Extreme Networks AP3917E Wireless 802.11 a/ac+b/g/n Access Point User Manual WiNG 5 9 1 WC CLI
Extreme Networks, Inc. Wireless 802.11 a/ac+b/g/n Access Point WiNG 5 9 1 WC CLI
Contents
- 1. User Manual-AP3917e
- 2. User Manual-AP7662
- 3. User Manual-AP3917e R1
- 4. User Manual-AP7662 R1
- 5. WiNG 5.9.1 System Reference Guide Part 1
- 6. WiNG 5.9.1 System Reference Guide Part 2
- 7. WiNG 5.9.1 System Reference Guide Part 3
- 8. WiNG 5.9.1 System Reference Guide Part 4
- 9. WiNG 5.9.1 CLI Reference Guide Part 1
- 10. WiNG 5.9.1 CLI Reference Guide Part 2
- 11. Extreme Wireless V10.41.06 User Guide Part 1
- 12. AP3917 User Manual
- 13. AP7662 User Manual
WiNG 5.9.1 CLI Reference Guide Part 2

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2227.1.36.3.5 ipinterface-config-vlan-instanceConfigures the VLAN interface’s IP settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [address|dhcp|helper-address|nat|ospf]ip helper-address <IP>ip address [<IP/M>|<NETWORK-ALIAS-NAME>|dhcp|zeroconf]ip address [<IP/M>|<NETWORK-ALIAS-NAME>|zeroconf] {secondary}ip address dhcpip dhcp client request options allip nat [inside|outside]ip ospf [authentication|authentication-key|bandwidth|cost|message-digest-key|priority]ip ospf authentication [message-digest|null|simple-password]ip ospf authentication-key simple-password [0 <WORD>|2 <WORD>]ip ospf [bandwidth <1-10000000>|cost <1-65535>|priority <0-255>]ip ospf message-digest-key key-id <1-255> md5 [0 <WORD>|2 <WORD>]Parameters• ip helper-address <IP>• ip address [<IP/M>|<NETWORK-ALIAS-NAME>|zeroconf] {secondary}helper-address <IP> Enables DHCP and BOOTP requests forwarding for a set of clients. Configure a helper address on the VLAN interface connected to the client. The helper address should specify the address of the BOOTP or DHCP servers to receive the requests. If you have multiple servers, configure one helper address for each server.• <IP> – Specify the IP address of the DHCP or BOOTP server.address Sets the VLAN interface’s IP address<IP/M> Specifies the interface IP address in the A.B.C.D/M format• secondary – Optional. Sets the specified IP address as a secondary address<NETWORK-ALIAS-NAME>Uses a pre-defined network alias to provide this VLAN interface’s IP address. Specify the network alias name.• secondary – Optional. Sets the network-alias provided IP address as the secondary addresszeroconf {secondary} Uses Zero Configuration Networking (zeroconf) to generate an IP address for this interfaceContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-4.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 223• ip address dhcp• ip dhcp client request options all• ip nat [inside|outside]• ip ospf authentication [message-digest|null|simple-password]• ip ospf authentication-key simple-password [0 <WORD>|2 <WORD>]• ip ospf [bandwidth <1-10000000>|cost <1-65535>|priority <0-255>]Zero configuration can be a means of providing a primary or secondary IP addresses for the virtual interface. Zero configuration (or zero config) is a wireless connection utility included with Microsoft Windows XP and later as a service dynamically selecting a network to connect based on a user's preferences and various default settings. Zero config can be used instead of a wireless network utility from the manufacturer of a computer's wireless networking device.• secondary – Optional. Sets the generated IP address as a secondary addressaddress Sets the VLAN interface’s IP addressdhcp Uses a DHCP client to obtain an IP address for this VLAN interfacedhcp Uses a DHCP client to configure a request on this VLAN interfaceclient Configures a DHCP clientrequest Configures DHCP client requestoptions Configures DHCP client request optionsall Configures all DHCP client request optionsnat [inside|outside] Defines NAT settings for the VLAN interface. NAT is disabled by default.• inside – Enables NAT on the inside interface. The inside network is transmitting data over the network to the intended destination. On the way out, the source IP address is changed in the header and replaced by the (public) IP address.• outside – Enables NAT on the outside interface. Packets passing through the NAT on the way back to the managed LAN are searched against the records kept by the NAT engine. There, the destination IP address is changed back to the specific internal private class IP address in order to reach the LAN over the network.ospf authentication Configures OSPF authentication scheme. Options are message-digest, null, and simple-password.message-digest Configures md5 based authenticationnull No authentication requiredsimple-password Configures simple password based authenticationospf authentication-keyConfigures an OSPF authentication keysimple-password[0 <WORD>|2 <WORD>]Configures a simple password OSPF authentication key• 0 <WORD> – Configures clear text key• 2 <WORD> – Configures encrypted keybandwidth<1-10000000>Configures bandwidth for the physical port mapped to this layer 3 interface• <1-10000000> – Specify the bandwidth from 1 - 10000000.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-5.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 224• ip ospf message-digest-key key-id <1-255> md5 [0 <WORD>|2 <WORD>]Examplerfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#ip address 10.0.0.1/8rfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#ip nat insiderfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#ip helper-address 172.16.10.3rfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#ip dhcp client request options allrfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#show context interface vlan8 description "This VLAN interface is configured for the Sales Team" ip address 10.0.0.1/8 ip dhcp client request options all ip helper-address 172.16.10.3 ip nat inside crypto map map1 dhcp-relay-incomingrfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#Related Commandscost <1-65535> Configures OSPF cost• <1-65535> – Specify OSPF cost value from 1 - 65535.priority <0-255> Configures OSPF priority• <0-255> – Specify OSPF priority value from 0 - 255.ospf message-digest Configures message digest authentication parameterskey-id <1-255> Configures message digest authentication key ID from 0 - 255md5[0 <WORD>|2 <WORD>]Configures md5 key• 0 <WORD> – Configures clear text key• 2 <WORD> – Configures encrypted keyno Removes or resets IP settings on this interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-6.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2257.1.36.3.6 ipv6interface-config-vlan-instanceConfigures the VLAN interface’s IPv6 settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 [accept|address|dhcp|enable|enforce-dad|mtu|redirects|request-dhcpv6-options|router-advertisements]ipv6 accept ra {(no-default-router|no-hop-limit|no-mtu)}ipv6 address [<IPv6/M>|autoconfig|eui-64|link-local|prefix-from-provider]ipv6 address [<IPv6/M>|autoconfig]ipv6 address eui-64 [<IPv6/M>|prefix-from-provider <WORD> <IPv6-PREFIX/PREFIX-LENGTH>]ipv6 address prefix-from-provider <WORD> <HOST-PORTION/LENGTH>ipv6 address link-local <LINK-LOCAL-ADD>ipv6 dhcp [client [information|prefix-from-provider <WORD>]|relay destination <DEST-IPv6-ADD>]ipv6 [enable|enforce-dad|mtu <1280-1500>|redirects|request-dhcpv6-options]ipv6 router-advertisements [prefix <IPv6-PREFIX>|prefix-from-provider <WORD>] {no-autoconfig|off-link|site-prefix|valid-lifetime}Parameters• ipv6 accept ra {(no-default-router|no-hop-limit|no-mtu)}ipv6 accept ra Enables processing of router advertisements (RAs) on this VLAN interface. This option is enabled by default.When enabled, IPv6 hosts can configure themselves automatically when connected to an IPv6 network using the neighbor discovery protocol via ICMPv6 router discovery messages. When first connected to a network, a host sends a link-local router solicitation multicast request for its configuration parameters; routers respond to the request with a router advertisement packet containing Internet layer configuration parameters.no-default-router Optional. Disables inclusion of routers on this interface in the default router selection process. This option is disabled by default.no-hop-limit Optional. Disables the use of RA advertised hop-count value on this interface. This option is disabled by default.no-mtu Optional. Disables the use of RA advertised MTU value on this interface. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-7.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 226• ipv6 address [<IPv6/M>|autoconfig]• ipv6 address eui-64 [<IPv6/M>|prefix-from-provider <WORD> <IPv6-PREFIX/PREFIX-LENGTH>]ipv6 address[<IPv6/M>|autoconfig]Configures IPv6 address related settings on this VLAN interface• <IPv6> – Specify the non-link local static IPv6 address and prefix length of the interface in the X:X::X:X/M format.• autoconfig – Enables stateless auto-configuration of IPv6 address, based on the prefixes received from RAs (with auto-config flag set). These prefixes are used to auto-configure the IPv6 address. This option is enabled by default. Use the no > ipv6 > address > autoconfig command to negate the use of prefixes received in RAs.ipv6 address eui-64 Configures the IPv6 prefix and prefix length. This prefix is used to auto-generate the static IPv6 address (for this interface) in the modified Extended Unique Identifier (EUI)-64 format.Implementing the IEEE's 64-bit EUI64 format enables a host to automatically assign itself a unique 64-bit IPv6 interface identifier, without manual configuration or DHCP. This is accomplished on a virtual interface by referencing the already unique 48-bit MAC address, and reformatting it to match the EUI-64 specification.In the EUI-64 IPv6 address the prefix and host portions are each 64 bits in length.<IPv6/M> Specify the IPv6 prefix and prefix length. This configured value is used as the prefix portion of the auto-generated IPv6 address, and the host portion is derived from the MAC address of the interface.Any bits of the configured value exceeding the prefix-length “M” are ignored and replaced by the host portion derived from the MAC address.For example:Prefix portion provided using this command: ipv6 > address > eui-64 > 2004:b055:15:dead::1111/64.Host portion derived using the interface’s MAC address (00-15-70-37-FB-5E): 215:70ff:fe37:fb5eAuto-configured IPv6 address using the above prefix and host portions: 2004:b055:15:dead:215:70ff:fe37:fb5e/64In this example, the host part “::1111” is ignored and replaced with the modified eui-64 formatted host address.prefix-from-provider <WORD> <IPv6-PREFIX/PREFIX-LENGTH>Configures the “prefix-from-provider” named object and the associated IPv6 prefix and prefix length. This configured value is used as the prefix portion of the auto-generated IPv6 address, and the host portion is derived from the MAC address of the interface.• <WORD> – Specify the IPv6 “prefix-from-provider” object’s name. This is the IPv6 general prefix (32 character maximum) name provided by the Internet service provider.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-8.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 227• ipv6 address prefix-from-provider <WORD> <HOST-PORTION/LENGTH>]• ipv6 address link-local <LINK-LOCAL-ADD>• ipv6 dhcp [client [information|prefix-from-provider <WORD>]|relay destination <DEST-IPv6-ADD>]• <IPv6-PREFIX/PREFIX-LENGTH> – Specify the IPv6 address subnet and host parts along with prefix length (site-renumbering).For example:Prefix portion provided using this command: ipv6 > address > eui-64 > prefix-from-provider > ISP1-prefix > 2002::/64Host portion derived using the interface’s MAC address (00-15-70-37-FB-5E): 215:70ff:fe37:fb5eAuto-configured IPv6 address using the above prefix and host portions: 2002::215:70ff:fe37:fb5e/64ipv6 address Configures the IPv6 address related settings on this VLAN interfaceprefix-from-provider <WORD> <HOST-PORTION/LENGTH>Configures the “prefix-from-provider” named object and the host portion of the IPv6 interface address. The prefix derived from the specified “prefix-from-provide” and the host portion (second parameter) are combined together (using the prefix-length of the specified “prefix-from-provide”) to generate the interface’s IPv6 address.• <WORD> – Provide the “prefix-from-provider” object’s name. This is the IPv6 general prefix (32 character maximum) name provided by the service provider.• <HOST-PORTION/LENGTH> – Provide the subnet number, host portion, and prefix length used to form the actual address along with the prefix derived from the “prefix-from-provider” object identified by the <WORD> keyword.ipv6 address Configures the IPv6 address related settings on this VLAN interfacelink-local <LINK-LOCAL-ADD>Configures IPv6 link-local address on this interface. The configured value overrides the default link-local address derived from the interface’s MAC address. Use the no > ipv6 > link-local command to restore the default link-local address derived from MAC address.It is mandatory for an IPv6 interface to always have a link-local address.ipv6 dhcp client [information|prefix-from-provider <WORD>]Configures DHCPv6 client-related settings on this VLAN interface• information – Configures stateless DHCPv6 client on this interface. When enabled. the device can request configuration information from the DHCPv6 server using stateless DHCPv6. This option is disabled by default.• prefix-from-provider – Configures prefix-delegation client on this interface. Enter the IPv6 general prefix (32 character maximum) name provided by the service provider. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-9.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 228• ipv6 [enable|enforce-dad|mtu <1280-1500>|redirects|request-dhcp-options]• ipv6 router-advertisements [prefix <IPv6-PREFIX>|prefix-from-provider <WORD>] {no-autoconfig|off-link|site-prefix <SITE-PREFIX>|valid-lifetime}relay destination <DEST-IPv6-ADD>Enables DHCPv6 packet forwarding on this VLAN interface• destination – Forwards DHCPv6 packets to a specified DHCPv6 relay• <DEST-IPv6-ADD> – Specify the destination DHCPv6 relay’s address.DHCPv6 relay enhances an extended DHCP relay agent by providing support in IPv6. DHCP relays exchange messages between a DHCPv6 server and client. A client and relay agent exist on the same link. When a DHCP request is received from the client, the relay agent creates a relay forward message and sends it to a specified server address. If no addresses are specified, the relay agent forwards the message to all DHCP server relay multicast addresses. The server creates a relay reply and sends it back to the relay agent. The relay agent then sends back the response to the client.ipv6 Configures IPv6 settings on this VLAN interfaceenable Enables IPv6 on this interface. This option is disabled by default.enforce-dad Enforces Duplicate Address Detection (DAD) on wired ports. This option is enabled by default.mtu <1280-1500> Configures the Maximum Transmission Unit (MTU) for IPv6 packets on this interface• <1280-1500> – Specify a value from 1280 - 1500. The default is 1500.redirects Enables ICMPv6 redirect messages sending on this interface. This option is enabled by default.request-dhcp-options Requests options from DHCPv6 server on this interface. This option is disabled by default.ipv6 router-advertisementsConfigures IPv6 RA related settings on this VLAN interfaceprefix <IPv6-PREFIX> Configures a static prefix and its related parameters. The configured value is advertised on RAs.• <IPv6-PREFIX> – Specify the IPv6 prefix.prefix-from-provider <WORD>Configures a static “prefix-from-provider” named object and its related parameters on this VLAN interface. The configured value is advertised on RAs.• <WORD> – Specify the “prefix-from-provider” named object’s nameno-autoconfig This parameter is common to the “general-prefix”, “prefix”, and “prefix-from-provider” keywords.• no-autoconfig – Optional. Disables the setting of the auto configuration flag in the prefix. When configured, the configured prefixes are not used for IPv6 address generation. The autoconfiguration option is enabled by default. Using no-autoconfig disables it.off-link This parameter is common to the “general-prefix”, “prefix”, and “prefix-from-provider” keywords.• off-link – Optional. Disables the setting of the on-link flag in the prefix. The on-link option is enabled by default. Using off-link disables it.site-prefix <SITE-PREFIX>This parameter is common to the “general-prefix”, “prefix”, and “prefix-from-provider” keywords.• site-prefix <SITE-PREFIX> – Configures subnet (site) prefix](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-10.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 229Examplerfs6000-81742D(config-profile-test-if-vlan4)#ipv6 enablerfs6000-81742D(config-profile-test-if-vlan4)#ipv6 accept ra no-mturfs6000-81742D(config-profile-test-if-vlan4)#ipv6 address eui-64 prefix-from-provider ISP1-prefix 2002::/64rfs6000-81742D(config-profile-test-if-vlan4)#show context interface vlan4 ipv6 enable ipv6 address eui-64 prefix-from-provider ISP1-prefix 2002::/64 ipv6 accept ra no-mturfs6000-81742D(config-profile-test-if-vlan4)#Related Commandsvalid-lifetime [<30-4294967294>|at|infinite] (preferred-lifetime)This parameter is common to the “general-prefix”, “prefix”, and “prefix-from-provider” keywords.• valid-lifetime – Configures the valid lifetime for the prefix• preferred-lifetime – Configures preferred lifetime for the prefix• <30-4294967294> – Configures the valid/preferred lifetime in seconds• at – Configures expiry time and date of the valid/preferred lifetime• infinite – Configures the valid/preferred lifetime as infiniteno Removes or resets IPv6 settings on this VLAN interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-11.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2307.1.36.3.7 n ointerface-config-vlan-instanceNegates a command or reverts to defaults. The no command, when used in the Config Interface VLAN mode, negates VLAN interface settings or reverts them to their default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [crypto|description|dhcp|dhcp-relay-incoming|ip|ipv6|shutdown|use]no dhcp client include client-identifierno [crypto map|description|dhcp-relay-incoming|shutdown]no ip [address|dhcp|helper-address|nat|ospf]no ip [helper-address <IP>|nat]no ip address {<IP/M> {secondary}|<NETWORK-ALIAS-NAME> {secondary}|dhcp|zeroconf {secondary}}no ip dhcp client request options allno ip ospf [authentication|authentication-key|bandwidth|cost|message-digest-key|priority]no ipv6 [accept|address|dhcp|enable|enforce-dad|mtu|redirects|request-dhcpv6-options|router-advertisement]no ipv6 [accept ra|enable|enforce-dad|mtu|redirects|request-dhcpv6-options]no ipv6 address [<IPv6/M>|autoconfig|eui-64|link-local|prefix-from-provider>]no ipv6 dhcp [client|relay]no ipv6 router-advertisement [prefix <WORD>|prefix-from-provider <WORD>]no use [bonjour-gw-discovery-policy>|ip-access-list in|ipv6-access-list in|ipv6-router-advertisement-policy|url-filter]Parameters• no <PARAMETERS>ExampleThe following example shows the VLAN interface settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#show context interface vlan8 description "This VLAN interface is configured for the Sales Team" ip address 10.0.0.1/8 ip dhcp client request options all ip helper-address 172.16.10.3 ip nat inside crypto map map1 dhcp-relay-incomingrfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#rfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#no crypto maprfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#no descriptionrfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#no dhcp-relay-incomingrfs6000-37FABE(config-profile-default-rfs6000-if-vlan8)#no ip dhcp client request options allno <PARAMETERS> Removes or reverts this VLAN interface’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-12.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2337.1.36.3.9 useinterface-config-vlan-instanceAssociates an IP (IPv4 and IPv6) access list, bonjour-gw-discovery policy, and an IPv6-router-advertisement policy with this VLAN interfaceSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [bonjour-gw-discovery-policy <POLICY-NAME>|ip-access-list in <IP-ACL-NAME>|ipv6-access-list in <IPv6-ACL-NAME>|ipv6-router-advertisement-policy <POLICY-NAME>|url-filter <URL-FILTER-NAME>]Parameters• use [bonjour-gw-discovery-policy <POLICY-NAME>|ip-access-list in <IP-ACL-NAME>|ipv6-access-list in <IPv6-ACL-NAME>|ipv6-router-advertisement-policy <POLICY-NAME>|url-filter <URL-FILTER-NAME>]bonjour-gw-discovery-policy <POLICY-NAME>Uses an existing Bonjour GW Discovery policy with this VLAN interface. When associated, the Bonjour GW Discovery policy is applied for the Bonjour requests coming over the VLAN interface.• <POLICY-NAME> – Specify the Bonjour GW Discovery policy name (should be existing and configured).For more information on Bonjour GW Discovery policy, see bonjour-gw-discovery-policy.ip-access-list in <IP-ACCESS-LIST-NAME>Uses a specified IPv4 access list with this interface• in – Applies IPv4 ACL to incoming packets• <IP-ACCESS-LIST-NAME> – Specify the IPv4 access list name.ipv6-access-list in <IPv6-ACCESS-LIST-NAME>Uses a specified IPv6 access list with this interface• in – Applies IPv6 ACL to incoming packets• <IPv6-ACCESS-LIST-NAME> – Specify the IPv6 access list name.ipv6-router-advertisement-policy <POLICY-NAME>Uses an existing IPv6 router advertisement policy with this VLAN interface.• <POLICY-NAME> – Specify the IPv6 router advertisement policy name (should be existing and configured).url-filter <URL-FILTER-NAME>Enforces URL filtering on this VLAN interface by associating a URL filter• <URL-FILTER-NAME> – Specify the URL filter name (should be existing and configured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-15.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2377.1.36.4.2 dupl exinterface-config-port-channel-instanceConfigures the duplex-mode (that is the data transmission mode) for this port channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxduplex [auto|half|full]Parameters• duplex [auto|half|full]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#duplex fullnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." duplex fullnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commandsduplex [auto|half|full] Configures the mode of data transmission as auto, full, or half• auto – Select this option to enable the controller, service platform, or access point to dynamically duplex as port channel performance needs dictate. This is the default setting.• full – Select this option to simultaneously transmit data to and from the port channel.• half – Select this option to send data over the port channel, then immediately receive data from the same direction in which the data was transmitted.no Reverts the duplex-mode to the default value (auto)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-19.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2387.1.36.4.3 i pinterface-config-port-channel-instanceConfigures ARP and DHCP related security parameters on this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [arp|dhcp]ip arp [header-mismatch-validation|trust]ip dhcp trustParameters• ip arp [header-mismatch-validation|trust]• ip dhcp trustExamplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#ip arp trustnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." duplex full ip arp trustnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commandsip arp [header-mismatch-validation|trust]Configures ARP related parameters on this port-channel interface• header-mismatch-validation – Enables a source MAC mismatch check in both the ARP and ethernet headers. This option is enabled by default.• trust – Enables ARP trust on this port channel. If enabled, ARP packets received on this port are considered trusted, and information from these packets is used to identify rogue devices. This option is disabled by default.ip dhcp trust Enables DHCP trust. If enabled, only DHCP responses are trusted and forwarded on this port channel, and a DHCP server can be connected only to a DHCP trusted port. This option is enabled by default.no Removes or reverts to default the ARP and DHCP security parameters configured](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-20.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2397.1.36.4.4 ipv6interface-config-port-channel-instanceConfigures IPv6 related parameters on this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 [dhcpv6|nd]ipv6 dhcpv6 trustipv6 nd [header-mismatch-validation|raguard|trust]Parameters• ipv6 dhcpv6 trust• ipv6 nd [header-mismatch-validation|raguard|trust]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#ipv6 nd header-mismatch-validationnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#ipv6 nd trustnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." duplex full ipv6 nd trust ipv6 nd header-mismatch-validation ip arp trustnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commandsipv6 dhcpv6 trust Enables DHCPv6 trust. If enabled, only DHCPv6 responses are trusted and forwarded on this port channel, and a DHCPv6 server can be connected only to a trusted port. This option is enabled by default.ipv6 nd [header-mismatch-validation|raguard|trust]Configures IPv6 neighbor discovery (ND) parameters• header-mismatch-validation – Enables a mismatch check for the source MAC in both the ND header and link layer options. This option is disabled by default.raguard Enables router advertisements or IPv6 redirects from this port. Router advertisements are periodically sent to hosts or are sent in response to solicitation requests. The advertisement includes IPv6 prefixes and other subnet and host information. This option is enabled by default.trust Enables DHCPv6 trust. If enabled, only DHCPv6 responses are trusted and forwarded on this port channel, and a DHCPv6 server can be connected only to a trusted port. This option is enabled by default.no Removes or reverts to default the IPv6 related parameters on this port-channel interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-21.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2407.1.36.4.5 p o rt-ch a nne linterface-config-port-channel-instanceConfigures client load balancing parameters on this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxport-channel load-balance [src-dst-ip|src-dst-mac]Parameters• port-channel load-balance [src-dst-ip|src-dst-mac]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#port-channel load-balance src-dst-macnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." duplex full ipv6 nd trust ipv6 nd header-mismatch-validation ip arp trust port-channel load-balance src-dst-macnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commandsport-channel load-balance [src-dst-ip|src-dst-mac]Specifies whether port channel load balancing is conducted using a source/destination IP or a source/destination MAC. • src-dst-ip – Uses a source/destination IP to conduct client load balancing. This is the default setting.• src-dst-mac – Uses a source/destination MAC to conduct client load balancingno Removes or reverts to default the client load balancing parameters on this port-channel interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-22.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2417.1.36.4.6 q o sinterface-config-port-channel-instanceConfigures Quality of Service (QoS) related parameters on this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxqos trust [802.1p|dscp]Parameters• qos trust [802.1p|dscp]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#qos trust dscpnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show contextRelated Commandsqos trust [802.1p|dscp]Configures the following QoS related parameters:•802.1p – Trusts 802.1p class of service (COS) values ingressing on this port channel. This option is enabled by default.• dscp – Trusts IP DSCP QOS values ingressing on this port channel. This option is enabled by default.no Removes the QoS related parameters configured on this port-channel interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-23.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2427.1.36.4.7 nointerface-config-port-channel-instanceRemoves or reverts to default this port-channel interface’s settingsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno beacon [description|duplex|ip|ipv6|port-channel|qos|shutdown|spanning-tree|speed|switchport|use]Parameters• no <PARAMETERS>ExampleThe following example shows the port-channel interface’s interface settings before the ‘no’ commands are executed:nx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show contextdescription "This port-channel is for enabling dynamic LACP." speed 100 duplex full switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1 use ip-access-list in BROADCAST-MULTICAST-CONTROL ipv6 nd trust ipv6 nd header-mismatch-validation spanning-tree portfast spanning-tree bpduguard enable spanning-tree bpdufilter enable spanning-tree mst 1 port-priority 1 spanning-tree mst 1 cost 20000 ip arp trust port-channel load-balance src-dst-macnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#nx9500-6C8809(config-profile-testNX9000-if-port-channel1)#no duplexnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#no ip arp trustnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#no ipv6 nd trustnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#no port-channel load-balanceno <PARAMETERS> Removes or reverts to default this port-channels interface’s settings based on the parameters passed• <PARAMETERS> – Specify the parameters.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-24.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2457.1.36.4.9 spanning-treeinterface-config-port-channel-instanceConfigures spanning-tree related parameters on this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxspanning-tree [bpdufilter|bpduguard|force-version|guard|link-type|mst|port-cisco-interoperability|portfast]spanning-tree [bpdufilter|bpduguard] [default|disable|enable]spanning-tree [force-version <0-3>|guard root|portfast|port-cisco-interoperability [disable|enable]]spanning-tree link-type [point-to-point|shared]spanning-tree mst <0-15> [cost <1-200000000>|port-priority <0-240>]]Parameters• spanning-tree [bpdufilter|bpduguard] [default|disable|enable]• spanning-tree [force-version <0-3>|guard root|portfast|port-cisco-interoperability [disable|enable]]spanning-tree [bpdufilter|bpduguard]Configures the following BPDU related parameters for this port channel:• bpdufilter – Configures the BPDU filtering options. The options are:• default – When selected, makes the bridge BPDU filter value to take effect. This isthe default setting.• disable – Disables BPDU filtering• enable – Enables BPDU filtering. Enabling the BPDU filter feature ensures this portchannel does not transmit or receive any BPDUs.• bpduguard – Configures the BPDU guard options. The options are• default – When selected, makes the bridge BPDU guard value to take effect. This isthe default setting.• disable – Disables guarding this port from receiving BPDUs• enable – Enables BPDU guarding. Enabling the BPDU guard feature means this portwill shutdown on receiving a BPDU. Thus, no BPDUs are processed.Execute the portfast command to ensure that fast transitions is enabled on this port channel before configuring BPDU filtering and guarding.spanning-tree [force-version <0-3>|guard root|portfast|port-cisco-interoperability [disable|enable]Configures the following MSTP related parameters for this port channel:• force-version <0-3> – Sets the protocol version to either STP(0), Not Supported(1), RSTP(2) or MSTP(3). MSTP is the default setting• guard root – Enforces root bridge placement. Setting the guard to Root ensures the port is a designated port. Typically, each guard root port is a designated port, unless two or more ports (within the root bridge) are connected together. Contd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-27.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 246• spanning-tree link-type [point-to-point|shared]• spanning-tree mst <0-15> [cost <1-200000000>|port-priority <0-240>]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#spanning-tree portfastnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#spanning-tree bpdufilter enablenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#spanning-tree bpduguard enablenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#spanning-tree force-version 3nx9500-6C8809(config-profile-testNX9000-if-port-channel1)#spanning-tree mst 1 cost 20000nx9500-6C8809(config-profile-testNX9000-if-port-channel1)#spanning-tree mst 1 port-priority 1If the bridge receives superior (BPDUs) on a guard root-enabled port, the guard root moves the port to a root-inconsistent STP state. This state is equivalent to a listening state. No data is forwarded across the port. Thus, the guard root enforces the root bridge position.• portfast – Enables fast transitions on this port channel. When enabled, BPDU filtering and guarding can be enforced on this port. Enable the portfast option and then use the ‘bpdufilter’ and bpduguard’ options to configure BPDU filtering and guarding parameters. This option is disabled by default.• port-cisco-interoperability [disable|enable] – Enables or disables interoperability with Cisco's version of MSTP, which is incompatible with standard MSTP. This option is disabled by default.spanning-tree link-type [point-to-point|shared]Configures the link type applicable on this port channel. The options are:• point-to-point – Configures a point-to-point link, which indicates the port should be treated as connected to a point-to-point link. Note, a port connected to the wireless device is a point-to-point link. This is the default setting.• shared – Configures a shared link, which indicates this port should be treated as having a shared connection. Note, A port connected to a hub is on a shared link.spanning-tree mst <0-15> [cost <1-200000000>|port-priority <0-240>]Configures the following Multiple Spanning Tree (MST) parameters on this port:• mst <0-15> – Select the MST instance from 0 - 15.• cost <1-200000000> – Configures the port cost from 1 - 200000000. The defaultpath cost depends on the user defined port speed.The cost helps determine the role ofthe port channel in the MSTP network. The designated cost is the cost for a packet totravel from this port to the root in the MSTP configuration. The slower the media, high-er the cost.• port-priority <0-240> – Configures the port priority from 0 - 240. The lower the priority, greater is the likelihood of the port becoming a designated port.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-28.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2487.1.36.4.10 speedinterface-config-port-channel-instanceConfigures the speed at which this port-channel interface receives and transmits dataSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxspeed [10|100|1000|auto]]]Parameters• speed [10|100|1000|auto]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#speed 100nx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." speed 100 duplex full ipv6 nd trust ipv6 nd header-mismatch-validation spanning-tree portfast spanning-tree bpduguard enable spanning-tree bpdufilter enable spanning-tree mst 1 port-priority 1 spanning-tree mst 1 cost 20000 ip arp trust port-channel load-balance src-dst-macnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commandsspeed [10|100|1000|auto]Configure the data receive-transmit speed for this port channel. The options are:• 10 – 10 Mbps• 100 – 100 mbps• 1000 – 1000 Mbps• auto – Enables the system to auto select the speed. This is the default setting.Select either of these options to establish a 10, 100 or 1000 Mbps data transfer rate for the selected half duplex or full duplex transmission over the port. The auto option enables the port-channel to automatically exchange information about data transmission speed and duplex capabilities. Auto negotiation is helpful in an environment where different devices are connected and disconnected on a regular basis.no Removes or reverts to default the speed at which this port-channel interface receives and transmits data](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-30.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2497.1.36.4.11 sw i tc hpor tinterface-config-port-channel-instanceConfigures the VLAN switching parameters for this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxswitchport [access|mode|trunk]switchport access vlan [<1-4094>|<VLAN-ALIAS-NAME>]switchport mode [access|trunk]switchport trunk [allowed|native]switchport trunk allowed vlan [<VLAN-ID>|add <VLAN-ID>|none|remove <VLAN-ID>]switchport trunk native [tagged|vlan [<1-4094>|<VLAN-ALIAS-NAME>]]Parameters• switchport access vlan [<1-4094>|<VLAN-ALIAS-NAME>]• switchport mode [access|trunk]• switchport trunk allowed vlan [<VLAN-ID>|add <VLAN-ID>|none|remove <VLAN-ID>]access vlan [<1-4094>|<VLAN-ALIAS-NAME>]Configures the VLAN to which this port-channel interface is mapped when the switching mode is set to access.• <1-4094> – Specify the SVI VLAN ID from 1 - 4094.• <VLAN-ALIAS-NAME> – Specify the VLAN alias name (should be existing and configured).mode [access|trunk] Configures the VLAN switching mode over the port channel• access – If selected, the port channel accepts packets only form the native VLANs. Frames are forwarded out the port untagged with no 802.1Q header. All frames received on the port are expected as untagged and are mapped to the native VLAN. This is the default setting.• trunk – If selected, the port channel allows packets from a list of VLANs you add to the trunk. A port channel configured as Trunk supports multiple 802.1Q tagged VLANs and one Native VLAN which can be tagged or untagged.trunk allowed If configuring the VLAN switching mode as trunk, use this option to configure the VLANs allowed on this port channel. Add VLANs that exclusively send packets over the port channel.vlan [<VLAN-ID>|add <VLAN-ID>|none|remove <VLAN-ID>Use this keyword to add/remove the allowed VLANs• <VLAN-ID> – Allows a group of VLAN IDs. Specify the VLAN IDs, can be either a range (55-60) or a comma-separated list (35, 41, etc.)• none – Allows no VLANs to transmit or receive through the layer 2 interfaceContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-31.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 250• switchport trunk native [tagged|vlan [<1-4094>|<VLAN-ALIAS-NAME>]]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#switchport mode trunknx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." speed 100 duplex full switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1 ipv6 nd trust ipv6 nd header-mismatch-validation spanning-tree portfast spanning-tree bpduguard enable spanning-tree bpdufilter enable spanning-tree mst 1 port-priority 1 spanning-tree mst 1 cost 20000 ip arp trust port-channel load-balance src-dst-macnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commands• add <VLAN-ID> – Adds VLANs to the current list• <VLAN-ID> – Specify the VLAN IDs. Can be either a range of VLAN (55-60) or alist of comma separated IDs (35, 41, etc.)• remove <VLAN-ID> – Removes VLANs from the current list• <VLAN-ID> – Specify the VLAN IDs. Can be either a range of VLAN (55-60) or alist of comma separated IDs (35, 41, etc.)Allowed VLANs are configured only when the switching mode is set to “trunk”.trunk If configuring the VLAN switching mode as trunk, use this option to configure the native VLAN on this port channel.native [tagged|vlan [<1-4094>|<VLAN-ALIAS-NAME>]]Configures the native VLAN ID for the trunk-mode portThe native VLAN allows an Ethernet device to associate untagged frames to a VLAN when no 802.1Q frame is included in the frame. Additionally, the native VLAN is the VLAN untagged traffic is directed over when using a port in trunk mode.• tagged – Tags the native VLAN. When a frame is tagged, the 12 bit frame VLAN ID is added to the 802.1Q header enabling upstream Ethernet devices to know which VLAN ID the frame belongs to. The device reads the 12 bit VLAN ID and forwards the frame to the appropriate VLAN. When a frame is received with no 802.1Q header, the upstream device classifies the frame using the default or native VLAN assigned to the Trunk port. A native VLAN allows an Ethernet device to associate untagged frames to a VLAN when no 802.1Q frame is included in the frame.• vlan [<1-4094>|<VLAN-ALIAS-NAME>] – Sets the native VLAN for classifying untagged traffic when the interface is in trunking mode. • <1-4094> – Specify a value from 1 - 4094.• <VLAN-ALIAS-NAME> – Specify the VLAN alias name used to identify theVLANs. The VLAN alias should be existing and configured.no Removes the packet switching parameters configured on this port-channel interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-32.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2517.1.36.4.12 useinterface-config-port-channel-instanceConfigures access controls on this port-channel interfaceSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [ip-access-list|ipv6-access-list|mac-access-list] in <IP/IPv6/MAC-ACCESS-LIST-NAME>]]Parameters• use [ip-access-list|ipv6-access-list|mac-access-list] in <IP/IPv6/MAC-ACCESS-LIST-NAME>]Examplenx9500-6C8809(config-profile-testNX9000-if-port-channel1)#use ip-access-list inBROADCAST-MULTICAST-CONTROLnx9500-6C8809(config-profile-testNX9000-if-port-channel1)#show context interface port-channel1 description "This port-channel is for enabling dynamic LACP." speed 100 duplex full switchport mode trunk switchport trunk native vlan 1 no switchport trunk native tagged switchport trunk allowed vlan 1 use ip-access-list in BROADCAST-MULTICAST-CONTROL ipv6 nd trust ipv6 nd header-mismatch-validation spanning-tree portfast--More--nx9500-6C8809(config-profile-testNX9000-if-port-channel1)#Related Commandsuse [ip-access-list|ipv6-access-list|mac-access-list] <IP/IPv6/MAC-ACCESS-LIST-NAME>]Associates an access list controlling the inbound traffic on this port channel.• ip-access-list – Specify the IPv4 specific firewall rules to apply to this profile’s port channel configuration. IPv4 is a connectionless protocol for packet switched networking. IPv4 operates as a best effort delivery method, as it does not guarantee delivery, and does not ensure proper sequencing or duplicate delivery (unlike (TCP). IPv4 hosts can use link local addressing to provide local connectivity.• ipv6-access-list – Specify the IPv6 specific firewall rules to apply to this profile’s port channel configuration. IPv6 is the latest revision of the Internet Protocol (IP) designed to replace IPv4. IPV6 provides enhanced identification and location information for computers on networks routing traffic across the Internet. IPv6 addresses are composed of eight groups of four hexadecimal digits separated by colons.• mac-access-list – Specify the MAC specific firewall rules to apply to this profile’s port channel configuration.• <IP/IPv6/MAC-ACCESS-LIST-NAME> – Provide the IPv4, IPv6, or MAC access listname based on the option selected. The access list specified should be existing andconfigured.no Removes the access controls configured on this port-channel interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-33.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2567.1.36.5.1 adaptivityinterface-config-radio-instanceConfigures an interval, in minutes, for avoiding channels detected with high levels of interferenceAs per the European Telecommunications Standards Institute’s (ETSI) EN 300 328 V1.8.1/ ETSI EN 301 893 V1.7.1 requirements, access points have to monitor interference levels on operating channels, and stop functioning on channels with interference levels exceeding ETSI-specified threshold values.This command configures the interval for which a channel is avoided on detection of interference, and is applicable only if the channel selection mode is set to ACS, Random, or Fixed.When configured, this feature ensures recovery by switching the radio to a new operating channel. Once adaptivity is triggered, the evacuated channel becomes inaccessible and is available again only after the adaptivity timeout, specified here, expires. In case of fixed channel, the radio switches back to the original channel of operation after the adaptivity timeout expires. On the other hand, ACS-enabled radios continue operating on the new channel even after the adaptivity timeout period expires.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxadaptivity [recovery|timeout <30-3600>]Parameters• adaptivity [recovery|timeout <30-3600>]Examplenx4500-5CFA2B(config-profile-testAP7532-if-radio1)#adaptivity timeout 200nx4500-5CFA2B(config-profile-testAP7532-if-radio1)#show context interface radio1 adaptivity timeout 200nx4500-5CFA2B(config-profile-testAP7532-if-radio1)#Related CommandsNOTE: If the channel selection mode is set to Smart, in the Smart-RF policy mode, use the avoidance-time > [adaptivity|dfs] > <30-3600> command to specify the interval for which a channel is avoided on detection of high levels of interference or radar. For more information, see avoidance-time.adaptivity Configures adaptivity parameters on the radio. These parameters are: recovery and timeout.recovery Enables switching of channels when an access point’s radio is in the adaptivity mode. In the adaptivity mode, an access point monitors interference on its set channel and stops functioning when the radio’s defined interference tolerance level is exceeded. When the defined adaptivity timeout is exceeded, the radio resumes functionality on adifferent channel. This option is enabled by default.timeout <30-3600>Configures an adaptivity timeout• <30-3600> – Specify a value from 30 - 3600 minutes. The default is 90 minutes.no Removes the configured adaptivity timeout value and disables adaptivity recovery](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-38.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2577.1.36.5.2 aeroscoutinterface-config-radio-instanceEnables Aeroscout multicast packet forwarding. This feature is disabled by default.Supported in the following platforms:• Access Points — AP6532, AP7502, AP7522Syntaxaeroscout [forward ip <IP> port <0-65535>|mac <MAC>]Parameters• aeroscout [forward ip <IP> port <0-65535>|mac <MAC>]Examplenx9500-6C8809(config-profile-ProfileTestAP7532-if-radio2)#aeroscout forward ip 10.233.84.206 port 22nx9500-6C8809(config-profile-ProfileTestAP7532-if-radio2)#show context interface radio2 aeroscout forward ip 10.233.84.206 port 22nx9500-6C8809(config-profile-ProfileTestAP7532-if-radio2)#Related Commandsaeroscout Enables Aeroscout packet forwarding and configures the packet forwarding parametersforward ip <IP> port <0-65535>Configures the following Aeroscout locationing engine details:• ip – Configures Aeroscout engine’s IP address• <IP> – Specify the Aeroscout engine’s IP address. When specified, the AP forwardsAeroscout beacons directly to the Aeroscout locationing engine without proxyingthrough the controller or RF Domain manager.• port – Configures the port on which the Aeroscout engine is reachable• <0-65535> – Specify the port number from 0 - 65535.mac <MAC> Configures the multicast MAC address to forward the Aeroscout packets• <MAC> – Specify the MAC address in the AA-BB-CC-DD-EE-FF format. The default value is 01-0C-CC-00-00-00.no Disables Aeroscout packet forwarding](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-39.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2587.1.36.5.3 aggregationinterface-config-radio-instanceConfigures 802.11n frame aggregation parameters. Frame aggregation increases throughput by sending two or more data frames in a single transmission. There are two types of frame aggregation: MAC Service Data Unit (MSDU) aggregation and MAC Protocol Data Unit (MPDU) aggregation. Both modes group several data frames into one large data frame.Supported in the following platforms:• Access Points — AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxaggregation [ampdu|amsdu]aggregation ampdu [rx-only|tx-only|tx-rx|none|max-aggr-size|min-spacing]aggregation ampdu [rx-only|tx-only|tx-rx|none]aggregation ampdu max-aggr-size [rx|tx]aggregation ampdu max-aggr-size rx [8191|16383|32767|65535]aggregation ampdu max-aggr-size tx <2000-65535>aggregation ampdu min-spacing [0|1|2|4|8|16]aggregation amsdu [rx-only|tx-rx]Parameters• aggregation ampdu [rx-only|tx-only|tx-rx|none]• aggregation ampdu max-aggr-size rx [8191|16383|32767|65535]aggregation Configures 802.11n frame aggregation parametersampdu Configures Aggregate MAC Protocol Data Unit (AMPDU) frame aggregation parametersAMPDU aggregation collects Ethernet frames addressed to a single destination. It wraps each frame in an 802.11n MAC header. This aggregation mode is less efficient, but more reliable in environments with high error rates. It enables the acknowledgement and retransmission of each aggregated data frame individually.tx-only Supports the transmission of AMPDU aggregated frames onlyrx-only Supports the receipt of AMPDU aggregated frames onlytx-rx Supports the transmission and receipt of AMPDU aggregated frames (default setting)none Disables support for AMPDU aggregationaggregation Configures 802.11n frame aggregation parametersampdu Configures AMPDU frame aggregation parametersAMPDU aggregation collects Ethernet frames addressed to a single destination. It wraps each frame in an 802.11n MAC header. This aggregation mode is less efficient, but more reliable in environments with high error rates. It enables the acknowledgement and retransmission of each aggregated data frame individually.max-aggr-size Configures AMPDU packet size limits. Configure the packet size limit on packets both transmitted and received.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-40.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 259• aggregation ampdu max-aggr-size tx <2000-65535>• aggregation ampdu min-spacing [0|1|2|4|8|16|auto]• aggregation amsdu [rx-only|tx-rx]rx [8191|16383|32767|65535]Configures the maximum limit (in bytes) advertised for received frames• 8191 – Advertises a maximum of 8191 bytes• 16383 – Advertises a maximum of 16383 bytes• 32767 – Advertises a maximum of 32767 bytes• 65535 – Advertises a maximum of 65535 bytes (default setting)aggregation Configures 802.11n frame aggregation parametersampdu Configures AMPDU frame aggregation parametersAMPDU aggregation collects Ethernet frames addressed to a single destination. It wraps each frame in an 802.11n MAC header. This aggregation mode is less efficient, but more reliable in environments with high error rates. It enables the acknowledgement and retransmission of each aggregated data frame individually.max-aggr-size Configures AMPDU packet size limits. Configure the packet size limit on packets both transmitted and received.tx <2000-65535> Configures the maximum size (in bytes) for AMPDU aggregated transmitted frames • <2000-65535> – Sets the limit from 2000 - 65535 bytes. The default is 65535 bytes.aggregation Configures 802.11n frame aggregation parametersampdu Configures AMPDU frame aggregation parametersAMPDU aggregation collects Ethernet frames addressed to a single destination. It wraps each frame in an 802.11n MAC header. This aggregation mode is less efficient, but more reliable in environments with high error rates. It enables the acknowledgement and retransmission of each aggregated data frame individually.mn-spacing [0|1|2|4|8|16]Configures the minimum gap, in microseconds, between AMPDU frames• 0 – Configures the minimum gap as 0 microseconds• 1 – Configures the minimum gap as 1 microseconds• 2 – Configures the minimum gap as 2 microseconds• 4 – Configures the minimum gap as 4 microseconds• 8 – Configures the minimum gap as 8 microseconds• 16 – Configures the minimum gap as 16 microseconds• auto – Auto configures the minimum gap depending on the platform and radio type (default setting)aggregation Configures 802.11n frame aggregation parametersamsdu Configures Aggregated MAC Service Data Unit (AMSDU) frame aggregation parameters. AMSDU aggregation collects Ethernet frames addressed to a single destination. But, unlike AMPDU, it wraps all frames in a single 802.11n frame.rx-only Supports the receipt of AMSDU aggregated frames only (default setting)tx-rx Supports the transmission and receipt of AMSDU aggregated frames](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-41.png)



