Extreme Networks AP3917E Wireless 802.11 a/ac+b/g/n Access Point User Manual WiNG 5 9 1 WC CLI
Extreme Networks, Inc. Wireless 802.11 a/ac+b/g/n Access Point WiNG 5 9 1 WC CLI
Contents
- 1. User Manual-AP3917e
- 2. User Manual-AP7662
- 3. User Manual-AP3917e R1
- 4. User Manual-AP7662 R1
- 5. WiNG 5.9.1 System Reference Guide Part 1
- 6. WiNG 5.9.1 System Reference Guide Part 2
- 7. WiNG 5.9.1 System Reference Guide Part 3
- 8. WiNG 5.9.1 System Reference Guide Part 4
- 9. WiNG 5.9.1 CLI Reference Guide Part 1
- 10. WiNG 5.9.1 CLI Reference Guide Part 2
- 11. Extreme Wireless V10.41.06 User Guide Part 1
- 12. AP3917 User Manual
- 13. AP7662 User Manual
WiNG 5.9.1 CLI Reference Guide Part 1




![ABOUT THIS GUIDEAccess Point, Wireless Controller and Service Platform CLI Reference Guide iii| The pipe symbol. This is used to separate the variables/keywords in a list.For example, the command,nx9500-6C8809> show .....is documented as:show [adoption|bluetooth|bonjour|boot|......where:• show – is the command – displays information• [adoption|bluetooth|bonjour|boot|.......] – indicates the different keywords that can be combined with the show command. However, only one of the above option can be used at a time.show adoption ...show bluetooth ...show bonjour ...[] Of the different keywords and variables listed inside a ‘[‘ & ‘]’ pair, only one can be used. Each choice in the list is separated with a ‘|’ (pipe) symbol.For example, the command,nx9500-6C8809#clear ...is documented as:clear [arp-cache|bonjour|cdp|counters|crypto|event-history|firewall|gre|ip|ipv6|l2tpv3-stats|lacp|license|lldp|logging|mac-address-table|mint|role|rtls|spanning-tree|traffic-shape|vrrp]where:• clear – is the command• [arp-cache|cdp|bonjour|counters|crypto|event-history|firewall|gre|ip|ipv6|l2tpv3-stats|lacp|license|lldp|logging|mac-address-table|mint|role|rtls|spanning-tree|traffic-shape|vrrp] – indicates that these keywords are available for this command. However, only one can be used at a time.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-23.png)








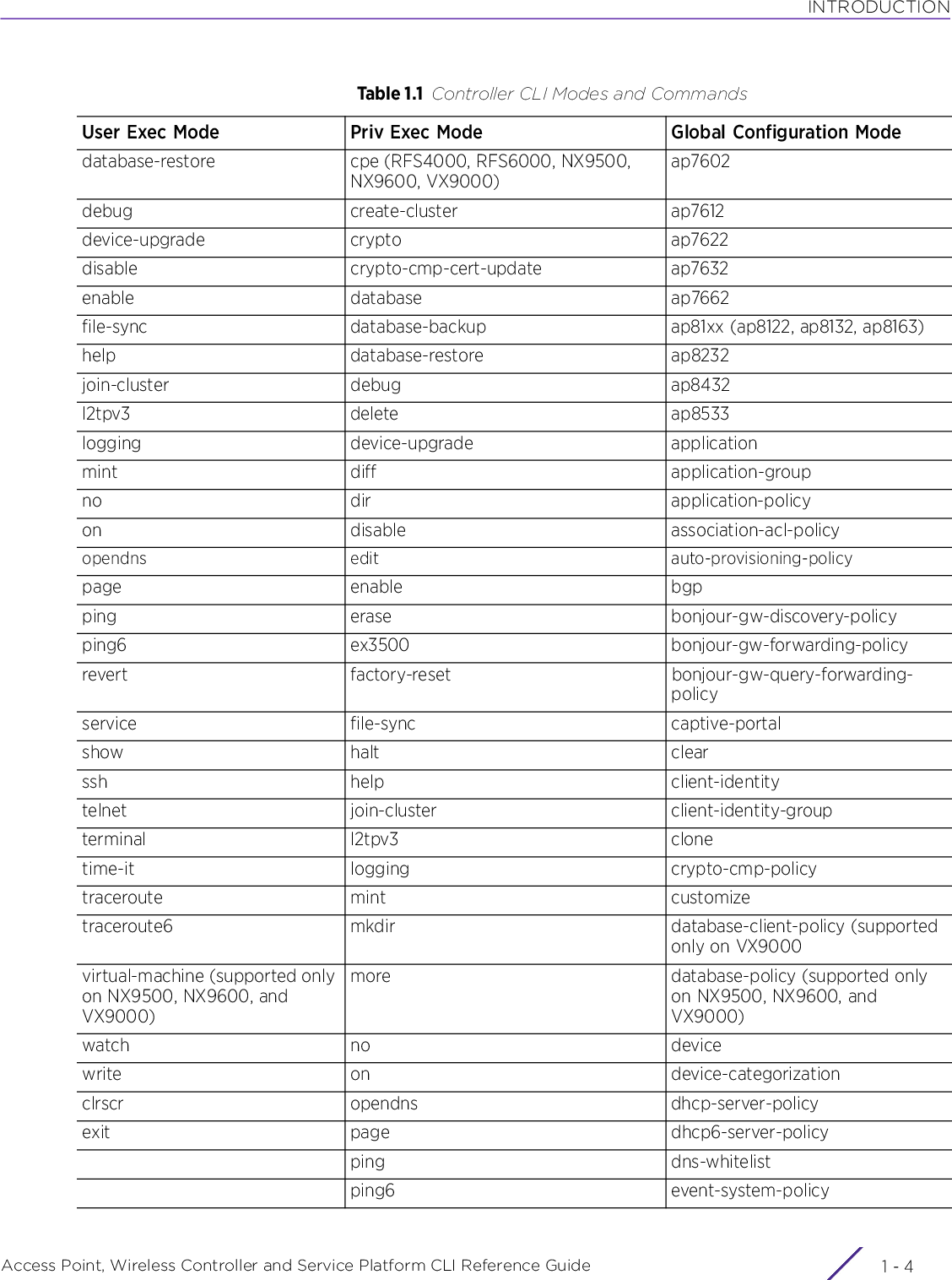
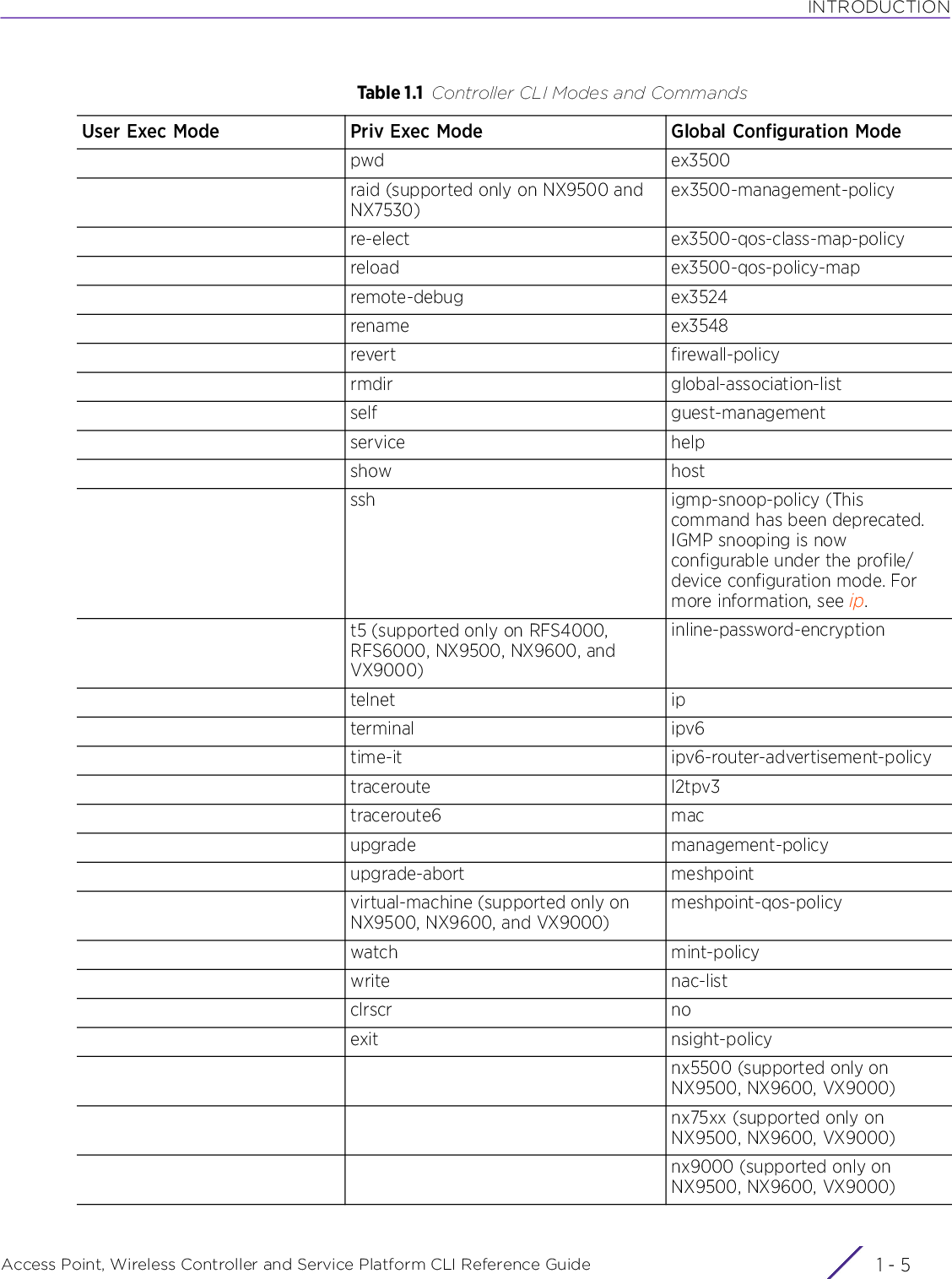
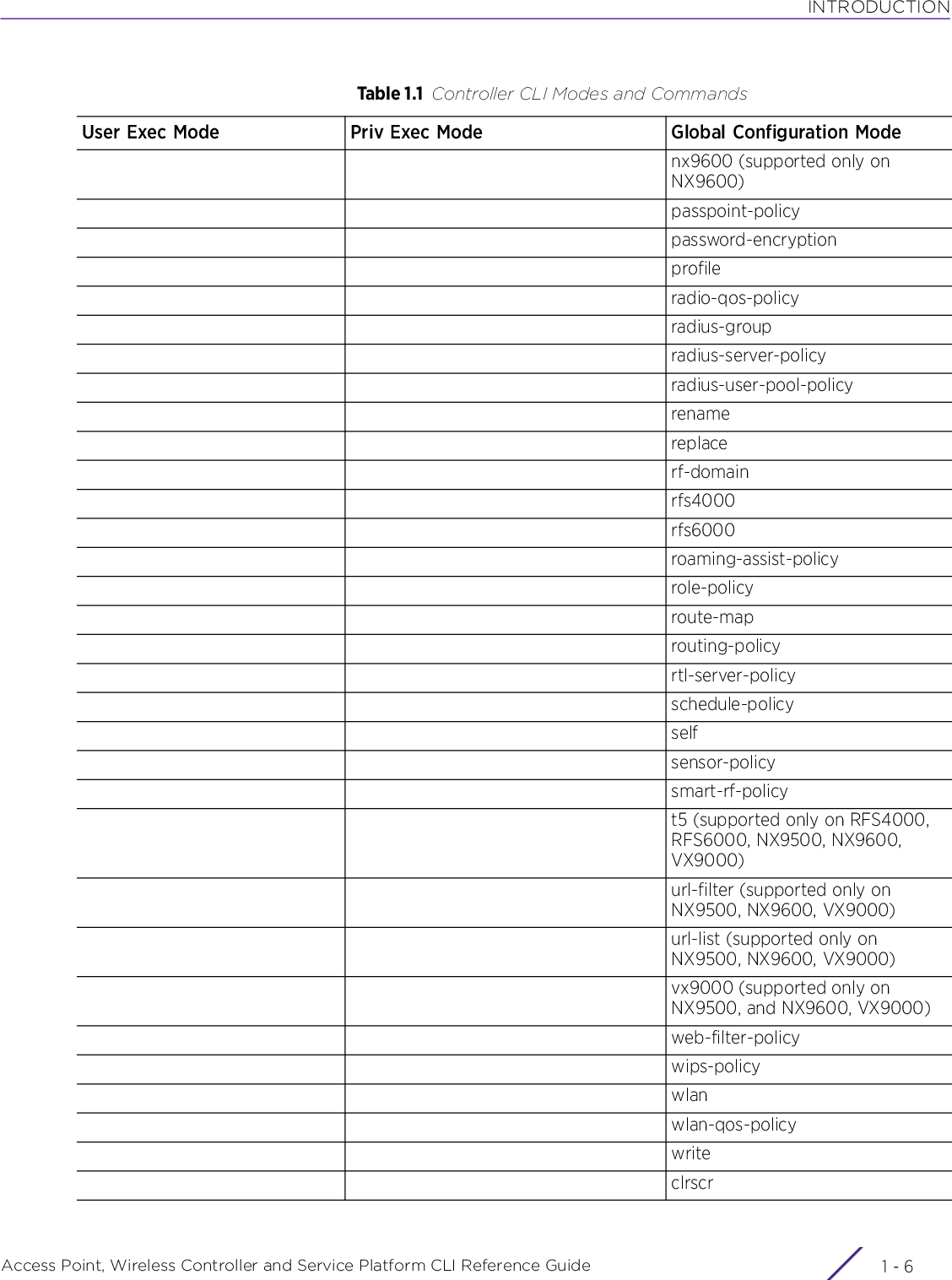
![INTRODUCTIONAccess Point, Wireless Controller and Service Platform CLI Reference Guide 1 - 71.2 Getting Context Sensitive HelpINTRODUCTIONEnter a question mark (?) at the system prompt to display a list of commands available for each mode. Obtain a list of arguments and keywords for any command using the CLI context-sensitive help.Use the following commands to obtain help specific to a command mode, command name, keyword or argument:commitdoendexitrevertserviceshowTable 1.1 Controller CLI Modes and CommandsUser Exec Mode Priv Exec Mode Global Configuration ModeCommand Description(prompt)#help Displays a brief description of the help system(prompt)#abbreviated-command-entry? Lists commands in the current mode that begin with a particular character string(prompt)#abbreviated-command-entry[TAB] Completes a partial command name(prompt)#? Lists all commands available in the command mode(prompt)#command ? Lists the available syntax options (arguments and keywords) for the command(prompt)#command keyword ? Lists the next available syntax option for the commandNOTE: The system prompt varies depending on the configuration mode.NOTE: Enter Ctrl + V to use ? as a regular character and not as a character used for displaying context sensitive help. This is required when the user has to enter a URL that ends with a ?NOTE: The escape character used through out the CLI is “\”. To enter a "\" use "\\" instead.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-37.png)


![INTRODUCTIONAccess Point, Wireless Controller and Service Platform CLI Reference Guide 1 - 11The CLI recognizes a command once you have entered enough characters to make the command unique. If you enter “conf” within the privileged EXEC mode, the CLI associates the entry with the configure command, since only the configure command begins with conf.In the following example, the CLI recognizes a unique string in the privileged EXEC mode when the Tab key is pressed:rfs6000-6DB5D4#conf[TAB]rfs6000-6DB5D4#configureWhen using the command completion feature, the CLI displays the full command name. The command is not executed until the [Return] or [Enter] key is pressed. Modify the command if the full command was not what you intended in the abbreviation. If entering a set of characters (indicating more than one command), the system lists all commands beginning with that set of characters.Enter a question mark (?) to obtain a list of commands beginning with a particular set of characters. Do not leave a space between the last letter and the question mark (?).In the following example, all commands, available in the current context, starting with the characters ‘co’ are listed:rfs6000-6DB5D4#co? commit Commit all changes made in this session configure Enter configuration mode connect Open a console connection to a remote device copy Copy from one file to anotherrfs6000-6DB5D4#1.4.3 Command Output PaginationUsing CLI Editing Features and ShortcutsOutput often extends beyond the visible screen length. For cases where output continues beyond the screen, the output is paused and a--More--prompt displays at the bottom of the screen. To resume the output, press the [Enter] key to scroll down one line or press the Spacebar to display the next full screen of output.1.5 Using CLI to Create Profiles and Enable Remote AdministrationINTRODUCTIONThe following sections describe the following essential procedures:•Creating Profiles•Changing the default profile by creating vlan 150 and mapping to ge3 Physical interface•Enabling Remote AdministrationNOTE: The characters entered before the question mark are reprinted to the screen to complete the command entry.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-41.png)
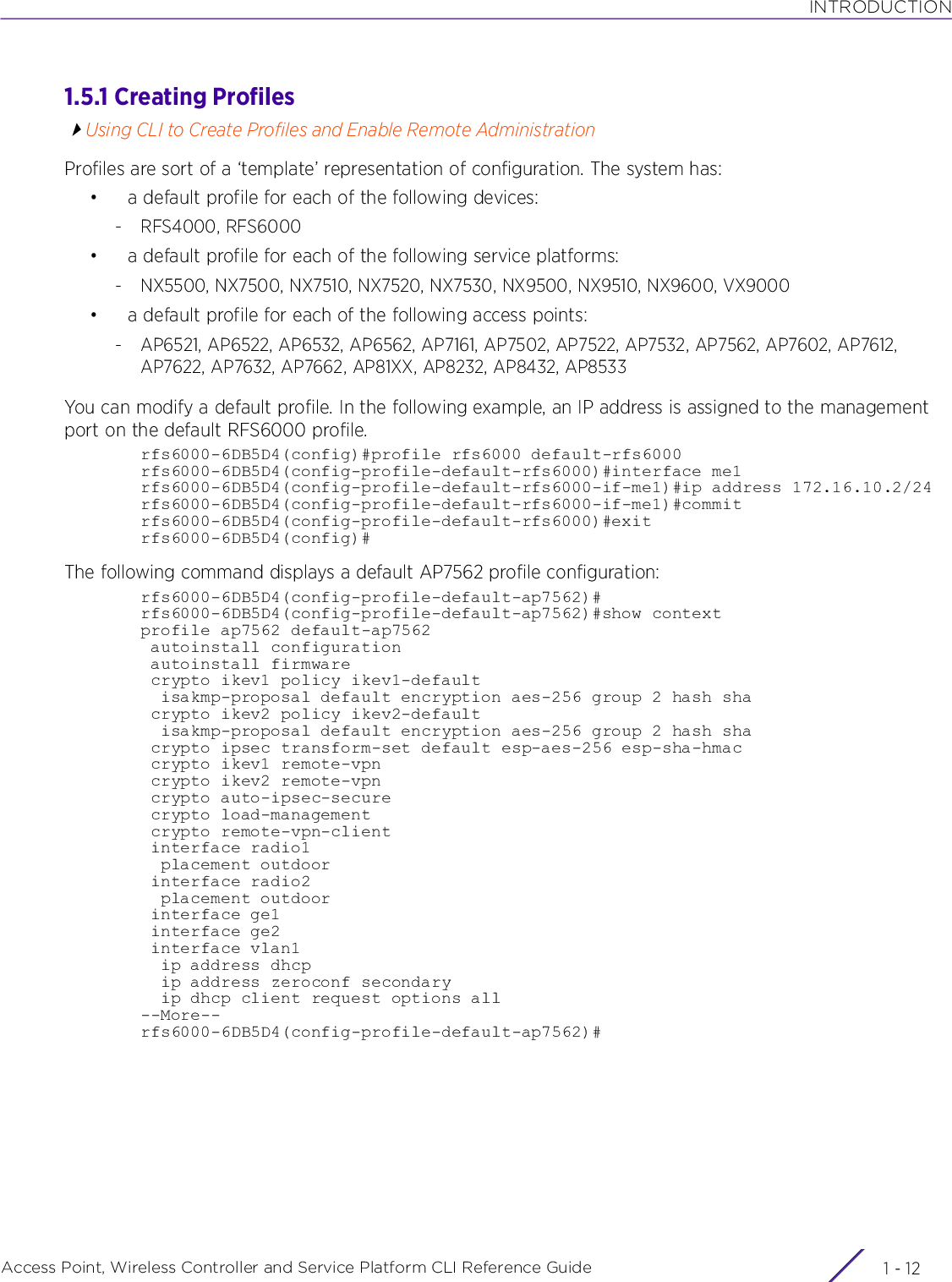
![INTRODUCTIONAccess Point, Wireless Controller and Service Platform CLI Reference Guide 1 - 131.5.2 Changing the default profile by creating vlan 150 and mapping to ge3 Physical interfaceUsing CLI to Create Profiles and Enable Remote AdministrationLogon to the controller in config mode and follow the procedure below:rfs6000-6DB5D4(config-profile-default-rfs6000)#interface vlan 150rfs6000-6DB5D4(config-profile-default-rfs6000-if-vlan150)#ip address 192.168.150.20/24rfs6000-6DB5D4(config-profile-default-rfs6000-if-vlan150)#exitrfs6000-6DB5D4(config-profile-default-rfs6000)#interface ge 3rfs6000-6DB5D4(config-profile-default-rfs6000-if-ge3)#switchport access vlan 150rfs6000-6DB5D4(config-profile-default-rfs6000-if-ge3)#commit writePlease Wait .[OK]rfs6000-6DB5D4(config-profile-default-rfs6000-if-ge3)#rfs6000-6DB5D4(config-profile-default-rfs6000-if-ge3)#show interface vlan 150Interface vlan150 is UP Hardware-type: vlan, Mode: Layer 3, Address: 00-15-70-81-74-2D Index: 6, Metric: 1, MTU: 1500 IP-Address: 192.168.150.20/24 input packets 0, bytes 0, dropped 0, multicast packets 0 input errors 0, length 0, overrun 0, CRC 0, frame 0, fifo 0, missed 0 output packets 2, bytes 140, dropped 0 output errors 0, aborted 0, carrier 0, fifo 0, heartbeat 0, window 0 collisions 0 IPv6 mode is disabledrfs6000-6DB5D4(config-profile-default-rfs6000-if-ge3)#1.5.2.1 Viewing Configured APsTo view previously configured APs, enter the following command:rfs6000-6DB5D4>show wireless ap configured-------------------------------------------------------------------------------- IDX NAME MAC PROFILE RF-DOMAIN ADOPTED-BY -------------------------------------------------------------------------------- 1 ap7532-80C2AC 84-24-8D-80-C2-AC default-ap7532 TechPubs 00-15-70-81-74-2D 2 ap8132-74B45C B4-C7-99-74-B4-5C default-ap81xx TechPubs 00-15-70-81-74-2D 3 ap7522-8330A4 84-24-8D-83-30-A4 default-ap7522 default 00-15-70-81-74-2D 4 ap8132-711728 B4-C7-99-71-17-28 default-ap81xx TechPubs 00-15-70-81-74-2D 5 ap8533-9A12DB 74-67-F7-9A-12-DB default-ap8533 default un-adopted 6 ap7562-84A224 84-24-8D-84-A2-24 default-ap7562 TechPubs 00-15-70-81-74-2D --------------------------------------------------------------------------------rfs6000-6DB5D4>](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-43.png)
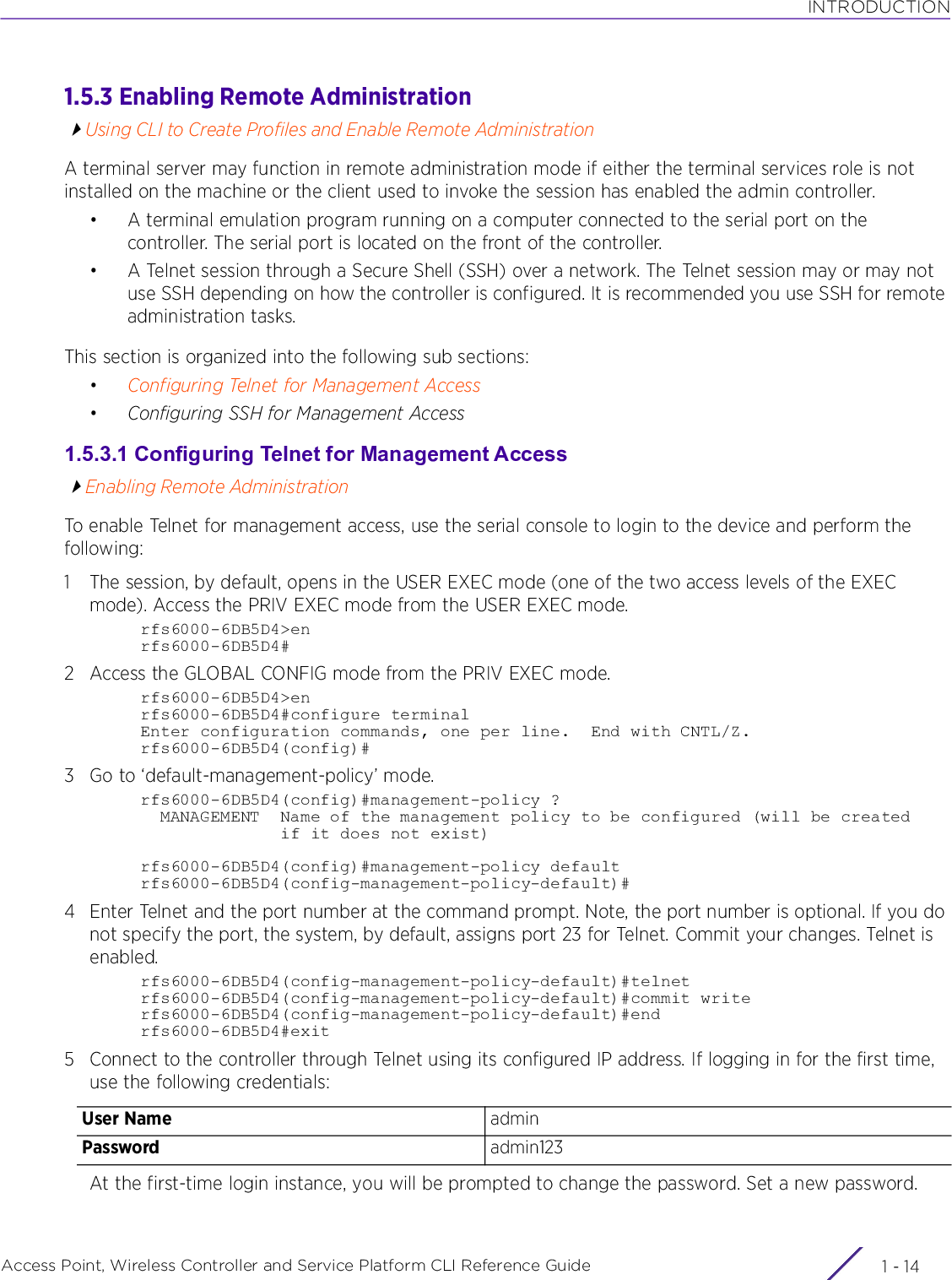
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 22.1 User Exec CommandsUSER EXEC MODE COMMANDSThe following table summarizes the User Exec Mode commands:Table 2.1 User Exec Mode CommandsCommand Description Referencecaptive-portal-page-uploadUploads captive portal advanced pages to adopted access points page 2-4change-passwd Changes the password of a logged user page 2-8clear Resets the last saved command page 2-9clock Configures the system clock page 2-20cluster Accesses the cluster context page 2-21connect Establishes a console connection to a remote device page 2-22create-cluster Creates a new cluster on a specified device page 2-23crypto Enables encryption and configures encryption related parameters page 2-24crypto-cmp-cert-updateTriggers a CMP certificate update on a specified device or devices page 2-33database Enables automatic repairing (vacuuming) and dropping of databases (Captive-portal and NSight)page 2-34database-backupBacks up captive-portal and/or NSight database to a specified location and file on an FTP or SFTP serverpage 2-38database-restoreRestores a previously exported database [captive-portal and/or NSight]. Previously exported databases (backed up to a specified FTP or SFTP server) are restored to the original database.page 2-40device-upgrade Configures device firmware upgrade settings page 2-41disable Turns off (disables) the privileged mode command set page 2-49enable Turns on (enables) the privileged mode command set page 2-50file-sync Configures parameters enabling syncing of PKCS#12 and wireless-bridge certificate between the staging-controller and adopted access pointspage 2-51join-cluster Adds a device (access point, wireless controller, or service platform) to an existing cluster of devicespage 2-54l2tpv3 Establishes or brings down Layer 2 Tunneling Protocol Version 3 (L2TPV3) tunnelspage 2-56logging Modifies message logging facilities page 2-58mint Configures MiNT protocol page 2-60no Negates a command or sets its default page 2-62on Executes the following commands in the RF Domain context: clrscr, do, end, exit, help, service, and showpage 2-64](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-48.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 42.1.1 captive-portal-page-uploadUser Exec CommandsUploads captive portal advanced pages to adopted access points. Use this command to provide access points with specific captive portal configurations, so that they can successfully provision login, welcome, and condition pages to clients attempting to access the wireless network using the captive portal.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcaptive-portal-page-upload [<CAPTIVE-PORTAL-NAME>|cancel-upload|delete-file|load-file]captive-portal-page-upload <CAPTIVE-PORTAL-NAME> [<MAC/HOSTNAME>|all|rf-domain]captive-portal-page-upload <CAPTIVE-PORTAL-NAME> [<MAC/HOSTNAME>|all] {upload-time <TIME>}captive-portal-page-upload <CAPTIVE-PORTAL-NAME> rf-domain [<DOMAIN-NAME>|all] {from-controller} {(upload-time <TIME>)}captive-portal-page-upload cancel-upload [<MAC/HOSTNAME>|all|on rf-domain [<DOMAIN-NAME>|all]]captive-portal-page-upload delete-file <CAPTIVE-PORTAL-NAME> <FILE-NAME>captive-portal-page-upload load-file <CAPTIVE-PORTAL-NAME> <URL>Parameters• captive-portal-page-upload <CAPTIVE-PORTAL-NAME> [<MAC/HOSTNAME>|all] {upload-time <TIME>}NOTE: Ensure that the captive portal pages uploaded are *.tar files.captive-portal-page-upload <CAPTIVE-PORTAL-NAME>Uploads advanced pages of the captive-portal identified by the <CAPTIVE-PORTAL-NAME> parameter• <CAPTIVE-PORTAL-NAME> – Specify the captive portal’s name (should be existing and configured).<MAC/HOSTNAME> Uploads to a specified AP• <MAC/HOSTNAME> – Specify AP’s MAC address or hostname.all Uploads to all APs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-50.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 5• captive-portal-page-upload <CAPTIVE-PORTAL-NAME> rf-domain [<DOMAIN-NAME>|all] {from-controller} {(upload-time <TIME>)}• captive-portal-page-upload cancel-upload [<MAC/HOSTNAME>|all|on rf-domain [<DOMAIN-NAME>|all]]• captive-portal-page-upload delete-file <CAPTIVE-PORTAL-NAME> <FILE-NAME>upload-time <TIME> Optional. Schedules an AP upload time• <TIME> – Specify upload time in the MM/DD/YYYY-HH:MM or HH:MM format.The scheduled upload time is your local system’s time. It is not the access point, controller, service platform, or virtual controller time and it is not synched with the device.To view a list of uploaded captive portal files, execute the show > captive-portal-page-upload > list-files <CAPTIVE-PORTAL-NAME> command.captive-portal-page-upload <CAPTIVE-PORTAL-NAME>Uploads advanced pages of the captive portal identified by the <CAPTIVE-PORTAL-NAME> parameter• <CAPTIVE-PORTAL-NAME> – Specify captive portal name (should be existing and configured).rf-domain [<DOMAIN-NAME>|all]Uploads to all APs within a specified RF Domain or all RF Domains• <DOMAIN-NAME> – Uploads to APs within a specified RF Domain. Specify the RF Domain name.• all – Uploads to APs across all RF Domainsfrom-controller Optional. Uploads captive-portal pages to APs via the controller to which the APs are adoptedupload-time <TIME> Optional. Schedules an AP upload time• <TIME> – Specify upload time in the MM/DD/YYYY-HH:MM or HH:MM format.The scheduled upload time is your local system’s time. It is not the access point, controller, service platform, or virtual controller time and it is not synched with the device.captive-portal-page-upload cancel-uploadCancels a scheduled AP uploadcancel-upload [<MAC/HOSTNAME>|all|on rf-domain [<DOMAIN-NAME>|all]]Select one of the following options:• <MAC/HOSTNAME> – Cancels scheduled upload to a specified AP. Specify the AP’s MAC address or hostname.• all – Cancels all scheduled AP uploads• on rf- domain – Cancels all scheduled uploads to APs within a specified RF Domain or all RF Domains• <DOMAIN-NAME> – Cancels scheduled uploads to APs within a specified RF Do-main. Specify RF Domain name.• all – Cancels scheduled uploads across all RF Domainscaptive-portal-page-upload delete-fileDeletes a specified captive portal’s uploaded captive-portal Web page files<CAPTIVE-PORTAL-NAME> <FILE-NAME>Identifies the captive-portal and Web pages to delete• <CAPTIVE-PORTAL-NAME> – Specify the captive portal name.• <FILE-NAME> – Specify the file name. The specified internal captive portal page isdeleted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-51.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 6• captive-portal-page-upload load-file <CAPTIVE-PORTAL-NAME> <URL>Exampleap6562-B1A214>captive-portal-page-upload load-file captive_portal_test tftp://89.89.89.17/pages_new_only.tarap6562-B1A214>ap6562-B1A214>show captive-portal-page-upload load-image-statusDownload of captive_portal_test advanced page file is completeap6562-B1A214>ap6562-B1A214>captive-portal-page-upload captive_portal_test all-------------------------------------------------------------------------------- CONTROLLER STATUS MESSAGE-------------------------------------------------------------------------------- FC-0A-81-B1-A2-14 Success Added 6 APs to upload queue--------------------------------------------------------------------------------ap6562-B1A214>captive-portal-page-upload load-fileLoads captive-portal advanced pages<CAPTIVE-PORTAL-NAME> <URL>Specify the captive portal name and location. The captive portal should be existing and configured.• <URL> – Specifies location of the captive-portal Web pages. Use one of the following formats to specify the location:IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileIPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileNote: The captive portal pages are downloaded to the controller from the location specified here. After downloading use the captive-portal-page-upload > <CAPTIVE-PORTAL-NAME> > <DEVICE-OR-DOMAIN-NAME> command to upload these pages to APs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-52.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 82.1.2 change-passwdUser Exec CommandsChanges the password of the logged user. When this command is executed without any parameters, the password can be changed interactively.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxchange-passwd {<OLD-PASSWORD>} <NEW-PASSWORD>Parameters• change-passwd {<OLD-PASSWORD>} <NEW-PASSWORD>Usage GuidelinesA password must be from 1 - 64 characters in length.Examplerfs6000-81742D>change-passwdEnter old password:Enter new password:Password for user 'admin' changed successfullyPlease write this password change to memory(write memory) to be persistent.rfs6000-81742D#write memoryOKrfs6000-81742D><OLD-PASSWORD> Optional. Specify the existing password.<NEW-PASSWORD> Specify the new password.Note: The password can also be changed interactively. To do so, press [Enter] after the command.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-54.png)
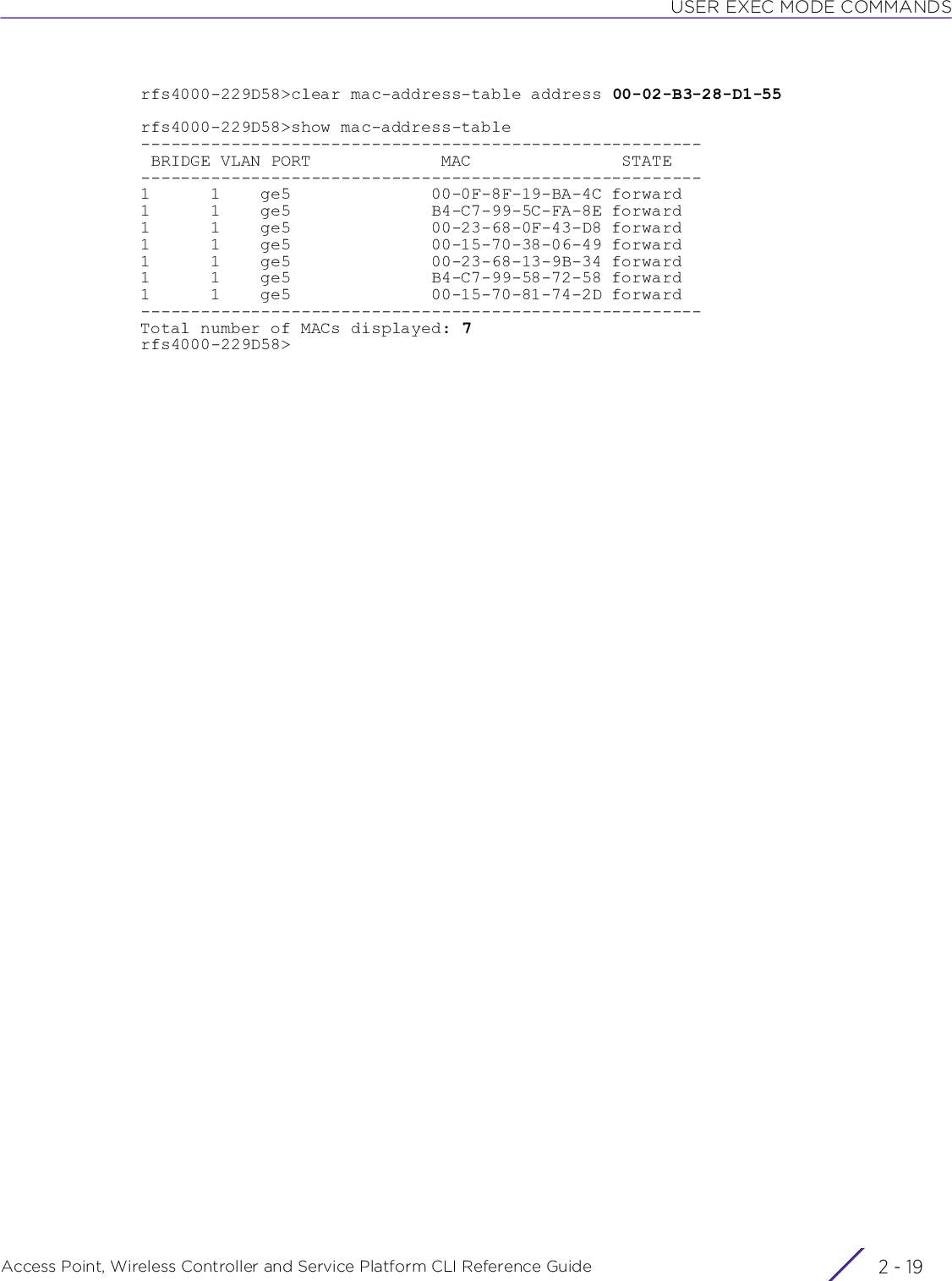
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 92.1.3 clearUser Exec CommandsClears parameters, cache entries, table entries, and other similar entries. The clear command is available for specific commands only. The information cleared, using this command, depends on the mode where the clear command is executed.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxclear [arp-cache|bonjour|cdp|counters|crypto|eguest|event-history|gre|ip|ipv6|lacp|lldp|mac-address-table|mint|role|rtls|spanning-tree|traffic-shape|vrrp]clear arp-cache {on <DEVICE-NAME>}clear bonjour cache {on <DEVICE-NAME>}clear [cdp|lldp] neighbors {on <DEVICE-NAME>}clear counters [ap|radio|wireless-client]clear counters [ap {<MAC>}|radio {<MAC/DEVICE-NAME>} {<1-X>}|wireless-client {<MAC>}] {(on <DEVICE-OR-DOMAIN-NAME>)}clear crypto [ike|ipsec] saclear crypto ike sa [<IP>|all] {on <DEVICE-NAME>}clear crypto ipsec sa {on <DEVICE-NAME>}clear eguest registration statisticsclear event-historyclear gre stats {on <DEVICE-NAME>}clear ip [bgp|dhcp|ospf]clear ip bgp [<IP>|all|external|process]clear ip bgp [<IP>|all|external] {in|on|out|soft}clear ip bgp [<IP>|all|external] {in prefix-filter} {on <DEVICE-NAME>}clear ip bgp [<IP>|all|external] {out} {(on <DEVICE-NAME>)}clear ip bgp [<IP>|all|external] {soft {in|out}} {on <DEVICE-NAME>}clear ip bgp process {on <DEVICE-NAME>}clear ip dhcp bindings [<IP>|all] {on <DEVICE-NAME>}clear ip ospf process {on <DEVICE-NAME>}clear ipv6 neighbor-cache {on <DEVICE-NAME>}clear lacp [<1-4> counters|counters]NOTE: When using the clear command, refer to the interface details provided in interface.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-55.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 10clear mac-address-table {address|interface|mac-auth-state|vlan} {on <DEVICE-NAME>}clear mac-address-table {address <MAC>|vlan <1-4094>} {on <DEVICE-NAME>}clear mac-address-table {interface [<IN-NAME>|ge <1-2>|port-channel <1-2>|vmif <1-8>]} {on <DEVICE-NAME>}clear mac-address-table mac-auth-state address <MAC> vlan <1-4094> {on <DEVICE-NAME>}clear mint mlcp history {on <DEVICE-NAME>}clear role ldap-stats {on <DEVICE-NAME>}clear rtls [aeroscout|ekahau]clear rtls [aeroscout|ekahau] {<MAC/DEVICE-NAME> {on <DEVICE-OR-DOMAIN-NAME>}|on <DEVICE-OR-DOMAIN-NAME>}clear spanning-tree detected-protocols {interface|on}clear spanning-tree detected-protocols {on <DEVICE-NAME>}clear spanning-tree detected-protocols {interface [<INTERFACE-NAME>|ge <1-X>|me1|port-channel <1-X>|pppoe1|up1|vlan <1-4094>|wwan1]} {on <DEVICE-NAME>}clear traffic-shape statistics class <1-4> {(on <DEVICE-NAME>)}clear vrrp [error-stats|stats] {on <DEVICE-NAME>}Parameters• clear arp-cache {on <DEVICE-NAME>}• clear bonjour cache {on <DEVICE-NAME>}• clear [cdp|lldp] neighbors {on <DEVICE-NAME>}arp-cache Clears Address Resolution Protocol (ARP) cache entries on a device. This protocol matches layer 3 IP addresses to layer 2 MAC addresses.on <DEVICE-NAME> Optional. Clears ARP cache entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.bonjour cache Clears all Bonjour cached statistics. Once cleared the system has to re-discover available Bonjour services.on <DEVICE-NAME> Optional. Clears all Bonjour cached statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.cdp Clears Cisco Discovery Protocol (CDP) table entrieslldp Clears Link Layer Discovery Protocol (LLDP) table entriesneighbors Clears CDP or LLDP neighbor table entries based on the option selected in the preceding stepon <DEVICE-NAME> Optional. Clears CDP or LLDP neighbor table entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-56.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 11• clear counters [ap {<MAC>}|radio {<MAC/DEVICE-NAME>} {<1-X>}|wireless-client {<MAC>}] {(on <DEVICE-OR-DOMAIN-NAME>)}• clear crypto ike sa [<IP>|all] {on <DEVICE-NAME>}• clear crypto ipsec sa {on <DEVICE-NAME>}counters Clears counters based on the parameters passed. The options are: AP, radio, and wireless clients.ap <MAC> Clears counters for all APs or a specified AP• <MAC> – Optional. Specify the AP’s MAC address.Note: If no MAC address is specified, all AP counters are cleared.radio <MAC/DEVICE-NAME> <1-X>Clears radio interface counters on a specified device or on all devices• <MAC/DEVICE-NAME> – Optional. Specify the device’s hostname or MAC address. Optionally, append the radio interface number (to the radio ID) using one of the following formats: AA-BB-CC-DD-EE-FF:RX or HOSTNAME:RX (where RX is the interface number).• <1-X> – Optional. Identifies the radio interface by its index. Specify the radio inter-face index, if not specified as part of the radio ID. Note, the number of radio interfacesavailable varies with the access point type.If no device name or MAC address is specified, all radio interface counters are cleared.wireless-client <MAC> Clears counters for all wireless clients or a specified wireless client• <MAC> – Optional. Specify the wireless client’s MAC address.If no MAC address is specified, all wireless client counters are cleared.on <DEVICE-OR-DOMAIN-NAME>The following option is common to all of the above keywords:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Clears AP, radio, or wireless client counters on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller,service platform, or RF Domain.crypto Clears encryption module’s cached statisticsike sa [<IP>|all] Clears Internet Key Exchange (IKE) security associations (SAs)• <IP> – Clears IKE SA entries for the peer identified by the <IP> keyword• all – Clears IKE SA entries for all peerson <DEVICE-NAME> Optional. Clears IKE SA entries, for a specified peer or all peers, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.crypto Clears encryption module’s cached statisticsipsec sa on <DEVICE-NAME>Clears Internet Protocol Security (IPSec) database SAs• on <DEVICE-NAME> – Optional. Clears IPSec SA entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-57.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 12• clear eguest registration statistics• clear gre stats {on <DEVICE-NAME>}• clear event-history• clear ip bgp [<IP>|all|external] {in prefix-filter} {on <DEVICE-NAME>}• clear ip bgp [<IP>|all|external] {out} {(on <DEVICE-NAME>)}eguest registration statisticsClears EGuest registration server counters. When cleared EGuest registration details are deleted, and the show > eguest > registration > statistics command output is null.This command is applicable only on the NX9500, NX9600, and VX9000 model service platforms.gre stats Clears GRE tunnel statisticson <DEVICE-NAME> Optional. Clears GRE tunnel statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.event-history Clears event history cache entriesip bgp [<IP>|all|external]Clears on-going BGP sessions based on the option selected• <IP> – Clears BGP session with the peer identified by the <IP> keyword. Specify the BGP peer’s IP address.• all – Clears all BGP peer sessions• external – Clears external BGP (eBGP) peer sessionsThis command is applicable only to the RFS4000, RFS6000, NX9500, NX9600, and VX9000 platforms.Modifications made to BGP settings (BGP access lists, weight, distance, route-maps, versions, routing policy, etc.) take effect only after on-going BGP sessions are cleared. The clear > ip > bgp command clears BGP sessions. To reduce lose of route updates during the process, use the ‘soft’ option. Soft reconfiguration stores inbound/outbound route updates to be processed later and updated to the routing table. This requires high memory usage.in prefix-filter Optional. Clears inbound route updates• prefix-filter – Optional. Clears the existing Outbound Route Filtering (ORF) prefix-liston <DEVICE-NAME> Optional. Clears route updates on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip bgp [<IP>|all|external]Clears on-going BGP sessions based on the option selected• <IP> – Clears BGP session with the peer identified by the <IP> keyword. Specify the BGP peer’s IP address.• all – Clears all BGP peer sessions• external – Clears eBGP peer sessionsThis command is applicable only to the RFS4000, RFS6000, NX9500, NX9600, and VX9000 platforms.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-58.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 13• clear ip bgp [<IP>|all|external] {soft {in|out}} {on <DEVICE-NAME>}• clear ip bgp process {on <DEVICE-NAME>}• clear ip dhcp bindings [<IP>|all] {on <DEVICE-NAME>}Modifications made to BGP settings (BGP access lists, weight, distance, route-maps, versions, routing policy, etc.) take effect only after on-going BGP sessions are cleared. The clear > ip > bgp command clears BGP sessions. To reduce lose of route updates during the process, use the ‘soft’ option. Soft reconfiguration stores inbound/outbound route updates to be processed later and updated to the routing table. This requires high memory usage.out Optional. Clears outbound route updates. Optionally specify the device on which to execute this command.on <DEVICE-NAME> The following keyword is recursive and optional.• on <DEVICE-NAME> – Optional. Clears BGP sessions on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip bgp [<IP>|all|external]Clears on-going BGP sessions based on the option selected• <IP> – Clears the BGP peer session with the peer identified by the <IP> keyword. Specify the BGP peer’s IP address.• all – Clears all BGP peer sessions• external – Clears eBGP peer sessionsThis command is applicable only to the RFS4000, RFS6000, NX9500, NX9600, and VX9000 platforms.soft {in|out} Optional. Initiates soft-reconfiguration of route updates for the specified IP address• in – Optional. Enables soft reconfiguration of inbound route updates• out – Optional. Enables soft reconfiguration of outbound route updatesModifications made to BGP settings (BGP access lists, weight, distance, route-maps, versions, routing policy, etc.) take effect only after on-going BGP sessions are cleared. The clear > ip > bgp command clears BGP sessions. To reduce loss of route updates during the process, use the ‘soft’ option. Soft reconfiguration stores inbound/outbound route updates to be processed later and updated to the routing table. This requires high memory usage.on <DEVICE-NAME> Optional. Initiates soft reconfiguration inbound/outbound route updates on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip bgp process Clears all BGP processes runningThis command is applicable only to the RFS4000, RFS6000, NX9500, NX9600, and VX9000 platforms.on <DEVICE-NAME> Optional. Clears all BGP processes on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip Clears a Dynamic Host Configuration Protocol (DHCP) server’s IP address binding entriesdhcp bindings Clears DHCP connections and server bindings<IP> Clears specific address binding entries. Specify the IP address to clear binding entries.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-59.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 14• clear ip ospf process {on <DEVICE-NAME>}• clear ipv6 neighbor-cache {on <DEVICE-NAME>}• clear lacp [<1-4> counters|counters]• clear mac-address-table {address <MAC>|vlan <1-4094>} {on <DEVICE-NAME>}all Clears all address binding entrieson <DEVICE-NAME> Optional. Clears a specified address binding or all address bindings on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ip ospf process Clears already enabled Open Shortest Path First (OSPF) process and restarts the processon <DEVICE-NAME> Optional. Clears OSPF process on a specified deviceOSPF is a link-state interior gateway protocol (IGP). OSPF routes IP packets within a single routing domain (autonomous system), like an enterprise LAN. OSPF gathers link state information from neighboring routers and constructs a network topology. The topology determines the routing table presented to the Internet Layer, which makes routing decisions based solely on the destination IP address found in IP packets.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.clear ipv6 neighbor-cacheClears IPv6 neighbor cache entrieson <DEVICE-NAME> Optional. Clears IPv6 neighbor cache entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.clear lacp [<1-4> counters|counters]Clears Link Aggregation Control Protocol (LACP) counters for a specified port-channel group or all port-channel groups configured• <1-4> counters – Clears LACP counters for a specified port-channel. Specify the port-channel index number from 1 - 4. Note, LACP is supported only on the NX5500, NX7500, and NX9500 model service platforms. However, the NX9500 series service platforms support only two (2) port-channels, and the other model service platforms support four (4) port-channels.• counters – Clears LACP counters for all configured port-channels on the devicemac-address-table Clears MAC address forwarding table data based on the parameters passedUse this command to clear the following: all or specified MAC addresses from the system, all MAC addresses on a specified interface, all MAC addresses on a specified VLAN, or the authentication state of a MAC address.address <MAC> Optional. Clears a specified MAC address from the MAC address table.• <MAC> – Specify the MAC address in one of the following formats: AA-BB-CC-DD-EE-FF or AA:BB:CC;DD:EE:FF or AABB.CCDD.EEFFIf executed without specifying any MAC address(es), all MAC addresses from the MAC address table will be removed.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-60.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 15• clear mac-address-table {interface [<IF-NAME>|ge <1-X>|port-channel <1-X>]} {on <DEVICE-NAME>}• clear mac-address-table mac-auth-state address <MAC> vlan <1-4904> {on <DEVICE-NAME>}vlan <1-4094> Optional. Clears all MAC addresses for a specified VLAN• <1-4094> – Specify the VLAN ID from 1 - 4094.on <DEVICE-NAME> Optional. Clears a single MAC entry or all MAC entries, for the specified VLAN on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.mac-address-table Clears MAC address forwarding table data based on the parameters passedUse this command to clear the following: all or specified MAC addresses from the system, all MAC addresses on a specified interface, all MAC addresses on a specified VLAN, or the authentication state of a MAC address.interface Clears all MAC addresses for the selected interface. Use the options available to specify the interface.<IF-NAME> Clears MAC address forwarding table for the specified layer 2 interface (Ethernet port)• <IF-NAME> – Specify the layer 2 interface name.ge <1-X> Clears MAC address forwarding table for the specified GigabitEthernet interface• <1-X> – Specify the GigabitEthernet interface index from 1 - X.The number of GE interfaces supported varies for different device types.port-channel <1-X> Clears MAC address forwarding table for the specified port-channel interface• <1-X> – Specify the port-channel interface index from 1 - X.The number of port-channel interfaces supported varies for different device types.on <DEVICE-NAME> Optional. Clears the MAC address forwarding table, for the selected interface, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.mac-address-table mac-auth-state address <MAC> vlan <1-4904>Clears MAC addresses learned from a particular VLAN when WLAN MAC authentication and captive-portal fall back is enabledAccess points/controllers provide WLAN access to clients whose MAC address has been learned and stored in their MAC address tables. Use this command to clear a specified MAC address on the MAC address table. Once cleared the client has to re-authenticate, and is provided access only on successful authentication.• <MAC> – Specify the MAC address to clear.• vlan <1-4904> – Specify the VLAN interface from 1 - 4094. In the AP/controller’sMAC address table, the specified MAC address is cleared on the specified VLAN in-terface.on <DEVICE-NAME> Optional. Clears the specified MAC address on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.If a device is not specified, the system clears the MAC address on all devices.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-61.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 16• clear mint mlcp history {on <DEVICE-NAME>}• clear role ldap-stats {on <DEVICE-NAME>}• clear rtls [aeroscout|ekahau] {<MAC/DEVICE-NAME> {on <DEVICE-OR-DOMAIN-NAME>}|on <DEVICE-OR-DOMAIN-NAME>}• clear spanning-tree detected-protocols {on <DEVICE-NAME>}• clear spanning-tree detected-protocols {interface [<INTERFACE-NAME>|ge <1-X>|me1|port-channel <1-X>|pppoe1|up1|vlan <1-4094>|wwan1]} {on <DEVICE-NAME>}mint Clears MiNT related informationmlcp history Clears MiNT Link Creation Protocol (MLCP) client historyon <DEVICE-NAME> Optional. Clears MLCP client history on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.role ldap-stats Clears Lightweight Directory Access Protocol (LDAP) server statisticson <DEVICE-NAME> Optional. Clears LDAP server statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.rtls Clears Real Time Location Service (RTLS) statisticsaeroscout Clears RTLS Aeroscout statisticsekahau Clears RTLS Ekahau statistics<MAC/DEVICE-NAME> This keyword is common to the ‘aeroscout’ and ‘ekahau’ parameters.• <MAC/DEVICE-NAME> – Optional. Clears Aeroscout or Ekahau RTLS statistics on a specified AP, wireless controller, or service platform. Specify the AP’s MAC address or hostname.on <DEVICE-OR-DOMAIN-NAME>This keyword is common to the ‘aeroscout’, ‘ekahau’, and <MAC/DEVICE-NAME> parameters.• on <DEVICE-OR-DOMAIN-NAME> – Optional. Clears Aeroscout or Ekahau RTLS statistics on a specified device• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller,service platform, or RF Domain.spanning-tree Clears spanning tree entries on an interface, and restarts protocol migrationdetected-protocols Restarts protocol migrationon <DEVICE-NAME> Optional. Clears spanning tree entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.spanning-tree Clears spanning tree entries on an interface and restarts protocol migrationdetected-protocols Restarts protocol migration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-62.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 17• clear traffic-shape statistics class <1-4> {(on <DEVICE-NAME>)}• clear vrrp [error-stats|stats] {on <DEVICE-NAME>}interface [<INTERFACE-NAME>|ge <1-X>|me1|port-channel <1-X>|pppoe1|up1|vlan <1-4094>|wwan1]Optional. Clears spanning tree entries on different interfaces• <INTERFACE-NAME> – Clears detected spanning tree entries on a specified interface. Specify the interface name.• ge <1-X> – Clears detected spanning tree entries for the selected GigabitEthernet interface. Select the GigabitEthernet interface index from 1 - X.• me1 – Clears FastEthernet interface spanning tree entries• port-channel <1-X> – Clears detected spanning tree entries for the selected port channel interface. Select the port channel index from 1 - X.The number of port-channel interfaces supported varies for different device types.• pppoe1 – Clears detected spanning tree entries for Point-to-Point Protocol over Ethernet (PPPoE) interface• up1 – Clears detected spanning tree entries for the WAN Ethernet interface• vlan <1-4094> – Clears detected spanning tree entries for the selected VLAN interface. Select a Switch Virtual Interface (SVI) VLAN ID from 1- 4094.• wwan1 – Clears detected spanning tree entries for wireless WAN interface.on <DEVICE-NAME> Optional. Clears spanning tree entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.traffic-shape statistics Clears traffic shaping statisticsclass <1-4> Clears traffic shaping statistics for a specific traffic class• <1-4> – Specify the traffic class from 1 - 4.Note: If the traffic class is not specified, the system clears all traffic shaping statistics.on <DEVICE-NAME> Optional. Clears traffic shaping statistics for the specified traffic class on a specified device• <DEVICE-NAME> – Specify the name of the access point, wireless controller, or service platform.Note: For more information on configuring traffic-shape, see traffic-shape.vrrp Clears a device’s Virtual Router Redundancy Protocol (VRRP) statisticsVRRP allows a pool of routers to be advertized as a single virtual router. This virtual router is configured by hosts as their default gateway. VRRP elects a master router, from this pool, and assigns it a virtual IP address. The master router routes and forwards packets to hosts on the same subnet. When the master router fails, one of the backup routers is elected as the master and its IP address is mapped to the virtual IP address.error-stats Clears global error statisticsstats Clears VRRP related statisticson <DEVICE-NAME> The following keywords are common to the ‘error-stats’ and ‘stats’ parameters:• on <DEVICE-NAME> – Optional. Clears VRRP statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-63.png)


![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 222.1.6 connectUser Exec CommandsBegins a console connection to a remote device using the remote device’s MiNT ID or nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxconnect [mint-id <MINT-ID>|<REMOTE-DEVICE-NAME>]Parameters• connect [mint-id <MINT-ID>|<REMOTE-DEVICE-NAME>]Examplerfs6000-81742D>show mint lsp-db9 LSPs in LSP-db of 19.6D.B5.D4:LSP 19.6C.88.09 at level 1, hostname nx9500-6C8809", 8 adjacencies, seqnum 1294555LSP 19.6D.B5.D4 at level 1, hostname "rfs6000-81742D", 8 adjacencies, seqnum 1915724LSP 19.74.B4.5C at level 1, hostname "ap8132-74B45C", 8 adjacencies, seqnum 1468229LSP 4D.80.C2.AC at level 1, hostname "ap7532-80C2AC", 8 adjacencies, seqnum 649244LSP 4D.83.30.A4 at level 1, hostname "ap7522-8330A4", 8 adjacencies, seqnum 202821LSP 4D.84.A2.24 at level 1, hostname "ap7562-84A224", 8 adjacencies, seqnum 380340LSP 68.88.0D.A7 at level 1, hostname "rfs4000-880DA7", 8 adjacencies, seqnum 1494523LSP 68.99.BB.7C at level 1, hostname "ap7131-99BB7C", 8 adjacencies, seqnum 831532rfs6000-81742D>rfs6000-81742D>connect mint-id 19.6C.88.09Entering character modeEscape character is '^]'.NX9500 release 5.9.1.0-012Dnx9500-6C8809 login:mint-id <MINT-ID> Connects to the remote system using its MiNT ID• <MINT-ID> – Specify the remote device’s MiNT ID.<REMOTE-DEVICE-NAME>Connects to the remote system using its name• <REMOTE-DEVICE-NAME> – Specify the remote device’s name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-68.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 232.1.7 create-clusterUser Exec CommandsCreates a new device cluster with the specified name and assigns it an IP address and routing levelA cluster (or redundancy group) is a set of controllers or service platforms (nodes) uniquely defined by a profile configuration. Within the cluster, members discover and establish connections to other members and provide wireless network self-healing support in the event of member's failure.A cluster's load is typically distributed evenly amongst its members. An administrator needs to define how often the profile is load balanced for radio distribution, as radios can come and go and members join and exit the cluster.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcreate-cluster name <CLUSTER-NAME> ip <IP> {level [1|2]}Parameters• create-cluster name <CLUSTER-NAME> ip <IP> {level [1|2]}Examplerfs6000-81742D>create-cluster name TechPubs ip 192.168.13.23 level 1... creating cluster... committing the changes... saving the changesPlease Wait .[OK]rfs6000-81742D>rfs6000-81742D>show context session-config include-factory | include cluster name TechPubs cluster name TechPubsrfs6000-81742D>Related Commandscreate-cluster Creates a clustername <CLUSTER-NAME>Configures the cluster name• <CLUSTER-NAME> – Specify a cluster name. Define a name for the cluster name unique to its configuration or profile support requirements. The name cannot exceed 64 characters.ip <IP> Specifies the device’s IP address used for cluster creation• <IP> – Specify the device’s IP address in the A.B.C.D format.level [1|2] Optional. Configures the cluster’s routing level• 1 – Configures level 1 (local) routing• 2 – Configures level 2 (inter-site) routingcluster Initiates cluster context. The cluster context provides centralized management to configure all cluster members from any one member.join-cluster Adds a device, as a member, to an existing cluster of devices](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-69.png)
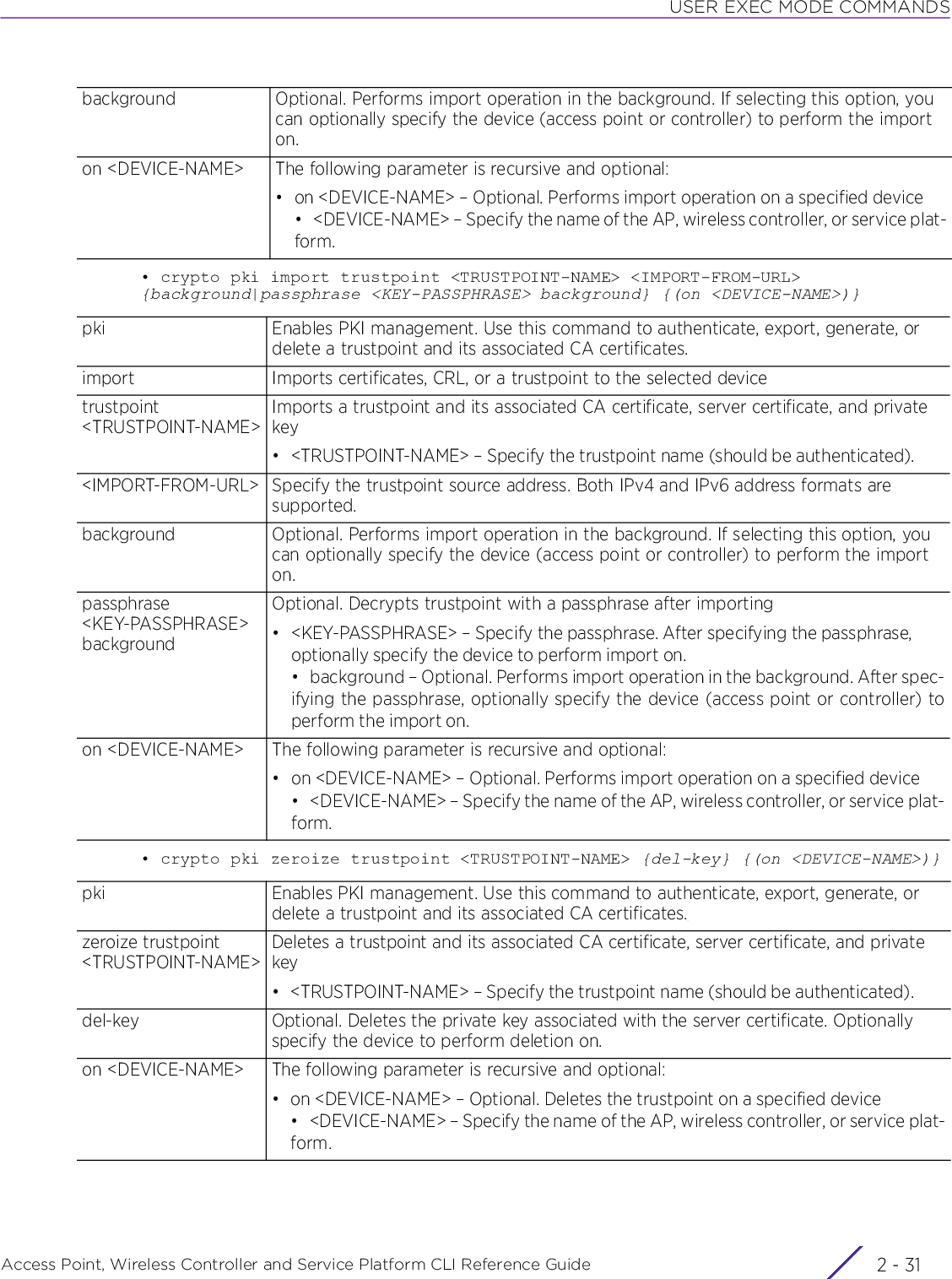
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 242.1.8 cryptoUser Exec CommandsEnables digital certificate configuration and RSA Keypair management. Digital certificates are issued by CAs and contain user or device specific information, such as name, public key, IP address, serial number, company name, etc. Use this command to generate, delete, export, or import encrypted RSA Keypairs and generate Certificate Signing Request (CSR).This command also enables trustpoint configuration. Trustpoints contain the CA’s identity and configuration parameters.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcrypto [key|pki]crypto key [export|generate|import|zeroize]crypto key export rsa <RSA-KEYPAIR-NAME> <EXPORT-TO-URL> {background|on|passphrase}crypto key export rsa <RSA-KEYPAIR-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}crypto key generate rsa <RSA-KEYPAIR-NAME> [2048|4096] {on <DEVICE-NAME>}crypto key import rsa <RSA-KEYPAIR-NAME> <IMPORT-FROM-URL> {background|on|passphrase}crypto key import rsa <RSA-KEYPAIR-NAME> <IMPORT-FROM-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}crypto key zeroize rsa <RSA-KEYPAIR-NAME> {force} {(on <DEVICE-NAME>)}crypto pki [authenticate|export|generate|import|zeroize]crypto pki authenticate <TRUSTPOINT-NAME> <LOCATION-URL> {background} {(on <DEVICE-NAME>)}crypto pki export [request|trustpoint]crypto pki export request [generate-rsa-key|short|use-rsa-key] <RSA-KEYPAIR-NAME> [autogen-subject-name|subject-name]crypto pki export request [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)crypto pki export request [generate-rsa-key|short [generate-rsa-key|use-rsa-key]|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)crypto pki export trustpoint <TRUSTPOINT-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME)}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-70.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 25crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> [autogen-subject-name|subject-name]crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name {(email <SEND-TO-EMAIL>, fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}crypto pki import [certificate|crl|trustpoint]crypto pki import [certificate|crl] <TRUSTPOINT-NAME> <IMPORT-FROM-URL> {background} {(on <DEVICE-NAME>})crypto pki import trustpoint <TRUSTPOINT-NAME> <IMPORT-FROM-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}crypto pki zeroize trustpoint <TRUSTPOINT-NAME> {del-key} {(on <DEVICE-NAME>)}Parameters• crypto key export rsa <RSA-KEYPAIR-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}• crypto key generate rsa <RSA-KEYPAIR-NAME> [2048|4096] {on <DEVICE-NAME>}key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.export rsa <RSA-KEYPAIR-NAME>Exports an existing RSA Keypair to a specified destination• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.<EXPORT-TO-URL> Specify the RSA Keypair destination address. Both IPv4 and IPv6 address formats are supported.After specifying the destination address (where the RSA Keypair is exported), configure one of the following parameters: background or passphrase.background Optional. Performs export operation in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the export on.passphrase <KEY-PASSPHRASE> backgroundOptional. Encrypts RSA Keypair before exporting• <KEY-PASSPHRASE> – Specify a passphrase to encrypt the RSA Keypair.• background – Optional. Performs export operation in the background. After spec-ifying the passphrase, optionally specify the device (access point or controller) toperform the export on.on <DEVICE-NAME> The following parameter is recursive and common to all of the above parameters:• on <DEVICE-NAME> – Optional. Performs export operation on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-71.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 26• crypto key import rsa <RSA-KEYPAIR-NAME> <IMPORT-FROM-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}• crypto key zeroize rsa <RSA-KEYPAIR-NAME> {force} {(on <DEVICE-NAME>)}generate rsa <RSA-KEYPAIR-NAME> [2048|4096]Generates a new RSA Keypair• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.• [2048|4096] – Sets the size of the RSA key in bits. The options are 2048 bits and4096 bits. The default size is 2048 bits.After specifying the key size, optionally specify the device (access point or controller) to generate the key on.on <DEVICE-NAME> Optional. Generates the new RSA Keypair on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.import rsa <RSA-KEYPAIR-NAME>Imports a RSA Keypair from a specified source• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.<IMPORT-FROM-URL> Specify the RSA Keypair source address. Both IPv4 and IPv6 address formats are supported.After specifying the source address (where the RSA Keypair is imported from), configure one of the following parameters: background or passphrase.background Optional. Performs import operation in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the import on.passphrase <KEY-PASSPHRASE> backgroundOptional. Decrypts the RSA Keypair after importing• <KEY-PASSPHRASE> – Specify the passphrase to decrypt the RSA Keypair.• background – Optional. Performs import operation in the background. After spec-ifying the passphrase, optionally specify the device (access point, controller, or ser-vice platform) to perform the import on.on <DEVICE-NAME> The following parameter is recursive and common to the ‘background’ and ‘passphrase’ keywords:• on <DEVICE-NAME> – Optional. Performs import operation on a specific device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.zeroize rsa <RSA-KEYPAIR-NAME>Deletes a specified RSA Keypair• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.Note: All device certificates associated with this key will also be deleted.force Optional. Forces deletion of all certificates associated with the specified RSA Keypair. Optionally specify a device on which to force certificate deletion.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-72.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 27• crypto pki authenticate <TRUSTPOINT-NAME> <URL> {background} {(on <DEVICE-NAME>)}• crypto pki export request [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)on <DEVICE-NAME> The following parameter is recursive and optional:• on <DEVICE-NAME> – Optional. Deletes all certificates associated with the RSA Keypair on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.pki Enables Private Key Infrastructure (PKI) management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated Certificate Authority (CA) certificates.authenticate <TRUSTPOINT-NAME>Authenticates a trustpoint and imports the corresponding CA certificate• <TRUSTPOINT-NAME> – Specify the trustpoint name.<URL> Specify CA’s location. Both IPv4 and IPv6 address formats are supported.Note: The CA certificate is imported from the specified location.background Optional. Performs authentication in the background. If selecting this option, you can optionally specify the device (access point, controller, or service platform) to perform the export on.on <DEVICE-NAME> The following parameter is recursive and optional:•on <DEVICE-NAME> – Optional. Performs authentication on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.export request Exports CSR to the CA for digital identity certificate. The CSR contains applicant’s details and RSA Keypair’s public key.[generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.autogen-subject-name Auto generates subject name from configuration parameters. The subject name identifies the certificate.<EXPORT-TO-URL> Specify the CA’s location. Both IPv4 and IPv6 address formats are supported.Note: The CSR is exported to the specified location.email <SEND-TO-EMAIL>Exports CSR to a specified e-mail address• <SEND-TO-EMAIL> – Specify the CA’s e-mail address.fqdn <FQDN> Exports CSR to a specified Fully Qualified Domain Name (FQDN)• <FQDN> – Specify the CA’s FQDN.ip-address <IP> Exports CSR to a specified device or system• <IP> – Specify the CA’s IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-73.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 28• crypto pki export request [generate-rsa-key|short [generate-rsa-key|use-rsa-key]|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)• crypto pki export trustpoint <TRUSTPOINT-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.export request Exports CSR to the CA for a digital identity certificate. The CSR contains applicant’s details and RSA Keypair’s public key.[generate-rsa-key|short [generate-rsa-key|use-rsa-key]|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• short [generate-rsa-key|use-rsa-key] – Generates and exports a shorter version of the CSR• generate-rsa-key – Generates a new RSA Keypair for digital authentication. If gen-erating a new RSA Keypair, specify a name for it.• use-rsa-key – Uses an existing RSA Keypair for digital authentication. If using anexisting RSA Keypair, specify its name.• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.subject-name <COMMON-NAME>Configures a subject name, defined by the <COMMON-NAME> keyword, to identify the certificate• <COMMON-NAME> – Specify the common name used with the CA certificate. The name should enable you to identify the certificate easily (2 to 64 characters in length).<COUNTRY> Sets the deployment country code (2 character ISO code)<STATE> Sets the state name (2 to 64 characters in length)<CITY> Sets the city name (2 to 64 characters in length)<ORGANIZATION> Sets the organization name (2 to 64 characters in length)<ORGANIZATION-UNIT>Sets the organization unit (2 to 64 characters in length)<EXPORT-TO-URL> Specify the CA’s location. Both IPv4 and IPv6 address formats are supported.The CSR is exported to the specified location.email <SEND-TO-EMAIL>Exports CSR to a specified e-mail address• <SEND-TO-EMAIL> – Specify the CA’s e-mail address.fqdn <FQDN> Exports CSR to a specified FQDN• <FQDN> – Specify the CA’s FQDN.ip-address <IP> Exports CSR to a specified device or system• <IP> – Specify the CA’s IP address.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-74.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 29• crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}export trustpoint <TRUSTPOINT-NAME>Exports a trustpoint along with CA certificate, Certificate Revocation List (CRL), server certificate, and private key• <TRUSTPOINT-NAME> – Specify the trustpoint name (should be authenticated).<EXPORT-TO-URL> Specify the destination address. Both IPv4 and IPv6 address formats are supported.The trustpoint is exported to the address specified here.background Optional. Performs export operation in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the export onpassphrase <KEY-PASSPHRASE> backgroundOptional. Encrypts the key with a passphrase before exporting• <KEY-PASSPHRASE> – Specify the passphrase to encrypt the trustpoint.• background – Optional. Performs export operation in the background. After spec-ifying the passphrase, optionally specify the device (access point or controller) toperform the export on.on <DEVICE-NAME> The following parameter is recursive and common to the ‘background’ and ‘passphrase’ keywords:• on <DEVICE-NAME> – Optional. Performs export operation on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated certificates.generate Generates a certificate and a trustpointself-signed <TRUSTPOINT-NAME>Generates a self-signed certificate and a trustpoint• <TRUSTPOINT-NAME> – Specify a name for the certificate and its trustpoint.[generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair, or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.autogen-subject-name Auto generates the subject name from the configuration parameters. The subject name helps to identify the certificate.email <SEND-TO-EMAIL>Optional. Exports the self-signed certificate to a specified e-mail address• <SEND-TO-EMAIL> – Specify the e-mail address.fqdn <FQDN> Optional. Exports the self-signed certificate to a specified FQDN• <FQDN> – Specify the FQDN.ip-address <IP> Optional. Exports the self-signed certificate to a specified device or system• <IP> – Specify the device’s IP address.on <DEVICE-NAME> Optional. Exports the self-signed certificate on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-75.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 30• crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}• crypto pki import [certificate|crl] <TRUSTPOINT-NAME> <IMPORT-FROM-URL> {background} {(on <DEVICE-NAME>)}pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated certificates.generate self-signed <TRUSTPOINT-NAME>Generates a self-signed certificate and a trustpoint• <TRUSTPOINT-NAME> – Specify a name for the certificate and its trustpoint.[generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair, or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.subject-name <COMMON-NAME>Configures a subject name, defined by the <COMMON-NAME> keyword, to identify the certificate• <COMMON-NAME> – Specify the common name used with this certificate. The name should enable you to identify the certificate easily and should not exceed 2 to 64 characters in length.<COUNTRY> Sets the deployment country code (2 character ISO code)<STATE> Sets the state name (2 to 64 characters in length)<CITY> Sets the city name (2 to 64 characters in length)<ORGANIZATION> Sets the organization name (2 to 64 characters in length)<ORGANIZATION-UNIT>Sets the organization unit (2 to 64 characters in length)email <SEND-TO-EMAIL>Optional. Exports the self-signed certificate to a specified e-mail address• <SEND-TO-EMAIL> – Specify the e-mail address.fqdn <FQDN> Optional. Exports the self-signed certificate to a specified FQDN• <FQDN> – Specify the FQDN.ip-address <IP> Optional. Exports the self-signed certificate to a specified device or system• <IP> – Specify the device’s IP address.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.import Imports certificates, Certificate Revocation List (CRL), or a trustpoint to the selected device[certificate|crl] <TRUSTPOINT-NAME>Imports a signed server certificate or CRL• certificate – Imports signed server certificate•crl – Imports CRL• <TRUSTPOINT-NAME> – Specify the trustpoint name (should be authenticated).<IMPORT-FROM-URL> Specify the signed server certificate or CRL source address. Both IPv4 and IPv6 address formats are supported.The server certificate or the CRL (based on the parameter passed in the preceding step) is imported from the location specified here.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-76.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 32Usage GuidelinesThe system supports both IPv4 and IPv6 address formats. Provide source and destination locations using any one of the following options:•IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/file•IPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileExamplerfs6000-81742D>crypto key generate rsa key 1025RSA Keypair successfully generatedrfs6000-81742D>rfs6000-81742D>crypto key import rsa test123 url passphrase word backgroundRSA key import operation is started in backgroundrfs6000-81742D>rfs6000-81742DE>crypto pki generate self-signed word generate-rsa-key word autogen-subject-name fqdn wordSuccessfully generated self-signed certificaterfs6000-81742D>rfs6000-81742D>crypto pki zeroize trustpoint word del-keySuccessfully removed the trustpoint and associated certificates%Warning: Applications associated with the trustpoint will start using default-trustpointrfs6000-81742D>rfs6000-81742D>crypto pki authenticate word url backgroundImport of CA certificate started in backgroundrfs6000-81742D>rfs6000-81742D>crypto pki import trustpoint word url passphrase wordImport operation started in backgroundrfs6000-81742D>Related Commandsno Removes server certificates, trustpoints and their associated certificates](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-78.png)

![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 342.1.10 databaseUser Exec CommandsEnables automatic repairing (vacuuming) and dropping of captive-portal and NSight databasesIf enforcing authenticated access to the database, use this command to generate the keyfile. Every keyfile has a set of associated users having a username and password. Access to the database is allowed only if the user credentials entered during database login are valid. For more information on enabling database authentication, see Enabling Database Authentication.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdatabase [drop|keyfile|repair]database drop [all|captive-portal|nsight]database repair {on <DEVICE-NAME>}database keyfile [export|generate|import|zerzoise]database keyfile generatedatabase keyfile [export|import] <URL>database keyfile zerzoiseParameters• database drop [all|captive-portal|nsight]• database repair {on <DEVICE-NAME>}database drop [all|captive-portal|nsight]Drops (deletes) all or a specified database. Execute the command on the database.• all – Drops all databases, captive portal and NSight• captive-portal – Drops the captive-portal database• nsight – Drops the NSight databasedatabase repair on <DEVICE-NAME>Enables automatic repairing of all databases. Repairing (vacuuming a database refers to the process of finding and reclaiming space left over from previous DELETE statements. Execute the command on the database host.• on <DEVICE-NAME> – Optional. Specifies the name of the database host. When specified, databases on the specified host are periodically checked to identify and remove obsolete data documents.• <DEVICE-NAME> – Specify the name of the access point, wireless controller, or ser-vice platform.Note: If no device is specified, the system repairs all databases.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-80.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 35• database keyfile generate• database keyfile [export|import] <URL>• database keyfile zerzoiseExamplenx9500-6C8809>database repair on nx9500-6C8809nx9500-6C8809>nx9500-6C8809>database keyfile generateDatabase keyfile successfully generatednx9500-6C8809>nx9500-6C8809>database keyfile zeroizeDatabase keyfile successfully removednx9500-6C8809>vx9000-1A1809>database keyfile generateDatabase keyfile successfully generatedvx9000-1A1809>vx9000-1A1809>database keyfile export ftp://1.1.1.111/db-keyDatabase keyfile successfully exportedvx9000-1A1809>database keyfile [generate|zerzoise]Enables database keyfile management. This command is part of a set of configurations required to enforce database authentication. Use this command to generate database keyfiles. After generating the keyfile, create the username and password combination required to access the database. For information on creating database users see, service. For information on enabling database authentication, see Enabling Database Authentication.• generate – Generates the keyfile. In case of a replica-set deployment, execute the command on the primary database host. Once generated, export the keyfile to a specified location from where it is imported on to the replica-set hosts.database keyfile [export|import] <URL>Enables database keyfile management. This command is part of a set of configurations required to enforce database authentication. Use this command to exchange keyfiles between replica set members.• export – Exports the keyfile to a specified location on an FTP/SFTP/TFTP server. Execute the command on the database host on which the keyfile has been generated.• import – Imports the keyfile from a specified location. Execute the command on the replica set members.The following parameter is common to both of the above keywords:• <URL> – Specify the location to/from where the keyfile is to be exported/imported.Use one of the following options to specify the keyfile location:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]/path/filetftp://<hostname|IP>[:port]/path/filedatabase keyfile zerzoiseEnables database keyfile management. Use this command to delete keyfiles• zerzoise – Deletes an existing keyfile.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-81.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 36vx9000-D031F2>database keyfile import ftp://1.1.1.111/db-keyDatabase keyfile successfully importedvx9000-D031F2>Example Enabling Database AuthenticationFollow the steps below to enable database authentication.1 On the primary database host,a Generate the database keyfile.Primary-DB-HOST>database keyfile generateDatabase keyfile successfully generatedPrimary-DB-HOST>bUse the show > database > keyfile command to view the generated keyfile.c Export the keyfile to an external location. This is required only in case of database replica-set deployment.Primary-DB-HOST>database keyfile export ftp://1.1.1.111/db-keyDatabase keyfile successfully exportedPrimary-DB-HOST>d Create the users that are allowed access to the database.Primary-DB-HOST#service database authentication create-user username techpubs password techPubs@123Database user [techpubs] created.Primary-DB-HOST#e View the database user account created.Primary-DB-HOST#show database users-------------------------------- DATABASE USER-------------------------------- techpubs--------------------------------Primary-DB-HOST#2 On the replica set host, import the keyfile from the location specified in Step 1 c. Secondary-DB-HOST#database keyfile import ftp://1.1.1.111/db-key3 In the database-policy context, --- (used on the NSight/EGuest database hosts)a Enable authentication.Primary-DB-HOST(config-database-policy-techpubs)#authenticationb Configure the user accounts created in Step 1 d.Primary-DB-HOST(config-database-policy-techpubs)#authentication username techpubs password S540QFZz9LzSOdX1ZJEqDgAAAAy3b7GtyO4Z/Ih2ruxnOYnrPrimary-DB-HOST(config-database-policy-techpubs)#show contextdatabase-policy techpubs authentication authentication username techpubs password 2 S540QFZz9LzSOdX1ZJEqDgAAAAy3b7GtyO4Z/Ih2ruxnOYnr replica-set member nx7500-A02B91 arbiter replica-set member vx9000-1A1809 priority 1](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-82.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 37 replica-set member vx9000-D031F2 priority 20Primary-DB-HOST(config-database-policy-techpubs)#4 In the database-client policy context --- (used on the NSight/EGuest server host),Note, this configuration is required only if the NSight/EGuest server and database are hosted on separate hosts.a Configure the user credentials created in Step 1 d.NOC-Controller(config-database-client-policy-techpubs)#authentication username techpubs password S540QFZz9LzSOdX1ZJEqDgAAAAy3b7GtyO4Z/Ih2ruxnOYnrb View the configuration.NOC-Controller(config-database-client-policy-techpubs)#show contextdatabase-client-policy techpubs authentication username techpubs password 2 S540QFZz9LzSOdX1ZJEqDgAAAAy3b7GtyO4Z/Ih2ruxnOYnrNOC-Controller(config-database-client-policy-techpubs)#Related Commandsdatabase-backup Backs up captive-portal and/or NSight database to a specified location and file on an FTP or SFTP serverdatabase-restore Restores a previously exported database [captive-portal and/or NSight]database-policy Documents database-policy configuration commands. Use this option to enable the database. database-client-policyDocuments database-client-policy configuration commands. Use this option to configure the database host details (IP address or hostname). If enforcing database authentication, use it to configure the users having database access. Once configured, use the policy in the NSight/EGuest server’s device config context.service Documents the database user account configuration details](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-83.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 382.1.11 database-backupUser Exec CommandsBacks up captive-portal and/or NSight database to a specified location and file on an FTP, SFTP, or TFTP server. Execute this command on the database host.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdatabase-backup database [captive-portal|nsight|nsight-placement-info] <URL>database-backup database [captive-portal|nsight] <URL>database-backup database nsight-placement-info <URL>Parameters• database-backup database [captive-portal|nsight] <URL>• database-backup database nsight-placement-info <URL>ExampleNS-DB-nx9510-6C87EF>database-backup database nsight tftp://192.168.9.50/testbckupNS-DB-nx9510-6C87EF>show database backup-statusLast Database Backup Status : In_Progress(Starting tftp transfer.)Last Database Backup Time : 2017-04-17 12:48:05NS-DB-nx9510-6C87EF>show database backup-statusLast Database Backup Status : SuccessfulLast Database Backup Time : Mon Apr 17 12:48:08 IST 2017NS-DB-nx9510-6C87EF>Apr 17 12:48:17 2017: NS-DB-nx9510-6C87EF : %DATABASE-6-OPERATION_COMPLETE: backup for database nsight successfulNS-DB-nx9510-6C87EF#database-backup database [captive-portal|nsight]Backs up captive portal and/or NSight database to a specified location. Select the database to backup:• captive-portal – Backs up captive portal database• nsight – Backs up NSight databaseAfter specifying the database type, configure the destination location.<URL> Configures the destination location. The database is backed up at the specified location. Specify the location URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzdatabase-backup database nsight-placement-info <URL>Backs up the NSight access point placement related details to a specified location• <URL> – Specify the URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gztftp://<hostname|IP>[:port]/path/file.tar.gz](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-84.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 39NS-DB-nx9510-6C87EF>database-backup database nsight-placement-info tftp://192.168.9.50/plmentinfoNS-DB-nx9510-6C87EF>show database backup-statusLast Database Backup Status : SuccessfulLast Database Backup Time : Mon Apr 17 12:48:48 IST 2017NS-DB-nx9510-6C87EF>Apr 17 12:49:03 2017: NS-DB-nx9510-6C87EF : %DATABASE-6-OPERATION_COMPLETE: backup for database nsight-placement-info successfulNS-DB-nx9510-6C87EF>Related Commandsdatabase Enables automatic repairing (vacuuming) and dropping of databases (captive-portal and/or NSight)database-restore Restores a previously exported (backed up) database (captive-portal and/or NSight)]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-85.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 402.1.12 database-restoreUser Exec CommandsRestores a previously exported database [captive-portal and/or NSight]. Previously exported databases (backed up to a specified FTP or SFTP server) are restored from the backed-up location to the original database.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdatabase-restore database [captive-portal|nsight] <URL>Parameters• database-restore database [captive-portal|nsight] <URL>Examplenx9500-6C8809>database-restore database nsight ftp://anonymous:anonymous@192.168.13.10/backups/nsight/nsight.tar.gzRelated Commandsdatabase-restore database [captive-portal|nsight]Restores previously exported (backed up) captive-portal and/or NSight database. Specify the database type:• captive-portal – Restores captive portal database• nsight – Restores NSight databaseAfter specifying the database type, configure the destination location and file name from where the files are restored.<URL> Configures the destination location. The database is restored from the specified location. Specify the location URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gztftp://<hostname|IP>[:port]/path/file.tar.gzdatabase Enables automatic repairing (vacuuming) and dropping of databases (captive-portal and NSight)database-backup Backs up captive-portal and/or NSight database to a specified location and file on an FTP or SFTP server](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-86.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 412.1.13 device-upgradeUser Exec CommandsEnables firmware upgrade on an adopted device or a set of adopted devices (access points, wireless controllers, and service platforms). In an hierarchically managed (HM) network, this command enables centralized device upgradation across the network. The WiNG HM network defines a three-tier structure, consisting of multiple wireless sites managed by a single Network Operations Center (NOC) controller. The NOC controller constitutes the first and the site controllers constitute the second tier of the hierarchy. The site controllers in turn adopt and manage access points that form the third tier of the hierarchy.Use the device-upgrade command to schedule firmware upgrades across adopted devices within the network. Devices are upgraded based on their device names, MAC addresses, or RF Domain. Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdevice-upgrade [<MAC/HOSTNAME>|all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap76232|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000|cancel-upgrade|load-image|rf-domain]device-upgrade <MAC/HOSTNAME> {no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}}NOTE: Hierarchical management allows the NOC controller to upgrade controllers and access points that are directly or indirectly adopted to it. However, ensure that the NOC controller is loaded with the correct firmware version.NOTE: If the persist-images option is selected, the RF Domain manager retains the old firmware image, or else deletes it. For more information on enabling device upgrade on profiles and devices (including the ‘persist-images’ option), see device-upgrade.NOTE: A NOC controller’s capacity is equal to, or higher than that of a site controller. The following devices can be deployed at NOC and sites:• NOC controller – NX95XX (NX9500 and NX9510), NX9600, VX9000• Site controller – RFS4000, RFS6000, NX5500, or NX95XXNOTE: Standalone devices have to be manually upgraded.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-87.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 42device-upgrade all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}device-upgrade [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap76232|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}device-upgrade cancel-upgrade [<MAC/HOSTNAME>|all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap76232|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000|on rf-domain [<RF-DOMAIN-NAME>|all]]device-upgrade load-image [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap76232|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx9000|nx9600|vx9000] {<IMAGE-URL>|on <DEVICE-OR-DOMAIN-NAME>}device-upgrade rf-domain [<RF-DOMAIN-NAME>|all|containing <WORD>|filter location <WORD>] [all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap76232|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] {(<MAC/HOSTNAME>|force|from-controller|no-reboot|reboot-time <TIME>|staggered-reboot|upgrade-time <TIME>)}Parameters• device-upgrade <MAC/HOSTNAME> {no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}}• device-upgrade all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}<MAC/HOSTNAME> Upgrades firmware on the device identified by the <MAC/HOSTNAME> keyword• <MAC/HOSTNAME> – Specify the device’s MAC address or hostname.no-reboot Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)reboot-time <TIME> Optional. Schedules an automatic reboot after a successful upgrade• <TIME> – Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.upgrade-time <TIME> {no-reboot|reboot-time <TIME>}Optional. Schedules an automatic device firmware upgrade on a specified day and time• <TIME> – Specify the upgrade time in the MM/DD/YYYY-HH:MM or HH:MM format. The following actions can be performed after a scheduled upgrade:• no-reboot – Optional. Disables automatic reboot after a successful upgrade (thedevice must be manually restarted)• reboot-time <TIME> – Optional. Schedules an automatic reboot after a successfulupgrade. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.all Upgrades firmware on all devicesforce Optional. Select this option to force upgrade on the selected device(s). When selected, the devices are upgraded even if they have the same firmware as the upgrading access point, wireless controller, or service platform. If forcing a device upgrade, optionally specify any one of the following options: no-reboot, reboot-time, upgrade-time, or staggered-reboot.no-reboot Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)reboot-time <TIME> Optional. Schedules an automatic reboot after a successful upgrade• <TIME> – Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-88.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 43• device-upgrade [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}upgrade-time <TIME> {no-reboot|reboot-time <TIME>}Optional. Schedules an automatic device firmware upgrade on all devices on a specified day and time• <TIME> – Specify the upgrade time in the MM/DD/YYYY-HH:MM or HH:MM format. The following actions can be performed after a scheduled upgrade:• no-reboot – Optional. Disables automatic reboot after a successful upgrade (thedevice must be manually restarted).• reboot-time <TIME> – Optional. Schedules an automatic reboot after a successfulupgrade. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.staggered-reboot This keyword is recursive and common to all of the above.• Optional. Enables staggered device reboot (one at a time) without network impactdevice-upgrade <DEVICE-TYPE> allUpgrades firmware on all devices of a specific type. Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX9500, NX9600, and VX9000.After selecting the device type, schedule an automatic upgrade and/or an automatic reboot.force Optional. Select this option to force upgrade on the selected device(s). When selected, the devices are upgraded even if they have the same firmware as the upgrading access point, wireless controller, or service platform. If forcing a device upgrade, optionally specify any one of the following options: no-reboot, reboot-time, upgrade-time, or staggered-reboot.no-reboot Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)reboot-time <TIME> Optional. Schedules an automatic reboot after a successful upgrade• <TIME> – Optional. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.upgrade-time <TIME> {no-reboot|reboot-time <TIME>}Optional. Schedules an automatic firmware upgrade on all devices, of the specified type, on a specified day and time• <TIME> – Specify the upgrade time in the MM/DD/YYYY-HH:MM or HH:MM format. The following actions can be performed after a scheduled upgrade:• no-reboot – Optional. Disables automatic reboot after a successful upgrade (thedevice must be manually restarted)• reboot-time <TIME> – Optional. Schedules an automatic reboot after a successfulupgrade. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.staggered-reboot This keyword is recursive and common to all of the above.• Optional. Enables staggered device reboot (one at a time) without network impact](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-89.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 44• device-upgrade cancel-upgrade [<MAC/HOSTNAME>|all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000|on rf-domain [<RF-DOMAIN-NAME>|all]]• device-upgrade load-image [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx500|nx9000|nx9600|vx9000] {<IMAGE-URL>|on <DEVICE-OR-DOMAIN-NAME>}cancel-upgrade Cancels a scheduled firmware upgrade based on the parameters passed. This command provides the following options to cancel scheduled firmware upgrades:• Cancels upgrade on specific device(s). The devices are identified by their MAC addresses or hostnames.• Cancels upgrade on all devices within the network• Cancels upgrade on all devices of a specific type. Specify the device type.• Cancels upgrade on specific device(s) or all device(s) within a specific RF Domain or all RF Domains. Specify the RF Domain name.cancel-upgrade [<MAC/HOSTNAME>|all]Cancels a scheduled firmware upgrade on a specified device or on all devices• <MAC/HOSTNAME> – Cancels a scheduled upgrade on the device identified by the <MAC/HOSTNAME> keyword. Specify the device’s MAC address or hostname.• all – Cancels scheduled upgrade on all devicescancel-upgrade <DEVICE-TYPE> allCancels scheduled firmware upgrade on all devices of a specific type. Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX9500, NX9600, and VX9000.cancel-upgrade on rf-domain [<RF-DOMAIN-NAME>|all]Cancels scheduled firmware upgrade on all devices in a specified RF Domain or all RF Domains• <RF-DOMAIN-NAME> – Cancels scheduled device upgrade on all devices in a specified RF Domain. Specify the RF Domain name.• all – Cancels scheduled device upgrade on all devices across all RF Domainsload-image <DEVICE-TYPE>Loads device firmware image from a specified location. Use this command to specify the device type and the location of the corresponding image file. • <DEVICE-TYPE> – Specify the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX9500, NX9600, and VX9000.After specifying the device type, provide the location of the required device firmware image.<IMAGE-URL> Specify the device’s firmware image location in one of the following formats:IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/file](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-90.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 45• device-upgrade rf-domain [<RF-DOMAIN-NAME>|all|containing <WORD>|filter location <WORD>] [all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] {(<MAC/HOSTNAME>|force|from-controller|no-reboot|reboot-time <TIME>|staggered-reboot|upgrade-time <TIME>)}IPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileon <DEVICE-OR-DOMAIN-NAME>Specify the name of the device or RF Domain. The image, of the specified device type is loaded from the device specified here. In case of an RF Domain, the image available on the RF Domain manager is loaded.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.rf-domain [<RF-DOMAIN-NAME>|all|containing <WORD>|filter location <WORD>]Upgrades firmware on devices in a specified RF Domain or all RF Domains. Devices within a RF Domain are upgraded through the RF Domain manager.• <RF-DOMAIN-NAME> – Upgrades devices in the RF Domain identified by the <RF-DOMAIN-NAME> keyword.• <RF-DOMAIN-NAME> – Specify the RF Domain name.• all – Upgrades devices across all RF Domains• containing <WORD> – Filters RF Domains by their names. RF Domains with names containing the sub-string identified by the <WORD> keyword are filtered. Devices on the filtered RF Domains are upgraded.• filter location <WORD> – Filters devices by their location. All devices with location matching the <WORD> keyword are upgraded.<DEVICE-TYPE> After specifying the RF Domain, select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX9500, NX9600, and VX9000.After specifying the RF Domain and the device type, configure any one of the following actions: force devices to upgrade, or initiate an upgrade through the adopting controller.<MAC/HOSTNAME> Optional. Use this option to identify specific devices for upgradation. Specify the device’s MAC address or hostname. The device should be within the specified RF Domain and of the specified device type. After identifying the devices to upgrade, configure any one of the following actions: force devices to upgrade, or initiate an upgrade through the adopting controller.Note: If no MAC address or hostname is specified, all devices of the type selected are upgraded.force Optional. Select this option to force upgrade for the selected device(s). When selected, the devices are upgraded even if they have the same firmware as the upgrading access point, wireless controller, or service platform. If forcing a device upgrade, optionally specify any one of the following options: no-reboot, reboot-time, upgrade-time, or reboot-time.from-controller Optional. Upgrades a device through the adopted device. If initiating an upgrade through the adopting controller, optionally specify any one of the following options: no-reboot, reboot-time, upgrade-time, or reboot-time.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-91.png)
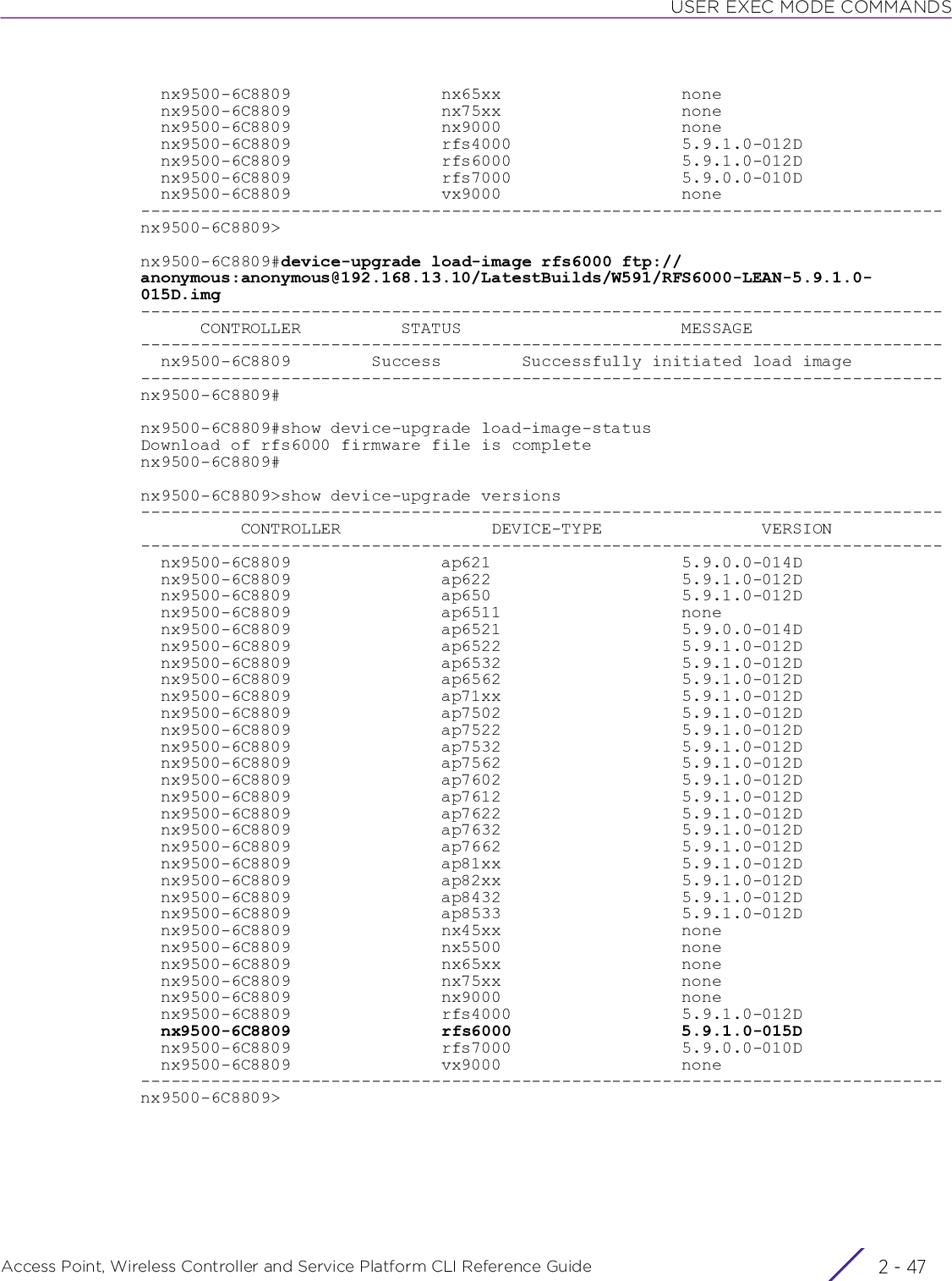
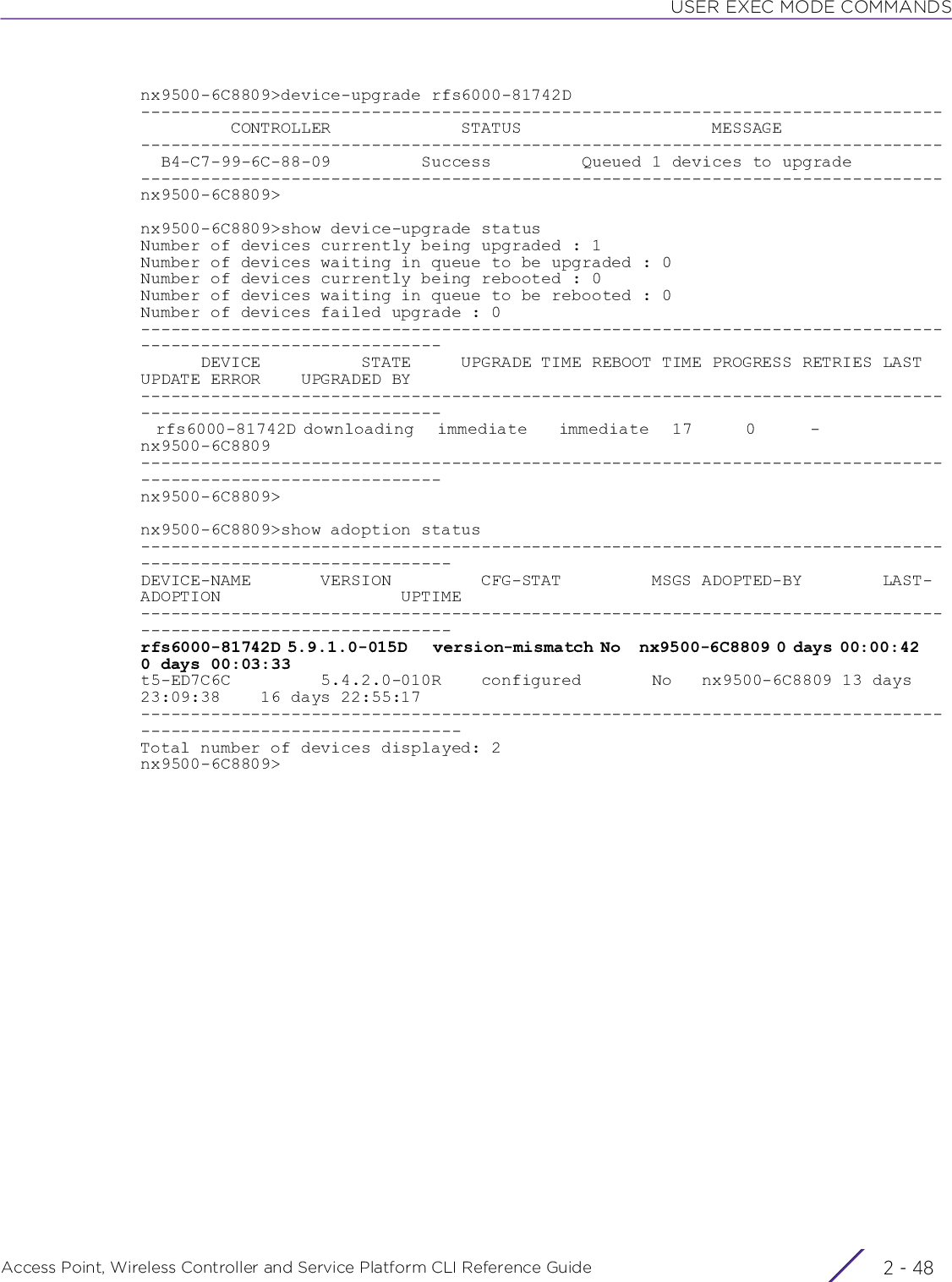

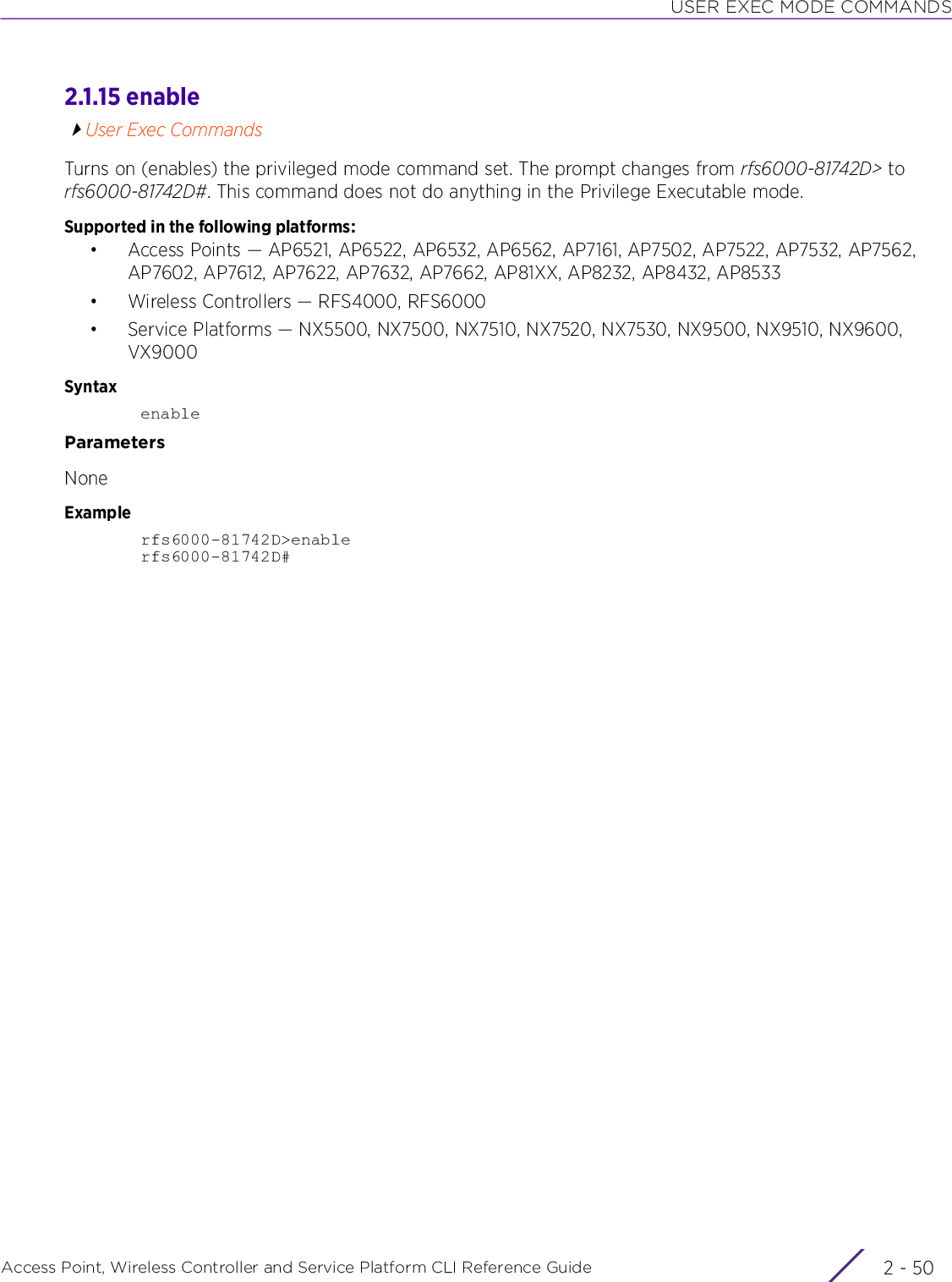
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 512.1.16 file-syncUser Exec CommandsSyncs trustpoint and/or EAP-TLS X.509 (PKCS#12) certificate between the staging-controller and adopted access points. When enabling file syncing, consider the following points:• The X.509 certificate needs synchronization only if the access point is configured to use EAP-TLS authentication.• Execute the command on the controller adopting the access points.• Ensure that the X.509 certificate file is installed on the controller.Syncing of trustpoint/wireless-bridge certificate can be automated. To automate file syncing, in the controller’s device/profile configuration mode, execute the following command: file-sync [auto|count <1-20>]. For more information, see file-sync.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632,AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxfile-sync [cancel|load-file|trustpoint|wireless-bridge]file-sync cancel [trustpoint|wireless-bridge]file-sync cancel [trustpoint|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all]]file-sync load-file [trustpoint|wireless-bridge]]file-sync load-file [trustpoint <TRUSTPOINT-NAME>|wireless-bridge] <URL>file-sync [trustpoint <TRUSTPOINT-NAME>|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all] {from-controller}] {reset-radio|upload-time <TIME>}Parameters• file-sync cancel [trustpoint|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all]]file-sync cancel [trustpoint|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all]]Cancels scheduled file synchronization• trustpoint – Cancels scheduled trustpoint synchronization on a specified AP, all APs, or APs within a specified RF Domain• wireless-bridge – Cancels scheduled wireless-bridge certificate synchronization on a specified AP, all APs, or APs within a specified RF Domain• <DEVICE-NAME> – Cancels scheduled trustpoint/certificate synchronization on aspecified AP. Specify the AP’s hostname or MAC address.• all – Cancels scheduled trustpoint/certificate synchronization on all APsContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-97.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 52• file-sync load-file [trustpoint|wireless-bridge] <URL>• file-sync [trustpoint <TRUSTPOINT-NAME>|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all] {from-controller}] {reset-radio|upload-time <TIME>}• rf-domain [<DOMAIN-NAME>|all] – Cancels scheduled trustpoint/certificate syn-chronization on all APs in a specified RF Domain or in all RF Domains• <DOMAIN-NAME> – Cancels scheduled trustpoint/certificate synchronization onall APs within a specified RF Domain. Specify the RF Domain’s name.• all – Cancels scheduled trustpoint/certificate synchronization on all RF Domainsfile-sync load-file [trustpoint|wireless-bridge] <URL>Loads the following files on to the staging controller:• trustpoint – Loads the trustpoint, including CA certificate, server certificate and private key• wireless-bridge – Loads the wireless-bridge certificate to the staging controllerUse this command to load the certificate to the controller before scheduling or initiating a certificate synchronization.• <URL> – Provide the trustpoint/certificate location using one of the following for-mats:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileNote: Both IPv4 and IPv6 address types are supported.file-sync trustpoint <TRUSTPOINT-NAME> [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all] from-controller]Configures file-syncing parameters• trustpoint <TRUSTPOINT-NAME> – Syncs a specified trustpoint between controller and its adopted APs• <TRUSTPOINT-NAME> – Specify the trustpoint name.• wireless-bridge – Syncs wireless-bridge certificate between controller and its adopted APsAfter specifying the file that is to be synced, configure following file-sync parameters:• <DEVICE-NAME> – Syncs trustpoint/certificate with a specified AP. Specify the AP’shostname or MAC address.• all – Syncs trustpoint/certificate with all APs• rf-domain [<DOMAIN-NAME>|all] – Syncs trustpoint/certificate with all APs in aspecified RF Domain or in all RF Domains• <DOMAIN-NAME> – Select to sync with APs within a specified RF Domain. Specifythe RF Domain’s name.• all – Select to sync with APs across all RF Domains• from-controller – Optional. Loads certificate to the APs from the adoptingcontroller and not the RF Domain managerAfter specifying the access points, specify the following options: reset-radio and upload-time.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-98.png)

![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 542.1.17 join-clusterUser Exec CommandsAdds a device (access point, wireless controller, or service platform), as a member, to an existing cluster of devices. Assign a static IP address to the device before adding to a cluster. Note, a cluster can be only formed of devices of the same model type.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxjoin-cluster <IP> user <USERNAME> password <WORD> {level|mode}join-cluster <IP> user <USERNAME> password <WORD> {level [1|2]|mode [active|standby]}Parameters• join-cluster <IP> user <USERNAME> password <WORD> {level [1|2]|mode [active|standby]}Usage GuidelinesTo add a device to an existing cluster:• Configure a static IP address on the device (access point, wireless controller, or service platform).• Provide username and password for superuser, network admin, system admin, or operator accounts.After adding the device to a cluster, execute the “write memory” command to ensure the configuration persists across reboots.Examplerfs4000-880DA7>join-cluster 192.168.13.15 user admin password superuser level 1mode standby... connecting to 192.168.13.15... applying cluster configuration... committing the changes... saving the changes[OK]rfs4000-880DA7>join-cluster Adds an access point, wireless controller, or service platform to an existing cluster<IP> Specify the cluster member’s IP address.user <USERNAME> Specify a user account with super user privileges on the new cluster memberpassword <WORD> Specify password for the account specified in the user parameterlevel [1|2] Optional. Configures the routing level• 1 – Configures level 1 routing• 2 – Configures level 2 routingmode [active|standby]Optional. Configures the cluster mode• active – Configures this cluster as active• standby – Configures this cluster to be on standby mode](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-100.png)
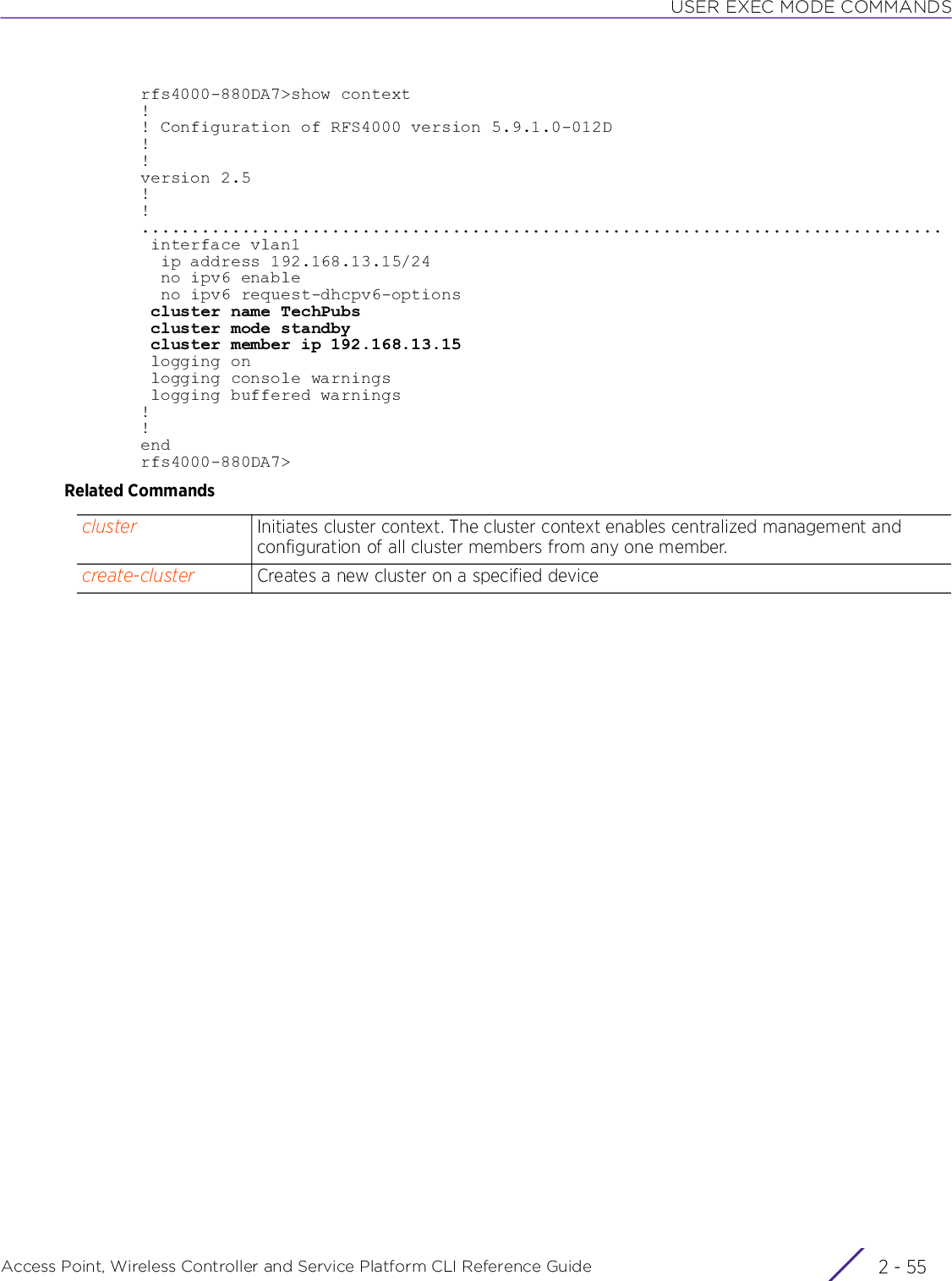
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 562.1.18 l2tpv3User Exec CommandsEstablishes and/or brings down a Layer 2 Tunnel Protocol Version 3 (L2TPV3) tunnelSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxl2tpv3 tunnel [<TUNNEL-NAME>|all]l2tpv3 tunnel <TUNNEL-NAME> [down|session|up]l2tpv3 tunnel <TUNNEL-NAME> [down|up] {on <DEVICE-NAME>}l2tpv3 tunnel <TUNNEL-NAME> session <SESSION-NAME> [down|up] {on <DEVICE-NAME>}l2tpv3 tunnel all [down|up] {on <DEVICE-NAME>}Parameters• l2tpv3 tunnel <TUNNEL-NAME> [down|up] {on <DEVICE-NAME>}• l2tpv3 tunnel <TUNNEL-NAME> session <SESSION-NAME> [down|up] {on <DEVICE-NAME>}• l2tpv3 tunnel all [down|up] {on <DEVICE-NAME>}l2tpv3 tunnel Establishes or brings down L2TPv3 tunnels<TUNNEL-NAME> [down|up]Specifies the tunnel name to establish or bring down• down – Brings down the specified tunnel• up – Establishes the specified tunnelon <DEVICE-NAME>Optional. Establishes or brings down a tunnel on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.l2tpv3 tunnel Establishes or brings down L2TPv3 tunnels<TUNNEL-NAME> [session <SESSION-NAME>] [down|up]Establishes or brings down a specified session inside an L2TPv3 tunnel• <TUNNEL-NAME> – Specify the tunnel name.• session <SESSION-NAME> – Identifies a specific session• <SESSION-NAME> – Specify the session name.• down – Brings down the session identified by the <SESSION-NAME> key-word• up – Establishes the session identified by the <SESSION-NAME> keywordon <DEVICE-NAME>Optional. Establishes or brings down a tunnel session on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.l2tpv3 tunnel Establishes or brings down L2TPv3 tunnelsall [down|up] Establishes or brings down all L2TPv3 tunnels• down – Brings down all tunnels• up – Establishes all tunnels](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-102.png)



![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 602.1.20 mintUser Exec CommandsUses MiNT protocol to perform a ping and traceroute to a remote deviceSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmint [ping|traceroute]mint ping <MINT-ID> {(count <1-10000>|size <1-64000>|timeout <1-10>)}mint traceroute <MINT-ID> {(destination-port <1-65535>|max-hops <1-255>|source-port <1-65535>|timeout <1-255>)}Parameters• mint ping <MINT-ID> {(count <1-10000>|size <1-64000>|timeout <1-10>)}• mint traceroute <MINT-ID> {(destination-port <1-65535>|max-hops <1-255>|source-port <1-65535>|timeout <1-255>)}ping <MINT-ID> Sends a MiNT echo message to a specified destination• <MINT-ID> – Specify the destination device’s MiNT ID.count <1-10000> Optional. Sets the pings to the MiNT destination• <1- 10000> – Specify a value from 1 - 10000. The default is 3.size <1-64000> Optional. Sets the MiNT payload size in bytes• <1-64000> – Specify a value from 1 - 640000 bytes. The default is 64 bytes.timeout <1-10> Optional. Sets a response time in seconds• <1-10> – Specify a value from 1 sec - 10 sec. The default is 1 second.traceroute <MINT-ID>Prints the route packets trace to a device• <MINT-ID> – Specify the destination device’s MiNT ID.destination-port <1-65535>Optional. Sets the Equal-cost Multi-path (ECMP) routing destination port• <1- 65535> – Specify a value from 1 - 65535. The default port is 45.max-hops <1-255> Optional. Sets the maximum number of hops a traceroute packet traverses in the forward direction• <1- 255> – Specify a value from 1 - 255. The default is 30.source-port <1-65535>Optional. Sets the ECMP source port• <1- 65535> – Specify a value from 1 - 65535. The default port is 45.timeout <1-255> Optional. Sets the minimum response time period in seconds• <1- 255> – Specify a value from 1 sec - 255 sec. The default is 30 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-106.png)
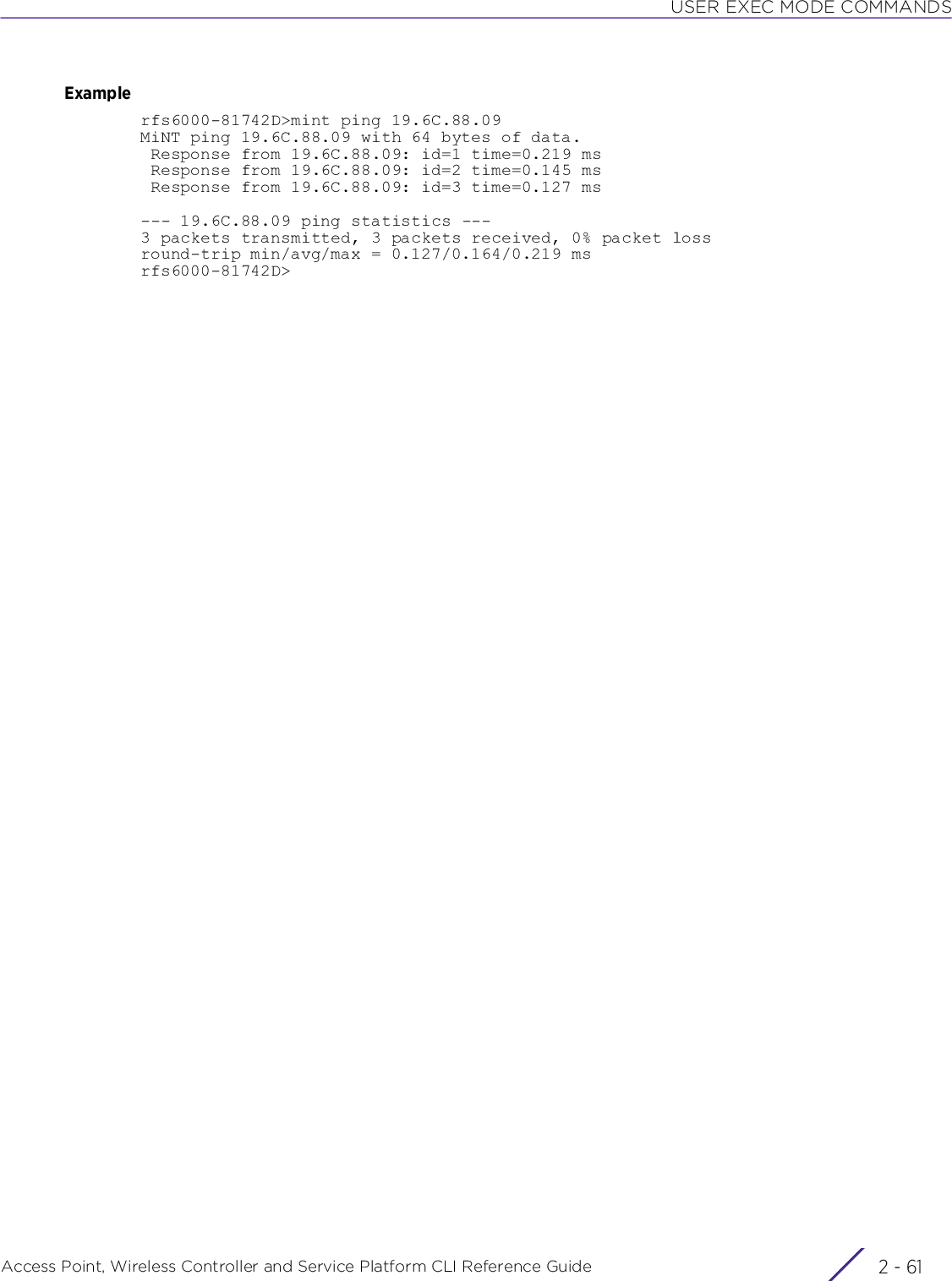
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 622.1.21 noUser Exec CommandsUse the no command to revert a command or to set parameters to their default. This command turns off an enabled feature or reverts settings to default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [adoption|captive-portal|crypto|debug|logging|page|service|terminal|virtual-machine|wireless]no adoption {on <DEVICE-OR-DOMAIN-NAME>}no captive-portal client [captive-portal <CAPTIVE-PORTAL-NAME>|mac <MAC>] {on <DEVICE-OR-DOMAIN-NAME>}no crypto pki [server|trustpoint]no crypto pki [server|trustpoint] <TRUSTPOINT-NAME> {del-key {on <DEVICE-NAME>}|on <DEVICE-NAME>}no logging monitorno pageno service [block-adopter-config-update|locator|snmp|ssm|wireless]no service snmp sysoid wing5no service block-adopter-config-updateno service ssm trace pattern {<WORD>} {on <DEVICE-NAME>}no service wireless [trace pattern {<WORD>} {on <DEVICE-NAME>}|unsanctioned ap air-terminate <BSSID> {on <DOMAIN-NAME>}]no service locator {on <DEVICE-NAME>}no terminal [length|width]no virtual-machine assign-usb-ports {on <DEVICE-NAME>}no wireless client [all|<MAC>]NOTE: The “no” command sub-set of commands changes with the context in which it is executed.NOTE: The no > adoption command resets the adoption state of a specified device (and all devices adopted to it) or devices within a specified RF Domain. When executed without specifying the device or RF Domain, the command resets the adoption state of the logged device and all devices, if any, adopted to it.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-108.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 63no wireless client all {filter|on}no wireless client all {filter [wlan <WLAN-NAME>]}no wireless client all {on <DEVICE-OR-DOMAIN-NAME>} {filter [wlan <WLAN-NAME>]}no wireless client mac <MAC> {on <DEVICE-OR-DOMAIN-NAME>}Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.Examplerfs4000-880DA7>no adoptionrfs4000-880DA7>no pageno <PARAMETERS> Resets or reverts settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-109.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 642.1.22 onUser Exec CommandsExecutes the following commands in the RF Domain context: clrscr, do, end, exit, help, service, and showSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxon rf-domain [<RF-DOMAIN-NAME>|all] Parameters• on rf-domain [<RF-DOMAIN-NAME>|all]Examplenx9500-6C8809>on rf-domain TechPubsnx9500-6C8809(TechPubs)>?on RF-Domain Mode commands: clrscr Clears the display screen do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system service Service Commands show Show running system informationnx9500-6C8809(TechPubs)>nx9500-6C8809(rf-domain-all)>?on RF-Domain Mode commands: clrscr Clears the display screen do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system service Service Commands show Show running system informationnx9500-6C8809(rf-domain-all)>on rf-domain [<RF-DOMAIN-NAME>|all]Enters the RF Domain context based on the parameter specified• <RF-DOMAIN-NAME> – Specify the RF Domain name. Enters the specified RF Domain context.• all – Specifies all RF Domains.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-110.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 652.1.23 opendnsUser Exec CommandsFetches the OpenDNS device_id from the OpenDNS site. Use this command to fetch the OpenDNS device_id. Once fetched, apply the device_id to WLANs that are to be OpenDNS enabled. OpenDNS is a free DNS service that enables swift Web navigation without frequent outages. It is a reliable DNS service that provides the following services: DNS query resolution, Web-filtering, protection against virus and malware attacks, performance enhancement, etc.This command is part of a set of configurations that are required to integrate WiNG devices with OpenDNS. When integrated, DNS queries going out of the WiNG device (access point, controller, or service platform) are re-directed to OpenDNS (208.67.220.220 or 208.67.222.222) resolvers that act as proxy DNS servers.For more information on integrating WiNG devices with OpenDNS site, see Enabling OpenDNS Support.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxopendns [APIToken|username]opendns APIToken <OPENDNS-APITOKEN>opendns username <USERNAME> password <OPENDNS-PSWD> label <LABEL>Note, as per the current implementation both of the above commands can be used to fetch the device_id from the OpenDNS site.Parameters• opendns APIToken <OPENDNS-APITOKEN>• opendns username <USERNAME> password <OPENDNS-PSWD> label <LABEL>opendns Fetches the device_id from the OpenDNS site using the OpenDNS API tokenAPIToken <OPENDNS-APITOKEN>Configures the OpenDNS APIToken. This is the token provided you by CISCO at the time of subscribing for their OpenDNS service.• <OPENDNS-APITOKEN> – Provide the OpenDNS API token (should be a valid token).For every valid OpenDNS API token provided a device_id is returned. Apply this device_id to WLANs that are to be OpenDNS enabled. Once applied, DNS queries originating from associating clients are appended with an additional 31 bytes of data (representing the device ID) at the end of the DNS packet. For information on configuring the device_id in the WLAN context, see opendns.opendns Fetches the device_id from the OpenDNS site using the OpenDNS credentialsusername <USERNAME>Configures the OpenDNS user name. This is your OpenDNS email ID provided by CISCO at the time of subscribing for their OpenDNS service.• <USERNAME> – Provide the OpenDNS user name (should be a valid OpenDNS username).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-111.png)


![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 682.1.25 pingUser Exec CommandsSends Internet Controller Message Protocol (ICMP) echo messages to a user-specified locationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxping <IP/HOSTNAME> {count <1-10000>|dont-fragment {count|size}|size <1-64000>|source [<IP>|pppoe|vlan <1-4094>|wwan]}Parameters• ping <IP/HOSTNAME> {count <1-10000>|dont-fragment {count|size}|size <1-64000>|source[<IP>|pppoe|vlan <1-4094>|wwan]}<IP/HOSTNAME> Specify the destination IP address or hostname. When entered without any parameters, this command prompts for an IP address or a hostname.count <1-10000> Optional. Sets the pings to the specified destination• <1-10000> – Specify a value from 1 - 10000. The default is 5.dont-fragment {count|size}Optional. Sets the don’t fragment bit in the ping packet. Packets with the dont-fragment bit specified are not fragmented. When a packet, with the dont-fragment bit specified, exceeds the specified maximum transmission unit (MTU) value, an error message is sent from the device trying to fragment it.• count <1-10000> – Optional. Sets the pings to the specified destination from 1 - 10000. The default is 5.• size <1-64000> – Optional. Sets the ping payload size from 1 - 64000 bytes. The default is 100 bytes.size <1-64000> Optional. Sets the ping payload size in bytes• <1-64000> – Specify the ping payload size from 1 - 64000. The default is 100 bytes.source [<IP>|pppoe|vlan <1-4094>|wwan]Optional. Sets the source address or interface name. This is the source of the ICMP packet to the specified destination.• <IP> – Specifies the source IP address• pppoe – Selects the PPP over Ethernet interface• vlan <1-4094> – Selects the VLAN interface from 1 - 4094• wwan – Selects the wireless WAN interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-114.png)
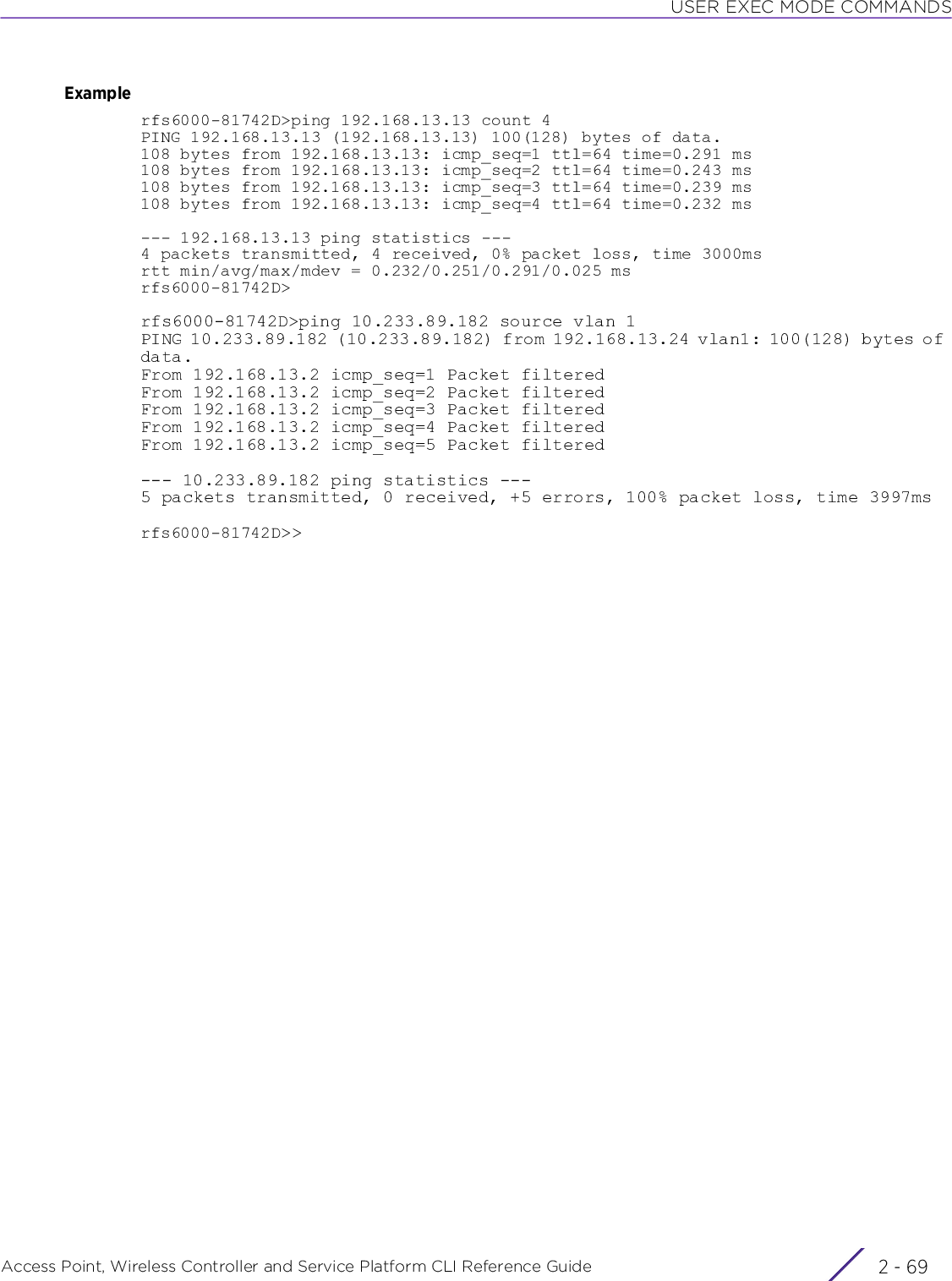


![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 722.1.28 telnetUser Exec CommandsOpens a Telnet session between two network devicesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtelnet <IP/HOSTNAME> {<TCP-PORT>} {<INTF-NAME>}Parameters• telnet <IP/HOSTNAME> {<TCP-PORT>} {<INTF-NAME>}Examplenx9500-6C8809#telnet 192.168.13.10Entering character modeEscape character is '^]'.Welcome to Microsoft Telnet Servicelogin:<IP/HOSTNAME> Configures the destination remote system’s IP (IPv4 or IPv6) address or hostname. The Telnet session is established between the connecting system and the remote system.• <IP/HOSTNAME> – Specify the remote system’s IPv4 or IPv6 address or hostname.<TCP-PORT> Optional. Specify the Transmission Control Protocol (TCP) port number.<INTF-NAME> Optional. Specify the interface name for the link local address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-118.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 732.1.29 terminalUser Exec CommandsSets the length and width of the CLI display window on a terminalSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxterminal [length|width] <0-512>Parameters• terminal [length|width] <0-512>Examplerfs6000-81742D>terminal length 150rfs6000-81742D>terminal width 215rfs6000-81742D>show terminalTerminal Type: xtermLength: 150 Width: 215rfs6000-81742D>Related Commandslength <0-512> Sets the number of lines displayed on the terminal window• <0-512> – Specify a value from 0 - 512.width <0-512> Sets the width (the number of characters displayed in one line) of the terminal window• <0-512> – Specify a value from 0 - 512.no Resets the width or length of the terminal window](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-119.png)

![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 752.1.31 tracerouteUser Exec CommandsTraces the route to a defined destinationUse ‘--help’ or ‘-h’ to display a complete list of parameters for the traceroute commandSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtraceroute <LINE>Parameters• traceroute <LINE>Examplerfs6000-81742D>traceroute --helpBusyBox v1.14.4 () multi-call binaryUsage: traceroute [-FIldnrv] [-f 1st_ttl] [-m max_ttl] [-p port#] [-q nqueries] [-s src_addr] [-t tos] [-w wait] [-g gateway] [-i iface] [-z pausemsecs] HOST [data size]Options: -F Set the don't fragment bit -I Use ICMP ECHO instead of UDP datagrams -l Display the ttl value of the returned packet -d Set SO_DEBUG options to socket -n Print hop addresses numerically rather than symbolically -r Bypass the normal routing tables and send directly to a host -v Verbose -m max_ttl Max time-to-live (max number of hops) -p port# Base UDP port number used in probes (default is 33434) -q nqueries Number of probes per 'ttl' (default 3) -s src_addr IP address to use as the source address -t tos Type-of-service in probe packets (default 0) -w wait Time in seconds to wait for a response (default 3 sec) -g Loose source route gateway (8 max)rfs6000-81742D>rfs6000-81742D>traceroute 192.168.13.13traceroute to 192.168.13.13 (192.168.13.13), 30 hops max, 38 byte packets 1 192.168.13.13 (192.168.13.13) 1.150 ms 0.261 ms 0.214 msrfs6000-81742D>traceroute <LINE> Traces the route to a destination IP address or hostname• <LINE> – Specify the destination IPv6 address or hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-121.png)

![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 772.1.33 virtual-machineUser Exec CommandsInstalls, configures, and monitors the status of virtual machines (VMs) installed on a WiNG controllerSupported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxvirtual-machine [assign-usb-ports|export|install|restart|set|start|stop|uninstall]virtual-machine assign-usb-ports team-vowlan {on <DEVICE-NAME>}virtual-machine export <VM-NAME> [<FILE>|<URL>] {on <DEVICE-NAME>}virtual-machine install [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}virtual-machine restart [<VM-NAME>|hard|team-urc|team-rls|team-vowlan]virtual-machine set [autostart|memory|vcpus|vif-count|vif-mac|vif-to-vmif|vnc]virtual-machine set [autostart [ignore|start]|memory <512-8192>|vcpus <1-4>|vif-count <0-2>|vif-mac <VIF-INDEX> <MAC-INDEX>|vif-to-vmif <VIF-INDEX> <VMIF-INDEX>| vnc [disable|enable]] [<VM-NAME>|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}The following virtual-machine commands are supported only on the VX9000 platform:virtual-machine volume-group [add-drive|replace-drive|resize-drive|resize-volume-group]virtual-machine volume-group [add-drive|replace-drive] <BLOCK-DEVICE-LABEL>virtual-machine volume-group replace-drive <BLOCK-DEVICE-LABLE> <NEW-BLOCK-DEVICE-LABEL>virtual-machine volume-group resize-volume-group <BLOCK-DEVICE-LABEL>Parameters• virtual-machine assign-usb-ports team-vowlan {on <DEVICE-NAME>}• virtual-machine export <VM-NAME> [<FILE>|<URL>] {on <DEVICE-NAME>}assign-usb-ports team-vowlanAssigns USB ports to TEAM-VoWLAN on a specified device•on <DEVICE-NAME> – Optional. Specify the device name.Note: Use the no > virtual-machine > assign-usb-ports to reassign the port to WiNG.Note: TEAM-RLS VM cannot be installed when USB ports are assigned to TEAM-VoWLAN.virtual-machine export Exports an existing VM image and settings. Use this command to export the VM to another <NX54XX> or <NX65XX> device in the same domain.• <VM-NAME> – Specify the VM name.• <FILE> – Specify the location and name of the source file (VM image). The VM im-age is retrieved and exported from the specified location.• <URL> – Specify the destination location. This is the location to which the VM im-age is copied. Use one of the following formats to provide the destination path:Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-123.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 78• virtual-machine install [<VM-NAME>|adsp|team-centro|team-rls|team-vowlan] {on <DEVICE-NAME>}• virtual-machine set [autostart [ignore|start]|memory <512-8192>|vcpus <1-4>|vif-count <0-2>|vif-mac <VIF-INDEX> <MAC-INDEX>|vif-to-vmif <VIF-INDEX> <VMIF-INDEX>|vnc [disable|enable]] [<VM-NAME>|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/file•on <DEVICE-NAME> – Optional. Executes the command on a specified device or devices•<DEVICE-NAME> – Specify the service platform name. In case of multiple devices, listthe device names separated by commas.Note: The VM should be in a stop state during the export process.Note: If the destination is a device, the image is copied to a predefined location (VM archive).virtual-machine install Installs the VM. The install command internally creates a VM template, consisting of the specified parameters, and starts the installation process. Select one of the following options:• <VM-NAME> – Installs a VM having name specified by <VM-NAME> keyword.• adsp – Installs ADSP• team-centro – Installs the VM TEAM-Centro image• team-rls – Installs the VM TEAM-RLS image• team-vowlan – Installs the VM TEAM-VoWLAN imageSpecify the device on which to install the VM.• on <DEVICE-NAME> – Optional. Executes the command on a specified device or devices• <DEVICE-NAME> – Specify the service platform name. In case of multiple devices,list the device names separated by commas.virtual-machine set Configures the VM settings•autostart – Specifies whether to autostart the VM on system reboot• ignore – Enables autostart on each system reboot• start – Disables autostart• memory – Defines the VM memory size• <512-8192> – Specify the VM memory from 512 - 8192 MB. The default is 1024 MB.• vcpus – Specifies the number of VCPUS for this VM• <1-4> – Specify the number of VCPUS from 1- 4.• vif-count – Configures or resets the VM's VIFs• <0-2> – Specify the VIF number from 0 - 2.• vif-mac – Configures the MAC address of the selected virtual network interface• <1-2> – Select the VIF• <1-8> – Specify the MAC index for the selected VIF• <MAC> – Specify the customized MAC address for the selected VIF in the AA-BB-CC-DD-EE-FF format.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-124.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 79• virtual-machine start [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}Each VM has a maximum of two network interfaces (indexed 1 and 2, referred to as VIF). By default, each VIF is automatically assigned a MAC from the range allocated for that device. However, you can use the ‘set’ keyword to specify the MAC from within the allocated range. Each of these VIFs are mapped to a layer 2 port in the dataplane (referred to as VMIF). These VMIFs are standard l2 ports on the DP bridge, supporting all VLAN and ACL commands. The WiNG software supports up to a maximum of 8 VMIFs. By default, a VM’s interface is always mapped to VMIF1. You can map a VIF to any of the 8 VMIFs. Use the vif-to-vmif command to map a VIF to a VMIF on the DP bridge.•vif-to-vmif – Maps the virtual interface (1 or 2) to the selected VMIF interface. Specify the VMIF interface index from 1 - 8.WiNG provides a dataplane bridge for external network connectivity for VMs. VM Interfaces define which IP address is associated with each VLAN ID the service platform is connected to and enables remote service platform administration. Each custom VM can have up to a maximum of two VM interfaces. Each VM interface can be mapped to one of the twelve ports for <NX9500> on the dataplane bridge. This mapping determines the destination for service platform routing.By default, VM interfaces are internally connected to the dataplane bridge via VMIF1. VMIF1, by default, is an untagged port providing access to VLAN 1 to support the capability to connect the VM interfaces to any of the VMIF ports. This provides the flexibility to move a VM interface onto different VLANs as well as configure specific firewall and QoS rules.•vnc – Disables/enables VNC port option for an existing VM. When enabled, provides remote access to VGA through the noVNC client.•disable – Disables VNC port• enable – Enables VNC portAfter configuring the VM settings, identify the VM to apply the settings.• <VM-NAME> – Applies these settings to the VM identified by the <VM-NAME> keyword. Specify the VM name.• adsp – Applies these settings to the ADSP VM• team-urc – Applies these settings to the VM TEAM-URC• team-rls – Applies these settings to the VM TEAM-RLS• team-vowlan – Applies these settings to the VM TEAM-VoWLANvirtual-machine start Starts the VM, based on the parameters passed. Select one of the following options:• <VM-NAME> – Starts the VM identified by the <VM-NAME> keyword. Specify the VM name.• adsp – Starts the ADSP VM• team-urc – Starts the VM TEAM-URC• team-rls – Starts the VM TEAM-RLS• team-vowlan – Starts the VM TEAM-VoWLANThe following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Executes the command on a specified device or devices• <DEVICE-NAME> – Specify the service platform name. In case of multiple devic-es, list the device names separated by commas.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-125.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 80• virtual-machine stop [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}• virtual-machine uninstall [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}• virtual-machine volume-group [add-drive|resize-drive] <BLOCK-DEVICE-LABEL>]virtual-machine stop hardStops the VM, based on the parameters passed. Select one of the following options:• <VM-NAME> – Stops the VM identified by the <VM-NAME> keyword. Specify the VM name.• ADSP – Stops the ADSP VM• team-urc – Stops the VM TEAM-URC• team-rls – Stops the VM TEAM-RLS• team-vowlan – Stops the VM TEAM-VoWLANThe following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Executes the command on a specified device ordevices• <DEVICE-NAME> – Specify the service platform name. In case of multiple de-vices, list the device names separated by commas.Note: The option ‘hard’ forces the selected VM to shutdown.virtual-machine uninstallUninstalls the specified VM• <VM-NAME> – Uninstalls the VM identified by the <VM-NAME> keyword. Specify the VM name.•ADSP – Uninstalls the ADSP VM• team-urc – Uninstalls the VM TEAM-URC• team-rls – Uninstalls the VM TEAM-RLS• team-vowlan – Uninstalls the VM TEAM-VoWLANThe following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Executes the command on a specified device ordevices• <DEVICE-NAME> – Specify the service platform name. In case of multiple de-vices, list the device names separated by commas.Note: This command releases the VM’s resources, such as memory, VCPUS, VNC port, disk space, and removes the RF Domain reference from the system.virtual-machine volume-group [add-drive|resize-drive] <BLOCK-DEVICE-LABEL>]Enables provisioning of logical volume-groups on the VX9000 platform. Logical volume-groups are created on the primary storage device, allowing the database storage to be expanded to include additional storage drives. However, volume-groups can be provisioned only on new VX9000 installation and cannot be added to existing VX9000 installation.Note: The logical volume-group is supported only on a VX9000 running the WiNG 5.9.1 image.• add-drive – Adds a new block-device to the VM. Note, currently a maximum of 3 (three) block devices can be added. To add a new drive, first halt the VM, In the Hypervisor, add a new storage disk to the VM and restart the VM. Once the VM comes up, use this command to add the new drive. To identify the new drive execute the show > virtual-machine > volume-group > status command.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-126.png)
![USER EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 2 - 81• virtual-machine volume-group replace-drive <BLOCK-DEVICE-LABEL> <NEW-BLOCK-DEVICE-LABEL>]• virtual-machine volume-group resize-volume-group <BLOCK-DEVICE-LABEL>]ExampleThe following examples show the VM installation process:Insatllation media: USB<DEVICE>#virtual-machine install <VM-NAME> type iso disk-size 8 install-media usb1://vms/win7.iso autostart start memory 512 vcpus 3 vif-count 2 vnc enableInstallation media: pre-installed disk image<DEVICE>#virtual-machine install <VM-NAME> type disk install-media flash:/vms/win7_disk.img autostart start memory 512 vcpus 3 vif-count 2 vnc-enable on <DEVICE-NAME>In the preceding example, the command is executed on the device identified by the <DEVICE-NAME> keyword. In such a scenario, the disk-size is ignored if specified. The VM has the install media as first boot device.Installation media: VM archive<DEVICE>#virtual-machine install type vm-archive install-media flash:/vms/<VM-NAME> vcpus 3• resize-drive - Resizes a drive in the VM’s volume group. To increase the size of a drive in the volume-group, first halt the VM. In the Hypervisor, increase the size of the existing secondary storage drive and restart the VM. Once the VM comes up, use this command to resize the drive. To identify the drive with the additional free space, execute the show > virtual-machine > volume-group > status command.The following keyword is common to all of the above parameters:• <BLOCK-DEVICE-LABEL> –Specify the block-device label to be added or resizeddepending on the action being performed. virtual-machine volume-group replace-drive <BLOCK-DEVICE-LABEL> <NEW-BLOCK-DEVICE-LABEL>]Enables provisioning of VMs as logical volume-groups on the VX9000 platform. Logical volume-group VMs are created on the primary storage device, allowing the database storage to be expanded to include additional storage drives.• replace-drive – Replaces an existing block-device with a new block-device in a volume-group. To replace a drive in the volume-group, first halt the VM. In the Hypervisor, add the new drive and restart the VM. Once the VM comes up, use this command to replace an existing drive with the new drive. To identify the drive with the additional free space, execute the show > virtual-machine > volume-group > status command• <BLOCK-DEVICE-LABEL> –Specify the block-device label to be replaced.• <BLOCK-DEVICE-LABEL> – Specify the replacement block-device label.virtual-machine volume-group resize-volume-group <BLOCK-DEVICE-LABEL>]Enables provisioning of VMs as logical volume-groups on the VX9000 platform. Logical volume-group VMs are created on the primary storage device, allowing the database storage to be expanded to include additional storage drives• resize-volume-group – Adds drive space to an existing block-device in the volume-group• <BLOCK-DEVICE-LABEL> –Specify the block-device label to which additionaldrive space is to be provided](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-127.png)
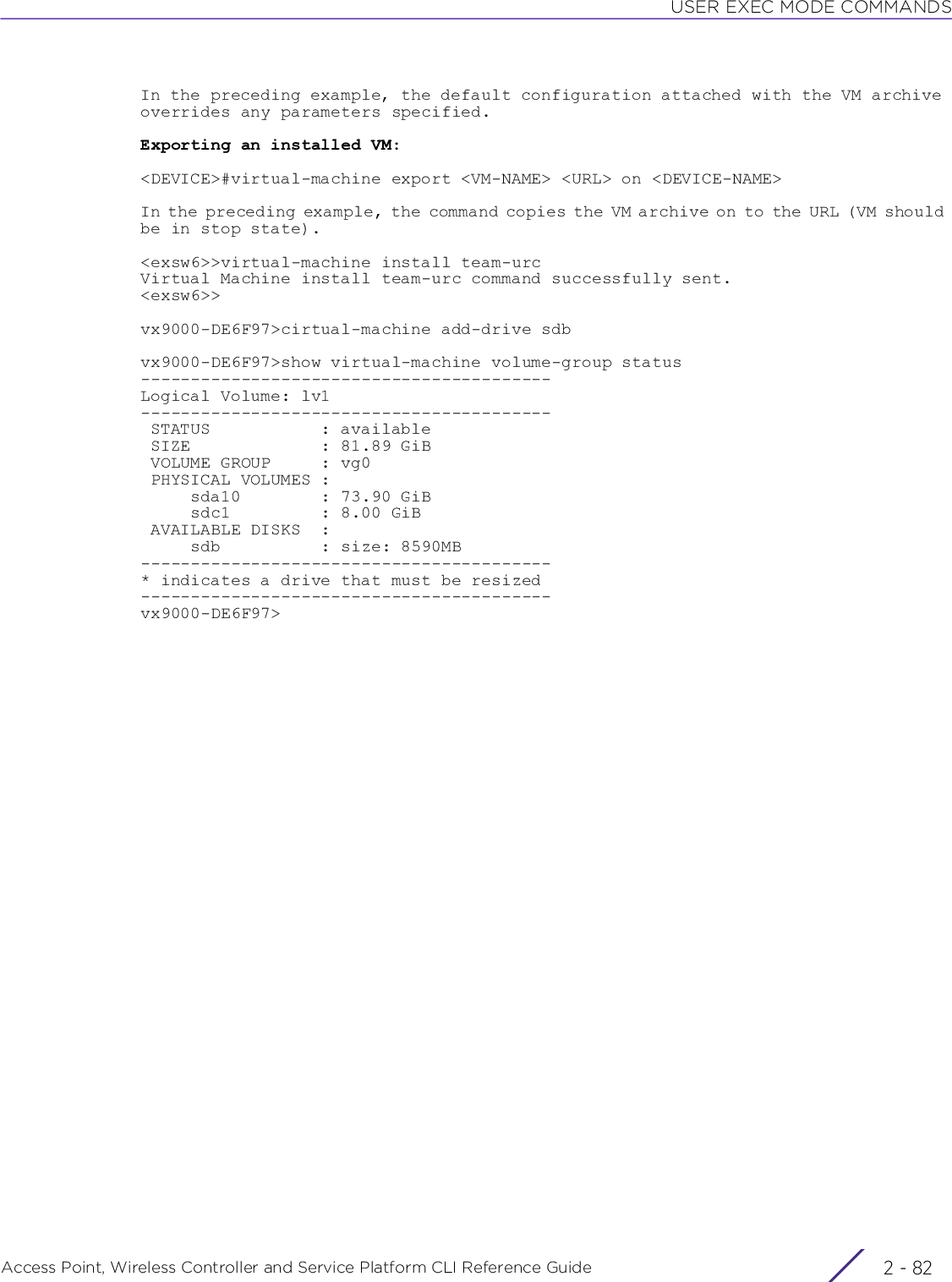


![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 33.1 Privileged Exec Mode CommandsPRIVILEGED EXEC MODE COMMANDSThe following table summarizes the PRIV EXEC Mode commands:Table 3.1 Privileged Exec CommandsCommand Description Referencearchive Manages file archive operations page 3-6boot Specifies the boot partition (primary or secondary). The device uses the image stored in the specified partition to boot.page 3-8captive-portal-page-uploadUploads captive portal advanced pages to adopted access points page 3-9cd Changes the current directory page 3-13change-passwd Changes the password of a logged user page 3-14clear Clears parameters, cache entries, table entries, and other similar entries page 3-15clock Configures the system clock page 3-28cluster Initiates a cluster context page 3-29configure Enters the global configuration mode page 3-30connect Begins a console connection to a remote device page 3-31copy Copies a file from any location to the wireless controller, service platform, or access pointpage 3-32cpe Enables adopted T5 Customer Premises Equipment (CPE) device(s) management. Use this command to perform the following operations on the CPEs: boot, reload, upgrade. This command is specific to the RFS4000, RFS6000, and NX9500 devices.page 3-33create-cluster Creates a new cluster on a specified device page 3-35crypto Enables encryption page 3-37crypto-cmp-cert-updateTriggers a CMP certificate update on a specified device or devices page 3-46database Enables automatic repairing (vacuuming) and dropping of databases (Captive-portal and NSight)page 3-47database-backupBacks up captive-portal and/or NSight database to a specified location and file on an FTP or SFTP serverpage 3-50database-restoreRestores a previously exported database [captive-portal and/or NSight]. Previously exported databases (backed up to a specified FTP or SFTP server) are restored to the original database.page 3-52delete Deletes a specified file from the system page 3-53device-upgrade Configures device firmware upgrade parameters page 3-54diff Displays the differences between two files page 3-60dir Displays the list of files on a file system page 3-61disable Disables the privileged mode command set page 3-62edit Enables ext file editing page 3-63](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-133.png)
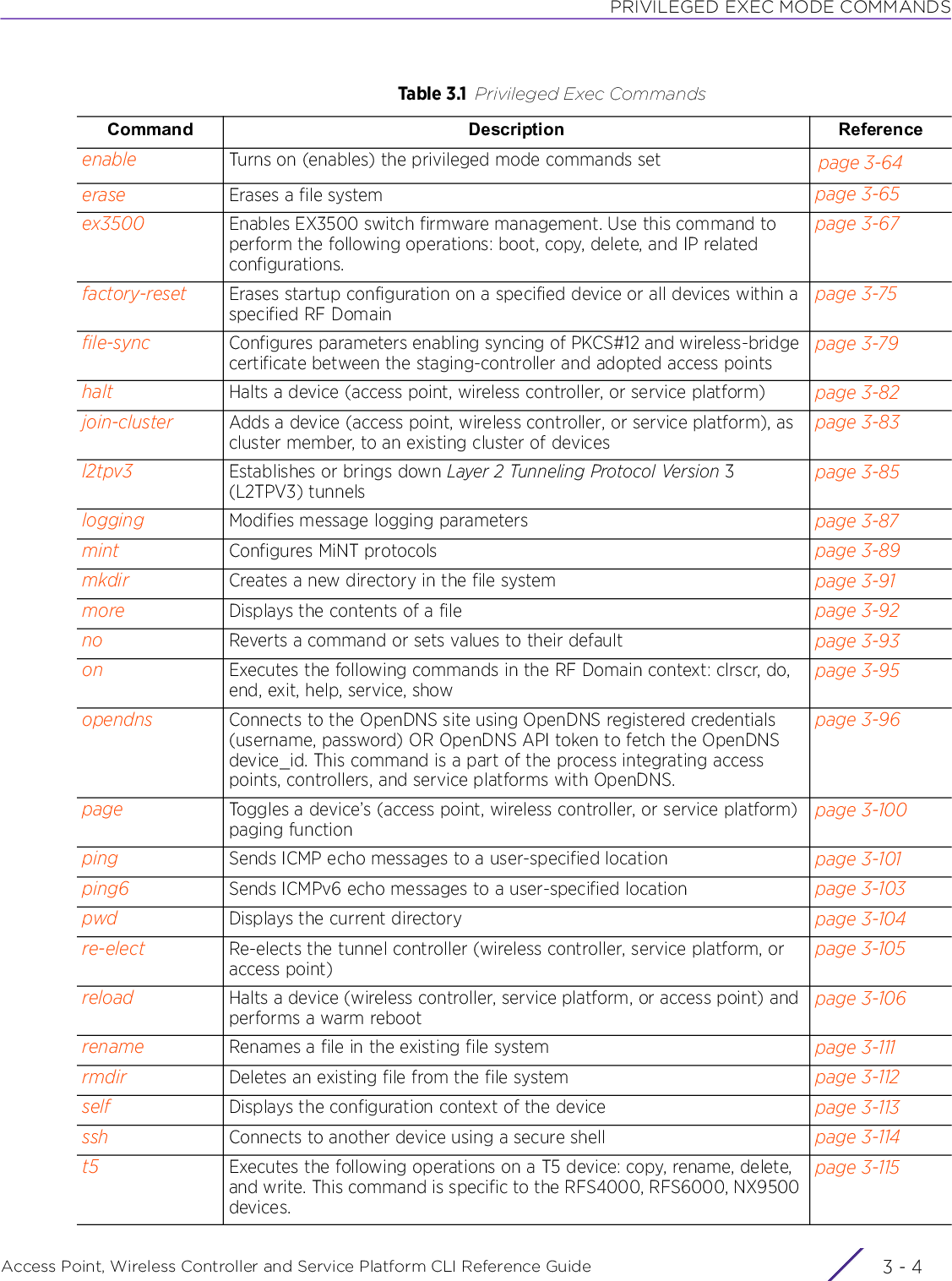
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 63.1.1 archivePrivileged Exec Mode CommandsManages file archive operationsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxarchive tar /table [<FILE>|<URL>]archive tar /create [<FILE>|<URL>] <FILE>archive tar /xtract [<FILE>|<URL>] <DIR>Parameters• archive tar /table [<FILE>|<URL>]• archive tar /create [<FILE>|<URL>] <FILE>• archive tar /xtract [<FILE>|<URL>] <DIR>tar Manipulates (creates, lists, or extracts) a tar file/table Lists the files in a tar file<FILE> Defines a tar filename<URL> Sets the tar file URLtar Manipulates (creates, lists or extracts) a tar file/create Creates a tar file<FILE> Defines tar filename<URL> Sets the tar file URLtar Manipulates (creates, lists or extracts) a tar file/xtract Extracts content from a tar file<FILE> Defines tar filename<URL> Sets the tar file URL<DIR> Specify a directory name. When used with /create, dir is the source directory for the tar file. When used with /xtract, dir is the destination file where contents of the tar file are extracted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-136.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 83.1.2 bootPrivileged Exec Mode CommandsSpecifies the image used after rebootSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxboot system [primary|secondary] {on <DEVICE-NAME>}Parameters• boot system [primary|secondary] {on <DEVICE-NAME>}Examplenx9500-6C8809#show boot-------------------------------------------------------------------------------- IMAGE BUILD DATE INSTALL DATE VERSION-------------------------------------------------------------------------------- Primary 03/26/2017 01:48:56 03/30/2017 15:02:18 5.9.0.0-012D Secondary 03/17/2017 13:13:38 03/22/2017 13:36:50 5.9.0.0-010D--------------------------------------------------------------------------------Current Boot : PrimaryNext Boot : PrimarySoftware Fallback : EnabledVM support : Not presentnx9500-6C8809#nx9500-6C8809#boot system secondaryUpdated system boot partitionnx9500-6C8809#nx9500-6C8809#show boot-------------------------------------------------------------------------------- IMAGE BUILD DATE INSTALL DATE VERSION-------------------------------------------------------------------------------- Primary 03/26/2017 01:48:56 03/30/2017 15:02:18 5.9.0.0-012D Secondary 03/17/2017 13:13:38 03/22/2017 13:36:50 5.9.0.0-010D--------------------------------------------------------------------------------Current Boot : PrimaryNext Boot : SecondarySoftware Fallback : EnabledVM support : Not presentnx9500-6C8809#system [primary|secondary]Specifies the image used after a device reboot• primary – Uses the primary image after reboot• secondary – Uses the secondary image after rebooton <DEVICE-NAME>Optional. Specifies the primary or secondary image location on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-138.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 93.1.3 captive-portal-page-uploadPrivileged Exec Mode CommandsUploads captive portal advanced pages to connected access points. Use this command to provide connected access points with specific captive portal configurations so they can successfully provision login, welcome, and condition pages to requesting clients attempting to access the wireless network using the captive portal.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcaptive-portal-page-upload [<CAPTIVE-PORTAL-NAME>|cancel-upload|delete-file|load-file]captive-portal-page-upload <CAPTIVE-PORTAL-NAME> [<MAC/HOSTNAME>|all|rf-domain]captive-portal-page-upload <CAPTIVE-PORTAL-NAME> [<MAC/HOSTNAME>|all] {upload-time <TIME>}captive-portal-page-upload <CAPTIVE-PORTAL-NAME> rf-domain [<DOMAIN-NAME>|all] {from-controller} {(upload-time <TIME>)}captive-portal-page-upload cancel-upload [<MAC/HOSTNAME>|all|on rf-domain {<DOMAIN-NAME>|all]]captive-portal-page-upload delete-file <CAPTIVE-PORTAL-NAME> <FILE-NAME>captive-portal-page-upload load-file <CAPTIVE-PORTAL-NAME> <URL>Parameters• captive-portal-page-upload <CAPTIVE-PORTAL-NAME> [<MAC/HOSTNAME>|all] {upload-time <TIME>}NOTE: Ensure that the captive portal pages to be uploaded are *.tar files.captive-portal-page-upload <CAPTIVE-PORTAL-NAME>Uploads advanced pages specified by the <CAPTIVE-PORTAL-NAME> parameter• <CAPTIVE-PORTAL-NAME> – Specify captive portal name (should be existing and configured).<MAC/HOSTNAME> Uploads to a specified AP• <MAC/HOSTNAME> – Specify the AP’s MAC address or hostname.all Uploads to all APs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-139.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 10• captive-portal-page-upload <CAPTIVE-PORTAL-NAME> rf-domain [<DOMAIN-NAME>|all] {from-controller} {(upload-time <TIME>)}• captive-portal-page-upload cancel-upload [<MAC/HOSTNAME>|all|on rf-domain [<DOMAIN-NAME>|all]]• captive-portal-page-upload delete-file <CAPTIVE-PORTAL-NAME> <FILE-NAME>upload-time <TIME> Optional. Schedules an upload time• <TIME> – Specify upload time in the MM/DD/YYYY-HH:MM or HH:MM format.The scheduled upload time is your local system’s time. It is not the access point, controller, service platform, or virtual controller time and it is not synched with the device.To view a list of uploaded captive portal files, execute the show > captive-portal-page-upload > list-files <CAPTIVE-PORTAL-NAME> command.captive-portal-page-upload <CAPTIVE-PORTAL-NAME>Uploads advanced pages specified by the <CAPTIVE-PORTAL-NAME> parameter• <CAPTIVE-PORTAL-NAME> – Specify captive portal name (should be existing and configured).rf-domain [<DOMAIN-NAME>|all]Uploads to all APs within a specified RF Domain or all RF Domains• <DOMAIN-NAME> – Uploads to APs within a specified RF Domain. Specify the RF Domain name.• all – Uploads to APs across all RF Domainsfrom-controller Optional. Uploads to APs from the adopted deviceupload-time <TIME> Optional. Schedules an AP upload• <TIME> – Specify upload time in the MM/DD/YYYY-HH:MM or HH:MM format.The scheduled upload time is your local system’s time. It is not the access point, controller, service platform, or virtual controller time and it is not synched with the device.captive-portal-page-upload cancel-uploadCancels a scheduled AP uploadcancel-upload[<MAC/HOSTNAME>|all|on rf-domain [<DOMAIN-NAME>|all]]Select one of the following options:• <MAC/HOSTNAME> – Cancels a scheduled upload to a specified AP. Specify the AP MAC address or hostname.• all – Cancels all scheduled AP uploads• on rf- domain – Cancels all scheduled uploads within a specified RF Domain or all RF Domains• <DOMAIN-NAME> – Cancels scheduled uploads within a specified RF Domain.Specify RF Domain name.• all – Cancels scheduled uploads across all RF Domainscaptive-portal-page-upload delete-fileDeletes a specified captive portal’s uploaded captive-portal internal page files<CAPTIVE-PORTAL-NAME> <FILE-NAME>Deletes a captive portal’s, identified by the <CAPTIVE-PORTAL-NAME> keyword, uploaded internal page files• <CAPTIVE-PORTAL-NAME> – Specify the captive portal’s name.• <FILE-NAME> – Specify the file name. The specified internal captive portal page isdeleted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-140.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 11• captive-portal-page-upload load-file <CAPTIVE-PORTAL-NAME> <URL>Exampleap6562-B1A214#captive-portal-page-upload load-file captive_portal_test tftp://89.89.89.17/pages_new_only.tarap6562-B1A214#ap6562-B1A214#show captive-portal-page-upload load-image-statusDownload of captive_portal_test advanced page file is completeap6562-B1A214#ap6562-B1A214#captive-portal-page-upload captive_portal_test all-------------------------------------------------------------------------------- CONTROLLER STATUS MESSAGE-------------------------------------------------------------------------------- FC-0A-81-B1-A2-14 Success Added 6 APs to upload queue--------------------------------------------------------------------------------ap6562-B1A214#captive-portal-page-upload load-fileLoads captive-portal advanced pages<CAPTIVE-PORTAL-NAME> <URL>Specify captive portal name (should be existing and configured) and location.• <URL> – Specifies location of the captive-portal's advanced pages. Use one of the following formats:IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileIPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileNote: The captive portal pages are downloaded to the controller from the location specified here. After downloading use the captive-portal-page-upload> <CAPTIVE-PORTAL-NAME> > <DEVICE-OR-DOMAIN-NAME> command to upload these pages to APs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-141.png)
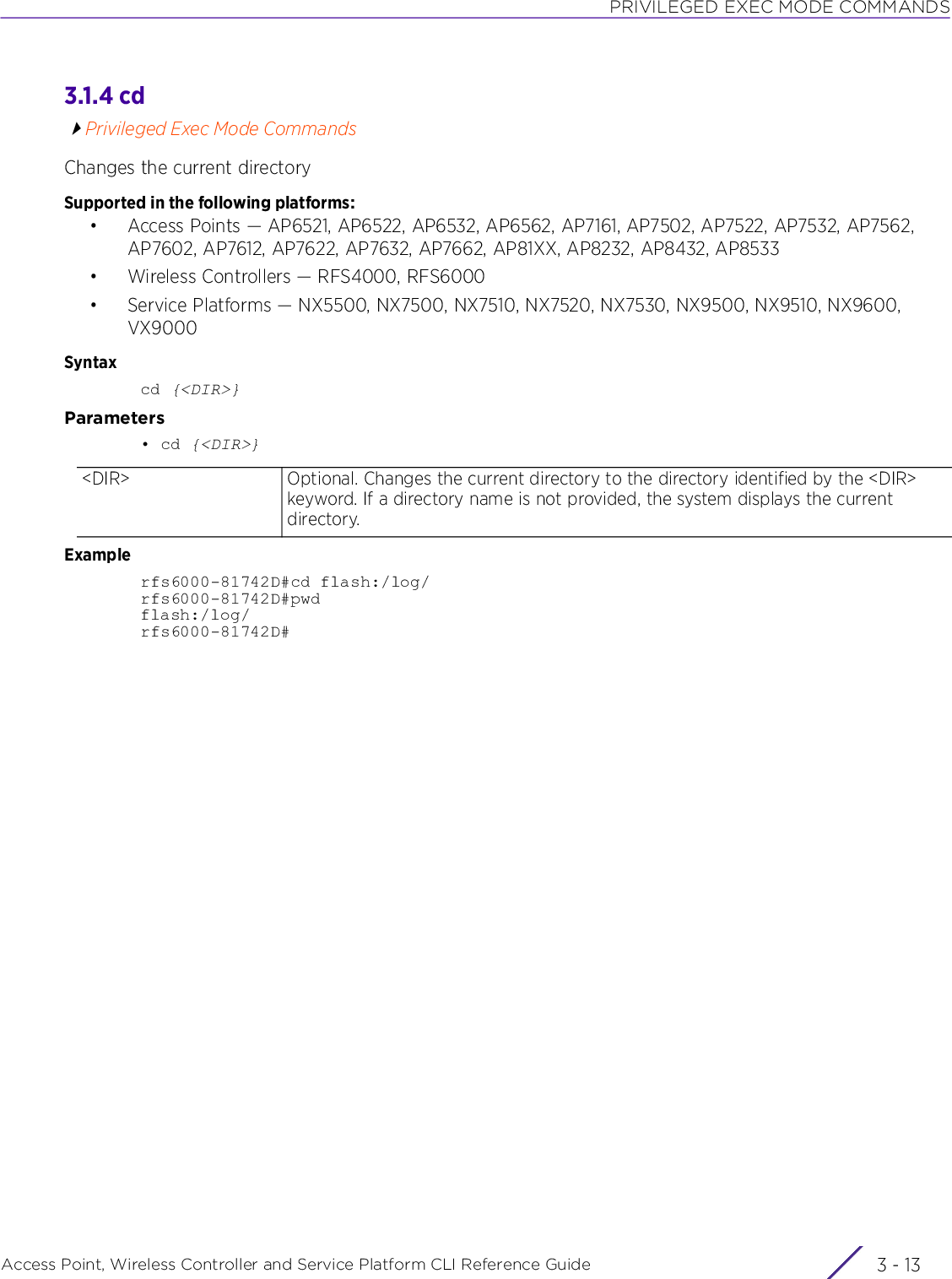
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 143.1.5 change-passwdPrivileged Exec Mode CommandsChanges the password of a logged user. When this command is executed without any parameters, the password can be changed interactively.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxchange-passwd <OLD-PASSWORD> <NEW-PASSWORD>Parameters• change-passwd <OLD-PASSWORD> <NEW-PASSWORD>Usage GuidelinesA password must be from 1 - 64 characters in length.Examplerfs6000-81742D#change-passwdEnter old password:Enter new password:Password for user 'admin' changed successfullyPlease write this password change to memory(write memory) to be persistent.rfs6000-81742D#write memoryOKrfs6000-81742D#<OLD-PASSWORD> Specify the password to be changed.<NEW-PASSWORD> Specify the new password.Note: The password can also be changed interactively. To do so, press [Enter] after the command.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-144.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 153.1.6 clearPrivileged Exec Mode CommandsClears parameters, cache entries, table entries, and other entries. The clear command is available for specific commands only. The information cleared using this command varies depending on the mode where the clear command is executed.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxclear [arp-cache|bonjour|cdp|counters|crypto|eguest|event-history|firewall|gre|ip|ipv6|l2tpv3-stats|lacp|license|lldp|logging|mac-address-table|mint|role|rtls|spanning-tree|traffic-shape|vrrp]clear arp-cache {on <DEVICE-NAME>}clear bonjour cache {on <DEVICE-NAME>}clear [cdp|lldp] neighbors {on <DEVICE-NAME>}clear counters [all|ap|bridge|interface|radio|router|thread|wireless-client]clear counters [all|bridge|router|thread]clear counters [ap|wireless-client] {<MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}clear counters interface [<INTERFACE-NAME>|all|ge <1-X>|me1|port-channel <1-X>|pppoe1|vlan <1-4094>|wwan1|xge <1-4>]clear counters radio {<MAC/HOSTNAME>|on}clear counters radio {<MAC/HOSTNAME> <1-X>} {(on <DEVICE-OR-DOMAIN-NAME>)}clear crypto [ike|ipsec]clear crypto ike sa [<IP>|all] {on <DEVICE-NAME>}clear crypto ipsec sa {on <DEVICE-NAME>}clear eguest registration statisticsclear event-historyclear firewall [dhcp snoop-table|dos stats|flows [ipv4|ipv6]|neighbors snoop-table] {on <DEVICE-NAME>}clear gre stats {on <DEVICE-NAME>}clear ip [bgp|dhcp|ospf]clear ip bgp [<IP>|all|external|process]NOTE: When using the clear command, refer to the interface details provided in interface.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-145.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 16clear ip bgp [<IP>|all|external] {in|on|out|soft}clear ip bgp [<IP>|all|external] {in prefix-filter} {on <DEVICE-NAME>}clear ip bgp [<IP>|all|external] {out} {(on <DEVICE-NAME>)}clear ip bgp [<IP>|all|external] {soft {in|out}} {on <DEVICE-NAME>}clear ip bgp process {on <DEVICE-NAME>}clear ip dhcp bindings [<IP>|all] {on <DEVICE-NAME>}clear ip ospf process {on <DEVICE-NAME>}clear ipv6 neighbor-cache {on <DEVICE-NAME>}clear lacp [<1-4> counters|counters]clear l2tpv3-stats tunnel <L2TPV3-TUNNEL-NAME> {session <SESSION-NAME>} {(on <DEVICE-NAME>)}clear license [borrowed|lent]clear license borrowed {on <DEVICE-NAME>}clear license lent to <DEVICE-NAME> {on <DEVICE-NAME>}clear logging {on <DEVICE-NAME>}clear mac-address-table {address|interface|mac-auth-state|vlan} {on <DEVICE-NAME>}clear mac-address-table mac-auth-state address <AMC> vlan <1-4094> {on <DEVICE-NAME>}clear mac-address-table {address <MAC>|vlan <1-4094>} {on <DEVICE-NAME>}clear mac-address-table interface [<IF-NAME>|ge <1-X>|port-channel <1-X>|t1e1 <1-4> <1-1>|up <1-X>|xge <1-4>] {on <DEVICE-NAME>}clear mint mlcp history {on <DEVICE-NAME>}clear role ldap-stats {on <DEVICE-NAME>}clear rtls [aeroscout|ekahau]clear rtls [aeroscout|ekahau] {<MAC/DEVICE-NAME> {on <DEVICE-OR-DOMAIN-NAME>}|on <DEVICE-OR-DOMAIN-NAME>}clear spanning-tree detected-protocols {interface|on <DEVICE-NAME>}clear spanning-tree detected-protocols {interface [<INTERFACE-NAME>|ge <1-x>|me1|port-channel <1-x>|pppoe1|vlan <1-4094>|wwan1|xge <1-4>]} {on <DEVICE-NAME>}clear traffic-shape statistics {class <1-4>} {(on <DEVICE-NAME>)}clear vrrp [error-stats|stats] {on <DEVICE-NAME>}The following clear command is specific to the NX95XX series service platforms:clear logging analytics {on <DEVICE-NAME>}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-146.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 17Parameters• clear arp-cache {on <DEVICE-NAME>}• clear bonjour cache {on <DEVICE-NAME>}• clear [cdp|lldp] neighbors {on <DEVICE-NAME>}• clear counters [all|bridge|router|thread]• clear counters [ap|wireless-client] {<MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}arp-cache Clears Address Resolution Protocol (ARP) cache entries on a device. This protocol matches layer 3 IP addresses to layer 2 MAC addresses.on <DEVICE-NAME> Optional. Clears ARP cache entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.bonjour cache Clears all Bonjour cached statistics. Once cleared, the system has to re-discover available Bonjour services.on <DEVICE-NAME> Optional. Clears all Bonjour cached statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.cdp Clears Cisco Discovery Protocol (CDP) table entriesldp Clears Link Layer Discovery Protocol (LLDP) neighbor table entriesneighbors Clears CDP or LLDP neighbor table entries based on the option selected in the preceding stepon <DEVICE-NAME> Optional. Clears CDP or LLDP neighbor table entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.counters [all|bridge|router|thread]Clears counters on a system• all – Clears all counters irrespective of the interface type• bridge – Clears bridge counters• router – Clears router counters• thread – Clears per-thread counterscounters [ap|wireless-client]Clears counters on a system• ap – Clears access point wireless counters• wireless-client – Clears wireless client counters<MAC> The following keyword is common to the ‘ap’ and ‘wireless-client’ parameters:• <MAC> – Optional. Clears counters of the AP/wireless client identified by the <MAC> keyword. Specify the MAC address of the AP or wireless client.The system clears all AP or wireless client counters, if no MAC address is specified.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-147.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 18• clear counters interface [<INTERFACE-NAME>|all|ge <1-X>|me1|port-channel <1-X>|pppoe1|vlan <1-4094>|wwan1|xge <1-4>]• clear counters radio {<MAC/HOSTNAME> <1-X>} {(on <DEVICE-OR-DOMAIN-NAME>)}• clear crypto ike sa [<IP>|all] {on <DEVICE-NAME>}on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and is applicable to the <MAC> parameter:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Clears AP/wireless-client counters on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller,service platform, or RF Domain.If no MAC address is specified, the system clears all AP or wireless client counters on the specified AP, wireless controller, service platform, or RF Domain.counters interface [<INTERFACE-NAME>|all|ge <1-X>|me1|port-channel <1-X>|pppoe1|vlan <1-4094>|wwan1|xge <1-4>]Clears interface counters for a specified interface• <INTERFACE-NAME> – Clears a specified interface counters. Specify the interface name.• all – Clears all interface counters• ge <1-X> – Clears GigabitEthernet interface counters. Specify the GigabitEthernet interface index from 1 - X.• me1 – Clears FastEthernet interface counters• port-channel <1- X> – Clears port-channel interface counters. Specify the port channel interface index from 1 - X.Note: The number of port-channel interfaces supported varies for different device types. For example, RFS4000 supports 3 port-channels.• pppoe1 – Clears Point-to-Point Protocol over Ethernet (PPPoE) interface counters• vlan <1-4094> – Clears interface counters. Specify the Switch Virtual Interface (SVI) VLAN ID from 1 - 4094.• wwan1 – Clears wireless WAN interface counters• xge <1-4> – Clears TenGigabitEthernet interface counters. Specify the GigabitEthernet interface index from 1 - 4.counters radio Clears wireless radio counters<MAC/HOSTNAME> <1-X>Clears counters of a radio identified by the <MAC/HOSTNAME> keyword.• <MAC/HOSTNAME> – Optional. Specify the hostname or MAC address. Optionally, append the interface number to form radio ID in the form of AA-BB-CC-DD-EE-FF:RX or HOSTNAME:RX• <1-X> – Optional. Specify the radio index (if not specified as part of the radio ID).The maximum number of radio antennas supported varies with the access pointtype.If no MAC address or radio index is specified, the system clears all radio counters.on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and is applicable to the <MAC> parameter:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Clears AP/wireless-client counters on a specified device or RF DomainIf no MAC address is specified, the system clears all AP or wireless client counters on the specified AP, wireless controller, service platform, or RF Domain.crypto Clears encryption module database](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-148.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 19• clear crypto ipsec sa {on <DEVICE-NAME>}• clear eguest registration statistics• clear event-history• clear firewall [dhcp snoop-table|dos stats|flows [ipv4|ipv6]|neighbors snoop-table] {on <DEVICE-NAME>}• clear gre stats {on <DEVICE-NAME>}ike sa [<IP>|all] Clears Internet Key Exchange (IKE) security associations (SAs)• <IP> – Clears IKE SAs for a certain peer• all – Clears IKE SAs for all peerson <DEVICE-NAME> Optional. Clears IKE SA entries, for a specified peer or all peers, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.crypto Clears encryption module databaseipsec sa {on <DEVICE-NAME>}Clears Internet Protocol Security (IPSec) database SAs• on <DEVICE-NAME> – Optional. Clears IPSec SA entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.eguest registration statisticsClears EGuest registration server counters. When cleared EGuest registration details are deleted, and the show > eguest > registration > statistics command output is null.This command is applicable only on the NX95XX, NX9600, and the VX9000 model platforms.event-history Clears event history cache entriesfirewall Clears firewall event entriesdhcp snoop-table Clears DHCP snoop table entriesdos stats Clears denial of service statisticsflows [ipv4|ipv6] Clears established IPv4 or IPv6 firewall sessionsneighbors snoop-table Clears IPv6 neighbors snoop-table entrieson <DEVICE-NAME> The following keywords are common to the DHCP, DOS, and flows parameters:• on <DEVICE-NAME> – Optional. Clears DHCP snoop table entries, denial of service statistics, or the established firewall sessions on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.gre stats Clears GRE tunnel statisticson <DEVICE-NAME> Optional. GRE tunnel statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-149.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 20• clear ip bgp [<IP>|all|external] {in prefix-filter} {on <DEVICE-NAME>}• clear ip bgp [<IP>|all|external] {out} {(on <DEVICE-NAME>)}• clear ip bgp [<IP>|all|external] {soft {in|out}} {on <DEVICE-NAME>}ip bgp [<IP>|all|external]Clears BGP routing table information based on the option selected• <IP> – Clears the BGP peer identified by the <IP> keyword. Specify the BGP peer’s IP address.• all – Clears Route Updates Received From All BGP Peers• external – Clears route updates received from external BGP peersThis command is applicable only to the RFS4000, RFS6000, NX95XX, and NX9600 series service platforms.In case of a change in routing policy it is necessary to clear BGP routing table entries in order for the new policy to take effect.in prefix-filter Optional. Clears soft-reconfiguration inbound route updates• prefix-filter – Optional. Clears the existing Outbound Route Filtering (ORF) prefix-list. on <DEVICE-NAME> Optional. Clears soft-reconfiguration inbound route updates on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip bgp [<IP>|all|external]Clears BGP routing table information based on the option selected• <IP> – Clears the BGP peer identified by the <IP> keyword. Specify the BGP peer’s IP address.• all – Clears route updates received from all BGP peers• external – Clears route updates received from external BGP peersThis command is applicable only to the RFS4000, RFS6000, and NX95XX series service platforms.In case of a change in routing policy it is necessary to clear BGP routing table entries in order for the new policy to take effect.out Optional. Clears soft-reconfiguration outbound route updates. Optionally specify the device on which to execute this command.on <DEVICE-NAME> The following keyword is recursive and optional.• on <DEVICE-NAME> – Optional. Clears BGP sessions on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip bgp [<IP>|all|external]Clears BGP routing table information based on the option selected• <IP> – Clears the BGP peer identified by the <IP> keyword. Specify the BGP peer’s IP address.• all – Clears route updates received from all BGP peers• external – Clears route updates received from external BGP peersThis command is applicable only to the RFS4000, RFS6000, and NX95XX series service platforms.In case of a change in routing policy it is necessary to clear BGP routing table entries in order for the new policy to take effect.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-150.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 21• clear ip bgp process {on <DEVICE-NAME>}• clear ip dhcp bindings [<IP>|all] {on <DEVICE-NAME>}• clear ip ospf process {on <DEVICE-NAME>}soft {in|out} Optional. Enables soft-reconfiguration of route updates for the specified IP address. This option allows routing tables to be reconfigured without clearing BGP sessions.• in – Optional. Enables soft reconfiguration of inbound route updates• out – Optional. Enables soft reconfiguration of outbound route updatesModifications made to BGP settings (BGP access lists, weight, distance, route-maps, versions, routing policy, etc.) take effect only after on-going BGP sessions are cleared. The clear > ip > bgp command clears BGP sessions. To reduce loss of route updates during the process, use the ‘soft’ option. Soft reconfiguration stores inbound/outbound route updates to be processed later and updated to the routing table. This requires high memory usage.on <DEVICE-NAME> Optional. Clears soft-reconfiguration inbound/outbound route updates on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip bgp process Clears all BGP processes runningThis command is applicable only to the RFS4000, RFS6000, NX95XX, NX9600 platforms.on <DEVICE-NAME> Optional. Clears all BGP processes on a specified device• <DEVICE-NAME> – Specify the name of the AP or service platform.ip Clears a Dynamic Host Configuration Protocol (DHCP) server’s IP address bindings entriesdhcp bindings Clears DHCP server’s connections and address binding entries<IP> Clears specific address binding entries. Specify the IP address to clear binding entries.all Clears all address binding entrieson <DEVICE-NAME> Optional. Clears a specified address binding or all address bindings on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ip ospf process Clears already enabled open shortest path first (OSPF) process and restarts the processon <DEVICE-NAME> Optional. Clears OSPF process on a specified deviceOSPF is a link-state interior gateway protocol (IGP). OSPF routes IP packets within a single routing domain (autonomous system), like an enterprise LAN. OSPF gathers link state information from neighbor routers and constructs a network topology. The topology determines the routing table presented to the Internet layer which makes routing decisions based solely on the destination IP address found in IP packets.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-151.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 22• clear ipv6 neighbor-cache {on <DEVICE-NAME>}• clear lacp [<1-4> counters|counters]• clear l2tpv3-stats tunnel <L2TPV3-TUNNEL-NAME> {session <SESSION-NAME>} {(on <DEVICE-NAME>)}• clear license borrowed {on <DEVICE-NAME>}• clear license lent to <DEVICE-NAME> {on <DEVICE-NAME>}clear ipv6 neighbor-cacheClears IPv6 neighbor cache entrieson <DEVICE-NAME> Optional. Clears IPv6 neighbor cache entries on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.clear lacp [<1-4> counters|counters]Clears Link Aggregation Control Protocol (LACP) counters for a specified port-channel group or all port-channel groups configured• <1-4> counters – Clears LACP counters for a specified port-channel. Specify the port-channel index number from 1 - 4. Note, LACP is supported only on the NX5500, NX7500, and NX9500 model service platforms. However, the NX9500 series service platforms support only two (2) port-channels, and the other model service platforms support four (4) port-channels.• counters – Clears LACP counters for all configured port-channels on the devicel2tpv3-stats Clears L2TPv3 tunnel session statisticstunnel <L2TPV3-TUNNEL-NAME>Clears all sessions associated with a specified L2TPv3 tunnel• <L2TPV3-TUNNEL-NAME> – Specify the L2TPv3 tunnel name.session <SESSION-NAME>Optional. Clears a specified L2TPv3 tunnel session, identified by the <SESSION-NAME> keyword• <SESSION-NAME> – Specify the session name.on <DEVICE-NAME> The following parameter is recursive and optional:• on <DEVICE-NAME> – Optional. Specifies the device running the L2TPv3 tunnel session• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.If no optional parameters are specified, the system clears all L2TPv3 tunnel session statistics.license borrowed {on <DEVICE-NAME>}Releases or revokes all licenses borrowed by a site controller• on <DEVICE-NAME> – Optional. Specifies the borrowing controller’s name.• <DEVICE-NAME> – Specify the wireless controller’s name.If no device name is specified, the system clears all borrowed licenses on the logged device.license lent NOC controller releases or revokes all licenses loaned to a site controllerto <DEVICE-NAME> Specifies the borrowing controller’s name• <DEVICE-NAME> – Specify the controller's name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-152.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 23• clear mac-address-table {address <MAC>|vlan <1-4094>} {on <DEVICE-NAME>}• clear mac-address-table interface [<IF-NAME>|ge <1-X>|port-channel <1-X>|t1e1 <1-4> <1-1>|up <1-X>|xge <1-4>] {on <DEVICE-NAME>}on <DEVICE-NAME> Optional. Specifies the controller’s name• <DEVICE-NAME> – Specify the wireless controller’s name.If no device name is specified, the system clears all loaned licenses on the logged device.mac-address-table Clears the MAC address forwarding tableaddress <MAC> Optional. Clears a specified MAC address from the MAC address table.• <MAC> – Specify the MAC address in one of the following formats: AA-BB-CC-DD-EE-FF or AA:BB:CC;DD:EE:FF or AABB.CCDD.EEFFvlan <1-4094> Optional. Clears all MAC addresses for a specified VLAN• <1-4094> – Specify the VLAN ID from 1 - 4094.on <DEVICE-NAME> Optional. Clears a single entry or all MAC entries for the specified VLAN in the MAC address forwarding table on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.mac-address-table Clears the MAC address forwarding tableinterface Clears all MAC addresses for the selected interface. Use the options available to specify the interface.<IF-NAME> Clears MAC address forwarding table for the specified layer 2 interface (Ethernet port)• <IF-NAME> – Specify the layer 2 interface name.ge <1-X> Clears MAC address forwarding table for the specified GigabitEthernet interface• <1-X> – Specify the GigabitEthernet interface index from 1 - X.port-channel <1-X> Clears MAC address forwarding table for the specified port-channel interface• <1-X> – Specify the port-channel interface index from 1 - X.up <1-X> Clears MAC address forwarding table for the WAN Ethernet interfaceThe number of WAN Ethernet interfaces supported varies for different devices. The RFS4000 and RFS6000 devices support 1 WAN Ethernet interface.xge <1-4> Clears MAC address forwarding table for the specified TenGigabitEthernet interface• <1-4> – Specify the GigabitEthernet interface index from 1 - 4.on <DEVICE-NAME> Optional. Clears the MAC address forwarding table, for the selected interface, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-153.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 24• clear mac-address-table mac-auth-state address <MAC> vlan <1-4904> {on <DEVICE-NAME>}• clear mint mlcp history {on <DEVICE-NAME>}• clear role ldap-stats {on <DEVICE-NAME>}• clear rtls [aeroscout|ekahau] {<MAC/DEVICE-NAME> {on <DEVICE-OR-DOMAIN-NAME>}|on <DEVICE-OR-DOMAIN-NAME>}mac-address-table mac-auth-state address <MAC> vlan <1-4904>Clears MAC addresses learned from a particular VLAN when WLAN MAC authentication and captive-portal fall back is enabledAccess points/controllers provide WLAN access to clients whose MAC address has been learned and stored in their MAC address tables. Use this command to clear a specified MAC address on the MAC address table. Once cleared the client has to re-authenticate, and is provided access only on successful authentication.• <MAC> – Specify the MAC address to clear.• vlan <1-4904> – Specify the VLAN interface from 1 - 4094. In the AP/controller’sMAC address table, the specified MAC address is cleared on the specified VLAN in-terface.on <DEVICE-NAME> Optional. Clears the specified MAC address on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.If a device is not specified, the system clears the MAC address from the MAC address table of all devices.mint Clears MiNT related informationmlcp history Clears MiNT Link Creation Protocol (MLCP) client historyon <DEVICE-NAME> Optional. Clears MLCP client history on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platformrole ldap-stats Clears role based Lightweight Directory Access Protocol (LDAP) server statisticson <DEVICE-NAME> Optional. Clears role based LDAP server statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.rtls Clears Real Time Location Service (RTLS) statisticsaeroscout Clears RTLS Aeroscout statisticsekahau Clears RTLS Ekahau statistics<MAC/DEVICE-NAME> This keyword is common to the ‘aeroscout’ and ‘ekahau’ parameters.• <MAC/DEVICE-NAME> – Optional. Clears Aeroscout or Ekahau RTLS statistics on a specified AP, wireless controller, or service platform. Specify the AP’s MAC address or hostname.on <DEVICE-OR-DOMAIN-NAME>This keyword is common to the ‘aeroscout’ and ‘ekahau’ parameters.• on <DEVICE-OR-DOMAIN-NAME> – Optional. Clears Aeroscout or Ekahau RTLS statistics on a specified device or RF Domain • <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-154.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 25• clear spanning-tree detected-protocols {on <DEVICE-NAME>}• clear spanning-tree detected-protocols {interface [<INTERFACE-NAME>|ge <1-X>|me1|port-channel <1-X>|pppoe1|vlan <1-4094>|wwan1|xge <1-4>]} {on <DEVICE-NAME>}• clear traffic-shape statistics {class <1-4>} {(on <DEVICE-NAME>)}• clear vrrp [error-stats|stats] {on <DEVICE-NAME>}spanning-tree Clears spanning tree protocols on an interface, and also restarts protocol migrationdetected-protocols Restarts protocol migrationon <DEVICE-NAME> Optional. Clears spanning tree protocols on a specified device• <DEVICE-NAME> – Optional. Specify the name of the AP, wireless controller, or service platform.spanning-tree Clears spanning tree protocols on an interface and restarts protocol migrationdetected-protocols Restarts protocol migrationinterface [<INTERFACE-NAME>|ge <1-X>|me1|port-channel <1-X>|pppoe1|vlan <1-4094>|wwan1|xge <1-4>]Optional. Clears spanning tree entries on different interfaces• <INTERFACE-NAME> – Clears detected spanning tree entries on a specified interface. Specify the interface name.• ge <1-X> – Clears detected spanning tree entries for the selected GigabitEthernet interface. Select the GigabitEthernet interface index from 1 - X• me1 – Clears FastEthernet interface spanning tree entries• port-channel <1- X> – Clears detected spanning tree entries for the selected port channel interface. Select the port channel index from 1 - X.The number of port-channel interfaces supported varies for different device types. For example, RFS4000 supports 3 port-channels.• pppoe1 – Clears detected spanning tree entries for PPPoE interface.• vlan <1-4094> – Clears detected spanning tree entries for the selected VLAN interface. Select a SVI VLAN ID from 1 - 4094.• wwan1 – Clears detected spanning tree entries for wireless WAN interface• xge <1-4> – Clears detected spanning tree entries for TenGigabitEthernet interfaces. Specify the GigabitEthernet interface index from 1 - 4.on <DEVICE-NAME> Optional. Clears spanning tree protocol entries on a selected device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.traffic-shape statistics Clears traffic shaping statisticsclass <1-4> Optional. Clears traffic shaping statistics for a specific traffic class• <1-4> – Specify the traffic class from 1 - 4.Note: If the traffic class is not specified, the system clears all traffic shaping statistics.on <DEVICE-NAME> Optional. Clears traffic shaping statistics for the specified traffic class on a specified device• <DEVICE-NAME> – Specify the name of the access point, wireless controller, or service platform.Note: For more information on configuring traffic-shape, see interface.vrrp Clears Virtual Router Redundancy Protocol (VRRP) statistics for a device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-155.png)
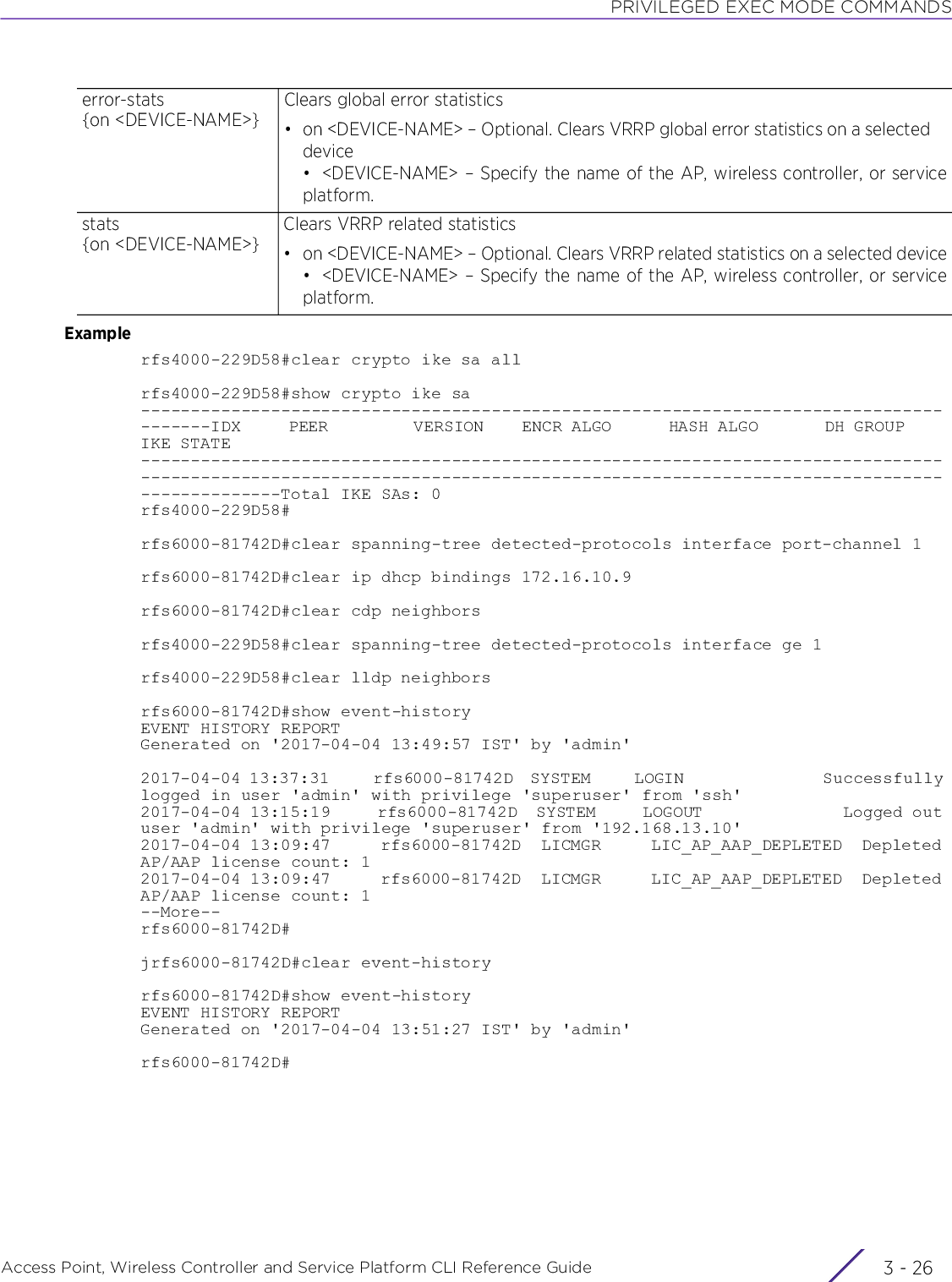
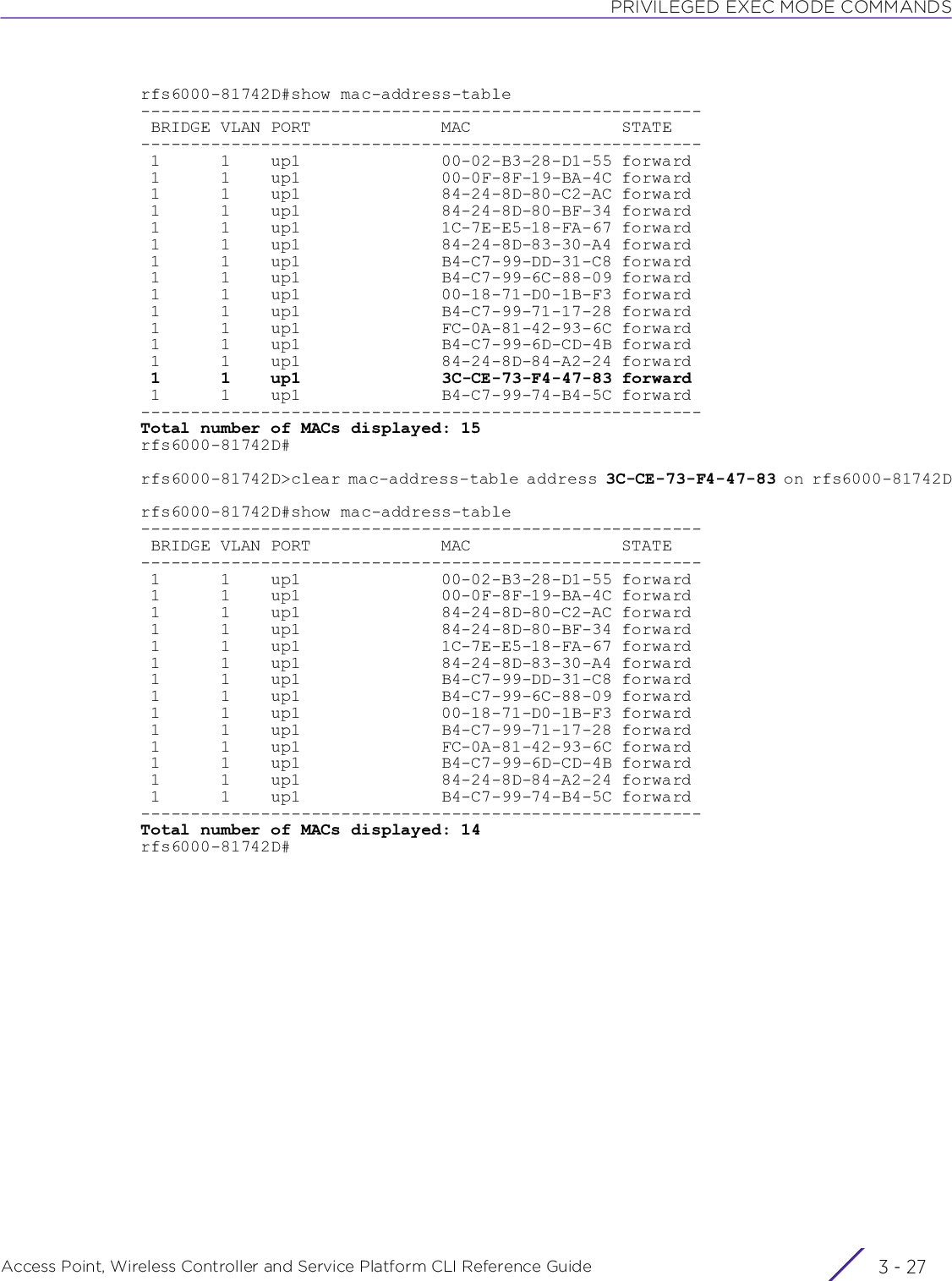

