data processing is utilised at the operational level of organisations
to handle transactions that were previously carried out by office workers. A major role of IT
is in cost reduction through improving operational efficiency in transaction processing.
The primary function of a transaction processing system is transaction handling and record
keeping as well as providing information. Transaction processing systems are used in
functional areas such as Sales, Purchasing, Accounts etc.
Management Information Systems (MIS)
Management information systems provide managers with reports based largely on data taken
from transaction processing systems. Those using management information systems (MIS)
require information on a periodic basis rather than a daily basis like those using a transaction
processing system. Managers also require information on an exception basis. That is, they
need to know if production is higher or lower than the targeted rate or if they are over or
under their budgets. They also need to know about trends.
MIS systems tend to have an internal orientation where the primary sources of information
are internal and the users are normally members of the organisation. MIS systems are
inclined to have limited flexibility in that they present information but usually don’t permit
manipulation of the information by the user.
The information presented by MIS systems is retrieved from files or databases and is
presented either on screen or in the form of a report. Figure 2.2 illustrates examples of a
number of different types of screen presentation utilised by MIS systems.
Examples of management information systems include sales management, inventory control
and annual budgeting.
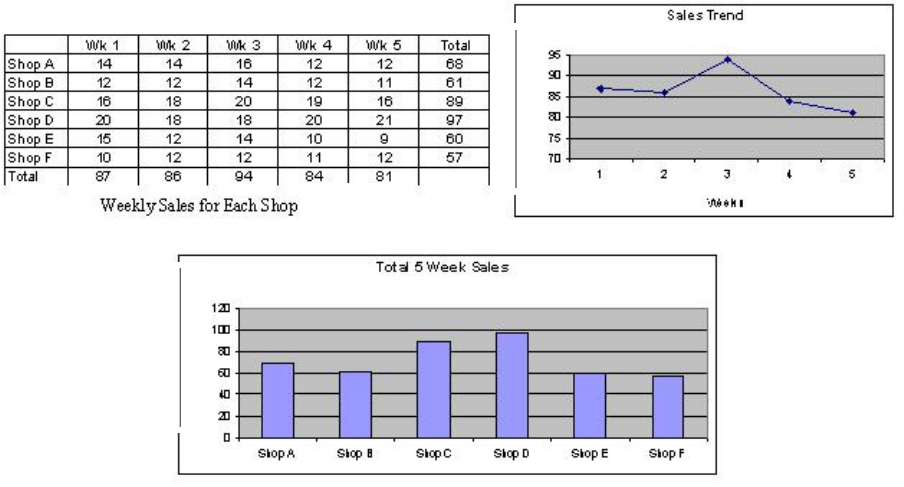
27
Figure 2.2: MIS display examples
Decision-Support Systems (DSSs)
Decision support systems (DSS) or business intelligence systems, assist managers with non-
routine decisions that are unique, rapidly changing and not easily specified in advance (semi-
structured decision-making). DSS are more analytical than MIS, as they use a variety of
models to analyse internal and external data or compress large quantities of data for analysis.
Decision-support systems are generally used at the middle management level.
Decision-support systems are used for complex “what-if” questions that necessitate internal
and external data. Decisions made at this management level are predominantly semi-
structured so the information system needs to be able to respond to the unique needs of the
managers.
A selection of decision-support systems includes sales region analysis, production
scheduling, profitability analysis and contract cost analysis. Decision-support systems are
discussed in more extensive detail in Chapter 8.
Executive Support Systems (ESSs)
Executive support systems (ESS) are used at the top levels of management. ESSs supply a
generalised computing and communications environment that assists senior managers in
addressing strategic issues and identifying long-term trends in the firm and its environment.
Typical decisions made at the strategic level are characteristically quite unstructured. Often
there is no specific question to address, but rather a series of undefined situations executives
may face. There are no straightforward, definable answers. These executives require
summarised, historical information collected from all other levels throughout the
organisation, together with large quantities of external data assembled from many sources.
ESS present graphs and data from a range of internal and external sources through an
interface that is uncomplicated for senior managers to use. The information is regularly
(RWF1000)
Sales in RWF1000
Sales in RWF1000
28
delivered to senior executives through a portal, which uses a Web interface to present
integrated personalised business content.
Executive-support systems are discussed in greater detail in Chapter 8.
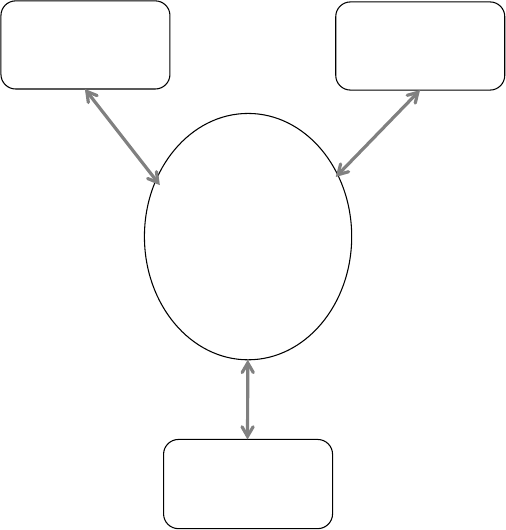
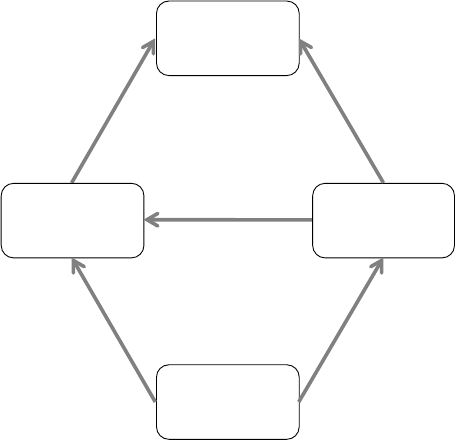
Relationship between Systems
The various forms of systems in the organisation exchange data with each another (See
Figure 2.3). TPS provide a major source of data for other systems, in particular MIS and
DSS, however these systems may also use other data. TPS are operational-level systems that
gather transaction data. Some examples of TPS include payroll or order processing that track
the flow of daily routine transactions that are essential for conducting business. DSS use data
from TPS and also MIS. MIS rely heavily on data from TPS.
ESSs acquire the majority of their internal data from MIS and DSS. These different types of
systems are loosely joined in most business firms, but increasingly firms are using new
technologies to integrate information that resides in many different systems.
Figure 2.3: Interrelationships among systems
Office Information Systems
This is a category of systems that combine hardware and software and networks to improve the
flow of information and enhance communications between employees in an organisation. These
systems support the office tasks of creating publishing and distributing information. Office
information systems include word processors, desktop publishers, e-mail, voicemail, fax,
teleconferencing, videoconferencing and groupware.
The terms “office automation systems” is also used to describe these systems.
MIS
TPS
ESS
DSS
29
C. SYSTEMS THAT SPAN THE ENTERPRISE
Enterprise Applications
Enterprise applications are systems that span functional areas, focus on carrying out business
processes across the business firm and encompass all levels of management. Enterprise
applications assist businesses in becoming more flexible and productive by coordinating their
business processes more closely.
There are four main enterprise applications:
1. Enterprise systems
2. Supply chain management systems
3. Customer relationship management systems
4. Knowledge management systems
Each of these enterprise applications integrates a related set of functions and business
processes to improve the performance of the organisation as a whole.
Enterprise Systems
Enterprise systems, or enterprise resource planning (ERP) systems, model and automate
many business processes, for instance filling an order or scheduling a shipment, with the
objective of integrating information throughout the company and eradicating complex,
costly links between computer systems in different areas of the business. Information that
was in the past split between different systems can now effortlessly flow throughout the
company, allowing it to be shared by business processes in manufacturing, accounting,
human resources and other areas of the organisation. Distinct business processes from sales,
production, finance and logistics can be integrated into company-wide business processes that
flow across organisational levels and functions.
The enterprise system assembles data from a range of key business processes and stores the
data in a single comprehensive data repository where it can be utilised by other parts of the
business. Managers are provided with information that is more accurate and timely for
assisting in the coordination of the daily operations of the business and a firm-wide view of
business processes and information flows.
Supply Chain Management Systems
Supply chain management (SCM) systems facilitate businesses with managing relationships
with their suppliers. These systems help suppliers, purchasing firms, distributors and logistics
companies share information about orders, production, inventory levels, and delivery of
products and services so that they can source, produce and deliver goods and services more
efficiently.
SCM systems increase firm profitability by reducing the costs associated with moving and
manufacturing products and by enabling managers to make better decisions about how to
organise and schedule sourcing, production and distribution.
Supply chain management systems are a form of inter-organisational system because they
automate the flow of information across organisational boundaries. Firms that carefully
30
manage their supply chains get the correct amount of products from their source to the point
of consumption in the minimum amount of time and at the lowest cost.
Customer orders, shipping notifications, optimised shipping plans and other supply chain
information, flow between the Warehouse Management System (WMS), Transportation
Management System (TMS), and its back-end corporate systems.
Customer Relationship Management Systems
Customer relationship management (CRM) systems focus on coordinating the business
processes regarding a firm's interactions with its customers in sales, marketing and service, to
fully optimise profits, customer satisfaction and customer retention. They merge customer
data from numerous sources and communication channels to enable firms to identify
profitable customers, acquire new customers, improve service and support and target
products and services more accurately to particular customers’ preferences.
Knowledge Management Systems
The value of a firm's products and services is based not only on its physical resources but also
on intangible knowledge assets. Some firms perform better than others because they have
superior knowledge regarding the creation, production, and delivery of products and services.
Knowledge management systems support processes for discovering, codifying, sharing, and
distributing knowledge, as well as processes for generating new knowledge and integrating
external sources of knowledge.
ERP, SCM and CRM systems are discussed in more detail in Chapter 9 while knowledge
management is discussed in Chapter 10.
Intranets and Extranets
Companies that do not boast the resources required to invest in enterprise applications can
still achieve some information integration through the use of intranets and extranets.
Intranets normally present information to employees through a private portal that supplies a
single point of access to information from numerous different systems and to documents
using a Web interface. Corporate portals regularly feature e-mail, collaboration tools and
tools for searching for internal corporate systems and documents. Companies can connect
their intranets to internal company transaction systems, allowing employees to carry out
actions fundamental to a company's operations, such as checking the status of an order or
granting a customer credit.
Extranets accelerate the flow of information between the firm and its suppliers and
customers. They can facilitate different firms working collaboratively on product design,
marketing and production. Intranets and Extranets are discussed in detail in Chapter 5.
Enterprise applications and technologies are transforming firms' relationships with customers,
employees, suppliers and logistic partners into digital relationships via networks and the
Internet.
E-Business, E-Commerce and E-Government
Electronic business, or e-business, refers to the use of digital technology and the Internet to
execute the major business processes in the organisation. E-business includes activities for
31
the internal management of the firm and for coordination with suppliers and other business
partners. It also includes electronic commerce or e-commerce.
E-commerce is the division of e-business that deals with buying and selling of goods and
services over the Internet. It encompasses activities that support these market transactions, for
example advertising, marketing, customer support, security, delivery and payment.
E-government (electronic government) refers to the use of the Internet and networking
technologies in digitally enabling government and public sector agencies' relationships with
citizens, businesses and other arms of government. In addition to enhancing delivery of
government services, e-government can make government operations more efficient,
transparent and accountable. Furthermore, it can empower citizens by allowing them easier
access to information. The different categories of e-government include:
• G2C – government to citizens
• G2B – government to business enterprises
• G2G – inter-agency relationship within government
E-business and e-commerce are discussed in greater detail in Chapter 7.
D. THE INFORMATION SYSTEMS FUNCTION
The Information Systems Department
In all but the smallest of firms, the information systems department is the formal
organisational unit responsible for information technology services. The information systems
department is in charge of maintaining the hardware, software, data storage and networks that
make up the firm's IT infrastructure. The information systems department proposes new
business strategies and new information-based products and services. It then coordinates both
the development of the technology and the planned changes in the organisation.
The information systems department consists of specialists, such as:
• Programmers: technical specialists who write the software instructions for computers.
• Systems analysts: the principal liaisons between the information systems groups and the
rest of the organisation.
• Information systems managers: leaders of teams of programmers and analysts, project
managers, physical facility managers, telecommunications managers or database
specialists.
In many companies, the information systems department is headed by a chief technology
officer; a senior manager who supervises the use of information technology in the firm. End
users are employees of departments outside of the information systems group who use the
information systems.
Small companies may not have a formal information systems group. Larger companies will
normally have a separate information systems department
32
E. Using Information Systems to Achieve Competitive Advantage
Firms with a competitive advantage over others, typically have access to special resources
that others do not or are have special competencies that enable them to use resources more
efficiently, or in ways that their competitors find difficult to imitate. Competitive advantage
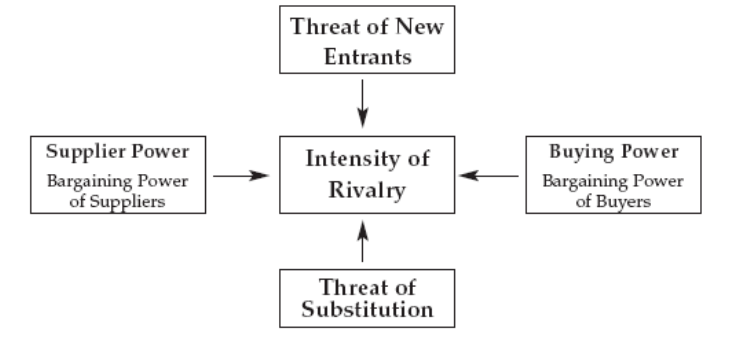
can be turned into higher profits for the company. Porters five forces model can be used to
understand the competitive force in an industry and how they affect profitability.
Porter’s Competitive Forces Model
Michael Porter's competitive forces model (Figure 2.4), describes five competitive forces that
shape the fate of the firm.
1. Intensity of Rivalry between competitors: Generally the strongest of the five forces.
Rivalry can be focused on such factors as; price, performance features, new product
innovation, quality, durability, warranties, after-sale service and brand image.
2. Threat of new market entrants: New companies have certain advantages, such as not
being locked into old equipment, as well as disadvantages, such as less expertise and little
brand recognition. Barriers to entry can include; economies of scale, capital costs, and
access to supplier, distributors, expertise and customer loyalty.
3. Threat of Substitute products and services: These are substitutes that customers might
use if prices become too high. For example, Internet telephone services can substitute for
traditional telephone services. The more substitute products and services available in an
industry, the harder it is to control price and the lower profit margins will be as a result.
4. Bargaining power of Customers: The power of customers grows if they can easily
switch to a competitor's products and services, or if they can force a business and its
competitors’ to compete on price alone where there is little product differentiation and all
prices are known instantly (such as on the Internet).
5. Bargaining power of Supplier’s: The more different suppliers that are available to a
firm, the greater control the firm can exercise over suppliers in terms of price, quality and
delivery schedules. Where there are many suppliers in an industry their power will be
low.
Figure 2.4: Porter’s Competitive Forces Model
33
Information System Strategies for dealing with Competitive Forces
Michael Porter developed a number of generic strategies that can be used by companies to
deal with competitive forces. A company will normally choose the particular strategy which
best suits the particular competitive advantage they want to pursue in the market place. The
following section shows how information systems can be used with each of the following
strategy options:
1. Low-cost leadership: Information systems can be used to achieve the lowest operational
costs and the lowest prices. For example, a supply chain management system can be used
to directly link customers to distribution, production and supply chains, helping lower
inventory and distribution costs.
2. Product differentiation: Information systems can enable new products and services, or
greatly change the customer convenience in using existing products and services. For
example; Dell uses mass customisation, offering individually tailored computers using the
same production resources as mass production, to customise computers to individual
customer needs.
3. Focus on market niche: Use information systems to enable a specific market focus and
serve this narrow target market better than competitors. Information systems support this
strategy by producing and analysing data for finely tuned sales and marketing techniques.
The Internet’s Impact on Competitive Advantage
The Internet has seriously damaged some industries and has severely threatened more. It has
also created entirely new markets and formed the basis for thousands of new businesses.
Because of the Internet, the traditional competitive forces are still at work, but competitive
rivalry has become much more intense. Internet technology is based on universal standards,
making it easy for rivals to compete on price alone and for new competitors to enter the
market. Because information is available to everyone, the Internet raises the bargaining
power of customers, who can quickly find the lowest-cost provider on the Web. Some
industries, such as the travel industry and the financial services industry, have been more
impacted than others. However, the Internet also creates new opportunities for building
brands and establishing very large and loyal customer bases, as is the case for Google,
Facebook and eBay.
Table 2.5 summarises some of the potential impacts of the Internet on the five competitive
forces identified by Porter.

34
Table 2.5: The impact of the internet on the five competitive forces
Five forces
Impact of the internet
Intensity of Rivalry The internet has had the effect of reducing differences between
companies and makes it more difficult for any one company to
maintain competitive advantage
Threat of new entrants The internet reduces the barriers to entry making it easier for a new
company to enter a market. E-commerce can be used
instead of
investing in new shops.
Threat of Substitutes The internet has enabled new substitutes to emerge and new ways
of meeting customer needs.
Bargaining power of
Customers
This is increasing as customers can use the internet to find cheaper
product and services.
Bargaining power of
Suppliers
Companies can use the internet to source new suppliers thus
reducing their power. Suppliers can also benefit from the power of
the internet to eliminate intermediaries and in some cases enables
them to sell directly to consumers.

35
Study Unit 3
Ethics Social and Political Issues of Information Systems
Contents
A.
Key Infrastructure Components
B.
Hardware Platforms
C.
Hardware Platform Trends
D.
Computer Software Platforms
E.
Software Platform Trends
F.
Management challenges posed by IT infrastructure
36
Introduction
The objectives of this chapter are to:
• Describe the Ethics Social and Political Issues of Information Systems
• Describe the impact of modern information systems and the Internet on the protection
of individual privacy and intellectual property.
• Give a brief overview of Data Protection legalisation
A. ETHICAL AND SOCIAL ISSUES RELATED TO SYSTEMS
Ethics creates theories about the nature of right and wrong, duty and obligation that
individuals can use to guide their behaviour. Individuals act within a social environment that,
in turn, exists within a political environment. Ethical dilemmas are problems that affect
society as a whole and are often dealt with in a political setting. The development of
Information systems can drive intense social change thereby raising new ethical questions for
both the individuals and societies involved. For example, new computer technology makes it
easier to gain private information about individuals, such as their shopping preferences,
names, addresses, phone numbers and e-mail addresses as well as bank and social security
details, creating an ethical dilemma for the potential user of that information (whether or not
to invade the privacy of the individual). Society will react by demanding new laws to regulate
the use and storage of data.
Ethical, Social, and Political Issues
Introducing a new technology can gives rise to new ethical, social and political issues that
must be dealt with on individual, social and political levels. These issues have five moral
dimensions: information rights and obligations, property rights and obligations, system
quality, quality of life and lastly accountability and control. Introducing a new Information
system can affect ethical issues that in turn lead to social issues and these subsequently cause
political issues. This demonstrates the tight relationship between ethical, social and political
issues in this modern information society and how introducing a new information system can
ultimately impact on them all.
Five Moral Dimensions of the Information Age
Laudon and Laudon (2010) describe five moral dimensions of information systems as
follows:
1. Information Rights: What information rights do individuals and organisations have with
respect to information about themselves? There are also moral obligations for those
dealing with this information.
2. Property Rights: How will intellectual property rights be protected in a digital society,
where traditional measures that protect property are no longer applicable?
3. Accountability and Control: Who can be held responsible for damage caused to
individual information and property?
4. System Quality: Data quality and system errors - No software program is perfect, errors
will be made, even if the errors have a low probability of occurring
37
5. Quality of Life: What values should be retained in an information society? Which
cultural values and practices are supported by the new information technology?
These dimensions pose useful ethical questions that a company should consider when
introducing a new technology.
These issues are discussed in more detail in Section 3.3.
Technology Trends That Raise Ethical Issues
There are a number of technological trends that generate ethical concerns including:
• Computing power has doubled every 18 months: This is enables growing numbers of
organisations to use information systems in their primary business practices. This is
increasing reliance on systems and increases vulnerability to system errors and reduced
data quality.
• Rapidly falling data storage costs and developments in data storage techniques: This
has led to big increases in the amount of data kept on individuals by private and public
organisations - allowing for violation of an individual’s privacy.
• Networking advances and the Internet: This enables personal data to be remotely
accessed. It is incredibly easy to copy data from one location to another. This raises the
issue of who actually owns the data? Furthermore, how can this ownership be protected?
• Advances in data analysis techniques: This has enabled companies and government
agencies to use profiling to establish detailed information about an individual's behaviour
and tastes and to create a record of this personal information.
• Non-obvious Relationship Awareness (NORA) is a new data analysis technology that
can locate obscure hidden connections between people or other entities by analysing
information from a range of sources to identify relationships. This technology is used by
governments and the private sector to provide powerful profiling. NORA can gather
information about people from many sources such as job applications, telephone records,
customer records, court record, tax records etc. This correlates relationships so that
hidden connections can be uncovered that might help identify criminals or terrorists.
NORA poses ethical questions in relation to privacy implications for individuals. In other
words the information that each of us generates about ourselves every day can be
correlated, manipulated, mined and sold, as it is very valuable. This is an intrusion into an
individual’s privacy and is a major ethical issue for our society
38
B. ETHICAL DILEMMAS IN THE INFORMATION SOCIETY
Responsibility, Accountability and Liability
The term responsibility means that an individual must accept the possible costs and
obligations for the decisions they make. Accountability is a feature of systems and social
institutions that establishes who is responsible. Liability is an aspect of political systems that
allows individuals to recover damages done to them by individuals or organisations that are
deemed responsible. Due-process requires that laws are known and understood by all and
that individuals can appeal to higher authorities to ensure laws were properly applied.
Ethical Analysis
If faced with a situation that poses ethical issues and dilemmas, the following five-step
analysis can be applied:
1. Identify and explain the facts clearly
2. Define the conflict or ethical dilemma posed and recognize the higher order values
concerned
3. Identify the stakeholders
4. Assess the options that can be reasonably taken
5. Identify the possible consequences of these options.
Ethical Principles
Once the 5-step analysis above has been carried out, the following six ethical principles can
be applied to aid in decision making:
1. The Golden Rule: It suggests doing unto others, as you would have them do unto you.
This ethical guideline is found in all major religions and traditions.
2. Immanuel Kant’s Categorical Imperative: Act on rules that you wish to apply to
yourself and universally. This suggests that if an action is not right for everyone to take,
then it is not right for anyone.
3. Descartes’ Rule of Change: This rule also known as the slippery slope rule, suggests
that if an action cannot be taken repeatedly, then it is not right to be taken at any time.
4. Utilitarian Principle: The Utilitarian Principle suggests taking the action that overall
achieves the higher or greater value. An action is good if it promotes ‘happiness’ over
‘pain’ between those affected by it.
5. Risk Aversion Principle: The Risk Aversion Principle suggests taking the action that
produces the least harm or the least potential cost
6. The Ethical “no free lunch rule”: This rule says that practically all tangible and
intangible objects are owned by someone unless there is a specific declaration to state
otherwise. If someone has created something of value to you, that person probably wants
some form of payment for your use.
39
Code of Conduct for Professionals
In declaring one-self to be a professional, special rights and obligations are taken on. Being a
professional, involves entering into constrained relationships with employers, customers, and
society due to special claims to knowledge, wisdom and respect. Professional codes of
conduct are propagated by associations of professionals in order to regulate entrance
qualifications and competencies and to establish codes of ethics. Codes of ethics are applied
by professions to regulate themselves in the general interest of society. For example
honouring property rights and including intellectual property rights.
Examples of Ethical Dilemmas - related to IT systems
The following are some real world examples of ethical dilemmas:
• Using IT systems to increase efficiency can have the knock-on effect of causing layoffs
and personal hardships
• Using IT systems to monitor employee e-mail in order to protect valuable company
assets, is coupled with the ethical dilemma of invading employee privacy
• Monitoring employees’ use of the Internet at work similarly decreases employee privacy
C. THE MORAL DIMENSIONS OF INFORMATION SYSTEMS
Information Rights
Privacy is defined as a state in which an individual is not being observed or disturbed by
other people or organisations. Claims to privacy involve the workplace as well as the home.
Information technology threatens the individual’s claims to privacy by making the invasion
of privacy cheap, profitable and effective. An example of Information technology affecting
the individual’s claims to privacy is the controversy related to Google Street view where
pictures of people’s homes and individual were displayed on the internet without their
consent.
Most European and American privacy law is based a set of principles called the Fair
Information Practices (FIP) which govern the collection and use of information about
individuals. The five FIP principles are:
(1) Notice/awareness;
(2) Choice/consent;
(3) Access/participation;
(4) Security;
(5) Enforcement.
For more details on the Fair Information Practices (FIP), see section 14.1 in Appendix 1
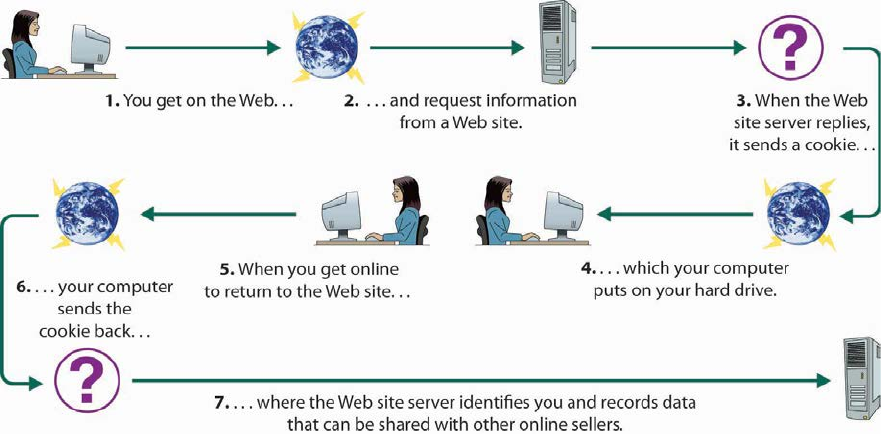
40
Data Protection
For example:
Privacy protection in Europe is far stricter than in the United States. In contrast to the US,
European countries do not permit the use of personally identifiable information by businesses
without the consumer’s prior consent.
How the Internet is challenging the protection of individual privacy
Internet technology creates new obstacles to the protection of an individuals’ privacy. When
information is sent over the Internet it may pass through a variety of different computer
systems before it finally reaches its intended destination. Each of these systems may
jeopardise the individuals’ privacy as they are capable of monitoring, recording and storing
information that pass through them.
Web sites can uncover an individual’s identity if they register on the web site in order
purchase a product or utilise a free service. Web sites can capture information about
individuals that visit their site without their knowledge using a technology called cookies (see
Figure 4.3).
Cookies are small files sent by a Web site to the user’s browser, which are subsequently used
to identify the visitors Web browser and track visits to the Web site. In this way the site can
customise its content to the interests of each particular visitor. For example if you purchase a
book on Amazon the Website will be able to recommend other books of interest based on
previous purchases. Most modern Web browsers allow users to decide whether to accept
cookies or not. However rejecting cookies may make some websites unusable.
Figure 4.3: How Cookies work (Collins, 2009).
Other malicious tools include Web bugs, which are small graphic files embedded in e-mail
messages and Web pages that record who is reading the e-mail message or Web page and
communicates this information to another computer.
41
Protecting the Individual privacy of Internet users
There are a range of approaches that can be implemented to protect the privacy of Internet
users, these include the following:
• Informed consent means that an individual visiting a Web site knowingly consents to the
collection of their data upon visiting the company’s Web site. Federal privacy laws in
United States help mediate the correct collection, usage and disclosure of information.
Similar laws exist in the majority of European countries.
• Self-regulation: Businesses have taken some steps to enhance protection of Internet users
privacy, including publishing statements regarding how their information will be used and
sometimes offering an opt-out right. However, few businesses offer an opt-in approach,
which is far more favourable for protection of privacy, whereby it is prohibited to collect
personal data unless the individual approves it.
• Laws and privacy legislation: These can help regulate the collection, usage, and
disclosure of information.
• Technical solutions: Several technology tools are available to combat privacy invasion
including e-mail encryption, anonymous e-mailing and surfing, cookie rejection and
Spyware detection. The Platform for Privacy Preferences (P3P) is a benchmark for
relating a Web site's privacy policy to its visitors to enable them to select the level of
privacy they desire to maintain while using the Web site.
Intellectual Property Rights
Intellectual property describes intangible property created by individuals or businesses.
Developments in Information technology has created obstacles to the protection of
intellectual property because of the ease with which information can be copied and circulated
over networks such as the Internet. Described below are three legal mechanisms that protect
property rights are trade secret, copyright and patent.
Protecting Property Rights
A trade secret is any intellectual work product used for a business purpose that can be
classified as belonging to that business, provided it is not based on information available in
the public domain. An obstacle to trade secret protection is that once an idea enters into the
public domain, it can no longer be protected as a trade secret.
A copyright is a statutory grant that protects creators of intellectual property against their
work being copied by others for any purpose.. A patent allows the owner a monopoly on the
ideas behind an invention for 20 years. While patent protection does grant a monopoly on the
underlying concepts and ideas, there is a challenge to passing stringent criteria of non-
obviousness, originality and novelty. The Internet makes it very easy to widely distribute and
reproduce intellectual property.
Challenges posed to Intellectual Property Rights
Digital media and software can now be so readily copied, altered, or transmitted, that it is
becoming increasingly difficult to protect with existing intellectual property safeguards.
Illegal copying of software and music and video files is a widespread problem with no
immediate solution or prevention.
42
While it is possible to protect against copying of software program code, copyright protection
can't prevent another person from using the underlying ideas behind a piece of software and
subsequently developing new software that follows the same fundamental concepts. Patent
protection protects the underlying ideas behind software. However a very limited amount of
software has received this protection because the software must first pass very stringent
criteria concerning the originality and novelty of the ideas involved in its design. The Internet
poses a huge challenge to Intellectual Property Rights because it makes it even easier to copy
intellectual property and transmit it freely around the world.
The Business Software Alliance (BSA) is a registered, non-profit trade association composed
of the worlds leading IT organisations and majors software publishers (such as Microsoft and
Oracle). The principle aims of the BSA involve promoting awareness among both the public
and businesses of proper software management practices and the value of software
compliance.
Methods are being developed for the sale and distribution of books, articles and other
intellectual property legally on the Internet. The Digital Millennium Copyright Act (DMCA)
of 1998 is supplying some copyright protection. The DMCA put into practice a World
Intellectual Property Organisation Treaty that makes it illegal to ignore technology-based
protection of copyrighting.
SOFTWARE PIRACY
Software piracy encompasses the unauthorised copying, distribution and/or use of
copyrighted software products. Huge financial loses occur each year to the software industry
as a result of software piracy.
FORMS OF SOFTWARE PIRACY
The following are the primary forms of software piracy:
• Illegal use by End users: This involves the use of copyrighted software without an
appropriate licence or allowing more users of the software than the licence permits.
• Illegal Copying: This consists of making unauthorised copies of software for installation
on other computers and also producing copies for private sale.
• Illegal Bundling: This is where hardware vendors without proper licensing install
copyrighted software onto computers they are selling to increase revenue.
• Professional Counterfeiting: This involves the illegal copying and sale of software
along with imitation logos, manuals and licences to disguise the illegal product.
SOURCES OF SOFTWARE PIRACY
The main sources of software piracy are the following:
• End users who purposely disobey the law or are ignorant of it
• Organisation that ignore the law
• Unprincipled hardware or software dealers
• Internet sites that sell counterfeit software or make them available for illegal download
43
Accountability, Liability and Control
As well as acting as obstacles to both privacy and property rights, modern information
technologies are challenging existing liability laws and social practices for holding
individuals and institutions accountable.
It is very difficult, if not impossible, to hold software producers liable for their software
products as it is only when software acts as a part of a defective product that stringent
liability pertains. However, if the software is strictly a service (not part of a product) these
laws do not apply.
Other interesting ethical issues are: Should an Internet Service Provider (ISP) be held liable
for the material that users transmit, when telephone companies are not held liable for the
messages that users transmit over the phone? Should the providers of online bulleting boards
(and blogs) be held liable for the content posed on these sites? Also should authorities do
more to control the cumbersome amounts of Spam in circulation? Spam is described as un-
requested junk e-mails sent to thousands of Internet users. The primary ethical issues raised
by new technology are whether or not the individuals and organisations that create, produce
and sell systems are morally responsible for the consequence of their use. Furthermore, what
liability should the users assume and what liability should the provider assume?
Note: A Blog is defined as a form the online diary or journal where people provide
commentary or articles on a particular subject. Blogs are continuing to grow exponentially in
number, popularity and content.
Causes of System Quality Problems
The primary sources of system quality problems are hardware and facility failures, software
bugs and errors, and low data quality. It is of note that while software companies generally
try to de-bug their products before releasing them to the public marketplace, they may
knowingly ship products with bugs due to the fact that the time and cost required to fix all
minor errors would prevent the product from ever being released as it would no longer be
financially viable. However while these software errors and bugs are a source of many
system quality problems, the most common cause is in fact data quality.
44
Quality of Life Impacts of Computers and Information Systems
Laudon and Laudon (2010) identified a number of quality of life impacts of computers and
information systems as described below:
1. Balancing power depicts the shift toward highly decentralised computing, coupled with
an ideology of "empowerment" of workers and decentralisation of decision making to
lower organisational levels. The problem with this idea is that the lower-level worker’s
involvement in decision-making still tends to be minor or trivial. Key policy decisions
largely remain as centralised as they were in the past.
2. The rapidity of change impact suggests that information systems have increased the
efficiency of the global marketplace. As a result of this efficiency, businesses no longer
have many years to adjust to competition. This has the negative effect of many
businesses being wiped out very rapidly before they can develop, meaning that jobs are
lost.
3. The maintaining boundaries impact proposes that the development of laptops and
telecommuting have created a situation where people can take their work anywhere with
them and do it at any time. This has negative connotations, for example workers may
find that their work is cutting into family time, vacations and leisure, weakening the
traditional institutions of family and friends and blurring the line between public and
private life.
4. The dependency and vulnerability impact indicates that businesses, governments,
schools and private associations are becoming increasingly dependent on information
systems leaving them highly vulnerable to the failure of those systems.
5. The computer crime and abuse impact suggests that computers have created new
medium for committing crimes and subsequently have themselves become the target of
criminal acts.
6. The employment impact implies that redesigning business processes may lead to
countless middle level managers and clerical workers losing their jobs. Worse still, if the
proposed re-engineering works as claimed, these workers will be unable to find similar
employment as the need for their skills will decline.
7. The equity and access impact proposes that access to computers and information
resources, like wealth, is not equally distributed throughout society. Access is distributed
inequitably along racial, economic and social class lines (in the same way as many other
information resources).
8. Health risks have been attributed to computers and information technologies. For
instance, businesses are reported to now spend $20 billion a year to compensate and treat
victims of computer-related occupational diseases. The most important occupational
disease today is repetitive stress injury (RSI). The largest single source of RSI is
considered to be computer keyboards. However, RSI is avoidable; workstations can be
designed for a neutral wrist position, with a wrist rest to support the wrists, proper
monitor stands and footrests. These measures collectively contribute to proper posture
and reduced incidence of RSI and should be enhanced with frequent rest breaks and
rotation of employees to different jobs.

45
Study Unit 4
Computer Hardware and Software
Contents
A.
Key Infrastructure Components
B.
Hardware Platforms
C.
Hardware Platform Trends
D.
Computer Software Platforms
E.
Software Platform Trends
F.
Management challenges posed by IT infrastructure
46
Introduction
The objectives of this chapter are to:
• Introduce the different types of IT infrastructure
• Describe the different hardware platform
• Highlight a number of emerging hardware technology trends
• Describe the different computer software platforms
• Highlight a number of emerging software technology trends
A. INFRASTRUCTURE
Information technology infrastructure is the shared technology resources that provide the
platform for the firm’s specific information systems. IT infrastructure includes hardware,
software and services that are shared across the entire firm.
Laudon and Loudon (2010) identified the following IT infrastructure elements:
• Computing platforms that are used to provide computing services.
• Telecommunications services that connect employees, customers and suppliers.
• Physical facilities management which develop and manage the physical installations
required for the computing, telecommunications and data management services.
• Application software services such as ERP, SCM, CRM and Knowledge management
systems that are shared across all business units.
• Data management services that manage the company’s data and make it available to
internal and external users as required.
• IT management services that plan, develop and manage the IT infrastructure.
• IT education and training services that train employees on how to properly use the
systems.
Different Levels of IT Infrastructure
IT infrastructure is organised at three major levels:
• Public: All firms are dependent on public IT infrastructure, which includes the Internet,
the Public Switched Telephone Network (PSTN) and other IT support facilities such as
cable systems and cellular networks.
• Enterprise-wide infrastructure: This includes services such as e-mail, a corporate Web
site, corporate intranets and a range of enterprise software applications.
• Business unit: This IT infrastructure is tailored to the particular line of business such as
specialised production systems, customer support systems, local order entry and other
transaction systems.
47
B. KEY INFRASTRUCTURE COMPONENTS
Information Technology is composed of seven key components:
1. Computer hardware platforms include client computers and servers.
2. Operating system platforms include Windows operating systems for client computers,
and UNIX or Linux operating system for servers. Operating systems are the software that
manage the hardware resources and activities of the computer and act as an interface for
the user.
3. Enterprise and other software applications include SAP and Oracle, and middleware
software that are used to link a firm's existing application systems.
