LINKSYS WRT54AG Wireless A/G Broadband Router User Manual WRT54AG ug Rev NC
LINKSYS LLC Wireless A/G Broadband Router WRT54AG ug Rev NC
LINKSYS >
Contents
- 1. Users Manual 1
- 2. Users Manual 2
- 3. Users Manual 3
- 4. Users Manual 4
Users Manual 2
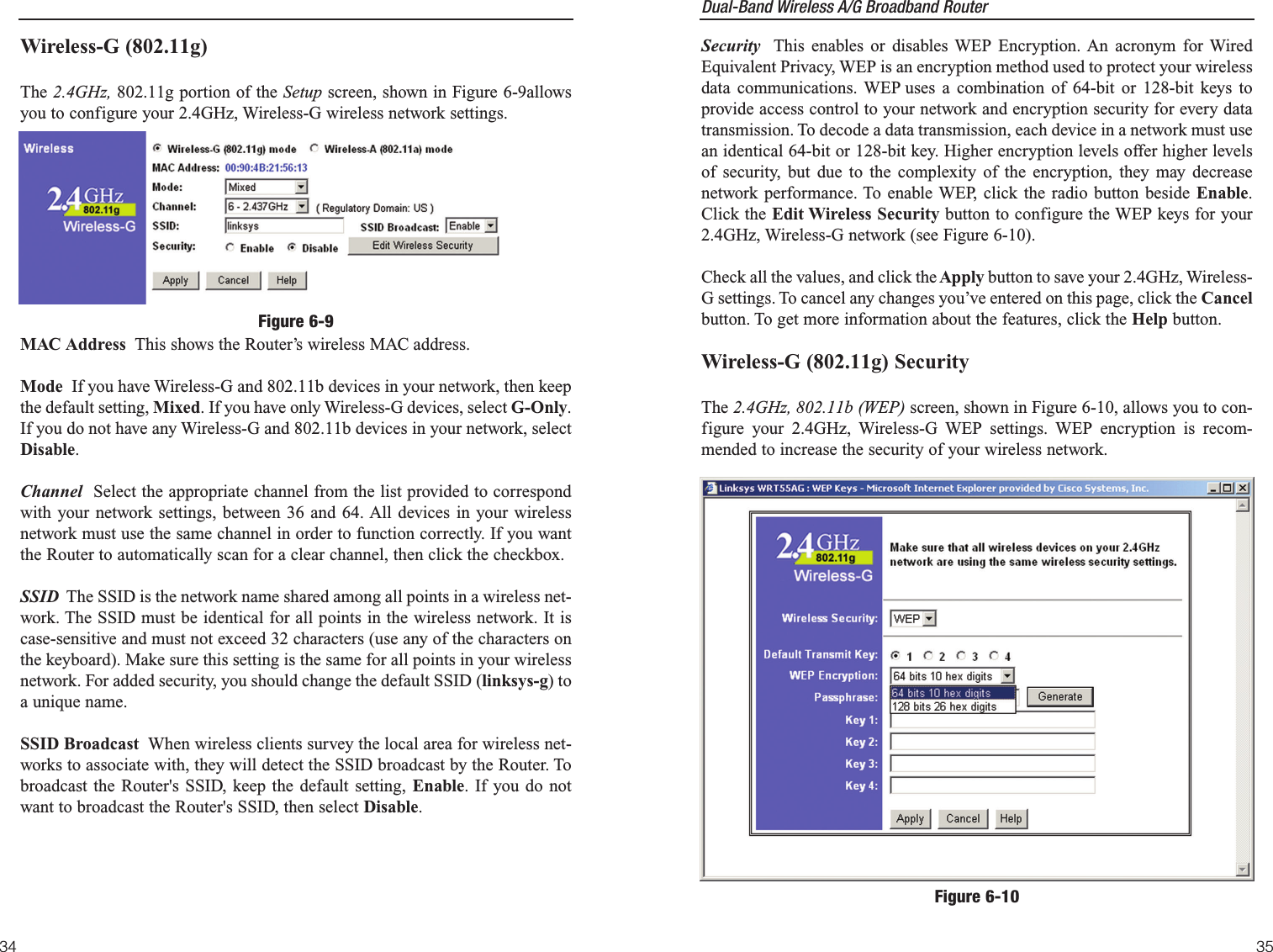
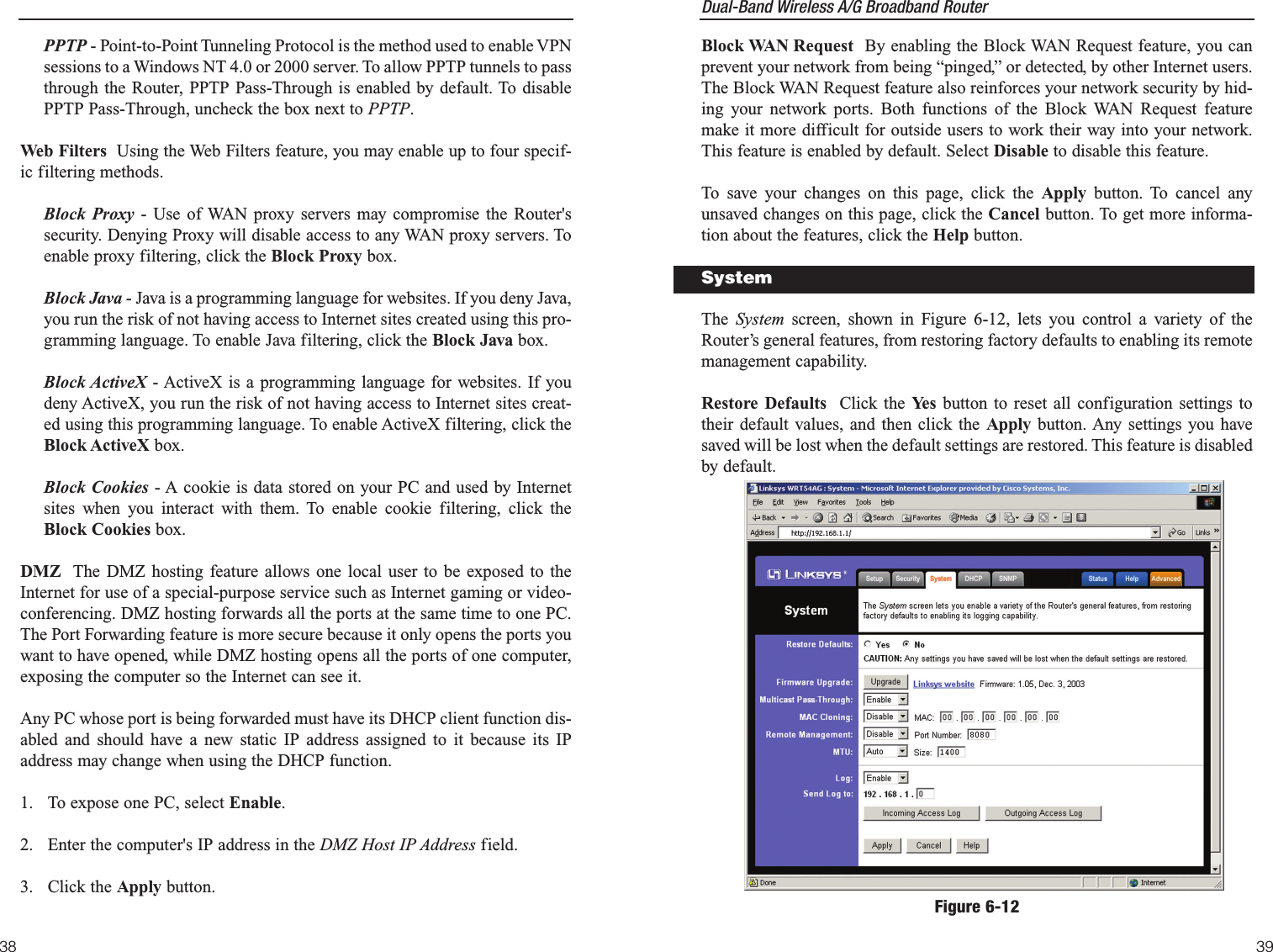
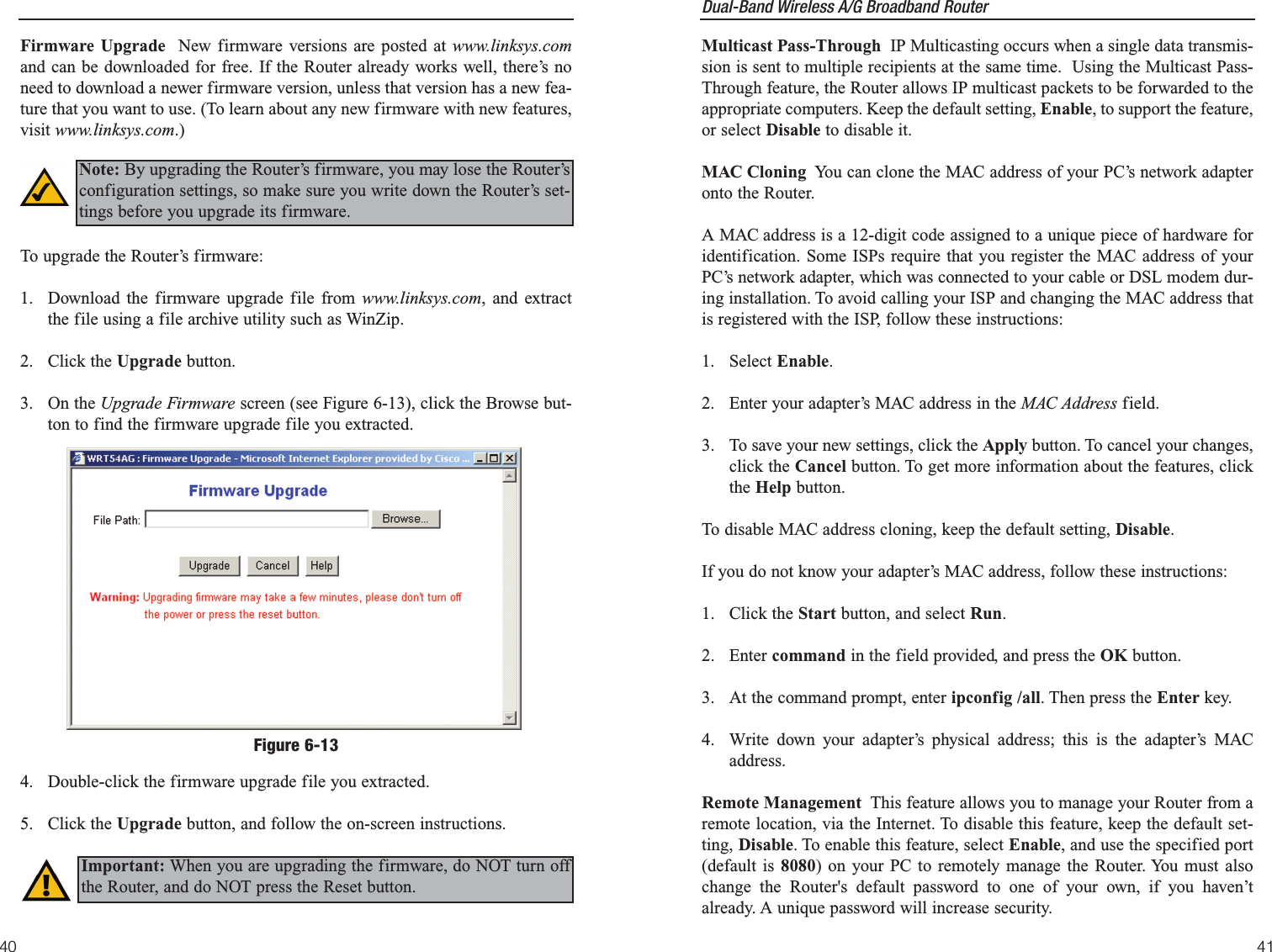
![Dual-Band Wireless A/G Broadband Router 37The Security screen, shown in Figure 6-11, allows you to change the Router’ssecurity settings. You should change the factory default password, which isadmin, to your own as soon as possible. All users who try to access theRouter’s web-based utility or Setup Wizard will be prompted for the Router’spassword.Router Password The new Password must not exceed 32 characters in lengthand must not include any spaces. Enter the new Password in the second field toconfirm it.VPN Pass-Through Virtual Private Networking (VPN) is typically used forwork-related networking. For VPN tunnels, the Router supports IPSec Pass-Through and PPTP Pass-Through. IPSec - Internet Protocol Security (IPSec) is a suite