Contents
- 1. User Manual.pdf
- 2. User Manual Part 1
- 3. User Manual Part 2
User Manual.pdf

ARRIS
®
NVG599 VDSL2 Gateway
ARRIS
®
Embedded Software Version 9.1.0
Administrator’s Handbook
Administrator’s Handbook
Copyright
©ARRIS Enterprises, Inc. 2013 All rights reserved. No part of this publication may be reproduced in any form or by any means or
used to make any derivative work (such as translation, transformation, or adaptation) without written permission from ARRIS
Enterprises, Inc. (“ARRIS”). ARRIS reserves the right to revise this publication and to make changes in content from time to time
without obligation on the part of ARRIS to provide notification of such revision or change.
ARRIS and the ARRIS logo are all trademarks of ARRIS Enterprises, Inc. Other trademarks and trade names may be used in this
document to refer to either the entities claiming the marks and the names of their products. ARRIS disclaims proprietary interest in
the marks and names of others. MOTOROLA and the Stylized M logo are trademarks or registered trademarks of Motorola
Trademark Holdings, LLC. and are used by ARRIS under license. All other product or service names are the property of their
respective owners.
ARRIS provides this guide without warranty of any kind, implied or expressed, including, but not limited to, the implied warranties of
merchantability and fitness for a particular purpose. ARRIS may make improvements or changes in the product(s) described in this
manual at any time.
The capabilities, system requirements and/or compatibility with third-party products described herein are subject to change without
notice.
EXCEPT AS INDICATED IN THE APPLICABLE SYSTEM PURCHASE AGREEMENT, THE SYSTEM, DOCUMENTATION AND
SERVICES ARE PROVIDED "AS IS", AS AVAILABLE, WITHOUT WARRANTY OF ANY KIND. ARRIS GROUP, INC. (“ARRIS”)
DOES NOT WARRANT THAT THE SYSTEM WILL MEET CUSTOMER'S REQUIREMENTS, OR THAT THEIR OPERATION WILL
BE UNINTERRUPTED OR ERROR-FREE, OR THAT ANY ERRORS CAN OR WILL BE FIXED. ARRIS HEREBY DISCLAIMS ALL
OTHER WARRANTIES, EXPRESS OR IMPLIED, ORAL OR WRITTEN, WITH RESPECT TO THE SYSTEM AND SERVICES
INCLUDING, WITHOUT LIMITATION, ALL IMPLIED WARRANTIES OF TITLE, NON-INFRINGEMENT, INTEGRATION,
MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE AND ALL WARRANTIES ARISING FROM ANY COURSE
OF DEALING OR PERFORMANCE OR USAGE OF TRADE.
EXCEPT AS INDICATED IN THE APPLICABLE SYSTEM PURCHASE AGREEMENT, ARRIS SHALL NOT BE LIABLE
CONCERNING THE SYSTEM OR SUBJECT MATTER OF THIS DOCUMENTATION, REGARDLESS OF THE FORM OF ANY
CLAIM OR ACTION (WHETHER IN CONTRACT, NEGLIGENCE, STRICT LIABILITY OR OTHERWISE), FOR ANY (A) MATTER
BEYOND ITS REASONABLE CONTROL, (B) LOSS OR INACCURACY OF DATA, LOSS OR INTERRUPTION OF USE, OR
COST OF PROCURING SUBSTITUTE TECHNOLOGY, GOODS OR SERVICES, (C) INDIRECT, PUNITIVE, INCIDENTAL,
RELIANCE, SPECIAL, EXEMPLARY OR CONSEQUENTIAL DAMAGES INCLUDING, BUT NOT LIMITED TO, LOSS OF
BUSINESS, REVENUES, PROFITS OR GOODWILL, OR (D) DIRECT DAMAGES, IN THE AGGREGATE, IN EXCESS OF THE
FEES PAID TO IT HEREUNDER FOR THE SYSTEM OR SERVICE GIVING RISE TO SUCH DAMAGES DURING THE 12-
MONTH PERIOD PRIOR TO THE DATE THE CAUSE OF ACTION AROSE, EVEN IF COMPANY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES. THESE LIMITATIONS ARE INDEPENDENT FROM ALL OTHER PROVISIONS OF THIS
AGREEMENT AND SHALL APPLY NOTWITHSTANDING THE FAILURE OF ANY REMEDY PROVIDED HEREIN.
All ARRIS products are furnished under a license agreement included with the product. If you are unable to locate a copy of the
license agreement, please contact ARRIS.
Part Number
591861-001-00
V9.1.0
TABLE 1.
Document Change Log
Draft version Firmware version Changes this draft
1 tbd First release

Table of Contents
Table of Contents
CHAPTER 1 - Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
About ARRIS Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Related Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Documentation Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
General . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Internal Web Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Command Line Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Organization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
A Word About Example Screens . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
CHAPTER 2 - Device Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Important Safety Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
POWER SUPPLY INSTALLATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
TELECOMMUNICATION INSTALLATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
COAX INSTALLATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
PRODUCT VENTILATION . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Status Indicator Lights . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Battery Installation (optional) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Battery Door Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Set up the ARRIS Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Microsoft Windows: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Macintosh MacOS 8 or higher or Mac OS X: . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Accessing the Web Management Interface . . . . . . . . . . . . . . . . . . . . 21
Broadband Network Redirect Pages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
IP Diagnostics Page Redirect. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Offline Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Device Status Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Device Access Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Tab Bar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Links Bar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Device List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
System Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Access Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Remote Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Battery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Restart Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Broadband Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Broadband Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Configure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
IGMP Stats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38

Administrator’s Handbook
Home Network Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39
Configure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
HPNA Configure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
WiFi . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Wireless Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
MAC Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Wireless Scan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Subnets & DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
IP Allocation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
HPNA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Voice . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
Line Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Call Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
Packet Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Working with Packet Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
NAT/Gaming . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Custom Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
IP Passthrough . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Firewall Advanced . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Update . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Resets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Syslog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Event Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
NAT Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
CHAPTER 3 - Basic Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Status Indicator Lights . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
LED Function Summary Matrix. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Factory Reset Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
Log Event Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .96
CHAPTER 4 - Command Line Interface . . . . . . . . . . . . . . . . . . . . . . . . . 101
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .103
Starting and Ending a CLI Session . . . . . . . . . . . . . . . . . . . . . . . . . . . .105
Logging In. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Ending a CLI Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Using the CLI Help Facility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .106
About SHELL Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .106
SHELL Prompt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
SHELL Command Shortcuts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .106
SHELL Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .107
Common Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
WPS Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116

Table of Contents
WAN Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
About CONFIG Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
CONFIG Mode Prompt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .118
Navigating the CONFIG Hierarchy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .118
Entering Commands in CONFIG Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .118
Guidelines: CONFIG Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .119
Displaying Current Gateway Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Step Mode: A CLI Configuration Technique. . . . . . . . . . . . . . . . . . . . . . . . . . . .119
Validating Your Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .120
CONFIG Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Connection Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .121
Filter Set Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .124
Global Filter Set (“IPv6 Firewall”) Commands. . . . . . . . . . . . . . . . . . . . . . . . . .128
Queue Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .129
IP Gateway Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .132
IPv6 Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .132
IP DNS Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .139
IP IGMP Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
NTP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .142
Application Layer Gateway (ALG) Commands . . . . . . . . . . . . . . . . . . . . . . . . . .142
Dynamic DNS Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Link Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
Remote Access Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .148
Physical Interfaces Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .150
PPPoE Relay Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .157
NAT Pinhole Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Security Stateful Packet Inspection (SPI) Commands . . . . . . . . . . . . . . . . . . . .158
VoIP Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .160
Targeted Ad Insertion Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .171
System Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .173
Debug Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Disclaimer and Warning Text . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .178
Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
TR-069 CLI CShell Commands (debug mode) . . . . . . . . . . . . . . . . . . . . . . . . . .178
CHAPTER 5 - Technical Specifications and Safety Information. . . . . . 179
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Power Supply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Environment. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .179
Software and protocols. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .179
Agency approvals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Manufacturer’s Declaration of Conformance . . . . . . . . . . . . . . . . . . 181
Important Safety Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
47 CFR Part 68 Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
FCC Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .184
FCC Statements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .184
RF Exposure Statement: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185

Administrator’s Handbook
Electrical Safety Advisory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .185
Caring for the Environment by Recycling . . . . . . . . . . . . . . . . . . . . . .186
Beskyttelse af miljøet med genbrug . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Umweltschutz durch Recycling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Cuidar el medio ambiente mediante el reciclaje . . . . . . . . . . . . . . . . . . . . . . . 186
Recyclage pour le respect de l'environnement. . . . . . . . . . . . . . . . . . . . . . . . . 186
Milieubewust recycleren . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Dba³oÊç o Êrodowisko - recykling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Cuidando do meio ambiente através da reciclagem . . . . . . . . . . . . . . . . . . . . 187
Var rädd om miljön genom återvinning. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Copyright Acknowledgments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .189
Open Source Software Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Appendix A - ARRIS Gateway Captive Portal Implementation . . . . . . 213
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .214
Captive Portal RPC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .215
X_00D09E_GetCaptivePortalParams RPC:. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
X_00D09E_SetCaptivePortalParams RPC: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Appendix B - Quality of Service (QoS) Examples . . . . . . . . . . . . . . . . . 217
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .218
Upstream QoS: Priority and Shaping . . . . . . . . . . . . . . . . . . . . . . . . .220
Downstream QoS: Ethernet Switch . . . . . . . . . . . . . . . . . . . . . . . . . .221
Downstream QoS: Egress queues . . . . . . . . . . . . . . . . . . . . . . . . . . . .221
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223

7
CHAPTER 1 Introduction
About ARRIS Documentation
This guide describes the wide variety of features and functionality of the ARRIS NVG599 Gateway, when used in Router
mode. The NVG599 device can also be delivered in Bridge mode. In Bridge mode, the NVG599 acts as a pass-through device
and allows the workstations on your LAN to have public addresses directly on the Internet. Documentation for the NVG599
in Bridge mode is available for download.
Related Documentation
ARRIS provides a suite of technical documents for its family of intelligent enterprise and consumer gateways.
This documentation consists of:
Administrator’s Handbook (this document)
Dedicated user manuals
Specific white papers covering related technology
The documents are available in electronic form as Portable Document Format (PDF) files. They can be viewed
(and printed) from Adobe Acrobat Reader, Exchange, or any other application that supports PDF files.
NOTE::
For the purposes of this manual the “ARRIS NVG599 Gateway” will be referred to as the “NVG599.”

Administrator’s Handbook
8
Documentation Conventions
This manual uses the following conventions to present information.
General
The following typographic conventions are used in this guide.
Internal Web Interface
The following graphic conventions are used when describing elements of the Web interface in this guide.
Command Line Interface
Syntax conventions for the command line interface are as follows.
Convention Description
bold sans serif Menu commands and button names
underlined sans serif Web GUI page links
terminal Computer display text
bold terminal User-entered text
Italic The complete titles of manuals
Convention (Graphics) Description
An excerpt from a Web page or the visual truncation of a Web page
An area of emphasis on a Web page
Convention Description
[ ] Optional command arguments are shown with straight brackets
{ } Alternative values for an argument are presented in curly ({ }) brack-
ets, with values separated by vertical bars (|).
bold User-entered text
italic Variables for which you supply your own values
blue border
solid rounded rectangle
with an arrow

9
Organization
This guide consists of five chapters, two appendixes, and an index. It is organized as follows:
Chapter 1, “Introduction” — Describes the ARRIS
®
document suite and the purpose of, audience for, and
structure of this guide. It includes a table of style conventions.
Chapter 2, “Device Configuration” — Describes how to get up and running with your NVG599.
Chapter 3, “Basic Troubleshooting” — Gives some simple suggestions for troubleshooting problems with
the initial configuration of your NVG599.
Chapter 4, “Command Line Interface” — Describes all the current text-based commands for both the SHELL
and CONFIG modes. A summary table and individual command examples for each mode are provided.
Chapter 5, “Technical Specifications and Safety Information” — Presents system and device specifications
and important compliance and safety statements.
Appendix A, "ARRIS Gateway Captive Portal Implementation" — Describes the ARRIS Gateway Captive Por-
tal Implementation.
Appendix B, "Quality of Service (QoS) Examples" — Describes the ARRIS Gateway Quality of Service (QoS)
Implementation.
A Word About Example Screens
This manual contains many example screen illustrations. Since ARRIS gateways offer a wide variety of features
and functionality, the example screens shown may not exactly match the screens for your particular device or
setup. The example screens are for illustrative and explanatory purposes, and should not be construed to
represent your own unique environment.

Administrator’s Handbook
10
11
CHAPTER 2 Device Configuration
Most users will find that the basic Quick Start configuration is sufficient to meet their needs. The Quick Start
section may be all that you need to configure and use your ARRIS NVG599 Gateway. For more advanced users,
a rich feature set is available. The following instructions cover installation in Router mode.
This chapter covers:
“Important Safety Instructions” on page 12
“Status Indicator Lights” on page 13
“Battery Installation (optional)” on page 16
“Battery Door Instructions” on page 17
“Set up the ARRIS Gateway” on page 18
“Accessing the Web Management Interface” on page 21
“Device Status Page” on page 24
“Tab Bar ” on page 27
“Broadband Tab” on page 34
“Home Network Tab” on page 39
“WiFi” on page 43
“Voice” on page 53
“Firewall” on page 59
“Diagnostics” on page 78

Administrator’s Handbook
12
Important Safety Instructions
POWER SUPPLY INSTALLATION
Connect the power supply cord to the power jack on the NVG599. Plug the power supply into an appropriate
electrical outlet. There is no power (on / off) switch to power off the device.
TELECOMMUNICATION INSTALLATION
When using your telephone equipment, basic safety precautions should always be followed to reduce the risk
of fire, electric shock, and injury, including the following:
Do not use this product near water, for example, near a bathtub, wash bowl, kitchen sink or laundry tub, in a
wet basement or near a swimming pool.
Avoid using a telephone (other than a cordless type) during an electrical storm. There may be a remote risk
of electrical shock from lightning.
Do not use the telephone to report a gas leak in the vicinity of the leak.
CAUTION: The external phone should be UL listed, and the connections should be made in accordance with
Article 800 of the NEC.
CAUTION: To reduce the risk of fire, use only No. 26 AWG or larger telecommunication line cord.
COAX INSTALLATION
Ensure that the outside coaxial cable system is grounded, so as to provide some protection against voltage
surges and built-up static charges. Article 820-20 of the NEC (Section 54, Part I of the Canadian Electrical Code)
provides guidelines for proper grounding and, in particular, specifies that the CATV cable ground be connected
to the grounding system of the building, as close to the point of cable entry as practical.
PRODUCT VENTILATION
The NVG599 is intended for use in a consumer's home. Ambient temperatures should not exceed 104°F (40°C).
The NVG599 should not be used in locations exposed to outside heat radiation or where it is subject to
trapping of its own heat. The product should have at least one inch of clearance on all sides except the bottom
when properly installed and should not be placed inside tightly enclosed spaces unless proper ventilation is
provided.
SAVE THESE INSTRUCTIONS
WARNING:
The power supply must be connected to a mains outlet with a protective earth connection. Do not defeat the
protective earth connection.
CAUTION:
Depending on the power supply provided with the product, either the direct plug-in power supply blades,
power supply cord plug or the appliance coupler serves as the mains power disconnect. It is important that
the direct plug-in power supply, socket-outlet or appliance coupler be located so it is readily accessible.
WARNING:
The battery used in this device may present a risk of fire or chemical burn if mistreated. Do not disassemble,
heat above manufacturer’s maximum temperature limit, or incinerate. Replace battery with ARRIS
P/N 586185-002-00 only. Use of another battery may present a risk of fire or explosion.
Dispose of used battery promptly. Keep away from children. Do not disassemble and do not dispose of in fire.
13
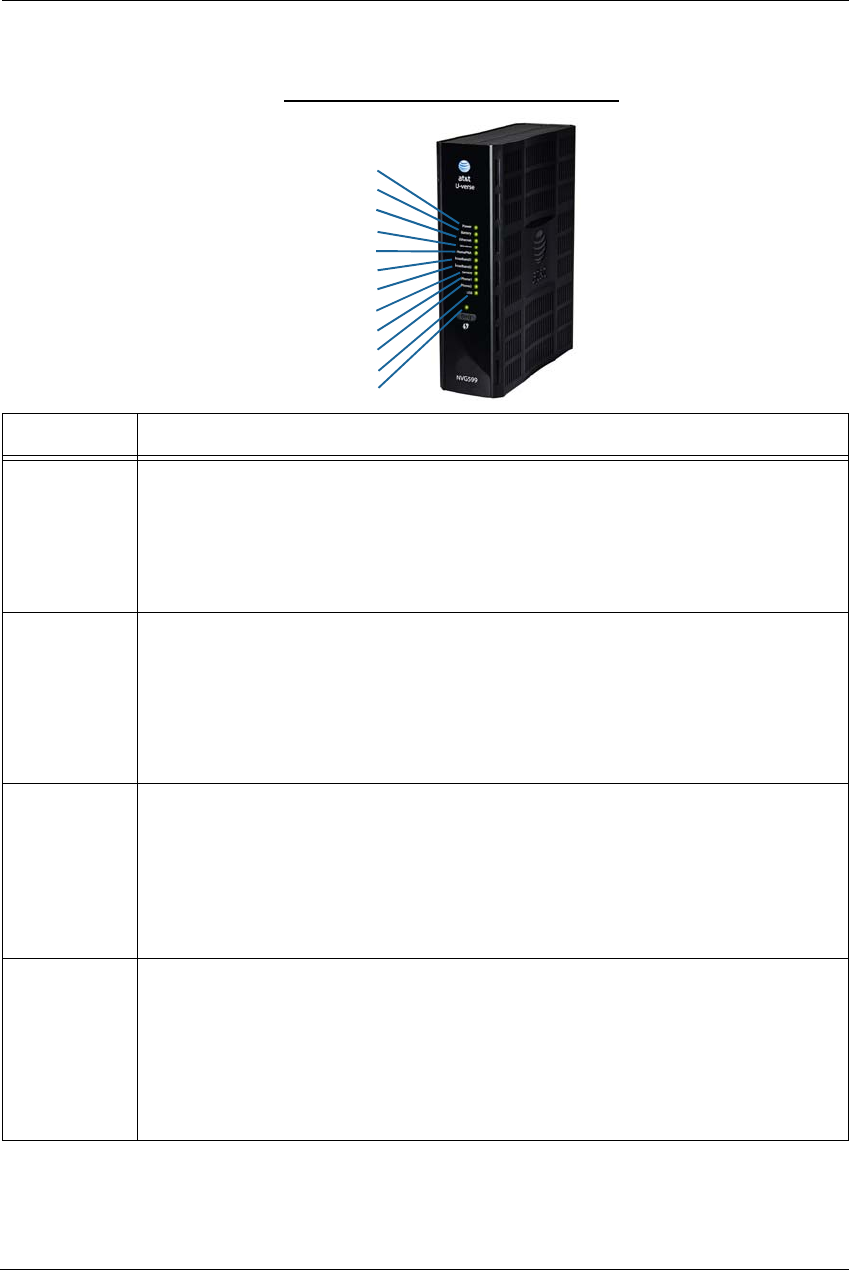
Status Indicator Lights
Colored LEDs on your NVG599 indicate the activity status of various ports.
ARRIS NVG599 Status Indicator Lights
LED Activity
Power
Solid Green = The device is powered.
Flashing Green = A power-on self-test (POST) is in progress
Flashing Red = A POST failure (not bootable) or device malfunction occurred.
Flashing Amber = Firmware upgrade in progress (see below)
Off = The unit has no AC power. If the battery is in use, the Battery LED will indicate battery status,
and all other LEDs will be off.
Power during
Firmware
Upgrade
During the software installation, you will lose Internet and phone service. The LEDs will function as
follows:
1. As firmware is being loaded into flash, the LEDs operate normally.
2. During the firmware upgrade, which takes a few minutes, the Power LED will flashes amber
(flash writing to memory), and all other LEDs are off.
3. The NVG599 restarts automatically.
As the device reboots, the LEDs display power-on behavior.
All during
Boot process
• Power LED = Flashing Green
• All other LEDs = Off
If the device does not boot and fails its self-test or fails to perform initial load of the bootloader:
• Power LED = Flashing Red
• ALL other LEDs = Off
If the device boots and then detects a failure:
Power LED = Flashing Green starting POST, and then all LEDs will flash red, including Power LED.
Battery
Solid Green = Battery in place but not being used.
Flashing Green = Battery charging.
Solid Red = Battery backup mechanism has a fault.
Flashing Red = Battery needs to be replaced.
Solid Amber = Battery in use.
Flashing Amber = Low battery.
Off = No battery, or battery has no charge.
Side View
Power
Battery
Ethernet
WiFi
HomePNA
USB
Broadband 1
Broadband 2
Service
Phone 1
Phone 2
WPS
Administrator’s Handbook
14
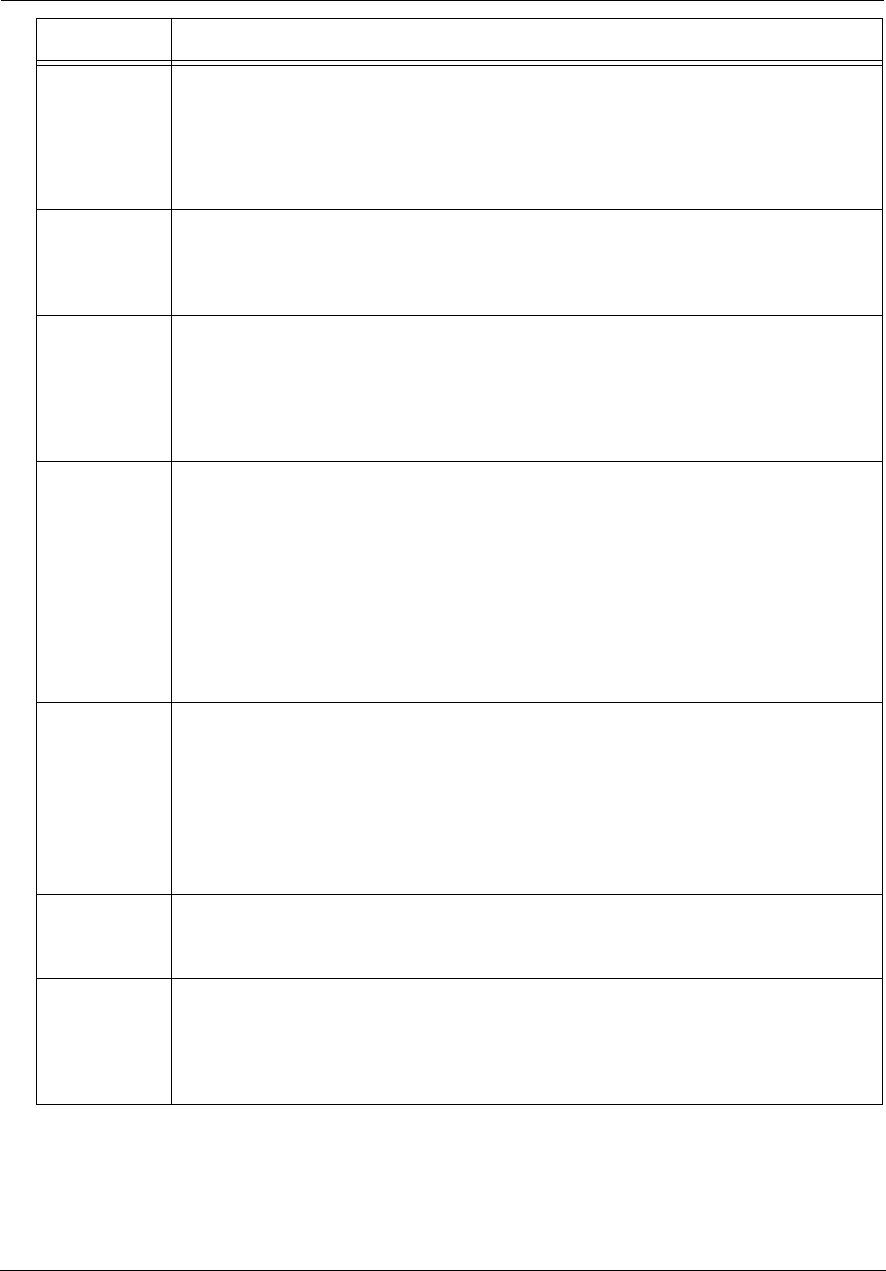
Ethernet
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, or no cable or no powered devices are connected to the associated
ports.
WiFi
Solid Green = Wi-Fi is powered.
Flickering Green = Activity seen from devices connected via Wi-Fi. The flickering of the light is syn-
chronized to actual data traffic.
Off = The device is not powered, or no powered devices are connected to the associated ports.
HomePNA
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, or no cable or no powered devices are connected to the associated
ports.
Broadband
1**, 2
Solid Green = Good broadband connection (good DSL sync or Gigabit Ethernet).
Flashing Green = Attempting broadband connection (DSL attempting sync).
Flashing Green and Red = If, after three consecutive minutes, the broadband connection fails to be
established, the LED switches to Flashing Green alternating with a five second steady Red while
attempting or waiting to establish a broadband connection. This pattern continues until the broad-
band connection is successfully established.
Flashing Red = No DSL signal on the line. This display is not used during times of temporary ‘no tone’
during the training sequence.
Off = The device is not powered.
** Broadband 1 LED is also the Gigabit Ethernet WAN LED when that is in play (and DSL is not).
Service
Solid Green = IP connected. The device has a WAN IP address from DHCP or 802.1x authentication
and the broadband connection is up.
Flashing Green = Attempting connection, attempting IEEE 802.1X authentication, or attempting to
obtain DHCP information.
Red = Device attempted to become IP connected and failed (no DHCP response, 802.1x authentica-
tion failed, no IP address from IPCP, etc.). The Red state times out after two minutes, and the Service
indicator light returns to the Off state.
Off = The device is not powered or the broadband connection is not present.
Phone 1, 2
Solid Green = The associated VoIP line has been registered with a SIP proxy server.
Flashing Green = Indicates a telephone is off-hook on the associated VoIP line.
Off = VoIP not in use, line not registered, or gateway power off.
USB
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, no cable or no powered devices connected to the associated ports.
LED Activity

15
Rear View
WPS
(appears after
using WPS
button)
Solid Green = Wi-Fi Protected Setup has been completed successfully. LED should stay on for 5 min-
utes or until push button is pressed again.
Flashing Green = Continues for 2 minutes, indicating when WPS is broadcasting.
Flashing Red = Continues for 2 minutes, indicating a Session overlap was detected (possible security
risk).
Solid Red = Error unrelated to security, such as failure to find a partner, or WPS is disabled. LED
should stay solid red for 5 minutes or until push button is pressed again.
Off = The device is not powered, or no cable or no powered devices are connected to the associated
ports.
LED Activity
Ethernet
1, 2, 3, 4
Flashing Amber = A Gigabit Ethernet device is connected to each port.
Solid Green = A 10/100 Ethernet device is connected.
Flickering Green = Ethernet traffic activity.
Off = The device is not powered, or no powered devices are connected to the associated ports.
NOTE:
The NVG599 supports two VoIP lines over one RJ14 (FXS) VoIP port. In order to
connect two phone lines, the supplied inner/outer pair splitter adapters must
be attached to the RJ14 (FXS) VoIP port in order to terminate both lines. This is
a special-purpose splitter. You must use only the inner/outer pair splitter
adapters supplied by AT&T.
LED Activity
Gigabit Ethernet (WAN)
USB
DSL (WAN)
Ethernet (LAN)
F-Connector (HPNA)
RJ14 (FXS)
Reset
Power Jack

Administrator’s Handbook
16
Battery Installation (optional)
The optional backup battery is located in a compartment on the bottom of the unit. Installing the battery door
requires some care.
1. Note the tab on the bottom of the battery.
2. Insert the battery into the compartment on the bottom of the unit, as shown, and press into place so that
the battery contacts seat securely in the unit.
3. Close the compartment door. See “Battery Door Instructions” on page 17.
CAUTION:
The battery used in this device may present a risk of fire or chemical burn if mistreated. Do not disassemble,
heat above manufacturer’s maximum temperature limit, or incinerate. Replace battery with ARRIS P/N
586185-002-00 only. Use of another battery may present a risk of fire or explosion.
Dispose of used battery promptly. Keep away from children. Do not disassemble and do not dispose of in fire.
Battery Compartment Door

17
Battery Door Instructions
1. Place NVG599 unit on a tabletop with the battery door side up.
2. Push in and upward to open the battery door as shown in Figure 1.
3. Swing back the battery door. See Figure 2.
4. Insert the battery in the compartment as shown in Figure 3.
5. Swing the door back down and snap closed.
Figure 1
Figure 2
Figure 3
Administrator’s Handbook
18
Set up the ARRIS Gateway
Refer to your Quick Start Guide for instructions on how to connect your NVG599 to your power source, PC, or
local area network, and your Internet access point, whether it is a dedicated DSL outlet or a DSL or cable
modem. Be sure to enable dynamic addressing on your PC. To set up the gateway, complete the following
steps:
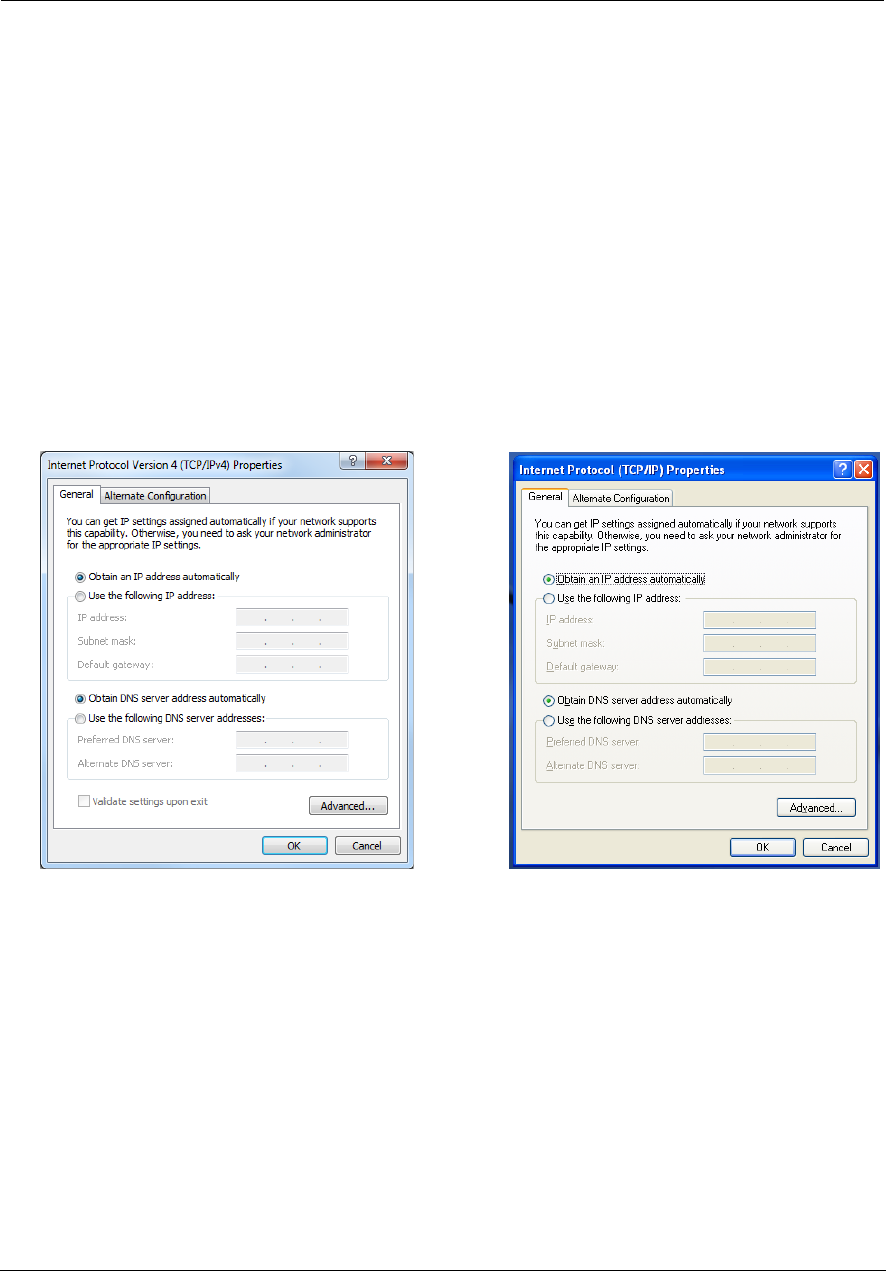
Microsoft Windows:
1. Navigate to the TCP/IP Properties control panel to configure the IP address using one of the suggested path-
ways that follow. Note that Windows Vista and Windows 7 obtain an IP address automatically by default.
You may not need to configure it at all.
Windows 7 follows a path like this: Start menu -> Control Panel -> Network and Sharing Center -> Change
adapter settings -> Local Area Connection -> Change settings of this connection -> Local Area Connection
Properties -> Internet Protocol (TCP/IP) -> Properties
Windows XP follows a path like this: Start menu -> Settings -> Control Panel -> Network Connections -> Local
Area Connection -> Internet Protocol [TCP/IP] -> Properties
2. Select Obtain an IP address automatically.
3. Select Obtain DNS server address automatically, if available.
4. Remove any previously configured gateways, if available.
5. OK the settings. Restart if prompted.
To check:
1. Open the Networking control panel and select Internet Protocol Version 4 (TCP/IPv4).
2. Click the Properties button. The Internet Protocol Version 4 (TCP/IPv4) Properties window should appear as
shown.
Windows 7 Windows XP
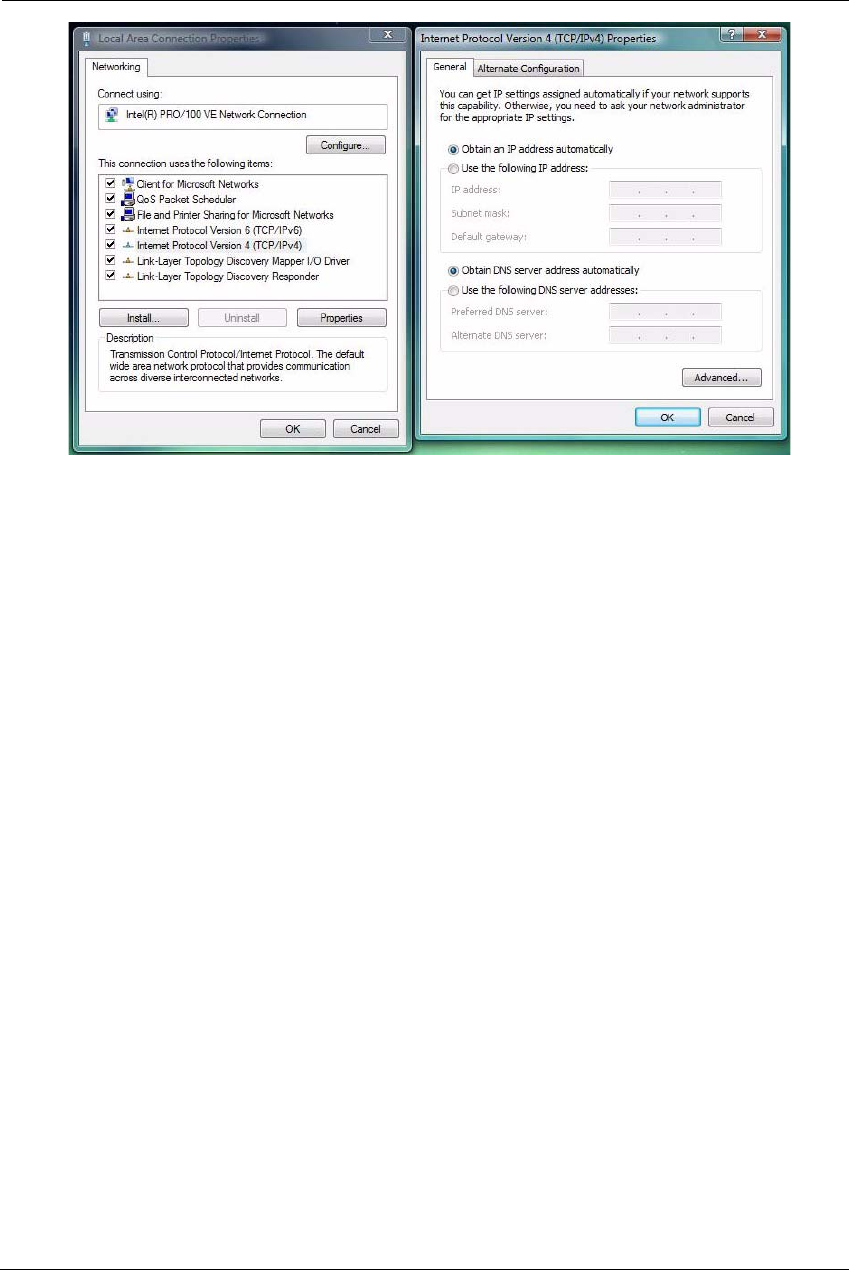
19
3. Set the radio buttons to the values shown above, and click the OK button.
Windows Vista
Administrator’s Handbook
20
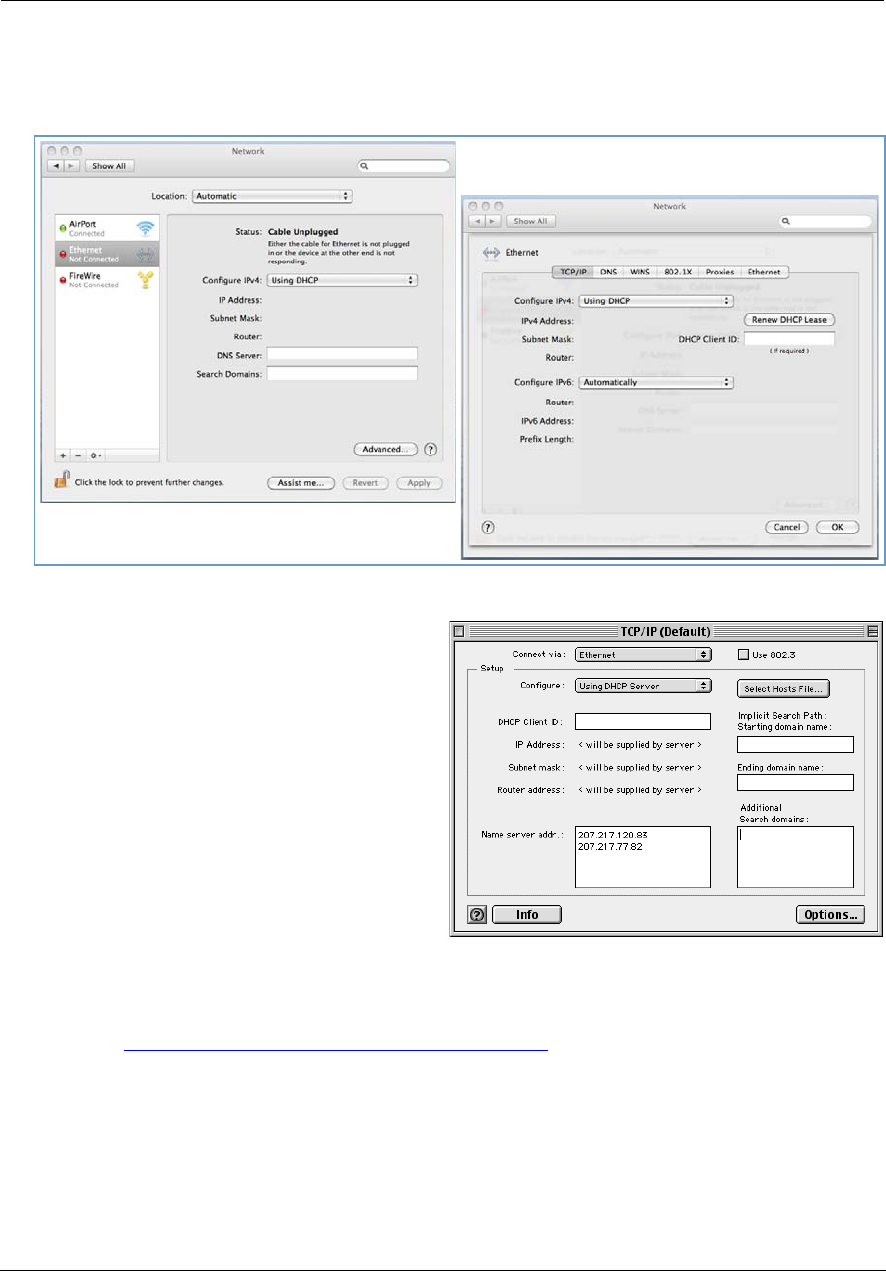
Macintosh MacOS 8 or higher or Mac OS X:
1. Access the TCP/IP or Network control panel.
Mac OS X follows a path like this:
Apple Menu -> System Preferences -> Network
MacOS Classic follows a path like this:
Apple Menu -> Control Panels -> TCP/IP Control
Panel
2. Select Ethernet.
3. Select Configure Using DHCP.
4. Close and save, if prompted.
Proceed to “Accessing the Web Management Interface” on page 21.
21
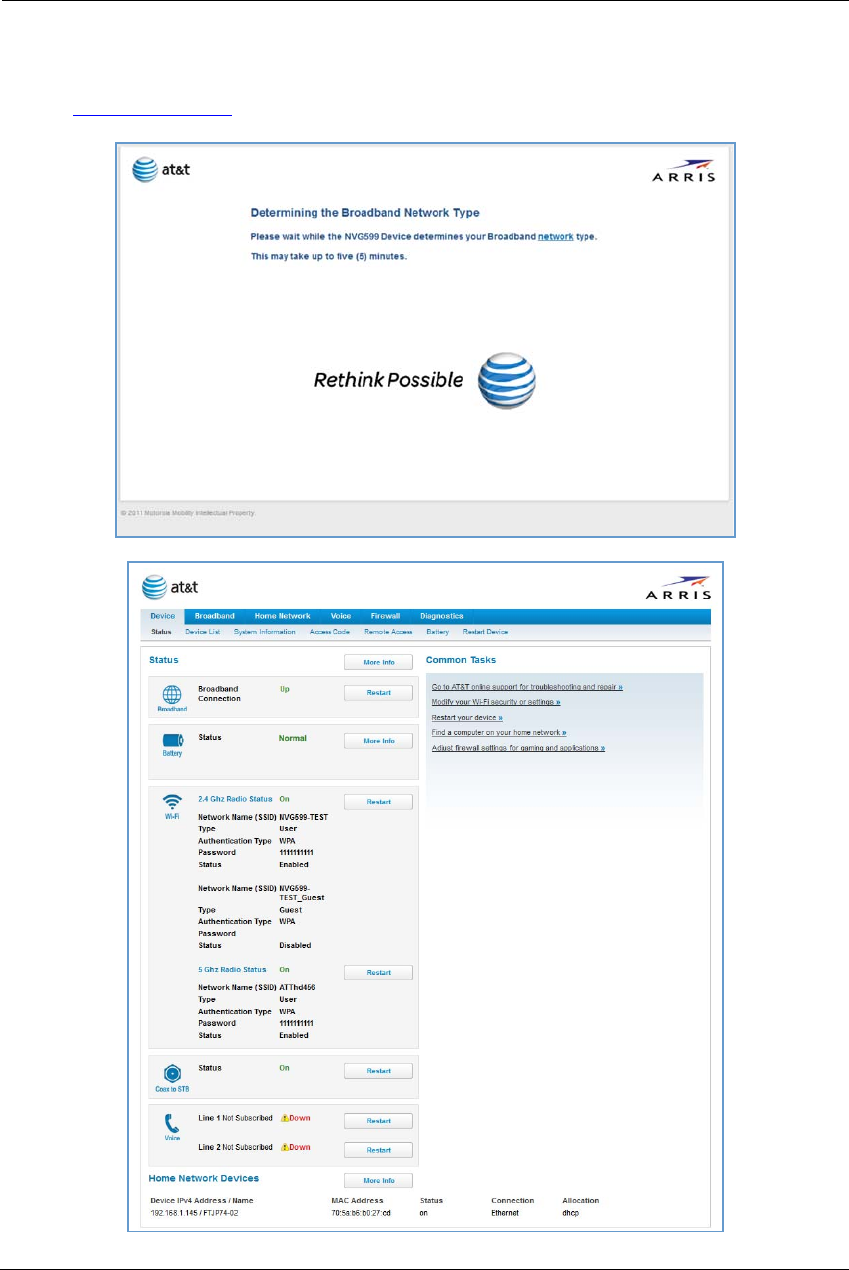
Accessing the Web Management Interface
1. Run your Web browser application, such as Firefox or Microsoft Internet Explorer, from the computer con-
nected to the NVG599 device.
2. Enter http://192.168.1.254 in the Location text box.
While the NVG599 is determining the broadband network type, the following screen appears.
The Device Status page appears.
Administrator’s Handbook
22
3. Check to make sure the Broadband and Service LEDs on your NVG599 device are lit GREEN to verify that the
connection to the Internet is active.
Congratulations! Your installation is complete. You can now surf to your favorite Web sites by typing a URL in
your browser’s location box or by selecting one of your favorite Internet bookmarks.
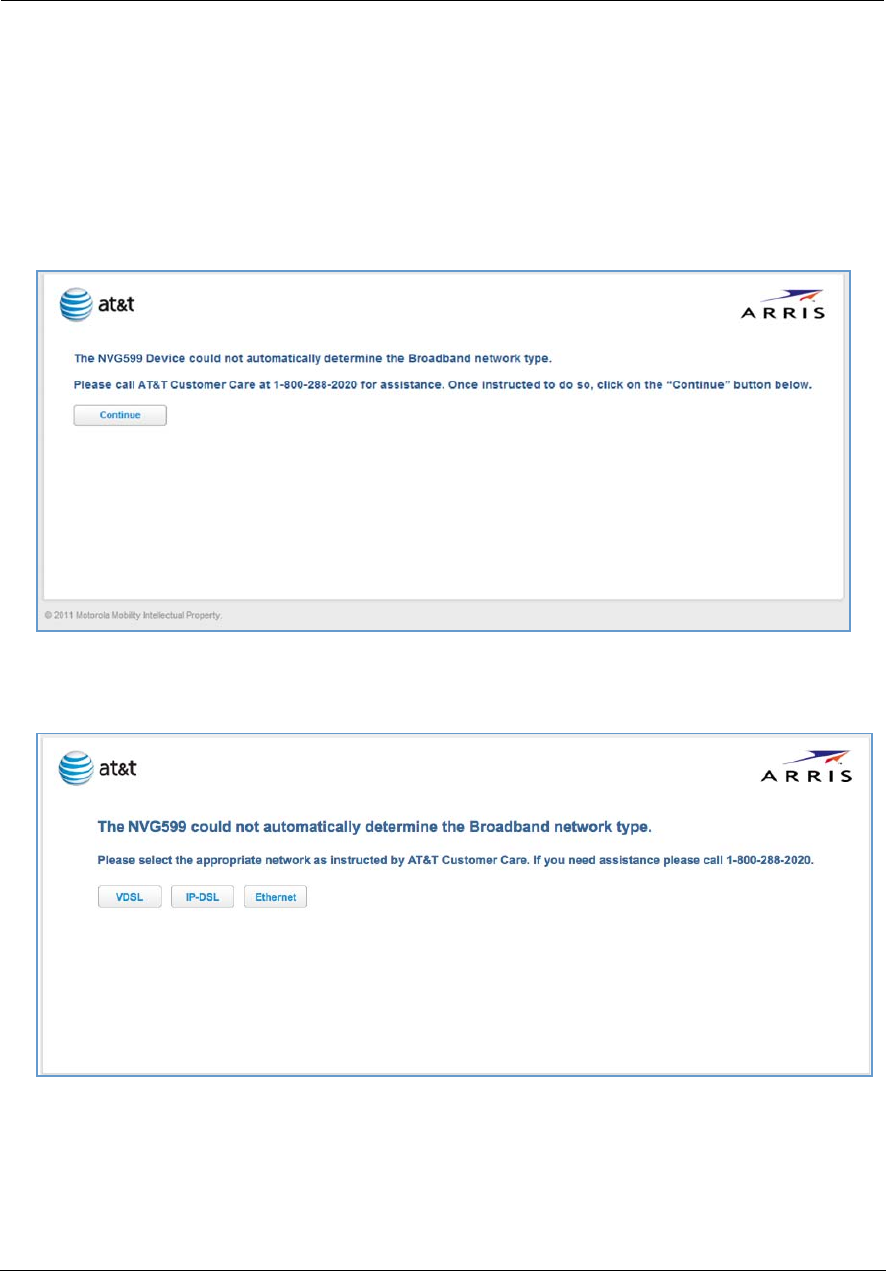
Broadband Network Redirect Pages
After a few minutes, if the broadband network cannot be determined, the following screen appears. Contact
AT&T Customer Care at the number shown on your screen for assistance.
If you click the Continue button, the following screen appears. Here you can manually select the broadband
network type, if you know it.
23
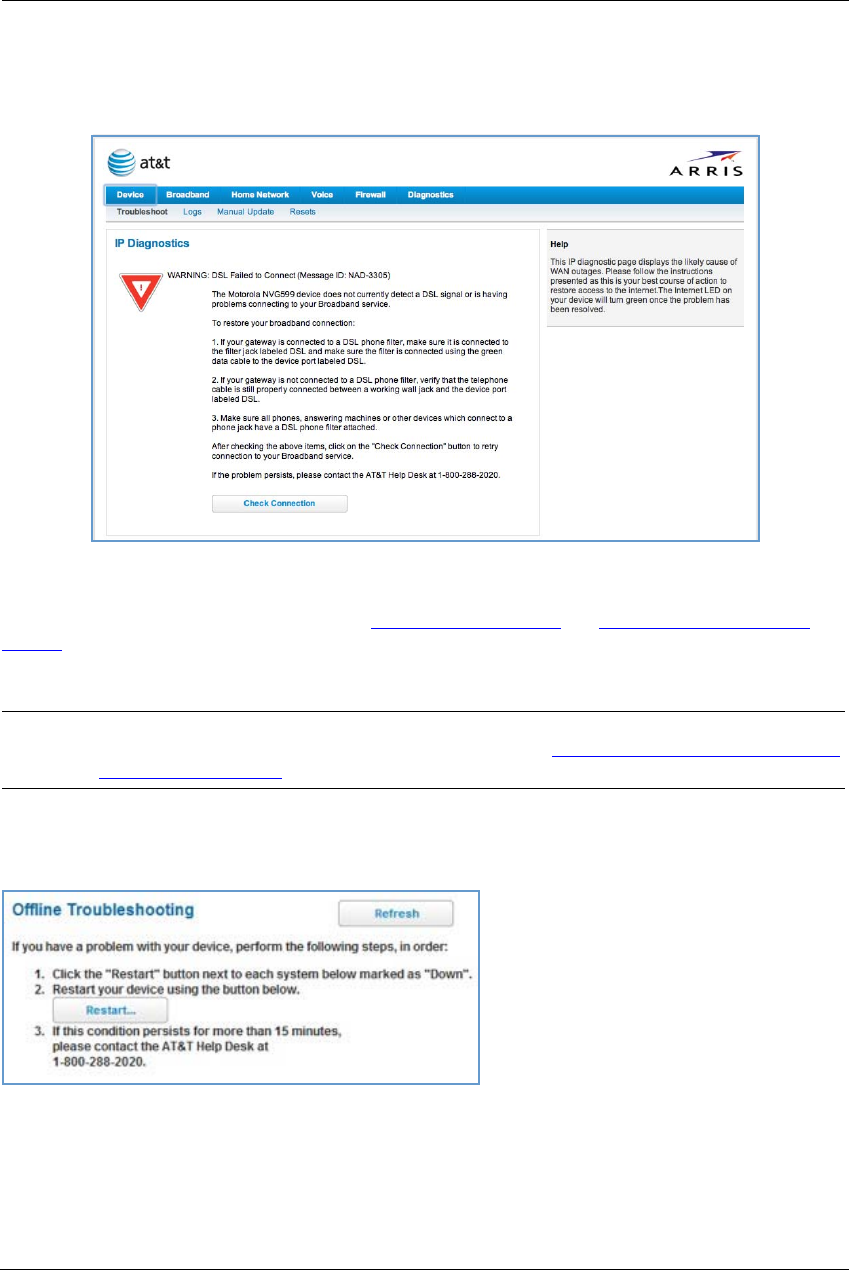
IP Diagnostics Page Redirect
In the event that your connection to the Internet fails, the Broadband LED on your NVG599 device flashes
RED and you are redirected to the IP Diagnostics page.
Follow the on-screen troubleshooting suggestions.
For additional troubleshooting information, see “Diagnostics” on page 78 and “Basic Troubleshooting” on
page 87.
When your connection is restored or the problem is resolved, the Broadband LED turns GREEN.
Offline Troubleshooting
If the WAN is down, the following information is displayed at the top of the page:
NOTE:
For AT&T this function is enabled by default. See the CLI command “set management lan-redirect enable
[ off | on ]” on page 149.
Administrator’s Handbook
24
Device Status Page
After you have performed the basic Easy Login configuration, any time you log in to your NVG599 you will
access the NVG599 Home page.
To access the Home page, type http://192.168.1.254 in your Web browser’s location box.
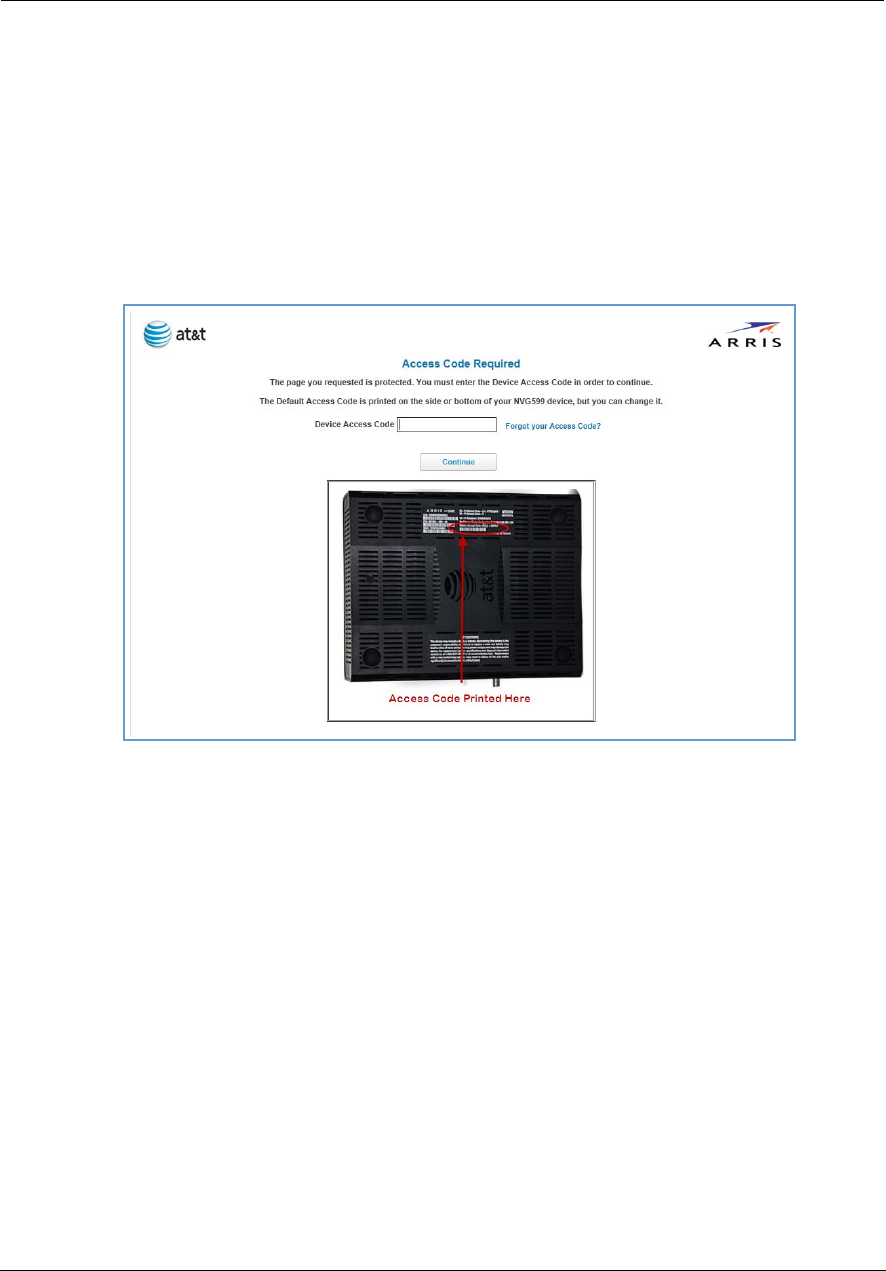
Device Access Code
On the Device Status page, you may be required to provide your device access code to access the Web
management configuration pages. The device access code is unique to your device. It is printed on a label on
the side of the NVG599.
Enter your device access code and click the Continue button.
25
The Device Status page appears.
DeviceStatusWindow
Administrator’s Handbook
26
The Device Status page displays the following information in the center section:
Some fields may or may not be displayed, depending on your particular setup.
The Diagnostics button will connect you to the Troubleshoot page. See “Diagnostics” on page 78.
The frame at right displays some links to commonly performed tasks for easy access.
(icon) Field Description
(Broadband)
Broadband
Connection
Waiting for DSL is displayed while the NVG599 is training. This
should change to Up within two minutes.
Up is displayed when the ADSL line is synched and the session is
established.
Down indicates inability to establish a connection; possible line fail-
ure.
(Battery)
Status May display any of these values: Normal, Low Battery,
Charging, Warning: No battery or battery has no
charge or Warning: Battery backup mechanism has a
fault.
(WiFi)
Status Your wireless signal may be On or Off.
Network ID (SSID) The name or ID that is displayed to a client scan. The default SSID for
the NVG599 is attxxx where xxx is the last 3 digits of the serial
number located on the side of the NVG599.
Authentication Type The type of wireless encryption security in use. May be Disabled,
WPA, WEP, Default Key, or Manual.
Network Key Wireless network encryption key in use.
(Coax to STB)
Status Off or On.
(Voice)
Line 1 Indication of VoIP or other phone connection.
Line 2 Indication of VoIP or other phone connection.
Display additional troubleshooting steps » - OR -
Go to AT&T online support for troubleshooting and repair
This link will connect you to the IP Diagnostics page with
help for troubleshooting and the AT&T Help Desk infor-
mation. See “IP Diagnostics Page Redirect” on page 23.
Modify your WiFi security or settings »
This link will connect you to the WiFi page. See “WiFi” on
page 43.
Restart your device »
This link will connect you to the Restart Device page. See
“Restart Device” on page 33.
Find a computer on your home network »
This link will connect you to the Device List page. See
“Device List” on page 28.
Adjust firewall settings for gaming and applications »
This link will connect you to the NAT/Gaming page. See
“NAT/Gaming” on page 67.
27
Tab Bar
The tab bar is located at the top of every page, allowing you to move freely about the site.
The tabs reveal a succession of pages that allow you to manage or configure several features of your Gateway.
Each tab is described in its own section.
Help
Online Help for your device is available in the rightmost frame on every page in the Web interface. For
example, the Help section at right is displayed on the System Information page.
Links Bar
The links bar appears at the top of each page, allowing you to configure aspects of the features displayed on
the page. For example, the links bar on the Home Summary page is as shown below:
The links bar on the Device Status page includes the following links. For more information about each link, see
the related section in this guide.
Status (see page 24)
Device List (see page 28)
System Information (see page 29)
Access Code (see page 30)
Remote Access (see page 31)
Battery (see page 32)