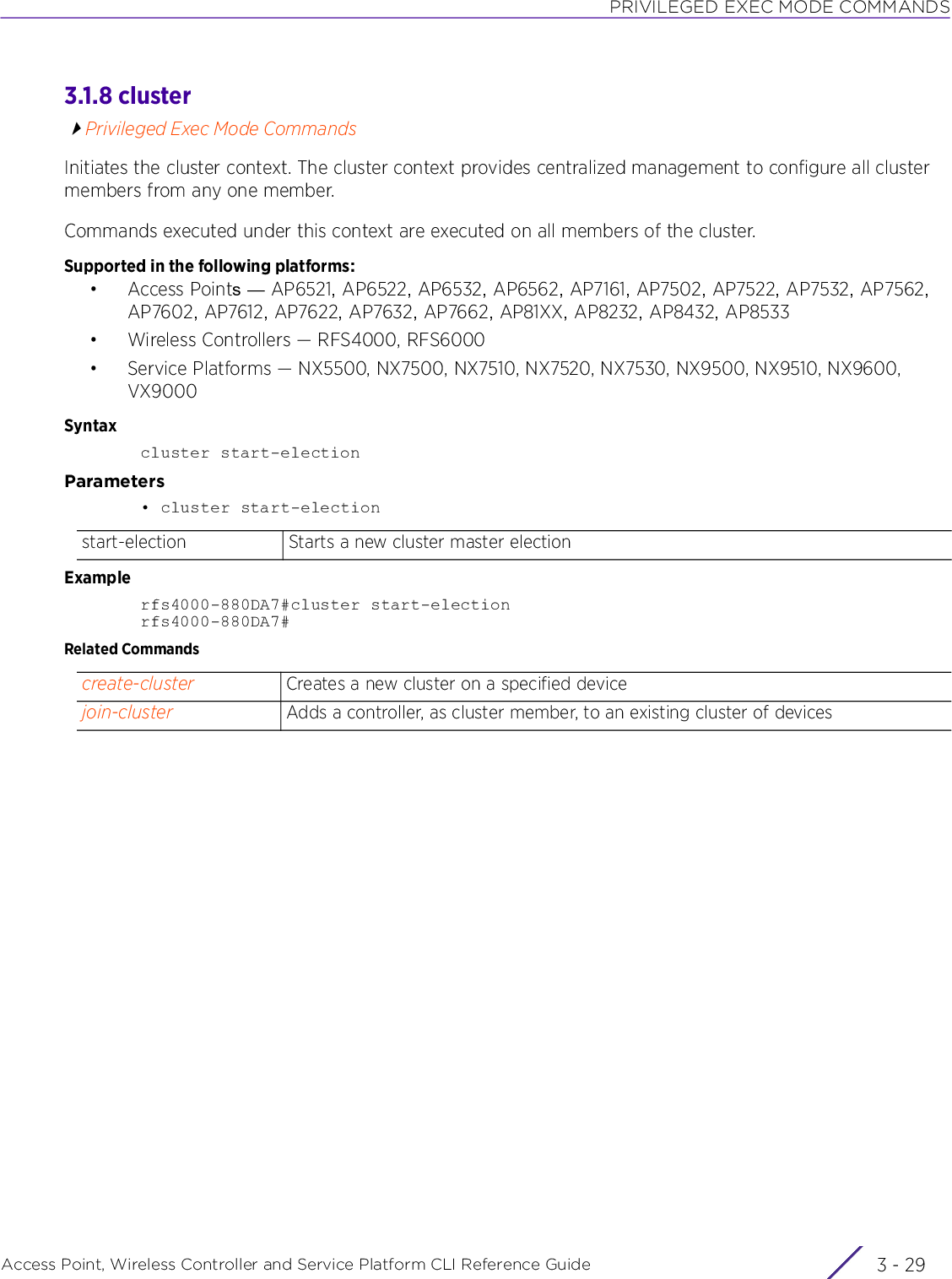

![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 313.1.10 connectPrivileged Exec Mode CommandsBegins a console connection to a remote device using the remote device’s MiNT ID or nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxconnect [mint-id <MINT-ID>|<REMOTE-DEVICE-NAME>]Parameters• connect [mint-id <MINT-ID>|<REMOTE-DEVICE-NAME>]Examplenx9500-6C8809#show mint lsp-db9 LSPs in LSP-db of 19.6C.88.09:LSP 19.6C.88.09 at level 1, hostname "nx9500-6C8809", 8 adjacencies, seqnum 1294552LSP 19.6D.B5.D4 at level 1, hostname "rfs6000-81742D", 8 adjacencies, seqnum 1915721LSP 19.74.B4.5C at level 1, hostname "ap8132-74B45C", 8 adjacencies, seqnum 1468227LSP 4D.80.C2.AC at level 1, hostname "ap7532-80C2AC", 8 adjacencies, seqnum 649241LSP 4D.83.30.A4 at level 1, hostname "ap7522-8330A4", 8 adjacencies, seqnum 202818LSP 4D.84.A2.24 at level 1, hostname "ap7562-84A224", 8 adjacencies, seqnum 380337LSP 68.88.0D.A7 at level 1, hostname "rfs4000-880DA7", 8 adjacencies, seqnum 1494520LSP 68.99.BB.7C at level 1, hostname "ap7131-99BB7C", 8 adjacencies, seqnum 831529nx9500-6C8809#nx9500-6C8809#connect mint-id ? MINT-ID MiNT ID of device to connect tonx9500-6C8809#connect mint-id 19.6D.B5.D4Entering character modeEscape character is '^]'.RFS6000 release 5.9.0.0-012Drfs6000-81742D login: adminPassword:rfs6000-81742D>mint-id <MINT-ID> Connects to a remote system using the MiNT ID• <MINT-ID> – Specify the remote device’s MiNT ID.<REMOTE-DEVICE-NAME>Connects to a remote system using its name• <REMOTE-DEVICE-NAME> – Specify the remote device’s name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-161.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 323.1.11 copyPrivileged Exec Mode CommandsCopies a file (config,log,txt...etc) from any location to the access point, wireless controller, or service platform and vice-versaSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcopy [<SOURCE-FILE>|<SOURCE-URL>] [<DESTINATION-FILE>|<DESTINATION-URL>]Parameters• copy [<SOURCE-FILE>|<SOURCE-URL>] [<DESTINATION-FILE>|<DESTINATION-URL>]ExampleTransferring file snmpd.log to remote TFTP server.rfs6000-81742D#copy flash:/log/snmpd.log tftp://10.233.89.183:/snmpd.logAccessing running-config file from remote TFTP server into switch running-config.rfs6000-81742D#copy tftp://10.233.89.183:/running-config running-configNOTE: Copying a new config file to an existing running-config file merges it with the existing running-config file on the wireless controller. Both the existing running-config and the new config file are applied as the current running-config.Copying a new config file to a start-up config file replaces the existing start-up config file with the parameters of the new file. It is better to erase the existing start-up config file and then copy the new config file to the startup config.<SOURCE-FILE> Specify the source file to copy.<SOURCE-URL> Specify the source file’s location (URL).<DESTINATION-FILE> Specify the destination file to copy to.<DESTINATION-URL> Specify the destination file’s location (URL).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-162.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 333.1.12 cpePrivileged Exec Mode CommandsEnables a WiNG controller to perform certain operations on Customer Premises Equipment (CPEs) through an adopted T5 controllerA T5 controller uses the IPX operating system to manage its connected radio devices, as opposed to the WiNG operating system used by RFS wireless controllers and NX service platforms. However, a T5 controller, once enabled as a supported external device, can provide data to WiNG to assist in a T5’s management within a WiNG supported subnet populated by both types of devices. The CPEs are the T5 controller managed radio devices using the IPX operating system. These CPEs use a Digital Subscriber Line (DSL) as their high speed Internet access mechanism using the CPE’s physical wallplate connection and phone jack.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcpe [boot|reload|upgrade]cpe boot system cpe [<1-24>|all] [primary|secondary] {on <T5-DEVICE-NAME>}cpe [reload|upgrade <IMAGE-LOCATION>] cpe [<1-24>|all] {on <T5-DEVICE-NAME>}Parameters• cpe boot system cpe [<1-24>|all] [primary|secondary] {on <T5-DEVICE-NAME>}NOTE: These commands can also be executed on the T5 profile and device context. For more information, see T5 Profile Config Commands.cpe boot system Changes the image used by a CPE to boot. When reloading, the CPE uses the specified image.cpe [<1-24>|all] Identifies the CPE(s) on which this change is implemented• <1-24> – Reloads only those CPEs whose IDs have been specified. Specify the ID from 1 - 24.• all – Reloads all CPEs[primary|secondary] Select the next boot image• primary – Uses the primary image when reloading• secondary – Uses the secondary image when reloadingon <T5-DEVICE-NAME>Optional. Performs this operation on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-163.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 34• cpe [reload|upgrade <IMAGE-LOCATION>] cpe [<1-24>|all] {on <T5-DEVICE-NAME>}Examplenx9500-6C8809#show t5 cpe boot on t5-ED7C6C---------------------------------------------------------------------------------------------------- DEVICE PRIMARY VERSION SECONDARY VERSION NEXT BOOT UPGRADE STATUS UPGRADE PROGRESS %---------------------------------------------------------------------------------------------------- cpe1 5.4.2.0-010R 5.4.2.0-006B primary none 0 cpe2 5.4.2.0-010R 5.4.2.0-006B primary none 0 ----------------------------------------------------------------------------------------------------nx9500-6C8809#nx9500-6C8809#cpe boot system cpe 1 secondary on t5-ED7C6CUpdated T5 CPE system boot partitionnx9500-6C8809#cpe [reload|upgrade <IMAGE-LOCATION>]Performs the following operations on CPEs• reload – Reloads the device• upgrade <IMAGE-LOCATION> – Upgrades the device• <IMAGE-LOCATION> – Specify the location of the firmware image. Both IPv4 and IPv6 addresses are supported. Use one of the following options to provide the location:IPv4 URLs: tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileIPv6 URLs: tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileNote: After specifying the operation to perform, identify the device(s).cpe [<1-24>|all] Identifies the CPE(s) on which the operation is performed• <1-24> – Configures the CPE’s ID from 1 - 24• all – Configures all CPEson <T5-DEVICE-NAME>Optional. Performs this operation on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-164.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 353.1.13 create-clusterPrivileged Exec Mode CommandsCreates a new device cluster, with the specified name, and assigns it an IP address and routing levelA cluster (or redundancy group) is a set of controllers or service platforms (nodes) uniquely defined by a profile configuration. Within the cluster, members discover and establish connections to other members and provide wireless network self-healing support in the event of member's failure.A cluster's load is typically distributed evenly amongst its members. An administrator needs to define how often the profile is load balanced for radio distribution, as radios can come and go and members join and exit the cluster.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcreate-cluster name <CLUSTER-NAME> ip <IP> {level [1|2]}Parameters• create-cluster name <CLUSTER-NAME> ip <IP> {level [1|2]}Examplerfs4000-229D58#create-cluster name TechPubs ip 192.168.13.8 level 2... creating cluster... committing the changes... saving the changesPlease Wait .[OK]rfs4000-229D58#rfs4000-229D58#show cluster configurationcreate-cluster Creates a clustername <CLUSTER-NAME>Configures the cluster name• <CLUSTER-NAME> – Specify a cluster name. Define a name for the cluster name unique to its configuration or profile support requirements. The name cannot exceed 64 characters.ip <IP> Specifies the device’s IP address used for cluster creation• <IP> – Specify the device’s IP address in the A.B.C.D format.level [1|2] Optional. Configures the routing level for this cluster• 1 – Configures level 1 (local) routing• 2 – Configures level 2 (inter-site) routing](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-165.png)
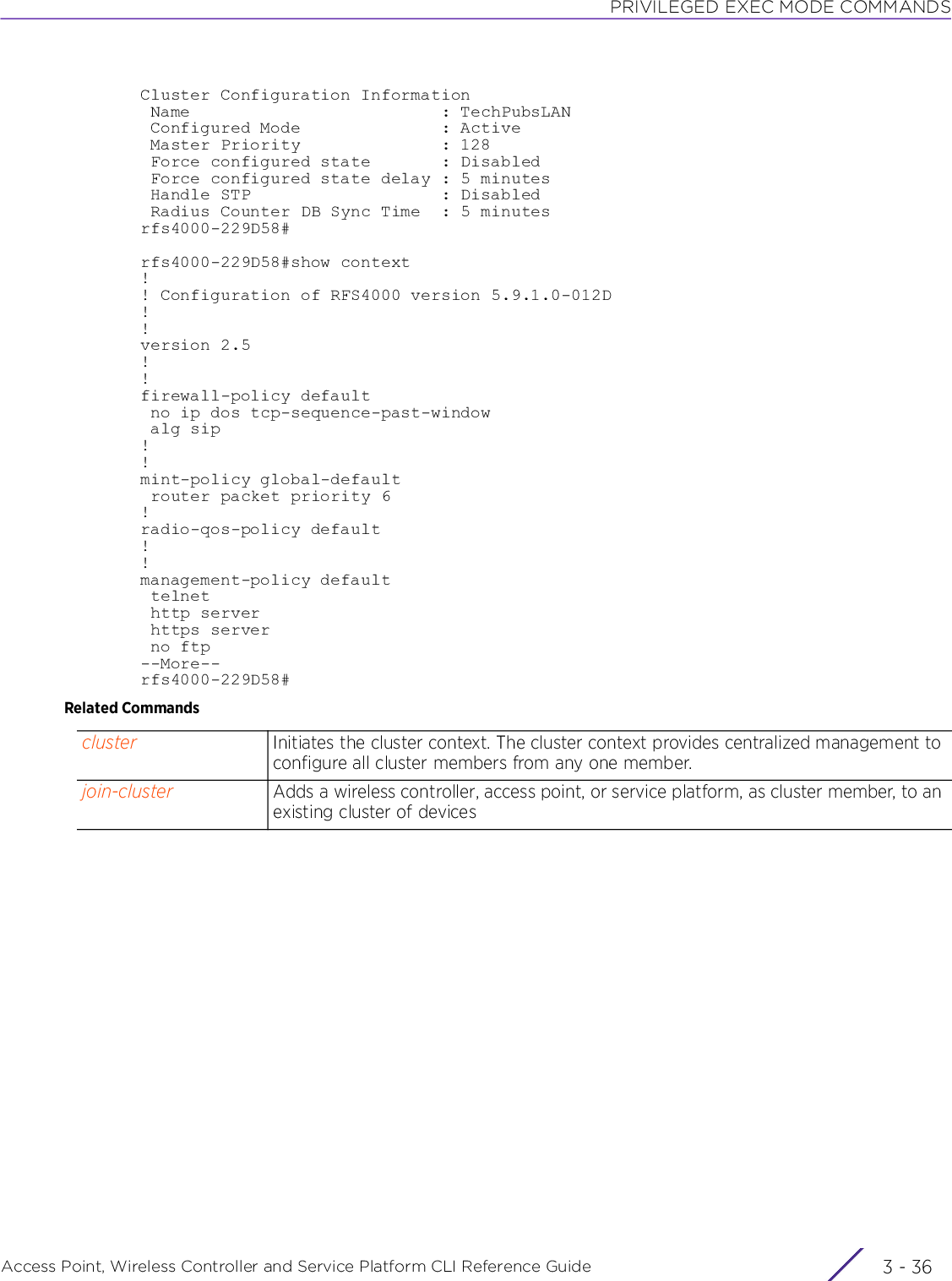
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 373.1.14 cryptoPrivileged Exec Mode CommandsEnables digital certificate configuration and RSA Keypair management. Digital certificates are issued by CAs and contain user or device specific information, such as name, public key, IP address, serial number, company name, etc. Use this command to generate, delete, export, or import encrypted RSA Keypairs and generate Certificate Signing Request (CSR).This command also enables trustpoint configuration. Trustpoints contain the CA’s identity and configuration parameters.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcrypto [key|pki]crypto key [export|generate|import|zeroize]crypto key export rsa <RSA-KEYPAIR-NAME> <EXPORT-TO-URL> {background|on|passphrase}crypto key export rsa <RSA-KEYPAIR-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}crypto key generate rsa <RSA-KEYPAIR-NAME> [2048|4096] {on <DEVICE-NAME>}crypto key import rsa <RSA-KEYPAIR-NAME> <IMPORT-FROM-URL> {background|on|passphrase}crypto key import rsa <RSA-KEYPAIR-NAME> <IMPORT-FROM-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}crypto key zeroize rsa <RSA-KEYPAIR-NAME> {force} {(on <DEVICE-NAME>)}crypto pki [authenticate|export|generate|import|zeroize]crypto pki authenticate <TRUSTPOINT-NAME> <LOCATION-URL> {background} {(on <DEVICE-NAME>)}crypto pki export [request|trustpoint]crypto pki export request [generate-rsa-key|short|use-rsa-key] <RSA-KEYPAIR-NAME> [autogen-subject-name|subject-name]crypto pki export request [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)crypto pki export request [generate-rsa-key|short [generate-rsa-key|use-rsa-key]|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)crypto pki export trustpoint <TRUSTPOINT-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME)}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-167.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 38crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> [autogen-subject-name|subject-name]crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}crypto pki import [certificate|crl|trustpoint]crypto pki import [certificate|crl] <TRUSTPOINT-NAME> <IMPORT-FROM-URL> {background} {(on <DEVICE-NAME>})crypto pki import trustpoint <TRUSTPOINT-NAME> <IMPORT-FROM-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}crypto pki zeroize trustpoint <TRUSTPOINT-NAME> {del-key} {(on <DEVICE-NAME>)}Parameters• crypto key export rsa <RSA-KEYPAIR-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}• crypto key generate rsa <RSA-KEYPAIR-NAME> [2048|4096] {on <DEVICE-NAME>}key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.export rsa <RSA-KEYPAIR-NAME>Exports an existing RSA Keypair to a specified destination• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.<EXPORT-TO-URL> Specify the RSA Keypair destination address. Both IPv4 and IPv6 address formats are supported.After specifying the destination address (where the RSA keypair is exported), configure one of the following parameters: background or passphrase.background Optional. Performs export operation in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the export on.passphrase <KEY-PASSPHRASE> backgroundOptional. Encrypts RSA Keypair before exporting• <KEY-PASSPHRASE> – Specify a passphrase to encrypt the RSA keypair.• background – Optional. Performs export operation in the background. After specifying the passphrase, optionally specify the device (access point or controller)to perform the export on.on <DEVICE-NAME> The following parameter is recursive and common to all of the above parameters:• on <DEVICE-NAME> – Optional. Performs export operation on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-168.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 39• crypto key import rsa <RSA-KEYPAIR-NAME> <IMPORT-FROM-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}• crypto key zeroize rsa <RSA-KEYPAIR-NAME> {force} {(on <DEVICE-NAME>)}generate rsa <RSA-KEYPAIR-NAME> [2048|4096]Generates a new RSA Keypair• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.• [2048|4096] – Sets the size of the RSA key in bits. The options are 2048 bits and4096 bits. The default size is 2048 bits.After specifying the key size, optionally specify the device (access point or controller) to generate the key on.on <DEVICE-NAME> Optional. Generates the new RSA Keypair on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.import rsa <RSA-KEYPAIR-NAME>Imports a RSA Keypair from a specified source• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.<IMPORT-FROM-URL> Specify the RSA Keypair source address. Both IPv4 and IPv6 address formats are supported.After specifying the source address (where the RSA Keypair is imported from), configure one of the following parameters: background or passphrase.background Optional. Performs import operation in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the import on.passphrase <KEY-PASSPHRASE> backgroundOptional. Decrypts the RSA Keypair after importing• <KEY-PASSPHRASE> – Specify the passphrase to decrypt the RSA keypair.• background – Optional. Performs import operation in the background. After specifying the passphrase, optionally specify the device (access point or controller)to perform the import on.on <DEVICE-NAME> The following parameter is recursive and common to the ‘background’ and ‘passphrase’ keywords:• on <DEVICE-NAME> – Optional. Performs import operation on a specific device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.key Enables RSA Keypair management. Use this command to export, import, generate, or delete a RSA key.zeroize rsa <RSA-KEYPAIR-NAME>Deletes a specified RSA Keypair• <RSA-KEYPAIR-NAME> – Specify the RSA Keypair name.Note: All device certificates associated with this key will also be deleted.force Optional. Forces deletion of all certificates associated with the specified RSA Keypair. Optionally specify a device on which to force certificate deletion.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-169.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 40• crypto pki authenticate <TRUSTPOINT-NAME> <URL> {background} {(on <DEVICE-NAME>)}• crypto pki export request [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)on <DEVICE-NAME> The following parameter is recursive and optional:• on <DEVICE-NAME> – Optional. Deletes all certificates associated with the RSA Keypair on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.pki Enables Private Key Infrastructure (PKI) management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated Certificate Authority (CA) certificates.authenticate <TRUSTPOINT-NAME>Authenticates a trustpoint and imports the corresponding CA certificate• <TRUSTPOINT-NAME> – Specify the trustpoint name.<URL> Specify CA’s location. Both IPv4 and IPv6 address formats are supported.Note: The CA certificate is imported from the specified location.background Optional. Performs authentication in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the authentication on.on <DEVICE-NAME> The following parameter is recursive and optional:•on <DEVICE-NAME> – Optional. Performs authentication on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.export request Exports CSR to the CA for digital identity certificate. The CSR contains applicant’s details and RSA Keypair’s public key.[generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.autogen-subject-name Auto generates subject name from configuration parameters. The subject name identifies the certificate.<EXPORT-TO-URL> Specify the CA’s location. Both IPv4 and IPv6 address formats are supported.Note: The CSR is exported to the specified location.email <SEND-TO-EMAIL>Exports CSR to a specified e-mail address• <SEND-TO-EMAIL> – Specify the CA’s e-mail address.fqdn <FQDN> Exports CSR to a specified Fully Qualified Domain Name (FQDN)• <FQDN> – Specify the CA’s FQDN.ip-address <IP> Exports CSR to a specified device or system• <IP> – Specify the CA’s IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-170.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 41• crypto pki export request [generate-rsa-key|short [generate-rsa-key|use-rsa-key]|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> (<EXPORT-TO-URL>,email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>)• crypto pki export trustpoint <TRUSTPOINT-NAME> <EXPORT-TO-URL> {background|passphrase <KEY-PASSPHRASE> background} {(on <DEVICE-NAME>)}pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.export request Exports CSR to the CA for a digital identity certificate. The CSR contains applicant’s details and RSA Keypair’s public key.[generate-rsa-key|short [generate-rsa-key|use-rsa-key]|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• short [generate-rsa-key|use-rsa-key] – Generates and exports a shorter version of the CSR• generate-rsa-key – Generates a new RSA Keypair for digital authentication. If gen-erating a new RSA Keypair, specify a name for it.• use-rsa-key – Uses an existing RSA Keypair for digital authentication. If using anexisting RSA Keypair, specify its name.• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.subject-name <COMMON-NAME>Configures a subject name, defined by the <COMMON-NAME> keyword, to identify the certificate• <COMMON-NAME> – Specify the common name used with the CA certificate. The name should enable you to identify the certificate easily (2 to 64 characters in length).<COUNTRY> Sets the deployment country code (2 character ISO code)<STATE> Sets the state name (2 to 64 characters in length)<CITY> Sets the city name (2 to 64 characters in length)<ORGANIZATION> Sets the organization name (2 to 64 characters in length)<ORGANIZATION-UNIT>Sets the organization unit (2 to 64 characters in length)<EXPORT-TO-URL> Specify the CA’s location. Both IPv4 and IPv6 address formats are supported.The CSR is exported to the specified location.email <SEND-TO-EMAIL>Exports CSR to a specified e-mail address• <SEND-TO-EMAIL> – Specify the CA’s e-mail address.fqdn <FQDN> Exports CSR to a specified FQDN• <FQDN> – Specify the CA’s FQDN.ip-address <IP> Exports CSR to a specified device or system• <IP> – Specify the CA’s IP address.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-171.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 42• crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> autogen-subject-name {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}export trustpoint <TRUSTPOINT-NAME>Exports a trustpoint along with CA certificate, Certificate Revocation List (CRL), server certificate, and private key• <TRUSTPOINT-NAME> – Specify the trustpoint name (should be authenticated).<EXPORT-TO-URL> Specify the destination address. Both IPv4 and IPv6 address formats are supported.The trustpoint is exported to the address specified here.background Optional. Performs export operation in the background. If selecting this option, you can optionally specify the device (access point or controller) to perform the export on.passphrase <KEY-PASSPHRASE> backgroundOptional. Encrypts the key with a passphrase before exporting• <KEY-PASSPHRASE> – Specify the passphrase to encrypt the trustpoint.• background – Optional. Performs export operation in the background. After specifying the passphrase, optionally specify the device (access point or controller)to perform the export on.on <DEVICE-NAME> The following parameter is recursive and common to the ‘background’ and ‘passphrase’ keywords:• on <DEVICE-NAME> – Optional. Performs export operation on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated certificates.generate Generates a certificate and a trustpointself-signed <TRUSTPOINT-NAME>Generates a self-signed certificate and a trustpoint• <TRUSTPOINT-NAME> – Specify a name for the certificate and its trustpoint.[generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair, or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.autogen-subject-name Auto generates the subject name from the configuration parameters. The subject name helps to identify the certificate.email <SEND-TO-EMAIL>Optional. Exports the self-signed certificate to a specified e-mail address• <SEND-TO-EMAIL> – Specify the e-mail address.fqdn <FQDN> Optional. Exports the self-signed certificate to a specified FQDN• <FQDN> – Specify the FQDN.ip-address <IP> Optional. Exports the self-signed certificate to a specified device or system• <IP> – Specify the device’s IP address.on <DEVICE-NAME> Optional. Exports the self-signed certificate on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-172.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 43• crypto pki generate self-signed <TRUSTPOINT-NAME> [generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME> subject-name <COMMON-NAME> <COUNTRY> <STATE> <CITY> <ORGANIZATION> <ORGANIZATION-UNIT> {(email <SEND-TO-EMAIL>,fqdn <FQDN>,ip-address <IP>,on <DEVICE-NAME>)}• crypto pki import [certificate|crl] <TRUSTPOINT-NAME> <IMPORT-FROM-URL> {background} {(on <DEVICE-NAME>)}pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated certificates.generate self-signed <TRUSTPOINT-NAME>Generates a self-signed certificate and a trustpoint• <TRUSTPOINT-NAME> – Specify a name for the certificate and its trustpoint.[generate-rsa-key|use-rsa-key] <RSA-KEYPAIR-NAME>Generates a new RSA Keypair, or uses an existing RSA Keypair• generate-rsa-key – Generates a new RSA Keypair for digital authentication• use-rsa-key – Uses an existing RSA Keypair for digital authentication• <RSA-KEYPAIR-NAME> – If generating a new RSA Keypair, specify a name for it.If using an existing RSA Keypair, specify its name.subject-name <COMMON-NAME>Configures a subject name, defined by the <COMMON-NAME> keyword, to identify the certificate• <COMMON-NAME> – Specify the common name used with this certificate. The name should enable you to identify the certificate easily and should not exceed 2 to 64 characters in length.<COUNTRY> Sets the deployment country code (2 character ISO code)<STATE> Sets the state name (2 to 64 characters in length)<CITY> Sets the city name (2 to 64 characters in length)<ORGANIZATION> Sets the organization name (2 to 64 characters in length)<ORGANIZATION-UNIT>Sets the organization unit (2 to 64 characters in length)email <SEND-TO-EMAIL>Optional. Exports the self-signed certificate to a specified e-mail address• <SEND-TO-EMAIL> – Specify the e-mail address.fqdn <FQDN> Optional. Exports the self-signed certificate to a specified FQDN• <FQDN> – Specify the FQDN.ip-address <IP> Optional. Exports the self-signed certificate to a specified device or system• <IP> – Specify the device’s IP address.pki Enables PKI management. Use this command to authenticate, export, generate, or delete a trustpoint and its associated CA certificates.import Imports certificates, Certificate Revocation List (CRL), or a trustpoint to the selected device[certificate|crl] <TRUSTPOINT-NAME>Imports a signed server certificate or CRL• certificate – Imports signed server certificate•crl – Imports CRL• <TRUSTPOINT-NAME> – Specify the trustpoint name (should be authenticated).<IMPORT-FROM-URL> Specify the signed server certificate or CRL source address. Both IPv4 and IPv6 address formats are supported.The server certificate or the CRL (based on the parameter passed in the preceding step) is imported from the location specified here.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-173.png)
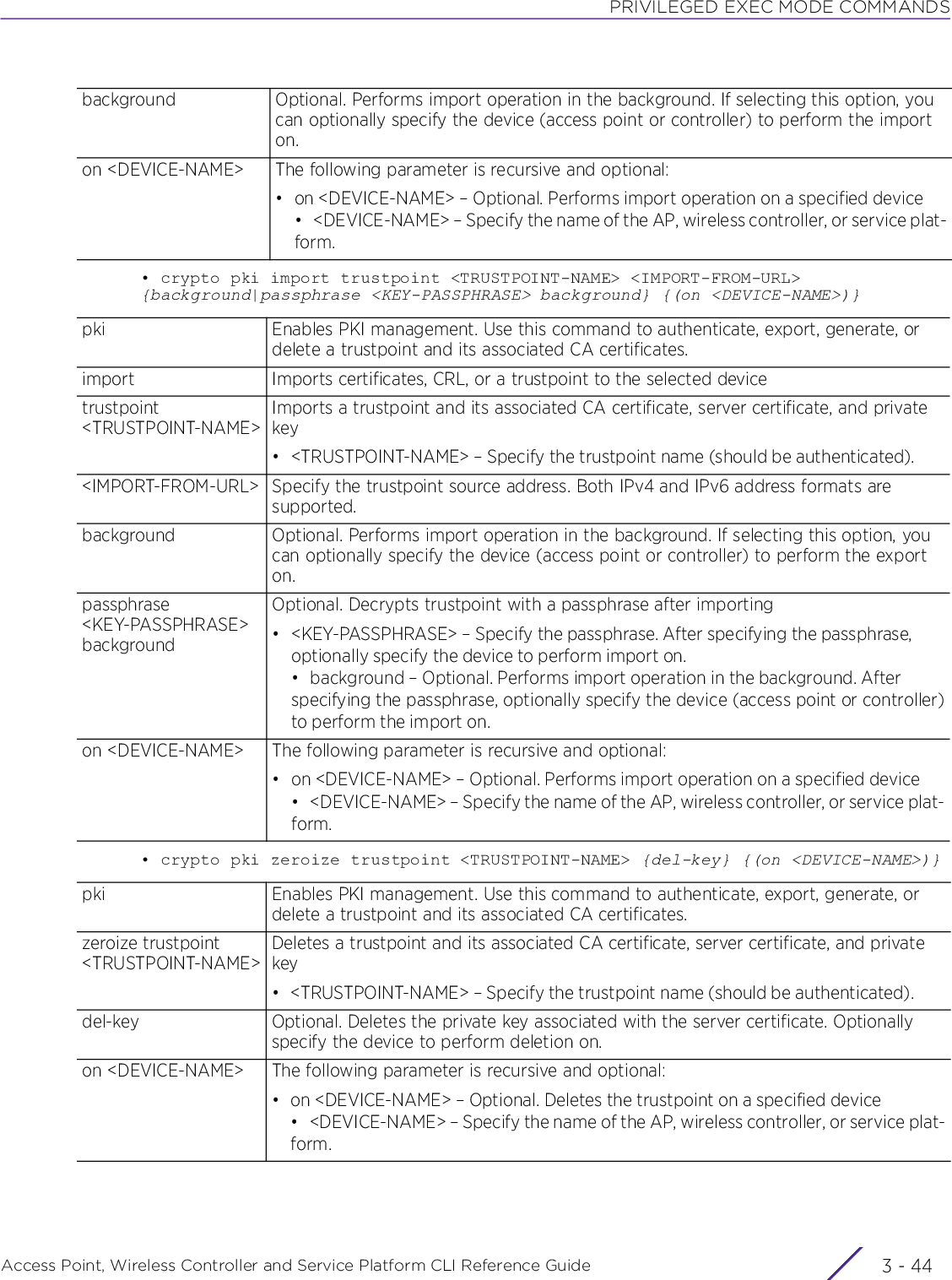
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 45Usage GuidelinesThe system supports both IPv4 and IPv6 address formats. Provide source and destination locations using any one of the following options:•IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/file•IPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileExamplerfs6000-81742D#crypto key generate rsa key 1025RSA Keypair successfully generatedrfs6000-81742D#rfs6000-81742D#crypto key import rsa test123 url passphrase word backgroundRSA key import operation is started in backgroundrfs6000-81742D#rfs6000-81742D#crypto pki generate self-signed word generate-rsa-key word autogen-subject-name fqdn wordSuccessfully generated self-signed certificaterfs6000-81742D#rfs6000-81742D#crypto pki zeroize trustpoint word del-keySuccessfully removed the trustpoint and associated certificates%Warning: Applications associated with the trustpoint will start using default-trustpointrfs6000-81742D#rfs6000-81742D#crypto pki authenticate word url backgroundImport of CA certificate started in backgroundrfs6000-81742D#rfs6000-81742D#crypto pki import trustpoint word url passphrase wordImport operation started in backgroundrfs6000-81742D#Related Commandsno Removes server certificates, trustpoints and their associated certificates](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-175.png)

![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 473.1.16 databasePrivileged Exec Mode CommandsEnables automatic repairing (vacuuming) and dropping of databases (Captive-portal and NSight). Vacuuming a database refers to the process of finding and reclaiming space left over from previous DELETE statements.If enforcing authenticated access to the database, use this command to generate the keyfile. Every keyfile has a set of associated users having a username and password. Database access is provided only if the keyfile and the user credentials entered during database longin match.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdatabase [drop|keyfile|repair]database drop [all|captive-portal|nsight]database repair {on <DEVICE-NAME>}database keyfile [export|generate|import|zerzoise]database keyfile generatedatabase keyfile [export|import] <URL>database keyfile zerzoiseParameters• database drop [all|captive-portal|nsight]• database repair {on <DEVICE-NAME>}NOTE: For information on enabling database authentication, see Enabling Database Authentication.database drop [all|captive-portal|nsight]Drops (deletes) all or a specified database. Execute the command on the database host.• all – Drops all databases, captive portal and NSight.• captive-portal – Drops captive-portal database only• nsight – Drops NSight database onlydatabase repair on <DEVICE-NAME>Enables automatic repairing of all databases. Execute the command on the database host.• on <DEVICE-NAME> – Optional. Specifies the name of the access point, wireless controller, or service platform hosting the database. When specified, databases on the specified device are periodically checked through to identify and remove obsolete data documents.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.If no device is specified, the system repairs all databases.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-177.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 48• database keyfile [generate|zerzoise]• database keyfile [export|import] <URL>• database keyfile zerzoiseExamplenx9500-6C8809#database repair on nx9500-6C8809nx9500-6C8809#nx9500-6C8809#database keyfile generateDatabase keyfile successfully generatednx9500-6C8809#nx9500-6C8809#database keyfile zeroizeDatabase keyfile successfully removednx9500-6C8809#vx9000-1A1809#database keyfile generateDatabase keyfile successfully generatedvx9000-1A1809#vx9000-1A1809#database keyfile export ftp://1.1.1.111/db-keyDatabase keyfile successfully exportedvx9000-1A1809#vx9000-D031F2#database keyfile import ftp://1.1.1.111/db-keyDatabase keyfile successfully importedvx9000-D031F2#database keyfile [generate|zerzoise]Enables management of database keyfiles. This command is part of a series of configurations that are required to enforce authentication on the database. Use this command to generate keyfiles associated with the database. After generating the keyfile, create the users having the database access. For information on creating database users, see service.• generate – Generates the keyfile. Execute the command on the primary database host.• zerzoise – Deletes a keyfile.database keyfile [export|import] <URL>Enables database keyfile management. This command is part of a series of configurations required to enforce database authentication. Use this command to exchange keyfiles between replica set members.• export – Exports the keyfile to a specified location on an FTP/SFTP/TFTP server. Execute the command on the primary database host.• import – Imports the keyfile from a specified location. Execute the command on the replica set members.The following parameter is common to both of the above keywords:• <URL> – Specify the location to/from where the keyfile is to be exported/imported.Use one of the following options:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]/path/filetftp://<hostname|IP>[:port]/path/filedatabase keyfile zerzoiseEnables the management of database keyfiles• zerzoise – Deletes an existing keyfile.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-178.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 49Related Commandsdatabase-backup Backs up captive-portal and/or NSight database to a specified location and file on an FTP or SFTP serverdatabase-restore Restores a previously exported database [captive-portal and/or NSight]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-179.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 503.1.17 database-backupPrivileged Exec Mode CommandsBacks up captive-portal/NSight database to a specified location and file on an FTP or SFTP serverSupported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxfdatabase-backup database [captive-portal|nsight|nsight-placement-info] <URL>database-backup database [captive-portal|nsight] <URL>database-backup database nsight-placement-info <URL>Parameters• database-backup database [captive-portal|nsight] <URL>• database-backup database nsight-placement-info <URL>ExampleNS-DB-nx9510-6C87EF#database-backup database nsight tftp://192.168.9.50/testbckupNS-DB-nx9510-6C87EF#show database backup-statusLast Database Backup Status : In_Progress(Starting tftp transfer.)Last Database Backup Time : 2017-04-17 12:48:05NS-DB-nx9510-6C87EF#show database backup-statusLast Database Backup Status : SuccessfulLast Database Backup Time : Mon Apr 17 12:48:08 T 2017NS-DB-nx9510-6C87EF#Apr 17 12:48:17 2017: NS-DB-nx9510-6C87EF : %DATABASE-6-OPERATION_COMPLETE: backup for database nsight successfulNS-DB-nx9510-6C87EF#NS-DB-nx9510-6C87EF#database-backup database nsight-placement-info tftp://192.168.9.50/plmentinfoNS-DB-nx9510-6C87EF#show database backup-statusLast Database Backup Status : SuccessfulLast Database Backup Time : Mon Apr 17 12:48:48 IST 2017NS-DB-nx9510-6C87EF#Apr 17 12:49:03 2017: NS-DB-nx9510-6C87EF : %DATABASE-6-OPERATION_COMPLETE: backup for database nsight-placement-info successfulNS-DB-nx9510-6C87EF#database-backup database [captive-portal|nsight]Backs up captive portal and/or NSight database to a specified location. Select the database to backup:• captive-portal – Backs up captive portal database• nsight – Backs up NSight databaseAfter specifying the database type, configure the destination location.<URL> Configures the destination location. The database is backed up at the specified location. Specify the location URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzdatabase-backup database nsight-placement-info <URL>Backs up the NSight access point placement related details to a specified location• <URL> – Specify the URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gztftp://<hostname|IP>[:port]/path/file.tar.gz](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-180.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 51Related Commandsdatabase Enables automatic repairing (vacuuming) and dropping of databases (captive-portal and NSight)database-restore Restores a previously exported (backed up) database [captive-portal and/or NSight]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-181.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 523.1.18 database-restorePrivileged Exec Mode CommandsRestores a previously exported database [captive-portal and/or NSight]. Previously exported databases (backed up to a specified FTP or SFTP server) are restored from the backed-up location to the original database.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdatabase-restore database [captive-portal|nsight] <URL>Parameters• database-restore database [captive-portal|nsight] <URL>Examplenx9500-6C8809#database-restore database nsight ftp://anonymous:anonymous@192.168.13.10/backups/nsight/nsight.tar.gzRelated Commandsdatabase-restore database [captive-portal|nsight]Restores previously exported (backed up) captive-portal and/or NSight database. Specify the database type:• captive-portal – Restores captive portal database• nsight – Restores NSight databaseAfter specifying the database type, configure the destination location and file name from where the files are restored.<URL> Configures the destination location. The database is restored from the specified location. Specify the location URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzdatabase Enables automatic repairing (vacuuming) and dropping of databases (captive-portal and NSight)database-backup Backs up captive-portal and/or NSight database to a specified location and file on an FTP or SFTP server](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-182.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 533.1.19 deletePrivileged Exec Mode CommandsDeletes a specified file from the device’s file systemSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdelete [/force <FILE>|/recursive <FILE>|<FILE>]Parameters• delete [/force <FILE>|/recursive <FILE>|<FILE>]Examplerfs6000-81742D#delete flash:/out.tar flash:/out.tar.gzDelete flash:/out.tar [y/n]? yDelete flash:/out.tar.gz [y/n]? yrfs6000-81742D#delete /force flash:/tmp.txtrrfs6000-81742D#rfs6000-81742D#delete /recursive flash:/backup/Delete flash:/backup//fileMgmt_350_180B.core[y/n]? yDelete flash:/backup//fileMgmt_350_18212X.core_bk [y/n]? nDelete flash:/backup//imish_1087_18381X.core.gz [y/n]? nrfs6000-81742D#/force <FILE> Forces deletion without a prompt/recursive <FILE> Performs a recursive delete<FILE> Specifies the file name• Deletes the file specified by the <FILE> parameter](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-183.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 543.1.20 device-upgradePrivileged Exec Mode CommandsEnables firmware upgrade on an adopted device or a set of adopted devices (access points, wireless controllers, and service platforms)Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdevice-upgrade [<MAC/HOSTNAME>|all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000|cancel-upgrade|load-image|rf-domain]device-upgrade <MAC/HOSTNAME> {no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}}device-upgrade all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}device-upgrade [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}device-upgrade cancel-upgrade [<MAC/HOSTNAME>|all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx75xx|nx9000|nx9600|vx9000|on rf-domain [<RF-DOMAIN-NAME>|all]]device-upgrade load-image [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] {<IMAGE-URL>|on <DEVICE-OR-DOMAIN-NAME>}device-upgrade rf-domain [<RF-DOMAIN-NAME>|all|containing <WORD>|filter location <WORD>] [all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] {(<MAC/HOSTNAME>|force|no-reboot|from-controller|reboot-time <TIME>|staggered-reboot|upgrade-time <TIME>)}Parameters• device-upgrade <MAC/HOSTNAME> {no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}}NOTE: A NOC controller’s capacity is equal to, or higher than that of a site controller. The following devices can be deployed at NOC and sites:• NOC controller – NX95XX (NX9500 and NX9510), NX9600• Site controller – RFS4000, RFS6000, NX5500, NX75XX, or NX95XX<MAC/HOSTNAME> Upgrades firmware on the device identified by the <MAC/HOSTNAME> keyword• <MAC/HOSTNAME> – Specify the device’s MAC address or hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-184.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 55• device-upgrade all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}• device-upgrade [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] all {force|no-reboot|reboot-time <TIME>|upgrade-time <TIME> {no-reboot|reboot-time <TIME>}} {(staggered-reboot)}no-reboot Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)reboot-time <TIME> Optional. Schedules an automatic reboot after a successful upgrade• <TIME> – Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.upgrade-time <TIME> {no-reboot|reboot-time <TIME>}Optional. Schedules an automatic device firmware upgrade on a specified day and time• <TIME> – Specify the upgrade time in the MM/DD/YYYY-HH:MM or HH:MM format. The following actions can be performed after a scheduled upgrade:• no-reboot – Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)• reboot-time <TIME> – Optional. Schedules an automatic reboot after a successful upgrade. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.all Upgrades firmware on all devicesforce Optional. Select this option to force upgrade on the selected device(s). When selected, the devices are upgraded even if they have the same firmware as the upgrading access point, wireless controller, or service platform. If forcing a device upgrade, optionally specify any one of the following options: no-reboot, reboot-time, upgrade-time, or staggered-reboot.no-reboot Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)reboot-time <TIME> Optional. Schedules an automatic reboot after a successful upgrade• <TIME> – Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.upgrade-time <TIME> {no-reboot|reboot-time <TIME>}Optional. Schedules an automatic device firmware upgrade on all devices on a specified day and time• <TIME> – Specify the upgrade time in the MM/DD/YYYY-HH:MM or HH:MM format. The following actions can be performed after a scheduled upgrade:• no-reboot – Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)• reboot-time <TIME> – Optional. Schedules an automatic reboot after a successful upgrade. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MMformat.staggered-reboot This keyword is recursive and common to all of the above.• Optional. Enables staggered device reboot (one at a time), without network impactdevice-upgrade <DEVICE-TYPE> allUpgrades firmware on all devices of a specific type. Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000.After selecting the device type, schedule an automatic upgrade and/or an automatic reboot.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-185.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 56• device-upgrade cancel-upgrade [<MAC/HOSTNAME>|all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000|on rf-domain [<RF-DOMAIN-NAME>|all]]force Optional. Select this option to force upgrade on selected device(s). When selected, the devices are upgraded even if they have the same firmware as the upgrading access point, wireless controller, or service platform. If forcing a device upgrade, optionally specify any one of the following options: no-reboot, reboot-time, upgrade-time, or staggered-reboot.no-reboot Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)reboot-time <TIME> Optional. Schedules an automatic reboot after a successful upgrade• <TIME> – Optional. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MM format.upgrade-time <TIME> {no-reboot|reboot-time <TIME>}Optional. Schedules an automatic firmware upgrade on all devices of the specified type, on a specified day and time• <TIME> – Specify the upgrade time in the MM/DD/YYYY-HH:MM or HH:MM format. The following actions can be performed after a scheduled upgrade:• no-reboot – Optional. Disables automatic reboot after a successful upgrade (the device must be manually restarted)• reboot-time <TIME> – Optional. Schedules an automatic reboot after a successful upgrade. Specify the reboot time in the MM/DD/YYYY-HH:MM or HH:MMformat.staggered-reboot This keyword is recursive and common to all of the above.• Optional. Enables staggered device reboot (one at a time), without network impactcancel-upgrade Cancels a scheduled firmware upgrade based on the parameters passed. This command provides the following options to cancel scheduled firmware upgrades:• Cancels upgrade on specific device(s). The devices are identified by their MAC addresses or hostnames.• Cancels upgrade on all devices within the network• Cancels upgrade on all devices of a specific type. Specify the device type.• Cancels upgrade on specific device or all device(s) within a specific RF Domain or all RF Domains. Specify the RF Domain name.cancel-upgrade [<MAC/HOSTNAME>|all]Cancels a scheduled firmware upgrade on a specified device or on all devices• <MAC/HOSTNAME> – Cancels a scheduled upgrade on the device identified by the <MAC/HOSTNAME> keyword. Specify the device’s MAC address or hostname.• all – Cancels scheduled upgrade on all devicescancel-upgrade <DEVICE-TYPE> allCancels scheduled firmware upgrade on all devices of a specific type. Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX9500, NX9600, and VX9000.cancel-upgrade on rf-domain [<RF-DOMAIN-NAME>|all]Cancels scheduled firmware upgrade on all devices in a specified RF Domain or all RF Domains• <RF-DOMAIN-NAME> – Cancels scheduled device upgrade on all devices in a specified RF Domain. Specify the RF Domain name.• all – Cancels scheduled device upgrade on all devices across all RF Domains](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-186.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 57• device-upgrade load-image [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] {<IMAGE-URL>|on <DEVICE-OR-DOMAIN-NAME>}• device-upgrade rf-domain [<RF-DOMAIN-NAME>|all|containing <WORD>|filter location <WORD>] [all|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000] {(<MAC/HOSTNAME>|force|from-controller|no-reboot|reboot-time <TIME>|staggered-reboot|upgrade-time <TIME>)}load-image <DEVICE-TYPE>Loads device firmware image from a specified location. Select the device type and provide the location of the required device firmware image.• <DEVICE-TYPE> – Specify the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000. After specifying the device type, provide the location of the required device firmware image.<IMAGE-URL> Specify the device’s firmware image location in one of the following formats:IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileIPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/fileon <DEVICE-OR-DOMAIN-NAME>Optional. Specifies the name of a device or RF Domain. The image, of the specified device type is loaded from the device specified here. In case of an RF Domain, the image available on the RF Domain manager is loaded.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.rf-domain [<RF-DOMAIN-NAME>|all|containing <WORD>|filter location <WORD>]Upgrades firmware on devices in a specified RF Domain or all RF Domains. Devices within a RF Domain are upgraded through the RF Domain manager.• <RF-DOMAIN-NAME> – Upgrades devices in the RF Domain identified by the <RF-DOMAIN-NAME> keyword.• <RF-DOMAIN-NAME> – Specify the RF Domain name.• all – Upgrades devices across all RF Domains• containing <WORD> – Filters RF Domains by their names. RF Domains with names containing the sub-string identified by the <WORD> keyword are filtered. Devices on the filtered RF Domains are upgraded.• filter location <WORD> – Filters devices by their location. All devices with locationmatching the <WORD> keyword are upgraded.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-187.png)
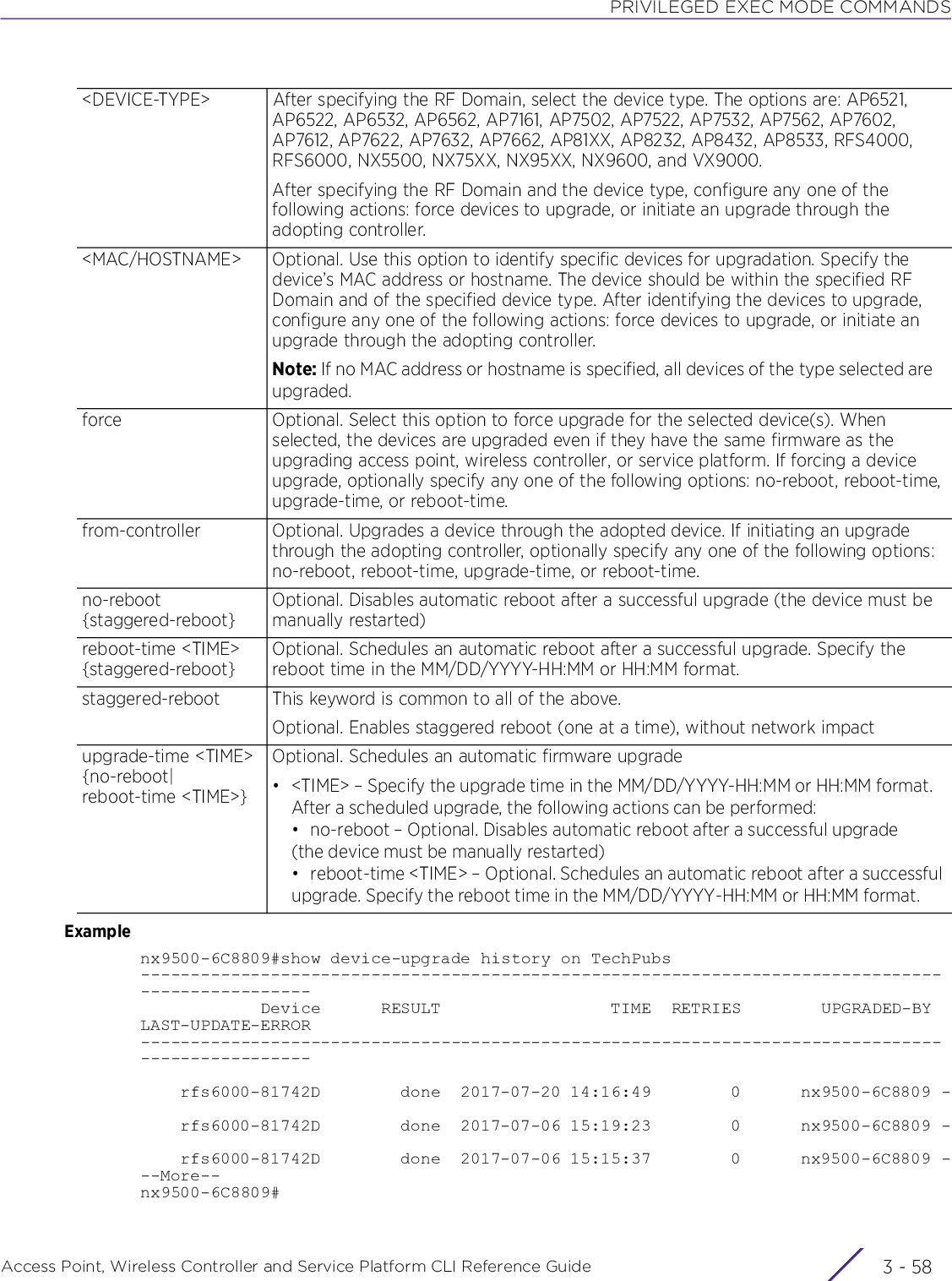
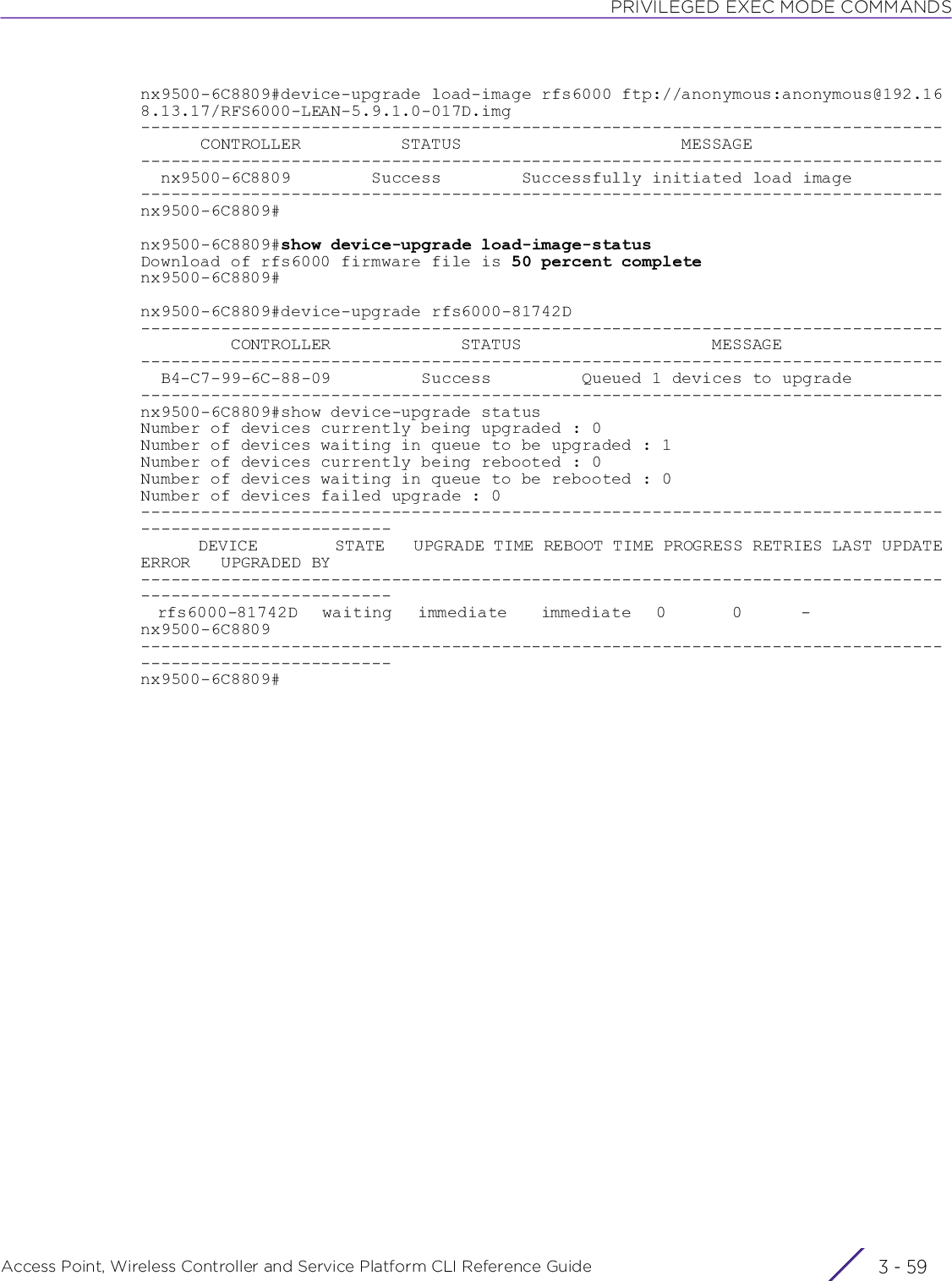
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 603.1.21 diffPrivileged Exec Mode CommandsDisplays the differences between two files on a device’s file system or a particular URLSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdiff [<FILE>|<URL>] [<FILE>|<URL>]Parameters• diff [<FILE>|<URL>] [<FILE>|<URL>]Examplenx9500-6C8809#diff startup-config running-config--- startup-config+++ running-config@@ -1,12 +1,10 @@+!### show running-config ! ! Configuration of NX9500 version 5.9.1.0-012D ! ! version 2.5 !-password-encryption-version 1.0-inline-password-encryption-password-encryption-key secret 2 776f9d6d5bb08fac753394d779cbc5a200000020a4ca26def55d4d77952308cd5e3afc66c06581bb1e5af6d6b033fd664c363522 ! client-identity-group default load default-fingerprints@@ -35,13 +33,13 @@ ! alias string $IN-Blr-EcoSpace-Floor-4 IBEF4 !-alias encrypted-string $READ 2 LKSXiTieTV5hybKxfbd6JwAAAAZ/lakoqHh/ZfyHLJWzluTH+alias encrypted-string $READ 2 1og6ZeMyEVJhybKxfbd6JwAAAAahnGq6RaJb70CEIbVpTYre--More--nx9500-6C8809#<FILE> The first <FILE> is the source file for the diff command. The second <FILE> is used for comparison.<URL> The first <URL> is the source file’s URL. The second <URL> is the second file’s URL.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-190.png)
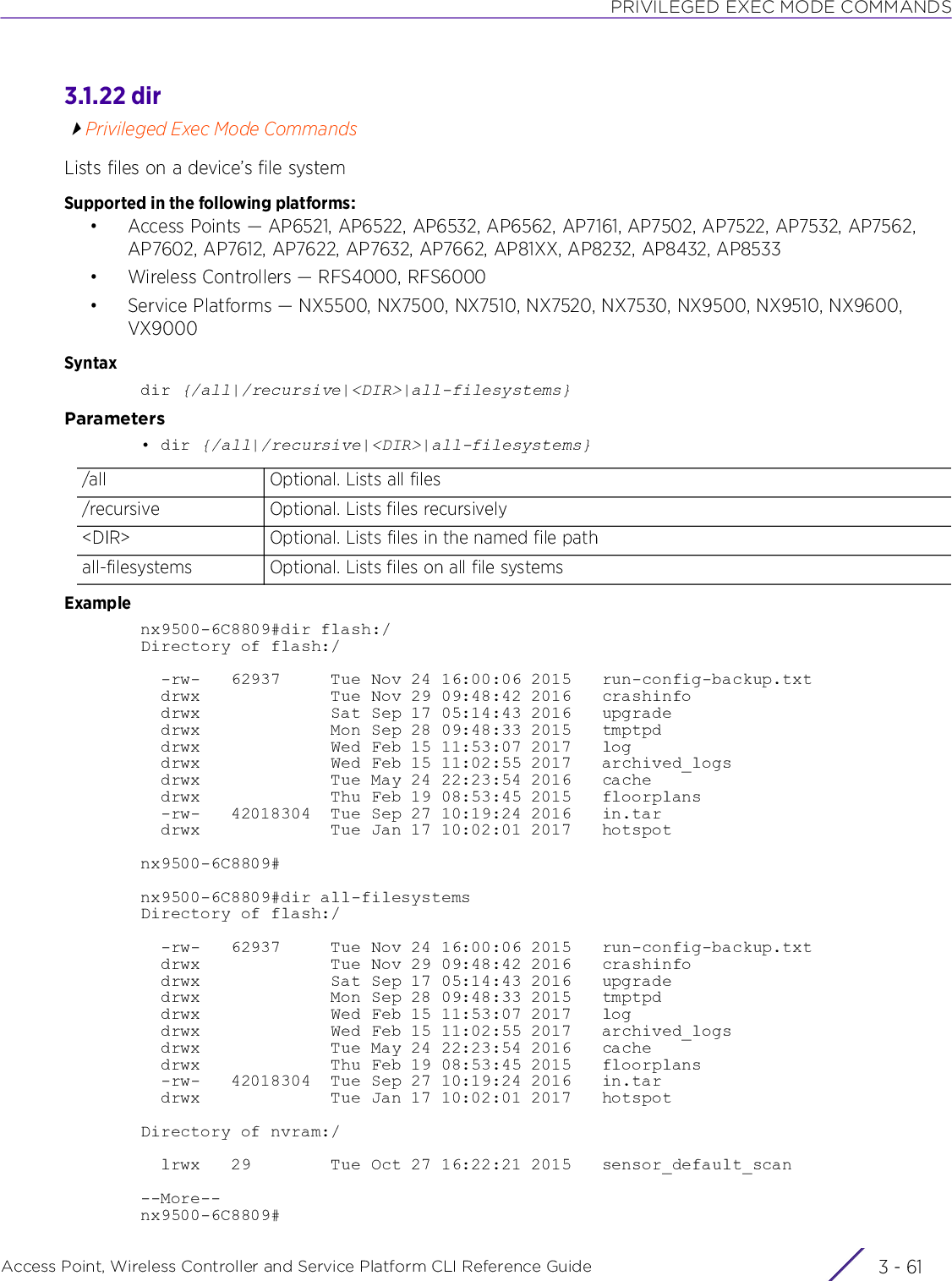
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 633.1.24 editPrivileged Exec Mode CommandsEdits a text file on the device’s file systemSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxedit <FILE>Parameters• edit <FILE>Examplerfs4000-880DA7#edit startup-config GNU nano 1.2.4 File: startup-config!! Configuration of RFS4000 version 5.9.1.0-015D!!version 2.5!password-encryption-version 1.0inline-password-encryptionno password-encryption-key!client-identity-group default load default-fingerprints!ip snmp-access-list default permit any!firewall-policy default no ip dos tcp-sequence-past-window! [ Read 400 lines ]^G Get Help ^O WriteOut ^R Read File ^Y Prev Page ^K Cut Text ^C Cur Pos^X Exit ^J Justify ^W Where Is ^V Next Page ^U UnCut Txt ^T To Spell<FILE> Specify the name of the file to modify.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-193.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 653.1.26 erasePrivileged Exec Mode CommandsErases a device’s (wireless controller, access point, and service platform) file system. Erases the content of the specified storage device. Also erases the startup configuration to restore the device to its default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxerase [flash:|nvram:|startup-config|usb1:|usb2:|usb3:|usb4:]erase [flash:|nvram:|usb1:|usb2:|usb3:|usb4:]erase startup-config {<HOSTNAME/MAC>|on <DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>}}Parameters• erase [flash:|nvram:|usb1:|usb2:|usb3:|usb4:]• erase startup-config {<HOSTNAME/MAC>|on <DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>}}flash: Erases everything in the device’s flash: filenvram: Erases everything in the device’s nvram: filestartup-config Erases the device’s startup configuration file. The startup configuration file is used to configure the device when it reboots.usb1: Erases everything in the device's usb1: fileusb2: Erases everything in the device's usb2: fileusb3: Erases everything in the device's usb3: fileusb4: Erases everything in the device's usb4: filestartup-config: Erases the startup configuration file on a specified device or devices in a specified RF Domain. The specified device(s) are reloaded after the startup configuration file is erased. Use the ‘<HOSTNAME/MAC>’ or ‘on <DOMAIN-NAME>’ options to identify the device or RF Domain respectively. Once executed, the configuration file, for the targeted device or for all device(s) in the targeted RF Domain, is also erased from the adopting controller’s configuration file. The are automatically reloaded once the startup configuration file has been erased.<HOSTNAME/MAC> Optional. Erases the startup configuration file on the device identified by the <HOSTNAME/MAC> keyword. Specify the device’s hostname or MAC address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-195.png)
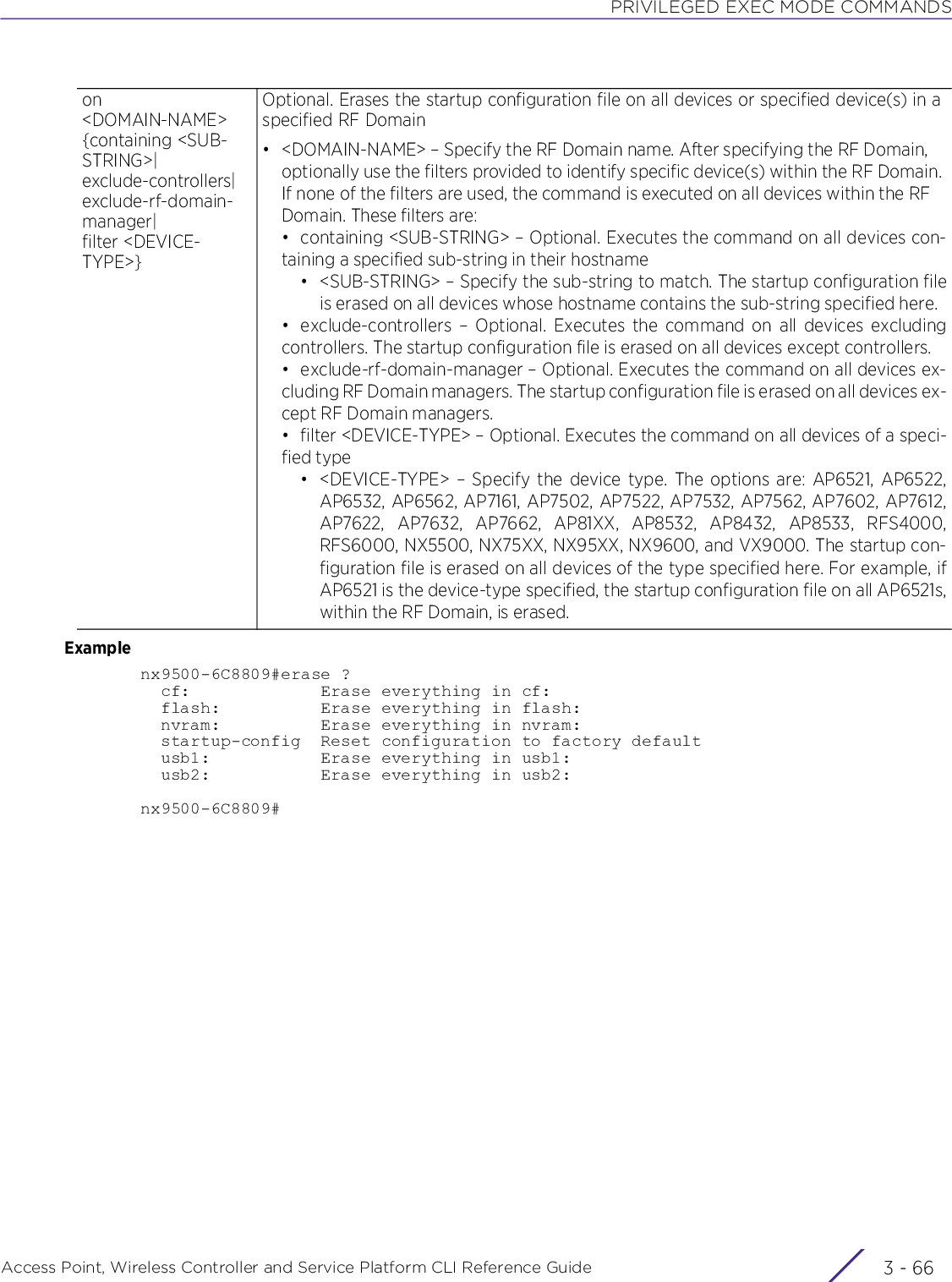
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 673.1.27 ex3500Privileged Exec Mode CommandsEnables EX3500 switch firmware management. Use this command to perform the following operations: boot, copy, delete, and IP-related configurations.The copy keyword provides multiple copy options. It allows you to upload or download code images or configuration files between the switch’s flash memory and an FTP/TFTP server. When you save the system code or configuration settings to a file on an FTP/TFTP server, that file can later be downloaded to the switch to restore system operation. The success of the file transfer depends on the accessibility of the FTP/TFTP server and the quality of the network connection.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600Syntaxex3500 [adoptd|boot|copy|delete|ip]ex3500 adoptd upgrade <URL> on <EX3500-DEVICE-NAME>ex3500 boot system <1-1> (config|opcode) <FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 copy [file|ftp|running-config|startup-config|tftp|unit]ex3500 copy [file file <SOURCE-FILE-NAME> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 copy [ftp|tftp] [add-to-running-config|file|https-certificate|public-key|running-config|startup-config]ex3500 copy [ftp|tftp] add-to-running-config <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> <SOURCE-FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 copy [ftp|tftp] file <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> [1|2] <SOURCE-FILE-NAME> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 copy [ftp|tftp] https-certificate <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> <SOURCE-CERT-FILE-NAME> <SOURCE-PVT-KEY-FILE-NAME> <PVT-PASS-WORD> on <EX3500-DEVICE-NAME>ex3500 copy [ftp|tftp] public-key <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> [1|2] <SOURCE-PUB-KEY-FILE-NAME> <USER-NAME> on <EX3500-DEVICE-NAME>ex3500 copy [ftp|tftp] [running-config|startup-config] <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> <SOURCE-CONFIG-FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 copy running-config [file <DEST-FILE-NAME>|ftp <FTP-SERVER-IP> <USER-NAME> <PASSWORD> <DEST-FILE-NAME>|startup-config|tftp <TFTP-SERVER-IP> <DEST-FILE-NAME>] on <EX3500-DEVICE-NAME>ex3500 copy startup-config [file <DEST-FILE-NAME>|ftp <FTP-SERVER-IP> <USER-NAME> <PASSWORD> <DEST-FILE-NAME>|running-config|tftp <TFTP-SERVER-IP> <DEST-FILE-NAME>] on <EX3500-DEVICE-NAME>ex3500 copy unit file <1-1> [1|2] <SOURCE-FILE-NAME> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 delete [file|public-key]ex3500 delete file [name <FILE-NAME>|unit <1-1> name <FILE-NAME>] on <EX3500-DEVICE-NAME>ex3500 delete public-key <USER-NAME> [dsa|rsa] on <EX3500-DEVICE-NAME>](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-197.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 68ex3500 ip ssh [crypto|save]ex3500 ip ssh crypto host-key generates [dsa|rsa] on <EX3500-DEVICE-NAME>ex3500 ip ssh crypto zeroize [dsa|rsa] on <EX3500-DEVICE-NAME>ex3500 ip ssh save host-key on <EX3500-DEVICE-NAME>Parameters• ex3500 adoptd upgrade <URL> on <EX3500-DEVICE-NAME>• ex3500 boot system <1-1> (config|opcode) <FILE-NAME> on <EX3500-DEVICE-NAME>• ex3500 copy file file <SOURCE-FILE-NAME> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME>ex3500 adoptd upgradeUpgrades an adopted EX3500 switchNote: After an upgrade, reboot the EX3500 switch to initiate the new image. To view an EX3500’s current image version, use the show > version > on <EX3500-DEVICE-NAME> command.<URL> Specifies the location and image file name in the following format:tftp://<IP>[/path]/fileon <EX3500-DEVICE-NAME>Executes the command on a specified EX3500 switch• <EX3500-DEVICE-NAME> – Specify the EX3500 switch’s hostname.ex3500 boot system Boots a EX3500 switch using a specified configuration file<1-1> Identifies the EX3500 unit by its ID number. Specify the EX3500 ID from 1 - 1.Note: As of now only one (1) EX3500 unit can be managed through a NOC controller.(config|opcode) <FILE-NAME>The following keywords are recursive:Specifies the image file to use for booting. The options are:• config – Uses the configuration file to boot the switch• opcode – Uses the Operation Code (opcode), which is the runtime code, to boot the switch. The opcode is like an operating system that enables the WiNG software to communicate with the EX3500 device.The following parameter is common to the ‘config’ and opcode’ keywords:• <FILE-NAME> – Specify the configuration/runtime-code file name.on <EX3500-DEVICE-NAME>Reloads a specified EX3500 switch• <EX3500-DEVICE-NAME> – Specify the EX3500 switch’s hostname. You can also specify its MAC address.ex3500 copy Copies a configuration file to another filefile file <SOURCE-FILE-NAME> <DEST-FILE-NAME>Copies a specified file (this is the source configuration file)• file – Copies the specified source file to a specified file (this is the destination configuration file)• <SOURCE-FILE-NAME> – Specify the source configuration file’s name• <DEST-FILE-NAME> – Specify the destination configuration file’s name.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-198.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 69• ex3500 copy [ftp|tftp] add-to-running-config <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> <SOURCE-FILE-NAME> on <EX3500-DEVICE-NAME>• ex3500 copy [ftp|tftp] file <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> [1|2] <SOURCE-FILE-NAME> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME>When specifying the destination file name, keep in mind the following points:- It should not contain slashes (\ or /),- It should not exceed 32 characters for files on the switch, or 127 characters for files on the server.on <EX3500-DEVICE-NAME>Copies the file to a specified EX3500 switch• <EX3500-DEVICE-NAME> – Specify the EX3500 switch’s hostname. The specified source file is copied to specified destination file on the EX3500 identified here.ex3500 copy [ftp|tftp] Copies files from a FTP or TFTP server. This command allows you to copy the following types of files: HTTPS certificate, running configuration, startup configuration, public key, etc. This command also allows you to add a remote system’s running configuration to the current system configuration.add-to-running-config Adds a remote system’s running configuration to the current system<FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD>Configures the FTP or TFTP server details (depending on the option selected in the previous step), such as IP address and user credentials. This is the device running the FTP/TFTP server.• <FTP/TFTP-SERVER-IP> – Specify the FTP or TFTP server’s IP address in the A.B.C.D format.• <USER-NAME> – If using a FTP server, specify the FTP server’s user name (shouldbe an authorized user)• <PASSWORD> – Specify the password applicable for the above specified FTPserver user name.<SOURCE-FILE-NAME>After specifying the server details, specify the name of the running configuration file.• <SOURCE-FILE-NAME> – Specify the source file’s name.on <EX3500-DEVICE-NAME>Copies the file to a specified EX3500 switch• <EX3500-DEVICE-NAME> – Specify the EX3500 switch’s hostname. The specified source file is copied to specified destination file on the EX3500 identified here.ex3500 copy [ftp|tftp] Copies files from a FTP or TFTP server. This command allows you to copy the following types of files: HTTPS certificate, running configuration, startup configuration, public key, etc. file Copies to a specified file system<FTP/TFTP-SERVER-IP> <USER-NAME> <PASS-WORD>Configures the FTP or TFTP server details (depending on the option selected in the previous step), such as IP address and user credentials. This is the device running the FTP/TFTP server.• <FTP/TFTP-SERVER-IP> – Specify the FTP or TFTP server’s IP address in the A.B.C.D format.• <USER-NAME> – If using a FTP server, specify the FTP server’s user name (shouldbe an authorized user)• <PASSWORD> – Specify the password applicable for the above specified FTPserver user name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-199.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 70• ex3500 copy [ftp|tftp] https-certificate <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> <SOURCE-CERT-FILE-NAME> <SOURCE-PVT-KEY-FILE-NAME> <PVT-PASS-WORD> on <EX3500-DEVICE-NAME>• ex3500 copy [ftp|tftp] public-key <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> [1|2] <SOURCE-PUB-KEY-FILE-NAME> <USER-NAME> on <EX3500-DEVICE-NAME>[1|2] <SOURCE-FILE-NAME> <DEST-FILE-NAME>After specifying the server details, select the file type and specify the name of the source and destination file names.• [1|2] – Select the file type from 1 - 2.• 1 – Copies the EX3500 configuration file.• 2 – Copies the opcode, which is the runtime code. The opcode is like an operatingsystem that enables the WiNG software to communicate with the EX3500 device.• <SOURCE-FILE-NAME> – Specify the source file’s name.• <DEST-FILE-NAME> – Specify the destination file’s name.on <EX3500-DEVICE-NAME>Copies the file to a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname. The specified source file is copied to specified destination file on the EX3500 identified here.ex3500 copy [ftp|tftp] Copies files from a FTP or TFTP server. This command allows you to copy the following types of files: HTTPS certificate, running configuration, startup configuration, public key, etc. https-certificate Copies HTTPS secure site certificate from the FTP or TFTP server to the switch<FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD>Configures the FTP or TFTP server details (depending on the option selected in the previous step), such as IP address and user credentials. This is the device running the FTP/TFTP server.• <FTP/TFTP-SERVER-IP> – Specify the FTP or TFTP server’s IP address in the A.B.C.D format.• <USER-NAME> – If using a FTP server, specify the FTP server’s user name (shouldbe an authorized user)• <PASSWORD> – Specify the password applicable for the above specified FTPserver user name.<SOURCE-CERT-FILE-NAME> <SOURCE-PVT-KEY-FILE-NAME> <PVT-PASS-WORD>After identifying the FTP or TFTP server, specify the following:• <SOURCE-CERT-FILE-NAME> – Specify the source HTTPS secure site certificate file name.• <SOURCE-PVT-KEY-FILE-NAME> – Specify the source private-key file name.• <PVT-PASS-WORD> – Specify the private password.on <EX3500-DEVICE-NAME>Copies the file to a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname.ex3500 copy [ftp|tftp] Copies files from a FTP or TFTP server. This command allows you to copy the following types of files: HTTPS certificate, running configuration, startup configuration, public key, etc. public-key Copies the SSH public key from the FTP or TFTP server to the switch](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-200.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 71• ex3500 copy [ftp|tftp] [running-config|startup-config] <FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME>• ex3500 copy unit file <1-1> [1|2] <SOURCE-FILE-NAME> <DEST-FILE-NAME> on <EX3500-DEVICE-NAME><FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD>Configures the FTP or TFTP server details (depending on the option selected in the previous step), such as IP address and user credentials. This is the device running the FTP/TFTP server.• <FTP/TFTP-SERVER-IP> – Specify the FTP or TFTP server’s IP address in the A.B.C.D format.• <USER-NAME> – If using a FTP server, specify the FTP server’s user name (shouldbe an authorized user)• <PASSWORD> – Specify the password applicable for the above specified FTPserver user name.[1|2] <SOURCE-PUB-KEY-FILE-NAME> <USER-NAME>After identifying the FTP or TFTP server, specify the following:• [1|2] – Configures the SSH public key type as RS or DSA• 1 – Configures the public key type as RSA• 2 – Configures the public key type as DSA• <SOURCE-PUB-KEY-FILE-NAME> – Specifies the source public key file name• <USER-NAME> – Specifies the public key’s user name.on <EX3500-DEVICE-NAME>Copies the public key to a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname.ex3500 copy [ftp|tftp] Copies files from a FTP or TFTP server. This command allows you to copy the following types of files: HTTPS certificate, running configuration, startup configuration, public key, etc.[running-config|startup-config]Copies the running or startup configuration file to one of the following destinations: file system, FTP server, or TFTP serverThe running configuration file can be copied to the startup configuration file and vice versa.<FTP/TFTP-SERVER-IP> <USER-NAME> <PASSWORD>If copying to a FTP/TFTP server, configure the following parameters: • <FTP/TFTP-SERVER-IP> – Specify the FTP or TFTP server’s IP address in the A.B.C.D format.• <USER-NAME> – If using a FTP server, specify the FTP server’s user name (shouldbe an authorized user)• <PASSWORD> – Specify the password applicable for the above specified FTPserver user name.<DEST-FILE-NAME> Configures the destination file name. The running or startup configuration file is copied to the specified destination file.• <DEST-FILE-NAME> – Specify the destination file name. You can also copy the running configuration file to the startup configuration file and vice versa.on <EX3500-DEVICE-NAME>Copies the running or startup configuration file on to a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname. ex3500 copy unit Copies from a EX3500 switch](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-201.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 72• ex3500 delete file [name <FILE-NAME>|unit <1-1> name <FILE-NAME>] on <EX3500-DEVICE-NAME>• ex3500 delete public-key <USER-NAME> [dsa|rsa] on <EX3500-DEVICE-NAME>file <1-1> [1|2] Copies the file system from the EX3500 switch identified by the unit number• <1-1> – Specify the unit number from 1 - 1.• [1|2] – Select the file type from 1 - 2.• 1 – Copies the selected unit’s configuration file.• 2 – Copies the selected unit’s opcode, which is the runtime code. The opcode islike an operating system that enables the WiNG software to communicate withthe EX3500 device.<SOURCE-FILE-NAME>Configures the source file name• <SOURCE-FILE-NAME> – Specify the source file name. You can copy the running configuration file to the startup configuration file and vice versa.<DEST-FILE-NAME> Configures the destination file name. The running or startup configuration file is copied to the specified file.• <DEST-FILE-NAME> – Specify the destination file name. You can copy the running configuration file to the startup configuration file and vice versa.on <EX3500-DEVICE-NAME>Copies the running or startup configuration file on to a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname. ex3500 delete file Deletes a file or image on a specified EX3500 devicename <FILE-NAME> Specifies the file to delete. The specified file is deleted.• <FILE-NAME> – Specify the file name.unit <1-1> name <FILE-NAME>Identifies the unit in the stackable system on which the file is located• <1-1> – Select the unit from 1 - 1.• name – After identifying the unit, specify the file to delete. The specified file is deleted.• <FILE-NAME> – Specify the file name.on <EX3500-DEVICE-NAME>Executes the command on a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname. ex3500 delete public-key <USER-NAME> [dsa|rsa]Deletes a specified user’s public key• <USER-NAME> – Specify the SSH user’s name.• dsa – Deletes the specified user’s DSA (version 2) key• rsa – Deletes the specified user’s RSA (version 1) keyon <EX3500-DEVICE-NAME>Executes the command on a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-202.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 73• ex3500 ip ssh crypto host-key generates [dsa|rsa] on <EX3500-DEVICE-NAME>• ex3500 ip ssh zeroize [dsa|rsa] <EX3500-DEVICE-NAME>• ex3500 ip ssh save host-key on <EX3500-DEVICE-NAME>Usage GuidelinesWhen using the ex3500 command and its parameters, keep in mind the following:• Destination file names should not:- Contain slashes (\ or /),- Exceed 32 characters for files on the switch, or 127 characters for files on the server• The FTP server’s default user name is set as “anonymous”.• The Boot ROM and Loader cannot be uploaded or downloaded from the FTP/TFTP server. Follow instructions provided in the release notes for new firmware, or contact your distributor for help.• The “Factory_Default_Config.cfg” can be used as the source to copy from, but cannot be used as the destination.• Although the switch supports only two operation code files, the maximum number of user-defined configuration files supported is 16.ex3500 ip ssh crypto host-key generates [dsa|rsa] Generates the host-key pair (public and private). This host key is used by the SSH server to negotiate a session key and encryption method with the client trying to connect to it.• dsa – Generates DSA (version 2) key type• rsa – Generates RSA (version 1) key typeNote: The RSA Version 1 is used only for SSHv1.5 clients, whereas DSA Version 2 is used only for SSHv2 clients.Note: This generated host-key pair is stored in the volatile memory (i.e RAM). To save the host-key pair in the flash memory, use the ex3500 > ip > ssh > save > host-key command.on <EX3500-DEVICE-NAME>Executes the command on a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname.ex3500 ip ssh zeroize [dsa|rsa]Removes the host-key (DSA and RSA) from the volatile memory (i.e. RAM)on <EX3500-DEVICE-NAME>Executes the command on a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname.ex3500 ip ssh save host-keySaves the host-key (DSA and RSA) to the flash memoryon <EX3500-DEVICE-NAME>Executes the command on a specified EX3500 device• <EX3500-DEVICE-NAME> – Specify the EX3500 device’s hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-203.png)
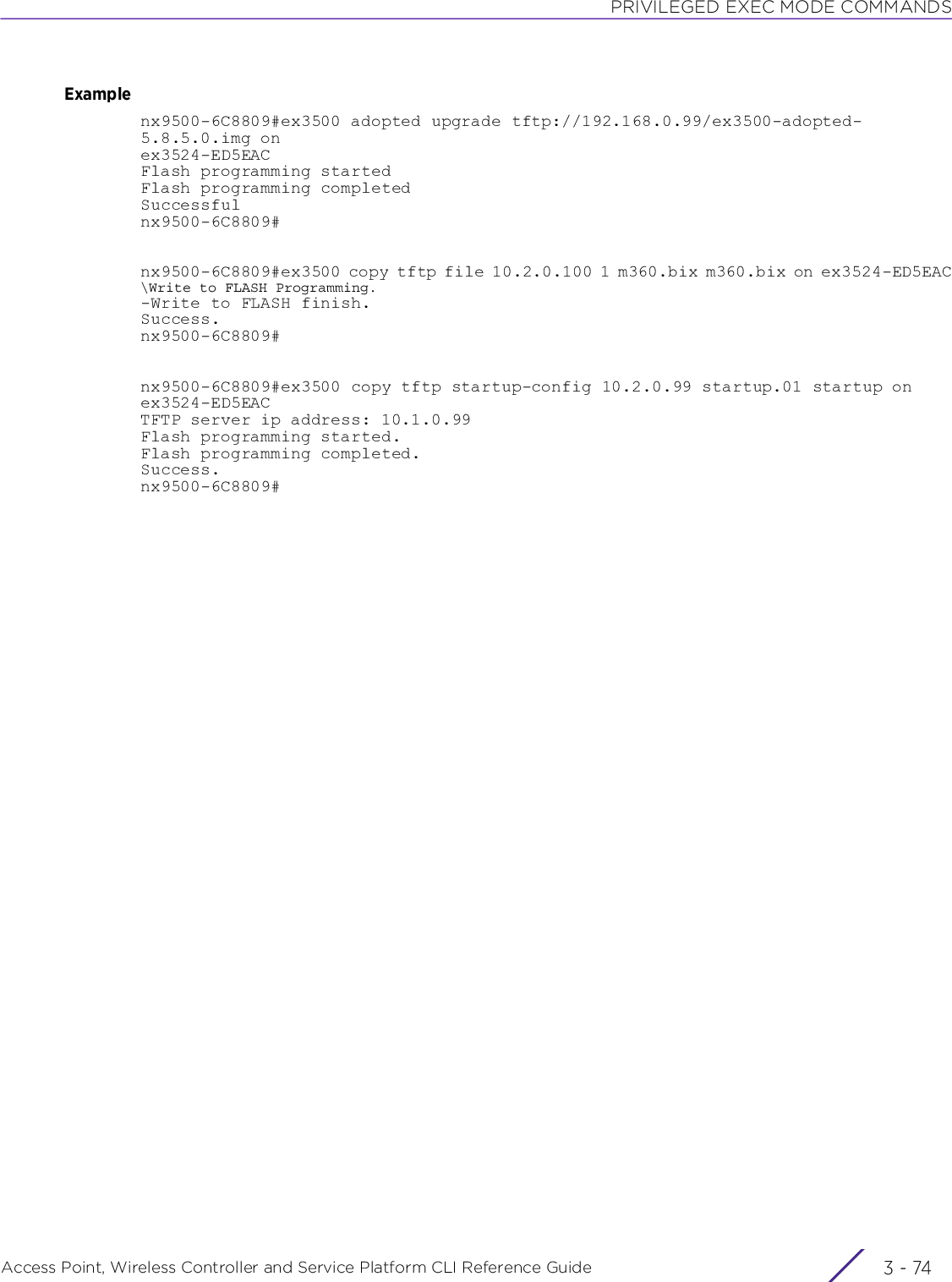
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 753.1.28 factory-resetPrivileged Exec Mode CommandsErases startup configuration on a specified device or all devices within a specified RF DomainSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxfactory-reset [<HOSTNAME/MAC>|config-all|config-device-only|on <RF-DOMAIN-NAME>]factory-reset <HOSTNAME/MAC> {<HOSTNAME/MAC>}factory-reset on <RF-DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>}factory-reset [config-all|config-device-only] [<HOSTNAME/MAC> {<HOSTNAME/MAC>}|on <RF-DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>}]Parameters• factory-reset <HOSTNAME/MAC> {<HOSTNAME/MAC>}• factory-reset on <RF-DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>}factory-reset Erases startup configuration and reloads device(s) based on the parameters passedFor more information on the actions performed by this command, see Actions performed by the factory-reset command.<HOSTNAME/MAC> {<HOSTNAME/MAC>}Erases startup configuration and reloads the device identified by the <HOSTNAME/MAC> keyword. Specify the device’s hostname or MAC address.• <HOSTNAME/MAC> – Optional. You can optionally specify multiple space-separated devices.factory-reset Erases startup configuration and reloads device(s) based on the parameters passedFor more information on the actions performed by this command, see Actions performed by the factory-reset command.on <RF-DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>]}Erases startup configuration and reloads all devices or specified device(s) within a specified RF Domain identified by the <RF-DOMAIN-NAME> keyword• <RF-DOMAIN-NAME> – Specify the RF Domain name. After specifying the RF Domain, optionally use the filters provided to identify specific device(s) within the RF Domain. If none of the filters are used, the command is executed on all devices within the RF Domain. These filters are:• containing <SUB-STRING> – Optional. Executes the command on all devices con-taining a specified sub-string in their hostname• <SUB-STRING> – Specify the sub-string to match.Contd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-205.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 76• factory-reset [config-all|config-device-only] [<HOSTNAME/MAC> {<HOSTNAME/MAC>}|on <RF-DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>}]• exclude-controllers – Optional. Executes the command on all devices excludingcontrollers. Since only a NOC controller is capable of adopting other controllers, usethis option when executing the command on a NOC controller.• exclude-rf-domain-manager – Optional. Executes the command on all devices ex-cluding RF Domain managers. Use this option when executing the command on theNOC, site controller, or RF Domain manager.• filter <DEVICE-TYPE> – Optional. Executes the command on all devices of a speci-fied type• <DEVICE-TYPE> – Specify the device type. The options are: AP6521, AP6522,AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612,AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000,RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000. The startup con-figuration is erased on all devices of the type specified here. For example, ifAP6521 is the device-type specified, the command is executed on all AP6521swithin the specified RF Domain.factory-reset Erases startup configuration and reloads device(s) based on the parameters passedFor more information on the actions performed by this command, see Actions performed by the factory-reset command.[config-all|config-device-only]Erases startup configuration and reloads only controller-adopted devices or the controller as well as its adopted devices• config-all – Erases startup configuration on the controller and all devices adopted by it• config-device-only – Erases startup configuration only on the devices adopted by the controller<HOSTNAME/MAC> {<HOSTNAME/MAC>}This parameter is common to the ‘config-all’ and ‘config-device-only’ keywords:• <HOSTNAME/MAC> – Erases startup configuration and reloads the device identified by the <HOSTNAME/MAC> keyword. Specify the device’s hostname or MAC address.• <HOSTNAME/MAC> – Optional. You can optionally specify multiple space-separated devices.The following parameters are common to the ‘config-all’ and ‘config-device-only’ keywords:• on <RF-DOMAIN-NAME> – Erases startup configuration and reloads all devices or specified device(s) within a specified RF Domain• <RF-DOMAIN-NAME> – Specify the RF Domain name. After specifying the RF Do-main, optionally use the filters provided to identify specific device(s) within the RF Do-main. If none of the filters are used, the command is executed on all devices within theRF Domain. These filters are:• containing <SUB-STRING> – Optional. Executes the command on all devices con-taining a specified sub-string in their hostname• <SUB-STRING> – Specify the sub-string to match.• exclude-controllers – Optional. Executes the command on all devices excludingcontrollers. Since only a NOC controller is capable of adopting other controllers,use this option when executing the command on a NOC controller.Contd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-206.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 77Usage Guidelines Actions performed by the factory-reset command.The action taken by this command depends on the parameters passed.•For the ‘factory-reset [<DEVICE-NAME>|on <RF-DOMAIN-NAME>]’ options, the command:- Erases startup configuration on the target device (or) all devices in the target RF Domain.- Erases the device configuration entries from the controller’s configuration for the target device (or) for all the devices in the target RF Domain.- Reloads the target device (or) all devices in the target RF Domain.•For the ‘factory-reset config-all [<DEVICE-NAME>|on <RF-DOMAIN-NAME>]’ options, the command:- Erases startup configuration on the target device (or) all devices in the target RF Domain.- Erases the device configuration entries from the controller’s configuration for the target device (or) for all the devices in the target RF Domain.•For the ‘factory-reset config-device-only [<DEVICE-NAME>|on <RF-DOMAIN-NAME>]’ options, the command:- Erases startup configuration on the target device (or) all devices in the target RF Domain.Examplenx7500-7F3609#factory-reset config-all ap6522-5A873CIn progress ....Erased startup-config - success 1 fail 0Successful device deletion - total 1nx7500-7F3609#rfs6000-18072B# factory-reset B4-C7-99-5A-87-3CIn progress ....Erased startup-config and initiated reload - success 1 fail 0Successful device deletion - total 1rfs6000-18072B#The following example displays the access points in the RF Domain ‘rfd1’:nx7500-7F3609#show wireless ap on rfd1--------------------------------------------------------------------------------------- MODE : radio modes - W = WLAN, S=Sensor, ' ' (Space) = radio not present------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ AP-NAME AP-LOCATION RF-DOMAIN AP-MAC #RADIOS MODE #CLIENT IPv4 IPv6---------------------------------------------------------------------------------------on <RF-DOMAIN-NAME> {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-manager|filter <DEVICE-TYPE>]}• exclude-rf-domain-manager – Optional. Executes the command on all devicesexcluding RF Domain managers. Use this option when executing the commandon the NOC, Site controller, or RF Domain manager.• filter <DEVICE-TYPE> – Optional. Executes the command on all devices of a spec-ified type•<DEVICE-TYPE> – Specify the device type. The options are: AP6521,AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562,AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432,AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, andVX9000. The startup configuration is erased on all devices of the typespecified here. For example, if AP6521 is the device-type specified, thecommand is executed on all AP6521s within the specified RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-207.png)

![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 793.1.29 file-syncPrivileged Exec Mode CommandsSyncs trustpoint and/or EAP-TLS X.509 (PKCS#12) certificate between the staging-controller and adopted access points. When enabling file syncing, consider the following points:• The X.509 certificate needs synchronization only if the access point is configured to use EAP-TLS authentication.• Execute the command on the controller adopting the access points.• Ensure that the X.509 certificate file is installed on the controller.Syncing of trustpoint/wireless-bridge certificate can to be automated. To automate file syncing, in the controller’s device/profile configuration mode, execute the following command: file-sync [auto|count <1-20>]. For more information, see file-sync.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxfile-sync [cancel|load-file|trustpoint|wireless-bridge]file-sync cancel [trustpoint|wireless-bridge]file-sync cancel [trustpoint|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all]]file-sync load-file [trustpoint|wireless-bridge]]file-sync load-file [trustpoint <TRUSTPOINT-NAME>|wireless-bridge] <URL>file-sync [trustpoint <TRUSTPOINT-NAME>|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all] {from-controller}] {reset-radio|upload-time <TIME>}Parameters• file-sync cancel [trustpoint|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all]]file-sync cancel [trustpoint|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all]]Cancels scheduled file synchronization• trustpoint – Cancels scheduled trustpoint synchronization on a specified AP, all APs, or APs within a specified RF Domain• wireless-bridge – Cancels scheduled wireless-bridge certificate synchronization on a specified AP, all APs, or APs within a specified RF Domain• <DEVICE-NAME> – Cancels scheduled trustpoint/certificate synchronization on aspecified AP. Specify the AP’s hostname or MAC address.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-209.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 80• file-sync load-file [trustpoint|wireless-bridge] <URL>• file-sync [trustpoint <TRUSTPOINT-NAME>|wireless-bridge] [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all] {from-controller}] {reset-radio|upload-time <TIME>}• all – Cancels scheduled trustpoint/certificate synchronization on all APs• rf-domain [<DOMAIN-NAME>|all] – Cancels scheduled trustpoint/certificate syn-chronization on all APs in a specified RF Domain or in all RF Domains• <DOMAIN-NAME> – Cancels scheduled trustpoint/certificate synchronization onall APs within a specified RF Domain. Specify the RF Domain’s name.• all – Cancels scheduled trustpoint/certificate synchronization on all RF Domainsfile-sync load-file [trustpoint|wireless-bridge] <URL>Loads the following files on to the staging controller:• trustpoint – Loads the trustpoint, including CA certificate, server certificate and private key• wireless-bridge – Loads the wireless-bridge certificate to the staging controllerUse this command to load the certificate to the controller before scheduling or initiating a certificate synchronization.• <URL> – Provide the trustpoint/certificate location using one of the following for-mats:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileNote: Both IPv4 and IPv6 address types are supported.file-sync trustpoint <TRUSTPOINT-NAME> [<DEVICE-NAME>|all|rf-domain [<DOMAIN-NAME>|all] from-controller]Configures file-syncing parameters• trustpoint <TRUSTPOINT-NAME> – Syncs a specified trustpoint between controller and its adopted APs• <TRUSTPOINT-NAME> – Specify the trustpoint name.• wireless-bridge – Syncs wireless-bridge certificate between controller and its adopted APsAfter specifying the file that is to be synced, configure following file-sync parameters:• <DEVICE-NAME> – Syncs trustpoint/certificate with a specified AP. Specify the AP’shostname or MAC address.• all – Syncs trustpoint/certificate with all APs• rf-domain [<DOMAIN-NAME>|all] from-controller – Syncs trustpoint/certificate withall APs in a specified RF Domain or in all RF Domains• <DOMAIN-NAME> – Select to sync with APs within a specified RF Domain. Specifythe RF Domain’s name.• all – Select to sync with APs across all RF Domains• from-controller – Optional. Loads certificate to the APs from the adoptingcontroller and not the RF Domain managerAfter specifying the access points, specify the following options: reset-radio and upload-time.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-210.png)


![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 833.1.31 join-clusterPrivileged Exec Mode CommandsAdds a device (access point, wireless controller, or service platform), as cluster member, to an existing cluster of devices. Assign a static IP address to the device before adding to a cluster. Note, a cluster can be only formed of devices of the same model type.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxjoin-cluster <IP> user <USERNAME> password <WORD> {level|mode}join-cluster <IP> user <USERNAME> password <WORD> {level [1|2]|mode [active|standby]}Parameters• join-cluster <IP> user <USERNAME> password <WORD> {level [1|2]|mode [active|standby]}Usage GuidelinesTo add a device to an existing cluster:• configure a static IP address on the device (access point, wireless controller, or service platform).• provide username and password for superuser, network admin, system admin, or operator accounts.After adding the device to a cluster, execute the “write memory” command to ensure the configuration persists across reboots.Examplerfs6000-81742D#join-cluster 192.168.13.16 user admin password superuser level 1 mode standby... connecting to 192.168.13.16... applying cluster configuration... committing the changes... saving the changes[OK]rfs6000-81742D#join-cluster Adds a access point, wireless controller, or service platform to an existing cluster<IP> Specify the cluster member’s IP address.user <USERNAME> Specify a user account with super user privileges on the new cluster member.password <WORD> Specify password for the account specified in the user parameter.level [1|2] Optional. Configures the routing level• 1 – Configures level 1 routing• 2 – Configures level 2 routingmode [active|standby] Optional. Configures the cluster mode• active – Configures cluster mode as active• standby – Configures cluster mode as standby](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-213.png)
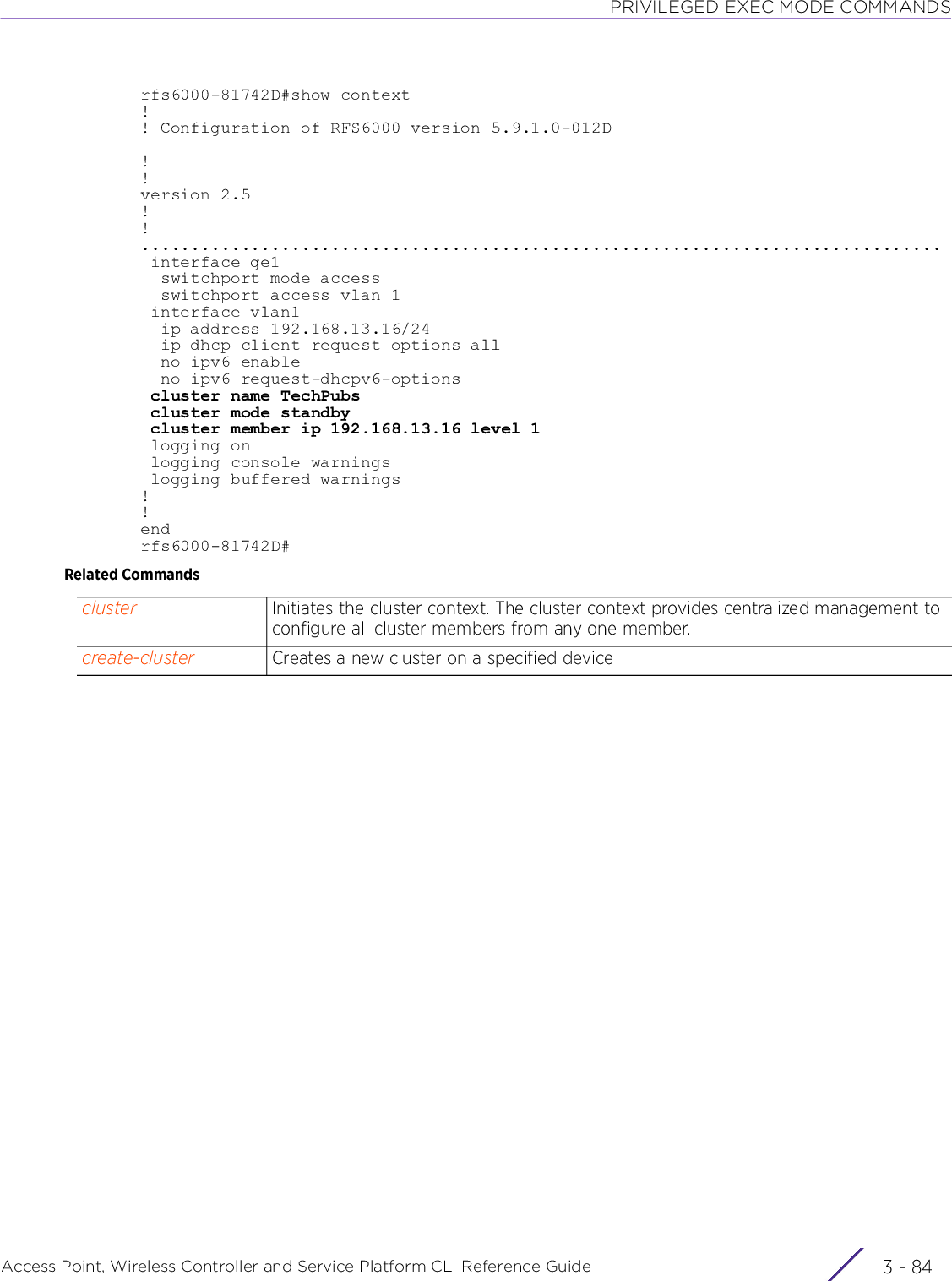
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 853.1.32 l2tpv3Privileged Exec Mode CommandsEstablishes or brings down an L2TPv3 tunnelSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxl2tpv3 tunnel [<TUNNEL-NAME>|all]l2tpv3 tunnel <TUNNEL-NAME> [down|session|up]l2tpv3 tunnel <TUNNEL-NAME> [down|up] {on <DEVICE-NAME>}l2tpv3 tunnel <TUNNEL-NAME> session <SESSION-NAME> [down|up] {on <DEVICE-NAME>}l2tpv3 tunnel all [down|up] {on <DEVICE-NAME>}Parameters• l2tpv3 tunnel <TUNNEL-NAME> [down|up] {on <DEVICE-NAME>}• l2tpv3 tunnel <TUNNEL-NAME> session <SESSION-NAME> [down|up] {on <DEVICE-NAME>}• l2tpv3 tunnel all [down|up] {on <DEVICE-NAME>}l2tpv3 tunnel<TUNNEL-NAME> [down|up]Establishes or brings down an L2TPv3 tunnel• <TUNNEL-NAME> – Specify the tunnel name.• down – Brings down the specified tunnel• up – Establishes the specified tunnelon <DEVICE-NAME> Optional. Establishes or brings down a tunnel on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.l2tpv3 tunnel <TUNNEL-NAME>Establishes or brings down an L2TPv3 tunnel• <TUNNEL-NAME> – Specify the tunnel name.session <SESSION-NAME> [down|up]Establishes or brings down a session in the specified tunnel• <SESSION-NAME> – Specify the session name.• down – Brings down the specified tunnel session• up – Establishes the specified tunnel sessionon <DEVICE-NAME> Optional. Establishes or brings down a tunnel session on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.l2tpv3 tunnel Establishes or brings down a L2TPv3 tunnelall [down|up] Establishes or brings down all L2TPv3 tunnels• down – Brings down all tunnels• up – Establishes all tunnels](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-215.png)

![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 893.1.34 mintPrivileged Exec Mode CommandsUses MiNT protocol to perform a ping and traceroute to a remote deviceSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmint [ping|traceroute]mint ping <MINT-ID> {count <1-10000>|size <1-64000>|timeout <1-10>}mint traceroute <MINT-ID> {destination-port <1-65535>|max-hops <1-255>|source-port <1-65535>|timeout <1-255>}Parameters• mint ping <MINT-ID> {count <1-10000>|size <1-64000>|timeout <1-10>}• mint traceroute <MINT-ID> {destination-port <1-65535>|max-hops <1-255>|source-port <1-65535>|timeout <1-255>}ping <MINT-ID> Sends a MiNT echo message to a specified destination• <MINT-ID> – Specify the destination device’s MiNT ID.count <1-10000> Optional. Sets the pings to the MiNT destination• <1-10000> – Specify a value from 1 - 60. The default is 3.size <1-64000> Optional. Sets the MiNT payload size in bytes• <1-64000> – Specify a value from 1 - 640000 bytes. The default is 64 bytes.timeout <1-10> Optional. Sets a response time in seconds• <1-10> – Specify a value from 1 - 10 seconds. The default is 1 second.traceroute <MINT-ID>Prints the route packets trace to a device• <MINT-ID> – Specify the destination device’s MiNT ID.destination-port <1-65535>Optional. Sets the Equal-cost Multi-path (ECMP) routing destination port• <1-65535> – Specify a value from 1 - 65535. The default port is 45.max-hops <1-255> Optional. Sets the maximum number of hops a traceroute packet traverses in the forward direction• <1-255> – Specify a value from 1 - 255. The default is 30.source-port <1-65535>Optional.Sets the ECMP source port• <1-65535> – Specify a value from 1 - 65535. The default port is 45.timeout <1-255> Optional. Sets the minimum response time period• <1-255> – Specify a value from 1 - 255 seconds. The default is 30 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-219.png)
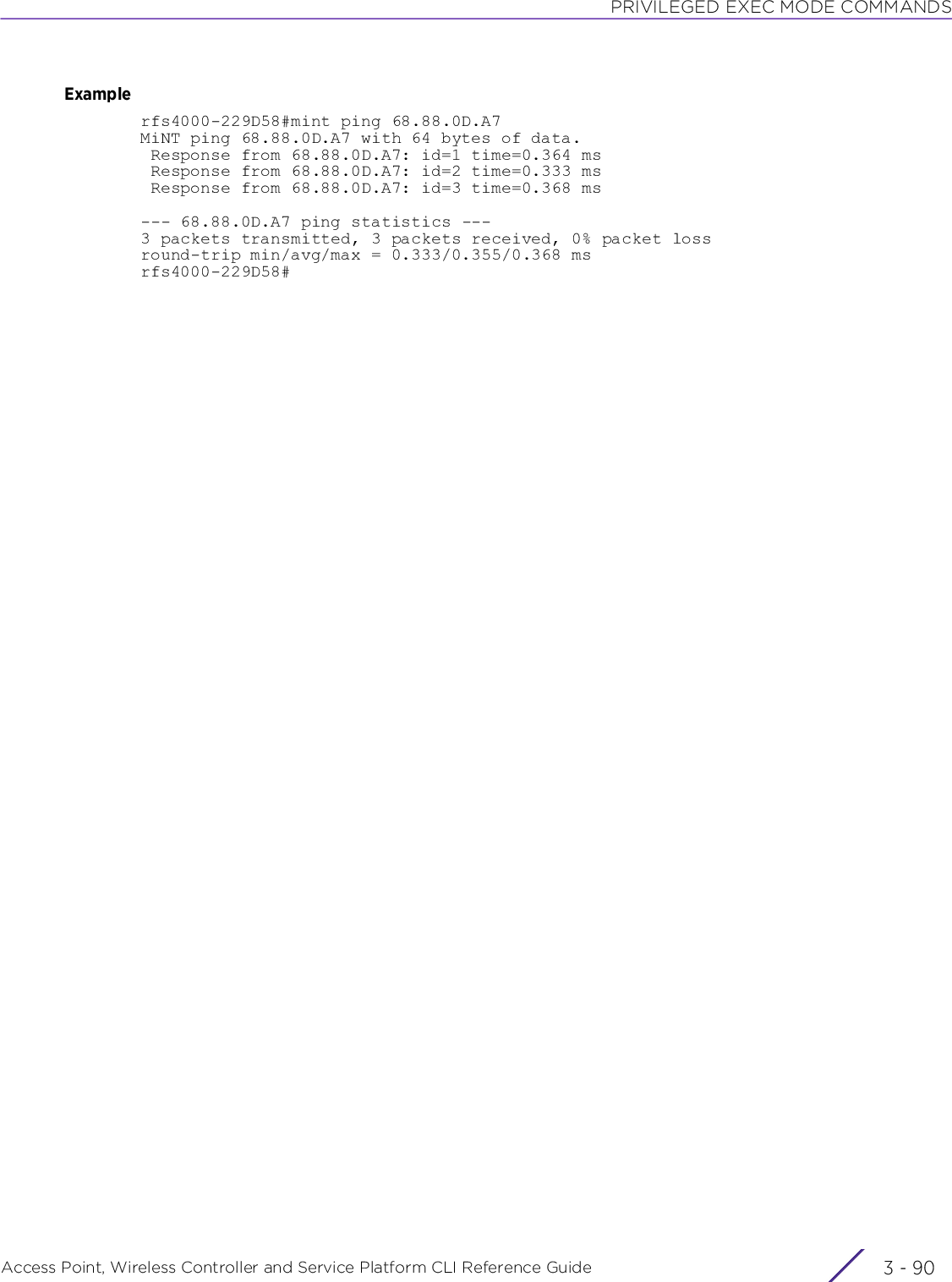
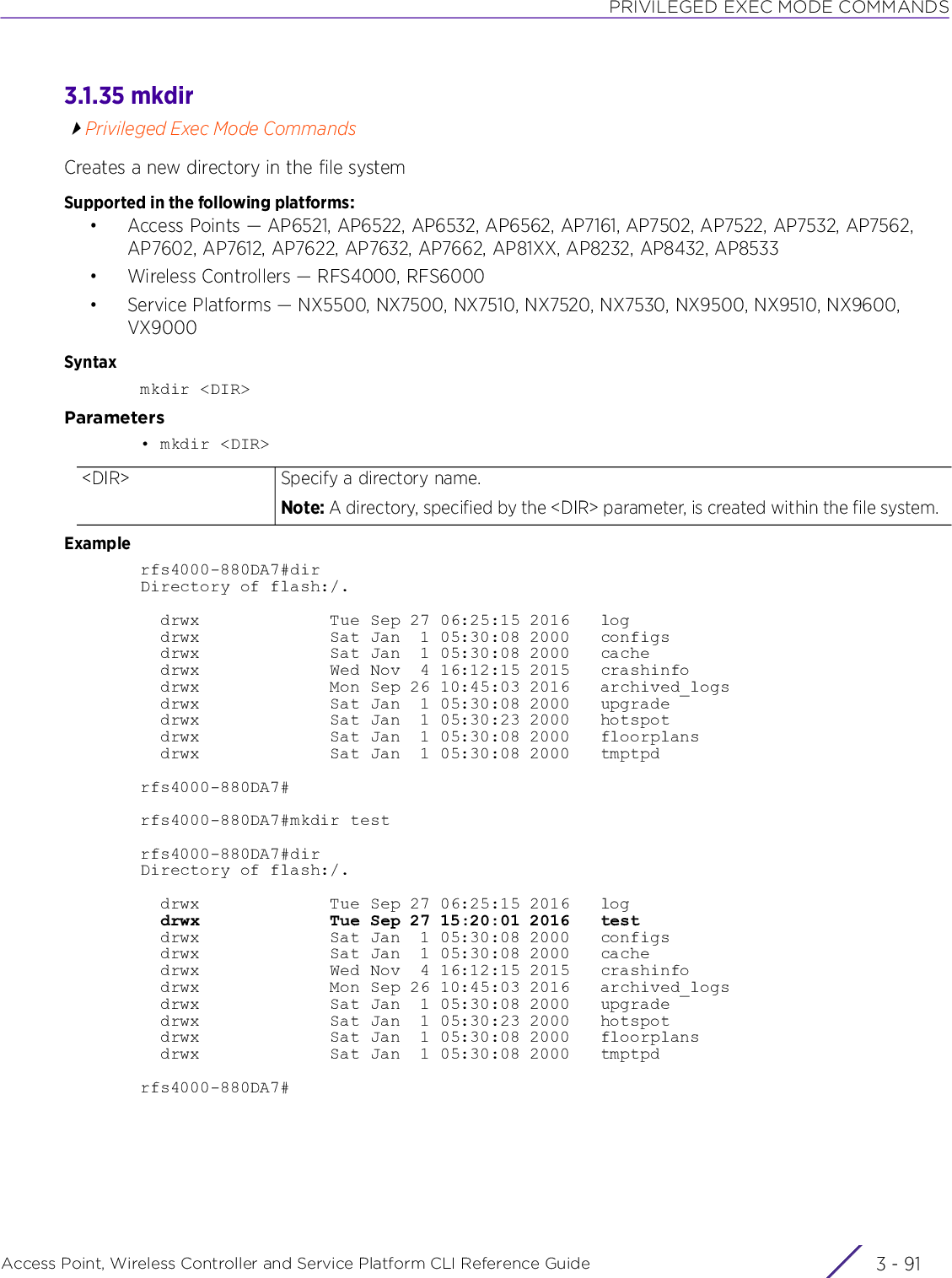
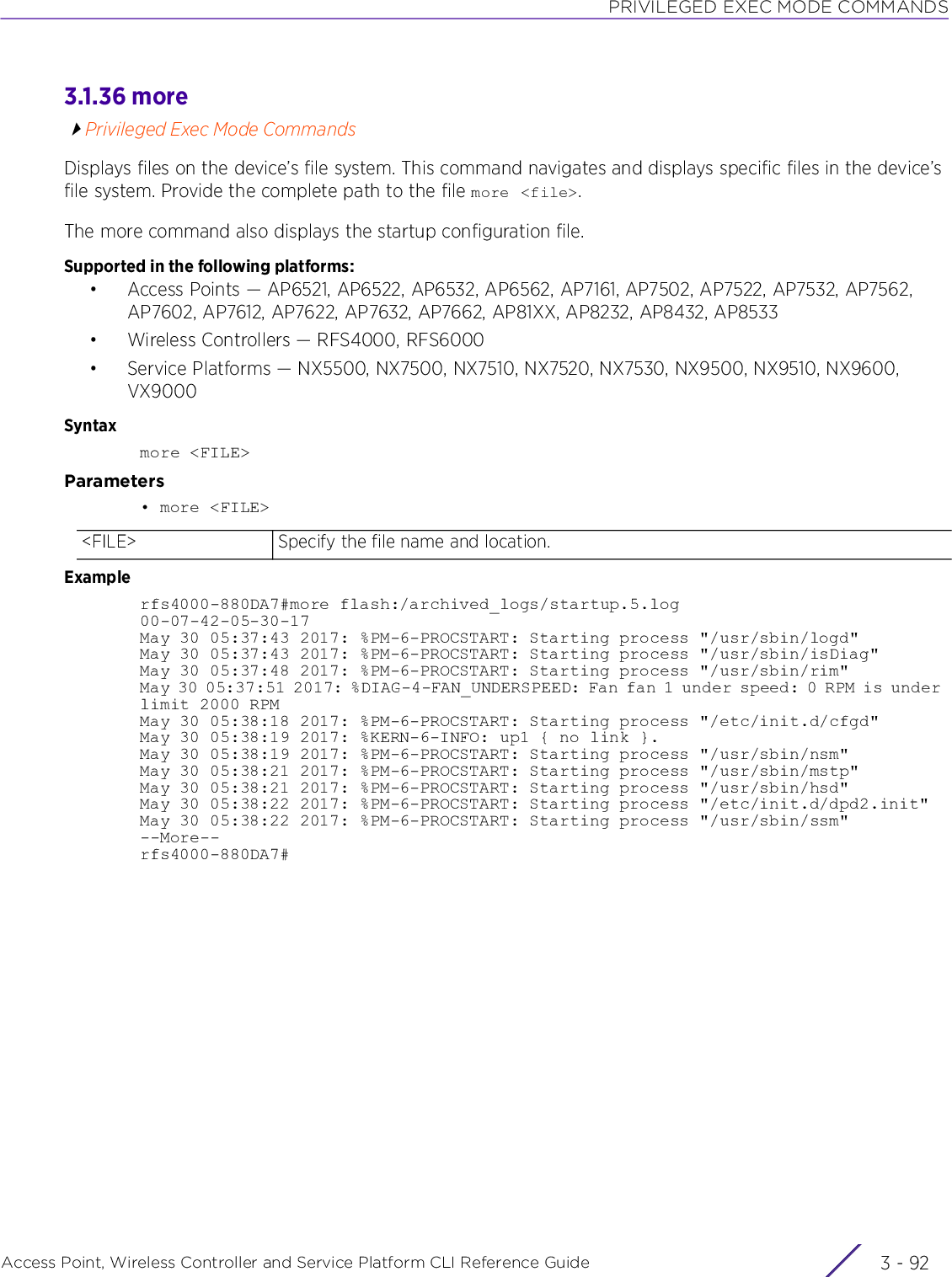
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 933.1.37 noPrivileged Exec Mode CommandsUse the no command to revert a command or a set of parameters to their default. This command is useful to turn off an enabled feature or to revert to default settings.The no commands have their own set of parameters that can be reset. These parameters depend on the context in which the command is being used.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [adoption|captive-portal|cpe|crypto|debug|logging|page|raid|service|terminal|upgrade|virtual-machine|wireless]no adoption {on <DEVICE-OR-DOMAIN-NAME>}no captive-portal client [captive-portal <CAPTIVE-PORTAL-NAME>|mac <MAC>] {on <DEVICE-OR-DOMAIN-NAME>}no crypto pki [server|trustpoint]no crypto pki [server|trustpoint] <TRUSTPOINT-NAME> {del-key {on <DEVICE-NAME>}| on <DEVICE-NAME>}no logging monitorno pageno service [block-adopter-config-update|locator|snmp|ssm|wireless]no service block-adopter-config-updateno service locator {on <DEVICE-NAME>}no service snmp sysoid wing5no service ssm trace pattern {<WORD>} {(on <DEVICE-NAME>)}no service wireless [trace pattern {<WORD>} {(on <DEVICE-NAME>)}|unsanctioned ap air-terminate <BSSID> {on <DOMAIN-NAME>}]no terminal [length|width]no upgrade <PATCH-NAME> {on <DEVICE-NAME>}no wireless client [all|<MAC>]NOTE: The no > adoption command resets the adoption state of a specified device (and all devices adopted to it) or devices within a specified RF Domain. When executed without specifying the device or RF Domain, the command resets the adoption state of the logged device and all devices, if any, adopted to it.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-223.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 94no wireless client all {filter|on}no wireless client all {filter [wlan <WLAN-NAME>]}no wireless client all {on <DEVICE-OR-DOMAIN-NAME>} {filter [wlan <WLAN-NAME>]}no wireless client mac <MAC> {on <DEVICE-OR-DOMAIN-NAME>}The following command is available only on the NX95XX series service platforms:no cpe led cpe [<1-24>|all] {on <T5-DEVICE-NAME>}no virtual-machine assign-usb-ports {on <DEVICE-NAME>}no raid locateParameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.Examplerfs4000-229D58#no adoptionrfs4000-229D58#rfs6000-81742D#no pagerfs6000-81742D#no <PARAMETERS> Resets or reverts settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-224.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 953.1.38 onPrivileged Exec Mode CommandsExecutes the following commands in the RF Domain context: clrscr, do, end, exit, help, service, and showSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxon rf-domain [<RF-DOMAIN-NAME>|all] Parameters• on rf-domain [<RF-DOMAIN-NAME>|all]Examplenx9500-6C8809#on rf-domain TechPubsnx9500-6C8809(TechPubs)#nx9500-6C8809(TechPubs)#?on RF-Domain Mode commands: clrscr Clears the display screen do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system service Service Commands show Show running system informationnx9500-6C8809(TechPubs)#?nx9500-6C8809(TechPubs)#show adoption timeline on TechPubs/ap7562-84A224------------------------------------------------------------------------------------- AP-NAME RF-DOMAIN LAST-ADOPTION-TIMESTAMP ADOPTED-SINCE------------------------------------------------------------------------------------- nx9500-6C8809 TechPubs 2016-09-09 00:00:14 7 days 05:19:49 rfs4000-880DA7 TechPubs 2016-09-08 23:59:57 7 days 05:20:06 rfs6000-81742D TechPubs 2016-09-08 05:52:04 7 days 23:27:58-------------------------------------------------------------------------------------Total number of devices displayed: 3nx9500-6C8809(TechPubs)#on rf-domain [<RF-DOMAIN-NAME>|all]Enters the RF Domain context based on the parameter specified• <RF-DOMAIN-NAME> – Specify the RF Domain name. Enters the specified RF Domain context.• all – Specifies all RF Domains.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-225.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 963.1.39 opendnsPrivileged Exec Mode CommandsFetches the OpenDNS device_id from the OpenDNS site. Use this command to fetch the OpenDNS device_id. Once fetched, apply the device_id to WLANs that are to be OpenDNS enabled. OpenDNS is a free DNS service that enables swift Web navigation without frequent outages. It is more reliable than other available DNS services, and provides the following services: DNS query resolution, Web-filtering, protection against virus and malware attacks, performance enhancement, etc.This command is part of a set of configurations that are required to integrate WiNG devices with OpenDNS. When integrated, DNS queries going out of the WiNG device (access point, controller, or service platform) are re-directed to OpenDNS (208.67.220.220 or 208.67.222.222) resolvers that act as proxy DNS servers. For more information on enabling OpenDNS support, see Enabling OpenDNS Support.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxopendns [APIToken|username]opendns APIToken <OPENDNS-APITOKEN>opendns username <USERNAME> password <OPENDNS-PSWD> label <LABEL>Note, you can use either of the above commands to fetch the device_id from the OpenDNS site. Parameters• opendns APIToken <OPENDNS-APITOKEN>• opendns username <USERNAME> password <OPENDNS-PSWD> label <LABEL>opendns Fetches the device_id from the OpenDNS site using the OpenDNS API tokenAPIToken <OPENDNS-APITOKEN>Configures the OpenDNS APIToken. This is the token provided you by CISCO at the time of subscribing for their OpenDNS service.• <OPENDNS-APITOKEN> – Provide the OpenDNS API token (should be a valid token).For every valid OpenDNS API token provided a device_id is returned. Apply this device_id to WLANs that are to be OpenDNS enabled. Once applied, DNS queries originating from associating clients are appended with an additional 31 bytes of data (representing the device ID) at the end of the DNS packet. For information on configuring the device_id in the WLAN context, see opendns.opendns Fetches the device_id from the OpenDNS site using the OpenDNS credentialsusername <USERNAME>Configures the OpenDNS user name. This is your OpenDNS email ID provided by CISCO at the time of subscribing for their OpenDNS service.• <USERNAME> – Provide the OpenDNS user name (should be a valid OpenDNS username).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-226.png)

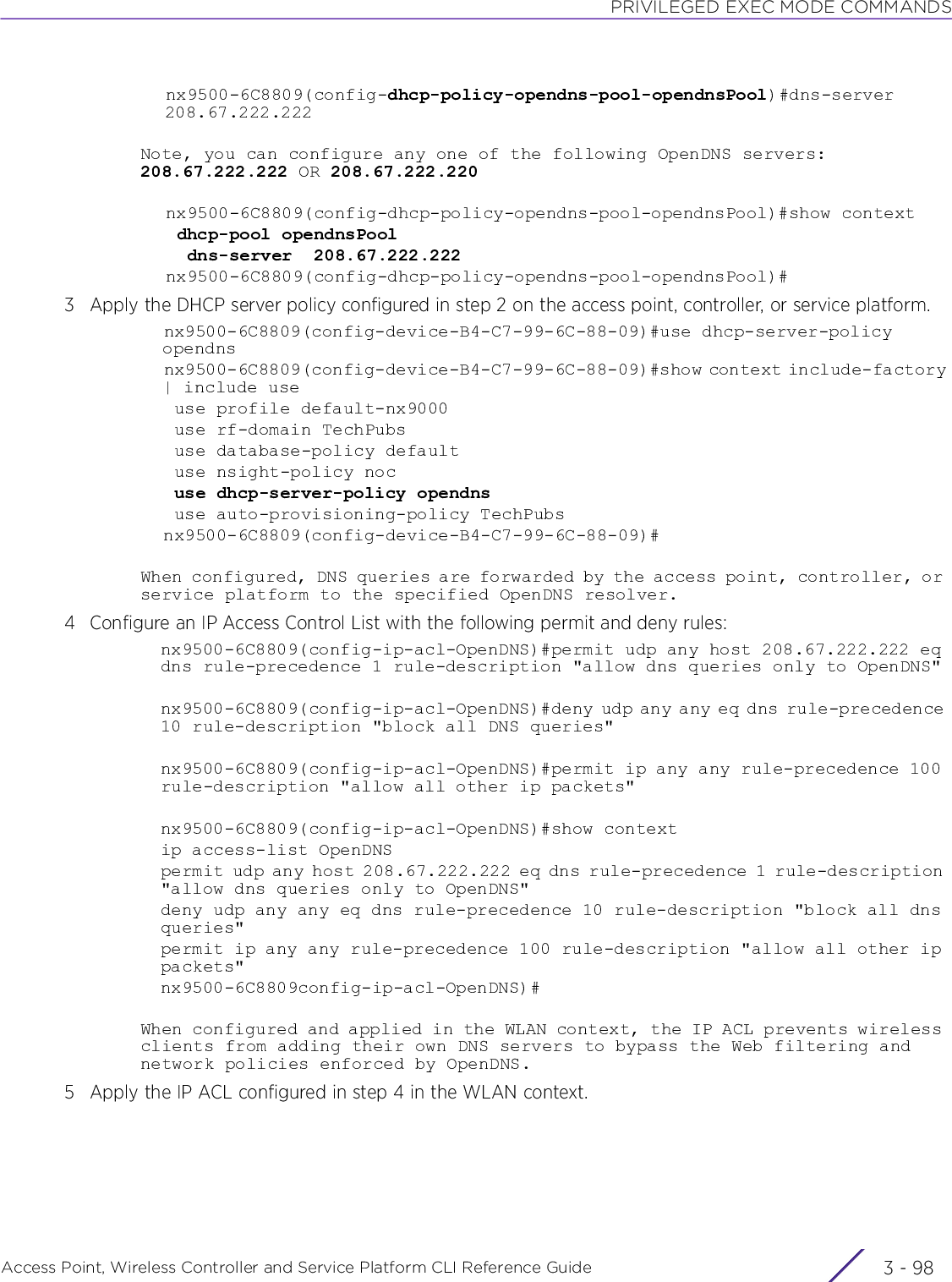
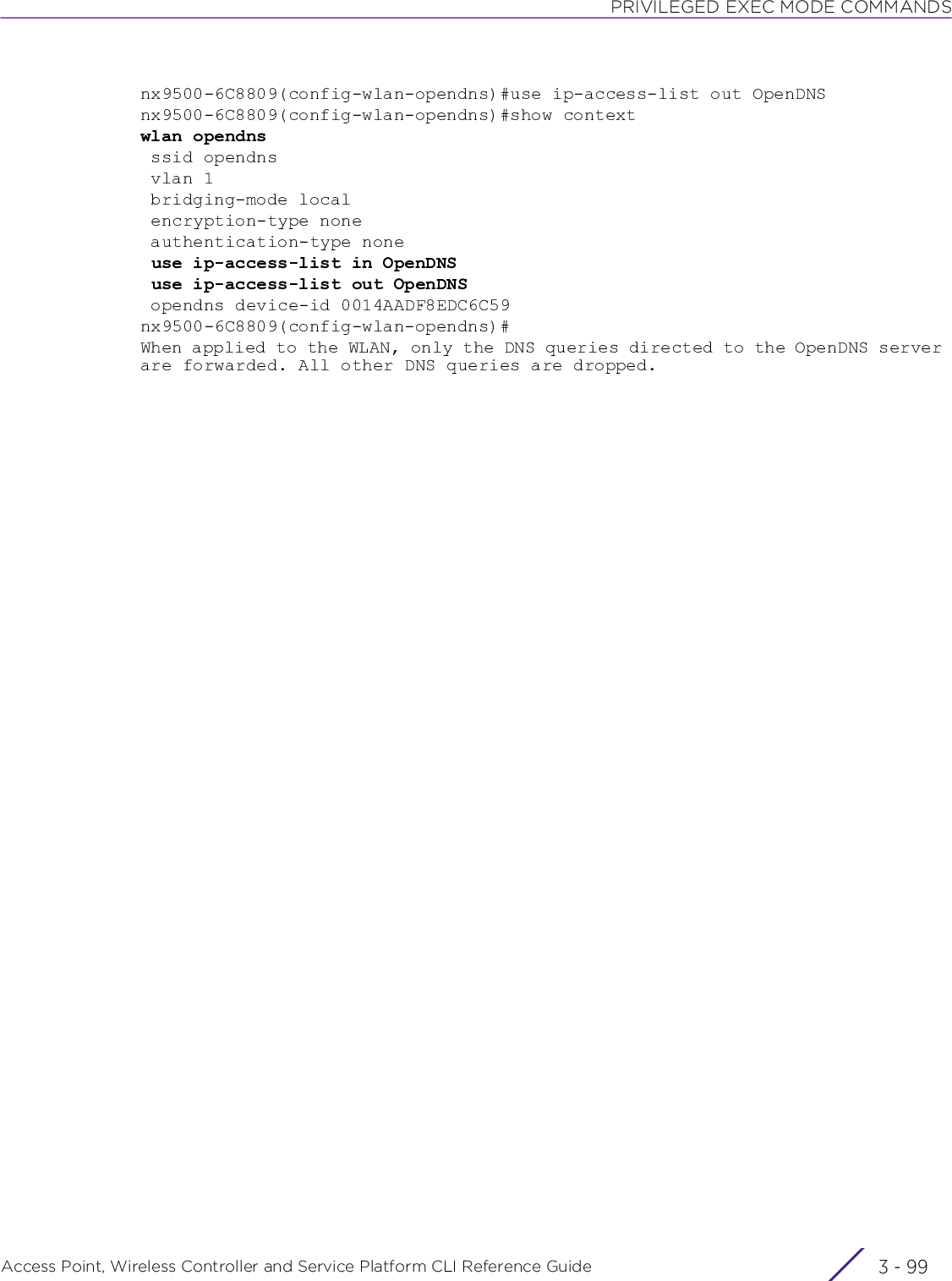
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1013.1.41 pingPrivileged Exec Mode CommandsSends Internet Controller Message Protocol (ICMP) echo messages to a user-specified locationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxping <IP/HOSTNAME> {count <1-10000>|dont-fragment {count|size}|size <1-64000>|source [<IP>|pppoe|vlan <1-4094>|wwan]}Parameters• ping <IP/HOSTNAME> {count <1-10000>|dont-fragment {count|size}|size <1-64000>|source [<IP>|pppoe|vlan <1-4094>|wwan]}<IP/HOSTNAME> Specify the destination IP address or hostname to ping. When entered without any parameters, this command prompts for an IP address or a hostname.count <1-10000> Optional. Sets the pings to the specified destination• <1-10000> – Specify a value from 1 - 10000. The default is 5.dont-fragment {count|size}Optional. Sets the dont-fragment bit in the ping packet. Packets with the dont-fragment bit specified, are not fragmented. When a packet, with the dont-fragment bit specified, exceeds the specified Maximum Transmission Unit (MTU) value, an error message is sent from the device trying to fragment it.• count <1-10000> – Sets the pings to the specified destination from 1 - 10000. The default is 5.• size – <1-64000> – Sets the size of ping payload size from 1 - 64000 bytes. The default is 100 bytes.size <1-64000> Optional. Sets the ping packet’s size in bytes• <1-64000> – Specify the ping payload size from 1 - 64000 bytes. The default is 100 bytes.source [<IP>|pppoe|vlan <1-4094>|wwan]Optional. Sets the source address or interface name. This is the source of the ICMP packet to the specified destination.• <IP> – Specifies the source IP address• pppoe – Selects the PPP over Ethernet interface• vlan <1-4094> – Selects the VLAN interface from 1 - 4094• wwan – Selects the wireless WAN interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-231.png)
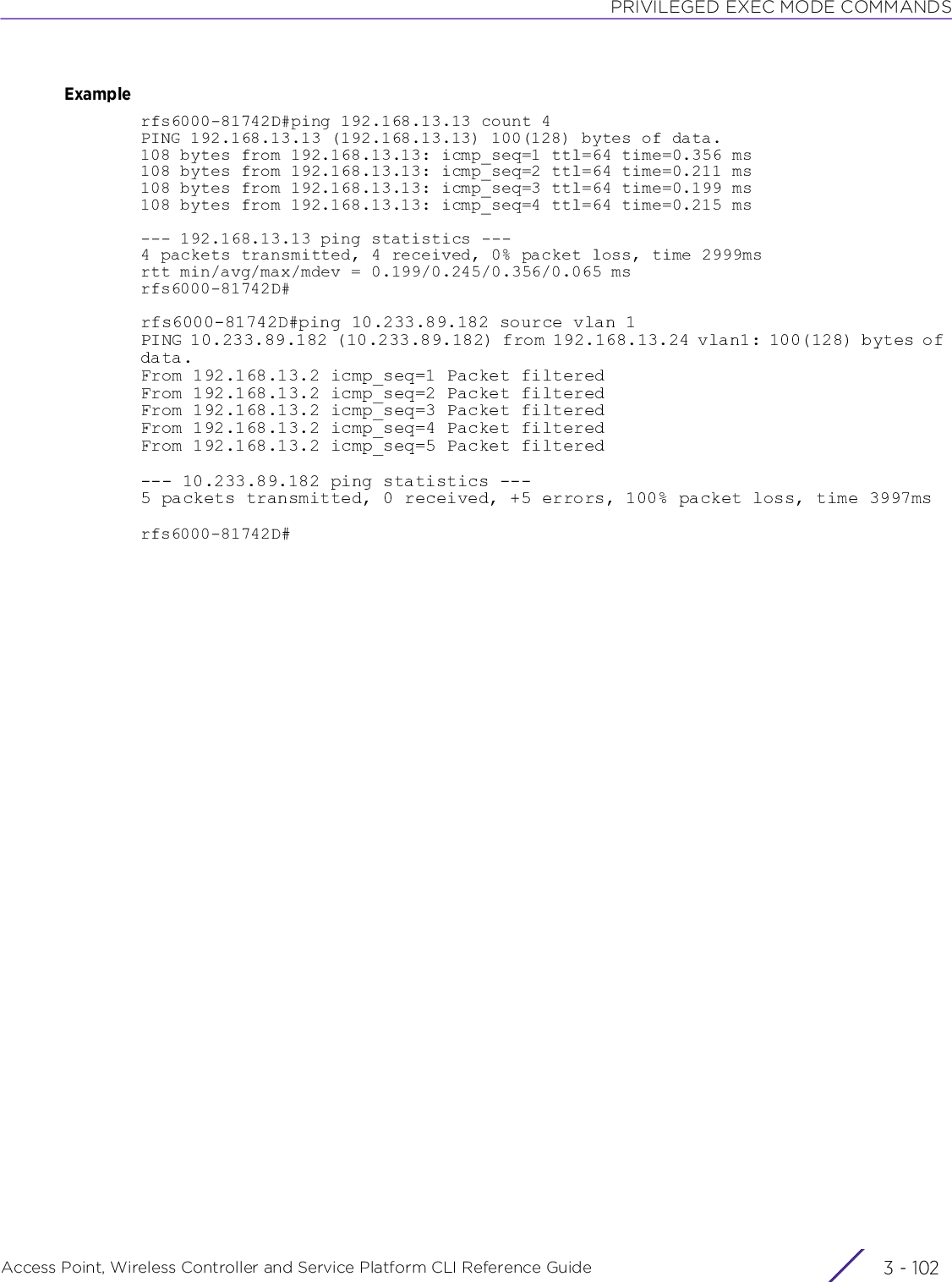




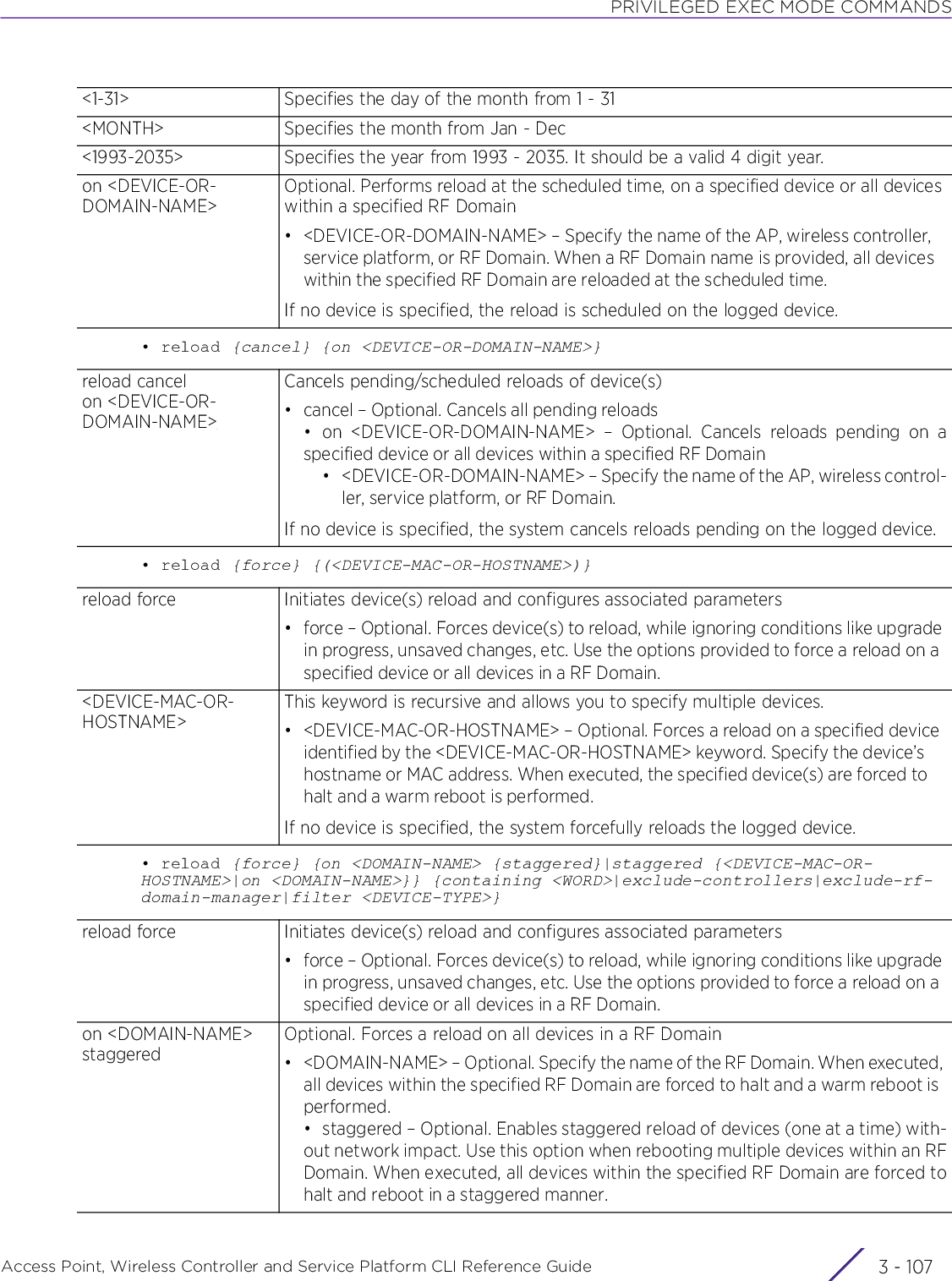




![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1153.1.50 t5Privileged Exec Mode CommandsExecutes following operations on a T5 device through the WiNG controller:• copy, rename, and delete files on the T5 device’s file system• write running configuration to the T5 device’s memoryThe T5 switch is a means of providing cost-effective, high-speed, wall-to-wall coverage across a building. The T5 switch leverages the in-building telephone lines to extend Ethernet and Wireless LAN networks without additional expenditure on re-wiring. This setup is ideally suited for hotels, providing high-speed Wi-Fi coverage to guest rooms.The entire setup consists of the DSL T5 switch, TW-510 Ethernet wallplates, and TW-511 wireless wallplate access points. Replace the phone jack plate in a room with the TW-511 delivers 802.11 a/b/g/n and extend wireless connectivity in that room and the neighboring rooms. These TW-511 wallplates (also referred to as the CPEs) are connected to the T5 switch over the DSL interface using a phone block.The T5 switch is adopted and managed through a WiNG controller. The connection between the T5 and WiNG switches is over a WebSocket.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxt5 [copy <SOURCE-FILE-NAME> <DEST-FILE-NAME>|delete <FILE-NAME>|rename <SOURCE-FILE-NAME> <DEST-FILE-NAME>|write memory] {on <T5-DEVICE-NAME>}Parameters• t5 [copy <SOURCE-FILE-NAME> <DEST-FILE-NAME>|delete <FILE-NAME>|rename <SOURCE-FILE-NAME> <DEST-FILE-NAME>|write memory] {on <T5-DEVICE-NAME>}NOTE: For more information on other T5 CPE related commands, see cpe.copy <SOURCE-FILE-NAME> <DEST-FILE-NAME>Copies file to an external server• <SOURCE-FILE-NAME> – Specify the source file name.• <DEST-FILE-NAME> – Specify the destination file name.The content from the source file is copied to the destination file.The source or destination files can be local or remote FTP or TFTP files. The source file also can be a pre-defined keyword. At least one of the files should be a local file. Use this command to copy the startup and/or running configurations to an external server.delete <FILE-NAME> Deletes files on the T5 device’s file system• <FILE-NAME> – Specify the file name. The specified file is deleted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-245.png)

![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1173.1.51 telnetPrivileged Exec Mode CommandsOpens a Telnet session between two network devicesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtelnet <IP/HOSTNAME> {<TCP-PORT>} {<INTF-NAME>}Parameters• telnet <IP/HOSTNAME> {<TCP-PORT>} {<INTF-NAME>}Usage GuidelinesTo exit the other device’s context, use the command relevant to that device.Examplenx9500-6C8809#telnet 192.168.13.22Entering character modeEscape character is '^]'.AP7131 release 5.9.0.0-012Dap7131-11E6C4 login: adminPassword:ap7131-11E6C4><IP/HOSTNAME> Configures the remote system’s IP (IPv4 or IPv6) address or hostname. The Telnet session will be established between the connecting system and the remote system.• <IP> – Specify the remote system’s IPv4 or IPv6 address or hostname.<TCP-PORT> Optional. Specify the Transmission Control Protocol (TCP) port.<INTF-NAME> Optional. Specify the interface name for the link local address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-247.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1183.1.52 terminalPrivileged Exec Mode CommandsSets the number of characters per line, and the number of lines displayed within the terminal windowSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxterminal [length|width] <0-512>Parameters• terminal [length|width] <0-512>Examplerfs6000-81742D#terminal length 150rfs6000-81742D#terminal width 215rfs6000-81742D#show terminalTerminal Type: xtermLength: 150 Width: 215rfs6000-81742D#Related Commandslength <0-512> Sets the number of lines displayed on the terminal window• <0-512> – Specify a value from 0 - 512.width <0-512> Sets the width or number of characters displayed on the terminal window• <0-512> – Specify a value from 0 - 512.no Resets the width of the terminal window or the number of lines displayed on a terminal window](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-248.png)


![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1223.1.56 upgradePrivileged Exec Mode CommandsUpgrades a device’s software imageSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxupgrade [<FILE>|<URL>|dhcp-vendor-options]upgrade [<FILE>|<URL>] {background|on <DEVICE-NAME>|on <RF-DOMAIN-NAME>}upgrade dhcp-vendor-options {<DEVICE-NAME>|on <RF-DOMAIN-NAME>}upgrade dhcp-vendor-options {<DEVICE-NAME>} {<DEVICE-NAME>}upgrade dhcp-vendor-options {on <RF-DOMAIN-NAME>} {containing <SUB-STRING>|exclude-controllers|exclude-rf-domain-managers|filter <DEVICE-TYPE>}Parameters• upgrade [<FILE>|<URL>] {background|on <DEVICE-NAME>|on <RF-DOMAIN-NAME>}<FILE> Specify the target firmware image location in the following format:cf:/path/fileusb1:/path/fileusb2:/path/fileusb<n>:/path/file<URL> Specify the target firmware image location. Use one of the following formats:IPv4 URLs:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/filecf:/path/fileusb<n>:/path/fileIPv6 URLs:tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filehttp://<hostname|[IPv6]>[:port]/path/filebackground Optional. Performs upgrade in the background](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-252.png)

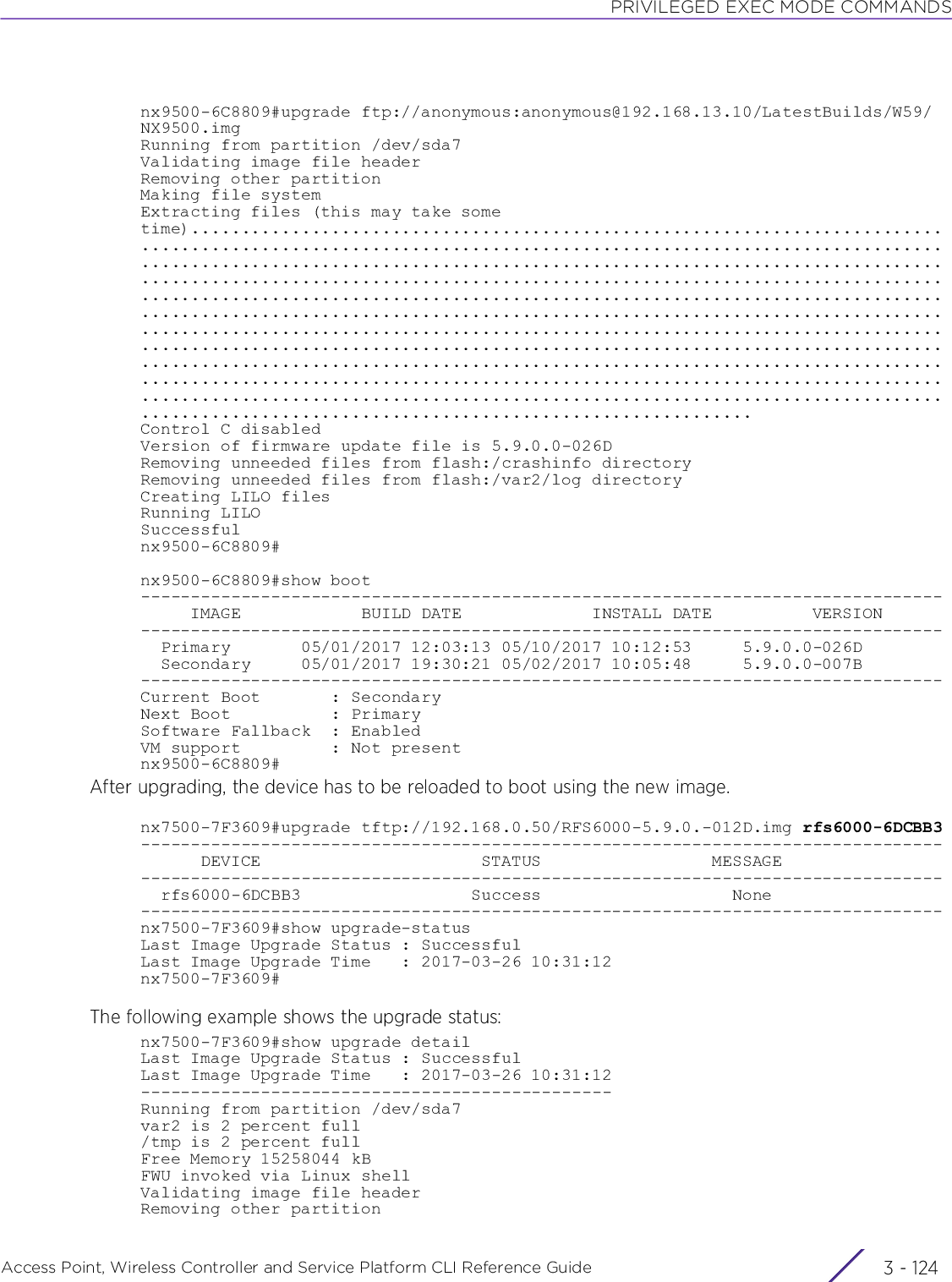
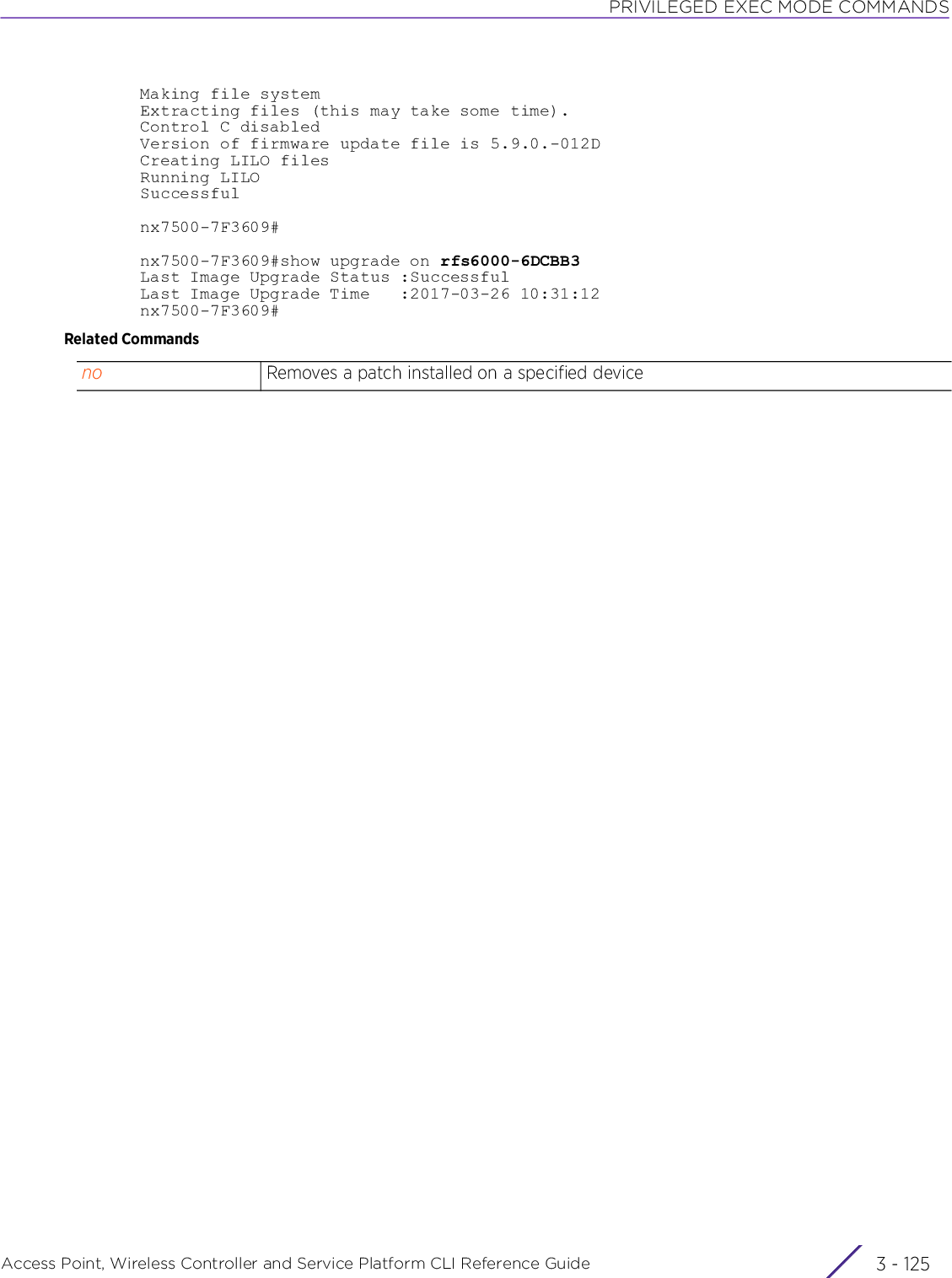

![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1273.1.58 virtual-machinePrivileged Exec Mode CommandsInstalls, configures, and monitors the status of virtual machines (VMs) installed on a WiNG controllerSupported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxvirtual-machine [assign-usb-ports|export|install|restart|set|start|stop|uninstall]virtual-machine assign-usb-ports team-vowlan {on <DEVICE-NAME>}virtual-machine export <VM-NAME> [<FILE>|<URL>] {on <DEVICE-NAME>}virtual-machine install [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}virtual-machine restart [<VM-NAME>|hard|team-urc|team-rls|team-vowlan]virtual-machine set [autostart|memory|vcpus|vif-count|vif-mac|vif-to-vmif|vnc]virtual-machine set [autostart [ignore|start]|memory <512-8192>|vcpus <1-4>|vif-count <0-2>|vif-mac <VIF-INDEX> <MAC-INDEX>|vif-to-vmif <VIF-INDEX> <VMIF-INDEX>| vnc [disable|enable]] [<VM-NAME>|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}The following virtual-machine commands are supported only on the VX9000 platform:virtual-machine volume-group [add-drive|replace-drive|resize-drive|resize-volume-group]virtual-machine volume-group [add-drive|replace-drive] <BLOCK-DEVICE-LABEL>virtual-machine volume-group replace-drive <BLOCK-DEVICE-LABLE> <NEW-BLOCK-DEVICE-LABEL>virtual-machine volume-group resize-volume-group <BLOCK-DEVICE-LABEL>Parameters• virtual-machine assign-usb-ports team-vowlan {on <DEVICE-NAME>}• virtual-machine export <VM-NAME> [<FILE>|<URL>] {on <DEVICE-NAME>}assign-usb-ports team-vowlan Assigns USB ports to TEAM-VoWLAN on a specified device•on <DEVICE-NAME> – Optional. Specify the device name.Note: Use the no > virtual-machine > assign-usb-ports to reassign the port to WiNG.Note: TEAM-RLS VM cannot be installed when USB ports are assigned to TEAM-VoWLAN.virtual-machine export Exports an existing VM image and settings. Use this command to export the VM to another <NX54XX> or <NX65XX> device in the same domain.• <VM-NAME> – Specify the VM name.• <FILE> – Specify the location and name of the source file (VM image). The VMimage is retrieved and exported from the specified location.• <URL> – Specify the destination location. This is the location to which the VM im-age is copied. Use one of the following formats to provide the destination path:Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-257.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 128• virtual-machine install [<VM-NAME>|adsp|team-centro|team-rls|team-vowlan] {on <DEVICE-NAME>}• virtual-machine set [autostart [ignore|start]|memory <512-8192>|vcpus <1-4>|vif-count <0-2>|vif-mac <VIF-INDEX> <MAC-INDEX>|vif-to-vmif <VIF-INDEX> <VMIF-INDEX>|vnc [disable|enable]] [<VM-NAME>|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/filehttp://<hostname|IP>[:port]/path/file•on <DEVICE-NAME> – Optional. Executes the command on a specified device or devices•<DEVICE-NAME> – Specify the service platform name. In case of multiple devices, listthe device names separated by commas.Note: The VM should be in a stop state during the export process.Note: If the destination is a device, the image is copied to a predefined location (VM archive).virtual-machine install Installs the VM. The install command internally creates a VM template, consisting of the specified parameters, and starts the installation process. Select one of the following options:• <VM-NAME> – Installs a VM having name specified by <VM-NAME> keyword.• adsp – Installs ADSP• team-centro – Installs the VM TEAM-Centro image• team-rls – Installs the VM TEAM-RLS image• team-vowlan – Installs the VM TEAM-VoWLAN imageSpecify the device on which to install the VM.• on <DEVICE-NAME> – Optional. Executes the command on a specified device or devices• <DEVICE-NAME> – Specify the service platform name. In case of multiple devices,list the device names separated by commas.virtual-machine set Configures the VM settings•autostart – Specifies whether to autostart the VM on system reboot• ignore – Enables autostart on each system reboot• start – Disables autostart• memory – Defines the VM memory size• <512-8192> – Specify the VM memory from 512 - 8192 MB. The default is 1024 MB.• vcpus – Specifies the number of VCPUS for this VM• <1-4> – Specify the number of VCPUS from 1- 4.• vif-count – Configures or resets the VM's VIFs• <0-2> – Specify the VIF number from 0 - 2.• vif-mac – Configures the MAC address of the selected virtual network interface• <1-2> – Select the VIF• <1-8> – Specify the MAC index for the selected VIF• <MAC> – Specify the customized MAC address for the selected VIF in the AA-BB-CC-DD-EE-FF format.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-258.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 129• virtual-machine start [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}Each VM has a maximum of two network interfaces (indexed 1 and 2, referred to as VIF). By default, each VIF is automatically assigned a MAC from the range allocated for that device. However, you can use the ‘set’ keyword to specify the MAC from within the allocated range. Each of these VIFs are mapped to a layer 2 port in the dataplane (referred to as VMIF). These VMIFs are standard l2 ports on the DP bridge, supporting all VLAN and ACL commands. The WiNG software supports up to a maximum of 8 VMIFs. By default, a VM’s interface is always mapped to VMIF1. You can map a VIF to any of the 8 VMIFs. Use the vif-to-vmif command to map a VIF to a VMIF on the DP bridge.•vif-to-vmif – Maps the virtual interface (1 or 2) to the selected VMIF interface. Specify the VMIF interface index from 1 - 8.WiNG provides a dataplane bridge for external network connectivity for VMs. VM Interfaces define which IP address is associated with each VLAN ID the service platform is connected to and enables remote service platform administration. Each custom VM can have up to a maximum of two VM interfaces. Each VM interface can be mapped to one of the twelve ports for <NX9500> on the dataplane bridge. This mapping determines the destination for service platform routing.By default, VM interfaces are internally connected to the dataplane bridge via VMIF1. VMIF1, by default, is an untagged port providing access to VLAN 1 to support the capability to connect the VM interfaces to any of the VMIF ports. This provides the flexibility to move a VM interface onto different VLANs as well as configure specific firewall and QoS rules.•vnc – Disables/enables VNC port option for an existing VM. When enabled, provides remote access to VGA through the noVNC client.•disable – Disables VNC port• enable – Enables VNC portAfter configuring the VM settings, identify the VM to apply the settings.• <VM-NAME> – Applies these settings to the VM identified by the <VM-NAME> keyword. Specify the VM name.• adsp – Applies these settings to the ADSP VM• team-urc – Applies these settings to the VM TEAM-URC• team-rls – Applies these settings to the VM TEAM-RLS• team-vowlan – Applies these settings to the VM TEAM-VoWLANvirtual-machine start Starts the VM, based on the parameters passed. Select one of the following options:• <VM-NAME> – Starts the VM identified by the <VM-NAME> keyword. Specify the VM name.• adsp – Starts the ADSP VM• team-urc – Starts the VM TEAM-URC• team-rls – Starts the VM TEAM-RLS• team-vowlan – Starts the VM TEAM-VoWLANThe following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Executes the command on a specified device or devices• <DEVICE-NAME> – Specify the service platform name. In case of multiple devic-es, list the device names separated by commas.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-259.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 130• virtual-machine stop [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}• virtual-machine uninstall [<VM-NAME>|adsp|team-urc|team-rls|team-vowlan] {on <DEVICE-NAME>}• virtual-machine volume-group [add-drive|resize-drive] <BLOCK-DEVICE-LABEL>]virtual-machine stop hardStops the VM, based on the parameters passed. Select one of the following options:• <VM-NAME> – Stops the VM identified by the <VM-NAME> keyword. Specify the VM name.• ADSP – Stops the ADSP VM• team-urc – Stops the VM TEAM-URC• team-rls – Stops the VM TEAM-RLS• team-vowlan – Stops the VM TEAM-VoWLANThe following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Executes the command on a specified device ordevices• <DEVICE-NAME> – Specify the service platform name. In case of multiple de-vices, list the device names separated by commas.Note: The option ‘hard’ forces the selected VM to shutdown.virtual-machine uninstallUninstalls the specified VM• <VM-NAME> – Uninstalls the VM identified by the <VM-NAME> keyword. Specify the VM name.•ADSP – Uninstalls the ADSP VM• team-urc – Uninstalls the VM TEAM-URC• team-rls – Uninstalls the VM TEAM-RLS• team-vowlan – Uninstalls the VM TEAM-VoWLANThe following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Executes the command on a specified device ordevices• <DEVICE-NAME> – Specify the service platform name. In case of multiple de-vices, list the device names separated by commas.Note: This command releases the VM’s resources, such as memory, VCPUS, VNC port, disk space, and removes the RF Domain reference from the system.virtual-machine volume-group [add-drive|resize-drive] <BLOCK-DEVICE-LABEL>]Enables provisioning of logical volume-groups on the VX9000 platform. Logical volume-groups are created on the primary storage device, allowing the database storage to be expanded to include additional storage drives. However, volume-groups can be provisioned only on new VX9000 installation and cannot be added to existing VX9000 installation.Note: The logical volume-group is supported only on a VX9000 running the WiNG 5.9.1 image.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-260.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 131• virtual-machine volume-group replace-drive <BLOCK-DEVICE-LABEL> <NEW-BLOCK-DEVICE-LABEL>]• virtual-machine volume-group resize-volume-group <BLOCK-DEVICE-LABEL>]• add-drive – Adds a new block-device to the VM. Note, currently a maximum of 3 (three) block devices can be added. To add a new drive, first halt the VM, In the Hypervisor, add a new storage disk to the VM and restart the VM. Once the VM comes up, use this command to add the new drive. To identify the new drive execute the show > virtual-machine > volume-group > status command.• resize-drive - Resizes a drive in the VM’s volume group. To increase the size of a drive in the volume-group, first halt the VM. In the Hypervisor, increase the size of the existing secondary storage drive and restart the VM. Once the VM comes up, use this command to resize the drive. To identify the drive with the additional free space, execute the show > virtual-machine > volume-group > status command.The following keyword is common to all of the above parameters:• <BLOCK-DEVICE-LABEL> –Specify the block-device label to be added or resizeddepending on the action being performed. virtual-machine volume-group replace-drive <BLOCK-DEVICE-LABEL> <NEW-BLOCK-DEVICE-LABEL>]Enables provisioning of VMs as logical volume-groups on the VX9000 platform. Logical volume-group VMs are created on the primary storage device, allowing the database storage to be expanded to include additional storage drives.• replace-drive – Replaces an existing block-device with a new block-device in a volume-group. To replace a drive in the volume-group, first halt the VM. In the Hypervisor, add the new drive and restart the VM. Once the VM comes up, use this command to replace an existing drive with the new drive. To identify the drive with the additional free space, execute the show > virtual-machine > volume-group > status command• <BLOCK-DEVICE-LABEL> –Specify the block-device label to be replaced.• <BLOCK-DEVICE-LABEL> – Specify the replacement block-device label.virtual-machine volume-group resize-volume-group <BLOCK-DEVICE-LABEL>]Enables provisioning of VMs as logical volume-groups on the VX9000 platform. Logical volume-group VMs are created on the primary storage device, allowing the database storage to be expanded to include additional storage drives• resize-volume-group – Adds drive space to an existing block-device in the volume-group• <BLOCK-DEVICE-LABEL> –Specify the block-device label to which additionaldrive space is to be provided](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-261.png)



![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 1353.1.61 raidPrivileged Exec Mode CommandsEnables Redundant Array of Independent Disks (RAID) managementRAID is a group of one or more independent, physical drives, referred to as an array or drive group, These physically independent drives are linked together and appear as a single storage unit or multiple virtual drives. Replacing a single, large drive system with an array, improves performance (input and output processes are faster) and increases fault tolerance within the data storage system. In an array, the drives can be organized in different ways, resulting in different RAID types. Each RAID type is identified by a number, which determines the RAID level. The common RAID levels are 0, 00, 1, 5, 6, 50 and 60. The WiNG MegaRAID implementation supports RAID-1, which provides data mirroring, but does not support data parity. RAID-1 consists of a two-drive array, where the data is simultaneously written on both drives, ensuring total data redundancy. In case of a drive failure the information on the other drive is used to rebuild the failed drive.An array is said to be degraded when one of its drives has failed. A degraded array continues to function and can be rebooted using the one remaining functional drive. When a drive fails, the chassis sounds an alarm (if enabled), and the CLI prompt changes to “RAID degraded”. The failed drive is automatically replaced with a hot spare (provided a spare is installed). The spare is used to re-build the array.Use this command to:• Verify the current array status• Start and monitor array consistency checks• Retrieve date and time of the last consistency check• Shut down drives before physically removing them• Install new drives• Assign drives as hot spares• Identify a degraded drive• Deactivate an alarm (triggered when a drive is removed from the array)Supported in the following platforms:• Service Platforms — NX7530, NX9500, NX9510Syntaxraid [check|install|locate|remove|silence|spare]raid [check|silence]raid [install|locate|remove|spare] drive <0-4>NOTE: RAID controller drive arrays are available within NX7530 and NX95XX series service platforms (NX9500 and NX9510 models) only. However, they can be administrated on behalf of a NX9500 profile by a different model service platform or controller. The NX9500 service platform includes a single Intel MegaRAID controller, configured to provide a single virtual drive. This virtual drive is of the RAID-1 type, and has a maximum of two physical drives. In addition to these two drives, there are three hot spares, which are used in case of a primary drive failure.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-265.png)
![PRIVILEGED EXEC MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 3 - 136Parameters• raid [check|silence]• raid [install|locate|remove|spare] drive <0-4>Examplenx9500-6C874D#raid install drive 0Error: Input Error: Drive 0 is already member of array, can't be addednx9500-6C874D#check Starts a consistency check on the RAID array. Use the show > raid command to view consistency check status.A consistency check verifies the data stored in the array. When regularly executed, it helps protect against data corruption, and ensures data redundancy. Consistency checks also warn of potential disk failures.silence Deactivates an alarmWhen enabled, an audible alarm is triggered when a drive in the array fails. The silence command deactivates the alarm (sound).Note: To enable RAID alarm, in the device configuration mode, use the raid > alarm > enable command. A NX9500 profile can also have the RAID alarm feature activated. For more information on the enabling RAID alarm, see raid.install <0-4> Installs a new drive, inserted in one of the available slots, in the array. Specify the drive number.Drives 0 and 1 are the array drives. Drives 2, 3, and 4 are the hot spare drives. You can include the new drive in a degraded array, or enable it as a hot spare.If the array is in a degraded state, the re-build process is triggered and the new drive is used to repair the degraded array.locate <0-4> Enables LEDs to blink on a specified drive. Specify the drive number.Blinking LEDs enable you correctly locate a drive.remove <0-4> Removes (shuts downs) a disk from the array, before it is physically removed from its slot. Specify the drive number containing the disk.Use this command to also remove a hot spare.spare <0-4> Converts an unused drive into a hot spare. Specify the drive number.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-266.png)
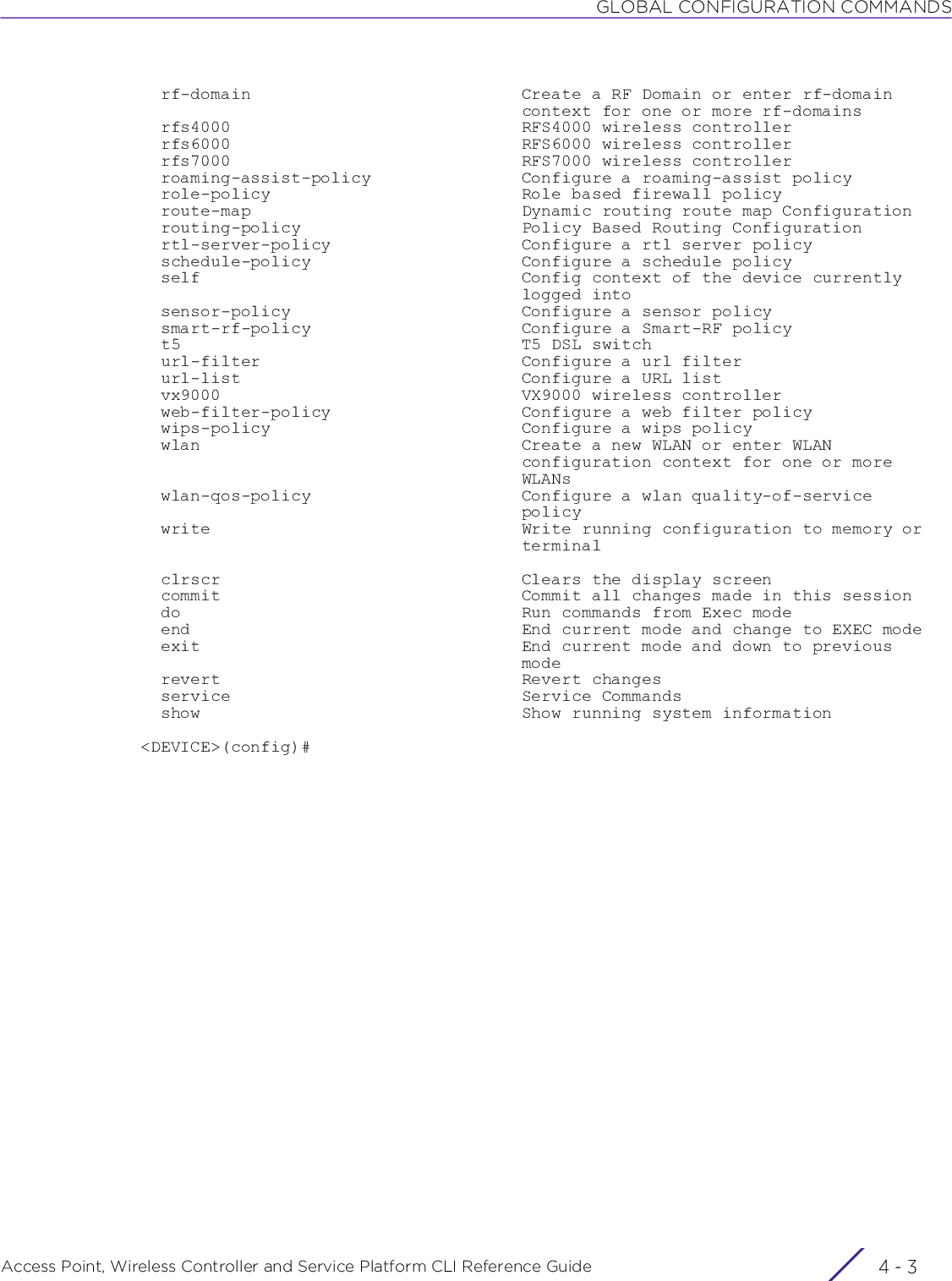
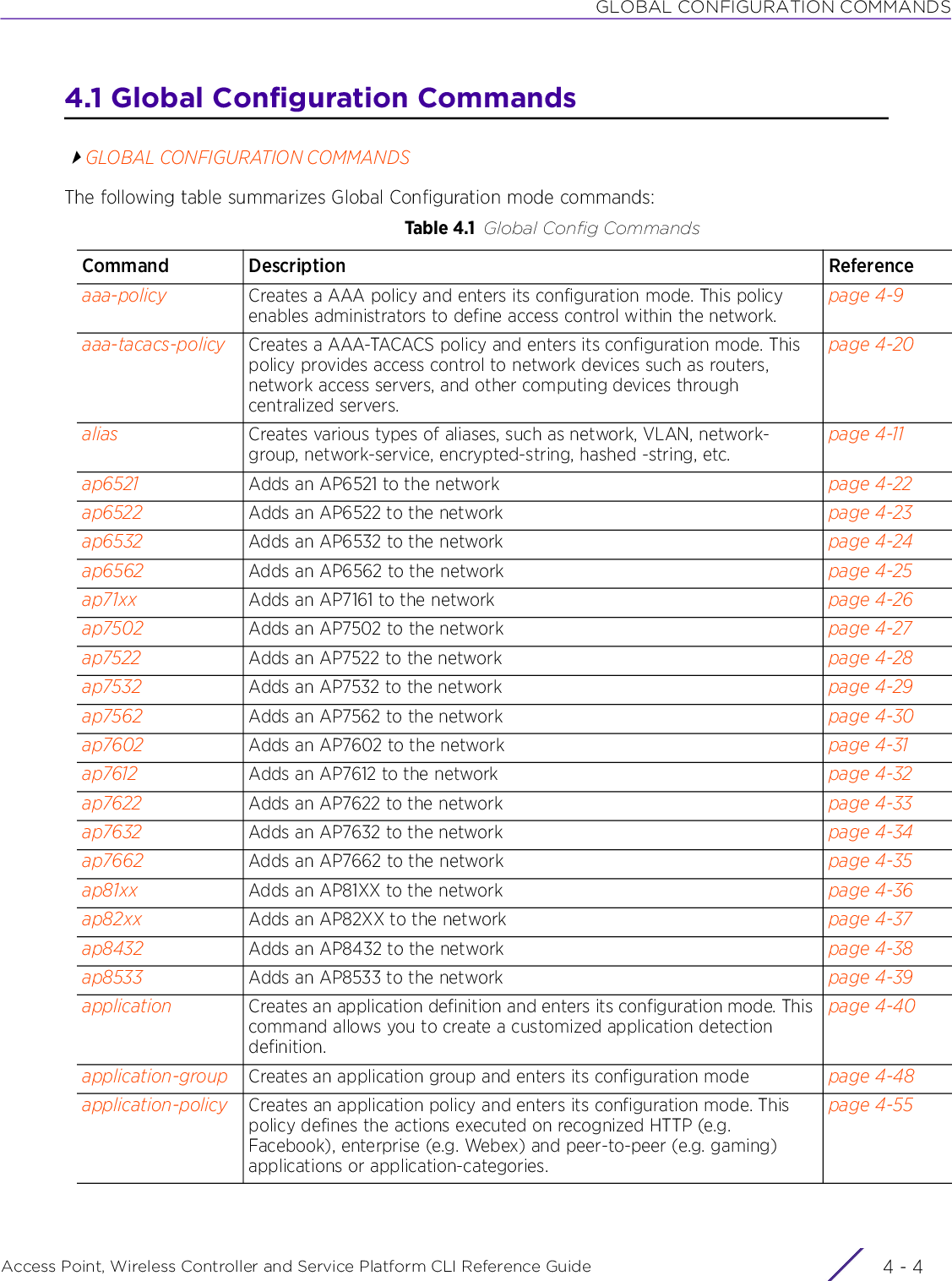
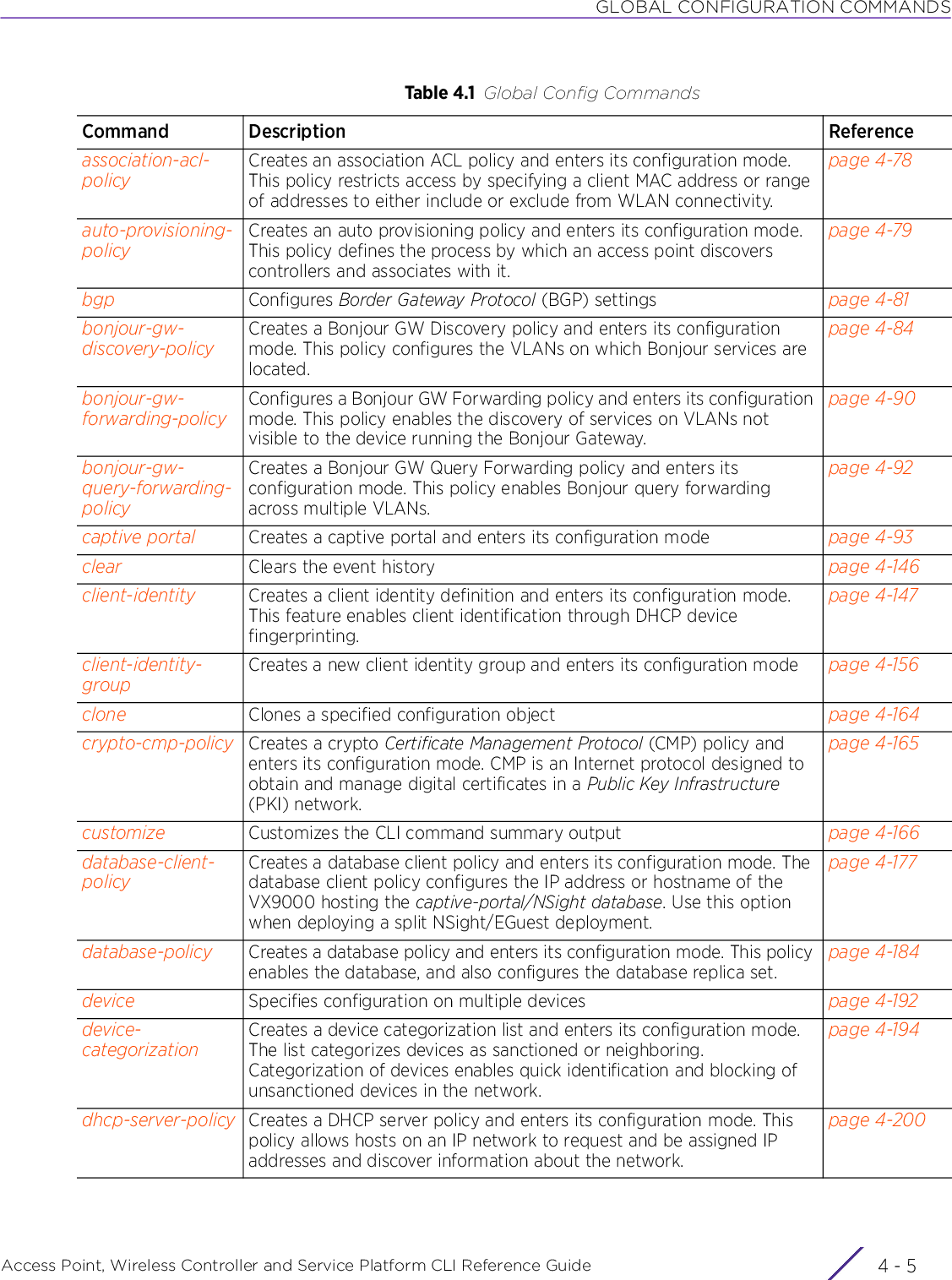
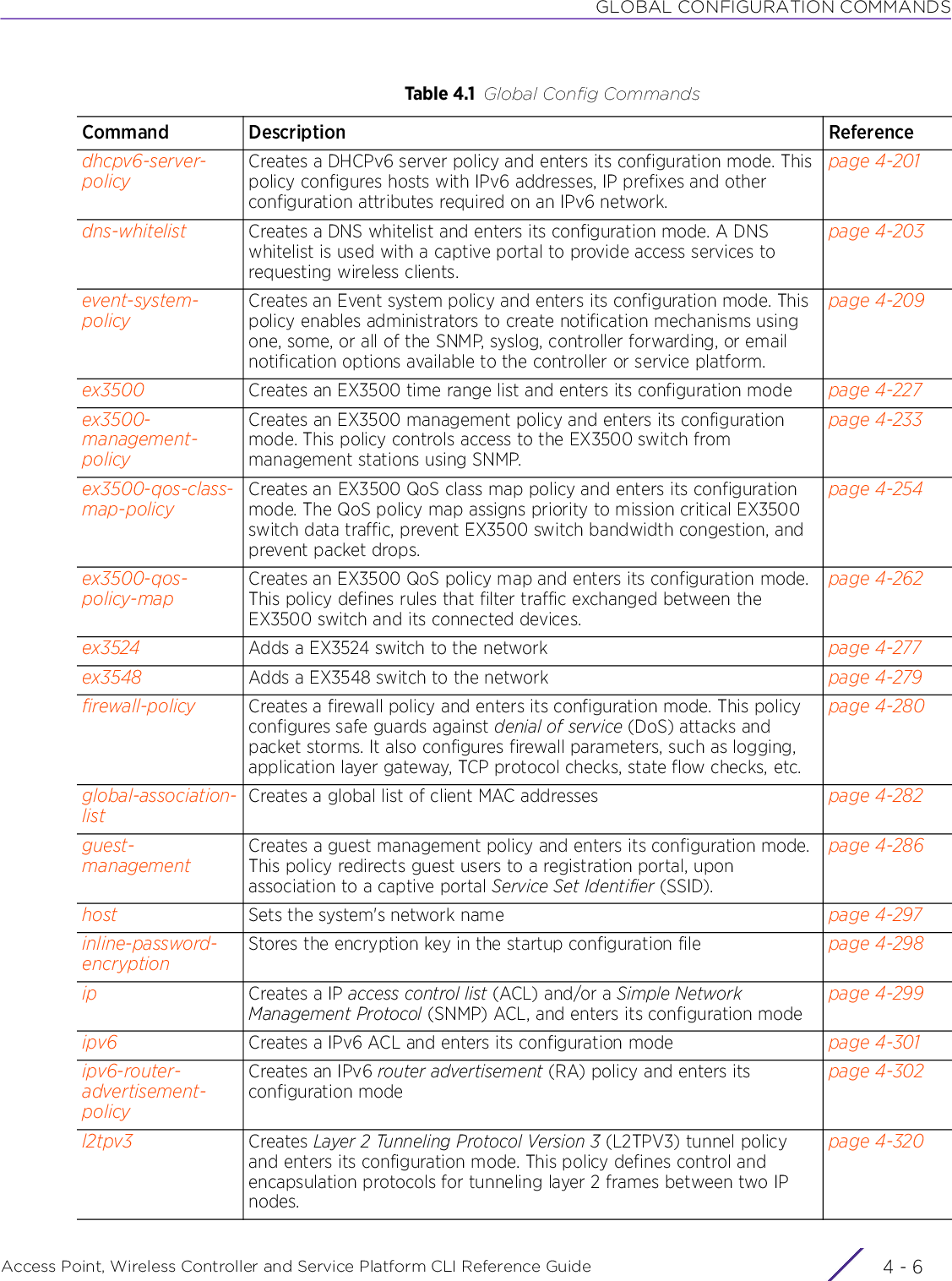
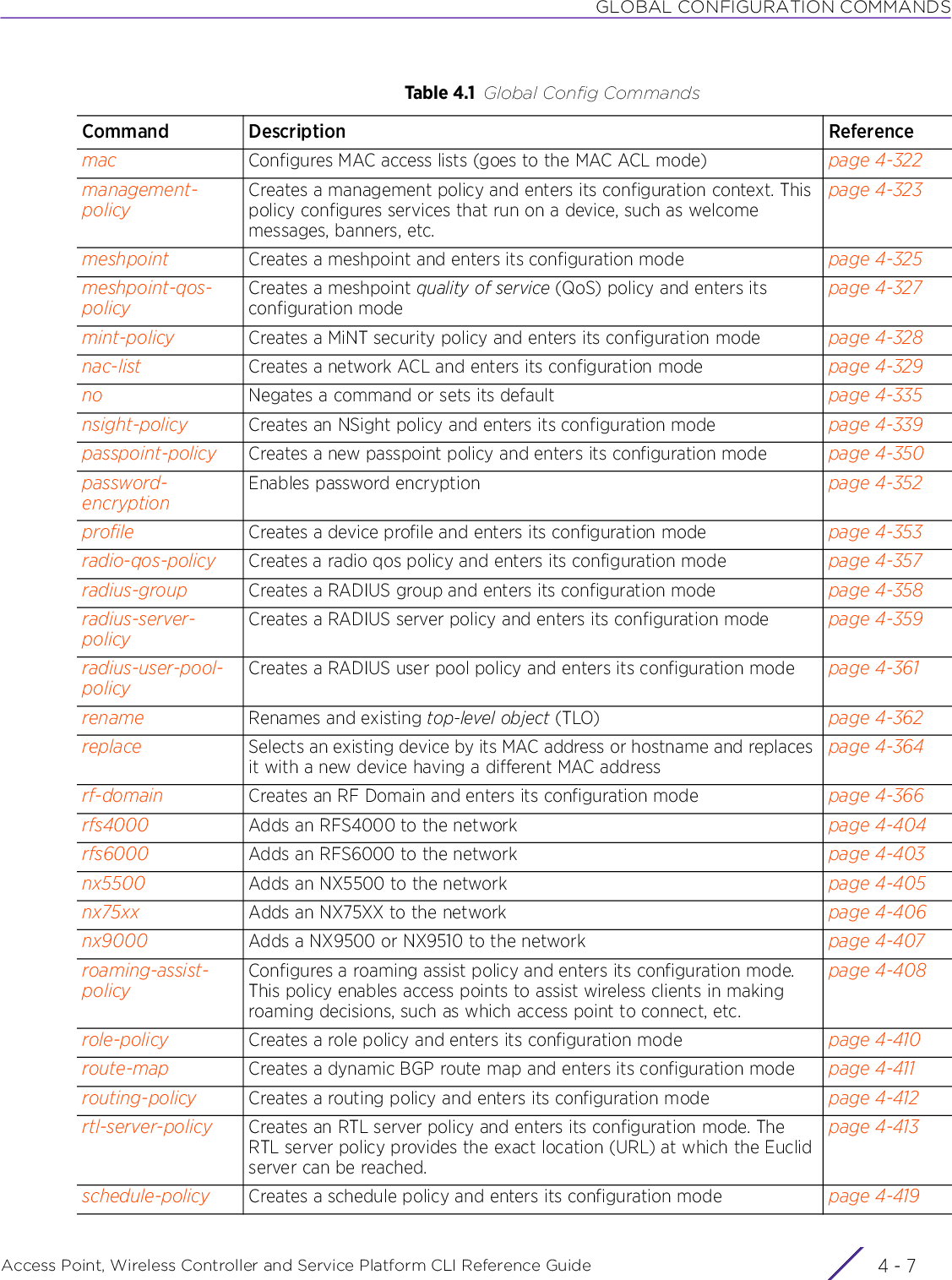

