Trilliant Networks CONN Wireless Mesh Wide Area Network CPE User Manual scout
Trilliant Networks, Inc. Wireless Mesh Wide Area Network CPE scout
Contents
Manual

SecureMesh Connector Installation
CONN-1000

© 2011 Trilliant, Inc. All rights reserved
This publication, or parts thereof, may not be reproduced in any form, by any method, for any purpose.
Product specifications are subject to change without notice. This material is provided for informational purposes only; Trilliant assumes no liability related
to its use and expressly disclaims any implied warranties of merchantability or fitness for any particular purpose.
Trilliant Trademarks
Trilliant™, CellReader®, CellGateway™, SecureMesh™, SerViewCom®, UnitySuite™, SkyPilot®, SyncMesh™, the Trilliant logo, and the SkyPilot logo are
trademarks of Trilliant Incorporated and/or its subsidiaries.
All other trademarks are the property of their respective owners.
This material is provided for informational purposes only; Trilliant assumes no liability related to its use and expressly disclaims any implied warranties of
merchantability or fitness for any particular purpose.
All specifications, descriptions, and information contained herein are subject to change without prior notice.
Third-Party Trademarks
Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries.
MySQL is a registered trademark of MySQL AB in the United States, the European Union, and other countries.
All other designated trademarks, trade names, logos, and brands are the property of their respective owners.
Third-Party Software Program Credits
This product includes software developed by the Apache Software Foundation (http://www.apache.org/), licensed under the Apache License.
This product includes the DHCP Server software from Internet Systems Consortium, licensed under the DHCP License. The DHCP Server software is copyright ©
2004 Internet Systems Consortium, Inc. (“ISC”). Copyright © 1995–2003 Internet Software Consortium. All rights reserved. Redistribution and use in source and
binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above
copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of
conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. Neither the name of ISC, ISC DHCP, nor the
names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS
PROVIDED BY INTERNET SYSTEMS CONSORTIUM AND CONTRIBUTORS “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN
NO EVENT SHALL ISC OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA,
OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes the FTP Server software from vsftpd (http://vsftpd.beasts.org/), licensed under the GNU General Public License.
This product includes Java software from Sun Microsystems, licensed under Sun Microsystems' Binary Code License Agreement. Copyright 2003, Sun
Microsystems, Inc. All rights reserved. Use is subject to license terms. Sun, Sun Microsystems, the Sun logo, Solaris, Java, the Java Coffee Cup logo, J2SE, and all
trademarks and logos based on Java are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries.
This product includes JBOSS Version 3.2.3 software from JBoss, licensed under the GNU Lesser General Public License. Some bundled products in JBOSS are
licensed under the Apache License.
This product contains Java Telnet Application (JTA 2.0).
This product contains the MibBrowser software from Mibble.
This product includes software the copyright of which is owned by and licensed from MySQLAB.
This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://www.openssl.org/). Copyright (c) 1998–2005 The
OpenSSL Project. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in
binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with
the distribution. 3. All advertising materials mentioning features or use of this software must display the following acknowledgment: “This product includes software
developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://www.openssl.org/)” 4. The names “OpenSSL Toolkit” and “OpenSSL Project” must not be
used to endorse or promote products derived from this software without prior written permission. For written permission, please contact openssl-core@openssl.org. 5.
Products derived from this software may not be called “OpenSSL” nor may “OpenSSL” appear in their names without prior written permission of the OpenSSL
Project. 6. Redistributions of any form whatsoever must retain the following acknowledgment: “This product includes software developed by the OpenSSL Project
for use in the OpenSSL Toolkit (http://www.openssl.org/)”. THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY EXPRESSED
OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY
WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes libraries developed by Eric Young and is licensed under the Original SSLeay License. This product includes cryptographic software written by
Eric Young (eay@cryptsoft.com). This product includes software written by Tim Hudson (tjh@cryptsoft.com). Copyright (C) 1995–1998 Eric Young
(eay@cryptsoft.com). All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following
conditions are met: 1. Redistributions of source code must retain the copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary
form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the
distribution. 3. All advertising materials mentioning features or use of this software must display the following acknowledgement: “This product includes
cryptographic software written by Eric Young (eay@cryptsoft.com)” The word 'cryptographic' can be left out if the routines from the library being used are not
cryptographic related:-). 4. If you include any Windows specific code (or a derivative thereof) from the apps directory (application code) you must include an
acknowledgement: “This product includes software written by Tim Hudson (tjh@cryptsoft.com)”. THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS''
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY
DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED
AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes SNMP software from WestHawk, licensed under the WestHawk License.
