D Link DIR628A2 RangeBooster N Dual Band Router User Manual 6
D Link Corporation RangeBooster N Dual Band Router 6
D Link >
Contents
User manual 6
69D-Link DIR-628 User Manual
Section 3 - Configuration
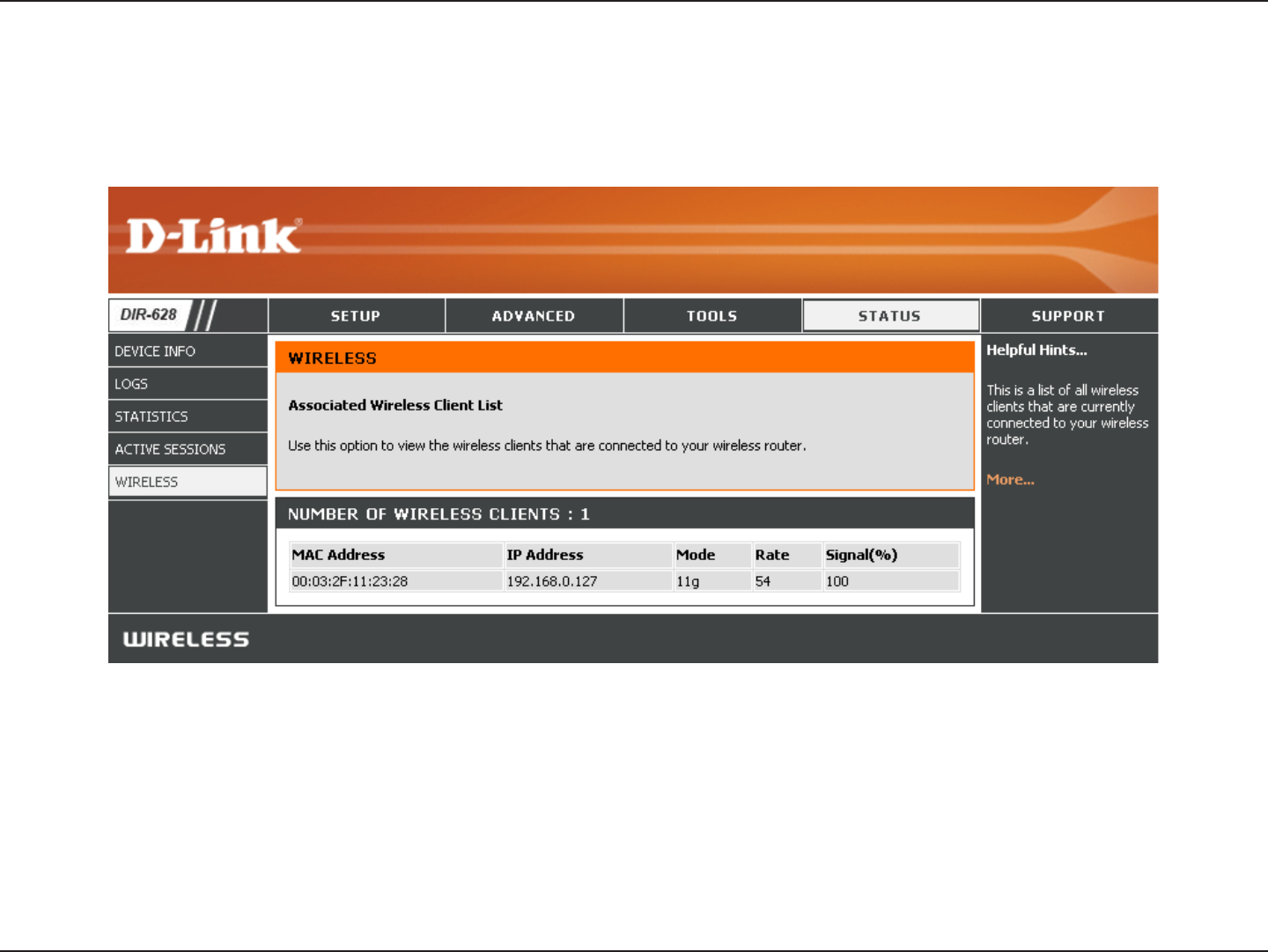
The wireless client table displays a list of current connected wireless clients. This table also displays the connection
time and MAC address of the connected wireless clients.
Wireless
70D-Link DIR-628 User Manual
Section 3 - Configuration
Support
71D-Link DIR-628 User Manual
Section 4 - Security
Wireless Security
This section will show you the different levels of security you can use to protect your data from intruders. The
DIR-655 offers the following types of security:
• WPA2 (Wi-Fi Protected Access 2) • WPA2-PSK (Pre-Shared Key)
• WPA (Wi-Fi Protected Access) • WPA-PSK (Pre-Shared Key)
What is WPA?
WPA, or Wi-Fi Protected Access, is a Wi-Fi standard that was designed to improve the security features of WEP (Wired
Equivalent Privacy).
The 2 major improvements over WEP:
• Improved data encryption through the Temporal Key Integrity Protocol (TKIP). TKIP scrambles the keys
using a hashing algorithm and, by adding an integrity-checking feature, ensures that the keys haven’t
been tampered with. WPA2 is based on 802.11i and uses Advanced Encryption Standard (AES) instead
of TKIP.
• User authentication, which is generally missing in WEP, through the extensible authentication protocol
(EAP). WEP regulates access to a wireless network based on a computer’s hardware-specific MAC
address, which is relatively simple to be sniffed out and stolen. EAP is built on a more secure public-key
encryption system to ensure that only authorized network users can access the network.
WPA-PSK/WPA2-PSK uses a passphrase or key to authenticate your wireless connection. The key is an alpha-numeric
password between 8 and 63 characters long. The password can include symbols (!?*&_) and spaces. This key must
be the exact same key entered on your wireless router or access point.