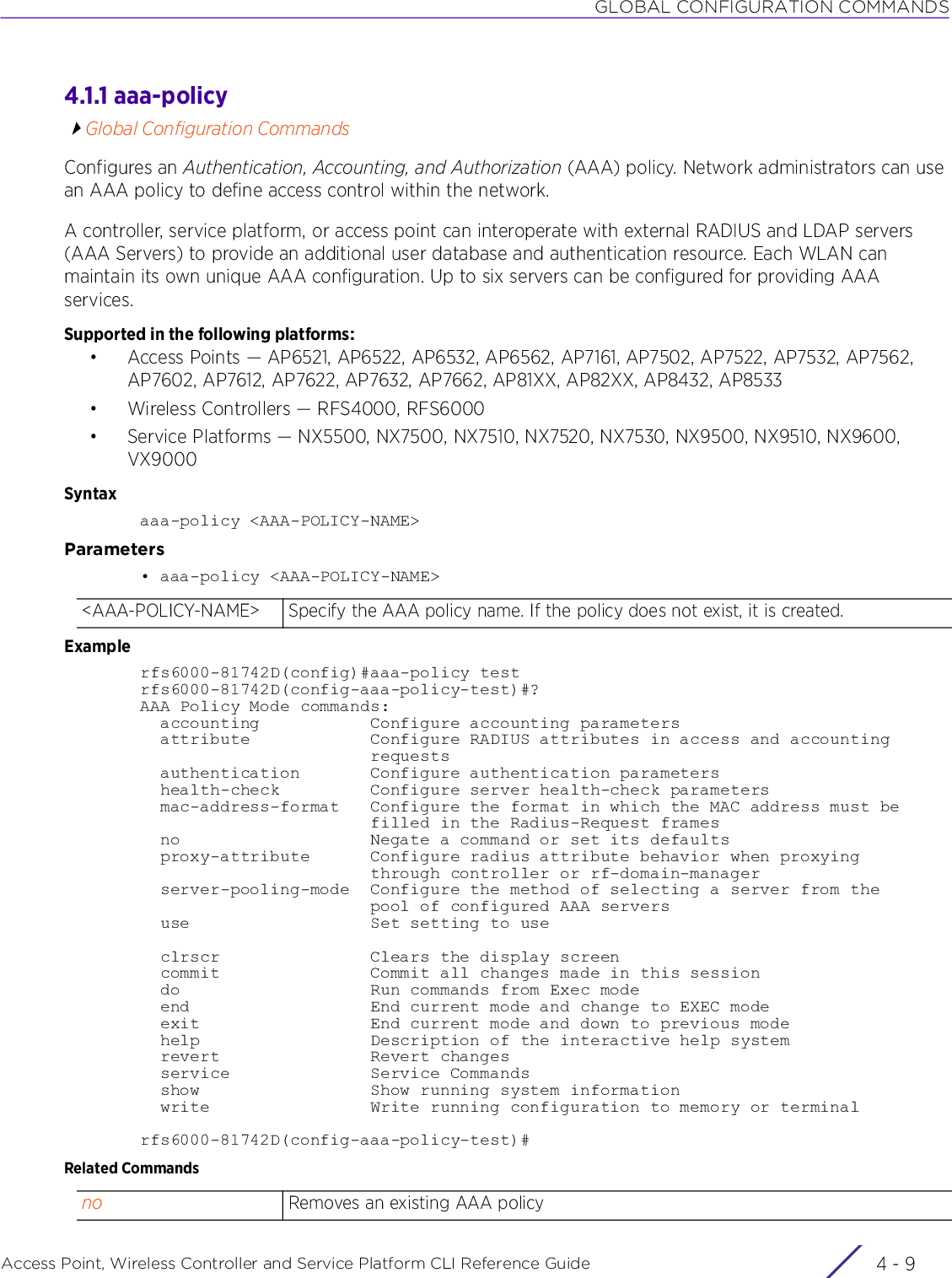


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 12A network-group alias can be used in IP firewall rules to substitute hosts, subnets, and IP address ranges.• network-service alias – Maps a user-friendly name to service protocols and ports. Both source and destination ports are configurable. For each protocol, up to 2 source port ranges and up to 2 destination port ranges can be configured. A maximum of 4 protocol entries can be configured per network-service alias. When used with an ACL, the network-service alias defines the service-specific components of the ACL rule. Overrides can be applied to the service alias, at the device level, without modifying the ACL. Application of overrides to the service alias allows an ACL to be used across sites.Use a network-service alias to associate more than one IP address to a network interface, providing multiple connections to a network from a single IP node.• number alias – Maps a user-friendly name to a number• vlan alias – Maps a user-friendly name to a VLAN ID. A VLAN alias can be used at different deployments. For example, if a named VLAN is defined as 10 for the central network, and the VLAN is set at 26 at a remote location, the VLAN can be overridden at the deployment location with an alias. At the remote deployment location, the network is functional with a VLAN ID of 26, but utilizes the name defined at the centrally managed network. A new VLAN need not be created specifically for the remote deployment.• string alias – Maps a user-friendly name to a specific string (for example, RF Domain name). A string alias can be utilized at different deployments. For example, if the main domain at a remote location is called loc1.domain.com and at another deployment location it is called loc2.domain.com, the alias can be overridden at the remote location to suit the local (but remote) requirement. At one remote location, the alias functions with the loc1.domain.com domain and at the other with the loc2.domain.com domain.• encrypted-string alias – Maps a user-friendly name to a string value. The string value of this alias is encrypted when "password-encryption" is enabled. Encrypted-string aliases can be used for string configuration parameters that are encrypted by the "password-encryption" feature.• hashed-string alias – Maps a user-friendly name to a hashed-string value. Hashed-string aliases can be used for string configuration parameters that are hashed, such as passwords.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxalias [address-range|encrypted-string|hashed-string|host|network|network-group|network-service|number|string|vlan]alias address-range <ADDRESS-RANGE-ALIAS-NAME> <STARTING-IP> to <ENDING-IP>alias encrypted-string <ENCRYPTED-STRING-ALIAS-NAME> [0|2] <LINE>alias hashed-string <HASHED-STRING-ALIAS-NAME> <LINE>alias host <HOST-ALIAS-NAME> <HOST-IP>alias network <NETWORK-ALIAS-NAME> <NETWORK-ADDRESS/MASK>alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range|host|network]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-278.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 13alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}|host <HOST-IP> {<HOST-IP>}|network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}]alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport|ssh|telnet|tftp|www)}alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}alias number <NUMBER-ALIAS-NAME> <0-4294967295>alias string <STRING-ALIAS-NAME> <LINE>alias vlan <VLAN-ALIAS-NAME> <1-4094>Parameters• alias address-range <ADDRESS-RANGE-ALIAS-NAME> <STARTING-IP> to <ENDING-IP>• alias encrypted-string <ENCRYPTED-STRING-ALIAS-NAME> [0|2] <LINE>address-range <ADDRESS-RANGE-ALIAS-NAME>Creates an address-range alias, defining a range of IP addresses• <ADDRESS-RANGE-ALIAS-NAME> – Specify the address-range alias name.Alias name should begin with ‘$’.<STARTING-IP> to <ENDING-IP>Associates a range of IP addresses with this address-range alias• <STARTING-IP> – Specify the first IP address in the range.• to <ENDING-IP> – Specify the last IP address in the range.encrypted-string <ENCRYPTED-STRING-ALIAS-NAME>Creates an alias for an encrypted string. Use this alias for string configuration values that are encrypted when "password-encryption" is enabled. For example, in the management-policy, use it to define the SNMP community string. For more information, see snmp-server.• <ENCRYPTED-STRING-ALIAS-NAME> – Specify the encrypted-string alias name.Alias name should begin with ‘$’.[0|2] <LINE> Configures the value associated with the alias name specified in the previous step• [0|2] <LINE> – Configures the alias valueNote, if password-encryption is enabled, in the show > running-config output, this clear text is displayed as an encrypted string, as shown below:nx9500-6C8809(config)#show running-config!...............................alias encrypted-string $enString 2 fABMK2is7UToNiZE3MQXbgAAAAxB0ZIysdqsEJwr6AH/Da//!--More--nx9500-6C8809In the above show > running-config output, the ‘2’ displayed before the encrypted-string alias value indicates that the displayed text is encrypted and not a clear text.Cotnd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-279.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 15• alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}|host <HOST-IP> {<HOST-IP>}|network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}]• alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}network <NETWORK-GROUP-ALIAS-NAME>Creates a network-group alias• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name.Alias name should begin with ‘$’.The network-group aliases are used in ACLs, to define the network-specific components. ACLs using aliases can be used across sites by re-defining the network-group alias elements at the device or profile level.After specifying the name, specify the following: a range of IP addresses, host addresses, or a range of network addresses.address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}Associates a range of IP addresses with this network-group alias• <STARTING-IP> – Specify the first IP address in the range.• to <ENDING-IP> – Specify the last IP address in the range.• <STARTING-IP> to <ENDING-IP> – Optional. Specifies more than one range of IPaddresses. A maximum of eight (8) IP address ranges can be configured.host <HOST-IP> {<HOST-IP>}Associates a single or multiple hosts with this network-group alias• <HOST-IP> – Specify the hosts’ IP address.• <HOST-IP> – Optional. Specifies more than one host. A maximum of eight (8) hostscan be configured.network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}Associates a single or multiple networks with this network-group alias• <NETWORK-ADDRESS/MASK> – Specify the network’s address and mask.• <NETWORK-ADDRESS/MASK> – Optional. Specifies more than one network. Amaximum of eight (8) networks can be configured.alias network-service <NETWORK-SERVICE-ALIAS-NAME>Configures an alias that specifies available network services and the corresponding source and destination software ports• <NETWORK-SERVICE-ALIAS-NAME> – Specify a network-service alias name.Alias name should begin with ‘$’.Network-service aliases are used in ACLs, to define the service-specific components. ACLs using aliases can be used across sites by re-defining the network-service alias elements at the device or profile level.proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp]Use one of the following options to associate an Internet protocol with this network-service alias:• <0-254> – Identifies the protocol by its number. Specify the protocol number from 0 - 254. This is the number by which the protocol is identified in the Protocol field of the IPv4 header and the Next Header field of IPv6 header. For example, the User Datagram Protocol’s (UDP) designated number is 17.• <WORD> – Identifies the protocol by its name. Specify the protocol name.• eigrp – Selects Enhanced Interior Gateway Routing Protocol (EIGRP). The protocol number 88.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-281.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 16•gre – Selects Generic Routing Encapsulation (GRE). The protocol number is 47.• igmp – Selects Internet Group Management Protocol (IGMP). The protocol number is 2.•igp – Selects Interior Gateway Protocol (IGP). The protocol number is 9.•ospf – Selects Open Shortest Path First (OSPF). The protocol number is 89.• vrrp – Selects Virtual Router Redundancy Protocol (VRRP). The protocol number is 112.{(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}After specifying the protocol, you may configure a destination port for this service. These keywords are recursive and you can configure multiple protocols and associate multiple destination and source ports.• <1-65535> – Optional. Configures a destination port number from 1 - 65535• <WORD> – Optional. Identifies the destination port by the service name provided. For example, the secure shell (SSH) service uses TCP port 22.• bgp – Optional. Configures the default Border Gateway Protocol (BGP) services port (179)• dns – Optional. Configures the default Domain Name System (DNS) services port (53)• ftp – Optional. Configures the default File Transfer Protocol (FTP) control services port (21)• ftp-data – Optional. Configures the default FTP data services port (20)• gopher – Optional. Configures the default gopher services port (70)• https – Optional. Configures the default HTTPS services port (443)• ldap – Optional. Configures the default Lightweight Directory Access Protocol (LDAP) services port (389)• nntp – Optional. Configures the default Newsgroup (NNTP) services port (119)• ntp – Optional. Configures the default Network Time Protocol (NTP) services port (123)• POP3 – Optional. Configures the default Post Office Protocol (POP3) services port (110)• proto – Optional. Use this option to select another Internet protocol in addition to the one selected in the previous step.• sip – Optional. Configures the default Session Initiation Protocol (SIP) services port (5060)• smtp – Optional. Configures the default Simple Mail Transfer Protocol (SMTP) services port (25)• sourceport [<1-65535>|<WORD>] – Optional. After specifying the destination port, you may specify a single or range of source ports.• <1-65535> – Specify the source port from 1 - 65535.• <WORD> – Specify the source port range, for example 1-10.• ssh – Optional. Configures the default SSH services port (22)• telnet – Optional. Configures the default Telnet services port (23)• tftp – Optional. Configures the default Trivial File Transfer Protocol (TFTP) services port (69)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-282.png)

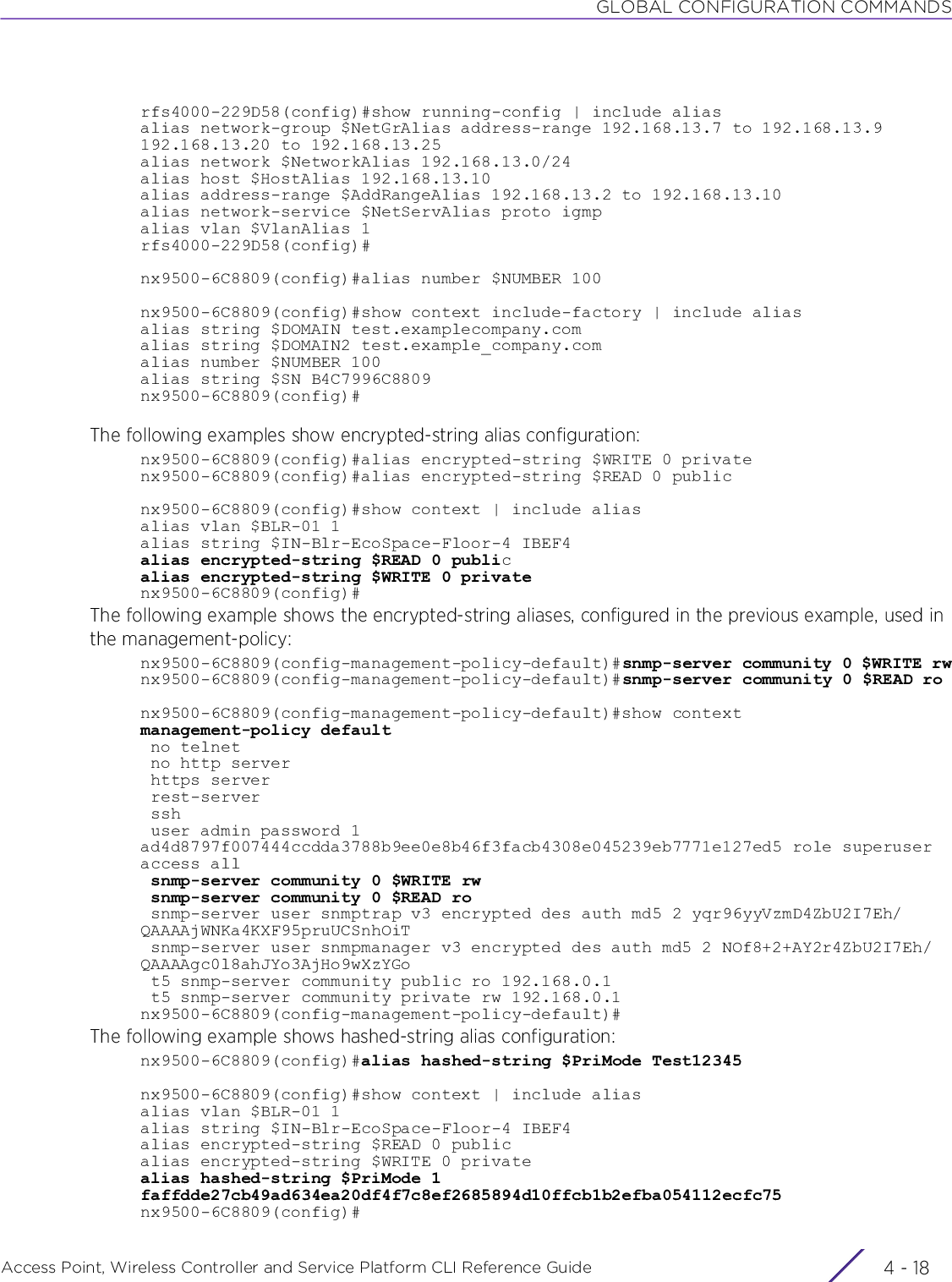
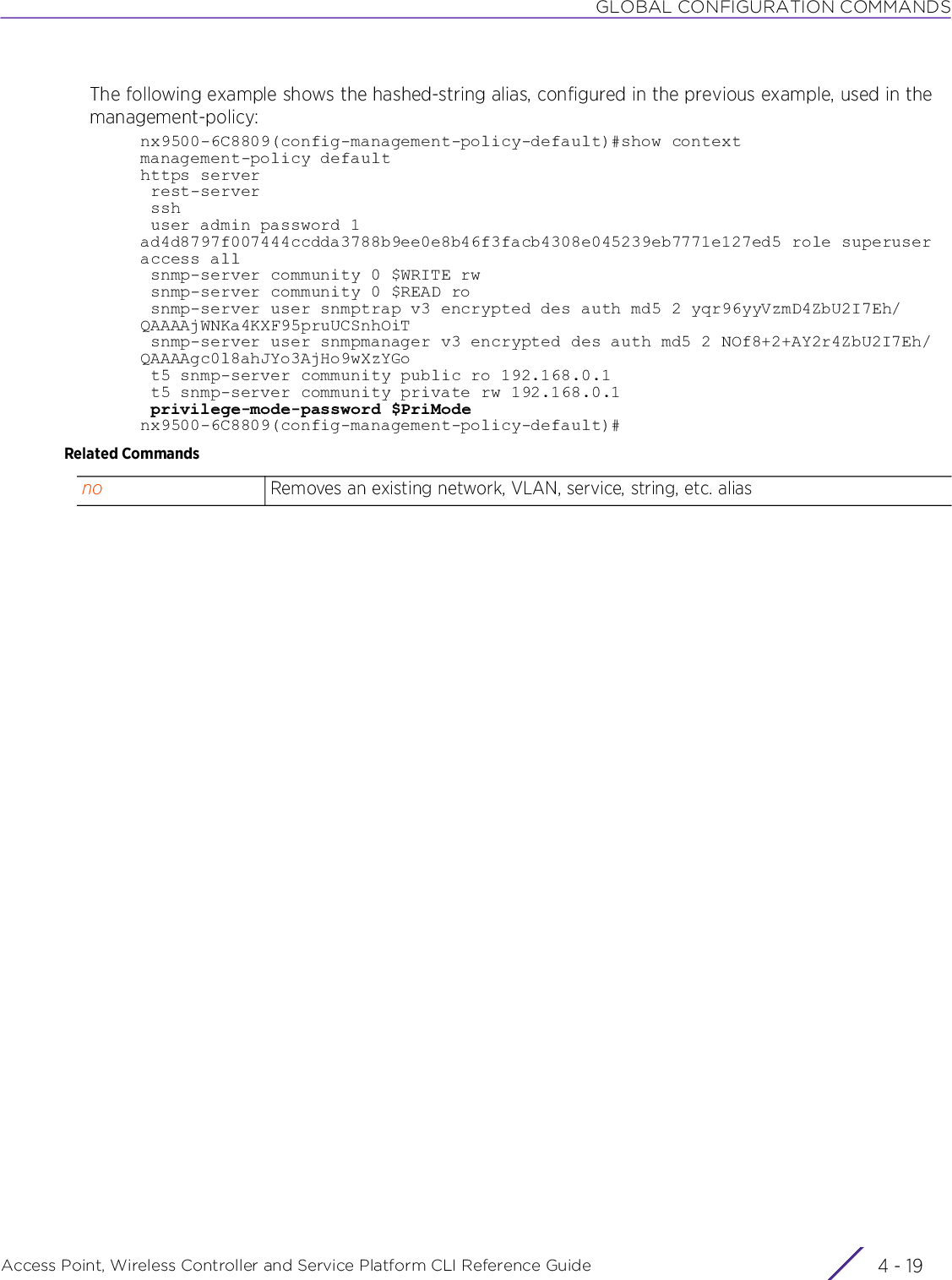



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 434.1.22.2.1 app-categoryapplication-config-mode commandsConfigures the category for this application definitionSupported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxapp-category <APP-CATEGORY-NAME>Parameters• app-category <APP-CATEGORY-NAME>Examplenx9500-6C8809(config-application-Bing)#app-category [TAB]business conference customdatabase filetransfer gaminggeneric im mailmobile network\ management otherp2p remote_control sharehostingsocial\ networking streaming tunnelvoip webnx9500-6C8809(config-application-Bing)#nx9500-6C8809(config-application-Bing)#app-category streamingnx9500-6C8809(config-application-Bing)#show contextapplication Bing app-category streamingnx9500-6C8809(config-application-Bing)#Related Commandsapp-category <APP-CATEGORY-NAME>Select the category best suited for this application definition. There are twenty three categories. These are: business, conference, custom, database, filetransfer, gaming, generic, im, mail, mobile, network\ management, other, p2p, remote_control, social\ networking, standard, streaming, tunnel, video, voip, and Web. The default setting is custom. Use this option to categorize your internal custom applications, so that they do not appear as unknown traffic.no Resets application category to default (custom)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-309.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 454.1.22.2.3 httpsapplication-config-mode commandsConfigures the HTTPS parameter type, attribute type, match criteria for the HTTPS server name and 64 character maximum server name attribute used in the HTTPS server message exchange Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxhttps server-cert common-name [contains|ends-with] <WORD>Parameters• https server-cert common-name [contains|ends-with] <WORD>Examplenx9500-6C8809(config-application-Bing)#https server-cert common-name exact bing.comnx9500-6C8809(config-application-Bing)#show contextapplication Bing description "Bing is Microsoft's web search engine" app-category streaming https server-cert common-name exact bing.comnx9500-6C8809(config-application-Bing)#Related Commandshttps server-cert Configures the HTTPS parameter type as server certificatecommon-name [contains|ends-with] <WORD>Configures the HTTPS attribute match criteria as common name. This is the only option applicable when the HTTPS parameter type is set to server-cert. Use one of the following options to provide the common-name attribute value used as the match criteria:• contains – Filters applications having common-name attributes containing the string specified here• ends-with – Filters applications ending with the string specified here• <WORD> – Specify the string to match (should not exceed 64 characters).no Removes the HTTPS common-name attribute value configured with this application category](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-311.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 464.1.22.2.4 useapplication-config-mode commandsAssociates a network-service alias or a URL list with this application definitionFor applications using protocols other than HTTPS, use this command to define the protocols, ports, and/or URL host name to match.Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [network-service <NETWORK-SERVICE-ALIAS-NAME>|url-list <URL-LIST-NAME>]Parameters• use [network-service <NETWORK-SERVICE-ALIAS-NAME>|url-list <URL-LIST-NAME>]Examplenx9500-6C8809(config-application-Bing)#use url-list Bingnx9500-6C8809(config-application-Bing)#show contextapplication Bing description "Bing is Microsoft's web search engine" app-category streaming use url-list Bing https server-cert common-name exact bing.comnx9500-6C8809(config-application-Bing)#Related Commandsuse Configures this application definition to use a network-service alias or a URL listnetwork-service <NETWORK-SERVICE-ALIAS-NAME>Associates a network-service alias with this application definition• <NETWORK-SERVICE-ALIAS-NAME> – Specify the network-service alias name (should be existing and configured). The network-service alias should specify the protocols and ports to match.url-list <URL-LIST-NAME>Associates a URL list with this application definition. URL lists are utilized for whitelisting and blacklisting Web application URLs from being launched and consuming bandwidth within the WiNG managed network.• <URL-LIST-NAME> – Specify the URL list name (should be existing and configured). The URL list should specify the HTTP URL host names to match.no Removes the network-service alias or the URL list associated with this application definition](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-312.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 474.1.22.2.5 noapplication-config-mode commandsRemoves or resets this application definition’s configured settingsSupported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [app-category|description|https|use]no [app-category|description]no https server-cert common-name [contains|ends-with] <WORD>no use [network-service <NETWORK-SERVICE-ALIAS-NAME>|url-list <URL-LIST-NAME>]Parameters• no <PARAMETERS>ExampleThe following example displays the application definition ‘Bing’ parameters before the ‘no’ commands are executed:nx9500-6C8809(config-application-Bing)#show contextapplication Bing description "Bing is Microsoft's web search engine" app-category streaming use url-list Bing https server-cert common-name exact bing.comnx9500-6C8809config-application-Bing)#nx9500-6C8809(config-application-Bing)#no descriptionnx9500-6C8809(config-application-Bing)#no https server-cert common-name exact bing.comThe following example displays the application definition ‘Bing’ parameters after the ‘no’ commands are executed:nx9500-6C8809(config-application-Bing)#show contextapplication Bing app-category streaming use url-list Bingnx9500-6C8809(config-application-Bing)#no <PARAMETERS> Removes or resets this application definition’s configured settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-313.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 514.1.23.2.1 applicationapplication-group-mode commandsAdds an application to this application group. You can add a system-provided or user-defined application.Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxapplication <APPLICATION-NAME>Parameters• application <APPLICATION-NAME>ExampleTo view all applications available in the system, use [TAB], as shown in the following example:nx9500-6C8809(config-app-group-test)#application [TAB]Display all 299 possibilities? (y or n)1-clickshare-com 1-upload-com1-upload-to 10upload-com--More--nx9500-6C8809(config-app-group-test)#Select the desired application from the list displayed, as shown in the following examples:nx9500-6C8809(config-app-group-amazon)#application amazon [TAB]amazon-prime-music amazon-prime-video amazon_cloud amazon_shopnx9500-6C8809(config-app-group-amazon)#nx9500-6C8809(config-app-group-amazon)#application amazon-prime-musicnx9500-6C8809(config-app-group-amazon)#application amazon-prime-videonx9500-6C8809(config-app-group-amazon)#application amazon_cloudnx9500-6C8809(config-app-group-amazon)#application amazon_shopnx9500-6C8809(config-app-group-amazon)#show contextapplication-group amazon application amazon-prime-music application amazon-prime-video application amazon_cloud application amazon_shopnx9500-6C8809(config-app-group-amazon)#Note, the system returns an error message if the application entered is not listed, as shown in the following example:nx9500-6C8809(config-app-group-test)#application bing% Error: application 'bing' is not definednx9500-6C8809(config-app-group-test)#application <APPLICATION-NAME>Configures the application to be added to this application group• <APPLICATION-NAME> – Provide the application name (should be available as an option in the system). A maximum of eight (8) applications can be added to a group.If the desired application is not available as an option, use the application command to add it.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-317.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 544.1.23.2.3 noapplication-group-mode commandsRemoves this application group’s configured parameters (application and/or description)Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [application <APPLICATION-NAME>|description]Parameters• no [application <APPLICATION-NAME>|description]ExampleThe following example displays the application-group ‘amazon’ configuration before the execution of ‘no’ commands:nx9500-6C8809(config-app-group-amazon)#show contextapplication-group amazon description "This application-group lists all Amazon applications." application amazon-prime-music application amazon-prime-video application amazon_cloud application amazon_shopnx9500-6C8809(config-app-group-amazon)#nx9500-6C8809(config-app-group-amazon)#no application amazon_cloudnx9500-6C8809(config-app-group-amazon)#no descriptionThe following example displays the application-group ‘amazon’ configuration after the execution of ‘no’ commands:nx9500-6C8809(config-app-group-amazon)#show contextapplication-group amazon application amazon-prime-music application amazon-prime-video application amazon_shopnx9500-6C8809(config-app-group-amazon)#no <PARAMETERS> Removes an application associated with this group, and removes this group’s description](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-320.png)


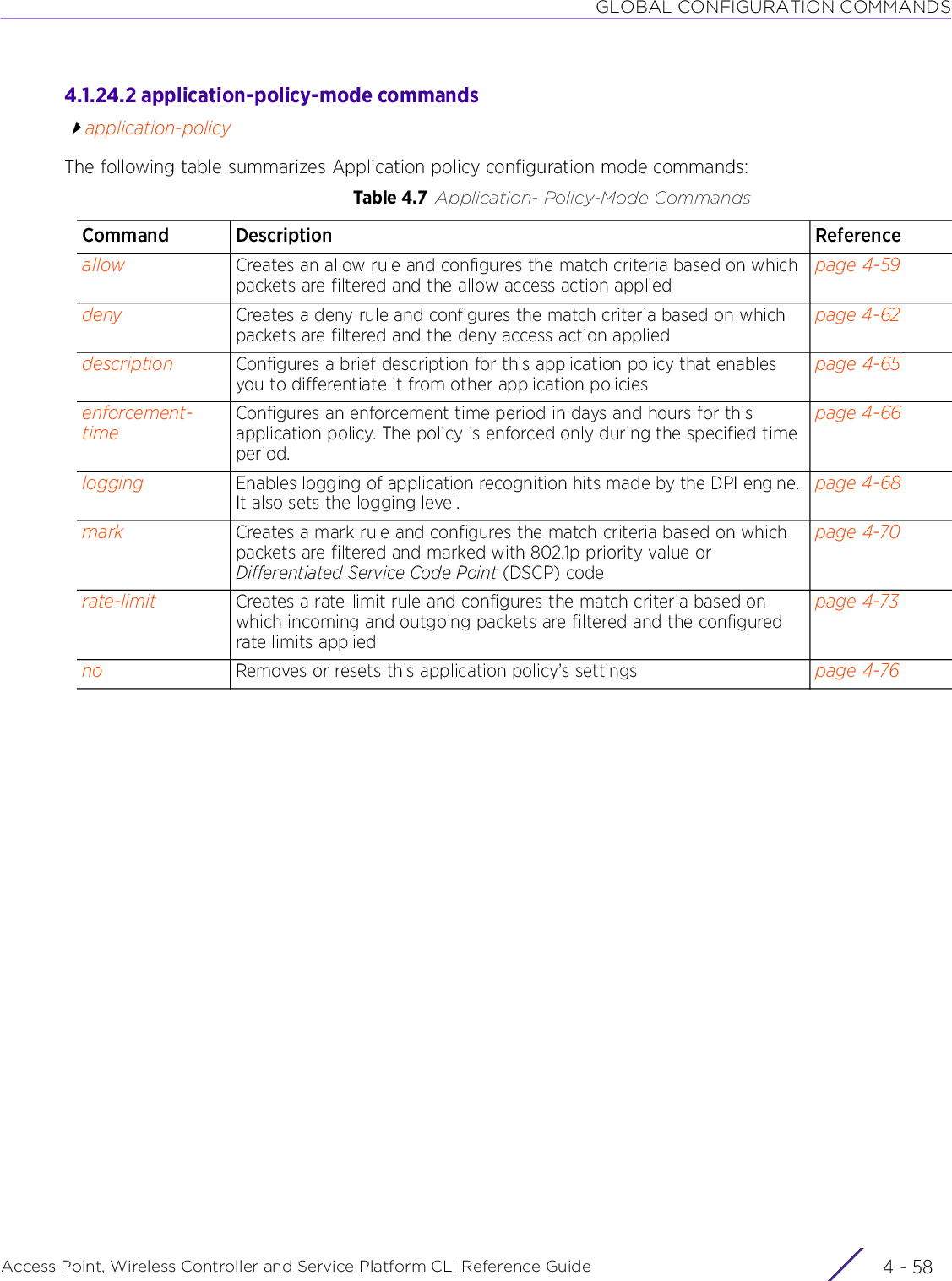
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 594.1.24.2.1 allowapplication-policy-mode commandsCreates an allow rule and configures the match criteria based on which packets are filtered and the allow access action appliedSupported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxallow [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)Parameters• allow [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)allow Creates an allow rule and configures the match criteria. The options are app-category and application.app-category [<APP-CATEGORY-NAME>|all]Uses application category as the match criteria• <APP-CATEGORY-NAME> – Specify the application category. The options are: antivirus\ update, audio, business, conference, custom, database, file transfer, gaming, generic, im, mail, mobile, network\ management, other, p2p, remote_control, social\ networking, standard, streaming, tunnel, video, voip, and web. Each packet’s app-category is matched with the value specified here. In case of a match, the system forwards the packet or else drops it.• all – The system forwards all packets irrespective of the application category.application <APPLICATION-NAME>Uses application name as the match criteria• <APPLICATION-NAME> – Specify the application name. Each packet’s application is matched with the application name specified here. In case of a match, the system forwards the packet.The WiNG database provides approximately 381 canned applications. In addition to these, the database also includes custom-made applications. These are application definitions created using the application command.schedule <SCHEDULE-POLICY-NAME>Schedules an enforcement time for this allow rule by associating a schedule policy with it. Use this parameter to apply rule-specific enforcement time.• schedule <SCHEDULE-POLICY-NAME> – Associates a schedule policy with the rule. When associated, the rule is enforced only on the days and time configured in the schedule policy. Without the association of a schedule policy, all rules within an application policy are enforced concurrently (defined by the application-policy > enforcement-time command). If scheduling a rule, ensure that the time configured in the schedule policy is a subset of the application policy’s enforcement time. In other words the application policy should be active when the rule is being enforced. For example, if the application policy is enforced on Mondays from 10:00 to 22:00 hours and the schedule policy time-rule is set for Fridays, then this rule will never be hit. When enforcing rules at different times the best practice would be to keep the application policy active at all time (i.e., retain the default enforcement-time setting as ‘all’).Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-325.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 60ExampleThe following example shows how to view all built-in, system provided applications:nx9500-6C8809(config-app-policy-test)#allow application [TAB]Display all 366 possibilities? (y or n)1-clickshare-com 1-upload-com1-upload-to 10upload-com123upload-pl 139pan-com163pan-com 1clickshare-net1fichier-com 1kxun2channel 2gis2shared-com 360mobile4fastfile-com 4share-wsDota\ 2 EA\ Origin--More--nx9500-6C8809(config-app-policy-test)#The following examples show two allow rules, allowing access to all packets belonging to the application category ‘business’ and the application ‘Bing’:nx9500-6C8809(config-app-policy-Bing)#allow application Bi [TAB]Bing BitTorrent BitTorrent_encryptedBitTorrent_plain BitTorrent_uTP BitTorrent_uTP_encryptednx9500-6C8809(config-app-policy-Bing)#Note: Bing is not one of the WiNG built-in database applications. It is a customized application created using the application command.nx9500-6C8809(config-app-policy-Bing)#allow application Bing precedence 1• <SCHEDULE-POLICY-NAME> – Specify the policy name (should be existing and configured). After applying a schedule policy, specify a precedence for the rule.In case of no schedule policy being applied, the rule is enforced as per the enforcement-time configured in the application policy. For more information, see enforcement-time.precedence <1-256> Assigns a precedence value for this allow rule. The precedence value differentiates between rules applicable to applications and the application categories to which they belong. The allow, deny, mark, rate-limit options are mutually exclusive. In other words, in an application policy, for a specific application or application category, you can create either an allow rule, or a deny rule, or a mark and rate-limit rule.Let us consider application youtube belonging to app-category streaming.The action required is: Allow youtube packets and deny all other applications belonging to app-category streaming.The rules can be defined as:#allow application youtube precedence 1#deny app-category streaming precedence 2The following configuration is incorrect:#deny app-category streaming precedence 1#allow application youtube precedence 2Once the deny app-category streaming precedence 1 rule is hit, all streaming packets, including youtube, are dropped. Consequently, there are no packets left to apply the subsequent allow rule.The mark and rate-limit rules are the only two actions that can be combined for a specific application or application category type.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-326.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 61nx9500-6C8809(config-app-policy-Bing)#allow app-category [TAB]all antivirus\ update audiobusiness conference customdatabase filetransfer gaminggeneric im mailmobile network\ management otherp2p remote_control social\ networkingstandard streaming tunnelvideo voip webnx9500-6C8809(config-app-policy-Bing)#nx9500-6C8809(config-app-policy-Bing)#allow app-category business precedence 2nx9500-6C8809(config-app-policy-Bing)#show contextapplication-policy Bing allow application Bing precedence 1 allow app-category business precedence 2nx9500-6C8809(config-app-policy-Bing)#The following example shows an application policy 'SocialNet' having an allow rule with an associated schedule policy named 'FaceBook':nx9500-6C8809(config-app-policy-SocialNet)#allow application facebook schedule Facebook precedence 1nx9500-6C8809(config-app-policy-SocialNet)#show contextapplication-policy SocialNet description "This application policy relates to Social Networking sites." allow application facebook schedule FaceBook precedence 1nx9500-6C8809(config-app-policy-SocialNet)#The schedule policy ‘FaceBook’ configuration is as follows. As per this policy, the above allow rule will apply to all FaceBook packets every Friday between 13:00 and 18:00 hours.nx9500-6C8809(config-schedule-policy-FaceBook)#show contextschedule-policy FaceBook description "Allows FaceBook traffic on Fridays." time-rule days friday start-time 13:00 end-time 18:00nx9500-6C8809(config-schedule-policy-FaceBook)#Related Commandsno Removes this allow rule from the application policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-327.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 624.1.24.2.2 denyapplication-policy-mode commandsCreates a deny rule and configures the match criteria based on which packets are filtered and the deny access action appliedSupported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)Parameters• deny [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)deny Creates a deny rule and configures the match criteria. The options are app-category and application.app-category [<APP-CATEGORY-NAME>|all]Uses application category as the match criteria• <APP-CATEGORY-NAME> – Specify the application category name. The options are: antivirus\ update, audio, business, conference, custom, database, file transfer, gaming, generic, im, mail, mobile, network\ management, other, p2p, remote_control, social\ networking, standard, streaming, tunnel, video, voip, and web. Each packet’s app-category is matched with the value specified here. In case of a match, the system drops the packet.• all – The system drops all packets irrespective of the application category.application <APPLICATION-NAME>Uses application name as the match criteria• <APPLICATION-NAME> – Specify the application name. Each packet’s application is matched with the application name specified here. In case of a match, the system drops the packet.There are approximately some 381 canned applications in the database. In addition to these, the database displays custom-made applications also. These are application definitions created using the application command.schedule <SCHEDULE-POLICY-NAME>Schedules an enforcement time for this deny rule by associating a schedule policy with it. Use this parameter to apply rule-specific enforcement time.• schedule <SCHEDULE-POLICY-NAME> – Associates a schedule policy with the rule. When associated, the rule is enforced only on the days and time configured in the schedule policy. Without the association of a schedule policy, all rules within an application policy are enforced concurrently (defined by the application-policy > enforcement-time command). If scheduling a rule, ensure that the time configured in the schedule policy is a subset of the application policy’s enforcement time. In other words the application policy should be active when the rule is being enforced. For example, if the application policy is enforced on Mondays from 10:00 to 22:00 hours and the schedule policy time-rule is set for Fridays, then this rule will never be hit. When enforcing rules at different times the best practice would be to keep the application policy active at all time (i.e., retain the default enforcement-time setting as ‘all’).Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-328.png)

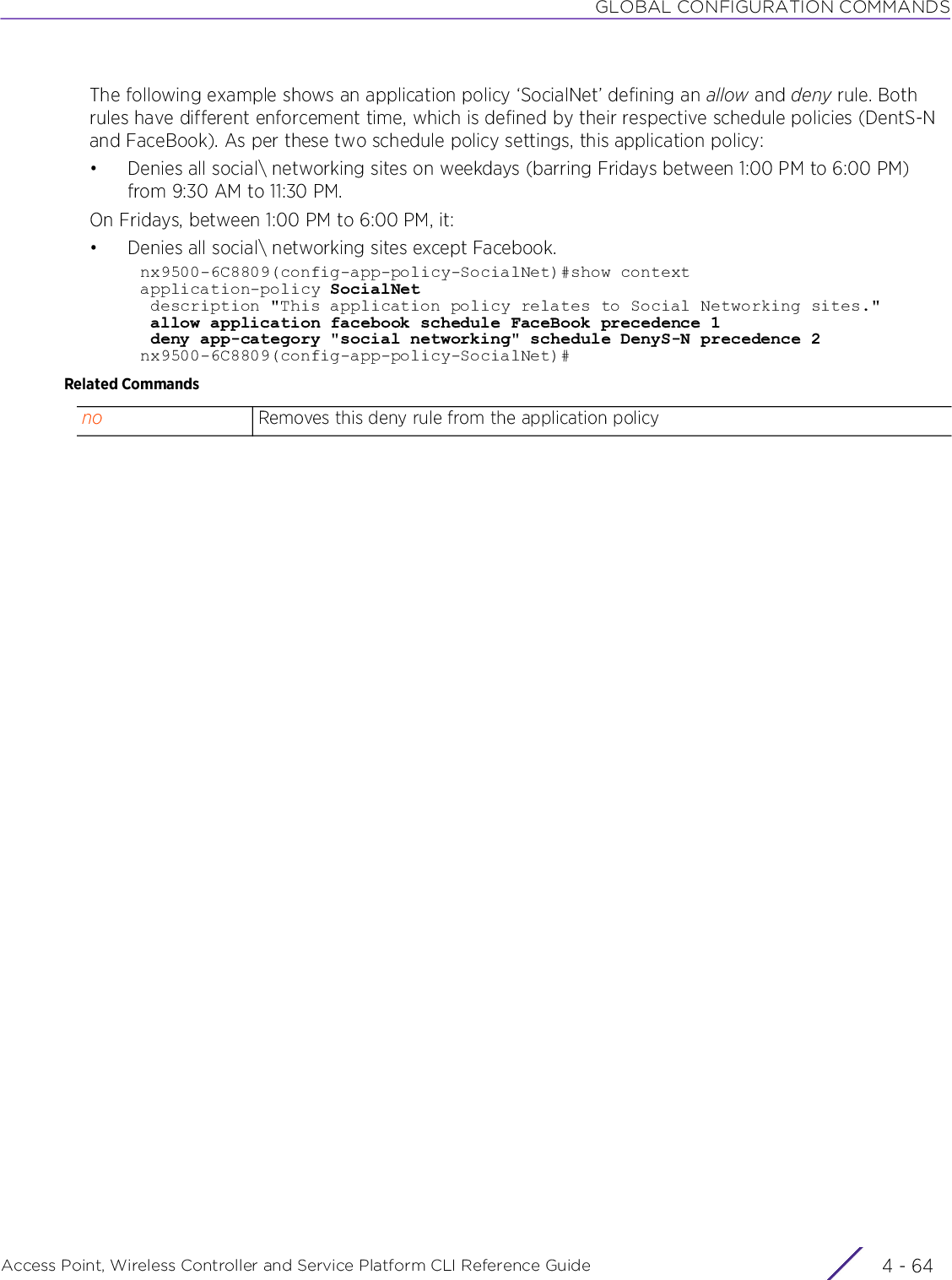

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 664.1.24.2.4 enforcement-timeapplication-policy-mode commandsConfigures an enforcement time period in days and hours for this application policy. The enforcement time is applicable only to those rules, within the application policy, that do not have a schedule policy associated. By default an application policy is enforced on all days.Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxenforcement-time days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays] {start-time <HH:MM> end-time <HH:MM>}Parameters• enforcement-time days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays] {start-time <HH:MM> end-time <HH:MM>}NOTE: Schedule policies are a means of enforcing allow/deny/mark/rate-limit rules at different time periods. If no schedule policy is applied, all rules within an application policy are enforced at the time specified using this enforcement-time command. For more information on configuring a schedule policy, see schedule-policy. enforcement-time daysEnforces this application policy on only on the days specified here• sunday – Enforces the policy only on Sundays• monday – Enforces the policy only on Mondays• tuesday – Enforces the policy only on Tuesdays• wednesday – Enforces the policy only on Wednesdays• thursday – Enforces the policy only on Thursdays• friday – Enforces the policy only on Fridays• saturday – Enforces the policy only on Saturdays• all – Enforces the policy on all days. This is the default setting.• weekends – Enforces the policy only on weekends• weekdays – Enforces the policy only on weekdaysIn case no enforcement time is specified, the application policy is enforced on all days (i.e., always active).If using schedule policies with the allow/deny/mark/rate-limit rules, the best practice would be to keep the application policy active at all time (i.e., retain the default enforcement-time setting of ‘all’).start-time <HH:MM> end-time <HH:MM>Optional. Configures this application policy’s enforcement period• start-time – Configures the start time. This is the time at which the application policy enforcement begins.• end-time – Configures the end time. This is the time at which the application policy enforcement ends.• <HH:MM> – Specify the start and end time in the HH:MM format.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-332.png)
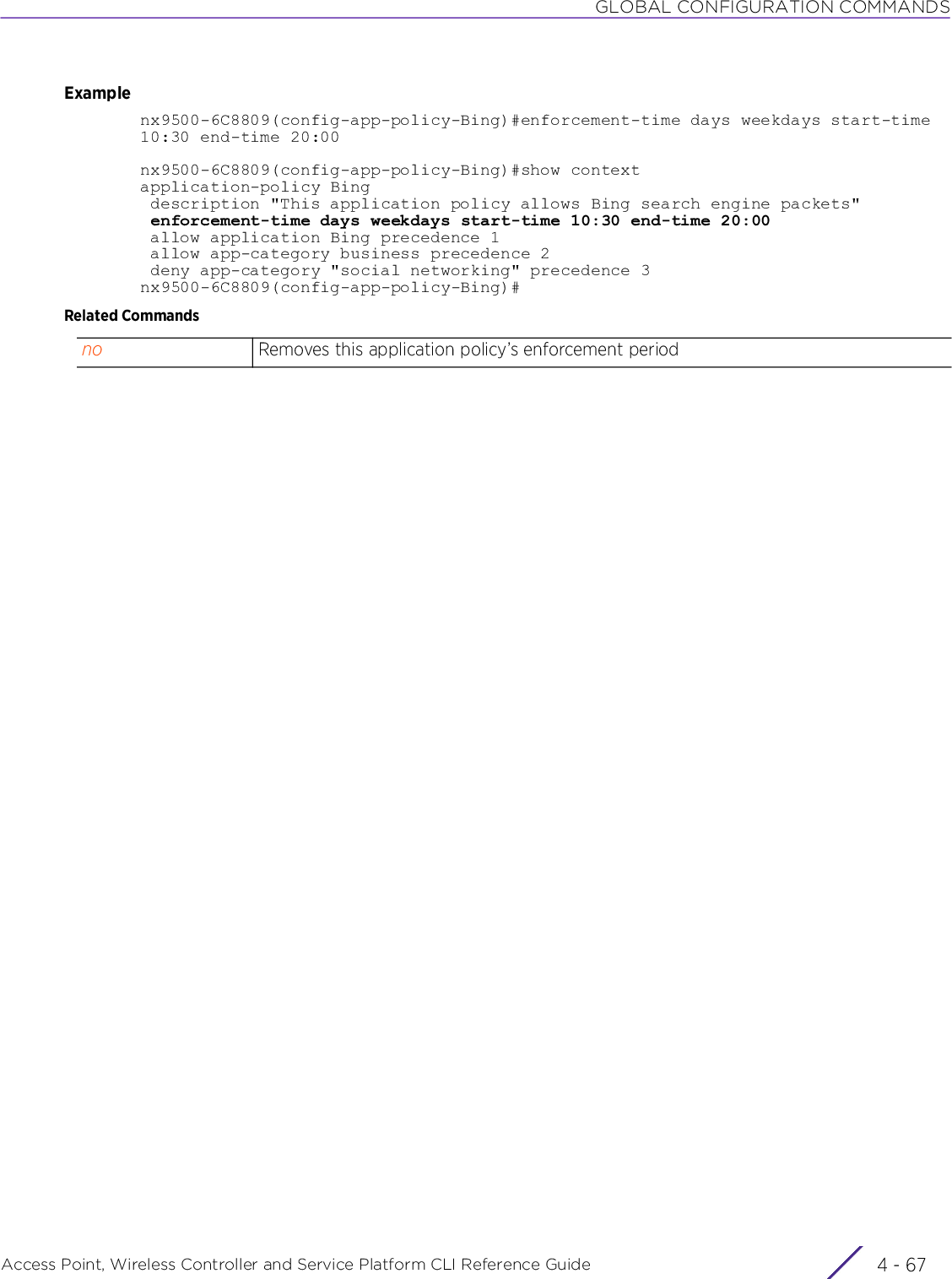
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 684.1.24.2.5 loggingapplication-policy-mode commandsEnables DPI application recognition logging. It also sets the logging level.DPI is an advanced packet analysis technique, which analyzes packet and packet content headers to determine the nature of network traffic. When enabled, DPI inspects packets of all flows to identify applications (such as, Netflix, Twitter, Facebook, etc.) and extract metadata (such as, host name, server name, TCP-RTT, etc.) for further use by the WiNG firewall.Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlogging [level|on]logging onlogging level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]Parameters• logging on• logging level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]logging on Enables logging of application recognition hits made by the DPI engine. This option is disabled by default.logging level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]Sets the logging level for application recognition hits made by the DPI engine. This option is disabled by default.• <0-7> – Sets the message logging severity level on a scale of 0 - 7• emergencies – Severity level 0: System is unusable• alerts – Severity level 1: Requires immediate action• critical – Severity level 2: Critical conditions• errors – Severity level 3: Error conditions• warnings – Severity level 4: Warning conditions• notifications – Severity level 5: Normal but significant conditions (this is the default setting)• informational – Severity level 6: Informational messages• debugging – Severity level 7: Debugging messages](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-334.png)
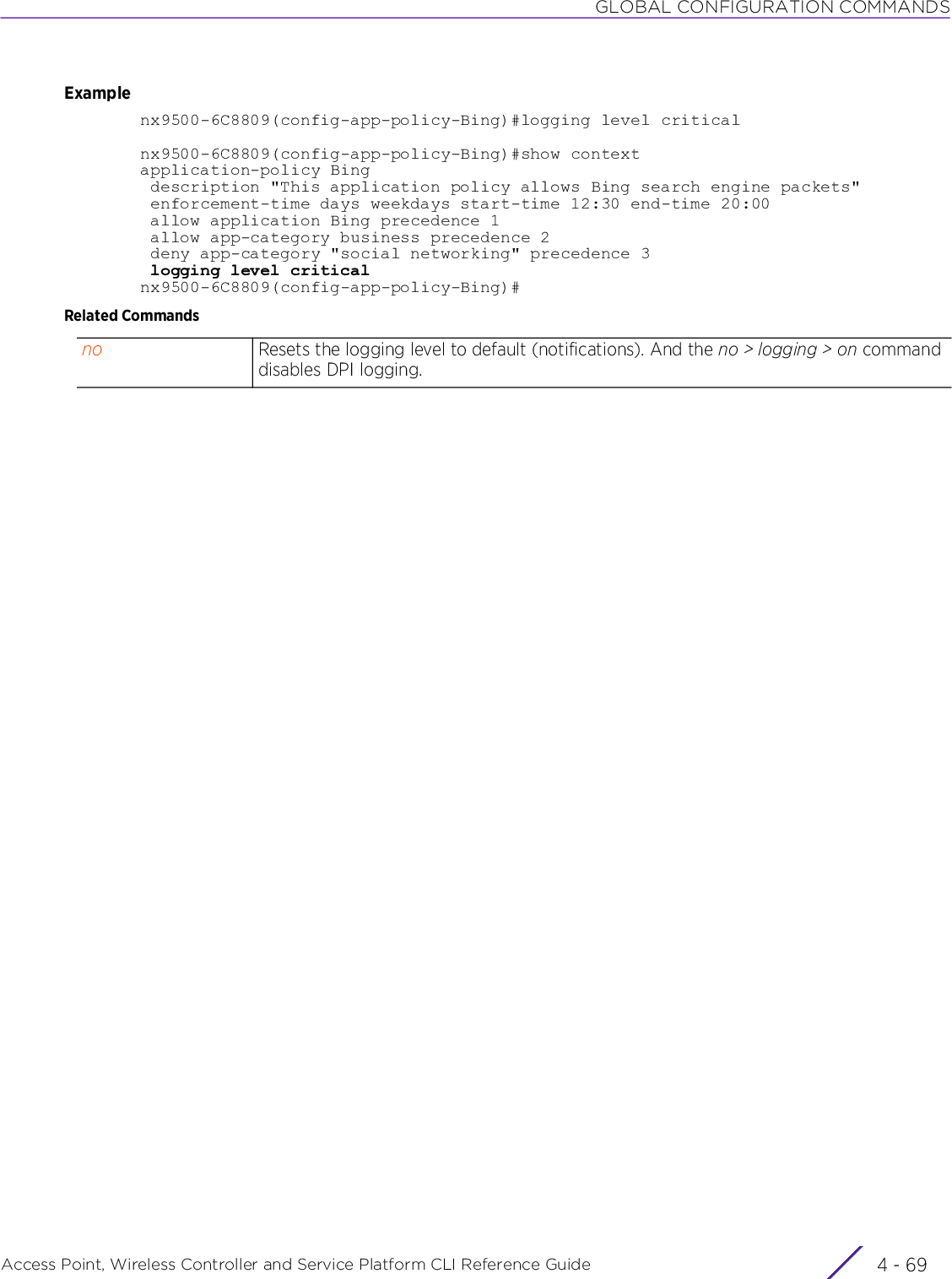
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 704.1.24.2.6 markapplication-policy-mode commandsCreates a mark rule and configures the match criteria based on which packets are markedMarks packets, matching a specified set of application categories or applications/protocols, with 802.1p priority level or Differentiated Services Code Point (DSCP) type of service (ToS) code. Marking packets is a means of identifying them for specific actions, and is used to provide different levels of service to different traffic types.Supported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmark [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] [8021p <0-7>|dscp <0-63>] schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)Parameters• mark [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] [8021p <0-7>|dscp <0-63>] schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)mark Creates a mark rule and configures the match criteria. When applied, the rule marks packets, matching the criteria configured here, with 802.1p priority value or DSCP code. The match criteria options are: app-category and application.app-category [<APP-CATEGORY-NAME>|all]Uses application category as the match criteria• <APP-CATEGORY-NAME> – Specify the application category. The options are: antivirus\ update, audio, business, conference, custom, database, file transfer, gaming, generic, im, mail, mobile, network\ management, other, p2p, remote_control, social\ networking, standard, streaming, tunnel, video, voip, and web. Each packet’s app-category is matched with the value specified here. In case of a match, the system marks the packet.• all – The system marks all packets irrespective of the application category.application <APPLICATION-NAME>Uses application name as the match criteria• <APPLICATION-NAME> – Specify the application name. Each packet’s application is matched with the application name specified here. In case of a match, the system marks the packet.The WiNG database provides approximately 381 canned applications. In addition to these, the database includes custom-made applications. These are application definitions created using the application command.8021p <0-7> Marks packets matching the specified criteria with 802.1p priority value• <0-7> – Specify a value from 0 - 7.The IEEE 802.1p signaling standard enables marking of layer 2 network traffic. Layer 2 network devices (such as switches), using 802.1p standards, group traffic into classes based on their 802.1p priority value, which is appended to the packet’s MAC header. In case of traffic congestion, packets with higher priority get precedence over lower priority packets and are forwarded first.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-336.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 734.1.24.2.7 rate-limitapplication-policy-mode commandsCreates a rate-limit rule and configures the match criteriaSupported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrate-limit [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] ([egress|ingress]) rate <50-1000000> max-burst-size <2-1024> schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)Parameters• rate-limit [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] ([egress|ingress]) rate <50-1000000> max-burst-size <2-1024> schedule <SCHEDULE-POLICY-NAME> (precedence <1-256>)rate-limit Creates a rate-limit rule and configures the match criteria. When applied, the rule applies a rate-limit to packets that match the criteria configured here. These packets could be incoming, outgoing, or both. The match criteria options are: app-category and application.app-category [<APP-CATEGORY-NAME>|all]Uses application category as the match criteria• <APP-CATEGORY-NAME> – Specify the application category. The options are: antivirus\ update, audio, business, conference, custom, database, file transfer, gaming, generic, im, mail, mobile, network\ management, other, p2p, remote_control, social\ networking, standard, streaming, tunnel, video, voip, and web. Each packet’s app-category is matched with the value specified here. In case of a match, the system rate-limits the packet.• all – The system rate-limits all packets irrespective of the application category.application <APPLICATION-NAME>Uses application name as the match criteria• <APPLICATION-NAME> – Specify the application name. Each packet’s application is matched with the application name specified here. In case of a match, the system rate-limits the packet.[egress|ingress] The egress and ingress parameters are recursive and can be used to rate limit either incoming, outgoing, or both incoming and outgoing traffic.• egress – Selects the traffic type as outgoing • ingress – Selects the traffic type as outgoingAfter selecting the traffic type (incoming/outgoing) configure the rate and maximum burst size. rate <50-1000000> The following parameters are common to the ‘egress’ and ‘ingress’ keywords:• rate – Configures the rate limit, in Kbps, for both incoming and outgoing packets• <50-1000000> – Specify the rate limit from 50 - 1000000 Kbps.max-burst-size The following parameters are common to the ‘egress’ and ‘ingress’ keywords:• max-burst-size – Configures the maximum burst size, in Kbytes, for both incoming and outgoing packets• <2-1024> – Specify the maximum burst size from 2 - 1024 Kbytes.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-339.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 764.1.24.2.8 noapplication-policy-mode commandsRemoves or resets this application policy’s settingsSupported in the following platforms:• Access Points — AP7522, AP7532• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [allow|deny|description|enforcement-time|logging|mark|rate-limit]no allow [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] precedence <1-256>no deny [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] precedence <1-256>no descriptionno enforcement-time days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays]no logging [level|on]no mark [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] precedence <1-256>no rate-limit [app-category [<APP-CATEGORY-NAME>|all]|application <APPLICATION-NAME>] precedence <0-256>Parameters• no <PARAMETERS>ExampleThe following example shows the application policy ‘Bing’ settings before the ‘no’ commands are executed:nx9500-6C8809(config-app-policy-Bing)#show contextapplication-policy Bing description "This application policy allows Bing search engine packets" enforcement-time days weekdays start-time 12:30 end-time 20:00 allow application Bing precedence 1 allow app-category business precedence 2 deny app-category "social networking" precedence 3 mark app-category video dscp 9 precedence 4 mark application facetime dscp 10 precedence 5 rate-limit application BGP ingress rate 100 max-burst-size 25 egress rate 50 max-burst-size 25 precedence 6 logging level criticalnx9500-6C8809(config-app-policy-Bing)#nx9500-6C8809(config-app-policy-Bing)#no allow app-category business precedence 2nx9500-6C8809(config-app-policy-Bing)#no deny app-category social\ networking precedence 3no <PARAMETERS> Removes or resets this application policy settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-342.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 814.1.27 bgpGlobal Configuration CommandsConfigures Border Gateway Protocol (BGP) settingsBGP is an inter-ISP routing protocol which establishes routing between Internet Service Providers (ISPs). ISPs use BGP to exchange routing and reachability information between Autonomous Systems (AS) on the Internet. BGP makes routing decisions based on paths, network policies and/or rules configured by network administrators. The primary role of a BGP system is to exchange network reachability information with other BGP peers. This information includes information on AS that the reachability information traverses. This information is sufficient to create a graph of AS connectivity from which routing decisions can be created and rules enforced.An AS is a set of routers under the same administration that use Interior Gateway Protocol (IGP) and common metrics to define how to route packets within the AS. AS uses inter-AS routing to route packets to other ASs. For an external AS, an AS appears to have a single coherent interior routing plan and presents a consistent picture of the destinations reachable through it.Routing information exchanged through BGP supports only destination based forwarding (it assumes a router forwards packets based on the destination address carried in the IP header of the packet).BGP uses TCP as its transport protocol. This eliminates the need to implement explicit update fragmentation, retransmission, acknowledgment, and sequencing. BGP listens on TCP port 179. The error notification mechanism used in BGP assumes that TCP supports a graceful close (all outstanding data is delivered before the connection is closed).Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxbgp [as-path-list|community-list|extcommunity-list|ip-access-list|ip-prefix-list] <LIST-NAME>Parameters• bgp [as-path-list|community-list|extcommunity-list|ip-access-list|ip-prefix-list] <LIST-NAME>as-path-list <LIST-NAME>Creates an AS path list and enters its configuration mode• <LIST-NAME> – Provide the AS-PATH-LIST name.community-list <LIST-NAME>Creates a community list and enters its configuration mode• <LIST-NAME> – Provide the COMMUNITY-LIST name.extcommunity-list <LIST-NAME>Creates an extended community list and enters its configuration mode• <LIST-NAME> – Provide the EXTCOMMUNITY-LIST name.ip-access-list <LIST-NAME>Creates a BGP IP access list and enters its configuration mode• <LIST-NAME> – Provide the BGP IP-ACCESS-LIST name.ip-prefix-list<LIST-NAME>Creates a BGP IP prefix list and enters its configuration mode• <LIST-NAME> – Provide the BGP IP-PREFIX-LIST name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-347.png)




![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 874.1.28.2.1 allow-servicebonjour-gateway-discovery-policy-mode commandsEnables discovery of Bonjour devices and the services they provide on Local or Tunneled VLANsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxallow-service <BONJOUR-SERVICE-NAME> [local|tunneled]allow-service <BONJOUR-SERVICE-NAME> local {instance-name contains <WORD>} ({service-vlans <WORD>})allow-service <BONJOUR-SERVICE-NAME> tunneled {instance-name contains <WORD>}Parameters• allow-service <BONJOUR-SERVICE-NAME> local {instance-name contains <WORD>} ({service-vlans <WORD>})allow-service <BONJOUR-SERVICE-NAME>Configures the services that can be discovered by the Bonjour gateway. And also configures the VLANs on which the selected services can be discovered.• <BONJOUR-SERVICE-NAME> – You can either select the Bonjour services from a set of system-provided, pre-defined Apple services, or use an existing alias to define a service not available in the predefined list.The predefined Apple services available are: Afp, AirPlay, AirPort, AirPrint, AirTunes, AppleTimeMachine, Chromecast, Daap, HomeSharing, Printer, and Scanner.Use the <WORD> keyword to define a service not included in the system-provided, pre-defined list. Ensure this device is registered with the Multicast DNS Responder (mDNSResponder).local Select to enable the discovery of the selected Bonjour Services on the local VLANinstance-name contains <WORD>Optional. Specifies the selected Bonjour service’s instance name. When specified, the Bonjour service discovery queries contain the instance name. of the service to be discovered.This option is useful especially in large distributed, enterprise networks. Use it to create different instances of a Bonjour service for the different organizations or departments (VLANS) within your network. Creating instances allows you to advertise specific service instances for a specific set of VLANs, instead of advertising top-level Bonjour Services to various allocated VLAN(s).• contains <WORD> – Specify the instance name. You can either directly specify the string value to be used as a match criteria, or use a string alias (for example, $BONJOUR-STRING) to identify the string to match. If using a string alias, ensure that it is existing and configured. For information on configuring a string alias, see alias.service-vlans <WORD>Optional. Configures a VLAN or a list of VLANs on which the selected service is discoverable. When specified, Bonjour discovery queries are delivered to all clients on the specified VLANs. Applicable only if enabling Bonjour Services discovery on local VLANs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-353.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 894.1.28.2.2 nobonjour-gateway-discovery-policy-mode commandsRemoves or modifies the Bonjour Gateway Discovery policy settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno allow-service <BONJOUR-SERVICE-NAME> [local|tunneled] {service-vlans <WORD>}Parameters• no allow-service <BONJOUR-SERVICE-NAME> [local|tunneled] {service-vlans <WORD>}ExampleThe following example shows the Bonjour GW Discovery policy ‘test’ settings before the ‘no’ command is executed:nx9500-6C8809(config-bonjour-gw-discovery-policy-test)#show contextbonjour-gw-discovery-policy test allow-service Printer local service-vlans 1-2 instance-name contains $Bonjour_Service allow-service Afp localnx9500-6C8809(config-bonjour-gw-discovery-policy-test)#nx9500-6C8809(config-bonjour-gw-discovery-policy-test1)#no allow-service Afp localThe following example shows the Bonjour GW Discovery policy ‘test’ settings after the ‘no’ command was executed:nx9500-6C8809(config-bonjour-gw-discovery-policy-test)#show contextbonjour-gw-discovery-policy test allow-service Printer local service-vlans 1-2 instance-name contains $Bonjour_Servicenx9500-6C8809(config-bonjour-gw-discovery-policy-test)#no <parameters> Removes allow-service rules in the selected Bonjour GW Discovery policy, based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-355.png)



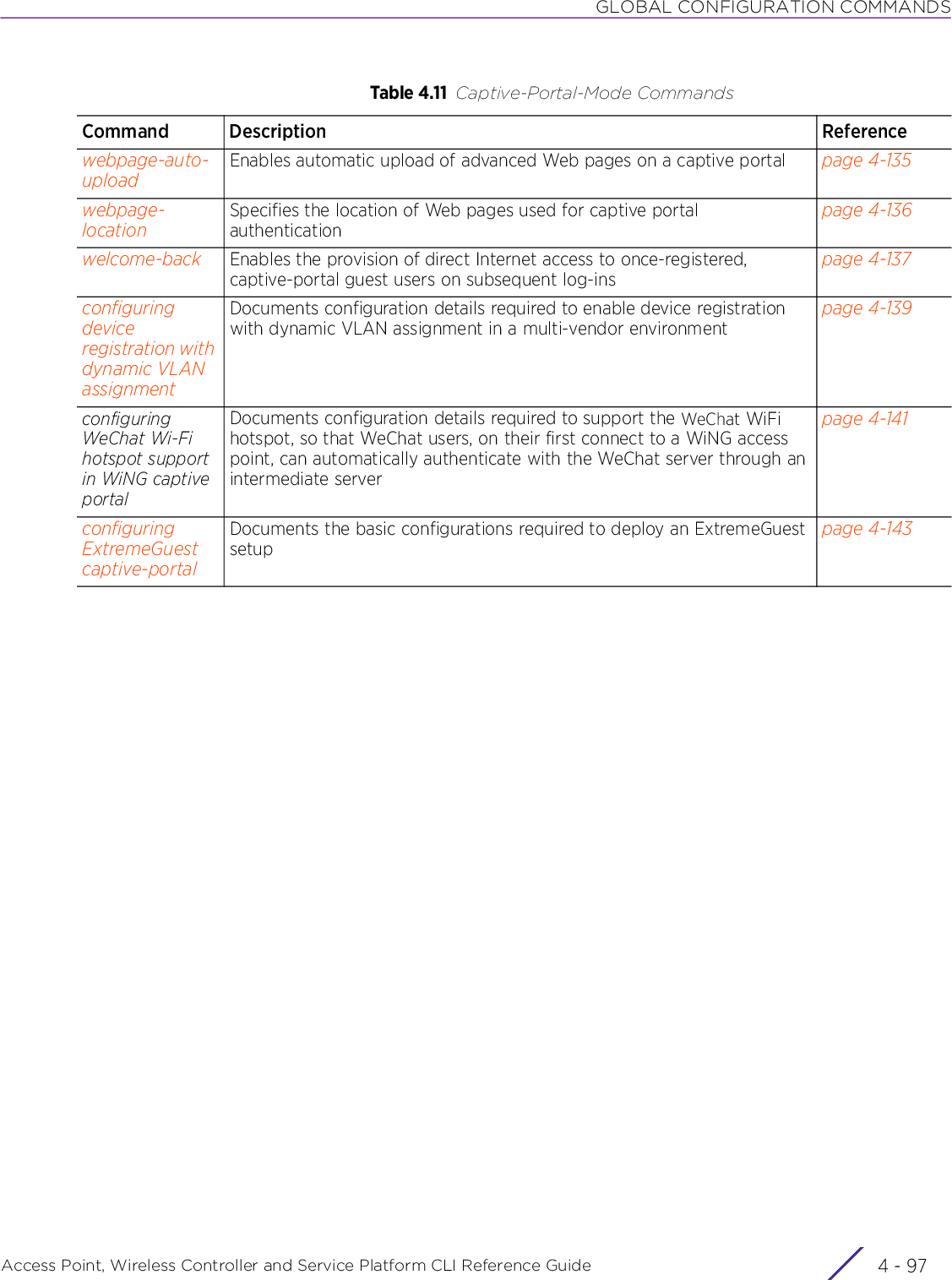

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 994.1.31.2.2 access-typecaptive-portal-mode commandsDefines the captive portal’s access type. The authentication scheme configured here is applied to wireless clients using this captive portal.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccess-type [custom-auth-radius|logging|no-auth|radius|registration]Parameters• access-type [custom-auth-radius|logging|no-auth|radius|registration]Examplerfs6000-81742D(config-captive-portal-test)#access-type loggingrfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test access-type logging access-time 35rfs6000-81742D(config-captive-portal-test)#Related Commandscustom-auth-radius Specifies the custom user information used for authentication (RADIUS lookup of given information, such as name, e-mail address, telephone, etc.). When configured, accessing clients are required to provide a 1-32 character lookup data string used to authenticate their credentials.When selecting this option, use the custom-auth command to configure the required user information.logging Provides users access without authentication. The system logs access details of users allowed access.no-auth Defines no authentication required for a guest (guest is redirected to welcome message). Provides users access to the captive portal without authentication.radius Enables RADIUS authentication for wireless clients. Provides captive portal access to successfully authenticated users only. This is the default setting.registration Enables captive portal’s clients to self register in the captive portal’s database. When configured, a requesting client’s user credentials require authentication locally or through social media credential exchange and validation.If enabled, use the webpage > internal > registration > field command to customize the registration page. If not customized, the default, built-in registration Web page is displayed.no Removes the captive portal access type or reverts to default (radius)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-365.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1004.1.31.2.3 accountingcaptive-portal-mode commandsEnables support for accounting messages for this captive portalWhen enabled, accounting for clients entering and exiting the captive portal is initiated. Accounting is the method of collecting and sending security server information for billing, auditing, and reporting user data. This data includes information, such as start and stop times, executed commands (such as PPP), number of packets and number of bytes transmitted, etc. Accounting enables tracking of captive portal services consumed by clients.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccounting [radius|syslog]accounting radiusaccounting syslog host <IP/HOSTNAME> {port <1-65535>} {proxy-mode [none|through-controller|through-rf-domain-manager]}Parameters• accounting radius• accounting syslog host <IP/HOSTNAME> {port <1-65535>} {proxy-mode [none|through-controller|through-rf-domain-manager]}radius Enables support for RADIUS accounting messages. When enabled, this option uses an external RADIUS resource for AAA accounting. This option is disabled by default.syslog host <IP/HOSTNAME>Enables support for syslog accounting messages. When enabled, data relating to wireless client usage of remote access services is logged on the specified external syslog resource. This information assists in differentiating between local and remote users. Remote user information can be archived to an external location for periodic network and user administration. This option is disabled by default.• host <IP/HOSTNAME> – Specifies the destination where accounting messages are sent. Specify the destination’s IP address or hostname.port <1-65535> Optional. Specifies the syslog server’s listener port• <1-65535> – Specify the UDP port from 1- 65535. The default is 514.proxy-mode [none|through-controller|through-rf-domain-manager]Optional. Specifies the mode of proxying the syslog server• none – Accounting messages are sent directly to the syslog server• through-controller – Accounting messages are sent through the controller configuring the device• through-rf-domain-manager – Accounting messages are sent through the local RF Domain manager](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-366.png)
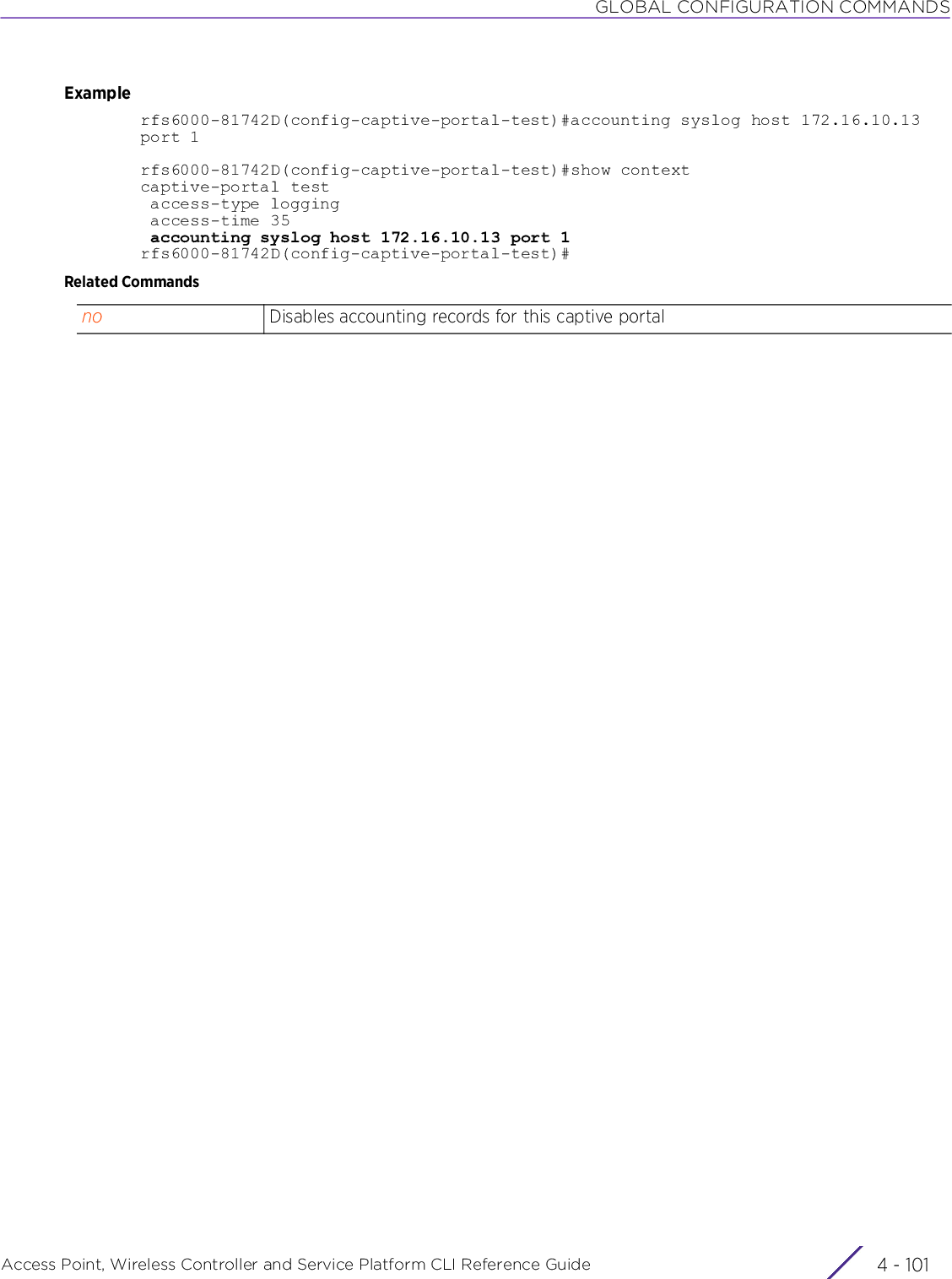

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1034.1.31.2.5 connection-modecaptive-portal-mode commandsConfigures a captive portal’s mode of connection to the Web server. HTTP uses plain unsecured connection for user requests. HTTPS uses an encrypted connection to support user requests.Both HTTP and HTTPS use the same Uniform Resource Identifier (URI), so controller and client resources can be identified. However, the use of HTTPS is recommended, as it affords controller and client transmissions some measure of data protection HTTP cannot provide.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxconnection-mode [http|https]Parameters• connection-mode [http|https]Examplerfs6000-81742D(config-captive-portal-test)#connection-mode httpsrfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test access-type logging access-time 35 connection-mode https accounting syslog host 172.16.10.13 port 1rfs6000-81742D(config-captive-portal-test)#Related Commandshttp Sets HTTP as the default connection mode. This is the default setting.https Sets HTTPS as the default connection modeHTTPS is a more secure version of HTTP, and uses encryption while sending and receiving requests.no Removes this captive portal’s connection mode](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-369.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1054.1.31.2.7 data-limitcaptive-portal-mode commandsEnforces data transfer limits on captive portal clients. This feature enables the tracking and logging of user usage. Users exceeding the allowed bandwidth are restricted from the captive portal.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdata-limit <1-102400> {action [log-and-disconnect|log-only]}Parameters• data-limit <1-102400> {action [log-and-disconnect|log-only]}Examplerfs6000-81742D(config-captive-portal-test)#data-limit 200 action log-and-disconnectrfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test data-limit 200 action log-and-disconnectrfs6000-81742D(config-captive-portal-test)#Related Commandsdata-limit <1-102400>Sets a captive portal client’s data transfer limit in megabytes. This limit is applicable for both upstream and downstream data transfer.• <1-102400> – Specify a value from 1 - 102400 MB.action [log-and-disconnect|log-only]Optional. Specifies the action taken when a client exceeds the configured data limit. The options are:• log-and-disconnect – When selected, an entry is added to the log file any time a captive portal client exceeds the data limit, and the client is disconnected.• log-only – When selected, an entry is added to the log file any time a captive portal client exceeds the data limit. the client, however, remains connected to the captive portal. This is the default setting.no Removes data limit enforcement for captive portal clients](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-371.png)

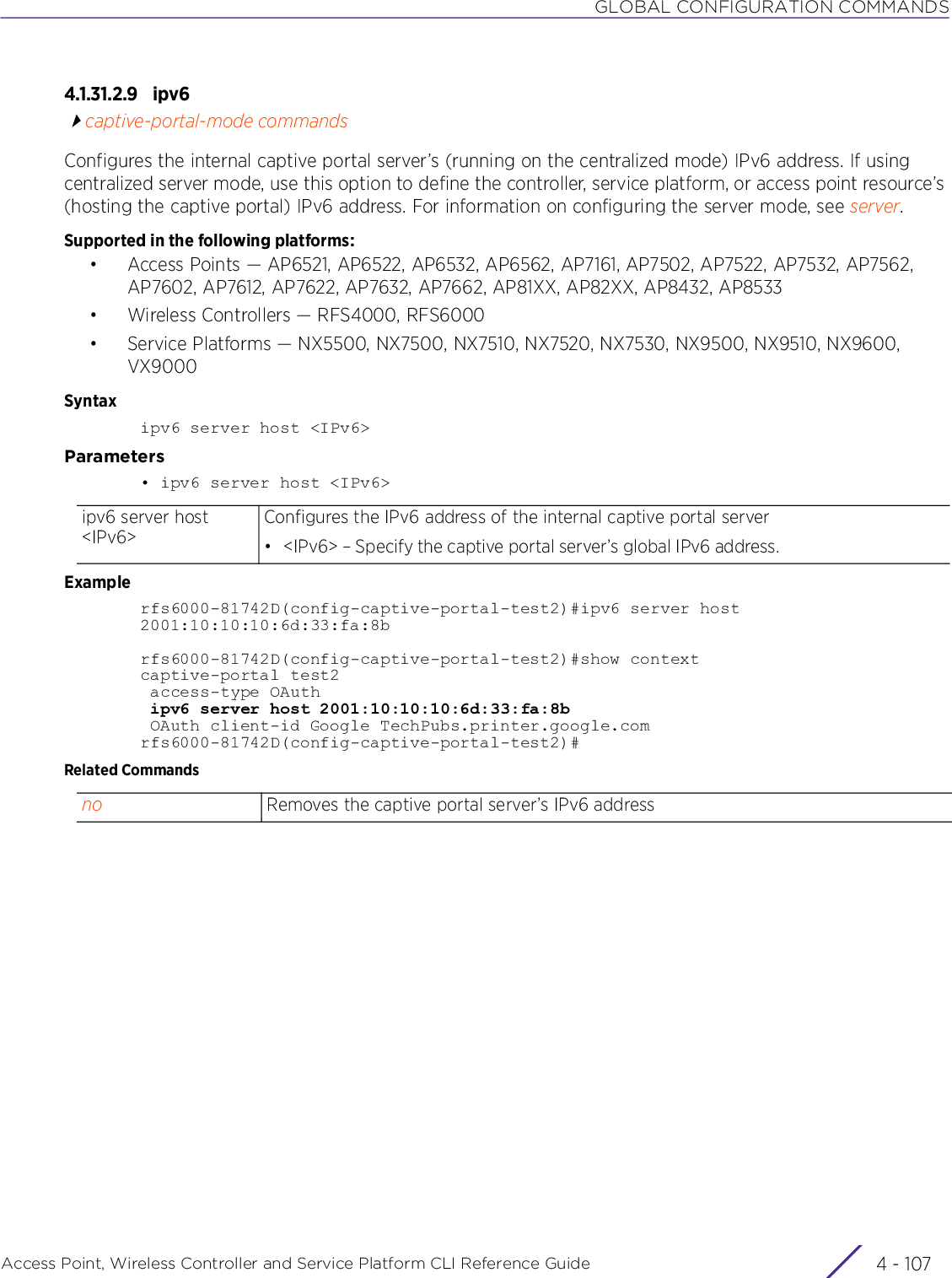
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1084.1.31.2.10 localizationcaptive-portal-mode commandsConfigures an FQDN address string that enables the client to receive localization parameters. Use this option to add a URL to trigger a one-time redirect on demand. The defined URL is triggered from a mobile application to derive location information from the wireless network so an application can be localized to a particular store or region.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlocalization [fqdn <WORD>|response <WORD>]Parameters• localization [fqdn <WORD>|response <WORD>]localization Configures an FQDN address string that enables the client to receive localization parameters. This command also allows the configuration of a response message.fqdn <WORD> Configures the FQDN address string, which is used to obtain localization parameters for the captive portal’s client.• <WORD> – Specify the FQDN address string. For example, local.guestaccess.comresponse <WORD> Configures a message, which is sent back to the client in response to the client’s localization HTTP requests• <WORD> – Specify the response message (should not exceed 512 characters in length). The following built-in query tags can be included in the response message:WING_TAG_CLIENT_IP' -Captive portal client IPv4 address'WING_TAG_CLIENT_MAC' - Captive portal client MAC address'WING_TAG_WLAN_SSID ' - Captive portal client WLAN ssid'WING_TAG_AP_MAC' - Captive portal client AP MAC address'WING_TAG_AP_NAME' - Captive portal client AP Name'WING_TAG_RF_DOMAIN' - Captive portal client RF Domain'WING_TAG_USERNAME' - Captive portal authentication username'WING_TAG_USERTYPE' - Captive portal usertype(new/return/refresh) Example:-<local><site>WING_TAG_RF_DOMAIN</site><ap>WING_TAG_AP_NAME</ap></local](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-374.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1114.1.31.2.12 nocaptive-portal-mode commandsThe no command reverts the selected captive portal’s settings or resets settings to default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [access-time|access-type|accounting|bypass|connection-mode|custom-auth|data-limit|inactivity-timeout|ipv6|localization|logout-fqdn|oauth|php-helper|post-authentication-vlan|radius-vlan-assignment|redirection|report-loyalty-application|server|simultaneous-users|terms-agreement|use|webpage|webpage-auto-upload|webpage-location|welcome-back]no [access-time|access-type|connection-mode|data-limit|inactivity-timeout|logout-fqdn|post-authentication-vlan|radius-vlan-assignment|report-loyalty-application|simultaneous-users|terms-agreement|webpage-auto-upload|webpage-location]no accounting [radius|syslog]no bypass captive-portal-detectionno custom-auth infono ipv6 server hostno localization [fqdn|response]no oauth {client-id}no php-helperno redirection portsno server hostno server mode {centralized-controller [hosting-vlan-interface]}no use [aaa-policy|dns-whitelist]no webpage external [acknowledgement|agreement|fail|login {post}|no-service|registration|welcome]no webpage internal [acknowledgement|agreement|fail|login|no-service|org-name|org-signature|registration|welcome]no webpage internal [org-name|org-signature]no webpage internal [acknowledgment|agreement|fail|login|no-service] [body-background-color|body-font-color|description|footer|header|main-logo|org-background-color|org-font-color|small-logo|title]no webpage internal registration [body-background-color|body-font-color|description|field|footer|header|main-logo|org-background-color|org-font-color|small-logo|title]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-377.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 112no webpage internal registration field [age-range|city|country|custom <FIELD-NAME>|disclaimer|dob|email|gender|member|mobile|name|optout|street|via-email|via-sms|zip] {enable}no webpage internal welcome [body-background-color|body-font-color|description|footer|header|main-logo|org-background-color|org-font-color|small-logo|title|use-external-success-url]no welcome-back pass-throughParameters• no <PARAMETERS>ExampleThe following example shows the captive portal ‘test’ settings before the ‘no’ commands are executed:rfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test access-type logging access-time 35 custom-auth info bob bob@examplecompany.com connection-mode https inactivity-timeout 750 accounting syslog host 172.16.10.13 port 1rfs6000-81742D(config-captive-portal-test)#rfs6000-81742D(config-captive-portal-test)#no accounting syslogrfs6000-81742D(config-captive-portal-test)#no access-typeThe following example shows the captive portal ‘test’ settings after the ‘no’ commands are executed:rfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test access-time 35 custom-auth info bob bob@examplecompany.com connection-mode https inactivity-timeout 750rfs6000-81742D(config-captive-portal-test)#no <PARAMETERS> Removes or resets this captive portal’s settings, based on the parameters passed.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-378.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1134.1.31.2.13 oauthcaptive-portal-mode commandsEnables OAuth-driven Google and/or Facebook authentication on captive portals that use internal Web pages. To enable Google and Facebook captive-portal authentication:• Enforce captive-portal authentication on the WLAN to which wireless-clients associate. For information, see captive-portal-enforcement.• Set captive-portal Web page location to internal. For more information, see webpage-location.• Register your captive-portal individually on Google/FaceBook APIs and generate a client-id and client-secret. The client-ids retrieved during registration are the IDs for the WiNG application running on the access point/controller. The WiNG application uses these client-ids to access the Google and Facebook Auth APIs, and authenticate the guest client on behalf of the user.If enabling OAuth-driven Google and/or Facebook authentication on the captive portal, use this command to configure the Google/Facebook client-ids. Once enabled, the captive portal landing page, displayed on the client’s browser, provides the Facebook and Google login buttons.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoauthoauth client-id [facebook|google] <WORD>Parameters• oauth• oauth client-id [facebook|google] <WORD>oauth Execute this command without the associated keywords to enable OAuth on this captive-portal. If enabling OAuth, ensure the captive-portal Web page location is configured as advanced or external.oauth client-id [facebook|google] <WORD>Configures the client-ids retrieved from the Google and Facebook API manager portals during registration• facebook – Configures the Facebook API client-id (is a 15 digit entity)• google – Configures the Google API client-id (is a 12 digit number)• <WORD> – Provide the Facebook/Google client-id.If the captive-portal Web page location is advanced or external, and you are enabling OAuth support, you need not configure the client-id. In such a scenario, the client-id is configured through the EGuest server UI and not the WiNG CLI.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-379.png)
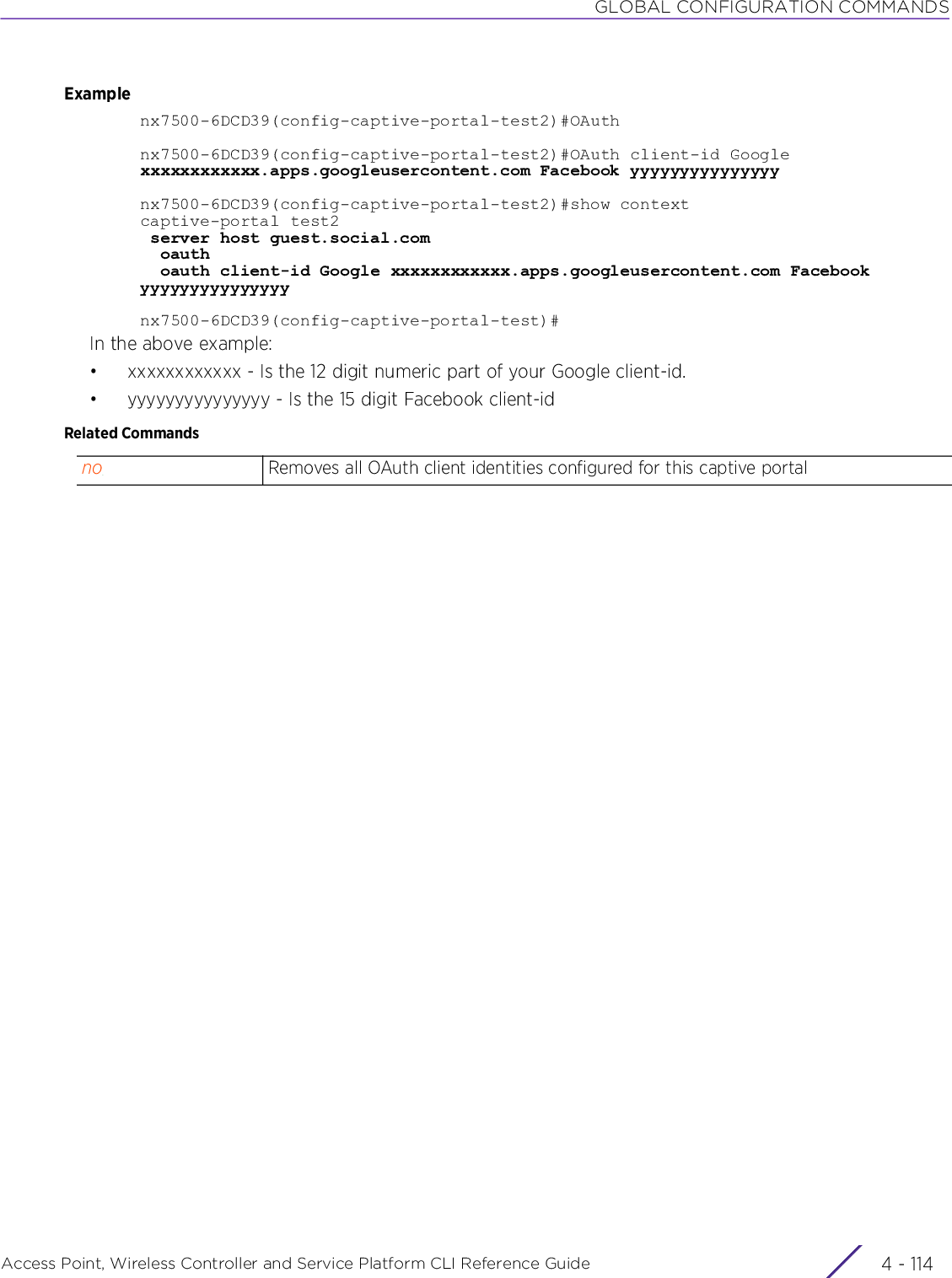
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1154.1.31.2.14 php-helpercaptive-portal-mode commandsConfigures a PHP helper to serve the PHP splash pages to guest users logging in to the captive portal using social-media credentials. Configure a PHP helper only if the following criteria are fulfilled:• OAuth-based authentication is enabled on the captive portal.• The captive-portal server mode is “self”.• The access point, hosting the captive-portal server, has low memory space (for example, the AP6511, AP6521, AP6522, AP6532, and AP7502 model access points).• A hotspot server, hosting the captive-portal PHP splash pages, is up and running.The WiNG software introduces HybridAuth support on captive portals. HybridAuth is an open-source, social-sign on PHP Library. In addition to Google and Facebook, it allows a variety of third-party social authentications, such as LinkedIn, Twitter, Live, Yahoo, OpenID, etc. However, HybridAuth uses space-consuming PHP splash pages that cannot be loaded on access points with low memory space. These access points can only serve the initial landing page, where guests clicking on a social login button are redirected by the php-helper to a PHP page hosted on the PHP-helper.To create PHP splash pages, use the splash template configuration tool available on the ExtremeGuest (EGuest) dashboard. Upload the generated tar to both the hotspot server and the php helper. Note, the EGuest dashboard can be launched from the WiNG controller (NX9500/NX9600/VX9000) enabled as the EGuest server. For more information on enabling the EGuest server, see eguest-server (VX9000 only).For more information on configuring an EGuest captive portal, see configuring ExtremeGuest captive-portal.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxphp-helper [controller|domain-manager]php-helper controller <IP/HOSTNAME> hosting-vlan-interface <0-4096>php-helper domain-manager <IP/HOSTNAME>Parameters• php-helper controller <IP/HOSTNAME> hosting-vlan-interface <0-4094>]php-helper Configures the php-helper parameterscontroller <IP/HOSTNAME>Configures the controller adopting the captive-portal access point as the php-helper• <IP/HOSTNAME> – Specify the adopting controller’s IP address or host name.hosting-vlan-interface <0-4096>Optional. Configures the VLAN on which the php-helper is reachable• <0-4096> – Specify the VLAN hosting the php-helper from 0 - 4096.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-381.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1174.1.31.2.15 post-authentication-vlancaptive-portal-mode commandsConfigures the VLAN that is assigned to this captive portal’s users upon successful authenticationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpost-authentication-vlan [<1-4096>|<VLAN-ALIAS>]Parameters• post-authentication-vlan [<1-4096>|<VLAN-ALIAS>]Examplerfs4000-229D58(config-captive-portal-test)#post-authentication-vlan 1rfs4000-229D58(config-captive-portal-test)#show contextcaptive-portal test post-authentication-vlan 1rfs4000-229D58(config-captive-portal-test)#Related Commandspost-authentication-vlan [<1-4096>|<VLAN-ALIAS>]Configures the post authentication VLAN. The VLAN specified here is assigned to this captive portal’s users after they have authenticated and logged on to the network. Provide the VLAN ID, or use an existing VLAN alias to identify the post authentication VLAN.• <1-4096> – Specify the VLAN’s number from 1 - 4096.• <VLAN-ALIAS> – Specify the VLAN alias (should be existing and configured).VLAN alias names begin with a ‘$’.no Removes the post authentication RADIUS VLAN assigned to this captive portal’s usersradius-vlan-assignmentEnables assignment of a RADIUS VLAN for this captive portal](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-383.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1214.1.31.2.19 servercaptive-portal-mode commandsConfigures captive portal server parameters, such as the hostname, IP address, and mode of operation. This is the captive-portal server hosting the captive portal Web pages.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxserver [host|mode]server host <IP/HOSTNAME>server mode [centralized|centralized-controller {hosting-vlan-interface <0-4096>}|self]Parameters• server host <IP/HOSTNAME>• server mode [centralized|centralized-controller {hosting-vlan-interface <0-4096>}|self]host <IP/HOSTNAME> Configures the internal captive portal server (wireless controller, access point, service platform)• <IP/HOSTNAME> – Specify the IPv4/IPv6 address or hostname of the captive portal server.For centralized-controller mode, the server host should be a virtual hostname and not an IP address.If enabling OAuth (social-media login) on the captive portal, configure the server’s hostname and not the IP address. This is because some social media do not allow IP address as redirect-uri. For more information, see oauth and php-helper.mode Configures the captive portal server mode. This parameter identifies the device that will capture and redirect a wireless user’s Web browser session to a landing page where the user has to provide login credentials in order to access the managed network. The WiNG captive portal implementation is very flexible and allows captive portal services to reside anywhere within the WiNG managed network. For example, the capture and redirection can be performed directly by the access points at the edge of the network, centrally on the controllers or service platforms managing the access points, or on dedicated wireless controller deployed within an isolated network.centralized Select this option if capture and redirection is provided by a designated wireless controller/service platform on the network defined using an IPv4/IPv6 address or hostname. This dedicated device can either be managing the dependent/independent access points or be a dedicated device deployed over the intermediate network.Ensure the IPv4 address or hostname of the WiNG wireless controller performing the capture and redirection is defined in the captive portal policy. And also, that the wireless controller is reachable via MINT.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-387.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1254.1.31.2.22 usecaptive-portal-mode commandsConfigures a AAA policy and DNS whitelist with this captive portal policy. AAA policies are used to configure authentication and accounting servers for this captive portal. DNS whitelists restrict users to a set of configurable domains on the Internet.For more information on AAA policies, see AAA-POLICY.For more information on DNS whitelists, see dns-whitelist.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [aaa-policy <AAA-POLICY-NAME>|dns-whitelist <DNS-WHITELIST-NAME>]Parameters• use [aaa-policy <AAA-POLICY-NAME>|dns-whitelist <DNS-WHITELIST-NAME>]Examplerfs6000-81742D(config-captive-portal-test)#use aaa-policy testrfs6000-81742D(config-captive-portal-test)#use dns-whitelist testrfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test access-time 35 custom-auth info bob bob@examplecompany.com connection-mode https inactivity-timeout 750 server host 172.16.10.9 simultaneous-users 5 terms-agreement use aaa-policy test use dns-whitelist testrfs6000-81742D(config-captive-portal-test)#aaa-policy <AAA-POLICY-NAME>Associates a AAA policy with this captive portal. AAA policies validate user credentials and provide captive portal access to the network.• <AAA-POLICY-NAME> – Specify the AAA policy name.dns-whitelist <DNS-WHITELIST-NAME>Associates a DNS whitelist to use with this captive portal. A DNS whitelist defines a set of allowed destination IP addresses. DNS whitelists restrict captive portal access.• <DNS-WHITELIST-NAME> – Specify the DNS whitelist name.To effectively host captive portal pages on an external Web server, the IP address of the destination Web server(s) should be added to the DNS whitelist.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-391.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1274.1.31.2.23 webpagecaptive-portal-mode commandsUse this command to define the appearance and flow of Web pages requesting clients encounter when accessing a controller, service platform, or access point managed captive portal. Define whether the Web pages are maintained locally or externally to the managing device as well as messages displayed requesting clients.Configures Web pages displayed when interacting with a captive portal. These pages are:• acknowledgment – This page displays details for the user to acknowledge• agreement – This page displays “Terms and Conditions” that a user accepts before allowed access to the captive portal.• fail – This page is displayed when the user is not authenticated.• login – This page is displayed when the user connects to the captive portal. It fetches login credentials from the user.• no-service – This page is displayed when a captive portal user is unable to access the captive portal due to unavailability of critical services.• registration – This page is displayed when users are redirected to a Web page where they have to register in the captive portal’s database.• welcome – This page is displayed to welcome an authenticated user to the captive portal.These Web pages, which interact with captive portal users, can be located either on the controller or an external location.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwebpage [external|internal]webpage external [acknowledgment|agreement|fail|login {post}|no-service|registration|welcome] <URL>webpage internal [acknowledgment|agreement|fail|login|no-service|org-name|org-signature|registration|welcome]webpage internal [acknowledgment|agreement|fail|login|no-service|registration|welcome] [description|footer|header|title] <CONTENT>webpage internal [acknowledgment|agreement|fail|login|no-service|registration|welcome] [body-background-color|body-font-color|org-background-color|org-font-color] <WORD>webpage internal [acknowledgment|agreement|fail|login|no-service|registration|welcome] [main-logo use-as-banner|small-logo] <URL>webpage internal registration field [age-range|city|country|custom|disclaimer|dob|email|gender|member|mobile|name|optout|street|via-email|via-sms|zip] type [checkbox|date|dropdown-menu|e-address|number|radio-button|text] enable {label <LINE>|mandatory|title <LINE>|placeholder <LINE>}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-393.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 128webpage internal welcome use-external-success-urlwebpage internal [org-name|org-signature] <LINE>Parameters• webpage external [acknowledgment|agreement|fail|login {post}|no-service|registration|welcome] <URL>external Indicates Web pages being served are hosted on an external (to the captive portal) server resourceacknowledgment Indicates the page is displayed for user acknowledgment of details. Users are redirected to this page to acknowledge information provided.agreement Indicates the page is displayed for “Terms & Conditions”The agreement page provides conditions that must be agreed to before captive portal access is permitted.fail Indicates the page is displayed for login failureThe fail page asserts authentication attempt has failed, the user is not allowed to access the Internet (using this captive portal) and must provide the correct login information again to access the Internet.login {post} Indicates the page is displayed for getting user credentials. This page is displayed by default.• post – Optional. Redirects users to post externally during authenticationThe login page prompts the user for a username and password to access the captive portal and proceed to either the agreement page (if used) or the welcome page.no-service Indicates the page is displayed when certain critical services are unavailable and the user fails to access the captive portal. The no-service page asserts the captive portal service is temporarily unavailable due to technical reasons. Once the services become available, the captive portal user is automatically connected back to the services available through the captive portal. The possible scenarios are:• The RADIUS server (on-board or external) is not reachable and the user cannot be authenticated• The external captive portal server is not reachable• The connectivity between the adopted AP and controller is lost• The external DHCP server is not reachableTo provide this service, enable the following:• External captive portal server monitoring• AAA server monitoring. This enables detection of RADIUS server failure.• External DHCP server monitoringFor more information on enabling these critical resource monitoring, see service.registration Indicates the page is displayed when users are redirected to a Web page where they have to register in the captive portal’s databaseGuest users are redirected to an internally (or) externally hosted registration page (registration.html) upon association to a captive portal SSID, where previously, not-registered guest users can register.welcome Indicates the page is displayed after a user has been successfully authenticatedThe welcome page asserts a user has logged in successfully and can access the captive portal.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-394.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 129• webpage internal [acknowledgment|agreement|fail|login|no-service|registration|welcome] [description|footer|header|title] <CONTENT><URL> This parameter is common to all of the above mentioned Web pages, and specifies the Web page URL. The Web page is retrieved and served from the specified external location.The URL can include following query tags:'WING_TAG_CLIENT_IP' - Captive portal client IPv4 address'WING_TAG_CLIENT_MAC' - Captive portal client MAC address'WING_TAG_WLAN_SSID ' - Captive portal client WLAN ssid'WING_TAG_AP_MAC' - Captive portal client AP MAC address'WING_TAG_AP_NAME' - Captive portal client AP Name'WING_TAG_RF_DOMAIN' - Captive portal client RF Domain'WING_TAG_CP_SERVER' - Captive portal server address'WING_TAG_USERNAME' - Captive portal authentication usernameExample:http://cportal.com/policy/login.html?client_ip=WING_TAG_CLIENT_IP&ap_mc=WING_TAG_AP_MAC.Use '&' or '?' character to separate field-value pair.Enter 'ctrl-v' followed by '?' to configure query string.internal Indicates the Web pages are hosted on an internal server resource. This is the default setting.acknowledgment Indicates the Web page is displayed for users to acknowledge the information providedagreement Indicates the page is displayed for “Terms & Conditions”fail Indicates the page is displayed for login failurelogin Indicates the page is displayed for entering user credentialsno-service Indicates the page is displayed when certain critical services are unavailable and the user fails to access the captive portal. The possible scenarios are:• The RADIUS server (on-board or external) is not reachable and the user cannot be authenticated• The external captive portal server is not reachable• The connectivity between the adopted AP and controller is lost• The external DHCP server is not reachableTo provide this service, enable the following:• External captive portal server monitoring• AAA server monitoring. This enables detection of RADIUS server failure.• External DHCP server monitoring• AP to controller connectivity monitoringFor more information on enabling these critical resource monitoring, see service.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-395.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 130• webpage internal [acknowledgment|agreement|fail|login|no-service|registration|welcome] [main-logo use-as-banner|small-logo] <URL>registration Indicates the page is displayed when users are redirected to a Web page where they have to register in the captive portal’s databaseGuest users are redirected to an internally (or) externally hosted registration page (registration.html) upon association to a captive portal SSID, where previously, not-registered guest users can register.welcome Indicates the page is displayed after a user has been successfully authenticateddescription Indicates the content is the description portion of each of the following internal Web pages: acknowledgment, agreement, fail, login, no-service, and welcomefooter Indicates the content is the footer portion of each of the following internal Web pages: acknowledgment, agreement, fail, no-service, and welcome page. The footer portion contains the signature of the organization that hosts the captive portal.header Indicates the content is the header portion of each of the following internal Web pages: acknowledgment, agreement, fail, no-service, and welcome page. The header portion contains the heading information for each of these pages.title Indicates the content is the title of each of the following internal Web pages: acknowledgment, agreement, fail, no-service, and welcome page. The title for each of these pages is configured here.<CONTENT> The following keyword is common to all of the above internal Web page options:• <CONTENT> – Specify the content displayed for each of the different components of the internal Web page. Enter up to 900 characters for the description and 256 characters each for header, footer, and title.internal Indicates the Web pages are hosted on an internal server resourceagreement Indicates the page is displayed for “Terms & Conditions”acknowledgment Indicates the Web page is displayed for users to acknowledge the information providedfail Indicates the page is displayed for login failurelogin Indicates the page is displayed for user credentialsno-service Indicates the page is displayed when certain critical services are unavailable and the user fails to access the captive portal. The possible scenarios are:• The RADIUS server (on-board or external) is not reachable and the user cannot be authenticated• The external captive portal server is not reachable• The connectivity between the adopted AP and controller is lost• The external DHCP server is not reachableTo provide this service, enable the following:• External captive portal server monitoring• AAA server monitoring. This enables detection of RADIUS server failure.• External DHCP server monitoring• AP to controller connectivity monitoringFor more information on enabling these critical resource monitoring, see wlan.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-396.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 131• webpage internal registration field [age-range|city|country|custom|disclaimer|dob|email|gender|member|mobile|name|optout|street|via-email|via-sms|zip] type [checkbox|date|dropdown-menu|e-address|number|radio-button|text] enable {label <LINE>|mandatory|title <LINE>|placeholder <LINE>}registration Indicates the page displayed is the registration page to which users are redirected in order to register in the captive portal’s databaseGuest users are redirected to an internally (or) externally hosted registration page (registration.html) upon association to a captive portal SSID, where previously, not-registered guest users can register.welcome Indicates the page is displayed after a user has been successfully authenticatedmain-logo use-as-bannerThe following keyword is common to all of the above internal Web page options:• main-logo – Indicates the main logo displayed in the header of each Web page• use-as-banner – Uses the image, specified here, as the Web page banner, in placeof the logo and organization namesmall-logo The following keyword is common to all of the above internal Web page options:• small-logo – Indicates the logo image displayed in the footer of each Web page, and constitutes the organization’s signature<URL> This parameter is common to the ‘main-logo’ and ‘small-logo’ keywords and provides the complete URL from where the main-logo and small-logo files are loaded and subsequently cached on the system.• <URL> – Specify the location and name of the main-logo and the small-logo image files.internal Indicates the Web pages are hosted on an internal server resourceregistration Allows you to customize the user registration page. Select this option if the captive-portal’s access-type is set to registration. Use the field and type options to define the input fields (for example, age-range, city, email, etc.) and the field type (for example, text, checkbox, dropdown-menu, radio-button, etc.)Guest users are redirected to an internally (or) externally hosted registration page (registration.html) upon association to a captive portal SSID, where previously, not-registered guest users can register.If the registration Web page is not customized, the built-in, default registration page is displayed to the client.field [age-range|city|country|custom <WORD >|disclaimer|]Configures the captive portal’s registration page fieldsFollowing are the available fields and the field type for each:• age-range – Creates the age-range input field (enabled by default and included in the built-in registration page)• dropdown-menu – Configures the age-range field as a drop-down menu• radio-button – Configures the age-range field as a radio button menu•city – Creates the postal address: city name input field (enabled by default and included in the built-in registration page)• text – Configures the city field as only alpha-numeric and special characters inputfieldContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-397.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 132• country – Creates the postal address: country name input field (disabled by default)• text – Configures the country field as only alpha-numeric and special characters in-put field• custom <WORD> – Creates a customized field (as per your requirement). Use the ‘custom’ option to create a field not included in the built-in list.• <WORD> – Provide a name for the field. On the registration page, the field is dis-played under the name specified here.• disclaimer – Creates client’s disclaimer-confirmation input field (disabled by default)• checkbox – Configures the disclaimer field as a check boxfield [dob|email|gender|member|mobile|name|optout|street|via-email|via-sms|zip]•dob – Creates the client’s date of birth (DoB) input field (disabled by default)• date – Configures the DoB field as only date-format input field• dropdown-menu – Configures the DoB field as a drop-down menu• text – Configures the DoB field as only alpha-numeric and special characters inputfield• email – Creates the e-mail address input field (enabled by default and included in the built-in registration page)• e-address – Configures the e-mail field as only e-mail address format input field• gender – Creates client’s gender input field (disabled by default)• dropdown-menu – Configures the gender field as a drop-down menu• radio-button – Configures the gender field as a radio button menu• member – Creates client’s loyalty or captive-portal membership card number input field (disabled by default)• number – Configures the member field as only-numeric characters input field• text – Configures the member field as only alpha-numeric and special characters input field• mobile – Creates the mobile number input field (enabled by default and included in the built-in registration page)• number – Configures the mobile field as only-numeric characters input field• text – Configures the mobile field as only alpha-numeric and special characters in-put field• name – Creates the client name input field (enabled by default and included in the built-in registration page)• text – Configures the name field as only alpha-numeric and special characters inputfield• optout – Creates an input field that enables clients to opt out from registering• checkbox – Configures the optout field as a check box• street – Creates the postal address: street name/number input field (enabled by default and included in the built-in registration page)• text – Configures the street field as only alpha-numeric and special characters inputfield• via-email – Creates the client’s preferred mode of communication as e-mail input field (enabled by default and included in the built-in registration page)• checkbox – Configures the via-email field as a check box• via-sms – Creates the client’s preferred mode of communication as SMS input field (enabled by default and included in the built-in registration page)• checkbox – Configures the via-sms field as a check boxContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-398.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 133• webpage internal welcome use-external-success-url• webpage internal [org-name|org-signature] <LINE>• zip – Creates the postal address: zip input field (enabled by default and included in the built-in registration page)• number – Configures the zip field as only-numeric characters input field• text – Configures the zip field as only alpha-numeric and special characters inputfieldtype [checkbox|date|dropdown-menu|e-address|number|radio-button|text]After specifying the field, configure the field type. The options displayed depend on the field selected in the previous step. These options are: checkbox, date, dropdown-menu, e-address, number, radio-button, and text.• checkbox – Configures the field as a check box• date – Configures the field as only date-format input field • dropdown-menu – Configures the field as a drop-down menu• e-address – Configures the field as an e-mail address input field• number – Configures the field as only-numeric characters input field• radio-button – Configures the field as a radio button• text – Configures the field as only alpha-numeric and special characters input fieldSome of the fields can have more than one field type options. For example, the field ‘zip’ can either be a numerical field or a text. Select the one best suited for your captive-portal.enable {label <LINE>|mandatory|title <LINE>|placeholder <LINE>}Enables the field. When enabled, the field is displayed on the registration page. After enabling the field, optionally configure the following parameters:• label <LINE> – Optional. Configures the field’s label• mandatory – Optional. Makes the field mandatory• title – Optional. Configures the comma-separated list of items to include in the drop-down menu.• placeholder <LINE> – Optional. Configures a string, not exceeding 300 characters, that is displayed within the field. If not configured, the field remains blank.internal Indicates the Web pages are hosted on an internal server resourcewelcome Indicates the page is displayed after a user has been successfully authenticateduse-external-success-urlWhen configured, redirects the user, on successful authentication, to an externally hosted success URL from the locally-hosted landing page.Use the webpage > external > welcome > <URL> command to specify the location of the Welcome page.internal Indicates the Web pages are hosted on an internal server resourceorg-name Specifies the company’s name, included on Web pages along with the main imageorg-signature Specifies the company’s signature information, included in the bottom of Web pages along with a small image<LINE> Specify the company’s name or signature depending on the option selected.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-399.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1364.1.31.2.25 webpage-locationcaptive-portal-mode commandsSpecifies the location of the Web pages used for authentication. These pages can either be hosted on the system or on an external Web server.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwebpage-location [advanced|external|internal]Parameters• webpage-location [advanced|external|internal]Examplerfs6000-81742D(config-captive-portal-test)#webpage-location externalrfs6000-81742D(config-captive-portal-test)#show contextcaptive-portal test access-time 35 custom-auth info bob bob@examplecompany.com connection-mode https inactivity-timeout 750 server host 172.16.10.9 simultaneous-users 5 terms-agreement webpage-location external use aaa-policy testrfs6000-81742D(config-captive-portal-test)#Related Commandsadvanced Uses Web pages for login, welcome, failure, and terms created and stored on the controller. Select advanced to use a custom-developed directory full of Web page content that can be copied in and out of the controller, service platform, or access point.If selecting advanced, enable the webpage-auto-upload option to automatically launch the advanced pages to requesting clients upon association. For more information, see webpage-auto-upload.external Uses Web pages for login, welcome, failure, and terms located on an external server. Provide the URL for each of these pages.internal Uses Web pages for login, welcome, and failure that are automatically generatedno Resets or disables captive portal Web page settingswebpage Configures a captive portal’s Web page (acknowledgment, agreement, login, welcome, fail, no-service, and terms) settingswebpage-auto-uploadEnables an automatic upload of advanced Web pages on a captive portal](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-402.png)

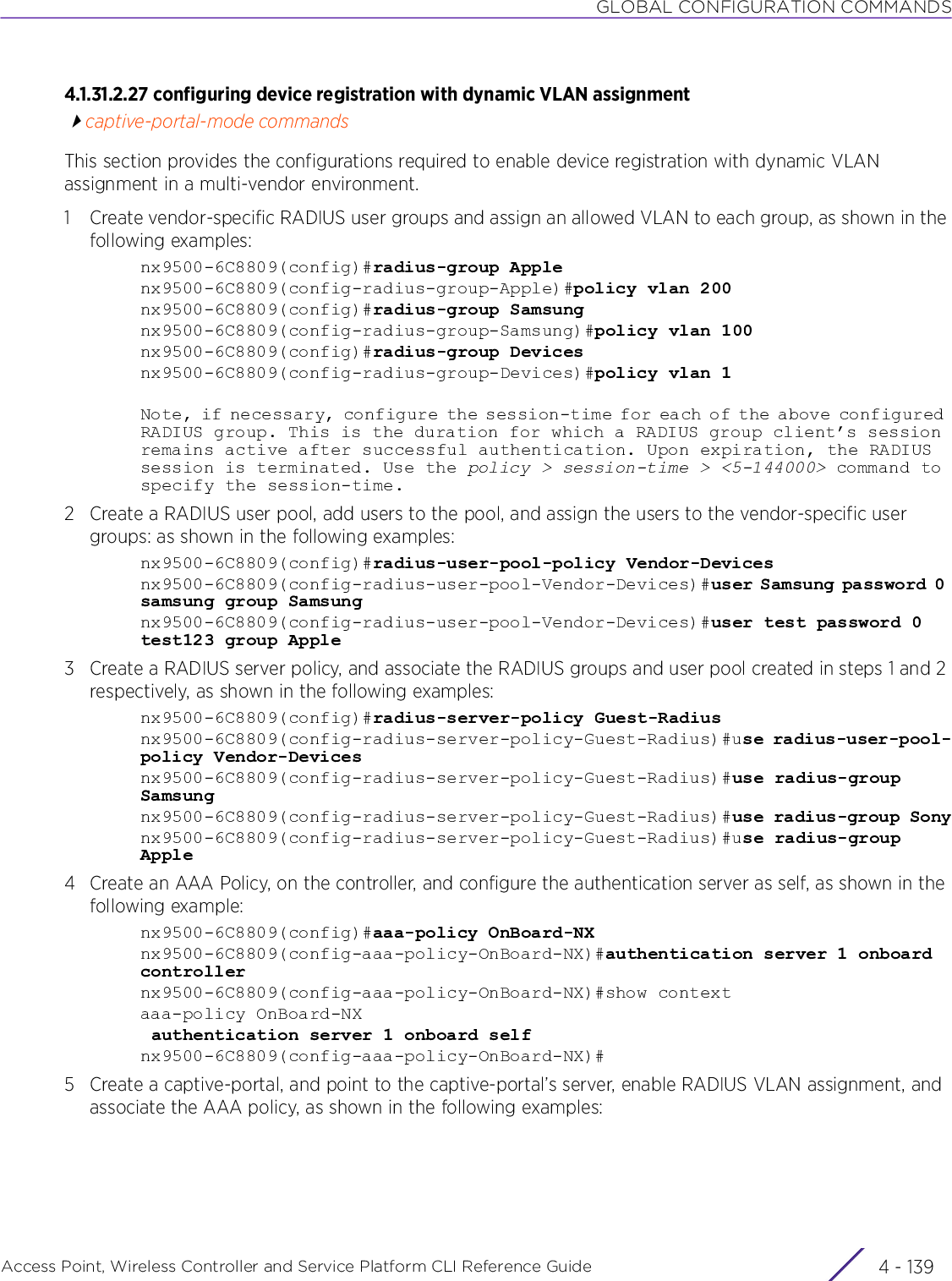
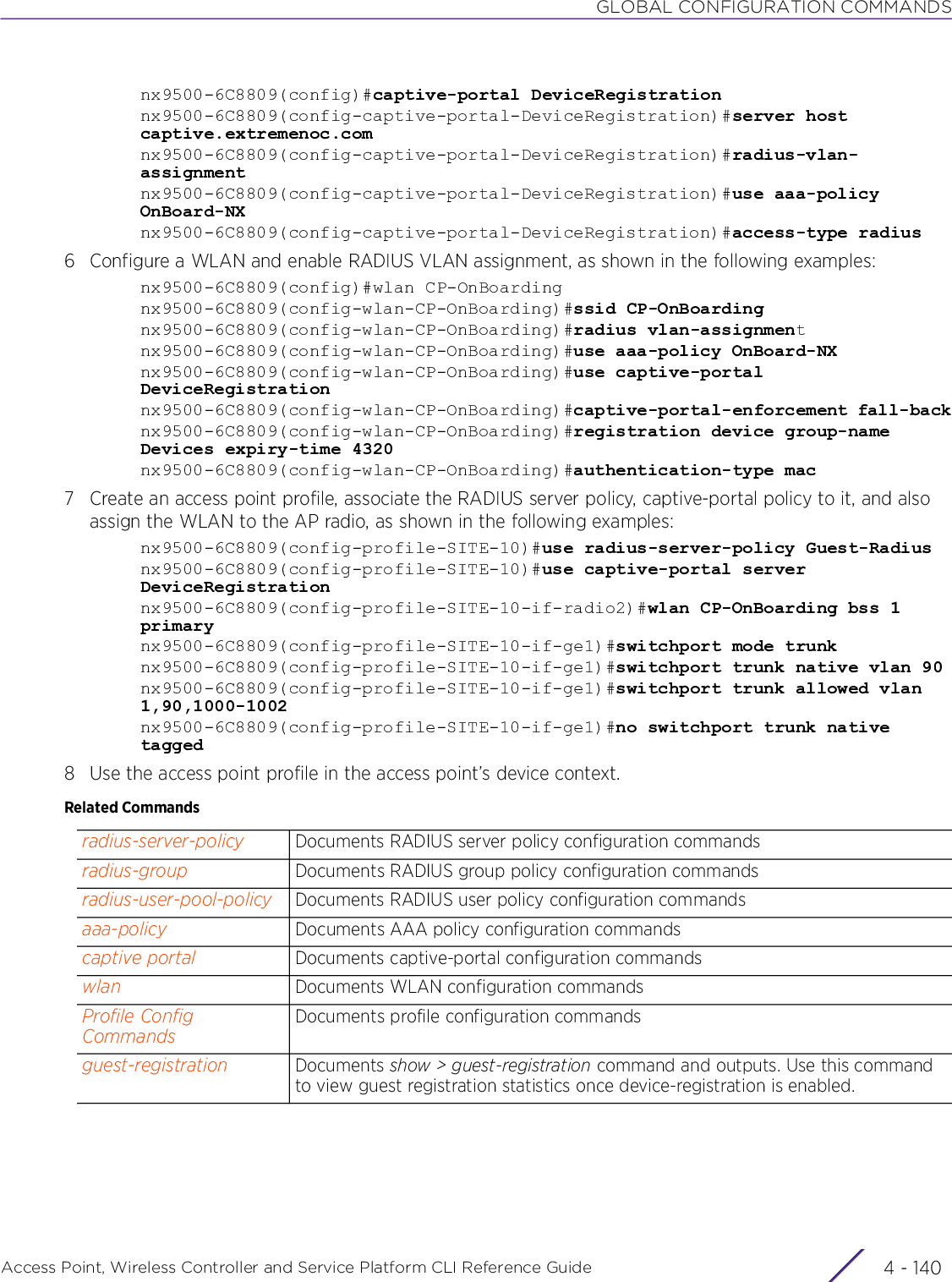
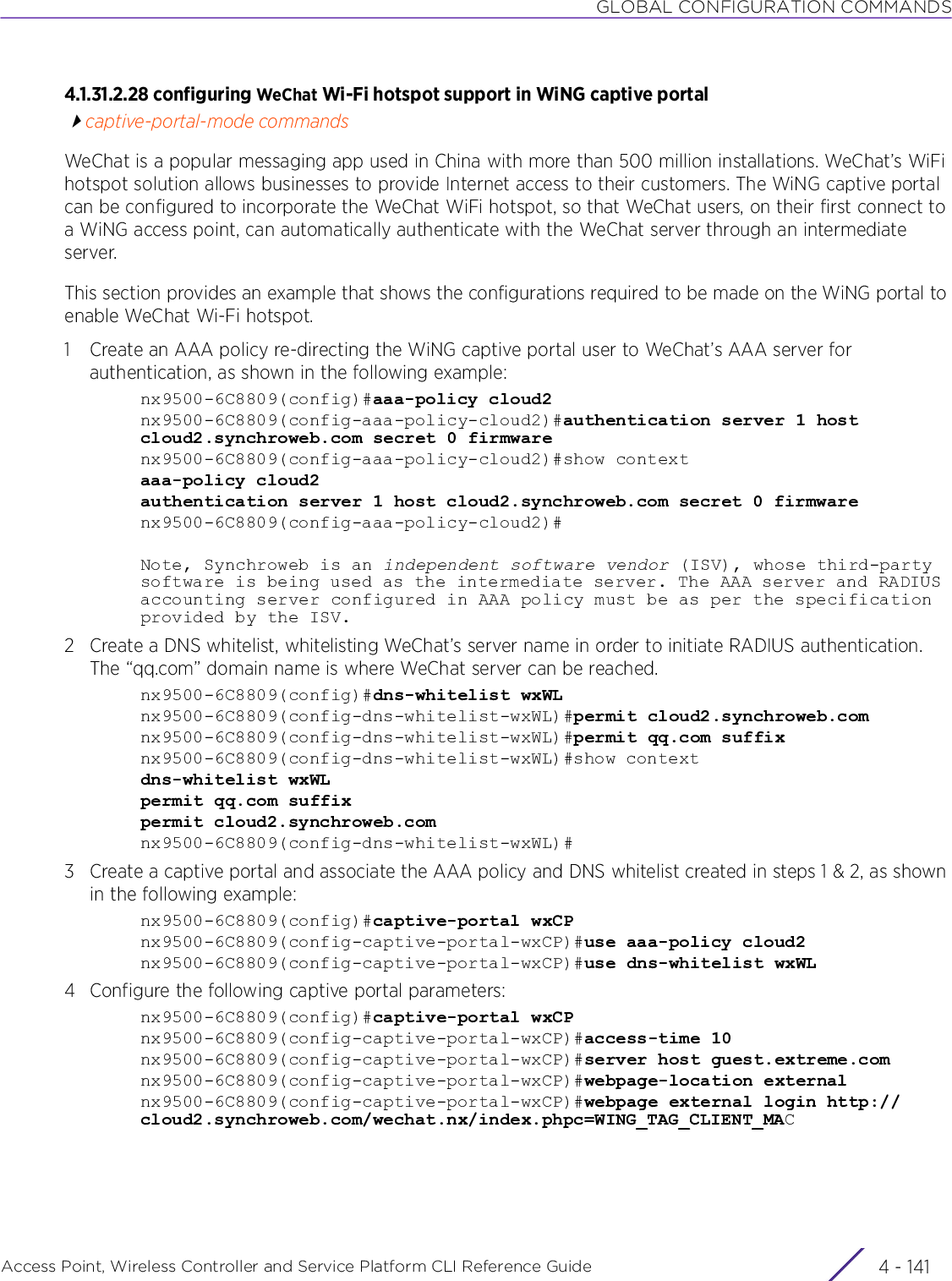
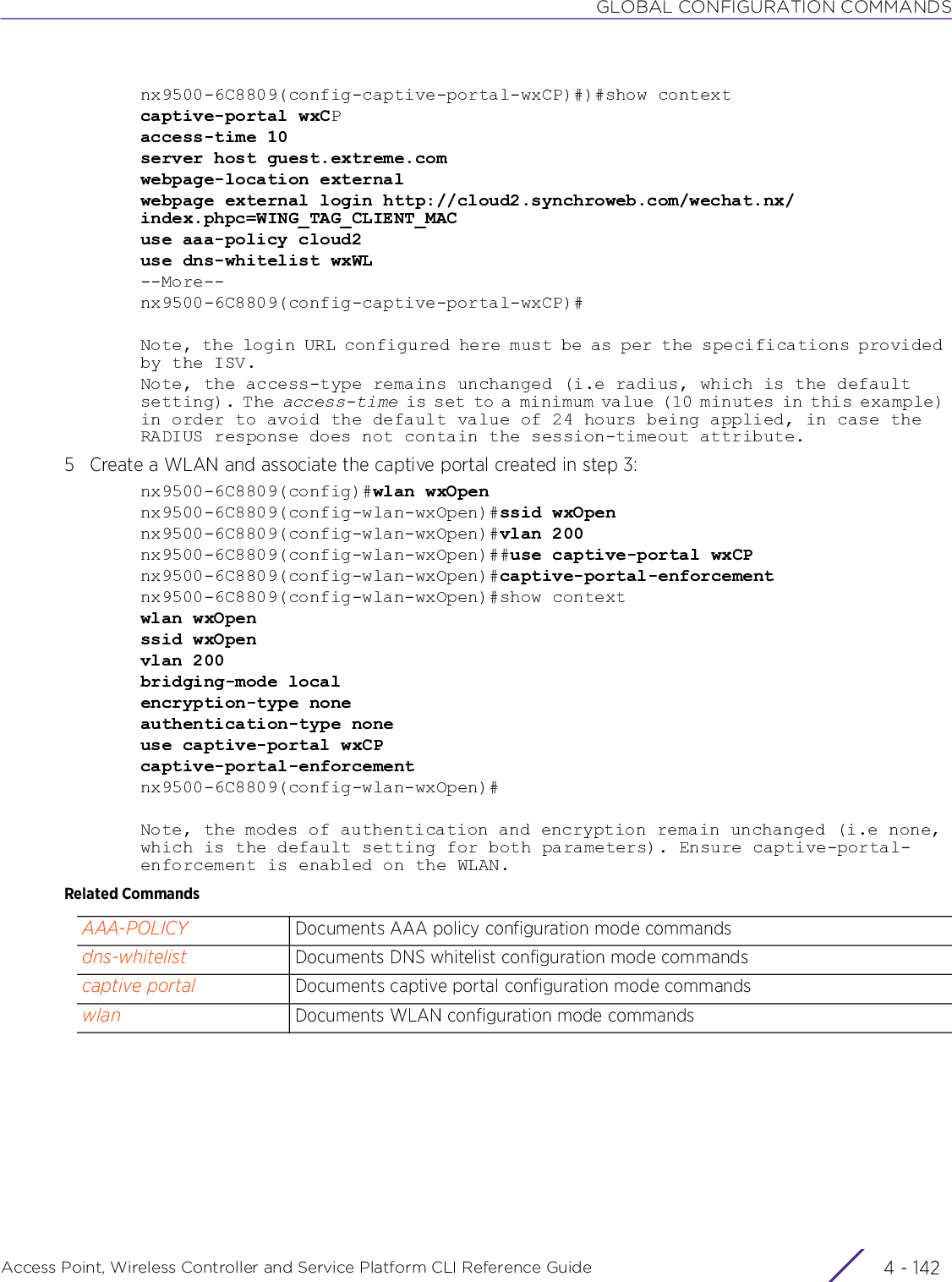



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1514.1.33.2.1 dhcpclient-identity-mode commandsConfigures the DHCP option match criteria (signature) for the discover and request message types received from wireless clientsWhen accessing a network, DHCP discover and request messages are passed between wireless clients and the DHCP server. These messages contain DHCP options and option values that differ from device to device and are based on the DHCP implementation in the device’s operating system (OS). Options and option values contained in a client’s messages are parsed and compared against the configured DHCP option values to identify the device. Once a device type is identified, the wireless client database is updated with the discovered device type.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdhcp <1-16> message-type [discover|request] [option|option-codes]dhcp <1-16> message-type [discover|request] [option <1-254>|option-codes] [contains|exact|starts-with] [ascii|hexstring] <WORD>Parameters• dhcp <1-16> message-type [discover|request] [option <1-254>|option-codes] [contains|exact|starts-with] [ascii|hexstring] <WORD>dhcp <1-16> Adds a DHCP option match criteria signature• <1-16> – Specify an index for this DHCP match criteria from 1 - 16.A maximum of 16 match criteria can be configured.message-type [discover|request]Specifies the message type to which this DHCP match criteria is applicable• discover – Applies this match criteria to DHCP discover messages only. Indicates that the fingerprint is only checked with any DHCP discover messages received from any device.• request – Applies this match criteria to DHCP request messages only. Indicates that the fingerprint is only checked with any DHCP request messages received from any device.It is recommended to configure client-identity with request messages, because clients rarely send discover messages.If the message type is not specified, the fingerprint is checked with all message types (DHCP request and DHCP discover).option <1-254> The following keywords are common to the ‘discover’ and ‘request’ message types:• option – Configures a DHCP option value, which is used as the match criteria• <1-254> – Configures a code for this DHCP option from 1 - 254 (except option 53)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-417.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1544.1.33.2.2 dhcp-match-message-typeclient-identity-mode commandsConfigures the DHCP message type to matchSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdhcp-match-message-type [all|any|discover|request]Parameters• dhcp-match-message-type [all|any|discover|request]Examplerfs4000-229D58(config-client-identity-test)#dhcp-match-message-type allrfs4000-229D58(config-client-identity-test)#show contextclient-identity test dhcp 2 message-type discover option 2 exact hexstring 012456c22c44 dhcp 1 message-type request option 60 exact ascii MSFT5.0 dhcp-match-message-type allrfs4000-229D58(config-client-identity-test)#Related Commandsdhcp-match-message-type [all|any|discover|request]Specifies the DHCP message type to consider for matching• all – Matches all message types: discover and request. Indicates that the fingerprint is checked with both the DHCP request and the DHCP discover message.• any – Matches any message type: discover or request. Indicates that the fingerprint is checked with either the DHCP request or the DHCP discover message.• discover – Matches discover messages only. Client matches the client identity only if the discover message sent by the client matches. Values configured for request messages are ignored.• request – Matches request messages only. Client matches the client identity only if the request message sent by the client matches. Values configured for discover messages are ignored.no Removes the DHCP message type to match](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-420.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1554.1.33.2.3 noclient-identity-mode commandsRemoves the DHCP options match criteria configurationsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [dhcp <1-16>|dhcp-match-message-type]Parameters• no [dhcp <1-16>|dhcp-match-message-type]ExampleThe following example shows the client identity ‘test’ settings before the ‘no’ commands are executed:rfs4000-229D58(config-client-identity-test)#show contextclient-identity test dhcp 2 message-type discover option 2 exact hexstring 012456c22c44 dhcp 1 message-type request option 60 exact ascii MSFT5.0 dhcp-match-message-type allrfs4000-229D58(config-client-identity-test)#The following example shows the client identity ‘test’ settings after the ‘no’ commands are executed:rfs4000-229D58(config-client-identity-test)#no dhcp 2rfs4000-229D58(config-client-identity-test)#no dhcp-match-message-typerfs4000-229D58(config-client-identity-test)#show contextclient-identity test dhcp 1 message-type request option 60 exact ascii MSFT5.0rfs4000-229D58(config-client-identity-test)#Related Commandsdhcp <1-16> Removes the DHCP option match criteria rule identified by the <1-16> keyword• <1-16> – Specify the DHCP option match criteria rule indexdhcp-match-message-typeRemoves the DHCP message type to matchdhcp Configures the DHCP option match criteria for device fingerprintingdhcp-match-message-typeConfigures the DHCP message type for device fingerprinting](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-421.png)





![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1634.1.34.2.3 noclient-identity-group-mode commandsRemoves the client identity associated with the client identity groupSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [client-identity|load]no client-identity <CLIENT-IDENTITY-NAME> precedence <1-10000>no load default-fingerprintsParameters• no client-identity <CLIENT-IDENTITY-NAME> precedence <1-10000>• no load default-fingerprintsExamplerfs4000-229D58(config-client-identity-group-test)#show contextclient-identity-group test client-identity test precedence 1rfs4000-229D58(config-client-identity-group-test)#rfs4000-229D58(config-client-identity-group-test)#no client-identity testrfs4000-229D58(config)#Related Commandsno client-identity <CLIENT-IDENTITY-NAME> precedence <1-10000>Disassociates a specified client identity from this client identity group• <CLIENT-IDENTITY-NAME> – Specify the client identity name.• precedence <1-10000> – Specify the above specified client identity’s precedencevalue from <1-10000>.The client identity rule is applied based on its precedence value. Lower the value, higher is the precedence. Therefore, a client identity with precedence 5 gets precedence over a client identity having precedence 20.no load default-fingerprintsDisables automatic loading of built-in, system-provided client identity fingerprintsclient-identity Associates an existing and configured client identity (device fingerprint) with this client identity groupload Loads default (built-in, system-provided) client identity fingerprints. This option is enabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-429.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1644.1.35 cloneGlobal Configuration CommandsCreates a replica of an existing object or device. The configuration of the new object or device is an exact copy of the existing object or device configuration. Use this command to copy existing configurations and then modifying only the required parameters.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxclone [TLO|device]clone TLO <EXISTING-OBJECT-NAME> <NEW-OBJECT-NAME>clone device <EXISTING-DEVICE-MAC/NAME> <NEW-DEVICE-MAC>Parameters• clone TLO <EXISTING-OBJECT-NAME> <NEW-OBJECT-NAME>• clone device <EXISTING-DEVICE-MAC/NAME> <NEW-DEVICE-MAC>Examplenx9500-6C8809(config)#clone rf_domain TechPubs Cloned_TechPubs2nx9500-6C8809(config)#show context!! Configuration of NX9500 version 5.9.1.0-008B!!version 2.5!................................................................................rf-domain TechPubs location SanJose timezone America/Los_Angeles country-code us!rf-domain Cloned_TechPubs2 location SanJose--More--nx9500-6C8809(config)#TLO <EXISTING-OBJECT-NAME> <NEW-OBJECT-NAME>Creates a new TLO by cloning an existing top-level object. The new object has the same configuration as the cloned object.• <EXISTING-OBJECT-NAME> – Specify the existing object’s (to be cloned) name• <NEW-OBJECT-NAME> – Provide the new object’s name.Enter clone and press Tab to list objects available for cloning.device <EXISTING-DEVICE-MAC/NAME> <NEW-DEVICE-MAC>Configures a new device based on an existing device configuration• <EXISTING-DEVICE-MAC/NAME> – Specify the existing device’s name or MAC address (the device to be cloned)• <NEW-DEVICE-MAC> – Provide the new device’s MAC address.Enter clone > device and press Tab to list devices available for cloning.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-430.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1664.1.37 customizeGlobal Configuration CommandsCustomizes the output of the summary CLI commands. Use this command to define the data displayed as a result of various show commands.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcustomize [cdp-lldp-info-column-width|hostname-column-width|show-adoption-status|show-wireless-client|show-wireless-client-stats|show-wireless-client-stats-rf|show-wireless-meshpoint|show-wireless-meshpoint-accelerated-multicast|show-wireless-meshpoint-neighbor-stats|show-wireless-meshpoint-neighbor-stats-rf|show-wireless-mint-client|show-wireless-mint-client-stats|show-wireless-mint-client-stats-rf|show-wireless-mint-portal|show-wireless-mint-portal-stats|show-wireless-mint-portal-stats-rf|show-wireless-radio|show-wireless-radio-stats|show-wireless-radio-stats-rf]customize [cdp-lldp-info-column-width|hostname-column-width] <1-64>customize show-adoption-status (adopted-by,ap-name <1-64>,cdp-lldp-info,config-status,last-adoption,msgs,uptime,version)customize show-wireless-client (ap-name <1-64>,auth,client-identity <1-32>,bss,enc,hostname <1-64>,ip,last-active,location <1-64>,mac,radio-alias <3-67>,radio-id,radio-type,role <1-32>,state,username <1-64>,vendor,vlan,wlan)customize show-wireless-client-stats (hostname <1-64>,mac,rx-bytes,rx-errors,rx-packets,rx-throughput,t-index,tx-bytes,tx-dropped,tx-packets,tx-throughput)customize show-wireless-client-stats-rf (average-retry-number,error-rate,hostname <1-64>,mac,noise,q-index,rx-rate,signal,snr,tx-rate)customize show-wireless-meshpoint-accelerated-multicast (ap-hostname,group-addr,mesh-name,neighbor-hostname,neighbor-ifid,radio-alias,radio-id,radio-mac,subscriptions)customize show-wireless-meshpoint (ap-mac,cfg-as-root,hops,hostname <1-64>,interface-ids,is-root,mesh-name <1-64>,mpid,next-hop-hostname <1-64>,next-hop-ifid,next-hop-use-time,path-metric,root-bound-time,root-hostname <1-64>,root-mpid)customize show-wireless-meshpoint-neighbor-stats (ap-hostname <1-64>,neighbor-hostname <1-64>,neighbor-ifid,rx-bytes,rx-errors,rx-packets,rx-throughput,t-index,tx-bytes,tx-dropped,tx-packets,tx-throughput)customize show-wireless-meshpoint-neighbor-stats-rf (ap-hostname <1-64>,average-retry-number,error-rate,neighbor-hostname <1-64>,neighbor-ifid,noise,q-index,rx-rate,signal,snr,t-index,tx-rate)customize show-wireless-mint-client (client-alias <1-64>,client-bss,portal-alias <1-64>,portal-bss,up-time)customize show-wireless-mint-client-stats (client-alias <1-64>,portal-alias <1-64>,portal-bss,rx-bytes,rx-errors,rx-packets,rx-throughput,t-index,tx-bytes,tx-dropped,tx-packets,tx-throughput)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-432.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 167customize show-wireless-mint-client-stats-rf (average-retry-number,client-alias <1-64>,error-rate,noise,portal-alias <1-64>,portal-bss,q-index,rx-rate,signal,snr,tx-rate)customize show-wireless-mint-portal (client-alias <1-64>,client-bss,portal-alias <1-64>,portal-bss,up-time)customize show-wireless-mint-portal-stats (client-alias <1-64>,client-bss,portal-alias <1-64>,rx-bytes,rx-errors,rx-packets,rx-throughput,t-index,tx-bytes,tx-dropped,tx-packets,tx-throughput)customize show-wireless-mint-portal-stats-rf (average-retry-number,client-alias <1-64>,client-bss,error-rate,noise,portal-alias <1-64>,q-index,rx-rate,signal,snr,tx-rate)customize show-wireless-radio (adopt-to,ap-name <1-64>,channel,location <1-64>,num-clients,power,radio-alias <3-67>,radio-id,radio-mac,rf-mode,state)customize show-wireless-radio-stats (radio-alias <3-67>,radio-id,radio-mac,rx-bytes,rx-errors,rx-packets,rx-throughput,tx-bytes,tx-dropped,tx-packets,tx-throughput)customize show-wireless-radio-stats-rf (average-retry-number,error-rate,noise,q-index,radio-alias <3-67>,radio-id,radio-mac,rx-rate,signal,snr,t-index,tx-rate)Parameters• customize [cdp-lldp-info-column-width|hostname-column-width] <1-64>• customize show-adoption-status (adopted-by,ap-name <1-64>,cdp-lldp-info,config-status,last-adoption,msgs,uptime,version)• customize show-wireless-client (ap-name <1-64>,auth,client-identity <1-32>,bss,enc,hostname <1-64>,ip,last-active,location <1-64>,mac,radio-alias <3-67>,radio-id,radio-type,role <1-32>,state,username <1-64>,vendor,vlan,wlan)hostname-column-width <1-64>Configures default width of the hostname column in all show command outputs• <1-64> – Sets the hostname column width from 1 - 64 characterscdp-lldp-info-column-width <1-64>Configures the column width in the show > cdp/lldp > [neighbor|report] command output• <1-64> – Sets the column width from 1 - 64 charactersshow-adoption-status Configures the information displayed in the show > adoption > status command output. Select the columns (information) displayed from the following options: adopted-by, ap-name, cdp-lldp-info, config-status, last-adoption, msgs, uptime, and version. These are recursive parameters and you can select multiple options at a time.The columns displayed by default are: Device-Name, Version, Config-Status, MSGS, Adopted-By, Last-Adoption, and Uptime.Where ever available, you can optionally use the <1-64> parameter to set the column width.show-wireless-client Customizes the show > wireless > client command outputThe columns displayed by default are: MAC, IPv4, Vendor, Radio-ID, WLAN. VLAN, and State.ap-name <1-64> Includes the ap-name column, which displays the name of the AP with which this client associates• <1-64> – Sets the ap-name column width from 1 - 64 charactersauth Includes the auth column, which displays the authorization protocol used by the wireless client](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-433.png)
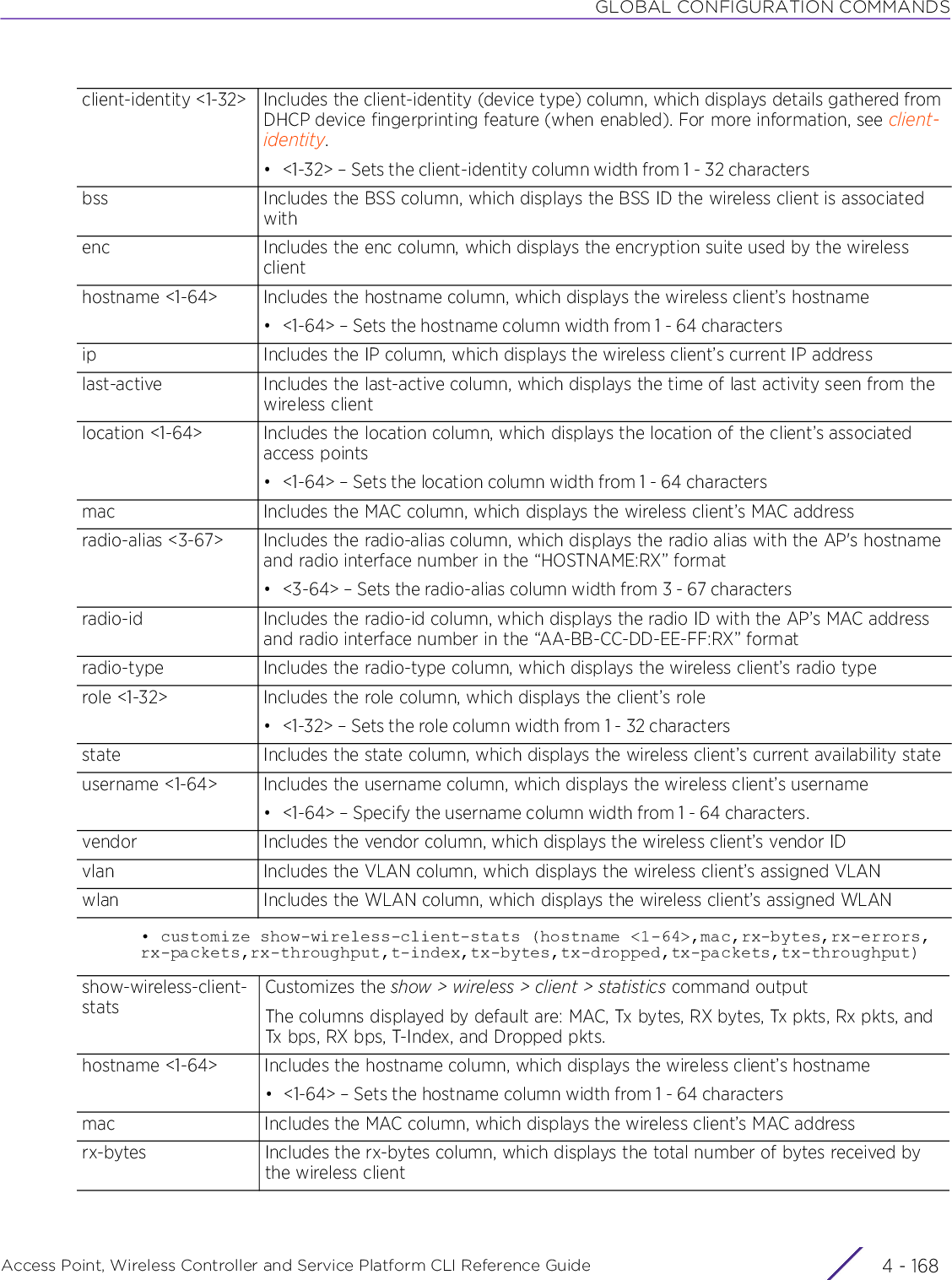
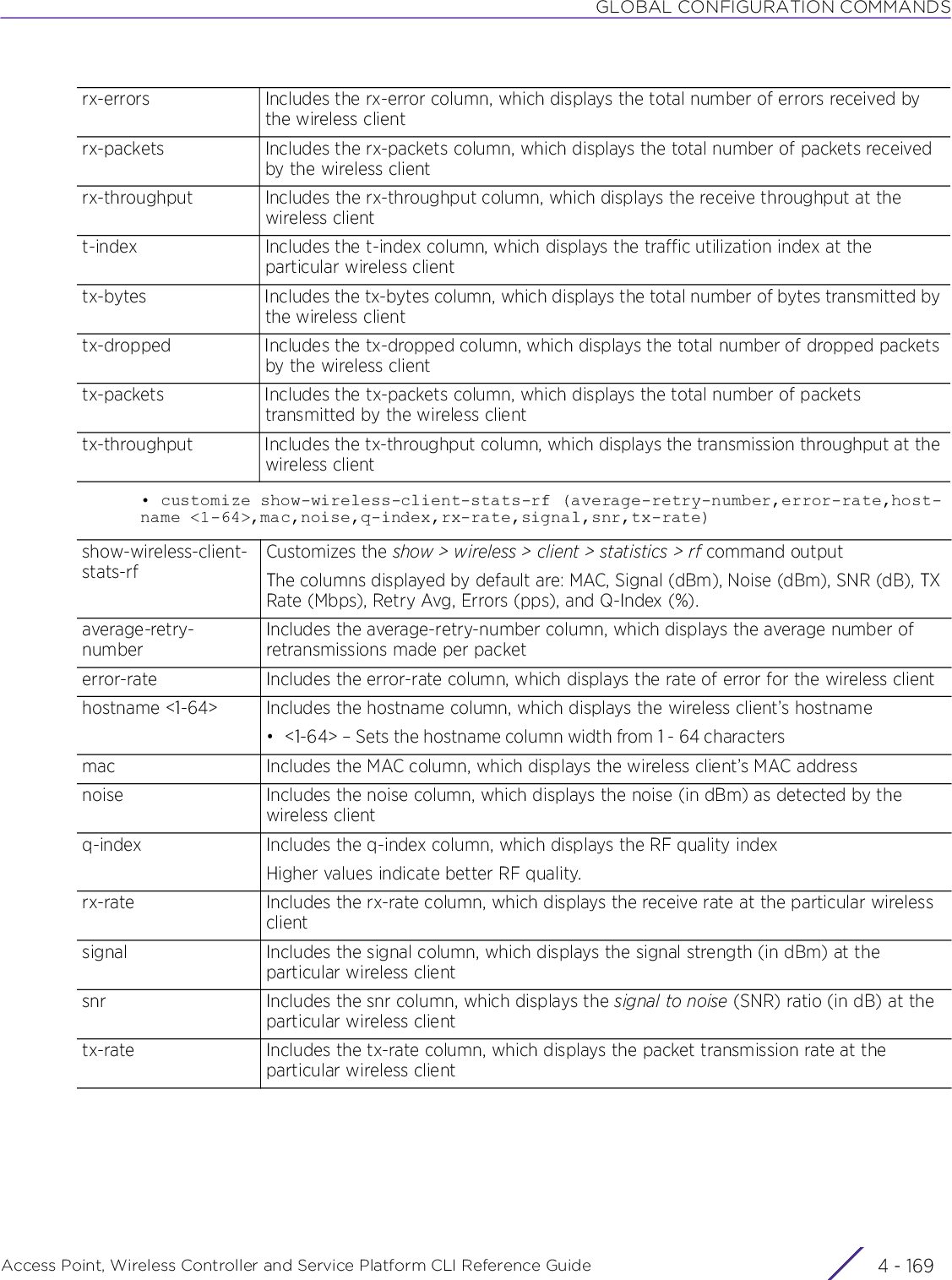
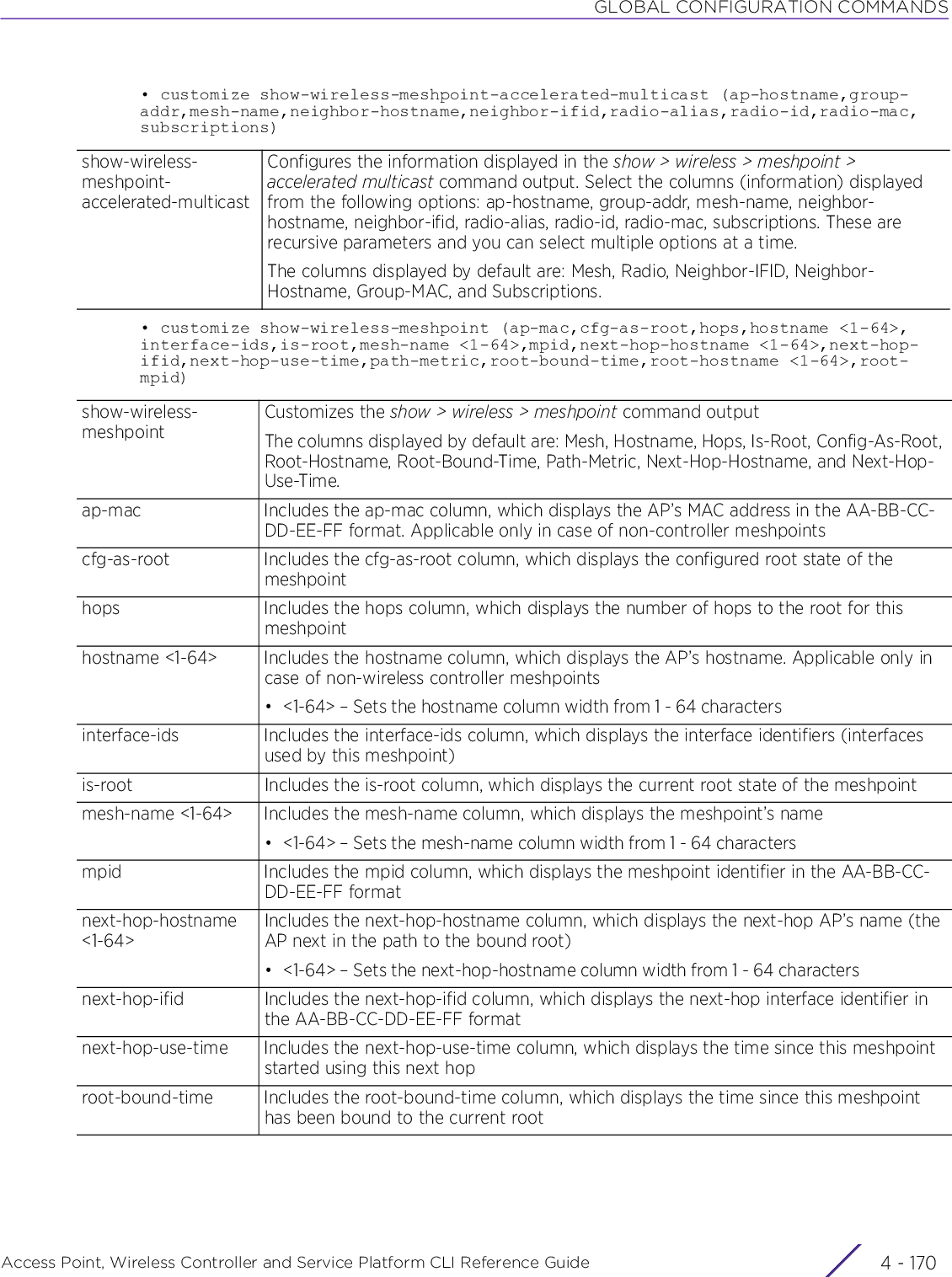
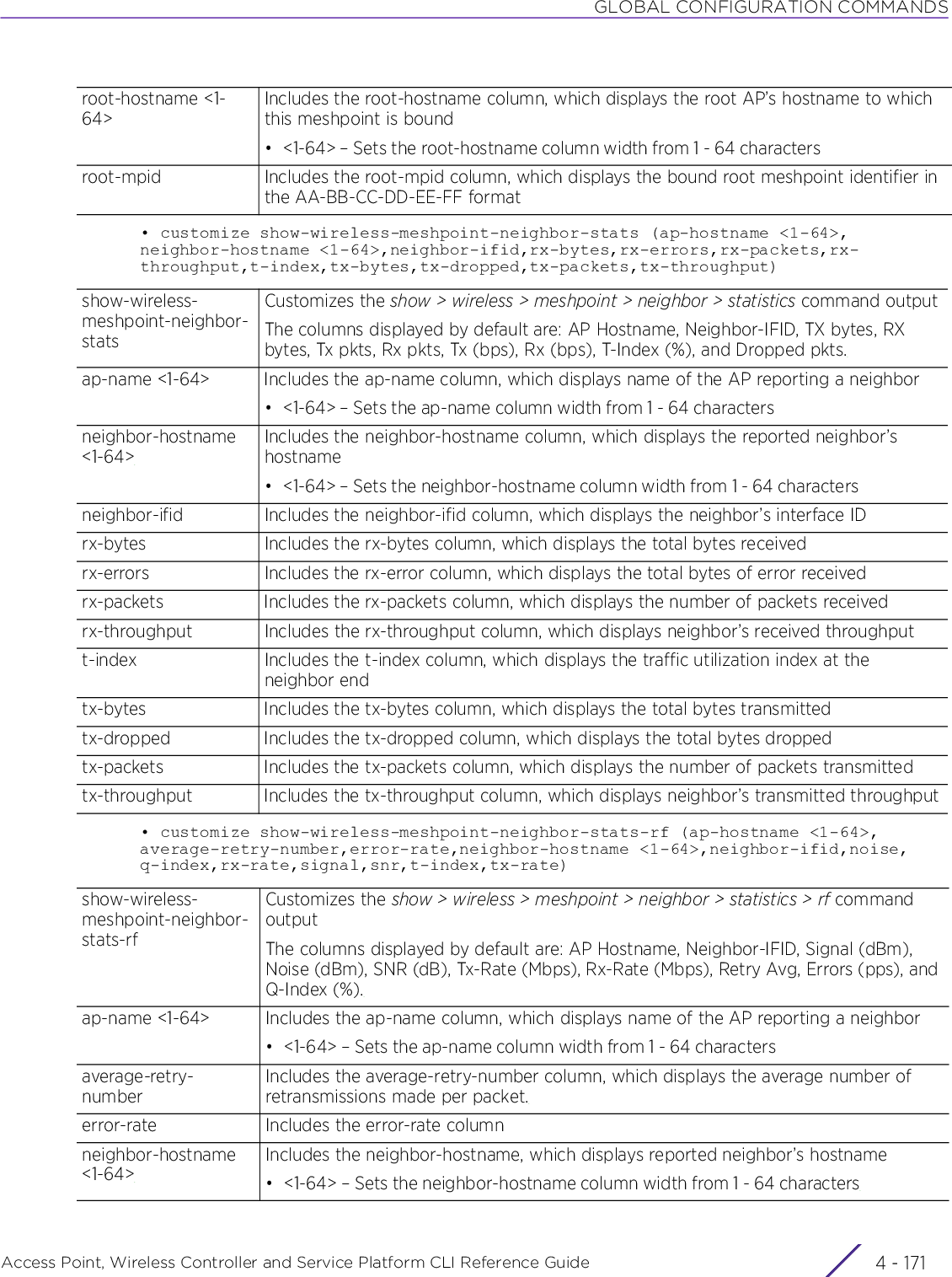






![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1824.1.38.2.2 database-serverdatabase-client-policy-mode commandsConfigures the IPv4/IPv6 address or hostname of the VM hosting the databaseSupported in the following platforms:• Service Platforms — VX9000Syntaxdatabase-server [<IP>|<HOSTNAME>|<IPv6>]Parameters• database-server [<IP>|<HOSTNAME>|<IPv6>]Examplevx9000-34B78B(config-database-client-policy-DBClientPolicy)#database-server 192.168.13.10vx9000-34B78B(config-database-client-policy-DBClientPolicy)#show contextdatabase-client-policy DBClientPolicydatabase-server 192.168.13.10vx9000-34B78B(config-database-client-policy-DBClientPolicy)#Related Commandsdatabase-server [<IP>|<HOSTNAME>|<IPv6>]Identifies the database host using one of the following options:• <IP> – Specifies the host’s IPv4 address• <HOSTNAME> – Specifies the host’s hostname• <IPv6> – Specifies the host’s IPv6 address.no Removes the database server’s (the VM hosting the database) IP/hostname configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-448.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1834.1.38.2.3 nodatabase-client-policy-mode commandsRemoves the database host’s IP/hostname configurationSupported in the following platforms:• Service Platforms — VX9000Syntaxno [authentication|database-server]no authentication username <USER-NAME>no database-server [<IP>|<HOST-NAME>|<IPv6>]Parameters• no [authentication|database-server]Examplevx9000-34B78B(config-database-client-policy-DBClientPolicy)#show contextdatabase-client-policy DBClientPolicydatabase-server 192.168.13.10vx9000-34B78B(config-database-client-policy-DBClientPolicy)#vx9000-34B78B(config-database-client-policy-DBClientPolicy)#no database-servervx9000-34B78B(config-database-client-policy-DBClientPolicy)#show contextdatabase-client-policy DBClientPolicyvx9000-34B78B(config-database-client-policy-DBClientPolicy)#no database-server Removes the database VM’s IPv4/Ipv6 address or hostname associated with this database client policy. Also removes database user details.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-449.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1884.1.39.2.2 replica-setdatabase-policy-mode commandsAdds a member to a database replica set. A replica-set is a group of devices (replica-set members) running the database instances that maintain the same data set. Replica sets provide redundancy and high availability and are the basis for all production deployments. The replica set usually consists of: an arbiter, a primary member, and one or more secondary members. The primary member and the secondary member(s) maintain replicas of the data set.Before deploying a replica set, ensure that each of the replica-set member:• has the DB instances installed, and• is able to communicate with every other member in the set.After ensuring the above,• Create a database policy (with identical replica-set configuration) on each of the member devices, and• Use the database policy in the member device’s configuration mode.These member devices elect a primary member, which begins accepting client-write operations. Remaining devices in the replica-set, with the exception of the arbiter, are designated as secondary members.Supported in the following platforms:• Service Platforms — NX9500, NX9600, VX9000, NX7500, NX5500Syntaxreplica-set member [<IP>|<FQDN>] {arbiter|priority <0-255>}Parameters• replica-set member [<IP>|<FQDN>] {arbiter|priority <0-255>}replica-set member [<IP>|<FQDN>] {arbiter|priority <0-255>}Adds a member to the database replica set. To identify the member, use one of the following options:• <IP> – Specify the member’s IP address.• <FQDN> – Specify the member’s Fully Qualified Domain Name (FQDN).After specifying the IP address or FQDN, specify the following:• arbiter – Optional. Select to configure the member as the arbiter.• priority <0-255> – Optional. Configures the priority of a non-arbiter member of thereplica set• <0-255> – Specify the priority from 0 - 255. This value determines the member’sposition within the replica set as primary or secondary. It also helps in electing thefall-back primary member in the eventuality of the current primary member beingunreachable.A replica set should have at least three members. The maximum number of members can go up to fifty (50). However, configuring a three-member replica set is recommended. Replica sets should have odd number of members. In case of an even-numbered replica set, add an arbiter to make the member count odd. This ensures that at least one member gets a majority vote in the primary-member election.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-454.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1914.1.39.2.4 nodatabase-policy-mode commandsRemoves or reverts the database policy settings to default values Supported in the following platforms:• Service Platforms — NX9500, NX9600, VX9000, NX7500, NX5500Syntaxno [authentication|replica-set|shutdown]no authentication {username <USER-NAME>}no replica-set member [<IP>|<FQDN>]no shutdownParameters• no <PARAMETERS>ExampleThe following example shows a three-member replica set:nx9500-6C8809(config-database-policy-test)#show contextdatabase-policy test replica-set member 192.168.13.12 priority 2 replica-set member 192.168.13.14 arbiter replica-set member 192.168.13.16 priority 1nx9500-6C8809(config-database-policy-test)#In the following example the arbiter is being removed, leaving the replica set with only two members:nx9500-6C8809(config-database-policy-test)#no replica-set member 192.168.13.14nx9500-6C8809(config-database-policy-test)#show contextdatabase-policy test replica-set member 192.168.13.12 priority 2 replica-set member 192.168.13.16 priority 1nx9500-6C8809(config-database-policy-test)#Since a replica set must have at least three members, another member must be added to this replica set. This member may or may not be an arbiter.nx9500-6C8809(config-database-policy-test)#replica-set member 192.168.13.8 priority 3nx9500-6C8809(config-database-policy-test)#show contextdatabase-policy test replica-set member 192.168.13.12 priority 2 replica-set member 192.168.13.16 priority 1 replica-set member 192.168.13.8 priority 3nx9500-6C8809(config-database-policy-test)#no <PARAMETERS> Removes a member from the database replica set, or brings up a database server that is down. Also disables database authentication and removes user](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-457.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1924.1.40 deviceGlobal Configuration CommandsEnables simultaneous configuration of multiple devicesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdevice {containing|filter}device {containing <STRING>} {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|t5|vx9000]}device {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|t5|vx9000]}Parameters• device {containing <STRING>} {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|t5|vx9000]}• device {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|t5|vx9000]}device Enters a device’s configuration mode. Use this command to simultaneously configure devices having similar configuration.containing <STRING> Optional. Configures the string to search for in the device’s hostname. All devices having hostnames containing the string specified here are filtered, and can be configured simultaneously.• <STRING> – Specify the string to search for in the device’s hostname.filter type <DEVICE-TYPE>Optional. Filters out a specific device type. After specifying the hostname string, select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, EX3524, EX3548, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, t5, and VX9000 (V-WLC).The t5 option is applicable only on the NX7500, NX7510, NX7520, NX7530, NX95XX, NX9500, NX9510, and NX9600 platforms.The VX9000 option is applicable only to the NX9500, NX9510, and NX9600 platforms.device Configures a basic device profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-458.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1974.1.41.2.1 mark-devicedevice-categorization-mode commandsAdds a device to the device categorization list as sanctioned or neighboring. Devices are further classified as AP or client.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmark-device <1-1000> [sanctioned|neighboring] [ap|client]mark-device <1-1000> [sanctioned|neighboring] ap {mac <MAC>|ssid <SSID> {mac <MAC>}}mark-device <1-1000> [sanctioned|neighboring] client {mac <MAC>}Parameters• mark-device <1-1000> [sanctioned|neighboring] ap {mac <MAC>|ssid <SSID> {mac <MAC>}}• mark-device [sanctioned|neighboring] client {mac <MAC>}<1-1000> Configures the device categorization entry index numbersanctioned Marks a device as sanctioned. A sanctioned device is authorized to use network resources.neighboring Marks a device as neighboring. A neighboring device is a neighbor in the same network as this device.ap{mac <MAC>|ssid <SSID>}Marks a specified AP as sanctioned or neighboring based on its MAC address or SSID• mac <MAC> – Optional. Specify the AP’s MAC address• ssid <SSID> – Optional. Specify the AP’s SSID. After specifying the SSID, you can optionally specify its MAC SSID.All APs are marked if no specific MAC address or SSID is provided.<1-1000> Configures the device categorization entry index numbersanctioned Marks the wireless client as sanctioned. A sanctioned device is authorized to use network resources.neighboring Marks the wireless client as neighboring. A neighboring device is a neighbor in the same network as this device.client {mac <MAC>} Marks a specified wireless client as sanctioned or neighboring based on its MAC address• mac <MAC> – Optional. Specify the wireless client’s MAC address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-463.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 1994.1.41.2.2 nodevice-categorization-mode commandsRemoves a device from the device categorization listSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno mark-device <1-1000> [neighboring|sanctioned] [ap|client]no mark-device <1-1000> [sanctioned|neighboring] client {mac <MAC>}no mark-device <1-1000> [sanctioned|neighboring] ap {mac <MAC>|ssid <SSID> {mac <MAC>}}Parameters• no <PARAMETERS>ExampleThe following example shows the device categorization list ‘rfs6000’ settings before the ‘no’ command is executed:rfs6000-81742D(config-device-categorization-rfs6000)#show contextdevice-categorization rfs6000 mark-device 1 sanctioned ap mac 11-22-33-44-55-66rfs6000-81742D(config-device-categorization-rfs6000)#rfs6000-81742D(config-device-categorization-rfs6000)#no mark-device 1 sanctioned ap mac 11-22-33-44-55-66The following example shows the device categorization list ‘rfs6000’ settings after the ‘no’ command is executed:rfs6000-81742D(config-device-categorization-rfs6000)#show contextdevice-categorization rfs6000rfs6000-81742D(config-device-categorization-rfs6000)#Related Commandsno <PARAMETERS> Removes a mark device (AP or wireless client) entry from this device categorization listmark-device Adds a device to a list of sanctioned or neighboring devices](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-465.png)






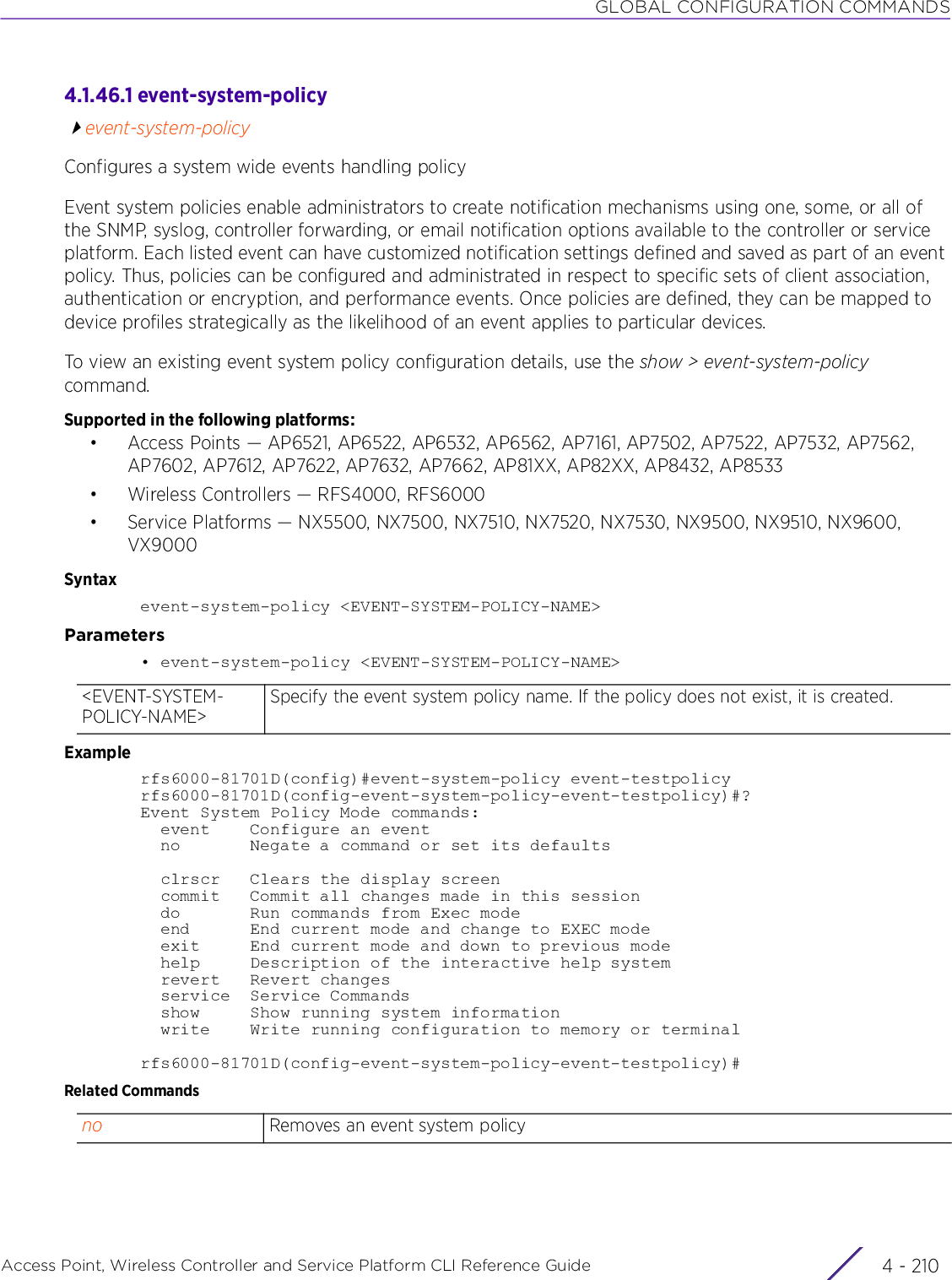
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2124.1.46.2.1 eventevent-system-policy-mode commandsConfigures an event and sets the action performed when the event happensSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxevent <EVENT-TYPE> <EVENT-NAME> (email,forward-to-switch,snmp,syslog) [default|on|off]The event types are:rfs6000-81742D(config-event-system-policy-testpolicy)#event ? aaa AAA/Radius module adapt Adaptivity Module adopt-service Adoption Service adv-wips Adv-wips module ap Access Point module bt Bluetooth captive-portal Captive Portal cdp Cisco Discovery Protocol certmgr Certificate Manager (Not valid for NCAP/MCN) cfgd Cfgd module cluster Cluster module crm Critical Resource Monitoring database Database Services device Device module dhcpsvr DHCP Configuration Daemon diag Diag module dot11 802.11 management module dot1x 802.1X Authentication fwu Firmware update module isdn Isdn module l2gre Layer 2 GRE Tunnel l2tpv3 Layer 2 Tunneling Protocol Version 3 licmgr License module lldp Link Layer Discovery Protocol mesh Mesh module mgmt Management Services nsm Network Services Module pm Process-monitor module radconf Radius Configuration Daemon rasst Roaming-Assist module radio Radio module smrt Smart-rf module smtpnot Smtpnot module system System module test Test module vrrp Virtual Router Redundancy Protocol webf Webf module wips Wireless IPS modulerfs6000-81742D(config-event-system-policy-testpolicy)#](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-478.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 213Parameters• event <EVENT-TYPE> <EVENT-NAME> (email,forward-to-switch,snmp,syslog) [default|on|off]NOTE: The parameter values for <EVENT-TYPE> and <EVENT-NAME> are summarized in the table under the Parameters section.<event-type> <event-name>aaa Enables and configures logging of the following authentication, authorization, and accounting related events:• radius-discon-msg – RADIUS disconnection• radius-session-expired – RADIUS session expired• radius-session-not-started – RADIUS session not started• radius-vlan-update – RADIUS VLAN updateadapt Enables and configures logging of the following adaptivity module related events:• adaptivity-change – Event adaptivity change• adaptivity-rehome – Event adaptivity rehomeadopt-services Enables and configures the logging of adopted services related eventsadv-wips Enables and configures the logging of advanced WIPS related eventsap Enables and configures logging of the following AP related events:• adopted – Event AP adopted• adopted-to-controller – Event AP adopted to wireless controller• ap-adopted – Event access port adopted• ap-autoup-done – Event AP autoup done• ap-autoup-fail – Event AP autoup fail• ap-autoup-needed – Event AP autoup needed• ap-autoup-no-need – Event AP autoup not needed• ap-autoup-reboot – Event AP autoup reboot• ap-autoup-timeout – Event AP autoup timeout• ap-autoup-ver – Event AP autoup version• ap-reset-detected – Event access port reset detected• ap-reset-request – Event access port user requested reset• ap-timeout – Event access port timed out• ap-unadopted – Event access port unadopted• image-parse-failure – Event image parse failure message• legacy-auto-update – Event legacy auto update• no-image-file – Event no image file•offline – Event AP detected as offline• online – Event offline AP detected as onlineContd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-479.png)


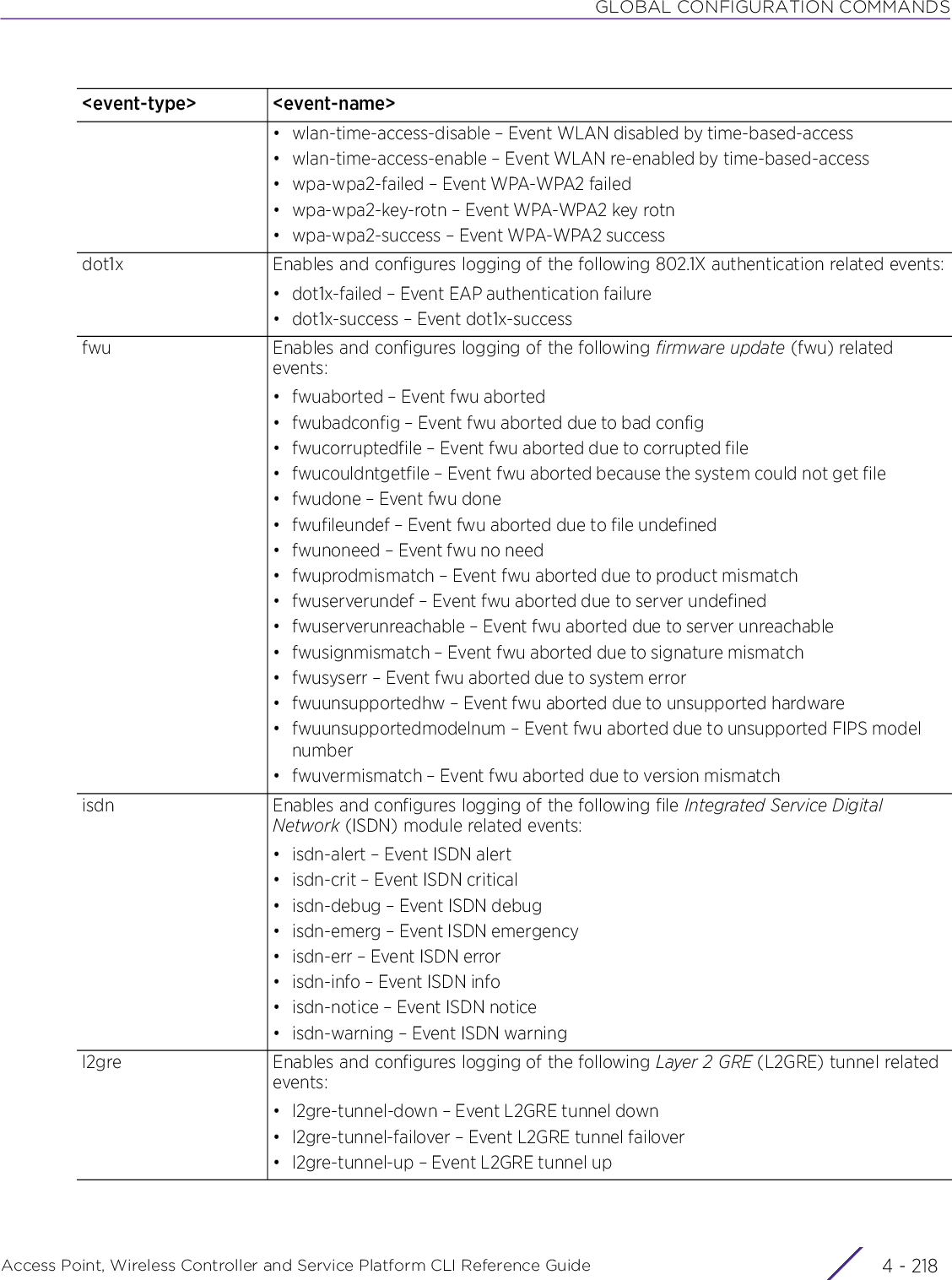
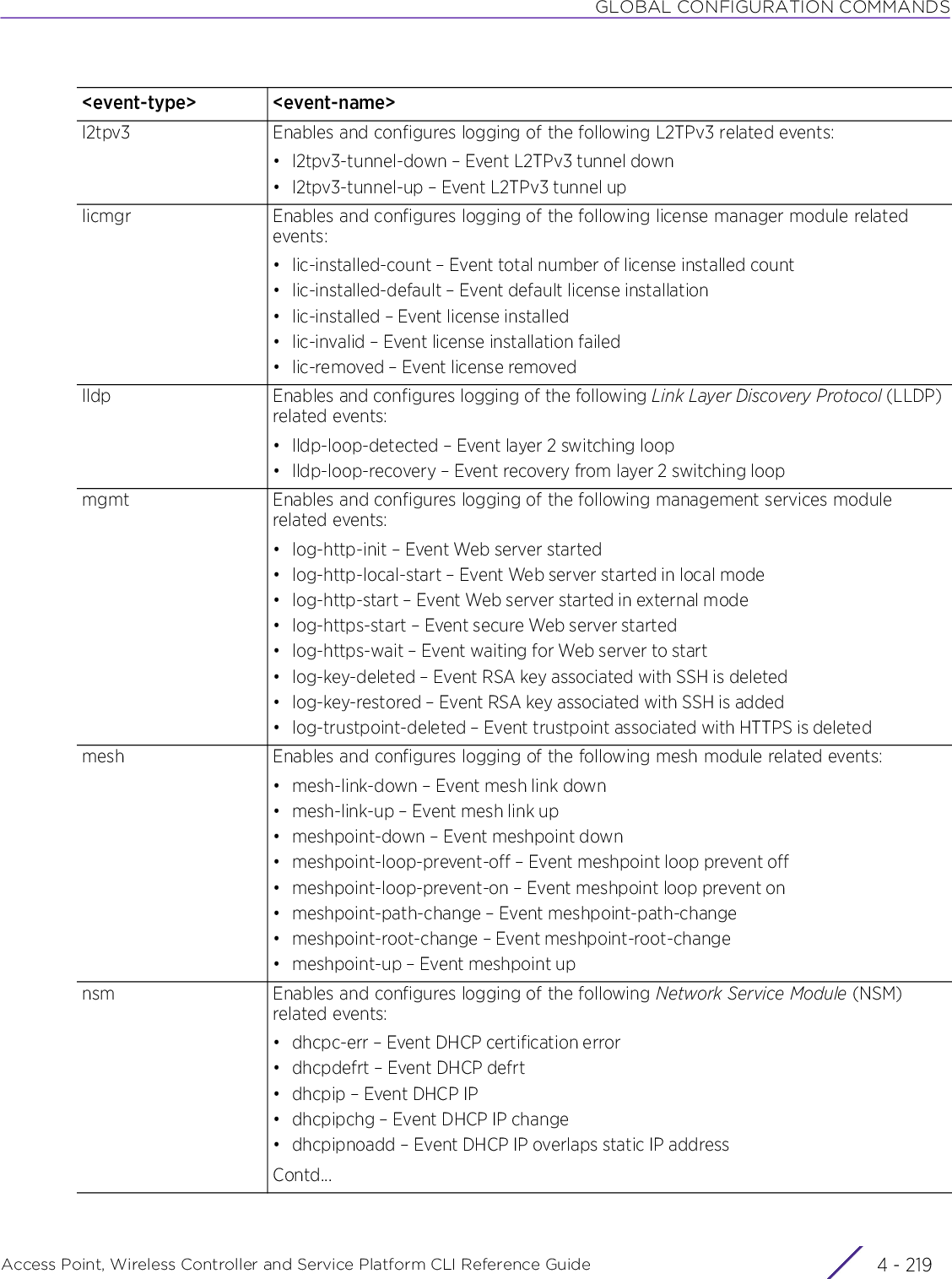
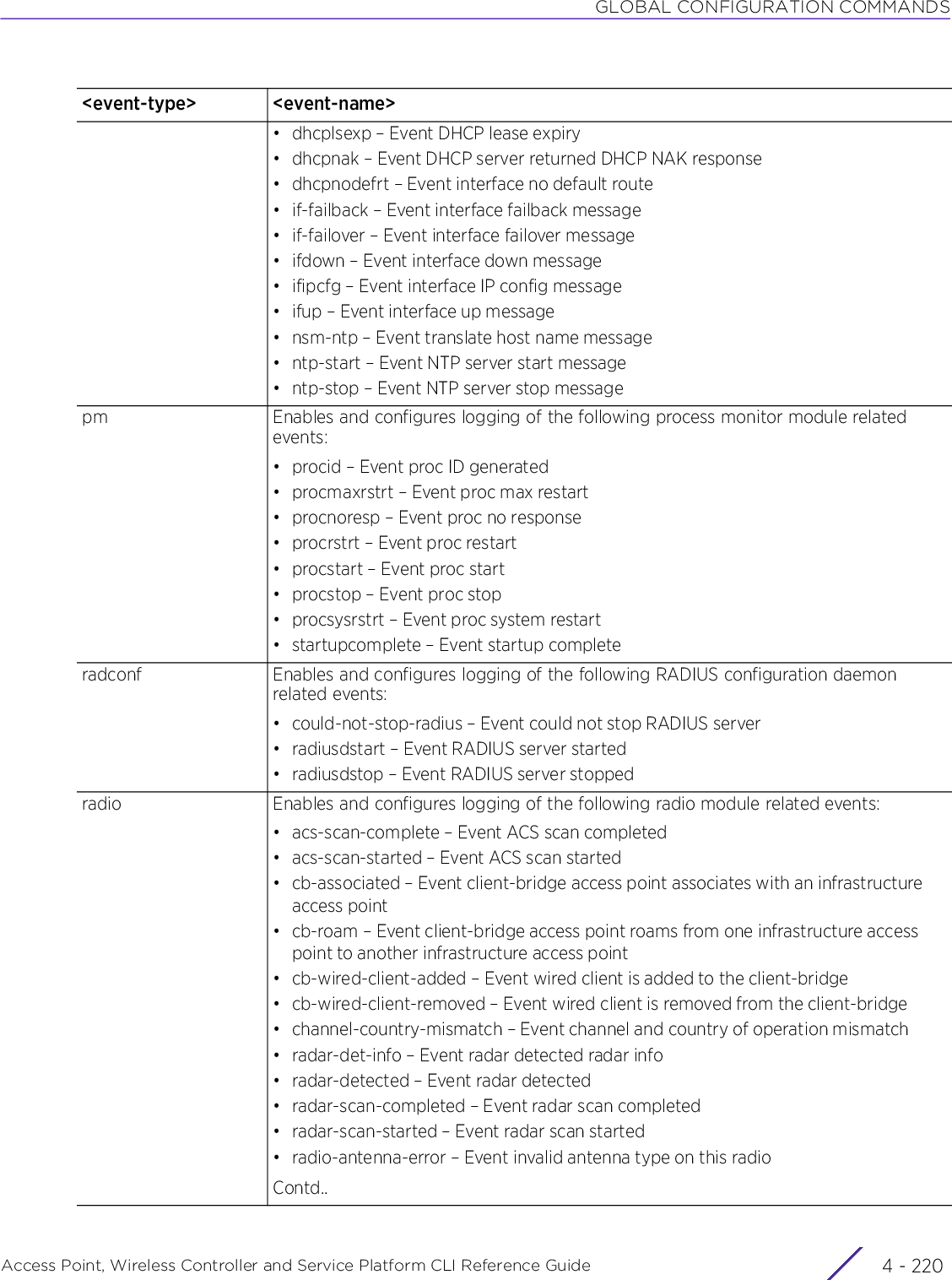
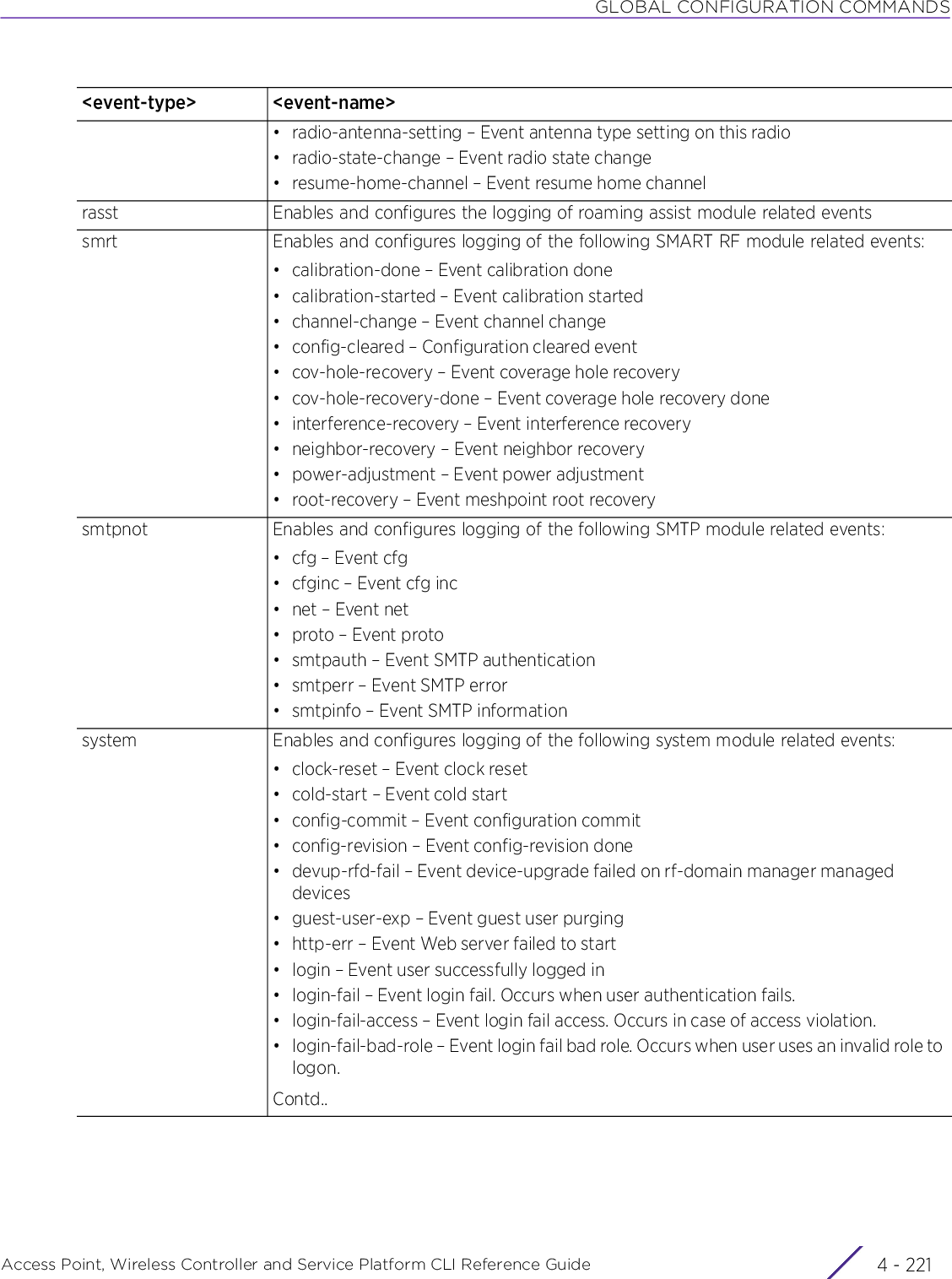