This product includes JFreeCharts from http://www.jfree.org/, licensed under GNU Lesser General Public License.
This product includes JasperReports from http://jasperreports.sourceforge.net/index.html, licensed under GNU Lesser Public License.
GOVERNMENT USE

SkyConnector Outdoor Installation | iii
Contents
About This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . v
Audience and Purpose . . . . . . . . . . . . . . . . . . . . . . . . . . . . . vi
How This Guide Is Organized . . . . . . . . . . . . . . . . . . . . . . . . . vi
Conventions Used in This Guide . . . . . . . . . . . . . . . . . . . . . . .vii
Chapter 1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Solution Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Mesh Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
SecureMesh Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
SecureMesh Extender Devices. . . . . . . . . . . . . . . . . . . . . . . . . 4
SecureMesh Connector and SecureMesh Connector DualBand. . . . 5
Chapter 2 Your SecureMesh Connector Kit . . . . . . . . . . . . . . . . . 7
Kit Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
What Else You Need . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Chapter 3 Installing a SecureMesh Connector . . . . . . . . . . . . . . .11
Planning Your Installation . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Cabling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Powering Up the SecureMesh Connector . . . . . . . . . . . . . . . . 15
Optimizing Location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Monitoring SecureMesh Connector Status . . . . . . . . . . . . . . . . 17
Mounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Configuring the SecureMesh Connector . . . . . . . . . . . . . . . . . 19
Accessing the Command-Line Interface . . . . . . . . . . . . . . . . . 20
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Appendix A Grounding Guidelines . . . . . . . . . . . . . . . . . . . . . . .23
General Grounding Strategy . . . . . . . . . . . . . . . . . . . . . . . . . 23
Adding Surge Protection . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Grounding Checklist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Appendix B FCC Statements . . . . . . . . . . . . . . . . . . . . . . . . . . .27
iv

SkyConnector Outdoor Installation | v
About This Guide
This guide explains how to install and set up a Trilliant™ SecureMesh
Connector™ to provide wireless network access to users of a Trilliant wireless
mesh network. It assumes administrator-level knowledge of IP networks and a
familiarity with configuring wireless devices.
Chapter Highlights
Audience and purpose
How this guide is organized
Conventions used in this guide
vi | About This Guide
Audience and Purpose
This guide provides directions for installing and setting up a Trilliant SecureMesh
Connector device that can provide access to users of a Trilliant wireless mesh
network.
This guide assumes administrator-level knowledge of IP networks and a
familiarity with configuring wireless devices.
How This Guide Is Organized
This guide is organized as follows:
Chapter 1, “Introduction,” provides an overview of the Trilliant solution,
describes the Trilliant devices, and then illustrates how they combine to form
a mesh network.
Chapter 2, “Your SecureMesh Connector Kit,” provides the information you
need before you begin your installation.
Chapter 3, “Installing a SecureMesh Connector,” provides instructions for the
physical installation of the SecureMesh Connector as well as background
information about configuration and references to associated procedures.
Appendix A, “Grounding Guidelines,” provides direction on protecting your
Trilliant device with proper grounding and surge protection.
Appendix B, “FCC Statements,” provides the FCC radio frequency
interference statements for the SecureMesh Connector
Conventions Used in This Guide | vii
Conventions Used in This Guide
This section describes the text and syntax conventions used throughout this guide.
Text Conventions
This guide uses the following text conventions:
Italic is used to introduce new terms.
Bold is used to indicate what you click or type in a graphical user interface
(for example, commands names or text being entered). In examples showing
user interaction with the command-line interface, bold is used to indicate user
input as opposed to command output.
A monospace font is used for code elements (variable names, data values,
function names, and so forth), command lines, scripts, and source code
listings.