WPA/WPA2 incorporates user authentication through the Extensible Authentication Protocol (EAP). EAP is built on a
more secure public key encryption system to ensure that only authorized network users can access the network.
72D-Link DIR-628 User Manual
Section 4 - Security
Wireless Security Setup Wizard
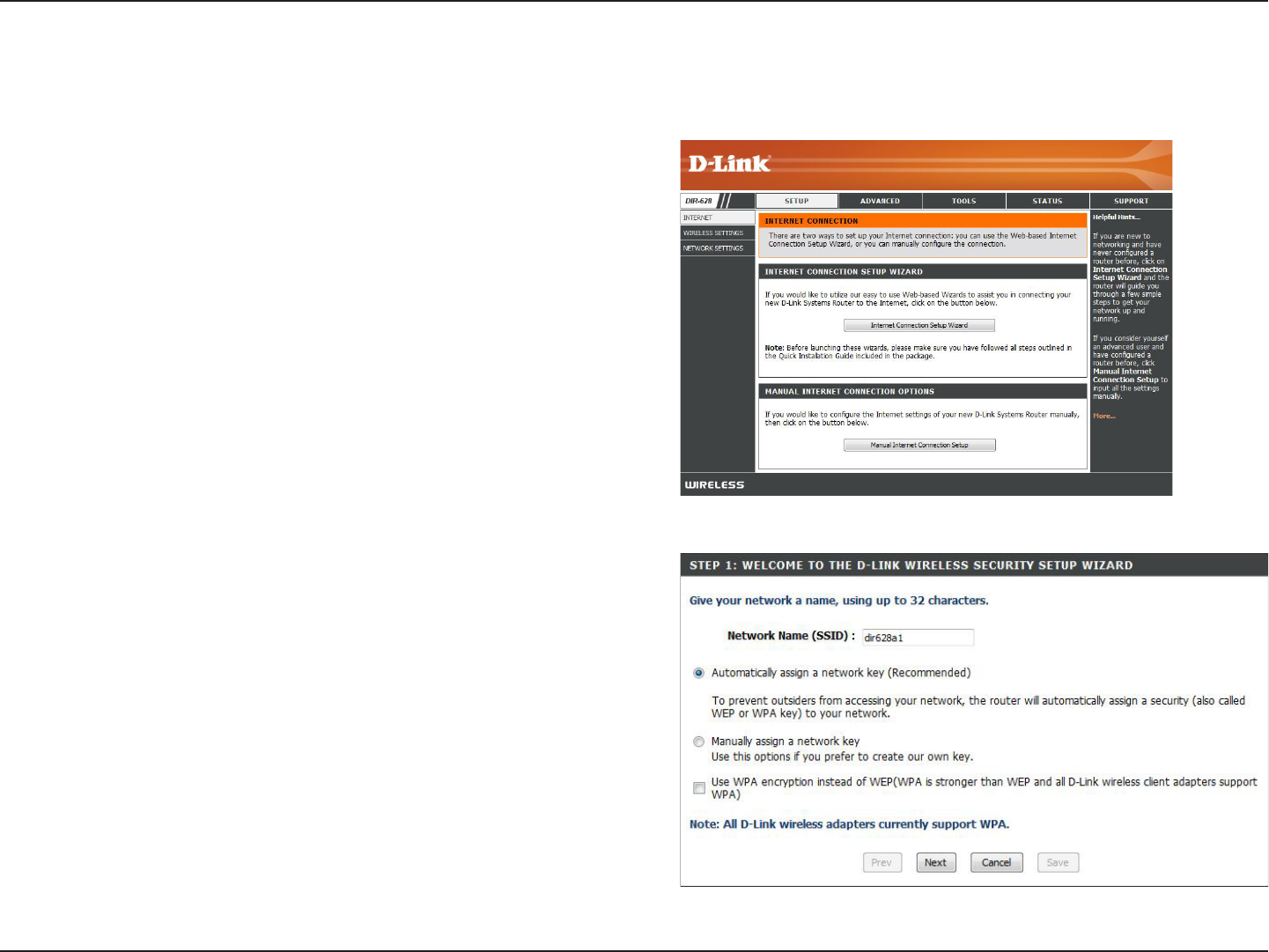
To run the security wizard, click on Setup at the top and then
click Launch Wireless Security Setup Wizard.
Type your desired wireless network name (SSID).
Automatically: Select this option to automatically
generate the router’s network key and click Next.
Manually: Select this option to manually enter your
network key and click Next.