![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2677.1.36.5.9 antenna-modeinterface-config-radio-instanceConfigures the antenna mode (the number of transmit and receive antennas) on the access pointThis command sets the number of transmit and receive antennas on the access point. The 1x1 mode is used for transmissions over just the single -A- antenna, 1xALL is used for transmissions over the -A- antenna and all three antennas for receiving. The 2x2 mode is used for transmissions and receipts over two antennas for dual antenna models. 3x3x3 is used for transmissions and receipts over three antennas for AP81XX models. The default setting is dynamic based on the access point model deployed and its transmit power settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxantenna-mode [1*1|1*ALL|2*2|3*3|default]Parameters• antenna-mode [1*1|1*ALL|2*2|default]Usage GuidelinesTo support STBC feature on AP7161 profile, the antenna-mode should not be configured to 1*1.Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#antenna-mode 2x2rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 antenna-gain 12.0 aggregation ampdu tx-only aeroscout forward antenna-mode 2x2 antenna-diversity airtime-fairness prefer-ht weight 6 antenna-downtiltrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandsantenna-mode Configures the antenna mode1*1 Uses only antenna A to receive and transmit1*ALL Uses antenna A to transmit and receives on all antennas2*2 Uses antennas A and C for both transmit and receive3*3 Uses antenna A, B, and C for both transmit and receivedefault Uses default antenna settings. This is the default setting.no Resets the radio antenna mode (the number of transmit and receive antennas) to its default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-49.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2687.1.36.5.10 ass o c - re s pons einterface-config-radio-instanceConfigures the parameters determining whether the access point ignores or responds to an association/authorization requestSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxassoc-response [deny-threshold <1-12>|rssi-threshold <-128--40>]Parameters• assoc-response [deny-threshold <1-12>|rssi-threshold <-128--40>]Examplerfs6000-37FABE(config-profile-71XXTestProfile-if-radio1)#assoc-response rssi-threshold -128rfs6000-37FABE(config-profile-71XXTestProfile-if-radio1)#show context interface radio1 assoc-response rssi-threshold -128rfs6000-37FABE(config-profile-71XXTestProfile-if-radio1)#Related Commandsassoc-response Configures the following thresholds, based on which the AP ignores or responds to an association/authorization request: deny-threshold and rssi-threshold. Both these options are disabled by default.deny-threshold <1-12>Configures the number of times the AP ignores association/authorization requests, if the RSSI is below the configured RSSI threshold value• <1-12> – Specify a value from 1 - 12.Note: The AP always ignores association/authorization requests when deny-threshold is not specified and rssi-threshold is specified.rssi-threshold <-128--40>Configures the RSSI threshold. If the RSSI is lower than the threshold configured here, the AP ignores the association/authorization request.• <128--40> – Specify the RSSI threshold from -128 - -40 dBi.no Removes the RSSI threshold, based on which an association/authorization request is either ignored or responded.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-50.png)
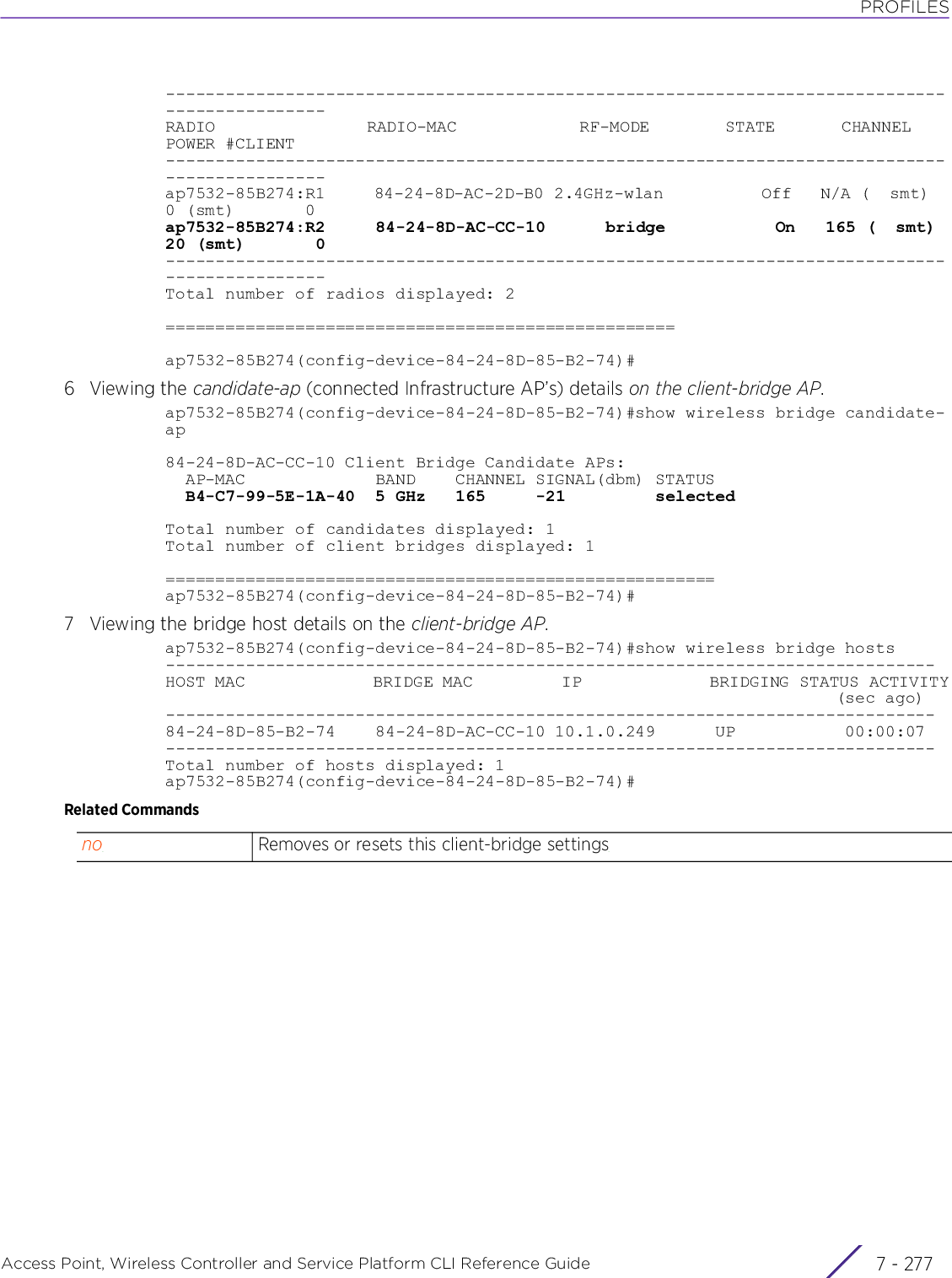
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2707.1.36.5.12 be a co ninterface-config-radio-instanceConfigures radio beacon parametersA beacon is a packet broadcasted by adopted radios to keep the network synchronized. Included in a beacon is information, such as the WLAN service area, the radio address, the broadcast destination addresses, a time stamp, and indicators about traffic and delivery such as a Delivery Traffic Indication Message (DTIM). Increase the DTIM/beacon settings (lengthening the time) to let nodes sleep longer and preserve battery life. Decrease these settings (shortening the time) to support streaming-multicast audio and video applications that are jitter sensitive.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxbeacon [dtim-period|period]beacon dtim-period [<1-50>|bss]beacon dtim-period [<1-50>|bss <1-16> <1-50>]beacon period [50|100|200]Parametersd• beacon dtim-period [<1-50>|bss <1-8> <1-50>]• beacon period [50|100|200]beacon Configures radio beacon parametersdtim-period Configures the radio DTIM interval. A DTIM is a message that informs wireless clients about the presence of buffered multicast or broadcast data. These are simple data frames that require no acknowledgement, so nodes sometimes miss them. Increase the DTIM/ beacon settings (lengthening the time) to let nodes sleep longer and preserve their battery life. Decrease these settings (shortening the time) to support streaming multicast audio and video applications that are jitter-sensitive.<1-50> Configures a single value to use on the radio. Specify a value between 1 and 50.bss <1-16> <1-50> Configures a separate DTIM for a Basic Service Set (BSS) on this radio interface• <1-16> – Sets the BSS number from 1 - 16• <1-50> – Sets the BSS DTIM from 1 - 50. The default is 2.period [50|100|200] Configures the beacon period (the interval between consecutive radio beacons)• 50 – Configures 50 K-uSec interval between beacons• 100 – Configures 100 K-uSec interval between beacons (default)• 200 – Configures 200 K-uSec interval between beacons](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-52.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2727.1.36.5.13 br i dgeinterface-config-radio-instanceConfigures the client-bridge parameters for radios with rf-mode set to bridge. When configured as a client bridge, the radio can authenticate and associate to the Wireless LAN (WLAN) hosted on the infrastructure access point. After successfully associating with the infrastructure WLAN, the client-bridge access point switches frames between its bridge radio and wired/wireless client(s) connected either to its GE port(s) or to the other radio, there by providing the clients access to the infrastructure WLAN resources.Supported in the following platforms:• Access Points — AP6522, AP6562, AP7522, AP7532, AP7562, AP7602, AP7622Syntaxbridge [authentication-type [eap|none]|channel-dwell-time <50-2000>|channel-list [2.4GHz|5GHz] <LIST>|connect-through-bridges|eap [password <PASSWORD>|type [peap-mschapv2|tls]|username <USERNAME>]|encryption-type [ccmp|none|tkip]|inactivity-timeout <0-864000>|keepalive [frame-type [null-data|wnmp]|interval <0-36000>]|max-clients <1-64>|on-link-loss shutdown-other-radio <1-1800>|on-link-up refresh-vlan-interface|roam-criteria [missed-beacons <1-60>|rssi-threshold <-128--40>]|ssid <SSID>|wpa-wpa2 psk [0|2|<LINE>]]Parameters• bridge [authentication-type [eap|none]|channel-dwell-time <50-2000>|channel-list [2.4GHz|5GHz] <LIST>|connect-through-bridges|eap [password <PASSWORD>]|type [peap-mschapv2|tls]|username <USERNAME>]|encryption-type [ccmp|none|tkip]|inactivity-timeout <0-864000>|keepalive [frame-type [null-data|wnmp]|interval <0-36000>]|max-clients <1-64>|on-link-loss shutdown-other-radio <1-1800>|on-link-up refresh-vlan-interface|roam-criteria [missed-beacons <1-60>|rssi-threshold <-128--40>]|ssid <SSID>|wpa-wpa2 psk [0|2|<LINE>]]NOTE: The radio interface configured to form the client-bridge will not be able to service wireless clients as its RF mode is set to bridge and not 2.5 GHz or 5.0 GHz.bridge Configures client-bridge related parameters on the selected radioPrior to configuring the client-bridge parameters, set the radio’s rf-mode to bridge.authentication-type [eap|none]Configures the authentication method used to authenticate with the infrastructure WLAN. The authentication mode specified here should be the same as that configured on the infrastructure WLAN. The options are:• eap – Uses EAP authentication (802.1X). If using EAP, use the ‘eap’ keyword to configure EAP related parameters.• none – Uses no authentication. This is the default setting.channel-dwell-time <50-2000>Configures the channel-dwell time in milliseconds. This is the time the client-bridge radio dwells on each channel (configured in the channel-list) when scanning for an infrastructure WLAN.• <50-2000> – Specify a value from 50 -2000 milliseconds. The default is 150 milliseconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-54.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 273channel-list [2.4GHz|5GHz] <LIST>Configures the list of channels the radio scans when scanning for an infrastructure WLAN access point to associate• 2.4GHz <LIST> – Configures a list of channels for scanning across all the channels in the 2.4GHz radio band• 5GHz <LIST> – Configures a list of channels for scanning across all the channels in the 5.0 GHz radio bandThe following parameter is common to both of the 2.5 GHz and 5.0 GHz bands:• <LIST> – Provide the list of channels separated by commas.connect-through-bridgesEnables the client-bridge access point radio to connect to an infrastructure WLAN, which already has other client-bridge radios associated with it. The client-bridge access points, in this scenario, are said to be daisy chained together.eap [password [<PASSWORD>]|type [peap-mschapv2|tls]|username <UESERNAME>]Configures EAP authentication parameters if the authentication mode is set as EAP• password [0|2|<PASSWORD>] – Configures the EAP authentication password to use with the infrastructure WLAN. The password type depends on the EAP authentication type configured.PEAP-MSCHAPv2 - PEAP passwordTLS – PKCS #12 certificate secretUse of EAP-TLS authentication is recommended since it is stronger than PEAP-MSCHAPv2.• <PASSWORD> – Enter the password.• type [peap-mschapv2|tls] – Configures the EAP authentication type as:• PEAP-MSCHAPv2 – Configures the EAP authentication type as PEAP-MSCHAPv2.This is the default setting.• TLS – Configures the EAP authentication type as TLS• username <USERNAME> – Configures the EAP authentication user name to use with the infrastructure WLAN.• <USERNAME> – Specify the EAP username.PEAP-MSCHAPv2 – PEAP username (example client-bridge)TLS – Username in the CN field of the installed PKCS #12 client certificate (example client-bridge@example.com)encryption-type [ccmp|none|tkip]Configures the encryption mode. The encryption mode specified here should be the same as that configured on the infrastructure WLAN. The options are:• ccmp – Uses WPA/WPA2 CCMP encryption• none – Uses no encryption method. This is the default setting.• tkip – Uses WPA/WPA2 TKIP encryptionIf using CCMP or TKIP, use the ‘wpa2-wpa2’ keyword to configure the pre-shared key (PSK).inactivity-timeout <0-864000>Configures the inactivity timeout for each bridge MAC address. This is the time for which the client-bridge access point waits before deleting a MAC address from which a frame has not been received for more than the time specified here. For example, if the inactivity time is set at 120 seconds, and if no frames are received from a MAC address for 120 seconds, it is deleted. The default value is 600 seconds.• <0-864000> – Specify a value from 0 - 864000 seconds. The default is 600 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-55.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 274keepalive [frame-type [null-data|wnmp]|interval <0-36000>]Configures the keep-alive frame type and interval• frame-type – Configures the keepalive frame type exchanged between the client-bridge access point and the infrastructure access point/controller. The options are:• null-data – Transmits 802.11 NULL data frames. This is the default setting.• wnmp – Transmits Wireless Network Management Protocol (WNMP) multicastpacket• interval <0-36000> – Configures the interval, in seconds, between two successive keep-alive frame transmission.• <0-36000> – Specify a value from 0 - 36000 seconds. The default is 300 seconds.max-clients <1-64> Configures the maximum number of clients that the client-bridge AP can support• <1-14> – Specify a value from 1 - 64. The default is 64.on-link-loss shutdown-other-radio <1-1800>Configures the radio-link behaviour when the link between the client-bridge and infrastructure access points is lost.• shutdown-other-radio – Enables shutting down of the non-client bridge radio (this is the radio to which wireless-clients associate) when the link between the client-bridge and infrastructure access points is lost. When enabled, clients associated with the non-client bridge radio are pushed to search for and associate with other access points having backhaul connectivity. This option is disabled by default.• <1-1800> – If enabling this option, use this parameter to configure the time, in sec-onds, for which the non-client bridge radio is shut down. Specify a value from 1 - 1800seconds.on-link-up refresh-vlan-interfaceConfigures the radio-link behaviour when the link between the client-bridge and infrastructure access points comes up.• refresh-vlan-interface – Enables the SVI to refresh on re-establishing client bridge link to infrastructure Access Point. And, if using a DHCP assigned IP address, causes a DHCP renew. This option is enabled by default.roam-criteria [missed-beacons <1-60>|rssi-threshold <-128--40>]Configures the following roaming criteria parameters• missed-beacons <1-60> – Configures the missed beacon interval from 0 - 60 seconds.This is the time for which the client-bridge Access Point waits for after missing a beacon from the associated infrastructure Access Point, before roaming to another infrastructure Access Point. For example, if the missed-beacon time is set to 30 seconds, and if more than 30 seconds have passed since the last received beacon, from the associated infrastructure Access Point, the client-bridge Access Point resumes scanning for another infrastructure Access Point. The default value s 20 seconds.• <1-60> – Specify a value from 1 - 60 seconds. The default is 20 seconds.• rssi-threshold <-128--40> – Configures the minimum signal strength, received from target AP, for the bridge connection to be maintained before roaming• <-128--40> – Specify a value from -128 - -40 dBm. If the RSSI value of signals re-ceived from the infrastructure access point falls below the specified value, the client-bridge access point resumes scanning for another infrastructure access point. Thedefault is -75 dBm.ssid <SSID> Configures the infrastructure WLAN SSID the client bridge connects to• <SSID> – Specify the SSID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-56.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 275Usage Guidelines EAP AuthenticationUse the following commands to view client-bridge configuration:1 show > wireless > bridge > configShows the current client bridge configuration.2 show > wireless > bridge > candidate-apShows the available infrastructure WLAN candidates that are found during the last scan.3 show > wireless > bridge > hostShows the wired/wireless clients that are being bridged.4 show > wireless > bridge > statistics > rfShows the client bridge RF statistics.5 show > wireless > bridge > statistics > trafficShows the client bridge traffic statistics.6 show > wireless > bridge > certificate > statusShows the client bridge authentication certificate status.ExampleThe following examples show the basic parameters that need to be configured on the Infrastructure and the client-bridge APs in order to enable the client-bridge AP to associate with the Infrastructure WLAN. Note, in this example, the authentication mode is set to ‘none’ and the encryption-type is set to ‘ccmp’. The authentication and encryption modes used will vary as per requirement.1 Configuring the Infrastructure WLAN:InfrastrNOC(config)#wlan cb-pskInfrastrNOC(config-wlan-cb-psk)#ssid cb-pskInfrastrNOC(config-wlan-cb-psk)#encryption-type ccmpInfrastrNOC(config-wlan-cb-psk)#wpa-wpa2 psk extreme@123InfrastrNOC(config-wlan-cb-psk)#authentication-type noneInfrastrNOC(config)#show running-config wlan cb-psk wlan cb-psk ssid cb-psk bridging-mode local encryption-type ccmp authentication-type none wpa-wpa2 psk 0 extreme@123InfrastrNOC(config)#2 Associating the ‘cb-psk’ WLAN to the Infrastructure AP’s radio.Infra7131-5F5078(config-device-B4-C7-99-5F-50-78-if-radio2)#wlan cb-pskwpa-wpa2 psk [0|2|<LINE>]Configures the encryption pre-shared key (PSK) to use with the infrastructure WLAN• 0 – Configures clear text psk• 2 – Configures encrypted psk• <LINE> – Enter the keyNote: Pre-shared keys are valid only when the authentication-type is set to none and the encryption-type is set to tkip or ccmp.Note: The PSK should be 8 - 32 characters in length.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-57.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2787.1.36.5.14 channelinterface-config-radio-instanceConfigures a radio’s channel of operationOnly a trained installation professional should define the radio channel. Select Smart for the radio to scan non-overlapping channels listening for beacons from other access points. After the channels are scanned, the radio selects the channel with the fewest access points. In case of multiple access points on the same channel, it selects the channel with the lowest average power level.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxchannel [smart|acs|random|1|2|3|4|-------]Parameters• channel [smart|acs|random|1|2|3|4|-------]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#channel 1rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 channel 1 beacon period 50 beacon dtim-period bss 1 5 beacon dtim-period bss 2 2 ........................................................................ beacon dtim-period bss 14 5 beacon dtim-period bss 15 5 beacon dtim-period bss 16 5 antenna-gain 12.0 aggregation ampdu tx-only aeroscout forward antenna-mode 2x2 antenna-diversity--More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#NOTE: Channels with a “w” appended to them are unique to the 40 MHz band. Channels with a “ww” appended to them are 802.11ac specific, and appear only when using an AP8232, and are unique to the 80 MHz band.channel Configures a radio’s channel of operation[smart|acs|random|1|2|3|4|-------]Configures a radio’s channel of operation. The options are:• smart – Uses Smart RF to assign a channel (uses uniform spectrum spreading if Smart RF is not enabled). This is the default setting.•acs – Uses automatic channel selection (ACS) to assign a channel• random – Randomly assigns a channel• 1 – Channel 1 in 20 MHz mode• 2 – Channel 2 in 20 MHz mode](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-60.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2807.1.36.5.15 data-ratesinterface-config-radio-instanceConfigures the 802.11 data rates on this radioThis command sets the rate options depending on the 802.11 protocol and the radio band selected. If 2.4 GHz is selected as the radio band, select separate 802.11b, 802.11g and 802.11n rates and define how they are used in combination. If 5.0 GHz is selected as the radio band, select separate 802.11a and 802.11n rates then define how they are used together.If dedicating the radio to either 2.4 or 5.0 GHz support, use the custom keyword to set a 802.11n modulation and coding scheme (MCS) in respect to the radio’s channel width and guard interval. A MCS defines (based on RF channel conditions) an optimal combination of rates, bonded channels, multiple spatial streams, different guard intervals and modulation types. Clients can associate as long as they support basic MCS (as well as non-11n basic rates).Data rates are fixed and not user configurable for radios functioning as sensors.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxdata-rates [b-only|g-only|a-only|bg|bgn|gn|an|default|custom|mcs]data-rates [b-only|g-only|a-only|bg|bgn|gn|an|default]data-rates custom [1|2|5.5|6|9|11|12|18|24|36|48|54|mcs-1s|mcs-2s|mcs-3s|basic-1|basic-2|basic-5.5|basic-6|basic-9|basic-11|basic-12|basic-18|basic-24|basic-36|basic-48|basic-54|basic-mcs-1s]data-rates mcs qam-onlyParameters• data-rates [b-only|g-only|a-only|bg|bgn|gn|an|default]NOTE: Use the rf-mode command to configure a radio’s mode of operation.NOTE: The MCS-1s and MCS-2s options are available for each supported access point. However, the MCS-3s option is only available to the AP8232 model access point, and its ability to provide 3x3x3 MIMO support.data-rates Configures the 802.11 data rates on this radiob-only Supports operation in the 802.11b mode only (applicable for 2.4 and 4.9 GHz bands)g-only Uses rates that support operation in the 802.11g mode only (applicable for 2.4 and 4.9 GHz bands)a-only Uses rates that support operation in the 802.11a mode only (applicable for 5.0 GHz band only)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-62.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 281• data-rates custom [1|2|5.5|6|9|11|12|18|24|36|48|54||mcs-1s|mcs-2s|mcs-3s|basic-1|basic-2|basic-5.5|basic-6|basic-9|basic-11|basic-12|basic-18|basic-24|basic-36|basic-48|basic-54|basic-mcs-1s]bg Uses rates that support 802.11b and 802.11g wireless clients (applicable for 2.4 and 4.9 GHz bands)bgn Uses rates that support 802.11b, 802.11g, and 802.11n wireless clients (applicable for 2.4 and 4.9 GHz bands)gn Uses rates that support 802.11g and 802.11n wireless clients (applicable for 2.4 and 4.9 GHz bands)an Uses rates that support 802.11a and 802.11n wireless clients (applicable for 5.0 GHz band only)default Enables the default data rates according to the radio’s band of operationdata-rates Configures the 802.11 data rates on this radiocustom Configures a list of data rates by specifying each rate individually. Use 'basic-' prefix before a rate to indicate it’s used as a basic rate (For example, 'data-rates custom basic-1 basic-2 5.5 11')• 1 – 1-Mbps• 2 – 2-Mbps• 5.5 – 5.5-Mbps• 6 – 6-Mbps• 9 – 9-Mbps• 11 – 11-Mbps• 12 – 12-Mbps• 18 – 18-Mbps• 24 – 24-Mbps• 36 – 36-Mbps• 48 – 48-Mbps• 54 – 54-Mbps• mcs-1s – Applicable to 1-spatial stream data rates• mcs-2s – Applicable to 2-spatial stream data rates• mcs-3s – Applicable to 3-spatial stream data rates (supported only on AP8232 for the MIMO feature)• basic-1 – Basic 1-Mbps• basic-2 – Basic 2-Mbps• basic-5.5 – Basic 5.5-Mbps• basic-6 – Basic 6-Mbps• basic-9 – Basic 9-Mbps• basic-11 – Basic 11-Mbps• basic-12 – Basic 12-Mbps• basic-18 – Basic 18-Mbps• basic-24 – Basic 24-Mbps• basic-36 – Basic 36-MbpsContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-63.png)
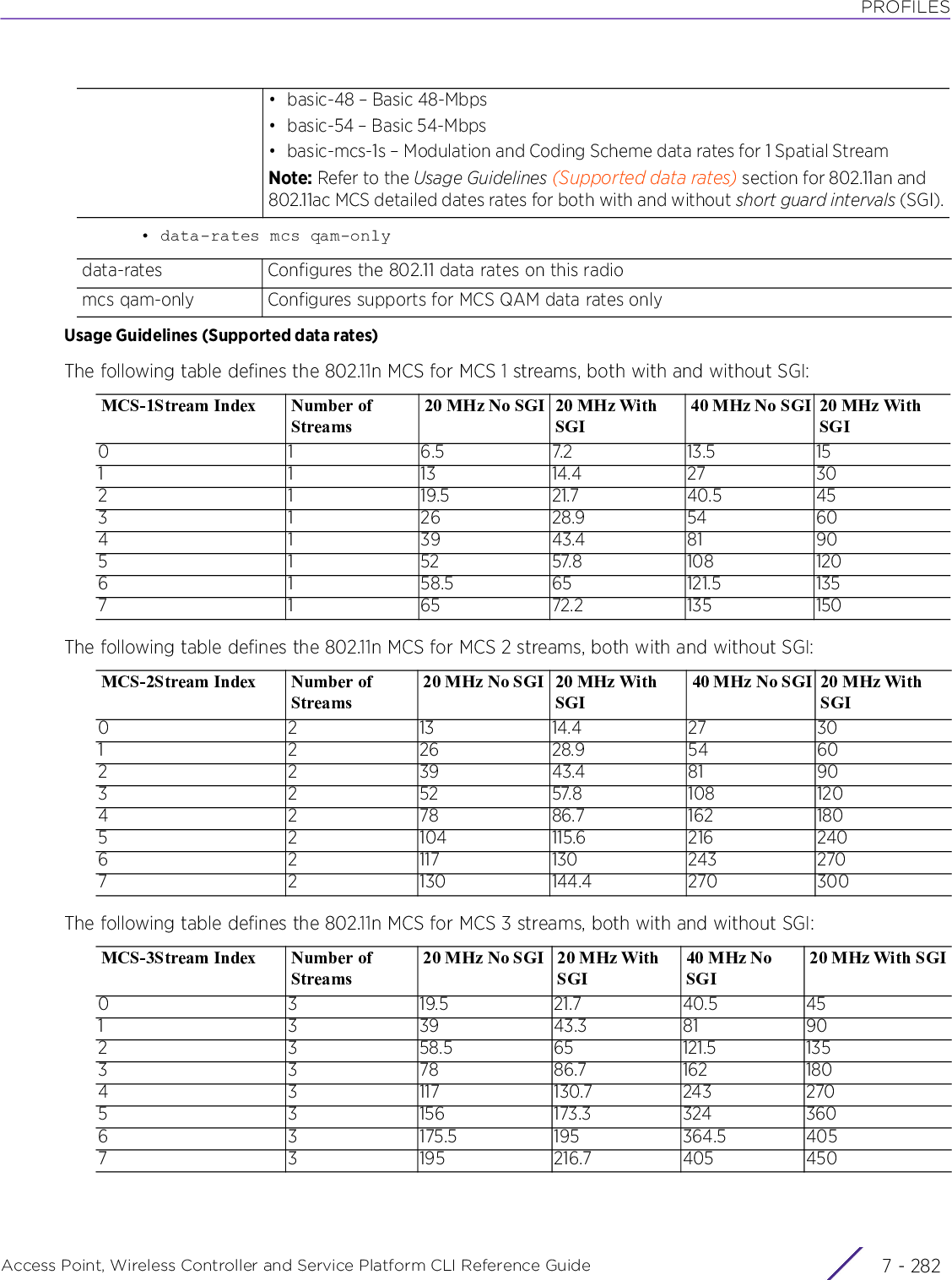
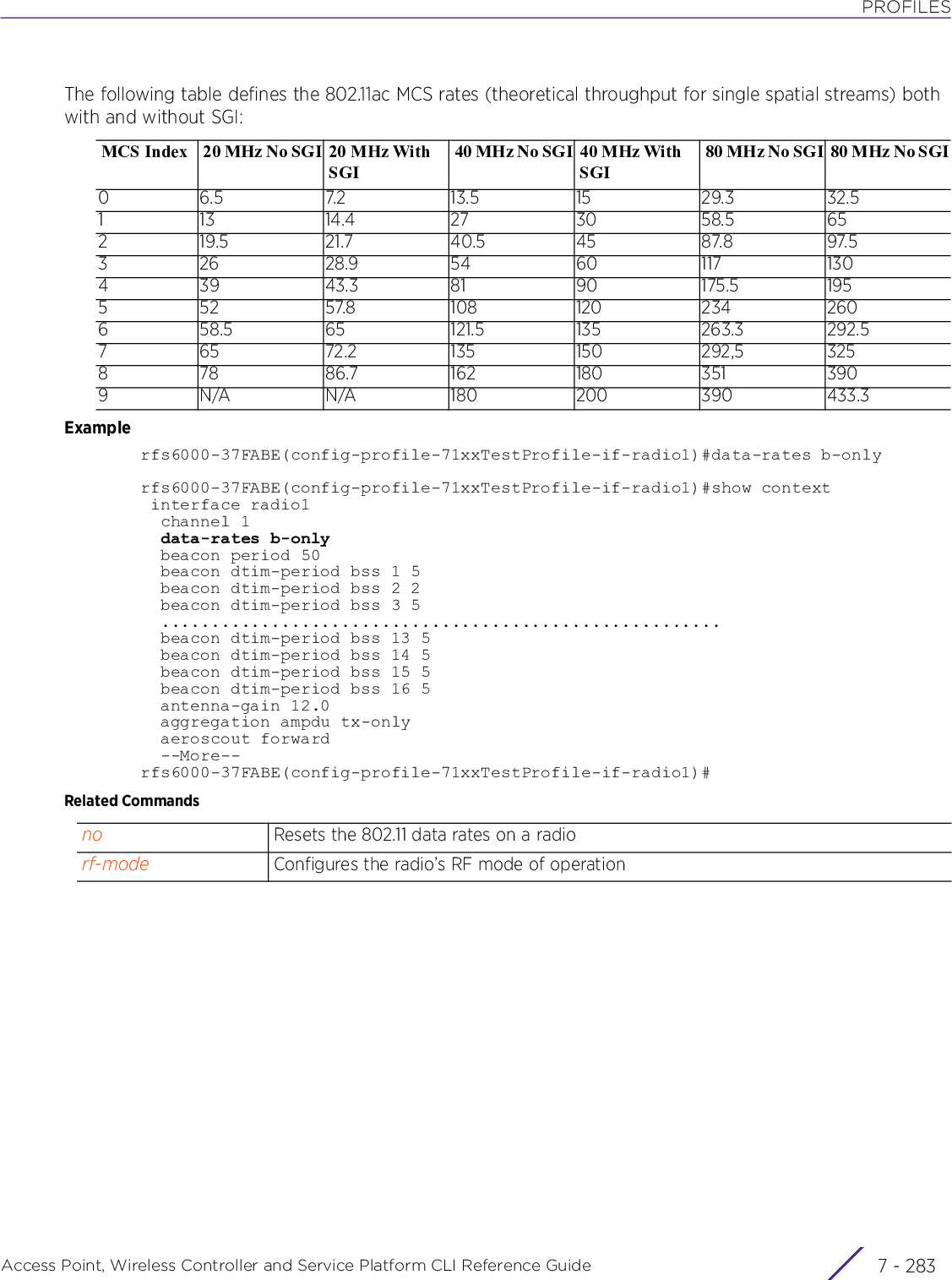
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2877.1.36.5.19 ekah a uinterface-config-radio-instanceEnables Ekahau multicast packet forwarding. When enabled, Ekahau small, battery powered Wi-Fi tags are attached to tracked assets or assets carried by people. Ekahau processes locations, rules, messages, and environmental data and turns the information into locationing maps, alerts and reports.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxekahau [forward ip <IP> port <0-65535>|mac <MAC>]Parameters• ekahau [forward ip <IP> port <0-65535>|mac <MAC>]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#ekahau forward ip 172.16.10.1 port 3rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 description "Primary radio to use" channel 1 data-rates b-only beacon period 50 beacon dtim-period bss 1 5 beacon dtim-period bss 2 2 beacon dtim-period bss 3 5 beacon dtim-period bss 4 5 beacon dtim-period bss 5 5 beacon dtim-period bss 6 5 beacon dtim-period bss 7 5................................................. beacon dtim-period bss 16 5 antenna-gain 12.0 aggregation ampdu tx-only aeroscout forward ekahau forward ip 172.16.10.1 port 3 antenna-mode 2x2--More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandsekahau Enables Ekahau multicast packet forwarding on this radioforward ip <IP>port <0-65535>Enables multicast packet forwarding to the Ekahau engine• ip <IP> – Configures the IP address of the Ekahau engine in the A.B.C.D format• port <0-65535> – Specifies the TaZman Sniffer Protocol (TZSP) port on Ekahau engine from 0 - 65535TZSP is an encapsulation protocol, which is generally used to wrap 802.11 wireless packets.mac <MAC> Configures the multicast MAC address to forward the Ekahau multicast packets• <MAC> – Specify the MAC address in the AA-BB-CC-DD-EE-FF format.no Uses default Ekahau multicast MAC address](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-69.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2897.1.36.5.21 fallback-channelinterface-config-radio-instanceConfigures the channel to which the radio switches in case of radar detection on the current channelSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxfallback-channel [100|100w|100ww|104|104w|104ww|108|108w...............]Parameters• fallback-channel [100|100w|100ww|104|104w|104ww|108|108w...............]Examplenx9500-6C8809(config-profile-testAP81XX-if-radio2)#fallback-channel 104NOTE: Functionality is supported only in the US regulatory domain and only a non-dfs channel can be configured as a fallback channelnx9500-6C8809(config-profile-testAP81XX-if-radio2)#show context interface radio2 fallback-channel 104nx9500-6C8809(config-profile-testAP81XX-if-radio2)#Related Commandsfallback-channel [100|100w|...........]Configures the fallback channel. This is the channel the radio switches to in case a radar is detected on the radio’s current operating channel.• [100|100w|100ww|...] – Select the fall back channel from the available options.Note: Channels with a “w” appended to them are unique to the 40 MHz band. Channels with a “ww” appended to them are 802.11ac specific, and appear only when using an AP8232, and are unique to the 80 MHz band.no Removes the fallback-channel configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-71.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2907.1.36.5.22 guard-intervalinterface-config-radio-instanceConfigures the 802.11n guard interval. A guard interval ensures distinct transmissions do not interfere with one another. It provides immunity to propagation delays, echoes and reflection of radio signals.The guard interval is the space between transmitted characters. The guard interval eliminates inter symbol interference (ISI). ISI which occurs when echoes or reflections from one symbol interferes with another. Adding time between transmissions allows echoes and reflections to settle before the next symbol is transmitted. A shorter guard interval results in shorter symbol times, which reduces overhead and increases data rates by up to 10%.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxguard-interval [any|long]Parameters• guard-interval [any|long]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#guard-interval longrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 description "Primary radio to use" channel 1 data-rates b-only beacon period 50 beacon dtim-period bss 1 5 beacon dtim-period bss 2 2 beacon dtim-period bss 3 5 beacon dtim-period bss 4 5 beacon dtim-period bss 5 5 beacon dtim-period bss 6 5 beacon dtim-period bss 7 5 beacon dtim-period bss 8 5 beacon dtim-period bss 9 5 beacon dtim-period bss 10 5 beacon dtim-period bss 11 5 beacon dtim-period bss 12 5 beacon dtim-period bss 13 5 beacon dtim-period bss 14 5 beacon dtim-period bss 15 5 beacon dtim-period bss 16 5 antenna-gain 12.0 guard-interval long--More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandsguard-interval Configures the 802.11n guard intervalany Enables the radio to use any short (400nSec) or long (800nSec) guard intervallong Enables the use of long guard interval (800nSec). This is the default setting.no Resets the 802.11n guard interval to default (long: 800nSec)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-72.png)
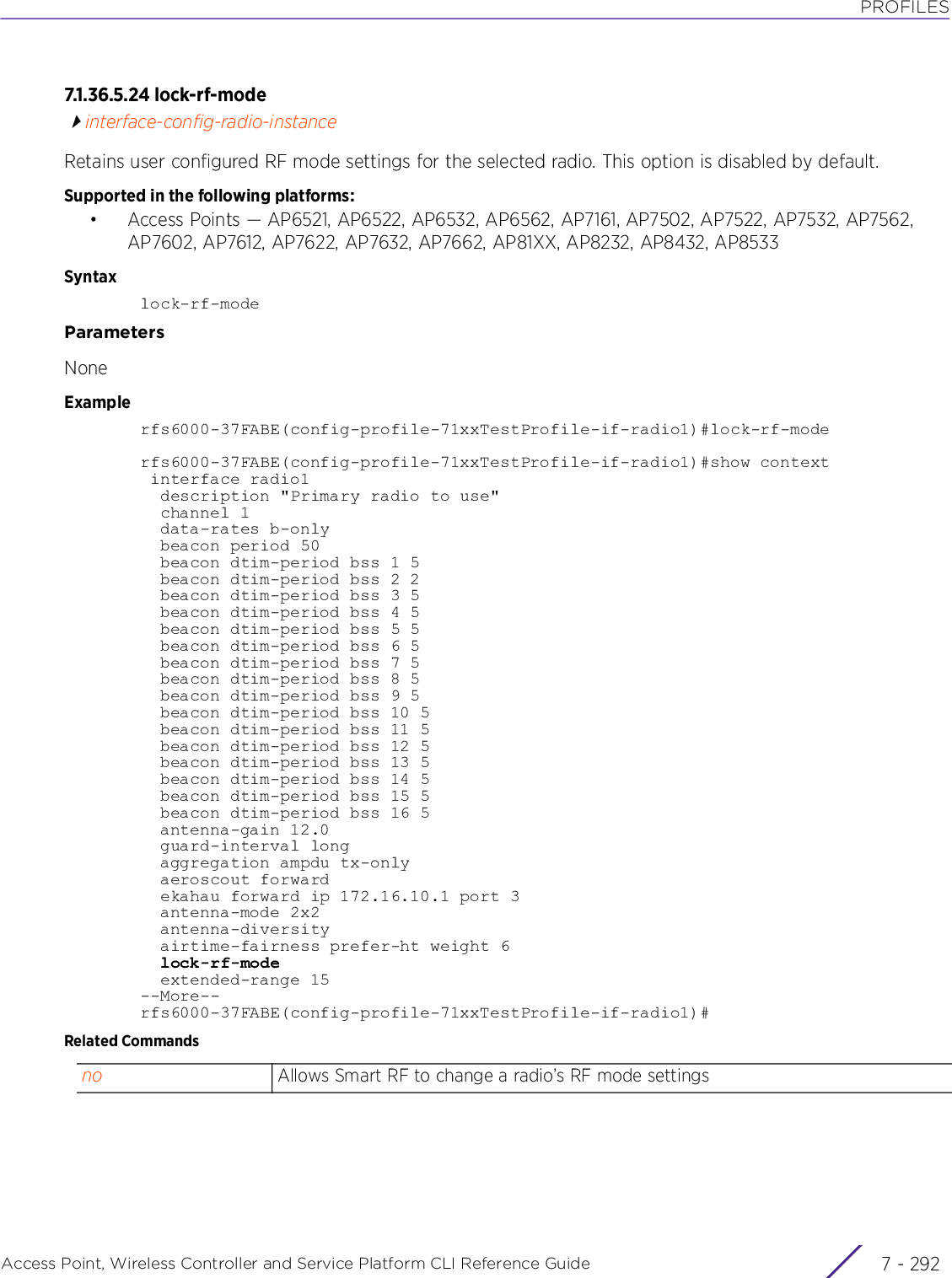
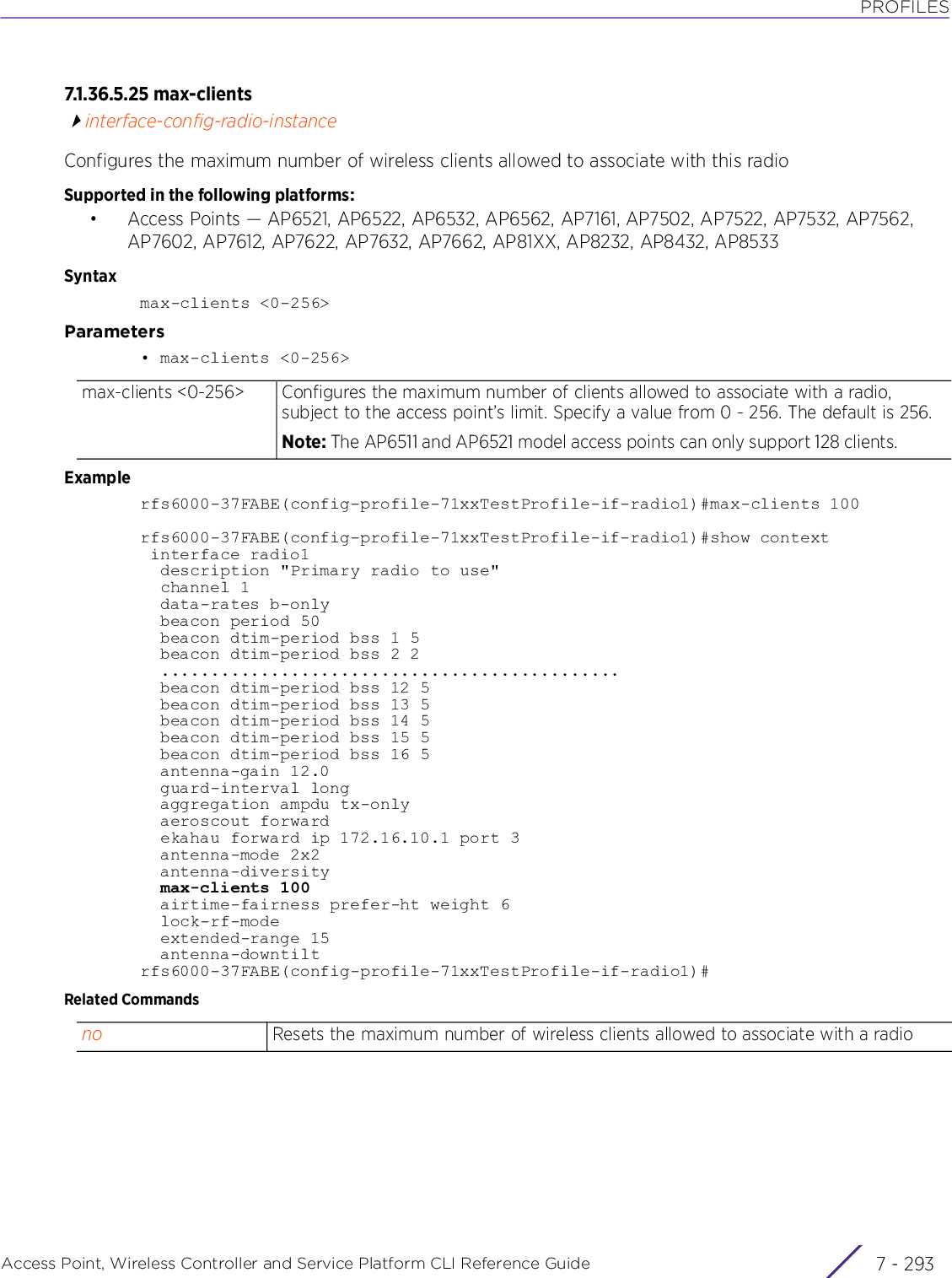
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 2947.1.36.5.26 meshinterface-config-radio-instanceUse this command to configure radio mesh parameters. A Wireless Mesh Network (WMN) is a network of radio nodes organized in a mesh topology. It consists of mesh clients, mesh routers, and gateways.Each radio setting can have a unique mesh mode and link configuration. This provides a customizable set of connections to other mesh supported radios within the same radio coverage area.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP8232, AP8432, AP8533Syntaxmesh [client|links|portal|preferred-peer|psk]mesh [client|links <1-6>|portal|preferred-peer <1-6> <MAC>|psk [0 <LINE>|2 <LINE>|<LINE>]]Parameters• mesh [client|links <1-6>|portal|preferred-peer <1-6> <MAC>|psk [0 <LINE>|2 <LINE>|<LINE>]]mesh Configures radio mesh parameters, such as maximum number of mesh links, preferred peer device, client operations, etc.client Enables operation as a clientSetting the mesh mode to ‘client’ enables the radio to operate as a mesh client that scans for and connects to mesh portals or nodes that are connected to portals.links <1-6> Configures the maximum number of mesh links a radio attempts to create• <1-6> – Sets the maximum number of mesh links from 1 - 6. The default is 6.portal Enables operation as a portalSetting the mesh mode to ‘portal’ turns the radio into a mesh portal. The radio starts beaconing immediately and accepts connections from other mesh nodes, typically the node with a connection to the wired network.preferred-peer <1-6> <MAC>Configures a preferred peer device• <1-6> – Configures the priority at which the peer node will be addedWhen connecting to the mesh infrastructure, nodes with lower priority are given precedence over nodes with higher priority.• <MAC> – Sets the MAC address of the preferred peer device (Ethernet MAC of either a AP, wireless controller, or service platform with onboard radios)psk [0 <LINE>|2 <LINE>| <LINE>]Configures the pre-shared key. Ensure this key is configured on the access point when staged for mesh, and added to the mesh client and to the portal access point’s configuration on the controller or service platform.• 0 <LINE> – Enter a clear text key• 2 <LINE> – Enter an encrypted key• <LINE> – Enter the pre-shared keyPre-shared keys should be 8 - 64 characters in length.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-76.png)