Italic-monospace is used for replaceable elements and placeholders
within code listings.
Syntax Conventions
This guide uses the following conventions when showing syntax:
Angle brackets, “<“and “>”, enclose mandatory elements. You must enter
these elements. For example:
ping <IP-address>
Square brackets, “[“and “]”, enclose optional elements. You can omit these
elements. For example:
show filter [filter-table-number]
Square brackets are also used to show the current value of parameters in the
output of some commands.
A vertical bar, “|”, separates choices. For example:
show bridge [cache | port]
viii

SkyConnector Outdoor Installation | 1
Introduction
This chapter provides an overview of the Trilliant solution, describes the Trilliant
devices, and then illustrates how they combine to form a mesh network.
Chapter Highlights
Solution overview
Mesh network
SecureMesh Gateway
SecureMesh Extender devices
SecureMesh Connector
1
2 | Chapter 1 Introduction
Solution Overview
Trilliant delivers a wireless, end-to-end broadband solution that seamlessly
supports high-capacity, high-coverage mesh networks. Designed for managed-
access networks and service providers, the Trilliant network takes broadband
wireless the “last mile” with a cost-effective, robust infrastructure solution.
Based on a high-performance architecture that deploys intelligent antenna arrays,
the Trilliant network delivers a dynamic broadband solution with significant
advantages for business and home users.
Trilliant wireless devices are simple to install and easily fit into any type of
wireless environment—metropolitan, business, or home.
The auto-discovery and rapid provisioning features of a Trilliant wireless mesh
network can greatly reduce deployment and maintenance costs. Multiple
topology options and network scalability create intriguing options for rapidly
expanding a metro Wi-Fi customer base.
Trilliant devices’ multiple antenna configurations work within mixed-use
environments of municipal applications and broadband Internet access,
supporting public-private partnerships such as public safety services.
Mesh Network
The typical configuration for a Trilliant network is a mesh topology, which uses
SecureMesh Extenders to extend range and add network flexibility. In a mesh
configuration, subscribers can either connect directly to the SecureMesh Gateway
or connect indirectly via SecureMesh Extenders (see Figure 1-1). In addition to
adding range, a mesh network allows connections from locations where
obstructions prevent line-of-sight access to a SecureMesh Gateway hub.
Mesh networks are ideal for dense subscriber environments, for filling in
coverage “holes,” and for reaching subscribers in areas where RF communication
is obstructed by hills, trees, buildings, or other obstacles.
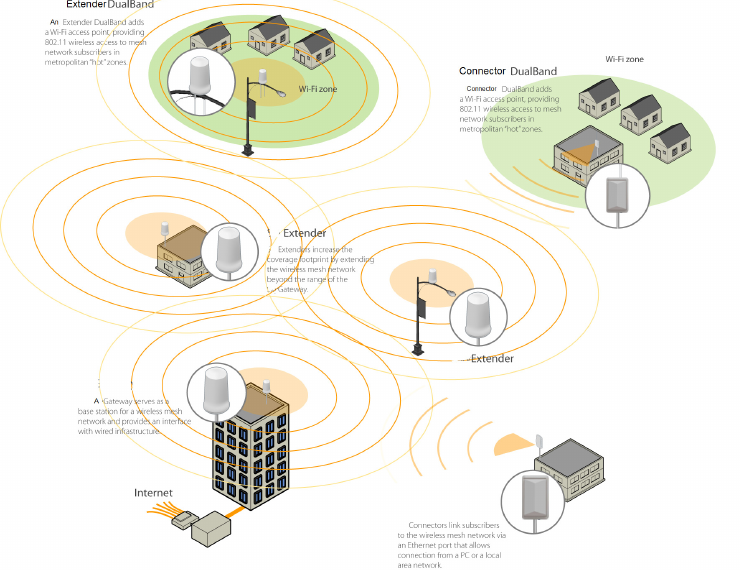
Mesh Network | 3
Figure 1-1. Trilliant wireless mesh network
4 | Chapter 1 Introduction
SecureMesh Gateway
The SecureMesh Gateway operates as a base station for a wireless mesh network.