Administrator’s Handbook
28
Restart Device (see page 33)
Link: Device List
When you click the Device List link, the Device List page appears.
The page displays the following summary information for each home network device connected to the NVG599
device on your local area network: IPv4 address, network name, MAC address, and other status information.
Home Network Devices
MAC Address Client device’s unique hardware address.
IPv4 Address / Name Client device’s IP address or device network name.
Last Activity Date and time of last traffic for this client device.
Status May be off or on.
Allocation Type of IP address assignment, for example, static or DHCP.
Connection Type Type of connection, for example, Ethernet or WiFi.
29
For WiFi client connections, the Device List page displays the familiar bars indicating signal strength, as
follows:
Click the Clear Device List button to update the Home Network Devices summary.
Click the Scan for Devices button to seek out other devices that have been connected since the last Home
Network Devices summary update.
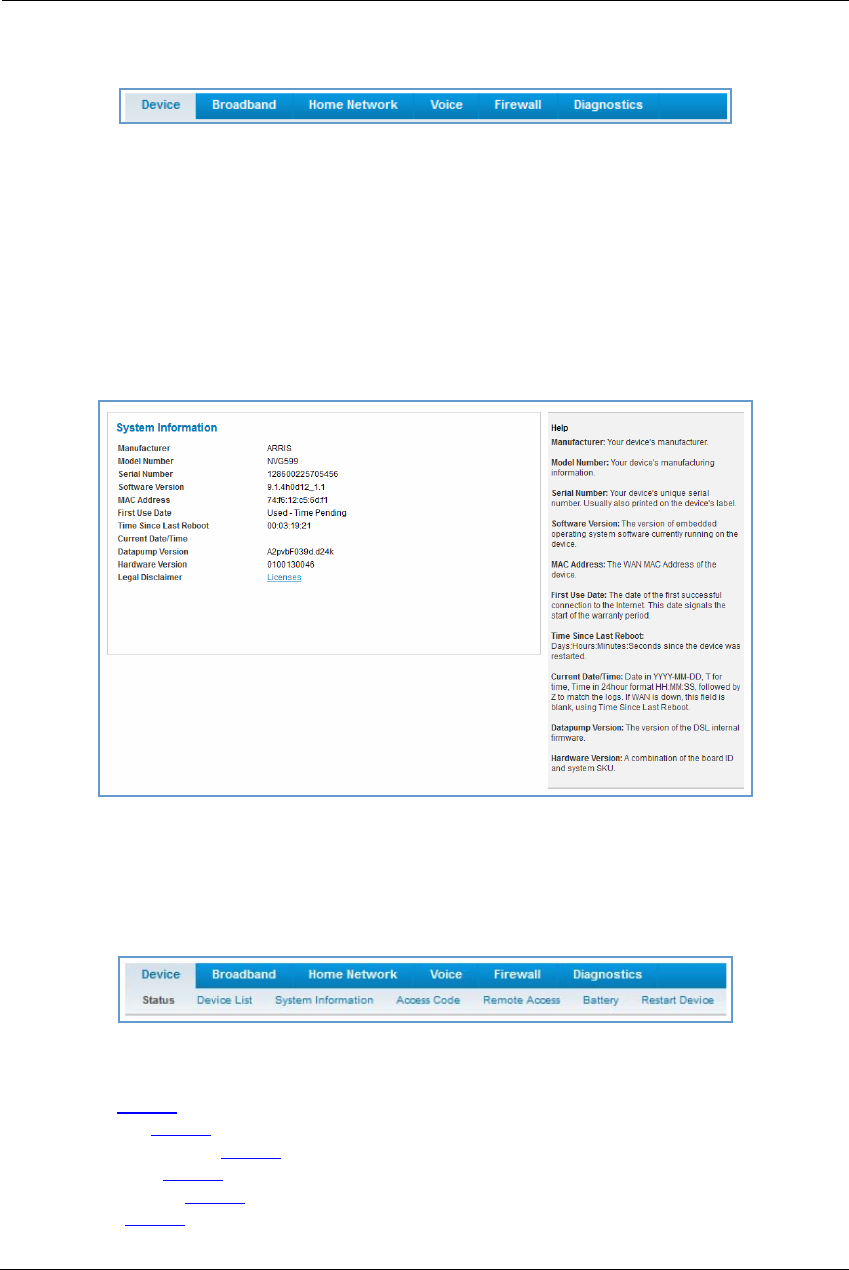
Link: System Information
When you click the System Information link, the System Information page appears.
The page displays the following information:
System Information
Manufacturer Manufacturer’s identifier name.
Model Number Manufacturer’s model number.
Serial Number Unique serial number of your device.
Software Version Version number of the current embedded software in your device.
MAC Address Unique hardware address of this NVG599 unit.
Administrator’s Handbook
30
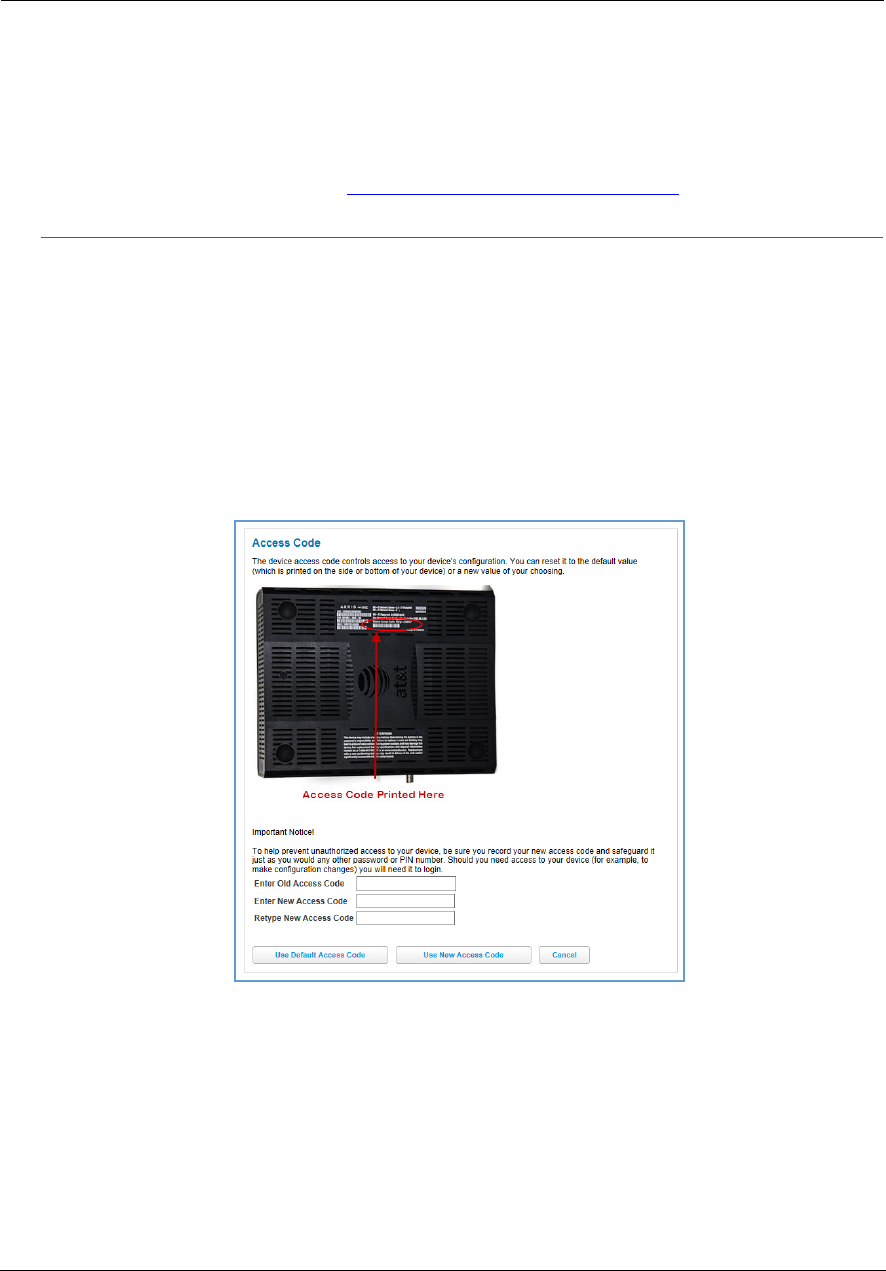
Link: Access Code
When you click the Access Code link, the Access Code page appears and allows changes to the code that
controls access to your device’s configuration. Access to your NVG599 device is controlled through an account
named Admin. The default Admin password for your device is the unique access code printed on the label on
the side of your device.
As the Admin, you can change this password to one of your own choosing between 8 and 20 characters long.
The new password must include two characters from any these categories: alpha, number, and special
characters.
Example: “fru1tfl13s_likeabanana”
Enter your old access code, your new access code, and click the Use New Access Code button. The new access
code takes effect immediately.
You can always return to the original default password by clicking the Use Default Access Code button.
First Use Date Date and time the NVG599 device is first used. This field changes to the current date
and time after a reset to factory defaults.
Time Since Last Reboot Elapsed time since last reboot of the device in days:hr:min:sec.
Current Date/Time Current system date and time in days:hr:min:sec.
Datapump Version Underlying operating system software datapump version.
Legal Disclaimer Clicking the Licenses link displays a listing of software copyright attributions, also
shown in “Copyright Acknowledgments” on page 189.
31
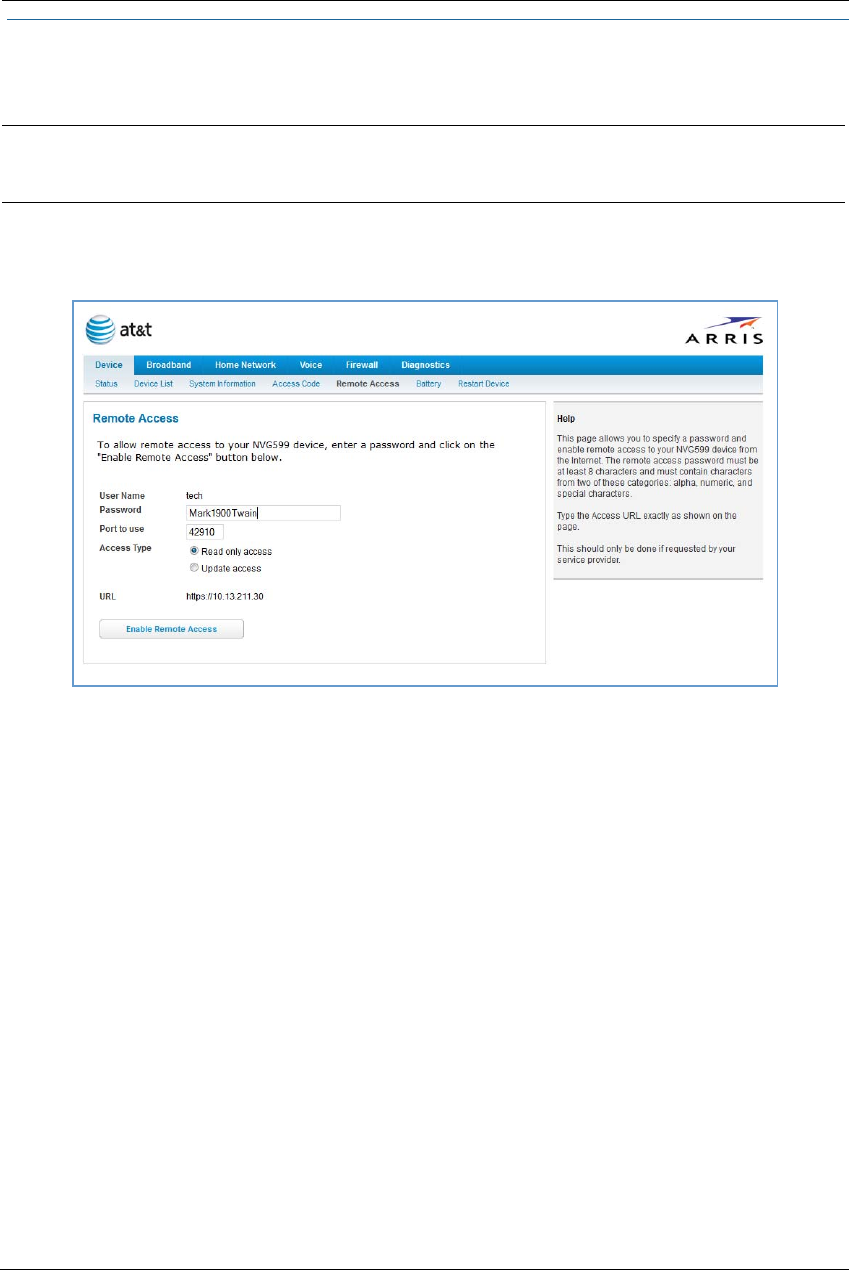
Link: Remote Access
The Remote Access page lets you grant access to your NVG599 device to other users on the WAN. This
function can be used for advanced troubleshooting or remote configuration.
If remote access is not currently enabled, the Remote Access page will let you configure and enable it. If
remote access has been enabled, the Remote Access page will indicate that, and provides a button to disable
it.
To enable remote access:
1. Type a password in the Password field. This password must be at least 8 characters long, and must include at
least two of the following types of characters:
Alphabetic (letter) characters
Numeric (number) characters
Special characters (! @ # $ % ^ & * , etc)
2. If necessary, set a custom port number for secure HTTP access to the NVG599 remote access session in the
Port Value field.
3. Click the radio button that describes the type of remote access to allow:
Read only access - to allow the remote access session to view, but not change, the configuration and col-
lected statistics of the gateway.
Update access - to allow the session to make changes to the gateway’s configuration.
4. Click the Enable Remote Access button.
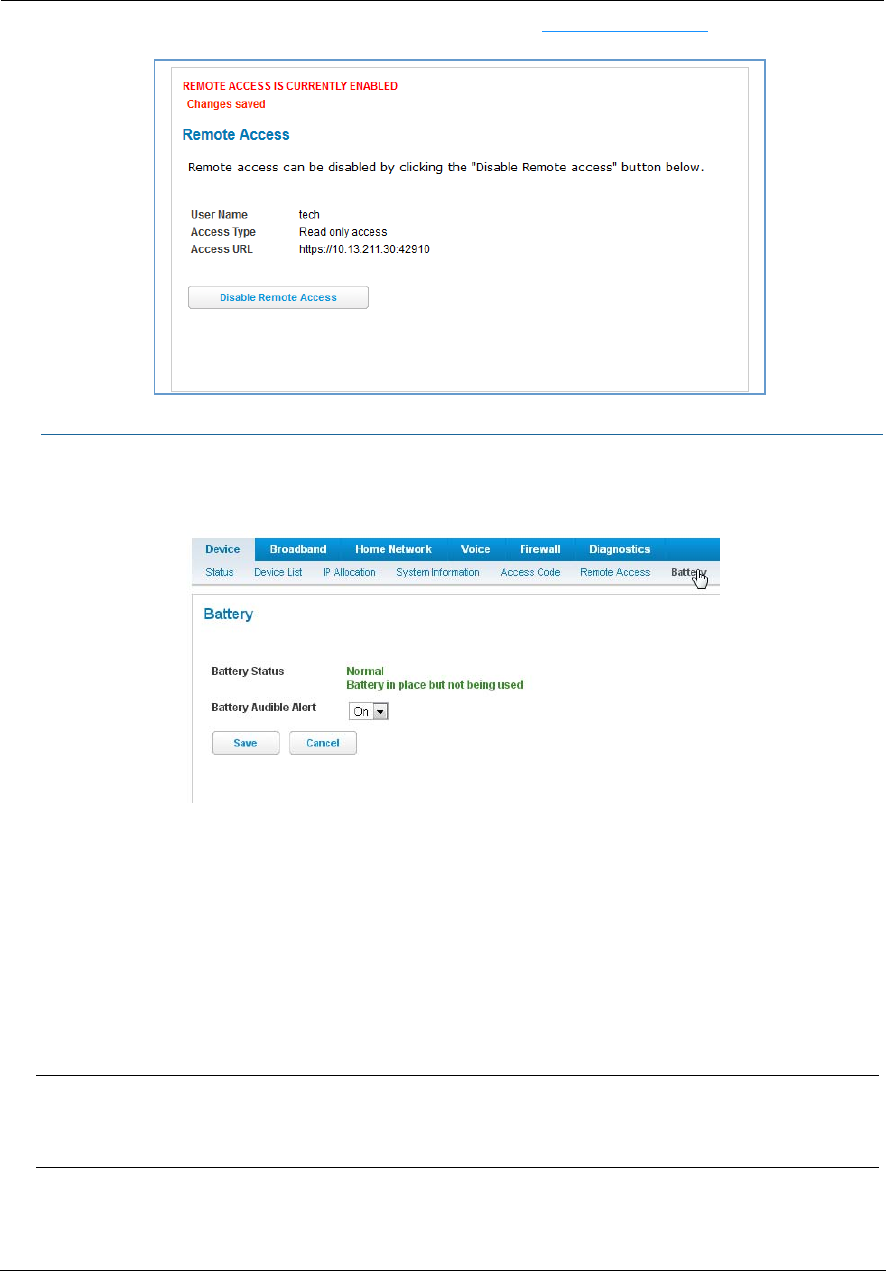
The NVG599 updates the Remote Access page and displays the current remote access settings, shows the URL
that a remote access client must use to connect to the remote access session, and provides a button for ending
the remote access session. The remote access client will need to connect to the URL shown on the Remote
Access page, and will need to log in with the user name “tech” and with the password configured when access
was enabled.
WARNING:
Enabling remote access allows anyone who knows or can determine the password, port ID, and URL
(address) of your NVG599 device to view any configuration settings or change the operation of your gateway.
Administrator’s Handbook
32
To end (disable) an existing remote access configuration, click the Disable Remote Access button, as shown
below:
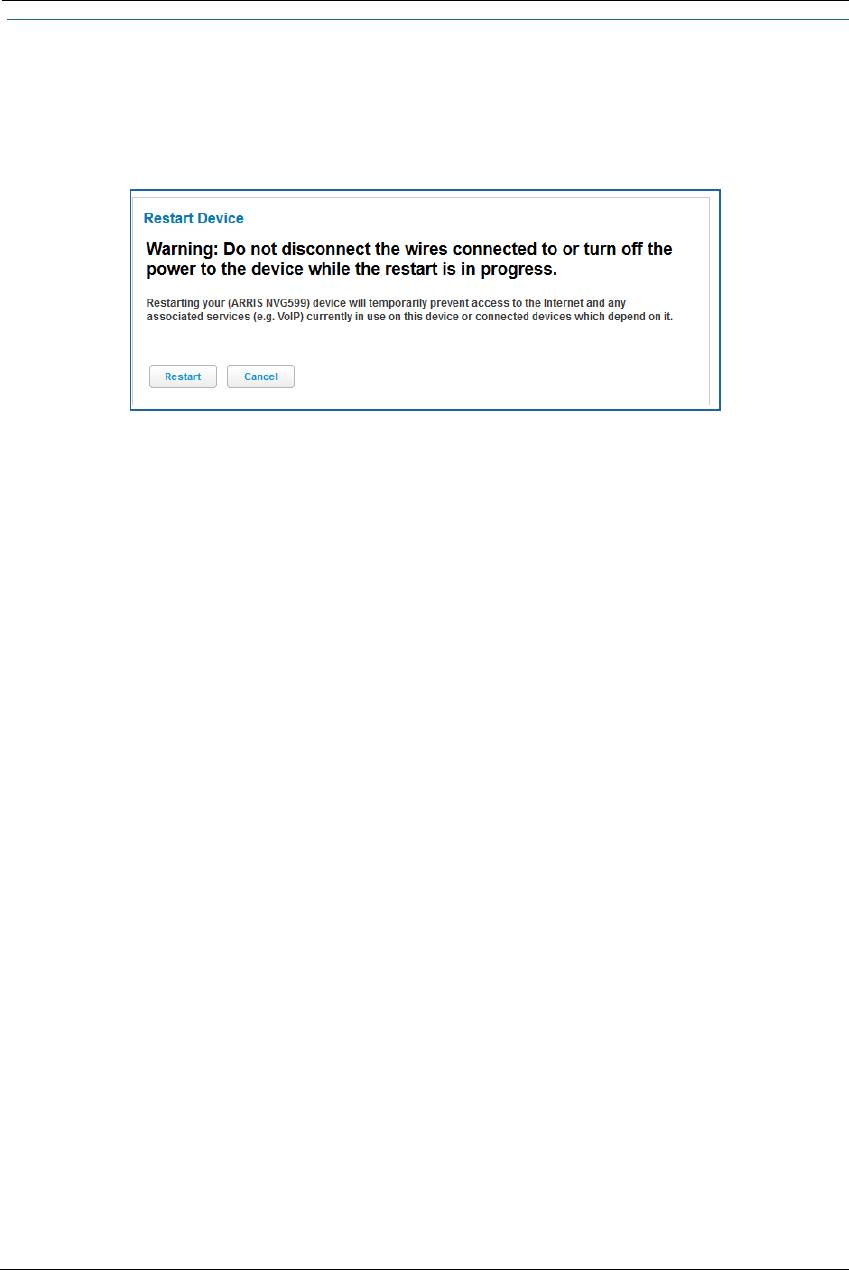
Link: Battery
The Battery page shows the condition and status of the NVG599 internal battery, and provides control over the
battery condition audible alarm.
The battery condition audible alarm provides an on-hook ringing signal on a connected telephone if the
NVG599 battery needs recharging or replacing. This alarm uses a distinctive “splash” ring pattern and a battery
notification message on phones with caller ID displays or announcers. Additionally, the NVG599 provides an
off-hook voice notification to the subscriber if the NVG599 battery is low (and needs recharging) or faulty (and
needs replacing). After playing the recorded voice notification, the NVG599 provides a dial tone.
The alarm is triggered when the NVG599 determines that the installed battery is:
Below 35% charge and in need of recharging, or
Unable to charge past 80% of capacity and in need of replacing.
To change the alarm setting, click the Battery Audible Alert drop-down menu, and select the setting (On or Off)
for the alarm. Click the Save button to save the new settings, or Cancel to discard them.
Note:
A subscriber may interrupt the voice notification by dialing. The voice notification may be turned off by a
subscriber phone dialing “*#103”. This capability is included in the VOIP digit map with the parameter
*#103<:@C06>
33
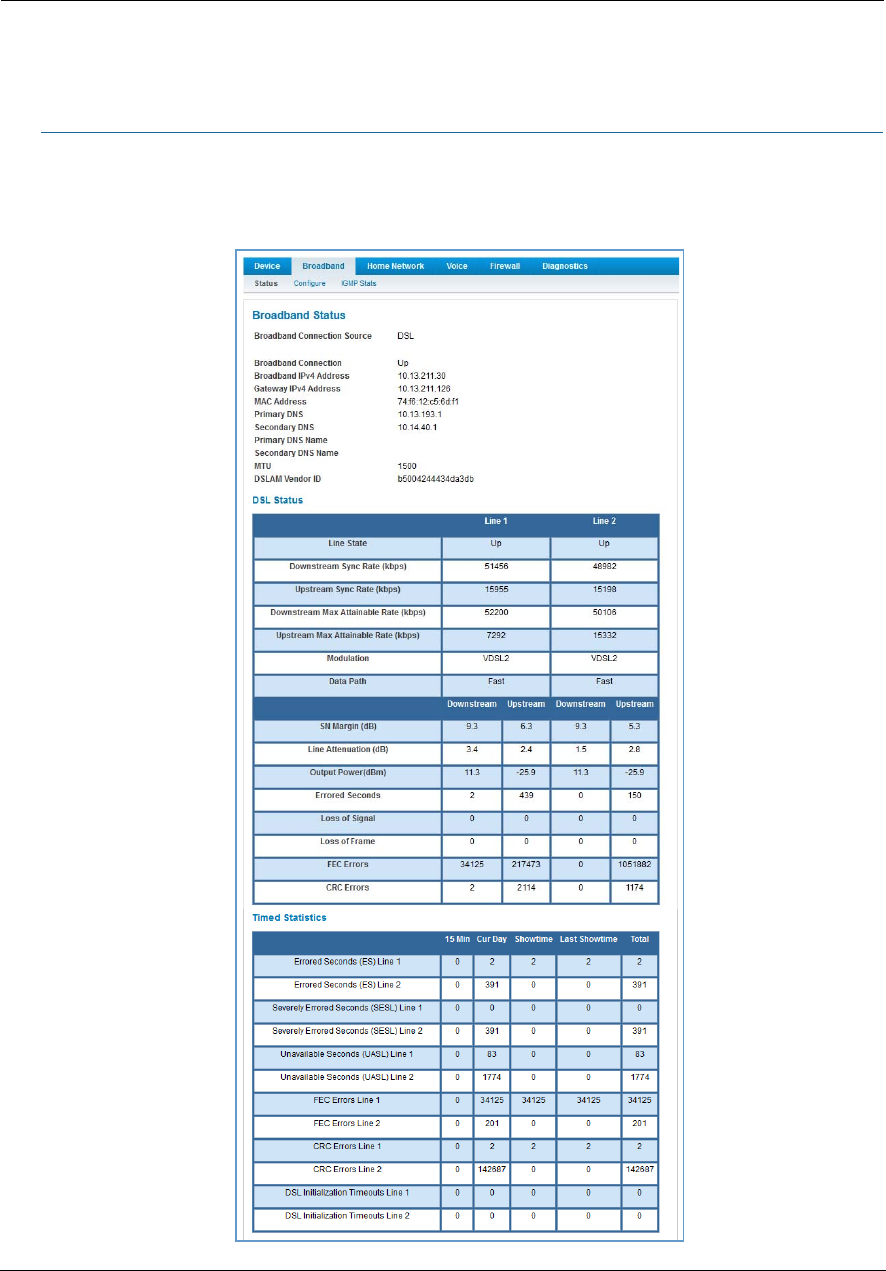
Link: Restart Device
When the NVG599 is restarted, it will disconnect all users, initialize all its interfaces, and load the operating
system software.
In some cases, when you make configuration changes, you may be required to restart for the changes to take
effect.
Administrator’s Handbook
34
Broadband Tab
Links available on the Broadband tab provide access to pages that allow you to view information about the
broadband connection and configure connection details.
Link: Broadband Status
When you click the Broadband tab, the Broadband Status page is the first to appear.

35
The Status page displays information about the NVG599 device’s WAN connection(s) to the Internet.
Broadband Status
Broadband Connection
Source
The communications technology providing the NVG599 broadband uplink.
Broadband Connection May be Up (connected) or Down (disconnected).
Broadband IPv4 Address The public IP address of your device, whether dynamically or statically assigned.
Gateway IPv4 Address Your ISP's gateway router IP address.
MAC Address Your device’s unique hardware address identifier.
Primary DNS The IP address of the primary Domain Name System (DNS) server.
Secondary DNS The IP address of the backup DNS server, if available.
Primary DNS Name The name of the primary DNS server.
Secondary DNS Name The name of the backup DNS server, if available.
MTU Maximum transmittable unit before packets are broken into multiple packets.
DSL Status (for each line)
Line State May be Up (connected) or Down (disconnected).
Downstream Sync Rate The rate at which your connection can download (receive) data on your DSL line, in
kilobits per second.
Upstream Sync Rate The rate at which your connection can upload (send) data on your DSL line, in kilobits
per second.
Modulation Method of regulating the DSL signal. DMT (discrete multi-tone) allows connections to
work better when certain radio transmitters are present.
Data Path Type of path used by the device's processor.
Downstream and Upstream Statistics (DSL WAN)
SN Margin (db) Signal-to-noise margin, in decibels. Reflects the amount of unwanted noise on the DSL
line.
Line Attenuation Amount of reduction in signal strength on the DSL line, in decibels.
Output Power (dBm) Measure of power output in decibels (dB) referenced to one milliwatt (mW).
Errored Seconds The number of uncorrected seconds after being down for seven consecutive seconds.

Administrator’s Handbook
36
Loss of Signal The absence of any signal for any reason, such as a disconnected cable or loss of
power.
Loss of Frame A signal is detected but the device cannot sync with signal because of mismatched
protocols, wrong ISP connection configuration, or faulty cable.
FEC Errors Forwarded Error Correction errors. Count of received errored packets that were fixed
successfully without a retry.
CRC Errors Number of times data packets have had to be resent because of errors in transmission
or reception.
Ethernet Statistics (Ethernet WAN)
Line State Up or Down
Current Speed Line speed
Current Duplex Full- or half-duplex
Receive Packets Number of packets received
Transmit Packets Number of packets sent
Receive Bytes Number of bytes received
Transmit Bytes Number of bytes sent
Receive Unicast Receive Unicast statistics
Transmit Unicast Transmit Unicast statistics
Receive Multicast Receive Multicast statistics
Transmit Multicast Transmit Multicast statistics
Receive Drops Received packets dropped
Transmit Drops Sent packets dropped
Receive Errors Count of received errored packets that were fixed successfully without a retry.
Transmit Errors Number of times data packets have had to be resent due to errors in transmission.
Collisions Count of packet collisions.
Aggregated Information
Bonded Downstream Rate The bonded channel receive rate.
Bonded Upstream Rate The bonded channel transmit rate.
IPv6
Status May be Enabled or Unavailable.
Global Unicast IPv6 Address The public IPv6 address of your device, whether dynamically or statically assigned.
Border Relay IPv4 Address The public IPv4 address of your device.
IPv4 Statistics
Transmit Packets IPv4 packets transmitted.
Transmit Errors Errors on IPv4 packets transmitted.
Transmit Discards IPv4 packets dropped.
IPv6 Statistics
Transmit Packets IPv6 packets transmitted.
Transmit Errors Errors on IPv6 packets transmitted.
Transmit Discards IPv6 packets dropped.
37
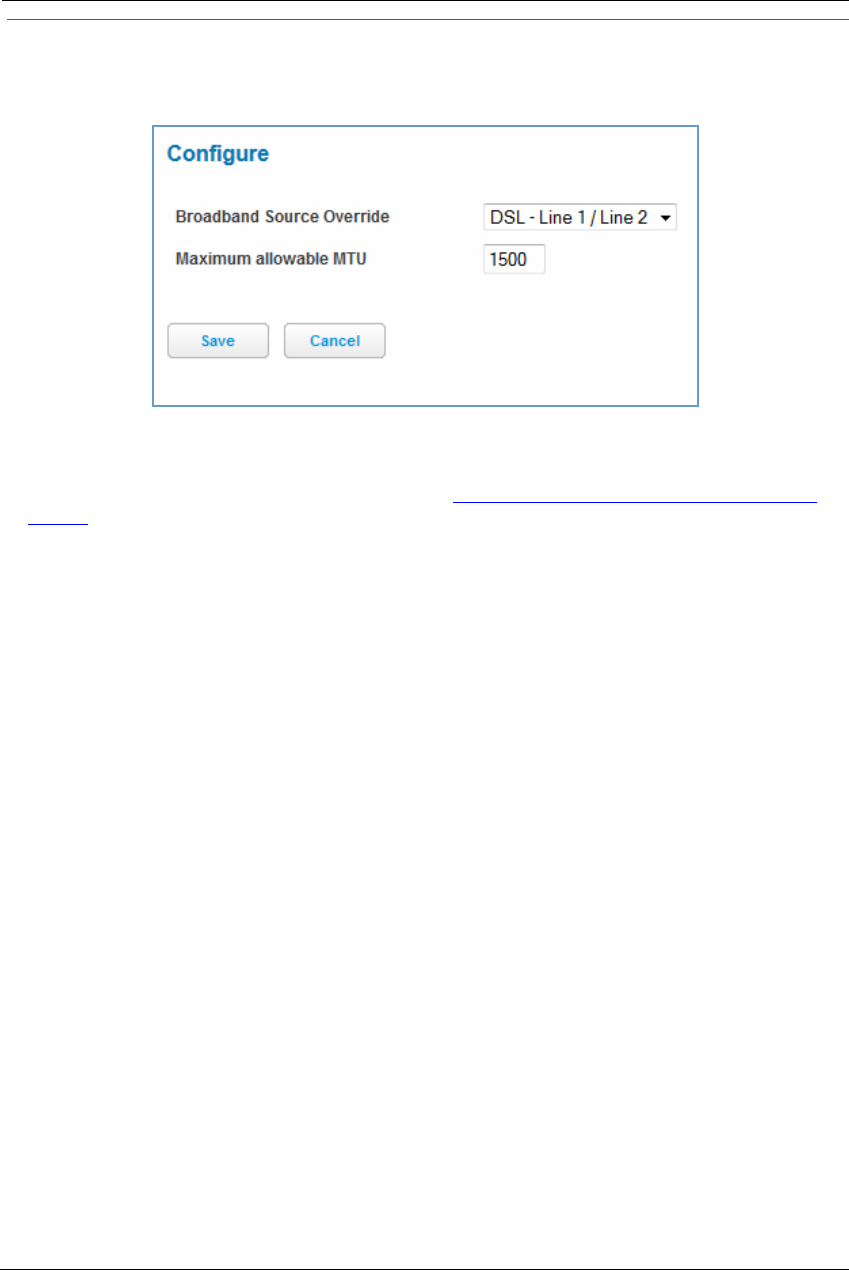
Link: Configure
When you click the Configure link, the Broadband Configure screen appears. Here you can reconfigure your
type of broadband connection should it change in the future.
Broadband Source Override - Auto (automatically detected), DSL - Line 1, DSL - Line 2, DSL - Line 1 / Line -2
(Bonded), or Ethernet WAN.
If you switch from DSL to Ethernet or from Ethernet to DSL, the device will prcoceed to reconnect as in its ini-
tial connection to the Internet, as described earlier. See “Accessing the Web Management Interface” on
page 21.
The WAN connection is automatically configured. However, you can adjust the Maximum allowable MTU
(maximum transmittable unit) value, if your service provider suggests it. The default 1500 is the maximum
value, but some services require other values (1492 is common).
If you make any change here, click the Save button.
Administrator’s Handbook
38
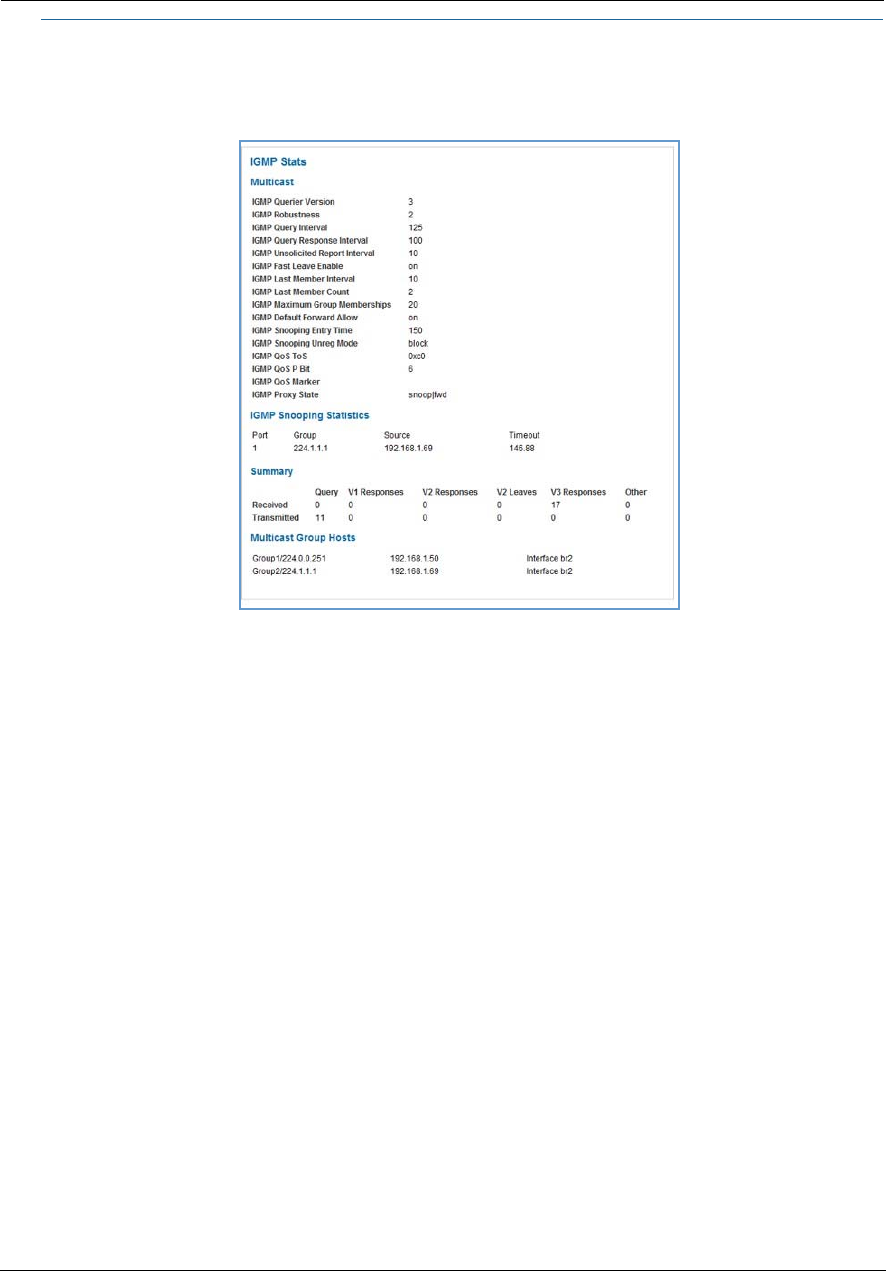
Link: IGMP Stats
When you click the IGMP Stats link, the IGMP Stats screen appears. The IGMP statistics screen reports IGMP
proxy groups and multicast forwarding information. It also displays a packet counter.
39
Home Network Tab
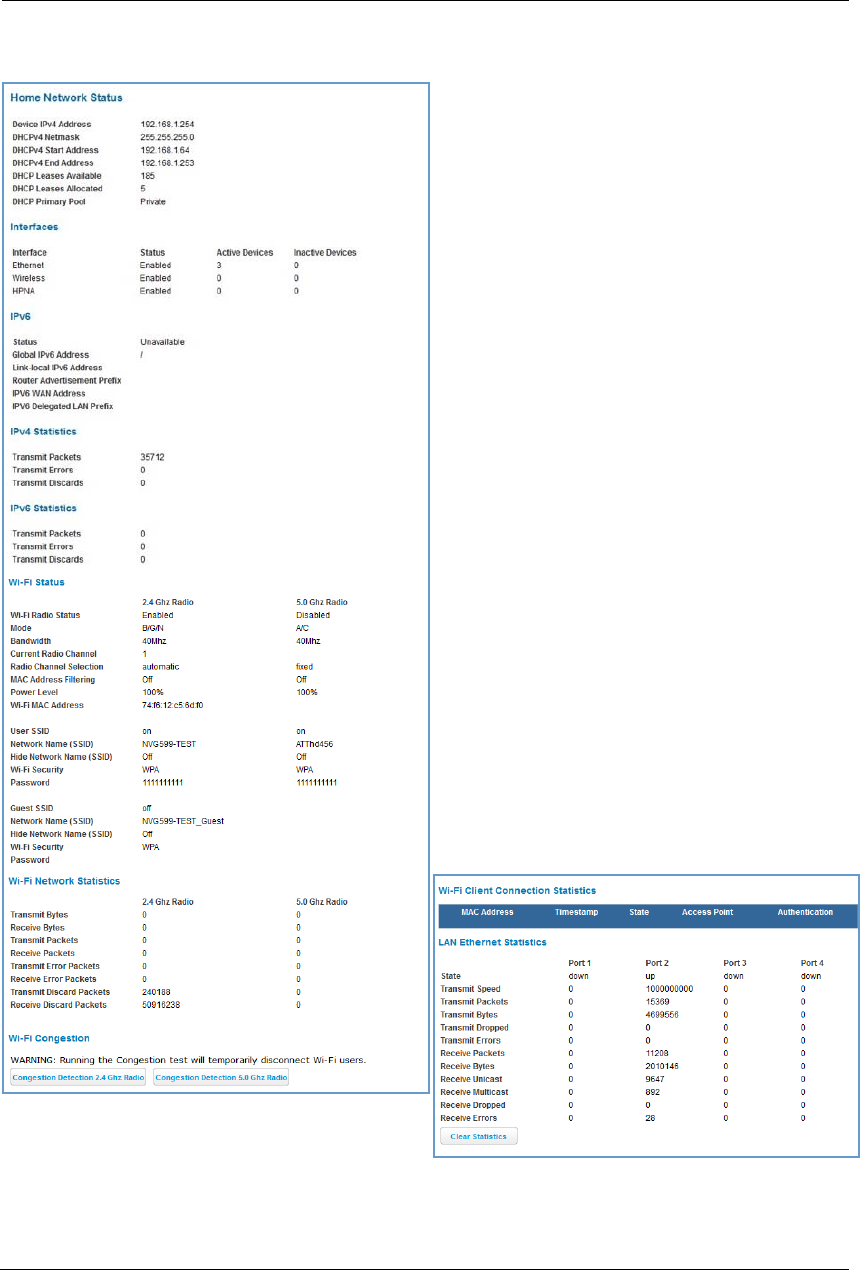
When you click the Home Network tab, the Home Network Status page appears.
The Home Network Status page displays information
about the NVG599 device’s local area network.
If you click the Run Congestion Detection button, the
device will generate statistics for each of the 11
channels available, displaying:
Channel number
AP (access point) count
Congestion score (1 - 10) - Note that higher val-
ues mean lower congestion.
The wireless congestion feature provides simple data
to the user to show the level of network congestion
in each wireless channel. This data can be used to
determine router placement or to determine which
channels to avoid.
The display tells the user how many access points
(APs) are active within each channel, and provides a
score of 1 - 10 to indicate how clear the channel is. A
higher score indicates less congestion in a channel;
thus, a 10 indicates a channel extremely clear of
wireless traffic and noise. Alternatively, a score of 1
indicates more severe congestion in a channel.
You can clear the current statistics information by
clicking the Clear Statistics button.
Administrator’s Handbook
40
Home Network Status
Device IPv4 Address The NVG599 device’s own IP address on the network.
DHCP Netmask The device’s own netmask on the network.
DHCPv4 Start Address The starting IP address of the DHCP range served by the device.
DHCPv4 End Address The ending IP address of the DHCP range served by the device.
DHCP Leases Available The number of IP addresses of the DHCP range available to be served by the device.
DHCP Leases Allocated The number of IP addresses of the DHCP range currently being served by the device.
DHCP Primary Pool Source pool of the IP addresses served by the NVG599 device, Public or Private.
IPv6
Status May be Enabled or Unavailable.
Global IPv6 Address The public IPv6 address of your device, whether dynamically or statically assigned.
Link-local IPv6 Address The private IPv6 address of your device, whether dynamically or statically assigned.
Router Advertisement Prefix The IPv6 prefix to include in router advertisements.
IPv6 Delegated LAN Prefix The IPv6 network address prefix that identifies the NVG599 network.
IPv4 Statistics
Transmit Packets IPv4 packets transmitted.
Transmit Errors Errors on IPv4 packets transmitted.
Transmit Discards IPv4 packets dropped.
IPv6 Statistics
Transmit Packets IPv6 packets transmitted.
Transmit Errors Errors on IPv6 packets transmitted.
Transmit Discards IPv6 packets dropped.
WiFi Status
WiFi Radio Status Status of the Wi-Fi radio: Enabled or Disabled.
Mode May be 802.11B only, 802.11G only, 802.11N only, 802.11 B/G or 802.11 B/G/N. For
the 5.0 Ghz radio, may be 802.11AC as well.
Bandwidth The capacity of the wireless LAN to carry traffic in megahertz.
Current Radio Channel The radio channel that your Wi-Fi network is broadcasting on.
Radio Channel Selection May be set to automatic or manually selected.
MAC Address Filtering May be either On or Off. If On, you can accept or block client devices from your WLAN
based on their MAC address.
Power Level May be adjusted up to 100%, lower if multiple wireless access points are in use, and
might interfere with each other.
WiFi MAC Address Shows the information of the MAC address of the wireless subsystem.
User SSID May be either On or Off for either frequency.
Guest SSID May be either On or Off for the 2.4 Ghz radio only.
Network Name (SSID) The name or ID that is displayed to a client scan. The default SSID for the NVG599 is
attxxx where xxx is the last 3 digits of the serial number located on the side of the
NVG599 device.
Hide SSID May be either On or Off. If On, your SSID will not appear in a client scan.
Wireless Security The type of wireless encryption security in use. May be Disabled, WPA, WEP,
Default Key, or Manual.
41
The links at the top of the Home Network page provide access to a series of pages that allow you to configure
and monitor features of your device.
The links bar on the Home Network page includes the following links. For more information about each link,
see the related section in this guide.
Configure (see page 42)
HPNA Configure (see page 42)
Wifi (see page 43)
MAC Filtering (see page 46)
Wireless Scan (see page 47)
Subnets & DHCP (see page 47)
IP Allocation (see page 49)
HPNA (see page 51)
Password Shows the information of the security encryption key in use.
WiFi Network Statistics
Transmit Bytes Number of bytes transmitted on the Wi-Fi network.
Receive Bytes Number of bytes received on the Wi-Fi network.
Transmit Packets Number of packets transmitted on the Wi-Fi network.
Receive Packets Number of packets received on the Wi-Fi network.
Transmit Error Packets The number of errors on packets transmitted on the Wi-Fi network.
Receive Error Packets The number of errors on packets received on the Wi-Fi network.
Transmit Discard Packets The number of packets transmitted on the Wi-Fi network that were dropped.
Receive Discard Packets The number of packets received on the Wi-Fi network that were dropped.
LAN Ethernet Statistics
State May be Up or Down.
Transmit Speed The maximum speed of which the port is capable.
Transmit Packets The number of packets sent out from the port.
Transmit Bytes The number of bytes sent out from the port.
Transmit Dropped The number of packets sent out from the port that were dropped.
Transmit Errors The number of errors on packets sent out from the port.
Receive Packets The number of packets received on the port.
Receive Bytes The number of bytes received on the port.
Receive Unicast The number of unicast packets received on the port.
Receive Multicast The number of multicast packets received on the port.
Receive Dropped The number of packets received on the port that were dropped.
Receive Errors The number of errors on packets received on the port.
Administrator’s Handbook
42
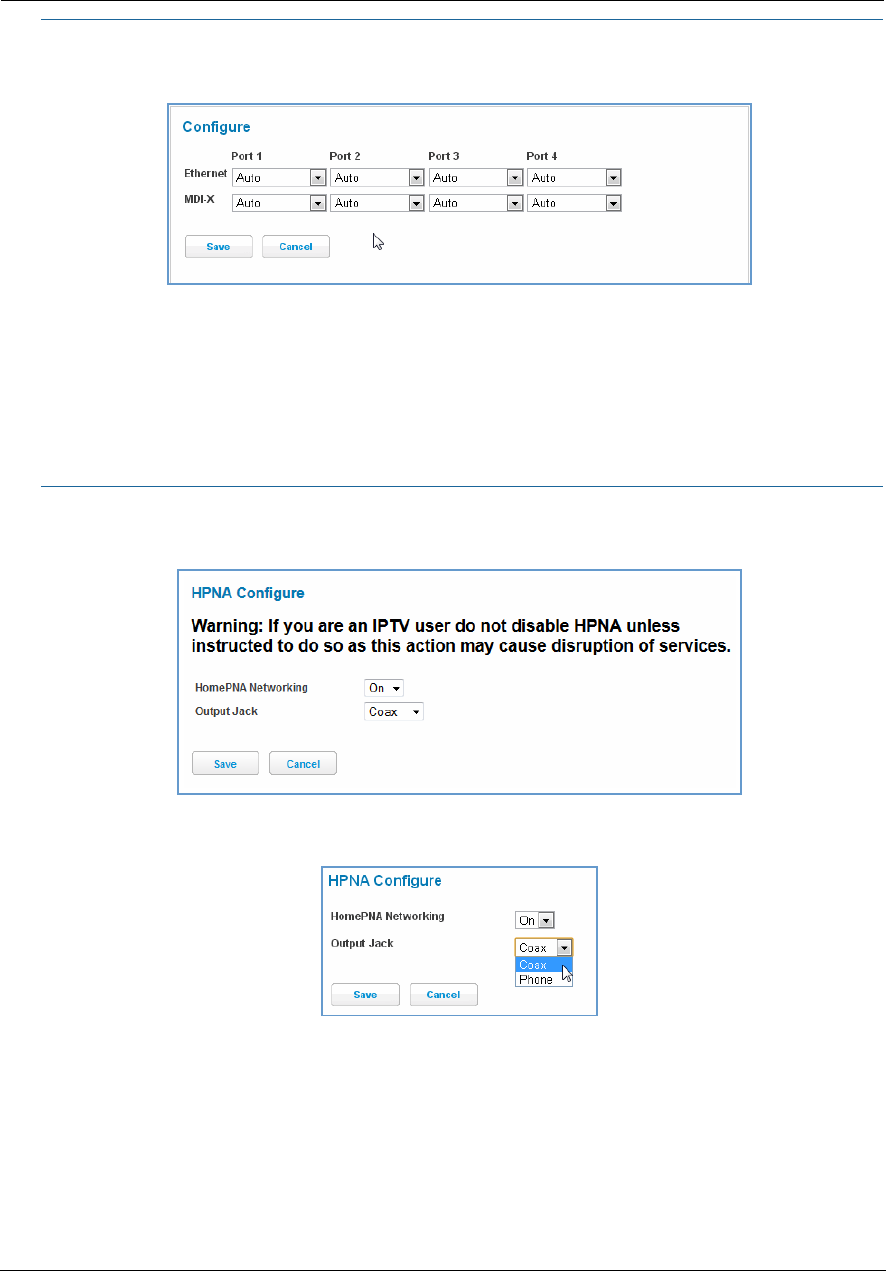
Link: Configure
When you click the Configure link, the Configure page for the Ethernet LAN appears.
For each Ethernet Port, 1 through 4, you can select:
Ethernet – Auto (the default self-sensing rate), 10M full- or half-duplex, 100M full- or half-duplex, or 1G
full- or half-duplex.
MDI-X – Auto (the default self-sensing crossover setting), Off, or On.
Click the Save button.
Link: HPNA Configure
When you click the HPNA Configure link, the HPNA Configure page for the HomePNA network appears.
Here you can set HomePNA Networking On or Off.
If desired, you can also set the Output Jack, as either the Coax jack or the Phone jack.
Click the Save button.
43
Link: WiFi
When you click the WiFi link, the WiFi page appears. The WiFi page displays the status of your wireless LAN
elements.
The WiFi page center section contains a summary of the configuration settings and operational status for the
wireless access point.
Summary Information
Field Status and/or Description
Radio Selection Display the settings for either the 2.4 Ghz or the 5.0 Ghz frequency radio.
WiFi Operation May be either On or Off.
Mode Wireless transmission mode. For the 2.4 Ghz radio, may be 802.11B only, 802.11G only,
802.11N only, 802.11 B/G or 802.11 B/G/N. For the 5.0 Ghz radio, may be 802.11AC as
well.
Bandwidth The capacity of the wireless LAN to carry traffic in megahertz, 20 or 40.
Channel The radio channel on which your Wi-Fi network is broadcasting.
Power Level May be adjusted up to 100%, lower if multiple wireless access points are in use, and
might interfere with each other.
User SSID Enable May be either On or Off for either frequency.
Guest SSID Enable May be either On or Off for the 2.4 Ghz radio only.
Network Name (SSID) The name or ID that is displayed to a client scan. The default SSID for the NVG599 is
attxxx where xxx is the last 3 digits of the serial number located on the side of the
device.
Hide SSID May be either Off or On. If On, your SSID will not appear in a client scan.
Security The type of wireless encryption security in use. May be OFF-No Privacy, WPA-
PSK, WEP, Default Key or Manual.
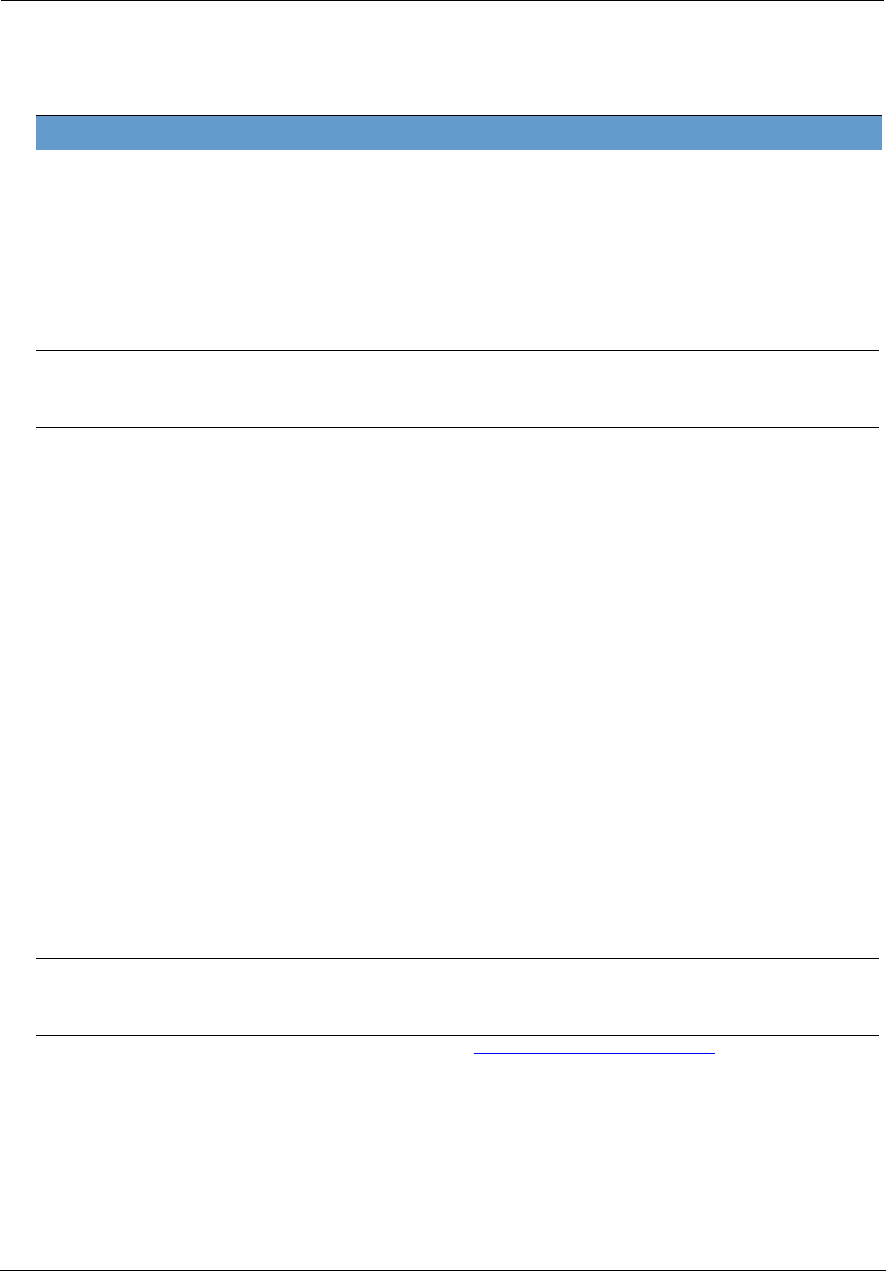
Administrator’s Handbook
44
WiFi Operation – Automatically enabled by default. If you deselect the checkbox, the WiFi options are dis-
abled, and the wireless access point will not provide or broadcast its wireless LAN services.
Mode – The drop-down menu allows you to select and lock the NVG599 into the wireless transmission mode
you want: A/C, B/G/N, B-only, B/G, G-only, or N-only.
For compatibility with clients using 802.11b (up to 11 Mbps transmission), 802.11g (up to 20+ Mbps),
802.11a (up to 54 Mbit/s using the 5 GHz band), or 802.11n (from 54 Mbit/s to 600 Mbit/s with the use of
four spatial streams at a channel width of 40 MHz), select B/G/N. To limit your wireless LAN to one mode or
the other, select the option that applies to your setup.
Bandwidth – Use a single 20-MHz channel (20MHz setting) , or combine two 20-MHz channels (40MHz set-
ting) to increase data speeds. The 40-MHz mode may only be selected if the Mode setting is 801.11 B/G/N
or 802.11 N-Only. To prevent interference with lower bandwidth clients, the wireless network will revert to
20MHz operation if non-compatible (802.11B, 802.11G, or 20-MHz 802.11N) clients are detected.
Channel – Channel (1 through 11, for North America) on which the network will broadcast. This is a fre-
quency range within the 2.4-Ghz or 5.0-Ghz band. The Automatic setting allows the wireless access point to
automatically determine the best channel for broadcast.
Power Level – Sets the wireless transmit power, scaling down the wireless access point’s wireless transmit
coverage by lowering its radio power output. Default is 100% power. Transmit power settings are useful in
large venues with multiple wireless routers where you want to reuse channels. Since there are only three
non-overlapping channels in the 802.11 spectrum, it helps to size the wireless access point cell to match the
location. This allows you to install a router to cover a small “hole” without conflicting with other routers
nearby.
Network Name (SSID) – Preset to a number unique to your unit. You can either leave it as is, or change it by
entering a freeform name of up to 32 characters, for example “Brian’s Wireless LAN.” In client PC software,
this might also be called the wireless ID. The Network Name is used to identify this particular wireless LAN.
Depending on their operating system or client wireless card, users must either:
• Select from a list of available wireless LANs that appear in a scanned list on their client.
• Enter this name on their clients in order to join this wireless LAN.
Hide SSID – If enabled, this mode hides the wireless network from the scanning features of wireless client
computers. Hiding the SSID prevents casual detection of your wireless network by unwanted neighbors and
passers-by. The gateway WLAN will not appear when clients scan for access points. If Hide SSID is enabled,
you must remember to enter your SSID when adding clients to the wireless LAN.
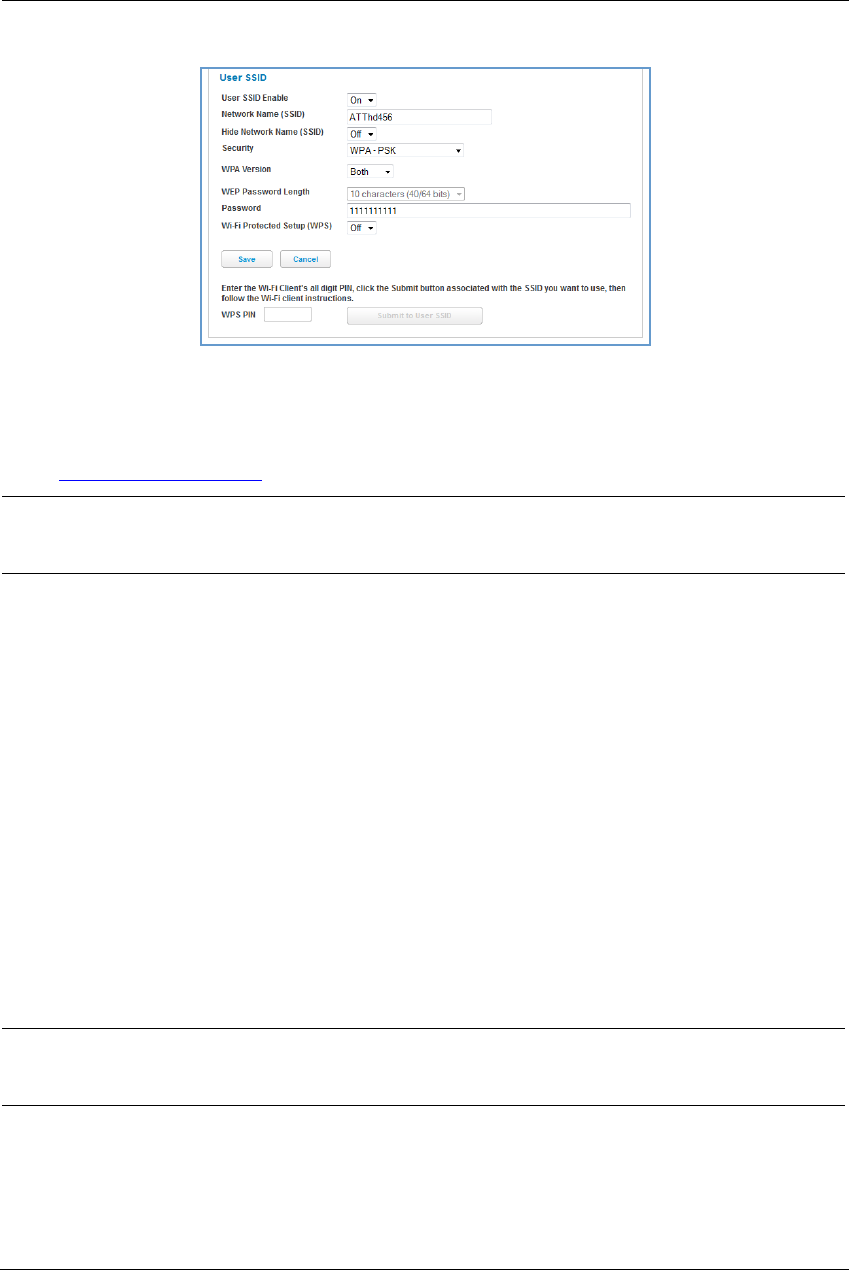
Security, WPA Version, WEP Key Length, Key – See “Wireless Security” on page 45.
WiFi Protected Setup (WPS) – Not a security protocol. WPS is an easier way to add and securely configure
new clients to your WLAN. By default, Privacy is set to WiFi Protected Access (WPA-PSK) with a 12-character
security key. WPS allows you to securely share your exact security configuration with a new client that you
are adding to the WLAN, without needing to look up and type this security key. Clients can be added using
the WPS button on the router, or by entering the client WPS PIN on this page. Not all client wireless devices
support WPS. Refer to their documentation.
To add a client: Enter your WPS PIN and click the Submit button. Follow the instructions that came with
your wireless client.
WPA Version If WPA is selected, may be Both, WPA-1, or WPA-2.
WEP Key Length May be 10 characters for 40/64-bit, or 26 characters for 128-bit WP encryption.
Key Here you can enter a manual encryption key.
WiFi Protected Setup (WPS) May be either On or Off.
General Information
NOTE:
If you choose to limit the operating mode to 802.11b or 802.11g only, clients using the mode you excluded
will not be able to connect.
NOTE:
While hiding the SSID may prevent casual discovery of your wireless network, enabling security is the only
true method of securing your network.
45
Wireless Security
By default, wireless security is set to WPA-PSK with a pre-defined WPA-Default Key.
Other options are available from the Security drop-down menu:
WEP - Manual: WEP security is a privacy option that is based on encryption between the router and any PCs
(clients) you have with wireless cards. For WEP-Manual encryption to work, both your wireless access point
and each client must share the same wireless ID (SSID), and both must be using the same encryption keys.
See “WEP-Manual” on page 45.
WPA-PSK: Allows you to enter your own key, the most secure option for your wireless network. The key
can be between 8 and 63 characters, but for best security it should be at least 20 characters. If you select
WPA-PSK as your privacy setting, the WPA Version drop-down menu allows you to select the WPA ver-
sion(s) that will be required for client connections. Choices are:
• Both, for maximum interoperability
• WPA-1, for backward compatibility
• WPA-2, for maximum security
All clients must support the version(s) selected in order to successfully connect. Be sure that your Wi-Fi cli-
ent adapter supports this option. Not all Wi-Fi clients support WPA-PSK.
OFF - No Privacy: Disables privacy on your network, allowing any wireless users to connect to your wireless
LAN. Select this option if you are using alternative security measures such as VPN tunnels, or if your network
is for public use.
Click the Save button.
WEP-Manual
You can provide a level of data security by enabling WEP (Wired Equivalent Privacy) for encryption of network
data. You can enable 40- or 128-bit WEP Encryption (depending on the capability of your client wireless card)
for IP traffic on your LAN.
WEP - Manual allows you to enter your own encryption keys manually. This is a difficult process, but only
needs to be done once. Avoid the temptation to enter all the same characters.
Key Length: The drop-down menu selects the length of each encryption key. The longer the key, the stronger
the encryption and the more difficult it is to break the encryption.
NOTE:
WEP is a less current and less secure authentication method than WPA-PSK. It may be required if your wire-
less clients do not support WPA.
NOTE:
WEP is a less current and less secure authentication method than WPA-PSK. It may be required if your wire-
less clients do not support WPA.
Administrator’s Handbook
46
Key: You must enter a key using hexadecimal digits. For 40/64-bit encryption, you need ten digits; 26 digits for
128-bit WEP. Hexadecimal characters are 0 – 9, and a – f.
Examples:
40 bits: 02468ACE02
128 bits: 0123456789ABCDEF0123456789
Any WEP-enabled client must have an identical key of the same length as the router, in order to successfully
receive and decrypt the traffic. Similarly, the client also has a default key that it uses to encrypt its
transmissions. In order for the router to receive the client’s data, it must likewise have the identical key of the
same length.
Click the Save button.
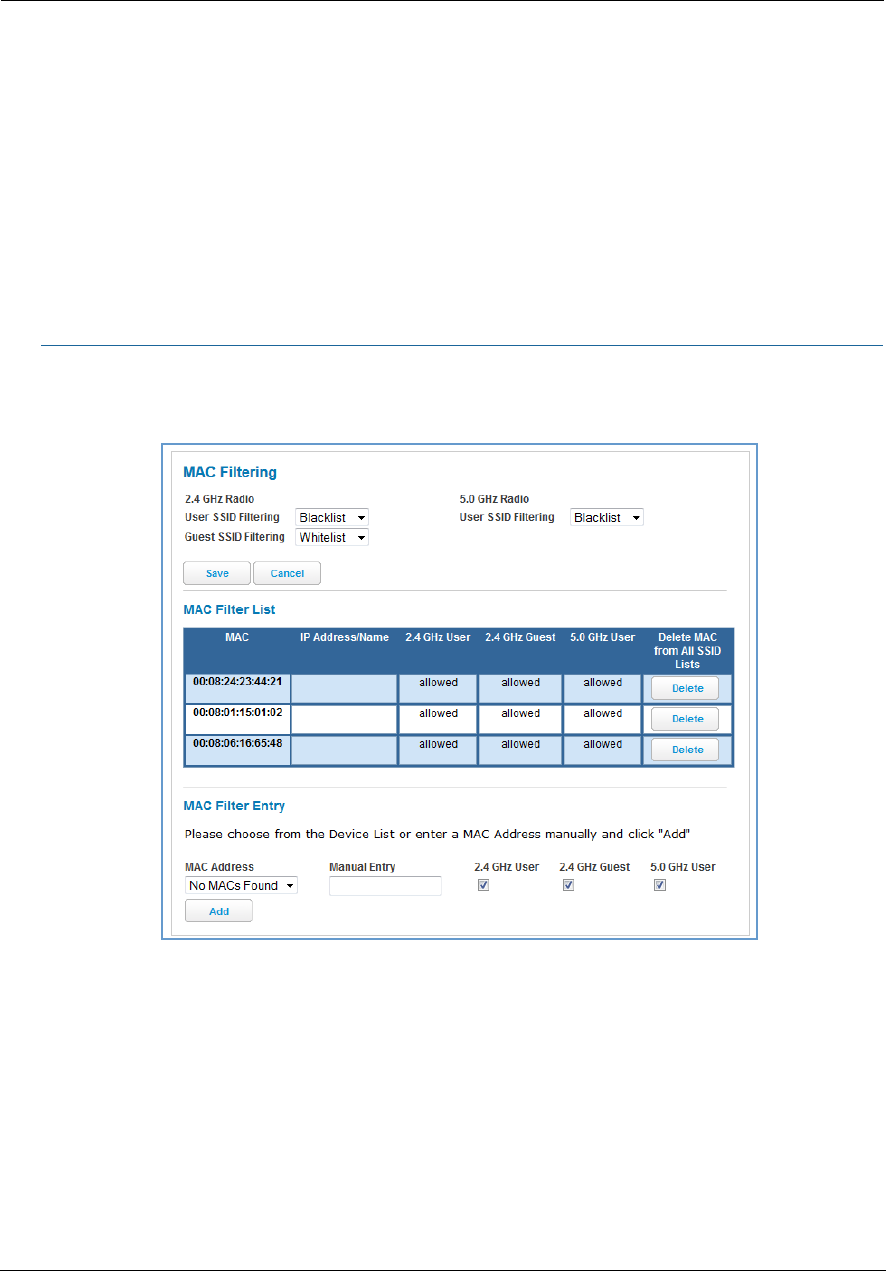
Link: MAC Filtering
When you click the MAC Filtering link the MAC Filtering page appears.
MAC filtering allows you to specify which client PCs are allowed to join the wireless LAN by unique hardware
(MAC) address.
To enable this feature, select Blacklist or Whitelist from the MAC Filtering Type menu. Blacklist means that
only MAC addresses you specify will be denied access; Whitelist means that only MAC addresses you specify
will be allowed access.
You add wireless clients that you want to whitelist or blacklist for your wireless LAN by selecting them from
the MAC Address drop-down list or by entering the MAC addresses in the Manual Entry field provided.
Click the Add button.
Your entries will be added to a list of clients that will be either authorized (whitelisted) or disallowed
(blacklisted) depending on your selection.
47
Click the Save button.
You can add or delete any of your entries later by returning to this page.
Link: Wireless Scan
Your device automatically checks for the best channel to broadcast wireless services. However, in some cases it
may be useful to switch to a different channel (1 through 11, for North America) on which the network will
broadcast.
The scan covers a frequency range within the 2.4 Ghz or 5.0 Ghz band. Channel selection depends on
government regulated radio frequencies that vary from region to region. Channel selection can have a
significant impact on performance, depending on other wireless activity close to this device. You need not
select a channel at any of the computers on your wireless network. They will automatically scan available
channels seeking a wireless device broadcasting on the SSID for which they are configured.
This scan will disconnect any wireless client devices from the wireless network.
If you want to scan for a different channel on which the device will broadcast, click the Continue button.
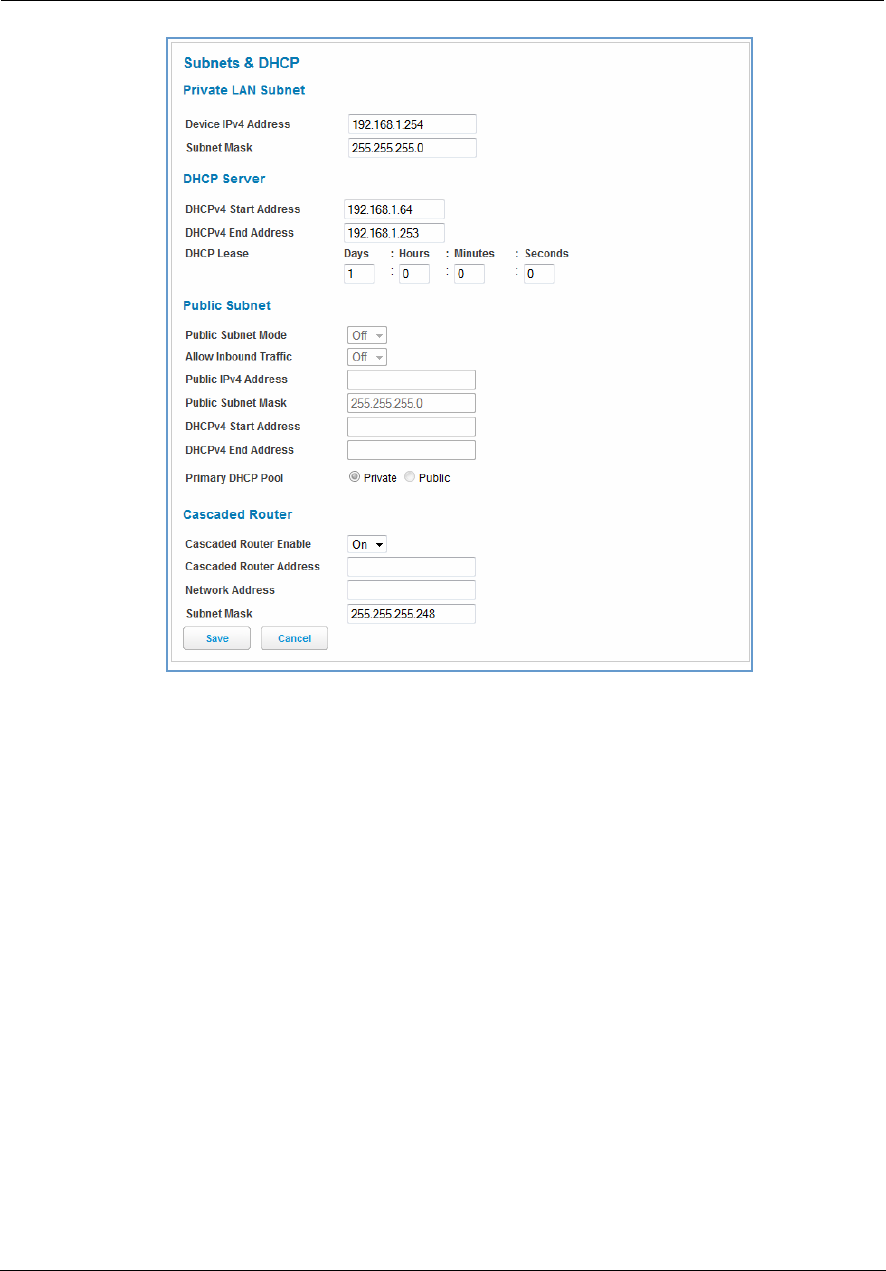
Link: Subnets & DHCP
When you click the Subnets & DHCP link, the Subnets & DHCP page appears.
Administrator’s Handbook
48
The server configuration determines the functionality of your DHCP settings. This functionality enables the
NVG599 to assign your LAN computer(s) a “private” IP address and other parameters that allow network
communication. This feature simplifies network administration because the NVG599 maintains a list of IP
address assignments. Additional computers can be added to your LAN without the need to configure an IP
address. This is the default mode for your NVG599 device.
Private LAN Subnet
Device IPv4 Address: The IP address of your device as seen from the LAN.
Subnet Mask: Subnet mask of your LAN.
DHCP
DHCPv4 Start Address: First IP address in the range being served to your LAN by the NVG599 DHCP server.
DHCPv4 End Address: Last IP address in the range being served to your LAN by the NVG599 DHCP server.
DHCP Lease: Specifies the default length for DHCP leases issued by the router. Enter lease time in
dd:hh:mm:ss (days/hours/minutes/seconds) format.
Public Subnet
Public Subnet Enable: If you select On from the drop-down menu, you can enable a second subnet to dis-
tribute public addresses to DHCP clients; this means that IP addresses assigned to LAN clients will be public
addresses.
Public IPv4 Address: The IP address of your NVG599 device as seen from the WAN.
Public Subnet Mask: Public subnet mask.
DHCPv4 Start Address: First IP address in the range being served from a DHCP public pool.
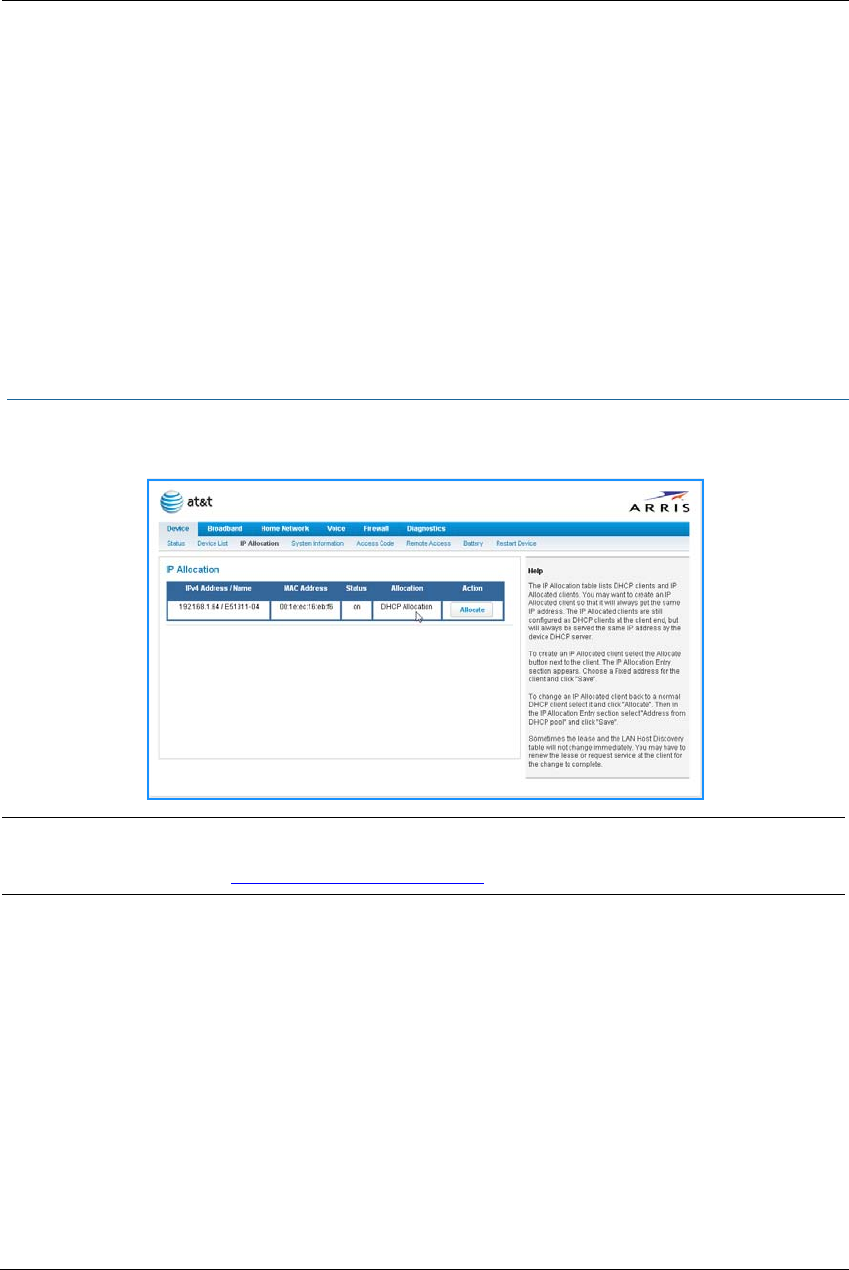
49
DHCPv4 End Address: Last IP address in the range being served from a DHCP public pool.
Primary DHCP Pool: Choose the source of the DHCP pool IP address assignment by selecting either Private
(local to your LAN) or Public (assigned remotely).
Cascaded Router
Cascaded Router Enable: If you have another router behind this device, choose On from the drop-down
menu.
Cascaded Router Address: If you chose On from the drop-down menu, enter the IP address of the router
you are using behind this device in the LAN private IP subnet range.
Network Address: If you chose On from the drop-down menu, enter the Network Address that defines the
range of IP addresses available to clients of the router you are using behind this device.
Subnet Mask: If you chose On from the drop-down menu, enter the subnet mask for the network address
that defines the range of IP addresses available to clients of the router you are using behind this device.
If you make any changes here, click the Save button, and if prompted, restart the NVG599 device.
Link: IP Allocation
When you click the IP Allocation link, the IP Allocation page appears.
The IP Allocation page lets you set aside or assign IP addresses to client devices on your network. With IP
allocation, you can configure known devices to either use DHCP for dynamic IP address assignment, or set
aside a specific IP address for a client device. When IP allocation is enabled for a client, that device is assigned
a pre-determined IP address by the DHCP server of the NVG599. IP allocation lets you set up client devices as
common DHCP systems, but ensures that they always receive the same IP address from the gateway.
The IP Allocation table shows a list of all identified and active client devices the NVG599 is serving.
To change the allocation method used by a client:
1. Locate the client in the IP Allocation table. The client may be identified by the Name value (in the IPv4
Address/Name column) or the device MAC address.
2. Click the Allocate button associated with the client entry.
NOTE:
IP Allocation functions require you to enter your NVG599 Gateway’s access code. Information on the device
code is provided in “Device Access Code” on page 24
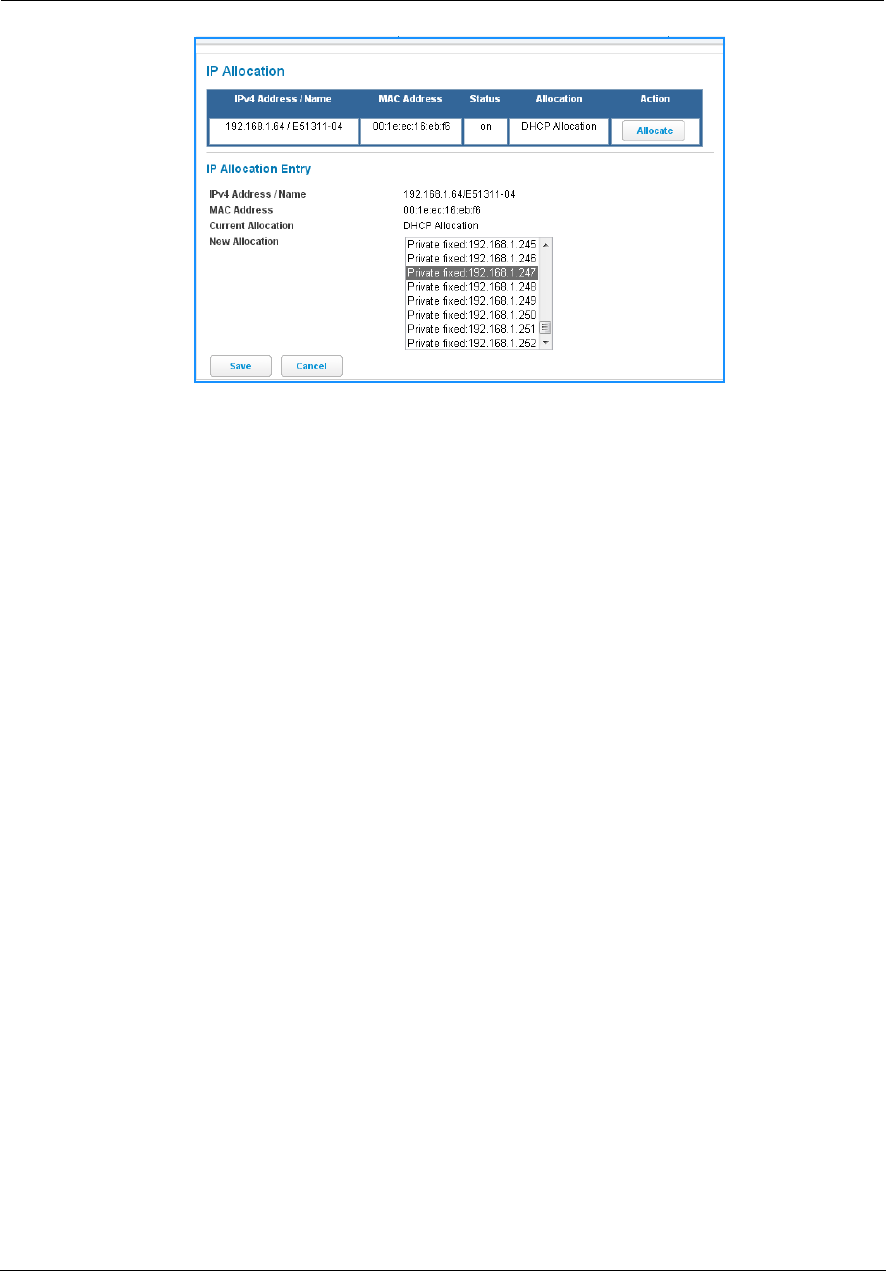
Administrator’s Handbook
50
The IP Allocation window for the client opens.
3. Scroll through the New Allocation values and select the address or method to use for the client’s DHCP
assignment:
•
Click Address from DHCP Pool to set the client to accept any valid DHCP address available (standard
operation).
•
Click any of the private fixed IP addresses (192.168.1.64 to 192.168.1.253) shown in the list to allocate
that IP address to the selected client.
4. Click the Save button to save the IP allocation settings. A red “Changes saved” message appears at the top of
the IP Allocation page.
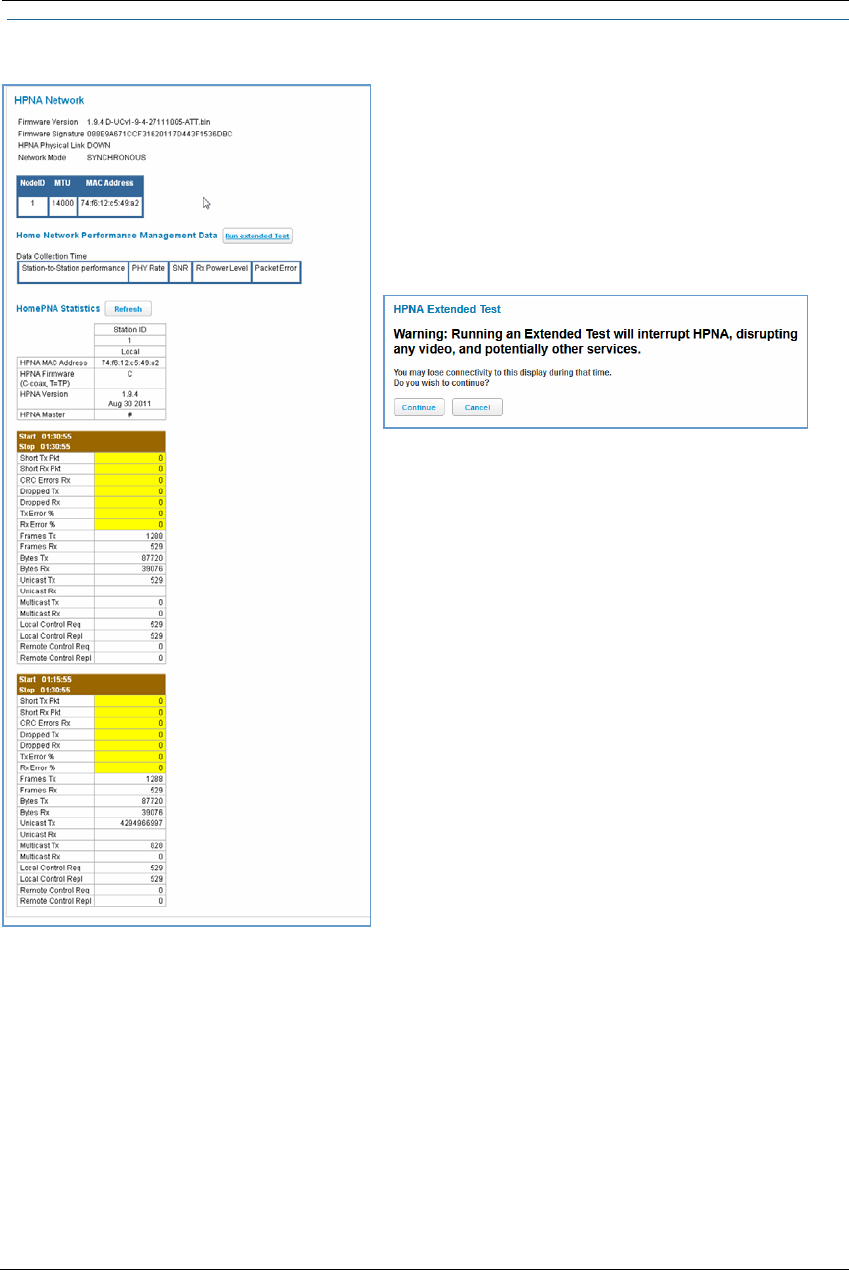
51
Link: HPNA
When you click the HPNA link, the HPNA Network page appears.
The HPNA Network page displays information about the
NVG599 gateway’s HPNA-connected devices in 15-minute
intervals. You can test the performance of each station to
station pair by clicking the Run extended Test button.
The following page appears as a warning about this invasive
test.
If you do not run the extended test, the station-to-station
performance section is not displayed.
You can generate updated statistics by clicking the Refresh
button.
HomePNA statistics for the current and previous intervals
are displayed below the following static values:
Station ID
HPNA MAC Address
HPNA Firmware (C-coax, T=TP)
HPNA Version
HPNA Master