73D-Link DIR-628 User Manual
Section 4 - Security
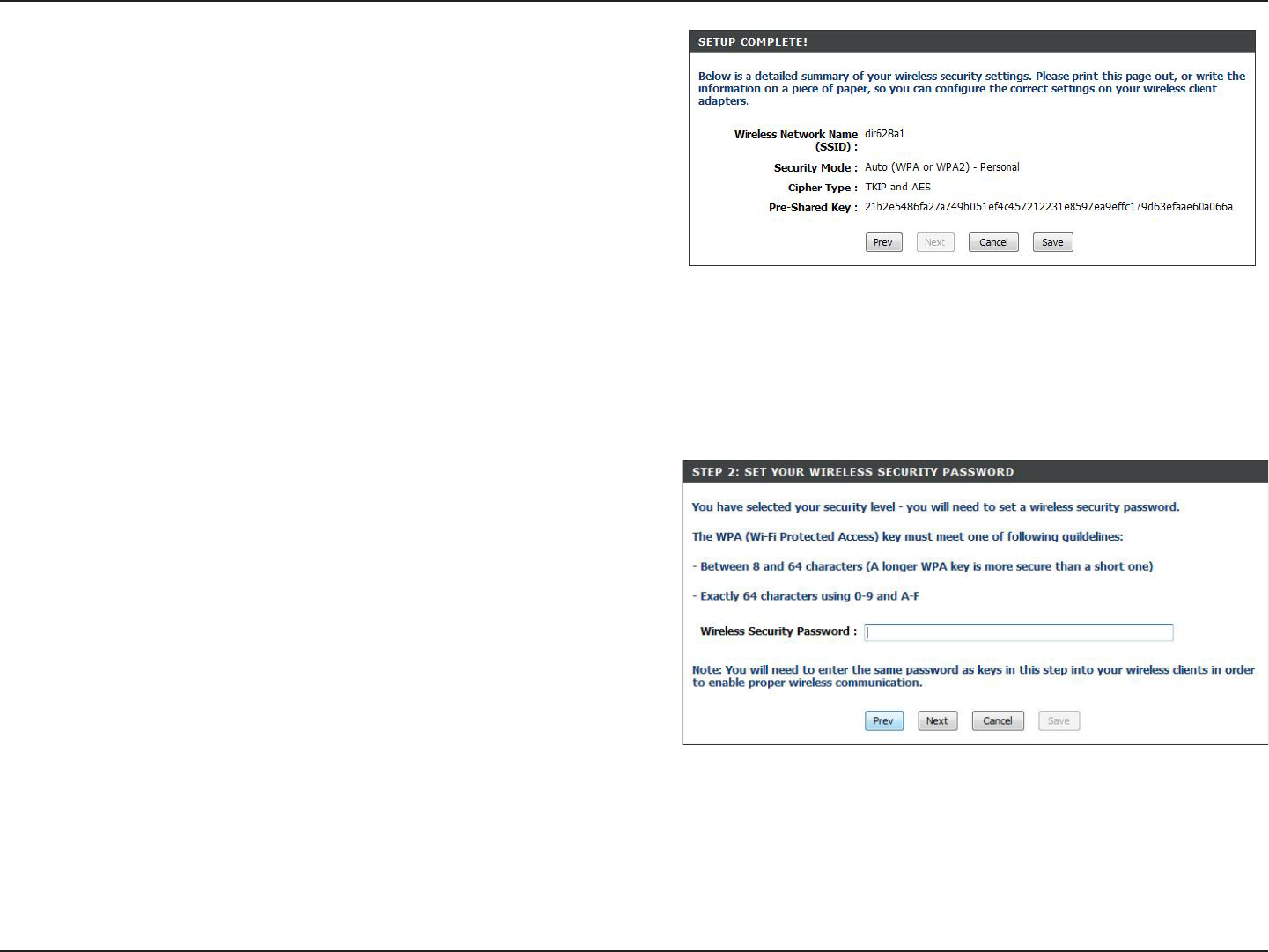
If you selected Automatically, the summary window will
display your settings. Write down the security key and
enter this on your wireless clients. Click Save to save your
settings.
If you selected Manually, the following screen will appear.
74D-Link DIR-628 User Manual
Section 4 - Security
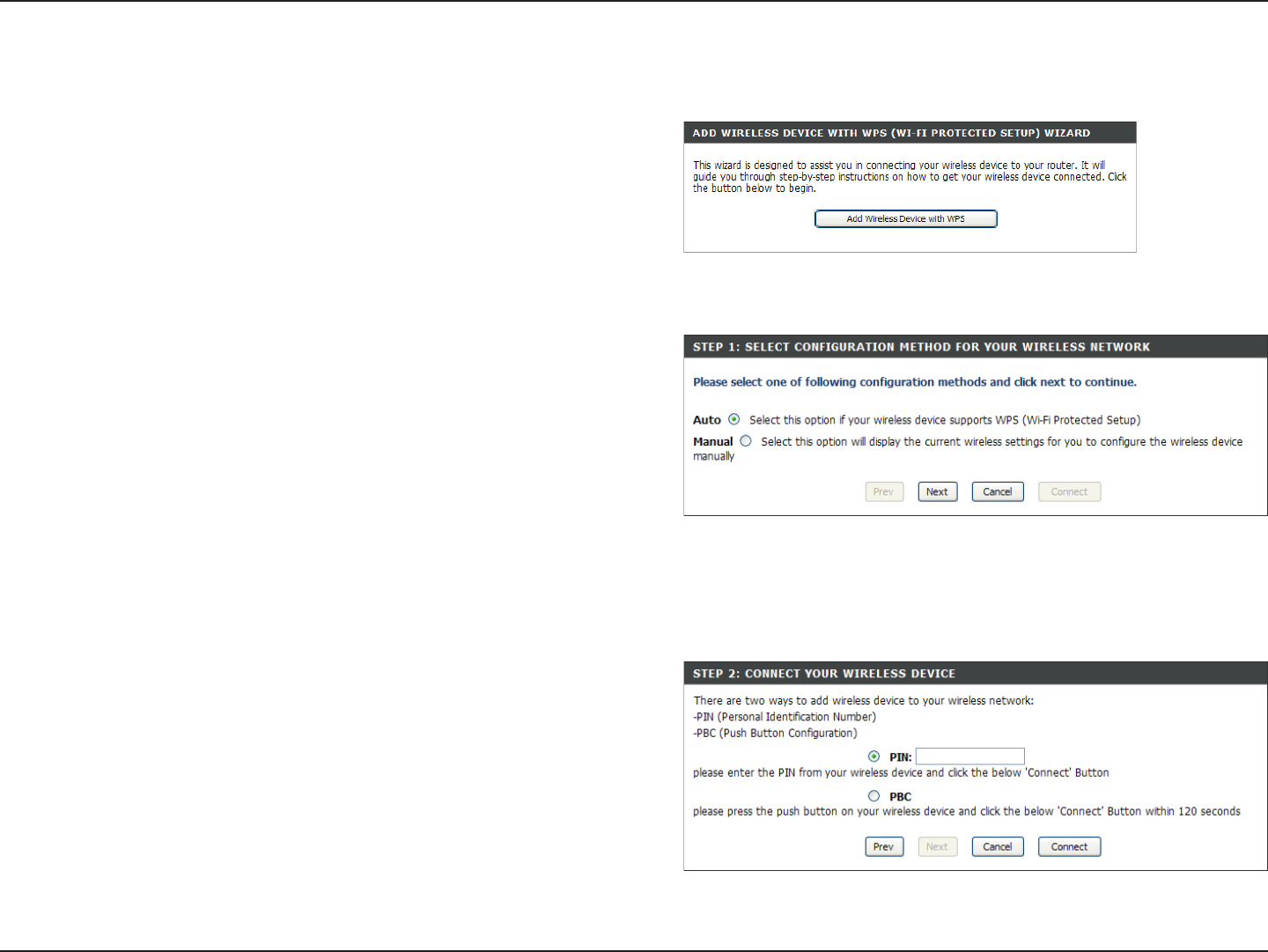
From the Basic > Wizard screen, click Add Wireless Device
with WPS.