4. Data management and storage is handled by database management software and
storage devices including traditional storage methods, such as disk arrays and tape
libraries, and newer network-based storage technologies such as storage area networks
(SANs). SANs connect multiple storage devices over dedicated high-speed networks.
5. Networking and telecommunications platforms include Windows server operating
systems; Novell, Linux, and UNIX. Nearly all LAN and many wide area networks
(WANs) use the TCP/IP standards for networking.
6. Internet platforms overlap with, and must interconnect with the firm's general
networking infrastructure, hardware and software platforms. Internet-related
infrastructure includes the hardware, software and services to maintain corporate Web
sites, intranets and extranets, including Web hosting services. A Web hosting service
maintains large Web servers and provides fee-paying customers with space to maintain
their Web sites.
7. Consulting and system integration services are employed to integrate a firm's legacy
systems with new technology and infrastructure and providing expertise in implementing
new infrastructure along with relevant changes in business processes, training and
software integration.
C. HARDWARE PLATFORMS
The term Hardware platform is used to describe the hardware equipment on which the
information system is installed.
The microprocessor is the heart of any computing device no matter how small or large. Two
companies produce most micro processing chips: Intel and Advanced Micro Devices (AMD).
The most widely used of these is Intel.
Since the network is becoming so commonplace and the heart of computing; network service
providers must have the correct type server in place to meet the increased demand. Blade
servers which are small compact highly efficient servers are meeting these needs while being
cheaper and easier to manage than traditional big-box servers.
48
Categories of Computer
The following are the main categories of computers:
• Microcomputers are the most important category of computer for business people and
consumers. Microcomputers are normally referred to as personal computers or PCs. Most
microcomputers are called desktop computers as they are designed to sit on a desk.
Another important type of microcomputer is the laptop, which is designed to suit those
who want a portable computer.
• Midrange computers including minicomputers and high-end network servers are multi-
user systems that can manage networks of PCs and terminals. Midrange computers can
support hundreds of users and are popular as industrial processing control and
manufacturing plant computers. Midrange computers have also become popular as
powerful network servers to help manage large Internet websites and corporate Intranets.
• Mainframe computers are large, fast and powerful computing systems. These systems
are normally found in large corporations who have significant transactions processing
volumes or complex computational problems. Major International banks, airlines, oil
companies and other large organisations used mainframe computers to process millions of
sales transactions and customer enquires each day.
D. HARDWARE PLATFORM TRENDS
Integration of Computing and Telecommunications Platforms
The Integration of Computing and Telecommunications Platforms is one of the most
dominant themes in hardware today where increasingly computing is taking place over the
network. Client level communications devices such as cell phones are taking on the functions
of handheld computers. An example is the smartphone which has all the functionality of a
cell phone coupled with the ability to send and receive e-mail as well as browse the internet.
The functionality of these devices has been further extended by the availability of thousands
of application programmes that can be installed in the smartphone. At the server and network
level, the growing success of Internet telephone systems shows how historically separate
telecommunications and computing platforms are converging towards a single network.
Cloud computing (also called on-demand computing)
On-demand computing, which is another term for cloud computing, provides necessary
infrastructure from centralised sources. Cloud computing enables firms to off-load the
demand for computing power to remote, large-scale data processing centres. By doing this
firms can reduce their investment in IT infrastructures, and pay for only as much computing
power as they require. It’s cheaper and helps companies reduce the total cost of ownership of
IT technology. They can also take advantage of newer technologies than what they are able to
buy and maintain on their own. Utility computing is another term for cloud computing.
49
Advantages of Cloud Computing
The advantages associated with cloud computing includes:
• It is not dependent on physical location of either resources or users.
• Users access computing resources on their own and are not necessarily dependent on IT
staff.
• It is based on standard network and Internet devices.
• Resources serve multiple users with computing virtually assigned according to need.
• Resources are increased or decreased according to demand.
• Charges are based on the amount of resources actually used.
• Large investments in IT infrastructure are not necessarily needed or investments are
significantly reduced.
• Firms can shift additional processing requirements to cloud computing during peak
business periods.
• It allows a more flexible IT infrastructure.
Disadvantages of Cloud Computing
The disadvantages associated with cloud computing includes:
• Responsibility for data storage and control is transferred away from the organization to a
third party.
• Security risks and chances of data compromises are increased.
• Risk diminishing system reliability.
• Increased dependency on a third party.
• Huge investments in proprietary systems supporting unique business processes may be at
risk.
Grid Computing
Grid computing involves connecting geographically remote computers into a single network
to create a computational grid that combines the computing power of all the computers on the
network to create a large computing platform. It allows companies to save money on
hardware and software, and increase computing and processing speeds to make the company
more agile.
Edge computing
Edge computing is a multi-tier, load-balancing scheme for Web-based applications in which
parts of the Web site content and processing are performed by smaller, less expensive servers
located near the computer. In an edge computing platform client requests are initially
processed by the edge servers, which may deliver static presentation content and reusable
code, while database and business logic components are delivered by the enterprise servers.
50
Autonomic computing
As companies rely more and more on IT to meet the demands of employees, customers,
suppliers, and business partners, they can’t afford to have any system downtime at all.
Autonomic computing is a step towards creating an IT infrastructure that is able to diagnose
and fix problems with very little human intervention. Autonomic computing features systems
that can:
• Configure themselves
• Optimise and tune themselves
• Repair themselves when broken
• Protect themselves from intruders and self-destruction
Although this type of computing is still relatively new, it promises to relieve the burden many
companies experience in trying to maintain large, complex IT infrastructures.
Virtualisation and Multi-core Processors
As companies deploy more and more servers, many have discovered that they are spending
more on electricity to power and cool their systems than they did on acquiring the hardware.
Power consumption can be lowered through virtualisation and multi-core processors.
Virtualisation is the process of presenting a set of computing resources (such as computing
power or data storage) so that they can all be accessed in ways that are not restricted by
physical configuration or geographic location. Server virtualisation enables companies to run
more than one operating system at the same time on a single machine. Most servers run at
just 10 to 15 percent of capacity, and virtualisation can boost server utilisation rates to 70
percent or higher.
A multi-core processor is an integrated circuit that contains two or more processors. This
technology enables two or more processing engines with reduced power requirements and
heat dissipation to perform tasks faster than a single-core processor.
Intel and Advanced Micro Devices (AMD) now make multi-core processors. SUN
Microsystems sells servers using its eight-core processor.
Green Computing
This is an approach to reduce the impact on the environment and reduce resources
consumption by using more efficient hardware and better software.
A few trends in green computing include:
• purchasing desktops that are built to reduce power needs;
• more efficient server computers;
• increase the use of virtualisation to reduce the number of servers needed;
• reducing power costs;
• turning off equipment that isn’t being used;
• recycling computer equipment;
• Using environmentally friendly materials in computer manufacture.
From a business perspective it makes sense to reduce costs, both in the short term and long
term.
51
The Growth of Mobile Platform:
Cell phones and smartphones (for example; BlackBerry, iPhone and Android phones) are
now being used for data transmission, Web surfing, sending and receiving e-mails and instant
messaging.
Other types of mobile devices include
• Netbooks which are small, low-cost lightweight notebooks that have optimised
wireless communication and core computing tasks
• Tablet computers (for example the iPad)
• Networked e-readers (such as the Kindle)
E. COMPUTER SOFTWARE PLATFORMS
Operating System Platforms
An operating system is the software that interacts with the hardware of the computer in order
to manage and direct the computer’s resources. Operating systems tell computers what to do,
when to do it, and how. Operations such as logging on, file management, and network
connectivity are controlled by the operating system. By far the most prolific operating system
is Microsoft Windows. Windows is also the operating system used by some non-traditional
computing devices such as hand-held devices and cell phones.
Unix and Linux are often associated with large networks that require less application
overheads and faster processing. Linux open-source software is becoming the operating
system of choice for organisations looking to save money. Businesses and governments
across the globe are adopting the Linux platform as a way to reduce IT spending and license
costs.
Application Software
Application software consists of programs that direct the computer to perform specific
information processing activities and that provide functionality for users. Because there are
many different types of users of computer systems there are a large number of different types
of application programs available.
Application Software can be subdivided into the following two groups:
• Application Specific Software
• General Purpose Application Programs
Application Specific Software
Application Specific Software packages support end users in business and other fields. For
example application specific software packages support business uses such as Transaction
Processing, decision support, accounting, sales management etc.
General Purpose Application Programs
There is a wide variety of general-purpose application programs available including: word-
processing and spreadsheet packages.
52
Enterprise Software Applications
Integrating applications into seamless processes across the organisation is the goal of
enterprise software applications. Customer relationship management and supply chain
management systems are the two most popular applications in this category.
Application Programming Languages
The following are the main application programming languages:
• COBOL (COmmon Business Oriented Language) was developed in the early 1960s. It
was designed with business administration in mind. It is used for processing large data
files with alphanumeric characters and for performing repetitive tasks such as payroll. It
is poor at complex mathematical calculations.
• C and C++ are powerful and efficient languages developed at AT&T’s Bell Labs. They
combine machine portability with tight control and efficient use of computer resources.
C++ is object-oriented.
• FORTRAN (FORmula translator) is useful in processing numeric data and is primarily
used for scientific and engineering applications.
• BASIC and Pascal are used primarily in education programming. Assembly language
resembles machine language, but it substitutes mnemonics for 1s and 0s, making it easier
to program (although it is perhaps the most difficult language). Assembly language is
designed for a specific machine and specific microprocessors.
Object-oriented Programming
Object-oriented programming combines data and specific procedures that operate on that data
into an object. Instead of passing data to procedures, programs send a message for an object
to perform a procedure that is already embedded in it. Programmers can focus on what they
want an object to do, and the object decides how to do it. Each object is an independent
software building block that can be used in many different systems without changing the
program code.
In traditional programming, data and procedures are treated as independent components and
are not combined as in object-oriented programming. A separate programming procedure
must be written every time someone wants to take an action on a particular piece of data.
Procedures act on data the program passes to them.
Data Management and Storage
Businesses and organisations are gathering more and more data on customers, employees and
even the business itself. Managing and storing the data so that they are easily accessible and
provide meaningful information to the organisation is becoming a complex task. The systems
that are responsible for organising and managing the storage of the firms are called Database
management Systems (DBMS). Data Management systems are discussed in detail in Chapter
6.
In addition to the traditional physical storage mediums of disk and tapes, many large firms
are turning to high speed network based storage solutions called Storage area networks
(SANs). SANs provide an interconnected, economical way to consolidate data from across
53
any and all systems within the business. Online users want instant access to data and SANs
help companies provide it.
Networking and telecommunications platforms
As we continue towards convergence of all forms of digital communications, networking and
telecommunications platforms are merging into one. Rather than having one platform for
networking computer devices and a separate platform for telecommunications, we’ll see one
company providing a combination of telephone services, cell phone connectivity, computers
and peripheral devices, handheld PDAs, and wireless services all rolled into one. Many
telecommunications companies are now merging with Internet service providers to offer a
complete package of digital services.
Internet Platforms
The Internet and its technology standards continue to expand the services businesses are able
to provide their employees, customers, suppliers and business partners. Intranets and
extranets built on Internet technologies giving businesses an easy and inexpensive method of
providing services.
Rather than purchase all of the hardware necessary to support Web sites, intranets, and
extranets, many small and medium-sized companies use Web hosting services instead. It’s
cheaper and easier to have these service providers take care of hardware, software and
security issues while the business concentrates on its core processes.
Consulting and System Integration Services
Systems used in many medium and large-sized companies and organisations are so complex
that most businesses simply can’t manage by themselves. Integration services provided by
companies like IBM and Hewlett-Packard are necessary to keep up with changes. It makes
more business sense for a small/medium company to concentrate on its core business and let
a service provider like HP take care of the technology issues.
These services become more critical as many companies merge their old legacy systems with
newer technologies such as wireless computing. Some legacy systems can’t be thrown away
but must work seamlessly with today’s technologies. Companies choose not to totally replace
legacy systems because it’s too expensive, involves too much training, and carries too much
organisational change and sometimes risk. It’s easier to use middleware and other
technologies to merge old and new systems.
F. SOFTWARE PLATFORM TRENDS
The main trends in contemporary software platforms are:
• Open source software
• Java
• Enterprise integration software
• Web services and service-oriented architecture
• Apps (Mobile)
• Software outsourcing
54
Open-Source Software
Open-source software is computer software for which the source code and certain other rights
normally reserved for copyright holders are provided under a software license that meets the
Open-Source definition or that is in the public domain. Open-source software is produced and
maintained by a global community of programmers and is downloadable for free. Users can
use, change, and improve the software, and redistribute it in modified or unmodified forms. It
is very often developed in a public, collaborative manner.
Linux is a powerful, resilient open-source operating system that can run on multiple
hardware platforms and is used widely to run Web servers. Linux is virtually free, meaning
expensive operating licenses are practically eliminated. Support is available through the
open-source Linux community. Other help is increasingly becoming more available as more
companies migrate towards this software.
Java
Java is a programming language that delivers only the software functionality needed for a
particular task. With Java, the programmer writes small programs called applets that can run
on another machine on a network. With Java, programmers write programs that can execute
on a variety of operating systems and environments. Further, any program could be a series
of applets that are distributed over networks as they are needed and as they are upgraded.
Java is important because of the dramatic growth of Web applications. Java is an operating
system that can run on multiple hardware platforms and is used widely to run Web servers. It
provides a standard format for data exchange and for Web page descriptions.
Enterprise integration software
Software for enterprise integration is needed by firms, who need to integrate existing legacy
systems with newer information systems and technologies. Replacing isolated systems that
cannot communicate with enterprise software is one solution. However, many companies
cannot simply discard essential legacy applications. Some integration can be achieved by
middleware, which is software that creates an interface or bridge between two different
systems. Firms increasingly purchase enterprise application integration (EAI) software
that enables multiple systems to exchange data through a single software hub.
EAI software uses special middleware that creates a common platform, which enables many
different applications to communicate with each other. EAI requires much less programming
and development than traditional point-to-point integration (See Figure 5.3).
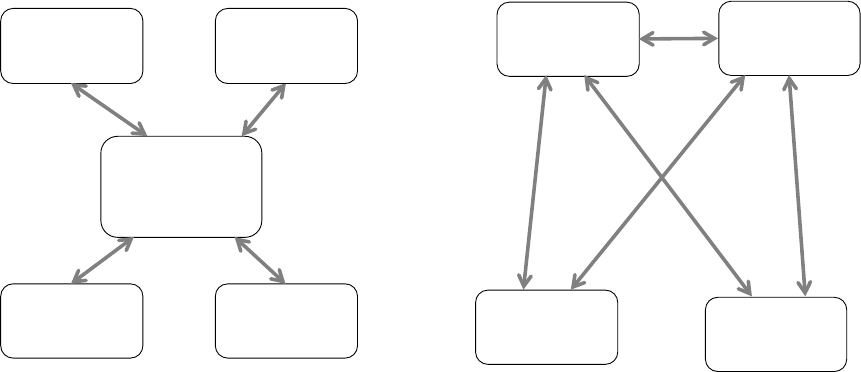
55
Figure 5.3: Enterprise application integration versus point to point integration.
Web Services and Service-Oriented Architecture
WEB SERVICES
Web services refer to a set of loosely coupled software components that exchange
information with each other using standard Web communication standards and languages.
Some of the characteristics of Web services include:
• They can exchange information between two different systems regardless of the
operating systems or programming languages on which the systems are based.
• They can be fused to build open standard Web-based applications linking systems of
two different organisations.
• They can be used to create applications that link disparate systems within a single
company.
• They are not tied to anyone operating system or programming language.
• Different applications can use them to communicate with each other in a standard way
without time-consuming custom coding.
The foundation technology of web services is XML – this is discussed below.
MARKUP LANGUAGES
Hypertext Markup Language (HTML) is a page description language for specifying
how text, graphics, video and sound are placed in a Web page document.
Extensible Markup Language (XML) provides a standard format for data exchange,
enabling Web services to pass data from one process to another. It was developed in 1996 by
the World Wide Web Consortium as a more flexible markup language than HTML. While
HTML is limited to describing how data should be presented in the form of a Web page,
Application
D
Application
C
Application
A
Application
B
Application
A
Middleware
Application
D
Application
C
Application
B
Point to Point IntegrationEnterprise Application Integration (EAI)
56
XML can perform presentation, communications, and storage of data. The tag in XML is able
to specify the type of data – for example it can specify if the piece of data is a price, a date or
a customer id etc.
By tagging selected elements of the content of a document with their meaning XML makes it
possible for computers to automatically manipulate and interpret the data and perform
operations on the data without human intervention.
XHTML (Extensible Hypertext Markup Language) combines HTML language with the
XML language to create a more powerful language for building more useful Web pages.
Four software standards and communication protocols provide easy access to data and
information via Web services in the first layer:
• XML (eXtensible Markup Language): describes data in Web pages and databases
• SOAP (Simple Object Access Protocol): allows applications to pass data and
applications to one another
• WSDL (Web Services Description Language): describes a Web service so that other
applications can use it
• UDDI (Universal Description, Discovery, and Integration): lists Web services in a
directory so it can be located
EXTENSIBLE BUSINESS REPORTING LANGUAGE (XBRL)
XBRL is a language for the electronic communication of business and financial data, which
is revolutionising business reporting around the world. It provides major benefits in the
preparation, analysis and communication of business information. It offers cost savings,
greater efficiency and improved accuracy and reliability to all those involved in supplying or
using financial data.
XBRL stands for eXtensible Business Reporting Language. It is one of a family of "XML"
languages which is becoming a standard means of communicating information between
businesses and on the internet.
The idea behind XBRL, eXtensible Business Reporting Language, is simple. Instead of
treating financial information as a block of text - as in a standard internet page or a printed
document - it provides an identifying tag for each individual item of data that is computer
readable. For example, company net profit has its own unique tag.
The introduction of XBRL tags enables automated processing of business information by
computer software, cutting out laborious and costly processes of manual re-entry and
comparison. Computers can treat XBRL data "intelligently": they can recognise the
information in a XBRL document, select it, analyse it, store it, exchange it with other
computers and present it automatically in a variety of ways for users. XBRL greatly
increases the speed of handling of financial data, reduces the chance of error and permits
automatic checking of information.
Companies can use XBRL to save costs and streamline their processes for collecting and
reporting financial information. Consumers of financial data, including investors, analysts,
financial institutions and regulators, can receive, find, compare and analyse data much more
rapidly and efficiently than if it is in XBRL format.

57
XBRL can handle data in different languages and accounting standards. It can flexibly be
adapted to meet different requirements and uses. Data can be transformed into XBRL by
suitable mapping tools or it can be generated in XBRL by appropriate software (Source -
http://www.xbrl.org/).
The XBRL format is governed and marketed by an international consortium (XBRL
International Incorporated) of approximately 600 organisations including; companies,
regulators, government agencies, infomediaries and software vendors.
XBRL International is supported by its jurisdictions—independent bodies, generally
organised on a country specific basis — that work to promote the adoption of XBRL and the
development of taxonomies that define the information requirements of their particular
domains. XBRL is being adopted around the world in order to migrate business information
process from paper-based and legacy electronic proprietary formats more fully onto Internet
oriented processes (both for external and internal reporting processes).
SERVICE – ORIENTED ARCHITECTURE
A service-oriented architecture is a set of self-contained services that communicate with
each other to create a working software application. Business tasks are accomplished by
executing a series of these services. Software developers are able to reuse these services in
other combinations to create other applications when needed.
Apps (Mobile)
Apps are Small pieces of software that run on the Internet, on your computer, or on your cell
phone. The most popular apps are available for the iPhone, BlackBerry, Android and
Windows smartphones and tablet computers. They are generally delivered over the Internet.
Software Outsourcing
Today most business firms continue to operate their legacy systems that continue to meet a
business need that would be very costly to replace. However they will purchase most of their
new software applications from external sources. There are three main external sources of
software:
• Software Packages from Software Vendor: A software package is a prewritten
commercially available set of software programs that eliminates the need for the business
to write its own software for certain functions such as payroll processing and order
handling.
• Software as a Service (SaaS) is a model of software deployment whereby a provider
licenses an application to customers for use as a service on demand. SaaS software
vendors (such as SalesForce.com) may host the application on their own web servers or
upload the application to the consumer device, disabling it after use or after the on-
demand contract expires. The on-demand function may be handled internally to share
licenses within a firm or by a third-party application service provider (ASP) sharing
licenses between firms. The sharing of end-user licenses and on-demand use may also
reduce investment in server hardware or the shift of server use to SaaS suppliers of
applications file services. Using a SaaS can allow companies to bootstrap business
necessities and reduce hiring costs (e.g. using onsip.com for a business telephone system
rather than hiring an IT/systems specialist to install a phone system.)
58
• Application Service Provider (ASP): An ASP is a business that delivers and manages
applications and computer services from remote computer centres to multiple users using
the Internet or private network. Instead of buying and installing the software programs,
subscribing companies can rent the same functions from the ASP. Users pay for the use of
this software either on a subscription or per-transaction basis.
• Outsourcing: This is where a firm contract out custom software development or
maintenance of existing legacy programs to outside firms, frequently to firms who
operate in low-wage areas of the world (outsourcing is described in detail in Chapter 12).
G. MANAGEMENT CHALLENGES POSED BY IT INFRASTRUCTURE
The objective of infrastructure management is to provide a coherent and balanced set of
computer based services to customers, employees and suppliers. To reach this objective
firms must deal with a number of issues:
• Cost of IT infrastructure
• Integration of information, applications and platforms
• Flexibility to respond to business environments
• Resilience
• Service levels
Creating and maintaining a coherent IT infrastructure raises multiple challenges including:
• Making wise infrastructure investments – IT infrastructure is a major capital
investment for the firm. If too much money is spent on infrastructure, it lies idle and
constitutes a drag on firm financial performance. If too little is spent, important business
services cannot be delivered and the firm’s competitors will outperform the under-
investing firm.
• Coordinating infrastructure components – Firms create IT infrastructures by choosing
combinations of vendors, people, and technology services and fitting them together so
they function as a coherent whole.
• Dealing with scalability and technology change – As firms grow, they can quickly
outgrow their infrastructure. As firms shrink, they can get stuck with excessive
infrastructure purchased in better times. Scalability refers to the ability of a computer,
product or system to expand to serve a larger number of users without breaking down.
• Management and governance – Involves who will control and manage the firm’s IT
infrastructure.
Total Cost of Ownership (TCO)
Total cost of ownership (TCO) is a financial estimate. Its purpose is to help consumers and
enterprise managers determine direct and indirect costs of a product or system. The total cost
of owning technology resources includes not only the original cost of acquiring and installing
hardware and software, but it also includes the ongoing administration costs for hardware and
upgrades, maintenance, technical support, training, and even utility and real estate costs for
running and housing the technology. When incorporated in any financial benefit analysis, it
provides a cost basis for determining the economic value of that investment.
59
TCO tries to offer a statement on the financial impact of deploying an information technology
product over its Lifecycle. These technologies include software and hardware, and training.
Some of the Total Cost of Ownership elements that can be considered in the deployment of
technology include the costs of the following:
• Computer hardware and programs
• Network hardware and software
• Server hardware and software
• Workstation hardware and software
• Installation and integration of hardware and software
• Purchasing research
• Warranties and licenses
• License tracking - compliance
• Other migration expenses
• Risks: susceptibility to vulnerabilities, availability of upgrades, patches and future
licensing policies, etc.
• Operation expenses
• Infrastructure (floor space)
• Electricity (for related equipment, cooling, backup power)
• Testing costs
• Downtime, outage and failure expenses
• Diminished performance (i.e. users having to wait, diminished money making
ability)
• Security (including breaches, loss of reputation, recovery and prevention)
• Backup and recovery process
• Technology training
• Audit (internal and external)
• Insurance
• Information technology related personnel
• Corporate Level Management time
• Long term expenses
• Replacement
• Future upgrade or scalability expenses
• Decommissioning
60
Study Unit 5
Telecommunications, Networks, the Internet and Wireless
Contents
A.
Networks and Communications
B.
Communication Networks
C.
The Internet
D.
Wireless Technology
E.
Management Opportunities and Challenges
61
Introduction
The objectives of this chapter are:
• To give an overview of the major trends in telecommunications
• To describe the different types of communication networks and technologies
• To illustrate the operation of the Internet and the services that are provided over it
• To describe Intranets and Extranets and their business benefit
• To explain wireless technology and how it can be utilised for business benefit
A. NETWORKS AND COMMUNICATIONS
Major Trends in Telecommunications
The major trends in telecommunications include:
• Rapid technological innovation has resulted in many new forms of business
communications, ranging from cell phones with Internet access to Wi-Fi wireless local
area networks.
• Continuing deregulation of telecommunications has driven competition leading to
lowered prices for telephone services, and an expansion of alternative phone services
such as wireless, cable, and Internet telephones.
• The line between telephone, cable television and Internet, has blurred as each different
type of network operator (fixed line, mobile and cable TV operator) tries to provide
video, voice, and data connectivity on a single network.
• Growing importance of Internet technologies in voice, video, and data communications.
• Increase in speed of broadband connections to homes and businesses.
• Rapid growth in wireless telephones, wireless computer networks, and mobile Internet
devices such as smartphones and tablet computers.
• Growth in communication based services and products such as Internet telephone and
video and TV over the internet. A new addition is telephone television, which is making
its way into the market.
Business Network Infrastructure
The network infrastructure used in businesses today to link departments, offices, and various
functions is a combination of many different networks. These include the public switched
telephone network, the Internet, wide area networks and local area networks linking
workgroups, departments, or office floors. The basic function of any telecommunications
networks is the transmission of information from the source device through the network(s) to
its correct destination while ensuring that the received message is free of errors.
Figure 7.1 shows a simple network that includes the major components found in a company
network. These components include:
• Computers (PCs), network interfaces, a connection medium network operating system
software, and either a hub or a switch.
62
• Each computer on the network contains a network interface device (NIC) that the
network is connected to.
• Connection medium for linking network components can be a copper wire, coaxial cable,
fibre optic cable, or radio signal in the case of wireless networks.
• Network operating systems manage the communications on the network between the
different network elements.
• Most networks contain a hub or switch acting as a connection device between the
computers or other devices on the network.
• To communicate with another network, the network would use a router which is a
special communications device used to route packets of data through different networks,
to ensure that any message sent gets to the correct address.
Figure 7.1: A simple network
The Complexity of Large Company Networks
Today’s enterprises have large complex networks usually consisting of a number of local-
area networks (LANs) linked to enterprise wide area network (WAN) for data and voice
communication. Many large servers are utilised for supporting company Web sites, an
intranet and extranets. The connect various applications and databases that support services
such as sales, ordering, and financial transactions, inventory control etc.. These large
enterprises may also have a number of enterprise applications such as supply chain
management and CRM systems. A challenge for organisations is the integration of these
networks and systems.
Server
Internet
SwitchHub or Switch Router
Company's Private
Network
NIC
NIC
NIC
NIC
PC
PC
PC
PC
Server running a
Network Operating
System
Network Interface Card (NIC)
63
Important Telecommunications Technologies
Modern digital networks and the Internet are based on three key technologies: (1)
Client/server computing; (2) the use of packet switching; (3) and the development of
widely used communications standards such as TCP/IP.
Client/Server Computing
A client/server arrangement involves client computers (PCs) and a server connected across a
network. The server has hard disks holding shared data, shared applications and may often
have other resources that can also be shared such as printers, etc. The clients are all the other
computers on the network. Under the client/server arrangement, processing is usually done by
the server, and only the results are sent to the client. However, some of the processing can be
shared with the client. For example, the client may request data from a database on the server;
the server then processes the request and sends the results to the client, who performs further
processing on the data.
The Client/server arrangement can help reduce the amount of data traffic on a network thus
allowing faster response for the client computers. Security can be controlled as clients can be
forced to authenticate to the server before being given access to resources. Authentication can
be achieved using login names and passwords. Because management of the network is
centralised, costs are lower. Since the server does most of the intensive processing, less
expensive computers can be used by the clients. The main disadvantages of the client server
model include the fact that if the server fails, the system fails
Packet Switching:
Packet switching makes efficient use of network capacity by breaking messages into small
packets that are sent independently along different paths in a network and are then
reassembled at their destination (see Figure 7.2).
When a user sends a message to another user on the Internet, the message is first decomposed
into packets using the TCP protocol. Each packet contains the destination address of the
message and sequence in the overall message. The packets are then sent from the client
computer to the network server and from there to various routers on the networks to arrive at
a specific destination computer address. The routers use the destination address of the packets
to select a route for each packet. At the destination address, the packets are finally
reassembled into the original message.
Packet Switching technology allows greater utilisation of available links and capacity.
64
Figure 7.2: Packet Switching Example – individual packets can take different routes to the
destination.
Communications Standards – Protocols
A protocol is a standard set of rules and procedures for the control of communication in a
network. Having a standard set of protocols provides a universally agreed upon method for
data transmission and supports communications between diverse hardware and software
equipment. Examples of protocols are:
• TCP/IP: Transmission Control Protocol/Internet Protocol is a suite of protocols that is
used on the Internet (and other networks) to control how the packets of data are sent and
received.
• Ethernet: The Ethernet protocol is widely used in networking. It specifies rules that
govern the communications between computers on a network.
TCP/IP is discussed in more detail later in this chapter.
B. COMMUNICATION NETWORKS
WANs, MANs and LANs
Wide Area Network (WAN): A WAN is a wide area telecommunications network, spanning
a large geographical distance. WANs may use a variety of media and a combination of
switched and dedicated lines.
Metropolitan Area Network (MAN): A MAN is a metropolitan area network that spans an
urban area, usually a city and its major suburbs.
Local Area Network (LAN): A LAN is a network that encompasses a limited distance,
usually one building or several buildings in close proximity. A router connects the LAN to
other networks (such as a WAN or MAN), so that the LAN can exchange information with
external networks.
Message received
& reassembled
Message to be sent
broken into packets
P3
P4
P4
P3
P2
P1
P1
P2
P4
P1
P3
P4
P2
P4
P3
P2
P1
Kigali
Kampala
Dar es Salaam
Bujumbura
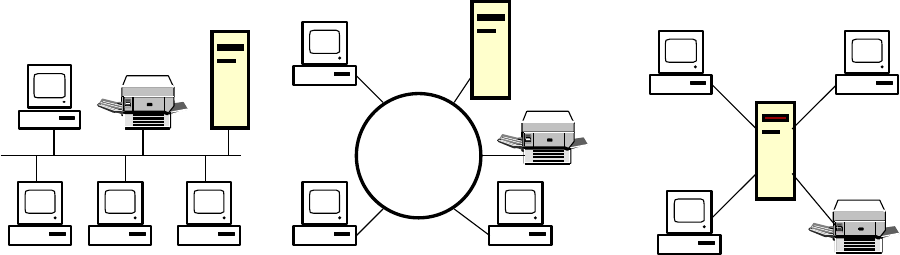
65
Network Topologies
There are three main types of network topologies as shown in figure 7.3:
• In a star topology, all devices on the network connect to a single hub and all network
traffic flows through the hub.
• In a bus topology, one station transmits signals, which travel in both directions along a
single transmission segment. All of the signals are broadcast in both directions to the
entire network, with special software to identify which device should receive each
message.
• A ring topology connects network devices in a closed loop. Messages pass from
computer to computer in only one direction around the loop and only one station at a time
may transmit.
Figure 7.3: Network Topologies
Transmission Media
Networks use different types of physical transmission media to carry messages from one
device to another, these include the following:
• Twisted pairs: Twisted pairs of copper wires are used mostly for analogue voice
signals but also for data.
• Coaxial cable: Coaxial cable consists of a single, thickly insulated and shielded
copper wire, which can transmit a large volume data than twisted pair.
• Fibre optic cable and Optical networks: Fibre optic cable is made up of strands of
glass fibre, each about the thickness of a human hair. The data is transformed into
pulses of light which are sent through the fibre optic cable at very high speed using a
laser light.
Optical networks are networking technologies for high-speed transmission of data in
the form of light pulses. They are becoming important because they can transmit all
types of traffic (voice, data, and video) over fibre cables and provide the massive
bandwidth for new types of services and software. One advantage of this type of
network is that there is very little degradation in quality, unlike transmission over
copper wire.
Bus Topology Star TopologyRing Topology
Server
Server
Server
66
Wireless Transmission Media and Devices
Wireless transmission involves sending signals through the air or space without the need for a
physical line. Each type of wireless transmission uses specific frequency ranges. Microwave
systems transmit high-frequency radio signals through the atmosphere. Other types of
wireless transmission such as cellular telephones are assigned a specific range of frequencies
by national regulatory agencies in line with international agreements.
Microwave systems transmit high-frequency radio signals through the atmosphere and are
widely used for high-volume, long distance and point-to-point communications. Microwave
signals follow a straight line and do not bend with the curvature of the earth. Therefore long
distance microwave transmission systems require transmission stations to be located
approximately 37 miles apart to increase the expense of microwave.
This problem can be solved by bouncing microwave signals off communication satellites,
enabling them to serve as relay stations communication satellites are used for geographically
dispersed organisations. However, using satellite communications can be very expensive for
a business.
Comparing the speed and cost of the different transmission media
Table 7.4 summarises typical speeds for the different telecommunications transmission
media.
Table 7.4: Telecommunications media
Medium
Speed
Twisted wire
Up to 100 Mbps
Microwave
Up to 600+ Mbps
Satellite
Up to 600+ Mbps
Coaxial cable
Up to 1 Gbps
Fiber-optic cable
Up to 6+ Tbps
Broadband (High Speed) Network Service Technologies
There are a number of services available to organisations that require high speed or
broadband transmission capabilities or access to the Internet. These include:
• Asynchronous Transfer Mode (ATM): ATM connects all the different parts of a
network into what will appear to the user as one network. It parcels data into uniform
cells for high-speed transmission. It can transmit data, video, and audio over the same
network. ATM equipment is expensive and as a result its popularity is declining.
• ISDN: Integrated Services Digital Network, an international communications standard for
sending voice, video, and data over digital telephone lines. ISDN supports data transfer
rates of 64 Kbps (64,000 bits per second). There are two types of ISDN:
o Basic Rate Access, which consists of two 64-Kbps B-channels and one D-
channel for transmitting control information.
67
o Primary Rate Access, which consists of 30 B-channels and one D-channel
(Europe) or 23 B-channels and one D-channel (U.S.).
• Leased Line: This is a permanent connection between two points normally set up by a
telecommunications company. Typically, leased lines are used by businesses to connect
geographically distant offices. Unlike normal dial-up connections, a leased line is always
active. The fee for the connection is a fixed monthly rate. The primary factors affecting
the monthly fee are the distance between end points and the speed of the circuit. Because
the connection doesn't carry anybody else's communications, the carrier (supplier) can
assure the business (customer) a certain level of quality.
• Digital Subscriber Line (DSL) Broadband: DSL technologies use sophisticated
modulation schemes to send data at high speeds over standard copper telephone wires.
DSL can be used to provide high-speed connection to the Internet. The term Broadband is
used to refer to a high-speed, high-capacity transmission mechanism that can be used to
carry voice, data or video.
• Cable modem is service for high-speed transmission of data over cable TV lines that are
shared by many users.
Connectivity to these different network transmission services are normally provided by the
telecommunications service provider.
Other Networking Terms
Bandwidth
Bandwidth describes (a) the speed of data on a given transmission path and (b) the width of
the range of frequencies that an electronic signal occupies on a given transmission medium.
The term bandwidth is applied to both digital and analogue signals.
Bandwidth is normally measured in the amount of data transmitted per second. For example:
it requires more bandwidth, to download a picture in one second than a one-line document. In
digital systems, bandwidth is measured in bits transmitted per second (BPS). The higher the
bandwidth, the more messages that can be transmitted or messages can be transmitted faster.
Some applications working over a network will require different bandwidth than others. For
example, the bandwidth required to view a video over a network is far higher than that
required to view a text document.
Bandwidth can be affected by many factors – the physical media that makes up the network,
the amount of network traffic, and the software protocols of the network and the network
connection. To increase bandwidth, we can have higher capacity media (normally cables), or
we can increase traffic speed.
Broadband
Broadband is a term used to refer to the high-speed transmission technology that can
generally transmit multiple channels of data simultaneously.
Converged Network
A converged network is a network that provides technology to enable voice and data to run
over a single network. These multi-service networks can potentially reduce networking costs
68
by eliminating the need to provide support services for each different type of network.
Multimedia networks can be attractive solutions for companies running multimedia
applications such as video, voice-data call centres, unified messaging or for firms with high
costs for separate voice and data services.
Peer to Peer Network
A peer-to-peer network is a group of computers that basically operate as equals. Each
computer is called a peer. The peers share resources, such as files and printers, but no
specialised servers exist. Each peer is responsible for its own security, and effectively each
peer is both a client (because it requests services from the other peers) and a server (because
it offers services to the other peers). Small networks may work well in this configuration. An
example might involve a company in which each department wants to maintain its own files
on its own computer, but allow other department to access these files.
The main disadvantages of a peer-to-peer network include lack of speed – as the number of
computers on the network grows, the performance decreases because of heavy traffic.
Security is also a problem as is the management of the network. Each computer owner is
responsible for the management of his or her machine.
Centralised and Distributed Processing
Centralised processing is where data processing is carried out at one point. The data for
processing can be gathered from several different locations. The output can then be
distributed over a wide area.