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2254.1.46.2.2 noevent-system-policy-mode commandsNegates an event monitoring configurationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno event <EVENT-TYPE> <EVENT-NAME> [email|forward-to-switch|snmp|syslog] [default|on|off]Parameters• no <PARAMETERS>Examplerfs4000-229D58(config-event-system-policy-TestPolicy)#event ap adopted syslog defaultrfs4000-229D58(config-event-system-policy-TestPolicy)#no event ap adopted syslogRelated Commandsno <PARAMETERS> Removes event monitoring and message forwarding activity based on the parameters passedThe system stops network monitoring for the occurrence of the specified event and no notification is sent if the event occurs.event Configures the action taken for each event](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-491.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2304.1.47.2.2 periodicex3500-time-range-config-mode commandsConfigures a periodic time range rule for this EX3500 time range listPeriodic time ranges are configured to recur based on periodicity such as daily, weekly, weekends, weekdays, and on specific week days, such as on every successive Sunday.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxperiodic [daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend] <0-23> <0-59> to [<023> <0-59>|daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend] <0-23> <0-59> rule-precedence <1-7>Parameters• periodic [daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend] <0-23> <0-59> to [<023> <0-59>|daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend] <0-23> <0-59> rule-precedence <1-7>periodic [daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend]Configures this periodic time range’s start day. The options are:•daily•Friday•Monday•Saturday•Sunday• Thursday•Tuesday•Wednesday•weekdays•weekend<0-23> <0-59> After specifying the start day, specify the start time in hours (24 hours format) and minutes• <0-23> – Specify the start time from 0 - 23 hours.• <0-59> – Specify the start time from 0 - 59 minutes.For example, if the values provided are 12 hours and 30 minutes, the start time is 12:30 A.M on the specified day.to [<023> <0-59>|daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend]Configures this periodic time range’s end day. This is the day when the time range ends. The options available changes depending on the start day configured. The options are:• <0-23> <0-59> – Select this option to end the time range on the same day as it starts. Specify the end hour from 0 - 23 hours and the minutes from 0 - 59 minutes.• daily – Select this option if the time range starts and ends every day at a specified time• friday – Select this option if the time range ends on FridaysContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-496.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2324.1.47.2.3 noex3500-time-range-config-mode commandsRemoves this EX3500 time range list settingsSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxno [absolute|periodic]no absoluteno periodic [daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend] <0-23> <0-59> to [<0-23> <0-59>|daily|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekend]Parameters• no <PARAMETERS>Examplenx9500-6C8809(config-ex3500-time-range-EX3500-TimeRange-01)#show contextex3500 time-range EX3500-TimeRange-01 periodic daily 1 10 to daily 23 10 rule-precedence 1 absolute start 1 0 1 june 2015 end 1 0 30 june 2016nx9500-6C8809(config-ex3500-time-range-EX3500-TimeRange-01)#nx9500-6C8809(config-ex3500-time-range-EX3500-TimeRange-01)#no periodic daily 110 to daily 23 10 rule-precedence 1nx9500-6C8809(config-ex3500-time-range-EX3500-TimeRange-01)#show contextex3500 time-range EX3500-TimeRange-01 absolute start 1 0 1 june 2015 end 1 0 30 june 2016nx9500-6C8809(config-ex3500-time-range-EX3500-TimeRange-01)#no <PARAMETERS> Removes this EX3500 time range list settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-498.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2374.1.48.2.1 enableex3500-management-policy config commandsConfigures an executive password for this EX3500 management policyEach EX3500 management policy can have a unique executive password with its own privilege level assigned. Utilize these passwords as specific EX3500 management sessions require priority over others.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxenable password [0|7|level]enable password [0|7] <PASSWORD>enable password level <0-15> [0 <PASSWORD>|7 <PASSWORD>]Parameters• enable password [0|7] <PASSWORD>• enable password level <0-15> [0 <PASSWORD>|7 <PASSWORD>]Examplenx9500-6C8809(config-ex3500-management-policy-test)#enable password level 3 7 12345678901020304050607080929291nx9500-6C8809(config-ex3500-management-policy-test)#show contextex3500-management-policy test enable password level 3 7 12345678901020304050607080929291 snmp-server notify-filter 1 remote 127.0.0.1nx9500-6C8809(config-ex3500-management-policy-test)#enable password [0|7] <PASSWORD>Creates a new executive password for this EX3500 management policy. The password could be in clear text or encrypted• 0 – Configures a clear text password using ASCII characters (should be 1 - 32 characters long)• 7 – Configures an encrypted password using HEX characters (should be 32 characters long)• <PASSWORD> – Specify the password.enable password level <0-15>Creates a new executive password for this EX3500 management policy and sets its privilege level• <0-15> – Specify the privilege level for this executive password from 0 - 15. Lower values have higher priority, to slot and prioritize executive passwords and EX3500 management sessions.[0|7] <PASSWORD> After setting the privilege level, configure the password, which could be in clear text or encrypted• 0 – Configures a clear text password using ASCII characters (should be 1 - 32 characters long)• 7 – Configures an encrypted password using HEX characters (should be 32 characters long)• <PASSWORD> – Specify the password.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-503.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2394.1.48.2.2 httpex3500-management-policy config commandsConfigures the HTTP server settings used to authenticate HTTP connection to a EX3500 switchManagement access to an EX3500 switch can be enabled/disabled as required using separate interfaces and protocols (HTTP, SSH). Disabling un-used and insecure interfaces and unused management services can dramatically reduce an attack footprint and free resources within an EX3500 management policy.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxhttp [port <1-65535>|secure-port <1-65535>|secure-server|server]Parameters• http [port <1-65535>|secure-port <1-65535>|secure-server|server]Examplenx9500-6C8809(config-ex3500-management-policy-test)#http secure-servernx9500-6C8809(config-ex3500-management-policy-test)#show contextex3500-management-policy test http secure-server enable password level 3 7 12345678901020304050607080929291 snmp-server notify-filter 1 remote 127.0.0.1nx9500-6C8809(config-ex3500-management-policy-test)#Related Commandshttp Configures following HTTP settings: port, secure-port, secure-server, and serverport <1-65535> Configures the HTTP port number. This is the port used to connect to the HTTP server.• <1-65535> – Specify a value from 1 - 65535. The default port is 80.secure-port <1-65535>Enables secure HTTP connection over a designated secure port. Ensure that the HTTP secure server is enabled before specifying the secure-server port.• <1-65535> – Specify the secure HTTP server port from 1 - 65535. The default port is 443.secure-server Enables HTTP secure server. This option is disabled by default.server Enables HTTP server. This option is enabled by default. Consequently, HTTP management access is allowed by default.no Reverts to default HTTP server settings (HTTP server enabled, HTTP port 80)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-505.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2404.1.48.2.3 memoryex3500-management-policy config commandsConfigures the EX3500’s memory utilization rising (upper) and falling (lower) threshold values. Once configured, the system sends a notification when the memory utilization exceeds the specified rising limit or falls below the specified falling limit.By customizing an EX3500’s memory and CPU utilization’s upper and lower thresholds, you can avoid over utilization of the EX3500’s processor capacity when sharing network resources with an NX series service platform or a WiNG VM.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxmemory [falling-threshold|rising-threshold] <1-100>Parameters• memory [falling-threshold|rising-threshold] <1-100>Examplenx9500-6C8809(config-ex3500-management-policy-test)#memory falling-threshold 50nx9500-6C8809(config-ex3500-management-policy-test)#memory rising-threshold 95nx9500-6C8809(config-ex3500-management-policy-test)#show contextex3500-management-policy test http secure-server enable password level 3 7 12345678901020304050607080929291 snmp-server notify-filter 1 remote 127.0.0.1 memory falling-threshold 50 memory rising-threshold 95nx9500-6C8809(config-ex3500-management-policy-test)#Related Commandsmemory Configures the EX3500’s memory utilization rising and falling threshold values. The system generates a notification when either of these limits is exceeded.falling-threshold <1-100>Configures the falling threshold for the EX3500 memory utilization• <1-100> – Specify the falling threshold as a percentage from 1 - 100. The default is 70%.rising-threshold <1-100>Configures the rising threshold for the EX3500’s memory utilization• <1-100> – Specify the rising threshold as a percentage from 1 - 100. The default is 90%.no Reverts the memory utilization's falling-threshold and/or rising threshold to 70% and 90% respectively](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-506.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2414.1.48.2.4 process-cpuex3500-management-policy config commandsConfigures the EX3500’s CPU (processor) utilization rising (upper) and falling (lower) threshold values. Once configured, the system sends a notification when the CPU utilization exceeds the specified rising limit or falls below the specified falling limit.By customizing an EX3500’s memory and CPU utilization’s upper and lower thresholds, you can avoid over utilization of the EX3500’s processor capacity when sharing network resources with an NX series service platform or a WiNG VM.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxprocess-cpu [falling-threshold|rising-threshold] <1-100>Parameters• process-cpu [falling-threshold|rising-threshold] <1-100>Examplenx9500-6C8809(config-ex3500-management-policy-test)#process-cpu falling-threshold 60nx9500-6C8809(config-ex3500-management-policy-test)#process-cpu rising-threshold 80nx9500-6C8809(config-ex3500-management-policy-test)#show contextex3500-management-policy test http secure-server enable password level 3 7 12345678901020304050607080929291 snmp-server notify-filter 1 remote 127.0.0.1 memory falling-threshold 50 memory rising-threshold 95 process-cpu falling-threshold 60 process-cpu rising-threshold 80nx9500-6C8809(config-ex3500-management-policy-test)#Related Commandsprocess-cpu Configures the EX3500’s CPU utilization rising and falling threshold values. The system generates a notification when either of these limits is exceeded.falling-threshold <1-100>Configures the falling threshold for the EX3500’s CPU utilization• <1-100> – Specify the falling threshold as a percentage from 1 - 100. The default is 70%.rising-threshold <1-100>Configures the rising threshold for the EX3500’s CPU utilization• <1-100> – Specify the rising threshold as a percentage from 1 - 100. The default is 90%.no Reverts the CPU utilization's falling-threshold and/or rising threshold to 70% and 90% respectively](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-507.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2424.1.48.2.5 snmp-serverex3500-management-policy config commandsConfigures Simple Network Management Protocol (SNMP) server settings. Once configured and applied on a EX3500 switch, the management policy controls access to the switch from management stations using SNMP.SNMP is an application layer protocol that facilitates the exchange of management information between the management stations and a managed EX3500 switch. SNMP-enabled devices listen on port 162 (by default) for SNMP packets from the management server. SNMP uses read-only and read-write community strings as an authentication mechanism to monitor and configure supported devices. The read-only community string is used to gather statistics and configuration parameters from a supported wireless device. The read-write community string is used by a management server to set device parameters. SNMP is generally used to monitor a system's performance and other parameters.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxsnmp-server {community|contact|enable|engine-id|group|host|location|notify-filter|user|view}snmp-server {community <STRING> {ro|rw}}snmp-server {contact <NAME>}snmp-server {enable traps {authentication|link-up-down}}snmp-server {engine-id [local <WORD>|remote <IP> <WORD>]}snmp-server {group <GROUP-NAME> [v1|v2c|v3 [auth|noauth|priv]] {notify <WORD>|read <WORD>|write <WORD>}}snmp-server {host <IP> [<STRING>|inform]}snmp-server {host <IP> <STRING> version [v1|v2c|v3 [auth|noauth|priv]] {udp-port <1-65535>}}snmp-server {host <IP> inform [retry <0-255>|timeout <0-2147483647>] <STRING> version [v2c|v3 [auth|noauth|priv]] {udp-port <1-65535>}}snmp-server {location <WORD>}snmp-server {notify-filter <WORD> remote <IP>}snmp-server {user <USER-NAME> <GROUP-NAME> [remote-host|v1|v2c|v3]}snmp-server {user <USER-NAME> <GROUP-NAME> remote-host <IP> v3 [auth|encrypted auth] [md5|sha] <WORD> {priv [3des|aes128|aes192|aes256|des56] <WORD>}}snmp-server {user <USER-NAME> <GROUP-NAME> [v1|v2c|v3]}snmp-server {view <VIEW-NAME> <OID-TREE-STRING> [excluded|included]}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-508.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 243Parameters• snmp-server {community <STRING> {ro|rw}}• snmp-server {contact <NAME>}• snmp-server {enable traps {authentication|link-up-down}}• snmp-server {engine-id [local <WORD>|remote <IP> <WORD>]}snmp-server community <STRING> {ro|rw}Configures SNMP-server related settings• community – Optional. Configures an SNMP community access string used to authorize management access by clients using SNMP v1, v2c, or v3• <STRING> – Specify the SNMP community access string (should not exceed 32 char-acters).After specifying the string, optionally specify the access type associated with it.• ro – Optional. Provides read-only access with this SNMP community string. Allows authorized clients to only retrieve Management Information Base (MIB) objects. This is the default setting.• rw – Optional. Provides read-write access with this SNMP community string. Allows authorized clients to retrieve as well as modify MIB objects.You can configure a maximum of five (5) community strings per EX3500 management policy.snmp-server contact <NAME>Configures SNMP-server related settings• contact – Optional. Configures the system’s contact information• <NAME> – Specify the contact person’s name (should not exceed 255 characters).snmp-server enable traps {authentication|link-up-down}Configures SNMP-server related settings• enable traps – Optional. Enables the EX3500 switch to send following SNMP traps or notifications:• authentication – Optional. Enables SNMP authentication trap. This option is disabledby default.• link-up-down – Optional. Enables SNMP link up and link down traps. This option isdisabled by default.If the command is executed without either of the above mentioned trap options, the system enables both authentication and link-up-down traps.If enabling SNMP traps, use the snmp-server > host command to specify the host(s) receiving the SNMP notifications.snmp-server engine-id [local <WORD>|remote <IP> <WORD>]Configures SNMP-server related settings• engine-id – Optional. Configures an identification string for the SNMPv3 engine. The SNMP engine is an independent SNMP agent residing either on the logged switch or on a remote device. It prevents message replay, delay, and redirection. In SNMPv3, the engine ID in combination with user passwords generates the security keys that is used for SNMPv3 packet authentication and encryption.• local – Configures the SNMP engine on the logged switch• <WORD> – Specify the hexadecimal engine ID string identifying the SNMP engine(should be 9 - 64 characters in length).Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-509.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 244• snmp-server {group <GROUP-NAME> [v1|v2c|v3 [auth|noauth|priv]] {notify <WORD>|read <WORD>|write <WORD>}}• snmp-server {host <IP> <STRING> version [v1|v2c|v3 [auth|noauth|priv]] {udp-port <1-65535>}}• remote <IP> <WORD> – Configures a remote device as the SNMP engine• <IP> – Specify the remote device’s IP address.• <WORD> – Specify the hexadecimal engine ID string identifying the SNMP engine (should be 9 - 64 characters in length).Configure the remote engine ID when using SNMPv3 informs. The remote ID configured here is used to generate the security digest for authentication and encryption of packets exchanged between the switch and the and the remote host user. SNMP passwords are localized using the engine ID of the authoritative agent. For informs, the authoritative SNMP agent is the remote agent. You therefore need to configure the remote agent’s SNMP engine ID before you can send proxy requests or informs to it.snmp-server group <GROUP-NAME>Configures SNMP-server related settings• group – Optional. Configures an SNMP user group, mapping SNMP users to SNMP views• <GROUP-NAME> – Specify the SNMP group name (should not exceed 32 charac-ters).[v1|v2c|v3 [auth|noauth|priv]] Configures the SNMP version used for authentication by this user group• v1 – Configures the SNMP version as v1.• v2c – Configures SNMP version as v2c• v3 – Configures the SNMP version as v3. If using SNMP v3, specify the authentication and encryption levels.• auth – Uses SNMP v3 with authentication and no privacy• noauth – Uses SNMP v3 with no authentication and no privacy • priv – Uses SNMP v3 with authentication and privacynotify <WORD> Optional. Configures the notification view string• <WORD> – Specify the string (should not exceed 32 characters).read <WORD> Optional. Configures the read view string• <WORD> – Specify the string (should not exceed 32 characters).write <WORD> Optional. Configures the write view string• <WORD> – Specify the string (should not exceed 32 characters).snmp-server host <IP>Configures SNMP-server related settings• host – Optional. Configures the host(s) receiving the SNMP notifications. At least one SNMP server host should be configured in order to configure the switch to send notifications • <IP> – Specify the SNMP host’s IP address.You can configure a maximum of five (5) SNMP trap recipients per EX3500 management policy.Ensure that SNMP trap notification is enabled.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-510.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 245• snmp-server {host <IP> inform [retry <0-255>|timeout <0-2147483647>] <STRING> version [v2c|v3 [auth|noauth|priv]] {udp-port <1-65535>}}<STRING> Configures the SNMP community string. You can configure the SNMP community string here, or else use the string configured using the snmp-server > community <STRING> > {ro|rw} command. It is recommended that you configure the SNMP community string prior to configuring the SNMP host.• <STRING> – Specify the community string. The string configured here is sent in the SNMP traps to the SNMPv1 or SNMPv2c hosts.version [v1|v2c|v3 [auth|noauth|priv]]Configures the SNMP version used• v1 – Configures the SNMP version as 1. This is the default setting.• v2c – Configures SNMP version as 2c• v3 – Configures the SNMP version as 3. If using SNMPv3, specify the authentication and encryption levels.• auth – Uses SNMP v3 with authentication and no privacy• noauth – Uses SNMP v3 with no authentication and no privacy • priv – Uses SNMP v3 with authentication and privacyudp-port <1-65535> Optional. After specifying the SNMP version, optionally specify the host UDP port• <1-65535> – Specify the UDP port. The default is 162.snmp-server host <IP>Configures SNMP-server related settings• host – Optional. Configures the host(s) receiving the SNMP notifications• <IP> – Specify the SNMP host’s IP address.You can configure a maximum of five (5) SNMP trap recipients per EX3500 management policy.Ensure that SNMP trap notification is enabled.inform [retry <0-255>|timeout <0-2147483647>]Enables sending of SNMP notifications as inform messages, and configures inform message settings.• retry <0-255> – Configures the maximum number attempts made to re-send an inform message in case the specified SNMP host does not acknowledge receipt.• <0-255> – Specify a value from 0 - 255. The default is 3.• timeout <0-2147483647> – Configures the interval, in seconds, to wait for an acknowledgment from the SNMP host before re-sending an inform message• <0-2147483647> – Specify a value from 0 - 2147483647 seconds. The default is 1500seconds.Inform messages are more reliable than trap messages since they include a request for acknowledgement of receipt. Using inform messages to communicate critical information would be good practice. However, since inform messages are retained in the memory until a response is received, they consume more memory and may also result in traffic congestion. Take into considerations these facts when configuring the notification format.<STRING> Configures the SNMP community string. You can configure the SNMP community string here, or else use the string configured using the snmp-server > community <STRING> > {ro|rw} command. It is recommended that you configure the SNMP community string prior to configuring the SNMP host.• <STRING> – Specify the community string. The string configured here is sent in the SNMP inform messages to the SNMPv2c or SNMPv3 hosts.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-511.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 246• snmp-server {location <WORD>}• snmp-server {notify-filter <WORD> remote <IP>}• snmp-server {user <USER-NAME> <GROUP-NAME> remote <IP> v3 {auth|encrypted auth} [md5|sha] <WORD> {priv [3des|aes128|aes192|aes256|des56] <WORD>}}version [v2c|v3 [auth|noauth|priv]]Configures the SNMP version used• v2c – Configures the SNMP version as v2c• v3 – Configures the SNMP version as v3. If using SNMP v3, specify the authentication and encryption levels.• auth – Uses SNMP v3 with authentication and no privacy• noauth – Uses SNMP v3 with no authentication and no privacy • priv – Uses SNMP v3 with authentication and privacySNMP inform messages are not supported on SNMP v1.udp-port <1-65535> Optional. After specifying the SNMP version, optionally specify the host UDP port• <1-65535> – Specify the UDP port. The default is 162.snmp-server location <WORD>Configures SNMP-server related settings• location – Optional. Configures the EX3500’s location string• <WORD> – Specify the location (should not exceed 255 characters).snmp-server notify-filter <WORD>Configures SNMP-server related settings• notify-filter – Optional. Modifies the SNMP server’s notify filter• <WORD> – Specify the SNMP notify-filter name.remote <IP> Optional. Configures the remote host’s IP address• <IP> – Specify the IP address in the A.B.C.D format.snmp-server user <USER-NAME> <GROUP-NAME>Configures SNMP-server related settings• user – Optional. Configures the name of the SNMP user (connecting to the SNMP agent) and adds the user to an existing SNMP group. It also specifies the SNMP version type used. In case of SNMP version 3, this command also configures the remote host’s IP address and the authentication type used.• <USER-NAME> – Specify the user’s name (should not exceed 32 characters).• <GROUP-NAME> – Specify the SNMP group name to which this user is assigned.remote <IP> v3 Configures the remote host on which the SNMPv3 engine is running• <IP> – Specify the remote host’s IP address.This option is available only for SNMPv3 engine.After configuring the remote host, optionally configure the authentication type and the corresponding authentication password used.{auth|encrypted auth} [md5|sha] <WORD> {priv [3des|aes128|aes192|aes256|des56] <WORD>}Optional. Configures authentication and encryption settings• auth – Specifies the authentication type used and configures the authentication password• encrypted – Enables encryption. When enabled all communications between the user and the SNMP engine are encrypted. After enabling encryption, specify the authentication type and configure the authentication password.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-512.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 247• snmp-server {user <USER-NAME> <GROUP-NAME> [v1|v2c|v3]}• snmp-server {view <VIEW-NAME> <OID-TREE-STRING> [excluded|included]}The following parameters are common to the ‘auth’ and ‘encrypted’ keywords:• md5 – Uses MD5 to authenticate the user• sha – Uses SHA to authenticate the userThe following parameter is common to the ‘md5’ and ‘sha’ keywords:• <WORD> – Specify the authentication password.If the ‘encrypted’ option is not being used, enter an 8 - 40 characters ASCII password. Whereas, in case of an encrypted password enter a HEX characters password of 32 characters.• priv – Optional. Uses SNMPv3 with privacy. Select one of the privacy options: des, aes128, aes192, aes256, des56• <WORD> – Configures the privacy password. If the ‘encrypted’ option is not beingused, enter an 8 - 40 characters long ASCII password. Whereas, the encrypted pass-word should be 32 HEX characters.snmp-server user <USER-NAME> <GROUP-NAME> [v1|v2c|v3]Configures SNMP-server related settings• user – Optional. Configures the name of the SNMP user (connecting to the SNMP agent) and adds the user to an existing SNMP group. It also specifies the SNMP version type used. In case of SNMPv3, this command also configures the authentication type used and the enables encryption.• <USER-NAME> – Specify the user’s name (should not exceed 32 characters).• <GROUP-NAME> – Specify the SNMP group name to which this user is assigned.• [v1|v2c|v3] – After specifying the group name, specify the SNMP versionused. The options are SNMP version v1, SNMP version 2c, and SNMP version3.If using SNMP version 3, optionally specify the authentication type and the corresponding authentication password used. Please see previous table for SNMPv3 authentication and encryption configuration details.snmp-server view <VIEW-NAME>Configures SNMP-server related settings• view – Optional. Creates an SNMP view. SNMP views are used to control user access to the MIB.• <VIEW-NAME> – Provide a name for this SNMP view (should not exceed 32 charac-ters).<OID-TREE-STRING> [excluded|included]Configures the object identifier (OID) of a branch within the MIB tree• excluded – Specifies an excluded view• included – Specifies an included view](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-513.png)
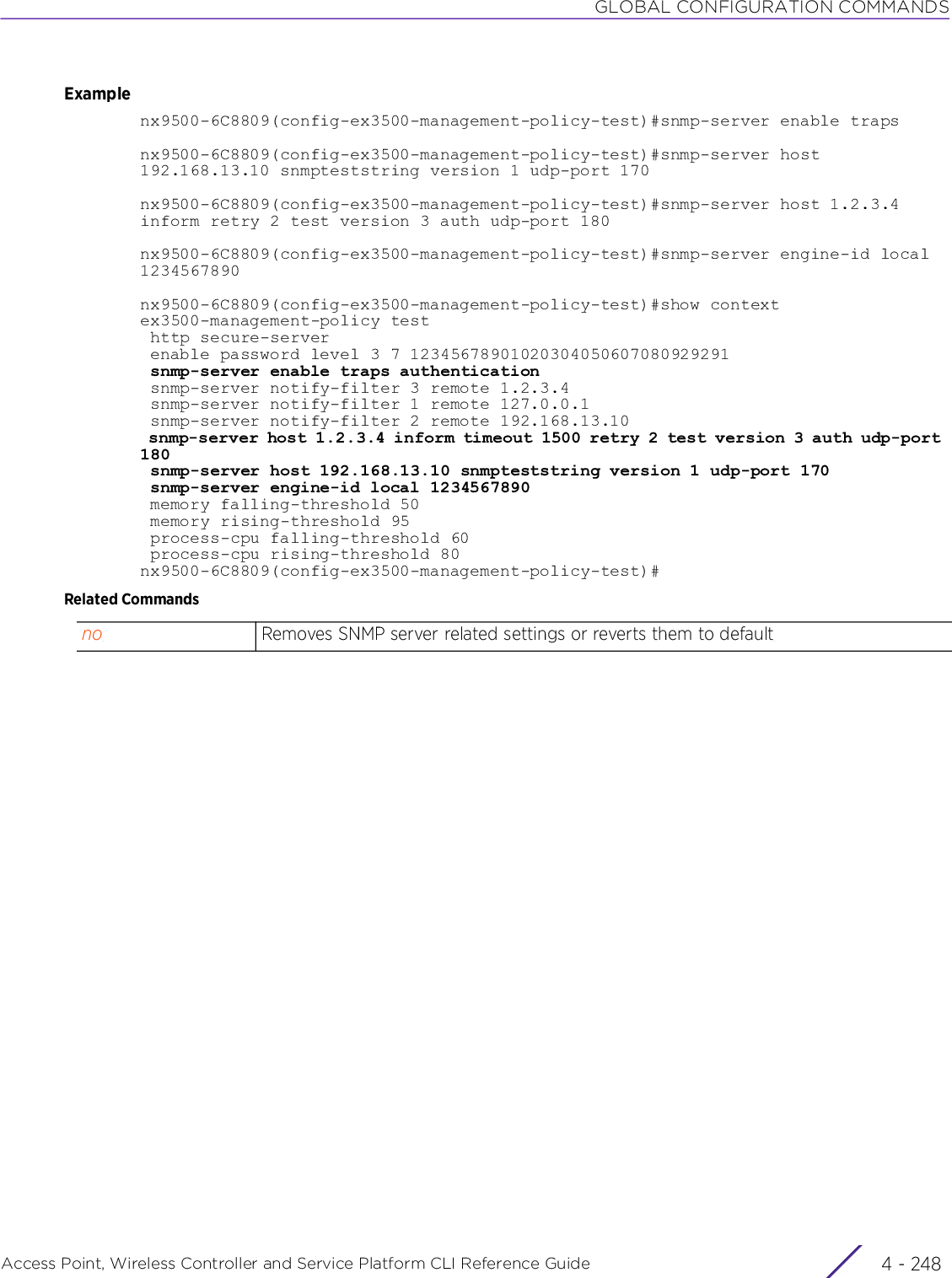
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2494.1.48.2.6 sshex3500-management-policy config commandsConfigures the SSH server settings used to authenticate Secure Shell (SSH) connection to a EX3500 switchManagement access to an EX3500 switch can be enabled/disabled as required using separate interfaces and protocols (HTTP, SSH). Disabling un-used and insecure interfaces and unused management services can dramatically reduce an attack footprint and free resources within an EX3500 management policy.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxssh [authentication-retries <1-5>|server|server-key size <512-1024>|timeout <1-120>]Parameters• ssh [authentication-retries <1-5>|server|server-key size <512-1024>|timeout <1-120>]Examplenx9500-6C8809(config-ex3500-management-policy-test)#ssh authentication-retries 4nx9500-6C8809(config-ex3500-management-policy-test)#ssh timeout 90nx9500-6C8809(config-ex3500-management-policy-test)#ssh server-key size 600nx9500-6C8809(config-ex3500-management-policy-test)#ssh servernx9500-6C8809(config-ex3500-management-policy-test)#show contextex3500-management-policy test ssh server ssh authentication-retries 4 ssh timeout 90 ssh server-key size 600 http secure-server enable password level 3 7 12345678901020304050607080929291 snmp-server enable traps authentication --More--nx9500-6C8809(config-ex3500-management-policy-test)#ssh Enables SSH management access to an EX3500 switch. This option is disabled by default. Use this command to configure SSH access settings.authentication-retries <1-5>Configures the maximum number of retries made to connect to the SSH server resource• <1-5> – Specify a value from 1 - 5. The default setting is 3.server Enables SSH server connectionserver-key size <512-1024>Configures the SSH server key size• <512-1024> – Specify the SSH server key from 512 - 1,024. The default length is 768.timeout <1-120> Configures the SSH server resource inactivity timeout value in seconds. When the specified time is exceeded, the SSH server resource becomes unreachable and must be re-authenticated. • <1-120> – Specify a value from 1 120 seconds. The default is 120 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-515.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2514.1.48.2.7 usernameex3500-management-policy config commandsConfigures a EX3500 switch user settingsThe EX3500 switch user details are stored in a local database on the NX9500, NX7500, or WiNG VM. You can configure multiple users, each having a unique name, access level, and password.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxusername <USER-NAME> [access-level <0-15>|nopassword|password [0|7] <PASSWORD>]Parameters• username <USER-NAME> [access-level <0-15>|nopassword|password [0|7] <PASSWORD>]Examplenx9500-6C8809(config-ex3500-management-policy-test)#username user1 access-level 5nx9500-6C8809(config-ex3500-management-policy-test)#username user1 password 0 user1@1234nx9500-nx9500-6C8809(config-ex3500-management-policy-test)#show contextex3500-management-policy test ssh server ssh authentication-retries 4 ssh timeout 90 ssh server-key size 600 http secure-server enable password level 3 7 12345678901020304050607080929291 username user1 access-level 5 username user1 password 7 5c4786c1e52f913d38168ce89154a079 snmp-server enable traps authentication snmp-server notify-filter 3 remote 1.2.3.4 snmp-server notify-filter 1 remote 127.0.0.1--More--nx9500-6C8809(config-ex3500-management-policy-test)#Related Commandsusername <USER-NAME>Configures the TACACS server port username• <USER-NAME> – Specify the user name (should not exceed 32 characters)access-level <0-15> Configures the access level for this user. This value determines the access priority of each user requesting access and interoperability with EX3500 switch.• <0-15> – Specify the access level from 0 - 15. The default is 0.nopassword Allows user to login without a passwordpassword [0|7] <PASSWORD>Configures the password for this user• 0 – Configures a plain text password• 7 – Configures an encrypted password (should be 32 characters in length)• <PASSWORD> – Specify the password.no Removes this SNMP user settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-517.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2524.1.48.2.8 noex3500-management-policy config commandsRemoves or reverts this EX3500 management policy settingsSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxno [enable|http|memory|process-cpu|snmp-server|ssh|username]no enable password {level <0-15>}no http [port|secure-port|secure-sever|server]no memory [falling-threshold|rising-threshold]no process-cpu [falling-threshold|rising-threshold]no snmp-server {community|contact|enable|engine-id|group|host|location|notify-filter|user|view}no snmp-server {community <STRING>}no snmp-server {contact}no snmp-server {enable traps {authentication|link-up-down}}no snmp-server {engine-id [local|remote <IP>]}no snmp-server {group <GROUP-NAME> [v1|v2c|v3 [auth|noauth|priv]]}no snmp-server {host <IP>}no snmp-server {location}no snmp-server {notify-filter <WORD> remote <IP>}no snmp-server {user <USER-NAME> [v1|v2c|v3]}no snmp-server {user <USER-NAME> <GROUP-NAME> remote-host <IP> v3}no snmp-server {view <VIEW-NAME> {<OID-TREE-STRING>}}no ssh [authentication-retries|server|server-key size <512-1024>|timeout]no usernameParameters• no <PARAMETERS>no <PARAMETERS> Removes this EX3500 management policy settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-518.png)
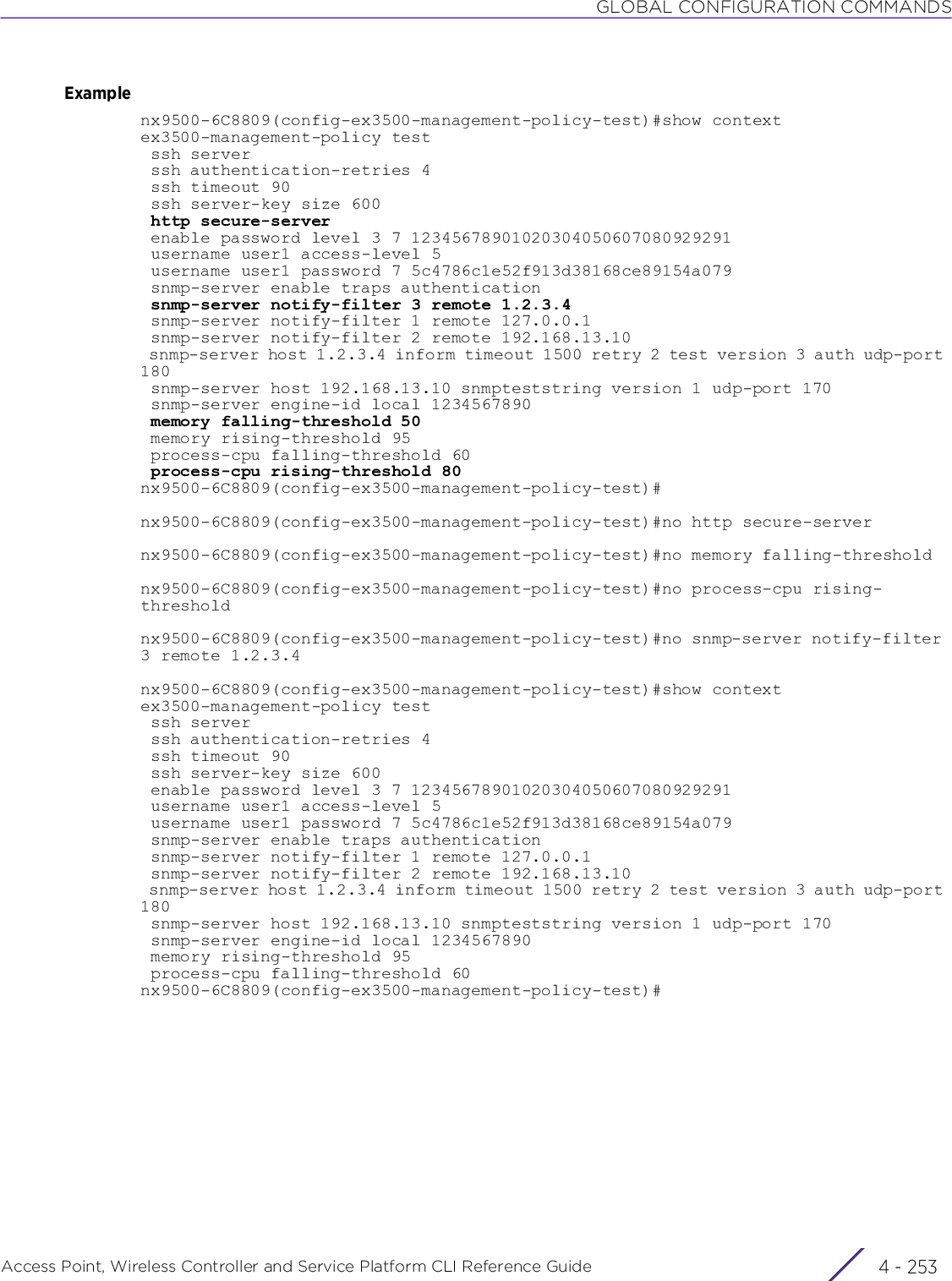
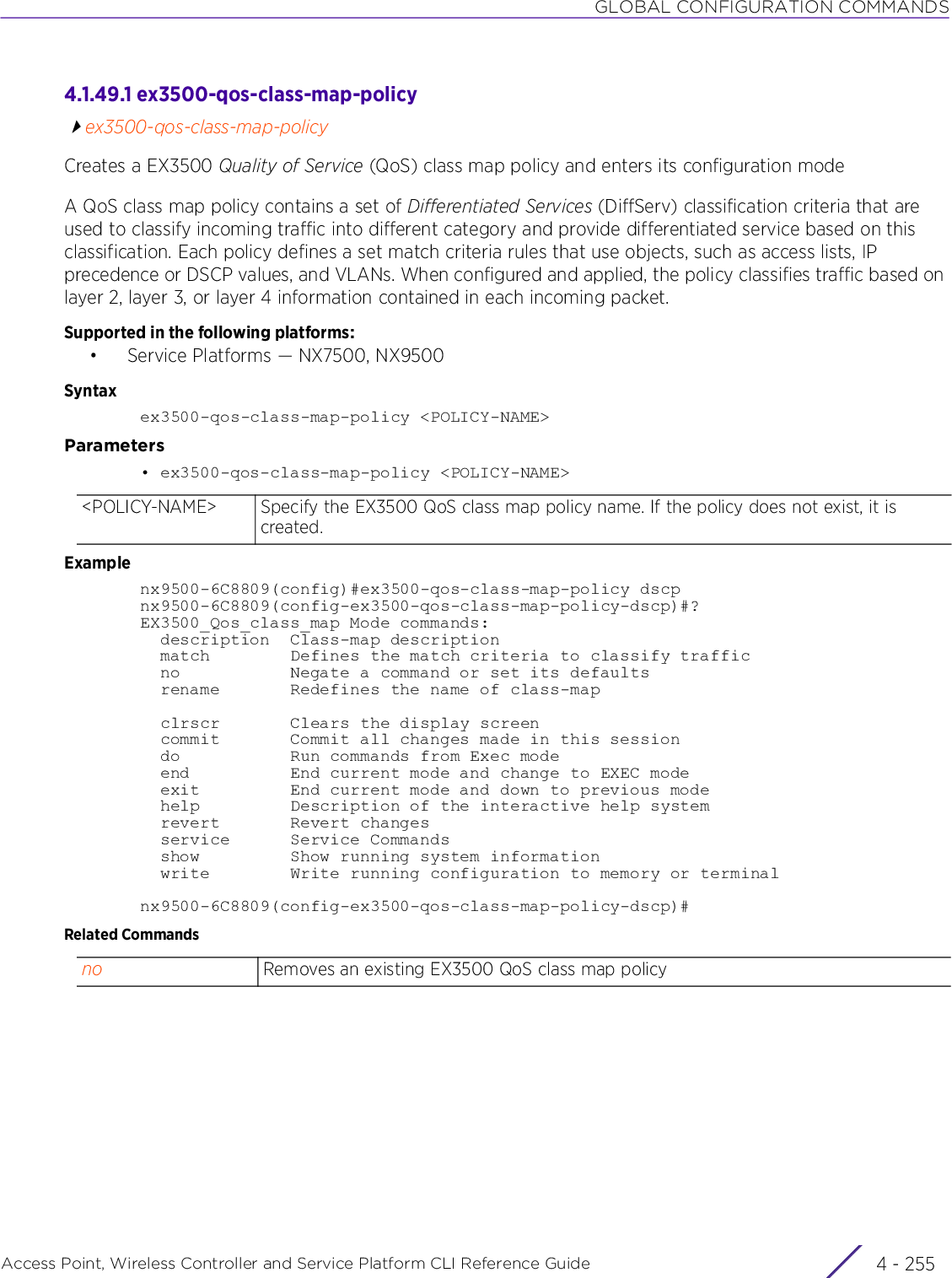

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2584.1.49.2.2 matchex3500-qos-class-map-policy config commandsConfigures match criteria rules used to classify trafficAccess lists, IP precedence, DSCP values, or VLANs are commonly used to classify traffic. Access lists select traffic based on layer 2, layer 3, or layer 4 information contained in each packet.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxmatch [access-list [ex3500-ext-access-list|ex3500-std-access-list|mac-acl] <ACL-NAME>|cos <0-7>|ip [dscp <0-63>|precedence <0-7>]|ipv6 dscp <0-63>|vlan <1-4094>]Parameters• match [access-list [ex3500-ext-access-list|ex3500-std-access-list|mac-acl] <ACL-NAME>|cos <0-7>|ip [dscp <0-63>|precedence <0-7>]|ipv6 dscp <0-63>|vlan <1-4094>]match Configures the match criteria. The options are: access-list, cos, ip, ipv6, vlanIncoming packets matching the specified criteria are included in this QoS class map.access-list [ex3500-ext-access-list|ex3500-std-access-list|mac-acl] <ACL-NAME>Uses access lists to provide the match criteria. You can use any one the following ACL types to classify traffic:• ex3500-ext-access-list – Uses an IPv4 EX3500 extended ACL• ex3500-std-access-list – Uses an IPv4 EX3500 standard ACL• mac-acl – Uses a MAC EX3500 ACLThe following keyword is common to all of the above ACL types:• <ACL-NAME> – Specify the ACL name (should be existing and configured).cos <0-7> Configures the class of service (CoS) value used to apply user priority. CoS is a form of QoS applicable only to layer 2 Ethernet frames. It uses 3-bits (8 values) of the 802.1Q tag to differentiate and shape network traffic.• <0-7> – Specify the CoS value from 0 - 7.Following are the 8 traffic classes based on the CoS value:000 (0) - Routine001 (1) - Priority010 (2) - Immediate011 (3) - Flash100 (4) - Flash Override101 (5) - Critical110 (6) - Internetwork Control111 (7) - Network Control](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-524.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 259Usage GuidelinesWhen configuring match entries, take into consideration the following points:• Deny rules included in an ACL (associated with a EX3500 QoS class map policy) are ignored whenever an incoming packet matches the ACL.• A class map policy cannot include both IP ACL or IP precedence rule and a VLAN rule.• A class map policy containing a MAC ACL or VLAN rule cannot include either an IP ACL or a IP precedence rule.• A class map policy can include a maximum of 16 match entries.Examplenx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#match ip dscp 3nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#show contextex3500-qos-class-map-policy dscp description "Matches packets marked for DSCP service 3" match ip dscp 3nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#nx9500-6C8809(config-ex3500-qos-class-map-policy-test2)#match ip precedence 1Related Commandsip [dscp <0-63>|precedence <0-7>]Configures the IPv4 DSCP value to match and/or the IP precedence value to match.• <0-63> – Specify the DSCP value from 0 - 63. Use this option to specify the type of service (ToS) field values included in the IP header. The ToS field exists between the header length and the total length fields. The DSCP constitutes the first 6 bits of the ToS field.• precedence <0-7> – Configures the IP precedence to match. Following are the 8 traffic classes based on the IP precedence values: 000 (0) - Routine001 (1) - Priority010 (2) - Immediate011 (3) - Flash100 (4) - Flash Override101 (5) - Critical110 (6) - Internetwork Control111 (7) - Network Controlipv6 dscp <0-63> Configures the IPv6 DSCP value to match• <0-63> – Specify the DSCP value from 0 - 63.vlan <1-4094> Configures the VLAN to match• <1-4094> – Specify the VLAN ID.no Removes match criteria rules configured for this EX3500 QoS class map policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-525.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2604.1.49.2.3 renameex3500-qos-class-map-policy config commandsRenames an existing EX3500 QoS class map policySupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxrename <EX3500-QOS-CLASS-MAP-POLICY-NAME> <NEW-EX3500-QOS-CLASS-MAP-POLICY-NAME>Parameters• rename <EX3500-QOS-CLASS-MAP-POLICY-NAME> <NEW-EX3500-QOS-CLASS-MAP-POLICY-NAME>Examplenx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#rename [TAB]dscp test test2nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#rename test2 IP_Precedencenx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#rename [TAB]dscp IP_Precedence testnx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#rename <EX3500-QOS-CLASS-MAP-POLICY-NAME> <NEW-EX3500-QOS-CLASS-MAP-NAME>Renames an existing EX3500 QoS class map• <EX3500-QOS-CLASS-MAP-POLICY-NAME> – Enter the EX3500 QoS class map’s current name.• <NEW-EX3500-QOS-CLASS-MAP-POLICY-NAME> – Enter the new name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-526.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2614.1.49.2.4 noex3500-qos-class-map-policy config commandsRemoves this EX3500 QoS class map policy’s description and match criteriaSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxno [description|match]no descriptionno match [access-list [ex3500-ext-access-list|ex3500-std-access-list|mac-acl] <ACL-NAME>|cos <0-7>|ip [dscp <0-63>|precedence <0-7>]|ipv6 dscp <0-63>|vlan <1-4094>]Parameters• no <PARAMETERS>ExampleThe following example shows the EX3500 QoS class map policy ‘test’ settings before the ‘no’ command are executed:nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#show contextex3500-qos-class-map-policy dscp description "Matches packets marked for DSCP service 3" match ip dscp 3nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#no descriptionnx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#no match ip dscpThe following example shows the EX3500 QoS class map policy ‘test’ settings after the ‘no’ command are executed:nx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#show contextex3500-qos-class-map-policy testnx9500-6C8809(config-ex3500-qos-class-map-policy-dscp)#no <PARAMETERS> Removes the EX3500 QoS class map policy’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-527.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2674.1.50.2.3 policeex3500-qos-policy-map-class-config commandsConfigures an enforcer for classified trafficSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxpolice [flow|srtcm-color-aware|srtcm-color-blind|trtcm-color-aware|trtcm-color-blind]police flow <0-1000000> <0-16000000> conform-action transmit violate-action [<0-63>|drop]police [srtcm-color-aware|srtcm-color-blind] <0-1000000> <0-16000000> <0-16000000> conform-action transmit exceed-action [<0-63>|drop] violate-action [<0-63>|drop]police [trtcm-color-aware|trtcm-color-blind] <0-1000000> <0-16000000> <0-1000000> <0-16000000> conform-action transmit exceed-action [<0-63>|drop] violate-action [<0-63>|drop]Parameters• police flow <0-1000000> <0-16000000> conform-action transmit violate-action [<0-63>|drop]police Configures an enforcer for classified trafficflow <0-1000000> <0-16000000>Configures an enforcer for classified traffic based on the metered flow rate• <0-1000000> – Configures the committed information rate (CIR) from 0 -1000000 kilobits per second.• <0-16000000> – Configures the committed burst size (BC) from 0 - 16000000bytes.Policing is based on a token bucket, where bucket depth (i.e., the maximum burst before the bucket overflows) is specified by the committed-burst field, and the average rate tokens are added to the bucket is specified by the committed-rate option. Note that the token bucket functions similar to that described in RFC 2697 and RFC 2698.The behavior of the meter is specified in terms of one token bucket (C), the rate at which the tokens are incremented CIR and the maximum size of the token bucket BC.The token bucket C is initially full, that is, the token count Tc(0) = BC. Thereafter, the token count Tc is updated CIR times per second as follows:• If Tc is less than BC, Tc is incremented by one, else• Tc is not incremented.When a packet of size B bytes arrives at time t, the following happens:• If Tc(t)-B > OR = 0, the packet is green and Tc is decremented by B down to the minimum value of 0, else• The packet is red and Tc is not decremented.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-533.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 268• police [srtcm-color-aware|srtcm-color-blind] <0-1000000> <0-16000000> <0-16000000> conform-action transmit exceed-action [<0-63>|drop] violate-action [<0-63>|drop]conform-action transmitConfigures the action applied when packets fall within the specified CIR and BC limits• transmit – Transmits packets falling within the specified CIR and BC limits. This is subject to there being enough tokens to service the packet, in which case the packet is set green.violate-action [<0-63>|drop]Configures the action applied when packets violate the specified CIR and BC limits• <0-63> – Applies a new DSCP value. Select the DSCP value from 0 - 63.• drops – Drops packets violating the specified CIR and BC limitspolice Configures an enforcer for classified traffic[srtcm-color-aware|srtcm-color-blind] <0-1000000> <0-16000000> <0-16000000>Configures an enforcer for classified traffic based on single rate three color meter (srTCM) mode. The srTCM as defined in RFC 2697 meters a traffic stream and processes its packets according to three traffic parameters – Committed Information Rate (CIR), Committed Burst Size (BC), and Excess Burst Size (BE).• srtcm-color-blind - Single rate three color meter in color-blind mode• srtcm-color-aware - Single rate three color meter in color-aware modeThe meter operates in one of two modes. In the color-blind mode, the meter assumes that the packet stream is uncolored. In color-aware mode the meter assumes that some preceding entity has pre-colored the incoming packet stream so that each packet is either green, yellow, or red. The marker (re)colors an IP packet according to the results of the meter. The color is coded in the DSfield [RFC 2474] of the packet.• <0-1000000> – Configures the CIR from 0 -1000000 kilobits per second.• <0-16000000> – Configures the BC from 0 - 1600000 bytes.• <0-16000000> – Configures the BE from 0 - 1600000 bytes.The behavior of the meter is specified in terms of its mode and two token buckets, C and E, which both share the common rate CIR. The maximum size of the token bucket C is BC and the maximum size of the token bucket E is BE.The token buckets C and E are initially full, that is, the token count Tc(0) = BC and the token count Te(0) = BE. Thereafter, the token counts Tc and Te are updated CIR times per second as follows:• If Tc is less than BC, Tc is incremented by one, else• If Te is less then BE, Te is incremented by one, else• neither Tc nor Te is incremented.When a packet of size B bytes arrives at time t, the following happens if srTCM is configured to operate in color-blind mode:• If Tc(t)-B > OR = 0, the packet is green and Tc is decremented by B down to the minimum value of 0, else• if Te(t)-B > OR = 0, the packets is yellow and Te is decremented by B down to the minimum value of 0,• else the packet is red and neither Tc nor Te is decremented.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-534.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 269• police [trtcm-color-aware|trtcm-color-blind] <0-1000000> <0-16000000> <0-1000000> <0-16000000> conform-action transmit exceed-action [<0-63>|drop] violate-action [<0-63>|drop]When a packet of size B bytes arrives at time t, the following happens if srTCM is configured to operate in color-aware mode:• If the packet has been pre-colored as green and Tc(t)-B ? 0, the packet is green and Tc is decremented by B down to the minimum value of 0, else• If the packet has been pre-colored as yellow or green and if• Te(t)-B > OR = 0, the packets is yellow and Te is decremented by B down to the minimum value of 0, else the packet is red and neither Tc nor Te is decremented.The metering policy guarantees a deterministic behavior where the volume of green packets is never smaller than what has been determined by the CIR and BC, that is, tokens of a given color are always spent on packets of that color. Refer to RFC 2697 for more information on other aspects of srTCM.conform-action transmit Configures the action applied when packet rates fall within the specified CIR and BC limits• transmit – Transmits packets falling within the specified CIR and BC limitsexceed-action [<0-63>|drop]Configures the action applied when packet rates exceed the specified CIR and BC limits• <0-63> – Applies a new DSCP value. Select the DSCP value from 0 - 63.• drops – Drops packets exceeding the specified CIR and BC limitsviolate-action [<0-63>|drop]Configures the action applied when packet rates exceed the specified BE limit• <0-63> – Applies a new DSCP value. Select the DSCP value from 0 - 63.• drops – Drops packets exceeding the specified BE limitpolice Configures an enforcer for classified traffic[trtcm-color-aware|trtcm-color-blind]<0-1000000> <0-16000000> <0-1000000> <0-16000000> Configures an enforcer for classified traffic based on a two rate three color meter (trTCM) mode. The trTCM as defined in RFC 2698 meters a traffic stream and processes its packets based on two rates – Committed Information Rate (CIR) and Peak Information Rate (PIR), and their associated burst sizes - Committed Burst Size (BC) and Peak Burst Size (BP).• trtcm-color-blind - Two rate three color meter in color-blind mode• trtcm-color-aware - Two rate three color meter in color-aware mode• <0-1000000> – Configures the CIR from 0 - 1000000 kilobits per second• <0-16000000> – Configures the BC from 0 - 1600000 bytes.• <0-1000000> – Configures the PIR from 0 - 1000000 kilobits per second• <0-16000000> – Configures the BP from 0 - 1600000 bytesThe meter operates in one of two modes. In the color-blind mode, the meter assumes that the packet stream is uncolored. In color-aware mode the meter assumes that some preceding entity has pre-colored the incoming packet stream so that each packet is either green, yellow, or red. The marker (re)colors an IP packet according to the results of the meter. The color is coded in the DS field [RFC 2474] of the packet.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-535.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 270Usage GuidelinesWhen configuring the traffic class enforcer parameters, take into consideration the following factors:• You can configure up to 200 enforcers/policers (i.e., class maps) for ingress ports.• The committed-rate cannot exceed the configured interface speed, and the committed-burst cannot exceed 16 Mbytes.The behavior of the meter is specified in terms of its mode and two token buckets, P and C, which are based on the rates PIR and CIR, respectively. The maximum size of the token bucket P is BP and the maximum size of the token bucket C is BC.The token buckets P and C are initially (at time 0) full, that is, the token count Tp(0) = BP and the token count Tc(0) = BC. Thereafter, the token count Tp is incremented by one PIR times per second up to BP and the token count Tc is incremented by one CIR times per second up to BC.When a packet of size B bytes arrives at time t, the following happens if trTCM is configured to operate in color-blind mode:• If Tp(t)-B < 0, the packet is red, else• if Tc(t)-B < 0, the packet is yellow and Tp is decremented by B, else• The packet is green and both Tp and Tc are decremented by B.When a packet of size B bytes arrives at time t, the following happens if trTCM is configured to operate in color-aware mode:• If the packet has been pre-colored as red or if Tp(t)-B < 0, the packet is red, else• if the packet has been pre-colored as yellow or if Tc(t)-B < 0, the packet is yellow and Tp is decremented by B, else• the packet is green and both Tp and Tc are decremented by B.The trTCM can be used to mark a IP packet stream in a service, where different, decreasing levels of assurances (either absolute or relative) are given to packets which are green, yellow, or red. Refer to RFC 2698 for more information on other aspects of trTCM.conform-action transmit Configures the action applied when packet rates fall within the specified CIR and BP limits• transmit – Transmits packets falling within the specified CIR and BC limitsexceed-action [<0-63>|drop]Configures the action applied when packet rates exceed the specified CIR limit, but are within the specified PIR limit• <0-63> – Applies a new DSCP value. Select the DSCP value from 0 - 63.• drops – Drops packets exceeding the specified CIR and BC limitviolate-action [<0-63>|drop]Configures the action applied when packet rates exceed the specified PIR limit• <0-63> – Applies a new DSCP value. Select the DSCP value from 0 - 63.• drops – Drops packets exceeding the specified BE limit](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-536.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2724.1.50.2.4 setex3500-qos-policy-map-class-config commandsSets class of service (CoS) value, per-hop behavior (PHB) value, and IP DSCP value in matching packetsSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxset [cos <0-7>|ip dscp <0-63>|phb <0-7>]Parameters• set [cos <0-7>|ip dscp <0-63>|phb <0-7>]ExampleThe following example uses the set > phb command to classify the service that incoming packets will receive, and then uses the police > trtcm-color-blind command to limit the average bandwidth to 100,000 Kbps, the committed burst rate to 4000 bytes, the peak information rate to 1,000,000 Kbps, the peak burst size to 6000 bytes, to remark any packets exceeding the committed burst size, and to drop any packets exceeding the peak information rate.nx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-test2)#set phb 3nx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-test2)#police trtcm-color-blind 100000 4000 1000000 6000 conform-action transmit exceed-action 0 violate-action dropnx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-test2)#showcontext class test2 set phb 3 police trtcm-color-blind 100000 4000 100000 6000 conform-action transmit exceed-action 0 violate-action dropnx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-test2)#set Sets the match criteria used to identify and classify traffic into different classes. The match criteria options are: CoS, IP DSCP, and PHB values.cos <0-7> Configures the CoS value for a matching packet (as specified by the match command) in the packet’s VLAN tag• <0-7> – Specify a value from 0 - 7. The CoS is modified to the value specified here.ip dscp <0-63> Modifies the IP DSCP value in a matching packet (as specified by the match command)• <0-63> – Specify a value from 0 - 63. The DSCP value is modified to the value specified here.phb <0-7> Configures a PHB value for a matching packets• <0-7> – Specify a value from 0 -7.The PHB label is composed of five bits, three bits for per-hop behavior, and two bits for the color scheme used to control queue congestion. A packet is marked green, yellow, or red as per the following:• green if it does not exceed the CIR and BC limits• yellow if it exceeds the CIR and BC limits, but not the BE limit, and • red otherwise.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-538.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2744.1.50.2.5 noex3500-qos-policy-map-class-config commandsRemoves this traffic classification’s settingsSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxno [police|set]no police [flow|srtcm-color-aware|srtcm-color-blind|trtcm-color-aware|trtcm-color-blind]no set [cos|ip dscp|phb]Parameters• no <PARAMETERS>Examplenx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-dscp)#show context class dscp set ip dscp 3 police flow 100000 4000 conform-action transmit violate-action dropnx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-dscp)#nx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-dscp)#no set ip dscpnx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-dscp)#no police flownx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-dscp)#show context class dscpnx9500-6C8809(config-ex3500-qos-policy-map-testPolicyMap-pmap-class-dscp)#no <PARAMETERS> Removes this traffic class settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-540.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2764.1.50.2.7 noex3500-qos-policy-map config commandsRemoves this EX3500 QoS policy map's settings. Use this keyword to remove the description and to remove the QoS traffic classification created.Supported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxno [class <EX3500-QoS-POLICY-MAP-NAME>|description]Parameters• no <PARAMETERS>ExampleThe following example shows the EX3500 QoS policy map ‘test’ settings before the ‘no’ command are executed:nx9500-6C8809(config-ex3500-qos-policy-map-test)#show contextex3500-qos-policy-map test description "This is a test EX3500 QoS Policy Map" class testnx9500-6C8809(config-ex3500-qos-policy-map-test)#nx9500-6C8809(config-ex3500-qos-policy-map-test)#no descriptionnx9500-6C8809(config-ex3500-qos-policy-map-test)#no class testThe following example shows the EX3500 QoS policy map ‘test’ settings after the ‘no’ command are executed:nx9500-6C8809(config-ex3500-qos-policy-map-test)#show contextex3500-qos-policy-map testnx9500-6C8809(config-ex3500-qos-policy-map-test)#no <PARAMETERS> Removes this EX3500 QoS policy map's settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-542.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2884.1.55.2.1 emailguest-management-mode commandsConfigures guest user e-mail notification settings. When configured, guest users can register themselves with their e-mail credentials as a primary key for authentication. The captive portal system provides the pass code for their registration. Guest users need to use their registered e-mail, mobile, or member ID and the received pass code for subsequent logins to the captive portal.This option is disabled by default. Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxemail [host|message|subject]email host [<IP/HOSTNAME>|<HOST-ALIAS-NAME>] sender <EMAIL-ADDRESS> security [none|ssl|starttls] username <USER-NAME> password <PASSWORD>email message <LINE>email subject <LINE>Parameters• email host [<IP/HOSTNAME>|<HOST-ALIAS-NAME>] sender <EMAIL-ADDRESS> security [none|ssl|starttls] username <USER-NAME> password <PASSWORD>email Configures guest user e-mail notification settingshost [<IP/HOSTNAME>|<HOST-ALIAS-NAME>]Configures the SMTP server’s IP address or hostname used for guest management e-mail traffic, guest user credential validation, and pass code reception. Optionally you can use an existing host alias to identify the SMTP server host.• <IP/HOSTNAME> – Specify the SMTP server’s IPv4 address or hostname.• <HOST-ALIAS-NAME> – Specify the host alias name (should be existing and configured). Consider providing the host as an alias. A host alias is a configuration item that maps the alias to a hostname. Once created, it can be used across different configuration modes. Where ever used the alias is replaced by the associated hostname.sender <EMAIL-ADDRESS>Configures the sender’s name for the guest user receiving the passcode required for registering their guest E-mail credentials using SMTP.• <EMAIL-SENDER> – Specify the sender’s name (should not exceed 100 characters).security [none|ssl|starttls]Configures the encryption protocol used by the SMTP server when communicating the pass code• none – No encryption used. Use if no additional user authentication is needed beyond the required username and password combination.• SSL – Uses SSL encryption. This is the default setting.• STARTTLS – Uses STARTTLS encryptionusername <USER-NAME>Configures a username unique to this SMS guest management configuration. After configuring the username, specify the associated password. Ensure that the password is correctly provided to receive the pass code required for registering guest user credentials with SMS.• <USER-NAME> – Specify the username (should not exceed 100 characters).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-554.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2914.1.55.2.3 guest-database-exportguest-management-mode commandsSchedules an export of the Guest Management user database to a specified external server. This option is enabled by default.Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxguest-database-export <TIME> frequency <1-168> url-directory <URL> {(format [csv|json]|last-visit-within <1-168>)}Parameters• guest-database-export <TIME> frequency <1-168> url-directory <URL> {(format [csv|json]|last-visit-within <1-168>)}Examplenx9500-6C8809(config-guest-management-gm1)#guest-database-export 10:30 frequency 6 url-directory ftp://admin:xxxxxx@192.168.13.10/dbe_dir format json last-visit-within 168nx9500-6C8809(config-guest-management-test)#show contextguest-management test guest-database-export 12:30 frequency 20 url-directory ftp://admin:xxxxxx@192.168.13.10/dbe_dir format json last-visit-within 168nx9500-6C8809(config-guest-management-test)#Related Commandsguest-database-export <TIME>Schedules an export of the Guest Management User collection to an external server• <TIME> – Configures the start time of the export operation in the HH:MM formatfrequency <1-168> Configures the user collection export frequency in hours• <1-168> – Configures the frequency from 1 - 168 hours. If the frequency is set at 3 hours, the user database is exported once in every 3 hours. The default is 4 hours.url-directory <URL> Configures external server’s URL and directory to where the collection is exported• <URL> – Specify the external server’s URLformat [csv|json] Optional. Configures the file format• csv – Exports collection to the specified location in CSV format. This is the default setting.• json – Exports collection to the specified location in JSON formatlast-visit-within <1-168>Configures a filters guest users who have last visited within a specified period of time• <1-168> – Specify a time period from 1 - 168 hours. If for example, the last-visit-within value is set at 2 hours, then only the last two hours guest user collections will be exported. The default is 4 hours.no Reverts the guest database export parameters to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-557.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2924.1.55.2.4 smsguest-management-mode commandsConfigures guest user SMS notification settingsWhen configured, guest users can register themselves with their e-mail or mobile device ID as the primary key for authentication. The captive portal provides the pass code for registration. Guest users use their registered e-mail or mobile device ID and the received pass code for subsequent logins to the captive portal.SMS is similar to MAC address-based self registration, but in addition the captive portal sends an SMS message, containing an access code, to the user’s mobile phone number provided at the time of registration. The captive portal verifies the code, returns the Welcome page and provides access. This allows the administrator to verify the phone number provided and can be traced back to a specific individual should the need arise.The default gateway used with SMS is Clickatell. A pass code can be sent with SMS to the guest user directly using Clickatell, or the pass code can be sent via e-mail to the SMS Clickatell gateway server, and Clickatell sends the pass code SMS to the guest user.Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsms [host|message]sms host clickatell username <USER-NAME> password <PASSWORD> api-id <ID> user-agent <PYCLICKATELL> {source-number <WORD>}sms message <LINE>Parameters• sms host clickatell username <USER-NAME> password <PASSWORD> api-id <ID> user-agent <PYCLICKATELL> {source-number <WORD>}NOTE: When using SMS, ensure that the WLAN’s mode of authentication is set to none and the mode of registration is set to user. In other words, captive portal authentication must always enforce guest registration.sms Configures guest user SMS notification settingshost clickatell By default, clickatell is the host SMS gateway server resource. Upon receiving the pass code e-mail, the SMS gateway sends the actual notification pass code SMS to the guest user.username <USER-NAME>Configures a username unique to this SMS guest management configuration. After configuring the username, specify the associated password. Ensure that the password is correctly provided to receive the pass code required for registering guest user credentials with SMS.• <USER-NAME> – Specify the username (should not exceed 32 characters).password <PASSWORD>Configures the password associated with the specified username • <PASSWORD> – Specify the password (should not exceed 63 characters).api-id <ID> Set a 32 character maximum API ID• <API-ID> – Specify the API ID (should not exceed 32 characters).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-558.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2944.1.55.2.5 sms-over-smtpguest-management-mode commandsConfigures an e-mail host server (for example: smtp.gmail.com) along with sender related credentials and the recipient gateway e-mail address to which the message is E-mailed. The gateway server converts the e-mail into SMS and sends the message to the guest users’s mobile device.When sending an e-mail, the e-mail client interacts with a SMTP server to handle the content transmission. The SMTP server on the host may have conversations with other SMTP servers to deliver the e-mail.Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsms-over-smtp [host|message|subject]sms-over-smtp host [<IP/HOSTNAME>|<HOST-ALIAS-NAME>] sender <EMAIL-ADDRESS> security [none|ssl|starttls] username <USER-NAME> password <PASSWORD> recipient <EMAIL-ADDRESS>sms-over-smtp message <LINE>sms-over-smtp subject <LINE>Parameters• sms-over-smtp host [<IP/HOSTNAME>|<HOST-ALIAS-NAME>] sender <EMAIL-ADDRESS> security [none|ssl|starttls] username <USER-NAME> password <PASSWORD> recipient <EMAIL-ADDRESS>sms-over-smtp Configures guest user SMS over SMTP notification settingshost [<IP/HOSTNAME>|<HOST-ALIAS-NAME>]Configures the SMS gateway server resource’s IPv4 address or hostname used for guest management SMS over SMTP traffic, guest user credential validation and pass code reception. Optionally you can use an existing host alias to identify the SMS gateway server resource.• <IP/HOSTNAME> – Specify the SMTP gateway server resource’s IP address or hostname.• <HOST-ALIAS-NAME> – Specify the host alias name (should existing and configured). Consider providing the host as an alias. A host alias is a configuration item that maps the alias to a hostname. Once created, it can be used across different configuration modes. Where ever used the alias is replaced by the associated hostname.sender <EMAIL-ADDRESS>Configures the sender’s e-mail address. The sender here is the guest user receiving the pass code. Guest users require this pass code for registering their guest e-mail credentials using SMTP.• <EMAIL-ADDRESS> – Specify the e-mail address (should not exceed 64 characters).security [none|ssl|starttls]Configures the encryption protocol used by the SMTP server when communicating the pass code• none – No encryption used. Use if no additional user authentication is needed beyond the required username and password combination.• SSL – Uses SSL encryption. This is the default setting.• STARTTLS – Uses STARTTLS encryption](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-560.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2964.1.55.2.6 noguest-management-mode commandsRemoves this guest management policy settingsSupported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [email|guest-database-backup|guest-database-export|sms|sms-over-smtp]no email [host|message|subject]no guest-database-backup enableno guest-database-exportno gmd report-generation enableno sms [host|message]no sms-over-smtp [host|message|subject]Parameters• no <PARAMETERS>Examplenx9500-6C8809(config-guest-management-test3)#show contextguest-management test3 sms-over-smtp host test sender bob@extremenetworks.com security ssl username bob password bob@123 recipient john@extremenetworks.comnx9500-6C8809(config-guest-management-test3)#nx9500-6C8809(config-guest-management-test)#no sms-over-smtp hostnx9500-6C8809(config-guest-management-test3)#show contextguest-management test3nx9500-6C8809(config-guest-management-test3)#no <PARAMETERS> Removes this guest management policy settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-562.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 2994.1.58 ipGlobal Configuration CommandsCreates a IP access control list (ACL) and/or a SNMP IP ACLAccess lists define access permissions to the network using a set of rules. Each rule specifies an action taken when a packet matches the rule. If the action is deny, the packet is dropped. If the action is permit, the packet is allowed.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [access-list|snmp-access-list]ip access-list <IP-ACL-NAME>ip snmp-access-list <IP-SNMP-ACL-NAME>Parameters• ip access-list <IP-ACL-NAME>• ip snmp-access-list <IP-SNMP-ACL-NAME>access-list <IP-ACL-NAME>Creates an IP ACL and enters its configuration mode• <IP-ACL-NAME> – Specify the ACL name. If the access list does not exist, it is created.snmp-access-list <IP-SNMP-ACL-NAME>Creates a SNMP IP ACL and enters its configuration mode. An SNMP IP ACL is an access control mechanism that uses a combination of IP ACL and SNMP community string.SNMP performs network management functions using a data structure called a Management Information Base (MIB). SNMP is widely implemented but not very secure, since it uses only text community strings for accessing controller or service platform configuration files.Use SNMP ACLs (firewalls) to help reduce SNMP’s vulnerabilities, as SNMP traffic can be easily exploited to produce a denial of service (DoS).• <IP-SNMP-ACL-NAME> – Specify the SNMP IP ACL name. If the access list does not exist, it is created. After creating the SNMP ACL, define the deny/permit rules based on the network and/or host IP addresses. Once created and configured, link this SNMP IP ACL with a SNMP community string.To link the SNMP community string with the SNMP IP ACL, in the management-policy-config-mode, use the following command: snmp-server > community <COMMUNITY-STRING> > [ro|rw] > ip-snmp-access-list <IP-SNMP-ACL-NAME>.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-565.png)
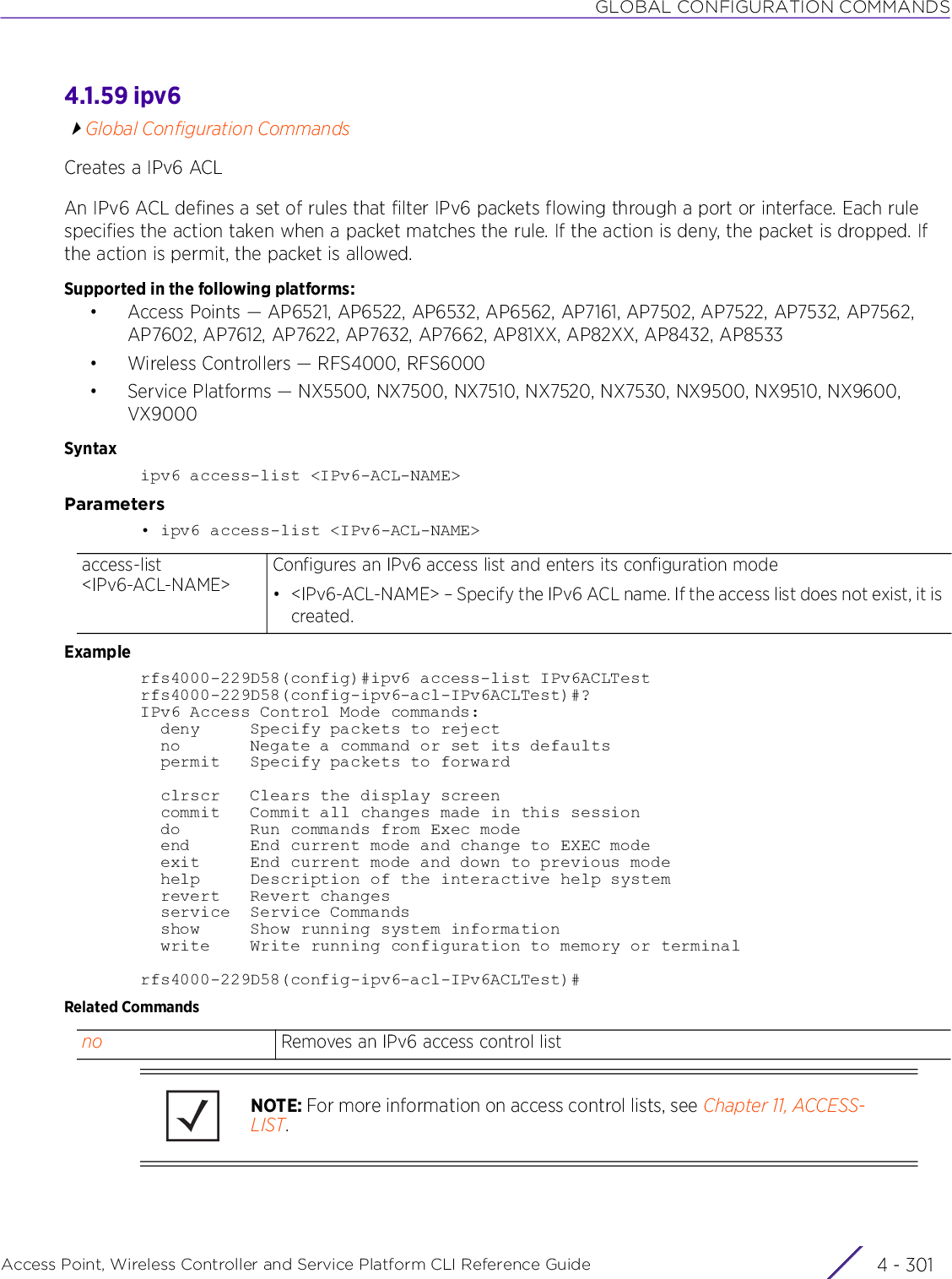

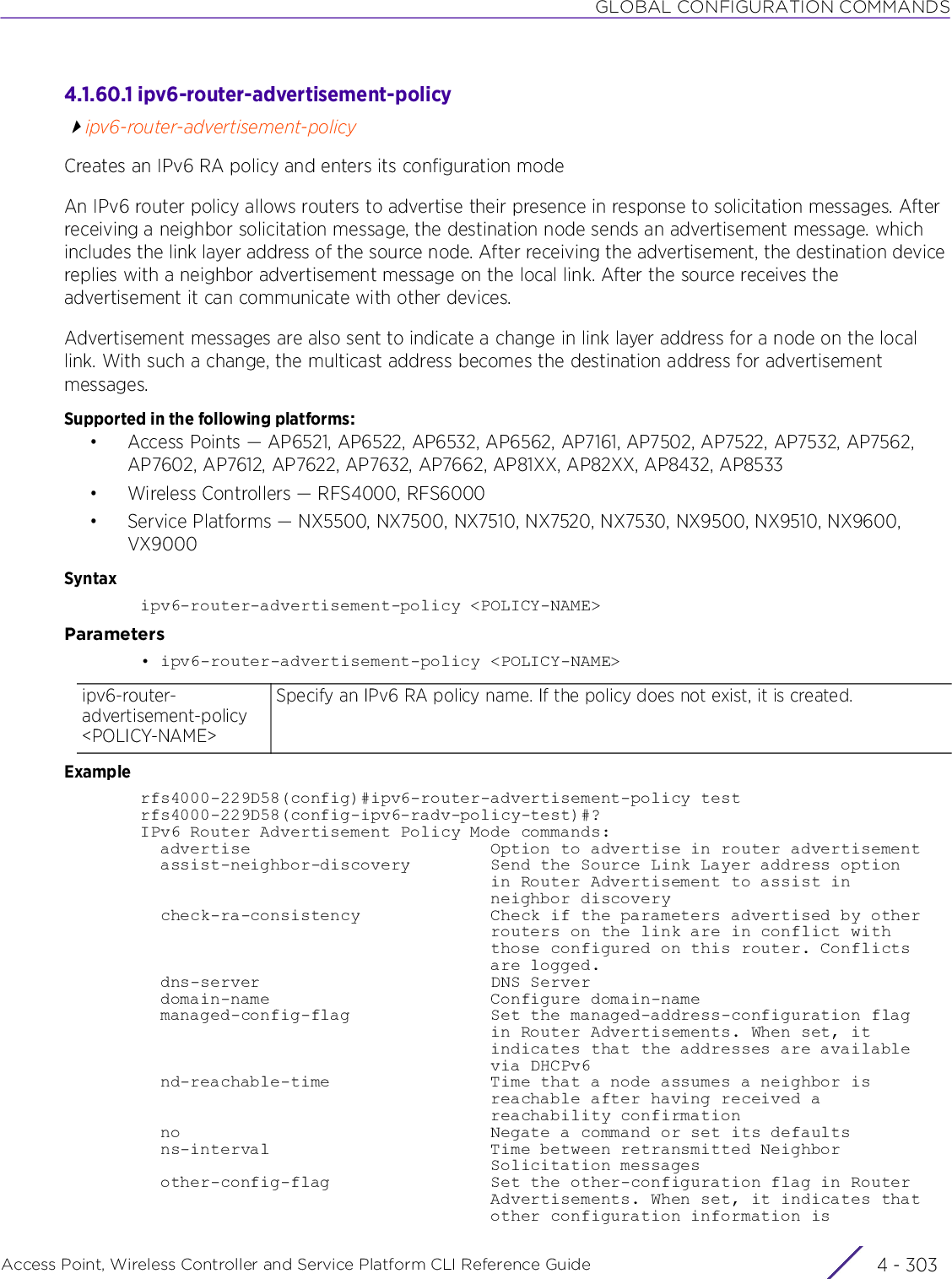
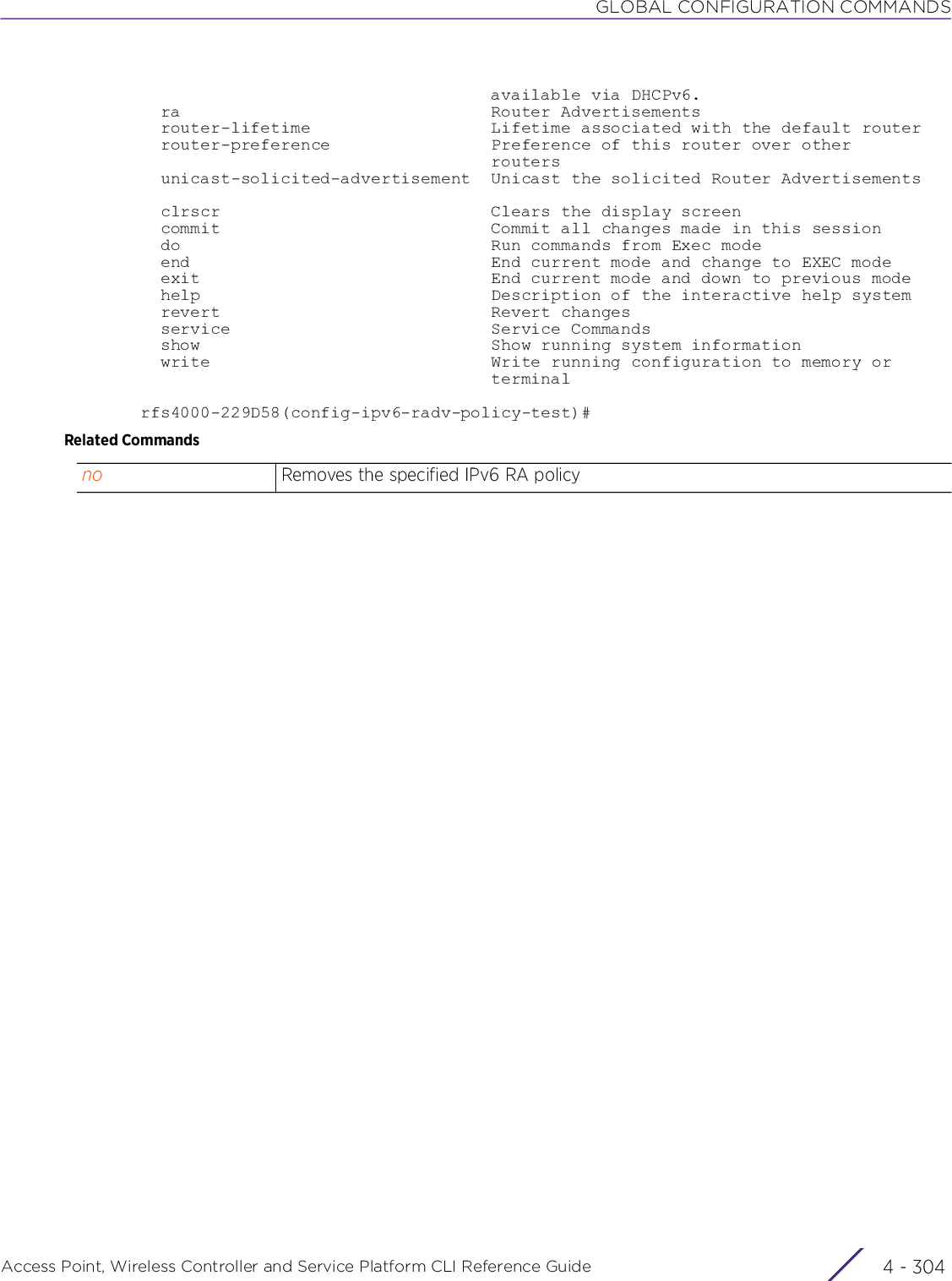
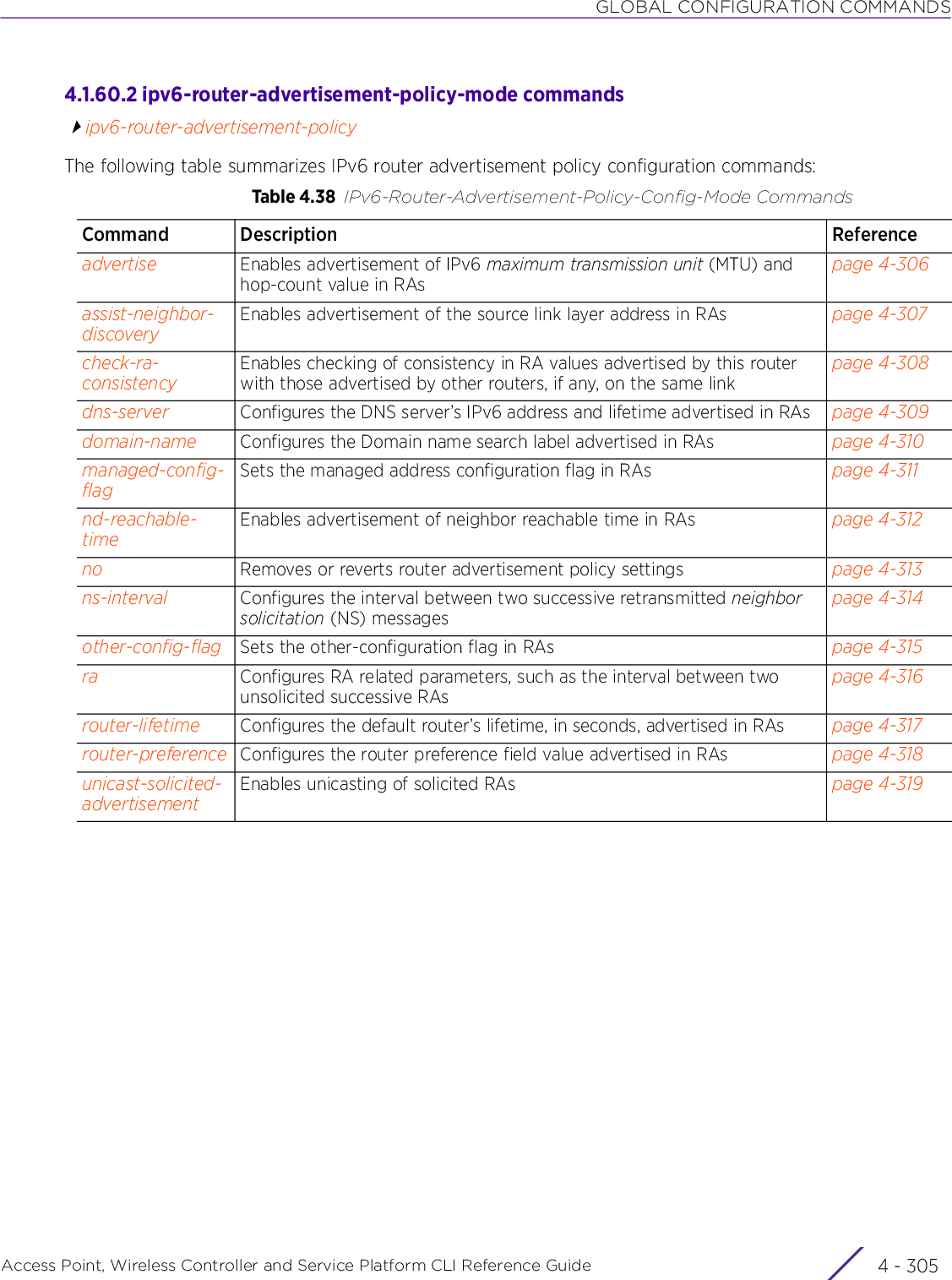
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3064.1.60.2.1 advertiseipv6-router-advertisement-policy-mode commandsEnables advertisement of IPv6 MTU and hop-count value in RAsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxadvertise [hop-limit|mtu]Parameters• advertise [hop-limit|mtu]Examplerfs6000-81742D(config-ipv6-radv-policy-test)#advertise hop-limitrfs6000-81742D(config-ipv6-radv-policy-test)#advertise mturfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test advertise mtu advertise hop-limitrfs6000-81742D(config-ipv6-radv-policy-test)#Related Commandsadvertise [hop-limit|mtu]Enables advertisement of IPv6 MTU and hop-count value in RAs. Both these features are disabled by default.no Disables advertisement of IPv6 MTU and hop-count value in RAs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-572.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3094.1.60.2.4 dns-serveripv6-router-advertisement-policy-mode commandsConfigures the DNS server’s IPv6 address and lifetime. The configured values are advertised in RAs.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdns-server <IPv6> {lifetime [<4-3600>|expired|infinite]}Parameters• dns-server <IPv6> {lifetime [<4-3600>|expired|infinite]}Examplerfs6000-81742D(config-ipv6-radv-policy-test)#dns-server 2002::2 lifetime 3000rfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test advertise mtu advertise hop-limit check-ra-consistency dns-server 2002::2 lifetime 3000rfs6000-81742D(config-ipv6-radv-policy-test)#Related Commandsdns-server <IPv6> Configures the DNS server’s IPv6 addressEnables the use of a DNS server to resolve host names to IPv6 addresses. When an IPv6 host is configured with the address of a DNS server, the host sends DNS name queries to the server for resolution.• <IPv6> – Specify the DNS server’s address. This address is advertised in RAs. A maximum of four (4) entries can be made per policy.lifetime [<4-3600>|expired|infinite]Optional. Configures the DNS server’s (identified by the <IPv6> parameter) lifetime• <4-3600> – Configures a lifetime in seconds. Specify a value form 4 - 3600 seconds. The default is 600 seconds.• expired – Advertises that this DNS server’s lifetime has expired and should not be used• infinite – Advertises that this DNS server’s lifetime is infiniteno Removes the DNS server settings advertised in RAs. Once removed these values are not advertised in RAs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-575.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3104.1.60.2.5 domain-nameipv6-router-advertisement-policy-mode commandsConfigures the Domain name search label advertised in RAsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdomain-name <WORD> {lifetime [<4-3600>|expired|infinite]}Parameters• domain-name <WORD> {lifetime [<4-3600>|expired|infinite]}Examplerfs6000-81742D(config-ipv6-radv-policy-test)#domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test advertise mtu advertise hop-limit check-ra-consistency dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#Related Commandsdomain-name <WORD>Configures the Domain name search label advertised in RAsEnter a fully qualified domain name (FQDN), which is an unambiguous domain name available in a router advertisement resource. To distinguish an FQDN from a regular domain name, a trailing period is added. For example, somehost.example.com.• <WORD> – Specify the Domain name search label. A maximum of four (4) entries can be made per policy.lifetime [<4-3600>|expired|infinite]Optional. Configures the Domain name search label's lifetime• <4-3600> – Configures a lifetime in seconds. Specify a value form 4 - 3600 seconds. The default is 600 seconds.• expired – Advertises that this Domain name search label's lifetime has expired and should not be used• infinite – Advertises that this Domain name search label's lifetime is infiniteno Removes the Domain name settings advertised in RAs. Once removed these values are not advertised in RAs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-576.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3124.1.60.2.7 nd-reachable-timeipv6-router-advertisement-policy-mode commandsEnables advertisement of neighbor discovery reachable time in RAs. This feature is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnd-reachable-time [<5000-3600000>|global]Parameters• nd-reachable-time [<5000-3600000>|global]Examplerfs6000-81742D(config-ipv6-radv-policy-test)#nd-reachable-time 6000rfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test managed-config-flag nd-reachable-time 6000 advertise mtu advertise hop-limit check-ra-consistency dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#Related Commandsnd-reachable-time [<5000-3600000>|global]Configures the interval, in milliseconds, that a node assumes a neighbor is reachable after receiving a reachability confirmation from the neighbor. Therefore, a neighbor is reachable, after being discovered, for a period specified here. This value is advertised in RAs. Use one of the following options:• <5000-3600000> – Configures an interface-specific value. Specify a value from 5000 - 3600000 milliseconds. The default is 5000 milliseconds.• global – Advertises the neighbor reachable time configured for the system. This is the value configured at the device configuration mode. For more information, see use.no Disables advertisement of neighbor reachable time in RAs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-578.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3134.1.60.2.8 noipv6-router-advertisement-policy-mode commandsRemoves or reverts router advertisement policy settings. Use the no command to remove or revert the interface-specific parameters that are advertised by link router.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [advertise [hop-limit|mtu]|assist-neighbor-discovery|check-ra-consistency|dns-server <IPv6>|domain-name <WORD>|managed-config-flag|nd-reachable-time|ns-interval|other-config-flag|ra [interval|suppress]|router-lifetime|unicast-solicited-advertisement]Parameters• no <PARAMETERS>Examplerfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test managed-config-flag nd-reachable-time global advertise mtu advertise hop-limit check-ra-consistency dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#rfs6000-81742D(config-ipv6-radv-policy-test)#no managed-config-flagrfs6000-81742D(config-ipv6-radv-policy-test)#no nd-reachable-timerfs6000-81742D(config-ipv6-radv-policy-test)#no check-ra-consistencyrfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test advertise mtu advertise hop-limit dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#no <PARAMETERS> Removes or reverts this IPv6 router advertisement policy’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-579.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3144.1.60.2.9 ns-intervalipv6-router-advertisement-policy-mode commandsConfigures the neighbor solicitation (NS) retransmit timer value advertised in RAs. This is the interval between two successive NS messages. When specified, it enables the sending of the specified value in RAs. This feature is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxns-interval [<1000-3600000>|global]Parameters• ns-interval [<1000-3600000>|global]Examplerfs6000-81742D(config-ipv6-radv-policy-test)#ns-interval 3000rfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test managed-config-flag nd-reachable-time global ns-interval 3000 advertise mtu advertise hop-limit check-ra-consistency dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#Related Commandsns-interval [<1000-3600000>|global]Configures the NS interval advertised in RAs. Use one of the following options:• <1000-3600000> – Specify a value from 1000 - 3600000 milliseconds. The default is 1000 milliseconds.• global – Advertises the NS interval configured for the system. This is configured on the device in the device configuration mode. For more information, see ipv6.no Disables advertisement of NS interval in RAs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-580.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3164.1.60.2.11 raipv6-router-advertisement-policy-mode commandsConfigures RA related parameters, such as the interval between two unsolicited successive RAs. It also allows suppression of RAs.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxra [interval <3-1800>|suppress]Parameters• ra [interval <3-1800>|suppress]Examplerfs6000-81742D(config-ipv6-radv-policy-test)#ra interval 200rfs6000-81742D(config-ipv6-radv-policy-test)#ra suppressrfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test ra suppress ra interval 200 managed-config-flag nd-reachable-time global advertise mtu advertise hop-limit check-ra-consistency dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#Related Commandsinterval <3-1800> Configures the interval, in seconds, between two unsolicited successive RAs• <3-1800> – Specify a value from 3 - 1800 seconds. The default is 300 seconds.The router-lifetime should be at least three times the specified router interval.suppress Enables the suppression of RAs. When enabled, the transmission of RAs in IPv6 packets is suppressed. This option is disabled by default. The no > ra > suppress command enables the sending of RAs.no Removes the RA interval, and enables the sending of RAs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-582.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3184.1.60.2.13 router-preferenceipv6-router-advertisement-policy-mode commandsConfigures the router preference field value advertised in RAs. The options are high, medium, and low. This value is used to prioritize and select the default router when multiple routers are discovered.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrouter-preference [high|medium|low]Parameters• router-preference [high|medium|low]Examplerfs6000-81742D(config-ipv6-radv-policy-test)#router-preference highrfs6000-81742D(config-ipv6-radv-policy-test)#show contextipv6-router-advertisement-policy test ra suppress ra interval 200 managed-config-flag nd-reachable-time global router-lifetime 2000 advertise mtu advertise hop-limit router-preference high check-ra-consistency dns-server 2002::2 lifetime 3000 domain-name TechPubs lifetime infiniterfs6000-81742D(config-ipv6-radv-policy-test)#router-preference [high|medium|low]Sets this router’s preference over other routers, in the link, to be the default router. The options are high, low, and medium. The default value is medium.The following points should be taken into consideration when configuring router preference:• For a router to be selected as a default router, the router’s lifetime should not be equal to “0”.• To enable default router selection, using router information contained in RAs, configure default router selection on that interface.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-584.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3254.1.64 meshpointGlobal Configuration CommandsCreates a new meshpoint and enters its configuration mode. Use this command to select and configure existing meshpoints.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmeshpoint [<MESHPOINT-NAME>|containing <WORD>]Parameters• meshpoint [<MESHPOINT-NAME>|containing <WORD>]Examplerfs6000-81742D(config)#meshpoint TestMeshpointrfs6000-81742D(config-meshpoint-TestMeshpoint)#?Mesh Point Mode commands: allowed-vlans Set the allowed VLANs beacon-format The beacon format of this meshpoint control-vlan VLAN for meshpoint control traffic data-rates Specify the 802.11 rates to be supported on this meshpoint description Configure a description of the usage of this meshpoint force Force suboptimal paths meshid Configure the Service Set Identifier for this meshpoint neighbor Configure neighbor specific parameters no Negate a command or set its defaults root Set this meshpoint as root security-mode The security mode of this meshpoint shutdown Shutdown this meshpoint use Set setting to use wpa2 Modify ccmp wpa2 related parameters clrscr Clears the display screen commit Commit all changes made in this session do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system revert Revert changes service Service Commands show Show running system information write Write running configuration to memory or terminalrfs6000-81742D(config-meshpoint-TestMeshpoint)#Related Commands<MESHPOINT-NAME> Specify the meshpoint name. If the meshpoint does not exist, it is created.containing <WORD> Selects existing meshpoints containing the sub-string <WORD> in their namesno Removes an existing meshpoint](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-591.png)



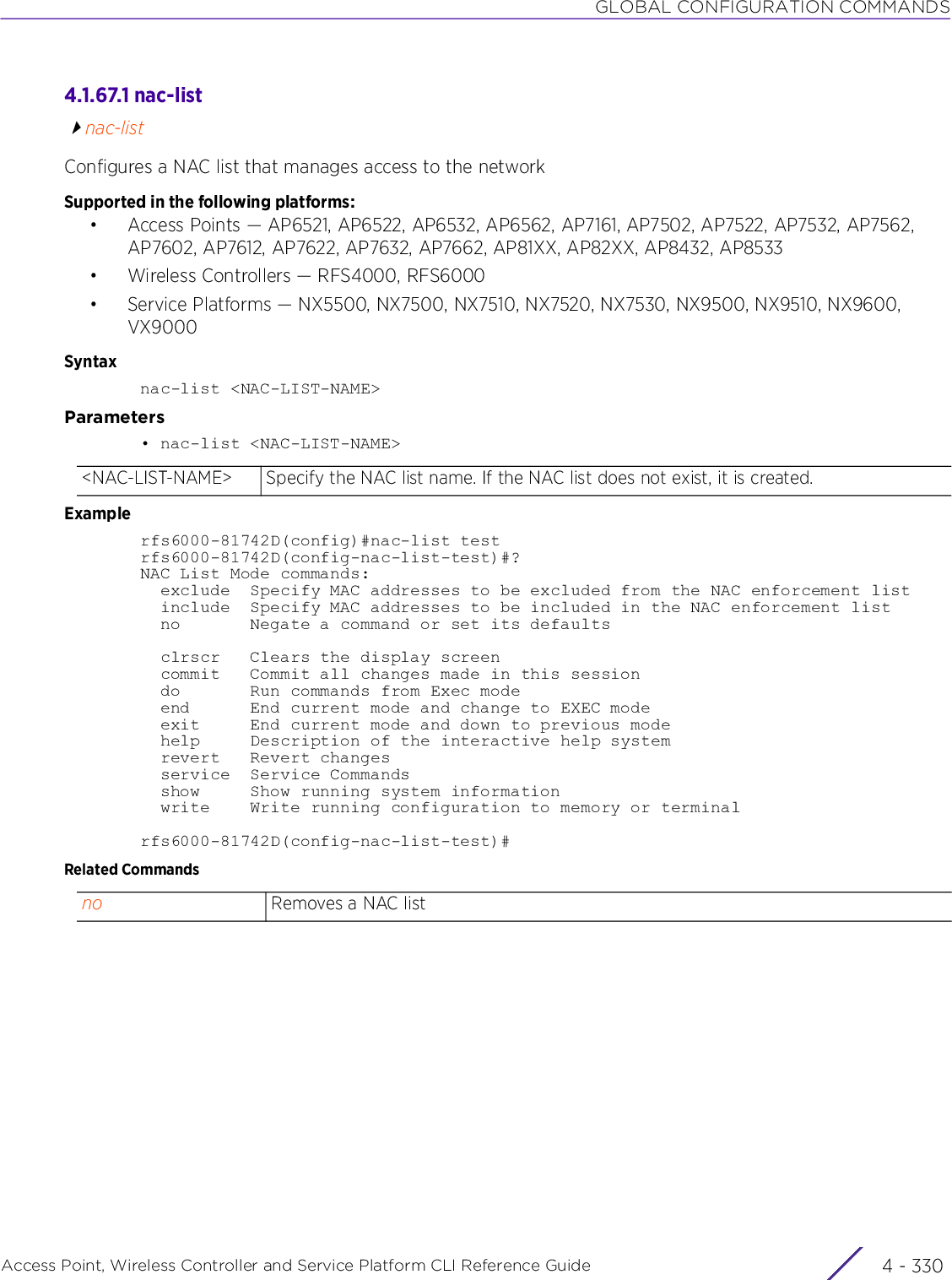
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3324.1.67.2.1 excludenac-list-mode commandsSpecifies the MAC addresses excluded from the NAC enforcement listSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxexclude <START-MAC> [<END-MAC> precedence <1-1000>|precedence <1-1000>]Parameters• exclude <START-MAC> [<END-MAC> precedence <1-1000>|precedence <1-1000>]Examplerfs6000-81742D(config-nac-list-test)#exclude 00-40-96-B0-BA-2A precedence 1rfs6000-81742D(config-nac-list-test)#show contextnac-list test exclude 00-40-96-B0-BA-2A 00-40-96-B0-BA-2A precedence 1rfs6000-81742D(config-nac-list-test)#<START-MAC> Specifies a range of MAC addresses or a single MAC address to exclude from the NAC enforcement list• <START-MAC> – Specify the first MAC address in the range.Use this parameter to specify a single MAC address.<END-MAC> Specifies the last MAC address in the range (optional if a single MAC is added to the list)• <END-MAC> – Specify the last MAC address in the range.precedence <1-1000>Sets the rule precedence. Exclude entries are checked in the order of their rule precedence.• <1-1000> – Specify a value from 1 - 1000.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-598.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3334.1.67.2.2 includenac-list-mode commandsSpecifies the MAC addresses included in the NAC enforcement listSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxinclude <START-MAC> [<END-MAC> precedence <1-1000>|precedence <1-1000>]Parameters• include <START-MAC> [<END-MAC> precedence <1-1000>|precedence <1-1000>]Examplerfs6000-81742D(config-nac-list-test)#include 00-15-70-38-06-49 precedence 2rfs6000-81742D(config-nac-list-test)#show contextnac-list test exclude 00-04-96-B0-BA-2A 00-04-96-B0-BA-2A precedence 1 include 00-15-70-38-06-49 00-15-70-38-06-49 precedence 2rfs6000-81742D(config-nac-list-test)#<START-MAC> Specifies a range of MAC addresses or a single MAC address to include in the NAC enforcement list• <START-MAC> – Specify the first MAC address in the range.Use this parameter to specify a single MAC address.<END-MAC> Specifies the last MAC address in the range (optional if a single MAC is added to the list)• <END-MAC> – Specify the last MAC address in the range.precedence <1-1000>Sets the rule precedence. Include entries are checked in the order of their rule precedence.• <1-1000> – Specify a value from 1 - 1000.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-599.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3344.1.67.2.3 nonac-list-mode commandsCancels an exclude or include NAC list ruleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [exclude|include]no [exclude|include] <START-MAC> [<END-MAC> precedence <1-1000>|precedence <1-1000>]Parameters• no <PARAMETERS>ExampleThe following example shows the NAC list ‘test’ settings before the ‘no’ command is executed:rfs6000-81742D(config-nac-list-test)#show contextnac-list test exclude 00-04-96-B0-BA-2A 00-04-96-B0-BA-2A precedence 1 include 00-15-70-38-06-49 00-15-70-38-06-49 precedence 2rfs6000-81742D(config-nac-list-test)#rfs6000-81742D(config-nac-list-test)#no exclude 00-40-96-B0-BA-2A precedence 1The following example shows the NAC list ‘test’ settings after the ‘no’ command is executed:rfs6000-81742D(config-nac-list-test)#show contextnac-list test include 00-15-70-38-06-49 00-15-70-38-06-49 precedence 2rfs6000-81742D(config-nac-list-test)#Related Commandsno <PARAMETERS> Removes or reverts this NAC list’s settings based on the parameters passedexclude Specifies MAC addresses excluded from the NAC enforcement listinclude Specifies MAC addresses included in the NAC enforcement list](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-600.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3354.1.68 noGlobal Configuration CommandsNegates a command, or reverts configured settings to their defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [aaa-policy|aaa-tacacs-policy|alias|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|nx5500|nx75xx|nx9000|nx9600|application|application-group|application-policy|association-acl-policy|auto-provisioning-policy|bgp|bonjour-gw-discovery-policy|bonjour-gw-forwarding-policy|bonjour-gw-query-forwarding-policy|captive-portal|client-identity|client-identity-group|crypto-cmp-policy|customize|database-policy|device|device-categorization|dhcp-server-policy|dhcpv6-server-policy|dns-whitelist|event-system-policy|ex3500|ex3500-management-policy|ex3500-qos-class-map-policy|ex3500-qos-policy-map|ex3524|ex3548|firewall-policy|global-association-list|guest-management|igmp-snoop-policy|inline-password-encryption|ip|ipv6|ipv6-router-advertisement-policy|l2tpv3|mac|management-policy|meshpoint|meshpoint-qos-policy|nac-list|nsight-policy|passpoint-policy|password-encryption|profile|radio-qos-policy|radius-group|radius-server-policy|radius-user-pool-policy|rf-domain|rfs4000|rfs6000|roaming-assist-policy|role-policy|route-map|routing-policy|rtl-server-policy|schedule-policy|t5|sensor-policy|smart-rf-policy|url-filter|url-list|vx9000|web-filter-policy|wips-policy|wlan|wlan-qos-policy|service]no alias [address-range <ADDRESS-RANGE-ALIAS-NAME>|host <HOST-ALIAS-NAME>|network <NETWORK-ALIAS-NAME>|network-group <NETWORK-GROUP-ALIAS-NAME> [address-range|host|network]|network-service <NETWORK-SERVICE-ALIAS-NAME>|number <NUMBER-ALIAS-NAME>|string <STRING-ALIAS-NAME>|vlan <VLAN-ALIAS-NAME>]no [aaa-policy|aaa-tacacs-policy|application-policy|auto-provisioning-policy|auto-provisioning-policy|bonjour-gw-discovery-policy|bonjour-gw-forwarding-policy|bonjour-gw-query-forwarding-policy|database-policy|captive-portal|crypto-cmp-policy|device-categorization|dhcp-server-policy|dhcpv6-server-policy|dns-whitelist|event-system-policy|ex3500|ex3500-management-policy|ex3500-qos-class-map-policy|ex3500-qos-policy|firewall-policy|global-association-list|guest-management|igmp-snoop-policy|inline-password-encryption|ip|ipv6|ipv6-router-advertisement-policy|l2tpv3|mac|management-policy|meshpoint|meshpoint-qos-policy|nac-list|nsight-policy|passpoint-policy|radio-qos-policy|radius-group|radius-server-policy|radius-user-pool-policy|roaming-assist-policy|role-policy|routing-policy|rtl-server-policy|schedule-policy|sensor-policy|smart-rf-policy|web-filter-policy|wips-policy|wlan-qos-policy] <POLICY-NAME>no application <APPLICATION-NAME>no application-group <APPLICATION-GROUP-NAME>no [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|rfs4000|rfs6000|t5|nx5500|nx75xx|nx9000|nx9600|vx9000] <MAC>no client-identity <CLIENT-IDENTITY-NAME>no client-identity-group <CLIENT-IDENTITY-GROUP-NAME>](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-601.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 336no device {containing <WORD>} {(filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|rfs4000|rfs6000|t5|nx5500|nx75xx|nx9000|nx9600|vx9000])}no customize [hostname-column-width|show-wireless-client|show-wireless-client-stats|show-wireless-client-stats-rf|show-wireless-meshpoint|show-wireless-meshpoint-neighbor-stats|show-wireless-meshpoint-neighbor-stats-rf|show-wireless-radio|show-wireless-radio-stats|show-wireless-radio-stats-rf]no password-encryption secret 2 <OLD-PASSPHRASE>no profile {ap6521|ap6522|ap6532|ap71xx|ap7502|ap7522|ap7532|ap7562|ap81xx|ap82xx|ap8432|ap8533|ex3524|ex3548|containing|filter|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|t5|vx9000} <PROFILE-NAME>no wlan [<WLAN-NAME>|all|containing <WLAN-NAME-SUBSTRING>]no service set [command-history|reboot-history|upgrade-history] {on <DEVICE-NAME>}The following ‘no’ commands are specific to the RFS4000, RFS6000, and NX95XX platforms:no t5 <T5-DEVICE-MAC>The following ‘no’ commands are specific to the RFS4000, RFS6000, and NX95XX platforms:no bgp [as-path-list|community-list|extcommunity-list|ip-access-list|ip-prefix-list] <LIST-NAME>The following ‘no’ commands are specific to the NX95XX series service platforms:no route-map <ROUTE-MAP-NAME>The following ‘no’ commands are specific to the AP6522, AP6532, AP7161, AP7502, AP7522, AP7532, AP8132, RFS4000, RFS6000 platforms:no url-filter <URL-FILTER-NAME>no url-list <URL-LIST-NAME>no web-filter-name <WEB-FILTER-NAME>The following ‘no’ command is specific to the VX9000 virtual machine platform:no database-client-policy <POLICY-NAME>Parameters• no <PARAMETERS>Example<DEVICE>(config)#no ? aaa-policy Delete a aaa policy aaa-tacacs-policy Delete a aaa tacacs policy alias Alias ap650 Delete an AP650 access point ap6511 Delete an AP6511 access point ap6521 Delete an AP6521 access point ap6522 Delete an AP6522 access point ap6532 Delete an AP6532 access point ap6562 Delete an AP6562 access point ap71xx Delete an AP7161 access point ap7502 Delete an AP7502 access point ap7522 Delete an AP7522 access point ap7532 Delete an AP7532 access point ap7562 Delete an AP7562 access point ap7602 Delete an AP7602 access point ap7612 Delete an AP7612 access point ap7622 Delete an AP7622 access point ap7632 Delete an AP7632 access point ap7662 Delete an AP7662 access point ap81xx Delete an AP81XX access pointno <PARAMETERS> Removes or resets settings, configurable in the global configuration mode, based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-602.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3444.1.69.2.2 event-history-sizensight-policy commandsConverts and sizes the NSight event history collection to a capped collection. The conversion occurs when upgrading. Use this command to define the NSight event history collection’s size and prevent its unbounded growth. Note, resizing the collection results in the collection contents being dropped.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxevent-history-size [high|low|medium]Parameters• event-history-size [high|low|medium]Examplenx9500-6C8809(config-nsight-policy-test)#event-history-size mediumnx9500-6C8809(config-nsight-policy-test)#show contextnsight-policy test event-history-size mediumnx9500-6C8809(config-nsight-policy-test)#Related Commandsevent-history-size [high|low|medium]Defines the size of the NSight event history collection. The options are:• high – Sets the size at approximately 10 M events• low – Sets the size at approximately 500 K events. This is the default setting.• medium – Sets the size at approximately 5 M eventsno Reverts the NSight event history collection size to default (5 M)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-610.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3454.1.69.2.3 history-ttlnsight-policy commandsConfigures the time-to-live (TTL), in days, for historical data related to clients, devices, and guest users. This is the duration for which clients, devices, or guest user related data is retained in the NSight database.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxhistory-ttl [clients|devices|guest-clients]history-ttl [clients|devices] <1-3650>history-ttl guest-clients <8-48>Parameters• history-ttl [clients|devices] <1-3650>• history-ttl guest-clients <8-48>Examplenx9500-6C8809(config-nsight-policy-test)#history-ttl clients 250nx9500-6C8809(config-nsight-policy-test)#show contextnsight-policy test history-ttl clients 250nx9500-6C8809(config-nsight-policy-test)#Related Commandshistory-ttl [client|devices] <1-3650>Configures the TTL for historical data related to clients and devices• clients – Configures the TTL for wireless clients related historical data• devices – Configures the TTL for devices (adopted access points or site controllers) related historical dataThe following is common to both the ‘clients’ and ‘devices’ keywords:• <1-3650> – Specify a value from 1 - 3650 days. The default for both (clients and de-vices) is 180 days.history-ttl guest-clients <8-48>Configures the TTL for historical data related to clients and devices• guest-clients – Configures the TTL for guest-client related historical data• <8-48> – Specify a value from 8 - 48 hours. The default is 8 hours.no Reverts the NSight clients or devices TTL duration to default (180 days)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-611.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3464.1.69.2.4 nsight-servernsight-policy commandsEnables NSight server functionality and configures the SMTP report delivery settings.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxnsight-server {smtp-report-delivery|standalone}nsight-server {smtp-report-delivery host <WORD> sender <EMAIL-ADD> [port <1-65535>|security [none|ssl|starttls]|username <USER-NAME> password [0|2|<WORD>]]}nsight-server {standalone}Parameters• nsight-server {smtp-report-delivery host <WORD> sender <EMAIL-ADD> [port <1-65535>|security [none|ssl|starttls]|username <USER-NAME> password [0|2|<WORD>]]}• nsight-server {standalone}nsight-server Enables NSight server functionality on the host using this NSight policysmtp-report-delivery host <WORD>Optional. Configures SMTP report delivery settings• host <WORD> – Configures the SMTP server host• <WORD> – Specify the SMTP server host’s IP address or hostname.sender <EMAIL-ADD>Optional. Configures the SMTP sender’s e-mail address• <EMAIL-ADD> – Specify the sender’s e-mail address.port <1-65535> Optional. Configures the SMTP server port• <1-65535> – Specify the port from 1 - 65535.security [none|ssl|starttls]Optional. Configures the encryption protocol used by the SMTP server. The options are:• none – Uses no encryption• ssl – Uses SSL encryption• starttls – Uses STARTTLS encryptionusername <USER-NAME> password [0|2|<WORD>]Optional. Configures the SMTP username• <USER-NAME> Specify the user name• password [0|2|<WORD>] – Configures the password associated with the above con-figured user• 0 – Configures a clear text password• 2 – Configures an encrypted password• <WORD> – Enter the password.nsight-server Enables NSight server functionality on the host using this NSight policystandalone Optional. Configures NSight server as standalone. Use this option in the split NSight deployment scenario where the NSight server and database are hosted on separate hosts.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-612.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3484.1.69.2.5 servernsight-policy commandsConfigures the NSight server host. This configuration is used by the NSight client to identify the NSight server host.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxserver host [<IP>|<HOSTNAME>|<X:X::X:X>] {http|https}Parameters• server host [<IP>|<HOSTNAME>|<X:X::X:X>] {http|https}Examplenx9510-6C8A5C(config-nsight-policy-test2)#server host 172.22.0.153 httpnx9510-6C8A5C(config-nsight-policy-test2)#show contextnsight-policy test2 server host 172.22.0.153 http nsight-servernx9510-6C8A5C(config-nsight-policy-test2)#Related Commandsserver host [<IP>|<HOSTNAME>|<X:X::X:X>]Configures the NSight server host’s address. Use one of the following options to identify the NSight server host:• <IP> – Configures the NSight server’s IPv4 address• <HOSTNAME> – Configures the NSight server’s hostname• <X:X::X:X> – Configures the NSight server’s IPv6 address{http|https} Optional. Configures the protocol used to communicate with the NSight server• http – Optional. Uses HTTP to communicate• https – Optional. Uses HTTPS to communicate (this is the default setting) no Removes NSight server host settings from this NSight policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-614.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3494.1.69.2.6 nonsight-policy commandsRemoves NSight policy settingsSupported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxno [enable|event-history-size|history-ttl [clients|devices|guest-clients]|nsight-server {smtp-report-delivery}|server host [<IP>|<HOSTNAME>|<X:X::X:X>]]Parameters• no <PARAMETERS>ExampleThe following example shows the NSight policy ‘test2’ settings before the ‘no’ command is executed:nx9510-6C8A5C(config-nsight-policy-test2)#show contextnsight-policy test2 server host 172.22.0.153 http nsight-servernx9510-6C8A5C(config-nsight-policy-test2)#nx9510-6C8A5C(config-nsight-policy-test2)#no server host 172.22.0.153The following example shows the NSight policy ‘test2’ settings after the ‘no’ command is executed:nx9500-6C8809(config-nsight-policy-test2)#show contextnsight-policy test2 nsight-servernx9510-6C8A5C(config-nsight-policy-test2)#no <PARAMETERS> Removes NSight policy settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-615.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3534.1.72 profileGlobal Configuration CommandsConfigures profile related commands. If no parameters are given, all profiles are selected.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxprofile {anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|containing|filter|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000}profile {anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000} <DEVICE-PROFILE-NAME>profile {containing <DEVICE-PROFILE-NAME>} {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx75xx|nx9000|vx9000]}profile {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000]}Parameters• profile {anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000} <DEVICE-PROFILE-NAME>• profile {containing <DEVICE-PROFILE-NAME>} {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000]}profile <DEVICE-TYPE> <DEVICE-PROFILE-NAME>Configures device profile commands. If no device profile is specified, the system configures all device profiles.• <DEVICE-TYPE> – Optional. Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000. After specifying the device type, specify the profile name.• <DEVICE-PROFILE-NAME> – Specify the profile name.Select ‘anyap’ to configure a profile applicable to any access point.The NX9600 profile option is only available on an NX9600 device.profile Configures device profile commandscontaining <DEVICE-PROFILE-NAME>Optional. Configures profiles that contain a specified sub-string in the hostname• <DEVICE-PROFILE-NAME> – Specify a substring in the profile name to filter profiles.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-619.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 354• profile {filter type [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600|vx9000]}Example<DEVICE>(config)#profile <DEVICE-TYPE> <PROFILE-NAME><DEVICE>(config-profile-<PROFILE-NAME>)#?Profile Mode commands: adopter-auto-provisioning-policy-lookup Use centralized auto-provisioning policy when adopted by another controller adoption Adoption configuration alias Alias application-policy Application Policy configuration area Set name of area where the system is located arp Address Resolution Protocol (ARP) auto-learn Auto learning autogen-uniqueid Autogenerate a unique id autoinstall Autoinstall settings bluetooth-detection Detect Bluetooth devices using the Bluetooth USB module - there will be interference on 2.4 Ghz radio in wlan mode bridge Ethernet bridge captive-portal Captive portal cdp Cisco Discovery Protocol cluster Cluster configuration configuration-persistence Enable persistence of configuration across reloads (startup config file) controller WLAN controller configuration critical-resource Critical Resource crypto Encryption related commands database Database command device-onboard Device-onboarding configuration device-upgrade Device firmware upgrade diag Diagnosis of packets dot1x 802.1X dpi Enable Deep-Packet-Inspection (Application Assurance) dscp-mapping Configure IP DSCP to 802.1p priority mapping for untaggedfilter type Optional. An additional filter used to configure a specific type of device profile. If no device type is specified, the system configures all device profiles.• type – Filters profiles by the device type. Select a device type from the following options: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000.The NX9600 profile option is only available on an NX9600 device.profile Configures device profile commandsfilter type Optional. An additional filter used to configure a specific type of device profile. If no device type is specified, the system configures all device profiles.• type – Filters profiles by the device type. Select a device type from the following options: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000.The NX9600 profile option is only available on an NX9600 device.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-620.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3644.1.78 replaceGlobal Configuration CommandsSelects an existing device by its MAC address or hostname and replaces it with a new device having a different MAC address. Internally, a new device is created with the new MAC address. The old device’s configuration is copied to the new device, and then removed from the controller’s configuration (i.e., the old device’s configuration is no longer staged on the controller).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxreplace device [<MAC-ADDRESS>|<HOSTNAME>] <NEW-MAC-ADDRESS>Parameters• replace device [<MAC-ADDRESS>|<HOSTNAME>] <NEW-MAC-ADDRESS>Examplerfs4000-882A17(config)#replace device ap7131-4BF364 ? AA-BB-CC-DD-EE-FF New device MAC addressrfs4000-882A17(config)#replace device ap7131-4BF364 00-15-0F-BB-98-30The following example shows an existing AP7502 (MAC: DD-AA-BB-88-12-43) configuration staged on a VX9000 controller:VX9000-NOC-DE9D(config-device-DD-AA-BB-88-12-43)#show contextap7502 DD-AA-BB-88-12-43 use profile default-ap7502 use rf-domain default hostname ap7502-881243 interface radio1 wlan theMOZART bss 1 primary interface radio2 wlan theMOZART bss 1 primary interface ge1 switchport mode access switchport access vlan 1 controller host 12.12.12.2VX9000-NOC-DE9D(config-device-DD-AA-BB-88-12-43)#replace device Replaces an existing device with a new device, such that the old device’s configuration is copied on to the new device[<MAC-ADDRESS>|<HOSTNAME>]Identifies the device to replace by its MAC address or hostname• <MAC-ADDRESS> – Identifies the device to replace by its MAC address. Specify the device’s existing MAC address.• <HOSTNAME> – Identifies the device to replace by its hostname. Specify the device’s hostname.<NEW-MAC-ADDRESS>Specifies the new device’s MAC addressBoth the new and old devices should of the same model type.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-630.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3704.1.79.2.1 aliasrf-domain-mode commandsConfigures network, VLAN, host, string, network-service, etc. aliases at the RF Domain levelFor information on aliases, see alias.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxalias [address-range|encrypted-string|hashed-string|host|network|network-group|network-service|number|string|vlan]alias encrypted-string <ENCRYPTED-STRING-ALIAS-NAME> [0|2] <LINE>alias hashed-string <HASHED-STRING-ALIAS-NAME> 1 <LINE>alias address-range <ADDRESS-RANGE-ALIAS-NAME> <STARTING-IP> to <ENDING-IP>alias host <HOST-ALIAS-NAME> <HOST-IP>alias network <NETWORK-ALIAS-NAME> <NETWORK-ADDRESS/MASK>alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range|host|network]alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}|host <HOST-IP> {<HOST-IP>}|network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}]alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport|ssh|telnet|tftp|www)}alias number <NUMBER-ALIAS-NAME> <0-4294967295>alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}alias string <STRING-ALIAS-NAME> <LINE>alias vlan <VLAN-ALIAS-NAME> <1-4094>Parameters• alias address-range <ADDRESS-RANGE-ALIAS-NAME> <STARTING-IP> to <ENDING-IP>address-range <ADDRESS-RANGE-ALIAS-NAME>Creates a new address-range alias for this RF Domain. Or associates an existing address-range alias with this RF Domain. An address-range alias maps a name to a range of IP addresses.• <ADDRESS-RANGE-ALIAS-NAME> – Specify the address range alias name.Alias name should begin with ‘$’.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-636.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 371• alias encrypted-string <ENCRYPTED-STRING-ALIAS-NAME> [0|2] <LINE>• alias hashed-string <HASHED-STRING-ALIAS-NAME> <LINE><STARTING-IP> to <ENDING-IP>Associates a range of IP addresses with this address range alias• <STARTING-IP> – Specify the first IP address in the range.• to <ENDING-IP> – Specify the last IP address in the range.Aliases defined at any given level can be overridden at the next lower level. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.encrypted-string <ENCRYPTED-STRING-ALIAS-NAME>Creates an alias for an encrypted string. Use this alias for string configuration values that are encrypted when "password-encryption" is enabled. For example, in the management-policy, use it to define the SNMP community string. For more information, see snmp-server.• <ENCRYPTED-STRING-ALIAS-NAME> – Specify the encrypted-string alias name.Alias name should begin with ‘$’.[0|2] <LINE> Configures the value associated with the alias name specified in the previous step• [0|2] <LINE> – Configures the alias valueNote, if password-encryption is enabled, in the show > running-config output, this clear text is displayed as an encrypted string, as shown below:nx9500-6C8809(config)#show running-config!...............................alias encrypted-string $enString 2 fABMK2is7UToNiZE3MQXbgAAAAxB0ZIysdqsEJwr6AH/Da//!--More--nx9500-6C8809In the above output, the ‘2’ displayed before the encrypted-string alias value indicates that the displayed text is encrypted and not a clear text.However, if password-encryption is disabled the clear text is displayed as is:nx9500-6C8809(config)#show running-config!...............................!alias encrypted-string $enString 0 test11223344!--More--nx9500-6C8809For more information on enabling password-encryption, see password-encryption.hashed-string <HASHED-STRING-ALIAS-NAME>Creates an alias for a hashed string. Use this alias for configuration values that are hashed string, such as passwords. For example, in the management-policy, use it to define the privilege mode password. For more information, see privilege-mode-password.• <HASHED-STRING-ALIAS-NAME> – Specify the hashed-string alias name.Alias name should begin with ‘$’.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-637.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 372• alias host <HOST-ALIAS-NAME> <HOST-IP>• alias network <NETWORK-ALIAS-NAME> <NETWORK-ADDRESS/MASK>• alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}|host <HOST-IP> {<HOST-IP>}|network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}]<LINE> Configures the hashed-string value associated with this alias.nx9500-6C8809(config)#show running-config!alias encrypted-string $WRITE 2 sBqVCDAoxs3oByF5PCSuFAAAAAd7HT2+EiT/l/BXm9c4SBDv!alias hashed-string $PriMode 1 faffdde27cb49ad634ea20df4f7c8ef2685894d10ffcb1b2efba054112ecfc75--More--nx9500-6C8809In the above show > running-config output, the ‘1’ displayed before the hashed-string alias value indicates that the displayed text is hashed and not a clear text.host <HOST-ALIAS-NAME>Creates a host alias for this RF Domain. Or associates an existing host alias with this RF Domain. A host alias maps a name to a single network host.• <HOST-ALIAS-NAME> – Specify the host alias name.Alias name should begin with ‘$’.<HOST-IP> Associates the network host’s IP address with this host alias• <HOST-IP> – Specify the network host’s IP address.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.network <NETWORK-ALIAS-NAME>Creates a network alias for this RF Domain. Or associates an existing network alias with this RF Domain. A network alias maps a name to a single network address.• <NETWORK-ALIAS-NAME> – Specify the network alias name.Alias name should begin with ‘$’.<NETWORK-ADDRESS/MASK>Associates a single network with this network alias• <NETWORK-ADDRESS/MASK> – Specify the network’s address and mask.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.network-group <NETWORK-GROUP-ALIAS-NAME>Creates a network-group alias for this RF Domain. Or associates an existing network-group alias with this RF Domain.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name.Alias name should begin with ‘$’.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-638.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 373• alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}After specifying the name, specify the following: a range of IP addresses, host addresses, or a range of network addresses.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}Associates a range of IP addresses with this network-group alias• <STARTING-IP> – Specify the first IP address in the range.• to <ENDING-IP> – Specify the last IP address in the range.• <STARTING-IP> to <ENDING-IP> – Optional. Specifies more than one range of IPaddresses. A maximum of eight (8) IP address ranges can be configured.host <HOST-IP> {<HOST-IP>}Associates a single or multiple hosts with this network-group alias• <HOST-IP> – Specify the hosts’ IP address.• <HOST-IP> – Optional. Specifies more than one host. A maximum of eight (8) hostscan be configured.network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}Associates a single or multiple networks with this network-group alias• <NETWORK-ADDRESS/MASK> – Specify the network’s address and mask.• <NETWORK-ADDRESS/MASK> – Optional. Specifies more than one network. Amaximum of eight (8) networks can be configured.alias network-service <NETWORK-SERVICE-ALIAS-NAME>Creates a network-service alias for this RF Domain. Or associates an existing network-service alias with this RF Domain. A network-service alias maps a name to network services and the corresponding source and destination software ports.• <NETWORK-SERVICE-ALIAS-NAME> – Specify a network-service alias name.Alias name should begin with ‘$’.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp]Use one of the following options to associate an Internet protocol with this network-service alias:• <0-254> – Identifies the protocol by its number. Specify the protocol number from 0 - 254. This is the number by which the protocol is identified in the Protocol field of the IPv4 header and the Next Header field of IPv6 header. For example, the User Datagram Protocol’s (UDP) designated number is 17.• <WORD> – Identifies the protocol by its name. Specify the protocol name.• eigrp – Selects Enhanced Interior Gateway Routing Protocol (EIGRP). The protocol number 88.•gre – Selects Generic Routing Encapsulation (GRE). The protocol number is 47.• igmp – Selects Internet Group Management Protocol (IGMP). The protocol number is 2.•igp – Selects Interior Gateway Protocol (IGP). The protocol number is 9.•ospf – Selects Open Shortest Path First (OSPF). The protocol number is 89.• vrrp – Selects Virtual Router Redundancy Protocol (VRRP). The protocol number is 112.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-639.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 374• alias number <NUMBER-ALIAS-NAME> <0-4294967295>{(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}After specifying the protocol, you may configure a destination port for this service. These keywords are recursive and you can configure multiple protocols and associate multiple destination and source ports.• <1-65535> – Optional. Configures a destination port number from 1 - 65535• <WORD> – Optional. Identifies the destination port by the service name provided. For example, the secure shell (SSH) service uses TCP port 22.• bgp – Optional. Configures the default Border Gateway Protocol (BGP) services port (179)• dns – Optional. Configures the default Domain Name System (DNS) services port (53)• ftp – Optional. Configures the default File Transfer Protocol (FTP) control services port (21)• ftp-data – Optional. Configures the default FTP data services port (20)• gopher – Optional. Configures the default gopher services port (70)• https – Optional. Configures the default HTTPS services port (443)• ldap – Optional. Configures the default Lightweight Directory Access Protocol (LDAP) services port (389)• nntp – Optional. Configures the default Newsgroup (NNTP) services port (119)• ntp – Optional. Configures the default Network Time Protocol (NTP) services port (123)• POP3 – Optional. Configures the default Post Office Protocol (POP3) services port (110)• proto – Optional. Use this option to select another Internet protocol in addition to the one selected in the previous step.• sip – Optional. Configures the default Session Initiation Protocol (SIP) services port (5060)• smtp – Optional. Configures the default Simple Mail Transfer Protocol (SMTP) services port (25)• sourceport [<1-65535>|<WORD>] – Optional. After specifying the destination port, you may specify a single or range of source ports.• <1-65535> – Specify the source port from 1 - 65535.• <WORD> – Specify the source port range, for example 1-10.• ssh – Optional. Configures the default SSH services port (22)• telnet – Optional. Configures the default Telnet services port (23)• tftp – Optional. Configures the default Trivial File Transfer Protocol (TFTP) services port (69)• www – Optional. Configures the default HTTP services port (80)alias number <NUMBER-ALIAS-NAME> <0-4294967295>Creates a new number alias or applies an existing number, identified by the <NUMBER-ALIAS-NAME> keyword, • <NUMBER-ALIAS-NAME> – Specify the number alias name.• <0-4294967295> – Specify the number, from 0 - 4294967295, assigned to thenumber alias created.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-640.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3774.1.79.2.2 channel-listrf-domain-mode commandsConfigures the channel list advertised by radios. This command also enables a dynamic update of a channel list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxchannel-list [2.4GHz|5GHz|dynamic]channel-list dynamicchannel-list [2.4GHz|5GHz] <CHANNEL-LIST>Parameters• channel-list dynamic• channel-list [2.4GHz|5GHz] <CHANNEL-LIST>Examplerfs6000-81742D(config-rf-domain-default)#channel-list 2.4GHz 1-10rfs6000-81742D(config-rf-domain-default)#show contextrf-domain default no country-code channel-list 2.4GHz 1,2,3,4,5,6,7,8,9,10rfs6000-81742D(config-rf-domain-default)#Related Commandsdynamic Enables a dynamic update of a channel list2.4GHz <CHANNEL-LIST>Configures the channel list advertised by radios operating in the 2.4 GHz mode• <CHANNEL-LIST> – Specify the list of channels separated by commas or hyphens.5GHz <CHANNEL-LIST>Configures the channel list advertised by radios operating in the 5.0 GHz mode• <CHANNEL-LIST> – Specify the list of channels separated by commas or hyphens.no Removes the list of channels configured on the selected RF Domain for 2.4 GHz and 5.0 GHz bands. Also disables dynamic update of a channel list.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-643.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3794.1.79.2.4 control-vlanrf-domain-mode commandsConfigures the VLAN designated for traffic control in this RF DomainSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcontrol-vlan [<1-4094>|<VLAN-ALIAS-NAME>]Parameters• control-vlan [<1-4094>|<VLAN-ALIAS-NAME>]Examplerfs6000-81742D(config-rf-domain-default)#control-vlan 1rfs6000-81742D(config-rf-domain-default)#show contextrf-domain default contact Bob+14082778691 no country-code channel-list 2.4GHz 1,2,3,4,5,6,7,8,9,10 control-vlan 1rfs6000-81742D(config-rf-domain-default)#Related Commands[<1-4094>|<VLAN-ALIAS-NAME>]Specify the VLAN ID from 1 - 4094. Alternately, use a vlan-alias to identify the control VLAN. If using a vlan-alias, ensure that the alias is existing and configured.no Disables the VLAN designated for controlling RF Domain traffic](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-645.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3834.1.79.2.8 layoutrf-domain-mode commandsConfigures the RF Domain layout in terms of area, floor, and location on a map. It allows users to place APs across the deployment map. A maximum of 256 layouts is permitted.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlayout [area|description|floor|map-location] {(area|description|floor|map-location)}layout [area <AREA-NAME>|description <LINE>|floor <FLOOR-NAME> {<1-4094>}|map-location <URL> units [feet|meters]] {(area <AREA-NAME>|description <LINE>|floor <FLOOR-NAME> {<1-4094>}|map-location <URL> units [feet|meters])}Parameters• layout [area <AREA-NAME>|description <LINE>|floor <FLOOR-NAME> {<1-4094>}|map-location <URL> units [feet|meters]] {(area <AREA-NAME>|description <LINE>|floor <FLOOR-NAME> {<1-4094>}|map-location <URL> units [feet|meters])}layout Configures the RF Domain’s layout in terms of area, floor, and location on a mapThese are recursive parameters and you can configure one or all of these parameters.area <AREA-NAME> Configures the RF Domain’s layout in terms of the area of location• <AREA-NAME> – Specify the area name.After configuring the RF Domain’s area of functioning, optionally specify the floor name (and number), description, and/or the location on map.description <LINE> Configures a description for this RF Domain• <LINE> – Specify a description that enables you to identify the RF Domain. For a multi-worded string, use double quotes.floor <FLOOR-NAME> <1-4094>Configures the RF Domain’s layout in terms of the floor name and number• <FLOOR-NAME> – Specify the floor name.• <1-4094> – Optional. Specifies the floor number from 1 - 4094. The default floornumber is 1.After configuring the RF Domain’s floor name (and number), optionally specify the area name, description, and/or the location on map.map-location <URL> units [feet|meters]Configures the location of the RF Domain on the map• <URL> – Specify the URL to configure the map location.• units [feet|meters] – Configures the map units. The options are: feet or meters• feet – Configures the map units in terms of feet• meters – Configures the map units in terms of meterAfter configuring the location of the RF Domain on the map, optionally specify the area name, floor name (and number), and/or description.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-649.png)
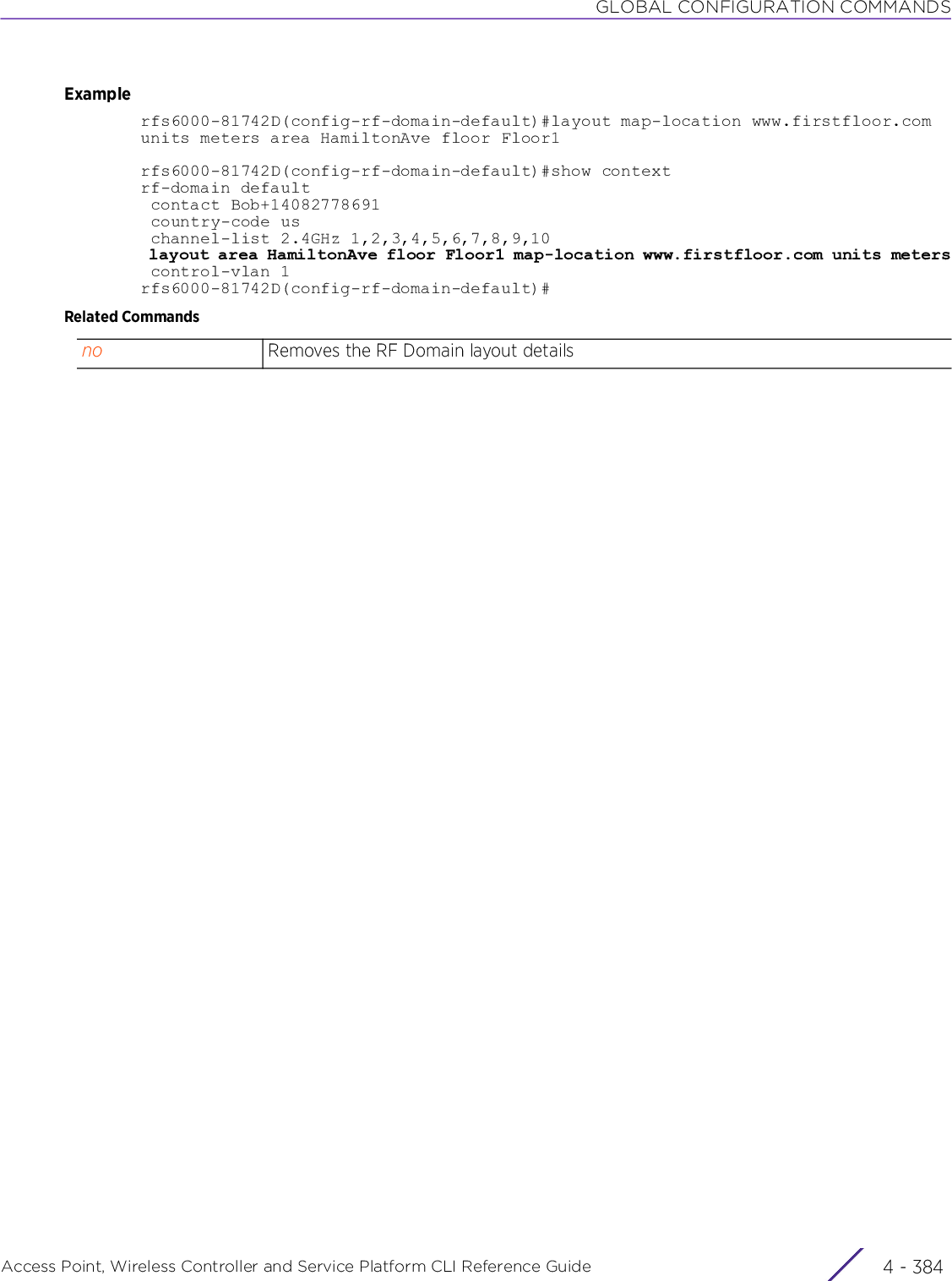

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3864.1.79.2.10 location-serverrf-domain-mode commandsConfigures the L-Sense server’s IP address or hostname on the selected RF Domain. When configured, the AP7522, AP7532, AP7562, AP8432 and AP8533 model access points, within the RF Domain, extract and forward client-location related data to the specified L-Sense server. L-Sense is a highly scalable indoor locationing platform that gathers location-related analytics, such as visitor trends, peak and off-peak times, dwell time, heat-maps, etc. to enable entrepreneurs deeper visibility at a venue. To enable the location tracking system, the L-Sense server should be up and running and the RF Domain Sensor configuration should point to the L-sense server.Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxlocation-server 1 ip <LSENSE-SERVER-IP/HOSTNAME> {port [443|<1-65535>]}Parameters• location-server 1 ip <LSENSE-SERVER-IP/HOSTNAME> {port [443|<1-65535>]}Examplenx9500-6C8809(config-rf-domain-test)#location-server 1 ip 192.168.13.20 port 200nx9500-6C8809(config-rf-domain-test)#show contextrf-domain test no country-code location-server 1 ip 192.168.13.20 port 200nx9500-6C8809(config-rf-domain-test)#Related Commandslocation-server 1 ip <LSENSE-SERVER-IP/HOSTNAME>Configures the LSENSE server parameters• 1 – Sets the server ID as 1. As of now only one L-Sense server can be configured.• ip <LSENSE-SERVER-IP/HOSTNAME> – Specify the server’s IPv4 address/host-name. This is the L-Sense server designated to receive RSSI scan data from a WiNGdedicated sensor.port [443|<1-65535>]Optional. Configures the port where the LSENSE server is reachable. The options are:• 443 – Configures port 443. This is the default setting.• <1-65535> – Alternately, specify a port as the LSENSE server port from 1 - 65535.no Removes the LSENSE server configurations](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-652.png)
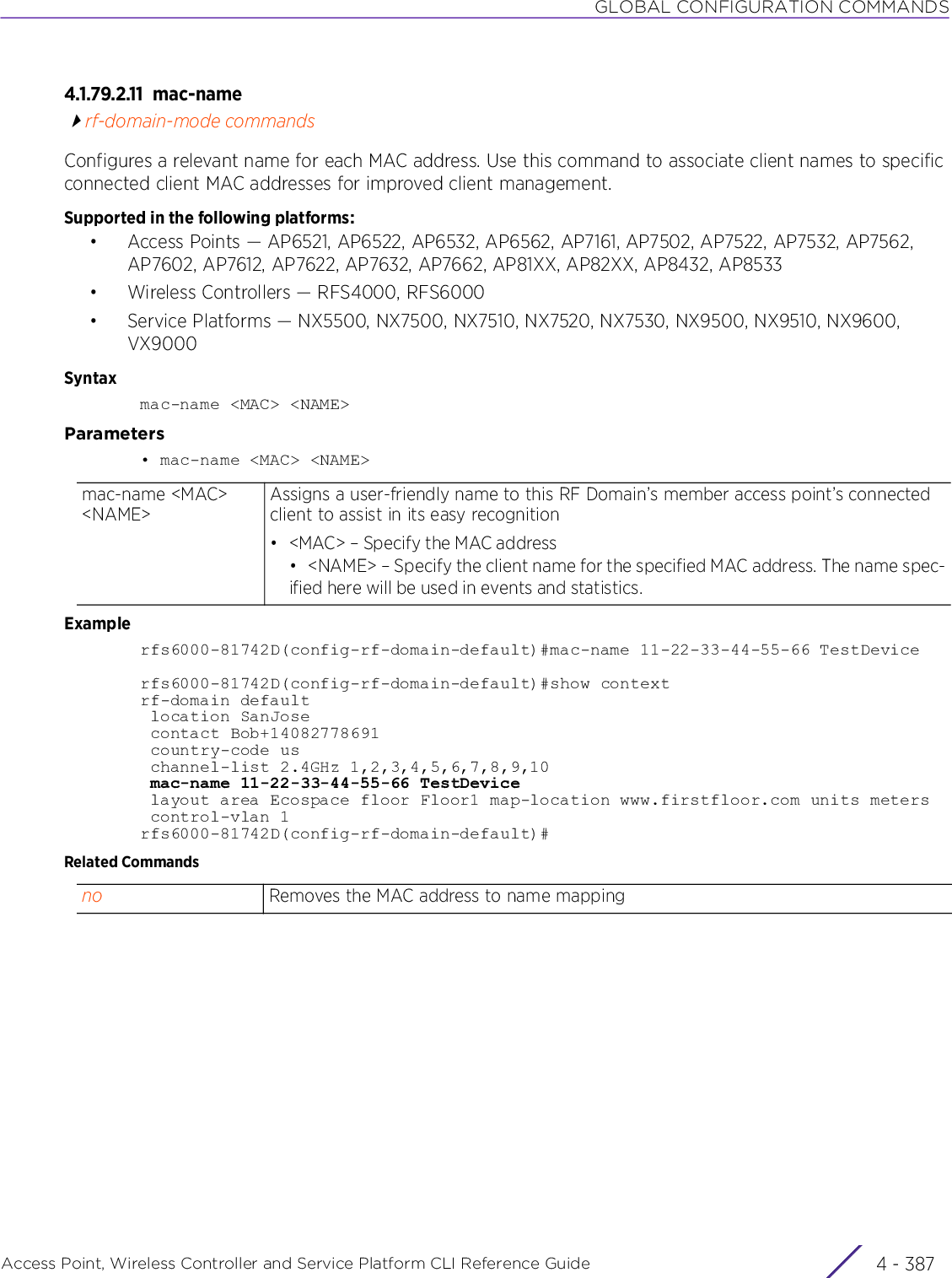
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3884.1.79.2.12 norf-domain-mode commandsNegates a command or reverts configured settings to their default. When used in the config RF Domain mode, the no command negates or reverts RF Domain settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [alias|channel-list|contact|control-vlan|controller-managed|country-code|geo-coordinates|layout|location|location-server|mac-name|nsight-sensor|override-smartrf|override-wlan|sensor-server|stats|timezone|tree-node|use]no [adoption-mode|channel-list [2.4GHz|5GHz|dynamic]|contact|control-vlan|controller-managed|country-code|location|location-server 1|mac-name <MAC>||nsight-sensor|sensor-server <1-3>|stats update-interval|timezone|tree-node]no alias [address-range|host|network|network-group [address-range|host|network]|network-service|number|string|vlan] <ALIAS-NAME>no layout {(area <AREA-NAME>|floor <FLOOR-NAME>)}no override-smartrf channel-list [2.4GHz|5GHz]no override-wlan <WLAN-NAME> [shutdown|ssid|template|vlan-pool [<1-4094>|all]|wep128 [key <1-3>|transmit-key]|wpa-wpa2-psk]no use [database-policy|license|nsight-policy|smart-rf-policy|wips-policy]Parameters• no <PARAMETERS>ExampleThe following example shows the default RF Domain settings before the ‘no’ commands are executed:rfs6000-81742D(config-rf-domain-default)#show contextrf-domain default location SanJose contact Bob+14082778691 country-code us channel-list 2.4GHz 1,2,3,4,5,6,7,8,9,10 mac-name 11-22-33-44-55-66 TestDevice layout area Ecospace floor Floor1 map-location www.firstfloor.com units meters control-vlan 1rfs6000-81742D(config-rf-domain-default)#rfs6000-81742D(config-rf-domain-default)#no channel-list 2.4GHz 1-10rfs6000-81742D(config-rf-domain-default)#no mac-name 11-22-33-44-55-66rfs6000-81742D(config-rf-domain-default)#no locationrfs6000-81742D(config-rf-domain-default)#no control-vlanno <PARAMETERS> Removes or reverts this RF Domain’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-654.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3904.1.79.2.13 override-smart-rfrf-domain-mode commandsEnables dynamic channel switching for Smart RF radios. This command allows you to configure an override list of channels that Smart RF can use for channel compensations on 2.4 GHz and 5.0 GHz radios.When a radio fails or is faulty, a Smart RF policy provides automatic recovery by instructing neighboring access points to increase their transmit power to compensate for the coverage loss. Once correct access point placement has been established, Smart-RF can optionally be leveraged for automatic detector radio selection. Smart-RF uses detector radios to monitor RF events and can ensure availability of adequate detector coverage.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoverride-smartrf channel-list [2.4GHz|5GHZ] <CHANNEL-LIST>Parameters• override-smartrf channel-list [2.4GHz|5GHZ] <CHANNEL-LIST>Examplerfs6000-81742D(config-rf-domain-default)#override-smartrf channel-list 2.4GHz 1,2,3rfs6000-81742D(config-rf-domain-default)#show contextrf-domain default contact Bob+14082778691 country-code us override-smartrf channel-list 2.4GHz 1,2,3 layout area Ecospace floor Floor1 map-location www.firstfloor.com units metersrfs6000-81742D(config-rf-domain-default)#Related Commandsoverride-smartrf Enables dynamic channel switching for Smart RF radioschannel-list Configures a list of channels for 2.4 GHz and 5.0 GHz Smart RF radios2.4GHz <CHANNEL-LIST>Selects the 2.4 GHz Smart RF radio channels• <CHANNEL-LIST> – Specify a list of channels separated by commas.5GHz <CHANNEL-LIST>Selects the 5.0 GHz Smart RF radio channels• <CHANNEL-LIST> – Specify a list of channels separated by commas.no Removes the override-smartrf list of channels configured for 2.4 GHz and 5.0 GHz radios](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-656.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3914.1.79.2.14 override-wlanrf-domain-mode commandsConfigures RF Domain level overrides for a WLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoverride-wlan <WLAN-NAME> [shutdown|ssid|template|vlan-pool|wep128|wpa-wpa2-psk]override-wlan <WLAN-NAME> [shutdown|ssid <SSID>|template <TEMPLATE-NAME>|vlan-pool <1-4094> {limit <0-8192>}]override-wlan <WLAN-NAME> wpa-wpa2-psk [0 <WORD>|2 <WORD>]override-wlan <WLAN-NAME> wep128 [key <1-4> hex [0 <WORD>|2 <WORD>]|transmit-key <1-4>]Parameters• override-wlan <WLAN-NAME> [shutdown|ssid <SSID>|template <TEMPLATE-NAME>|vlan-pool <1-4094> {limit <0-8192>}]<WLAN-NAME> Configures the WLAN nameIf applying RF Domain level overrides to an existing WLAN, specify its name. If creating a new WLAN, specify a name not exceeding 32 characters and representing the WLAN’s coverage area. After creating the WLAN, configure its override parameters.shutdown Shuts down WLAN operation on all mapped radiosssid <SSID> Configures a override SSID associated with this WLAN• <SSID> – Specify the SSID (should not exceed 32 characters in length).Each WLAN provides associated wireless clients with a SSID. This has limitations, because it requires wireless clients to associate with different SSIDs to obtain QoS and security policies. However, a WiNG-managed RF Domain can have WLANs assigned and advertise a single SSID, and yet allow users to inherit different QoS or security policies.template <TEMPLATE-NAME>Configures a template name for this RF Domain• <TEMPLATE-NAME> – Specify the template name (should not exceed 32 characters in length).vlan-pool <1-4094> {limit <0-8192>}Configures the override VLANs available to this WLAN• <1-4094> – Specify the VLAN ID from 1 - 4094.• limit <0-8192> – Optional. Sets a limit to the number of users on this VLAN from 0 -8192. The default is 0.Controllers and service platforms allow the mapping of a WLAN to more than one VLAN. Wireless clients associating with a WLAN are assigned VLANs, from the pool representative of the WLAN, in a way that ensures proper load balancing across VLANs. Clients are tracked per VLAN, and assigned to the least used/loaded VLAN. Client VLAN usage is tracked on a per-WLAN basis. The maximum allowed client limit is 8192 per VLAN.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-657.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 392• override-wlan <WLAN-NAME> wpa-wpa2-psk [0 <WORD>|2 <WORD>]• override-wlan <WLAN-NAME> wep128 [key <1-4> hex [0 <WORD>|2 <WORD>]|transmit-key <1-4>]<WLAN-NAME> Configures the WLAN nameIf applying RF Domain level overrides to an existing WLAN, specify its name. If creating a new WLAN, specify a name not exceeding 32 characters and representing the WLAN’s coverage area. After creating the WLAN, configure its override parameters.wpa-wpa2-psk <PASSPHRASE>Overrides a WLAN’s existing WPA-WPA2 pre-shared key or passphrase at the RF Domain level. WPA2 is a newer 802.11i standard that provides wireless security that is stronger than Wi-Fi Protected Access (WPA) and WEP.• <PASSPHRASE> – Specify a WPA-WPA2 key or passphrase. It is an alphanumeric string of 8 to 64 ASCII characters or 64 HEX characters as the primary string, which both the transmitting and receiving authenticators must share in this new override PSK. The alphanumeric string allows character spaces. The string is converted to a numeric value. This passphrase saves the you the necessity of entering the 256-bit key each time keys are generated.<WLAN-NAME> Configures the WLAN nameIf applying RF Domain level overrides to an existing WLAN, specify its name. If creating a new WLAN, specify a name not exceeding 32 characters and representing the WLAN’s coverage area. After creating the WLAN, configure its override parameters.wep128 Overrides a WLAN’s existing WEP128 keys at the RF Domain level (not the profile level). WEP128 uses a 104 bit key, which is concatenated with a 24-bit initialization vector (IV) to form the RC4 traffic key. WEP may be all a small-business user needs for the simple encryption of wireless data on the WLAN. However, networks that require more security are at risk from a WEP flaw. WEP is only recommended if there are client devices incapable of using higher forms of security. The existing 802.11 standard alone offers administrators no effective method to update keys.key <1-4> hex [0 <WORD>|2 <WORD>]Configures the WEP128 key.A total of four keys can be configured. • <1-4> – Select the key index from 1- 4.• hex – Configures a hexadecimal key• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted keyThe following parameter is common to both clear-text and encrypted key options:• <WORD> – Specify the WEP128/Keyguard key (should not exceed 26 hexadecimal characters in length).transmit-key <1-4>Configures transmit WEP/Keyguard key settings• <1-4> – Transmit the key identified by the key index specified here. Specify the index from 1 - 4.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-658.png)
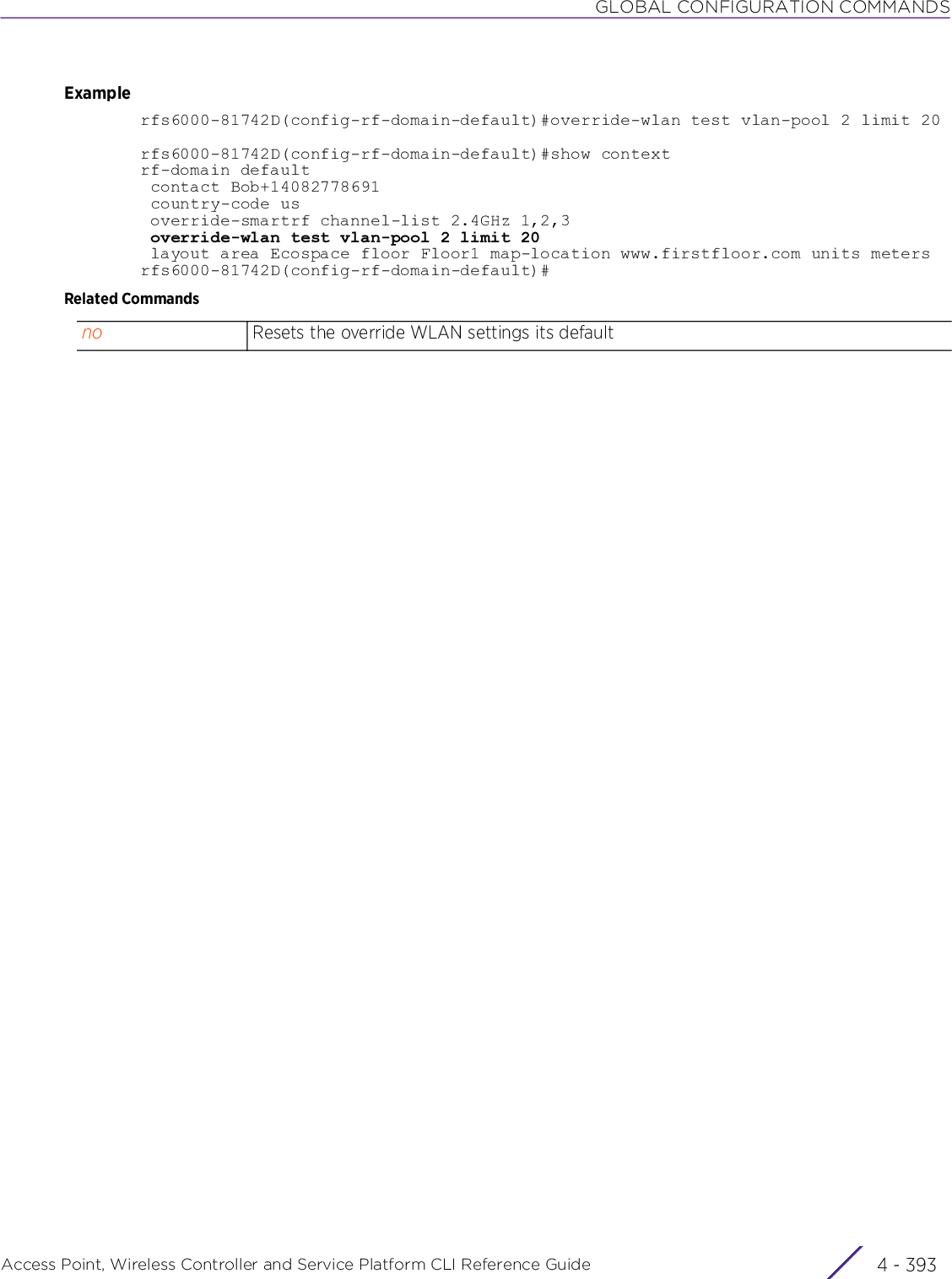
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3944.1.79.2.15 sensor-serverrf-domain-mode commandsConfigures an AirDefense sensor server on this RF Domain. Sensor servers allow network administrators to monitor and download data from multiple sensors remote locations using Ethernet TCP/IP or serial communications. This enables administrators to respond quickly to interferences and coverage problems.The Wireless Intrusion Protection System (WIPS) protects the controller managed network, wireless clients and access point radio traffic from attacks and unauthorized access. WIPS provides tools for standards compliance and around-the-clock wireless network security in a distributed environment. WIPS allows administrators to identify and accurately locate attacks, rogue devices and network vulnerabilities in real time and permits both a wired and wireless lockdown of wireless device connections upon acknowledgement of a threat.In addition to dedicated AirDefense sensors, an access point radio can function as a sensor and upload information to a dedicated WIPS server (external to the controller). Unique WIPS server configurations can be used by RF Domains to ensure a WIPS server configuration is available to support the unique data protection needs of individual RF Domains.WIPS is not supported on a WLAN basis, rather sensor functionality is supported on the access point radio(s) available to each controller managed WLAN. When an access point radio is functioning as a WIPS sensor, it is able to scan in sensor mode across all legal channels within the 2.4 and 5.0 GHz bands. Sensor support requires a AirDefense WIPS Server on the network. Sensor functionality is not provided by the access point alone. The access point works in conjunction with a dedicated WIPS server.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsensor-server <1-3> ip <IP/HOSTNAME> {port [443|<1-65535>]}Parameters• sensor-server <1-3> ip <IP/HOSTNAME> {port [443|<1-65535>]}sensor-server <1-3> Configures an AirDefense sensor server parameters• <1-3> – Select the server ID from 1 - 3. The server with the lowest defined ID is reached first. The default is 1.ip <IP/HOSTNAME> Configures the (non DNS) IPv4 address of the sensor server• <IP/HOSTNAME> – Specify the sensor server’s IPv4 address or hostname.port [443|<1-65535>] Optional. Configures the sensor server port. The options are:• 443 – Configures port 443, the default port used by the AirDefense server. This is the default setting.• <1-65535> – Allows you to select a WIPS/AirDefense sensor server port from 1 - 65535](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-660.png)
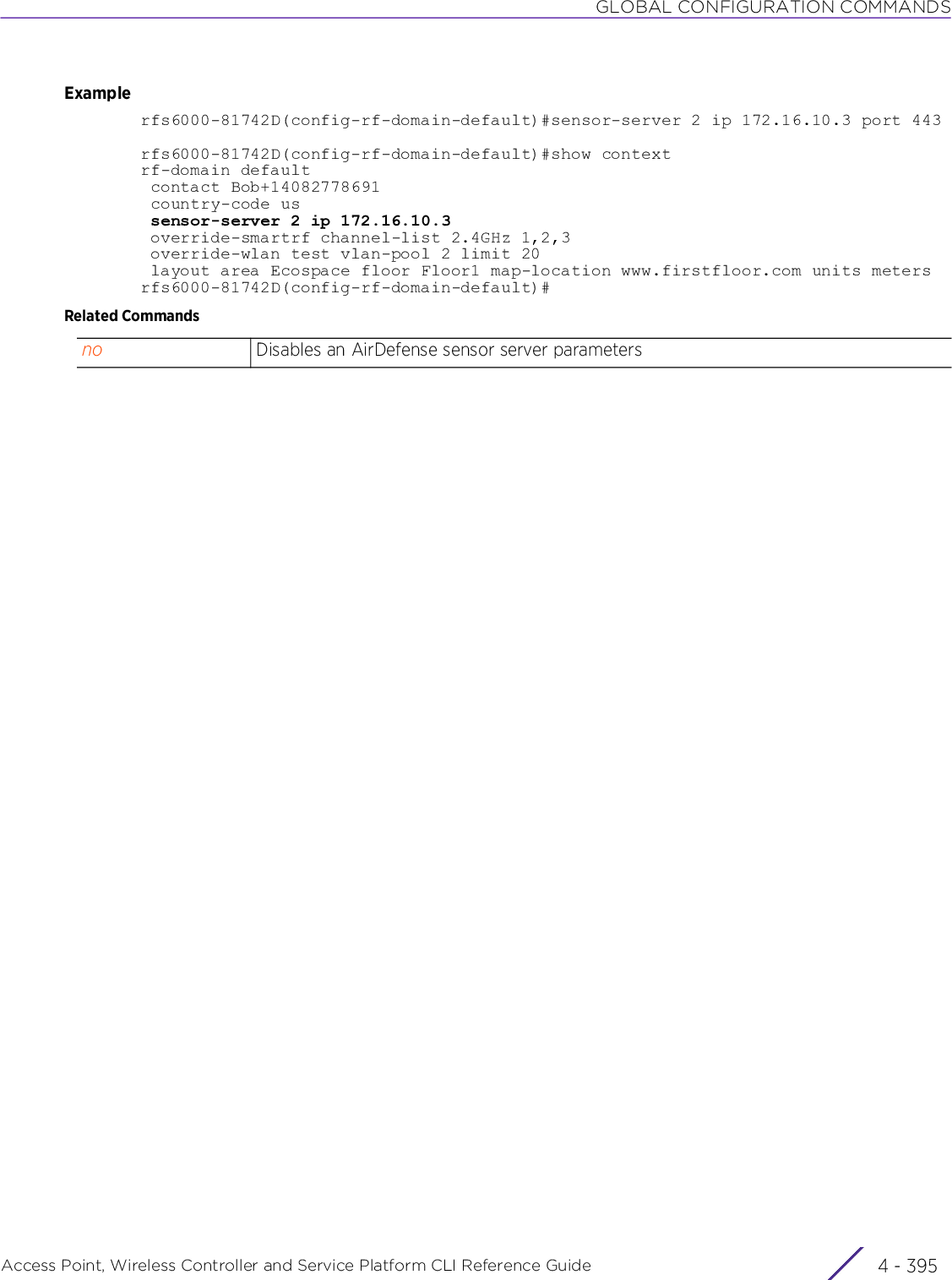
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3964.1.79.2.16 statsrf-domain-mode commandsConfigures stats settings that define how RF Domain statistics are updatedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxstats update-intervalstats update-interval [<5-300>|auto]Parameters• stats update-interval [<5-300>|auto]Examplerfs6000-81742D(config-rf-domain-default)#stats update-interval 200rfs6000-81742D(config-rf-domain-default)#show contextrf-domain default contact Bob+14082778691 stats update-interval 200 country-code us sensor-server 2 ip 172.16.10.3 override-smartrf channel-list 2.4GHz 1,2,3 override-wlan test vlan-pool 2 limit 20 layout area Ecospace floor Floor1 map-location www.firstfloor.com units metersrfs6000-81742D(config-rf-domain-default)#Related Commandsstats Configures stats related settings on this RF Domainupdate-interval [<5-300>|auto]Configures the interval at which RF Domain statistics are updated. The options are:• <5-300> – Specify an update interval from 5 - 300 seconds.• auto – The RF Domain manager automatically adjusts the update interval based on the load. This is the default setting.no Resets stats related settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-662.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 3994.1.79.2.18 tree-noderf-domain-mode commandsConfigures the hierarchical (tree-node) structure under which this RF Domain is locatedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtree-node [campus|city|country|region] {(campus|city|country|region)}Parameters• tree-node [campus|city|country|region] {(campus|city|country|region)}Usage GuidelinesThe following points need to be taken into consideration when creating the tree-node structure:• Adding a country first is a good idea since region, city, and campus can all be added as sub-nodes in the tree structure. However, the selected country is an invalid tree node until a RF Domain is mapped.• A city and campus can be added in the tree structure as sub-nodes under a region. An RF Domain can be mapped anywhere down the hierarchy for a region and not just directly under a country. For example, a region can have city, campus, and one RF Domain mapped.• Only a campus can be added as a sub-node under a city. The city is an invalid tree node until a RF Domain is mapped somewhere within the directory tree.• A campus is the last node in the hierarchy before a RF Domain, and it is not valid unless it has a RF Domain mapped.• After creating the tree structure do a commit and save for the tree configuration to take effect and persist across reboots.tree-node Configures the hierarchical tree structure defining the RF Domain’s location. The tree node hierarchy can be configured in any order, but will always appear as: country > region > city > campus. Further, a higher node, such as country, cannot be defined under a lower node, such as region. An RF Domain can be placed under any one of the tree nodes. But, an RF Domain at the country level may have all four nodes defined. Whereas, an RF Domain restricted to a campus, cannot have the country, city, and region nodes.At least one of these four nodes must be defined. This feature is disabled by default.campus Configures the campus name for this RF Domaincity Configures the city for this RF Domaincountry Configures the country for this RF Domainregion Configures the region for this RF Domain](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-665.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4014.1.79.2.19 userf-domain-mode commandsAssociates the following with an RF Domain: database policy, NSight policy, sensor policy, Smart RF policy, WIPS policy, RTL server policy, and Web filtering license.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [database-policy|license|nsight-policy|rtl-server-policy|sensor-policy|smart-rf-policy|wips-policy]use [database-policy <DATABASE-POLICY-NAME>|license <WEB-FILTERING-LICENSE>|nsight-policy <NSIGHT-POLICY-NAME>|rtl-server-policy <RTL-SERVER-POLICY-NAME>sensor-policy <SENSOR-POLICY-NAME>|smart-rf-policy <SMART-RF-POLICY-NAME>|wips-policy <WIPS-POLICY-NAME>]Parameters• use [database-policy <DATABASE-POLICY-NAME>|license <WEB-FILTERING-LICENSE>|nsight-policy <NSIGHT-POLICY-NAME>|rtl-server-policy <RTL-SERVER-POLICY-NAME>|sensor-policy <SENSOR-POLICY-NAME>|smart-rf-policy <SMART-RF-POLICY-NAME>|wips-policy <WIPS-POLICY-NAME>]use Associates the following policies with the RF Domain: database policy, NSight policy, sensor policy, Smart RF policy, WIPS policy. It also applies a Web filtering license to the selected RF Domain.database-policy <DATABASE-POLICY-NAME>Associates a database policy with the selected RF Domain• <DATABASE-POLICY-NAME> – Specify the database policy name (should be existing and configured).license <WEB-FILTERING-LICENSE>Obtains the specified Web filtering license from the adopting controller• <WEB-FILTERING-LICENSE> – Specify the WEBF license name.nsight-policy <NSIGHT-POLICY-NAME>Associates an NSight policy to this RF Domain• Specify the NSight policy name (should be existing and configured). When applied, it enables the RF Domain manager to gather statistical data from access points within the domain and forward to the NOC running the NSight server. For information on configuring NSight policy, see nsight-policy.rtl-server-policy <RTL-SERVER-POLICY-NAME>Associates an Real Time Locationing (RTL) server policy with the selected RF Domain• <RTL-SERVER-POLICY-NAME> – Specify the RTL server policy name (should be existing and configuredsensor-policy <SENSOR-POLICY-NAME>Associates a sensor policy with the selected RF Domain• <SENSOR-POLICY-NAME> – Specify the sensor policy name (should be existing and configured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-667.png)





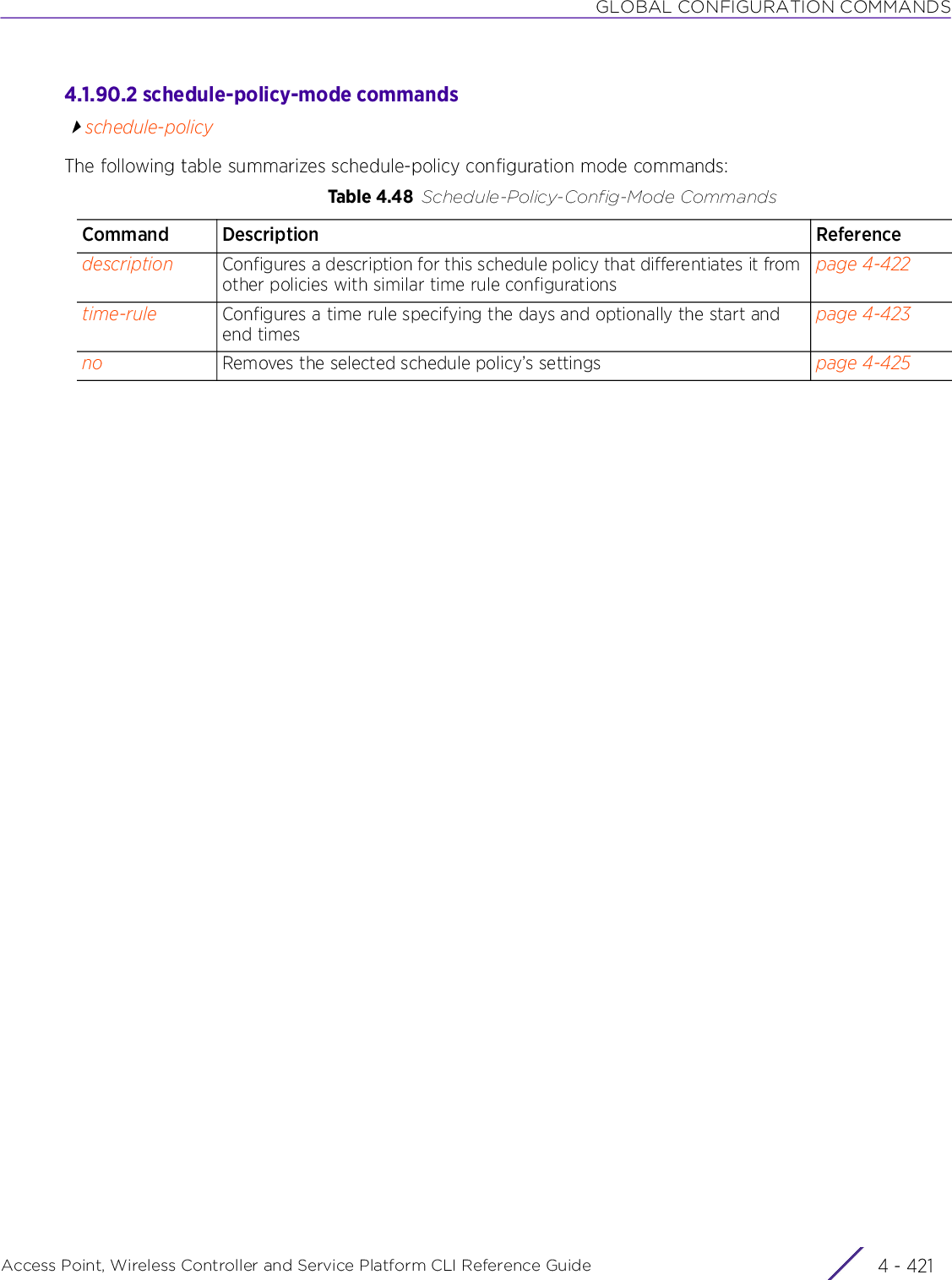
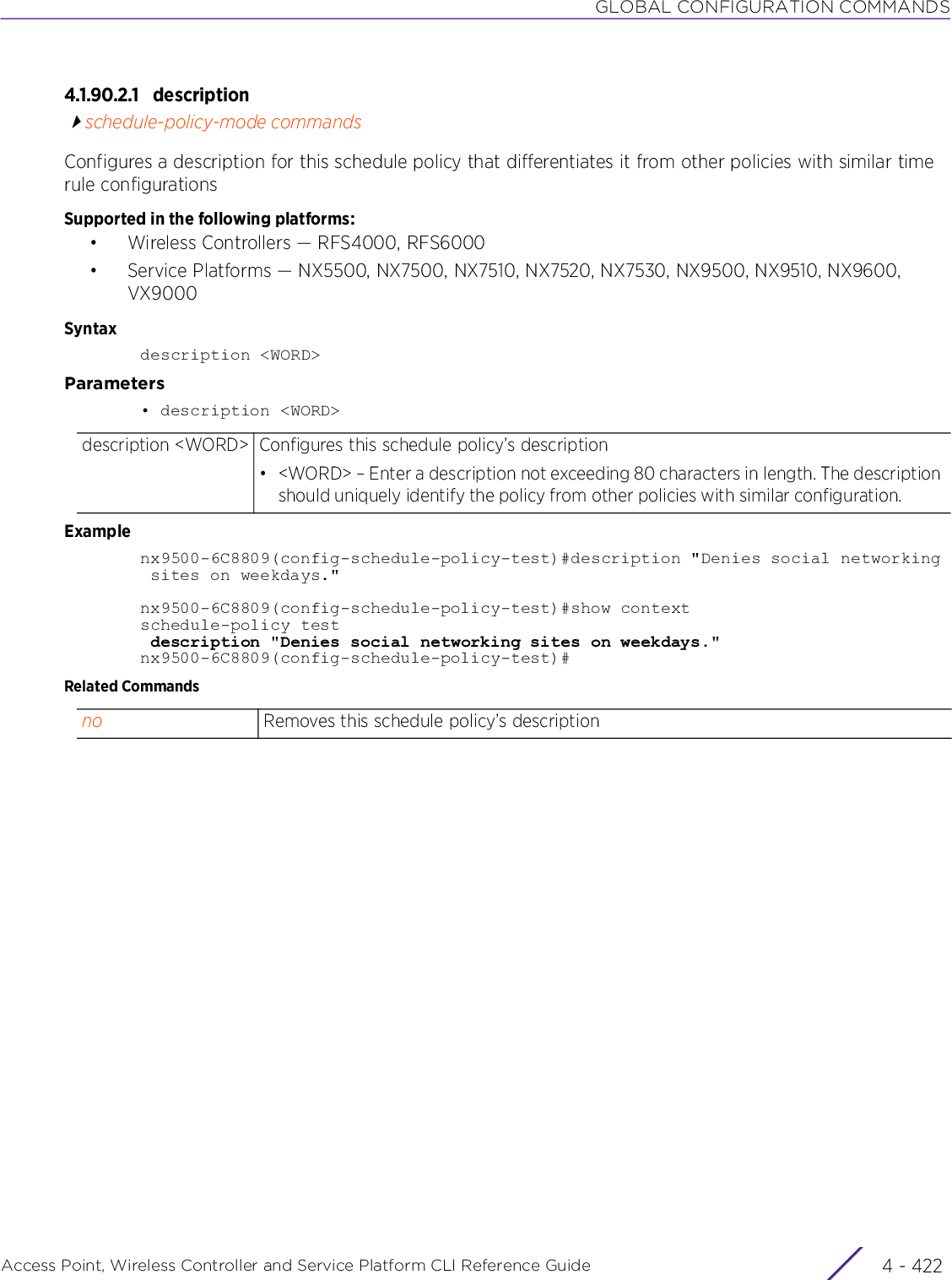
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4234.1.90.2.2 time-ruleschedule-policy-mode commandsConfigures a time rule specifying the days and optionally the start and end times. When applied to an application-policy rule, the schedule policy defines the enforcement time of the rule. For more information, see application-policy.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtime-rule days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays] {start-time <HH:MM> [end-time <HH:MM>]}Parameters• time-rule days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays] {start-time <HH:MM> [end-time <HH:MM>]}time-rule Configures a time rule in days and hours and minutesA schedule policy can have more than one non-overlapping time-rules. The following time-rules, having overlapping time periods, are invalid: ‘weekdays, start-time 9:30 am, end-time 11:30 pm’ and ‘all, start-time 12:00 am, end-time 12:00 pm’.days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays]Specifies the days on which the time rule is applicable• sunday – Applicable on Sundays only• monday – Applicable on Mondays only• tuesday – Applicable on Tuesdays only• wednesday – Applicable on Wednesdays only• thursday – Applicable on Thursdays only• friday – Applicable on Fridays only• saturday – Applicable on Saturdays only• weekends – Applicable on weekends only• weekdays – Applicable on weekdays only• all – Applicable on all daysstart-time <HH:MM> [end-time <HH:MM>]After specifying the days of enforcement, specify the following:• start-time – Optional. Specifies the enforcement start time• <HH:MM> – Specify the start time in hours and minutes in the HH:MM format.If no start time is specified, the time rule is enforced, on the specified days, at all time.• end-time – Specifies the enforcement end time• <HH:MM> – Specify the time in hours and minutes in the HH:MM format.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-689.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4254.1.90.2.3 noschedule-policy-mode commandsRemoves the selected schedule policy’s settingsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [description|time-rule]no descriptionno time-rule days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays]Parameters• no <PARAMETERS>ExampleThe following example displays the schedule policy ‘test’ settings before the ‘no’ commands have been executed:nx9500-6C8809(config-schedule-policy-test)#show contextschedule-policy test description "Denies social networking sites on weekdays." time-rule days weekdays start-time 10:00 end-time 23:30nx9500-6C8809(config-schedule-policy-test)#The following example displays the schedule policy ‘test’ settings after the ‘no’ commands have been executed:nx9500-6C8809(config-schedule-policy-test)#no descriptionnx9500-6C8809(config-schedule-policy-test)#no time-rule days weekdaysnx9500-6C8809(config-schedule-policy-test)#show contextschedule-policy testnx9500-6C8809(config-schedule-policy-test)#no <PARAMETERS> Removes the schedule policy’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-691.png)



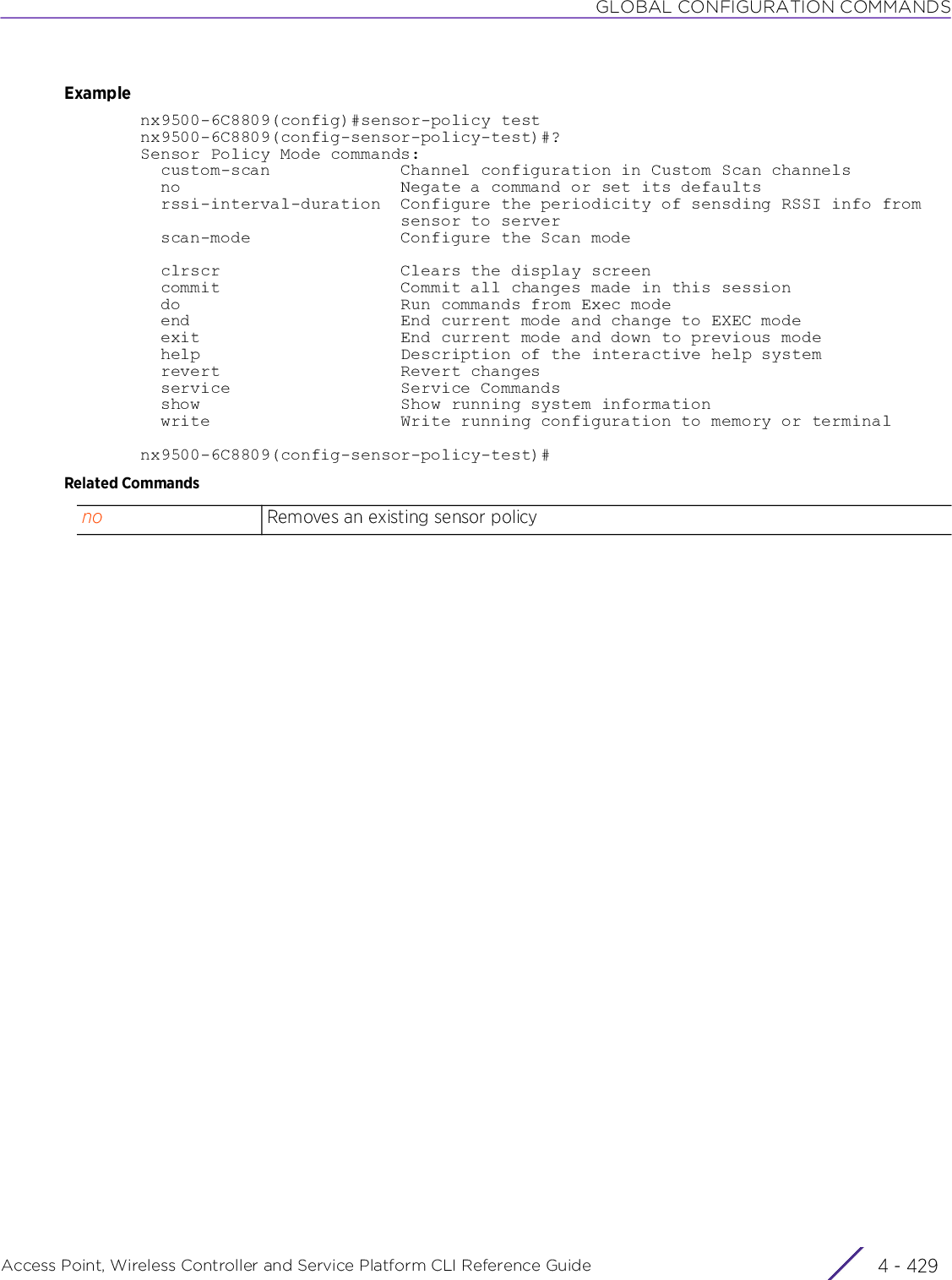
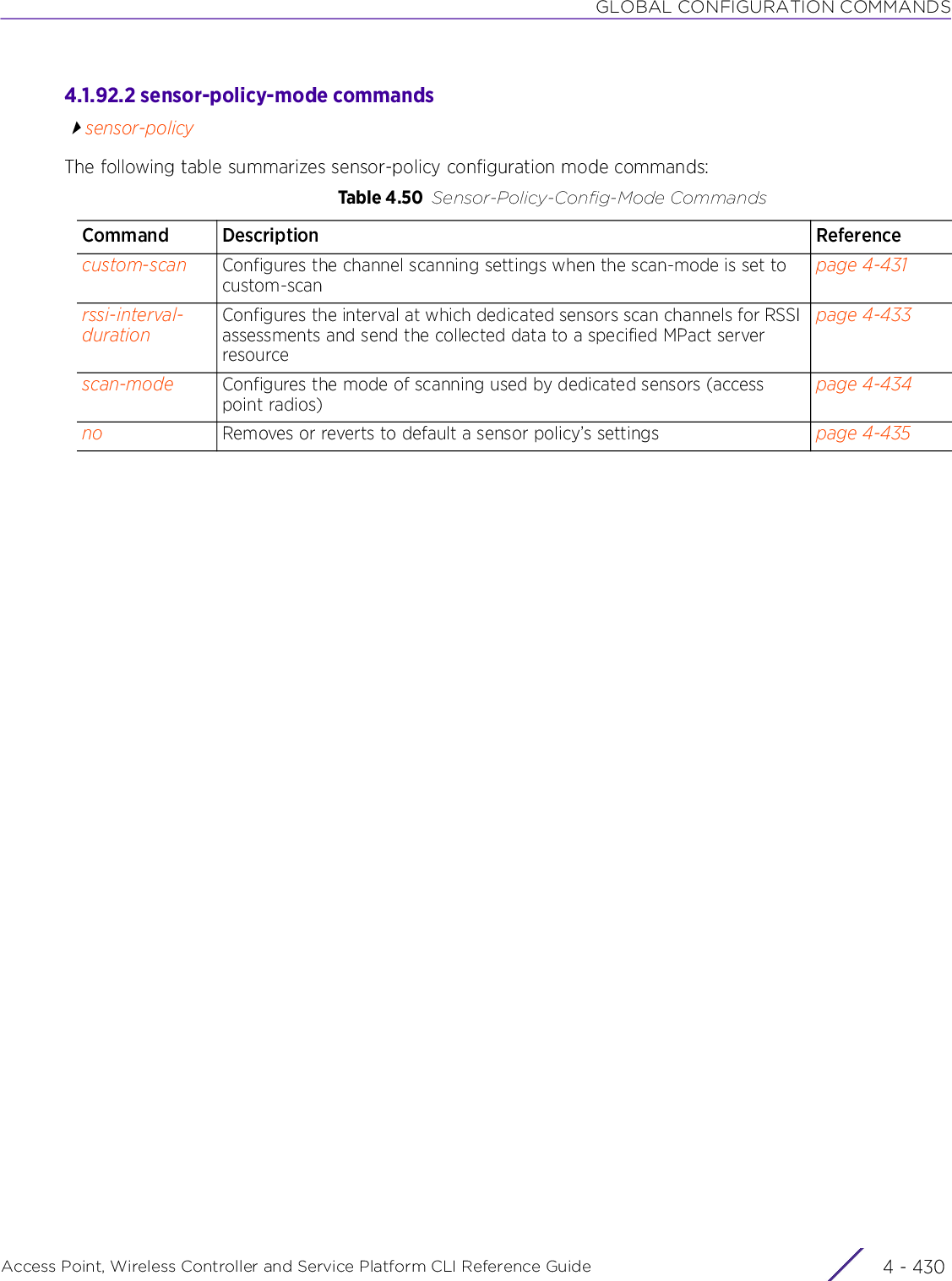
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4314.1.92.2.1 custom-scansensor-policy-mode commandsConfigures the channel scanning settings when the scan-mode is set to custom-scanSupported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcustom-scan channel-frequency <CHANNEL-FREQUENCY> width [20MHz|40MHz-Bth|40MHz-Lower|40MHz-Upper|80MHz] scan-weight <SCAN-WEIGHT>Parameters• custom-scan channel-frequency <CHANNEL-FREQUENCY> width [20MHz|40MHz-Both|40MHz-Lower|40MHz-Upper|80MHz] scan-weight <SCAN-WEIGHT>Examplenx9500-6C8809(config-sensor-policy-test)#custom-scan channel-frequency 2412 width 20MHz scan-weight 1000nx9500-6C8809(config-sensor-policy-test)#custom-scan channel-frequency 2417 width 20MHz scan-weight 1000NOTE: If the mode of scanning is set to Custom-Scan, use this command to configure the channels to be scanned. To set the mode of scanning to custom-scan, use the scan-mode > Custom-Scan command. For more information, see scan-mode.custom-scan Configures the custom-scan channel frequency, channel width, and scan weightchannel-frequency <CHANNEL-FREQUENCY>Configures the channel frequency. A list of unique channels in the 2.4, 4.9, 5 and 6 GHzband can be collectively or individually enabled for customized channel scans and RSSI reporting.• <CHANNEL-FREQUENCY> – Specify a single or multiple, ‘comma-separated’ channel frequencies.width [20MHz|40MHz-Both|40MHz-Lower|40MHz-Upper|80MHz]Configures the channel width. When custom channels are selected for RSSI scans,each selected channel can have its own width defined. Numerous channels have their width fixed at 20MHz, 802.11a radios support 20 and 40 MHz channel widths.• 20MHz – Sets the channel width as 20 Mhz• 40Mhz-Both – Sets the channel width as 40Mhz-Both• 40Mhz-Lowe – Sets the channel width as 40Mhz-Lower• 40Mhz-Upper – Sets the channel width as 40Mhz-Upper• 80Mhz – Sets the channel width as 80Mhzscan-weight <SCAN-WEIGHT>Configures the scan-weight (scanning duration) for each of the selected channels. Each selected channel can have its weight prioritized in respect to the amount of time a scan is permitted within the defined RSSI scan interval.• <SCAN-WEIGHT> – Specify the scan weightage given to each selected channel.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-697.png)

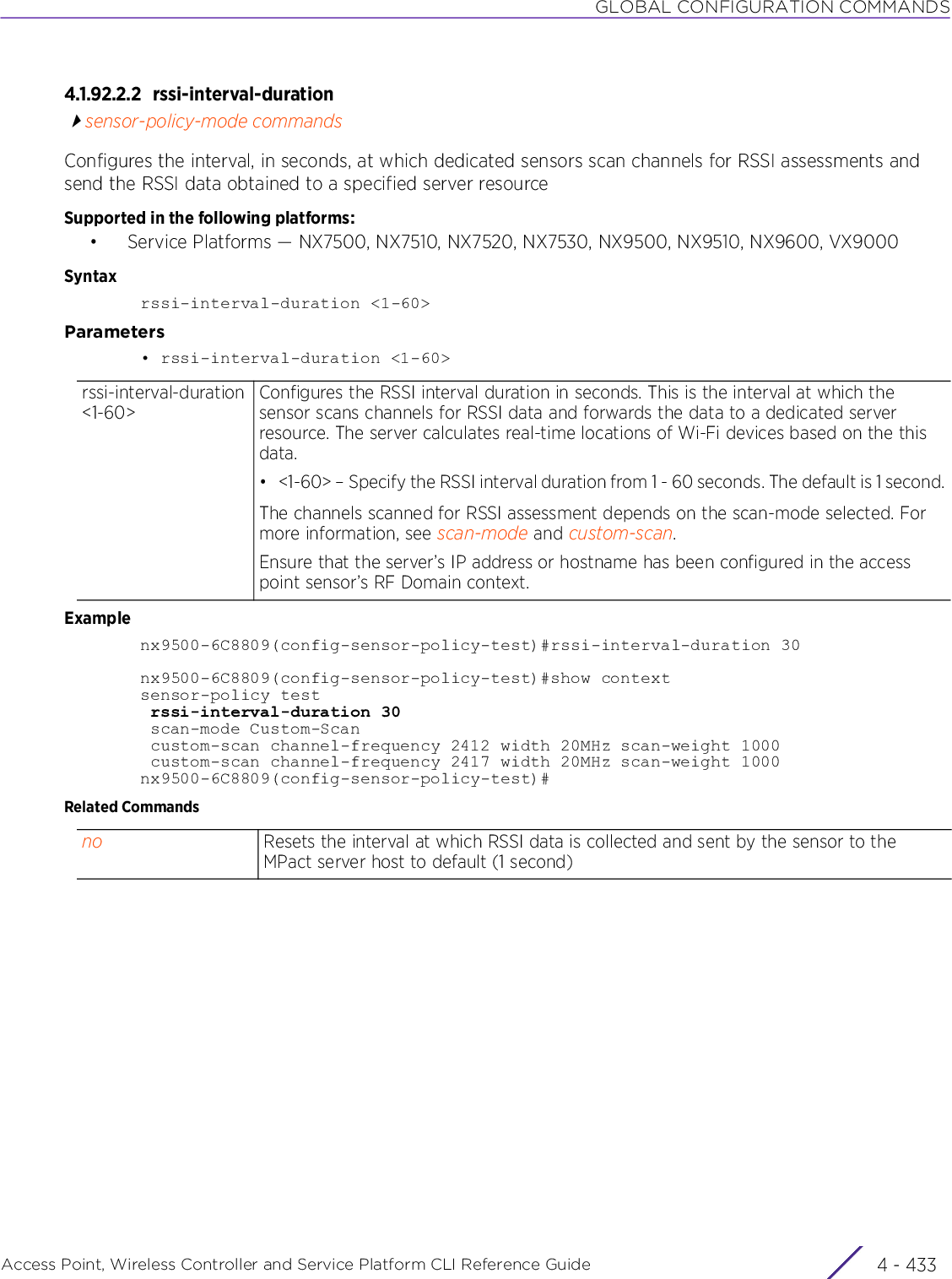
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4344.1.92.2.3 scan-modesensor-policy-mode commandsConfigures the mode of scanning used by dedicated sensors (access point radios)Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxscan-mode [Channel-Lock|Custom-Scan|Default-Scan]scan-mode Channel-Lock lock-frequency <LOCK-FREQUENCY>scan-mode [Custom-Scan|Default-Scan]Parameters• scan-mode Channel-Lock lock-frequency <LOCK-FREQUENCY>• scan-mode [Custom-Scan|Default-Scan]Examplenx9500-6C8809(config-sensor-policy-test)#scan-mode Custom-Scannx9500-6C8809(config-sensor-policy-test)#show contextsensor-policy test rssi-interval-duration 30 scan-mode Custom-Scan custom-scan channel-frequency 2412 width 20MHz scan-weight 1000 custom-scan channel-frequency 2417 width 20MHz scan-weight 1000nx9500-6C8809(config-sensor-policy-test)#Related Commandsscan-mode Configures the mode of scanning used by the sensors to scan system-defined or user-defined channels for RSSI assessments. The options are: Channel-Lock, Custom-Scan, and Default-Scan.Channel-Lock lock-frequency <LOCK-FREQUENCY>Configures the mode of scanning as Channel-Lock• lock-frequency <LOCK-FREQUENCY> – Locks scanning for RSSI data to one specific channel identified by the <LOCK-FREQUENCY> parameter. • <LOCK-FREQUENCY> – Specify the channel frequency in MHz. When specified, thesensor scans only this specified channel.scan-mode Configures the mode of scanning used by the sensor. The options are: channel-lock, custom-scan, and default-scan.Custom-Scan Configures the mode of scanning as Custom-ScanSelect this option to restrict scanning to user-defined channels. If selecting this option, use the custom-scan > channel-frequency command to configure the channels scanned by the dedicated sensor. For more information, see custom-scan.Default-Scan Configures the mode of scanning as Default-Scan. This is the default setting.By default the system has a fixed, built-in list of channels that are scanned. These channels are hard coded in a spread pattern of 1, 6, 11, 36, 40, 44, and 48. When selected, the dedicated sensor scans only these default channels.no Reverts the scan-mode to default (Default-Scan)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-700.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4354.1.92.2.4 nosensor-policy-mode commandsRemoves or reverts to default a sensor policy’s settingsSupported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [custom-scan|rss1-interval-duration|scan-mode]no custom-scan channel-frequency <CHANNEL-FREQUENCY-LIST>no rssi-interval-durationno scan-modeParameters• no <PARAMETERS>ExampleThe following example shows the sensor-policy ‘test’ settings before the ‘no’ commands are executed:nx9500-6C8809(config-sensor-policy-test)#show contextsensor-policy test rssi-interval-duration 30 scan-mode Custom-Scan custom-scan channel-frequency 2412 width 20MHz scan-weight 1000 custom-scan channel-frequency 2417 width 20MHz scan-weight 1000nx9500-6C8809(config-sensor-policy-test)#The scan-mode is reverted back to the default setting of 'Default-Scan', as show in the following output:nx9500-6C8809(config-sensor-policy-test)#no scan-modenx9500-6C8809(config-sensor-policy-test)#show contextsensor-policy test rssi-interval-duration 30 scan-mode Default-Scan custom-scan channel-frequency 2412 width 20MHz scan-weight 1000 custom-scan channel-frequency 2417 width 20MHz scan-weight 1000nx9500-6C8809(config-sensor-policy-test)#nx9500-6C8809(config-sensor-policy-test)#no custom-scan channel-frequency 2412nx9500-6C8809(config-sensor-policy-test)#no custom-scan channel-frequency 2417nx9500-6C8809(config-sensor-policy-test)#show contextsensor-policy test rssi-interval-duration 30 scan-mode Default-Scannx9500-6C8809(config-sensor-policy-test)#no <PARAMETERS> Removes or reverts to default a sensor policy settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-701.png)
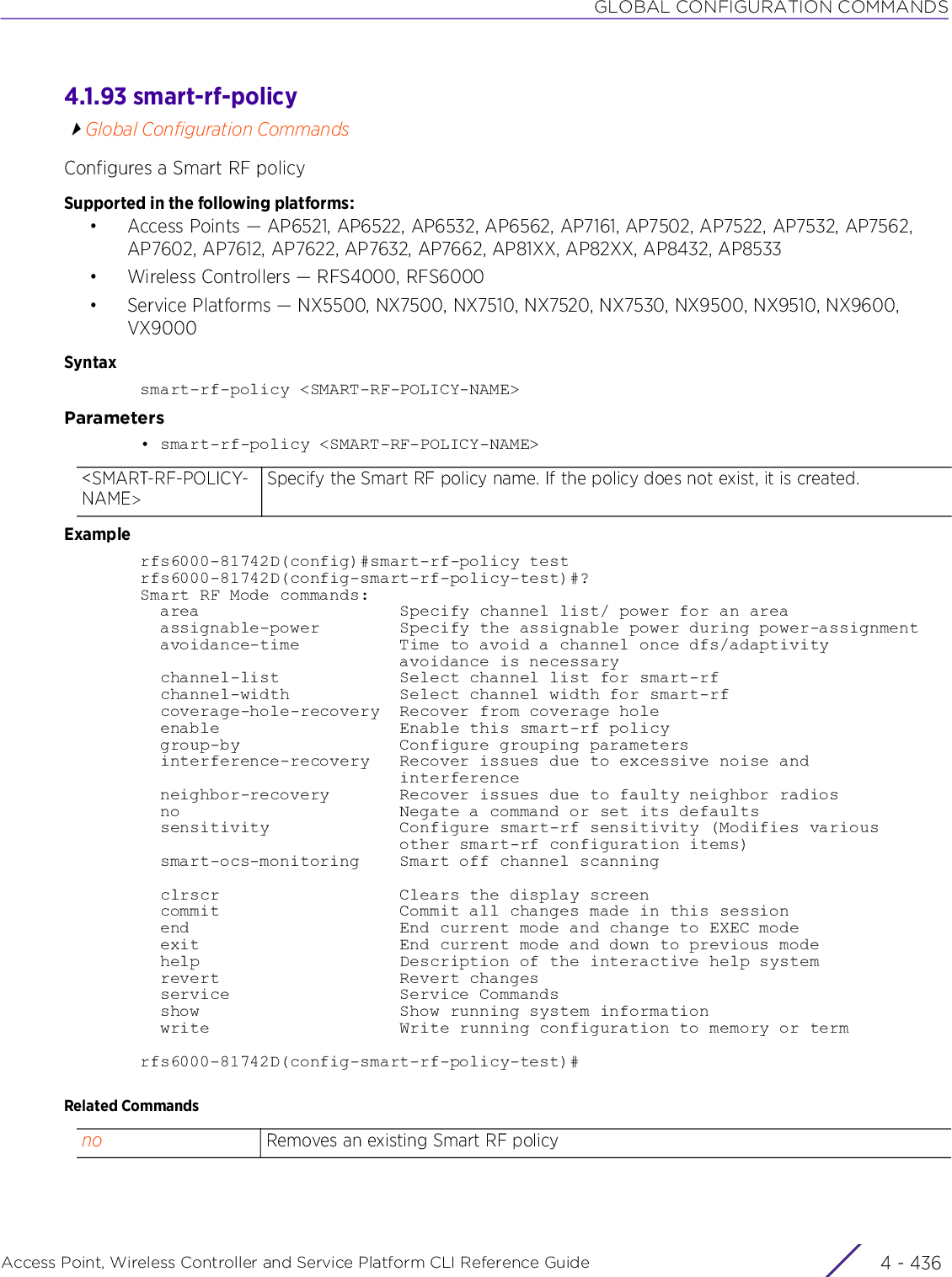