Administrator’s Handbook
52
Interval statistic fields supply the following information:
Label Statistic Displayed
Short Tx Pkt Transmitted Packets
Short Rx Pkt Received Packets
CRC Errors Rx Receipt errors
Dropped Tx Transmit packets dropped
Dropped Rx Receipt packets dropped
Tx Error % Percentage of transmitted errors
Rx Error % Percentage of receipt errors
Frames Tx Number of frames transmitted
Frames Rx Number of frames received
Bytes Tx Bytes transmitted
Bytes Rx Bytes received
Unicast Tx Number of unicast packets transmitted
Unicast Rx Number of unicast packets received
Multicast Tx Number of multicast packets transmitted
Multicast Rx Number of multicast packets received
Local Control Req Number of requests made to the device by local control
Local Control Repl Number of replies made by the device to local control
Remote Control Req Number of requests made to the device by remote control
Remote Control Repl Number of replies made by the device to remote control
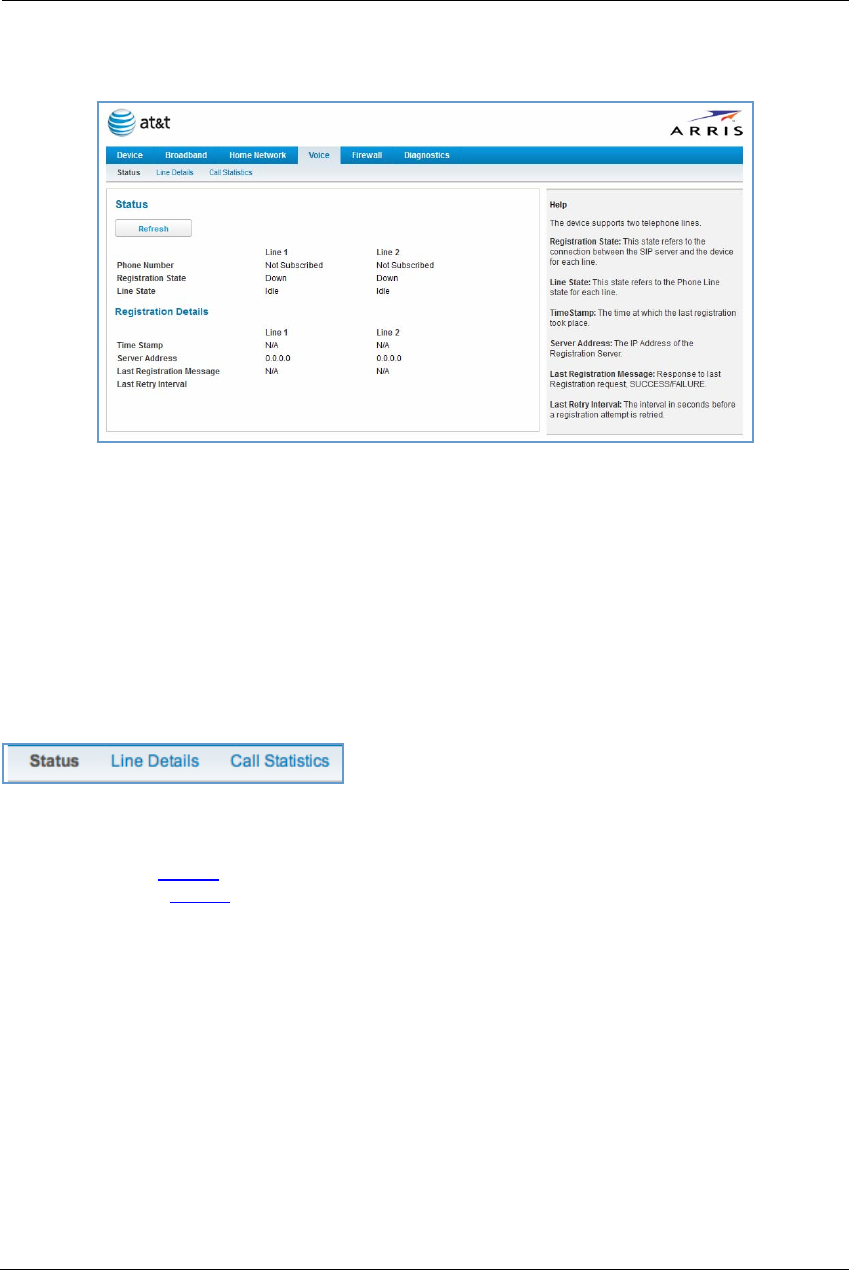
53
Voice
When you click the Voice tab, the Voice Status page appears.
Voice-over-IP (VoIP) refers to voice telephone calls transmitted over the Internet. This type of service differs
from traditional phone service that uses the Public Switched Telephone Network (PSTN). VoIP calls use an
Internet protocol, Session Initiation Protocol (SIP), to transmit sound over a network or the Internet in the form
of data packets.
The Voice page displays information about your VoIP phone lines, if configured. Your device supports two
phones, Line 1 and Line 2.
If either one or both are registered with a SIP server by your service provider or not registered, the Voice
page will display their Registration Details.
The links at the top of the Voice page provide access to a series of pages that allow you to configure and
monitor features of your device.
The links bar on the Voice page includes the following links. For more information about each link, see the
related section in this guide.
Line Details (see page 54)
Call Statistics (see page 55)
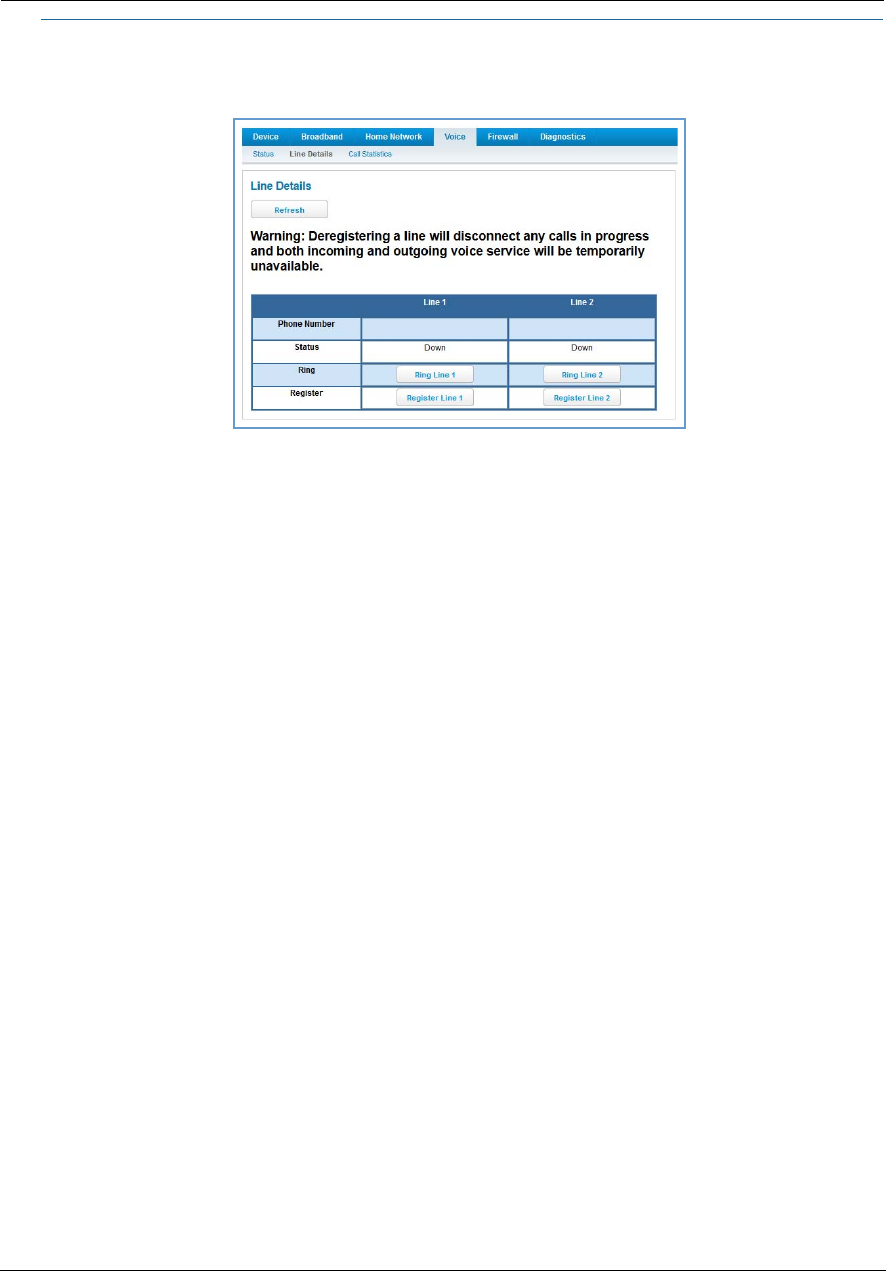
Administrator’s Handbook
54
Link: Line Details
When you click the Line Details link, the Line Details page appears.
If your service provider has enabled your VoIP phone lines, you can register them by clicking the Register
Line 1 or Register Line 2 button.
To test if the lines are enabled, click the Ring Line 1 or Ring Line 2 button. If enabled and registered, the
respective phone will ring for 30 seconds.
To clear the current state of each phone line, click the Reset Line 1 or Reset Line 2 button. This will disconnect
any calls currently in progress as well.
To update the display, click the Refresh button.
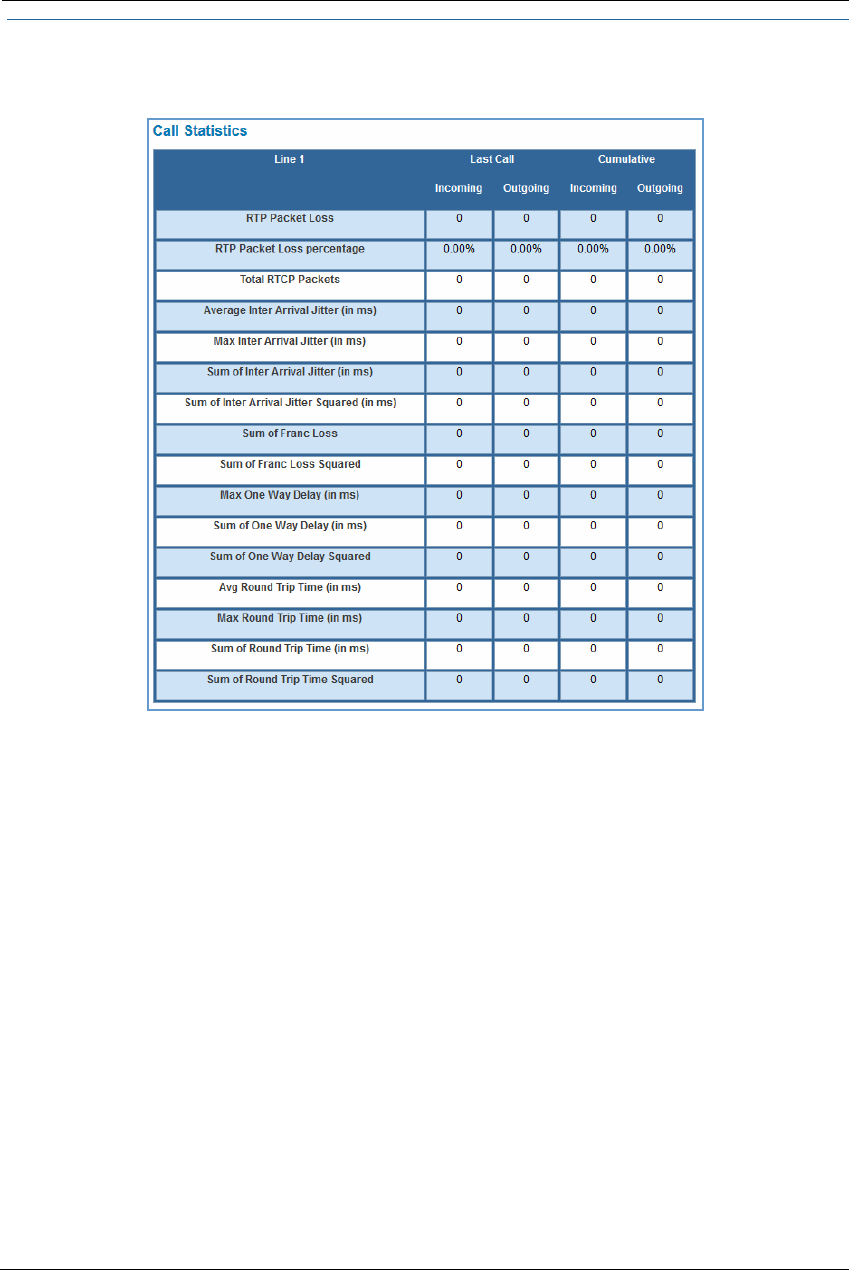
55
Link: Call Statistics
When you click Call Statistics, the Call Statistics page appears.

Administrator’s Handbook
56
For Line 1 and Line 2, the two available phone lines, the Call Statistics page displays the following information:
Call Statistics - Line 1 and Line 2
Last Call/Cumulative – Incoming/Outgoing
RTP Packet Loss Real-time Transport Protocol packets dropped
RTP Packet Loss percentage Percent of Real-time Transport Protocol packets dropped
Total RTCP Packets Total Real-time Transport Control Protocol packets
Average Inter Arrival Jitter Calculated continuously in milliseconds as each data packet is received and averaged.
Max Inter Arrival Jitter The maximum value in milliseconds recorded as each data packet is received.
Sum of Inter Arrival Jitter Calculated continuously in milliseconds as each data packet is received and totalled.
Sum of Inter Arrival Jitter
Squared
Calculated continuously in milliseconds as each data packet is received and the total is
squared.
Sum of Franc Loss Fraction Lost: The fraction of RTP data packets lost since the previous SR or RR packet
was sent. This fraction is defined to be the number of packets lost divided by the num-
ber of packets expected. This number will be calculated on every RTCP SR packet. Sum
of the fraction lost is calculated with all the RTCP packets.
Sum of Franc Loss Squared Fraction lost is squared with every RTCP SR or RR packet. Sum of all values will give the
Sum of Franc Loss Squared.
Max One Way Delay One-way delay will be calculated in milliseconds on every RTCP SR or RR packet. This
value is (systime - lsr - dslr) / 2
lsr means last SR timestamp
dslr means delay since last SR.
Sum of One Way Delay The sum of all the one-way delays calculated in milliseconds on every RTCP packet is
displayed as Sum of One Way Delay.
Sum of One Way Delay
Squared
One-way delay is squared with every RTCP SR or RR packet. Sum of all values will give
the Sum of One Way Delay Squared.
Avg Round Trip Time Average time in milliseconds from this local source to destination address and back
again for all logged calls
Max Round Trip Time Maximum amount of time in milliseconds from this local source to destination
address and back again for all logged calls
Sum of Round Trip Time Sum of time in milliseconds from this local source to destination address and back
again for all logged calls
Sum of Round Trip Time
Squared
Sum squared of time from this local source to destination address and back again for
all logged calls
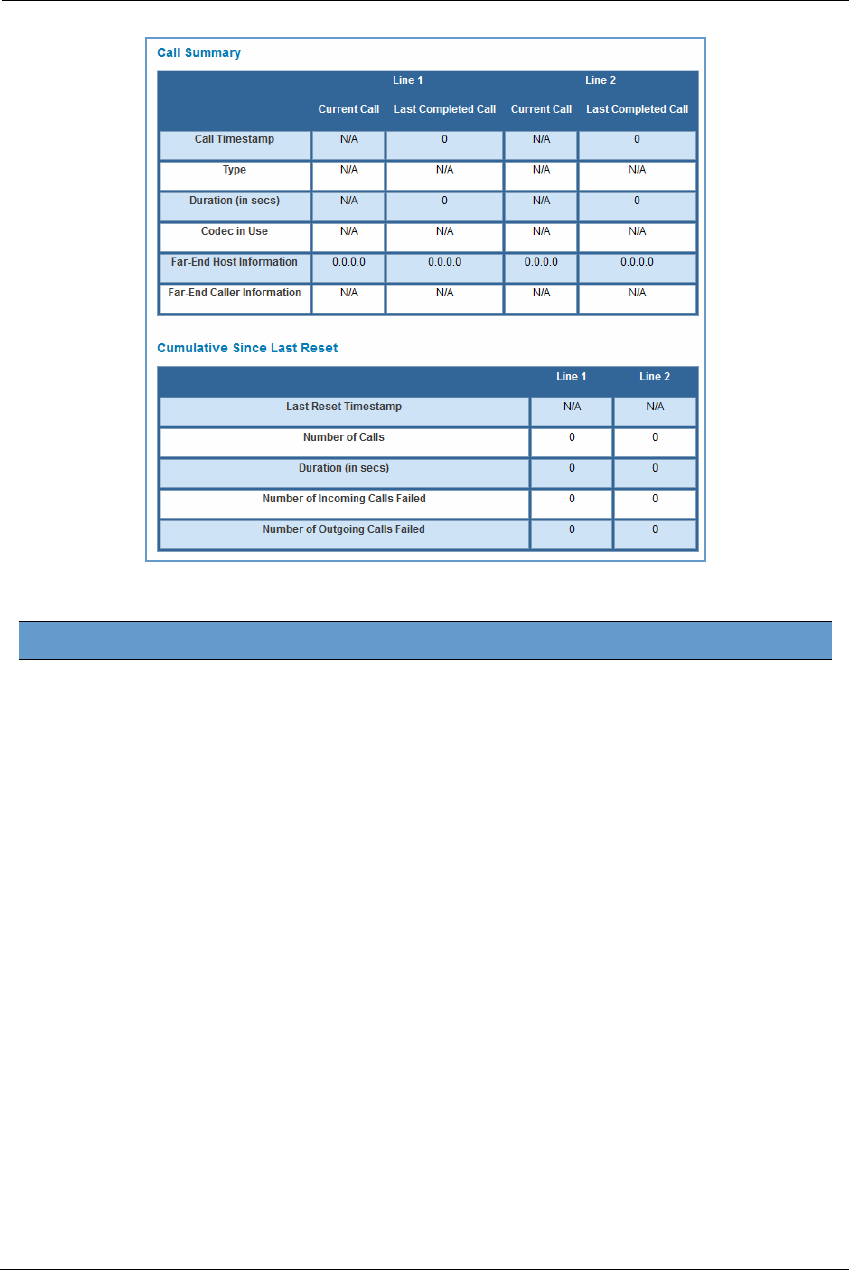
57
For Line 1 and Line 2, the two available phone lines, the Call Summary section displays the following
information:
Call Summary - Line 1 and Line 2
Current Call/Last Completed Call
Call Timestamp Date and time of the current call
Type May be Incoming or Outgoing
Duration Length of time in seconds of call connection
Codec in Use Audio codec used for decoding the call packet traffic.
Far-End Host Information SIP server IP information: IP address and port number
Far-End Caller Information Caller ID information, if available
Cumulative Since Last Reset
Last Reset Timestamp Date and time of the last call
Number of Calls Total number of calls for each VoIP line
Duration Time in seconds since the last call
Number of Incoming Calls Failed Number of incoming calls that fail to connect
Number of Outgoing Calls Failed Number of outgoing calls that fail to connect
Administrator’s Handbook
58
The following table shows VoIP line states during various conditions.
The following table provides the state changes during the boot-up procedure.
VoIP Line
1/2 Hook state WAN IP Reg-state FXS
Voltage Tone LED
Disabled On/Off-hook Up Idle Off N/A Off
Enabled On-hook Up Registered On N/A Solid
Enabled Off-hook Up Registered On Dial tone Blink
Enabled On/Off hook Up Failure Off N/A Off
Enabled On/Off hook Down Idle Off N/A Off
VoIP Line
1/2 WAN Status Hook State Reg-state FXS
Voltage Tone LED
Disabled Down Off-hook Idle On-to-off Off Off
Enabled Down On/Off-hook Idle On Congestion Off
Enabled Up Off-hook Registered On Congestion.
Dial Tone played
after the hook
state is
changed.
On
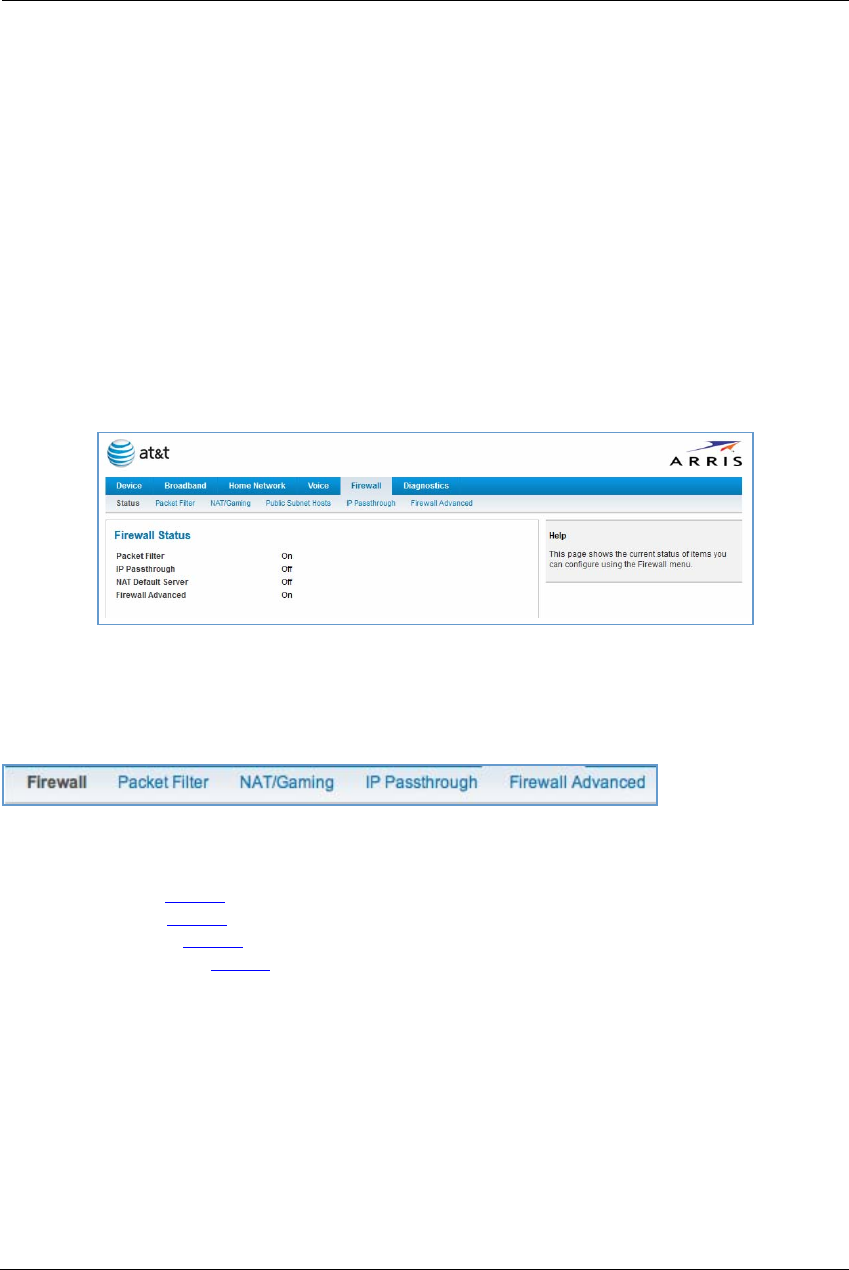
59
Firewall
When you click the Firewall tab, the Firewall Status page appears. The Firewall page displays the status of your
system firewall elements.
All computer operating systems are vulnerable to attack from outside sources, typically at the operating
system or Internet Protocol (IP) layers. Stateful Inspection firewalls intercept and analyze incoming data
packets to determine whether they should be admitted to your private LAN, based on multiple criteria, or
blocked. Stateful inspection improves security by tracking data packets over a period of time, examining
incoming and outgoing packets. Outgoing packets that request specific types of incoming packets are tracked;
only those incoming packets constituting a proper response are allowed through the firewall.
Stateful inspection is a security feature that prevents unsolicited inbound access when network address
translation (NAT) is disabled. You can configure UDP and TCP “no-activity” periods that will also apply to NAT
timeouts if stateful inspection is enabled on the interface. Stateful Inspection parameters are active on a WAN
interface only if enabled on your system. Stateful inspection can be enabled on a WAN interface whether NAT
is enabled or not.
The Firewall Status page shows whether the each firewall feature is On or Off.
The links at the top of the Firewall page provide access to series of pages that allow you to configure security
features of your device.
The links bar on the Firewall page includes the following links. For more information about each link, see the
related section in this guide.
Packet Filter (see page 60)
NAT/Gaming (see page 67)
IP Passthrough (see page 73)
Firewall Advanced (see page 76)
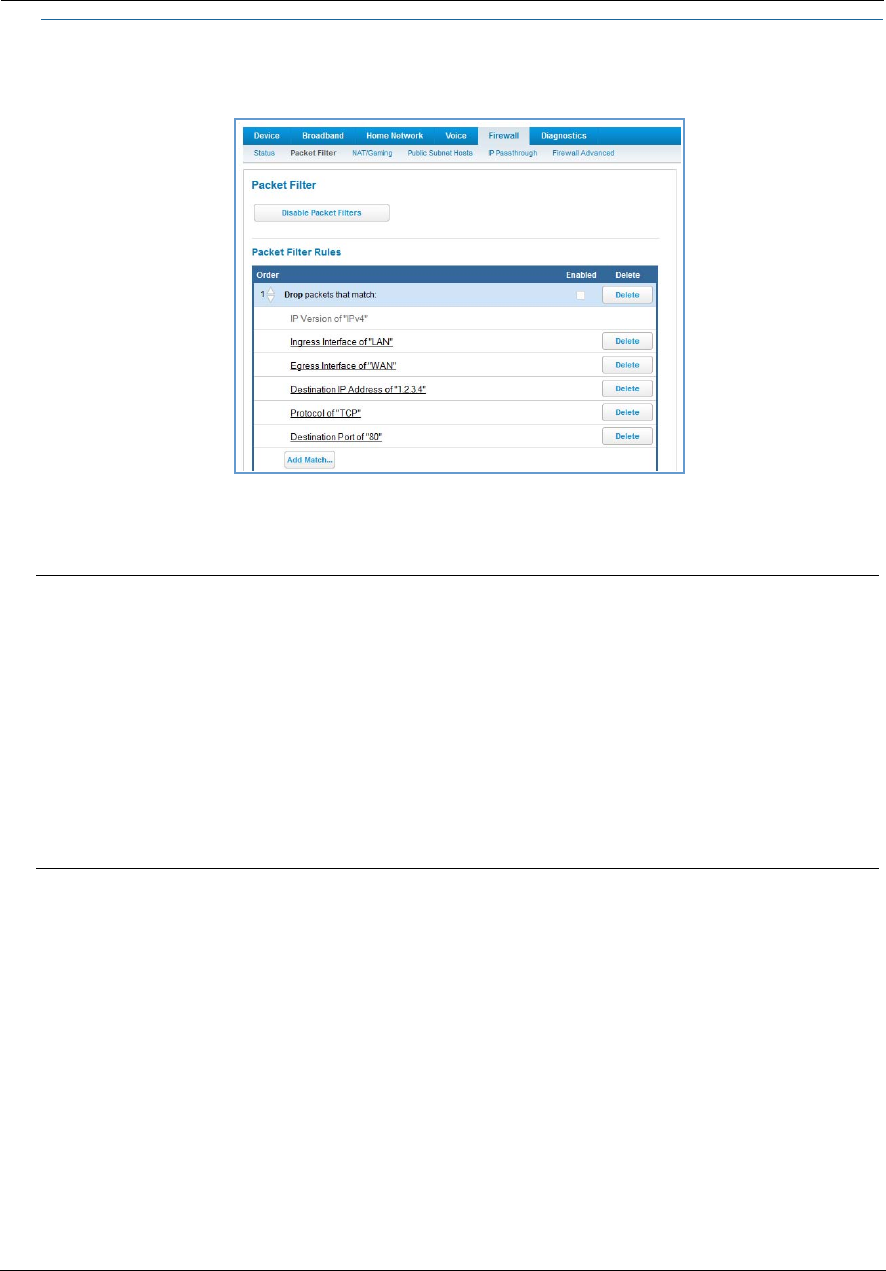
Administrator’s Handbook
60
Link: Packet Filter
When you click the Packet Filter link, the Packet Filter page appears.
Security should be a high priority for anyone administering a network connected to the Internet. Using packet
filters to control network communications can greatly improve your network’s security. The Packet Filter
engine allows creation of a maximum of eight filtersets. Each filterset can have up to eight rules configured.
ARRIS’s packet filters are designed to provide security for the Internet connections made to and from your
network. You can customize the NVG599 device’s filtersets for a variety of packet filtering applications. Typically,
you use filters to selectively admit or refuse TCP/IP connections from certain remote networks and specific
hosts. You will also use filters to screen particular types of connections. This is commonly called firewalling
your network.
Before creating filtersets, you should read the next few sections to learn more about how these powerful
security tools work.
WARNING:
Before attempting to configure filters and filtersets, please read and understand this entire section thor-
oughly. The ARRIS NVG599 device incorporating NAT has advanced security features built in. Improperly add-
ing filters and filtersets increases the possibility of loss of communication with the device and the Internet.
Never attempt to configure filters unless you are local to the NVG599 device.
Although using filtersets can enhance network security, there are disadvantages:
• Filters are complex. Combining them in filtersets introduces subtle interactions, increasing the likelihood of
implementation errors.
• Enabling a large number of filters can have a negative impact on performance. Processing of packets will
take longer if they have to go through many checkpoints in addition to NAT.
• Too much reliance on packet filters can cause too little reliance on other security methods. Filtersets are
not a substitute for password protection, effective safeguarding of passwords, and general awareness of how
your network may be vulnerable.