Distributed processing on the other hand, allows the data processing to be distributed. There
are several independent but interacting processors. These processors can be used to process
the data near the source. Processors’ workloads can be balanced so if one processor is
overloaded and then the load can be redistributed to another processor. Because the
processing is spread between several points, if a processor fails, the other sites can continue
working independently. It might be possible to off-load the work of the affected processor to
the other processors in the system, thus minimising downtime.
Router
A router is a network communications device that routes messages through different network
and ensures that it gets to the correct address.
C. THE INTERNET
The Internet, which is the largest computer network in the world, is actually a network of
networks. It is a collection of hundreds of thousands of different individual network owned
by governments, universities, and businesses. These interconnected networks interchange
information seamlessly by using the same open, non-proprietary standards and protocol. The
Internet has opened up new possibilities that challenge the existing ways of interacting,
communicating and doing business.
Operation of the Internet
The Internet is a packet switched network where each message is broken into packets. Each
packet contains the address of the sending and receiving machine as well as sequencing
information about its location relative to other packets in the message. Individual packets

69
may follow different routes across the network but when all the packets arrive at the
receiving computer they are reassembled into the complete message.
Connecting to the Internet
The most common methods of connecting to the Internet include DSL, Leased Line, cable
modem, dial-up access using a modem, and Wireless access to an Internet Service Provider
(ISP).
How the Domain Name and IP Addressing System works
A domain name system converts IP addresses to domain names. A name identifies one or
more IP addresses. For example, the domain name Microsoft.com represents about a dozen
IP addresses. Domain names are used in Uniform Resource Locators (URLs) to identify
particular Web pages. For example, in the http://www.cpaireland.ie, the domain name is
cpaireland.ie. Every domain name has a suffix that indicates which top-level domain (TLD)
it belongs to. There are only a limited number of such suffixes. For example:
• gov - Government agencies
• edu - Educational institutions
• org - Organisations (non-profit)
• mil - Military
• com - commercial business
• net - Network organisations
An IP addressing system is an identifier for a computer or device on a TCP/IP network.
Networks using the TCP/IP protocol route messages based on the IP address of the
destination. The format of an IP address is a 32-bit numeric address written as four numbers
separated by periods. Each number can be zero to 255. For example, 1.10.10.220 could be an
IP address.
Because the Internet is based on IP addresses not domain names, every Web server requires a
Domain Name System (DNS) server to translate domain names into IP addresses. When a
user sends a message to another user on the Internet, the message is first decomposed into
packets using the TCP protocol. Each packet contains its destination IP address. The packets
are then sent from the client to the network server and from there to the next server until it
arrives at its destination address. At the destination address, the packets are reassembled into
the original message.
TCP/IP
Transmission Control Protocol/Internet Protocol (TCP/IP) is the basic communication
language or protocol of the Internet. It can also be used as a communications protocol in a
private network (either an intranet or an extranet). Every computer with direct access to the
Internet will have a copy of the TCP/IP program running on their computer.
TCP/IP is a two-layer protocol. The higher layer, Transmission Control Protocol, manages
the assembling of a message or file into smaller packets that are transmitted over the Internet
and received by a TCP layer at the distant machine which reassembles the packets into the
original message. The lower layer, Internet Protocol, handles the address part of each packet
70
so that it gets to the right destination. Each gateway computer on the network checks this
address to see where to forward the message. Even though some packets from the same
message are routed differently than others, they are reassembled at the destination. TCP/IP
uses the client/server model of communication in which a computer user (a client) requests
and is provided a service (such as sending a Web page) by another computer (a server) in the
network. TCP/IP communication is primarily point-to-point, meaning each communication is
from one point (or host computer) in the network to another point or host computer.
Internet Services
This section provides an overview on some of the main internet services and communications
tools.
Communication Services
ELECTRONIC MAIL
Electronic mail systems are used by most organisations to send and messages. The Internet is
the most important e-mail system because it connects so many companies and individuals.
Users can attach text files, graphics, spreadsheets or even application files to a mail message.
Not all networks use the same e-mail format so a computer called a gateway translates the e-
mail message to a format that the next network understands.
The components of a typical e-mail address are:
Individual Name @ Domain.Function/location
joeblogs@gmail.com
NEWSGROUPS
Newsgroups are international discussion groups in which people share information and ideas
on a particular topic. Many newsgroups exist on the Internet. Discussion in newsgroups takes
place on electronic bulletin boards where anyone can post messages for others to read.
CHATTING
Chatting allows two or more people who are simultaneously connected to the Internet to hold
live interactive written conversations. Chat groups are divided into channels, each assigned
its own topic of conversation.
Note: Both newsgroups and chat groups have decreased in popularity with the phenomenal
growth in social networking.
TELNET
Telnet is a protocol that establishes a link between two computers. Telnet allows users to be
on one computer while doing work on another. Users can log on to their office computer
from their home. Also users can logon to, and use, third party computers that have been made
accessible to them.
71
INTERNET TELEPHONY
Internet telephony (also called Voice over IP or VoIP) lets users talk across the Internet to
any personal computer equipped to receive the call for the price of only the Internet
connection. However sound quality can be poor due to delays in the transmission process
when large amounts of data clog the Internet at certain times.
STREAMING AUDIO AND VIDEO
Streaming allows Internet users to see and hear data as it is transmitted from the host server
instead of waiting until the entire file is downloaded.
Streaming audio enables the broadcast of radio programs, music, press conferences,
speeches and news programs over the Internet.
Streaming video has business application including training, entertainment, communication,
advertising and marketing.
Information Retrieval
Information retrieval over the Internet allows users to access thousands of online library
catalogues and databases that have been opened to the public by companies, government
agencies and academic intuitions. Also many users can download free software made
available over the Internet.
File Transfer Protocol (FTP) enables users to access a remote computer and retrieve files
from it.
The World Wide Web
While the Internet and the World Wide Web are closely related they are not the same thing.
The Internet functions as a transport mechanism and the World Wide Web (also called the
Web and WWW) is an application that uses those transport functions. Other applications such
as e-mail also run on the Internet.
The Web is a system with universally accepted standards for storing, retrieving, and
displaying information via client/server architecture. The technology supporting the World
Wide Web was created by Timothy Berners-Lee who in 1989 proposed a global network of
hypertext documents that would allow physics researchers to work together.
HYPERTEXT
The Web is based on a standard hypertext language called Hypertext Markup Language
(HTML), which formats documents and incorporates dynamic hypertext links to other
documents, which can be stored on the same or different computers. To use a hypertext link a
user clicks on the highlighted word (usually coloured blue and underlined) and is then
transported to another document.
HYPERMEDIA
Hypermedia is a term created by Ted Nelson in 1970. It is an extension of the term hypertext,
in which graphics, audio, video, plain text and hyperlinks are intertwined in the same medium
of information. Hypermedia also involves hyper-linked pages. The World Wide Web is an
example of hypermedia.
72
WEB SITES AND HOME PAGES
Organisations or individuals who wish to offer information on the Web need to establish a
home page. A home page is a text and graphical screen display that explains the organisation
that has established the page and provides links to other pages. All the pages of a particular
organisation or individual are known as a Web site. The person in charge of the Web site is
called the Webmaster.
URLS AND HTTP
To access a Web site a user must specify the uniform resource locator (URL), which points
to the address of a specific resource on the Web. The HTTP stands for Hypertext Transport
Protocol, which is the transport protocol, used to transfer pages across the WWW portion of
the Internet. HTTP defines how messages are formatted and transmitted and what action Web
servers and browsers should take in response to various commands.
BROWSERS
Users will normally access the Web through software applications called browsers. The
browser is capable of communicating via HTTP, managing HTML and displaying graphical
data types such as GIF (Graphical Interchange Format) and JPEG (Joint Photographic Expert
Group).
There are a number of popular browsers such as Internet Explorer from Microsoft, Firefox,
Safari and Google Chrome.
SEARCH ENGINES
‘Search’ is one of the Webs most popular activity. Search engines are programs that return a
list of Web sites or pages that match the selected criteria. To use a search engine a user will
navigate to the search engines Web site and enter the details of the subject to be searched for.
The search engine will then return the URLs of sites that match the subject entered by the
user. Some of the most popular search engines are Google and Yahoo.
Unified Communications (UC)
In the past each of a firm’s networks for wired, wireless, voice and data operated
independently of each other and had to be management separately by the IT department.
Now organisations are able to merge different communication modes into a single universally
accessible service using Unified communications.
Unified communications technology integrates separate channels for voice communications,
data communications, instant messaging, e-mail, and electronic conferencing into a single
experience where users can switch back and forth between different communications modes.
Presence technology can show whether a person is available to receive a call or is occupied.
Firms will need to examine how this technology can be incorporated into work flows and
business processes and what alternations are needed.
Rather than having separate systems for voice mail, e-mail, conference calling, and instant
messaging, the Unified communications technology can bring everything together into a
more cohesive package.
73
Unified communications can help accelerate information sharing and allows everyone to
make faster, better decisions.
Web 2.0
A Web 2.0 site allows users to interact with other users or to change website content, in
contrast to non-interactive websites where users are limited to the passive viewing of
information that is provided.
Web 2.0 refers to second-generation, interactive Internet-based services, such as:
• Blogs: Informal yet structured Web site where subscribing individuals can publish stories,
opinions, and links to other Web sites of interest
• RSS: RSS (Rich Site Summary, or Really Simple Syndication) technology pulls specified
content from Web sites and feeds it automatically to users' computers, where it can be
stored for later viewing
• Wikis: Collaborative Web sites where visitors can add, delete, or modify content on the
site, including the work of previous authors
Services such as the photo sharing website Flickr, the social networking site Facebook,
video-sharing site YouTube and the collaborative encyclopaedia Wikipedia are all examples
of Web 2.0.
VIRTUAL PRIVATE NETWORK
A Virtual Private Network (VPN) is a secure network that uses the Internet (or a public
network owned by a telephone company) as the backbone network but uses firewalls and
other security features to secure connections between distant locations. A VPN offers the
advantages of a private network but at a cheaper cost.
A VPN can be a private network of computers linked using a secure “tunnel” connection over
the Internet. It protects data transmitted over the public Internet by encoding the data to hide
its content, to provide what is a virtual private connection that travels through the public
Internet.
Intranets and Extranets
Intranets
An Intranet is a private network inside an organisation that uses Internet technologies such as
web browsers and servers, TCP/IP network protocols, HTML hypermedia document
publishing and databases. Companies use Intranets to provide an Internet-like environment
within the enterprise for information sharing, communications, collaboration, and the support
of business processes.
USE OF INTRANETS IN ORGANISATIONS
In sales and marketing, intranets help oversee and coordinate the activities of the sales
force. The sales force can obtain updates on pricing, promotions, rebates, customers, or
information about competitors. The sales force can also access presentation and sales
documents, which they can customise for specific customers.
74
In the human resources area, intranets keep employees informed of company issues and
policies, allow employees to access and update their personnel records, and take online
competency tests. Further, job postings and internal job information can be made available to
employees. Employees can enrol in health care, benefit plans, or company training seminars.
In finance and accounting, intranets provide an online, integrated view of financial and
accounting information in an easy-to-use format.
In the manufacturing area, intranets integrate complex information across the plant floors or
many plants, particularly in managing work flow and process control.
Business Value of Intranets
There are a number ways in which an intranet can provide business value which include:
• Intranets can significantly improve communications and collaboration within an
enterprise. Regardless of location, intranets allow organisational members to exchange
ideas, share information, and work together on common projects and assignments.
• Intranets lower cost of publishing and accessing multimedia business information
internally via intranet web sites. Examples include: employee manuals, documents,
company policies, business standards, company news, staff directories, product
information including pricing, competitor profiles and even training material, can all be
accessed using browser software on a standard computer. This is one of the main reasons
for the rapid growth in the use of intranets in business.
• Intranets can be used to integrate information from different sources into a common view.
• Intranets are being used as the platform for developing and implementing business
applications to support business operations and managerial decision making. Employees
within the company, or external business partners can access and run such applications
using web browsers from anywhere on the network.
• A company’s Intranet can also be accessed through the Intranets of customers, suppliers,
and other business partners via extranet links.
Extranets
An extranet is a type of inter-organisational information system. Extranets enable people who
are located outside a company to work together with the company's internally located
employees. Extranets are network links that use Internet technologies to interconnect the
Intranet of a business with the Intranets of its customers, suppliers, or other business partners.
The word extranet comes from extended intranet. The main purpose of extranets is to foster
collaboration between selected suppliers, customers and other business partners.
Companies can:
• Establish direct private network links between themselves, or create private secure
Internet links between them called virtual private networks.
• Use the unsecured Internet as the extranet link between its Intranet and consumers and
others, but rely on encryption of sensitive data and its own firewall systems to provide
adequate security.
75
Business Value of Extranets
The business value of extranets is derived from several factors:
• The web browser technology of extranets makes customer and supplier access of intranet
resources a lot easier and faster than previous business methods.
• Extranets enable a company to offer new kinds of interactive Web-enabled services to
their business partners. Thus, extranets are another way that a business can build and
strengthen strategic relationships with its customers and suppliers.
• Extranets enable and improve collaboration by a business with its customers and other
business partners.
• Extranets facilitate an online, interactive product development, marketing, and customer-
focused process that can bring better designed products to market faster.
Extranets provide the privacy and security of an Intranet with the global reach of the Internet.
Extranets are becoming the major platform for B2B (Business-to-Business) electronic
commerce, replacing or supplementing Electronic Data Interchange (EDI).
Electronic Data Interchange (EDI)
Electronic Data Interchange (EDI) is a communications standard that enables businesses to
exchange business documents such as purchase orders, invoices, and shipment schedules
electronically with other businesses. EDI formats the documents according to an agreed data
standard and transmits the message. The messages can be sent over a value added network
(VAN) or over the Internet. The transaction data is sent automatically from the computer
systems of one business to the computer of the other business, eliminating the handling of
paper and the manual re-input of data. EDI offers a number of benefits over manual systems
such as reduced data entry error, better security, increased productivity and improved
customer service.
D. WIRELESS TECHNOLOGY
Wireless communications helps businesses stay in touch with customers, suppliers and
employees and supports more flexible arrangements for organising work. Wireless
technology has also led to the creation of new products and services.
The Growth in Wireless Communications
Increasingly individuals and businesses are turning to wireless devices such as cell phones,
wireless handheld devices, and laptops with wireless network connections to communicate
and to obtain information and data.
Mobile phones are cheaper, more powerful and usage has exploded world wide. According to
the International Telecommunication Union (ITU); as of Dec 2010, there are some 5.5 billion
mobile subscribers worldwide, as well as about 1.268 fixed access lines, with the vast
majority of new subscriptions being mobile as opposed to fixed. The number of mobile
subscribers is expected to top 6 billion in 2012.
Mobile phones are no longer used exclusively for voice communications; they have become
mobile platforms for delivering digital data, used for recording and downloading photos,
video and music, Internet access and sending and receiving e-mail. An array of technologies
76
are available that provide high-speed wireless access to the Internet for PCs, mobile phones
and other wireless handheld devices. Businesses are increasingly using wireless networks and
applications to cut costs, increase productivity and flexibility, and create new products and
services.
Business Value of Wireless Networking
There are a number ways in which wireless technology can provide business value which
includes:
• Wireless technology helps businesses stay more easily in touch with customers, suppliers,
and employees and provides more flexible arrangements for organising work.
• Wireless technology increases productivity and worker output by providing anytime,
anywhere communication and access to information.
• Companies can save on wiring offices and conference rooms by using wireless networks
because they do not have to pull cables through walls. Wireless networks also make
additions, moves, and changes much easier.
• Wireless technology has also been the source of new products, services, and sales
channels in a variety of businesses.
Devices for Wireless Transmission
Devices for wireless transmission include:
E-mail hand held devices: These devices include a small display screen and a keypad for
typing short messages. Some versions of these devices have a built in organiser, web and
voice transmission features and the ability to integrate with corporate applications. An
example of an E-mail wireless handheld device is the Blackberry.
Cellular telephones (Cell phones): These work by using radio waves to communicate
with radio antennas (usually located in towers or masts) placed within adjacent
geographical areas called cells. A telephone message is transmitted to the local cell by the
cellular telephone and then passed to the cell of its destination where it is transmitted to
the receiving telephone. As the cellular signal travels from one cell into another (as the
location of the mobile phones moves) a computer that monitors signals from the cells
switches the conversation to a radio channel assigned to the next cell.
Short message service (SMS) is a text message service used by a number of digital cell
phone systems to send and receive short alphanumeric messages less than 160 characters
in length. Like e-mail, SMS messages can be forwarded and stored for retrieval later.
Smart phones: This class of digital communications device combine the functionality of
a Personal Digital Assistant (PDA) with a digital cell phone and require a cellular phone
service connection. These smart phones can handle voice transmission and e-mail, save
addresses, store schedules, access a private corporate network, and access information
from the Internet. Smart phones include Web browser software that enable digital cellular
phones to access Web pages formatted to send text or other information that is suitable
for small screens. Increasingly smartphones are also fitted with built in WiFi which can
be used to provide high speed access to the Internet at a designated WiFi enabled
location.
77
Personal computers are also starting to be used in wireless transmissions – most new laptops
are now Wi-Fi enabled.
Cellular Network Standards and Generations
Major cellular standards include Code Division Multiple Access (CDMA), which is used
primarily in the United States, and Global System for Mobile Communication (GSM),
which is the standard in Europe and much of the rest of the world.
Cellular networks have evolved from slow-speed (1G) analogue networks to high-speed high-
bandwidth digital packet-switched third-generation (3G) networks with speeds ranging from
144 Kbs to over 2 Mbps for data transmission. Second-generation (2G) cellular networks are
digital networks used primarily for voice transmission, but they can also transmit data at
ranges from 9.6 to 14.4 Kbps. 2.5G networks are packet-switched, use many existing
infrastructure elements and have data transmission rates ranging from 50 to 144 Kbps. A
2.5G service called General Packet Radio Service (PRS) transports data over GSM wireless
networks and improves wireless Internet access. 2.5G also improves data transmission rates
for CDMA. See figure 7.5 for a summary of these generations.
Generation
Capacity
Description
1G
Low
Analogue cellular networks for voice communication
2G 10 to14Kbps
Digital wireless networks, primarily for voice
communication; limited data transmission capability
2.5G 50 to144 Kbps Interim step toward 3G in the US similar to GPRS in
Europe
3G 144 Kbps to 2+ Mbps
High speed, mobile, supports video and other rich
media, always on for e- mail, Web browsing, instant
messaging
4G Up to 100Mbps
This is the next evolution of wireless cellular
networks
Figure 7.5: Wireless Cellular Generations
Wireless Computer Networks and Internet Access
This section discusses the major standards for wireless networks and for wireless Internet
access. The Institute of Electrical and Electronics Engineers (IEEE) has established a
hierarchy of related standards for wireless computer networks. These include:
• Bluetooth (802.15) for small personal area networks,
• Wi-FI (802.11) for Local Area Networks (LANs),
• WiMax (802.16) for Metropolitan Area Networks (MANs).
Bluetooth
Bluetooth is a telecommunications industry specification that describes how mobile phones,
computers, and personal digital assistants (PDAs) can be easily interconnected using a short-
78
range wireless connection. Bluetooth can link up to eight devices within a 10-meter area
using low-power, radio-based communication and can transmit up to 722 Kbps in the 2.4
GHz band. Wireless phones, keyboards, computers, printers, and PDAs using Bluetooth can
communicate with each other and even operate with each other without direct user
intervention. Through this technology, users of cellular phones, pagers, and personal digital
assistants can buy a three-in-one phone that can double as a portable phone at home or in the
office, get quickly synchronised with information in a desktop or notebook computer, initiate
the sending or receiving of a fax, initiate a print-out, and, in general, have all mobile and
fixed computer devices coordinated completely.
Bluetooth is designed for personal area networks that are limited to a 10-meter area. It has
low power requirements, so it is better for battery-powered appliances.
Wi-Fi
Wi-Fi stands for Wireless Fidelity and refers to the 802.11 family of wireless networking
standards.
The 802.11a standard can transmit up to 54Mbps in the unlicensed 5GHz frequency range
and has an effective distance of 10 to 30 meters. The 802.11b standard can transmit up to 11
Mbps in an unlicensed 2.4 GHz band and has an effective distance of 30 - 50 meter area,
providing a low-cost flexible technology for creating wireless LANs and providing wireless
Internet access.
A Wi-Fi system can operate in two different modes:
• Infrastructure Mode: In this mode, wireless devices communicate with a wired LAN
using access points. An access point is box consisting of a radio receiver/transmitter and
antennas that link to a wired network, router, or hub. Each access point and its wireless
devices are known as a Basic Service Set (BSS).
• Ad-hoc Mode: In this mode, also known as peer-to-peer mode, wireless devices
communicate with each other directly and do not use an access point. Most Wi-Fi
communications use an infrastructure mode.
Wi-Fi hotspots which are located in hotels, restaurants, airports, libraries, college campuses,
and other public places provide mobile access to the Internet. Hotspots generally consist of
one or more access points positioned on a ceiling, wall or other spot in a public place to
provide maximum wireless coverage for a specific area. Users within range of the hotspot can
then access the internet from their laptop or mobile device. Most laptops, smart phones and
tablet computers come equipped with wireless network interface card (NIC) built–in radio
that can send and receive Wi-Fi signals.
Wi-Fi networking costs have declined so that a basic network can be setup relatively cheaply.
Benefits of Using Wi-Fi
The benefit of Wi-Fi include:
• Can be used create low-cost wireless LANs and to provide Internet access from
conference rooms and temporary workstations.
• Helps individual companies extend their networking to new areas and obtain Internet
services at a low cost.
79
Challenges of Using Wi-Fi
The challenges of using Wi-Fi include:
• Transforming Wi-Fi from a wireless hit-or-miss phenomenon into a sustainable
business.
• Users cannot freely roam between hotspots if they use different Wi-Fi network
services.
• Public and private hotspots need to be transformed into interoperable, dependable
networks with billing systems, roaming agreements, and technical standards that will
enable users to plug into hotspots at will.
• Overcoming weak security features that make Wi-Fi wireless networks vulnerable to
intruders.
• Susceptibility to interference from nearby systems operating in the same spectrum.
WiMax
WiMax, which stands for Worldwide Interoperability for Microwave Access, is the popular
term for IEEE Standard 802.16, which is known as the “Air Interface for Fixed Broadband
Wireless Access Systems.”
WiMax antennas are able to beam high-speed Internet connections to rooftop antennas of
homes and businesses that are miles away. WiMax has a wireless access range of up to 31
miles and a data transfer rate of up to 75 Mbps, making it suitable for providing broadband
Internet access in areas lacking DSL and cable lines. Whereas Wi-Fi is vulnerable to
penetration by outsiders, WiMax (802.16) has robust security and quality of service features
to support voice and video.
Radio Frequency Identification (RFID)
Radio frequency identification (RFID) systems use tiny tags that have embedded microchips
that contain data about an item and its location. The tag transmits radio signals over a short
distance to special RFID readers. The RFID readers then pass the data over a network to a
computer for processing (As shown in Figure 5.6). This technology provides value to a
business by capturing data on the movement of goods as these events take place and by
providing detailed, immediate information as goods move through the supply chain.
RFID and Privacy Issues
Privacy activists have objected to RFID technology applications that could lead to more
tracking and monitoring of individual behaviour. They fear it could someday enable
marketers, the government, or insurers to compile details about individuals’ shopping habits
or even assist in tracking people’s movements.
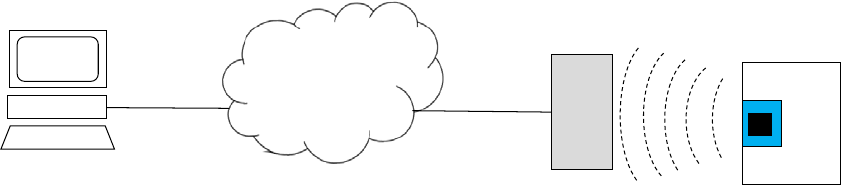
80
Figure 5.6: A Radio frequency identification (RFID) system
Wireless in Health Care
Health care systems have traditionally been dominated by paper based processes. The vast
majority of hospitals have communications networks but still have problems getting essential
information to the right place at the right time.
Mobile technology can provide some solutions. Some Hospitals are installing wireless LANs
in emergency rooms and treatment areas and are equipping staff with Wi-Fi enabled laptop
computers or wireless handheld devices and Smart phones.
E. MANAGEMENT OPPORTUNITIES AND CHALLENGES
Some businesses will benefit from incorporating wireless technology into their business
strategy, while others may not. Before investing heavily in wireless technology, firms must
address a series of technology and organisational issues.
Opportunities
Wireless technology opens up new opportunities to business which include:
• Wireless technology gives firms more flexibility and the ability to innovate.
• Wireless systems support business processes that are not limited by time or location,
extending the company's reach and saving employees and customers substantial amounts
of time.
• The technology provides a new channel for connecting with customers.
• It can also be a source of exciting new products and services.
Management Challenges
The principal challenges posed by wireless technology are integrating this technology into the
firm’s IT infrastructure and maintaining security and privacy.
Tag fitted to item
being tracked
Network RFID
Reader
Tag
Computer
Reader pick up the data
from the tag and send it to
the computer or network
Computer processes
the data from the tag
and updates a system
such as a supply chain
management system
The data originating from the
tag may be sent over a network
Radio signal
from the tag
81
Integrating Wireless Technology into the Firm’s IT Infrastructure
A large enterprise may have hundreds of wireless access points and many thousands of
wireless devices to configure and monitor, similar to a desktop environment. It will be a
challenge to integrate this new network infrastructure with the firm's existing infrastructure
and applications. Central coordination and oversight are required.
Some companies have found that the savings they expected from using wireless technology
did not materialise due to unexpected costs. Gains in productivity and efficiency from
equipping employees with wireless mobile computing devices must be balanced with
increased costs associated with integrating these devices into the firm's IT infrastructure and
providing technical support.
Maintaining Security and Privacy
Maintaining security and privacy poses special challenges for users of wireless technology.
Wi-Fi security is not well developed, making such systems especially vulnerable to
infiltration from outsiders. Wireless systems are easily susceptible to interference from other
devices in the same bandwidth.
One of the unique benefits of wireless technology is its location-tracking capability.
However, this same capability worries privacy advocates who fear the technology could be
used to continuously monitor where users are going and what they are doing. These privacy
issues are particularly relevant to RFID technology and mobile phones.

82
Study Unit 6
Managing Data and Information Resources
Contents
A.
The Importance of Data
B.
File Organisation
C.
The Database Approach to Data Management
D.
Using Databases to Improve Business Performance & Decision Making
E.
Managing Data Resources
F.
Management Challenges and Solutions
83
Introduction
The objectives of this chapter are to:
• Explain the importance of data
• Describe the traditional file method of data storage
• Describe the database approach to data storage
• Compare and contrast the advantages and disadvantages of both the file and database
methods of data storage
• Describe the principal types of databases
• Provide an overview of database design
• Explain how databases can improve business performance
• Discuss the management of data resources and data quality
A. THE IMPORTANCE OF DATA
Data is a vital organisational resource that needs to be carefully managed. The following are
some of issues that impact on the management of organisational data:
• The amount of data being generated in information systems is growing at a phenomenal
rate.
• Data must be stored for a long period of time, both for legal reasons and so it can be
analysed to aid business decision making.
• Data is collected by many groups within in the organisation using different methods and
technology.
• Data is stored using different servers, systems, databases and formats.
• Only a small fraction of an organisation’s data is appropriate for aiding any specific
decision.
• An increasing amount of external data needs to be considered when making decisions.
• Data security, quality, and integrity are critical issues for those managing organisational
data.
These issues highlight the need for careful planning and management of data within an
organisation.
Most organisational data is associated with applications systems. The data may be inputted
into the system or created during processing. Data is generally stored by the applications
using one of two means:
• Files
• Databases
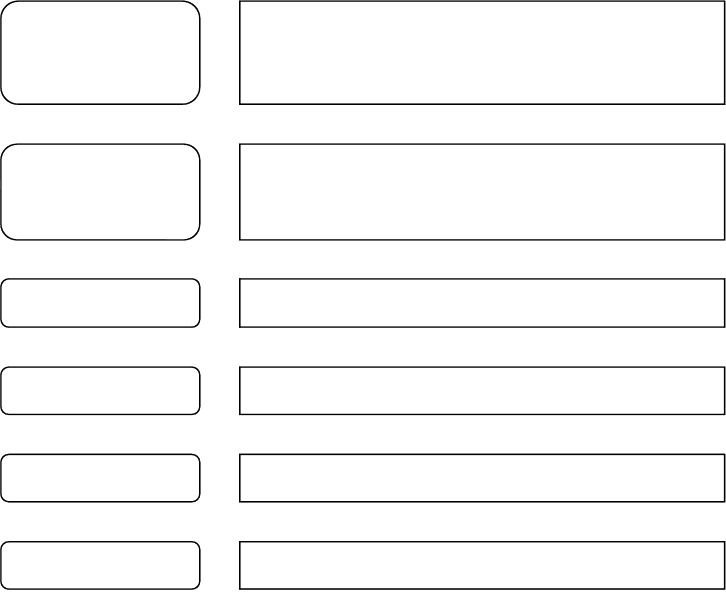
84
B. FILE ORGANISATION
The Traditional File Environment
Information cannot be used effectively if it is stored in a disorganised, inflexible manner.
Without proper file management, it may be difficult or even impossible to extract information
from an automated system. Retrieving a simple report can be timely and costly, if the
information is not properly managed. File management must also be flexible enough to
accommodate new pieces of information or to combine different pieces of information in
changing ways. When computer files are poorly managed it will result in poor performance,
high costs, and minimal flexibility.
The Hierarchy of Data
The data hierarchy, as depicted in Figure 6.1, includes bits, bytes, fields, records, files, and
databases. Data are organised in a hierarchy that starts with the bit, which is represented by
either a 0 or 1. Bits can be grouped to form a byte to represent one character, number, or
symbol. Bytes can be grouped to form a field, such as a name or date, and related fields can
be grouped to form a record. Related records are combined to form files, and related files can
be organised into a database.
Figure 6.1: Hierarchy of Data
Entities, Attributes, and Key fields
An entity is a person, place, thing or event from which information can be obtained. An
attribute is a piece of information describing a particular entity. A key field is a field in a
record that uniquely identifies the record so that it can be retrieved, updated, or sorted (See
Bit
Byte
File
Database
Field
Record
1
01000001 (Binary for letter A)
3025 (Part Number)
Part Number
Part Description Unit Price Supplier Num
3025 80 mm bolt RWF1 201
Parts File
Supplier File
Customer File
Part Number
Part Description Unit Price Supplier Num
3025 80 mm bolt RWF1.50 201
3040 50 mm bolt RWF1.00 201
3128 6 mm nut RWF0.20 218
85
Figure 6.2). For example, a product description may not be unique but a product number can
be designed to be unique
Figure 6.2: Entities, Attributes, and Key fields
Methods of File Organisation
There are three main methods of file organisation:
• Sequential file organisation: In this method of file organisation records are organised in
order of the key field. If a particular record is required in a sequential file, all the prior
records must be read before the required record is reached.
• Direct file organisation: Direct file processing or direct access allows the computer to go
directly to the desired record by using a record key. To retrieve a record a formula is
applied to the record key. The result is the disk address of the particular record. This
operation is referred to as hashing. The record key is generated by the system. Direct
access retrieves specific records quickly.
• Indexed file organisation: This method of file organisation is a form of compromise
between the sequential and direct methods. The indexed file is made up of two files. The
first file is a sequential file where the data is stored. The second file is an index file. It
contains entries consisting of the key to each record and the address of that record. For a
record to be accessed directly the key must be located in the index file and the address
retrieved. The address is then used to retrieve the required record.
Problems associated with the File Environment
The use of a traditional approach to file processing encourages each functional area in a
corporation to develop specialised applications and files. Each application requires its own
unique data file.
The problems with the traditional file environment include data redundancy and confusion,
program-data dependence, lack of flexibility, poor security, and lack of data sharing and
availability.
Data redundancy is the presence of duplicate data in multiple data files. In this situation,
confusion results because the data can have different meanings in different files.
Program-data dependence is the tight relationship between data stored in files and the
specific programs required to update and maintain those files. This dependency is very
Part Number
Part Description
Unit Price
Supplier Num
3025
80 mm bolt
RWF1.50
201
Entity = Parts
Attributes
Field
Key field
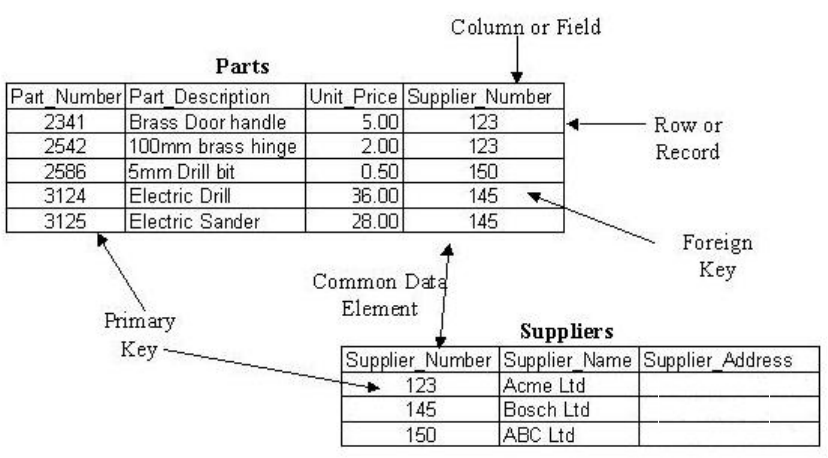
86
inefficient, resulting in the need to make changes in many programs when a piece of data, has
to be changed (e.g. changing the length of a data field).
Lack of flexibility refers to the fact that it is very difficult to create new reports from data
when needed. Ad-hoc reports are impossible to generate and a new report may require
programmers to modify the application so it can search the file for the particular information
and output the report required.
Poor security results from the lack of control over the data because the data are so
widespread.
Data sharing is virtually impossible because it is distributed in so many different files
around the organisation and each file can only be accessed by its own application.
C. THE DATABASE APPROACH TO DATA MANAGEMENT
A database is an integrated collection of logically related data elements. A database
consolidates records previously stored in separate files into a common pool of data elements
that provides data for many applications. The data stored in a database is independent of the
application programs using them and of the type of storage device on which they are kept.
Therefore a single database can serve multiple applications. All the data is consolidated into a
single database eliminating data duplication and redundancy. The data can therefore be
shared by multiple applications.
Database Structure
Database records are stored in tables with each table row representing a separate record. One
field is designated the primary key and must hold a unique value for each record. A key
field that identifies records in a different table is called a foreign key. Figure 6.3 shows an
example of a simple database structure with two tables (Parts and Suppliers).
Figure 6.3: Database Structure
RWF
RWF
RWF
RWF
RWF
Kigali
Butare
Kibuye
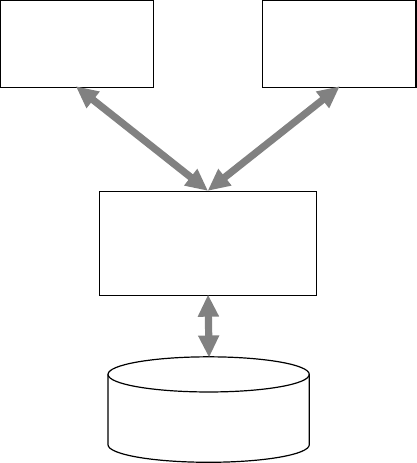
87
Database Software
A database is a store of data, while the software application that controls access to the
database, is called the Database Management System (DBMS).
A Database Management System (DBMS)
The DBMS (see Figure 6.4) serves as an interface between the Physical database and the
applications programs that use it. When an application calls for a data item, the DBMS
locates it in the database and presents it to the application program. There is no need for the
application to specify to the DBMS where the data is physically stored. The DBMS looks
after the job of physically reading and writing of the data, which simplifies the job of the
application program. However the application programs will still need to understand the
logical structure of the data.
Figure 6.4: The Database Environment
A database management system (DBMS) is a collection of programs that enable users to
create and maintain a database. The DBMS is a software system that facilitates the process
of defining, constructing and manipulating databases
Defining a database involves specifying the data types, structures and constraints for the data
to be stored in the database
Constructing the database is the process of storing the data itself on some storage medium
that is controlled by the DBMS
Manipulating the database includes such functions as querying the database to retrieve
specific data, updating the database to reflect changes to the data, and generating reports from
the data.
Database
Application
B
Application
A
Database
Management
System
88
The capabilities of the DBMS include the following:
• Controlling redundancy of persistent data
• Providing efficient ways to access a large amount of data
• Supporting a logical data model
• Supporting high-level languages to define the structure of data, access data and
manipulate data
• Enabling concurrent access to data by multiple users
• Maintaining the integrity of the data
• Protecting the data from unauthorised access and malicious use
• Recovering from failures without losing data
• Being able to represent complex relationships among data
• Enforcing integrity constraints
• Providing persistent storage for program objects and data structures
Benefits of a DBMS
A database management system (DBMS) can:
• Reduce the complexity of the information systems environment
• Reduce data redundancy and inconsistency
• Eliminate data confusion
• Create program-data independence
• Reduce program development and maintenance costs
• Enhance flexibility
• Enable ad-hoc retrieval of information, improve access and availability of information
• Allow for the centralised management of data, their use, and security.
