Motorola Solutions 89FT7629 Access Point/CPE User Manual User Guide Part 1
Motorola Solutions, Inc. Access Point/CPE User Guide Part 1
Contents
- 1. User Guide Part 1
- 2. User Guide Part 2
- 3. User Guide Part 3
- 4. User Guide Part 4
- 5. User Guide Part 5
User Guide Part 1

March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Canopy® System
Release 8
User Guide,
Issue 2
Sys8-UG-en
Issue 2
November 2007
Sections:
Planning Guide
Installation and
Configuration Guide
Operations Guide
Reference
Information
R
New in Issue 2:
Release 8.2 Features
Canopy OFDM

March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Notices
See the following information:
◦ important regulatory and legal notices in Section 36 on Page 487.
◦ personal safety guidelines in Section 15 on Page 169.
Trademarks, Product Names, and Service Names
MOTOROLA, the stylized M Logo and all other trademarks indicated as such herein are
trademarks of Motorola, Inc.® Reg. U.S. Pat & Tm. Office. Canopy is a registered
trademark and MOTOwi4 is a trademark of Motorola, Inc. All other product or service
names are the property of their respective owners.
Adobe Reader is a registered trademark of Adobe Systems Incorporated.
Java and all other Java-based marks are trademarks or registered trademarks of Sun
Microsystems, Inc. in the U.S. and other countries.
Microsoft and Windows are registered trademarks of Microsoft Corporation, and Windows
XP is a trademark of Microsoft Corporation.
© 2007 Motorola, Inc. All rights reserved.
http://www.motorola.com/canopy

March 200 Through Software Release 6.
Draft 5 for Regulatory Review
TABLE OF SECTIONS
Guide To This User Guide
31
Overview of Canopy Networks
43
Planning Guide
127
Installation and Configuration Guide
167
Operations Guide
361
Reference Information
483
Glossary
503
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
TABLE OF CONTENTS
G
G
G
G
G
GU
U
U
U
U
UI
I
I
I
I
ID
D
D
D
D
DE
E
E
E
E
E
T
T
T
T
T
TO
O
O
O
O
O
T
T
T
T
T
TH
H
H
H
H
HI
I
I
I
I
IS
S
S
S
S
S
U
U
U
U
U
US
S
S
S
S
SE
E
E
E
E
ER
R
R
R
R
R
G
G
G
G
G
GU
U
U
U
U
UI
I
I
I
I
ID
D
D
D
D
DE
E
E
E
E
E.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.3
3
31
1
1
1 New in This Issue .................................................................................................... 33
1.1 New Products and Features Described in Issue 2 .......................................... 33
1.2 New Descriptions and Revisions in Issue 2 .................................................... 33
1.3 MOTOwi4 Portfolio......................................................................................... 33
1.4 Products Covered by This User Guide ........................................................... 33
1.5 Products Not Covered by This User Guide..................................................... 34
1.6 Software Compatibility Described in This User Guide..................................... 34
2 Using This User Guide............................................................................................ 35
2.1 Finding the Information You Need .................................................................. 35
2.1.1 Becoming Familiar with This User Guide ...........................................................35
2.1.2 Searching This User Guide .................................................................................38
2.1.3 Finding Parameter and Field Definitions for Module Web Pages ....................38
2.2 Interpreting Typeface and Other Conventions ................................................ 41
2.3 Getting Additional Help................................................................................... 42
2.4 Sending Feedback ......................................................................................... 42
O
O
OV
V
VE
E
ER
R
RV
V
VI
I
IE
E
EW
W
W
O
O
OF
F
F
C
C
CA
A
AN
N
NO
O
OP
P
PY
Y
Y
N
N
NE
E
ET
T
TW
W
WO
O
OR
R
RK
K
KS
S
S.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.4
4
43
3
3
3 Advancing from Research to Implementation ...................................................... 45
4 Realizing a Wireless Backhaul Network ................................................................ 47
5 Exploring the Scope of Solutions .......................................................................... 49
5.1 Components................................................................................................... 49
5.1.1 Canopy Access Point Module and Canopy OFDM Access Point Module.......49
5.1.2 Advantage Access Point Module ........................................................................49
5.1.3 Canopy Access Point Cluster and Canopy OFDM Access Point Cluster........50
5.1.4 Canopy Subscriber Module.................................................................................50
5.1.5 Advantage Subscriber Module............................................................................51
5.1.6 Canopy Lite Subscriber Module..........................................................................51
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
5.1.7 900-MHz AP and SM...........................................................................................52
5.1.8 Canopy .................................................................................................................53
5.1.9 Backhaul Module .................................................................................................53
5.1.10 Radio Adjustable Power Capabilities ...............................................................53
5.1.11 Cluster Management Module-2 (Part 1008CK-2)............................................53
5.1.12 Cluster Management Module micro (Part 1070CK) ........................................54
5.1.13 GPS Antenna .....................................................................................................55
5.1.14 Surge Suppressor (Part 600SS) .......................................................................55
5.1.15 Accessory Components ....................................................................................55
5.2 Frequency Band Ranges................................................................................ 59
5.3 Canopy Product Comparisons........................................................................ 60
5.3.1 Canopy Product Applications ..............................................................................60
5.3.2 Link Performance and Encryption Comparisons ...............................................61
5.3.3 Cluster Management Product Comparison........................................................63
5.4 Antennas for Connection to 900-MHz Modules .............................................. 64
5.4.1 Certified Connectorized Flat Panel Antennas....................................................64
5.4.2 Third-party Certified Connectorized Flat Panel Antenna ..................................65
5.5 Adjunctive Software Products......................................................................... 65
5.6 Bandwidth and Authentication Manager ......................................................... 66
5.7 Prizm.............................................................................................................. 67
5.7.1 Network Definition and Element Discovery........................................................67
5.7.2 Monitoring and Fault Management.....................................................................68
5.7.3 Element Management .........................................................................................68
5.7.4 BAM Subsystem in Prizm....................................................................................68
5.7.5 Northbound Interface ...........................................................................................69
5.8 License Management ..................................................................................... 69
5.9 Specifications and Limitations ........................................................................ 71
5.9.1 Radios...................................................................................................................71
5.9.2 Cluster Management Products ...........................................................................71
5.9.3 300SS and 600SS Surge Suppressors ..............................................................73
6 Differentiating Among Components...................................................................... 75
6.1 Interpreting Model (Part) Number................................................................... 75
6.2 Sorted Model Numbers .................................................................................. 78
6.3 Interpreting Electronic Serial Number (ESN) .................................................. 79
6.4 Finding the Model (Part) Number and ESN .................................................... 79
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
7 Canopy Link Characteristics .................................................................................. 81
7.1 Understanding Bandwidth Management......................................................... 81
7.1.1 Downlink Frame Contents...................................................................................81
7.1.2 Uplink Frame Contents........................................................................................81
7.1.3 Default Frame Structures ....................................................................................82
7.1.4 Media Access Control and AP Capacity ............................................................83
7.1.5 Canopy Slot Usage..............................................................................................83
7.1.6 Data Transfer Capacity........................................................................................83
7.1.7 Maximum Information Rate (MIR) Parameters..................................................84
7.1.8 Committed Information Rate ...............................................................................86
7.1.9 Bandwidth from the SM Perspective ..................................................................86
7.1.10 Interaction of Burst Allocation and Sustained Data Rate Settings .................86
7.1.11 High-priority Bandwidth .....................................................................................86
7.1.12 Hardware Scheduling ........................................................................................88
7.1.13 2X Operation ......................................................................................................89
7.1.14 3X Operation (Canopy OFDM modules only) ..................................................92
7.2 Understanding Synchronization...................................................................... 92
7.2.1 GPS Synchronization ..........................................................................................93
7.2.2 Passing Sync in a Single Hop.............................................................................95
7.2.3 Passing Sync in an Additional Hop.....................................................................95
8 Meeting Link Requirements ................................................................................... 99
8.1 AP-SM Links .................................................................................................. 99
8.2 BH-BH Links ................................................................................................ 101
9 Previewing Network Configurations .................................................................... 103
9.1 Viewing Typical Layouts............................................................................... 103
9.2 Viewing Case Studies .................................................................................. 105
10 Accessing Features ............................................................................................ 107
10.1 Activating Features..................................................................................... 114
10.1.1 Fixed License Keys..........................................................................................114
10.2 Enabling Features ...................................................................................... 115
11 Acquiring Proficiencies ...................................................................................... 117
11.1 Understanding RF Fundamentals ............................................................... 117
11.2 Understanding IP Fundamentals ................................................................ 117
11.3 Acquiring a Canopy Demonstration Kit ....................................................... 117
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
11.3.1 900-MHz with Integrated Antenna and Band-pass Filter Demonstration Kit117
11.3.2 900-MHz with Connectorized Antenna Demonstration Kit ...........................117
11.3.3 2.4-GHz with Adjustable Power Set to Low Demonstration Kit...................118
11.3.4 2.4-GHz with Adjustable Power Set to High Demonstration Kit ...................118
11.3.5 5.1-GHz Demonstration Kit .............................................................................119
11.3.6 5.2-GHz Demonstration Kit .............................................................................119
11.3.7 5.4-GHz Demonstration Kit .............................................................................119
11.3.8 5.7-GHz with Integrated Antenna Demonstration Kit ....................................120
11.3.9 5.7-GHz with Connectorized Antenna and Adjustable Power Set to Low ...120
11.3.10 Demonstration Kit Part Numbers ....................................................................120
11.4 Acquiring a Canopy Starter Kit.................................................................... 121
11.4.1 900-MHz with Integrated Antenna and Band-pass Filter Starter Kit ............121
11.4.2 900-MHz with Connectorized Antenna Starter Kit.........................................122
11.4.3 2.4-GHz with Adjustable Power Set to Low Starter Kit .................................122
11.4.4 2.4-GHz with Adjustable Power Set to High Starter Kit ................................122
11.4.5 5.1-GHz Starter Kit ..........................................................................................123
11.4.6 5.2-GHz Starter Kit ..........................................................................................123
11.4.7 5.4-GHz Starter Kit ..........................................................................................123
11.4.8 5.7-GHz with Integrated Antenna Starter Kit .................................................124
11.4.9 5.7-GHz with Connectorized Antenna and Adjustable Power Set to Low ...124
11.4.10 Starter Kit Part Numbers .................................................................................124
11.5 Evaluating Canopy Training Options........................................................... 125
11.6 Attending On-line Knowledge Sessions ...................................................... 125
P
P
PL
L
LA
A
AN
N
NN
N
NI
I
IN
N
NG
G
G
G
G
GU
U
UI
I
ID
D
DE
E
E.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.1
1
12
2
27
7
7
12 Engineering Your RF Communications ............................................................. 129
12.1 Anticipating RF Signal Loss........................................................................ 129
12.1.1 Understanding Attenuation..............................................................................129
12.1.2 Calculating Free Space Path Loss .................................................................129
12.1.3 Calculating Rx Signal Level ............................................................................129
12.1.4 Calculating Fade Margin .................................................................................130
12.2 Analyzing the RF Environment ................................................................... 131
12.2.1 Mapping RF Neighbor Frequencies ...............................................................131
12.2.2 Anticipating Reflection of Radio Waves .........................................................132
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
12.2.3 Noting Possible Obstructions in the Fresnel Zone ........................................132
12.2.4 Radar Signature Detection and Shutdown.....................................................132
12.3 Using Jitter to Check Received Signal Quality (Canopy FSK Only)............. 134
12.4 Using Link Efficiency to Check Received Signal Quality ............................. 135
12.4.1 Comparing Efficiency in 1X Operation to Efficiency in 2X Operation ..........135
12.4.2 When to Switch from 2X to 1X Operation Based on 60% Link Efficiency ...135
12.5 Considering Frequency Band Alternatives .................................................. 136
12.5.1 900-MHz Channels ..........................................................................................137
12.5.2 2.4-GHz Channels ...........................................................................................137
12.5.3 5.2-GHz Channels ...........................................................................................138
12.5.4 5.4-GHz Channels ...........................................................................................138
12.5.5 5.4-GHz OFDM Channels ...............................................................................139
12.5.6 5.7-GHz Channels ...........................................................................................139
12.5.7 Channels Available for PTP 400 and PTP 600 radios ..................................140
12.5.8 Example Channel Plans for AP Clusters........................................................140
12.5.9 Multiple Access Points Clusters......................................................................142
12.6 Selecting Sites for Network Elements ......................................................... 142
12.6.1 Resources for Maps and Topographic Images..............................................143
12.6.2 Surveying Sites ................................................................................................144
12.6.3 Assuring the Essentials ...................................................................................144
12.6.4 Finding the Expected Coverage Area ............................................................145
12.6.5 Clearing the Radio Horizon .............................................................................145
12.6.6 Calculating the Aim Angles .............................................................................145
12.7 Collocating Canopy Modules ...................................................................... 146
12.8 Deploying a Remote AP ............................................................................. 147
12.8.1 Remote AP Performance ................................................................................148
12.8.2 Example Use Case for RF Obstructions ........................................................148
12.8.3 Example Use Case for Passing Sync.............................................................149
12.8.4 Physical Connections Involving the Remote AP............................................150
12.9 Diagramming Network Layouts................................................................... 151
12.9.1 Accounting for Link Ranges and Data Handling Requirements ...................151
12.9.2 Avoiding Self Interference ...............................................................................151
12.9.3 Avoiding Other Interference ............................................................................153
13 Engineering Your IP Communications .............................................................. 155
13.1 Understanding Addresses .......................................................................... 155
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
13.1.1 IP Address ........................................................................................................155
13.2 Dynamic or Static Addressing..................................................................... 155
13.2.1 When a DHCP Server is Not Found ...............................................................155
13.3 Network Address Translation (NAT) ........................................................... 156
13.3.1 NAT, DHCP Server, DHCP Client, and DMZ in SM......................................156
13.3.2 NAT and VPNs.................................................................................................161
13.4 Developing an IP Addressing Scheme........................................................ 161
13.4.1 Address Resolution Protocol...........................................................................162
13.4.2 Allocating Subnets ...........................................................................................162
13.4.3 Selecting Non-routable IP Addresses ............................................................162
14 Engineering VLANs............................................................................................. 165
14.1 SM Membership in VLANs.......................................................................... 165
14.2 Priority on VLANs (802.1p) ......................................................................... 166
I
I
IN
N
NS
S
ST
T
TA
A
AL
L
LL
L
LA
A
AT
T
TI
I
IO
O
ON
N
N
A
A
AN
N
ND
D
D
C
C
CO
O
ON
N
NF
F
FI
I
IG
G
GU
U
UR
R
RA
A
AT
T
TI
I
IO
O
ON
N
N
G
G
GU
U
UI
I
ID
D
DE
E
E.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.1
1
16
6
67
7
7
15 Avoiding Hazards ................................................................................................ 169
15.1 Exposure Separation Distances.................................................................. 169
15.1.1 Details of Exposure Separation Distances Calculations and Power
Compliance Margins ........................................................................................169
15.2 Grounding Canopy Equipment.................................................................... 171
15.2.1 Grounding Infrastructure Equipment ..............................................................171
15.2.2 Grounding SMs ................................................................................................172
15.3 Conforming to Regulations ......................................................................... 174
15.4 Protecting Cables and Connections............................................................ 174
16 Testing the Components .................................................................................... 177
16.1 Unpacking Components ............................................................................. 177
16.2 Configuring for Test .................................................................................... 177
16.2.1 Configuring the Computing Device for Test ...................................................177
16.2.2 Default Module Configuration .........................................................................178
16.2.3 Component Layout ..........................................................................................178
16.2.4 Diagnostic LEDs ..............................................................................................179
16.2.5 CMM2 Component Layout ..............................................................................180
16.2.6 CMMmicro Component Layout .......................................................................180
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
16.2.7 Standards for Wiring ........................................................................................182
16.2.8 Best Practices for Cabling ...............................................................................182
16.2.9 Recommended Tools for Wiring Connectors.................................................182
16.2.10 Wiring Connectors ...........................................................................................182
16.2.11 Alignment Tone—Technical Details ...............................................................184
16.3 Configuring a Point-to-Multipoint Link for Test ............................................ 184
16.3.1 Quick Start Page of the AP .............................................................................185
16.3.2 Time Tab of the AP..........................................................................................191
16.3.3 Session Status Tab of the AP .........................................................................193
16.3.4 Beginning the Test of Point-to-Multipoint Links .............................................197
16.3.5 Remote Subscribers Tab of the AP ................................................................197
16.3.6 General Status Tab of the SM ........................................................................198
16.3.7 Continuing the Test of Point-to-Multipoint Links ............................................200
16.3.8 General Status Tab of the AP .........................................................................201
16.3.9 Concluding the Test of Point-to-Multipoint Links ...........................................203
16.4 Configuring a Point-to-Point Link for Test ................................................... 204
16.4.1 Quick Start Page of the BHM..........................................................................205
16.4.2 Time Tab of the BHM ......................................................................................206
16.4.3 Beginning the Test of Point-to-Point Links.....................................................210
16.4.4 Continuing the Test of Point-to-Point Links....................................................212
16.4.5 General Status Tab of the BHM......................................................................213
16.4.6 Concluding the Test of Point-to-Point Links...................................................215
16.5 Configuring a CMMmicro for Test ............................................................... 216
16.5.1 Setting up a CMMmicro...................................................................................216
16.5.2 Status Page of the CMMmicro ........................................................................221
16.5.3 Configuration Page of the CMMmicro ............................................................224
16.5.4 Configuring Modules for Connection to CMMmicro ......................................231
16.5.5 Event Log Page of the CMMmicro..................................................................231
16.5.6 GPS Status Page of the CMMmicro...............................................................231
16.5.7 Port MIB Page of the CMMmicro ....................................................................232
17 Preparing Components for Deployment............................................................ 233
17.1 Correlating Component-specific Information ............................................... 233
17.2 Ensuring Continuing Access to the Modules............................................... 233
18 Configuring for the Destination ......................................................................... 235
18.1 Configuring an AP for the Destination......................................................... 235
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
18.1.1 General Tab of the AP.....................................................................................235
18.1.2 IP Tab of the AP...............................................................................................239
18.1.3 Radio Tab of the AP ........................................................................................241
18.1.4 SNMP Tab of the AP .......................................................................................246
18.1.5 Quality of Service (QoS) Tab of the AP .........................................................249
18.1.6 Security Tab of the AP.....................................................................................251
18.1.7 VLAN Tab of the AP ........................................................................................253
18.1.8 VLAN Membership Tab of the AP ..................................................................255
18.1.9 DiffServe Tab of the AP...................................................................................256
18.1.10 Unit Settings Tab of the AP.............................................................................258
18.2 Configuring an SM for the Destination ........................................................ 259
18.2.1 General Tab of the SM ....................................................................................260
18.2.2 NAT and IP Tabs of the SM with NAT Disabled ............................................262
18.2.3 NAT and IP Tabs of the SM with NAT Enabled.............................................268
18.2.4 Radio Tab of the SM........................................................................................273
18.2.5 SNMP Tab of the SM.......................................................................................276
18.2.6 Quality of Service (QoS) Tab of the SM.........................................................279
18.2.7 Security Tab of the SM ....................................................................................282
18.2.8 VLAN Tab of the SM........................................................................................284
18.2.9 VLAN Membership Tab of the SM..................................................................286
18.2.10 DiffServe Tab of the SM ..................................................................................287
18.2.11 Protocol Filtering Tab of the SM .....................................................................289
18.2.12 NAT Port Mapping Tab of the SM ..................................................................290
18.2.13 Unit Settings Tab of the SM ............................................................................291
18.3 Setting the Configuration Source ................................................................ 292
18.4 Configuring a BH Timing Master for the Destination ................................... 294
18.4.1 General Tab of the BHM .................................................................................295
18.4.2 IP Tab of the BHM ...........................................................................................298
18.4.3 Radio Tab of the BHM .....................................................................................300
18.4.4 SNMP Tab of the BHM ....................................................................................303
18.4.5 Security Tab of the BHM .................................................................................306
18.4.6 DiffServe Tab of the BHM ...............................................................................308
18.4.7 Unit Settings Tab of the BHM .........................................................................310
18.5 Configuring a BH Timing Slave for the Destination ..................................... 312
18.5.1 General Tab of the BHS ..................................................................................312
18.5.2 IP Tab of the BHS ............................................................................................315
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
18.5.3 Radio Tab of the BHS......................................................................................316
18.5.4 SNMP Tab of the BHS.....................................................................................319
18.5.5 Quality of Service (QoS) Tab of the BHS.......................................................321
18.5.6 Security Tab of the BHS..................................................................................322
18.5.7 DiffServe Tab of the BHS ................................................................................324
18.5.8 Unit Settings Tab of the BHS ..........................................................................325
18.6 Adjusting Transmitter Output Power ........................................................... 326
19 Installing Components........................................................................................ 329
19.1 PDA Access to Canopy Modules ................................................................ 329
19.2 Installing an AP........................................................................................... 332
19.3 Installing a Connectorized Flat Panel Antenna ........................................... 333
19.4 Installing a GPS Antenna............................................................................ 334
19.4.1 Recommended Materials for Cabling the GPS Antenna ..............................335
19.4.2 Cabling the GPS Antenna ...............................................................................335
19.5 Installing a CMM2....................................................................................... 335
19.5.1 CMM2 Installation Temperature Range .........................................................335
19.5.2 Recommended Tools for Mounting a CMM2 .................................................335
19.5.3 Mounting a CMM2 ...........................................................................................336
19.5.4 Cabling a CMM2 ..............................................................................................336
19.5.5 Verifying CMM2 Connections .........................................................................340
19.6 Installing a CMMmicro ................................................................................ 340
19.6.1 CMMmicro Temperature Range .....................................................................341
19.6.2 Recommended Tools for Mounting a CMMmicro..........................................341
19.6.3 Mounting a CMMmicro ....................................................................................341
19.6.4 Installing the Power Supply for the CMMmicro..............................................341
19.6.5 Cabling a CMMmicro .......................................................................................342
19.6.6 Verifying CMMmicro Connections ..................................................................343
19.7 Installing an SM.......................................................................................... 344
19.8 Verifying an AP-SM Link............................................................................. 347
19.9 Installing a Reflector Dish ........................................................................... 350
19.9.1 Both Modules Mounted at Same Elevation....................................................350
19.9.2 Modules Mounted at Different Elevations ......................................................351
19.9.3 Mounting Assembly .........................................................................................351
19.10 Installing a BH Timing Master ..................................................................... 352
19.11 Installing a BH Timing Slave ....................................................................... 354
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
19.12 Upgrading a BH Link to BH20..................................................................... 355
19.13 Verifying a BH Link ..................................................................................... 355
20 Verifying System Functionality .......................................................................... 359
O
O
OP
P
PE
E
ER
R
RA
A
AT
T
TI
I
IO
O
ON
N
NS
S
S
G
G
GU
U
UI
I
ID
D
DE
E
E.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.3
3
36
6
61
1
1
21 Growing Your Network ....................................................................................... 363
21.1 Monitoring the RF Environment .................................................................. 363
21.1.1 Spectrum Analyzer (Not available for Canopy OFDM) ................................363
21.1.2 Graphical Spectrum Analyzer Display (Not available for Canopy OFDM) ..364
21.1.3 Using the AP as a Spectrum Analyzer (Not available for Canopy OFDM).364
21.2 Considering Software Release Compatibility .............................................. 365
21.2.1 Designations for Hardware in Radios.............................................................365
21.2.2 CMMmicro Software and Hardware Compatibility.........................................366
21.2.3 MIB File Set Compatibility ...............................................................................367
21.3 Redeploying Modules ................................................................................. 367
21.3.1 Wiring to Extend Network Sync ......................................................................367
22 Securing Your Network....................................................................................... 369
22.1 Isolating APs from the Internet.................................................................... 369
22.2 Encrypting Canopy Radio Transmissions ................................................... 369
22.2.1 DES Encryption................................................................................................369
22.2.2 AES Encryption ................................................................................................369
22.2.3 AES-DES Operability Comparisons ...............................................................370
22.3 Managing Module Access by Passwords.................................................... 371
22.3.1 Adding a User for Access to a Module ...........................................................371
22.3.2 Overriding Forgotten IP Addresses or Passwords on AP, SM, or BH .........373
22.3.3 Overriding Forgotten IP Addresses or Passwords on CMMmicro ...............375
22.4 Requiring SM Authentication ...................................................................... 375
22.5 Filtering Protocols and Ports....................................................................... 376
22.5.1 Port Filtering with NAT Enabled......................................................................376
22.5.2 Protocol and Port Filtering with NAT Disabled ..............................................376
22.6 Encrypting Downlink Broadcasts ................................................................ 378
22.7 Isolating SMs.............................................................................................. 378
22.8 Filtering Management through Ethernet...................................................... 379
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
22.9 Allowing Management from Only Specified IP Addresses........................... 379
22.10 Configuring Management IP by DHCP ....................................................... 379
23 Managing Bandwidth and Authentication ......................................................... 381
23.1 Managing Bandwidth without BAM ............................................................. 381
23.2 Bandwidth and Authentication Manager (BAM) Services and Features ...... 381
23.2.1 Bandwidth Manager Capability .......................................................................381
23.2.2 Authentication Manager Capability.................................................................383
24 Managing the Network From a Management Station (NMS) ............................ 385
24.1 Roles of Hardware and Software Elements ................................................ 385
24.1.1 Role of the Agent .............................................................................................385
24.1.2 Role of the Managed Device...........................................................................385
24.1.3 Role of the NMS...............................................................................................385
24.1.4 Dual Roles for the NMS...................................................................................385
24.1.5 Simple Network Management Protocol (SNMP) Commands .......................385
24.1.6 Traps from the Agent.......................................................................................386
24.1.7 AP SNMP Proxy to SMs ..................................................................................386
24.2 Management Information Base (MIB) ......................................................... 386
24.2.1 Cascading Path to the MIB .............................................................................386
24.2.2 Object Instances ..............................................................................................387
24.2.3 Management Information Base Systems and Interface (MIB-II) ..................387
24.2.4 Canopy Enterprise MIB ...................................................................................388
24.3 Configuring Modules for SNMP Access ...................................................... 389
24.4 Objects Defined in the Canopy Enterprise MIB........................................... 389
24.4.1 AP, SM, and BH Objects .................................................................................389
24.4.2 AP and BH Timing Master Objects.................................................................392
24.4.3 SM and BH Timing Slave Objects ..................................................................396
24.4.4 CMMmicro Objects ..........................................................................................399
24.5 Objects Defined in the PTP 400 and PTP 600 series Bridges MIB ............. 402
24.6 Objects Supported in the Canopy 30/60-Mbps BH...................................... 403
24.7 Objects Supported in the Canopy 150/300-Mbps BH.................................. 403
24.8 Interface Designations in SNMP ................................................................. 403
24.9 Traps Provided in the Canopy Enterprise MIB ............................................ 404
24.10 Traps Provided in the PTP 400 Series Bridge MIB ..................................... 404
24.11 Traps Provided in the PTP 600 Series Bridge MIB ..................................... 404
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
24.12 MIB Viewers ............................................................................................... 405
25 Using the Canopy Network Updater Tool (CNUT)............................................. 407
25.1 CNUT Functions ......................................................................................... 407
25.2 Network Element Groups............................................................................ 407
25.3 Network Layers........................................................................................... 407
25.4 Script Engine .............................................................................................. 408
25.5 Software Dependencies for CNUT.............................................................. 408
25.6 CNUT Download......................................................................................... 408
26 Using Informational Tabs in the GUI.................................................................. 409
26.1 Viewing General Status (All) ....................................................................... 409
26.2 Viewing Session Status (AP, BHM) ............................................................ 409
26.3 Viewing Remote Subscribers (AP, BHM).................................................... 410
26.4 Interpreting Messages in the Event Log (All) .............................................. 410
26.4.1 Time and Date Stamp......................................................................................410
26.4.2 Event Log Data Collection...............................................................................410
26.4.3 Messages that Flag Abnormal Events ...........................................................412
26.4.4 Messages that Flag Normal Events ...............................................................412
26.5 Viewing the Network Interface Tab (All)...................................................... 413
26.6 Interpreting Radio Statistics in the Scheduler Tab (All) ............................... 414
26.7 Viewing the List of Registration Failures (AP, BHM) ................................... 415
26.8 Interpreting Data in the Bridging Table (All) ................................................ 416
26.9 Translation Table (SM) ............................................................................... 417
26.10 Interpreting Data in the Ethernet Tab (All)................................................... 417
26.11 Interpreting RF Control Block Statistics in the Radio Tab (All) .................... 420
26.12 Interpreting Data in the VLAN Tab (AP, SM)............................................... 421
26.13 Data VC (All) .............................................................................................. 423
26.14 Filter (SM)................................................................................................... 424
26.15 NAT Stats (SM) .......................................................................................... 425
26.15.1 NAT DHCP Statistics (SM)..............................................................................426
26.15.2 Interpreting Data in the GPS Status Page (AP, BHM) ..................................427
27 Using Tools in the GUI........................................................................................ 429
27.1 Using the Spectrum Analyzer Tool (SM, BHS)............................................ 429
27.2 Using the Alignment Tool (SM, BHS).......................................................... 429
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
27.3 Using the Link Capacity Test Tool (All) ....................................................... 432
27.4 Using the AP Evaluation or BHM Evaluation Tool (SM, BHS) ..................... 434
27.5 Using the Frame Calculator Tool (All) ......................................................... 438
27.6 Using the SM Configuration Tool (AP, BHM) .............................................. 443
27.7 Using the BER Results Tool (SM, BHS) ..................................................... 444
28 Maintaining Your Canopy Software ................................................................... 445
28.1 History of System Software Upgrades ........................................................ 445
28.1.1 Canopy Release 8 Features ...........................................................................445
28.1.2 Canopy Release 8 Fixes .................................................................................445
28.2 History of CMMmicro Software Upgrades................................................... 445
28.3 Typical Contents of Release Notes............................................................. 445
28.4 Typical Upgrade Process............................................................................ 445
28.4.1 Downloading Software and Release Notes ...................................................446
29 Rebranding Module Interface Screens .............................................................. 447
30 Toggling Remote Access Capability.................................................................. 451
30.1 Denying All Remote Access........................................................................ 451
30.2 Reinstating Remote Access Capability ....................................................... 451
31 Setting Up a Protocol Analyzer on Your Canopy Network ............................... 453
31.1 Analyzing Traffic at an SM.......................................................................... 453
31.2 Analyzing Traffic at an AP or BH with No CMM .......................................... 454
31.3 Analyzing Traffic at an AP or BH with a CMM............................................. 454
31.4 Example of a Protocol Analyzer Setup for an SM ....................................... 455
32 Troubleshooting.................................................................................................. 463
32.1 General Planning for Troubleshooting ........................................................ 463
32.2 General Fault Isolation Process.................................................................. 463
32.3 Questions to Help Isolate the Problem........................................................ 464
32.4 Secondary Steps ........................................................................................ 464
32.5 Procedures for Troubleshooting.................................................................. 465
32.5.1 Module Has Lost or Does Not Establish Connectivity...................................465
32.5.2 NAT/DHCP-configured SM Has Lost or Does Not Establish Connectivity ..466
32.5.3 SM Does Not Register to an AP .....................................................................468
32.5.4 BHS Does Not Register to the BHM...............................................................469
32.5.5 Module Has Lost or Does Not Gain Sync ......................................................470