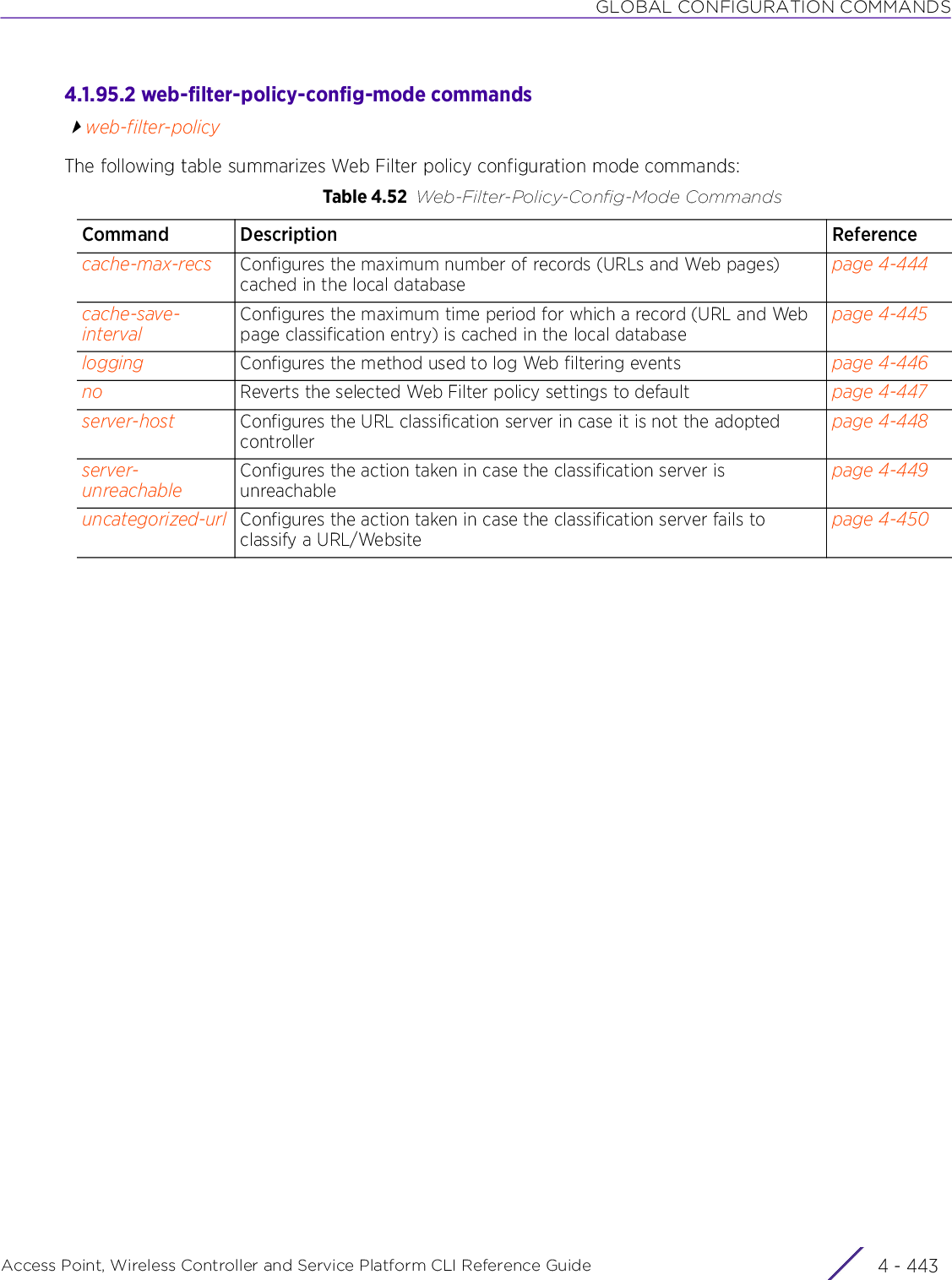

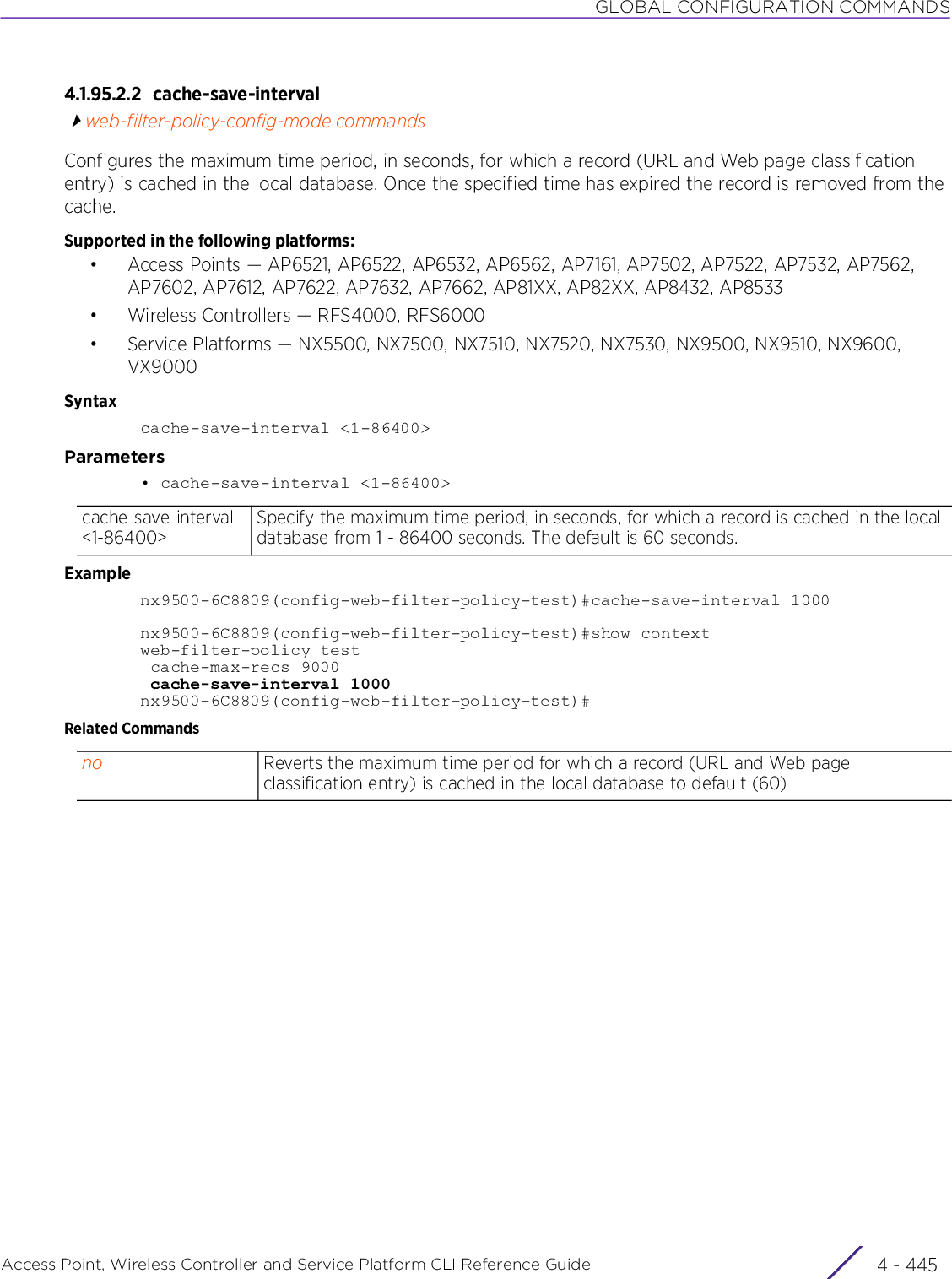
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4464.1.95.2.3 loggingweb-filter-policy-config-mode commandsConfigures the method used to log Web filtering eventsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlogging [logfile|syslog]Parameters• logging [logfile|syslog]Examplenx9500-6C8809(config-web-filter-policy-test)#logging logfilenx9500-6C8809(config-web-filter-policy-test)#show contextweb-filter-policy test logging logfilenx9500-6C8809(config-web-filter-policy-test)#logging [logfile|syslog]Selects the method used to log Web filtering events. The options are:• logfile – Logs to a file.• syslog – Logs to the syslog server. This is the default setting.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-712.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4474.1.95.2.4 noweb-filter-policy-config-mode commandsReverts the selected Web Filter policy settings to default, based on the parameters passedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [cache-max-recs|cache-save-interval|server-host|server-unreachable|uncategorized-url]Parameters• no <PARAMETERS>ExampleThe following example shows the Web Filter policy ‘test’ settings before the ‘no’ command is executed:nx9500-6C8809(config-web-filter-policy-test)#show contextweb-filter-policy test cache-max-recs 9000 cache-save-interval 1000 uncategorized-url block server-unreachable block server-host ip-address 192.168.13.13nx9500-6C8809(config-web-filter-policy-test)#nx9500-6C8809(config-web-filter-policy-test)#no cache-max-recsnx9500-6C8809(config-web-filter-policy-test)#no server-unreachablenx9500-6C8809(config-web-filter-policy-test)#no uncategorized-urlThe following example shows the Web Filter policy ‘test’ settings after the ‘no’ command has been executed:nx9500-6C8809(config-web-filter-policy-test)#show contextweb-filter-policy test cache-save-interval 1000 server-host ip-address 192.168.13.13nx9500-6C8809(config-web-filter-policy-test)#no <PARAMETERS> Reverts the selected Web Filter policy settings to default, based on the parameters passed. Specify the parameters to revert back to default value.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-713.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4484.1.95.2.5 server-hostweb-filter-policy-config-mode commandsConfigures the URL classification server in case it is not the adopted controllerSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxserver-host [host-name <SERVER-HOST-NAME>|ip-address <SERVER-IPv4>|mint-id <SERVER-MiNT-ID>]Parameters• server-host [host-name <SERVER-HOST-NAME>|ip-address <SERVER-IPv4>|mint-id <SERVER-MiNT-ID>]Examplenx9500-6C8809(config-web-filter-policy-test)#server-host ip-address 192.168.13.13nx9500-6C8809(config-web-filter-policy-test)#show contextweb-filter-policy test cache-max-recs 9000 cache-save-interval 1000 server-host ip-address 192.168.13.13nx9500-6C8809(config-web-filter-policy-test)#Related Commandsserver-host [host-name <SERVER-HOST-NAME>|ip-address <SERVER-IPv4>|mint-id <SERVER-MiNT-ID>]Use one of the following options to identify the URL classification server:• host-name <SERVER-HOST-NAME> – Identifies the classification server by its hostname.• ip-address <SERVER-IPv4> – Identifies the classification server by its IP address.• mint-id <SERVER-MiNT-ID> – Identifies the classification server by its MiNT ID.no Removes the URL classification server’s configured details, such as hostname, ip-address, or MiNT ID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-714.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4494.1.95.2.6 server-unreachableweb-filter-policy-config-mode commandsConfigures the action taken in case the classification server is unreachable. Based on the value configured the an end user’s request for a URL/Website is either blocked or passed.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxserver-unreachable [block|pass]Parameters• server-unreachable [block|pass]Examplenx9500-6C8809(config-web-filter-policy-test)#server-unreachable blocknx9500-6C8809(config-web-filter-policy-test)#show contextweb-filter-policy test cache-max-recs 9000 cache-save-interval 1000 server-unreachable block server-host ip-address 192.168.13.13nx9500-6C8809(config-web-filter-policy-test)#Related Commandsserver-unreachable [block|pass]Configures the action taken in case the classification server is unreachable. The options are:• block – Denies access to the requested URL/Website• pass – Allows access to the requested URL/Website. This is the default value.no Reverts the action taken in case the classification server is unreachable to default (pass)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-715.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4504.1.95.2.7 uncategorized-urlweb-filter-policy-config-mode commandsConfigures the action taken in case the classification server fails to classify a URL/Website. Based on the value configured the an end user’s request for a non-classified URL/Website is either blocked or passed.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuncategorized-url [block|pass]Parameters• uncategorized-url [block|pass]Examplenx9500-6C8809(config-web-filter-policy-test)#uncategorized-url blocknx9500-6C8809(config-web-filter-policy-test)#show contextweb-filter-policy test cache-max-recs 9000 cache-save-interval 1000 uncategorized-url block server-unreachable block server-host ip-address 192.168.13.13nx9500-6C8809(config-web-filter-policy-test)#Related Commandsuncategorized-url [block|pass]Configures the action taken in case the classification server fails to classify a URL/Website. The options are:• block – Denies access to the requested non-classified URL/Website• pass – Allows access to the requested non-classified URL/Website. This is the default value.no Reverts the action taken in case the classification server fails to classify a URL/Website to default (pass)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-716.png)
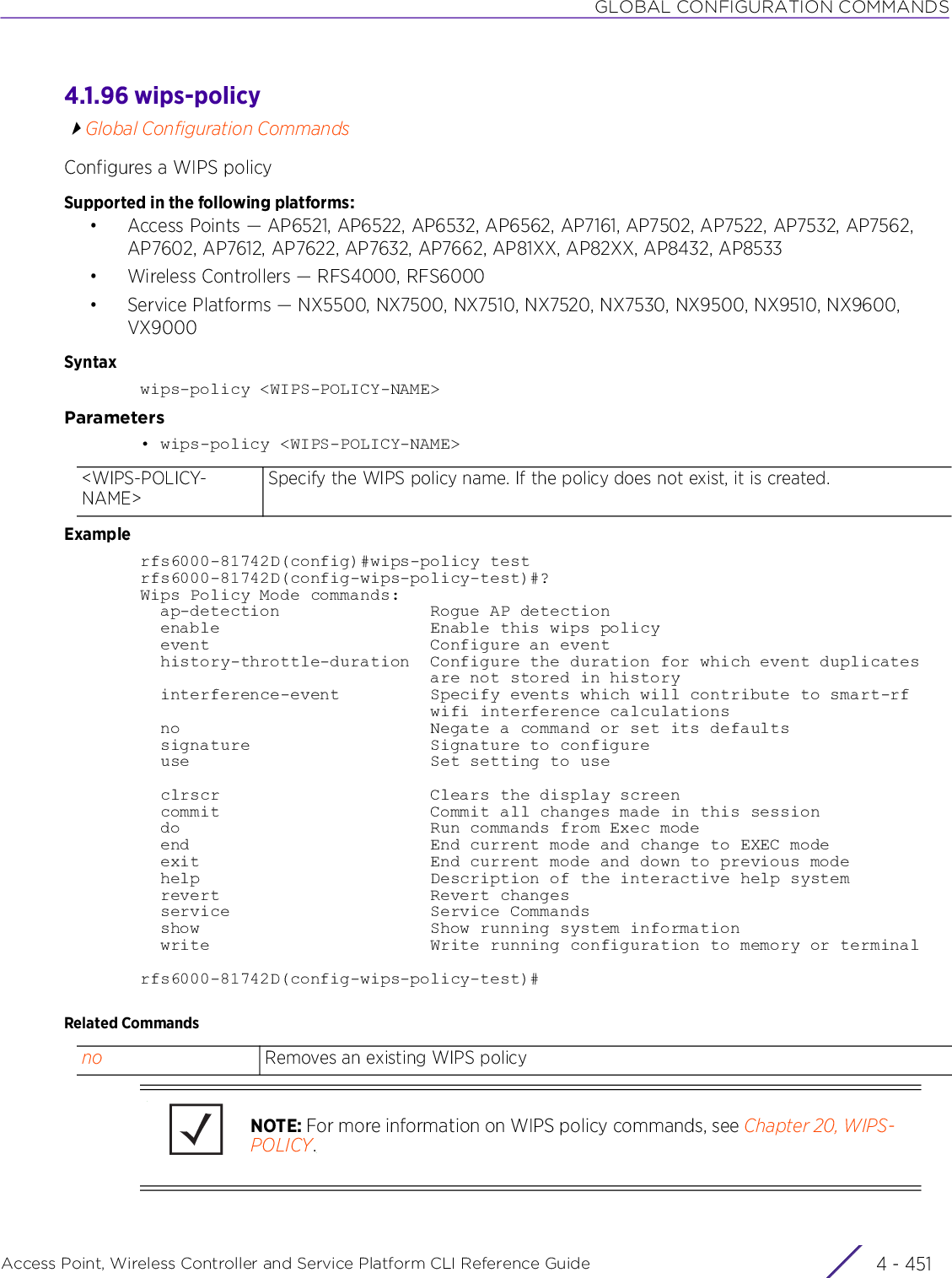
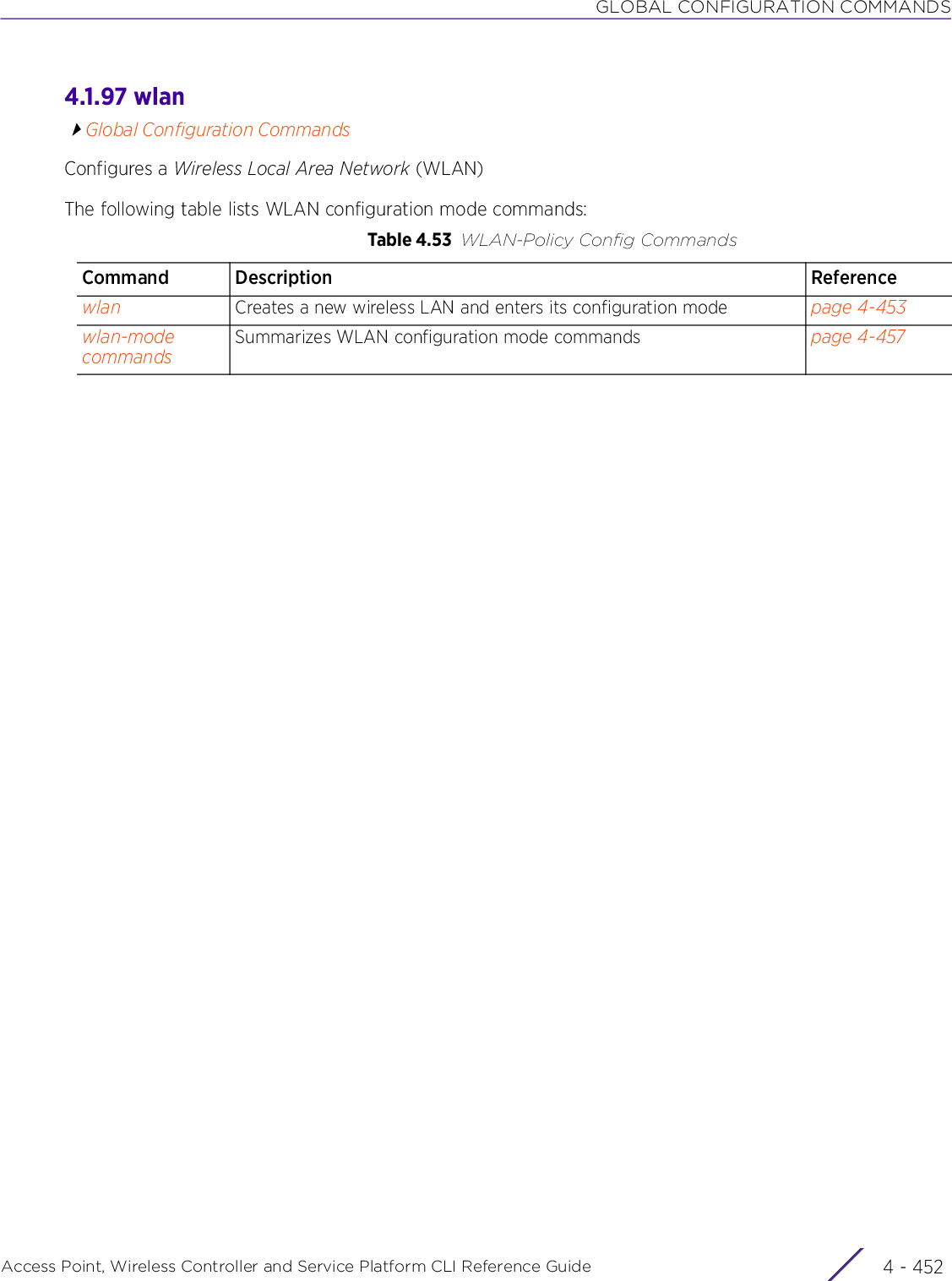

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 454Parameters• wlan {<WLAN-NAME>|containing <WLAN-NAME>}Examplerfs6000-81742D(config)#wlan 1rfs6000-81742D(config-wlan-1)#?Wireless LAN Mode commands: accounting Configure how accounting records are created for this wlan acl Actions taken based on ACL configuration [packet drop being one of them] answer-broadcast-probes Include this wlan when responding to probe requests that do not specify an SSID assoc-response Association response threshold association-list Configure the association list for the wlan authentication-type The authentication type of this WLAN bridging-mode Configure how packets to/from this wlan are bridged broadcast-dhcp Configure broadcast DHCP packet handling broadcast-ssid Advertise the SSID of the WLAN in beacons captive-portal-enforcement Enable captive-portal enforcement on the wlan client-access Enable client-access (normal data operations) on this wlan client-client-communication Allow switching of frames from one wireless client to another on this wlan client-load-balancing Configure load balancing of clients on this wlan controller-assisted-mobility Enable controller assisted mobility to determine wireless clients' VLAN assignment data-rates Specify the 802.11 rates to be supported on this wlan description Configure a description of the usage of this wlan downstream-group-addressed-forwarding Enable downstream group addressed forwarding of packets dpi Deep-Packet-Inspection (Application Assurance) dynamic-vlan-assignment Dynamic VLAN assignment configuration eap-types Configure client access based on eap-type used for authentication encryption-type Configure the encryption to use on this wlan enforce-dhcp Drop packets from Wireless Clients with static IP address fast-bss-transition Configure support for 802.11r Fastwlan <WLAN-NAME>Configures a new WLAN• <WLAN-NAME> – Optional. Specify the WLAN name.The WLAN name could be a logical representation of its coverage area (for example, engineering, marketing, etc.).The name cannot exceed 32 characters.containing <WLAN-NAME>Optional. Configures an existing WLAN’s settings• <WLAN-NAME> – Specify a sub-string in the WLAN name. Use this parameter to filter a WLAN. This option allows you to select and enter the configuration mode of one or more WLANs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-720.png)

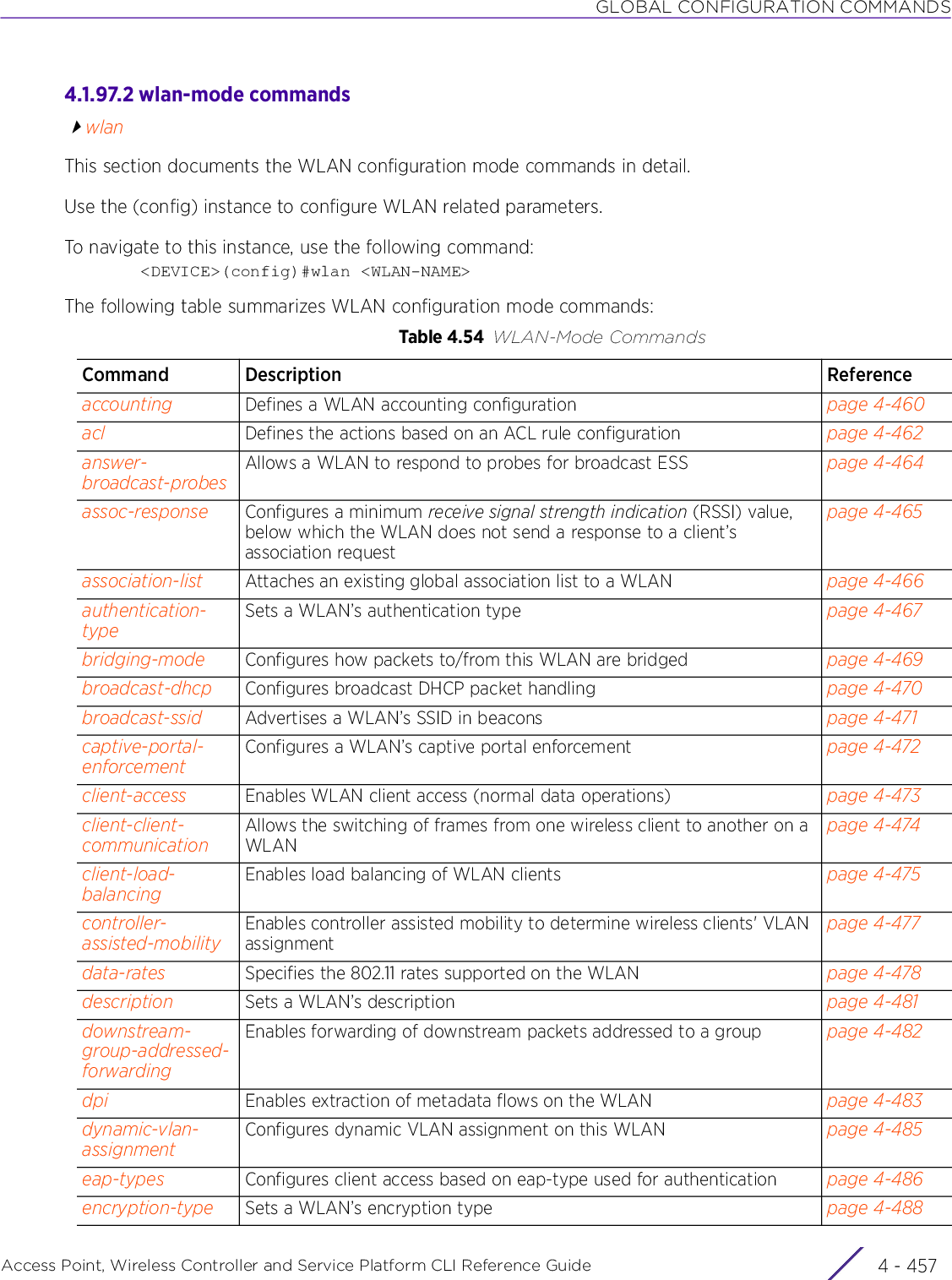
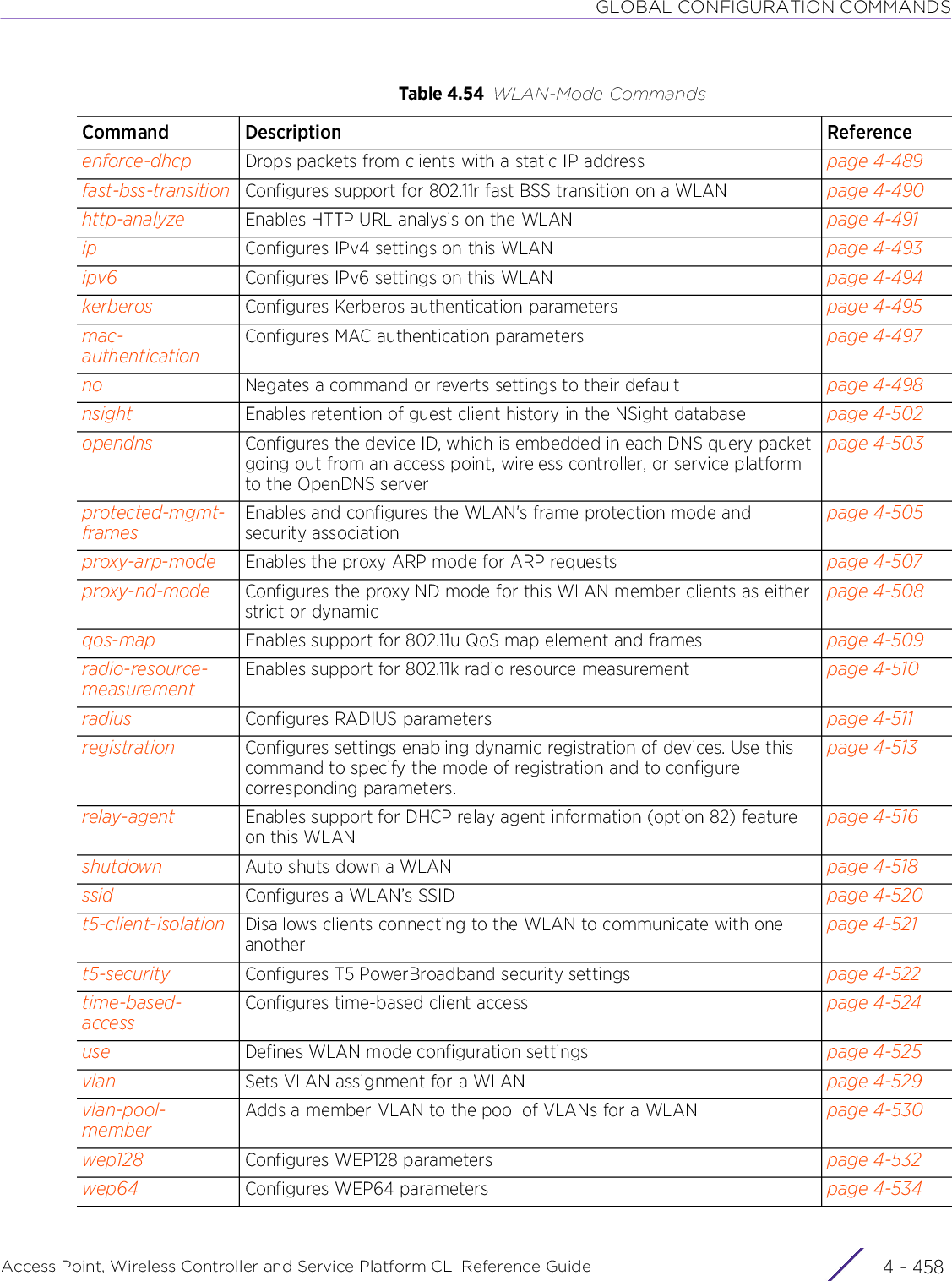
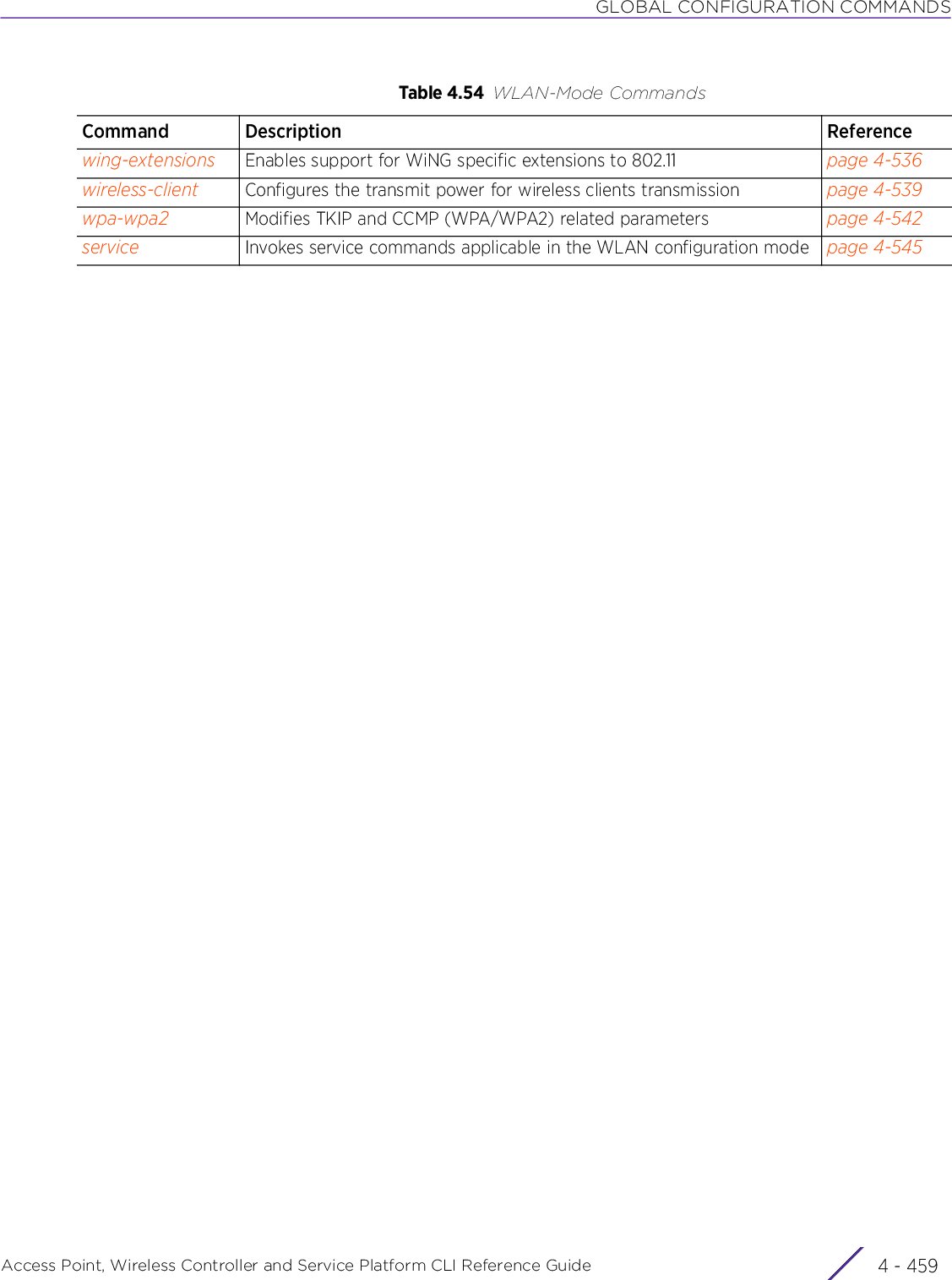
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4604.1.97.2.1 accountingwlan-mode commandsDefines the WLAN’s accounting configurationAccounting is the method of collecting user data, such as start and stop times, executed commands (for example, PPP), number of packets and number of bytes received and transmitted. This data is sent to the security server for billing, auditing, and reporting purposes. Accounting enables wireless network administrators to track the services and network resources accessed and consumed by users. When enabled, this feature allows the network access server to report and log user activity to a RADIUS security server in the form of accounting records. Each accounting record is comprised of AV pairs and is stored on the access control server. The data can be analyzed for network management, client billing, and/or auditing. Accounting methods must be defined through AAA policies.Accounting can be enabled and applied to access point, wireless controller, or service platform managed WLANs. Once enabled, it uniquely logs accounting events specific to the managed WLAN. Accounting logs contain information about the use of remote access services by users. This information is of great assistance in partitioning local versus remote users and how to best accommodate each. Remote user information can be archived to a location outside of the access point for periodic network and user permission administration.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccounting [radius|syslog|wait-client-ip]accounting [radius|wait-client-ip]accounting syslog [host|mac-address-format]accounting syslog host <IP/HOSTNAME> {port <1-65535>} {proxy-mode [none|through-controller|through-rf-domain-manager]}accounting syslog mac-address-format [middle-hyphen|no-delim|pair-colon|pair-hyphen|quad-dot] case [lower|upper]Parameters• accounting [radius|wait-client-ip]accounting radius Enables support for WLAN RADIUS accounting messages. This option is disabled by default.When enabled, the WLAN uses an external RADIUS resource for accounting.Use the use > aaa-policy > <AAA-POLICY-NAME> command to associate an appropriate AAA policy with this WLAN. This AAA policy should be existing and should define the accounting, authentication, and authorization parameters.accounting wait-client-ipEnables waiting for client’s IP before commencing the accounting procedure](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-726.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 461• accounting syslog host <IP/HOSTNAME> {port <1-65535>} {proxy-mode [none|through-controller|through-rf-domain-manager]}• accounting syslog mac-address-format [middle-hyphen|no-delim|pair-colon|pair-hyphen|quad-dot] case [lower|upper]Examplerfs6000-81742D(config-wlan-test)#accounting syslog host 172.16.10.4 port 2 proxy-mode nonerfs6000-81742D(config-wlan-test)#show contextwlan test ssid test bridging-mode tunnel encryption-type none authentication-type none accounting syslog host 172.16.10.4 port 2rfs6000-81742D(config-wlan-test)#Related Commandsaccounting syslog Enables support for WLAN syslog accounting messages in standard syslog format (RFC 3164). This option is disabled by default.host <IP/HOSTNAME>Configures a syslog destination hostname or IP address for accounting records• <IP/HOSTNAME> – Specify the IP address or name of the destination host.port <1-65535> Optional. Configures the syslog server’s UDP port (this port is used to connect to the server)• <1-65535> – Specify the port from 1 - 65535. Default port is 514.proxy-mode[none|through-controller|through-rf-domain-manager]Optional. Configures the request proxying mode• none – Requests are directly sent to the server from the device• through-controller – Proxies requests through the controller (access point, wireless controller, or service platform) configuring the device• through-rf-domain-manager – Proxies requests through the local RF Domain manageraccounting syslog Enables support for WLAN syslog accounting messagesmac-address-format Configures the MAC address format used in syslog messagesmiddle-hyphen Configures the MAC address format with middle hyphen (AABBCC-DDEEFF)no-delim Configures the MAC address format without delimitors (AABBCCDDEEFF)pair-colon Configures the MAC address format with pair-colon delimitors (AA:BB:CC:DD:EE:FF)pair-hyphen Configures the MAC address format with pair-hyphen deli mi tors (AA-BB-CC-DD-EE-FF). This is the default setting.quad-dot Configures the MAC address format with quad-dot delimitors (AABB.CCDD.EEFF)case [lower|upper] The following keywords are common to all:• case – Specifies MAC address case (upper or lower)• lower – Specifies MAC address is filled in lower case (for example, aa-bb-cc-dd-ee-ff)• upper – Specifies MAC address is filled in upper case (for example, AA-BB-CC-DD-EE-FF)no Disables sending of accounting message to the RADIUS server, disables syslog accounting, or disables waiting for client’s IP before sending accounting messages](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-727.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4654.1.97.2.4 assoc-responsewlan-mode commandsConfigures the deny-threshold and rssi-threshold values. These threshold values are considered when responding to a client’s association/authentication request.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxassoc-response [deny-threshold <1-12>|rssi-threshold <-100--40>]Parameters• assoc-response [deny-threshold <1-12>|rssi-threshold <-100--40>]Examplenx9500-6C8809(config-wlan-test)#assoc-response rssi-threshold -60nx9500-6C8809(config-wlan-test)#assoc-response deny-threshold 4nx9500-6C8809(config-wlan-test)#show contextwlan test ssid test bridging-mode local encryption-type none authentication-type none assoc-response rssi-threshold -60 assoc-response deny-threshold 4 registration user group-name guest expiry-time 2000 agreement-refresh 14400nx9500-6C8809(config-wlan-test)#Related Commandsassoc-response Configures the association response thresholdsdeny-threshold <1-12>Configures the number of times association/authentication request, from a client, is ignored if the RSSI is less than the configured RSSI threshold. This option is disabled by default.• <1-12> – Specify the deny-threshold from 1 - 12.rssi-threshold <-100--40>Configures an association response RSSI threshold value. If the RSSI is below the configured threshold value, the client’s association/authentication request is ignored. This option is disabled by default.• rssi-threshold <-100--40> – Specify a value from -100 - -40 dBm. no Removes the configured deny-threshold and rssi-threshold values](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-731.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4674.1.97.2.6 authentication-typewlan-mode commandsSets the WLAN’s authentication typeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthentication-type [eap|eap-mac|eap-psk|kerberos|mac|none]Parameters• authentication-type [eap|eap-mac|eap-psk|kerberos|mac|none]authentication-type Configures a WLAN’s authentication typeThe authentication types are: EAP, EAP-MAC, EAP-PSK, Kerberos, MAC, and none.eap Configures EAP authentication (802.1X)EAP is the de-facto standard authentication method used to provide secure authenticated access to controller managed WLANs. EAP provides mutual authentication, secured credential exchange, dynamic keying and strong encryption. 802.1X EAP can be deployed with WEP, WPA or WPA2 encryption schemes to further protect user information forwarded over controller managed WLANs.The EAP process begins when an unauthenticated supplicant (client device) tries to connect with an authenticator (in this case, the authentication server). An access point passes EAP packets from the client to an authentication server on the wired side of the access point. All other packet types are blocked until the authentication server (typically, a RADIUS server) verifies the client’s identity.If using EAP authentication ensure that a AAA policy is mapped to the WLAN.eap-mac Configures EAP or MAC authentication depending on client. (This setting is valid only with the None encryption type.EAP-MAC is useful when in a hotspot environment, as some clients support EAP and an administrator may want to authenticate based on just the MAC address of the device.eap-psk Configures EAP authentication or pre-shared keys depending on client (This setting is only valid with Temporal Key Integrity Protocol (TKIP) or Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) encryption types).When using PSK with EAP, the controller sends a packet requesting a secure link using a pre-shared key. The controller and authenticating device must use the same authenticating algorithm and pass code during authentication. EAP-PSK is useful when transitioning from a PSK network to one that supports EAP.If using eap-psk authentication ensure that a AAA policy is mapped to the WLAN.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-733.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4694.1.97.2.7 bridging-modewlan-mode commandsConfigures how packets are bridged to and from a WLANUse this command to define which VLANs are bridged, and how local VLANs are bridged between the wired and wireless sides of the network.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxbridging-mode [local|tunnel]Parameters• bridging-mode [local|tunnel]Examplerfs6000-81742D(config-wlan-test)#bridging-mode localrfs6000-81742D(config-wlan-test)#show contextwlan test ssid test bridging-mode local encryption-type none authentication-type eap accounting syslog host 172.16.10.4 port 2 acl exceed-rate wireless-client-denied-traffic 20 disassociaterfs6000-81742D(config-wlan-test)#bridging-mode Configures how packets are bridged to and from a WLAN. The options are local and tunnel.local Bridges packets between WLAN and local ethernet ports. This is the default mode.tunnel Tunnels packets to other devices (typically a wireless controller or service platform)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-735.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4754.1.97.2.13 client-load-balancingwlan-mode commandsEnforces client load balancing on a WLAN’s access point radios. AP6522, AP6532, AP6562, AP81XX, and AP82XX models can support 256 clients per access point. AP6511 and AP6521 models can support up to 128 clients per access point. When enforced, loads are balanced by ignoring association and probe requests. Probe and association requests are not responded to, forcing a client to associate with another access point radio.This feature is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxclient-load-balancing {allow-single-band-clients|band-discovery-intvl|capability-ageout-time|max-probe-req|probe-req-invl}client-load-balancing {allow-single-band-clients [2.4ghz|5ghz]|band-discovery-intvl <0-10000>|capability-ageout-time <0-10000>}client-load-balancing {max-probe-req|probe-req-intvl} [2.4ghz|5ghz] <0-10000>Parameters• client-load-balancing {allow-single-band-clients [2.4ghz|5ghz]|band-discovery-intvl <0-10000>|capability-ageout-time <0-10000>}• client-load-balancing {max-probe-req|probe-req-intvl} [2.4ghz|5ghz] <0-10000>client-load-balancing Configures client load balancing on a WLANallow-single-band-clients [2.4ghz|5ghz]Optional. Allows single band clients to associate even during load balancing• 2.4ghz – Enables load balancing across 2.4 GHz channels• 5ghz – Enables load balancing across 5.0 GHz channelsThis option is enabled by default for 2.4 and 5.0 GHz radios.band-discovery-intvl <0-10000>Optional. Configures the interval to discover a client's band capability before connection• <0-10000> – Specify a value from 0 - 10000 seconds. The default is 10 seconds.capability-ageout-time <0-10000>Optional. Configures a client's capability ageout interval. This is the time for which a client’s capabilities are retained in the device’s internal table. Once this time is exceeded the client’s capabilities are aged out.• <0-10000> – Specify a value from 0 - 10000 seconds. The default is 3600 seconds.client-load-balancing Configures WLAN client load balancingmax-probe-req [2.4ghz|5ghz] <0-10000>Optional. Configures client probe request interval limits for device association• 2.4ghz – Configures maximum client probe requests on 2.4 GHz radios• 5ghz – Configures maximum client probe requests on 5.0 GHz radios• <0-10000> – Specify a client probe request threshold from 0 - 10000. The defaultfor both 2.4 and 5.0 GHz radios is 60.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-741.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 476Examplerfs6000-81742D(config-wlan-test)#client-load-balancing band-discovery-intvl 2rfs6000-81742D(config-wlan-test)#client-load-balancing probe-req-intvl 5ghz 5rfs6000-81742D(config-wlan-test)#show contextwlan test ssid test bridging-mode local encryption-type none authentication-type eap accounting syslog host 172.16.10.4 port 2 client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 captive-portal-enforcement fall-back acl exceed-rate wireless-client-denied-traffic 20 disassociate broadcast-dhcp validate-offerrfs6000-81742D(config-wlan-test)#Related Commandsprobe-req-intvl [2.4ghz|5ghz] <0-10000>Optional. Configures client probe request interval limits for device association• 2.4ghz – Configures the client probe request interval on 2.4 GHz radios• 5ghz – Configures the client probe request interval on 5.0 GHz radios• <0-10000> – Specify a value from 0 - 10000. The default for both 2.4 and 5.0 GHzradios is 10 seconds.no Disables client load balancing on a WLAN’s access point radios](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-742.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4784.1.97.2.15 data-rateswlan-mode commandsSpecifies the 802.11 rates supported on a WLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdata-rates [2.4GHz|5GHz]data-rates 2.4GHz [b-only|bg|bgn|custom|default|g-only|gn]data-rates 2.4GHz custom [1|11|12|18|2|24|36|48|5.5|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|basic-mcs-1s|mcs-1s|mcs-2s|mcs-3s]data-rates 5GHz [a-only|an|custom|default]data-rates 5GHz custom [12|18|24|36|48|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|basic-mcs-1s|mcs-1s|mcs2s|mcs3s]Parameters• data-rates 2.4GHz [b-only|bg|bgn|default|g-only|gn]• data-rates 5GHz [a-only|an|default]• data-rates [2.4GHz|5GHz] custom [1|11|12|18|2|24|36|48|5.5|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|basic-mcs-1s|mcs-1s|mcs-2s|mcs-3s]data-rates Specifies the 802.11 rates supported when mapped to a 2.4 GHz radiob-only Uses rates that support only 11b clientsbg Uses rates that support both 11b and 11g clientsbgn Uses rates that support 11b, 11g and 11n clientsdefault Uses the default rates configured for a 2.4 GHz radiog-only Uses rates that support operation in 11g onlygn Uses rates that support 11g and 11n clientsdata-rates Specifies the 802.11 rates supported when mapped to a 5.0 GHz radioa-only Uses rates that support operation in 11a onlyan Uses rates that support 11a and 11n clientsdefault Uses default rates configured for a 5.0 GHzdata-rates [2.4GHz|5GHz]Specifies the 802.11 rates supported when mapped to a 2.4 GHz or 5.0 GHz radio](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-744.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 479custom Configures a data rates list by specifying each rate individually. Use 'basic-' prefix before a rate to indicate it is used as a basic rate (For example, 'data-rates custom basic-1 basic-2 5.5 11').The data-rates for 2.4 GHz and 5.0 GHz channels are the same with a few exceptions. The 2.4 GHz channel has a few extra data rates: 1, 11, 2, and 5.5.1,11,2,5.5 The following data rates are specific to the 2.4 GHz channel:• 1 – 1-Mbps• 11 – 11-Mbps• 2 – 2-Mbps• 5.5 – 5.5-Mbps[12,18,24,36,48,54,6,9,basic-1,basic-11,basic-12,basic-18,basic-2,basic-36,basic-48,basic-5.5,basic-54,basic-6,basic-9,basic-mcs-1s,mcs-1s,mcs2s,mcs-3s]The following data rates are common to both the 2.4 GHz and 5.0 GHz channels:•12 – 12 Mbps•18 – 18-Mbps•24 – 24 Mbps• 36 – 36-Mbps• 48 – 48-Mbps• 54 – 54-Mbps•6 – 6-Mbps•9 – 9-Mbps• basic-1 – basic 1-Mbps• basic-11 – basic 11-Mbps• basic-12 – basic 12-Mbps• basic-18 – basic 18-Mbps• basic-2 – basic 2-Mbps• basic-36 – basic 36-Mbps• basic-48 – basic 48-Mbps• basic-5.5 – basic 5.5-Mbps• basic-54 – basic 54-Mbps• basic-6 – basic 6-Mbps• basic-9 – basic 9-Mbps• basic-mcs-1s – Modulation and coding scheme data rates for 1 Spatial Stream• mcs-1s – Applicable to 1-spatial stream data rates• mcs-2s – Applicable to 2-spatial stream data rates• mcs-3s – Applicable to 3-spatial stream data rates](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-745.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4834.1.97.2.18 dpiwlan-mode commandsEnables DPI on this WLAN. When enabled, all traffic is subjected to DPI for detection of applications, application categories, custom applications, and metadata extraction.DPI is an advanced packet analysis technique, which analyzes packet and packet content headers to determine the nature of network traffic. When enabled, DPI inspects packets of all flows to identify applications (such as, Netflix, Twitter, Facebook, etc.) and extract metadata (such as, host name, server name, TCP-RTT, etc.) for further use by the WiNG firewall.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdpi metadata [http|ssl|tcp-rtt|voice-video]Parameters• dpi metadata [http|ssl|tcp-rtt|voice-video]dpi metadata [http|ssl|tcp-rtt|voice-video]Enables extraction of the following metadata flows:• http – Extracts HTTP flows. When enabled, administrators can track HTTP Websites accessed by both internal and guest clients and visualize HTTP data usage, hits, active time and total clients on the NSight application’s dashboard. This setting is disabled by default.• ssl – Extracts SSL flows. When enabled, administrators can track SSL Websites accessed by both internal and guest clients and visualize SSL data usage, hits, active time and total clients on the NSight application’s dashboard.This setting is disabled by default• tcp-rtt – Extracts Round Trip Time (RTT) information from Transmission Control Protocol (TCP) flows. However, this TCP-RTT metadata is viewable only on the NSight dashboard. Therefore, ensure the NSight server is up and NSight analytics data collection is enabled.• voice-video – Extracts voice and video flows. When enabled, voice and video calls can be tracked by extracting parameters, such as packets transferred and lost, jitter, and application name. Most Enterprise VoIP applications like facetime, skype for business and VoIP terminals can be monitored for call quality and visualized on the NSight dashboard in manner similar to HTTP and SSL. Call quality and metrics can only be determined from calls established unencrypted. This setting is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-749.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4864.1.97.2.20 eap-typeswlan-mode commandsConfigures client access based on the EAP type usedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxeap-types [allow|deny] [aka|all|fast|peap|sim|tls|ttls] {(aka|all|fast|peap|sim|tls|ttls)}Parameters• eap-types [allow|deny] [aka|all|fast|peap|sim|tls|ttls] {(aka|all|fast|peap|sim|tls|ttls)}eap-types [allow|deny]Configures a list of allowed or denied EAP types• allow – Configures a list of EAP types allowed for WLAN client authentication• deny – Configures a list of EAP types not allowed for WLAN client authentication[aka|all|fast|peap|sim|tls|ttls]The following EAP types are common to the ‘allow’ and ‘deny’ keywords:• aka – Configures EAP Authentication and Key Agreement (AKA) and EAP-AKA’ (AKA Prime). EAP-AKA is one of the methods in the EAP authentication framework. It uses Universal Mobile Telecommunications System (UMTS) and Universal Subscriber Identity Module (USIM) for client authentication and key distribution.• all – Allows or denies usage of all EAP types on the WLAN. This is the default setting.• fast – Configures EAP Flexible Authentication via Secure Tunneling (FAST). EAP-FAST establishes a Transport Layer Security (TLS) tunnel, to verify client credentials, using Protected Access Credentials (PAC).•peap – Configures Protected Extensible Authentication Protocol (PEAP). PEAP or Protected EAP uses encrypted and authenticated TLS tunnel to encapsulate EAP.• sim – Configures EAP Subscriber Identity Module (SIM). EAP-SIM uses Global System for Mobile Communications (GSMC) SIM for client authentication and key distribution.• tls – Configures EAP Transport Layer Security (TLS). EAP-TLS is an EAP authentication method that uses PKI to communicate with a RADIUS server or any other authentication server.• ttls – Configures Tunneled Transport Layer Security (TTLS). EAP-TTLS is an extension of TLS. Unlike TLS, TTLS does not require every client to generate and install a CA- signed certificate.These options are recursive, and more than one EAP type can be selected. The selected options are added to the allowed or denied EAP types list.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-752.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4884.1.97.2.21 encryption-typewlan-mode commandsSets a WLAN’s encryption typeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxencryption-type [ccmp|keyguard|none|tkip-ccmp|wep128|web128-keyguard|wep64]Parameters• encryption-type [ccmp|keyguard|none|tkip-ccmp|wep128|web128-keyguard|wep64]Examplerfs6000-81742Dconfig-wlan-test)#encryption-type tkip-ccmprfs6000-81742D(config-wlan-test)#show contextwlan test description TestWLAN ssid test bridging-mode local encryption-type tkip-ccmp authentication-type eap accounting syslog host 172.16.10.4 port 2 data-rates 2.4GHz gn client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 captive-portal-enforcement fall-back acl exceed-rate wireless-client-denied-traffic 20 disassociate broadcast-dhcp validate-offerrfs6000-81742D(config-wlan-test)#Related Commandsencryption-type Configures the WLAN’s data encryption parametersccmp Configures Advanced Encryption Standard (AES) Counter Mode CBC-MAC Protocol (AES-CCM/CCMP)keyguard Configures Keyguard-MCM (Mobile Computing Mode)none No encryption used. This is the default setting.tkip-ccmp Configures the TKIP and AES-CCM/CCMP encryption modeswep128 Configures WEP with 128 bit keyswep128-keyguard Configures WEP128 as well as Keyguard-MCM encryption modeswep64 Configures WEP with 64 bit keys. A WEP64 configuration is insecure when two WLANs are mapped to the same VLAN, and one uses no encryption while the other uses WEP.no Resets the WLAN’s encryption type to default (none)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-754.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4914.1.97.2.24 http-analyzewlan-mode commandsEnables HTTP URL analysis on the WLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxhttp-analyze [filter|syslog]http-analyze filter [images|post|query-string]http-analyze syslog host <IP/HOSTNAME> {port <1-65535>} {proxy-mode [none|through-controller|through-rf-domain-manager]}Parameters• http-analyze filter [images|post|query-string]• http-analyze syslog host <IP/HOSTNAME> {port <1-65535>} {proxy-mode [none|through-controller|through-rf-domain-manager]}filter Filters URLs, based on the parameters set, before forwarding themimages Filters out URLs referring to images (does not forward URL requesting images)post Filters out URLs requesting POST (does not forward POST requests). This option is disabled by default.query-string Removes query strings from URLs before forwarding them (forwards requests and no data). This option is disabled by default.syslog host <IP/HOSTNAME>Forwards client and URL information to a syslog server• host <IP/HOSTNAME> – Specify the syslog server’s IP address or hostnameport <1-65535> Optional. Specifies the UDP port to connect to the syslog server from 1 - 65535proxy-mode [none|through-controller|through-rf-domain-manager]Optional. Specifies if the request is to be proxied through another device• none – Requests are sent directly to syslog server from device• through-controller – Proxies requests, to the syslog server, through the controller configuring the device• through-rf-domain-manager – Proxies requests, to the syslog server, through the local RF Domain manager](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-757.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4934.1.97.2.25 ipwlan-mode commandsConfigures Internet Protocol (IP) settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [arp|dhcp]ip arp [header-mismatch-validation|trust]ip dhcp trustParameters• ip arp [header-mismatch-validation|trust]• ip dhcp trustExamplerfs6000-81742D(config-wlan-test)#ip dhcp trustrfs6000-81742D(config-wlan-test)#show contextwlan test description TestWLAN ssid test bridging-mode local encryption-type tkip-ccmp authentication-type eap accounting syslog host 172.16.10.4 port 2 data-rates 2.4GHz gn client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 captive-portal-enforcement fall-back ip dhcp trust acl exceed-rate wireless-client-denied-traffic 20 disassociate enforce-dhcp broadcast-dhcp validate-offer http-analyze controllerrfs6000-81742D(config-wlan-test)#Related Commandsip arp Configures the IP settings for ARP packetsheader-mismatch-validationVerifies mismatch of source MAC address in the ARP and Ethernet headers. This option is enabled by default.trust Sets ARP responses as trusted for a WLAN/range. This option is disabled by default.ip dhcp Configures the IP settings for DHCP packetstrust Sets DHCP responses as trusted for a WLAN/range. This option is disabled by default.no Resets IP ARP or DHCP trust parameters to default. ARP trust is disabled, ARP mismatch verification is enabled, or DHCP trust is disabled.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-759.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4944.1.97.2.26 ipv6wlan-mode commandsSets the DHCPv6 and ICMPv6 neighbor discovery (ND) components for this WLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 [dhcpv6|nd]ipv6 dhcpv6 trustipv6 nd [header-mismatch-validation|raguard|trust]Parameters• ipv6 dhcpv6 trust• ipv6 nd [header-mismatch-validation|raguard|trust]Examplerfs6000-81742D(config-wlan-test)#ipv6 dhcpv6 trustrfs6000-81742D(config-wlan-test)#ipv6 nd trustrfs6000-81742D(config-wlan-test)#show contextwlan test ssid test vlan 1 bridging-mode tunnel encryption-type none authentication-type none ipv6 dhcpv6 trust ipv6 nd trustrfs6000-81742D(config-wlan-test)#Related Commandsipv6 dhcpv6 trust Enables DHCPv6 trust state for DHCPv6 responses on this WLAN. When enabled, all DHCPv6 responses received on this WLAN are trusted and forwarded. This option is disabled by default.ipv6 nd Sets the IPv6 ND settings for this WLANheader-mismatch-validationChecks for mismatch of source MAC address in the ICMPv6 ND message and Ethernet header (link layer option). This option is enabled by default.raguard Allows redirection of router advertisements (RAs) and ICMPv6 packets originating on this WLAN. This option is disabled by default.trust Enables trust state for ND requests received on this WLAN. When enabled, all ND requests on an IPv6 firewall, on this WLAN, are trusted. This option is disabled by default.no Resets IPv6 ND or DHCPv6 trust parameters to default. ND request trust is disabled, ND header mismatch verification is enabled, ND RA and ICMPv6 redirection is disabled, or DHCPv6 trust is disabled.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-760.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4954.1.97.2.27 kerberoswlan-mode commandsConfigures Kerberos authentication parameters on a WLANKerberos (designed and developed by MIT) provides strong authentication for client/server applications using secret-key cryptography. Using Kerberos, a client must prove its identity to a server (and vice versa) across an insecure network connection.Once a client and server use Kerberos to validate their identity, they encrypt all communications to assure privacy and data integrity. Kerberos can only be used on the access point with 802.11b clients. Kerberos uses Network Time Protocol (NTP) for synchronizing the clocks of its Key Distribution Center (KDC) server(s).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxkerberos [password|realm|server]kerberos password [0 <LINE>|2 <LINE>|<LINE>]kerberos realm <REALM>kerberos server [primary|secondary|timeout]kerberos server [primary|secondary] host <IP/HOSTNAME> {port <1-65535>}kerberos server timeout <1-60>Parameters• kerberos password [0 <LINE>|2 <LINE>|<LINE>]• kerberos realm <REALM>kerberos Configures a WLAN’s Kerberos authentication parametersThe parameters are: password, realm, and server.password Configures a Kerberos KDC server password. The password should not exceed 127 characters. The password options are:• 0 <LINE> – Configures a clear text password• 2 <LINE> – Configures an encrypted password•<LINE> – Specify the password.kerberos Configures a WLAN’s Kerberos authentication parametersThe parameters are: password, realm, and server.realm <REALM> Configures a Kerberos KDC server realm. The REALM should not exceed 127 characters.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-761.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 496• kerberos server [primary|secondary] host <IP/HOSTNAME> {port <1-65535>}• kerberos server timeout <1-60>Examplerfs6000-81742D(config-wlan-test)#kerberos server timeout 12rfs6000-81742D(config-wlan-test)#kerberos server primary host 172.16.10.2 port 88rfs6000-81742D(config-wlan-test)#show contextwlan test description TestWLAN ssid test bridging-mode local encryption-type tkip-ccmp authentication-type eap kerberos server timeout 12 kerberos server primary host 172.16.10.2 accounting syslog host 172.16.10.4 port 2 data-rates 2.4GHz gn client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 captive-portal-enforcement fall-back ip dhcp trust acl exceed-rate wireless-client-denied-traffic 20 disassociate enforce-dhcp broadcast-dhcp validate-offer http-analyze controllerrfs6000-81742D(config-wlan-test)#Related Commandskerberos Configures a WLAN’s Kerberos authentication parametersThe parameters are: password, realm, and server.server [primary|secondary]Configures the primary and secondary KDC server parameters• primary – Configures the primary KDC server parameters• secondary – Configures the secondary KDC server parametershost <IP/HOSTNAME> Sets the primary or secondary KDC server address• <IP/HOSTNAME> – Specify the IP address or name of the KDC server.port <1-65535> Optional. Configures the UDP port used to connect to the KDC server• <1-65535> – Specify the port from 1 - 65535. The default is 88.kerberos Configures a WLAN’s Kerberos authentication parametersThe parameters are: password, realm, and server.timeout <1-60> Modifies the Kerberos KDC server‘s timeout parameters• <1-60> – Specifies the wait time for a response from the Kerberos KDC server before retrying. Specify a value from 1 - 60 seconds.no Removes Kerberos authentication related parameters on a WLAN](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-762.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4974.1.97.2.28 mac-authenticationwlan-mode commandsEnables MAC authentication. When enabled, the system uses cached credentials (RADIUS server lookups are skipped) to authenticate clients.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmac-authentication [cached-credentials|enforce-always]Parameters• mac-authentication [cached-credentials|enforce-always]Examplerfs4000-229D58(config-wlan-test)#mac-authentication cached-credentialsrfs4000-229D58(config-wlan-test)#Related Commandsmac-authentication Enables MAC authentication on this WLAN and configures related parameterscached-credentials Uses cached credentials to skip RADIUS lookups. This option is disabled by default.enforce-always Enforces MAC authentication on this WLAN. When enabled, MAC authentication is enforced, each time a client logs in, even when the authentication type specified (using the authentication-type command) is not MAC authentication. This option is disabled by default.no Disables MAC authentication related parameters: Disables use of cached credentials to skip RADIUS lookups, or disables enforcement of MAC authentication on this WLAN.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-763.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 4984.1.97.2.29 nowlan-mode commandsNegates WLAN mode commands and reverts values to their defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [accounting|acl|answer-broadcast-probes|assoc-response|association-list|authentication-type|broadcast-dhcp|broadcast-ssid|captive-portal-enforcement|client-access|client-client-communication|client-load-balancing|controller-assisted-mobility|data-rates|description|downstream-group-addressed-forwarding|dpi|dynamic-vlan-assignment|eap-types|encryption-type|enforce-dhcp|fast-bss-transition|http-analyze|ip|ipv6|kerberos|mac-authentication|nsight|opendns|protected-mgmt-frames|proxy-arp-mode|proxy-nd-mode|qos-map|radio-resource-measurement|radius|registration|relay-agent|shutdown|ssid|t5-client-isolation|t5-security|time-based-access|use|vlan|vlan-pool-member|wep128|wep64|wing-extensions|wireless-client|wpa-wpa2|service]no accounting [radius|syslog|wait-client-ip]no acl exceed-rate wireless-client-denied-trafficno [answer-broadcast-probes|association-list global|authentication-type|broadcast-dhcp validate-offer|broadcast-ssid|captive-portal-enforcement|client-access|client-client-communication|client-load-balancing allow-single-band-clients|controller-assisted-mobility|data-rates [2.4GHz|5GHz]|description|downstream-group-addressed-forwarding|dynamic-vlan-assignment allowed-vlans|eap-types|encryption-type|enforce-dhcp|fast-bss-transition over-ds|opendns device-id|protected-mgmt-frames {sa-query}|proxy-arp-mode|proxy-nd-mode|qos-map|ssid|t5-client-isolation|t5-security|vlan]no assoc-response [deny-threshold|rssi-threshold]no http-analyze {filter|syslog}no http-analyze {filter [images|post|query-string]}no ip [arp|dhcp]no ip arp [header-mismatch-validation|trust]no ip dhcp trustno dpi metadata [http|ssl|voice-video]no ipv6 [dhcpv6|nd]no ipv6 dhcpv6 trustno ipv6 nd [header-mismatch-validation|raguard|trust]no kerberos [password|realm|server]no kerberos server [primary host|secondary host|timeout]no mac-authentication [cached-credentials|enforce-always]no nsight client-historyno radio-resource-measurement {channel-report|neighbor-report {hybrid}}no radius [dynamic-authorization|nas-identifier|nas-port-id|vlan-assignment]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-764.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 499no registration {external}no relay-agent [dhcp-option82|dhcpv6-ldra]no shutdown {on-critical-resource|on-meshpoint-loss|on-primary-port-link-loss|on-unadoption}no time-based-access days [all|friday|monday|saturday|sunday|thursday|tuesday|wednesday|weekdays|weekends]no use [aaa-policy|association-acl-policy|bonjour-gw-discovery-policy|captive-portal|ip-access-list|ipv6-access-list|mac-access-list|passpoint-policy|roaming-assist-policy|url-filter|wlan-qos-policy]no vlan-pool-member [<1-40 95>|<VLAN-ALIAS-NAME>]no [wep128|wep64] [key {1-4}|transmit-key]no wing-extension [move-command|smart-scan|wing-load-information|wmm-load-information]no wireless-client [count-per-radio|cred-cache-ageout|hold-time|inactivity-timeout|max-firewall-sessions|reauthentication|roam-notification|t5-inactivity-timeout|tx-power|vlan-cache-ageout]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.Examplerfs6000-81742D(config-wlan-test)#no ? accounting Configure how accounting records are created for this wlan acl Actions taken based on ACL configuration [ packet drop being one of them] answer-broadcast-probes Do not Include this wlan when responding to probe requests that do not specify an SSID assoc-response Association response threshold association-list Configure the association list for the wlan authentication-type Reset the authentication to use on this wlan to default (none/Pre-shared keys) broadcast-dhcp Configure broadcast DHCP packet handling broadcast-ssid Do not advertise the SSID of the WLAN in beacons captive-portal-enforcement Configure how captive-portal is enforced on the wlan client-access Disallow client access on this wlan (no data operations) client-client-communication Disallow switching of frames from one wireless client to another on this wlan client-load-balancing Disable load-balancing of clients on this wlan controller-assisted-mobility Disable configure assisted mobilityno <PARAMETERS> Removes or reverts this WLAN’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-765.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5054.1.97.2.32 protected-mgmt-frameswlan-mode commandsConfigures the WLAN's frame protection mode and security association (SA) query parameters802.11w provides protection for both unicast management frames and broadcast/multicast management frames. The ‘robust management frames’ are action, disassociation, and deauthentication frames. The standard provides one security protocol CCMP for protection of unicast robust management frames. Protected management frames (PMF) protocol only applies to robust management frames after establishment of RSNA PTK. Robust management frame protection is achieved by using CCMP for unicast management frames, broadcast/multicast integrity protocol (BIP) for broadcast/multicast management frames and SA query protocol for protection against (re)association attacks.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxprotected-mgmt-frames [mandatory|optional|sa-query [attempts <1-10>|timeout <100-1000>]]Parameters• protected-mgmt-frames [mandatory|optional|sa-query [attempts <1-10>|timeout <100-1000>]]protected-mgmt-framesEnables and configures WLAN's frame protection mode and SA query parameters. Use this command to specify whether management frames are continually or optionally protected. Frame protection mode is disabled by default.mandatory Enforces protected management frames (PMF) on this WLAN (management frames are continually optionally protected)optional Provides PMF only for those clients that support PMF (management frames are optionally protected)sa-query [attempts <1-10>|timeout <100-1000>]Configures the following SA parameters:• attempts <1-10> – Configures the number of SA query attempts from 1 - 10. The default is 5.• timeout <100-1000> – Configures the interval, in milliseconds, used to timeout association requests that exceed the defined interval. Specify a value from 100 - 1000 milliseconds. The default value is 201 milliseconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-771.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5074.1.97.2.33 proxy-arp-modewlan-mode commandsEnables proxy ARP mode for handling ARP requestsProxy ARP is the technique used to answer ARP requests intended for another system. By faking its identity, the access point accepts responsibility for routing packets to the actual destination.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxproxy-arp-mode [dynamic|strict]Parameters• proxy-arp-mode [dynamic|strict]Examplerfs6000-81742D(config-wlan-test)#proxy-arp-mode strictrfs6000-81742D(config-wlan-test)#show contextwlan test ssid test bridging-mode local encryption-type none authentication-type none protected-mgmt-frames mandatory wing-extensions wmm-load-information client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 acl exceed-rate wireless-client-denied-traffic 20 disassociate proxy-arp-mode strict broadcast-dhcp validate-offer http-analyze controllerrfs6000-81742D(config-wlan-test)#Related Commandsproxy-arp-mode Enables proxy ARP mode for handling ARP requests. The options available are dynamic and strict.dynamic Forwards ARP requests to the wireless side (for which a response could not be proxied). This is the default setting.strict Does not forward ARP requests to the wireless sideno Reverts the proxy ARP mode to default (dynamic)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-773.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5084.1.97.2.34 proxy-nd-modewlan-mode commandsConfigures the proxy ND mode for this WLAN member clients as either strict or dynamicND proxy is used in IPv6 to provide reachability by allowing a client to act as proxy. Proxy certificate signing can be done either dynamically (requiring exchanges of identity and authorization information) or statically when the network topology is defined.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxproxy-nd-mode [dynamic|strict]Parameters• proxy-nd-mode [dynamic|strict]Examplerfs6000-81742D(config-wlan-test)#proxy-nd-mode strictrfs6000-81742D(config-wlan-test)#show contextwlan test ssid test bridging-mode tunnel encryption-type none authentication-type none wpa-wpa2 server-only-authentication proxy-nd-mode strict opendns device-id 44-55-66rfs6000-81742D(config-wlan-test)#Related Commandsproxy-nd-mode [dynamic|strict]Configures the proxy ND mode for this WLAN member clients. The options are: dynamic and strict• dynamic – Forwards ND request to wireless for which a response could not be proxied. This is the default value.• strict – Does not forward ND requests to the wireless sideno Reverts the proxy ND mode to default (dynamic)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-774.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5114.1.97.2.37 radiuswlan-mode commandsConfigures RADIUS related parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxradius [dynamic-authorization|nas-identifier|nas-port-id|vlan-assignment]radius [dynamic-authorization|nas-identifier <NAS-ID>|nas-port-id <NAS-PORT-ID>|vlan-assignment]Parameters• radius [dynamic-authorization|nas-identifier <NAS-ID>|nas-port-id <NAS-PORT-ID>|vlan-assignment]dynamic-authorization Enables support for disconnect and change of authorization messages (RFC5176)When enabled, this option extends the RADIUS protocol to support unsolicited messages from the RADIUS server. These messages allow administrators to issue change of authorization (CoA) messages, which affect session authorization, or disconnect messages (DM) that terminate a session immediately. This option is disabled by default.nas-identifier <NAS-ID>Configures the network access server (NAS) identifier attribute, a value that identifies the access point or controller where the RADIUS messages originate. The value specified here is included in the RADIUS NAS-Identifier field for WLAN authentication and accounting packets.• <NAS-ID> – Specify the NAS identifier attribute (should not exceed 256 characters in length).nas-port-id <NAS-PORT-ID>Configures the NAS port ID attribute, a value that identifies the port from where the RADIUS messages originate• <NAS-PORT-ID> – Specify the NAS port ID attribute (should not exceed 256 characters in length).The profile database on the RADIUS server consists of user profiles for each connected NAS port. Each profile is matched to a username representing a physical port. When authorizing users, it queries the user profile database using a username representative of the physical NAS port making the connection. Set the numeric port value from 0 - 4294967295.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-777.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5134.1.97.2.38 registrationwlan-mode commandsConfigures settings enabling dynamic registration and validation of devices by their MAC addresses. When configured, this option registers a device’s MAC address, and allows direct access to a previously registered device.This command also configures the external guest registration and validation server details. If using an external server to perform guest registration, authentication and accounting, use this command to configure the external server’s IP address/hostname. When configured, access points and controllers forward guest registration requests to the specified registration server. In case of EGuest deployment, this external resource should point to the EGuest registration server.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxregistration [device|device-OTP|external|user]registration [device|device-OTP|user] group-name <RAD-GROUP-NAME> {agreement-refresh <0-144000>|expiry-time <1-43800>}registration external [follow-aaa|host]registration external follow-aaa {send-mode [http|https|udp]}registration external host <IP/HOSTNAME> {proxy-mode|send-mode}registration external host <IP/HOSTNAME> {proxy-mode [none|through-controller|through-rf-domain-manager|through-centralized-controller]|send-mode [https|https|udp]}Parameters• registration external follow-aaa {send-mode [http|https|udp]}registration Enables dynamic guest-user registration and validation. This option is disabled by default.external Specifies that the guest registration is handled by an external resource. Access points/controllers send registration requests to the external registration server.follow-aaa Uses an AAA policy to point to the guest registration, authentication, and accounting server. When used, guest registration is handled by the RADIUS server specified in the AAA policy used in the WLAN context.In case of EGuest deployment, the RADIUS authentication and accounting server configuration in the AAA policy should point to the EGuest server. The use of ‘follow-aaa’ option is recommended in EGuest replica-set deployments.For more information on enabling the EGuest server, see eguest-server (VX9000 only).For more information on configuring an EGuest deployment, see configuring ExtremeGuest captive-portal.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-779.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 514• registration external host <IP/HOSTNAME> {proxy-mode [none|through-controller|through-rf-domain-manager|through-centralized-controller]|send-mode [https|https|udp]}• registration [device|device-OTP|user] group-name <RAD-GROUP-NAME> {agreement-refresh <0-144000>|expiry-time <1-43800>}send-mode [https|https|udp]Optional. Specifies the protocol used to forward registration requests to the external AAA policy servers. The options are;• HTTPS – Sends registration requests as HTTPS packet• HTTP – Sends registration requests as HTTP packet• UDP – Sends registration requests as UDP packet, using the UPD port 12322. This is the default setting.registration Configures dynamic guest registration and validation parameters. This option is disabled by default.external Specifies that the guest registration is handled by an external resource. Access points/controllers send registration requests to the external registration server.host <IP/HOSTNAME>Specifies the external registration server’s IP address or hostname. When configured, access points/ controllers forward guest registration requests to the external registration server specified here.proxy-mode{none|through-controller|through-rf-domain-manager|through-centralized-controller}Optional. Specifies the proxy mode. If a proxy is needed for connection, specify the proxy mode as through-controller, through-rf-domain. If no proxy is needed, select none.• none – Optional. Requests are sent directly to the controller from the requesting device• through-controller – Optional. Requests are proxied through the controller configuring the device• through-rf-domain-manager – Optional. Requests are proxied through the local RF Domain manager• through-centralized-controller – Optional. Request are proxied through one of the controllers in a cluster.that is operating as the designated forwarder. Select this option if capture and redirection is on a cluster of wireless controller/service platforms managing dependent/independent access points when redundancy is required.After specifying the proxy-mode, optionally specify the protocol used to send the requests to the external registration server host.send-mode [https|https|udp]Optional. Specifies the communication protocol used. The options are;• HTTPS – Sends registration requests as HTTPS packets• HTTP – Sends registration requests as HTTP packets• UDP – Sends registration requests as UDP packet, using the UPD port 12322. This is the default setting.registration Configures dynamic guest registration and validation parameters. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-780.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 515Examplenx9500-6C8809(config-wlan-test)#registration user group-name guest agreement-refresh 14400 expiry-time 2000nx9500-6C8809(config-wlan-test)#show contextwlan test ssid test bridging-mode local encryption-type none authentication-type none registration user group-name guest expiry-time 2000 agreement-refresh 14400nx9500-6C8809(config-wlan-test)#Related Commands[device|device-OTP|user]Configures the mode used to register guest users of this WLAN. Options include device, external, user, and device-OTP• device-OTP – Registers a device by its MAC address. During registration, the user, using the registered device, has to provide the e-mail address, mobile number, or member id, and the one-time-passcode (OTP) sent to the registered e-mail id or mobile number to complete registration. On subsequent logins, the user has to enter the OTP. If the MAC address of the device attempting login and the OTP combination matches, the user is allowed access. If using this option, set the WLAN authentication type as MAC authentication.• device – Registers a device by its MAC address. On subsequent logins, already registered MAC addresses are allowed access. If using this option, set the WLAN authentication type as MAC authentication.• user – Registers guest users using one of the following options: e-mail address, mobile-number, or member-id.If using any one of the above modes of registration, specify the RADIUS group to which the registered device or user is to be assigned post authentication.group-name <RAD-GROUP-NAME>Configures the RADIUS group name to which registered users are associated. When left blank, users are not associated with a RADIUS group.• <RAD-GROUP-NAME> – Specify the RADIUS group name (should not exceed 64 characters).expiry-time <1-43800>Optional. Configures the amount of time, in hours, before registered addresses expire and must be re-entered• <1-43800> – Specify a value from 1 - 43800 hrs. The default is 1500 hrs.agreement-refresh <0-144000>Optional. Sets the time, in minutes, after which an inactive user has to refresh the WLAN’s terms of agreement. For example, if the agreement refresh period is set to 1440 minutes, a user, who has been inactive for more than 1440 minutes (1 day) is served the agreement page, and is allowed access only after refreshing the terms of agreement.• <0-100> – Specify a value from 0 - 144000. The default is 0 minutes.no Disables dynamic user registration and removes associated configurations. ALso disables forwarding of user information to an external device.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-781.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5164.1.97.2.39 relay-agentwlan-mode commandsEnables support for DHCP/DHCPv6 relay agent information (option 82 and DHCPv6-LDRA) feature on this WLAN. This option is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrelay-agent [dhcp-option82|dhcpv6-ldra]Parameters• relay-agent [dhcp-option82|dhcpv6-ldra]Examplerfs4000-229D58(config-wlan-test)#relay-agent dhcp-option82rfs4000-229D58(config-wlan-test)#show contextwlan test ssid test vlan 1 bridging-mode tunnel encryption-type none authentication-type none radio-resource-measurement relay-agent dhcp-option82 controller-assisted-mobilityrfs4000-229D58(config-wlan-test)#rfs6000-81701D(config-wlan-test)#relay-agent dhcpv6-ldrarfs6000-81701D(config-wlan-test)#show contextwlan test ssid test bridging-mode tunnel encryption-type none authentication-type none relay-agent dhcpv6-ldrarfs6000-81701D(config-wlan-test)#relay-agent Enables support for the following DHCP and DHCPv6 options: option 82 and Lightweight DHCPv6 Relay Agent (LDRA) respectively. When enabled, this feature allows the DHCP/DHCPv6 relay agent to insert the relay agent information option (option 82, LDRA) in client requests forwarded to the DHCP/DHCPv6 server.This information provides the following:• circuit ID suboption – Provides the SNMP port interface index• remote ID – Provides the controller’s MAC addressdhcp-option82 Enables DHCP option 82. DHCP option 82 provides client physical attachment information. This option is disabled by default.dhcpv6-ldra Enables the DHCPv6 relay agent. The LDRA feature allows DHCPv6 messages to be transmitted on existing networks that do not currently support IPv6 or DHCPv6. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-782.png)



![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5224.1.97.2.43 t5-securitywlan-mode commandsConfigures T5 PowerBroadband security settingsA T5 controller uses the IPX operating system to manage its connected radio devices, as opposed to the WiNG operating system used by RFS controllers and NX service platforms. However, a T5 controller, once enabled as a supported external device, can provide data to WiNG to assist in a T5’s management within a WiNG supported subnet populated by both types of devices. The CPEs are the T5 controller managed radio devices using the IPX operating system. These CPEs use DSL as their high speed Internet access mechanism using the CPE’s physical wallplate connection and phone jack.Supported in the following platforms:• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxt5-security [static-wep|wpa-enterprise|wpa-personal]t5-security static-wep encryption-type [wep128|wep64] [hex <STRING>|passphrase <STRING>]t5-security [wpa-enterprise|wpa-personal] encryption-type [ccmp|tkip|tkip-ccmp] version [mixed|wpa|wpa2]Parameters• t5-security static-wep encryption-type [wep128|wep64] [hex <STRING>|passphrase <STRING>]• t5-security [wpa-enterprise|wpa-personal] encryption-type [ccmp|tkip|tkip-ccmp] version [mixed|wpa|wpa2]NOTE: This setting is applicable only when this WLAN supports T5 controllers and their connected CPEs.t5-security static-wep Configures the T5 WLAN security type as static-wepencryption-type [wep128|wep64]Applies one of the following encryption algorithms to the T5 support WLAN configuration: WEP64 or WEP128hex <STRING> Configures the hex password (used to derive the security key)• <STRING> – Specify the hex password (should not exceed the 10 - 26 characters).passphrase <STRING> Configures the passphrase shared by both transmitting and receiving authenticators• <STRING> – Specify the passphrase. It could either be an alphanumeric string of 8 to 63 ASCII characters or 64 HEX characters. The alphanumeric string allows character spaces. This string is converted to a numeric value. Configuring a passphrase saves you the need to create a 256-bit key each time keys are generated.t5-security [wpa-enterprise|wpa-personal]Configures the T5 WLAN security type as: wpa-enterprise OR wpa-personal](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-788.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 523Examplenx9500-6C8809(config-wlan-test)#t5-security wpa-enterprise encryption-type ccmpversion wpanx9500-6C8809(config-wlan-test)#show contextwlan test ssid test bridging-mode local encryption-type none authentication-type none t5-security wpa-enterprise encryption-type ccmp version wpa t5-client-isolationnx9500-6C8809(config-wlan-test)#Related Commandsencryption-type [ccmp|tkip|tkip-ccmp]The following parameters are common to the wpa-enterprise and wpa-personal keywords:Applies one of the following encryption algorithms to the T5 support WLAN configuration: CCMP, TKIP, or TKIP-CCMPversion [mixed|wpa|wpa2]The following parameters are common to the wpa-enterprise and wpa-personal keywords:• version – Applies one of the following encryption schemes to the T5 support WLAN configuration: WPA, WPA2, or mixed no Removes the configured T5 PowerBroadband security settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-789.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5244.1.97.2.44 time-based-accesswlan-mode commandsConfigures time-based client access to the network resourcesAdministrators can use this feature to assign fixed days and time of WLAN access for wireless clientsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtime-based-access days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays] {start <START-TIME>} [end <END-TIME>]Parameters• time-based-access days [sunday|monday|tuesday|wednesday|thursday|friday|saturday|all|weekends|weekdays] {start <START-TIME>} [end <END-TIME>]Examplerfs6000-81742D(config-wlan-test)#time-based-access days weekdays start 10:00 end 16:30rfs6000-81742D(config-wlan-test)#show contextwlan test ssid testWLAN1 bridging-mode local encryption-type none authentication-type none protected-mgmt-frames mandatory radius vlan-assignment time-based-access days weekdays start 10:00 end 16:30 --More--rfs6000-81742D(config-wlan-test)#Related Commandsday <option> Specifies the day or days on which the client can access the WLAN• sunday – Allows access on Sundays only• monday – Allows access on Mondays only• tuesday – Allows access on Tuesdays only• wednesday – Allows access on Wednesdays only• thursday – Allows access on Thursdays only• friday – Allows access on Fridays only• saturday – Allows access on Saturdays only• weekends – Allows access on weekends only• weekdays – Allows access on weekdays only• all – Allows access on all daysstart <START-TIME> Optional. Specifies the access start time in hours and minutes (HH:MM)end <END-TIME> Specifies the access end time in hours and minutes (HH:MM)no Removes the configured time-based-access settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-790.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5254.1.97.2.45 usewlan-mode commandsThis command associates an existing captive portal with a WLAN.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [aaa-policy|application-policy|association-acl-policy|bonjour-gw-discovery-policy|captive-portal|ip-access-list|ipv6-access-list|mac-access-list|passpoint-policy|roaming-assist-policy|url-filter|wlan-qos-policy]use [aaa-policy <AAA-POLICY-NAME>|application-policy <POLICY-NAME>|association-acl-policy <ASSOCIATION-POLICY-NAME>|bonjour-gw-discovery-policy <POLICY-NAME>|captive-portal <CAPTIVE-PORTAL-NAME>|passpoint-policy <PASSPOINT-POLICY-NAME>|roaming-assist-policy <POLICY-NAME>|url-filter <URL-FILTER-NAME>|wlan-qos-policy <WLAN-QOS-POLICY-NAME>]use ip-access-list [in|out] <IP-ACCESS-LIST-NAME>use ipv6-access-list [in|out] <IPv6-ACCESS-LIST-NAME>use mac-access-list [in|out] <MAC-ACCESS-LIST-NAME>Parameters• use [aaa-policy <AAA-POLICY-NAME>|application-policy <POLICY-NAME>|association-acl-policy <ASSOCIATION-POLICY-NAME>|bonjour-gw-discovery-policy <POLICY-NAME>|captive-portal <CAPTIVE-PORTAL-NAME>|passpoint-policy <PASSPOINT-POLICY-NAME>|roaming-assist-policy <POLICY-NAME>|url-filter <URL-FILTER-NAME>|wlan-qos-policy <WLAN-QoS-POLICY-NAME>]aaa-policy <AAA-POLICY-NAME>Uses an existing AAA policy with a WLAN• <AAA-POLICY-NAME> – Specify the AAA policy name.application-policy <POLICY-NAME>Uses an existing application policy with a WLAN. An application policy defines actions to perform on a packet when it matches a specified set of pre-defined applications or application categories. For more information, see application-policy.• <POLICY-NAME> – Specify the policy name.association-acl <ASSOCIATION-POLICY-NAME>Uses an existing association ACL policy with a WLAN• <ASSOCIATION-POLICY-NAME> – Specify the association ACL policy name.bonjour-gw-discovery-policy <POLICY-NAME>Uses an existing Bonjour GW Discovery policy with a WLAN. When associated, the Bonjour GW Discovery policy defines a list of services clients can discover across subnets.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-791.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 526• use ip-access-list [in|out] <IP-ACCESS-LIST-NAME>• use ipv6-access-list [in|out] <IPv6-ACCESS-LIST-NAME>Bonjour enables discovery of services on a LAN. Bonjour allows the setting up a network (without any configuration) in which services such as printers, scanners and file-sharing servers can be found using Bonjour. Bonjour only works within a single broadcast domain. However, with a special DNS configuration, it can be extended to find services across broadcast domains.• <POLICY-NAME> – Specify the Bonjour GW Discovery policy name (should be existing and configured).For more information on Bonjour GW Discovery policy, see bonjour-gw-discovery-policy.captive-portal <CAPTIVE-PORTAL-NAME>Specifies the captive-portal policy to use if enforcing captive-portal authentication on this WLAN• <CAPTIVE-PORTAL-NAME> – Specify the captive-portal policy name. Should be existing and configured.passpoint-policy<PASSPOINT-POLICY-NAME>Associates a passpoint policy (Hotspot2 configuration) with this WLAN• <PASSPOINT-POLICY-NAME> – Specify the Hotspot 2.0 policy name.For more information on passpoint policy, see passpoint-policy.Map a passpoint policy to a WLAN. Since the configuration gets applied to the radio by BSS, only the Hotspot 2.0 configuration of primary WLANs on a BSSID is used. Incoming Hotspot 2.0 GAQ/ANQP requests from clients are identified by their destination MAC addresses and are handled by the passpoint policy from the primary WLAN on that BSS.Define one passpoint policy for every WLAN configured.roaming-assist-policy <POLICY-NAME>Associates an existing roaming assist policy with this WLAN• <POLICY-NAME> – Specify the Roaming Assist policy name.For more information on roaming assist policy, see roaming-assist-policy.url-filter <URL-FILTER-NAME>Associates an existing URL list with this WLAN• <URL-FILTER-NAME> – Specify the URL filter name.For more information on configuring a URL list, see url-list.wlan-qos-policy <WLAN-QOS-POLICY-NAME>Uses an existing WLAN QoS policy with a WLAN• <wlan-qos-policy-name> – Specify the WLAN QoS policy name.ip-access-list [in|out] <IP-ACCESS-LIST-NAME>Specifies the IP access list for incoming and outgoing packets• in – Applies the IP ACL to incoming packets• out – Applies IP ACL to outgoing packets• <IP-ACCESS-LIST-NAME> – Specify the IP access list name.ipv6-access-list [in|out] <IPv6-ACCESS-LIST-NAME>Specifies the IPv6 access list for incoming and outgoing packets• in – Applies the IPv6 ACL to incoming packets• out – Applies IPv6 ACL to outgoing packets• <IPv6-ACCESS-LIST-NAME> – Specify the IPv6 access list name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-792.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 527• use mac-access-list [in|out] <MAC-ACCESS-LIST-NAME>Usage GuidelinesIP and MAC ACLs act as firewalls within a WLAN. WLANs use ACLs as firewalls to filter or mark packets based on the WLAN from which they arrive, as opposed to filtering packets on layer 2 ports. An ACL contains an ordered list of Access Control Entries (ACEs). Each ACE specifies a set of conditions (rules) and the action taken in case of a match. The action can be permit, deny, or mark. Therefore, when a packet matches an ACE’s conditions, it is either forwarded, dropped, or marked depending on the action specified in the ACE. The order of conditions in the list is critical since filtering is stopped after the first match.IP ACLs contain deny and permit rules specifying source and destination IP addresses. Each rule has a precedence order assigned. Both IP and non-IP traffic on the same layer 2 interface can be filtered by applying both an IP ACL and a MAC.Additionally, you can filter layer 2 traffic on a physical layer 2 interface using MAC addresses. A MAC firewall rule uses source and destination MAC addresses for matching operations, where the result is a typical allow, deny, or mark designation to WLAN packet traffic.Keep in mind IP and non-IP traffic on the same layer 2 interface can be filtered by applying both an IP ACL and a MAC ACL to the interface.Examplerfs6000-81742D(config-wlan-test)#use aaa-policy testrfs6000-81742D(config-wlan-test)#use association-acl-policy testrfs6000-81742D(config-wlan-test)#show contextwlan test ssid testWLAN1 bridging-mode local encryption-type none authentication-type none protected-mgmt-frames mandatory radius vlan-assignment time-based-access days weekdays start 10:00 end 16:30 wing-extensions wmm-load-information client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 use aaa-policy test use association-acl-policy test acl exceed-rate wireless-client-denied-traffic 20 disassociate proxy-arp-mode strict broadcast-dhcp validate-offer shutdown on-unadoption http-analyze controllerrfs6000-81742D(config-wlan-test)#mac-access-list [in|out] <MAC-ACCESS-LIST-NAME>Specifies the MAC access list for incoming and outgoing packets.• in – Applies the MAC ACL to incoming packets• out – Applies MAC ACL to outgoing packets• <MAC-ACCESS-LIST-NAME> – Specify the MAC access list name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-793.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5294.1.97.2.46 vlanwlan-mode commandsSets the VLAN where traffic from a WLAN is mappedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxvlan [<1-4094>|<VLAN-ALIAS-NAME>]Parameters• vlan [<1-4094>|<VLAN-ALIAS-NAME>]Examplerfs6000-81742D(config-wlan-test)#vlan 4rfs6000-81742D(config-wlan-test)#show contextwlan test ssid testWLAN1 vlan 4 bridging-mode local encryption-type none authentication-type none protected-mgmt-frames mandatory radius vlan-assignment time-based-access days weekdays start 10:00 end 16:30 wing-extensions wmm-load-information client-load-balancing probe-req-intvl 5ghz 5 client-load-balancing band-discovery-intvl 2 use aaa-policy test use association-acl-policy test acl exceed-rate wireless-client-denied-traffic 20 disassociate proxy-arp-mode strict broadcast-dhcp validate-offer shutdown on-unadoption http-analyze controllerrfs6000-81742D(config-wlan-test)#Related Commands<1-4094> Sets a WLAN’s VLAN ID. This command starts a new VLAN assignment for a WLAN index. All prior VLAN settings are erased.Use this command to assign just one VLAN to the WLAN. Utilizing a single VLAN per WLAN is a more typical deployment scenario than using a VLAN pool.<VLAN-ALIAS-NAME> Assigns a VLAN alias to the WLAN. The VLAN alias should to existing and configured.A VLAN alias maps a name to a VLAN ID. When applied to ports (for example GE ports) using the trunk mode, a VLAN alias denies or permits traffic, on the port, to and from the VLANs specified in the alias. For more information on aliases, see alias.no Removes a WLAN’s default VLAN mapping](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-795.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5324.1.97.2.48 wep128wlan-mode commandsConfigures WEP128 parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwep128 [key|keys-from-passkey|transmit-key]wep128 key <1-4> [ascii|hex] [0 <WORD>|2 <WORD>|<WORD>]wep128 keys-from-passkey <WORD>wep128 transmit-key <1-4>Parameters• wep128 key <1-4> [ascii|hex] [0 <WORD>|2 <WORD>|<WORD>]• wep128 keys-from-passkey <WORD>• wep128 transmit-key <1-4>wep128 Configures WEP128 parameters. The parameters are: key, key-from-passkey, and transmit-key.key <1-4> Configures pre-shared hex keys• <1-4> – Configures a maximum of four key indexes. Select the key index from 1 - 4.ascii [0 <WORD>|2 <WORD>||<WORD>]Sets keys as ASCII characters (5 characters for WEP64, 13 for WEP128)• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted key• <WORD> – Configures keys as 13 ASCII characters converted to hex, or 26 hexadecimal charactershex [0 <WORD>|2 <WORD>|<WORD>]Sets keys as hexadecimal characters (10 characters for WEP64, 26 for WEP128)• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted key• <WORD> – Configures keys as 13 ASCII characters converted to hex, or 26 hexadecimal characterskeys-from-passkey <WORD>Specifies a passphrase from which keys are derived• <WORD> – Specify a passphrase from 4 - 32 characters.transmit-key <1-4> Configures the key index used for transmission from an AP to a wireless client or service platform• <1-4> – Specify a key index from 1 - 4.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-798.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5344.1.97.2.49 wep64wlan-mode commandsConfigures WEP64 parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwep64 [key|keys-from-passkey|transmit-key]wep64 key <1-4> [ascii|hex] [0 <WORD>|2 <WORD>|<WORD>]wep64 keys-from-passkey <WORD>wep64 transmit-key <1-4>Parameters• wep64 key <1-4> [ascii|hex] [0 <WORD>|2 <WORD>|<WORD>]• wep64 keys-from-passkey <WORD>• wep64 transmit-key <1-4>wep64 Configures WEP64 parametersThe parameters are: key, key-from-passkey, and transmit-key.key <1-4> Configures pre-shared hex keys• <1-4> – Configures a maximum of four key indexes. Select a key index from 1 - 4.ascii [0 <WORD>|2 <WORD>|<WORD>]Sets keys as ASCII characters (5 characters for WEP64, 13 for WEP128)• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted key• <WORD> – Configures key (10 hex or 5 ASCII characters for WEP64, 26 hex or 13 ASCII characters for WEP128).hex [0 <WORD>|2 <WORD>|<WORD>]Sets keys as hexadecimal characters (10 characters for WEP64, 26 for WEP128)• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted key• <WORD> – Configures the key (10 hex or 5 ASCII characters for WEP64, 26 hex or 13 ASCII characters for WEP128)keys-from-passkey <WORD>Specifies a passphrase from which keys are derived• <WORD> – Specify a passphrase from 4 - 32 characters.transmit-key <1-4> Configures the key index used for transmission from an AP to a wireless client or service platform• <1-4> – Specify a key index from 1 - 4.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-800.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5364.1.97.2.50 wing-extensionswlan-mode commandsEnables support for WiNG-specific client extensions to the IEEE 802.11x WLAN standards that potentially increase client roaming reliability and handshake speedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwing-extensions [ap-attributes-information {include-hostname}|coverage-hole-detection {11k-clients|offset <5-20>|threshold <-80--60}|ft-over-ds-aggregate|move-command|scan-assist {channel-info-interval <6-9>}|smart-scan|wing-load-information|wmm-load-information]Parameters• wing-extensions [ap-attributes-information {include-hostname}|coverage-hole-detection {11k-clients|offset <5-20>|offset <5-20>|threshold <-80--60}|ft-over-ds-aggregate|move-command|scan-assist {channel-info-interval <6-9>}|smart-scan|wing-load-information|wmm-load-information]wing-extensions Enables support for inclusion of WiNG-specific client extensions in radio transmissionsap-attributes-information {include-hostname}Enables support for AP attributes information element (IE)• include-hostname – Optional. When enabled, includes AP’s hostname, as a sub-element, in the AP attributes IE.The AP attributes IE is vendor-specific and, when enabled, is added to beacons and probe responses. Inclusion of AP attributes IE allows Extreme Networks terminals to:- Recognize Extreme APs- Determine if the AP supports PAN BU features, irrespective of whether these features are enabled or not.AP attributes IE is not added to beacons and probe responses by default.overage-hole-detection {11k-clients|offset <5-20>|threshold <-80--60>}Enables coverage hole detection (CHD) and configures CHD parameters. When enabled, allows clients (MUs) to inform an access point when it experiences a coverage hole. A coverage hole is an area of poor wireless coverage not supported by a WiNG managed access point radio. Enable radio resource measurement prior to enabling CHD. For enabling radio resource measurement, see radio-resource-measurement. CHD is disabled by default. After enabling CHD, optionally configure the following parameters:• 11k-clients – Optional. Provides coverage hole detection to 802.11k-only-capable clients. This is a reduced set of coverage hole detection capabilities (standard 11k messages and behaviors). This option is disabled by default.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-802.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5394.1.97.2.51 wireless-clientwlan-mode commandsConfigures the transmit power indicated to clientsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwireless-client [count-per-radio|cred-cache-ageout|hold-time|inactivity-timeout|max-firewall-sessions|reauthentication|roam-notification|t5-inactivity-timeout|tx-power|vlan-cache-ageout]wireless-client [count-per-radio <0-256>|cred-cache-ageout <60-86400>|hold-time <1-86400>|inactivity-timeout <60-86400>|max-firewall-sessions <10-10000>|reauthentication <30-86400>|t5-inactivity-timeout <60-86400>|tx-power <0-20>|vlan-cache-ageout <60-86400>]wireless-client roam-notification [after-association|after-data-ready|auto]Parameters• wireless-client [count-per-radio <0-256>|cred-cache-ageout <60-86400>|hold-time <1-86400>|inactivity-timeout <60-86400>|max-firewall-sessions <10-10000>|reauthentication <30-86400>|t5-inactivity-timeout <60-86400>|tx-power <0-20>|vlan-cache-out <60-86400>]wireless-client Configures the transmit power indicated to wireless clients for transmissioncount-per-radio<0-256>Configures the maximum number of clients allowed on this WLAN per radio• <0-256> – Specify a value from 0 - 256.cred-cache-ageout <60-86400>Configures the timeout period for which client credentials are cached across associations• <60-86400> – Specify a value from 60 - 86400 seconds.hold-time <1-86400> Configures the time period for which wireless client state information is cached post roaming• <1-86400> – Specify a value from 1 - 86400 seconds.inactivity-timeout <60-86400>Configures an inactivity timeout period in seconds. If a frame is not received from a wireless client for this period of time, the client is disassociated.• <60-86400> – Specify a value from 60 - 86400 seconds.max-firewall-sessions <10-10000>Configures the maximum firewall sessions allowed per client on a WLAN• <10-10000> – Specify the maximum number of firewall sessions allowed from 10 - 10000.reauthentication <30-86400>Configures periodic reauthentication of associated clients• <30-86400> – Specify the client reauthentication interval from 30 - 86400 seconds.t5-inactivity-timeout <60-86400>Configures and inactivity timeout, in seconds, for T5 devices. When configured, the T5 device is disassociated if the time lapsed after the last frame received from it exceeds the value specified here.• <60-86400> – Specify a value from 60 - 86400 seconds. The default is 60 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-805.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 540• wireless-client roam-notification [after-association|after-data-ready|auto]Examplerfs6000-81742D(config-wlan-test)#wireless-client cred-cache-ageout 65rfs6000-81742D(config-wlan-test)#wireless-client hold-time 200rfs6000-81742D(config-wlan-test)#wireless-client max-firewall-sessions 100rfs6000-81742D(config-wlan-test)#wireless-client reauthentication 35rfs6000-81742D(config-wlan-test)#wireless-client tx-power 12rfs6000-81742D(config-wlan-test)#show contextwlan test ssid testWLAN1 vlan-pool-member 1 limit 1 vlan-pool-member 2 limit 1 vlan-pool-member 3 limit 1 vlan-pool-member 4 limit 1 vlan-pool-member 5 limit 1 vlan-pool-member 6 limit 1 vlan-pool-member 7 limit 1 vlan-pool-member 8 limit 1 vlan-pool-member 9 limit 1 vlan-pool-member 10 limit 1 bridging-mode local encryption-type none authentication-type none wireless-client hold-time 200 wireless-client cred-cache-ageout 65 wireless-client max-firewall-sessions 100 protected-mgmt-frames mandatory wireless-client reauthentication 35 wep64 key 1 hex 0 7465737431 wep128 key 1 hex 0 25f6e7ed9718918a87a75acc75 wep128 key 2 hex 0 2b3fb36924b22dffe98c86c315 wep128 key 3 hex 0 1ebf3394431700194762ebd5b2 wep128 key 4 hex 0 e3de75be311bd787aeac5e4e8b radius vlan-assignment time-based-access days weekdays start 10:00 end 16:30 wing-extensions wmm-load-information wireless-client tx-power 12 client-load-balancing probe-req-intvl 5ghz 5--More--rfs6000-81742D(config-wlan-test)#tx-power <0-20> Configures the transmit power indicated to clients• <0-20> – Specify a value from 0 - 20 dBm.vlan-cache-ageout <60-86400>Configures the timeout period for which client VLAN information is cached across associations.• <60-86400> – Specify a value from 60 - 86400 seconds.wireless-client Configures the transmit power indicated to wireless clients for transmissionroam-notification Configures when a roam notification is transmittedafter-association Transmits a roam notification after a client has associatedafter-data-ready Transmits a roam notification after a client is data-ready (after completion of authentication, handshakes, etc.)auto Transmits a roam notification upon client association (if the client is known to have authenticated to the network)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-806.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5424.1.97.2.52 wpa-wpa2wlan-mode commandsModifies TKIP-CCMP (WPA/WPA2) related parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwpa-wpa2 [exclude-wpa2-tkip|handshake|key-rotation|opp-pmk-caching|pmk-caching|preauthentication|server-only-authentication|psk|tkip-countermeasures|use-sha256-akm]wpa-wpa2 [exclude-wpa2-tkip|opp-pmk-caching|pmk-caching|preauthentication|server-only-authentication|use-sha256-akm]wpa-wpa2 handshake [attempts|init-wait|priority|timeout]wpa-wpa2 handshake [attempts <1-5>|init-wait <5-1000000>|priority [high|normal]|timeout <10-5000> {10-5000}]wpa-wpa2 key-rotation [broadcast|unicast] <30-86400>wpa-wpa2 psk [0 <LINE>|2 <LINE>|<LINE>]wpa-wpa2 tkip-countermeasures holdtime <0-65535>Parameters• wpa-wpa2 [exclude-wpa2-tkip|opp-pmk-caching|pmk-caching|preauthentication|server-only-authentication|use-sha256-akm]• wpa-wpa2 handshake [attempts <1-5>|init-wait <5-1000000>|priority [high|normal]|timeout <10-5000> {10-5000}]wpa-wpa2 Modifies TKIP-CCMP (WPA/WPA2) related parametersexclude-wpa2-tkip Excludes the Wi-Fi Protected Access II (WPA2) version of TKIP. It supports the WPA version of TKIP only. This option is disabled by default.opp-pmk-caching Uses opportunistic key caching (same Pairwise Master Key (PMK) across APs for fast roaming with EAP.802.1x. This option is enabled by default.pmk-caching Uses cached pair-wise master keys (fast roaming with eap/802.1x). This option is enabled by default.preauthentication Uses pre-authentication mode (WPA2 fast roaming)server-only-authenticationUses online sign up server-only-authenticated encryption network. This option is disabled by default.use-sha256-akm Uses sha256 authentication key management suite. This option is disabled by default.wpa-wpa2 Modifies TKIP-CCMP (WPA/WPA2) related parametershandshake Configures WPA/WPA2 handshake parametersattempts <1-5> Configures the total number of times a message is transmitted towards a non-responsive client• <1-5> – Specify a value from 1 - 5. The default is 2.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-808.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 543• wpa-wpa2 key-rotation [broadcast|unicast] <30-86400>• wpa-wpa2 psk [0 <LINE>|2 <LINE>|<LINE>]• wpa-wpa2 tkip-countermeasures holdtime <0-65535>init-wait <5-1000000>Configures a minimum wait-time period, in microseconds, before the first handshake message is transmitted from the AP. This option is disabled by default.• <5-1000000> – Specify a value from 5 - 1000000 microseconds.priority [high|normal]Configures the relative priority of handshake messages compared to other data traffic• high – Treats handshake messages as high priority packets on a radio. This is the default setting.• normal – Treats handshake messages as normal priority packets on a radiotimeout <10-5000><10-5000>Configures the timeout period, in milliseconds, for a handshake message to retire. Once this period is exceed, the handshake message is retired.• <10-5000> – Specify a value from 10 - 5000 milliseconds. The default is 500 milliseconds.• <10-5000> – Optional. Configures a different timeout between the second and third attemptswpa-wpa2 Modifies TKIP-CCMP (WPA/WPA2) related parameterskey-rotation Configures parameters related to periodic rotation of encryption keys. The periodic key rotation parameters are broadcast, multicast, and unicast traffic.broadcast <30-86400>Configures the periodic rotation of keys used for broadcast and multicast traffic. This parameter specifies the interval, in seconds, at which keys are rotated. This option is disabled by default.• <30-86400> – Specify a value from 30 - 86400 seconds.unicast <30-86400> Configures a periodic interval for the rotation of keys, used for unicast traffic. This option is disabled by default.• <30-86400> – Specify a value from 30 - 86400 seconds.wpa-wpa2 Modifies TKIP-CCMP (WPA/WPA2) related parameterspsk Configures a pre-shared key. The key options are: 0, 2, and LINE0 <LINE> Configures a clear text key2 <LINE> Configures an encrypted key<LINE> Enter the pre-shared key either as a passphrase not exceeding 8 - 63 characters, or as a 64 character (256bit) hexadecimal valuewpa-wpa2 Modifies TKIP-CCMP (WPA/WPA2) parameterstkip-countermeasuresConfigures a hold time period for implementation of TKIP counter measuresholdtime <0-65535> Configures the amount of time a WLAN is disabled when TKIP counter measures are invoked• <0-65535> – Specify a value from 0 - 65535 seconds. The default is 60 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-809.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5454.1.97.2.53 servicewlan-mode commandsInvokes service commands applicable in the WLAN configuration modeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxservice [allow-ht-only|allow-open-passpoint|client-load-balancing|cred-cache|eap-mac-mode|eap-mac-multicopy|eap-mac-multikeys|eap-throttle|enforce-pmkid-validation|key-index|monitor|radio-crypto|reauthentication|session-timeout|tx-deauth-on-roam-detection|unresponsive-client|wpa-wpa2|show]service [allow-ht-only|allow-open-passpoint|cred-cache [clear-on-4way-timeout|clear-on-disconnect]|eap-mac-multicopy|eap-mac-multikeys|enforce-pmkid-validation|radio-crypto|reauthentication seamless|session-timeout mac|tx-deauth-on-roam-detection|show cli]service eap-mac-mode [mac-always|normal]service eap-throttle <0-254>service key-index eap-wep-unicast <1-4>service monitor [aaa-server|adoption|captive-portal|dhcp|dns]service monitor [aaa-server|adoption vlan <1-4094>|captive-portal external-server]service monitor [dhcp|dns] crm <RESOURCE-NAME> vlan <1-4094>service unresponsive-client [attempts <1-1000>|ps-detect {threshold <1-1000>}|timeout <1-60>]service wpa-wpa2 exclude-ccmpParameters• service [allow-ht-only|allow-open-passpoint|cred-cache [clear-on-4way-timeout|clear-on-disconnect]|eap-mac-multicopy|eap-mac-multikeys|enforce-pmkid-validation|radio-crypto|reauthentication seamless|session-timeout mac|tx-deauth-on-roam-detection|show cli]allow-ht-only Only allows clients capable of High Throughput (802.11n) data rates to associate. This option is disabled by default.allow-open-passpoint Enables non-WPA2 security for passpoint WLANs. This option is disabled by default.For more information on passpoint policy and configuration, see PASSPOINT POLICY.cred-cache [clear-on-4way-timeout|clear-on-disconnect]Clears credential cache based on the parameter passed• clear-on-4way-timeout – Clears cached client credentials after the 4way handshake with a client has timed out. This option is enabled by default.• clear-on-disconnect – Clears cached client credentials after the client has disconnected from the network. This option is disabled by default.eap-mac-multicopy Enables sending of multiple copies of broadcast and unicast messages. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-811.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 546• service eap-mac-mode [mac-always|normal]• service eap-throttle <0-254>• service key-index eap-wep-unicast <1-4>• service wpa-wpa2 exclude-ccmpeap-mac-multikeys Enables configuration of different key indices for MAC authentication. This option is disabled by default.enforce-pmkid-validationValidates the Predictive real-time pairwise master key identifier (PMKID) contained in a client’s association request against the one present in the wpa-wpa2 handshake. This option is enabled by default.This functionality is based on the Proactive Key Caching (PKC) extension of the 802.11i EEEE standard. Whenever a wireless client successfully authenticates with a AP it receives a pairwise master key (PMK). PKC allows clients to cache this PMK and reuse it for future re-authentications with the same AP. The PMK is unique for every client and is identified by the PMKID. The PMKID is a combination of the hash of the PMK, a string, the station and the MAC addresses of the AP.radio-crypto Uses radio hardware for encryption and decryption. This is applicable only for devices using Counter Cipher Mode with Block Chaining Message Authentication Code Protocol (CCMP) encryption mode. This option is enabled by default.reauthentication seamlessEnables seamless EAP client reauthentication without disconnecting client after the session has timed out. This option is enabled by default.session-timeout mac Enables reauthentication of MAC authenticated clients without disconnecting client after the session has timed out. This option is enabled by default.tx-deauth-on-roam-detectionTransmits a deauthentication on the air while disassociating a client because its roam is detected on the wired side. This option is disabled by default.show cli Displays the CLI tree of the current mode. When used in the WLAN mode, this command displays the WLAN CLI structure.eap-mac-mode Configures the EAP and/or MAC authentication mode used with this WLAN. This option is enabled by default.mac-always Enables both EAP and MAC authentication. MAC authentication is performed first, followed by EAP authentication. Clients are granted access based on the EAP authentication result. If a client does not have EAP, the MAC authentication result is used to grant access.normal Grants client access if the client clears either EAP or MAC authentication. This is the default setting.eap-throttle <0-254> Enables EAP request throttling. Use this command to specify the maximum number of parallel EAP sessions allowed on this WLAN. Once this specified value is exceeded, all incoming EAP session requests are throttled. This option is enabled by default.• <0-254> – Specify a value from 0 - 254. This default value is 0.key-index eap-wep-unicast <1-4>Configures an index with each key during EAP authentication with WEP. This option is enabled by default.• <1-4> – Select a index from 1 - 4. The default value is 1.wpa-wpa2 exclude-ccmpConfigures exclusion of CCMP requests when the authentication mode is set to tkip-ccmp. When enabled, it provides compatibility for client devices not compliant with tkip-ccmp. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-812.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 547• service monitor [aaa-server|adoption vlan <1-4094>|captive-portal external-server]• service monitor [dhcp|dns] crm <RESOURCE-NAME> vlan <1-4094>]monitor Enables critical resource monitoring. In a WLAN, service monitoring enables regular monitoring of external AAA servers, captive portal servers, access point adoption, DHCP and DNS servers. When enabled, it allows administrators to notify users of a service’s availability and make resource substitutions in case of unavailability of a service.aaa-server Enables external AAA server failure monitoring. When enabled monitors an external RADIUS server resource’s AAA activity and ensures its adoption and availability. This feature is disabled by default.adoption vlan <1-4094>Enables adoption failure monitoring on an adopted AP. Also configures a adoption failover VLAN. This feature is disabled by default.• VLAN <1-4094> – Specify the VLAN on which clients are placed when the connectivity between the AAP and the controller is lost.Configure a DHCP pool and gateway for the failover VLAN. Ensure the DHCP server is running on the AP. Also ensure that the DHCP pool is configured to have less lease time.When this feature is enabled on a WLAN, it allows adopted APs to monitor their connectivity with the controller. If and when this connectivity is lost, all new clients are placed in the configured adoption failover VLAN. They are served an IP by the DHCP server running on the AP. In this situation if a client tries to access a Web URL, the AP redirects the client to a page stating that the service is down.When the AAP’s link to the switch is restored, clients are placed back in the WLAN’s configured VLAN, and are served an IP from the corresponding configured DHCP server (external or on the AP/controller).captive-portal external-serverEnables external captive portal server failure monitoring. When enabled, monitors externally hosted captive portal activity, and user access to the controller or service platform managed network. This feature is disabled by default.When enabled, this feature enables APs to display, to an externally located captive portal’s user, the no-service page when the captive portal’s server is not reachable.monitor Enables DHCP and/or DNS server monitoring on this WLAN.dhcp Enables monitoring of a specified DHCP server. When the connection to the DHCP server is lost, captive portal users automatically migrate to a pre-defined VLAN. The feature is disabled by default.Use the crm keyword to specify the DHCP server to monitor.dns Enables monitoring of a specified DNS server. When the connection to the DNS server is lost, captive portal users automatically migrate to a pre-defined VLAN. The feature is disabled by default.Use the crm keyword to specify the DNS server to monitor.crm <RESOURCE-NAME>This keyword is common to the ‘dhcp’ and ‘dns’ parameters.• crm – Identifies the DHCP and/or DNS server to monitor• <RESOURCE-NAME> – Specify the name of the DHCP or DNS server.Once enabled, the CRM server monitors the DHCP/DNS server and updates their status as ‘up’ or ‘down’ depending on the availability of the resource. When either of these resources is down the wireless client is mapped to the failover VLAN and served with the ‘no-service’ page through the access point.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-813.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 548• service unresponsive-client [attempts <1-1000>|ps-detect {threshold <1-1000>}|timeout <1-60>]Examplerfs4000-229D58(config-wlan-test)#service allow-ht-onlyrfs4000-229D58(config-wlan-test)#service monitor aaa-serverrfs4000-229D58(config-wlan-test)#show contextwlan test ssid test vlan 1 bridging-mode tunnel encryption-type none authentication-type none service monitor aaa-server service allow-ht-only controller-assisted-mobilityrfs4000-229D58(config-wlan-test)#Related Commandsvlan <1-4094> This keyword is common to the ‘dhcp’ and ‘dns’ parameters.After specifying the DHCP/DNS sever resource, specify the failover VLAN.• VLAN <1-4094> – Configures the failover VLAN from 1 - 4094.When the DHCP server resource becomes unavailable, the device falls back to the VLAN defined here. This VLAN has a DHCP server configured that provides a pool of IP addresses with a lease time less than the main DHCP server.When this DNS server resource becomes unavailable, the device falls back to the VLAN defined here. This VLAN has a DNS server configured that provides DNS address resolution until the main DNS server becomes available.eap-mac-mode Configures handling of unresponsive clientsattempts <1-1000> Configures the maximum number of successive packets that failed transmission• <1-1000> – Specify a value from 1 - 1000. The default is 7.ps-detect {threshold <1-1000>}Enables the detection of power-save mode clients, whose PS stats has not been updated on the AP. This option is enabled by default.• threshold – Optional. Configures the threshold at which power-save client detection is triggered• <1-1000> – Configures the number of successive unacknowledged packets received before power-save detection is triggered. Specify a value from 1 - 1000. Thedefault is 3.timeout <1-60> Configures the interval, in seconds, for successive packets not acknowledged by the client• <1-60> – Specify a value from 1 - 60 seconds. The default is 3 seconds.no Removes or reverts to default WLAN settings configured using the ‘service’ command](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-814.png)




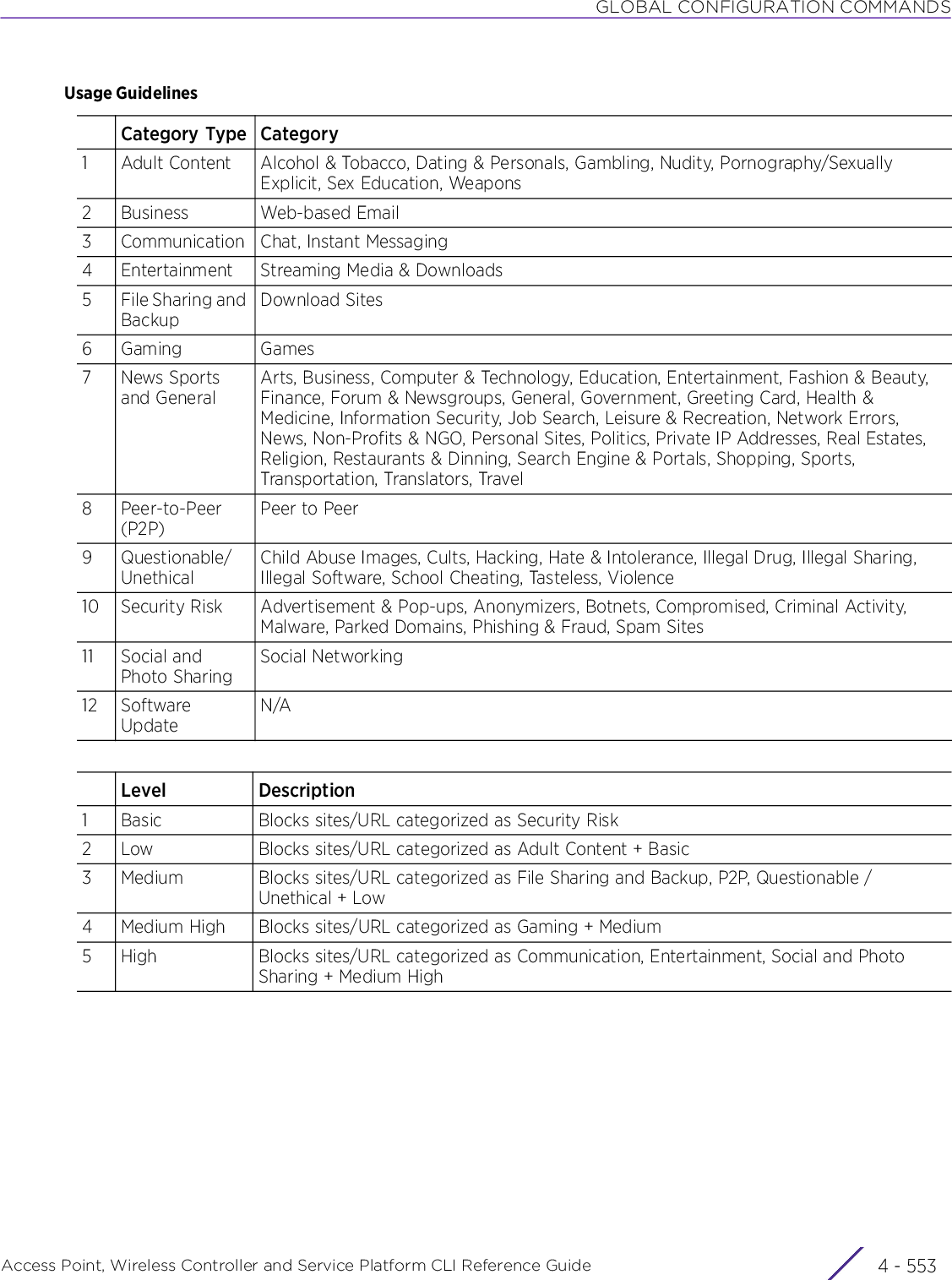
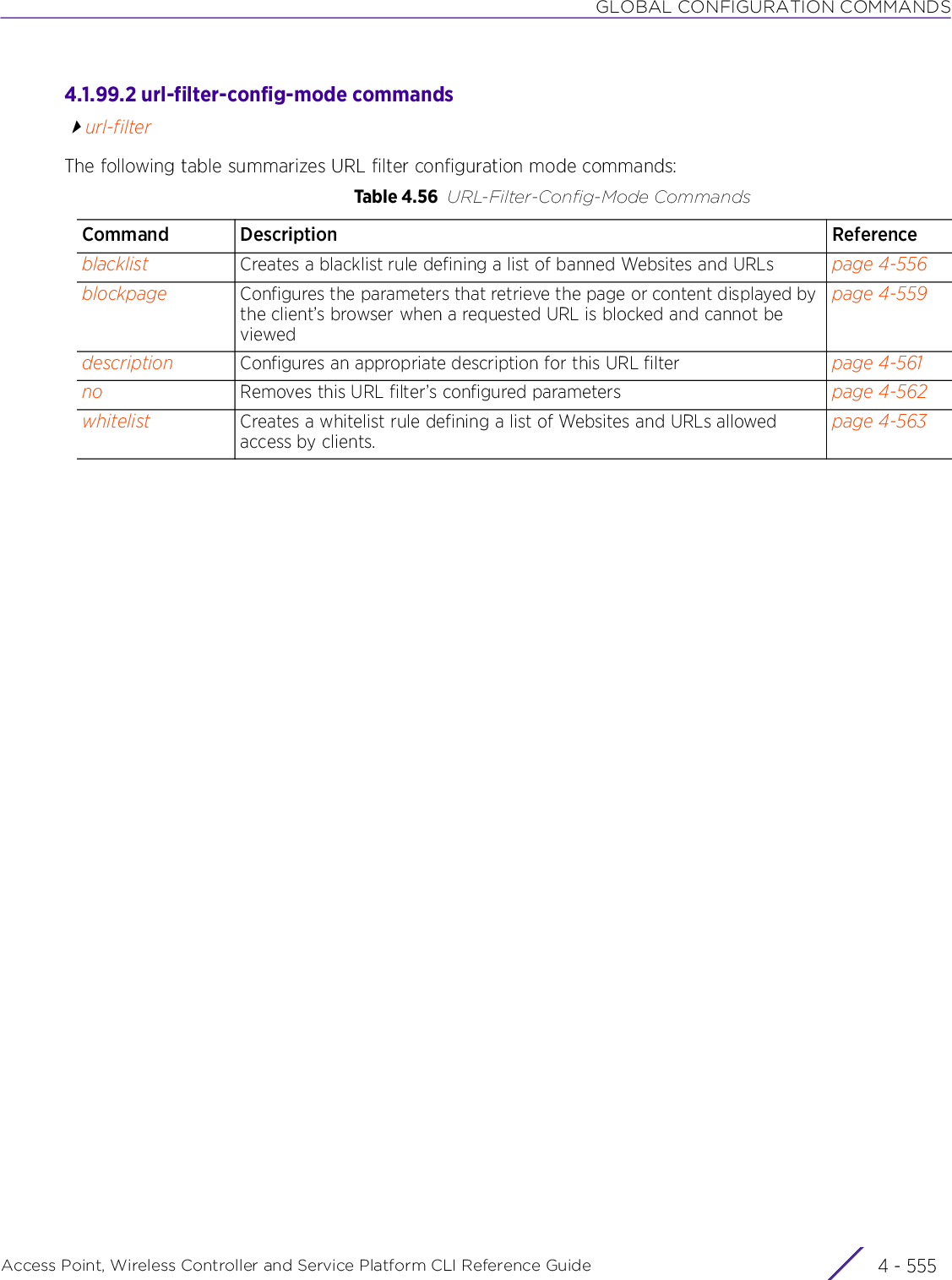
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5564.1.99.2.1 blacklisturl-filter-config-mode commandsCreates a blacklist rule. A blacklist is a list of Websites and URLs denied access by clients. Clients requesting blacklisted URLs are presented with a page displaying the ‘Web page blocked’ message. Parameters relating to this page are configured using the ‘blockpage’ option.URL filtering is based on the classification of Websites into pre-defined category-types. Some of the category-types are further divided into multiple categories. Currently available are 12 built-in category types, and 64 categories. These built-in category-types and categories cannot be modified.Use the available options to identify the URL category-types and categories to include in the blacklist.In addition to identifying URLs by the categories and category-types they are classified into, the system also provides five (5) levels of Web filtering (basic, high, low, medium, and medium-high). Each level identifies a specific set of URL categories to blacklist. For more information on category-types, categories, and URL filtering levels, see url-filter.Supported in the following platforms:• Access Points — AP6522, AP6532, AP7131, AP7502, AP7522, AP7532, AP7562, AP8132• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxblacklist [category-type|level|url-list]blacklist category-type [adult-content|all|business|communication|entertainment|file-sharing-backup|gaming|news-sports-general|p2p|questionable|security-risk|social-photo-sharing|software-updates] precedence <1-500> {description <LINE>}blacklist level [basic|high|low|medium|medium-high] precedence <1-500> {description <LINE>}blacklist url-list <URL-LIST-NAME> precedence <1-500> {description <LINE>}Parameters• blacklist category-type [adult-content|all|business|communication|entertainment|file-sharing-backup|gaming|news-sports-general|p2p|questionable|security-risk|social-photo-sharing|software-updates] precedence <1-500> {description <LINE>}blacklist category-type <SELECT-CATEGORY-TYPE>Selects the category-type to blacklist. A category is a pre-defined URL list available in the WiNG software. Categories are based on an external database, and cannot be modified or removed. Custom categories can created with the URL List and added to the database.Websites have been classified into the following 12 category types:adult-content, business, communication, entertainment, file-sharing-backup, gaming, news-sports-general, p2p, questionable, security-risk, social-photo-sharing, and software-updatesContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-822.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 557• blacklist level [basic|high|low|medium|medium-high] precedence <1-500> {description <LINE>}• blacklist url-list <URL-LIST-NAME> precedence <1-500> {description <LINE>}Examplerfs6000-81742D(config-url-filter-test)#blacklist level medium-high precedence 10rfs6000-81742D(config-url-filter-test)#blacklist category-type adult-content category alcohol-tobacco precedence 1rfs6000-81742D(config-url-filter-test)#blacklist category-type security-risk category botnets precedence 3Select ‘all’ to blacklist all category-types.Some of the category-types are further classified into categories. For example, the ‘adult-content’ category-type is differentiated into the following categories:• alcohol-tobacco, dating-personals, gambling, nudity, pornography-sexually-explicit, sex-education, and weapons.The system blocks all categories (URLs falling within their limits) within the selected category-type.precedence <1-500>Configures the precedence value for this blacklist rule. Rules are applied in the increasing order of their precedence. Therefore, rules with lower precedence are applied first.description <LINE> Optional. Configures a description (not exceeding 80 characters) for this blacklist rule. Enter a description that allows you to identify the purpose of the rule.blacklist level [basic|high|low|medium|medium-high]Configures the Web filtering level as basic, high, low, medium, or medium-high. Each of these filter-levels are pre-configured to use a set of category types and this mapping cannot be modified. precedence <1-500>Configures the precedence value for this blacklist rule. Rules are applied in the increasing order of their precedence. Therefore, rules with lower precedence are applied first.description <LINE> Optional. Configures a description (not exceeding 80 characters) for this blacklist rule. Enter a description that allows you to identify the purpose of the rule.blacklist url-list <URL-LIST-NAME>Associates a URL list with this URL filter. When associated with a blacklist rule, all URLs listed in the specified URL list are blacklisted.URL lists are customized categories included in the custom filter-level setting. URL lists enable an administrator to blacklist or whitelist URLs in addition to the built-in categories. For more information on configuring a URL list, see url-list.• <URL-LIST-NAME> – Enter URL list name (should be existing and configured)precedence <1-500>Configures the precedence value for this blacklist rule. Rules are applied in the increasing order of their precedence. Therefore, rules with lower precedence are applied first.description <LINE> Optional. Configures a description (not exceeding 80 characters) for this blacklist rule. Enter a description that allows you to identify the purpose of the rule.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-823.png)

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5594.1.99.2.2 blockpageurl-filter-config-mode commandsConfigures the parameters that retrieve the page or content displayed by the client’s browser when a requested URL is blocked and cannot be viewedSupported in the following platforms:• Access Points — AP6522, AP6532, AP7131, AP7502, AP7522, AP7532, AP7562, AP8132• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxblockpage [external|internal|path]blockpage path [external|internal]blockpage external url <URL>blockpage internal [content|footer|header|main-logo|org-name|org-signature|small-logo|title] <LINE/IMAGE-URL>Parameters• blockpage path [external|internal]• blockpage external url <URL>• blockpage internal [content|footer|header|main-logo|org-name|org-signature|small-logo|title] <LINE/IMAGE-URL>blockpage path [external|internal]Specifies if the location of the page displayed, to the client when a requested URL is blocked, is external or internal• external – Indicates the page displayed is hosted on an external Web server resource. If selecting this option, use the blockpage > external > url <URL> command to provide the path to the external Web server hosting the page.internal – Indicates the page displayed is hosted internally. This is the default setting. If selecting this option, use the blockpage > internal > <SELECT-PAGE-TYPE> > <LINE/IMAGE-URL> command to define the page configuration.blockpage external url <URL>Configures the URL of the external Web server hosting the page (displayed to the client when a requested URL is blocked). • url <URL> – Specify the URL of the Web server and the blocking page nameValid URLs should begin with http:// or https://The URL can contain query strings.Use '&' or '?' character to separate field-value pair.Enter 'ctrl-v' followed by '?' to configure query stringsblockpage internal [content|footer|header|main-logo|org-name|org-signature|small-logo|title] <LINE/IMAGE-URL>Configures the internally hosted blocking page parameters, such as the content displayed, page footer and header, organization (the organization enforcing the Web page blocking) details (name, signature, and logo), and page title• content – Configures the text (message) displayed on the blocking page• footer – Configures the text displayed as the blocking page footerContd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-825.png)
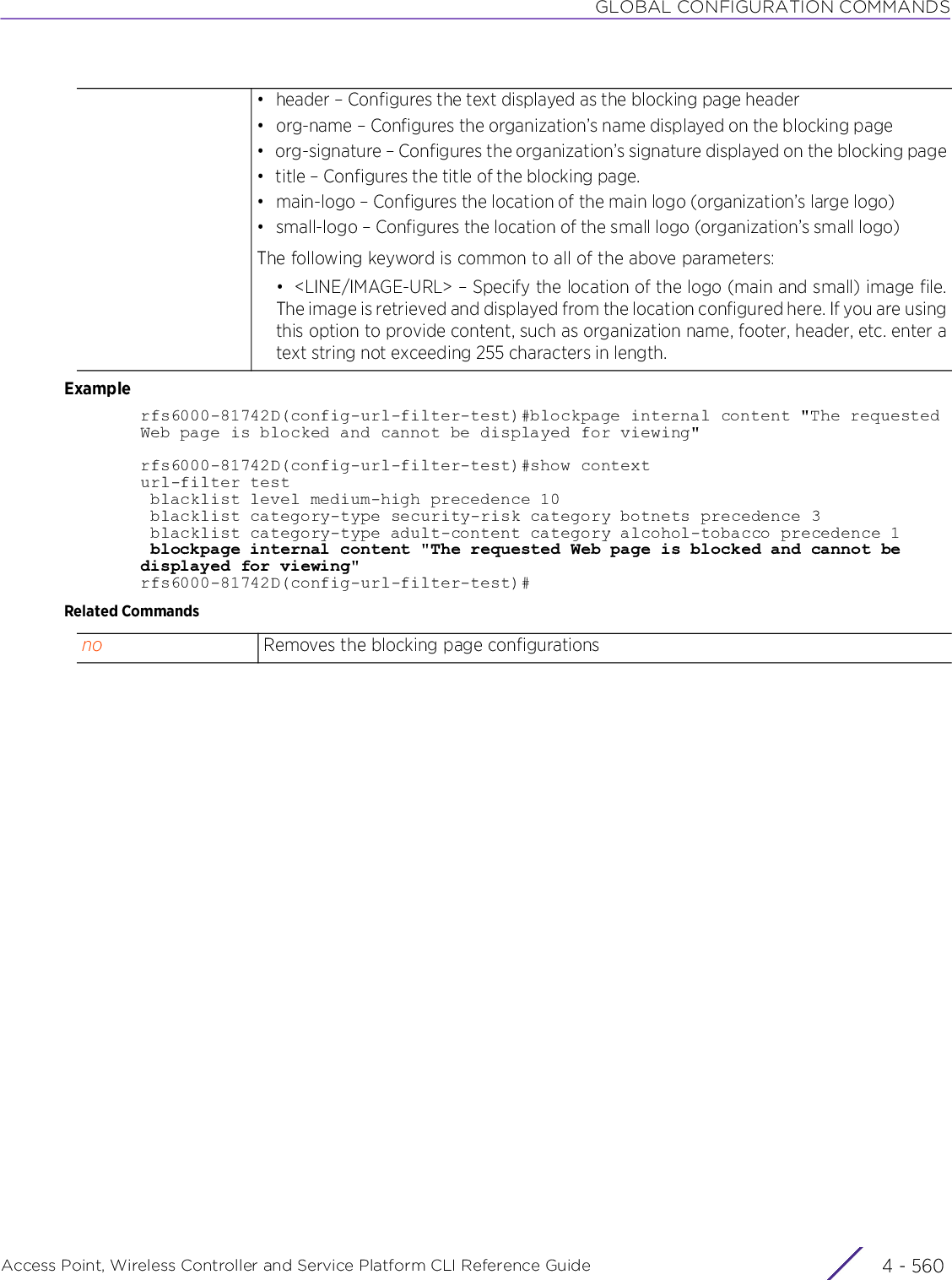

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5624.1.99.2.4 nourl-filter-config-mode commandsUse the no command to remove this URL filter’s configured parametersSupported in the following platforms:• Access Points — AP6522, AP6532, AP7131, AP7502, AP7522, AP7532, AP7562, AP8132• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [blacklist|blockpage|description|whitelist]no blacklist [category-type|level|url-list]no blacklist [category-type <SELECT-CATEGORY-TYPE>|level <SELECT-LEVEL>|url-list <URL-LIST-NAME>] precedence <1-500>no blockpage [external|internal [content|footer|header|main-logo|org-name|org-signature|small-logo|title]|path]no descriptionno whitelist [category-type|url-list]no whitelist [category-type <SELECT-CATEGORY-TYPE>|url-list <URL-LIST-NAME>] precedence <1-500>Parameters• no <PARAMETERS>ExampleThe following example displays the URL filter ‘test’ settings before the ‘no’ is executed:rfs6000-81742D(config-url-filter-test)#show contexturl-filter test description "Blacklists sites inappropriate for children and are security risks." blacklist level medium-high precedence 10 whitelist category-type communication category chat precedence 7 blacklist category-type security-risk category botnets precedence 3 blacklist category-type adult-content category alcohol-tobacco precedence 1 blockpage internal content "The requested Web page is blocked and cannot be displayed for viewing"rfs6000-81742D(config-url-filter-test)#rfs6000-81742D(config-url-filter-test)#no descriptionrfs6000-81742D(config-url-filter-test)#no blacklist category-type adult-contentcategory alcohol-tobacco precedence 1rfs6000-81742D(config-url-filter-test)#no whitelist category-type communicationcategory chat precedence 7The following example displays the URL filter ‘test’ settings after the ‘no’ is executed:rfs6000-81742D(config-url-filter-test)#show contexturl-filter test blacklist level medium-high precedence 10 blacklist category-type security-risk category botnets precedence 3 blockpage internal content "The requested Web page is blocked and cannot be displayed for viewing"rfs6000-81742D(config-url-filter-test)#no <PARAMETERS> Removes this URL filter’s configured parameters based on the values passed here](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-828.png)
![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5634.1.99.2.5 whitelisturl-filter-config-mode commandsCreates a whitelist rule. A whitelist is a list of Websites and URLs allowed access by clients.URL filtering is based on the classification of Websites into pre-defined category-types. Some of the category-types are further divided into multiple categories. Currently available are 12 built-in category types, and 64 categories. These built-in category-types and categories cannot be modified.Use the available options to identify the category-types and categories to include in the whitelist.Supported in the following platforms:• Access Points — AP6522, AP6532, AP7131, AP7502, AP7522, AP7532, AP7562, AP8132• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwhitelist [category-type|url-list]whitelist category-type [adult-content|all|business|communication|entertainment|file-sharing-backup|gaming|news-sports-general|p2p|questionable|security-risk|social-photo-sharing|software-updates] precedence <1-500> {description <LINE>}whitelist url-list <URL-LIST-NAME> precedence <1-500> {description <LINE>}Parameters• whitelist category-type [adult-content|all|business|communication|entertainment|file-sharing-backup|gaming|news-sports-general|p2p|questionable|security-risk|social-photo-sharing|software-updates] precedence <1-500> {description <LINE>}whitelist category-type <SELECT-CATEGORY-TYPE>Selects the category-type to add to this whitelist. A category is a pre-defined URL list available in the WiNG software. Categories are based on an external database, and cannot be modified or removed. Custom categories can created with the URL List and added to the database.Websites have been classified into the following 12 category types: adult-content, business, communication, entertainment, file-sharing-backup, gaming, news-sports-general, p2p, questionable, security-risk, social-photo-sharing, and software-updates.Select ‘all’ to whitelist all category-types.Some of the category-types are further classified into categories. For example, the ‘adult-content’ category-type is differentiated into the following categories:• alcohol-tobacco, dating-personals, gambling, nudity, pornography-sexually-explicit, sex-education, and weapons.The system allows all categories (URLs falling within their limits) within the selected category-type.precedence <1-500>Configures the precedence value for this whitelist rule. Rules are applied in the increasing order of their precedence. Therefore, rules with lower precedence are applied first.description <LINE> Optional. Configures a description (not exceeding 80 characters) for this whitelist rule. Enter a description that allows you to identify the purpose of the rule.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-829.png)


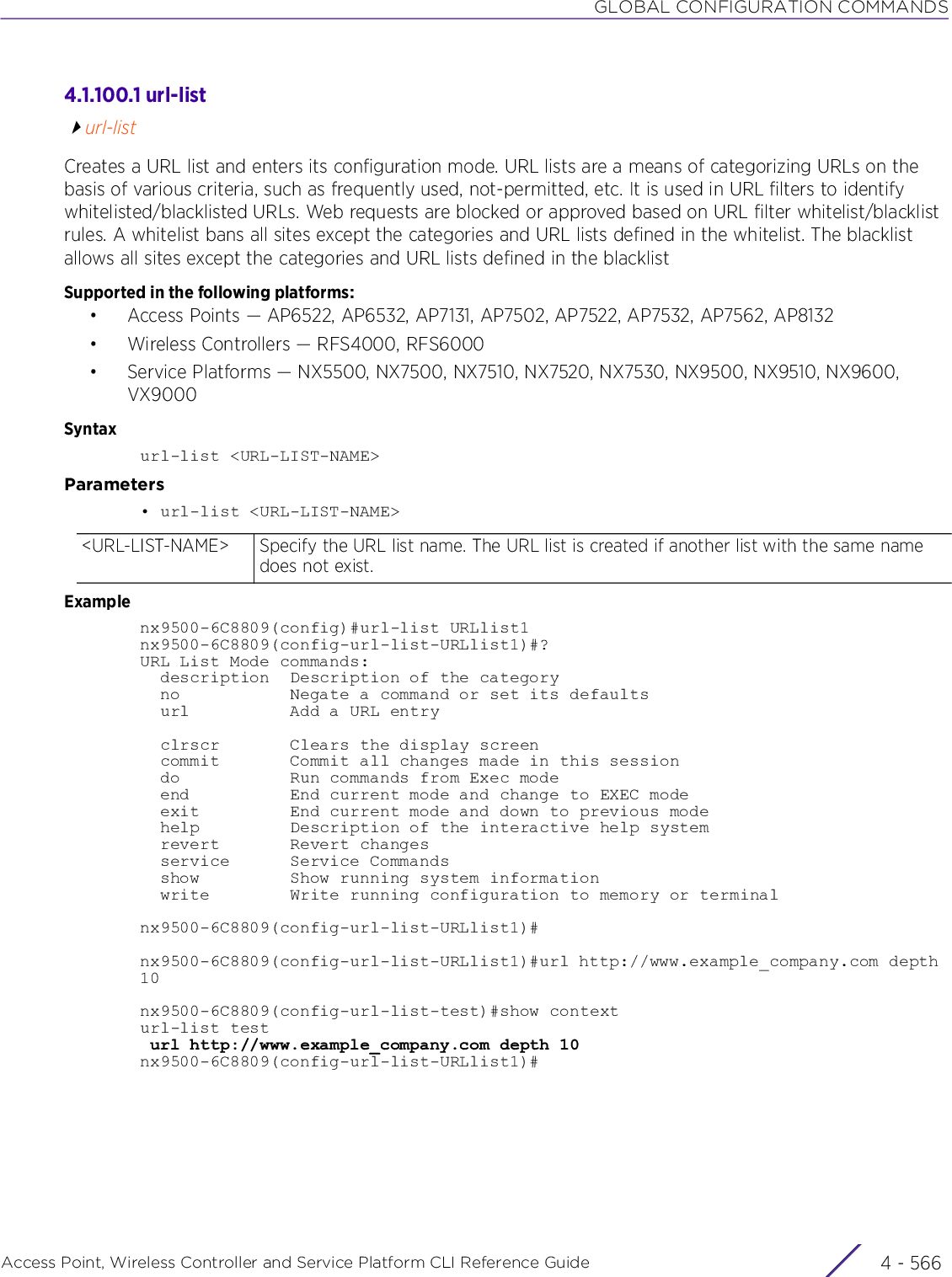
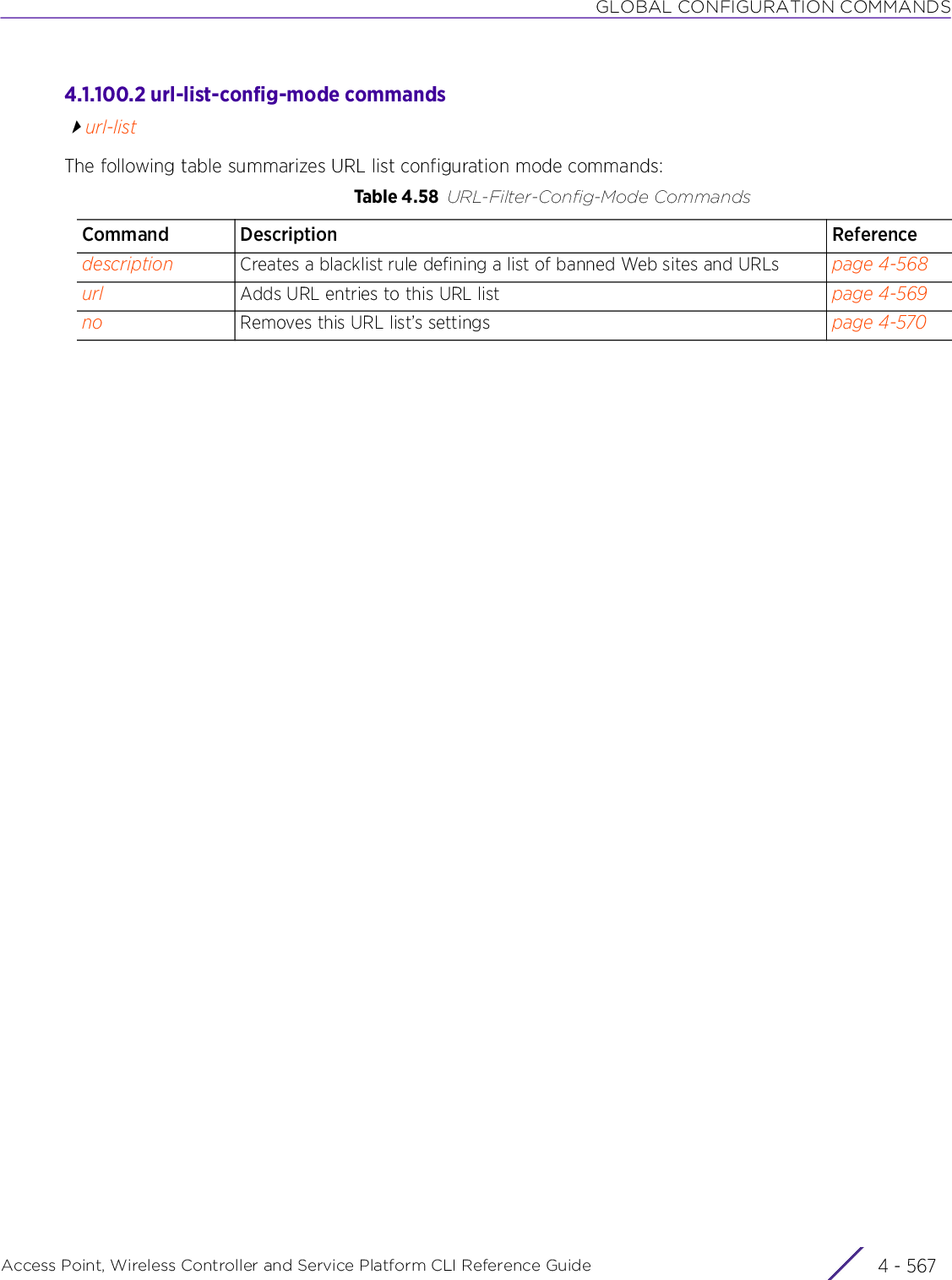

![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 5704.1.100.2.3 nourl-list-config-mode commandsRemoves this URL list’s settingsSupported in the following platforms:• Access Points — AP6522, AP6532, AP7131, AP7502, AP7522, AP7532, AP7562, AP8132• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [description|url]no descriptionno url <WORD>Parameters• no <PARAMETERS>ExampleThe following example displays the URL list ‘test’ settings before the ‘no’ command is executed:nx9500-6C8809(config-url-list-test)#show contexturl-list test description “This URL list contains social communication URLS” url https://www.facebook.com depth 5nx9500-6C8809(config-url-list-test)#nx9500-6C8809(config-url-list-test)#no url www.facebook.comThe following example displays the URL list ‘test’ settings after the ‘no’ command is executed:nx9500-6C8809(config-url-list-test)#show contexturl-list test description “This URL list contains social communication URLS”nx9500-6C8809(config-url-list-test)#no <PARAMETERS> Removes this URL’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-836.png)


![GLOBAL CONFIGURATION COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 4 - 574 previous mode help Description of the interactive help system revert Revert changes service Service Commands show Show running system information write Write running configuration to memory or terminalnx9500-6C8809(config-device-11-22-33-44-55-66)#vx-0099CC(config-device-00-0C-29-00-99-CC)~*#license ? WORD Feature name (AP/AAP/ADSEC/HTANLT/VX) for which license is to be addedvx-0099CC(config-device-00-0C-29-00-99-CC)~*#license vx 80ee9649eddc94b48b5a35d7eaf8e73b376a51649291714d04c84769b0fc4b3766816878d2739c24vx-0099CC(config-device-00-0C-29-00-99-CC)~*#com wrJan 16 13:48:11 2014: vx-0099CC : %SYSTEM-6-CONFIG_COMMIT: Configuration commit by user 'root' (mapsh) from 'Console'Jan 16 13:48:11 2014: vx-0099CC : %SYSTEM-6-CONFIG_REVISION: Configuration revision updated to 9 from 8Jan 16 13:48:12 2014: vx-0099CC : %LICMGR-6-LIC_INSTALLED: VX license installed[OK]vx-0099CC(config-device-00-0C-29-00-99-CC)~*#Jan 16 13:48:12 2014: vx-0099CC : %SYSTEM-6-CONFIG_REVISION: Configuration revision updated to 10 from 9vx-0099CC(config-device-00-0C-29-00-99-CC)~*#vx-0099CC(config-device-00-0C-29-00-99-CC)~*#vx-0099CC(config-device-00-0C-29-00-99-CC)~*#sh licenses Serial Number : 000C290099CCC0A80001WARNING: Recommended minimum system resource requirements not met for the current license pack or cluster configs. Please check user guide and reconfigure the systemDevice Licenses: AP-LICENSE String : Value : 10240 AAP-LICENSE String : Value : 10240 ADVANCED-SECURITY String : DEFAULT-ADV-SEC-LICENSE VX-LICENSE String : 80ee9649eddc94b48b5a35d7eaf8e73b376a51649291714d04c84769b0fc4b3766816878d2739c24Cluster Licenses: AP-LICENSE Value : 10240 Used : 0 AAP-LICENSE Value : 10240 Used : 0Cluster MAX AP Capacity: Value : 10240 Used : 0Active Members:---------------------------------------------------------------------------------------------------MEMBER SERIAL LIC TYPE VALUE BORROWED TOTAL NO.APS NO.AAPS ---------------------------------------------------------------------------------------------------00-0C-29-00-99-CC 000C290099CCC0A80001 AP 10240 0 10240 0 0](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-840.png)



![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 45.1.2 commitCommon CommandsCommits changes made in the active session. Use the commit command to save and invoke settings entered during the current transaction.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcommit {write}{memory}Parameters• commit {write}{memory}Examplenx9500-6C8809#commit write memory[OK]nx9500-6C8809#write Optional. Commits changes made in the current sessionmemory Optional. Writes to memory. This option ensures current changes persist across reboots.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-845.png)



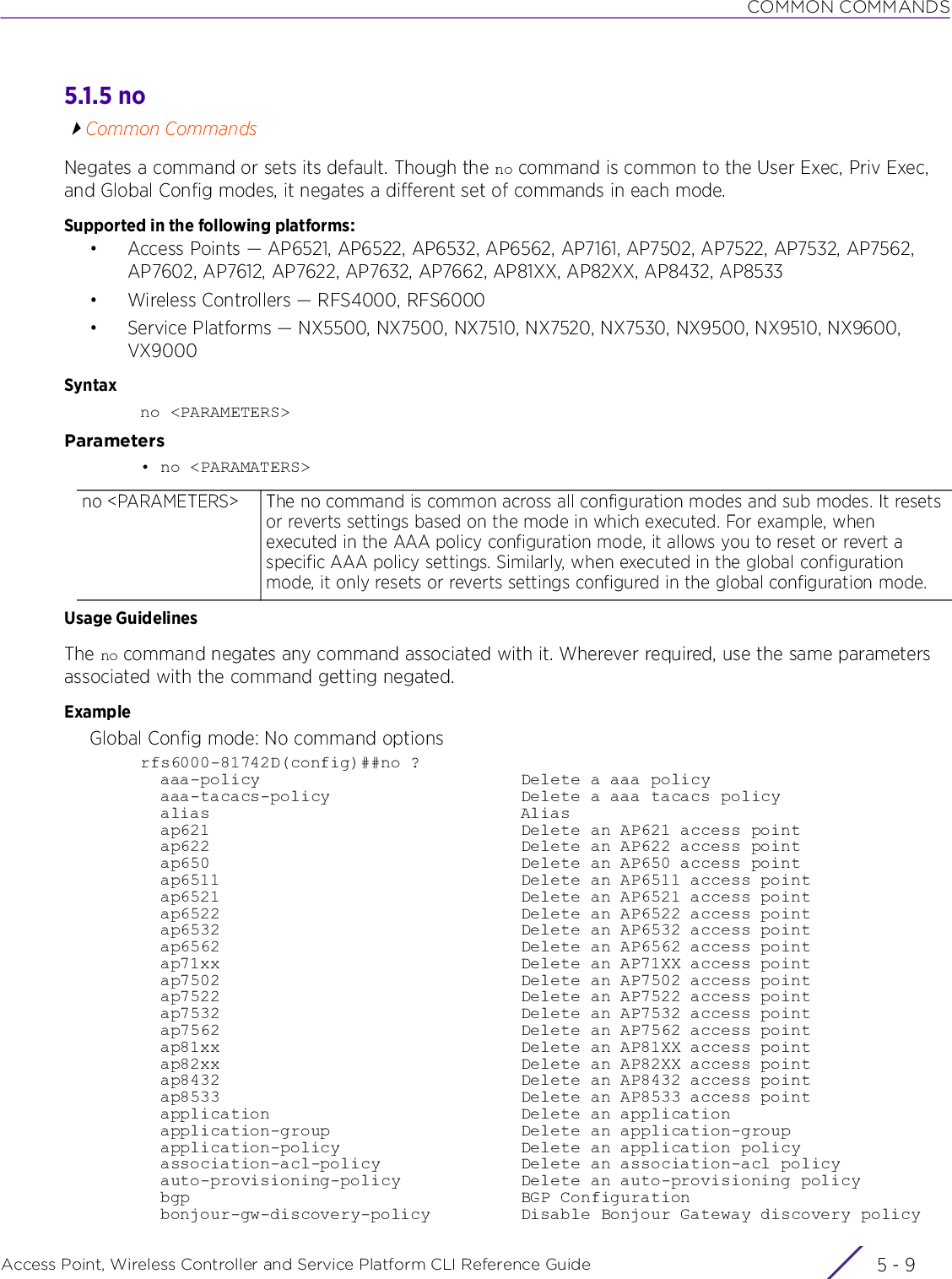
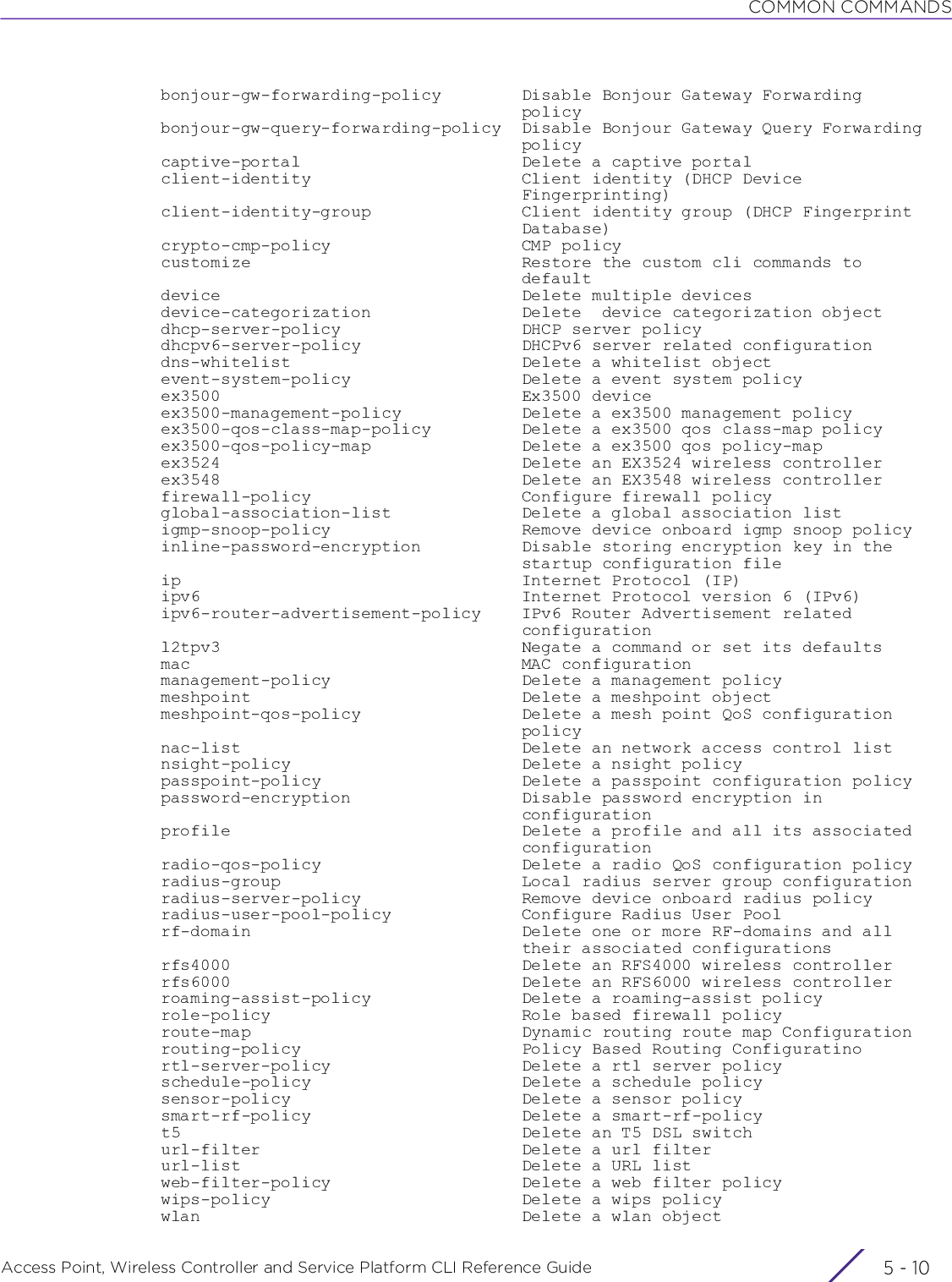
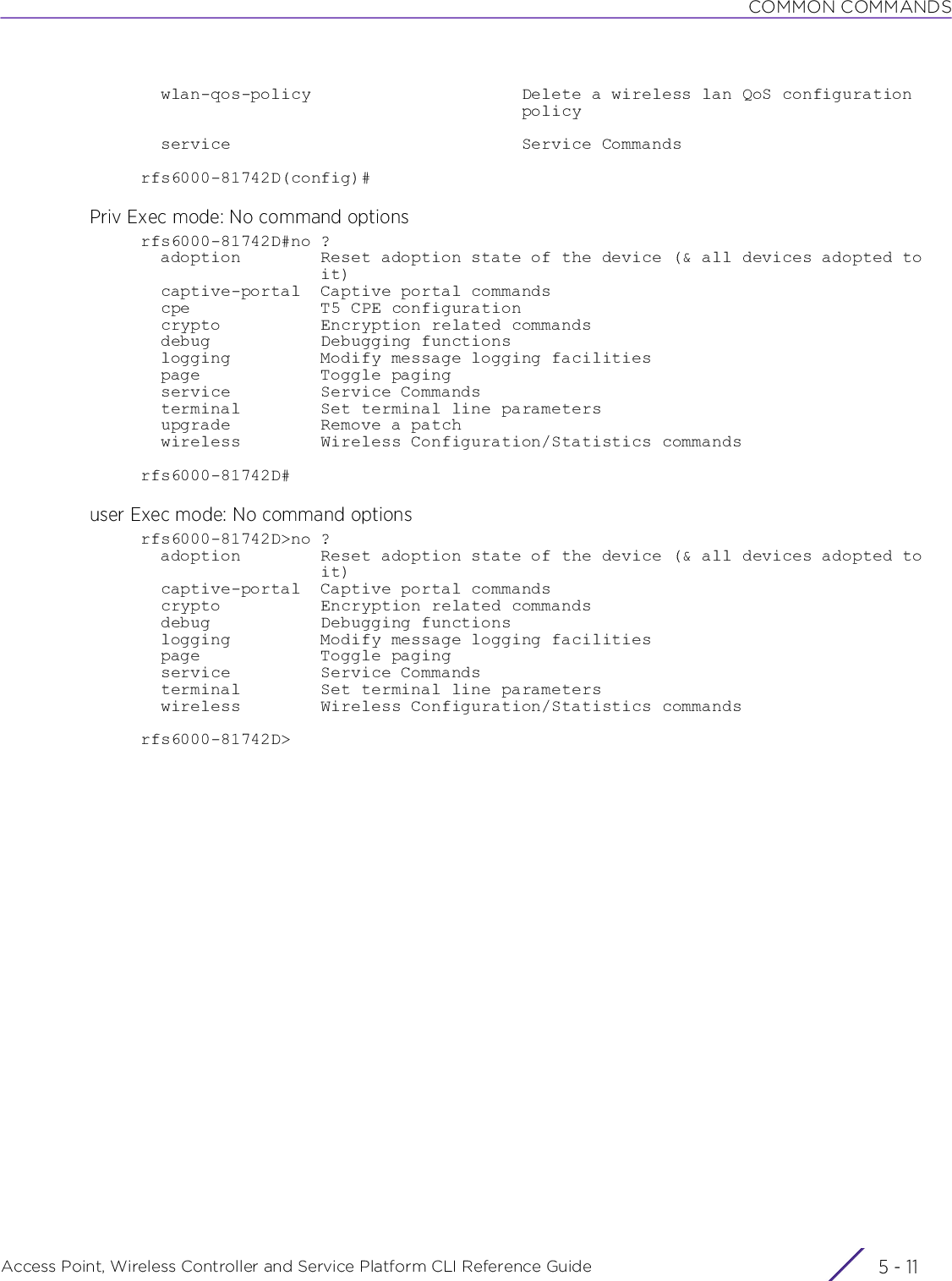

![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 135.1.7 serviceCommon CommandsService commands are used to view and manage configurations. The service commands and their corresponding parameters vary from mode to mode. The User Exec mode and Priv Exec mode commands provide same functionalities with a few minor changes. The Global Config service command sets the size of history files. It also enables viewing the current mode’s CLI tree.This section consists of the following sub-sections:•Syntax (User Exec Mode)•Syntax (Privilege Exec Mode)•Syntax (Privilege Exec Mode: NX9500 and NX9510)Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntax (User Exec Mode)service [block-adopter-config-update|clear|cli-tables-skin|cluster|database|delete-offline-aps|force-send-config|force-update-vm-stats|guest-registration|load-balancing|load-ssh-authorized-keys|locator|nsight|radio|radius|request-full-config-from-adopter|set|show|smart-rf|ssm|snmp|syslog|wireless]service [block-adopter-config-update|request-full-config-from-adopter]service clear [adoption|captive-portal-page-upload|command-history|device-upgrade|diag|dpi|file-sync|noc|reboot-history|unsanctioned|upgrade-history|virtual-machine-history|web-filter|wireless|xpath]service clear adoption history {on <DEVICE-NAME>}service clear device-upgrade history {on <DOMAIN-NAME>}service clear dpi [all|app|app-category] stats {on <DEVICE-OR-DOMAIN-NAME>}service clear diag pktsservice clear file-sync history {on <DOMAIN-NAME>}service clear captive-portal-page-upload history {on <DOMAIN-NAME>}service clear [command-history|reboot-history|upgrade-history|virtual-machine-history] {on <DEVICE-NAME>}service clear noc statisticsservice clear unsanctioned aps {on <DEVICE-OR-DOMAIN-NAME>}service clear web-filter cache {on <DEVICE-NAME>}service clear wireless [ap|client|controller-mobility-database|dns-cache|radio|wlan]service clear wireless controller-mobility-databaseservice clear wireless [ap|client] statistics {<MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}service clear wireless dns-cache on {(on <DEVICE-OR-DOMAIN-NAME)}service clear wireless radio statistics {<MAC/HOSTNAME>} {<1-3>} {(on <DEVICE-OR-DOMAIN-NAME>)}service clear wireless wlan statistics {<WLAN-NAME>} {(on <DEVICE-OR-DOMAIN-NAME)}service clear xpath requests {<1-100000>}service cli-tables-skin [ansi|hashes|minimal|none|percent|stars|thick|thin|utf-8] {grid}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-854.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 14service cluster force [active|configured-state|standby]service database [authentication|start-shell]service database authentication [create-user|delete-user]service database authentication create-user username <USER-NAME> password <PASSWORD>service database authentication delete-user username <USER-NAME>Note, the other service > database command options are documented latter in this section under the (Privilege Exec Mode) section.service database start-shellservice delete-offline-aps [all|offline-for]service delete-offline-aps offline-for days <0-999> {time <TIME>}service force-send-config {on <DEVICE-OR-DOMAIN-NAME>}service force-update-vm-stats {on <DEVICE-NAME>}service guest-registration [backup|delete|export|import]service guest-registration backup [delete|restore]service guest-registration delete [all|email <EMAIL-ADD>|group <RAD-GROUP-NAME>|mac <MAC>|mobile <MOBILE-NUMBER>|name <CLIENT-FULL-NAME>|non-social|offline-for days <1-999>|otp-incomplete-for days <1-999>|social [facebook|google]|wlan <WLAN-NAME>]service guest-registration export format [csv|json] <DEST-URL> {(rfdomain <DOMAIN-NAME>|time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]|wlan <WLAN-NAME>)}service guest-registration import format <JSON> <SOURCE-URL>service load-balancing clear-client-capability [<MAC>|all] {on <DEVICE-NAME>}service load-ssh-authorized-keys <PUBLIC-KEY> {on <DEVICE-NAME>}service locator {<1-60>} {(on <DEVICE-NAME>)}service nsight clear-offline [all|offline-for days <0-999> {time <TIME>}]service radio <1-3> [adaptivity|channel-switch|dfs]service radio <1-3> adaptivityservice radio <1-3> channel-switch <36-196> [160|20|40|80]service radio <1-3> dfs simulator-radar [extension|primary]service radius test [<IP>|<HOSTNAME>] [<WORD>|port]service radius test [<IP>|<HOSTNAME>] <WORD> <USERNAME> <PASSWORD> {wlan <WLAN-NAME> ssid <SSID>} {(on <DEVICE-NAME>)}service radius test [<IP>|<HOSTNAME>] port <1024-65535> <WORD> <USERNAME> <PASSWORD> {wlan <WLAN-NAME> ssid <SSID>} {(on <DEVICE-NAME>)}service set validation-mode [full|partial] {on <DEVICE-NAME>}service show [block-adopter-config-update|captive-portal|cli|client-identity-defaults|command-history|configuration-revision|crash-info|dhcp-lease|diag|fast-switching|fib|fib6|guest-registration|info|ip-access-list|mac-vendor|mem|mint|noc|nsight|pm|process|reboot-history|rf-domain-manager|sites|snmp|ssh-authorized-keys|startup-log|sysinfo|top|upgrade-history|virtual-machine-history|watch-dog|wireless|xpath-history]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-855.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 15service show block-adopter-config-updateservice show captive-portal [log-internal|servers|user-cache]service show captive-portal log-internalservice show captive-portal [servers|user-cache] {on <DEVICE-NAME>}service show [cli|client-identity-defaults|configuration-revision|mac-vendor <OUI/MAC>|noc diag|snmp session|xpath-history]service show [command-history|crash-info|info|mem|process|reboot-history|startup-log|ssh-authorized-keys|sysinfo|top|upgrade-history|watchdog] {on <DEVICE-NAME>}service show ip-access-list wlan <WLAN-NAME> status {detail} {on <DEVICE-OR-DOMAIN-NAME>}service show dhcp-lease {<INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1} (on <DEVICE-NAME>)}service show diag [fds|led-status|pkts|psu|stats]service show diag [fds|pkts]service show diag [led-status|psu|stats] {on <DEVICE-NAME>}service show fast-switching {on <DEVICE-NAME>}service show [fib|fib6] {table-id <0-255>}service show guest-registration [export-status|import-status|restore-status]service show mint [adopted-devices {on <DEVICE-NAME>}|ports]service show pm {history} {(on <DEVICE-NAME>)}service show rf-domain-manager [diag|info] {<MAC/HOSTNAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}service show sitesservice show virtual-machine-history {on <DEVICE-NAME>}service show wireless [aaa-stats|adaptivity-status|client|config-internal|credential-cache|dns-cache|log-internal|meshpoint|neighbors|radar-status|radio-internal|reference|stats-client|vlan-usage]service show wireless [aaa-stats|adaptivity-status|credential-cache|dns-cache|radar-status|vlan-usage] {on <DEVICE-NAME>}service show wireless [config-internal|log-internal|neighbors]service show wireless [client|meshpoint neighbor] proc [info|stats] {<MAC>} {{on <DEVICE-OR-DOMAIN-NAME>)}service show wireless radio-internal [radio1|radio2] <LINE>service show wireless reference [channels|frame|handshake|mcs-rates|reason-codes|status-codes]service show wireless stats-client diag {<MAC/HOSTNAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}service smart-rf [clear-config|clear-history|clear-interfering-aps|save-config]service smart-rf clear-config {<MAC>|<DEVICE-NAME>|on <DOMAIN-NAME>}service smart-rf [clear-history||clear-interfering-aps|save-config] {on <DOMAIN-NAME>}service snmp sysoid wing5](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-856.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 16service ssm [dump-core-snapshot|trace]service ssm trace pattern <WORD> {on <DEVICE-NAME>}service syslog test {level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]} {(on <DEVICE-NAME>)}service wireless [client|dump-core-snapshot|meshpoint|qos|trace|unsanctioned|wips]service wireless client [beacon-request|quiet-element|trigger-bss-transition|trigger-wnm]service wireless client beacon-request <MAC> mode [active|passive|table] ssid [<SSID>|any] channel-report [<CHANNEL-LIST>|none] {on <DEVICE-NAME>}service wireless client quiet-element [start|stop]service wireless client trigger-bss-transition mac <MAC> {timeout <0-65535>} {url <URL>} {on <DEVICE-OR-DOMAIN-NAME>}service wireless client trigger-wnm mac <MAC> type [deauth-imminent|subscription-remediation] {uri <WORD>}service wireless dump-core-snapshotservice wireless meshpoint zl <MESHPOINT-NAME> [on <DEVICE-NAME>] {<ARGS>|timeout <1-65535>}service wireless qos delete-tspec <MAC> tid <0-7>service wireless trace pattern <WORD> {on <DEVICE-NAME>}service wireless unsanctioned ap air-terminate <MAC> {on <DOMAIN-NAME>}service wireless wips [clear-client-blacklist|clear-event-history|dump-managed-config]service wireless wips clear-client-blacklist [all|mac <MAC>]service wireless wips clear-event-history {on <DEVICE-OR-DOMAIN-NAME>}Parameters (User Exec Mode)service• service [block-adopter-config-update|request-full-config-from-adopter]• service clear adoption history {on <DEVICE-NAME>}block-adopter-config-updateBlocks the configuration updates sent from the NOC serverrequest-full-config-from-adopterConfigures a request for full configuration updates from the adopter deviceIn an hierarchically managed (HM) network devices are deployed in two levels. The first level consists of the Network Operations Center (NOC) controllers. The second level consists of the site controllers that can be grouped to form clusters. The NOC controllers adopt and manage the site controllers. Access points within the network are adopted and managed by the site controllers. The adopted devices (access points and site controllers) are referred to as the adoptee. The devices adopting the adoptee are the ‘adopters’.clear adoption history Clears adoption history on this device and its adopted access points](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-857.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 17• service clear device-upgrade history {on <DOMAIN-NAME>}• service clear diag pkts• service clear dpi [all|app|app-category] stats {on <DEVICE-OR-DOMAIN-NAME>}• service clear file-sync history {on <DOMAIN-NAME>}• service clear captive-portal-page-upload history {on <DOMAIN-NAME>}on <DEVICE-NAME> Optional. Clears adoption history on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.clear device-upgrade historyClears device upgrade historyon <DOMAIN-NAME> Optional. Clears all firmware upgrade history in a specified RF Domain• <DOMAIN-NAME> – Specify the RF Domain name.clear diag pkts Clears the looped packets queue logged by the dataplane. The dataplane logs up to 16 looped packets at a time in a separate queue, which has to be manually cleared to make space for new packet logging.For more information on viewing logged looped packet information execute the service > show > diag > pkts command.clear dpi Clears Deep Packet Inspection (DPI) statisticsWhen enabled, DPI allows application and/or application category recognition. The DPI statistics are maintained by the system for every hit registered by the DPI engine.[all|app|app-category] statsUse the following filter options to clear all or specific DPI statistics:• all – Clears all DPI related (application and app-category) statistics• app – Clears only application related statistics• app-category – Clears only app-category related statisticson <DEVICE-OR-DOMAIN-NAME>Optional. Clears DPI statistics based on the parameters passed on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the access point, controller, service platform, or RF Domain.clear file-sync history Clears client-bridge certificate synchronization statisticsWhen an AP6522/AP6562 access point is configured as a client bridge, the EAP-TLS X.509 (PKCS#12) certificate is synchronized between the staging-controller and adoptee AP6522/AP6562 client-bridge access points. This command allows you to clear client-bridge certificate synchronization statistics.on <DOMAIN-NAME> Optional. Clears file synchronization history on all devices within a specified RF Domain• <DOMAIN-NAME> – Specify the RF Domain name.clear captive-portal-page-upload historyClears captive portal page upload historyon <DOMAIN-NAME> Optional. Clears captive portal page upload history on a specified RF Domain• <DOMAIN-NAME> – Specify the RF Domain name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-858.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 18• service clear [command-history|reboot-history|upgrade-history|virtual-machine-history] {on <DEVICE-NAME>}• service clear noc statistics• service clear unsanctioned aps {on <DEVICE-OR-DOMAIN-NAME>}• service clear wireless [ap|client] {<MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}• service clear wireless controller-mobility-database• service clear web-filter cache {on <DEVICE-NAME>}clear [command-history|reboot-history|upgrade-history]Clears command history, reboot history, or device upgrade historyclear virtual-machine-historyClears virtual-machine history on the logged device or a specified deviceThis command is applicable only on the NX9500 and NX9510 series service platforms.on <DEVICE-NAME> Optional. Clears history on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.When executing the clear virtual-machine-history command, provide the name of the service platform running the VMs.clear noc statistics Clears Network Operations Center (NOC) applicable statistics countersclear unsanctioned apsClears the unsanctioned APs liston <DEVICE-OR-DOMAIN-NAME>Optional. Clears the unsanctioned APs list on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.clear wireless [ap|client] statisticsClears wireless statistics counters based on the parameters passed• ap statistics – Clears applicable AP statistics counters• client statistics – Clears applicable wireless client statistics counters• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller,service platform, or RF Domain.<MAC> {on <DEVICE-OR-DOMAIN-NAME>}The following keywords are common to the ‘ap’ and ‘client’ parameters:• <MAC> – Optional. Clears statistics counters for a specified AP or client. Specify the AP/client MAC address.• on <DEVICE-OR-DOMAIN-NAME> – Optional. Clears AP/client statistics counterson a specified device or RF Domain. Specify the name of the AP, wireless controller,service platform, or RF Domain.clear wireless controller-mobility-databaseClears the controller assisted mobility databaseclear web-filter cache Clears the cache used for Web filtering](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-859.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 19• service clear wireless radio statistics {<MAC/HOSTNAME>} {<1-3>} {(on <DEVICE-OR-DOMAIN-NAME>)}• service clear wireless wlan statistics {<WLAN-NAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}• service clear xpath requests {<1-100000>}• service cli-tables-skin [ansi|hashes|minimal|none|percent|stars|thick|thin|utf-8] {grid}on <DEVICE-NAME> Optional. Clears the Web filtering cache on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.clear wireless radio statisticsClears applicable wireless radio statistics counters<MAC/HOSTNAME> <1-3>Optional. Specify the MAC address or hostname of the radio, or append the interface number to form the radio ID in the AA-BB-CC-DD-EE-FF:RX or HOSTNAME:RX format.• <1-3> – Optional. Specify the radio interface index, if not specified as part of the radio ID.on <DEVICE-OR-DOMAIN-NAME> Optional. This is a recursive parameter, which clears wireless radio statistics on a specified device or RF Domain. Specify the name of the device.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.clear wireless wlan statisticsClears WLAN statistics counters<WLAN-NAME> Optional. Clears statistics counters on a specified WLAN. Specify the WLAN name.on <DEVICE-OR-DOMAIN-NAME>Optional. This is a recursive parameter, which clears WLAN statistics on a specified device or RF Domain. Specify the name of the device.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.clear xpath Clears XPATH related informationrequests Clears pending XPATH get requests<1-100000> Optional. Specifies the session number (cookie from show sessions)• <1-100000> – Specify the session number from 1 - 100000.Note: Omits clearing the current session’s pending XPATH get requests.cli-tables-skin [ansi|hashes|minimal|none|percent|stars|thick|thin|uf-8]Selects a formatting layout or skin for CLI tabular outputs• ansi – Uses ANSI characters for borders• hashes – Uses hashes (#) for borders• minimal – Uses one horizontal line between title and data rows• none – Displays space separated items with no decoration• percent – Uses the percent sign (%) for borders• stars – Uses asterisks (*) for borders• thick – Uses thick lines for bordersContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-860.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 20• service cluster force [active|configured-state|standby]• service database authentication create-user username <USER-NAME> password <PASSWORD>• database authentication delete-user username <USER-NAME>• service database start-shell• service delete-offline-aps all• service delete-offline-aps offline-for days <0-999> {time <TIME>}• thin – Uses thin lines for borders• utf-8 – Uses UTF-8 characters for bordersgrid Optional. Uses a complete grid instead of just title linescluster Enables cluster protocol managementforce Forces action commands on a cluster (active, configured-state, and standby)active Changes the cluster run status to activeconfigured-state Restores a cluster to the configured statestandby Changes the cluster run status to standbydatabase Performs database related actionsThis command is supported only on the NX95XX, NX9600, and VX9000 platforms.authentication create-user username <USER-NAME> password <PASSWORD>Creates users having access rights to the database. Execute this command on the database host. However, before creating users, on the database, generate the database keyfile. For more information on generating the keyfile, see database.• username <USER-NAME> – Configures databse username• password <PASSWORD> – Configures a password for the username specifiedaboveIn the database-policy ensure that authentication is enabled and username and password is configured. The database-client-policy also should have the same username and password configured. For more information on database-policy and database-client-policy, see database-policy and database-client-policy.database Performs database related actionsThis command is supported only on the NX95XX, NX9600, and VX9000 platforms.database authentication delete-user username <USER-NAME>Deletes the username requires to access rights the captive-portal/NSight database• username <USER-NAME> – Deletes the username identified by the <USER-NAME> keywordOnce deleted, the database cannot be accessed using the specified combination of username and password.database Performs database related actionsThis command is supported only on the NX95XX, NX9600, and VX9000 platforms.start-shell Starts the database shelldelete-offline-aps all Deletes all off-line access pointsdelete-offline-aps Deletes off-line access points for a specified interval](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-861.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 21• service force-send-config {on <DEVICE-OR-DOMAIN-NAME>}• service force-update-vm-stats {on <DEVICE-NAME>}• service guest-registration backup [delete|restore]• service guest-registration delete [all|email <EMAIL-ADD>|group <RAD-GROUP-NAME>|mac <MAC>|mobile <MOBILE-NUMBER>|name <CLIENT-FULL-NAME>|non-social|offline-for days <1-999>|wlan <WLAN-NAME>|otp-incomplete-for days <1-999>|social [facebook|google]day <0-999> Deletes off-line access points for a specified number of days• <0-999> – Specify the number of off-line days from 0 - 999.time <TIME> Optional. Deletes off-line access points for a specified time• <TIME> – Specify the time in HH:MM:SS format.force-send-config Resends configuration to device(s)on <DEVICE-OR-DOMAIN-NAME>Optional. Resends configuration to a specified device or all devices in a specified RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.force-update-vm-stats Forcefully pushes VM statistics on to the NOCon <DEVICE-NAME> Optional. Executes the command on a specified device• <DEVICE-NAME> – Specify the name of the device.service guest-registration backup [delete|restore]Deletes or restores all guest registration backup snapshots based on the parameter passed• delete – Deletes all guest registration backup snapshots• restores – Restores all guest registration backup snapshotsNote: To view the status of the restore process, use the service > show > guest-registration > restore-status command.service guest-registration deleteDeletes a specified user or all user records from the guest-registration databaseTo delete a specific user, use one of the following options as an identification parameter: email, group, mac, mobile number, name, offline-for, wlan, otp-incomplete-for, or social.[all|email <EMAIL-ADD>|group <RAD-GROUP-NAME>|mac <MAC>|mobile <MOBILE-NUMBER>|name <CLIENT-FULL-NAME>]|non-social|offline-for days <1-999>|wlan <WLAN-NAME>|otp-incomplete-for days <1-999>|social [facebook|google]Following are the user filtering options: The user identified by one of the following parameters is deleted from the guest-registration database.• email <EMAIL-ADD> – Identifies user by the e-mail address• <EMAIL-ADD> – Provide the user’s e-mail address.• mac <MAC> – Identifies user by the MAC address• <MAC> – Provide the user’s MAC address.• group <RAD-GROUP-NAME> – Identifies users by their RADIUS group association• <RAD-GROUP-NAME> – Specify the RADIUS group name.• mobile <MOBILE-NUMBER> – Identifies user by the registered mobile number• <MOBILE-NUMBER> – Provide the user’s mobile number.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-862.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 22• service guest-registration export format [csv|json] <DEST-URL> {(rfdomain <DOMAIN-NAME>|time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]|wlan <WLAN-NAME>)}• name <CLIENT-FULL-NAME> – Identifies user by the registered full name• <CLIENT-FULL-NAME> – Provide the user’s full name.• non-social – Identifies users that have not registered through social authentication• offline-for days <1-999> – Filters users who have not accessed the network for a specified number of days• days <1-999> – Specify the number of days from 1 - 999.• wlan <WLAN-NAME> – Identifies users accessing a specified WLAN• <WLAN-NAME> – Specify the WLAN name.• otp-incomplete-for days <1-999> – Identifies records of users that have not used their one-time-password (OTP) to complete registration within a specified number of days• days <1-999> – Specify the number of days from 1 - 999.• social [facebook|google] – Identifies users using either Facebook or Google credentials to access the network• facebook – Identifies users using Facebook authentication• google – Identifies users using Google authenticationservice guest-registration exportExports guest registration user data files in the Comma-Separated Values (CSV) or JavaScript Object Notation (JSON) formatUse the ‘rfdomain’, ‘wlan’, and ‘time’ options to filter users for a specified RF Domain, WLAN, and/or time period. These are recursive parameters and you can apply all or any of these three filters.format [csv|json] Specifies the file format. The options are:• csv – Exports user data files in the CSV format• json – Exports user data files in the JSON format<DEST-URL> Configures the destination URL. The files are exported to the specified location. Both IPv4 and IPv6 address formats are supported.IPv4 URLs: tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/fileIPv6 URLs: tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/filerfdomain <DOMAIN-NAME>Optional. Filters user data based on RF Domain name. Only the filtered data are exported.• <DOMAIN-NAME> – Specify the RF Domain name.wlan <WLAN-NAME>Optional. Filters user data based on WLAN name. Only the filtered data are exported.• <WLAN-NAME> – Specify the WLAN name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-863.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 23• service guest-registration import format json <SOURCE-URL>• service load-balancing clear-client-capability [<MAC>|all] {on <DEVICE-NAME>}• service load-ssh-authorized-keys <PUBLIC-KEY> {on <DEVICE-NAME>}time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]Optional. Filters user data for a specified time period. Only the filtered data are exported.• 1-Day – Filters and exports previous day’s data• 1-Month – Filters and exports previous month’s data• 1-Week – Filters and exports previous week’s data• 2-Hours – Filters and exports last 2 hours data• 30-Mins – Filters and exports last 30 minutes data• 5-Hours – Filters and exports last 5 hours data• all – Exports the entire databaseservice guest-registration importImports user data from a specified locationformat json Specifies the file format• json – Imports user data files in the JSON format<SOURCE-URL> Configures the Source URL. The files are imported from the specified location. Both IPv4 and IPv6 address formats are supported.IPv4 URLs: tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>:<passwd>@<hostname|IP>[:port]>/path/fileIPv6 URLs: tftp://<hostname|[IPv6]>[:port]/path/fileftp://<user>:<passwd>@<hostname|[IPv6]>[:port]/path/filesftp://<user>:<passwd>@<hostname|[IPv6]>[:port]>/path/fileload-balancing Enables wireless load balancing by clearing client capability recordsclear-client-capability[<MAC>|all]Clears a specified client or all client’s capability records• <MAC> – Clears capability records of a specified client. Specify the client’s MAC address in the AA-BB-CC-DD-EE-FF format.• all – Clears the capability records of all clientson <DEVICE-NAME> Optional. Clears client capability records on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.load-ssh-authorized-keysLoads SSH public (client) key on a device<PUBLIC-KEY> Enter the public key. The public key should be in the OpenSSH rsa/dsa format.on <DEVICE-NAME> Optional. Loads the specified public key on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-864.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 24• service locator {<1-60>} {(on <DEVICE-NAME>)}• service nsight clear-offline [all|offline-for days <0-999> {time <TIME>}]• service radio <1-3> adaptivity• service radio <1-3> channel-switch <36-196> [160|20|40|80|80-80]• service radio <1-3> dfs simulate-radar [extension|primary]locator Enables LEDs<1-60> Sets LED flashing time from 1 - 60 seconds.on <DEVICE-NAME> The following keyword is recursive and common to the <1-60> parameter:• on <DEVICE-NAME> – Optional. Enables LEDs on a specified device• <DEVICE-NAME> – Specify name of the AP, wireless controller, or service plat-form.nsight clear-offline [all|offline-for days <0-999> {time <TIME>}]Clears NSight data received from offline controllers, based on the parameters passed. Select one of the following options:• all – Clears NSight data received from all offline controllers• offline-for days <0-999> time <TIME> – Clears NSight data received from controllers that have been offline for a specified time period• days <0-999> – Specifies the number of days controllers have been offline• <0-999> – Specify the number of days from 0 - 999 days. Select “0” to identifycontrollers offline less than 24 hours.• time <TIME> – Optional. Specifies the total time for which controllers havebeen offline• <TIME> – Specify the time in HH:MM:SS format.Note: This command is applicable only to the NX95XX, NX9600, and VX9000 platforms.radio <1-3> Configures radio’s parameters• <1-3> – Specify the radio index from 1 - 3.adaptivity Simulates the presence of interference on the current channelradio <1-3> Configures radio’s parameters• <1-3> – Specify the radio index from 1 - 3.channel-switch <36-196> [160|20|40|80|80-80]Enables channel switching• <36-196> – Specifies the channel to switch to from 36 - 196.• 160|20|40|80|80-80] – Specifies the bandwidth for the above specified channel.Select the appropriate option.radio <1-3> Configures radio’s parameters• <1-3> – Specify the radio index from 1 - 3.dfs Enables Dynamic Frequency Selection (DFS)simulate-radar [extension|primary]Simulates the presence of a radar on a channel. Select the channel type from the following options:• extension – Simulates a radar on the radio’s current extension channel• primary – Simulates a radar on the radio’s current primary channel](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-865.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 25• service radius test [<IP>|<HOSTNAME>] <WORD> <USERNAME> <PASSWORD> {wlan <WLAN-NAME> ssid <SSID>} {(on <DEVICE-NAME>)}• service radius test [<IP>|<HOSTNAME>] port <1024-65535> <WORD> <USERNAME> <PASSWORD> {wlan <WLAN-NAME> ssid <SSID>} {(on <DEVICE-NAME>)}• service set validation-mode [full|partial] {on <DEVICE-NAME>}radius test Tests RADIUS server’s account. This command sends an access-request packet to the RADIUS server. Use this command to confirm time and data/bandwidth parameters for valid wireless clients.• test – Tests the RADIUS server’s account with user provided parameters[<IP>|<HOSTNAME>] Sets the RADIUS server’s IP address or hostname• <IP> – Specifies the RADIUS server’s IP address• <HOSTNAME> – Specifies the RADIUS server’s hostname<WORD> Specify the RADIUS server’s shared secret.<USERNAME> Specify username for authentication.<PASSWORD> Specify the password.wlan <WLAN-NAME> ssid <SSID>Optional. Tests the RADIUS server on the local WLAN. Specify the local WLAN name.• ssid <SSID> – Specify the local RADIUS server’s SSID.on <DEVICE-NAME> Optional. This is a recursive parameter also applicable to the WLAN parameter. Performs tests on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.radius test Tests a RADIUS server’s account. This command sends an access-request packet to the RADIUS server. Use this command to confirm time and data/bandwidth parameters for valid wireless clients.• test – Tests the RADIUS server’s account with user provided parameters[<IP>|<HOSTNAME>] Sets the IP address or hostname of the RADIUS server• <IP> – Specify the RADIUS server’s IP address.• <HOSTNAME> – Specify the RADIUS server’s hostname.port <1024-65535> Specify the RADIUS server port from 1024 - 65535. The default port is 1812.<WORD> Specify the RADIUS server’s shared secret.<USERNAME> Specify username for authentication.<PASSWORD> Specify the password.wlan <WLAN-NAME> ssid <SSID>Optional. Tests the RADIUS server on the local WLAN. Specify the local WLAN name.• ssid <SSID> – Specify the RADIUS server’s SSID.on <DEVICE-NAME> Optional. This is a recursive parameter also applicable to the WLAN parameter. Performs tests on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.set Sets the validation mode for running configuration validation](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-866.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 26• service show block-adopter-config-update• service show captive-portal log-internal• service show captive-portal [servers|user-cache] {on <DEVICE-NAME>}• service show [cli|client-identity-defaults|configuration-revision|mac-user-import-status|mac-vendor <OUI/MAC>|noc diag|snmp session|xpath-history]validation-mode [full|partial]Sets the validation mode• full – Performs a full configuration validation• partial – Performs a partial configuration validationon <DEVICE-NAME> Optional. Performs full or partial configuration validation on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.show Displays running system statistics based on the parameters passedblock-adopter-config-updateDisplays NOC configuration blocking statusshow Displays running system statistics based on the parameters passedcaptive-portal Displays captive portal informationlog-internal Displays recent captive portal debug logs (information and above severity level)show Displays running system statistics based on the parameters passedcaptive-portal Displays captive portal informationservers Displays server information for active captive portalsuser-cache Displays cached user details for a captive portalon <DEVICE-NAME> Optional. Displays server information or cached user details on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.show Displays running system statistics based on the parameters passedcli Displays CLI tree of the current modeclient-identity-defaultsDisplays default client-identities and their configurationconfiguration-revision Displays current configuration revision numbermac-user-import-statusDisplays status of file import initiated by a MAC-usermac-vendor <OUI/MAC>Displays vendor name for a specified MAC address or Organizationally Unique Identifier (OUI) part of the MAC address• <OUI/MAC> – Specify the MAC address or its OUI. The first six digits of the MAC address is the OUI. Use the AABBCC or AA-BB-CC format to provide the OUI.noc diag Displays NOC diagnostic detailssnmp session Displays SNMP session detailsxpath-history Displays XPath history](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-867.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 27• service show [command-history|crash-info|info|mem|process|reboot-history|startup-log|ssh-authorized-keys|sysinfo|top|upgrade-history|watchdog] {on <DEVICE-NAME>}• service show ip-access-list wlan <WLAN-NAME> status {detail} {on <DEVICE-OR-DOMAIN-NAME>}• service show dhcp-lease {<INTERFACE-NAME>|on|pppoe1|vlan <1-4094>|wwan1} {(on <DEVICE-NAME>)}show Displays running system statistics based on the parameters passedcommand-history Displays command history (lists all commands executed)crash-info Displays information about core, panic, and AP dump filesinfo Displays snapshot of available support informationmem Displays a system’s current memory usage (displays the total memory and available memory)process Displays active system process information (displays all processes currently running on the system)reboot-history Displays the device’s reboot historystartup-log Displays the device’s startup logssh-authorized-keys Displays all devices (device hostnames) that have ssh authorized keys loadedsysinfo Displays system’s memory usage informationtop Displays system resource informationupgrade-history Displays the device’s upgrade history (displays details, such as date, time, and status of the upgrade, old version, new version, etc.)watchdog Displays the device’s watchdog statuson <DEVICE-NAME> The following keywords are common to all of the above:• on <DEVICE-NAME> – Optional. Displays information for a specified device. If no device is specified, the system displays information for logged device(s)• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.show ip-access-list Displays status of IP Access Control List (ACL) to WLAN mappings on a specified device or all devices within a specified RF Domain. This command also displays if IP ACLs are properly applied in the dataplane.wlan <WLAN-NAME> Specifies the WLAN, for which the IP ACL to WLAN mapping status is required• <WLAN-NAME> – Specify the WLAN name.status detail Displays only failed IP ACL to WLAN mappings• details – Optional. Displays all (failed as well as successful) IP ACL to WLAN mapping statuson <DEVICE-OR-DOMAIN-NAME>Optional. Specifies the device name or the RF Domain name.• <DEVICE-OR-DOMAIN-NAME> – Specify the device name or the RF Domain. When specified, the system displays IP ACL to WLAN mapping status on the specified device or all devices within the specified RF Domain.show Displays running system statistics based on the parameters passeddhcp-lease Displays DHCP lease information received from the server](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-868.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 28• service show diag [fds|pkts]• service show diag [led-status|psu|stats] {(on <DEVICE-NAME>)}<INTERFACE-NAME> Optional. Displays DHCP lease information for a specified router interface• <INTERFACE-NAME> – Specify the router interface name.on Optional. Displays DHCP lease information for a specified devicepppoe1 Optional. Displays DHCP lease information for a PPP over Ethernet interfacevlan <1-4094> Optional. Displays DHCP lease information for a VLAN interface• <1-4094> – Specify a VLAN index from 1 - 4094.wwan1 Optional. Displays DHCP lease information for a Wireless WAN interfaceon <DEVICE-NAME> The following keywords are common to all of the above:• on <DEVICE-NAME> – Optional. Displays DHCP lease information for a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.show diag Displays diagnostic statistics, such as LED status, fan speed, sensor temperature, open file descriptors, looped packets etc. fds Displays the number of file descriptors (fds) opened by key processes, such as the CFGD. When executed, the command displays only the file name and FD. pkts Displays details of looped packets captured by the dataplane and pushed to a separate queue. These queued packets are written to a log file (named loop_pkt_info.log) available at the /var2/log/ directory. Use the service > start-shell command and enter the path ‘cat /var2/log/’ to view if the loop_pkt_info.log file exists. However, looped packet logging has to be enabled in the profile/device context. For more information, see diag. The dataplane can log up to 16 looped packets at a time. Once the queue is full, no new loop packet is logged until the existing queue is cleared. To clear the logged looped packet queue execute the service > clear > diag > pkts command.Following are the loop codes and the corresponding loop reasons: (5) - "pkt looping in dataplane"(51) - "loop in packet path"(367) - "wispe encapsulation loop"(432) - "mcx loop prevention"(532) - "Port loop detected"(536) - "packet loop detected by wireless bridge"(41) - "IPv4 TTL exceeded"(493) - "IPv6 TTL exceeded"(540) - "mint TTL exceeded"show Displays running system statistics based on the parameters passeddiag Displays diagnostic statistics, such as LED status, fan speed, and sensor temperatureled-status Displays LED state variables and the current statepsu Displays power supply information](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-869.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 29• service show guest-registration [export-status|import-status|restore-status]• service show fast-switching {on <DEVICE-NAME>}• service show [fib|fib6] {table-id <0-255>}• service show mint [adopted-devices {on <DEVICE-NAME>}|ports]stats Displays fan speed and sensor temperature statisticson <DEVICE-NAME> Optional. Displays diagnostic statistics for a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.show Displays running system statistics based on the parameters passedguest-registration Displays status of the guest-registration database snapshot related processes (export, import, and restore)Note: To export, import, or restore a guest-registration database, use the service > guest-registration > [backup|export|import] command.]export-status Displays the status of the latest export process initiatedimport-status Displays the status of the latest import process initiatedexport-status Displays the status of the latest restore process initiatedshow Displays running system statistics based on the parameters passedfast-switching Displays fast switching state (enabled or disabled)on <DEVICE-NAME> Optional. Displays fast switching state for a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.show Displays running system statistics based on the parameters passedfib Displays entries in the Forwarding Information Base (FIB)fib6 Displays FIB IPv6 static routing entriesThe WiNG software allows the IPv6 FIB to maintain only IPv6 static and interface routes.FIB is a collection of routing entries. A route entry consists of IPv6 network (which can also be a host) address, the prefix length for the network (for IPv6 routes this is between 0 - 128), and the next hop’s (gateway) IPv6 address. Since a destination can be reached through multiple next hops, you can configure multiple routes to the same destination with multiple next hops.table-id <0-255> Optional. Displays FIB information maintained by the system based on the table ID• <0-255> – Specify the table ID from 0 - 255.show Displays running system statistics based on the parameters passedmint Displays MiNT protocol details](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-870.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 30• service show pm {history} {(on <DEVICE-NAME>)}• service show rf-domain-manager [diag|info] {<MAC/HOSTNAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}• service show sites• service show virtual-machine-history {on <DEVICE-NAME>}• service show wireless [aaa-stats|adaptivity-status|credential-cache|dns-cache|radar-status|vlan-usage] {on <DEVICE-NAME>}adopted-deviceson <DEVICE-NAME>Displays adopted devices status in dpd2• on <DEVICE-NAME> – Optional. Displays MiNT protocol details for a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.ports Displays MiNT ports used by various services and featuresshow Displays running system statistics based on the parameters passedpm Displays the Process Monitor (PM) controlled process detailshistory Optional. Displays process change history (the time at which the change was implemented, and the events that triggered the change)on <DEVICE-NAME> Optional. Displays process change history for a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.show Displays running system statistics based on the parameters passedrf-domain-manager Displays RF Domain manager informationdiag Displays RF Domain manager related diagnostics statisticsinfo The following keyword is common to the ‘diag’ and ‘info’ parameters:Displays RF Domain manager related information<MAC/HOSTNAME> Optional. Specify the MAC address or hostname of the RF Domain manager.on <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘diag’ and ‘info’ parameters:Optional. Displays diagnostics statistics on a specified device or domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.show Displays running system statistics based on the parameters passedsites Displays NOC sites related informationshow virtual-machine-historyDisplays virtual machine history based on the parameters passedThis command is applicable only to the NX9500, and NX9510 series service platforms. It is also available on the Privilege Executable Mode of these devices.on <DEVICE-NAME> Optional. Displays virtual machine history on a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the service platform.show Displays running system statistics based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-871.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 31• service show wireless [config-internal|log-internal|neighbors]• service show wireless [client|meshpoint neighbor] proc [info|stats] {<MAC>} {(on <DEVICE-OR-DOMAIN-NAME)}wireless Displays WLAN statistics (WLAN AAA policy, configuration parameters, VLAN assignment, etc.)aaa-stats Displays AAA policy statisticsadaptivity-status Displays the current list of channels (with interference levels exceeding the configured threshold resulting in adaptivity kicking in) and time when adaptivity kicked in on a devicecredential-cache Displays clients cached credentials statistics (VLAN, keys, etc.)dns-cache Displays cache of resolved names of servers related to wireless networkingradar-status Displays radar discovery status. This option displays following information:• If a radar has been discovered by the AP•The time of discoveryvlan-usage Displays VLAN statistics across WLANson <DEVICE-NAME> The following keywords are common to all of the above:• on <DEVICE-NAME> – Optional. Displays running system statistics on a specified device. If no device is specified, the system displays information for the logged device.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.show Displays running system statistics based on the parameters passedwireless Displays WLAN statistics (WLAN AAA policy, configuration parameters, VLAN usage, etc.)config-internal Displays internal configuration parameterslog-internal Displays recent internal wireless debug logs (info and above severity)neighbors Displays neighboring device statistics for roaming and flow migrationshow Displays running system statistics based on the parameters passedwireless Displays WLAN statistics (WLAN AAA policy, configuration parameters, VLAN usage, etc.)client Displays WLAN client statisticsmeshpoint neighbor Displays meshpoint related proc entriesproc The following keyword is common to client and meshpoint neighbor parameters:• proc – Displays dataplane proc entries based on the parameter selectedNote: These proc entries provide statistics on each wireless client on the WLAN.Note: For the meshpoint parameter, it displays proc entries about neighbors.info This parameter is common to client and meshpoint neighbor parameters. Displays information for a specified device (wireless client or neighbor) or RF Domainstats This parameter is common to client and meshpoint neighbor parameters. Displays information for a specified device (wireless client or neighbor) or RF Domain](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-872.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 32• service show wireless radio-internal [radio1|radio2] <LINE>• service show wireless reference [channels|frame|handshake|mcs-rates|reason-codes|status-codes]• service show wireless stats-client diag {<MAC/HOSTNAME>} {(on <DEVICE-OR-DOMAIN-NAME)}• service smart-rf clear-config {<MAC>|<DEVICE-NAME>|on <DOMAIN-NAME>}<MAC> Displays information for a specified device (wireless client or neighbor) or RF Domainon <DEVICE-OR-DOMAIN-NAME>This parameter is common to client and meshpoint neighbor parameters. Displays information for a specified device (wireless client or neighbor) or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.show Displays running system statistics based on the parameters passedwireless Displays WLAN statistics (WLAN AAA policy, configuration parameters, VLAN usage, etc.)radio-internal [radio1|radio2]Displays radio internal debug logs. Select the radio from the following options:•radio1 – Selects radio 1• radio2 – Selects radio 2.<LINE> Specify the radio internal debug command to enable.show Displays running system statistics based on the parameters passedwireless Displays WLAN statistics (WLAN AAA policy, configuration parameters, VLAN usage, etc.)reference Displays look up reference information related to standards, protocols, etc.channels Displays 802.11 channels informationframe Displays 802.11 frame structurehandshake Displays a flow diagram of 802.11 handshakesmcs-rates Displays MCS rate informationreason-codes Displays 802.11 reason codes (for deauthentication, disassociation, etc.)status-codes Displays 802.11 status codes (for association response)show Displays running system statistics based on the parameters passedwireless Displays WLAN statistics (WLAN AAA policy, configuration parameters, VLAN usage, etc.)stats-client Displays managed AP statistics<MAC/HOSTNAME> Optional. Specify the MAC address or hostname of the AP.on <DEVICE-OR-DOMAIN-NAME>Optional. Displays statistics on a specified AP, or all APs on a specified domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.smart-rf Enables Smart RF managementclear-config Clears WLAN Smart RF configuration on a specified device or on all devices](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-873.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 33• service smart-rf [clear-history|clear-interfering-aps|save-config] {on <DOMAIN-NAME>}• service snmp sysoid wing5• service ssm dump-core-snapshot• service syslog test {level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]} {(on <DEVICE-NAME>)}<MAC> Optional. Clears WLAN Smart RF configuration on a device identified by its MAC address. Specify the device’s MAC address in the AA-BB-CC-DD-EE-FF format.<DEVICE-NAME> Optional. Clears WLAN Smart RF configuration on a device identified by its hostname. Specify the device’s hostname.on <DOMAIN-NAME> Optional. Clears WLAN Smart RF configuration on all devices in a specified RF Domain• <DOMAIN-NAME> – Specify the RF Domain name.smart-rf Enables Smart RF managementclear-history Clears WLAN Smart RF history on all devicesclear-interfering-aps Clears Smart-RF interfering APssave-config Saves the Smart RF configuration on all devices, and also saves the history on the RF Domain Manageron <DOMAIN-NAME> Optional. Clears WLAN Smart RF configuration on all devices in a specified RF Domain• <DOMAIN-NAME> – Specify the RF Domain name.snmp sysoid wing5 Configures a new sysObjectID (sysoid), in the MIB, for devices running WiNG 5.X devicesWhen configured, the SNMP manager returns sysoid for WiNG 5.X OS. Hardwares running the WiNG 4.X and WiNG 5.X images have different sysoids. For example, the sysoid for a RFS4000 using the WiNG 4.X image differs from another RFS4000 running the WiNG 5.X image.This command is applicable only to RFS4000 and RFS6000 platforms, since they have the same sysoid supported in WiNG 4.X and WiNG 5.X.The WiNG 4.X sysoids are:• RFS4000 – 1.3.6.1.4.1.388.18• RFS6000 – 1.3.6.1.4.1.388.16The WiNG 5.X sysoids are:• RFS4000 – 1.3.6.1.4.1.388.50.1.1.35• RFS6000 – 1.3.6.1.4.1.388.50.1.1.36ssm dump-core-snapshotTriggers a debug core dump of the SSM modulesyslog test Sends a test message to the syslog server to confirm server availability](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-874.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 34• service ssm trace pattern <WORD> {on <DEVICE-NAME>}• service wireless client beacon-request <MAC> mode [active|passive|table] ssid [<SSID>|any] channel-report [<CHANNEL-LIST>|none] {on <DEVICE-NAME>}level Optional. Sets the logging level. In case syslog server is unreachable, an event is logged based on the logging level defined. This is an optional parameter, and the system configures default settings, if no logging severity level is specified.• <0-7> – Optional. Specify the logging severity level from 0-7. The various levels and their implications are as follows:• alerts – Optional. Immediate action needed (severity=1)• critical – Optional. Critical conditions (severity=2)• debugging – Optional. Debugging messages (severity=7)• emergencies – Optional. System is unusable (severity=0)• errors – Optional. Error conditions (severity=3)• informational – Optional. Informational messages (severity=6)• notifications – Optional. Normal but significant conditions (severity=5)• warnings – Optional. Warning conditions (severity=4). This is the default setting.on <DEVICE-NAME> Optional. Executes the command on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ssm trace Displays the SSM module trace based on parameters passedpattern <WORD> Configures the pattern to match• <WORD> – Specify the pattern to match.on <DEVICE-NAME> Optional. Displays the SSM module trace on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.wireless client beacon-requestsSends beacon measurement requests to a wireless client<MAC> Specify the wireless client’s MAC address.mode [active|passive|table]Specifies the beacon measurement mode. The following modes are available:• Active – Requests beacon measurements in the active mode• Passive – Requests beacon measurements in the passive mode• Table – Requests beacon measurements in the table modessid [<SSID>|any] Specifies if the measurements have to be made for a specified SSID or for any SSID• <SSID> – Requests beacon measurement for a specified SSID• any – Requests beacon measurement for any SSIDchannel-report [<CHANNEL-LIST>|none]Configures channel report in the request. The request can include a list of channels or can apply to all channels.• <CHANNEL-LIST> – Request includes a list of channels. The client has to send beacon measurements only for those channels included in the request• none – Request applies to all channelson <DEVICE-NAME> Optional. Sends requests on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-875.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 35• service wireless client quiet-element [start|stop]• service wireless client trigger-bss-transition mac <MAC> {timeout <0-65535} {url <URL>} {on <DEVICE-OR-DOMAIN-NAME>}• service wireless client trigger-wnm mac <MAC> type [deauth-imminent|subscription-remediation] {uri <WORD>}• service wireless dump-core-snapshot• service wireless meshpoint zl <MESHPOINT-NAME> [on <DEVICE-NAME>] {<ARGS>|timeout <1-65535>}wireless client quiet-elementEnables the quite-element information in beacons sent to wireless clientsstart Enables the quite-element information in beacons sent to wireless clients. This is the interval for which all wireless clients are to remain quiet.stop Disables the quite-element information in beacons sent to wireless clients. Once disabled, this information is no longer included in beacons.wireless client trigger-bss-transitionSends a 80211v-Wireless Network Management BSS transition request to a clientmac <MAC> Specifies the wireless client’s MAC addresstimeout <0-65535> Specifies the time remaining, for this client. before BSS transition is initiated. In other words on completion of the specified time period, BSS transition is triggered.• <0-65535> – Specify a time from 0 -65535 seconds.url <URL> Optional. Specifies session termination URLon <DEVICE-OR-DOMAIN-NAME>Optional. Sends request on a specified device• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.wireless client trigger-wnmSends a WNM notification (action frame) to a wireless clientmac <MAC> Specifies the wireless client’s MAC addresstype [deauth-imminent|subscription-remediation]Configures the WNM notification type• deauth-imminent – Sends a de-authentication imminent frame• subscription-remediation – Sends a subscription remediation needed frameuri <WORD> Optional. Specifies the unique resource identifier (URI)wireless client dump-core-snapshotTriggers a debug core dump of the wireless moduleservice wireless meshpoint zlTriggers a zonal level debug of a specified meshpoint’s modules<MESHPOINT-NAME> Specify the meshpoint nameon <DEVICE-NAME> Triggers zonal level debug of a specified meshpoint’s modules on a specified device• <DEVICE-NAME> – Specify the name of the device (AP, wireless controller, or service platform)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-876.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 36• service wireless qos delete-tspec <MAC> tid <0-7>• service wireless trace pattern <WORD> {on <DEVICE-NAME>}• service wireless unsanctioned ap air-terminate <MAC> {on <DOMAIN-NAME>}• service wireless wips clear-client-blacklist [all|mac <MAC>]• service wireless wips clear-event-history {on <DEVICE-OR-DOMAIN-NAME}<ARGS> Optional. Specifies the zonal arguments. These zonal arguments represent the meshpoint modules identified by the zonal and subzonal arguments passed here. Also specify the debug level from 0 -7. Please see the Examples section, at the end of this topic, for more information.timeout <1-65535> Optional. Specifies a timeout value from 1 - 65535 seconds. When specified, meshpoint logs are debugged for the time specified here.wireless qos delete-tspecSends a delete TSPEC request to a wireless client<MAC> Specify the MAC address of the wireless client.tid <0-7> Deletes the Traffic Identifier (TID)• <0-7> – Select the TID from 0 - 7.wireless trace Displays the wireless module trace based on parameters passedpattern <WORD> Configures the pattern to match• <WORD> – Specify the pattern to match.on <DEVICE-NAME> Optional. Displays the wireless module trace on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.wireless unsanctioned ap air-terminateEnables unsanctioned access points termination<MAC> Configures the unsanctioned access points’ BSSID (MAC address)on <DOMAIN-NAME> Optional. Specifies the RD Domain of the access point• <DOMAIN-NAME> – Specify the name of the RF Domain.wireless wips Enables management of WIPS parametersclear-client-blacklist [all|mac <MAC>]Removes a specified client or all clients from the blacklist• all – Removes all clients from the blacklist• mac <MAC> – Removes a specified client form the blacklist• <MAC> – Specify the wireless client’s MAC address.wireless wips Enables WIPS managementclear-event-history Clears event historyon <DEVICE-OR-DOMAIN-NAME>Optional. Clears event history on a device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-877.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 37Syntax (Privilege Exec Mode)serviceservice [block-adopter-config-updates|clear|cli-tables-skin|cluster|copy|database|delete|delete-offline-aps|force-send-config|force-update-vm-stats|guest-registration|load-balancing|locator|mint|pktcap|pm|radio|radius|request-full-config-from-adopter|restore|set|show|signal|smart-rf|snmp|ssm|start-shell|syslog|trace|wireless]service clear crash-info {on <DEVICE-NAME>}service copy [stats-report|tech-support]service copy stats-report [global|rf-domain <DOMAIN-NAME>] (<FILE>|<URL>)service copy tech-support [<FILE>|<URL>]service database [authentication|compact|drop|maintenance-mode|primary-stepdown|remove-all-files|replica-set|server|start-shell]service database authentication [create-user|delete-user]service database authentication create-user username <USER-NAME> password <PASSWORD>service database authentication delete-user username <USER-NAME>service database compact [all|captive-portal|nsight]service database drop [captive-portal|nsight] collection <COLLECTION-NAME>service database [maintenance-mode|primary-stepdown|remove-all-files|start-shell]service database replica-set [add|delete]service database replica-set add member [<IP>|<FQDN>] [arbiter|priority <0-255>]service database replica-set delete member [<IP>|<FQDN>]service database server [restart|start|stop]service delete sessions <SESSION-COOKIES>service mint [clear|debug-log|expire|flood]service mint [clear [lsp-db|mlcp]|debug-log [flash-and-syslog|flash-only]|expire [lsp|spf]|flood [csnp|lsp]]service pktcap on [bridge|deny|drop|ext-vlan|interface|radio|rim|router|vpn|wireless]service pktcap on [bridge|deny|drop|ext-vlan|rim|router|vpn|wireless] {(acl-name <ACL>,count <1-1000000>,direction [any|inbound|outbound],filter <LINE>,hex,rate <1-100>,snap <1-2048>,tcpdump,verbose,write [file|url|tzsp [<IP/TZSP-HOSTNAME>])}service pktcap on interface [<INTERFACE-NAME>|ge <1-4>|me1|port-channel <1-2>|pppoe1|vlan <1-4094>|wwan1] {(acl-name <ACL>,count <1-1000000>,direction [any|inbound|outbound],filter <LINE>,hex,rate <1-100>,snap <1-2048>,tcpdump,verbose,write [file|url|tzsp [<IP/TZSP-HOSTNAME>])}NOTE: The “service” command of the Priv Exec Mode is the same as the service command in the User Exec Mode. There a few modifications that have been documented in this section. For the syntax and parameters of the other commands refer to the (User Exec Mode) syntax and (User Exec Mode) parameters sections of this chapter.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-878.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 38service pktcap on radio [<1-1024>|all] {(acl-name <ACL>,count <1-1000000>,direction [any|inbound|outbound],filter <LINE>,hex,promiscuous,rate <1-100>,snap <1-2048>,tcpdump,verbose,write [file|url|tzsp [<IP/TZSP-HOSTNAME>])}service pm stop {on <DEVICE-NAME>}service restore analytics-support [<FILE>|<URL>]service show last-passwdservice signal [abort <PROCESS-NAME>|kill <PROCESS-NAME>]service start-shellservice trace <PROCESS-NAME> {summary}Parameters (Privilege Exec Mode)service• service copy tech-support [<FILE>|<URL>]• service copy stats-report [global|rf-domain <DOMAIN-NAME>] (<FILE>|<URL>)• service clear crash-info {on <DEVICE-NAME>}copy tech-support Copies extensive system information used for troubleshooting<FILE> Specify the location to copy file using the following format:•usbX:/path/file<URL> Specify the location URL to copy file. Both IPv4 andIPv6 address formats are supported.tftp://<hostname|IPv4/IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]/path/filesftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]>/path/filecopy stats-report Copies extensive statistical data useful for troubleshooting[global|rf-domain <DOMAIN-NAME>]Identifies the RF Domain to copy statistical data• global – Copies extensive statistical data of all configured RF Domains• rf-domain <DOMAIN-NAME> – Copies extensive statistical data of a specified RF Domain. Specify the domain name.<FILE> Specify the location to copy file using the following format:•usbX:/path/file<URL> Specify the location URL to copy file. Both IPv4 andIPv6 address formats are supported.tftp://<hostname|IPv4/IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]/path/filesftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]>/path/fileclear crash-info Clears all crash fileson <DEVICE-NAME> Optional. Clears crash files on a specified device. These crash files are core, panic, and AP dump.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-879.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 39• service database authentication create-user username <USER-NAME> password <PASSWORD>• database authentication delete-user username <USER-NAME>• service database compact [all|captive-portal|nsight]• service database drop [captive-portal|nsight] collection <COLLECTION-NAME>database Performs captive-portal/NSight database related actionsThis command is supported only on the NX95XX, NX9600, and VX9000 platforms.database authentication create-user username <USER-NAME> password <PASSWORD>Creates the username and password required to access the database. Execute this command on the database host. However, before creating users, on the database, generate the database keyfile. For more information on generating the keyfile, see database.• username <USER-NAME> – Configures a database username• password <PASSWORD> – Configures a password for the username createdaboveIn the database-policy context, enable authentication and configure this username and password. The database-client-policy also should have the same user credentials configured. For more information on database-policy and database-client-policy, see database-policy and database-client-policy.database Performs database related actionsThis command is supported only on the NX95XX, NX9600, and VX9000 platforms.database authentication delete-user username <USER-NAME>Deletes existing users having access rights to the database• username <USER-NAME> – Identifies the user to delete by the username• <USER-NAME> – Specify the user name.Once deleted, the database cannot be accessed using the specified combination of username and password.database Performs database related actionsNote: This command is supported only on the NX95XX, NX9600, and VX9000 platforms.compact [all|captive-portal|nsight]Compacts collections within the database. Each database (captive-portal and NSight) contains one or more collection, where each collection is a set of records. Use this command to make a single compact set of all collections within a database.• all – Compacts collections within all databases (captive-portal and NSight) being maintained• captive-portal – Compacts all collections within the captive portal database only• nsight – Compacts all collections within the NSight database onlydatabase Performs database related actionsNote: This command is supported only on the NX95XX, NX9600, and VX9000 platforms.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-880.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 40• service database [maintenance-mode|primary-stepdown|remove-all-files|start-shell]• service database replica-set add member [<IP>|<FQDN>] [arbiter|priority <0-255>]drop [captive-portal|nsight] collection <COLLECTION-NAME>Drops the specified collection from the selected database. Select the database type and specify the collection.• captive-portal – Drops a captive portal database collection• nsight – Drops an NSight database collectionThe following keyword is common to both the ‘captive-portal’ and ‘NSight’ databases:• collection <COLLECTION-NAME> – Drops the collection identified by the <COL-LECTION-NAME> parameter.• <COLLECTION-NAME> – Specify the collection name.database Performs database related actionsNote: This command is supported only on the NX95XX, NX9600, and VX9000 platforms.maintenance-mode Places the database server in the maintenance modeprimary-stepdown Requests the primary replica-set to step down. For more information on replica-sets and its creation, see database-policy.remove-all-files Removes all database-server related files (captive-portal and NSight). Use in a scenario where complete removal of all database related files is necessary, such as when downgrading to 5.8.1 or 5.8.0 version. Extreme caution is recommended when using this command.start-shell Starts the database shelldatabase Performs database related actionsNote: This command is supported only on the NX95XX, NX9600, and VX9000 platforms.replica-set Adds members to the database replica set. A replica set is a group of devices running the database instances that maintain the same data set. Replica sets provide redundancy and high availability, and are the basis for all production deployments. The replica set can contain a maximum of fifty (50) members, with each member (with the exception of the arbiter) hosting an instance of the database. For more information on creating replica sets, see database-policy.add member [<IP>|<FQDN>]Adds members to the database replica set• <IP> – Identifies the member by its IP address. Specify the member’s IP address.• <FQDN> – Identifies the member by its Fully Qualified Domain Name (FQDN). Specify the member’s FQDN address.Note: Ensure that the identified members have the database instance running prior to being added to the replica set.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-881.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 41• service database replica-set delete member [<IP>|<FQDN>]• service database server [restart|start|stop]• service delete sessions <SESSION-COOKIES>• service mint [clear [lsp-dp|mlcp]|debug-log [flash-and-syslog|flash-only]|expire [lsp|spf]|flood [csnp|lsp]][arbiter|priority <0-255>]After identifying the new member, optionally specify if the member is the arbiter or not. If not the arbiter, specify the member’s priority value.• arbiter – Identifies the new member as the arbiter. The arbiter does not maintain a data set and is added to the replica set to facilitate the election of the fall-back primary member. It provides that one extra vote required in the election of the primary member.• priority <0-255> – Identifies the new member as not being the arbiter and configures its priority value.• <0-255> – Specify the priority value from 0 - 255. Not applicable for the arbiter.The priority value determines the member’s position within the replica set as primary or secondary. It also helps in electing the fall-back primary member in the eventuality of the current primary member being unreachable.All identified members should have the database instances running prior to being added to the replica set.database Performs database related actionsNote: This command is supported only on the NX95XX, NX9600, and VX9000 platforms.replica-set Allows deletion of members in a database replica set. For each database a single three-member replica-set can be created and maintained. For more information on creating replica sets, see database-policy.delete member [<IP>|<FQDN>]Deletes members from an existing database replica set• <IP> – Identifies the member by its IP address. Specify the member’s IP address.• <FQDN> – Identifies the member by its FQDN. Specify the member’s FQDN address.database Performs database related actionsNote: This command is supported only on the NX95XX, NX9600, and VX9000 platforms.server [restart|start|stop]Performs the following actions on the database server:• restart – Restarts the server• start – Starts the server• stop – Stops the serverdelete sessions <SESSION-COOKIES>Deletes session cookies• <SESSION-COOKIES> – Provide a list of cookies to delete.mint Enables MiNT protocol management (clears LSP database, enables debug logging, enables running silence, etc.)clear [lsp-dp|mlcp] Clears LSP database and MiNT Link Control Protocol (MLCP) links• lsp-dp – Clears MiNT Label Switched Path (LSP) database• mlcp – Clears MLCP links](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-882.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 42• service pm stop {on <DEVICE-NAME>}• service pktcap on [bridge|deny|drop|ext-vlan|rim|router|vpn|wireless] {(acl-name <ACL>,count <1-1000000>,direction [any|inbound|outbound],filter,hex,rate <1-100>,snap <1-2048>,tcpdump,verbose,write [file|url|tzsp <IP/TZSP-HOSTNAME>])}debug-log [flash-and-syslog|flash-only]Enables debug message logging• flash-and-syslog – Logs debug messages to the flash and syslog files• flash-only – Logs debug messages to the flash file onlyexpire [lsp|spf] Forces expiration of LSP and recalculation of Shortest Path First (SPF)• lsp – Forces expiration of LSP• spf – Forces recalculation of SPFflood [csnp|lsp] Floods control packets• csnp – Floods our Complete Sequence Number Packets (CSNP)• lsp – Floods our LSPpm Stops the Process Monitor (PM)stop Stop the PM from monitoring all daemonson <DEVICE-NAME> Optional. Stops the PM on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.pktcap on Captures data packets crossing at a specified location• on – Defines the packet capture locationbridge Captures packets transiting through the Ethernet bridgedeny Captures packets denied by an Access Control List (ACL)drop Captures packets at the drop locationsext-vlan Captures packets forwarded to or from an extended VLANrim Captures packets at the Radio Interface Module (RIM)router Captures packets transiting through an IP routervpn Captures packets forwarded to or from a VPN linkwireless Captures packets forwarded to or from a wireless deviceacl-name <ACL> Optional. Specify the ACL that matches the acl-name for the 'deny' locationcount <1-1000000> Optional. Limits the captured packet count. Specify a value from 1 -1000000.direction [any|inbound|outbound]Optional. Changes the packet direction with respect to a device. The direction can be set as any, inbound, or outbound.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-883.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 43filter [<LINE>|arp|capwap|cdp|dot11|dropreason|dst|ether|failed|host|icmp|icmp6|igmp|ip|ipv6|l2|l3|l4|lldp|mint|net|not|port|priority|radio|rssi|src|stp|tcp|tcp6|udp|udp6|vlan|wlan]Optional. Filters packets based on the option selected (must be used as a last option)The filter options are:• <LINE> – Defines user defined packet capture filter• arp – Matches ARP packets• capwap – Matches CAPWAP packets• cdp – Matches CDP packets• dot11 – Matches 802.11 packets• dropreason – Matches packet drop reason• dst – Matches IP destination• ether – Matches Ethernet packets• failed – Matches failed 802.11 transmitted frames• host – Matches host destination• icmp – Matches ICMP packets• icmp6 – Matches ICMPv6 frames• ip – Matches IPV4 packets• ipv6 – Matches IPV6 packets• l2 – Matches L2 header• l3 – Matches L3 header•l4 – Matches L4 header• mint – Matches MiNT packets• lldp – Matches LLDP packets• net – Matches IP in subnet• not – Filters out any packet that matches the filter criteria (For example, if not TCP is used, all tcp packets are filtered out)• port – Matches TCP or UDP port• priority – Matches packet priority•radio – Matches radio•rssi – Matches Received Signal Strength Indication (RSSI) of received radio signals• src – Matches IP source•stp – Matches STP packets•tcp – Matches TCP packets• tcp6 – Matches TCP over IPv6 packets• udp – Matches UDP packets• udp6 – Matches UDP over IPv6 packets•vlan – Matches VLAN•wlan – Matches WLANhex Optional. Provides binary output of the captured packetsrate <1-100> Optional. Specifies the packet capture rate• <1-100> – Specify a value from 1 - 100 seconds.snap <1-2048> Optional. Captures the data length• <1-2048> – Specify a value from 1 - 2048 characters.tcpdump Optional. Decodes tcpdump. The tcpdump analyzes network behavior, performance, and infrastructure. It also analyzes applications that generate or receive traffic.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-884.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 44• service pktcap on radio [<1-1024>|all] {(acl-name <ACL>,count <1-1000000>,direction [any|inbound|outbound],filter <LINE>,hex,promiscuous,rate <1-100>,snap <1-2048>,tcpdump,verbose,write [file|url|tzsp <IP/TZSP-HOSTNAME>])}verbose Optional. Displays full packet bodywrite Captures packets to a specified file. Specify the location to capture file:FILE – flash:/path/fileusbX:/path/filevram:startup-configURL – Specify the location URL to capture file. Both IPv4 and IPv6 address formats are supported.tftp://<hostname|IPv4/IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]/path/filesftp://<user>@<hostname|IPv4/IPv6>[:port]>/path/filetzsp – Tazman Sniffer Protocol (TZSP) host. Specify the TZSP host’s IP address or hostname.pktcap on radio Captures data packets on a radio (802.11)<1-1024> Captures data packets on a specified radio• <1-1024> – specify the radio index from 1 - 1024.all Captures data packets on all radiosacl-name <ACL> Optional. Specify the ACL that matches the ACL name for the 'deny' locationcount <1-1000000> Optional. Sets a specified number of packets to capture• <1-1000000> – Specify a value from 1 - 1000000.direction [any|inbound|outbound]Optional. Changes the packet direction with respect to a device. The direction can be set as any, inbound, or outbound.filter <LINE> Optional. Filters packets based on the option selected (must be used as a last option)• <LINE> – Define a packet capture filter or select any one of the available options.hex Optional. Provides binary output of the captured packetsrate <1-100> Optional. Specifies the packet capture rate• <1-100> – Specify a value from 1 - 100 seconds.snap <1-2048> Optional. Captures the data length• <1-2048> – Specify a value from 1 - 2048 characters.tcpdump Optional. Decodes the TCP dumpverbose Optional. Provides verbose output](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-885.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 45• service pktcap on interface [<INTERFACE>|ge <1-4>|me|port-channel <1-2>|vlan <1-4094>] {(acl-name <ACL>,count <1-1000000>,direction [any|inbound|outbound],filter <LINE>,hex,rate <1-100>,snap <1-2048>,tcpdump,verbose,write [file|url|tzsp <IP/TZSP-HOSTNAME>])}write Captures packets to a specified file. Specify the location to capture file:FILE – flash:/path/fileusbX:/path/filenvram:startup-configURL – Specify the location URL to capture file. Both IPv4 and IPv6 address formats are supported.tftp://<hostname|IPv4/IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]/path/filesftp://<user>@<hostname|IPv4/IPv6>[:port]>/path/filetzsp – The TZSP host. Specify the TZSP host’s IP address or hostname.pktcap on Captures data packets at a specified interface• on – Specify the capture location.interface [<INTERFACE>|ge <1-4>|me1|port-channel <1-2>|vlan <1-4094>]Captures packets at a specified interface. The options are:• <INTERFACE> – Specify the interface name.• ge <1-4> – Selects a GigabitEthernet interface index from 1 - 4• me1 – Selects the FastEthernet interface• port-channel <1-2> – Selects a port-channel interface index from 1- 2• vlan <1-4094> – Selects a VLAN ID from 1 - 4094acl-name <ACL> Optional. Specify the ACL that matches the ACL name for the 'deny' locationcount <1-1000000> Optional. Sets a specified number of packets to capture• <1-1000000> – Specify a value from 1 - 1000000.direction [any|inbound|outbound]Optional. Changes the packet direction with respect to a device. The direction can be set as any, inbound, or outbound.filter <LINE> Optional. Filters packets based on the option selected (must be used as a last option)• <LINE> – Define a packet capture filter or select any one of the available options.hex Optional. Provides binary output of the captured packetsrate <1-100> Optional. Specifies the packet capture rate• <1-100> – Specify a value from 1 - 100 seconds.snap <1-2048> Optional. Captures the data length• <1-2048> – Specify a value from 1 - 2048 characters.tcpdump Optional. Decodes the TCP dumpverbose Optional. Provides verbose output](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-886.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 46• service show last-passwd• service signal [abort <PROCESS-NAME>|kill <PROCESS-NAME>]• service start-shell• service trace <PROCESS-NAME> {summary}Syntax (Privilege Exec Mode: NX9500 and NX9510)serviceThe following service commands are specific to the NX9500 and NX9510 series service platforms:service copy analytics-support [<FILE>|<URL>]Parameters (Privilege Exec Mode: NX9500 and NX9510)• service copy analytics-support [<FILE>|<URL>]write Captures packets to a specified file. Specify the location to capture file:FILE – flash:/path/fileusbX:/path/filenvram:startup-configURL – Specify the location URL to capture file. Both IPv4 and IPv6 address formats are supported.tftp://<hostname|IPv4/IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]/path/filesftp://<user>@<hostname|IPv4/IPv6>[:port]>/path/filetzsp – The TZSP host. Specify the TZSP host’s IP address or hostname.show Displays running system statistics based on the parameters passedlast-passwd Displays the last password used to enter shellsignal Sends a signal to a process• tech-support – Copies extensive system information useful for troubleshootingabort Sends an abort signal to a process, and forces it to dump to core• <PROCESS-NAME> – Specify the process name.kill Sends a kill signal to a process, and forces it to terminate without a core• <PROCESS-NAME> – Specify the process name.start-shell Provides shell accesstrace Traces a process for system calls and signals<PROCESS-NAME> Specifies the process namesummary Optional. Generates summary report of the specified processcopy analytics-supportEnables copying of analytics information to a specified. Use one of the following options to specify the file:This information is useful to troubleshoot issues by the Technical Support team.<FILE> Specify the file name and location using one of the following formats:usb1:/path/fileusb2:/path/file](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-887.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 47Usage GuidelinesThe NX9500 and NX9510 model service platforms (NOC) provide granular and robust analytic reporting for a RFS4000 or RFS6000 device managed network. The data analyzed is collected at intervals specified by the administrator.To enable data analytics, procure and apply a separate hot spare analytics license at the NOC. The license restricts the number of access point streams processed at the NOC or forwarded to partner systems for further processing. The analytics feature can be turned on at select APs by enabling them in configuration. This way the customer can enable analytics on a select set of APs and not the entire system as long as the number of APs on which it is enabled is less than or equal to the total number of AP analytics licenses available at the NOC controller.In an NOC managed network, the analytics engine parses and processes Smart RF events as they are received. The analytics engine parses the new channel and power information from the Smart RF event, as opposed to retrieving the event from the devices themselves.Syntax (Global Config Mode)serviceservice [set|show cli]service set [command-history <10-300>|upgrade-history <10-100>|reboot-history <10-100>|virtual-machine-history <10-200>] {on <DEVICE-NAME>}service show cliParameters (Global Config Mode)• service set [command-history <10-300>|upgrade-history <10-100>|reboot-history <10-100>|virtual-machine-history <10-200>] {on <DEVICE-NAME>}<URL> Specify the location URL to copy file. Both IPv4 and IPv6 formats are supported.tftp://<hostname|IPv4/IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]/path/filesftp://<user>:<passwd>@<hostname|IPv4/IPv6>[:port]>/path/fileset Sets the size of history filescommand-history <10-300>Sets the size of the command history file• <10-300> – Specify a value from 10 - 300. The default is 200.upgrade-history <10-100>Sets the size of the upgrade history file• <10-100> – Specify a value from 10 - 100. The default is 50.reboot-history <10-100>Sets the size of the reboot history file• <10-100> – Specify a value from 10 - 100. The default is 50.virtual-machine-history <10-200>Sets the size of the virtual-machine history file• <10-200> – Specify a value from 10 - 200. The default is 100.This command is applicable only to the NX9500 and NX9510 series service platforms. Use the no > service > set > virtual-machine-history > {on <DEVICE-NAME>} command to revert the history file size to 100.on <DEVICE-NAME> Optional. Sets the size of history files on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-888.png)
![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 48• service show cliExamplerfs6000-81742D>service show cliCommand mode: +-do+-help [help] +-search +-WORD [help search WORD (|detailed|only-show|skip-show|skip-no)] +-detailed [help search WORD (|detailed|only-show|skip-show|skip-no)] +-only-show [help search WORD (|detailed|only-show|skip-show|skip-no)] +-skip-show [help search WORD (|detailed|only-show|skip-show|skip-no)] +-skip-no [help search WORD (|detailed|only-show|skip-show|skip-no)]+-show +-commands [show commands] +-adoption +-log +-adoptee [show adoption log adoptee(|on DEVICE-NAME)] +-on +-DEVICE-NAME [show adoption log adoptee(|on DEVICE-NAME)] +-adopter [show adoption log adopter (|mac AA-BB-CC-DD-EE-FF)(|on DEVICE-NAME)] +-mac +-AA-BB-CC-DD-EE-FF [show adoption log adopter (|mac AA-BB-CC-DD-EE-FF)(|on DEVICE-NAME)] +-on +-DEVICE-NAME [show adoption log adopter (|mac AA-BB-CC-DD-EE-FF)(|on DEVICE-NAME)]--More--rfs6000-81742D>rfs6000-81742D#service signal abort testprocessSending an abort signal to testprocessrfs6000-81742D#nx9500-6C8809*#service show crash-info-------------------------------------------------------------------------------- CRASH FILE SIZE LAST MODIFIED-------------------------------------------------------------------------------- cfgd.log_NX9500_5.9.0.0-014D.error.1 8369 Tue Apr 12 03:54:54 2017--------------------------------------------------------------------------------nx9500-6C8809*#rfs6000-81742D#service show command-historyConfigured size of command history is 200 Date & Time User Location Command=====================================================================Apr 12 09:31:41 2017 admin 192.168.13.10 22 rf-domain testApr 11 03:00:56 2017 admin 192.168.13.10 93 reload forceApr 11 03:00:35 2017 admin 192.168.13.10 93 write memoryApr 11 03:00:31 2017 admin 192.168.13.10 93 commitApr 11 03:00:24 2017 admin 192.168.13.10 93 no cluster nameApr 10 21:29:50 2017 admin 192.168.13.10 93 commitApr 10 21:29:48 2017 admin 192.168.13.10 93 use rf-domain TechPubsApr 10 21:29:44 2017 admin 192.168.13.10 93 selfApr 10 21:29:40 2017 admin 192.168.13.10 93 write memoryApr 10 21:29:34 2017 admin 192.168.13.10 93 commitApr 10 21:29:27 2017 admin 192.168.13.10 93 use license WEBFApr 10 21:29:27 2017 admin 192.168.13.10 93 controller-managedApr 10 21:29:27 2017 admin 192.168.13.10 93 control-vlan 1--More--rfs6000-81742D#show cli Displays running system configuration details• cli – Displays the CLI tree of the current mode](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-889.png)

