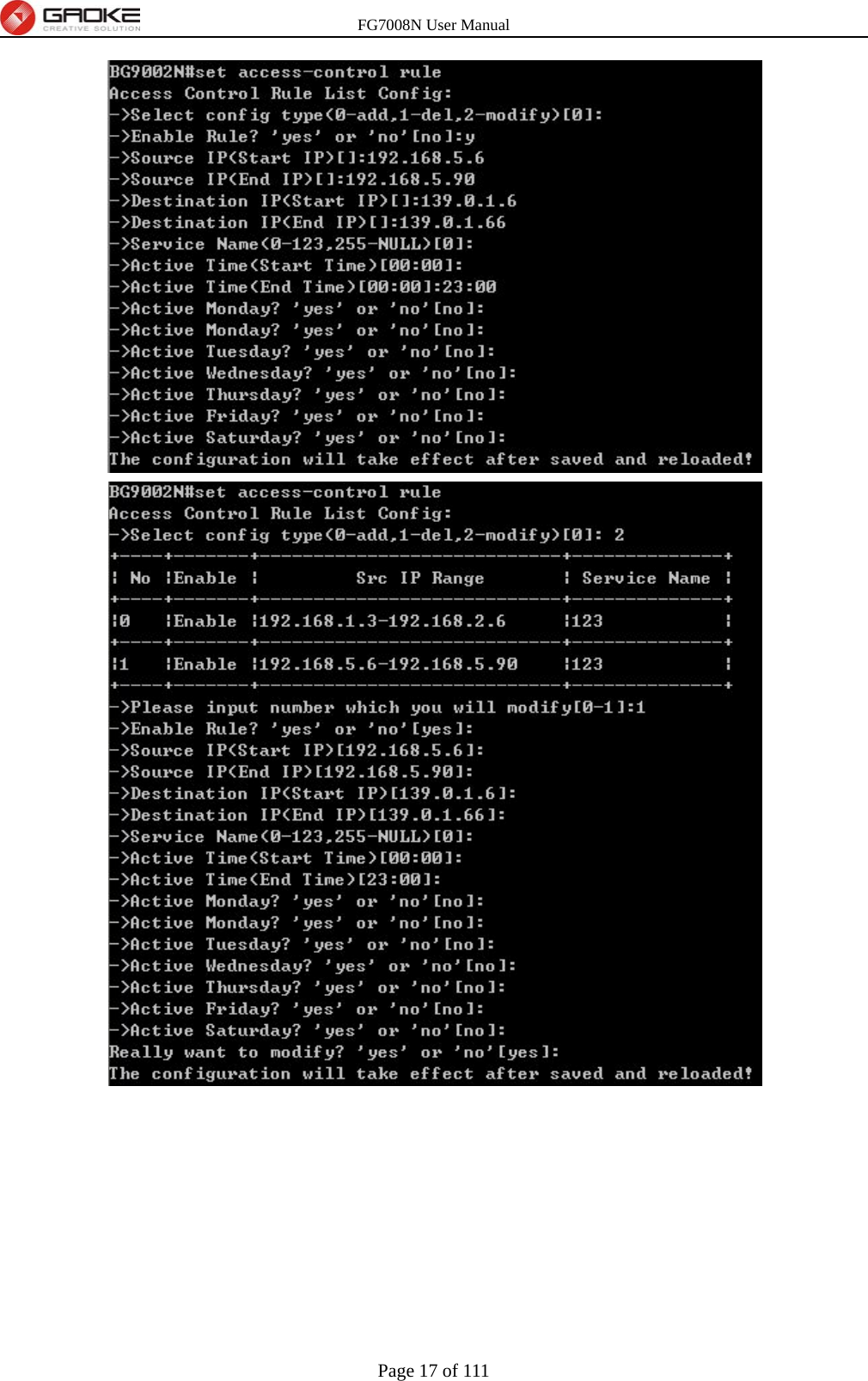
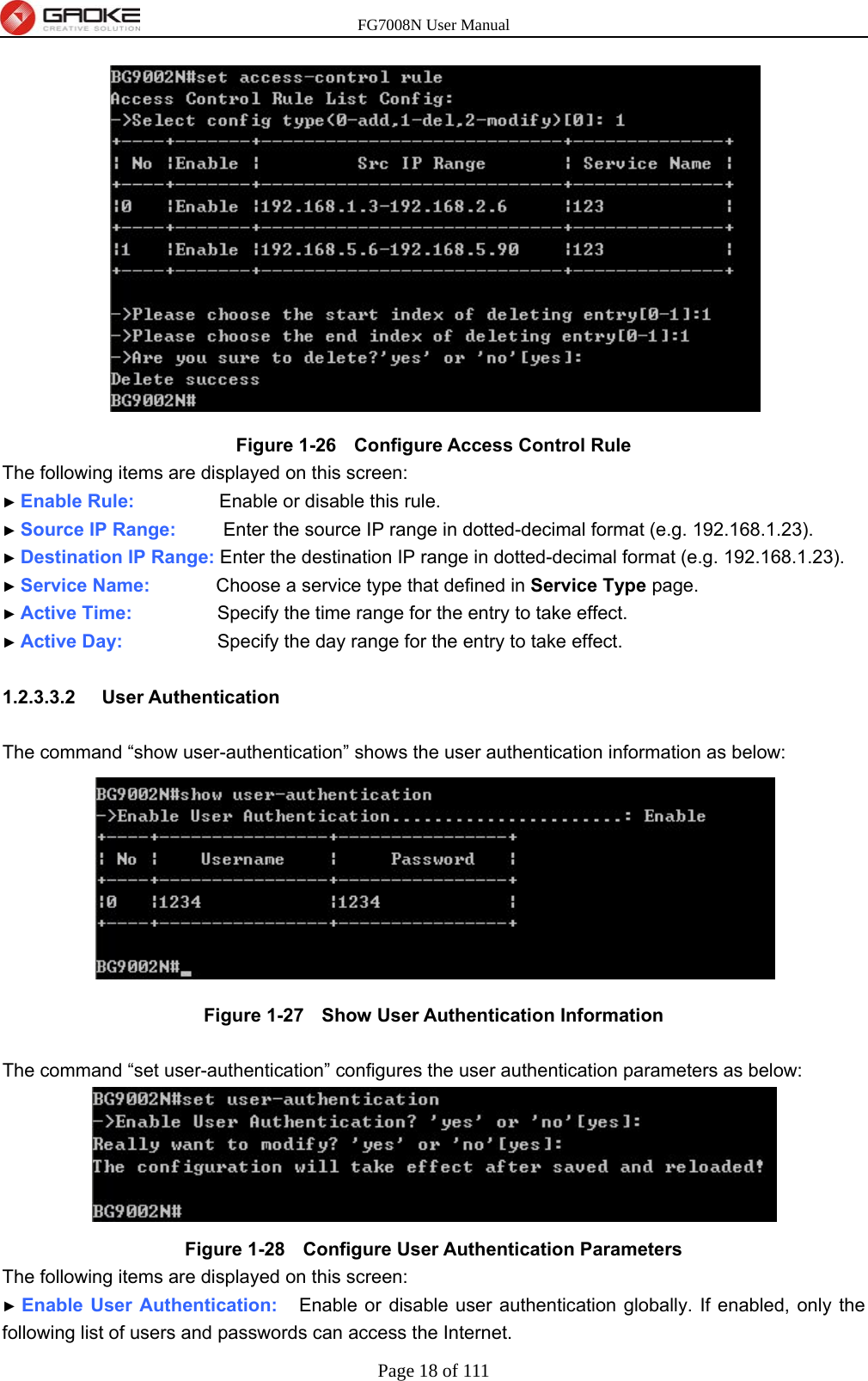
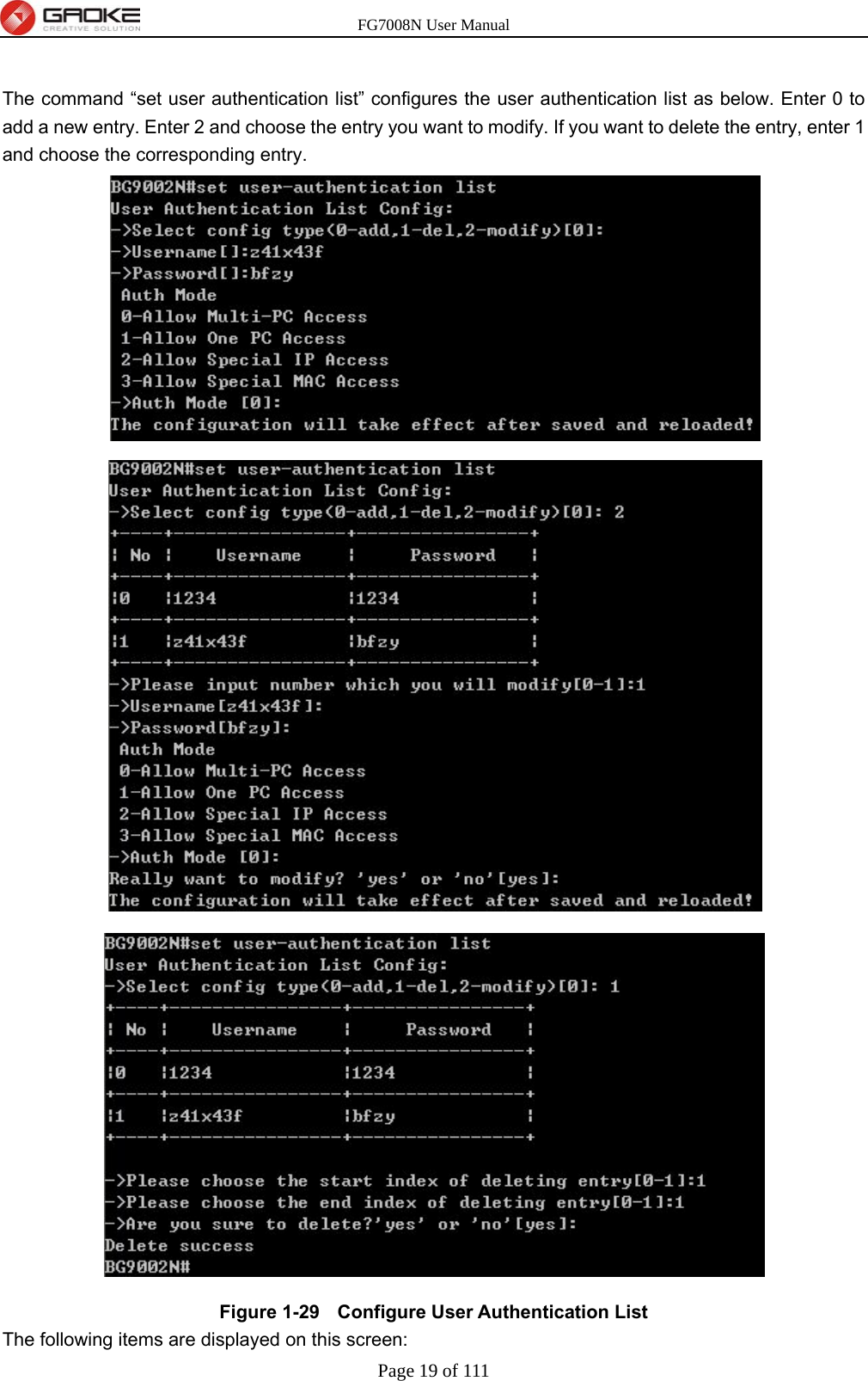
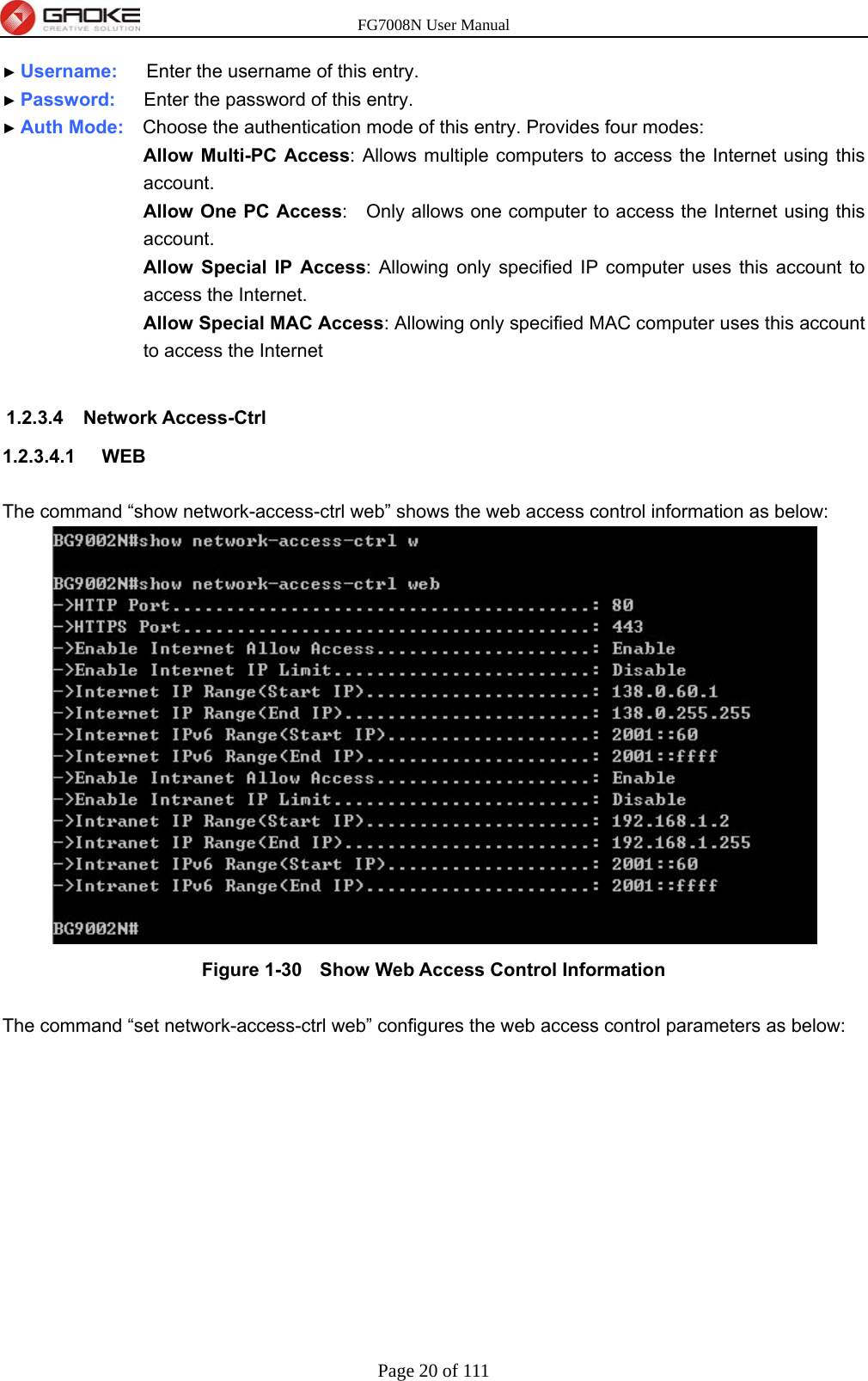