61
Parts of a Filter
A filter consists of criteria based on packet attributes. A typical filter can match a packet on any one of the
following attributes:
The source IP address (where the packet was sent from)
The destination IP address (where the packet is going)
The type of higher-layer Internet protocol the packet is carrying, such as TCP or UDP
Other Filter Attributes
There are three other attributes to each filter:
The filter’s order (i.e., priority) in the filterset
Whether the filter is currently active
Whether the filter is set to forward packets or to block (discard) packets
Design Guidelines
Careful thought must go into designing a new filterset. You should consider the following guidelines:
Be sure the filterset’s overall purpose is clear from the beginning. A vague purpose can lead to a faulty set,
and that can actually make your network less secure.
Be sure each individual filter’s purpose is clear.
Determine how filter priority will affect the set’s actions. Test the set (on paper) by determining how the fil-
ters would respond to a number of different hypothetical packets.
Consider the combined effect of the filters. If every filter in a set fails to match on a particular packet, the
packet is:
• Forwarded if all the filters are configured to discard (not forward)
• Discarded if all the filters are configured to forward
• Discarded if the set contains a combination of forward and discard filters
An Approach to Using Filters
The ultimate goal of network security is to prevent unauthorized access to the network without compromising
authorized access. Using filtersets is part of reaching that goal.
Each filterset you design will be based on one of the following approaches:
That which is not expressly prohibited is permitted.
That which is not expressly permitted is prohibited.
We strongly recommend that you take the latter, and safer, approach to all of your filterset designs.
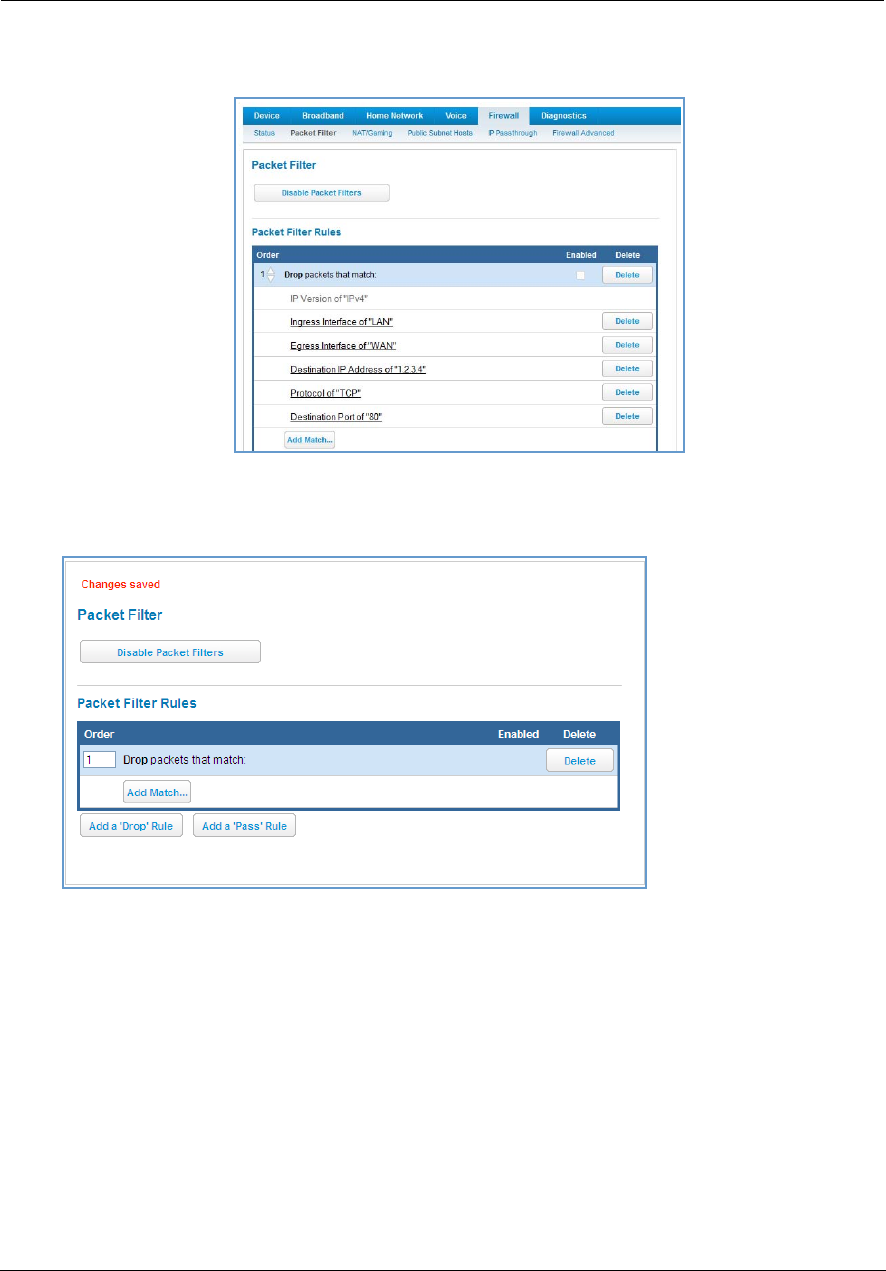
Administrator’s Handbook
62
Working with Packet Filters
To work with filters:
1. Accessing the Packet Filter page by clicking the Packet Filter link.
2. Globally turn filters on or off by clicking the Enable/Disable Packet Filters button.
3. Select the type of packet filter rule by clicking either the Add a ‘Drop’ Rule or Add a ‘Pass’ Rule button.
• If you select a drop rule, the specified packets will be blocked.
• If you select a pass rule, the specified packets will be forwarded.
4. Click the Add Match button to enter the source IP address or destination IP address this filter will match on.
As you create new matches, the list items change. There can only be one match from each match type for a
given rule. Match types like Source Port, Destination Port, and TCP Flags are only available if other matches
(for example, Protocol =TCP) have previously been created.
5. Select a protocol, if necessary, from the pull-down menu: ICMP, TCP, UDP, or None to specify any another IP
transport protocol.
If you chose by number, enter the Protocol by number here.
If you chose by name, enter the Protocol by name here.
Enter the Source Port this filter will match on.
Enter the Destination Port this filter will match on.
If you selected ICMP, enter the ICMP Type here.
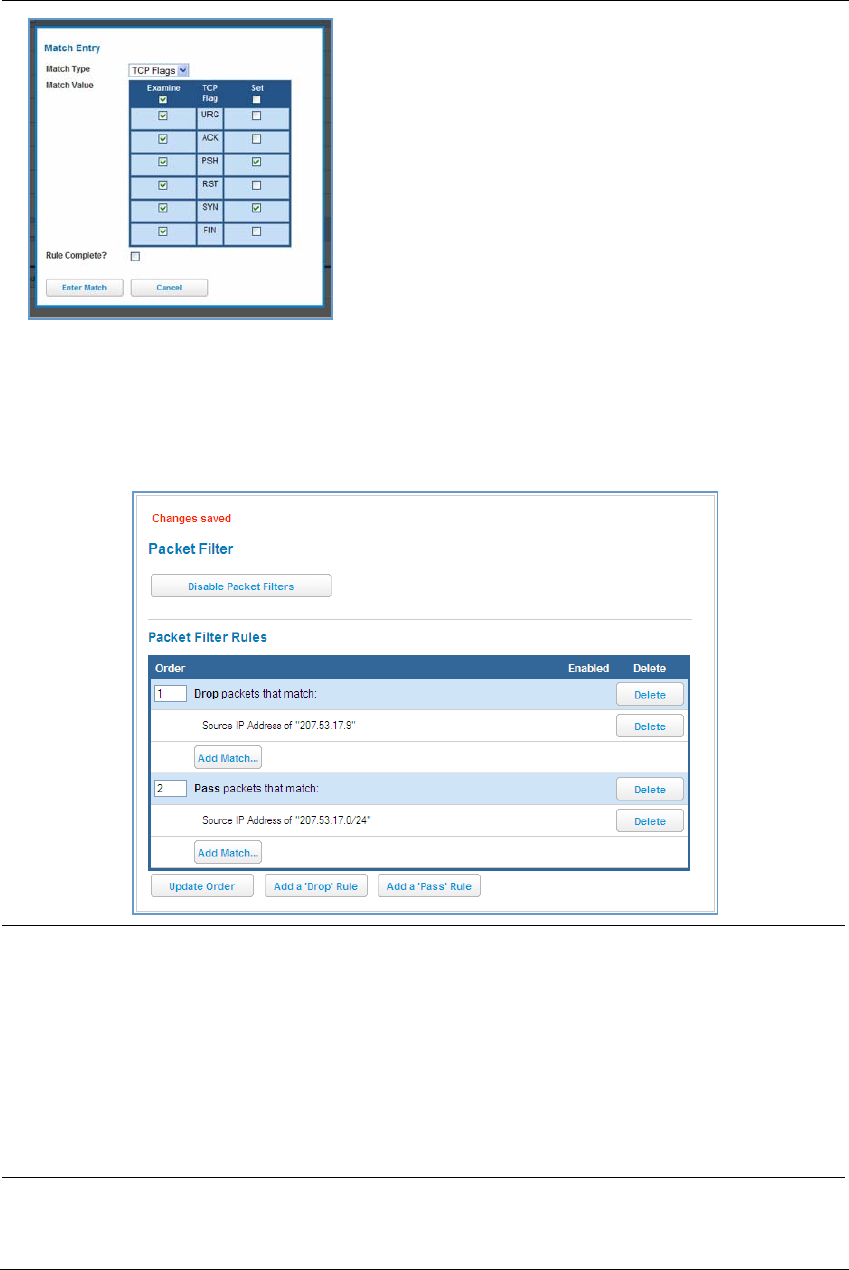
63
When you are finished configuring the filter, click the Enter Match button.
The filter is automatically saved.
Packet Filter Rules List
Your entries to the packet filter rules list are displayed as a table.
NOTE:
Default Forwarding Filter
If you create one or more filters that have a matching action of forward, then action on a packet matching
none of the filters is to block any traffic.
Therefore, if the behavior you want is to force the routing of a certain type of packet and pass all others
through the normal routing mechanism, you must configure one filter to match the first type of packet and
apply Force Routing. A subsequent filter is required to match and forward all other packets.
Management IP traffic
If the Force Routing filter is applied to source IP addresses, it may inadvertently block communication with
the router itself. You can avoid this by preceding the Force Routing filter with a filter that matches the desti-
nation IP address of the NVG599 device itself.
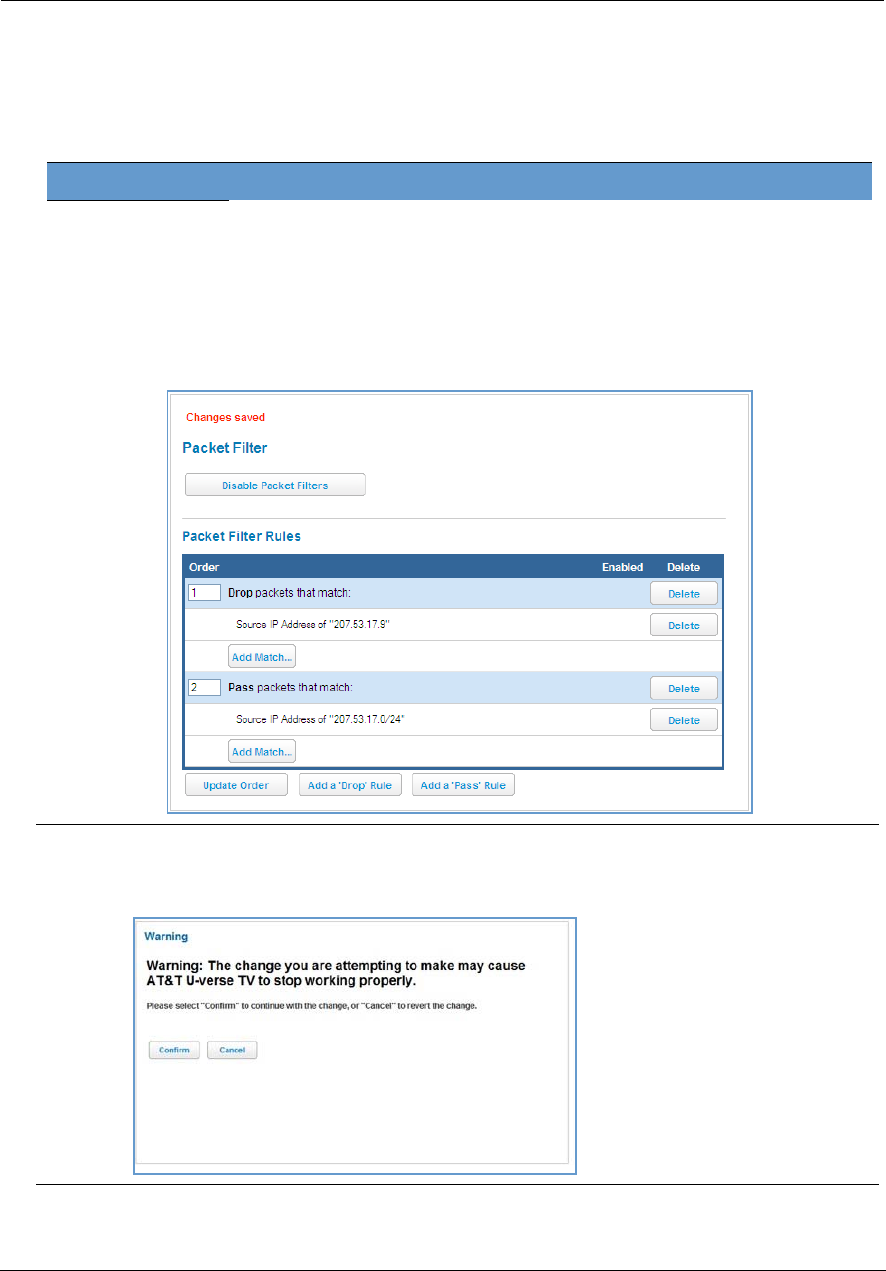
Administrator’s Handbook
64
Example:
Assume a configured Custom Service/Hosted Application for an internal web server whose global port range is
8080-8080. Also assume that we want to allow only one external subnet access to this internal server:
207.53.17.0/24. And finally, assume that we want to disallow one IP address on that subnet, 207.53.17.9, from
access to that same server (perhaps they were abusing the system in some way). We would need the following
rules:
Input Rules
Rule
Order Action Source IP Destination IP Protocol Source
Port
Destination
Port
1 Drop 207.53.17.9 - TCP 8080
2 Pass 207.53.17.0/24 - TCP 8080
3 Drop - - TCP 8080
Caution:
If the packet filter or port forwarding rule involves TCP port 80 or 3389; or UDP port 47806, 43962, 69, 123,
or 53; or if you attempt to add or change a match such that this occurs and you are running in VDSL/Ethernet
mode, the following warning will appear.
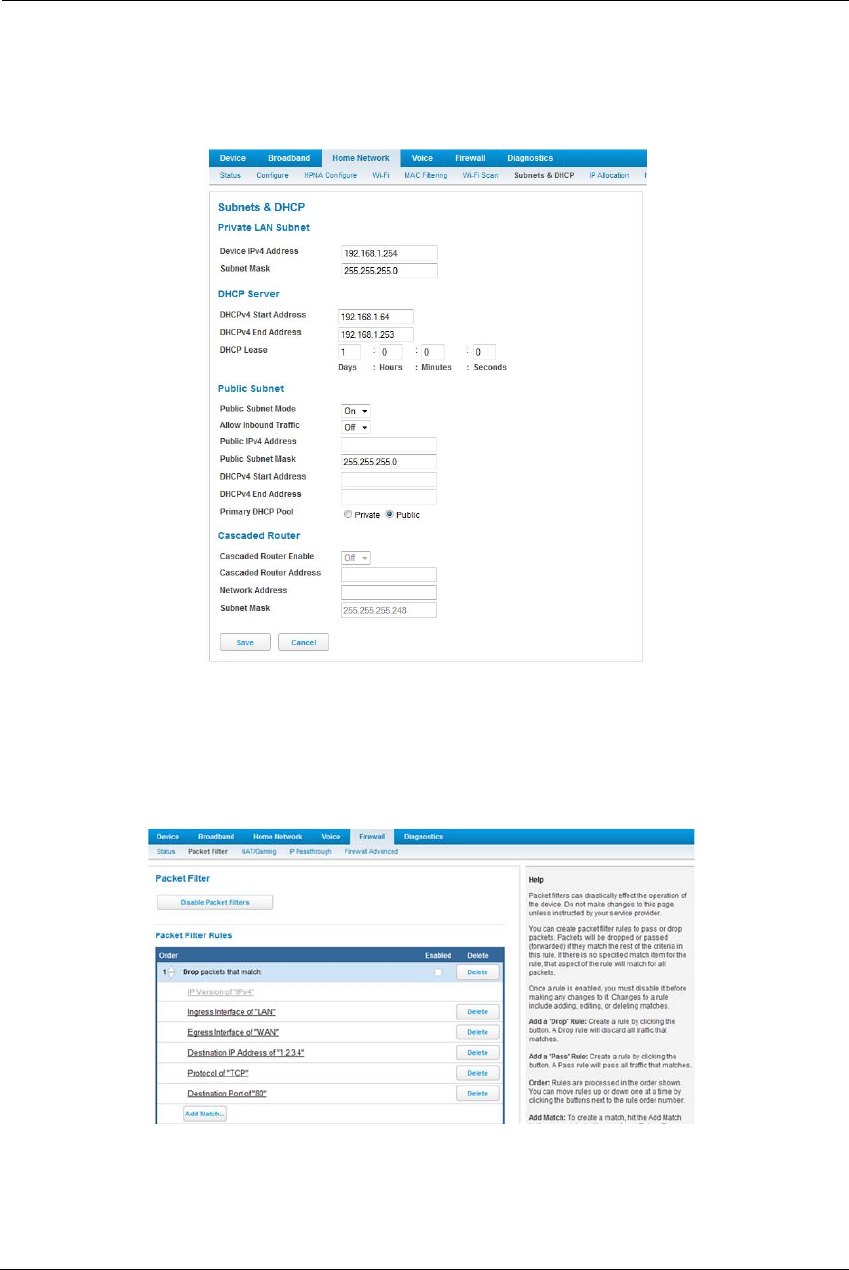
65
Example 2
The following example uses the GUI to detail how to create a public subnet.
1. Select Home Network -> Subnets & DHCP from the Web management GUI.
2. Select On from the Public Subnet Enable drop-down menu.
3. Enter all applicable public subnet IP address information and select Save at the bottom of the view.
4. Select Firewall -> Packet Filter to create a packet filter that will allow specific traffic to flow to a public LAN
client.
5. Scroll to the bottom of the screen and select Add a Pass Rule. This rule will allow traffic to flow through the
public subnet based on the match criteria that will be set up next.
The new rule will be at the bottom of the Packet Rules list (as shown below).
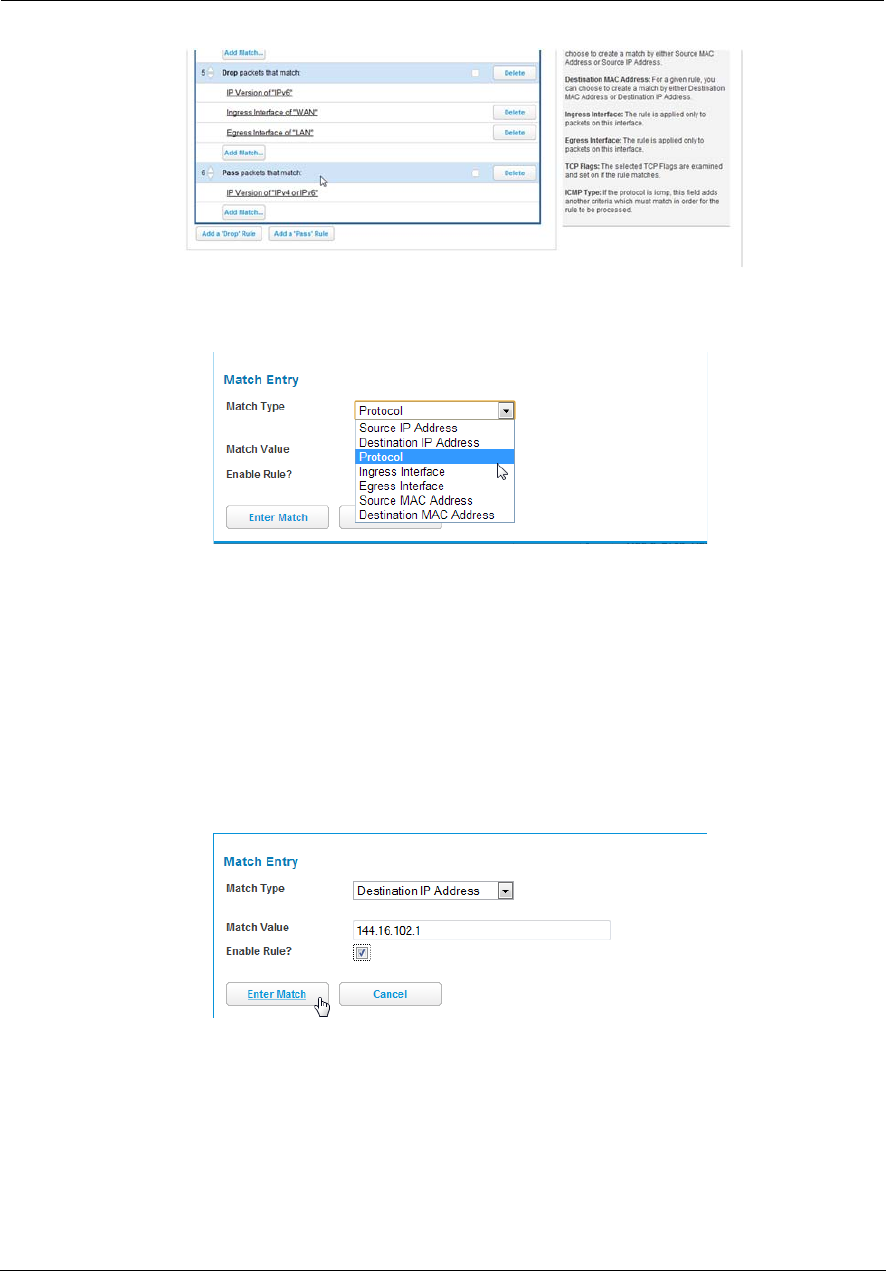
Administrator’s Handbook
66
6. Select the Add Match button below the new rule created above. This opens the Match Entry view.
7. For this example, the filter will be made based on a TCP port. Select Protocol from the Match Type drop-
down menu. This automatically fills in TCP in the Match Value field. At this point do not enable the rule until
all criteria have been entered.
8. Click Enter Match. This will return the GUI to the Packet Rules list.
9. Select Add Match below the rule created earlier.
10.Select Destination Port from the Match Type drop-down menu and enter 21 (this value corresponds to FTP)
in the Match Value entry box.
11.Click Enter Match.
12.Select Add Match below the same rule created earlier.
13.Select Destination IP Address from the Match Type drop-down menu and enter the IP address entered in
Step 3 of this procedure.
14.Select the Enable Rule check box and click Enter Match. The GUI returns to the Packet Rules list and the rule
is active and grayed out. It cannot be edited without first disabling the rule.
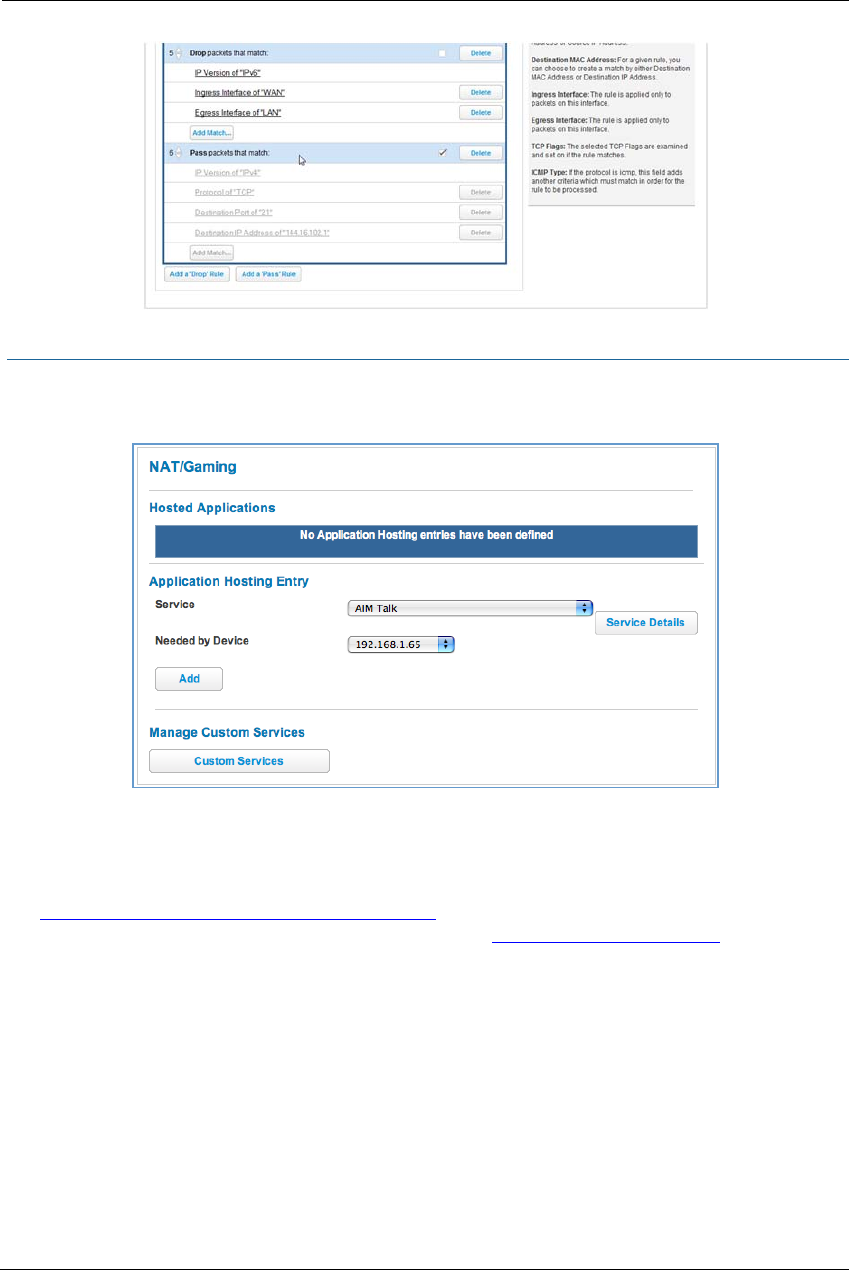
67
Link: NAT/Gaming
When you click the NAT/Gaming link, the NAT/Gaming page appears.
The NAT/Gaming feature allows you to host internet applications when NAT (network address translation) is
enabled. You can host different games and software on different PCs.
From the Service drop-down menu, you can select any of a large number of predefined games and software.
(See “List of Supported Games and Software” on page 71.) In addition to choosing from these predefined
services you can also select a user defined custom service. (See “Custom Services” on page 69.)
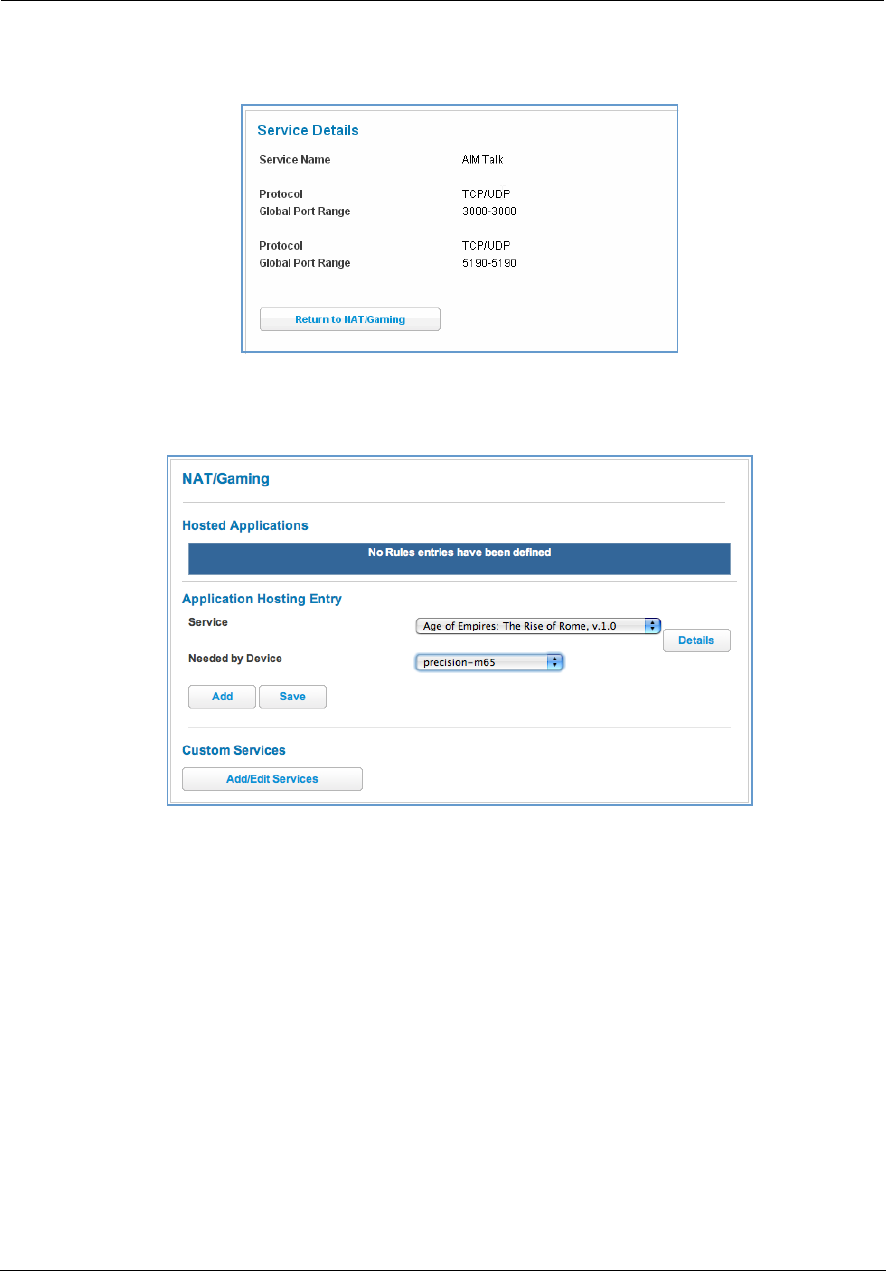
Administrator’s Handbook
68
For each supported game or service, you can view the protocols and port ranges used by the game or service
by clicking the Service Details button. For example:
1. Select a hosting device from the Needed by Device drop-down menu.
2. Once you choose a software service or game, click Add.
3. Select a PC to host the software from the Select Host Device drop-down menu and click Save.
Each time you enable a software service or game, your entry will be added to the list of Service names dis-
played on the NAT Configuration page.
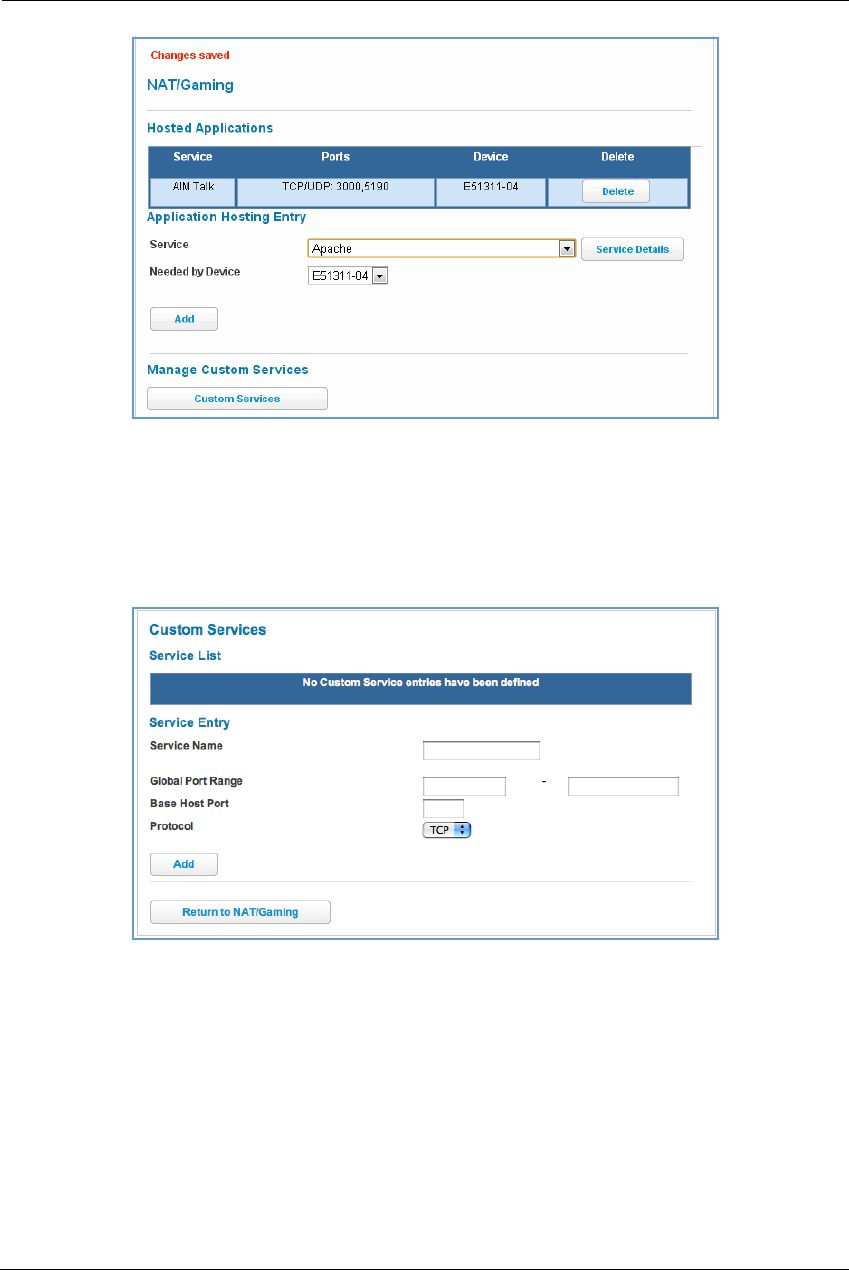
69
To remove a game or software from the hosted list, choose the game or software you want to remove and
click the Remove button.
Custom Services
To configure a custom service, click the Add/Edit Services button. The Custom Services page appears.
Enter the following information:
Service Name: A unique identifier for the custom service.
Global Port Range: Range of ports on which incoming traffic will be received.
Base Host Port: The port number at the start of the port range your NVG599 device should use when for-
warding traffic of the specified type(s) to the internal IP address.
Protocol: Protocol type of Internet traffic, TCP or UDP.
Once you define a custom service it becomes available in the Application Hosting Entry Service menu as one of
the services to select.
Click the Add button.
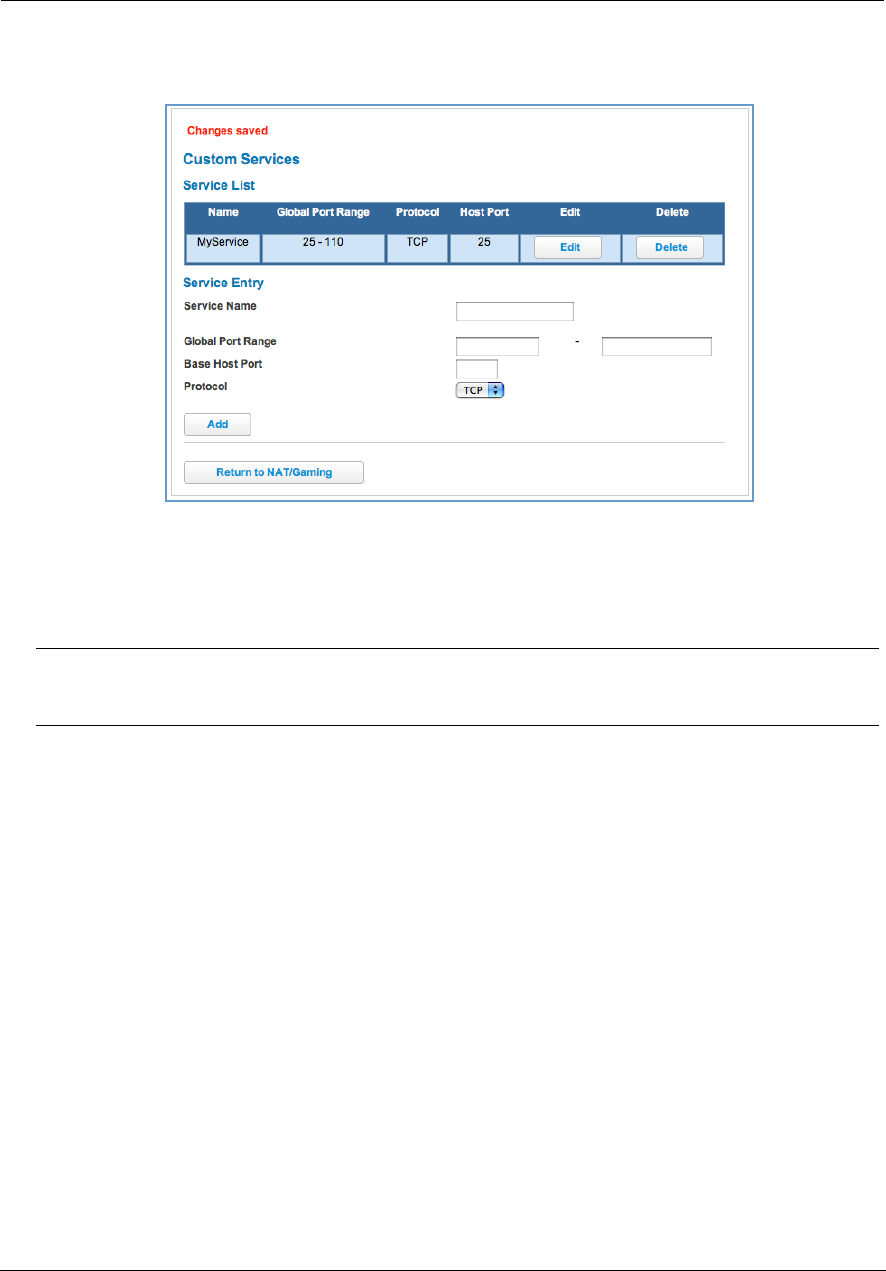
Administrator’s Handbook
70
Each time you add a custom service, your entry will be added to the list of service names displayed on the
Custom Services page.
Changes are saved immediately.
To remove this Service, click the Delete button.
To edit this Service, click the Edit button.
NOTE:
You cannot edit a custom service if that service is active; it must be inactive before it can be edited.
71
List of Supported Games and Software
AIM Talk Act of War - Direct Action Age of Empires II
Age of Empires, v.1.0 Age of Empires: The Rise of Rome,
v.1.0
Age of Mythology
Age of Wonders America's Army Apache
Asheron's Call Azureus Baldur's Gate I and II
Battlefield 1942 Battlefield Communicator Battlefield Vietnam
BitTornado BitTorrent Black and White
Blazing Angels Online Brothers in Arms - Earned in Blood Brothers in Arms Online
Buddy Phone CART Precision Racing, v 1.0 Calista IP Phone
Call of Duty Citrix Metaframe/ICA Client Close Combat III: The Russian Front,
v 1.0
Close Combat for Windows 1.0 Close Combat: A Bridge Too Far, v
2.0
Combat Flight Sim 2: WWII Pacific
Thr, v 1.0
Combat Flight Sim: WWII Europe
Series, v 1.0
Counter Strike DNS Server
Dark Reign Delta Force (Client and Server) Delta Force 2
Delta Force Black Hawk Down Diablo II Server Dialpad
DirecTV STB 1 DirecTV STB 2 DirecTV STB 3
Doom 3 Dues Ex Dune 2000
Empire Earth Empire Earth 2 F-16, Mig 29
F-22, Lightning 3 FTP Far Cry
Fighter Ace II GNUtella Grand Theft Auto 2 Multiplayer
H.323 compliant (Netmeeting,
CUSeeME)
HTTP HTTPS
Half Life Half Life 2 Steam Half Life 2 Steam Server
Half Life Steam Half Life Steam Server Halo
Hellbender for Windows, v 1.0 Heretic II Hexen II
Hotline Server ICQ 2001b ICQ Old
IMAP Client IMAP Client v.3 IPSec IKE
Internet Phone Jedi Knight II: Jedi Outcast Kali
KazaA Lime Wire Links LS 2000
Lord of the Rings Online MSN Game Zone MSN Game Zone DX
MSN Messenger Mech Warrior 3 MechWarrior 4: Vengeance
Medal of Honor Allied Assault Microsoft Flight Simulator 2000 Microsoft Flight Simulator 98
Microsoft Golf 1998 Edition, v 1.0 Microsoft Golf 1999 Edition Microsoft Golf 2001 Edition
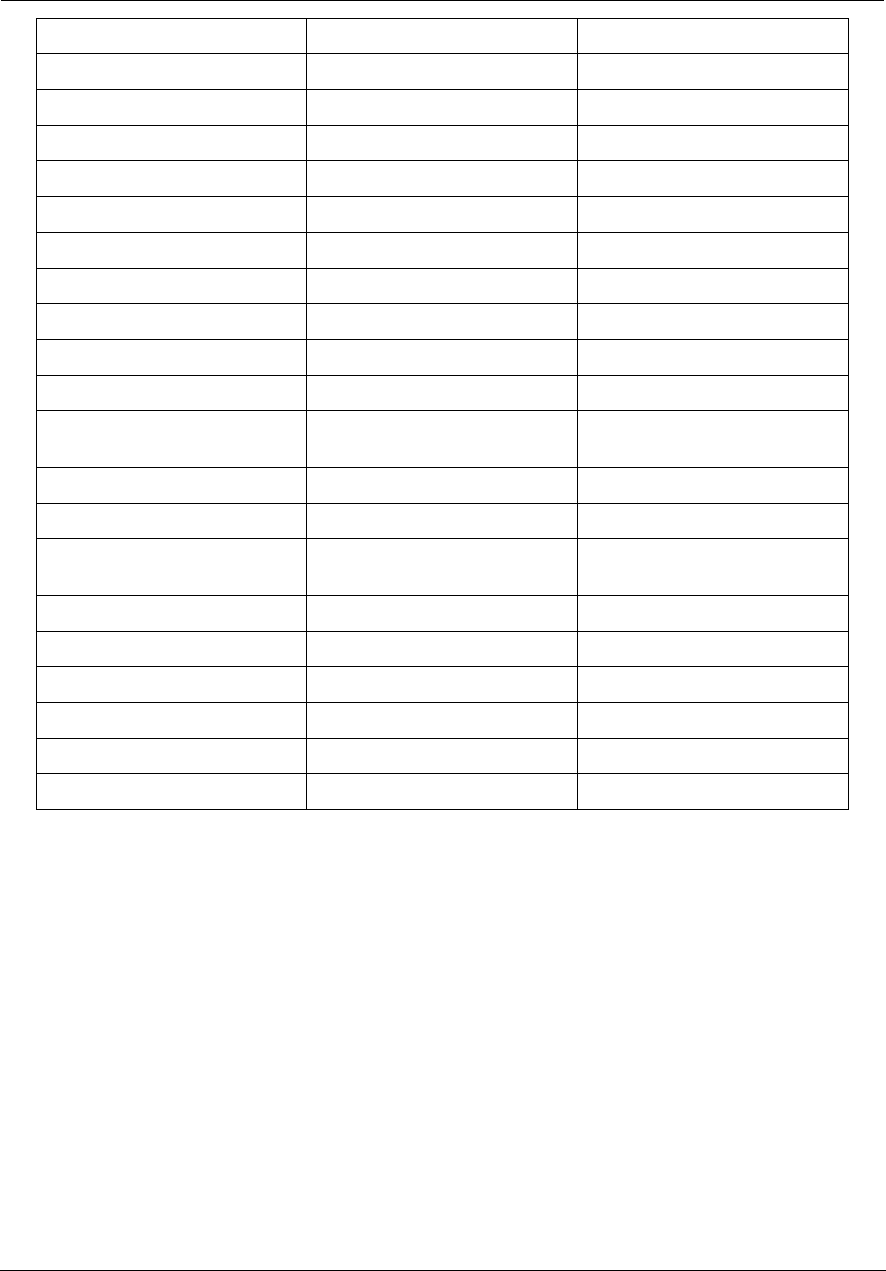
Administrator’s Handbook
72
Midtown Madness, v 1.0 Monster Truck Madness 2, v 2.0 Monster Truck Madness, v 1.0
Motocross Madness 2, v 2.0 Motocross Madness, v 1.0 NNTP
Need for Speed 3, Hot Pursuit Need for Speed, Porsche Net2Phone
Operation FlashPoint Outlaws POP-3
PPTP PlayStation Network Quake 2
Quake 3 Quake 4 Rainbow Six
RealAudio Return to Castle Wolfenstein Roger Wilco
Rogue Spear SMTP SNMP
SSH server ShoutCast Server SlingBox
Soldier of Fortune StarCraft StarLancer, v 1.0
Starfleet Command TFTP TeamSpeak
Telnet Tiberian Sun: Command and Con-
quer
Timbuktu
Total Annihilation Ultima Online Unreal Tournament Server
Urban Assault, v 1.0 VNC, Virtual Network Computing Warlords Battlecry
Warrock Westwood Online, Command and
Conquer
Win2000 Terminal Server
Wolfenstein Enemy Territory World of Warcraft X-Lite
XBox 360 Media Center XBox Live 360 Yahoo Messenger Chat
Yahoo Messenger Phone ZNES eDonkey
eMule eMule Plus iTunes
mIRC Auth-IdentD mIRC Chat mIRC DCC - IRC DCC
pcAnywhere (incoming)
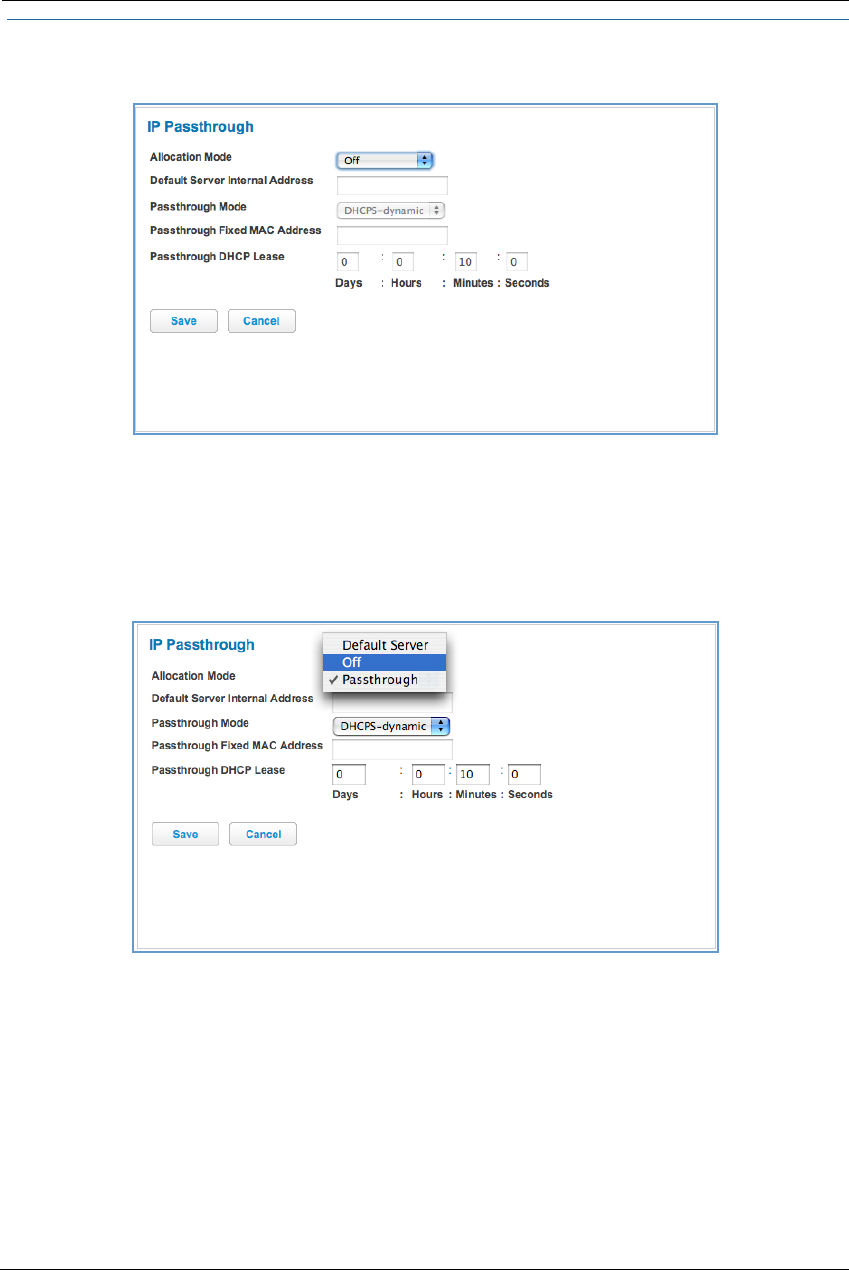
73
Link: IP Passthrough
When you click the IP Passthrough link, the IP Passthrough page appears.
IP Passthrough
The IP Passthrough feature allows a single PC on the LAN to have the ARRIS Gateway’s public address assigned
to it. It also provides PAT (port address translation) (or NAPT – network address and port translation) via the
same public IP address for all other hosts on the private LAN subnet.
Using IP Passthrough, the public WAN IP is used to provide IP address translation for private LAN computers.
The public WAN IP is assigned and reused on a LAN computer.
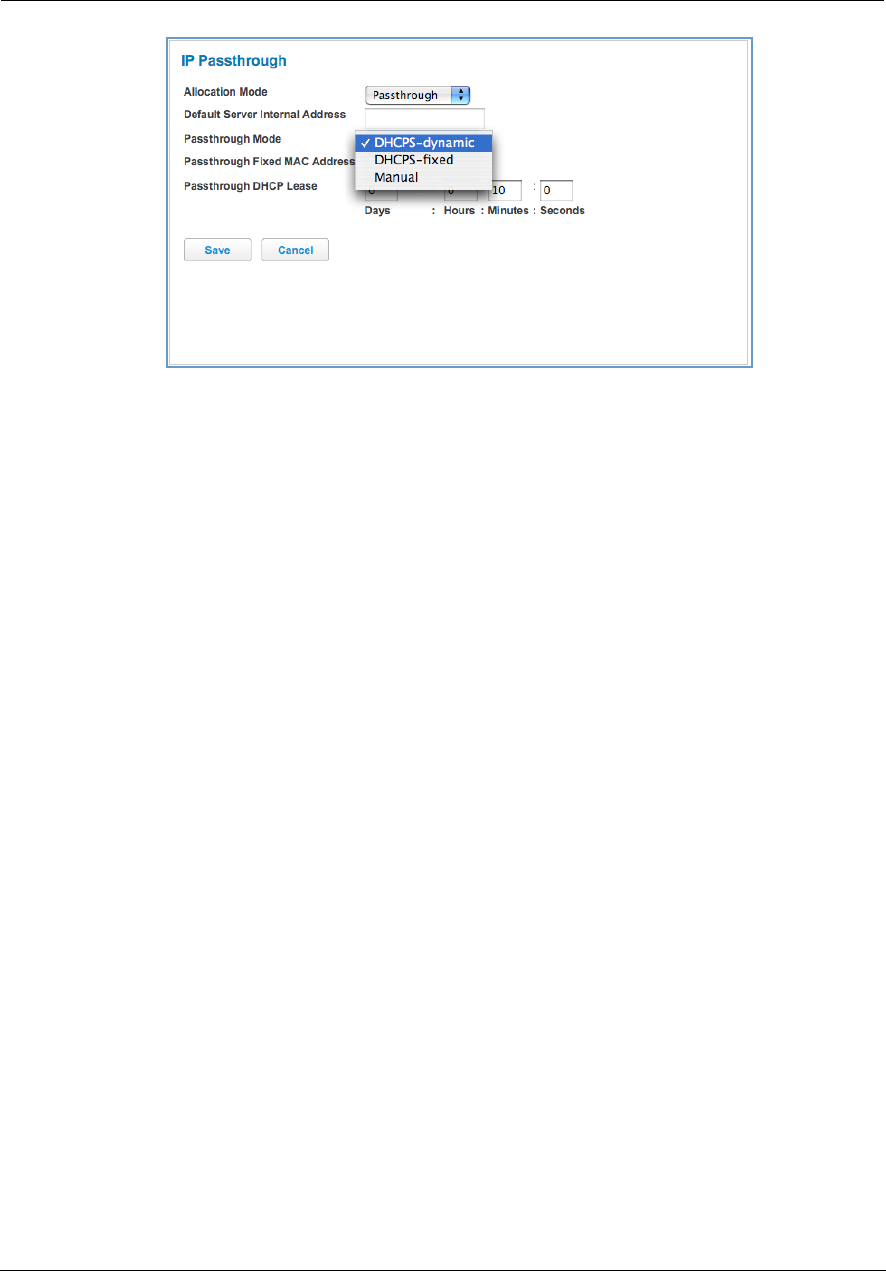
Administrator’s Handbook
74
DHCP address serving can automatically serve the WAN IP address to a LAN computer.
When DHCP is used for addressing the designated passthrough PC, the acquired or configured WAN address is
passed to DHCP, which will dynamically configure a single-servable-address subnet, and reserve the address
for the configured PC’s MAC address. This dynamic subnet configuration is based on the local and remote
WAN address and subnet mask.
The two DHCP modes assign the needed WAN IP information to the client automatically.
• You can select the MAC address of the PC you want to be the IP Passthrough client with fixed mode, or,
• with “first-come-first-served” – dynamic – the first client to renew its address will be assigned the WAN IP.
Manual mode is like statically configuring your PC. With Manual mode, you configure the TCP/IP Properties
of the LAN client PC you want to be the IP Passthrough client. You then manually enter the WAN IP address,
gateway address, and so on that matches the WAN IP address information of your ARRIS device. This mode
works the same as the DHCP modes. Unsolicited WAN traffic will get passed to this client. The client is still
able to access the ARRIS NVG599 device and other LAN clients on the 192.168.1.x network, etc.
The Passthrough DHCP Lease – By default, the passthrough host's DHCP leases will be shortened to two min-
utes. This allows for timely updates of the host's IP address, which will be a private IP address before the
WAN connection is established. After the WAN connection is established and has an address, the
passthrough host can renew its DHCP address binding to acquire the WAN IP address. You may alter this set-
ting.
Click Save. Changes take effect upon restart.
A Restriction
Because both the NVG599 device and the passthrough host will use the same IP address, new sessions that
conflict with existing sessions will be rejected by the NVG599. For example, suppose you are a teleworker using
an IPSec tunnel from the router and from the passthrough host. Both tunnels go to the same remote endpoint,
such as the VPN access concentrator at your employer’s office. In this case, the first one to start the IPSec
traffic will be allowed; the second one – because, from the WAN, it is indistinguishable – will fail.
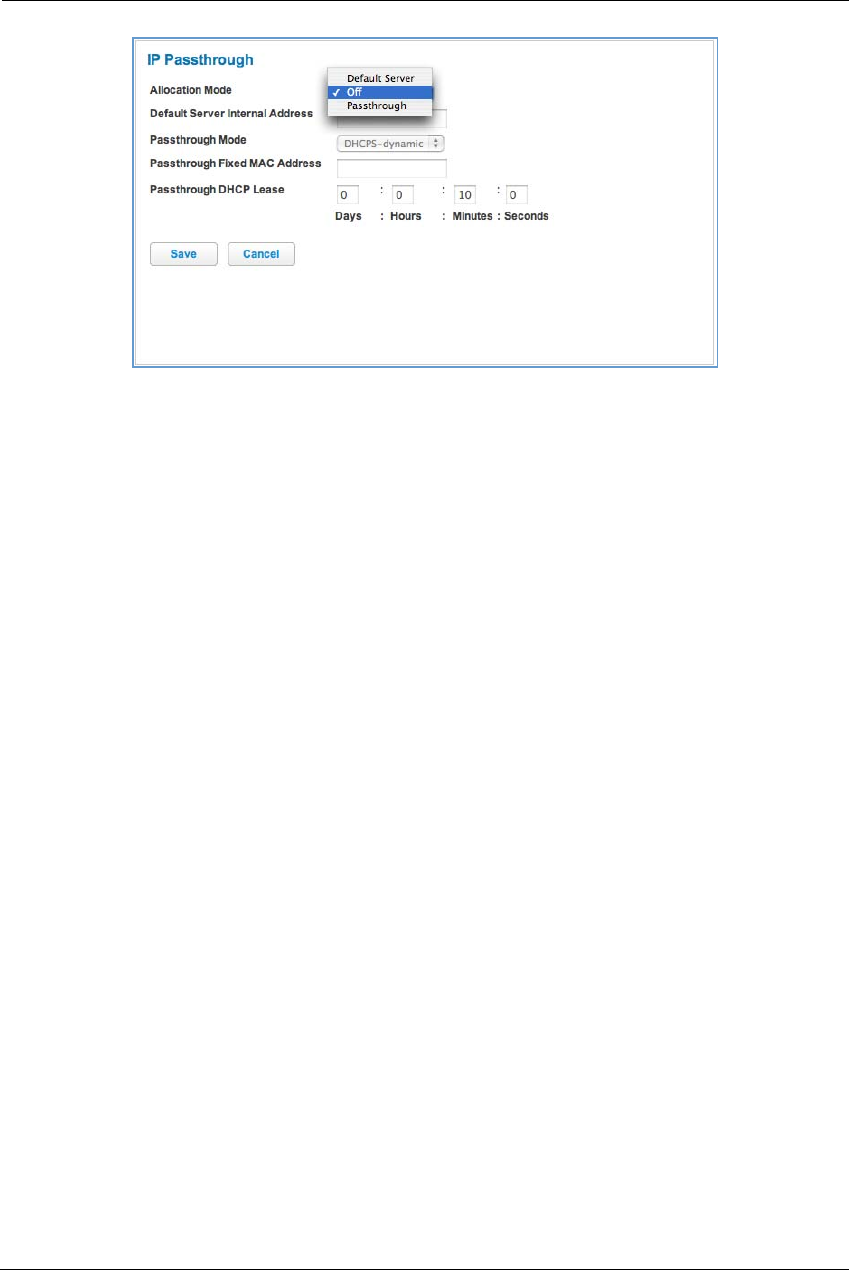
75
NAT Default Server
The NAT default server feature allows you to:
Direct your NVG599 device to forward all externally initiated IP traffic (TCP and UDP protocols only) to a
default host on the LAN, specified by your entry in the Internal Address field.
Enable the default server for certain situations:
– Where you cannot anticipate what port number or packet protocol an in-bound application might use. For
example, some network games select arbitrary port numbers when a connection is opened.
– When you want all unsolicited traffic to go to a specific LAN host.
This feature allows you to direct unsolicited or non-specific traffic to a designated LAN station. With NAT on in
the device, these packets normally would be discarded. For instance, this feature could be used for application
traffic where you do not know in advance the port or protocol that will be used. Some game applications fit
this profile.
Click Save. Changes take effect immediately.
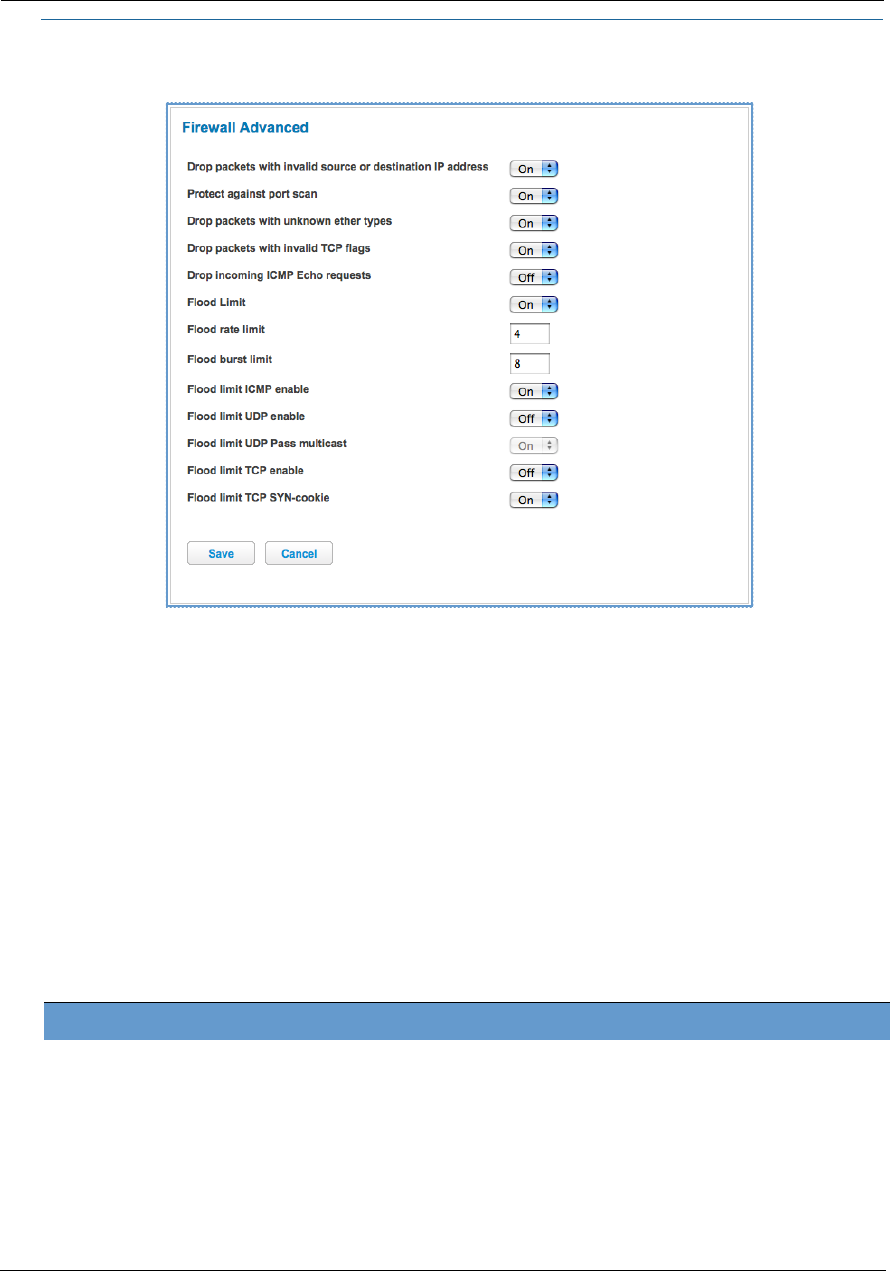
Administrator’s Handbook
76
Link: Firewall Advanced
When you click the Firewall Advanced link the Firewall Advanced screen appears.
All computer operating systems are vulnerable to attack from outside sources, typically at the operating
system or Internet Protocol (IP) layers. Stateful inspection firewalls intercept and analyze incoming data
packets to determine whether they should be admitted to your private LAN, based on multiple criteria, or
blocked. Stateful inspection improves security by tracking data packets over a period of time, examining
incoming and outgoing packets. Outgoing packets that request specific types of incoming packets are tracked;
only those incoming packets constituting a proper response are allowed through the firewall.
Stateful inspection is a security feature that prevents unsolicited inbound access when NAT is disabled. You can
configure UDP and TCP “no-activity” periods that will also apply to NAT timeouts if stateful inspection is
enabled on the interface. Stateful Inspection parameters are active on a WAN interface only if enabled on your
NVG599 device. Stateful inspection can be enabled on a WAN interface whether NAT is enabled or not.
DoS Protection – Denial-of-service (DoS) attacks are common on the Internet, and can render an individual PC
or a whole network practically unusable by consuming all its resources. Your NVG599 includes default settings
to block the most common types of DoS attacks. For special requirements or circumstances, a variety of
additional blocking characteristics are offered. See the following table.
Menu item Function
Drop packets with invalid source or desti-
nation IP address
Whether packets with invalid source or destination IP address(es) are to be
dropped
Protect against port scan Whether to detect and drop port scans.
Drop packets with unknown ether types Whether packets with unknown ether types are to be dropped
Drop packets with invalid TCP flags Whether packets with invalid TCP flag settings (NULL, FIN, Xmas, etc.)
should be dropped
Drop incoming ICMP Echo requests Whether all ICMP echo requests are to be dropped; On or Off.

77
If you make any changes here, click the Save button.
Flood Limit Whether packet flooding should be detected and offending packets be
dropped; On or Off.
Flood rate limit Specifies the number limit of packets per second before dropping the
remainder.
Flood burst limit Specifies the number limit of packets in a single burst before dropping the
remainder.
Flood limit ICMP enable Whether ICMP traffic packet flooding should be detected and offending
packets be dropped; On or Off.
Flood limit UDP enable Whether UDP traffic packet flooding should be detected and offending
packets be dropped; On or Off.
Flood limit UDP Pass multicast Allows exclusion of UDP multicast traffic. On by default.
Flood limit TCP enable Allows exclusion of TCP traffic. Off by default.
Flood limit TCP SYN-cookie Allows TCP SYN cookies flooding to be excluded.
Neighbor Discovery Attack protection Prevents downstream traffic from an upstream device that sends excessive
traffic but receives no replies; On or Off.
ESP Header Forwarding Allows the use of Encapsulating Security Payload (ESP) data payload encryp-
tion for IP Secure (IPsec) from qualifying endpoints; On or Off.
Authentication Header Forwarding Accept and forward IPSec packets with Authencation Headers, which may
be used by some IPSec implementations to validate packet sources ; On or
Off.
Reflexive ACL When IPv6 is enabled, Reflexive Access Control Lists can deny inbound IPv6
traffic unless this traffic results from returning outgoing packets (except as
configured through firewall rules).
Menu item Function
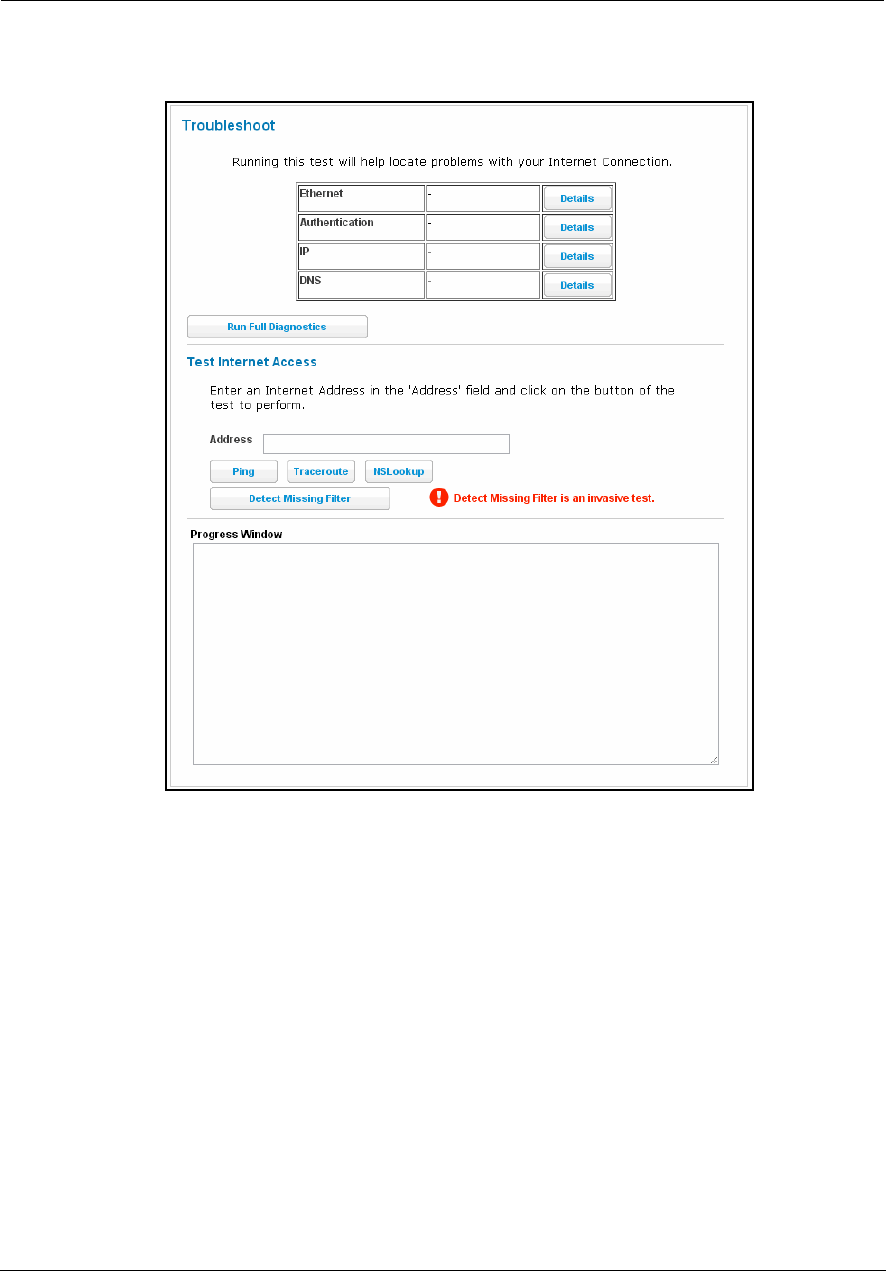
Administrator’s Handbook
78
Diagnostics
When you click the Diagnostics tab, the Troubleshoot page appears.
This automated multi-layer test examines the functions of the router from the physical connections to the data
traffic being sent by users through the router.
You can run all the tests in order by clicking the Run Full Diagnostics button.
The device will automatically test a number of components to determine any problems. You can see detailed
results of the tests by clicking the Details buttons for each item. The details presented depend on the
configuration of your router and your network type.
79
Here is an example of the Ethernet Details screen.
Test Internet Access
Internet access tests send a ping from the modem to either the LAN or WAN to verify connectivity. A ping could
be either an IP address (163.176.4.32) or domain name (www.arris.com). You enter a Web address URL or an IP
address in the respective field.
Click the Ping, Trace, NSLookup, or Detect Missing Filter button.
Results will be displayed in the Progress Window as they are generated.
Ping - tests the reachability of a particular network destination by sending an ICMP echo request and waiting
for a reply.
Traceroute - displays the path to a destination by showing the number of hops and the router addresses of
these hops.
NSLookup - converts a domain name to its IP address and vice versa.
Detect Missing Filter - if you click the Detect Missing Filter button, a warning message appears at the top
since the detection takes up to 2 minutes. When completed the Progress area might look like following.
To use the ping capability, type a destination address (domain name or IP address) in the text box and click the
Ping, Trace, or Lookup button. The results are displayed in the Progress Window.
This sequence of tests takes approximately one minute to generate results. Be sure to wait for the test to run to
completion.
Administrator’s Handbook
80
Each test generates one of the following result codes:
Below are some specific tests:
Result Meaning
* PASS: The test was successful.
* FAIL: The test was unsuccessful.
* SKIPPED: The test was skipped because a test on which it depended failed.
* PENDING: The test timed out without producing a result. Try running the test again.
* WARNING: The test was unsuccessful. The service provider equipment your modem connects to may not
support this test.
Action If Ping Fails, Possible Causes Are:
From the Check Connection Page:
Ping the Internet default gateway IP address DSL is down, DSL settings are incorrect; gateway’s IP
address or subnet mask are wrong; gateway router is
down.
Ping an Internet site by IP address Site is down.
Ping an Internet site by name Servers are down; site is down.
From a LAN PC:
Ping the modem’s LAN IP address IP address and subnet mask of PC are not on the same
scheme as the modem; cabling or other connectivity
issue.
Ping an Internet site by IP address PC's subnet mask may be incorrect, site is down.
Ping an Internet site by name DNS is not properly configured on the PC, site is down.
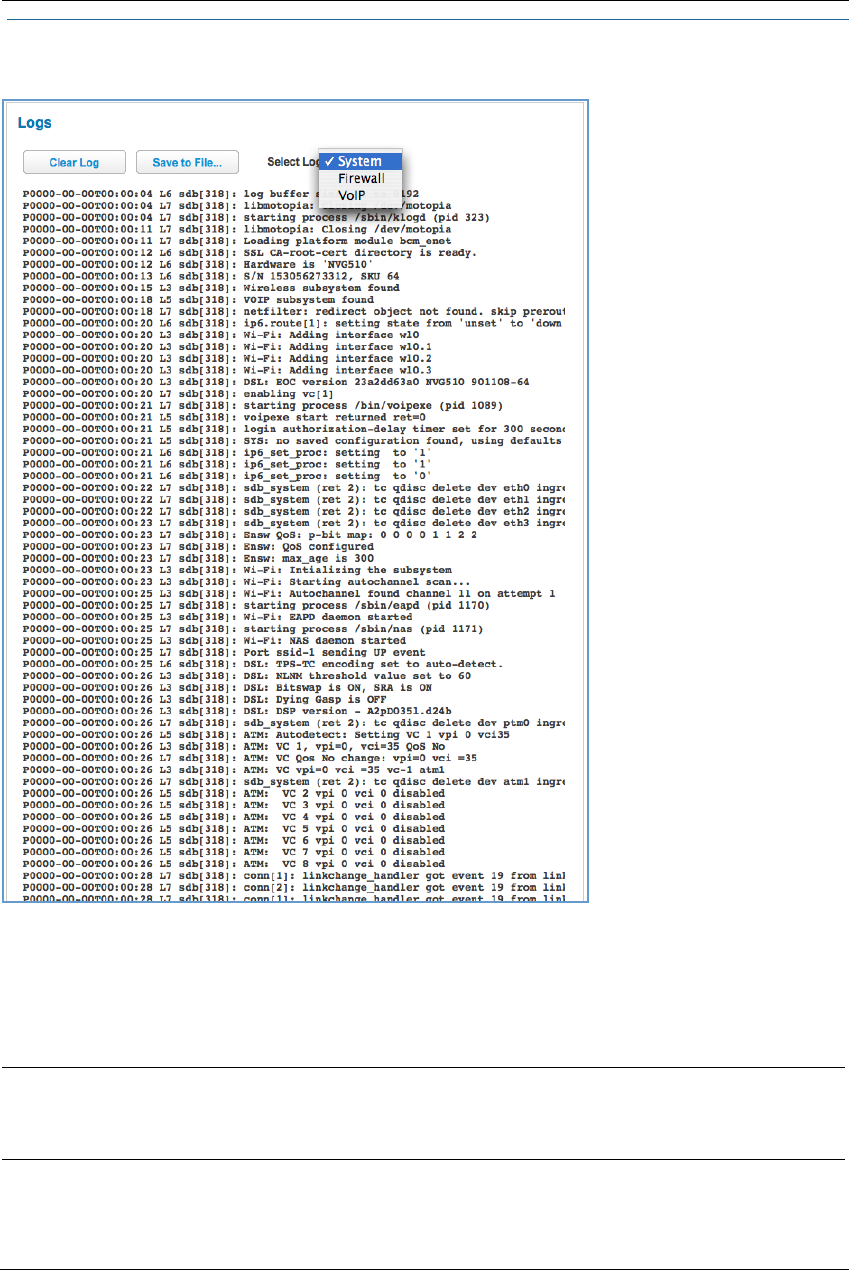
81
Link: Logs
When you click Logs, the Logs page appears.
The current status of the device is displayed for all logs: System, Firewall, or VoIP. Choose the log you want to
display from the drop-down menu.
You can clear all log entries by clicking the Clear Log button.
You can save logs to a text (.TXT) file by clicking the Save to File button. This will download the file to your
browser’s default download location on your hard drive. The file can be opened with your favorite text edi-
tor.
NOTE:
Some browsers, such as Internet Explorer for Windows XP, require that you specify the ARRIS device’s URL as
a “Trusted site” in “Internet Options: Security.” This is necessary to allow the download of the log text file to
the PC.
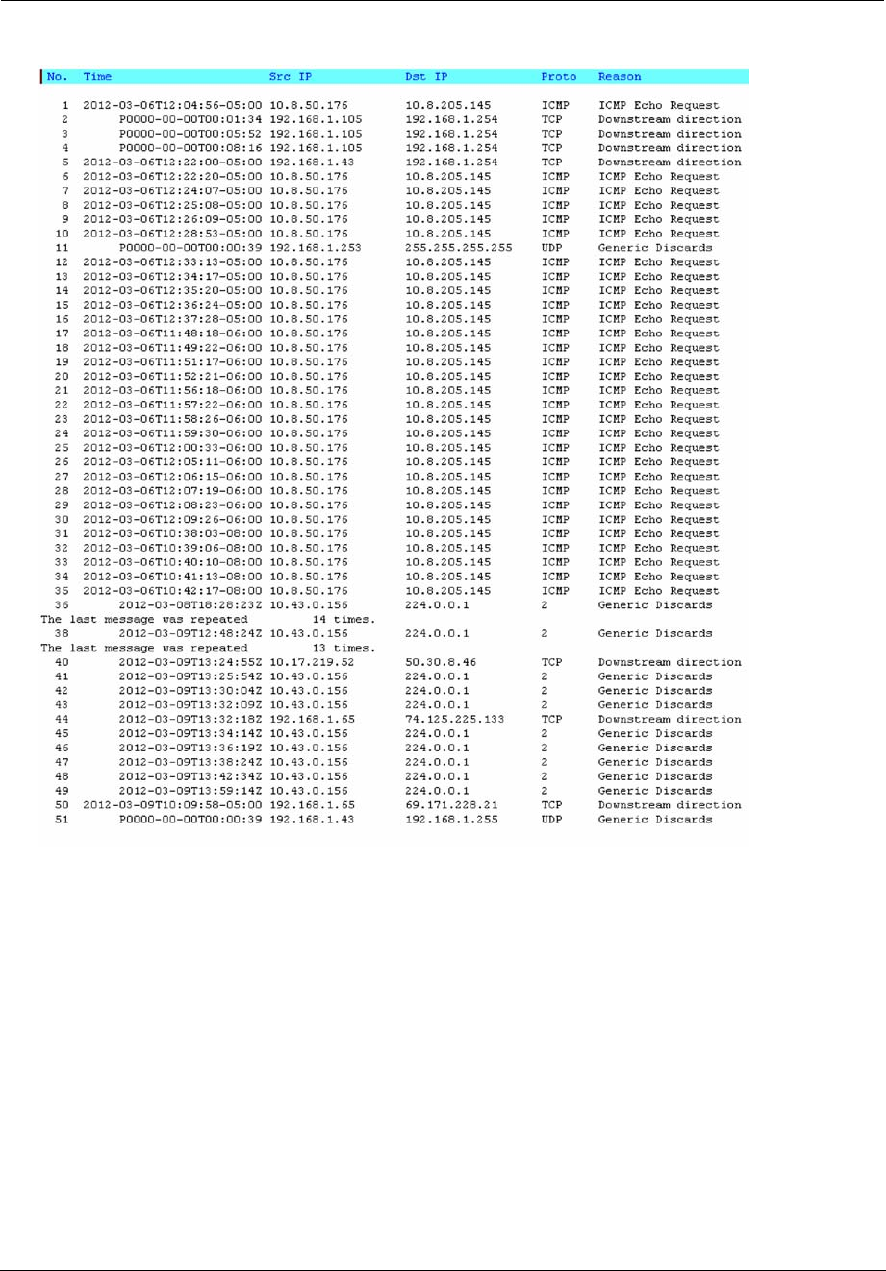
Administrator’s Handbook
82
The following is an example log portion saved as a .TXT file:
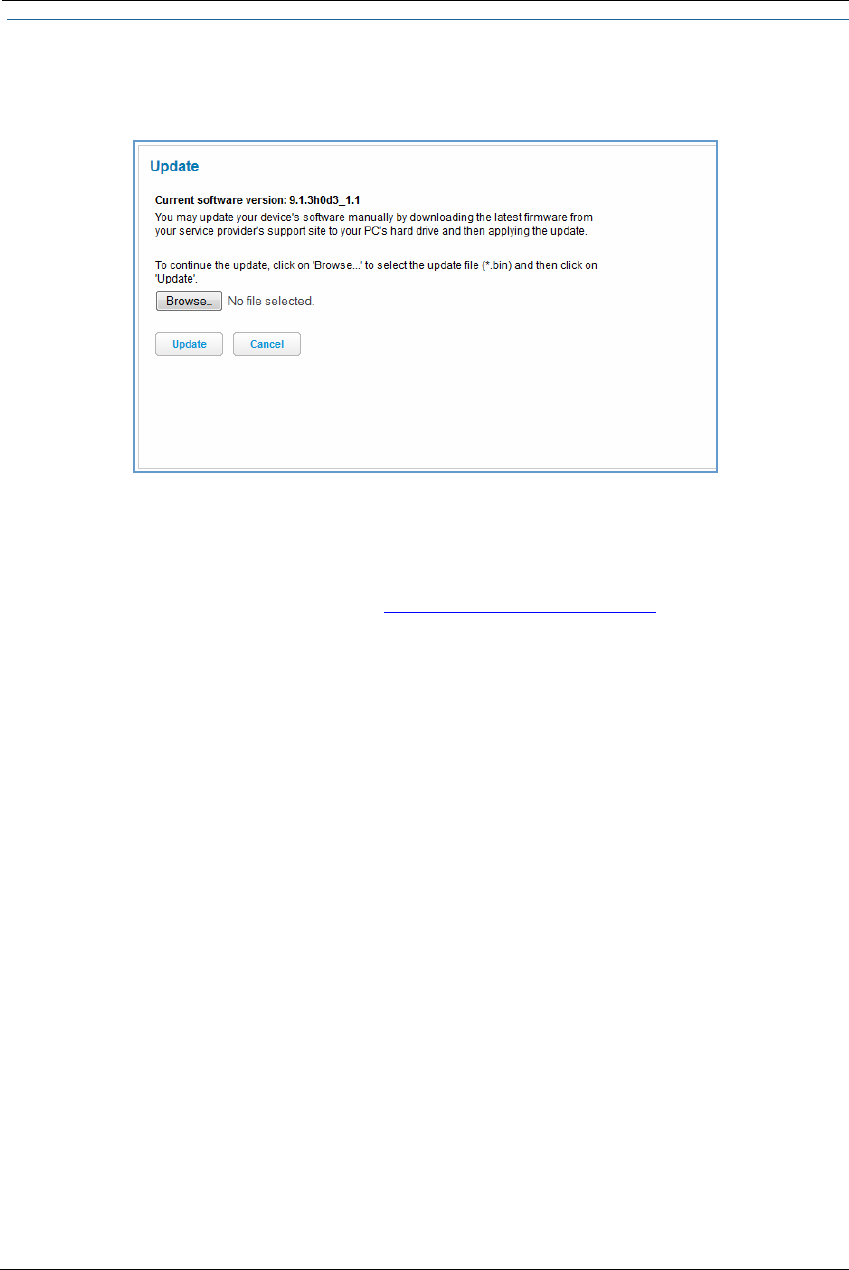
83
Link: Update
When you click Update, the Update page appears.
Operating system software is what makes your NVG599 device run, and occasionally it needs to be updated.
Your Current software version is displayed at the top of the page.
To update your software from a file on your PC, you must first download the software from your service
provider's support site to your PC's hard drive.
1. Browse your computer for the operating system file you downloaded and select the file.
2. Click the Update button.
The LEDs will operate normally as described in “Status Indicator Lights” on page 88.
3. The installation may take a few minutes and the Web page will indicate a 3-part countdown before returning
you to the Home page; wait for it to complete. During the software installation, you will lose Internet and
phone service. The LEDs will function as follows:
•
The Power LED will flash Orange/Amber during firmware upgrade (flash writing to memory) and all
other LEDs will be off.
4. The Gateway will restart automatically.
As the device reboots, the LEDs display power-on behavior.
5. Your new operating system will then be running.
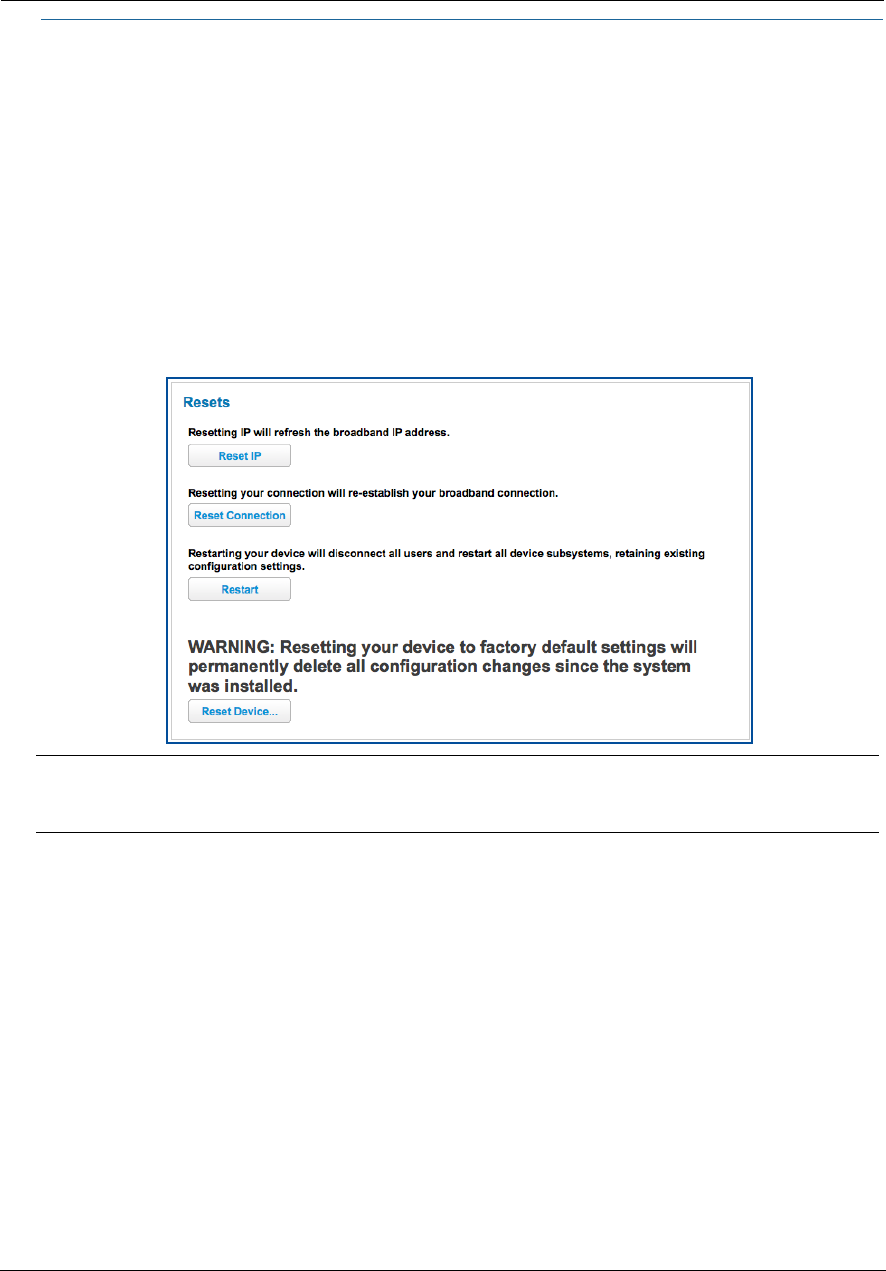
Administrator’s Handbook
84
Link: Resets
When you click the Resets link, the Resets page appears.
In some cases, you may need to clear all the configuration settings and start over again to program the
ARRIS NVG599 device. You can perform a factory reset to do this.
It might also be useful to reset your connection to the Internet without deleting all of your configuration
settings.
Click the Reset IP button to refresh your Internet WAN IP address. LAN-side users will be briefly disconnected
from the Internet, but will otherwise be unaffected.
Click the Reset Connection button to disconnect and reconnect all of your connections, including your VoIP
phones.
Click the Reset Device button to reset the Gateway back to its original factory default settings.
Click the Restart button to reboot the device. Previous configuration settings are still retained.
NOTE:
Exercise caution before performing a factory reset. This will erase any configuration changes that you may
have made and allow you to reprogram your NVG599 device.
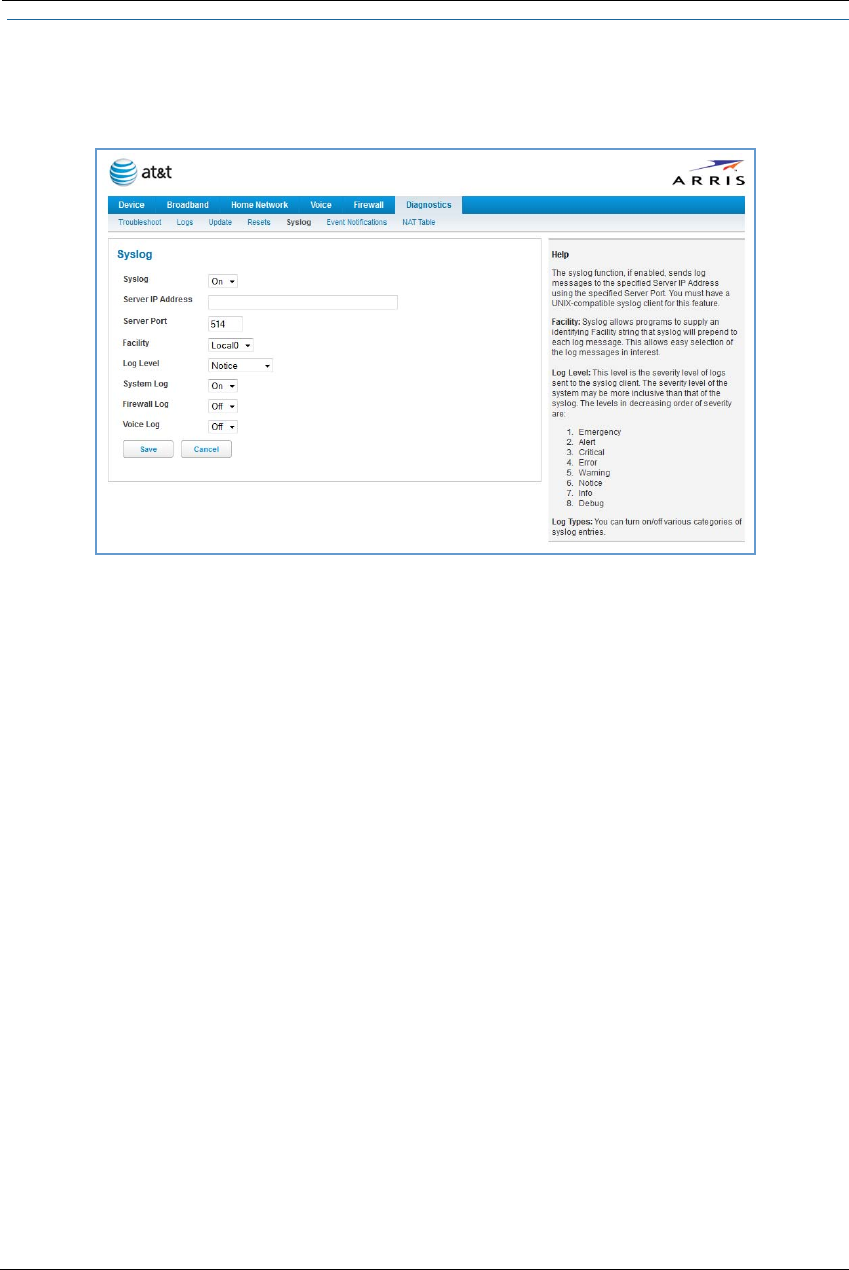
85
Link: Syslog
When you click the Syslog link the Syslog configuration page appears. You can configure a UNIX-compatible
(BSD Syslog protocol - RFC 3164) Syslog client to report a number of subsets of the events entered in the device
logs.
You can enable or disable the Syslog client dynamically. When enabled, it will report any appropriate and
previously unreported events.
You can specify the Syslog server’s address and port, if required, either in dotted decimal format or as a DNS
name of up to 63 characters.
You can specify the UNIX Syslog facility to use by selecting from the Facility drop-down menu.
From the Log Level drop-down menu, you can select a level from a list organized in decreasing severity level:
Emergency, Alert, Critical, Error, Warning, Notice, Info, or Debug.
By toggling each event descriptor to either On or Off, you can determine which ones are logged and which
are ignored.
You will need to install a Syslog client daemon program on your PC and configure it to report the events you
specified in the Syslog configuration screen.
Click the Save button.
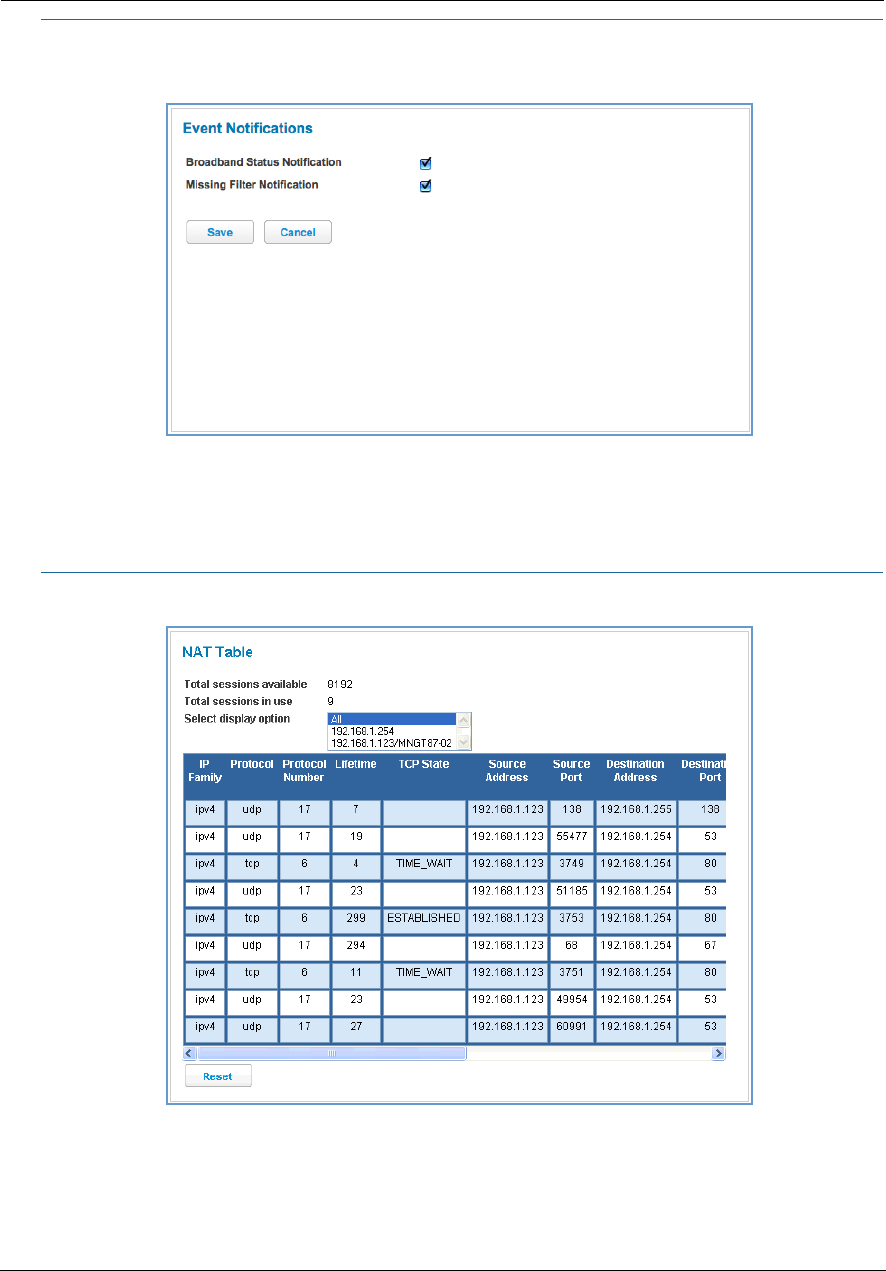
Administrator’s Handbook
86
Link: Event Notifications
When you click the Event Notifications link, the Event Notifications page appears.
If you select the Broadband Status Notification checkbox, the device will alert users on your network if the
connection to the Internet should fail. In that event, troubleshooting suggestions will display.
If you select the Missing Filter Notification checkbox, the device will alert users on your network if hardware
line filters are either missing or improperly installed. In that event, troubleshooting suggestions will display.
Link: NAT Table
When you click the NAT Table link, the NAT Table page appears.
The NAT Table page displays the network address translation sessions in use by the NVG599 device. You can
use the drop-down menu to limit the displayed sessions to selected IP addresses.
To refresh all the sessions displayed, click the Reset button.