![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 56WLAN: XPO-Guest-PSK use ip-access-list in guest_access_inbound : fail use ip-access-list out BC-MC-CONTROL : success--------------------------------------------------------------------------------WLAN: PartnerNet use ip-access-list in guest_access_inbound : success use ip-access-list out BC-MC-CONTROL : success--------------------------------------------------------------------------------================================================================================Reporting Device: AP02--------------------------------------------------------------------------------WLAN: PartnerNet use ip-access-list in guest_access_inbound : success use ip-access-list out BC-MC-CONTROL : success--------------------------------------------------------------------------------================================================================================Reporting Device: AP03--------------------------------------------------------------------------------WLAN: PartnerNet use ip-access-list in guest_access_inbound : success use ip-access-list out BC-MC-CONTROL : success--------------------------------------------------------------------------------Total reporting devices: 3SW01#Scenario 4: AP in RF Domain is unreachable or does not support this functionality.SW01#service show ip-access-list wlan status on guest-domainReporting Device: AP01 - unreachableReporting Device: AP02 - successReporting Device: AP03 - successTotal reporting devices: 3SW01# SW01#service show ip-access-list wlan status detail on guest-domain================================================================================Reporting Device: AP01Timed out waiting for remote device: xpath=wing-stats/device/00-23-68-0B-86-38/firewall/ip_acl_intf_status/wlan[mac='*']================================================================================Reporting Device: AP02--------------------------------------------------------------------------------WLAN: PartnerNet use ip-access-list in guest_access_inbound : success use ip-access-list out BC-MC-CONTROL : success--------------------------------------------------------------------------------================================================================================Reporting Device: AP03--------------------------------------------------------------------------------WLAN: PartnerNet](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-897.png)


![COMMON COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 5 - 605.1.9 writeCommon CommandsWrites the system running configuration to memory or terminalSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwrite [memory|terminal]Parameters• write [memory|terminal]Examplenx9500-6C8809>write memory[OK]nx9500-6C8809>memory Writes to the non-volatile (NV) memoryterminal Writes to the terminal](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-901.png)



![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 106.1.2 adoptionshow commandsDisplays adoption related information, and is common to the User Exec, Priv Exec, and Global Config modes.In an hierarchically managed (HM) network devices are deployed in two levels. The first level consists of the Network Operations Center (NOC) controllers. The second level consists of the site controllers. that can be grouped to form clusters. The NOC controllers adopt and manage the site controllers. Access points within the network are adopted and managed by the site controllers.Use this command to confirm if a device is an adoptee or an adopter. This command also allows you to determine the devices adopted by an adopter device. Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow adoption [config-errors|controllers|history|info|log|offline|pending|status|timeline]show adoption offlineshow adoption config-errors <DEVICE-NAME>show adoption log [adoptee|adopter {<MAC>}] {on <DEVICE-NAME>}show adoption [controllers {include-ipv6}|history|info|pending|status {summary}|timeline] {on <DEVICE-NAME>}Parameters• show adoption offline• show adoption config-errors <DEVICE-NAME>• show adoption log [adoptee|adopter {<MAC>}] {on <DEVICE-NAME>}NOTE: A NOC controller’s capacity is equal to or higher than a site controller’s capacity. The following devices can be deployed at NOC and sites:• NOC controller – RFS6000, NX65XX, NX9500, NX9510, or NX9600.• Site controller – RFS6000 or RFS4000.adoption Displays adoption related information. It also displays configuration errors.offline Displays non-adopted status of the logged device and its adopted access pointsadoption Displays adoption related information. It also displays configuration errors.config-errors <DEVICE-NAME>Displays configuration errors for a specified adopted device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.adoption Displays adoption related information. It also displays configuration errors.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-911.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 11• show adoption [history|controllers {include-ipv6}|info|pending|status {summary}|timeline] {on <DEVICE-NAME>}log [adoptee|adopter {MAC}] {on <DEVICE-NAME>}Displays adoption logs, for the specified device. If no device name is specified, the system displays logs for the logged device.• adoptee – Displays adoption logs for adoptee devices (APs, wireless controllers, and service platforms). To view logs for a specified adoptee, specify the device’s name. If no device name is specified, the system displays logs for the logged device. If the logged device is not an adoptee, the system states that the device is a controller. For example, 2013-01-19 22:00:13:MLCP_TAG_CLUSTER_MASTER not present and this device is a controller. Ignoring• on <DEVICE-NAME> – Optional. Displays adoptee status and details for the deviceidentified by the <DEVICE-NAME> keyword• <DEVICE-NAME> – Specify the device’s name.• adopter – Displays adoption logs for adopter devices (APs, wireless controllers, and service platforms). To view logs for a specified adopter, specify the device’s name. If no device name is specified, the system displays logs for the logged device.• <MAC> – Optional. Filters adopters by the adoptee device’s MAC address. Specifythe adoptee device’s MAC address. The system displays logs for the device that hasadopted the device identified by the <MAC> keyword.• on <DEVICE-NAME> – Optional. Displays adopter status and details for the deviceidentified by the <DEVICE-NAME> keyword.• <DEVICE-NAME> – Specify the adopter device’s name.A wireless controller or service platform cannot be configured as an adoptee and an adopter simultaneously. In other words, an adopted wireless controller or service platform cannot be configured to adopt another device and vice versa.adoption Displays adoption related information. It also displays configuration errors.controllers {include-ipv6}Displays information about adopted controllers. This is applicable in a Hierarchically managed network, where site controllers are adopted by the NOC controllers.• include-ipv6 – Optional. Displays the controller’s IPv6 address, if assigned, in the outputhistory Displays adoption history of the logged device and its adopted access pointsinfo Displays adopted device informationpending Displays information for devices pending adoptionstatus {summary} Displays adoption status for the logged device. When executed without using the ‘on <DEVICE-NAME>’ parameter, this command displays detailed information of all devices adopted by the device on which the command is executed.• summary – Optional. Displays a summary of all devices adopted by the logged device.timeline Displays the logged device’s adoption timeline. It also shows the adoption time for logged device’s adopted APs. To view the adoption timeline of a specific device, use the on <device-name> option to specify the device.on <DEVICE-NAME> The following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Displays a device’s adoption information, based on the parameter passed.• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-912.png)
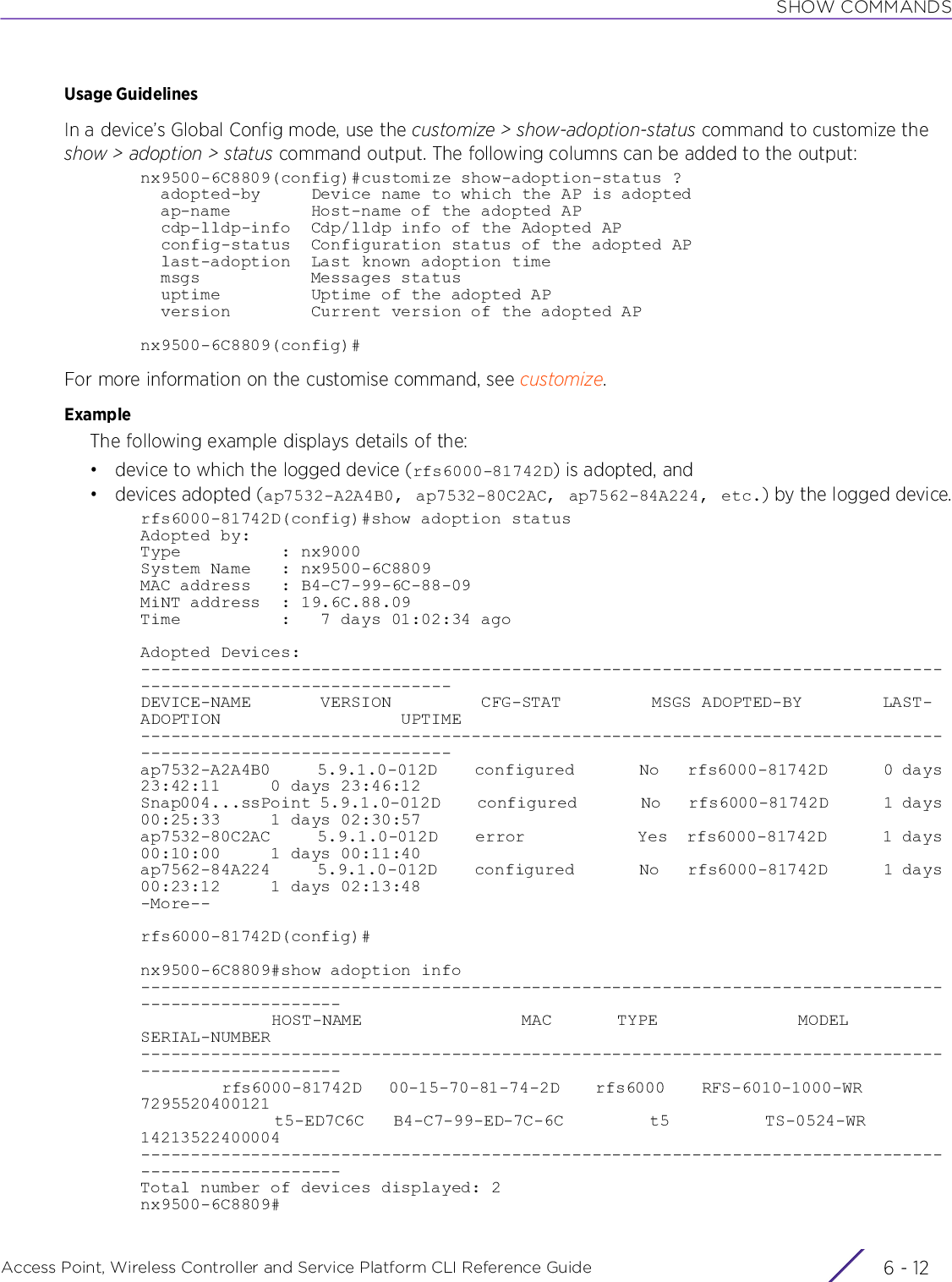
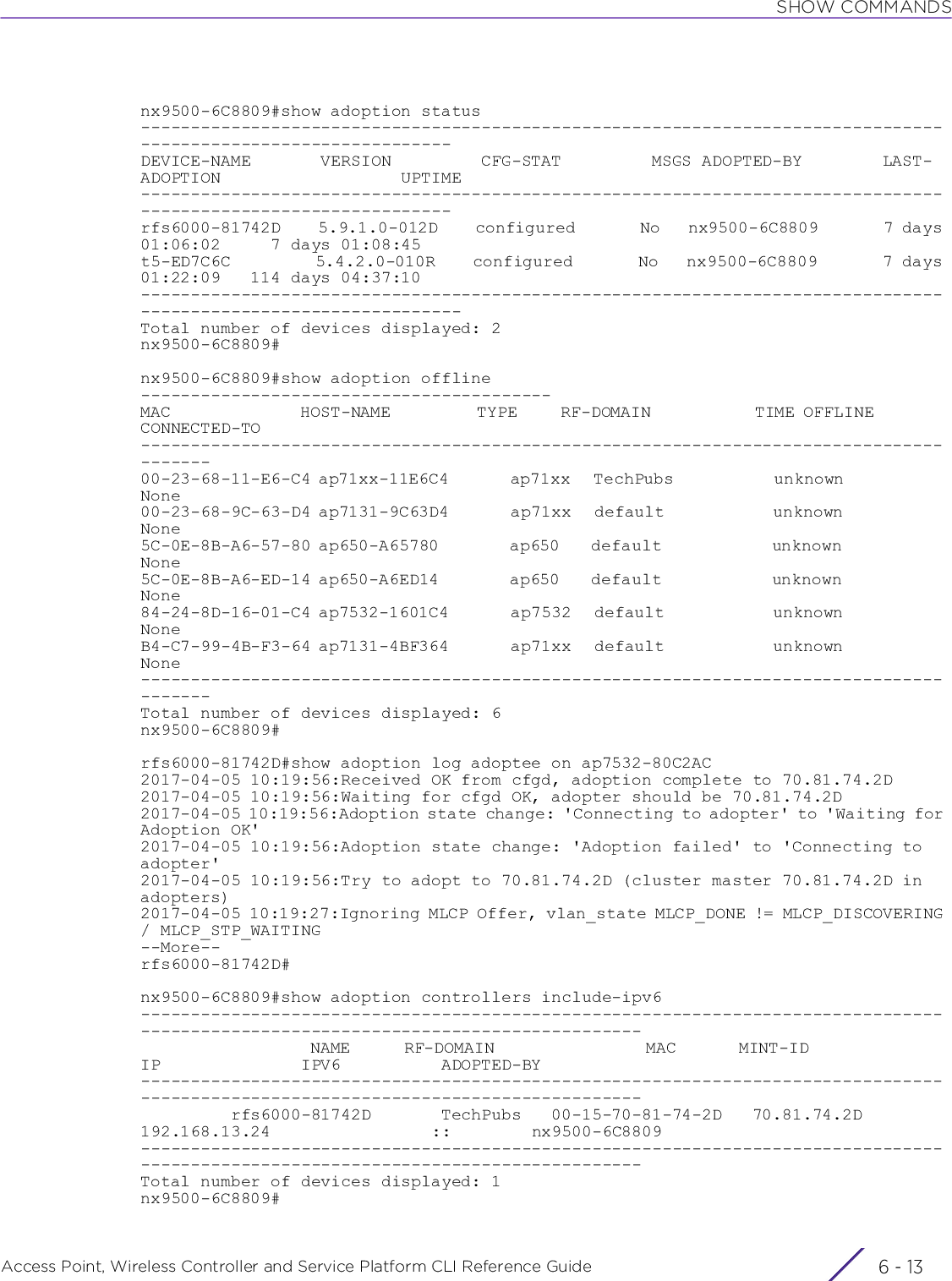
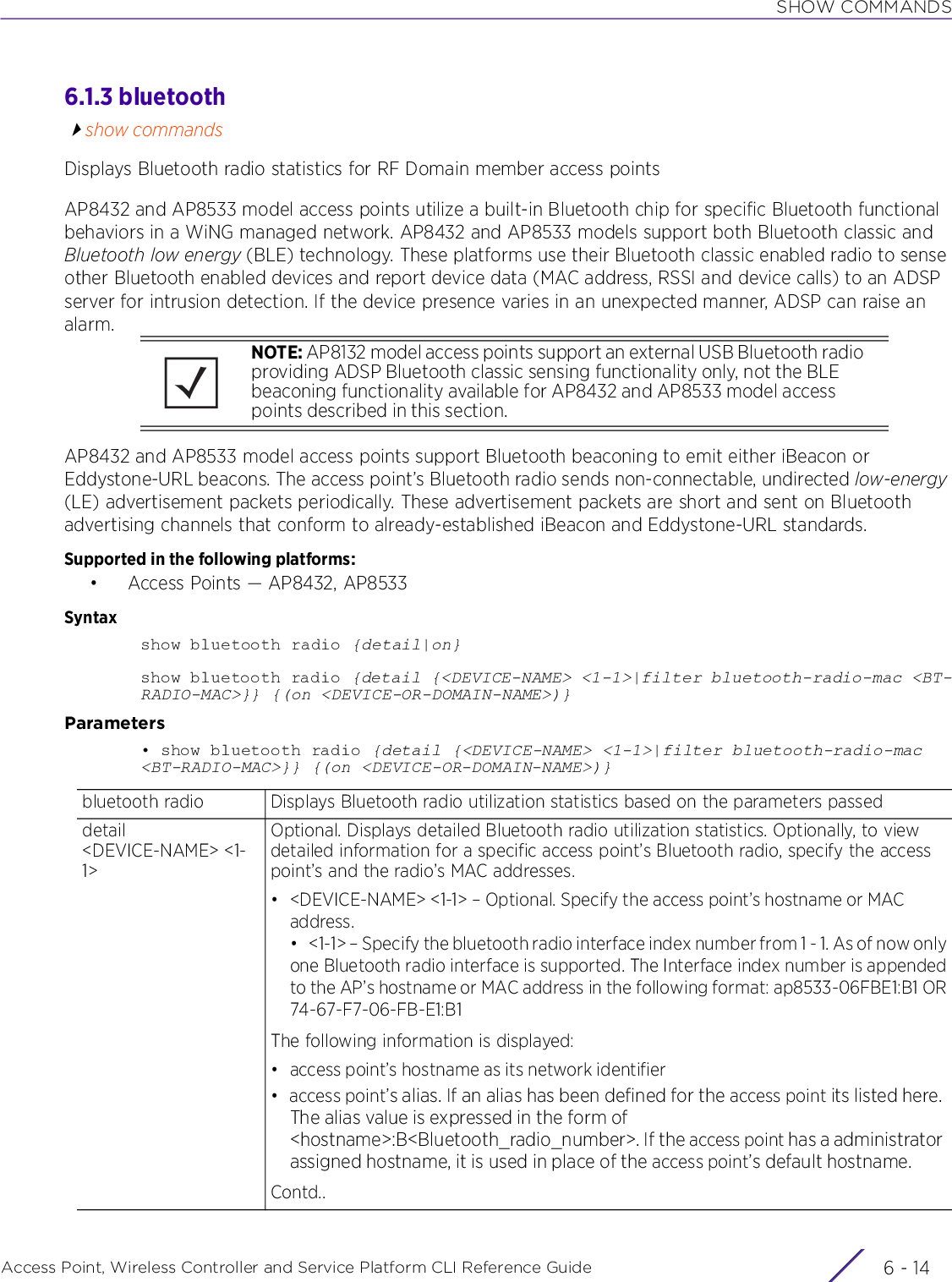
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 15Examplenx9500-6C8809(config)#show bluetooth radio on ap8533-06F808----------------------------------------------------------------------------- BLUETOOTH RADIO RADIO MAC MODES STATE-----------------------------------------------------------------------------ap8533-06F808:B1 74-67-F7-08-A3-B0 BLE-Beacon On-----------------------------------------------------------------------------Total number of Bluetooth radios displayed: 0nx9500-6C8809(config)#nx9500-6C8809(config)#show bluetooth radio detail 74-67-F7-06-F8-08 1Radio: 74-67-F7-06-F8-08:B1, alias ap8533-06F808:B1 STATE : Off [shutdown in cfg] PHY INFO : MAC: 74-67-F7-08-A3-B0 ACCESS POINT : Name: ap8533-06F808 Location: default Placement: Indoor ENABLED MODES : BLE-Beacon BEACON TYPES : Eddystone-URL BEACON PERIOD : 1000ms Last error : nx9500-6C8809(config)#contd.. • access point’s factory encoded MAC address• access point and bluetooth radio’s administrator assigned area of deployment (the AP’s geographical location)• bluetooth radio’s state (on/off)• bluetooth radio’s reason for inactivity (in case the radio is off)• bluetooth radio’s factory encoded MAC address serving as this device’s hardware identifier on the network• bluetooth radio’s functional mode: bt-sensor or le-beacon• bluetooth radio’s beacon period• bluetooth radio’s beacon type• descriptive text on any error that’s preventing the Bluetooth radio from operatingfilter bluetooth-radio-mac <BT-RADIO-MAC>Optional. Specifies additional filters to get table values. Filters data based on the Bluetooth radio’s MAC address.• <BT-RADIO-MAC> – Specify the Bluetooth radio’s MAC address. The system only displays statistics related to the specified Bluetooth radio.on <DEVICE-OR-DOMAIN-NAME>The following keywords are recursive and common to all of the above.• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays Bluetooth radio statistics on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the device or RF Domain. Ifthe device name is explicitly given, the results display data for the specified AP only.If the RF Domain is explicitly given, the results display data for all APs within the spec-ified RF Domain.If no device/RF Domain is specified, the results include data for all Bluetooth radios within the controller’s RF Domain.If the controller is in the “on rf-domain all” mode, the results include data for all Bluetooth radios for all APs in each domain known to the controller.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-916.png)
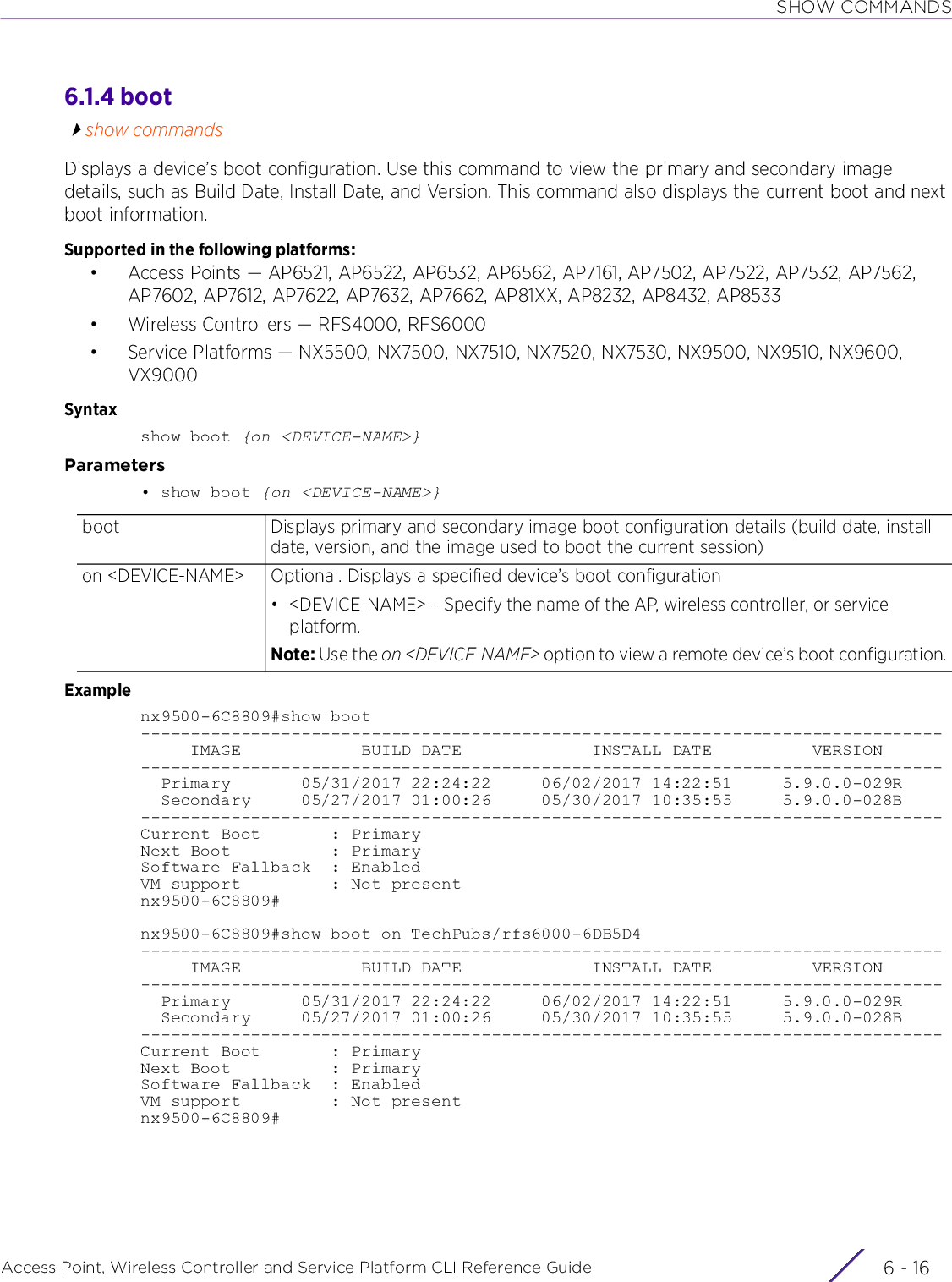

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 186.1.6 captive-portalshow commandsDisplays WLAN captive portal information. Use this command to view a configured captive portal’s client information.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow captive-portal sessions {include-ipv6|on <DEVICE-OR-DOMAIN-NAME>|statistics} {(filter [captive-portal [<CAPTIVE-PORTAL>|not <CAPTIVE-PORTAL>]|ip [<IPv4>|not <IPv4>]|ipv6 [<IPv6>|not <IPv6>]|state [pending|success|not [pending|success]|vlan [<VLAN-ID>|not <VLAN-ID>]|wlan [<WLAN-NAME>|not <WLAN-NAME>]])}Parameters• show captive-portal sessions {include-ipv6|on <DEVICE-OR-DOMAIN-NAME>|statistics} {(filter [captive-portal [<CAPTIVE-PORTAL>|not <CAPTIVE-PORTAL>]|ip [<IPv4>|not <IPv4>]|ipv6 [<IPv6>|not <IPv6>]|state [pending|success|not [pending|success]|vlan [<VLAN-ID>|not <VLAN-ID>]|wlan [<WLAN-NAME>|not <WLAN-NAME>]])}captive-portal sessionsDisplays active captive portal client session detailsinclude-ipv6 Optional. Includes IPv6 address (if known) of captive portal clientsBy default the system only displays IPv4 addresses. The include-ipv6 parameter includes IPv6 address (if known) of each client.statistics Optional. Displays statistical information regarding client sessionson <DEVICE-OR-DOMAIN-NAME>Optional. Displays active captive portal session details on a specified device or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.filter This parameter is recursive and can be used with any of the above parameters to define additional filters.Optional. Defines additional filters. Use one of the following options: captive-portal, ip, ipv6, state, vlan, or wlan.captive-portal [<CAPTIVE-PORTAL>|not <CAPTIVE-PORTAL>]Optional. Displays captive portal client and client session information, based on the captive portal name passed• <CAPTIVE-PORTAL> – Specify the captive portal name. Displays client details for the specified captive portal.• not <CAPTIVE-PORTAL> – Inverts the match selection. Displays client details for all captive portals other than the specified captive portal.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-919.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 19Examplerfs4000-229D58#show captive-portal sessions=======================================================================================CLIENT IPv4 CAPTIVE-PORTAL WLAN/PORT VLAN STATE SESSION TIME---------------------------------------------------------------------------------------00-26-55-F4-5F-79 192.168.3.99 cappo rfs4000-229D58:ge2 400 Success 23:58:35=======================================================================================Total number of captive portal sessions displayed: 1rfs4000-229D58#ip [<IPv4>|not <IPv4>]Optional. Displays captive portal client/client sessions information, based on the IPv4 address passed• <IPv4> – Specify the client’s IPv4 address. Displays information of the client identified by the <IPv4> parameter• not <IPv4> – Inverts the match selection. Displays client details for all clients other than the one identified by the <IPv4> parameter.ipv6 [<IPv6>|not <IPv6>]This filter option is available only for the ‘include-ipv6’ keyword.Optional. Displays captive portal client/client sessions information, based on the IPv6 address passed• <IPv6> – Specify the client’s IPv6 address. Displays information of the client identified by the <IPv6> parameter• not <IPv6> – Inverts the match selection. Displays client details for all clients other than the one identified by the <IPv6> parameter.state [pending|success|not [pending|success]]Optional. Filters clients/client sessions based on the client’s authentication state• pending – Displays information of clients redirected for authentication• success – Displays information of successfully authenticated clients• not [pending|success] – Inverts match selection• pending – Displays information of successfully authenticated clients (opposite ofpending authentication)• success – Displays information of clients redirected for authentication (opposite ofsuccessful authentication)vlan [<VLAN-ID>|not <VLAN-ID>]Optional. Displays captive portal client/client sessions information based on the VLAN ID passed• <VLAN-ID> – Specify the VLAN ID. Displays client details for the specified VLAN.• not <VLAN-ID> – Inverts match selection. Displays client details for all VLANs other than the one identified by the <VLAN-ID> parameter.wlan [<WLAN-NAME>|not <WLAN-NAME>]Optional. Displays captive portal client/client sessions information based on the WLAN name passed• <WLAN-NAME> – Specify the WLAN name. Displays client details for the specified WLAN.• not <WLAN-NAME> – Inverts match selection. Displays client details for all WLANs other than the one identified by the <WLAN-NAME> parameter.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-920.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 206.1.7 captive-portal-page-uploadshow commandsDisplays captive portal page information, such as upload history, upload status, and page file download statusSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow captive-portal-page-upload [history|list-files|load-image-status|status]show captive-portal-page-upload load-image-statusshow captive-portal-page-upload history {on <RF-DOMAIN-NAME>}show captive-portal-page-upload status {on [<RF-DOMAIN-NAME>|<RF-DOMAIN-MANAGER>]}show captive-portal-page-upload list-files <CAPTIVE-PORTAL-NAME>Parameters• show captive-portal-page-upload load-image-status• show captive-portal-page-upload history {on <RF-DOMAIN-NAME>}• show captive-portal-page-upload status {on [<RF-DOMAIN-NAME>|<RF-DOMAIN-MANAGER>]}• show captive-portal-page-upload list-files <CAPTIVE-PORTAL-NAME>load-image-status Displays captive portal advanced page file download status on the logged devicehistory {on <RF-DOMAIN-NAME>}Displays captive portal page upload history• on <RF-DOMAIN-NAME> – Optional. Displays captive portal page upload history within a specified RF Domain. Specify the RF Domain name.status {on <RF-DOMAIN-NAME>|on <RF-DOMAIN-MANAGER>}Displays captive portal page upload status• on <RF-DOMAIN-NAME> – Optional. Displays captive portal page upload status within a specified RF Domain. Specify the RF Domain name.• on <RF-DOMAIN-MANAGER> – Optional. Displays captive portal page upload status for a specified RF Domain Manager. Specify the RF Domain Manager name.list-files <CAPTIVE-PORTAL-NAME>Displays a list of all captive portal Web page files, of a specified captive portal, uploaded (internal and advanced page files) • <CAPTIVE-PORTAL-NAME> – Specify the captive portal name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-921.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 226.1.8 cdpshow commandsDisplays the Cisco Discovery Protocol (CDP) neighbor tableSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow cdp [neighbors|report] {detail {on <DEVICE-NAME>}|on <DEVICE-NAME>}Parameters• show cdp [neighbors|report] {detail {on <DEVICE-NAME>}|on <DEVICE-NAME>}ExampleThe following example shows detailed CDP neighbors table:nx9500-6C8809#show cdp neighbors detail-------------------------Device ID: ap8132-74B45CEntry address(es): IP Address: 192.168.13.26Platform: AP-8132-66040-WR, Capabilities: Router SwitchInterface: ge1, Port ID (outgoing port): ge1Hold Time: 165 secadvertisement version: 2Native VLAN: 1Duplex: fullVersion :5.8.6.0-008B-------------------------Device ID: ap7532-80C2ACEntry address(es): IP Address: 192.168.13.28Platform: AP-7532-67040-WR, Capabilities: Router SwitchInterface: ge1, Port ID (outgoing port): ge1Hold Time: 169 sec--More--nx9500-6C8809#cdp [neighbors|report] Displays CDP neighbors table or aggregated CDP neighbors tabledetail {on <DEVICE-NAME>}Optional. Displays detailed CDP neighbors table or aggregated CDP neighbors table• on <DEVICE-NAME> – Optional. Displays table details on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.on <DEVICE-NAME> Optional. Displays table details on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-923.png)
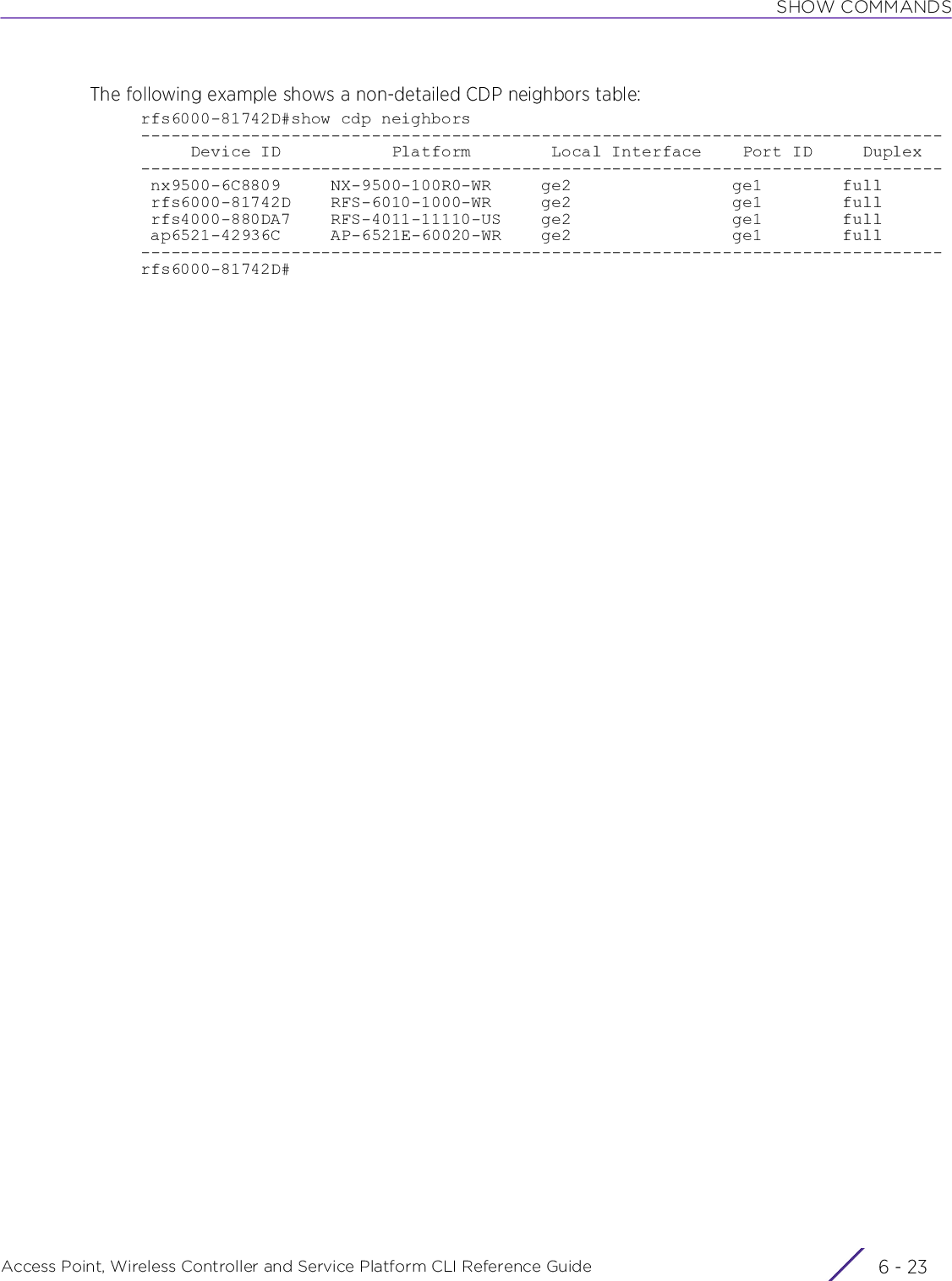
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 246.1.9 classify-urlshow commandsDisplays a specified URL’s category. Use this command to query the category of a specific URL. The query is sent to a configured classification server. This option is available only if a valid URL filter license is available.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow classify-url [<URL-TO-QUERY>|datacenter <URL-TO-QUERY>]Parameters• show classify-url [<URL-TO-QUERY>|datacenter <URL-TO-QUERY>]Examplenx9500-6C8809#show classify-url www.google.com Categories: search-engines-portals, Custom Categories:nx9500-6C8809#nx9500-6C8809#show classify-url www.ndtv.com Categories: news, Custom Categories: list1,nx9500-6C8809#classify-url Queries the category of a specified URL<URL-TO-QUERY> Specify the URL to query. The query is sent to the configured classification server.datacenter <URL-TO-QUERY>The query is sent to a global classification datacenter• <URL-TO-QUERY> – Specify the URL to query.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-925.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 266.1.11 clustershow commandsDisplays cluster information (cluster configuration parameters, members, status, etc.)Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow cluster [configuration|history|members|status]show cluster [configuration|history {on <DEVICE-NAME>}|members {detail}|status]Parameters• show cluster [configuration|members {detail}|status]Examplerfs6000-380649(config)#show cluster configurationCluster Configuration Information Name : SiteConRFS6k Configured Mode : Active Master Priority : 128 Force configured state : Disabled Force configured state delay : 5 minutes Handle STP : Disabled Radius Counter DB Sync Time : 5 minutesrfs6000-380649(config)#rfs6000-380649(config)#show cluster members detail--------------------------------------------------------------------------------------- ID MAC MODE AP COUNT AAP COUNT AP LICENSE AAP LICENSE VERSION---------------------------------------------------------------------------------------70.38.06.49 00-15-70-38-06-49 Active 0 1 0 0 5.8.6.0-008B70.81.74.2D 00-15-70-81-74-2D Active 0 0 1 0 5.8.6.0-008B---------------------------------------------------------------------------------------rfs6000-380649(config)#cluster Displays cluster informationconfiguration Displays cluster configuration detailshistory on <DEVICE-NAME>Displays cluster history status• <DEVICE-NAME> – Optional. Specify the controller or access point name. If the device name is not specified, the system displays all cluster history.members {detail} Displays cluster members configured on the logged device• detail – Optional. Displays detailed information of known cluster membersstatus Displays cluster status](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-927.png)
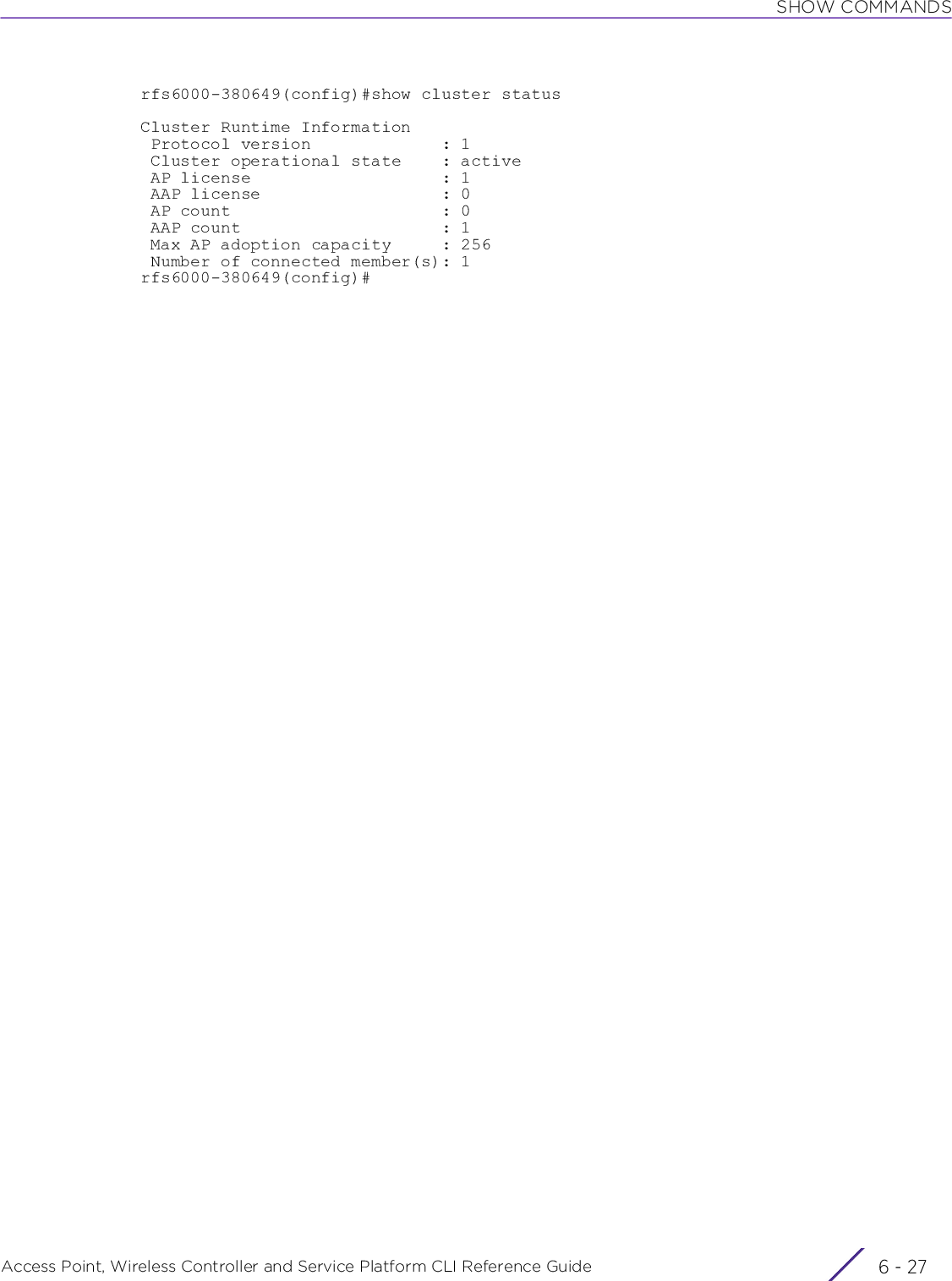



![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 326.1.16 cryptoshow commandsDisplays encryption mode informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow crypto [cmp|ike|ipsec|key|pki]show crypto cmp request statusshow crypto ike sa {detail|on|peer|version}show crypto ike sa {detail|peer <IP>} {on <DEVICE-NAME>}show crypto ike sa {version [1|2]} {peer <IP>} {(on <DEVICE-NAME>)}show crypto ipsec sa {detail|on|peer}show crypto ipsec sa {detail} {on <DEVICE-NAME>}show crypto ipsec sa {peer <IP>} {detail} {(on <DEVICE-NAME>)}show crypto key rsa {on|public-key-detail}show crypto key rsa {public-key-detail} {(on <DEVICE-NAME>)}show crypto pki trustpoints {<TRUSTPOINT-NAME>|all|on}show crypto pki trustpoints {<TRUSTPOINT-NAME>|all} {(on <DEVICE-NAME>)}Parameters• show crypto cmp request status• show crypto ike sa {detail|peer <IP>} {on <DEVICE-NAME>}crypto cmp request statusDisplays current status of in-progress certificate management protocol (CMP) requestsFor more information, see CRYPTO-CMP-POLICY.crypto ike sa Displays Internet Key Exchange (IKE) security association (SA) statisticsdetail Displays detailed IKE SA statisticspeer <IP> Optional. Displays IKE SA statistics for a specified peer• <IP> – Specify the peer’s IP address in the A.B.C.D formaton <DEVICE-NAME> Optional. Displays IKE SA statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-933.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 33• show crypto ike sa {version [1|2]} {peer <IP>} {(on <DEVICE-NAME>)}• show crypto ipsec sa {detail} {on <DEVICE-NAME>}• show crypto sa {peer <IP>} {detail} {(on <DEVICE-NAME>)}• show crypto key rsa {public-key-detail} {(on <DEVICE-NAME>)}• show crypto pki trustpoints {<TRUSTPOINT-NAME>|all} {(on <DEVICE-NAME>)}crypto ike sa Displays IKE SA detailsversion [1|2] Optional. Displays IKE SA version statistics•1 – Displays IKEv1 statistics• 2 – Displays IKEv2 statisticspeer <IP> Optional. Displays IKE SA version statistics for a specified peer• <IP> – Specify the peer’s IP address in the A.B.C.D formaton <DEVICE-NAME> The following keyword is recursive and common to the ‘peer ip’ parameter:• on <DEVICE-NAME> – Optional. Displays IKE SA statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.crypto ipsec sa Displays Internet Protocol Security (IPSec) SA statistics. The IPSec encryption authenticates and encrypts each IP packet in a communication sessiondetail Optional. Displays detailed IPSec SA statisticson <DEVICE-NAME> Optional. Displays IPSec SAs on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.crypto ipsec sa Displays IPSec SA statistics. The IPSec encryption authenticates and encrypts each IP packet in a communication sessionpeer <IP> detail Optional. Displays IPSec SA statistics for a specified peer• <IP> – Specify the peer’s IP address in the A.B.C.D format.• detail – Displays detailed IPSec SA statistics for the specified peeron <DEVICE-NAME> The following keyword is recursive:• on <DEVICE-NAME> – Optional. Displays IPSec SAs on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.crypto key rsa Displays RSA public keyspublic-key-detail Optional. Displays public key in the Privacy-Enhanced Mail (PEM) formaton <DEVICE-NAME> The following keyword is recursive:• on <DEVICE-NAME> – Optional. Displays public key on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.crypto pki Displays PKI related informationtrustpoints Displays WLAN trustpointsThis command displays all trustpoints including CMP-generated trustpoints.<TRUSTPOINT-NAME> Optional. Displays a specified trustpoint details. Specify the trustpoint name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-934.png)
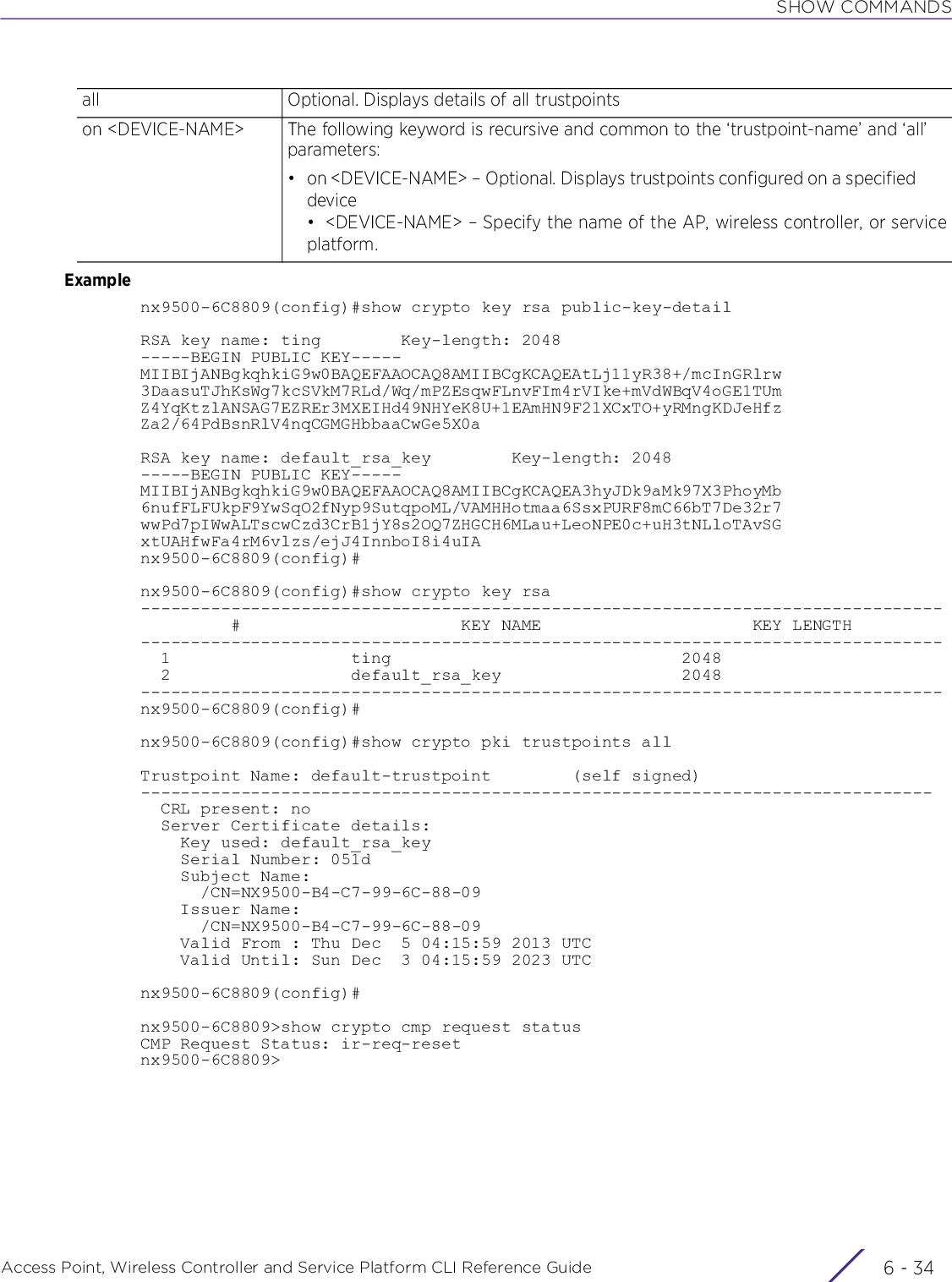
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 356.1.17 databaseshow commandsDisplays database-related statistics and statusSupported in the following platforms:• Service Platforms — NX9500, NX9510, VX9000Syntaxshow database [backup-status|keyfile|restore-status|statistics|status|users] {on <DEVICE-NAME>}Parameters• show database [backup-status|keyfile|restore-status|statistics|status|users] {on <DEVICE-NAME>}Examplevx9000-D031F2(config)#show database backup-status detailLast Database Backup Status : Failed(Error in ftp: 1)Last Database Backup Time : 2017-04-11 08:03:10-----------------------------------------------Starting backup of mart ...connected to: 127.0.0.12015-05-20T14:02:46.340+0530 DATABASE: mart to dump/mart2015-05-20T14:02:46.341+0530 mart.system.indexes to dump/mart/system.indexes.bson2015-05-20T14:02:46.341+0530 61 documents2015-05-20T14:02:46.341+0530 mart.wlan_info to dump/mart/wlan_info.bson2015-05-20T14:02:46.341+0530 5 documents2015-05-20T14:02:46.342+0530 Metadata for mart.wlan_info to dump/mart/wlan_info.metadata.json2015-05-20T14:02:46.342+0530 mart.rf_domain_info to dump/mart/rf_domain_info.bson2015-05-20T14:02:46.342+0530 21 documents2015-05-20T14:02:46.342+0530 Metadata for mart.rf_domain_info to dump/mart/rf_domain_info.metadata.json--More--vx9000-D031F2(config)#database Displays all configured database-related statistics and statusbackup-status Displays the last database backup statuskeyfile Displays the keyfiles generated on the database host to enable authenticated database accessback-restore Displays the last database restore statusstatistics Displays database-related statistics, such as name of the database (NSight or captive portal), data size, storage size, free disk space available, etc.status Displays database status, such as online time.users Displays database users created. These are the users that can access the databases.on <DEVICE-NAME> Optional. Displays database-related information on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-936.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 36vx9000-D031F2(config)#show database status-------------------------------------------------------------------------------- MEMBER STATE ONLINE TIME-------------------------------------------------------------------------------- localhost PRIMARY 2 days 3 hours 45 min 24 sec-------------------------------------------------------------------------------- Authentication: Disabled Authentication User: None--------------------------------------------------------------------------------[*] indicates this device.vx9000-D031F2(config)#vx9000-D031F2(config)#show database statistics-------------------------------------------------------------------------------- DATABASE STORAGE SIZE DATA SIZE INDEX SIZE DISK FREE-------------------------------------------------------------------------------- admin 32k 335 48k 594.5G captive-portal 4k 0 24k 594.5G nsightcache 96k 2.0k 264k 594.5G nsight 26.1M 136.6M 18.9M 594.5G--------------------------------------------------------------------------------vx9000-D031F2(config)#nx9500-6C8809#show database keyfileSLz6lVXyi9vyTCChUKs04THRo3mWOjZheM58Dt6NC0MDkdgV+5+wWN9/IT6zfy1sKPut4BPpUWyM8MEaRmapg4kRrN/SMSMlH6sPITMGTLMu6wRYFEUgKgO01Wn/BohE5n+uuhY0xiZQsN0LS7IaA8Yb9rX859YRQ7v9By5aEpi1NIDR4KX09Xs3TqIB+5v2jE3vv7OsKK+LX63bCIoYo35MX251T2pHdL+fMdLfKPMt8ZbzYzx2b22Yvukfg0gmxHsMCB+bLAsfkjeCPgHCAq/WWi3Kxna6ysFjp8J4US2Bm+GL1COvALbCQBwkPPN+o7M90qT40AubibBkeID2S9rkQkKcXqGESbL5xG6ip+26jIxiLv7GP6/SQZGFOqC/ZZEkCNhGhkiyktiOIxBfoXwoy66sqQ4KBwLF449eqBe7Svel/dzpFPNfYZpW8SMYLD6iLTPR9BddjsBBej8kGGc5R+M0R6lgQFEew2WX6Rqz45YTGEcfOkl8c9wl3taDxn4imhI/esjMppFDu5muxRHF5RHa5RncTGnsMfc7ndvUl78QaGHLZvDqjNLBUnuPc8QmyohEnKf70TYx/ruG9Vb2AP0Jw5OODTNh2lmaoFjicKYQr+xIHUJpHc0qY43C5WzlWf84CK67cu7kOPiJoaxvufzSXhJB18BiCXTuv40+ZZ6e3PcisZuIrPXxCZupGJ3KpuHq61IJyVCydFd5zl4Fho+RGaQ9dlDIlaLjbW+YT4CEH1bTiUmreUt+D/X2zcB9nec77wIIAcdfl2qysgGIqmkI3jRI89d3XM5Y7Kc2TuXBVZOazYldPj+qE/yiEgVWcbtvyS834jit35MGbVXhvQ2d45qgo42WZwdTVLXC9memzoKa3YIZoj32uP3UiOrzD8E1gMte4gDE/KmGkYya+hsWswBmKC1v0gj5NQ6TejYS4z+nefqLHUSVXbQ8NxRel1huGi8P1ns4dWCwClWp8GpxUTa7GuN1DySA7/l2OJM=nx9500-6C8809#](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-937.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 376.1.18 device-upgradeshow commandsDisplays device firmware upgradation information for devices adopted by a wireless controller or access pointSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow device-upgrade [history|load-image-status|status|versions]show device-upgrade [history {on <DOMAIN-NAME>}|load-image-status|versions {on <DEVICE-OR-DOMAIN-NAME>}show device-upgrade status {on [<DOMAIN-NAME>|rf-domain-manager]|summary {on <DOMAIN-NAME>}}Parameters• show device-upgrade [history {on <DOMAIN-NAME>}|load-image-status|versions {on <DEVICE-OR-DOMAIN-NAME>}]• show device-upgrade status {on [<DOMAIN-NAME>|rf-domain-manager]|summary {on <DOMAIN-NAME>}}]device-upgrade Displays device upgrade information based on the parameters passedhistory {on <DOMAIN-NAME>}Displays device upgrade history• on <DOMAIN-NAME> – Optional. Displays upgrade history for all devices within a specified RF Domain. Specify the RF Domain name.load-image-status Displays firmware image loading status. The output displays the <DEVICE> image loading status in percentage.For example:#show device-upgrade load-image-status Download of ap81xx firmware file is 47 percent completeversions {on <DEVICE-OR-DOMAIN-NAME>}Displays firmware image versions• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays firmware image versions loaded on specified device or RF Domain. Specify the name of the AP, wireless controller, service platform, or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the AP, wireless controller, service plat-form, or RF Domain name.device-upgrade Displays device upgrade information based on the parameters passedstatus Displays in progress device upgrade statuson [<DOMAIN-NAME>|rf-domain-manager]Optional. Displays in progress upgrade status of all devices within a specified RF Domain, or all devices upgraded by the RF Domain manager. Use this option to view upgrade status of multiple devices.• <DOMAIN-NAME> – Specify the RF Domain name.• rf-domain-manager – Select to view devices upgraded by the RF Domain manager.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-938.png)
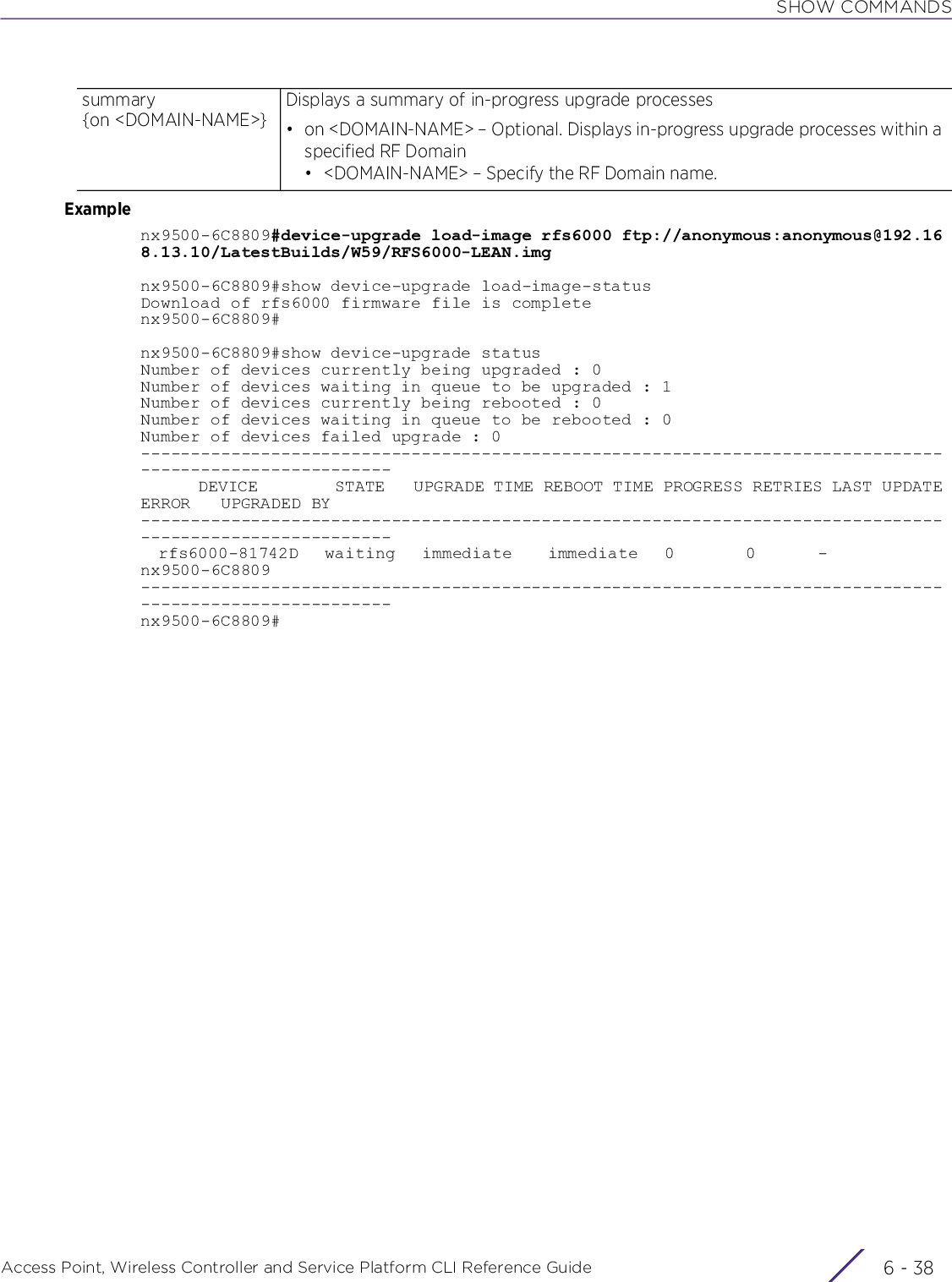

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 40• show dot1x {interface [<INTERFACE-NAME>|ge <1-4>|port-channel <1-2>]} {on <DEVICE-NAME>}Examplerfs6000-81742D#show dot1x all802.1X information------------------------------ SysAuthControl : disabled Guest-Vlan : disabled AAA-Policy : none Holdtime : 60802.1X information for interface GE1--------------------------------------Supplicant MAC N/A Auth SM State : FORCE AUTHORIZED Bend SM State : REQUEST Port Status : AUTHORIZED Host Mode : SINGLE Auth Vlan : None Guest Vlan : None802.1X information for interface GE2--------------------------------------Supplicant MAC N/A Auth SM State : FORCE AUTHORIZED Bend SM State : REQUEST Port Status : AUTHORIZED--More--rfs6000-81742D#rfs6000-81742D#show dot1x interface ge 1802.1X information for interface GE1--------------------------------------Supplicant MAC N/A Auth SM State : FORCE AUTHORIZED Bend SM State : REQUEST Port Status : AUTHORIZED Host Mode : SINGLE Auth Vlan : None Guest Vlan : Nonerfs6000-81742D#dot1x {on <DEVICE-NAME>}Optional. Displays dot1x information for interfaces on a specified device• <DEVICE-NAME> – Specify the name of AP, wireless controller, or service platform.dot1x interface Optional. Displays dot1x information for a specified interface or interface type<INTERFACE-NAME> Displays dot1x information for the layer 2 (Ethernet port) interface specified by the <INTERFACE-NAME> parameterge <1-4> Displays dot1x for a specified GigabitEthernet interface• <1-4> – Select the interface index from 1 - 4.port-channel <1-2> Displays dot1x for a specified port channel interface• <1-2> – Select the interface index from 1 - 2.on <DEVICE-NAME> The following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Displays dot1x interface information on a specified device• <DEVICE-NAME> – Specify the name of AP, wireless controller, or service plat-form.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-941.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 416.1.20 dpishow commandsDisplays Deep Packet Inspection (DPI) statistics for all configured and canned applications. DPI is an advanced packet analysis technique, which analyzes packet and packet content headers to determine the nature of network traffic. When DPI is enabled, packets of all flows are subjected to DPI to get accurate results. DPI identifies applications (such as, Netflix, Twitter, Facebook, etc.) and also extracts metadata (such as, host name, server name, TCP-RTT, etc.) for further use by the WiNG firewall.Supported in the following platforms:• Access Points — AP7522, AP7532, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow dpi [app|app-category|application|application-policy|per-category]show dpi app wireless-clients stats <MAC> {on <DEVICE-OR-DOMAIN-NAME>}show dpi [app|app-category] stats [<APPLICATION/APP-CATEGORY-NAME>|all] {on <DEVICE-OR-DOMAIN-NAME>}show dpi application-policy stats <APPLICATION-POLICY-NAME> {on <DEVICE-OR-DOMAIN-NAME>}show dpi application briefshow dpi per-category stats <APP-CATEGORIES> [bytes-in|bytes-out|total-bytes] {on <DEVICE-OR-DOMAIN-NAME>}Parameters• show dpi app wireless-clients stats <MAC> {<DEVICE-OR-DOMAIN-NAME>}NOTE: The show > dpi command returns results only if executed on a device that supports DPI and has DPI logging enabled. DPI logging can be enabled either on the device or on the profile applied to the device. For more information, see dpi.dpi app wireless-clients <MAC>Displays application-related statistics for all or a specified wireless clients• <MAC> – Displays statistics for a specified wireless client. Specify the client’s MAC address.on <DEVICE-OR-DOMAIN-NAME>Optional. Displays statistical data on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the access point, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-942.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 42• show dpi [app|app-category] stats [<APPLICATION/APP-CATEGORY-NAME>|all] {on <DEVICE-OR-DOMAIN-NAME>}• show dpi application-policy stats <APPLICATION-POLICY-NAME> {on <DEVICE-OR-DOMAIN-NAME>}• show dpi application brief• show dpi per-category stats <APP-CATEGORIES> [bytes-in|bytes-out|total-bytes] {on <DEVICE-OR-DOMAIN-NAME>}dpi [app|app-category] statsDisplays statistics for a application or application category• app – Displays statistics for a specified application or all applications• app-category – Displays statistics for a specified application category or all categories.Note: The applications are the RF Domain member allowed applications whose data (bytes) are passing through the WiNG managed network. And, the application categories are existing WiNG or user defined application groups (video, streaming, mobile, audio, etc.) that assist administrators to permit or deny forwarding of application data.[<APPLICATION/APP-CATEGORY-NAME>|all]This parameter is common to the ‘app’ and ‘app-category’ keywords.• <APPLICATION/APP-CATEGORY-NAME> – Displays statistics for a specified application or application category, depending on the option selected in the previous step. Specify the application name or application category name.• all – Displays statistics for all applications or application categories, depending on the option selected in the previous stepon <DEVICE-OR-DOMAIN-NAME>Optional. Displays statistical data on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the access point, wireless controller, service platform, or RF Domain.dpi application-policy statsDisplays statistics for an existing application policy<APPLICATION-POLICY-NAME>Displays statistics for a specified application-policy. Specify the application-policy name.on <DEVICE-OR-DOMAIN-NAME>Optional. Displays application-policy related statistical data on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the access point, wireless controller, service platform, or RF Domain.dpi application brief Displays a brief summary of applications their status and configurationdpi per-category statsDisplays statistics for the top ten applications based on the application category and the Sort ID specified. The Sort ID options are: bytes-in, bytes-out or total-bytes.<APP-CATEGORIES> Specify the application category name. The system displays statistics for the top ten applications in this category.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-943.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 43Examplenx9500-6C8809>show dpi application brief 1-clickshare-com This application recognizes DirectDownloadLink 1-clickshare traffic Application Category : filetransfer Predefined Application : Yes 1-upload-com This application recognizes DirectDownloadLink 1-upload-com traffic Application Category : filetransfer Predefined Application : Yes 1-upload-to This application recognizes DirectDownloadLink 1-upload-to traffic Application Category : filetransfer Predefined Application : Yes 10upload-com This application recognizes DirectDownloadLink 10upload-com traffic Application Category : filetransfer Predefined Application : Yes 123upload-pl This application recognizes DirectDownloadLink 123upload-pl traffic--More--nx9500-6C8809>[bytes-in|bytes-out|total-bytes]Filters and displays statistical data for the top ten utilized applications in respect to the following:• bytes-in – Displays total data bytes uploaded through the controller managed network. If this application data is not aligned with application utilization expectations, consider allowing or denying additional applications and categories or adjusting their precedence (priority).• bytes-out – Displays total data bytes downloaded through the controller managed network. If this application data is not aligned with application utilization expectations, consider allowing or denying additional applications and categories or adjusting their precedence (priority).• total-bytes – Displays total data bytes (uploaded and downloaded) through the controller managed network. These are only the administrator allowed applications approved for proliferation within the managed network.on <DEVICE-OR-DOMAIN-NAME>Optional. Displays statistical data on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the access point, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-944.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 446.1.21 eguestshow commandsDisplays EGuest server status and EGuest registration statisticsSupported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxeguest [registration statistics|status]Parameters• eguest [registration statistics|status]Examplevx-eguest-primary#show eguest status-----------------------------------pid process-----------------------------------2521 gmd2529 regserver2539 acct_server2569 guest_manager2636 acct_server2642 acct_server2643 acct_server2649 acct_server2655 acct_server2708 acct_server-helper2770 guest_manager2776 guest_manager2777 guest_manager2783 guest_manager3628 gmd3630 gmd3631 gmd3632 gmd3633 gmd3634 gmd5729 radiusd-----------------------------------Database server is localDatabase server is reachablevx-eguest-primary#vx-eguest-primary#show eguest registration statisticsmsg_received - number of registration messages receiveduser_try_to_add - number of database add attemptsuser_added - number of messages succesfully added to dbuser_failed - number of messages failed adding to db------------------------------------------------------------------------msg_received user_try_to_add user_added user_failed------------------------------------------------------------------------189 11 11 0vx-eguest-primary#registration statisticsDisplays the EGuest registration statisticsstatus Displays the current status of EGuest servers](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-945.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 456.1.22 environmental-sensorshow commandsDisplays environmental sensor’s recorded data. The environmental sensor has to be enabled and configured in order to collect data related to humidity, light, motion, and temperature.Supported in the following platforms:• Access Points — AP8132Syntaxshow environmental-sensor [history|humidity|light|motion|summary|temperature|version]show environmental-sensor history {<1-HOUR>|<20-MINUTE>|<24-HOUR>}show environmental-sensor [humidity|light|motion|summary|temperature|version]Parameters• show environmental-sensor history {<1-HOUR>|<20-MINUTE>|<24-HOUR>}• show environmental-sensor [humidity|light|motion|summary|temperature|version]NOTE: The environmental senor is supported only on an AP8132. When executed on any controller (other than an AP8132), the show > environmental-sensor > <parameters> command displays environmental-sensor details for adopted AP8132s (if any).environmental-sensor historyDisplays environmental sensor history once in every hour, 20 minutes, or 24 hoursHistory includes the humidity, light, motion, and temperature data recorded by the sensor at specified time interval.1-hour Optional. Displays environmental sensor history once in every 1 (one) hour20-minute Optional. Displays environmental sensor history once in every 20 minutes24-hour Optional. Displays environmental sensor history once in every 24 hoursenvironmental-sensorDisplays environmental sensor’s recorded data, based on the parameters passed. The system displays the specified recorded data.The environmental sensor records data at the following intervals: 20 minutes, 1 hour, and 24 hours.humidity Displays the minimum, average, and maximum humidity recorded light Displays the minimum, average, and maximum light recordedmotion Displays the minimum, average, and maximum motion recordedtemperature Displays the minimum, average, and maximum temperature recordedversion Displays the hardware and firmware versionssummary Displays a summary of the data recorded at following intervals:](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-946.png)
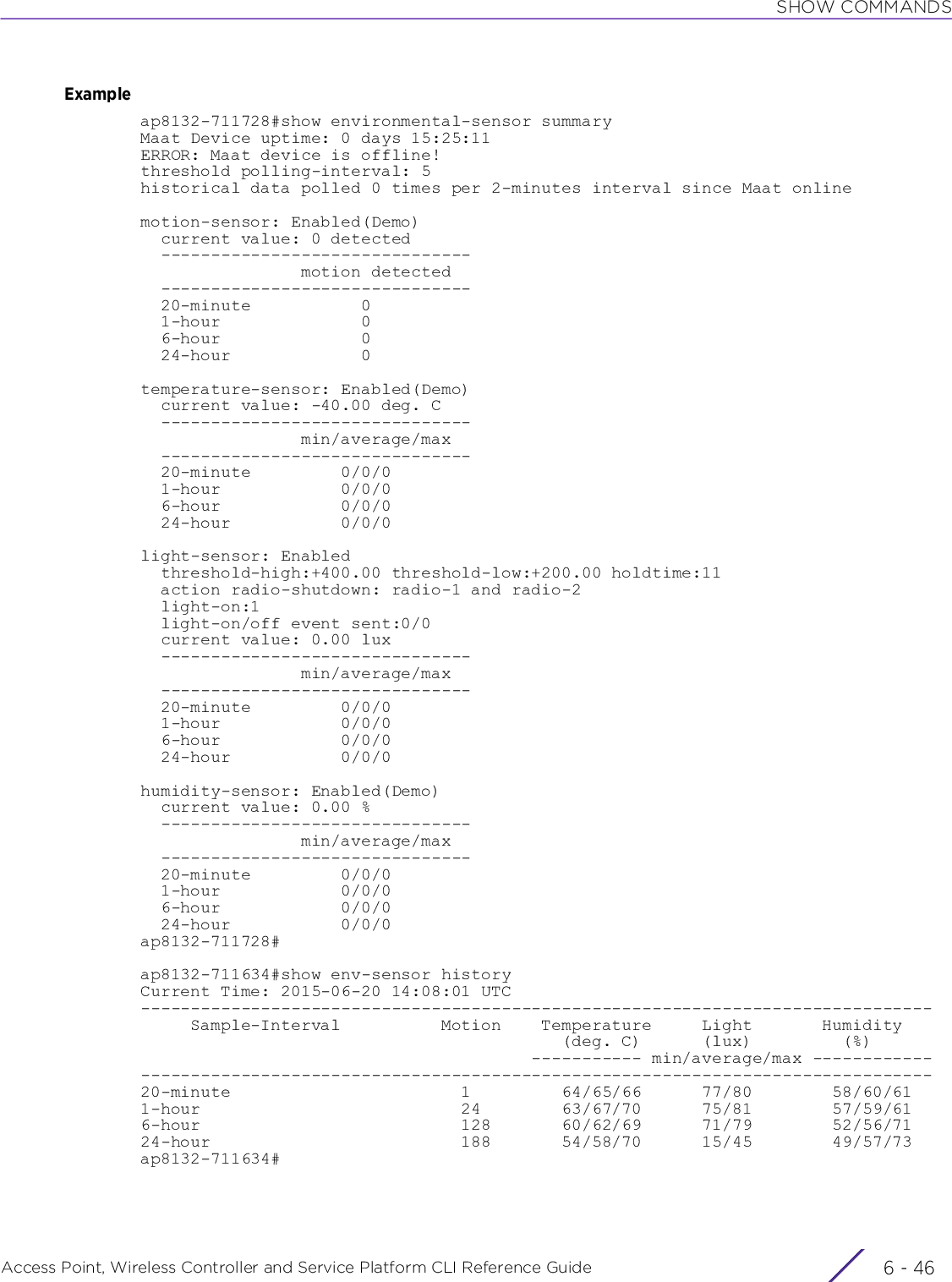
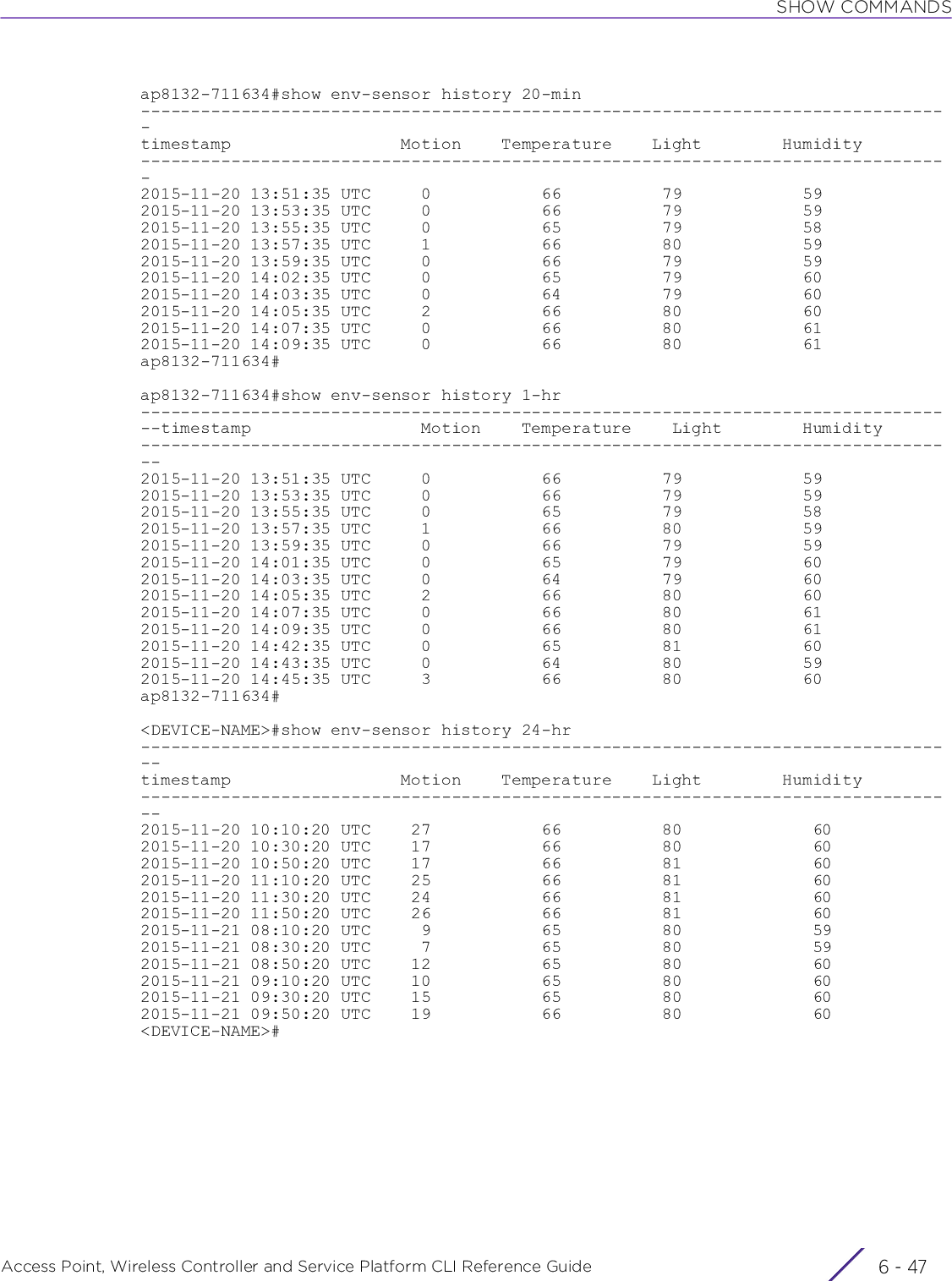
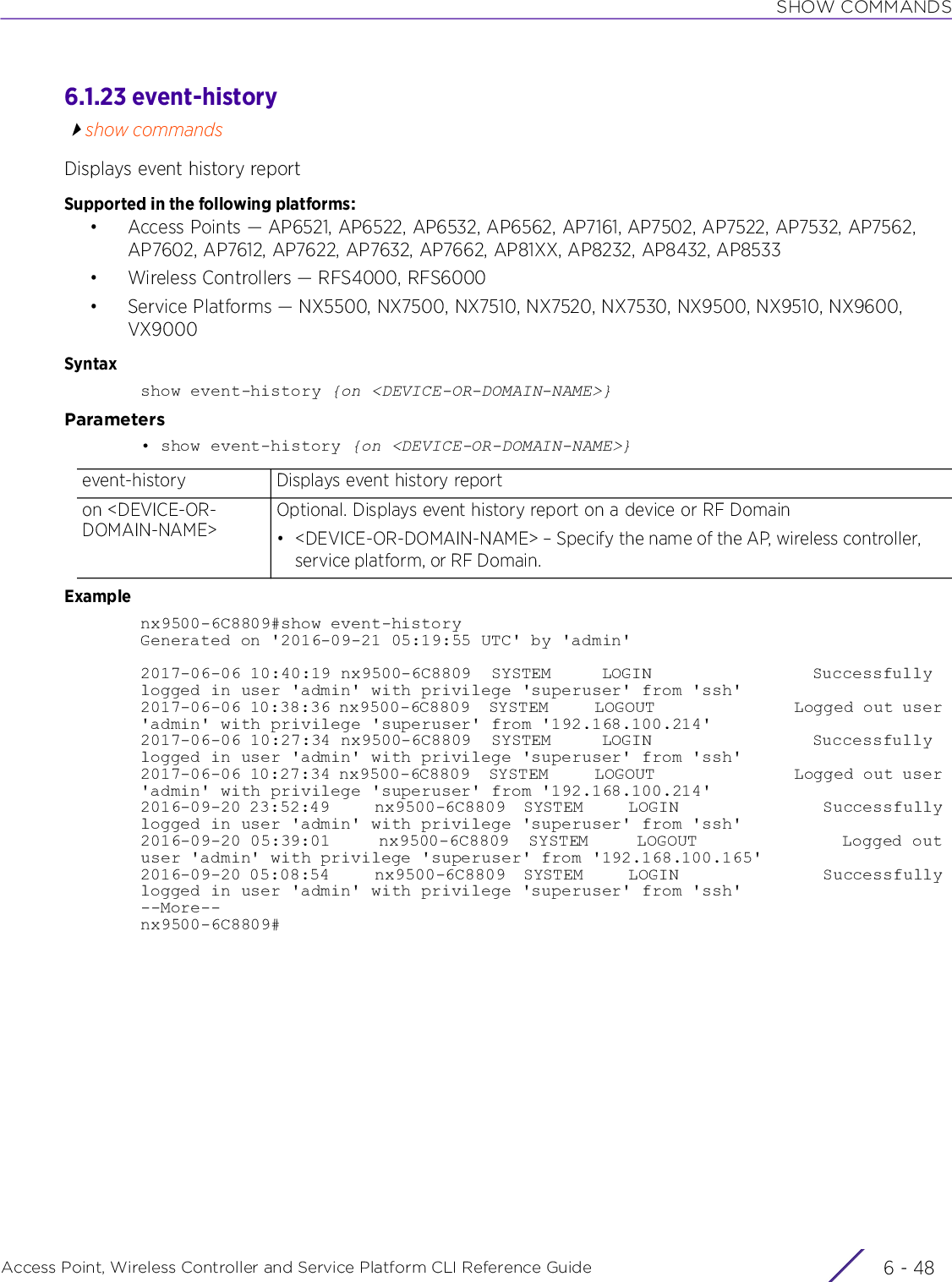
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 496.1.24 event-system-policyshow commandsDisplays detailed event system policy configurationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow event-system-policy [config|detail] <EVENT-SYSTEM-POLICY-NAME>Parameters• show event-system-policy [config|detail] <EVENT-SYSTEM-POLICY-NAME>Examplerfs6000-81742D(config)#show event-system-policy config testpolicy--------------------------------------------------------------------------MODULE EVENT SYSLOG SNMP FORWARD EMAIL--------------------------------------------------------------------------aaa radius-discon-msg on on on default--------------------------------------------------------------------------rfs6000-81742D(config)#event-system-policy Displays event system policy configurationconfig Displays configuration for a specified policydetail Displays detailed configuration for a specified policy<EVENT-SYSTEM-POLICY-NAME>Specify the event system policy name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-950.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 506.1.25 ex3500show commandsDisplays EX3500-related statistical dataSupported in the following platforms:• Service Platforms — NX7500, NX9500Syntaxshow ex3500 [dir|interfaces|system|upgrade|version|whichboot]show ex3500 dir {boot-rom|config|on|opcode} {<FILE-NAME>} {on <EX3500-DEVICE-NAME>}show ex3500 interfaces counters [ether-like stats|ethernet <1-1> <1-52>|ext-if-table stats|if-table stats|portUtil stats|rmon stats] {on <EX3500-DEVICE-NAME>}show ex3500 [system|upgrade|version|whichboot] {on <EX3500-DEVICE-NAME>}Parameters• show ex3500 dir {boot-rom|config|on|opcode} {<FILE-NAME>} {on <EX3500-DEVICE-NAME>}• show ex3500 interfaces counters [ether-like stats|ethernet <1-1> <1-52>|ext-if-table stats|if-table stats|portUtil stats|rmon stats] {on <EX3500-DEVICE-NAME>}ex3500 dir Displays EX3500 directory information based on the option selected. The options are: boot-rom, config, opcodeNote: If none of the specified options is selected, all EX3500 system-related information is displayed.boot-rom Optional. Displays only the Boot-ROM informationconfig Optional. Displays only the configuration fileopcode Optional. Displays only the run-time operation code<FILE-NAME> Displays the contents of a specified file identified by the <FILE-NAME> keyword. This is the name of configuration file or code image.on <EX3500-DEVICE-NAME>Optional. Executes the command on a specified EX3500 device• <DEVICE-NAME> – Specify the device’s name.ex3500 interfaces countersDisplays EX3500 interface counter information based on the option selected. The options are: ether-like, ethernet, ext-if-table, if-table, portUtil, rmonether-like stats Displays Managed Information Base (MIB) object statistics for Ethernet-like interfacesethernet <1-1> <1-52> Displays the Ethernet port statistics based on the unit identifier and port number selected• <1-1> – Specify the EX3500 unit’s identifier from 1 - 1.• <1-52> – Specify the port number from 1 - 52. This range varies for the EX3524 (1-28) and EX3548 (1-52) devices.Note: This option displays the following for the selected Ethernet interface: extended interface table stats, interface table stats, port utilization information, and remote monitoring stats.ext-if-table stats Displays only the extended interface table statistics](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-951.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 51• show ex3500 [system|upgrade|version|whichboot] {on <EX3500-DEVICE-NAME>}Examplenx9500-6C8809#show ex3500 interfaces counters ethernet 1 17Ethernet 1/ 17===== IF table Stats =====2166458 Octets Input14734059 Octets Output14707 Unicast Input19806 Unicast Output0 Discard Input0 Discard Output0 Error Input0 Error Output0 Unknown Protocols Input0 QLen Output===== Extended Iftable Stats =====23 Multi-cast Input5525 Multi-cast Output170 Broadcast Input11 Broadcast Output===== Ether-like Stats =====0 Alignment Errors0 FCS Errors0 Single Collision Frames0 Multiple Collision Frames0 SQE Test Errors0 Deferred Transmissions0 Late Collisions0 Excessive Collisions0 Internal Mac Transmit Errors0 Internal Mac Receive Errors0 Frames Too Long0 Carrier Sense Errors0 Symbol Errors0 Pause Frames Input0 Pause Frames Output===== RMON Stats =====0 Drop Events16900558 Octets40243 Packetsif-table stats Displays only the interface table statisticsportUtil stats Displays only the port utilization informationrmon stats Displays only remote monitoring (RMon) statisticson <EX3500-DEVICE-NAME>Optional. Executes the command on a specified EX3500 device• <DEVICE-NAME> – Specify the device’s name.ex3500 Displays the following information for a specified EX3500 device or all EX3500 devices in the managed networksystem Displays EX3500 system information, such as device description, OID string, up time, name, location, contact, MAC address, etc. Some of these information (example, system name) are configurable items, and if not configured are left blank.upgrade Displays the opcode upgrade configuration settingsversion Displays hardware and software version information for a EX3500 systemwhichboot Displays boot informationon <EX3500-DEVICE-NAME>Optional. Executes the command on a specified EX3500 device• <DEVICE-NAME> – Specify the device’s name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-952.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 546.1.27 file-syncshow commandsDisplays file synchronization settings and status on a controllerThe file-sync command syncs wireless-bridge certificate and trustpoint between the staging-controller and its adopted access points. The show > file-sync command displays information related to this process.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxshow file-sync [configuration|history|load-file-status|status] {on <DEVICE-OR-DOMAIN-NAME>}Parameters• show file-sync [configuration|history|load-file-status|status] {on <DEVICE-OR-DOMAIN-NAME>}file-sync Displays the following file-synchronization (trustpoint and wireless-bridge certificate) related information: configuration, history, load-file-status, and statusconfiguration Displays the following file-synchronization configuration details:• automatic file-syncing enabled or disabled. The default setting is disabled.The X.509 certificate needs synchronization only if the access point’s radio2 is configured to use EAP-TLS authentication. In which case PKCS#12 certificate needs to be pushed on AP adoption. To enable automatic file syncing, in the controller’s device/profile configuration mode, execute the file-sync > auto command. For more information, see file-sync.• Number of access points to which the certificate can be simultaneously uploaded. The default is 10.To modify the number of simultaneous uploads, in the controller’s device/profile configuration mode, execute the file-sync > count <1-20> command. For more information, see file-sync.• Scheduled certificate upload, if any, details, such time and date of upload.To schedule certificate upload, use the file-sync > wireless-certificate command. For more information, see file-sync.history Displays file synchronization history. Use this option to view statistical data relating to wireless-bridge certificate synchronization between staging controller and its access points. When executed, a list of all certificate transfers made to the APs is displayed, with the latest transfer listed at the top.load-file-status Displays the status of the file upload to the controller. Use this command to view the status of a in-progress certificate upload, For more information on initiating a PKCS#12 certificate upload, see file-sync.status Displays status of the file synchronization between the controller and its adopted access point.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-955.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 566.1.28 firewallshow commandsDisplays wireless firewall information, such as Dynamic Host Configuration Protocol (DHCP) snoop table entries, denial of service statistics, active session summaries, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow firewall [dhcp|flows|neighbors]show firewall dhcp snoop-table {on <DEVICE-NAME>}show firewall flows {filter|management|on|stats|wireless-client}show firewall flows {filter} {(dir|dst port <1-65535>|ether|flow-type|icmp|icmpv6|igmp|ip|ipv6|max-idle|min-bytes|min-idle|min-pkts|not|port|src|tcp|udp)}show firewall flows {management {on <DEVICE-NAME>}|stats {on <DEVICE-NAME>}|wireless-client <MAC>|on <DEVICE-NAME>}show firewall neighbors snoop-table {on <DEVICE-NAME>}Parameters• show firewall dhcp snoop-table {on <DEVICE-NAME>}• show firewall flows {filter} {(dir|dst|ether|flow-type|icmp|icmpv6|igmp|ip|ipv6|max-idle|min-bytes|min-idle|min-pkts|not|port|src|tcp|udp)}firewall dhcp snoop-tableDisplays DHCP snoop table entries• snoop-table – Displays DHCP snoop table entriesDHCP snooping acts as a firewall between non-trusted hosts and the DHCP server. Snoop table entries contain MAC address, IP address, lease time, binding type, and interface information of non-trusted interfaces.on <DEVICE-NAME> The following keyword is common to the ‘DHCP snoop table’ and ‘DoS stats’ parameters:• on <DEVICE-NAME> – Optional. Displays snoop table entries, or DoS stats on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.firewall flows Notifies a session has been establishedfilter Optional. Defines additional firewall flow filter parametersdir [wired-wired|wired-wireless|wireless-wired|wireless-wireless] Optional. Matches the packet flow direction• wired-wired – Wired to wired flows• wired-wireless – Wired to wireless flows• wireless-wired – Wireless to wired flows• wireless-wireless – Wireless to wireless flows](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-957.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 57dst port <1-65535>Optional. Matches the destination port with the specified port• port <1-65535> – Specifies the destination port number from 1 - 65535ether [dst <MAC>|host <MAC>|src <MAC>|vlan <1-4094>]Optional. Displays Ethernet filter options• dst <MAC> – Matches only the destination MAC address• host <MAC> – Matches flows containing the specified MAC address• src <MAC> – Matches only the source MAC address• vlan <1-4094> – Matches the VLAN number of the traffic with the specified value. Specify a value from 1- 4094.flow-type [bridged|natted|routed|wired|wireless]Optional. Matches the traffic flow type• bridged – Bridged flows•natted – Natted flows•routed – Routed flows• wired – Flows belonging to wired hosts• wireless – Flows containing a mobile uniticmp {code|type} Optional. Matches flows with the specified Internet Control Message Protocol (ICMP) version 4 code and type• code – Optional. Matches flows with the specified ICMPv4 code• type – Optional. Matches flows with the specified ICMPv4 typeicmpv6 {code|type} Optional. Matches flows with the specified ICMP version 6 code and type• code – Optional. Matches flows with the specified ICMPv6 code• type – Optional. Matches flows with the specified ICMPv6 typeigmp Optional.Matches Internet Group Management Protocol (IGMP) flowsip [dst <IP>|host <IP>|proto <0-254>|src <IP>] Optional. Filters firewall flows based on the IPv4 parameters passed• dst <IP> – Matches destination IP address• host <IP> – Matches flows containing IPv4 address• proto <0-254> – Matches the IPv4 protocol number with the specified number• src <IPv4> – Matches source IP addressipv6 [dst <IPv6>|host <IPv6>|proto <0-254>|src <IPv6>]Optional. Filters firewall flows based on the IPv6 parameters passed• dst <IPv6> – Matches destination IPv6 address• host <IPv6> – Matches flows containing IPv6 address• proto <0-254> – Matches the IPv6 protocol number with the specified number• src <IPv6> – Matches source IPv6 addressmax-idle<1-4294967295>Optional. Filters firewall flows idle for at least the specified duration. Specify a max-idle value from 1 - 4294967295 bytes.min-bytes<1-4294967295>Optional. Filters firewall flows with at least the specified number of bytes. Specify a min-bytes value from 1 - 4294967295 bytes.min-idle<1-4294967295>Optional. Filters firewall flows idle for at least the specified duration. Specify a min-idle value from 1 - 4294967295 bytes.min-pkts<1-4294967295>Optional. Filters firewall flows with at least the given number of packets. Specify a min-bytes value from 1 - 4294967295 bytes.not Optional. Negates the filter expression selected](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-958.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 606.1.29 globalshow commandsDisplays global information for network devices based on the parameters passedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow global [device-list|domain]show global device-list {filter {offline|online|rf-domain}}show global device-list {filter {offline|online}}show global device-list {filter rf-domain [<DOMAIN-NAME>|not <DOMAIN-NAME>]}show global domain managersParameters• show global device-list {filter {offline|online}}• show global device-list {filter rf-domain [<DOMAIN-NAME>|not <DOMAIN-NAME>]}• show global domain managersglobal device-list Displays global information for all network devices. Use the following keywords to specify additional filters: offline, online, and rf-domain.filter {offline|online} Optional. Specifies additional filters• offline – Optional. Displays global information for offline devices only• online – Optional. Displays global information for online devices onlyglobal device-list Displays global information for all network devices. Use the following keywords to specify additional filters: offline, online, and rf-domain.filter rf-domain [<DOMAIN-NAME>|not <DOMAIN-NAME>]Optional. Specifies additional filters• rf-domain – Optional. Displays global information for all devices in a specified RF Domain• <DOMAIN-NAME> – Optional. Displays information of all devices within the domainidentified by the <DOMAIN-NAME> keyword• not <DOMAIN-NAME> – Optional. Displays information of all devices in domains notmatching the <DOMAIN-NAME> keywordglobal domain managersDisplays global information for all RF Domains and managers in the network](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-961.png)
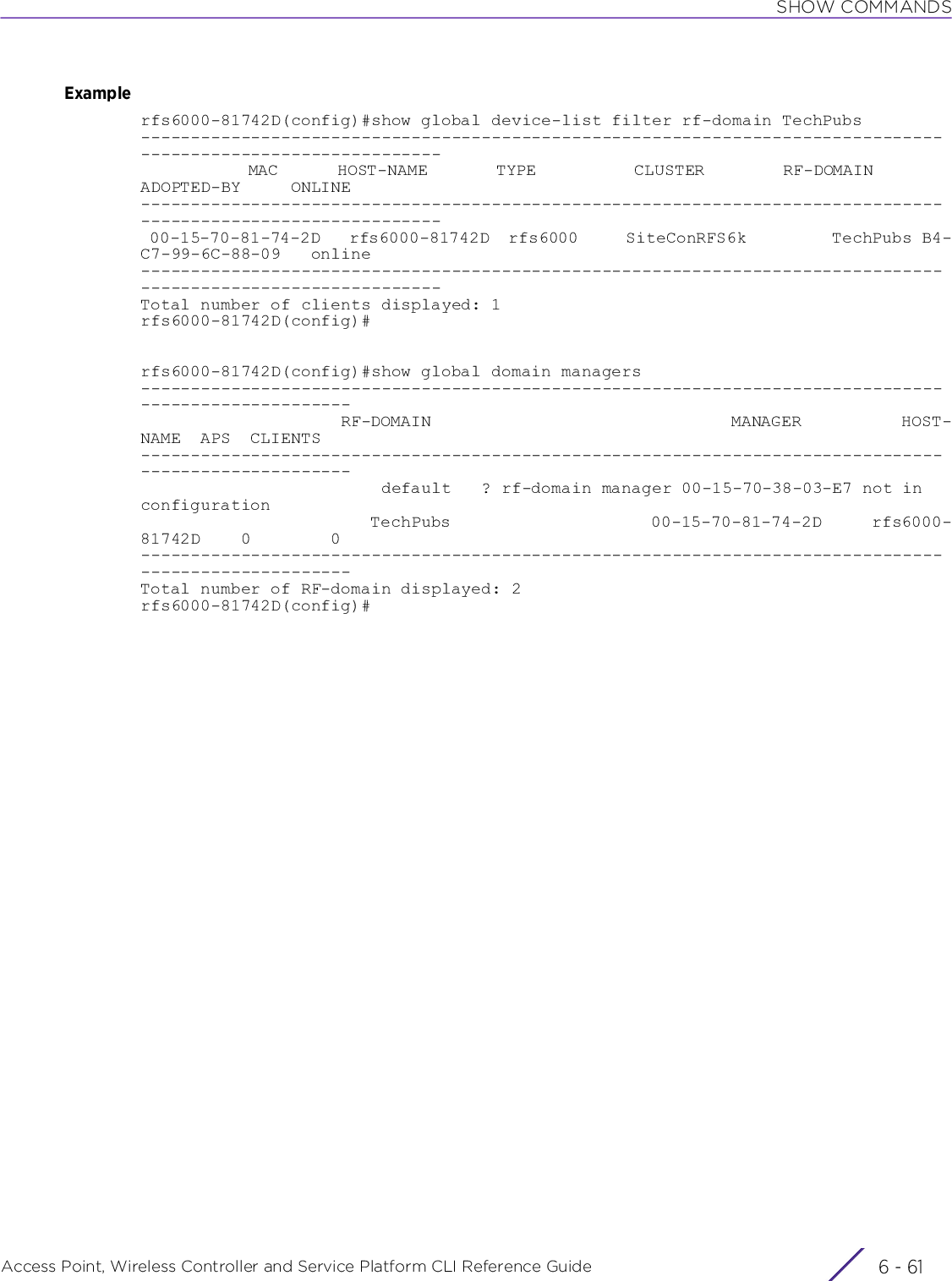

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 636.1.31 guest-registrationshow commandsDisplays information on the performance of clients using guest access permissions to obtain network resources within the WiNG network. The reporting timeline can be adjusted as needed, as can the RF Domain(s) and WLAN(s) used to filter and report guest client statistics.Supported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxshow guest-registration [age-range|backup-snapshots|browsers|client|devices|gender|loyalty-app-status|notification-status|os|social|user-trends|visitors] {on <DEVICE-NAME>}show guest-registration backup-snapshotsshow guest-registration [age-range|browsers|devices|gender|os|user-trends|visitors] time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all] {(rfdomain <DOMAIN-NAME>|wlan <WLAN-NAME>)}show guest-registration client [email|mac|member|mobile|name|time]show guest-registration client [email <EMAIL-ADDRESS>|mac <MAC>|member <MEMBER-ID>|mobile <MOBILE-NUMBER>|name <NAME>]show guest-registration client time [1-Hour|10-Mins|15-Mins|2-Mins|30-Mins|30-Secs|5-Mins] {(rfdomain <DOMAIN-NAME>|wlan <WLAN-NAME>)}show guest-registration loyalty-app-status time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all] {rfdomain <RF-DOMAIN-NAME>|wlan <WLAN-NAME>}show guest-registration notification-statusshow guest-registration social time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all] {(facebook|rfdomain <DOMAIN-NAME>|wlan <WLAN-NAME>|google)}Parameters• show guest-registration backup-snapshots• show guest-registration [age-range|browsers|devices|gender|os|user-trends|visitors] time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all] {(rfdomain <DOMAIN-NAME>|wlan <WLAN-NAME>)}guest-registration Displays guest registration statistics based on the parameters passedbackup-snapshots Displays a list of periodically backed up snapshots of the database. By default, the system maintains a snapshot of the database on a daily basis.Note: Use the service > guest-registration > backup [delete|restore] command to delete these snapshots and to restore deleted snapshots. For more information, see service.guest-registration Displays guest registration statistics based on the parameters and time entered. Optionally, use the ‘rfdomain’ and/or ‘wlan’ keywords to view guest registration statistics for a specified RF Domain and/or WLAN.age-range Displays the age ranges of logged guest users for a selected time periodbrowsers Displays the browsers used by guest users logged in within a selected time perioddevices Displays the device types used by guest users logged in within a selected time period](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-964.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 64• show guest-registration client [email <EMAIL-ADDRESS>|mac <MAC>|member <MEMBER-ID>|mobile <MOBILE-NUMBER>|name <NAME>] gender Displays the gender of guest users logged in within a selected time periodos Displays the operating system (OS) of devices logged in within a selected time perioduser-trends Displays guest user login trends for a selected time period. It displays statistical data, such as number of new users, number of return users, and total of number users.visitors Displays type of visitors logged in within a selected time periodtime [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]Displays guest registration statistics, for a specified time period. The stats displayed depends on the option selected in the previous step. Specify the time period using one of the following options:• 1-Day – Displays previous day’s statistics• 1-Month – Displays previous month’s statistics• 1-Week – Displays previous week’s statistics• 2-Hours – Displays last 2 hours statistics• 30-Mins – Displays last 30 minutes statistics• 5-Hours – Displays last 5 hours statistics• all – Displays statistics from the day the database was created[rfdomain <DOMAIN-NAME|wlan <WLAN-NAME>]Use the following options as additional filters:• rfdomain <DOMAIN-NAME> – Optional. Displays guest registration statistics for a specified RF Domain.• <DOMAIN-NAME> – Specify the RF Domain name.• wlan <WLAN-NAME> – Optional. Displays guest registration statistics for a specified WLAN.• <WLAN-NAME> – Specify the WLAN name.guest-registration Displays guest registration statistics based on the parameters and time entered. Optionally, use the ‘rfdomain’ and/or ‘wlan’ keywords to view guest registration statistics for a specified RF Domain and/or WLAN.client Displays statistical data for a specific client. Use the e-mail, mac, member, mobile, name to provide a match criteria.email <EMAIL-ADDRESS>Displays statistical data for the client with e-mail address matching the <EMAIL-ADDRESS> parameter• <EMAIL-ADDRESS> – Specify the client’s e-mail address.mac <MAC> Displays statistical data for the client with MAC address matching the <MAC> parameter• <MAC> – Specify the client’s MAC addressmember <MEMBER-ID>Displays statistical data for the client with member ID matching the <MEMBER-ID> parameter• <MEMBER-ID> – Specify the client’s member ID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-965.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 65• show guest-registration client time [1-Hour|10-Mins|15-Mins|2-Mins|30-Mins|30-Secs|5-Mins] {(rfdomain <DOMAIN-NAME>|wlan <WLAN-NAME>)}• show guest-registration loyalty-app-status time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all] {rfdomain <RF-DOMAIN-NAME>|wlan <WLAN-NAME>}mobile <MOBILE-NUMBER>Displays statistical data for the client with mobile number matching the <MOBILE-NUMBER> parameter• <MOBILE-NUMBER> – Specify the client’s mobile number.name <NAME> Displays statistical data for the client with name matching the <NAME> parameter• <MOBILE-NUMBER> – Specify the client’s name.guest-registration Displays guest registration statistics based on the parameters and time entered. Optionally, use the ‘rfdomain’ and/or ‘wlan’ keywords to view guest registration statistics for a specified RF Domain and/or WLAN.client Displays statistical data for all clients logged in within a specified time periodtime [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]Use one of the following options to specify the time period:• 1-Day – Displays previous day’s statistics• 1-Month – Displays previous month’s statistics• 1-Week – Displays previous week’s statistics• 2-Hours – Displays last 2 hours statistics• 30-Mins – Displays last 30 minutes statistics• 5-Hours – Displays last 5 hours statistics• all – Displays entire statistics, from the day the database was created[rfdomain <DOMAIN-NAME|wlan <WLAN-NAME>]Use the following options as additional filters:• rfdomain <DOMAIN-NAME> – Optional. Displays guest registration statistics for a specified RF Domain.• <DOMIAIN-NAME> – Specify the RF Domain name.• wlan <WLAN-NAME> – Optional. Displays guest registration statistics for a specified WLAN.• <WLAN-NAME> – Specify the WLAN name.guest-registration Displays guest registration statistics based on the parameters and time enteredloyalty-app-status Displays captive portal clients’ Loyalty Application analytics, such as the number of guest clients with loyalty application detection enabled, associating with the captive portal’s access point during a specified time periodLoyalty application detection occurs on the access point to which the guest client is associated, allowing a retail administrator to assess whether a captive portal client is using specific retail (loyalty) applications in their captive portal.For more information on enabling loyalty application detection on a captive portal, see report-loyalty-application.time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]Specifies the time period, using one of the following options:• 1-Day – Displays previous day’s captive portal clients’ Loyalty Application analytics• 1-Month – Displays previous month’s captive portal clients’ Loyalty Application analyticsContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-966.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 66• show guest-registration notification-status• show guest-registration social time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all] {(facebook|rfdomain <DOMAIN-NAME>|wlan <WLAN-NAME>|google)}• 1-Week – Displays previous week’s captive portal clients’ Loyalty Application analytics• 2-Hours – Displays last 2 hours captive portal clients’ Loyalty Application analytics• 30-Mins – Displays last 30 minutes captive portal clients’ Loyalty Application analytics• 5-Hours – Displays last 5 hours captive portal clients’ Loyalty Application analytics• all – Displays the entire Loyalty Application analytics, from the day the database was created{rfdomain <RF-DOMAIN-NAME>|wlan <WLAN-NAME>}Optional. Specifies the ‘rfdomain’ and/or ‘wlan’ to view guest registration statistics for a specified RF Domain and/or WLAN• rfdomain <RF-DOMAIN-NAME> – Displays Loyalty App analytics for a specified RF Domain• <RF-DOMAIN-NAME> – Specify the RF Domain name.• wlan <WLAN-NAME> – Displays Loyalty App analytics for a specified WLAN• <WLAN-NAME> – Specify the WLAN name.guest-registration Displays guest registration statistics based on the parameters and time entered. Optionally, use the ‘rfdomain’ and/or ‘wlan’ keywords to view guest registration statistics for a specified RF Domain and/or WLAN.notification-status Displays guest registration notification statusguest-registration social Displays the social sites used by guests to register. Optionally, use the ‘rfdomain’ and/or ‘wlan’ keywords to view social site used by guests of a specified RF Domain and/or WLAN.time [1-Day|1-Month|1-Week|2-Hours|30-Mins|5-Hours|all]Displays social site statistics for a specified time period. Use one of the following time options:• 1-Day – Displays previous day’s statistics• 1-Month – Displays previous month’s statistics• 1-Week – Displays previous week’s statistics• 2-Hours – Displays last 2 hours statistics• 30-Mins – Displays last 30 minutes statistics• 5-Hours – Displays last 5 hours statistics• all – Displays the entire databasefacebook Displays guest users using Facebook to log inrfdomain <DOMAIN-NAME>Displays guest users for a specific RF Domain• <DOMAIN-NAME> – Specify the RF Domain name.wlan <WLAN-NAME> Displays guest users for a specific WLAN• <WLAN-NAME> – Specify the WLAN name.google Displays guest users using Google to log in](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-967.png)
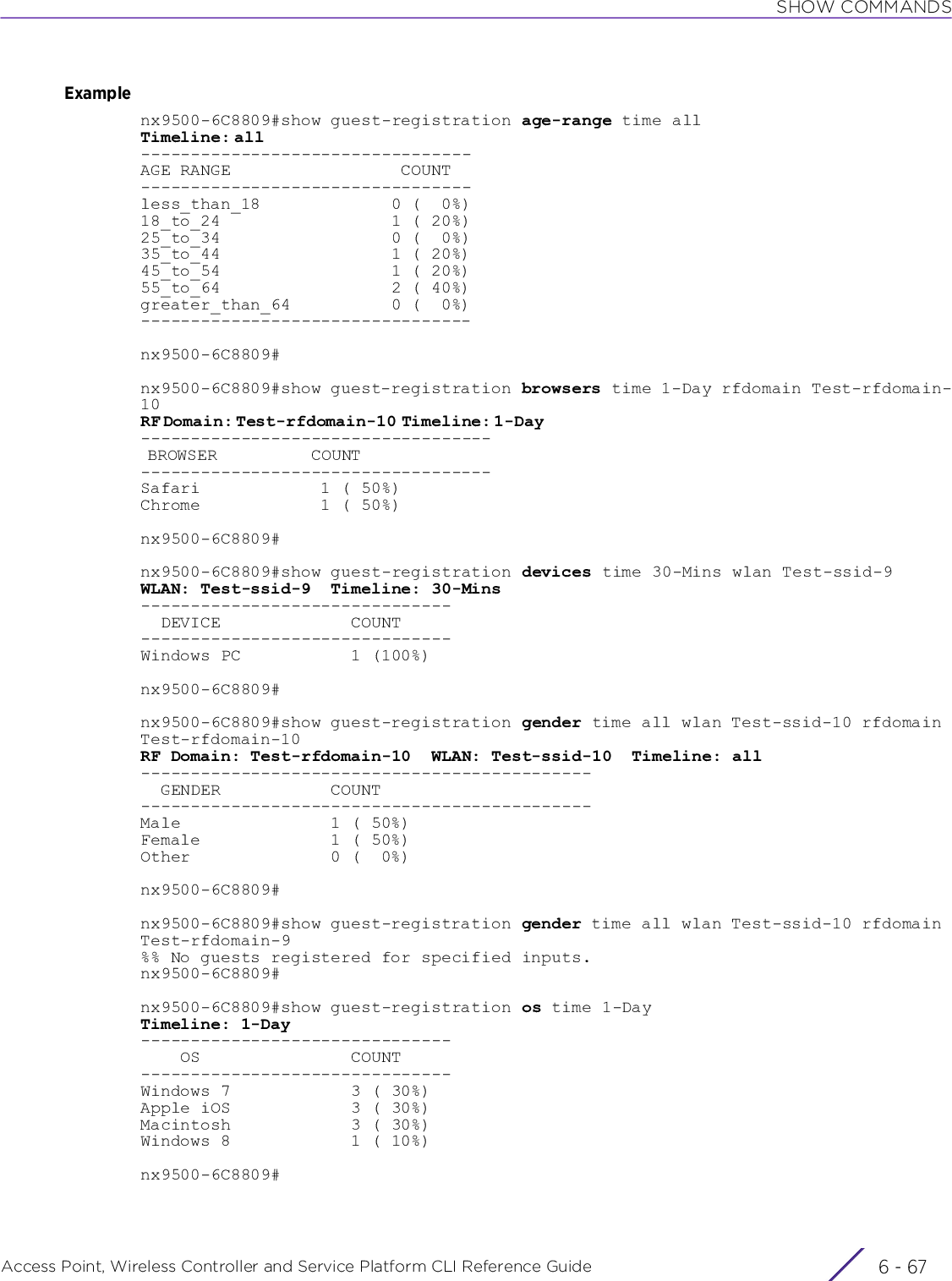
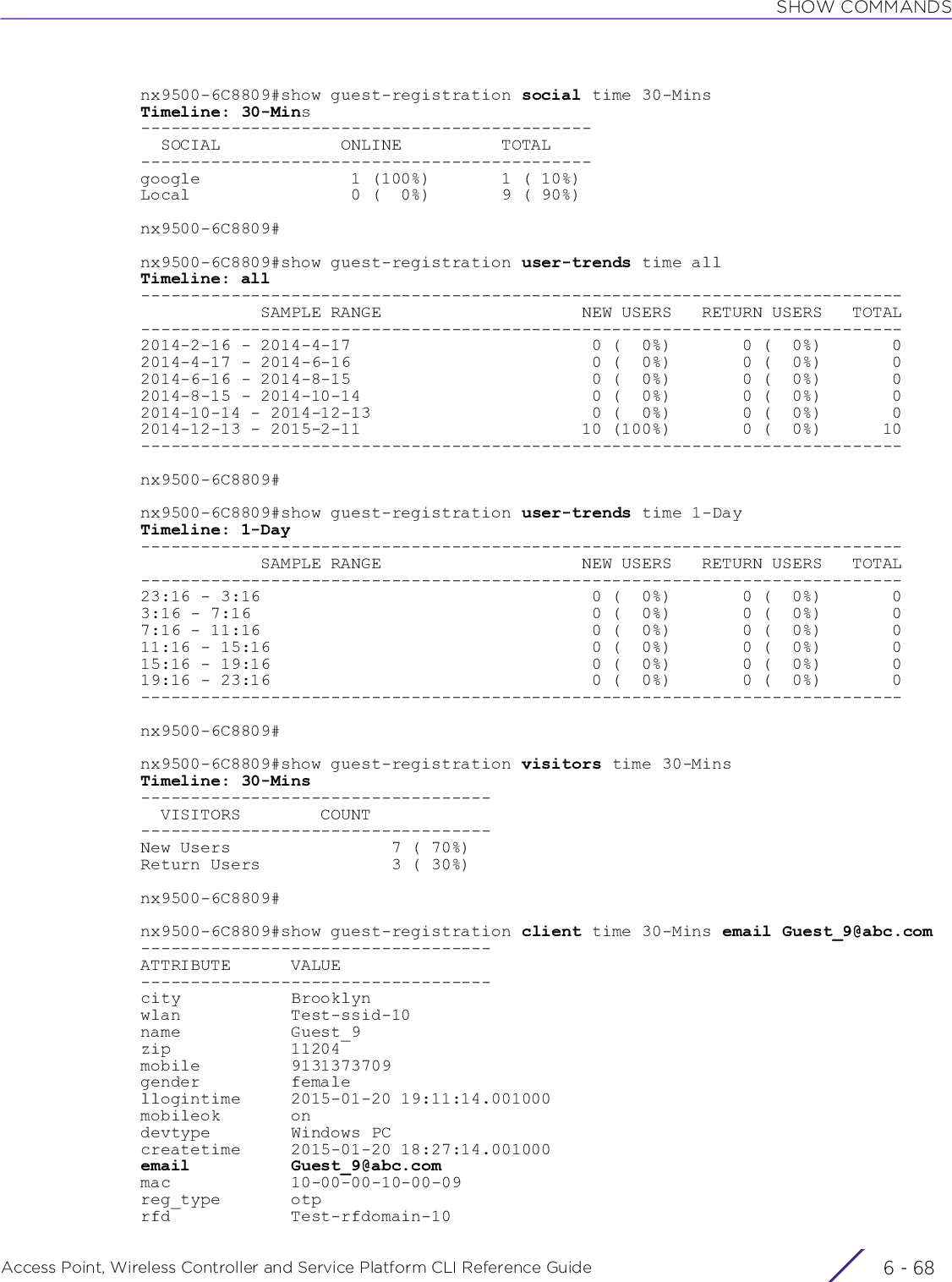
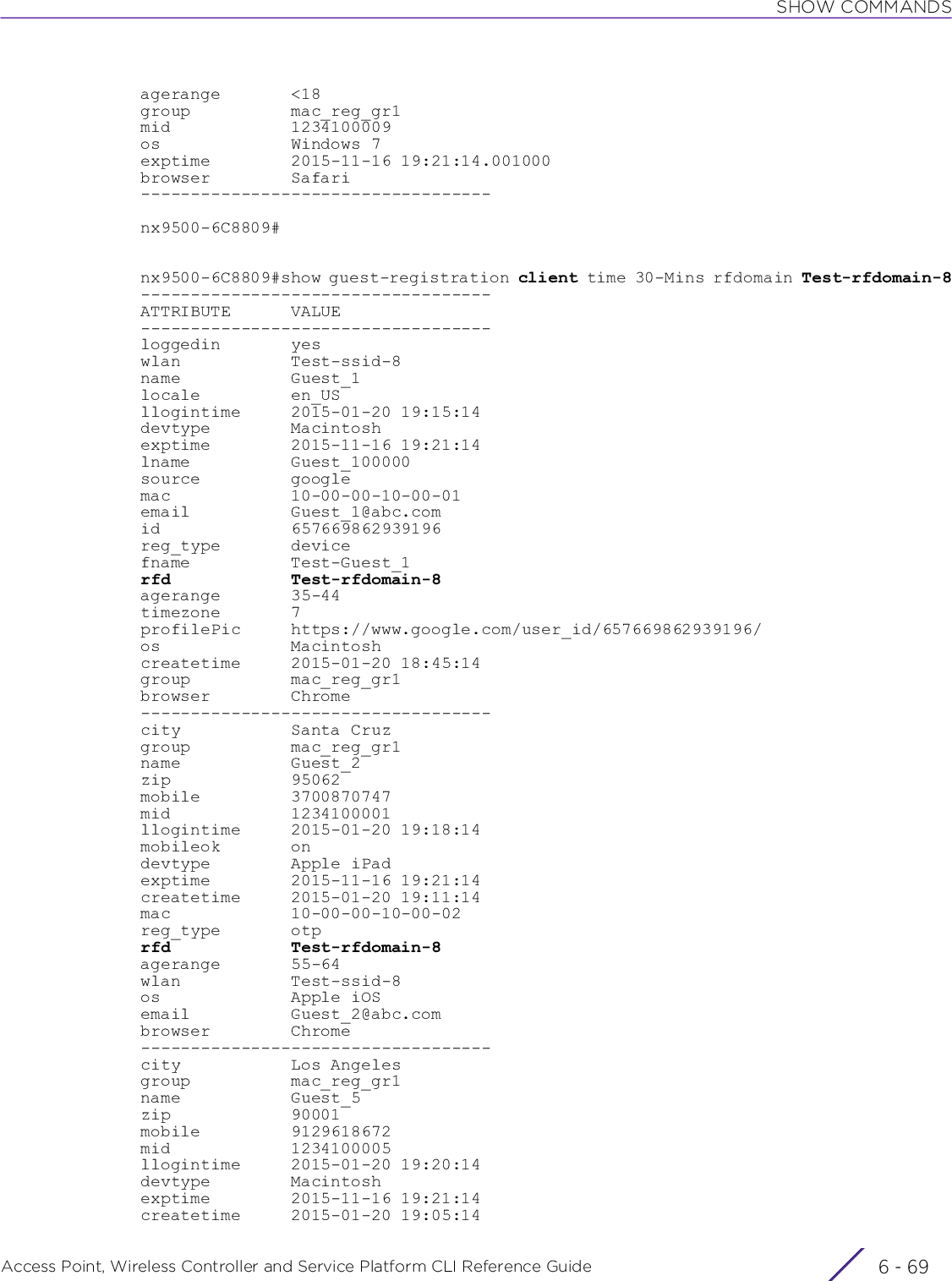
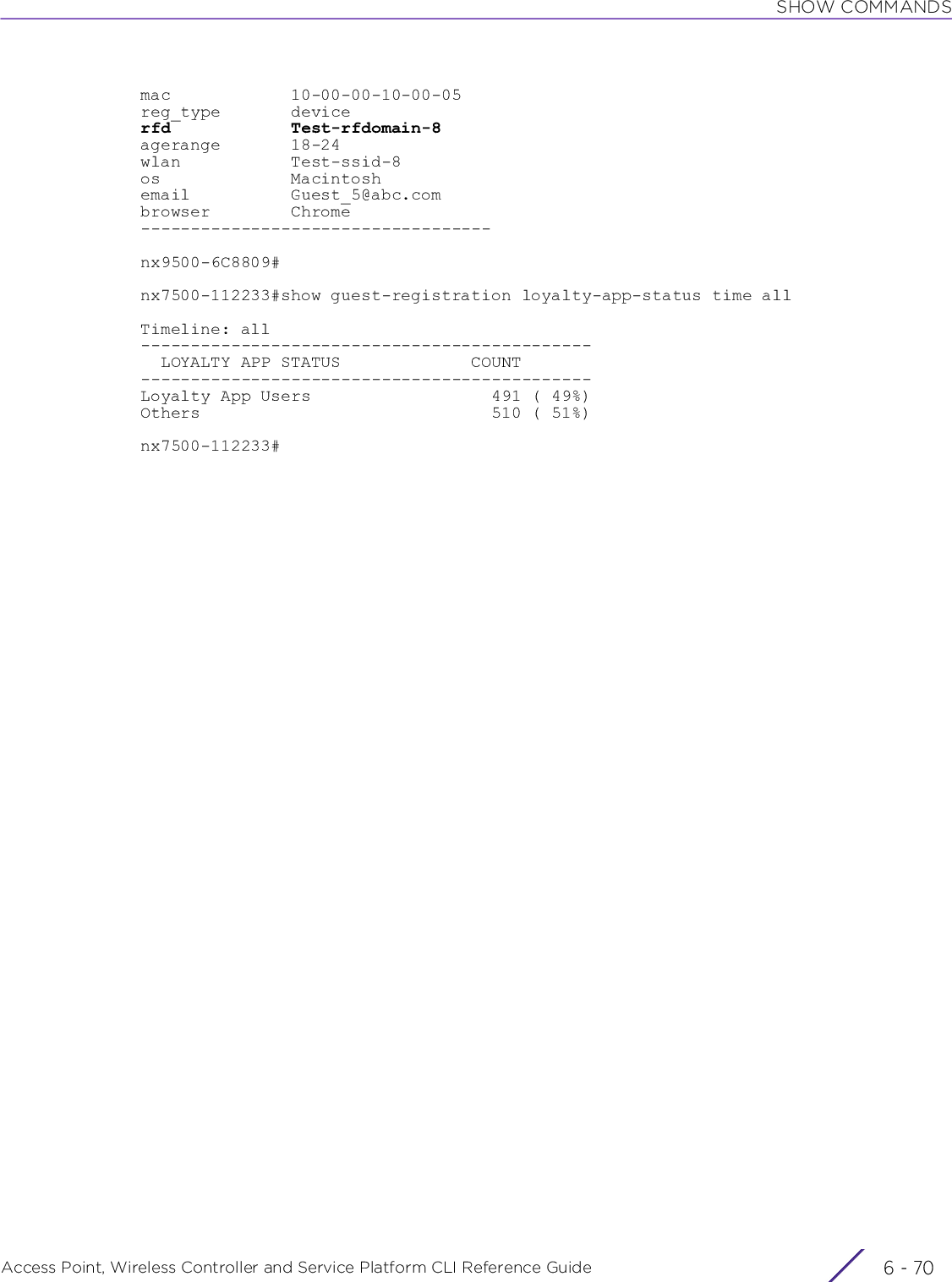

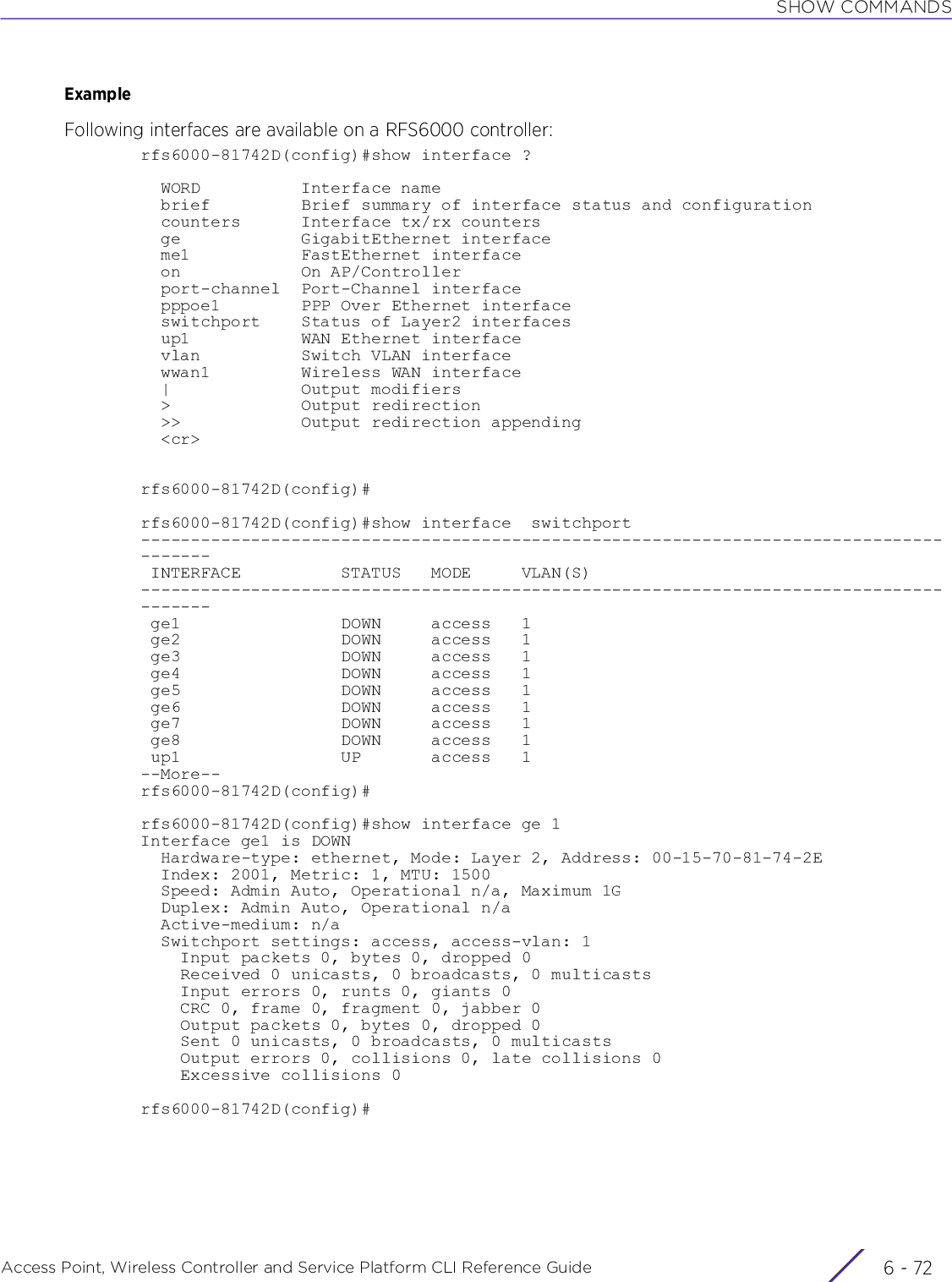
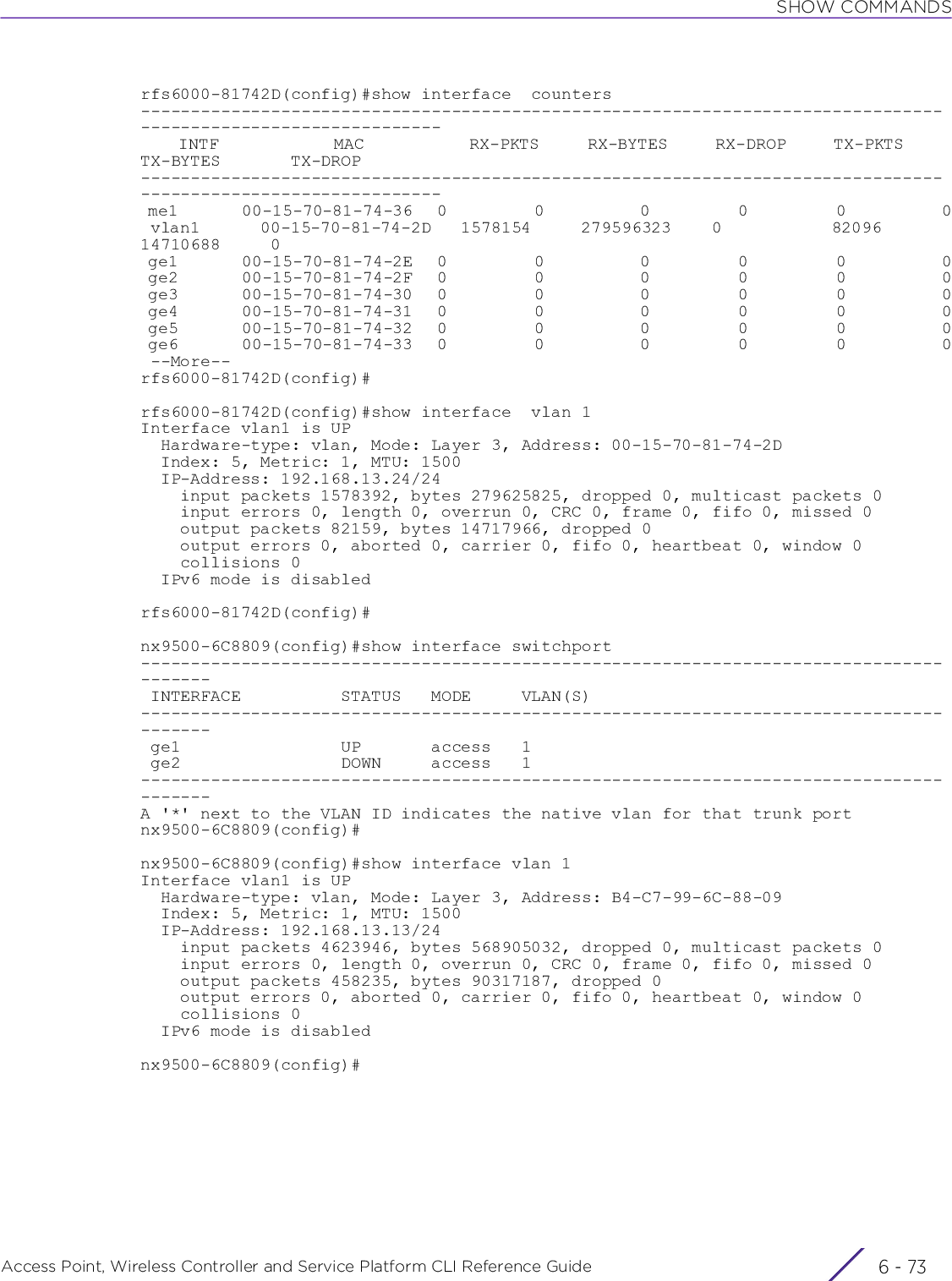
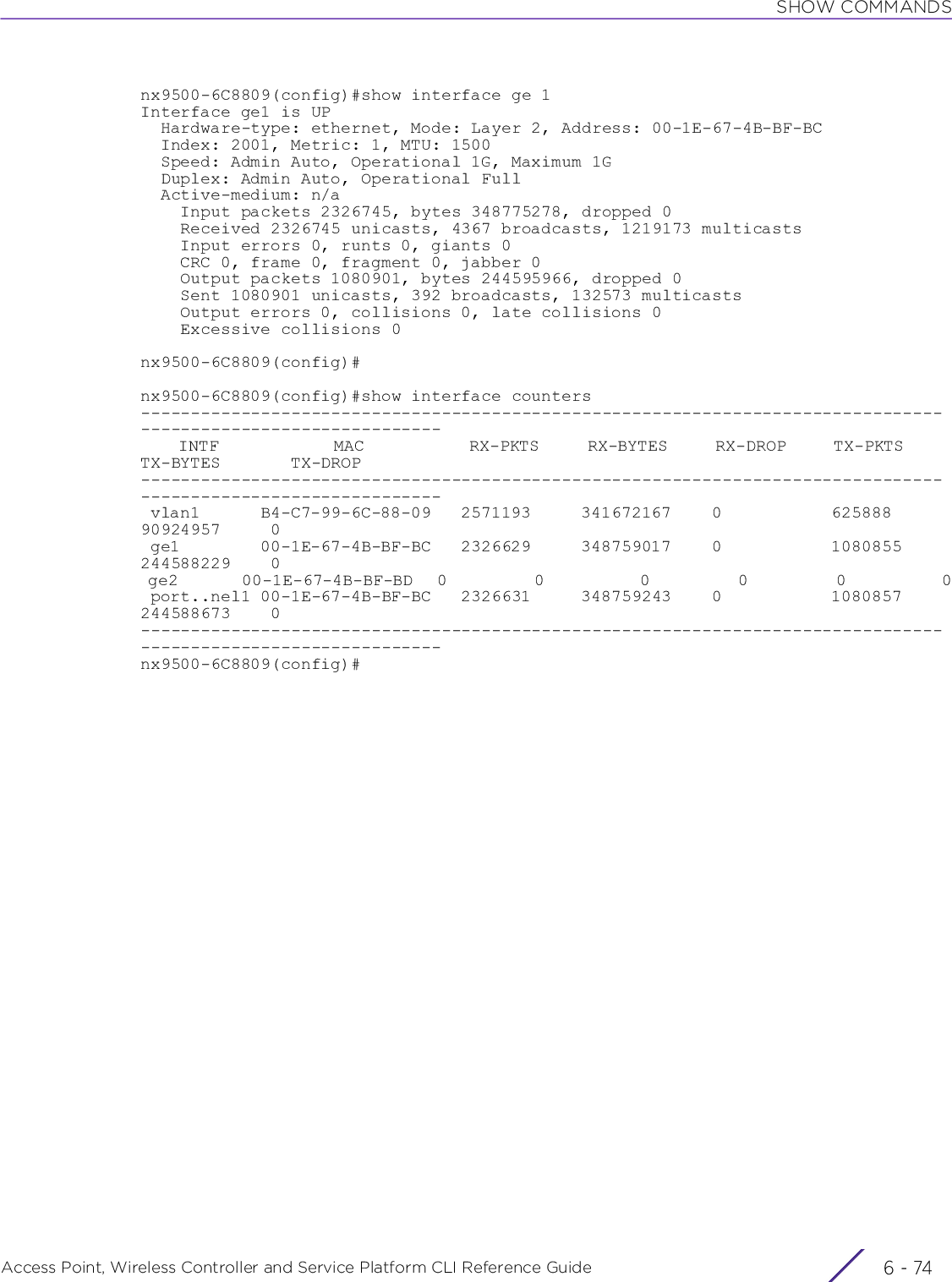
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 756.1.33 ipshow commandsDisplays IP related informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow ip [arp|bgp|ddns|default-gateways|dhcp|dhcp-vendor-options|domain-name|extcommunity-list|igmp|interface|name-server|nat|ospf|route|routing]show ip arp {<VLAN-NAME>} {(on <DEVICE-NAME>)}show ip bgp {<IP>|<IP/M>|community|community-list|filter-list|neighbors|on|paths|prefix-list|regexp|route-map|state|summary}show ip ddns bindings {on <DEVICE-NAME>}show ip dhcp [binding|networks|status]show ip dhcp binding {manual} {(on <DEVICE-NAME>)}show ip dhcp [networks|status] {on <DEVICE-NAME>}show ip [default-gateways|dhcp-vendor-options|domain-name|name-server|routing] {on <DEVICE-NAME>}show ip extcommunity-list [<1-500>|<NAME>]show ip igmp snooping [mrouter|querier|vlan]show ip igmp snooping [mrouter|querier] vlan <1-4095> {on <DEVICE-NAME>}show ip igmp snooping vlan <1-4095> {<IP>} {(on <DEVICE-NAME>)}show ip interface {<INTERFACE-NAME>|brief|on}show ip interface {<INTERFACE-NAME>|brief} {(on <DEVICE-NAME>)}show ip nat translations verbose {on <DEVICE-NAME>}show ip route {<INTERFACE-NAME>|ge|me1|on|port-channel|pppoe1|vlan|wwan1}show ip route {<INTERFACE-NAME>|ge <1-4>|me1|port-channel <1-2>|vlan <1-4094>|pppoe1|wwan1} {(on <DEVICE-NAME>)}show ip ospf {border-router|interface|neighbor|on|route|state}show ip ospf {border-router|neighbor|route|on|state} {on <DEVICE-NAME>}show ip ospf {interface} {vlan|on}show ip ospf {interface} {vlan <1-4094>} {(on <DEVICE-NAME>)}Parameters• show ip arp {<VLAN-NAME>} {(on <DEVICE-NAME>)}NOTE: The show ip ospf command is also available under the ‘profile’ and ‘device’ modes.ip arp Displays Address Resolution Protocol (ARP) mappings<VLAN-NAME> Optional. Displays ARP mapping on a specified VLAN. Specify the VLAN name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-976.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 77• show ip ddns bindings {on <DEVICE-NAME>}• show ip dhcp [networks|status] {on <DEVICE-NAME>}• show ip dhcp binding {manual} {(on <DEVICE-NAME>)}• show ip extcommunity-list [<1-500>|<NAME>]• show ip [default-gateways|dhcp-vendor-options|domain-name|name-server|routing] {on <DEVICE-NAME>}regexp <LINE> Optional. Displays routes matching the specified AS path regular expression• <LINE> – Specify the regular expression.route-map <ROUTE-MAP-NAME>Optional. Displays routes matching the specified route map• <ROUTE-MAP-NAME> – Specify the route map name.ip ddns Displays Dynamic Domain Name Server (DDNS) configuration detailsbindings {on <DEVICE-NAME>}Displays DDNS address bindings• on <DEVICE-NAME> – Optional. Displays address bindings on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.ip dhcp Displays DHCP server related details, such as network and statusnetworks Displays DHCP server network detailsstatus Displays DHCP server statuson <DEVICE-NAME> The following keyword is common to all of the above parameters:• on <DEVICE-NAME> – Optional. Displays server status and network details on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.ip dhcp Displays the DHCP server configuration detailsbindings Displays DHCP address bindingsmanual Optional. Displays static DHCP address bindingson <DEVICE-NAME> The following keyword is recursive and common to the ‘manual’ parameter:• on <DEVICE-NAME> – Optional. Displays DHCP address bindings on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.ip extcommunity-list [<1-500>|<NAME>]Displays the specified extended community list details• <1-500> – Specify the extended community number from 1 - 500.• <NAME> – Specify the extended community name.This command is applicable to the RFS4000, RFS6000, NX95XX model devices.ip default-gateways Displays all learnt default gatewaysip dhcp-vendor-optionsDisplays DHCP 43 parameters received from the DHCP server. This output includes the interface from which the option was learned.ip domain-name Displays the DNS default domain](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-978.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 78• show ip igmp snooping [mrouter|querier] vlan <1-4095> {on <DEVICE-NAME>}• show ip igmp snooping vlan <1-4095> {<IP>} {(on <DEVICE-NAME>)}• show ip interface {<INTERFACE-NAME>|brief} {(on <DEVICE-NAME>)}• show ip nat translations verbose {on <DEVICE-NAME>}ip name-server Displays the DNS name server detailsip routing Displays routing statuson <DEVICE-NAME> The following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Displays IP related information, based on the parameters passed, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.ip igmp snooping Displays the IGMP snooping configurationmrouter Displays the IGMP snooping multicast router (mrouter) configurationquerier Displays the IGMP snooping multicast querier configurationvlan <1-4095> {on <DEVICE-NAME>}Displays the IGMP snooping multicast router configuration for a VLAN• <1-4095> – Specify the VLAN ID from 1 - 4095.• on <DEVICE-NAME> – Optional. Displays the IGMP snooping mrouter configuration on a specified device• <DEVICE-NAME> – Specify the name of the AP or wireless controller.ip igmp snooping Displays the IGMP snooping configurationvlan <1-4095> Displays the VLAN IGMP snooping configuration• <1-4095> – Specify the VLAN ID from 1 - 4095.<IP> Optional. Specifies the multicast group IP addresson <DEVICE-NAME> The following keyword is recursive and common to the ‘ip’ parameter:• on <DEVICE-NAME> – Optional. Displays configuration details on a specified device• <DEVICE-NAME> – Specify the name of the AP or wireless controller.ip interface Displays an administrative and operational status of all layer 3 interfaces or a specified layer 3 interface<INTERFACE-NAME> Optional. Displays a specified interface status. Specify the interface name.brief Optional. Displays a brief summary of all interface status and configurationon <DEVICE-NAME> The following keyword is recursive and common to the ‘interface-name’ and ‘brief’ parameters:• on <DEVICE-NAME> – Optional. Displays interface status and summary, based on the parameters passed, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.ip nat translations Displays Network Address Translation (NAT) translationsverbose Displays detailed NAT translations• on <DEVICE-NAME> – Optional.Displays NAT translations on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-979.png)
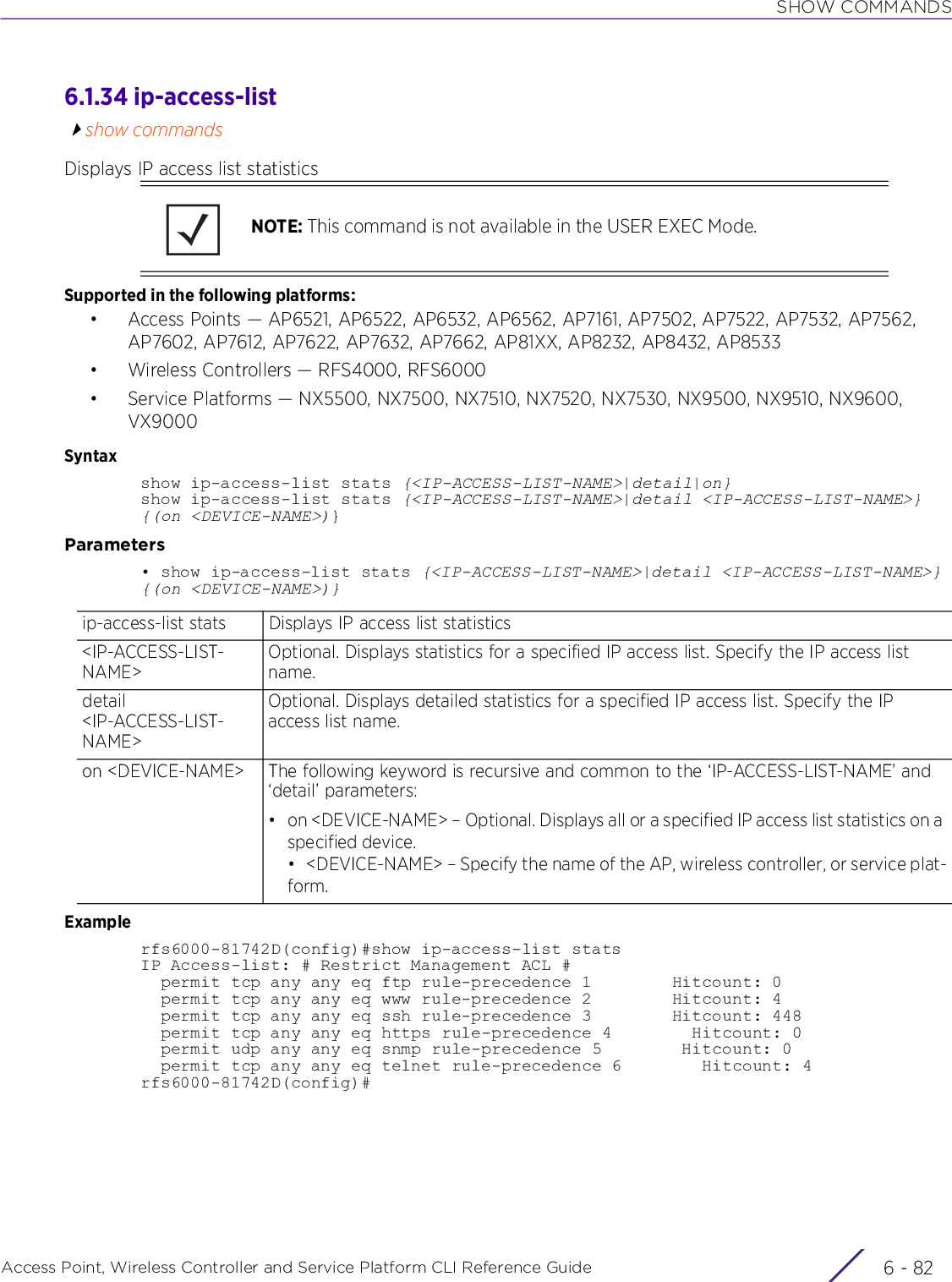
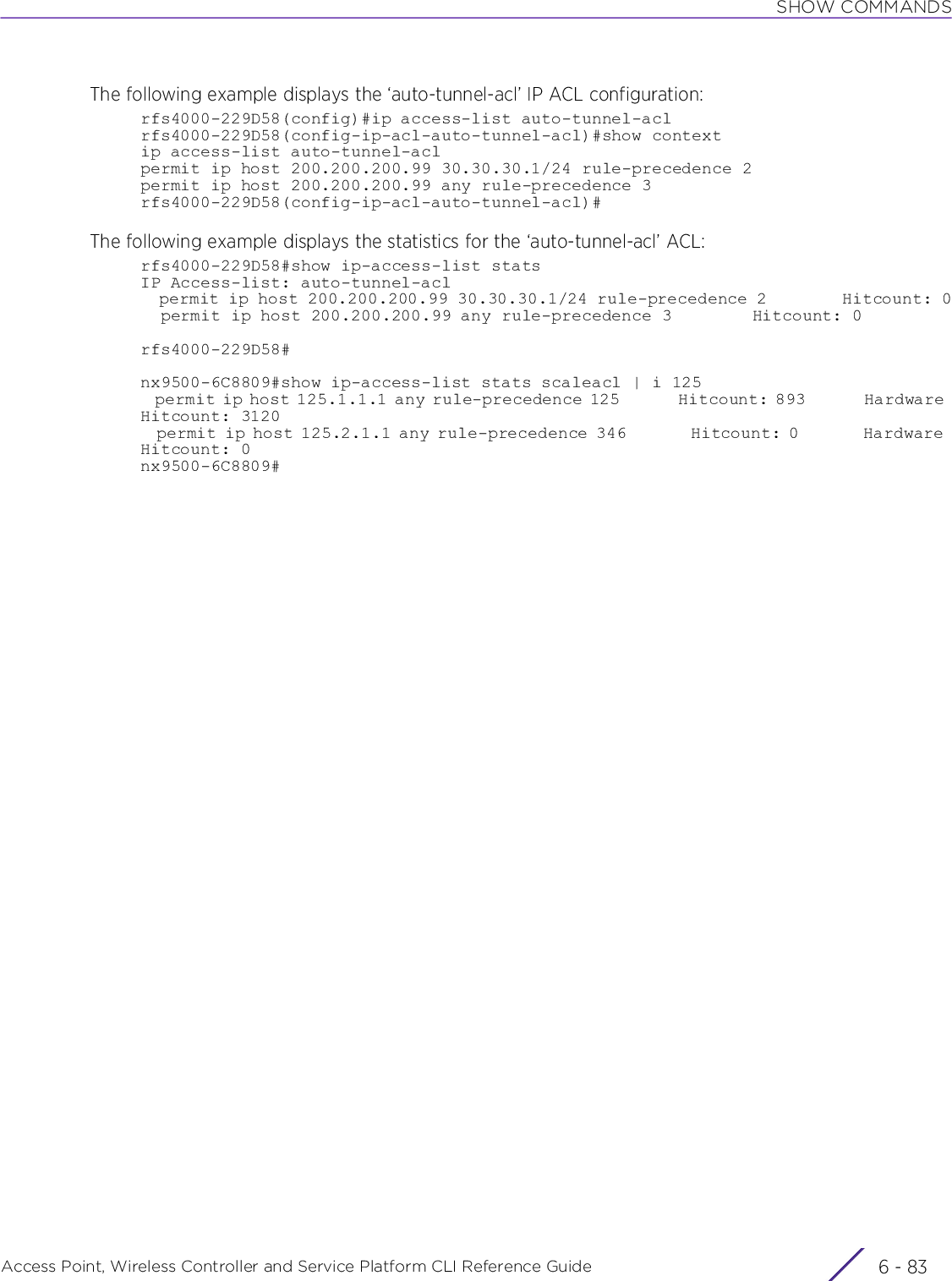
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 846.1.35 ipv6show commandsDisplays IPv6 related informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow ipv6 [default-gateways|delegated-prefix|dhcp|hop-limit|interface|mld|name-server|neighbors|route]show ipv6 [default-gateways|delegated-prefix|hop-limit|name-server] {on <DEVICE-NAME>}show ipv6 dhcp [client received-options|relay status|status] {on <DEVICE-NAME>}show ipv6 interface {<IF-NAME>|brief} {(on <DEVICE-NAME>)}show ipv6 mld snooping [mrouter vlan <1-4095>|querier vlan <1-4095>|vlan <1-4095>] {on <DEVICE-NAME>}show ipv6 neighbors <VLAN-NAME> {(on <DEVICE-NAME>)}show ipv6 route {<IF-NAME>|ge <1-X>|me1|port-channel <1-2>|ppppoe1|serial <1-4>|t1e1 <1-4> <1-1>|up|vlan <1-4095>|wwan1|xge} {(on <DEVICE-NAME>)}Parameters• show ipv6 [default-gateways|delegated-prefix|hop-limit|name-server] {on <DEVICE-NAME>}• show ipv6 dhcp [client received-options|relay status|status] {on <DEVICE-NAME>}ipv6 Displays IPv6 related informationdefault-gateways Displays all learnt default gatewaysdelegated-prefix Displays prefix delegation informationhop-limit Displays the configured IPv6 hop count valuename-server Displays DNS name serverson <DEVICE-NAME> This parameter is common to all of the above keywords.• on <DEVICE-NAME> – Optional. Displays the specified information on a device (access point, wireless controller, or service platform)• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ipv6 Displays IPv6 related informationdhcp Displays DHCPv6 related informationclient received-options Displays DHCP options received from clientsrelay status Displays the DHCPv6 relay agent’s running statusstatus Displays the DHCPv6 stateless server daemon’s status. In case the DHCPv6 server is up and running, it also displays interface names.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-985.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 85• show ipv6 interface {<IF-NAME>|brief} {(on <DEVICE-NAME>)}• show ipv6 mld snooping [mrouter vlan <1-4095>|querier vlan <1-4095>|vlan <1-4095>] {on <DEVICE-NAME>}• show ipv6 neighbors <VLAN-NAME> {(on <DEVICE-NAME>)}• show ipv6 route {<IF-NAME>|ge <1-X>|me1|port-channel <1-2>|ppppoe1|serial <1-4>|t1e1 <1-4> <1-1>|up|vlan <1-4095>|wwan1|xge} {(on <DEVICE-NAME>)}on <DEVICE-NAME> This parameter is common to all of the above keywords.• on <DEVICE-NAME> – Optional. Displays the specified information on a device (access point, wireless controller, or service platform)<DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ipv6 Displays IPv6 related informationinterface {<IF-NAME>|brief}Displays IPv6 status and configuration on a specified interface related information• <IF-NAME> – Optional. Specify the interface name.• brief – Optional. Displays a brief summary of IPv6 status and configuration on the specified interfaceon <DEVICE-NAME> This parameter is common to all of the above keywords.• on <DEVICE-NAME> – Optional. Displays the specified information on a device (access point, wireless controller, or service platform)<DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ipv6 Displays IPv6 related informationmld snooping Displays Multicast Listener Discovery Protocol (MLD) snooping related informationmrouter vlan <1-4095>Displays IPv6 multicast router information on the specified VLANquerier vlan <1-4095>Displays IPv6 multicast querier information on the specified VLANvlan <1-4095> Displays MLD snooping related information on the specified VLANon <DEVICE-NAME> This parameter is common to all of the above keywords.• on <DEVICE-NAME> – Optional. Displays the specified information on a device (access point, wireless controller, or service platform)<DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ipv6 Displays IPv6 related informationneighbors <VLAN-NAME>Displays IPv6 neighbors on the specified VLANon <DEVICE-NAME> Optional. Displays IPv6 neighbors on a specified device (access point, wireless controller, or service platform)<DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.ipv6 Displays IPv6 related information](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-986.png)
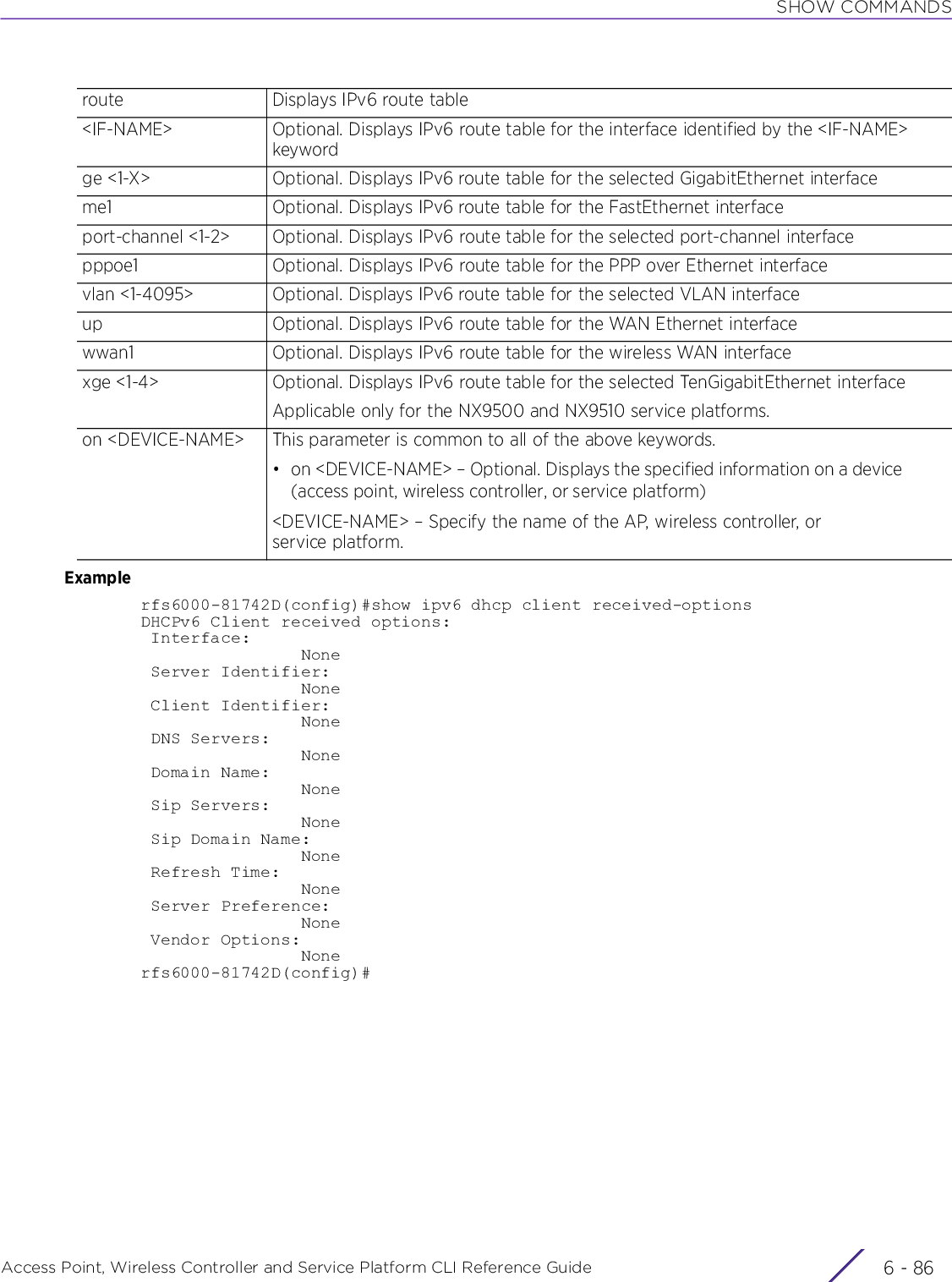
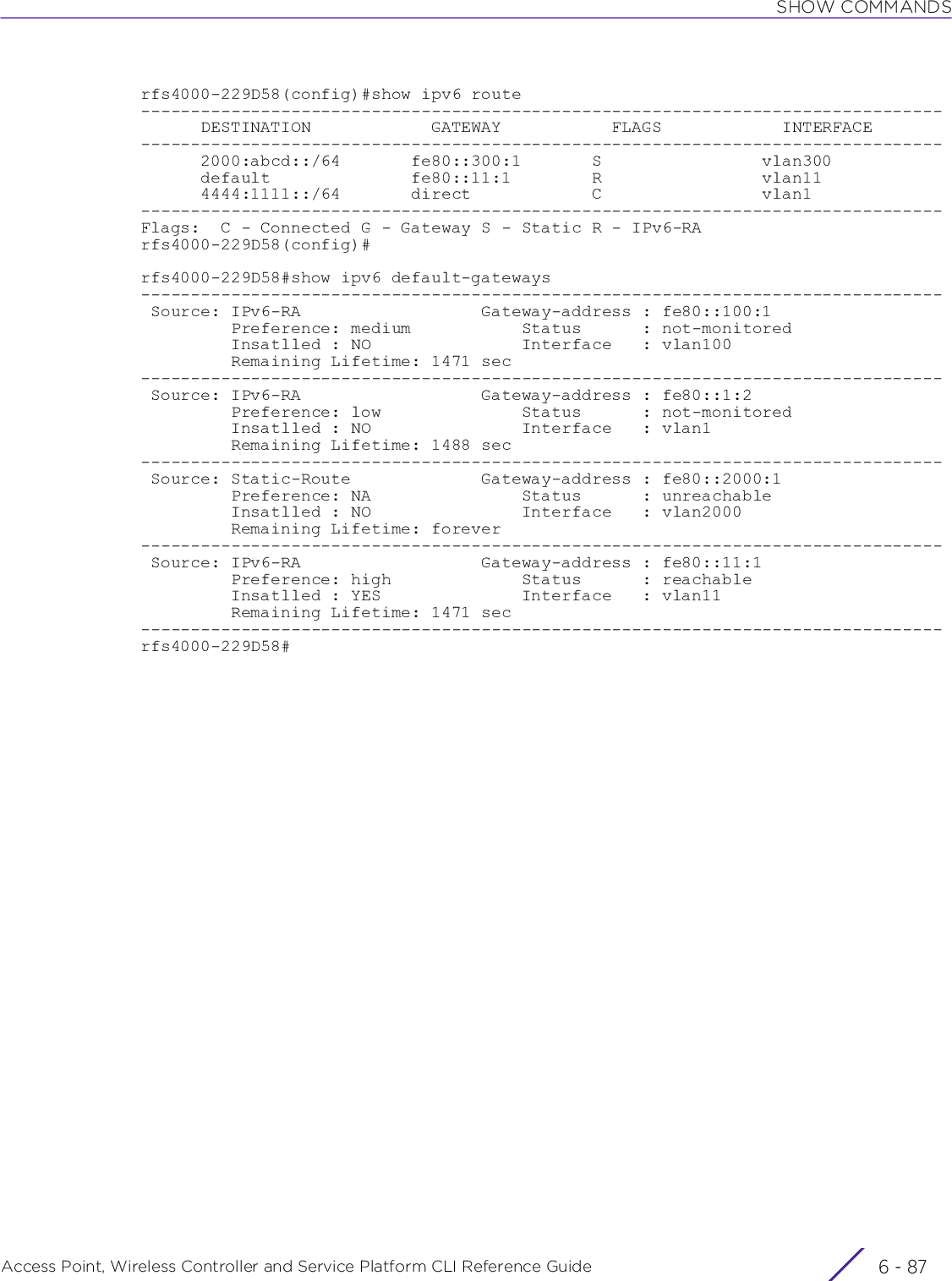