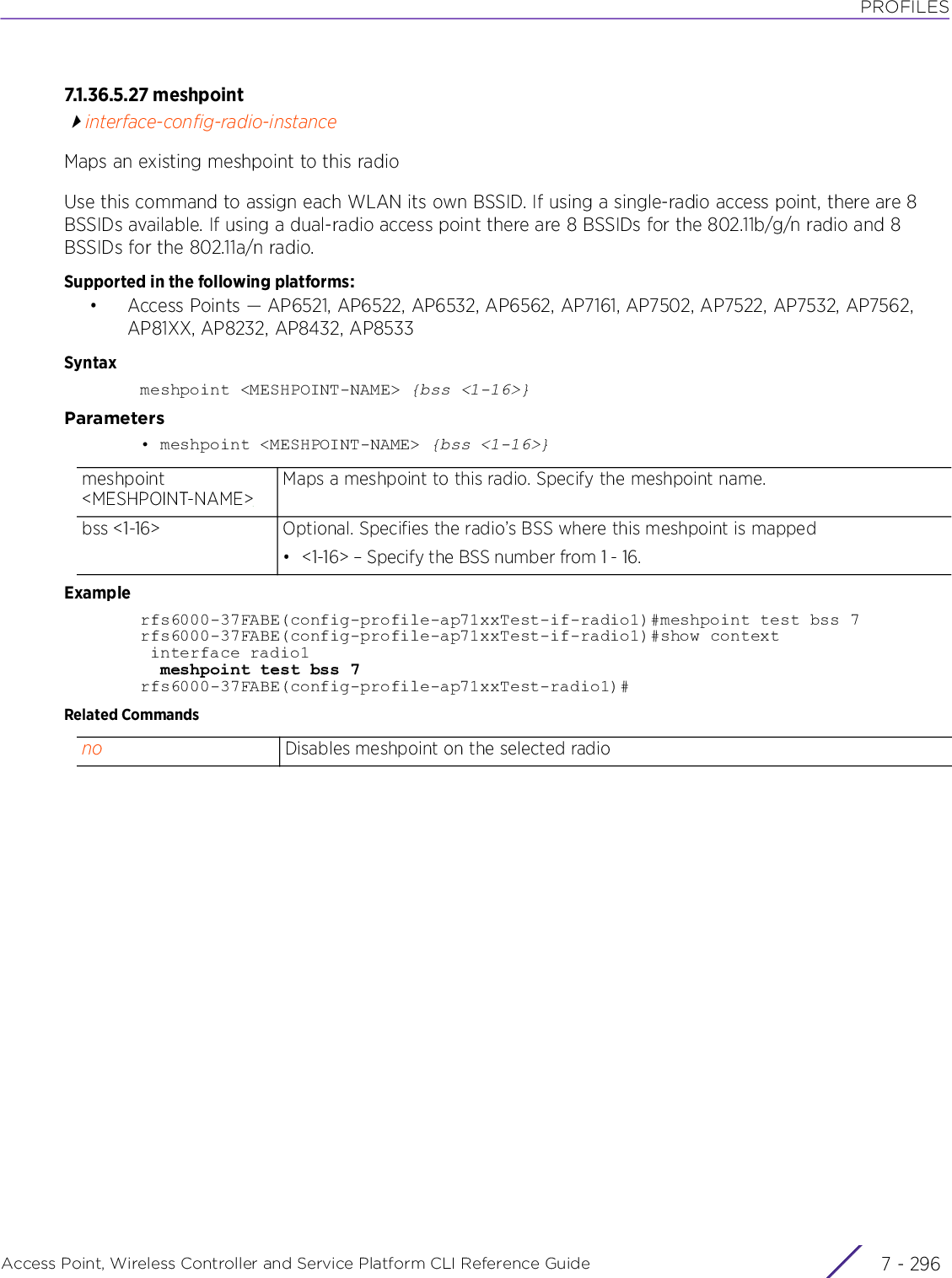
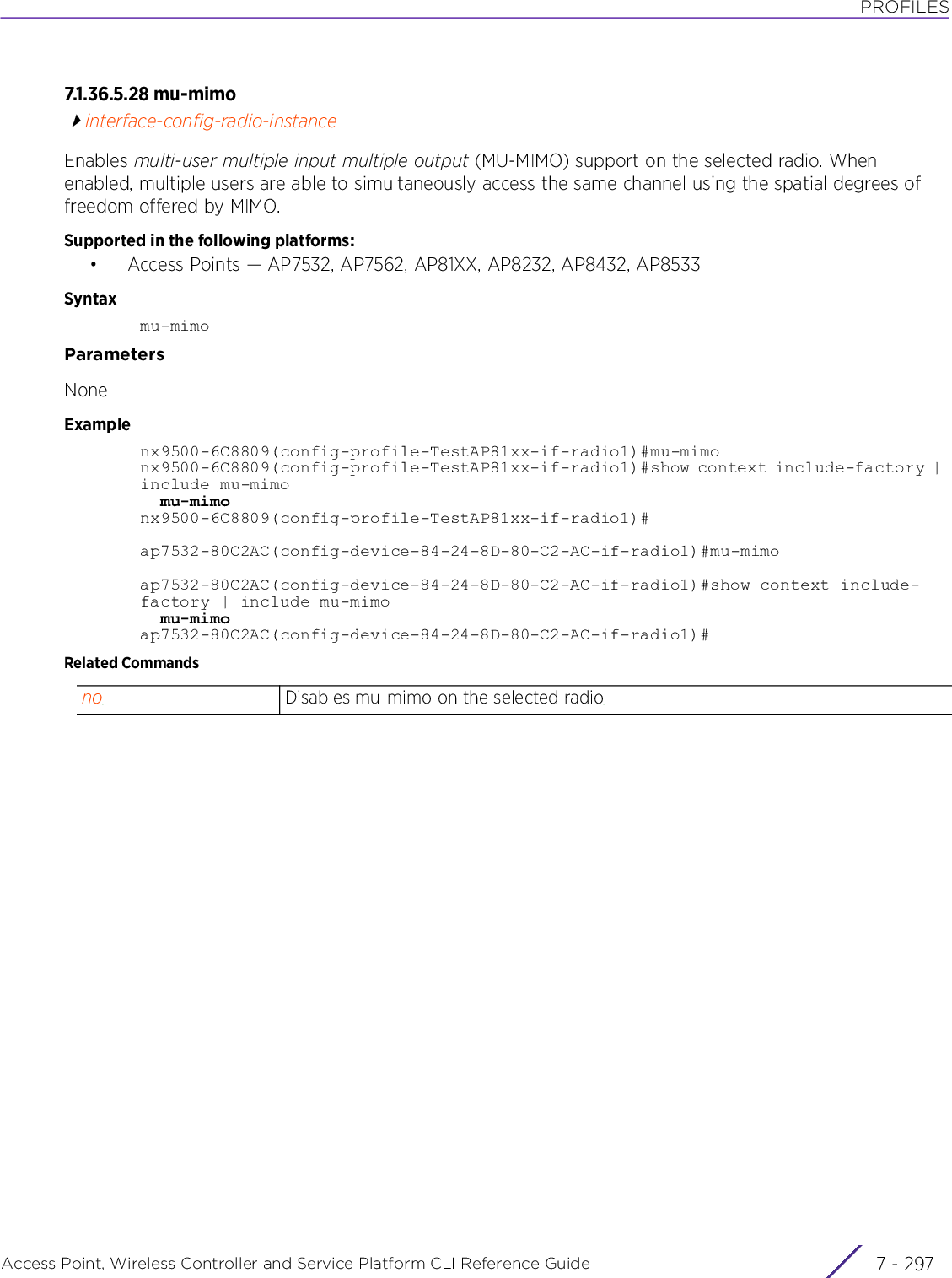