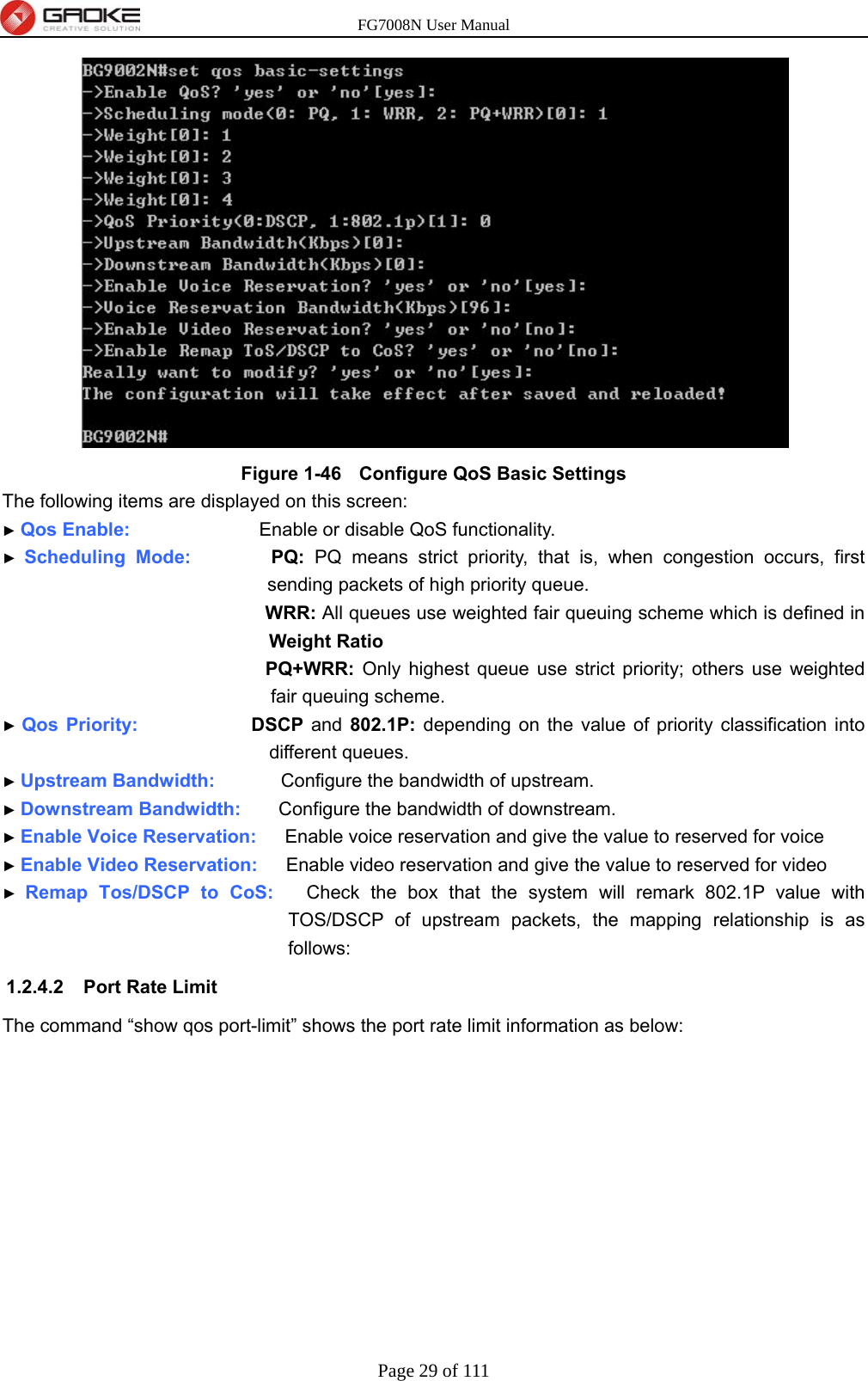
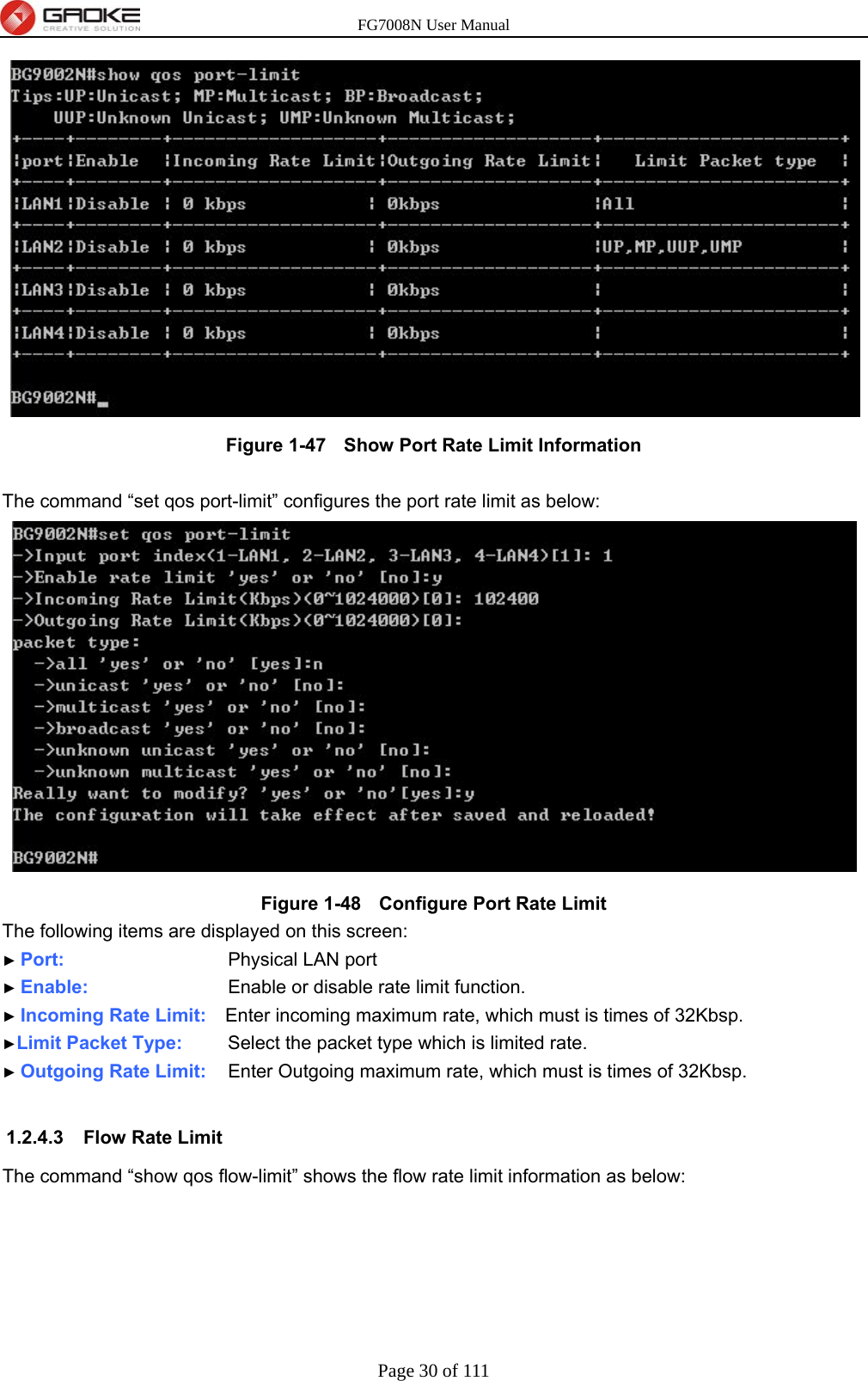
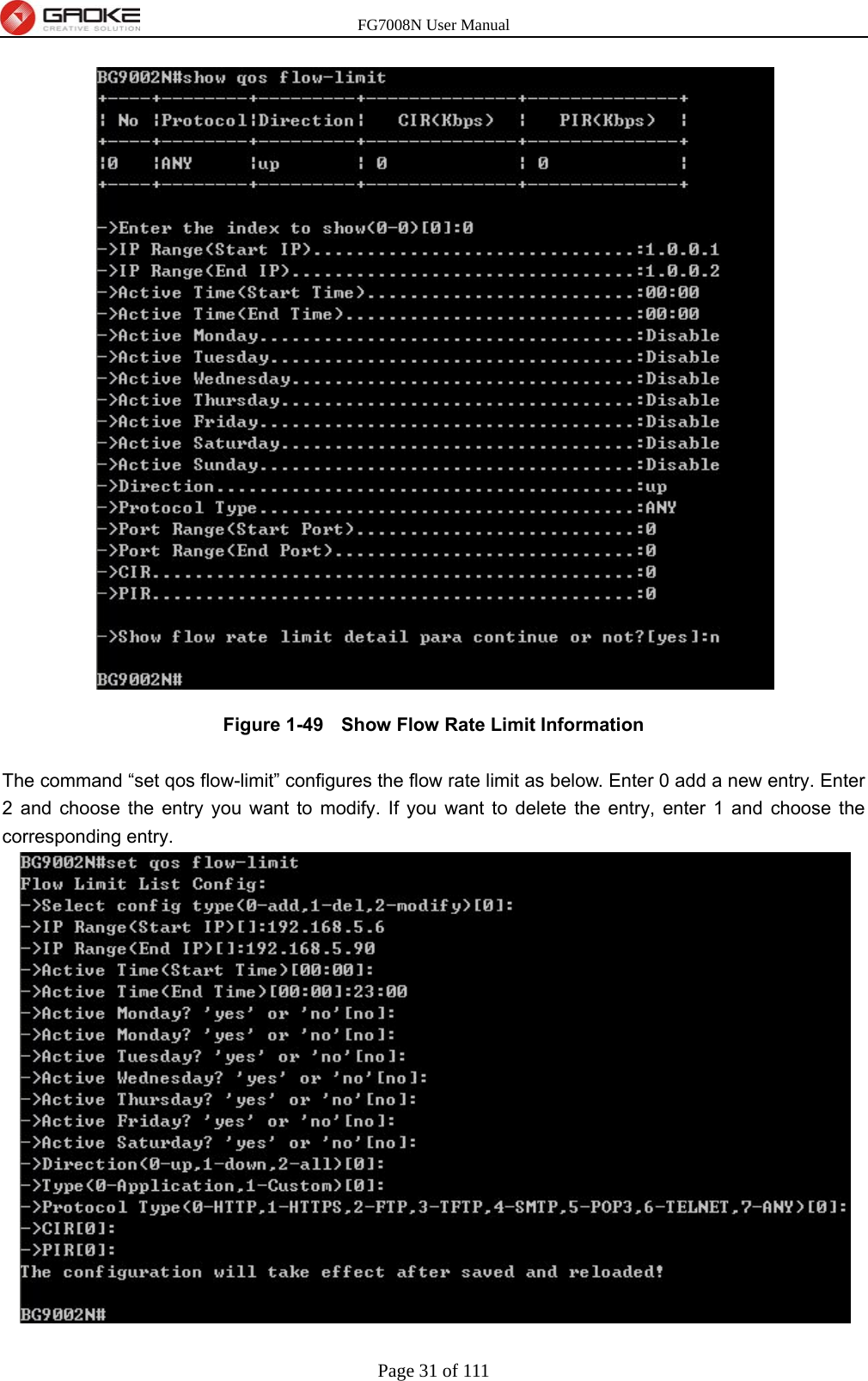
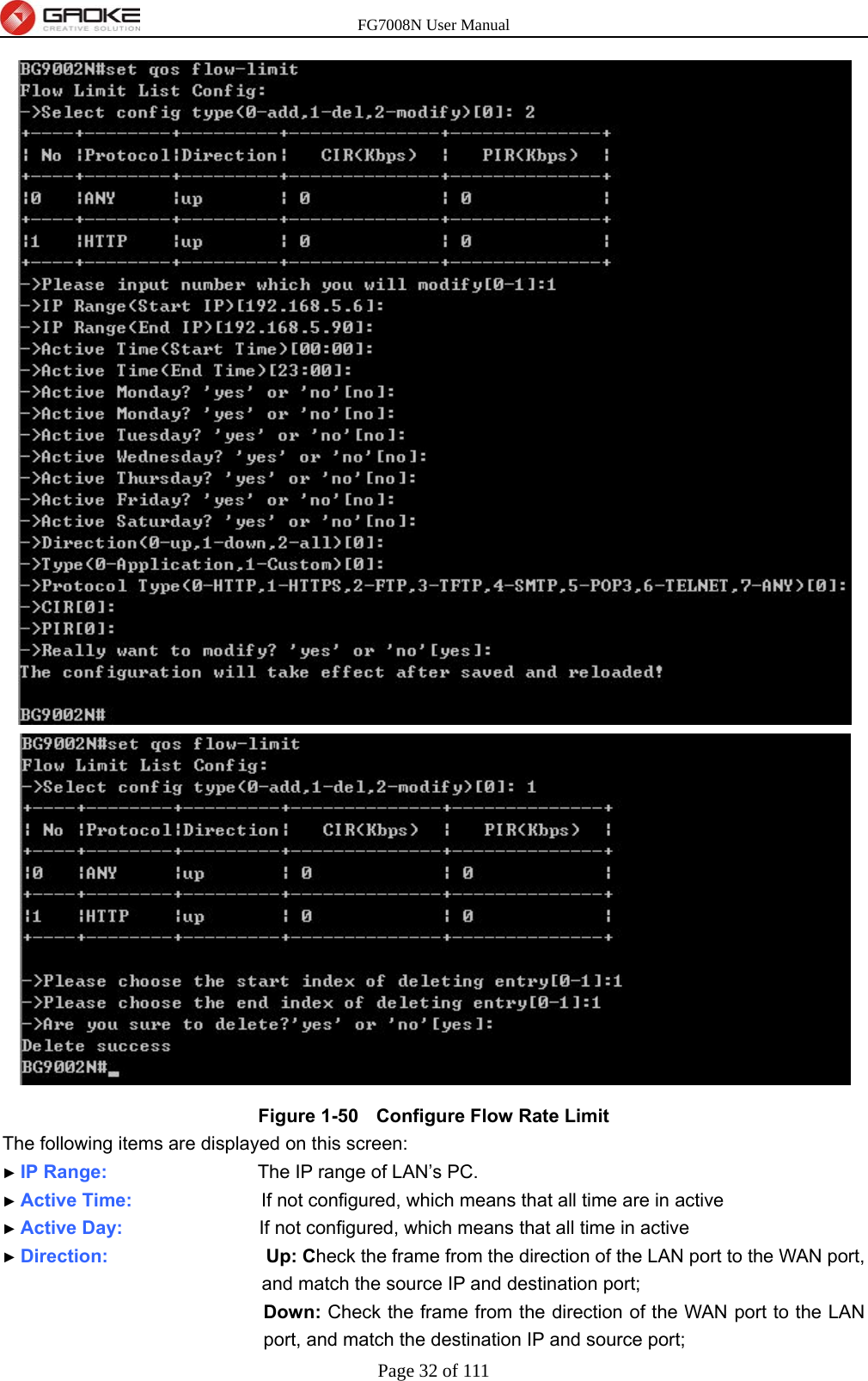
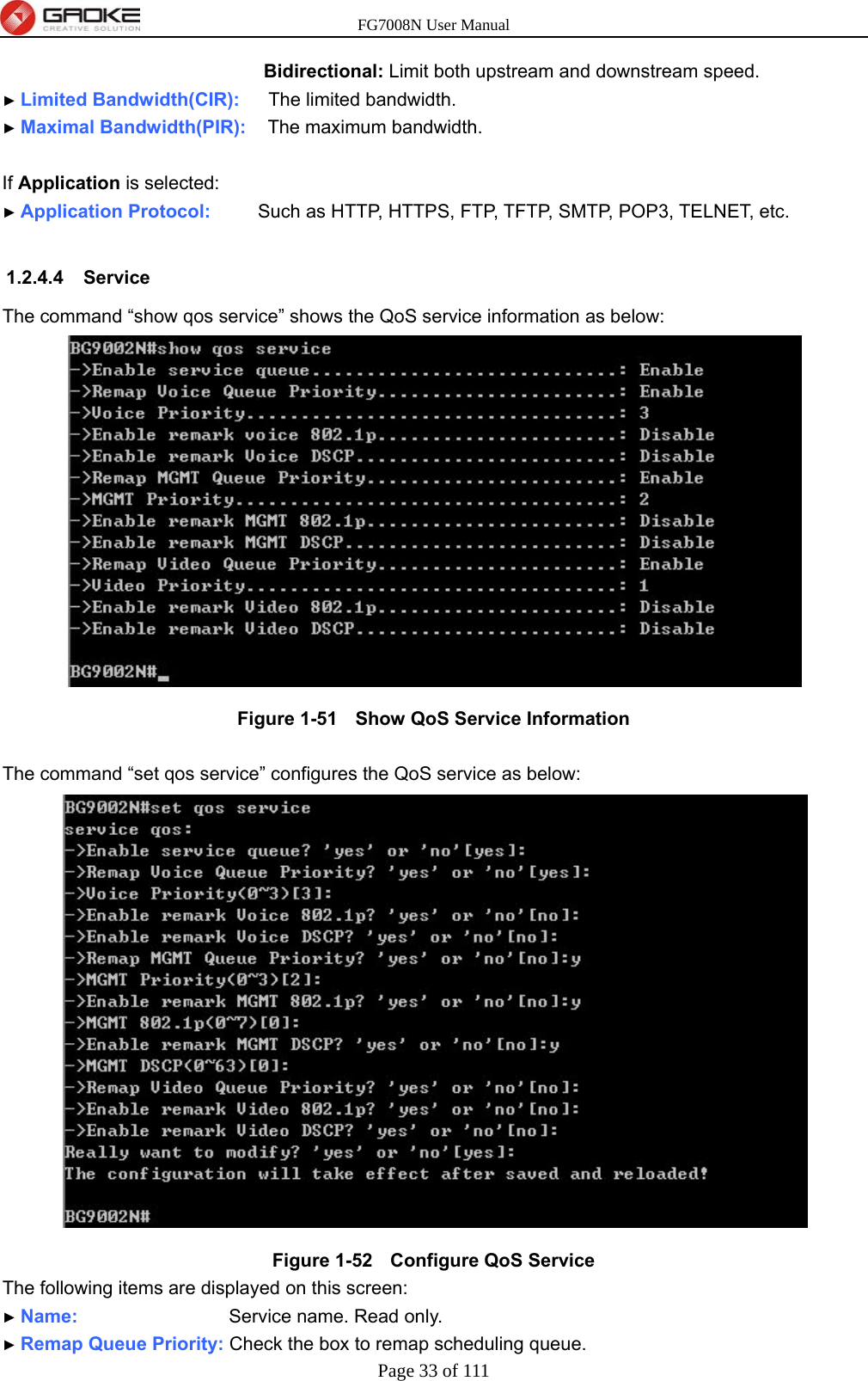