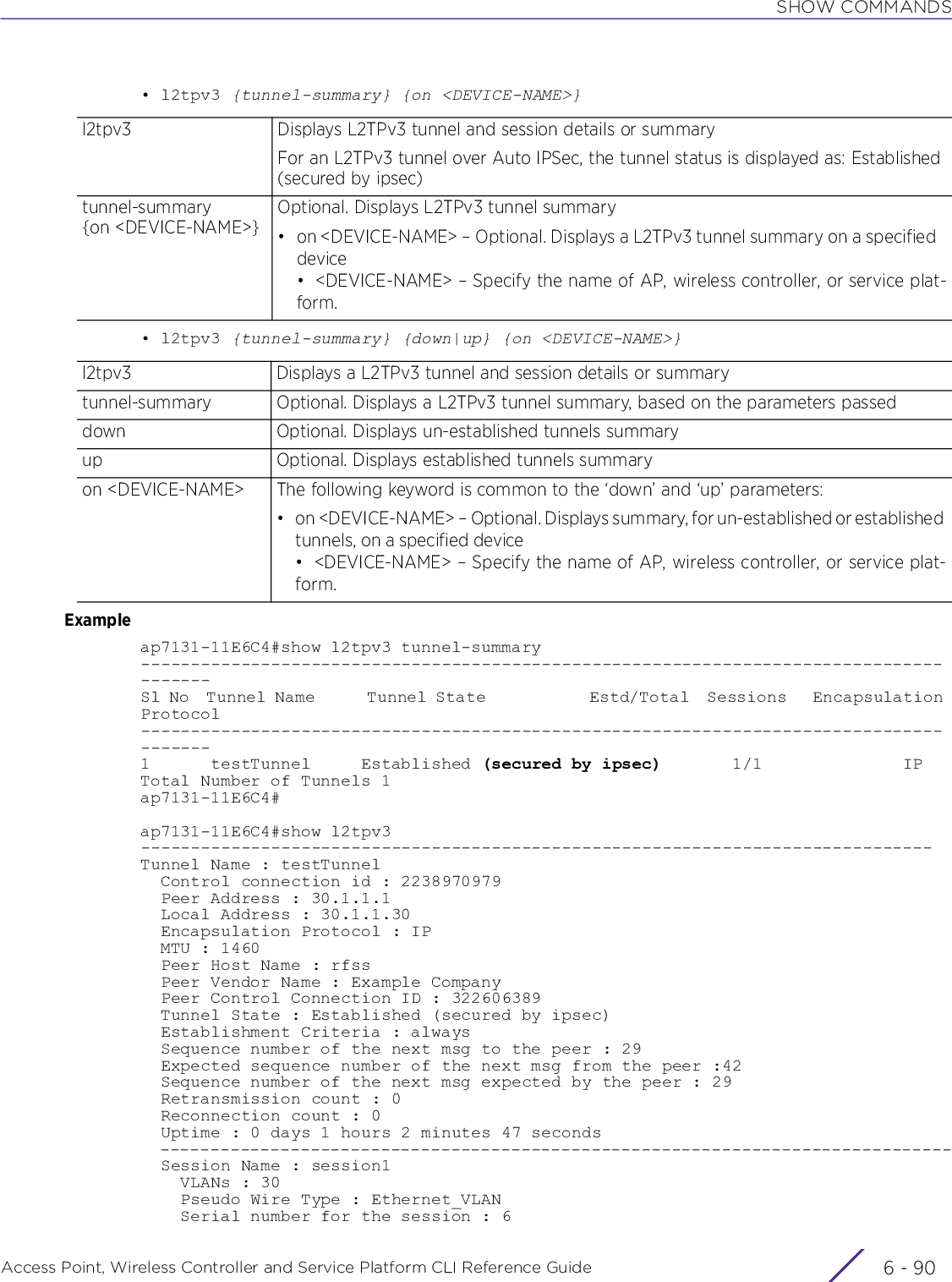
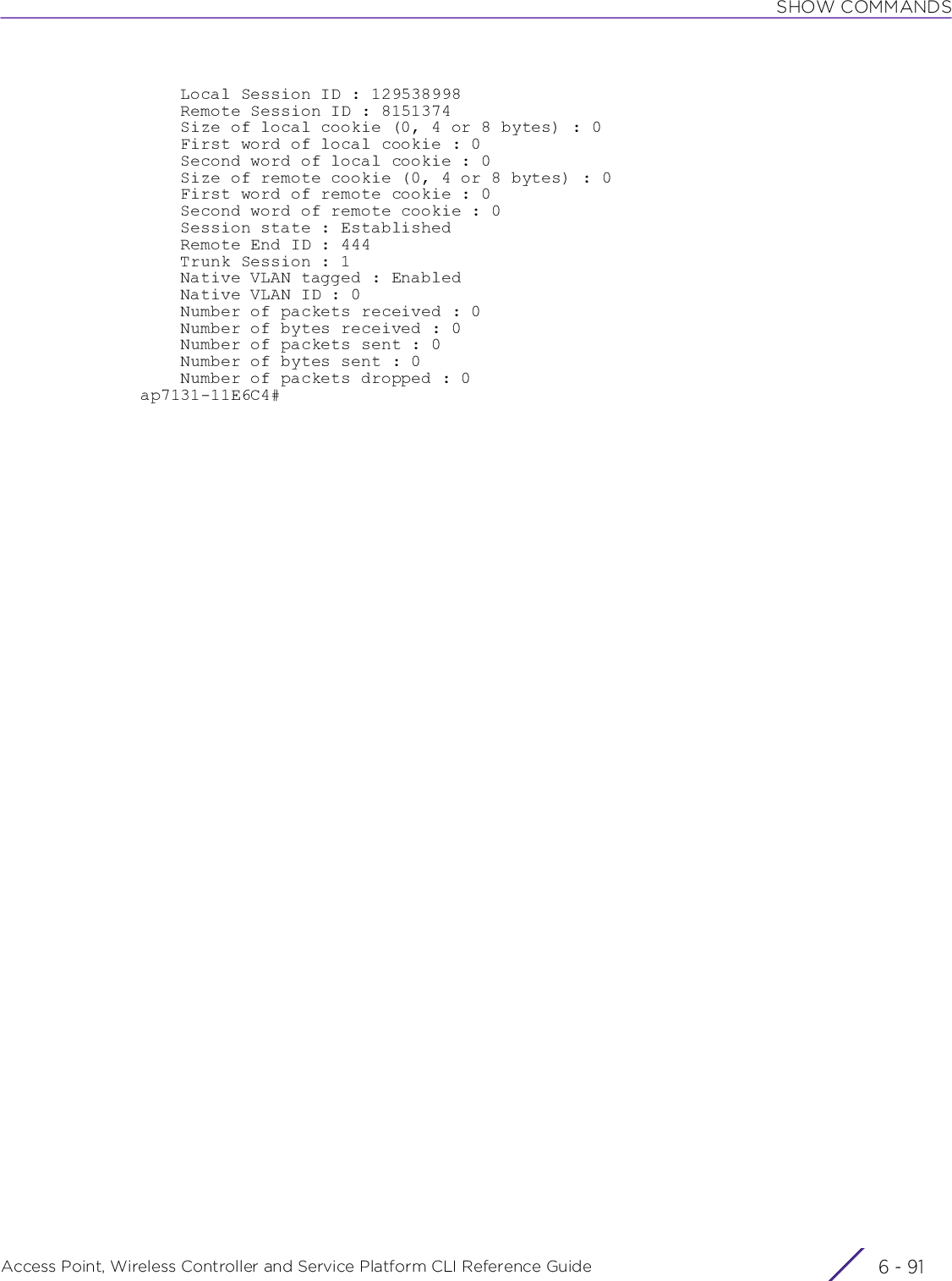
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 926.1.38 lacpshow commandsDisplays Link Aggregation Control Protocol (LACP) related informationSupported in the following platforms:• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow lacp [<1-4>|counters|details|sys-id]show lacp <1-4> ([counters|details])show lacp sys-idParameters• show lacp <1-4> ([counters|details])• show lacp sys-idNOTE: For more information on enabling dynamic LACP, see lacp, lacp-channel-group, and lacp.show lacp <1-4> Shows the LACP related information for a specified port-channel or all port-channels using LACP• <1-4> – Select the port-channel index number from 1 - 4. Note, LACP is supported only on the NX5500, NX7500, and NX9500 model service platforms. However, the NX9500 series service platforms support only two (2) port-channels. Where as the other model service platforms support four (4) port-channels.If the port-channel index number is not specified, the system displays LACP counters and details for all port-channels configured on the device.counters Shows LACP counters for LACP-enabled port-channels. When passed without the <1-4> keyword, the system displays LACP counters for all configured port-channels. However, if the port-channel index number is specified, the system displays LACP counters only for the specified port-channel.details Shows details for LACP-enabled port-channels. When passed without the <1-4> keyword, the system displays LACP details for all configured port-channels. However, if the port-channel index number is specified, the system displays LACP details only for the specified port-channel.show lacp sys-id Shows the LACP related information for all LACP-enabled port-channels• sys-id – Shows the LACP system identifier and priority. This is the identifier assigned to the LACP peers (devices).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-993.png)
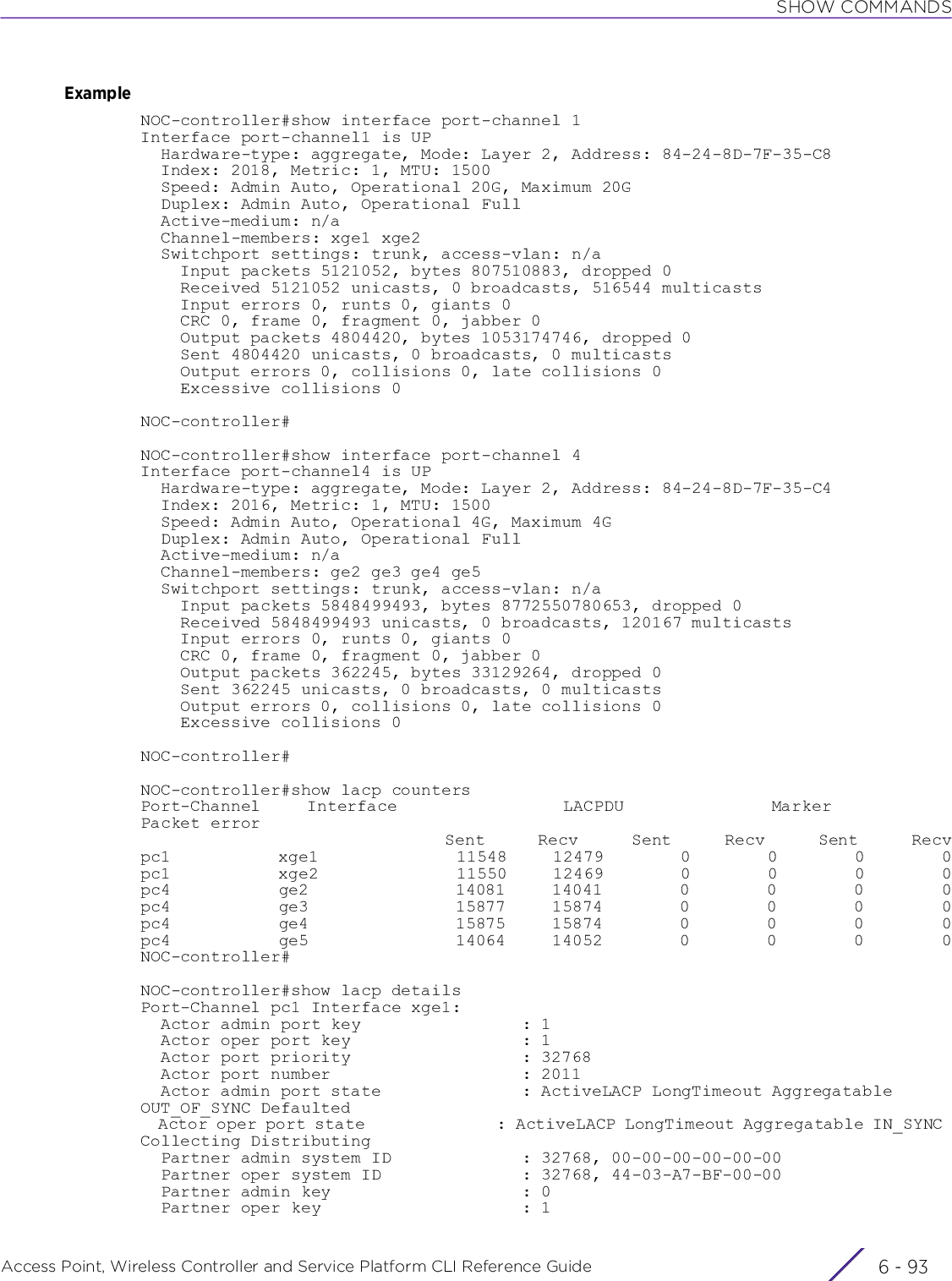



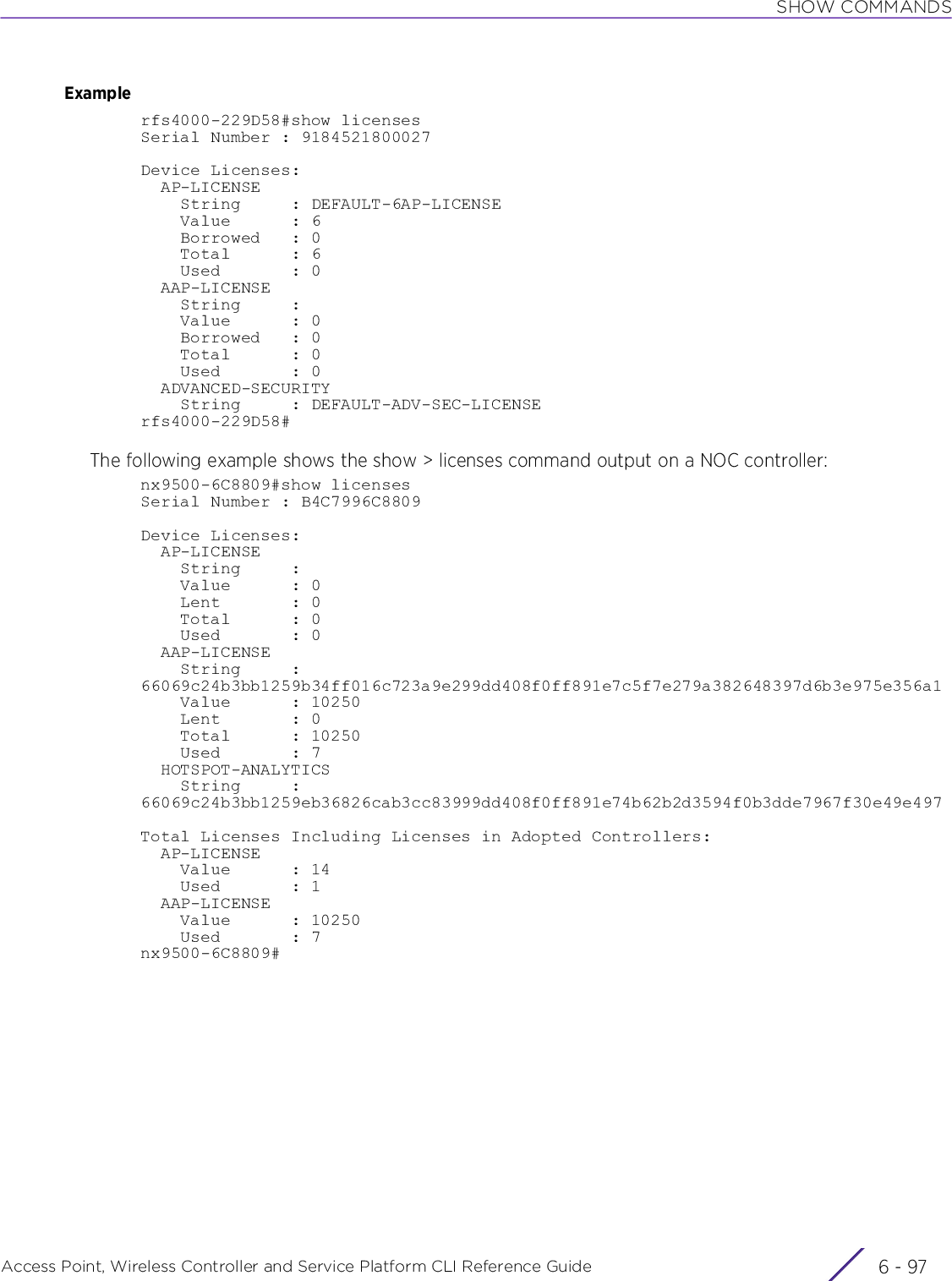
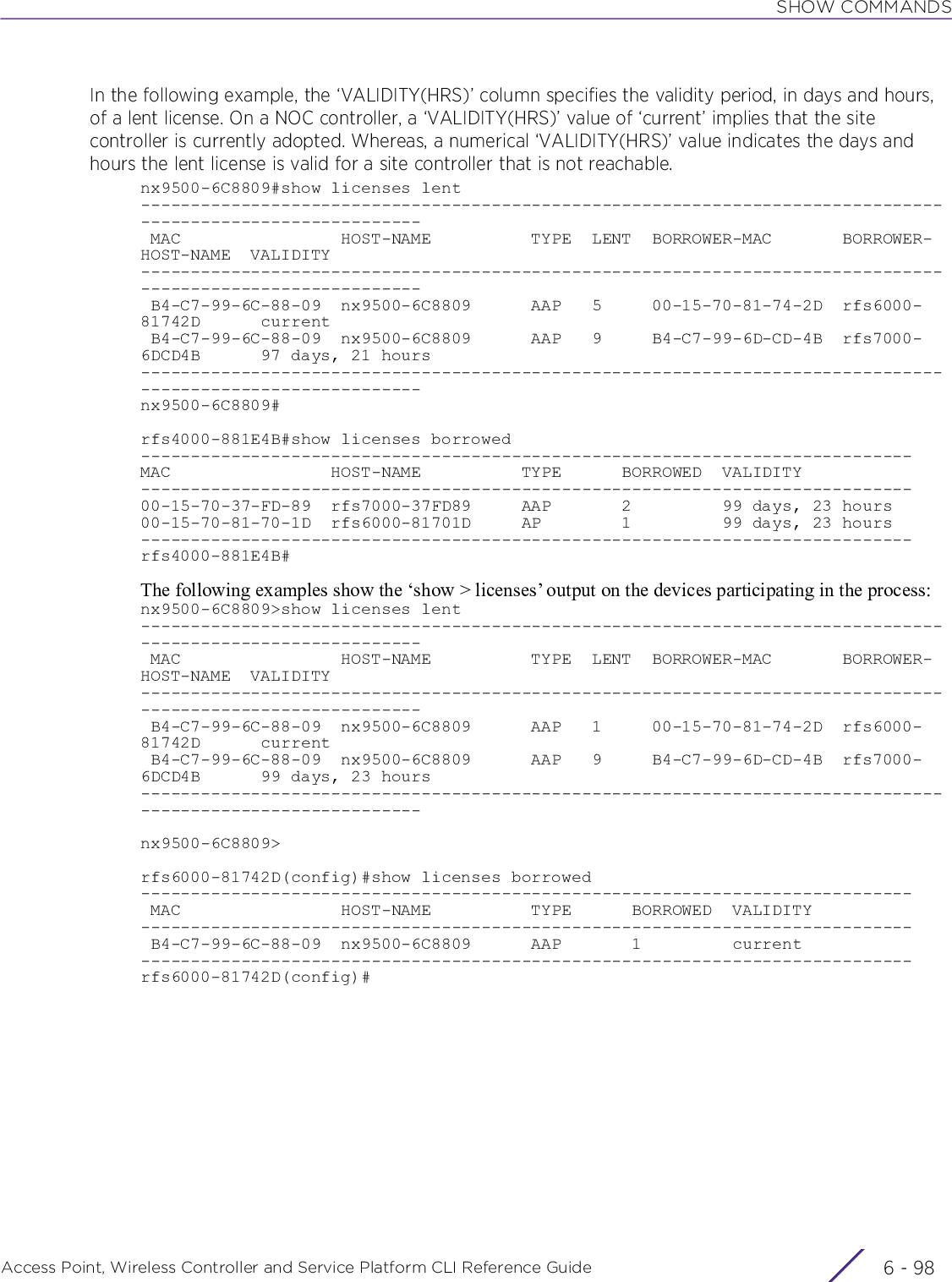
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 996.1.41 lldpshow commandsDisplays Link Layer Discovery Protocol (LLDP) informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow lldp [neighbors|report]show lldp neighbors {on <DEVICE-NAME>}show lldp report {detail|on}show lldp report {detail} {(on <DEVICE-OR-DOMAIN-NAME>)}Parameters• show lldp neighbors {on <DEVICE-NAME>}• show lldp report {detail} {(on <DEVICE-OR-DOMAIN-NAME>)}Examplenx9500-6C8809#show lldp neighbors-------------------------Chassis ID: 00-18-71-D0-0B-00System Name: TechPubs-ProCurve-SwitchPlatform: ProCurve J8697A Switch 5406zl, revision K.12.1X, ROM K.11.03 (/sw/code/build/btm(sw_esp1))Capabilities: Bridge RouterEnabled Capabilities: BridgeLocal Interface: ge1, Port ID(Port Description) (outgoing port): 5(A5)TTL: 113 secManagement Addresses: 192.168.13.40nx9500-6C8809#lldp Displays an LLDP neighbors table or aggregated LLDP neighbors tableneighbors Displays an LLDP neighbors tableon <DEVICE-NAME> Optional. Displays an LLDP neighbors table on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.lldp Displays an LLDP neighbors table or aggregated LLDP neighbors tablereport detail Displays an aggregated LLDP neighbors table• detail – Optional. Displays detailed aggregated LLDP neighbors tableNote: If the ‘on’ keyword is used without the ‘detail’ keyword, the system displays LLDP neighbors table summary on the specified device or RF Domain.on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and common to the ‘report detail’ parameter:• on <DEVICE-OR-DOMAIN-NAME> – Displays an aggregated LLDP neighbors table on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller,service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1000.png)



![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1036.1.45 mac-authshow commandsDisplays details of wired ports that have MAC address authentication enabledUse this command to view MAC authentication configuration and authentication state. The command displays the current authentication state of the wired host, the authorization state of the Ge1 port, and the wired hosts’ MAC address. The port status displays as Authorized if the wired host has successfully authenticated and Not Authorized if the wired host has not authenticated or has failed MAC authentication.For more information on enabling MAC address authentication on a wired port, see mac-auth.Supported in the following platforms:• Access Points — AP6511• Wireless Controllers — RFS4000, RFS6000Syntaxshow mac-auth {all|interface|on}show mac-auth {all|interface [<INTERFACE-NAME>|ge <1-5>|port-channel <1-3>|t1e1 <1-4>|up <1-2>|xge <1-4>]} {(on <DEVICE-NAME>)}Parameters• show mac-auth {all|interface [<INTERFACE-NAME>|ge <1-5>|port-channel <1-3>|t1e1 <1-4>|up <1-2>|xge <1-4>]} {(on <DEVICE-NAME>)}mac-auth Displays MAC authentication related information for all interfaces or all interfacesall Optional. Displays MAC authentication related information for all interfacesinterface [<INTERFACE-NAME>|ge <1-5>|port-channel <1-3>|t1e1 <1-4>|up <1-2>|xge <1-4>]Optional. Displays MAC authentication related information for a specified interface. Specify the interface using one of the following options:• <INTERFACE-NAME> – Selects the interface identified by the <INTERFACE-NAME> keyword• ge <1-5> – Selects the GigabitEthernet interface identified by the index number• port-channel <1-3> – Selects the port channel interface identified by the index number• t1e1 <1-4> – Selects the layer 2 interface (Ethernet port)• up <1-2> – Selects the WAN Ethernet interface identified by the index number• xge <1-4> – Selects the TenGigabitEthernet interface identified by the index numberon <DEVICE-NAME> The following keywords are common to the ‘all’ and ‘interface’ parameters:• on <DEVICE-NAME> – Optional. Displays MAC authentication related information on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.Note: When the ‘on’ keyword is used exclusively, without the ‘all’ and ‘interface’ options, the system displays MAC authentication related information for interfaces configured on the specified device.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1004.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1056.1.46 mac-auth-clientsshow commandsDisplays MAC authenticated clientsSupported in the following platforms:• Access Points — AP6511• Wireless Controllers — RFS4000, RFS6000Syntaxshow mac-auth-clients [all|interface]show mac-auth-clients all {on <DEVICE-NAME>}show mac-auth-clients interface {<INF-NAME>|ge <1-X>|port-channel <1-2>|xge <1-4>}Parameters• show mac-auth-clients all {on <DEVICE-NAME>}• show mac-auth-clients interface {<INF-NAME>|ge <1-X>|port-channel <1-2>|xge <1-4>}mac-auth-clients Displays MAC authenticated clients based on the parameters passed. The options are: all and interface.all Displays MAC authenticated clients for all interfaceson <DEVICE-NAME> Optional. Displays MAC authenticated clients for all interfaces on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.mac-auth-clients Displays MAC authenticated clients based on the parameters passed. The options are: all and interface.interface [<INF-NAME>|ge <1-X>|port-channel <1-2>|xge <1-4>]Displays MAC authenticated clients for the specified interface. Select the interface type from the following options:• <INF-NAME> – Optional. Displays MAC authenticated clients for the interface identified by the <INF-NAME> keyword. Specify the layer 2 (ethernet port) interface name.• ge <1-X> – Optional. Displays MAC authenticated clients for the selected GigabitEthernet interface. Specify the GE interface index from 1 - X. This will vary for different device types.• port-channel <1-2> – Optional. Displays MAC authenticated clients for the selected port channel interface. Specify the port channel interface index from 1 - 2.• xge <1-4> – Optional. Displays MAC authenticated clients for the selected TenGigabitEthernet interface. Specify the interface index from 1 - 4.on <DEVICE-NAME> Optional. Displays MAC authenticated clients for the specified interface on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1006.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1076.1.47 mintshow commandsDisplays MiNT protocol related statisticsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow mint [config|dis|id|info|known-adopters|links|lsp|lsp-db|mlcp|neighbors|route|stats|tunnel-controller|tunneled-vlans]show mint [config|id|info|known-adopters|route|stats|tunneled-vlans] {on <DEVICE-NAME>}show mint [dis|links|neighbors|tunnel-controller] {details} {(on <DEVICE-NAME>)}show mint lspshow mint lsp-db {details <MINT-ADDRESS>} {(on <DEVICE-NAME>)}show mint mlcp {history} {(on <DEVICE-NAME>)}Parameters• show mint [config|id|info|known-adopters|route|stats|tunneled-vlans] {on <DEVICE-NAME>}• show mint [dis|links|neighbors|tunnel-controller] {details} {(on <DEVICE-NAME>)}mint Displays MiNT protocol information based on the parameters passedconfig Displays MiNT configurationid Displays local MiNT IDinfo Displays MiNT statusknown-adopters Displays known, possible, or reachable adoptersroute Displays MiNT route table detailsstats Displays MiNT related statisticstunneled-vlans Displays MiNT tunneled VLAN detailson <DEVICE-NAME> The following keywords are common to all of the above parameters:• on <DEVICE-NAME> – Optional. Displays MiNT protocol details on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.mint Displays MiNT protocol information based on the parameters passeddis Displays MiNT network Designated Intermediate Systems (DISes) and Ethernet Virtualization Interconnects (EVISes)links Displays MiNT networking link detailsneighbors Displays adjacent MiNT peer details](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1008.png)
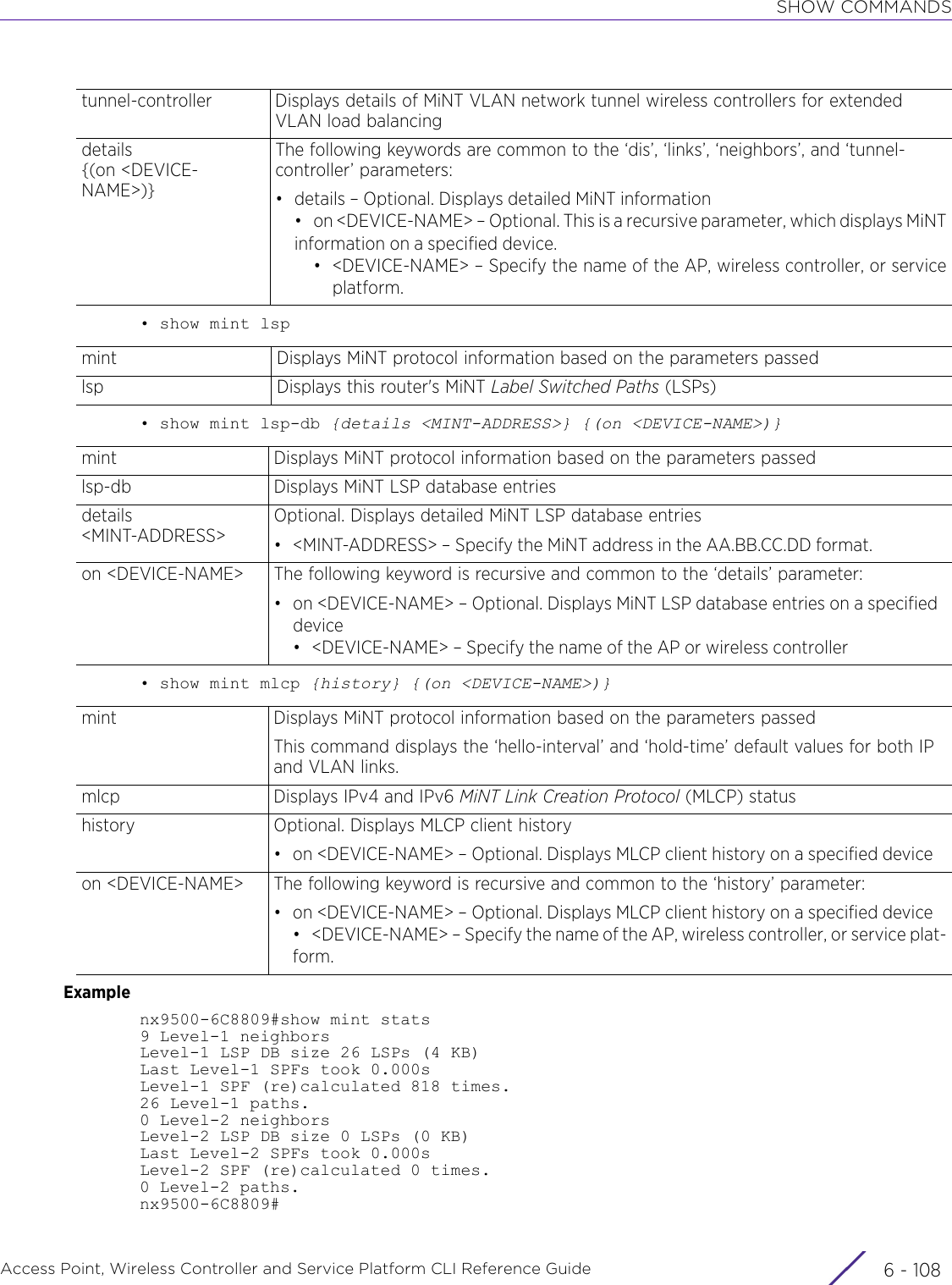
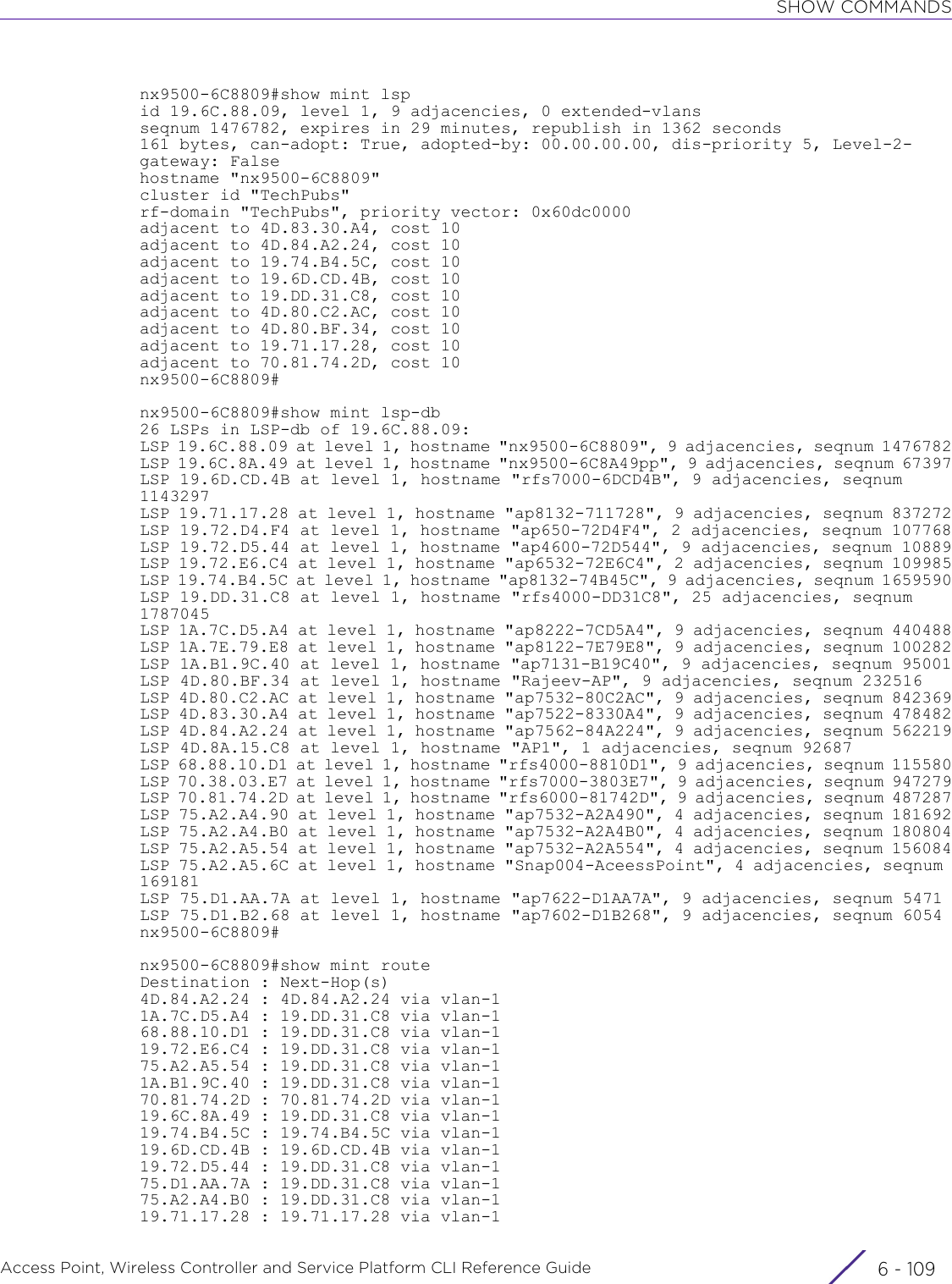

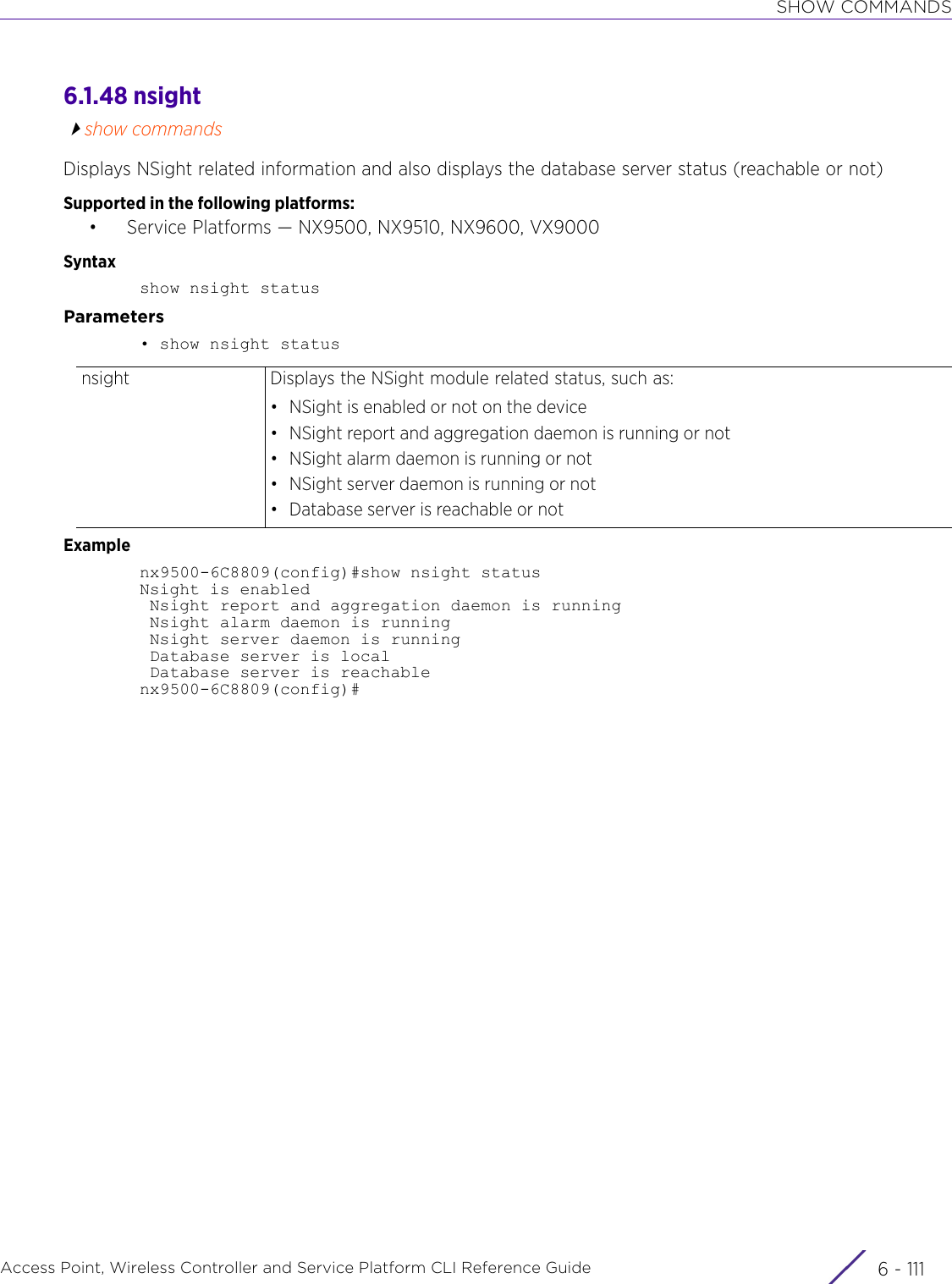
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1126.1.49 ntpshow commandsDisplays Network Time Protocol (NTP) information. NTP enables clock synchronization within a network.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow ntp [associations|status]show ntp [associations {detail|on}|status {on <DEVICE-NAME>}]Parameters• show ntp [associations {detail|on}|status {on <DEVICE-NAME>}]ntp associations {detail|on}Displays existing NTP associations. The interaction between the controller or service platform and a SNTP server constitutes an association. SNTP associations are of two kinds:- peer associations - where a controller or service platform synchronizes to another system or allows another system to synchronize to it, or - server associations - where only the controller or service platform synchronizes to the SNTP resource, not the other way around.• detail – Optional. Displays detailed NTP associations• on <DEVICE-NAME> – Optional. Displays NTP associations on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.Note: If the ‘on’ keyword is used without the ‘detail’ keyword, the system displays a summary of existing NTP associations on the specified device or RF Domain.ntp status {on <DEVICE-NAME>}Displays the performance (status) information relative to the NTP association status. Use this command to view the access point, controller, or service platform’s current NTP resource.• on <DEVICE-NAME> – Optional. Displays NTP association status on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1013.png)
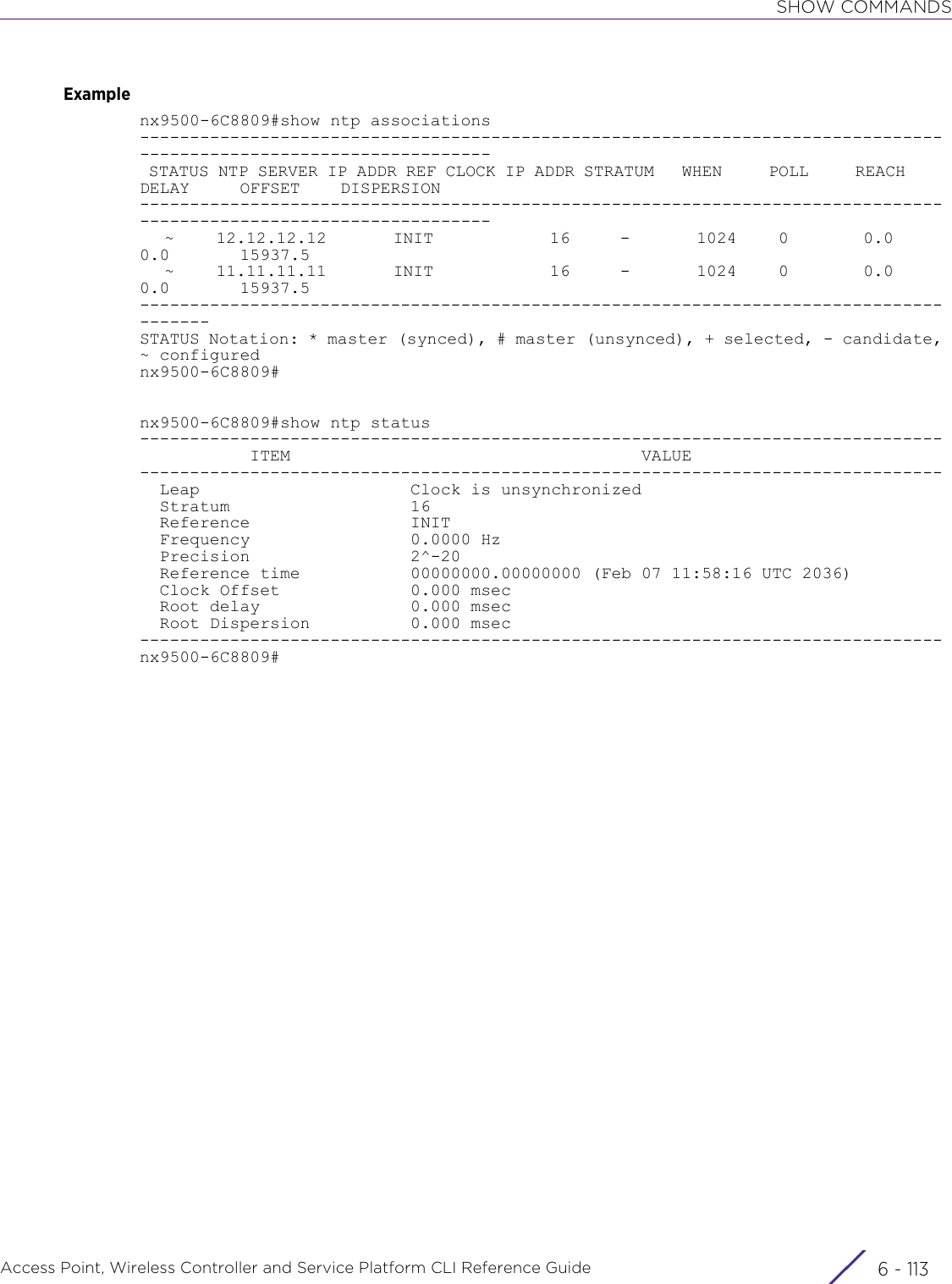
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1156.1.51 pppoe-clientshow commandsDisplays Point-to-Point Protocol over Ethernet (PPPoE) client informationUse this command to view PPPoE statistics derived from access to high-speed data and broadband networks. PPPoE uses standard encryption, authentication, and compression methods as specified by the PPPoE protocol. PPPoE enables point-to-points connection to an ISP over existing Ethernet interface.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow pppoe-client [configuration|status] {on <DEVICE-NAME>}Parameters• show pppoe-client [configuration|status] {on <DEVICE-NAME>}Examplenx9500-6C8809#show pppoe-client configuration PPPoE Client Configuration:+-------------------------------------------| Mode : Disabled| Service Name :| Auth Type : pap| Username :| Password : fJx5O+5duPjaOaPuXmtLDQAAAAAmvgEXcQ1+eUK4ByHK4aRi| Idle Time : 600| Keepalive : Disabled| Local n/w : vlan1| Static IP : __wing_internal_not_set__| MTU : 1492+-------------------------------------------nx9500-6C8809#pppoe-client Displays PPPoE client information (configuration and status)configuration Displays detailed PPPoE client configurationstatus Displays detailed PPPoE client statuson <DEVICE-NAME> The following keywords are common to ‘configuration’ and ‘status’ parameters:• on <DEVICE-NAME> – Optional. Displays detailed PPPoE client status or configuration on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1016.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1176.1.53 radiusshow commandsDisplays the amount of access time consumed and the amount of access time remaining for all guest users configured on a RADIUS serverEvery captive portal guest user can access the captive portal for a specified duration. This results in following three scenarios:• Scenario 1: Access duration not specified (in this case the default of 1440 minutes is applied)• Scenario 2: Access duration is specified and is greater than 0• Scenario 3: Access duration is specified and equals to 0 (in this case the guest user has unlimited access)In all the three scenarios the access time consumed is the duration for which the guest user has logged.But the access time remaining varies. It is calculated as follows:• Scenarios 1 & 2 - It is the lesser of the following two values: difference between the configured access duration and the time consumed AND the time until user account expiration.• Scenario 3 - It is the time until user account expirationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow radius [guest-users|server]show radius guest-users {brief|<GUEST-USER-NAME>}show radius serverParameters• show radius guest-users {brief|<GUEST-USER-NAME>}radius guest-users {brief|<GUEST-USER-NAME>}Displays RADIUS server’s guest user’s access details: total time for which the user has logged in, and the amount of access time remaining.• brief – Displays the total number of guest users provided RADIUS access• <GUEST-USER-NAME> – Optional. Provide the name of the guest user (whose access details are to be viewed). If no name is provided, the system displays details of all guest users who have successfully logged in at least once.Use this command in the captive-portal context to view time and data statistics for guest user(s) having bandwidth-based or time-based vouchers configured. In such a scenario, the system displays the following information: data configured, data remaining, configured and current bandwidths (for both downlink and uplink), time configured, and time remaining. Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1018.png)
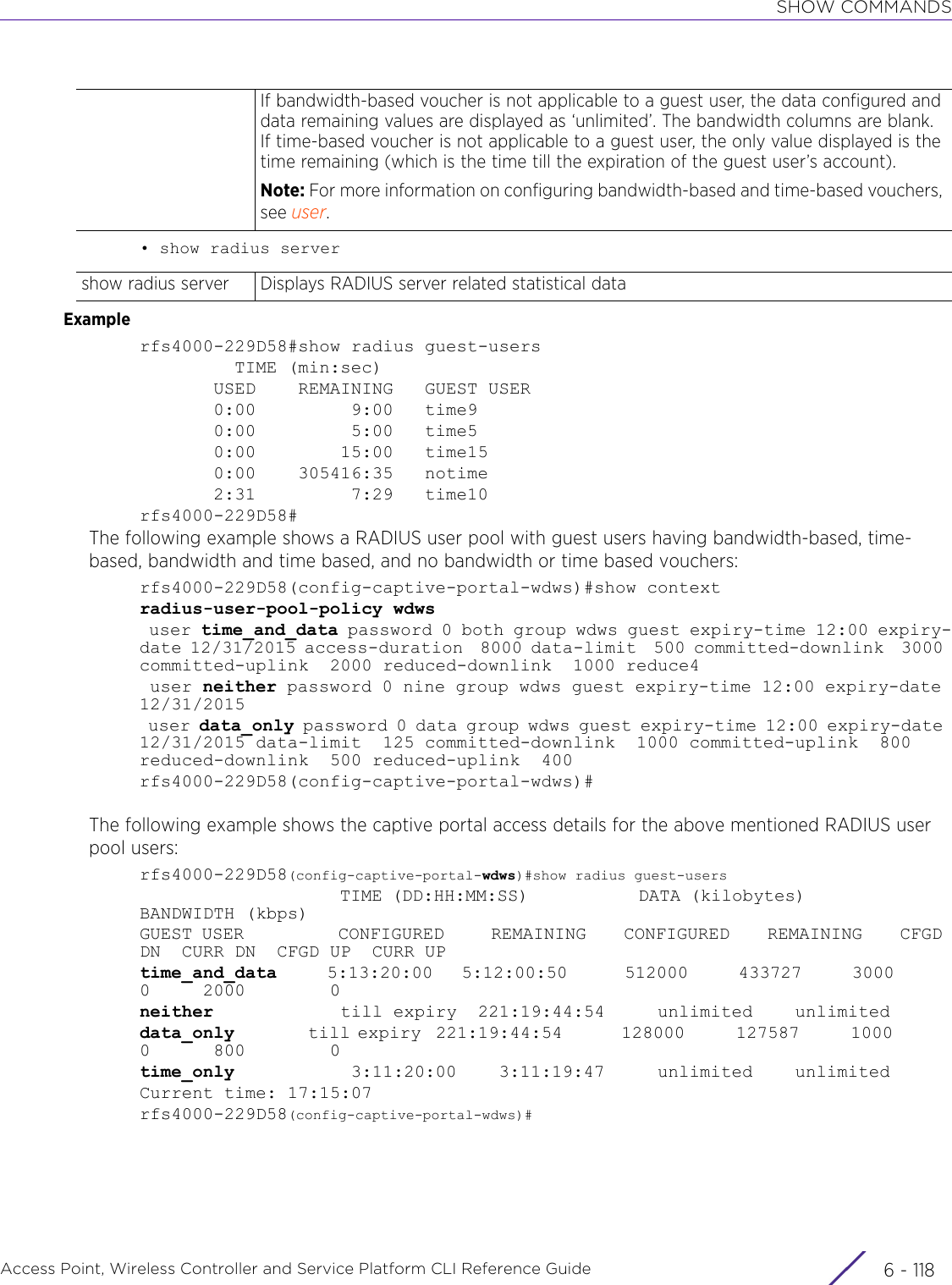

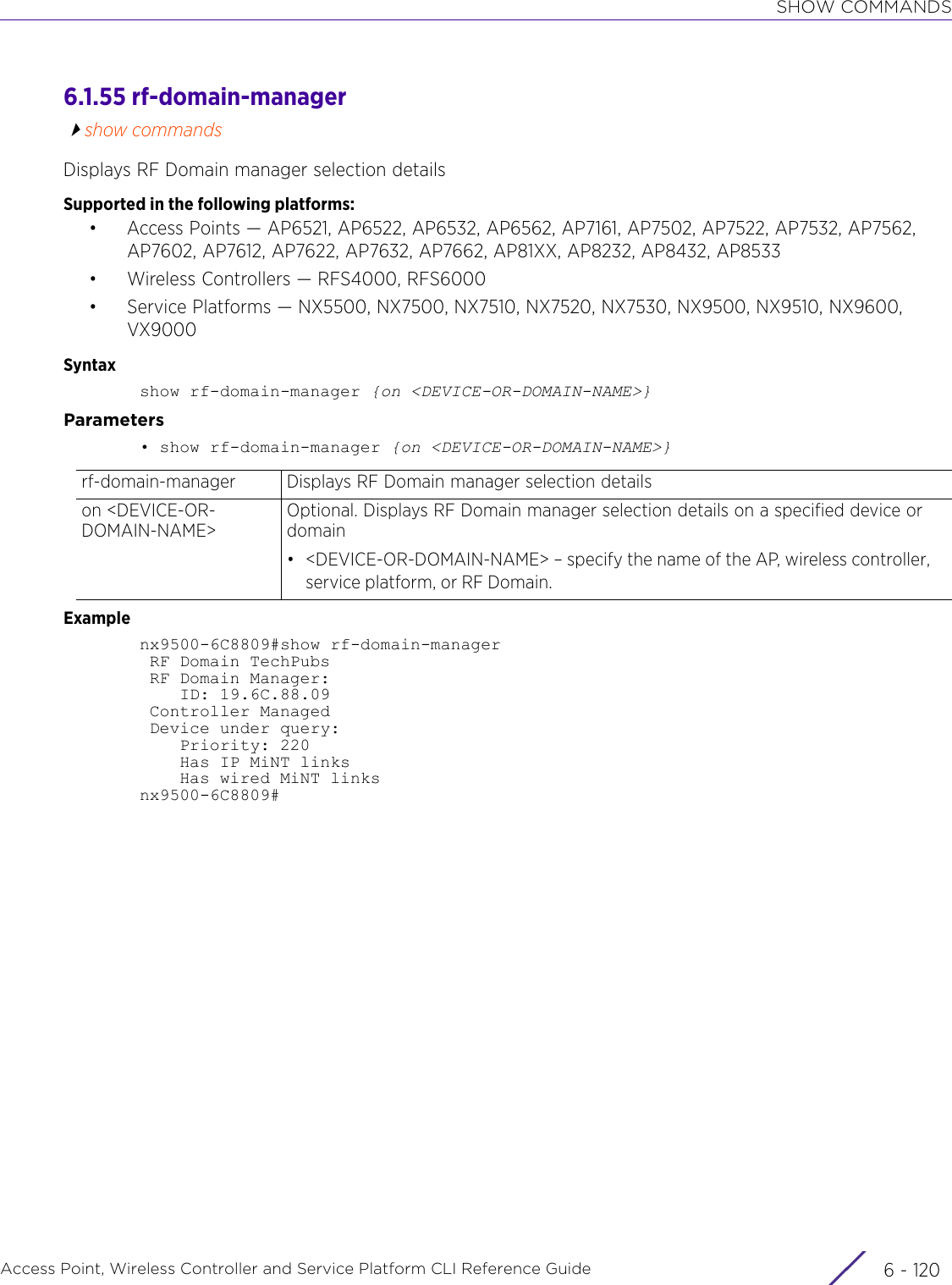
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1216.1.56 roleshow commandsDisplays role based firewall informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow role [ldap-stats|wireless-clients]show role [ldap-stats|wireless-clients] {on <DEVICE-NAME>}Parameters• show role [ldap-stats|wireless-clients] {on <DEVICE-NAME>}Examplenx9500-6C8809(config)#show role wireless-clientsNo ROLE statistics found.nx9500-6C8809(config)#role ldap-stats Displays LDAP server status and statisticsrole wireless-clients Displays clients associated with roleson <DEVICE-NAME> The following parameters are common to the ‘ldap-stats’ and ‘wireless-clients’ keywords:• on <DEVICE-NAME> – Optional. Displays clients associated with roles on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, and serviceplatform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1022.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1236.1.58 rtlsshow commandsDisplays Real Time Location Service (RTLS) statistics for access points contributing locationing informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow rtls [aeroscout|ekahau|omnitrail] {<MAC/HOSTNAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}Parameters• show rtls [aeroscout|ekahau|omnitrail] {<MAC/HOSTNAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}Examplerfs4000-229D58(config)#show rtls aeroscout Aeroscout Engine IP: 0.0.0.0 Port: 0 Send Count : 0 Recv Count : 0 Tag Reports : 0 Nacks : 0 Acks : 0 Lbs : 0 AP Status : 0 AP Notif : 0 Send Err : 0 Errmsg Count : 0Total number of APs displayed: 1rfs4000-229D58(config)#rtls Displays access point RTLS statisticsaeroscout Displays access point Aeroscout statisticsekahau Displays access point Ekahau statisticsomnitrail Displays access point Omnitrail statistics<MAC/HOSTNAME> Optional. Displays Aeroscout or Ekahau statistics for a specified access point. Specify the MAC address or hostname of the access point.on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and common to ‘Aeroscout’ and ‘Ekahau’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays Aeroscout or Ekahau statistics on a specified device or domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1024.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1256.1.59 running-configshow commandsDisplays configuration files (where all configured MAC and IP access lists are applied to an interface)Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow running-config {aaa-policy|application|application-group|application-policy|association-acl-policy|auto-provisioning-policy|captive-portal-policy|device|database-client-policy|database-policy|device|device-overrides|dhcp-server-policy|dhcpv6-server-policy|ex3500-management-policy|ex3500-qos-class-map-policy|ex3500-qos-policy-map|exclude-devices|firewall-policy|flag-unwritten-changes|guest-management-policy|hide-encrypted-values|include-factory|interface|ip-access-list|ipv6-access-list|mac-access-list|management-policy|meshpoint|nsight-policy|profile|radio-qos-policy|rf-domain|roaming-assist-policy|rtl-server-policy|schedule-policy|smart-rf-policy|url-filter|url-list|web-filter-policy|wlan|wlan-qos-policy}show running-config {aaa-policy|application-policy|association-acl-policy|auto-provisioning-policy|captive-portal-policy|database-client-policy|database-policy|dhcp-server-policy|dhcpv6-server-policy|ex3500-management-policy|ex3500-qos-class-map-policy|ex3500-qos-policy-map|guest-management-policy|firewall-policy|management-policy|nsight-policy|radio-qos-policy|roaming-assist-policy|rtl-server-policy|schedule-policy|smart-rf-policy|web-filter-policy|wlan-qos-policy} <POLICY-NAME> {include-factory}show running-config {flag-unwritten-changes}show running-config {application <APPLICATION-NAME>|application-group <APPLICATION-GROUP-NAME>}show running-config exclude-devicesshow running-config {device [<MAC>|self]} {include-factory}show running-config {device-overrides {brief}}show running-config {hide-encrypted-values {exclude-devices|include-factory}}show running-config {include-factory}show running-config {interface} {<INTERFACE-NAME>|ge|include-factory|me|port-channel|pppoe1|vlan|wwan1}show running-config {interface} {<INTERFACE-NAME>|ge <1-4>|include-factory|me1|port-channel <1-2>|pppoe1|vlan <1-4094>|wwan1} {include-factory}show running-config {ip-access-list <IP-ACCESS-LIST-NAME>|ipv6-access-list <IPv6-ACCESS-LIST-NAME>|mac-access-list <MAC-ACCESS-LIST-NAME} {include-factory}show running-config {meshpoint <MESHPOINT-NAME>} {include-factory}show running-config {profile [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600] <PROFILE-NAME>} {include-factory}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1026.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 127• show running-config {application <APPLICATION-NAME>|apllication-group <APPLICATION-GROUP-NAME>}• show running-config {device [<MAC>|self]} {include-factory}• show running-config {hide-encrypted-values {exclude-devices|include-factory}}include-factory The following keyword is common to all policies:• include-factory – Optional. Includes factory defaultsrunning-config Displays current running configurationOptionally, execute the command along with one of the associated keywords to view the running configuration for that top-level object. For example, to view a policy and its configuration, specify the policy type and provide the policy name.If the command is executed without a keyword, the system displays the entire running configuration.application <APPLICATION-NAME>Displays an application’s configuration. The application can be system-provided or user-defined.• <APPLICATION-NAME> – Specify the application name (should be existing).application-group <APPLICATION-GROUP-NAME>Displays an application-group’s configuration• <APPLICATION-GROUP-NAME> – Specify the application-group name (should be existing and configured).running-config Displays current running configurationOptionally, execute the command along with one of the associated keywords to view the running configuration for that top-level object. For example, to view a policy and its configuration, specify the policy type and provide the policy name.If the command is executed without a keyword, the system displays the entire running configuration.device [<MAC>|self] Optional. Displays device configuration• <MAC> – Displays a specified device configuration. Specify the MAC address of the device.• self – Displays the logged device’s configurationinclude-factory The following keyword is common to the ‘<MAC>’ and ‘self’ parameters:• Optional. Displays factory defaultsrunning-config Displays current running configurationOptionally, execute the command along with one of the associated keywords to view the running configuration for that top-level object. For example, to view a policy and its configuration, specify the policy type and provide the policy name.If the command is executed without a keyword, the system displays the entire running configuration.hide-encrypted-values {exclude-devices|include-factory}Optional. Replaces all encrypted passwords with the standard characters ****** in the show > running-config output• exclude-devices – Optional. Excludes devices from the running configuration displayed• include-factory – Optional. Includes factory default values in the running configuration displayed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1028.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 129• show running-config {meshpoint <MESHPOINT-NAME>} {include-factory}• show running-config {profile [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600] <PROFILE-NAME>} {include-factory}• show running-config {rf-domain <DOMAIN-NAME>} {include-factory}• show running-config {wlan <WLAN-NAME>} {include-factory}• show running-config url-filter <URL-FILTER-NAME>include-factory The following keyword is common to the ‘ip-access-list’ and ‘mac-access-list’ parameters:• Optional. Includes factory defaultsrunning-config Displays current running configurationmeshpoint <MESHPOINT-NAME>Optional. Displays meshpoint configuration• <MESHPOINT-NAME> – Specify the meshpoint nameinclude-factory Optional. Includes factory defaults along with running configuration detailsrunning-config Displays current running configurationprofile <DEVICE-TYPE> <PROFILE-NAME>Optional. Displays current configuration for a specified profile. Select the device type, and then specify the profile name.• <DEVICE-TYPE> – Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, and VX9000.• <PROFILE-NAME> – Specify the profile name for the selected <DEVICE-TYPE>.Note: Select the ‘anyap’ option to view the running configuration of any type of device.include-factory Optional. This parameter is common to all profiles. When selected, it includes factory defaults in the output.running-config Displays current running configurationrf-domain <DOMAIN-NAME>Optional. Displays current configuration for a RF Domain• <DOMAIN-NAME> – Displays current configuration for a specified RF Domain. Specify the RF Domain name.include-factory Optional. Includes factory defaultsrunning-config Displays current running configurationwlan <WLAN-NAME> Optional. Displays current configuration for a WLAN• <WLAN-NAME> – Displays current configuration for a specified WLAN. Specify the WLAN name.include-factory Optional. Includes factory defaultsrunning-config Displays current running configurationurl-filter <URL-FILTER-NAME>Optional. Displays current configuration for the URL filter identified by the <URL-FILTER-NAME> keyword• <URL-FILTER-NAME> – Specify the URL filter’s name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1030.png)

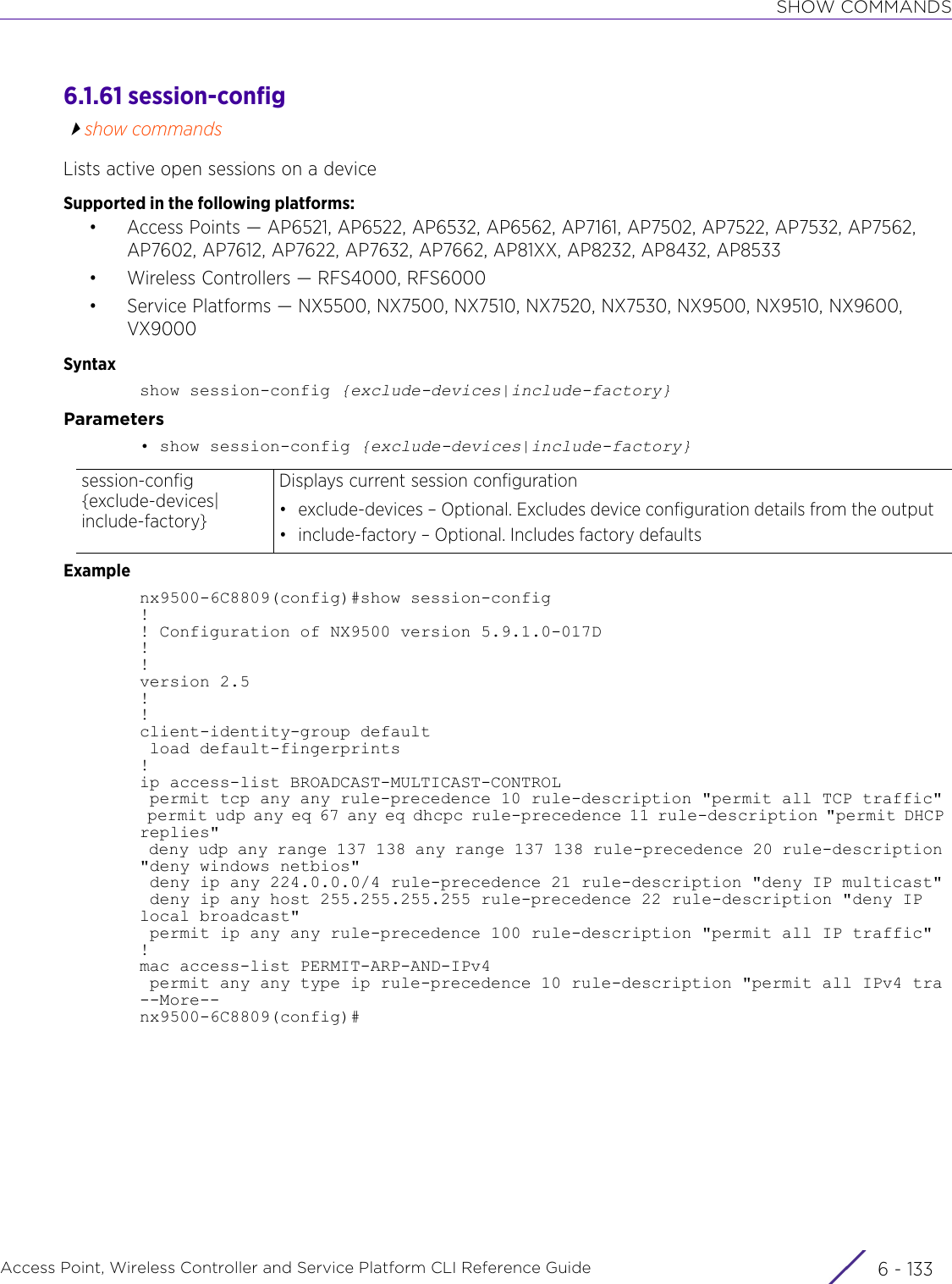
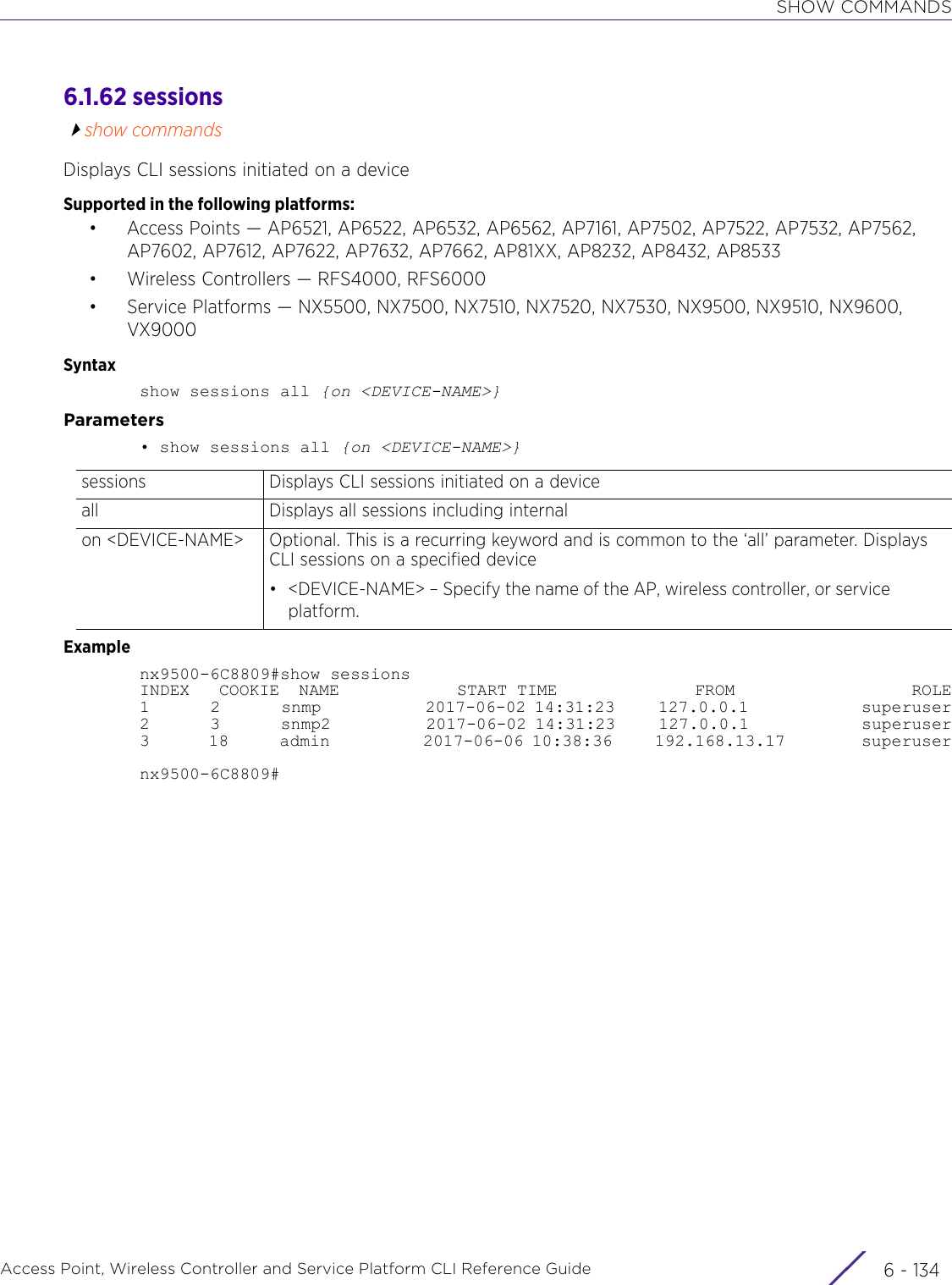

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1366.1.64 smart-rfshow commandsDisplays Self-Monitoring At Run Time (Smart RF) statistical history to assess adjustments made to device configurations to compensate for detected coverage holes or device failuresWhen invoked by an administrator, Smart RF instructs access point radios to change to a specific channel and begin beaconing using the maximum available transmit power. Within a well-planned deployment, any RF Domain member access point radio should be reachable by at least one other radio. Smart RF records signals received from its neighbors as well as signals from external, un-managed radios. AP-to-AP distance is recorded in terms of signal attenuation. The information from external radios is used during channel assignment to minimize interference.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow smart-rf [ap|channel-distribution|history|history-timeline|interfering-ap|interfering-neighbors|radio]show smart-rf ap {<MAC>|<DEVICE-NAME>|activity|energy|neighbors|on <DOMAIN-NAME>}show smart-rf ap {<MAC>|<DEVICE-NAME>} {on <DOMAIN-NAME>}show smart-rf ap (activity|energy|neighbors} [<MAC>|<DEVICE-NAME>] {(on <DOMAIN-NAME>)}show smart-rf [channel-distribution|history|history-timeline] {on <DOMAIN-NAME>}show smart-rf radio {<MAC>|activity|all-11an|all-11bgn|channel|energy|neighbors|on <DOMAIN-NAME>}show smart-rf radio {<MAC>|all-11an|all-11bgn|energy <MAC>} {on <DOMAIN-NAME>}show smart-rf radio {activity|neigbors} {<MAC>|all-11an|all-11bgn} {on <DOMAIN-NAME>}show smart-rf interfering-ap {<MAC>|<DEVICE-NAME>|on <DOMAIN-NAME>}show smart-rf interfering-neighbors {<MAC>|<DEVICE-NAME>|on <DOMAIN-NAME>|threshold <50-100>}Parameters• show smart-rf ap {<MAC>|<DEVICE-NAME>} {on <DOMAIN-NAME>}smart-rf Displays Smart RF related informationap Displays access point related Smart RF information<MAC> Optional. Uses MAC addresses to identify access points. Displays all access points, if no MAC address is specified.<DEVICE-NAME> Optional. Uses an administrator defined name to identify an access pointon <DOMAIN-NAME> Optional. Displays access point details on a specified RF Domain• <DOMAIN-NAME> – Specify the domain name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1037.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 137• show smart-rf ap (activity|energy|neighbors} [<MAC>|<DEVICE-NAME>] {(on <DOMAIN-NAME>)}• show smart-rf [channel-distribution|history|history-timeline] {on <DOMAIN-NAME>}smart-rf Displays Smart RF related informationap Displays AP related Smart RF informationactivity Optional. Displays Smart RF activity related informationUse this option to view the following:• Time-period – Lists the frequency Smart RF activity is trended for the RF Domain. Trending periods include the current hour, last 24 hours, or the last seven days. Comparing Smart RF adjustments versus the last seven days enables an administrator to assess whether periods of interference and poor performance were relegated to just specific periods.• Power changes – Displays the number of Smart RF initiated power level changes needed for RF Domain member devices during each of the three trending periods. Determine whether power compensations were relegated to known device outages or if compensations were consistent over the course of a day or week.• Channel changes – Lists the number of Smart RF initiated channel changes needed for RF Domain member devices during each of the three trending periods. Determine if channel adjustments were relegated to known device count increases or decreases over the course of a day or week.• Coverage changes – Displays the number of Smart RF initiated coverage changes needed for RF Domain member devices during each of the three trending periods. Determine if coverage changes were relegated to known device failures or known periods of interference over the course of a day or week.energy Optional. Displays AP energy for a specified AP or all APsUse this option to view an RF Domain member access point’s operating channels, noise level and neighbor count. This information helps assess whether Smart RF neighbor recovery is needed in respect to poorly performing access points.neighbors Optional. Displays AP neighborsUse this option to view attributes of neighbor radio resources available for Smart RF radio compensations for other RF Domain member device radios.{<MAC>|<DEVICE-NAME>}The following keywords are common to all of the above parameters:• <MAC> – Displays all of the above mentioned information for a specified AP, identified by its MAC address. Specify the AP’s MAC address.• <DEVICE-NAME> – Displays all of the above mentioned information for a specified AP, identified by its hostname. Specify the AP’s hostname.on <DOMAIN-NAME> Optional.Displays access point details on a specified RF Domain• <DOMAIN-NAME> – Specify the domain name.smart-rf Displays Smart RF related informationchannel-distribution Displays Smart RF channel distribution information. This provides an overview of how RF Domain member devices are utilizing different channels to optimally support connect devices and avoid congestion and interference with neighboring devices. Assess whether the channel spectrum is being effectively utilized and whether channel changes are warranted to improve RF Domain member device performance.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1038.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1406.1.65 spanning-treeshow commandsDisplays spanning tree utilization informationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow spanning-tree mst {configuration|detail|instance|on <DEVICE-NAME>}show spanning-tree mst {configuration} {(on <DEVICE-NAME>)}show spanning-tree mst {detail} {interface|on}show spanning-tree mst {detail} interface {<INTERFACE-NAME>|ge <1-4>|me1|port-channel <1-2>|pppoe1|vlan <1-4094>|wwan1} {(on <DEVICE-NAME>)}show spanning-tree mst {instance <1-15>} {interface <INTERFACE-NAME>} {(on <DEVICE-NAME>)}Parameters• show spanning-tree mst {configuration} {(on <DEVICE-NAME>)}• show spanning-tree mst {detail} interface {<INTERFACE-NAME>|ge <1-4>|me1|port-channel <1-2>|pppoe1|vlan <1-4094>|wwan1} {(on <DEVICE-NAME>)}spanning-tree Displays spanning tree utilization informationmst Displays Multiple Spanning Tree (MST) related informationconfiguration {on <DEVICE-NAME>}Optional. Displays MST configuration• on <DEVICE-NAME> – Optional. Displays MST configuration on a specified device• <DEVICE-NAME> – Specify the name of the AP or wireless controller.Note: If the ‘on’ keyword is used without any of the other options, the system displays a summary of spanning tree utilization information on the specified device.spanning-tree Displays spanning tree informationmst Displays MST configurationdetail Optional. Displays detailed MST configuration, based on the parameters passedinterface [<INTERFACE>|ge <1-4>|me1|port-channel <1-2>|pppoe1|vlan <1-4094>wwan1]Displays detailed MST configuration for a specified interface• <INTERFACE> – Displays detailed MST configuration for a specified interface. Specify the interface name.• ge <1-4> – Displays GigabitEthernet interface MST configuration• <1-4> – Select the GigabitEthernet interface index from 1 - 4.• me1 – Displays FastEthernet interface MST configuration• port-channel – Displays port channel interface MST configuration• <1-2> – Select the port channel interface index from 1 - 2.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1041.png)

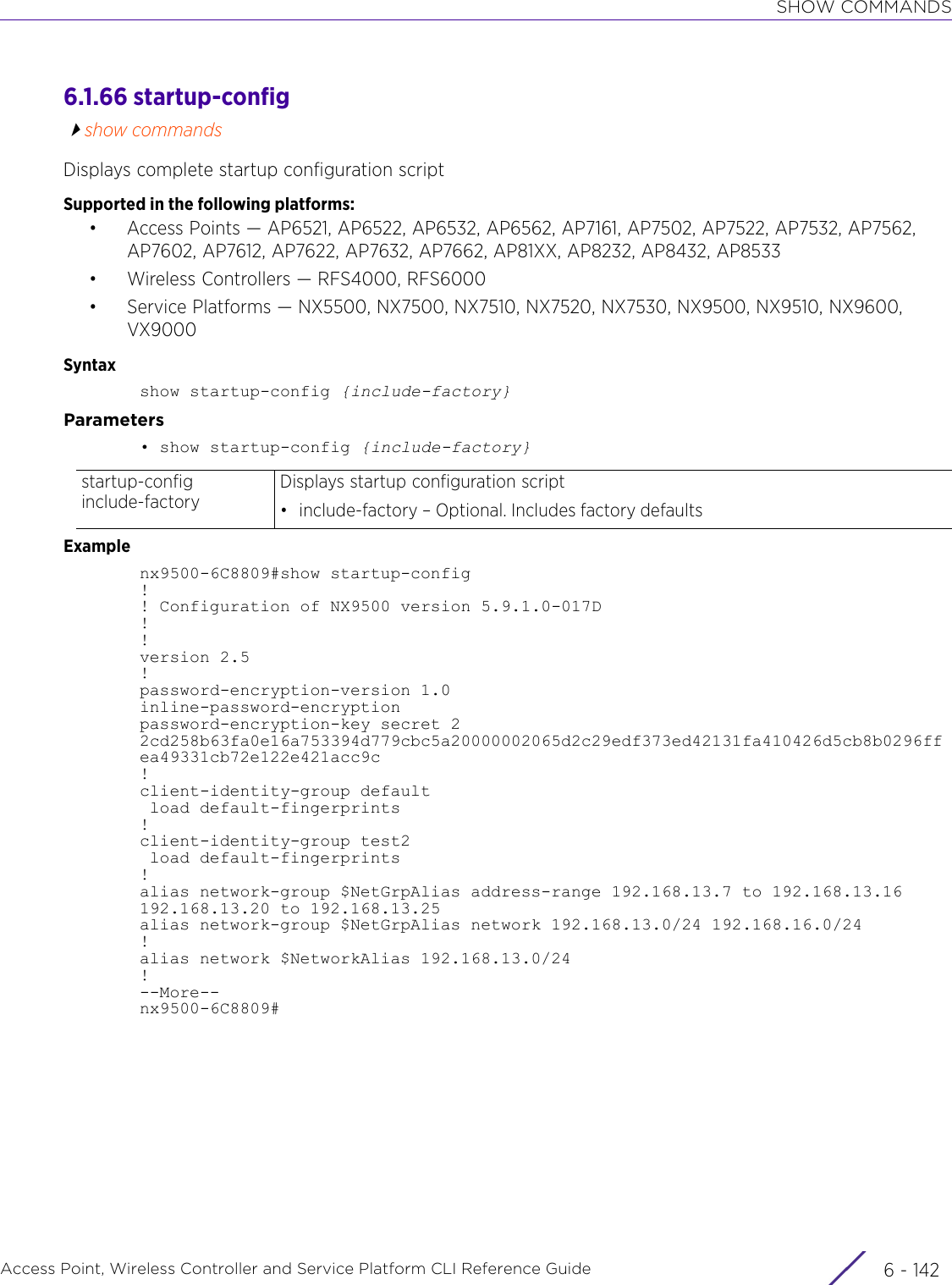
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1436.1.67 t5show commandsDisplays adopted T5 controller statisticsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7510, NX7520, NX9500, NX9510, NX9600, VX9000Syntaxshow t5 [boot|clock|cpe|interface|mac|system|temperature|uptime|version|wireless] {on <T5-DEVICE-NAME>}show t5 [boot|clock|system|temperature|uptime|version] {on <T5-DEVICE-NAME>}show t5 cpe [address|boot|ether port status|led|reset|system|uptime|version] {on <T5-DEVICE-NAME>}show t5 interface [dsl|fe|ge|radio]show t5 interface [dsl|fe|ge] [counter|description|errors|status|utilization] {on <T5-DEVICE-NAME>}show t5 interface dsl custom [avg|dses|dsses|peak|uses|usses] {on <T5-DEVICE-NAME>}show t5 interface radio [stats|status|wlam-map] {on <T5-DEVICE-NAME>}show t5 mac table [filter name [dsl<1-24>|ge <1-2>|vlan <1-4094>|wlan <1-24>] {on <T5-DEVICE-NAME>}]show t5 wireless [client|wlan]show t5 wireless client {filter name [association-status|authentication-status|bss|mac-address|retry-percentage|rssi-value]} {on <T5-DEVICE-NAME>}show t5 wireless wlan counters [qos|rate|size] {on <T5-DEVICE-NAME>}Parameters• show t5 [boot|clock|system|temperature|uptime|version] {on <T5-DEVICE-NAME>}NOTE: This command is applicable only on WiNG controllers with adopted and managed T5 controllers.t5 Displays adopted T5 controller statisticsboot Displays the T5 device’s boot details. Use this option to view the primary and secondary image files available to use for booting up.clock Displays the T5 controller’s system time, as reported from the controller itself or its remote NTP time resourcesystem Displays T5 controller’s system information, which includes the T5 controller’s hostname, MAC address, RF Domain, system clock, uptimetemperature Displays T5 controller’s current temperatureuptime Displays the T5 controller’s uptime (the time it has been actively deployed and operational)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1044.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 144• show t5 cpe [address|boot|ether port status|led|reset|system|uptime|version] {on <T5-DEVICE-NAME>}• show t5 interface [dsl|fe|ge] [counter|description|errors|status|utilization] {on <T5-DEVICE-NAME>}version Displays the T5 controller’s primary and secondary firmware imageson <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticscpe Displays the T5 controller managed Customer Premises Equipment (CPE) statistics based on the parameters passed. Use this command to verify each CPE address credentials and whether currently disconnected or ready for radio coverage area support.address Displays each linked CPE's current IP address used as its network identifierboot Displays the primary and secondary firmware versions available to each CPE, along with status of the most recent upgrade operation detailsether port status Displays Ethernet port statusled Displays whether the CPEs currently have their LEDs enabled or disabled. In places like hospitals, its not uncommon for access points to be operational, but their LEDs off as to not disturb patients.reset Displays the number times a CPE has been resetsystem Displays device hardware and SKU information for each CPE. Use this information to assess whether a controller is managing the correct CPE devices out of the total number of CPEs available.uptime Displays the time each CPE device has been actively deployed and operationalversion Displays the application and boot versions utilized by the CPE deviceson <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticsinterface Displays T5 interface-related statistics based on the interface selected[dsl|fe|ge|radio] [counter|description|errors|status|utilization]Select the interface type. The options are: dsl, fe, ge.• dsl – Displays Digital Subscriber Line (DSL) interface related information•fe – Displays Fast Ethernet (FE) interface related information• ge – Displays Gigabit Ethernet (GE) interface related informationThe system displays the following information for the DSL, GE, and FE ports:• counter – Displays the following:• Number of octets (bytes) received and transmitted on this port• Number of data packets received and transmitted on this port• Number of flow control (layer 2) packets received and transmitted on this portContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1045.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 145• show t5 interface dsl custom [avg|dses|dsses|peak|uses|usses] {on <T5-DEVICE-NAME>}contd.. • description – Displays the following:•The selected port’s name• The numeric index assignable to each port• The 64 character maximum, unique, administrator-assigned description to eachport• errors – Displays the following DSL interface related errors:• The name of the DSL utilized by each T5 controller connected CPE device.• The number of FECs detected in the downstream direction.Forward Error Correction (FEC) or channel coding is used for controlling errors overunreliable or noisy communication channels.• The number of CPE DSL coding violations (badly coded packets) detected in thedownstream direction.• The number of FECs detected in the upstream direction.• The number of CPE DSL coding violations (badly coded packets) detected in theupstream direction.• status – Displays the following:•The selected port’s name• Whether the port is currently up or down as a T5 controller transmit and receiveresource• The port's current speed in MB• Whether pause packet utilization is currently off or on for the selected port• Whether each listed port is enabled or disabled by the administrator• utilization – Displays the following:•The selected port’s name• The port’s receive and transmit data rates (in Kbps)• The packet per second port receive and transmit rates (p/s)• Each port's receive and transmit direction utilization as a percentage of the totaltransmit bandwidth available.on <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticsinterface Displays T5 interface-related statistics based on the interface selecteddsl Selects A T5 controller’s DSL interface. A T5 controller uses the operating system to manage its connected radio devices, as opposed to the WiNG operating used by RFS controllers and NX service platforms. However, a T5 controller, once enabled as a supported external device, can provide data to WiNG to assist in a T5’s management within a WiNG supported subnet populated by both types of devices. The CPEs are the T5 controller managed radio devices using the operating system. These CPEs use a DSL as their high speed Internet access mechanism using the CPE’s physical wallplate connection and phone jack.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1046.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 146• show t5 interface radio [stats|status|wlam-map] {on <T5-DEVICE-NAME>}custom [avg|dses|dsses|peak|uses|usses]Displays following custom CPE DSL data:• avg – Each DSL's average response time in microseconds• dses – The number of seconds downstream DSL transmissions were negatively impacted by code violations.• dsses – The number of seconds downstream DSL transmissions were severely negatively impacted by code violations.• peak – Each DSL's maximum (best to date since the screen was refreshed) response time in microseconds.• uses – The number of seconds upstream DSL transmissions were negatively impacted by code violations.• usses – The number of seconds upstream DLS transmissions were severely negatively impacted by code violations.on <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticsinterface Displays T5 interface-related statistics based on the interface selectedradio [stats|status|wlan-map]Displays following radio interface related information:• stats – Displays T5 radio interface statistics. A T5 controller uses the operating system to manage its connected radio devices, as opposed to the WiNG operating used by RFS controllers and NX service platforms. However, a T5 controller, once enabled as a supported external device, can provide data to WiNG to assist in a T5’s management within a WiNG supported subnet populated by both types of devices. The CPEs are the T5 controller managed radio devices using the operating system. Use this option to view the following:• name – The administrator assigned name of each listed CPE radio as its uniqueidentifier• Rx (Kbps) – The listed CPE radio's receive data rate (in Kbps). Use this informationto assess RF activity versus other T5 managed CPE radios in the same radio cover-age area.• Rx Octets – The number of octets (bytes) received with no errors by the listed T5controller managed CPE radio.• Rx Packets – The number of data packets received for the listed T5 managed CPEradio since this screen was last refreshed.• Tx (Kbps) – The listed CPE radio's transmit data rate (in Kbps). Use this informa-tion to assess RF activity versus other T5 managed CPE radios in the same radiocoverage area.• Tx Octets – Displays the number of octets (bytes) transmitted with no errors bythe listed T5 controller managed CPE radio.• Tx Packets – The number of data packets transmitted from the listed T5 managedCPE radio since this screen was last refreshed.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1047.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 147• show t5 mac table [filter name [dsl<1-24>|ge <1-2>|vlan <1-4094>|wlan <1-24>] {on <T5-DEVICE-NAME>}• show t5 wireless client {filter name [association-status|authentication-status|bss|mac-address|retry-percentage|rssi-value]} {on <T5-DEVICE-NAME>}contd.. • status – Displays T5 radio interface status information• name – The administrator assigned name of each listed CPE radio as its uniqueidentifier.• Operational status – The radio interface’s operational status (enabled/disabled).• mac – The T5 radio interface's MAC address.• transmit power – The T5 radio interface’s transmit power.• Channel – The T5 radio interface’s channel of operation.• wlan-map – Displays WLAN map membership data for T5 controller managed CPE radio devices. Use this option to view the following:• name – The administrator assigned name of each listed CPE radio as its uniqueidentifier.• status – Whether a CPE radio is currently enabled or disabled as a radio resourcefor the WLAN(s) the CPE radio has been mapped to.• wlan-radio-mapping – The managed WLAN(s) each listed radio has beenmapped to.on <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticsmac table [dsl<1-24>|ge <1-2>|vlan <1-4094>|wlan <1-24>]Displays T5 MAC address table. The T5 MAC table displays a dynamic list of MAC addresses learned by the T5 controller over its ethernet interfaces. Use this information to identify devices and the interfaces on which they can be found.Use the following additional filters to filter on the basis of the VLAN or DSL interface:• dsl <1-24> – Filters information on the basis of the selected DSL port• ge <1-2> – Filters information on the basis of the selected GE port• vlan <1-4094 – Filters information on the basis of the selected VLAN port• wlan <1-24> – Filters on the basis of the selected CPEon <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticswireless client Displays the T5 wireless client and WLAN related statistics• client – Displays read-only device information for wireless clients associated with the selected T5 controller and its connected CPE device radios. Use this information to assess if configuration changes are required to improve client performance.Use the additional filters available to view specific client-related information. The options are:• association-statusContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1048.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 148• show t5 wireless wlan counters [qos|rate|size] {on <T5-DEVICE-NAME>}ExampleThe following examples are for show commands executed on the ‘t5-ED7C6C’ controller adopted by the ‘nx9500-6C8809’ wireless controller:nx9500-6C8809(config)#show t5 boot on t5-ED7C6CPrimary Version: 5.4.2.0-010RSecondary Version: 5.4.2.0-006BNext Boot: PrimaryUpgrade Status: noneUpgrade Progress %: 0nx9500-6C8809(config)#nx9500-6C8809(config)#show t5 version on t5-ED7C6CBootloader Version: 5.4.2.0-010RApplication Version: 5.4.2.0-010Rnx9500-6C8809(config)#• authentication-status•bss• retry-percentage• rssi-valueon <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.t5 Displays adopted T5 controller statisticswireless wlan [qos|rate|size]Displays the T5 wireless WLAN related statistics• wlan – Displays following T5 controller traffic counter statistics:• qos – T5 controller WLAN QoS utilization. Displays the number of background(low priority) and best-effort packets received and transmitted on each listed T5controller managed WLANs• rates – Displays T5 controller's WLAN utilization data rate statistics• Lists the number of data packets received and transmitted in the WLAN thathave been relegated to a 1 Mbps data rate• Lists the number of data packets received and transmitted in the WLAN by T5 controller connected devices at 54Mbps• size – Displays the number of data packets received and transmitted, in each listed WLAN, greater than 1024 byteson <T5-DEVICE-NAME>Optional. Executes the command on a specified T5 device• <T5-DEVICE-NAME> – Specify the T5 device’s hostname. An error message is displayed if no T5 device name is specified.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1049.png)
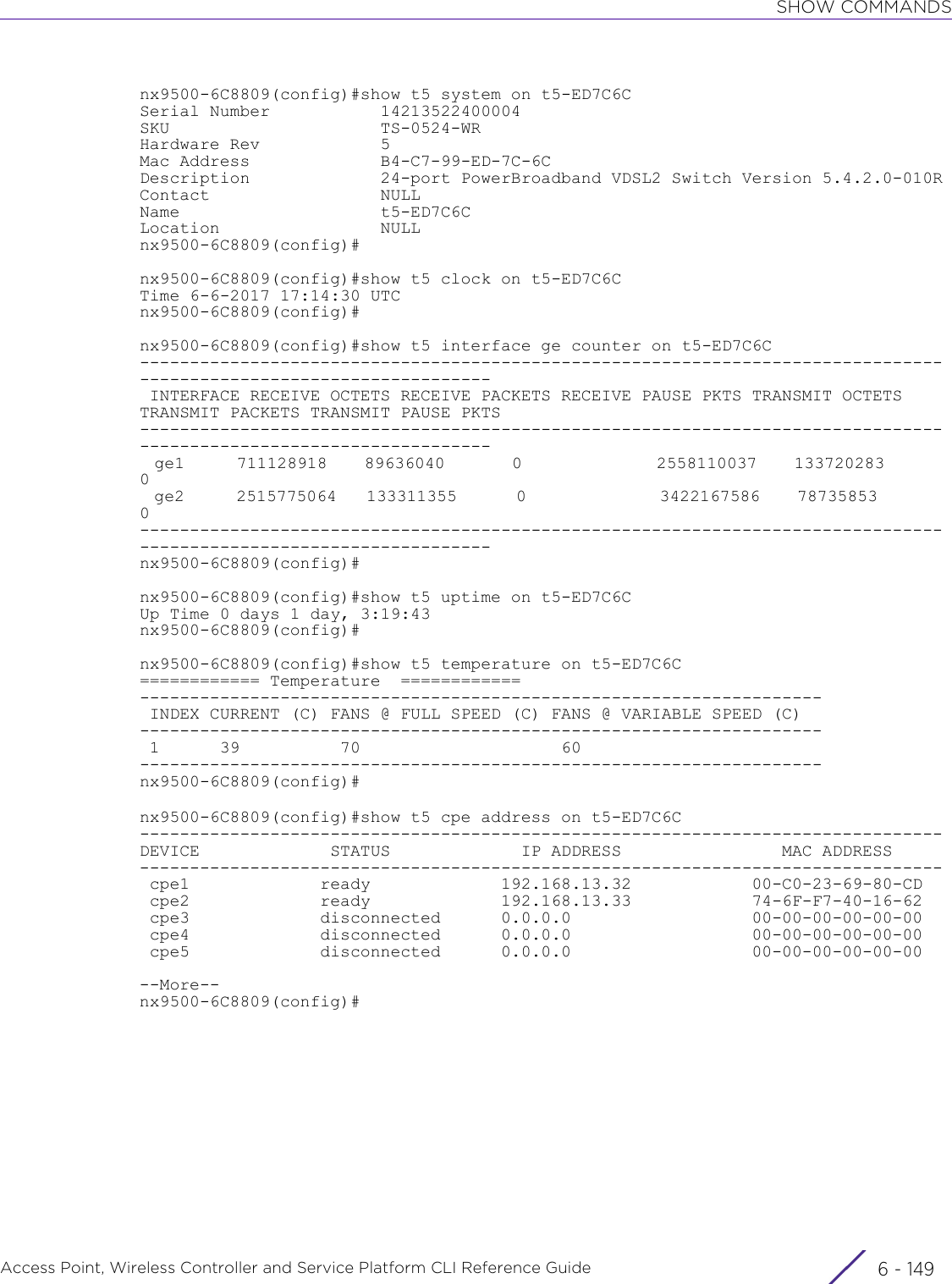
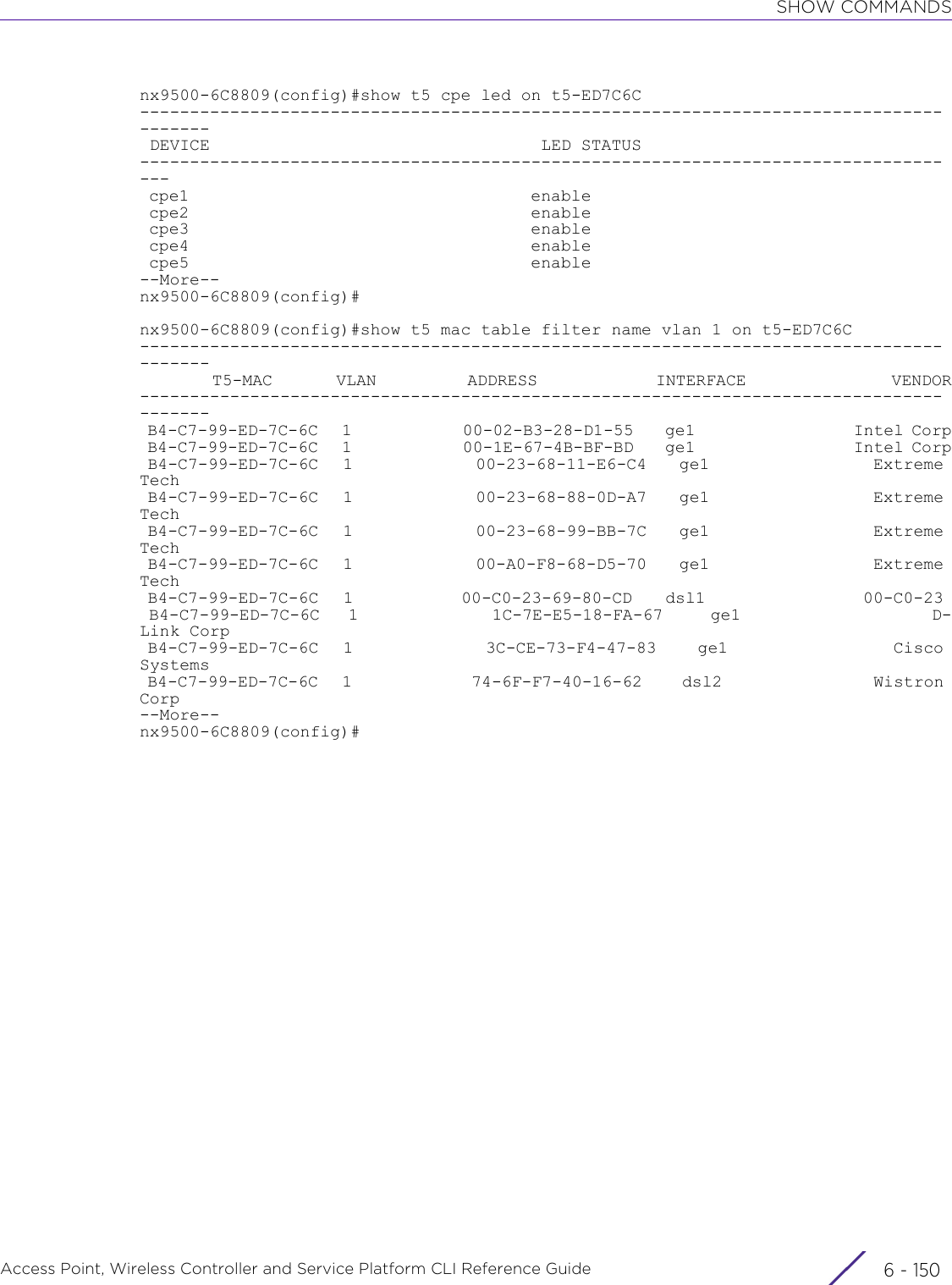

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1536.1.70 traffic-shapeshow commandsDisplays traffic-shaping related configuration details and statisticsTraffic shaping regulates network data transfers to ensure a specific performance level. Traffic shaping delays the flow of packets defined as less important than prioritized traffic streams. Traffic shaping enables traffic control out an interface to match its flow to the speed of a remote target’s interface and ensure traffic conforms applied policies. Traffic can be shaped to meet downstream requirements and eliminate network congestion when data rates are in conflict.Apply traffic shaping to specific applications to apply application categories. When application and ACL rules are conflicting, ACL rules take precedence for the traffic shaping class. Using traffic shaping, an application takes precedence over an application category.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530Syntaxshow traffic-shape [priority-map|statistics {class <1-4>}|status] {on <DEVICE-NAME>}Parameters• show traffic-shape [priority-map|statistics {class <1-4>}|status] {on <DEVICE-NAME>}traffic-shape Displays traffic-shaping related configuration details and statisticspriority-map Displays the traffic shaper queue priority. There are 8 queues (0 - 7), and traffic is queued in each based on incoming packets 802.1p markings.statistics class <1-4> Displays traffic-shaping related statistics for all traffic shaper classes or for a selected class• class <1-4> – Optional. Specify the traffic class from 1 - 4. The system displays traffic shaping statistics for the selected class. If not selected, the system statistics for all classes.status Displays the controller or service platform’s traffic shaping status (whether running or not)on <DEVICE-NAME> Optional. Displays traffic-shaping related configuration details and statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1054.png)



![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1576.1.73 vrrpshow commandsDisplays the following Virtual Router Redundancy Protocol (VRRP) related statistics: configuration error, router redundancy information in brief and detail. VRRP configuration errors include mismatch of authentication credentials, invalid packet checksums, invalid packet types, invalid virtual route IDs, TTL errors, packet length errors and invalid (non matching) VRRP versions.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow vrrp [brief|details|error-stats|stats]show vrrp [brief|details|stats] {<1-255>} {(on <DEVICE-NAME>)}show vrrp error-stats {on <DEVICE-NAME>}Parameters• show vrrp [brief|details|stats] {<1-255>} {(on <DEVICE-NAME>)}• show vrrp error-stats {on <DEVICE-NAME>}vrrp Displays VRRP related statistics in brief or in detail depending on the option selectedbrief Displays virtual router information in briefdetails Displays virtual router information in detailstats Displays virtual router statistics<1-255> The following keyword is common to all of the above parameters:• <1-255> – Optional. Displays information for a specified Virtual Router. Specify the router's ID from 1 - 255.on <DEVICE-NAME> The following keyword is recursive and common to the ‘<1-255>’ parameter:• on <DEVICE-NAME> – Optional. Displays specified router information on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.vrrp Displays VRRP related statistics in brief or in detail depending on the option selectederror-stats{on <DEVICE-NAME>}Displays global error statistics• on <DEVICE-NAME> – Optional. Displays global error statistics on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or service plat-form.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1058.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1596.1.74 web-filtershow commandsDisplays Web filtering related information Use this command to view information on Web requests for content and whether the requests were blocked or approved based on URL filter settings defined for the selected controller or service platform. A URL filter is comprised of several filter rules. A whitelist bans all sites except the categories and URL lists defined in the whitelist. The blacklist allows all sites except the categories and URL lists defined in the blacklist.Supported in the following platforms:• Access Points — AP6522, AP6532, AP7161, AP7502, AP7522, AP7532, AP7562, AP8132• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow web-filter [category|category-type|config|filter-level [basic|high|low|medium|medium-high]|statistics {on <DEVICE-NAME>}|status]Parameters• show web-filter [category|category-type|config|filter-level [basic|high|low|medium|medium-high]|statistics {on <DEVICE-NAME>}|status]web-filter Displays an existing and configured Web filter detailscategory Displays Web filter categories. A category is a pre-defined URL list available in the WiNG software.category-type Displays the Web filter category types. This is a pre-configured list of categories and sub-categories in to which commonly accessed URLs have been classified.config Displays all existing Web filters and their configuration detailsfilter-level [basic|high|low|medium|medium-high]Displays category types for the selected filter-level. Each filter level is pre-configured to use a set of category types. You cannot change the categories in the category types used for these pre-configured filter-level setting. Nor can you add, modify, or remove the category types mapped to a filter-level setting.The options are:• basic – Displays all category types configured for the basic filter-level• high – Displays all category types configured for the high filter-level• low – Displays all category types configured for the low filter-level• medium – Displays all category types configured for the medium filter-level• medium-high – Displays all category types configured for the medium-high filter-levelstatistics {on <DEVICE-NAME>}Displays Web filter statistics on a specified device• on <DEVICE-NAME> – Optional. Specifies the device name• <DEVICE-NAME> – Specify the name of the AP, controller, or service platform.Note: Web filtering is a licensed feature, and only when enforced can the system display Web filtering statistics.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1060.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1616.1.75 whatshow commandsDisplays details of a specified search phrase (performs global search)Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow what [contain|is] <WORD> {on <DEVICE-OR-DOMAIN-NAME>}Parameters• show what [contain|is] <WORD> {on <DEVICE-OR-DOMAIN-NAME>}Examplerfs4000-229D58#show what contain default----------------------------------------------------------------------------------------------------------------------------------------------------NO. CATEGORY MATCHED OTHER KEY INFO (1) OTHER KEY INFO (2) OTHER KEY INFO (3) NAME/VALUE NAME/VALUE NAME/VALUE NAME/VALUE---------------------------------------------------------------------------------------------------------------------------------------------------- https-trustpoint type mac rf_domain_name 1 device-cfg default-trustpoint rfs4000 00-23-68-22-9D-58 default __obj_name__ name 2 firewall_policy default default __obj_name__ name https idle_session_timeout 3 management_policy default default True 30 qos_policy name control_vlan beacon_format --More--rfs4000-229D58#contain <WORD> Searches on all the items that contain a specified word• <WORD> – Specify a word to search (for example, MAC address, hostname, etc.).is <WORD> Searches on an exact match• <WORD> – Specify a word to search (for example, MAC address, hostname, etc.).on <DEVICE-OR-DOMAIN-NAME>Optional. Performs global search on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1062.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1626.1.76 wirelessshow commandsDisplays wireless configuration parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow wireless [ap|bridge|client|coverage-hole-incidents|meshpoint|mint|mobility-database|radio|regulatory|rf-domain|sensor-server|unsanctioned|wips|wlan]show wireless ap {configured|detail|load-balancing|on <DEVICE-NAME>}show wireless ap {configured}show wireless ap {detail} {<MAC/HOST-NAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless ap {load-balancing} {client-capability|events|neighbors} {(on <DEVICE-NAME>)}show wireless bridge {candidate-ap|certificate|config|hosts|on|statistics}show wireless bridge {candidate-ap} {<MAC/HOSTNAME> {<1-3>}} {(filter radio-mac <RADIO-MAC>)} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless bridge {certificate} status {on <DEVICE-NAME>}show wireless bridge {config}show wireless bridge {hosts} {on <DEVICE-OR-DOMAIN-NAME>}show wireless bridge {statistics} {rf|traffic} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless client {association-history|detail|filter|include-ipv6|on <DEVICE-OR-DOMAIN-NAME>|statistics|tspec}show wireless client {association-history <MAC>} {on <DEVICE-OR-DOMAIN-NAME>}show wireless client {detail <MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless client {filter [ip|on|state|wlan]}show wireless client {filter} {ip [<IP>|not <IP>]} {on <DEVICE-OR-DOMAIN-NAME>}show wireless client {filter} {on <DEVICE-OR-DOMAIN-NAME>}show wireless client {filter} {state [data-ready|not [data-ready|roaming]|roaming]} {on <DEVICE-OR-DOMAIN-NAME>}show wireless client {filter} {wlan [<WLAN-NAME>|not <WLAN-NAME>]} {on <DEVICE-OR-DOMAIN-NAME>}show wireless client {include-ipv6} {detail|on|filter}show wireless client {include-ipv6} {detail <MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless client {include-ipv6} {filter {ip|ipv6|state|wlan}}show wireless client {statistics} {detail|on|rf|window-data}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1063.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 163show wireless client {statistics} {detail <MAC>|rf|window-data <MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless client {tspec <MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless coverage-hole-incidents [detail|on|summary]show wireless coverage-hole-incidents detail {filter [ap <MAC/HOSTNAME>|client-mac <MAC>]|summary} {(on <DOMAIN-NAME>)}]show wireless meshpoint {config|detail|multicast|neighbor|on|path|proxy|root|security|statistics|tree|usage-mappings}show wireless meshpoint {config} {filter [device <DEVICE-NAME>|rf-domain <DOMAIN-NAME>]}show wireless meshpoint {detail} {<MESHPOINT-NAME>}show wireless meshpoint {on <DEVICE-OR-DOMAIN-NAME>}show wireless meshpoint {multicast|path|proxy|root|security|statistics} [<MESHPOINT-NAME>|detail] {on <DEVICE-OR-DOMAIN-NAME>}show wireless meshpoint neighbor [<MESHPOINT-NAME>|detail|statistics {rf}] {on <DEVICE-OR-DOMAIN-NAME>}show wireless meshpoint {tree} {on <DEVICE-OR-DOMAIN-NAME>}show wireless meshpoint {usage-mappings}show wireless mobility-database {on <DEVICE-NAME>}show wireless mint [client|detail|links|portal]show wireless [client|detail] {on|portal-candidates {<DEVICE-NAME>|filter <RADIO-MAC>}|statistics} (<DEVICE-OR-DOMAIN-NAME>)show wireless mint links {on <DEVICE-OR-DOMAIN-NAME>}show wireless mint portal statistics {on <DEVICE-OR-DOMAIN-NAME>}show wireless radio {detail|on <DEVICE-OR-DOMAIN-NAME>|statistics|tspec|wlan-map}show wireless radio {detail} {<DEVICE-NAME>|filter|on <DEVICE-OR-DOMAIN-NAME>}show wireless radio {detail} {<DEVICE-NAME> {<1-3>|filter|on}}show wireless radio {detail} {filter <RADIO-MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless radio {statistics} {detail|on|rf|windows-data}show wireless radio {statistics} {on <DEVICE-OR-DOMAIN-NAME>|rf {on <DEVICE-OR-DOMAIN-NAME>}}show wireless radio {statistics} {detail|window-data} {<DEVICE-NAME>} {<1-3>|filter <RADIO-MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless radio {tspec} {<DEVICE-NAME>|filter|on <DEVICE-OR-DOMAIN-NAME>|option}show wireless radio {wlan-map} {on <DEVICE-OR-DOMAIN-NAME>}show wireless regulatory [channel-info <WORD>|country-code <WORD>|device-type]show wireless regulatory device-type [ap6521|ap6522|ap6532|ap6562|ap7131|ap7161|ap7181|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap8132|ap8163|ap82xx|ap8432|ap8533|rfs4000] <WORD>show wireless rf-domain statistics {detail} {(on <DEVICE-OR-DOMAIN-NAME>)}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1064.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 164show wireless sensor-server {on <DEVICE-OR-DOMAIN-NAME>}show wireless unsanctioned aps {detail|statistics} {(on <DEVICE-OR-DOMAIN-NAME>)}show wireless wips [client-blacklist|event-history] {on <DEVICE-OR-DOMAIN-NAME>}show wireless wlan {config|detail <WLAN>|on <DEVICE-OR-DOMAIN-NAME>|policy-mappings|statistics|usage-mappings}show wireless wlan {detail <WLAN>|on <DEVICE-OR-DOMAIN-NAME>|policy-mappings|usage-mappings}show wireless {config filter {device <DEVICE-NAME>|rf-domain <DOMAIN-NAME>}}show wireless wlan statistics {<WLAN>|detail|traffic} {on <DEVICE-OR-DOMAIN-NAME>}Parameters• show wireless ap {configured}• show wireless ap {detail} {<MAC/HOST-NAME>} {(on <DEVICE-OR-DOMAIN-NAME>)}• show wireless ap {load-balancing} {client-capability|events|neighbors} {(on <DEVICE-NAME)}wireless Displays wireless configuration parametersap Displays managed access point informationconfigured Optional. Displays configured AP information, such as name, MAC address, profile, RF Domain, and adoption statuswireless Displays wireless configuration parametersap Displays managed access point informationdetail <MAC/HOST-NAME>Optional. Displays detailed information for all APs or a specified AP• <MAC/HOST-NAME> – Optional. Displays information for a specified AP. Specify the AP’s MAC address.on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and common to the ‘detail <MAC/HOST-NAME>’ parameter:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays information on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parametersap Displays managed access point informationload-balancing {client-capability|events|neighbors}Optional. Displays load balancing status. Use additional filters to view specific details.• client-capability – Optional. Displays client band capability• events – Optional. Displays client events• neighbors – Optional. Displays neighboring clientson <DEVICE-NAME> The following keyword is recursive and common to the ‘client-capability’, ‘events’, and ‘neighbors’ parameters:• on <DEVICE-NAME> – Optional. Displays load balancing information, based on the parameters passed, on a specified device• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1065.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 166• show wireless bridge {statistics} {rf|traffic} {(on <DEVICE-OR-DOMAIN-NAME>)}• show wireless client {association-history <MAC>} {on <DEVICE-OR-DOMAIN-NAME>}• show wireless client {detail <MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}• show wireless client {filter ip [<IP>|not <IP>]} {on <DEVICE-OR-DOMAIN-NAME>}on <DEVICE-OR-DOMAIN-NAME>Optional. Executes the command on a specified device or devices within a specified RF Domain• <DEVICE-OR-DOMAIN-NAME> – Optional. Specify the AP, controller, service platform, or Domain name.wireless Displays wireless configuration statisticsbridge statistics Optional. Displays the client-bridge related statisticsrf Optional. Displays the client-bridge related RF statisticsThe output displays the signal, noise, SNR, TX/RX rates, retries, and errors.traffic Optional. Displays the client-bridge related traffic statisticsThe output displays TX/RX bytes, TX/RX packets, TX/RX bits/second, and dropped packets.on <DEVICE-OR-DOMAIN-NAME>Optional. Executes the command on a specified device or devices within a specified RF Domain• on <DEVICE-OR-DOMAIN-NAME> – Optional. Specify the AP, controller, service platform, or Domain name.wireless Displays wireless configuration parametersclient Displays client information based on the parameters passedassociation-history <MAC>Optional. Displays association history for a specified client• <MAC> – Specify the MAC address of the client.on <DEVICE-OR-DOMAIN-NAME>Optional. Displays association history on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.wireless Displays wireless configuration parametersclient Displays client information based on the parameters passeddetail <MAC> Optional. Displays detailed wireless client(s) information• <MAC> – Optional. Displays detailed information for a specified wireless client. Specify the MAC address of the client.on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and common to the ‘detail <MAC>’ parameter:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays detailed information on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.wireless Displays wireless configuration parametersclient Displays client information based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1067.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 167• show wireless client {filter} {state [data-ready|not [data-ready|roaming]|roaming]} {on <DEVICE-OR-DOMAIN-NAME>}• show wireless client {filter} {wlan [<WLAN-NAME>|not <WLAN-NAME>]} {on <DEVICE-OR-DOMAIN-NAME>}• show wireless client {statistics} {detail <MAC>|rf|window-data <MAC>} {(on <DEVICE-OR-DOMAIN-NAME>)}filter IP [<IP>|not <IP>]Optional. Uses IP addresses to filter wireless clients• <IP> – Selects clients with IP address matching the <IP> parameter• not <IP> – Inverts the match selectionon <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘IP’ and ‘not IP’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays selected wireless client information on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parametersclient Displays client information based on the parameters passedfilter state [data-ready|not [data-ready|roaming]|roaming]Optional. Filters clients based on their state• data-ready – Selects wireless clients in the data-ready state• not [data-ready|roaming] – Inverts match selection. Selects wireless clients neither ready nor roaming• Roaming – Selects roaming clientson <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘ready’, ‘not’, and ‘roaming’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays selected client details on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parametersclient Displays client information based on the parameters passedfilter wlan [<WLAN-NAME>|not <WLAN-NAME>]Optional. Filters clients on a specified WLAN• <WLAN-NAME> – Specify the WLAN name.• not <WLAN-NAME> – Inverts the match selectionon <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘WLAN and ‘not’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Filters clients on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parametersclient Displays client information based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1068.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 169• show wireless coverage-hole-incidents {detail} {filter [ap <MAC/HOSTNAME>|client-mac <MAC>]|summary} {(on <DOMAIN-NAME>)}include-ipv6 {filter} Optional. Includes IPv6 address (if known) of wireless clients• filter – Optional. Defines additional filters. Use one of the following options to filter clients: ip, ipv6, state, and wlanBy default the system only displays the IPv4 address of clients. The include-ipv6 parameter includes the known IPv6 address of each client.ip [<IPv4>|not <IPv4>] Optional. Displays wireless client information based on the IPv4 address passed• <IPv4> – Displays information of the client identified by the <IPv4> parameter• not <IPv4> – Inverts the match selectionipv6 [<IPv6>|not <Pv6>]Optional. Displays wireless client information based on the IPv6 address passed• <IPv6> – Displays information of the client identified by the <IPv6> parameter• not <IPv6> – Inverts the match selectionfilter state [data-ready|not [data-ready|roaming]|roaming]Optional. Filters wireless client information based on their state• data-ready – Displays information of wireless clients in the data-ready state• not [data-ready|roaming] – Inverts match selection. Displays information of wireless clients neither ready nor roaming• Roaming – Displays information of roaming clientswlan [<WLAN-NAME>|not <WLAN-NAME>]Optional. Displays wireless client information based on the WLAN name passed• <WLAN-NAME> – Specify the WLAN name.• not <WLAN-NAME> – Inverts match selectionwireless Displays wireless configuration parameters. Use this option to view coverage-hole related incidents encountered by wireless clients and reported to associated access points.coverage-hole-incidents Displays coverage-hole related statisticsdetail filters[ap <MAC/HOSTNAME>|client-mac <MAC>]Optional. Displays detailed coverage-hole related statistics• filters – Optional. Displays detailed coverage-hole related statistics on a per access point or wireless-client basis• ap <MAC/HOSTNAME> – Displays detailed coverage-hole related statistics fora specified access point• <MAC/HOSTNAME> – Specify the access point’s device name or MAC ad-dress.• client-mac <MAC> – Displays detailed coverage-hole related statistics encoun-tered by a specified wireless client• <MAC> – Specify the wireless client’s MAC addressNote: If the command is executed without any parameters being included, the system displays all coverage-hole related statistics.summary Optional. Displays a summary of coverage-hole related statisticson <DOMAIN-NAME> This parameter is recursive and is common to the ‘detail’ and ‘summary’ keywords:• on <DOMAIN-NAME> – Optional. Displays detailed or summary coverage-hole related statistics on a specified RF Domain• <DOMAIN-NAME> – Specify the domain name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1070.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 170• show wireless meshpoint {config} {filter [device <DEVICE-NAME>|rf-domain <DOMAIN-NAME>]}• show wireless meshpoint {detail} {<MESHPOINT-NAME>}• show wireless meshpoint {multicast|path|proxy|root|security|statistics} [<MESHPOINT-NAME>|detail] {on <DEVICE-OR-DOMAIN-NAME>}wireless Displays wireless configuration parameters. Use this option to view detailed statistics on each Mesh-capable client available within controller’s adopted access point’s radio coverage area.A mesh network is where one where each node is able to communicate with other nodes and maintain more then one path to the other mesh nodes within the mesh network. A mesh network provides robust, reliable and redundant connectivity to all the members of the mesh network. When one member of the mesh network becomes unavailable, the other mesh nodes are still able to communicate with one another either directly or indirectly through intermediate nodes.meshpoint Displays meshpoint related informationconfig Optional. Displays all meshpoint configurationfilters[device <DEVICE-NAME>|rf-domain <DOMAIN-NAME>]Optional. Provides additional filter options, such as device name and RF Domain name.• device <DEVICE-NAME> – Displays meshpoints applied to a specified device• <DEVICE-NAME> – Specify the device name.• rf-domain – <DOMAIN-NAME> – Displays meshpoints applied to a specified RF Domain• <DOMAIN-NAME> – Specify the domain name.wireless Displays wireless configuration parametersmeshpoint Displays meshpoint related information. Use this option to view detailed statistics on each Mesh-capable client available within controller’s adopted access point’s radio coverage area.A mesh network is where one where each node is able to communicate with other nodes and maintain more then one path to the other mesh nodes within the mesh network. A mesh network provides robust, reliable and redundant connectivity to all the members of the mesh network. When one member of the mesh network becomes unavailable, the other mesh nodes are still able to communicate with one another either directly or indirectly through intermediate nodes.detail<MESHPOINT-NAME>Optional. Displays detailed information for all meshpoints or a specified meshpoint• <MESHPOINT-NAME> – Optional. Displays detailed information for a specified meshpoint. Specify the meshpoint name.wireless Displays wireless configuration parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1071.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 171• show wireless meshpoint {neighbor} [<MESHPOINT-NAME>|detail|statistics {rf}] {on <DEVICE-OR-DOMAIN-NAME>}meshpoint Displays meshpoint related information. Use this option to view detailed statistics on each Mesh-capable client available within controller’s adopted access point’s radio coverage area.A mesh network is where one where each node is able to communicate with other nodes and maintain more then one path to the other mesh nodes within the mesh network. A mesh network provides robust, reliable and redundant connectivity to all the members of the mesh network. When one member of the mesh network becomes unavailable, the other mesh nodes are still able to communicate with one another either directly or indirectly through intermediate nodes.multicast Optional. Displays meshpoint multicast informationpath Optional. Displays meshpoint path informationproxy Optional. Displays meshpoint proxy informationroot Optional. Displays meshpoint root informationsecurity Optional. Displays meshpoint security informationstatistics Optional. Displays meshpoint statistics[<MESHPOINT-NAME>|detail]The following keywords are common to all of the above parameters:• <MESHPOINT-NAME> – Displays meshpoint related information for a specified meshpoint. Specify the meshpoint name.• detail – Displays detailed multicast information for all meshpointson <DEVICE-OR-DOMAIN-NAME>The following keyword is common to all of the above parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays detailed multicast information on a specified device or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parametersmeshpoint Displays meshpoint related information. Use this option to view detailed statistics on each Mesh-capable client available within controller’s adopted access point’s radio coverage area.A mesh network is where one where each node is able to communicate with other nodes and maintain more then one path to the other mesh nodes within the mesh network. A mesh network provides robust, reliable and redundant connectivity to all the members of the mesh network. When one member of the mesh network becomes unavailable, the other mesh nodes are still able to communicate with one another either directly or indirectly through intermediate nodes.neighbor Optional. Displays meshpoint neighbor information, based on the parameters passed[<MESHPOINT-NAME>|detail|statistics {rf}]Select one of the following parameter to view neighbor related information• <MESHPOINT-NAME> – Displays detailed multicast information for a specified meshpoint. Specify the meshpoint name.• detail – Displays detailed multicast information for all meshpoints• statistics – Displays neighbors related statistics• rf – Optional. Displays RF related statistics for neighbors](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1072.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 172• show wireless meshpoint {tree} {on <DEVICE-OR-DOMAIN-NAME>}• show wireless meshpoint {usage-mappings|on <DEVICE-OR-DOMAIN-NAME>}• show wireless mobility-database {on <DEVICE-NAME>}• show wireless mint [client|detail] {portal-candidates {<DEVICE-NAME>|filter <RADIO-MAC>}|statistics} (on <DEVICE-OR-DOMAIN-NAME>)on <DEVICE-OR-DOMAIN-NAME>The following keyword is common to all of the above parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays meshpoint neighbor information, based on the parameters passed, on a specified device or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parametersmeshpoint Displays meshpoint related informationNote: The show > wireless > meshpoint > tree command can be executed only from a wireless controller.tree Optional. Displays meshpoint network treeon <DEVICE-OR-DOMAIN-NAME>Optional. Displays meshpoint network tree on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Optional. Specify the name of AP, wireless controller, service platform, or RF Domainwireless Displays wireless configuration parametersmeshpoint Displays meshpoint related informationusage-mappings Optional. Lists all devices and profiles using the meshpointon <DEVICE-OR-DOMAIN-NAME>Optional. Displays meshpoint applied to a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Optional. Specify the name of AP, wireless controller,service platform, or RF Domainwireless Displays wireless configuration parametersmobility-database Displays controller-assisted mobility databaseon <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and common to the ‘filter <RADIO-MAC>’ parameter:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays detailed radio operation status for all or a specified radio on a specified device or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless mint [client|detail]Displays radio MiNT-mesh related statistics• client – Displays MiNT-mesh client related information. Use the ‘client’ option to view detailed statistics on each Mesh capable client available within the selected access point’s radio coverage area.• detail – Displays detailed MiNT-mesh related informationportal-candidates Displays detailed information about portal candidates for a MiNT-mesh. Mesh points connected to an external network and forwarding traffic in and out are Mesh portals. Mesh points must find paths to a portal to access the Internet. When multiple portals exist, the mesh point must select one.Use the additional filter option to view specific portal candidate details.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1073.png)
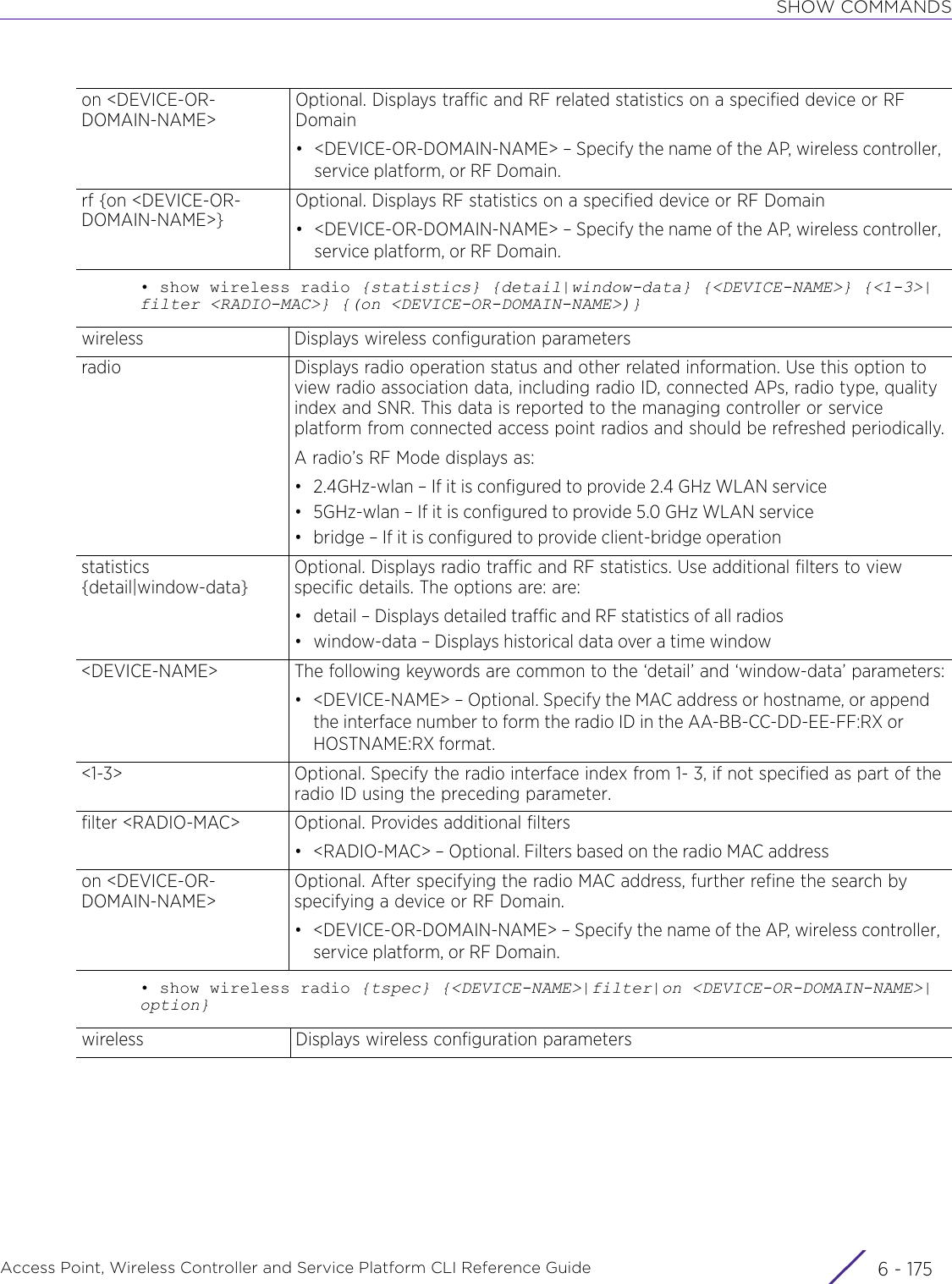
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 176• show wireless regulatory [channel-info <WORD>|county-code <WORD>]• show wireless regulatory device-type [ap6521|ap6522|ap6532|ap6562|ap7131|ap7161|ap7181|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap8132|ap8163|ap82xx|ap8432|ap8533|rfs4000] <WORD>• show wireless rf-domain statistics {detail} {(on <DEVICE-OR-DOMAIN-NAME>)}radio Displays radio operation status and other related information. Use this option to view radio association data, including radio ID, connected APs, radio type, quality index and Signal to Noise Ratio (SNR). This data is reported to the managing controller or service platform from connected access point radios and should be refreshed periodically.A radio’s RF Mode displays as:• 2.4GHz-wlan – If it is configured to provide 2.4 GHz WLAN service• 5GHz-wlan – If it is configured to provide 5.0 GHz WLAN service• bridge – If it is configured to provide client-bridge operationtspec Optional.Displays TSPEC information on a radio<DEVICE-NAME> Optional. Specify the MAC address or hostname, or append the interface number to form the radio ID in the AA-BB-CC-DD-EE-FF:RX or HOSTNAME:RX format.filter Optional. Provides additional filters• <RADIO-MAC> – Optional. Filters based on the radio MAC addresson <DEVICE-OR-DOMAIN-NAME>Optional. After specifying the radio MAC address, further refine the search by specifying a device or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.wireless Displays wireless configuration parametersregulatory Displays wireless regulatory informationchannel-info <WORD> Displays channel information• <WORD> – Specify the channel number.country-code <WORD> Displays country code to country name information• <WORD> – Specify the two letter ISO-3166 country code.wireless Displays wireless configuration parametersregulatory Displays wireless regulatory informationdevice-type <DEVICE-TYPE> <WORD>Displays wireless regulatory information based on the device type selected. Select the device type. The options are:AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP8132, AP8163, AP8232, AP8432, AP8533 and RFS4000.After specifying the device type, specify the country code.• <WORD> – Specify the two letter ISO-3166 country code.wireless Displays wireless configuration parametersrf-domain statistics Displays RF Domain statisticsdetails Optional. Displays detailed RF Domain statistics](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1077.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 177• show wireless sensor-server {on <DEVICE-OR-DOMAIN-NAME>}• show wireless unsanctioned aps {detailed|statistics} {(on <DEVICE-OR-DOMAIN-NAME>)}• show wireless wips [client-blacklist|event-history] {on <DEVICE-OR-DOMAIN-NAME>}• show wlan {detail <WLAN>|on <DEVICE-OR-DOMAIN-NAME>|policy-mappings|usage-mappings}on <DEVICE-OR-DOMAIN-NAME>The following keyword is recursive and common to the ‘detail’ parameter:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays RF Domain statistics on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parameterssensor- server {on <DEVICE-OR-DOMAIN-NAME>}Displays AirDefense sensor server configuration details• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays AirDefense sensor server configuration on a specified device or RF Domainwireless Displays wireless configuration parametersunsanctioned aps Displays unauthorized APs. Use additional filters to view specific details.detailed Optional. Displays detailed unauthorized APs informationstatistics Optional. Displays channel statisticson <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘detailed’ and ‘statistics’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Specify the name of the AP, wireless controller, service platform, or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parameterswips [client-blacklist|event-history]Displays the WIPS details• client-blacklist – Displays blacklisted clients• event-history – Displays event historyon <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘client-blacklist’ and ‘event-history’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays the WIPS details on a specified device or RF Domain.• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless control-ler, service platform, or RF Domain.wireless Displays wireless configuration parameterswlan Displays WLAN related information based on the parameters passeddetail <WLAN> Optional. Displays WLAN configuration• <WLAN> – Specify the WLAN name.on <DEVICE-OR-DOMAIN-NAME>Optional. Displays WLAN configuration on a specified device or RF Domain• <DEVICE-OR-DOMAIN-NAME> – Specify the name of the AP, wireless controller, service platform, or RF Domain.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1078.png)

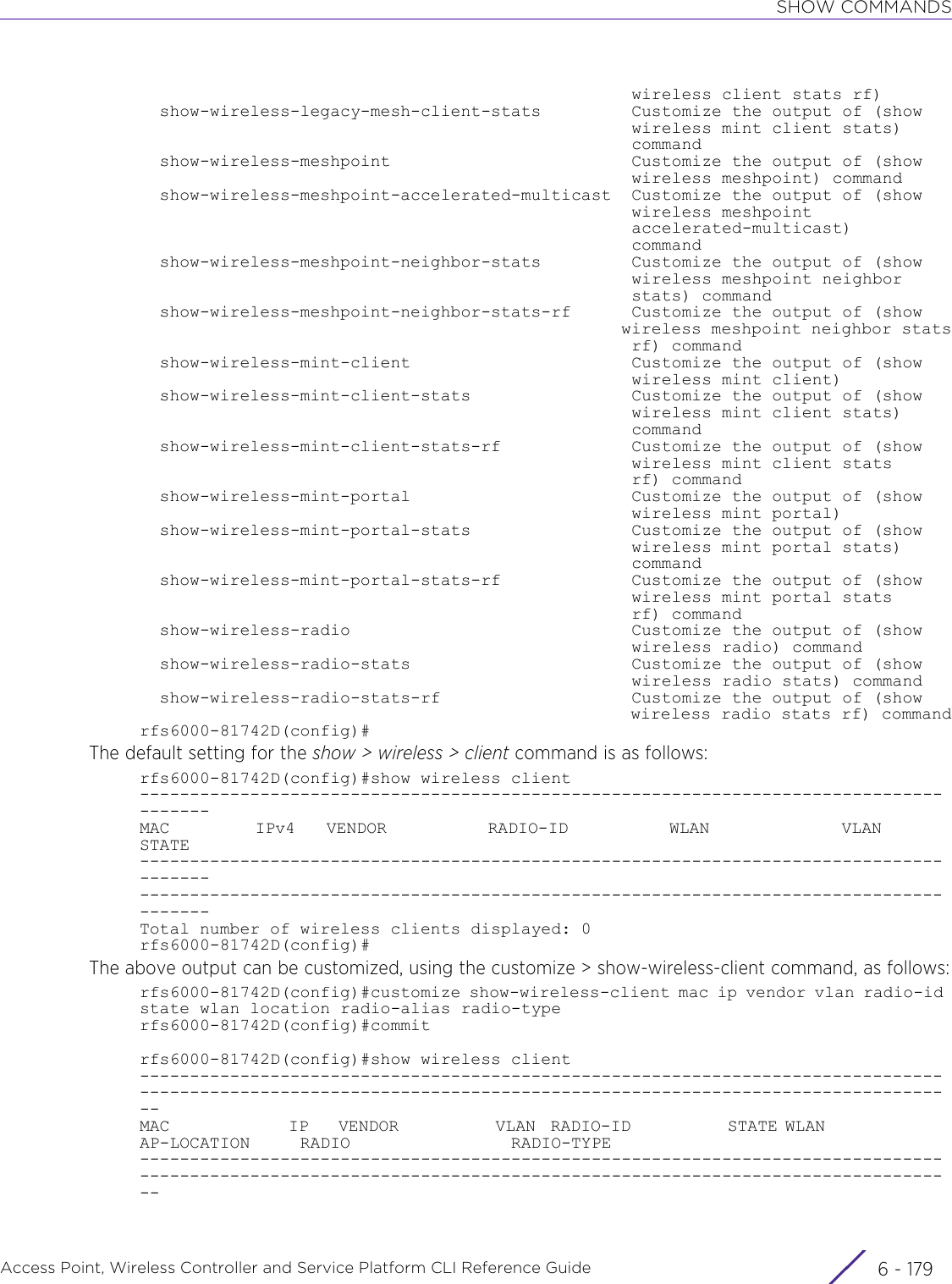
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 181rfs6000-81742D#show wire ap detailAP: 84-24-8D-84-A2-24 AP Name : ap7562-84A224 Location : Bangalore RF-Domain : TechPubs Type : ap7562 Model : AP-7562-67040-US IP : 192.168.13.29 IPv6 : :: Num of radios : 2 Num of clients : 0 Last Smart-RF time : not done Stats update mode : auto Stats interval : 30 Radio Modes : radio-1 : wlan radio-2 : wlan Country-code : not-set Site-Survivable : True Last error : in [India] not supported on hardware model AP-7562-67040-US Fault Detected : False Power management information for ap7562:--More--rfs6000-81742D#nx9500-6C8809#show wireless ap load-balancing on rfs6000-81742D Column Name Reference: Ap-Ld : Load of the AP as reported by it. Avg-Ld : Average AP load in the AP's neighborhood. 2.4g-Ld : 2.4GHz band load in the AP's neighborhood. 5g-Ld : 5GHz band load in the AP's neighborhood. Ap-2.4g-Ch-Ld : Load in the AP's 2.4GHz channel in its neighborhood. Avg-2.4g-Ch-Ld : Average load of a 2.4GHz channel in AP's neighborhood. Ap-5g-Ch-Ld : Load in the AP's 5GHz channel in its neighborhood. Avg-5g-Ch-Ld : Average load of a 5GHz channel in AP's neighborhood. Allow-2.4g-Req : AP responds to client requests on 2.4ghz radio Allow-5g-Req : AP responds to client requests on 5ghz radio-------------------------------------------------------------------------------------------------------------------------------- No. Ap-Name Ap- Avg- 2.4g- 5g- Band Cfgd- Ap- Ap- Avg- Avg- Allow Allow Load Load Load Load Ratio Band 2.4g- 5g- 2.4g- 5g- 2.4g- 5g- Ratio Ch-Ld Ch-Ld Ch-Ld Ch-Ld Req Req-------------------------------------------------------------------------------------------------------------------------------- 1 rfs6000-81742D 0% 0% 0% 0% 0:0 0:1 182% 240% 0% 70% yes yes--------------------------------------------------------------------------------------------------------------------------------nx9500-6C8809#nx9600-7F5124#show wireless meshpoint tree on PTP-APIn progress .......1:PTP-Radio2 [7 MPs(2 roots, 5 bound)]|-ap7562-84A484-ROOT1| |-ap7562-84A2CC-VMM| |-ap7532-80C28C-NR| |-ap7532-82CCA4-NR| |-ap7562-84A22C-NR2| |-ap7532-160114|-ap7562-84A280-ROOT2Total number of meshes displayed: 1nx9600-7F5124#](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1082.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 182ap6532-000001#show wireless meshpoint multicast detailMulticast Paths @00-23-68-00-00-01 (ap6532-000001), mesh1 [00-23-68-2E-64-B2]-------------------------------------------------------------------------------- Group-Addr Subscriber Name Subscriber MPID Timeout (mSecs)--------------------------------------------------------------------------------01-00-5E-01-01-01 ap6532-000001 00-23-68-2E-64-B2 N/A--------------------------------------------------------------------------------Total number of meshpoint displayed: 1ap6532-000001#ap6532-000001#show wireless meshpoint neighbor detailNeighbors @00-23-68-00-00-01 (ap6532-000001), mesh1 [00-23-68-2E-64-B2]-----------------------------------------------------------------------------------------------------------------------------------------------------------Neighbor Name Neighbor MPID.IFID Root Name Root MPID RMet Hops Type Interface Auth-State Resourced Rank LQ% LMet Age----------------------------------------------------------------------------------------------------------------------------------------------------------- 5C-0E-8B-21-76-22.5C-0E-8B-21-74-40 00-23-68-2E-97-60 115 1 Fixed 00-23-68-00-00-01:R2 Enabled Yes 0 97 87 20 00-23-68-30-F7-82.00-23-68-30-F8-F0 00-23-68-2E-97-60 99 1 Fixed 00-23-68-00-00-01:R2 Init Yes 0 97 86 30 00-23-68-30-F7-82.00-23-68-30-F7-82 00-23-68-2E-97-60 99 1 Fixed 00-23-68-00-00-01:R1 Enabled Yes 0 96 94 0 5C-0E-8B-21-76-22.5C-0E-8B-21-76-22 00-23-68-2E-97-60 115 1 Fixed 00-23-68-00-00-01:R1 Enabled Yes 0 96 93 30 00-23-68-2E-AB-50.00-23-68-2E-AB-50 00-23-68-2E-AB-50 0 0 Root 00-23-68-00-00-01:R2 Enabled Yes 7 96 87 40 00-23-68-2E-97-60.00-23-68-2E-97-60 00-23-68-2E-97-60 0 0 Root 00-23-68-00-00-01:R2 Enabled Yes 8 94 90 10-----------------------------------------------------------------------------------------------------------------------------------------------------------Total number of meshpoint displayed: 1ap6532-000001#ap6532-000001#show wireless meshpoint proxy detailProxies @00-23-68-00-00-01 (ap6532-000001), mesh1 [00-23-68-2E-64-B2]-------------------------------------------------------------------------------- Destination Addr Owner Name Owner MPID Persist VLAN Age--------------------------------------------------------------------------------00-23-68-00-00-01 ap6532-000001 00-23-68-2E-64-B2 Permanent 101 18065431000-1E-E5-A6-66-E2 ap6532-000001 00-23-68-2E-64-B2 Untimed 103 231920--------------------------------------------------------------------------------Total number of meshpoint displayed: 1ap6532-000001#ap6532-000001#show wireless meshpoint multicast mesh1Multicast Paths @00-23-68-00-00-01 (ap6532-000001), mesh1 [00-23-68-2E-64-B2]-------------------------------------------------------------------------------- Group-Addr Subscriber Name Subscriber MPID Timeout (mSecs)--------------------------------------------------------------------------------01-00-5E-01-01-01 ap6532-000001 00-23-68-2E-64-B2 -1--------------------------------------------------------------------------------Total number of meshpoint displayed: 1ap6532-000001#](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1083.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 183ap6532-000001#show wireless meshpoint path detailPaths @00-23-68-00-00-01 (ap6532-000001), mesh1 [00-23-68-2E-64-B2]-------------------------------------------------------------------------------------------------------------------------------------------------Destination Name Destination Addr Next Hop Name Next Hop IFID State Hops Type Binding Metric Timeout Path-Timeout Sequence MiNT ID ------------------------------------------------------------------------------------------------------------------------------------------------- 00-23-68-2E-AB-50 00-23-68-2E-AB-50 Valid 1 Root Bound 89 8730 0 23847 68.31.19.58 00-23-68-2E-97-60 00-23-68-2E-97-60 Valid 1 Root Unbound 92 5200 0 3481 68.31.1A.80 -------------------------------------------------------------------------------------------------------------------------------------------------ap6532-000001#rfs4000-22A24E#show wireless client-----------------------------------------------------------------------------------------------------------------Report start on RF-Domain: qs1MAC IP VENDOR RADIO-ID WLAN VLAN STATE -----------------------------------------------------------------------------------------------------------------Report end on RF-Domain: qs1----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Report start on RF-Domain: Store-1MAC IP VENDOR RADIO-ID WLAN VLAN STATE -----------------------------------------------------------------------------------------------------------------00-01-02-03-04-10 2.3.4.16 3Com Corp 00-01-02-03-04-00:R1 sim-wlan-1 1 Data-Ready 00-01-02-03-05-10 2.3.5.16 3Com Corp 00-01-02-03-04-00:R2 sim-wlan-1 1 Data-Ready Report end on RF-Domain: Store-1----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Report start on RF-Domain: default database not availableReport end on RF-Domain: default-----------------------------------------------------------------------------------------------------------------Total number of clients displayed: 2rfs4000-22A24E#The following examples show client-bridge related information:NX9500(config)#show adoption status---------------------------------------------------------------------------------------DEVICE-NAME VERSION CFG-STAT MSGS ADOPTED-BY LAST-ADOPTION UPTIME---------------------------------------------------------------------------------------ap6562-167598 5.9.1.0-017DB configured No NX9500 0 days 00:01:59 0 days 00:03:22---------------------------------------------------------------------------------------Total number of devices displayed: 1NX9500(config)#](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1084.png)

![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1856.1.77 wwanshow commandsDisplays wireless WAN statusSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow wwan [configuration|status] {on <DEVICE-OR-DOMAIN-NAME>}Parameters• show wwan [configuration|status] {on <DEVICE-OR-DOMAIN-NAME>}Examplerfs4000-229D58(config-device-00-23-68-22-9D-58)#show wwan configuration>>> WWAN Configuration:+-------------------------------------------| Access Port Name : isp.cingular| User Name : testuser| Cryptomap : map1+-------------------------------------------rfs4000-229D58(config-device-00-23-68-22-9D-58)#rfs4000-229D58(config-device-00-23-68-22-9D-58)#show wwan status>>> WWAN Status:+-------------------------------------------| State : ACTIVE| DNS1 : 209.183.54.151| DNS2 : 209.183.54.151+-------------------------------------------rfs4000-229D58(config-device-00-23-68-22-9D-58)#wwan Displays wireless WAN configuration and status detailsconfiguration Displays wireless WAN configuration informationstatus Displays wireless WAN status informationon <DEVICE-OR-DOMAIN-NAME>The following keyword is common to the ‘configuration’ and ‘status’ parameters:• on <DEVICE-OR-DOMAIN-NAME> – Optional. Displays configuration or status details on a specified device or RF Domain<DEVICE-OR-DOMAIN-NAME> – Specify the AP, wireless controller, service platform, or RF Domain name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1086.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 1866.1.78 virtual-machineshow commandsDisplays the virtual-machine (VM) configuration, logs, and statisticsSupported in the following platforms:• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxshow virtual-machine [configuration|debugging|export|statistics]show virtual-machine [configuration|statistics] {<VM-NAME>|team-urc|team-rls|team-vowlan} {(on <DEVICE-NAME>)}show virtual-machine debugging {level|on}show virtual-machine debugging {level [debug|error|info|warning]} {on <DEVICE-NAME>}show virtual-machine export <VM-NAME> {on <DEVICE-NAME>}show virtual-machine [configuration|statistics] {<VM-NAME>|adsp|team-cmt}Parameters• show virtual-machine [configuration|statistics] {<VM-NAME>|team-urc|team-rls|team-vowlan} {(on <DEVICE-NAME>)}• show virtual-machine [configuration|statistics] {<VM-NAME>|adsp|team-cmt}{(on <DEVICE-NAME>)}virtual-machine Displays the following VM-related information: configuration or statistics configuration Displays detailed VM configurationstatistics Displays VM statistics[<VM-NAME>|team-urc|team-rls|team-vowlan]The following keywords are common to the ‘configuration’ and ‘statistics’ parameters:• <VM-NAME> – Optional. Displays VM configuration or statistics for the virtual machine identified by the <VM-NAME> keyword. Specify the VM name.• team-urc – Optional. Displays TEAM-URC (IP-PBX) VM configuration/statistics• team-rls – Optional. Displays TEAM-RLS (Radio Link Server) VM configuration/statistics• team-vowlan – Optional. Displays TEAM-VoWLAN (Voice over WLAN) VM configuration/statisticson <DEVICE-NAME> Optional. Specifies the name of the device on which the command is executed• <DEVICE-NAME> – Specify the name of the service platform.virtual-machine Displays the following VM-related information: configuration or statistics configuration Displays detailed VM configurationstatistics Displays VM statistics](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1087.png)
![SHOW COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 6 - 187• show virtual-machine debugging {level[debug|error|info|warning]} {on <DEVICE-NAME>}• show virtual-machine export <VM-NAME> {on <DEVICE-NAME>}[<VM-NAME>|adsp|team-cmt]The following keywords are common to the ‘configuration’ and ‘statistics’ parameters:• <VM-NAME> – Optional. Displays VM configuration or statistics for the virtual machine identified by the <VM-NAME> keyword. Specify the VM name.• adsp – Optional. Displays Air-Defense Services Platform (ADSP) VM configuration/statistics• team-cmt – Optional. Displays TEAM-CMT VM configuration/statisticsThese keywords are specific to the NX9500 and NX9510 service platforms.on <DEVICE-NAME> Optional. Specifies the name of the device on which the command is executed• <DEVICE-NAME> – Specify the name of the service platform.virtual-machine Displays the following VM-related information: configuration or statistics debugging Displays VM logslevel [debug|error|info|warning]Optional. Displays VM logs based on the level selected. The available options are:• debug – Displays VM logs of level debug and above• error – Displays VM logs of level error• info – Displays VM logs of level Info and above• warning – Displays logs of level warning and aboveThe NX9500 and NX9510 series service platforms will display ADSP and TEAM-CMT VM debugging logs.on <DEVICE-NAME> Optional. Specifies the name of the device on which the command is executed• <DEVICE-NAME> – Specify the name of the service platform.virtual-machine Displays the following VM-related information: configuration or statistics export Displays VM configuration export related information<VM-NAME> Displays VM configuration export related information for the virtual machine identified by the <VM-NAME> keyword. Specify the VM name.The NX9500 and NX9510 series service platforms will display ADSP and TEAM-CMT VM configuration export informationon <DEVICE-NAME> Optional. Specifies the name of the device on which the command is executed• <DEVICE-NAME> – Specify the name of the service platform.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1088.png)
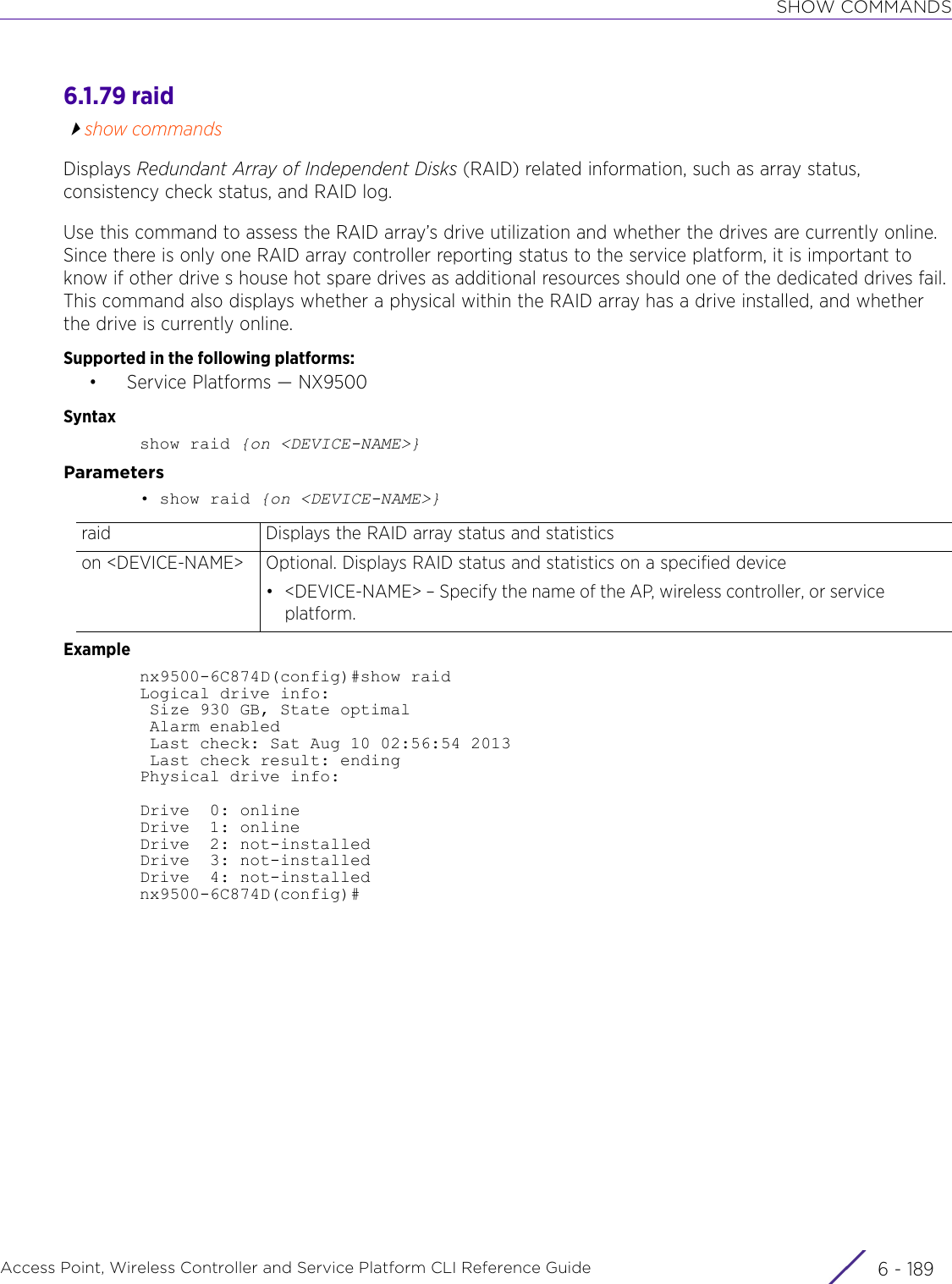


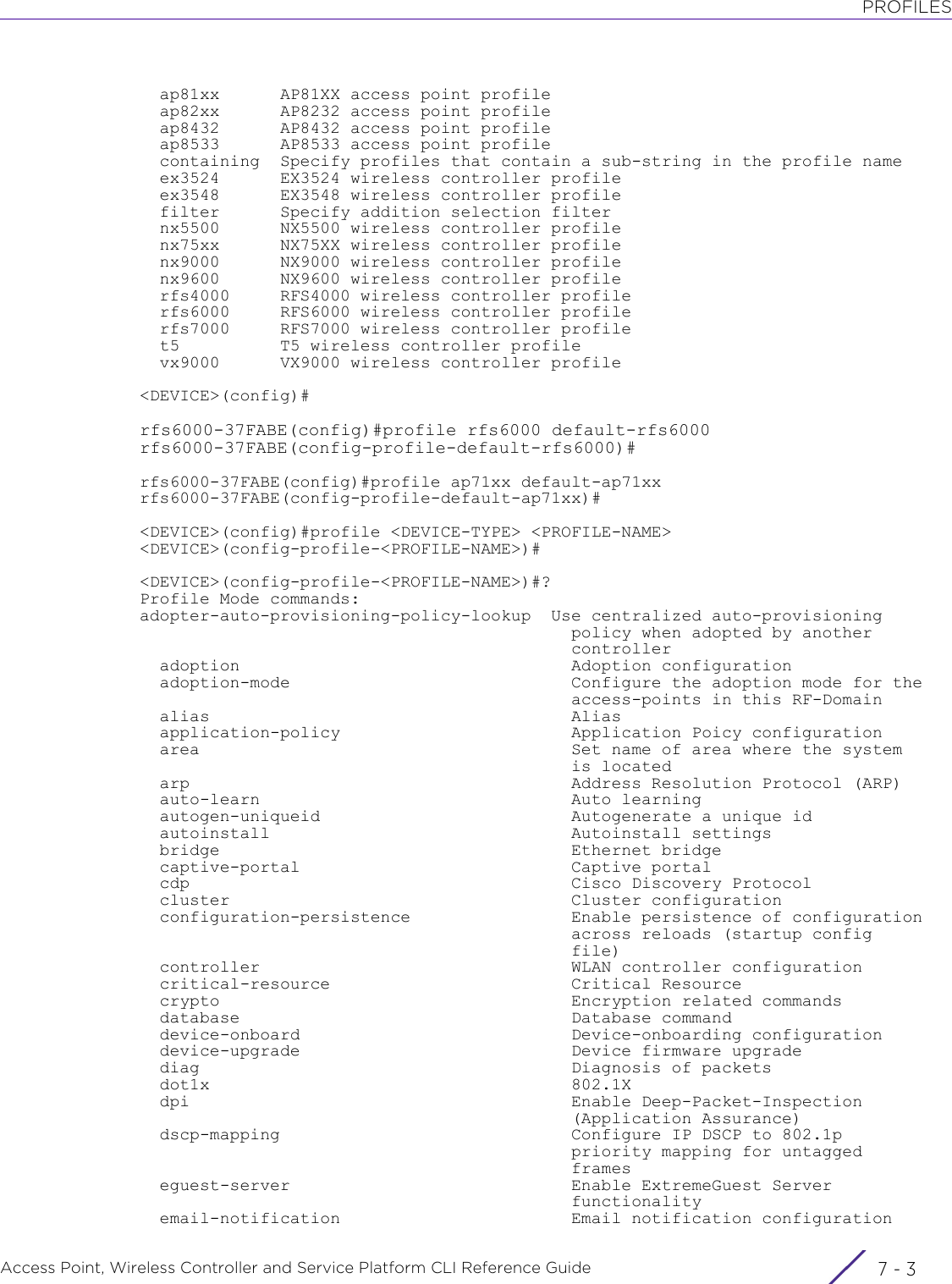
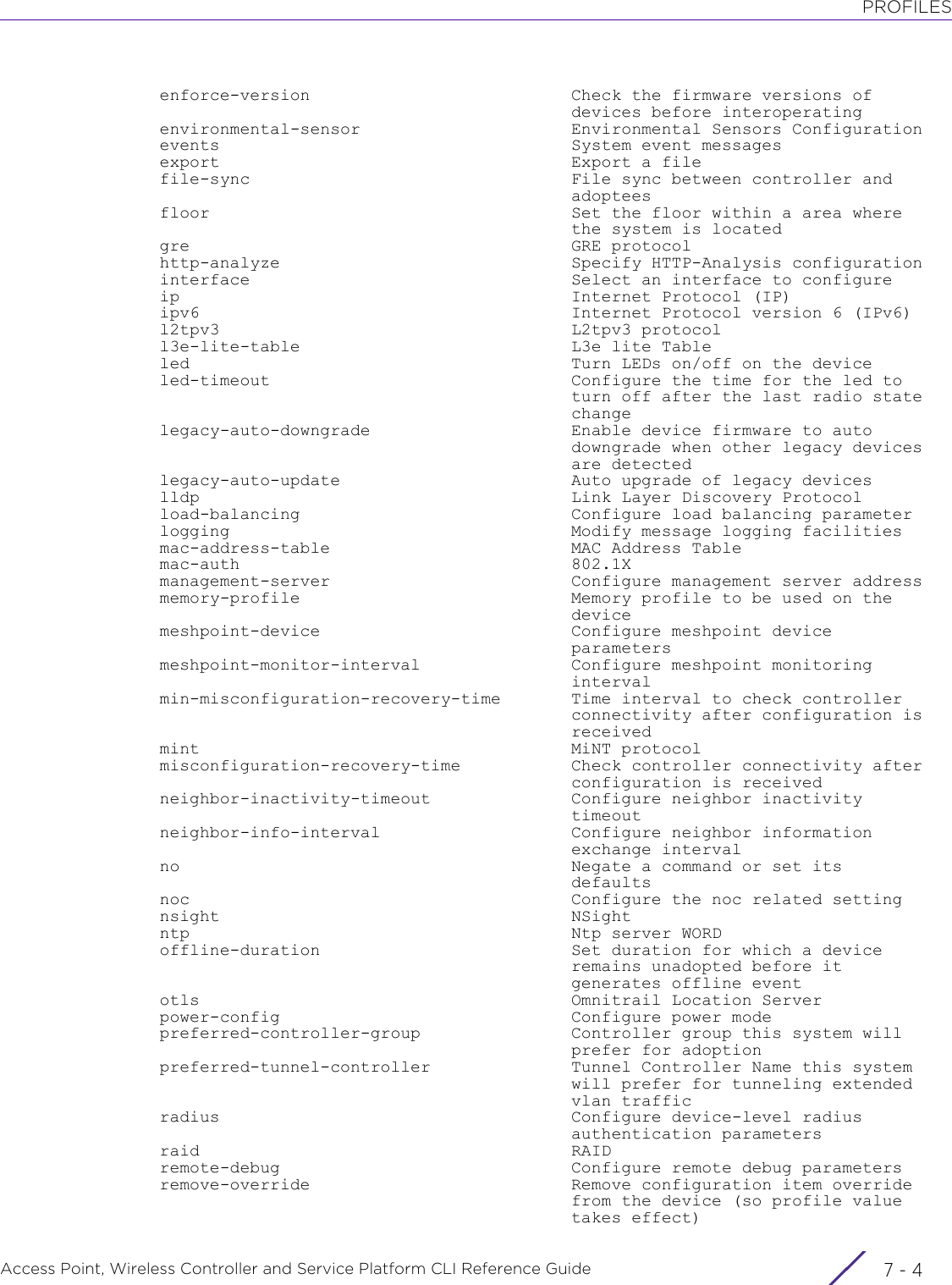

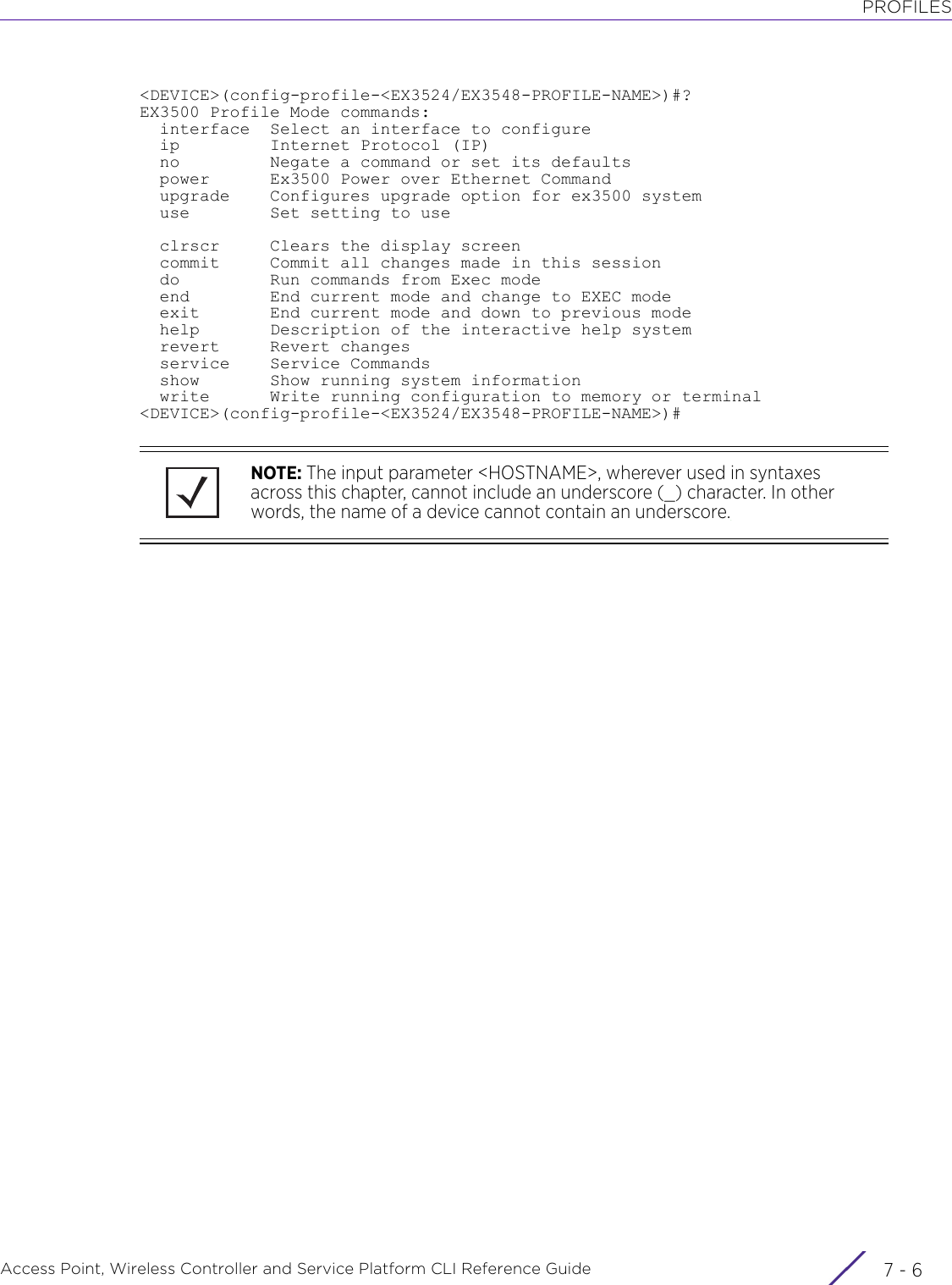
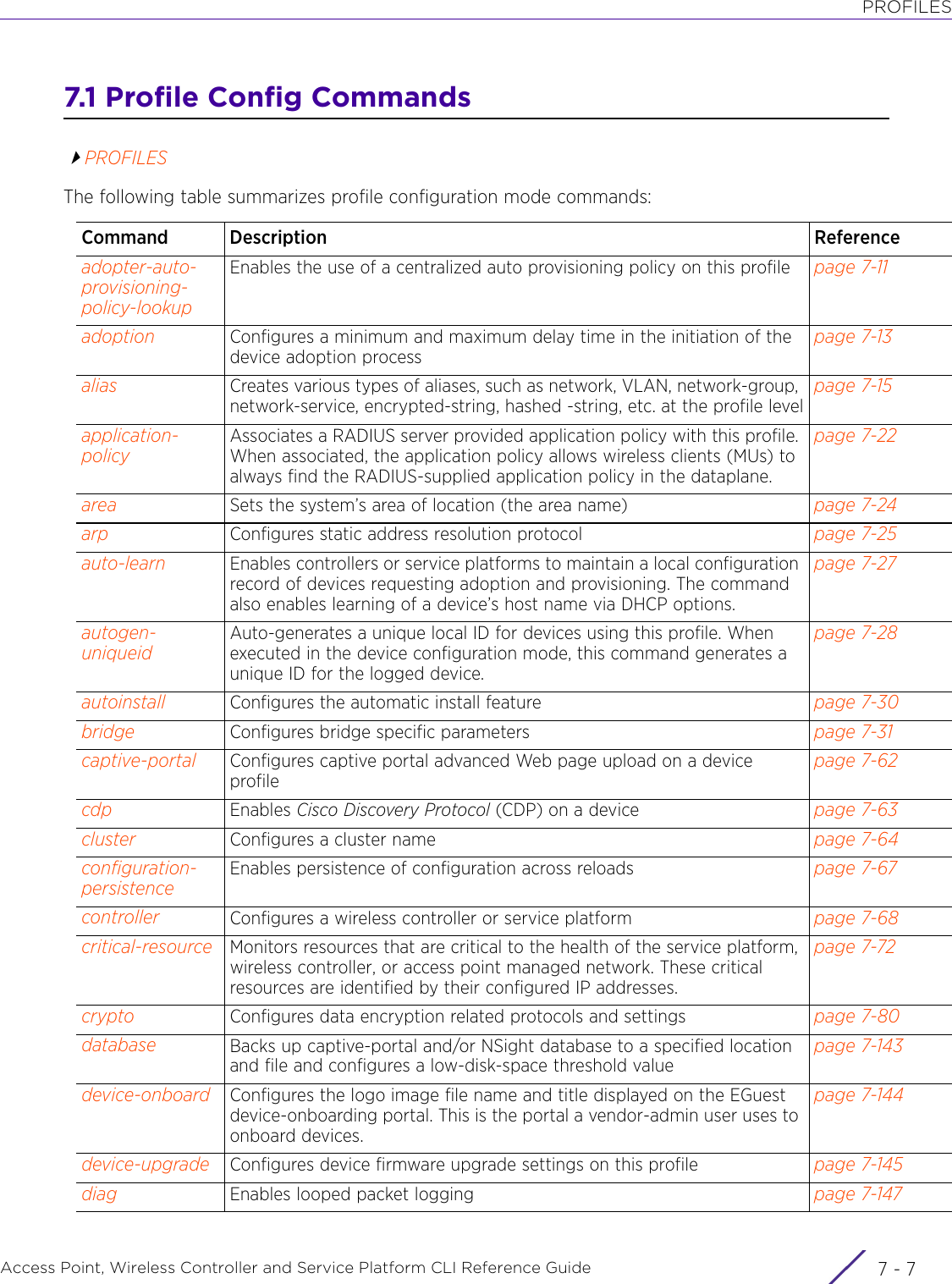
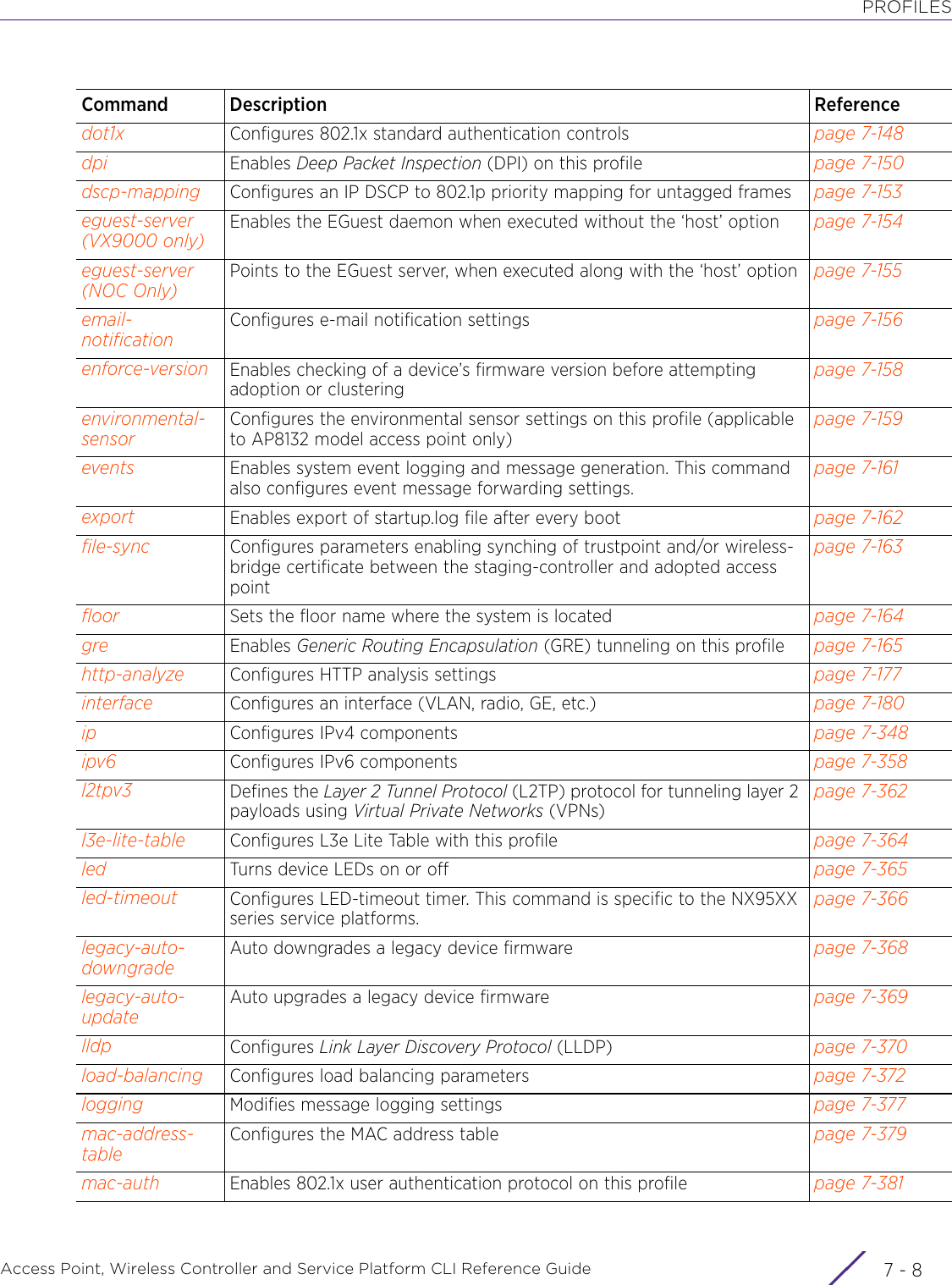
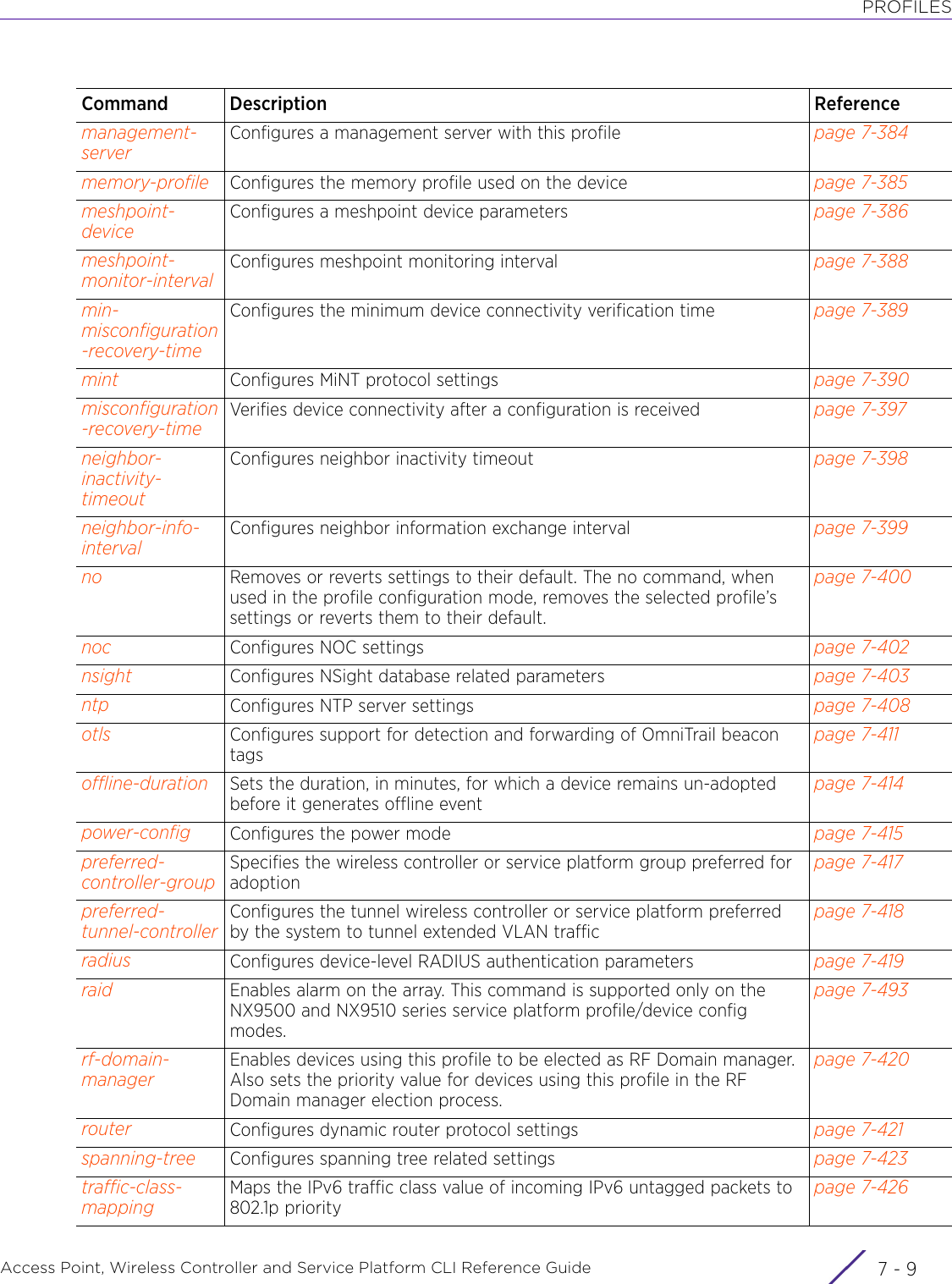
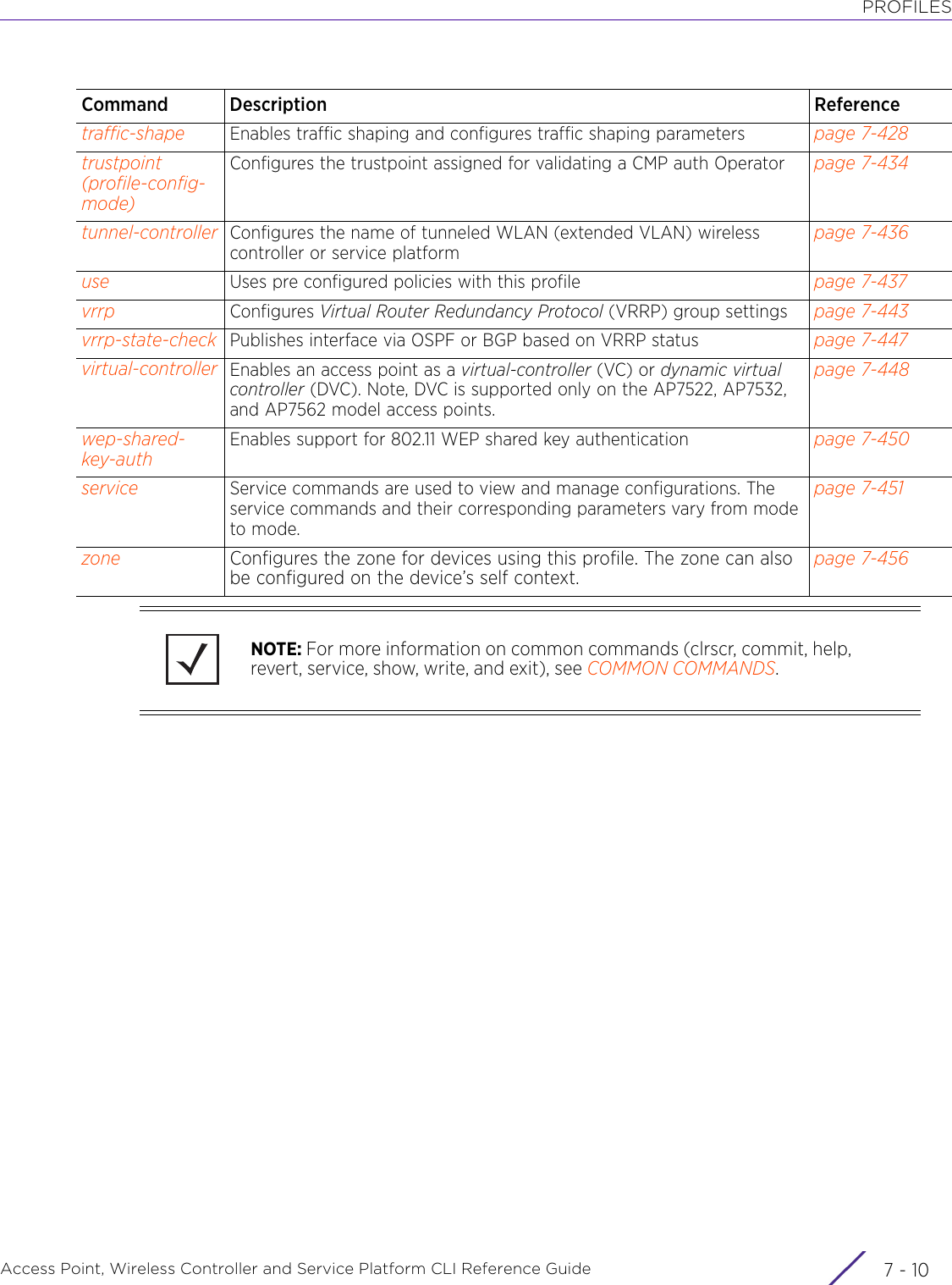
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 157.1.3 aliasProfile Config CommandsConfigures network, VLAN, and service aliases. The aliases defined on this profile applies to all devices using this profile. Aliases can be also defined at the device level.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxalias [address-range|encrypted-string|hashed-string|host|network|network-group|network-service|number|string|vlan]alias address-range <ADDRESS-RANGE-ALIAS-NAME> <STARTING-IP> to <ENDING-IP>alias encrypted-string <ENCRYPTED-STRING-ALIAS-NAME> [0|2] <LINE>alias hashed-string <HASHED-STRING-ALIAS-NAME> <LINE>alias host <HOST-ALIAS-NAME> <HOST-IP>alias network <NETWORK-ALIAS-NAME> <NETWORK-ADDRESS/MASK>alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range|host|network]alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}|host <HOST-IP> {<HOST-IP>}|network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}]alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport|ssh|telnet|tftp|www)}alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}alias number <NUMBER-ALIAS-NAME> <0-4294967295>alias string <STRING-ALIAS-NAME> <LINE>alias vlan <VLAN-ALIAS-NAME> <1-4094>Parameters• alias address-range <ADDRESS-RANGE-ALIAS-NAME> <STARTING-IP> to <ENDING-IP>NOTE: You can apply overrides to aliases at the device level. Overrides applied at the device level take precedence. For more information on aliases, see alias.address-range <ADDRESS-RANGE-ALIAS-NAME>Creates a new address-range alias for this profile. Or associates an existing address-range alias with this profile. An address-range alias maps a name to a range of IP addresses. Use this option to create unique address-range aliases for different deployment scenarios. Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1105.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 16• alias encrypted-string <ENCRYPTED-STRING-ALIAS-NAME> [0|2] <LINE>For example, if an ACL defines a pool of network addresses as 192.168.10.10 through 192.168.10.100 for an entire network, and a remote location’s network range is 172.16.13.20 through 172.16.13.110, the remote location’s ACL can be overridden using an alias. At the remote location, the ACL works with the 172.16.13.20-110 address range. A new ACL need not be created specifically for the remote deployment location.• <ADDRESS-RANGE-ALIAS-NAME> – Specify the address range alias name.Note: Alias name should begin with ‘$’.<STARTING-IP> to <ENDING-IP>Associates a range of IP addresses with this address range alias• <STARTING-IP> – Specify the first IP address in the range.• to <ENDING-IP> – Specify the last IP address in the range.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.encrypted-string <ENCRYPTED-STRING-ALIAS-NAME>Creates an alias for an encrypted string. Use this alias for string configuration values that are encrypted when "password-encryption" is enabled. For example, in the management-policy, use it to define the SNMP community string. For more information, see snmp-server.• <ENCRYPTED-STRING-ALIAS-NAME> – Specify the encrypted-string alias name.Alias name should begin with ‘$’.[0|2] <LINE> Configures the value associated with the alias name specified in the previous step• [0|2] <LINE> – Configures the alias valueNote, if password-encryption is enabled, in the show > running-config output, this clear text is displayed as an encrypted string, as shown below:nx9500-6C8809(config)#show running-config!...............................alias encrypted-string $enString 2 fABMK2is7UToNiZE3MQXbgAAAAxB0ZIysdqsEJwr6AH/Da//!--More--nx9500-6C8809In the above output, the ‘2’ displayed before the encrypted-string alias value indicates that the displayed text is encrypted and not a clear text.However, if password-encryption is disabled the clear text is displayed as is:nx9500-6C8809(config)#show running-config!...............................!alias encrypted-string $enString 0 test11223344!--More--nx9500-6C8809For more information on enabling password-encryption, see password-encryption.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1106.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 18• alias network-group <NETWORK-GROUP-ALIAS-NAME> [address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}|host <HOST-IP> {<HOST-IP>}|network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}]• alias network-service <NETWORK-SERVICE-ALIAS-NAME> proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp] {(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}<NETWORK-ADDRESS/MASK>Associates a single network with this network alias• <NETWORK-ADDRESS/MASK> – Specify the network’s address and mask.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.network <NETWORK-GROUP-ALIAS-NAME>Creates a new network-group alias for this profile. Or associates an existing network-group alias with this profile.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name.Alias name should begin with ‘$’.The network-group aliases are used in ACLs, to define the network-specific components. ACLs using aliases can be used across sites by re-defining the network-group alias elements at the device or profile level.After specifying the name, specify the following: a range of IP addresses, host addresses, or a range of network addresses.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.address-range <STARTING-IP> to <ENDING-IP> {<STARTING-IP> to <ENDING-IP>}Associates a range of IP addresses with this network-group alias• <STARTING-IP> – Specify the first IP address in the range.• to <ENDING-IP> – Specify the last IP address in the range.• <STARTING-IP> to <ENDING-IP> – Optional. Specifies more than one range of IPaddresses. A maximum of eight (8) IP address ranges can be configured.host <HOST-IP> {<HOST-IP>}Associates a single or multiple hosts with this network-group alias• <HOST-IP> – Specify the hosts’ IP address.• <HOST-IP> – Optional. Specifies more than one host. A maximum of eight (8) hostscan be configured.network <NETWORK-ADDRESS/MASK> {<NETWORK-ADDRESS/MASK>}Associates a single or multiple networks with this network-group alias• <NETWORK-ADDRESS/MASK> – Specify the network’s address and mask.• <NETWORK-ADDRESS/MASK> – Optional. Specifies more than one network. Amaximum of eight (8) networks can be configured.alias network-service <NETWORK-SERVICE-ALIAS-NAME>Creates a new network-service alias for this profile. Or associates an existing network-service alias with this profile. A network service alias is a set of configurations that consist of protocol and port mappings. Both source and destination ports are configurable. For each protocol, up to 2 source port ranges and up to 2 destination port ranges can be configured. A maximum of 4 protocol entries can be configured per network service alias.• <NETWORK-SERVICE-ALIAS-NAME> – Specify a network-service alias name.Alias name should begin with ‘$’.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1108.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 19The network-service aliases are used in ACLs, to define the service-specific components. ACLs using aliases can be used across sites by re-defining the network-service alias elements at the device or profile level.Note: Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.proto [<0-254>|<WORD>|eigrp|gre|igmp|igp|ospf|vrrp]Use one of the following options to associate an Internet protocol with this network-service alias:• <0-254> – Identifies the protocol by its number. Specify the protocol number from 0 - 254. This is the number by which the protocol is identified in the Protocol field of the IPv4 header and the Next Header field of IPv6 header. For example, the User Datagram Protocol’s (UDP) designated number is 17.• <WORD> – Identifies the protocol by its name. Specify the protocol name.• eigrp – Selects Enhanced Interior Gateway Routing Protocol (EIGRP). The protocol number 88.•gre – Selects Generic Routing Encapsulation (GRE). The protocol number is 47.• igmp – Selects Internet Group Management Protocol (IGMP). The protocol number is 2.•igp – Selects Interior Gateway Protocol (IGP). The protocol number is 9.•ospf – Selects Open Shortest Path First (OSPF). The protocol number is 89.• vrrp – Selects Virtual Router Redundancy Protocol (VRRP). The protocol number is 112.{(<1-65535>|<WORD>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|proto|sip|smtp|sourceport [<1-65535>|<WORD>]|ssh|telnet|tftp|www)}After specifying the protocol, you may configure a destination port for this service. These keywords are recursive and you can configure multiple protocols and associate multiple destination and source ports.• <1-65535> – Optional. Configures a destination port number from 1 - 65535• <WORD> – Optional. Identifies the destination port by the service name provided. For example, the secure shell (SSH) service uses TCP port 22.• bgp – Optional. Configures the default Border Gateway Protocol (BGP) services port (179)• dns – Optional. Configures the default Domain Name System (DNS) services port (53)• ftp – Optional. Configures the default File Transfer Protocol (FTP) control services port (21)• ldap – Optional. Configures the default Lightweight Directory Access Protocol (LDAP) services port (389)• ftp-data – Optional. Configures the default FTP data services port (20)• gopher – Optional. Configures the default gopher services port (70)• https – Optional. Configures the default HTTPS services port (443)• nntp – Optional. Configures the default Newsgroup (NNTP) services port (119)• ntp – Optional. Configures the default Network Time Protocol (NTP) services port (123)• proto – Optional. Use this option to select another Internet protocol in addition to the one selected in the previous step.• sip – Optional. Configures the default Session Initiation Protocol (SIP) services port (5060).Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1109.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 20• alias number <NUMBER-ALIAS-NAME> <0-4294967295>• alias string <STRING-ALIAS-NAME> <LINE>• alias vlan <VLAN-ALIAS-NAME> <1-4094>• sourceport [<1-65535>|<WORD>] – Optional. After specifying the destination port, you may specify a single or range of source ports.• <1-65535> – Specify the source port from 1 - 65535.• <WORD> – Specify the source port range, for example 1-10.• ssh – Optional. Configures the default SSH services port (22)• telnet – Optional. Configures the default Telnet services port (23)• tftp – Optional. Configures the default Trivial File Transfer Protocol (TFTP) services port (69)• www – Optional. Configures the default HTTP services port (80)alias number <NUMBER-ALIAS-NAME> <0-4294967295>Creates a number alias identified by the <NUMBER-ALIAS-NAME> keyword. Number aliases map a name to a numeric value. For example, ‘alias number $NUMBER 100’• The number alias name is: $NUMBER• The value assigned is: 100The value referenced by alias $NUMBER, wherever used, is 100.• <NUMBER-ALIAS-NAME> – Specify the number alias name.• <0-4294967295> – Specify the number, from 0 - 4294967295, assigned to thenumber alias created.Alias name should begin with ‘$’.alias string <STRING-ALIAS-NAME>Creates a new string alias for this profile. Or associates an existing string alias with this profile. String aliases map a name to an arbitrary string value. Use this option to create unique string aliases for different deployment scenarios. For example, if the main domain at a remote location is called loc1.domain.com and at another deployment location it is called loc2.domain.com, the alias can be overridden at the remote location to suit the local (but remote) requirement. At one remote location, the alias functions with the loc1.domain.com domain and at the other with the loc2.domain.com domain.• <VLAN-ALIAS-NAME> – Specify the string alias name.• <LINE> – Specify the string value.Alias name should begin with ‘$’.Aliases defined at any given level can be overridden at the next lower levels. For example, a global alias can be redefined on a selected set of RF Domains, profiles, or devices. Overrides applied at the device level take precedence.alias vlan <VLAN-ALIAS-NAME>Creates a new VLAN alias for this profile. Or associates an existing VLAN alias with this profile. A VLAN alias maps a name to a VLAN ID. A VLAN alias is a configuration for optimal VLAN re-use and management for local and remote deployments. Use this option to create unique VLANs aliases for different deployment scenarios. For example, if a VLAN ID is set as 10 for the central network, and the VLAN is set as 26 at a remote location, the VLAN can be overridden at the remote location using an alias. Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1110.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 257.1.6 arpProfile Config CommandsAdds a static Address Resolution Protocol (ARP) IP address in the ARP cacheThe ARP protocol maps an IP address to a hardware MAC address recognized on the network. ARP provides protocol rules for making this correlation and providing address conversion in both directions.When an incoming packet destined for a host arrives, ARP finds a physical host or MAC address that matches the IP address. ARP looks in its ARP cache and, if it finds the address, provides it so the packet can be converted to the right packet length, formatted, and sent to its destination. If no entry is found for the IP address, ARP broadcasts a request packet in a special format on the LAN to locate a device that recognizes the IP address. A device that recognizes the IP address as its own returns a reply indicating it. ARP updates the ARP cache for future reference and then sends the packet to the MAC address that replied.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxarp [<IP>|timeout]arp <IP> <MAC> arpa [<L3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1|serial <1-4> <1-1> <1-1>] {dhcp-server|router}arp timeout <15-86400>Parameters• arp <IP> <MAC> arpa [<L3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1|serial <1-4> <1-1> <1-1>] {dhcp-server|router}arp <IP> Adds a static ARP IPv4 address in the ARP cache• <IP> – Specify the static IP address.<MAC> Specify the MAC address associated with the IP and the Switch Virtual Interface (SVI).arpa Sets ARP encapsulation type to ARPA<L3-INTERFACE-NAME>Configures static ARP entry for a specified router interface• <L3-INTERFACE-NAME> – Specify the router interface name.pppoe1 Configures static ARP entry for PPP over Ethernet interfacevlan <1-4094> Configures static ARP entry for a VLAN interface• <1-4094> – Specify a SVI VLAN ID from 1 - 4094.wwan1 Configures static ARP entry for Wireless WAN interface{dhcp-server|router} The following keywords are common to all off the above interface types:• dhcp-server – Optional. Sets ARP entries for a DHCP server• router – Optional. Sets ARP entries for a router](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1115.png)
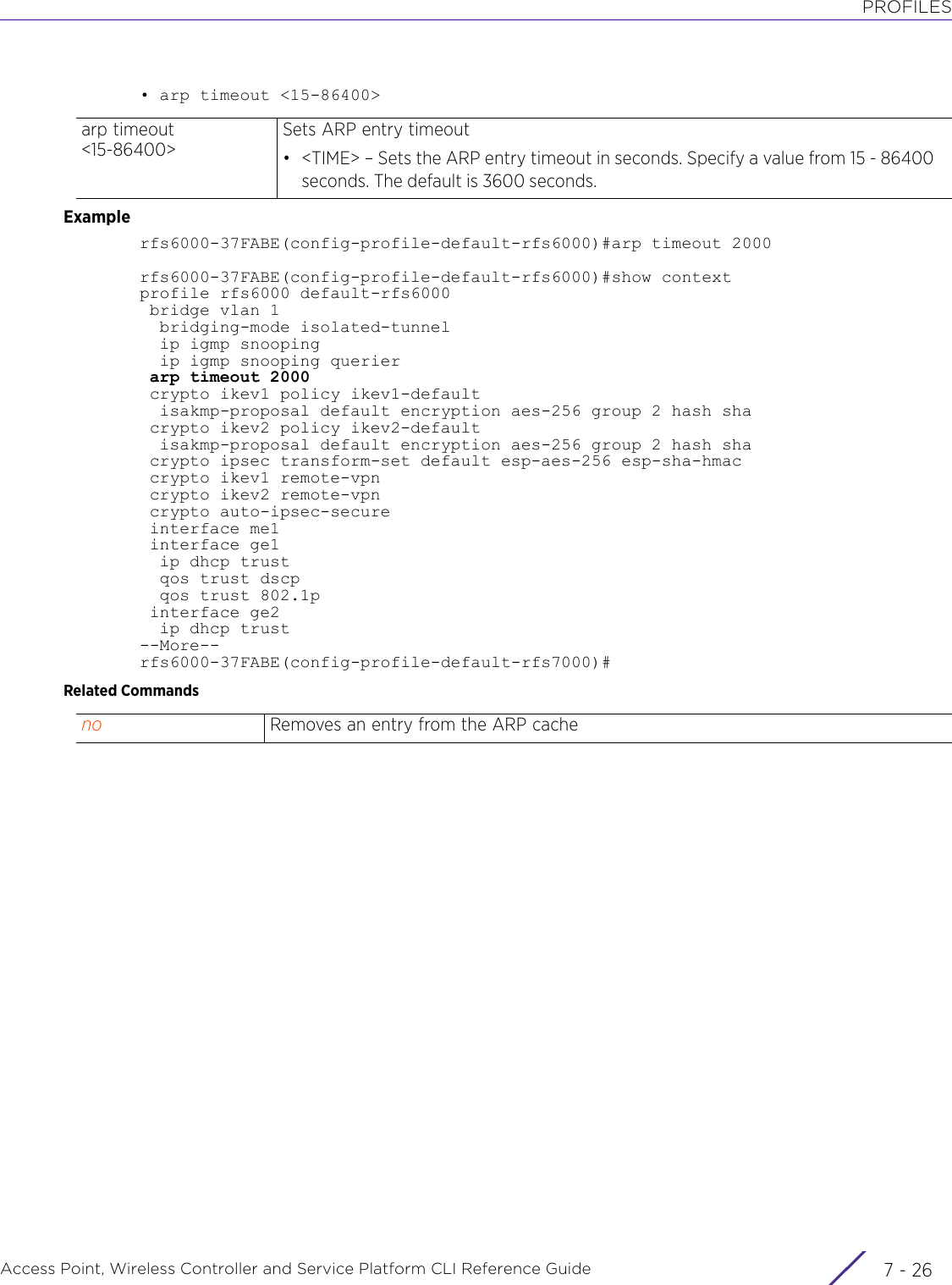
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 277.1.7 auto-learnProfile Config CommandsEnables controllers or service platforms to maintain a local configuration record of devices requesting adoption and provisioning. The command also enables learning of a device’s host name via DHCP options.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauto-learn [host-name-via-dhcp <WORD>|staging-config]Parameters• auto-learn [host-name-via-dhcp <WORD>|staging-config]Examplenx9500-6C8809(config-profile-test)#auto-learn staging-confignx9500-6C8809(config-profile-test)#show context include-factory | include auto-learn auto-learn staging-config no auto-learn host-name-via-dhcpnx9500-6C8809(config-profile-test)#Related Commandsauto-learn [host-name-via-dhcp <WORD>|staging-config]Enables auto-learning of:• host-name-via-dhcp – A device’s host name via DHCP option.• <WORD> – Provide the optional template with substitution token. For example,'outdoor-$DHCP[1:3]-ap', where the $DHCP token references DHCP Option value re-ceived by the adopting device. The $DHCP token should be present. This option is dis-abled by default.• staging-config – The network configuration of devices requesting adoption. Thisoption is enabled by default. For dependent access points that are pre-staged priorto deployment, it is recommended that the auto-learn-staging-config parameter re-mains enabled so that hostnames, VLAN and IP addressing configuration can bemaintained upon initial adoption. However, if dependent access points are to be cen-trally managed and configured, it is recommended that the auto-learn-staging-configparameter be disabled.no Disables automatic recognition of devices’ hostname and devices pending adoption](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1117.png)