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3017.1.36.5.30 non-unicastinterface-config-radio-instanceConfigures support for forwarding of non-unicast (multicast and broadcast) frames on this radioSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxnon-unicast [forwarding|queue|tx-rate]non-unicast forwarding [follow-dtim|power-save-aware]non-unicast queue [<1-200>|bss]non-unicast queue [<1-200>|bss <1-16> <1-200>]non-unicast tx-rate [bss <1-16>|dynamic-all|dynamic-basic|highest-basic|lowest-basic]non-unicast tx-rate bss <1-16> [dynamic-all|dynamic-basic|highest-basic|lowest-basic]Parameters• non-unicast forwarding [follow-dtim|power-save-aware]• non-unicast queue [<1-200>|bss <1-16> <1-200>]• non-unicast tx-rate [bss <1-16>|dynamic-all|dynamic-basic|highest-basic|lowest-basic]non-unicast forwarding Enables non-unicast frame forwarding on this radio. Once enabled, select one of the available options to specify whether these frames should always follow DTIM, or only follow DTIM when using power save aware mode.follow-dtim Specifies frames always wait for the DTIM interval to time out. The DTIM interval is configured using the beacon command. This is the default setting.power-save-aware Enables immediate forwarding of frames only if all associated wireless clients are in the power save modenon-unicast queue Enables non-unicast frame forwarding on this radio. Once enabled, specify the number of broadcast packets queued per BSS on this radio. This option is enabled by default.This command also enables you to override the default on a specific BSS.<1-200> Specify a number from 1 - 200. This value applies to all BSSs. The default is 50 frames per BSS.bss <1-16> <1-200> Overrides the default on a specified BSS• <1-16> – Select the BSS number from 1 - 16.• <1-200> – Specify the number of broadcast packets queued for the selected BSSfrom 1 - 200.non-unicast tx-rate Enables non-unicast frame forwarding on this radio. Once enabled, use one of the available options to configure the rate at which these frames are transmitted.bss <1-16> Overrides the default on a specified BSS• <1-16> – Select the BSS number from 1 - 16. The transmit rate selected is applied only to the BSS specified here. The tx-rate options are: dynamic-all, dynamic-basic, highest-basic, lowest-basic.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-83.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3037.1.36.5.31 off-channel-scaninterface-config-radio-instanceEnables off channel scanning on this radio. This option is disabled by default.Channel scanning uses the access point’s resources and is time consuming. Therefore, enable this option only if the radio has the bandwidth to support channel scan without negatively impacting client support.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxoff-channel-scan {channel-list|max-multicast|scan-interval|sniffer-redirect}off-channel-scan {channel-list [2.4Ghz|5Ghz]} {<CHANNEL-LIST>}off-channel-scan {max-multicast <0-100>|scan-interval <2-100>}off-channel-scan {sniffer-redirect tzsp <IP>}Parameters• off-channel-scan {channel-list [2.4Ghz|5Ghz]} {<CHANNEL-LIST>}• off-channel-scan {max-multicast <0-100>|scan-interval <2-100>}• off-channel-scan {sniffer-redirect tzsp <IP>}off-channel-scan Enables off-channel scanning and configures related parameters. These parameters are optional, and the system configures default settings if no values are specified.channel-list [2.4GHz|5GHz]Optional. Selects the 2.4GHz or 5GHz access point radio band. Restricting off channel scans to specific channels frees bandwidth otherwise utilized for scanning across all channels.• 2.4GHz – Selects the 2.4 GHz band• 5GHz – Selects the 5.0 GHz band<CHANNEL-LIST> Optional. Specifies a list of 20 MHz, 40 MHz, or 80 MHz channels for the selected band (the channels are separated by commas or hyphens)off-channel-scan Enables off-channel scanning and configures related parameters. These parameters are optional, and the system configures default settings if no values are specified.max-multicast <0-100> Optional. Configures the maximum multicast/broadcast messages used to perform OCS• <0-100> – Specify a value from 0 - 100. The default is 4.scan-interval <2-100> Optional. Configures the scan interval in dtims• <2-100> – Specify a value from 2 - 100. The default is 20 dtims.off-channel-scan Enables off-channel scanning and configures related parameters. These parameters are optional, and the system configures default settings if no values are specified.sniffer-redirect tzsp <IP> Optional. Captures and redirects packets to a host running a packet capture/analysis tool. Use this command to configure the IP address of the host.• tzsp – Encapsulates captured packets in TZSP before redirecting to the specified host• <IP> – Specify the destination device IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-85.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3057.1.36.5.32 placementinterface-config-radio-instanceDefines the radio’s location (whether the radio is deployed indoors or outdoors). The radio’s placement should depend on the country of operation selected and its regulatory domain requirements for radio emissions.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxplacement [indoor|outdoor]Parameters• placement [indoor|outdoor]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#placement outdoorrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 data-rates b-only placement outdoor mesh client off-channel-scan channel-list 2.4GHz 1 guard-interval long aggregation ampdu tx-only aeroscout forward ekahau forward ip 172.16.10.1 port 3 non-unicast tx-rate bss 1 dynamic-all non-unicast tx-rate bss 2 highest-basic non-unicast tx-rate bss 3 highest-basic non-unicast tx-rate bss 4 highest-basic non-unicast tx-rate bss 5 highest-basic non-unicast tx-rate bss 6 highest-basic non-unicast tx-rate bss 7 highest-basic non-unicast tx-rate bss 8 highest-basic non-unicast tx-rate bss 9 highest-basic non-unicast tx-rate bss 10 highest-basic non-unicast tx-rate bss 11 highest-basic non-unicast tx-rate bss 12 highest-basic non-unicast tx-rate bss 13 highest-basic non-unicast tx-rate bss 14 highest-basic--More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandsplacement Defines the radio’s locationindoor Radio is deployed indoors (uses indoor regulatory rules). This is the default setting.outdoor Radio is deployed outdoors (uses outdoor regulatory rules)no Resets a radio’s deployment location](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-87.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3067.1.36.5.33 powerinterface-config-radio-instanceConfigures the radio’s transmit power settingThe transmit power control (TPC) mechanism automatically reduces the used transmission output power when other networks are within range. Reduced power results in reduced interference issues and increased battery capacity.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxpower [<1-30>|smart]Parameters• power [<1-30>|smart]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#power 12rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 power 12 data-rates b-only placement outdoor mesh client off-channel-scan channel-list 2.4GHz 1 guard-interval long aggregation ampdu tx-only aeroscout forward ekahau forward ip 172.16.10.1 port 3 non-unicast tx-rate bss 1 dynamic-all non-unicast tx-rate bss 2 highest-basic non-unicast tx-rate bss 3 highest-basic non-unicast tx-rate bss 4 highest-basic non-unicast tx-rate bss 5 highest-basic non-unicast tx-rate bss 6 highest-basic non-unicast tx-rate bss 7 highest-basic --More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandspower Configures a radio’s transmit power<1-30> Configures the transmit power from 1 - 30 dBm (actual power could be lower based on regulatory restrictions)For APs with dual or three radios, each radio should be configured with a unique transmit power in respect to its intended client support function.smart Enables Smart RF to determine the optimum transmit power needed. By default APs use Smart RF to determine transmit power.no Resets a radio’s transmit power](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-88.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3087.1.36.5.35 probe-responseinterface-config-radio-instanceConfigures transmission parameters for probe response framesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxprobe-response [rate|retry|rssi-threshold]probe-response retryprobe-response rate [follow-probe-request|highest-basic|lowest-basic]probe-response rssi-threshold <-128--40>Parameters• probe-response retry• probe-response rate [follow-probe-request|highest-basic|lowest-basic]• probe-response rssi-threshold <-128--40>Examplenx9500-6C8809(config-profile-testAP7161-if-radio1)#probe-response rate highest-basicnx9500-6C8809(config-profile-testAP7161-if-radio1)#probe-response retrynx9500-6C8809(config-profile-testAP7161-if-radio1)#probe-response rssi-threshold -60nx9500-6C8809(config-profile-testAP7161-if-radio1)#show context interface radio1 probe-response rate highest-basic probe-response rssi-threshold -60nx9500-6C8809(config-profile-testAP7161-if-radio1)#Related Commandsprobe-response retry Enables retransmission of probe-response frames if no acknowledgement is received from the client. This option is enabled by default.probe-response rate Configures the rates used for transmission of probe response frames. The tx-rate options available for transmitting probe response frames are: follow-probe-request, highest-basic, lowest-basic.follow-probe-request Transmits probe responses at the same rate as the received request (default setting)highest-basic Uses the highest configured basic ratelowest-basic Uses the lowest configured basic rateprobe-response rssi-threshold <-128--40>Ignores probe request from client if the received signal strength is less than the RSSI threshold specified here<-128--40> – Specify a value from -128 - -40.no Resets transmission parameters for probe response frames](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-90.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3097.1.36.5.36 radio-resource-measurementinterface-config-radio-instanceEnables 802.11k radio resource measurement. When enabled, the radio station sends channel and neighbor reports.The IEEE 802.11 Task Group k defined a set of specifications regarding radio resource measurements. These specifications specify the radio resources to be measured and the mechanism used to communicate measurement requests and results.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxradio-resource-measurement [attenuation-threshold <1-199>|max-entries <1-12>]Parameters• radio-resource-measurement [attenuation-threshold <1-199>|max-entries <1-12>]Examplerfs4000-229D58(config-device-00-23-68-22-9D-58-if-radio1)#radio-resource-measurement attenuation-threshold 20rfs4000-229D58(config-device-00-23-68-22-9D-58-if-radio1)#radio-resource-measurement max-entries 10rfs4000-229D58(config-device-00-23-68-22-9D-58-if-radio1)#show context interface radio1 radio-resource-measurement max-entries 10 radio-resource-measurement attenuation-threshold 20rfs4000-229D58(config-device-00-23-68-22-9D-58-if-radio1)#Related Commandsradio-resource-measurementEnables 802.11k radio resource measurement on the radioattenuation-threshold <1-199>Configures the neighbor attenuation threshold, considered when generating channel and neighbor reports• <1-199> – Specify the attenuation threshold from 1 -199. The default is 90.max-entries <1-12> Configures the maximum number of entries to include in channel and neighbor reports• <1-12> – Specify a value from 1 - 12. The default is 6.no Disables 802.11k radio resource measurement support](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-91.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3107.1.36.5.37 radio-share-modeinterface-config-radio-instanceConfigures the radio’s mode of operation as radio share. A radio operating in the radio share mode services clients and also performs sensor functions (defined by the radio’s AirDefense Services Platform (ADSP) licenses and profiles).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533Syntaxradio-share-mode [inline|off|promiscuous]Parameters• radio-share-mode [inline|off|promiscuous]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#radio-share-mode promiscuousrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 power 12 data-rates b-only placement outdoor mesh client off-channel-scan channel-list 2.4GHz 1 preamble-short guard-interval long ......................................................... non-unicast queue bss 16 50 antenna-diversity max-clients 100 radio-share-mode promiscuous airtime-fairness prefer-ht weight 6 lock-rf-mode extended-range 15 antenna-downtiltrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related CommandsNOTE: The sensor capabilities of the radio are restricted to the channel and WLANs defined on the radio.radio-share-mode Enables sharing of packets, switched by this radio, with the WIPS sensor module. There are two radio-share modes, these are: inline and promiscuousinline Enables sharing of all WLAN packets (matching the BSSID of the radio) serviced by the radio with the WIPS sensor module.off Disables radio share (no packets shared with the WIPS sensor module)promiscuous Enables the promiscuous radio share mode. In this mode the radio is configured to receive all packets on the channel irrespective of whether the destination address is the radio or not, and shares these packets with the WIPS sensor module for analysis (i.e. without filtering based on BSSI).no Resets the radio share mode for this radio to its default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-92.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3117.1.36.5.38 rate-selectioninterface-config-radio-instanceSets the data-rate selection mode to standard or opportunisticSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxrate-selection [opportunistic|standard]Parameters• rate-selection [opportunistic|standard]Examplenx9500-6C8809(config-profile-testAP7161-if-radio1)#rate-selection opportunisticnx9500-6C8809(config-profile-testAP7161-if-radio1)#show context interface radio1 rate-selection opportunisticnx9500-6C8809(config-profile-testAP7161-if-radio1)#Related Commandsrate-selection Sets the rate selection mode to standard or opportunisticstandard Configures the monotonic rate selection mode. This is the default setting.opportunistic Configures the opportunistic radio link adaptation (ORLA) rate selection modeThe ORLA algorithm is designed to select data rates that provide best throughput. Instead of using local conditions to decide whether a data rate is acceptable or not, ORLA pro-actively probes other rates to determine if greater throughput is available. If these other rates do provide improved throughput, ORLA intelligently adjusts its selection tables to favour higher performance. ORLA provides improvements both on the client side of a mesh network as well as in the backhaul capabilities.Note: The ORLA rate selection mode is supported only on the AP7161 and AP8163 model access points.no Resets the rate selection mode to standard (monotonic)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-93.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3127.1.36.5.39 rf-modeinterface-config-radio-instanceConfigures the radio’s RF mode of operationThis command sets the mode to either 2.4 GHz WLAN or 5.0 GHz WLAN support depending on the radio’s intended client support. If you are currently licensed to use 4.9 GHz, configure the 4.9 GHz-WLAN option. Set the mode to sensor if using the radio for rogue device detection. The radio cannot support rogue detection when one of the other radios is functioning as a WIPS sensor. To set a radio as a detector, disable sensor support on the other access point radios.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxrf-mode [2.4GHz-wlan|4.9GHz-wlan|5GHz-wlan|bridge|scan-ahead|sensor]Parameters• rf-mode [2.4GHz-wlan|4.9GHz-wlan|5GHz-wlan|bridge|scan-ahead|sensor]rf-mode Configures the radio’s RF mode of operation2.4GHz-wlan Provides WLAN service in the 2.4 GHz bandwidth4.9GHz-wlan Provides WLAN service in the 4.9 GHz bandwidth5GHz-wlan Provides WLAN service in the 5.0 GHz bandwidthbridge Enables this radio to operate as client bridge that can authenticate and associate to a defined infrastructure Wireless LAN (WLAN) access pointNote: This option is applicable only on the AP6522, AP6562, AP7522, AP7532, and AP7562 model access points. Enable this option only if the access point is to provide client-bridge support. Once enabled, configure the client-bridge parameters. For more information, see bridge.scan-ahead Enables this radio to operate as a scan-ahead radioA radio functioning in the scan-ahead mode is used for forward scanning only. The radio does not support WLAN or mesh services.The scan ahead feature is used in Dynamic Frequency Selection (DFS) aware countries for infrastructure devices, static, and vehicular mounted modems (VMMs). It enables a secondary radio to scan ahead for an active channel for backhaul transmission, in the event of a radar trigger on the primary radio. The device then switches radios allowing transmission to continue. This is required in environments where handoff is required and DFS triggers are common.With a secondary radio dedicated for forward scanning, the primary radio, in case of radar hit, hands over the channel availability check (CAC) function to the secondary radio. This avoids a break in data communication, which would have resulted if the primary radio was to do CAC itself.The secondary radio periodically does a scan of the configured channel list, searching for the other available meshpoint roots. When configured on the root meshpoint, the scan-ahead feature also scans for cleaner channels.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-94.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3147.1.36.5.40 rifsinterface-config-radio-instanceConfigures Reduced Interframe Spacing (RIFS) parameters on this radioThis value determines whether interframe spacing is applied to access point transmitted or received packets, both, or none. Inter-frame spacing is the interval between two consecutive Ethernet frames that enable a brief recovery between packets and allow target devices to prepare for the reception of the next packet.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxrifs [none|rx-only|tx-only|tx-rx]Parameters• rifs [none|rx-only|tx-only|tx-rx]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#rifs tx-onlyrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 rf-mode sensor placement outdoor mesh client off-channel-scan channel-list 2.4GHz 1 guard-interval long aggregation ampdu tx-only rifs tx-only aeroscout forward ekahau forward ip 172.16.10.1 port 3 non-unicast tx-rate bss 1 dynamic-all non-unicast tx-rate bss 2 highest-basic non-unicast tx-rate bss 3 highest-basic non-unicast tx-rate bss 4 highest-basic--More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandsrifs Configures RIFS parametersnone Disables support for RIFSConsider setting the value to None for high-priority traffic to reduce packet delay.rx-only Supports RIFS possession onlytx-only Supports RIFS transmission onlytx-rx Supports both RIFS transmission and possession (default setting)no Disables radio’s RIFS parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-96.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3167.1.36.5.42 serv iceinterface-config-radio-instanceEnables dynamic control function. This dynamic function controls performance of the radio receiver's low noise amplifiers (LNAs).When enabled, the control function, in the presence of very strong received signals, improves the receiver’s performance on radio 1. Strong signals are caused if the distance between the WiFi client and the AP is within two (2) meters. When disabled, the control function is a useful debug tool in case the uplink throughput is less than expected and the AP-to-client separation is greater than two (2) meters. Disabling the control function does not affect the receive sensitivity of the radio.Supported in the following platforms:• Access Points — AP6522, AP6562Syntaxservice radio-lna [agc|ms]Parameters• service radio-lna [agc|ms]Examplenx9500-6C8809(config-profile-testAP6522-if-radio1)#service radio-lna msnx9500-6C8809(config-profile-testAP6522-if-radio1)#show context interface radio1 service radio-lna msnx9500-6C8809(config-profile-testAP6522-if-radio1)#Related Commandsservice radio-lna [agc|ms]Enables dynamic control function• agc – Enables dynamic LNA control function. This is the default setting.• ms – Disables dynamic LNA control functionno Reverts radio-lna mode to default (agc)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-98.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3187.1.36.5.44 smar t- rfinterface-config-radio-instanceOverrides Smart RF channel width setting on this radio. When configured, the radio overrides the Smart RF selected channel setting and operates in the channel configured using this command.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxsmart-rf preferred-channel-width [20MHz|40MHz|80MHz]Parameters• smart-rf preferred-channel-width [20MHz|40MHz|80MHz]Examplenx9500-6C8809(config-profile-testAP7161-if-radio1)#smart-rf preferred-channel-width 40MHznx9500-6C8809(config-profile-testAP7161-if-radio1)#show context interface radio1 smart-rf preferred-channel-width 40MHz rate-selection opportunisticnx9500-6C8809(config-profile-testAP7161-if-radio1)#Related Commandssmart-rf preferred-channel-width [20MHz|40MHz|80MHz]Configures the preferred channel width. The options are:• 20MHz – Sets 20 MHz as the preferred channel of operation• 40MHz – Sets 40MHz as the preferred channel of operation• 80MHz – Sets 80MHz as the preferred channel of operation (default setting)no Enables use of Smart RF selected channel of operation](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-100.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3197.1.36.5.45 sniffer-redirectinterface-config-radio-instanceCaptures and redirects packets to an IP address running a packet capture/analysis toolSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxsniffer-redirect [omnipeek|tzsp] <IP> channel [1|10|100|100w --------] {snap <1-65535> (append descriptor)}Parameters• sniffer-redirect [omnipeek|tzsp] <IP> channel [1|10|100|100w ---------] {snap <1-65535> (append descriptor)}Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#sniffer-redirect omnipeek 172.16.10.1 channel 1rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 rf-mode sensor placement outdoor mesh client rts-threshold 100 off-channel-scan channel-list 2.4GHz 1 guard-interval long aggregation ampdu tx-only rifs tx-only sniffer-redirect omnipeek 172.16.10.1 channel 1 aeroscout forward ekahau forward ip 172.16.10.1 port 3sniffer-redirect Captures and redirects packets to an IP address running a packet capture/analysis toolomnipeek Encapsulates captured packets in proprietary header (used with OmniPeek and plug-in)tzsp Encapsulates captured packets in TZSP (used with WireShark and other tools)<IP> Specify the IP address of the device running the capture/analysis tool (the host to which captured off channel scan packets are redirected)[1|10|100|100w ----------] Specify the channel to capture packets• 1 – Channel 1 in 20 MHz mode (default setting)• 10 – Channel 10 in 20 MHz mode• 100 – Channel 100 in 20 MHz mode• 100w – Channels 100w in 40 MHz mode (channels 100*,104)snap <1-65535> Optional. Allows truncating of large captured frames at a specified length (in bytes). This option is useful when capturing traffic with large frames. Use this option when only headers are needed for analysis, since it reduces the bandwidth needed for sniffing, and (for typical values) eliminates any fragmentation of the outer packet.• <1-65535> – Specify the maximum truncated byte length of captured packets.append descriptor Optional – Enables appending of the radio's receive descriptor to the captured packet](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-101.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3217.1.36.5.46 st bcinterface-config-radio-instanceConfigures the radio’s Space Time Block Coding (STBC) mode. STBC is a pre-transmission encoding scheme providing an improved SNR ratio (even at a single RF receiver). STBC transmits multiple data stream copies across multiple antennas. The receiver combines the copies into one to retrieve data from the signal. These transmitted data versions provide redundancy to increase the odds of receiving data streams with a good data decode (especially in noisy environments).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxstbc [auto|none|tx-only]Parameters• stbc [auto|none|tx-only]Examplerfs6000-37FABE(config-profile-81xxTestProfile-if-radio1)#stbc tx-onlyrfs6000-37FABE(config-profile-81xxTestProfile-if-radio1)#show context interface radio1 stbc tx-onlyrfs6000-37FABE(config-profile-81xxTestProfile-if-radio1)#Related CommandsNOTE: STBC requires the radio has at least two antennas with the capability to transmit two streams. If the antenna mode is configured to 1x1 (or falls back to 1x1 for some reason), STBC support is automatically disabled.stbc Configures the radio’s STBC modeauto Autoselects STBC settings based on the platform type and other radio interface settings. This is the default setting.none Disables STBC supporttx-only Configures the AP radio to format and broadcast the special stream (enables STBC support for transmit only)no Disables STBC support](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-103.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3237.1.36.5.48 useinterface-config-radio-instanceApplies an association ACL policy and a radio QoS policy on this radio interfaceAn association ACL is a policy-based Access Control List (ACL) that either prevents or allows wireless clients from connecting to a controller managed access point radio. An ACL is a sequential collection of permit and deny conditions that apply to controller packets. When a packet is received on an interface, the controller compares the fields in the packet against any applied ACLs to verify the packet has the required permissions to be forwarded, based on the criteria specified in the access lists. If a packet does not meet any of the criteria specified in the ACL, the packet is dropped.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxuse [association-acl-policy|radio-qos-policy]use [association-acl-policy <ASSOC-ACL-POLICY-NAME>|radio-qos-policy <RADIO-QOS-POLICY-NAME>]Parameters• use [association-acl-policy <ASSOC-ACL-POLICY-NAME>|radio-qos-policy <RADIO-QOS-POLICY-NAME>]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#use association-acl-policy testrfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 rf-mode sensor placement outdoor mesh client rts-threshold 100 off-channel-scan channel-list 2.4GHz 1 guard-interval long aggregation ampdu tx-only rifs tx-only use association-acl-policy test sniffer-redirect omnipeek 172.16.10.1 channel 1 aeroscout forward ekahau forward ip 172.16.10.1 port 3 --More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandsuse Applies an association ACL policy and a radio QoS policy on this radio interfaceassociation-acl-policy Uses a specified association ACL policy with this radio interface• <ASSOC-ACL-POLICY-NAME> – Specify the association ACL policy name (should be existing and fully configured).radio-qos-policy Uses a specified radio QoS policy with this radio interface• <RADIO-QoS-POLICY-NAME> – Specify the radio QoS policy name (should be existing and fully configured).no Dissociates the specified association ACL policy and radio QoS policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-105.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3257.1.36.5.50 wireless-clientinterface-config-radio-instanceConfigures wireless client parameters on this radioSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533Syntaxwireless-client tx-power [<0-20>|mode]wireless-client <0-20>wireless-client tx-power mode [802.11d {wing-ie}|wing-ie {802.11d}]Parameters• wireless-client tx-power <0-20>• wireless-client tx-power mode [802.11d {wing-ie}|wing-ie {802.11d}]Examplerfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#wireless-client tx-power 20rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#show context interface radio1 rf-mode sensor placement outdoor mesh client rts-threshold 100 wireless-client tx-power 20 off-channel-scan channel-list 2.4GHz 1 guard-interval long aggregation ampdu tx-only --More--rfs6000-37FABE(config-profile-71xxTestProfile-if-radio1)#Related Commandswireless-client Configures wireless client parameterstx-power <0-20> Configures the transmit power indicated to wireless clients. If using a dual or three radio model access point, each radio should be configured with a unique transmit power in respect to its intended client support function. A setting of 0 defines the radio as using Smart RF to determine its output power. 20 dBm is the default value.• <0-20> – Specify transmit power from 0 - 20 dBm.wireless-client Configures wireless client parameterstx-power[802.11d|wing-ie]Configures the transmit power indicated to wireless clients• 802.11d – Advertises in the IEEE 802.11d country information element• wing-ie – Optional. Advertises in the WiNG information element (173)• wing-ie – Advertises in the WiNG information element (173). This is the default setting.• 802.11d – Optional. Advertises in the IEEE 802.11d country information elementno Resets the transmit power indicated to wireless clients](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-107.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3297.1.36.6.2 a uth- t ypeinterface-config-wwan-instanceConfigures the authentication type used by the cellular data providerSupported in the following platforms:• Access Point — AP7161, AP81XX, AP8232• Wireless Controllers — RFS4000, RFS6000Syntaxauth-type [chap|mschap|mschap-v2|pap]Parameters• auth-type [chap|mschap|mschap-v2|pap]Examplenx9500-6C8809(config-profile-testRFS6000-if-wwan1)#auth-type mschap-v2nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#show context interface wwan1 apn AT&T auth-type mschap-v2nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#Related Commandsauth-type Configures the authentication protocol used on this interface. The options are: PAP, CHAP, MSCHAP, and MSCHAP-v2chap Configures Challenge-Handshake Authentication Protocol (CHAP). This is the default value.mschap Configures Microsoft Challenge-Handshake Authentication Protocol (MSCHAP)mschapv2 Configures Microsoft Challenge-Handshake Authentication Protocol (MSCHAP) version 2pap Configures Password Authentication Protocol (PAP)no Removes the authentication protocol configured on this interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-111.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3317.1.36.6.4 ipinterface-config-wwan-instanceConfigures IP related settings on this interfaceSupported in the following platforms:• Access Point — AP7161, AP81XX, AP8232• Wireless Controllers — RFS4000, RFS6000Syntaxip [default-gateway|nat]ip default-gateway priority <1-8000>ip nat [inside|outside]Parameters• ip default-gateway priority <1-8000>• ip nat [inside|outside]Examplenx9500-6C8809(config-profile-testRFS6000-if-wwan1)#ip default-gateway priority 1nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#ip nat insidenx9500-6C8809(config-profile-testRFS6000-if-wwan1)#show context interface wwan1 apn AT&T auth-type mschap-v2 crypto map test ip nat inside ip default-gateway priority 1nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#Related Commandsip Configures IP related settings on this interfacedefault-gateway priority <1-8000>Configures the default-gateway’s (learned by the wireless WAN) priority. • <1-8000> – Specify a value from 1 - 8000. The default is 3000.ip Configures IP related settings on this interfacenat [inside|outside] Configures the NAT settings. This option is disabled by default.• inside – Marks this WWAN interface as NAT inside. The inside network is transmitting data over the network to its intended destination. On the way out, the source IP address is changed in the header and replaced by the (public) IP address.• outside – Marks this WWAN interface as NAT outside. Packets passing through the NAT on the way back to the controller or service platform managed LAN are matched against the records kept by the NAT engine. There, the destination IP address is changed back to the specific internal private class IP address in order to reach the LAN over the network.no Removes IP related settings on this interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-113.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3327.1.36.6.5 n ointerface-config-wwan-instanceRemoves or reverts the WWAN interface settingsSupported in the following platforms:• Access Point — AP7161, AP81XX, AP8232• Wireless Controllers — RFS4000, RFS6000Syntaxno [all|apn|auth-type|crypto|description|ip|password|shutdown|use|username]no [all|apn|auth-type|description|password|shutdown|username]no crypto mapno ip [default-gateway priority|nat]no use ip-access-list inParameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.ExampleThe following example displays the WWAN interface settings before the ‘no’ commands are executed:nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#show context interface wwan1 apn AT&T auth-type mschap-v2 crypto map test ip nat inside ip default-gateway priority 1nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#no apnnx9500-6C8809(config-profile-testRFS6000-if-wwan1)#no auth-typeThe following example displays the WWAN interface settings after the ‘no’ commands are executed:nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#show context interface wwan1 crypto map test ip nat inside ip default-gateway priority 1nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#no <PARAMETERS> Removes or reverts this WWAN interface’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-114.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3337.1.36.6.6 passwordinterface-config-wwan-instanceConfigures a password for this WWAN interface. The configured value is used for authentication support by the cellular data carrier.Supported in the following platforms:• Access Point — AP7161, AP81XX, AP8232• Wireless Controllers — RFS4000, RFS6000Syntaxpassword [2 <WORD>|<WORD>]Parameters• password [2 <WORD>|<WORD>]Examplenx9500-6C8809(config-profile-testRFS6000-if-wwan1)#password 2 TechPubsTesting@123nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#show context interface wwan1 password TechPubsTesting@123 crypto map test ip nat inside ip default-gateway priority 1nx9500-6C8809(config-profile-testRFS6000-if-wwan1)#Related Commandspassword Configures a password for this WWAN interface2 <WORD> Configures an encrypted password. Use this option when copy pasting the password from another device.<WORD> Enter the password string (should not exceed 32 characters in length.no Removes the configured password](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-115.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3397.1.36.7.1 b e aco ninterface-config-bluetooth-instanceConfigures the Bluetooth radio’s beacon’s emitted transmission pattern for Bluetooth radios functioning in the low energy beacon (le-beacon) mode. This option is applicable only if the Bluetooth radio’s operational mode is set to le-beacon.Supported in the following platforms:• Access Points – AP8432, AP8533Syntaxbeacon [pattern|period]beacon pattern [eddystone-url1|eddystone-ulr2|ibeacon]beacon period <100-10000>Parameters• beacon pattern [eddystone-url1|eddystone-ulr2|ibeacon]• beacon period <100-10000>beacon pattern [eddystone-url1|eddystone-ulr2|ibeacon]When the beacon mode is set to ‘le-beacon’, use this command to configure the Bluetooth radio’s beacon’s emitted transmission pattern. Select one of the following beacon patterns:• eddystone-url1 – Transmits an Eddystone-URL beacon using URL 1. This is the default setting.• eddystone-url2 – Transmits an Eddystone-URL beacon using URL 2An Eddystone-URL frame broadcasts a URL using a compressed encoding scheme to better fit within a limited advertisement packet. Once decoded, the URL can be used by a client for Internet access. If an Eddystone-URL beacon broadcasts https:anysite, clients receiving the packet can access that URL. If setting the transmission pattern as ‘eddystone-url1’ or ‘eddystone-ulr2’, use the ‘eddystone’ keyword to configure Eddystone beacon payload parameters. For more information, see eddystone.• ibeacon – Transmits an ibeacon beacon. iBeacon was created by Apple for use in iPhone OS (iOS) devices (beginning with iOS version 7.0). There are three data fields Apple has made available to iOS applications, a Universally Unique IDentifier (UUID) for device identification, a Major value for device class and a Minor value for more refined information like product category. If setting the transmission pattern as ‘ibeacon’, use the ‘ibeacon’ keyword to configure ibeacon beacon payload parameters. For more information, see ibeacon.For more information on configuring the Bluetooth radio’s operational mode, see mode.beacon period <100-10000>Configures the Bluetooth radio’s beacon transmission period, in milliseconds, from 100 - 10000. As the defined period increases, so does the CPU processing time and the number of packets incrementally transmitted (typically one per minute).• <100-10000> – Specify a value from 100 - 10000 milliseconds. The default value is 1000 milliseconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-121.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3427.1.36.7.3 edd ysto neinterface-config-bluetooth-instanceConfigures Eddystone beacon payload parameters. Configure these parameters only if the Bluetooth radio interface’s operational mode is set to ‘le-beacon’, and the beacon’s emitted transmission pattern is set to either ‘eddystone-url1’ or ‘eddystone-ulr2’.Supported in the following platforms:• Access Points – AP7602, AP7612, AP7622, AP7632, AP7662, AP8432, AP8533Syntaxeddystone [calibration-rssi <-127-127>|url [1|2] <WORD>]Parameters• eddystone [calibration-rssi|url [1|2] <WORD>]Examplenx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#eddystone calibration-rssi -120nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#show context interface bluetooth1 shutdown description AP8432-BLE-Radio1 mode le-beacon beacon pattern eddystone-url2 beacon period 900 eddystone calibration-rssi -120nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#Related Commandseddystone [calibration-rssi <-127-127>|url [1|2] <WORD>]If the Beacon transmission pattern has been set to either ‘eddystone-url1’ or ‘eddystone-url2’, configure the following Eddystone parameters:• calibration-rssi – Configures the Eddystone beacon measured calibration signal strength, from -127 to 127 dBm, at 0 meters. Mobile devices can approximate their distance to beacons based on received signal strength. However, distance readings can fluctuate since they depend on several external factors. The closer you are to a beacon, the more accurate the reported distance. This setting is the projected calibration signal strength at 0 meters.• <-127-127> – Specify a value from -127 - 127 dBm. The default value is -19 dBm.• url [1|2] <WORD> – Configures the Eddystone URL as URL1 OR URL2• 1 – Selects the Eddystone URL number 1• 2 – Selects the Eddystone URL number 2The following keyword is common to the ‘eddystone-url1’ and ‘eddystone-url2’ keywrods:• <WORD> – Enter a 64 character maximum eddystone-URL1/eddystone-URL2.The URL must be 18 characters or less once auto-encoding is applied. URL encoding is used when placing text in a query string to avoid confusion with theURL itself. It is typically used when a browser sends data to a Web server.no Removes or reverts to default this Bluetooth radio’s Eddystone beacon payload configurations](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-124.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3437.1.36.7.4 ibe a coninterface-config-bluetooth-instanceConfigures iBeacon beacon payload parameters. Configure these parameters only if the Bluetooth radio interface’s operational mode is set to ‘le-beacon’, and the beacon’s emitted transmission pattern is set to ‘ibeacon’.Supported in the following platforms:• Access Points – AP7602, AP7612, AP7622, AP7632, AP7662, AP8432, AP8533Syntaxibeacon [calibration-rssi <-127-127>|major <0-65535>|minor <0-65535>|uuid <WORD>]ibeacon [calibration-rssi <-127-127>|uuid <WORD>]ibeacon [major|minor] <0-65535>Parameters• ibeacon [calibration-rssi <-127-127>|major <0-65535>|minor <0-65535>|uuid <WORD>]Examplenx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#ibeacon calibration-rssi -70nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#ibeacon major 1110nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#ibeacon minor 2210nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#ibeacon uuid f2468da65fa82e841134bc5b71e0893eibeacon Configures following iBeacon beacon payload parameters: calibration-rssi, major, minor, and uuidcalibration-rssi <-127-127>Configures the ibeacon measured calibration signal strength, from -127 to 127 dBm, at 1 meter. Mobile devices can approximate their distance to beacons based on received signal strength. However, distance readings can fluctuate since they depend on several external factors. The closer you are to a beacon, the more accurate the reported distance. This setting is the projected calibration signal strength at 1 meter.• <-127-127> – Specify a value from -127 - 127 dBm. The default value is -60 dBm.major <0-65535> Configures the iBeacon Major value from 0 - 65535. Major values identify and distinguish groups. For example, each beacon on a specific floor in a building could be assigned a unique major value.• <0-65535> – Specify a value from 0 - 65535. The default value is 1111.minor <0-65535> Configures the iBeacon Minor value from 0 - 65535. Minor values identify and distinguish individual beacons. Minor values help identify individual beacons within a group of beacons assigned a major value. The default setting is 2,222.• <0-65535> – Specify a value from 0 - 65535. The default value is 2222.uuid <WORD> Configures a 32 hex character maximum UUID. The UUID classification contains 32 hexadecimal digits, split into 5 groups, separated by dashes. For example, f2468da65fa82e841134bc5b71e0893e. The UUID distinguishes iBeacons in the network from all other beacons in networks outside of your direct administration.• <WORD> – Specify the UUID (should not exceed 32 hexadecimal characters). The default value is 01F101F101F101F101F101F101F101F1.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-125.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3457.1.36.7.5 mo d einterface-config-bluetooth-instanceConfigures the Bluetooth radio interface’s mode of operation as bt-sensor or le-beaconSupported in the following platforms:• Access Points – AP7602, AP7612, AP7622, AP7632, AP7662, AP8432, AP8533Syntaxmode [bt-sensor|le-beacon|le-tracking]Parameters• mode [bt-sensor|le-beacon|le-tracking]Examplenx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#mode le-beaconnx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#show context interface bluetooth1 shutdown mode le-beacon beacon pattern ibeacon ibeacon calibration-rssi -70 ibeacon major 1110 ibeacon minor 2210 ibeacon uuid f2468da65fa82e841134bc5b71e0893enx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#Related Commandsmode Configures the Bluetooth radio interface’s mode of operation. The options are:• bt-sensor – Select this option to provide Bluetooth support for legacy devices. bt-sensors are Bluetooth classic sensors providing robust wireless connections for legacy devices. Typically these connections are not ideally suited for the newer Bluetooth low energy (BLE) technology supported devices. This is the default setting.• le-beacon – Select this option to provide Bluetooth support for newer BLE technology supported devices. le-beacons are newer Bluetooth low energy beacons ideal for applications requiring intermittent or periodic transfers of small amounts of data. le-beacons are not designed as replacements for classic beacon sensors. If selecting this option, use the beacon keyword to configure the Beacon transmission period and Beacon transmission pattern.• le-tracking – Select this option to provide Bluetooth support for BLE asset tracking. When enabled, it uses the AP’s Bluetooth radio to detect BLE ‘asset tags’ within the managed network. This information is reported to a back-end server (NSight server).no Reverts this Bluetooth radio’s mode of operation to le-beacon](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-127.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3477.1.36.7.7 n ointerface-config-bluetooth-instanceRemoves or reverts to default this AP8432/AP8533 Bluetooth radio interface’s settingsSupported in the following platforms:• Access Points – AP7602, AP7612, AP7622, AP7632, AP7662, AP8432, AP8533Syntaxno [beacon|description|eddystone|ibeacon|mode|shutdown]no beacon [pattern|period]no descriptionno eddystone [calibration-rssi|url [1|2]no ibeacon [calibration-rssi|major|minor|uuid]no modeno shutdownParameters• no <PARAMETERS>ExampleThe following example shows the AP8432 default profile’s Bluetooth radio interface settings:nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#show context interface bluetooth1 shutdown mode le-beacon beacon pattern ibeacon ibeacon calibration-rssi -70 ibeacon major 1110 ibeacon minor 2210 ibeacon uuid f2468da65fa82e841134bc5b71e0893enx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#no shutdownnx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#no ibeacon minornx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#no ibeacon calibration-rssiThe following example shows the AP8432 default profile’s Bluetooth radio interface settings after the ‘no’ commands are executed:nx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#show context interface bluetooth1 no shutdown mode le-beacon beacon pattern ibeacon ibeacon major 1110 ibeacon uuid f2468da65fa82e841134bc5b71e0893enx9500-6C8809(config-profile-default-ap8432-if-bluetooth1)#no <PARAMETERS> Removes or reverts to default this Bluetooth radio interface’s settings based on the parameters passed• <PARAMETERS> – Specify the parameters.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-129.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3497.1.37.1 ipipConfigures IPv4 routing components, such as default gateway, DHCP, DNS server forwarding, name server, domain name, routing standards, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxip [default-gateway|dhcp|dns-server-forward|domain-lookup|domain-name|igmp|name-server|nat|route|routing]ip default-gateway [<IP>|<HOST-ALIAS-NAME>|failover|priority [dhcp-client <1-1800>|static-route <1-1800>]]ip [dns-server-forward|domain-lookup|domain-name <DOMAIN-NAME>|name-server <IP>|routing]ip dhcp client [hostname|persistent-lease]ip igmp snooping {fast-leave|forward-unknown-multicast|querier}ip igmp snooping {fast-leave|forward-unknown-multicast}ip igmp snooping {querier} {max-response-time <1-25>|query-interval <1-18000>|robustness-variable <1-7>|timer expiry <60-300>|version <1-3>}ip nat [crypto|inside|outside|pool]ip nat [crypto source pool|pool] <NAT-POOL-NAME>ip nat [inside|outside] [destination|source]ip nat [inside|outside] destination static <ACTUAL-IP> <1-65535> [tcp|udp] [(<NATTED-IP> {<1-65535>})]ip nat [inside|outside] source [list|static]ip nat [inside|outside] source static <ACTUAL-IP> <1-65535> [tcp|udp] [(<NATTED-IP> {<1-65535>})]ip nat [inside|outside] source list <IP-ACCESS-LIST-NAME> interface [<INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1] [(address <IP>|interface <L3-IF-NAME>|overload|pool <NAT-POOL-NAME>)]ip route <IP/M> [<IP>|<HOST-ALIAS-NAME>]Parameters• ip default-gateway [<IP>|<HOST-ALIAS-NAME>|failover|priority [dhcp-client <1-1800>|static-route <1-1800>]]NOTE: The command ‘ip igmp snooping’ can be configured under bridge VLAN context also. For example: rfs7000-37FABE(config-device 00-15-70-37-FA-BE-bridge-vlan-1)#ip igmp snooping forward-unknown-multicastip Configures IPv4 routing components](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-131.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 350• ip [dns-server-forward|domain-lookup|domain-name <DOMAIN-NAME>|name-server <IP>|routing]• ip dhcp client [hostname|persistent-lease]default-gateway Configures default gateway (next-hop router) parameters<IP> Configures default gateway’s IP address• <IP> – Specify the default gateway’s IP address.failover Configures failover to the gateway (with next higher priority) when the current default gateway is unreachable (In case of multiple default gateways). This option is enabled by default.<HOST-ALIAS-NAME> Configures the host alias mapped to the required default gateway• <HOST-ALIAS-NAME> – Specify the host alias name (should be existing and configured). Host alias names begin with a ‘$’.priority [dhcp-client <1-1800>|static-route <1-1800>]Configures default gateway priority• dhcp-client <1-1800> – Defines a priority for the default gateway acquired by the DHCP client on the VLAN interface. The default setting is 1000.• static-route <1-1800> – Defines the weight (priority) assigned to this static route versus others that have been defined to avoid potential congestion. The default setting is 100.The following keyword is common to ‘dhcp-client’ and ‘static-route’ parameters:• <1-1800> – Specify the priority from 1 - 18000 (lower the value higher is the priority).ip Configures IPv4 routing componentsdns-server-forward Enables DNS forwarding. This command enables the forwarding of DNS queries to DNS servers outside of the network. This option is disabled by default.domain-lookup Enables domain lookup. When enabled, human friendly domain names are converted into numerical IP destination addresses. The option is enabled by default.domain-name <DOMAIN-NAME>Configures a default domain name• <DOMAIN-NAME> – Specify a name for the DNS (should not exceed 64 characters in length).name-server <IP> Configures the name server’s IP address• <IP> – Specify the IP address of the name server.routing Enables IP routing of logically addressed packets from their source to their destination. IPv4 routing is enabled by default.ip Configures IPv4 routing componentsdhcp Configures the DHCP client and hostclient[hostname|persistent-lease]Sets the DHCP client• hostname – Includes the hostname in the DHCP lease for the requesting client. This option is enabled by default.• persistent-lease – Retains the last lease across reboots if the DHCP server is unreachable. A persistent DHCP lease assigns the same IP address and other network information to the device each time it renews its DHCP lease. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-132.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 351• ip igmp snooping {fast-leave|forward-unknown-multicast}• ip igmp snooping {querier} {max-response-time <1-25>|query-interval <1-18000>|robustness-variable <1-7>|timer expiry <60-300>|version <1-3>}• ip nat [crypto source pool|pool <NAT-POOL-NAME>]• ip nat [inside|outside] destination static <ACTUAL-IP> <1-65535> [tcp|udp] [(<NATTED-IP> {<1-65535>})]ip Configures IPv4 routing componentsfats-leave Optional. Enables fast leave processing. When enabled, leave messages are processed quickly, preventing the host from receiving further traffic. Should be configured for one (wired) host network only. This option is disabled by default.This feature is supported only on the AP7502, AP8232, AP8533 model access points.igmp snooping forward-unknown-multicastOptional. Enables unknown multicast data packets to be flooded in the specified VLAN. This option is disabled by default.ip Configures IPv4 routing componentsigmp snooping querierOptional. Enables the IGMP querier functionality for the specified VLAN. By default IGMP snooping querier is disabled.max-response-time <1-25>Configures the IGMP maximum query response interval used in IGMP V2/V3 queries for the given VLAN. The default is 10 seconds.query-interval <1-18000>Configures the IGMP querier query interval in seconds. Specify a value from 1 - 18000 seconds. The default is 60 seconds.robustness-variable <1-7>Configures the IGMP robustness variable from 1 - 7. The default is 2.timer expiry <60-300>Configures the other querier time out value for the given VLAN. The default is 60 seconds.version <1-3> Configures the IGMP query version for the given VLAN. The default is 3.ip Configures IPv4 routing componentsnat Configures the NAT parameterscrypto source pool <NAT-POOL-NAME>Configures the NAT source address translation settings for IPSec tunnels• <NAT-POOL-NAME> – Specify a NAT pool name.pool <NAT-POOL-NAME>Configures a pool of IP addresses for NAT• <NAT-POOL-NAME> – Specify a name for the NAT pool.ip Configures IPv4 routing componentsnat Configures the NAT parameters[inside|outside] Configures inside and outside address translation for the destination• inside – Configures inside address translation• outside – Configures outside address translationdestination static <ACTUAL-IP>The following keywords are common to the ‘inside’ and ‘outside’ parameters:• destination – Specifies destination address translation parameters• static – Specifies static NAT local to global mapping• <ACTUAL-IP> – Specify the actual outside IP address to map.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-133.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 352• ip nat [inside|outside] source static <ACTUAL-IP> <1-65535> [tcp|udp] [(<NATTED-IP> {<1-65535>})]• ip nat [inside|outside] source list <IP-ACCESS-LIST-NAME> interface [<INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1] [(address <IP>|interface <L3-IF-NAME>|overload|pool <NAT-POOL-NAME>)]<1-65535> [tcp|udp] • <1-65535> – Configures the actual outside port. Specify a value from 1 - 65535.• tcp – Configures Transmission Control Protocol (TCP) port• udp – Configures User Datagram Protocol (UDP) port<NATTED-IP> <1-65535>Enables configuration of the outside natted IP address• <NATTED-IP> – Specify the outside natted IP address.• <1-65535> – Optional. Configures the outside natted port. Specify a value from 1 - 65535.ip Configures IPv4 routing componentsnat Configures the NAT parameters[inside|outside] Configures inside and outside address translation for the source• inside – Configures inside address translation• outside – Configures outside address translationsource static <ACTUAL-IP> The following keywords are common to the’ inside’ and ‘outside’ parameters:• source – Specifies source address translation parameters• static – Specifies static NAT local to global mapping• <ACTUAL-IP> – Specify the actual inside IP address to map.<1-65535> [tcp|udp] • <1-65535> – Configures the actual outside port. Specify a value from 1 - 65535.• tcp – Configures Transmission Control Protocol (TCP) port• udp – Configures User Datagram Protocol (UDP) port<NATTED-IP> <1-65535>Enables configuration of the outside natted IP address• <NATTED-IP> – Specify the outside natted IP address.• <1-65535> – Optional. Configures the outside natted port. Specify a value from 1 - 65535.ip Configures IPv4 routing componentsnat Configures the NAT parameters[inside|outside] Configures inside and outside IP access listsource list <IP-ACCESS-LIST-NAME>Configures an access list describing local addresses• <IP-ACCESS-LIST-NAME> – Specify a name for the IP access list.interface [<INTERFACE-NAME>|pppoe1|vlan <1-4094>|wwan1]Selects an interface to configure. Select a layer 3 router interface or a VLAN interface.• <INTERFACE-NAME> – Selects a layer 3 interface. Specify the layer 3 router interface name.• vlan – Selects a VLAN interface• <1-4094> – Set the SVI VLAN ID of the interface.• pppoe1 – Selects PPP over Ethernet interface• wwan1 – Selects Wireless WAN interfaceaddress <IP> The following keyword is recursive and common to all interface types:• address <IP> – Configures the interface IP address used with NAT](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-134.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 353• ip route <IP/M> [<IP>|<HOST-ALIAS-NAME>]Examplerfs6000-37FABE(config-profile-default-rfs6000)#ip default-gateway 172.16.10.4rfs6000-37FABE(config-profile-default-rfs6000)#ip dns-server-forwardrfs6000-37FABE(config-profile-default-rfs6000)#ip nat inside source list test interface vlan 1 pool pool1 overloadrfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 bridging-mode isolated-tunnel ip igmp snooping ip igmp snooping querier ip default-gateway 172.16.10.4 autoinstall configuration autoinstall firmware crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac ........................................................ qos trust 802.1p interface ge3 ip dhcp trust qos trust dscp qos trust 802.1p interface ge4 ip dhcp trust qos trust dscp qos trust 802.1p interface pppoe1 use firewall-policy default ip dns-server-forward ip nat inside source list test interface vlan1 pool pool1 overload service pm sys-restart router ospfrfs6000-37FABE(config-profile-default-rfs6000)#interface <L3-IF-NAME>The following keyword is recursive and common to all interface types:• interface <L3-IF-NAME> – Configures a wireless controller or service platform’s VLAN interface• <L3IFNAME> – Specify the SVI VLAN ID of the interface.overload The following keyword is recursive and common to all interface types:• overload – Enables use of global address for many local addressespool <NAT-POOL-NAME>The following keyword is recursive and common to all interface types:• pool <NAT-POOL-NAME> – Specifies the NAT pool• <NAT-POOL-NAME> – Specify the NAT pool name.ip Configures IPv4 routing componentsroute Configures the static routes<IP/M> Specify the IP destination prefix in the A.B.C.D/M format.<IP> Specify the IP address of the gateway.<HOST-ALIAS-NAME> Configures the host alias mapped to the required default gateway• <HOST-ALIAS-NAME> – Specify the host alias name (should be existing and configured). Host alias names begin with a ‘$’.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-135.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3567.1.37.2.1 addressnat-pool-config-instanceConfigures NAT pool of IP addressesDefine a range of IP addresses hidden from the public Internet. NAT modifies network address information in the defined IP range while in transit across a traffic routing device. NAT only provides IP address translation and does not provide a firewall. A branch deployment with NAT by itself will not block traffic from being potentially routed through a NAT device. Consequently, NAT should be deployed with a stateful firewall.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxaddress [<IP>|range <START-IP> <END-IP>]Parameters• address [<IP>|range <START-IP> <END-IP>]Examplerfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#address range 172.16.10.2 172.16.10.8rfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#show context ip nat pool pool1 address range 172.16.10.2 172.16.10.8rfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#Related Commandsaddress <IP> Adds a single IP address to the NAT poolrange <START-IP> <END-IP>Adds a range of IP addresses to the NAT pool• <START-IP> – Specify the starting IP address of the range.• <END-IP> – Specify the ending IP address of the range.no Removes address(es) configured with this NAT pool](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-138.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3577.1.37.2.2 nonat-pool-config-instanceRemoves address(es) configured with this NAT poolSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxno address [<IP>|range <START-IP> <END-IP>]Parameters• no address [<IP>|range <START-IP> <END-IP>]Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.Examplerfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#show context ip nat pool pool1 address range 172.16.10.2 172.16.10.8rfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#rfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#no address range 172.16.10.2 172.16.10.8rfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#show context ip nat pool pool1rfs6000-37FABE(config-profile-default-rfs6000-nat-pool-pool1)#Related Commandsno address [<IP>|range <START-IP> <END-IP>]Removes a single IP address or a range of IP addresses from this NAT pooladdress Configures NAT pool IP address(es)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-139.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3587.1.38 ipv6Profile Config CommandsConfigures IPv6 routing components, such as default gateway, DNS server forwarding, name server, routing standards, etc. These IPv6 settings are applied to all devices using this profile.You can also configure IPv6 settings on a device, using the device’s configuration mode.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxipv6 [default-gateway|dns-server-forward|hop-limit|mld|name-server|nd-reachable-time|neighbor|ns-interval|ra-convert|route|ula-reject-route|unicast-routing]ipv6 [default-gateway <IPv6> {vlan <VLAN-ID>}|dns-server-forward|hop-limit <1-255>|name-server <IPv6>|nd-reachable-time <5000-3600000>|ns-interval <1000-3600000>|ula-reject-route|unicast-routing]ipv6 ra-convert {throttle interval <3-1800> max-RAs <1-256>}ipv6 mld snooping {forward-unknown-multicast|querier}ipv6 mld snooping {forward-unknown-multicast}ipv6 mld snooping {querier} {max-response-time <1-25000>|query-interval <1-18000>|robustness-variable <1-7>|timer expiry <60-300>|version <1-2>}ipv6 neighbor [<IPv6>|timeout]ipv6 neighbor <IPv6> <MAC> [<INTF-NAME>|pppoe1|vlan <1-4094>|wwan1] {dhcp-server|router}ipv6 neighbor timeout <15-86400>ipv6 route <DEST-IPv6-PREFIX/PREFIX-LENGTH> <IPv6-GATEWAY-ADDRESS> {vlan <VLAN-ID>}Parameters• ipv6 [default-gateway <IPv6> {vlan <VLAN-ID>}|dns-server-forward|hop-limit <1-255>|name-server <IPv6>|nd-reachable-time <5000-3600000>|ns-interval <1000-3600000>|ula-reject-route|unicast-routing]NOTE: The IPv6 settings configured at the profile/device level are global configuration settings and not interface-specific.ipv6 Configures IPv6 routing componentsdefault-gateway <IPv6> {vlan <VLAN-ID>}Configures IPv6 default gateway’s address in the ::/0 format• vlan <VLAN-ID> – Optional. Specify the VLAN interface’s ID through which the default gateway is accessible.dns-server-forward Enables DNS server forwarding. This command enables the forwarding of DNS queries to DNS servers outside of the network. This feature is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-140.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 360• ipv6 mld snooping {querier} {max-response-time <1-25000>|query-interval <1-18000>|robustness-variable <1-7>|timer expiry <60-300>|version <1-2>}• ipv6 neighbor <IPv6> <MAC> [<INTF-NAME>|pppoe1|vlan <1-4094>|wwan1] {dhcp-server|router}• forward-unknown-multicast – Optional. Enables unknown multicast forwarding. This feature is enabled by default.ipv6 Configures IPv6 routing componentsmld snooping querier Enables MLD protocol snooping• querier – Optional. Enables the on-board MLD querier. When enabled, IPv6 devices send query messages to discover which network devices are members of a given multicast group.This option is disabled by default.max-response-time <1-25000>Configures the MLD querier’s maximum query response time. This is the time for which the querier waits before sending a responding report. Queriers use MLD reports to join and leave multicast groups and receive group traffic.• <1-25000> – Specify a value from 1 - 25000 milliseconds. The default is 10 milliseconds.query-interval <1-18000>Configures the interval, in seconds, between two consecutive MLD querier’s queriesThe robustness variable is an indication of how susceptible the subnet is to lost packets. MLD can recover from robustness variable minus 1 lost MLD packets.• <1-18000> – Specify a value from 1 - 18000 seconds. The default is 60 seconds.robustness-variable <1-7>Configures the MLD IGMP robustness variable. This value is used by the sender of a query.• <1-7> – Select a value from 1 - 7. The default is 2.timer expiry <60-300>Configures the MLD other querier (any external querier) timeout• <60-300> – Specify a value from 60 - 300 seconds. The default is 60 seconds.version <1-2> Configures the MLD querier’s version. MLD version 1 is based on IGMP version 2 for IPv4. MLD version 2 is based on IGMP version 3 for IPv4 and is fully backward compatible. IPv6 multicast uses MLD version 2.• <1-2> – Select the MLD version from 1 - 2. The default is 2.ipv6 Configures IPv6 routing componentsneighbor Configures static IPv6 neighbor entries<IPv6> Specify the IPv6 address for which a static neighbor entry is created.<MAC> Specify the MAC address associated with the specified IPv6 address.[<INTF-NAME>|pppoe1|vlan <1-4094>|wwan1] Specify the following interface settings:• <INTF-NAME> – Selects the layer 3 router interface. Specify the interface name.• pppoe1 – Selects the PPP over Ethernet interface• vlan <1-4094> – Selects the VLAN interface. Specify the VLAN interface index.• wwan1 – Selects the wireless WAN interface{dhcp-server|router} After specifying interface type, you can optionally specify the device type for this neighbor solicitation.• dhcp-server – Optional. States this neighbor entry is for a DHCP server• router – Optional. States this neighbor entry is for a router](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-142.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3627.1.39 l2tpv3Profile Config CommandsDefines the L2TPV3 settings for tunneling layer 2 payloads using VPNsL2TPv3 is an IETF standard that defines the control and encapsulation protocol settings for tunneling layer 2 frames in an IP network (and access point profile) between two IP nodes. Use L2TPv3 to create tunnels for transporting layer 2 frames. L2TPv3 enables WiNG supported controllers and access points to create tunnels for transporting Ethernet frames to and from bridge VLANs and physical ports. L2TPv3 tunnels can be defined between WiNG devices and other vendor devices supporting the L2TPv3 protocol.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxl2tpv3 [hostname <HOSTNAME>|inter-tunnel-bridging|logging|manual-session|router-id [<1-4294967295>|<IP>]|tunnel|udp-listen-port <1024-65535>]l2tpv3 logging ip-address [<IP>|any] hostname [<HOSTNAME>|any] router-id [<IP>|<WORD>|any]Parameters• l2tpv3 [hostname <HOSTNAME>|inter-tunnel-bridging|manual-session|router-id [<1-4294967295>|<IP>]|tunnel|udp-listen-port <1024-65535>]• l2tpv3 logging ip-address [<IP>|any] hostname [<HOSTNAME>|any] router-id [<IP>|<WORD>|any]l2tpv3 Configures the L2TPv3 protocol settings for a profilehostname <HOSTNAME>Configures the host name sent in the L2TPv3 signalling messages. Tunnel establishment involves exchanging 3 message types (SCCRQ, SCCRP and SCCN) with the peer. Tunnel IDs and capabilities are exchanged during the tunnel establishment with the host.• <HOSTNAME> – Specify the L2TPv3 specific host name.inter-tunnel-bridging Enables inter tunnel bridging of packets. This feature is disabled by default.manual-session Creates/modifies L2TPv3 manual sessionsFor more information, see l2tpv3-manual-session-commands.router-id [<1-4294967295>|<IP>]Configures the router ID sent in the L2TPv3 signaling messages. These signaling (AVP) messages help to identify tunneled peers.• <1-4294967295> – Configures the router ID in decimal format from 1 - 4294967295• <IP> – Configures the router ID in the IP address (A.B.C.D) formattunnel Creates/modifies a L2TPv3 tunnelFor more information, see l2tpv3-tunnel-commands.udp-listen-port <1024-65535>Configures the UDP port used to listen for incoming traffic• <1024-65535> – Specify the UDP port from 1024 - 65535 (default is 1701)l2tpv3 Configures L2TPv3 protocol settings for a profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-144.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 363Examplerfs6000-37FABE(config-profile-default-rfs6000)#l2tpv3 hostname l2tpv3Host1rfs6000-37FABE(config-profile-default-rfs6000)#l2tpv3 inter-tunnel-bridgingrfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 bridging-mode isolated-tunnel ip igmp snooping ip igmp snooping querier ................................................. l2tpv3 hostname l2tpv3Host1 l2tpv3 inter-tunnel-bridgingrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandslogging Enables L2TPv3 tunnel event logging and debugging. When enabled, all events relating to Ethernet frames to and from bridge VLANs and physical ports on a specified IP address, host or router ID are logged. This option is disabled by default.ip-address [<IP>|any]Configures the L2TPv3 peer tunnel IP address for which event logging is enabled. The options are:• <IP> – Specify the peer’s IP address. L2TPv3 events are captured and logged for the specified peer.• any – Peer’s IP address is not specified. Enables event logging for all incoming connections from any IP address.hostname [<HOSTNAME>|any] Configures the L2TPv3 peer tunnel hostname for which event logging is enabled. The options are:• <HOSTNAME> – Specify the peer’s host name. L2TPv3 events are captured and logged for specified host.• any – Peer’s hostname is not specified. Enables debugging for all incoming connections from any host.router-id [<IP>|<WORD>|any]Configures the L2TPv3 tunnel router ID for which event logging is enabled. The options are:• <IP> – Specify the router ID in the IP address format.• <WORD> – Specify the router ID in the form of an integer or range. For example 100-200.• any – Router ID is not specified. Enables debugging for all incoming connections from any L2TPv3 router.no Negates a L2TPv3 tunnel settings on this profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-145.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3667.1.42 led-timeoutProfile Config CommandsConfigures the LED-timeout timer in the device or profile configuration modeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxled-timeout [<15-1440>|shutdown]Parameters• led-timeout [<15-1440>|shutdown]Examplenx9500-6C8809(config-device-B4-C7-99-6C-88-09)#led-timeout 25nx9500-6C8809(config-device-B4-C7-99-6C-88-09)#show contextnx9000 B4-C7-99-6C-88-09 use profile default-nx9000 use rf-domain default hostname nx9500-6C8809 license AAP 66069c24b3bb1259b34ff016c723a9e299dd408f0ff891e7c5f7e279a382648397d6b3e975e356a1 license HTANLT 66069c24b3bb1259eb36826cab3cc83999dd408f0ff891e74b62b2d3594f0b3dde7967f30e49e497 no autogen-uniqueid ip default-gateway 192.168.13.2 led-timeout 25 --More--nx9500-6C8809(config-device-B4-C7-99-6C-88-09)#nx9500-6C8809(config-device-B4-C7-99-6C-88-09)#led-timeout shutdownnx9500-6C8809(config-device-B4-C7-99-6C-88-09)#show contextnx9000 B4-C7-99-6C-88-09 use profile default-nx9000 use rf-domain default hostname nx9500-6C8809 license AAP 66069c24b3bb1259b34ff016c723a9e299dd408f0ff891e7c5f7e279a382648397d6b3e975e356a1 license HTANLT 66069c24b3bb1259eb36826cab3cc83999dd408f0ff891e74b62b2d3594f0b3dde7967f30e49e497 no autogen-uniqueid ip default-gateway 192.168.13.2 led-timeout shutdown crypto ikev2 peer IKEv2Peer1--More--nx9500-6C8809(config-device-B4-C7-99-6C-88-09)#led-time [<15-1440>|shutdown]Sets the LED-timeout timer. The value provided here determines the interval (time to lapse) for which a device’s LEDs are turned off after the last radio state change. For example, if set at 15 minutes, the LEDs are turned off for 15 minutes after the last radio state change.• <15-1440> – Specify a value from 15 - 1400 minutes. The default is 30 minutes.• shutdown – Shuts down the LED-timeout timer. The device LEDs are not turned off.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-148.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3697.1.44 legacy-auto-updateProfile Config CommandsAuto updates an AP7161 legacy access point firmwareSupported in the following platforms:• Access Points — AP7161 Syntaxlegacy-auto-update ap71xx image <FILE>]Parameters• legacy-auto-update ap71xx image <FILE>Examplerfs6000-37FABE(config-profile-default-rfs6000)#legacy-auto-update ap71xx image flash:/ap47d.imgRelated Commandslegacy-auto-update Updates a legacy AP7161 access point firmwareap71xx image <FILE>Auto updates legacy AP7161 firmware• image – Sets the path to the firmware image• <FILE> – Specify the path and filename in the flash:/ap.img format.no Disables automatic legacy firmware upgrade](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-151.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3707.1.45 lldpProfile Config CommandsEnables LLDP on this profile and configures LLDP settingsLLDP or IEEE 802.1AB is a vendor-neutral Data Link Layer protocol used by network devices for advertising of (announcing) identity, capabilities, and interconnections on a IEEE 802 LAN network. The protocol is formally referred to by the IEEE as Station and Media Access Control Connectivity Discovery. Both LLDP snooping and ability to generate and transmit LLDP packets is provided.Information obtained via CDP and LLDP snooping is available in the UI. Information obtained using LLDP is provided during the adoption process, so the layer 2 device detected by the access point can be used as a criteria in the provisioning policy.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlldp [holdtime|med-tlv-select|run|timer]lldp [holdtime <10-1800>|run|timer <5-900>]lldp med-tlv-select [inventory-management|power-management {auto}]Parameters• lldp [holdtime <10-1800>|run|timer <5-900>]• lldp med-tlv-select [inventory-management|power-management {auto}]lldp Enables LLDP on this profile and configures LLDP settingsholdtime <10-1800> Sets the holdtime for transmitted LLDP PDUs. This command specifies the time a receiving device holds information before discarding.• <10-1800> – Specify a holdtime from 10 - 1800 seconds. The default is 180 seconds.run Enables LLDP on this profiletimer <5-900> Sets the transmit interval. This command specifies the transmission frequency of LLDP updates in seconds.• <5-900> – Specify transmit interval from 5 - 900 seconds. The default is 60 seconds.lldp Enables LLDP on this profile and configures LLDP settingsmed-tlv-select [inventory-management|power-management {auto}]Provides additional media endpoint device TLVs to enable inventory and power management discovery. Specifies the LLDP MED TLVs to send or receive.• inventory-management – Enables inventory management discovery. Allows an endpoint to convey detailed inventory information about itself. This information includes details, such as manufacturer, model, and software version, etc. This option is enabled by default.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-152.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3727.1.46 load-balancingProfile Config CommandsConfigures load balancing parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxload-balancing [advanced-params|balance-ap-loads|balance-band-loads|balance-channel-loads|band-control-startegy|band-ratio|group-id|neighbor-selection-strategy]load-balancing advanced-params [2.4GHz-load|5GHz-load|ap-load|equality-margin|hiwater-threshold|max-neighbors|max-preferred-band-load|min-common-clients|min-neighbor-rssi|min-probe-rssi]load-balancing advanced-params [2.4GHz-load|5GHz-load|ap-load] [client-weightage|throughput-weightage] <0-100>load-balancing advanced-params equality-margin [2.4GHz|5GHz|ap|band] <0-100>load-balancing advanced-params hiwater-threshold [ap|channel-2.4GHz|channel-5GHz]<0-100>load-balancing advanced-params max-preferred-band-load [2.4GHz|5GHz] <0-100>load-balancing advanced-params [max-neighbors <0-16>|min-common-clients <0-256>|min-neighbor-rssi <-100-30>|min-probe-rssi <-100-30>]load-balancing [balance-ap-loads|balance-band-loads|balance-channel-loads [2.4GHz|5GHz]]load-balancing band-control-strategy [distribute-by-ratio|prefer-2.4GHz|prefer-5GHz]load-balancing band-ratio [2.4GHz|5GHz] [0|<1-10>]load-balancing group-id <GROUP-ID>load-balancing neighbor-selection-strategy [use-common-clients|use-roam-notification|use-smart-rf]Parameters• load-balancing advanced-params [2.4GHz-load|5GHz-load|ap-load] [client-weightage|throughput-weightage] <0-100>load-balancing advanced-paramsConfigures advanced load balancing parameters2.4GHz-load [client-weightage|throughput-weightage] <0-100>Configures 2.4 GHz load calculation weightages• client-weightage – Specifies weightage assigned to the client-count when calculating the 2.4 GHz loadContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-154.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 373• load-balancing advanced-params equality-margin [2.4GHz|5GHz|ap|band] <0-100>• throughput-weightage – Specifies weightage assigned to throughput, when calculating the 2.4 GHz loadThe following keyword is common to the ‘client-weightage’ and ‘throughput-weightage’ parameters:• <0-100> – Sets the margin as a load percentage from 1 - 100. The default client-weightage is 90%. The default throughput-weightage is 10%.5GHz-load [client-weightage|throughput-weightage] <0-100>Configures 5.0 GHz load calculation weightages• client-weightage – Specifies weightage assigned to the client-count when calculating the 5.0 GHz load• throughput-weightage – Specifies weightage assigned to throughput, when calculating the 5.0 GHz loadThe following keyword is common to the ‘client-weightage’ and ‘throughput-weightage’ parameters:• <0-100> – Sets the margin as a load percentage from1 - 100. The default client-weightage is 90%. The default throughput-weightage is 10%.ap-load [client-weightage|throughput-weightage] <0-100>Configures AP load calculation weightages• client-weightage – Specifies weightage assigned to the client-count, when calculating the AP load• throughput-weightage – Specifies weightage assigned to throughput, when calculating the AP loadThe following keyword is common to the ‘client-weightage’ and ‘throughput-weightage’ parameters:• <0-100> – Sets the margin as a load percentage from 1 - 100. The default client-weightage is 90%. The default throughput-weightage is 10%.load-balancing advanced-paramsConfigures advanced load balancing parametersequality-margin [2.4GHz|5GHz|ap|band] <0-100>Configures the maximum load difference considered equal. The load is compared for different 2.4 GHz channels, 5.0 GHz channels, APs, or bands.• 2.4GHz – Configures the maximum load difference considered equal when comparing loads on different 2.4 GHz channels• 5GHz – Configures the maximum load difference considered equal when comparing loads on different 5.0 GHz channels• ap – Configures the maximum load difference considered equal when comparing loads on different APs• band – Configures the maximum load difference considered equal when comparing loads on different bandsThe following keyword is common to 2.4 GHz channels, 5.0 GHz channels, APs, and bands:• <0-100> – Sets the margin as a load percentage from 1 - 100. The default equality-margin for 2.5 GHz, 5.0 GHz, ap, and band loads is 1%.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-155.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 374• load-balancing advanced-params hiwater-threshold [ap|channel-2.4GHz|channel-5GHz] <0-100>• load-balancing advanced-params max-preferred-band-load [2.4GHGz|5GHzd] <0-100>• load-balancing advanced-params [max-neighbors <0-16>|min-common-clients <0-256>|min-neighbor-rssi <-100-30>|min-probe-rssi <-100-30>]load-balancing advanced-paramsConfigures advanced load balancing parametershiwater-threshold Configures the load beyond which load balancing is invoked[ap|channel-2.4GHz|channel-5GHz] <0-100>Select one of the following options:• ap – Configures the AP load beyond which load balancing begins• channel-2.4GHz – Configures the AP load beyond which load balancing begins (for APs on 2.4 GHz channel)• channel-5GHz – Configures the AP load beyond which load balancing begins for (APs on 5.0 GHz channel)The following keyword is common for the ‘AP’, ‘channel-2.4GHz’, and ‘channel-5GHz’ parameters:• <0-100> – Sets the load threshold as a number from 1 - 100. The default hiwater-threshold for channel-2.5GHz, channel-5GHz, and ap loads is 5.load-balancing advanced-paramsConfigures advanced load balancing parametersmax-preferred-band-loadConfigures the maximum load on the preferred band, beyond which the other band is equally preferred[2.4GHz|5GHz] <0-100>Select one of the following options:• 2.4GHz – Configures the maximum load on 2.4 GHz, when it is the preferred band• 5GHz – Configures the maximum load on 5.0 GHz, when it is the preferred bandThe following keyword is common to the 2.4 GHz and 5.0 GHz bands:• <0-100> – Configures the maximum load as a percentage from 0 - 100. The de-fault value for 2.4GHz and 5.GHz is 75%.load-balancing advanced-paramsConfigures advanced load balancing parametersmax-neighbors <0-16> Configures the maximum number of confirmed neighbors to balance• <0-16> – Specify a value from 0 - 16. Optionally configure a minimum of 0 neighbors and a maximum of 16 neighbors. The default is 16.min-common-clients <0-256>Configures the minimum number of common clients that can be shared with the neighbor for load balancing• <0-256> – Specify a value from 0 - 256. Optionally configure a minimum of 0 clients and a maximum of 256 clients. The default is 0.min-neighbor-rssi <-100-30>Configures the minimum signal strength (RSSI) of a neighbor detected• <-100-30> – Sets the signal strength in dBm. Specify a value from -100 - 30 dBm. The default is -65 dBm.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-156.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 375• load-balancing [balance-ap-loads|balance-band-loads|balance-channel-loads [2.4GHz|5GHz]]• load-balancing band-control-strategy [distribute-by-ratio|prefer-2.4GHz|prefer-5GHz]• load-balancing band-ratio [2.4GHz|5GHz] [0|<1-10>]min-probe-rssi <-100-30>Configures the minimum received probe signal strength required to qualify the sender as a common client• <0-100> – Sets the signal strength in dBm. Specify a value from -100 - 30 dBm. The default is -100 dBm.load-balancing Configures the following load balancing parameters: ap-loads, band-loads, and channel-loads.balance-ap-loads Enables neighbor AP load balancing. This option distributes the access point’s radio load amongst other controller managed access point radios. This option is disabled by default.balance-band-loads Enables balancing of the total band load amongst neighbors. This option balances the access point’s radio load by assigning a ratio to both the 2.4 GHz and 5.0 GHz bands. Balancing radio load by band ratio allows an administrator to assign a greater weight to radio traffic on either the 2.4 GHz or 5.0 GHz band. This option is disabled by default.balance-channel-loads [2.4GHz|5GHz]Enables the following:• 2.4GHz – Channel load balancing on 2.4 GHz band. This option is disabled by default.Balances the access point’s 2.4 GHz radio load across channels supported within the country of deployment. This can prevent congestion on the 2.4 GHz radio if a channel is over utilized.• 5GHz – Channel load balancing on 5.0 GHz band. This option is disabled by default.Balances the access point’s 5.0 GHz radio load across channels supported within the country of deployment. This can prevent congestion on the 5.0 GHz radio if a channel is over utilized.load-balancing band-control-strategyConfigures a band control strategyBy default, this option steers 5.0 GHz-capable clients to the 5.0 GHz band. When an access point hears a request from a client to associate on both the 2.4 GHz and 5.0 GHz bands, it knows the client is capable of operation in 5.0 GHz. Band steering steers the client by responding only to the 5.0 GHz association request and not the 2.4 GHz request. Consequently, the client only associates in the 5.0 GHz band.distribute-by-ratio Distributes clients to either band according to the band-ratioprefer-2.4GHz Nudges all dual-band clients to 2.4 GHz bandprefer-5GHz Nudges all dual-band clients to 5.0 GHz band. This is the default setting.load-balancing band-ratioConfigures the relative loading of 2.4 GHz band and 5.0 GHz band.This allows an administrator to weight client traffic load if wishing to prioritize client traffic load on the 2.4 GHz or the radio band. The higher the value set, the greater the weight assigned to radio traffic load on the 2.4 GHz or 5.0 GHz radio band.2.4GHz [0|<1-10>] Configures the relative loading of 2.4 GHz band• 0 – Selecting ‘0’ steers all dual-band clients preferentially to the other band• <0-10> – Configures a relative load as a number from 0 - 10. The default is 0.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-157.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 376• load-balancing group-id <GROUP-ID>• load-balancing neighbor-selection-strategy [use-common-clients|use-roam-notification|use-smart-rf]Examplerfs6000-37FABE(config-profile-default-rfs6000)#load-balancing advanced-params 2.4ghz-load throughput-weightage 90rfs6000-37FABE(config-profile-default-rfs6000)#load-balancing advanced-params hiwater-threshold ap 90rfs6000-37FABE(config-profile-default-rfs6000)#load-balancing balance-ap-loadsrfs7000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 bridging-mode isolated-tunnel ip igmp snooping ip igmp snooping querier ip default-gateway 172.16.10.4 autoinstall configuration autoinstall firmware load-balancing advanced-params 2.4ghz-load throughput-weightage 90 load-balancing advanced-params hiwater-threshold ap 90 load-balancing balance-ap-loads--More--rfs6000-37FABE(config-profile-default-rfs6000)#Related Commands5ghz [0|<1-10>] Configures the relative loading of 5.0 GHz band• 0 – Selecting ‘0’ steers all dual-band clients preferentially to the other band• <0-10> – Configures a relative load as a number from 0 - 10. The default is 1.load-balancing group-id <GROUP-ID>Configures group ID to facilitate load balancing• <GROUP-ID> – Specify the group ID. This option is enabled only when a group ID is configured.load-balancing neighbor-selection-strategyConfigures a neighbor selection strategy. The options are: use-common-clients, use-roam-notification, and use-smart-rfuse-common-clients Selects neighbors based on probes from clients common to neighbors. This option is enabled by default.use-roam-notification Selects neighbors based on roam notifications from roamed clients. This option is enabled by default.use-smart-rf Selects neighbors detected by Smart RF. This option is enabled by default.no Disables load balancing on this profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-158.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3777.1.47 loggingProfile Config CommandsEnables message logging and configures logging settings. When enabled, the profile logs individual system events to a user-defined log file or a syslog server. Message logging is disabled by default.Enabling message logging is recommended, because system event logs can be analyzed to determine an overall pattern that may be negatively impacting performance.This command can also be executed in the device configuration mode.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlogging [aggregation-time|buffered|console|facility|forward|host|on|syslog]logging [aggregation-time <1-60>|host [<IPv4>|<IPv6>] {port <1-65535>}|on]logging [buffered|console|syslog|forward] [<0-7>|emergencies|alerts|critical|errors|warnings|notifications|informational|debugging]logging facility [local0|local1|local2|local3|local4|local5|local6|local7]Parameters• logging [aggregation-time <1-60>|host [<IPv4>|<IPv6>] {port <1-65535>}|on]• logging [buffered|console|syslog|forward] [<0-7>|emergencies|alerts|critical|errors|warnings|notifications|informational|debugging]logging Enables message logging and configures logging settingsaggregation-time <1-60>Sets the number of seconds for aggregating repeated messages. This is the interval at which system events are logged on behalf of this profile. The shorter the interval, the sooner the event is logged.• <1-60> – Specify a value from 1 - 60 seconds. The default value is 0.host [<IPv4>|<IPv6>] {port <1-65535>}Configures a remote host to receive log messages. Defines numerical (non DNS) IPv4 or IPv6 addresses for external resources where logged system events can be sent on behalf of the profile (or device). A maximum of four entries can be made.• <IPv4> – Specify the IPv4 address of the remote host.• <IPv6> – Specify the IPv6 address of the remote host.• port <1-65535> – Optional. Configures the syslog port• <1-65535> – Specify the syslog port from 1 - 65535. The default port is 514.on Enables the logging of system messageslogging Enables message logging and configures logging settingsbuffered Sets the buffered logging levelconsole Sets the console logging levelsyslog Sets the syslog server’s logging level](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-159.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 378• logging facility [local0|local1|local2|local3|local4|local5|local6|local7]Examplerfs6000-37FABE(config-profile-default-rfs6000)#logging facility local4rfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 bridge vlan 1 ................................................... ip dns-server-forward logging facility local4 ip nat pool pool1 address range 172.16.10.2 172.16.10.8 ip nat inside source list test interface vlan1 pool pool1 overload lldp timer 20 service pm sys-restart router ospf l2tpv3 hostname l2tpv3Host1 l2tpv3 inter-tunnel-bridgingrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsforward Forwards system debug messages to the wireless controller or service platform[<0-7>|alerts|criticail|debugging|emergencies|errors|informational|notifications|warnings]The following keywords are common to the buffered, console, syslog, and forward parameters.All incoming messages have different severity levels based on their importance. The severity level is fixed on a scale of 0 - 7.• <0-7> – Sets the message logging severity level on a scale of 0 - 7• emergencies – Severity level 0: System is unusable• alerts – Severity level 1: Requires immediate action• critical – Severity level 2: Critical conditions• errors – Severity level 3: Error conditions• warnings – Severity level 4: Warning conditions (default)• notifications – Severity level 5: Normal but significant conditions• informational – Severity level 6: Informational messages• debugging – Severity level 7: Debugging messageslogging Enables message logging and configures logging settingsfacility [local0|local1|local2|local3|local4|local5|local6|local7]Enables the syslog to decide where to send the incoming messageThere are 8 logging facilities, from syslog0 to syslog7.• local0 – Syslog facility local0• local1 – Syslog facility local1• local2 – Syslog facility local2• local3 – Syslog facility local3• local4 – Syslog facility local4• local5 – Syslog facility local5• local6 – Syslog facility local6• local7 – Syslog facility local7no Disables logging on this profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-160.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3797.1.48 mac-address-tableProfile Config CommandsConfigures the MAC address table. Use this command to create MAC address table entries by assigning a static address to the MAC address table.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmac-address-table [aging-time|detect-gateways|static]mac-address-table aging-time [0|<10-1000000>]mac-address-table detect-gatewaysmac-address-table static <MAC> vlan <1-4094> interface [<L2-INTERFACE>|ge <1-4>|port-channel <1-2>]Parameters• mac-address-table aging-time [0|<10-1000000>]• mac-address-table detect-gateways• mac-address-table static <MAC> vlan <1-4094> interface [<L2-INTERFACE>|ge <1-4>|port-channel <1-2>]mac-address-table aging-time [0|<10-1000000>]Sets the duration a learned MAC address persists after the last update• 0 – Entering the value ‘0’ disables the aging time• <10-1000000> – Sets the aging time from 10 -100000 seconds. The default is 300 seconds.mac-address-table detect-gatewaysEnables automatic detection of gateways. Detected gateways are remembered in the MAC address table.mac-address-table static <MAC>Creates a static MAC address table entry• <MAC> – Specifies the static address to add to the MAC address table. Specify the MAC address in the AA-BB-CC-DD-EE-FF, AA:BB:CC:DD:EE:FF, or AABB.CCDD.EEFF format.vlan <1-4094> Assigns a static MAC address to a specified VLAN port• <1-4094> – Specify the VLAN index from 1 - 4094.interface [<L2-INTERFACE>|ge <1-4>|port-channel <1-2>]Specifies the interface type. The options are: layer 2 Interface, GigabitEthernet interface, and a port channel interface• <L2-INTERFACE> – Specify the layer 2 interface name.• ge – Specifies a GigabitEthernet interface• <1-4> – Specify the GigabitEthernet interface index from 1 - 4.• port-channel – Specifies a port channel interface• <1-2> – Specify the port channel interface index from 1 - 2.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-161.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3817.1.49 mac-authProfile Config CommandsEnables authentication of a client’s MAC address on wired ports. When configured, MAC authentication will be enabled on devices using this profile.To enable MAC address authentication on a device, enter the device’s configuration mode and execute the mac-auth command.When enabled, the source MAC address of a device, connected to the specified wired port, is authenticated with the RADIUS server. Once authenticated the device is permitted access to the managed network and packets from the authenticated source are processed. If not authenticated the device is either denied access or provided guest access through the guest VLAN (provided guest VLAN access is configured on the port).Enabling MAC authentication requires you to first configure a AAA policy specifying the RADIUS server. Configure the client’s MAC address on the specified RADIUS server. Attach this AAA policy to a profile or a device. Finally, enable MAC authentication on the desired wired port of the device or device-profile.Only one MAC address is supported for every wired port. Consequently, when one source MAC address is authenticated, packets from all other sources are dropped.To enable client MAC authentication on a wired port:1 Configure the user on the RADIUS server. The following examples create a RADIUS server user entry.a <DEVICE>(config)#radius-group <RAD-GROUP-NAME><DEVICE>(config-radius-group-<RAD-GROUP-NAME>)#policy vlan <VLAN-ID>b <DEVICE>(config)#radius-user-pool-policy <RAD-USER-POOL-NAME><DEVICE>(config-radius-user-pool-<RAD-USER-POOL-NAME>)#user <USER-NAME> password <PASSWORD> group <RAD-GROUP-OF-STEP-A>Note: The <USER-NAME> and <PASSWORD> should be the client’s MAC address. This address will be matched against the MAC address of incoming traffic at the specified wired port.c <DEVICE>(config)#radius-server-policy <RAD-SERVER-POL-NAME><DEVICE>(config-radius-server-policy-<RAD-SERVER-POL-NAME>)#use radius-user-pool-policy <RAD-USER-POOL-OF-STEP-B>2 Configure a AAA policy exclusively for wired MAC authentication and specify the authentication (RADIUS) server settings. The following example creates a AAA policy ‘macauth’ and enters its configuration mode:<DEVICE-A>(config)#aaa-policy macauth<DEVICE-A>(config-aaa-policy-macauth)#...a Specify the RADIUS server details.<DEVICE-A>(config)#aaa-policy macauth<DEVICE-A>(config-aaa-policy-macauth)#authentication server <1-6> [host <IP>|onboard]3 Attach the AAA policy to the device or profile. When attached to a profile, the AAA policy is applied to all devices using this profile.<DEVICE>(config-device-aa-bb-cc-dd-ee)#mac-auth use aaa-policy macauth<DEVICE>(config-profile-<DEVICE-PROFILE-NAME>)#mac-auth use aaa-policy macauth](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-163.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3857.1.51 memory-profileProfile Config CommandsConfigures memory profile used on the deviceSupported in the following platforms:• Access Points — AP6511, AP6521 Syntaxmemory-profile [adopted|standalone]Parameters• memory-profile [adopted|standalone]Examplenx9500-6C8809(config-profile-testAP6511)#memory-profile adoptedNote: memory-profile change will take effect after device rebootnx9500-6C8809(config-profile-testAP6511)#Related Commandsmemory-profile Configures memory profile used on the deviceadopted Configures adopted mode (no GUI and higher MiNT routes, firewall flows)standalone Configures standalone mode (GUI and fewer MiNT routes, firewall flows)no Resets device's memory profile configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-167.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3907.1.55 mintProfile Config CommandsConfigures MiNT protocol parameters required for MiNT creation and adoptionMiNT links are required for adoption of a device (APs, wireless controller, and service platform) to a controller. The MiNT link is created on both the adoptee and the adopter. WiNG provides several commands to configure MiNT links and establish adoption for both IPv4 and IPv6 addresses.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmint [dis|inter-tunnel-bridging|level|link|mlcp|rate-limit|spf-latency|tunnel-across-extended-vlan|tunnel-controller-load-balancing]mint dis [priority-adjustment <-255-255>|strict-evis-reachability]mint inter-tunnel-bridgingmint level 1 area-id [<1-16777215>|<NUMBER-ALIAS-NAME>]mint link [force|ip|listen|vlan]mint link force ip [<IPv4>|<IPv6>] [<1-65535> level 2|level 2] {adjacency-hold-time <2-600>|cost <1-10000>|hello-interval <1-120>|ipsec-secure {gw [<IP>|<HOST-NAME>]}}mint link [listen ip [<IPv4>|<IPv6>|<HOST-ALIAS-NAME>]|vlan <1-4094>] {adjacency-hold-time <2-600>|cost <1-10000>|hello-interval <1-120>|ipsec-security {gw [<IP>|<HOST-NAME>]}|level [1|2]}mint link ip [<IPv4>|<IPv6>|<HOST-ALIAS-NAME>] {<1-65535>|adjacency-hold-time <2-600>|cost <1-10000>|hello-interval <1-120>|ipsec-security {gw [<IP>|<HOST-NAME>]}|level [1|2]}mint mlcp [ip|ipv6|vlan]mint rate-limit level2 [link|mlcp]mint rate-limit level2 [link [ip [<IPv4>|<IPv6>] <1-65535>|vlan <1-4094>]|mlcp [ip|ipv6|vlan]] rate <50-1000000> max-burst-size <2-1024> {red-threshold [background|best-effort|video|voice] <0-100>}mint spf-latency <0-60>mint tunnel-across-extended-vlanmint tunnel-controller-load-balancing level1Parameters• mint dis [priority-adjustment <-255-255>|strict-evis-reachability]mint Configures MiNT protocol parameters required for MiNT link creation and adoption](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-172.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 391• mint inter-tunnel-bridging• mint level 1 area-id [<1-16777215>|<NUMBER-ALIAS-NAME>]• mint link force ip [<IPv4>|<IPv6>] [<1-65535> level 2|level 2] {adjacency-hold-time <2-600>|cost <1-10000>|hello-interval <1-120>|ipsec-security {gw [<IP>|<HOST-NAME>]}}dis priority-adjustment <-255-255>Sets the relative priority for the router to become DIS (designated router)• priority-adjustment – Sets priority adjustment added to base priorityThe Designated IS (DIS) priority adjustment is the value added to the base level DIS priority to influence the DIS election. A value of +1 or greater increases DISiness.• <-255-255> – Specify a value from -255 - 255. The default is 0.Higher numbers result in higher prioritiesstrict-evis-reachability Enables reaching Ethernet Virtualization Interconnect (EVIS) election winners through MiNT. This option is enabled by default.mint Configures MiNT protocol parameters required for MiNT link creation, adoption and communicationinter-tunnel-bridging Enables forwarding of broadcast multicast (BCMC) packets between devices communicating via Level 2 MiNT links. When enabled, MiNT tunnels across Level 2, adopted access points are bridged. One of the advantages of inter-tunnel bridging is the enabling of roaming between these access points. This option is disabled by default.If enabling this option, use ACLs to filter unwanted BCMC traffic.mint Configures MiNT protocol parameters required for MiNT link creation and adoptionlevel 1 Configures local MiNT routing settings• 1 – Configures local MiNT routing levelarea-id [<1-16777215>|<NUMBER-ALIAS-NAME>]Specifies the level 1 routing area identifier. Use one of the following options to specify the area ID:• <1-16777215> – Specify a value from 1 - 16777215.• <NUMBER-ALIAS-NAME> – Specify a number alias (should be existing and configured). Aliases are configuration items that can be defined once and used in different configuration contexts. For more information on creating a number alias, see alias.mint Configures MiNT protocol parameters required for MiNT link creation and adoptionlink force Creates a MiNT routing link as a forced link• force – Forces a MiNT routing link to be created even if not necessaryip [<IPv4>|<IPv6>] Creates a MiNT tunnel over UDP/IPv4 or IPv6Use this keyword to specify the IP address (IPv4 or IPv6) used by peers for inter-operation when supporting the MINT protocol.• <IPv4> – Specify the MiNT tunnel peer’s IPv4 address.• <IPv6> – Specify the MiNT tunnel peer’s IPv6 address.After specifying the MiNT peer’s address, configure the following MiNT link parameters: UDP port, adjacency-hold-time, cost, hello-interval, IPSec security gateway, and routing level.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-173.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 392• mint link [listen ip [<IPv4>|<IPv6>|<HOST-ALIAS-NAME>]|vlan <1-4094>] {adjacency-hold-time <2-600>|cost <1-10000>|hello-interval <1-120>|level [1|2]|ipsec-security {gw [<IP>|<HOST-NAME>]}}<1-65535> level 2 Optional. Specifies a custom UDP port for MiNT links. Specify the port from 1 - 65535.• level – Specifies the routing level• 2 – Configures level 2 inter-site MiNT routingadjacency-hold-time <2-600>Optional. Specifies the adjacency lifetime after hello packets cease• <2-600> – Specify a value from 2 - 600 seconds. The default is 46 seconds.cost <1-100000> Optional. Specifies the link cost in arbitrary units• <1-100000> – Specify a value from 1 - 100000. The default is 100.hello-interval <1-120> Optional. Specifies the interval, in seconds, between successive hello packets• <1-120> – Specify a value from 1 - 120 seconds. The default is 15 seconds.ipsec-security {gw [<IP>|<HOST-NAME>]}Optional. Enables IPSec secure peer authentication on the MiNT link connection (link). This option is disabled by default.• gw [<IP>|<HOSTNAME>] – Optional. Configures the IPSec secure gateway. When enabling IPSec, you can optionally specify the IPSec secure gateway’s numerical IP address or administrator defined hostname.mint Configures MiNT protocol parameters required for MiNT link creation and adoptionlink listen ip [<IPv4>|<IPv6>|<HOST-ALIAS-NAME>]Creates a MiNT routing link• listen – Creates a MiNT listening link• ip – Creates a MiNT listening link over UDP/IP or IPv6• <IPv4> – Specify the IPv4 address of the listening UDP/IP link.• <IPv6> – Specify the IPv6 address of the listening UDP/IP link.• <HOST-ALIAS-NAME> – Specify the host alias identifying the MiNT link ad-dress. The host alias should existing and configured.UDP/IP links can be created by configuring a matching pair of links, one on each end point. However, that is error prone and does not scale. So UDP/IP links can also listen (in the TCP sense), and dynamically create connected UDP/IP links when contacted. The typical configuration is to have a listening UDP/IP link on the IP address S.S.S.S, and for all the APs to have a regular UDP/IP link to S.S.S.S.link vlan <1-4094> Enables MiNT routing on VLAN• vlan – Defines a VLAN ID used by peers for inter-operation when supporting the MINT protocol.• <1-4094> – Select VLAN ID from 1 - 4094.adjacency-hold-time <2-600>This parameter is common to the ‘listen’ and ‘vlan’ parameters:• adjacency-hold-time <2-600> – Optional. Specifies the adjacency lifetime after hello packets cease• <2-600> – Specify a value from 2 - 600 seconds. The default is 46 seconds.For MiNT VLAN routing, the default is 13 seconds.cost <1-100000> This parameter is common to the ‘listen’ and ‘vlan’ parameters:• cost <1-100000> – Optional. Specifies the link cost in arbitrary units• <1-100000> – Specify a value from 1 - 100000. The default is 100. For MiNT VLAN routing, the default is 10.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-174.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 393• mint link ip [<IPv4>|<IPv6>|<HOST-ALIAS-NAME>] {<1-65535>|adjacency-hold-time <2-600>|cost <1-10000>|hello-interval <1-120>|level [1|2]|ipsec-security {gw [<IP>|<HOST-NAME>]}}hello-interval <1-120> This parameter is common to the ‘listen’ and ‘vlan’ parameters:• hello-interval <1-120> – Optional. Specifies the interval, in seconds, between successive hello packets• <1-120> – Specify a value from 1 - 120. The default is 15 seconds.For MiNT VLAN routing the default is 4 seconds.level [1|2] This parameter is common to the ‘listen’ and ‘vlan’ parameters:Optional. Specifies the routing levels for this routing link. The options are:• 1 – Configures local routing• 2 – Configures inter-site routingipsec-security {gw [<IP>|<HOST-NAME>]}This parameter is common to the ‘listen’ and ‘vlan’ parameters:• ipsec-security – Optional. Enables IPSec secure peer authentication on the MiNT connection (link). This option is disabled by default.• gw [<IP>|<HOSTNAME>] – Optional. Configures the IPSec secure gateway. Whenenabling IPSec, you can optionally specify the IPSec secure gateway’s numerical IPaddress or administrator defined hostname.mint Configures MiNT protocol parameters required for MiNT link creation and adoptionlink ip [<IPv4>|<IPv6>|<HOST-ALIAS-NAME>]Creates a MiNT routing link• ip – Creates a MiNT tunnel over UDP/IP or IPv6Use this keyword to specify the IP address (IPv4 or IPv6) used by peers for inter-operation when supporting the MINT protocol.• <IPv4> – Specify the IPv4 address used by peers.• <IPv6> – Specify the IPv6 address used by peers.• <HOST-ALIAS-NAME> – Specify the host alias identifying the MiNT tunnel peer’saddress. The host alias should existing and configured.<1-65535> Select the peer UDP port from 1 - 65535.adjacency-hold-time <2-600>Optional. Specifies the adjacency lifetime after hello packets cease• <2-600> – Specify a value from 2 - 600 seconds. The default is 46 seconds.cost <1-100000> Optional. Specifies the link cost in arbitrary units• <1-100000> – Specify a value from 1 - 100000. The default is 100.hello-interval <1-120> Optional. Specifies the interval, in seconds, between successive hello packets<1-120> – Specify a value from 1 - 120. The default is 15 seconds.level [1|2] Optional. Specifies the routing levels for this routing link. The options are:• 1 – Configures local routing• 2 – Configures inter-site routingipsec-security {gw [<IP>|<HOST-NAME>]}Optional. Enables IPSec secure peer authentication on the MiNT connection (link). This option is disabled by default.• gw [<IP>|<HOSTNAME>] – Optional. Configures the IPSec secure gateway. When enabling IPSec, you can optionally specify the IPSec secure gateway’s numerical IP address or administrator defined hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-175.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 394• mint mlcp [ip|ipv6|vlan]• mint rate-limit level2 [link [ip [<IPv4>|<IPv6>] <1-65535>|vlan <1-4094>]|mlcp [ip|ipv6|vlan]] rate <50-1000000> max-burst-size <2-1024> {red-threshold [background|best-effort|video|voice] <0-100>}mint Configures MiNT protocol parameters required for MiNT link creation and adoptionmlcp [ip|ipv6|vlan] Configures the MLCP using the IP address or VLAN. MLCP is used to create a UDP/IP link from the device to a neighbor. The neighboring device does not need to be a wireless controller or service platform, it can be another access point with a path to the wireless controller or service platform.• vlan – Enables MLCP over layer 2 (VLAN) links• ip – Enables MLCP over layer 3 (UDP/IP) links. When enabled, allows adoption over IPv4 address.• ipv6 – Enables MLCP over layer 3 (UDP/IPv6) links. When enabled, allows adoption over IPv6 address.mint Configures MiNT protocol parameters required for MiNT link creation and adoptionmint rate-limit level2 Applies rate limits on extended VLAN trafficExcessive traffic can cause performance issues on an extended VLAN. Excessive traffic can be caused by numerous sources including network loops, faulty devices, or malicious software.Rate limiting reduces the maximum rate sent or received per wireless client. It prevents any single user from overwhelming the wireless network, and also provides differential service for service providers. Uplink and downlink rate limits are usually configured on a RADIUS server using vendor specific attributes. Rate limits are extracted from the RADIUS server’s response. When such attributes are not present, the settings defined on the controller, service platform or access point are applied. You can set separate QoS rate limit configurations for data types transmitted from the network (upstream) and data transmitted from a wireless clients back to associated radios (downstream).link [ip <IPv4/IPv6> <1-65535>|vlan <1-4094>]Configures rate limit parameters applicable for all statically configured MiNT links on level2. Select the link-type as ‘IP’ or ‘VLAN’.• ip <IPv4/IPv6> – Configures rate limits for MiNT link traffic over UDP/IP• <IPv4/IPv6> – Specify the MiNT peer’s IPv4 or IPV6 address in the A.B.C.D andX:X::X:X formats respectively.• <1-65535> – Configures the virtual port used for rate limiting traffic. Specify theUDP port from 1 - 65535.• vlan <1-4094 – Configures rate limits for MiNT link traffic on specified VLAN• <1-4094> – Specify the VLAN ID from 1 - 4094.mlcp [ip|ipv6|vlan] Configures rate limit parameters applicable for MLCPMLCP creates a UDP/IP link from the device to a neighbor. The neighboring device does not need to be a controller or service platform, it can be an access point with a path to the controller or service platform.• ip – Configures rate-limits for MLCP over UDP/IPv4 links• ipv6 – Configures rate-limits for MLCP over UDP/IPv6 links• vlan – Configures rate-limits for MLCP over VLAN links](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-176.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 395• mint spf-latency <0-60>• mint tunnel-across-extended-vlanrate <50-1000000> Configures the rate limit from 50 - 1000000 KbpsThis limit constitutes a threshold for the maximum number of packets transmitted or received (from all access categories). Traffic exceeding the defined rate is dropped and a log message is generated. The default setting is 5000 Kbps.max-burst-size <2-1024> Configures the maximum burst size from 0 - 1024 KbytesSmaller the burst size, lesser is the probability of the upstream packet transmission resulting in congestion for the WLAN’s client destinations. By trending the typical number of ARP, broadcast, multicast and unknown unicast packets over a period of time, the average rate for each access category can be obtained. Once a baseline is obtained, add a 10% margin (minimally) to allow for traffic bursts. The default burst size is 320 Kbytes.red-threshold [background|best-effort|video|voice] <0-100>Optional. Configures the random early detection (RED) threshold (as a percentage) for the following traffic types:• background – Configures the RED threshold for low priority background traffic. Background packets are dropped and a log message generated if the rate exceeds the set value. Background traffic consumes the least bandwidth of any access category, so this value can be set to a lower value once a general upstream rate is known by the network administrator (using a time trend analysis). The default setting is 50%.• best-effort – Configures the RED threshold for low priority best-effort traffic. Best-effort packets are dropped and a log message generated if the rate exceeds the set value. Best effort traffic consumes little bandwidth, so this value can be set to a lower value once a general upstream rate is known by the network administrator (using a time trend analysis).The default setting is 50%.• video – Configures the RED threshold for high priority video traffic. Video packets are dropped and a log message generated if the rate exceeds the set value. Video traffic consumes significant bandwidth, so this value can be set to a higher value once a general upstream rate is known by the network administrator (using a time trend analysis).The default setting is 25%.• voice – Configures the RED threshold for high priority voice traffic. Voice packets are dropped and a log message generated if the rate exceeds the set value. Voice applications consume significant bandwidth, so this value can be set to a higher value once a general upstream rate is known by the network administrator (using a time trend analysis).The default setting is 0%.• <0-100> – After selecting the traffic type, specify the RED threshold from 0 - 100%.mint Configures MiNT protocol parameters required for MiNT link creation and adoptionspf-latency <0-60> Specifies the latency of SPF routing recalculationThis option allows you to set the latency of routing recalculation option (within the Shortest Path First (SPF) field). This option is disabled by default.• <0-60> – Specify the latency from 0 - 60 seconds.mint Configures MiNT protocol parameters required for MiNT link creation and adoptiontunnel-across-extended-vlanEnables tunneling of MiNT protocol packets across an extended VLAN. This setting is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-177.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 3977.1.56 misconfiguration-recovery-timeProfile Config CommandsVerifies connectivity after a configuration is receivedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmisconfiguration-recovery-time [0|<60-300>]Parameters• misconfiguration-recovery-time [0|<60-300>]Examplerfs6000-37FABE(config-profile-default-rfs6000)#misconfiguration-recovery-time 65rfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 mint link ip 1.2.3.4 mint level 1 area-id 88 bridge vlan 1 bridging-mode isolated-tunnel ................................................. qos trust 802.1p interface pppoe1 use firewall-policy default misconfiguration-recovery-time 65 service pm sys-restart router ospfrfs6000-37FABE(config-profile-default-rfs6000)#Related Commands<60-300> Sets the recovery time from 60 - 300 seconds (default is 180 seconds)0 Disables recovery from misconfigurationno Reverts to default (180 seconds)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-179.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4007.1.59 noProfile Config CommandsNegates a command or resets values to their defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [adopter-auto-provisioning-policy-lookup|adoption|alias||application-policy|area|arp|auto-learn|autogen-uniqueid|autoinstall|bluetooth-detection|bridge|cdp|cluster|configuration-persistence|controller|critical-resource|crypto|database-backup|device-upgrade|diag|dot1x|dpi|dscp-mapping|eguest-server|email-notification|environmental-sensor|events|export|file-sync|floor|gre|http-analyze|interface|ip|ipv6|lacp|l2tpv3|l3e-lite-table|led|led-timeout|legacy-auto-downgrade|legacy-auto-update|lldp|load-balancing|logging|mac-address-table|mac-auth|management-server|memory-profile|meshpoint-device|meshpoint-monitor-interval|min-misconfiguration-recovery-time|mint|misconfiguration-recovery-time|noc|ntp|otls|offline-duration|power-config|preferred-controller-group|preferred-tunnel-controller|radius|raid|rf-domain-manager|router|spanning-tree|traffic-class-mapping|traffic-shape|trustpoint|tunnel-controller|use|virtual-controller|vrrp|vrrp-state-check|zone|wep-shared-key-auth|service]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.Examplerfs6000-81742D(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 autoinstall configuration autoinstall firmware crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac crypto ikev1 remote-vpn crypto ikev2 remote-vpn crypto auto-ipsec-secure crypto remote-vpn-client interface me1 interface up1 interface ge1 interface ge2 interface ge3 interface ge4 interface ge5 interface ge6 interface ge7no <PARAMETERS> Removes or reverts this profile’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-182.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4027.1.60 nocProfile Config CommandsConfigures Network Operations Center (NOC) statistics update interval. This is the interval at which statistical updates are sent by the RF Domain manager to its adopting controller (the NOC controller).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnoc update-interval [<5-3600>|auto]Parameters• noc update-interval [<5-3600>|auto]Examplerfs6000-37FABE(config-profile-default-rfs6000)#noc update-interval 25rfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 mint link ip 1.2.3.4 mint level 1 area-id 88 bridge vlan 1 bridging-mode isolated-tunnel ip igmp snooping ip igmp snooping querier ................................................... interface pppoe1 use firewall-policy default misconfiguration-recovery-time 65 noc update-interval 25 service pm sys-restart router ospfrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsnoc update-interval [<5-3600>|auto]Configures NOC statistics update interval• <5-3600> – Specify the update interval from 5 - 3600 seconds.• auto – The NOC statistics update interval is automatically adjusted by the wireless controller or service platform based on load. This option is enabled by default.no Resets NOC related parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-184.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4037.1.61 nsightProfile Config CommandsConfigures NSight database related parameters. Use this command to configure the data-update periodicity, number of applications posted to the NSight server for a wireless client, and the duration for which data is stored in the NSight database’s buckets. These parameters impact the amount of data stored in the NSight DB and interval at which data is aggregated and expired within the NSight DB. For more information on data aggregation and expiration, see (Data Aggregation and Expiration).Configure these parameters in the NSight server’s profile configuration mode. These parameters are also configurable on the NSight server’s device configuration mode.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxnsight database [statistics|summary]nsight database statistics [avc-update-interval|max-apps-per-client|max-http-usage-metadata|max-http-visits-metadata|max-ssl-usage-metadata|max-ssl-visits-metadata|update-interval|wireless-clients-update-interval]nsight database statistics [avc-update-interval|update-interval|wireless-clients-update-interval] [120|30|300|60|600]nsight database statistics max-apps-per-client <1-1000>nsight database statistics [max-http-usage-metadata|max-http-visits-metadata|max-ssl-usage-metadata|max-ssl-visits-metadata] <1-1000>nsight database summary duration <1-24> <1-168> <1-2160> <24-26280>Parameters• nsight database statistics [avc-update-interval|update-interval|wireless-clients-update-interval] [120|30|300|60|600]nsight database statisticsConfigures NSight database statistics related parametersavc-update-interval Configures the interval, in seconds, at which Application Visibility and Control (AVC) statistics is updated to the NSight database. This interval represents the rate at which AVC-related data is inserted in the NSight database’s first bucket. This first bucket data is referred to as the RAW records. A bucket is a database collection that holds statistical data on a per RF Domain basis. For more information, see (Data Aggregation and Expiration).When configured, RF Domain managers posting AVC-related data to the NSight server receive a reply from the NSight server intimating the next update time. The NSight server calculates the ‘next update time’ based on the avc-update-interval configured here.update-interval Configures the interval, in seconds, at which data is updated to the NSIght server. This interval represents the rate at which data (excluding AVC and wireless-clients related statistics) is inserted in the NSight database’s first bucket. This first bucket data is referred to as the RAW records. A bucket is a database collection that holds statistical data on a per RF Domain basis. For more information, see (Data Aggregation and Expiration).Contd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-185.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 404• nsight database statistics max-apps-per-client <1-1000>• nsight database statistics [max-http-usage-metadata|max-http-visits-metadata|max-ssl-usage-metadata|max-ssl-visits-metadata] <1-1000>contd.. When configured, RF Domain managers posting data to the NSight server receive a reply from the NSight server intimating the next update time. The NSight server calculates the ‘next update time’ based on the update-interval configured here.Note: Use the ‘avc-update-interval’ and ‘wireless-clients-update-interval’ keywords to configure update interval for AVC-related and wireless-clients related information respectively.wireless-clients-update-intervalConfigures the interval, in seconds, at which wireless-client statistics is updated to the NSIght server. This interval represents the rate at which wireless-clients related statistics is inserted in the NSight database’s first bucket. This first bucket data is referred to as the RAW records. A bucket is a database collection that holds statistical data on a per RF Domain basis. For more information, see (Data Aggregation and Expiration).When configured, RF Domain managers posting wireless-client related data to the NSight server receive a reply from the NSight server intimating the next update time. The NSight server calculates the ‘next update time’ based on the wireless-clients-update-interval configured here.[120|30|300|60|600] The following keywords are common to all of the above parameters:• 120 – Sets the data-update periodicity as 120 seconds (2 minutes)• 30 – Sets the data-update periodicity as 30 seconds• 300 – Sets the data-update periodicity as 300 seconds (5 minutes). This is the default setting for the ‘avc-update-interval’ and ‘wireless-clients-update-interval’ parameters.• 60 – Sets the data-update periodicity as 60 seconds (1 minute). This is the default setting for the ‘update-interval’ parameter.• 600 – Sets the data-update periodicity as 600 seconds (10 minutes)nsight database statisticsConfigures NSight database statistics related parametersmax-apps-per-client Configures the maximum number of applications per wireless-client to be posted to the NSight server within the configured data-update interval. This information is included in the AVC statistics posted by RF Domain managers to the NSight server.<1-1000> Specify the number of applications posted from 1 - 1000. The default is 10 applications per wireless client.nsight database statisticsConfigures NSight database statistics related parameters[max-http-usage-metadata|max-http-visits-metadata|max-ssl-usage-metadata|max-ssl-visits-metadata]Configures the number of HTTP and/or SSL metadata posted within an update interval• max-http-usage-metadata – Configures the NSight database maximum http-metadata by usage (rx+tx) to be posted in an update-interval• max-http-visits-metadata – Configures the NSight database’s maximum http-metadata by the number of visits to be posted within an update-interval• max-ssl-usage-metadata – Configures the NSight database maximum ssl-metadata by usage (rx+tx) to be posted in an update-intervalContd...](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-186.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4087.1.62 ntpProfile Config CommandsConfigures the Network Time Protocol (NTP) server settingsNTP manages time and/or network clock synchronization within the network. NTP is a client/server implementation. Controllers, service platforms, and access points (NTP clients) periodically synchronize their clock with a master clock (an NTP server). For example, a controller resets its clock to 07:04:59 upon reading a time of 07:04:59 from its designated NTP server.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxntp server <PEER-IP/HOSTNAME> {autokey|key|maxpoll|minpoll|prefer|version}ntp server <PEER-IP/HOSTNAME> {autokey}ntp server <PEER-IP/HOSTNAME> {maxpoll [1024|2048|4096|8192]}ntp server <PEER-IP/HOSTNAME> {minpoll [1024|128|256|512|64]}ntp server <PEER-IP> {key <1-65534> md5 [0 <WORD>|2<WORD>|<WORD>]}ntp server <PEER-IP/HOSTNAME> {prefer version <1-4>|version <1-4> prefer}Parameters• ntp server <PEER-IP/HOSTNAME> {autokey} {prefer version <1-4>|version <1-4>}• ntp server <PEER-IP/HOSTNAME> {maxpoll [1024|2048|4096|8192]}ntp server <PEER-IP/HOSTNAME>Configures NTP server resources that are used to obtain system time• <PEER-IP/HOSTNAME> – Identifies the NTP server resource by its IP address or hostname. Specify the NTP server’s IP address or hostname. autokey Optional. Enables automatic configuration of authentication key for the specified NTP server. This option is disabled by default. If not enabled, use the ‘key’ option to configure an authentication key for the NTP server.ntp server <PEER-IP/HOSTNAME>Configures NTP server resources that are used to obtain system time• <PEER-IP/HOSTNAME> – Identifies the NTP server resource by its IP address or hostname. Specify the NTP server’s IP address or hostname. maxpoll [1024|2048|4096|8192]Optional. Configures the maximum polling interval. Once set, the specified NTP server is polled no later than the defined interval. Select one of the following options:• 1024 – Configures the maximum polling interval as 1024 seconds. This is the default setting.• 2048 – Configures the maximum polling interval as 2048 seconds• 4096 – Configures the maximum polling interval as 4096 seconds• 8192 – Configures the maximum polling interval as 8192 seconds](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-190.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 409• ntp server <PEER-IP/HOSTNAME> {minpoll [1024|128|256|512|64]}• ntp server <PEER-IP/HOSTNAME> {key <1-65534> md5 [0 <WORD>|2<WORD>|<WORD>]}• ntp server <PEER-IP/HOSTNAME> {prefer version <1-4>|version <1-4> prefer}ntp server <PEER-IP/HOSTNAME>Configures NTP server resources that are used to obtain system time• <PEER-IP/HOSTNAME> – Identifies the NTP server resource by its IP address or hostname. Specify the NTP server’s IP address or hostname. minpoll [1024|128|256|512|64]Optional. Configures the minimum polling interval. Once set, the specified NTP server is polled no sooner than the defined interval. Select one of the following options:• 1024 – Configures the minimum polling interval as 1024 seconds• 128 – Configures the minimum polling interval as 128 seconds• 256 – Configures the minimum polling interval as 256 seconds• 512 – Configures the minimum polling interval as 512 seconds• 64 – Configures the minimum polling interval as 64 seconds. This is the default setting.ntp server <PEER-IP/HOSTNAME>Configures NTP server resources that are used to obtain system time• <PEER-IP/HOSTNAME>> – Identifies the NTP server resource by its IP address or hostname. Specify the NTP server’s IP address or hostname. key <1-65534> md5 [0 <WORD>|2 <WORD>|<WORD>]Optional. Defines the authentication key for the specified NTP server. This option is used to configure the key when ‘autokey’ configuration is not enabled.• <1-65534> – Specify the peer key number. Should not exceed 64 characters in length.• md5 – Sets MD5 authentication• 0 <WORD> – Configures a clear text password• 2 <WORD> – Configures an encrypted password• <WORD> – Sets an authentication keyntp server <PEER-IP/HOSTNAME>Configures NTP server resources that are used to obtain system time• <PEER-IP/HOSTNAME> – Identifies the NTP server resource by its IP address or hostname. Specify the NTP server’s IP address or hostname. prefer version <1-4> Optional. Designates the specified NTP server as a preferred NTP resource. This setting is disabled by default.• version – Optional. Configures the NTP version• <1-4> – Select the NTP version from 1 - 4. If not specified, the default value of ‘0’ is applied, which implies that the NTP server’s version is ignored.version <1-4> prefer Optional. Configures the version number used by the specified NTP server resource• <1-4> – Select the NTP version from 1 - 4. The default setting is 0. A value of ‘0’ implies that the NTP server’s version is ignored.• prefer – Optional. Designates the specified NTP server as a preferred NTP resource.This setting is disabled by default. The NTP version number specified using the ‘ver-sion <1-4>’ keyword is applied to this preferred NTP resource.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-191.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4117.1.63 otlsProfile Config CommandsEnables support for OmniTrail Location Server (OTLS) beacon identificationOmniTrail (offered by OmniTrail technologies) is a Wi-Fi based locationing protocol used in positioning and tracking location solutions. Access points supporting OTLS beacon identification lock their radios to scan channels for beacons with OTLS tags. Beacons received by the access point are matched for the OTLS signature, and in case of a match, the beacons are forwarded to the OTLS server as UDP payload.Use this command to configure OTLS server details on the AP and enable OTLS data forwarding. Alternately, OTLS parameters can be configured in the AP’s profile on the controller or service platform, and pushed to adopted access points. When configured, APs establish connection with the OTLS server and forward OTLS locationing feeds to the server.Supported in the following platforms:• Access Points — AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP8432, AP8533Syntaxotls [apid|control-port|data-port|forward|server-ip]otls apid <WORD>otls control-port <0-65535>otls data-port [2.4GHz|5GHz] <0-65535>otls forward [2.4GHz|5GHz] [disable|enable]otls server-ip <OTLS-SERVER-IP>Parameters• otls apid <WORD>• otls control-port <0-65535>otls apid <WORD> Configures a unique identification for the OTLS-enabled access point. The access point identifier (APID) enables the OTLS server to identify the AP forwarding the OTLS tag.• <WORD> – Specify an ID for the AP.To ensure that OTLS-enabled APs have unique OTLS ID, it is recommended that the APID is configured in the device context of each AP.otls control-port <0-65535>Configures the port used by the AP to establish and maintain connection with the OTLS server• <0-65535> – Specify the control port from 0 - 655635.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-193.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 412• otls data-port [2.4GHz|5GHz] <0-65535>• otls forward [2.4GHz|5GHz] [disable|enable]• otls server-ip <OTLS-SERVER-IP>Exampleap8533-84A224(config-device-84-24-8D-84-A2-24)#otls apid 112233ap8533-84A224(config-device-84-24-8D-84-A2-24)#otls forward 2.4GHz enableap8533-84A224(config-device-84-24-8D-84-A2-24)#otls forward 5GHz enableap8533-84A224(config-device-84-24-8D-84-A2-24)#otls control-port 8890ap8533-84A224(config-device-84-24-8D-84-A2-24)#otls data-port 2.4GHz 8888ap8533-84A224(config-device-84-24-8D-84-A2-24)#otls data-port 5GHz 8889ap8533-84A224(config-device-84-24-8D-84-A2-24)#otls server-ip 192.168.13.10ap8533-84A224(config-device-84-24-8D-84-A2-24)#show context include-factory | include otls otls forward 5GHz enable otls forward 2.4GHz enable otls server-ip 192.168.13.10 otls control-port 8890 otls data-port 2.4GHz 8888 otls data-port 5GHz 8889 otls apid 112233ap8533-84A224(config-device-84-24-8D-84-A2-24)otls data-port [2.4GHz|5GHz] <0-65535>Configures the port used by the AP to forward OTLS beacons to the OTLS server. However, OTLS data forwarding has to be enabled on the APs. Use the otls > forward > [2.4GHz|5GHz] > [disable|enable] command to enable data forwarding.• 2.4GHz – Configures the port used to forward OTLS beacons received on the 2.4 GHz band• 5.0GHz – Configures the port used to forward OTLS beacons received on the 5.0 GHz bandThe following keyword is common to the above parameters:• <0-65535> – Specify a data-forwarding port from 0 - 65535. otls forward [2.4GHz|5GHz] [disable|enable]Enables or disables OTLS tag forwarding• 2.4GHz – Enables or disables forwarding of OTLS beacons received on the 2.4 GHz band• 5GHz – Enables or disables forwarding of OTLS beacons received on the 5.0 GHz bandThe following keywords are common to the above parameters:• disable – Disables OTLS tag forwarding. By default OTLS beacon forwarding is dis-abled for both 2.4 GHz and 5.0 GHz bands.• enable – Enables OTLS tag forwardingotls server-ip <OTLS-SERVER-IP>Configures the OTLS server’s IP address• <OTLS-SERVER-IP> – Specify the OTLS server’s IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-194.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4157.1.65 power-configProfile Config CommandsConfigures the power option mode. Use this command in the profile configuration mode to configure the transmit output power of access point radios. This command is also available in the device-config mode.Single radio model access points always operate using a full power configuration. The power management configurations described in this section do not apply to single radio models. When an access point is powered on for the first time, the system determines the power budget available to the access point. If 802.3af is selected, the access point assumes 12.95 watts is available. If the mode is changed, the access point requires a reset to implement the change. If 802.3at is selected, the access point assumes 23 - 26 watts is available.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpower-config [af-option|at-option|mode]power-config [af-option|at-option] [range|throughput]power-config mode [auto|3af]Parameters• power-config [af-option|at-option] [range|throughput]NOTE: Single radio model access points (AP6511 and AP6521) always operate using a full power configuration. The power management configurations described in this section do not apply to single radio models.The access point has to be restarted for power management changes to take effect.power-config Configures the power option modeaf-option [range|throughput]Configures the 802.3.af power mode option. The options are:• range – Configures the af power range mode. This mode provides higher power but fewer transmission (tx) chains.Select range when range is preferred over performance for broadcast/multicast (group) traffic. The data rates used for range are the lowest defined basic rates.• throughput – Configures the af power throughput mode. This mode provides lower power but has more tx chains. This is the default setting.Select throughput to transmit packets at the radio’s highest defined basic rate (based on the radio’s current basic rate settings). This option is optimal in environments where transmission range is secondary to broadcast/multicast transmission performance.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-197.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 416• power-config mode [auto|3af]Examplenx9500-6C8809(config-profile-testAP7161)#power-config mode 3afnx9500-6C8809(config-profile-testAP7161)#power-config af-option rangenx9500-6C8809(config-profile-testAP7161)#show contextprofile ap71xx testAP7161 no autoinstall configuration no autoinstall firmware power-config mode 3af power-config af-option range crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac --More--nx9500-6C8809(config-profile-testAP7161)#Related Commandsat-option [range|throughput]Configures the 802.3 at power mode option. The options are:• range – Configures the at power range mode. This mode provides higher power but fewer tx chains.Select range when range is preferred over performance for broadcast/multicast (group) traffic. The data rates used for range are the lowest defined basic rates.• throughput – Configures the at power throughput mode. This mode provides lower power but has more tx chains. This is the default setting.Select throughput to transmit packets at the radio’s highest defined basic rate (based on the radio’s current basic rate settings). This option is optimal in environments where transmission range is secondary to broadcast/multicast transmission performance.power-config Configures the power option modemode [auto|3af] Configures the AP power mode• 3af – Forces an AP to power up in the 802.3af power mode• auto – Sets the detection auto mode (default setting)The automatic power-config mode enables an access point to automatically determine the best power configuration based on the available power budget.no Reverts the power mode setting on this profile to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-198.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4197.1.68 radiusProfile Config CommandsConfigures device level RADIUS authentication parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxradius [nas-identifier|nas-port-id] <WORD>Parameters• radius [nas-identifier|nas-port-id] <WORD>Examplerfs6000-37FABE(config-profile-default-rfs6000)#radius nas-port-id 1rfs6000-37FABE(config-profile-default-rfs6000)#radius nas-identifier testrfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 mint link ip 1.2.3.4 mint level 1 area-id 88 bridge vlan 1 bridging-mode isolated-tunnel ip igmp snooping ip igmp snooping querier radius nas-identifier test radius nas-port-id 1 neighbor-info-interval 6 neighbor-inactivity-timeout 500--More--rfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsradius Configures RADIUS authentication parametersnas-identifier <WORD>Specifies the RADIUS Network Access Server (NAS) identifier attribute used by this device• <WORD> – Specifies the NAS identifiernas-port-id <WORD> Specifies the RADIUS NAS port ID attribute used by this device• <WORD> – Specifies the NAS port IDno Disables or reverts settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-201.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4207.1.69 rf-domain-managerProfile Config CommandsConfigures the RF Domain manager election criteriaSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrf-domain-manager [capable|priority <1-255>]Parameters• rf-domain-manager [capable|priority <1-255>]Examplerfs6000-37FABE(config-profile-default-rfs6000)#rf-domain-manager priority 9rfs6000-37FABE(config-profile-default-rfs6000)#show contextprofile rfs6000 default-rfs6000 mint link ip 1.2.3.4 mint level 1 area-id 88 .............................................. rf-domain-manager priority 9 preferred-controller-group testGroup misconfiguration-recovery-time 65 noc update-interval 25 service pm sys-restart preferred-tunnel-controller testtunnel router ospfrfs6000-37FABE(config-profile-default-rfs6000)#Related Commandsrf-domain-manager Configures the RF Domain manager election criteriacapable Enables devices using this profile capable of being elected as the RF Domain manager. The RF Domain manager stores and provisions configuration and firmware images for other members of the RF Domain. It also updates state changes, if any, to RF Domain members. This option is enabled by default.priority <1-255> Assigns a priority value for devices using this profile in the RF Domain manager election process. The higher the number set, higher is the device’s priority in the RF Domain manager election process.• <1-255> – Select a priority value from 1 - 255.no Disables or reverts settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-202.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4217.1.70 routerProfile Config CommandsEnables dynamic routing (BGP and/or OSPF) and enters the routing protocol configuration modeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrouter [bgp|ospf]Parameters• router [bgp|ospf]NOTE: BGP is supported only on RFS4000, RFS6000, NX75XX, and NX9500 model controllers and service platforms.The NX9500 and NX9510 service platforms do not support OSPF routing.The access points only support OSPF routing.router Enables dynamic routing and enters the routing protocol configuration modebgp Enables BGP dynamic routing and configures relevant settingsBGP is an inter-ISP routing protocol, which establishes routing between ISPs. ISPs use BGP to exchange routing and reachability information between Autonomous Systems (AS) on the Internet. BGP uses TCP as its transport protocol, eliminating the need to implement explicit update fragmentation, retransmission, acknowledgement, and sequencing.Routing information exchanged through BGP supports destination based forwarding only. It assumes a router forwards packets based on the destination address carried in the IP header of the packet.An AS is a set of routers under the same administration that use Interior Gateway Protocol (IGP) and common metrics to define how to route packets within the AS.For more information on dynamic BGP routing configurations, see BORDER GATEWAY PROTOCOL.ospf Enables OSPF dynamic routing and configures relevant settings. Changes configuration mode to router modeOSPF is a link-state IGP. OSPF routes IP packets within a single routing domain (autonomous system), like an enterprise LAN. OSPF gathers link state information from neighbor routers and constructs a network topology. The topology determines the routing table presented to the Internet Layer which makes routing decisions based solely on the destination IP address found in IP packets.For more information on dynamic OSPF routing configurations, see ROUTER-MODE COMMANDS.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-203.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4237.1.71 spanning-treeProfile Config CommandsEnables spanning tree commands. Use these commands to configure the errdisable, multiple spanning tree and portfast settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxspanning-tree [errdisable|mst|portfast]spanning-tree errdisable recovery [cause bpduguard|interval <10-1000000>]spanning-tree mst [<0-15>|cisco-interoperability|enable|forward-time|hello-time|instance|max-age|max-hops|region|revision]spanning-tree mst [<0-15> priority <0-61440>|cisco-interoperability [enable|disable]|enable|forward-time <4-30>|hello-time <1-10>|instance <1-15>|max-age <6-40>|max-hops <7-127>|region <LINE>|revision <0-255>]spanning-tree portfast [bpdufilter|bpduguard] defaultParameters• spanning-tree errdisable recovery [cause bpduguard|interval <10-1000000>]• spanning-tree mst [<0-15> priority <0-61440>|cisco-interoperability [enable|disable]|enable|forward-time <4-30>|hello-time <1-10>|instance <1-15>|max-age <6-40>|max-hops <7-127>|region <LINE>|revision <0-255>]spanning-tree Configures spanning-tree related parameterserrdisable Disables or shuts down ports where traffic is looping, or ports with traffic in one directionrecovery Enables the timeout mechanism for a port to be recovered. This option is disabled by default.cause bpduguard Specifies the reason for errdisable• bpduguard – Recovers from errdisable due to bpduguardinterval <10-1000000>Specifies the interval after which a port is enabled• <10-1000000> – Specify a value from 10 - 1000000 seconds. The default is 300 seconds.spanning-tree Configures spanning-tree related parametersmst Configures Multiple Spanning Tree (MST) commandsThe MSTP provides an extension to STP to optimize the usefulness of VLANs. MSTP allows for a separate spanning tree for each VLAN group, and blocks all but one of the possible alternate paths within each spanning tree topology.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-205.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 424• spanning-tree portfast [bpdufilter|bpduguard] default<0-15> priority <0-61440>Specifies the number of instances required to configure MST. Select a value from 0 -15.• priority – Sets the bridge priority to the specified value. This value is used to determine the root bridge. Use the no parameter with this command to restore the default bridge priority value.• <0-61440> – Sets the bridge priority in increments (Lower priority indicates greaterlikelihood of becoming root)cisco interoperability [enable|disable]Enables CISCO interoperabilityEnables interoperability with CISCO’s version of MSTP, which is incompatible with standard MSTP. This setting is disabled by default.enable Enables MST protocolforward-time <4-30> Specifies the forwarding delay time in seconds• <4-30> – Specify a value from 4 - 30 seconds. The default is 15 seconds.hello-time <1-10> Specifies the hello BDPU interval in seconds• <1-10> – Specify a value from 1 - 10 seconds. The default is 2 seconds.instance <1-15> Defines the instance ID to which the VLAN is associated• <1-15> – Specify an instance ID from 1 - 10.max-age <6-40> Defines the maximum time to listen for the root bridge• <6-40> – Specify a value from 4 - 60 seconds. The default is 20 seconds.max-hops <7-127> Defines the maximum hops when BPDU is valid• <7-127> – Specify a value from 7 - 127. The default is 20.region <LINE> Specifies the MST region• <LINE> – Specify the region name.revision <0-255> Sets the MST bridge revision number. This enables the retrieval of configuration information.• <0-255> – Specify a value from 0 - 255. This default is 0.spanning-tree Configures spanning-tree related parametersportfast [bpdufilter| bpduguard] defaultEnables PortFast on a bridge• bpdufilter default – Sets the BPDU filter for the port. The BPDU filter is disabled by default. The spanning tree protocol sends BPDUs from all ports. Enabling the BPDU filter ensures that PortFast enabled ports do not transmit or receive BPDUs.• bpduguard default – Guards PortFast ports against BPDU receive. The BPDU guard is disabled by default.Enabling the BPDU guard means this port will shutdown on receiving a BPDU.• default – Enables the BPDU filter and/or BPDU guard on PortFast enabled ports bydefault](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-206.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4287.1.73 traffic-shapeProfile Config CommandsEnables traffic shaping and configures traffic shaping parameters. This command is applicable to both the profile and device configuration modes.Traffic shaping is a means of regulating data transfers and ensuring a specific level of performance within a network. Traffic shaping does the following:• Controls flow of packets based on their priority value. Prioritized traffic streams are given priority over less important traffic.• Controls traffic on an interface to match its flow to the speed of a remote target’s interface and ensure traffic conforms to applied policies• Shapes traffic to meet downstream requirements and eliminate network congestion when data rates are in conflict.Use this option to apply traffic shaping to specific applications or application categories. Note, in scenarios where a traffic class is matched against an application, application-category, and ACL rule, the application rule will be applied first, followed by the application-category, and finally the ACL. Further, using traffic shaping, an application takes precedence over an application category.To enable traffic shaping, configure QoS values on the basis of which priority of service is provided to some packets over others. For example, VoIP packets get higher priority than data packets to provide a better quality of service for high priority voice traffic. For configuring IPv6 traffic class mappings, see traffic-class-mapping. And for configuring DSCP traffic class mappings, see dscp-mapping.Supported in the following platforms:• Access Points — AP6522, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530Syntaxtraffic-shape [activation-criteria|app-category|application|class|enable|priority-map|total-bandwidth]traffic-shape activation-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]traffic-shape app-category <APP-CATEGORY-NAME> class <1-4>traffic-shape application <APPLICATION-NAME> class <1-4>traffic-shape class <1-4> [max-buffers|max-latency|rate]traffic-shape class <1-4> max-buffers <1-400> {red-level <1-400>|red-percent <1-100>}traffic-shape class <1-4> max-latency <1-1000000> [msec|usec]traffic-shape class <1-4> rate [<1-250000> [Kbps|Mbps]|total-bandwidth-percent <1-100>]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-210.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 429traffic-shape priority-map <0-7>traffic-shape total-bandwidth <1-1000000> [Kbps|Mbps]traffic-shape enableParameters• traffic-shape activation-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]• traffic-shape app-category <APP-CATEGORY-NAME> class <1-4>NOTE: The available range for the ‘rate’ field will vary depending on the unit selected. It is 250 - 250000 for Kbps and 1 - 250 for Mbps.NOTE: The available range for the ‘total-bandwidth’ field will vary depending on the unit selected. It is 250 - 1000000 for Kbps and 1 - 1000 for Mbps.traffic-shape activation-criteriaConfigures traffic-shape activation criteria that determines when the device invokes traffic shapingalways Always invokes traffic shaping. This is the default setting.cluster-master Invokes traffic shaping when the device is the cluster master. The solitary cluster master (elected using a priority assignment scheme) is a cluster member that provides management configuration and Smart RF data to other members within the cluster. Cluster requests go through the elected master before dissemination to other cluster members.rf-domain-manager Invokes traffic shaping when the device is the RF Domain manager. The RF Domain manager is the elected member capable of storing and provisioning configuration and firmware images for other members of the RF Domain.vrrp-master <1-255> Invokes traffic shaping when the device is the VRRP master. As the VRRP master, the device responds to ARP requests, forwards packets with a destination link MAC layer address equal to the virtual router MAC layer address, rejects packets addressed to the IP associated with the virtual router and accepts packets addressed to the IP associated with the virtual router.• <1-255> – Specify the VRRP group ID from 1 - 255.traffic-shape app-category <APP-CATEGORY-NAME> class <1-4>Configures an application category to traffic-class mapping. Use this option to apply an application category to traffic-shaper class mapping. Naming and categorizing applications that do not fall into existing groups is an additional means of filtering and potentially limiting network airtime to consumptive non required applications negatively impacting network performance.Note: app-category <APP-CATEGORY-NAME> – Specify the application category name. To list the available application categories, press [TAB] after entering app-category. Select the required category from the displayed list.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-211.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 430• traffic-shape application <APPLICATION-NAME> class <1-4>• traffic-shape class <1-4> max-buffers <1-400> {red-level <1-400>|red-percent <1-100>}• class <1-4> – Map the specified application category to a traffic-shaper class from 1- 4.Before configuring an application category to class mapping, ensure that the specified classes have been configured. Use the ‘class > [max-buffers|max-latency|rate]’ option available with this command to configure a traffic shaper class. For more information, see following parameter tables.traffic-shape app-category <APPLICATION-NAME> class <1-4>Configures an application to traffic-class mapping. Use this option to apply an application to traffic-shaper class mapping.• app-category <APPLICATION-NAME> – Specify the application name.• class <1-4> – Map the specified application to a traffic-shaper class from 1 - 4.Note: Before configuring an application to class mapping, ensure that the specified classes have been configured. Use the ‘class > [max-buffers|max-latency|rate] option available with this command to configure a traffic shaper class. For more information, see following tables.traffic-shape class <1-4> max-buffers <1-400>Configures the queue length limit for different traffic-shaper class• class <1-4> – Specify the traffic-shaper class from 1 - 4.• max-buffers <1-400> – Configures the maximum queue lengths for packets of dif-ferent priority queues, after which the queue starts to drop packets. • <1-400> – Configure the queue length limit from 1 - 400 for packets of priorityqueues 0, 1, 2, 3, 4, 5, 6, and 7.Note: For access points the upper queue length limit is 400.red-level <1-400> Optional. Performs Random Early Drop (RED) when a specified queue length in packets is reached• <1-400> – Configure the queue length limit from 1 - 400 for packets of priority queues 0, 1, 2, 3, 4, 5, 6, and 7.The RED algorithm is a queuing technique for congestion avoidance. RED monitors the average queue size and drops or marks packets. If the buffer is near empty, all incoming packets are accepted. When the queue grows, the probability for dropping an incoming packet also grows. When the buffer is full, the probability has reached 1 and all incoming packets are dropped.Note: For more information on default values, see the Usage Guidelines section in this topic.red-percent <1-100> Optional. Performs RED when a specified value, which is a percentage of the max-buffers configured, is reached• <1-100> – Configure the percentage of the maxi-buffers from 1 - 100 for packets of priority queues 0, 1, 2, 3, 4, 5, 6, and 7.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-212.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 431• traffic-shape class <1-4> max-latency <1-1000000> [msec|usec]• traffic-shape class <1-4> rate [<1-250000> [Kbps|Mbps]|total-bandwidth-percent <1-100>]• traffic-shape priority-map <0-7>traffic-shape class <1-4> max-latency <1-1000000> [msec|usec]Configures the max-latency for different traffic-shaper class. Max latency specifies the time limit after which packets start dropping (maximum packet delay in the queue). The maximum number of entries is 8.• class <1-4> – Specify the traffic-shaper class from 1 - 4.• max-latency <1-1000000> – Configures the max-latency for packets of differentpriority queues, after which the queue starts to drop packets. • <1-1000000> – Configure the max-latency from 1 - 100000 for packets of priorityqueues 0, 1, 2, 3, 4, 5, 6, and 7.• [msec|usec] – Configures the unit for measuring latency as milliseconds(msec) or microseconds (usec). The default setting is msec.traffic-shape class <1-4> rate Configures traffic rate, in either Kbps, Mbps or percentage, for the different traffic shaper class. Specify rates for different traffic shaper class to control the maximum traffic rate sent or received on an interface. Consider this form of rate limiting on interfaces at the edge of a network to limit traffic into or out of the network. Traffic within the set limit is sent and traffic exceeding the set limit is dropped or sent with a different priority.• class <1-4> – Specify the traffic-shaper class from 1 - 4.<1-250000> [Kbps|Mbps]Configures the traffic rate, in Kbps, Mbps, for the class specified in the previous step• <1-250000> – Specify the rate from 1 - 250000.• [Kbps|Mbps] – Configures the unit for measuring bandwidth as Kbps or Mbps. Thedefault setting is Kbps.Note: The range varies depending on the unit selected. It is 1 - 250 Mbps, or 250 - 250000 Kbps.total-bandwidth-percent <1-100>Configures the traffic rate, as a percentage of the total available bandwidth, for the class specified in the previous first step• <1-100> – Specify the traffic rate from 1 - 100% of the total bandwidth.traffic-shape priority-map <0-7>Configures the traffic-shaper queues, within a class, having different priority values (0, 1, 2, 3, 4, 5, 6, and 7). There are 8 queues (0 - 7), and traffic is queued in each based on the incoming packet’s 802.1p 3-bit priority markings.• priority-map <0-7> – Specify the priority from 0 - 7 for priority levels 0, 1, 2, 3, 4, 5, 6, and 7.The IEEE 802.1p standards sets a 3-bit value in the MAC header to indicate prioritization. This 3-bit value provides priority levels ranging from 0 to 7 (i.e., a total of 8 levels), with level 7 representing the highest priority. This permits packets to cluster and form different traffic classes. In case of network congestion, packets with higher priority receive preferential treatment while low priority packets are kept on hold.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-213.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 432• traffic-shape total-bandwidth <1-1000000> [Kbps|Mbps]• traffic-shape enableUsage GuidelinesFollowing are the default max-buffers set for the traffic shaper classes:traffic-shape class 1 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10traffic-shape class 2 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10traffic-shape class 3 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10traffic-shape class 4 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10Following is the default priority-map settings:traffic-shape priority-map 2 0 1 3 4 5 6 7Examplenx9500-6C8809(config-profile-ProfileNX5500)#show context include-factory | include traffic-shape traffic-shape priority-map 2 0 1 3 4 5 6 7 traffic-shape class 1 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10 traffic-shape class 2 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10 traffic-shape class 3 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10 traffic-shape class 4 max-buffers 35 35 35 30 25 20 15 10 red-level 27 27 27 23 25 20 15 10 traffic-shape activation-criteria always traffic-shape total-bandwidth 10 Mbps no traffic-shape enablenx9500-6C8809(config-profile-ProfileNX5500)#nx9500-6C8809(config-profile-ProfileNX5500)#traffic-shape enablenx9500-6C8809(config-profile-ProfileNX5500)#traffic-shape class 1 rate 250 Mbpsnx9500-6C8809(config-profile-ProfileNX5500)#traffic-shape application Bing class 1nx9500-6C8809(config-profile-ProfileNX5500)#traffic-shape total-bandwidth 200 Mbpstraffic-shape total-bandwidth <1-1000000> [Kbps|Mbps]Configures the total-bandwidth for traffic shaping• <1-1000000> – Specify the value from 1 - 1000000 Kbps/Mbps. The default value is 10 Mbps.• [Kbps|Mbps] – Configures the unit for measuring bandwidth as Kbps or Mbps. Thedefault setting is Mbps.Note: The range varies depending on the unit selected. It is 1 - 1000 Mbps, or 250 - 1000000 Kbps.traffic-shape enable Enables traffic shaping using the defined bandwidth, rate and class mappings configured using this commandNote: Traffic shaping is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-214.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4347.1.74 trustpoint (profile-config-mode)Profile Config CommandsConfigures the trustpoint assigned for validating a CMP auth OperatorA certificate links identity information with a public key enclosed in the certificate.A CA is a network authority that issues and manages security credentials and public keys for message encryption. The CA signs all digital certificates it issues with its own private key. The corresponding public key is contained within the certificate and is called a CA certificate. A browser must contain the CA certificate in its Trusted Root Library so it can trust certificates signed by the CA's private key.Depending on the public key infrastructure, the digital certificate includes the owner's public key, the certificate expiration date, the owner's name and other public key owner information.Each certificate is digitally signed by a trustpoint. The trustpoint signing the certificate can be a certificate authority, corporation or individual. A trustpoint represents a CA/identity pair containing the identity of the CA, CA-specific configuration parameters, and an association with an enrolled identity certificate.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtrustpoint [cmp-auth-operator|https|radius-ca|radius-server] <TRUSTPOINT-NAME>Parameters• trustpoint [cmp-auth-operator|https|radius-ca|radius-server] <TRUSTPOINT-NAME>NOTE: Certificates/trustpoints used in this command should be verifiable as existing on the device.NOTE: For information on configuring trustpoints on a device, see trustpoint (device-config-mode).trustpoint Assigns an existing trustpoint to validate CMP auth operator, client certificates, and RADIUS server certificatehttps Assigns an existing trustpoint to validate HTTPS requests](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-216.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4377.1.76 useProfile Config CommandsAssociates existing policies with this profile. This command is also applicable to the device configuration mode.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntax Profiles Modeuse [auto-provisioning-policy|bonjour-gw-forwarding-policy|bonjour-gw-query-forwarding-policy|captive-portal|client-identity-group|crypto-cmp-policy|database-client-policy|dhcp-server-policy|dhcpv6-server-policy|event-system-policy|firewall-policy|global-association-list|guest-management|ip-access-list|ipv6-access-list|management-policy|radius-server-policy|role-policy|routing-policy|web-filter-policy] <POLICY-NAME>use ip/ipv6-access-list <IP/IPv6-ACL-NAME> traffic-shape class <1-4>Syntax Device Modeuse [auto-provisioning-policy|bonjour-gw-forwarding-policy|bonjour-gw-query-forwarding-policy|captive-portal|client-identity-group|crypto-cmp-policy|database-client-policy|database-policy|dhcp-server-policy|dhcpv6-server-policy|enterprise-ui|event-system-policy|firewall-policy|global-association-list|guest-management|ip-access-list|ipv6-access-list|license|management-policy|nsight-policy|profile|radius-server-policy|rf-domain|role-policy|routing-policy|rtl-server-policy|sensor-policy|web-filter-policy||wips-policy] <POLICY-NAME>Parameters Profiles Mode• use [auto-provisioning-policy|bonjour-gw-forwarding-policy|bonjour-gw-query-forwarding-policy|captive-portal|client-identity-group|crypto-cmp-policy|database-client-policy|dhcp-server-policy|dhcpv6-server-policy|event-system-policy|firewall-policy|global-association-list|guest-management|ip-access-list|ipv6-access-list|management-policy|radius-server-policy|role-policy|routing-policy|web-filter-policy] <POLICY-NAME>NOTE: The following tables contain the ‘use’ command parameters for the Profile and Device configuration modes.use Associates the specified policies with this profileThe specified policies should be existing and configured.auto-provisioning-policy <POLICY-NAME>Associates an auto provisioning policy• <POLICY-NAME> – Specify the auto provisioning policy name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-219.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 439Parameters Device Mode• use [auto-provisioning-policy|bonjour-gw-forwarding-policy|bonjour-gw-query-forwarding-policy|captive-portal|client-identity-group|crypto-cmp-policy|database-client-policy|database-policy|dhcp-server-policy|dhcpv6-server-policy|enterprise-ui|event-system-policy|firewall-policy|global-association-list|guest-management|ip-access-list|ipv6-access-list|license|management-policy|nsight-policy|profile|radius-server-policy|rf-domain|role-policy|routing-policy|rtl-server-policy|sensor-policy|wips-policy|smart-rf-policy|web-filter-policy] <POLICY-NAME>ip/ipv6-access-list <IP/IPv6-ACL-NAME> traffic-shape class <1-4>Associates an IP and/or IPv6 ACL with this profile and applies it as a firewall for the selected traffic-shape class• <IP/IPv6-ACL-NAME> – Specify the IP/IPv6 ACL name (should be existing and configured)• traffic-shape class <1-4> – Selects the traffic-shape class to apply the above spec-ified IP/IPv6 ACL• <1-4> – Select the traffic-shape class from 1 - 4.management-policy <MNGT-POLICY>Associates a management policy• <MNGT-POLICY> – Specify the management policy name.radius-server-policy <RADIUS-POLICY>Associates a device onboard RADIUS policy• <RADIUS-POLICY> – Specify the RADIUS policy name.role-policy <ROLE-POLICY>Associates a role policy• <ROLE-POLICY> – Specify the role policy name.routing-policy <ROUTING-POLICY>Associates a routing policy• <ROUTING-POLICY> – Specify the routing policy name.•web-filter-policy <POLICY-NAME>Associates an existing Web Filter policy with a profile or device• <POLICY-NAME> – Specify the policy name.use Associates the following policies with this device:auto-provisioning-policy <POLICY-NAME>Associates an auto provisioning policy• <POLICY-NAME> – Specify the auto provisioning policy name.bonjour-gw-forwarding-policy <POLICY-NAME>Uses an existing Bonjour GW Forwarding policy with a profile or device• <POLICY-NAME> – Specify the Bonjour GW Forwarding policy name (should be existing and configured).For more information on Bonjour GW Forwarding policy, see bonjour-gw-forwarding-policy.bonjour-gw-query-forwarding-policy <POLICY-NAME>Uses an existing Bonjour GW Query Forwarding policy with a profile or device• <POLICY-NAME> – Specify the Bonjour GW Query Forwarding policy name (should be existing and configured).captive-portal server <CAPTIVE-PORTAL>Configures access to a specified captive portal• <CAPTIVE-PORTAL> – Specify the captive portal name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-221.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4437.1.77 vrrpProfile Config CommandsConfigures VRRP group settingsA default gateway is a critical resource for connectivity. However, it is prone to a single point of failure. Thus, redundancy for the default gateway is required. If WAN backhaul is available, and a router failure occurs, then the controller should act as a router and forward traffic on to its WAN link.Define an external VRRP configuration when router redundancy is required in a network requiring high availability.Central to VRRP configuration is the election of a VRRP master. A VRRP master (once elected) performs the following functions:• Responds to ARP requests• Forwards packets with a destination link layer MAC address equal to the virtual router’s MAC address• Rejects packets addressed to the IP address associated with the virtual router, if it is not the IP address owner• Accepts packets addressed to the IP address associated with the virtual router, if it is the IP address owner or accept mode is true.The nodes that lose the election process enter a backup state. In the backup state they monitor the master for any failures, and in case of a failure one of the backups, in turn, becomes the master and assumes the management of the designated virtual IPs. A backup does not respond to an ARP request, and discards packets destined for a virtual IP resource.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxvrrp [<1-255>|version]vrrp <1-255> [delta-priority|description|interface|ip|monitor|preempt|priority|sync-group|timers]vrrp <1-255> [delta-priority <1-253>|description <LINE>|ip <IP> {<IP>}|preempt {delay <1-65535>}|priority <1-254>|sync-group]vrrp <1-255> interface vlan <1-4094>vrrp <1-255> monitor [<IF-NAME>|critical-resource|pppoe1|vlan|wwan1]vrrp <1-255> monitor [<IF-NAME>|pppoe1|vlan <1-4094>|wwan1] {(<IF-NAME>|critical-resource|pppoel|vlan|wwan1)}vrrp <1-255> monitor critical-resource <CRM-NAME1> <CRM-NAME2> <CRM-NAME3> <CRM-NAME4> (action [decrement-priority|increment-priority] {<IF-NAME>|pppoe1|vlan|wwan1})vrrp <1-255> timers advertise [<1-255>|centiseconds <25-4095>|msec <250-999>]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-225.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 444vrrp version [2|3]Parameters• vrrp <1-255> [delta-priority <1-253>|description <LINE>|vrrp ip <IP> {<IP>}|preempt {delay <1-65535>}|priority <1-254>|sync-group]• vrrp <1-255> interface vlan <1-4094>• vrrp <1-255> monitor critical-resource <CRM-NAME1> <CRM-NAME2> <CRM-NAME3> <CRM-NAME4> (action [decrement-priority|increment-priority] {<IF-NAME>|pppoe1|vlan|wwan1})vrrp <1-255> Configures the virtual router ID from 1- 255. Identifies the virtual router the packet is reporting status for.delta-priority <1-253> Configures the priority to decrement (local link monitoring and critical resource monitoring) or increment (critical resource monitoring). When the monitored interface is down, the configured priority decrements by a value defined by the delta-priority option. When monitoring critical resources, the value increments by the delta-priority option.• <1-253> – Specify the delta priority level from 1- 253.description <LINE> Configures a text description for the virtual router to further distinguish it from other routers with similar configuration• <LINE> – Provide a description (a string from 1- 64 characters in length)ip <IP-ADDRESSES> Identifies the IP address(es) backed by the virtual router. These are IP addresses of Ethernet switches, routers, and security appliances defined as virtual router resources.• <IP-ADDRESSES> – Specify the IP address(es) in the A.B.C.D format.This configuration triggers VRRP operation.preempt {delay <1-65535>}Controls whether a high priority backup router preempts a lower priority master. This field determines if a node with higher priority can takeover all virtual IPs from a node with lower priority. This feature is disabled by default.• delay – Optional. Configures the pre-emption delay timer from 1 - 65535 seconds (default is 0 seconds). This option can be used to delay sending out the master advertisement or, in case of monitored link coming up, adjusting the VRRP priority by priority delta.priority <1-254> Configures the priority level of the router within a VRRP group. This value determines which node is elected as the Master. Higher values imply higher priority, value 254 has the highest precedence (default is 100).sync-group Adds this VRRP group to a synchronized group. To trigger VRRP failover, it is essential all individual groups within a synchronized group have failover. VRRP failover is triggered if an advertisement is not received from the virtual masters that are part of this VRRP sync group. This feature is disabled by default.vrrp <1-255> Configures the virtual router ID from 1- 255. Identifies the virtual router the packet is reporting status for.interface vlan <1-4094>Enables VRRP on the specified switch VLAN interface (SVI)• vlan <1-4094> – Specify the VLAN interface ID from 1 - 4094.vrrp <1-255> Configures the virtual router ID from 1- 255. Identifies the virtual router the packet is reporting status for.monitor Enables link monitoring or Critical Resource Monitoring (CRM)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-226.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 445• vrrp <1-255> timers advertise [<1-255>|centiseconds <25-4095>|msec <250-999>]• vrrp version [2|3]critical-resource <CRM-NAME1>Specifies the name of the critical resource to monitor. VRRP can be configured to monitor maximum of four critical resources. Use the <CRM-NAME2>, <CRM-NAME3>, and <CRM-NAME4> to provide names of the remaining three critical resources.By default VRRP is configured to monitor all critical resources on the device.action [decrement-priority|increment-priority]Sets the action on critical resource down event. It is a recursive parameter that sets the action for each of the four critical resources being monitored.• decrement-priority – Decrements the priority of virtual router on critical resource down event• increment-priority – Increments the priority of virtual router on critical resource down event<IF-NAME> Optional. Enables interface monitoring• <IF-NAME> – Specify the interface name to monitorpppoe1 Optional. Enables Point-to-Point Protocol (PPP) over Ethernet interface monitoringvlan <1-4094> Optional. Enables VLAN (switched virtual interface) interface monitoring• <1-4094> – Specify the VLAN interface ID from 1- 4094.wwan1 Optional. Enables Wireless WAN interface monitoringvrrp <1-255> Configures the virtual router ID from 1- 255. Identifies the virtual router the packet is reporting status for.timers Configures the timer that runs every intervaladvertise [<1-255>|centiseconds <25-4095>|msec <250-999>]Configures the VRRP advertisements time interval. This is the interval at which a master sends out advertisements on each of its configured VLANs.• <1-255> – Configures the timer interval from 1- 255 seconds. (applicable for VRRP version 2 only)• centiseconds <25-4095> – Configures the timer interval in centiseconds (1/100th of a second). Specify a value between 25 - 4095 centiseconds (applicable for VRRP version 3 only).• msec <250-999> – Configures the timer interval in milliseconds (1/1000th of a second). Specify a value between 250 - 999 msec (applicable for VRRP version 2 only).Default is 1 second.vrrp version [2|3] Configures one of the following VRRP versions:• 2 – VRRP version 2 (RFC 3768). This is the default setting.• 3 – VRRP version 3 (RFC 5798 only IPV4)The VRRP version determines the router redundancy. Version 3 supports sub-second (centisecond) VRRP failover and support services over virtual IP.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-227.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4487.1.79 virtual-controllerProfile Config CommandsEnables an access point as a virtual-controller (VC) or a dynamic virtual controller (DVC)When configured without the ‘auto’ option, this command manually enables an AP as a VC. The ‘auto’ option allows dynamic enabling of APs as VCs. When DVC is enabled on an AP’s device or profile context, the AP is dynamically enabled as the VC on being elected as the RF-Domain manager.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxvirtual-controller {auto|management-interface}virtual-controller autovirtual-controller {management-interface [ip address <IP/M>|vlan <1-4094>]}Parameters• virtual-controller autoNOTE: The DVC feature is supported only on the AP7522, AP7532, AP7562, AP8432, and AP8533 model access points.virtual-controller auto Enables an AP as a virtual-controller• auto – Enables AP as a DVC. When enabled, the AP on being elected as the RF Domain manager takes on the role of the virtual controller. In an RF-Domain, DVC can be enabled on multiple access points. However, only the current RF-Domain manager AP has a running instance of the DVC. This option is applicable only if enabling DVC.Note: MLCP discovery does not function on APs enabled as VC or DVCs. Do an explicit “mint link vlan X” on the AP’s device/profile context, or “control-vlan X” in the AP’s RF-Domain context, to establish MiNT links between the VC and its adopted APs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-230.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 449• virtual-controller {management-interface [ip address <IP/M>|vlan <1-4094>]}Exampleap8533-9A1529(config-device-74-67-F7-9A-15-29)#virtual-controller autoap8533-9A1529(config-device-74-67-F7-9A-15-29)#virtual-controller management-interface ip address 110.110.110.120/24ap8533-9A1529(config-device-74-67-F7-9A-15-29)#virtual-controller management-interface vlan 100ap8533-9A1529(config-device-74-67-F7-9A-15-29)#show context | include virtual-controllervirtual-controller autovirtual-controller management-interface ip address 110.110.110.120/24virtual-controller management-interface vlan 100ap8533-9A1529(config-device-74-67-F7-9A-15-29)#The following example shows the management interface VLAN IP address being configured as the secondary IP address.ap8533-9A1529(config-device-74-67-F7-9A-15-29)#show ip interface brief-------------------------------------------------------------------------------INTERFACE IP-ADDRESS/MASK TYPE STATUS PROTOCOL-------------------------------------------------------------------------------vlan1 10.1.1.11/24 primary UP upvlan100 110.110.110.110/24 primary UP upvlan100 110.110.110.120/24 secondary UP up-------------------------------------------------------------------------------virtual-controller {management-interface [ip address <IP/M>|vlan <1-4094>]}Enables an AP as a virtual-controller. If enabling DVC, use this option to configure management interface details.• management-interface – Configures the management interface for the DVC. Configuring the management interface ensures failover in case the RF Domain manager is unreachable.• ip address <IP/M> – Specify the management interface IP address. Due to the ran-dom nature of DVC, specifying an explicit management interface IP address makesit easier to manage VCs. In case of fail over, this IP address is installed as the second-ary IP address on the new VC.• vlan <1-4094> – Optional. Specifies the VLAN from 1 - 4094 on which the man-agement interface IP address is configured.Note: For DVC, configuring management-interface ip address is mandatory. However, VLAN configuration is optional. If you configure the ip address without specifying the VLAN, the system configures the specified ip address as secondary ip on VLAN 1.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-231.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4517.1.81 serviceProfile Config CommandsService commands are used to view and manage configurations. The service commands and their corresponding parameters vary from mode to mode.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxservice [captive-portal-server|cluster|critical-resource|fast-switching|enable|global-association-list|lldp|memory|meshpoint|pm|power-config|radius|remote-config|rss-timeout|watchdog|wireless|show]service captive-portal-server connections-per-ip <3-64>service cluster master-election immediateservice critical-resource port-mode-source-ip <IP>service enable [l2tpv3|pppoe|radiusd]service global-association-list blacklist-interval <1-65535>service lldp loop-detectionservice memory kernel decreaseservice meshpoint loop-prevention-port [<L2-INTERFACE-NAME>|ge <1-5>|port-channel <1-2>|up1]service pm sys-restartservice power-config [3af-out|force-3at]service radius dynamic-authorization additional-port <1-65535>service remote-config apply-delay <0-600>service rss-timeout <0-86400>service watchdogservice wireless [anqp-frag-always|anqp-frag-size|ap650|client|cred-cache-sync|inter-ap-key|noise-immunity|reconfig-on-tx-stall|test|wispe-controller-port]service wireless anqp-frag-alwaysservice wireless anqp-frag-size <100-1500>service wireless ap650 legacy-auto-update-image <FILE>service wireless client tx-deauth on-radar-detectservice wireless cred-cache-sync [full|interval <30-864000>|never|partial]service wireless test [max-rate|max-retries|min-rate]service wireless test [max-rate|min-rate] [1,2,5.5,6,11,12,18,24,36,48,54,mcs0,mcs1,............mcs23]service wireless inter-ap-key [0 <WORD>|2 <WORD>|<WORD>]service wireless noise-immunityservice wireless reconfig-on-rx-stallservice wireless test max-retries <0-15>service wireless wispe-controller-port <1-65535>](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-233.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 452service show cliParameters• service captive-portal-server connections-per-ip <3-64>• service cluster master-election immediate• service critical-resource port-mode-source-ip <IP>• service enable [l2tpv3|pppoe|radiusd]• service global-association-list blacklist-interval <1-65535>• service lldp loop-detectioncaptive-portal-server connections-per-ip <3-64>Configures the maximum number of simultaneous captive portal connection allowed per IP address• <3-64> – Specify the maximum number of connections per IP address from 3 - 64. The default is 3.Note: This command is applicable only to the NX9XXX and NX9600 service platform profiles.cluster master-election immediateInitiates and completes cluster master election as soon as just one cluster member comes on and is active. This option is disabled by default.critical-resource port-mode-source-ip <IP>Hard codes a source IP for critical resource management The default is 0.0.0.0Use this option to define the IP address used as the source address in ARP packets used to detect a critical resource on a layer 2 interface. By default, the source address used in ARP packets to detect critical resources is 0.0.0.0. However, some devices do not support the above IP address and drop the ARP packets. Use this field to provide an IP address specifically used for this purpose. The IP address used for port-mode-source-ip monitoring must be different from the IP address configured on the device.service enable l2tpv3 Enables L2TPv3 on this profileThe L2TPV3 enable/disable option is not supported on AP6522, AP6532, AP6562, AP7161, AP81XX, AP8232, AP8432, AP8533, RFS4000, RFS6000, and NX95XX model devices.It is supported only on AP6521.service enable pppoe Enables PPPoE features. When executed on a device, enables PPPoE on the logged device. When executed on a profile, enables PPPoE on all devices using that profile.service enable radiusd Enables RADIUSD features. When executed on a device, enables RADIUSD on the logged device. When executed on a profile, enables RADIUSD on all devices using that profile.service global-association-listConfigures global association list related parametersblacklist-interval <1-65535>Configures the period for which a client is blacklisted. A client is considered blacklisted after being denied access by the server.• <1-65535> – Specify a value from 1 - 65535 seconds. The default is 60 seconds.lldp loop-detection Enables network loop detection via LLDP. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-234.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 453• service memory kernel decrease• service meshpoint loop-prevention-port [<L2-INTERFACE-NAME>|ge <1-4>|port-channel <1-2>]• service pm sys-restart• service power-config [3af-out|force-3at]• service radius dynamic-authorization additional-port <1-65535>• service remote-config apply-delay <0-600>• service rss-timeout <0-86400>service memory kernel decreaseEnables reduction in kernel memory usage. When enabled, firewall flows are reduced by 75% resulting in reduced kernel memory usage. A reboot is required for the option to take effect. This option is disabled by default.meshpoint loop-prevention-portLimits meshpoint loop prevention to a single port<L2-INTERFACE-NAME>Limits meshpoint loop prevention on a specified Ethernet interface• <L2-INTERFACE-NAME> – Specify the layer 2 Ethernet interface name.ge <1-4> Limits meshpoint loop prevention on a specified GigabitEthernet interface• ge <1-4> – Specify the GigabitEthernet interface index from 1 - 4.port-channel <1-2> Limits meshpoint loop prevention on a specified port-channel interface• port-channel <1-2> – Specify the port-channel interface index from 1 - 2.pm sys-restart Enables the process monitor (PM) to restart the system when a process fails. This option is enabled by default.power-config 3af-out Enables LLDP power negotiation, but uses 3af power. This option is disabled by default.power-config force-3at Disables LLDP negotiation and forces 802.3at power configuration. This option is disabled by default.radius dynamic-authorization additional-port <1-65535>Configures an additional UDP port used by the device to listen for dynamic authorization messages• <1-65535> – Specify a value from 1 - 65535. The default is 3799.The Cisco Identity Services Engine (ISE) server uses port 1700.remote-config apply-delay <0-600>Delays configuration of a remote device (after it becomes active) by the specified time period• <0-600> – Specify a value from 0 - 600 seconds. The default is 0 seconds.rss-timeout <0-86400>Configures the duration, in seconds, for which an adopted access point will continue to provide wireless functions even after loosing controller adoption.• <0-86400> – Specify a value from 0 - 86400 seconds. The default is 300 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-235.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 454• service watchdog• service wireless anqp-frag-always• service wireless anqp-frag-size <100-1500>• service wireless client tx-deauth on-radar-detection• service wireless cred-cache-sync [full|interval <30-864000>|never|partial]• service wireless inter-ap-key [0 <WORD>|2 <WORD>|<WORD>]• service wireless noise-immunity• service wireless reconfig-on-rx-stallwatchdog Enables the watchdog. This feature is enabled by default.Enabling the watchdog option implements heartbeat messages to ensure other associated devices are up and running and capable of effectively inter-operating with the controller.wireless anqp-frag-alwaysEnables fragmentation of all ANQP packets. This option is disabled by default.wireless anqp-frag-size <100-1500>Configures the ANQP packet fragment size• <100-1500> – Specify a value from 100 - 1500. The default is 1200.wireless client Configures wireless client and stations related settingstx-deauth on-radar-detectionEnables access points to transmit deauth to clients when changing channels on radar detection. This option is enabled by default.wireless cred-cache-sync Configures the credential cache’s synchronization parameters. The parameters are: full, interval, never, and partial.full Enables synchronization of all credential cache entriesinterval <30-864000> Sets the interval, in seconds, at which the credential cache is synchronized• <30-864000> – Specify a value from 30 - 864000 seconds. The default is 1200 seconds.never Disables credential cache entry synchronization for all associated clients other than roaming clients. This is the default setting.partial Enables partial synchronization of parameters for associated clients, with credential cache close to aging outwireless inter-ap-key Configure encryption key used for securing inter-ap messages. This option is disabled by default.[0<WORD>|2<WORD>|<WORD>]Specify a clear text or encrypted key.wireless noise-immunityPolls for status and reconfigures radio in case of receive stall. This option is enabled by default.wireless reconfig-on-rx-stallEnables noise immunity on the radio](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-236.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 455• service wireless test [max-rate|min-rate] [1,2,5.5,6,11,12,18,24,36,48,54,mcs0,mcs1,............mcs23]• service wireless test max-retries <0-15>• service wireless wispe-controller-port <1-65535>• service show cliExamplerfs6000-37FABE(config-profile-testrfs6000)#service radius dynamic-authorization additional-port 1700rfs6000-37FABE(config-profile-testrfs6000)#show contextprofile rfs6000 testrfs6000 service radius dynamic-authorization additional-port 1700 no autoinstall configuration no autoinstall firmware crypto ikev1 policy ikev1-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ikev2 policy ikev2-default isakmp-proposal default encryption aes-256 group 2 hash sha crypto ipsec transform-set default esp-aes-256 esp-sha-hmac crypto ikev1 remote-vpn crypto ikev2 remote-vpn--More--rfs6000-37FABE(config-profile-testrfs6000)#Related Commandswireless test Configures the serviceability parameters used for testing[max-rate|min-rate] Configures the maximum and minimum data rates for clients using rate-scaling. The ‘max-rate’ and min-rate’ options are disabled by default.[1,2,5.5,....mcs23] Select the maximum and minimum data rates applicable.wireless test Configures the serviceability parameters used for testingmax-retries <0-15> Configures the maximum number of retries per packet from 0 - 15. The default is 0.wispe-controller-port <1-65535>Resets the WIreless Switch Protocol Enhanced (WISPe) controller port. This is the UDP port used to listen for WISPe.• <1-65535> – Specify a value from 1 - 65535. The default is 24756.show cli Displays running system configuration details• cli – Displays the CLI tree of the current modeno Removes or resets service command parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-237.png)