It provides an interface between wired infrastructure and a wireless network of
subscribers who enjoy secure, high-speed access to the Internet or to wide area
networks.
A Trilliant wireless network requires at least one SecureMesh Gateway for
operation. If necessary, you can add additional SecureMesh Gateways to increase
network capacity or provide redundancy.
The SecureMesh Gateway typically resides at a location with easy access to
wired infrastructure—usually a POP (point of presence) or data center.
For optimal performance, install the SecureMesh Gateway on an elevated site
such as a cell tower or the top of a tall building.
SecureMesh Extender Devices
SecureMesh Extenders, SecureMesh Extender DualBand provide a cost-effective
way to add capacity and balance network loads by operating as “repeaters” to
extend the wireless range of a SecureMesh Gateway (see Figure 1-1). You can
add any SecureMesh Extender device to your network to expand your coverage
footprint and provide redundancy through Trilliant’s mesh networking features.
SecureMesh Extender devices (except DualBands) can provide subscribers with a
direct connection to the wireless network via the device’s Ethernet port.
SecureMesh Extender DualBand is a dual-radio solution that combines Trilliant’s
long-range, high-capacity 5 GHz mesh backhaul with a high-powered 2.4 GHz
802.11b/g access point that allows service providers and municipalities to offer
standard Wi-Fi services over great distances—for targeted hot zones or dense,
ubiquitous coverage patterns.
For optimal performance, install the SecureMesh Extender in an elevated location
such as a roof, tower, or utility pole.
SecureMesh Connector and SecureMesh Connector DualBand | 5
SecureMesh Connector and SecureMesh
Connector DualBand
SecureMesh Connectors link your subscribers to the Trilliant wireless network.
An Ethernet port on the device allows a connection to a subscriber’s computer, or
to a local area network (LAN) via a data switch or router. Designed for
installation by the service provider, the SecureMesh Connector attaches to an
external structure such as an eave, roof, or pole.
The SecureMesh Connector DualBand offers the same features as a SecureMesh
Connector, plus a Wi-Fi access point that enables service providers and
municipalities to provide standard 802.11 wireless access over great distances,
for targeted hot zones, or for dense coverage patterns.
6

SkyConnector Outdoor Installation | 7
Your SecureMesh Connector Kit
Your Trilliant SecureMesh Connector installation kit provides the basic
equipment you need to install the device and configure it for operation on a
Trilliant wireless mesh network. This chapter describes that equipment and lists
additional items you should have on hand before starting installation.
Chapter Highlights
Kit contents
What else you need
2

8 | Chapter 2 Your SecureMesh Connector Kit
Kit Contents
Figure 2-1 shows the contents of the SecureMesh Connector installation kit.
Figure 2-1. Trilliant installation kit
Trilliant separately offers accessories for different types of installation, including
a surge suppressor and a tilt mount kit. For more information, visit the Trilliant
website at www.Trilliant.com/support/.
What Else You Need
Before starting installation, you also need the following:
For basic mounting:
Phillips screwdriver
For pole mounting:
Magnetic level
Steel pole between 1 1/8” (2.87 cm) and 1 3/8” (3.48 cm) in diameter
What Else You Need | 9
For network cabling:
Spool of CAT-5 network cable (shielded cable is recommended)
IMPORTANTEthernet cabling must comply with NEC/CEC
requirements for CAT-5 cables. The cabling’s outer jacket
must be clearly marked as CAT-5e per ANSI/TIA/EIA-568-
B.2.
Crossover cable (for connecting to a an access point, switch, or router)
RJ-45 connectors (connectors without a protective “boot” are
recommended)
RJ-45 crimping tool
For configuration:
Computer with a serial port, a terminal emulation program, a network
interface card, and a Web browser (laptop recommended for convenience)
10

SkyConnector Outdoor Installation | 11
Installing a SecureMesh
Connector
This chapter provides instructions for planning and performing the physical
installation of a SecureMesh Connector.
Chapter Highlights
Planning your installation
Cabling
Powering up the SecureMesh Connector
Optimizing location
Monitoring SecureMesh Connector status
Mounting
Configuring the SecureMesh Connector
Accessing the command-line interface
Troubleshooting
3
12 | Chapter 3 Installing a SecureMesh Connector
Planning Your Installation
In a typical wide area wireless mesh network, you’ll install a SecureMesh
Connector on a utility pole or the roof of a building. The effective range of a
SecureMesh Connector is usually proportional to the height of the installation.