Add Wireless Device with WPS Wizard
PIN: Select this option to use PIN method. In order to use this
method you must know the wireless client’s 8 digit PIN and
click Connect.
PBC: Select this option to use PBC (Push Button) method to
add a wireless client. Click Connect.
Select Auto to add a wireless client using WPS (Wi-Fi Protected
Setup). Once you select Auto and click Connect, you will have
a 120 second time limit to apply the settings to your wireless
client(s) and successfully establish a connection.
If you select Manual, a settings summary screen will appear.
Write down the security key and enter this on your wireless
clients.
75D-Link DIR-628 User Manual
Section 4 - Security
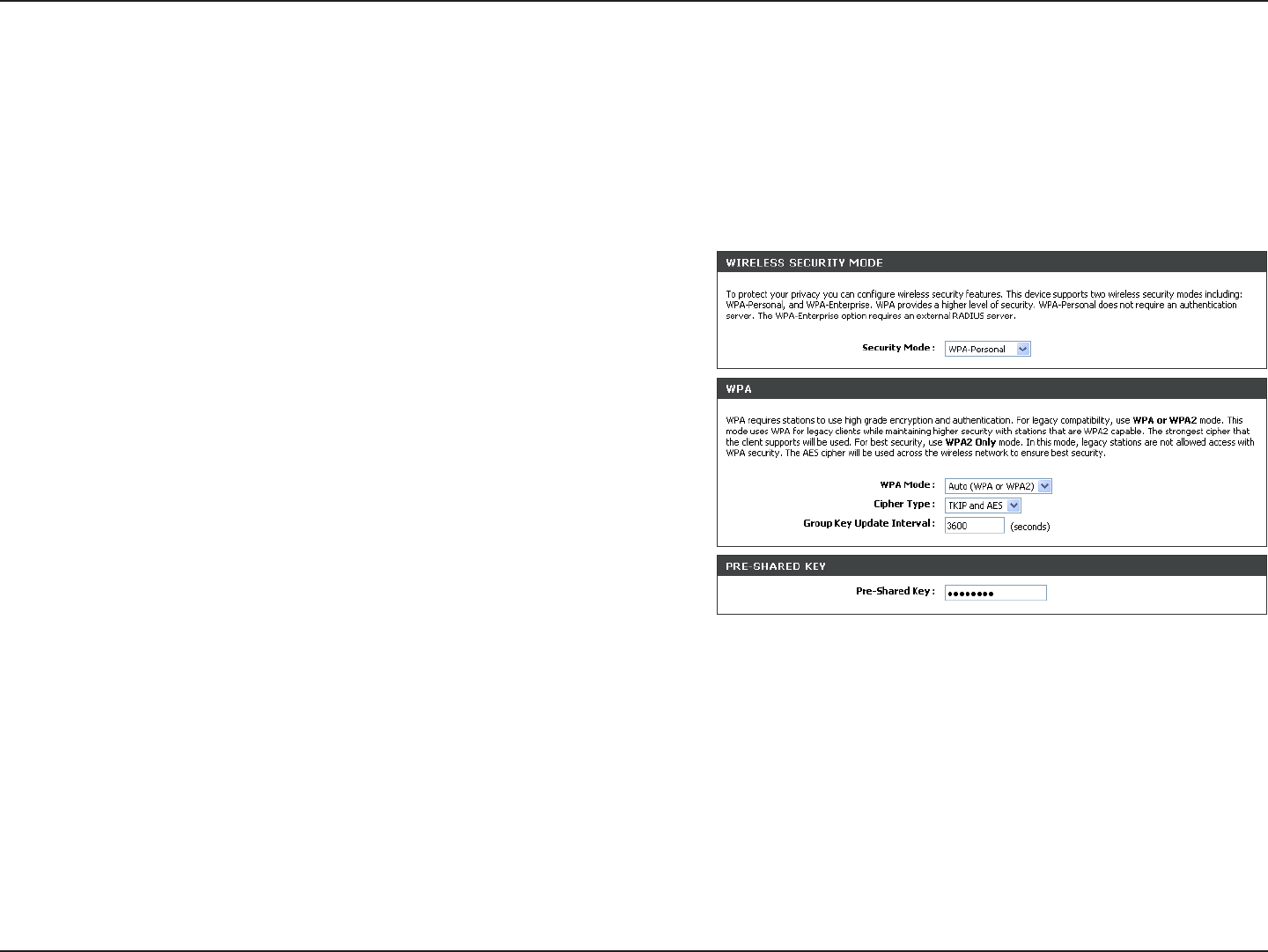
Configure WPA-Personal (PSK)
It is recommended to enable encryption on your wireless router before your wireless network adapters. Please establish
wireless connectivity before enabling encryption. Your wireless signal may degrade when enabling encryption due to
the added overhead.
1. Log into the web-based configuration by opening a web browser
and entering the IP address of the router (192.168.0.1). Click
on Setup and then click Wireless Settings on the left side.