March 200 Through Software Release 6.
Draft 5 for Regulatory Review
32.5.6 Module Does Not Establish Ethernet Connectivity........................................471
32.5.7 Module Does Not Power Up ...........................................................................472
32.5.8 Power Supply Does Not Produce Power .......................................................472
32.5.9 CMM2 Does Not Power Up.............................................................................473
32.5.10 CMM2 Does Not Pass Proper GPS Sync to Connected Modules ...............473
32.5.11 Module Software Cannot be Upgraded..........................................................474
32.5.12 Module Functions Properly, Except Web Interface Became Inaccessible ..474
33 Obtaining Technical Support ............................................................................. 475
34 Getting Warranty Assistance ............................................................................. 481
R
R
RE
E
EF
F
FE
E
ER
R
RE
E
EN
N
NC
C
CE
E
E
I
I
IN
N
NF
F
FO
O
OR
R
RM
M
MA
A
AT
T
TI
I
IO
O
ON
N
N.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.4
4
48
8
83
3
3
35 Administering Modules through telnet Interface .............................................. 485
36 Regulatory and Legal Notices ............................................................................ 487
36.1 Important Note on Modifications ................................................................. 487
36.2 National and Regional Regulatory Notices.................................................. 487
36.2.1 U.S. Federal Communication Commission (FCC) Notification.....................487
36.2.2 Industry Canada (IC) Notification....................................................................489
36.2.3 Regulatory Requirements for CEPT Member States (www.cept.org)..........490
36.2.4 European Union Notification for 5.7 GHz Product.........................................491
36.2.5 Equipment Disposal.........................................................................................492
36.2.6 EU Declaration of Conformity for RoHS Compliance....................................492
36.2.7 UK Notification .................................................................................................492
36.2.8 Belgium Notification .........................................................................................492
36.2.9 Luxembourg Notification..................................................................................492
36.2.10 Czech Republic Notification ............................................................................492
36.2.11 Norway Notification ..........................................................................................493
36.2.12 Greece Notification ..........................................................................................493
36.2.13 Brazil Notification .............................................................................................493
36.2.14 Australia Notification ........................................................................................493
36.2.15 Labeling and Disclosure Table for China .......................................................494
36.3 RF Exposure .............................................................................................. 495
36.4 Legal Notices.............................................................................................. 495
36.4.1 Software License Terms and Conditions .......................................................495
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
36.4.2 Hardware Warranty in U.S. .............................................................................497
36.4.3 Limit of Liability.................................................................................................497
37 Additional Resources ......................................................................................... 499
38 History of Documentation................................................................................... 501
G
G
GL
L
LO
O
OS
S
SS
S
SA
A
AR
R
RY
Y
Y.
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
..
.
.5
5
50
0
03
3
3
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
LIST OF FIGURES
Figure 1: Canopy Advantage Platform GUI logo.............................................................. 49
Figure 2: Pole-mounted AP cluster.................................................................................. 50
Figure 3: OFDM AP - Antenna and Radio ....................................................................... 50
Figure 4: Structure-mounted SM ..................................................................................... 50
Figure 5: OFDM SM, front and side views....................................................................... 51
Figure 6: Examples of flat panel antennas with 900-MHz modules.................................. 52
Figure 7: Dish-mounted 10- or 20-Mbps BH.................................................................... 53
Figure 8: CMM2 enclosure .............................................................................................. 54
Figure 9: CMM2 pole-mounted........................................................................................ 54
Figure 10: Motorola GPS antenna................................................................................... 55
Figure 11: 600SS surge suppressor................................................................................ 55
Figure 12: ACPS110-03A power supply.......................................................................... 56
Figure 13: ACPSSW-09A power supply .......................................................................... 56
Figure 14: 27RD with mounted module ........................................................................... 56
Figure 15: SMMB1 SM support bracket........................................................................... 57
Figure 16: ACATHS-01 alignment headset ..................................................................... 59
Figure 17: HSG-01 Housing ............................................................................................ 59
Figure 18: Uplink data slot usage .................................................................................... 83
Figure 19: TDD dividing Canopy frames.......................................................................... 84
Figure 20: Uplink and downlink rate caps adjusted to apply aggregate cap..................... 85
Figure 21: Uplink and downlink rate cap adjustment example ......................................... 85
Figure 22: Canopy frame structure.................................................................................. 88
Figure 23: One unsynchronized AP in cluster.................................................................. 94
Figure 24: GPS timing throughout the Canopy network (Canopy FSK shown) ................ 95
Figure 25: Additional link to extend network sync, Design 3 ............................................ 96
Figure 26: Additional link to extend network sync, Design 4 ............................................ 96
Figure 27: Additional link to extend network sync, Design 5 ............................................ 97
Figure 28: Typical network layout with no BH................................................................ 103
Figure 29: Typical network layout with BH..................................................................... 104
Figure 30: Typical multiple-BH network layout............................................................... 104
Figure 31: Determinants in Rx signal level .................................................................... 130
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Figure 32: Example layout of 7 Access Point clusters ................................................... 142
Figure 33: Fresnel zone ................................................................................................ 145
Figure 34: Variables for calculating angle of elevation (and depression) ....................... 145
Figure 35: Double-hop backhaul links ........................................................................... 147
Figure 36: Remote AP deployment ............................................................................... 148
Figure 37: Example 900-MHz remote AP behind 2.4-GHz SM ...................................... 149
Figure 38: Remote AP wired to SM that also serves a customer ................................... 150
Figure 39: Remote AP wired to SM that serves as a relay ............................................ 151
Figure 40: NAT Disabled implementation ...................................................................... 157
Figure 41: NAT with DHCP Client and DHCP Server implementation ........................... 158
Figure 42: NAT with DHCP Client implementation ........................................................ 159
Figure 43: NAT with DHCP Server implementation ....................................................... 160
Figure 44: NAT without DHCP implementation.............................................................. 161
Figure 45: Example of IP address in Class B subnet..................................................... 162
Figure 46: Canopy base cover, attached and detached ................................................ 178
Figure 47: Canopy CMM2, bottom view ........................................................................ 180
Figure 48: Cluster Management Module micro.............................................................. 181
Figure 49: RJ-45 pinout for straight-through Ethernet cable .......................................... 183
Figure 50: RJ-45 pinout for crossover Ethernet cable.................................................... 183
Figure 51: RJ-11 pinout for straight-through sync cable ................................................ 184
Figure 52: Quick Start tab of AP, example .................................................................... 186
Figure 53: Radio Frequency Carrier tab of AP, example ............................................... 187
Figure 54: Synchronization tab of AP, example............................................................. 188
Figure 55: LAN IP Address tab of AP, example............................................................. 189
Figure 56: Review and Save Configuration tab of AP, example .................................... 190
Figure 57: Time tab of AP, example .............................................................................. 191
Figure 58: Session Status tab data from AP, example .................................................. 193
Figure 59: Remote Subscribers tab of AP, example...................................................... 197
Figure 60: General Status tab of SM, example.............................................................. 198
Figure 61: General Status tab of AP, example .............................................................. 201
Figure 62: Quick Start tab of BHM, example ................................................................. 205
Figure 63: Time tab of BHM, example........................................................................... 207
Figure 64: Remote Subscribers tab of BHM, example................................................... 209
Figure 65: General Status tab of BHS, example............................................................ 210
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Figure 66: General Status tab of BHM, example ........................................................... 213
Figure 67: CMMmicro layout ......................................................................................... 216
Figure 68: CMMmicro door label ................................................................................... 218
Figure 69: CMMmicro circuit board ............................................................................... 219
Figure 70: CMMmicro connections................................................................................ 220
Figure 71: Status page of CMMmicro, example............................................................. 221
Figure 72: Configuration page of CMMmicro, example.................................................. 224
Figure 73: GPS Status page of CMMmicro, example .................................................... 231
Figure 74: Port MIB page of CMMmicro, example......................................................... 232
Figure 75: General tab of AP, example ......................................................................... 236
Figure 76: IP tab of AP, example................................................................................... 239
Figure 77: Radio tab of AP (900 MHz), example ........................................................... 241
Figure 78: SNMP tab of AP, example............................................................................ 246
Figure 79: Quality of Service (QoS) tab of AP, example................................................ 249
Figure 80: Security tab of AP, example ......................................................................... 251
Figure 81: VLAN tab of AP, example............................................................................. 253
Figure 82: VLAN Membership tab of AP, example ........................................................ 255
Figure 83: DiffServe tab of AP, example ....................................................................... 256
Figure 84: Unit Settings tab of AP, example.................................................................. 258
Figure 85: General tab of SM, example......................................................................... 260
Figure 86: NAT tab of SM with NAT disabled, example................................................. 263
Figure 87: IP tab of SM with NAT disabled, example..................................................... 266
Figure 88: NAT tab of SM with NAT enabled, example ................................................. 268
Figure 89: IP tab of SM with NAT enabled, example ..................................................... 272
Figure 90: Radio tab of SM, example ............................................................................ 273
Figure 91: SNMP tab of SM, example ........................................................................... 276
Figure 92: Quality of Service (QoS) tab of SM, example ............................................... 279
Figure 93: Security tab of SM, example......................................................................... 282
Figure 94: VLAN tab of SM, example ............................................................................ 284
Figure 95: VLAN Membership tab of SM, example........................................................ 286
Figure 96: DiffServe tab of SM, example....................................................................... 287
Figure 97: Protocol Filtering tab of SM, example........................................................... 289
Figure 98: NAT Port Mapping tab of SM, example ........................................................ 290
Figure 99: Unit Settings tab of SM, example ................................................................. 291
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Figure 100: General tab of BHM, example .................................................................... 295
Figure 101: IP tab of BHM, example ............................................................................. 298
Figure 102: Radio tab of BHM, example........................................................................ 300
Figure 103: SNMP tab of BHM, example....................................................................... 303
Figure 104: Security tab of BHM, example .................................................................... 306
Figure 105: DiffServe tab of BHM, example .................................................................. 308
Figure 106: Unit Settings tab of BHM, example............................................................. 310
Figure 107: General tab of BHS, example..................................................................... 312
Figure 108: IP tab of BHS, example .............................................................................. 315
Figure 109: Radio tab of BHS, example ........................................................................ 317
Figure 110: SNMP tab of BHS, example ....................................................................... 319
Figure 111: Quality of Service (QoS) tab of BHS, example ........................................... 321
Figure 112: Security tab of BHS, example..................................................................... 322
Figure 113: DiffServe tab of BHS, example................................................................... 324
Figure 114: Unit Settings tab of BHS, example ............................................................. 325
Figure 115: PDA Quick Status tab, example ................................................................. 330
Figure 116: PDA Spectrum Analyzer tab of SM, example ............................................. 330
Figure 117: PDA Spectrum Results tab of SM, example ............................................... 331
Figure 118: PDA Information tab of SM, example ......................................................... 331
Figure 119: PDA AP Evaluation tab of SM, example ..................................................... 332
Figure 120: PDA Aim tab of SM, example ..................................................................... 332
Figure 121: Detail of GPS antenna mounting ................................................................ 335
Figure 122: Detail of pole mounting............................................................................... 336
Figure 123: Location of 115-/230-volt switch ................................................................. 337
Figure 124: Layout of logical connections in CMM2 ...................................................... 338
Figure 125: Canopy CMM2, front view .......................................................................... 339
Figure 126: Port indicator LED on Ethernet switch ........................................................ 340
Figure 127: SM attachment to reflector arm .................................................................. 344
Figure 128: SM grounding per NEC specifications ........................................................ 345
Figure 129: Internal view of Canopy 300SS Surge Suppressor..................................... 346
Figure 130: Audible Alignment Tone kit, including headset and connecting cable ......... 347
Figure 131: AP/SM link status indications in the AP Session Status tab........................ 349
Figure 132: Correct mount with reflector dish ................................................................ 350
Figure 133: Incorrect mount with reflector dish.............................................................. 351
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Figure 134: Mounting assembly, exploded view ............................................................ 352
Figure 135: BH attachment to reflector arm................................................................... 353
Figure 136: Session Status tab of BHM......................................................................... 357
Figure 137: Spectrum Analyzer tab of SM, example...................................................... 364
Figure 138: General Status tab view for GUEST-level account ..................................... 372
Figure 139: Add User tab of SM, example..................................................................... 373
Figure 140: RJ-11 pinout for the override plug .............................................................. 374
Figure 141: Categorical protocol filtering ....................................................................... 377
Figure 142: Session Status tab data, example .............................................................. 409
Figure 143: Event Log tab data, example...................................................................... 411
Figure 144: Network Interface tab of AP, example ........................................................ 413
Figure 145: Network Interface tab of SM, example........................................................ 413
Figure 146: Scheduler tab of SM, example ................................................................... 414
Figure 147: SM Registration Failures tab of AP, example ............................................. 415
Figure 148: Bridging Table tab of AP, example ............................................................. 416
Figure 149: Translation Table tab of SM, example ........................................................ 417
Figure 150: Ethernet tab of AP, example....................................................................... 418
Figure 151: Radio tab of Statistics page in SM, example .............................................. 420
Figure 152: VLAN tab of AP, example........................................................................... 422
Figure 153: Data VC tab of SM, example ...................................................................... 423
Figure 154: Filter tab on SM, example .......................................................................... 425
Figure 155: Nat Stats tab on SM, example.................................................................... 426
Figure 156: NAT DHCP Statistics tab in SM, example .................................................. 426
Figure 157: Alignment tab of BHS, example.................................................................. 429
Figure 158: Link Capacity Test tab with 1522-byte packet length, example................... 432
Figure 159: Link Capacity Test tab with 64-byte packet length, example....................... 433
Figure 160: AP Evaluation tab of SM, example ............................................................. 435
Figure 161: Frame Calculator tab, example .................................................................. 439
Figure 162: Calculated Frame Results section of Frame Calculator tab, example ......... 442
Figure 163: SM Configuration tab of AP, example......................................................... 443
Figure 164: BER Results tab of SM, example ............................................................... 444
Figure 165: Example ftp session to transfer custom logo file......................................... 448
Figure 166: Example telnet session to activate custom logo file .................................... 449
Figure 167: Example telnet session to clear custom files .............................................. 450
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Figure 168: Protocol analysis at SM.............................................................................. 453
Figure 169: Protocol analysis at AP or BH not connected to a CMM ............................. 454
Figure 170: Protocol analysis at AP or BH connected to a CMM ................................... 455
Figure 171: IP tab of SM with NAT disabled and local accessibility ............................... 456
Figure 172: Local Area Connection Properties window ................................................. 457
Figure 173: Internet Protocol (TCP/IP) Properties window ............................................ 457
Figure 174: Ethereal Capture Options window .............................................................. 458
Figure 175: Ethereal Capture window ........................................................................... 459
Figure 176: <capture> - Ethereal window, Packet 1 selected ........................................ 460
Figure 177: <capture> - Ethereal window, Packet 14 selected ...................................... 461
Figure 178: NAT Table tab of SM, example .................................................................. 467
Figure 179: NAT DHCP Statistics tab of SM, example .................................................. 468
Figure 180: Event Log tab of SM, example ................................................................... 470
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
LIST OF TABLES
Table 1: Canopy User Guide organization scheme ......................................................... 36
Table 2: Examples of where to find information in this user guide ................................... 37
Table 3: Locations of screen captures and associated documentation ............................ 38
Table 4: Font types ......................................................................................................... 41
Table 5: Admonition types............................................................................................... 41
Table 6: Essential user guide elements for new backhaul network implementation ......... 47
Table 7: Power supply descriptions................................................................................. 55
Table 8: Recommended outdoor UTP Category 5E cables ............................................. 57
Table 9: Recommended indoor UTP Category 5E cables ............................................... 58
Table 10: Recommended antenna cables ....................................................................... 58
Table 11: Product applications per frequency band range............................................... 60
Table 12: Products with encryption options available per frequency band, PTMP links ... 61
Table 13: Typical range and throughput per frequency band, PTMP links ....................... 62
Table 14: Typical range and throughput per frequency band, PTP links.......................... 63
Table 15: Cluster management product similarities and differences ................................ 63
Table 16: Canopy applications and tools......................................................................... 65
Table 17: Correct placement of license keys................................................................... 70
Table 18: CMM2 specifications and limitations................................................................ 71
Table 19: CMMmicro specifications and limitations ......................................................... 72
Table 20: Canopy model numbers .................................................................................. 78
Table 21: Labels and locations of model (part) numbers and ESNs ................................ 79
Table 22: Characteristics of hardware scheduling ........................................................... 89
Table 23: Effect of 2X operation on throughput for the SM .............................................. 90
Table 24: Effects of network conditions on PTMP throughput ....................................... 100
Table 25: Comparison of SM products with Canopy Advantage AP .............................. 100
Table 26: Canopy features............................................................................................ 107
Table 27: Demonstration Kit part numbers .................................................................... 121
Table 28: Starter Kit part numbers ................................................................................ 124
Table 29: Signal quality levels indicated by jitter ........................................................... 134
Table 30: Recommended courses of action based on Efficiency in 2X operation .......... 135
Table 31: Example 900-MHz channel assignment by sector ......................................... 140
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Table 32: Example 2.4-GHz channel assignment by sector .......................................... 141
Table 33: Example 5.2-GHz channel assignment by sector .......................................... 141
Table 34: Example 5.4-GHz channel assignment by sector .......................................... 141
Table 35: Example 5.7-GHz channel assignment by sector .......................................... 142
Table 36: VLAN filters in point-to-multipoint modules .................................................... 166
Table 37: Exposure separation distances...................................................................... 169
Table 38: Calculated exposure distances and power compliance margins .................... 170
Table 39: Statistical incidence of current from lightning strikes...................................... 172
Table 40: LEDs in AP and BHM .................................................................................... 179
Table 41: LEDs in SM and BHS .................................................................................... 179
Table 42: Port Configuration selections for CMMmicro.................................................. 226
Table 43: When changes become effective in CMMmicro ............................................. 230
Table 44: Control slot settings for all APs in cluster....................................................... 243
Table 45: Recommended combined settings for typical operations ............................... 293
Table 46: Where feature values are obtained for an SM with authentication required ... 293
Table 47: Where feature values are obtained for an SM with authentication disabled ... 294
Table 48: Total gain per antenna................................................................................... 327
Table 49: Patch antenna and reflector gain................................................................... 327
Table 50: Transmitter output power settings, example cases ........................................ 328
Table 51: Wire size for CMMmicro power runs of longer than 9 feet (2.8 m) ................. 342
Table 52: Hardware series by MAC address ................................................................. 365
Table 53: Hardware series differences .......................................................................... 366
Table 54: AP/BH compatibility with CMMmicro.............................................................. 366
Table 55: Ports filtered per protocol selections.............................................................. 378
Table 56: Example times to download for typical tiers of service with Canopy AP ......... 382
Table 57: Example times to download for typical tiers of service with Advantage AP .... 383
Table 58: Categories of MIB-II objects .......................................................................... 387
Table 59: Canopy Enterprise MIB objects for APs, SMs, and BHs ................................ 389
Table 60: Canopy Enterprise MIB objects for APs and BH timing masters .................... 392
Table 61: Canopy Enterprise MIB objects for SMs and BH timing slaves ...................... 396
Table 62: Canopy Enterprise MIB objects for CMMmicros ............................................ 399
Table 63: PTP 400 and PTP 600 series bridge MIB objects .......................................... 402
Table 64: Event Log messages for abnormal events..................................................... 412
Table 65: Event Log messages for normal events......................................................... 412
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Table 66: Basic site information for technical support.................................................... 476
Table 67: Supported telnet commands for module administration ................................. 485
Table 68: US FCC IDs and Industry Canada Certification Numbers and Covered
Configurations ........................................................................................................ 488
Table 69: Disclosure Table............................................................................................ 495
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
LIST OF PROCEDURES
Procedure 1: Modifying a fixed license key for a module IP address ............................. 114
Procedure 2: Analyzing the spectrum............................................................................ 131
Procedure 3: Reducing transmitter output power .......................................................... 152
Procedure 4: Wrapping the cable .................................................................................. 175
Procedure 5: Setting up the AP for Quick Start ............................................................. 184
Procedure 6: Bypassing proxy settings to access module web pages ........................... 185
Procedure 7: Using Quick Start to configure a standalone AP for test ........................... 187
Procedure 8: Setting up the SM for test......................................................................... 192
Procedure 9: Retrying to establish a point-to-multipoint link .......................................... 193
Procedure 10: Verifying and recording information from SMs........................................ 200
Procedure 11: Verifying and recording information from the AP .................................... 203
Procedure 12: Setting up the BH for Quick Start ........................................................... 204
Procedure 13: Using Quick Start to configure the BHs for test ...................................... 206
Procedure 14: Setting up the BHS for test..................................................................... 208
Procedure 15: Verifying and recording information from the BHS.................................. 212
Procedure 16: Verifying and recording information from the BHM ................................. 215
Procedure 17: Setting up a CMMmicro.......................................................................... 217
Procedure 18: Setting CMMmicro parameters for test................................................... 225
Procedure 19: Installing the AP..................................................................................... 332
Procedure 20: Mounting the GPS antenna.................................................................... 334
Procedure 21: Mounting the CMM2............................................................................... 336
Procedure 22: Cabling the CMM2 ................................................................................. 337
Procedure 23: Verifying CMM2 connections ................................................................. 340
Procedure 24: Mounting the CMMmicro........................................................................ 341
Procedure 25: Installing the Power Supply for the CMMmicro....................................... 342
Procedure 26: Cabling the CMMmicro .......................................................................... 342
Procedure 27: Verifying CMMmicro connections........................................................... 343
Procedure 28: Installing the SM .................................................................................... 344
Procedure 29: Verifying performance for an AP-SM link ............................................... 347
Procedure 30: Installing the BHM.................................................................................. 352
Procedure 31: Installing the BHS .................................................................................. 354
March 200 Through Software Release 6.
Draft 5 for Regulatory Review
Procedure 32: Verifying performance for a BH link........................................................ 355
Procedure 33: Verifying system functionality................................................................. 359
Procedure 34: Using the Spectrum Analyzer in AP feature ........................................... 365
Procedure 35: Extending network sync ......................................................................... 367
Procedure 36: Fabricating an override plug................................................................... 374
Procedure 37: Regaining access to a module ............................................................... 374
Procedure 38: Using the override switch to regain access to CMMmicro ...................... 375
Procedure 39: Installing the Canopy Enterprise MIB files .............................................. 388
Procedure 40: Performing a Link Capacity Test ............................................................ 433
Procedure 41: Using the Frame Calculator ................................................................... 441
Procedure 42: Replacing the Canopy logo on the GUI with another logo ...................... 447
Procedure 43: Changing the URL of the logo hyperlink................................................. 449
Procedure 44: Returning a module to its original logo and hyperlink ............................. 449
Procedure 45: Denying all remote access ..................................................................... 451
Procedure 46: Reinstating remote access capability ..................................................... 451
Procedure 47: Setting up a protocol analyzer................................................................ 456
Procedure 48: Troubleshooting loss of connectivity ...................................................... 465
Procedure 49: Troubleshooting loss of connectivity for NAT/DHCP-configured SM ...... 466
Procedure 50: Troubleshooting SM failing to register to an AP ..................................... 468
Procedure 51: Troubleshooting BHS failing to register to a BHM .................................. 469
Procedure 52: Troubleshooting loss of sync.................................................................. 470
Procedure 53: Troubleshooting loss of Ethernet connectivity ........................................ 471
Procedure 54: Troubleshooting failure to power up ....................................................... 472
Procedure 55: Troubleshooting failure of power supply to produce power..................... 472
Procedure 56: Troubleshooting CMM2 that malfunctions .............................................. 473
Procedure 57: Troubleshooting CMM2 not passing sync .............................................. 473
Procedure 58: Troubleshooting an unsuccessful software upgrade............................... 474
Procedure 59: Restoring the web interface to a module ................................................ 474

Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 31
G
G
G
G
G
GU
U
U
U
U
UI
I
I
I
I
ID
D
D
D
D
DE
E
E
E
E
E
T
T
T
T
T
TO
O
O
O
O
O
T
T
T
T
T
TH
H
H
H
H
HI
I
I
I
I
IS
S
S
S
S
S
U
U
U
U
U
US
S
S
S
S
SE
E
E
E
E
ER
R
R
R
R
R
G
G
G
G
G
GU
U
U
U
U
UI
I
I
I
I
ID
D
D
D
D
DE
E
E
E
E
E

Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 33
1 NEW IN THIS ISSUE
1.1 NEW PRODUCTS AND FEATURES DESCRIBED IN ISSUE 2
Issue 2 adds the following products and features
◦ Release 8.2 features, including US and Canada DFS (Dynamic Frequency
Selection) support for 5.4 GHz modules
◦ Canopy OFDM in the 5.4 GHz band
1.2 NEW DESCRIPTIONS AND REVISIONS IN ISSUE 2
This section is a placeholder where other new descriptions, as wells as clarifications and
corrections, will be listed in future issues.
1.3 MOTOwi4 PORTFOLIO
The MOTOwi4™ portfolio of wireless broadband solutions provides a range of flexible,
mix-and-match options including
◦ wi4 Fixed
− Canopy unlicensed point-to-multipoint solutions
− Point-to-point solutions, including
− PTP 100 series Canopy backhauls
− PTP 400 and PTP 600 series bridges
− Expedience licensed point-to-multipoint solutions
◦ wi4 Indoor
− Broadband over Powerline (BPL) solutions
− Enterprise Wireless LAN (WLAN) solutions
◦ wi4 Mesh, including the MOTOMESH series of products
◦ wi4 WiMAX, including infrastructure, CPE and devices, services, and IP core
1.4 PRODUCTS COVERED BY THIS USER GUIDE
Products covered by this user guide include
◦ Canopy Access Points (APs), Subscriber Modules (SMs), and Backhauls (BHs)
in the following frequency bands:
− 900 MHz
− 2.4 GHz
− 5.1 GHz
− 5.2 GHz
− 5.4 GHz
− 5.7 GHz
◦ Canopy OFDM APs and SMs in the 5.4 GHz band
◦ Cluster Management Module micro (CMMmicro)
◦ Surge Suppressor
◦ Canopy 900 MHz Indoor SMs

Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 34
1.5 PRODUCTS NOT COVERED BY THIS USER GUIDE
Canopy products with their own user guides include
◦ Cluster Management Module 4 (CMM4)
◦ Canopy LENS
All the non-Canopy wi4 products and solutions are covered by their own user guides and
documentation.
1.6 SOFTWARE COMPATIBILITY DESCRIBED IN THIS USER GUIDE
The following sections of this document provide details and caveats about the
compatibility of Canopy products:
◦ Designations for Hardware on Page 365
◦ CMMmicro Software and Hardware Compatibility on Page 366
◦ MIB File Set Compatibility on Page 367

Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 35
2 USING THIS USER GUIDE
This document should be used with Canopy features through Software Release 8.2,
Canopy OFDM, and CMMmicro Release 2.2.1. The audience for this document includes
system operators, network administrators, and equipment installers.
2.1 FINDING THE INFORMATION YOU NEED
2.1.1 Becoming Familiar with This User Guide
This is a guide to the guide. A high-level overview of the guide and some examples of
where to look provide insight into how information is arranged and labeled.
The Table of Contents provides not only a sequential index of topics but also a visual
glance at the organization of topics in this guide. A few minutes spent with the Table of
Contents in either the paper or the electronic version of this guide can save much more
time in finding information now and in the future. The List of Procedures may be
especially useful in the paper version of this guide, particularly where you mark those
procedures that you wish to frequently see.
In contrast, the List of Figures and List of Tables are most useful for automated searches
on key words in the electronic version of this guide. If a match is present, the match is the
first instance that the search finds.
Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 36
Quick Reference
The Canopy User Guide comprises six sections, as described in Table 1.
Table 1: Canopy User Guide organization scheme
Section
Purpose
Guide to This User Guide
(this section)
Identifies
◦ products covered by this user guide.
◦ products covered by their own separate user guides.
◦ how this user guide is organized.
◦ where to find module web pages and parameter
descriptions.
◦ what the various typefaces and admonitions indicate.
◦ how to contact Canopy.
Overview of Canopy Networks
Provides
◦ references to RF and networking theory.
◦ a list of sections to see if you are building only a backhaul
network.
◦ overviews and comparisons of Canopy products and how
they communicate.
◦ descriptions of data handling and synchronization.
◦ a review of Canopy optional features.
◦ resources for developing familiarity and proficiencies with
Canopy networks.
Planning Guide
Provides essential information for
◦ evaluating an area for a Canopy network.
◦ specifying the IP addresses and frequency band ranges to
use for each type of link.
Installation and Configuration Guide
Provides systematic approaches for
◦ avoiding hazards from RF and natural causes.
◦ testing, storing, and deploying Canopy equipment.
Operations Guide
Provides guidance for
◦ expanding network coverage.
◦ improving the security of Canopy wireless links.
◦ distributing bandwidth resources.
◦ monitoring and changing variables through SNMP.
Reference Information
Provides supplemental information such as
◦ authorizations, approvals, and notices.
◦ a bibliography of adjunctive information sources.
◦ a history of changes in Canopy documentation.
Glossary
Defines terms and concepts that are used in this user guide.
Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 37
Examples
A list of common tasks and references to information that supports each task is provided
in Table 2.
Table 2: Examples of where to find information in this user guide
If you want to know…
then see…
because…
Avoiding Self Interference
on Page 151
this topic is important to RF
planning.
what the Spectrum Analyzer in
SM and BHS feature does
Monitoring the RF
Environment on Page 363
this topic is also important to
managing the network.
what types of slots compose the
Canopy frame
Understanding Bandwidth
Management on Page 81
this information is helpful for
understanding Canopy networks.
how to calculate whether an
object will interfere with a signal
Noting Possible
Obstructions in the Fresnel
Zone on Page 132
this topic is important to RF
planning.
Cables on Page 35
cables are accessory
components.
how long a cable you can use
from the GPS antenna to the
CMM
Procedure 20 on Page 334
or Procedure 24 on Page
341
the advisory applies to mounting
GPS antennas and CMMs.
how to react to a WatchDog
Event Log message
Messages that Flag
Abnormal Events on Page
412 and Messages that
Flag Normal Events on
Page 412
together, these two sections
document all significant Event
Log messages.
what beam angle the passive
reflector dish produces
Specifications and
Limitations on Page 70,
then downward to a table
for a Canopy Part Number
that includes “RF.”
the beam angle is a specification.
how to aim the passive reflector
dish
Installing a Reflector Dish
on Page 350
aiming is associated with
Backhaul Module installation.
how to set Differentiated
Services values so that traffic
with original ToS byte formatting
continues to be prioritized as it
was before DSCP fields.
High-priority Bandwidth
on Page 86
DSCP fields specify the level of
priority that the device is
requesting for the packet.

Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 38
2.1.2 Searching This User Guide
To search this document and the software release notes of supported releases, look in
the Table of Contents for the topic and in the Adobe Reader® search capability for
keywords that apply.1 These searches are most effective when you begin the search from
the cover page because the first matches may be in titles of sections, figures, tables, or
procedures.
2.1.3 Finding Parameter and Field Definitions for Module Web Pages
Because this user guide is sequentially arranged to support tasks, and various tasks
require different settings and readings, parameter and field definitions are scattered
according to the tasks that they support. The locations of these are provided in Table 3.
Table 3: Locations of screen captures and associated documentation
Tab or Web Page Displayed
Page
Add User tab of SM, example
373
Alignment tab of BHS, example
429
AP Evaluation tab of SM, example
435
BER Results tab of SM, example
444
Bridging Table tab of AP, example
416
Calculated Frame Results section of Frame Calculator tab, example
442
Configuration page of CMMmicro, example
224
DiffServe tab of AP, example
256
DiffServe tab of BHM, example
308
DiffServe tab of BHS, example
324
DiffServe tab of SM, example
287
Ethernet tab of AP, example
418
Event Log tab data, example
411
Event Log tab of SM, example
470
Frame Calculator tab, example
439
General Status tab of AP, example
201
General Status tab of BHM, example
213
General Status tab of BHS, example
210
General Status tab of SM, example
198
General Status tab view for GUEST-level account
372
General tab of AP, example
236
General tab of BHM, example
295
General tab of BHS, example
312
1 Reader is a registered trademark of Adobe Systems, Incorporated.
Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 39
Tab or Web Page Displayed
Page
General tab of SM, example
260
GPS Status page of CMMmicro, example
231
IP tab of AP, example
239
IP tab of BHM, example
298
IP tab of BHS, example
315
IP tab of SM with NAT disabled and local accessibility
456
IP tab of SM with NAT disabled, example
266
IP tab of SM with NAT enabled, example
272
LAN IP Address tab of AP, example
189
Link Capacity Test tab with 1522-byte packet length, example
432
Link Capacity Test tab with 64-byte packet length, example
433
NAT DHCP Statistics tab of SM, example
468
NAT Port Mapping tab of SM, example
290
NAT tab of SM with NAT disabled, example
263
NAT tab of SM with NAT enabled, example
268
NAT Table tab of SM, example
467
PDA Aim tab of SM, example
332
PDA AP Evaluation tab of SM, example
332
PDA Information tab of SM, example
331
PDA Quick Status tab, example
330
PDA Spectrum Analyzer tab of SM, example
330
PDA Spectrum Results tab of SM, example
331
Port MIB page of CMMmicro, example
232
Protocol Filtering tab of SM, example
289
Quality of Service (QoS) tab of AP, example
249
Quality of Service (QoS) tab of BHS, example
321
Quality of Service (QoS) tab of SM, example
279
Quick Start tab of AP, example
186
Quick Start tab of BHM, example
205
Radio Frequency Carrier tab of AP, example
187
Radio tab of AP (900 MHz), example
241
Radio tab of BHM, example
300
Radio tab of BHS, example
317
Radio tab of SM, example
273
Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 40
Tab or Web Page Displayed
Page
Remote Subscribers tab of AP, example
197
Remote Subscribers tab of BHM, example
209
Review and Save Configuration tab of AP, example
190
Scheduler tab of SM, example
414
Security tab of AP, example
251
Security tab of BHM, example
306
Security tab of BHS, example
322
Security tab of SM, example
282
Session Status tab data from AP, example
193
Session Status tab data, example
409
SM Configuration tab of AP, example
443
SM Registration Failures tab of AP, example
415
SNMP tab of AP, example
246
SNMP tab of BHM, example
303
SNMP tab of BHS, example
319
SNMP tab of SM, example
276
Spectrum Analyzer tab of SM, example
364
Status page of CMMmicro, example
221
Synchronization tab of AP, example
188
Time tab of AP, example
191
Time tab of BHM, example
207
Unit Settings tab of AP, example
258
Unit Settings tab of BHM, example
310
Unit Settings tab of BHS, example
325
Unit Settings tab of SM, example
291
VLAN Membership tab of AP, example
255
VLAN Membership tab of SM, example
286
VLAN tab of AP, example
253
VLAN tab of SM, example
284

Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 41
2.2 INTERPRETING TYPEFACE AND OTHER CONVENTIONS
This document employs distinctive fonts to indicate the type of information, as described
in Table 4.
Table 4: Font types
Font
Type of Information
variable width bold
Selectable option in a graphical user interface or settable
parameter in the web-based interface to a Canopy component.
constant width regular
Literal system response in a command-line interface.
constant width italic
Variable system response in a command-line interface.
constant width bold
Literal user input in a command-line interface.
constant width bold italic
Variable user input in a command-line interface.
This document employs specific imperative terminology as follows:
◦ Type means press the following characters.
◦ Enter means type the following characters and then press Enter.
This document also employs a set of consistently used admonitions. Each of these types
of admonitions has a general purpose that underlies the specific information in the box.
These purposes are indicated in Table 5.
Table 5: Admonition types
Admonition
Label
General Message
NOTE:
informative content that may
◦ defy common or cursory logic.
◦ describe a peculiarity of the Canopy implementation.
◦ add a conditional caveat.
◦ provide a reference.
◦ explain the reason for a preceding statement or provide prerequisite
background for what immediately follows.
RECOMMENDATION:
suggestion for an easier, quicker, or safer action or practice.
Release 8 Guide To This User Guide
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 42
Admonition
Label
General Message
IMPORTANT!
informative content that may
◦ identify an indication that you should watch for.
◦ advise that your action can disturb something that you may not want
disturbed.
◦ reiterate something that you presumably know but should always
remember.
CAUTION!
a notice that the risk of harm to equipment or service exists.
WARNING!
a notice that the risk of harm to person exists.
2.3 GETTING ADDITIONAL HELP
Help is available for problems with supported products and features. Obtaining Technical
Support on Page 475 provides the sequence of actions that you should take if these
problems arise.
2.4 SENDING FEEDBACK
We welcome your feedback on Canopy system documentation. This includes feedback
on the structure, content, accuracy, or completeness of our documents, and any other
comments you have. Send your comments to
technical-documentation@canopywireless.com.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 43
O
O
OV
V
VE
E
ER
R
RV
V
VI
I
IE
E
EW
W
W
O
O
OF
F
F
C
C
CA
A
AN
N
NO
O
OP
P
PY
Y
Y
N
N
NE
E
ET
T
TW
W
WO
O
OR
R
RK
K
KS
S
S
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 45
3 ADVANCING FROM RESEARCH TO
IMPLEMENTATION
Before you begin to research a possible Canopy implementation, you should have both
◦ basic knowledge of RF theory. See
− Understanding RF Fundamentals on Page 117.
− Engineering Your RF Communications on Page 129.
◦ network experience. See
− Canopy Link Characteristics on Page 81.
− Understanding IP Fundamentals on Page 117.
− Engineering Your IP Communications on Page 155.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 47
4 REALIZING A WIRELESS BACKHAUL NETWORK
Canopy backhaul modules (BHs) can connect Canopy access point clusters to the point
of presence or be the backbone of a Metro WiFi mesh network. In other applications,
the backhaul modules can be used to provide connectivity for
◦ cell sites, in lieu of leased T1/E1 telecommunications lines.
◦ buildings in corporate or institutional campuses.
◦ remote sites, including temporary sites set up for relief efforts.
These BHs are available in 10- or 20-Mbps modulation rates from the factory. The rate is
distinguished as BH10 or BH20 in the Software Version field of the General Status tab
(in the Home page) of the module GUI.
For these and any other backhaul networks, Table 6 provides a quick reference to
information that you would need to establish and maintain the Canopy wireless backhaul
network.
Table 6: Essential user guide elements for new backhaul network implementation
Element
Title
Page
Section 1.5
Products Not Covered by This User Guide
34
Section 5.1.8
Canopy
Backhaul Module
52
Section 5.1.11
Cluster Management Module-2 (Part 1008CK-2)
53
Section 5.1.12
Cluster Management Module micro (Part 1070CK)
54
Table 14
Typical range and throughput per frequency band, PTP links
63
Section 8.2
BH-BH Links
99
Figure 30
Typical multiple-BH network layout
104
Section 12.2
Analyzing the RF Environment
131
Section 12.5
Considering Frequency Band
136
Section 15
Avoiding Hazards
169
Section 16.4
Configuring a Point-to-Point Link for Test
204
Section 17
Preparing Components for Deployment
233
Section 18.4
Configuring a BH Timing Master for the Destination
294
Section 18.5
Configuring a BH Timing Slave for the Destination
312
Section 19.4
Installing a GPS Antenna
334
Section 19.5
Installing a CMM2
335
Section 19.6
Installing a CMMmicro
340
Section 19.9
Installing a Reflector Dish
350
Section 19.10
Installing a BH Timing Master
352
Section 19.11
Installing a BH Timing Slave
354
Section 19.13
Verifying a BH Link
355

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 48
Section 21.2.2
CMMmicro Software and Hardware Compatibility
366
Section 22.2
Encrypting Canopy Radio Transmissions
369
Section 22.3
Managing Module Access
371
Section 24.6
Objects Supported in the Canopy 30/60-Mbps BH
403
Section 24.7
Objects Supported in the Canopy 150/300-Mbps BH
403
Section 24.10
Traps Provided in the PTP 400 Series Bridge MIB
404
Section 24.11
Traps Provided in the PTP 600 Series Bridge MIB
404
Section 25
Using the Canopy Network Updater Tool (CNUT)
407
Section 28.3
Typical Contents of Release Notes
445
Section 28.4
Typical Upgrade Process
445
Section 31.2
Analyzing Traffic at an AP or BH with No CMM
454
Section 31.3
Analyzing Traffic at an AP or BH with a CMM
454
Section 32
Troubleshooting
463
Section 33
Obtaining Technical Support
475
Section 34
Getting Warranty
481

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 49
5 EXPLORING THE SCOPE OF SOLUTIONS
Canopy wireless broadband applications include:
◦ local area network (LAN) extensions
◦ Internet subscriber service
◦ high-bandwidth point-to-point connections
◦ multicast video (for instruction or training, for example)
◦ private branch exchange (PBX) extensions
◦ point-to-multipoint data backhaul
◦ redundant network backup
◦ video surveillance
◦ voice over IP (VoIP)
◦ TDM over Ethernet (for legacy voice and data)
5.1 COMPONENTS
Canopy networks use some or all of the following components. For the components that
provide a graphical user interface (GUI), access to the GUI is through a web browser. In
Release 8 and later, cascading style sheets (CSS) configure the GUI. Thus an operator is
able to customize the GUI by editing these style sheets.
5.1.1 Canopy Access Point Module and Canopy OFDM Access Point Module
The Canopy Access Point (AP) module provides broadband connectivity in a 60° sector.
The Canopy OFDM AP provides broadband connectivity in a 90° sector. Either supports
up to 200 subscribers and 4,096 MAC addresses, which may be directly-connected PCs,
IP appliances, gateways, Subscriber Modules (SMs), and the AP, except that no limit
applies behind subscriber network address translation (NAT) gateways. The AP is
configurable through a web interface. A Canopy AP can only communicate with a Canopy
SM, not also an Advantage SM or a Canopy Lite SM. A Canopy OFDM AP can only
communicate with a Canopy OFDM SM.
5.1.2 Advantage Access Point Module
The Canopy Advantage AP distributes services as broadly as the Canopy AP. However,
the Advantage AP provides greater throughput and less latency. Each tab in the GUI for
Canopy Advantage modules displays the distinctive branding shown in Figure 1.
Figure 1: Canopy Advantage Platform GUI logo
The Advantage AP communicates with all Canopy SMs in its frequency band range:
Canopy SMs, Advantage SMs, and Canopy Lite SMs.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 50
5.1.3 Canopy Access Point Cluster and Canopy OFDM Access Point Cluster
Figure 2: Pole-mounted AP cluster
An AP cluster covers as much as 360°.
The Canopy FSK AP cluster consists of
two to six APs that provide broadband
connectivity to 1,200 or fewer subscribers.
Each AP transmits and receives in a 60°
sector.
The Canopy OFDM AP cluster consists of
two to four APs that provide broadband
connectivity to 800 or fewer subscribers.
Each AP transmits and receives in a 90°
sector.
The variety of available APs, Advantage
APs, and OFDM APs in frequency band
range, power adjustability, and antenna
configuration is shown under Acquiring a
Canopy Demonstration Kit, beginning on
Page 117.
An AP cluster is pictured in Figure 2.
An OFDM AP, showing the antenna in front
and the radio attached to it, is pictured in
Figure 3.
Figure 3: OFDM AP - Antenna and
Radio
5.1.4 Canopy Subscriber Module
The Subscriber Module (SM) is a
customer premises equipment (CPE)
device that provides broadband
services through communication with
an AP. The SM is configurable
through a web interface.
The variety of available SMs,
Advantage SMs, and OFDM SMs in
frequency band range, power
adjustability, and antenna
configuration is shown under
Acquiring a Canopy Demonstration
Kit, beginning on Page 117.
Figure 4: Structure-mounted SM