87
CHAPTER 3 Basic Troubleshooting
This chapter gives some simple suggestions for troubleshooting problems with your NVG599 VDSL2 Gateway’s
initial configuration. This chapter covers the following topics:
Status Indicator Lights on page 88
Factory Reset Switch on page 95
Event Log Messages on page 96
Before troubleshooting, make sure you have:
Read this guide
Plugged in all the necessary cables
Set your PC’s TCP/IP controls to obtain an IP address automatically
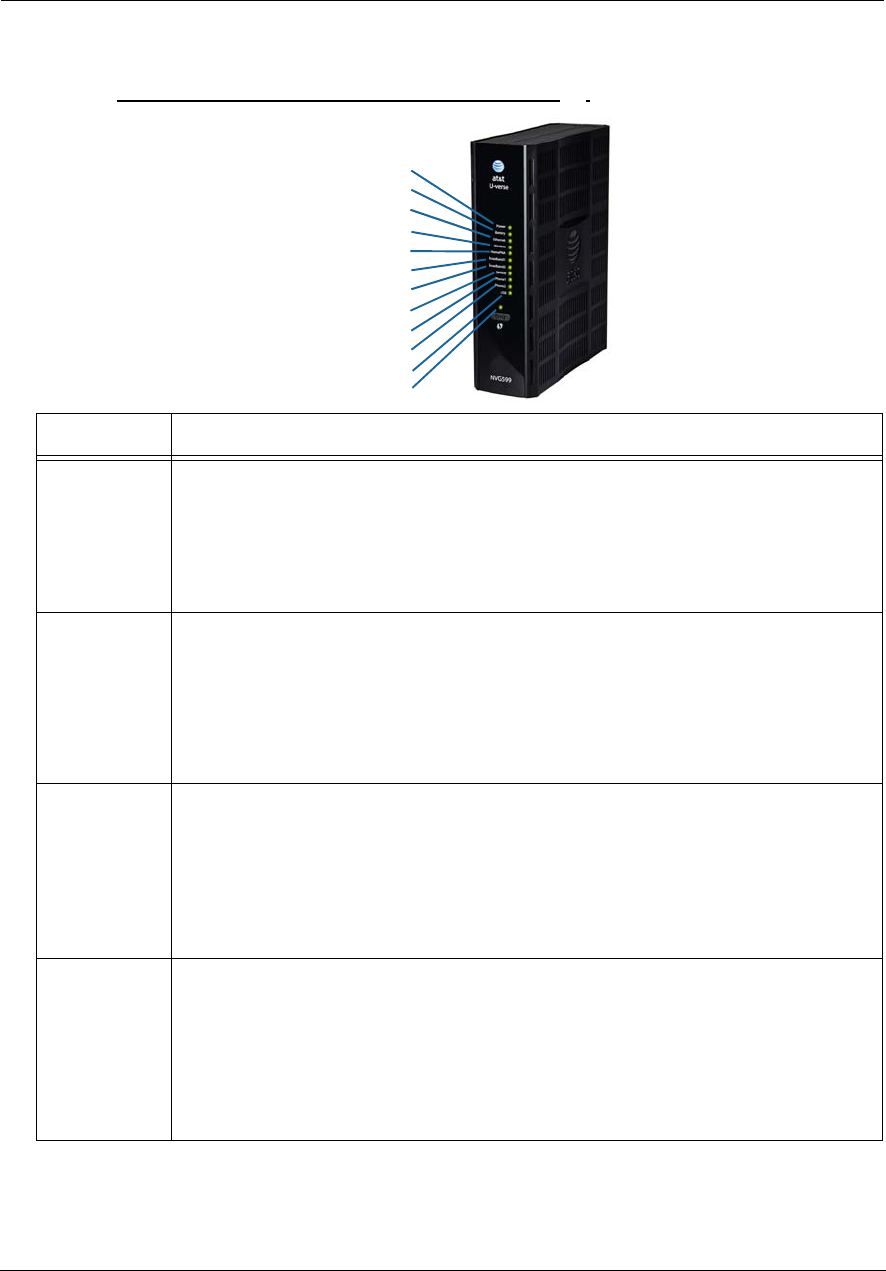
Administrator’s Handbook
88
Status Indicator Lights
The first step in troubleshooting is to check the status indicator lights (LEDs) in the order outlined below.
ARRIS NVG599 VDSL2 Gateway Status Indicator Lights
LED Activity
Power
Solid Green = The device is powered.
Flashing Green = A power-on self-test (POST) is in progress
Flashing Red = A POST failure (not bootable) or device malfunction occurred.
Flashing Amber = Firmware upgrade in progress (see below)
Off = The unit has no AC power. If the battery is in use, the Battery LED will indicate battery status,
and all other LEDs will be off.
Power during
Firmware
Upgrade
During the software installation, you will lose Internet and phone service. The LEDs will function as
follows:
1. As firmware is being loaded into flash, the LEDs operate normally.
2. During the firmware upgrade, which takes a few minutes, the Power LED will flashes amber
(flash writing to memory), and all other LEDs are off.
3. The NVG599 restarts automatically.
As the device reboots, the LEDs display power-on behavior.
All during
Boot process
• Power LED = Flashing Green
• All other LEDs = Off
If the device does not boot and fails its self-test or fails to perform initial load of the bootloader:
• Power LED = Flashing Red
• ALL other LEDs = Off
If the device boots and then detects a failure:
Power LED = Flashing Green starting POST, and then all LEDs will flash red, including Power LED.
Battery
Solid Green = Battery in place but not being used.
Flashing Green = Battery charging.
Solid Red = Battery backup mechanism has a fault.
Flashing Red = Battery needs to be replaced.
Solid Amber = Battery in use.
Flashing Amber = Low battery.
Off = No battery, or battery has no charge.
Side View
Power
Battery
Ethernet
Wireless
HomePNA
USB
Broadband 1
Broadband 2
Service
Phone 1
Phone 2
WPS

89
Ethernet
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, or no cable or no powered devices are connected to the associated
ports.
WiFi
Solid Green = Wi-Fi is powered.
Flickering Green = Activity seen from devices connected via Wi-Fi. The flickering of the light is syn-
chronized to actual data traffic.
Off = The device is not powered, or no powered devices are connected to the associated ports.
HomePNA
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, or no cable or no powered devices are connected to the associated
ports.
Broadband
1**, 2
Solid Green = Good broadband connection (good DSL sync or Gigabit Ethernet).
Flashing Green = Attempting broadband connection (DSL attempting sync).
Flashing Green and Red = If, after three consecutive minutes, the broadband connection fails to be
established, the LED switches to Flashing Green alternating with a five second steady Red while
attempting or waiting to establish a broadband connection. This pattern continues until the broad-
band connection is successfully established.
Flashing Red = No DSL signal on the line. This display is not used during times of temporary ‘no tone’
during the training sequence.
Off = The device is not powered.
** Broadband 1 LED is also the Gigabit Ethernet WAN LED when that is in play (and DSL is not).
Service
Solid Green = IP connected. The device has a WAN IP address from DHCP or 802.1x authentication
and the broadband connection is up.
Flashing Green = Attempting connection, attempting IEEE 802.1X authentication, or attempting to
obtain DHCP information.
Red = Device attempted to become IP connected and failed (no DHCP response, 802.1x authentica-
tion failed, no IP address from IPCP, etc.). The Red state times out after two minutes, and the Service
indicator light returns to the Off state.
Off = The device is not powered or the broadband connection is not present.
Phone 1, 2
Solid Green = The associated VoIP line has been registered with a SIP proxy server.
Flashing Green = Indicates a telephone is off-hook on the associated VoIP line.
Off = VoIP not in use, line not registered, or NVG599 power off.
USB
Solid Green = Powered device connected to the associated port (includes devices with wake-on-LAN
capability where a slight voltage is supplied to the Ethernet connection).
Flickering Green = Activity seen from devices associated with the port. The flickering of the light is
synchronized to actual data traffic.
Off = The device is not powered, no cable or no powered devices connected to the associated ports.
LED Activity

Administrator’s Handbook
90
Rear View
WPS
(appears after
using WPS
button)
Solid Green = Wi-Fi Protected Setup has been completed successfully. LED should stay on for 5 min-
utes or until push button is pressed again.
Flashing Green = Continues for 2 minutes, indicating when WPS is broadcasting.
Flashing Red = Continues for 2 minutes, indicating a Session overlap was detected (possible security
risk).
Solid Red = Error unrelated to security, such as failure to find a partner, or WPS is disabled. LED
should stay solid red for 5 minutes or until push button is pressed again.
Off = The device is not powered, or no cable or no powered devices are connected to the associated
ports.
LED Action
Ethernet
1,2 3,4
Flashing Amber = A Gigabit Ethernet device is connected to each port.
Solid Green = A 10/100 Ethernet device is connected.
Flickering Green = Ethernet traffic activity.
Off = The device is not powered, or no powered devices are connected to the associated ports.
NOTE:
The NVG599 supports two VoIP lines over one RJ11 VoIP port. In order to con-
nect two phone lines the supplied inner/outer pair splitter adapters must be
attached to the RJ11 VoIP port in order to terminate both lines. This is a spe-
cial-purpose splitter. You must only use the inner/outer pair splitter adapters
supplied by AT&T.
LED Activity
Gigabit Ethernet (WAN)
USB
DSL (WAN)
Ethernet (LAN)
F-Connector (HPNA)
RJ14 (FXS)
Reset
Power Jack
91
LED Function Summary Matrix
Power Solid Green =
The device is
powered.
Flashing Green =
A power-on self-
test (POST) is in
progress.
Orange/Amber =
Firmware
upgrade (see
“Power during
Firmware
Upgrade” on
page 88)
Flashing Red = A
POST failure (not
bootable) or
device malfunc-
tion occurred.
*
When the
device encoun-
ters a POST fail-
ure, all indicator
lights on the
front of the
device continu-
ously flash.
Off = The unit
has no AC power.
Battery Solid Green =
Battery in place
but not being
used.
Flashing Green =
Battery charging.
Solid Amber =
Battery in use.
Flashing Amber =
Low battery.
Solid Red = Bat-
tery backup
mechanism has a
fault.
Flashing Red =
Battery needs to
be replaced.
Off = No battery
or battery has no
charge.
Cycle between
all colors = Bat-
tery conducting
self-test.
Ethernet Solid Green =
Powered device
connected to the
associated port
(includes devices
with wake-on-
LAN capability
where a slight
voltage is sup-
plied to the
Ethernet connec-
tion).
Flashing Green =
Activity seen
from devices
associated with
the port. The
flickering of the
light is synchro-
nized to actual
data traffic.
Off = The device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
WiFi Solid Green = Wi-
Fi is powered.
Flashing Green =
Activity seen
from devices
connected via
Wi-Fi. The flick-
ering of the light
is synchronized
to actual data
traffic.
Off = The device
is not powered
or no powered
devices con-
nected to the
associated ports.
HomePNA Solid Green =
Powered device
connected to the
associated port
(includes devices
with wake-on-
LAN capability
where a slight
voltage is sup-
plied to the
Ethernet connec-
tion).
Flickering Green
= Activity seen
from devices
associated with
the port. The
flickering of the
light is synchro-
nized to actual
data traffic.
Off = The device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
Administrator’s Handbook
92
Broadband
1**, 2
Solid Green =
Good broadband
connection (i.e.,
good DSL Sync).
** Broadband 1
LED is also the
Gigabit ethernet
WAN LED when
that is in play
(and DSL is not).
Flashing Green =
Attempting
broadband con-
nection (i.e., DSL
attempting sync).
Flashing Green &
Red = If the
broadband con-
nection fails to
be established
for more than
three consecu-
tive minutes the
LED switches to
Flashing Green
when attempt-
ing or waiting to
establish a
broadband con-
nection alternat-
ing with a five
second steady
Red. This pattern
continues until
the broadband
connection is
successfully
established.
Flashing Red =
No DSL signal on
the line. This is
only used when
there is no signal,
not during times
of temporary ‘no
tone’ during the
training
sequence.
Off = The device
is not powered.
Service Solid Green = IP
connected (The
device has a
WAN IP address
from DHCP or
802.1x authenti-
cation and the
broadband con-
nection is up).
Flashing Green =
Attempting PPP
connection.þ
Attempting IEEE
802.1X authenti-
cation or
attempting to
obtain DHCP
information.
Red = Device
attempted to
become IP con-
nected and failed
(no DHCP
response, 802.1x
authentication
failed, no IP
address from
IPCP, etc.). The
Red state times
out after two
minutes and the
Service indicator
light returns to
the Off state.
Off = The device
is not powered
or the broad-
band connection
is not present.
Phone 1, 2 Solid Green =
The associated
VoIP line has
been registered
with a SIP proxy
server.
Flashing Green =
Indicates a tele-
phone is off-hook
on the associated
VoIP line.
Off = VoIP not in
use, line not reg-
istered or
NVG599 power
off.
93
USB Solid Green =
Powered device
connected to the
associated port
(includes devices
with wake-on-
LAN capability
where a slight
voltage is sup-
plied to the
Ethernet connec-
tion).
Flickering Green
= Activity seen
from devices
associated with
the port. The
flickering of the
light is synchro-
nized to actual
data traffic.
Off = The device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
WPS Solid Green = Wi-
Fi Protected
Setup has been
completed suc-
cessfully. It
should stay on
for 5 minutes or
until push but-
ton is pressed
again.
Flashing Green =
Indicates when
WPS is broad-
casting.
Solid Red = Error
unrelated to
security, such as
failed to find any
partner, or proto-
col prematurely
aborted. It
should stay Solid
Red for 5 min or
until push but-
ton is pressed
again.
Flashing Red =
Session overlap
detected (possi-
ble security risk)
in Scenario.
Off = WPS is not
active, the device
is not powered,
no cable or no
powered devices
connected to the
associated ports.
Administrator’s Handbook
94
If a status indicator light does not look correct, look for these possible problems:
LED Not Lit Possible Problems
Power Make sure the power adapter is plugged into the DSL modem properly.
Try a known good wall outlet.
If a power strip is used, make sure it is switched on.
Broadband Make sure that any telephone has a microfilter installed.
Make sure that you are using the correct cable. The DSL cable is the thinner stan-
dard telephone cable and is labeled “Data Cable.”
Make sure the DSL cable is plugged into the correct wall jack.
Make sure the DSL cable is plugged into the DSL port on the DSL modem.
Make sure the DSL line has been activated at the central office DSLAM.
Make sure the DSL modem is not plugged into a micro filter.
Ethernet Make sure the you are using the yellow Ethernet cable, not the DSL cable. The
Ethernet cable is thicker than the standard telephone cable.
Make sure the Ethernet cable is securely plugged into the Ethernet jack on the PC.
Make sure the Ethernet cable is securely plugged into the Ethernet port on the DSL
modem.
Make sure you have Ethernet drivers installed on the PC.
Make sure the PC’s TCP/IP properties for the Ethernet network control panel are
set to obtain an IP address via DHCP.
Make sure the PC has obtained an address in the 192.168.1.x range. (You may have
changed the subnet addressing.)
Make sure the PC is configured to access the Internet over a LAN.
Disable any installed network devices (Ethernet, HomePNA, wireless) that are not
being used to connect to the DSL modem.

95
Factory Reset Switch
Lose your access code? This section shows how to use the factory reset switch to reset the NVG599 so that you
can access the configuration screens once again.
If you don't have an access code, the only way to access the NVG599 is to follow these steps:
1. Referring to the diagram below, find the round Reset switch opening.
2. Carefully insert the point of a pen or an unwound paperclip into the opening.
If you press the factory reset switch for less than ten seconds, the device will be rebooted.
The indicator lights on the device will respond immediately and start blinking red within one second of the
reset switch being pressed.
The lights will blink whether the switch is still being pressed or has been released. The indicator lights will
flash for a minimum of five seconds, even if the reset switch is released within five seconds of being pressed.
If the reset switch is held for more than five seconds, it will continue to blink until released or until ten sec-
onds have elapsed (see below).
If you press the factory reset switch for a longer period of time, the device will be reset to the factory
default shipped settings. If the switch is held for ten seconds, the Power indicator continues to blink for an
additional five seconds, and then the indicator lights return to their normal operating mode, whether or not
the reset switch is still depressed.
NOTE:
Keep in mind that all of your settings will need to be reconfigured.
Reset Switch

Administrator’s Handbook
96
Log Event Messages
The system generates the log messages described in the following tables for events related to administrative
access, system operation, DSL issues, packet access, or firewall issues.
Administration-Related Log Messages
1. administrative access attempted: This log message is generated whenever the user attempts to access the
router's management interface.
2. administrative access authenti-
cated and allowed:
This log message is generated whenever the user attempts to access the
router's management interface and is successfully authenticated and
allowed access to the management interface.
3. administrative access allowed: If for some reason, a customer does not want password protection for the
management interface, this log message is generated whenever any user
attempts to access the router's management interface and is allowed access
to the management interface.
4. administrative access denied -
invalid user name:
This log message is generated whenever the user tries to access the router's
management interface and authentication fails because of an incorrect
username.
5. administrative access denied -
invalid password:
This log message is generated whenever the user tries to access the router's
management interface and authentication fails because of an incorrect
password.
6. administrative access denied -
telnet access not allowed:
This log message is generated whenever the user tries to access the router's
Telnet management interface from a public interface and is not permitted
because remote management is disabled.
7. administrative access denied -
web access not allowed:
This log message is generated whenever the user tries to access the router's
HTTP management interface from a public interface and is not permitted
because remote management is disabled.
System Log Messages
1. Received NTP Date and Time: This log message is generated whenever NTP receives date and time from
the server.
2. EN: IP up: This log message is generated whenever Ethernet WAN comes up.
3. WAN: Ethernet WAN1 activated
at 100000 Kbps:
This log message is generated when the Ethernet WAN link is up.
4. Device Restarted: This log message is generated when the router has been restarted.

97
DSL Log Messages (Most Common)
1. WAN: Data link
activated at <Rate> Kbps (rx/tx)
This log message is generated when the DSL link comes up.
2.WAN: Data link deactivated This log message is generated when the DSL link goes down.
3. RFC1483 up This log message is generated when RFC1483 link comes up.
4. RFC1483-<WAN-instance>: IP
down
This log message is generated when RFC1483 link goes down.
5. PPP: Channel <ID> up Dialout
Profile name: <Profile Name>
This log message is generated when a PPP channel comes up.
6. PPP-<WAN Instance> down:
<Reason>
This log message is generated when a PPP channel goes down. The reason
for the channel going down is displayed as well.
Access-Related Log Messages
1. permitted: This log message is generated whenever a packet is allowed to traverse
router interfaces or allowed to access the router itself.
2. attempt: This log message is generated whenever a packet attempts to traverse
router interfaces or attempts to access the router itself.
3. dropped - violation of security
policy:
This log message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped by the firewall because it violates
the expected conditions.
4. dropped - invalid checksum: This log message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped because of invalid IP checksum.
5. dropped - invalid data length: This log message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped because the IP length is greater than
the received packet length or if the length is too small for an IP packet.
6. dropped - fragmented packet: This log message is generated whenever a packet, traversing the router, is
dropped because it is fragmented, stateful inspection is turned ON on the
packet's transmit or receive interface, and the deny-fragment option is
enabled.
7. dropped - cannot fragment: This log message is generated whenever a packet traversing the router is
dropped because the packet cannot be sent without fragmentation, but the
do-not-fragment bit is set.
8. dropped - no route found: This log message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped because no route is found to for-
ward the packet.
9. dropped - invalid IP version: This log message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped because the IP version is not 4.
10. dropped - possible land attack: This log message is generated whenever a packet, traversing the router or
destined to the router itself, is dropped because the packet is a TCP/UDP
packet and the source IP address and source port equals the destination IP
address and destination port.
11. TCP SYN flood detected: This log message is generated whenever a SYN packet destined to the
router's management interface is dropped because the number of SYN-sent
and SYN-receive messages exceeds one-half the number of allowable con-
nections in the router.
Administrator’s Handbook
98
12. Telnet receive DoS attack -
packets dropped:
This log message is generated whenever TCP packets destined to the
router's Telnet management interface are dropped due to overwhelming
receive data.
13. dropped - reassembly timeout: This log message is generated whenever packets, traversing the router or
destined to the router itself, are dropped because of reassembly timeout.
14. dropped - illegal size: This log message is generated whenever packets, traversing the router or
destined to the router itself, are dropped during reassembly because of ille-
gal packet size in a fragment.
Firewall Log Messages Detail (AT&T Requirement #841)
Reason Enumeration ( C ) Log Text Representation Why the Packet Was Logged
NM_LOGDROP_CAT_DIR DIRECTION Direction (generic)
NM_LOGDROP_CAT_DIR_UP DIRECTION-UP Upstream direction
NM_LOGDROP_CAT_DIR_DOWN DIRECTION-DOWN Downstream direction
NM_LOGDROP_CAT_ETH ETH Ethernet header (generic)
NM_LOGDROP_CAT_ETH_SRC_ADDR ETH-SRC Ethernet source MAC address
NM_LOGDROP_CAT_ETH_DST_ADDR ETH-DST Ethernet destination MAC address
NM_LOGDROP_CAT_ETH_PROT ETH-PROTOCOL Ethernet Protocol
NM_LOGDROP_CAT_ETH_VLAN ETH-VLAN Ethernet VLAN ID (where applica-
ble)
NM_LOGDROP_CAT_IP IP IP header (generic)
NM_LOGDROP_CAT_IP_SRC IP-SRC IP source address
NM_LOGDROP_CAT_IP_DST IP-DST IP destination address
NM_LOGDROP_CAT_IP_PROT IP-PROTOCOL IP Protocol
NM_LOGDROP_CAT_IP_SPOOF IP-SPOOF IP address is spoofed (could not
have been sent by a device legiti-
mately with the address in the
source address field)
NM_LOGDROP_CAT_IP_ILL IP-ILLEGAL IP address is illegal (either src or
dest)
NM_LOGDROP_CAT_TCP TCP TCP header (generic)
NM_LOGDROP_CAT_TCP_SRC_PORT TCP-SRC-PORT TCP source port
NM_LOGDROP_CAT_TCP_DST_PORT TCP-DST-PORT TCP destination port
NM_LOGDROP_CAT_TCP_FLAGS TCP-FLAGS TCP flags field
NM_LOGDROP_CAT_UDP UDP UDP header (generic)
NM_LOGDROP_CAT_UDP_SRC_PORT UDP-SRC-PORT UDP source port
NM_LOGDROP_CAT_UDP_DST_PORT UDP-DST-PORT UDP destination port
NM_LOGDROP_CAT_ICMP ICMP ICMP packet (generic)
NM_LOGDROP_CAT_ICMP_TYPE ICMP-TYPE ICMP Type field
NM_LOGDROP_CAT_ICMP_CODE ICMP-CODE ICMP Code field
NM_LOGDROP_CAT_ICMP6 ICMPv6 ICMPv6 (generic)
Access-Related Log Messages
99
NM_LOGDROP_CAT_POLICY POLICY Policy (generic). This currently
includes filterset rules, restricted
hosts, IPv6 profiles.
NM_LOGDROP_CAT_POLICY_INPUT POLICY-INPUT-GEN-DISCARD Packets destined for the CPE that
are generically discarded (we spec-
ify the packets we do want; the rest
are discarded.)
NM_LOGDROP_CAT_POLICY_WAN_MGMT POLICY-WAN-MGMT-ACCESS 1) Trying to access CPE service from
WAN side using LAN-side port
2) Trying to access CPE service from
LAN side using WAN-side IP address
3) Trying to access CPE service from
WAN side using IPv6
NM_LOGDROP_CAT_POLICY_ICMP_ECHO POLICY-ICMP-ECHO ICMP echo request discarded (more
specific than
NM_LOGDROP_CAT_ICMP_TYPE)
NM_LOGDROP_CAT_POLICY_UWC_RESTRICT POLICY-UWC-RESTRICT Packets dropped because of “Uni-
versal Wi-Fi Configuration” restric-
tions (currently unused)
NM_LOGDROP_CAT_POLICY_RESTRICTED_HO
ST
POLICY-RESTRICTED-HOST Packets dropped because of
“Restricted Host” feature (either
content or time restrictions) (cur-
rently unused)
NM_LOGDROP_CAT_POLICY_WAN_DNS_QUE
RY
POLICY-WAN-SIDE-DNS-
QUERY
DNS query packets received on a
WAN interface
NM_LOGDROP_CAT_POLICY_WAN_DHCP_TO
SRVR
POLICY-WAN-SIDE-DHCP-TO-
SRVR
DHCP Discover request received on
a WAN interface
NM_LOGDROP_CAT_POLICY_AH POLICY-IPV6-AH IPv6 packets with AH header (if so
configured)
NM_LOGDROP_CAT_POLICY_ESP POLICY-IPV6-ESP IPv6 packets with ESP header (if so
configured)
NM_LOGDROP_CAT_POLICY_DEP_HEADER POLICY-DEPRECATED-
HEADER
IPv6 packets with deprecated
header (currently this only includes
routing extension header type 0)
NM_LOGDROP_CAT_POLICY_CAPT_PORTAL POLICY-CAPTIVE-PORTAL [IPv6] packets dropped because
captive portal is enabled.
NM_LOGDROP_CAT_FLOW FLOW Packets rejected as a result of analy-
sis of multiple related packets
(generic)
NM_LOGDROP_CAT_FLOW_FLOOD FLOOD Packets rejected because of flood-
limiting
NM_LOGDROP_CAT_FLOW_PORTSCAN PORTSCAN Packets rejected because of port-
scan detection
NM_LOGDROP_CAT_FLOW_DOS_OTHER OTHER-DoS Packets rejected because of other
DoS detection. Currently this
includes downstream flows that
don't generate upstream responses
- specifically addressing IPv6 Neigh-
bor Discovery DoS attacks.
Firewall Log Messages Detail (AT&T Requirement #841)
Reason Enumeration ( C ) Log Text Representation Why the Packet Was Logged

Administrator’s Handbook
100

101
CHAPTER 4 Command Line Interface
The NVG599 VDSL2 Gateway operating software includes a command line interface (CLI) that lets you access
your NVG599 device over a Telnet connection. You can use the command line interface to enter and update the
unit’s configuration settings, monitor its performance, and restart it.
This chapter covers the following topics:
“Overview” on page 103
“Starting and Ending a CLI Session” on page 105
“Using the CLI Help Facility” on page 106
“About SHELL Commands” on page 106
“SHELL Commands” on page 107
“About CONFIG Commands” on page 118
“CONFIG Commands” on page 121
“Debug Commands” on page 178
Administrator’s Handbook
102
CONFIG Commands
“Connection Commands” on page 121
“Filter Set Commands” on page 124
“Queue Commands” on page 129
“IP Gateway Commands” on page 132
“IPv6 Commands” on page 132
“IP DNS Commands” on page 139
“IP IGMP Commands” on page 139
“NTP Commands” on page 142
“Application Layer Gateway (ALG) Commands” on page 142
“Dynamic DNS Commands” on page 143
“Link Commands” on page 143
“Management Commands” on page 146
“Remote Access Commands” on page 148
“Physical Interfaces Commands” on page 150
“PPPoE Relay Commands” on page 157
“NAT Pinhole Commands” on page 157
“Security Stateful Packet Inspection (SPI) Commands” on page 158
“VoIP Commands” on page 160
“System Commands” on page 173
103
Overview
The CLI has two major command modes: SHELL and CONFIG. Summary tables that list the commands are
provided below. Details of the entire command set follow in this section.
SHELL Commands
Command Description
arp Send ARP request
clear Erase all stored configuration information
clear_certificate Remove an SSL certificate that has been installed
clear_https_certkey Remove a secure HTTP certificate key value
clear_firewall_log Empty the contents of the firewall event log
clear_log Erase all stored log info in flash memory
configure Configure unit's options
diagnose Run self-test
download Download config file
exit Quit this shell
ffbb Show the number of POST fault states
help Get more: “help all” or “help help”
install Download and program an image into flash
log Add a message to the diagnostic log
loglevel Report or change diagnostic log level
netstat Show IP information
nslookup Send DNS query for host
ping Send ICMP echo request
quit Quit this shell
6rd-check Send a 6rd loopback packet to the border gateway
reset Reset subsystems
restart Restart unit
show Show system information
start Start subsystem
status Show basic status of unit
telnet Telnet to a remote host
traceroute Send traceroute probes
upload Upload config file
view Show configuration information
who Show who is using the shell
wps Enter Wireless Protection Settings mode
Administrator’s Handbook
104
CONFIG Commands
Command Verbs Description
delete Delete configuration list data
help Display a list of Help command options
save Save configuration data
script Print configuration data
set Set configuration data
validate Validate configuration settings
view View configuration data
Keywords
conn Connection options
ip TCP/IP protocol options
ip6 IPv6 protocol options
dns Domain Name System options
gfs Global filter set options
igmp IGMP configuration options
ntp Network Time Protocol options
gateway Gateway options
link WAN link options
management System management options
physical Physical interface options
dsl DSL configuration options
enet Ethernet options
pinhole Pinhole options
pppoe-relay Point to Point Protocol over Ethernet relay options
preferences Shell environment preferences
queue Queue options
security Security (firewall) options
system Gateway’s system options
target-ad-insertion Targeted Ad Insertion (TAI) options
voip IP Voice (VoIP) configuration options
log System activity logging options
Command Utilities
top Go to top level of configuration mode
quit Exit from configuration mode; return to shell mode
exit Exit from configuration mode; return to shell mode

105
Starting and Ending a CLI Session
To start a CLI session, you need to open a Telnet connection from a workstation on your network.
You initiate a Telnet connection by issuing the following command from an IP host that supports Telnet, for
example, a personal computer running a Telnet application such as NCSA Telnet.
telnet <ip_address>
You must know the IP address of the NVG599 device before you can make a Telnet connection to it. By default,
your NVG599 uses 192.168.1.254 as the IP address for its LAN interface. You can use a Web browser to
configure the NVG599 IP address.
Logging In
The command line interface log-in process emulates the log-in process for a UNIX host. To log in, enter the user
name and your password.
Entering the administrator password lets you display and update all NVG599 settings.
When you have logged in successfully, the command line interface lists the user name and the security level
associated with the password you entered in the diagnostic log.
Ending a CLI Session
You end a command line interface session by typing quit from the SHELL node of the command line interface
hierarchy.

Administrator’s Handbook
106
Using the CLI Help Facility
The help command displays online help for SHELL and CONFIG commands. To display a list of the commands
available to you from your current location within the command line interface hierarchy, type help or a
question mark (
?
).
To obtain help for a specific CLI command, type help <command>. You can truncate the help command to h
or a question mark when you request help for a CLI command.
About SHELL Commands
Begin in SHELL mode when you start a CLI session. SHELL mode lets you perform the following tasks:
Monitor NVG599 performance
Display and reset NVG599 device statistics
Issue administrative commands to restart NVG599 device functions
SHELL Prompt
When you are in SHELL mode, the CLI prompt is the name of the NVG599 device followed by a right angle
bracket (>). For example, if you open a CLI connection to the NVG599 device named “ARRIS-3000/9437188,”
you would see ARRIS-3000/9437188> as your CLI prompt.
SHELL Command Shortcuts
You can truncate most commands in the CLI to their shortest unique string. For example, you can use the
truncated command q in place of the full quit command to exit the CLI. However, you would need to enter rese
for the reset command, since the first characters of reset are common to the restart command.
The only commands you cannot truncate are restart and clear. To prevent accidental interruption of
communications, you must enter the restart and clear commands in their entirety.
You can use the Up and Down arrow keys to scroll backward and forward through recent commands you have
entered. Alternatively, you can use the !! command to repeat the last command you entered.

107
SHELL Commands
Common Commands
arp nnn.nnn.nnn.nnn
Sends an Address Resolution Protocol (ARP) request to match the nnn.nnn.nnn.nnn IP address to an Ethernet
hardware address.
clear [ yes ]
Clears the configuration settings in an NVG599 device. You are prompted to confirm the clear command by
entering yes.
clear_certificate
Removes an SSL certificate that has been installed.
clear_https_certkey
Removes any Secure HTTP certificate key value installed in the NVG599.
configure
Puts the command line interface into Configure mode, which lets you configure your NVG599 with config
commands. The config commands are described starting on page 121.
download [ server_address ] [ filename ] [ confirm ]
Installs a file of configuration parameters into the NVG599 device from a TFTP (Trivial File Transfer Protocol)
server. The TFTP server must be accessible on your Ethernet network.
You can include one or more of the following arguments with the download command. If you omit arguments,
the console prompts you for this information.
The server_address argument identifies the IP address of the TFTP server from which you want to copy the
NVG599 configuration file.
The filename argument identifies the path and name of the configuration file on the TFTP server.
If you include the optional confirm keyword, the download begins as soon as all information is entered.
You can also download an SSL certificate file from a trusted certification authority (CA), on platforms that
support SSL, as follows:
download [-cert] [server_address ] [filename] [confirm]
ffbb
Displays the number of times that the NVG599 device has entered a Power-On Self-Test (POST) fault state.
install [ server_address ] [ filename ] [ confirm ]
Downloads a new version of the NVG599 operating software from a TFTP (Trivial File Transfer Protocol) server,
validates the software image, and programs the image into the NVG599 memory. After you install new
operating software, you must restart the NVG599 device.
Administrator’s Handbook
108
The server_address argument identifies the IP address of the TFTP server on which your NVG599 operating
software is stored. The filename argument identifies the path and name of the operating software file on the
TFTP server.
If you include the optional keyword confirm, you will not be prompted to confirm whether or not you want to
perform the operation.
log message_string
Adds the message in the message_string argument to the NVG599 diagnostic log.
loglevel [ level ]
Displays or modifies the types of log messages you want the NVG599 to record. If you enter the loglevel
command without the optional level argument, the command line interface displays the current log level
setting.
You can enter the loglevel command with the level argument to specify the types of diagnostic messages you
want to record. All messages with a level number equal to or greater than the level you specify are recorded.
For example, if you specify log level 3, the diagnostic log will retain high-level informational messages (level 3),
warnings (level 4), and failure messages (level 5).
Use the following values for the level argument:
1 or low – Low-level informational messages or greater; includes trivial status messages.
2 or medium – Medium-level informational messages or greater; includes status messages that can help
monitor network traffic.
3 or high – High-level informational messages or greater; includes status messages that may be significant
but do not constitute errors.
4 or warning – Warnings or greater; includes recoverable error conditions and useful operator information.
5 or failure – Failures; includes messages describing error conditions that may not be recoverable.
netstat -i
Displays the IP interfaces for your NVG599.
netstat -r
Displays the IP routes stored in your NVG599.
nslookup [ hostname | ip_address ]
Performs a domain name system lookup for a specified host.
The hostname argument is the name of the host for which you want DNS information; for example,
nslookup klaatu.
The ip_address argument is the IP address, in dotted decimal notation, of the device for which you want
DNS information.
ping [-s size] [-c count ] [ hostname | ip_address ]
Causes the NVG599 to issue a series of ICMP Echo requests for a device with the specified name or IP address.
The hostname argument is the name of the device you want to ping; for example,
ping ftp.arris.com.
The ip_address argument is the IP address, in dotted decimal notation, of the device you want to locate. If a
host using the specified name or IP address is active, it returns one or more ICMP echo replies, confirming
that it is accessible from your network.

109
The -s size argument lets you specify the size of the ICMP packet.
The -c count argument lets you specify the number of ICMP packets generated for the ping request. Values
greater than 250 are truncated to 250.
You can use the ping command to determine whether a hostname or IP address is already in use on your
network. You cannot use the ping command to ping the NVG599 device’s own IP address.
quit
Exits the NVG599 command line interface.
6rd-check [-s size] [-c count] conn_name
Generates and sends 6rd (IPv6 Rapid Deployment) loopback packets to the 6rd gateway.
reset arp
Clears the Address Resolution Protocol (ARP) cache on your unit.
reset crash
Clears crash-dump information, which identifies the contents of the NVG599 registers at the point of system
malfunction.
reset dhcp server
Clears the DHCP lease table in the NVG599 device.
reset enet [ all ]
Resets Ethernet statistics to zero. Resets individual LAN switch port statistics as well as wireless and WAN
Ethernet statistics (where applicable).
reset firewall-log
Rewinds the firewall log to the first entry.
reset ipmap
Clears the IPMap table (NAT).
reset log
Rewinds the diagnostic log display to the top of the existing NVG599 diagnostic log. The reset log command
does not clear the diagnostic log. The next show log command will display information from the beginning of
the log file.
reset wan
This function resets WAN interface statistics.
Administrator’s Handbook
110
restart [ seconds ]
Restarts your NVG599 device. If you include the optional seconds argument, your NVG599 will restart when
the specified number of seconds have elapsed. You must enter the complete restart command to initiate a
restart.
show all-info
Displays all settings currently configured in the NVG599 device.
show bridge interfaces
Displays bridge interfaces maintained by the NVG599 device.
show bridge table
Displays the bridging table maintained by the NVG599 device.
show config
Dumps the ARRIS Gateway’s configuration script just as the script command does in Configure mode.
show crash
Displays the most recent crash information, if any, for your NVG599 device.
show dhcp server leases
Displays the DHCP leases stored in RAM by your NVG599 device.
show dhcp client
Displays the DHCP clients stored in RAM by your NVG599 device.
show dsl [ all ]
Displays DSL port statistics, such as upstream and downstream connection rates and noise levels.
show dslf device-association
Displays LAN devices that conform with the TR111 Gateway requirement. It displays IP address, manufacture
OUI, and serial number.
show enet [ all ]
Displays Ethernet interface statistics maintained by the NVG599 device. Supports display of individual LAN
switch port statistics as well as WAN Ethernet statistics (where applicable).
Example:
Ethernet driver full statistics - LAN
10/100/1000 Ethernet
Port Status: Link up

111
General:
Transmit OK : 253
Receive OK : 22
Tx Errors : 0
Rx Errors : 0
Receiver:
Dropped Packets : 0
Transmitter:
Collisions : 0
Dropped Packet : 0
Upper Layers:
Rx No Handler : 0
Rx No Message : 0
Rx Octets : 4781
Rx Unicast Pkts : 22
Rx Multicast Pkts : 0
Tx Discards : 0
Tx Octets : 17204
10/100/1000 Ethernet port 1
Port Status: Link down
10/100/1000 Ethernet port 2
Port Status: Link up
Duplex: Full
Speed: 1000BASE-T
Transmit OK : 253
Transmit unicastpkts : 0
Tx Octets : 16192
Tx Collision : 0
Receive OK : 24
Receive unicastpkts : 0
Receive errors : 0
Rx Octets : 4781
10/100/1000 Ethernet port 3
Port Status: Link down
10/100/1000 Ethernet port 4
Port Status: Link down
HPNA port 5 (counter values include management traffic)
Port Status: Link up
Duplex: Full
Speed: 200 MBPS
Transmit OK : 1702
Transmit unicastpkts : 1173
Tx Octets : 226117
Tx Collision : 0
Receive OK : 1168
Receive unicastpkts : 1168
Receive errors : 0
Rx Octets : 202156
Ethernet driver statistics - Wireless
Port Status: Link down
Ethernet driver full statistics - PTM WAN
Port Status: Link down

Administrator’s Handbook
112
Ethernet driver full statistics - WAN
10/100/1000 Ethernet
Port Status: Link down
Ethernet driver full statistics - 10/100 Ethernet
Port Status: Link up
Type: 100BASET Duplex: Full
General:
Transmit OK : 434
Receive OK : 267
Tx Errors : 0
Rx Errors : 0
Receiver:
Incompl Packet Errors : 0
No RBD's For Packet : 0
Carrier Sense Lost : 0
Deferred Replen : 0
Transmitter:
TX Retries : 0
Single Collisions : 0
No Buf For Packet : 0
Upper Layers:
Rx No Handler : 0
Rx No Message : 0
Rx Octets : 30773
Rx Unicast Pkts : 267
Rx Multicast Pkts : 0
Tx Discards : 0
Tx Octets : 31692
10/100 Ethernet phy.enet.port
Port Status: Link up
Duplex: Full-duplex active
Speed: 100BASE-T
Transmit OK : 434
Transmit unicastpkts : NA
Receive OK : 267
Receive unicastpkts : 267
show enet tx-queue
"show enet tx-queue"
This is an output of what is should look like:
NOS/128600225699776/UNLOCKED> show enet tx-queue
No transmit software queue configured on Ethernet port 1
No transmit software queue configured on Ethernet port 2
No transmit software queue configured on Ethernet port 3
No transmit software queue configured on Ethernet port 4
No transmit software queue configured on Ethernet port 5
No transmit software queue configured on Ethernet port 6
Ethernet switch queue stats:
Port 1:
TxQ1: 54257
TxQ2: 0

113
TxQ3: 0
TxQ4: 508
Port 2:
TxQ1: 55767
TxQ2: 0
TxQ3: 0
TxQ4: 508
Port 3:
TxQ1: 0
TxQ2: 0
TxQ3: 0
TxQ4: 0
Port 4:
TxQ1: 0
TxQ2: 0
TxQ3: 0
TxQ4: 0
Port 5:
TxQ1: 92950
TxQ2: 0
TxQ3: 0
TxQ4: 508
show group-mgmt
Displays the IGMP Snooping table. See “IP IGMP Commands” on page 139 for detailed explanation.
show ip arp
Displays the Ethernet address resolution table stored in your NVG599 device.
show ip igmp
Displays the contents of the IGMP Group Address table and the IGMP Report table maintained by your NVG599
device.
show ip interfaces
Displays the IP interfaces for your NVG599 device.
show ip firewall
Displays firewall statistics.
show ip lan-discovery
Displays the LAN Host Discovery table of hosts on the wired or wireless LAN, and whether or not they are
currently online.
show ip routes
Displays the IP routes stored in your NVG599 device.
show ipmap
Displays IPMap table (NAT).

Administrator’s Handbook
114
show ipv6 interfaces
Displays IPv6 interfaces.
show ipv6 routes
Displays the IPv6 route table.
show ipv6 neighbors
Displays the IPv6 neighbor table.
show ipv6 dhcp server leases
Displays the DHCPv6 server lease table.
show ipv6 statistics
Displays IPv6 statistics information.
show log
Displays blocks of information from the NVG599 diagnostic log. To see the entire log, you can repeat the show
log command, or you can enter show log all.
show firewall-log
Displays blocks of information from the NVG599 firewall log.
show memory [ all ]
Displays memory usage information for your NVG599 device. If you include the optional all argument, your
NVG599 will display a more detailed set of memory statistics.
show ptm
Displays statistics information for each PTM session.
show post-results
Displays Power-On Self-Test results.
show pppoe
Displays status information for each PPPoE socket, such as the socket state, service names, and host ID values.
show rootcert
Dumps the Subject line for the list of all the trusted root certificates for the 802.1x supplicant.
show rtsp
Displays RTSP ALG session activity data.

115
show status
Displays the current status of an NVG599 device, the device's hardware and software revision levels, a
summary of errors encountered, and the length of time the device has been running since it was last restarted.
Identical to the status command.
show summary
Displays a summary of WAN, LAN, and gateway information.
show vlan
Displays detail of VLAN status and statistics.
show wireless [ all ]
Shows wireless status and statistics.
show wireless clients [ MAC_address ]
Displays details on connected clients, or more details on a particular client if the MAC address is added as an
argument.
show voip
Displays VoIP call statistics.
show voiplog
Displays VoIP event logs.
telnet [ hostname | ip_address ] [ port ]
Lets you open a Telnet connection to the specified host through your NVG599 device.
The hostname argument is the name of the device to which you want to connect, for example, telnet
ftp.arris.com.
The ip_address argument is the IP address, in dotted decimal notation, of the device to which you want to
connect.
The port argument is the number of the port over which you want to open a Telnet session.
traceroute ( ip_address | hostname )
Traces the routing path to an IP destination.
upload [ server_address ] [ filename ] [ confirm ]
Copies the current configuration settings of the NVG599 to a TFTP (Trivial File Transfer Protocol) server. The
TFTP server must be accessible on your Ethernet network. The server_address argument identifies the IP
address of the TFTP server on which you want to store the NVG599 settings. The filename argument identifies
the path and name of the configuration file on the TFTP server. If you include the optional confirm keyword,
you will not be prompted to confirm whether or not you want to perform the operation.
view config
Dumps the NVG599 device’s configuration just as the view command does in Configure mode.

Administrator’s Handbook
116
who
Displays the names of the current shell and PPP users.
wps
Enters the wireless WPS (Wi-Fi Protected Setup) mode.
WPS Commands
The following commands are available in WPS mode:
pushbutton
Sets the NVG599 device to WPS “pushbutton” mode, initiating protected setup.
pin
Sets the NVG599 device to PIN mode, enabling authorized devices to be identified and added by MAC address
personal identification number.
list
Lists the WPS-ready client devices (enrollees) known to the NVG599.
self-pin
Displays the NVG599’s own Personal Identification Number (PIN) value.
WAN Commands
atmping vccn [ segment | end-to-end ]
Lets you check the ATM connection reachability and network connectivity. This command sends five
Operations, Administration, and Maintenance (OAM) loopback calls to the specified VPI/VCI destination. There
is a five second total timeout interval.
Use the segment argument to ping a neighbor switch.
Use the end-to-end argument to ping a remote end node.
reset dhcp client release [ vcc-id ]
Releases the DHCP lease the NVG599 device is currently using to acquire the IP settings for the specified DSL
port. The vcc-id identifier is an “index” letter in the range B-I, and does not directly map to the VCC in use.
Enter the reset dhcp client release command without the variable to see the letter assigned to each virtual
circuit.
reset dhcp client renew [ vcc-id ]
Renews the DHCP lease the NVG599 device is currently using to acquire the IP settings for the specified DSL
port. The vcc-id identifier is an “index” letter in the range B-I, and does not directly map to the VCC in use.
Enter the reset dhcp client release command without the variable to see the letter assigned to each virtual
circuit.
117
reset dsl
Resets any open DSL connection.
reset ppp vccn
Resets the point-to-point connection over the specified virtual circuit. This command only applies to virtual
circuits that use PPP framing.
show atm [all]
Displays ATM statistics for the NVG599 device. The optional all argument displays a more detailed set of ATM
statistics.
show ppp [{ stats | lcp | ipcp }]
Displays information about open PPP links. You can display a subset of the PPP statistics by including an
optional stats, lcp, or ipcp argument for the show ppp command.
start ppp vccn
Opens a PPP link on the specified virtual circuit.

Administrator’s Handbook
118
About CONFIG Commands
You can reach the Configuration mode of the command line interface by typing configure (or any truncation of
configure, such as con or config) at the CLI SHELL prompt.
CONFIG Mode Prompt
When you are in CONFIG mode, the CLI prompt consists of the name of the NVG599 device followed by your
current node in the hierarchy and two right angle brackets (>>). For example, when you enter CONFIG mode
(by typing config at the SHELL prompt), the prompt
ARRIS-3000/9437188 (top)>>
reminds you
that you are at the top of the CONFIG hierarchy. If you move to the IP node in the CONFIG hierarchy (by typing
ip at the CONFIG prompt), the prompt changes to
ARRIS-3000/9437188 (ip)>>
to identify your
current location.
Some CLI commands are not available until certain conditions are met. For example, you must enable IP for an
interface before you can enter IP settings for that interface.
Navigating the CONFIG Hierarchy
Moving from CONFIG to SHELL — You can navigate from anywhere in the CONFIG hierarchy back to the
SHELL level by entering quit at the CONFIG prompt and pressing Enter.
ARRIS-3000/9437188 (top)>> quit
ARRIS-3000/9437188 >
Moving from top to a subnode — You can navigate from the top node to a subnode by entering the node
name (or the significant letters of the node name) at the CONFIG prompt and pressing R
ETURN
. For example,
you move to the IP subnode by entering
ip
and pressing Enter.
ARRIS-3000/9437188 (top)>> ip
ARRIS-3000/9437188 (ip)>>
As a shortcut, you can enter the significant letters of the node name in place of the full node name at the
CONFIG prompt. The significant characters of a node name are the letters that uniquely identify the node. For
example, since only one CONFIG node starts with “b,” you could enter the letter “b” to move to the bridge
node.
Jumping down several nodes at once — You can jump down several levels in the CONFIG hierarchy by
entering the complete path to a node.
Moving up one node — You can move up through the CONFIG hierarchy one node at a time by entering the
up command.
Jumping to the top node — You can jump to the top level from anywhere in the CONFIG hierarchy by enter-
ing the top command.
Moving from one subnode to another — You can move from one subnode to another by entering a partial
path that identifies how far back to climb.
Moving from any subnode to any other subnode — You can move from any subnode to any other subnode
by entering a partial path that starts with a top-level CONFIG command.
Scrolling backward and forward through recent commands — You can use the Up and Down arrow keys
to scroll backward and forward through recent commands you have entered. When the command you want
appears, press Enter to execute it.
Entering Commands in CONFIG Mode
CONFIG commands consist of keywords and arguments. Keywords in a CONFIG command specify the action
you want to take or the entity on which you want to act. Arguments in a CONFIG command specify the values
appropriate to your site. For example, the following CONFIG command consists of three keywords (ip, dns and
domain-name) and one argument (domain_name_value).
119
set ip dns domain-name domain_name_value
When you use the command to configure your NVG599 device, you would replace the argument with a value
appropriate to your site.
For example:
set ip dns domain-name arris.com
Guidelines: CONFIG Commands
The following table provides guidelines for entering and formatting CONFIG commands.
If a command is ambiguous or miskeyed, the CLI prompts you to enter additional information. For example,
you must specify which virtual circuit you are configuring when you are setting up an NVG599 device.
Displaying Current Gateway Settings
You can use the view command to display the current CONFIG settings for your NVG599. If you enter the view
command at the top level of the CONFIG hierarchy, the CLI displays the settings for all enabled functions. If you
enter the view command at an intermediate node, you see settings for that node and its subnodes.
Step Mode: A CLI Configuration Technique
The NVG599 command line interface includes a step mode to automate the process of entering configuration
settings. When you use the CONFIG step mode, the command line interface prompts you for all required and
optional information. You can then enter the configuration values appropriate for your site without having to
enter complete CLI commands.
When you are in step mode, the command line interface prompts you to enter required and optional settings.
If a setting has a default value or a current setting, the command line interface displays the default value for
the command in parentheses. If a command has a limited number of acceptable values, those values are
presented in brackets, with each value separated by a vertical line.
Command
Component Rules for Entering CONFIG Commands
Command Verbs CONFIG commands must start with a command verb (set, view, delete).
You can truncate CONFIG verbs to three characters (set, vie, del).
CONFIG verbs are case-insensitive. You can enter SET, Set, or set.
Keywords Keywords are case-insensitive. You can enter Ethernet, ETHERNET, or ethernet as a keyword with-
out changing its meaning.
Keywords can be abbreviated to the length that they are differentiated from other keywords.
Argument Text Text strings can be as many as 64 characters long, unless otherwise specified. In some cases they
may be as long as 255 bytes.
Special characters are represented using backslash notation.
Text strings can be enclosed in double (“) or single (‘) quotation marks. If the text string includes
an embedded space, it must be enclosed in quotation marks.
Special characters are represented using backslash notation.
Numbers Enter numbers as integers, or in hexadecimal format, where so noted.
IP Addresses Enter IP addresses in dotted decimal notation (0 to 255).

Administrator’s Handbook
120
For example, the following CLI step command indicates that the default value is
off
and that valid entries are
limited to
on
and
off
.
option (off) [on | off]:
on
You can accept the default value for a field by pressing the Enter key. To use a different value, type it and press
Enter.
You can enter the CONFIG step mode by entering set from the top node of the CONFIG hierarchy. You can enter
step mode for a particular service by entering set service_name. In stepping set mode (press Control-X Enter)
to exit. For example:
ARRIS-3000/9437188 (top)>> set system
...
system
name (“ARRIS-3000/9437188”): Mycroft
Diagnostic Level (High): medium
Stepping mode ended.
Validating Your Configuration
You can use the validate CONFIG command to make sure that your configuration settings have been entered
correctly. If you use the validate command, the NVG599 device verifies that all required settings for all services
are present and that settings are consistent.
ARRIS-3000/9437188 (top)>> validate
Error: Subnet mask is incorrect
Global Validation did not pass inspection!
You can use the validate command to verify your configuration settings at any time. Your NVG599 device
automatically validates your configuration any time you save a modified configuration.