![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4667.2.3 channel-listDevice Config CommandsConfigures the channel list advertised to wireless clientsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxchannel-list [2.4GHz|5GHz|dynamic]channel-list [2.4GHz <CHANNEL-LIST>|5GHz <CHANNEL-LIST>|dynamic]Parameters• channel-list [2.4GHz <CHANNEL-LIST>|5GHz <CHANNEL-LIST>|dynamic]Examplerfs7000-37FABE(config-device-00-04-96-4A-A7-08)#channel-list 2.4GHz 1,2rfs7000-37FABE(config-device-00-04-96-4A-A7-08)#show contextap71xx 00-04-96-4A-A7-08 use profile default-ap71xx use rf-domain default hostname ap7131-4AA708 area RMZEcospace channel-list 2.4GHz 1,2rfs7000-37FABE(config-device-00-04-96-4A-A7-08)#Related Commandschannel-list Configures the channel list advertised to wireless clients2.4GHz <CHANNEL-LIST>Configures the channel list advertised by radios operating in 2.4 GHz• <CHANNEL-LIST> – Specify a list of channels separated by commas or hyphens.5GHz <CHANNEL-LIST>Configures the channel list advertised by radios operating in 5.0 GHz• <CHANNEL-LIST> – Specify a list of channels separated by commas or hyphens.dynamic Enables dynamic (neighboring access point based) update of configured channel listno Resets the channel list configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-248.png)