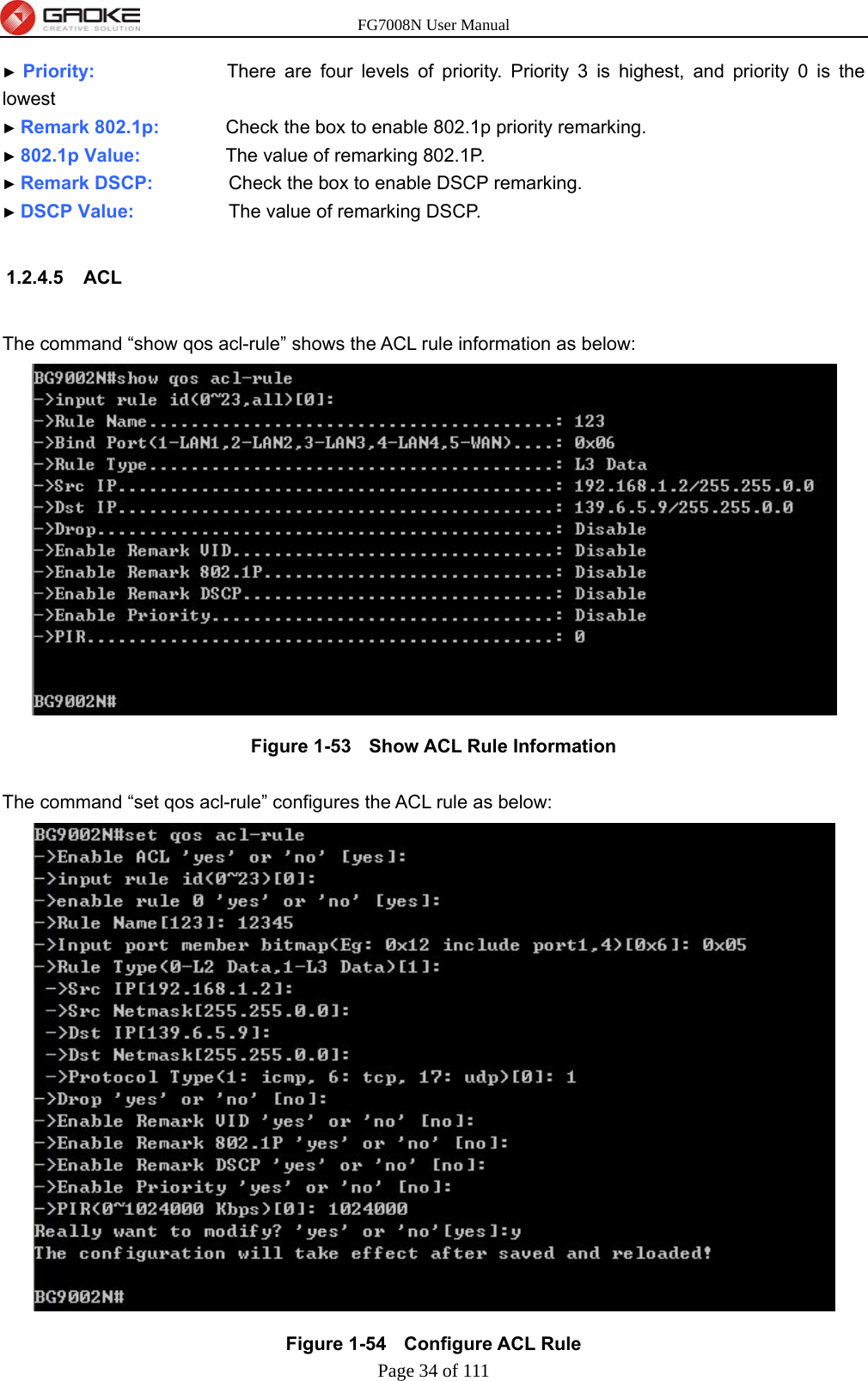
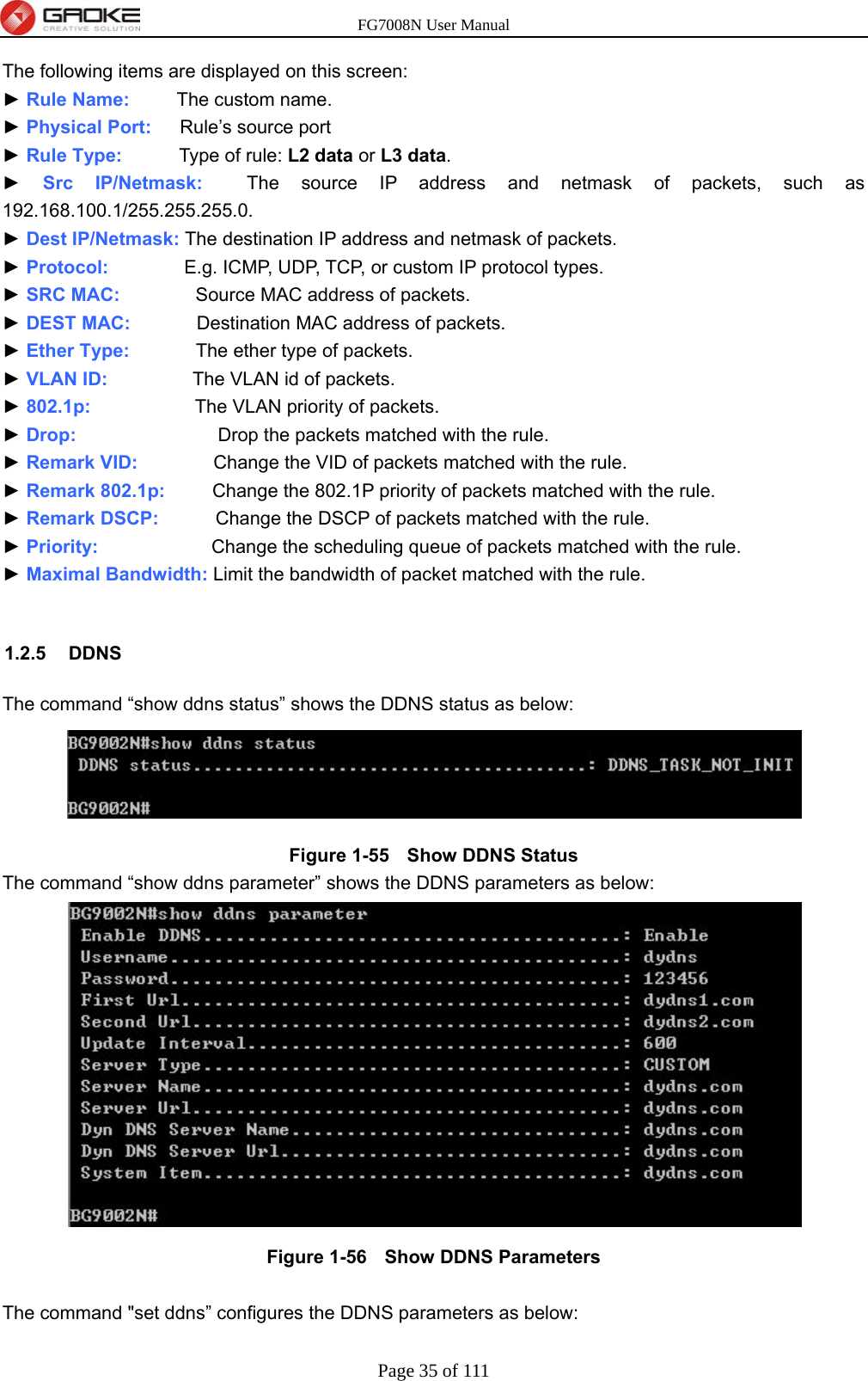
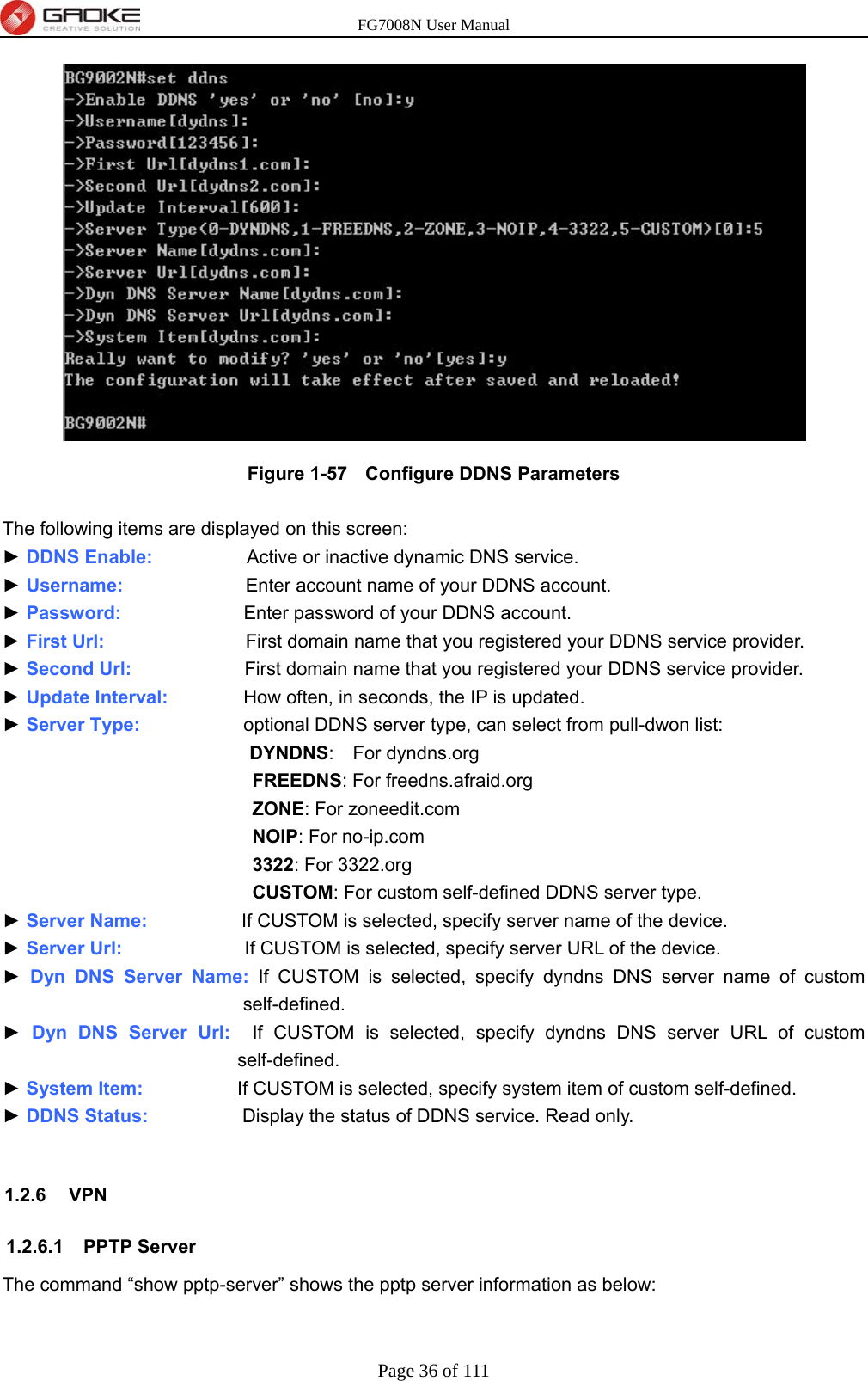
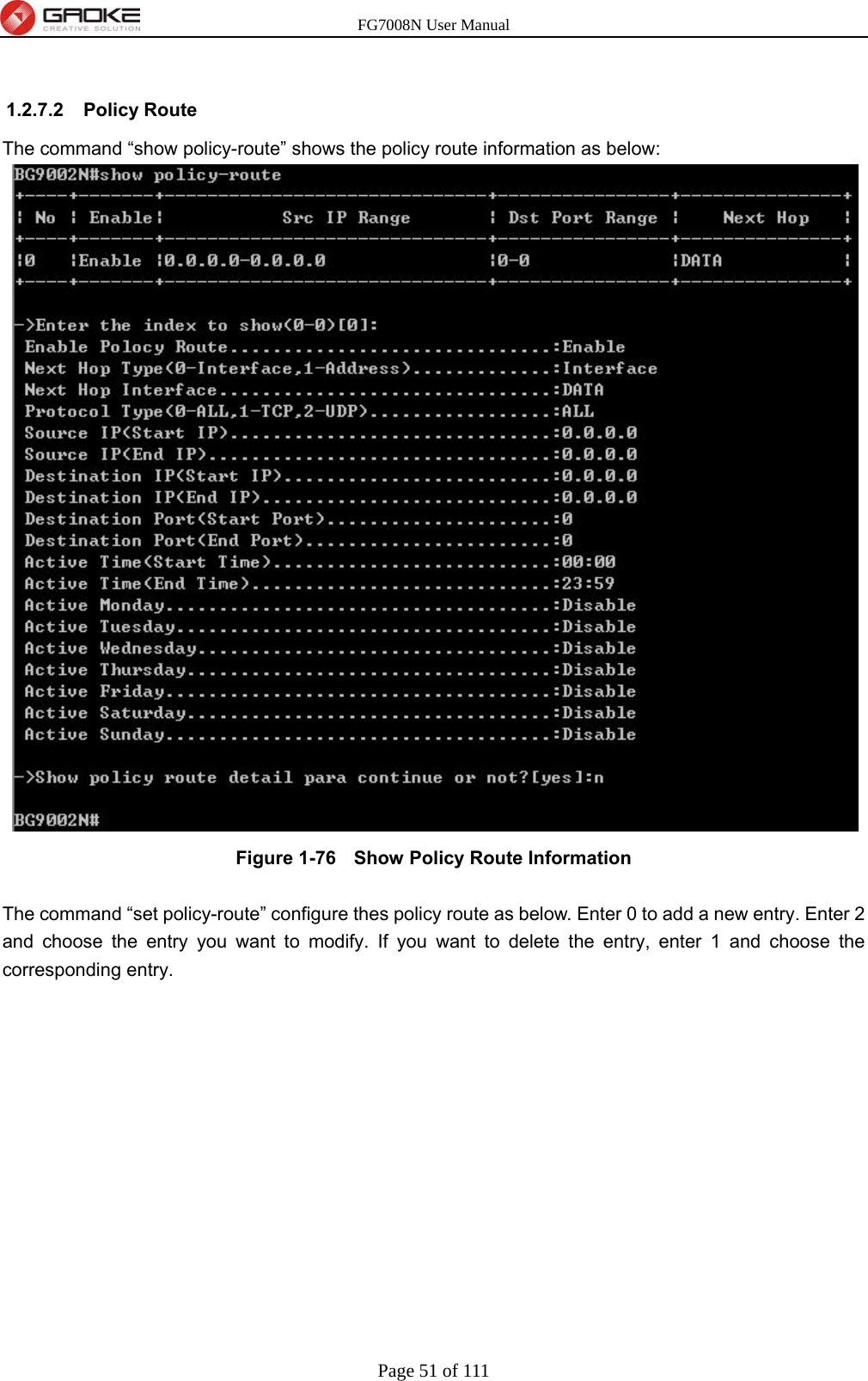