121
CONFIG Commands
This section describes the keywords and arguments for the various CONFIG commands.
Connection Commands
The conn commands are used to create connections, for example, a WAN or LAN connection. There may be
more than one of each depending on your model. The name commands correspond to the system object IDs
(OIDs), but you can name them yourself.
set conn name name link-oid value
Sets the connection named name to point to an associated link specified by the link-oid value.
set conn name name type [ static | dhcpc | ppp ]
Specifies whether the type of the connection named name is static, DHCPC, or PPP.
set conn name name side [ lan | wan ]
Specifies whether this connection is LAN- or WAN-side. A connection can be either lan or wan.
set conn name name lan-type [ private | public | public-delegated ]
Specifies whether this connection’s LAN is private, public, or public-delegated. The default is private, the usual
type of local network.
set conn name name dhcp-server-enable [ on | off ]
Turns the DHCP server for this connection on or off. The DHCP server can be enabled per connection. The
default is on.
set conn name name mcast-forwarding [ off | on ]
Turns IP IGMP multicast forwarding for this connection off or on. The default is off.
set conn name name rip-send [ off | v1 | v2 | v1-compat | v2-md5 ]
Specifies whether the device should use Routing Information Protocol (RIP) broadcasts to advertise its routing
tables to other gateways. RIP Version 2 (RIP-2) is an extension of the original Routing Information Protocol (RIP-
1) that expands the amount of useful information in the RIP packets. While RIP-1 and RIP-2 share the same
basic algorithms, RIP-2 supports several additional features, including inclusion of subnet masks in RIP packets
and implementation of multicasting instead of broadcasting (which reduces the load on hosts that do not
support routing protocols. RIP-2 with MD5 authentication is an extension of RIP-2 that increases security by
requiring an authentication key when routes are advertised. Depending on your network needs, you can
configure your device to support RIP-1, RIP-2, or RIP-2MD5.
If you specify v2-MD5, you must also specify a rip-send-key. Keys are ASCII strings with a maximum of 31
characters, and must match the other gateway keys for proper operation of MD5 support. The default is off.
set conn name name rip-receive [ off | v1 | v2 | v1-compat | v2-md5 ]
Specifies whether the device should use Routing Information Protocol (RIP) broadcasts to update its routing
tables with information received from other gateways on the other side of the connection. If you specify v2-
md5, you must also specify a rip-receive-key. Keys are ASCII strings with a maximum of 31 characters, and must
match the other gateway keys for proper operation of MD5 support. The default is off.

Administrator’s Handbook
122
set conn name name icmp-echo-drop [ off | on ]
If set to on, drops echo-requests received on the particular interface. The default is off.
set conn name name icmp-err-suppress [ off | on ]
An additional option to suppress ICMP error messages on WAN IP interfaces. The default is off.
set conn name name static ipaddr ipaddr
Specifies a static IP address when the connection type has been set to static. The default is 192.168.1.254.
Example:
NOS/128600225634272/conf
Config Mode v1.3
NOS/128600225634272 (top)>> conn
NOS/128600225634272 (conn)>> set
conn
(conn) node list ...
"LAN"
"WAN"
Select (name) node to modify from list,
or enter new (name) to create.
conn name (?):
name "LAN"
link-oid ("LAN") [ LAN | WAN | PPPoE | ]:
type (static) [ static | dhcpc | ppp ]:
side (lan) [ lan | wan ]:
lan-type (private) [ private | public | public-delegated ]:
mcast-forwarding (off) [ off | on ]:
rip-send (off) [ off | v1 | v2 | v1-compat | v2-md5 ]:
rip-receive (off) [ off | v1 | v2 | v1-compat | v2-md5 ]:
fs-egress ("") [ Security | QosUpstream | WanEgress | ]:
fs-ingress ("") [ Security | QosUpstream | WanEgress | ]:
static
ipaddr ("192.168.1.254"):
netmask ("255.255.255.0"):
dhcp-server-enable (on) [ off | on ]:
dhcp-server
start-addr ("192.168.1.64"):
end-addr ("192.168.1.253"):
lease-time (01:00:00:00):
subnet-order (1) [ 1 - 8 ]:
gen-option
(gen-option) node list ...
Select (name) node to modify from list,
or enter new (name) to create.
gen-option name (?):
option-group
(option-group) node list ...
Select (name) node to modify from list,
or enter new (name) to create.
option-group name (?):
NOTE:
You must also set the gateway address OR turn it off, otherwise the settings cannot be saved. See “IP Gate-
way Commands” on page 132.

123
filterset
(filterset) node list ...
Select (name) node to modify from list,
or enter new (name) to create.
filterset name (?):
name "WAN"
link-oid ("WAN") [ LAN | WAN | PPPoE | ]:
type (dhcpc) [ static | dhcpc | ppp ]: static
side (wan) [ lan | wan ]:
mcast-forwarding (off) [ off | on ]:
nat-enable (on) [ off | on ]:
rip-receive (off) [ off | v1 | v2 | v1-compat | v2-md5 ]:
icmp-echo-drop (on) [ off | on ]:
icmp-err-suppress (off) [ off | on ]:
fs-egress ("WanEgress") [ Security | QosUpstream | WanEgress | ]:
fs-ingress ("") [ Security | QosUpstream | WanEgress | ]:
static
ipaddr (""): 10.3.53.100
netmask ("255.255.255.0"):
NOS/128600225634272 (conn)>> set ip gateway address 10.3.53.1
NOS/128600225634272 (conn)>> save
If you do not want the gateway use this command to turn it off:
set ip gateway enable off
set conn name name static netmask netmask
Specifies a static netmask when the connection type has been set to static. The default is 255.255.255.0.
set conn name name dhcp-server start-addr ipaddr
If dhcp-server-enable is set to on, specifies the first address in the DHCP address range. The NVG599 can
reserve a sequence of up to 253 IP addresses within a subnet, beginning with the specified address for dynamic
assignment. The default is 192.168.1.64
set conn name name dhcp-server end-addr ipaddr
If dhcp-server-enable is set to on, specifies the last address in the DHCP address range. The default is
192.168.1.253
set conn name name dhcp-server lease-time seconds
If dhcp-server-enable is set to on, specifies the default length for DHCP leases issued by the NVG599. Lease
time is in seconds. Default is 3600.
set conn name name dhcp-server subnet-order [1... 8]
If dhcp-server-enable is set to on, specifies the order in which to address the first of 8 possible subnets.
Ordinarily, this is the first one, the default 1.
set conn name name nat-enable [ on | off ]
Specifies whether you want the NVG599 device to use network address translation (NAT) when communicating
with remote gateways. NAT lets you conceal details of your network from remote gateways. It also permits all
LAN devices to share a single IP address. By default, address NAT is turned on.

Administrator’s Handbook
124
set conn name name dhcp-client discover-time seconds
The DHCP client parameters appear when the connection type has been set to dhcpc. The discover-time value
is in seconds; the default is 30.
set conn name name dhcp-client dns-enable [ on | off ]
Allows you to enable or disable the default behavior of acting as a DNS proxy. The default is on.
set conn name name dhcp-client dns-override [ off | on ]
Allows you to enable or disable overriding default DNS behavior. The default is off.
set conn name name dhcp-client vendor-class string
The vendor-class default information varies by model and components. This is information that identifies the
unit.
set conn name name fs-egress filterset_name
Attaches a user filterset to a connection, which is applied to transmitted packets. See “Filter Set Commands”
on page 124.
set conn name name fs-ingress filterset_name
Attaches a user filter set to a connection, which is applied to received packets. See “Filter Set Commands” on
page 124.
Filter Set Commands
Filter sets provide packet filtering and QoS configuration. Packets are identified by characteristics that allow
QoS and forwarding decisions to be made. These characteristics can be at the MAC layer, IP layer, TCP | UDP |
ICMP layer(s), or (in applicable circumstances) 802.1q/p (VLAN-tagging) layer.
Your NVG599 device is capable of adding and stripping 802.1Q tags to and from frames before transmission on
its LAN interfaces. See also “Link Commands” on page 143 for more information.
A maximum of 8 filter sets are supported. Each filter set can have up to 8 rules configured. A maximum 8
egress queues are supported. Each queue can have up to 8 entries.
A filter set rule identifies packet attributes to match with its match parameters. It acts on these packets using
its default action parameters.
set filterset name filterset_name rule number order number
Determines order of execution of filter set rules (1 before 2, etc). If order is unspecified, the value of order is
set to 1 more than the last order in the filter set. If order is set to an already existing order value, order values
of other rules are incremented automatically.
set filterset name filterset_name rule number enable [ on | off ]
Dynamically enables or disables the specified filter set rule.

125
set filterset name filterset_name rule number match-eth-proto number
Matches Ethernet protocol field to the supplied value.
set filterset name filterset_name rule number match-eth-length number
Matches Ethernet length field to the supplied value.
set filterset name filterset_name rule number match-eth-p-bits number
Matches VLAN priority bits.
set filterset name filterset_name rule number match-eth-vid number
Matches VLAN ID number.
set filterset name filterset_name rule number match-eth-src-mac-addr
mac_address
Matches supplied source MAC address field.
set filterset name filterset_name rule number match-eth-dst-mac-addr
mac_address
Matches supplied destination MAC address field.
set filterset name filterset_name rule number match-src-ip-addr
ip_address_range
Matches supplied value with packet's source IP address field.
set filterset name filterset_name rule number match-dst-ip-addr
ip_address_range
Matches supplied value with packet's destination IP address field.
set filterset name filterset_name rule number match-protocol protocol_string
Matches supplied value with packet's protocol field.
set filterset name filterset_name rule number match-tos [ number |
descriptive_value ]
Matches TOS field from numeric value 0-255; or one of the following descriptive values:
Minimize-Delay (0x10)
Maximize-Throughput (0x08)
Maximize-Reliability (0x04)
Minimize-Cost (0x02)
Normal-Service (0x00)
set filterset name filterset_name rule number match-dscp [ number |
diffserv_class_string ]
Matches DiffServ class with supplied numerical value, which can be in decimal (ex: 32) or in Hex (ex: 0x20);

Administrator’s Handbook
126
Or match the supplied DiffServ class. This value may be any of the BE, EF, AFxx or CSx classes. A full list is:
{ "CS0", 0x00 }
{ "CS1", 0x08 }
{ "CS2", 0x10 }
{ "CS3", 0x18 }
{ "CS4", 0x20 }
{ "CS5", 0x28 }
{ "CS6", 0x30 }
{ "CS7", 0x38 }
{ "BE", 0x00 }
{ "AF11", 0x0a }
{ "AF12", 0x0c }
{ "AF13", 0x0e }
{ "AF21", 0x12 }
{ "AF22", 0x14 }
{ "AF23", 0x16 }
{ "AF31", 0x1a }
{ "AF32", 0x1c }
{ "AF33", 0x1e }
{ "AF41", 0x22 }
{ "AF42", 0x24 }
{ "AF43", 0x26 }
{ "EF", 0x2e }
set filterset name filterset_name rule number match-src-port number [ number ]
Matches TCP|UDP source port field or port range.
set filterset name filterset_name rule number match-dst-port number
[number ]
Matches TCP|UDP destination port field or port range.
set filterset name filterset_name rule number match-tcp-flags tcp_flag_string
Matches TCP flags in a packet. The flag string is comma-delimited.
set filterset name filterset_name rule number match-packet-length number
[number ]
Matches packet length against value or range.
set filterset name filterset_name rule number action forward [ pass | drop |
reject ]
Executes the named filter set’s default action: pass, drop, or reject.
set filterset name filterset_name rule number match-qos-marker-enable [ off |
on ]
Turns the function of tagging the packet according to the queue marker name on or off. Default is off.

127
set filterset name filterset_name rule number action set-qos-marker
qos_marker_string
Tags the packet according to the queue marker name. See “Queue Commands” on page 129.
set filterset name filterset_name rule number action set-tos number
Sets the packet TOD field to the supplied value.
set filterset name filterset_name rule number action set-dscp [ number |
diffserv_class_string ]
Sets the DSCP field to the supplied value.
set filterset name filterset_name rule number action set-eth-p-bits number
Sets VLAN priority bits to the supplied value.
set filterset filterset_name rule number action do-filterset name
Executes the supplied filter set.
Default Actions
If a packet passes through all of a filter's rules without a match, then the filter set's default actions come into
play. These behave the same way that rule actions behave.
set filterset name filterset_name default-action set-qos-marker
qos_marker_string
Tags the packet according to the queue marker name.
set filterset name filterset_name default-action set-tos number
Sets the packet TOS field to the supplied value.
set filterset name filterset_name default-action set-dscp [ number
|diffserv_class_string ]
Sets the DSCP field to the supplied value.
set filterset name filterset_name default-action set-eth-p-bits number
Sets VLAN priority bits to the supplied value.
set filterset name filterset_name default-action do-filterset name
Executes the supplied filter set.
set filterset name filterset_name default-action forward [ pass | drop | reject ]
Executes the named filter set’s default action: pass, drop, or reject.
Administrator’s Handbook
128
Global Filter Set (“IPv6 Firewall”) Commands
Global filter sets exist at the root level of the hierarchy, outside the umbrella of both the “ip” and “ip6”
subtrees, since they pertain to both.
Global filter set rules allow for the specification of these match attributes:
IP Protocol
Source and/or destination port:
UDP
TCP
TCP flags, for rules that specify TCP traffic
ICMP type, for IP-protocol types 1 (ICMP) and 58 (IPv6-ICMP)
LAN-side device/range:
By MAC address (or current IPv4/6 address, host name, equivalently)
IPv4 address, range, or subnet
IPv6 address or subnet
WAN-side range:
IPv4 address, range, or subnet
IPv6 address or subnet
Ingress and egress interface, by link-oid (such as “LAN”)
set gfs name filterset_name enable [ on | off ]
Dynamically enables or disables the specified filter set rule.
set gfs name filterset_name default-action value [ pass | drop ]
Executes the named filter set’s default action: pass or drop.
set gfs name filterset_name rule number enable [ on | off ]
Dynamically enables or disables the specified filter set rule.
set gfs name filterset_name rule number active [ on | off ]
Activates or deactivates the specified filter set rule.
set gfs name filterset_name rule number type [ either | ipv4 | ipv6 ]
Specifies whether the named filter set rule applies to IPv4, IPv6, or both (either).
set gfs name filterset_name rule number action value [ pass | drop | accept ]
Executes the named filter set’s action: pass, drop, or accept.
set gfs name filterset_name rule number order number
Determines order of execution of filter set rules (1 before 2, etc). If order is unspecified, the value of order is
set to 1 more than the last order in the filter set. If order is set to an already existing order value, order values
of other rules are incremented automatically.
set gfs name filterset_name rule number match number category [ src-ip-addr |
dst-ip-addr | ip-proto | src-port | dst-port | tcp-flags | src-host-mac | dst-host-
mac | in-link-oid
129
| out-link-oid | icmp-type ]
Matches on the following categories:
set gfs name filterset_name rule number match number value [ value (category-
specific) ]
Queue Commands
Queue configuration typically requires a classification component to set a QoS marker to a packet and a
queueing component to schedule the marked packets to the link. This is accomplished using filter sets (“Filter
Set Commands” on page 124).
The basic queue's size and length are controls for how many packets and total bytes can be enqueued before it
is considered to be full. Once it is full, any attempts to enqueue another packet will result in a “tail-drop.”
Both constraints are simultaneously used, such that the queue is full when either packet count or byte count
exceeds the limit. This allows flexibility in obtaining a balance, where a large number of small packets, but only
a small number of large packets can be enqueued.
If there are no tail-drops – that is, the queue is not blocked from sending and doesn't over-fill and dump
packets – then these queue size/bytes parameters do not affect anything. Their only function is to adjust the
threshold at which the queue is considered full, which dictates when tail-drops will occur. So if there are no
tail-drops, then increasing the queue length will have no effect. Increasing the queue length has no effect
unless there are tail-drops.
The maximum size/bytes of a queue balances how much burstiness can be buffered versus having a queue that
is simply too long.
Burstiness smoothing requires queueing up the buffers. For example, if the upstream line rate is 1 mbps, but
the traffic source sends 100 mbps bursts for 10 ms every second (which coincidentally averages 1 mbps) then
src-ip-addr (ip[4|6] address or subnet spec (type ip4 or ip6 only))
dst-ip-addr (ip[4|6] address or subnet spec (type ip4 or ip6 only))
ip-proto (0-255 or iana-defined string equivalents)
src-port (1-65535[:1-65535], only if ip-proto == TCP or UDP)
dst-port (1-65535[:1-65535], only if ip-proto == TCP or UDP)
tcp-flags (only if ip-proto == TCP)
icmp-type (only if ip-proto == ICMP or IPv6 ICMP)
src-host-mac (MAC address of src)
dst-host-mac (MAC address of dest)
in-link-oid (oid of ingress link oid)
out-link-oid (oid of egress link oid)
NOTE:
A rule cannot contain data that specifies both IPv6 and IPv4 at the same time, and thus be applicable to nei-
ther iptables nor ip6tables; however, a rule can be IP-version agnostic, in which case it will be applied to both
iptables and ip6tables, given the proper conditions. For instance, if a LAN-side device has both an IPv4
address and a routable IPv6 address, then one can specify a rule for this device by referring to its MAC
address, and if no other match attributes of the rule preclude its use in both tables, the rule will be applied to
both iptables and ip6tables (given the assumption that the LAN Host Discovery database contains both
addresses).
Administrator’s Handbook
130
the router will have to buffer enough (about a full second worth of traffic) so that the burst of traffic doesn't
get tail-dropped when it arrives and is enqueued at the same time in the same burst.
On the other hand, it is undesirable to buffer too much data in the queue(s) since the packets may be stale by
the time they are sent. It may be desirable to drop the traffic sufficiently that there are queuing disciplines
such as Random Early Discard (RED) that do not drop packets from the tail of the queue. Instead, RED drops
packets towards the front of the queue, so that the congestion is noticed more quickly in order for the sender
to scale back bandwidth usage to avoid drops.
The following types of queue “building blocks” are supported:
basic queue
ingress queue
priority queue
wfq (weighted fair queue)
Basic queues have three different packet dropping options:
byte|packet fifo (bpfifo)
random early discard (red)
stochastic fairness queuing (sfq)
set queue name queue_name type [ basic | ingress | priority | wfq ]
Sets the type of queue.
set queue name queue_name options [ off | red | sfq ]
Sets the queue packet dropping options.
set queue name queue_name size [ 1... 64 ]
Sets the maximum number of packets that can be enqueued.
set queue name queue_name bytes [ 2048... 131072 ]
Sets the maximum total number of bytes that can be enqueued.
set queue name queue_name perturb [ 0... 100 ]
Sets the interval in seconds for queue algorithm perturbation when queue option is sfq.
set queue name queue_name police-rate [ 0... 100000000 ]
Sets the rate in milliseconds that is used for policing traffic when the queue type is ingress.
set queue name queue_name police-burst [ 0... 100000000 ]
Sets the burst rate in milliseconds that is used for policing traffic when the queue type is ingress.
set queue name queue_name bw-sharing [ on | off ]
Enables or disables bandwidth sharing, when the queue type is either priority or wfq.

131
set queue nam
ip-proto
-mode [ bps | relative ]
Sets the mode of the weighted fair queue. The bps keyword indicates that weights are defined as bits-per-
second. The relative keyword indicates that weights are defined as a proportion of the sum of the weights of
all inputs to the wfq.
set queue name queue_name entry number input queue_name
Sets the input to a priority or weighted fair queue.
set queue name queue_name entry number marker queue_marker
Sets the marker with which packets must be marked to be directed to this queue entry's input queue when the
type is priority or wfq.
set queue name queue_name entry number priority [ 0... 255 ]
Sets the priority level of this queue. A lower value indicates a higher priority. All entries of equal priority will be
subject to a round robin algorithm.
For (strict) priority queue, the higher priority gets link resource first.
For wfq queue, each entry gets reserved bandwidth according to its weight. If different priority is given, any
excess bandwidth is offered to higher priority entry first; otherwise any excess bandwidth is distributed to
the weights ratio.
set queue name queue_name entry number weight [ 0... 100 ]
Sets the weight level of this weighted fair queue. Weight units are dependent on bps-mode setting.
If bps-mode is set to bps, then setting the weight to 0 will allocate the remaining available bandwidth to the
queue entry.
If no priority specified, excess bandwidth will be distributed proportionately to the weight ratio.
set queue name queue_name entry number peak [ 0... 100,000,000 ]
Sets the peak level of this weighted fair queue. The peak parameter is a number from 0 through 100,000,000 in
bits/second. It must be at least 50,000 for best effect. It is the peak data rate allowed on the queue entry, and
usually supports bandwidth sharing, that is, if other queues are not busy and there is spare bandwidth, then a
busy queue is allowed to go up to the peak rate.
set queue name queue_name default-entry queue_name
Indicates the input queue used if there is no match between the packet queue marker and the configured
markers in any of the queue's inputs when the queue type is priority or wfq.
Administrator’s Handbook
132
IP Gateway Commands
set ip gateway enable [ on | off ]
Specifies the conn of the gateway. Normally, this would be the WAN connection. Specifies whether the
NVG599 should send packets to a default gateway if it does not know how to reach the destination host.
set ip gateway conn-oid value
Sets the default gateway to point to an associated link specified by the conn-oid value.
set ip gateway address ip_address
Specifies the IP address of a host on a local or remote network in standard dotted-quad format.
IPv6 Commands
set ip6 enable [ on | off ]
Enables/disables IPv6 globally. The default is off. When enabled, the following default configuration is created:
set ip6 enable on
set ip6 conn name "WANv6" enable on
set ip6 conn name "WANv6" type rd
set ip6 conn name "WANv6" mtu 1472
set ip6 conn name "WANv6" side wan
set ip6 conn name "WANv6" mcast-forwarding off
set ip6 conn name "WANv6" icmp-echo-drop on
set ip6 conn name "WANv6" traffic-class-clear on
set ip6 conn name "WANv6" 6rd-tunnel type cpe
set ip6 conn name "WANv6" 6rd-tunnel ipv4-conn "WAN"
set ip6 conn name "WANv6" 6rd-tunnel use-dhcp-values off
set ip6 conn name "WANv6" 6rd-tunnel prefix "::"
set ip6 conn name "WANv6" 6rd-tunnel prefix-length 1
set ip6 conn name "WANv6" 6rd-tunnel ipv4-common-bits 0
set ip6 conn name "WANv6" 6rd-tunnel relay-ipv4-addr "0.0.0.0"
set ip6 conn name "WANv6" 6rd-tunnel ipv4-tx-tos-mode off
set ip6 conn name "WANv6" 6rd-tunnel force-tx-to-br on
set ip6 conn name "WANv6" 6rd-tunnel anti-spoof-enable on
set ip6 conn name "WANv6" 6rd-tunnel tx-df-bit-set on
set ip6 conn name "LANv6" enable off
set ip6 gateway enable on
set ip6 gateway conn "WANv6"
set ip6 gateway address "::"
set ip6 dhcp-server enable on
set ip6 dhcp-server information-only off
set ip6 dhcp-server preference 255
set ip6 dhcp-server authoritative on
set ip6 dhcp-server rapid-commit on
set ip6 dhcp-server unicast off
set ip6 dhcp-server leasequery off
set ip6 dhcp-server pd-enable on
set ip6 dhcp-server default-lease-time 2592000
set ip6 dhcp-server preferred-lifetime 604800
set ip6 dhcp-server T1 302400
set ip6 dhcp-server T2 483840

133
set ip6 dhcp-server info-refresh-time 86400
set ip6 dns primary-address ""
set ip6 dns secondary-address ""
Default IPv6 security configuration values:
set security spi ip6 src-mcast-drop off
set security spi ip6 invalid-mcast-scope-drop on
set security spi ip6 forbidden-addr-drop on
set security spi ip6 deprecated-ext-hdr-drop on
set security spi ip6 src-addr-from-lan-unassigned-drop on
set security spi ip6 lan-assigned-src-addr-from-wan-drop on
set security spi ip6 ula-drop on
set security spi ip6 ignore-dns-from-wan on
set security spi ip6 ignore-dhcp-from-wan on
set security spi ip6 esp-hdr-drop on
set security spi ip6 ah-hdr-drop on
set security spi ip6 allow-inbound off
set security spi ip4 invalid-addr-drop on
set security spi ip4 private-addr-drop off
set security spi flood-limit enable off
set security ip6 firewall-level low
set security ip6 enable on
ip6 gateway conn
set ip6 gateway enable [ on | off ]
Enables or disables IPv6 default gateway.
set ip6 gateway conn value
Sets the default gateway to point to an associated link specified by the conn-oid value. Normally, this would be
the WAN connection.
set ip6 gateway address ipv6_address
Specifies the IPv6 address of a host on a local or remote network in standard IPv6 format.
ip6 conn
set ip6 conn name name enable [ on | off ]
Enables/disables the IPv6 connection named name.
set ip6 conn name name type [ static | autoconf | rd | dp | aiccu ]
Type of connection. See below for connection types.
set ip6 conn name name mtu octets
Specified MTU of connection.
set ip6 conn name name side [ lan | wan ]
Specified whether the connection is LAN side or WAN side.
Administrator’s Handbook
134
set ip6 conn name name mcast-fwding [ off | on ]
Turns IPv6 multicast forwarding for this connection off or on. The default is off. (not yet implemented)
set ip6 conn name name old-prefix-purge-timer
The time in seconds for which old, invalid prefixes are advertised with a lifetime of zero. The intent is to “flush
out” global prefixes on attached IPv6 hosts that suddenly become invalid.
Static Connections
ip6 conn (type = static): Statically configured IPv6 connection.
set ip6 conn name name static link-oid link_name
Sets the connection named name to point to an associated link specified by the link-oid link_name.
set ip6 conn name name static ipaddr ipv6_address
Specifies a static IPv6 address.
set ip6 conn name name static prefix-length value
Specifies the prefix length of the connection's static IPv6 address. Default is 64.
6rd Connections
ip6 conn (type = rd, side = wan). This WAN connection type is a 6rd tunnel over an IPv4 conn in
accordance with RFC 5569.
set ip6 conn name name 6rd-tunnel type [ cpe | gateway ]
The 6rd connection can operate in “cpe” or “gateway” mode as configured by the type parameter. “cpe” mode
is used when operating as a CPE; “gateway” mode is used when operating as a “6rd relay,” as per RFC 5569.
set ip6 conn name name 6rd-tunnel ipv4-conn-oid ipv4_name
Sets the 6rd connection named name to tunnel over an associated IPv4 connection named ipv4_name.
set ip6 conn name name 6rd-tunnel use-dhcp-values [ off | on ]
If this parameter is on, 6rd-provisioned parameters are obtained via the underlying DHCPv4 client associated
with the IPv4 connection named ipv4-name. See the Internet Engineering Task Force document, “draft-ietf-
softwire-ipv6-6rd-10” for DHCP format description.
ip6 conn (type = rd, 6rd-tunnel use-dhcp-values = off).
set ip6 conn name name 6rd-tunnel prefix IPv6_address
6rd domain prefix.
set ip6 conn name name 6rd-tunnel prefix-length value [ 1 - 63 ]
6rd domain prefix length.

135
set ip6 conn name name 6rd-tunnel ipv4-common-bits value [ 0 - 31 ]
The number of bits common to all IPv4 addresses within the 6rd domain. The top-most bits of the IPv4 address
will be “subtracted” from the 6rd address. If the whole 32-bit IPv4 address is contained in the 6rd IPv6 address,
this value is set to zero. Default is 0, meaning all 42 bits of the IPv4 address are embedded in the 6rd prefix.
set ip6 conn name name 6rd-tunnel relay-ipv4-addr IPv4_address
The IPv4 anycast address of the 6rd border gateway.
set ip6 conn name name 6rd-tunnel ipv4-tx-tos-mode [ off | use-ipv6 ]
The off parameter sets the TOS field in the IPv4 header to zero for transmitted 6rd packets. The keyword use-
ipv6 sets the the TOS field in the IPv4 headerto the DS field of the 6rd-encapsulated IPv6 packet.
set ip6 conn name name 6rd-tunnel ipv4-tx-to-br [ off | on ]
If the off parameter is used, each packet set to a destination IPv6 address within the originating 6rd domain is
sent directly to the 6rd endpoint. If the keyword on is used, all packets are transmitted to the 6rd border
gateway.
AICCU (SixXS tunnel broker) Connections
ip6 conn (type = aiccu, side = wan). This connection type enables an IPv6 connection to the IPv6 Internet
over an IPv4/NAT/UDP tunnel to a tunnel endpoint administered by tunnel broker SIXXS (www.sixxs.net).
You set up an account with SIXXS, and subsequently get assigned a tunnel and a subnet (usually a /48 subnet).
set ip6 conn name name aiccu username username
Sets the connection’s SIXXS user name.
set ip6 conn name name aiccu password password
Sets the connection’s SIXXS password.
Delegated Prefix Connections
ip6 conn (type = dp, side = lan). A connection of type “delegated prefix” obtains its global prefix
information from one or more prefixes from another IPv6 connection (typically a WAN), if available. For a
delegated prefix connection to become fully operational, its underlying link must be up and the IPv6
connection that delegates the prefix must have created one or more prefixes from which to draw the delegated
prefix connection's global prefix.
set ip6 conn name name dp link-oid link_name
Sets the connection to obtain its prefix from the specified link.
set ip6 conn name name dp conn-oid ipv6_conn_name
Sets the delegated prefix connection named name to obtain its prefix from IPv6 connection named
ipv6_conn_name.
Administrator’s Handbook
136
set ip6 conn name name dp subnet-length value [ 0 - 16 ]
The length of the subnet portion of the delegated prefix. Default is 0.
set ip6 conn name name dp subnet-id value [ 0 - 65535 ]
If a subnet length is specified, the value that would occupy the of the subnet portion of the connection's IPv6
prefix. Default is 0.
set ip6 conn name name dp stay-up [ off | on ]
If the delegated prefix parameter stay-up is set to on, the global prefix assigned from the connection
delegating the prefix remains active in the event that the connection delegating the prefix goes down, and the
prefix becomes invalid. This enables local LAN-side hosts to continue to use the global prefix uninterrupted. If
parameter stay-up is set to off, the connection's delegated prefix becomes invalid when the connection named
ipv6-conn-name delegating the prefix goes down.
Router Advertisement and DHCPv6 Server
ip6 conn (side = lan). Router advertisements and the DHCPv6 server are available on LAN-side connections
as the means to provide clients with stateful or stateless IPv6 prefixes and addresses, as well as addition client
parameters such as MTU size and IPv6-addressable DNS servers.
set ip6 conn name name radv enable [ off | on ]
The on parameter sets router advertisement to enabled for this connection.
set ip6 conn name name radv min-rtr-adv-interval seconds [ 3 - 1350 ]
The minimum time allowed between sending unsolicited multicast router advertisements from the link, in
seconds.
set ip6 conn name name radv max-rtr-adv-interval seconds [ 4 - 1800 ]
The maximum time allowed between sending unsolicited multicast router advertisements from the interface,
in seconds.
set ip6 conn name name dhcp-server enable [ off | on ]
The on parameter sets the DHCPv6 server to enabled for this connection.
set ip6 conn name name dhcp-server addr-count value [ 0 - 256 ]
The number of IPv6 addresses available to serve to DHCPv6 stateful clients. If the addr-count parameter is set
to zero, the DHCPv6 server operates in “stateless” mode.
set ip6 conn name name dhcp-server start-addr-offset value [ 0 - 65536 ]
If the addr-count parameter is greater than zero, the start address is an offset from the base address of the
prefix that is assigned to the LAN connection.
set ip6 conn name name dhcp-server lease-time seconds [ 180 - 8553600 ]
DHCPv6 lease time.

137
set ip6 conn name name dhcp-server dns-server optional IPv6 address
IPv6 address of advertised DNS server (optional).
IPv6 DHCP Server
set ip6 dhcp-server enable [ on | off ]
Globally enables or disables DHCPv6 servers on all IPv6 LAN connections. The default is on.
set ip6 dhcp-server information-only [ off | on ]
The on parameter sets DHCPv6 servers on all IPv6 LAN connections to operate in stateless “information-only”
mode. The default is off.
set ip6 dhcp-server preference 255
Sets the preference option, as defined in RFC1315, sec. 22.8. The preference option in the server’s Advertise
message may assist a DHCPv6 client in selecting from more than one server on the LAN.
set ip6 dhcp-server authoritative [ on | off ]
If a client requests an IP address on a given network segment that the server knows is not valid for that
segment, and authoritative is set to on, the server will respond with a DHCPNAK message, causing the client to
forget its IP address and try to get a new one. If authoritative is set to off, the server will ignore the client’s
request. The default is on.
set ip6 dhcp-server rapid-commit [ on | off ]
Enables or disables the rapid commit option per RFC 3315 Section 22.14. The default is on.
set ip6 dhcp-server unicast [ off | on ]
Enables or disables server unicast option per RFC 3315 Section 22.12. The default is off.
set ip6 dhcp-server leasequery [ off | on ]
Enables or disables DHCPv6 Leasequery option per RFC 5007. The default is off.
set ip6 dhcp-server pd-enable [ on | off }
Enables or disables prefix delegation globally on all DHCPv6 servers on all IPv6 LAN connections, overriding
individual DHCPv6 server settings. The default is on.
set ip6 dhcp-server default-lease-time seconds
Sets the global DHCPv6 lease time setting in seconds. The default is 2592000 (30 days).
set ip6 dhcp-server preferred-lifetime seconds
Sets the global DHCPv6 preferred lifetime of prefixes in seconds, per RFC 3633. The default is 604800 (7 days).
Administrator’s Handbook
138
set ip6 dhcp-server T1 seconds
set ip6 dhcp-server T2 seconds
Sets global DHCPv6 T1, T2 values, per RFC 3315 for local NA addresses:
And also per global DHCPv6 T1, T2 values, per RFC 3633 for PD prefixes:
set ip6 dhcp-server info-refresh-time seconds
In seconds, per RFC 4242: The information refresh time option specifies an upper bound for how long a client
should wait before refreshing information retrieved from DHCPv6 in stateless mode. The default is 86400 (24
hours).
Static Routes
ip6 static-route
set ip6 static-route name conn-oid ipv6_conn_name
Route is directed to IPv6 connection named ipv6_conn_name.
set ip6 static-route name nexthop IPv6_address
Next-hop IPv6 address for forwarding. Can be a global or link-local address.
set ip6 static-route name prefix IPv6_prefix
IPv6 prefix.
set ip6 static-route name prefix-length value [ 1 - 64 ]
IPv6 prefix-length.
set ip6 static-route name metric value [ 0 - 255 ]
Metric assigned to route.
T1
The time at which the client contacts the server from which the addresses in the IA_NA were obtained to
extend the lifetimes of the addresses assigned to the IA_NA; T1 is a time duration relative to the current
time expressed in seconds. Defaults to 302400 (3.5 days).
T2
The time at which the client contacts any available server to extend the lifetimes of the addresses
assigned to the IA_NA; T2 is a time duration relative to the current time expressed in seconds. Defaults to
483840 (5.6 days).
T1
The time at which the requesting router should contact the delegating router from which the prefixes in
the IA_PD were obtained to extend the lifetimes of the prefixes delegated to the IA_PD; T1 is a time dura-
tion relative to the current time expressed in seconds.
T2
The time at which the requesting router should contact any available delegating router to extend the life-
times of the prefixes assigned to the IA_PD; T2 is a time duration relative to the current time expressed in
seconds.
139
IP DNS Commands
set ip dns domain-name domain_name
Specifies the default domain name for your network. When an application needs to resolve a host name, it
appends the default domain name to the host name and asks the DNS server if it has an address for the fully
qualified host name.
set ip dns primary-address ip_address
Specifies the IP address of the primary DNS name server.
set ip dns secondary-address ip_address
Specifies the IP address of the secondary DNS name server. Enter 0.0.0.0 if your network does not have a
secondary DNS name server.
set ip dns proxy-enable [ on | off ]
Allows you to disable the default behavior of acting as a DNS proxy. The default is on.
IP IGMP Commands
Multicasting is a method for transmitting large amounts of information to many, but not all, computers over an
internet. One common use is to distribute real-time voice, video, and data services to the set of computers
which have joined a distributed conference. Other uses include updating the address books of mobile
computer users in the field, or sending out company newsletters to a distribution list.
Since a router should not be used as a passive forwarding device, NVG599 devices use a protocol for
forwarding multicasting: Internet Group Management Protocol (IGMP).
NVG599 devices support IGMP Version 1, Version 2, or Version 3.
IGMP “Snooping” is a feature of Ethernet Layer 2 switches that “listens in” on the IGMP conversation between
computers and multicast routers. Through this process, it builds a database of locations where the multicast
routers reside by noting IGMP general queries used in the querier selection process and by listening to other
router protocols.
From the host point of view, the snooping function listens at a port level for an IGMP report. The switch then
processes the IGMP report and starts forwarding the relevant multicast stream onto the host's port. When the
switch receives an IGMP leave message, it processes the leave message, and if appropriate, stops the multicast
stream to that particular port. Basically, customer IGMP messages although processed by the switch are also
sent to the multicast routers.
In order for IGMP snooping to function with IGMP Version 3, it must always track the full source filter state of
each host on each group, as was previously done with Version 2 only when fast leave support was enabled.
IGMP Version 3 supports source filtering, which is the ability for group memberships to incorporate source
address filtering. This ability allows source-specific multicast (SSM). By adding source filtering, a gateway that
proxies IGMP can more selectively join the specific multicast group for which there are interested LAN
multicast receivers.
These features require no user configuration on the gateway.

Administrator’s Handbook
140
You can set the following options:
IGMP Snooping – Enables the NVG599 to “listen in” to IGMP traffic. The NVG599 discovers multicast group
membership for the purpose of restricting multicast transmissions to only those ports which have requested
them. This restriction helps to reduce overall network traffic from streaming media and other bandwidth-
intensive IP multicast applications.
Robustness – A way of indicating how sensitive to lost packets the network is. IGMP can recover from
robustness minus 1 lost IGMP packet. The default value is 2.
Query Interval – The amount of time in seconds between IGMP General Query messages sent by the querier
gateway. The default query interval is 125 seconds.
Query Response Interval – The maximum amount of time in tenths of a second that the IGMP gateway waits
to receive a response to a General Query message. The default query response interval is 10 seconds and
must be less than the query interval.
Unsolicited Report Interval – The amount of time in seconds between repetitions of a particular computer’s
initial report of membership in a group. The default unsolicited report interval is 10 seconds.
Querier Version – Version of the IGMP querier: version 1, version 2, or version 3. If you know you will be
communicating with other hosts that are limited to v1 or v2, for backward compatibility, select accordingly;
otherwise, allow the default v3.
Last Member Query Interval – The amount of time in tenths of a second that the IGMP gateway waits to
receive a response to a Group-Specific Query message. The last member query interval is also the amount of
time in seconds between successive Group-Specific Query messages. The default last member query interval
is 1 second (10 deci-seconds).
Last Member Query Count – The number of Group-Specific Query messages sent before the gateway
assumes that there are no members of the host group being queried on this interface. The default last mem-
ber query count is 2.
Fast Leave – Set to off by default, fast leave enables a non-standard expedited leave mechanism. The querier
keeps track of which client is requesting which channel by IP address. When a leave message is received, the
querier can check its internal table to see if there are any more clients on this group. If there are none, it
immediately sends an IGMP leave message to the upstream querier.
Log Enable – If set to on, all IGMP messages on both the LAN and the WAN will be logged.
Wireless Multicast to Unicast conversion – Only available if IGMP snooping is enabled. If set to on, the gate-
way replaces the multicast MAC address with the physical MAC address of the wireless client. If there is
more than one wireless client interested in the same multicast group, the gateway will revert to multicasting
the stream immediately. When one or more wireless clients leave a group, and the gateway determines that
only a single wireless client is interested in the stream, it will once again unicast the stream.
set ip igmp querier-version [ 1 | 2 | 3 ]
Sets the IGMP querier version: version 1, version 2, or version 3. If you know you will be communicating with
other hosts that are limited to v1, for backward compatibility, select 1; otherwise, allow the default 3.
set ip igmp robustness value
Sets IGMP robustness range: 2 – 255. The default is 2.
set ip igmp query-interval value
Sets the query-interval range: 10 seconds – 600 seconds. The default is 125 seconds.
NOTE:
IGMP querier version is relevant only if the gateway is configured for IGMP forwarding. If any IGMP v1 rout-
ers are present on the subnet, the querier must use IGMP v1. The use of IGMP v1 must be administratively
configured, since there is no reliable way of dynamically determining whether IGMP v1 routers are present
on a network. IGMP forwarding is enabled per the IP profile and the WAN connection profile.

141
set ip igmp query-response-interval value
Sets the query-response interval range in deci-seconds (tenths of a second): 5 – 255. The default is 100 deci-
seconds.
set ip igmp unsolicited-report-interval value
Sets the unsolicited report interval: the amount of time in seconds between repetitions of a particular
computer’s initial report of membership in a group. The default is 10 seconds.
set ip igmp fast-leave [ off | on ]
Sets fast leave on or off. Set to on by default, fast leave enables a non-standard expedited leave mechanism.
The querier keeps track of which client is requesting which channel by IP address. When a leave message is
received, the querier can check its internal table to see if there are any more clients on this group. If there are
none, it immediately sends an IGMP leave message to the upstream querier.
set ip igmp max-group-memberships value
Sets the maximum number of IGMP group memberships. Default is 20.
set ip igmp fwd-admin-groups [ off | on ]
Turns Admin group forwarding off or on. Default is off.
set ip igmp last-member-interval value
Sets the last member query interval: the amount of time in tenths of a second that the IGMP gateway waits to
receive a response to a Group-Specific Query message. The last member query interval is also the amount of
time in seconds between successive Group-Specific Query messages. The default is 1 second (10 deci-seconds).
set ip igmp last-member-count value
Sets the last member query count: the number of Group-Specific Query messages sent before the gateway
assumes that there are no members of the host group being queried on this interface. The default is 2.
set ip igmp default-fwd-allow [ on | off ]
Turns default forwarding on or off. The default is on.
set ip igmp snoop-entry-time seconds
The snoop-entry-time value is the amount of time an entry will remain in the snooping table (in seconds) after
being added. An entry is added when a join is seen from a multicast client. Any new joins (triggered by
upstream queries) will reset the timeout back to the value of seconds. If no additional joins are seen, the entry
will expire after the value of seconds. Default is 130.
set ip igmp snooping-unreg-mode [ block | flood ]
The snooping-unreg-mode value can be set to block or flood. This value indicates what should happen to
unregistered multicast traffic – traffic that hasn't been subscribed to by any clients. If set to flood, the traffic
will be sent to all LAN ports. If set to block, the traffic will not be sent to any LAN ports; it will be dropped.
Default is block.
Administrator’s Handbook
142
NTP Commands
set ip ntp enable [ on | off ]
Enables or disables acquiring the time of day from an NTP (Network Time Protocol) server.
set ip ntp server-address server_address
set ip ntp alt-server-address alt_server_address
Specifies the NTP server(s) to use for time updates. The NTP server-address and alt-server-address values can
be entered as DNS names as well as IP addresses.
set ip ntp update-period minutes
Specifies how often, in minutes, the gateway should update the clock. Default is 1440.
Application Layer Gateway (ALG) Commands
These commands allow you to enable or disable the router’s support for a variety of application layer gateways
(ALGs). An application layer gateway (ALG) is a NAT component that helps certain application sessions to pass
cleanly through NAT. Each ALG has a slightly different function based on the particular application’s protocol-
specific requirements.
An internal client first establishes a connection with the ALG. The ALG determines if the connection should be
allowed or not and then establishes a connection with the destination computer. All communications go
through two connections – client to ALG and ALG to destination. The ALG monitors all traffic against its rules
before deciding whether or not to forward it. Because the ALG is the only address seen by the public Internet,
the internal network is concealed. In some situations, it may be desirable to disable some of the ALGs.
set ip alg esp-enable [ on | off ]
Turns the ESP (Encapsulating Security Payload) ALG for file transfers on or off. Default is on.
set ip alg esp-setup-timeout value
Specifies the timeout value for the ESP ALG setup. Default is 180.
set ip alg esp-stream-timeout value
Specifies the timeout value for the ESP ALG streaming. Default is 300.
set ip alg ftp-enable [ on | off ]
Turns the FTP (File Transfer Protocol) ALG for file transfers on or off. Default is on.
set ip alg h323-enable [ on | off ]
Turns the H323 ALG for audio, video, and data communications across IP-based networks on or off. Default is
on.
set ip alg pptp-enable [ on | off ]
Turns the PPTP (Point-to-Point Transfer Protocol) ALG for authentication on or off. Default is on.
143
set ip alg sip-enable [ on | off ]
Turns the SIP (Session Initiation Protocol) ALG for voice communication initiation on or off. Default is on.
set ip alg tftp-enable [ on | off ]
Turns the TFTP (Trivial File Transfer Protocol) ALG for simple file transfers and firmware updates on or off.
Default is on.
Dynamic DNS Commands
set ip dynamic-dns enable [ off | on ]
Enables or disables dynamic DNS. Dynamic DNS support allows you to use the free services of
www.dyndns.org. Dynamic DNS automatically directs any public Internet request for your computer's name to
your current dynamically-assigned IP address. This allows you to get to the IP address assigned to your
gateway, even though your actual IP address may change as a result of a PPPoE connection to the Internet.
set ip dynamic-dns service-type [ dyndns ]
set ip dynamic-dns username myusername
set ip dynamic-dns password mypassword
set ip dynamic-dns hostname myhostname
set ip dynamic-dns retries [ 1 - 64 ]
Enables or disables dynamic DNS services. The default is off. If you specify dyndns.org, you must supply your
host name, user name for the service, and password. Number of retries defaults to 5.
Default Server Settings
set ip wan-allocation mode [ normal | defaultserver ]
Sets the WAN mode to direct your NVG599 to forward all externally initiated IP traffic (TCP and UDP protocols
only) to a default host on the LAN, otherwise this feature is disabled. Default is normal.
Link Commands
The link commands represent physical connections. Currently, port-based VLAN support is provided at this
level. Your NVG599 device is capable of adding and stripping 802.1Q tags to and from frames before
transmission on its LAN interfaces. See also “Filter Set Commands” on page 124 and “Queue Commands” on
page 129 for more information.
set link name name type [ ethernet | ppp ]
Specifies whether the type of the link named name is ethernet or ppp.
set link name name mtu-override [ 0 - 1500 ]
Specifies whether the maximum transmission unit value should be set to other than the standard 1500. A
setting of 0 (zero) turns off override.
set link name name igmp-snooping [ off | on ]
Turns igmp-snooping off or on on the link named name.
Administrator’s Handbook
144
set link name name port-vlan ports [ lan-1... 4 | hpna | ssid-1...4 | ptm | vc-1 | vc-
2 ]
Specifies a port-based VLAN on the selected ports on the link named name.
set link name name port-vlan priority [ 0 - 7 ]
Specifies the 802.1p priority bit. If you set this to a value greater than 0, all packets of this VLAN with unmarked
priority bits (pbits) will be re-marked to this priority.
set link name name tagged-vlan name integer ports
[ lan-1... 4 | hpna | ssid-1...4 | ptm | vc-1 | vc-2 ]
Specifies a tagged VLAN on the selected port on the link named name. Default is ptm.
set link name name tagged-vlan name integer vid vlan_id
Specifies a VLAN ID (VID) on the selected link named name. Default is 0.
set link name name tagged-vlan name integer priority [ 0 - 7 ]
Specifies the 802.1p priority bit. If you set this to a value greater than 0, all packets of this VLAN with unmarked
priority bits (pbits) will be re-marked to this priority.
set link name name supplicant type [ none | eap-tls ]
Specifies whether the EAP TLS supplicant is enabled on the link named name. Default is eap-tls.
set link name name supplicant priority [ 0 - 7 ]
Sets the supplicant priority on the link named name when supplicant type is eap-tls. Default is 0.
set link name name ppp sub-link link_name
Specifies a name link_name for this secondary link when one is required.
set link name name ppp auth-type [ on | off ]
Enables or disables PPP login authorization.
set link name name ppp username uname
Specifies a user name uname for authentication on the specified link when ppp auth-type is set to on.
set link name name ppp password pwd
Specifies a password pwd for authentication on the specified link when ppp auth-type is set to on.
set link name name ppp magic-number [ on | off ]
Enables or disables LCP magic number negotiation.

145
set link name name ppp protocol-compression [ off | on ]
Specifies whether you want the NVG599 to compress the PPP Protocol field when it transmits datagrams over
the PPP link.
set link name name ppp max-failures integer
Specifies the maximum number of Configure-NAK messages the PPP module can send without having sent a
Configure-ACK message. The integer argument can be any number between 1 and 20.
set link name name ppp max-configures integer
Specifies the maximum number of unacknowledged configuration requests that your NVG599 will send. The
integer argument can be any number between 1 and 20.
set link name name ppp max-terminates integer
Specifies the maximum number of unacknowledged termination requests that your NVG599 will send before
terminating the PPP link. The integer argument can be any number between 1 and 10.
set link name name ppp restart-timer integer
Specifies the number of seconds the NVG599 should wait before retransmitting a configuration or termination
request. The integer argument can be any number between 1 and 30.
set link name name ppp connection-type [ instant-on | always-on ]
Specifies whether a PPP connection is maintained by the NVG599 device when it is unused for extended
periods. If you specify always-on, the NVG599 never shuts down the PPP link. If you specify instant-on, the
NVG599 shuts down the PPP link after the number of seconds specified in the timeout setting (below) if no
traffic is moving over the circuit.
set link name name ppp echo-request [ on | off ]
Specifies whether you want your NVG599 to send LCP echo requests. You should turn off LCP echoing if you do
not want the NVG599 to drop a PPP link to a nonresponsive peer.
set link name name ppp echo-failures integer
Specifies the maximum number of lost echoes the NVG599 should tolerate before bringing down the PPP
connection. The integer argument can be any number from between 1 and 20.
set link name name ppp echo-interval integer
Specifies the number of seconds the NVG599 should wait before sending another echo from an LCP echo
request. The integer argument can be any number from between 5 and 300 (seconds).
set link name name ppp mru integer
Specifies the maximum receive unit (MRU) for the PPP interface. The integer argument can be any number
between 128 and 1492 for PPPoE; 1500 otherwise.
Administrator’s Handbook
146
set link name name ppp peer-dns [ on | off ]
Controls whether the NVG599 accepts name server addresses from the peer.
The default is on, which means the NVG599 expects to get name server addresses when the PPP link comes
up. This especially applies when the primary WAN connection is PPP.
However, there are some unusual situations where the PPP connection is not the primary WAN, for example
when the connection is used only for management. In that situation it may be desirable to not pick up more
name server addresses. You can do that by setting the parameter to off.
Specifies an ISP name or a class or quality of service. The service name tells the access concentrator which
network service the NVG599 is trying to reach.
set link name name pppoe ac-name name
Specifies this particular access concentrator (AC) unit from all others. Some access provider networks may
have multiple PPPoE servers, and having the NVG599 indicate an AC name specifies to which one the NVG599
is trying to connect.
Management Commands
All management related items are grouped in this section.
set management account administrator username username
Specifies the username for the administrative user. The default is admin.
set management account user username username
Specifies the username for the non-administrative user. The default is user.
set management cwmp enable [ off | on ]
Turns cwmp (TR-069 CPE WAN Management Protocol) on or off. TR-069 allows a remote auto-config server
(ACS) to provision and manage the NVG599 device. TR-069 protects sensitive data on the NVG599 by not
advertising its presence, and by password protection.
set management cwmp acs-url acs_url:port_number
set management cwmp acs-username acs_username
set management cwmp acs-password acs_password
If TR-069 WAN-side management services are enabled, specifies the auto-config server URL and port number.
A user name and password must also be supplied, if TR-069 is enabled.
NOTE:
This is an expert-mode setting that will rarely be used. The setting should be left on, unless you are an expert
user who knows you do not want the NVG599 to acquire any name server addresses from this PPP connec-
tion.

147
The auto-config server is specified by URL and port number. The format for the ACS URL is as follows:
http://some_url.com:port_number
or
http://123.45.678.910:port_number
On units that support SSL, the format for the ACS URL can also be:
https://some_url.com:port_number
or
https://123.45.678.910:port_number
TR-064
DSL Forum TR-064 (“LAN Side CPE Configuration”) is an extension of UPnP (Universal Plug-and-Play). It defines
more services to locally manage the NVG599 device. While UPnP allows open access to configure the device's
features, TR-064 requires a password to execute any command that changes the device's configuration.
set management lanmgmt enable [ off | on ]
Turns TR-064 LAN side management services on or off. The default is off.
set management shell idle-timeout [ 1...120 ]
Specifies a timeout period of inactivity for Telnet access to the NVG599 device, after which a user must re-log
in to the NVG599. Default is 15 minutes for Telnet.
set management shell ssh-port [ 1 - 65534 ]
Specifies the port number for secure shell (SSH) communication with the NVG599. Defaults to port 0 (off).
set management shell telnet-port [ 1 - 65534 ]
Specifies the port number for Telnet (CLI) communication with the NVG599 device. Because port numbers in
the range 0-1024 are used by other protocols, you should use numbers in the range 1025-65534 when
assigning new port numbers to the NVG599 Telnet configuration interface. A setting of 0 (zero) will turn the
server off.
set management upnp enable [ off | on ]
Turns Universal Plug-and-Play (UPnP) on or off.
set management web http-port [ 1 - 65534 ]
Specifies the port number for HTTP (Web) communication with the NVG599 device. Because port numbers in
the range 0-1024 are used by other protocols, you should use numbers in the range 1025-65534 when
assigning new port numbers to the NVG599 Web configuration interface. A setting of 0 (zero) will turn the
server off.
set management web https-port [ 1 - 65534 ]
Sets the secure Web access port for secure management of the NVG599. Default is port 443.
Administrator’s Handbook
148
set management web https-cert-cn string
Specifies a certificate from a trusted certificate authority to identify the secure Web access.
set management web idle-timeout [ 1...120 ]
Specifies a timeout period of inactivity for HTTP access to the NVG599 device, after which a user must log in to
the NVG599. Default is 5 minutes for HTTP.
set management web isp-help-desk phone_number_string
Specifies the ISP Help Desk phone number as it appears in the Web UI. For AT&T, the default is: 1-800-288-
2020.
Remote Access Commands
set management remote-access http-port [ 1 - 65534 ]
Sets the Web access port for remote access management of the NVG599. Default is port 51003.
set management remote-access http-idle-timeout [ 1...120 ]
Specifies a timeout period of inactivity for remote HTTP access to the NVG599, after which a user must log in
to the device. Default is 20 minutes for HTTP.
set management remote-access http-total-timeout [ 1...120 ]
Specifies a total timeout period of inactivity for remote HTTP access to the NVG599, after which a user must
log in to the device. Default is 20 minutes for HTTP.
set management remote-access http-max-clients number
Specifies the maximum number of client sessions for remote Web access management. Defaults to 1 (one).
set management remote-access https-port [ 1 - 65534 ]
Sets the secure Web access port for remote access management of the NVG599. Default is port 51443.
set management remote-access https-idle-timeout [ 1...120 ]
Specifies a timeout period of inactivity for secure remote HTTPS access to the NVG599 device, after which a
user must log in to the device. Default is 20 minutes for HTTPS.
set management remote-access https-total-timeout [ 1...120 ]
Specifies a total timeout period of inactivity for secure remote HTTPS access to the NVG599 device, after which
a user must log in to the device. Default is 20 minutes for HTTPS.
set management remote-access https-max-clients number
Specifies the maximum number of client sessions for secure remote Web access management. Defaults to 1.
NOTE:
You cannot specify a port setting of 0 (zero) for both the Web and Telnet ports at the same time. This would
prevent you from accessing the NVG599.

149
set management remote-access telnet-port [ 1 - 65534 ]
Specifies the port number for remote access Telnet (CLI) communication with the NVG599 device. Because
port numbers in the range 0-1024 are used by other protocols, you should use numbers in the range 1025-
65534 when assigning new port numbers to the NVG599 Telnet configuration interface. A setting of 0 (zero)
will turn the server off. Defaults to port 0.
set management remote-access telnet-idle-timeout [ 1...120 ]
Specifies a timeout period of inactivity for remote Telnet access to the NVG599 device, after which a user must
log in to the device. Default is 5 minutes for Telnet.
set management remote-access telnet-total-timeout [ 1...120 ]
Specifies a total timeout period of inactivity for remote Telnet access to the NVG599 device, after which a user
must log in to the device. Default is 20 minutes for Telnet.
set management remote-access telnet-max-clients number
Specifies the maximum number of client sessions for remote Telnet access management. Defaults to 4.
set management remote-access ssh-port [ 1 - 65534 ]
Specifies the port number for secure shell (SSH) communication with the NVG599. Defaults to port 22.
set management remote-access ssh-idle-timeout [ 1...120 ]
Specifies a timeout period of inactivity for remote secure shell (SSH) access to the NVG599 device, after which
a user must log in to the device. Default is 5 minutes for SSH.
set management remote-access ssh-total-timeout [ 1...120 ]
Specifies a total timeout period of inactivity for remote secure shell (SSH) access to the NVG599 device, after
which a user must log in to the device. Default is 20 minutes for SSH.
set management remote-access ssh-max-clients number
Specifies the maximum number of client sessions for remote secure shell (SSH) access management. Defaults
to 4.
set management lan-redirect enable [ off | on ]
If set to on and a WAN failure condition is detected, the LAN client's browser is redirected to a Web page of
failure and Help text information. The redirect will only occur once, as the Web UI maintains a state variable to
determine whether the redirect has occurred; to continually redirect would block the user from reconfiguring
the router.
set management lan-redirect missing-filter-notify [ on | off ]
If set to on and a missing filter on the line is detected, the LAN client's browser is redirected to a Web page of
failure and Help text information. The redirect will only occur once, as the Web UI maintains a state variable to
determine whether the redirect has occurred; to continually redirect would block the user from reconfiguring
the router.
Administrator’s Handbook
150
set management lan-access wan-cpe-mgmt-block [ off | web | all ]
Blocks management of the device from the LAN via the Web or all interface(s).
TR-064
DSL Forum TR-064 (“LAN Side CPE Configuration”) is an extension of UPnP (Universal Plug-and-Play). It defines
more services to locally manage the NVG599 device. While UPnP allows open access to configure the device's
features, TR-064 requires a password to execute any command that changes the device's configuration.
set management lanmgmt enable [ off | on ]
Turns TR-064 LAN-side management services on or off. The default is off.
Physical Interfaces Commands
DSL interfaces
set physical dsl enable [ off | on ]
Turns the physical DSL interface off or on. Default is on.
set physical dsl dsl-mode [ auto | single | bonded ]
Sets the mode for the DSL connection, whether a single line or bonded. If the default auto is set, the device
will try both single and bonded, attempting to detect and lock on the mode in use.
set physical dsl loopback [ off | on ]
Turns the DSL loopback mode off or on. Default is off.
set physical dsl annexm [ off | on ]
Turns optional DSL Annex M off or on. Default is off. If enabled, data rates can be as high as 12 or 24 Mbit/s
downstream and 3 Mbit/s upstream depending on the distance from the DSLAM to the customer's premises.
set physical dsl modulation auto [ off | on ]
Turns automatic DSL modulation off or on. Default is off.
set physical dsl modulation vdsl2 [ off | on ]
Turns VDSL2 DSL modulation off or on. Default is on.
set physical dsl modulation adsl2 [ off | on ]
Turns ADSL2 DSL modulation off or on. Default is on.
set physical dsl modulation adsl2+ [ off | on ]
Turns ADSL2+ DSL modulation off or on. Default is on.
set physical dsl modulation annex-l [ off | on ]
Turns Annex-l DSL modulation off or on. Default is off.

151
set physical dsl modulation annex-m [ off | on ]
Turns Annex-M DSL modulation off or on. Default is off.
set physical dsl profile-8a [ on | off ]
Enables or disables VDSL2 profile 8a governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-8b [ on | off ]
Enables or disables VDSL2 profile 8b governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-8c [ on | off ]
Enables or disables VDSL2 profile 8c governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-8d [ on | off ]
Enables or disables VDSL2 profile 8d governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-12a [ on | off ]
Enables or disables VDSL2 profile 12a governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-12b [ on | off ]
Enables or disables VDSL2 profile 12b governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-17a [ on | off ]
Enables or disables VDSL2 profile 17a governing upstream and downstream bandwidth. Default is on.
set physical dsl profile-30a [ on | off ]
Enables or disables VDSL2 profile 30a governing upstream and downstream bandwidth. Default is off.
set physical dsl bit-swap [ on | off ]
Turns DSL bit-swapping on or off. Bit-swapping is resilient to loss of hand-shake commands. Default is on.
set physical dsl trellis [ on | off ]
Turns trellis error correction encoding on or off. Default is on.
set physical dsl vectoring-enable [ off | on ]
Enables or disables VDSL2 vectoring. Vectoring enables VDSL2 to achieve its highest potential data rates,
exceeding 100 Mbps. Default is off.
set physical dsl vectoring-timeout-ms milliseconds
If vectoring-enable is set to on, specifies a timeout interval in milliseconds. Default is 5000.
Administrator’s Handbook
152
set physical dsl nlnm-threshold [ 0 - 480 ]
Specifies the New Low Noise Model (NLNM) value between 0 and 480. Default is 60.
set physical dsl transport [ atm | ptm | auto | off ]
Sets the DSL transport mode: Asynchronous (atm), Packet (ptm), Automatic (auto), or none (off). Default is
ptm.
set physical dsl atm vcc 1 enable [ off | on ]
Turns ATM on or off on vcc 1. Default is on.
set physical dsl atm vcc 1 aal-type [ aal5 | aal0pkt | aal0cell ]
Sets the ATM Adaptation Layer type (aal-type): AAL5, AAL0-packet, or AAL0-cell. Default is aal5.
set physical dsl atm vcc 1 datapath [ phy0fast | phy0interleaved ]
Sets the ATM datapath, Fast Path or Interleaved. Default is phy0fast.
set physical dsl atm vcc 1 encap-type [ llcsnap-eth | llcsnap-rtip | llcencaps-ppp
| vcmux-eth | vcmux-ipoa | vcmux-pppoa ]
Specifies the data link encapsulation type. Default is llcsnap-eth.
set physical dsl atm vcc 1 vpi [ 0 - 255 ]
Sets the virtual path identifier (VPI) for the circuit. Default is 0.
set physical dsl atm vcc 1 vci [ 32 - 65535 ]
Sets the virtual channel identifier (VCI) for the circuit. Default is 35.
set physical dsl atm vcc 2 enable [ off | on ]
Turns ATM on or off on vcc 2. Default is on.
set physical dsl atm vcc 2 aal-type [ aal5 | aal0pkt | aal0cell ]
Sets the ATM adaptation layer type (aal-type): AAL5, AAL0-packet, or AAL0-cell. Default is aal5.
set physical dsl atm vcc 2 datapath [ phy0fast | phy0interleaved ]
Sets the ATM datapath, Fast Path or Interleaved. Default is phy0fast.
set physical dsl atm vcc 2 encap-type [ llcsnap-eth | llcsnap-rtip | llcencaps-ppp
| vcmux-eth | vcmux-ipoa | vcmux-pppoa ]
Specifies the data link encapsulation type. Default is llcsnap-eth.
set physical dsl atm vcc 2 vpi [ 0 - 255 ]
Sets the virtual path identifier (VPI) for the circuit. Default is 8.

153
set physical dsl atm vcc 2 vci [ 32 - 65535 ]
Sets the virtual channel identifier (VCI) for the circuit. Default is 35.
set physical dsl atm vcc vcc_num tx-queue queue_name
Attaches the egress queue template to the ATM VC when the queue type is egress.
set physical dsl atm vcc vcc_num rx-queue queue_name
Attaches the ingress queue to the ATM VC when the queue type is ingress.
set physical dsl ptm datapath [ phy0fast | phy0interleaved ]
Sets the ATM datapath, Fast Path or Interleaved. Default is phy0fast.
set physical dsl ptm priority [ low | high ]
Sets the packet transfer mode (PTM) priority. Default is low.
set physical dsl ptm tx-queue queue_name
Attaches the egress queue template to the PTM interface when the queue type is egress.
set physical dsl ptm rx-queue queue_name
Attaches the ingress queue to the PTM interface when the queue type is ingress.
set physical dsl atm vcc 1 auto-vpi-vci [ on | off ]
Turns automatic VPI/VCI detection on or off. If you leave the default on, the device will try a series of VPI/VCI
pairs that are commonly used by service providers. When one pair succeeds, the device will use this one for
future connections.
set physical dsl atm vcc 1 vpi-vci-list vpi_vci_pairs
Specifies the series of VPI/VCI pairs that the device will use to attempt a connection. The default set ("0/35 8/35
0/43 0/51 0/59 8/43 8/51 8/59") can be changed.
set physical dsl atm vcc 1 qos enable [ off | on ]
Turns QoS off or on on the virtual circuit. Default is off.
set physical dsl power-save enable [ off | on ]
Turns power saving mode off or on. Default is off.