2. Next to Security Mode, select WPA-Personal.
3. Next to WPA Mode, select Auto, WPA2 Only, or WPA Only. Use
Auto if you have wireless clients using both WPA and WPA2.
4. Next to Cypher Type, select TKIP and AES, TKIP, or AES.
5. Next to Group Key Update Interval, enter the amount of time
before the group key used for broadcast and multicast data is
changed (3600 is default).
6. Next to Pre-Shared Key, enter a key (passphrase). The key is entered as a pass-phrase in ASCII format at both ends
of the wireless connection. The pass-phrase must be between 8-63 characters.
7. Click Save Settings to save your settings. If you are configuring the router with a wireless adapter, you will lose
connectivity until you enable WPA-PSK on your adapter and enter the same passphrase as you did on the router.
76D-Link DIR-628 User Manual
Section 4 - Security
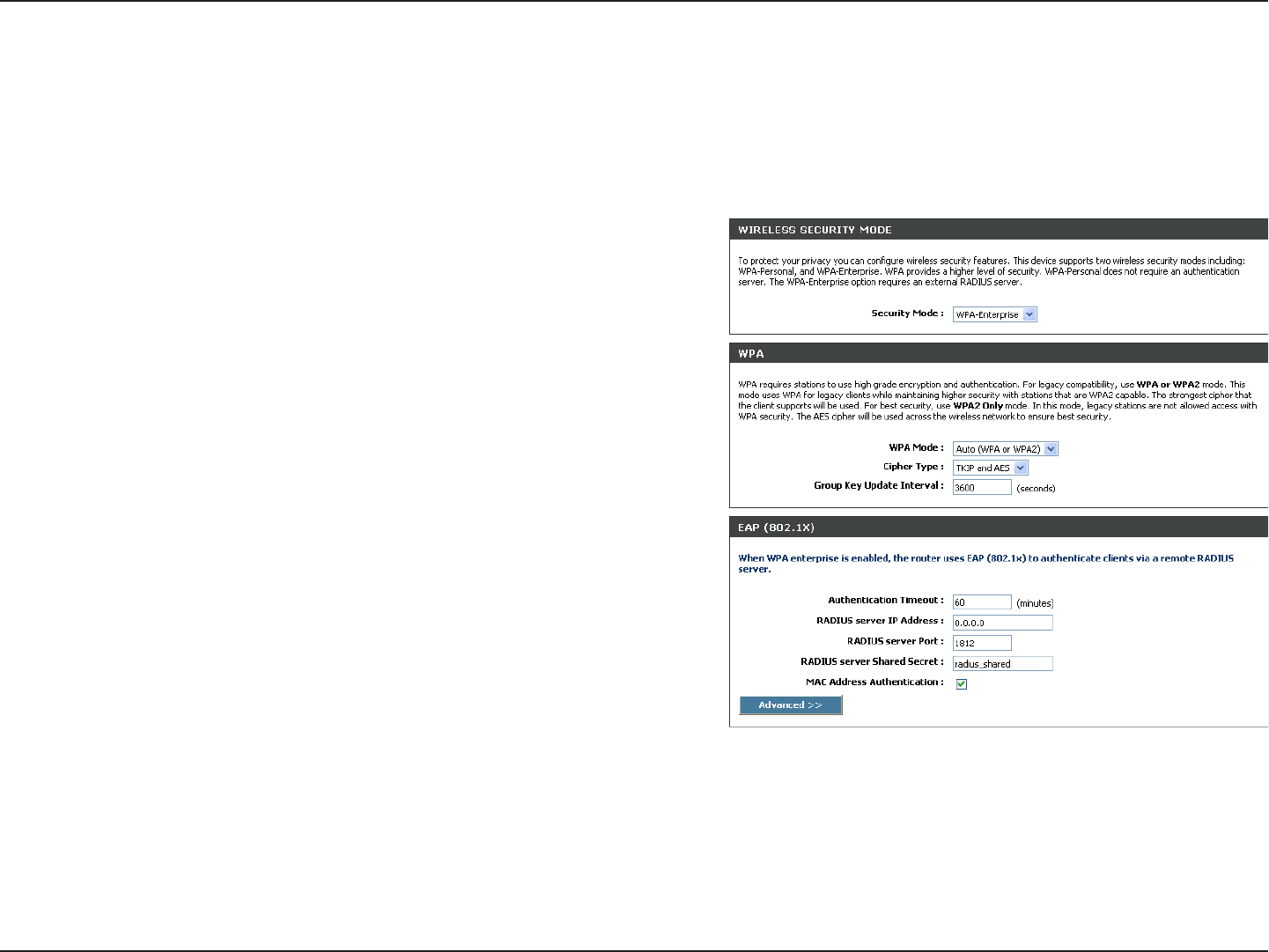
It is recommended to enable encryption on your wireless router before your wireless network adapters. Please establish
wireless connectivity before enabling encryption. Your wireless signal may degrade when enabling encryption due to
the added overhead.
1. Log into the web-based configuration by opening a web browser
and entering the IP address of the router (192.168.0.1). Click
on Setup and then click Wireless Settings on the left side.
2. Next to Security Mode, select WPA-Enterprise.
3. Next to WPA Mode, select Auto, WPA2 Only, or WPA Only. Use
Auto if you have wireless clients using both WPA and WPA2.
4. Next to Cypher Type, select TKIP and AES, TKIP, or AES.
5. Next to Group Key Update Interval, enter the amount of time
before the group key used for broadcast and multicast data is
changed (3600 is default).