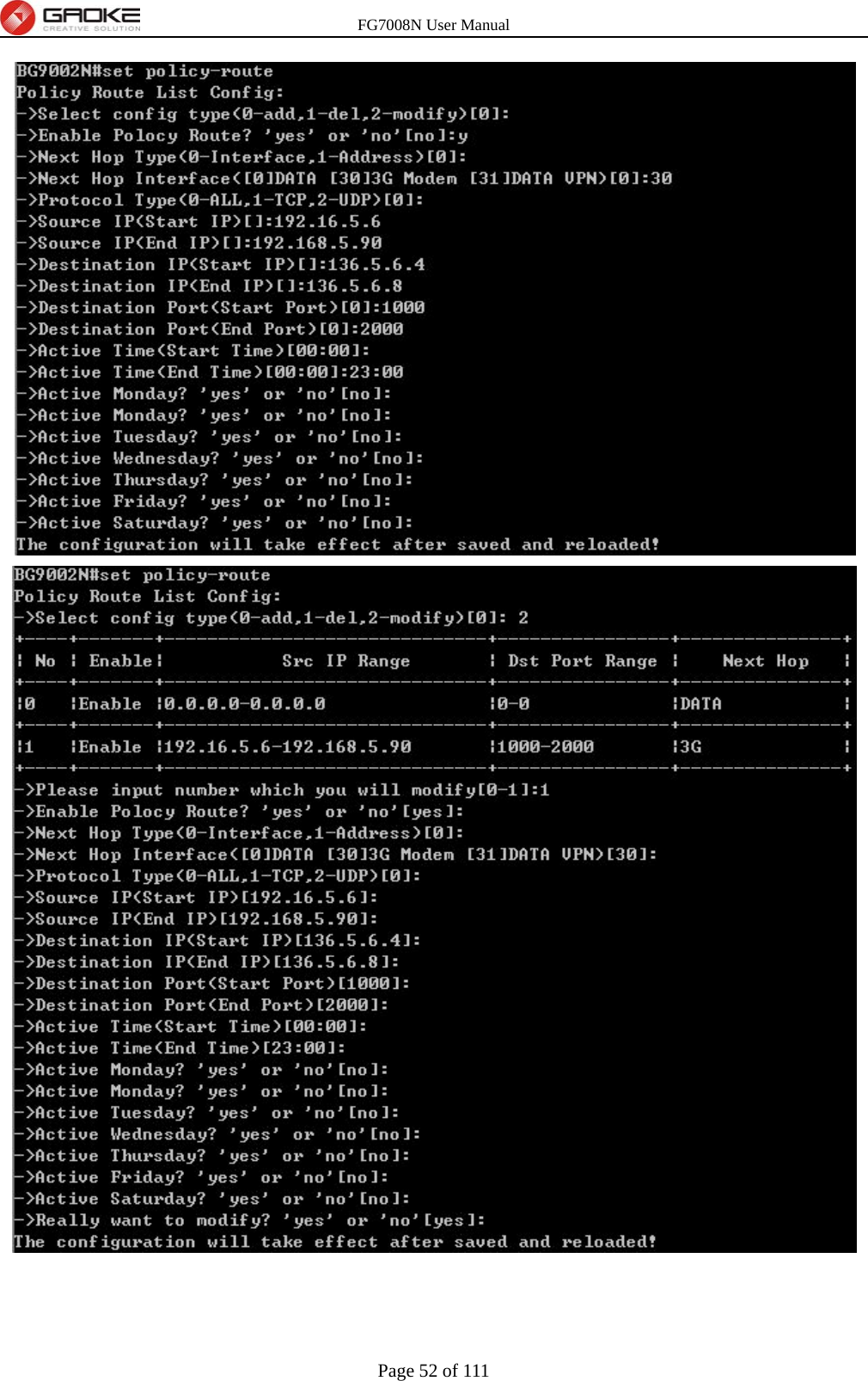
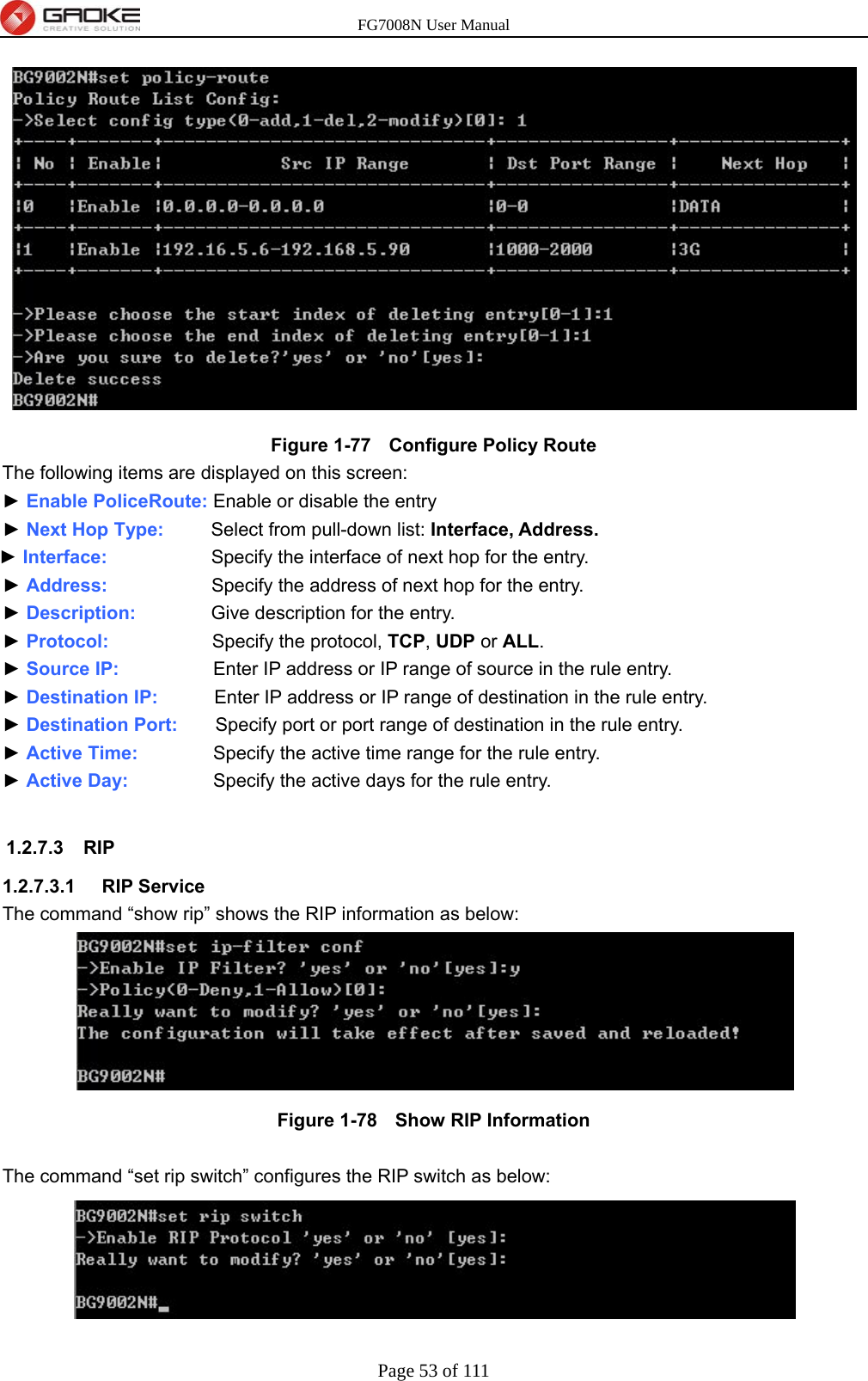
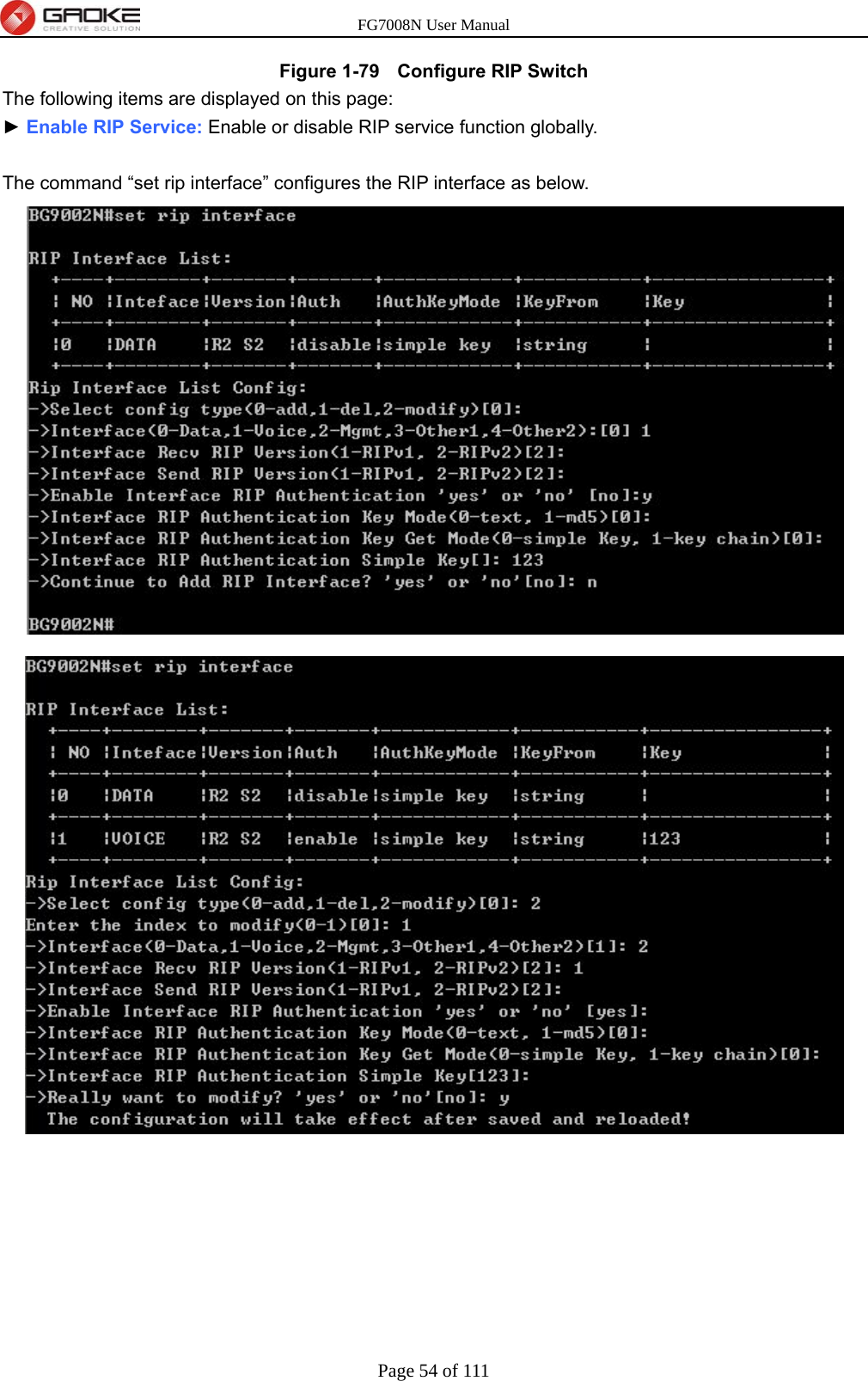
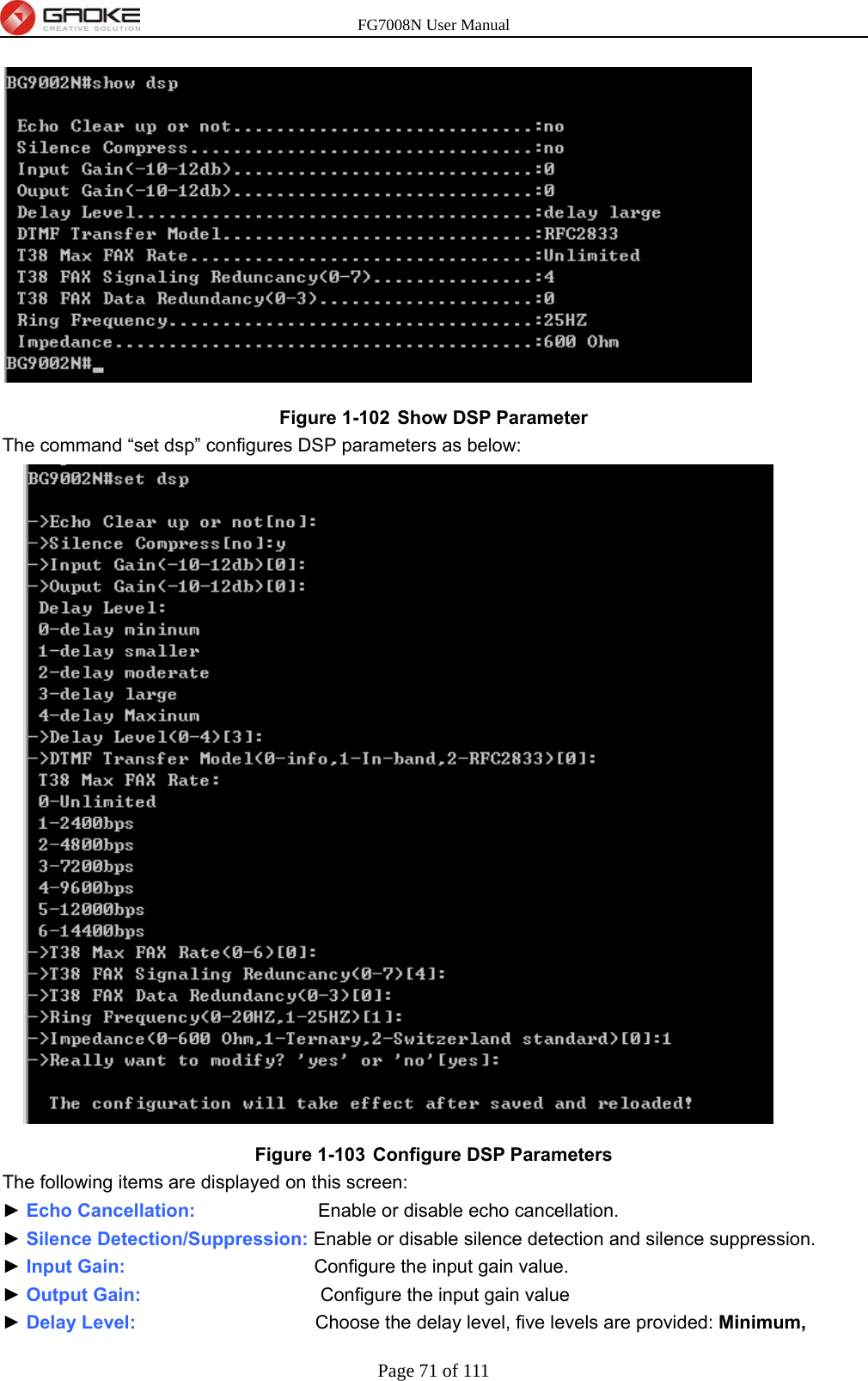
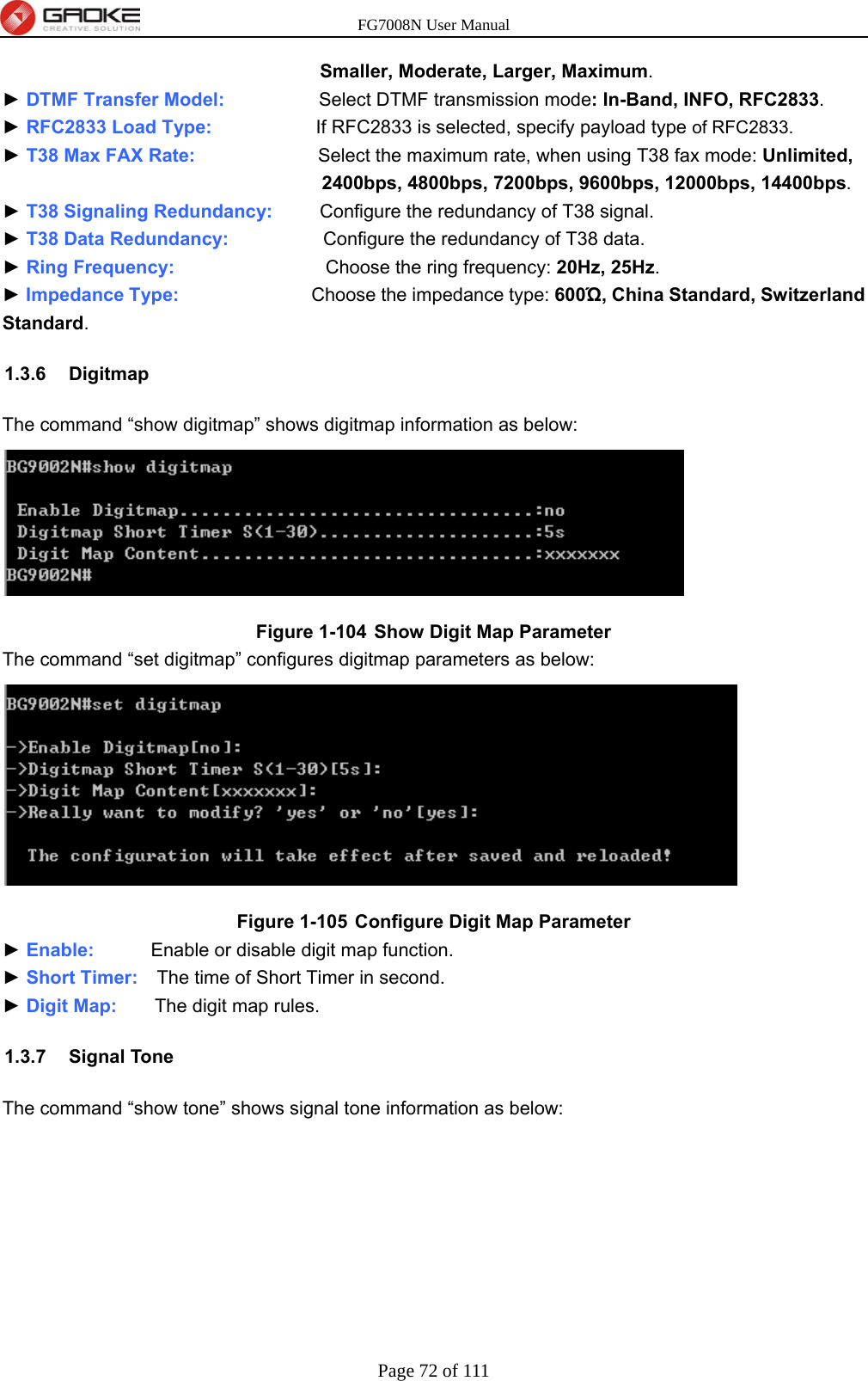