When choosing a site for a SecureMesh Connector, consider the radio frequency
(RF) environment and the physical layout of the area.
Trees, buildings, and hills can attenuate or block a wireless signal. When
assessing a site, examine the overall topology of the wireless path for possible
obstructions—both existing and planned—as well as seasonal changes of foliage
and tree growth. The RF environment is dynamic, and can deteriorate over time
as structures appear or are relocated.
Plan to use test signals to determine the suitability of the link topology for target
applications. Interference on your desired frequency results in overlapping
signals, causing outages or intermittent drops in throughput.
Once you’ve identified a potential site, use a topographic map or path profile
software to ensure that terrain or obstacles will not interfere with the links.
Your site survey should include an RF scan to identify available frequencies. You
should also check your preferred frequency at all locations. A frequency that’s
clear at one location may be crowded at another. Frequency planning is a critical
factor in planning and implementing a wireless network. (For device operating
frequencies, see Appendix C, “Specifications.”)
The site survey process should be ongoing. To verify that a site is relatively free
of interference, make site audits every six to twelve months, scheduling regular
maintenance visits to coincide with the site audits.
IMPORTANTPlan to configure the SecureMesh Connector before mounting it.
Some steps, such as those requiring serial console access, are easier
if the device is more accessible. For information about
configuration, see “Configuring the SecureMesh Connector” on
page 20.
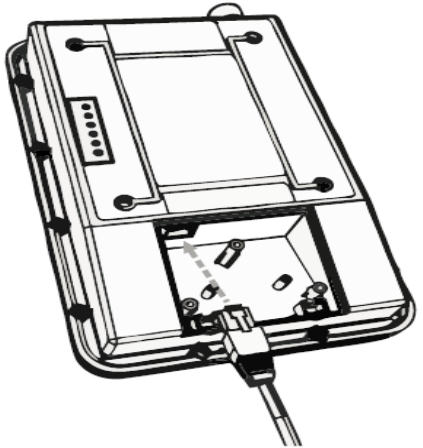
Cabling | 13
Cabling
Ethernet cabling provides power and data connectivity for the SecureMesh
Connector. This section provides instructions for attaching CAT5 cable to the
device.
To install CAT-5 cabling:
Figure 3-1. Connecting CAT-5 cable to the SecureMesh Connector
1Terminate the appropriate grade and length of CAT-5 cable with an RJ-45
connector, and plug it into the RJ-45 port on the back of the SecureMesh
Connector.
2Make sure the fit is snug
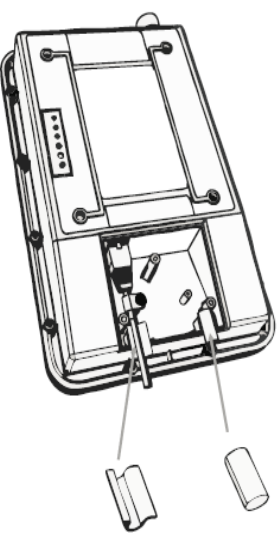
14 | Chapter 3 Installing a SecureMesh Connector
Securing cable placement
Figure 3-2. Securing the CAT-5 cable to the SecureMesh Connector
1Fit the CAT-5 cable in between the guide posts to fit in place
2Use a screw to tighten the cable guide to secure the CAT-5 cable in place
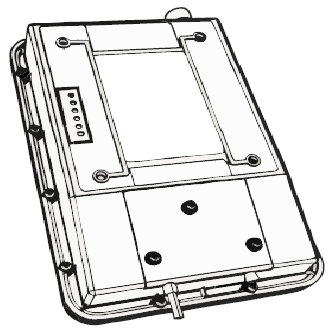
Powering Up the SecureMesh Connector | 15
Figure 3-3. Attaching weather gasket and metal cover
1Tighten the cover with three screws
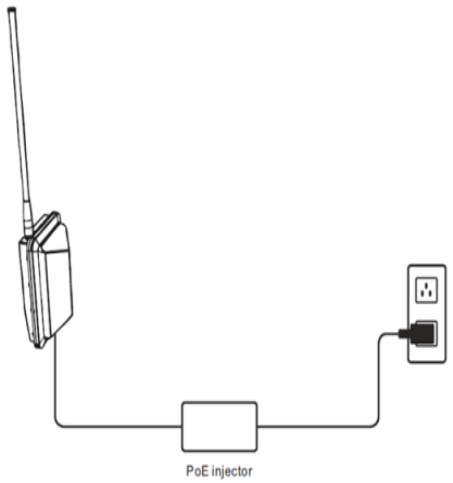
Powering Up the SecureMesh Connector
Before mounting the SecureMesh Connector, first power on the unit so you can
use the status LEDs to determine optimal location placement.