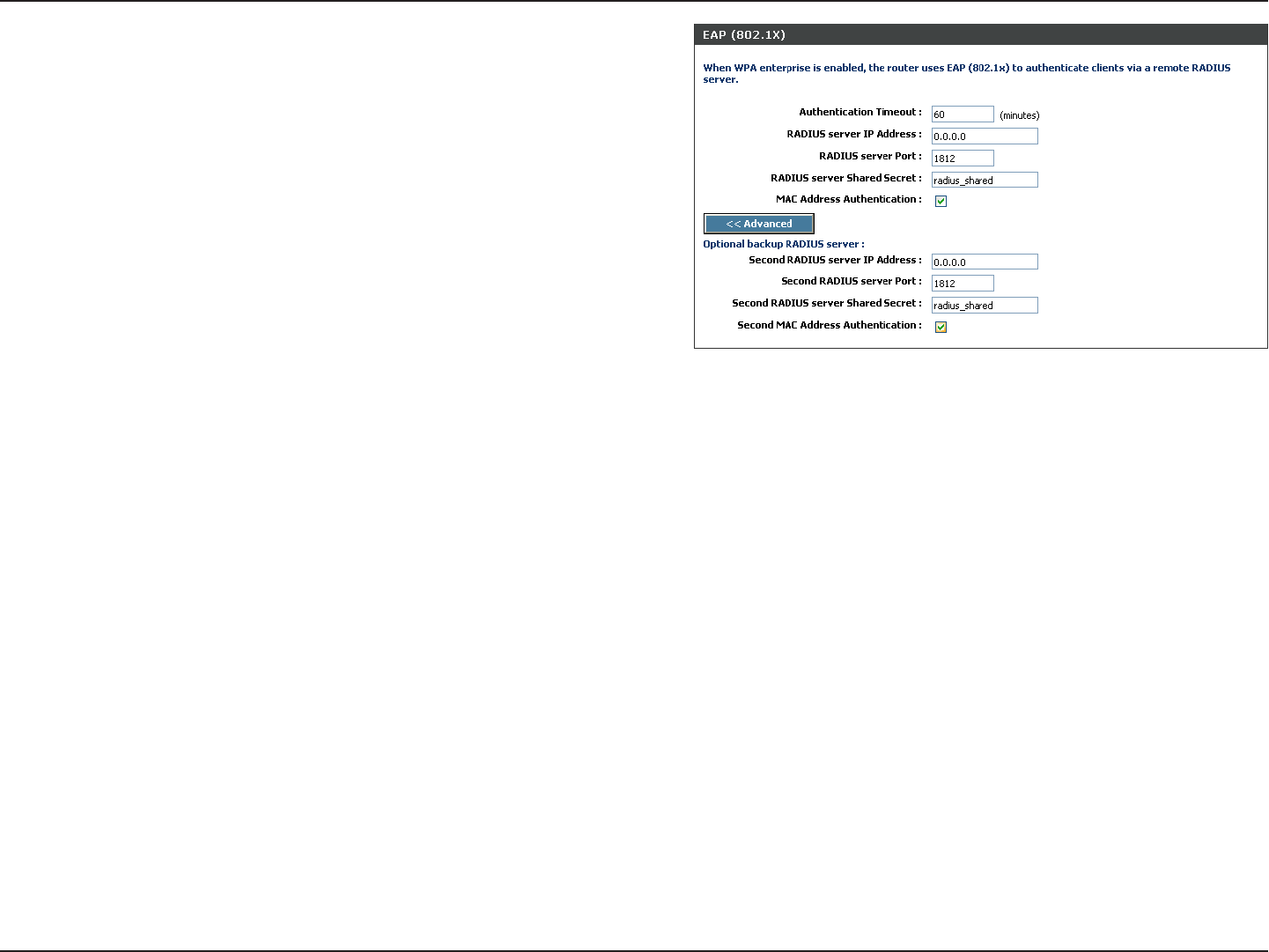
6. Next to Authentication Timeout, enter the amount of time before
a client is required to re-authenticate (60 minutes is default).
7. Next to RADIUS Server IP Address enter the IP Address of your RADIUS server.
Configure WPA-Enterprise (RADIUS)
77D-Link DIR-628 User Manual
Section 4 - Security
8. Next to RADIUS Server Port, enter the port you are using with
your RADIUS server. 1812 is the default port.
9. Next to RADIUS Server Shared Secret, enter the security
key.
10. If the MAC Address Authentication box is selected then the
user will need to connect from the same computer whenever
logging into the wireless network.
11. Click Advanced to enter settings for a secondary RADIUS
Server.
12. Click Apply Settings to save your settings.
78D-Link DIR-628 User Manual
Section 4 - Security
Connect to a Wireless Network
Using Windows Vista®
Windows Vista® users may use the built-in wireless utility. If you are using another company’s utility or Windows® 2000,
please refer to the user manual of your wireless adapter for help with connecting to a wireless network. Most utilities
will have a “site survey” option similar to the Windows Vista® utility as seen below.
