Fortress Technologies ES210 The ES210 is a single radio access point/bridge. User Manual ES210 Secure Wireless Bridge User Guide DRAFT
Fortress Technologies, Inc. The ES210 is a single radio access point/bridge. ES210 Secure Wireless Bridge User Guide DRAFT
Contents
Manual






![Fortress ES210vigovernment licenses. The transfer or export of the software outside the U.S. may require a license from the Bureau of Industry and Security. For questions call BIS at 202-482-4811.U.S Government CustomersThe Software and associated documentation were developed at private expense and are delivered and licensed as “commercial computer software” as defined in DFARS 252.227-7013, DFARS 252.227-7014, or DFARS 252.227-7015 as a “commercial item” as defined in FAR 2.101(a), or as “Restricted computer software” as defined in FAR 52.227-19. All other technical data, including manuals or instructional materials, are provided with “Limited Rights” as defined in DFAR 252.227-7013 (a) (15), or FAR 52.227-14 (a) and in Alternative II (JUN 1987) of that clause, as applicable. Limited WarrantyThe warranties provided by Fortress in this Statement of Limited Warranty apply only to Fortress Products purchased from Fortress or from a Fortress Solution Provider for internal use on Customer's computer network. “Product” means a Fortress software product, upgrades, or firmware, or any combination thereof. The term “Product” also includes Fortress software programs, whether pre-loaded with the Fortress hardware Product, installed subsequently or otherwise. Unless Fortress specifies otherwise, the following warranties apply only in the country where Customer acquires the Product. Nothing in this Statement of Warranty affects any statutory rights of consumers that cannot be waived or limited by contract. Customer is responsible for determining the suitability of the Products in Customer's network environment. Unless otherwise agreed, Customer is responsible for the Product's installation, set-up, configuration, and for password and digital signature management. Fortress warrants the Products will conform to the published specifications and will be free of defects in materials and workmanship. Customer must notify Fortress within the specified warranty period of any claim of such defect. The warranty period for software is one (1) year commencing from the ship date to Customer [and in the case of resale by a Fortress Solution Provider, commencing not more than (90) days after original shipment by Fortress]. Date of shipment is established per the shipping document (packing list) for the Product that is shipped from Fortress location. Customer shall provide Fortress with access to the Product to enable Fortress to diagnose and correct any errors or defects. If the Product is found defective by Fortress, Fortress' sole obligation under this warranty is to remedy such defect at Fortress' option through repair, upgrade or replacement of product. Services and support provided to diagnose a reported issue with a Fortress Product, which is then determined not to be the root cause of the issue, may at Fortress’ option be billed at the standard time and material rates. Warranty ExclusionsThe warranty does not cover Fortress Hardware Product or Software or any other equipment upon which the Software is authorized by Fortress or its suppliers or licensors, which (a) has been damaged through abuse or negligence or by accident, (b) has been altered except by an authorized Fortress representative, (c) has been subjected to abnormal physical or electrical stress (i.e., lightning strike) or abnormal environmental conditions, (d) has been lost or damaged in transit, or (e) has not been installed, operated, repaired or maintained in accordance with instructions provided by Fortress.The warranty is voided by removing any tamper evidence security sticker or marking except as performed by a Fortress authorized service technician.Fortress does not warrant uninterrupted or error-free operation of any Products or third party software, including public domain software which may have been incorporated into the Fortress Product. Fortress will bear no responsibility with respect to any defect or deficiency resulting from accidents, misuse, neglect, modifications, or deficiencies in power or operating environment.Unless specified otherwise, Fortress does not warrant or support non-Fortress products. If any service or support is rendered such support is provided WITHOUT WARRANTIES OF ANY KIND. D R A F T D O C U M E N T](https://usermanual.wiki/Fortress-Technologies/ES210.Manual/User-Guide-1190376-Page-7.png)

![Fortress ES210viiiFORTRESS OR ITS SOLUTION PROVIDER IS INFORMED OF THEIR POSSIBILITY. SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OR LIMITATION OF INCIDENTAL OR CONSEQUENTIAL DAMAGES, SO THE ABOVE LIMITATION OR EXCLUSION MAY NOT APPLY TO CUSTOMER. Telephone SupportDuring the warranty period, Fortress or its Solution Provider will provide a reasonable amount of telephone consultation to the Customer. This support shall include assistance in connection with the installation and routine operation of the Product, but does not include network troubleshooting, security consultation, design and other services outside of the scope of routine Product operation. Warranty services for the Products shall be available during Fortress' normal U.S. (EST) business days and hours.Extended Warranty ServiceIf the Customer purchases an extended warranty service agreement with Fortress, service will be provided in accordance to said agreement's terms and conditions.Access and ServiceCustomer must provide Fortress or Solution Provider with access to the Product to enable Fortress or Solution Provider to provide the service. Access may include access via the Internet, on-site access or Customer shall be responsible for returning the Product to Fortress or Solution Provider. Fortress or Solution Provider will notify the Customer to obtain authorization to perform any repairs. If, during the warranty period, as established by the date of shipment [and in the case of resale by a Fortress Solution Provider, commencing not more than (90) days after original shipment by Fortress], the Customer finds any significant defect in materials and workmanship under normal use and operating conditions, the Customer shall notify Fortress Customer Service in accordance with the Fortress Service Policies in effect at that time which can be located on the Fortress web site: www.fortresstech.com.D R A F T D O C U M E N T](https://usermanual.wiki/Fortress-Technologies/ES210.Manual/User-Guide-1190376-Page-9.png)