Administrator’s Handbook
154
Ethernet Interfaces
set physical enet [ 1 - 4 ] mac-addr-override mac_addr
You can override your NVG599 device’s Ethernet MAC address with any necessary setting. Some ISPs require
your account to be identified by the MAC address, among other things. Enter your 12-character Ethernet MAC
override address as instructed by your service provider, for example: 12 34 AB CD 19 64
set physical enet [ 1 - 4 ] port media [ auto | 100-fd | 100-hd | 10-fd | 10-hd ]
Sets the Ethernet port’s media flow control: Automatic, 100 Mbps Full-Duplex, 100 Mbps Half-Duplex, 10 Mbps
Full-Duplex, or 10 Mbps Half-Duplex. Default is auto.
set physical enet [ 1 - 4 ] port mdix [ auto | on | off ]
Sets the Ethernet port’s crossover detection. Default is off.
set physical enet [ 1 - 4 ] tx-queue queue_name
Attaches the egress queue template to the Ethernet interface when the queue type is egress.
set physical enet [ 1 - 4 ] rx-queue queue_name
Attaches the ingress queue to the Ethernet interface when the queue type is ingress.
set physical enet [ 1 - 4 ] port power-save enable ""
Turns power saving mode off or on.
set physical ensw max-age seconds
Sets the maximum delay on the Ethernet switch in seconds. Default is 300 (5 minutes).
set physical ensw qos-mode [ off | p-bit ]
Sets QoS up on Ethernet switch, classified by priority-bit mapping. Default is off. When p-bit is selected,
packets will be mapped from their priority (even if untagged) to one of four queues per-port in the Ethernet
switch.
See “Quality of Service (QoS) Examples” on page 217 for more information.
set physical ensw p-bit-map pbit-to-4queue-map
Sets the mapping from the 8 priority-bits to the four queues in the Ethernet switch. The lowest priority queue
is “1”, and the highest priority queue is “4”.
Example: Mapping is “1 1 2 2 3 3 4 4", where priority bit values 0 and 1 would map to queue 1, and values 2
and 3 would map to queue 2, etc.
NOTE:
This setting only applies to packets sent from the host CPU to a switch port; it does not apply to port-to-port
traffic.

155
Wireless Interfaces
set physical wireless enable [ on | off ]
Enables or disables the wireless capability for supported Wi-Fi devices. Default is on.
set physical wireless standard [ bg | b-only | g-only | bgn | n-only | an | a-only ]
Sets and locks the NVG599 into the wireless transmission mode you want: bg, b-only, g-only, bgn, n-only, an,
or a-only. For compatibility with clients using 802.11b (up to 11 Mbps transmission), 802.11g (up to 20+
Mbps), 802.11a (up to 54 Mbit/s using the 5 GHz band), or 802.11n (from 54 Mbit/s to 600 Mbit/s with the use
of four spatial streams at a channel width of 40 MHz), select b/g/n. To limit your wireless LAN to one mode or
the other, select g-only, n-only, a-only, or b-only, or some combination that applies to your setup. Default is
bgn.
set physical wireless auto-channel [ off | on ]
Turns auto-channel selection on or off.
set physical wireless bandwidth [ narrow | wide ]
Specifies whether the Wi-Fi channel is narrow or wide band. Default is narrow in compliance with FCC
requirements.
set physical wireless default-channel [ 1... 11 ]
(1 through 11, for North America) on which the network will broadcast. This is a frequency range within the
2.4 Ghz band. Channel selection can have a significant impact on performance, depending on other wireless
activity close to this router. Channel selection is not necessary at the client computers; the clients will scan the
available channels seeking access points using the same SSID as the client. Defaults to 6.
set physical wireless power [ 1 - 100 ]
Sets some value lower than 100 percent transmit power if your NVG599 device is located close to other Wi-Fi
devices and causes interference. Defaults to 100 (percent).
set physical wireless mul2uni [ off | on ]
Turns wireless “many-to-one” packet scheduling off or on. Default is off.
set physical wireless ssid 1 enable [ on | off ]
Enables or disables the first (default) Wi-Fi SSID.
set physical wireless ssid 1 name name
Specifies a name for the first Wi-Fi SSID. Defaults to a unique value per router of the form “ATTxxx”.
set physical wireless ssid 1 access-type [ none | allow | deny ]
Specifies the type of address list for defining MAC address filtering. If set to allow, only hosts with the specified
addresses will be permitted to join the WLAN of the specified SSID. If set to deny, any hosts except those with
the specified addresses will be permitted to join the specified SSID. Default is none.

Administrator’s Handbook
156
set physical wireless ssid 1 access-list mac_address
Specifies the MAC address of devices controlled by MAC address filtering.
set physical wireless ssid 1 hidden [ off | on ]
Enables or disables SSID hiding for the specified SSID. If set to on, the specified SSID will not appear on client
scans. Clients must log into the SSID with the exact SSID name and credentials specified for that SSID.
set physical wireless ssid 1 isolate [ off | on ]
If set to on, blocks wireless clients from communicating with other wireless clients on the WLAN side of the
NVG599. Defaults to off.
set physical wireless ssid 1 security [ none | wep | wpa ]
Sets the wireless privacy type: none, wep, or wpa-psk. Default is none.
set physical wireless ssid 2 enable [ off | on ]
Enables or disables the second available SSID.
set physical wireless ssid 3 enable [ off | on ]
Enables or disables the third available SSID.
set physical wireless ssid 4 enable [ off | on ]
Enables or disables the fourth available SSID.
set physical wireless wps [ on | off ]
Enables or disables Wi-Fi Protected Setup (WPS) for simplified security configuration with Wi-Fi clients that
support it.
set physical wireless wmm enable [ off | on ]
Enables or disables Wi-Fi multimedia settings for multimedia queueing characteristics.
set physical wireless wmm power-save [ off | on ]
Turns power saving mode off or on for wireless multimedia when wmm enable is on. Default is on.

157
PPPoE Relay Commands
set pppoe-relay enable [ on | off ]
Allows the NVG599 device to forward PPPoE packets. Default is on.
set pppoe-relay max-sessions [ 0... 4 ]
Specifies the maximum number of PPPoE relay sessions. Default is 4.
NAT Pinhole Commands
NAT pinholes let you pass specific types of network traffic through the NAT interfaces on the NVG599. NAT
pinholes allow you to route selected types of network traffic, such as FTP requests or HTTP (Web) connections,
to a specific host behind the NVG599 transparently.
To set up NAT pinholes, you identify the type(s) of traffic you want to redirect by port number, and you specify
the internal host to which each specified type of traffic should be directed.
The following list identifies protocol type and port number for common TCP/IP protocols:
FTP (TCP 21)
Telnet (TCP 23)
SMTP (TCP 25),
TFTP (UDP 69)
set pinhole name name protocol [ tcp | udp ]
Specifies the identifier for the entry in the NVG599 device's pinhole table. You can name pinhole table entries
sequentially (1, 2, 3), by port number (21, 80, 23), by protocol, or by some other naming scheme. Specifies the
type of protocol being redirected.
set pinhole name name ext-port-range [ 0 - 49151 ]
Specifies the first and last port number in the range being translated.
set pinhole name name int-addr ipaddr
Specifies the IP address of the internal host to which traffic of the specified type should be transferred.
set pinhole name name int-start-port [ 0 - 65535 ]
Specifies the port number your NVG599 device should use when forwarding traffic of the specified type. Under
most circumstances, you would use the same number for the external and internal port.
NOTE:
When configuring a PPPoE connection, you must also configure the required PPPoE authentication details
(such as user name and password combinations) on the client computer.

Administrator’s Handbook
158
Security Stateful Packet Inspection (SPI) Commands
set security firewall-level [ low | high | off ]
All computer operating systems are vulnerable to attack from outside sources, typically at the operating
system or Internet Protocol (IP) layers. Stateful inspection firewalls intercept and analyze incoming data
packets to determine whether they should be admitted to your private LAN, based on multiple criteria, or
blocked. Stateful inspection improves security by tracking data packets over a period of time, examining
incoming and outgoing packets. Outgoing packets that request specific types of incoming packets are tracked;
only those incoming packets constituting a proper response are allowed through the firewall.
The high setting is recommended, but for special circumstances, a low level of firewall protection is available.
You can also turn all firewall protection off. Defaults to low.
set security spi ip4 invalid-addr-drop [ on | off ]
Enables or disables whether broadband packets with invalid source or destination addresses should be
dropped. Default is on.
set security spi ip4 private-addr-drop [ on | off ]
Enables or disables whether broadband packets with private source or destination addresses should be
dropped. Default is off.
set security spi unknown-ethertypes-drop [ on | off ]
Enables or disables whether packets with unknown ether types are to be dropped. Default is on.
set security spi portscan-protect [ on | off ]
Enables or disables whether to detect and drop port scans. Default is on.
set security spi invalid-tcp-flags-drop [ on | off ]
Enables or disables whether packets with invalid TCP flag settings (NULL, FIN, Xmas, etc.) are to be dropped.
Default is on.
set security spi ip4 invalid-addr-drop [ on | off ]
Blocks broad sets of addresses that should not be used as either source or destination addresses, or both.
These include the following:
The default is on.
IP address/mask Source or destination
10.0.0.0/8 source
192.168.0.0.0/16 source
169.254.0.0/16 source
172.16.0.0/12 source
224.0.0.0/4 Source / destination
224.0.0.0/5 Source / destination
0.0.0.0/8 Source / destination
255.255.255.255 destination

159
set security spi ip4 private-addr-drop [ off | on ]
Drops packets sourced or destined for private IPv4 addresses. The default is off.
set security spi flood-limit enable [ on | off ]
Enables or disables whether packet flooding should be detected and offending packets be dropped. Default is
on.
set security spi flood-limit limit pps_value
Sets a maximum packets-per-second (PPS) value for packet flood criterion. Defaults to 4.
set security spi flood-limit burst-limit max_value
Sets a maximum value in a packet-burst for packet flood criterion. Defaults to 8.
set security spi flood-limit icmp enable [ on | off ]
Enables or disables whether ICMP packet flooding should be detected and offending packets be dropped.
Defaults to on.
set security spi flood-limit udp enable [ off | on ]
Enables or disables whether UDP packet flooding should be detected and offending packets be dropped.
Defaults to off.
set security spi flood-limit tcp enable [ off | on ]
Enables or disables whether TCP packet flooding should be detected and offending packets be dropped.
Defaults to off.
set security spi flood-limit tcp syn-cookie [ on | off ]
Allows TCP SYN cookies flooding to be excluded. Defaults to on.
Reflexive ACL
set security spi ip6 allow-inbound [ on | off ]
Turns reflexive ACL on or off for IPv6.
Reflexive access control lists (ACL) provide that Layer 4 session information is used to make decisions about
what packets to route. Reflexive ACL reduces exposure to spoofing and denial-of-service attacks, because
desired inbound packet flows are usually in response to outbound traffic.
ARRIS 9.x DSL gateways use the relevant session information about whether the packet flow was initiated from
the LAN side (upstream) or WAN side (downstream). If the parameter security.spi.ip6.allow-inbound is set to
off, then sessions which are initiated from the WAN side are disallowed. Upstream sessions are never
precluded because of reflexive ACL. (Of course there may be other reasons that particular packets are
dropped.)
For IPv4, NAT is generally enabled, thus reflexive ACL is usually not an issue.

Administrator’s Handbook
160
VoIP Commands
(supported models only)
Voice-over-IP (VoIP) refers to the ability to make voice telephone calls over the Internet. This differs from
traditional phone calls that use the public switched telephone network (PSTN). VoIP calls use an Internet
protocol, Session Initiation Protocol (SIP), to transmit sound over a network or the Internet in the form of data
packets. Certain ARRIS gateway models have one or more voice ports for connecting telephone handsets.
These models support VoIP. If your gateway is a VoIP model, you can configure the VoIP features.
VoIP Profile Settings
set voip profile [ 1 - 4 ] prof-enable [ on | off ]
Enables or disables the use and configuration of the specified VoIP profile on the NVG599.
set voip profile [ 1 - 4 ] proxy-server address
Specifies the IP address or fully-qualified domain name of the SIP proxy server that stations using the profile
will connect to.
set voip profile [ 1 - 4 ] proxy-port port
Sets the well-known port number the station using the profile will use to connect to the SIP proxy. Default is
5060.
set voip profile [ 1 - 4 ] proxy-transport udp
Assigns a proxy transport protocol to the VoIP profile. Default is udp.
set voip profile [ 1 - 4 ] registrar-server address
Specifies the IP address or fully-qualified domain name of the SIP registrar (server) that stations using the
profile will connect to.
set voip profile [ 1 - 4 ] registrar-port portnumber
Sets the well-known port number the user agent using the profile will use to connect to the SIP registrar.
Default is 5060.
set voip profile [ 1 - 4 ] registrar-transport [ tcp | udp | tls ]
Assigns a registrar transport protocol to the VoIP profile. Default is udp.
set voip profile [ 1 - 4 ] sip-expires [ 0 – 65535 ]
Specifies the SIP registration server timeout duration from 0 – 65535 seconds for the specified profile. Default
is 3600 (1 hour).
set voip profile [ 1 - 4 ] outbound-proxy-server address
Specifies the SIP outbound proxy server for the specified profile by fully qualified server name or IP address.
set voip profile [ 1 - 4 ] outbound-proxy-port portnumber
Specifies the SIP outbound proxy server port for the specified profile. Default is 5060.

161
set voip profile [ 1 - 4 ] sip-user-domain name
Sets the SIP user domain value to be used by the VoIP profile.
set voip profile [ 1 - 4 ] sip-user-port [ 1 - 65535 ]
Specifies the SIP user port for the specified phone, Default is 5060.
set voip profile [ 1 - 4 ] sip-user-transport [ tcp | udp ]
Assigns a transport protocol to the identified VoIP SIP profile. Default is udp.
set voip profile [ 1 - 4 ] invite-expires seconds
Assigns the “lifespan” of a SIP INVITE message for the identified profile.
set voip profile [ 1 - 4 ] reinvite-expires seconds
Sets the amount of time a SIP user agent with the named profile will consider a re-INVITE message valid.
set voip profile [ 1 - 4 ] reg-retry-interval seconds
Specifies the number of seconds that must elapse before a SIP user agent using the named profile may attempt
to retry registration.
set voip profile [ 1 - 4 ] reg-min-expires seconds
Assign the profile a minimum length of time until a registration expires and must be renewed.
set voip profile [ 1 - 4 ] registration-period seconds
Sets the amount of time that a registration remains valid.
set voip profile [ 1 - 4 ] max-retrans-invite times
Assigns the profile a maximum number of INVITE message retries. Default: 3.
set voip profile [ 1 - 4 ] max-retrans-non-invite times
Assigns the profile a maximum number of non-INVITE message retransmissions. Default: 4.
set voip profile [ 1 - 4 ] sip-publish-method PUBLISH
Sets the specified profile’s SIP event state publication method to PUBLISH.
set voip profile [ 1 - 4 ] sip-publish-destination "DEFAULT"
Sets the specified profile’s SIP event state published destination to DEFAULT.
set voip profile [ 1 - 4 ] sip-publish-destination2 "NULL"
Clears (assign to NULL) the specified SIP profile’s second published destination.
Administrator’s Handbook
162
set voip profile [ 1 - 4 ] sip-publish-invocation never
Sets the specified profile to never invoke PUBLISH.
set voip profile [ 1 - 4 ] sip-publish-interval seconds
Assigns the publication interval to the specified profile.
set voip profile [ 1 - 4 ] sip-publish-count -1
Sets the number of SIP publication events for the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-hk-flash-mode info
Assigns a SIP HK Flash mode to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-session-refresher auto
Assigns a SIP session refresh method to the identified profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-session-timer-value [value]
Configures the SIP session timer value for the profile. Default: 2280.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-dynamic-payload [value]
Sets the dynamic payload value for the identified profile. Default: 101.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-dtmf-mode [inband | rfc2833 |
info]
Assigns a DTMF signaling mode for the SIP profile.
inband: sends the DTMF digits as a normal inband tone.
rfc2833: (default) sends the DTMF digits as an event as part of the RTP packet header information.
info: sends the DTMF digits in the SIP INFO message.
Default: rfc2833.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-digit-map
"O=15,I=6,S=3(*#101<:@C03>|*#103<:@C06>|T0|T*xx|T*xxx|E[2-
9]11|E[01]911|1[2-9]xxxxxxxxx|T[2-9]xxxxxx|[2-9]xxxxxxxxx|n.)"
Assigns the specified digit map to the SIP profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-compact-header [ on | off ]
Sets the profile to use compact format when set to on. Sends the SIP messages with compact headers,
reducing the size of the SIP messages.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-q-value [ 0 - 10 ]
Assigns a prioritizing SIP q-value to the profile. Default: 10.

163
set voip profile [ 1 - 4 ] sip-advanced-setting sip-qos-tos [ 0 - 255 ]
Specifies the SIP DiffServ type of service (ToS) values for Quality of Service (QoS) assignment. Default: 160.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-qos-p-bit [ 0 - 7 ]
Assigns a Quality of Service priority bit (p-bit) value to the SIP profile. Default: 6.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-qos-marker [ value ]
Assigns a QoS packet marker to the SIP profile. Default: VO.
set voip profile [ 1 - 4 ] sip-advanced-setting fax-redundancy-level [ 0 - 1 ]
Specifies the level of fax redundancy for t38 fax data rate management. Default: 1.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-init-de-register [ on | off ]
Turns SIP de-registration on or off for the profile. Default: or both.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-known-ip-list "[string]"
Specifies a known IP address list of SIP servers for the SIP profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-allow-ip-list "[string]"
Defines a string of named SIP servers that the profile may use.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-t1-timer-value 500
Assigns a SIP t1 (estimated round trip time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-t2-timer-value 4000
Assigns a SIP t2 (maximum non-INVITE retransmit time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-t4-timer-value 5000
Assigns a SIP t4 (message clear time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-a-value 500
Assigns a SIP A timer (UDP INVITE retransmit interval) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-b-value 32000
Assigns a SIP B timer (INVITE transaction timeout) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-c-value 0
Assigns a SIP C timer value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-d-value 32000
Assigns a SIP D timer (response retransmission time) value to the profile.

Administrator’s Handbook
164
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-e-value 500
Assigns a SIP E timer (UDP non-INVITE retransmit interval) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-f-value 32000
Assigns a SIP F timer (non-INVITE retransmit interval) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-g-value 500
Assigns a SIP G timer (INVITE response retransmit interval) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-h-value 32000
Assigns a SIP H timer (ACK reciept wait time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-i-value 5000
Assigns a SIP I timer (ACK retransmit wait time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-j-value 32000
Assigns a SIP J timer (non-INVITE retransmit request wait time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-k-value 0
Assigns a SIP K timer (response retransmission wait time) value to the profile.
set voip profile [ 1 - 4 ] sip-advanced-setting sip-reset-code "code"
Sets the SIP reset code for the profile. Default: 101
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-shortinterdigit-value
[value]
Sets an interdigit (short) timer value for the profile. Default: 0
set voip profile [ 1 - 4 ] sip-advanced-setting sip-timer-interdigit-value [value]
Sets an interdigit timer value to the profile. Default: 0.
set voip profile [ 1 - 4 ] rtp-advanced-setting rtp-qos-tos [value]
Assigns a Real Time Protocol terms of service number code to the VoIP profile. Default: 184.
set voip profile [ 1 - 4 ] rtp-advanced-setting rtp-qos-p-bit [ 0 - 7]
Sets a Real Time Protocol Priority bit (P-bit) value to the VoIP profile. Default: 6.
set voip profile [ 1 - 4 ] rtp-advanced-setting rtp-qos-marker "string"
Assigns a Real Time Protocol QoS packet marker to the VoIP profile. Default VO.

165
set voip profile [ 1 - 4 ] rtp-advanced-setting rtp-port-range-start [value]
Defines the beginning of the VoIP Real Time Protocol port range assigned to the profile. Default: 6002.
set voip profile [ 1 - 4 ] rtp-advanced-setting rtp-port-range-end [value]
Defines the end of the VoIP Real Time Protocol port range assigned to the profile. Default: 6200.
set voip profile [ 1 - 4 ] rtp-advanced-setting rtcp-option [ on | off ]
Configures the Real Time Control Protocol (RTCP) setting for the VoIP profile.
set voip profile [ 1 - 4 ] rtp-advanced-setting rtcp-repeat-interval [value]
Assigns a Real Time Control Protocol repeat interval value to the VoIP RTP profile. Default: 5000
set voip profile [ 1 - 4 ] advanced-telephony-setting fxs-port-setting-for-fxo [
none | fxs1 | fxs2 | both | emgncy ]
Sets a port to be used for the FXS (foreign exchange station) interface port to the FXO (foreign exchange office)
interface—the phone—port. Default is none.
set voip profile [ 1 - 4 ] advanced-telephony-setting t38-option [ on | off ]
Enables or disables T.38 fax capability for the VoIP profile.
set voip profile [ 1 - 4 ] advanced-telephony-setting sip-dynamic-line-selection
[ on | off ]
Turns dynamic (next available) line selection off or on for the identified VoIP profile. Default is off.
set voip profile [ 1 - 4 ] advanced-telephony-setting sip-dns-ns [ on | off ]
Enables or disables SIP DNS NS records (for Authoritative Name Server zone specification).
set voip profile [ 1 - 4 ] advanced-telephony-setting sip-dns-naptr [ on | off ]
Enables or disables the Name Authority Pointer (NAPTR) DNS function in the SIP profile.
set voip profile [ 1 - 4 ] advanced-telephony-setting sip-dns-srv [ on | off ]
Enables or disables the use of DNS Service Locator (SRV) functions in the profile.
set voip profile [ 1 - 4 ] advanced-telephony-setting announcement-setting
announcement-battery-alert-option [ on | off ]
Enables or disables the autonomous announcement of battery alert conditions in the VoIP profile.
set voip profile [ 1 - 4 ] advanced-telephony-setting battery-notification-setting
battery-notification-interval [value]
Specifies the number of seconds between battery notification messages.
Administrator’s Handbook
166
set voip profile [ 1 - 4 ] advanced-telephony-setting battery-notification-setting
battery-notification-tod-start "[HH:MM]AM | [HH:MM]PM"
Assigns a start time for battery notification message generation to the profile.
set voip profile [ 1 - 4 ] advanced-telephony-setting battery-notification-setting
battery-notification-tod-end "[HH:MM]AM | [HH:MM]PM"
Assigns an end time for battery notification message generation to the profile.
set voip profile [ 1 - 4 ] advanced-telephony-setting testline-setting voip-
testline-mode Always
Assigns a line test mode to the VoIP profile specified.
set voip profile [ 1 - 4 ] advanced-telephony-setting testline-setting
voip-testline-maxlenX5s [value]
Sets the maximum X5s length to the profile’s testline settings. Default: 6.
set voip profile [ 1 - 4 ] advanced-telephony-setting testline-setting
voip-testline-maxfreq [value]
Sets the maximum frequency of line tests for the VoIP profile. Default: 10.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] enable [ on | off ]
Enables or disables the identified VoIP user account (individual account) on the specified VoIP profile.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] voip-testline-option [ on | off ]
Enables or disables the test line option for the named user account on the VoIP profile. Default: off.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] fxs-line 1
Sets a line in the user account to support FXS (foreign exchange station) interface. Default is none.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-user-disp-name “[string]”
Assigns a display name for the identified user account on the specified VoIP profile. Default: 1000.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-user-name “[string]”
Adds a user name value to the VoIP profile SIP user account. Default: 1000.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-user-password “[string]”
Sets the SIP password for the user account on the VoIP profile.
NOTE:
User account settings may be specified for disabled user accounts, but the features will not be available
unless the account is enabled.

167
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-user-auth-id “[string]”
Defines a user authentication ID value for the user account on the VoIP profile. Default: 1000.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-uri ""
Assigns a SIP Uniform Resource Identifier (URI) to the specified user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-subscribe-expires [time]
Sets the expiration timer value for SIP subscriptions by the identified user account. Default: 3600.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] sip-service-outage-detect [ on | off]
Enables or disables the detection of SIP service outages by the user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G711U priority [ 1 - 7 | none ]
Assigns a priority value to the Mu-law (G711U) codec on the user account. Default: 1
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G711U packetization-time
[value]
Assigns a packetization time value to the Mu-law (G711U) codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G711A priority [ 1 - 7 | none ]
Assigns a priority value to the a-law (G711A) codec on the user account. Default: 2
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G711A packetization-time
[value]
Assigns a packetization time value to the a-law (G711A) codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G729 priority [ 1 - 7 | none ]
Assigns a priority value to the G.729 codec on the user account. Default: 7
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G729 packetization-time
[value]
Assigns a packetization time value to the G.729 codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G729 annexb-support [ on |
off ]
Enables or disables G.729 Annex-B support on the specified user account. Default: off.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_16 priority [ 1 - 7 |
none ]
Assigns a priority value to the 16 kbit/s G.726 codec on the user account. Default: 3.
Administrator’s Handbook
168
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_16 payload-type
[value]
Assigns a payload value to the 16 kbit/s G.726 codec on the user account. Default: 102.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_16 packetization-time
[value]
Assigns a packetization time value to the 16 kbit/s G.726 codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_24 priority [ 1 - 7 | none
]
Assigns a priority value to the 24 kbit/s G.726 codec on the user account. Default: 4
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_24 payload-type
[value]
Assigns a payload value to the 24 kbit/s G.726 codec on the user account. Default: 103
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_24 packetization-time
[value]
Assigns a packetization time value to the 24 kbit/s G.726 codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_32 priority [ 1 - 7 | none
]
Assigns a priority value to the 32 kbit/s G.726 codec on the user account. Default: 5.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_32 packetization-time
[value]
Assigns a packetization time value to the 32 kbit/s G.726 codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_40 priority [ 1 - 7 | none
]
Assigns a priority value to the 40 kbit/s G.726 codec on the user account. Default: 6.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_40 payload-type
[value]
Assigns a payload value to the 40 kbit/s G.726 codec on the user account. Default: 105.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec G726_40 packetization-time
[value]
Assigns a packetization time value to the 40 kbit/s G.726 codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec AMR priority [ 1 - 7 | none ]
Assigns a priority value to the Adaptive Multi-Rate (AMR) - Narrowband audio codec on the user account.
Default: none.

169
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec AMR payload-type [value]
Assigns a payload value to the AMR codec on the user account. Default: 120
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec AMR packetization-time
[value]
Assigns a packetization time value to the AMR codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec AMR_WB priority [ 1 - 7 |
none ]
Assigns a priority value to the Adaptive Multi-Rate Wideband (AMR-WB) audio codec on the user account.
Default: none.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec AMR_WB payload-type
[value]
Assigns a payload value to the AMR-WB codec on the user account. Default: 122
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] codec AMR_WB packetization-time
[value]
Assigns a packetization time value to the AMR-WB codec on the user account. Default: 20
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature
call-forwarding-all-option [ on | off ]
Turns unconditional call forwarding on or off for the specified user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature
call-forwarding-on-busy-option [ on | off ]
Enables or disables call forwarding when the line is busy for the specified user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature
call-forwarding-on-no-answer-option [ on | off ]
Turns no-answer call forwarding on or off for the specified user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature call-waiting-option [ on
| off ]
Eanbles or disables call waiting for the specified user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature call-conferencing-
option [ on | off ]
Enables or disables 3-way conferencing for the user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature do-not-disturb-option [
on | off ]
Activates or deactivates the ring-prevention (do not disturb) option for the specified user account.
Administrator’s Handbook
170
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature subscribe-mwi-option [
on | off ]
Enables or disables the message waiting indicator for the user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature subscribe-send-mes-
sage [ on | off ]
Enables or disables message sending for the user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature
anonymous-call-block-option [ on | off ]
Sets the user account to block (on) or accept (off) calls from unidentified sources.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature call-transfer-option
[ on | off ]
Enables or disables the call transfer function on the user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature
call-disconnsupervision-option [ on | off ]
Enables or disables disconnection supervision on the user account.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] call-feature call-osi-signaldur [
value ]
Assigns an OSI signal duration value to the account. Default: 800.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] dsp-settings
echo-option [ echo-off | echo-on | echo-on-nlp |echo-on-cng-nlp ]
Specifies the conditions under which the user account will invoke or disable echo cancellation. Default: echo-
on-cng-nlp
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] dsp-settings echo-tail-length 0
Specifies the length of the Digital Signal Processor (DSP) echo tail in milliseconds. Default: 0.
set voip profile [ 1 - 4 ] user-account [ 1 - 4 ] dsp-settings vad-option [ on | off ]
Enables or disables voice activity deetection (VAD) in the DSP for the user account.

171
Targeted Ad Insertion Commands
set targeted-ad-insertion enable [ on | off ]
Turns targeted ad insertion on or off. Default is on.
set targeted-ad-insertion v-zone-ad [ on | off ]
Specifies whether the targeted ad is zone-specific. Default is on.
set targeted-ad-insertion sender-ssrc [ 0... n ]
Specifies the synchronization source identifier for the sender.
set targeted-ad-insertion carousel-ip-address ip_address
Specifies the IP address of the ad carousel server.
set targeted-ad-insertion carousel-port [ 0... n ]
Specifies the port of the ad carousel server.
set targeted-ad-insertion vcc-group-id [ 0... n ]
Specifies the VCC group identifier of the ad carousel server.
set targeted-ad-insertion key-identification-counter [ 0... n ]
Sets a counter value for the ad key indentifier.
set targeted-ad-insertion authentication-key string
Specifies an authentication key for the targeted ads.
set targeted-ad-insertion channel-change-notification [ on | off ]
Turns the “change the channel’ notification on or off. Default is on.
set targeted-ad-insertion retransmit [ on | off ]
Turns ad retransmission on or off. Default is on.
set targeted-ad-insertion unicast-filter [ on | off ]
Turns unicast filtering on or off. Default is on.
set targeted-ad-insertion blocked-unicast-sources string
Specifies names of unicast targeted ad sources to be blocked.
set targeted-ad-insertion hello-interval seconds
Specifies an interval for ad insertion in seconds. Default is 7200 (2 hours).

Administrator’s Handbook
172
set targeted-ad-insertion hello-retransmit-min seconds
Specifies a minimum interval for retransmission of ad insertion in seconds. Default is 15 seconds.
set targeted-ad-insertion hello-retransmit-max seconds
Specifies a maximum interval for retransmission of ad insertion in seconds. Default is 300 seconds.
set targeted-ad-insertion vcc-ip-address ip_address
Specifies the VCC IP address of the ad carousel server.
set targeted-ad-insertion vcc-port [ 0... n ]
Specifies the VCC port of the ad carousel server.
set targeted-ad-insertion zones zone_number
Specifies the zone for targeted ads when v-zone-ad is set to on.
set targeted-ad-insertion during-ad-timeout value
Sets a timeout value. Default is 25,000.

173
System Commands
set system name name
Specifies the name of your NVG599 device. Each NVG599 is assigned a name as part of its factory initialization.
The default name for an NVG599 device consists of the word “ARRIS-7000/XXX” where “XXX” is the serial
number of the device; for example, ARRIS-7000/9437188. A system name can be 1 – 255 characters long. Once
you have assigned a name to your NVG599, you can enter that name in the address text field of your browser
to open a connection to your NVG599.
set system time-zone [ UTC | HST10 | AKST9AKDT | YST8 | PST8PDT |
MST7MDT | MST7 | CST6CDT | CST6 | EST5EDT | AST4ADT | NST3:30NDT ]
A time-zone setting of 0 is Coordinated Universal Time (UTC); options are -12 through 12 (+/- 1 hour
increments from UTC time).
set system auto-daylight-savings [ on | off ]
Time zones honoring Daylight Saving Time may be automatically designated.
set system firewall-log enable [ on | off ]
Turns firewall logging on or off. The firewall log tracks attempted violations of the firewall rules. Default is on.
set system firewall-log persist [ on | off ]
When set to on, causes the log information to be kept in flash memory. Default is off.
set system firewall-log file-size [ 4096... 65536 ]
Specifies a size for the firewall logs. The most recent entries are posted to the beginning of the log. When the
log becomes full, the oldest entries are dropped. The default is 16384.
set system firewall-log file-count [ 2... 8 ]
Specifies the number of possible log files. The default is 4.
set system fastpath software-enable [ on | off ]
Enables or disables the fastpath accelerator processor. Fastpath works on only TCP and UDP. Default is on.
set system fastpath hardware-enable [ off | on ]
Enables or disables the fastpath accelerator processor. Default is off.
set system fastpath mcast-mode 3
Sets the mode for multicast on the fastpath accelerator processor.
NOTE:
Some broadband cable-oriented service providers use the system name as an important identification and
support parameter. If your NVG599 device is part of this type of network, do not alter the system name
unless specifically instructed by your service provider.

Administrator’s Handbook
174
set system scheduler enable [ off | on ]
Turns the system scheduler feature on or off. The default is off.
set system scheduler enable-time hr:min
Specifies a time at which to turn the system on. Default is midnight (00:00). The enable-time parameter must
be supplied in 24-hour military time, colon separated, for example “05:21”.
set system scheduler disable-time hr:min
Specifies a time at which to turn the system off. Default is 5 o’clock (05:00). The disable-time parameter must
be supplied in 24-hour military time, colon separated, for example “21:44”.
set system calendar-update enable [ on | off ]
Turns the calendar update feature on or off. The device will periodically poll the update server for new
operating system software. The default is on.
set system calendar-update interval [ monthly | biweekly ]
Specifies how often the device should poll the update server, monthly or biweekly. The default is monthly.
set system calendar-update protocol [ http | https | tftp ]
Specifies the protocol for accessing the update server. The default is http.
set system calendar-update server server_address
Specifies the address of the update server by name or IP address. The default is "cpems.bellsouth.net".
set system calendar-update username string
Specifies the user name for the update server. The default is anonymous.
set system calendar-update password string
Specifies the password for the update server. The default is guest.
set system calendar-update fwverfile filename
Specifies the firmware version filename to the update server. For the AT&T NVG599 the file is
netopiaNVG599_64.txt.
set system calendar-update day day_of_month
Specifies the numerical day of the month for the update server to be polled, for example, 21.
set system calendar-update time hr:min_AMPM
Specifies the time of day for the update server to be polled, in the format HOUR:MINUTEAM/PM. For example:
06:00AM.

175
set system supplicant enable [ on | off ]
Turns on the 802.1x supplicant functionality. You must set the corresponding type field in the WAN link to
activate it:
NOS/142253966608 (top)>> set link name WAN supplicant
supplicant
type (none) [ none | eap-tls ]:
priority (0) [ 0 - 7 ]:
Default is on.
set system supplicant dest-broadcast [ off | on ]
Mostly useful for debugging. If this is set to on, the destination MAC address FF:FF:FF:FF:FF:FF is used when
the supplicant sends 802.lx packets. If this is off, the EAPOL-specific destination address of 01:80:C2:00:00:03 is
used. Default is off.
set system supplicant eap-tls-identity string
Sets the identity sent by the supplicant in response to an Identity request from an 802.1x authenticator.
set system supplicant server-cert-check [ on | off ]
If set to on, examines the certificate chain sent by an 802.1x authenticator for validation, and ensures that the
root cert of this chain is accepted by the CPE (is in its trust list). Default is on.
set system syslog enable [ on | off ]
Enables or disables the NVG599 Syslog function. The Syslog function is disabled by default. If Syslog is enabled,
the following additional Syslog settings may be configured:
set system syslog server-ip <IPv4/IPv6 Address>
set system syslog server-port <port>
set system syslog facility [ local0 ... local7 ]
set system syslog level [ 0 ... 7 ]
set system syslog log-system [ on | off ]
set system syslog log-firewall [ on | off ]
set system syslog log-igmp [ on | off ]
set system syslog log-voice [ on | off ]
You must specify the Syslog server’s IP address and any custom UDP port number to identify system logging
messages with the set system syslog server-ip <IPv4/IPv6 Address> and set system syslog server-port <port>
commands. After the Syslog server is specified, you may turn on any or all of the logging categories.
The receiving server must have a properly configured Syslog server package active.
set system syslog server-ip <IPv4/IPv6 Address>
Specifies the IP address (in IPv4 dotted decimal notation or IPv6 colon-separated hexadecimal notation) of the
server that Syslog messages will be sent to.
set system syslog server-port <port>
Customizes the UDP port number that the Syslog function marks messages to the logging server package with
(range: 1 - 65535, default: 514).

Administrator’s Handbook
176
set system syslog facility [ local0 ... local7 ]
Specifies the local facility number that Syslog messages are sent to (range: local0 - local7, default: local0).
set system syslog level [ 0 ... 7 ]
Sets the severity level of Syslog messages the NVG599 will send to the Syslog server. Each severity level
includes all higher-level messages (e.g; a level of 2 [Critical] will also send Alert and Emergency messages). The
severity levels are arranged and enumerated as follows:
0 : Emergency
1 : Alert
2 : Critical
3 : Error
4 : Warning
5 : Notice (default)
6 : Info
7 : Debug
set system syslog log-system [ on | off ]
Enables or disables the generation of system log messages for the Syslog server. If the Syslog function is
enabled, system log is enabled (on) by default.
set system syslog log-firewall [ on | off ]
Enables or disables the delivery of firewall log messages to the Syslog server. Firewall log is disabled by default.
set system syslog log-igmp [ on | off ]
Enables or disables the delivery of IGMP log messages to the Syslog server. The IGMP log is disabled by default.
set system syslog log-voice [ on | off ]
Enables or disables the generation of voice log messages for the Syslog server. Voice log is disabled by default.
set system voice-check enable [ off | on ]
When this is set to on, and a voice call is in progress when a software update is scheduled, the software update
is deferred for the voice-check interval until the call is completed, that is, the call state becomes “idle.” If set to
off, and a voice call is in progress when an update is scheduled, the call is torn down. The default is on.
set system voice-check interval [ 60 - 86400 ]
Specifies the interval in seconds for the device to wait before attempting a software update, when a software
update is scheduled but a voice call is in progress, when voice-check enable is set to on. The default is 300 (5
minutes).
set system voice-check max-time [ 300 - 604800 ]
Specifies the maximum time in seconds for the device to continue to attempt a scheduled software update if a
voice call is in progress and voice-check enable is set to on. The default is 3600 (1 hour).

177
set system log buffer-size [ 4096... 65536 ]
Specifies a size for the system log. The most recent entries are posted to the beginning of the log. When the log
becomes full, the oldest entries are dropped. The default is 16384.
set system log level [ low | medium | high | alerts | failures ]
Specifies the types of log messages you want the NVG599 device to record. All messages with a level equal to
or greater than the level you specify are recorded. For example, if you specify set system diagnostic-level
medium, the diagnostic log will retain medium-level informational messages, alerts, and failure messages.
Use the following guidelines:
low - Low-level informational messages or greater; includes trivial status messages.
medium - Medium-level informational messages or greater; includes status messages that can help monitor
network traffic.
high - High-level informational messages or greater; includes status messages that may be significant but do
not constitute errors. The default.
alerts - Warnings or greater; includes recoverable error conditions and useful operator information.
failures - Failures; includes messages describing error conditions that may not be recoverable.
Administrator’s Handbook
178
Debug Commands
When you are in SHELL mode, the Debug prompt consists of the name of the NVG599 device followed by the
word “DEBUG” and a right angle bracket (>). For example, if you open a CLI connection to the NVG599 named
“ARRIS-3000/9437188” and then type debug you would see ARRIS-3000/9437188/DEBUG> as your
prompt.
Debug level is available for field debugging purposes. There is no service and quality level guarantee from
ARRIS. This level is intended for SEs or Telco lab personnel, not for normal operation at home for end users.
More commands are available. To display the options, type help all.
Disclaimer and Warning Text
The following is displayed when entering Debug level from normal Config level.
“Warning: Accessing these commands may impact the normal operation of this device. Exit now if you
entered by mistake.”
Commands
console
Makes this session the console.
mirror <src-port> <dst-port>
Mirrors one port's traffic to another. Causes traffic transmitted or received on <src-port> to be mirrored on
<dst-port>. Ports must support Ethernet (IPoA and PPPoA ATM ports are not supported).
mirror off
Turns off port mirroring.
show fastpath
Displays entries in fastpath.
show cpu
Displays CPU usage as a percentage and CPU load averages over 1, 5, and 15 minute periods.
TR-069 CLI CShell Commands (debug mode)
tr69 GetParameterValues <path>
tr69 SetParameterValues <path> = <value>
tr69 GetParameterNames <path> <nextlevel>
tr69 Addobject <path>
tr69 Deleteobject <path>
Example:
tr69 GetParameterValues InternetGatewayDevice.
NOTE:
CLI and ACS sessions are mutually exclusive and should not be used at the same time

179
CHAPTER 5 Technical Specifications and Safety
Information
Description
Dimensions:
10 in H x 7.25 in L x 1.63 in W (25.4 cm H x 18.4 cm L x 4.1 cm W)
1.28 lbs (.58 kg) (without integrated battery)
1.77 lbs (.80 kg) (with integrated battery)
Communications interfaces: The ARRIS Gateways have a 4-port 10/100/1000Base-T Ethernet switch for
your LAN connections, an FXS port for VoIP connections, a HomePNA 3.1 coax port, a USB 2.0 network port,
and a 400 mW wireless radio for Wi-Fi connections.
WAN interfaces: Bonded VDSL2/single line VDSL2/bonded ADSL2+/single line ADSL, RJ-14; One-port 10/100/
1000 Ethernet, RJ-45
Power Supply
115VAC 36W/12VDC@3A (2phone,5REN, RINGING)
Environment
Operating temperature: 0°C to 42°C (32° F to 107° F); 8% to 95% (Non Condensing) Relative Humidity
Storage temperature: –20° C to 85° C (–4° F to 185° F)
Relative storage humidity: 20 to 80% noncondensing
Software and protocols
Software media: Software preloaded on internal flash memory; field upgrades done via download to
internal flash memory via CLI or web upload.
Routing: IPv4 , IPv6/6rd; DHCP server/relay; DNS Proxy, Dynamic DNS Support; Multiple subnet support
WAN support: PPPoA, DHCP, static IP address; ADSL, ADSL2/2+, ADSL2 Reach Extended protocol (ITU G.992.3
annex L)

Administrator’s Handbook
180
Security: Stateful Packet Inspection Firewall; Virtual DMZ/IP pass-through; Denial of Service (DoS)
protection; VPN Pass-through (PPTP, L2TP, IPSec)
Wi-Fi Security. WEP (64-bit, 128-bit, 256-bit) encryption 802.1x, WPA, WPA-PSK, 802.11i/WPA2, WPA2-PSK
EAP-TLS, EAP-TTLS, EAP-SIM MAC Address filtering
Management/configuration methods: HTTP (Web server), telnet command line interface
Diagnostics: Ping, event logging, routing table displays, statistics counters, web-based management,
traceroute, nslookup, and diagnostic commands.
Agency approvals
North America
Safety Approvals:
United States – UL 60950, Third Edition
Canada – CSA: CAN/CSA-C22.2 No. 60950-00
EMC:
United States – FCC Part 15 Class B
Canada – ICES-003
Telecom:
United States – 47 CFR Part 68
Canada – CS-03
Integrated Battery:
Hazardous Materials Regulations and Procedures CFR Title 49, Section 173,
Subsection 185
UL60950/CAN/CSA-C22.2 No. 60950—Recognized component (U.S. and Canada)
UL 2054—Recognized component (U.S. and Canada)
UN Manual of test and Criteria, sect. 38.3, CE, IEC62133
California Code of Regulation Title 20

181
Manufacturer’s Declaration of Conformance
United States. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions:
1. This device may not cause harmful interference, and
2. this device must accept any interference received, including interference that may cause undesired opera-
tion.
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to
Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates, uses, and can radiate radio frequency
energy and, if not installed and used in accordance with the instructions, may cause harmful interference to
radio communications. However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or television reception, which can be
determined by turning the equipment off and on, the user is encouraged to try to correct the interference by
one or more of the following measures:
Reorient or relocate the device.
Increase the distance between the equipment being interfered with and the device.
Connect the device to an outlet on a circuit different from the outlet to which the equipment being inter-
fered with is connected.
Consult the retailer or an experienced radio/TV technician for help.
FCC Caution: Any changes or modifications not expressly approved by the party responsible for compliance
could void the user’s authority to operate this equipment.
This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.
Operations within the 5.15 ~ 5.25GHz band are restricted to indoor use only.
Radiation Exposure Statement: This equipment complies with FCC radiation exposure limits as set forth
for an uncontrolled environment. This equipment should be installed and operated maintaining a minimum
distance of 20cm between the device and your body.
Service requirements. In the event of equipment malfunction, if under warranty we will exchange a
product deemed defective. Under FCC rules, no customer is authorized to repair this equipment. This
restriction applies regardless of whether the equipment is in or out of warranty.
Technical Support for Hardware Products
1-877-466-8646
http://www.arrisi.com/consumer
WARNING:
This is a Class B product. In a domestic environment this product may cause radio interference, in which case
the user may be required to take adequate measures. Adequate measures include increasing the physical dis-
tance between this product and other electrical devices.
Changes or modifications to this unit not expressly approved by the party responsible for compliance could
void the user’s authority to operate the equipment.
IMPORTANT:
This product was tested for FCC compliance under conditions that included the use of shielded cables and
connectors between system components. Changes or modifications to this product not authorized by the
manufacturer could void your authority to operate the equipment.

Administrator’s Handbook
182
Canada. This Class B digital apparatus meets all requirements of the Canadian Interference -Causing
Equipment Regulations.
Cet appareil numérique de la classe B respecte toutes les exigences du Réglement sur le matériel brouilleur du
Canada.
Declaration for Canadian users
NOTICE: The Canadian Industry Canada label identifies certified equipment. This certification means that the
equipment meets certain telecommunications network protective, operation, and safety requirements. The
Department does not guarantee the equipment will operate to the user’s satisfaction.
Before installing this equipment, users should ensure that it is permissible to be connected to the facilities
of the local telecommunications company. The equipment must also be installed using an acceptable
method of connection. In some cases, the company’s inside wiring associated with a single line individual
service may be extended by means of a certified connector assembly (telephone extension cord). The
customer should be aware that compliance with the above conditions may not prevent degradation of
service in some situations.
Repairs to the certified equipment should be made by an authorized Canadian maintenance facility
designated by the supplier. Any repairs or alterations made by the user to this equipment, or equipment
malfunctions, may give the telecommunications company cause to request the user to disconnect the
equipment.
Users should ensure for their own protection that the electrical ground connections of the power utility,
telephone lines, and internal metallic water pipe system, if present, are connected together. This precaution
may be particularly important in rural areas.
Caution
Users should not attempt to make such connections themselves, but should contact the appropriate electric
inspection authority, or electrician, as appropriate.
The Ringer Equivalence Number (REN) assigned to each terminal device provides an indication of the
maximum number of terminals allowed to be connected to a telephone interface. The termination on an
interface may consist of any combination of devices subject only to the requirement that the sum of the Ringer
Equivalence Numbers of all the devices does not exceed 5.

183
Important Safety Instructions
Caution
DO NOT USE BEFORE READING THE INSTRUCTIONS: Do not connect the Ethernet ports to a carrier or carriage
service provider’s telecommunications network or facility unless: a) you have the written consent of the
network or facility manager, or b) the connection is in accordance with a connection permit or connection
rules.
Connection of the Ethernet ports may cause a hazard or damage to the telecommunication network or facility,
or persons, with consequential liability for substantial compensation.
Caution
The direct plug-in power supply serves as the main power disconnect; locate the direct plug-in power supply
near the product for easy access.
For use only with CSA Certified Class 2 power supply, rated 12VDC, 1.0A.
Telecommunication installation cautions
Never install telephone wiring during a lightning storm.
Never install telephone jacks in wet locations unless the jack is specifically designed for wet locations.
Never touch uninsulated telephone wires or terminals unless the telephone line has been disconnected at
the network interface.
Use caution when installing or modifying telephone lines.
Avoid using a telephone (other than a cordless type) during an electrical storm. There may be a remote risk
of electric shock from lightning.
Do not use the telephone to report a gas leak in the vicinity of the leak.

Administrator’s Handbook
184
47 CFR Part 68 Information
FCC Requirements
1. The Federal Communications Commission (FCC) has established Rules which permit this device to be directly
connected to the telephone network. Standardized jacks are used for these connections. This equipment should not be
used on party lines or coin phones.
2. If this device is malfunctioning, it may also be causing harm to the telephone network; this device should be
disconnected until the source of the problem can be determined and until repair has been made. If this is not done, the
telephone company may temporarily disconnect service.
3. The telephone company may make changes in its technical operations and procedures; if such changes affect the
compatibility or use of this device, the telephone company is required to give adequate notice of the changes. You will
be advised of your right to file a complaint with the FCC.
4. If the telephone company requests information on what equipment is connected to their lines, inform them of:
a. The telephone number to which this unit is connected.
b. The ringer equivalence number. [0.XB]
c. The USOC jack required. [RJ11C]
d. The FCC Registration Number. [XXXUSA-XXXXX-XX-E]
Items (b) and (d) are indicated on the label. The Ringer Equivalence Number (REN) is used to determine how many
devices can be connected to your telephone line. In most areas, the sum of the REN's of all devices on any one line
should not exceed five (5.0). If too many devices are attached, they may not ring properly.
FCC Statements
a) This equipment complies with Part 68 of the FCC rules and the requirements adopted by the ACTA. On the
bottom of this equipment is a label that contains, among other information, a product identifier in the format
US:AAAEQ##TXXXX. If requested, this number must be provided to the telephone company.
b) List all applicable certification jack Universal Service Order Codes (“USOC”) for the equipment: RJ11.
c) A plug and jack used to connect this equipment to the premises wiring and telephone network must comply
with the applicable FCC Part 68 rules and requirements adopted by the ACTA. A compliant telephone cord and
modular plug is provided with this product. It is designed to be connected to a compatible modular jack that is
also compliant. See installation instructions for details.
d) The REN is used to determine the number of devices that may be connected to a telephone line. Excessive
RENs on a telephone line may result in the devices not ringing in response to an incoming call. In most but not
all areas, the sum of RENs should not exceed five (5.0). To be certain of the number of devices that may be
connected to a line, as determined by the total RENs, contact the local telephone company. For products
approved after July 23, 2002, the REN for this product is part of the product identifier that has the format
US:AAAEQ##TXXXX. The digits represented by ## are the REN without a decimal point (e.g., 03 is a REN of 0.3).
For earlier products, the REN is separately shown on the label.
e) If this equipment, the NVG599 device, causes harm to the telephone network, the telephone company will
notify you in advance that temporary discontinuance of service may be required. But if advance notice isn’t
practical, the telephone company will notify the customer as soon as possible. Also, you will be advised of your
right to file a complaint with the FCC if you believe it is necessary.
f) The telephone company may make changes in its facilities, equipment, operations or procedures that could
affect the operation of the equipment. If this happens the telephone company will provide advance notice in
order for you to make necessary modifications to maintain uninterrupted service.
g) If trouble is experienced with this equipment, theNVG599 device, for warranty information, please contact:

185
Technical Support for Hardware Products
1-877-466-8646
http://moto.force.com/customercare360
If the equipment is causing harm to the telephone network, the telephone company may request that you
disconnect the equipment until the problem is resolved.
h) This equipment not intended to be repaired by the end user. In case of any problems, please refer to the
troubleshooting section of the Product User Manual before calling ARRIS Technical Support.
i) Connection to party line service is subject to state tariffs. Contact the state public utility commission, public
service commission or corporation commission for information.
j) If your home has specially wired alarm equipment connected to the telephone line, ensure that the
installation of this ARRIS NVG599 VDSL2 Gateway does not disable your alarm equipment. If you have
questions about what will disable alarm equipment, consult your telephone company or qualified installer.
RF Exposure Statement:
NOTE: Installation of the wireless models must maintain at least 20 cm between the wireless NVG599 device
and any body part of the user to be in compliance with FCC RF exposure guidelines.
Electrical Safety Advisory
Telephone companies report that electrical surges, typically lightning transients, are very destructive to
customer terminal equipment connected to AC power sources. This has been identified as a major nationwide
problem. Therefore it is advised that this equipment be connected to AC power through the use of a surge
arrestor or similar protection device.
Administrator’s Handbook
186
Caring for the Environment by Recycling
Recycling your ARRIS Equipment
Please do not dispose of this product with your
residential or commercial waste. Some countries
or regions, such as the European Union, have set
up systems to collect and recycle electrical and
electronic waste items. Contact your local
authorities for information about practices
established for your region. If collection systems
are not available, call ARRIS Customer Service for
assistance.
Genbrug af dit ARRIS-udstyr
Dette produkt må ikke bortskaffes sammen med husholdningsaffald eller
erhvervsaffald. Nogle lande eller områder, f.eks. EU, har oprettet systemer
til indsamling og genbrug af elektriske og elektroniske affaldsprodukter.
Kontakt de lokale myndigheder for oplysninger om gældende
fremgangsmåder i dit område. Hvis der ikke findes tilgængelige
indsamlingssystemer, kan du kontakte ARRIS Kundeservice.
Recycling bei Geräten von ARRIS
Bitte entsorgen Sie dieses Produkt nicht als gewöhnlichen Haus- oder
Büromüll. In einigen Ländern und Gebieten, z. B. in der Europäischen Union,
wurden Systeme für die Rücknahme und Wiederverwertung von
Elektroschrott eingeführt. Erkundigen Sie sich bitte bei Ihrer Stadtoder
Kreisverwaltung nach der geltenden Entsorgungspraxis. Falls bei Ihnen noch
kein Abfuhroder Rücknahmesystem besteht, wenden Sie sich bitte an den
Kundendienst von ARRIS.
Reciclaje de su equipo ARRIS
No deseche este producto junto con sus residuos residenciales o
comerciales. Algunos países o regiones, tales como la Unión Europea, han
organizado sistemas para recoger y reciclar desechos eléctricos y
electrónicos. Comuníquese con las autoridades locales para obtener
información acerca de las prácticas vigentes en su región. Si no existen
sistemas de recolección disponibles, solicite asistencia llamando el Servicio
al Cliente de ARRIS.
Recyclage de votre équipement ARRIS
Veuillez ne pas jeter ce produit avec vos ordures ménagères ou vos rebuts
d'entreprise. Certains pays ou certaines régions comme l'Union Européenne
ont mis en place des systèmes de collecte et de recyclage des produits
électriques et électroniques mis au rebut. Veuillez contacter vos autorités
locales pour vous informer des pratiques instaurées dans votre region. Si
aucun système de collecte n'est disponible, veuillez appeler le Service
clientèle de ARRIS qui vous apportera son assistance.
When you see this symbol on
an ARRIS product, do not
dispose of the product with
residential or commercial
waste.
Beskyttelse af miljøet med
genbrug
Når du ser dette symbol på et
ARRIS-produkt, må produktet
ikke bortskaffes sammen med
husholdningsaffald eller
erhvervsaffald.
Umweltschutz durch
Recycling
Wenn Sie dieses Zeichen auf
einem Produkt von ARRIS
sehen, entsorgen Sie das
Produkt bitte nicht als
gewöhnlichen Hausoder
Büromüll.
Cuidar el medio ambiente
mediante el reciclaje
Cuando vea este símbolo en un
producto ARRIS, no lo deseche
junto con residuos residenciales
o comerciales.
Recyclage pour le respect
de l'environnement
Lorsque vous voyez ce symbole
sur un produit ARRIS, ne le jetez
pas avec vos ordures ménagères
ou vos rebuts d'entreprise.

187
Uw ARRIS-materiaal recycleren.
Gooi dit product niet bij het huishoudelijk afval het of bedrijfsafval. In
sommige landen of regio's zoals de Europese Unie, zijn er bepaalde
systemen om elektrische of elektronische afvalproducten in te zamelen en
te recycleren. Neem contact op met de plaatselijke overheid voor
informatie over de geldende regels in uw regio. Indien er geen systemen
bestaan, neemt u contact op met de klantendienst van ARRIS.
Recykling posiadanego sprz´tu ARRIS
Produktu nie nale″y wyrzucaç do komunalnych pojemników na Êmieci. W
niektórych krajach i regionach, np. w Unii Europejskiej, istniejà systemy
zbierania i recyklingu sprz´tu elektrycznego i elektronicznego. Informacje o
utylizacji tego rodzaju odpadów nale″y uzyskaç od w³adz lokalnych. JeÊli w
danym regionie nie istniejà systemy zbierania odpadów elektrycznych i
elektronicznych, informacje o utylizacji nale″y uzyskaç od biura obs³ugi
klienta firmy ARRIS (ARRIS Customer Service).
Reciclagem do seu equipamento ARRIS
Não descarte este produto junto com o lixo residencial ou comercial. Alguns
países ou regiões, tais como a União Européia, criaram sistemas para
colecionar e reciclar produtos eletroeletrônicos. Para obter informações
sobre as práticas estabelecidas para sua região, entre em contato com as
autoridades locais. Se não houver sistemas de coleta disponíveis, entre em
contato com o Serviço ao Cliente da ARRIS para obter assistência.
Återvinning av din ARRIS-utrustning
Kasta inte denna produkt tillsammans med det vanliga avfallet. Vissa länder
eller regioner, som t.ex. EU, har satt upp ett system för insamling och
återvinning av el- och elektronikavfall. Kontakta dina lokala myndigheter för
information om vilka regler som gäller i din region. Om det inte finns något
insamlingssystem ska du kontakta ARRIS kundtjänst för hjälp.
Milieubewust recycleren
Als u dit symbool op een ARRIS-
product ziet, gooi het dan niet
bij het huishoudelijk afval of het
bedrijfsafval.
Dba³oÊç o Êrodowisko -
recykling
Produktów ARRIS oznaczonych
tym symbolem nie nale″y
wyrzucaç do komunalnych
pojemników na Êmieci.
Cuidando do meio
ambiente através da
reciclagem
Quando você ver este símbolo
em um produto ARRIS, não
descarte o produto junto com
lixo residencial ou comercial.
Var rädd om miljön
genom återvinning
När du ser den här symbolen på
en av ARRIS produkter ska du
inte kasta produkten
tillsammans med det vanliga
avfallet.

Administrator’s Handbook
188

189
Copyright Acknowledgments
Because ARRIS Group, Inc. has included certain software source code in this product, ARRIS includes the
following text required by the respective copyright holders:
Open Source Software Information
For instructions on how to obtain a copy of any source code being made publicly available by ARRIS related to software
used in this ARRIS product you may send your request in writing to:
ARRIS Group, Inc.
OSS Management
2450 Walsh Avenue
Santa Clara, CA 95051
USA
The ARRIS website opensource.arrisi.com also contains information regarding ARRIS’s use of open source. ARRIS has
created the opensource.arrisi.com to serve as a portal for interaction with the software community-at-large.
This document contains additional information regarding licenses, acknowledgments and required copyright notices for
open source packages used in this ARRIS product.
aiccu 2007.01.15
The SixXS License - http://www.sixxs.net/
Copyright (C) SixXS <info@sixxs.net>
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. Neither the name of SixXS nor the names of its contributors may be used to endorse or promote products derived from
this software without specific prior permission.
THIS SOFTWARE IS PROVIDED BY SIXXS AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL SIXXS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
ASN.1 object dumping code
Copyright (c) Peter Gutmann
c-ares async resolver library
http://daniel.haxx.se/projects/c-ares/
Original ares library by Greg Hudson, MIT
ftp://athena-dist.mit.edu/pub/ATHENA/ares
Copyright 1998 by the Massachusetts Institute of Technology.

Administrator’s Handbook
190
Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is
hereby granted, provided that the above copyright notice appear in all copies and that both that copyright notice and this
permission notice appear in supporting documentation, and that the name of M.I.T. not be used in advertising or publicity
pertaining to distribution of the software without specific, written prior permission. M.I.T. makes no representations about
the suitability of this software for any purpose. It is provided "as is" without express or implied warranty.
dhcpcd - DHCP client daemon 5.5.0
Copyright (c) 2006-2010 Roy Marples <roy@marples.name>
All rights reserved
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
Copyright (c) ARRIS India Electronics
dhcp (dhcp-isc) 4.1.1-P1
Copyright © 2004-2011 by Internet Systems Consortium, Inc. ("ISC")
Copyright © 1995-2003 by Internet Software Consortium
Permission to use, copy, modify, and/or distribute this software for any purpose with or without fee is hereby granted,
provided that the above copyright notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND ISC DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL ISC BE LIABLE FOR ANY SPECIAL,
DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
dhcpcd - DHCP client daemon 5.5.0
Copyright (c) 2006-2011 Roy Marples <roy@marples.name>
All rights reserved
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
dhcpcv6
Copyright (C) 1998-2004 WIDE Project.

191
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. Neither the name of the project nor the names of its contributors may be used to endorse or promote products derived
from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE PROJECT AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE PROJECT OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
Encryption
Aaron D. Gifford License
Copyright (c) 2000-2001, Aaron D. Gifford
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. Neither the name of the copyright holder nor the names of contributors may be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTOR(S) ``AS IS'' AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTOR(S) BE LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
RSA Data Security License
Copyright (C) 1990, RSA Data Security, Inc. All rights reserved.
License to copy and use this software is granted provided that it is identified as the "RSA Data Security, Inc. MD5 Message-
Digest Algorithm" in all material mentioning or referencing this software or this function.
License is also granted to make and use derivative works provided that such works are identified as "derived from the RSA
Data Security, Inc. MD5 Message-Digest Algorithm" in all material mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either the merchantability of this software or the suitability of
this software for any particular purpose. It is provided "as is" without express or implied warranty of any kind. These
notices must be retained in any copies of any part of this documentation and/or software.
Copyright (c) Broadcom Corporation
Copyright (c) The Internet Society
expat 1.95.7
Copyright (c) 1998, 1999, 2000 Thai Open Source Software Center Ltd and Clark Cooper
Copyright (c) 2001, 2002 Expat maintainers.

Administrator’s Handbook
192
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation
files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy,
modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT
LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
GNU General Public License 2.0 (GPL)
This ARRIS product contains the following open source software packages licensed under the terms of the GPL 2.0 license:
• Linux 2.6.30
• Arptables 0.0.3-4 (also Copyright (c) Jay Fenlason)
• bridge-utils 1.2 (also Copyright (c) Stephen Hemminger, Copyright (c) Lennery Buytenhek)
• busybox 1.18.3 (also Copyright (C) 1999-2004 by Erik Andersen <andersen@codepoet.org>)
• conntrack 1.0.1
• dnsmasq 2.45 (also Copyright (c) Simon Kelley)
• ebtables 2.0.10-2 (also Copyright (c) Bart De Schuymer)
• ez-ipupdate 3.0.11b7 (also Copyright (c) Angus Mackay)
• haserl 0.9.26 (also Copyright (c) 2003-2007 Nathan Angelacos)
• inetd (also Copyright (c) Kenneth Albanowski Copyright (c) D. Jeff Dionne Copyright (c) Lineo, Inc.)
• iproute2 (also Copyright (c) Rusty Russell, Copyright (c) The Regents of the University of California, Copyright (c) USAGI
WIDE Project, Copyright (c) Free Software Founcation, Copyright (c) Intel Corp. Copyright (c) Robert Olsson Uppsala Univer-
sity Sweden, Copyright (c) Harald Welte)
• iptables 1.4.0 (also Copyright (c) Netfilter Core Team)
• libnetfilter_conntrack (also (C) 2005-2011 Pablo Neira Ayuso)
• libnfnetlink (also "(c) 2001-2005 Netfilter Core Team, (c) 2008 by Pablo Neira Ayuso <pablo@netfilter.org>, (c) 2004 by
Astaro AG, written by Harald Welte, (c) 2002-2006 by Harald Welte <laforge@gnumonks.org>")
• mtd-utils 1.4.9 (also Copyright Texas Instruments)
• ntpclient 2003_194 (also Copyright (c) Larry Doolittle)
• pppd 2.4.4 (also Copyright Fred N. van Kempen, <waltje@uWalt.NL.Mugnet.ORG>, Copyright Donald Becker,
<becker@super.org>, Copyright Alan Cox, <alan@lxorguk.ukuu.org.uk>, Copyright Steve Whitehouse,
<gw7rrm@eeshack3.swan.ac.uk>)
• rp-pppoe 3.10
• samba 3.0.25a (also Copyright (c) Ricky Poulten 1995-1998, Copyright (c) Richard Sharpe 1998)
• udev 136 (also Copyright (C) Kay Sievers)
• vconfig 1.6 (also Copyright (c) Ben Greear)
• wget 1.10.2 (also copyright (c) GNU Wget Authors)
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.,
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU
General Public License is intended to guarantee your freedom to share and change free software--to make sure the
software is free for all its users. This General Public License applies to most of the Free Software Foundation's software and
to any other program whose authors commit to using it. (Some other Free Software Foundation software is covered by the
GNU Lesser General Public License instead.) You can apply it to your programs, too.

193
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to
make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish), that you
receive source code or can get it if you want it, that you can change the software or use pieces of it in new free programs;
and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to ask you to surrender
the rights. These restrictions translate to certain responsibilities for you if you distribute copies of the software, or if you
modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients all the
rights that you have. You must make sure that they, too, receive or can get the source code. And you must show them
these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license which gives you legal
permission to copy, distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain that everyone understands that there is no warranty
for this free software. If the software is modified by someone else and passed on, we want its recipients to know that what
they have is not the original, so that any problems introduced by others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger that redistributors of
a free program will individually obtain patent licenses, in effect making the program proprietary. To prevent this, we have
made it clear that any patent must be licensed for everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the copyright holder saying it may
be distributed under the terms of this General Public License. The "Program", below, refers to any such program or work,
and a "work based on the Program" means either the Program or any derivative work under copyright law: that is to say, a
work containing the Program or a portion of it, either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in the term "modification".) Each licensee is addressed as
"you".
Activities other than copying, distribution and modification are not covered by this License; they are outside its scope. The
act of running the Program is not restricted, and the output from the Program is covered only if its contents constitute a
work based on the Program (independent of having been made by running the Program). Whether that is true depends on
what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in any medium, provided
that you conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of warranty;
keep intact all the notices that refer to this License and to the absence of any warranty; and give any other recipients of the
Program a copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty protection in
exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work based on the Program, and
copy and distribute such modifications or work under the terms of Section 1 above, provided that you also meet all of
these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the files and the date of any
change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is derived from the
Program or any part thereof, to be licensed as a whole at no charge to all third parties under the terms of this License.