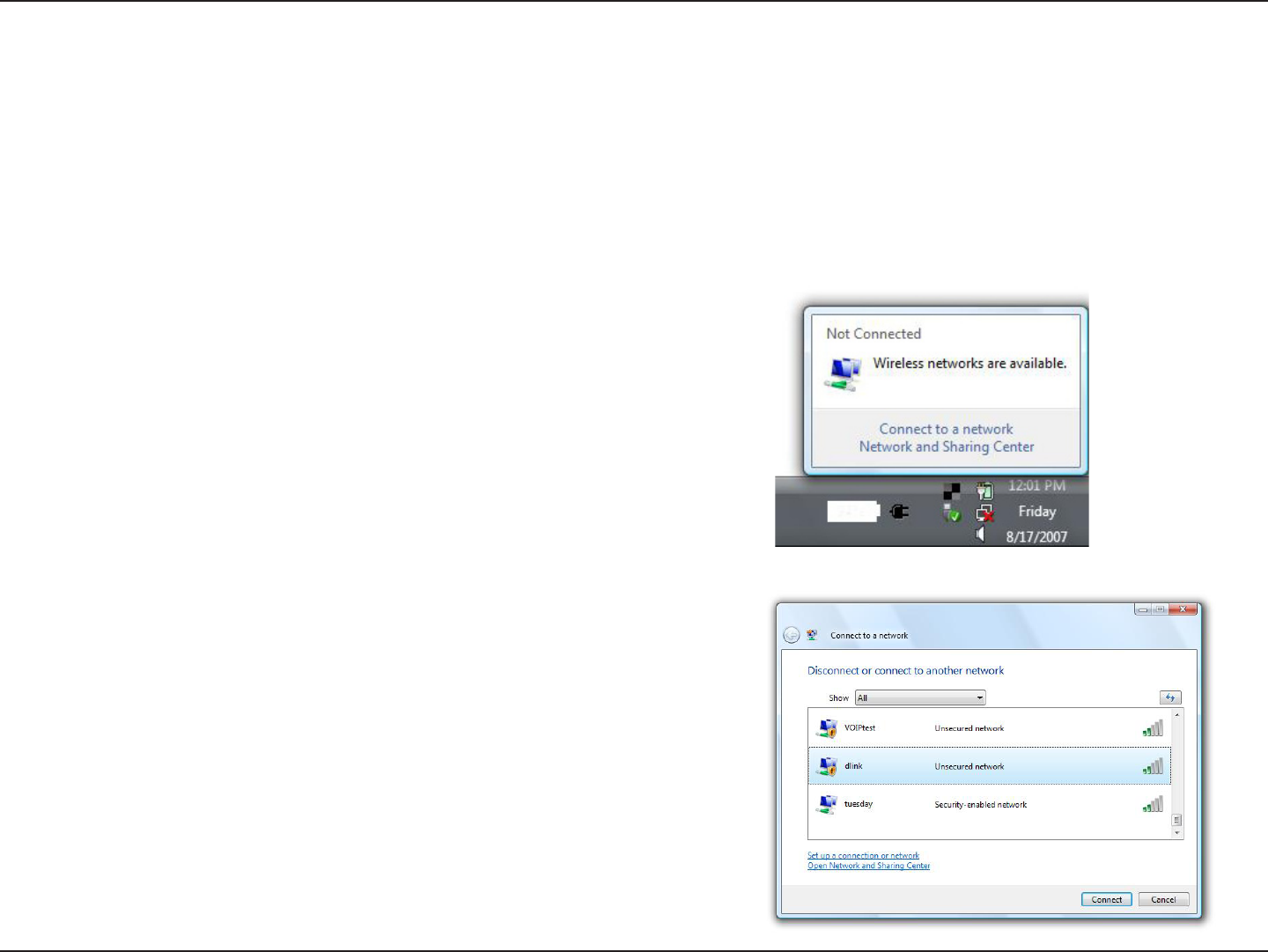
Right-click on the wireless computer icon in your system tray
(lower-right corner next to the time). Select Connect to a
network.
If you receive the Wireless Networks Detected bubble, click
on the center of the bubble to access the utility.
or
The utility will display any available wireless networks in your
area. Click on a network (displayed using the SSID) and click
the Connect button.
If you get a good signal but cannot access the Internet, check you
TCP/IP settings for your wireless adapter. Refer to the Networking
Basics section in this manual for more information.
79D-Link DIR-628 User Manual
Section 4 - Security
Configure Wireless Security
It is recommended to enable wireless security (WPA/WPA2) on your wireless router or access point before configuring
your wireless adapter. If you are joining an existing network, you will need to know the security key or passphrase
being used.
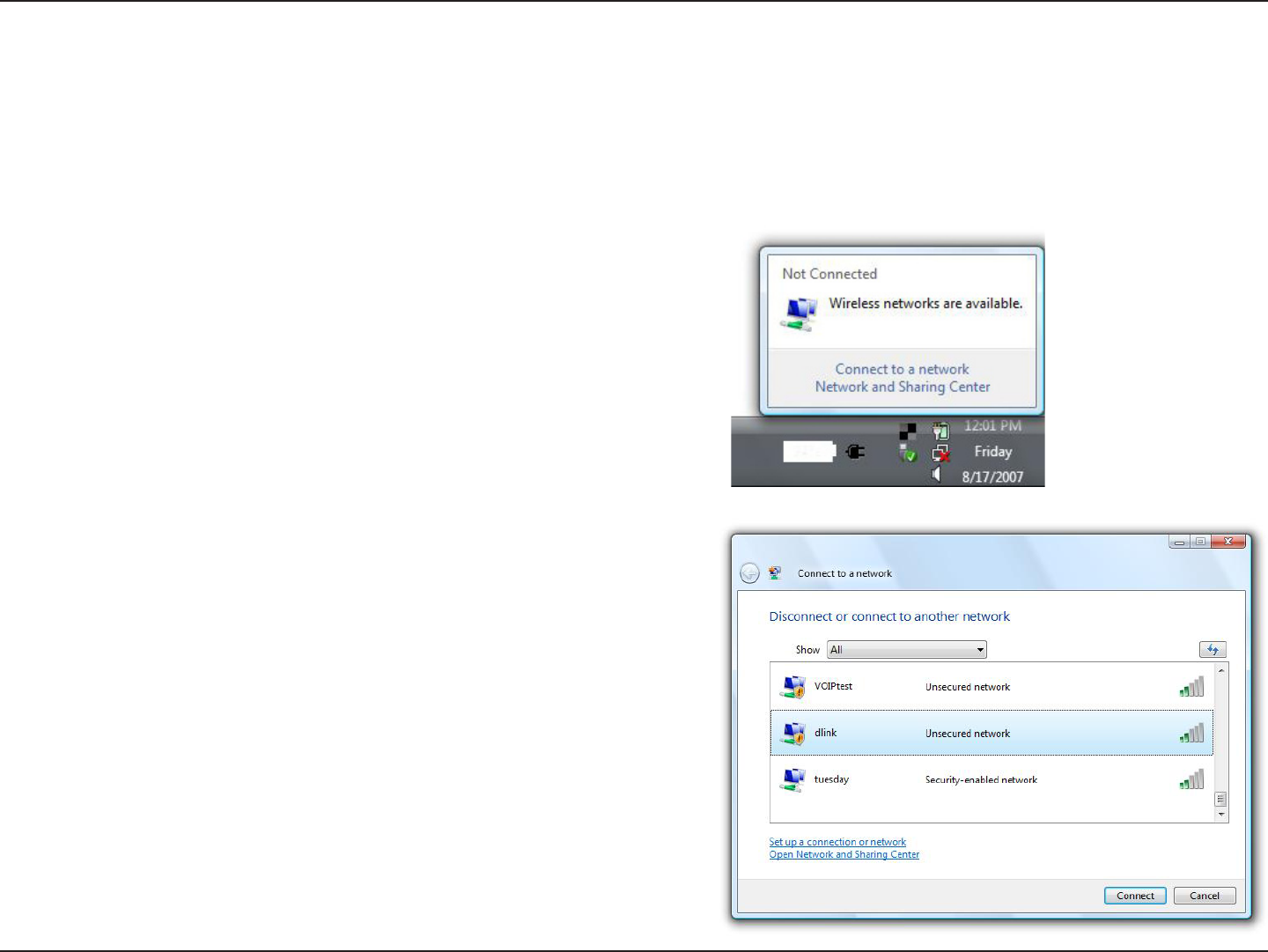
2. Highlight the wireless network (SSID) you would like to
connect to and click Connect.