![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4797.2.14 noDevice Config CommandsNegates a command or resets values to their defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [adopter-auto-provisioning-policy-lookup|adoption-site|alias|application-policy|area|arp|auto-learn-staging-config|autoinstall|bridge|captive-portal|cdp|channel-list|cluster|configuration-persistence|contact|controller|country-code|critical-resource|crypto|database-backup|device-upgrade|dot1x|dpi|dscp-mapping|email-notification|environmental-sensor|events|export|file-sync|floor|geo-coordinates|gre|hostname|http-analyze|interface|ip|ipv6|l2tpv3|l3-lite-table|lacp|layout-coordinates|led|led-timeout|legacy-auto-downgrade|legacy-auto-update|license|lldp|load-balancing|location|logging|mac-address-table|mac-auth|mac-name|management-server|memory-profile|meshpoint-device|meshpoint-monitor-interval|min-misconfiguration-recovery-time|mint|mirror|misconfiguration-recovery-time|mpact-server|noc|nsight||ntp|offline-duration|override-wlan|power-config|preferred-controller-group|preferred-tunnel-controller|radius|raid|rf-domain-manager|router|rsa-key|sensor-server|slot|spanning-tree|timezone|traffic-class-mapping|traffic-shape|trustpoint|tunnel-controller|use|vrrp|vrrp-state-check|wep-shared-key-auth|service]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negatedExamplerfs7000-37FABE(config-device-00-04-96-4A-A7-08)#no arearfs7000-37FABE(config-device-00-04-96-4A-A7-08)#no contactno <PARAMETERS> Removes or resets the logged device’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-261.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4807.2.15 nsightDevice Config CommandsConfigures NSight database related parameters. Use this command to configure the data-update periodicity, number of applications posted to the NSight server for a wireless client, and the duration for which data is stored in the NSight database’s buckets. These parameters impact the amount of data stored in the NSight DB and interval at which data is aggregated and expired within the NSight DB. For more information on data aggregation and expiration, see (Data Aggregation and Expiration).Configure these parameters in the NSight server’s device configuration mode.Supported in the following platforms:• Service Platforms — NX9500, NX9510, NX9600, VX9000Syntaxnsight database [statistics|summary]nsight database statistics [avc-update-interval|max-apps-per-client|update-interval|wireless-clients-update-interval]nsight database statistics [avc-update-interval|update-interval|wireless-clients-update-interval] [120|30|300|60|600]nsight database statistics max-apps-per-client <1-1000>nsight database summary duration <1-24> <1-168> <1-2160> <24-26280>Parameters• nsight database statistics [avc-update-interval|update-interval|wireless-clients-update-interval] [120|30|300|60|600]nsight database statisticsConfigures NSight database statistics related parametersavc-update-interval Configures the interval, in seconds, at which Application Visibility and Control (AVC) statistics is updated to the NSight database. This interval represents the rate at which AVC-related data is inserted in the NSight database’s first bucket. This first bucket data is referred to as the RAW records. A bucket is a database collection that holds statistical data on a per RF Domain basis. For more information, see (Data Aggregation and Expiration).When configured, RF Domain managers posting AVC-related data to the NSight server receive a reply from the NSight server intimating the next update time. The NSight server calculates the ‘next update time’ based on the avc-update-interval configured here.update-interval Configures the interval, in seconds, at which data is updated to the NSIght server. This interval represents the rate at which data (excluding AVC and wireless-clients related statistics) is inserted in the NSight database’s first bucket. This first bucket data is referred to as the RAW records. A bucket is a database collection that holds statistical data on a per RF Domain basis. For more information, see (Data Aggregation and Expiration).When configured, RF Domain managers posting data to the NSight server receive a reply from the NSight server intimating the next update time. The NSight server calculates the ‘next update time’ based on the update-interval configured here.Note: Use the ‘avc-update-interval’ and ‘wireless-clients-update-interval’ keywords to configure update interval for AVC-related and wireless-clients related information respectively.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-262.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 481• nsight database statistics max-apps-per-client <1-1000>• nsight database summary duration <1-24> <1-168> <1-2160> <24-26280>wireless-clients-update-intervalConfigures the interval, in seconds, at which wireless-client statistics is updated to the NSIght server. This interval represents the rate at which wireless-clients related statistics is inserted in the NSight database’s first bucket. This first bucket data is referred to as the RAW records. A bucket is a database collection that holds statistical data on a per RF Domain basis. For more information, see (Data Aggregation and Expiration).When configured, RF Domain managers posting wireless-client related data to the NSight server receive a reply from the NSight server intimating the next update time. The NSight server calculates the ‘next update time’ based on the wireless-clients-update-interval configured here.[120|30|300|60|600] The following keywords are common to all of the above parameters:• 120 – Sets the data-update periodicity as 120 seconds (2 minutes)• 30 – Sets the data-update periodicity as 30 seconds• 300 – Sets the data-update periodicity as 300 seconds (5 minutes). This is the default setting for the ‘avc-update-interval’ and ‘wireless-clients-update-interval’ parameters.• 60 – Sets the data-update periodicity as 60 seconds (1 minute). This is the default setting for the ‘update-interval’ parameter.• 600 – Sets the data-update periodicity as 600 seconds (10 minutes)nsight database statisticsConfigures NSight database statistics related parametersmax-apps-per-client Configures the maximum number of applications per wireless-client to be posted to the NSight server within the configured data-update interval. This information is included in the AVC statistics posted by RF Domain managers to the NSIght server.<1-1000> Specify the number of applications posted from 1 - 1000. The default is 10 applications per wireless client.nsight database summaryConfigures the NSight database’s per-bucket data storage durationduration <1-24> <1-168> <1-2160> <24-26280>Configures the duration for which data is stored on a per-bucket basis• <1-24> – Specify the bucket 1 duration from 1 - 24 hours (i.e. 1 hour to 1 day). The default is 8 hours.• <1-168> – Specify the bucket 2 duration from 1 - 168 hours (i.e. 1 hour to 7 days).The default is 24 hours.• <1-2160> – Specify the bucket 3 duration from 1 - 2160 hours (i.e. 1 hour to 90days). The default is 7 days (168 hours).• <24-26280> – Specify the bucket 4 duration from 24 - 26280 hours (i.e. 1day to 3 years). The default is 365 days (1 year).Note: A bucket is a database collection that holds statistical data for each RF Domain within the network. (Note, only those RF Domain’s that are using an NSight policy with the NSight server host configured will post data to the NSight server. For more information, see use in the RF Domain configuration mode.) NSight database has four (4) buckets. The data from each bucket is aggregated and pushed to the next bucket once the data storage duration, specified for the bucket, has exceeded. For more information on data aggregation, see (Data Aggregation and Expiration).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-263.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4847.2.16 override-wlanDevice Config CommandsConfigures WLAN’s RF Domain level overridesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoverride-wlan <WLAN> [shutdown|ssid|vlan-pool|wep128|wpa-wpa2-psk]override-wlan <WLAN> [shutdown|ssid <SSID>|vlan-pool <1-4094> {limit <0-8192>}|wpa-wpa2-psk <WORD>]override-wlan <WLAN> wep128 [key <1-4> hex [0<WORD>|2 <WORD>]|transmit-key <1-4>]Parameters• override-wlan <WLAN> [shutdown|ssid <SSID>|vlan-pool <1-4094> {limit <0-8192>}|wpa-wpa2-psk <WORD>]• override-wlan <WLAN> wep128 [key <1-4> hex [0<WORD>|2 <WORD>]|transmit-key <1-4>]<WLAN> Specify the WLAN name.Configure the following WLAN parameters: SSID, VLAN pool, and WPA-WPA2 key.shutdown Shuts down the WLAN’s (identified by the <WLAN> keyword) operations on all mapped radiosSSID <SSID> Configures the WLAN’s Service Set Identifier (SSID)• <SSID> – Specify an SSID ID.vlan-pool <1-4094> {limit <0-8192>}Configures a pool of VLANs for the selected WLAN• <1-4094> – Specifies a VLAN pool ID from 1 - 4094.• limit – Optional. Limits the number of users on this VLAN pool• <0-8192> – Specify the user limit from 0 - 8192.Note: The VLAN pool configuration overrides the VLAN configuration.wpa-wpa2-psk <WORD>Configures the WLAN WPA-WPA2 key or passphrase for the selected WLAN• <WORD> – Specify a WPA-WPA2 key or passphrase.<WLAN> Specify the WLAN name.wep128 [key <1-4> hex [0<WORD>|2 <WORD>]|transmit-key <1-4>Configures the WEP128 key for this WLAN, and also enables key transmissionWired Equivalent Privacy (WEP) is a security protocol specified in the IEEE Wireless Fidelity (Wi -Fi) standard. WEP 128 uses a 104 bit key, which is concatenated with a 24-bit initialization vector (IV) to form the RC4 traffic key. This results in a level of security and privacy comparable to that of a wired LAN.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-266.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4897.2.19 sensor-serverDevice Config CommandsConfigures an AirDefense sensor server resource for client terminations and WIPS event logging. This is the server that supports WIPS events on behalf of the controller or service platform.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsensor-server <1-3> ip <IP/HOSTNAME> {port [443|<1-65535>]}Parameters• sensor-server <1-3> ip <IP/HOSTNAME> {port [443|<1-65535>]}Examplerfs7000-37FABE(config-device-00-04-96-4A-A7-08)#sensor-server 1 ip 172.16.10.7rfs7000-37FABE(config-device-00-04-96-4A-A7-08)#show contextap71xx 00-04-96-4A-A7-08 use profile default-ap71xx use rf-domain default hostname TechPubAP7131 floor 5thfloor layout-coordinates 1.0 2.0 license AP aplicenseley@1234 aplicensekey@123 rsa-key ssh rsa-key1 location SanJose no contact country-code us sensor-server 1 ip 172.16.10.7 channel-list 2.4GHz 1,2 override-wlan test vlan-pool 8 mac-name 00-04-96-4A-A7-08 5.8TestAP neighbor-info-interval 50rfs7000-37FABE(config-device-00-04-96-4A-A7-08)#Related Commandssensor-server <1-3> Sets a numerical index to differentiate this AirDefense sensor server from other servers. A maximum of 3 (three) sensor server resources can be defined.ip <IP/HOSTNAME> Configures the AirDefense sensor server’s IP address or hostname• <IP/HOSTNAME> – Specify the IP address.port [443|<1-65535>] Optional. Configures the port. The options are:• 443 – The default port used by the AirDefense server. This is the default setting.• <1-65535> – Manually sets the port number of the AirDefense server from 1 - 65535no Removes configured sensor server settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-271.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4917.2.21 trustpoint (device-config-mode)Device Config CommandsAssigns trustpoints to validate various services, such as HTTPS, RADIUS CA, RADIUS server, external LDAP server, etc.For more information on digital certificates and certificate authorities, see trustpoint (profile-config-mode).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8232, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtrustpoint [cloud-client|cmp-auth-operator|https|radius-ca|radius-ca-ldaps|radius-server|radius-server-ldaps] <TRUSTPOINT-NAME>Parameters• trustpoint [cloud-client|cmp-auth-operator|https|radius-ca|radius-ca-ldaps|radius-server|radius-server-ldaps] <TRUSTPOINT-NAME>NOTE: Certificates/trustpoints used in this command should be verifiable as existing on the device.trustpoint Assigns trustpoints to validate various services. The assigned trustpoint is used as the CA for validating the services.cloud-client Assigns trustpoint to validate cloud client. The trustpoint should be existing and installed on the device.Use this option on cloud-enabled access points and cloud-adopted, to secure the communication between the cloud AP and cloud client. The trustpoint should be existing and installed on the AP. The cloud-enabled access points are AP7502, AP7522, AP7532, and AP7562. For local-controller adopted APs, this configuration is not required,cmp-auth-operator Assigns an existing trustpoint to validate CMP auth operator. Once validated, CMP is used to obtain and manage digital certificates in a PKI network. Digital certificates link identity information with a public key enclosed within the certificate, and are issued by the CA.Use this command to specify the CMP-assigned trustpoint. When specified, devices send a certificate request to the CMP supported CA server, and download the certificate directly from the CA server. CMP supports multiple request options through for device communicating to a CMP supported CA server. The device can initiate a request for getting the certificates from the server. It can also auto update the certificates which are about to expire.Note: When configured, this cmp-auth-operator trustpoint setting overrides the profile-level configuration.https Assigns an existing trustpoint to validate HTTPSradius-ca Assigns an existing trustpoint to validate client certificates in EAP](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-273.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4957.3.1 cpeT5 Profile Config CommandsConfigures T5 CPE related settings. This command is available both in the T5 profile and T5 device contextsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510Syntax T5 Profile & T5 Device Contextcpe [address led]cpe address vlan <1-4094> <START-IP> <END-IP>cpe led cpe <cpe1-24>The following commands are specific to the T5 device context:cpe [boot|reload|upgrade]cpe boot system <cpe1-24> <primary|secondary>cpe reload <cpe1-24>cpe <cpe1-24> upgrade <IMAGE-LOCATION>Parameters• cpe address vlan <1-4094> <START-IP> <END-IP>• cpe led cpe <cpe1-24>• cpe boot system <cpe1-24> <primary|secondary>cpe address Configures the range of addresses that can be assigned to adopted CPEsvlan <1-4094> Configures the VLAN assigned to the CPEs managed by this T5 controller<START-IP> <END-IP>Configures the range of IP addresses that can be assigned to the CPEs managed by this T5 controller• <START-IP> – Specify the first IP address in the range.• <END-IP> – Specify the last IP address in the range.cpe led Enables flashing of LEDs on specified CPEscpe <cpe1-24> Identifies the CPE(s) on which the operation is performed• <cpe1-24> – Configures the CPE’s ID from cpe1 - cpe24. To enable led flashing on all adopted CPEs, enter cpe1-X, where X is the total number of adopted CPEs. For example, if CPEs 1, 2, 3, 4, & 5 are adopted and ready, then enter this value as cpe1-5.cpe boot system Changes the image used by a CPE to boot. When reloading, the CPE uses the specified image.<cpe1-24> Identifies the CPE(s) on which the operation is performed• <cpe1-24> – Configures the CPE’s ID from cpe1 - cpe24. To enable led flashing on all adopted CPEs, enter cpe1-X, where X is the total number of adopted CPEs. For example, if CPEs 1, 2, 3, 4, & 5 are adopted and ready, then enter this value as cpe1-5.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-277.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 4977.3.2 interfaceT5 Profile Config CommandsConfigures the T5 controller’s interfacesSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510Syntaxinterface [<WORD>|dsl|fe|ge|radio|vlan]interface [<WORD>|dsl <1-24>|fe <1-24> <1-2>|ge <1-2>|radio <1-24> <1-2>|vlan <1-4094>]Parameters• interface [<WORD>|dsl <1-24>|fe <1-24> <1-2>|ge <1-2>|radio <1-24> <1-2>|vlan <1-4094>]<WORD> Configures the interface identified by the <WORD> keyworddsl <1-24> Configures the specified DSL interface. A T5 controller uses the IPX operating system to manage its connected radio devices, as opposed to the WiNG operating used by controllers and NX service platforms. However, a T5 controller, once enabled as a supported external device, can provide data to WiNG to assist in a T5’s management within a WiNG supported subnet populated by both types of devices. The CPEs are the T5 controller managed radio devices using the IPX operating system. These CPEs use DSL as their high speed Internet access mechanism using the CPE’s physical wallplate connection and phone jack.• <1-24> – Specify the DSL port index from 1 - 24.fe <1-24> <1-2> Configures the specified FastEthernet interface. The T5 controller has the following FastEthernet port designations: fe1-fe2 (fe1-fe2 are for up to 24 CPE devices managed by a T5 controller).• <1-24> – Specify the DSL port index from 1 - 24.• <1-2> – Specify the FastEthernet interface to configure.In the FastEthernet interface configuration mode, specify the interface settings.ge <1-2> Configures the specified GigabitEthernet interface.T5 controllers have two Ethernet port designations, These are ge1 and ge2.The GE ports can be RJ-45 or fiber ports supporting 10/100/1000Mbps.• <1-2> – Specify the interface index from 1 - 2.In the GigabitEthernet interface configuration mode, specify the interface settings.radio <1-24> <1-2> Configures the specified radio interface. T5 controller managed CPE device radios can have their radio configurations overridden once their radios have successfully associated and have been provisioned by the adopting controller, service platform, or peer model AP controller access point.• <1-24> – Specify the radio interface index from 1 - 24.• <1-2> – Allows the second radio to be specified as a radio interface. For example,this is “interface radio X Y” where ‘X’ is the DSL line number and ‘Y’ is the radio interface (number).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-279.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5007.3.4 noT5 Profile Config CommandsRemoves or reverts this T5 controller profile settingsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510Syntaxno [cpe|interface|ntp|override-wlan|t5-logging|use]no cpe led cpe <1-24>no interface vlan <2-4094>no ntp server <IP>no override-wlan <WLAN-NAME> vlanno t5-logging host <IP>no use management-policyParameters• no <PARAMETERS>Examplenx9500-6C8809(config-profile-t5Profile)#show contextprofile t5 t5Profile ip default-gateway 192.168.13.7 no autoinstall configuration no autoinstall firmware interface vlan1 interface vlan4090.................................................... use firewall-policy default ntp server 192.168.13.2 service pm sys-restartnx9500-6C8809(config-profile-t5Profile)#nx9500-6C8809(config-profile-t5Profile)#no ntp server 192.168.13.2nx9500-6C8809(config-profile-t5Profile)#show contextprofile t5 t5Profile ip default-gateway 192.168.13.7 no autoinstall configuration no autoinstall firmware interface vlan1 interface vlan4090.................................................... use firewall-policy default service pm sys-restartnx9500-6C8809(config-profile-t5Profile)#no <PARAMETERS> Removes or reverts to default the selected T5 profile’s or device’s settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-282.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5047.3.8 t5-loggingT5 Profile Config CommandsConfigures a maximum of 5 (five) remote hosts capable of receiving syslog messages from this selected T5 controllerSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510Syntaxt5-logging host <IP> severity [error|info|notice|trace|warning] facility [local0|local1|local2|local3|local4|local5|local6|local7]Parameters• t5-logging host <IP> severity [error|info|notice|trace|warning] facility [local0|local1|local2|local3|local4|local5|local6|local7]Examplenx9500-6C8809(config-profile-T5TestProfile)#t5-logging host 192.168.13.10 severity warning facility local6nx9500-6C8809(config-profile-T5TestProfile)#show contextprofile t5 T5TestProfile t5-logging host 192.168.13.10 severity warning facility local6 no autoinstall configuration............................................................................. no autoinstall firmware t5 country-code US cpe address vlan 200 192.168.13.26 192.168.13.30nx9500-6C8809(config-profile-T5TestProfile)#Related Commandst5-logging host <IP>Configures syslog message logging settings• host <IP> – Configures the external syslog remote host resource’s IP address. This is the host dedicated to receive T5 syslog messages.severity [error|info|notice|trace|warning]Configures the syslog message filtering severity level. The options are:• Error – Only forwards error and above syslog event messages.• Info – Only forwards informational and above syslog event messages.• notice – Only forwards syslog notices relating to general device operational events. These are events that are of more interest than the “info” events. • trace – Only forwards trace routing event messages• warning – Only forwards warnings and above syslog event messagesfacility [local0|local1|local2|local3|local4|local5|local6|local7]Configures the facility level for log messages sent to the syslog server. The facility level specifies the type of program logging the message. Specifying the facility level allows the configuration file to specify that message handling will vary with varying facility type. The options are: local0, local1, local2, local3, local4, local5, local5, local6, local7. The default value is local7.no Modifies message logging severity level and facilities](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-286.png)