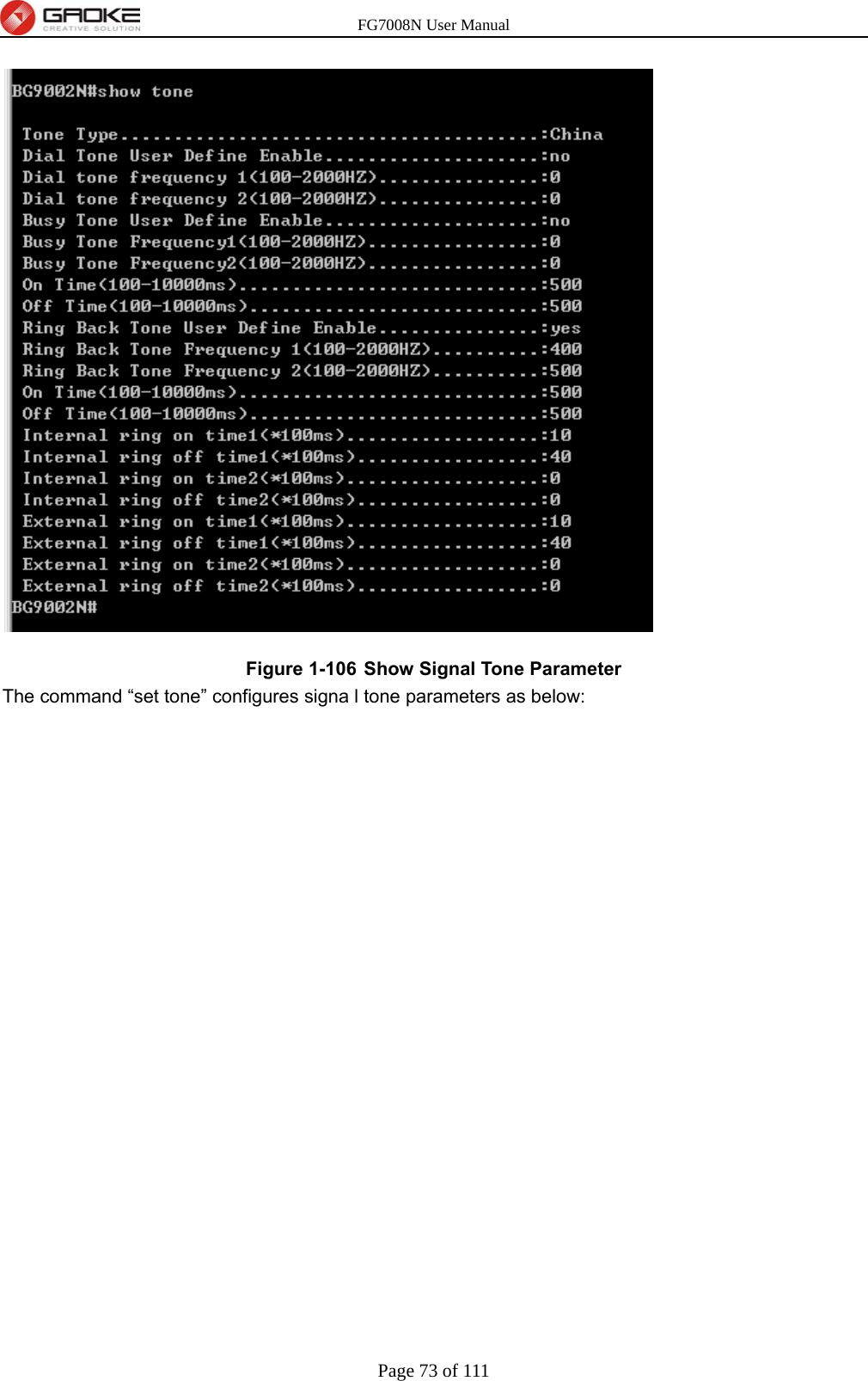
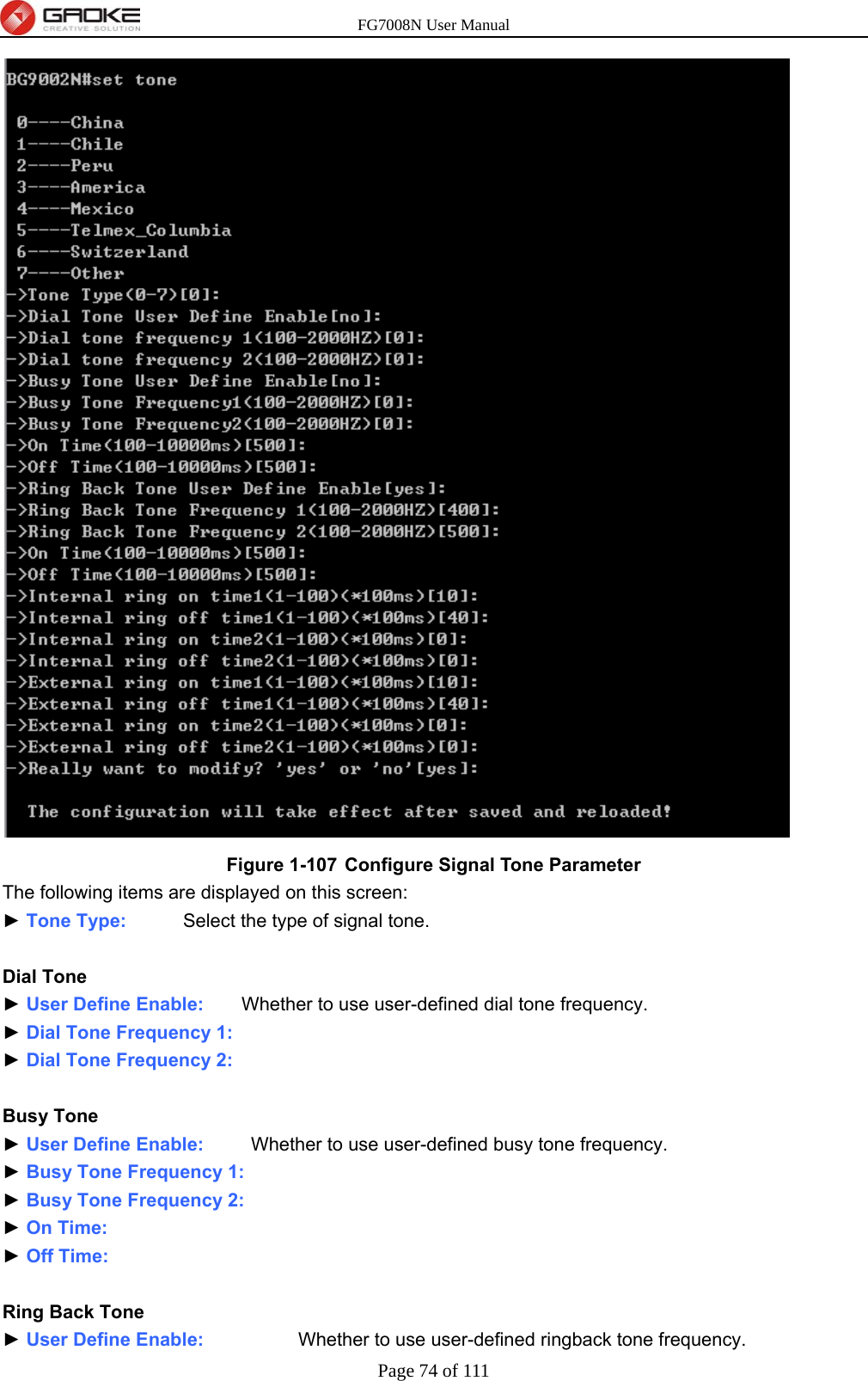
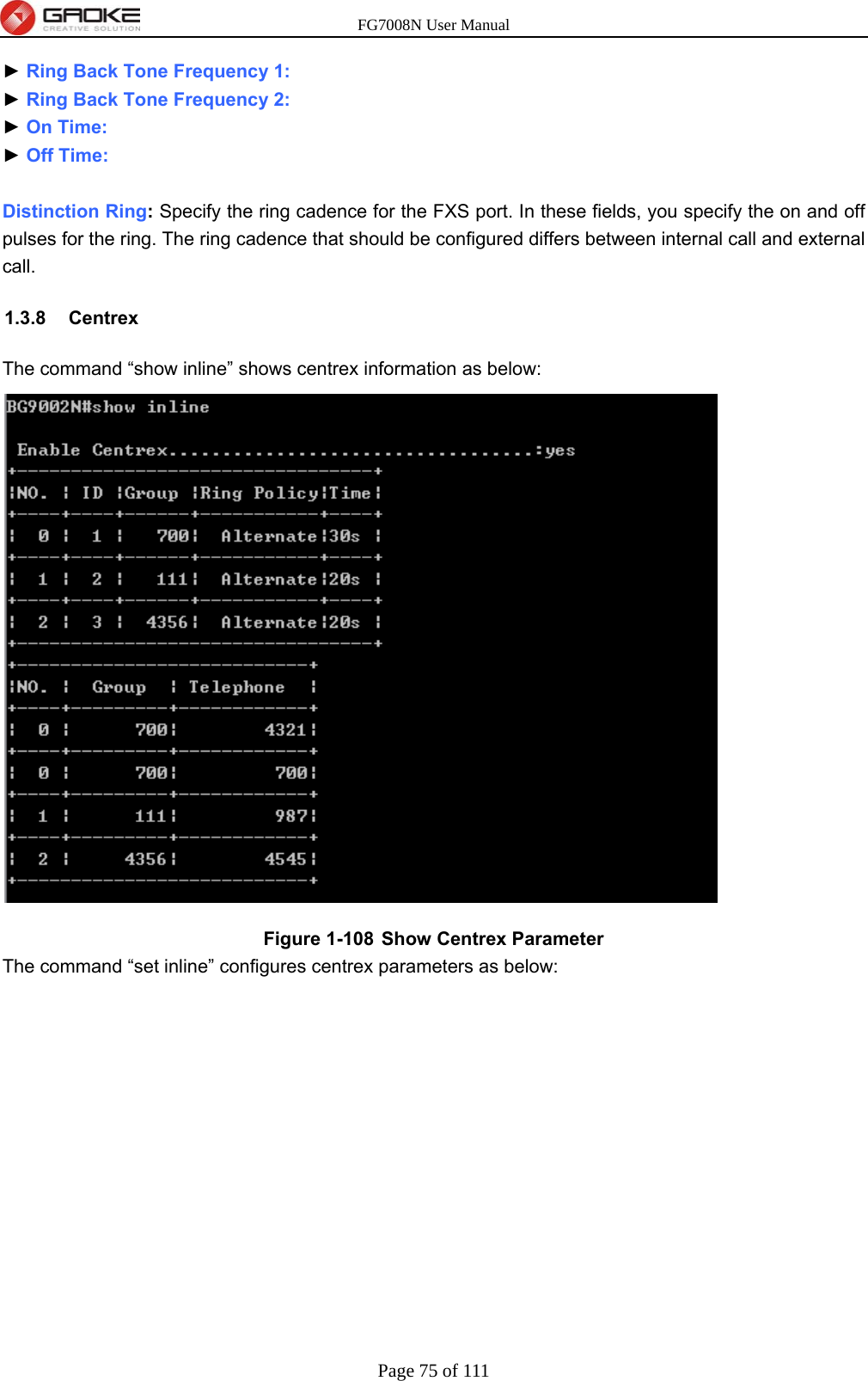
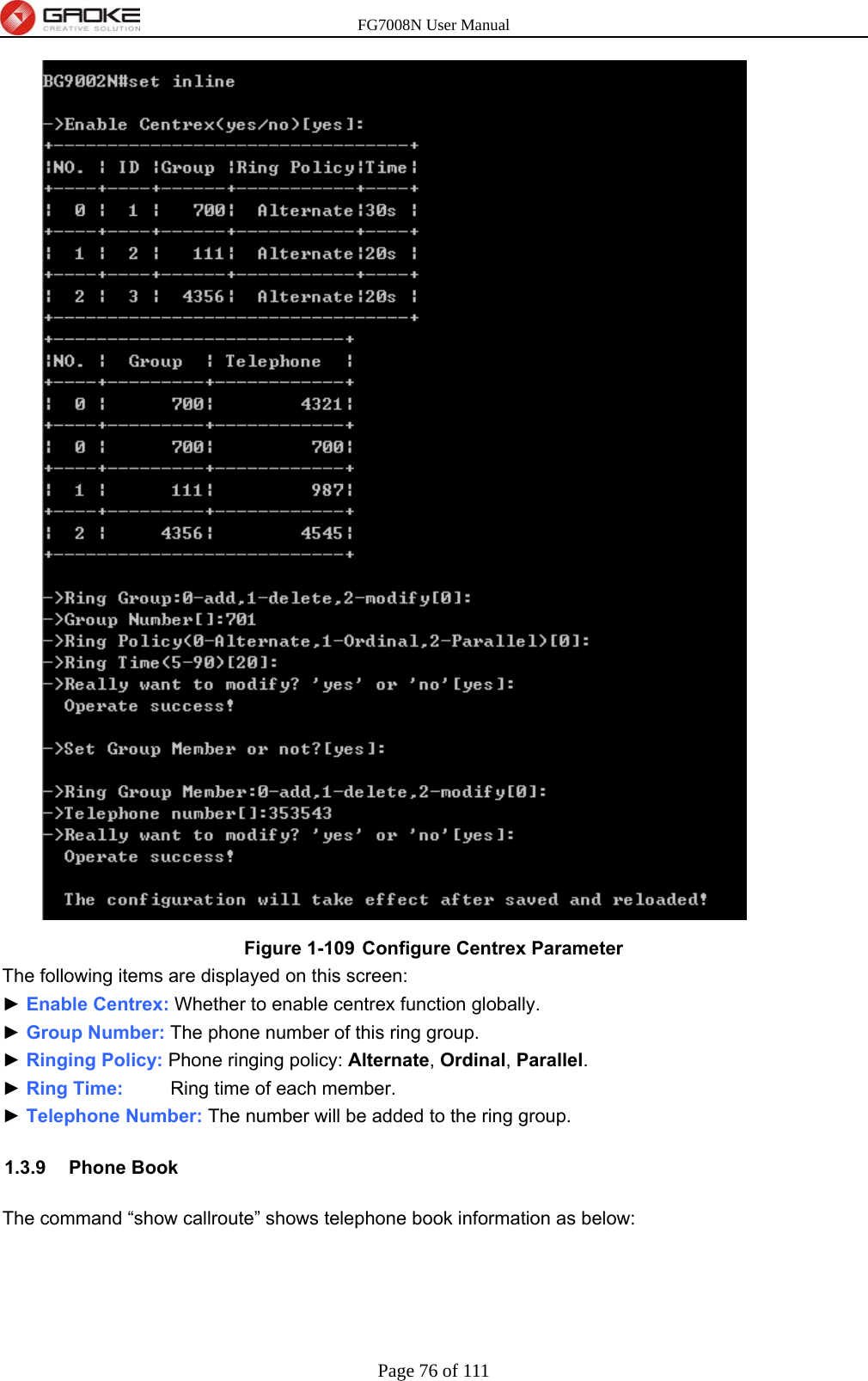