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 51
A Canopy SM can communicate with
either a Canopy AP or an Advantage
AP. A Canopy OFDM SM can
communicate with only a Canopy
OFDM AP.
An SM mounted directly to a structure
is pictured in Figure 4.
An OFDM SM is shown in Figure 5 in
both front and side views.
Figure 5: OFDM SM, front and side
views
5.1.5 Advantage Subscriber Module
The Canopy Advantage SM provides the same configurability and services as the
Canopy SM. However, in a link with an Advantage AP, the Advantage SM provides
uncapped sustained 2X throughput. See 2X Operation on Page 89. An Advantage SM
can only communicate with an Advantage AP.
5.1.6 Canopy Lite Subscriber Module
Canopy Lite SMs cost less and provide less throughput than regular Canopy SMs. They
support the same radio frequencies, interference tolerance, and product reliability. They
give operators the additional option to serve cost-sensitive customers who want standard
services (web browsing, email, VoIP, and downloads), but do not require the higher
throughput that is available with a regular Canopy SM. Canopy Lite SMs support an
aggregate(uplink plus downlink) throughput of 512 kbps. Through purchased floating
licenses that Prizm manages, they are upgradeable to 1, 2, 4, or 7 Mbps aggregate
throughput. A Canopy Lite SM can communicate with only a Canopy Advantage AP.
A comparison of the Canopy Lite SM to the Canopy SM and Advantage SM is provided in
Table 25 on Page 100.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 52
5.1.7 900-MHz AP and SM
Canopy 900 MHz AP and SM modules operate at a 3.3 Mbps carrier rate (compared to
10 Mbps for other Canopy frequency bands).
Figure 6: Examples of flat panel antennas with 900-MHz modules
These 900-MHz modules run the same software and provide the same parameters,
network features, and connections as all other Canopy APs and SMs. The physics of
longer-wavelength 900 MHz, the power allowed by regulatory authorities, and the low
required level of Canopy Carrier-to-Interference (C/I) ratio combine to support
◦ line of sight (LOS) range of up to 40 miles (over 64 km)
◦ increased non-line of sight (NLOS) range, depending on RF considerations such
as foliage, topography, and obstructions.
When collocated with a Canopy SM of another frequency band range, the 900-MHz AP
may serve, without a tower or BH, as a remote AP (see Deploying a Remote AP on
Page 147). 900-MHz AP/SM links are logical choices for extending radio networks where
you wish to
◦ add subscriber-handling capacity to a tower that is either
− fully used in the other frequency band ranges.
− not available to any other frequency band range.
◦ reach sparsely populated areas.
◦ penetrate foliage.
◦ add a remote AP behind an SM that operates in another frequency band range.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 53
5.1.8 Canopy
5.1.9 Backhaul Module
A pair of Backhaul Modules (BHs) provide point-to-point
connectivity as either
◦ a standalone link
◦ a link through a cluster management module to an
AP cluster.
You must configure a BH as either a timing master (BHM)
or timing slave (BHS). The BHM provides synchronization
signal (sync) to the BHS.
A BH mounted to a passive reflector dish is pictured in
Figure 7. Carrier applications for these modules include
reaching remote AP clusters, interconnecting campus
buildings or remote branch offices, extending private
branch exchange (PBX) circuits, backhauling cell sites, and
extending central office T1s/E1s.
These BHs are supported by this user guide. See Realizing
a Wireless Backhaul Network on Page 47.
Figure 7: Dish-mounted
10- or 20-Mbps BH
5.1.10 Radio Adjustable Power Capabilities
Canopy offers adjustable power radios in all frequency bands.See Adjusting Transmitter
Output Power on Page 326 to ensure that your radios do not exceed the maximum
permitted EIRP.
5.1.11 Cluster Management Module-2 (Part 1008CK-2)
The Cluster Management Module-2 (CMM2) provides power, GPS timing from an
antenna that is included, and networking connections for an AP cluster. The CMM2 can
also connect to a BH, in which case the CMM2 is the central point of connectivity for the
entire site. The CMM2 can connect as many as eight collocated modules—APs, BHMs,
BHSs—and an Ethernet feed.
The CMM2 requires two cables for each connected module:
◦ One provides Ethernet communications and power. This cable terminates in an
RJ-45 connector.
◦ The other provides synchronization (sync), GPS status, and time and date in a
serial interface. This cable terminates in an RJ-11 connector.
A CMM2 is pictured in Figure 8. A CMM2 as part of a mounted Canopy system is
pictured in Figure 9.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 54
Figure 8: CMM2 enclosure
Figure 9: CMM2 pole-mounted
5.1.12 Cluster Management Module micro (Part 1070CK)
The Cluster Management Module micro (CMMmicro) provides power, GPS timing, and
networking connections for an AP cluster. Unlike the CMM2, the CMMmicro is
configurable through a web interface.
The CMMmicro contains an 8-port managed switch that supports Power over Ethernet
(PoE) on each port and connects any combination of APs, BHMs, BHSs, or Ethernet
feed. Canopy PoE differs from 803.3af PoE, and the two should not be intermixed. The
CMMmicro can auto-negotiate speed to match inputs that are either
100Base-TX or 10Base-T, and either full duplex or half duplex, where the connected
device is set to auto-negotiate. Alternatively, these parameters are settable.
A CMMmicro requires only one cable, terminating in an RJ-45 connector, for each
connected module to distribute
◦ Ethernet signaling.
◦ power to as many as 8 collocated modules—APs, BHMs, or BHSs. Through a
browser interface to the managed switch, ports can be powered or not.
◦ sync to APs and BHMs. The CMMmicro receives 1-pulse per second timing
information from Global Positioning System (GPS) satellites through an antenna
(included) and passes the timing pulse embedded in the 24-V power to the
connected modules.
GPS status information is available at the CMMmicro, however
◦ CMMmicro provides time and date information to BHMs and APs if both the
CMMmicro is operating on CMMmicro Release 2.1 or later and the AP/BHM is
operating on Canopy System Release 4.2 or later.
See Time Tab of the AP on Page 191.
◦ CMMmicro does not provide time and date information to BHMs and APs if either
the CMMmicro is operating on a release earlier than CMMmicro Release 2.1 or
the AP/BHM is operating on a release earlier than Canopy System Release 4.2.
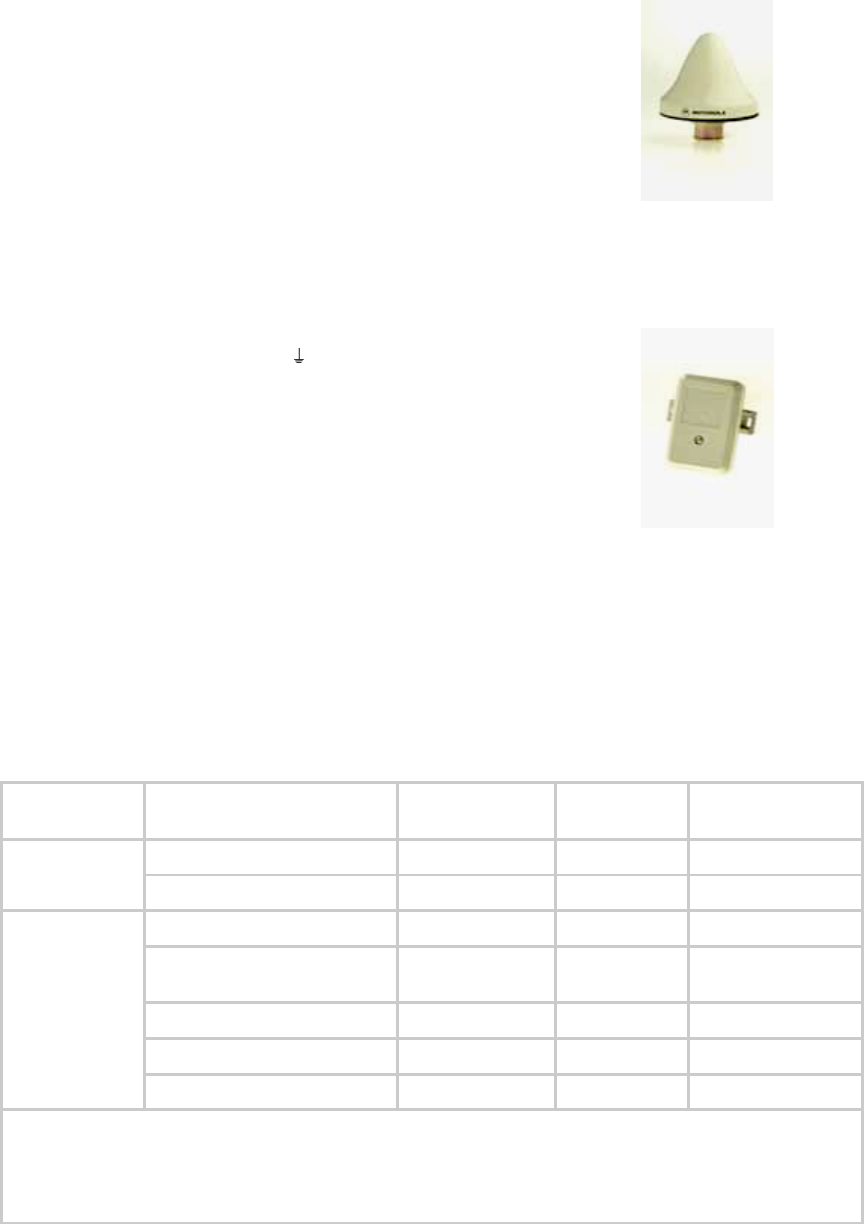
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 55
5.1.13 GPS Antenna
The Motorola GPS antenna provides either
◦ timing pulses to the CMMmicro.
◦ timing pulses and positioning information to
the CMM2.
The GPS antenna is pictured in Figure 10.
Figure 10: Motorola GPS antenna
5.1.14 Surge Suppressor (Part 600SS)
The 600SS Surge Suppressor provides a path to
ground (Protective Earth
) that reduces the risk to
persons, buildings, and inside equipment from
over-currents and over-voltages associated with
lightning strikes. A 600SS is pictured in Figure 11.
Figure 11: 600SS surge suppressor
5.1.15 Accessory Components
In addition to the above modules, the following accessories are available.
Power Supplies
The various power supplies available for Canopy modules are listed in Table 7.
Table 7: Power supply descriptions
For Use With
Part
Number
Voltage (AC)
Cycles per
Second (Hz)
Includes
ACPS81WA
100 to 240
50 to 60
US IEC line cord
CMMmicro
ACPS81W-02A
100 to 240
50 to 60
no IEC line cord
ACPS110-03A1
120
50 to 60
US plug
ACPSSW-09A3
90 to 240
50 to 60
US, Euro, and UK
adaptors
ACPSSW-10A3
90 to 240
50 to 60
Argentina adaptor
ACPSSW-11A3
90 to 240
50 to 60
Australia adaptor
Canopy radio2
ACPSSW-12A3
90 to 240
50 to 60
China adaptor
NOTES:
1. Pictured in Figure 12.
2. Single transceiver.
3. Pictured in Figure 13.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 56
Figure 12: ACPS110-03A power supply
Figure 13: ACPSSW-09A power supply
Passive Reflector Dish Assembly
A 27RD Passive Reflector Dish on both ends of
a BH link extends the distance range of the link
and provides a narrower beam width, which
can reduce both received and transmitted
interference. A 27RD on an SM extends the
distance range in some bands (notably 5.7-
GHz and 2.4-GHz) and can reduce both
received and transmitted interference in all
bands. An SMMThe module support tube
provides the proper offset focus angle. See
Figure 14.
For 5.x-GHz radios, the reflector gain is 18dB
and the 3 dB beam width is 6° in both azimuth
and elevation. For 2.4-GHz radios, the reflector
gain is 11dB and the 3 dB beam width is 17° in
both azimuth and elevation.
Figure 14: 27RD with mounted module
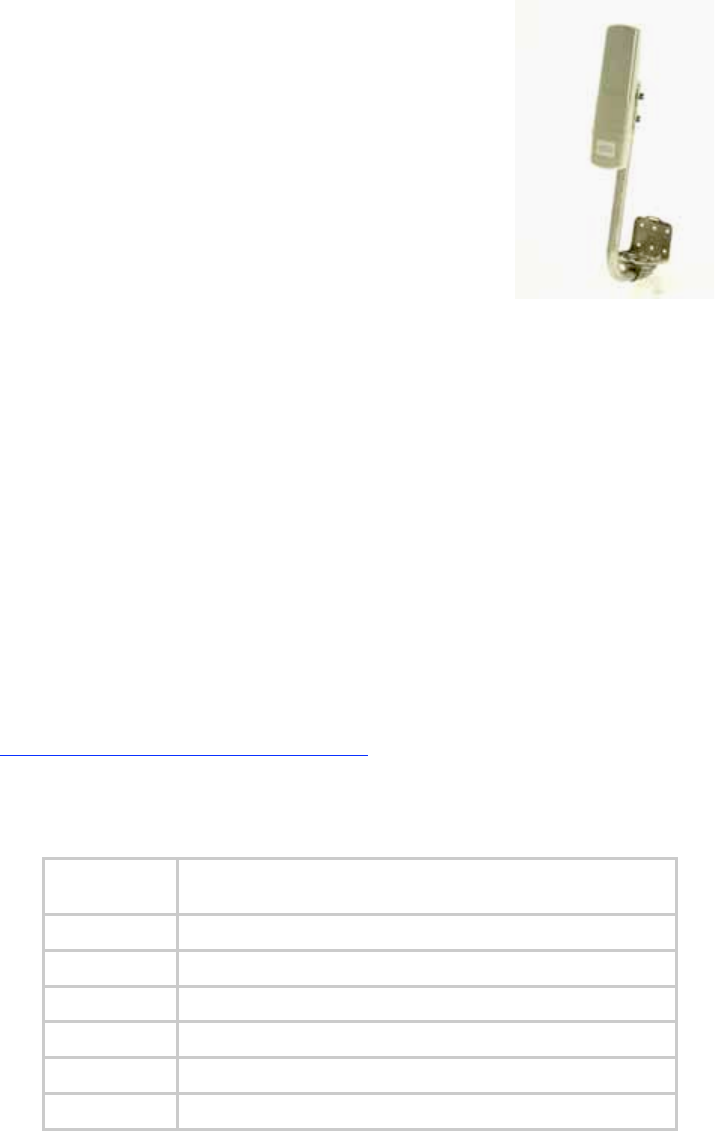
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 57
Module Support Brackets
The SMMB1 support bracket facilitates
mounting the SM to various surfaces of a
structure and has slots through which chimney
straps can be inserted. An SMMB1 is pictured
in Figure 15.
The SMMB2 is a heavy duty mounting bracket
that comes with the 900-MHz integrated SM or
AP, and with the 27D passive reflector. It is
also available separately for use with 900-MHz
connectorized SMs and APs, other
connectorized modules, and OFDM SMs.
The BH1209 is a pole-mount bracket kit for
Canopy backhaul modules.
Figure 15: SMMB1 SM support bracket
Cables
Canopy modules that are currently or recently sold can auto-sense whether the Ethernet
cable is wired as straight-through or crossover. Some modules that were sold earlier
cannot. The MAC address, visible on the module, distinguishes whether the module can.
All CMMmicros can auto-sense the cable scheme.
Where a non auto-sensing module is deployed
◦ a straight-through cable must be used for connection to a network interface card
(NIC).
◦ a crossover cable must be used for connection to a hub, switch, or router.
Canopy-recommended Ethernet and sync cables can be ordered in lengths up to 328 ft
(100 m) from Best-Tronics Manufacturing, Inc. at
http://www.best-tronics.com/motorola.htm. These cables are listed in Table 8 and
Table 9.
Table 8: Recommended outdoor UTP Category 5E cables
Best-Tronics
Part #
Description
BT-0562
RJ-45 TO RJ-45; straight-through Ethernet cable
BT-0562S
RJ-45 TO RJ-45; shielded straight-through Ethernet cable
BT-0565
RJ-45 TO RJ-45; crossover Ethernet cable
BT-0565S
RJ-45 TO RJ-45; shielded crossover Ethernet cable
BT-0563
RJ-11 TO RJ-11; sync cable
BT-0563S
RJ-11 TO RJ-11; shielded sync cable
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 58
NOTE:
Shielded cable is strongly recommended for all AP cluster and BH installations.
Table 9: Recommended indoor UTP Category 5E cables
Best-Tronics
Part #
Description
BT-0596
RJ-45 TO RJ-45; straight-through Ethernet cable
BT-0595
RJ-45 TO RJ-45; crossover Ethernet cable
Approved Ethernet cables can also be ordered as bulk cable:
◦ CA-0287
◦ CA-0287S (shielded)
Canopy-approved antenna cables can be ordered in lengths up to 100 ft (30.4 m),
as listed in Table 10.
Table 10: Recommended antenna cables
Best-Tronics
Part #
Description
BT-0564
N TO N GPS antenna cable for CMM2
BT-0716
BNC TO N GPS antenna cable for CMMmicro
Category 5 Cable Tester
For purchase within the U.S.A., the CTCAT5-01 Cable Tester is available.
Override Plug
An override plug (sometimes called a default plug) is available to provide access to a
module whose password and/or IP address have been forgotten. This plug allows the AP,
SM, or BH to be accessed using IP address 169.254.1.1 and no password. During the
override session, you can assign any new IP address and set either or both user
passwords (display-only and/or full access) as well as make other parameter changes.
This plug is available from Best-Tronics Manufacturing, Inc. at
http://www.best-tronics.com/motorola.htm as Part BT-0583 (RJ-11 Default Plug).
Alternatively if you wish, you can fabricate an override plug. For instructions, see
Procedure 36 on Page 374 and the pinout in Figure 140 on Page 374.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 59
Alignment Headset
The ACATHS-01 Alignment Headset facilitates the
operation of precisely aiming an SM toward an AP (or
a BHS toward a BHM). This device produces infinitely
variable
◦ pitch, higher when the received signal is
stronger.
◦ volume, louder when jitter is less.
An ACATHS-01 is pictured in Figure 16.
Pinouts for an alternative listening device are provided
under Alignment Tone—Technical Details on
Page 184.
Figure 16: ACATHS-01
alignment headset
Module Housing
The HSG-01 Canopy Plastic Housing is available for
replacement of a damaged housing on a module that is
otherwise functional. The HSG-01 is pictured in
Figure 17.
The HSG-01 and all module housings of this design
provide clearances for cable ties on the Ethernet and sync
cables.
RECOMMENDATION:
Use 0.14” (40-lb tensile strength) cable ties
to secure the Ethernet and sync cables to
the cable guides on the module housing.
For the Ethernet cable tie, the Ethernet cable groove is
molded lower at the top edge. For the sync cable tie,
removal of a breakaway plug provides clearance for the
sync cable, and removal of two breakaway side plates
provides clearance for the sync cable tie.
Figure 17: HSG-01 Housing
5.2 FREQUENCY BAND RANGES
In the 2.4-, 5.2-, 5.1-, 5.4-, and 5.7-GHz frequency band ranges, Canopy APs, SMs, and
BHs are available. Additionally, in the 900-MHz frequency band range, Canopy APs and
SMs are available. National restrictions may apply. See Regulatory and Legal Notices on
Page 487.
To avoid self-interference, a Canopy network typically uses two or more of these ranges.
For example, where properly arranged, all AP clusters and their respective SMs can use
the 2.4-GHz range where the BH links use the 5.7-GHz range. In this scenario,
subscriber links can span as far as 5 miles (8 km) with no reflector dishes, and the BH
links can span as far as 35 miles (56 km) with reflector dishes on both ends.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 60
Within this example network, wherever the 2.4-GHz module is susceptible to interference
from other sources, AP clusters and their linked SMs may use the 5.2-GHz range to span
as far as 2 miles (3.2 km) with no reflector dishes. The network in this example takes
advantage of frequency band range-specific characteristics of Canopy modules as
follows:
◦ The 900-MHz modules cover a larger area, albeit with lower throughput, than
modules of the other frequency bands. The 900-MHz modules can be used to
− penetrate foliage
− establish links that span greater distances
− add subscribers
− add overall throughput where modules of other frequency bands cannot be
used (such as where interference would result or space on a tower is
limited).
◦ The 2.4-GHz frequency band range supports AP/SM links of greater than 2-mile
spans (with no reflectors).
◦ The 5.7-GHz frequency band range supports BH links that span as far as 35
miles.
5.3 CANOPY PRODUCT COMPARISONS
5.3.1 Canopy Product Applications
The product applications per frequency band range are is summarized in Table 11.
Table 11: Product applications per frequency band range
Frequency Band Range
Product
900
MHz
2.4 GHz
5.1 GHz
5.2 GHz
5.4 GHz
5.7 GHz
5.4 GHz
OFDM
Access Point Module
●
●
●
●
●
●
●
Subscriber Module
●
●
●
●
●
●
●
Subscriber Module with
Reflector1
●
●
●
●
Backhaul Module
●
●
●
●
●
Backhaul Module with
Reflector1
●
●
●
●
●
CMM2
●
●
●
●
●
●
CMMmicro
●
●
●
●
●
●
●
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 61
Frequency Band Range
Product
900
MHz
2.4 GHz
5.1 GHz
5.2 GHz
5.4 GHz
5.7 GHz
5.4 GHz
OFDM
Power supply
●
●
●
●
●
●
●
Surge suppressor
●
●
●
●
●
●
●
NOTES:
1. National or regional regulations may limit EIRP to the same as without a reflector, and therefore
require Transmit Output Power to be reduced. In these cases
◦ the reflector used with an SM reduces beamwidth to reduce interference, but does not increase
the range of the link.
◦ the reflector on both ends of a BH link reduces beamwidth to reduce interference and also
increases the range of the link.
5.3.2 Link Performance and Encryption Comparisons
Encryption options are summarized in Table 12. Typical Line-of-Site (LOS) range and
aggregate useful throughput for Canopy PTMP links are summarized in Table 13. Typical
Line-of-Site (LOS) range and aggregate useful throughput for Canopy PTP links are
summarized in Table 14.
Table 12: Products with encryption options available per frequency band, PTMP links
Products available with the following
encryption options
Frequency Band
DES or none
AES or none
900 MHz
●
●
2.4 GHz @100 mW
(ETSI)
●
●
2.4 GHz @ 1W
●
●
5.1 GHz
●
5.2 GHz
●
●
5.4 GHz
●
●
5.7 GHz
●
●
5.4 GHz OFDM
●
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 62
Table 13: Typical range and throughput per frequency band, PTMP links
Advantage AP
Canopy AP
Range
Range
Frequency
Band
no SM
Reflector
mi (km)
with SM
Reflector
mi (km)
Aggregate
Throughput
Mbps
Round-
trip
Latency
msec
no SM
Reflector
mi (km)
with SM
Reflector
mi (km)
Aggregate
Throughput3
Mbps
Round-
trip
Latency
msec
0.3 (0.5)
0.3 (0.5) 1
14
6
2.4 GHz
ETSI
0.6 (1)
0.6 (1) 1
7
6
0.6 (1)
0.6 (1) 1
7
20
2.5 (4)
7.5 (12)
14
6
2.4 GHz
5 (8)
15 (24)
7
6
5 (8)
15 (24)
7
20
1 (1.6)
na
14
6
5.1 GHz
2 (3.2)
na
7
6
2 (3.2)
na
7
20
1 (1.6)
na2
14
6
5.2 GHz
2 (3.2)
na2
7
6
2 (3.2)
na2
7
20
1 (1.6)
1 (1.6) 1
14
6
5.4 GHz
2 (3.2)
2 (3.2) 1
7
6
2 (3.2)
2 (3.2)1
7
20
1 (1.6)
5 (8)
14
6
5.7 GHz
2 (3.2)
10 (16)
7
6
2 (3.2)
10 (16)
7
20
900 MHz4
40 (64)
na
4
15
1X
5 (8)
7
tbd
2X
2.5 (4)
14
tbd
5.4
GHz
OFDM
3X
1.25 (2)
21
tbd
NOTES:
2. In Europe, 2.4-GHz ETSI and 5.4-GHz SMs can have a reflector added to focus the antenna pattern and reduce
interference, but transmit output power must be reduced to maintain the same EIRP as without a reflector, so
the throughput and range specs for PTMP links remain the same.
3. In the USA and Canada, the use of a reflector with a full power radio in the 5.2-GHz frequency band is not
allowed.
4. These values assume a hardware series P9 AP running hardware scheduler. When running software scheduler
on a series P7, P8, or P9 AP, aggregate throughput drops to 6.2 Mbps, and only 4 Mbps is available to any one
SM. (Series P7 and P8 APs can only run software scheduler.)
5. All 900-MHz APs are Advantage APs.
GENERAL NOTES:
Range is affected by RF conditions, terrain, obstacles, buildings, and vegetation.
An Advantage AP in other than 900 MHz has an aggregate (sum of uplink plus downlink) throughput or capacity of
14 Mbps, if RF conditions, range, and SM hardware version permit.
An Advantage SM in other than 900 MHz has an aggregate sustained throughput of 14 Mbps if RF conditions and
range permit.
A regular SM can burst to 14 Mbps if RF conditions and range permit, then run at 7 Mbps sustained throughput.
An OFDM SM has an aggregate throughput or capacity of XX Mbps, if RF conditions and range permit.d