To power on the SecureMesh Connector:
1Attach the power supply.
aConnect the AC power cord to the AC adapter, and plug it into an AC
outlet.
bConnect the Ethernet cable to the port labeled “CPE” on the power
injector.
16 | Chapter 3 Installing a SecureMesh Connector
IMPORTANTBe careful not to plug the Ethernet cable connected to
the SecureMesh Connector into the port labeled
“Computer.”
cPlug the AC adapter into the power injector.
dGround the PoE injector
2Check the LEDs on the SecureMesh Connector.
If the connections are correct, the SecureMesh Connector’s power LED
(labeled “PWR”) should illuminate and the WAN activity LED (labeled
“WAN Act”) should blink on and off. (For details about the LED status lights,
see Table 3-1 on page 18.)
Figure 3-4. Checking the SecureMesh Connector LEDs
Optimizing Location
After powering up the SecureMesh Connector, use the device’s LEDs to identify
the optimal location for mounting. (For details about the LED status lights, see
Table 3-1 on page 18.)
Optimizing Location | 17
To optimize a SecureMesh Connector’s location:
1Confirm signal acquisition.
aPosition the SecureMesh Connector near the intended mounting location
and watch the “WAN Act” LED for activity. The LED starts blinking
when it acquires a signal from the network and is attempting to make a
connection.
If the LED doesn’t start blinking within 30 seconds, try changing the
orientation of the SecureMesh Connector or walk to a new location.
Repeat the process until the LED starts blinking.
bWhen the LED starts blinking, make minor adjustments to find the
location where the signal is strongest. (The faster the LED blinks, the
stronger the signal.)
When the LED blinks steadily at a high rate, you have an optimal signal.
2Verify network connection.
Watch the “WLAN Link” LED for activity. Within 90 seconds of locating a
signal, the LED should start to blink—first slowly, then more quickly, and
finally it should remain steadily lit.
When the “WAN Link” LED is steadily lit and the “WAN Act” LED is
blinking, SecureMesh Connector has established an authorized connection to
the network, indicating that the current location is suitable for mounting.
If both the “WAN Link” LED and the “WAN Act” LED continue blinking, a
signal is available but isn’t strong enough for reliable service. Keep trying
different locations until you can confirm a network connection.
NOTE To optimize your SecureMesh Connector installation, ask your
network administrator (at the Network Operations Center) to
measure signal strength on the node to which SecureMesh Connector
has established a link.
18 | Chapter 3 Installing a SecureMesh Connector
Monitoring SecureMesh Connector Status
Table 3-1 provides detailed descriptions of SecureMesh Connector states
indicated by the LED lights. When both LED lights are lit and steady, the
SecureMesh Connector is successfully connected to the wireless network.
Table 3-1. SecureMesh Connector LED Status Lights
LED LED state Device state
LAN
Link
Steady illumination SecureMesh Connector is connected to
another device via its Ethernet port.
LAN Act Blinking SecureMesh Connector is transmitting
or receiving data via its Ethernet port.
PWR Steady illumination SecureMesh Connector is powered up.
WAN
Link
Blinking (fast blink
when SecureMesh
Connector is in standby
mode)
SecureMesh Connector is attempting to
establish an authorized connection on
the wireless network.