![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5087.4.1.1 interfaceinterfaceSelects the EX35XX interface type and enters the selected interface’s configuration modeSupported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxinterface [ge 1 <1-48>|vlan <1-4094>]Parameters• interface [ge 1 <1-48>|vlan <1-4094>]Examplenx4500-5CFA8E(config-profile-testEX35XX)#interface vlan 1nx4500-5CFA8E(config-profile-testEX35XX-if-vlan1)#? commands: ip Internet Protocol (IP) no Negate a command or set its defaults clrscr Clears the display screen commit Commit all changes made in this session do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system revert Revert changes service Service Commands show Show running system information write Write running configuration to memory or terminalnx4500-5CFA8E(config-profile-testEX35XX-if-vlan1)#nx4500-5CFA8E(config-profile-testEX35XX)#interface ge 1 1nx4500-5CFA8E(config-profile-testEX35XX-if-ge1-1)#? commands: access-group Access group to bind a port to an ACL name no Negate a command or set its defaults port Configures the characteristics of the port power EX3500 Power over Ethernet Command shutdown Shutdown the selected interface speed-duplex Configures speed and duplex operation switchport Configures switch mode characteristics use Set setting to useinterface Selects the EX35XX interface type and enters its configuration mode. The interface options available are: GE and VLANge 1 <1-48> Selects a GE interface to configure• 1 – Configures the GE interface unit identifier as 1• <1-48> – Configures the physical port number from 1 - 24/48Note: For the EX3524 model switch the GE port range is 1-24, and for the EX3548 it is 1-48.vlan <1-4094> Selects a VLAN interface to configure• <1-4094> – Specify the VLAN interface ID from 1 - 4094.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-290.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5117.4.1.2.1 access-groupinterface-ge-config commandsBinds an EX3500 ACL to the selected portWhen applied to the port, the ACL takes effect. Only one ACL can be bound to a port at a time. In case you bind a new ACL to a port with an existing ACL binding, the old binding is replaced with the new one.Supported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxaccess-group [ex3500-ext-access-list|ex3500-std-access-list|mac-access-list] <ACL-NAME> in {time-range <TIME-RANGE-NAME>}Parameters• access-group [ex3500-ext-access-list|ex3500-std-access-list|mac-access-list] <ACL-NAME> in {time-range <TIME-RANGE-NAME>}Examplenx9500-6C8809(config-profile-testEX3524-if-ge1-20)#access-group ex3500-ext-access-list EX3500_ACL_EXT_1 in time-range EX3500_TimeRange_01nx9500-6C8809(config-profile-testEX3524-if-ge1-20)#show context interface ge 1 20 access-group ex3500-ext-access-list EX3500_ACL_EXT_1 in time-range EX3500_TimeRange_01nx9500-6C8809(config-profile-testEX3524-if-ge1-20)#Related Commandsaccess-group Binds a EX3500 ACL with this GE port. Select ACL type and specify the ACL name. The ACL should be existing and configured.ex3500-ext-access-list <ACL-NAME>Binds an existing and configured EX3500 extended ACL• <ACL-NAME> – Specify the ACL name.ex3500-std-access-list <ACL-NAME>Binds an existing and configured EX3500 standard ACL• <ACL-NAME> – Specify the ACL name.mac-access-list <ACL-NAME>Binds an existing and configured EX3500 MAC ACL• <ACL-NAME> – Specify the MAC ACL name.in Applies the specified ACL to all incoming packetstime-range <TIME-RANGE-NAME>Optional. Associates a EX3500 absolute or periodic time range with this access group. The specified ACL is bound to the port during the time period specified by the associated time range.• <TIME-RANGE-NAME> – Specify the time range name (should be existing and configured).no Removes the GE port EX3500 ACL binding](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-293.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5127.4.1.2.2 po rtinterface-ge-config commandsEnables port monitoring on the selected port. This allows the port to monitor specified ports and/or MAC address(es). When enabled, the switch sends a copy of the network packets seen on the specified switch port (or VLAN interface) to the monitoring switch port. These packets are analyzed and debugged to provide vital information, such as network performance, intrusion alerts, etc.Supported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxport monitor [ethernet|ex3500-ext-access-list|ex3500-std-access-list|mac-access-list|mac-address|vlan]port monitor ethernet 1 <1-52> {both|rx|tx}port monitor [ex3500-ext-access-list|ex3500-std-access-list|mac-access-list] <ACL-NAME>port monitor mac-address <MAC>port monitor vlan <1-4094>Parameters• port monitor ethernet 1 <1-52> {both|rx|tx}• port monitor [ex3500-ext-access-list|ex3500-std-access-list|mac-access-list]<ACL-NAME>• port monitor mac-address <MAC>port monitor ethernet 1 <1-52>Configures the characteristics of this GE port• monitor – Enables monitoring of another port• ethernet 1 – Selects Ethernet interface and configures the port identifier as 1• <1-52> – Configures the Ethernet unit number from 1 - 52{both|rx|tx} After specifying the port, optionally configure the following:• both – Optional. Monitors both incoming and outgoing traffic• rx – Optional. Monitors only incoming traffic• tx – Optional. Monitors only outgoing trafficport monitor Configures the characteristics of this GE port• monitor – Enables monitoring of another port[ex3500-ext-access-list|ex3500-std-access-list|mac-access-list]<ACL-NAME>After specifying the port, apply one of the following ACLs:• ex3500-ext-access-list – Applies a EX3500 extended ACL• ex3500-std-access-list – Applies a EX3500 standard ACL• mac-access-list – Applies a MAC ACL with EX3500 deny or permit rules• <ACL-NAME> – Specify the ACL name (should be existing and configured).port monitor Configures the characteristics of this GE port• monitor – Enables monitoring of another port](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-294.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5147.4.1.2.3 powe rinterface-ge-config commandsEnables power allocation to the selected port. When enabled, the power is allocated to this port. Use the command to configure the power allocation settings, such as maximum power allocated, priority level of this port in connection with power allocation, and the time range within which these power settings are applied.This option is enabled by default.Supported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxpower inline {maximum|priority|time-range}power inline {maximum allocation milliwatts <3000-34200>}power inline {priority [critical|high|low]}power inline {time-range <TIME-RANGE-NAME>}Parameters• power inline {maximum allocation milliwatts <3000-34200>}• power inline {priority [critical|high|low]}• power inline {time-range <TIME-RANGE-NAME>}power inline Turns power on or off for the selected port. This option is enabled by default.maximum allocation milliwatts <3000-34200>Optional. Configures the maximum power allocation, in milliwatts, for this port• <3000-34200> – Specify a value from 3000 - 34200 milliwatts. The default is 34200 milliwatts.power inline Turns power on or off for the selected port. This option is enabled by default.priority [critical|high|low]Optional. Configures the PoE power priority as:• critical – Configures the PoE power priority as critical• high – Configures the PoE power priority as high• low - Configures the PoE power priority as low (this is the default setting)power inline Turns power on or off for the selected port. This option is enabled by default.time-range <TIME-RANGE-NAME>Optional. Binds a EX3500 time range to this port• <TIME-RANGE-NAME> – Specify the time range name (should be existing and configured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-296.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5177.4.1.2.5 speed-duplexinterface-ge-config commandsConfigures the speed and duplex mode of the selected port when auto-negotiation is disabled. Auto-negotiation is enabled by default.This option is disabled by default.Supported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxspeed-duplex [100full|100half|10full|10half]Parameters• speed-duplex [100full|100half|10full|10half]Examplenx9500-6C8809(config-profile-testEX3524-if-ge1-20)#speed-duplex 100halfnx9500-6C8809(config-profile-testEX3524-if-ge1-20)#show context interface ge 1 20 shutdown speed-duplex 100half power inline maximum allocation milliwatts 30000 power inline priority critical power inline time-range EX3500_TimeRange_01 access-group ex3500-ext-access-list EX3500_ACL_EXT_1 in time-range EX3500_TimeRange_01 port monitor vlan 20nx9500-6C8809(config-profile-testEX3524-if-ge1-20)#Related Commandsspeed-duplex [100full|100half|10full|10half]Configures the speed and duplex mode of the selected port to one of the following modes:• 100full – Forces 100 Mbps full-duplex operation• 100half – Forces 100 Mbps half-duplex operation• 10full – Force 10 Mbps full-duplex operation• 10half – Force 10 Mbps half-duplex operationWhen configured, forces the switch to operate at the specified speed and mode.no Removes the speed and duplex settings configured for this EX35XX profile](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-299.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5187.4.1.2.6 sw i tc h- po r tinterface-ge-config commandsConfigures the switch mode characteristics of the selected portSupported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxswitchport [allowed|l2protocol-tunnel|mode|native]switchport allowed [add <VLAN-ID>|none|remove <VLAN-ID>]switchport l2protocol-tunnel [cdp|lldp|pvst+|spanning-tree|vtp]switchport mode [access|hybrid|trunk]switchport native Parameters• switchport allowed [add <VLAN-ID>|none|remove <VLAN-ID>]• switchport l2protocol-tunnel [cdp|lldp|pvst+|spanning-tree|vtp]• switchport mode [access|hybrid|trunk]switchport allowed [add <VLAN-ID>|none|remove <VLAN-ID>]Configures VLAN groups on the selected interface.• add <VLAN-ID> – Configures the list of VLAN identifiers to add. When the add option is used, the interface is assigned to the specified VLANs, and membership in all previous VLANs is retained.• <VLAN-ID> – Specify the list of VLANs to add.• none – Removes all VLANs from the current list• remove <VLAN-ID> – Configures the list of VLAN identifiers to remove. When the remove option is used, the specified VLANs are removed from the current list.• <VLAN-ID> – Specify the list of VLANs to remove.switchport l2protocol-tunnel [cdp|lldp|pvst+|spanning-tree|vtp]Enables layer 2 protocol tunneling (L2PT) for the specified protocol. Specify the protocol:• cdp – Cisco Discovery Protocol• lldp – Link Layer Discovery Protocol• pvst+ – Cisco Per VLAN Spanning Tree Plus• spanning-tree – Spanning Tree (STP, RSTP, MSTP)• vtp – Cisco VLAN Trunking ProtocolL2PT is disabled for all of the above specified protocols by default.switchport mode [access|hybrid|trunk]Configures the VLAN membership mode for this port• access – The port is configured as an access VLAN interface. It transmits and receives packets untagged frames on a single VLAN.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-300.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5217.4.1.2.8 n ointerface-ge-config commandsRemoves or reverts the selected port’s settingsSupported in the following platforms:• Switches — EX3524, EX3548Syntaxno [access-group|port|power|shutdown|speed-duplex|switchport|use]no access-group [ex3500-ext-access-list|ex3500-std-access-list|mac-access-list] <ACL-NAME> inno port monitor [ethernet|ex3500-ext-access-list|ex3500-std-access-list|mac-access-list|mac-address|vlan]no port monitor ethernet 1 <1-52>no port monitor [ex3500-ext-access-list|ex3500-std-access-list|mac-access-list] <ACL-NAME>no port monitor mac-address <MAC>no port monitor vlan <1-4094>no power inline {maximum allocation|priority|time-range}no shutdownno speed-duplexno switchport [l2protocol-tunnel [cdp|lldp|pvst+|spanning-tree|vtp]|native vlan]no use ex3500-policy-map inParameters• no <PARAMETERS>ExampleThe following example shows the EX3524 profile’s GE port 20’s settings before the ‘no’ commands are executed:nx9500-6C8809(config-profile-testEX3524-if-ge1-20)#show context interface ge 1 20 shutdown speed-duplex 100half switchport mode access use ex3500-policy-map in test power inline maximum allocation milliwatts 30000 power inline priority critical power inline time-range EX3500_TimeRange_01 access-group ex3500-ext-access-list EX3500_ACL_EXT_1 in time-range EX3500_TimeRange_01 port monitor vlan 20nx9500-6C8809(config-profile-testEX3524-if-ge1-20)#nx9500-6C8809(config-profile-testEX3524-if-ge1-20)#no shutdownnx9500-6C8809(config-profile-testEX3524-if-ge1-20)#no power inline maximum allocationnx9500-6C8809(config-profile-testEX3524-if-ge1-20)#no use ex3500-policy-map inno <PARAMETERS> Removes or reverts the selected port’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-303.png)


![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5247.4.1.3.1 ipinterface-vlan-config commandsConfigures IP related settings for this VLAN interfaceSupported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers – RFS4000, RFS6000• Service Platforms – NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxip address [<IP/M>|bootp|dhcp]ip address <IP/M> {default-gateway <IP>|secondary <IP>}ip address [bootp|dhcp]Parameters• ip address <IP/M> {default-gateway <IP>|secondary <IP>}• ip address [bootp|dhcp]ip address <IP/M> {default-gateway <IP>|secondary <IP>}Manually configures the selected VLAN interface’s primary and secondary IPv4 addresses. It also allows to optionally configure the default gateway.• <IP/M> – Manually configures this VLAN interface’s IP address in the A.B.C.D/M format. Network mask for the associated IP subnet. This mask identifies the host address bits used for routing to specific subnets. The network mask can be either in the traditional format xxx.xxx.xxx.xxx or use classless format with the range /5 to /32. For example the subnet 255.255.224.0 would be /19.• default-gateway <IP> – Optional. Configures the default gateway’s IP address. Thisis the gateway through which this switch can reach other subnets not found in the lo-cal routing table. Before specifying the default gateway, ensure that the network in-terface directly connecting to the gateway is configured on the route. By default nogateway is specified.• <IP> – Specify the IP address in the A.B.C.D address.• secondary <IP> – Optional. Configures this VLAN interface’s secondary IP address• <IP> – Specify the secondary IP address in the A.B.C.D addressip address [bootp|dhcp]Enables a DHCP or Bootp server to provide the primary IPv4 address for the selected VLAN interface• bootp – Enables the VLAN interface to get its IP address from a Bootp server• dhcp – Enables the VLAN interface to get its IP address from a DHCP serverIf selecting DHCP/Bootp, ensure that a server on the network has been configured to provide the necessary configuration to the switch. Using DHCP or Bootp results in frequent connectivity loss between the browser interface and the switch. Further, DHCP and Bootp cannot configure secondary IP addresses needed for multinetting.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-306.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5267.4.1.3.2 nointerface-vlan-config commandsRemoves the IP related settings configured for this VLAN interfaceSupported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers – RFS4000, RFS6000• Service Platforms – NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxno ip address [<IP/M>|bootp|dhcp]Parameters• no <PARAMETERS>ExampleThe following example shows the interface VLAN 20 setting before the ‘no’ command is executed:nx9500-6C8809(config-profile-testEX3524-if-vlan20)#show context interface vlan 20 ip address 192.168.13.28/24 default-gateway 192.168.13.13nx9500-6C8809(config-profile-testEX3524-if-vlan20)#nx9500-6C8809(config-profile-testEX3524-if-vlan20)#no ip address 192.168.13.28/24The following example shows the interface VLAN 20 setting after the ‘no’ command is executed:nx9500-6C8809(config-profile-testEX3524-if-vlan20)#show context interface vlan 20nx9500-6C8809(config-profile-testEX3524-if-vlan20)#no <PARAMETERS> Removes this EX3500’s selected VLAN’s settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-308.png)
![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5297.4.4 upgradeEX3524 & EX3548 Profile/Device Config CommandsConfigures adopted EX35XX switch upgrade settingsFor a EX35XX switch to adopt to and be managed by a WiNG controller, you need to upload two images on the switch. An operation code (opcode) image and an adopted image. The opcode image functions as an operating system that enables the WiNG controller to communicate with the EX35XX switch. This command allows you to configure the EX35XX’s opcode image upgrade settings.Supported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000, RFS7000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxupgrade opcode [auto|path <LINE>|reload]Parameters• upgrade opcode [auto|path <LINE>|reload]Example<EX35XX-DEVICE>#show versionsUnit 1Serial Number : 14136520900352Hardware Version : R01EPLD Version : 0.00Number of Ports : 28Main Power Status : UpRole : MasterLoader Version : 5.0.0.1-01ALinux Kernel Version : 2.6.22.18Boot ROM Version : 0.0.0.1Operation Code Version : 5.0.0.0-03DAdoptd Version : 5.8.3.0-024D<EX35XX-DEVICE>#nx9500-6C8809(config-profile-testEX3524)#upgrade autonx9500-6C8809(config-profile-testEX3524)#upgrade reloadnx9500-6C8809(config-profile-testEX3524)#upgrade opcode path ftp://anonymous:anonymous@192.168.13.10/ex35xx/EX3524.imgnx9500-6C8809(config-profile-testEX3524)#show contextprofile ex3524 testEX3524 ip default-gateway 192.168.13.13 power inline compatible............................................. use firewall-policy default service pm sys-restart upgrade opcode auto upgrade opcode path ftp://anonymous:anonymous@192.168.13.10/ex35xx/EX3524.img upgrade opcode reloadnx9500-6C8809(config-profile-testEX3524)#upgrade opcode Configures the opcode image upgrade settingsauto Enables automatic upgradepath <LINE> Configures the location of the opcode imagereload Enables automatic reload after successful loading of the opcode image](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-311.png)

![PROFILESAccess Point, Wireless Controller and Service Platform CLI Reference Guide 7 - 5317.4.6 noEX3524 & EX3548 Profile/Device Config CommandsRemoves or reverts this EX3500 profile’s settingsSupported in the following platforms:• Switches — EX3524, EX3548• Wireless Controllers — RFS4000, RFS6000, RFS7000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600Syntaxno [interface vlan <1-4094>|default-gateway {<IP>}|power inline compatible|upgrade opcode [auto|path|reload]|use ex3500-management-policy]Parameters• no <PARAMETERS>Examplenx9500-6C8809(config-profile-testEX3524)#show contextprofile ex3524 testEX3524 ip default-gateway 192.168.13.13 power inline compatible no autoinstall configuration no autoinstall firmware interface ge 1 17 interface ge 1 16 interface ge 1 15 interface ge 1 14 interface ge 1 13 interface ge 1 12 interface ge 1 11 interface ge 1 10 interface ge 1 24 interface ge 1 22 interface vlan 20 interface ge 1 23--More-- use ex3500-management-policy test use firewall-policy default service pm sys-restart upgrade opcode auto upgrade opcode path ftp://anonymous:anonymous@192.168.13.10/ex35xx/EX3524.img upgrade opcode reloadnx9500-6C8809(config-profile-testEX3524)#nx9500-6C8809(config-profile-testEX3524)#no use ex3500-management-policynx9500-6C8809(config-profile-testEX3524)#no upgrade opcode reloadnx9500-6C8809(config-profile-testEX3524)#no interface vlan 20nx9500-6C8809(config-profile-testEX3524)#show contextprofile ex3524 testEX3524 ip default-gateway 192.168.13.13 power inline compatible no autoinstall configuration--More-- use firewall-policy default service pm sys-restart upgrade opcode auto upgrade opcode path ftp://anonymous:anonymous@192.168.13.10/ex35xx/EX3524.imgnx9500-6C8809(config-profile-testEX3524)#no <PARAMETERS> Removes or reverts this EX3500 profile settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-313.png)

![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 48.1.1 accountingaaa-policyConfigures the server type and interval at which interim accounting updates are sent to the server. A maximum of 6 accounting servers can be configured.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccounting [interim|server|type]accounting interim interval <60-3600>accounting server [<1-6>|preference]accounting server preference [auth-server-host|auth-server-number|none]accounting server <1-6> [dscp|host|nai-routing|onboard|proxy-mode|retry-timeout-factor|timeout]accounting server <1-6> [dscp <0-63>|retry-timeout-factor <50-200>]accounting server <1-6> host <IP/HOSTNAME/HOST-ALIAS> secret [0 <SECRET>|2 <SECRET>|<SECRET>] {port <1-65535>}accounting server <1-6> nai-routing realm-type [prefix|suffix] realm <REALM-TEXT> {strip}accounting server <1-6> onboard [centralized-controller|self|controller]accounting server <1-6> proxy-mode [none|through-centralized-controller|through-controller|through-mint-host <HOSTNAME/MINT-ID>|through-rf-domain-manager]accounting server <1-6> timeout <1-60> {attempts <1-10>}accounting type [start-interim-stop|start-stop|stop-only]Parameters• accounting interim interval <60-3600>• accounting server preference [auth-server-host|auth-server-number|none]interim Configures the interim accounting interval. This is the interval at which interim accounting updates are posted to the accounting server.interval <60-3000> Specify the interim interval from 60 - 3600 seconds. The default is 1800 seconds.server Configures a RADIUS accounting server’s settingspreference Configures the accounting server’s preference mode. Authentication requests are forwarded to a accounting server, from the pool, based on the preference mode selected.auth-server-host Sets the authentication server as the accounting server. This is the default setting.This parameter indicates the same server is used for authentication and accounting. The server is identified by its hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-317.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 5• accounting server <1-6> [dscp <0-63>|retry-timeout-factor <50-200>]• accounting server <1-6> host <IP/HOSTNAME/HOST-ALIAS> secret [0 <SECRET>|2 <SECRET>|<SECRET>] {port <1-65535>}• accounting server <1-6> nai-routing realm-type [prefix|suffix] realm <REALM-TEXT> {strip}auth-server-number Sets the authentication server as the accounting serverThis parameter indicates the same server is used for authentication and accounting. The server is identified by its index or number.none Indicates the accounting server is independent of the authentication serverserver <1-6> Configures an accounting server. Up to 6 accounting servers can be configured.dscp <0-63> Sets the Differentiated Services Code Point (DSCP) value for Quality of Service (QOS) monitoring. This value is used in generated RADIUS packets.• <0-63> – Sets the DSCP value from 0 - 63. The default value is 34.retry-timeout-factor <50-200>Sets the scaling factor for retransmission timeouts. The timeout at each attempt is a function of this retry-timeout factor and the attempt number.• <50-200> – Specify a value from 50 - 200. The default is 100.If the scaling factor is 100, the interval between two consecutive retries remains the same, irrespective of the number of retries.If the scaling factor is less than 100, the interval between two consecutive retires reduces with subsequent retries.If this scaling factor is greater than 100, the interval between two consecutive retries increases with subsequent retries.server <1-6> Configures an accounting server. Up to 6 accounting servers can be configured.host <IP/HOSTNAME/HOST-ALIAS>Configures the accounting server’s hostname IP address, or host-aliasThe host alias should be existing and configured.secret [0 <SECRET>|2 <SECRET>|<SECRET>]Configures a common secret key used to authenticate with the accounting server• 0 <SECRET> – Configures a clear text secret key• 2 <SECRET> – Configures an encrypted secret key• <SECRET> – Specify the secret key. This shared secret should not exceed 127 characters.port <1-65535> Optional. Configures the accounting server’s UDP port (the port used to connect to the accounting server)• <1-65535> – Sets the port number from 1 - 65535 (default port is 1813)server <1-6> Configures an accounting server. Up to 6 accounting servers can be configured.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-318.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 6• accounting server <1-6> onboard [centralized-controller|self|controller]• accounting server <1-6> proxy-mode [none|through-centralized-controller|through-controller|through-mint-host <HOSTNAME/MINT-ID>|through-rf-domain-manager]nai-routing Enables Network Access Identifier (NAI) routing. This option is disabled by default.The NAI is a character string in the format of an e-mail address as either user or user@realm but it need not be a valid e-mail address or a fully qualified domain name. AAA servers identify clients using the NAI. The NAI can be used either in a specific or generic form. The specific form, which must contain the user portion and may contain the @realm portion, identifies a single user. Using the generic form allows all users to be configured on a single command line, irrespective of whether the users are within a realm or not. Each user still needs a unique security association, but these associations can be stored on a AAA server. The original purpose of the NAI was to support roaming between dial up ISPs. With NAI, an ISP does not have the accounts for all of its roaming partners in a single RADIUS database. RADIUS servers can proxy requests to remote servers as need be.realm-type Specifies whether the prefix or suffix of the username is used as the match criteria. For example, if the option selected is prefix, the username’s prefix is matched to the realm.[prefix|suffix] Select one of the following options:• prefix – Matches the prefix of the username (For example, username is of type DOMAIN/user1, DOMAIN/user2). This is the default setting.• suffix – Matches the suffix of the username (For example, user1@DOMAIN, user2)@DOMAIN)realm <REALM-TEXT>Configures the text matched against the username. Enter the realm name (should not exceed 50 characters). When the RADIUS accounting server receives a request for a user name, the server references a table of user names. If the user name is known, the server proxies the request to the RADIUS server.• <REALM-TEXT> – Specifies the matching text including the delimiter (a delimiter is typically '' or '@')strip Optional. When enabled, strips the realm from the username before forwarding the request to the RADIUS server. This option is disabled by default.server <1-6> Configures an accounting server. Up to 6 accounting servers can be configured.onboard Selects an onboard server instead of an external hostcentralized-controllerConfigures the server on the centralized controller managing the networkself Configures the onboard server on a AP, wireless controller, or service platform (where the client is associated)controller Configures local RADIUS server settingsserver <1-6> Configures an accounting server. Up to 6 accounting servers can be configured.proxy-mode Select the mode used to proxy requests. The options are: none, through-controller, and through-rf-domain-manager.none No proxy required. Sends the request directly using the IP address of the device. This is the default setting.through-centralized-controllerProxy requests through the centralized controller that is configuring and managing the network](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-319.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 7• accounting server <1-6> timeout <1-60> {attempts <1-10>}• accounting type [start-interim-stop|start-stop|stop-only]Examplerfs6000-37FABE(config-aaa-policy-test)#accounting interim interval 65rfs6000-37FABE(config-aaa-policy-test)#accounting server 2 host 172.16.10.10 secret test1 port 1rfs6000-37FABE(config-aaa-policy-test)#accounting server 2 timeout 2 attempts 2rfs6000-37FABE(config-aaa-policy-test)#accounting type start-stoprfs6000-37FABE(config-aaa-policy-test)#accounting server preference auth-server-numberrfs6000-37FABE(config-aaa-policy-test)#show contextaaa-policy test accounting server 2 host 172.16.10.10 secret 0 test1 port 1 accounting server 2 timeout 2 attempts 2 accounting interim interval 65 accounting server preference auth-server-numberrfs6000-37FABE(config-aaa-policy-test)#Related Commandsthrough-controller Proxies requests through the controller (access point, wireless controller, or service platform) configuring the devicethrough-mint-host <HOSTNAME/MINT-ID>Proxies requests through a neighboring MiNT device. Provide the device’s MiNT ID or hostname.through-rf-domain-managerProxies requests through the local RF Domain Managerserver <1-6> Configures an accounting server. Up to 6 accounting servers can be configured.timeout <1-60> Configures the timeout for each request sent to the RADIUS server• <1-60> – Specify a value from 1 - 60 seconds. The default is 5 seconds.attempts <1-10> Optional. Specifies the number of times a transmission request is attempted• <1-10> – Specify a value from 1 - 10. The default is 3.type Configures the type of RADIUS accounting packets sent. The options are: start-interim-stop, start-stop, and stop-only.start-interim-stop Sends accounting-start and accounting-stop messages when the session starts and stops. This parameter also sends interim accounting updates.start-stop Sends accounting-start and accounting-stop messages when the session starts and stops. This is the default setting.stop-only Sends an accounting-stop message when the session endsno Removes or resets accounting server parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-320.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 88.1.2 attributeaaa-policyConfigures RADIUS Framed-MTU attribute used in access and accounting requests. The Framed-MTU attribute reduces the Extensible Authentication Protocol (EAP) packet size of the RADIUS server. This command is useful in networks where routers and firewalls do not perform fragmentation.To ensure network security, some firewall software drop UDP fragments from RADIUS server EAP packets. Consequently, the packets are large. Using Framed MTU reduces the packet size. EAP authentication uses Framed MTU to notify the RADIUS server about the Maximum Transmission Unit (MTU) negotiation with the client. The RADIUS server communications with the client do not include EAP messages that cannot be delivered over the network.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622,, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxattribute [acct-delay-time|acct-multi-session-id|chargeable-user-identity|cisco-vsa|framed-ip-address|framed-mtu|location-information|nas-ip-address|nas-ipv6-address|operator-name|service-type]attribute acct-delay-timeattribute acct-multi-session-idattribute chargeable-user-identityattribute cisco-vsa audit-session-idattribute framed-ip-addressattribute framed-mtu <100-1500>attribute location-information [include-always|none|server-requested]attribute nas-ip-address <WORD>attribute nas-ipv6-addressattribute operator-name <OPERATOR-NAME>attribute service-type [framed|login]Parameters• attribute acct-delay-time• attribute acct-multi-session-idacct-delay-time Enables support for accounting-delay-time attribute in accounting requests. When enabled, this attribute indicates the number of seconds the client has been trying to send a request to the accounting server. By subtracting this value from the time the packet is received by the server, the system is able to calculate the time of a request-generating event. Note, the network transit time is ignored. This option is disabled by default.Including the acct-delay-time attribute in accounting requests updates the acct-delay-time value whenever the packet is retransmitted, This changes the content of the attributes field, requiring a new identifier and request authenticator.acct-multi-session-id Enables support for accounting-multi-session-id attribute. When enabled, it allows linking of multiple related sessions of a roaming client. This option is useful in scenarios where a client roaming between access points sends multiple RADIUS accounting requests to different access points. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-321.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 9• attribute chargeable-user-identity• attribute cisco-vsa audit-session-id• attribute framed-ip-address• attribute framed-mtu <100-1500>• attribute location-information [include-always|none|server-requested]• attribute nas-ip-address <WORD>chargeable-user-identityEnables support for chargeable-user-identity attribute. This option is disabled by default.cisco-vsa audit-session-idConfigures the CISCO Vendor Specific Attribute (VSA) attribute included in access requests. This feature s disabled by default.This VSA allows CISCO’s Identity Services Engine (ISE) to validate a requesting client’s network compliance, such as the validity of virus definition files (anti virus software or definition files for an anti-spyware software application).• audit-session-id – Includes the audit session ID attribute in access requestsThe audit session ID is included in access requests when Cisco ISE is configured as an authentication server.Note: If the Cisco VSA attribute is enabled, configure an additional UDP port to listen for dynamic authorization messages from the Cisco ISE server. For more information, see service.framed-ip-address Enables inclusion of framed IP address attribute in access requests. This option is disabled by default.framed-mtu <100-1500>Configures Framed-MTU attribute used in access requests• <100-1500> – Specify the Framed-MTU attribute from 100 - 1500. The default value is 1400.location-information [include-always|none|server-requested]Enables support for RFC5580 location information attribute, based on the option selected. The various options are:• include-always – Always includes location information in RADIUS authentication and accounting messages• none – Disables sending of location information in RADIUS authentication and accounting messages. This is the default setting.• server-requested – Includes location information in RADIUS authentication and accounting messages only when requested by the serverWhen enabled, location information is exchanged in authentication and accounting messages.nas-ip-address <WORD>Enables configuration of an IP address, which is used as the RADIUS attribute 4, NAS-IP-Address, without changing the source IP address in the IP header of the RADIUS packets. If you are using a cluster of small network access servers (NASs) to simulate a large NAS, use this option to improve scalability. The IP address configured using this option allows the NASs to behave as a single RADIUS client from the perspective of the RADIUS server.• <WORD> – Provide the IPv4 address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-322.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 10• attribute nas-ipv6-address• attribute operator-name <OPERATOR-NAME>• attribute service-type [framed|login]Examplerfs6000-37FABE(config-aaa-policy-test)#attribute framed-mtu 110rfs6000-37FABE(config-aaa-policy-test)#show contextaaa-policy test accounting server 2 host 172.16.10.10 secret 0 test1 port 1 accounting server 2 timeout 2 attempts 2 accounting interim interval 65 accounting server preference auth-server-number attribute framed-mtu 110rfs6000-37FABE(config-aaa-policy-test)#rfs6000-37FABE(config-aaa-policy-test1)#attribute cisco-vsa audit-session-idrfs6000-37FABE(config-aaa-policy-test1)#show contextaaa-policy test attribute cisco-vsa audit-session-idrfs6000-37FABE(config-aaa-policy-test)#Related Commandsnas-ipv6-address Enables support for NAS IPv6 address. This option is disabled by default.When enabled, IPv6 addresses are assigned to hosts. The length of IPv4 and IPv6 addresses is 32-bit and 128-bit respectively. Consequently, an IPv6 address requires a larger address space.operator-name <OPERATOR-NAME>Enables support for RFC5580 operator name attribute. When enabled, the network operator’s name is included in all RADIUS authentication and accounting messages and uniquely identifies the access network owner. This option is disabled by default.• <OPERATOR-NAME> – Specify the network operator’s name (should not exceed 63 characters in length). service-type [framed|login]Configures the service-type (6) attribute value. This attribute identifies the following: the type of service requested and the type of service to be provided.• framed – Sets service-type to framed (2) in the authentication packets. When enabled, a framed protocol, Point-to-Point Protocol (PPP) or Serial Line Internet Protocol (SLIP), is started for the client. This is the default setting.• login – Sets service-type to login (1) in the authentication packets. When enabled, the client is connected to the host.no Resets values or disables commands](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-323.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 118.1.3 authenticationaaa-policyConfigures user authentication parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthentication [eap|protocol|server]authentication eap wireless-client [attempts <1-10>|identity-request-retry-timeout <10-5000>|identity-request-timeout <1-60>|retry-timeout-factor <50-200>|timeout <1-60>]authentication protocol [chap|mschap|mschapv2|pap]authentication server <1-6> [dscp|host|nac|nai-routing|onboard|proxy-mode|retry-timeout-factor|timeout]authentication server <1-6> dscp <0-63>authentication server <1-6> host <IP/HOSTNAME/HOST-ALIAS> secret [0 <SECRET>|2 <SECRET>|<SECRET>] {port <1-65535>}authentication server <1-6> nacauthentication server <1-6> nai-routing realm-type [prefix|suffix] realm <REALM-NAME>{strip}authentication server <1-6> onboard [centralized-controller|controller|self]authentication server <1-6> proxy-mode [none|through-centralized-controller|through-controller|through-mint-host <HOSTNAME/MINT-ID>|through-rf-domain-manager]authentication server <1-6> retry-timeout-factor <50-200>authentication server <1-6> timeout <1-60> {attempts <1-10>}Parameters• authentication eap wireless-client [attempts <1-10>|identity-request-retry-timeout <10-5000>|identity-request-timeout <1-60>|retry-timeout-factor <50-200>|timeout <1-60>]eap Configures EAP authentication parameterswireless-client Configures wireless client’s EAP parametersattempts <1-10> Configures the maximum number of attempts allowed to authenticate a wireless client• <1-10> – Specify a value from 1 - 10. The default is 3.identity-request-retry-timeout <10-5000>Configures the interval, in milliseconds, after which an EAP-identity request to the wireless client is retried• <10-5000> – Specify a value from 10 - 5000 milliseconds. The default is 1000 milliseconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-324.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 12• authentication protocol [chap|mschap|mschapv2|pap]• authentication server <1-6> dscp <0-63>• authentication server <1-6> host <IP/HOSTNAME/HOST-ALIAS> secret [0 <SECRET>|2 <SECRET>|<SECRET>] {port <1-65535>}identity-request-timeout <1-60>Configures the timeout, in seconds, after the last EAP-identity request message retry attempt (to allow time to manually enter user credentials)• <1-60> – Specify a value from 1 - 60 seconds. The default is 30 seconds.retry-timeout-factor <50-200>Configures the spacing between successive EAP retries• <50-200> – Specify a value from 50 - 200. The default is 100.A value of 100 indicates the interval between two consecutive retires remains the same irrespective of the number of retries.A value lesser than 100 indicates the interval between two consecutive retries reduces with each successive retry.A value greater than 100 indicates the interval between two consecutive retries increases with each successive retry.timeout <1-60> Configures the interval, in seconds, between successive EAP-identity request sent to a wireless client• <1-60> – Specify a value from 1 - 60 seconds. The default is 3 seconds.protocol [chap|mschap|mschapv2|pap]Configures one of the following protocols for non-EAP authentication:• chap – Uses Challenge Handshake Authentication Protocol (CHAP)• mschap – Uses Microsoft Challenge Handshake Authentication Protocol (MS-CHAP)• mschapv2 – Uses MS-CHAP version 2•pap – Uses Password Authentication Protocol (PAP) (default authentication protocol used)server <1-6> Configures a RADIUS authentication server. Up to 6 RADIUS servers can be configured.• <1-6> – Specify the RADIUS server index from 1 - 6.dscp <0-63> Configures the Differentiated Service Code Point (DSCP) quality of service parameter generated in RADIUS packets. The DSCP value specifies the class of service provided to a packet, and is represented by a 6-bit parameter in the header of every IP packet.• <0-63> – Specify the value from 0 - 63. The default is 46.server <1-6> Configures a RADIUS authentication server. Up to 6 RADIUS servers can be configured.• <1-6> – Specify the RADIUS server index from 1 - 6.host <IP/HOSTNAME/HOST-ALIAS>Sets the RADIUS authentication server’s IP address, hostname, or host-aliasThe host alias should be existing and configured.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-325.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 13• authentication server <1-6> nac• accounting server <1-6> nai-routing realm-type [prefix|suffix] realm <REALM-NAME> {strip}secret [0 <SECRET>|2 <SECRET>|<SECRET>]Configures the RADIUS authentication server’s secret. This key is used to authenticate with the RADIUS server.• 0 <SECRET> – Configures a clear text secret• 2 <SECRET> – Configures an encrypted secret• <SECRET> – Specify the secret key. The shared key should not exceed 127 characters in length.port <1-65535> Optional. Specifies the RADIUS authentication server’s UDP port (this port is used to connect to the RADIUS server)• <1-65535> – Specify a value from 1 - 65535. The default port is 1812.server <1-6> Configures a RADIUS authentication server. Up to 6 RADIUS servers can be configured.• <1-6> – Specify the RADIUS server index from 1 - 6.nac Enables Network Access Control (NAC) on the RADIUS authentication server identified by the <1-6> parameter.Using NAC, the controller hardware and software grant access to specific network resources. NAC performs a user and client authorization check for resources that do not have a NAC agent. NAC verifies the client’s compliance with the controller’s security policy. The controller supports only the EAP/802.1x type of NAC. However, the controller also provides a means to bypass NAC authentication for client’s that do not have NAC 802.1x support (printers, phones, PDAs, etc.).server <1-6> Configures a RADIUS authentication server. Up to 6 RADIUS servers can be configured. • <1-6> – Specifies the RADIUS server index from 1 - 6.nai-routing Enables NAI routing. When enabled, AAA servers identify clients using NAI. This option is disabled by default.The NAI is a character string in the format of an e-mail address as either user or user@realm but it need not be a valid e-mail address or a fully qualified domain name. AAA servers identify clients using the NAI. The NAI can be used either in a specific or generic form. The specific form, which must contain the user portion and may contain the @realm portion, identifies a single user. Using the generic form allows all users to be configured on a single command line, irrespective of whether the users are within a realm or not. Each user still needs a unique security association, but these associations can be stored on a AAA server. The original purpose of the NAI was to support roaming between dial up ISPs. With NAI, an ISP does not have the accounts for all of its roaming partners in a single RADIUS database. RADIUS servers can proxy requests to remote servers as need be.realm-type [prefix|suffix]Configures the realm-type used for NAI authentication• prefix – Sets the realm prefix. For example, in the realm name ‘AC\JohnTalbot’, the prefix is ‘AC’ and the user name ‘JohnTalbot’.• suffix – Sets the realm suffix. For example, in the realm name ‘JohnTalbot@AC.org’ the suffix is ‘AC.org’ and the user name is ‘JohnTalbot’.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-326.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 14• authentication server <1-6> onboard [centralized-controller|controller|self]• authentication server <1-6> proxy-mode [none|through-centralized-controller|through-controller|through-mint-host <HOSTNAME/MINT-ID>|through-rf-domain-manager]realm <REALM-NAME>Sets the realm information used for RADIUS authentication. The realm name should not exceed 64 characters in length. When the wireless controller or access point’s RADIUS server receives a request for a user name the server references a table of usernames. If the user name is known, the server proxies the request to the RADIUS server.• <REALM-NAME> – Sets the realm used for authentication. This value is matched against the user name provided for RADIUS authentication. Example:Prefix - AC\JohnTalbotSuffix - JohnTalbot@AC.orgstrip Optional. Indicates the realm name must be stripped from the user name before sending it to the RADIUS server for authentication. For example, if the complete username is ‘AC\JohnTalbot’, then with the strip parameter enabled, only the ‘JohnTalbot’ part of the complete username is sent for authentication. This option is disabled by default.server <1-6> Configures a RADIUS authentication server. Up to 6 RADIUS servers can be configured.• <1-6> – Specify the RADIUS server index from 1 - 6.onboard [centralized-controller|controller|self]Selects the onboard RADIUS server for authentication instead of an external host• centralized-controller – Configures the server on the centralized controller managing the network• controller – Configures the wireless controller, to which the AP is adopted, as the onboard wireless controller• self – Configures the onboard server on the device (AP or wireless controller) where the client is associated as the onboard wireless controllerserver <1-6> Configures a RADIUS authentication server. Up to 6 RADIUS servers can be configured.• <1-6> – Specify the RADIUS server index from 1 - 6.proxy-mode [none|through-centralized-controller|through-controller|through-mint-host <HOSTNAME/MINT-ID>|through-rf-domain-manager]Configures the mode for proxying a request• none – Proxying is not done. The packets are sent directly using the IP address of the device. This is the default setting.• through-centralized-controller – The traffic is proxied through the centralized controller that is configuring and managing the network.• through-controller – The traffic is proxied through the wireless controller configuring this device.• through-mint-host <HOSTNAME/MINT-ID> – The traffic is proxied through a neighboring MiNT device. Provide the device’s hostname or MiNT ID.• through-rf-domain-manager – The traffic is proxied through the local RF Domain manager.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-327.png)

![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 178.1.5 mac-address-formataaa-policyConfigures the format MAC addresses are filled in RADIUS request framesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmac-address-format [middle-hyphen|no-delim|pair-colon|pair-hyphen|quad-dot]mac-address-format [middle-hyphen|no-delim|pair-colon|pair-hyphen|quad-dot] case [lower|upper] attributes [all|username-password]Parameters]• mac-address-format [middle-hyphen|no-delim|pair-colon|pair-hyphen|quad-dot] case [lower|upper] attributes [all|username-password]Examplerfs6000-37FABE(config-aaa-policy-test)#mac-address-format quad-dot case upper attributes username-passwordrfs6000-37FABE(config-aaa-policy-test)#show contextaaa-policy test authentication server 5 host 172.16.10.10 secret 0 test1 port 1 authentication server 5 timeout 10 accounting server 2 host 172.16.10.10 secret 0 test1 port 1 accounting server 2 timeout 2 attempts 2 mac-address-format quad-dot case upper attributes username-password authentication protocol chap --More--rfs6000-37FABE(config-aaa-policy-test)#middle-hyphen Configures the MAC address format as AABBCC-DDEEFFno-delim Configures the MAC address format as AABBCCDDEEFF (without delimiters)pair-colon Configures the MAC address format as AA:BB:CC:DD:EE:FFpair-hyphen Configures the MAC address display format as AA-BB-CC-DD-EE-FF (default setting)quad-dot Configures the MAC address display format as AABB.CCDD.EEFFcase [lower|upper] Indicates the case the MAC address is formatted• lower – Indicates MAC address is in lower case. For example, aa:bb:cc:dd:ee:ff• upper – Indicates MAC address is in upper case. For example, AA:BB:CC:DD:EE:FF (default setting)attributes [all|username-password]Configures RADIUS attributes to which this MAC format is applicable• all – Applies to all attributes with MAC addresses such as username, password, calling-station-id, and called-station-id• username-password – Applies only to the username and password fields (default setting)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-330.png)

![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 198.1.6 noaaa-policyNegates a AAA policy command or sets its defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [accounting|attribute|authentication|health-check|mac-address-format|proxy-attribute|server-pooling-mode|use]no accounting interim intervalno accounting server preferenceno accounting server <1-6> {dscp|nai-routing|proxy-mode|retry-timeout-factor|timeout}no accounting typeno attribute [acct-delay-time|acct-multi-session-id|chargeable-user-identity|cisco-vsa audit-session-id|framed-ip-address|framed-mtu|location-information|nas-ipv6-address|operator-name|service-type]no authentication [eap|protocol|server]no authentication eap wireless-client [attempts|identity-request-retry-timeout|identity-request-timeout|retry-timeout-factor|timeout]no authentication protocolno authentication server <1-6> {dscp|nac|nai-routing|proxy-mode|retry-timeout-factor|timeout}no health-check intervalno mac-address-formatno proxy-attribute [nas-identifier|nas-ip-address]no server-pooling-modeno use nac-listParameters• no <PARAMETERS>no <PARAMETERS> Negates a AAA policy command or sets its default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-332.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 218.1.7 proxy-attributeaaa-policyConfigures RADIUS server’s attribute behavior when proxying through a wireless controller or a RF Domain managerSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxproxy-attribute [nas-identifier|nas-ip-address]proxy-attribute [nas-identifier [originator|proxier]|nas-ip-address [none|proxier]]Parameters• proxy-attribute [nas-identifier [originator|proxier]|nas-ip-address [none|proxier]]Examplerfs6000-37FABE(config-aaa-policy-test)#proxy-attribute nas-ip-address proxierrfs6000-37FABE(config-aaa-policy-test)#proxy-attribute nas-identifier originatorRelated Commandsnas-identifier[originator|proxier]Uses NAS identifier• originator – Configures the NAS identifier as the originator of the RADIUS request. The originator could be an AP, or a wireless controller with radio. This is the default setting.• proxier – Configures the proxying device as the NAS identifier. The device could be a controller or a RF Domain manager.nas-ip-address[none|proxier]Uses NAS IP address• none – NAS IP address attribute is not filled• proxier – NAS IP address is filled by the proxying device.The device could be a controller or a RF Domain manager. This is the default setting.no Resets RADIUS server’s proxying attributes](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-334.png)
![AAA-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 8 - 228.1.8 server-pooling-modeConfigures the server selection method from a pool of AAA servers. The available methods are failover and load-balance.In the failover scenario, when a configured AAA server goes down, the server with the next higher index takes over for the failed server.In the load-balance scenario, when a configured AAA server goes down, the remaining servers distribute the load amongst themselves.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxserver-pooling-mode [failover|load-balance]Parameters• server-pooling-mode [failover|load-balance]Examplerfs6000-37FABE(config-aaa-policy-test)#server-pooling-mode load-balancerfs6000-37FABE(config-aaa-policy-test)#show contextaaa-policy test authentication server 5 host 172.16.10.10 secret 0 test2 port 1 authentication server 5 timeout 10 accounting server 2 host 172.16.10.10 secret 0 test1 port 1 server-pooling-mode load-balance mac-address-format quad-dot case upper attributes username-password accounting server preference auth-server-number health-check interval 4000rfs6000-37FABE(config-aaa-policy-test)#Related Commandsfailover Sets the pooling mode to failover. This is the default setting.When a configured AAA server fails, the server with the next higher index takes over the failed server’s load.load-balance Sets the pooling mode to load balancingWhen a configured AAA server fails, all servers in the pool share the failed server’s load transmitting requests in a round-robin fashion.no Resets the method of selecting a server, from the pool of configured AAA servers](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-335.png)