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 63
Table 14: Typical range and throughput per frequency band, PTP links
Throughput
Frequency Band
Modulation
Rate (Mbps)
No Reflectors
Both Reflectors
10
7.5 Mbps to 2 km
7.5 Mbps to 16 km
2.4 GHz @100 mW
(ETSI)
20
14 Mbps to 1 km
14 Mbps to 8 km
10
7.5 Mbps to 5 mi (8 km)
7.5 Mbps to 35 mi (56 km)
2.4 GHz @ 1W
20
14 Mbps to 3 mi (5 km)
14 Mbps to 35 mi (56 km)
10
7.5 Mbps to 2 mi (3.2 km)
5.1 GHz
20
14 Mbps to 2 mi (3.2 km)
10
7.5 Mbps to 2 mi (3.2 km)
5.2 GHz
20
10
7.5 Mbps to 10 mi (16 km)
5.2 GHz ER
20
14 Mbps to 5 mi (8 km)
10
7.5 Mbps to 2 mi (3.2 km)
7.5 Mbps to 10 mi (16 km)1
5.4 GHz
20
14 Mbps to 1 mi (1.6 km)
14 Mbps to 5 mi (8 km)1
10
7.5 Mbps to 2 mi (3.2 km)
7.5 Mbps to 35 mi (56 km)
5.7 GHz
20
14 Mbps to 1 mi (1.6 km)
14 Mbps to 35 mi (56 km)
NOTES:
1. These ranges are with power reduced to within 1 W (30 dBm) EIRP.
2. Use the Link Estimator tool to estimate throughput for a given link.
5.3.3 Cluster Management Product Comparison
Canopy offers a choice between two products for cluster management: CMM2 and
CMMmicro. Your choice should be based on the installation environment and your
requirements. The similarities and differences between these two products are
summarized in Table 15.
Table 15: Cluster management product similarities and differences
Characteristic
CMM2
CMMmicro
Approximate size
17” H x 13” W x 6.5” D
(43 cm H x 33 cm W x 7 cm D)
12” H x 10” W x 3” D
(30 cm H x 25 cm W x 8 cm D)
Approximate weight
25 lb ( 11.3 kg)
8 lb (3.5 kg)
Cabling
◦ one Ethernet/power cable per
radio.
◦ one sync cable per radio.
one Ethernet/power/sync cable per
radio.
Canopy network
interconnection
8 Ethernet ports
8 Ethernet ports
Data throughput
auto-negotiates to full or half duplex
auto-negotiates to full or half duplex
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 64
Characteristic
CMM2
CMMmicro
Ethernet operating
speed standard
auto-negotiates to 10Base-T or
100Base-TX
auto-negotiates to 10Base-T or
100Base-TX
Additional Ethernet
ports
one for data feed
one for local access
(notebook computer)
none
Power supply
integrated 24-V DC to power APs,
BHs, and GPS receiver
external 24-V DC to power APs, BHs,
and GPS receiver
SNMP management
capability
none
provided
Sync (to prevent
self-interference)
carried by the additional serial cable
to each AP and BHM
embedded in power-over-Ethernet
cable
Time & Date
carried by the additional serial cable
to each AP and BHM
provided by NTP (Network Time
Protocol). CMMmicro can be an NTP
server.
Weatherized
enclosure and power supply
only the enclosure (not the power
supply)
Web interface
none
web pages for status, configuration,
GPS status, and other purposes
NOTE:
Auto-negotiation of data throughput and Ethernet operating speed depend on the connected device
being set to auto-negotiate as well.
5.4 ANTENNAS FOR CONNECTION TO 900-MHz MODULES
Like the 2.4-, 5.2-, 5.4-, and 5.7-GHz module, the 900-MHz connectorized module has
◦ the same housing.
◦ a covered Ethernet port.
◦ a utility port for alignment headset, sync cable to CMM2, or override plug.
The 900-MHz AP or SM is available either
◦ as a connectorized unit with a 16-inch (approximately 40-cm) cable with a male
N-type connector for connection to the antenna.
◦ with an integrated horizontally-polarized antenna in a different form factor.
5.4.1 Certified Connectorized Flat Panel Antennas
Motorola has certified four connectorized flat panel antenna options. Motorola resells one
of these, whose attributes include
◦ gain—10 dBi
◦ dimensions—8.8 x 8.1 x 1.6 inches (22.4 x 20.6 x 4.06 cm)
◦ weight—1.2 lbs (0.54 kg)
◦ polarization—vertical or horizontal
◦ cable—12-inch (30.5 cm)
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 65
◦ connector—female N-type
◦ beamwidth—approximately 60° vertical and 60° horizontal at 3 dBm
Motorola has certified three other antennas, which are available through Canopy
resellers. The attributes of one of these other certified antennas include
◦ gain—10 dBi
◦ dimensions—12 x12 x 1 inches (30.5 x 30.5 x 2.5 cm)
◦ weight—3.3 lbs (1.5 kg)
◦ polarization—vertical or horizontal
◦ connector—female N-type
◦ beamwidth—approximately 60° vertical and 60° horizontal at 3 dBm
Examples of these antennas are pictured in Figure 6 on Page 52.
5.4.2 Third-party Certified Connectorized Flat Panel Antenna
A third party may certify additional antennas for use with the Canopy connectorized
900-MHz module.
5.5 ADJUNCTIVE SOFTWARE PRODUCTS
The capabilities of available applications and tools are summarized for comparison in
Table 16. In this table CNUT represents Canopy Network Updater Tool, Release 1.1 or
later, and BAM represents Bandwidth and Authentication Manager, Release 2.0 or later.
Table 16: Canopy applications and tools
Application or Tool
Capability
Prizm
CNUT
BAM
authenticates SMs
●
●
controls authentication in APs
●
●
manages Committed Information Rate (CIR)
●
●
has dependency on another application3
●
automatically discovers elements
●
●
exports network information with hierarchy
●
●
supports user-defined folder-based operations
●
●
senses FPGA version on an element
●
●
upgrades FPGA version on an element
●
enables/disables hardware scheduling
●
manages the high-priority channel
●
●
imports network information with hierarchy
●
●
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 66
Application or Tool
Capability
Prizm
CNUT
BAM
interface to a higher-level network management
system (NMS)
●
interface to an operations support system (OSS)
●
manages Maximum Information Rate (MIR)
●
●
automatically works from root (highest) level
●
element selection can be individual or multiple
●
●
●
element selection can be criteria based
●
element selection can be user-defined branch
●
●
senses software release on an element
●
●
upgrades software release on an element
●
manages VLAN parameters
●
●
provides access to element web interface
●
5.6 BANDWIDTH AND AUTHENTICATION MANAGER
Canopy Bandwidth and Authentication Manager (BAM) software allows you to use
◦ a primary server to distribute bandwidth resources per subscriber, require SMs to
authenticate per AP, and deny service to unauthorized SMs.
◦ a secondary server to redundantly store identical SM bandwidth and
authentication data and become governing if the primary server goes out of
service.
◦ an optional tertiary server to do the same if both the primary and secondary
servers go out of service.
In BAM Release 2.1, subscriber administration for an SM or batch of SMs is performed
as follows:
◦ Insert the ESNs.
◦ Specify MIR and Security attributes.
◦ Specify CIR attributes.
◦ Specify whether BAM should send its stored CIR attributes.
◦ Specify VLAN attributes.
◦ Specify whether BAM should send its stored VLAN attributes.
◦ Specify VLAN IDs to associate with the SM(s).
This product is supported by the dedicated document Canopy Bandwidth and
Authentication Manager Release 2.1 User Guide and associated release notes.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 67
The upgrade path from BAM Release 2.1 is Prizm Release 2.0. See Motorola Canopy
Prizm User Guide, Issue 3, and Motorola Canopy Prizm Release 2.0 Release Notes.
5.7 Prizm
The product name PrizmEMS is changed to Prizm in Release 2.0 and later, to reflect that
the product capabilities are expanded beyond those of the element management system
(EMS). Throughout this user guide, the name change applies to text for Release 2.0 and
for multiple releases that include 2.0. It does not apply to text that is for a previous
release. Case by case, software elements such as the GUI in the client application and
XML files on the server may retain the PrizmEMS syntax.
5.7.1 Network Definition and Element Discovery
Prizm allows the user to partition the entire Canopy network into criteria-based subsets
that can be independently managed. To assist in this task of defining networks, Prizm
auto discovers Canopy network elements that are in
◦ user-defined IP address ranges
◦ SM-to-AP relationships with APs in the user-defined range
◦ BHS-to-BHM relationships with BHMs in the user-defined range.
◦ PLV Modem-to-PLV Bridge relationships with PLV Bridges in the user-defined
range.
For a Canopy AP, SM, BHM, BHS, PLV Bridge, PLV Modem, or CMMmicro, Prizm
◦ auto discovers the element to the extent possible.
◦ includes the element in the network tree.
◦ shows general information.
◦ shows Canopy information.
◦ supports Canopy-specific operations.
For a generic element, Prizm
◦ auto discovers the element as only a generic network element.
◦ includes the element in the network tree.
◦ shows general information.
◦ shows events and alerts.
◦ charts port activity.
For passive elements (such as CMM2 or a non-manageable switch or hub), Prizm allows
you to enter into the network tree a folder/group with name, asset/owner information, and
descriptive information.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 68
Supported element types include
Canopy Access Point Module
Canopy Backhaul Master Module
Canopy Backhaul Slave Module
Canopy PrizmEMS
Canopy Subscriber Module
Cluster Management Module micro
Cluster Management Module-4
Cluster Management Module-4 Switch
Generic Group
Generic SNMP Device
Generic SNMP Device (08 Port)
Generic SNMP Device (16 Port)
Generic SNMP Device (24 Port)
Generic SNMP Device (26 Port)
High-Speed Backhaul Master Module 150/300 Mbps
High-Speed Backhaul Master Module 30/60 Mbps
High-Speed Backhaul Slave Module 150/300 Mbps
High-Speed Backhaul Slave Module 30/60 Mbps
PLV Bridge Unit
PLV Modem Unit
Ultra Light Access Point
Ultra Light Outdoor Subscriber Unit
5.7.2 Monitoring and Fault Management
Prizm receives the traps that Canopy elements send and generates an alert for each of
these. Prizm also allows the user to establish sets of criteria that would generate other
alerts and trigger email notifications. Optionally, the user can specify a trap template. In
this case, Prizm receives traps for non-Canopy elements in the network.
For any individual element that the user selects, Prizm offers text and graphed displays of
element configuration parameters and performance statistics from an interval that the
user specifies.
5.7.3 Element Management
Prizm allows the user to perform any of the following operations on any specified element
or group of elements:
◦ Manage
− large amounts of SNMP MIB data.
− module passwords.
− IP addresses.
− other communications setup parameters.
− site information: Site Name, Site Location, and Site Contact parameters.
◦ Reset the element.
5.7.4 BAM Subsystem in Prizm
Prizm Release 2.0 and later integrates Canopy Bandwidth and Authentication Manager
(BAM) functionality and supports simple migration of a pre-existing BAM data into the
Prizm database. These releases also support the maintenance of authentication and
bandwidth data on a RADIUS server, to the same extent that BAM Release 2.1 (the final
release of BAM) did.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 69
Either of the following modes is available for the Prizm server, subject to licensing:
◦ BAM-only functionality, which manages only
− authentication, bandwidth service plans, and VLAN profiles of SMs.
− authentication of Powerline LV modems.
◦ Full Prizm functionality, which manages attributes for all elements and
authentication of SMs and Powerline LV modems.
One difference between a service plan (or VLAN profile) and a configuration template
that has the identical set of attributes is that the former is a long-term association
whereas the latter is a one-time push to the element. When a service plan or VLAN
profile is modified, the change is automatically applied to all elements that have the
association. Another difference is that a configuration template cannot overwrite any
values that a service plan or VLAN profile has set in an element.
5.7.5 Northbound Interface
In Release 1.1 and later, Prizm provides three interfaces to higher-level systems:
◦ a Simple Network Management Protocol (SNMP) agent for integration with a
network management system (NMS).
◦ a Simple Object Access Protocol (SOAP) XML-based application programming
interface (API) for web services that supports integration with an operations
support systems (OSS) such as a customer relationship management (CRM),
billing, or provisioning system.
◦ console automation that allows such higher-level systems to launch and
appropriately display the Prizm management console in GUI that is custom
developed, using the PrizmEMS™ Software Development Kit (SDK), which
Canopy provides for this purpose.
Together these interfaces constitute the Northbound Interface feature. Prizm server
administrator tasks and GUI developer information are provided in the PrizmEMS™
Software Development Kit (SDK). This SDK also describes the how to define new
element types and customize the Details views.
All other features of the Prizm product are supported by the dedicated document
Motorola Canopy Prizm User Guide and associated release notes.
5.8 LICENSE MANAGEMENT
Under the original licensing regime for Canopy networks, licenses were permanently tied
to the Media Access Control (MAC) address of the equipment that was licensed or that
used the licensed feature. Thus, they were not transferable. Under server-based license
management, for some functionalities, Canopy offers licenses that
◦ float upon demand within the network.
◦ are tied to only the osted (MAC address) of the license management server for
which they were ordered.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 70
In Release 4.2.3 and later, server-based license management adds flexibility and makes
available licenses that previously would have been held by de-commissioned equipment.
License management technology from Macrovision, based on a FLEXnet™ Publisher
license management model, provides the platform for Canopy server-based licensing.
Canopy capabilities that are authorized by licenses on this platform are FLEXenabled
products.
In this platform, the license management server checks and then either assigns or
declines to assign a license in real time. See the Canopy Networks License Manager
User Guide.
The total number of floating license keys that you need for any feature is the highest
number that you will ever want to have simultaneously in use. The proper placement of
these keys and the number and placement of fixed Canopy licenses are listed in
Table 17.
Table 17: Correct placement of license keys
In This
Release
License
Key
Must Be in Directory
If This
Platform
On This
Server
Device
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
LM 1.0
License
Manager
Server
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
Server
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
Server1
BAM 2.0
BAM
Server,
AP Auth
Server
(APAS),
Cap 2
/usr/local/canopy/include
Enterprise
Linux
BAM
Server2
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
Server1
BAM 2.1
BAM
Server,
AP Auth
Server
(APAS),
Cap 2
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
BAM
Server2
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
Server3
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
PrizmEMS
1.0
PrizmEMS
Server,
Element
Pack
/usr/local/Canopy/Prizm/license_files
Enterprise
Linux
PrizmEMS
Server4
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
PrizmEMS
1.1
PrizmEMS
Server,
Element
Pack
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
Server3
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 71
In This
Release
License
Key
Must Be in Directory
If This
Platform
On This
Server
Device
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
Prizm 2.0
and 2.1
for full
mgmt
PrizmEMS
Server,
Element
Pack
BAM
Server,
AP Auth
Server
(APAS),
Cap 2
Canopy
Lite
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
server5
C:\Program Files\Motorola\Canopy\FLEXnet\license_files
Windows
Prizm 2.0
and 2.1
for BAM-
only or
redundant
BAM
BAM
Server,
AP Auth
Server
(APAS),
Cap 2
Canopy
Lite
/usr/local/Canopy/FLEXnet/license_files
Enterprise
Linux
LM
server1
NOTES:
1. One key required per each deployed BAM server.
2. Copied here so that BAM can find License Manager. No additional charge for using this copy.
3. One key required per each deployed PrizmEMS server.
4. Copied here so that PrizmEMS can find License Manager. No additional charge for using this copy.
5. One BAMServer key and one PrizmEMSServer key required per each full management Prizm server.
5.9 SPECIFICATIONS AND LIMITATIONS
5.9.1 Radios
Canopy radio specifications are provided at
http://motorola.canopywireless.com/products/specshome.php.
5.9.2 Cluster Management Products
Table 18: CMM2 specifications and limitations
Specification or Limitation
Canopy System Range
Max length from Cluster Management
Module to any radio
328 cable feet (100 meters)
Max length from Cluster Management
Module to GPS antenna
100 cable feet (30.5 meters)
Dimensions
17.00” H x 12.88” W x 6.50” D
(43.18 cm H x 32.72 cm W x 16.51 cm D)
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 72
Specification or Limitation
Canopy System Range
Weight
25.0 lbs. (11.3 kg)
Operation Temperature
-40°F to +131°F (-40°C to +55°C)
Overall
Meets CE IP44 according to EN60529:2000
AC Input Voltage and Frequency
100 V – 240 V~, 0.7 A – 0.35 A, settable to either 230 V or 115 V
nominal input.
50 Hz – 60 Hz
Note: Applying 230 V to a unit that is set to 115 V may damage
the unit.
AC Input Power
Nominal 66 watts, max 92 watts with 8 modules connected to the
CMM at max cable length.
24-V DC Input Voltage
18 to 32 V DC, measured at CMM
24-V DC Input Power
Nominal 60 watts. Maximum 84 watts with 8 modules connected
to the CMM at maximum cable length. 9A inrush upon start-up.
24-V DC Usage
If using a typical “24V +/-5%” power supply, ensure that CMM is
within 400 cable feet (120 m) of the power supply. Use minimum
12 AWG (4 mm2) copper wire.
12-V DC Input Voltage
11.5 to 32 VDC, measured at CMM
12-V DC Usage
If using a 12V power source (typically an automobile battery in a
test or emergency situation), use 12 AWG (4 mm2) wire between
the power supply and the CMM, ensure that the CMM is within 10
cable feet (3 m) of the power supply, and ensure the modules are
within 20 cable feet (6 m) of the CMM.
Ethernet, GPS Sync, and GPS Coax
Cables
The use of cables that conform to the operational temperature of
the product as well as being UV light protected is mandatory.
Table 19: CMMmicro specifications and limitations
Specification or Limitation
Canopy System Range
Enclosure Size
Approximately 12” H x 10” W x 3” D
(Approximately 30 cm H x 25 cm W x 7.5 cm D)
CMMmicro Weight (without DC power
supply)
Approximately 8 lb
(Approximately 3.5 k)
Max length from Cluster Management
Module to any radio
328 cable feet (100 meters)
Max length from Cluster Management
Module to GPS antenna
100 cable feet (30.5 meters)
Operating Temperature
-40°F to +131°F (-40°C to +55°C)
Provided DC Power Converter Input
Voltage
100 – 240 V~