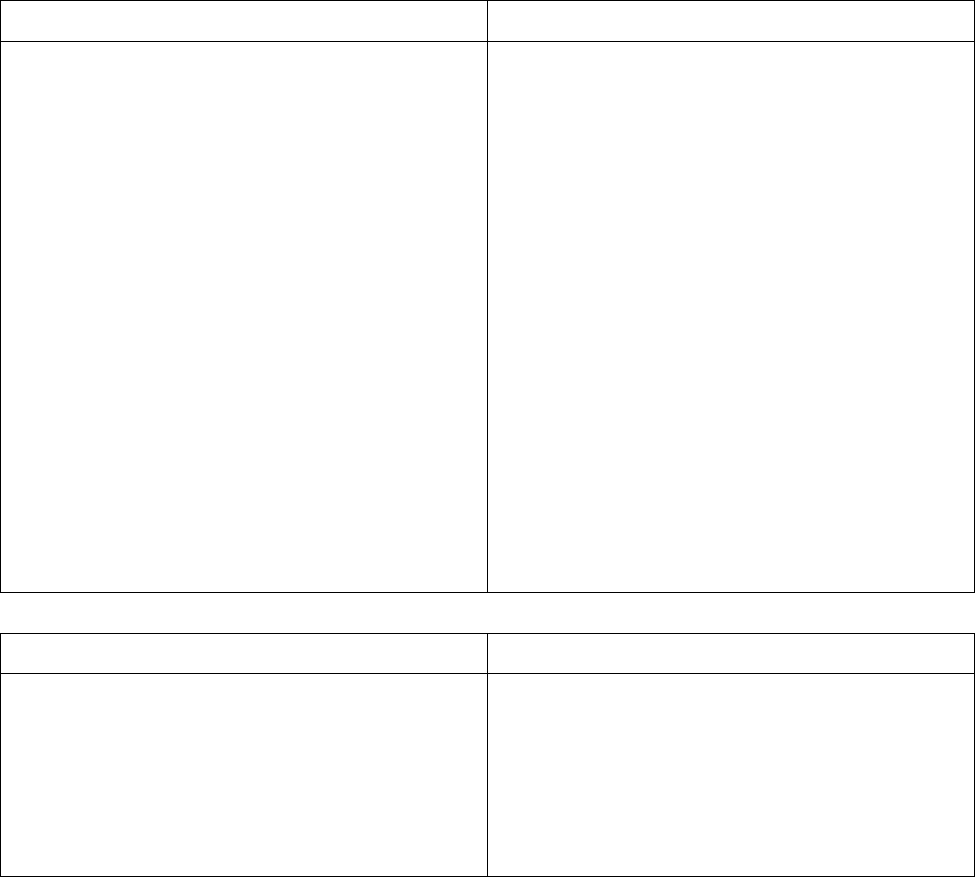
89
Database Management Systems (DBMS) Versus File Organisation Methods
Table 6.5 below summarises the advantages and disadvantages of both the database and file
approaches.
Table 6.5: Comparing the Advantages and Disadvantages of DBMS and Flat File approaches
DBMS Advantages over Flat file
FLAT FILE Advantages over DBMS
1.
Superior mechanism of retaining,
controlling and
managing tens, hundreds,
thousands or millions of database records.
2.
DBMS serve as an interface between
application programs and a set of co-
ordinated and integrated physical files
called a database.
3. Data independence
4. Program independence
5. User not concerned
with physical location
of Data
6.
View all data associated with a Unique
search of Query
7. Generated Report options are excellent
8.
Better revision control and maintenance of
data and records (limited or no Data
redundancy)
9. Back up of Data is centrally located
1.
Very cheap when compared to DBMS
pricing
2. Does not require a Database Administrator
(DBA)
3.
Does not require expensive high
performance computers (servers)
DBMS Disadvantages over Flat file
FLAT FILE Disadvantages over DBMS
1. Requires considerable resources
2. Initial cost of the Database
3. Generally requires a DBA
4. Staff Training Costs
1. Data Redundancy
2. Program / Data Dependency
3. Lack Of Flexibility
4. Poor Security
5. Lack Of Data sharing and availability
6. Lack Of Data integration
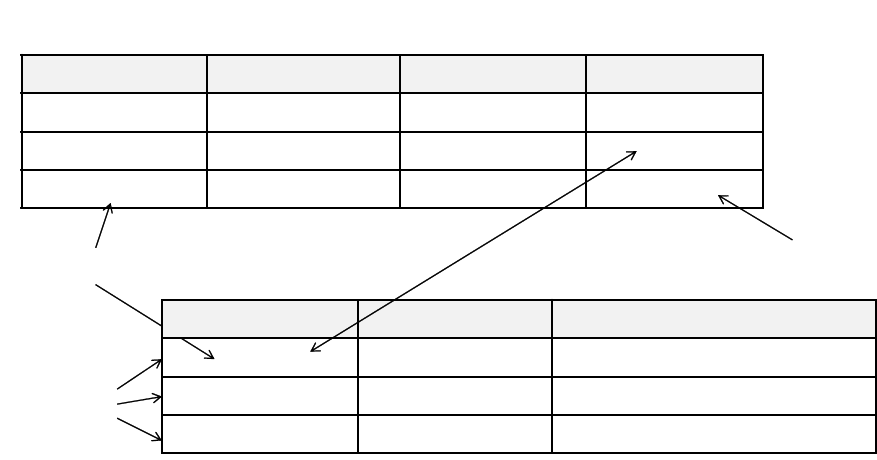
90
Principal Types of Databases and Advantages and Disadvantages of Each
The principal types of databases include relational, hierarchical, network, and object-oriented.
Relational Database
The relational database model organises data into two-dimensional tables (see Figure 6.6).
The relational model can relate any piece of information in one table to any piece of
information in another table as long as the two tables share a common data element (such as a
Supplier Number). Because relational DBMS can easily combine information from different
sources, they are more flexible than the other DBMS structures. They can easily respond to
ad-hoc inquiries. The main problem with relational DBMS is poor processing efficiency.
Response time can be very slow if large numbers of accesses to data are required to select,
join, and extract data from tables. Developments in relational technology, such as indexing,
can overcome this problem.
Figure 6.6: Relational Database Model
Hierarchical Database
The hierarchical database model stores data logically in a vertical hierarchy resembling a
tree-like structure. An upper record is connected logically to a lower record in a parent-child
relationship. A parent segment can have more than one child, but a child can only have one
parent. Hierarchical databases are good for treating one-to-many relationships. They can store
large numbers of segments and process information efficiently, but they can only deliver
information if a request follows the linkages of the hierarchy. Their disadvantages are their
low user-friendliness, inflexibility and programming complexity. They are advantageous for
high-volume, rapid response systems.
Part Number
Part Description
Unit Price
Supplier Num
3025
80 mm bolt
RWF1.50
201
3040
50 mm bolt
RWF1.00
201
3128
6 mm nut
RWF0.20
218
PARTS Table
Each Row
is a Record
Primary Key
Supplier Num
Supplier Name
Address
201
ABC Ltd
Kigali
203
Apple Industries
Butare
218
Oakpark
Ltd
Kibuye
Foreign Key
Linked
SUPPLIERS Table
91
Network Database
The network model stores data logically in a structure that permits many-to-many
relationships. Through extensive use of pointers, a child segment can have more than one
parent. Network databases reduce redundancy and, like hierarchical databases, they process
information efficiently. However, they are inflexible and are very complex to maintain and
program.
Object-oriented Database
The object-oriented database stores data and the procedures acting on the data as objects that
can be automatically retrieved and shared. Object-oriented databases can store complex types
of information, but are slower at processing larger numbers of transactions when compared to
relational DBMS.
Database Terms
Data Dictionary
A data dictionary is a collection of descriptions of the data items. The data dictionary defines
the format needed to enter data into the database. The data dictionary contains information
about each attribute in the database, such as its name, whether it’s a primary key or not and
the type of data it is (numeric, alphanumeric, data, currency etc). For certain attributes a
possible predefined set of values may be listed. A data dictionary would also contain
information about who used the attribute (e.g. form, reports, applications etc).
Most database management systems keep the data dictionary hidden from users to prevent
them from accidentally damage to its contents.
Structured Query Language (SQL)
Structured Query Language (SQL) pronounced either see-kwell or as separate letters SQL, is
a standardised query language for requesting information from a database. Structured Query
Language allows users to query a database and set up Ad-Hoc Reports.
The three most important SQL commands are SELECT, FROM, and WHERE.
• SELECT lists the columns from tables that the user wishes to see in a result table.
• FROM identifies the tables or views from which the columns will be selected.
• WHERE includes conditions for selecting specific records within a single table and
conditions for joining multiple tables.
Example:
SELECT Part_Number, Part_Description, Unit_Price
FROM Parts
WHERE Unit_Price > RWF10
Data Redundancy
Data stored in separate files, as opposed to in a database, tends to repeat some of the same
data over and over. Data redundancy occurs when different areas and groups within an
92
organisation independently collect the same piece of information. Because it is collected and
maintained in so many different places, the same data item may have different meanings in
different. Different parts of the organisation and different names may be used for the same
item. Also, the fields into which the data is gathered may have different field names, different
attributes, or different constraints.
End User Involvement in selection and of a database management system
End users should be involved in the selection of a database management system and the
database design. Developing a database environment requires much more than just selecting
the technology. It requires a change in the company’s attitude toward information. The
organisation must develop a data administration function and a data planning approach. The
end-user involvement can be important in reducing resistance to sharing information that has
been previously controlled by one organisational group.
The Role of the Database Administrator (DBA)
The role of the Database Administrator (DBA) is to:
• Maintain a data dictionary. The data dictionary defines the meaning of each data item
stored in the database and describes interrelations between data items.
• Determine and maintain the physical structure of the database.
• Provide the updating and changing the database, including the deletion of inactive
records.
• Create and maintain edit controls regarding changes and additions to the database.
• Develop retrieval methods to meet the user’s needs.
• Implement security & disaster recovery procedures.
• Control configuration of the database and ensure that changes requested by one user must
be first approved by the other users of the database before they are implemented.
• Assign user access rights in order to prevent unauthorised use of data.
• A DBA will work closely with users to create, maintain, and prevent damage to the
database.
Database Design
To create a database environment, you must understand the relationship among the data, the
type of data that will be stored in the database and how the data will be used. Database design
must also consider how the organisation will use the data in the future, including sharing data
with its business partners.
The creation of a new database involves two design stages; a logical design and a physical
design stage. The logical design of a database is a model of the database from a business
perspective, whereas the physical design shows how the database is arranged in the storage
devices. The logical design requires a detailed description of the business information needs
of the end users of the database.
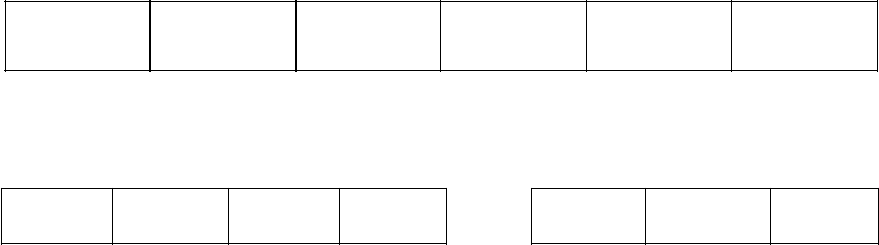
93
The logical database design describes how the data elements in the database are to be
grouped. The design process identifies relationships among data elements and the most
efficient way of grouping data elements. Groups of data are organised and refined until an
overall logical view of the relationships among all data elements in the database emerge.
To use a relational database, complex groupings of data must be simplified. The process of
creating small, flexible data structures from complex groups of data is called normalisation.
This process is illustrated in Figure 6.7 and 6.8. The advantage of normalisation is that it
reduces redundancy and improves efficiency. In the example of the unnormalised relation
(Figure 6.7) the supplier details would have to be recorded for each part they supply, while in
the normalised tables (Figure 6.8) each suppliers details is only recorded once in the supplier
table and is linked to each part using the “Supplier Num” field in the Parts table.
Figure 6.7: An unnormalised relation for PARTS
Figure 6.8: Normalised tables created from PARTS
ENTITY RELATIONSHIP DIAGRAMS
Database designers document their data model using an Entity Relational Diagram as shown
in Figure 6.9. The diagram shows the relationship between the entities Salesperson,
Customer, Orders, and Invoices. The boxes represent entities. The lines connecting the boxes
represent relationships. A line connecting two entities that ends with a crow’s foot topped by
a short mark indicates a one-to-many relationship. A line connecting two entities that end
with no crow’s foot designates a one-to-one relationship. Figure 6.9 shows that one
Salesperson can serve many Customers. Each Customer can place many orders but each order
can only be placed by one customer. Each order generates only on Invoice.
PARTS
Part
Number
Part
Description
Unit Price
Supplier
Num
Supplier
Name
Address
Part
Number
Part
Description
Unit Price
Supplier
Num
Supplier
Num
Supplier
Name
Address
PARTS SUPPLIER
94
Figure 6.9: An Entity-Relationship Diagram (Stair & Reynolds 2012)
Distributing Databases
A distributed database is one that is stored in more than one physical location. A distributed
database can be partitioned or replicated (duplicated). A partitioned database is divided
into partitions so that there is local access to the data that it needs to serve its local area.
These databases can be updated locally and later synchronised with the central database.
With replication, the database is duplicated at various remote locations. The central database
can be partitioned so that each remote processor has the necessary data to serve its local area.
Changes in local files are synchronised with the central. The central database can be
replicated at all remote locations. Any change made to the database at one location is
automatically replicated at all the other locations.
D. USING DATABASES TO IMPROVE BUSINESS PERFORMANCE
& DECISION MAKING
Businesses use their databases to:
• Keep track of basic transactions
• Provide information that will help the company run the business more efficiently
• Help managers and employees make better decisions
In companies with large databases and multiple systems, special technologies are needed to
access data from the multiple systems and for analysing vast quantities of data. These
technologies include data warehousing, data mining, and tools for accessing databases
through the web.
Salesperson
Customer
Orders
Invoice
Serves
Generates
Places
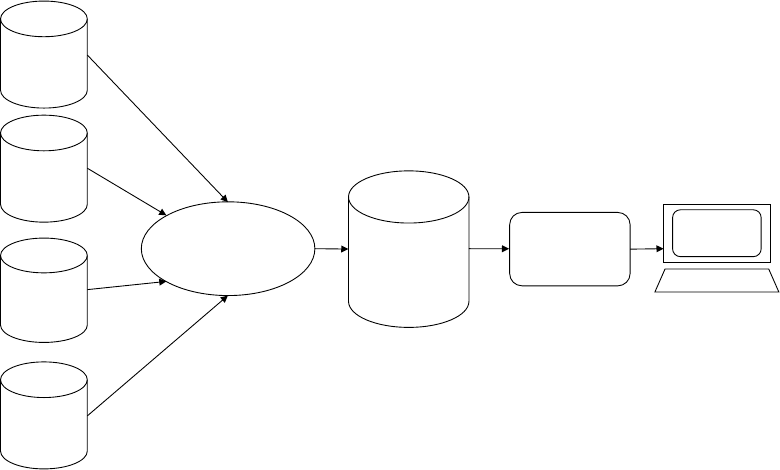
95
Data Warehousing
A data warehouse is a centralised data repository (storage for data), which can be queried for
business benefit. A data warehouse is a database that stores current and historical data that is
of interest to the organisation. This data originates in many different information systems and
from external sources, each with different data models. The data from the diverse
applications are copied into the warehouse database as often as needed (hourly, daily, weekly
etc). The data are transformed into a common data model and consolidated so that they can
be used across the enterprise for management analysis and decision-making. The data are
available for anyone to access as needed. Data warehouses are specifically designed to allow
the warehouse users to:
• Extract archived operational data
• Overcome inconsistencies between different legacy data formats
• Integrate data from throughout an enterprise, regardless of location or format
• Incorporate additional information
The data warehouse concept is shown in Figure 6.10. The data warehouse is designed to
provide the information to aid essential business decisions. The firm may need to change its
business processes to benefit from the information in the warehouse.
Companies can build enterprise-wide warehouses where a central data warehouse serves the
entire organisation. The company can also create smaller warehouses which focus on a single
area of the company or individual information system, which are called data marts.
A data mart is a subset of a data warehouse in which a summarised or highly focused portion
of the organisation's data is placed in a separate database where it can be accessed by a
specific group of users. A data mart will typically focus on a single subject area or line of
business, so it usually can be constructed quicker and at lower cost than an enterprise wide
data warehouse.
Figure 6.10: Components of a Data Warehouse
Data
Warehouse
External
Databases
Application
Data
Inventory
Application
Data
Orders
Application
Data
Payroll
Data
Extraction Data
Analysis
User Interface
•Queries
•Report
•OLAP
•Data mining
96
Business Intelligence, Data Analysis and Data Mining
Business intelligence refers to a series of analytical tools which works with data stored in
databases to find patterns and insights for helping managers and employees make better
decisions and improve organisational performance. Business intelligence provides
organisation with the capability to collect and store information, develop knowledge about
operations, and change decision-making behaviour, so as to achieve business objectives.
Technologies such as data mining can be used to obtain knowledge and insight from
analysing large quantities of data which is stored in databases. Business intelligence is
discussed in more detail in Chapter 8.
Data Analysis
Data warehouses support multidimensional data analysis, also known as online analytical
processing (OLAP). OLAP represents relationships among data as a multidimensional
structure, which can be visualised as cubes of data, enabling more sophisticated data analysis.
Data Mining
Data mining is the analysis of data for hidden relationships. For example, the sales data for a
particular brand of beer, is analysed and related to other market data, and may show a
seasonal correlation with the purchase of other types of alcohol by the same individuals.
Data mining results include:
• Associations: when one occurrence can be correlated to another occurrence.
• Sequences: or one event leads to another event.
• Recognition of patterns and the creation of new organisation of data - for example
analysing purchases to create customer profiles.
• Forecasting future trends as a result of finding patterns in the data.
Text Mining and Web Mining
Text mining and Web mining differ from conventional data mining in that the data is
unstructured and comes from a variety of sources, where as conventional data mining focuses
on structured data in databases and files.
TEXT MINING
Text mining focused on finding patterns and trends in unstructured data in text files. The data
may be in email, memos, survey responses, legal cases, service reports etc. Text mining tools
extract key elements from large unstructured data sets, discover patterns and relationships,
and summarise the information.
WEB MINING
WEB mining can be used by businesses to understand customer behaviour, evaluate the
effectiveness of a particular Web site, and measure the success of a marketing campaign.
There are a number of different aspects to web mining:
• Web mining looks for patterns in data
• Web content mining extracts knowledge from the content of Web pages
97
• Web structure mining inspects data related to the structure of a particular site
• Web usage mining examines user interaction data recorded by a Web server whenever
requests for a Web site’s resources are received.
Databases and the Web
Databases play an important role in making organisations information resources available on
the World Wide Web. A series of middleware and other software products have been
developed to help users gain access to organisations’ legacy data through the Web. For
example a customer with a Web browser might want to search an online retailer’s database
for product information. Figure 6.11 shows how a customer might access the retailer’s
internal database over the Web. The user would access the Web site over the Internet using
Web browser on their PC. The Web browser requests data from the organisations database
via the WEB server who in turn calls the application service who passes the request on to the
Database Server. The following is a summary of the function of each server:
Database server
The database server runs the DBMS to process SQL statements and perform database
management tasks.
Application server
This application system is installed on this server – this software handles all application
operations. It also translates HTML commands into SQL so that they can be processed by the
DBMS.
Web server
This server presents WEB pages to users & passes user requests for data to the application
server. The WEB server also delivers data in the form of web pages back to the user.
Figure 6.11: Accessing Databases over the Web
ADVANTAGES OF THIS APPROACH
This approach is a cost effective flexible approach. The WEB site can be setup without
making changes to the internal database. Also, it costs much less to add a web interface in
front of a legacy system than to redesign and rebuild the system to improve user access.
Database
Application
Server
WEB
Server
Browser
Database
Server
98
E. MANAGING DATA RESOURCES
Data planning may need to be performed to make sure that the organisation's data model
delivers information efficiently for its business processes and enhances organisational
performance. There can sometimes be resistance in organisations to the sharing of
information that has been previously controlled by one group. Creating a database
environment is a long-term endeavour that requires significant investments and organisational
change.
Information Policies
An information policy specifies the company’s rules for acquiring, classifying, standardising
and sharing, information, and includes procedures and roles.
Data administration is responsible for the specific information policies and procedures
through which data can be managed.
The Importance of Data Quality
Data residing in any database that is not accurate, timely, or does not contain relevant
information will limit the effectiveness of an organisation. Organisations need to identify and
correct faulty data and establish routines to edit and update data once a database becomes
operational. Analysis of the quality of the data involves doing a data quality audit.
A data quality audit, involves a structured survey of the accuracy and level of completeness
of the data in an information system. Data cleansing consists of activities for detecting and
correcting data in a database that are incorrect or redundant. Data cleansing not only corrects
data but also enforces consistency among different sets of data that originated in separate
information systems.
Database design should include efforts to maximise data quality and eliminate error. Some
data quality problems result from redundant and inconsistent data, but most stem from errors
in data input. Organisations need to identify and correct faulty data and establish better
controls for input and editing.
F. MANAGEMENT CHALLENGES AND SOLUTIONS
Developing a database environment requires much more than selecting database technology.
It requires a formal information policy governing the maintenance, distribution, and use of
information in the organisation. The organisation must also develop a data administration
function and a data-planning. Data-planning is needed to make sure that the organisation’s
data provides the information efficiently for its business processes and organisational
decision making and contributes to enhanced performance. Resistance to the sharing of data
must also be addressed.

99
Study Unit 7
E-Commerce
Contents
A.
Introduction to Electronic Commerce
B.
Electronic Commerce
C.
Mobile E-Commerce (M-Commerce)
D.
E-Commerce Payment Systems
E.
Management Challenge
F.
Management Decision Support Systems
G.
Decision Making
H.
Business Intelligence
I.
Systems to Support Decision Making
J.
Executive Support Systems (ESS)
K.
Group Decision Support Systems (GDSS)
L.
Challenges
100
Introduction
The objectives of this chapter are to:
• Describe Electronic Commerce
• Describe M-Commerce
• Provide an overview of the main E-Commerce Payment Systems
A. INTRODUCTION TO ELECTRONIC COMMERCE
Electronic commerce (e-commerce) can be defined as the process of buying, selling,
transferring, or exchanging products, services or information via computer networks
including the internet (Rainer, Turban etal 2007).
E-commerce has grown dramatically over the last ten years and continues to grow at a very
high rate. Some of the reasons for this growth are discussed in the next two sections.
E-business is a broader concept as in addition to buying and selling of goods and services it
also includes servicing customers, collaborating with business partners and performing
electronic transactions both within and outside an organisation.
Internet Technology and the Digital Firm
The Internet is an international network of networks connecting many millions of people
from most countries in the world. It is the largest information superhighway in the world. The
Internet provides a universal and easy-to-use set of technologies and standards that can be
adopted by all organisations, no matter what computer system or information technology
platform they are using. It provides a much lower cost and easier-to-use alternative for
coordinating activities than proprietary networks, it reduces organisational transaction and
agency costs and increases communication, including electronic mail, online forums, and
chatting. Additionally it provides access to increased information and information retrieval
from many thousands of online databases around the world and increases market potential
with online offerings of information and products through the easy-to-use World Wide Web.
The Internet is changing how companies do business
The Internet radically reduces the cost of creating, sending, and storing information while
making that information more widely available. The Internet reduces search costs, allowing
customers to locate products, suppliers, prices, and delivery terms. The Internet enables
companies to collect and analyse more detailed and accurate information about their
customers, allowing these companies to more effectively target their products and services to
a suitable market. The Internet has transformed the richness and reach of information. It can
help companies create and capture profits in new ways by adding extra value to existing
products and services. It also provides the foundation for new products and services. The
Internet permits personalisation (targeting personal messages to consumers) and
customisation (changing a product or service based on consumer preference or history).

101
Digital Goods and Digital Markets
Digital Goods
Digital goods are products that can be created, stored, delivered and sold as purely digital
products and can be delivered over a digital network such as the internet. They include music,
video, newspapers books and software. When compared to traditional goods, the marginal
cost of producing another unit of a digital good is approximately zero and delivery costs over
the Internet are very low. However while the marketing costs of digital goods are similar to
physical goods the methods of marketing have change significantly with the phenomenal
growth of internet marketing. The pricing of digital goods is far more flexible and can be
varied depending on demand conditions and customer profile. Digital goods are sold in
digital markets.
Digital Markets
Digital markets are very flexible and efficient because they allow the following:
• Reduced search and transaction costs
• Lower costs of changing prices
• Price discrimination
• Dynamic pricing (prices changing based on the demand characteristics of the customer or
the seller's supply situation)
• Disintermediation: Elimination of intermediaries such as wholesalers or retailers
Disintermediation
The typical distribution channel has several intermediary layers, each of which adds to the
final cost of a product (see Figure 10.1.). Removing layers such as wholesalers and retailers
lowers the final cost of the product or service to the consumer. Disintermediation or
removing the intermediaries, has allowed many companies to improve their profits while
reducing prices. For example Airlines have reduced their costs by using the internet to sell
flights directly to their customers thereby removing the travel agent from transactions with
customers. As a result the cost of flights to consumers have been a significant reduced.
Figure 10.1: Three different distribution channels
Channel 1
Channel 2
Channel 3
Manufacturer
¦
¦
¦
¦
¦
Consumer
Manufacturer
¦
Wholesaler
¦
Retailer
¦
Consumer
Manufacturer
¦
¦
¦
Retailer
¦
Consumer
102
Internet business models for electronic commerce
Laudon and Laudon (2010) identified the following eight Internet business models:
1. Virtual storefront: These sell physical products directly to consumers or individual
businesses. Online retail stores are also called e-tailers.
2. Information broker: These provide product, pricing, and information to individuals and
businesses. They generate revenue from advertising and from directing buyers to sellers.
3. Transaction broker: The transaction broker processes online sale transactions for
consumers and generates a fee each time.
4. Online marketplace: An online marketplace provides a digital environment where
buyers and sellers meet, search for and display products, and set prices for those products.
It can also provide online auctions facilities to users.
5. Content provider: A content provider creates revenue by providing digital content, such
as digital news, music, photos, or video on the Web. Some newspapers and magazines are
now pursuing this online strategy.
6. Online service provider: The online service provider supplies online services for
individuals and businesses and generates revenue from subscription or transaction fees
and from advertising. An example of an online service provider is salesforce.com who
provides a Web based Customer Relationship Management (CRM) solution for
businesses.
7. Virtual community: The virtual community provides an online meeting place where
people with similar interests can communicate and find useful information. These include
YouTube, and social networking sites such as Facebook and MySpace.
8. Portal: The portal provides an initial point of entry to the Web along with specialised
content and other services. Examples of portals include Google, Bing, Yahoo, MSN etc.
Many of these new business models generate revenue from:
• Sales of traditional or digital goods
• Selling advertising space for banner ads and pop-up ads
• Transaction fees
• Sales of marketing information collected by users
• Directing buyers to sellers and charging a referral fee or percentage of the revenue from
resulting sales
• Charging a subscriptions fee to access content and service
• Offering a basic service for free and charging a premium for special features.
103
PURE-PLAY AND CLICKS-AND-MORTAR BUSINESS MODELS
A pure-play business model is based purely on the Internet. An example of a company using
this business model is Amazon.com A clicks-and-mortar business model has a Web site that
is an extension of a traditional bricks-and-mortar business.
B. ELECTRONIC COMMERCE
Categories of Electronic Commerce
The three major types of electronic commerce are:
1. Business-to-Consumer (B2C): Business-to-consumer e-commerce involves retailing
products and services to individual shoppers. Amazon.com is an example of business-to-
consumer electronic commerce.
2. Business-to-Business (B2B): Business-to-business e-commerce involves the sale of
goods and services among businesses. In this type of e-commerce all participants are
businesses. B2B is an efficient tool for connecting business partners in a virtual supply
chain to cut costs and supply times.
3. Consumer-to-consumer (C2C): Consumer-to-consumer e-commerce involves
consumers selling directly to consumers. eBay.com is an example of consumer-to-
consumer e-commerce company
Electronic commerce transactions can also be categorised based on the participants’ physical
connections to the Web. Participants can use wired networks or mobile commerce (m-
commerce).
Distinctive features of retailing using the Internet
The Internet enables companies to create closer, cost-effective relationships with its
customers. The company can use the Internet to provide information, services, support, and in
many instances deliver the product over the Web. The Internet facilitates direct sales over
the Web, interactive marketing and personalisation, blogs and customer self-service.
The Internet digitally enables the firm. The firm can link to customers and suppliers so that
electronic commerce, business-to-business transactions such as invoices, purchase orders, and
payments can be carried out.
Direct Sales
The customer can purchase a product or service directly from a company’s Web site. A Web
site also allows potential customers to obtain information about the products and services and
also about who distributes them. A frequently asked questions (FAQ) section on the Web site
can be used to provide cost effective support for the product and customer.
Interactivity
The Internet provides a number of ways for companies to interact and communicate with
customers and build relationships with them.
104
Personalisation and Customisation
Marketers can use the interactive features of Web pages to keep consumers engaged and to
capture information about their tastes and interests as they move around the Web site. This
information may be obtained by asking visitors to "register" online and provide information
about themselves. Companies can then analyse this information to develop more precise
profiles of their customers and modify the web pages presented to each customer. This web
feature is called personalisation and involves directly tailoring the Web content to the specific
user interests to achieve the benefits of personal treatment but at much lower cost than having
an individual salesperson deal with each customer. Personalisation can help firms build long
lasting relationship with the customer.
Another Web personalisation technique used in online marketing compares information
collected about specific user behaviour at a web site such as what links they clicked on and
pages they visited to information stored about other customers with similar interests. This
information can be used to predict what the user may want to see next. Amazon use similar
technology to suggest suitable books or other products to a shopper – “Customers Who
Bought This Item Also Bought…” Or when a regular shopper logs in Amazon will present a
set of recommendations which are based on what that particular customer purchased in the
past.
Blogs
Blogs (short for Weblog) are usually maintained by an individual with regular entries of
commentary, descriptions of events, etc. Businesses are increasingly using blogs to
communicate with customers and suppliers to announce new products or services and to get
feedback about company services.
Social Networks
Businesses are realising the value of providing easy ways for interaction with customers to
enable a sharing of ideas and collaborate with each other. Starbucks is an example of a
company that has started to leverage this emerging social computing trend. My Starbucks
Idea (http://mystarbucksidea.force.com/) gives customers an opportunity to share ideas on
how the company can make improvements. Social computing has the potential to transform
business as dramatically as the Internet has already done.
Using the Internet to support Customer Service
Customer service starts with the ease that customers have in researching products themselves,
and then the ease of purchasing them. After the product has been delivered (whether physical
or digital product), the customer can obtain help and support on using the product over the
Internet. This support could include information on how to assemble or use the products or
services. Answers to questions can be e-mailed from the Web site without making customers
wait for telephone support.
105
Business to Business e-Commerce
Much of B2B e-commerce is still based on electronic data interchange (EDI). Electronic data
interchange (EDI) enables automated computer-to-computer exchange between two
organisations of standard transactions such as invoices, shipment schedules, or purchase
orders. Companies use EDI to automate transactions for B2B e-commerce and supply chain
management transactions. Suppliers can automatically send data about shipments to
purchasing firms. The purchasing firms can use EDI to send details of inventory requirements
and payment data to suppliers.
Today companies are progressively moving to the Internet for this purpose because it
provides a much more flexible and low-cost platform for linking to other firms. Business-to-
business transactions can occur via a company’s Web site, net marketplace, or private
exchange and utilise intranets and extranets.
Private Industrial Networks (Private Exchanges)
These typically consist of a large firm using an extranet to link to its suppliers and other
business partners. The Volkswagen Group opted for a private industry network (private
exchange) instead of an industry sponsored net marketplace because it wanted to have control
over supplier relationships and because of its business processes for supply chain
management.
Net Marketplaces
A net marketplace is a single digital marketplace based on Internet technology linking many
buyers to many sellers. The net marketplace is a business model for B2B e-commerce and
some net marketplaces serve vertical markets for specific industries (such as the chemical and
steel industries), while other net marketplaces serve horizontal markets, selling goods that are
available in many different industries. Also, net marketplaces can sell either direct goods or
indirect goods.
Benefits of E-Commerce
The benefits of e-commerce have started to materialise but will increase in significance as e-
commerce expands. Both organisations and consumers can benefit from e-commerce.
BENEFITS TO ORGANISATIONS
The benefits to the organisation include:
• Global reach: e-commerce expands the company's marketplace to national and
international markets.
• Cheaper supplies: Enables companies to buy materials and services from other
companies rapidly and at less cost.
• Reduced Costs: Decreases the cost of creating, processing, distributing, storing, and
retrieving information by digitising the process.
• Speeds up the flow of goods: Allows businesses to carry lower levels of inventories
by facilitating just in time strategies.
106
• Improved customer service: It enables companies to provide product support and
creates the possibility of a 24 hour service. It also allows companies to provide
enhanced services to customers.
• Others: It helps small businesses compete against large companies and it provides
advertising opportunities.
BENEFITS TO CONSUMERS
The benefits to the consumer include:
• Providing less expensive products and services by allowing customers to do quick
online comparisons
• Enabling customers to shop or make other transactions 24 hours a day from almost
any location
• Giving customers more choices in terms of products and suppliers
• Delivering relevant and detailed information quickly
• Enabling consumers to get customised products such as PCs
Limitations of E-Commerce
The limitations of e-commerce include:
• Lack of universally accepted standards for quality, security and reliability
• Difficulty in integrating e-commerce software with some existing applications and
databases
• Unresolved legal issues related to fraud and buyer and seller protection
• Customer resistance to changing from real to virtual stores
• Perception that e-Commerce is expensive and unsecured
• Increasing incidence of internet fraud and other crimes
C. MOBILE E-COMMERCE (M-COMMERCE)
M-commerce uses the Internet for purchasing goods and services as well as for transmitting
messages using wireless mobile devices. It is especially well suited for location-based
applications, such as finding local hotels and restaurants, monitoring local traffic and
weather, and providing personalised location-based marketing.
Mobile computing increases productivity and worker output by providing communication
and access to information regardless of location. Mobile communication helps businesses
stay more easily in touch with customers, suppliers, and employees and provides more
flexible ways of working.
107
M-Commerce Services and Applications
The following are categories of m-commerce services:
• Information-based services: Applications include instant messaging, e-mail, searching
for a movie or restaurants using a smartphone or handheld device.
• Transaction-based services: Applications include purchasing concert tickets, music, or
games. It includes searching for the best price for an item using a smartphone and buying
it from an e-commerce site.
• Financial Services: Many banks now allow customer to use their mobile phone to check
account balances, transfer funds between accounts and pay bills.
• Location Based services: Services that anticipate what a customer wants based on that
person’s location or data profile, such as traffic information and location of the closest
hotels. There are many smartphone applications that offer services that enable mobile
phone users to access relevant traffic information, calculate journey lengths, and search
for nearby garages, hotels and restaurants.
• Wireless Advertising: In this form of marketing, a company will send a text based add to
thousands of mobile users or tailor advertising on Web sites based on the location of the
user when they access those sites.
• Games and Entertainment: Many mobile phone services offer downloadable digital
games and ring tones. Many smartphone phone users can view TV programs, store digital
music and download and watch video clips on their phone.
Accessing Information from the Wireless Web
Although cell phones and other handheld devices can access the Web at any time and from
any place, the amount of information that can be handled at any one time is still limited.
Some web sites have been specially designed for m-commerce. They feature Web pages with
very few graphics and only enough information to fit on a small mobile handheld screen.
These wireless portals feature content and services optimised for mobile devices to steer
users to the information they are most likely to need. Many sites are developing smartphone
apps that can be installed on the mobile phone and will optimise how the site appears on the
mobile device.
Voice portals accept voice commands for accessing Web content, e-mail, and other
electronic applications from a cell phone or standard telephone. Sophisticated voice
recognition software processes the requests, and the responses are translated back into speech
for the customer.
M-Commerce Challenges
M-commerce represents a tiny fraction of all online purchases because wireless mobile
devices can’t display merchandise very well. There are a number of factors that contribute to
this including:
• Keyboards and screens on cell phones are still small and awkward to use
• Relatively slow data transfer speeds on cellular networks, even on third generation
networks, results in higher costs to customer
• Limited memory and power supplies
108
• More Web sites need to be designed specifically for small wireless devices.
M-commerce will benefit from new payment systems for wireless devices and faster wireless
networks to support more data-rich communications.
D. E-COMMERCE PAYMENT SYSTEMS
Special electronic payment systems have been developed to pay for goods electronically on
the Internet. Electronic payment systems for the Internet include systems for credit card
payments, digital cash, digital wallets, accumulated balance payment systems, stored value
payment systems, peer-to-peer payment systems, electronic checks, and electronic billing
presentment and payment systems (Laudon and Laudon 2010). The following section
describes the main electronic payment systems used on the Internet.
Credit Card
Credit cards are still used for a large proportion of online payments for online purchases.
Digital credit card payment systems extend the functionality of credit cards so they can be
used for online shopping payments. They make credit cards safer and more convenient for
online merchants and consumers by providing mechanisms for authenticating the purchaser's
credit card to make sure it is valid and arranging for the bank that issued the credit card to
deposit money for the amount of the purchase in the seller’s bank account.
Digital Wallets
Digital wallets make paying for purchases over the Web more efficient by eliminating the
need for shoppers to enter their credit card information each time they buy something. A
digital wallet securely stores credit card and owner identification information and provides
that information at an e-commerce site's "checkout" facility. The digital wallet enters the
shopper's name, credit card number, and shipping information automatically when invoked to
complete the purchase. Amazon.com’s “One-Click Shopping”, which enables a consumer to
fill in shipping and credit card information automatically by clicking one button, uses digital
wallet technology.