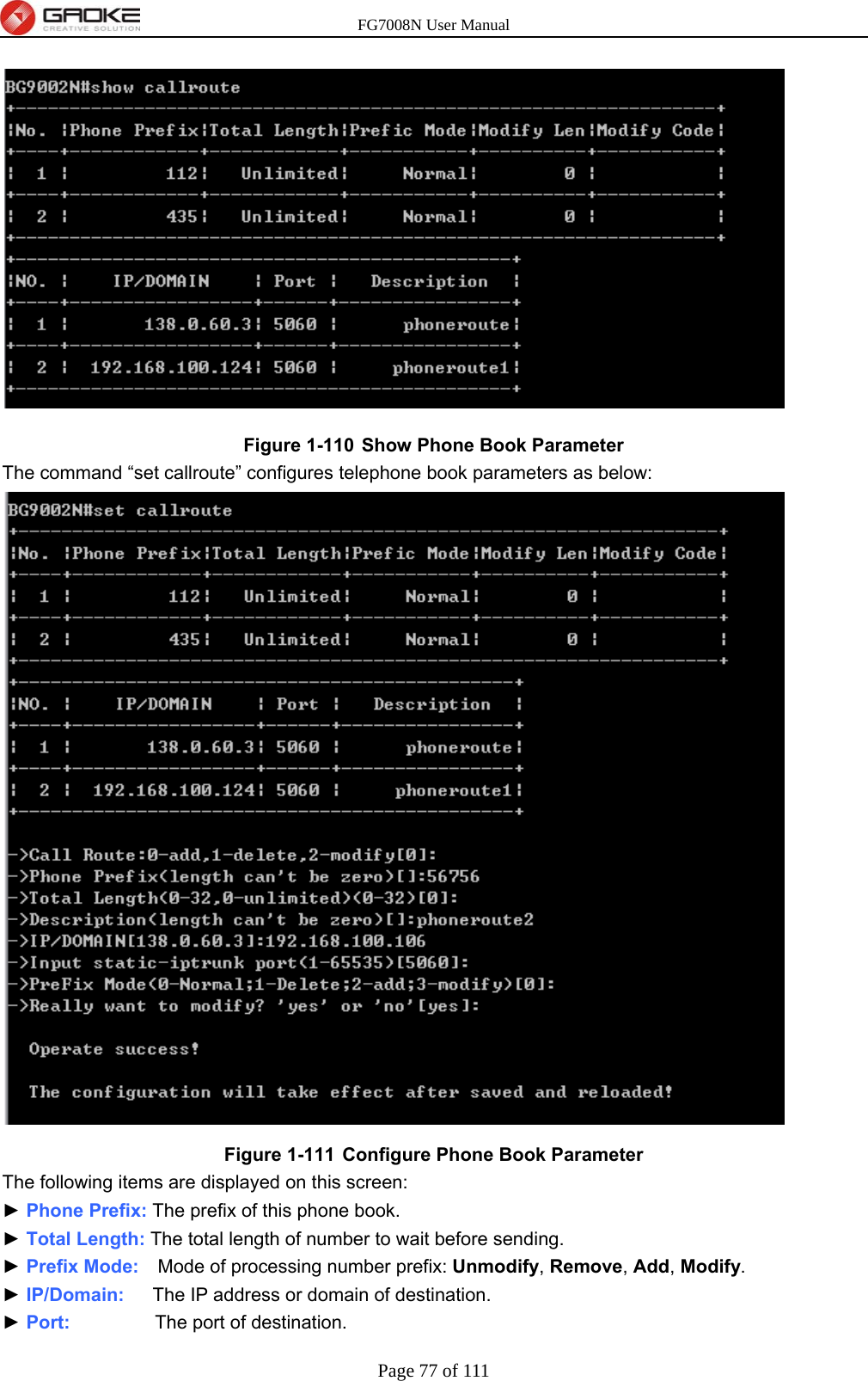
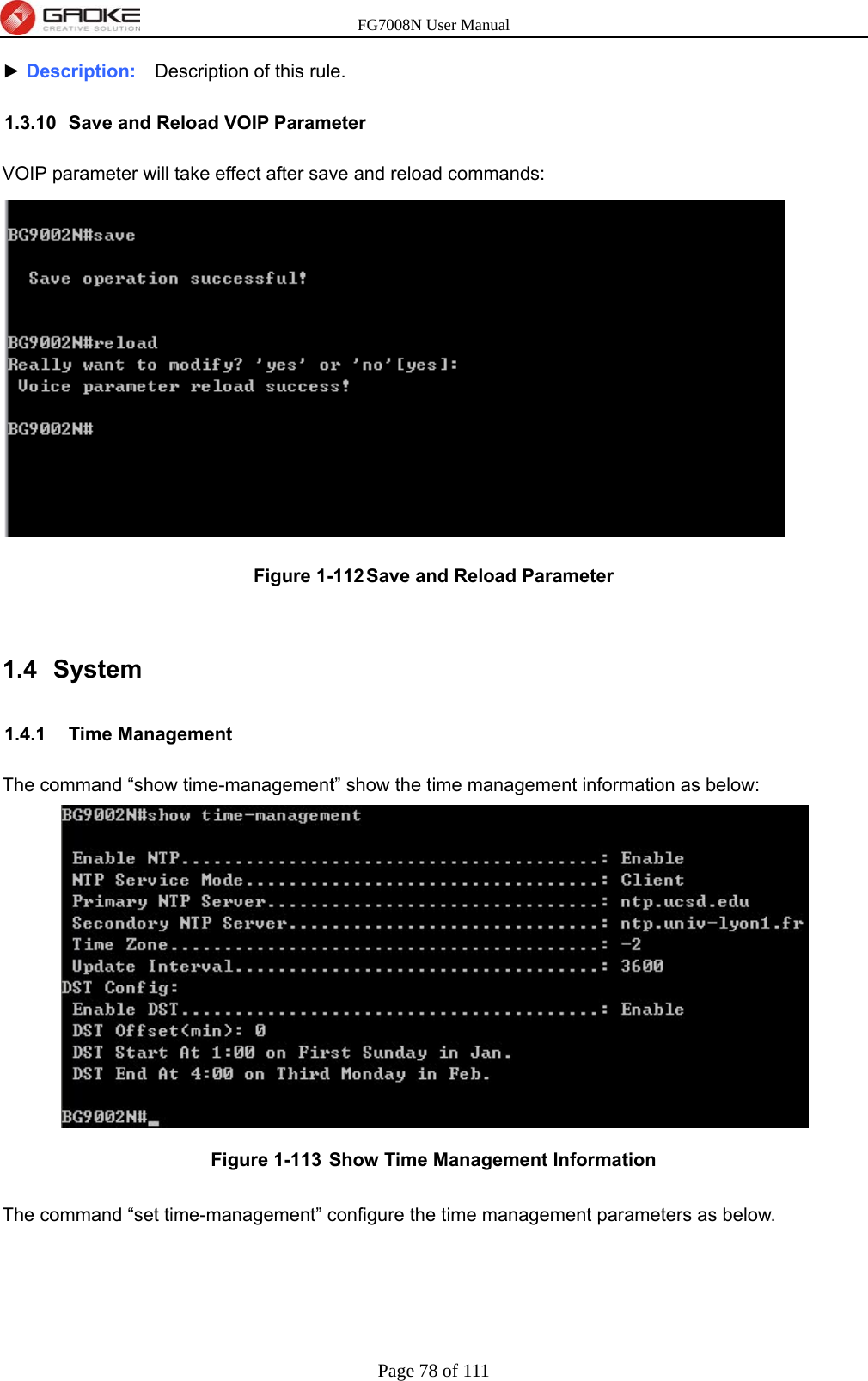
GUANGZHOU GAOKE COMMUNICATIONS TECHNOLOGY FG700X FIBER GATEWAY (Router) User Manual FG7008N USER S MANUAL2x
