Wistron NeWeb VM43B WLAN 802.11a + b combo mini-PCI User Manual Acrobat Distiller Job 2
Wistron NeWeb Corporation WLAN 802.11a + b combo mini-PCI Acrobat Distiller Job 2
Manual

1
1
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
Software User Guide
Version : 1.0
Date : 2002/08/09

2
2
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
Main Frame Description................................................................................................ 4
Configuration Setting .................................................................................................... 5
Security Setting ............................................................................................................. 7

3
3
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class
B digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and can radiate radio
frequency energy and, if not installed and used in accordance with the
instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and
on, the user is encouraged to try to correct the interference by one of the
following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that to which
the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: To assure continued compliance, (example - use only shielded
interface cables when connecting to computer or peripheral devices) any
changes or modifications not expressly approved by the party responsible for
compliance could void the user's authority to operate this equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) This device may not cause harmful interference,
and (2) this device must accept any interference received, including
interference that may cause undesired operation.
Statement Needed to be Shown on End Product
Since this module is installed inside the end product, the end product should
be affixed a label on visible area showing that this product contain a RF
module, and also its FCC ID.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an
uncontrolled environment. This equipment should be installed and operated
with minimum distance 20cm between the radiator & your body.
This transmitter must not be co-located or operating in conjunction with any
other antenna or transmitter.
4
4
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
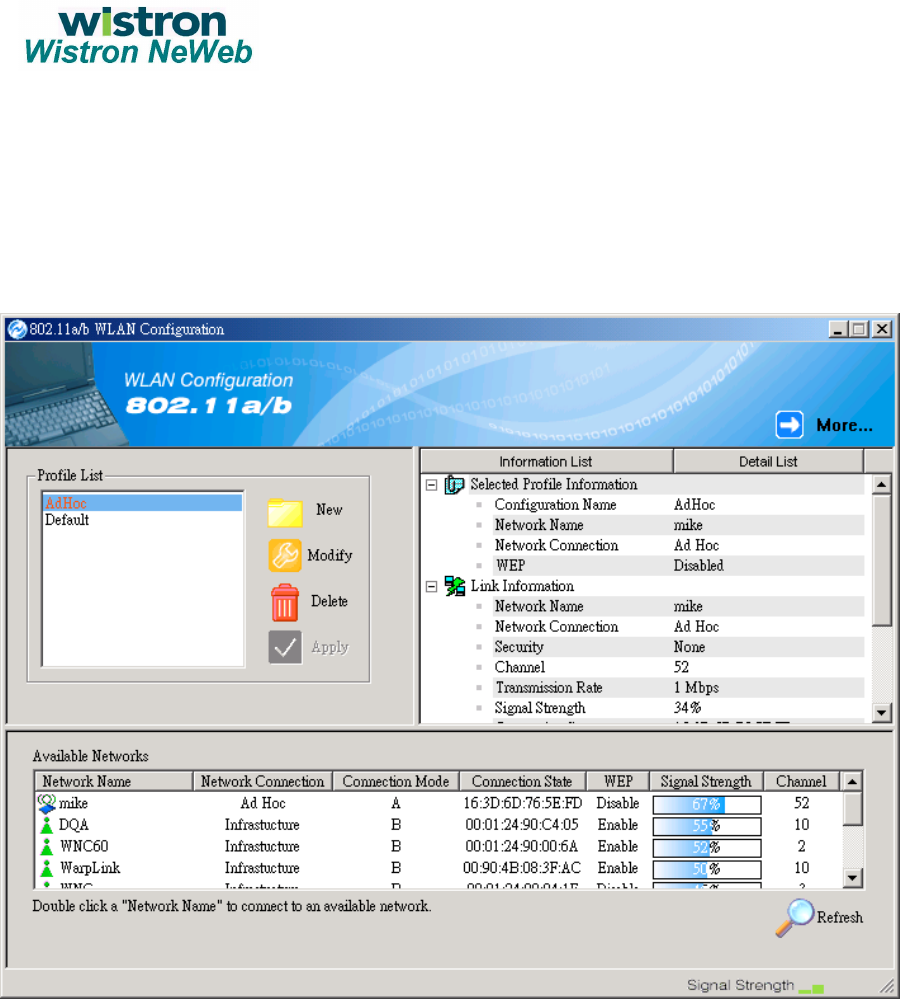
Main Frame Description
The main frame specifies three lists: Profile List, Information List, and Available
Network List. In the Profile List, you can create a new profile or modify / delete
the selected profile or set one of the profiles. After configuring the wireless
network adapter, you can get some information from Information List. This
Information List contains Selected Profile Information, Link Information, and
TCP/IP Information. At Available Network List, you can find all of the IEEE
802.11a and 802.11b wireless networks in range. You can press Refresh
button to refresh the available networks or double-click the network name to
connect to it. You also can get some information about manufacturer from
More button.
5
5
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
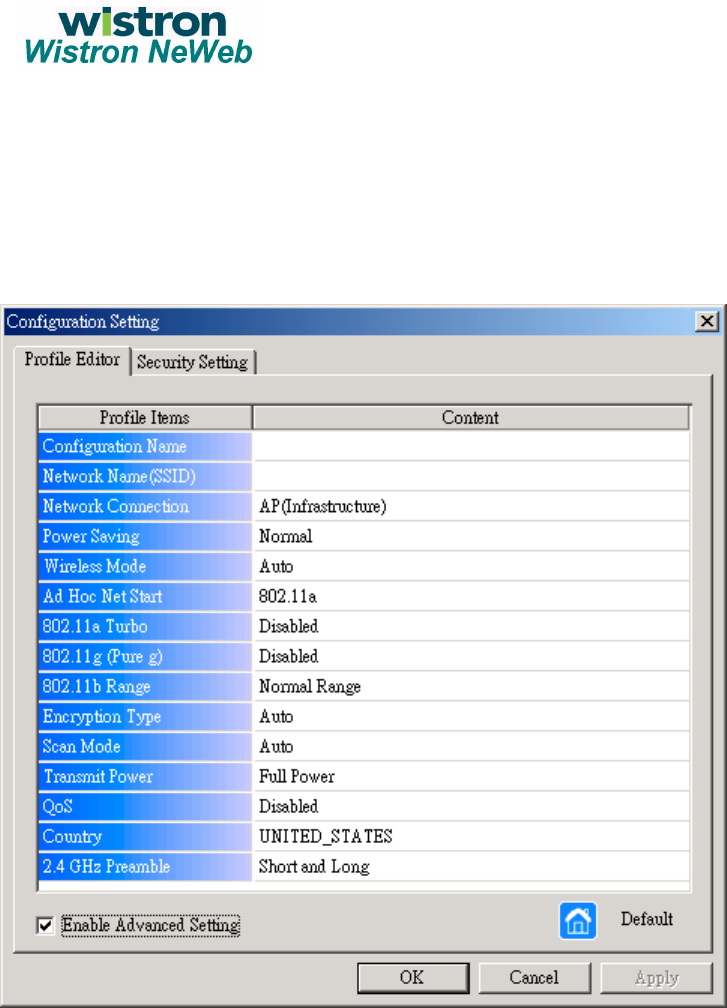
Configuration Setting
Configuration Name: This field identifies the configuration. This name
must be unique. Configuration names are case insensitive.
Network Name: This is the name of the IEEE 802.11a or 802.11b wireless
network, for example, “IEEE 802.11a Wireless Network”. This field has a
maximum limit of 32 characters.
Network Connection: This field defines whether the adapter is
configured for an ad hoc or infrastructure network.
Power Saving: This field allows the configuration of power management
options. The options are Off, Normal, and Maximum. Power management
is disabled when ad hoc mode is selected in the Network Connection field.
9 When the Power Saving setting is Off, the adapter

