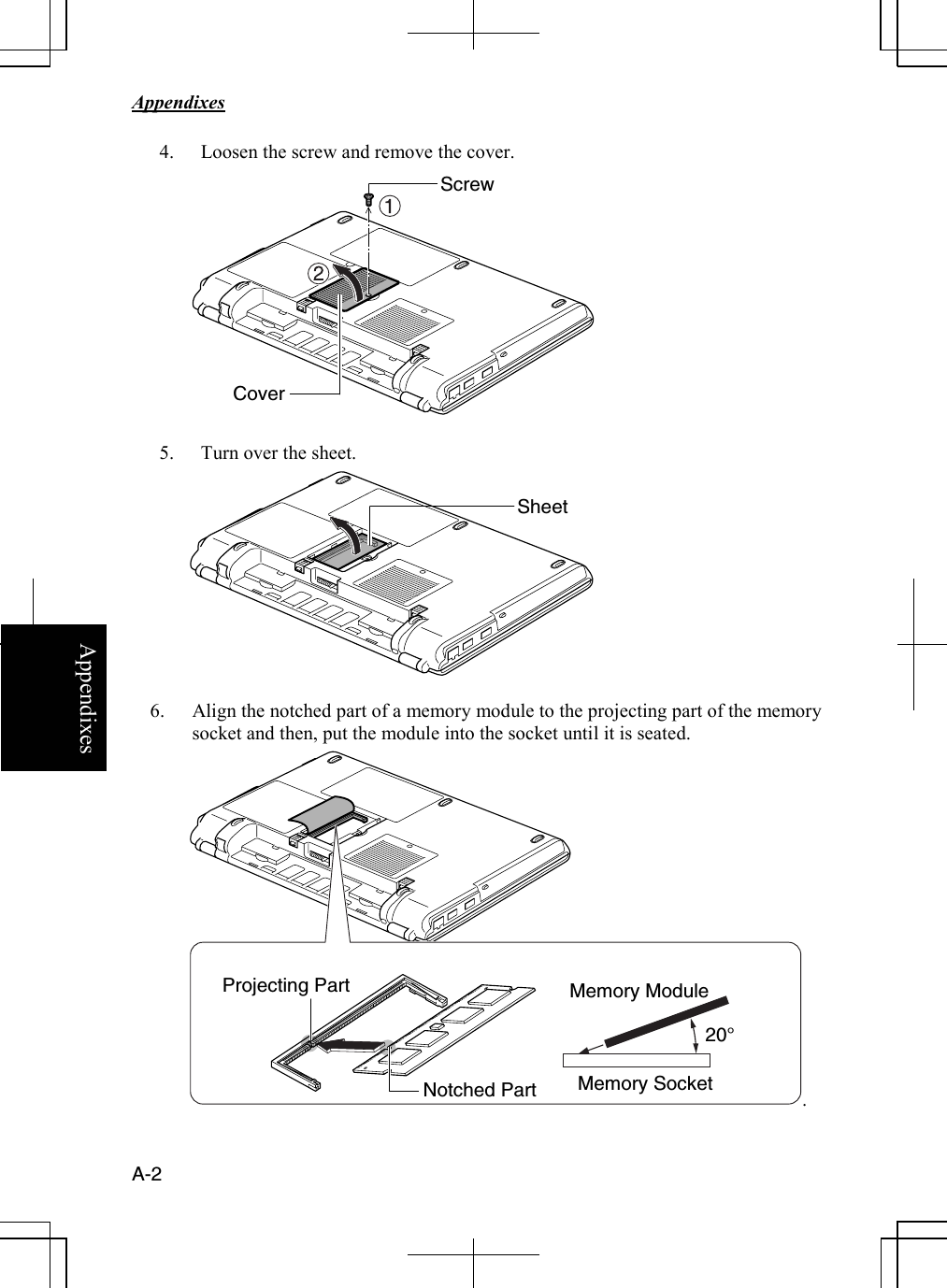
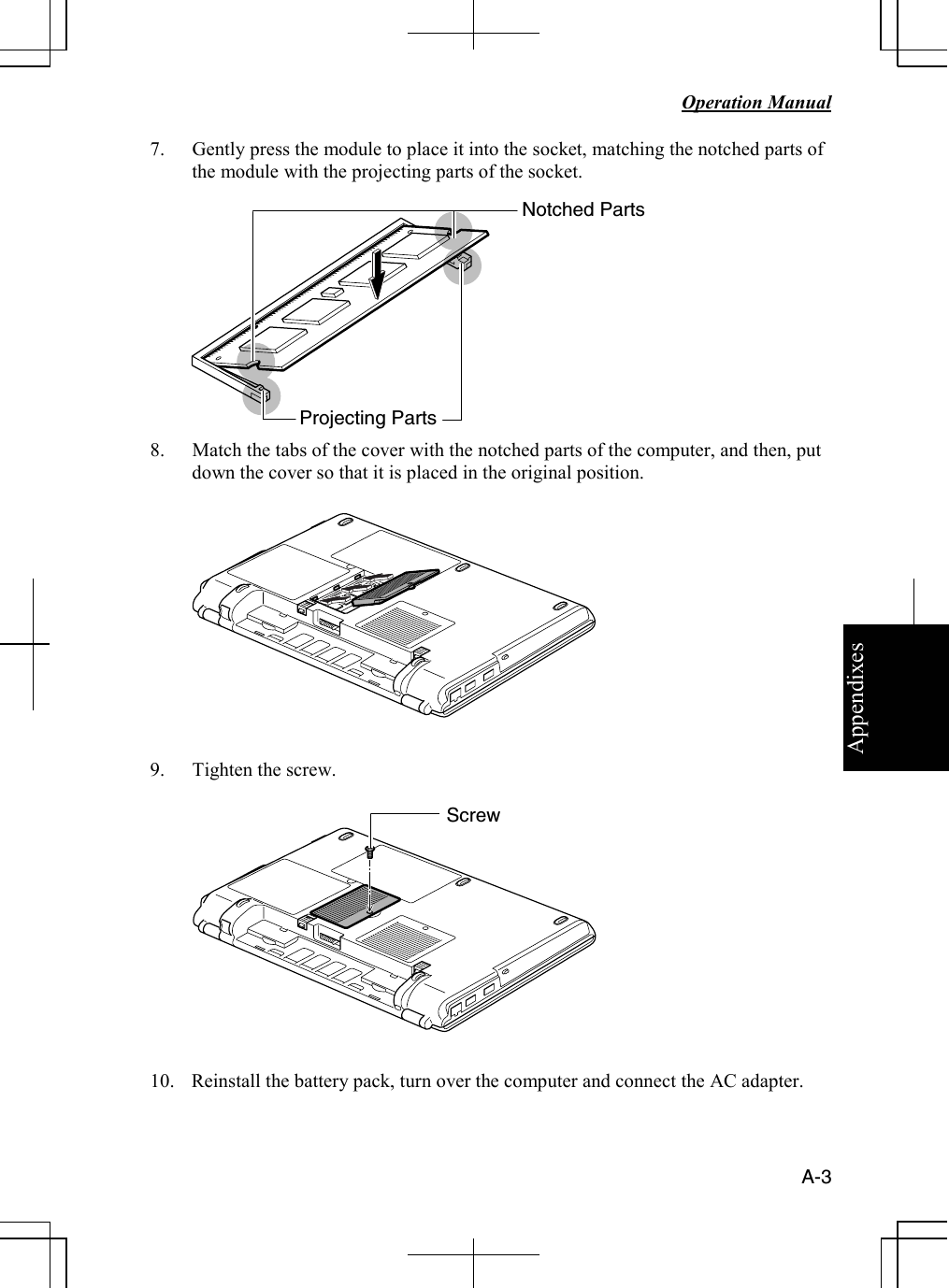
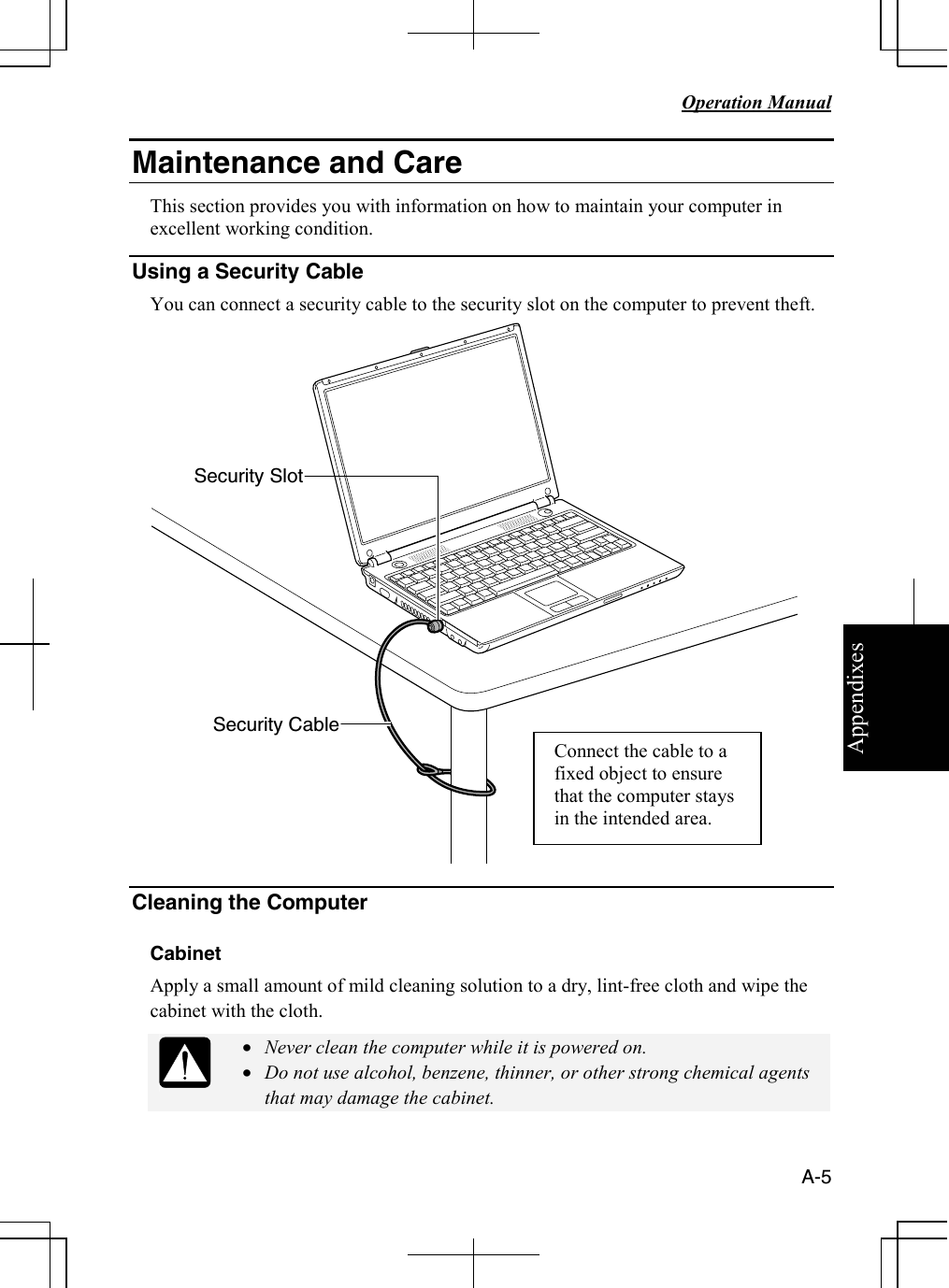
Sharp NAR0059 Laptop Computer with Integral 802.11 Transmitter User Manual safety m4000
Sharp Corporation Laptop Computer with Integral 802.11 Transmitter safety m4000
Sharp >
Contents
- 1. Users Manual part 1
- 2. Users Manual part 2
Users Manual part 2