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 73
Specification or Limitation
Canopy System Range
Provided DC Power Converter Input
Frequency
50 – 60 Hz
CMMmicro Power Input Voltage
21.5 – 26.5 V DC
CMMmicro Power Current
3.36 A @ 24 V DC (3.75 – 3.0 A over voltage range)
Ethernet, GPS sync, and GPS coax
cables
The use of cables that conform to the operational temperature of
the product as well as having UV light protection is mandatory.
Cables can be ordered from Best-Tronics Manufacturing, Inc. at
http://www.best-tronics.com/motorola.htm.
5.9.3 300SS and 600SS Surge Suppressors
Canopy Surge Suppressor specifications are provided at
http://motorola.canopywireless.com/products/specshome.php.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 75
6 DIFFERENTIATING AMONG COMPONENTS
6.1 INTERPRETING MODEL (PART) NUMBER
The part number of a module typically represents
◦ the model number, which may indicate
− radio frequency band range.
− link distance range.
− whether the module is Canopy Advantage.
− the factory-set encryption standard.
◦ the module type.
◦ whether the reflector dish is included.
◦ the antenna scheme of the module.
◦ whether adjustable power in the module is preset to low.
◦ the modulation capability.
Radio Frequency Band Range
The leading digits usually indicate the frequency band range in which the module can
operate. For example, if the part number is 5700BH, then the frequency band range of
the module is 5.7 GHz.
↓
5
7
0
0
B
H
An exception to this general rule is that the leading digits in the part number of 5.1-GHz
modules are 52. These modules are differentiated from 5.2-GHz modules by the leading
four digits (5202 for 5.1 GHz, 5200 for 5.2 GHz).
You cannot change the frequency band range of the module.
Link Distance Range or Canopy Advantage
The third digit in the part number may indicate whether the module is an extended range,
Canopy Advantage, or Canopy model. 1 indicates extended range. For example, if the
part number is 5210BH, then the module is an extended range module. If the part
number is 5200BH, then the module is not an extended range model.
↓
5
2
0
0
B
H
6 in the third position (5760SM, for example) indicates Canopy Lite. 5 in the third position
(5250AP, for example) indicates that the module is Canopy Advantage. 0 in the third
position (5200AP, for example) indicates that the module is Canopy. However, part
numbering for 900-MHz APs and SMs differs from this general rule. All APs and SMs in
this frequency band range are Canopy Advantage, but none of their part numbers use 5
in the third position.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 76
You cannot change the link distance range of the module. However, you can license a
Canopy SM to uncap its aggregate throughput (a capability of the Advantage SM).
Encryption Standard or Frequency Band Range
The fourth digit in the part number usually indicates the encryption standard that was
preset at the factory. 1 indicates the Advanced Encryption Standard (AES). 0 indicates
the Data Encryption Standard (DES) standard. For example, if the part number is
5201BH, then transmissions from the module are encrypted according to AES. If the part
number is 5200BH, then transmissions from the module are encrypted according to DES.
↓
5
7
0
0
B
H
An exception to this general rule is that the fourth digit in the part number of 5.1-GHz
modules is 2. These modules are differentiated from 5.2-GHz modules by the leading
four digits (5202 for 5.1 GHz, 5200 for 5.2 GHz).
You cannot change the encryption basis (from DES to AES, for example), but you can
enable or disable the encryption.
Module Type
The next two alpha characters indicate the module type. For example, CK indicates that
the module is a Cluster Management Module.
↓
1
0
0
8
C
K
The module type cannot be changed.
Reflector Added
In specifications tables and price lists, the trailing characters RF or RF20 indicate that the
associated information applies to the module being
◦ mounted to the 27RD Passive Reflector Dish, in the case of specifications.
◦ ordered with the 27RD Passive Reflector Dish, in the case of price lists.
↓
2
4
0
0
B
H
R
F
2
0
However, this designation is not shown on either label of the module, and a module
ordered with the dish can be deployed without the dish.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 77
Antenna Scheme
In specifications tables and price lists, the trailing character C indicates that the module is
connectorized for an external antenna.
↓
9
0
0
0
S
M
C
An F in this position indicates that the module has an internal antenna with a band-pass
filter (for example, 9000APF).
You cannot transform a module from connectorized to internal antenna or from internal
antenna to connectorized, but you may have flexibility in what external antenna you
deploy with it.
Adjustable Power Preset to High or Low
A trailing WL can indicate that the module had adjustable power that is preset to low.
↓
2
4
0
0
A
P
W
L
However, the 5700SMC and 5700APC are connectorized, but also have adjustable
power preset to low. No special designation is made for adjustable power that is set to
high (no trailing letters are used; for example, 5252AP).
You can reset power to higher in a module with adjustable power that is preset to low, but
you are constrained by applicable regulations in your region and or nation.
Modulation Capability
A trailing 20 indicates that the module is capable of being set to either
◦ 20-Mbps modulation (aggregate throughput of 14 Mbps)
◦ 10-Mbps modulation (aggregate throughput of 7 Mbps).
↓
2
4
0
0
B
H
R
F
2
0
The absence of a trailing 20 indicates that the module is capable of only 10-Mbps
modulation.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 78
6.2 SORTED MODEL NUMBERS
Model numbers of Canopy modules are listed in Table 20. Not all models are available in
all markets. Please check with your Canopy distributor or reseller for availability.
Table 20: Canopy model numbers
Integrated Antenna
Connectorized for Antenna
Canopy
Advantage
Canopy
Advantage
Range
DES
AES
DES
AES
DES
AES
DES
AES
5.7
GHz
5700AP
5700APHZ
5700SM
5760SM
5700SMMHZ
5700BH
5700BH20
5700BHRF
5700BHRF20
5701AP
5701SM
5701BH
5701BH20
5701BHRF
5701BHRF20
5750AP
5750APHZ
5750SM
5750SMHZ
5751AP
5751SM
5700APC
5700SMC
5700BHC
5700BHC20
5701APC
5701SMC
5701BHC
5701BHC20
5750APC
5750SMC
5751APC
5751SMC
5.4
GHz
5400AP
5400SM
5460SM
5400BH
5400BH20
5400BHRF
5400BHRF20
5401AP
5401SM
5401BH
5401BH20
5401BHRF
5401BHRF20
5450AP
5450SM
5451AP
5451SM
5400APC
5400SMC
5400BHC
5400BHC20
5401APC
5401SMC
5401BHC
5401BHC20
5450APC
5450SMC
5451APC
5451SMC
5.1
GHz
5202AP
5202SM
5202BH
5212BH20
5212BHRF20
5252AP
5252SM
5.2
GHz
5200AP
5200APHZ
5200SM
5260SM
5200SMHZ
5200BH
5210BHRF
5210BHRF20
5201AP
5201SM
5201BH
5211BH20
5211BHRF
5211BHRF20
5250AP
5250APHZ
5250SM
5250SMHZ
5251AP
5251SM
2.4
GHz
2400AP
2400APWL
2400SM
2400SMWL
2460SM
2400SMLP
2400BH
2400BH20
2400BHRF
2400BHRF20
2400BHWL
2400BHWL20
2400BHWLRF
2400BHWLRF20
2401AP
2401APWL
2401SM
2401SMWL
2401BH
2401BH20
2401BHRF
2401BHRF20
2401BHWL
2401BHWL20
2401BHWLRF
2401BHWLRF20
2450AP
2450APWL
2450SM
2450SMWL
2451AP
2451APWL
2451SM
2451SMWL
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 79
Integrated Antenna
Connectorized for Antenna
Canopy
Advantage
Canopy
Advantage
Range
DES
AES
DES
AES
DES
AES
DES
AES
900
MHz
9000AP
9000APF
9000SM
9000SMF
9001AP
9001APF
9001SM
9001SMF
9000APC
9000SMC
9001APC
9001SMC
5.4
GHz
OFDM
5440AP
5440APC
5440SM
6.3 INTERPRETING ELECTRONIC SERIAL NUMBER (ESN)
Canopy module labels contain a product serial number that could be significant in your
dealings with Motorola or your supply chain. This is the electronic serial number (ESN),
also known as the Media Access Control (MAC) address, of the module. This
hexadecimal number identifies the module in
◦ communications between modules.
◦ the data that modules store about each other (for example, in the Registered To
field).
◦ the data that the BAM software applies to manage authentication and bandwidth.
◦ Prizm auto discovery of SMs through the AP (or BHS through the BHM).
◦ software upgrades performed by the Canopy Network Updater Tool (CNUT).
◦ information that CNUT passes to external tools.
6.4 FINDING THE MODEL (PART) NUMBER AND ESN
The labels and locations of Canopy module model (part) numbers and ESNs are shown
in Table 21.
Table 21: Labels and locations of model (part) numbers and ESNs
Label and Location
Numeric
String
Older Modules
Newer Modules
Model number
PN outside
Model # outside
ESN/MAC address
S/N inside
ESN outside
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 81
7 CANOPY LINK CHARACTERISTICS
7.1 UNDERSTANDING BANDWIDTH MANAGEMENT
7.1.1 Downlink Frame Contents
The AP broadcasts downlink frames that contain control information, allocating slots in
succeeding or future uplink frames to SMs that have requested service. The downlink
frame also contains a beacon frame, control information, and data that specific SMs have
requested. Each SM
◦ examines the downlink frame to distinguish whether data is addressed to
that SM.
◦ retrieves data addressed to that SM.
◦ directs such data to the appropriate end user.
7.1.2 Uplink Frame Contents
Uplink frames contain control information from each SM that request service on
succeeding uplink frames. SMs insert data into the uplink frames in an amount that the
AP has established.
Optionally, you can configure the AP to change the source MAC address in every packet
it receives from its SMs to the MAC address of the SM that bridged the packet, before
forwarding the packet toward the public network. If you do, then
◦ not more than 10 IP devices at any time are valid to send data to the AP from
behind the SM.
◦ the AP populates the Translation Table tab of its Statistics web page, displaying
the MAC address and IP address of all the valid connected devices.
◦ each entry in the Translation Table is associated with the number of minutes that
have elapsed since the last packet transfer between the connected device and
the SM.
◦ if 10 are connected, and another attempts to connect
− and no Translation Table entry is older than 255 minutes, the attempt is
ignored.
− and an entry is older than 255 minutes, the oldest entry is removed and the
attempt is successful.
◦ the Send Untranslated ARP parameter in the General tab of the Configuration
page can be
− disabled, so that the AP will overwrite the MAC address in Address
Resolution Protocol (ARP) packets before forwarding them.
− enabled, so that the AP will forward ARP packets regardless of whether it
has overwritten the MAC address.
This is the Translation Bridging feature, which you can enable in the General tab of the
Configuration web page in the AP. When this feature is disabled, the setting of the Send
Untranslated ARP parameter has no effect, because all packets are forwarded
untranslated (with the source MAC address intact).
See Address Resolution Protocol on Page 162.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 82
7.1.3 Default Frame Structures
With a 64-byte slot size, the default Canopy frame in hardware scheduling consists of
◦ variable numbers of uplink and downlink data slots, subject to the following
factors:
− Maximum range decreases the number of available slots to 32.
− Background bit error rate (BER) mode decreases the number of available
data slots by one (and bandwidth by 200 kbps).
− Every two control slots that are allocated decrease the number of available
data slots by one.
◦ 0 to 10 control slots, subject to operator setting
◦ 0 to 9 downlink acknowledgement slots, dynamically assigned
◦ 0 to 9 uplink acknowledgement slots, dynamically assigned
◦ 1 uplink schedule slot
◦ 1 beacon slot, which identifies the
− timing and distribution for the SMs
− ratio of uplink to downlink allocation
− ESN of the AP
− color code
− protocol (point-to-point or point-to-multipoint)
− number of registered SMs
− frame number
− control slot information
◦ air delay, subject to the value of the Max Range parameter in the AP
Control Slots
The Radio tab of the Configuration web page in the AP displays the total of control slots
(default 3, maximum 7 in the 900-MHz frequency band range2 and 16 in all others).
These control slots are contention slots. If too many SMs contend for these slots, then
the number of control slots may be increased.
Frame Scheduling
When an SM boots, the following sequence occurs:
1. The SM finds this beacon slot from an AP.
2. The SM synchronizes with the AP.
3. If BAM is configured on the AP and the AP is licensed for authentication, then
a. the AP sends a Registration Request message to Prizm for authentication.
b. following a successful challenge, Prizm returns an Authentication Grant
message to the AP.
c. the AP sends a Registration Grant to the SM.
2 In the 900-MHz frequency band range, the frame size is 16,667 bits. In all others, the frame size
is 25,000 bits. The smaller frame does not provide enough space to allocate more than 7 control
slots.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 83
If BAM is not configured on the AP or the AP is not licensed for authentication,
then the AP simply returns the Registration Grant to the SM.
This Registration Grant includes the distance between the AP and SM. The SM uses the
distance to distinguish when to transmit data in the uplink frame. The AP performs
advance scheduling of up to 1024 frames that each SM will be permitted to use in the
uplink frame.
7.1.4 Media Access Control and AP Capacity
Regardless of whether the maximum number of SMs (200) all request service at the
same time, the reservation Media Access Control (MAC) system allows the AP to give a
reservation slot to each SM that requests service.
Regardless of the distance between any SM and the AP, the reservation MAC system
ensures that all SM data slots are free of contention. For this reason
◦ all SMs are equally able to compete for uplink and downlink bandwidth.
◦ the capacity of the AP is not degraded by distance from the SMs.
7.1.5 Canopy Slot Usage
The frame illustrated in Figure 18 shows both packet fragments (yellow) and unused slot
space (red) typical of uplink traffic. Packet sizes smaller than 64 bytes cause unused slot
spaces.
Figure 18: Uplink data slot usage
The following statistics apply to Canopy frame slot usage:
◦ Slot capacity is 64 bytes.
◦ The optimum Ethernet packet size is 1518 bytes.
◦ The maximum downlink throughput for one AP to one SM is 1800 packets per
second (pps).
◦ The maximum uplink throughput for one AP to one SM is 300 pps.
◦ The maximum backhaul throughput is 3000 pps.
7.1.6 Data Transfer Capacity
Canopy modules use Time Division Duplex (TDD) on a common frequency to divide
frames for uplink (orange) and downlink (green) usage, as shown in Figure 19.
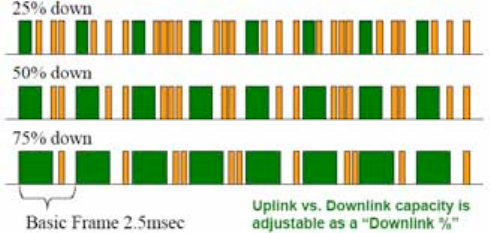
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 84
Figure 19: TDD dividing Canopy frames
7.1.7 Maximum Information Rate (MIR) Parameters
Canopy point-to-multipoint links use the following four MIR parameters for bandwidth
management:
◦ Sustained Uplink Data Rate (kbps)
◦ Uplink Burst Allocation (kb)
◦ Sustained Downlink Data Rate (kbps)
◦ Downlink Burst Allocation (kb)
You can independently set each of these parameters per AP or per SM.
Token Bucket Algorithm
The Canopy software uses a token bucket algorithm that
◦ stores credits (tokens) for the SM to spend on bandwidth for reception or
transmission.
◦ drains tokens during reception or transmission.
◦ refills with tokens at the sustained rate set by the network operator.
For each token, the SM can send toward the network in the uplink (or the AP can send
toward the SM in the downlink) an equivalent number of kilobits. Two buckets determine
the permitted throughput: one in the SM for uplink and one in the AP for downlink.
The applicable set of Uplink Burst Allocation and Downlink Burst Allocation
parameters determine the number of tokens that can fill each bucket. When the SM
transmits (or the AP transmits) a packet, the equivalent number of tokens is removed
from the uplink (or downlink) bucket.
Except when full, the bucket is continuously being refilled with tokens at rates that the
applicable set of Sustained Uplink Data Rate and Sustained Downlink Data Rate
parameters specify. The bucket often drains at a rate that is much faster than the
sustained data rate but can refill at only the sustained data rate. Thus, the effects of the
allocation and rate parameters on packet delay are as follows:
◦ the burst allocation affects how many kilobits are processed before packet delay
is imposed.
◦ the sustained data rate affects the packet delay that is imposed.
Which set of these MIR parameters are applicable depends on the interactions of other
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 85
parameter values. These interactions are described under Setting the Configuration
Source on Page 292. Also, where the Configuration Source parameter setting in the AP
specifies that BAM values should be used, they are used only if Prizm is configured to
send the values that it stores for the MIR parameters.
MIR Data Entry Checking
Uplink and downlink MIR is enforced as shown in Figure 20.
NOTE:
In these figures, entry refers to the setting in the data rate parameter, not the
burst allocation parameter.
uplink cap enforced =
uplink entry x aggregate cap for the SM
uplink entry + downlink entry
downlink cap enforced =
downlink entry x aggregate cap for the SM
uplink entry + downlink entry
Figure 20: Uplink and downlink rate caps adjusted to apply aggregate cap
For example, in the Canopy SM, if you set the Sustained Uplink Data Rate parameter to
2,000 kbps and the Sustained Downlink Data Rate parameter to 10,000 kbps, then the
uplink and downlink MIR that will be enforced for the SM can be calculated as shown in
Figure 21.
uplink cap enforced =
2,000 kbps x 7,000 kbps
2,000 kbps + 10,000 kbps
= 1,167 kbps
downlink cap enforced =
10,000 kbps x 7,000 kbps
2,000 kbps + 10,000 kbps
= 5,833 kbps
Figure 21: Uplink and downlink rate cap adjustment example
In this example case, the derived 1,167-kbps uplink and 5,833-kbps downlink MIR sum to
the fixed 7,000-kbps aggregate cap of the Canopy SM.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 86
7.1.8 Committed Information Rate
The Committed Information Rate (CIR) capability feature enables the service provider to
guarantee to any subscriber that bandwidth will never decrease to below a specified
minimum, unless CIR is oversubscribed. Bandwidth can be, and typically will be, higher
than the minimum, but this guarantee helps the WISP to attract and retain subscribers.
In BAM Release 2.1 and in Prizm Release 2.0, CIR configuration is supported as follows:
◦ The GUI allows you to view and change CIR configuration parameters per SM.
◦ When an SM successfully registers and authenticates, if BAM or Prizm has CIR
configuration data for the SM, then messages make the CIR configuration
available to the SM, depending on the Configuration Source setting. (See Setting
the Configuration Source on Page 292.)
◦ The operator can disable the CIR feature in the SM without deleting the CIR
configuration data.
7.1.9 Bandwidth from the SM Perspective
In the Canopy SM, normal web browsing, e-mail, small file transfers, and short streaming
video are rarely rate limited with practical bandwidth management (QoS) settings. When
the SM processes large downloads such as software upgrades and long streaming video
or a series of medium-size downloads, the bucket rapidly drains, the burst limit is
reached, and some packets are delayed. The subscriber experience is more affected in
cases where the traffic is more latency sensitive.
Example download times for various arbitrary tiers of service are shown in Table 56 on
Page 382 and Table 57 on Page 383.
7.1.10 Interaction of Burst Allocation and Sustained Data Rate Settings
If the Burst Allocation is set to 1200 kb and the Sustained Data Rate is set to 128 kbps, a
data burst of 1000 kb is transmitted at full speed because the Burst Allocation is set high
enough. After the burst, the bucket experiences a significant refill at the Sustained Data
Rate. This configuration uses the advantage of the settable Burst Allocation.
If both the Burst Allocation and the Sustained Data Rate are set to 128 kb, a burst is
limited to the Burst Allocation value. This configuration does not take advantage of the
settable Burst Allocation.
If the Burst Allocation is set to 128 kb and the Sustained Data Rate is set to 256 kbps, the
actual rate will be the burst allocation (but in kbps). As above, this configuration does not
take advantage of the settable Burst Allocation.
7.1.11 High-priority Bandwidth
To support low-latency traffic such as VoIP (Voice over IP) or video, the Canopy system
implements a high-priority channel. This channel does not affect the inherent latencies in
the Canopy system but allows high-priority traffic to be immediately served. The high-
priority pipe separates low-latency traffic from traffic that is latency tolerant, such as
standard web traffic and file downloads.
A Canopy module prioritizes traffic by
◦ reading the Low Latency bit (Bit 3) in the IPv4 Type of Service (ToS) byte in a
received packet.
◦ reading the 802.1p field of the 802.1Q header in a received packet, where VLAN
is enabled on the module.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 87
◦ comparing the 6-bit Differentiated Services Code Point (DSCP) field in the ToS
byte of a received packet to a corresponding value in the DiffServe tab of the
Configuration page of the module.
Low Latency Bit
Bit 3 is set by a device outside the Canopy system. In the uplink frame, the SM monitors
Bit 3. If this bit is set, then
◦ the SM prioritizes this traffic in its high-priority queue according to AP
configuration settings for the high-priority channel.
◦ the system sends the packet on the high-priority channel and services this
channel before any normal traffic.
802.1P Field
See Priority on VLANs (802.1p) on Page 166.
DSCP Field
Like Bit 3 of the original IPv4 ToS byte, the DSCP field (Bits 0 through 5) in the redefined
ToS byte is set by a device outside the Canopy system. A packets contains no flag that
indicates whether the encoding is for the Low Latency bit or the DSCP field. For this
reason, you must ensure that all elements in your trusted domain, including routers and
endpoints, set and read the ToS byte with the same scheme.
Canopy modules monitor ToS bytes with DSCP fields, but with the following differences:
◦ The 6-bit length of the field allows it to specify one of 64 service differentiations.
◦ These correlate to 64 individual (CodePoint) parameters in the DiffServe tab of
the Configuration page.
◦ Per RFC 2474, 3 of these 64 are preset and cannot be changed. (See
http://www.faqs.org/rfcs/rfc1902.html.)
◦ For any or all of the remaining 61 CodePoint parameters, you can specify a value
of
− 0 through 3 for low-priority handling.
− 4 through 7 for high-priority handling.
RECOMMENDATION:
Ensure that your Differentiated Services domain boundary nodes mark any
entering packet, as needed, so that it specifies the appropriate Code Point for
that traffic and domain. This prevents theft of service level.
An example of the DiffServe tab in the Configuration page and parameter descriptions
are provided under DiffServe Tab of the AP on Page 256. This tab and its rules are
identical from module type to module type in Canopy. However, any of the 61
configurable Code Points can be set to a different value from module to module, thus
defining unique per-hop behavior for some traffic.
This tab in the AP and BHM sets the priorities for the various packets in the downstream
(sent from the public network). This tab in the SM and BHS sets the priorities for the
various packets in the upstream (sent to the public network).
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 88
Typically in the Canopy network, some SMs attach to older devices that use the ToS byte
as originally formatted, and others to newer devices that use the DSCP field. The default
values in the DiffServe tab allow your modules to prioritize traffic from the older devices
roughly the same as they traditionally have. However, these default values may result in
more high-priority traffic as DSCP fields from the newer devices are read and handled.
So, after making any changes in the DiffServe tab, carefully monitor the high-priority
channel for high packet rates
◦ in SMs that you have identified as those to initially set and watch.
◦ across your Canopy network when you have broadly implemented Code Point
values, such as via SNMP.
The Canopy frame structure is illustrated in Figure 22.
Con-
trol
Beacon Data
AP Transmit (Downlink ) AP Receive (Uplink )
DataAck
Con-
trol Ack Con-
trol
Beacon Data
AP Transmit (Downlink ) AP Receive (Uplink )
DataAck
Con-
trol Ack
Figure 22: Canopy frame structure
7.1.12 Hardware Scheduling
Canopy Release 8 supports only hardware scheduling. Hardware scheduling always
sends high-priority traffic first, even to the exclusion of other traffic.
IMPORTANT!
The number of channels available to the AP is reduced by the number of SMs
configured for the high-priority channel. With this feature enabled on all SMs, an
AP can support 100 SMs (instead of 200).
Canopy Release 8 requires APs, BHs, and AES SMs to be Series P9 or later hardware.3
The characteristics of hardware scheduling in a Canopy sector are summarized in
Table 22.
3 See Designations for Hardware in Radios on Page 365.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 89
Table 22: Characteristics of hardware scheduling
Category
Factor
Treatment
Aggregate throughput, less
additional overhead
14 Mbps
Throughput
ACK slots in downlink used
for data except when request
for uplink is present
Yes
Number of frames required
for the scheduling process
1
Round-trip latency1
≈ 6 ms
Latency
AP broadcast the download
schedule
No
Allocation for uplink high-
priority traffic on amount of
high-priority traffic
Dynamic, based
on amount of
high-priority
traffic
Allocation for downlink high-
priority traffic on amount of
high-priority traffic
Dynamic, based
on amount of
high-priority
traffic
High-priority
Channel
Order of transmission
1. CIR high-priority
2. CIR low-priority
3. Other high-priority
4. Other low-priority
Transmit
Frame
Spreading
Support for Transmit Frame
Spreading feature
In Release 7.0 and
later
CIR
Capability
In all releases
NOTES:
1. For 2.4- and 5.n-GHz modules.
CAUTION!
Power requirements for modules that run hardware scheduling affect the
recommended maximums for power cord length feeding the CMMmicro. See
Table 51 on Page 342. However, the requirements do not affect the maximums
for the CMM2.
Packets that have a priority of 4 to 7 in either the DSCP or a VLAN 802.1p tag are
automatically sent on the high-priority channel, but only where the high-priority channel is
enabled.
7.1.13 2X Operation
A General tab option in both Advantage SMs and hardware series P9 and greater
Canopy SMs provides double the aggregate throughput for SMs that are nearer than half
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 90
of the maximum typical range from the AP. The requirements of this feature are as
follows:
◦ The AP must be an Advantage AP.
◦ The SM must be near the AP, roughly half the range of 1X.
◦ The SM must be of the P9 hardware series or later and enabled for hardware
scheduling. See Designations for Hardware on Page 365.
◦ The 2X Rate parameter in the SM must be set to enabled. This is the default
setting.
◦ The amount of noise and multipath must be low enough to allow the receiver in
the 6 dB less sensitive (2X) state to maintain a high carrier-to-interference (C/I)
ratio.
The flexibility of this feature is as follows:
◦ At the time of registration, signaling is at the 1X rate. However, if the above
requirements are all met, then the SM switches to 2X.
◦ Thereafter, whenever RF conditions are unfavorable for 2X operation, the SM
switches to 1X. When favorable RF conditions allow, the SM switches back to
2X, if user data is present at that time.
◦ Similarly, whenever no user data is present, the SM switches to 1X. When user
data flow resumes, the SM switches back to 2X, if RF conditions allow.
◦ Both links for the SM (uplink and downlink) are independent for this feature.
(One can be operating at 2X operation while the other is operating at 1X.)
◦ Other SMs in the sector can be communicating with the AP at the other
modulation rate.
◦ Although subscribers with Canopy SMs realize higher bursts, and subscribers
with Advantage SMs realize both higher burst and higher sustained throughput,
the network operator realizes higher sector throughput capacity in the AP.
The effect of 2X operation on aggregate throughput for the SM is indicated in Table 23.
Table 23: Effect of 2X operation on throughput for the SM
Typical Aggregate Rates1
Type of SM
Sustained2
Burst2
900 MHz3
4 Mbps
4 Mbps
Advantage SM
Any other frequency
band range
14 Mbps
14 Mbps
Regular SM
(at least P9 Hardware Series)
Any frequency band
range except 900 MHz
7 Mbps
14 Mbps
NOTES:
1. Subject to competition among all SMs in the sector.
2. Can be less if limited by the value of Downlink Data set in the
Radio tab of the Configuration page in the AP.
3. All 900-MHz modules are Advantage.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 91
Competition for Bandwidth
When multiple SMs vie for bandwidth, the AP divides its bandwidth among them,
considering their effective CIR and MIR values. However, 2X operation uses bandwidth
twice as efficiently as 1X, even where MIR values apply. This is because, in 2X
operation, the modules transmit their data in 4-level frequency shift keying (FSK), not
2-level as they would in 1X operation. This moves twice the data per slot. Thus, for the
sum of all bandwidth that 2X-eligible customers use, the bandwidth available to the
remaining customers increases by half of that sum when these eligible customers are
transmitting and receiving in 2X operation.
Engineering for 2X Operation
The following priorities should guide your implementation of 2X operation:
◦ In the near half of the distance range of the AP
− identify the customers who use the most bandwidth.
− enable their SMs first for 2X operation.
◦ When you have deployable Canopy P7 and P8 SMs, do not deploy Canopy
Advantage SMs or Canopy P9 SMs beyond half the distance range of the AP.
At this distance, steady and reliable 2X operation typically is not achievable.
Deploy the Canopy P7 and P8 SMs here.
◦ Wherever practical, implement 25 MHz of channel separation for 2X operation.
Checking Link Efficiencies in 2X Operation
Unlike in 1X operation, efficiencies below 90% on the Link Capacity Test tab in the Tools
web page of the SM may be acceptable for stable operation. An efficiency of 60% in 2X
operation is equivalent to an efficiency of 120% in 1X. If you read efficiency between 60%
and 90%, check the status of 2X operation (as described below) to confirm that the link is
operating at 2X.
Since received signal strength typically varies over time, you should perform link tests at
various times of day and on various days of the week. Efficiencies should consistently be
60% or greater for 2X operation. You may be able to achieve better efficiencies by re-
aiming the SM, mounting it elsewhere, or adding a reflector dish.
Checking the Status of 2X Operation
The Session Status tab in the Home page of the AP provides operation status information
about each SM-to-AP link. Under the MAC address of each SM, the data in this tab
includes a line such as the following:
RATE : VC 19 Rate 2X/2X VC 255 Rate 2X/1X
Interpret this information is as follows:
◦ VC means virtual channel. If one VC is displayed, the high-priority channel is
disabled. If two are displayed, the high-priority channel is enabled and is using
the higher number VC (255 in the above example).
◦ 2X/2X indicates that the SM-to-AP link is in 2X operation.
◦ 2X/1X indicates that the SM is capable of 2X operation but the SM-to-AP link is in
1X operation. This can be for either of the following reasons:
− The SM has not sent data on the channel yet.
− The received signal does not support 2X operation.

Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 92
◦ 1X/1X indicates that the SM is capable of only 1X operation. This can be for
either of the following reasons:
− The SM does not support 2X operation (SM is of the hardware series P7
or P8).
− The 2X Rate parameter is disabled in the General tab of the Configuration
page in the SM or the AP.
CAUTION!
2X operation requires approximately 3 to 5% more power than 1X operation.
This additional power affects the recommended maximum for power cord length
feeding the CMMmicro. See Table 51 on Page 342. However, 2X operation
does not affect the maximums for the CMM2.
Disabling 2X Operation
Disabling 2X operation for an SM can be helpful for alignment, troubleshooting, or
preventing frequent automatic switches between 2X and 1X, where RF conditions are
only marginally favorable to 2X. The ability to disable 2X for an SM is inherent since the
2X Operation feature was introduced.
Disabling 2X operation for a sector can be helpful for identifying a baseline for 1X-to-2X
comparison, broader troubleshooting activities, or forcing all SMs to 1X rather than
disabling 2X in each SM. Release 8 provides a 2X Rate parameter in the General tab of
the Configuration page in the AP:
◦ If you click Disable, then Save Changes and Reboot, 2X operation is disabled
for the sector, regardless of the 2X Rate setting in each SM.
◦ If you later click Enable, then Save Changes and Reboot, 2X operation is
enabled in the sector for SMs with 2X Rate enabled on their
Configuration>General page. SMs with 2X Rate disabled on their
Configuration>General page (or P7 or P8 SMs that don’t support 2X Rate) will
only operate at 1X.
7.1.14 3X Operation (Canopy OFDM modules only)
Canopy OFDM modules offer an additional modulation scheme that provides 3X
operation in addition to 1X and 2X operation. In clear space, 3X operation is possible
over half the range of 2X (which means it is possible over ¼ the range of 1X). However,
in NLOS installations (typical for Canopy OFDM), multipathing may be the predominant
RF issue, not free-space attenuation, so the relationship between 1X, 2X, and 3X range
may differ from clear space situations.
3X operation is configured on a Canopy OFDM module’s Configuration => General page
using the Dynamic Rate Adapt pop-up under Mac Control Parameters.
7.2 UNDERSTANDING SYNCHRONIZATION
The system usesTime Division Duplexing (TDD) - one channel alternately transmits and
receives - rather than using one channel for transmitting and a second channel for
receiving. To accomplish TDD, the AP must provide sync to its SMs – it must keep them
in sync. Furthermore, collocated APs must be synced together - an unsynchronized AP
that transmits during the receive cycle of a collocated AP can prevent that second AP
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 93
from being able to decode the signals from its SMs. In addition, across a geographical
area, APs that can “hear” each other benefit from using a common sync to further reduce
self-interference within the network.
7.2.1 GPS Synchronization
The Navigation Satellite Timing and Ranging (NAVSTAR) Global Positioning System
(GPS) uses 24 satellites to relay information for precise derivation of position and time.
The Canopy Cluster Management Module (CMM) contains a Motorola Oncore GPS
Receiver. The CMM is a critical element in the operation of the Canopy system. At one
AP cluster site or throughout an entire wireless system, the CMM provides a GPS timing
pulse to each module, synchronizing the network transmission cycles.
The Oncore GPS Receiver tracks eight or more satellites. The CMM uses the signal from
at least four of these satellites to generate a one-second interval clock that has a rise
time of 100 nsec. This clock directly synchronizes APs and BHMs which, in turn,
synchronize the SMs and BHSs in the Canopy network.
The Oncore GPS Receiver also provides
◦ the latitude and longitude of the GPS antenna (collocated with the CMM)
◦ the number of satellites that are being tracked
◦ the number of satellites that are available
◦ the date
◦ the time in Universal Coordinated Time (UCT)
◦ the altitude of the GPS antenna
◦ other information that can be used to diagnose network problems.
Alternative to GPS Sync
A Canopy link can operate without GPS sync, but cannot operate without sync. The
alternative to GPS sync is to configure the AP or BHM in the link to generate a sync pulse
to pass to the SM or BHS, respectively. Depending on the RF environment in which the
link operates, this latter alternative may or may not be plausible.
For example, in Figure 23, AP4
◦ is not synchronized with any of the other APs.
◦ is transmitting nearby the other APs while they are expecting to receive SM
transmissions from a maximum distance.
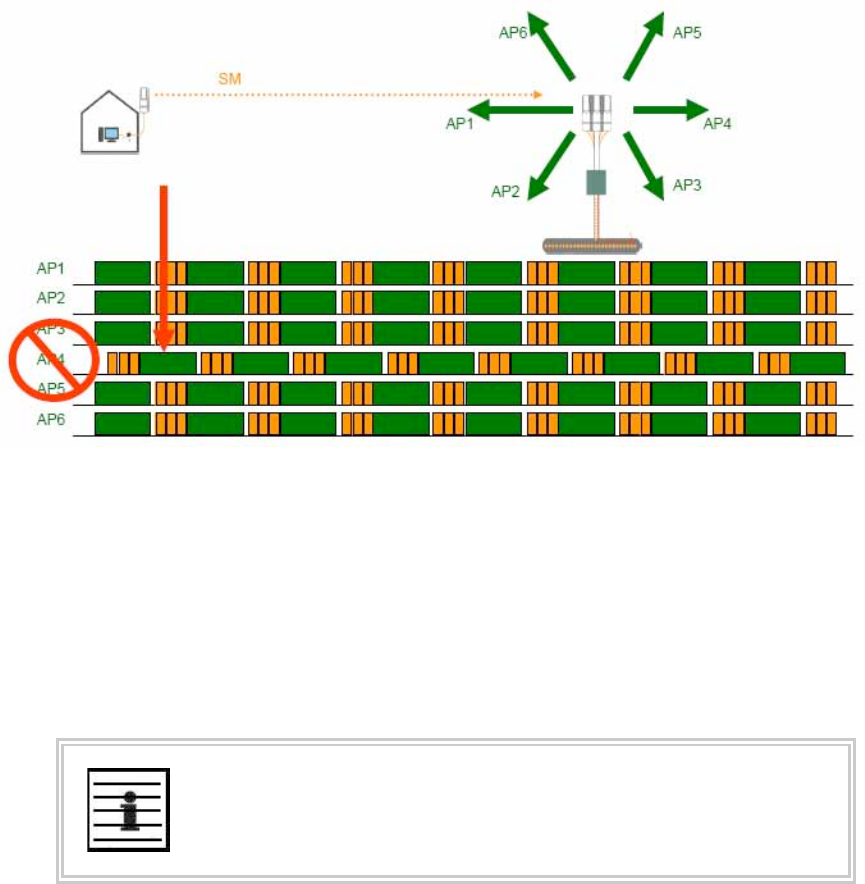
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 94
Figure 23: One unsynchronized AP in cluster
The result is self-interference. In this scenario, the self-interference can be avoided only
by synchronizing the TDD transmit cycles of all APs that operate in the same frequency
band.
An AP that is isolated by at least 5 miles (8 km) from any other Canopy equipment, or a
BHM in an isolated standalone BH link can generate and pass sync pulse without GPS
timing and not risk that interference will result from the generated sync. In any other type
of Canopy link, sync should be derived from GPS timing.
NOTE:
The OFDM Series BHMs generate their own sync. For more information about
these modules, see the user guides that support them. Titles are listed under
Products Not Covered by This User Guide on Page 34.
Advantage of GPS Sync
Although the embedded timing generation capability of the Canopy AP and BHM keeps a
precise clock, no trigger exists to start the clock at the same moment in each AP of a
cluster. So, the individual AP can synchronize communications between itself and
registered SMs, but cannot synchronize itself with other Canopy modules, except by GPS
timing (shown in Figure 24).
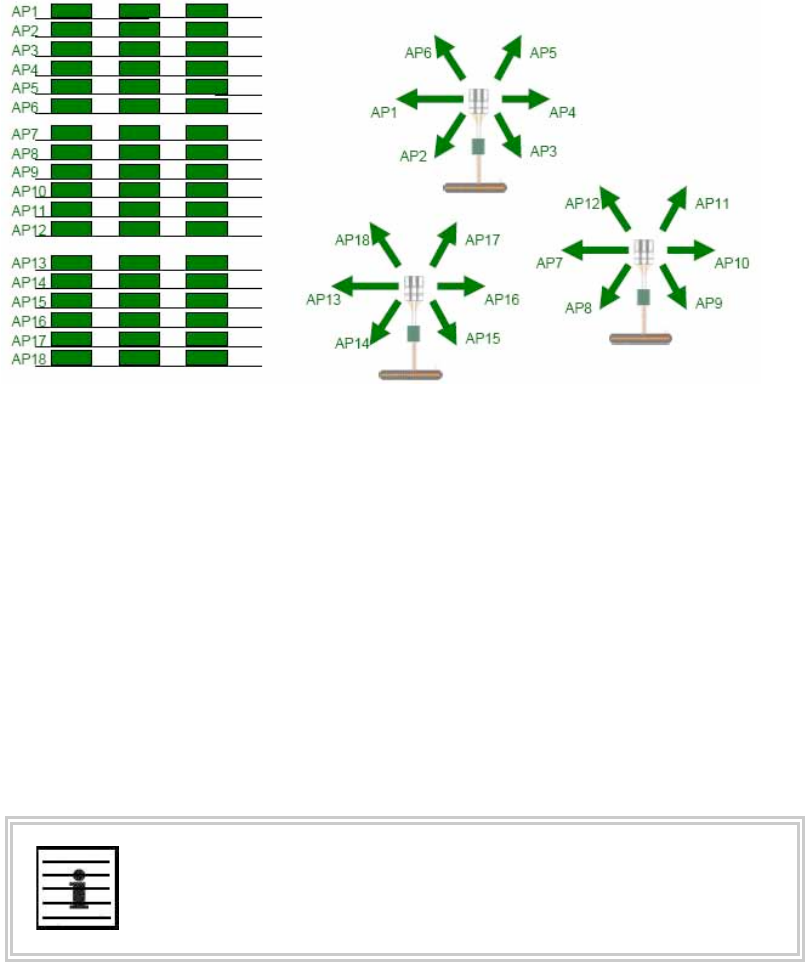
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 95
Figure 24: GPS timing throughout the Canopy network (Canopy FSK shown)
7.2.2 Passing Sync in a Single Hop
Network sync can be passed in a single hop in the following network designs:
◦ Design 1
1. A CMM provides sync to a collocated AP.
2. This AP sends the sync over the air to SMs.
◦ Design 2
1. A CMM provides sync to a collocated BH timing master.
2. This BH timing master sends the sync over the air to a BH timing slave.
7.2.3 Passing Sync in an Additional Hop
Network sync can be extended by one additional link in any of the following network
designs:
NOTE:
In each of these following designs, Link 2 is not on the same frequency band as
Link 4. (For example, Link 2 may be a 5.2-GHz link while Link 4 is a 5.7- or 2.4-
GHz link.)
◦ Design 3
1. A CMM provides sync to a collocated AP.
2. This AP sends the sync over the air to an SM.
3. This SM delivers the sync to a collocated AP.
4. This AP passes the sync in the additional link over the air to SMs.
This design is illustrated in Figure 25.
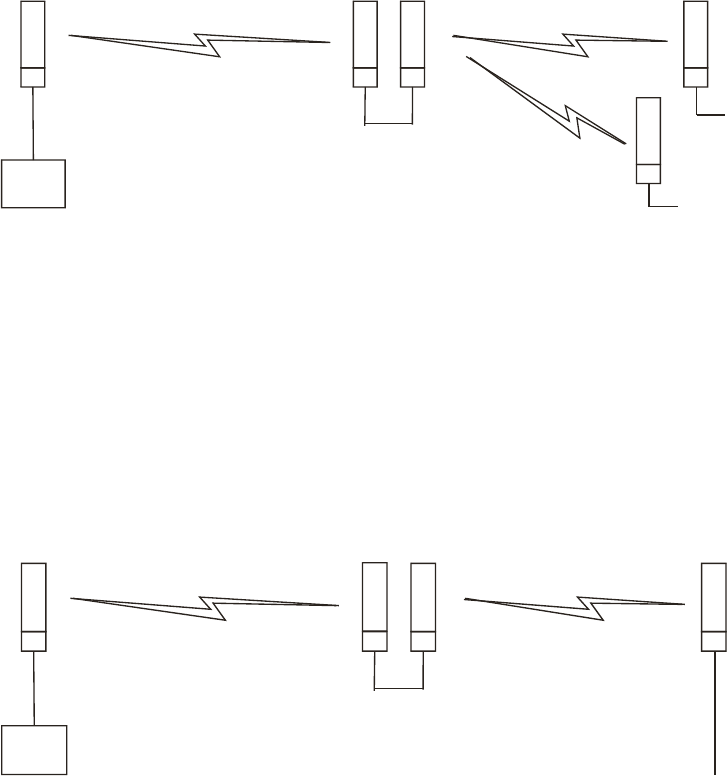
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 96
CMM
AP APSM SM
SM
2
1
3
4
4
Figure 25: Additional link to extend network sync, Design 3
◦ Design 4
1. A CMM provides sync to a collocated AP.
2. This AP sends the sync over the air to an SM.
3. This SM delivers the sync to a collocated BHM.
4. This BHM passes the sync in the additional link over the air to a BHS.
This design is illustrated in Figure 26.
CMM
BH
-M-
AP BH
-S-
SM
2
1
3
4
Figure 26: Additional link to extend network sync, Design 4
◦ Design 5
1. A CMM provides sync to a collocated BHM or the BHM generates timing.
2. This BHM sends the sync over the air to a BHS.
3. This BHS delivers the sync to a collocated AP.
4. This AP passes the sync in the additional link over the air to SMs.
This design is illustrated in Figure 27.
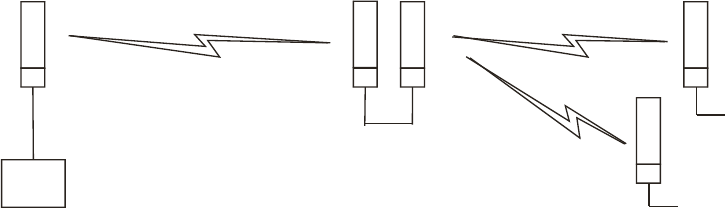
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 97
CMM
BH
-M- AP
BH
-S- SM
SM
2
1
3
4
4
Figure 27: Additional link to extend network sync, Design 5
Wiring and configuration information for this sync extension is described under Wiring to
Extend Network Sync on Page 367.
All Canopy radios support the remote AP functionality. The BHS and the SM can reliably
pass the sync pulse, and the BHM and AP can reliably receive it. The sync is passed in a
cable that connects Pins 1 and 6 of the RJ-11 timing ports of the two modules. (The sync
cable is described under Cables on Page 57.) When you connect modules in this way,
you must also adjust configuration parameters to ensure that
◦ the AP is set to properly receive sync.
◦ the SM will not propagate sync to the AP if the SM itself ceases to receive sync.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 99
8 MEETING LINK REQUIREMENTS
8.1 AP-SM LINKS
APs communicate with SMs using a point-to-multipoint protocol. An AP-SM link has lower
throughput and higher latency than a backhaul link for two reasons:
◦ Many endpoints are involved.
◦ The bandwidth request and reservation process consumes bandwidth.
In the 900-MHz frequency band range, round-trip latency is typically
◦ 40 msec with software scheduling.
◦ 15 msec with hardware scheduling.
In all other Canopy frequency band ranges, round-trip latency is typically
◦ 15 msec with software scheduling.
◦ 6 msec with hardware scheduling.
At range settings of greater than 40 miles (64 km) in the 900-MHz AP, more time elapses
between transmit and receive cycles to compensate for greater air delay. In each frame,
this reduces the number of data slots, which slightly reduces the aggregate throughput of
the link. However, the throughput is as predictable as in other Canopy point-to-multipoint
links.
Throughput is a factor of the Max Range parameter in the AP and is effective for all SMs,
regardless of their distance from the AP. Throughput includes all downlink data to all SMs
and all uplink data from all SMs that link to the AP. For throughput with hardware
scheduling, see Table 13 on Page 62.
End user perspective of throughput is based on both bandwidth in the sending direction
and the return of TCP acknowledgement packets in the other. Where sufficient downlink
bandwidth exists to support downlink traffic and overhead, transient traffic congestion in
the uplink can cause some TCP acknowledgement packets to be dropped, and the end
user to perceive a reduction in throughput. This can also occur with sufficient uplink
bandwidth and dropping acknowledgment packets in the downlink.
However, a Canopy network operator can optionally enable the Prioritize TCP ACK
parameter in the AP and BHM, giving these packets priority over other packet types.
This results in fewer of them being dropped.
The effects of changing network conditions on PTMP throughput are indicated in
Table 24.
Release 8 Overview of Canopy Networks
March 200 Through Software Release 6.
Issue 2, November 2007 Draft 5 for Regulatory Review 100
Table 24: Effects of network conditions on PTMP throughput
Changing Network Condition
Effect on AP Aggregate Throughput
Increasing the Max Range
parameter setting1 in the AP
somewhat decreased2
Increasing the number of SMs that
register in the AP
Increase in downlink traffic
Increase in uplink traffic
no effect
Increasing the average bandwidth
allotted to the SMs that register in
the AP
no effect, even when the additional
bandwidth is used.
NOTES:
1. For non 900-MHz APs, the AP accepts a Max Range value of up to 30
miles (48 km). See Max Range on Page 242.
2. To avoid a decrease of unnecessary proportion, set to not much further
than the distance between the AP and the furthest SM that registers in
the AP.
A comparison of SM products in link with a Canopy Advantage AP is shown in Table 25.
Table 25: Comparison of SM products with Canopy Advantage AP
Product
Maximum Sustained
Aggregate
Throughput
to a Single SM
Burst
Cap on
Committed
Information
Rate
Upgradability
VoIP
Channels
Supported
Canopy Advantage SM
14 Mbps
14 Mb
none
none
multiple
Canopy SM
7 Mbps
14 Mb
none
to Advantage SM
capabilities
multiple
Canopy Lite SM as
purchased
512 kbps
768 kb
100 kbps
to 1, 2, 4, or
7 Mbps
1
Canopy Lite SM
upgraded to 1 Mbps
1 Mbps
1.5 Mb
100 kbps
none
1
Canopy Lite SM
upgraded to 2 Mbps
2 Mbps
3 Mb
100 kbps
none
1
Canopy Lite SM
upgraded to 4 Mbps
4 Mbps
7 Mb
200 kbps
none
2
Canopy Lite SM
upgraded to 7 Mbps
7 Mbps
7 Mb
200 kbps
none
2