Accumulated Balance Digital Payment Systems
Micropayment systems have been developed for purchases of involving small amounts of
money, such as downloads ring tones that would be too small for normal credit card
payments. Accumulated balance payment systems or stored value payment systems are useful
for such purposes.
Accumulated balance digital payment systems enable users to make micropayments for
purchases on the Web, accumulating a balance that they must pay periodically on their credit
card or monthly telephone bills.
Stored Value Payment Systems
Stored value payment systems enable consumers to make instant online payments to
merchants and other individuals based on value stored in a digital account. Online stored
value systems rely on the value (money or credit) stored in a consumer's bank, or credit card
account.
109
Smart Cards
Smart cards are another type of stored value system used for micropayments. A smart card is
a plastic card the size of a credit card that stores digital information. The smart card can store
identification data, and can serve as an "electronic purse" in place of cash. These are contact
smart cards that require use of special card-reading devices whenever the cards need to
transfer cash to either an online or offline merchant. To pay for a Web purchase, the user
would swipe the smart card through the card reader.
Digital cash
Digital cash (also known as electronic cash or e-cash) can also be used for micropayments or
larger purchases. Digital cash is currency represented in electronic form and is different from
paper currency or credit cards. Users are supplied with client software and can exchange
money with another e-cash user over the Internet or with a retailer accepting e-cash. In
addition to facilitating micropayments, digital cash can be useful for people who do not have
credit cards and wish to make Web purchases.
Peer-to-Peer Payment systems
Web-based peer-to-peer payment systems were initially used to serve people who want to
send money to vendors or individuals who are not set up to accept credit card payments. The
person sending money uses their credit card to create an account with the payment at a peer-
to-peer payment Web site. The recipient accesses the payment by visiting the Web site and
supplying information about where to send the payment (e.g. a bank account). PayPal is a
widely used peer-to-peer payment system.
Digital Checking
Digital checking payment systems, such as eCheck, extend the functionality of existing
checking accounts so they can be used for online payments. Digital checks are less expensive
than credit cards and much faster than traditional paper-based checks. These checks are
encrypted with a digital signature that can be verified and used for payments in electronic
commerce. Electronic checking systems are useful in business-to-business electronic
commerce.
Electronic Billing Presentment and Payment Systems
Electronic billing presentment and payment systems are used for paying routine monthly
bills. They enable users to view their bills electronically and pay them through electronic
fund transfers from bank or credit card accounts. These services support payment for online
and physical store purchases of goods or services after the purchase has taken place. They
notify purchasers about bills that are due, present the bills, and process the payments. Table
10.2 below summarises the features of some of these payment systems.

110
Table 10.2: Examples of electronic payment systems for e-commerce (Laudon & Laudon.
2010).
Payment System
Description
Commercial
Example
Digital credit card
payment systems
Secure services for credit card payments on the Internet
that protect informatio
n transmitted among users,
merchant sites, and processing banks
eCharge
Digital wallet
Software that stores credit card and other information to
facilitate payment for goods on the Web
Q*Wallet
Accumulated
balance payment
systems
Accumulates micropayment purchases as a debit balance
that must be paid periodically on credit card or telephone
bills
QPass, Valista,
Peppercoin
Stored value
payment systems
Enables consumers to make instant payments to
merchants based on value stored in a digital account
eCount, Mondex
card
Digital cash
Digital currency that can be used for micropayments or
larger purchases
ClearBit
Peer-to-peer
payment systems
Sends money using the Web to individuals or vendors
who are not set up to accept credit card payments
PayPal
Digital Checking
Electronic check with a secure digital signature
ECheck
Electronic billing
presentment and
payment systems
Supports electronic payment for online and physical
store purchases of goods or services after the purchase
has taken place
CheckFree, Yahoo
Bill Pay,
Digital Payment Systems and M-Commerce
M-commerce requires special digital payment systems geared to the type of transactions that
are taking place using cell phones, and other small handheld devices. These transactions are
mainly small and frequent purchases for items such as sports results, mobile games, ring
tones and concert tickets which involve relatively small amounts of money that are not well
suited to credit card billing.
Micropayment system
Micropayment systems are where the mobile operator or internet service provider handles the
small payments by adding them up and presenting them on a single bill such as the mobile
telephone bill.
Mobile Wallets (m-Wallets)
Mobile wallets speed up purchases by storing online shoppers’ personal information and
credit card numbers that can be used in online transactions.
E. MANAGEMENT CHALLENGE
Electronic commerce and electronic business pose several management challenges, including
inadequate security, given the sensitive and nature of information that people might want to
communicate through the Internet. Electronic commerce and electronic business require
careful coordination of the firm’s divisions, production sites, and sales offices. It also requires
closer relationships with customers, suppliers, and other business partners in its network of
value creation.
111
Study Unit 8
Management Decision Support Systems
Contents
A.
Decision Making
B.
Business Intelligence
C.
Systems to Support Decision Making
D.
Executive Support Systems (ESS)
E.
Group Decision Support Systems (GDSS)
F.
Challenges
112
Introduction
Decision making is no longer the preserve of senior management as it is now common at all
levels on the organisation.
The objectives of this chapter are to:
• Differentiate between structured and non-structured decisions
• Explain the decision making process
• Describe Decision Support Systems
• Describe Graphic Information Systems (GIS) and Customer Decision Support
Systems (CDSS)
• Describe Executive Support Systems (ESS)
• Describe Group Decision Support Systems(GDSS)
A. DECISION MAKING
Traditionally in many organisations decision making was the job of management. However it
is now common for lower level employees to be responsible for some decision making. This
is in part made possible because information systems have made information available to
lower levels of the business.
Decisions are made at all levels of the firm. Some decisions are very common and routine but
very valuable. Although the value of improving any single one of these decisions may be
small, improving hundreds of these small decisions can add up to a very large annual value.
Types of Decisions – Unstructured, Structured and Semi-Structured
Decisions can be classified according to type: Unstructured, structured and semi-structured
(see Figure 12.1).
Unstructured decisions are non-routine decisions where the decision-maker must provide
judgement and evaluations for which there is no standard procedure for the solution. These
decisions are non-routine requiring unique solutions. Examples are an airline deciding on
whether to start a new route, or a book retailer deciding whether to close the book shop and
move to selling on-line.
Structured decisions are repetitive and routine where the decision maker can follow
standard procedures for solutions. These tend to occur at the operational level of the
organisation and are generally low risk. An example of a structured decision would be a
supermarket manager deciding how many staff to have on duty on a Saturday.
Semi-structured decisions are those where only part of the problem has a clear answer
which is provided by a standard procedure (structured part) and other components of the
problem are the unstructured part. There is a level of human judgement required in the
decision making process.
113
These different types of decisions tend to be required at different levels in the organisation
which can be summarised as follows:
• Senior management have to make many unstructured decisions.
• Middle management faces more structured decisions but these decisions may include an
unstructured part and are generally referred to as semi-structured decisions.
• Operational management and operational staff tend to make more structured decisions.
Figure 12.1: Decision Types at the different Management Levels
The Decision Making Process
The following are the four stages in the decision-making process (see Figure 12.2) and how
each can be supported by information systems:
1) Intelligence: This stage involves identifying and understanding the problems that are
present in the organisation and their root cause and effect. MIS systems that provide a
wide range of detailed reports and information can help in identifying problems. MISs
that provide exception reports are particularly useful for identifying problems.
2) Design: This stage involves identifying and investigating a number of possible
approaches and solutions to the problem. DSSs are ideal in this stage for exploring
Decision Type
Senior
Management
Semistructured
Key Decision-Making
Groups in an Organisation
Middle Management
Operational Management
Unstructured
Structured
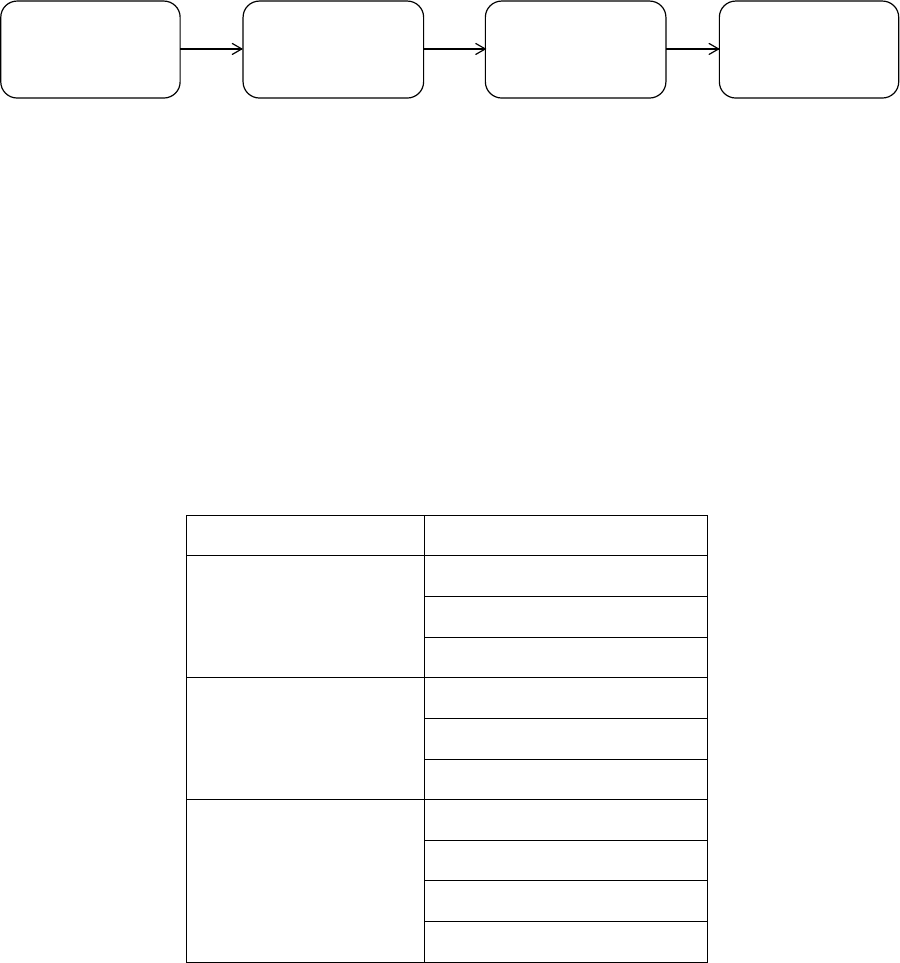
114
alternatives because they include tools for analysing and modelling data, thus enabling
users to explore various options quickly.
3) Choice: This stage involves choosing from alternative solutions. DSSs can support
managers in choosing the optimal solution. These DSSs can use complex analytic models
to look at the various potential outcomes.
4) Implementation: This stage involves implementing the chosen solution and monitoring
to establish if the solution works. An MIS can be used to provide managers with routine
reports on the progress of the solution.
Figure 12.2: The stages in the Decision making process
In the real world, the stages of decision-making do not necessarily follow the serial four stage
path described above. For example, during the implementing stage you may discover that the
solution is not working. In such cases you will be forced to repeat the design choice stages
and sometimes even the intelligence stage.
Managers and Decision Making
The classical model of management (Fayol, 1916) saw managers perform five management
functions: planning, organising, commanding, controlling and co-ordinating. A contemporary
model of management (Mintzberg, 1973) suggested that rather than looking at the functions
of managers that we should look at the roles they perform. Mintzberg identified ten roles that
all managers perform and grouped these roles into three categories as shown in Figure 12.3.
Category
Role
Interpersonal Role
Figurehead
Leader
Liaison
Information Role
Monitor (nerve centre)
Disseminator
Spokesperson
Decisional Role
Entrepreneur
Disturbance Handler
Resource Allocator
Negotiator
Figure 12.3: Mintzberg roles of management
Intelligence Choice
Design Implementation
115
Interpersonal Role
A key aspect of a managers job involves interacting with other people. As a figurehead
managers represent the organisation by performing ceremonial and symbolic activities. As a
leader managers must be able to motivate, communicate with and influence people. In the
role of a liaison a manager needs to be able to develop relations with groups both inside and
outside the organisation. These groups could include customers, trade unions and government
departments.
Information Role
Information is a very important resource of any organisation. The monitor role refers to the
acquiring of information from internal and external resources. The disseminator role refers to
the transmitting of information to those who require it. As a spokesman a manager delivers
information to groups outside the organisation such as the media.
Decisional Role
As an entrepreneur a manager must seek out new ways to deal with problems and find
opportunities for the organisations. The disturbance handler role involves resolving conflicts
between individuals and teams.
As a resource allocator the manager must make decisions on how to allocate resources such
as people, materials and time, to best achieve the objectives of the organisation. As a
negotiator a manager will negotiate with various interest groups such as customers, suppliers
and other managers.
Information systems can support managers in some of these roles while in other roles no
support exists. There is little information support for the roles of figurehead, leader,
entrepreneur, disturbance handler and negotiator. The following roles are supported:
• The role of liaison is supported by electronic communication system,
• The role of monitor is supported by management information systems (MIS) and ESS
• The role of disseminator is supported e-mail, office systems,
• The role of spokesperson is supported by office and professional system,
• The role of resource allocator is supported by DSSs (define)
While information systems can be helpful in improving decision making in some roles, it
should be noted that even in these areas, investment in information systems does not always
produce positive results. Laudon & Laudon (2012) suggests three main reasons:
1. Information quality: High-quality decisions require high-quality information. There are
seven dimensions of information quality that are important when designing decision-
support systems: Accuracy, integrity, consistency, completeness, validity, timeliness, and
accessibility.
2. Management filters: Managers filter by turning off to information they do not want to
hear because it does not conform to their prior views.
3. Organisational inertia and politics: Organisations are bureaucracies with limited
capacity and skills for acting decisively. When environments change and new business
116
models should be followed, strong forces within organisations resist making decisions
which require major change.
B. BUSINESS INTELLIGENCE
This topic was introduced in Chapter 6, where the focus was on the data as the source of
business intelligence. In this chapter the focus is on the business intelligence tools and
techniques that provide managers with the information to help them make better decisions.
Chaudhuri et al. (2011) described business intelligence software as a collection of decision
support technologies for the enterprise, aimed at enabling executives, managers and analysts
to make better and faster decisions.
Business intelligence can be described as the infrastructure for collecting, storing and
analysing data produced by a business. The data will come from databases, data warehouses
and data marts.
A related topic is business analytics which are the tools and techniques for analysing data.
These tools and techniques include OLAP, statistics, models and data mining.
Laudon & Laudon, (2012) describe the BI environment as comprising of six elements:
• Data from the business environment
• Business intelligence infrastructure
• Business analytics toolset
• Managerial users and methods
• Delivery platform – MIS, DSS, ESS
• User interface
Functionality Provided by Business Intelligence
The aim of business intelligence systems it to provide managers and decision makers with
accurate, real time information so as to enable them to make better decisions. According to
Laudon and Laudon (2012) Business intelligences systems will typically provide some or all
of the following functionality:
• Predefined reports
• Customisable reports
• Graphical presentation of data – e.g. Dashboards
• Ad-hoc query and report
• Drill down – to detailed information
The users of Business intelligence
The majority of BI users depend on predefined reports. At the different management levels
BI is used for different purposes:
• Senior executives use it to monitor operations and often rely on graphical outputs
such dashboards to see summaries.
117
• Middle managers tend to use ad-hoc queries and analysis to get a deeper
understanding of what is happening in the organisation.
• Operational managers and staff rely on predefined reports such as sales forecasts,
order delivery, inventory levels, etc.
C. SYSTEMS TO SUPPORT DECISION MAKING
The four main types of systems that support the different levels and types of decisions are:
1. Management Information systems (MIS)
2. Decision Support Systems (DSS)
3. Executive Support Systems (ESS)
4. Group Decision Support Systems (GDSS)
Management Information Systems (MIS)
MISs, which were previously discussed in Chapter 2, help managers monitor and control the
business by providing information on the firm’s performance. They produce routine summary
reports and exception reports for various purposes, based on date data extracted from
transaction processing systems. Examples include sales performance and inventory control.
MIS systems are mainly focused on supporting routing structured decision making.
Decision Support Systems (DSS)
A DSS is a computer system that supports managers in decision-making tasks. DSSs are
particularly suited to non-routine decision-making. While a spreadsheet program could be
designed for DSS purposes, the term ‘decision support system’ is normally applied to a more
specialised kind of software designed to create mathematical models of business situations.
From a management point of view there are four major functions of a DSS, which include;
“What if” analysis, model building, goal seeking and graphical analysis. “What if” analysis is
where the user can change the value of a particular parameter to examine the effect on over
all performance.
In general MIS provide routine, pre-specified, and formatted reports based on data extracted
and summarised from the firm's TPS. These reports provide information on the firm's
performance and are used to help monitor and control the business.
In contrast, DSS provide capabilities for addressing non-routine decisions. DSS are more
flexible and are better able to handle changing situations, as they are based on models and
support add-hoc queries and analysis. Also, MIS primarily addresses structured problems,
while DSS focus more on supporting semi-structured and unstructured problems.
There are two broad categories of DSS - data driven DSSs and model driven DSSs.
Data Driven DSS
A data driven DSS is a system that supports decision making by allowing users to extract and
analyse useful information that was previously buried in large databases. These systems
analyse large pools of data found in major organisational systems. Often data from
transaction processing systems are collected in data warehouses for this purpose. OLAP (a
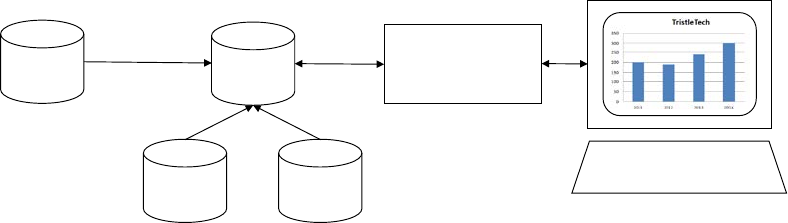
118
data analysis technique) and data mining can then be used to analyse the data. Both OLAP
and Data Mining are discussed in Chapter 5.
Model Driven DSS
A model-driven DSS is primarily a stand-alone system that has a model at its heart, perhaps a
mathematical or spreadsheet representation. It allows users to perform "what-if", sensitivity
and other kinds of analysis. Their analysis capabilities are based on models combined with a
good user interface to make the model easy to use.
While in a particular DSS the primary emphasise may be on modelling the data or the data
itself, in reality many DSS now use a combination of both approaches.
Components of a DSS
The following are the Main Components of a DSS (see Figure 12.4):
• Database Management System: This is a set of programs that creates, manages,
protects, and provides access to the database. A database management system of a DSS
gets data from a variety of internal and external databases. The data in a DSS database are
generally copies of production databases so that DSS does not interfere with the
operational systems.
• DSS Model: A key part of a DSS is its ability to apply mathematical models to data. The
analysis of DSSs depends on the nature of the models used. Examples include:
• Financial analysis – capital investment analysis
• Forecasting sales demand
A model is a representation of reality. It can be a mathematical model such as an equation
that models the relationship between variables. Each DSS is built for a specific set or
purpose and will utilise different models depending on those purposes.
• Supporting tools / interface tools: These ease the interaction between the DSS and the
user. Examples include: a) Report generators, b) User interface
Figure 12.4: Main parts of a DSS
The most widely used models include sensitivity analysis models that ask "what-if" questions
to determine the impact of changes in one or more factors. For example, sensitivity analysis
might be used to analyse what would happen to revenues in the company raised prices by say
DSS
Database
TPS
Data
DSS models
& analysis tools
User Interface
TPS
Data
External
Databases
119
5, 10, or 15 percent, or how much must the price of the product be reduced to increase sales
by 20 percent?
Using Spread sheets to support decision making
Spreadsheet software is also useful for helping managers detect and understand patterns in
data. Spreadsheet software uses a tool called pivot table that categorises and summarises data
very quickly. A pivot table is simply a table that displays two or more dimensions of data in a
convenient format.
Business Value of DSS
DSS have become very powerful and sophisticated, providing detailed information for
decisions that enable the firm to coordinate both internal and external business processes
much more accurately. Some DSS are helping companies with decisions in supply chain
management or customer relationship management. Some DSSs utilise the company-wide
data provided by enterprise systems. DSS today can also take advantage of the interactive
capabilities of the Web to provide decision-support tools to both employees and customers.
Geographic Information Systems (GIS)
Geographic information systems (GIS) are a special category of DSS that use data
visualisation technology to analyse and display data for planning and decision making in the
form of digitised maps. The software can assemble, store, manipulate, and display
geographically referenced information, tying data to points, lines, and areas on a map. GIS
can thus be used to support decisions that require knowledge about the geographic
distribution of people or other resources, resource management, and development planning.
For example, GIS might be used to help governments and emergency services calculate
emergency response times to natural disasters or to help banks identify the best locations for
installing new branches or ATM terminals. GIS tools have become affordable even for small
businesses and some can be used on the Web.
Customer Decision-Support System
A customer decision-support system (CDSS) supports the decision-making process of the
organisation’s existing and potential customers. The data can come from both internal and
external sources, including enterprise systems and the Web. The Web and Internet can
provide online access to various database and information pools along with software for data
analysis. For example the site Homes.com enables visitors to find out which mortgages they
qualify for and calculate the maximum mortgage they can afford and alternative monthly
mortgage payments. Web-based DSSs have become especially popular in the financial
services area because many people are trying to manage their own assets and investments.
D. EXECUTIVE SUPPORT SYSTEMS (ESS)
Executive Support Systems (ESSs); also referred to as Executive Information Systems (EIS)
are computerised systems designed specifically to meet the information need of senior
executive. The emphasis is on graphical displays and an easy to use interface that provides
quick easy access to timely information including direct access to management report. They
offer strong reporting and drill-down capabilities.
120
The following is a summary of the capabilities of ESSs:
• ESSs are specifically tailored to the needs of the senior executive.
• ESSs provide access data on specific issues and problems of interest to the executive as
well as general reports.
• ESSs provide a range of on-line analysis tools including trend analysis, exception
reporting and "drilldown" capacity.
• ESSs access a range of internal and external data.
ESSs are intended to help senior executives find problems, identify opportunities, forecast
trends and make decisions. ESSs usually enable managers to "drill down" for more
information. Executive Support Systems access data from transaction processing systems and
from warehouses.
Balanced Scorecard software can be used to create an ESS. ESS can be considered enterprise-
wide DSSs that help senior managers analyse, compare, and highlight trends in important
variables. They help managers monitor performance and identify opportunities and problems.
Benefits of Using an ESS
Executive support systems provide information to the executive. The executive is free to
select information, manipulate it and extrapolate from it as required. The ESS is not limited
to a set number and type of queries and they are generally not designed with any specific
problem in mind. Instead ESSs are designed to support the decision-making of the user.
The top executive’s information requirements should be met with an ESS. There is no need
for intermediaries to prepare the information in a format suitable for the executives’
requirements. The executive gets the information immediately from the ESS. The information
is also not influenced by the views of the intermediary. The monitoring facility of an ESS
allows executives to monitor their own areas of responsibility more successfully. The system
can warn when there are problems, allowing the executive more time for other tasks.
The ability to zone in on problem areas and to drill-down through the data to find the problem
means that executives can save time searching through data and initiate actions to address the
problem earlier.
E. GROUP DECISION SUPPORT SYSTEMS (GDSS)
A GDSS is an interactive computer-based system that facilitates the solution of unstructured
problems by a set of people working together as a group. GDSS have been developed in
response to the growing concern over the quality and effectiveness of meetings. In general,
DSS focus on individual decision making, whereas GDSS support decision making by
groups.
The underlying problems related to group decision making that have led to the development
of GDSS are the growth in the number and frequency of decision-maker meetings, the
growing length of these meetings, and the increased number of people attending these
meetings.
121
Components of a GDSS
GDSS consists of three basic elements, hardware, software tools, and people. Hardware
includes the electronic conference facility itself (virtual room) that is laid out to support
group collaboration. It also includes electronic hardware such as electronic display boards as
well as audio-visual, computer and networking equipment. Software tools include electronic
questionnaires, electronic brainstorming tools, tools for voting or setting priorities,
stakeholder identification and analysis tools, and group dictionaries. People include the
participants, a trained facilitator, and the staff to support the hardware and software.
Overview of a GDSS Meeting
• In a GDSS electronic meeting, each attendee has a networked workstation,
• All data sent from the workstations to the group are saved on the file server,
• The facilitator controls the use of tools during the meeting.
Benefits of GDSS
GDSS enable more people to attend and participate in a meeting, and at the same time can
increase meeting productivity. This increase in productivity is realised since the attendees can
contribute simultaneously. A GDSS can guarantee anonymity, follow structured methods for
organising and evaluating ideas, preserve the results of meetings, and can increase the
number of ideas generated and the quality of decisions made, while producing the desired
results in fewer meetings. A GDSS can support idea generation, complex problem analysis
and large groups.
F. CHALLENGES
Systems to support decision-making do not always lead to better decisions or improved
organisational performance. It can be difficult to understand managerial problems that
require unstructured decisions. Managers may have difficulties changing their approach to
decision making, to one based on data analysis and measurement. This is something they will
need to do to fully utilise the power of these support systems. There may be some resistance
to ESS at lower levels of the organisation if senior management is using them to monitor
performance carefully. These systems are more likely to be successful if they are designed
and built to be flexible and if they have adequate management support and training provided.
122
Study Unit 9
Enterprise Systems
Contents
A.
Enterprise Resources Planning (ERP) Systems
B.
Customer Relationship Management Systems
C.
Supply Chain Management Systems
D.
Enterprise Integration Trends
E.
Challenges
123
Introduction
The growing trend in businesses is to integrate business functions to ensure seamless transfer
of information between functions which will improve both the efficiency of the organisation
and its ability to respond to change. Businesses are also integrated with other companies such
as suppliers, customers and partners. Enterprise systems can enable this integration.
The objectives of this chapter are to:
• Describe Enterprise Resource Planning (ERP) Systems)
• Describe Customer Relationship Management (CRM) Systems
• Describe Supply Chain Management (SCM) Systems
• Comment on enterprise integration trends
A. ENTERPRISE RESOURCES PLANNING (ERP) SYSTEMS
Enterprise resource planning (ERP) systems (sometimes referred to as Enterprise systems)
are large complex systems that integrate the planning, management and use of all resources
within an organisation. These systems are typically based on a suite of integrated application
modules linked to a common central database and are accessible through a single user
interface. The suite of application modules support all the main business activities of the
organisation. There are a broad range of application modules that support the main functional
areas of Sales and Marketing, HR, Finance & Accounting and Manufacturing & Production.
For example there are modules for sales ordering, payroll, inventory management,
purchasing, accounts payable and receivable, etc. The database collects data from and feeds
it into the various application modules to support the organisation’s business processes and
activities. A major advantage of ERP system is that they enable application modules to share
data between functions and business processes for improved organisational coordination and
control. Organisations implementing ERP systems will select the application modules they
want to use and then they will need to change their business processes to align with the
predefined business processes in the software. Table 9.1 lists the major business processes
supported by ERP systems. The two leading ERP software vendors are SAP and Oracle.
Table 9.1: Examples of the business processes supported by ERP modules (adapted from
Rainer, Turban et al., 2007)
Functional Area
Business Process Module
Sales & Marketing
Order processing, pricing, billing, sales planning
Finance &
Accounting
General ledger, accounts payable, account receivable, cost accounting,
credit management, financial reporting
Manufacturing &
Production
Production scheduling, inventory management, purchasing, production
scheduling, material requirement planning,
Human Resources
Payroll, personnel admin, HR planning, performance management
124
Business Value of ERP Systems
Organisations can gain substantial benefits from implementing ERP systems. These benefits
include:
• Improved access to data for management reporting and decision making
• Helping to create a more disciplined organisational culture where decisions are based
on accurate timely information
• Helping to provide management with a single organisational wide view
• Removal of inflexible legacy systems than can be expensive to change
• Improvement of work processes and making cross functional processes possible
• Enabling sharing of information across business functions
• Improvement of the technology infrastructure of the organisation
• The possibility to help an organisation become more customer focused
Challenges of ERP Systems
There are a number of challenges associated with implementing ERP systems for example:
• ERP systems are very expensive to purchase and implement
• Extensive change is required to existing process
• It can be difficult to integrate the ERP systems with existing legacy systems
• There is an inherent risk associated with having a single vendor for all information
systems
• The risk and impact of implementation failure is increased
• The conversion of data to the ERP systems from legacy systems is a complex process
• The time and resources required to implement ERP systems are substantial
B. CUSTOMER RELATIONSHIP MANAGEMENT SYSTEMS
Introduction to Customer Relationship Management
Customer relationship management involves the use of information systems to coordinate all
of the business processes surrounding the firm’s interaction with its customers in sales,
marketing, service and finance.
Historically each of the business functions that interact with the customers such as sales,
services, marketing and finance had their own information systems and as a result customer
data was held in different systems in the various functions. CRM applications are designed to
address this issue.
Customer Relationship Management Applications
Customer Relationship Management (CRM) systems integrate customer data from all over
the organisation to provide a single enterprise view of the customer that can be used for
125
improving both sales and customer service. CRM systems can also provide customers with a
single view of the company.
CRM applications are designed to provide information and tools to deliver superior customer
experience and to maximise customer lifetime value to the business.
CRM software can also be used to increase customer loyalty through customer service by
identifying valued customers and providing them with enhanced services or offers.
CRM Applications
CRM systems normally provide software tools for sales, marketing and service:
SALES
Sales Force Automation (SFA) modules in CRM systems help sales staff increase their
productivity by focusing sales efforts on the most profitable customers, those who are good
candidates for sales. The SFA system provides information such as sales prospects, contact
information and product related information. The SFA software brings together all the
information the organisation has about a particular customer enabling the sales person to
tailor their message to match the customer
MARKETING
CRM systems support direct-marketing campaigns by providing capabilities for capturing
prospect and customer data, for providing product and service information, and sales leads
for targeted marketing (to specific customers or prospects), and for scheduling and tracking
direct-marketing mailings or e-mail. They also support initiatives for cross-selling and up-
selling to existing customers. Cross-selling involves the marketing of complementary
products to existing customer. For example those customers who purchased a new laptop
computer might be encouraged to purchase accidental damage insurance. Up-selling is the
marketing of higher value products to customers. For example a mobile phone customer who
already has a basic phone service may be targeted with marketing of a data contract and
smartphone.
SERVICE
Customer service modules in CRM systems provide information and tools to make call
centres and customer support staff more efficient. They could also include a Web-based self-
service option.
Operational and Analytical CRM
Laudon and Laudon, (2010) have divided the CRM application into two categories called
Operational and Analytical CRM.
Operational CRM includes customer-facing applications such as tools for sales force
automation, call centre and customer service support and marketing automation.
Analytical CRM includes applications that analyse customer data generated by operational
CRM applications and provide information for improving business performance
management. Analytical CRM applications analyse the data from data warehouses which
contains data from the various operational CRM systems. Analytical CRM applications can
126
identify customer buying patterns and create segments for target marketing and also generate
individual customer profiles.
The focus of CRM systems is to retain customers and help the organisation sell more to
customer as efficiently as possible. This is related to the concept of customer lifetime value.
Wireless Applications for Customer Relationship Management
Mobile CRM applications provide additional support for sales and service activities at the
point of customer interaction. Wireless CRM enables sales and field service professionals to:
• Access customer account records and information at any time or location
• Update customer accounts and deal information to update customer database
instantaneously
• Receive alerts to important events
• Enter, perform and update transactions and product information
Mobile CRM applications are increasingly utilising Smartphones to enable remote access to
information and updating of transactions.
Business Value of Customer Relationship Management Systems
Companies with effective customer relationship management systems can realise many
benefits, including increased customer satisfaction, reduced direct marketing costs, more
effective marketing, and lower costs of customer acquisition and retention. Information from
CRM systems can increase sales revenue by identifying the most profitable customers and
segments for focused marketing, cross-selling, and up-selling. CRM systems can help reduce
rates at which customers leave the company and go to a competitor.
C. SUPPLY CHAIN MANAGEMENT SYSTEMS
Introduction to Supply Chain Management
A supply chain is a network of organisations and business processes for procuring materials,
transforming raw materials into products, and distributing the finished products to retailers
and customers. The supply chain links suppliers to manufacturing plants to distribution
centres and retail outlets and finally to customers for the purpose of creating and delivering
products and services from source to point of consumption. The upstream section of the
supply chain includes the suppliers, their suppliers and the related processes that deliver the
raw materials and parts to the manufacturing plant. The downstream section is made up of the
companies and processes that distribute the products and services to the customers (See
Figure 9.2).
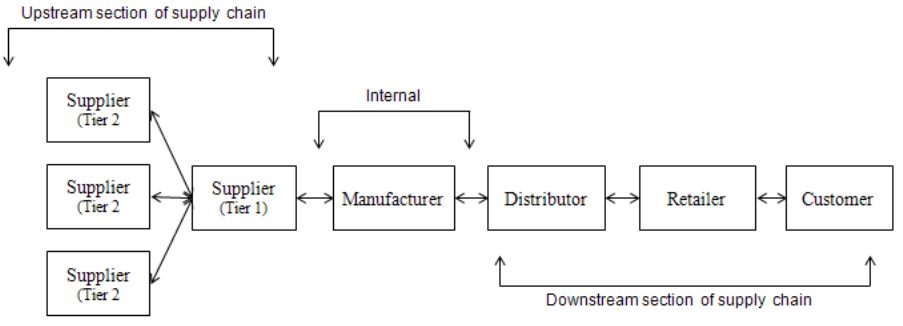
127
Figure 9.2: An example of a Supply Chain
Main Supply Chain Processes
The five major supply chain processes are:
• Plan: This consists of processes that balance supply and demand with the objective of
meeting sourcing, production and delivery requirements.
• Source: This consists of processes that procure goods and services needed to create the
particular product or service.
• Make: This consists of processes that create the finished product in quantities sufficient
to meet demand.
• Deliver: This consists of processes that distribute the finished goods and services to the
point of consumption.
• Return: This consists of processes associated with handling returned products.
Supply Chain Management
The purpose of supply chain management is to plan, organise and optimise the supply chain
activities to ensure the right amount of product arrives at the point of consumption in the least
amount of time and at the lowest cost while minimising inventory levels along the supply
chain. Supply chain management involves coordinating the flow of materials and information
(orders, forecasts etc) within and between the companies that make up the supply chain.
Problems along the supply chain
Problems along the supply chain include; the product not being delivered when the customer
needs it and high inventory costs. These problems can be as a result of poor coordination of
activities along the supply chain and poor demand management. A particular problem
relating to inventory levels is called the bullwhip effect.
The bullwhip effect occurs when information about the demand for a product gets distorted
and the distortion gets magnified as the information passes from one point to the next across
the supply chain. It can also occur when a retailer present manufacturers or suppliers with an
inaccurate forecast of consumer demand. The bullwhip effect can result in stockpiling at
various points on the supply chain. This can be addressed by reducing doubts or inaccuracies
128
about levels of demand and providing all of the supply chain participants with accurate and
up-to-date information.
To improve supply chain management organisations utilise supply chain management
systems.
Supply Chain Management Systems
There are two broad categories of supply chain management system; systems for planning the
supply chain and systems that execute the supply chain activities.
Supply Chain Planning Systems
Supply chain planning systems enable the firm to generate demand forecasts for a product
and to develop sourcing and manufacturing plans for that product. They help companies
decide how much of a specific product to manufacture in a particular time period and the
inventor levels (for raw materials, intermediate products, and finished goods) to hold. The
functions involved include order planning, advanced scheduling, demand planning,
distribution planning and transportation planning.
Supply Chain Execution Systems
Supply chain execution systems manage the flow of products through distribution centres to
ensure that products are delivered to the right locations as efficiently as possible. These
systems track the physical status of goods, the management of materials, warehouse and
transportation operations. These functions are referred to as order commitments, production,
and replenishment of stock and distribution management.
Supply Chain Management Using the Internet and Internet Technology
Firms use intranets to improve coordination among their internal supply chain processes, and
they can use extranets to coordinate supply chain processes shared with their business
partners. Intranet and extranet technology can enable all members of the supply chain to
communicate with each other, use up-to-date information to adjust purchasing, logistics,
manufacturing, packaging, and schedules. Using an extranet link a manager can connect to a
supplier’s systems to determine whether inventory and production capabilities match demand
for the products. Business partners can use Web-based supply chain management tools to
collaborate on forecasts. Sales representatives can access suppliers’ production schedules and
logistics information to check on a customer’s order status.
Wireless Technology and Supply Chain Management
Mobile wireless technology facilitates supply chain management by capturing data on the
movement of goods as these events take place and by providing detailed, up-to-date
information as goods move along the supply chain.
Warehouse managers can use mobile handheld devices to perform tasks such as picking,
packing, freight loading and unloading checks, and inventory checks. Some of these activities
are supported by radio frequency identification technology (RFID).
129
Push-Based and Pull-Based Supply Chain Models
The push-based model refers to a supply chain driven by production master schedules based
on forecasts or best guesses of demand for products. Earlier supply chain management
systems were driven by a push-based model (also known as build-to-stock).
The pull-based model refers to a supply chain driven by actual customer orders or purchases
so that members of the supply chain produce and deliver only what customers have ordered.
The pull-based model is also known as a demand driven model or build to order model.