If both WAN Link and WAN Act
continue blinking, either the signal isn’t
strong enough to support reliable
service or there’s a provisioning
problem that’s preventing SecureMesh
Connector from coming online. Contact
your network administrator for
assistance.
Steady illumination SecureMesh Connector is connected to
the wireless network.
WAN Act None Device cannot detect a wireless
network.
Blinking Device is within the coverage area of a
wireless network. Blink rate
communicates signal strength:
Fast (8x/second) = excellent
Medium (4x/second) = good
Slow (<1x/second) = poor
None = no reception
Mounting | 19
Mounting
After determining an optimal location for your SecureMesh Connector, you can
mount the device and run the appropriate cables.
To mount the SecureMesh Connector:
1Disconnect the CAT-5 cable from the power injector.
2Power down the SecureMesh Connector.
3Attach a magnetic level to the 1 1/8" (2.87 cm) and 1 3/8" (3.48 cm) diameter
steel mounting pole to verify that the pole is plumb (straight).
IMPORTANTIt is the installer’s responsibility to verify that the support
pole and its installation method are of sufficient strength to
withstand onsite weather conditions. (The supplied mounting
bracket and screws are certified to withstand a 125 mph wind
force.)
4Use the provided clamps and screws (provided in the accessory kit) to attach
the SecureMesh Connector to the mounting pole (see Figure 3-5).
Before clamping down the bracket, check that the mounting pole is still
plumb and that the SecureMesh Connector is level.
NOTE If the device is not level, performance may be degraded.

20 | Chapter 3 Installing a SecureMesh Connector
Figure 3-5. Attaching the SecureMesh Connector
5Reconnect the CAT-5 cable to the port labeled “CPE” on the SecureMesh
Connector power injector.
Configuring the SecureMesh Connector
To operate on the wireless mesh network, the SecureMesh Gateway requires a
network configuration.
A SecureMesh Connector will not transmit a wireless signal until it’s configured,
and it will not be able to connect to other network devices without a
configuration.
Trilliant offers two modes for provisioning devices with a configuration:
Automatic—Requires the use of Trilliant EMS software to create
configurations that an unattended central server can distribute to devices on
the wireless mesh network. Although automatic provisioning requires more
setup time than manual provisioning, it greatly simplifies the administration
of a growing network.
Manual—Usually performed in the field, manual provisioning permits the
configuration of a single device at a time, creating the minimum settings
required for a wireless link and storing them in the device’s flash (nonvolatile)

Accessing the Command-Line Interface | 21
memory. Manual provisioning is a logical choice if you’re installing a test
network or rolling out a small-scale installation that isn’t expected to expand.
For more information about provisioning modes and procedures, refer to Getting
Started with the SecureMesh Network and SecureMesh Network Administration,
available from the Trilliant website at www.Trilliant.com/support/.
Accessing the Command-Line Interface
Trilliant devices include a command-line interface which you can use for manual
provisioning and troubleshooting.
You can connect to a device and access its command-line interface through Telnet
over an Ethernet connection or via a terminal session from a console connected to
the device’s RJ-45 serial port. After logging in (by supplying a password), you
can enter commands at the command prompt.
For detailed cabling and access instructions for the command-line interface, refer
to the SecureMesh Command-Line Interface Reference.
Troubleshooting
After making an Ethernet or serial connection to the SecureMesh Connector, you
can manage and troubleshoot the device using a wide range of commands
available through the command-line interface.
For detailed troubleshooting procedures, refer to the “Troubleshooting” section in
SecureMesh Network Administration. There you’ll find troubleshooting
procedures for:
Power-on problems
Ethernet connectivity problems
IP connectivity problems
SecureMesh Gateway transmission problems
Link failure problems
22

SkyConnector Outdoor Installation | 23
Grounding Guidelines
This appendix provides some guidelines for properly grounding the Trilliant
Connector.
Proper grounding protects both your Trilliant device and equipment connected to
it. For the surge protection circuitry built into the Trilliant equipment to be
effective, proper grounding of the unit is necessary. This is especially true if
you’re installing devices on tall structures, or in areas subject to lightning.
NOTE The techniques described in this appendix are intended as general
guidelines only and do not constitute a comprehensive guide covering all
installation scenarios. For maximum protection, contact a qualified
installation specialist who is familiar with your operating environments.