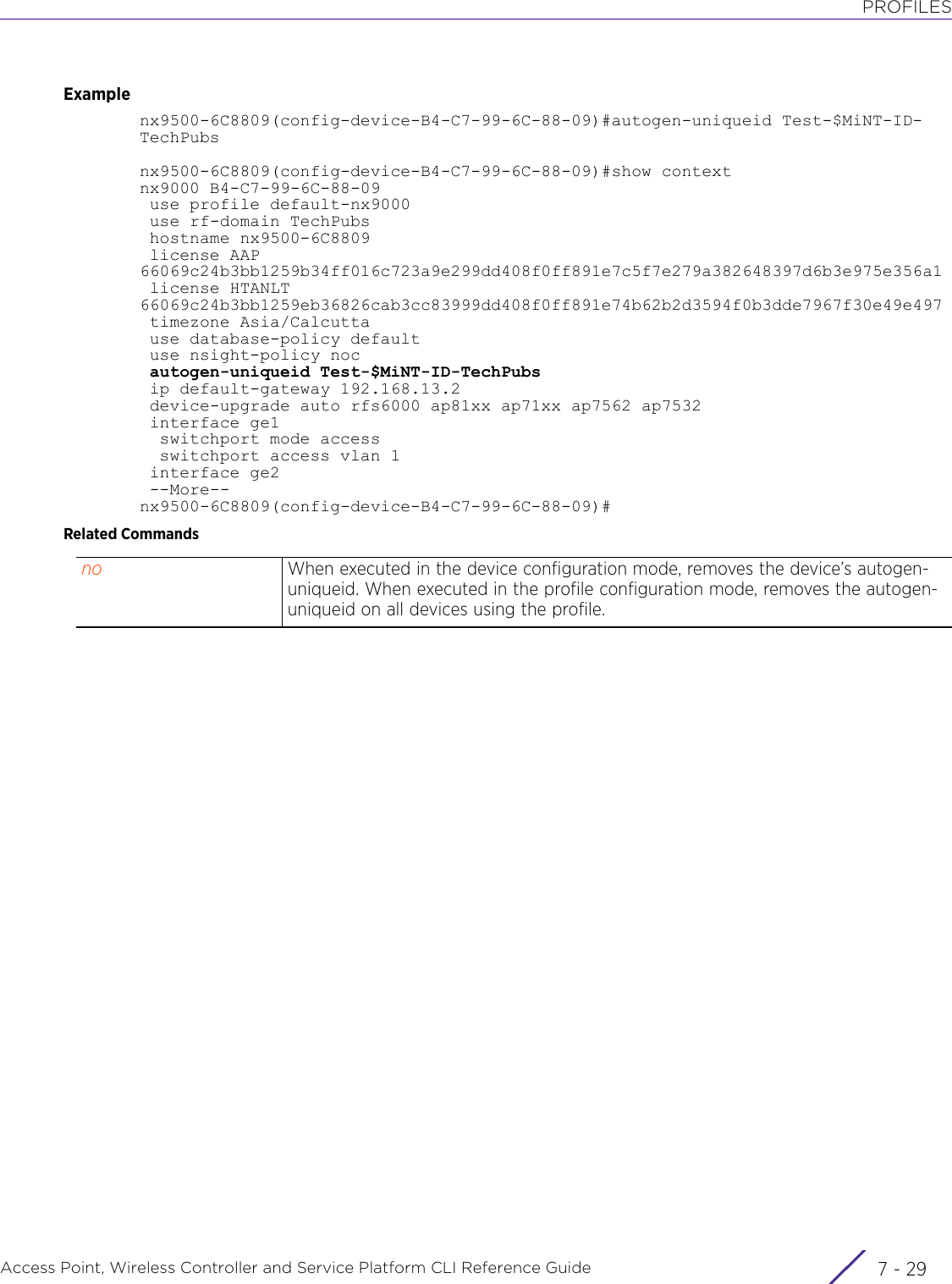
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 307.1.9 autoinstallProfile Config CommandsAutomatically installs firmware image and startup configuration parameters on to the selected device.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxautoinstall [configuration|firmware|start-interval <WORD>]Parameters• autoinstall [configuration|firmware|start-interval <WORD>]Examplerfs6000-37FABE(config-profile-default-rfs6000)#autoinstall configurationrfs6000-37FABE(config-profile-default-rfs6000)#autoinstall firmwarerfs7000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 bridging-mode isolated-tunnel ip igmp snooping ip igmp snooping querier arp timeout 2000 autoinstall configuration autoinstall firmware crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac crypto ikev1 remote-vpn crypto ikev2 remote-vpn crypto auto-ipsec-secure interface me1 interface ge1 ip dhcp trust--More--rfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsconfiguration Autoinstalls startup configuration. Setup parameters are automatically configured on devices using this profile. This option is disabled by default.firmware Autoinstalls firmware image. Firmware images are automatically installed on devices using this profile. This option is disabled by default.start-interval<WORD>Configures the interval between system boot and start of autoinstall process (this is the time, from system boot, after which autoinstall should start)• <WORD> – Specify the interval in minutes. The default is 10 minutes.Note: Zero (0) implies firmware or startup configuration installation can start any time.no Disables the auto install settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1120.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 33Syntaxbridge [nat|vlan]bridge nat source list <IP-ACCESS-LIST-NAME> precedence <1-500> interface [<LAYER3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1] [(address|interface|overload|pool <NAT-POOL-NAME>)]bridge vlan [<1-4094>|<VLAN-ALIAS-NAME>]Parameters• bridge nat source list <IP-ACCESS-LIST-NAME> precedence <1-500> interface [<LAYER3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1] [(address|interface|overload|pool <NAT-POOL-NAME>)]• bridge vlan [<1-4094>|<VLAN-ALIAS-NAME>]Usage GuidelinesCreating customized filter schemes for bridged networks limits the amount of unnecessary traffic processed and distributed by the bridging equipment.If a bridge does not hear Bridge Protocol Data Units (BPDUs) from the root bridge within the specified interval, defined in the max-age (seconds) parameter, assume the network has changed and recomputed the spanning-tree topology.nat Configures bridge NAT parameterssource Configures NAT source addresseslist <IP-ACCESS-LIST-NAME>precedence <1-500>Associates an access control list (ACL) with this bridge NAT policy. The ACL specifies the IP address permit/deny rules applicable to this bridge NAT policy.• <IP-ACCESS-LIST-NAME> – Specify access list name.• precedence <1-500> – Specifies a precedence value for this bridge NAT policy.interface[<LAYER3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1]Selects one of the following as the primary interface (between the source and destination points):• <LAYER3-INTERFACE-NAME> – A router interface. Specify interface name.• pppoe1 – A PPP over Ethernet interface.• vlan <1-4094> – A VLAN interface. Specify the VLAN interface index from 1 - 4094.• wwan1 – A Wireless WAN interface.[(address|interface|overload|pool <NAT-POOL-NAME>)]The following keywords are recursive and common to all interface types:• address – Configures the interface IP address used for NAT• interface – Configures the failover interface (default setting)• overload – Enables use of one global address for multiple local addresses (terminates command)• pool <NAT-POOLNAME> – Configures the NAT pool used with this bridge NAT policy. Specify the NAT pool name. For more information on configuring a NAT pool, see nat-pool-config-instance.vlan <1-4094> Configures the numerical identifier for the Bridge VLAN when it was initially created.• <1-4094> – Specify a VLAN index from 1 - 4094.vlan <VLAN-ALIAS-NAME>Configures the VLAN alias (should be existing and configured) identifying the bridge VLAN• <VLAN-ALIAS-NAME> – Specify a VLAN alias name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1123.png)
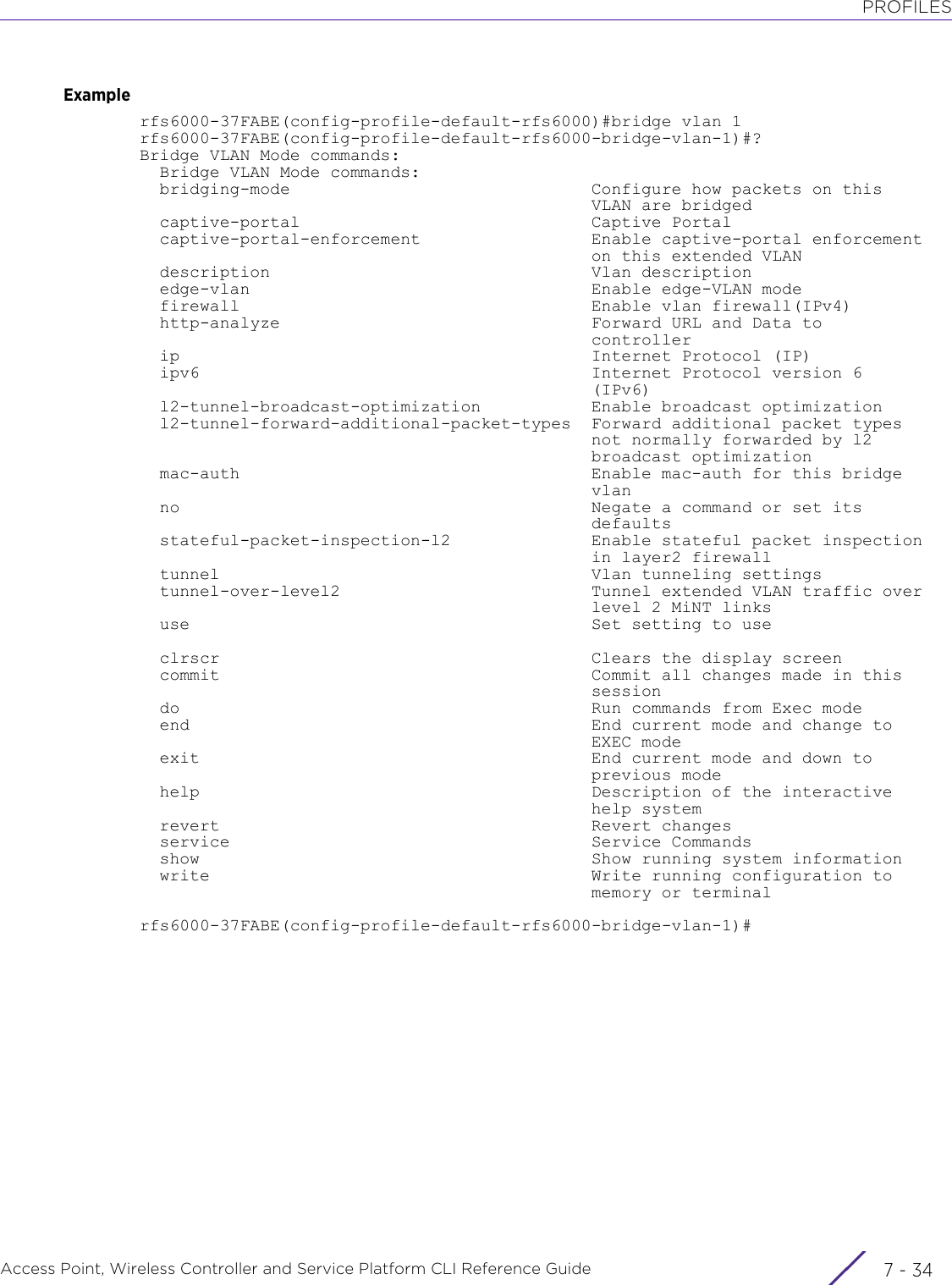
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 367.1.10.2.1 bridging-modebridge-vlan-mode commandsConfigures how packets are bridged on the selected VLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxbridging-mode [auto|isolated-tunnel|local|tunnel]Parameters• bridging-mode [auto|isolated-tunnel|local|tunnel]Usage GuidelinesACLs can only be used with tunnel or isolated-tunnel modes. They do not work with the local and automatic modes.bridging-mode Configures the VLAN bridging modeauto Automatically selects the bridging mode to match the WLAN, VLAN and bridging mode configurations. When selected, the controller or access point determines the best bridging mode for the VLAN. (default setting)isolated-tunnel Bridges packets between local Ethernet ports and local radios, and passes tunneled packets through without de-tunnelingSelect this option for a dedicated tunnel for bridging VLAN traffic.local Bridges packets normally between local Ethernet ports and local radios (if any)Local mode is typically configured in remote branch offices where traffic on remote private LAN segments need to be bridged locally. Local mode implies that traffic, wired and wireless, is to be bridged locally.tunnel Bridges packets between local Ethernet ports, local radios, and tunnels to other APs, wireless controllers, or service platformsSelect this option to use a shared tunnel for bridging VLAN traffic.In tunnel mode, the traffic at the AP is always forwarded through the best path. The APs decide the best path to reach the destination and forward packets accordingly. Setting the VLAN to tunnel mode ensures packets are bridged between local Ethernet ports, any local radios, and tunnels to other APs, wireless controllers, and service platforms.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1126.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 387.1.10.2.2 capti ve - po r talbridge-vlan-mode commandsEnables IP (IPv4 and IPv6) packet snooping on wired captive portals, and also configures the subnet to snoop. When enabled, IP packets received from wired captive portal clients, on the specified subnet, are snooped to learn IP to MAC mapping.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcaptive-portal [ipv4-snooping|ipv6-snooping] subnet <IPv4/M|IPv6/M> {excluded-address <IPv4|IPv6>}Parameters• captive-portal [ipv4-snooping|ipv6-snooping] subnet <IPv4/M|IPv6/M> {excluded-address <IPv4|IPv6>}Examplenx9500-6C8809(config-profile NX9500Test-bridge-vlan-4)#captive-portal ip-snooping subnet 192.168.13.0/24 excluded-address 192.168.13.7nx9500-6C8809(config-profile NX9500Test-bridge-vlan-4)#show context bridge vlan 4 captive-portal ip-snooping subnet 192.168.13.0/24 excluded-address 192.168.13.7 ip igmp snooping ip igmp snooping querier ipv6 mld snooping ipv6 mld snooping queriernx9500-6C8809(config-profile NX9500Test-bridge-vlan-4)#Related Commandscaptive-portal [ipv4-snooping|ipv6-snooping]Enables snooping of IPv4 or IPv6 packets (based on the option selected) for wired captive portal clientssubnet <IPv4/M|IPv6/M>Enables IPv4 or IPv6 packet snooping on a specified subnet• <IPv4/M|IPv6/M> – Specify the subnet address in the A.B.C.D/M or X:X::X:X/M format to identify an IPv4 or IPv6 subnet respectively. When specified, this is the IPv4/IPv6 subnet on which IP packets are to be snooped.excluded-address <IPv4|IPv6>Optional. Configures the IPv4 or IPv6 address excluded from snooping within the specified IPv4|IPv6 subnet.• <IPv4|IPv6> – Specify the IPv4 or IPv6 address. Use this parameter to configure the gateway’s address.no Disables IP packet snooping on wired captive portals](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1128.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 437.1.10.2.7 http-analyzebridge-vlan-mode commandsEnables the analysis of URLs and data traffic on this Bridge VLAN. When enabled, URLs and data are forwarded to the controller running the HTTP analytics engine.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxhttp-analyze {filter [images|post|query-string]}Parameters• http-analyze {filter [images|post|query-string]}Examplerfs4000-229D58(config-device 00-23-68-22-9D-58-bridge-vlan-4)#http-analyze filter imagesrfs4000-229D58(config-device 00-23-68-22-9D-58-bridge-vlan-4)#show context bridge vlan 4 http-analyze filter imagesrfs4000-229D58(config-device 00-23-68-22-9D-58-bridge-vlan-4)#Related Commandshttp-analyze filter [images|post|query-string]Enables URL and HTTP data analysis. Optionally use the filter keyword to filter out specific URLs• filter – Optional. Filters out specific URLs• images – Filters out URLs referring to images• post – Filters out URLs referring to POSTs• query-string – Filters out query strings received from URLsno Disables forwarding of URLs and data to the controller running the HTTP analytics engine](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1133.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 447.1.10.2.8 ipbridge-vlan-mode commandsConfigures VLAN bridge IP componentsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [arp|dhcp|igmp]ip [arp|dhcp] trustip igmp snooping {fast-leave|forward-unknown-multicast|last-member-query-count|mrouter|querier}ip igmp snooping {fast-leave|forward-unknown-multicast|last-member-query-count <1-7>}ip igmp snooping {mrouter [interface|learn]}ip igmp snooping {mrouter [interface <INTERFACE-LIST>|learn pim-dvmrp]}ip igmp snooping {querier} {address|max-response-time|timer|version}ip igmp snooping {querier} {address <IP>|max-response-time <1-25>|timer expiry <60-300>|version <1-3>}Parameters• ip [arp|dhcp] trust• ip igmp snooping {fast-leave|forward-unknown-multicast|last-member-query-count <1-7>}ip Configures the VLAN bridge IP parametersarp trust Configures the ARP trust parameter. Trusted ARP packets are used to update the DHCP snoop table to prevent IP spoof and arp-cache poisoning attacks. This option is disabled by default.• trust – Trusts ARP responses on the VLAN bridgedhcp trust Configures the DHCP trust parameter. Uses DHCP packets, from a DHCP server, as trusted and permissible within the access point, wireless controller, or service platform managed network. DHCP packets are used to update the DHCP snoop table to prevent IP spoof attacks. This feature is enabled by default.• trust – Trusts DHCP responses on the VLAN bridgeip Configures the VLAN bridge IP parametersigmp snooping Configures Internet Group Management Protocol (IGMP) snooping parameters. IGMP snooping is enabled by default.IGMP establishes and maintains multicast group memberships for interested members. Multicasting allows a networked device to listen to IGMP network traffic and forward IGMP multicast packets to radios on which the interested hosts are connected. The device also maintains a map of the links that require multicast streams, there by reducing unnecessary flooding of the network with multicast traffic.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1134.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 45• ip igmp snooping {mrouter [interface <INTERFACE-LIST>|learn pim-dvmrp]}• ip igmp snooping {querier} {address <IP>|max-response-time <1-25>|timer expiry <60-300>|version <1-3>}fast-leave Optional. Enables fast leave processing. When enabled, layer 2 LAN interfaces are removed from the IGMP snooping forwarding table entry without initially sending IGMP group-specific queries to the interface. When receiving a group specific IGMPv2 leave message, IGMP snooping removes the interface from the Layer 2 forwarding table entry for that multicast group, unless a multicast router was learned on the port. Fast-leave processing enhances bandwidth management for all hosts on the network. This option is disabled by default.This feature is supported only on the AP7502, AP8232, AP8533 model access points.forward-unknown-multicastOptional. Enables forwarding of multicast packets from unregistered multicast groups. If disabled, the unknown multicast forward feature is also disabled for individual VLANs. This option is enabled by default.last-member-query-count <1-7>Optional. Configures the last member query count used in determining the number of group-specific queries sent before removing the snoop entry• <1-7> – Specify the count from 1 - 7. The default value is 2.ip Configures the VLAN bridge IP parametersigmp snooping Configures the IGMP snooping parametersmrouter Optional. Configures the multicast router parametersinterface <INTERFACE-LIST>Configures the multicast router interfaces. This option is disabled by default.• <INTERFACE-LIST> – Specify a comma-separated list of interface names.learn pim-dvmrp Configures the multicast router learning protocols. This option is disabled by default.• pim-dvmrp – Enables Protocol-Independent Multicast (PIM) and Distance-Vector Multicast Routing Protocol (DVMRP) snooping of packetsip Configures the VLAN bridge IP parametersigmp snooping Configures the IGMP snooping parametersquerier Optional. Configures the IGMP querier parameters. This option is disabled by default.Enables IGMP querier. IGMP snoop querier keeps host memberships alive. It is primarily used in a network where there is a multicast streaming server and hosts subscribed to the server and no IGMP querier present. The access point, wireless controller, or service platform performs the IGMP querier role. An IGMP querier sends out periodic IGMP query packets. Interested hosts reply with an IGMP report packet. IGMP snooping is only conducted on wireless radios. IGMP multicast packets are flooded on wired ports. IGMP multicast packet are not flooded on the wired port. IGMP membership is also learnt on it and only if present, then it is forwarded on that port.address <IP> Optional. Configures the IGMP querier source IP address. This address is used as the default VLAN querier IP address.• <IP> – Specify the IGMP querier source IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1135.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 477.1.10.2.9 ipv6bridge-vlan-mode commandsConfigures this VLAN bridge’s IPv6 componentsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 [dhcpv6|firewall|mld|nd]ipv6 dhcpv6 trustipv6 firewallipv6 mld snooping {forward-unknown-multicast|mrouter|querier}ipv6 mld snooping {forward-unknown-multicast}ipv6 mld snooping {mrouter [interface|learn]}ipv6 mld snooping {mrouter [interface <INTERFACE-LIST>|learn pim-dvmrp]}ipv6 mld snooping {querier} {max-response-time|timer|version}ipv6 mld snooping {querier} {max-response-time <1-25000>|timer expiry <60-300>|version <1-2>}ipv6 nd raguardParameters• ipv6 dhcpv6 trust• ipv6 firewall• ipv6 mld snooping {forward-unknown-multicast}ipv6 Configures the VLAN bridge IPv6 parametersdhcpv6 trust Enables the DHCPv6 trust option. When enabled all DHCPv6 responses are trusted on this bridge VLAN. This option is enabled by default.• trust – Trusts DHCPv6 responses on this bridge VLANipv6 Configures the VLAN bridge IPv6 parametersfirewall Enables IPv6 firewall on this bridge VLAN. This option is enabled by default.Devices utilizing IPv6 addressing require firewall protection unique to IPv6 traffic.IPv6 addresses are composed of eight groups of four hexadecimal digits separated by colons. IPv6 hosts can configure themselves automatically when connected to an IPv6 network using the neighbor discovery (ND) protocol via ICMPv6 router discovery messages. When first connected to a network, a host sends a link-local router solicitation multicast request for its configuration parameters. Routers respond to such a request with a router advertisement (RA) packet that contains Internet layer configuration parameters.ipv6 Configures the VLAN bridge IPv6 parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1137.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 48• ipv6 mld snooping {mrouter [interface <INTERFACE-LIST>|learn pim-dvmrp]}• ipv6 mld snooping {querier} {max-response-time <1-25000>|timer expiry <60-300>|version <1-2>}mld snooping Configures Multicast Listener Discovery Protocol (MLD) snooping parametersMLD snooping enables a access point, wireless controller, or service platform to examine MLD packets and make forwarding decisions based on the content. MLD is used by IPv6 devices to discover devices wanting to receive multicast packets destined for specific multicast addresses. MLD uses multicast listener queries and multicast listener reports to identify which multicast addresses have listeners and join multicast groups.MLD snooping caps the flooding of IPv6 multicast traffic on controller, service platform or access point VLANs. When enabled, MLD messages between hosts and multicast routers are examined to identify the hosts receiving multicast group traffic. The access point, wireless controller, or service platform forward multicast traffic only to those interfaces connected to interested receivers instead of flooding traffic to all interfaces.This option is enabled by default.forward-unknown-multicastOptional. Enables forwarding of multicast packets from unregistered multicast groups. If disabled, the unknown multicast forward feature is also disabled for individual VLANs. This option is enabled by default.ipv6 Configures the VLAN bridge IPv6 parametersmld snooping Configures MLD snooping parameters. This option is enabled by default.mrouter Optional. Configures the multicast router parameters, such as interfaces and learning protocol used.interface <INTERFACE-LIST>Configures the multicast router interfaces. This option is disabled by default.• <INTERFACE-LIST> – Specify a comma-separated list of interface names.learn pim-dvmrp Configures the multicast router learning protocols. This option is disabled by default.• pim-dvmrp – Enables PIM and DVMRP snooping of packetsipv6 Configures the VLAN bridge IPv6 parametersmld snooping Configures IPv6 MLD snooping parameters. This option is disabled by default.querier Optional. Enables and configures the MLD querier parameters. When enabled, the device (access point, wireless controller, and service platform) sends query messages to discover which network devices are members of a given multicast group. This option is disabled by default.max-response-time <1-25000>Optional. Configures the IPv6 MLD querier’s maximum response time. This option is disabled by default.• <1-25000> – Specify the maximum response time from 1 - 25000 milliseconds.timer expiry <60-300> Optional. Configures the IPv6 MLD other querier’s timeout. This option is disabled by default.• <60-300> – Specify the MLD other querier’s timeout from 60 - 300 seconds.version <1-2> Optional. Configures the IPv6 MLD querier version. This option is disabled by default.• <1-2> – Specify the MLD version. The versions are 1- 2.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1138.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 517.1.10.2.11 mac-a u t hbridge-vlan-mode commandsEnables source MAC authentication for Extended VLAN and tunneled traffic (MiNT and L2TPv3) on this bridge VLANSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmac-auth {attempts <1-5>|throttle <0-255>}Parameters• mac-auth {attempts <1-5>|throttle <0-255>}]Usage Guidelines Applying AAA Policy for MAC AuthenticationTo enable MAC authentication, • Create an AAA policy.nx9500-6C8809(config)#aaa-policy MAC-Auth• Use the AAA policy on the device for MAC Authentication.nx9500-6C8809(config-device-B4-C7-99-6C-88-09)#mac-auth use aaa-policy MAC-Auth• In the bridge VLAN context, enable MAC Authentication,nx9500-6C8809(config-device B4-C7-99-6C-88-09-bridge-vlan-20)#mac-auth• Optionally, configure the following MAC Authentication parameters. If not specified, default values are applied.nx9500-6C8809(config-device B4-C7-99-6C-88-09-bridge-vlan-20)#mac-auth attempts 2nx9500-6C8809(config-device B4-C7-99-6C-88-09-bridge-vlan-20)#mac-auth throttle 100Usage Guidelines Enabling Fall-back Captive Portal AuthenticationTo enable fall-back captive-portal authentication on the bridge VLAN, • apply a captive-portal policy to the bridge VLAN.nx9500-6C8809(config-device B4-C7-99-6C-88-09-bridge-vlan-20)#use captive-portal testNOTE: If enabling MAC authentication, ensure that an AAA policy is configured and for enforcing MAC Authentication.mac-auth Enables MAC Authenticationattempts <1-5> Optional. Configures the maximum number of retries allowed for MAC authentication requests.• <1-5> – Specify the maximum allowed authentication retries from 1 - 5. The default is 3.throttle <0-255> Optional. Configures the throttle value for MAC authentication requests• <0-255> – Specify the MAC authentication request throttle value from 0 -255. The default is 64.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1141.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 547.1.10.2.13 nobridge-vlan-mode commandsNegates a command or reverts settings to their default. The no command, when used in the bridge VLAN mode, negates the VLAN bridge settings or reverts them to their default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [bridging-mode|captive-portal|captive-portal-enforcement|description|edge-vlan|firewall|http-analyze|ip|ipv6|l2-tunnel-broadcast-optimization|l2-tunnel-forward-additional-packet-types|mac-auth|stateful-packet-inspection-l2|tunnel|tunnel-over-level2|use]no [bridging-mode|captive-portal-enforcement|description|edge-vlan|firewall|l2-tunnel-broadcast-optimization|l2-tunnel-forward-additional-packet-types|mac-auth|stateful-packet-inspection-l2|tunnel-over-level2]no captive-portal [ip-snooping|ipv6-snooping] subnet <IPv4/M|IPv6/M> {excluded-address <IPv4|IPv6>}no http-analyze {filter [images|post|query-string]}no ip [arp|dhcp|igmp]no ip [arp|dhcp] trustno ip igmp snooping {fast-leave|forward-unknown-multicast|last-member-query-count|mrouter|querier}no ip igmp snooping {forward-unknown-multicast}no ip igmp snooping {mrouter [interface <INTERFACE-LIST>|learn pin-dvmrp]}no ip igmp snooping {querier} {address|max-response-time|timer expiry|version}no ipv6 [dhcpv6|firewall|mld|nd]no ipv6 dhcpv6 trustno ipv6 firewallno ipv6 mld snooping {forward-unknown-multicast}no ipv6 mld snooping {mrouter [interface <INTERFACE-LIST>|learn pin-dvmrp]}no ipv6 mld snooping {querier} {max-response-time|timer expiry|version}no ipv6 nd raguardno tunnel [rate-limit level2|unknown-unicast]no use [application-policy|captive-portal|ip-access-list|ipv6-access-list|mac-access-list|url-list] tunnel outParameters• no <PARAMETERS>no <PARAMETERS> Resets or reverts this bridge VLAN’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1144.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 577.1.10.2.15 tunnelbridge-vlan-mode commandsEnables tunneling of unicast messages, to unknown MAC destinations, on the selected VLAN bridgeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtunnel [rate-limit|unknown-unicast]tunnel rate-limit level2 rate <50-1000000> max-burst-size <2-1024> {red-threshold [background <0-100>|best-effort <0-100>|video <0-100>|voice <0-100>]}tunnel unknown-unicastParameters• tunnel rate-limit level2 rate <50-1000000> max-burst-size <2-1024> {red-threshold [background <0-100>|best-effort <0-100>|video <0-100>|voice <0-100>]}• tunnel unknown-unicasttunnel rate-limit level2 rate <50-1000000> max-burst-size <2-1024>Configures a rate-limit parameters (max-burst-size and rate) for tunneled VLAN traffic over level 2 MiNT links• rate – Optional. Configures the data rate, in kilobits per second, for the incoming and outgoing extended VLAN traffic tunneled over MiNT level 2 links• <50-1000000> – Specify a value from 50 - 1000000 Kbps. The default is 5000Kbps.• max-burst-size – Optional. Configures the maximum burst size• <2-1024> – Specify the maximum burst size from 2 - 1024 kbytes. The de-fault is 320 kbytes.After specifying the max-burst-size, optionally specify the red-threshold value for the different traffic types. The red-threshold is configured as a % of the specified max-burst-size.• red-threshold – Optional. Configures the random early detection (red) threshold for the different traffic types• background – Configures the red-threshold for low priority traffic from 0 - 100. Thedefault is 50% of the specified max-burst-size.• best-effort – Configures the red-threshold for normal priority traffic from 0 - 100.The default is 50% of the specified max-burst-size.• video – Configures the red-threshold for video traffic from 0 - 100. The default is25% of the specified max-burst-size.• voice – Configures the red-threshold for voice traffic from 0 - 100. The default is 0%of the specified max-burst-size.tunnel unknown-unicastEnables tunneling of unicast packets destined for unknown MAC addresses](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1147.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 607.1.10.2.17 usebridge-vlan-mode commandsAssociates a captive-portal, access control list (IPv4, IPv6, or MAC), and/or a URL filter with this bridge VLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [application-policy|captive-portal|ip-access-list|ipv6-access-list|mac-access-list|url-filter]use application-policy <APP-POLICY-NAME>use captive-portal <CAPTIVE-PORTAL-NAME>use [ip-access-list|ipv6-access-list|mac-access-list] tunnel out <IP/ipv6/MAC-ACCESS-LIST-NAME>use url-filter <URL-FILTER-NAME>Parameters• use application-policy <APP-POLICY-NAME>• use captive-portal <CAPTIVE-PORTAL-NAME>• use [ip-access-list|ipv6-access-list|mac-access-list] tunnel out <IP/IPv6/MAC-ACCESS-LIST-NAME>use application-policy <APP-POLICY-NAME>Enforces application detection on this VLAN bridge• <APP-POLICY-NAME> – Specify the application policy name (should be existing and configured).• For more information on application definitions and application policies, see application and application-policy.use captive-portal Applies an existing captive portal configuration to restrict access to the bridge VLAN configurationA captive portal is an access policy for providing temporary and restrictive access using a standard Web browser. Captive portals provide authenticated access by capturing and re-directing a wireless user's Web browser session to a captive portal login page where the user must enter valid credentials to access to the network. Once logged into the captive portal, additional terms and agreement, welcome, fail, and no-service pages provide the administrator with a number of options on captive portal screen flow and user appearance.• <CAPTIVE-PORTAL-NAME> – Specify the captive portal name.use Sets this VLAN bridge policy to use an IPv4/IPv6 access list or a MAC access listip-access-list Associates a pre-configured IPv4 access list with this VLAN-bridge interfaceipv6-access-list Associates a pre-configured IPv6 access list with this VLAN-bridge interfacemac-access-list Associates a pre-configured MAC access list with this VLAN- bridge interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1150.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 637.1.12 cdpProfile Config CommandsEnables Cisco Discovery Protocol (CDP), a proprietary data link layer network protocol implemented in Cisco networking equipment and used to share network information amongst different vendor wireless devicesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcdp [holdtime|run|timer]cdp [holdtime <10-1800>|run|timer <5-900>]Parameters• cdp [holdtime <10-1800>|run|timer <5-900>]Examplerfs6000-37FABE(config profile-default-rfs6000)#cdp runrfs6000-37FABE(config profile-default-rfs6000)#cdp holdtime 1000rfs7000-37FABE(config profile-default-rfs6000)#cdp timer 900rfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 no edge-vlan l2-tunnel-broadcast-optimization ............................................................. qos trust 802.1p interface pppoe1 use firewall-policy default cdp holdtime 1000 cdp timer 900 service pm sys-restart router ospfrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsholdtime <10-1800> Specifies the holdtime after which transmitted packets are discarded• <10-1800> – Specify a value from 10 - 1800 seconds. The default is 180 seconds.run Enables CDP sniffing and transmit globally. This feature is enabled by default.timer <5-900> Specifies the interval, in seconds, between successive CDP packet transmission• <5-900> – Specify a value from 5 - 900 seconds. The default is 60 seconds.no Disables CDP on this profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1153.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 647.1.13 clusterProfile Config CommandsSets the cluster configurationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcluster [force-configured-state|force-configured-state-delay|handle-stp|master-priority|member|mode|name|radius-counter-db-sync-time]cluster [force-configured-state|force-configured-state-delay <3-1800>|handle-stp|master-priority <1-255>]cluster member [ip|vlan]cluster member [ip <IP> {level [1|2]}|vlan <1-4094>]cluster mode [active|standby]cluster name <CLUSTER-NAME>cluster radius-counter-db-sync-time <1-1440>Parameters• cluster [force-configured-state|force-configured-state-delay <3-1800>|handle-stp|master-priority <1-255>]force-configured-state Forces adopted APs to auto revert when a failed wireless controller or service platform (in a cluster) restartsWhen an active controller (wireless controller, or service platform) fails, a standby controller in the cluster takes over APs adopted by the failed active controller. If the failed active controller were to restart, it starts a timer based on the ‘force-configured-state-delay’ interval specified. At the expiration of this interval, the standby controller releases all adopted APs and goes back to a monitoring mode. If the active controller fails during this interval, the ‘force-configured-state-delay’ timer is stopped. The timer restarts as soon as the active controller comes back up.This feature is disabled by default.force-configured-state-delay <3-1800>Forces cluster transition to the configured state after a specified interval• <3-1800> – Specify a delay from 3 - 1800 minutes. The default is 5 minutes.This is the interval a standby controller waits before releasing adopted APs when a failed primary controller becomes active again.handle-stp Enables Spanning Tree Protocol (STP) convergence handling. This feature is disabled by default.In layer 2 networks, this protocol is enabled to prevent network looping. If enabled, the network forwards data only after STP convergence. Enabling STP convergence delays the redundancy state machine execution until the STP convergence is completed (the standard protocol value for STP convergence is 50 seconds). Delaying the state machine is important to load balance APs at startup.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1154.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 65• cluster member [ip <IP> {level [1|2]}|vlan <1-4094>]• cluster mode [active|standby]• cluster name <CLUSTER-NAME>• cluster radius-counter-db-sync-time <1-1440>master-priority <1-255>Configures cluster master priority• <1-255> – Specifies cluster master election priority. Assign a value from 1 - 255. Higher the value higher is the precedence. The default is 128.In a cluster environment one device from the cluster is elected as the cluster master. A device’s master priority value decides the device’s priority to become cluster master.member Adds a member to the cluster. It also configures the cluster VLAN where members can be reached.ip <IP> level [1|2] Adds IP address of the new cluster member• <IP> – Specify the IP address.• level – Optional. Configures routing level for the new member. Select one of the fol-lowing routing levels:• 1 – Level 1, local routing• 2 – Level 2, In-site routingvlan <1-4094> Configures the cluster VLAN where members can be reached•<1-4094> – Specify the VLAN ID from 1- 4094.mode [active|standby] Configures cluster member’s mode as active or standby• active – Configures cluster mode as active. This is the default setting.• standby – Configures cluster mode as standbyA member can be in either an Active or Standby mode. All active member controllers can adopt access points. Standby members only adopt access points when an active member has failed or sees an access point not adopted by a controller.name <CLUSTER-NAME>Configures the cluster name• <CLUSTER-NAME> – Specify the cluster name.radius-counter-db-sync-time <1-1440>Configures the interval, in minutes, at which the RADIUS counter database is synchronized with the dedicated NTP server resource.• <1-1440> – Specify a value from 1 - 1440 minutes. The default is 5 minutes.Use the show > cluster > configuration command to view RADIUS counter DB sync time.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1155.png)
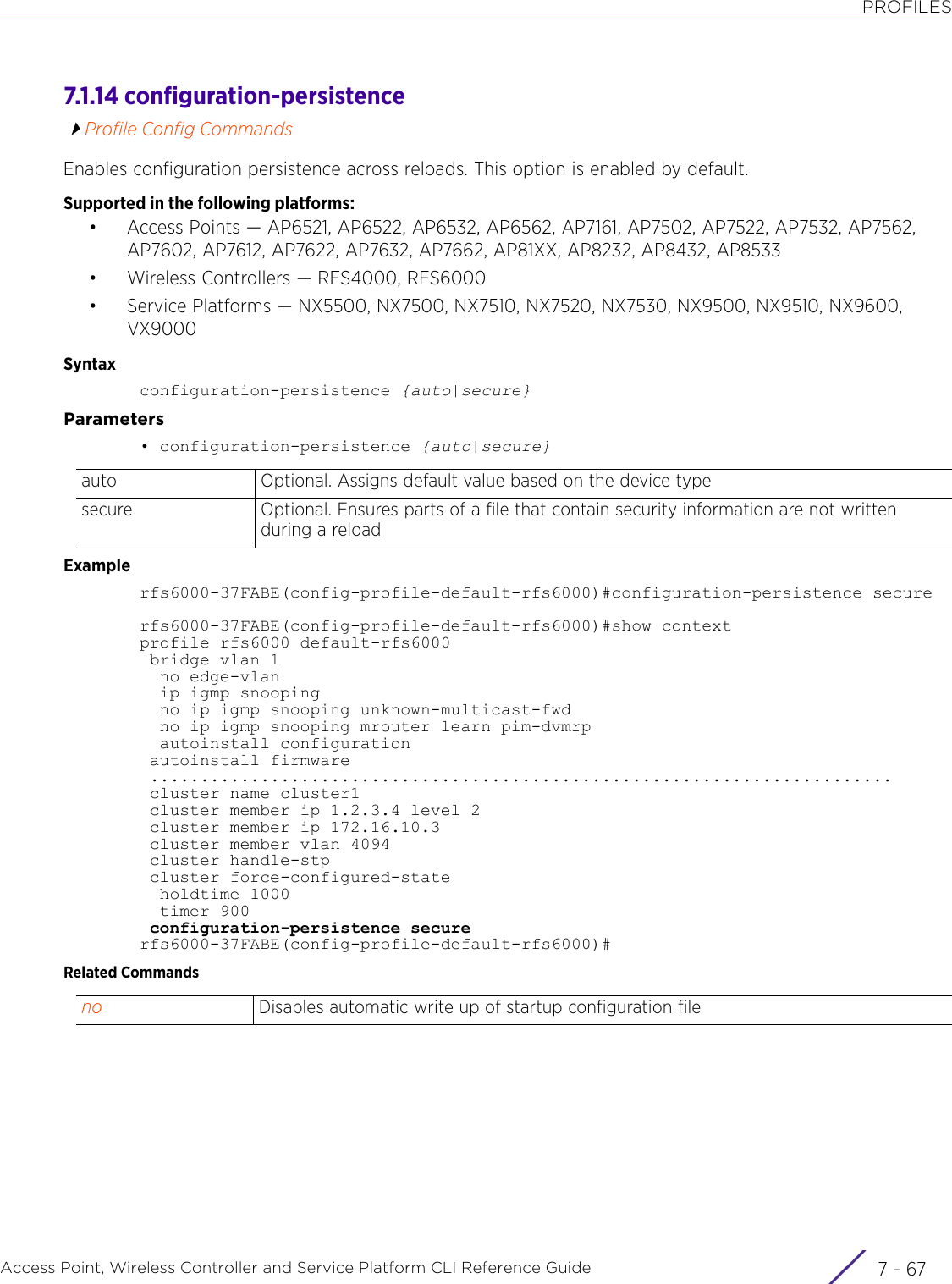
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 687.1.15 controllerProfile Config CommandsConfigures the WiNG controller (wireless controller or service platform) adoption settingsAdoption is the process a controller or service platform uses to discover available access points and/or peer controllers/service platforms, establish an association and provision the adopted device. Adoption settings are configurable and supported within a profile and applied to all devices supported by the profile.Use this command to add a controller to a pool and group. This command also enables and disables adoption on controllers, and specifies the device types that can be adopted by a controller.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcontroller [adopted-devices|adoption|group|hello-interval|vlan|host]controller adopted-devices [aps {controllers}|controllers {aps}|external-devices|external-devices-monitoring-only]helcontroller adoptioncontroller [group <CONTROLLER-GROUP-NAME>|vlan <1-4094>]controller hello-interval <1-120> adjacency-hold-time <2-600>controller host [<IPv4>|<IPv6>|<HOSTNAME>] {ipsec-secure|level|pool|remote-vpn-client}controller host [<IPv4>|<IPv6>|<HOSTNAME>] {ipsec-secure} {gw [<IP>|<HOSTNAME>]}controller host [<IPv4>|<IPv6>|<HOSTNAME>] {level [1|2]|pool <1-2> level [1|2]} {ipsec-secure {gw [<IP>|<HOSTNAME>]}|remote-vpn-client}controller host [<IPv4>|<IPv6>|<HOSTNAME>] {remote-vpn-client}Parameters• controller adopted-devices [aps {controllers}|controllers {aps}|external-devices|external-devices-monitoring-only]controller Configures the WLAN’s controller adoption settingsadopted-devices Configures the types of device (AP/controller) this controller can adoptaps {controllers} Enables the adoption of network access points by this controller. This option is enabled by default.• controllers – Optional. Enables the adoption of peer controllers by this controllerAll adopted devices (referred to as adoptee) receive complete configuration from the adopting controller (referred to as adopter).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1158.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 69• controller adoption• controller [group <CONTROLLER-GROUP-NAME>|vlan <1-4094>]• controller hello-interval <1-120> adjacency-hold-time <2-600>• controller host [<IPv4>|<IPv6>|<HOSTNAME>] {ipsec-secure} {gw [<IP>|<HOSTNAME>]}controllers {aps} Enables the adoption of peer controllers by this controllers• aps – Optional. Enables the adoption of network access points by this controllerA controller cannot be configured as an adoptee and an adopter simultaneously. In other words, an adopted controller (adoptee) cannot be configured to adopt another controller.Use the no > controller > adopted-devices command to remove this setting.external-devices Enables adoption of external devices by this controller. This option is disabled by default.When enabled, a WiNG controller can adopt and manage T5 controllers and EX3500 switches (using the IPX operating system) within a WiNG managed device subnet. This setting is disabled by default.To disable T5 or EX3500 adoption, use the no > controller > external-devices command.This feature is supported only on RFS4000, NX9500, NX9510, NX9600, and VX9000 platforms.external-devices-monitoring-onlyEnables only monitoring of external devices by this controller or service platform. This option is disabled by default.controller adoption Enables the adoption of the logged device (wireless controller or service platform) by other controllers. This option is disabled by default.Use the no > controller > adoption command to disable adoption.controller Configures the WLAN’s controller adoption settingsgroup <CONTROLLER-GROUP-NAME>Configures the wireless controller or service platform group• <CONTROLLER-GROUP-NAME> – Specify the wireless controller or service platform group name.vlan <1-4094> Configures the wireless controller or service platform VLAN• <1-4094> – Specify the VLAN ID from 1 - 4094.controller Configures the WLAN’s controller settingshello-interval <1-120> Configures the hello-interval in seconds. This is the interval between consecutive hello packets exchanged between AP and wireless controller or service platform.• <1-120> – Specify a value from 1 - 120 seconds.adjacency-hold-time<2-600>Configures the adjacency hold time in seconds. This is the time since the last received hello packet, after which the adjacency between wireless controller or service platform and AP is lost, and the link is re-established.• <2-600> – Specify a value from 2 - 600 seconds.controller Configures the WLAN’s controller adoption settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1159.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 70• controller host [<IPv4>|<IPv6>|<HOSTNAME>] {level [1|2]|pool <1-2> level [1|2]} {ipsec-secure {gw [<IP>|<HOSTNAME>]}|remote-vpn-client}host [<IPv4>|<IPv6>|<HOSTNAME>]Configures wireless controller or service platform’s IPv4/IPv6 address or hostname• <IPv4> – Configures wireless controller or service platform’s IPv4 address• <IPv6> – Configures wireless controller or service platform’s IPv6 address• <HOSTNAME> – Configures wireless controller or service platform’s hostnameipsec-secure {gw [<IP>|<HOSTNAME>]}Optional. Enables Internet Protocol Security (IPSec) peer authentication on the connection (link) between the adopting devices. This option is disabled by default.• gw – Optional. Specifies a IPSec gateway other than the wireless controller or service platform• <IP> – Use this option to specify the IPSec gateway’s IP address.• <HOSTNAME> – Use this option to specify the IPSec gateway’s hostname.If the gateway’s IP address or hostname is not specified, the system assumes the logged controller as the IPSec gateway.controller Configures the WLAN’s controller adoption settingshost [<IPv4>|<IPv6>|<HOSTNAME>]Configures wireless controller or service platform’s IPv4/IPv6 address or name• <IPv4> – Configures wireless controller or service platform’s IPv4 address• <IPv6> – Configures wireless controller or service platform’s IPv6 address• <HOSTNAME> – Configures wireless controller or service platform’s namelevel [1|2] The following keywords are common to the ‘IP’, ‘IPv6’, and ‘hostname’ parameters:Optional. After providing the wireless controller or service platform’s address, optionally select one of the following routing levels:• 1 – Optional. Level 1, local routing• 2 – Optional. Level 2, inter-site routingNote: After specifying the routing level, you can, optionally enable IPSec Secure authentication and remote VPN client.pool <1-2> level [1|2] The following keywords are common to the ‘IP’, ‘IPv6’, and ‘hostname’ parameters:Optional. Sets the wireless controller or service platform’s pool• <1-2> – Select either 1 or 2 as the pool. The default is 1. After selecting the pool, optionally select one of the following two routing levels:• 1 – Optional. Level 1, local routing• 2 – Optional. Level 2, inter-site routing{ipsec-secure {gw [<IP>|<HOSTNAME>]}|remote-vpn-client}After specifying the routing level and or device’s pool, you can optionally specify the following:• ipsec-secure – Optional. Enables IPSec peer authentication on the connection (link) between the adopting devices. This option is disabled by default.• gw – Optional. Specifies a IPSec gateway other than the wireless controller or service platform• <IP> – Use this option to specify the IPSec gateway’s IP address.• <HOSTNAME> – Use this option to specify the IPSec gateway’s hostname.Note: If the gateway’s IP address or hostname is not specified, the system assumes the logged controller as the IPSec gateway.Contd....](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1160.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 71• controller host [<IPv4>|<IPv6>|<HOSTNAME>] {remote-vpn-client}Examplerfs6000-37FABE(config-profile-default-rfs6000)controller group testrfs6000-37FABE(config-profile-default-rfs6000)#controller host 1.2.3.4 pool 2rfs7000-37FABE(config-profile-default-rfs7000)#show contextprofile rfs6000 default-rfs6000 no autoinstall configuration no autoinstall firmware crypto isakmp policy default crypto ipsec transform-set default esp-aes-256 esp-sha-hmac.......................................................... interface ge4 ip dhcp trust qos trust dscp qos trust 802.1p use firewall-policy default controller host 1.2.3.4 pool 2 controller group test service pm sys-restart--More--rfs6000-37FABE(config-profile-default-rfs6000)#rfs4000-229D58(config-profile-testRFS4000)#controller adopted-devices aps controllersrfs4000-229D58(config-profile-testRFS4000)#show contextprofile rfs4000 testRFS4000 autoinstall configuration.................................................................... logging on service pm sys-restart router ospf controller adopted-devices aps controllersrfs4000-229D58(config-profile-testRFS4000)#Related Commands• remote-vpn-client – Forces MiNT link creation protocol (MLCP) to use remote VPN connection on the controllerThe controller uses remote VPN tunnel for this traffic. If multiple controller hosts are configured, either all the hosts should use remote-vpn-client or none.When enabled, an MLCP connection is not initiated until remote VPN connection is UP and virtual IP, DNS server, source route, etc. are installed on the AP.controller Configures the WLAN’s controller settingshost [<IPv4>|<IPv6>|<HOSTNAME>]Configures wireless controller or service platform’s IPv4/IPv6 address or hostname• <IP> – Configures wireless controller or service platform’s IPv4 address• <IPv6> – Configures wireless controller or service platform’s IPv6 address• <HOSTNAME> – Configures wireless controller or service platform’s nameremote-vpn-client Forces MLCP to use remote VPN connection on the controllerThe controller uses remote VPN tunnel for this traffic. If multiple controller hosts are configured, either all the hosts should use remote-vpn-client or none.When enabled, an MLCP connection is not initiated until remote VPN connection is UP and virtual IP, DNS server, source route, etc. are installed on the AP. no Disables or reverts settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1161.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 727.1.16 critical-resourceProfile Config CommandsEnables monitoring of resources critical to the health of the service platform, wireless controller, or access point managed network. These critical resources are identified by their configured IP addresses. When enabled, the system monitors these devices regularly and logs their status. Use this command to create a critical resource monitoring (CRM) policy.A critical resource can be a gateway, AAA server, WAN interface, any hardware, or a service on which the stability of the network depends. Monitoring these resources is therefore essential. When enabled, this feature pings critical resources regularly to ascertain their status. If there is a connectivity issue, an event is generated stating a critical resource is unavailable. By default, there is no enabled critical resource policy and one needs to be created and implemented.Critical resources can be monitored directly through the interfaces on which they are discovered. For example, a critical resource on the same subnet as an AP8132 access point can be monitored by its IP address. However, a critical resource located on a VLAN must continue to be monitored on that VLAN.Critical resource monitoring can be enabled on service platforms, wireless controllers, and access points through their respective device profiles.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcritical-resource [<CR-NAME>|monitor|retry-count]critical-resource <CR-NAME> [monitor|monitor-using-flows]critical-resource <CR-NAME> monitor [direct|via]critical-resource <CR-NAME> monitor direct [all|any] [<IP/HOST-ALIAS-NAME>|sync-adoptees] {<IP/HOST-ALIAS-NAME>|arp-only vlan [<1-4094>|<VLAN-ALIAS-NAME>]{<IP/HOST-ALIAS-NAME>|port [<LAYER2-IF-NAME>|ge <1-4>|port-channel <1-2>]}}critical-resource <CR-NAME> monitor via [<IP/HOST-ALIAS-NAME>|<LAYER3-INTERFACE-NAME>|pppoe1|vlan|wwan1]critical-resource <CR-NAME> monitor via [<IP/HOST-ALIAS-NAME>|<LAYER3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1] [all|any] [<IP/HOST-ALIAS-NAME>|sync-adoptees] {<IP/HOST-ALIAS-NAME>|arp-only [vlan <1-4094>|<VLAN-ALIAS-NAME>] {<IP/HOST-ALIAS-NAME>|port [<LAYER2-IF-NAME>|ge <1-4>|port-channel <1-2>]}}critical-resource <CR-NAME> monitor-using-flows [all|any] [criteria|dhcp|dns|sync-adoptees]critical-resource <CR-NAME> monitor-using-flows [all|any] criteria [all|cluster-master|rf-domain-manager] (dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>) {dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}critical-resource <CR-NAME> monitor-using-flows [all|any] dhcp vlan <1-4094> {dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1162.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 73critical-resource <CR-NAME> monitor-using-flows [all|any] dns <IP/HOST-ALIAS-NAME> {dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}critical-resource <CR-NAME> monitor-using-flows [all|any] sync-adoptees criteria [all|cluster-master|rf-domain-manager] (dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>) {dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}critical-resource monitor interval <5-86400>critical-resource retry-count <0-10>Parameters• critical-resource <CR-NAME> monitor direct [all|any] [<IP/HOST-ALIAS-NAME>|sync-adoptees] {<IP/HOST-ALIAS-NAME>|arp-only [vlan <1-4094>|<VLAN-ALIAS-NAME>] {<IP/HOST-ALIAS-NAME>|port [<LAYER2-IF-NAME>|ge <1-4>|port-channel <1-2>]}}<CR-NAME> Identifies the critical resource to be monitored. Provide the name of the critical resource.monitor Enables critical resource(s) monitoringdirect [all|any] [<IP/HOST-ALIAS-NAME>|sync-adoptees]Monitors critical resources using the default routing engine• all – Monitors all resources that are going down (generates an event when all specified critical resources are unreachable)• any – Monitors any resource that is going down (generates an event when any one of the specified critical resource is unreachable)• <IP/HOST-ALIAS-NAME> – Configures the IP address of the critical resourcebeing monitored (for example, the DHCP or DNS server). Specify the IP address inthe A.B.C.D format. You can use a host-alias to identify the critical resource. If us-ing a host-alias, ensure that the host-alias is existing and configured.• sync-adoptees – Syncs adopted access points with the controller. In the stand-alone AP scenario, where the CRM policy is running on the AP, the AP is directlyintimated in case a critical resource goes down. On the other hand, when an AP isadopted to a controller (running the CRM policy), it is essential to enable the sync-adoptees option in order to sync the AP with the controller regarding the latest CRM status.arp-onlyvlan [<1-4094>|<VLAN-ALIAS-NAME>]{<IP/HOST-ALIAS-NAME>|port [<LAYER2-IFNAME>|ge|port-channel]}The following keywords are common to the ‘all’ and ‘any’ parameters:• arp-only vlan <1-4094> – Optional. Uses ARP to determine if the IP address is reachable (use this option to monitor resources that do not have IP addresses). ARP is used to resolve hardware addresses when only the network layer address is known.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Specifies the VLAN ID on which tosend the probing ARP requests. Specify the VLAN ID from 1 - 4094. Alternately,use a vlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias isexisting and configured.• <IP/HOST-ALIAS-NAME> – Optional. Limits ARP to a device specified by the<IP> parameter. You can use a host-alias to specify the IP address. If using ahost-alias, ensure that the host-alias is existing and configured.• port [<LAYER2-IF-NAME>|ge|port-channel] – Optional. Limits ARP to aspecified port](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1163.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 74• critical-resource <CRM-POLICY-NAME> monitor via [<IP/HOST-ALIAS-NAME>|<LAYER3-INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1] [all|any] [<IP/HOST-ALIAS-NAME>|sync-adoptees] {<IP/HOST-ALIAS-NAME>|arp-only vlan [<1-4094>|<VLAN-ALIAS-NAME>] {<IP>|port [<LAYER2-IFNAME>|ge|port-channel]}}<CR-NAME> Identifies the critical resource to be monitored. Provide the name of the critical resource.monitor Enables critical resource(s) monitoringvia Specifies the interface or next-hop via which the ICMP pings should be sent.Configures the interface or next-hop via which ICMP pings are sent. This does not apply to IP addresses configured for arp-only. For interfaces which learn the default-gateway dynamically (like DHCP clients and PPP interfaces), use an interface name for VIA, or use an IP address.<IP/HOST-ALIAS-NAME> Specify the IP address of the next-hop via which the critical resource(s) are monitored. Configures up to four IP addresses for monitoring. All the four IP addresses constitute critical resources. You can use a host-alias to specify the IP address. If using a host-alias, ensure that the host-alias is existing and configured.<LAYER3-INTERFACE-NAME>Specify the layer 3 Interface name (router interface)pppoe1 Specifies PPP over Ethernet interfacevlan [<1-4094>|<VLAN-ALIAS-NAME>]Specifies the wireless controller or service platform’s VLAN interface. Specify VLAN ID from 1 - 4094. Alternately, use a vlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existing and configured.wwan1 Specifies Wireless WAN interface[all|any] [<IP/HOST-ALIAS-NAME>|sync-adoptees]Monitors critical resources using the default routing engine• all – Monitors all resources that are going down (generates an event when all specified critical resource IP addresses are unreachable)• any – Monitors any resource that is going down (generates an event when any one of the specified critical resource IP address is unreachable)• <IP/HOST-ALIAS-NAME> – Configures the IP address of the critical resourcebeing monitored (for example, the DHCP or DNS server). Specify the IP address inthe A.B.C.D format. You can use a host-alias to specify the IP address. If using ahost-alias, ensure that the host-alias is existing and configured.• sync-adoptees – Syncs adopted access points with the controller. In the stand-alone AP scenario, where the CRM policy is running on the AP, the AP is directlyintimated in case a critical resource goes down. On the other hand, when an AP isadopted to a controller (running the CRM policy), it is essential to enable the sync-adoptees option in order to sync the AP with the controller regarding the latestCRM status.arp-onlyvlan [<1-4094>|<VLAN-ALIAS-NAME>]{<IP/HOST-ALIAS-NAME>|port [<LAYER2-IFNAME>|ge|port-channel]}The following keywords are common to the ‘all’ and ‘any’ parameters:• arp-only vlan <1-4094> – Optional. Uses ARP to determine if the IP address is reachable (use this option to monitor resources that do not have IP addresses). ARP is used to resolve hardware addresses when only the network layer address is known.Contd....](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1164.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 75• critical-resource <CRM-POLICY-NAME> monitor-using-flows [all|any] criteria [all|cluster-master|rf-domain-manager] (dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>) {dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Specifies the VLAN ID to send theprobing ARP requests. Specify the VLAN ID from 1 - 4094. Alternately, use a vlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existing andconfigured.• <IP’HOST-ALIAS-NAME> – Optional. Limits ARP to a device specified by the<IP> parameter. You can use a host-alias to specify the IP address. If using ahost-alias, ensure that the host-alias is existing and configured.• port [<LAYER2-IF-NAME>|ge|port-channel] – Optional. Limits ARP to aspecified port<CR-NAME> Identifies the critical resource to be monitored. Provide the name of the critical resource.monitor-using-flows Enables critical resource(s) monitoring using message flows for DHCP or DNS (DHCP discover, DHCP offer, etc.) instead of ICMP or ARP packets in order to reduce the amount of traffic on the network.[all|any] Configures how critical resource event messages are generated. Options include all and any.• all – Monitors all resources that are going down (generates an event when all specified critical resources are unreachable)• any – Monitors any resource that is going down (generates an event when any one of the specified critical resource is unreachable)criteria [all|cluster-master|rf-domain-manager]Configures the resource that will monitor critical resources and update the rest of the devices in a group. Options include all, rf-domain-manager, or cluster-master.• all – Configures all devices within a group (cluster or RF Domain) as the monitoring resource• cluster-master – Configures the cluster master as the monitoring resource• rf-domain-manager – Configures the RF Domain manager as the monitoring resourcedhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]The following parameters are recursive and common to the ‘all’, ‘cluster-master’, and ‘rf-domain-manager’ keywords:• dhcp – Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which thecritical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use avlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existing and configured.dns <IP/HOST-ALIAS-NAME>The following parameters are recursive and common to the ‘all’, ‘cluster-master’, and ‘rf-domain-manager’ keywords:• dns – Configures DNS as the mode of monitoring critical resources. When configured, DNS message flows are used instead of ICMP or ARP packets to confirm critical resource availability.• <IP/HOST-ALIAS-NAME> – Configures the IPv4 address or host alias of the crit-ical resource. Specify the IPv4 address or host alias name (should be existing andconfigured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1165.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 76• critical-resource <CRM-POLICY-NAME> monitor-using-flows [all|any] dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>] {dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}{dhcp [vlan <1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}The ‘dhcp’ and ‘dns’ parameters are recursive and you can optionally configure multiple VLANs and critical resource IPv4 addresses (or host alias names).• dhcp – Optional. Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which thecritical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use avlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existingand configured.• dns – Optional. Configures DNS as the mode of monitoring critical resources. When configured, DNS message flows are used instead of ICMP or ARP packets to confirm critical resource availability.• <IP/HOST-ALIAS-NAME> – Configures the IPv4 address or host alias of the crit-ical resource. Specify the IPv4 address or host alias name (should be existing andconfigured).<CR-NAME> Identifies the critical resource to be monitored. Provide the name of the critical resource.monitor-using-flows Enables critical resource(s) monitoring using message flows for DHCP or DNS (DHCP Discover, DHCP Offer, etc.) instead of ICMP or ARP packets in order to reduce the amount of traffic on the network.[all|any] Configures how critical resource event messages are generated. Options include all and any.• all – Monitors all resources that are going down (generates an event when all specified critical resources are unreachable)• any – Monitors any resource that is going down (generates an event when any one of the specified critical resource is unreachable)dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability. • vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which the critical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use a vlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existing and configured.{dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}The following parameters are recursive and optional. Use them to configure multiple VLANs and critical resource IPv4 addresses (or host alias names):• dhcp – Optional. Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which thecritical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use avlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existingand configured.Contd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1166.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 77• critical-resource <CRM-POLICY-NAME> monitor-using-flows [all|any] dns <IP/HOST-ALIAS-NAME> {dhcp vlan [<1-4094><VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}• critical-resource <CRM-POLICY-NAME> monitor-using-flows [all|any] sync-adoptees criteria [all|cluster-master|rf-domain-manager] (dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>) {dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}• dns – Optional. Configures DNS as the mode of monitoring critical resources. When configured, DNS message flows are used instead of ICMP or ARP packets to confirm critical resource availability.• <IP/HOST-ALIAS-NAME> – Configures the IPv4 address or host alias of the crit-ical resource. Specify the IPv4 address or host alias name (should be existing andconfigured).<CR-NAME> Identifies the critical resource to be monitored. Provide the name of the critical resource.monitor-using-flows Enables critical resource(s) monitoring using message flows for DHCP or DNS (DHCP Discover, DHCP Offer, etc.) instead of ICMP or ARP packets in order to reduce the amount of traffic on the network.[all|any] Configures how critical resource event messages are generated. Options include all and any.• all – Monitors all resources that are going down (generates an event when all specified critical resources are unreachable)• any – Monitors any resource that is going down (generates an event when any one of the specified critical resource is unreachable)dns <IP/HOST-ALIAS-NAME>Configures DNS as the mode of monitoring critical resources. When configured, DNS message flows are used instead of ICMP or ARP packets to confirm critical resource availability. • <IP/HOST-ALIAS-NAME> – Configures the IPv4 address or host alias of the critical resource. Specify the IPv4 address or host alias name (should be existing and configured).{dhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>|dns <IP/HOST-ALIAS-NAME>}The following parameters are recursive and optional. Use them to configure multiple VLANs and critical resource IPv4 addresses (or host alias names):• dhcp – Optional. Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which thecritical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use avlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existingand configured.• dns – Optional. Configures DNS as the mode of monitoring critical resources. When configured, DNS message flows are used instead of ICMP or ARP packets to confirm critical resource availability.• <IP/HOST-ALIAS-NAME> – Configures the IPv4 address or host alias of the critical resource. Specify the IPv4 address or host alias name (should be existingand configured).<CR-NAME> Identifies the critical resource to be monitored. Provide the name of the critical resource.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1167.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 78monitor-using-flows Enables critical resource(s) monitoring using message flows for DHCP or DNS (DHCP Discover, DHCP Offer, etc.) instead of ICMP or ARP packets in order to reduce the amount of traffic on the network.[all|any] Configures how critical resource event messages are generated. Options include all and any.• all – Monitors all resources that are going down (generates an event when all specified critical resources are unreachable)• any – Monitors any resource that is going down (generates an event when any one of the specified critical resource is unreachable)syn-adoptees Syncs adopted access points with the controller. In the stand-alone AP scenario, where the CRM policy is running on the AP, the AP is directly intimated in case a critical resource goes down. On the other hand, when an AP is adopted to a controller (running the CRM policy), it is essential to enable the sync-adoptees option in order to sync the AP with the controller regarding the latest CRM status.criteria [all|cluster-master|rf-domain-manager]Configures the resource that will monitor critical resources and update the rest of the devices in a group. Options include all, rf-domain-manager, or cluster-master.• all – Configures all devices within a group (cluster or RF Domain) as the monitoring resource• cluster-master – Configures the cluster master as the monitoring resource• rf-domain-manager – Configures the RF Domain manager as the monitoring resourcedhcp vlan [<1-4094>|<VLAN-ALIAS-NAME>]The following parameters are recursive and common to the ‘all’, ‘cluster-master’, and ‘rf-domain-manager’ keywords:• dhcp – Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability. • vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which thecritical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use avlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existing and configured.dns <IP/HOST-ALIAS-NAME>The following parameters are recursive and common to the ‘all’, ‘cluster-master’, and ‘rf-domain-manager’ keywords:• dns – Configures DNS as the mode of monitoring critical resources. When configured, DNS message flows are used instead of ICMP or ARP packets to confirm critical resource availability.• <IP/HOST-ALIAS-NAME> – Configures the IPv4 address or host alias of the critical resource. Specify the IPv4 address or host alias name (should be existingand configured).{dhcp vlan {<1-4094>|<VLAN-ALIAS-NAME>]|dns <IP/HOST-ALIAS-NAME>}The ‘dhcp’ and ‘dns’ parameters are recursive and you can optionally configure multiple VLANs and critical resource IPv4 addresses (or host alias names).• dhcp – Optional. Configures DHCP as the mode of monitoring critical resources. When configured, DHCP message flows (DHCP Discover, DHCP Offer, etc.) are used instead of ICMP or ARP packets to confirm critical resource availability.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Configures the VLAN on which thecritical resource(s) is available. Specify the VLAN from 1 - 4094. Alternately, use avlan-alias to identify the VLAN. If using a vlan-alias, ensure that the alias is existing and configured.Contd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1168.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 817.1.17.1 cryptocryptoUse the crypto command to define a system-level local ID for ISAKMP negotiation and enter the ISAKMP policy, ISAKMP client, or ISAKMP peer configuration mode.A crypto map entry is a single policy that describes how certain traffic is secured. There are two types of crypto map entries: ipsec-manual and ipsec-ike entries. Each entry is given an index (used to sort the ordered list).When a non-secured packet arrives on an interface, the crypto map associated with that interface is processed (in order). If a crypto map entry matches the non-secured traffic, the traffic is discarded.When a packet is transmitted on an interface, the crypto map associated with that interface is processed. The first crypto map entry that matches the packet is used to secure the packet. If a suitable Security Association (SA) exists, it is used for transmission. Otherwise, IKE is used to establish a SA with the peer. If no SA exists (and the crypto map entry is “respond only”), the packet is discarded.When a secured packet arrives on an interface, its Security Parameter Index (SPI) is used to look up a SA. If a SA does not exist (or if the packet fails any of the security checks), it is discarded. If all checks pass, the packet is forwarded normally.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcrypto [auto-ipsec-secure|enable-ike-uniqueids|ike-version|ikev1|ikev2|ipsec|load-management|map|pki|plain-text-deny-acl-scope|remote-vpn-client]crypto [auto-ipsec-secure|enable-ike-uniqueids|load-management]crypto ike-version [ikev1-only|ikev2-only]crypto ikev1 [dpd-keepalive <10-3600>|dpd-retries <1-100>|nat-keepalive <10-3600>|peer <IKEV1-PEER>|policy <IKEV1-POLICY-NAME>|remote-vpn]crypto ikev2 [cookie-challenge-threshold <1-100>|dpd-keepalive <10-3600>|dpd-retries <1-100>|nat-keepalive <10-3600>|peer <IKEV2-PEER>|policy <IKEV2-POLICY-NAME>|remote-vpn]crypto ipsec [df-bit|security-association|transform-set]crypto ipsec df-bit [clear|copy|set]crypto ipsec security-association lifetime [kilobytes <500-2147483646>|seconds <120-86400>]crypto ipsec transform-set <TRANSFORM-SET-TAG> [esp-3des|esp-aes|esp-aes-192|esp-aes-256|esp-des|esp-null] [esp-aes-xcbc-mac|esp-md5-hmac|esp-sha-hmac|esp-sha256-hmac]crypto map <CRYPTO-MAP-TAG> <1-1000> [ipsec-isakmp {dynamic}|ipsec-manual]crypto pki import crl <TRUSTPOINT-NAME> URL <1-168>crypto plain-text-deny-acl-scope [global|interface]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1171.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 82crypto remote-vpn-clientParameters• crypto [auto-ipsec-secure|enable-ike-uniqueids|load-management]• crypto ike-version [ikev1-only|ikev2-only]• crypto ikev1 [dpd-keepalive <10-3600>|dpd-retries <1-100>|nat-keepalive <10-3600>|peer <IKEV1-PEER>|policy <IKEV1-POLICY-NAME>|remote-vpn]• crypto ikev2 [cookie-challenge-threshold <1-100>|dpd-keepalive <10-3600>|dpd-retries <1-100>|nat-keepalive <10-3600>|peer <IKEV2-PEER>|policy <IKEV2-POLICY-NAME>|remote-vpn]auto-ipsec-secure Configures the Auto IPSec Secure parameter settings. For Auto IPSec tunnel configuration commands, see crypto-auto-ipsec-tunnel commands.enable-ike-uniqueids Enables Internet Key Exchange (IKE) unique ID checkFor more information on IKE unique IDs, see remotegw.load-management Configures load management for platforms using software cryptographyike-version [ikev1-only|ikev2-only]Selects and starts the IKE daemon• ikev1-only – Enables support for IKEv1 tunnels only• ikev2-only – Enables support for IKEv2 tunnels onlyikev1 Configures the IKE version 1 parametersdpd-keepalive <10-3600>Sets the global Dead Peer Detection (DPD) keep alive interval from 10 - 3600 seconds. This is the interval between successive IKE keep alive messages sent to detect if a peer is dead or alive. The default is 30 seconds.dpd-retries <1-1000> Sets the global DPD retries count from 1 - 1000. This is the number of keep alive messages sent to a peer before the tunnel connection is declared as dead. The default is 5.nat-keepalive <10-3600>Sets the global NAT keep alive interval from 10 - 3600 seconds. This is the interval between successive NAT keep alive messages sent to detect if a peer is dead or alive. The default is 20 seconds.peer <IKEV1-PEER> Specify the name/Identifier for the IKEv1 peer. For IKEV1 peer configuration commands, see crypto-ikev1/ikev2-peer commands.policy <IKEV1-POLICY-NAME>Configures an ISKAMP policy. Specify the name of the policy.The local IKE policy and the peer IKE policy must have matching group settings for successful negotiations.For IKEV1 policy configuration commands, see crypto-ikev1/ikev2-policy commands.remote-vpn Specifies the IKEV1 remote-VPN server configuration (responder only)ikev2 Configures the IKE version 2 parameterscookie-challenge-threshold <1-100>Starts the cookie challenge mechanism after the number of half open IKE SAs exceeds the specified limit. Specify the limit from 1 - 100. The default is 5. dpd-keepalive <10-3600>Sets the global DPD keepalive interval from 10 - 3600 seconds. The default is 30 seconds.dpd-retries <1-100> Sets the global DPD retries count from 1 - 100. The default is 5.nat-keepalive <10-3600>Sets the global NAT keepalive interval from 10 - 3600 seconds. The default is 20 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1172.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 83• crypto ipsec df-bit [clear|copy|set]• crypto ipsec security-association lifetime [kilobytes <500-2147483646>|seconds <120-86400>]• crypto ipsec transform-set <TRANSFORM-SET-TAG> [esp-3des|esp-aes|esp-aes-192|esp-aes-256|esp-des|esp-null] [esp-aes-xcbc-mac|esp-md5-hmac|esp-sha-hmac|esp-sha256-hmac]peer <IKEV2-PEER> Specify the name/Identifier for the IKEv2 peerpolicy <IKEV2-POLICY-NAME>Configures an ISKAMP policy. Specify the policy name.The local IKE policy and the peer IKE policy must have matching group settings for successful negotiations.remote-vpn Specifies an IKEv2 remote-VPN server configuration (responder only)ipsec Configures the IPSec policy parametersdf-bit [clear|copy|set] Configures Don’t-Fragment (DF) bit handling for encapsulating header. The options are:• clear – Clears the DF bit in the outer header and ignores in the inner header• copy – Copies the DF bit from the inner header to the outer header. This is the default setting.• set – Sets the DF bit in the outer headeripsec Configures the IPSec policy parameterssecurity-association Configures the IPSec SAs parameterslifetime [kilobyte |seconds]Defines the IPSec SAs lifetime (in kilobytes and/or seconds). Values can be entered in both kilobytes and seconds, which ever limit is reached first, ends the SA. When the SA lifetime ends it is renegotiated as a security measure.• kilobytes – Specifies a volume-based key duration (minimum is 500 KB and maximum is 2147483646 KB)• <500-2147483646> – Specify a value from 500 - 2147483646 KB. The default is4608000 KB.• seconds – Specifies a time-based key duration (minimum is 120 seconds and maximum is 86400 seconds)• <120-86400> – Specify a value from 120 - 86400 seconds. The default is 3600seconds.The security association lifetime can be overridden under crypto maps.ipsec Configures the IPSec policy parameterstransform-set <TRANSFORM-SET-TAG>Defines the transform set configuration (authentication and encryption) for securing data. A transform set is a combination of security protocols, algorithms and other settings applied to IPSec protected traffic.• <TRANSFORM-SET-TAG> – Specify the transform set name.After specifying the transform set used by the IPSec transport connection, set the encryption method and the authentication scheme used with the transform set.The encryption methods are: DES, 3DES, AES, AES-192 and AES-256.Note: The authentication schemes available are: esp-md5-hmac and esp-sha-hmac.esp-3des Configures the ESP transform using 3DES cipher (168 bits). The transform set is assigned to a crypto map using the map’s set > transform-set command.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1173.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 84• crypto map <CRYPTO-MAP-TAG> <1-1000> [ipsec-isakmp {dynamic}|ipsec-manual]• crypto pki import crl <TRUSTPOINT-NAME> <URL> <1-168>esp-aes Configures the ESP transform using Advanced Encryption Standard (AES) cipher. The transform set is assigned to a crypto map using the map’s set > transform-set command.esp-aes-192 Configures the ESP transform using AES cipher (192 bits). The transform set is assigned to a crypto map using the map’s set > transform-set command.esp-aes-256 Configures the ESP transform using AES cipher (256 bits). The transform set is assigned to a crypto map using the map’s set > transform-set command. This is the default setting.esp-des Configures the ESP transform using Data Encryption Standard (DES) cipher (56 bits). The transform set is assigned to a crypto map using the map’s set > transform-set command.esp-null Configures the ESP transform with no encryption[esp-aes-xcbc-mac|esp-md5-hmac|esp-sha-hmac|esp-sha256-hmac]The following keywords are common to all of the above listed transform sets.After specifying the transform set type, configure the authentication scheme used to validate identity credentials. The options are:• esp-aes-xcbc-mac – Configures ESP transform using AES-XCBC authorization• esp-md5-hmac – Configures ESP transform using HMAC-MD5 authorization• esp-sha-hmac – Configures ESP transform using HMAC-SHA authorization. This is the default setting.• esp-sha256-hmac – Configures ESP transform using HMAC-SHA256 authorizationmap <CRYPTO-MAP-TAG>Configures the crypto map, a software configuration entity that selects data flows that require security processing. The crypto map also defines the policy for these data flows.• <CRYPTO-MAP-TAG> – Specify a name for the crypto map. The name should not exceed 32 characters. For crypto map configuration commands, see crypto-map-ipsec-manual-instance.<1-1000> Defines the crypto map entry sequence. Each crypto map uses a list of entries, each entry having a specific sequence number. Specifying multiple sequence numbers within the same crypto map provides the flexibility to connect to multiple peers from the same interface. Specify a value from 1 - 1000.ipsec-isakmp {dynamic}Configures IPSEC w/ISAKMP.• dynamic – Optional. Configures dynamic map entry (remote VPN configuration) for XAUTH with mode-config or ipsec-l2tp configurationipsec-manual Configures IPSEC w/manual keying. Remote configuration is not allowed for manual crypto map.pki Configures certificate parameters. The Public Key Infrastructure (PKI) protocol creates encrypted public keys using digital certificates from certificate authorities.import Imports a trustpoint related configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1174.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 85• crypto plain-text-deny-acl-scope [global|interface]• crypto remote-vpn-clientExamplerfs6000-37FABE(config-profile-default-rfs6000)#crypto ipsec transform-set tpsec-tag1 esp-aes-256 esp-md5-hmacrfs6000-37FABE(config-profile-default-rfs6000)#crypto map map1 10 ipsec-isakmp dynamicrfs6000-37FABE(config-profile-default-rfs6000)#crypto plain-text-deny-acl-scope interfacerfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 tunnel-over-level2 ip igmp snooping ip igmp snooping querier no autoinstall configuration no autoinstall firmware device-upgrade persist-images crypto ikev1 dpd-retries 1 crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac crypto ipsec transform-set tpsec-tag1 esp-aes-256 esp-md5-hmac crypto map map1 10 ipsec-isakmp dynamic crypto ikev1 remote-vpncrl <TRUSTPOINT-NAME>Imports a Certificate Revocation List (CRL). Imports a trustpoint including either a private key and server certificate or a certificate authority (CA) certificate or both.A CRL is a list of revoked certificates that are no longer valid. A certificate can be revoked if the CA had improperly issued a certificate, or if a private-key is compromised. The most common reason for revocation is the user no longer being in sole possession of the private key.• <TRUSTPOINT-NAME> – Specify the trustpoint name.<URL> Specify the CRL source address in the following format. Both IPv4 and IPv6 address formats are supported.tftp://<hostname|IPv4 or IPv6>[:port]/path/fileftp://<user>:<passwd>@<hostname|IPv4 or IPv6>[:port]/path/filesftp://<user>:<passwd>@<hostname|IPv4 or IPv6>[:port]>/path/filehttp://<hostname|IPv4 or IPv6>[:port]/path/filecf:/path/fileusb<n>:/path/file<1-168> Sets command replay duration from 1 - 168 hours. This is the interval (in hours) after which devices using this profile copy a CRL file from an external server and associate it with a trustpoint.plain-text-deny-acl-scopeConfigures plain-text-deny-acl-scope parametersglobal Applies the plain text deny ACL globally. This is the default setting.interface Applies the plain text deny ACL to the interface onlyremote-vpn-client Configures remote VPN client settings. For more information, see crypto-remote-vpn-client commands.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1175.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 887.1.17.2.1 groupidcrypto-auto-ipsec-tunnel commandsSpecifies the identity string used for IKE authenticationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxgroupid <WORD> [psk|rsa]groupid <WORD> [psk [0 <WORD>|2 <WORD>|<WORD>]|rsa]Parameters• groupid <WORD> [psk [0 <WORD>|2 <WORD>|<WORD>]|rsa]Examplerfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#groupid testgroup@123 rsarfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#show context crypto auto-ipsec-secure groupid testgroup@123 rsarfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#<WORD> Specify a string not exceeding 64 characters. This is the group identity used for IKE exchange for auto IPSec secure peers. After providing a group ID, specify the authentication method used to authenticate peers on the auto IPSec secure tunnel. The options are: psk and rsa.psk [0 <WORD>|2 <WORD>|<WORD>]Configures the pre-shared key (PSK) as the authentication type for secure peer authentication on the auto IPSec secure tunnel• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted key• <WORD> – Specify a string value from 8 - 21 characters.rsa Configures the Rivest-Shamir-Adleman (RSA) key.RSA is an algorithm for public key cryptography. It is the first algorithm known to be suitable for signing, as well as encryption. This is the default setting.NOTE: Only one group ID is supported on the controller or service platform. All APs, controllers, and service platform must use the same group ID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1178.png)



![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 927.1.17.2.5 remotegwcrypto-auto-ipsec-tunnel commandsDefines the IKE version used for auto IPSEC tunnel negotiation with the IPSec remote gateway other than the controllerSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxremotegw ike-version [ikev1-aggr|ikev1-main|ikev2] {uniqueid}Parameters• remotegw ike-version [ikev1-aggr|ikev1-main|ikev2] {uniqueid}Examplerfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#remotegw ike-version ikev2 uniqueidrfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#show context crypto auto-ipsec-secure remotegw ike-version ikev2 uniqueidrfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#remotegw ike-versionConfigures the IKE version used for initiating auto IPSec tunnel with secure gateways other than the controllerikev1-aggr Aggregation mode is used by the auto IPSec tunnel initiator to set up the connectionikev1-main Main mode is used by the auto IPSec tunnel initiator to establish the connectionikev2 IKEv2 is the preferred method when wireless controller/AP only is useduniqueid This keyword is common to all of the above parameters.• uniqueid – Optional. Enables the assigning of a unique ID to APs (using this profile) behind a router by prefixing the MAC address to the group IDProviding a unique ID enables the access point, wireless controller, or service platform to uniquely identify the destination device. This is essential in networks where there are multiple APs behind a router, or when two (or more) APs behind two (or more) different routers have the same IP address. For example, let us consider a scenario where there are two APs (A and B) behind two routers (1 and 2). AP ‘A’ is behind router ‘1’. And AP ‘B’ is behind router ‘2’. Both these APs have the same IP address (192.168.13.8). In such a scenario, the controller fails to establish an Auto IPSec VPN tunnel to either APs, because it is unable to uniquely identify them.After enabling unique ID assignment, enable IKE unique ID check. For more information, see crypto.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1182.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 937.1.17.2.6 nocrypto-auto-ipsec-tunnel commandsRemoves or resets this auto IPSec tunnel settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [groupid|ike-lifetime|ikev2 peer reauth|ip nat crypto]Parameters• no <PARAMETERS>ExampleThe following example shows the Auto IPSec VLAN bridge settings before the ‘no’ command is executed:rfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#show context crypto auto-ipsec-secure groupid testpassword@123 rsarfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#rfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#no groupidThe following example shows the Auto IPSec VLAN bridge settings after the ‘no’ command is executed:rfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#show context crypto auto-ipsec-securerfs6000-37FABE(config-profile-default-rfs6000-crypto-auto-ipsec-secure)#no <PARAMETERS> Removes or resets this auto IPSec tunnel’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1183.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 987.1.17.3.3 isakmp-proposalcrypto-ikev1/ikev2-policy commandsConfigures ISAKMP proposals and their parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxisakmp-proposal <WORD> encryption [3des|aes|aes-192|aes-256] group [14|2|5] hash [aes-xcbc-mac|md5|sha|sha256]Parameters• isakmp-proposal <WORD> encryption [3des|aes|aes-192|aes-256] group [14|2|5] hash [aes-xcbc-mac|md5|sha|sha256]<WORD> Assigns the target peer (tunnel destination) a 32 character maximum name to distinguish it from others with a similar configuration.encryption [3des|aes|aes-192|aes-256]Configures the encryption method used by the tunneled peers to securely inter-operate• 3des – Configures triple data encryption standard• aes – Configures AES (128 bit keys)• aes-192 – Configures AES (192 bit keys)• aes-256 – Configures AES (256 bit keys). This is the default setting.group [14|2|5] Specifies the Diffie-Hellman (DH) group identifier used by VPN peers to derive a shared secret password without having to transmit. DH groups determine the strength of the key used in key exchanges. The higher the group number, the stronger and more secure the key. Options include 2, 5 and 14.• 14 – Configures DH group 14• 2 – Configures DH group 2. This is the default setting.• 5 – Configures DH group 5hash [maes-xcbc-mac|md5|sha|sha256]Specifies the hash algorithm used to authenticate data transmitted over the IKE SA. The hash algorithm specified here is used by VPN peers to exchange credential information.• aes-xcbc-mac – Uses AES XCBC Auth hash algorithm. This option is applicable only to the IKEv2 policy configuration context.•md5 – Uses Message Digest 5 (MD5) hash algorithm• sha – Uses Secure Hash Authentication (SHA) hash algorithm. This is the default setting.• sha256 – Uses Secure Hash Standard 2 algorithm](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1188.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1017.1.17.3.5 modecrypto-ikev1/ikev2-policy commandsConfigures the IPSec mode of operation for the IKEv1 policy. This option is not available for IKEv2 policy.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmode [aggresive|main]Parameters• mode [aggresive|main]Examplerfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#mode aggressiverfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#show context crypto ikev1 policy testpolicy dpd-keepalive 11 dpd-retries 10 lifetime 655 isakmp-proposal default encryption aes-256 group 2 hash sha isakmp-proposal testpraposal encryption aes group 2 hash sha mode aggressiverfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#mode [aggresive|main] Sets the mode of the tunnels• aggressive – Initiates the aggressive mode• main – Initiates the main modeIf configuring the IKEv1 IPSec policy, define the IKE mode as either main or aggressive. In the aggressive mode, 3 messages are exchanged between the IPSec peers to setup the SA. On the other hand, in the main mode, 6 messages are exchanged. The default setting is main.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1191.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1027.1.17.3.6 nocrypto-ikev1/ikev2-policy commandsRemoves or reverts IKEv1/IKEv2 policy settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [dpd-keepalive|dpd-retries|isakmp-proposal <WORD>|lifetime|mode]Parameters• no <PARAMETERS>ExampleThe following example shows the IKEV1 Policy settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#show context crypto ikev1 policy testpolicy dpd-keepalive 11 dpd-retries 10 lifetime 655 isakmp-proposal default encryption aes-256 group 2 hash sha isakmp-proposal testpraposal encryption aes group 2 hash sha mode aggressiverfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#rfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#no moderfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#no dpd-keepaliverfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#no dpd-retriesThe following example shows the IKEV1 Policy settings after the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#show context crypto ikev1 policy testpolicy lifetime 655 isakmp-proposal default encryption aes-256 group 2 hash sha isakmp-proposal testpraposal encryption aes group 2 hash sharfs6000-37FABE(config-profile-default-rfs6000-ikev1-policy-ikev1-testpolicy)#no <PARAMETERS> Removes or reverts this IKEv1/IKEv2 policy settings based on parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1192.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1057.1.17.4.1 authenticationcrypto-ikev1/ikev2-peer commandsConfigures IKEv1/IKEv2 peer’s authentication mode and the pre-shared keySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthentication [psk|rsa]authentication psk [0 <WORD>|2 <WORD>|<WORD>] {local|remote}authentication rsaParameters• authentication psk [0 <WORD>|2 <WORD>|<WORD>] {local|remote}• authentication rsaExamplerfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#authentication rsarfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#authenticationpsk 0 key@123456rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#show context crypto ikev2 peer peer1 authentication psk 0 key@123456 local authentication psk 0 key@123456 remoterfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#psk [0 <WORD>|2 <WORD>|<WORD>] {local|remote}Configures the authentication mode as pre-shared key (PSK). The PSK is a string, 8 - 12 characters long. It is shared by both ends of the VPN tunnel connection. If using IKEv2, both a local and remote string must be specified for handshake validation at both ends (local and remote) of the VPN connection.• 0 <WORD> – Configures a clear text key• 2 <WORD> – Configures an encrypted key• <WORD> – Configures the pre-shared keyThe following keywords are available only in the IKEv2 peer configuration mode:• local – Optional. Uses the specified key for local peer authentication only• remote – Optional. Uses the specified key for remote peer authentication onlyNote: In case the peer type is not specified, this string is used for authenticating both local and remote peers.rsa Configures the authentication mode as Rivest, Shamir, and Adleman (RSA) This is the default setting (for both IKEv1 and IKEv2).RSA is the first known public-key cryptography algorithm designed signing and encryption. If configuring the IKEv2 peer, the ‘rsa’ option allows you to enable authentication at both ends of the VPN connection (local and remote).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1195.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1067.1.17.4.2 ipcrypto-ikev1/ikev2-peer commandsSets the IP address or Fully Qualified Domain Name (FQDN) of the IPSec VPN peer used in the tunnel setup Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [address <IP>|fqdn <WORD>]Parameters• ip [address <IP>|fqdn <WORD>]Examplerfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#ip address 172.16.10.12rfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#show context crypto ikev1 peer peer1 ip address 172.16.10.12rfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#ip address 192.168.10.6rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#show context crypto ikev2 peer peer1 ip address 192.168.10.6 authentication psk 0 test@123456 local authentication psk 0 test@123456 remoterfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#address <IP> Specify the peer device’s IP address.fqdn <WORD> Specify the peer device’s FQDN hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1196.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1077.1.17.4.3 localidcrypto-ikev1/ikev2-peer commandsSets a IKEv1/IKEv2 peer’s local identity. This local identifier is used with this peer configuration for an IKE exchange with the target VPN IPSec peer.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlocalid [address|autogen-uniqueid|dn|email|fqdn|string]localid [address <IP>|autogen-uniqueid <WORD>|dn <WORD>|email <WORD>|fqdn <WORD>|string <WORD>]Parameters• localid [address <IP>|dn <WORD>|email <WORD>|fqdn <WORD>|string <WORD>]Examplerfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#localid email bob@examplecompany.comrfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#show context crypto ikev1 peer peer1 ip address 172.16.10.12 localid email bob@examplecompany.comrfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#address <IP> Configures the peer’s IP address. The IP address is used as local identity.autogen-uniqueid <WORD>Generates a localid using the device's unique identity. The system prefixes the device's unique identity to the string provided here. The device’s unique identity should be existing and configured. For more information on configuring a device’s unique identity, see autogen-uniqueid.• <WORD> – Provide the string.dn <WORD> Configures the peer’s distinguished name. (for example, "C=us ST=<state> L=<location> O=<organization> OU=<org unit>". The maximum length is 128 characters.email <WORD> Configures the peer’s e-mail address. The maximum length is 128 characters.fqdn <WORD> Configures the peer’s FQDN. The maximum length is 128 characters.string <WORD> Configures the peer’s identity string. The maximum length is 128 characters. This is the default setting.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1197.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1087.1.17.4.4 rem o tei dcrypto-ikev1/ikev2-peer commandsConfigures a IKEv1/IKEV2 peer’s remote identity. This remote identifier is used with this peer configuration for an IKE exchange with the target VPN IPSec peer.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxremoteid [address <IP>|dn <WORD>|email <WORD>|fqdn <WORD>|string <WORD>]Parameters• remoteid [address <IP>|dn <WORD>|email <WORD>|fqdn <WORD>|string <WORD>Examplerfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#remoteid dn SanJoserfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#show context crypto ikev1 peer peer1 ip address 172.16.10.12 remoteid dn SanJose localid email bob@examplecompany.comrfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#rfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#remoteid address 157.235.209.63rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#show context crypto ikev2 peer peer1 remoteid address 157.235.209.63rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#address <IP> Configures the remote IKEv1/IKEV2 peer’s IP address. The IP address is used as the peer’s remote identity.dn <WORD> Configures the remote peer’s distinguished name. For example, "C=us ST=<state> L=<location> O=<organization> OU=<org unit>". The maximum length is 128 characters.email <WORD> Configures the remote peer’s e-mail address. The maximum length is 128 characters.fqdn <WORD> Configures a peer’s FQDN. The maximum length is 128 characters.string <WORD> Configures a peer’s identity string. The maximum length is 128 characters.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1198.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1107.1.17.4.6 nocrypto-ikev1/ikev2-peer commandsRemoves or reverts IKEv1/IKEv2 peer settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [authentication|ip|localid|remoteid|use <IKEv1/IKEv2-POLICY-NAME>]Parameters• no <PARAMETERS>ExampleThe following example shows the Crypto IKEV1 peer1 settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#show context crypto ikev1 peer peer1 ip address 172.16.10.12 remoteid dn SanJose localid email bob@examplecompany.com use ikev1-policy test-ikev1policyrfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#rfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#no localidrfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#no remoteidThe following example shows the Crypto IKEV1 peer1 settings after the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#show context crypto ikev1 peer peer1 ip address 172.16.10.12 use ikev1-policy test-ikev1policyrfs6000-37FABE(config-profile-default-rfs6000-ikev1-peer-peer1)#The following example shows the Crypto IKEV2 peer1 settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#show context crypto ikev2 peer peer1 remoteid address 157.235.209.63 use ikev2-policy testrfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#The following example shows the Crypto IKEV2 peer1 settings after the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs7000-ikev2-peer-peer1)#no use ikev2-policyrfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#show context crypto ikev2 peer peer1 remoteid address 157.235.209.63rfs6000-37FABE(config-profile-default-rfs6000-ikev2-peer-peer1)#no <PARAMETERS> Removes or reverts IKEv1/IKEv2 peer settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1200.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1117.1.17.5 crypto-map-config-commandscryptoThis section explains crypto map configuration mode commands in detail.A crypto map entry is a single policy that describes how certain traffic is secured. There are two types of crypto map entries: ipsec-manual and ipsec-ike. Each entry is given an index (used to sort the ordered list).IPSec VPN provides a secure tunnel between two networked peers. Administrators can define which packets are sent within the tunnel, and how they're protected. When a tunneled peer sees a sensitive packet, it creates a secure tunnel and sends the packet through the tunnel to its remote peer destination.Tunnels are sets of SA between two peers. SAs define the protocols and algorithms applied to sensitive packets and specify the keying mechanisms used by tunneled peers. SAs are unidirectional and exist in both the inbound and outbound direction. SAs are established per the rules and conditions of defined security protocols (AH or ESP).IKE is a key management protocol standard used in conjunction with IPSec. IKE enhances IPSec by providing additional features, flexibility, and configuration simplicity for the IPSec standard. IKE automatically negotiates IPSec SAs, and enables secure communications without time consuming manual pre-configuration.Use crypto maps to configure IPSec VPN SAs. Crypto maps combine the elements comprising IPSec SAs. Crypto maps also include transform sets. A transform set is a combination of security protocols, algorithms and other settings applied to IPSec protected traffic. One crypto map is utilized for each IPSec peer, however for remote VPN deployments one crypto map is used for all the remote IPSec peers.Use the (config) instance to enter the crypto map configuration mode. To navigate to the crypto-map configuration instance, use the following commands:In the device-config mode:<DEVICE>(config-device-<DEVICE-MAC>)#crypto map <CRYPTO-MAP-TAG> <1-1000> [ipsec-isakmp {dynamic}|ipsec-manual]In the profile-config mode:<DEVICE>(config-profile-<PROFILE-NAME>)#crypto map <CRYPTO-MAP-TAG> <1-1000> [ipsec-isakmp {dynamic}|ipsec-manual]There are three different configurations defined for each listed crypto map: site-to-site manual (ipsec-manual), site-to-site-auto tunnel (ipsec-isakmp), and remote VPN client (ipsec-isakmp dynamic). With site-to-site deployments, an IPSec tunnel is deployed between two gateways, each at the edge of two different remote networks. With remote VPN, an access point located at remote branch defines a tunnel with a security gateway. This facilitates the end points in the branch office to communicate with the destination endpoints (behind the security gateway) in a secure manner.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1201.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1177.1.17.5.4 mod e conf i gcrypto-map auto-vpn-tunnel/remote-vpn-client instanceConfigures the mode config method (pull or push) associated with the remote VPN clientSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmodeconfig [pull|push]Parameters• modeconfig [pull|push]ExampleRemote VPN client:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#modeconfig pullrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#show context crypto map test 2 ipsec-isakmp dynamic modeconfig pullrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)modeconfig [pull|push]Configures the mode config method associated with a remote VPN client. The options are: pull and push.The mode (pull or push) defines the method used to assign a virtual IP. This setting is relevant for IKEv1 only, since IKEv2 always uses the configuration payload in pull mode. The default setting is push.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1207.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1187.1.17.5.5 peercrypto-map auto-vpn-tunnel/remote-vpn-client instanceConfigures the IKEv1 or IKEv2 peer for the auto site-to-site VPN tunnel or remote VPN client. The peer device can be specified either by its hostname or by its IP address. A maximum of three peers can be configured.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpeer <1-3> [ikev1|ikev2] <IKEv1/IKEv2-PEER-NAME>Parameters• peer <1-3> [ikev1|ikev2] <IKEv1/IKEv2-PEER-NAME>ExampleSite-to-site tunnel:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#peer 1 ikev2 ikev2Peer1rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#show context crypto map test 1 ipsec-isakmp peer 1 ikev2 ikev2Peer1 local-endpoint-ip 192.168.13.10 ip nat cryptorfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#Remote VPN client:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#peer 1 ikev1 RemoteIKEv1Peer1rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#show context crypto map test 2 ipsec-isakmp dynamic peer 1 ikev1 RemoteIKEv1Peer1 local-endpoint-ip 157.235.204.62rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#peer <1-3> Creates a new peer and configures the peer’s priority level. Peer ‘1’ is the primary peer, and peer ‘3’ is redundant.ikev1 <IKEv1-PEER-NAME>Configures an IKEv1 peer• <IKEv1-PEER-NAME> – Specify the IKEv1 peer’s name.ikev2<IKEv2-PEER-NAME>Configures an IKEv2 peer• <IKEv2-PEER-NAME> – Specify the IKEv2 peer’s name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1208.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1197.1.17.5.6 pfscrypto-map auto-vpn-tunnel/remote-vpn-client instanceConfigures Perfect Forward Secrecy (PFS) for the auto site-to-site VPN tunnel or remote VPN clientPFS is the key-establishment protocol, used to secure VPN communications. If one encryption key is compromised, only data encrypted by that specific key is compromised. For PFS to exist, the key used to protect data transmissions must not be used to derive any additional keys. Options include 2, 5 and 14. This option is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpfs [14|2|5]Parameters• pfs [14|2|5]ExampleSite-to-site VPN tunnel:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#pfs 5rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#show context crypto map test 1 ipsec-isakmp peer 1 ikev2 ikev2Peer1 local-endpoint-ip 192.168.13.10 pfs 5 ip nat cryptorfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#Remote VPN client:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#pfs 14rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#show context crypto map test 2 ipsec-isakmp dynamic peer 1 ikev1 RemoteIKEv1Peer1 local-endpoint-ip 157.235.204.62 pfs 14rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#pfs [14|2|5] Configures PFS• 14 – Configures D-H Group14 (2048-bit modp)• 2 – Configures D-H Group2 (1024-bit modp)• 5 – Configures D-H Group5 (1536-bit modp)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1209.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1207.1.17.5.7 remo te-typ ecrypto-map auto-vpn-tunnel/remote-vpn-client instanceConfigures the remote VPN client type as either None or XAuthSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxremote-type [none|xauth]Parameters• remote-type [none|xauth]ExampleRemote VPN client:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#remote-type nonerfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#show context crypto map test 2 ipsec-isakmp dynamic peer 1 ikev1 RemoteIKEv1Peer1 local-endpoint-ip 157.235.204.62 pfs 14 remote-type nonerfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#2)#remote-type [none|xauth]Specify the remote VPN’s client type• none – Configures remote VPN client with No XAUTH• xauth – Configures remote VPN client as using XAUTH (applicable only for IKEv1). This is the default setting.XAuth (extended authentication) provides additional authentication validation by permitting an edge device to request extended authentication information from an IPSec host. This forces the host to respond with additional authentication credentials. The edge device respond with a failed or passed message.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1210.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1217.1.17.5.8 security-associationcrypto-map auto-vpn-tunnel/remote-vpn-client instanceDefines the IPSec SA’s (created by this auto site-to-site VPN tunnel or remote VPN client) settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsecurity-association [inactivity-timeout|level|lifetime]security-association [inactivity-timeout <120-86400>|level perhost]security-association lifetime [kilobytes <500-2147483646>|seconds <120-86400>]Parameters• security-association [inactivity-timeout <120-86400>|level perhost]• security-association lifetime [kilobytes <500-2147483646>|seconds <120-86400>]ExampleSite-to-site tunnel:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#security-association inactivity-timeout 200rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#security-association level perhostrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#security-association lifetime kilobytes 250000inactivity-timeout <120-86400>Specifies an inactivity period, in seconds, for this IPSec VPN SA. Once the set value is exceeded, the association is timed out.• <120-86400> – Specify a value from 120 - 86400 seconds. The default is 900 seconds.level perhost Specifies the granularity level for this IPSec VPN SA• perhost – Sets the IPSec VPN SA’s granularity to the host levellifetime [kilobytes <500-2147483646>|seconds <120-86400>]Defines the IPSec SA’s lifetime (in kilobytes and/or seconds). Values can be entered in both kilobytes and seconds. Which ever limit is reached first, ends the security association.• kilobytes <500-2147483646> – Defines volume based key duration. Specify a value from 500 - 2147483646 kilobytes. Select this option to define a connection volume lifetime (in kilobytes) for the duration of the IPSec VPN SA. Once the set volume is exceeded, the association is timed out. This option is disabled by default.• seconds <120-86400> – Defines time based key duration. Specify the time frame from 120 - 86400 seconds. Select this option to define a lifetime (in seconds) for the duration of the IPSec VPN SA. Once the set value is exceeded, the association is timed out. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1211.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1257.1.17.5.11 n ocrypto-map auto-vpn-tunnel/remote-vpn-client instanceRemoves or reverts the auto site-to-site VPN tunnel or remote VPN client settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [ip|local-endpoint-ip|modeconfig|peer|pfs|remote-type|security-association|transform-set|use]Parameters• no <PARAMETERS>ExampleThe following example shows the IPSec site-to-site VPN tunnel ‘test’ settings before the ‘no’ commands are executed:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#show context crypto map test 1 ipsec-isakmp use ip-access-list test security-association level perhost peer 1 ikev2 ikev2Peer1 local-endpoint-ip 192.168.13.10 pfs 5 security-association lifetime kilobytes 250000 security-association inactivity-timeout 200 transform-set AutVPN ip nat cryptorfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#no use ip-access-listrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#no security-association level perhostrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#no ip nat cryptorfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#no pfsrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#no local-endpoint-ipThe following example shows the IPSec site-to-site VPN tunnel ‘test’ settings after the ‘no’ commands are executed:rfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#show context crypto map test 1 ipsec-isakmp peer 1 ikev2 ikev2Peer1 security-association lifetime kilobytes 250000 security-association inactivity-timeout 200 transform-set AutoVPNrfs4000-229D58(config-device-00-23-68-22-9D-58-cryptomap-test#1)#no <PARAMETERS> Removes or resets this auto site-to-site/remote VPN settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1215.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1297.1.17.5.14 m od ecrypto-map-ipsec-manual-instanceSets the crypto map tunnel modeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmode [transport|tunnel]Parameters• mode [transport|tunnel]Examplerfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#mode transportrfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#show context crypto map map1 1 ipsec-manual mode transportrfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#mode [transport|tunnel] Sets the mode of the tunnel for this crypto map• transport – Initiates transport mode• tunnel – Initiates tunnel mode (default setting)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1219.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1317.1.17.5.16 security-associationcrypto-map-ipsec-manual-instanceDefines the lifetime (in kilobytes and/or seconds) of IPSec SAs created by this crypto mapSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsecurity-association lifetime [kilobytes <500-2147483646>|seconds <120-86400>]Parameters• security-association lifetime [kilobytes <500-2147483646>|seconds <120-86400>]Examplerfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map2#2)#security-association lifetime seconds 123rfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map2#2)#show context Command not applicable to this crypto maprfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map2#2)#lifetime [kilobytes <500-2147483646>|seconds <120-86400>]Values can be entered in both kilobytes and seconds. Which ever limit is reached first, ends the security association.• kilobytes <500-2147483646> – Defines volume based key duration. Specify a value from 500 - 2147483646 bytes.• seconds <120-86400> – Defines time based key duration. Specify the time frame from 120 - 86400 seconds.NOTE: This command is not applicable to the ipsec-manual crypto map.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1221.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1327.1.17.5.17 s essi o n -keycrypto-map-ipsec-manual-instanceDefines encryption and authentication keys for this crypto map Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsession-key [inbound|outbound] [ah|esp] <256-4294967295>session-key [inbound|outbound] ah <256-4294967295> [0|2|authenticator [md5|sha]] <WORD>session-key [inbound|outbound] esp <256-4294967295> [0|2|cipher [3des|aes|aes-192|aes-256|des|esp-null]] <WORD> authenticator [md5|sha] <WORD>Parameters• session-key [inbound|outbound] ah <256-4294967295> [0|2|authenticator [md5|sha]] <WORD>• session-key [inbound|outbound] esp <256-4294967295> [0|2|cipher [3des|aes|aes-192|aes-256|des|esp-null]] <WORD> authenticator [md5|sha] <WORD>session-key [inbound|outbound]Defines the manual inbound and outbound security association key parametersah <256-4294967295>Configures authentication header (AH) as the security protocol for the security session• <256-4294967295> – Sets the SPI for the security association from 256 - 4294967295The SPI (in combination with the destination IP address and security protocol) identifies the security association.[0|2|authenticator [md5|sha] <WORD>]Specifies the key type•0 – Sets a clear text key•2 – Sets an encrypted key• authenticator – Sets AH authenticator details• md5 <WORD> – AH with MD5 authentication• sha <WORD> – AH with SHA authentication• <WORD> – Sets security association key value. The following key lengths (in hexcharacters) are required (w/o leading 0x).AH-MD5: 32, AH-SHA: 40session-key [inbound|outbound]Defines the manual inbound and outbound security association key parametersesp <256-4294967295>Configures Encapsulating Security Payloads (ESP) as the security protocol for the security session. This is the default setting.• <256-4294967295> – Sets the SPI for the security association from 256 - 4294967295The SPI (in combination with the destination IP address and security protocol) identifies the security association.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1222.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 133Examplerfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#session-key inbound esp 273 cipher esp-null authenticator sha 58768979rfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#show context crypto map map1 1 ipsec-manual peer 172.16.10.2 mode transport session-key inbound esp 273 0 cipher esp-null authenticator sha 58768979rfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#[0|2|cipher [3des|aes|aes-192|aes-256|des|esp-null]]•0 – Sets a clear text key•2 – Sets an encrypted key• cipher – Sets encryption/decryption key details• 3des – ESP with 3DES encryption• aes – ESP with AES encryption• aes-192 – ESP with AES-192 encryption• aes-256 – ESP with AES-256 encryption• des – ESP with DES encryption• esp-null – ESP with no encryption• authenticator – Specify ESP authenticator details• md5 <WORD> – ESP with MD5 authentication•sha <WORD> – ESP with SHA authentication• <WORD> – Sets security association key value. The following key lengths(in hex characters) are required (w/o leading 0x).AH-MD5: 32, AH-SHA:40](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1223.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1357.1.17.5.19 n ocrypto-map-ipsec-manual-instanceRemoves or resets this crypto map’s settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [local-endpoint-ip|mode|peer|security-association|session-key|use]Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#show context crypto map map1 1 ipsec-manual use ip-access-list test peer 172.16.10.12 mode transport session-key inbound esp 273 0 cipher esp-null authenticator sha 5876897rfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#rfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#no use ip-access-listrfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#no peerrfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#no moderfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#show context crypto map map1 1 ipsec-manual session-key inbound esp 273 0 cipher esp-null authenticator sha 58768979rfs6000-37FABE(config-profile-default-rfs6000-cryptomap-map1#1)#no <PARAMETERS> Removes or resets this crypto map settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1225.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1387.1.17.6.1 d h c p- p ee rcrypto-remote-vpn-client commandsConfigures DHCP peer’s local ID and authentication settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdhcp-peer [authentication|localid]dhcp-peer authentication [psk [0 <WORD>|2 <WORD>|<WORD>]|rsa]dhcp-peer localid [autogen-uniqueid <WORD>|string <WORD>]Parameters• dhcp-peer authentication [psk [0 <WORD>|2 <WORD>|<WORD>]|rsa]• dhcp-peer localid [autogen-uniqueid <WORD>|string <WORD>]Examplerfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#dhcp-peer authentication psk 0 @123testingrfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#show context crypto remote-vpn-client dhcp-peer authentication psk 0 @123testingrfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#dhcp-peer authentication psk[0 <WORD>|2 <WORD>|<WORD>]Configures the DHCP peer’s authentication type as PSK• 0 <WORD> – Configures a clear text authentication key• 2 <WORD> – Configures an encrypted authentication key• <WORD> – Provide a 8 - 21 character shared key password for DHCP peer authenticationdhcp-peer authentication rsaConfigures the DHCP peer’s authentication type as RSA. This is the default setting.dhcp-peer localid [autogen-uniqueid <WORD>|string <WORD>]Configures the DHCP peer's localid using one of the following options:• autogen-uniqueid - Generates a localid using the device's unique identity. The system prefixes the device's unique identity to the string provided here. The device’s unique identity should be existing and configured. For more information on configuring a device’s unique identity, see autogen-uniqueid.• <WORD> – Provide the string.• string - Uses the value provided here as the DHCP peer’s localid.• <WORD> - Provide the string.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1228.png)



![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1427.1.17.6.5 nocrypto-remote-vpn-client commandsRemoves the remote VPN client settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [dhcp-peer|peer <1-3>|shutdown|transform-set]no dhcp-peer [authentication|localid]no peer <1-3>no shutdownno transform-setParameters• no <PARAMETERS>Examplerfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#show context crypto remote-vpn-client peer 1 ikev2 peer5rfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#rfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#no peer 1rfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#show context crypto remote-vpn-clientrfs4000-229D58(config-profile-testRFS4000-crypto-ikev2-remote-vpn-client)#no <PARAMETERS> Removes or resets this remote VPN client settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1232.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1437.1.18 databaseProfile Config CommandsBacks up captive-portal and/or NSight database to a specified location and file. When applied to devices, this profile will enable the back up of the specified database. This command also enables you to configures a low-disk-space threshold value.These parameters can also be configured in the device configuration context of an NX95XX series service platform.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdatabase [backup|low-disk-space-threshold]database backup database [captive-portal|nsight] <URL>database low-disk-space-threshold <10-50>Parameters• database backup database [captive-portal|nsight] <URL>• database low-disk-space-threshold <10-50>Examplenx9500-6C8809(config-profile-testNX9500)#database backup database nsight ftp://anonymous:anonymous@192.168.13.10/backups/nsight/nsight.tar.gzRelated Commandsdatabase backup database [captive-portal|nsight]Backs up captive portal and/or NSight database to a specified location and file. Select the database to backup.• database – Selects the database to backup• captive-portal – Backs up captive portal database• nsight – Backs up NSight databaseAfter specifying the database type, configure the destination location and file name.<URL> Configures the destination location. The database is backed up at the specified location. Specify the location URL in one of the following formats:ftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gzsftp://<user>:<passwd>@<hostname|IP>[:port]/path/file.tar.gztftp://<hostname|IP>[:port]/pathdatabase low-disk-space-threshold <10-50>Configures the low disk space threshold for syslog warning. Once the threshold value configured here is reached a syslog warning is sent.• <10-50> – Specify the threshold from 10 - 50. The default is 30.no Removes database backup configurations](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1233.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1447.1.19 device-onboardProfile Config CommandsConfigures the logo image file name and title displayed on the EGuest device-onboarding portal. The EGuest UI can be accessed only by vendor-admin users.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxdevice-onboard [logo|title] <WORD>Parameters• device-onboard [logo|title] <WORD>ExampleSplit-EG-Server(config-device-00-0C-29-09-3C-CC)#device-onboard logo extremenetworks.pngSplit-EG-Server(config-device-00-0C-29-09-3C-CC)#device-onboard title EXTREME NETWORKS ONBOARDING UISplit-EG-Server(config-device-00-0C-29-09-3C-CC)#show context include-factory | include device-onboard device-onboard title EXTREME NETWORKS ONBOARDING UI device-onboard logo extremenetworks.pngSplit-EG-Server(config-device-00-0C-29-09-3C-CC)#Following example shows a Management Policy, vendor-admin user configuration:EC-NOC(config-management-policy-EGuest)#show context include-factory | include user user onboard-user password 1 1d5e9d60425bde727261b66b5e7eb0236058e7aae45225961ce7b872ea238240 role vendor-admin group Samsung,Philips,Nest1,Orbit1EC-NOC(config-management-policy-EGuest)#Related CommandsNOTE: Vendor admin users are configured in the Management policy context. For more information, see user.device-onboard [logo|title] <WORD>Configures the logo and page title displayed on the device-onboarding portal• logo – Specify the logo image file name. Note, logo image dimensions must not exceed 109 pixel and 52 pixel in width and height respectively.• title – Specify the UI portal title. Note, the title should not exceed 32 characters in length.The following keyword is common to both of the above parameters:• <WORD> – Specify the logo image file name/page title.no Removes the device-onboarding UI portal’s logo image file name and title configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1234.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1457.1.20 device-upgradeProfile Config CommandsConfigures device firmware upgrade settings on this profileAdministrators can customize profiles with unique device configuration file and firmware upgrade support. In a clustered environment, operations performed on one device are propagated to each member of the cluster and then onwards to devices managed by each cluster member. The number of concurrent device upgrades and their start times can be customized to ensure a sufficient number of devices remain in duty while upgrades are administered to others.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdevice-upgrade [add-auto|auto|count|persist-images]device-upgrade add-auto [(ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600)]device-upgrade auto {(ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600)}device-upgrade count <1-128>device-upgrade persist-imagesParameters• device-upgrade add-auto[(ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx75xx|nx9000|nx9600)]device-upgrade add-autoConfigures a list of devices types for automatic firmware upgradeThis command specifies the types of devices that can be automatically upgraded (if enabled). To enable automatic device firmware upgrade, use the ‘auto’ command. When enabled, access points, wireless controllers, and service platforms, using this profile, will automatically upgrade firmware on adopted devices that match the specified device types.[<DEVICE-TYPE>] Specifies the type of devices to be upgraded. Select the device type. The options are: AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, NX9600, VX9000.Note: Multiple device types can be added to the add-auto list.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1235.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1487.1.22 dot1xProfile Config CommandsConfigures 802.1x standard authentication controlsDot1x (or 802.1x) is an IEEE standard for network authentication. It enables media-level (layer 2) access control, providing the capability to permit or deny connectivity based on user or device identity. Dot1x allows port-based access using authentication. An dot1x enabled port can be dynamically enabled or disabled depending on user identity or device connection.Devices supporting dot1x allow the automatic provision and connection to the wireless network without launching a Web browser at login. When within range of a dot1x network, a device automatically connects and authenticates without needing to manually login.Before authentication, the endpoint is unknown, and traffic is blocked. Upon authentication, the endpoint is known and traffic is allowed. The controller or service platform uses source MAC filtering to ensure only the authenticated endpoint is allowed to send traffic.Dot1x authentication capabilities is supported on the following platforms:Supported in the following platforms:• Access Points — AP6511, AP6521, AP6522, AP6562, AP7161, AP7502, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432• Wireless Controllers — RFS4000, RFS6000, NX5500, NX7500Dot1x supplicant capabilities is supported on the following platforms:Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, NX5500, NX7500Syntaxdot1x [guest-vlan|holdtime|system-auth-control|use]dot1x holdtime <0-600>dot1x system-auth-controldot1x guest-vlan supplicantdot1x use aaa-policy <AAA-POLICY-NAME>Parameters• dot1x system-auth-control• dot1X holdtime <0-600>system-auth-control Enables system auth control. Enables dot1x authorization globally for the controller. This feature is disabled by default.holdtime <0-600> Configures a holdtime value. This is the interval after which an authentication attempt is ignored or failed.• <0-600> – Specify a value from 0 - 600 seconds. A value of ‘0’ indicates no holdtime. The default is 600 seconds or 10 minutes.Adding a hold time at startup allows time for the network to converge before receiving or transmitting 802.1x authentication packets.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1238.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1507.1.23 dpiProfile Config CommandsEnables Deep Packet Inspection (DPI) on this profile. DPI is an advanced packet analysis technique, which analyzes packet and packet content headers to determine the nature of network traffic. When enabled, DPI inspects packets of all flows to identify applications (such as, Netflix, Twitter, Facebook, etc.) and extract metadata (such as, host name, server name, TCP-RTT, etc.) for further use by the WiNG firewall.This command is also available in the device configuration mode.Supported in the following platforms:• Access Points — AP7522, AP7532, AP7602, AP7612, AP7622, AP7632, AP7662• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxdpi {custom-app|logging|metadata}dpi {custom-app <CUSTOM-APP-NAME>}dpi {logging [level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]|on]}dpi {metadata [http|ssl|tcp-rtt|voice-video]}dpi {metadata [http|ssl|voice-video]}dpi {metadata tcp-rtt {app-group <APPLICATION-GROUP-NAME>}}Parameters• dpi {custom-app <CUSTOM-APP-NAME>}• dpi {logging [level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]|on]}dpi Enables DPI on this profile/device context and configures DPI settings. When enabled, all flow traffic is subjected to DPI for detection of applications, application categories, custom applications, and metadata extraction. custom-app <CUSTOM-APP-NAME>Optional. Adds custom application to this profile• <CUSTOM-APP-NAME> – Specify custom application name (should be existing and configured)If no custom application is specified, the system detects the PACE built-in applications.Note: For more information on application categories and application detection, see application.dpi Enables DPI on this profile/device context and configures DPI settings. When enabled, all flow traffic is subjected to DPI for detection of applications, application categories, custom applications, and metadata extraction.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1240.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 151• dpi {metadata [http|ssl|voice-video]}• dpi {metadata tcp-rtt {app-group <APPLICATION-GROUP-NAME>}}logging [level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]|on] Optional. Enables DPI logging and sets the logging level• level – Configures the DPI logging level. Use one of the following options to specify the logging level:• <0-7> Logging severity level• alerts Immediate action needed (1)• critical Critical conditions (2)• debugging Debugging messages (7)• emergencies System is unusable (0)• errors Conditions (3)• nformational Informational messages (6)• notifications Normal but significant conditions (5) - Default setting• warnings Warning conditions (4)Either specify the logging level index (from 0 - 7) or the description. For example, to log all alerts either enter ‘1’ or ‘alerts’.• on – Enables application detection event logging. DPI logging is disabled by de-fault.dpi Enables DPI on this profile/device context and configures DPI settings. When enabled, all flow traffic is subjected to DPI for detection of applications, application categories, custom applications, and metadata extraction.metadata [http|ssl|voice-video]Optional. Enables metadata extraction from following flows:• http – HTTP flows. This option is disabled by default.• ssl – SSL flows. This option is disabled by default.• voice-video – Voice and video classified flows. This option is disabled by default.dpi Enables DPI on this profile/device context and configures DPI settings. When enabled, all flow traffic is subjected to DPI for detection of applications, application categories, custom applications, and metadata extraction. metadata tcp-rtt {app-group <APPLICATION-GROUP-NAME>}Optional. Enables Transmission Control Protocol - Round Trip Time (TCP-RTT) metadata collection for application groups. Before executing this command, ensure that you have created at least one application group.Enable this option in the profile/device contexts of the AP7522, AP7532, AP7562, AP8432, AP8533 access point models, as only these APs support TCP-RTT metadata collection.• app-group – Optional. Specifies the customized application-group name containing the applications for which TCP-RTT is to be collected• <APPLICATION-GROUP-NAME> – Specify the app-group name (should be existingand configured). If not specified, the system collects TCP-RTT metadata for all thecustomized app-groups created. You can enable TCP-RTT metadata collection oneight (8) application groups at a time.For more information on creating customized application-groups, see application-group.The TCP-RTT metadata is viewable only on the NSight dashboard. Therefore, ensure the NSight server and database is up and NSight analytics data collection is enabled.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1241.png)



![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1567.1.27 email-notificationProfile Config CommandsConfigures e-mail notification settings. When a system event occurs e-mail notifications are sent (provided message logging is enabled) based on the settings configured here. Use this option to configure the outgoing SMTP server settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxemail-notification [host|recipient]email-notification recipient <RECIPIENT-NAME>email-notification host <SMTP-SERVER-IP/HOSTNAME> sender <SENDER-EMAIL> [port|security|username]email-notification host <SMTP-SERVER-IP/HOSTNAME> sender <SENDER-EMAIL> [(port <1-65535>, security [none|ssl|starttls], username <SMTP-USERNAME> password [2 <WORD>|<WORD>])]Parameters• email-notification recipient <RECIPIENT-EMAIL>• email-notification host <SMTP-SERVER-IP/HOSTNAME> sender <SENDER-EMAIL> [(port <1-65535>, security [none|ssl|starttls], username <SMTP-USERNAME> password [2 <WORD>|<WORD>])]recipient<RECIPIENT-EMAIL>Defines the recipient’s e-mail address. A maximum of 6 (six) e-mail addresses can the configured.• <RECIPIENT-EMAIL> – Specify the recipient’s e-mail address (should not exceed 64 characters in length).host <SMTP-SERVER-IP/HOSTNAME>Configures the host SMTP server’s IP address or hostname• <SMTP-SERVER-IP/HOSTNAME> – Specify the SMTP server’s IP address or hostname.sender <SENDER-EMAIL>Defines the sender’s e-mail address. This is the from address on notification e-mails.• <SENDER-EMAIL> – Specify the sender’s e-mail address (should not exceed 64 characters in length). Use the email-notification > recipient > <EMAIL-ADDRESS> command to configure the recipient's address.port <1-65535> This option is recursive and applicable to the ‘security‘ and ‘username’ parameters.Configures the SMTP server port. Use this option to configure a non-standard SMTP port on the outgoing SMTP server. The standard SMTP port is 25.• <1-65535> – Specify the port from 1 - 65535.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1246.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 157Examplerfs6000-37FABE(config-profile-default-rfs6000)#email-notification recipient test@examplecompany.comrfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs7000 default-rfs7000 dscp-mapping 20 priority 7 no autoinstall configuration no autoinstall firmware ............................................................. interface ge4 ip dhcp trust qos trust dscp qos trust 802.1p use firewall-policy default email-notification recipient test@examplecompany.com service pm sys-restartrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandssecurity [none|ssl|starttls]This option is recursive and applicable to the ‘port‘ and ‘username’ parameters.Configures the SMTP encryption type used• none – No encryption used•ssl – Uses Secure Sockets Layer (SSL) encryption between the SMTP server and the client• starttls – Uses STARTTLS encryption between the SMTP server and the clientusername <SMTP-USERNAME> password [2 <WORD>|<WORD>]This option is recursive and applicable to the ‘port‘ and ‘security’ parameters.Configures the SMTP sender’s username. Many SMTP servers require users to authenticate with a username and password before sending e-mail through the server.• <SMTP-USERNAME> – Specify the SMTP username (should not exceed 64 characters in length).• password – Configures the SMTP server password. Specify the password associ-ated with the username of the sender on the outgoing SMTP server.• 2 <WORD> – Configures an encrypted password• <WORD> – Specify the password (should not exceed 127 characters inlength).no Disables or reverts settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1247.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1587.1.28 enforce-versionProfile Config CommandsEnables checking of a device’s firmware version before attempting adoption or clusteringSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxenforce-version [adoption|cluster] [full|major|minor|none|strict]Parameters• enforce-version [adoption|cluster] [full|major|minor|none|strict]Examplenx9500-6C8809(config-profile-test-nx5500)#enforce-version cluster fullnx9500-6C8809(config-profile-test-nx5500)#enforce-version adoption majornx9500-6C8809(config-profile-test-nx5500)#show contextprofile nx5500 test-nx5500 no autoinstall configuration no autoinstall firmware crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha ....................................................interface pppoe1 use firewall-policy default enforce-version adoption major enforce-version cluster full service pm sys-restart router ospf router bgp dot1x system-auth-control dot1x use aaa-policy OnBoardingnx9500-6C8809(config-profile-test-nx5500)#Related Commandsadoption Verifies firmware versions before adopting. This option is enabled by default.cluster Verifies firmware versions before clustering. This option is enabled by default.full Allows adoption or clustering when the first four octets of the firmware versions match (for example 5.8.6.0)major Allows adoption or clustering when the first two octets of the firmware versions match (for example 5.8)minor Allows adoption or clustering when the first three octets of the firmware versions match (for example 5.8.6)none Allows adoption or clustering between any firmware versionsstrict Allows adoption or clustering only when firmware versions exactly match (for example 5.8.6.0-008B). This is the default setting for both ‘adoption’ and ‘cluster’ options.no Disables or reverts settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1248.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1597.1.29 environmental-sensorProfile Config CommandsConfigures the environmental sensor settingsAn AP8132 sensor module is a USB environmental sensor extension to an AP8132 model access point. It provides a variety of sensing mechanisms, allowing the monitoring and reporting of the AP8132's radio coverage area.Supported in the following platforms:• Access Points — AP8132Syntaxenvironmental-sensor [humidity|light|motion|polling-interval|temperature]environmental-sensor [humidity|motion|polling-interval <1-100>|temperature]environmental-sensor light {holdtime|radio-shutdown|threshold}environmental-sensor light {holdtime <10-201>|radio-shutdown [all|radio-1|radio-2]}environmental-sensor light {threshold [high <100-10000>|low <0-1000>]}Parameters• environmental-sensor [humidity|motion|polling-interval <1-100>|temperature]• environmental-sensor light {holdtime <10-201>|radio-shutdown [all|radio-1|radio-2]}environmental-sensorConfigures environmental sensor settings on this profilehumidity Enables (turns on) humidity sensors. This setting is enabled by default.motion Enables (turns on) motion sensors.This setting is enabled by default.polling-interval <1-100>Configures polling interval, in seconds, on all sensors. This is the interval after which the sensor module polls its environment to assess the various parameters, such as light intensity.• <1-100> – Specify a value from 1 - 100 seconds. The default is 5 seconds.temperature Enables (turns on) temperature sensors. This setting is enabled by default.environmental-sensorConfigures environmental sensor settings on this profilelight Enables (turns on) light sensors and specifies its settingsWhen enabled, the sensor module polls the environment to determine the light intensity. Based on the reading, the system determines whether the AP8132’s deployment location has lights on or off. Light intensity also helps determine whether the access point’s deployment location is currently populated with clients.holdtime <10-201>Optional. Configures a holdtime, in seconds, for the light sensor• <10-201> – Specify a value from 10 - 201 seconds. The default value is 11 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1249.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 160• environmental-sensor light {threshold [high <100-10000>|low <0-1000>]}Examplerfs4000-229D58(config-profile-testRFS4000)#environmental-sensor humidityrfs4000-229D58(config-profile-testRFS4000)#environmental-sensor polling-interval 60rfs4000-229D58(config-profile-testRFS4000)#environmental-sensor light radio-shutdown allrfs4000-229D58(config-profile-testRFS4000)#environmental-sensor light threshold high 300rfs4000-229D58(config-profile-testRFS4000)#environmental-sensor light threshold low 100rfs4000-229D58(config-profile-testRFS4000)#show contextprofile rfs4000 testRFS4000 bridge vlan 1 tunnel-over-level2 ip igmp snooping ip igmp snooping querier environmental-sensor polling-interval 60 environmental-sensor light threshold high 300 environmental-sensor light threshold low 100 environmental-sensor light radio-shutdown all no autoinstall configuration no autoinstall firmware device-upgrade persist-images--More--rfs4000-229D58(config-profile-testRFS4000)#Related Commandsradio-shutdown [all|radio1|radio2]Optional. Shuts down the sensor’s radios• all – Shuts down all radios. This is the default setting.• radio1 – Shuts down radio 1•radio2 – Shuts down radio 2AP8132’s using this profile have their radios shut down, when the radio’s power falls below the specified threshold. Use the environmental-sensor > light > threshold > [high|low] command to set the threshold values.environmental-sensorConfigures environmental sensor settings on this profilelight Enables (turns on) light sensors and specifies its settingsthreshold Optional. Configures the upper and lower thresholds for the amount of light in the environmenthigh <100-10000>Specifies the upper threshold from 100 - 10000 lux. This value determines whether lighting is on in the AP8132’s deployment location. The radios are turned off if the average reading value is lower than the value set here. The default is 400 lux.The light sensor triggers an event if the amount of light exceeds the specified value.low <0-1000> Specifies the lower threshold from 0 - 1000 lux. This value determines whether lighting is off in the AP8132’s deployment location. The radios are turned on when the average value is higher than the value set here. The default is 200 lux.The light sensor triggers an event if the amount of light drops below the specified value.no Removes the environmental sensor’s settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1250.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1617.1.30 eventsProfile Config CommandsDisplays system event messagesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxevents [forward on|on]Parameters• events [forward on|on]Examplerfs6000-37FABE(config-profile-default-rfs6000)#events forward onrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsforward on Forwards system event messages to the wireless controller, service platform, or cluster members. This feature is enabled by default.• on – Enables forwarding of system eventson Generates system events. This feature is enabled by default.no Disables or reverts settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1251.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1627.1.31 exportProfile Config CommandsEnables export of startup.log file after every bootSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxexport startup-log [max-retries|retry-interval|url]export startup-log [max-retries <2-65535>|retry-interval <30-86400>|url <URL>]Parameters• export startup-log [max-retries <2-65535>|retry-interval <30-86400>|url <URL>]Examplenx9500-6C8809(config-profile-test-nx5500)#export startup-log max-retries 10 retry-interval 30 url ftp://anonymous:anonymous@192.168.13.10/log/startup.lognx9500-6C8809(config-profile-test-nx5500)#show contextprofile nx5500 test-nx5500 no autoinstall configuration no autoinstall firmware crypto ikev1 policy ikev1-default ....................................................... interface ge5 interface ge6 interface pppoe1 use firewall-policy default export startup-log max-retries 10 retry-interval 30 url ftp://anonymous:anonymous@192.168.13.10/log/startup.log enforce-version adoption major enforce-version cluster full service pm sys-restart--More--gnx9500-6C8809(config-profile-test-nx5500)#Related Commandsexport startup-log Enables export of the startup.log file after every boot. This option is disabled by default.max-retries <2-65535>Configures the maximum number of retries in case the export process fails• <2-65535> – Specify a value from 2 - 65535.retry-interval <30-86400>Configures the interval between two consecutive retries• <30-86400> – Specify a value from 30 - 86400 seconds.url <URL> Configures the destination URL in the following format:tftp://<hostname|IP>[:port]/path/fileftp://<user>:<passwd>@<hostname|IP>[:port]/path/filesftp://<user>@<hostname|IP>[:port]>/path/fileno Disables export of startup.log file](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1252.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1637.1.32 file-syncProfile Config CommandsConfigures parameters enabling auto syncing of trustpoint/wireless-bridge certificate between the staging-controller and its adopted access pointsThis command is applicable to the access point’s profile as well as device configuration modes.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxfile-sync [auto|count <1-20>]Parameters• file-sync [auto|count <1-20>]Examplenx9500-6C8809(config-profile-default-rfs6000)#file-sync autonx9500-6C8809(config-profile-default-rfs6000)#file-sync count 8nx9500-6C8809(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 no autoinstall configuration no autoinstall firmware no device-upgrade auto file-sync count 8 file-sync auto crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac --More--nx9500-6C8809(config-profile-default-rfs6000)#Related Commandsfile-sync [auto|count <1-20>]Configures the following file-synching parameters:• auto – Enables the staging controller to autoinstall trustpoint/wireless-bridge certificate on an access point when it comes up for the first time and adopts to the controller. Prior to enabling file syncing, ensure that the wireless-bridge certificate is present on the staging controller. To upload the certificate on the controller, in the user or privilege executable modes, execute the following command: file-sync > load-file > <URL>. • count <1-20> – Configures the maximum number of access points that can be concurrently auto-installed.• <1-20> – Specify a value from 1 - 20. The default is 10 access points.For the NX95XX service platforms the count-range is from 1 - 128.no Disables automatic file syncing between the staging-controller and its access points](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1253.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1697.1.34.2.1 d s c pgre-config-instanceSets the GRE tunnel’s DSCP / 802.1q priority value from encapsulated packets to the outer packet IPv4 header.This option is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdscp [<0-63>|reflect]Parameters• dscp [<0-63>|reflect]Examplerfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#dscp 20rfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#show context gre tunnel testGRETunnel dscp 20rfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#Related Commandsdscp <0-63> Specifies the DSCP 802.1q priority value for outer packets from 0 - 63. The default is 1.dscp reflect Copies the DSCP 802.1q value from inner packetsno Removes the GRE tunnel settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1259.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1707.1.34.2.2 establishment-criteriagre-config-instanceConfigures the GRE tunnel establishment criteriaIn a multi-controller RF domain, it is always the master node that establishes the tunnel. The tunnel is created only if the tunnel device is designated as one of the following: vrrp-master, cluster-master, or rf-domain-manager.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxestablishment-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]Parameters• establishment-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]Examplenx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#establishment-criteria rf-domain-managernx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#show context gre tunnel testGREtunnel establishment-criteria rf-domain-managernx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#establishment-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]Configures the GRE tunnel establishment criteria. The options are:• always – Always automatically establishes tunnel (default setting). The tunnel device need not be a cluster master, RF Domain manager, or VRRP master to establish the GRE tunnel. This is the default setting.• cluster-master – Establishes tunnel only if the tunnel device is designated as the cluster master• rf-domain-manager – Establishes tunnel only if the tunnel device is designated as the RF Domain manager• vrrp-master <1-255> – Establishes tunnel only if the tunnel device is designated as the Virtual Router Redundancy (VRRP) master• <1-255> – Configures the VRRP group ID from 1 - 255. A VRRP group enables thecreation of a group of routers as a default gateway for redundancy. Clients can pointto the IP address of the VRRP virtual router as their default gateway and utilize a dif-ferent group member if a master becomes unavailable.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1260.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1727.1.34.2.4 mtugre-config-instanceConfigures the MTU for IPv4/IPv6 L2GRE tunnel endpointsThe MTU is the largest physical packet size (in bytes) transmittable within the tunnel. Any messages larger than the configured MTU are divided into smaller packets before transmission. Larger the MTU greater is the efficiency because each packet carries more user data, while protocol overheads, such as headers or underlying per-packet delays remain fixed; the resulting higher efficiency means a slight improvement in bulk protocol throughput. A larger MTU results in the processing of fewer packets for the same amount of data.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmtu [ipv4 <900-1476>|ipv6 <1236-1456>]Parameters• mtu [ipv4 <900-1476>|ipv6 <1236-1456>]Examplenx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#mtu ipv4 1200nx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#mtu ipv6 1300nx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#show context gre tunnel testGREtunnel mtu ipv4 1200 mtu ipv6 1300 establishment-criteria rf-domain-managernx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#mtu [ipv4 <900-1476>|ipv6 <1236-1456>]Configures the MTU for L2GRE tunnel endpoints• ipv4 <900-1476> – Configures IPv4 L2GRE tunnel endpoint MTU from 900 - 1476. The default is 1476.• ipv6 <1236-1456> – Configures IPv6 L2GRE tunnel endpoint MTU from 1236 - 1456. The default is 1456.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1262.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1737.1.34.2.5 nativegre-config-instanceConfigures native trunking settings for this GRE tunnelSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnative [tagged|vlan <1-4094>]Parameters• native [tagged|vlan <1-4094>]Examplenx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#native taggednx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#native vlan 20nx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#show context gre tunnel testGREtunnel native vlan 20 native tagged mtu ipv4 1200 mtu ipv6 1300 establishment-criteria rf-domain-managernx9500-6C8809(config-profile testNX9500-gre-tunnel-testGREtunnel)#Related Commandsnative tagged Enables native VLAN taggingThe IEEE 802.1Q specification is supported for tagging frames and coordinating VLANs between devices. IEEE 802.1Q adds four bytes to each frame identifying the VLAN ID for upstream devices that the frame belongs. If the upstream Ethernet device does not support IEEE 802.1Q tagging, it does not interpret the tagged frames. When VLAN tagging is required between devices, both devices must support tagging and be configured to accept tagged VLANs. When a frame is tagged, the 12 bit frame VLAN ID is added to the 802.1Q header so upstream Ethernet devices know which VLAN ID the frame belongs to. The device reads the 12 bit VLAN ID and forwards the frame to the appropriate VLAN. When a frame is received with no 802.1Q header, the upstream device classifies the frame using the default or native VLAN assigned to the Trunk port. The native VLAN allows an Ethernet device to associate untagged frames to a VLAN when no 802.1Q frame is included in the frame. This feature is disabled by default.native vlan <1-4094> Specifies a numerical VLAN ID (1 - 4094) for the native VLANThe native VLAN allows an Ethernet device to associate untagged frames to a VLAN, when no 802.1q frame is included in the frame. Additionally, the native VLAN is the VLAN untagged traffic is directed over when using a port in trunk mode.no Removes the GRE tunnel settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1263.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1747.1.34.2.6 nogre-config-instanceRemoves or resets the GRE tunnel settings based on the parameters passedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [dscp|establishment-criteria|failover|mtu|native|peer|tunneled-vlan]no [dscp|establishment-criteria|failover|tunneled-vlan]no mtu [ipv4|ipv6]no native [tagged|vlan]no peer <1-2>Parameters• no <PARAMETERS>ExampleThe following example shows the GRE tunnel ‘testGRETunnel’ settings before the no commands are executed:rfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#show context gre tunnel testGRETunnel peer 1 ip 192.168.13.6 native vlan 1 tunneled-vlan 1,10 native tagged dscp 20 failover interval 200 retry 5rfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#rfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#no dscprfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#no native vlanrfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#no tunneled-vlanrfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#no failoverThe following example shows the GRE tunnel ‘testGRETunnel’ settings after the no commands are executed:rfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#show context gre tunnel testGRETunnel peer 1 ip 192.168.13.6 native taggedrfs4000-229D58(config-device 00-23-68-22-9D-58-gre-tunnel-testGRETunnel)#no <PARAMETERS> Removes or resets the GRE tunnel’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1264.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1777.1.35 http-analyzeProfile Config CommandsEnables forwarding of HTTP request related data to the HTTP analytics engineWireless clients (MUs) connect to APs and route their HTTP requests through the APs. These APs extract and forward HTTP request packets, through MiNT, to the NX series controller. The NX series controller uses a new analytic daemon to cache, format, and forward information to the analytics engine. Currently the analytics daemon is supported only on the NX series service platform. Therefore, it is essential that all APs should use an NX series service platform as controller.In a hierarchically organized network, HTTP analytics data forwarding is a simple and transparent process. The site controllers receive the HTTP data from adopted APs adopted. This data is compressed and forwarded to the Network Operations Center (NOC) controller. There is no need for a separate configuration to enable this feature.Use this command to configure the mode and interval at which data is sent to the controller and the external analytics engine. This command also configures the external engine’s details, such as URL, credentials, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxhttp-analyze [compress|external-server|update-interval <1-3600>]http-analyze [compress|update-interval <1-3600>http-analyze external-server [password <WORD>|proxy <URL>|update-interval <1-3600>|url <URL>|username <WORD>|validate-server-certificate]Parameters• http-analyze [compress|update-interval <1-3600>]• http-analyze external-server [password <WORD>|proxy <URL>|update-interval|url|username|validate-server-certificate]NOTE: The Analytics module helps gather data about customer behavior such as web sites visited, search terms used, mobile device types, number of new users vs. repeat users. This data provides a better understanding of pricing strategies and promotions being run by competitors.http-analyze Configures HTTP analysis related parameterscompress Compresses update files before forwarding to the controller. This option is disabled by default.update-interval <1-3600>Configures the interval, in seconds, at which buffered packets are pushed to the controller• <1-3600> – Specify the interval from 1 - 3600 seconds. The default is 60 seconds.http-analyze external-serverConfigures the external HTTP analytics engine’s parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1267.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1817.1.36.1 interfaceinterfaceSelects an interface to configureA profile’s interface configuration can be defined to support separate physical Ethernet configurations both unique and specific to RFS4000, RFS6000 controllers and NX7500 and NX95XX series service platforms. Ports vary depending on the platform, but controller or service platform models do have some of the same physical interfaces.A controller or service platform requires its virtual interface be configured for layer 3 (IP) access or layer 3 service on a VLAN. A virtual interface defines which IP address is associated with each VLAN ID the controller or service platform is connected to. If the profile is configured to support an access point radio, an additional radio interface is available, unique to the access point’s radio configuration.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntax Service Platformsinterface [<INTERFACE-NAME>|fe <1-4>|ge <1-24>|me1|port-channel <1-4>|pppoe1|radio [1|2|3]|serial <1-4>|t1e1 <1-4>|up <1-2>|vlan <1-4094>|wwan1|xge <1-4>]Syntax Access Points and Wireless Controllersinterface [<INTERFACE-NAME>|bluetooth <1-1>|fe <1-4>|ge <1-8>|me1|port-channel <1-4>|pppoe1|radio [1|2|3]|up1|vlan <1-4094>|wwan1|xge <1-4>]Parameters• interface [<INTERFACE-NAME>|bluetooth <1-1>|fe <1-4>|ge <1-8>|me1|port-channel <1-4>|radio [1|2|3]|serial <1-4>|t1e1 <1-4>|up <1-2>|vlan <1-4094>|wwan1|xge <1-4>]<INTERFACE-NAME> Enters the configuration mode of the interface identified by the <INTERFACE-NAME> keywordbluetooth <1-1> Selects the Bluetooth radio interface• <1-1> – Specify the Bluetooth radio interface index from 1 - 1. As of now only one Bluetooth radio interface is supported.This interface is applicable only for the AP8432 and AP8533 model access points.fe <1-4> Selects a FastEthernet interface• <1-4> – Specify the interface index from 1 - 4.ge <1-24> Selects a GigabitEthernet interface• <1-24> – Specify the interface index from 1 - 24. (4 for RFS7000 and 8 for RFS6000).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1271.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 182Usage GuidelinesThe ports available on a device vary depending on the model. For example, the following ports are available on RFS4000, RFS6000 and RFS7000 model wireless controllers:• RFS4000 - ge1, ge2, ge3, ge4, ge5, up1• RFS6000 - ge1, ge2, ge3, ge4, ge5, ge6, ge7, ge8, me1, up1GE ports on are RJ-45 supporting 10/100/1000Mbps..ME ports are available on RFS6000 platforms. ME ports are out-of-band management ports used to manage the controller via CLI or Web UI, even when the other ports on the controller are unreachable.The ports available on service platforms also vary depending on the model. For example, the following ports are available on NX series service platforms:• NX7500 - ge1-ge10, xge1-xge2• NX95XX series - ge1, ge2, xge1-xge4• EX3500 – ge1-1 to ge1-24• EX3548 – ge1-1 to ge1-48GE ports are available on devices, such as RFS4000 and RFS6000controllers. GE ports are RJ-45 supporting 10/100/1000Mbps. ME ports are available on RFS6000 platforms. ME ports are out-of-band management ports used to manage the controller via CLI or Web UI, even when the other ports on the controller are unreachable.me1 Selects a management interfaceNot applicable for RFS4000 model devices.The management interface is applicable only for RFS6000 and RFS7000 model controllers.port-channel <1-4> Selects the port channel interface• <1-4> – Specify the interface index from 1 - 4.pppoe1 Selects the PPP over Ethernet interface to configureradio [1|2|3] Selects a radio interface• 1 – Selects radio interface 1•2 – Selects radio interface 2• 3 – Selects radio interface 3The radio interface is not available on wireless controllers or service platforms.up1 Selects the uplink GigabitEthernet interfacevlan <1-4094> Selects a VLAN interface• <1-4094> – Specify the SVI VLAN ID from 1 - 4094.wwan1 Selects a Wireless WAN interfaceThis interface is applicable only to AP7161, AP81XX, AP8232, RFS4000, RFS6000 model access points and controllers.xge <1-4> Selects a TenGigabitEthernet interface• <1-2> – Specify the interface index from 1 - 4.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1272.png)

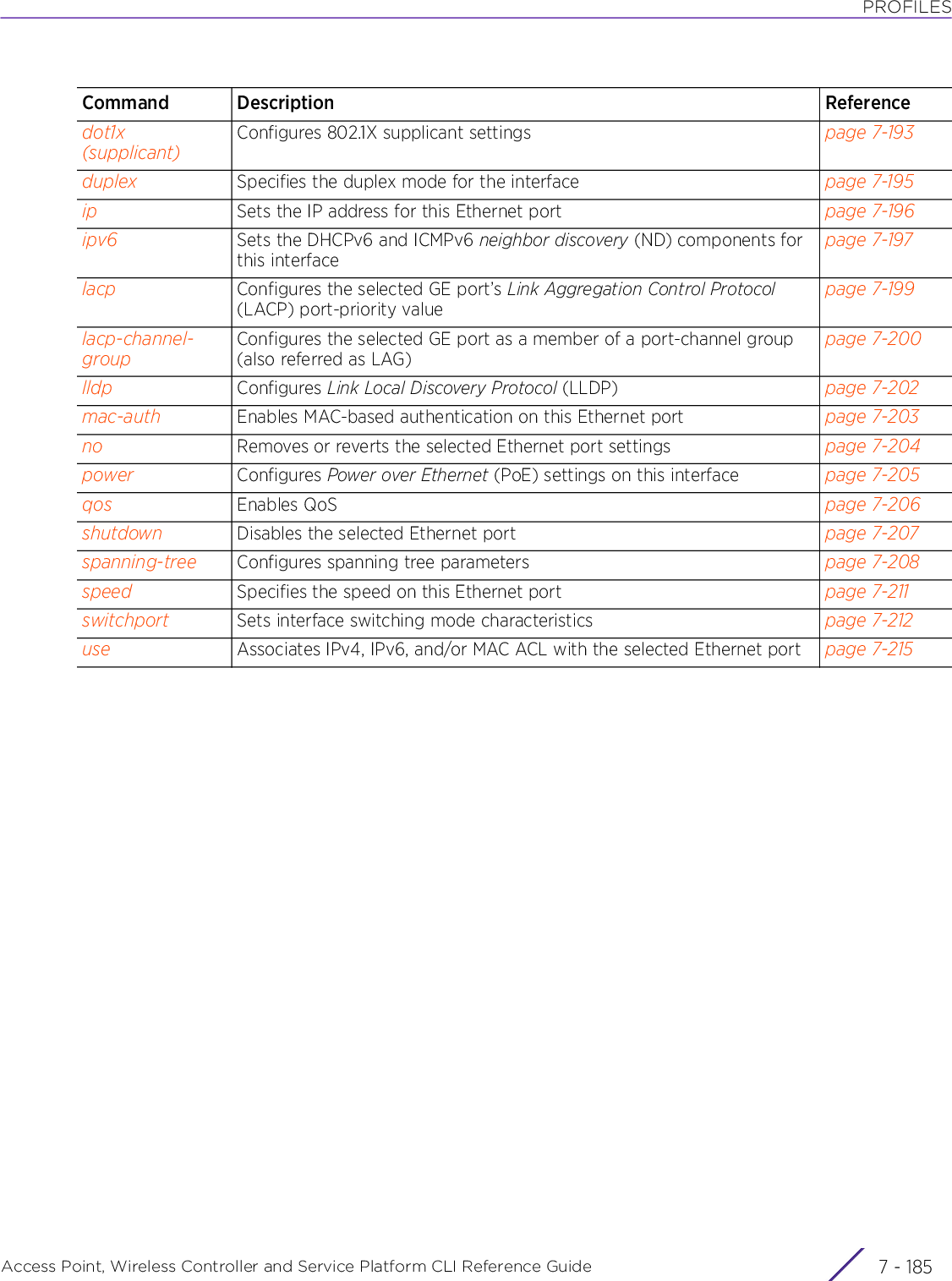

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1877.1.36.2.2 cdpinterface-config-ge-instanceEnables CDP on the selected GE portSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcdp [receive|transmit]Parameters• cdp [receive|transmit]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#cdp transmitRelated Commandsreceive Enables CDP packet snooping on this interface. When enabled, the port receives periodic interface updates from a multicast address. This option is enabled by default.transmit Enables CDP packet transmission on this interface. When enabled, the port sends out periodic interface updates to a multicast address to advertise its presence to neighbors. This option is enabled by default.no Disables CDP packet snooping on the controller or service platform’s selected GE ports](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1277.png)
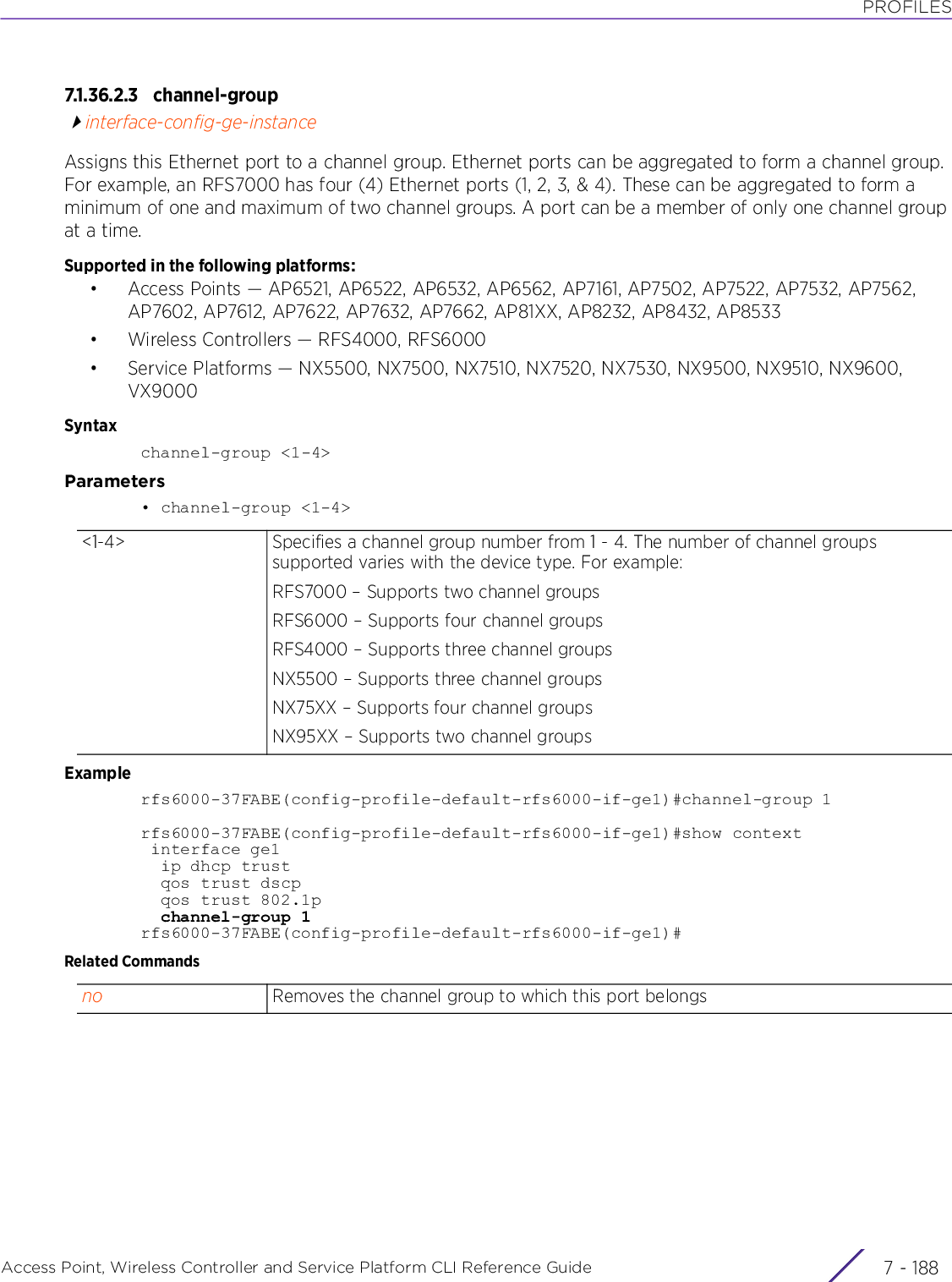
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1897.1.36.2.4 descriptioninterface-config-ge-instanceConfigures a description for this Ethernet portSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdescription [<LINE>|<WORD>]Parameters• description [<LINE>|<WORD>]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#description “This is GigabitEthernet interface for Royal King”rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#show context interface ge1 description "This is GigabitEthernet interface for Royal King" ip dhcp trust qos trust dscp qos trust 802.1p channel-group 1rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#Related Commands<LINE> Configures the maximum length (number of characters) of the interface description<WORD> Configures a unique description for this interface. The description should not exceed the length specified by the <LINE> parameter.no Removes the interface description](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1279.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1907.1.36.2.5 dot1x (authenticator)interface-config-ge-instanceConfigures 802.1X authenticator settingsDot1x (or 802.1x) is an IEEE standard for network authentication. It enables media-level (layer 2) access control, providing the capability to permit or deny connectivity based on user or device identity. Dot1x allows port-based access using authentication. An dot1x enabled port can be dynamically enabled or disabled depending on user identity or device connection.Devices supporting dot1x allow the automatic provision and connection to the wireless network without launching a Web browser at login. When within range of a dot1x network, a device automatically connects and authenticates without needing to manually login.Before authentication, the endpoint is unknown, and traffic is blocked. Upon authentication, the endpoint is known and traffic is allowed. The controller or service platform uses source MAC filtering to ensure only the authenticated endpoint is allowed to send traffic.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6562, AP7161, AP7502, AP81XX, AP8232, AP8432• Wireless Controllers — RFS4000, RFS6000, NX5500, NX7500Syntaxdot1x authenticator [guest-vlan|host-mode|max-reauth-req|port-control|reauthenticate|timeout]dot1x authenticator [guest-vlan <1-4094>|host-mode [multi-host|single-host]|max-reauth-req <1-10>|port-control [auto|force-authorized|force-unauthorized]|reauthenticate|timeout [quiet-period|reauth-period] <1-65535>]Parameters• dot1x authenticator [guest-vlan <1-4094>|host-mode [multi-host|single-host]|max-reauth-req <1-10>|port-control [auto|force-authorized|force-unauthorized]|reauthenticate|timeout [quiet-period|reauth-period]]NOTE: The dot1x (802.1x) supplicant settings are documented in the next section.dot1x authenticator Configures 802.1x authenticator settingsguest-vlan <1-4094> Configures the guest VLAN for this interface. This is the VLAN, traffic is bridged on if this port is unauthorized and the guest VLAN is globally enabled. Select the VLAN index from 1 - 4094.host-mode [multi-host|single-host]Configures the host mode for this interface• multi-host – Configures multiple host mode• single-host – Configures single host mode. This is the default setting.max-reauth-req <1-10>Configures maximum number of re-authorization retries for the supplicant. This is the maximum number of re-authentication attempts made before this port is moved to unauthorized.• <1-10> – Specify a value from 1 -10. The default is 2.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1280.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 191Examplerfs4000-229D58(config-profile-testRFS4000-if-ge1)#dot1x authenticator guest-vlan 2rfs4000-229D58(config-profile-testRFS4000-if-ge1)#dot1x authenticator host-mode multi-hostrfs4000-229D58(config-profile-testRFS4000-if-ge1)#dot1x authenticator max-reauth-req 6rfs4000-229D58(config-profile-testRFS4000-if-ge1)#dot1x authenticator reauthenticaterfs4000-229D58(config-profile-testRFS4000-if-ge1)#show context interface ge1 dot1x authenticator host-mode multi-host dot1x authenticator guest-vlan 2 dot1x authenticator reauthenticate dot1x authenticator max-reauth-count 6 ip dhcp trust qos trust dscp qos trust 802.1prfs4000-229D58(config-profile-testRFS4000-if-ge1)#The following examples show the configurations made on an RFS6000 to enable it as a dot1X authenticator:1 Configure AAA policy on the authenticator, and identify the authentication server as onboard (self):rfs6000-817379(config-aaa-policy-aaa-wireddot1x)#show contextaaa-policy aaa-wireddot1xauthentication server 1 onboard controllerrfs6000-817379(config-aaa-policy-aaa-wireddot1x)#This AAA policy is used in the authenticator’s self configuration mode as shown in the last step.2 Configure RADIUS user policy on the authenticator:rfs6000-817379(config-radius-user-pool-wired-dot1x-users)#show conradius-user-pool-policy wired-dot1x-usersuser bob password 0 bob1234rfs6000-817379(config-radius-user-pool-wired-dot1x-users)#The user name and password configured here should match that of the supplicant. For more information, see the examples provided in the dot1x (supplicant) section.3 Configure RADIUS server policy on the authenticator, and associate the RADIUS user policy created in the previous step:port-control[auto|force-authorized|force-unauthorized]Configures port control state• auto – Configures auto port state• force-authorized – Configures authorized port state. This is the default setting.• force-unauthorized – Configures unauthorized port statereauthenticate Enables re-authentication for this port. When enabled, clients are forced to re-authenticate on this port. The setting is disabled by default. Therefore, clients are not required to re-authenticate for connection over this port until this setting is enabled.timeout [quiet-period|reauth-period] <1-65535>Configures timeout settings for this interface• quiet-period – Configures the quiet period timeout in seconds. This is the interval, in seconds, between successive client authentication attempts.• reauth-period – Configures the time after which re-authentication is initiatedThe following option is common to ‘quiet-period’ and ‘reauth-period’ keywords:• <1-65535> – Specify a ‘quiet-period’ or ‘reauth-period’ from 1 - 65535 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1281.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1937.1.36.2.6 dot1x (supplicant)interface-config-ge-instanceConfigures 802.1X supplicant (client) settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, NX5500, NX7500Syntaxdot1x supplicant username <USERNAME> password [0 <WORD>|2 <WORD>|<WORD>]Parameters• dot1x supplicant username <USERNAME> password [0 <WORD>|2 <WORD>|<WORD>]Examplerfs4000-229D58(config-profile-testRFS4000-if-ge1)#dot1x supplicant username bobpassword 0 test@123rfs4000-229D58(config-profile-testRFS4000-if-ge1)#show context interface ge1 dot1x supplicant username bob password 0 test@123 dot1x authenticator host-mode multi-host dot1x authenticator guest-vlan 2 dot1x authenticator reauthenticate dot1x authenticator max-reauth-count 6 ip dhcp trust qos trust dscp qos trust 802.1prfs4000-229D58(config-profile-testRFS4000-if-ge1)#The following example shows the configuration made on an AP7522 to enable it as a dot1X supplicant:ap7522-85B19C(config-device-84-24-8D-85-B1-9C-if-ge2)#dot1x supplicant username bob password 0 bob1234ap7522-85B19C(config-device-84-24-8D-85-B1-9C)#show contextuse profile default-ap7522use rf-domain defaulthostname ap7522-85B19Cno adoption-modeinterface ge1 switchport mode access switchport access vlan 1 dot1x supplicant username bob password 0 bob1234logging onlogging console debugging--More--ap7522-85B19C(config-device-84-24-8D-85-B1-9Cdot1x supplicant Configures 802.1x suppliant settingsusername <USERNAME>Sets the username for authentication• <USERNAME> – Specify the supplicant’s username.password [0 <WORD>|2 <WORD>|<WORD>]Sets the password associated with the supplicant’s username. Select any one of the following options:• 0 <WORD> – Sets a clear text password• 2 <WORD> – Sets an encrypted password•<WORD> – Specify the password.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1283.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1957.1.36.2.7 d u pl exinterface-config-ge-instanceConfigures duplex mode (for the flow of packets) on this Ethernet portSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxduplex [auto|half|full]Parameters• duplex [auto|half|full]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#duplex fullrfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#show context interface ge1 description "This is GigabitEthernet interface for Royal King" duplex full dot1x supplicant username Bob password 0 test@123 ip dhcp trust qos trust dscp qos trust 802.1p channel-group 1rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#Related Commandsauto Enables automatic duplexity on an interface port. The port automatically detects whether it should run in full or half-duplex mode. (default setting)half Sets the port to half-duplex mode. Allows communication in one direction only at any given time. When selected, data is sent over the port, then immediately data is received from the direction in which the data was transmitted.full Sets the port to full-duplex mode. Allows communication in both directions simultaneously. When selected, the port can send data while receiving data as well.no Reverts to default (auto)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1285.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1967.1.36.2.8 ipinterface-config-ge-instanceSets the ARP and DHCP components for this Ethernet portSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [arp|dhcp]ip [arp [header-mismatch-validation|trust]|dhcp trust]Parameters• ip [arp [header-mismatch-validation|trust]|dhcp trust]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#ip dhcp trustrfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#ip arp header-mismatch-validationrfs7000-37FABE(config-profile-default-rfs6000-if-ge1)#show context interface ge1 description "This is GigabitEthernet interface for Royal King" duplex full dot1x supplicant username Bob password 0 test@123 ip dhcp trust ip arp header-mismatch-validation qos trust dscp qos trust 802.1p channel-group 1rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#Related Commandsarp [header-mismatch-validation|trust]Configures ARP packet settings• header-mismatch-validation – Enables matching of source MAC address in the ARP and Ethernet headers to check for mismatch. This option is disabled by default.• trust – Enables trust state for ARP responses on this interface. When enabled, ARP packets received on this port are considered trusted and information from these packets is used to identify rogue devices within the network. This option is disabled by default.dhcp trust Enables trust state for DHCP responses on this interface. When enabled, only DHCP responses are trusted and forwarded on this port, and a DHCP server can be connected only to a DHCP trusted port. This option is enabled by default.no Removes the ARP and DHCP components configured for this interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1286.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 1977.1.36.2.9 ipv6interface-config-ge-instanceSets the DHCPv6 and ICMPv6 neighbor discovery (ND) components for this interfaceThe ICMPv6 ND protocol uses ICMP messages and solicited multicast addresses to track neighboring devices on the same local network. These messages are used to discover a neighbor’s link layer address and to verify if a neighboring device is reachable.The ICMP messages are neighbor solicitation (NS) and neighbor advertisement (NA) messages. When a destination host receives an NS message from a neighbor, it replies back with a NA. The NA contains the following information:• Source address – This is the IPv6 address of the device sending the NA• Destination address – This is the IPv6 address of the device from whom the NS message is received• Data portion – Includes the link layer address of the device sending the NANS messages are used to verify a neighbor’s (whose ink layer address is known) reachability. To confirm a neighbor’s reachability a node sends an NS message in which the neighbor’s unicast address is specified as the destination address. If the neighbor sends back an acknowledgment on receipt of the NS message it is considered reachable.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 [dhcpv6|nd]ipv6 dhcpv6 trustipv6 nd [header-mismatch-validation|raguard|trust]Parameters• ipv6 dhcpv6 trust• ipv6 nd [header-mismatch-validation|raguard|trust]ipv6 dhcpv6 trust Enables trust state for DHCPv6 responses on this interface. When enabled, all DHCPv6 responses received on this port are trusted and forwarded. This option is enabled by default.A DHCPv6 server can be connected to a DHCPv6 trusted port.ipv6 nd Configures IPv6 ND settingsheader-mismatch-validationEnables matching of source MAC address in the ICMPv6 ND and Ethernet headers (link layer option) to check for mismatch. This option is disabled by default.raguard Allows redirection of router advertisements (RAs) and ICMPv6 packets originating on this interface. When selected, RAs are periodically sent to hosts or sent in response to neighbor solicitation requests. The advertisement includes IPv6 prefixes and other subnet and host information. This option is enabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1287.png)
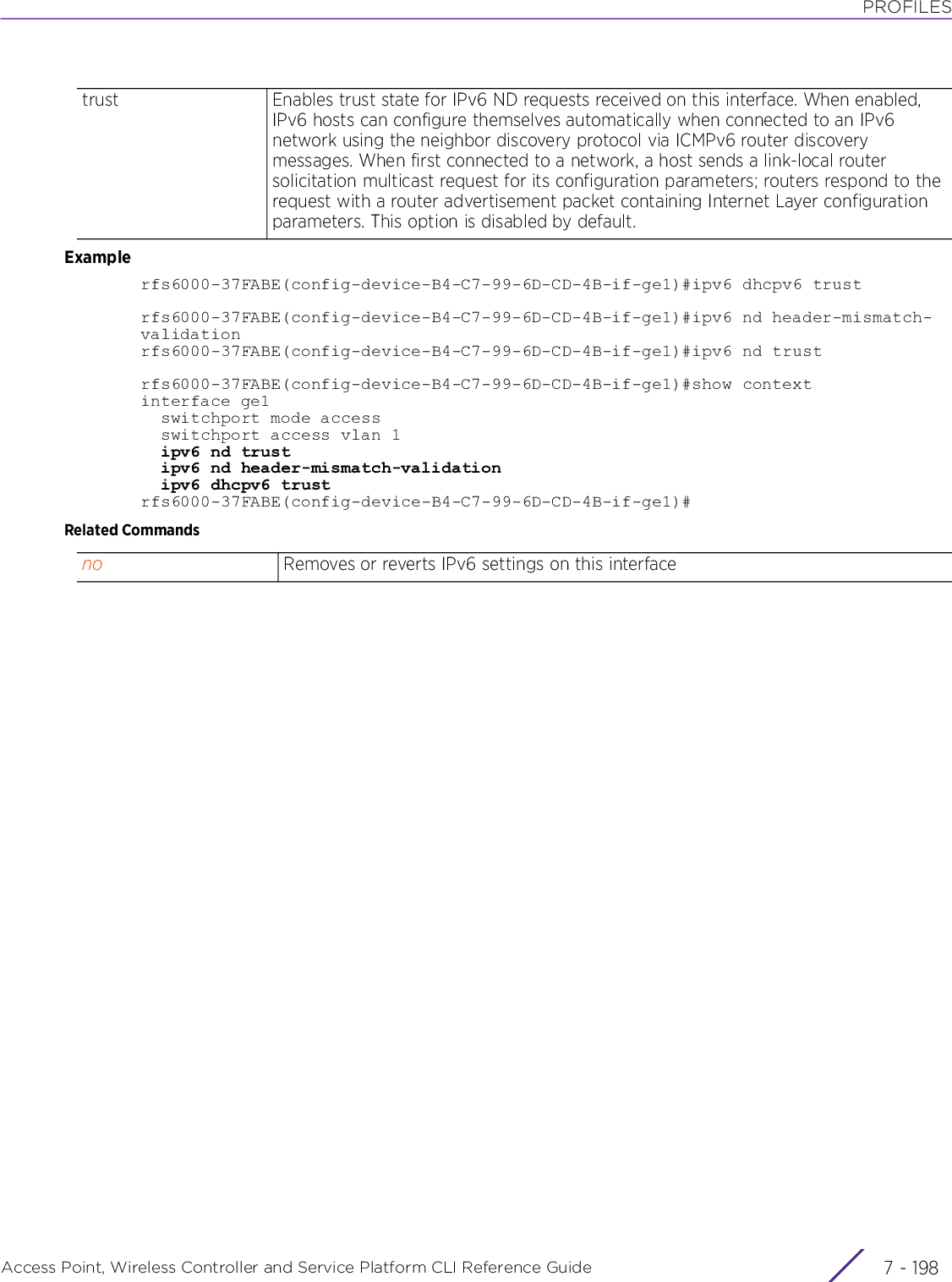
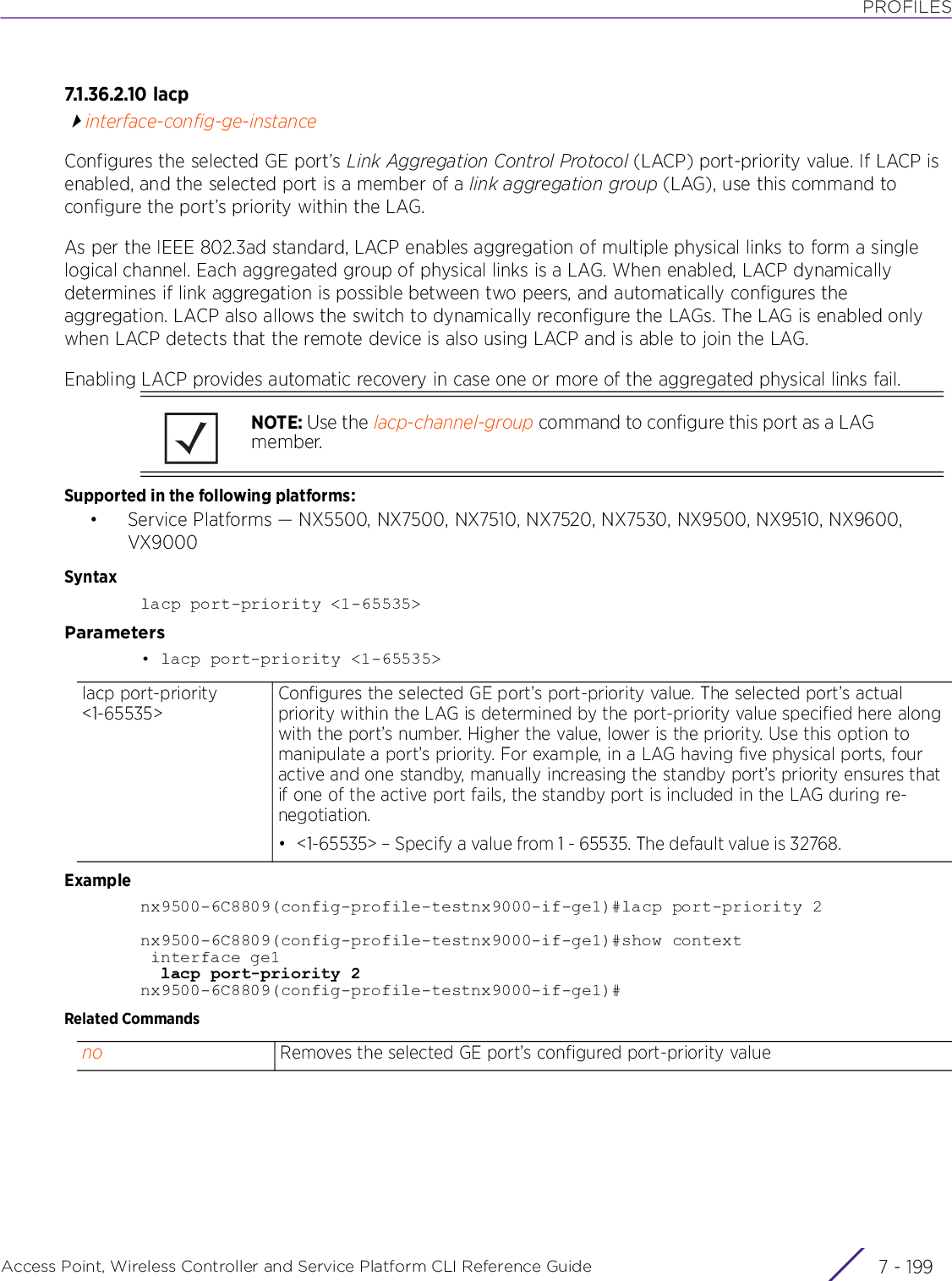
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2007.1.36.2.11 lacp-channel-groupinterface-config-ge-instanceConfigures the selected GE port as a member of a port channel group (also referred as LAG)As per the IEEE 802.3ad standard, LACP enables the aggregation of multiple physical links (ethernet ports) to form a single logical channel. When enabled, LACP dynamically determines if link aggregation is possible and then automatically configures the aggregation. LACP also allows the switch to dynamically reconfigure the LAGs. The LAG is enabled only when LACP detects that the remote device is also using LACP and is able to join the LAG.Supported in the following platforms:• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlacp-channel-group <1-4> mode [active|passive]Parameters• lacp-channel-group <1-4> mode [active|passive]Examplenx9500-6C8809(config-profile-testnx9000-if-ge1)#lacp-channel-group 2 mode activenx9500-6C8809(config-profile-test2nx9000-if-ge1)#show context interface ge1 lacp-channel-group 2 mode active lacp port-priority 2nx9500-6C8809(config-profile-test2nx900-if-ge1)#NOTE: Successful aggregation of two or more physical links is feasible only if the aggregating physical links are configured identically. To ensure uniformity in configuration across LAG members, implement configuration changes (such as changes in the switching mode, speed, etc.) on the logical port (the port-channel) and not on the physical port. Changes made on the port-channel will cascade down to each member of the LAG thereby retaining uniformity.lacp-channel-group <1-4>Associates this GE port with an existing port-channel group• <1-4> – Specify a value from 1 - 4.Use the interface > port-channel > <1-4> command to configure a port-channel group. For more information, see interface-config-port-channel-instance.mode [active|passive] After configuring the selected port as a LAG member, specify whether the port is an active or passive member within the group. An active member initiates and participates in LACP negotiations.• active – Configures the port as an active member. When set to active, the port always transmits LACPDU irrespective of the remote device’s port mode.• passive – Configures the port as passive member. When set to passive, the port will only respond to LACPDU received from its corresponding Active port.At least one port within a LAG, on either of the two negotiating peers, should be in the active mode. LACP negotiations are not initiated if all LAG member ports are passive. Further, the peer-to-peer LACP negotiations are always initiated by the peer with the lower system-priority value. For more information on configuring the system-priority, see lacp.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1290.png)
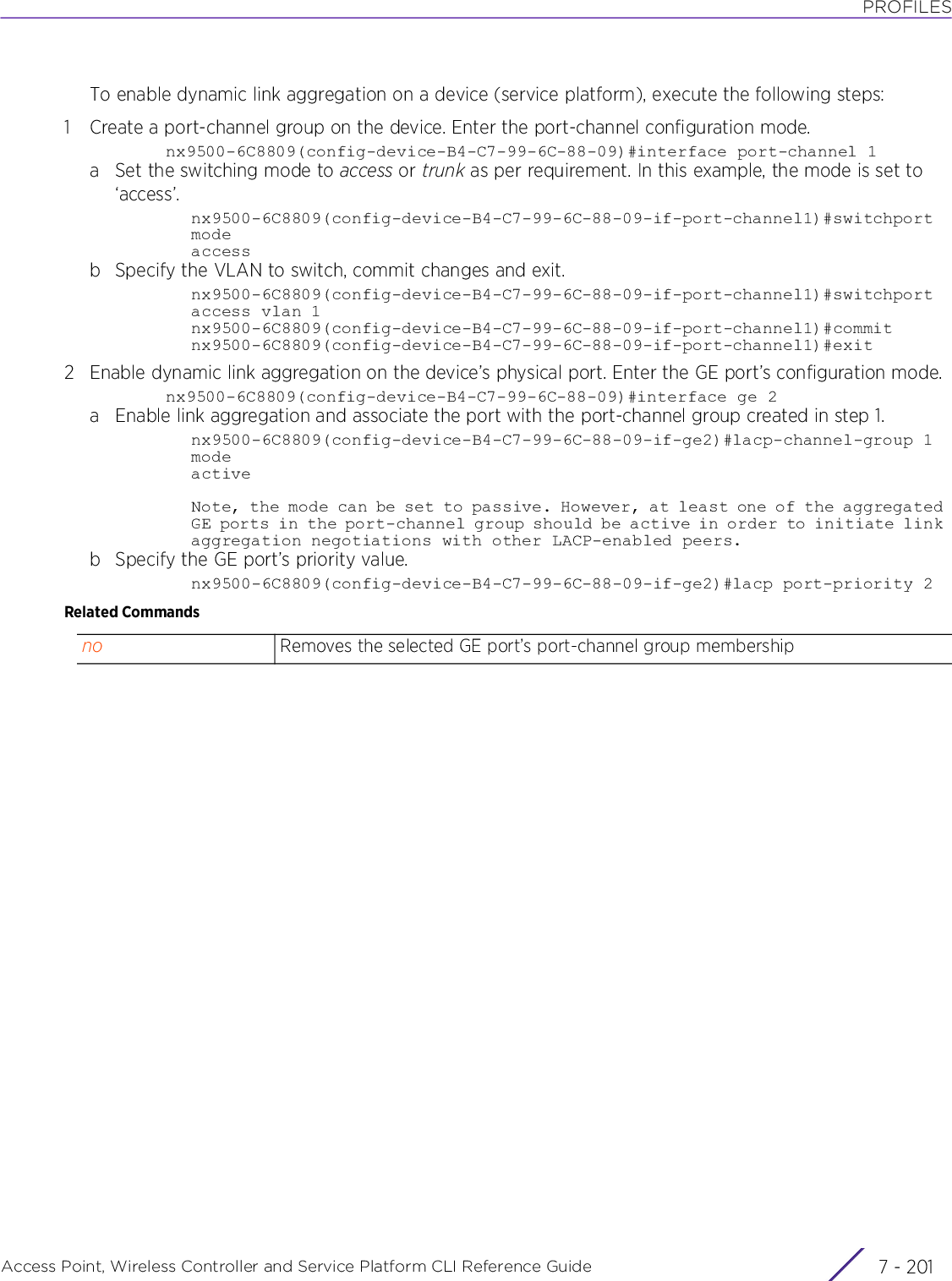
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2027.1.36.2.12 lldpinterface-config-ge-instanceConfigures Link Local Discovery Protocol (LLDP) parameters on this Ethernet portSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlldp [receive|transmit]Parameters• lldp [receive|transmit]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#lldp transmitRelated Commandsreceive Enables LLDP Protocol Data Units (PDUs) snooping. When enabled, the port receives periodic updates from a multicast address informing about presence of neighbors. This option is enabled by default.transmit Enables LLDP PDU transmission. When enabled, the port sends out periodic interface updates to a multicast address to advertise its presence to neighbors. This option is enabled by default.no Disables or reverts interface settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1292.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2047.1.36.2.14 n ointerface-config-ge-instanceRemoves or reverts the selected Ethernet port settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [captive-portal-enforcement|cdp|channel-group|description|dot1x|duplex|ip|ipv6|lacp|lacp-channel-group|lldp|mac-auth|power|qos|shutdown|spanning-tree|speed|switchport|use]no [captive-portal-enforcement|channel-group|description|duplex|mac-auth|shutdown|speed]no [cdp|lldp] [receive|transmit]no dot1x [authenticator [guest-vlan|host-mode|max-reauth-req|port-control|reauthentication|timeout [quiet-period|reauth-period]]|supplicant]no ip [arp [header-mismatch-validation|trust]|dhcp trust]no ipv6 [dhcpv6 trust|nd [header-mismatch-validation|raguard|trust]]no [lacp port-priority|lacp-channel-group]no power {best-effort|limit|priority}no qos trust [802.1p|cos|dscp]no spanning-tree [bpdufilter|bpduguard|force-version|guard|link-type|mst|portfast]no switchport [access vlan|mode|trunk native tagged]no use [ip-access-list|ipv6-access-list|mac-access-list] inParameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#no cdprfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#no duplexno <PARAMETERS> Removes or reverts this Ethernet port settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1294.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2057.1.36.2.15 p owe rinterface-config-ge-instanceConfigures Power over Ethernet (PoE) settings on this interfaceWhen configured, this option allows the selected port to use Power over Ethernet. When enabled, the controller supports 802.3af PoE on each of its GE ports. PoE allows users to monitor port power consumption and configure power usage limits and priorities for each GE port.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000Syntaxpower {best-effort|limit <0-40>|priority [critical|high|low]}Parameters• power {best-effort|limit <0-40>|priority [critical|high|low]}Examplerfs4000-229D58(config-profile-testRFS4000-if-ge1)#power limit 30rfs4000-229D58(config-profile-testRFS4000-if-ge1)#power priority criticalrfs4000-229D58(config-profile-testRFS4000-if-ge1)#show context interface ge1 ip dhcp trust qos trust dscp qos trust 802.1p power limit 30 power priority criticalrfs4000-229D58(config-profile-testRFS4000-if-ge1)#Related Commandspower Configures power related thresholds for this interfacebest-effort Optional. Enables power when the device is not operating from an 802.3at class 4 power sourcelimit <0-40> Optional. Configures the PoE power limit from 0 - 40 Watts. The default is 30 Watts.priority [critical|high|low]Optional. Configures the PoE power priority on this interface. This is the priority assigned to this port versus the power requirements of the other ports available on the controller.• critical – Sets PoE priority as critical• high – Sets PoE priority as high• low – Sets PoE priority as low. This is the default setting.no Removes PoE settings on this interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1295.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2067.1.36.2.16 q o sinterface-config-ge-instanceDefines Quality of Service (QoS) settings on this Ethernet portSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxqos trust [802.1p|cos|dscp]Parameters• qos trust [802.1p|cos|dscp]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#qos trust dscprfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#qos trust 802.1prfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#show context interface ge1 description "This is GigabitEthernet interface for Royal King" duplex full dot1x supplicant username Bob password 0 test@123 ip dhcp trust ip arp header-mismatch-validation qos trust dscp qos trust 802.1p channel-group 1rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#Related Commandstrust [802.1p|cos|dscp] Trusts QoS values ingressing on this interface• 802.1p – Trusts 802.1p COS values ingressing on this interface• cos – Trusts 802.1p COS values ingressing on this interface. This option is enabled by default.• dscp – Trusts IP DSCP QOS values ingressing on this interface. This option is enabled by default.no Removes QoS settings on the selected interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1296.png)
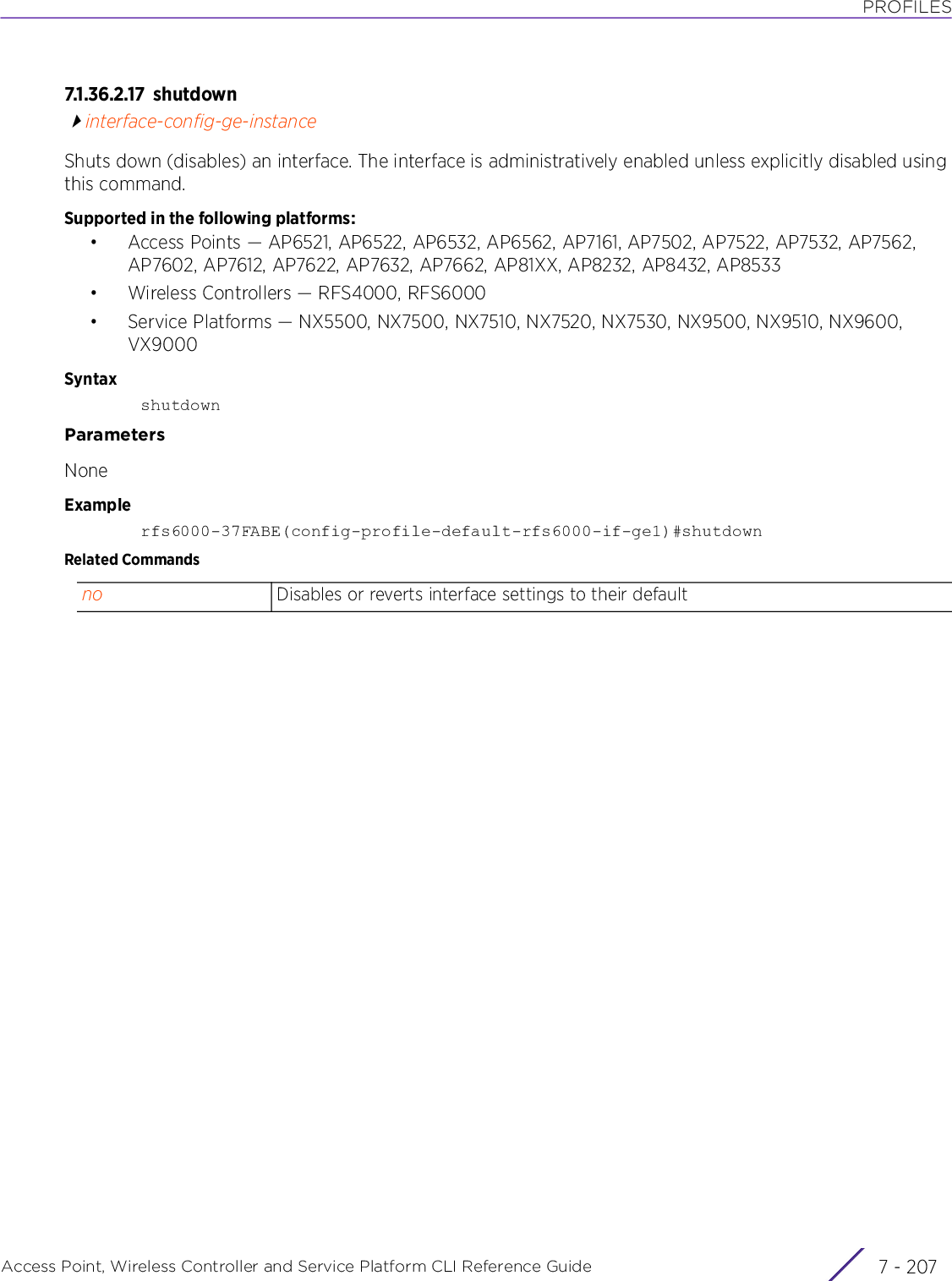
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2087.1.36.2.18 spanning-treeinterface-config-ge-instanceConfigures spanning tree parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxspanning-tree [bpdufilter|bpduguard|force-version|guard|link-type|mst|port-cisco-interoperability|portfast]spanning-tree [force-version <0-3>|guard root|portfast]spanning-tree [bpdufilter|bpduguard] [default|disable|enable]spanning-tree link-type [point-to-point|shared]spanning-tree mst <0-15> [cost <1-200000000>|port-priority <0-240>]spanning-tree port-cisco-interoperability [disable|enable]Parameters• spanning-tree [force-version <0-3>|guard root|portfast]• spanning-tree [bpdufilter|bpduguard] [default|disable|enable]force-version <0-3> Specifies the spanning tree force version. A version identifier of less than 2 enforces the spanning tree protocol. Select one of the following versions:•0 – Spanning Tree Protocol (STP)• 1 – Not supported•2 – Rapid Spanning tree Protocol (RSTP)•3 – Multiple Spanning Tree Protocol (MSTP). This is the default settingguard root Enables Root Guard for the portThe Root Guard disables superior Bridge Protocol Data Unit (BPDU) reception. The Root Guard ensures the enabled port is a designated port. If the Root Guard enabled port receives a superior BPDU, it moves to a discarding state (root-inconsistent STP state). This state is equivalent to a listening state, and data is not forwarded across the port. Therefore, enabling the guard root enforces the root bridge position. Use the no parameter with this command to disable the Root Guard.portfast Enables rapid transitions. Enabling PortFast allows the port to bypass the listening and learning states.bpdufilter [default|disable|enable]Sets a PortFast BPDU filter for the portUse the no parameter with this command to revert the port BPDU filter to its default. The spanning tree protocol sends BPDUs from all ports. Enabling the BPDU filter ensures PortFast enabled ports do not transmit or receive BPDUs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1298.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 209• spanning-tree link-type [point-to-point|shared]• spanning-tree mst <0-15> [cost <1-200000000>|port-priority <0-240>]• spanning-tree port-cisco-interoperability [disable|enable]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#spanning-tree bpdufilter disablerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#spanning-tree bpduguard enablerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#spanning-tree force-version 1rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#spanning-tree guard rootrfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#spanning-tree mst 2 port-priority 10bpduguard [default|disable|enable]Enables BPDU guard on a portUse the no parameter with this command to set BPDU guard to its default.When the BPDU guard is set for a bridge, all PortFast-enabled ports that have the BPDU guard set to default shut down upon receiving a BPDU. If this occurs, the BPDU is not processed. The port can be brought back either manually (using the no shutdown command), or by configuring the errdisable-timeout to enable the port after a specified interval.link-type [point-to-point|shared]Enables point-to-point or shared link types• point-to-point – Enables rapid transition. This option indicates the port should be treated as connected to a point-to-point link. A port connected to a controller is a point-to-point link.• shared – Disables rapid transition. This option indicates this port should be treated as having a shared connection. A port connected to a hub is on a shared link,mst <0-15> Configures MST on a spanning treecost <1-200000000> Defines path cost for a port from 1 - 200000000. The default path cost depends on the speed of the port. The cost helps determine the role of the port in the MSTP network. The designated cost is the cost for a packet to travel from this port to the root in the MSTP configuration. The slower the media, the higher the cost.port-priority <0-240> Defines port priority for a bridge from 1 - 240. Lower the priority greater is the likelihood of the port becoming a designated port. Applying a higher value impacts the port's likelihood of becoming a designated port.port-cisco-interoperabilityEnables interoperability with Cisco's version of MSTP (which is incompatible with standard MSTP)enable Enables CISCO Interoperabilitydisable Disables CISCO Interoperability. The default is disabled.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1299.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2117.1.36.2.19 speedinterface-config-ge-instanceSpecifies the speed of a FastEthernet (10/100) or GigabitEthernet (10/100/1000) port. This is the speed at which the port can receive and transmit the data.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxspeed [10|100|1000|auto]Parameters• speed [10|100|1000|auto]Usage GuidelinesSet the interface speed to auto detect and use the fastest speed available. Speed detection is based on connected network hardware.Examplerfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#speed 10rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#show context interface ge1 description "This is GigabitEthernet interface for Royal King" speed 10 duplex full spanning-tree bpduguard enable spanning-tree bpdufilter disable spanning-tree force-version 1 spanning-tree guard root spanning-tree mst 2 port-priority 10 dot1x supplicant username Bob password 0 test@123 ip dhcp trust ip arp header-mismatch-validation qos trust dscp qos trust 802.1p channel-group 1rfs6000-37FABE(config-profile-default-rfs6000-if-ge1)#Related Commands10 Forces 10 Mbps operation100 Forces 100 Mbps operation1000 Forces 1000 Mbps operationauto Port automatically detects its operational speed based on the port at the other end of the link. Select this option to enable the port to automatically exchange information about data transmission speed and duplex capabilities. Auto negotiation is helpful when in an environment where different devices are connected and disconnected on a regular basis.no Resets speed to default (auto)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1301.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2127.1.36.2.20 switchpo r tinterface-config-ge-instanceSets switching mode characteristics for the selected interfaceSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxswitchport [access|mode|trunk]switchport access vlan [<1-4094>|<VLAN-ALIAS-NAME>]switchport mode [access|trunk]switchport trunk [allowed|native]switchport trunk allowed vlan [<VLAN-ID>|add <VLAN-ID>|none|remove <VLAN-ID>]switchport trunk native [tagged|vlan [<1-4094>|<VLAN-ALIAS-NAME>]]Parameters• switchport access vlan [<1-4094>|<VLAN-ALIAS-NAME>]• switchport mode [access|trunk]• switchport trunk allowed vlan [<VLAN-ID>|add <VLAN-ID>|none|remove <VLAN-ID>]access vlan [<1-4094>|<VLAN-ALIAS-NAME>]Sets the VLAN when interface is in the access mode. You can either directly specify the native VLAN ID or use a VLAN alias to identify the native VLAN.• <1-4094> – Specify the SVI VLAN ID from 1 - 4094.• <VLAN-ALIAS-NAME> – Specify the VLAN alias name (should be existing and configured).An Ethernet port in the access mode accepts packets only from the native VLAN. Frames are forwarded out the port untagged with no 802.1Q header. All frames received on the port are expected as untagged and are mapped to the native VLAN.mode [access|trunk] Sets the interface’s switching mode to access or trunk (can only be used on physical - layer 2 - interfaces)• access – If access mode is selected, the access VLAN is automatically set to VLAN1. In this mode, only untagged packets in the access VLAN (vlan1) are accepted on this port. All tagged packets are discarded.• trunk – If trunk mode is selected, tagged VLAN packets are accepted. The native VLAN is automatically set to VLAN1. Untagged packets are placed in the native VLAN by the wireless controller or service platform. Outgoing packets in the native VLAN are sent untagged. The default mode for both ports is trunk.trunk allowed Sets trunking mode, allowed VLANs characteristics of the port. Use this option to add VLANs that exclusively send packets over the listed port.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1302.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 213• switchport trunk native [tagged|vlan [<1-4094>|<VLAN-ALIAS-NAME>]]Usage GuidelinesInterfaces ge1 - ge4 can be configured as trunk or in access mode. An interface configured as “trunk” allows packets (from the given list of VLANs) to be added to the trunk. An interface configured as “access” allows packets only from native VLANs.Use the [no] switchport (access|mode|trunk) to undo switchport configurations. vlan [<VLAN-ID>|add <VLAN-ID>|none|remove <VLAN-ID>Sets allowed VLAN options. The options are:• <VLAN-ID> – Allows a group of VLAN IDs. Specify the VLAN IDs, can be either a range (55-60) or a comma-separated list (35, 41, etc.)• none – Allows no VLANs to transmit or receive through the layer 2 interface• add <VLAN-ID> – Adds VLANs to the current list• <VLAN-ID> – Specify the VLAN IDs. Can be either a range of VLAN (55-60) or alist of comma separated IDs (35, 41, etc.)• remove <VLAN-ID> – Removes VLANs from the current list• <VLAN-ID> – Specify the VLAN IDs. Can be either a range of VLAN (55-60) or alist of comma separated IDs (35, 41, etc.)Allowed VLANs are configured only when the switching mode is set to “trunk”.trunk Sets trunking mode characteristics of the switchportnative [tagged|vlan [<1-4094>|<VLAN-ALIAS-NAME>]]Configures the native VLAN ID for the trunk-mode portThe native VLAN allows an Ethernet device to associate untagged frames to a VLAN when no 802.1Q frame is included in the frame. Additionally, the native VLAN is the VLAN untagged traffic is directed over when using a port in trunk mode.• tagged – Tags the native VLAN. When a frame is tagged, the 12 bit frame VLAN ID is added to the 802.1Q header enabling upstream Ethernet devices to know which VLAN ID the frame belongs to. The device reads the 12 bit VLAN ID and forwards the frame to the appropriate VLAN. When a frame is received with no 802.1Q header, the upstream device classifies the frame using the default or native VLAN assigned to the Trunk port. A native VLAN allows an Ethernet device to associate untagged frames to a VLAN when no 802.1Q frame is included in the frame.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Sets the native VLAN for classifying untagged traffic when the interface is in trunking mode. • <1-4094> – Specify a value from 1 - 4094.• <VLAN-ALIAS-NAME> – Specify the VLAN alias name used to identify theVLANs. The VLAN alias should be existing and configured.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1303.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2157.1.36.2.21 us einterface-config-ge-instanceSpecifies the IP (IPv4 and IPv6) access list and MAC access list used with this Ethernet port. The associated ACL firewall inspects IP and MAC traffic flows and detects attacks typically not visible to traditional wired firewall appliances.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [ip-access-list in <IPv4-ACCESS-LIST-NAME>|ipv6-access-list <IPv6-ACCESS-LIST-NAME>|mac-access-list in <MAC-ACCESS-LIST-NAME>]Parameters• use [ip-access-list in <IPv4-ACCESS-LIST-NAME>|ipv6-access-list <IPv6-ACCESS-LIST-NAME>|mac-access-list in <MAC-ACCESS-LIST-NAME>]ip-access-list in <IPv4-ACCESS-LIST-NAME>Associates an IPv4 access list with this Ethernet port. IPv4 is a connectionless protocol for packet switched networking. IPv4 operates as a best effort delivery method, as it does not guarantee delivery, and does not ensure proper sequencing or duplicate delivery (unlike (TCP). IPv4 hosts can use link local addressing to provide local connectivity.• in – Applies the IPv4 ACL on incoming packets• <IPv4-ACCESS-LIST-NAME> – Specify the IPv4 access list name (it should be anexisting and configured).ipv6-access-list in <IPv6-ACCESS-LIST-NAME>Associates an IPv6 access list with this Ethernet port. IPv6 is the latest revision of the IP designed to replace IPv4. IPV6 provides enhanced identification and location information for computers on networks routing traffic across the Internet. IPv6 addresses are composed of eight groups of four hexadecimal digits separated by colons.• in – Applies the IPv6 ACL on incoming packets• <IPv6-ACCESS-LIST-NAME> – Specify the IPv6 access list name (it should be anexisting and configured).mac-access-list in <MAC-ACCESS-LIST-NAME>Associates a MAC access list with this Ethernet port. MAC ACLs filter/mark packets based on the MAC address from which they arrive, as opposed to filtering packets on layer 2 ports.• in – Applies the MAC ACL on incoming packets• <MAC-ACCESS-LIST-NAME> – Specify the MAC access list name (it should be anexisting and configured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1305.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2177.1.36.3 interface-config-vlan-instanceinterfaceUse the config-profile-<DEVICE-PROFILE-NAME> mode to configure Ethernet, VLAN and tunnel settings.To switch to this mode, use the following commands:<DEVICE>(config-profile-default-<DEVICE-TYPE>)#interface [<INTERFACE-NAME>|fe <1-4>|ge <1-24>|me1|port-channel <1-4>|pppoe1|radio [1|2|3]|up1|vlan <1-4094>|wwan1|xge <1-24>]The following example uses the config-profile-default-rfs7000 instance to configure a VLAN interface:rfs6000-37FABE(config-profile-default-rfs6000)#interface vlan 8rfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#rfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#?SVI configuration commands: crypto Encryption module description Vlan description dhcp Dynamic Host Configuration Protocol (DHCP) dhcp-relay-incoming Allow on-board DHCP server to respond to relayed DHCP packets on this interface ip Interface Internet Protocol config commands ipv6 Internet Protocol version 6 (IPv6) no Negate a command or set its defaults shutdown Shutdown the selected interface use Set setting to use clrscr Clears the display screen commit Commit all changes made in this session do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system revert Revert changes service Service Commands show Show running system information write Write running configuration to memory or terminalrfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#The following table summarizes interface VLAN configuration commands:Commands Description Referencecrypto Defines the encryption module used with this VLAN interface page 7-218description Defines the VLAN interface description page 7-219dhcp Enables inclusion of optional fields (client identifier) in DHCP client requestspage 7-220dhcp-relay-incomingAllows an onboard DHCP server to respond to relayed DHCP packets on this interfacepage 7-221ip Configures the VLAN interface’s IP settings page 7-222ipv6 Configures the VLAN interface’s IPv6 settings page 7-225no Removes or reverts this VLAN interface’s settings to default page 7-230shutdown Shuts down this VLAN interface page 7-232use Associates an IP (IPv4 and IPv6) access list, bonjour-gw-discovery policy, and an IPv6-route-advertisement policy with this VLAN interfacepage 7-233](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-1/User-Guide-3831161-Page-1307.png)