Benefits of Supply Chain Management Systems
Effective use supply chain management systems can enhance organisational performance in
the following areas:
• More accurate management information for supply chain planning and execution
• Improved customer service and responsiveness through efficient supply chain and
improved delivery speed
• Cost reduction through reduced inventory level
• Cash utilisation
• Reduced time to market for new products
• Improved supply chain control
• Increased sales through better product availability
D. ENTERPRISE INTEGRATION TRENDS
Businesses are now focusing on cross-functional process integration. This is difficult to
achieve with traditional functional applications. They are using SCM, CRM and enterprise
systems to integrate with the systems of their customers, suppliers and business partners.
Extending Enterprise Applications
The major enterprise software vendors have developed Web-enables applications for
customer relationship management, supply chain management and their enterprise
applications to create what are called “enterprise solutions” or enterprise suites. Examples of
these systems are SAP’s “mySAP” and Oracle’s “e-Business Suite”
The latest trend in enterprise systems is the growth in cloud based CRM solutions.
Salesforce.com is the leader in cloud based CRM but SAP and Oracle also have cloud based
version of their ERP systems. Cloud-based software solutions are discussed in more detail
Chapter 4.
E. CHALLENGES
Enterprise applications are very difficult to implement successfully. They require extensive
organisational and process change, significant investments in software and related
implementation activities and a careful evaluation of how these systems will enhance
organisational performance.

130
Study Unit 10
Knowledge Management
Contents
A.
Introduction
B.
Description of Knowledge
C.
Enterprise knowledge management systems:
D.
Knowledge Work Systems
E.
Intelligent Systems and Techniques
F.
Management Challenges and Solutions
131
Introduction
The objectives of this chapter are to:
• Identify important dimensions of knowledge
• Explain what is meant by knowledge management
• Describe three types of knowledge management systems;
– Enterprise knowledge management systems
– Knowledge work systems
– Intelligent systems and techniques
• Identify the main challenges to implementing knowledge management systems
A. INTRODUCTION
There has been strong growth in knowledge management and investment in knowledge
management systems. Knowledge management has become an important subject at many
large firms as managers realise that much of their firm’s value depends on their ability to
create and manage knowledge. Creating and using knowledge is not limited to information-
based companies. It is essential for all organisations, regardless of industry or sector to
embrace knowledge management. It’s not enough to make good products; companies must
make products that are better, less expensive to produce and more desirable than those of
their competitors’. Using corporate and individual knowledge assets will help companies’
fulfil these requirements.
B. DESCRIPTION OF KNOWLEDGE
Data Information and Knowledge
Knowledge is different from data and information. Data are collections of facts and
measurements, while information is organised or processed data. Data by itself has no
meaning but is the first step in the creation of knowledge. Knowledge includes concepts,
experience and insight that provide a framework for creating, evaluating and using
information. Wisdom is the collective and individual experience of applying knowledge to
the solution of problems. Knowledge can be explicit or tacit. Explicit knowledge is
knowledge that has been documented (codified) and can be made available to others. Explicit
knowledge includes procedures, guides, reports, guides, policies, etc. A process description is
an example of explicit knowledge. Tacit (implicit) knowledge is the expertise, experience,
skills know-how, understanding, insights and learning of organisational members that has not
been formally documented. Tacit knowledge is slow, difficult and costly to capture and
document as it tends to be very personalised.
What is Knowledge Management?
Knowledge management is the set of processes developed in an organisation to create, gather,
store, maintain, disseminate and apply the firm’s knowledge. Knowledge management
promotes organisational learning as it defines and makes explicit the organisation’s
knowledge base. Knowledge management enables the organisation to learn from its
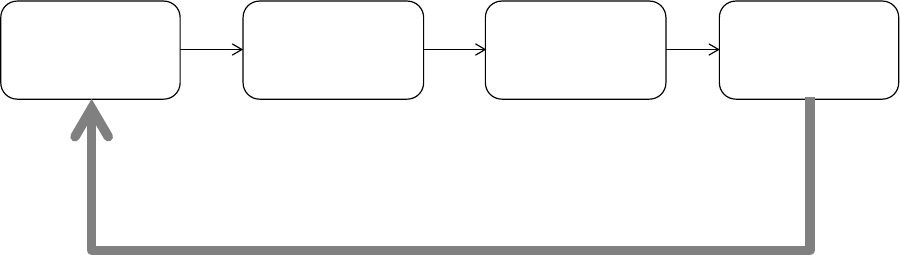
132
environment and incorporate this new knowledge into its business processes. Knowledge
management systems facilitate the creation and support of knowledge networks, knowledge
repositories and communities of practice. Moreover, knowledge networks enable people to
be linked, so that experts in a given area can be easily identified and share tacit knowledge.
Knowledge management streamlines the workflow and provides tools for creating a
knowledge repository.
The knowledge management cycle includes four main steps that transform data and
information into usable knowledge (see Figure 10.1).
Figure 10.1: The Knowledge Management Cycle
Acquisition
Knowledge comes from a variety of sources. Companies are using more sophisticated
technologies to gather information and knowledge from emails, transaction-processing
systems, and outside sources such as news reports and government statistical data. It’s
important to remember that while there are many internal sources of knowledge some
knowledge should come from external sources. This is important as it brings new knowledge
into the company and helps inform the organisation of the changes that are happening in its
external environment.
Storage
As knowledge is created and captured it must be stored efficiently and effectively and in a
way that allows it to be accessed by others. Document management systems are an easy way
to digitise, index and tag documents so that employees can retrieve them without too much
difficulty. For a knowledge system to be effective employees and management need to
support and contribute and not feel threatened by it. All the people in the organisation need to
realise how important a resource a knowledge management system is.
Dissemination
Once the system has acquired and stored the knowledge, it must be made straightforward and
efficient for employees to access the knowledge. People often complain nowadays of having
too much information. The organisation needs to make knowledge available in a useful
format for whoever needs it, when the need it and wherever it is needed. If not it will be
ignored or under-utilised.
Acquire Disseminate
Store Apply
133
Application
If the organisation is to gain business benefit from its investment in knowledge management
then employees and managers needs to apply the knowledge. The more people that apply the
knowledge to solve organisational problems the greater the benefit that accrues. One way to
ensure the knowledge is applied is to build the knowledge dissemination into every functional
area and every system used throughout the organisation. As old information systems are
upgraded or new ones deployed, attention must be given to how knowledge can be drawn into
them. The digital firm also needs to explore how it can use the knowledge system to build
new processes for its suppliers and employees or new products for its customers.
Types of Knowledge Management Systems
Laudon & Laudon, (2010) identified three main categories of knowledge management
systems as follows:
• Enterprise knowledge management systems
• Knowledge work systems
• Intelligent systems and techniques.
C. ENTERPRISE KNOWLEDGE MANAGEMENT SYSTEMS:
Enterprise knowledge management systems are integrated systems that acquire, store and
disseminate knowledge across the organisation. These systems provide databases and tools
for organising and storing structured and unstructured documents and other knowledge
objects, directories, as well as tools for locating employees with particular expertise. These
systems includes knowledge network systems, email systems, office work systems, group
ware and collaboration tools, and document management systems
The structured knowledge systems were the first to capture knowledge and making it easily
available to a wider range of people inside the organisation. These were effectively document
management systems.
As people started using newer forms of communications such as emails, voice mail, and
digital reports, graphics and presentations, organisations had to adapt their systems to
accommodate for this semi-structured knowledge. These semi-structured knowledge
systems sat on top of the more rigidly structured knowledge systems to incorporate a wider
range of information. These systems are also referred to as digital asset management systems.
Organisations can create a centralised knowledge repository by building upon document
management systems and including information from the structured and semi-structured
knowledge systems. The knowledge repository is then easily accessed by employees
throughout the organisation. However it also needs to be properly managed by a senior
person in the organisation who is responsible for the firms’ knowledge management program.
Because it’s simply too expensive and too time-consuming to try to capture all the
organisations knowledge, firms are turning to knowledge networks systems in an attempt to
link those who hold the knowledge with those that need the knowledge. Employees who have
the tacit knowledge about a product, service or process in their head (expertise) need to be
connected with those employees who need this knowledge. Users are easily connected to the
experts through these networks and can communicate and collaborate on a variety of subjects.
.
134
There are three main categories on enterprise-wide knowledge management system:
1. Structured Knowledge Systems
2. Semi-structured Knowledge Systems
3. Knowledge Network System
Structured Knowledge Systems
Structured knowledge is knowledge that has been captured and recorded in structured
documents and reports.
Businesses have realised over the years that most problems or situations are in most cases
new versions of previously experienced difficulties. By creating structured knowledge
systems, employees can research how the problem was solved in the past and can then adapt
the old solution to the current situation. This saves time, money, and frustration. It also
allows the organisation to re-use solutions to previous problems instead of trying to create a
new solution every time.
A structured knowledge system organises structured knowledge in a repository where it can
be accessed throughout the organisation. The capabilities of this system include being able to
develop large online databases with case-based rules that employees can easily access.
Semi-structured Knowledge Systems
A semi-structured knowledge system is a system for organising and storing less structured
information, such as e-mail, voice mail, videos, graphics and brochures. A centralised
repository can be created to pull data from employees, customers, partners, and suppliers and
feed it back into the company through a portal. E-mails are also codified using case-based
rules that allow for easy searching.
Note: The (U.S) Sarbanes-Oxley Act of 2002 requires financial service firms to maintain all
forms of communications. It also meant that new knowledge management systems were
required by companies in order to comply with the law.
Classifying and Tagging Organising Knowledge
Taxonomy is a scheme for classifying information and knowledge in such a way that it can be
easily accessed. Each firm has to develop its own taxonomy to classify documents. Once
knowledge taxonomy is produced, documents are tagged with the proper classification
(generally using XML tags); then the documents can be retrieved through a Web-based
system. There are several tools available that perform “auto tagging” and reduce the need for
managers to develop their own unique taxonomies. These tools identify key phrases in
documents that can be used to assign appropriate tags. The documents are then organised into
categories and the tags are created.
Knowledge Network System
A major problem for organisations is the difficulties they experience in accessing
undocumented knowledge. Because knowledge cannot be conveniently found, employees use
up significant time and energy rediscovering knowledge.
135
Knowledge network systems seek to turn tacit unstructured and undocumented knowledge
into explicit knowledge that can be stored in a database. Knowledge networks provide an
online directory of corporate experts in well-defined knowledge domains and use
communication technologies to make it easy for employees to find the appropriate expert in a
company. Solutions that are developed by experts and others in the firm are added to the
knowledge database. This new knowledge can be stored as an answer in a database of
frequently asked questions. Figure 10.2 shows the basic components of a knowledge network
system.
Figure 10.2: A simplified model of a knowledge network system
D. KNOWLEDGE WORK SYSTEMS
Many of the systems discussed in the previous section centred on how to collect, store,
distribute and apply knowledge. In this section we look at systems that can be used by those
classified as knowledge workers to create knowledge.
Knowledge Workers and Knowledge Work
Knowledge workers include researchers, designers, architects, scientists and engineers who
create knowledge and information for the organisation. Knowledge workers will usually have
high levels of education. Knowledge workers perform three key roles in an organisation:
• They keep the organisation up to date in knowledge as it develops in the external world;
in technology, science and the arts. They monitor the changes taking place, identifying
opportunities and threats.
• They serve as internal consultants in the areas appropriate to their knowledge.
• They act as change agents; appraising, initiating, and promoting change projects.
136
Knowledge workers will rely on office systems, such as word processors, voice mail, e-mail
and video conferencing systems, which are designed to increase worker productivity in the
office. However knowledge workers also require specialised knowledge work systems. These
knowledge work systems are designed to support the creation of knowledge and to ensure
that new knowledge and technical expertise are properly integrated into the business and
made available to others.
Knowledge Work Systems
Knowledge work systems provide knowledge workers with the specialised tools they need,
which include:
• Graphics tools
• Analytical tools
• Communication tools
• Document management tools
• User friendly interfaces
They must have adequate computing power to handle the specialised tasks and complex
calculations, provide easy access to external databases to support research, and present a
user-friendly interface. These systems highlight the special needs of knowledge workers.
Examples of Knowledge Work Systems
Laudon and Laudon, (2010) identified the following examples of knowledge work systems:
• Computer-aided design (CAD) tools automate the creation and revision of designs,
using computers and sophisticated graphics software. CAD applications are used by
design engineers to build new products or improve old ones. Modern CAD systems have
significantly reduced the time required to design new cars and airplanes and are
ultimately saving the car companies and aircraft manufactures millions.
• Virtual reality systems have sophisticated visualisation, and simulation capabilities that
go far beyond conventional CAD systems. They use computer generated simulations that
attempt to be as close to reality as possible. In many virtual reality systems users are
required to wear special equipment that records the user’s movements and feeds them
back to the computer so that it can plan its responses to the user input. Virtual reality is
beginning to provide benefits in educational, scientific and business.
• VRML (Virtual Reality Modelling Language) is a set of specifications for interactive
3-D modelling on the Web. Some companies are putting their training systems on the
Internet so that people can have access to the latest information and can use it when they
need it. Some Web sites use Java applets to help process the programs on the local
workstation.
• Investment workstations: These are used in the financial sector to analyse trading
situations instantaneously and facilitate portfolio management.
137
E. INTELLIGENT SYSTEMS AND TECHNIQUES
Artificial intelligence (AI) technology consists of computer-based systems (hardware and
software) that attempt to emulate intelligent human behaviour. Such systems are able to learn
languages, accomplish physical tasks, and emulate human expertise and decision-making.
While AI systems are limited to very narrow domains they play an important role in modern-
day knowledge management.
Artificial intelligence and database technology provide a number of intelligent systems and
techniques that organisations can use to capture individual and collective knowledge and to
extend their knowledge base. Expert systems, case based reasoning, and fuzzy logic are
used for capturing tacit knowledge. Neural networks and data mining are used for
knowledge discovery. These can discover underlying patterns, categories, and behaviours in
large quantities of data that could not be discovered by managers alone or simply through
experience. Genetic algorithms have the ability to search for solutions to problems that are
too large and complex for human beings to analyse on their own. Intelligent agents can
automate routine tasks to help firms search and filter information for use in electronic
commerce, supply chain management and other activities.
Data mining, which is discussed in Chapter 4, helps organisations capture undiscovered
knowledge hidden in large databases, providing managers with new insights into problems
for improving business performance. Data mining is also an important tool for management
decision-making.
The following intelligent systems and techniques are discussed here:
• Expert Systems
• Organisational Intelligence: Case-Based Reasoning
• Fuzzy Logic
• Neural Networks
• Genetic Algorithms
Expert Systems
An expert system is a system that uses human knowledge captured in a computer to solve
problems that ordinarily require human expertise. An expert system can be used in the
following situations:
• By non-experts to improve their problem-solving capabilities
• To propagate scarce knowledge resources for improved consistent results
• Where the area of expertise is limited to a narrow area (referred to as the domain)
• As a tool to improve productivity and quality
• To support strategic decisions
An expert system is a computer program that simulates the judgement and behaviour of a
human or an organisation that has expert knowledge and experience in a particular field.
Typically, such a system consists of a knowledge base containing the accumulated experience
and a set of rules for applying the knowledge base to each particular situation that is
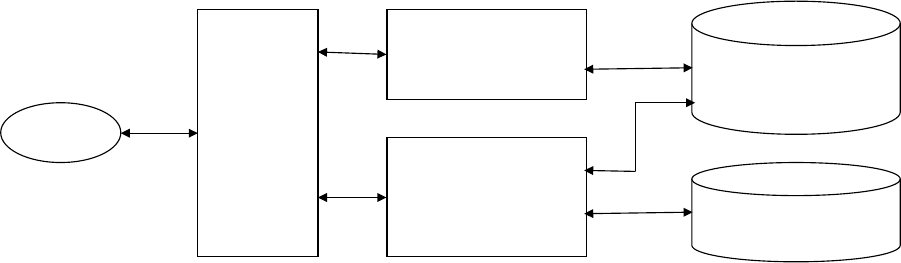
138
described to the program. Sophisticated expert systems can be enhanced with additions to the
knowledge base or to the set of rules.
While Expert systems (Figure 10.3) lack the breath of knowledge and the understanding of a
human expert, they can provide benefits, helping organisations make high quality decisions
with fewer people. Today expert systems are used in business in distinct highly structured
decision-making situations.
Figure 10.3: A simplified model of an Expert System
The Components of an Expert System
An expert system will generally contain the following components:
Knowledge base: The knowledge base contains the knowledge of humans experts based on
their experiences and knowledge built up over many years. The knowledge base also requires
a set of rules that direct the use of the knowledge to solve specific problems in a particular
domain.
Inference engine: The inference engine is a computer that draws inferences from the results
of applying the user supplied facts to the rules in the knowledge base. It then proceeds to the
next fact-rule combination. The inference engine is considered the “brain” of the system.
User interface: The user interface allows the user to communicate with the system. The
system communicates with the user using a question and answer format. This communication
drives the inference engine to match the symptoms of the problem with the knowledge in the
base so that a conclusion is drawn and a recommendation is made to solve the problem.
Explanation facility: This feature of the expert system gives it the ability to explain its
recommendation.
Current Data storage: This is a storage area set aside for input data related to the current
problem.
Knowledge engineer: The person who pulls the data from the human expert and fits it into
the expert system is called the knowledge engineer.
Benefits of an Expert System
The benefits of an expert system include the following:
• Reduced errors
• Reduced cost and reduced training time
User
Interface
Knowledge Base
Explanation
Facility
Inference Engine
User
Current Problem
Data
139
• Improved decision making
• Improved quality and services
• Improved user and customer satisfaction
Organisational Intelligence: Case-Based Reasoning
Expert systems primarily capture the tacit knowledge of individual experts, but organisations
also have collective knowledge and expertise that they have built up over the years. This
organisational knowledge can be captured and stored using case-based reasoning systems. In
case-based reasoning (CBR), descriptions of past experiences represented as cases, are
stored in a database for later retrieval when the user encounters a new case with similar
characteristics. The system searches for stored cases with problem characteristics similar to
the new one. It finds the closest fit, and applies the solutions of the old case to the new case.
Successful solutions are tagged to the new case and both are stored together with the other
cases in the knowledge base. Unsuccessful solutions are also added to the case database along
with explanations as to why the solutions did not work (See Figure 10.4).
Expert systems work by applying a set of IF-THEN-ELSE rules against a knowledge base,
both of which are extracted from human experts. Case-based reasoning, in contrast,
represents knowledge as a series of cases, and this knowledge base is continuously updated
by users of the system.
Figure 10.4: A simplified model of a Case-based reasoning system
User inputs problem
description
Case
Database
System searches
database for similar
case
System asks user for
more information
System finds case
that is best match &
returns solution
Does solution
solve problem
System stores
problem and solution
140
Fuzzy Logic
Fuzzy logic is a rule-based artificial intelligence technology that handles uncertainty, by
mimicking the process of human reasoning and allows computers to handle incomplete or
ambiguous data. Fuzzy logic represents more closely the way people actually think than
traditional IF-THEN rules. Decision making often involve situations that are neither black
nor white. They are grey at best with the term fuzzy often being suitable. Fuzzy logic systems
are only starting to be applied to business situations.
Neural Networks
Neural networks are systems of programs and data structures that attempt to model the
capabilities of the human brain. Neural Networks are an array of interconnected processors
operating in parallel in which knowledge is represented by the pattern of interconnections
among them and by adjustable weights of these connections. They have good pattern
recognition techniques and can identify hidden patterns in data and can also deal with
incomplete input. They also have an ability to learn new information and behaviour.
A neural network uses rules it “learns” from patterns in data to construct a hidden layer of
logic. The hidden layer then processes more inputs and categorises them based on the
experience of the model.
Difference between Neural Networks and Expert Systems
Table 10.5 provides a summary of the differences between neural networks and expert
systems
Table 10.5: Summary of the differences between neural networks and expert systems
Expert Systems
Neural Networks
Expert systems emulate human
decision-making.
Neural networks
learn human thought
processes and reasoning patterns.
Expert systems use rules and frames of
reference in which they make their
decisions.
Neural networks adjust to inputs and
outputs.
Expert systems require humans to
update their database of knowledge.
Neural networks continue to expand their
own base of knowledge
Genetic Algorithms
The concept of genetic algorithms was developed by John Holland in the US in the 1970s.
The concept of genetic algorithms is taken from nature and is based on the idea of natural
selection and genetics. Genetic algorithms are search procedures that can be used to find the
optimal solution to a specific problem by searching through a very large number of possible
solutions to that problem. Genetic algorithms involve adaptive computation where possible
solutions can evolve and can even be combined to form a new population of solutions. As
solutions alter and combine, the worst ones are discarded and the better ones survive to go on
and produce even better solutions.
141
Genetic algorithms are particularly suited to the areas of optimisation and search. They are
used to solve problems that are complex, changing and usually involve large numbers of
variables.
F. MANAGEMENT CHALLENGES AND SOLUTIONS
The difficulties of implementing knowledge management systems include:
• Insufficient resources available to structure and update the stored content
• Poor quality and high variability of content because of insufficient validation
• Document and content stores lack context, making documents difficult to understand
• Individual employees are not rewarded for contributing knowledge, and many are
resistant to sharing knowledge with others
• Search engines return too much information, reflecting lack of knowledge structure or
mechanism for tagging documents
Laudon and Laudon, (2010) suggest that for businesses to obtain value for knowledge
management systems they should use the following steps:
• Develop in stages
• Choose a high-value business process
• Choose the right audience
• Measure return on investment during initial implementation
• Use the result of the measurements to establish the organisational wide values.
142
Study Unit 11
Information Systems Security and Control
Contents
A.
System Vulnerability and Threats
B.
Security and Controls
C.
Organisational and Managerial Framework for Security and Control
D.
Tools and Technologies for Protecting Information Resources
E.
Management Challenges
143
Introduction
The objectives of this chapter are to:
• Explain why computer systems are venerable to attack
• Explain why the internet and Wi-Fi networks are so difficult to secure.
• Describe the main threats to information systems.
• Describe the business value of security and control.
• Describe the security controls mechanisms that can be employed to protect
information systems
• Briefly describe what is involved in disaster recovery planning.
• Describe the tools and technologies for protecting information systems
• Identify the challenges posed by information systems security and control
A. SYSTEM VULNERABILITY AND THREATS
Why Systems are Vulnerable
Computer based systems tend to be more vulnerable to damage, error, and fraud than manual
systems for the following reasons:
• Data are stored in electronic format and are therefore not visible or easily auditable.
• Data are concentrated in electronic files and databases. A disaster such as a hardware or
software fault, power failure or fire can be more far-reaching. An organisation’s entire
record-keeping system could be destroyed.
• There may not be a visible trail to indicate what occurred for every computer process so
errors entered in data can be very difficult to detect.
• Computer programs are also vulnerable as errors can be accidentally introduced when
updates to the programs are installed. It can also be possible for programmers to make
unauthorised changes to working systems.
• Many information systems can be accessed through telecommunications, and
telecommunications can produce errors in data transmission.
• Data in files or databases can be accessed and manipulated directly in online systems. The
data can be stolen, corrupted or damaged by hackers and computer viruses.
• Hardware equipment can be stolen – this is a growing problem because of the growth in
mobile computing.
Why are the Internet and Wi-Fi networks so difficult to secure?
The Internet is difficult to secure because:
• The Internet is designed to be an open system so anyone can access it.
• Cable modems or Digital Subscriber Lines (DSL) modems use fixed IP addresses that can
be identified by hackers making them venerable to attack.
144
• Internet technology is vulnerable to interception unless run over a secure private network.
Voice over IP (VoIP) traffic sent over the public Internet is not encrypted, so
conversations can be intercepted.
• E-mail messages can contain viruses and other forms of malware.
Wi-Fi networks are difficult to secure because:
• Wi-Fi networks are vulnerable because they use radio frequency bands to communicate
between devices; these can be easily scanned.
• Wi-Fi networks can be penetrated by outsiders using sniffer programs.
• Sometimes Wi-Fi networks do not have basic security protections activated to prevent
unauthorised access.
The initial security standard developed for Wi-Fi, called Wired Equivalent Privacy (WEP), is
not as effective as the enhanced WAP encryption.
Types of Threats
Malicious Software
Malicious software, also referred to as Malware, is any program or file that is harmful to a
computer user. Malware includes computer viruses, computer worms, Trojan horses, spyware
and keyloggers.
Virus: A computers virus is a small program or programming code that replicates itself by
being copied or initiating its copying from one file to another. They can spread to other
computers by infecting files on a shared file system.
Worms: A computer worm is a self-replicating virus that resides in active memory and
duplicates itself but does not alter files. A worm can exploit security weaknesses to spread
itself automatically to other computers on a network.
Trojan horse: A Trojan horse is a program in which malicious or harmful code is contained
inside what appears to be harmless programming or data in such a way that it can get control
and execute some form of damage to the computer system. A Trojan can also give a hacker
remote access to a targeted computer system.
Like a virus, Worms and Trojan horses can also harm a computer system's data or
performance.
Spyware: These are programmes that are resident in computers and gather information about
a computer user without their knowledge. Spyware can collect different types of data,
including personal information like Internet surfing habits, user logins and bank or credit
account information.
Keyloggers: These record keystrokes made on a computer by the person using the keyboard
to discover login names and passwords, bank account numbers etc. The tracking or logging is
typically done in a hidden manner so that the person using typing is unaware that their actions
are being monitored.
145
Hackers
A hacker is an individual who intends to gain unauthorised access to a computer system.
Hackers gain access to the systems by finding weaknesses in the security protections
employed by Web sites or information systems. Hackers may be motivated by many reasons,
such as challenge, protest or profit. Hackers can steal goods and information, deface, disrupt
or damage a Website or information system.
There are many different types of hackers with different motives such as:
• A white hat hacker attempts to break into a system for non-malicious reasons, such as
testing the security of the system.
• A black hat hacker is a hacker who breaches the computer security of a system for
personal gain, such as to steal data or information.
DENIAL OF SERVICE (DOS) ATTACK
This is where hackers flood a network or Web server with thousands of false requests for
service in order to crash the network of server. A DOS attack will normally involve the use of
many computers to overpower a network from many different launch points. Although DOS
attacks do not destroy information they can cause a Web site to shut down thus restricting
access to that site by legitimate users.
SPOOFING AND SNIFFING
Spoofing involves hiding of a hacker’s identity or email addresses, or redirecting a Web link
to a different web site setup up by the hacker. The aim of spoofing is to trick users to provide
information such as login names and passwords and account information to the outsider.
A sniffer is an eavesdropping program that monitors network information and can enable
hackers to steal information transmitting over the network. The sniffer program searches for
passwords or other content in packet of data as they pass through the Internet or other
network.
Identity Theft and Phishing
Identity theft is a crime in which someone uses the personal information of others such as a
bank account number, driver’s license number, or credit card numbers, to create a false
identity or impersonate someone else, for the purpose of committing some type of fraud. The
information may be used to obtain credit, goods or services in the name of the victim.
The Internet has made entity theft easier because goods can be purchased online without any
personal interaction. Hackers are increasingly targeting personal information and Credit card
details on e-commerce sites.
Phishing is an attempt to use deception to unlawfully acquire sensitive information such as
bank account details, systems login names and passwords. It normally involves setting up
fake Web sites or sending bogus e-mail messages that look like they have originated for the
official businesses to deceive users into divulging confidential personal data. The e-mail
usually asks recipients to update or confirm records by bank and credit card information, and
other confidential data by entering the information at a fake Web site.
146
Internet Click Fraud
This term refers to a collection of scams and deceptions that inflate advertising bills for
companies who are engaging in online advertising. Two common types of click fraud are:
• This type of fraud takes place when another user or competitor purposely clicks on an
pay-per-click advertisement
• This type occurs when advertising sites force paid views or clicks to advertisements on
their own websites via Spyware. The affiliate is then paid a commission on the cost-per-
click that was artificially generated.
With the phenomenal growth in pay-per-click advertising, this form of Internet fraud is on the
increase.
Threats from Employee
Some of the largest threats to businesses come from employees. These can include
disruptions to service, errors in data entry, accidental deletion if data and diversion of
customer credit data and personal information. Employees have access to privileged
information, and if internal security procedures are weak, they are often able to stray
throughout an organisation’s systems.
Many employees forget their passwords to access computer systems or allow other members
of staff to use them, which can compromise the system. Employees can introduce errors by
entering faulty data or by not following instructions for processing data and using computer
equipment. Information system specialists can also create software errors as they design and
develop new software or maintain existing programs.
Software Errors
Software errors pose a constant threat to information systems as they can cause the system to
crash, or slow down operation and can lead to large losses in productivity and in some cases
cause losses of data. Software can contain hidden bugs in the program code which in addition
to impacting performance can open system to hackers.
To correct software flaws once they are identified, the software vendor normally creates
segment code called patches to repair the defect in the software.
B. SECURITY AND CONTROLS
Security
The term Security is used to refer to the policies, rules, procedures and technical solutions
that can be used to prevent the following:
• Unauthorised access to systems,
• Alteration of data or software,
• Theft of data, software or equipment,
• Physical damage to information systems hardware.
147
The Business Value of Security and Controls
Security and control are an important area of information system. Companies that rely on
computer systems to support their main business functions can be seriously impacted if a
problem occurs with their information systems. For example an organisation relying on an e-
commerce site for online sales would by seriously impacted by a security breach that affected
the operation of that site. If data stored on information systems such as employee records,
trade secrets, customer data were to become accessible to people outside the organisation it
would undermine the business, damage its reputation and open the firm to legal liability.
Laws such as the Sarbanes-Oxley Act in the US and data protection legalisation in many
countries require companies to practice strict electronic records management (ERM) and
stick to exacting standards for security privacy and control. Electronic records management
(ERM) consists of policies, procedures and tools for managing the retention, destruction, and
storage of electronic records.
Electronic Evidence
An increasing amount of the evidence presented in legal cases today is in electronic form.
This includes information in hard disks, CDs and digital media as well as e-mail and records
of e-commerce transactions. E-mail is currently the most common type of electronic
evidence.
In a legal case, a firm may have to respond to a discovery request for access to information
that may be used as evidence, and the company is required by law to produce the data. The
cost of responding to a discovery request can be high if the company has difficulty collecting
the required data or the data have been deleted. Courts can impose stern financial and
criminal penalties for improper destruction of electronic documents.
Computer Forensics
Computer forensics is the scientific approach to collection, examination, authentication,
preservation and analysis of data held on or retrieved from computer storage media so that
the information can be used as evidence in a court of law.
Information System Controls
Computer systems are controlled by a combination of general controls and application
controls.
General Controls
There are six principal general controls, which include software controls, hardware controls,
computer operations controls, data security controls, system implementation controls and
administrative controls.
• Computer software security can be promoted by program security controls to prevent
unauthorised changes to programs in production systems. Software security is also
promoted by system software controls that prevent unauthorised access to system
software and log all system activities.
148
• Computer hardware security can be promoted by locating hardware in restricted rooms
where only authorised individuals can access it. Special safeguards against fire, high
temperature, and electric power disruptions can be implemented.
• Computer operations controls oversee the work of the computer department, ensuring
that procedures for storage and processing of data are followed. Computer operations
controls include the setup of computer processing jobs, computer operations and
computer backup and restore procedures.
• Data security controls prevent unauthorised changes, deletion or access to data while the
data is in use or in storage. Data security software can be configured to restrict access to
individual files, data fields or groups of records. Data security software often features
logs that record users who access or update files. Data storage media can be physically
secured to prevent access by unauthorised personnel.
• System implementation controls ensure that the systems development process is
properly controlled and managed. A system development audit checks that formal
reviews and signoff were done by users and management at the various stages of the
development process. The audit should look for the use of controls and quality assurance
techniques for program development, conversion and testing and for complete system
documentation.
• Administrative controls are formalised standards, rules, procedures and control
disciplines to ensure the organisations general and application controls are properly
executed and enforced.
Application Controls
These are specific controls that are associated with each application system such as payroll
systems. Their purpose is to ensure that only authorised data enters the system. They can
include both automated and manual controls.
There are three principal application controls, which are called input controls, processing
controls and output controls.
• Input controls are procedures to check data for accuracy and completeness when they
enter the system.
• Processing controls are the routines for establishing that data are complete and accurate
during updating. Common controls include control totals, computer matching and run
control totals.
• Output controls are measures to ensure that the outputs after processing are accurate,
complete and distributed to the correct recipients.
C. ORGANISATIONAL AND MANAGERIAL FRAMEWORK FOR
SECURITY AND CONTROL
Risk Assessment
A risk assessment determines the level of risk to the firm if a specific activity or process is
not properly protected or controlled. It involves determining the value of information
149
resources, their points of vulnerability, the likely occurrence of a problem and the potential
for damage.
Security risk analysis involves determining what needs to be protected, what it needs to be
protected from and how to protect it and the level of protection that is justified. The aim is to
make cost-effective decisions about what needs to be protected. There are two important
elements of a risk analysis:
1. Identify the assets
2. Identify the threats.
The risk analysis process prioritises those assets that need to be protected based on the value
of the asset, the probability of the threat, the likely impact of the threat in terms of potential
loss and the estimated cost of protection. Once the risks have been prioritised the system
builders can concentrate on the control point with the greatest vulnerability and potential for
loss.
The following are a list of categories of assets that may need to be assessed:
• Hardware: keyboards, terminals, workstations, personal computers, laptops, printers, disk
drives, communication lines, servers, routers, hubs etc.
• Software: source programs, object programs, utilities, diagnostic programs, operating
systems, communication programs.
• Data: during execution, stored online, archived off-line, backups, audit logs, databases,
and in-transit over communication links.
• People: users, internal IT professionals, external support organisations.
• Documentation: on programs, hardware, systems and local administrative procedures.
• Supplies: paper and digital storage media.
The end result of risk assessment is a plan to implement controls that minimise overall cost
while maximise defences.
RISK MITIGATION
Risk mitigation is where the organisation takes specific steps against the risk. They can
implement controls that are likely to reduce or eliminate the risk or they can develop some
way of recovering the asset if a breach occurs.
The following are three risk mitigation strategies that an organisation could adopt:
• Risk acceptance - continuing without controls and accept any loss that occurs
• Risk limitation - implement some controls to reduce the risk
• Risk transference - use other means to compensate for possible loss like purchasing
insurance
Security Policy, Acceptable Use Policy and Authorisation Policy
Larger firms typically have a formal corporate security function headed by a chief security
officer (CSO). The security group educates and trains users, keeps management aware of
150
security threats and breakdowns and maintains the tools chosen to implement security. The
chief security officer is responsible for enforcing the firm's security policy.
A security policy contains a set of statements that rank information risks to a company. The
policy will also specify what the acceptable security goals are and the level of risk that
management are willing to accept. It should also identify how these goals will be achieved.
An acceptable use policy (AUP; also sometimes referred to as acceptable usage policy)
defines what is considered to be acceptable uses of the firm’s information resources. These
resources would typically include computers, telephones, e-mail and the Internet. The policy
should set out the company policy regarding privacy, user responsibility and personal use of
company equipment.
New staff members will generally be expected to sign an AUP document before they are
given access to the information systems. The AUP should also specify what sanctions will be
applied if a user does not comply with the AUP.
Authorisation policy determines differing levels of access to information assets for different
levels of users. Authorisation management systems establish where and when a user is
permitted to access certain parts of a Web site or a corporate database.
Identity management is a much broader concept that includes business processes and tools to
identify valid users of system and control access to the systems. It specifies the level of
access the different categories of users have.
Ensuring Business Continuity
As companies increasingly rely on digital networks and systems for their business, they need
to take added steps to ensure that their systems and applications are always available.
Downtime refers to periods of time in which a system is not operational. Several techniques
can be used by companies to reduce downtime.
Fault Tolerant Systems
Fault Tolerant Systems are important in environments where interruption on processing has
highly undesirable effects, such as in hospital information systems or in securities trading i.e.
where interruption to processing is not acceptable. These systems continue to operate after
some of their processing components fails. Fault Tolerant Systems are built with redundant
components; they generally include several processors in a multiprocessing configuration. If
one of the processors fails, the other (or others) can provide degraded, yet effective, service.
High-Availability Computing
High-availability computing, although also designed to maximise application and system
availability, helps firms recover quickly from a crash. Fault tolerance promises continuous
availability and the elimination of recovery time altogether. High-availability computing
environments are a minimum requirement for firms with heavy electronic commerce
requirements.
Load Balancing
This involves distributing large numbers of access requests across multiple servers. The
requests are directed to the most available server so that no single device is overwhelmed. If
151
any server starts to get swamped access requests are forwarded to another server with more
capacity.
Mirroring
Mirroring involves the use of a backup server that duplicates all the processes and
transactions of the primary server. If for any reason the primary server fails the backup server
can take its place without any interruption to service. This approach is quite expensive,
because every server must be mirrored by an identical server, whose only purpose is to take
its place in the event of a failure.
Recovery-Oriented Computing
Researchers are looking at ways to make computer systems recover more rapidly when
mishaps occur. This approach, which is called recovery-oriented computing, involves
designing computing systems to recover quickly from mishaps and putting in place
capabilities and tools to help operators identify the source of the fault to allow the problem to
be easily corrected.
Disaster Recovery Planning
Disaster recovery planning involves specifying plans for the restoration of computing and
communications services after they have been disrupted by a natural event such as an
earthquake, flood, or some human activity. Disaster recovery plans focus primarily on the
technical issues involved in getting the systems up and running, such as which files to back
up and the maintenance of backup computer systems and having backup telecommunications
links in place.
With the increasing importance of information technology for the continuation of business
critical functions, combined with the increasing need to have systems operational 24/7, the
importance of protecting an organisations data and IT infrastructure in the event of a
disruption has become an ever increasing business priority in recent years.