1. Open the Windows Vista® Wireless Utility by right-clicking
on the wireless computer icon in your system tray (lower
right corner of screen). Select Connect to a network.
80D-Link DIR-628 User Manual
Section 4 - Security
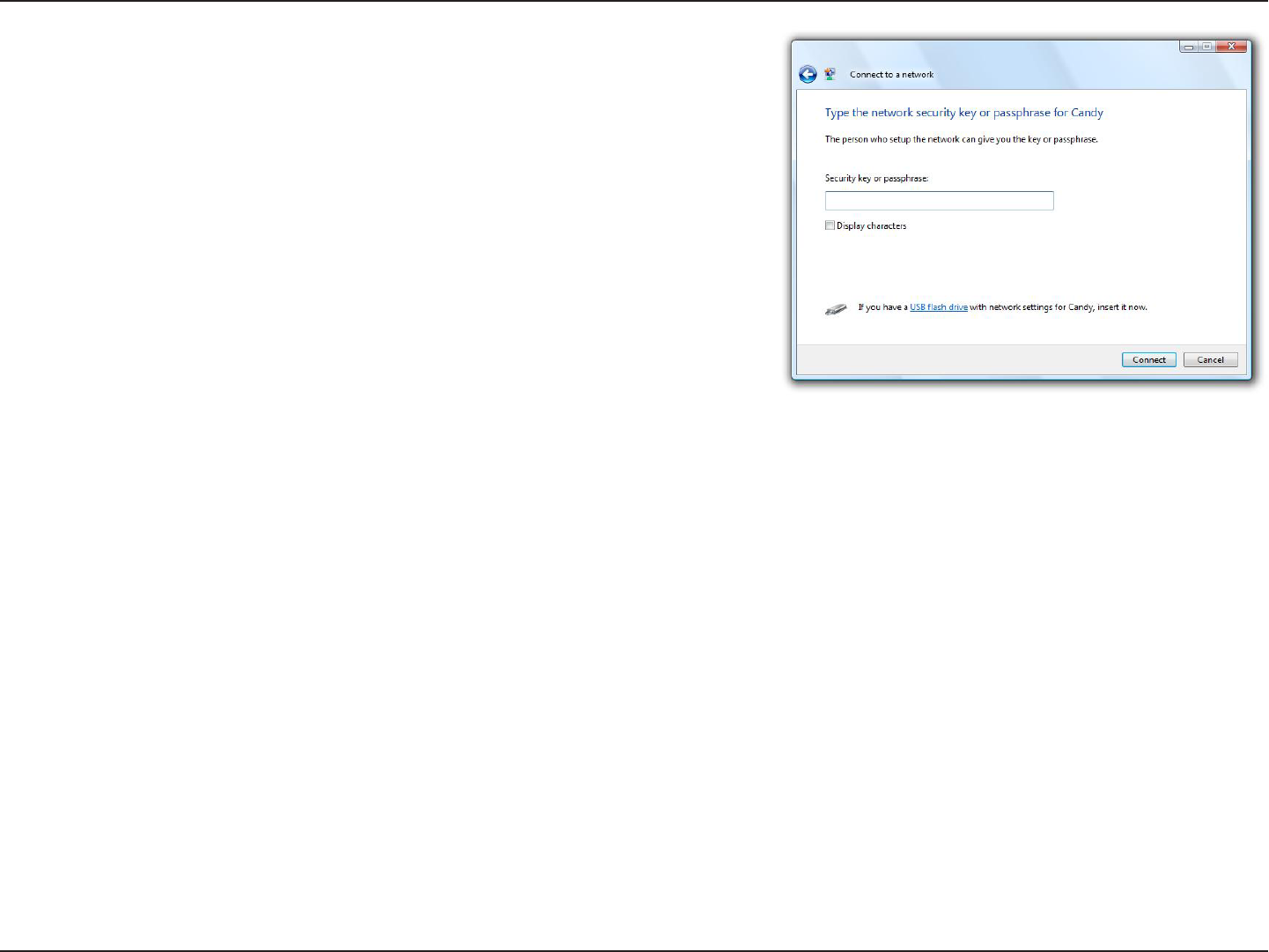
3. Enter the same security key or passphrase that is on your router
and click Connect.
It may take 20-30 seconds to connect to the wireless network. If the
connection fails, please verify that the security settings are correct.
The key or passphrase must be exactly the same as on the wireless
router.