of protocols used toimplement secure exchange of packets at the IP layer. To allow IPSec tun-nels to pass through the Router, IPSec Pass-Through is enabled by default.To disable IPSec Pass-Through, uncheck the box next to IPSec.L2TP - Layer Two Tunneling Protocol is an extension of the Point-to-PointTunneling Protocol (PPTP) used by to enable the operation of a virtual pri-vate network (VPN) over the Internet.SecurityFigure 6-1136Default Transmit Key Select which WEP key (1-4) will be used when theRouter sends data. Make sure the receiver is using the same key.WEP Encryption Keys 1-4 offer 64-bit or 128-bit encryption; select the typeof encryption you want from the drop-down box. To disable WEP Encryption,select Disable.Passphrase Instead of manually entering WEP keys, you can enter aPassphrase. This Passphrase is used to generate one or more WEP keys. It iscase-sensitive and should not be longer than 16 alphanumeric characters. ThisPassphrase function is compatible with Linksys wireless products only. [If youwant to communicate with non-Linksys wireless products, enter the WEPkey(s) manually on the non-Linksys wireless products.] After you enter thePassphrase, click the Generate button to create WEP keys. Keys 1-4 WEP keys enable you to create an encryption scheme for wirelessLAN transmissions. Manually enter a set of values. (Do not leave a key fieldblank, and do not enter all zeroes. These are not valid key values.) Keys 1-4offer 64-bit or 128-bit encryption.If you are using 64-bit WEP encryption, then the key must be exactly 10 hexa-decimal characters in length. If you are using 128-bit WEP encryption, then thekey must be exactly 26 hexadecimal characters in length. Valid hexadecimalcharacters are “0”-“9” and “A”-“F”.Check all the values, and click theApply button to save your 2.4GHz, Wireless-G WEP settings.To apply any of the settings you change on this page, click the Apply button.To cancel any changes you’ve entered on this page, click the Cancel button. Toget more information about the features, click the Help button.Note: All Wireless devices in your network must use the samePassphrase or WEP key.](https://usermanual.wiki/LINKSYS/WRT54AG.Users-Manual-2/User-Guide-402256-Page-2.png)