6
6
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
receives full power from the PC.
9 When the Power Saving setting is Normal, the driver
turns off power to the adapter for brief periods over
briefly-spaced time intervals.
9 When the Power Saving setting is Maximum, the driver
turns off power to the adapter for longer periods over
more widely-spaced time intervals.
Wireless Mode: Specifies 802.11a, 802.11b, or auto-select operation.
Auto-select allows the use of both 802.11a and 802.11b modes.
Ad-Hoc Net Start: Specifies a band to establish an ad-hoc network if no
matching SSID is found after scanning all available modes.
802.11a Turbo: Turbo mode for 802.11a radio space. Once enabled,
channel for 802.11a turbo modes are scanned.
802.11b Range: Specifies the normal range or extended range on the 2.4
GHz.
Encryption Type: Specifies the encryption type.
9 WEP – use only WEP encryption
9 AES – only associate with Access Points that can
successfully negotiate AES encryption.
9 Auto – allow the STA and AP to negotiate the
encryption type.
Scan Mode: Specifies passive, or auto scanning (use country code to
select the type of scan, active or passive).
Transmit Power: Selects 100%, 50%, 25%, 12.5%, or lowest transmit
power.
QoS: Disable or enable the station to cooperate in a network using Quality
of Service.
Country: You can select the country code and these regions represent
three regulatory domains, namely the FCC, ETSI, and MKK.
2.4GHz Preamble: Specifies short & long, or long preamble. Allows ad-
hoc compatibility with other 2.4 GHz devices.
7
7
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
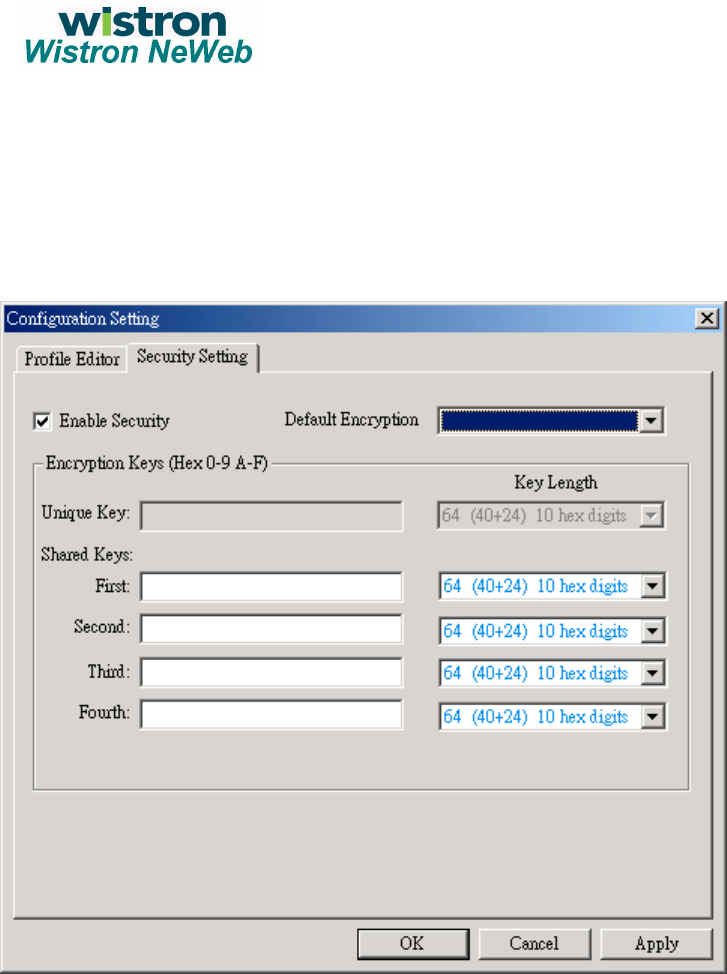
Security Setting
Enable Security: This field completely enables or disables the IEEE
802.11 wired equivalent privacy (WEP) security feature.
Default Encryption Key: This field defines the type of encryption key to
use (either Unique Key or Shared Keys). This field allows you to select
only a key (Unique, First, Second, Third, or Fourth) whose corresponding
field has been completed.
Unique Keys: This field defines the unique encryption key for security for
the current network configuration. In ad hoc mode, this encryption key
type is not used. To enable security using a Unique Key, this field must be
populated.
Shared Key: These fields define a set of shared encryption keys. To
enable security using Shared Keys, at least one Shared Key field must be

8
8
啟碁科技股份有限公司
啟碁科技股份有限公司啟碁科技股份有限公司
啟碁科技股份有限公司
No. 10-1 , Li-hsin Road I
Science-based Industrial Park ,
Hsinchu 300,Taiwan, R.O.C.
Tel: 886-3-6667799
Fax: 886-3-6667711
Web site: www.wneweb.co
m
populated.
Key Length: This field defines the length for each encryption key. As the
Key Length is changed, the number of available characters in the field is
changed automatically. If after a key is entered the length is adjusted to a
smaller number, the key is automatically truncated to fit. If the length is
increased again, the field is not automatically updated to its previous
value.