If lightning is a threat in your area, consider a consultation with a
lightning and transient protection specialist.
General Grounding Strategy
To ensure optimal reliability, properly ground the metal base of the Trilliant device. The
most efficient way to ground the device is to use an 8 GA or larger wire to connect it to a
ground point on the structure or tower.
The three most common ground points are:
A cold-water pipe. Make sure it is well connected to earth.
The primary grounding point of the AC electrical system of the building.
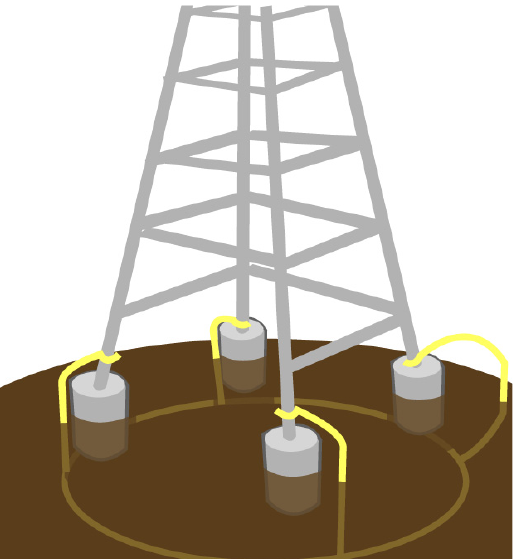
A 10-foot or longer copper-clad ground rod driven into the earth. For a tower
with multiple legs, you need one ground rod per leg and a ground wire loop
connecting each of the rods; see Figure 12.
A
24 | Appendix A Grounding Guidelines
Figure 12. Ground wire loop
Making Connections “Gas-Tight”
Regardless of the grounding point you use, make sure the connections are “gas-
tight”—capable of retaining low resistance and integrity over time and with
exposure to the elements.
Use of an antioxide compound and proper sealing is essential. For protection
against corrosion, wrap all connections with Scotch® 130C tape.
Checking Cold-Water Pipe Integrity
If you’re using a cold-water pipe for grounding, verify the integrity of the ground.
In some cases, sections of metal cold-water pipes may have been repaired or
extended with PVC material. PVC material or a dielectric union will render a
cold-water pipe ground unacceptable for grounding.
A

Adding Surge Protection | 25
Measuring Resistance
Verify that there is no more than 5 ohms of resistance between any two ground
points in the entire system. Also make sure that all ground points on a structure
are tied together. For example, if you use a ground rod and a cold-water pipe as
grounding points at different locations on the same structure, you must tie them
together.
Adding Surge Protection
If you’re installing a Trilliant device in an area that’s subject to lightning storms,
Trilliant recommends installing a surge protection device (SPD) at both ends of
the Ethernet cable—one at the Trilliant device and one at the point of entry to a
building or enclosure.
Trilliant offers SPDs with bracket and cabling designed for use with Trilliant
equipment. For more information, visit Trilliant customer support at
www.Trilliant.com/support/ to view accessory guides for Trilliant-branded surge
protection solution. (You may also purchase SPDs from third-party vendors.)
Grounding Checklist
When grounding a Trilliant device, use the following checklist to confirm that
your installation is adequately protected from power surges and lightning.
Connect a ground wire from the Trilliant device to a ground system on the
building or tower.
Use shielded CAT5 cabling and connect the drain wire of the shield to ground
at the Trilliant device. (Leave the other end of the drain wire unconnected.)
Use the proper size down lead to connect a Trilliant device on a roof or tower
to the ground system of indoor equipment.
Verify that all points of the ground system are tied together with less than 5
ohms resistance between any two points.
A
26 | Appendix A Grounding Guidelines
Run the CAT5 cable inside the tower structure, tying the cable to the tower leg
at every 4 feet of length. For increased protection, run the CAT5 cable through
metallic conduit installed on the tower.
Bleed off any static charge by installing a streamer-delaying, static-dissipation
array above the Trilliant device.
Install all lightning and surge protection devices in accordance with UL 96A
installation requirements for lightning protection systems and the NFPA 780
standard for lightning protection.
A