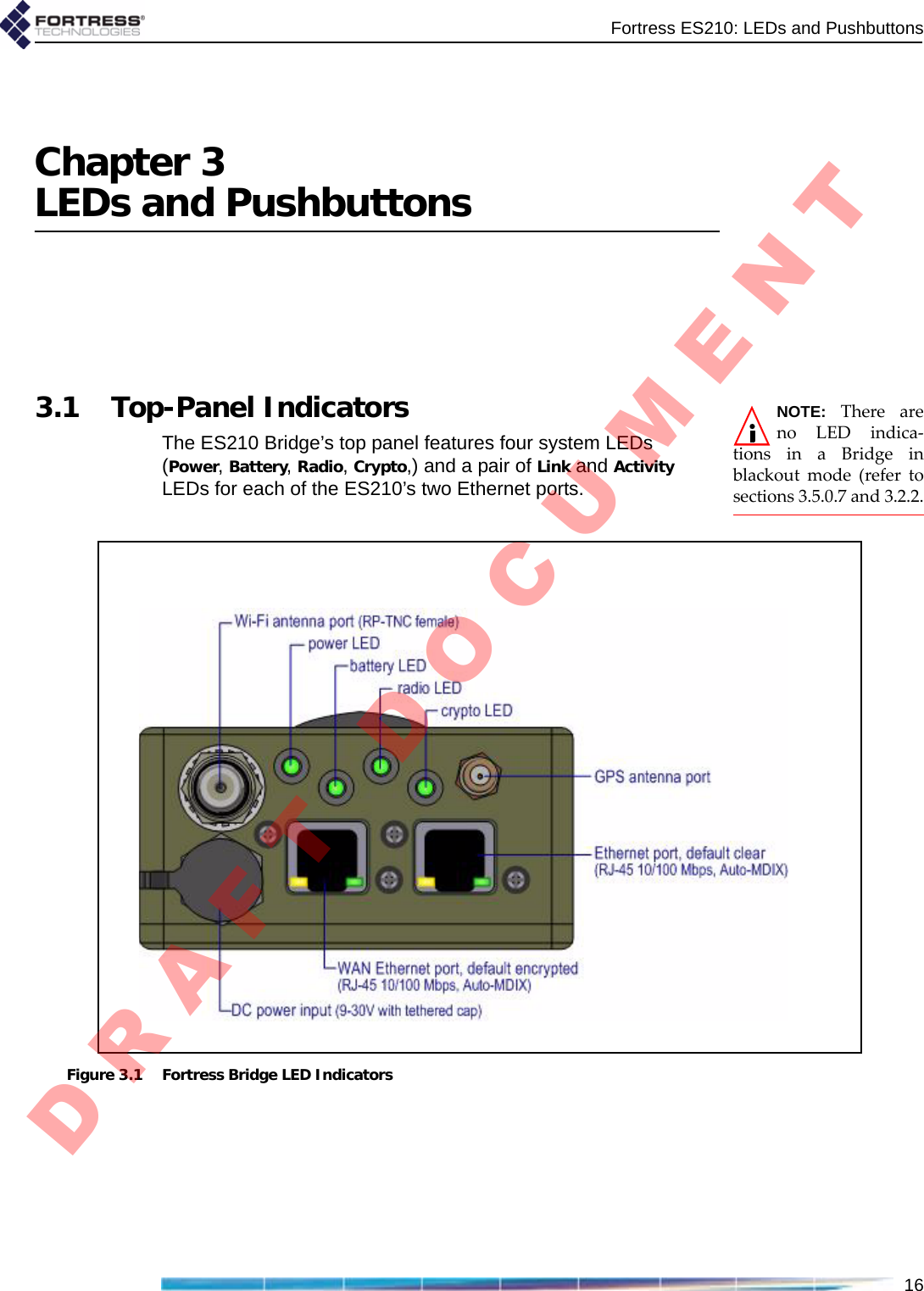
![Fortress ES210: LEDs and Pushbuttons173.1.1 System LEDsPower can exhibit:solid green - Bridge is powered on.off - Bridge is powered off.slow-flash green - Bridge is booting.fast-flash green - Bridge has a battery fault.Battery can exhibit:The Battery LED is reserved for a future function on the Bridge.Radio can exhibit:solid green - Bridge’s RF Kill function is enabled.intermittent green - Bridge’s 802.11a/b/g radio is passing traffic.Crypto can exhibit:solid green - Bridge has a FIPS failure.fast-flash green - Bridge is passing cleartext traffic (unencrypted data) in the encrypted zone.3.1.2 Port LEDsThe ES210 Bridge’s top-panel Ethernet ports are equipped with link/activity LEDs. Lnk/Act can exhibit:solid green - A link has been established for the port.intermittent green - Traffic is passing on the link.off - The port is not connected.color behavior Powerpower Batterybattery Radio802.11a/b/g Cryptoencryptiongreensolid unit on[reserved]RF kill activated FIPS failureslow flash booting - -fast flash battery fault - cleartext in encrypted zoneintermittent - passing traffic -off unit off radio off -D R A F T D O C U M E N T](https://usermanual.wiki/Fortress-Technologies/ES210.Manual/User-Guide-1190376-Page-28.png)