It is estimated that most large companies spend between 2% and 4% of their IT budget on
disaster recovery planning, with the aim of avoiding larger losses in the event that the
business cannot continue to function due to loss of IT infrastructure and data. Of companies
that had a major loss of business data, up to half don’t reopen, and a high percentage close
within two years.
Business Continuity Planning
Business continuity planning focuses on how the company can restore business operations
after a disaster occurs. The business continuity plan identifies critical business processes and
sets out the actions to be taken to enable mission-critical functions to continue to operate after
a disaster occurs and systems stop working.
MIS Audit
To check that its security and controls are effective, an organisation must conduct regular
systematic audits. A MIS audit identifies all of the controls that govern individual
information systems and assesses their effectiveness.
152
The auditor must acquire a thorough understanding of the operations, physical facilities,
telecommunications, control systems, data security objectives, organisational structure,
personnel, manual procedures and individual applications of the company.
The auditor usually interviews key individuals, who use and operate the specific information
system being audited, about their normal activities and procedures. The audit will examine
the various controls that are in place. The auditor will typically trace the flow of sample
transactions through the system. The output of the audit lists and ranks all control weaknesses
and estimates the probability of threat occurring and estimates the financial and
organisational impact of each threat. Management is expected to draw up a plan to address
any major threats or weaknesses highlighted in the audit.
D. TOOLS AND TECHNOLOGIES FOR PROTECTING
INFORMATION RESOURCES
There are a range of tools and techniques to help firms protect against or monitor intrusions.
These include tools for authentication, firewalls, intrusion detection systems, antivirus
software and encryption.
Access Control
Access control is all the policies and procedures that a company uses to prevent access to
systems by unauthorised insiders and outsiders. To gain access a user must be authorised and
authenticated. Authentication refers to the ability to know that a person is who they claim to
be. Authentication is often established by using passwords to log on to a computer system
and also by using passwords to access particular systems and files. However users often
forget passwords, share them with colleges or choose passwords that are easy to guess, all of
which compromises security. Passwords can also be sniffed when transmitted over a network.
Sometimes systems use tokens (physical devices) such as smart cards for access control.
Firewalls, Intruder Detection Systems and Antivirus Software
Firewalls
Firewalls are used to prevent unauthorised access to private networks or systems (see Figure
8.3). As many organisations are now connecting their networks to the Internet, firewalls are
becoming an essential element of an organisation’s defences against unauthorised access. A
firewall is a combination of hardware and software that inspects and controls the flow of
incoming and outgoing traffic. The firewall is normally placed between the organisation's
private internal networks and an external network such as the Internet. Firewalls can also be
used to protect a particular segment of a company's network from the rest of the network
153
Figure 8.3: A Firewall
The firewall is a bit like a gatekeeper that inspects the credentials of each access request
before access to the network is granted. The firewall identifies names, Internet Protocol (IP)
addresses, applications and other characteristics of incoming traffic. It checks this
information against the access rules that have been programmed into the system by the
network administrator. The firewall prevents unauthorised communication into and out of the
network, allowing the organisation to enforce a security policy on traffic flowing between its
network and other networks, including the Internet.
In large organisations, the firewall often resides on a specially designated computer separate
from the rest of the network so no incoming request can directly access private network
resources. There are a number of firewall screening technologies, including static packet
filtering, stateful inspection, Network Address Translation and application proxy filtering.
The following techniques are used in combination to provide firewall protection
Packet filtering examines selected fields in the headers of data packets flowing back and
forth between the trusted network and the Internet, examining individual packets in isolation.
This filtering technology can miss many types of attacks.
Stateful inspection provides additional security by determining whether packets are part of
an ongoing dialogue between a sender and a receiver. It sets up state tables to track
information over multiple packets. Packets are accepted or rejected based on whether they are
part of an approved conversation or whether they are attempting to establish a legitimate
connection.
Network Address Translation (NAT) provides an additional level of protection when
implemented along static packet filtering and stateful inspection. NAT hides the IP address of
the organisation's internal host computer(s) to prevent sniffer programs outside the firewall
from determining their identity and using that information to penetrate internal system. The
internal private IP address is temporarily assigned a public IP address for the duration of the
communication. Messages inside the firewall will utilise the hosts own IP address but once
the message passes through the firewall it uses the public IP address. The IP address
translation occurs in the firewall.
Application proxy filtering examines the application content of packets. A proxy server
stops data packets originating outside the organisation, inspects them, and passes a proxy to
the other side of the firewall. If a user outside the company wants to communicate with a user
inside the organisation, the outside user first "talks" to the proxy application and the proxy
Comp
any
Netw
ork
154
application communicates with the firm's internal computer. Likewise, a computer user inside
the organisation goes through the proxy to talk with computers on the outside.
To create a good firewall, an administrator must specify and maintain the internal rules
identifying the people, applications, or addresses that are allowed through the firewall those
that should be rejected. Firewalls can only deter intruders from penetrating a network. It will
not be able to fully prevent intrusions, so it should only be viewed as one element in an
overall security plan. To deal effectively with Internet security, a number of additional
methods are required.
Intruder Detection Systems
Intrusion detection systems monitor the most vulnerable points in a network to detect and
deter unauthorised intruders. These systems also monitor events, as they happen to look for
security attacks in progress. An alarm can be notified to network administrators if suspicious
activity is detected. These detection systems can be programmed to shut down a part of a
network if unauthorised traffic is detected.
Antivirus Software
Antivirus software checks the computer systems and hard drives for the presence of computer
viruses. The software detects and removes the virus from the infected area. To be effective,
antivirus software must be continually updated. Some of the companies providing antivirus
software include: AVG, McAfee, Symantec and Zone Alarm.
Anti-Spyware Software
Anti-spyware programs protect against spyware software by either preventing its installation
or detecting and removing spyware already installed on a computer system. Many providers
of anti-virus products also include anti-spyware functions in their products. Some also supply
stand alone anti spyware solutions.
Wireless Networks Security
Wi-Fi security is more easily penetrated because it uses radio waves to transmit data. Unless
users take rigorous precautions to protect their computers, it is possible for hackers to obtain
access to files. Stronger encryption and authentications systems for Wi-Fi, other than the
original Wired Equivalent Privacy (WEP) are being installed in newer systems.
WiFi Protected Access (WPA) and the Wi-Fi Alliance industry trade group's 802.11i
specification help tighten security for wireless LANs. These authentication and encryption
systems are used to help protect data travelling between devices over the airwaves.
Encryption and Digital Certificates
Encryption
Encryption is the coding and scrambling of messages to prevent their access by unauthorised
individuals. Encryption offers protection by keeping messages or packets hidden from the
view of unauthorised readers. Encryption is crucial for ensuring the success of electronic
155
commerce between the organisation and its customers, and between the organisation and its
suppliers and business partners.
Many companies use the Secure Socket Layer (SSL) security method and its successor
Transport Layer Security (TLS) that automatically encrypts data passing between your
web browser and a merchant’s server. Secure Hypertext Transfer Protocol (S-HTTP) is
another protocol used for encrypting data flowing over the Internet, but it is limited to
individual messages.
PUBLIC KEY ENCRYPTION
Public-key encryption, also known as asymmetrical encryption, uses two keys; a public key
and a private key. The two keys are created using the same mathematical formula meaning
that a message encrypted with one key can only be decrypted with the other key.
The sender locates the recipient's public key in a public directory and uses it to encrypt a
message. The message is sent in its encrypted form over the Internet or a private network.
When the encrypted message arrives, the recipient uses their private key to decrypt the data
and read the message.
Digital Signatures
Digital signatures are digital codes attached to an electronically transmitted message that are
used to verify the origins and content of the message. It provides a way to associate a
message with a sender, performing a similar function to a written signature.
Digital signature software can create a method of verifying that the message, document, or
file has not been altered between the time it left the sender and you received it. The
Electronic Signatures in Global and National Commerce Act (U.S) authorised the use of
digital signatures and promises to enhance electronic commerce and make it easier to do
business digitally.
Digital Certificate
A digital certificate is a data file used to establish the identity of people and electronic assets
so as to protect online transactions. It uses a third party known as a certificate authority to
validate the user’s identity. There are many certificate authorities around the world such as
VeriSign.
The certificate authority verifies a digital certificate user’s identity off-line. This information
is put into a certificate authority server, which generates an encrypted digital certificate
containing owner identification information and a copy of the owner’s public key. The
certificate authority makes its own public key available publicly either in print or on the
Internet. The recipient of an encrypted message uses the certificate authority’s public key to
decode the digital certificate attached to the message, verifies it was issued by the certificate
authority and then obtains the sender’s public key and identification information contained in
the certificate. The recipient of the encrypted message can use this information to send an
encrypted reply.
156
Public key infrastructure (PKI)
This is the use of public key encryption in combination with a certificate authority. This
approach is now widely used in e-commerce.
E. MANAGEMENT CHALLENGES
Establishing a good framework for security and control requires skilful balancing of risks,
rewards and the firm’s operational capabilities. Designing systems that are neither over-
controlled nor under-controlled and implementing an effective security policy are major
management challenges. To address these issues management need to make security and
control a higher priority within the firm. Management need to determine what is an
appropriate level of control for the organisation.
157
Study Unit 12
Information Systems Development and Acquisition
Contents
A.
Building Systems and Planned Organisational Change
B.
System Development
C.
Alternative Approaches to Developing and Acquiring Systems
D.
Contemporary Approaches to Application Development
E.
Management Challenges
158
Introduction
Building new systems is about more than new hardware and software - it may also include
changes to processes, jobs, skills, management and organisations.
The objectives of this chapter are to:
• Describe the relationship between system development and organisational change
• Explain business process re-engineering and process improvement
• Briefly describe Total Quality, Six Sigma and Benchmarking
• Provide an overview of system development
• Describe Systems Investigation; Systems Analysis; Systems design; Programming;
Testing; Implementation; Production and Maintenance
• Describe various system development approaches
– Traditional System Development Life Cycle; Prototyping; End-User
Development; Application Software Packages; Outsourcing
• Provide an overview of some contemporary approaches to application development
– JAD: RAD; Component-based Development and Web Services
A. BUILDING SYSTEMS AND PLANNED ORGANISATIONAL
CHANGE
The process of building and implementing a new information system will bring about change
in the organisation. The introduction of new information systems has a far greater impact that
the purchase and deployment of new pieces of technology. It also includes changes to
business processes, jobs, skills and even the structure of the organisation. System builders
must consider how the nature of work and business processes will change.
System Development and Organisational Change
According to Laudon & Laudon (2010) information technology can enable the following four
kinds of organisational change;
1. Automation: this involves using computers to speed up the performance of existing tasks
by eliminating the need for manual activity. This approach to organisational change may
release staff to other jobs, reduce the number of employees needed, or enable the
organisation to process more transactions.
2. Rationalisation of procedures refers to the streamlining of standard operating
procedures and eliminating some tasks in a process removing any blockages.
3. Business process reengineering refers to the radical redesign of business processes. It
can involve combining tasks in a process to cut waste and eliminating repetitive, labour-
intensive tasks in order to improve cost and quality and to maximise the benefits of
information technology.
4. A paradigm shift is a radical change in the business and the organisation. The strategy
of the business can be changed and sometimes even the business the company is in.
159
Business Process Re-engineering
Business process re-engineering (BPR) is a management practice that aims to improve the
efficiency of the business processes. Reengineering is a fundamental rethinking and radical
redesign of business processes to achieve major improvements in performance, cost, quality,
speed and service.
Companies should next identify a few core business processes to be redesigned, focusing on
those with the greatest potential return. Identifying the business processes with the highest
priority includes looking at those which are crucial to the business strategy of the company
and those where there are already issues and problems.
After identification of the core processes for re-designing, the business process itself must be
analysed in terms of its inputs and outputs, flow of products or services, activities, resources
etc. The performance of the existing processes must be measured and used as a baseline.
Business processes are typically measured along the following dimensions:
• Process cost
• Process time
• Process quality
• Process flexibility
Rather than designing the process in isolation and then looking at how Information
technology can support it, information technology should be allowed to influence process
design from the start. Once a business process is understood, a variety of techniques or
principles can be used to improve it, such as:
• Replace sequential steps in the process with parallel steps
• Enrich jobs by enhancing decision authority and concentrating information
• Enable information sharing throughout to all participants
• Eliminate delays
• Transform batch processing and decision making into continuous flow processes
• Automate decision tasks where possible
Following these steps does not guarantee that reengineering will always be successful
because the required organisational changes are often very difficult to manage. Therefore
companies will also need to develop a change management strategy to deal with the
resistance to changes that is likely to occur among the people impacted by the planned
changes.
New information system software provides businesses with new tools to support process
redesign. Work flow management offers the opportunity to streamline procedures for
companies whose primary business was traditionally focused on processing paperwork.
Instead of multiple people handling a single customer in serial fashion, work flow
management software speeds up the process, by allowing several people to work on the
electronic form of the document at the same time, and it can also decrease the total number of
people who handle it.
160
Process Improvement
While business process re-engineering might be a once off effort that focuses on processes
that need radical change, organisations have many business processes that must be constantly
revised to keep the business competitive. Business process management and quality
improvement programs provide opportunities for more incremental and ongoing types of
business process change.
Business Process Management (BPM)
Business Process Management (BPM) is an effort to help organisation manage process
change that are required in many areas of the business. Business process management (BPM)
involves analysing every task in a business and helping firms continually optimise them.
BPM includes work flow management, business process modelling, quality management,
change management and standardising processes throughout the organisation. Every business
should continually analyse how they accomplish each task and look for possible ways to
improve them.
Total Quality Management
In addition to business process management, Total Quality Management (TQM) is used to
make a series of continuous improvements rather than dramatic bursts of change. Many
organisations are using TQM to make quality control the responsibility of all the people and
functions within the organisation. Traditionally quality was the responsibility of the quality
control department, whose job was to identify and remove mistakes after they had occurred.
However trying to control mistakes after they had occurred is very difficult, as many quality
defects are embedded in the finished product and are essentially hidden, making them more
difficult to discover. Despite an organisations best efforts certain mistakes remained hidden
and undetected. The Total Quality Management (TQM) approach emphasised preventing
mistakes rather than finding and correcting them. To achieve this goal the responsibility for
quality is moved from the quality control department to everyone in the organisation.
Deming and Juran who are considered to be the fathers of TQM were both Americans but it
was the Japanese in the 1950s that embraced their ideas. Deming’s view was that by
improving quality, costs would be reduced due to less reworking, fewer mistakes, fewer
delays and better use of time. He believed this approach would lead to greater productivity
and enable the company to gain a larger share of the market because of lower costs and
higher quality. As maintaining quality became embedded in the organisation over time it
would cost less.
The successful application of the TQM concepts by Japanese companies in the 1970s and
there subsequent success in world markets led to organisations across the world taking on
board total quality initiatives in an attempt to cope with increased competition.
TQM is an all-encompassing approach to managing quality where the organisation tries to
achieve total quality products/services through the involvement of the entire organisation,
with customer satisfaction as the driving force.
161
Six Sigma
Six Sigma is another improvement approach that stresses quality by designating a set of
methodologies and technologies for improving quality and reducing costs.
Six Sigma is a set of practices originally developed by Motorola to systematically improve
processes by eliminating defects. A defect is defined as nonconformity of a product or service
to its specifications.
While the particulars of the methodology were originally formulated by Bill Smith at
Motorola in 1986, Six Sigma was heavily inspired by six preceding decades of quality
improvement methodologies such as quality control, TQM, and Zero Defects. Like its
predecessors, Six Sigma asserts the following:
• Continuous efforts to reduce variation in process outputs is fundamental to
business success
• Manufacturing and business processes can be measured, analysed, improved and
controlled
• Succeeding at achieving sustained quality improvement requires commitment
from the entire organisation, particularly from top-level management
The term "Six Sigma" refers to the ability of highly capable processes to produce output
within specification. In particular, processes that operate with Six Sigma quality produce
products with defect levels below 3.4 defects per (one) million opportunities (DPMO). Six
Sigma's implicit goal is to improve all processes to this level of quality or better.
The basic methodology consists of the following five steps:
• Define the process improvement goals that are consistent with customer demands
and business strategy.
• Measure the current process and use this for future comparison.
• Analyse to verify relationship between factors. Determine what the relationship is
and attempt to ensure that all factors have been considered.
• Improve or optimise the process based upon the earlier analysis. In this phase,
project teams seek the optimal solution and develop and test a plan of action for
implementing and confirming the solution.
• Control to ensure that any variances are corrected before they result in defects.
Set up pilot runs to establish process capability, move to full production and
continuously measure the process.
Benchmarking
Benchmarking involves setting strict standards for products, services and other activities and
then measuring performance against those standards. Companies may use external industry
standards, standards set by competitors, internally generated standards or a combination of all
three.
162
B. SYSTEM DEVELOPMENT
The set of activities that are involved in producing an information system are called system
development. The activities involved in system development include:
• System Investigation (including feasibility study)
• Systems analysis
• Systems design
• Programming
• Testing
• Implementation (including conversion or changeover)
• Production and maintenance.
This phased approach to system development is referred to as the System Development Life
Cycle (SDLC). A number of alternative software development approaches are described later
in this chapter.
Note: The number of steps in traditional systems development might vary from one company
to the next but most approaches have five common steps or phases: investigation, analysis,
design, programming/testing, implementation and lastly maintenance and review.
System Investigation
The system investigation (sometimes referred to as system definition) is the first stage of
SDLC. At this stage the business problem (or business opportunity) is investigated to define
the problem, to identify why a new system is need and to define the objectives of the
proposed system. The problem may relate to an existing system that is not able to handle the
workload, is not working properly or is not capable of handling some new product or service.
The system investigation stage will look at the feasibility of a system solution to the business
problem.
Feasibility Study
The systems investigation stage would include a feasibility study to determine whether the
proposed solution is feasible or not. The feasibility is assessed from a number of
perspectives:
• Financial feasibility: This involves investigating the costs and benefits of the proposed
system. The aim is to establish whether or not the proposed system is a good investment
and if the organisation can afford the expense. A number of different methods can be used
to assess the cost-benefit of the different system proposals. The methods include break-
even analysis, return on investment calculations or time value of money calculations.
Each method involves calculating the total tangible costs and benefits of a new system.
Typical costs include development, new hardware and training. Typical benefits include
savings from improved efficiency, improved stock control and reduced staffing costs. It
may also be necessary to establish intangible costs and benefits. Even though these can be
difficult to estimate, they can be important indicators of a system’s feasibility. An
example of an intangible costs might be the disruption to the organisation during and for a
163
short time after the implementing of a new ERP system, while an improved image of the
company as a result of launching a new e-commerce site could be an intangible benefit
• Technical feasibility: This relates to the ability of the organisation to construct and
implement the particular system in terms of expertise and knowledge of the technology
involved. It is important to assess the IT departments’ experience and skills in relation to
systems development and the software and hardware being used. Questions to be
addressed include; is the technology needed by the system available and does the
organisational have the expertise available to handle such technology.
• Organisational feasibility: This involves investigating how the new system or changes
to the existing system will support the current and future business strategy, plans and
objectives.
• Operational feasibility: This involves examining the ability of the organisation to accept
and use the new system. The issues that should be examined under operational feasibility
include company culture and workforce skill and possible existing agreements with
unions that could be impacted upon.
• Schedule feasibility: This looks at the time frame of the proposed development. For example
is there a critical date that needs to be met for the systems implementation and can it be
realistically achieved.
Typically several alternative solutions will be investigated. The feasibility of each solution is
assessed and a report is written identifying the costs and benefits and advantages and
disadvantages of each. It is then up to management or a steering group to determine which
proposed solution represents the best alternative. A typical feasibility report might contain the
following:
• Project background and objectives of the proposed system
• A description of the current system and problems experienced with it
• An outline of a number of possible solutions and an evaluation of the feasibility of each
• A recommendation for a particular solution.
After the feasibility report is presented to the steering committee or senior management (if no
steering committee exists) then a decision is made on whether or not to proceed with the
system development project. If the decision is to proceed then the systems analysis phase
begins.
System Analysis
Once the system development has been approved then the systems analysis stage can begin.
Systems analysis is the examination of the problem that the organisation is trying to solve
with an information system. This stage involves defining the problem in more detail,
identifying its causes, specifying solutions, and identifying the information requirements that
must be satisfied by a system solution.
To understand the business problem the analysis must gain an understanding of the various
processes. The analyst examines documents and procedures, observes end users operating the
system and interviews key users of the existing systems to identify the problem areas and
objectives the solution should aim to achieve. The solution could involve building a new
information system or making changes to an existing system.
164
Capturing Information Requirements
Information requirements capture involves identifying what information is needed, who
needs it, where, when and in what formats. The requirements define the objectives of the new
or modified system and contain a detailed description of the functions the new system must
perform. Gathering information requirements is a difficult task of the systems analyst and
faulty requirements capture and analysis can lead to system failure and high systems
development costs as major changes may be needed to the systems after implementation.
Information requirements are difficult to determine because business functions can be very
complex and are often poorly defined. Processes may vary from individual to individual, and
users may even disagree on what the process is or how things should be done. Defining
information requirements is a demanding job that can require a large amount of research by
the analyst. A number of tools are used by the analyst to document the existing and proposed
systems including Data Flow Diagrams (DFDs).
System Analysis Tools
DATA FLOW DIAGRAMS (DFD’S)
A data flow diagram (DFD) is a graphical method of showing the flow of data through a
system (see Figure 12.1). It is used to show processes and data flows. Although data flow
diagrams can be used in the design process, they are also useful during the analysis phased to
enable users and analysts to gain a shared understanding of the system. Data flow diagrams
enable the systems analyst to document systems using what is referred to as a structured
approach to systems development. Only four symbols are needed for data flow diagrams:
entity, process, data flow and data storage.
• Entity Symbol: This is the source or destination of a data or information flow. An entity
can be a person, a group of people or even a place.
• Process Symbol: Each process symbol contains a description of a function to be
performed. Typical processes include Enter Data, Verify Data and Update Record.
• Data Flow: The flow line indicates the flow of data or information.
• Data Store: These symbols identify storage locations for data, which could be a file or
database.
Because the notation is simple, users easily understand it. Users can check the DFDs for
problems or inaccuracies so that they can be changed before other design work begins.
Data flow diagrams allow the analyst to examine the data that enters a process and the data
that leaves the process and to see how it has been changed. This can help the analyst gain a
fuller understanding of the process.
Data flow diagrams are part of the system documentation. They show the logical view of the
system. They show what is happening, not how that event occurs.
Data flow diagrams describe the system in a top-down approach. High-level DFDs can be
drawn to give a high-level, summarised view of the system. More detailed DFDs can be
drawn for particular parts of the system, where more detail is required.
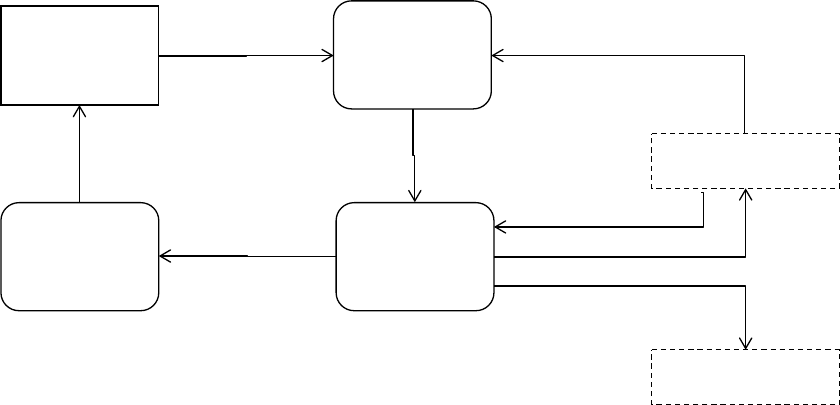
165
Figure 12.1: A Data Flow Diagram example of College Registration System. Adapted from
Laudon & Laudon. 2010
The advantage of using data flow diagrams is that they can be used to show a very general,
high-level view of the system or a very detailed view of a part of the system using the same
tools. Anyone can view the overall system and then drill down through the DFD diagrams to
lower levels of the system.
DECISION TABLES
A decision table is a tabular format for recording logical decisions that involves specifying a
set of conditions and the corresponding actions. Decision tables are useful in cases that
involve a series of interrelated decisions as they help to ensure that no alternatives are
overlooked. A decision table can provide a greater level of detail about a process that using a
process diagram on its own.
DECISION TREES
A decision tree is an alternative approach for analysing decisions whereby decision options
are represented as branches on a tree-like diagram. They are particularly usefully where a lot
of complex decision choices needs to be taken into account. They provide an effective
structure in which alternative decisions and the implications of taking those decisions can be
represented. Decision trees can be used to define what the decisions are, their sequence and
outcomes.
Systems Design
The purpose of the systems design phase is to show how the system will fulfil the information
requirements specified in the system analysis phase. The system designer draws up
specifications that will deliver the functionality identified during the systems analysis phase.
The systems design specification should contain details of system inputs, outputs and
interfaces. It should also contain specifications for hardware, software, databases,
telecommunications, networks, processes and people.
Course details
Student file
Check
Course
Availability
Enrol
Student
Confirm
Student
Registration
Course file
Available
courses
Enrolment details
Student details
Student
Confirmation
notification
Registration details
Course
Acceptance
166
Walkthrough
A walkthrough is a review by a small group of people of a system development project
usually presented by the creator of the document or item being reviewed. Walkthroughs can
be used to review a data-flow diagram, a structure chart, form designs, systems screens etc.
Walkthroughs generally include specification walkthroughs, design walkthroughs and test
walkthroughs.
Logical design
This involves laying out the parts of the system and their relationship to each other as they
would appear to users. The emphasis on what the system will provide in terms of
functionality rather than how the system will be implemented physically. The logical design
will include inputs, outputs, processing, controls etc.
Physical Design
The physical system design specifies how the system will perform its functions and will
include physical specifications such as design of hardware (computers, routers etc),
telecommunications, etc.
Data Driven and Process Driven Development
The term process-driven refers to an emphasis on the functions or activities of an enterprise
that the system is being designed for. By improving how a process is performed, it is hoped
that the system becomes more efficient. Techniques used in such a methodology concentrate
on describing the processes and the input-output flows. The processes are mapped using
process flow diagrams to gain a full understanding of the process. During the design phase
the process is changed to take advantage of the system functionality being developed.
Data-driven development focuses on modelling the data in a system because data is less
likely to change than processes. Data-driven methodologies describe the system in terms of
entities, attributes and relationships. Entities are things of interest to the system in the real
world, such as customers, products etc. Attributes are properties that describe the entity such
as customer name, address or product description. Relationships are ways that the entities
interact. Techniques used here are similar to those used in entity-relationship modelling
(discussed in Chapter 6). Data-driven development techniques are often associated with the
development of database systems.
Programming
Programming translates the design specification into software (program code) that provides
instructions for the computer. Many organisations no longer do their own programming but
instead outsource the building of the systems to an external software development company.
They also have the option to purchase of-the-shelf software applications that meets their
specific requirements from an external software vendor.
167
Testing
Testing is critical to the success of a system because it checks that the system will produce
the expected results under specific conditions. The testing will find any errors (bugs) in the
computer code. Comprehensive testing can be a time consuming and expensive process.
However the cost of implementing a system with underlying errors could be far greater for
the organisation. There are normally three stages of information system testing: unit testing,
system testing and acceptance testing.
• Unit testing (program testing) involves testing the smallest piece of testable software in
the application, usually the individual programs. The purpose of this testing is to locate
errors in the code so that they can be corrected. Unit testing is normally carried out by the
programmers.
• System testing which is normally carried out on a complete integrate system, involves
testing the functionality of the information system as a whole to determine whether
program modules are interacting as planned and to establish that the system meets its
specified requirements.
• Acceptance testing is normally the final stage of testing performed on a system. Its
purpose is to establish that the requirements defined in the analysis and design stages
have been met. Acceptance testing is normally carried out by the end users of the system.
Other types of testing include Regression testing which is normally carried out after changes
have been made to existing code. The aim of regression testing is to determine whether the
changes made to the code interfere with anything that worked prior to the change.
Performance testing is testing executed to determine how a system performs in terms of
responsiveness and consistency under a particular load.
Test Plan
Before testing is carried out a test plan must be created. The test plan details the approach that
will be used to ensure that the system meets its design specifications and requirements for the
tests to be carried out. A set of tests will be prepared which are generally derived for the
requirements. This approach to testing is called requirements-based testing. The individuals
who will carry out the testing must also be decided.
As the testing progresses, the testers formally document the results of each test, and provide
error (defect) reports to the system developers. The developers correct the defects and the
systems are re-tested.
Implementation
As part of the system implementation phase new hardware may need to be acquired and if not
already developed in house software will also need to be acquired. A critical part of the
implementation phase is the data conversion or changeover.
System conversion or changeover is the process involved in changing from the old system to
the new system. There are four main approaches to conversion: parallel running, direct
cutover, the pilot study and phased approach.
• Direct Cutover: The direct cutover or Big Bang approach involves fully replacing the old
system with a new system in one move. This is generally the fastest and cheapest method
of conversion, and in many situations it may be the only practical approach. However it is
168
also the most risky method as there is no fallback if a serious problem is discovered with
the new system after it has gone live.
• Parallel Running: The parallel approach involves running the old system and the new
system together for a period until there is reassurance that the new system is operating
correctly. This is the safest approach because if serious errors are discovered in the new
system, users can revert back to the old system until the problems are resolved. However
this approach is very expensive in terms of effort and resources required to update two
systems at the same time with every transaction.
• Pilot Study: The pilot study involves the new system going live in one location only or
within just one part of the organisation initially. When the system is working correctly in
the pilot area, it is then rolled out to the remainder of the organisation. In many cases this
is not a practical approach as the new system must go live across the whole organisation
simultaneously.
• Phased Approach: The phased approach introduces the new system in stages which could
be one module at a time or part of the functionality in stages. This approach reduces the
risk inherent in a direct changeover of the full system in one go.
Before the new system is implemented, end users are normally trained to use the new system.
Documentation must be prepared on the operation and use of the new system and this will be
used during training and in normal operations. Inadequate training and poor or non-existent
documentation can be major factors in contributing to system failure.
Production and Maintenance
Production is the operation of the system after it has been implemented and the conversion is
totally finished. During production the system will be reviewed by both users and IT
specialists to determine how well it has fulfilled the original requirements, if there are any
bugs in the systems, and to decide whether any changes are needed. A formal post
implementation review may be carried out.
Maintenance is the carrying out of modifications to a production system to correct errors,
meet new requirements, and improve efficiency of the system. The quality of the systems
analysis and design and testing phases will impact the level of system maintenance required.
For example if the requirement are not fully captured or understood at the analysis stage, then
the resulting system will not meet user requirement and may need significant changes during
the maintenance phase.
Modelling and Designing Systems – Structured and Object-Oriented Approaches
There are a number of alternative methodologies for modelling and designing systems. Some
such as data flow diagrams have already been described. Structured methodologies and object
oriented development are two common methods.
Structured Methodologies
Structured methods are generally step by step, with each step building on the previous one.
Traditionally, systems have been structured in an organised way. The methods used design
and build systems begins at the top and then moving on to the lower levels of detail, always
ensuring that the data and processes were kept separate. The designers can use data flow
169
diagrams (DFDs) to model how the data moves through the system and the relationships
between the processes. Data flow diagrams (DFD) are discussed earlier in this chapter.
Two other structured methodologies are process specifications and structure charts. The aim
of process specifications is to describe the processes within the data flow diagrams. They
detail the logic for each process. The structure chart shows each level of design in a top-
down approach; its relationship to the other levels and its place in the overall design of the
system. The structured design approach first looks at the main function of a system and then
splits this function into sub-functions. It then further breaks each sub-function down until the
lowest level of detail has been reached.
The Object-Oriented Approach to System Development
The traditional structured methodology focuses on what the new system is intended to do and
then develops the procedures and data to do it. Object-oriented development de-emphasises
system procedures and instead creates a model of a system composed of individual objects
that combine data and procedures. The objects are independent of any specific system. These
objects can then be placed into any system being built that needs to make use of the data and
functions. In addition, in traditional structured methodologies all work is done serially, with
work on each phase beginning only when the previous phase is completed. Object-oriented
development theoretically allows simultaneous work on design and programming. These
systems usually are easier to build and more flexible. Moreover, any objects created this way
are reusable for other programs.
Computer Aide Software Engineering (CASE)
Computer-Aided Software Engineering is a development approach that provides tools to
automate many of the tasks involved in software development. It includes software tools to
assist in systems planning, analysis, designing, programming testing, operation and
maintenance. In fact CASE tools can help automate the later stages of the SDLC –
programming, testing and operation. For example if data flow diagrams were produced and
stored within the CASE tools along with a data dictionary (data definitions) the CASE tools
could be used to automatically create the program code.
Case tools can provide a number of advantages in system development, such as speed up the
development process, help the analyst create a full set of requirements specifications, help
produce systems that better match user requirements and ensure system documentation is
provided.
C. ALTERNATIVE APPROACHES TO DEVELOPING AND
ACQUIRING SYSTEMS
A number of different system-building approaches have been developed. The organisation
also has the option of outsourcing, developing or purchasing ready-made application software
packages.
This section describes the following approaches:
• Traditional Systems Life Cycle
• Prototyping
• End-User Development
170
• Application Software Packages
• Outsourcing
Traditional Systems Life Cycle
The traditional systems life cycle (also referred to as the system development lifecycle
(SDLC)) is a formal methodology for managing the development of systems and is still the
primary methodology for medium and large projects. The overall development process is
divided into distinct stages or phases. The stages are usually gone through sequentially with
formal “sign-off” agreements among end users and the system specialists at the end of each
stage. This ensures that each stage has been completed. The approach is slow, expensive,
inflexible and may not be appropriate for many small systems.
The systems life cycle consists of systems analysis, systems design, programming, testing,
conversion, and production and maintenance. These stages are outlined earlier in this chapter.
Advantages of the SDLC Approach
The advantages of using this method for building information systems include; it is highly
structured and brings a formality to requirements collection and specifications of the system.
It is suitable for building large complex systems and where tight control of the development
process is required.
Disadvantages of the SDLC Approach
The disadvantages include; it is very costly and time consuming, it is inflexible and
discourages change to the requirements during the latter stages of the cycle. It is not suited to
situations where requirements are difficult to define.
Prototyping
Information system prototyping is an interactive system design methodology that builds a
model prototype of a system as a means of determining information requirements.
Prototyping involves defining an initial set of user requirements and building a prototype
system; then improving upon the system in a series of iterations based on feedback from the
end users. An initial model of a system or important parts of the system is built rapidly for
users to experiment with. The prototype is modified and refined until it conforms precisely to
what users want. Information requirements and design are determined as users interact with
and assess the prototype.
The steps in prototyping include identifying the users basic requirements; developing a
working prototype of the system outlined in the basic requirements, using the prototype, and
revising and enhancing the prototype based on the user’s feedback. Laudon and Laudon
(2010) suggest a four step prototyping process, where the steps are repeated many times if
necessary. The steps in prototyping are summarised as follows:
Step 1: Identify the user’s basic requirements.
Step 2: Develop an initial prototype.
Step 3 Use the prototype.
Step 4: Revise and enhance the prototype.
171
The users check that the prototype meets their needs. If it does not meet their needs the
prototype is revised. The third and fourth steps are repeated until users are satisfied with the
prototype. The process of repeating the steps to build a system over and over again is referred
to as an iterative process. Prototyping is best suited for smaller applications. Large systems
with complex processing may only be able to have limited features prototyped such as screen
inputs and outputs.
Benefits of Prototyping
• Prototyping is very useful for determining unclear requirements and where the design
solution is unclear.
• Prototyping is especially helpful for designing end-user interfaces (screens and
reports).
• End user involvement in the development process means that the systems are more
likely to meet end user requirements.
• Prototyping can help reduce development costs by capturing requirements more
accurately at an earlier stage in the development process.
Limitations of Prototyping
• Because prototypes can be built rapidly, documentation and testing may be minimal
or not completed.
• It can result in poorly designed systems that are not scalable to handle large data
volumes.
• Prototyping can result in a large number of iterations that can end up consuming the
time that it was supposed to save.
• Problem can also arise when the prototype is adopted as the production version of the
system.
End-User Development
End-user development refers to the development of information systems by end users without
involvement of systems analysts or programmers. End user can utilise a number of user-
friendly software tools to create basic but functional systems. Key tools used in end-user
development include fourth generation languages.
FOURTH-GENERATION LANGUAGES
Fourth-generation languages (4GLs) are sophisticated languages, which enable end-users to
perform programming tasks with little or no professional programmer assistance. They can
also be used by professional programmers. The 4GLs are essentially shorthand programming
languages that simplify the task writing programs typically reducing the amount of code
required in a program over what would be needed if a third-generation language was used.
Laudon & Laudon (2010) identifies a number of categories of fourth-generation language
tools which are:
172
• Query languages: This is a high-level language that is used to retrieve data from
database and file. It can be used for ad-hoc queering for information.
• Report generators: These enable the extracting data from files or databases to create
reports.
• Graphics languages: These are used to display data from files or databases in
graphic format.
• Application generators: These are modules that can be used to generate
programming code for input, processing, update and reporting once the users provide
specifications for an application.
• Very high-level programming languages: These can be used to perform coding with
far fewer instructions than conventional programming languages.
• General purpose software tools: These include software packages such as word
processing, data management, graphics, desktop publishing and spreadsheet software
that can be utilised by end user developers to build basic systems.