Guangzhou Gaoke Communications Technology Co., Ltd FIBER GATEWAY (Router) FG7008N USER S MANUAL2x
Contents
- 1. FG7008N User Manual-Part 2
- 2. FG7008N User Manual -Part1
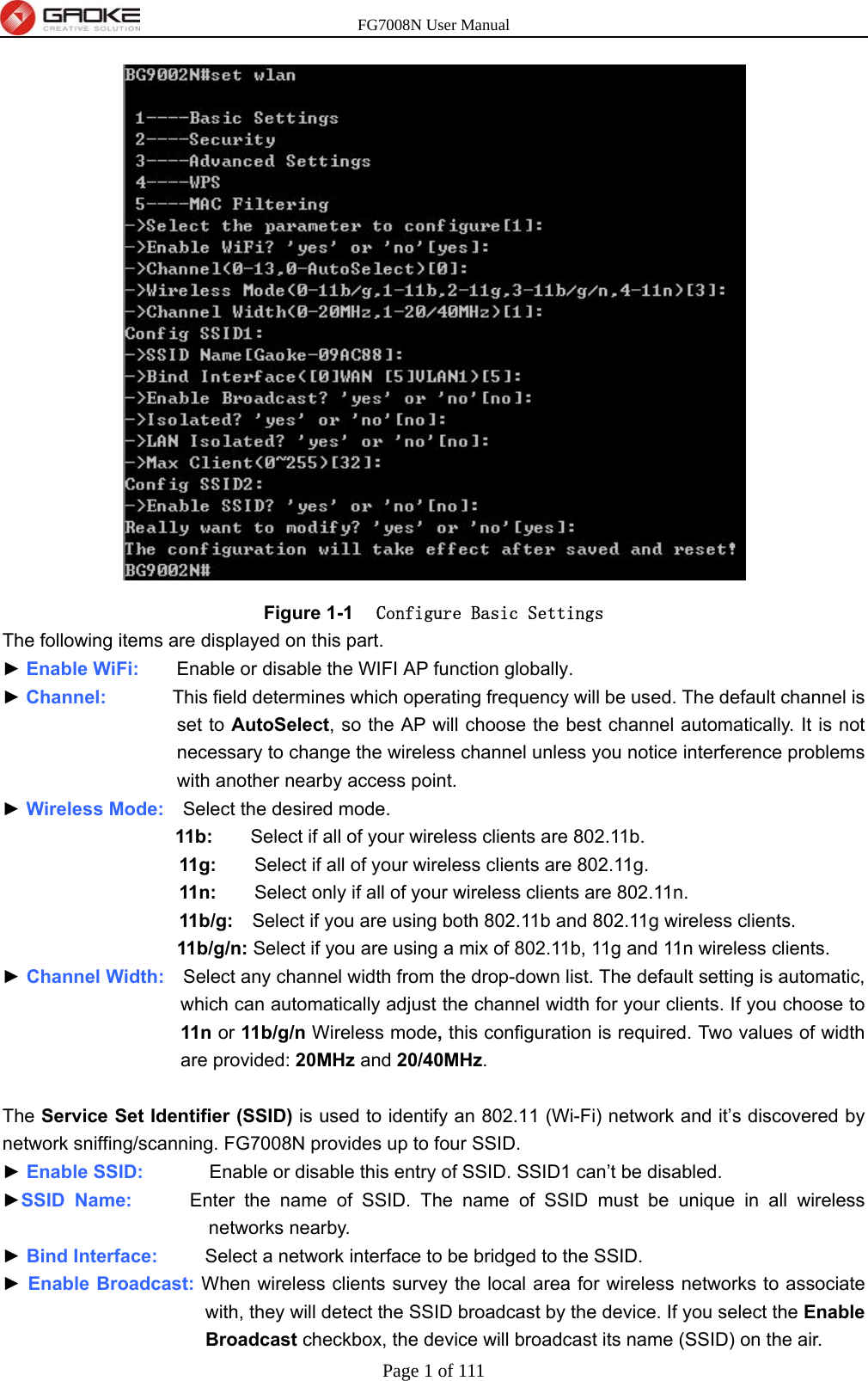
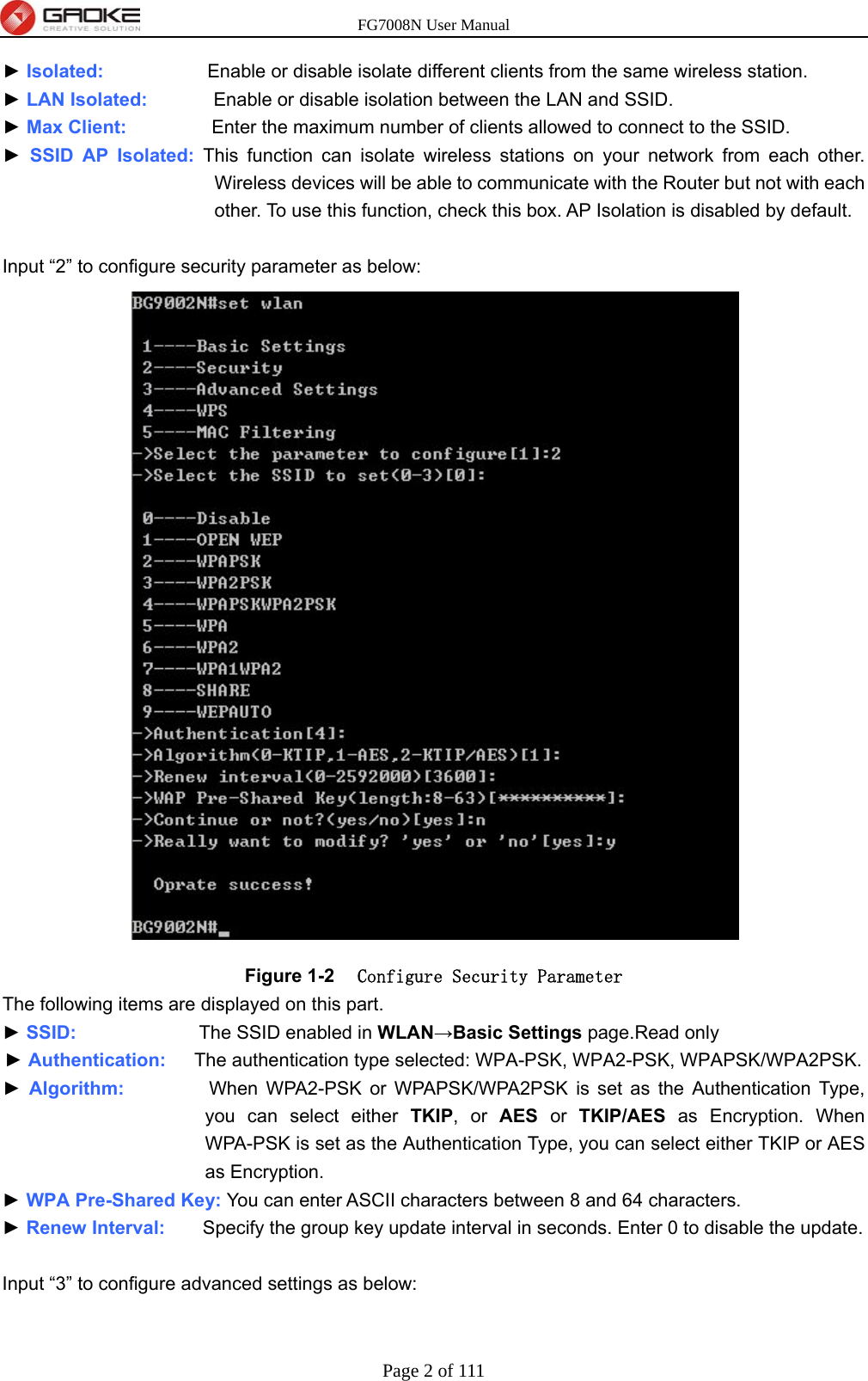
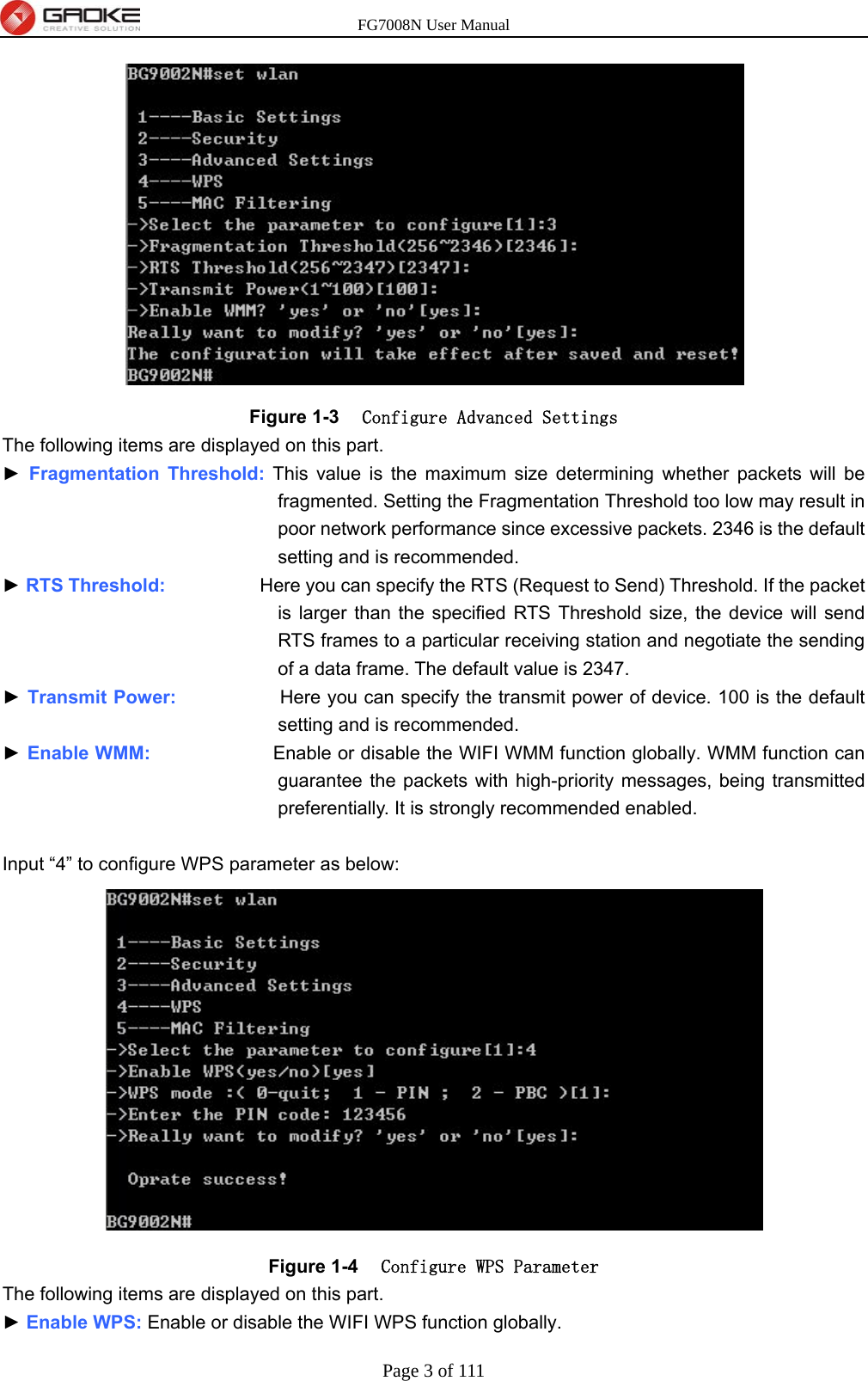
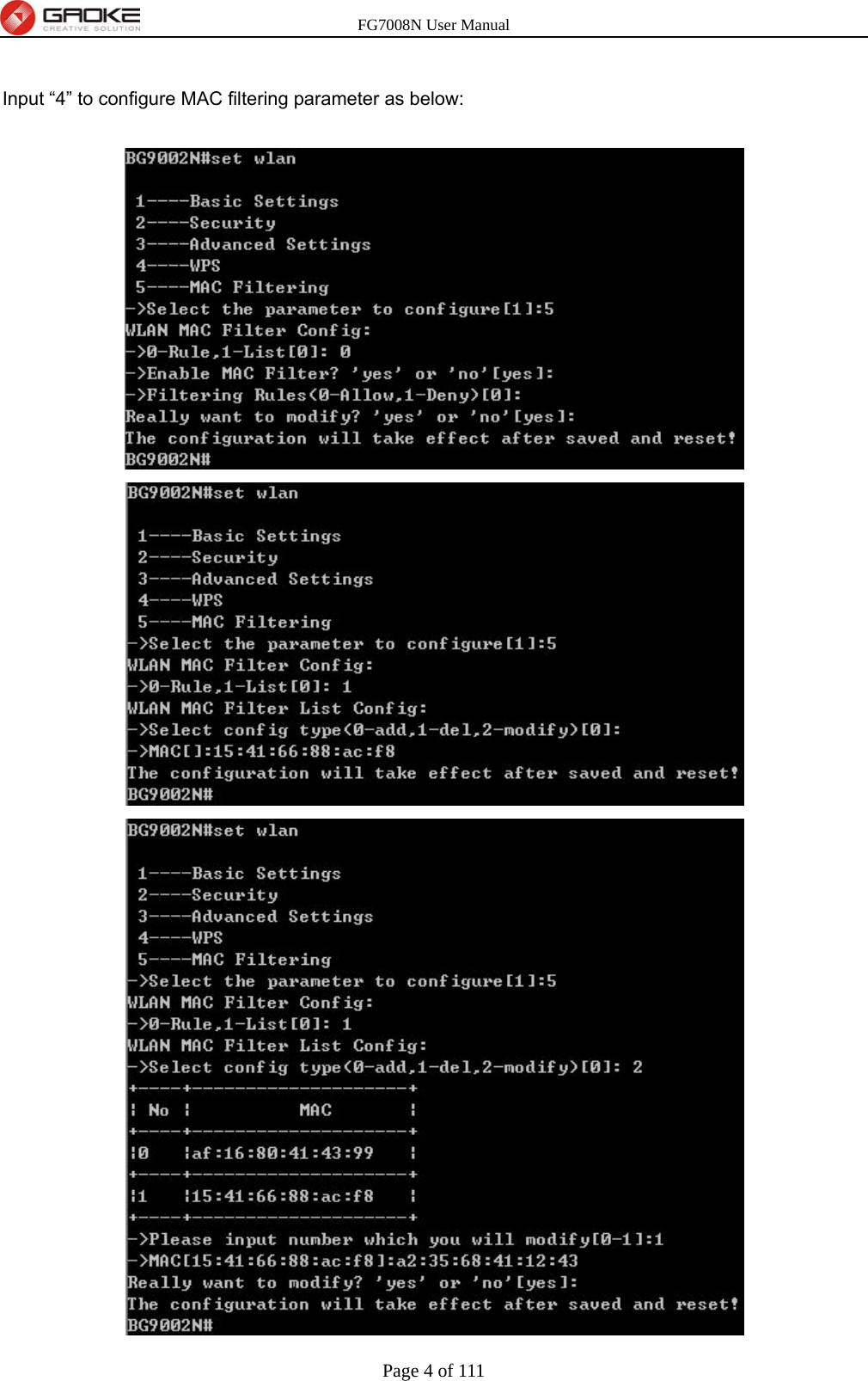
FG7008N User Manual-Part 2