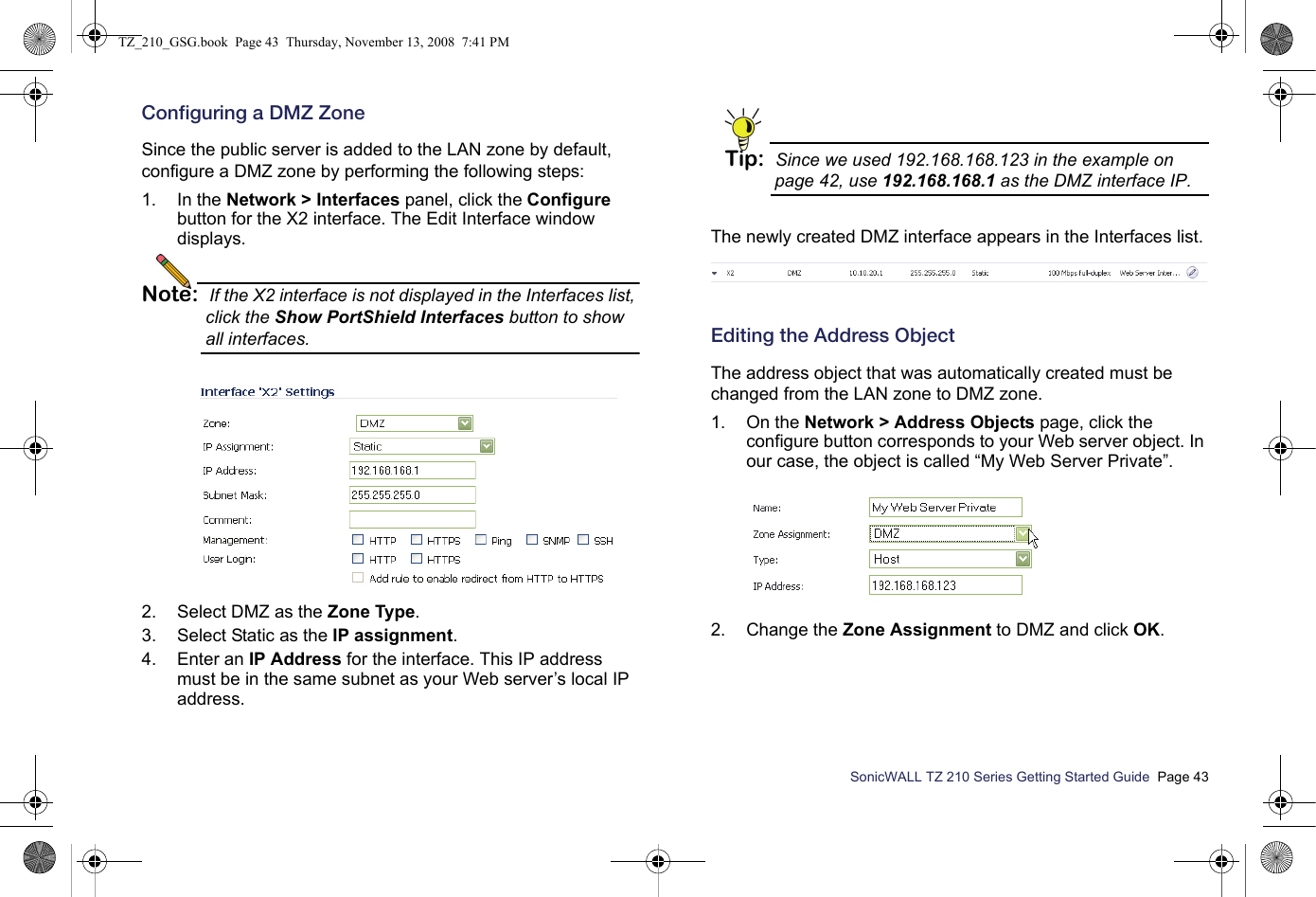
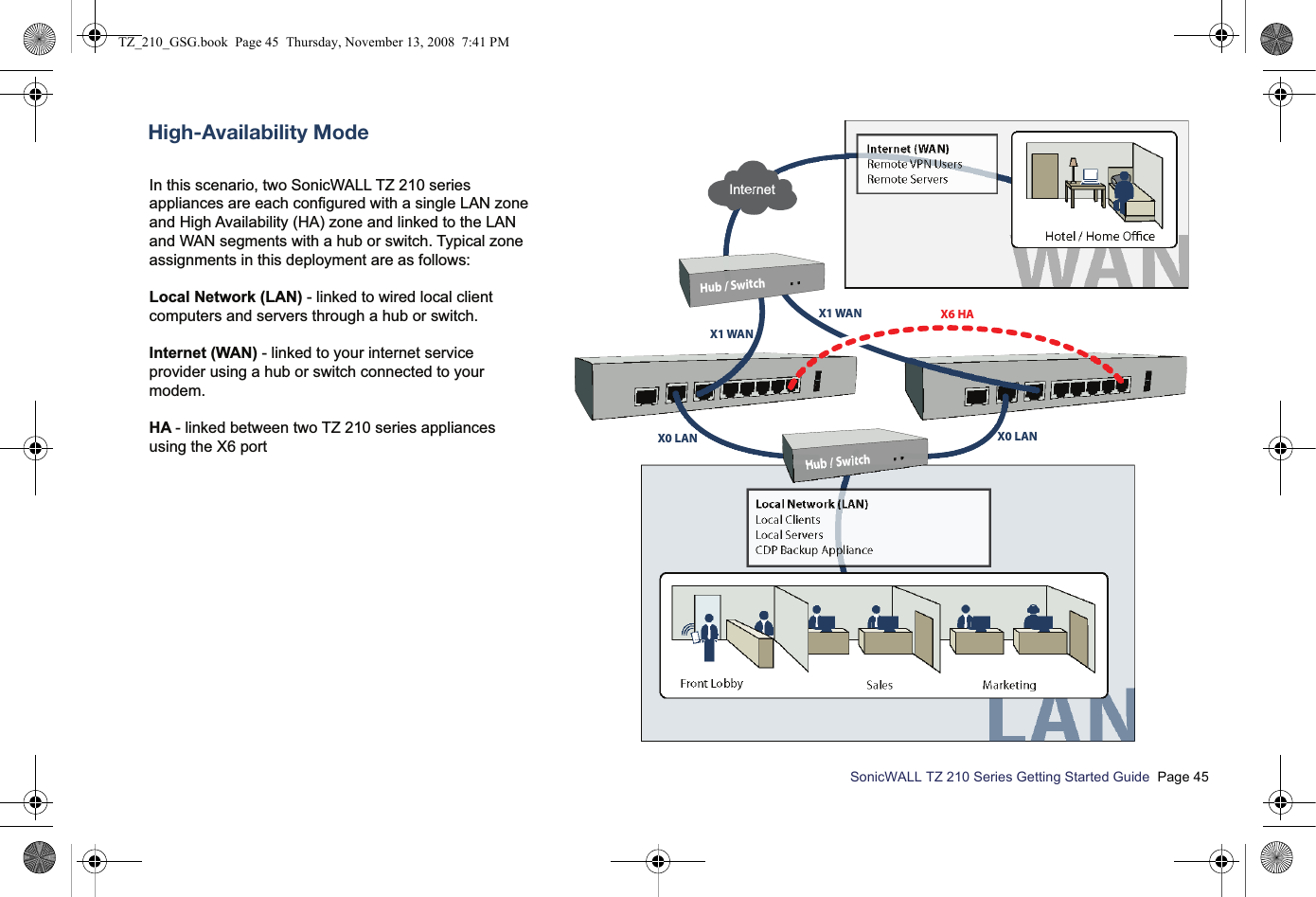
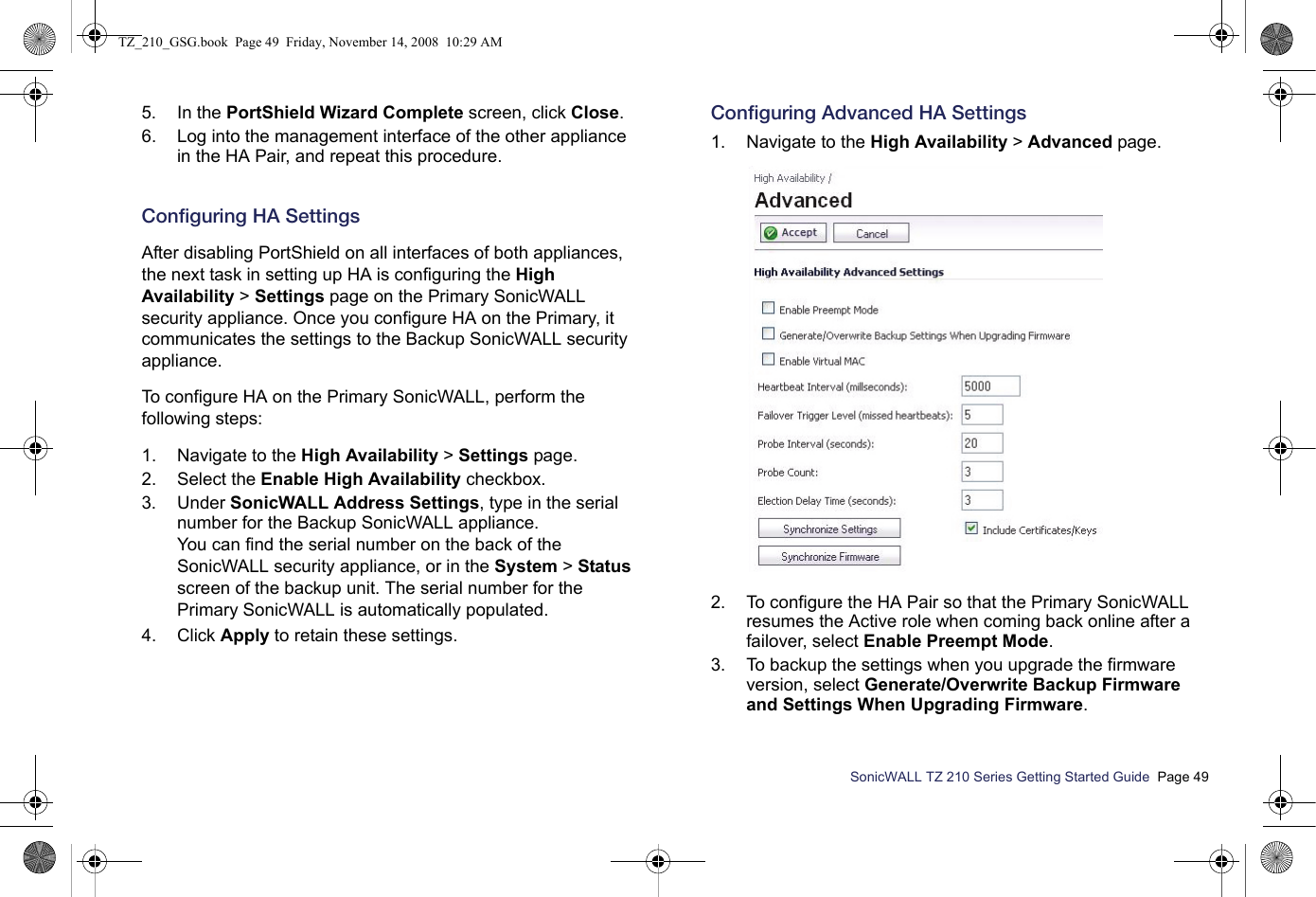
Sonicwall 06C 802.11b/g/n Router User Manual SonicWALL TZ 210 Series Getting Started Guide
Sonicwall, Inc. 802.11b/g/n Router SonicWALL TZ 210 Series Getting Started Guide
Contents
- 1. Manual Part 1
- 2. Manual Part 2
- 3. Manual Part 3
- 4. Manual Part 4
Manual Part 2