Administrator’s Handbook
194
c) If the modified program normally reads commands interactively when run, you must cause it, when started running for
such interactive use in the most ordinary way, to print or display an announcement including an appropriate copyright
notice and a notice that there is no warranty (or else, saying that you provide a warranty) and that users may redistribute
the program under these conditions, and telling the user how to view a copy of this License. (Exception: if the Program
itself is interactive but does not normally print such an announcement, your work based on the Program is not required to
print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the
Program, and can be reasonably considered independent and separate works in themselves, then this License, and its
terms, do not apply to those sections when you distribute them as separate works. But when you distribute the same
sections as part of a whole which is a work based on the Program, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the entire whole, and thus to each and every part regardless
of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by you; rather, the
intent is to exercise the right to control the distribution of derivative or collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with a work based on the
Program) on a volume of a storage or distribution medium does not bring the other work under the scope of this License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code or executable form
under the terms of Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code, which must be distributed under the
terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a charge no more than your
cost of physically performing source distribution, a complete machine-readable copy of the corresponding source code, to
be distributed under the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding source code. (This
alternative is allowed only for noncommercial distribution and only if you received the program in object code or
executable form with such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to it. For an executable work,
complete source code means all the source code for all modules it contains, plus any associated interface definition files,
plus the scripts used to control compilation and installation of the executable. However, as a special exception, the source
code distributed need not include anything that is normally distributed (in either source or binary form) with the major
components (compiler, kernel, and so on) of the operating system on which the executable runs, unless that component
itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated place, then offering
equivalent access to copy the source code from the same place counts as distribution of the source code, even though third
parties are not compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided under this License. Any
attempt otherwise to copy, modify, sublicense or distribute the Program is void, and will automatically terminate your
rights under this License. However, parties who have received copies, or rights, from you under this License will not have
their licenses terminated so long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else grants you permission
to modify or distribute the Program or its derivative works. These actions are prohibited by law if you do not accept this
License. Therefore, by modifying or distributing the Program (or any work based on the Program), you indicate your
acceptance of this License to do so, and all its terms and conditions for copying, distributing or modifying the Program or
works based on it.

195
6. Each time you redistribute the Program (or any work based on the Program), the recipient automatically receives a
license from the original licensor to copy, distribute or modify the Program subject tothese terms and conditions. You may
not impose any further restrictions on the recipients' exercise of the rights granted herein. You are not responsible for
enforcing compliance by third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to
patent issues), conditions are imposed on you (whether by court order, agreement orotherwise) that contradict the
conditions of this License, they do not excuse you from the conditions of this License. If you cannot distribute so as to
satisfy simultaneously your obligations under this License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent license would not permit royalty-free redistribution of the
Program by all those who receive copies directly or indirectly through you, then the only way you could satisfy both it and
this License would be to refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the balance of the section
is intended to apply and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims or to contest validity
of any such claims; this section has the sole purpose of protecting the integrity of the free software distribution system,
which is implemented by public license practices. Many people have made generous contributions to the wide range of
software distributed through that system in reliance on consistent application of that system; it is up to the author/donor
to decide if he or she is willing to distribute software through any other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by patents or by copyrighted
interfaces, the original copyright holder who places the Program under this License may add an explicit geographical
distribution limitation excluding those countries, so that distribution is permitted only in or among countries not thus
excluded. In such case, this License incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the General Public License from time to
time. Such new versions will be similar in spirit to the present version, but may differ in detail toaddress new problems or
concerns.
Each version is given a distinguishing version number. If the Program specifies a version number of this License which
applies to it and "any later version", you have the option of following the terms and conditions either of that version or of
any later version published by the Free Software Foundation. If the Program does not specify a version number of this
License, you may choose any version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution conditions are different,
write to the author to ask for permission. For software which is copyrighted by the Free Software Foundation, write to the
Free Software Foundation; we sometimes make exceptions for this. Our decision will be guided by the two goals of
preserving the free status of all derivatives of our free software and of promoting the sharing and reuse of software
generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT
PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR
OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR
ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU
FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE
OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY
OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.

Administrator’s Handbook
196
END OF TERMS AND CONDITIONS
GNU Lesser General Public License 2.1 (LGPL)
This ARRIS product contains the following open source software packages licensed under the terms of the LGPL 2.1 license:
• uClibc 0.9.27 (also Copyright (C) 2000-2006 Erik Andersen <andersen@uclibc.org>)
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
[This is the first released version of the Lesser GPL. It also counts as the successor of the GNU Library Public License,
version 2, hence the version number 2.1.]
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU
General Public Licenses are intended to guarantee your freedom to share and change free software--to make sure the
software is free for all its users.
This license, the Lesser General Public License, applies to some specially designated software packages--typically libraries--
of the Free Software Foundation and other authors who decide to use it. You can use it too, but we suggest you first think
carefully about whether this license or the ordinary General Public License is the better strategy to use in any particular
case, based on the explanations below.
When we speak of free software, we are referring to freedom of use, not price. Our General Public Licenses are designed to
make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish); that you
receive source code or can get it if you want it; that you can change the software and use pieces of it in new free programs;
and that you are informed that you can do these things.
To protect your rights, we need to make restrictions that forbid distributors to deny you these rights or to ask you to
surrender these rights. These restrictions translate to certain responsibilities for you if you distribute copies of the library
or if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you must give the recipients all the rights
that we gave you. You must make sure that they, too, receive or can get the source code. If you link other code with the
library, you must provide complete object files to the recipients, so that they can relink them with the library after making
changes to the library and recompiling it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the library, and (2) we offer you this license, which gives
you legal permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that there is no warranty for the free library. Also, if the library is
modified by someone else and passed on, the recipients should know that what they have is not the original version, so
that the original author's reputation will not be affected by problems that might be introduced by others.
Finally, software patents pose a constant threat to the existence of any free program. We wish to make sure that a
company cannot effectively restrict the users of a free program by obtaining a restrictive license from a patent holder.
Therefore, we insist that any patent license obtained for a version of the library must be consistent with the full freedom of
use specified in this license.
Most GNU software, including some libraries, is covered by the ordinary GNU General Public License. This license, the GNU
Lesser General Public License, applies to certain designated libraries, and is quite different from the ordinary General Public
License. We use this license for certain libraries in order to permit linking those libraries into non-free programs.
When a program is linked with a library, whether statically or using a shared library, the combination of the two is legally
speaking a combined work, a derivative of the original library. The ordinary General Public License therefore permits such
linking only if the entire combination fits its criteria of freedom. The Lesser General Public License permits more lax criteria
for linking other code with the library.
We call this license the "Lesser" General Public License because it does Less to protect the user's freedom than the ordinary
General Public License. It also provides other free software developers Less of an advantage over competing non-free
programs. These disadvantages are the reason we use the ordinary General Public License for many libraries. However, the
Lesser license provides advantages in certain special circumstances.
For example, on rare occasions, there may be a special need to encourage the widest possible use of a certain library, so
that it becomes a de-facto standard. To achieve this, non-free programs must be allowed to use the library. A more
frequent case is that a free library does the same job as widely used non-free libraries. In this case, there is little to gain by
limiting the free library to free software only, so we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free programs enables a greater number of people to use a
large body of free software. For example, permission to use the GNU C Library in non-free programs enables many more
people to use the whole GNU operating system, as well as its variant, the GNU/Linux operating system.
Although the Lesser General Public License is Less protective of the users' freedom, it does ensure that the user of a
program that is linked with the Library has the freedom and the wherewithal to run that program using a modified version
of the Library.

197
The precise terms and conditions for copying, distribution and modification follow. Pay close attention to the difference
between a "work based on the library" and a "work that uses the library". The former contains code derived from the
library, whereas the latter must be combined with the library in order to run.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License Agreement applies to any software library or other program which contains a notice placed by the copyright
holder or other authorized party saying it may be distributed under the terms of this Lesser General Public License (also
called "this License"). Each licensee is addressed as "you".
A "library" means a collection of software functions and/or data prepared so as to be conveniently linked with application
programs (which use some of those functions and data) to form executables.
The "Library", below, refers to any such software library or work which has been distributed under these terms. A "work
based on the Library" means either the Library or any derivative work under copyright law: that is to say, a work containing
the Library or a portion of it, either verbatim or with modifications and/or translated straightforwardly into another
language. (Hereinafter, translation is included without limitation in the term "modification".)
"Source code" for a work means the preferred form of the work for making modifications to it. For a library, complete
source code means all the source code for all modules it contains, plus any associated interface definition files, plus the
scripts used to control compilation and installation of the library.
Activities other than copying, distribution and modification are not covered by this License; they are outside its scope. The
act of running a program using the Library is not restricted, and output from such a program is covered only if its contents
constitute a work based on the Library (independent of the use of the Library in a tool for writing it). Whether that is true
depends on what the Library does and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library's complete source code as you receive it, in any medium,
provided that you conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of
warranty; keep intact all the notices that refer to this License and to the absence of any warranty; and distribute a copy of
this License along with the Library.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty protection in
exchange for a fee.
2. You may modify your copy or copies of the Library or any portion of it, thus forming a work based on the Library, and
copy and distribute such modifications or work under the terms of Section 1 above, provided that you also meet all of
these conditions:
* a) The modified work must itself be a software library.
* b) You must cause the files modified to carry prominent notices stating that you changed the files and the date of any
change.
* c) You must cause the whole of the work to be licensed at no charge to all third parties under the terms of this License.
* d) If a facility in the modified Library refers to a function or a table of data to be supplied by an application program that
uses the facility, other than as an argument passed when the facility is invoked, then you must make a good faith effort to
ensure that, in the event an application does not supply such function or table, the facility still operates, and performs
whatever part of its purpose remains meaningful.
(For example, a function in a library to compute square roots has a purpose that is entirely well-defined independent of the
application. Therefore, Subsection 2d requires that any application-supplied function or table used by this function must be
optional: if the application does not supply it, the square root function must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the
Library, and can be reasonably considered independent and separate works in themselves, then this License, and its terms,
do not apply to those sections when you distribute them as separate works. But when you distribute the same sections as
part of a whole which is a work based on the Library, the distribution of the whole must be on the terms of this License,
whose permissions for other licensees extend to the entire whole, and thus to each and every part regardless of who wrote
it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by you; rather, the
intent is to exercise the right to control the distribution of derivative or collective works based on the Library.
In addition, mere aggregation of another work not based on the Library with the Library (or with a work based on the
Library) on a volume of a storage or distribution medium does not bring the other work under the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public License instead of this License to a given copy of the
Library. To do this, you must alter all the notices that refer to this License, so that they refer to the ordinary GNU General
Public License, version 2, instead of to this License. (If a newer version than version 2 of the ordinary GNU General Public
License has appeared, then you can specify that version instead if you wish.) Do not make any other change in these
notices.
Once this change is made in a given copy, it is irreversible for that copy, so the ordinary GNU General Public License applies
to all subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of the Library into a program that is not a library.
4. You may copy and distribute the Library (or a portion or derivative of it, under Section 2) in object code or executable
form under the terms of Sections 1 and 2 above provided that you accompany it with the complete corresponding
machine-readable source code, which must be distributed under the terms of Sections 1 and 2 above on a medium
customarily used for software interchange.
If distribution of object code is made by offering access to copy from a designated place, then offering equivalent access to
copy the source code from the same place satisfies the requirement to distribute the source code, even though third
parties are not compelled to copy the source along with the object code.

Administrator’s Handbook
198
5. A program that contains no derivative of any portion of the Library, but is designed to work with the Library by being
compiled or linked with it, is called a "work that uses the Library". Such a work, in isolation, is not a derivative work of the
Library, and therefore falls outside the scope of this License.
However, linking a "work that uses the Library" with the Library creates an executable that is a derivative of the Library
(because it contains portions of the Library), rather than a "work that uses the library". The executable is therefore covered
by this License. Section 6 states terms for distribution of such executables.
When a "work that uses the Library" uses material from a header file that is part of the Library, the object code for the work
may be a derivative work of the Library even though the source code is not. Whether this is true is especially significant if
the work can be linked without the Library, or if the work is itself a library. The threshold for this to be true is not precisely
defined by law.
If such an object file uses only numerical parameters, data structure layouts and accessors, and small macros and small
inline functions (ten lines or less in length), then the use of the object file is unrestricted, regardless of whether it is legally
a derivative work. (Executables containing this object code plus portions of the Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may distribute the object code for the work under the terms of
Section 6. Any executables containing that work also fall under Section 6, whether or not they are linked directly with the
Library itself.
6. As an exception to the Sections above, you may also combine or link a "work that uses the Library" with the Library to
produce a work containing portions of the Library, and distribute that work under terms of your choice, provided that the
terms permit modification of the work for the customer's own use and reverse engineering for debugging such
modifications.
You must give prominent notice with each copy of the work that the Library is used in it and that the Library and its use are
covered by this License. You must supply a copy of this License. If the work during execution displays copyright notices, you
must include the copyright notice for the Library among them, as well as a reference directing the user to the copy of this
License. Also, you must do one of these things:
* a) Accompany the work with the complete corresponding machine-readable source code for the Library including
whatever changes were used in the work (which must be distributed under Sections 1 and 2 above); and, if the work is an
executable linked with the Library, with the complete machine-readable "work that uses the Library", as object code and/or
source code, so that the user can modify the Library and then relink to produce a modified executable containing the
modified Library. (It is understood that the user who changes the contents of definitions files in the Library will not
necessarily be able to recompile the application to use the modified definitions.)
* b) Use a suitable shared library mechanism for linking with the Library. A suitable mechanism is one that (1) uses at run
time a copy of the library already present on the user's computer system, rather than copying library functions into the
executable, and (2) will operate properly with a modified version of the library, if the user installs one, as long as the
modified version is interface-compatible with the version that the work was made with.
* c) Accompany the work with a written offer, valid for at least three years, to give the same user the materials specified in
Subsection 6a, above, for a charge no more than the cost of performing this distribution.
* d) If distribution of the work is made by offering access to copy from a designated place, offer equivalent access to copy
the above specified materials from the same place.
* e) Verify that the user has already received a copy of these materials or that you have already sent this user a copy.
For an executable, the required form of the "work that uses the Library" must include any data and utility programs needed
for reproducing the executable from it. However, as a special exception, the materials to be distributed need not include
anything that is normally distributed (in either source or binary form) with the major components (compiler, kernel, and so
on) of the operating system on which the executable runs, unless that component itself accompanies the executable.
It may happen that this requirement contradicts the license restrictions of other proprietary libraries that do not normally
accompany the operating system. Such a contradiction means you cannot use both them and the Library together in an
executable that you distribute.
7. You may place library facilities that are a work based on the Library side-by-side in a single library together with other
library facilities not covered by this License, and distribute such a combined library, provided that the separate distribution
of the work based on the Library and of the other library facilities is otherwise permitted, and provided that you do these
two things:
* a) Accompany the combined library with a copy of the same work based on the Library, uncombined with any other
library facilities. This must be distributed under the terms of the Sections above.
* b) Give prominent notice with the combined library of the fact that part of it is a work based on the Library, and
explaining where to find the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute the Library except as expressly provided under this License.
Any attempt otherwise to copy, modify, sublicense, link with, or distribute the Library is void, and will automatically
terminate your rights under this License. However, parties who have received copies, or rights, from you under this License
will not have their licenses terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not signed it. However, nothing else grants you permission to
modify or distribute the Library or its derivative works. These actions are prohibited by law if you do not accept this
License. Therefore, by modifying or distributing the Library (or any work based on the Library), you indicate your
acceptance of this License to do so, and all its terms and conditions for copying, distributing or modifying the Library or
works based on it.
10. Each time you redistribute the Library (or any work based on the Library), the recipient automatically receives a license
from the original licensor to copy, distribute, link with or modify the Library subject to these terms and conditions. You may
not impose any further restrictions on the recipients' exercise of the rights granted herein. You are not responsible for
enforcing compliance by third parties with this License.

199
11. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to
patent issues), conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the
conditions of this License, they do not excuse you from the conditions of this License. If you cannot distribute so as to
satisfy simultaneously your obligations under this License and any other pertinent obligations, then as a consequence you
may not distribute the Library at all. For example, if a patent license would not permit royalty-free redistribution of the
Library by all those who receive copies directly or indirectly through you, then the only way you could satisfy both it and
this License would be to refrain entirely from distribution of the Library.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the balance of the section
is intended to apply, and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims or to contest validity
of any such claims; this section has the sole purpose of protecting the integrity of the free software distribution system
which is implemented by public license practices. Many people have made generous contributions to the wide range of
software distributed through that system in reliance on consistent application of that system; it is up to the author/donor
to decide if he or she is willing to distribute software through any other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in certain countries either by patents or by copyrighted
interfaces, the original copyright holder who places the Library under this License may add an explicit geographical
distribution limitation excluding those countries, so that distribution is permitted only in or among countries not thus
excluded. In such case, this License incorporates the limitation as if written in the body of this License.
13. The Free Software Foundation may publish revised and/or new versions of the Lesser General Public License from time
to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems
or concerns.
Each version is given a distinguishing version number. If the Library specifies a version number of this License which applies
to it and "any later version", you have the option of following the terms and conditions either of that version or of any later
version published by the Free Software Foundation. If the Library does not specify a license version number, you may
choose any version ever published by the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free programs whose distribution conditions are incompatible
with these, write to the author to ask for permission. For software which is copyrighted by the Free Software Foundation,
write to the Free Software Foundation; we sometimes make exceptions for this. Our decision will be guided by the two
goals of preserving the free status of all derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE LIBRARY, TO THE EXTENT
PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR
OTHER PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE LIBRARY IS WITH YOU. SHOULD THE LIBRARY
PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR
ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU FOR
DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR
INABILITY TO USE THE LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE
OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER
SOFTWARE), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
libtecla 1.6.1
Martin C. Shepherd License
Copyright (c) 2000, 2001, 2002, 2003, 2004 by Martin C. Shepherd.
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation
files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy,
modify, merge, publish, distribute, and/or sell copies of the Software, and to permit persons to whom the Software is
furnished to do so, provided that the above copyright notice(s) and this permission notice appear in all copies of the
Software and that both the above copyright notice(s) and this permission notice appear in supporting documentation. THE
SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESSOR IMPLIED, INCLUDING BUT NOT LIMITED
TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD
PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY
CLAIM, OR ANY SPECIAL INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM
LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE. Except as contained in this
notice, the name of a copyright holder shall not be used in advertising or otherwise to promote the sale, use or other
dealings in this Software without prior written authorization of the copyright holder.

Administrator’s Handbook
200
lua 5.1
Lua is licensed under the terms of the MIT license reproduced below. This means that Lua is free software and can be used
for both academic and commercial purposes at absolutely no cost.
For details and rationale, see http://www.lua.org/license.html .
Copyright (C) 1994.2012 Lua.org, PUC-Rio.
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation
files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy,
modify, merge, publish, distribute, sublicense, and/or sellcopies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT
LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
miniupnp 20070228
Thomas BERNARD License
Copyright (c) 2006-2007, Thomas BERNARD
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* The name of the author may not be used to endorse or promote products derived from this software without specific
prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED
TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
muhttp 1.1.3
Copyright (c) 2005 Robbert Haarman
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation
files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy,
modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT
LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.

201
OpenSSL 0.9.8k
OpenSSL SSLeay License
LICENSE ISSUES
The OpenSSL toolkit stays under a dual license, i.e. both the conditions of the OpenSSL License and the original SSLeay
license apply to the toolkit. See below for the actual license texts. Actually both licenses are BSD-style Open Source
licenses. In case of any license issues related to OpenSSL please contact openssl-core@openssl.org.
OpenSSL License
-----------------------
Copyright (c) 1998-2008 The OpenSSL Project. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgment:
"This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://
www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to endorse or promote products derived from
this software without prior written permission. For written permission, please contact openssl-core@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor may "OpenSSL" appear in their names without
prior written permission of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment:
"This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit (http://
www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim Hudson (tjh@cryptsoft.com).
Original SSLeay License
-----------------------
Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The
following conditions apply to all code found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just the SSL
code. The SSL documentation included with this distribution is covered by the same copyright terms except that the holder
is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young's, and as such any Copyright notices in the code are not to be removed. If this package is used
in a product, Eric Young should be given attribution as the author of the parts of the library used. This can be in the form of
a textual message at program startup or in documentation (online or textual) provided with the package. Redistribution
and use in source and binary forms, with or without modification, are permitted provided that the following conditions are
met:
1. Redistributions of source code must retain the copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement:
"This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)"
The word 'cryptographic' can be left out if the rouines from the library being used are not cryptographic related :-).

Administrator’s Handbook
202
4. If you include any Windows specific code (or a derivative thereof) from the apps directory (application code) you must
include an acknowledgement:
"This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
HIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE MPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. The
licence and distribution terms for any publically available version or derivative of this code cannot be changed. i.e. this
code cannot simply be copied and put under another distribution licence [including the GNU Public Licence.]
pcre 5.0
PCRE is a library of functions to support regular expressions whose syntax and semantics are as close as possible to those of
the Perl 5 language. Release 5 of PCRE is distributed under the terms of the "BSD" licence, as specified below. The
documentation for PCRE, supplied in the "doc" directory, is distributed under the same terms as the software itself.
Written by: Philip Hazel <ph10@cam.ac.uk>
University of Cambridge Computing Service,
Cambridge, England. Phone: +44 1223 334714.
Copyright (c) 1997-2004 University of Cambridge
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
* Neither the name of the University of Cambridge nor the names of its contributors may be used to endorse or promote
products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BELIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED
TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
PPPD Composite Licenses
Copyright (c) 1984-2000 Carnegie Mellon University. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The name "Carnegie Mellon University" must not be used to endorse or promote products derived from this software
without prior written permission. For permission or any legal details, please contact
Office of Technology Transfer
Carnegie Mellon University
5000 Forbes Avenue
Pittsburgh, PA 15213-3890
(412) 268-4387, fax: (412) 268-7395
tech-transfer@andrew.cmu.edu

203
4. Redistributions of any form whatsoever must retain the following acknowledgment:
"This product includes software developed by Computing Services at Carnegie Mellon University (http://www.cmu.edu/
computing/)."
CARNEGIE MELLON UNIVERSITY DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL CARNEGIE MELLON UNIVERSITY BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
------------------------------------------------------------------------------
Copyright (c) 1999-2004 Paul Mackerras. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. The name(s) of the authors of this software must not be used to endorse or promote products derived from this
software without prior written permission.
3. Redistributions of any form whatsoever must retain the following acknowledgment:
"This product includes software developed by Paul Mackerras
<paulus@samba.org>".
THE AUTHORS OF THIS SOFTWARE DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL THE AUTHORS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
------------------------------------------------------------------------------
Author: Arvin Schnell <arvin@suse.de> . (No copyright, but listed the author for attribution.)
------------------------------------------------------------------------------
Copyright (C) 2002 Roaring Penguin Software Inc.
This plugin may be distributed according to the terms of the GNU General Public License, version 2 or (at your option) any
later version.
Copyright (C) 2002 Roaring Penguin Software Inc.
Copyright (C) 1996, Matjaz Godec <gody@elgo.si>
Copyright (C) 1996, Lars Fenneberg <in5y050@public.uni-hamburg.de>
Copyright (C) 1997, Miguel A.L. Paraz <map@iphil.net>
Copyright (C) 1995,1996,1997,1998 Lars Fenneberg <lf@elemental.net>
Copyright (C) 2002 Roaring Penguin Software Inc.
MPPE support is by Ralf Hofmann, <ralf.hofmann@elvido.net>, with modification from Frank Cusack,
<frank@google.com>.
This plugin may be distributed according to the terms of the GNU General Public License, version 2 or (at your option) any
later version.
------------------------------------------------------------------------------
Author: Ben McKeegan ben@netservers.co.uk

Administrator’s Handbook
204
Copyright (C) 2002 Netservers
This plugin may be distributed according to the terms of the GNU General Public License, version 2 or (at your option) any
later version. See the respective source files to find out which copyrights apply.
------------------------------------------------------------------------------
Copyright (C) 2002 Roaring Penguin Software Inc.
Permission to use, copy, modify, and distribute this software for any purpose and without fee is hereby granted, provided
that this copyright and permission notice appear on all copies and supporting documentation, the name of Roaring
Penguin Software Inc. not be used in advertising or publicity pertaining to distribution of the program without specific prior
permission, and notice be given in supporting documentation that copying and distribution is by permission of Roaring
Penguin Software Inc.. Roaring Penguin Software Inc. makes no representations about the suitability of this software for
any purpose. It is provided "as is" without express or implied warranty.
------------------------------------------------------------------------------
Copyright (C) 1995,1996,1997,1998 Lars Fenneberg <lf@elemental.net>
Permission to use, copy, modify, and distribute this software for any purpose and without fee is hereby granted, provided
that this copyright and permission notice appear on all copies and supporting documentation, the name of Lars Fenneberg
not be used in advertising or publicity pertaining to distribution of the program without specific prior permission, and
notice be given in supporting documentation that copying and distribution is by permission of Lars Fenneberg. Lars
Fenneberg makes no representations about the suitability of this software for any purpose. It is provided "as is" without
express or implied warranty.
------------------------------------------------------------------------------
Copyright 1992 Livingston Enterprises, Inc.
Livingston Enterprises, Inc. 6920 Koll Center Parkway Pleasanton, CA 94566
Permission to use, copy, modify, and distribute this software for any purpose and without fee is hereby granted, provided
that this copyright and permission notice appear on all copies and supporting documentation, the name of Livingston
Enterprises, Inc. not be used in advertising or publicity pertaining to distribution of the program without specific prior
permission, and notice be given in supporting documentation that copying and distribution is by permission of Livingston
Enterprises, Inc. Livingston Enterprises, Inc. makes no representations about the suitability of this software for any
purpose. It is provided "as is" without express or implied warranty.
------------------------------------------------------------------------------
[C] The Regents of the University of Michigan and Merit Network, Inc. 1992, 1993, 1994, 1995 All Rights Reserved
Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is
hereby granted, provided that the above copyright notice and this permission notice appear in all copies of the software
and derivative works or modified versions thereof, and that both the copyright notice and this permission and disclaimer
notice appear in supporting documentation. THIS SOFTWARE IS PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND,
EITHER EXPRESS OR IMPLIED, INCLUDING WITHOUT LIMITATION WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE. THE REGENTS OF THE UNIVERSITY OF MICHIGAN AND MERIT NETWORK, INC. DO NOT WARRANT
THAT THE FUNCTIONS CONTAINED IN THE SOFTWARE WILL MEET LICENSEE'S REQUIREMENTS OR THAT OPERATION WILL
BE UNINTERRUPTED OR ERROR FREE. The Regents of the University of Michigan and Merit Network, Inc. shall not be liable
for any special, indirect, incidental or consequential damages with respect to any claim by Licensee or any third party
arising from use of the software.
------------------------------------------------------------------------------
Copyright (C) 1990, 1991-2, RSA Data Security, Inc. Created 1991.
All rights reserved.

205
License to copy and use this software is granted provided that it is identified as the "RSA Data Security, Inc. MD5 Message-
Digest Algorithm" in all material mentioning or referencing this software or this function.
License is also granted to make and use derivative works provided that such works are identified as "derived from the RSA
Data Security, Inc. MD5 Message-Digest Algorithm" in all material mentioning or referencing the derived work. RSA Data
Security, Inc. makes no representations concerning either the merchantability of this software or the suitability of this
software for any particular purpose. It is provided "as is" without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this documentation and/or software.
------------------------------------------------------------------------------
Copyright (c) 2000 by Sun Microsystems, Inc.
All rights reserved.
Permission to use, copy, modify, and distribute this software and its documentation is hereby granted, provided that the
above copyright notice appears in all copies.
SUN MAKES NO REPRESENTATION OR WARRANTIES ABOUT THE SUITABILITY OF THE SOFTWARE, EITHER EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR
PURPOSE, OR NON-INFRINGEMENT. SUN SHALL NOT BE LIABLE FOR ANY DAMAGES SUFFERED BY LICENSEE AS A RESULT OF
USING, MODIFYING OR DISTRIBUTING THIS SOFTWARE OR ITS DERIVATIVES
------------------------------------------------------------------------------
Copyright (c) 1985, 1986 The Regents of the University of California.
All rights reserved.
This code is derived from software contributed to Berkeley by James A. Woods, derived from original work by Spencer
Thomas and Joseph Orost.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement: This
product includes software developed by the University of California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
Copyright (c) 1989 Regents of the University of California.
All rights reserved.

Administrator’s Handbook
206
Redistribution and use in source and binary forms are permitted provided that the above copyright notice and this
paragraph are duplicated in all such forms and that any documentation, advertising materials, and other materials related
to such distribution and use acknowledge that the software was developed by the University of California, Berkeley. The
name of the University may not be used to endorse or promote products derived from this software without specific prior
written permission. THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTIBILITY AND FITNESS FOR A PARTICULAR
PURPOSE.
Van Jacobson (van@helios.ee.lbl.gov), Dec 31, 1989:
- Initial distribution.
Modified June 1993 by Paul Mackerras, paulus@cs.anu.edu.au, so that the entire packet being decompressed doesn't have
to be in contiguous memory (just the compressed header).
--------------------------------------
Copyright 1995-2000 EPFL-LRC/ICA, and are licensed under the GNU Lesser General Public License.
Written 1995-2000 by Werner Almesberger, EPFL-LRC/ICA */
Copyright 2000 Mitchell Blank Jr.
Based in part on work from Jens Axboe and Paul Mackerras.
Updated to ppp-2.4.1 by Bernhard Kaindl
Updated to ppp-2.4.2 by David Woodhouse 2004.
- disconnect method added
- remove_options() abuse removed.
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License
as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version.
------------------------------------------------------------------------------
Copyright (C) 1995 Jean-loup Gailly and Mark Adler
This software is provided 'as-is', without any express or implied warranty. In no event will the authors be held liable for any
damages arising from the use of this software. Permission is granted to anyone to use this software for any purpose,
including commercial applications, and to alter it and redistribute it freely, subject to the following restrictions: 1. The
origin of this software must not be misrepresented; you must not claim that you wrote the original software. If you use this
software in a product, an acknowledgment in the product documentation would be appreciated but is not required. 2.
Altered source versions must be plainly marked as such, and must not be misrepresented as being the original software.
3. This notice may not be removed or altered from any source distribution.
Jean-loup Gailly Mark Adler
gzip@prep.ai.mit.edu madler@alumni.caltech.edu
---------------------------------------
Copyright (C) 2003 Andrew Bartlet <abartlet@samba.org>
Copyright 1999 Paul Mackerras, Alan Curry.
Copyright (C) 2002 Roaring Penguin Software Inc.
Copyright (C) 1996, Matjaz Godec <gody@elgo.si>
Copyright (C) 1996, Lars Fenneberg <in5y050@public.uni-hamburg.de>
Copyright (C) 1997, Miguel A.L. Paraz <map@iphil.net>
Copyright (C) 1995,1996,1997,1998 Lars Fenneberg <lf@elemental.net>
Copyright (C) 2002 Roaring Penguin Software Inc.
Copyright (C) 2003, Sean E. Millichamp <sean at bruenor dot org>
This plugin may be distributed according to the terms of the GNU General Public License, version 2 or (at your option) any
later version.

207
------------------------------------------------------------
Copyright (C) 2000 by Roaring Penguin Software Inc.
This program may be distributed according to the terms of the GNU General Public License, version 2 or (at your option)
any later version.
------------------------------------------------------------
Copyright (C) 2000-2001 by Roaring Penguin Software Inc.
Copyright (C) 2004 Marco d'Itri <md@linux.it>
This program may be distributed according to the terms of the GNU General Public License, version 2 or (at your option)
any later version.
----------------------------------------------------------------
Copyright (c) 2001 by Sun Microsystems, Inc.
All rights reserved.
Non-exclusive rights to redistribute, modify, translate, and use this software in source and binary forms, in whole or in part,
is hereby granted, provided that the above copyright notice is duplicated in any source form, and that neither the name of
the copyright holder nor the author is used to endorse or promote products derived from this software.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND WITHOUT ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, WITHOUT
LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTIBILITY AND FITNESS FOR A PARTICULAR PURPOSE.
Original version by James Carlson
---------------------------------------------------------------------------
Copyright (c) 2002 Google, Inc.
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The name(s) of the authors of this software must not be used to endorse or promote products derived from this
software without prior written permission.
THE AUTHORS OF THIS SOFTWARE DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL THE AUTHORS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
---------------------------------------------------------------------------
Copyright (c) 1999 Tommi Komulainen. All rights reserved.

Administrator’s Handbook
208
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The name(s) of the authors of this software must not be used to endorse or promote products derived from this
software without prior written permission.
4. Redistributions of any form whatsoever must retain the following acknowledgment:
"This product includes software developed by Tommi Komulainen
<Tommi.Komulainen@iki.fi>".
THE AUTHORS OF THIS SOFTWARE DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL THE AUTHORS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Original version, based on RFC2023 :
Copyright (c) 1995, 1996, 1997 Francis.Dupont@inria.fr, INRIA Rocquencourt,
Alain.Durand@imag.fr, IMAG,
Jean-Luc.Richier@imag.fr, IMAG-LSR.
Copyright (c) 1998, 1999 Francis.Dupont@inria.fr, GIE DYADE,
Alain.Durand@imag.fr, IMAG,
Jean-Luc.Richier@imag.fr, IMAG-LSR.
Ce travail a été fait au sein du GIE DYADE (Groupement d'Intérêt Économique ayant pour membres BULL S.A. et l'INRIA). Ce
logiciel informatique est disponible aux conditions usuelles dans la recherche, c'est-à-dire qu'il peut être utilisé, copié,
modifié, distribué à l'unique condition que ce texte soit conservé afin quel'origine de ce logiciel soit reconnue. Le nom de
l'Institut National de Recherche en Informatique et en Automatique (INRIA), de l'IMAG, ou d'une personne morale ou
physique ayant participé à l'élaboration de ce logiciel ne peut être utilisé sans son accord préalable explicite. Ce logiciel est
fourni tel quel sans aucune garantie, support ou responsabilité d'aucune sorte. Ce logiciel est dérivé de sources d'origine
"University of California at Berkeley" et "Digital Equipment Corporation" couvertes par des copyrights. L'Institut
d'Informatique et de Mathématiques Appliquées de Grenoble (IMAG) est une fédération d'unités mixtes de recherche du
CNRS, de l'Institut National Polytechnique de Grenoble et de l'Université Joseph Fourier regroupant sept laboratoires dont
le laboratoire Logiciels, Systèmes, Réseaux (LSR).
This work has been done in the context of GIE DYADE (joint R & D venture between BULL S.A. and INRIA). This software is
available with usual "research" terms with the aim of retain credits of the software. Permission to use, copy, modify and
distribute this software for any purpose and without fee is hereby granted, provided that the above copyright notice and
this permission notice appear in all copies, and the name of INRIA, IMAG, or any contributor not be used in advertising or
publicity pertaining to this material without the prior explicit permission. The software is provided "as is" without any
warranties, support or liabilities of any kind. This software is derived from source code from "University of California at
Berkeley" and "Digital Equipment Corporation" protected by copyrights. Grenoble's Institute of Computer Science and
Applied Mathematics (IMAG) is a federation of seven research units funded by the CNRS, National Polytechnic Institute of
Grenoble and University Joseph Fourier. The research unit in Software, Systems, Networks (LSR) is member of IMAG.
------------------------------------------------------------------------------
Copyright (c) 1995 Eric Rosenquist. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. The name(s) of the authors of this software must not be used to endorse or promote products derived from this
software without prior written permission.

209
THE AUTHORS OF THIS SOFTWARE DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL THE AUTHORS BE LIABLE FOR ANY
SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGESWHATSOEVER RESULTING FROM LOSS OF USE, DATA
OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
-----------------------------------------------------------------------
Copyright (C) Andrew Tridgell 1999-2004
Copyright (C) Anton Blanchard 2001
Copyright (C) Paul `Rusty' Russell 2000
Copyright (C) Jeremy Allison 2000-2003
** NOTE! The following LGPL license applies to the tdb library. This does NOT imply that all of Samba is released under the
LGPL
This library is free software; you can redistribute it and/or modify it under the terms of the GNU Lesser General Public
License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied
warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Lesser General Public License for
more details.
You should have received a copy of the GNU Lesser General Public License along with this library; if not, write to the Free
Software Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
radvd 1.8.3
radvd license
The author(s) grant permission for redistribution and use in source and binary forms, with or without modification, of the
software and documentation provided that the following conditions are met:
0. If you receive a version of the software that is specifically labelled as not being for redistribution (check the version
message and/or README), you are not permitted to redistribute that version of the software in any way or form.
1. All terms of all other applicable copyrights and licenses must be followed.
2. Redistributions of source code must retain the authors' copyright notice(s), this list of conditions, and the following
disclaimer.
3. Redistributions in binary form must reproduce the authors' copyright notice(s), this list of conditions, and the following
disclaimer in the documentation and/or other materials provided with the distribution.
4. All advertising materials mentioning features or use of this software must display the following acknowledgement with
the name(s) of the authors as specified in the copyright notice(s) substituted where indicated: This product includes
software developed by the authors which are mentioned at the start of the source files and other contributors.
5. Neither the name(s) of the author(s) nor the names of its contributors may be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY ITS AUTHORS AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHORS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
SimCList Component
Copyright (c) 2007,2008 Mij
Dropbear - a SSH2 server 0.52
Copyright (c) 2002-2008 Matt Johnston
Portions copyright (c) 2004 Mihnea Stoenescu
All rights reserved.

Administrator’s Handbook
210
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation
files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy,
modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice
shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS ORIMPLIED, INCLUDING BUT NOT
LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
=====
LibTomCrypt and LibTomMath are written by Tom St Denis, and are Public Domain.
=====
sshpty.c is taken from OpenSSH 3.5p1,
Copyright (c) 1995 Tatu Ylonen <ylo@cs.hut.fi>, Timo Rinne <tri@iki.fi>,Espoo, Finland
All rights reserved
"As far as I am concerned, the code I have written for this software can be used freely for any purpose. Any derived versions
of this software must be clearly marked as such, and if the derived work is incompatible with the protocol description in
the RFC file, it must be called by a name other than "ssh" or "Secure Shell". "
=====
loginrec.c is written primarily by Andre Lucas, Jason Downs, Theo de Raadt:
Copyright (c) 2000 Andre Lucas.
Portions copyright (c) 1998 Todd C. Miller
Portions copyright (c) 1996 Jason Downs
Portions Copyright (c) 1996 Theo de Raadt.
loginrec.h is written by Andre Lucas:
Copyright (c) 2000 Andre Lucas.
atomicio.h,atomicio.c written by Theo de Raadt (1995-1999)
Copyright (c) 1995,1999 Theo de Raadt.
And are licensed under the following terms:
Copyright (c) <YEAR>, <OWNER>
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met: Redistributions of source code must retain the above copyright notice, this list of conditions and the
following disclaimer.
Redistributions in binary form must reproduce the above copyright notice,this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED
TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
=====

211
strlcat() is (c) Todd C. Miller (included in util.c -- ) are from OpenSSH 3.6.1p2, and are licensed
under the BSD-Modified license:
Copyright (c) 1998 Todd C. Miller , < OWNER > All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met: Redistributions of source code must retain the above copyright notice, this list of conditions and the
following disclaimer. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and
the following disclaimer in the documentation and/or other materials provided with the distribution. Neither the name of
the < ORGANIZATION > nor the names of its contributors may be used to endorse or promote products derived from this
software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE
COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT
OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
=====
Import code in keyimport.c is modified from PuTTY's import.c, licensed as follows:
PuTTY is copyright 1997-2003 Simon Tatham.
Portions copyright Robert de Bath, Joris van Rantwijk, Delian Delchev, Andreas Schultz, Jeroen Massar, Wez Furlong,
Nicolas Barry, Justin Bradford, and CORE SDI S.A.
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation
files (the "Software"), to deal in the Software without restriction,including without limitation the rights to use, copy,
modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice
shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT
LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE
USE OR OTHER DEALINGS IN THE SOFTWARE.
WIDE-DHCPv6
Copyright (C) 2002 WIDE Project.
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. Neither the name of the project nor the names of its contributors may be used to endorse or promote products derived
from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE PROJECT AND CONTRIBUTORS ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE PROJECT OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
Copyright (C)2000 YOSHIFUJI Hideaki
Copyright (c) 1995, 1999 Berkeley Software Design, Inc.

Administrator’s Handbook
212
zlib 1.2.3
Copyright (C) 1995-2005 Jean-loup Gailly and Mark Adler
This software is provided 'as-is', without any express or implied warranty. In no event will the authors be held liable for
any damages arising from the use of this software. Permission is granted to anyone to use this software for any purpose,
including commercial applications, and to alter it and redistribute it freely, subject to the following restrictions:
1. The origin of this software must not be misrepresented; you must not claim that you wrote the original software. If you
use this software in a product, an acknowledgment in the product documentation would be appreciated but is not
required.
2. Altered source versions must be plainly marked as such, and must not be misrepresented as being the original software.
3. This notice may not be removed or altered from any source distribution.
Copyright (c) Mark Adler
Portions Copyright ARRIS Group, Inc. 2009-2012
Portions Copyright Broadcom Corporation
Portions Copyright AltoCom, Inc.

213
Appendix A ARRIS Gateway Captive Portal
Implementation
This section contains information about the ARRIS Gateway Captive Portal Support.

Administrator’s Handbook
214
Overview
ARRIS follows the 2Wire RPC specification for implementation of Captive Portal.
The Captive Portal feature redirects all TCP traffic destined to port 80 and redirects it to a Captive Portal URL. A
White-IP address list can be configured to avoid the captive portal redirect. All HTTP traffic destined to the IP
addresses within this white IP address list will not be redirected to the Captive Portal. Any Changes to the
Captive Portal parameters will take place immediately and do not require a reboot.
PortalURL can be a maximum of 512 characters long.
A maximum of 500 White-IP addresses are supported. The White-IP address list takes a comma-separated
string, which can be Individual IP addresses or a range of IP addresses. For a range of IP addresses, a subnet
mask is required.
The following formats of IP address are accepted:
• Individual IP address - 144.130.120.62 or 144.130.120.62/32
• Range of 64 IP addresses - 144.130.120.64/26
The White-IP address list gets rewritten on any changes.
Clearing the Captive Portal URL disables Captive Portal. Turning off the enable parameter can also disable
Captive Portal functionality.
Captive Portal is disabled by default and enabled via TR-069
The white list can be a combination of FQDN (fully qualified domain names) and White-IP address/CIDR.
FQDNs will be resolved to IP addresses on boot and whenever a new list is pushed.
For the NVG599, Captive Portal implementation only redirects port 80 traffic. Traffic to port 443 is allowed.
DNS Traffic will not be blocked.

215
Captive Portal RPC
RPC supported per 2Wire requirements that will set Captive Portal parameters.
<xs:schema xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:tns="urn:dslforum-org:cwmp-1-0"
targetNamespace="urn:dslforum-org:cwmp-1-0"
elementFormDefault="unqualified"
attributeFormDefault="unqualified">
<xs:import namespace="http://schemas.xmlsoap.org/soap/envelope/"
schemaLocation="soapenv.xsd"/>
<xs:import namespace="http://schemas.xmlsoap.org/soap/encoding/"
schemaLocation="soapenc.xsd"/>
<xs:complexType name="CaptivePortalParamStruct">
<xs:sequence>
<xs:element name="Enable" type="soapenc:boolean">
<xs:annotation>
<xs:documentation>If true, the Captive Portal is enabled.<
xs:documentation>
<xs:documentation>If false, the Captive Portal is
disabled.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="RedirectURL">
<xs:annotation>
<xs:documentation>the URL to be redirected to.<
xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:maxLength value="512"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
<xs:element name="WhiteList" type="tns:WhiteList">
<xs:annotation>
<xs:documentation>a list of sites and IP address to be
escaped by the Captive Portal.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
X_00D09E_GetCaptivePortalParams RPC:
<!-- X_00D09E_GetCaptivePortalParams -->
<xs:element name="X_00D09E_GetCaptivePortalParams">
<xs:annotation>
<xs:documentation>X_00D09E_GetCaptivePortalParams message is
to get the Captive Portal parameters on a CPE.</xs:documentation>
</xs:annotation>
<xs:complexType/>
</xs:element>

Administrator’s Handbook
216
<!-- X_00D09E_GetCaptivePortalParamsResponse -->
<xs:element name="X_00D09E_GetCaptivePortalParamsResponse">
<xs:annotation>
<xs:documentation>X_00D09E_GetCaptivePortalParamsResponse
response message for X_00D09E_GetCaptivePortalParams request.<
xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="CaptivePortalParamStruct"
type="tns:CaptivePortalParamStruct"/>
</xs:sequence>
</xs:complexType>
</xs:element>
X_00D09E_SetCaptivePortalParams RPC:
<!-- X_00D09E_SetCaptivePortalParams -->
<xs:element name="X_00D09E_SetCaptivePortalParams">
<xs:annotation>
<xs:documentation>X_00D09E_SetCaptivePortalParams message to
set the Captive Portal parameters on a CPE.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="CaptivePortalParamStruct"
type="tns:CaptivePortalParamStruct"/>
</xs:sequence>
</xs:complexType>
</xs:element>
<!-- X_00D09E_SetCaptivePortalParamsResponse -->
<xs:element name="X_00D09E_SetCaptivePortalParamsResponse">
<xs:annotation>
<xs:documentation>X_00D09E_SetCaptivePortalParamsResponse
response message is a response for X_00D09E_SetCaptivePortalParams
request.</xs:documentation>
</xs:annotation>
<xs:complexType/>
</xs:element>

217
Appendix B Quality of Service (QoS) Examples
This section contains information about the ARRIS Gateway QoS implementation.
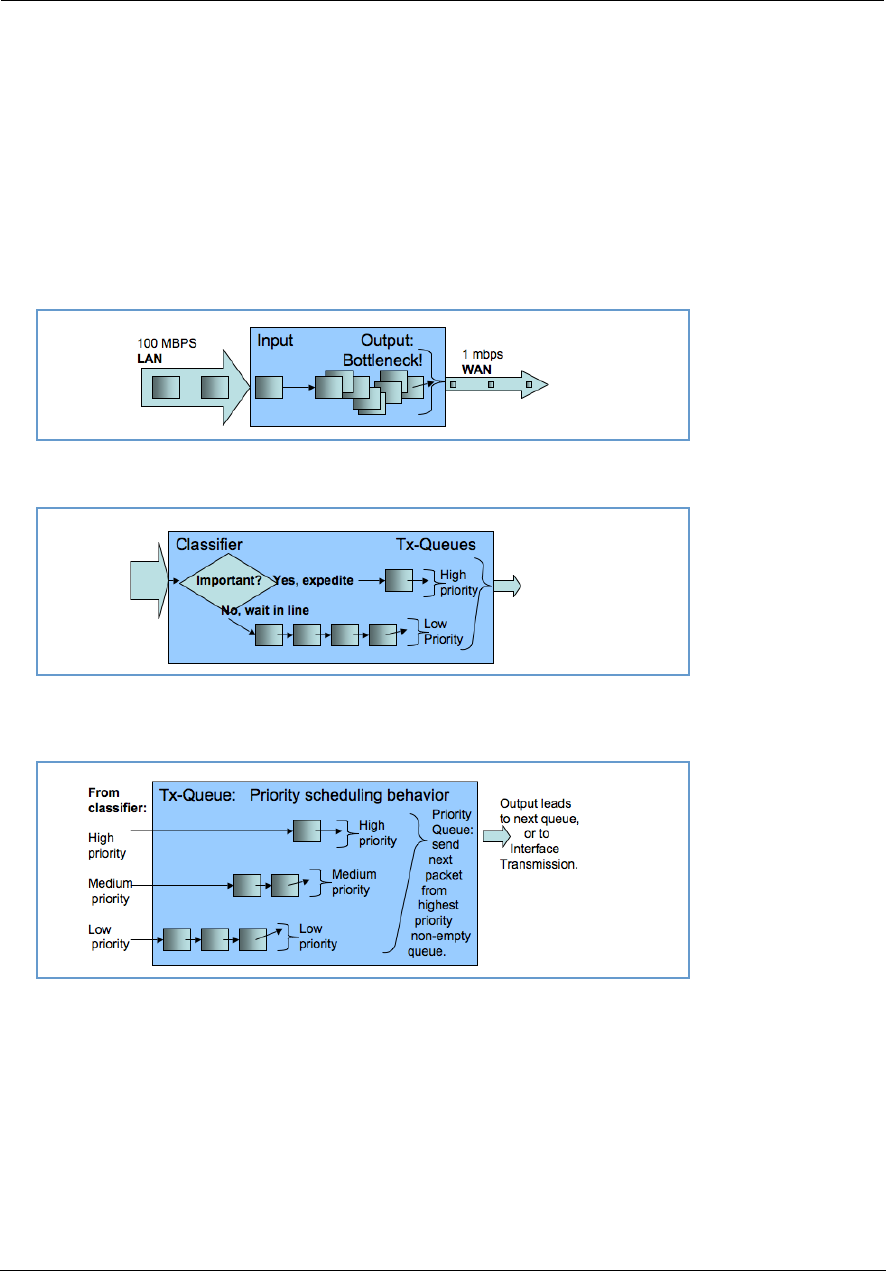
Administrator’s Handbook
218
Overview
When packets arrive on a high speed interface and are forwarded to a low speed interface, there is contention
for bandwidth. This is the use case for QoS: to make effective use of bandwidth.
The basic steps for Quality of Service are to match and identify packets as belonging to a class of traffic, and to
give each class of traffic a certain behavior such as priority queuing or bandwidth shaping across critical
networking bottlenecks.
Packets forwarded through the system are classified using sets of filter rules to match various criteria, for
example p-bit, DSCP, IP address, port, etc. The matching rule can set the classification, which is the name of the
queue that is to be used.
Figure 1. Illustration of upstream congestion, all traffic is consistently delayed.
Figure 2. Illustration of classification and transmit queue in a simple high/low priority scheme. Low priority may transmit
only when high priority is completely empty.
Figure 3. Illustration of priority scheduling
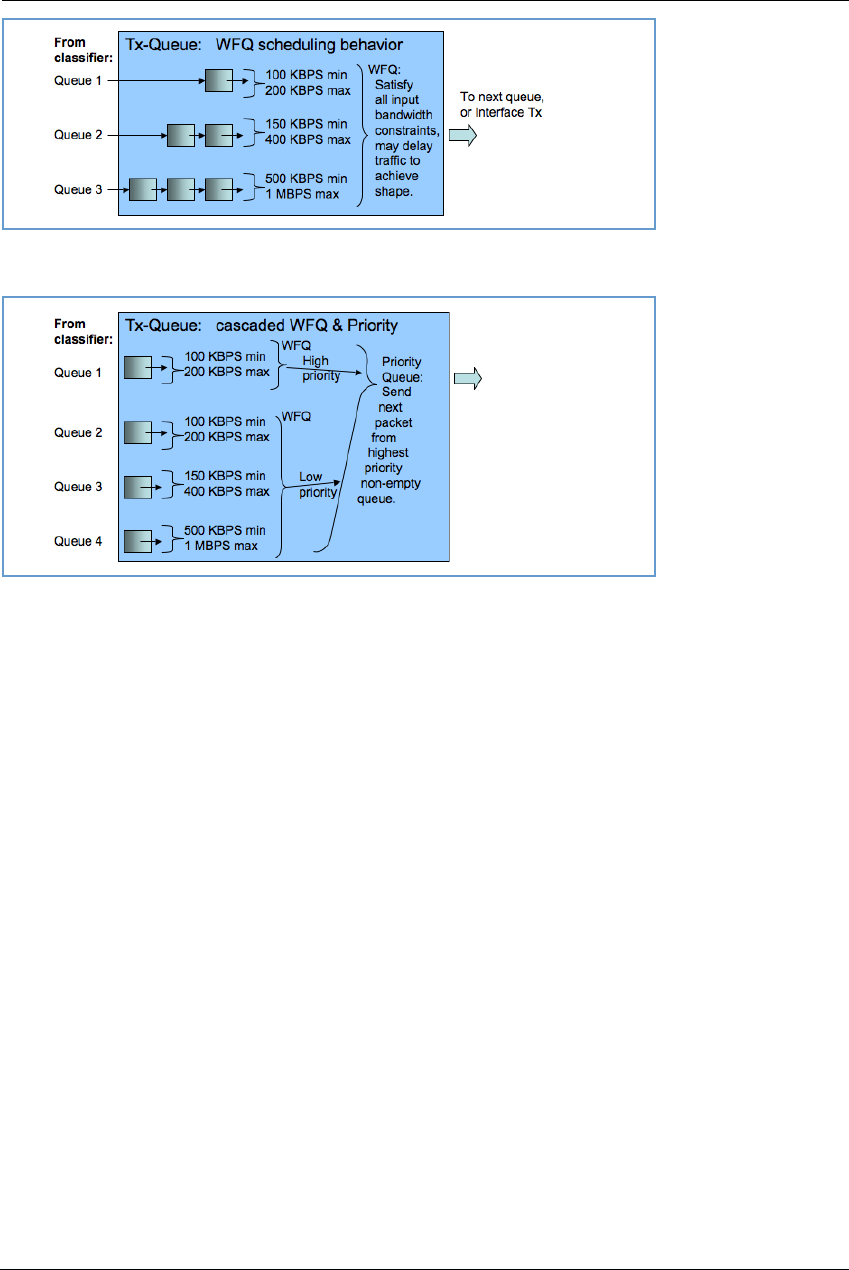
219
Figure 4. Illustration of weighted fair queue scheduling
Figure 5. Illustration of a hybrid queue that is both priority and WFQ, to both constrain bandwidth usage and expedite one of
the queues.
After the packet has been classified, it can be put in the proper queue. Queues are assigned to interfaces and
can be constructed of several queue components to deliver the desired behavior. The components of an
interface queue are these building blocks:
basic queues: a 1 input 1 output packet list with a length of 64 packets by default. Packets will tail-drop
when the enqueued to a full basic queue.
priority queue: 2 or more input, 1 output. Schedules the packets from the various inputs strictly according to
input's priority.
weighted fair queue: 1 or more input, 1 output. Schedules the packets according to bandwidth constraints
Packets are enqueued to basic queues, and only to basic queues. Basic queues are output to priority queues
and weighted fair queues, which act as “plumbing” elements that alter the dequeuing order and rate,
respectively. Priority queues and weighted fair queues can contain one another.
Weighted fair queues are used to constrain bandwidth. For example, consider a weighted fair queue with three
basic queues as inputs, EF, AF and BE:
WFQ
Input 1: EF
Input 2: AF
Input 3: BE
Each input entry is configured with a weight value, which is the rate at which to limit the traffic. This weight can
be either absolute (bps) or a relative percentage of the interface's data-rate. This allows dedicating a split
amount of bandwidth to each queue. A special value for the weight parameter is zero, which will use the
remainder of unclaimed bandwidth.
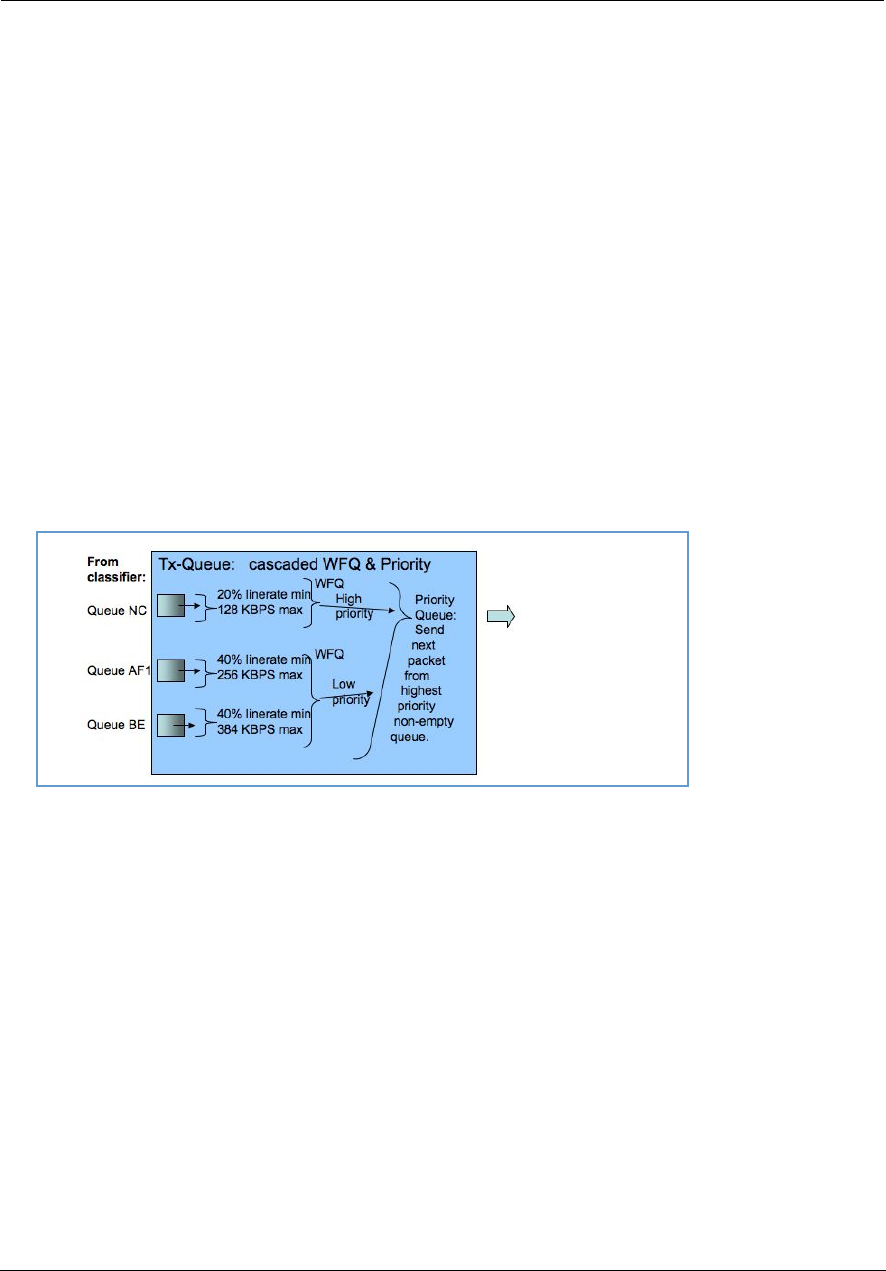
Administrator’s Handbook
220
There is an option to enable bandwidth sharing, so that unused bandwidth in idle queues can be shared to
other queues. When the traffic resumes in the previously idle queue, the previously shared-out bandwidth is
taken back.
When bandwidth sharing is enabled, a secondary rate configuration appears on each input entry, the peak
parameter. This is a hard limit on the amount of bandwidth that the particular input entry can use. This rate
will not be exceeded, even if there is an excess pool of idle bandwidth that could otherwise be shared.
Upstream QoS: Priority and Shaping
The gateway uses the DSL sync rate to determine traffic shaping requirements for WAN traffic. In this case
there are 6 basic queues, and a hierarchy of both priority queue and weighted fair queue (WFQ) with
bandwidth sharing and dual rate shaping. First the packets are classified via the filterset, to set the QoS-marker
with the name of the desired basic queues. The queues are shown here, with packets traveling from left to
right. Each basic queue feeds into a WFQ entry, and is shaped between the minimum bandwidth defined by
weight, and the maximum rate defined by peak. If there is sufficient bandwidth, the WFQ entry shapes at the
peak rate. If there is no spare bandwidth available for sharing, then the queue is shaped at the weight rate.
The weight rate is defined either as a bps value, or as a percentage of line-rate that is determined once the
upstream WAN data-rate is acquired. This weight value behaves as a committed information rate (CIR), and the
peak value behaves as a peak information rate (PIR.)
Figure 6. Illustration of default queues used for AT&T
Packet Rx > Filterset Rules:
Match Rule 1? Set QoS marker = EF
Match Rule 2? Set QoS marker = AF1
Match Rule 3? Set QoS marker = BE
EF CIR/PIR -> wfq_hi -> PQ1 \
AF4 CIR/PIR \ > PQ output to interface Tx
AF3 CIR/PIR \ /
AF2 CIR/PIR > wfq_lo > PQ2 /
AF1 CIR/PIR /
BE CIR/PIR /

221
Downstream QoS: Ethernet Switch
The simplest way of handling downstream QoS (from WAN to LAN) is to use the per-port queues that are
present in the Ethernet switch. This achieves the greatest efficiency since the queues are handled in the switch
hardware, and should be used when a strict priority queue with 4 priorities is sufficient.
The traffic is classified by priority-bit value. This can be the value retained from WAN ingress (assuming WAN is
tagged,) or it can be a value that is set via a filter rule, which allows for advanced classification criteria to be
used. Even though the LAN interface might not be tagged, there is still an internal priority field which is used to
convey this information to the switch.
Downstream QoS: Egress queues
The secondary method of downstream QoS is to assign egress queues to the LAN port configuration. This is less
efficient, however it allows more advanced queue scheduling algorithms to be used. Packets are classified by
QoS markers set by filter rules.
NOTE:
This method is typically not recommended for deployment configuration as this mechanism can
consume a large amount of CPU processing bandwidth.

Administrator’s Handbook
222
223
Index
Symbols
!! command
106
A
Access Code
30
Address resolution table
113
Administrator password
105
Arguments, CLI
118
ARP
Command
107, 116
B
basic queues
219
Broadband Network Redirect
22
Broadband Status
34
Broadband Status Notification
86
C
Call Statistics
55
Captive Portal
213
CLI
101
!! command
106
Arguments
118
Command shortcuts
106
Command truncation
118
Configuration mode
118
Keywords
118
Navigating
118
Prompt
106, 118
Restart command
106
SHELL mode
106
View command
119
Command
ARP
107, 116
Ping
108
Telnet
115
Command line interface (see CLI)
CONFIG
Command List
104
Configuration mode
118
Connection commands
121
Custom Service
69
D
Default Server
75
designing a new filter set
61
Detect Missing Filter
79
Device Access Code
24
Device List
28
DHCP lease table
109
Diagnostic log
109, 114
Diagnostics
78
Documentation conventions
8
Downstream QoS
221
E
Ethernet statistics
109
Event Notifications
86
F
filter
parts
61
parts of
61
filter sets
using
62
filters
using
61, 62
firewall
113
Firewall Advanced
76
Firewall Status
59
G
Global Filterset
128
H
Help
27
Home Network
39
HPNA
51
HPNA Configure
42
Administrator’s Handbook
224
I
ICMP Echo
108
IGMP
139
IGMP Snooping
140
IGMP Stats
38
IP DNS commands
139
IP Gateway commands
132
IP IGMP commands
139
IP interfaces
113
IP Passthrough
73
IP routes
113
IPMap table
113
K
Keywords, CLI
118
L
LAN Ethernet Statistics
41
LAN Host Discovery Table
113
LEDs
13
Link commands
143
links bar
27
Log
114
Logging in
105
Logs
81
M
MAC Filtering
46
Management commands
146
Memory
114
Missing Filter Notification
86
N
NAT Pinhole commands
157
NAT Table
86
NAT/Gaming
67
NSLookup
79
NTP commands
142
P
Packet Filters
60
Password
Administrator
105
User
105
Physical interfaces commands
150
Ping
79
Ping command
108
PPP
117
priority queue
219
Prompt, CLI
106, 118
Q
QoS
217
Quality of Service
217
R
Redirect page
23, 149
Reset Connection
84
Reset Device
84
Reset IP
84
Resets
84
Restart
84, 110
Restart command
106
Restart Modem
33
S
Safety Instructions
12
Security
filters
60
Session Initiation Protocol
160
SHELL
Command Shortcuts
106
Commands
106
Prompt
106
SHELL level
118
SHELL mode
106
show config
110
Show ppp
117
SIP
160
Step mode
119
Subnets & DHCP
47
Supported Games and Software
71
Syslog
85
System commands
173
System Information
29
225
T
tab bar
27
Targeted Ad Insertion
171
Telnet
105
Telnet command
115
Test Web Access
79
TFTP server
108
Traceroute
79
Trivial File Transfer Protocol
107
Troubleshoot
78
Truncation
118
U
Update
83
Upstream QoS
220
User name
105
User password
105
V
View command
119
view config
115
Voice
53
Voice-over-IP
160
VoIP
160
W
weighted fair queue
219
WiFi-Key
45
Wireless
43
Wireless Security
45

Administrator’s Handbook
226

227
ARRIS
®
DSL Gateways
ARRIS Enterprises, Inc.
600 North U.S. Highway 45
Libertyville, Illinois 60048 USA
Telephone: +1 847 523 5000
December 6, 2013

Administrator’s Handbook
228