Benefits of End-user Developments
The benefits of end user development include:
• Delivery of systems quickly and overcoming backlog in formal system development
• User requirement are better understood
• It is suited to developing low-transaction systems
• Lower cost development option.
Limitations of End-user Developments
The limitations of end user development include:
• Not suited to large complex systems
• Quality and testing standards are not always followed
• Poor documentation
• Can lead to data duplication and uncontrolled data
• System security is often poor or non existent
• Systems may lack basic data backup recovery capabilities
• These systems are not scalable and can suffer from poor performance as number of
users or transactions grows.
Application Software Packages
An application software package is a set of prewritten, pre-coded application software
programs that are available for sale or lease. Packages range from very simple programs to
very large and complex systems such as ERP systems. Packages are normally used when
functions are common to many companies and when resources for in-house development are
not available. Examples of application packages include payroll packages, accounting
packages, inventory control applications and supply chain applications.
173
Advantages of Software Packages
Software packages provide several advantages:
• They are generally available for use straight away
• Programs are pre-tested and will generally have few errors, cutting down testing time and
technical problems
• They are generally established, well-proven products that incorporate best practices
• The applications will have documentation and the vendor will normally provide training
for the application
• The vendor often installs or assists in the installation of the package
• Periodic enhancement or updates are supplied by the vendor
• The vendors have support staff which reduces the need for individual organisations to
have in-house expertise
• Packages are generally cheaper for the organisation than developing custom-built systems
Disadvantages of Software Packages
There are a number of disadvantages associated with software packages:
• There can be high conversion costs when moving from a custom legacy system to an off-
shelf application package.
• They are not always an optimal solution and as a result packages may require widespread
and expensive customisation to meet unique requirements
• Customisation is possible but can be costly, time-consuming and risky
Outsourcing
Outsourcing of information systems is the process of subcontracting the development and
sometimes the operation of information systems to a third party company who provide these
services. The work is done by the vendor rather than the organisation’s internal information
systems staff. Outsourcing is an option often considered when the cost of information
systems technology has risen too high. Outsourcing is seen as a way to control costs or to
develop applications when the firm lacks its own technology resources to do this work.
Benefits of Outsourcing
Organisations can realise the following benefits from outsourcing:
• Cost savings: Outsourcing can lower the overall cost of the service to the business.
Increasingly using outsourcing to low cost economies through off-shore outsourcing.
• Improve quality: By contracting out the development to specialist developer the quality
of the systems is improved.
• Knowledge: Outsourcing provides access to wider experience and knowledge.
• Contract: Services will be provided to a legally binding contract with financial penalties
and legal redress. This is not the case with internal services.
174
• Operational expertise: Access to operational best practice.
• Staffing issues: Outsourcing provides access to a larger talent pool in a cost effect way as
the capacity management becomes the responsibility of the supplier and the cost of any
excess capacity is borne by them.
• Catalyst for change: An organisation can use an outsourcing agreement as a catalyst for
change that it would not achieve on its own. It can bring new innovations that will drive
change in organisations.
• Reduce time to market: The speeding of system development that are required to
support new product and service can reduce the time for these products and services.
• Risk management: By working closely with the outsourcer on risk management many
types of risks can be lessened.
• Time zone: In the case of off-shore outsourcing work can be done in different time zones
thus speeding up the development process and keeping costs down.
Risks Associated with Outsourcing of Application Systems Development
There are a number of risks associated with outsourcing which must be understood and
evaluated to establish if outsourcing is appropriate in the particular situation. The risks
include:
• Many companies underestimate the costs associated with outsourcing.
• Outsourcing introduces new demands and costs such as RFI costs, travel expenses,
negotiating contracts and project management.
• Issues can arise if the vendor doesn’t fully understand the business.
• Offshore outsourcing can introduce issues related to cultural differences.
• If requirements are not fully documented or understood, this can lead to substantial
costs if changes are needed late in the development project.
• There is also the potential risk of the vendor going out of business at some stage after
the application is in operation, leaving the application unsupported.
Factors that Influence which Development Approach to Adopt
The approach that is adopted to develop the system will depend on certain factors. Some
examples of these factors are:
Knowledge and experience of the developers
If the analysts and designers have a good knowledge of the business sector in which the
system is being implemented they will be in a better position to adopt the traditional (SDLC)
approach. The input of users in this case is less critical that in a situation where the analysts
and designers are unfamiliar with the business.
Nature of system being developed
Large and complex systems may require the iterative approach that prototyping uses to
gradually extract and refine requirements. However large and complex systems also require
175
tight control of the development process which would favour the use of the SDLC.
Prototyping may be suitable for parts of the systems stuck at the user interface.
Clarity of the system requirements
If requirements are clear, well defined and understood then there is less scope for
misunderstanding. Therefore the traditional approach may be suitable. If requirements are
vague and unclear then the prototyping approach is more suitable as it ensures that the system
requirements are clearly understood and the system is developed to meet these requirements.
Experience of the user community
If users are experienced with computer systems they may be able to identify and express
requirements more clearly, thus allowing the traditional approach or end-user development
approaches to be used. If users are inexperienced with computer systems, it is sensible to
show users a version of the system as early as possible in the development process to aid the
understanding of requirements. Prototyping is therefore suitable for inexperienced users.
Timescale involved
Prototyping can be used in development projects with short timescales. If managed correctly,
prototyping can help to ensure speedy system development. If the timescale is short,
prototyping may be more suitable than the traditional approach. However if not tightly
managed prototyping can also lead to overruns as it can get bogged down in cycles of review
and changes. If the user is concerned about overruns then the traditional approach may be
better.
D. CONTEMPORARY APPROACHES TO APPLICATION
DEVELOPMENT
In the digital environment where the digital firm operates, organisations need to be able to
change their technology capability very quickly to respond to new threats and opportunities.
Companies are using shorter more informal development processes for many of their e-
commerce and e-business applications. A number of techniques can be used to speed up the
development process. These include joint application development (JAD), prototyping
techniques such as rapid application development (RAD) and reusable standardised software
components.
Joint Application Development (JAD)
This is an alternative approach to identifying and specifying requirements that was developed
in the late 1970s. The JAD approach is a collaborative method that involves bringing together
key users, managers and systems analysts for group sessions. Requirements are collected
from a number of key people, at the same time allowing the analyst to see areas where there
is agreement around requirements and areas of difference. JAD sessions are usually
conducted away from where people normally work in specially designed conference rooms
that are suitably equipped. The typical participants include:
• A JAD Session Leader
• Operational Level Users
• Managerial Level Users
176
• Systems Analysts
• Secretary - takes noted and records decisions
• Sponsor - A JAD sponsor would typically be a senior manager to highlight its importance
When probably managed and planned, JADF sessions can speed up the analysis and design
phases of a system development project.
Rapid Application Development (RAD)
Rapid Application Development (RAD) is an iterative approach to application development
similar to prototyping. Capturing requirements, analysis, design and the building of system
itself are developed in a sequence of refinements. The RAD approach was developed initially
by James Martin in 1991.
The developers enhance and extend the initial version through multiple iterations until it is
suitable for operational use. Unlike prototyping, RAD produces functional components of a
final system rather than a limited scale version.
One of the big advantages of RAD is that it reduces the time it takes to build systems. Like
other methods RAD does have disadvantages. The method’s speeded-up approach to systems
analysis and design may result in systems with limited functionality and flexibility for change
and often suffer quality issues.
Component-based Development and Web Services
Component-based development is a practice of developing reusable components that are
commonly found in many software programs. For example, the graphic user interface can be
created just once and then used in several applications or several parts of the same
application. This approach saves development time and also creates functions that users have
to learn only once and use multiple times.
Web services are reusable software components that enable one application to communicate
with another (share data and services) without the need for custom program code. In addition
to supporting the integration of systems, Web services can be used to build new information
system applications. Web services create software components that are deliverable over the
Internet and can be used to link an organisation's systems to those of another organisation.
E. MANAGEMENT CHALLENGES
Challenges
Businesses today are required to build applications very quickly if they are to remain
competitive. This is particularly true in relation to e-commerce and e-business applications.
The new systems are more likely to be integrated with systems belonging to suppliers,
customers and business partners.
Possible Solutions
Companies are turning to rapid application design, joint application design (JAD), and
reusable software components to improve the systems development processes. Rapid
application development (RAD) uses object-oriented software, prototyping, and fourth-
177
generation tools for quick creation of systems. Component-based development speeds up
application development by providing software components that can be combined (and
reused) to create large business applications.
Web services delivered over the Internet can by utilised for building new systems or
integrating existing systems. Web services enable organisations to link their systems together
independent of the technology platform the individual systems were created on.

178
Study Unit 13
Business Value of Systems and Managing Change
Contents
A.
Importance of Project management
B.
Selecting Projects
C.
Establishing the Business Value of Information Systems
D.
Change Management
E.
Management Challenges
F.
Information Systems Problem Areas
179
Introduction
In the previous chapter we discussed building information systems. In this chapter looks at
what is involved in managing an entire information system project to make sure a company
realises the intended benefits from its investment. Management need to ensure that the system
solves problems for the organisation rather than create new ones.
The objectives of this chapter are to:
• Explain the management of information system projects
• Describe how information system projects are selected for development
• Explain how the business value of Information Systems is established
• Explain the importance of change management when implementing systems
• Identify the problem areas in system development and implementation
A. IMPORTANCE OF PROJECT MANAGEMENT
Whether the project entails building a new information system or enhancing an existing
system, it is important to be able to measure the business benefits of these investments and
make sure that these systems will work successfully in your organisation. The success of any
project will depend on how well it is managed.
Poor Project Management
Only about a third of all technology investment projects are completed on time, on budget,
and with all features and functions originally specified, with another third of all software
projects far exceeding schedules and budgets.
A systems development project without proper management will most likely suffer the
following consequences:
• Costs that significantly exceed budgets
• Unexpected time slippage
• Technical performance that is less than expected
• Failure to obtain anticipated benefits
Other types of project failings include:
• Systems not being used as intended
• Failure to deliver business requirements
• Poor user interface
• Poor data quality
Without proper management, a systems development project takes longer to complete and
will likely exceed the allocated budget.
180
Project Management Objectives
A project is a planned series of related activities for achieving specific business objectives.
Project management refers to the application of knowledge, skills, tools and techniques to
achieve specific targets within specified budget and time constraints.
Project management activities include:
• Planning the work
• Assessing risk
• Estimating resources required to accomplish the work
• Organising the work
• Acquiring human and material resources
• Assigning tasks
• Directing activities
• Controlling project execution
• Reporting progress
• Analysing the results.
Good project management is essential for ensuring that systems are delivered on time, on
budget and provide real business benefits.
Project management for information systems must deals with five major variables:
• Scope: This defines what work is and is not included in a project
• Time: The amount of time required to complete the project
• Cost: This depends on the time to complete a project and the cost of human and other
resources required
• Quality: This relates to how well the end result of a project satisfy the objectives
specified
• Risk: This refers to potential problems that may threaten the success of a project
Factors that impact Project Risk
The level of risk inherent in an information systems development project risk is influenced by
three main factors:
• Project size: The larger or more complex the project, the greater the risk and the
greater the failure rate. Large projects will require large budgets; a large project team
will be involved; an extended timeframe will be required and will likely impact on a
number of organisational units. All these factors will contribute to the level of project
risk. A further complication is that there are few reliable techniques for estimating the
181
time and cost to develop large-scale information systems, meaning that large projects
run a very high risk of going over budget and over allocated time.
• Project structure: Highly structured projects carry lower risks than those with
relatively undefined and constantly changing requirements and scope. In some
situations the requirements are difficult to tie down because the users continually
change what they want or sometimes different users cannot agree on what they want.
• Experience with technology: The less experience the project team has with the
hardware and/or software, the higher the risk of project failure.
Project Management Software Tools
Project management software tools provide support for many aspects of project management.
Project management software typically features capabilities for defining and ordering tasks,
assigning resources to tasks, establishing starting and ending dates to tasks, tracking progress,
and facilitating modifications to tasks and resources and creating Gantt and PERT charts.
Microsoft Project has become the most widely used project management software today.
PERT ANALYSIS
A PERT analysis of the tasks involved in completing a project gives an estimate of the time
needed to complete each task and calculates the minimum time required to complete the
whole project. The minimum time needed to complete the total project is calculated on the
basis of the critical path, which is the series of tasks that take the longest time to complete.
GANTT CHARTS
Gantt charts are graphical means of representing the tasks involved in a project and their
interdependencies. The Gantt chart shows at what stage in the project each task can begin and
how long it will take. Gantt charts provide a means of comparing planned performance
against actual performance.
B. SELECTING PROJECTS
Because there are far more ideas for systems projects than there are resources, it is important
to select projects that promise the greatest benefit to the business and supports the firm's
business strategy.
Management Structure for Information System Projects
In a large corporation, the management structure for information systems projects helps
ensure that the most important projects are given priority. Each level of management in the
hierarchy is responsible for specific aspects of systems projects.
At the top of the structure is the corporate strategic planning group which is responsible for
developing the organisation’s strategic plan, which may need new information systems or
changes to existing systems.
The information systems steering committee is the senior management group responsible
for systems development and operation. It is made up of managers of departments from both
182
end-user and information systems areas. The steering committee reviews and approves plans
for all systems.
The project management group is made up of information systems managers and end user
managers and is responsible for overseeing specific information systems projects and
supervising the project team.
The project teams are responsible for the individual systems project. A team is made up of
systems analysts, specialists from the relevant end user business areas, programmers and
database experts.
System Projects must be linked to Business Plans
To identify the information systems projects that will deliver the most business value,
organisations need to develop an information systems plan that supports the overall business
plan and demonstrates which strategic systems are part of high level strategic planning. The
information systems plan is a road map indicating the direction of systems development, the
logic underlying the plan, the current systems, new developments being considered, the
management strategy and the budget. Other important components of an information systems
plan include target dates and milestones. These will help evaluate the plan's future progress
and drive management decisions regarding hardware and organisational change.
Establishing Organisational Information System Requirements
Enterprise Analysis
Two approaches called enterprise analysis and critical success factors (CSF) can be used
to establish organisation-wide information systems requirements. Both approaches attempt to
gain a clear understanding of the organisations long and short-term information requirements.
Both use interviews of managers to gain an understanding of the requirements.
Enterprise analysis looks at the entire organisation in terms of organisational units,
functions, processes, and the information they use. This approach involves taking a large
sample of managers and asking them the following questions:
• How do they use information?
• Where do they get the information from?
• What are their environments like?
• What are their objectives?
• How do they make decisions?
• What are their critical information needs?
The data collected is combined to enable conclusions to be drawn about the organisation-
wide information systems requirements.
The strength of enterprise analysis is in its complete picture of the way the organisation
conducts its business. The weakness of the enterprise analysis is that it produces so much
data that it is expensive to conduct and difficult to organise and analyse. A further weakness
is that the enterprise analysis tends to look at the way existing information is used and not at
the fact that new approaches may be needed in the future.
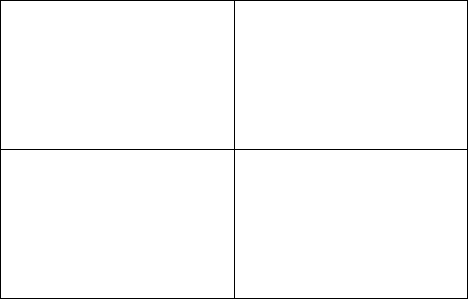
183
Critical Success Factors (CSFs)
Critical Success Factors (CSFs) are simply the goals managers feel will make the
organisation a success. The CSF approach involves interviewing a smaller number of top
managers who are asked to identify their goals and the objectives essential to those goals.
These critical success factors (CSFs) are combined to develop a picture of the overall
organisations CSFs. Systems that are needed to deliver these critical success factors are then
built.
The advantage of this method centres on the fact that the smaller sampling of data involved
makes it easier to develop an information plan. It tends to be faster than enterprise analysis
and therefore less expensive. The plan will revolve around a few CSFs instead of a large
number of information requirements.
Using the CSF method also takes into account how the external business environment affects
information needs. Usually top management are the organisational level most involved in this
type of analysis as they have a better idea of the environmental effects than lower levels of
management.
The main weakness of this method is in the process for analysing and combining the data as it
can be difficult to merge individual CSFs into a clear company blueprint. A second problem
is that there is often confusion between individual and organizational CSFs, as what can be
critical for a particular manager may not be important to the entire organisation. Finally, the
CSF approach is biased toward top managers because they are usually the only ones
interviewed.
Portfolio Analysis
This approach can be used to select and evaluate information systems investments using
strategic and other non-financial considerations. Portfolio analysis compares a portfolio of
potential projects based upon the projects expected risks and benefits. Projects are
categorised as high or low-risk and high or low-benefits. Thus, four ratings are available:
high-risk/high-benefits, high-risk/low-benefits, low-risk/high-benefits, and low-risk/low-
benefits. High-benefit/low-risk projects are generally preferred, whereas low-benefit/high-
risk projects are to be avoided. These four rating are summarise in Figure 13.1.
Figure 13.1: Portfolio analysis
Examine
(treat with caution)
Routine
Develop
Avoid
Expected Risks
Expected
Benefit
High
High Low
Low
184
Scoring Models
The scoring model is a quick method for deciding among alternative systems based on a
system of ratings for selected objectives. Criteria are listed and weighted and then alternative
projects are rated using these criteria by those involved in judging the projects. Scoring
models are meant to be relatively objective techniques, but involve many qualitative
judgments. They are used most commonly to confirm and support decisions rather than to
make decisions. The challenge with this method is on getting agreement on criteria to be used
to judge the system.
C. ESTABLISHING THE BUSINESS VALUE OF INFORMATION
SYSTEMS
It is not sufficient for a project to support strategic goals and meet user’s information
requirements; it also needs to be a good investment for the organisation. The value of systems
from a financial perspective is mainly concerned with the return on capital invested in the
system.
The Costs and Benefits of Information Systems
The benefits that can be gained from investing in information systems include both tangible
and intangible benefits. The tangible benefits of information systems can be quantified and
allocated a financial value. Intangible benefits, such as superior customer service or improved
decision making, cannot be immediately quantified but may lead to quantifiable gains in the
long run.
Total cost of ownership (TCO) is an approach designed to identify and measure all the
different pieces of information technology expenditures including those that come after the
initial costs of acquiring the hardware and software.
Capital Budgeting Models
Capital budgeting models are techniques used in assessing long-term capital investments. The
process of analysing and selecting proposals for capital expenditure is called capital
budgeting. Information systems are considered long-term capital investment projects. This
section describes six capital budgeting models. These models include:
• Payback method,
• Accounting rate of return on investment,
• Cost-benefit ratio,
• Net present value,
• Profitability index,
• Internal rate of return.
185
Payback Method
The payback method measures the time required to pay back the initial investment in the
project. This method is good for high-risk projects where useful life is difficult to know.
However, it ignores the time value of money, the cash flow after the payback period, the
disposal value and the profitability of the investment. The payback period is calculated as
follows:
Accounting Rate Of Return On Investment (ROI)
The accounting rate of return on investment (ROI) calculates the return from an investment
by adjusting the project inflows produced by the investment for depreciation. The rate of
return must equal or exceed the cost of capital in the marketplace. This model approximates
the accounting income that would be earned by the project. To calculate the ROI the average
net benefit is first calculated as follows:
The net benefit is then divided be the total initial investment to get the ROI as follows:
Cost-Benefit Ratio
The cost-benefit ratio is a method for calculating the returns from a capital expenditure by
dividing total benefits by total costs. Any value above 1.0 is a positive ratio. The method can
be used to rank several projects for comparison. The ratio can be calculated using present
values to account for the time value of money. The cost-benefit ratio is calculated as follows:
Net Present Value
Net present value is the amount of money an investment is worth, taking into account its cost,
earnings and the time value of money. By subtracting the cost of the project from the net
present value of its benefits, one can determine one measure of profitability. The present
value is first calculated using the following formula:
The net present value is then calculated as follows:
Present value of expected cash flows - Initial investment cost = Net present value
Original Investment
Annual net cash inflow
=
Number of years to pay back
Original Investment
Annual net cash inflow
=
Number of years to pay back
(Total benefits -Total cost -Depreciation)
Useful life
=
Net benefit
(Total benefits -Total cost -Depreciation)
Useful life
=
Net benefit
Net benefit
Total initial investment
=
ROI
Net benefit
Total initial investment
=
ROI
Total benefits
Total costs
=
Cost-benefit ratio
Total benefits
Total costs
=
Cost-benefit ratio
1 -(1+interest)-n
Interest =
Payment x Present value
1 -(1+interest)-n
Interest =
Payment x Present value
186
Profitability Index
The profitability index is calculated by dividing the present value of the total cash inflow by
the initial cost of the investment. The result is a profitability measure that, unlike the net
present value, can be used to compare with alternative investments. The profitability index is
calculated as follows:
Internal Rate Of Return
The internal rate of return is defined as the rate of return or profit an investment is expected
to earn taking into account the time value of money.
Real Options Pricing Models (ROPM)
Some information system projects are highly uncertain, especially investments in IT
infrastructure. While the costs of the investment can be calculated not all the benefits can be
calculated in advance because the future benefits are often unclear.
Methods such as real options pricing models (ROPM) can be applied to evaluate the
information system when the benefits cannot be easily established in advance. Real options
pricing models apply techniques used in valuing financial options to systems investments.
This approach can help managers think about the potential future benefits and value that IT
investments can generate.
An option gives the entitlement, but it does not compel one to take action at a future date. For
example a share option gives a person the right to purchase particular shares at a fixed price
on or before a specified date, but they are not obliged to purchase the shares if they don’t
want.
ROPM values information systems projects similar to stock options, where an initial
investment in information technology creates the right, (not the obligation) to gain benefits in
the future when further system developments are carried out. Management has the option in
the future not to go ahead with additional developments.
ROPM allows managers to systematically take account for the uncertainty in the value of
information technology projects over time.
The disadvantages of this model relate to the difficulties in estimating all the key elements,
such as the expected future cash flows from the investment, and changes that are likely in the
cost of implementing the technology and systems.
Limitations of financial models for establishing the value of information systems
Financial models assume all relevant alternatives have been examined, that all costs and
benefits are known and that these costs and benefits can be expressed in terms of money.
These assumptions are seldom met in reality. Only tangible benefits can be quantified and
assigned a monetary value. Intangible benefits cannot be easily quantified, but may lead to
monetary gains in the future. It should also be noted that financial models can be selectively
used to support decisions made for reasons that have nothing to do with the cost and benefits
of a system.
Present value of cash inflows
Investment
=
Profitability index
Present value of cash inflows
Investment
=
Profitability index
187
Financial models do not always express the risks and uncertainty of their own cost and
benefit estimates. They also fail to consider the fact that costs are usually incurred up-front,
while benefits tend to be realised in the future.
In addition, firms can invest in capital projects for many non-economic reasons that are not
captured by financial models. They may be undertaken to support strategic considerations or
to comply with government regulations.
Information Technology Investments and Productivity
Productivity is a measure of the firm’s efficiency in converting inputs to outputs. Many of the
studies into the relationship between IT investment and improved productivity have been
inconclusive. The term “productivity paradox” was created to describe such findings.
However, some studies have found evidence that when IT investment is complemented with
organisational and process change then productivity has indeed increased.
D. CHANGE MANAGEMENT
Change Management and Implementation
To effectively manage the organisational change surrounding the introduction of a new
information system, you must look at the implementation process. In the implementation
process, the systems analyst should act as a change agent. As well as developing technical
solutions the analyst also needs to consider the organisational structure, the relationships
between the various impacts by the new system and the business process that the new system
will support. It is highly likely that all these will need to be changed as part of the
implementation. The analyst is effectively the driver of the entire change process and is
responsible for ensuring that all parties involved accept the changes created by a new system.
The change agent communicates with users, negotiates between competing interest groups,
and ensures that the organisational changes required are achieved.
End Users Involvement
System implementation generally depends on user involvement and management support. A
high level of user involvement ensures that the system better reflects user needs, as well as
creating a positive reaction to the system by users. An important consideration is the
difference between the technical focus of the system designers and the business focus of end-
users. This can often result in a communication gap. Systems development projects run a very
high risk of failure when there is an obvious gap between users and technical specialists and
when these two groups pursue different goals.
Management Support
Commitment of management on every level in the organisation to an information system will
ensure it is viewed in a positive way by both the users and the technical specialist staff. If a
particular manager in seen to support an information systems project then their staff will also
treat it as a priority. Also management support will ensure that the information project
receives sufficient funding and resources to be successful.
188
Change Management Challenges
Implementing applications that span the enterprise (enterprise applications) usually requires
extensive organisational and business process changes and are therefore very demanding.
They often replace old technologies and legacy systems. Many are damaged by poor
implementation and change managements. These types of projects must address employee
concerns about the change, their fears and worries and the resistance that is generated.
E. INFORMATION SYSTEMS PROBLEM AREAS
An information system failure rarely means a catastrophic system failure; it usually means
that the system does not perform as expected, is not operational at a specified time or cannot
be used in the way it was intended. Therefore it is often under-utilised or not used as
intended. Users may have to develop parallel manual procedures to make the system work
properly. The major problem areas are:
• Design - the system may fail to capture essential business requirements or improve
organisational performance. Information may not be provided quickly enough to be
helpful; it may be in a poor format or it may represent a wrong piece of data. The system
may be designed with poor user interface. If the system is not compatible with the
structure, culture and goals of the organisation as a whole, it is unlikely to be a success.
• Data - the data may be inaccurate or inconsistent. The information in certain fields may
be erroneous or ambiguous. The data may not be organised properly. Information
required for a specific business function may be inaccessible because the data are
incomplete.
• Cost - some systems operate well but their implementation cost may have gone way over
budget. Other system projects may be too costly to complete. In either case, the excessive
expenditures cannot be justified by the business value of the information they provide.
• Operations – the system does not run well. Information is not available in a timely and
efficient manner. Jobs fail too often, leading to excessive reruns and late or missed
schedules for delivery of information. The response time may be too long.
Causes of Implementation of Success and Failure
System failure can be due to external or internal factors. An organisation may be faced with
external, environmental pressures that cannot be met. However in many instances, system
failure and poor implementations are caused by factors within the organisations control.
According to Laudon and Laudon (2010) implementation success or failure can be
determined by the following factors:
• The role of users in the implementation process
– End user need to be involved so the requirements are understood
– Need to address users concerns about change and also deal with resistance
• Level of management support and commitment
– Strong management support will facilitate the organisational change required
• The level of complexity and risk involved in the implementation project
– The principal risk factors include:
1. Project size;
189
2. Project structure;
3. Experience with the technology
• The quality of management of the implementation process
– Good project management is required to ensure systems are delivered:
– On time, on budget, of good quality and provided business benefits
Implementation Process Issues
In relation to information systems implementations the entire process of introducing,
building, and installing the system can be considered a complex organisational change
initiative. One of the most important determinants in a system success and failure is how the
implementation process is carried out and managed. Some of the key facets in the
implementation process are:
• Conflicts between the technical focus of information systems specialists and the
organisational or business focus of users.
• The impact of information systems on organisational structures, work groups, processes
and behaviour.
• The planning and management of systems development activities.
• The degree of user participation in the design and development process
Increasing End User Involvement Overcoming End User Resistance
Projects with little structure and many undefined requirements require heavy user
involvement at all stages and implementation activities. For example users can become active
members of the project team, take on leadership roles and take charge of installation and
training. It is important to promote cohesion and unity within the implementation team. This
is particularly important when projects involve a high level of technical complexity.
Involvement of end users in the implementation activities may not be enough to overcome
resistance to organisational change. End-user resistance to information system projects can be
reduced using following strategies:
• Promote user participation in the project to obtain commitment as well as to improve
design
• Provide user education and training
• Management pronouncement and policies, including management sponsorship of the
project
• Provide incentives for those who cooperate
• Improve user interfaces design
• Solve organisational problems prior to implementation
• Engage in process change initiative before implementation
190
F. MANAGEMENT CHALLENGES
Building successful systems is a very complex and demanding activity. It is becoming
increasingly difficult to determine the costs and benefits of systems, especially those in which
benefits are primarily intangible or those that are interrelated with other systems and projects
in the firm. Implementing large-scale systems and obtaining benefits from such investments
are especially challenging. Management solutions include developing ways of measuring
return on investments and processes to make sure information systems investments provide
business value. There is also a need for a more dynamic and rigorous approach to project
management and a greater use of project management tools.

191
Appendix 1
Contents
A.
Fair Information Practice Principles
B.
Finance and IT - a special relationship?
192
A. Fair Information Practice Principles Generally
Over the past quarter century, government agencies in the United States, Canada, and Europe
have studied the manner in which entities collect and use personal information -- their
"information practices" -- and the safeguards required to assure those practices are fair and
provide adequate privacy protection. The result has been a series of reports, guidelines, and
model codes that represent widely-accepted principles concerning fair information practices.
Common to all of these documents [hereinafter referred to as "fair information practice
codes"] are five core principles of privacy protection: (1) Notice/Awareness; (2)
Choice/Consent; (3) Access/Participation; (4) Integrity/Security; and (5)
Enforcement/Redress.
1. Notice/Awareness
The most fundamental principle is notice. Consumers should be given notice of an entity's
information practices before any personal information is collected from them. Without notice,
a consumer cannot make an informed decision as to whether and to what extent to disclose
personal information. Moreover, three of the other principles discussed below --
choice/consent, access/participation, and enforcement/redress -- are only meaningful when a
consumer has notice of an entity's policies, and his or her rights with respect thereto.
While the scope and content of notice will depend on the entity's substantive information
practices, notice of some or all of the following have been recognised as essential to ensuring
that consumers are properly informed before divulging personal information:
• identification of the entity collecting the data;
• identification of the uses to which the data will be put;
• identification of any potential recipients of the data;
• the nature of the data collected and the means by which it is collected if not obvious
(passively, by means of electronic monitoring, or actively, by asking the consumer to
provide the information);
• whether the provision of the requested data is voluntary or required, and the
consequences of a refusal to provide the requested information; and
• the steps taken by the data collector to ensure the confidentiality, integrity and quality
of the data.
Some information practice codes state that the notice should also identify any available
consumer rights, including: any choice respecting the use of the data; whether the consumer
has been given a right of access to the data; the ability of the consumer to contest
inaccuracies; the availability of redress for violations of the practice code; and how such
rights can be exercised.
In the Internet context, notice can be accomplished easily by the posting of an information
practice disclosure describing an entity's information practices on a company's site on the
Web. To be effective, such a disclosure should be clear and conspicuous, posted in a
prominent location, and readily accessible from both the site's home page and any Web page
where information is collected from the consumer. It should also be unavoidable and
understandable so that it gives consumers meaningful and effective notice of what will
happen to the personal information they are asked to divulge.
193
2. Choice/Consent
The second widely-accepted core principle of fair information practice is consumer choice or
consent. At its simplest, choice means giving consumers options as to how any personal
information collected from them may be used. Specifically, choice relates to secondary uses
of information -- i.e., uses beyond those necessary to complete the contemplated transaction.
Such secondary uses can be internal, such as placing the consumer on the collecting
company's mailing list in order to market additional products or promotions, or external, such
as the transfer of information to third parties.
Traditionally, two types of choice/consent regimes have been considered: opt-in or opt-out.
Opt-in regimes require affirmative steps by the consumer to allow the collection and/or use of
information; opt-out regimes require affirmative steps to prevent the collection and/or use of
such information. The distinction lies in the default rule when no affirmative steps are taken
by the consumer. Choice can also involve more than a binary yes/no option. Entities can, and
do, allow consumers to tailor the nature of the information they reveal and the uses to which
it will be put. Thus, for example, consumers can be provided separate choices as to whether
they wish to be on a company's general internal mailing list or a marketing list sold to third
parties. In order to be effective, any choice regime should provide a simple and easily-
accessible way for consumers to exercise their choice.
In the online environment, choice easily can be exercised by simply clicking a box on the
computer screen that indicates a user's decision with respect to the use and/or dissemination
of the information being collected. The online environment also presents new possibilities to
move beyond the opt-in/opt-out paradigm. For example, consumers could be required to
specify their preferences regarding information use before entering a Web site, thus
effectively eliminating any need for default rules.
3. Access/Participation
Access is the third core principle. It refers to an individual's ability both to access data about
him or herself -- i.e., to view the data in an entity's files -- and to contest that data's accuracy
and completeness. Both are essential to ensuring that data are accurate and complete. To be
meaningful, access must encompass timely and inexpensive access to data, a simple means
for contesting inaccurate or incomplete data, a mechanism by which the data collector can
verify the information, and the means by which corrections and/or consumer objections can
be added to the data file and sent to all data recipients.
4. Integrity/Security
The fourth widely accepted principle is that data be accurate and secure. To assure data
integrity, collectors must take reasonable steps, such as using only reputable sources of data
and cross-referencing data against multiple sources, providing consumer access to data, and
destroying untimely data or converting it to anonymous form.
Security involves both managerial and technical measures to protect against loss and the
unauthorised access, destruction, use, or disclosure of the data. Managerial measures include
internal organisational measures that limit access to data and ensure that those individuals
with access do not utilise the data for unauthorised purposes. Technical security measures to
prevent unauthorised access include encryption in the transmission and storage of data; limits
on access through use of passwords; and the storage of data on secure servers or computers
that are inaccessible by modem.
194
5. Enforcement/Redress
It is generally agreed that the core principles of privacy protection can only be effective if
there is a mechanism in place to enforce them. Absent an enforcement and redress
mechanism, a fair information practice code is merely suggestive rather than prescriptive, and
does not ensure compliance with core fair information practice principles. Among the
alternative enforcement approaches are industry self-regulation; legislation that would create
private remedies for consumers; and/or regulatory schemes enforceable through civil and
criminal sanctions.
195
B. Finance and IT - a special relationship?
Article published on the CPAI site
People often perceive the Finance and IT functions to be inseparable. Some would even say
that there is a special relationship between these two functions.
If a special relationship exists then this bond could be based on the fact that in a lot of
businesses there is a perception that every ill that could possibly befall a business is usually
the fault of IT or Finance. Of course IT and Finance have responsibilities within a business
and are at fault when some things go wrong but not everything!
Being the convenient fall guy could explain the special relationship between IT and Finance.
However a special relationship between IT and Finance also exists in the quest for successful
IT implementation in the SME.
Achieving Successful IT Implementation in the SME
An essential weapon in any business’ arsenal is information. Having the information however
is only half the battle; making proper use of it is the real challenge. If properly designed and
well implemented, Information Systems can prove an invaluable investment in the long-term
success of your business.
In common with any other production process raw material is required and in this case the
raw material is data. Information therefore, is the product of applying Information
Technology to data, which must be entered into a computer system in a consistent fashion.
Whilst this may appear to be stating the obvious, this consistency, or lack of it, is a major
reason why Information Systems implementations fail.
Critical success factors for successful IT implementations
• Systems analysis - are the requirements clearly stated?
Operating needs - Functionality required from a system?
Storage needs - Data that needs to be recorded and held in the system for future use?
Information needs - What information do you need to be available from the system?
• System development / sourcing - does it fit?
One key objective in sourcing any system is that it is compatible and will integrate
into the existing or planned operating environment.
• User commitment - are users on board?
To achieve success, it is imperative that use of any system be based on clearly defined
procedures developed in conjunction with the users and taking into account current
and future user requirements.
• Training and communication - what training is planned and when?
It is human nature to resist change and employees often fear the implications. Having
defined the changes required everyone must be kept fully informed and trained before
the changes are implemented.
• System hand over and user acceptance
196
How and when will the end of the project be identified?
This is arguably the most important phase of any project. The system must be
formally handed over to the users at the end of the implementation phase. From then
on, it is the user's responsibility to operate the system.
• Standards and Infrastructure
Ironically one of the easiest things to do on Information Systems projects is deliver
the technology. Many Information Systems projects suffer though because of the
quality and standard of the technology applied. There is no point in buying cheap and
paying later in terms of lost time for users and extra technical support costs, i.e. the
much talked about ‘Cost of Ownership’.
All personal computers are not the same. All printers are not the same. All software is
not the same, etc. Cheap technology is a major factor why IT projects fail. Computers,
which are of a suitable quality and correctly implemented, should not need constant
fixing. If you find yourself in this situation then maybe its time to seek outside help to
audit your systems and put a plan in place to rectify the root causes of the constant
fixing.
• Maintenance
Be aware of the critical parts of your system - It’s not always just the server!
Assessing the needs of your maintenance contracts is similar to assessing your
insurance needs. You are seeking to predict and minimise exposure to risk in your
business. You can get cheap insurance, which, on paper will discharge your
responsibility to carry it, but it may not deliver when you most need it. The same is
true of maintenance contracts. It is one of the hidden costs of stable computer
systems. When choosing a service partner make sure that they have the staffing levels
and skills to deliver on the commitments they make to you. Be prepared to pay
reasonable rates to get the best contract.
• Outsourcing IT
Depending on the business there may or may not need to be staff dedicated to the IT
function. One of the cardinal sins of smaller businesses is to dump the responsibility
for IT on the shoulders of the manager who finds it easiest to turn on a PC. The end
result of this is a stressed out member of staff struggling to do the job they are paid to
do combined with maintaining computer systems.
Outsourcing the technical support aspects of the computer systems is a good way of
dealing with this problem of competing priorities.
• Conclusion
Many Finance and IT people have a relationship which is based on a mutual
disrespect and would find it hard to consider the cooperation required for this special
relationship. They are wrong. By making this relationship work both parties can
achieve their objectives and make an invaluable contribution to the success of the
business, especially in the case of successful IT implementation in the SME.
197