![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 59.1.1 adoptauto-provisioning-policyAdds device adoption rulesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxadopt [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600]adopt [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [profile|rf-domain]adopt [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7632|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [profile <DEVICE-PROFILE-NAME>|rf-domain <RF-DOMAIN-NAME>] [any|area|cdp-match|dhcp-option|floor|fqdn|ip|ipv6|lldp-match|mac|model-number|rf-domain|serial-number|vlan]adopt [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [profile <DEVICE-PROFILE-NAME>|rf-domain <RF-DOMAIN-NAME>] anyadopt [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [profile <DEVICE-PROFILE-NAME>|rf-domain <RF-DOMAIN-NAME>] [area <AREA-NAME>|cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|floor <FLOOR-NAME>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|serial-number <SERIAL-NUMBER>|rf-domain <RF-DOMAIN-NAME>|vlan <VLAN-ID>]Parameters• adopt [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [profile <DEVICE-PROFILE-NAME>|rf-domain <RF-DOMAIN-NAME>] anyadopt Adds an adopt device rule. The rule applies to the selected device types. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX7500, NX7510, NX7520, NX7530 NX95XX, VX9000, and NX9600.Note: ‘anyap’ is used in auto provisioning policies to create rules that are applicable to any AP regardless of the model type.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-341.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 6• adopt[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx9000|vx9000|nx9600] precedence <1-10000> [profile <DEVICE-PROFILE-NAME>|rf-domain <RF-DOMAIN-NAME>] [area <AREA-NAME>|cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|floor <FLOOR-NAME>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|serial-number <SERIAL-NUMBER>|rf-domain <RF-DOMAIN-NAME>|vlan <VLAN-ID>]precedence <1-10000>Sets the rule precedence from 1 - 10000. A rule with a lower value has a higher precedence.profile <DEVICE-PROFILE-NAME>Sets the device profile for this provisioning policy. The selected device profile must be appropriate for the device being provisioned. For example, use an AP7502 device profile for an AP7502. Using an inappropriate device profile can result in unpredictable results. Provide a device profile name.Provide a device profile name (should be existing and configured). Or a template with appropriate substitution tokens, such as 'campus-$MODEL[1:6]', 'FQDN[1:4]-indoor'.Please see the Usage Guidelines section Built-in Tokens & Alias for the different types of built in tokens available in the system.rf-domain <RF-DOMAIN-NAME>Sets the RF Domain for this auto provisioning policy. The provisioning policy is only applicable to devices that try to become a part of the specified RF Domain. Provide the full RF Domain name OR use a string alias to identify the RF Domain.Provide the full RF Domain name or an alias (should be existing and configured). Or a template with appropriate substitution tokens, such as '$CDP[1:7]', '$DNS-SUFFIX[1:5]'Please see the Usage Guidelines section Built-in Tokens & Alias for the different types of built in tokens available in the system.Note: Use the built-in string alias or a user-defined string alias. String aliases allow you to configure APs in the same RF Domain as the adopting controller. A string alias maps a name to an arbitrary string value, for example, ‘alias string $DOMAIN test.example_company.com’. In this example, the string-alias $DOMAIN is mapped to the string: test.example_company.com. For more information, see alias.any Indicates any device. Any device seeking adoption is adopted.adopt Adds an adopt device rule. The rule applies to the selected device types. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7502, AP7522, AP7532, AP7562, AP7161, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX7500, NX7510, NX7520, NX7530, NX95XX, VX9000, and NX9600.Note: ‘anyap’ is used in auto provisioning policies to create rules that are applicable to any AP regardless of the model type.precedence <1-10000>Sets the rule precedence. A rule with a lower value has a higher precedence.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-342.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 7profile <DEVICE-PROFILE-NAME>Sets the device profile for this provisioning policy. The selected device profile must be AP7502 for the device being provisioned. For example, use an AP7502 device profile for an AP7502. Using an inappropriate device profile can result in unpredictable results.Provide a device profile name (should be existing and configured). Or a template with appropriate substitution tokens, such as 'campus-$MODEL[1:6]', 'FQDN[1:4]-indoor'Please see the Usage Guidelines section Built-in Tokens & Alias for the different types of built in tokens available in the system.rf-domain <RF-DOMAIN-NAME>Sets the RF Domain for this auto provisioning policy. The provisioning policy is only applicable to devices that try to become a part of the specified RF Domain.Provide the full RF Domain name or an alias (should be existing and configured). Or a template with appropriate substitution tokens, such as '$CDP[1:7]', '$DNS-SUFFIX[1:5]'.Please see the Usage Guidelines section Built-in Tokens & Alias for the different types of built in tokens available in the system.Note: Use the built-in string alias or a user-defined string alias. String aliases allow you to configure APs in the same RF Domain as the adopting controller. A string alias maps a name to an arbitrary string value, for example, ‘alias string $DOMAIN test.example_company.com’. In this example, the string-alias $DOMAIN is mapped to the string: test.example_company.com. For more information, see alias.area <AREA-NAME> Matches the area of deployment. This option is not applicable to the ‘rf-domain’ parameter.• <AREA-NAME> – Enter a 64 character maximum deployment area name assigned to this policy. Devices with matching area names are adopted.cdp-match <LOCATION-SUBSTRING>Matches a substring in a list of CDP snoop strings (case insensitive). For example, if an access point snooped 3 devices: controller1.example.com, controller2.example.com, and controller3.example.com, 'controller1', ‘example’, 'example.com', are examples of the substrings that will match.• <LOCATION-SUBSTRING> – Specify the value to match. Devices matching the specified value are adopted.dhcp-option <DHCP-OPTION>Matches the value found in DHCP vendor option 191 (case insensitive). DHCP vendor option 191 can be setup to communicate various configuration parameters to an AP. The value of the option in a string in the form of tag=value separated by a semicolon, for example 'tag1=value1;tag2=value2;tag3=value3'. The access point includes the value of tag 'rf-domain', if present.• <DHCP-OPTION> – Specify the DHCP option. Devices matching the specified value are adopted.floor <FLOOR-NAME>Matches the floor name. This option is not applicable to the ‘rf-domain’ parameter.• <FLOOR-NAME> – Enter a 32 character maximum deployment floor name assigned to this policy. Devices with matching floor names are adopted. fqdn <FQDN> Matches a substring to the Fully Qualified Domain Name (FQDN) of a device (case insensitive)FQDN is a domain name that specifies its exact location in the DNS hierarchy. It specifies all domain levels, including its top-level domain and the root domain. This parameter allows a device to adopt based on its FQDN value.• <FQDN> – Specify the FQDN. Devices matching the specified value are adopted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-343.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 8ip [<START-IP> <END-IP>|<IP/MASK>]Adopts a device if its IP address matches the specified IPv4 address or is within the specified IP address range. Or if the device is a part of the specified subnet.• <START-IP> – Specify the first IPv4 address in the range.• <END-IP> – Specify the last IPv4 address in the range.• <IP/MASK> – Specify the IPv4 subnet and mask to match against the device’s IP address.ipv6 [<START-IP> <END-IP>|<IP/MASK>]Adopts a device if its IP v6 address matches the specified IPv6 address or is within the specified IP address range. Or if the device is a part of the specified subnet.• <START-IP> – Specify the first IPv6 address in the range.• <END-IP> – Specify the last IPv6 address in the range.• <IP/MASK> – Specify the IPv6 subnet and mask to match against the device’s IPv6 address.lldp-match <LLDP-STRING>Matches a substring in a list of Link Layer Discovery Protocol (LLDP) snoop strings (case insensitive). For example, if an access point snooped 3 devices: controller1.example.com, controller2.example.com, and controller3.example.com,'controller1', 'example', 'example.com', are examples of the substrings that will match.LLDP is a vendor neutral link layer protocol that advertises a network device’s identity, capabilities, and neighbors on a local area network.• <LLDP-STRING> – Specify the LLDP string. Devices matching the specified value are adopted.mac <START-MAC> {<END-MAC>}Adopts a device if its MAC address matches the specified MAC address or is within the specified MAC address range• <START-MAC> – Specify the first MAC address in the range. Provide this MAC address if you want to match for a single device.• <END-MAC> – Optional. Specify the last MAC address in the range.model-number <MODEL-NUMBER>Adopts a device if its model number matches <MODEL-NUMBER>• <MODEL-NUMBER> – Specify the model number.rf-domain <RF-DOMAIN-NAME>Adopts a device if its RF Domain matches <RF-DOMAIN-NAME><RF-DOMAIN-NAME> – Specify the RF Domain name. You can use a string alias to specify a RF Domain.Provide the full RF Domain name or an alias (should be existing and configured). Or a template with appropriate substitution tokens, such as '$CDP[1:7]', '$DNS-SUFFIX[1:5]'Please see the Usage Guidelines section Built-in Tokens & Alias for the different types of built in tokens available in the system.Note: Use the built-in string alias or a user-defined string alias. String aliases allow you to configure APs in the same RF Domain as the adopting controller. A string alias maps a name to an arbitrary string value, for example, ‘alias string $DOMAIN test.example_company.com’. In this example, the string-alias $DOMAIN is mapped to the string: test.example_company.com. For more information, see alias.serial-number <SERIAL-NUMBER>Adopts a device if its serial number matches <SERIAL-NUMBER>• <SERIAL-NUMBER> – Specify the serial number.vlan <VLAN-ID> Adopts a device if its VLAN matches <VLAN-ID>• <VLAN-ID> – Specify the VLAN ID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-344.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 109.1.2 auto-create-rfd-templateauto-provisioning-policyEnables auto creation of an RF Domain:• when tokens are used to select the RF Domain to apply to devices matching the adoption criteria, and• the token-specified RF Domain does not exist.During device adoption, if the token-specified RF Domain (configured using the ‘adopt’ rule) is not found, the system auto creates a new RF Domain based on an existing RF Domain template specified using this command. This option is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauto-create-rfd-template <RF-DOMAIN-NAME>Parameters• auto-create-rfd-template <RF-DOMAIN-NAME>ExampleThe following example configures an adopt rule for adopting any AP7532 and applying an RF Domain matching the token “$MODEL[1:5]” to the adopted AP:nx9500-6C8809(config-auto-provisioning-policy-test)#adopt ap7532 precedence 20 rf-domain $MODEL[1:5] anynx9500-6C8809(config-auto-provisioning-policy-test)#show contextauto-provisioning-policy test adopt ap7532 precedence 20 rf-domain $MODEL[1:5] anynx9500-6C8809(config-auto-provisioning-policy-test)#The following example enables auto creation of the following RF Domain using an existing RF Domain ‘rfd-AP’ as template:• RF Domain name “AP-75”: Applicable to any AP7532nx9500-6C8809(config-auto-provisioning-policy-test)#auto-create-rfd-template rfd-APnx9500-6C8809(config-auto-provisioning-policy-test)#show contextauto-provisioning-policy test adopt ap7532 precedence 20 rf-domain $MODEL[1:5] any auto-create-rfd-template rfd-APnx9500-6C8809(config-auto-provisioning-policy-test)#auto-creates-rfd-template <RF-DOMAIN-NAME>Auto creates a new RF Domain based on an existing RF Domain template• <RF-DOMAIN-NAME> – Specify the RF Domain name (should be existing and configured). The new RF Domain created is saved with the token name specified in the ‘adopt’ command.Note: For more information on configuring tokens, see adopt.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-346.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 11As per the above configurations, when an AP7532 comes up for first-time adoption, the system:• Checks for an RF Domain matching the options provided in the ‘adopt’ rule, and if not found• auto creates the RF Domain only if:- A token is specified in the ‘adopt’ rule. For example, $MODEL[1:5], and- the ‘auto-create-rfd-template’ option is configured• Uses the ‘RF Domain’ specified in the auto-create-rfd-template command as a template. Therefore, the specified RF Domain should be existing and configured.• Applies the new RF Domain to the AP.Related Commandsno Disables auto creation of an RF Domain](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-347.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 139.1.4 denyauto-provisioning-policyDefines a deny device adoption ruleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600]deny [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [any|cdp-match|dhcp-option|fqdn|ip|ipv6|lldp-match|mac|model-number|serial-number|vlan]deny [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> anydeny [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|serial-number <SERIAL-NUMBER>|vlan <VLAN-ID>]Parameters• deny[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|aap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> anydeny Adds a deny adoption rule. The rule applies to the selected device types. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, VX9000, and NX9600 series.Note: ‘anyap’ is used in auto provisioning policies to create rules that are applicable to any AP regardless of the model type.precedence <1-10000> Sets the rule precedence. A rule with a lower value has a higher precedence.any Indicates any device. Any device seeking adoption is denied adoption.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-349.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 14• deny[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-1000> [cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|serial-number <SERIAL-NUMBER>|vlan <VLAN-ID>]deny Adds a deny adoption rule. The rule applies to the selected device types. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, VX9000, and NX9600.precedence <1-10000>Sets the rule precedence. A rule with a lower value has a higher precedence.After specifying the rule precedence, specify the match criteria. Devices matching the specified criteria are denied adoption.cdp-match <LOCATION-SUBSTRING>Matches a substring in a list of CDP snoop strings (case insensitive). For example, if an access point snooped 3 devices: controller1.example.com, controller2.example.com and controller3.example.com, 'controller1', ‘example’, 'example.com', are examples of the substrings that will match.• <LOCATION-SUBSTRING> – Specify the value to match. Devices matching the specified value are denied adoption.dhcp-option <DHCP-OPTION>Matches the value found in DHCP vendor option 191 (case insensitive). DHCP vendor option 191 can be setup to communicate various configuration parameters to an AP. The value of the option in a string in the form of tag=value separated by a semicolon, for example 'tag1=value1;tag2=value2;tag3=value3'. The access point includes the value of tag 'rf-domain', if present.• <DHCP-OPTION> – Specify the DHCP option value to match. Devices matching the specified value are denied adoption.fqdn <FQDN> Matches a substring to the FQDN of a device (case insensitive)FQDN is a domain name that specifies its exact location in the DNS hierarchy. It specifies all domain levels, including its top-level domain and the root domain.• <FQDN> – Specify the FQDN. Devices matching the specified value are denied adoption.ip [<START-IP> <END-IP>|<IP/MASK>]Denies adoption if a device's IP address matches the specified IPv4 address or is within the specified IP address range• <START-IP> – Specify the first IPv4 address in the range.• <END-IP> – Specify the last IPv4 address in the range.• <IP/MASK> – Specify the IPv4 subnet and mask to match against the device’s IP address.ipv6 [<START-IP> <END-IP>|<IP/MASK>]Denies adoption if a device's IPv6 address matches the specified IP address or is within the specified IP address range• <START-IP> – Specify the first IPv6 address in the range.• <END-IP> – Specify the last IPv6 address in the range.• <IP/MASK> – Specify the IPv6 subnet and mask to match against the device’s IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-350.png)

![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 179.1.6 redirectauto-provisioning-policyAdds a rule redirecting device adoption to another controller within the system. Devices seeking adoption are redirected to a specified controller based on the redirection parameters specified.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxredirect[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600]redirect [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> controller [<CONTROLLER-IP>|<CONTROLLER-HOSTNAME>] [any|cdp-match|dhcp-option|fqdn|ip|ipv6|level|lldp-match|mac|model-number|pool|serial-number|vlan]redirect [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> controller [<CONTROLLER-IP>|<CONTROLLER-HOSTNAME>|ipv6] anyredirect[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> controller [<CONTROLLER-IP>|<CONTROLLER-HOSTNAME>|ipv6] [cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|level [1|2]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|pool <1-2>|serial-number <SERIAL-NUMBER>|vlan <VLAN-ID>] {upgrade}Parameters• redirect[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> controller [<CONTROLLER-IP>|<CONTROLLER-HOSTNAME>|ipv6] anyredirect Adds a redirect adoption rule. The rule applies to the device type selected. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, VX9000, AP7632, AP7662, NX9600 series.Note: ‘anyap’ is used in auto provisioning policies to create rules that are applicable to any AP regardless of the model type.Note: An adoptee controller, such as RFS4000 and RFS6000 can be redirected to another controller (configured to adopt controllers) with a capacity equal to or higher than its own. For more information, see controller.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-353.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 18• redirect [ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-1000> controller [<CONTROLLER-IP>| <CONTROLLER-HOSTNAME>|ipv6] [cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6[<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|pool <1-2>|serial-number <SERIAL-NUMBER>|vlan <VLAN-ID>] {upgrade}precedence <1-10000>Sets the rule precedence. Rules with lower values get precedence over rules with higher values.controller [<CONTROLLER-IP>|<CONTROLLER-HOSTNAME>|ipv6]Configures the controller to which the adopting devices are redirected. Specify the controller’s IP address or hostname.• <CONTROLLER-IP> – Specifies the controller’s IP address• <CONTROLLER-HOSTNAME> – Specifies the controller’s hostname• ipv6 – Specify the controller’s IPv6 addressany Indicates any device. Any device seeking adoption is redirected.redirect Adds a redirect adoption rule. The rule applies to the device type selected. Specify the device type and assign a precedence to the rule.The different device type options are: anyap, AP6521, AP6522, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, VX9000, and NX9600.Note: An adoptee controller, such as RFS4000, RFS6000, and RFS7000, can be redirected to another controller (configured to adopt controllers) with a capacity equal to or higher than its own. For more information, see controller.precedence <1-10000>Sets the rule precedence. Rules with lower values get precedence over rules with higher values.controller [<CONTROLLER-IP>|<CONTROLLER-HOSTNAME>|ipv6]Configures the controller to which the adopting devices are redirected. Specify the controller’s IP address or hostname.• <CONTROLLER-IP> – Specifies the controller’s IP address• <CONTROLLER-HOSTNAME> – Specifies the controller’s hostname• ipv6 – Specify the controller’s IPV6 address.After specifying the rule precedence and the controller, specify the match criteria.cdp-match <LOCATION-SUBSTRING>Configures the device location to match, based on CDP snoop strings• <LOCATION-SUBSTRING> – Specify the location. Devices matching the specified string are redirected.dhcp-option <DHCP-OPTION>Configures the DHCP options to matchDHCP options identify the vendor and DHCP client functionalities. This information is used by the client to convey to the DHCP server that the client requires extra information in a DHCP response.• <DHCP-OPTION> – Specify the DHCP option value. Devices matching the specified value are redirected.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-354.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 19fqdn <FQDN> Configures the FQDN to matchFQDN is a domain name that specifies its exact location in the DNS hierarchy. It specifies all domain levels, including its top-level domain and the root domain.• <FQDN> – Specify the FQDN. Devices matching the specified value are redirected.ip [<START-IP> <END-IP>|<IP/MASK>]Configures a range of IP addresses and subnet address. Devices having IPv4 addresses within the specified range or are part of the specified subnet are redirected.• <START-IP> – Specify the first IPv4 address in the range.• <END-IP> – Specify the last IPv4 address in the range.• <IP/MASK> – Specify the IPv4 subnet and mask to match against the device’s IP address.level[1|2] Configures the routing level• level1 – Specifies level 1 as local routing• level2 – Specifies level2 as inter-site routingipv6 [<START-IP> <END-IP>|<IP/MASK>]Redirects if a device's IPv6 address matches the specified IP address or is within the specified IP address range• <START-IP> – Specify the first IPv6 address in the range.• <END-IP> – Specify the last IPv6 address in the range.• <IP/MASK> – Specify the IPv6 subnet and mask to match against the device’s IP address.lldp-match <LLDP-STRING>Configures the device location to match, based on LLDP snoop stringsLLDP is a vendor neutral link layer protocol used to advertise a network device’s identity, capabilities, and neighbors on a local area network.• <LLDP-STRING> – Specify the location. Devices matching the specified string are redirected.mac <START-MAC> {<END-MAC>}Configures a single or a range of MAC addresses. Devices matching the specified values are redirected.• <START-MAC> – Specify the first MAC address in the range. Provide only this MAC address to filter a single device.• <END-MAC> – Optional. Specify the last MAC address in the range.model-number <MODEL-NUMBER>Configures the device model number• <MODEL-NUMBER> – Specify the model number. Devices matching the specified model number are redirected.pool <1-2> Configures the controller pool• <1-2> – Configures the pool to which the specified controller belongs to. The default pool value is 1. serial-number <SERIAL-NUMBER>Configures the device’s serial number• <SERIAL-NUMBER> – Specify the serial number. Devices matching the specified serial number are redirected.vlan <VLAN-ID> Configures the VLAN ID• <VLAN-ID> – Specify the VLAN ID. Devices assigned to the specified VLAN are redirected.upgrade Optional. Upgrades APs before redirecting the device for adoption within the system](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-355.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 219.1.7 upgradeauto-provisioning-policyAdds a device upgrade rule to this auto provisioning policy. When applied to a controller, the upgrade rule ensures adopted devices, of the specified type, are upgraded automatically. Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxupgrade[anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600]upgrade [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [any|cdp-match|dhcp-option|fqdn|ip|ipv6|lldp-match|mac|model-number|serial-number|vlan]upgrade [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> anyupgrade [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|rfs7000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|serial-number <SERIAL-NUMBER>|vlan <VLAN-ID>]Parameters• upgrade [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> anyupgrade Adds a device upgrade rule. The rule applies to the device type selected. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, VX9000, and NX9600 series.precedence <1-10000>Sets the rule precedence. Rules with lower values get precedence over rules with higher values.any Indicates any device. Any device, of the selected type, is upgraded.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-357.png)
![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 22• upgrade [anyap|ap6521|ap6522|ap6532|ap6562|ap71xx|ap7502|ap7522|ap7532|ap7562|ap7602|ap7612|ap7622|ap7632|ap7662|ap81xx|ap82xx|ap8432|ap8533|rfs4000|rfs6000|nx5500|nx7500|nx7510|nx7520|nx7530|nx9000|vx9000|nx9600] precedence <1-10000> [cdp-match <LOCATION-SUBSTRING>|dhcp-option <DHCP-OPTION>|fqdn <FQDN>|ip [<START-IP> <END-IP>|<IP/MASK>]|ipv6 [<START-IP> <END-IP>|<IP/MASK>]|lldp-match <LLDP-STRING>|mac <START-MAC> {<END-MAC>}|model-number <MODEL-NUMBER>|serial-number <SERIAL-NUMBER>|vlan <VLAN-ID>]redirect Adds a device upgrade rule. The rule applies to the device type selected. Specify the device type and assign a precedence to the rule.The different device types are: anyap, AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533, RFS4000, RFS6000, NX5500, NX75XX, NX95XX, VX9000, and NX9600 series.Note: ‘anyap’ is used in auto provisioning policies to create rules that are applicable to any AP regardless of the model type.precedence <1-10000>Sets the rule precedence. Rules with lower values get precedence over rules with higher values.cdp-match <LOCATION-SUBSTRING>Configures the device location to match, based on CDP snoop strings• <LOCATION-SUBSTRING> – Specify the location. Devices matching the specified string are upgraded.dhcp-option <DHCP-OPTION>Configures the DHCP options to matchDHCP options identify the vendor and DHCP client functionalities. This information is used by the client to convey to the DHCP server that the client requires extra information in a DHCP response.• <DHCP-OPTION> – Specify the DHCP option value. Devices matching the specified value are upgraded.fqdn <FQDN> Configures the FQDN to matchFQDN is a domain name that specifies its exact location in the DNS hierarchy. It specifies all domain levels, including its top-level domain and the root domain.• <FQDN> – Specify the FQDN. Devices matching the specified value are upgraded.ip [<START-IP> <END-IP>|<IP/MASK>]Configures a range of IP addresses and subnet address. Devices having IPv4 addresses within the specified range or are part of the specified subnet are upgraded.• <START-IP> – Specify the first IPv4 address in the range.• <END-IP> – Specify the last IPv4 address in the range.• <IP/MASK> – Specify the IPv4 subnet and mask to match against the device’s IP address.ipv6 [<START-IP> <END-IP>|<IP/MASK>]Upgrades if a device's IPv6 address matches the specified IP address or is within the specified IP address range• <START-IP> – Specify the first IPv6 address in the range.• <END-IP> – Specify the last IPv6 address in the range.• <IP/MASK> – Specify the IPv6 subnet and mask to match against the device’s IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-358.png)

![AUTO-PROVISIONING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 9 - 249.1.8 noauto-provisioning-policyRemoves a deny, permit, or redirect rule from the specified auto provisioning policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [adopt|auto-create-rfd-template|default-adoption|deny|evaluate-always|redirect|upgrade]no adopt precedence <1-10000>no auto-create-rfd-templateno deny precedence <1-10000>no evaluate-alwaysno default-adoptionno redirect precedence <1-10000>no upgrade precedence <1-10000>Parameters• no <PARAMETERS>ExampleThe following example shows the auto-provisioning-policy ‘test’ settings before the ‘no’ commands are executed:rfs4000-229D58(config-auto-provisioning-policy-test)#show contextauto-provisioning-policy test default-adoption adopt ap81xx precedence 1 profile default-ap81xx vlan 1 deny ap71xx precedence 2 model-number AP7131N deny ap71xx precedence 3 ip 192.168.13.23 192.168.13.23 redirect ap81xx precedence 4 controller 192.168.13.10 ip 192.168.13.25 192.168.13.25 redirect ap81xx precedence 5 controller 192.168.13.10 model-number AP-8132-66040-USrfs4000-229D58(config-auto-provisioning-policy-test)#rfs4000-229D58(config-auto-provisioning-policy-test)#no default-adoptionrfs4000-229D58(config-auto-provisioning-policy-test)#no deny precedence 2rfs4000-229D58(config-auto-provisioning-policy-test)#no deny precedence 3rfs4000-229D58(config-auto-provisioning-policy-test)#no deny precedence 5The following example shows the auto-provisioning-policy ‘test’ settings after the ‘no’ commands are executed:rfs4000-229D58(config-auto-provisioning-policy-test)#show contextauto-provisioning-policy test adopt ap81xx precedence 1 rf-domain TechPubs vlan 1 redirect ap81xx precedence 4 controller 192.168.13.10 ip 192.168.13.25 192.168.13.25rfs4000-229D58(config-auto-provisioning-policy-test)#no <PARAMETERS> Removes a deny, permit, or redirect rule from the specified auto provisioning policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-360.png)
![ASSOCIATION-ACL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 10 - 310.1.1 denyassociation-acl-policyCreates a list of devices denied access to the managed network. Devices are identified by their MAC address. A single MAC address or a range of MAC addresses can be denied access. This command also sets the precedence on how deny rules are applied. Up to a thousand (1000) deny rules can be defined for every association ACL policy. Each rule has a unique sequential precedence value assigned, and is applied to packets on the basis of the precedence value. Lower the precedence, higher is the priority. This results in the rule with the lowest precedence being applied first. No two rules can have the same precedence. The default precedence is 1, prioritize ACLs accordingly as they are added.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny <STARTING-MAC> [<ENDING-MAC>|precedence]deny <STARTING-MAC> precedence <1-1000>deny <STARTING-MAC> <ENDING-MAC> precedence <1-1000>Parameters• deny <STARTING-MAC> precedence <1-1000>• deny <STARTING-MAC> <ENDING-MAC> precedence <1-1000>Usage GuidelinesEvery rule has a unique sequential precedence value. You cannot add two rules with the same precedence. Rules are applied in an increasing order of precedence. That means the rule with precedence 1 is applied first, then the rule with precedence 2 and so on.deny Adds a single device or a set of devices to the deny list<STARTING-MAC> To add a single device, enter its MAC address in the <STARTING-MAC> parameter.precedence <1-1000>Sets a precedence rule. Rules are applied in an increasing order of precedence.• <1-1000> – Specify a precedence value from 1 - 1000.deny Adds a single device or a set of devices to the deny listTo add a set of devices, provide the range of MAC addresses.<STARTING-MAC> Specify the first MAC address in the range.<ENDING-MAC> Specify the last MAC address in the range.precedence <1-1000>Sets a precedence rule. Rules are applied in an increasing order of precedence.• <1-1000> – Specify a value from 1 - 1000.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-364.png)
![ASSOCIATION-ACL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 10 - 510.1.2 noassociation-acl-policyRemoves a deny or permit rule from this association ACL policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [deny|permit]no deny <STARTING-MAC> precedence <1-1000>no deny <STARTING-MAC> <ENDING-MAC> precedence <1-1000>no permit <STARTING-MAC> precedence <1-1000>no permit <STARTING-MAC> <ENDING-MAC> precedence <1-1000>Parameters• no <PARAMETERS>ExampleThe following example shows the association ACL policy ‘test’ settings before the ‘no’ commands is executed:rfs6000-37FABE(config-assoc-acl-test)#show contextassociation-acl-policy test deny 11-22-33-44-55-01 11-22-33-44-55-FF precedence 150 deny 11-22-33-44-56-01 11-22-33-44-56-01 precedence 160rfs6000-37FABE(config-assoc-acl-test)#rfs6000-37FABE(config-assoc-acl-test)#no deny 11-22-33-44-56-01 11-22-33-44-56-FF precedence 160The following example shows the association ACL policy ‘test’ settings after the ‘no’ commands is executed:rfs6000-37FABE(config-assoc-acl-test)#show contextassociation-acl-policy test deny 11-22-33-44-55-01 11-22-33-44-55-FF precedence 150rfs6000-37FABE(config-assoc-acl-test)#no <PARAMETERS> Removes a deny or permit rule from this association ACL policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-366.png)
![ASSOCIATION-ACL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 10 - 610.1.3 permitassociation-acl-policyCreates a list of devices allowed access to the managed network. Devices are permitted access based on their MAC address. A single MAC address or a range of MAC addresses can be specified. This command also sets the precedence on how permit list rules are applied. Up to a thousand (1000) permit rules can be defined for every association ACL policy. Each rule has a unique sequential precedence value assigned, and are applied to packets on the basis of this precedence value. Lower the precedence of a rule, higher is its priority. This results in the rule with the lowest precedence being applied first. No two rules can have the same precedence. The default precedence is 1, so be careful to prioritize ACLs accordingly as they are added.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpermit <STARTING-MAC> [<ENDING-MAC>|precedence]permit <STARTING-MAC> precedence <1-1000>permit <STARTING-MAC> <ENDING-MAC> precedence <1-1000>Parameters• permit <STARTING-MAC> precedence <1-1000>• permit <STARTING-MAC> <ENDING-MAC> precedence <1-1000>Usage GuidelinesEvery rule has a unique sequential precedence value. You cannot add two rules with the same precedence. Rules are applied to packets in an increasing order of precedence. That means the rule with precedence 1 is applied first, then the rule with precedence 2 and so on.permit Adds a single device or a set of devices to the permit list<STARTING-MAC> To add a single device, enter its MAC address in the <STARTING-MAC> parameter.precedence <1-1000>Specifies a rule precedence. Rules are applied in an increasing order of precedence.• <1-1000> – Specify a value from 1 - 1000.permit Adds a single device or a set of devices to the permit listTo add a set of devices, provide the MAC address range.<STARTING-MAC> Specify the first MAC address of the range.<ENDING-MAC> Specify the last MAC address of the range.precedence <1-1000>Specifies a rule precedence. Rules are applied in an increasing order of precedence.• <1-1000> – Specify a value from 1 - 1000.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-367.png)


![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 511.1.1 denyip-access-listCreates a deny rule that rejects packets from a specified source IP and/or to a specified destination IP. You can also use this command to modify an existing deny rule.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny [<NETWORK-SERVICE-ALIAS-NAME>|dns-name|icmp|ip|proto|tcp|udp]deny <NETWORK-SERVICE-ALIAS-NAME> [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|any|host <DEST-HOST-IP>|<NETWORK-GROUP-ALIAS-NAME>] (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}deny dns-name [contains|exact|suffix]deny dns-name [contains|exact|suffix] <WORD> (log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny icmp [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (<ICMP-TYPE> <ICMP-CODE>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny ip [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igmp|igp|ospf|vrrp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny [tcp|udp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|eq <SOURCE-PORT>|host <DEST-HOST-IP>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}NOTE: Use a decimal value representation to implement a permit/deny designation for a packet. The command set for IP ACLs provides the hexadecimal values for each listed EtherType. Use the decimal equivalent of the EtherType listed for any other EtherType.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-373.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 6Parameters• deny <NETWORK-SERVICE-ALIAS-NAME> [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|any|host <DEST-HOST-IP>|<NETWORK-GROUP-ALIAS-NAME>] (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}<NETWORK-SERVICE-ALIAS-NAME>Applies this deny rule to packets based on service protocols and ports specified in the network-service alias• <NETWORK-SERVICE-ALIAS-NAME> – Specify the network-service alias name (should be existing and configured).A network-service alias defines service protocols and ports to match. When used with an ACL, the network-service alias defines the service-specific components of the ACL deny rule.Note: For more information on configuring network-service alias, see alias.<SOURCE-IP/MASK>Specifies the source IP address and mask (A.B.C.D/M) to match. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified network are dropped.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. Packets, matching the service protocols and ports specified in the network-service alias, received from the addresses identified by the network-group alias are dropped.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).A network-group alias defines a single or a range of addresses of devices, hosts, and networks. When used with an ACL, the network-group alias defines the network-specific component of the ACL rule (permit/deny).any Specifies the source as any source IP address. Packets, matching the service protocols and ports specified in the network-service alias, received from any source are dropped.from-vlan <VLAN-ID>Specifies a single VLAN or a range of VLANs as the match criteria. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified VLAN(s) are dropped.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLANs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified host are dropped.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> Specifies the destination IP address and mask (A.B.C.D/M) to match. Packets, matching the service protocols and ports specified in the network-service alias, addressed to the specified network are dropped.any Specifies the destination as any destination IP address. Packets, matching the service protocols and ports specified in the network-service alias, addressed to any destination are dropped.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-374.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 7• deny dns-name [contains|exact|suffix] <WORD> (log,rule-precedence <1-5000>) {(rule-description <LINE>)}host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. Packets, matching the service protocols and ports specified in the network-service alias, addressed to the specified host are dropped.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the destination IP addresses. Packets, matching the service protocols and ports specified in the network-service alias, destined for the addresses identified by the network-group alias are dropped.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).log Logs all deny events matching this entry. If a source and/or destination IP address is matched (i.e. if any specified type of packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.mark [8021p <0-7>|dscp <0-63>]Specifies packets to mark• 8021p <0-7> – Marks packets by modifying 802.1.p VLAN user priority• dscp <0-63> – Marks packets by modifying DSCP TOS bits in the headerrule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).dns-name Applies this deny rule to packets based on dns-names specified in the network-servicecontains Matches any hostname which has this DNS label. (for example, *.test.*)exact Matches an exact hostname as specified in the network-servicesuffix Matches any hostname as suffix (for example, *.test)<WORD> Identifies a specific host (as the source to match) by its domain name. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified host are dropped.log Logs all deny events matching this dns entry. If a dns-name is matched an event is logged.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-375.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 8• deny icmp [<SOURCE-IP/MASK>|<NETWORK-GROUP-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-NAME>|any|host <DEST-HOST-IP>](<ICMP-TYPE> <ICMP-CODE>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).icmp Applies this deny rule to Internet Control Message Protocol (ICMP) packets only<SOURCE-IP/MASK>Specifies the source IP address and mask (A.B.C.D/M) to match. ICMP packets received from the specified sources are dropped.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. ICMP packets received from the addresses identified by the network-group alias are dropped.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).any Specifies the source as any IP address. ICMP packets received from any source are dropped.from-vlan <VLAN-ID>Specifies a single VLAN or a range of VLANs as the match criteria. ICMP packets received from the VLANs identified here are dropped.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLANs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. ICMP packets received from the specified host are dropped.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> Specifies the destination IP address and mask (A.B.C.D/M) to match. ICMP packets addressed to specified destinations are dropped.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the destination IP addresses. ICMP packets destined for addresses identified by the network-group alias are dropped.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).any Specifies the destination as any IP address. ICMP packets addressed to any destination are dropped.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. ICMP packets addressed to the specified host are dropped.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-376.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 9• deny ip [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}<ICMP-TYPE> Defines the ICMP packet typeFor example, an ICMP type 0 indicates it is an ECHO REPLY, and type 8 indicates it is an ECHO.<ICMP-CODE> Defines the ICMP message typeFor example, an ICMP code 3 indicates “Destination Unreachable”, code 1 indicates “Host Unreachable”, and code 3 indicates “Port Unreachable.”Note: After specifying the source and destination IP address(es), the ICMP message type, and the ICMP code, specify the action taken in case of a match.log Logs all deny events matching this entry. If a source and/or destination IP address is matched (i.e. a ICMP packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.• rule-description – Optional. Configures a description for this deny rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).ip Applies this deny rule to IP packets only<SOURCE-IP/MASK>Specifies the source IP address and mask (A.B.C.D/M) to match. IP packets received from the specified networks are dropped.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. IP packets received from the addresses identified by the network-group alias are dropped.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).any Specifies the source as any IP address. IP packets received from any source are dropped.from-vlan <VLAN-ID>Specifies a single VLAN or a range of VLANs as the match criteria. IP packets received from the specified VLANs are dropped.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLAN IDs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. IP packets received from the specified host are dropped.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> Specifies the destination IP address and mask (A.B.C.D/M) to match. IP packets addressed to the specified networks are dropped.any Specifies the destination as any IP address. IP packets addressed to any destination are dropped.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-377.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 10• deny proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igmp|igp|ospf|vrrp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. IP packets addressed to the specified host are dropped.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. IP packets destined for addresses identified by the network-group alias are dropped.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).log Logs all deny events matching this entry. If a source and/or destination IP address is matched (i.e. a IP packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).proto Configures the ACL for additional protocolsAdditional protocols (other than IP, ICMP, TCP, and UDP) must be configured using this parameter<PROTOCOL-NUMBER>Filters protocols using their Internet Assigned Numbers Authority (IANA) protocol number• <PROTOCOL-NUMBER> – Specify the protocol number.<PROTOCOL-NAME>Filters protocols using their IANA protocol name• <PROTOCOL-NAME> – Specify the protocol name.eigrp Identifies the Enhanced Internet Gateway Routing Protocol (EIGRP) protocol (number 88)EIGRP enables routers to maintain copies of neighbors’ routing tables. Routers use this information to determine the fastest route to a destination. When a router fails to find a route in its stored route tables, it sends a query to neighbors who in turn query their neighbors till a route is found. EIGRP also enables routers to inform neighbors of changes in their routing tables.gre Identifies the General Routing Encapsulation (GRE) protocol (number 47)GRE is a tunneling protocol that enables transportation of protocols (IP, IPX, DEC net, etc.) over an IP network. GRE encapsulates the packet at the source and removes the encapsulation at the destination.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-378.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 12• deny [tcp|udp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|eq <SOURCE-PORT>|host <DEST-HOST-IP>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}any Specifies the destination as any IP address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to any destination are dropped.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addresses to the specified host are dropped.• <SOURCE-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the destination IP addresses. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to the destinations identified in the network-group alias are dropped.• <NETWORK-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).Note: After specifying the source and destination IP address(es), specify the action taken in case of a match.log Logs all deny events matching this entry. If a source and/or destination IP address is matched (i.e. a packet (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).tcp Applies this deny rule to TCP packets onlyudp Applies this deny rule to UDP packets only<SOURCE-IP/MASK>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the source IP address and mask (A.B.C.D/M) to match. TCP/UDP packets received from the specified sources are dropped.<NETWORK-GROUP-ALIAS-NAME>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Applies a network-group alias to identify the source IP addresses. TCP/UDP packets received from the VLANs identified here are dropped.• <NETWORK-ALIAS-GROUP-NAME> – Specify the network-group alias name (should be existing and configured).After specifying the source and destination IP address(es), specify the action taken in case of a match.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-380.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 14Usage GuidelinesUse this command to deny traffic between networks/hosts based on the protocol type selected in the access list configuration. The following protocols are supported:•IP•ICMP•TCP•UDP• PROTO (any Internet protocol other than TCP, UDP, and ICMP)eq [<1-65535>|<SERVICE-NAME>||bgp|dns|ftp|ftp-data|gropher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]Identifies a specific destination or protocol port to match• <1-65535> – The destination port is designated by its number• <SERVICE-NAME> – Specifies the service name• bgp – The designated Border Gateway Protocol (BGP) protocol port (179)• dns – The designated Domain Name System (DNS) protocol port (53)• ftp – The designated File Transfer Protocol (FTP) protocol port (21)• ftp-data – The designated FTP data port (20)• gropher – The designated GROPHER protocol port (70)• https – The designated HTTPS protocol port (443)• ldap – The designated Lightweight Directory Access Protocol (LDAP) protocol port (389)• nntp – The designated Network News Transfer Protocol (NNTP) protocol port (119)•ntp – The designated Network Time Protocol (NTP) protocol port (123)• pop3 – The designated POP3 protocol port (110)• sip – The designated Session Initiation Protocol (SIP) protocol port (5060)• smtp – The designated Simple Mail Transfer Protocol (SMTP) protocol port (25)• ssh – The designated Secure Shell (SSH) protocol port (22)• telnet – The designated Telnet protocol port (23)• tftp – The designated Trivial File Transfer Protocol (TFTP) protocol port (69)• www – The designated www protocol port (80)range <START-PORT> <END-PORT>Specifies a range of destination ports• <START-PORT> – Specify the first port in the range.• <END-PORT> – Specify the last port in the range.log Logs all deny events matching this entry. If a source and/or destination IP address or port is matched (i.e. a TCP/UDP packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-382.png)

![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 1711.1.2 disableip-access-listDisables an existing deny or permit rule without removing it from the ACL. A disabled rule is inactive and is not used to filter packets.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdisable [deny|insert|permit]disable [deny|insert [deny|permit]|permit] [<NETWORK-SERVICE-ALIAS-NAME>|dns-name|icmp|ip|proto|tcp|udp]disable [deny|insert [deny|permit]|permit] [<NETWORK-SERVICE-ALIAS-NAME>|dns-name [contains|exact|suffix]|icmp|ip|proto <PROTOCOL-OPTIONS>|tcp|udp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence)Parameters• disable [deny|insert [deny|permit]|permit] [<NETWORK-SERVICE-ALIAS-NAME>|dns-name [contains|exact|suffix]|icmp|ip|proto <PROTOCOL-OPTIONS>|tcp|udp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence)disable [deny|insert [deny|permit]|permit]Disables a deny or permit access rule without removing it from the ACLThis command also enables the insertion of a disable deny or permit rule without overwriting an existing rule in the IP ACL.Note: To disable an existing deny/permit rule, provide the exact values used to configure the deny or permit rule.<NETWORK-SERVICE-ALIAS-NAME>Specifies the network-service alias, identified by the <NETWORK-SERVICE-ALIAS-NAME> keyword, associated with the deny/permit ruledns-name [contains|exact|suffix]Specifies the packets to reject based on the dns-name match. Applies this deny rule to packets based on dns-names specified in the network-serviceicmp Disables a rule applicable to ICMP packets onlyip Disables a rule applicable to IP packets onlyproto <PROTOCOL-OPTIONS>Disables a rule applicable to any Internet protocol other than TCP, UDP, or ICMP packets• <PROTOCOL-OPTIONS> – Identify the Internet protocol using the options available.tcp Disables a rule applicable to TCP packets only](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-385.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 18ExampleThe following example shows the ‘auto-tunnel-acl’ settings before the disable command is executed:rfs6000-37FABE(config-ip-acl-auto-tunnel-acl)#show contextip access-list auto-tunnel-acl permit ip host 200.200.200.99 30.30.30.1/24 rule-precedence 2 permit ip host 200.200.200.99 any rule-precedence 3rfs6000-37FABE(config-ip-acl-auto-tunnel-acl)#rfs6000-37FABE(config-ip-acl-auto-tunnel-acl)#disable permit ip host 200.200.200.99 any rule-precedence 3rfs6000-37FABE(config-ip-acl-auto-tunnel-acl)#The following example shows the ‘auto-tunnel-acl’ settings after the disable command is executed:rfs6000-37FABE(config-ip-acl-auto-tunnel-acl)#show contextip access-list auto-tunnel-acl permit ip host 200.200.200.99 30.30.30.1/24 rule-precedence 2udp Disables a rule applicable to UDP packets onlyNote: After specifying the packet type, specify the source and destination devices and network address(es) to match.<SOURCE-IP/MASK>Specify the source IP address and mask in the A.B.C.D/M format.<NETWORK-GROUP-ALIAS-NAME>Specifies the network-group alias, identified by the <NETWORK-GROUP-ALIAS-NAME> keyword, associated with this deny/permit ruleany Select ‘any’ if the rule is applicable to any source IP address.from-vlan <VLAN-ID>Specify the VLAN IDs.host <SOURCE-HOST-IP>Specify the source host’s exact IP address.<DEST-IP/MASK> Specify the destination IP address and mask in the A.B.C.D/M format.<NETWORK-GROUP-ALIAS-NAME>Specifies the network-group alias, identified by the <NETWORK-GROUP-ALIAS-NAME> keyword, associated with this deny/permit ruleany Select ‘any’ if the rule is applicable to any destination IP address.host <DEST-HOST-IP>Specify the destination host’s exact IP address.log Select log, if the rule has been configured to log records in case of a match.mark [8021p <0-7>|dscp <0-63>]Specifies packets to mark• 8021p <0-7> – Marks packets by modifying 802.1.p VLAN user priority• dscp <0-63> – Marks packets by modifying DSCP TOS bits in the headerrule-precedence <1-5000>Specify the rule precedence. The deny or permit rule with the specified precedence is disabled.Note: To enable a disabled rule, enter the rule again without the ‘disable’ keyword.Note: The no > disable command removes a disabled rule from the ACL.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-386.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 2011.1.3 insertip-access-listEnables the insertion of a rule in an IP ACL without overwriting or replacing an existing rule having the same precedenceThe insert option allows a new rule to be inserted within a IP access list. Consider an IP ACL consisting of rules having precedences 1, 2, 3, 4, 5, and 6. You want to insert a new rule with precedence 4, without overwriting the existing precedence 4 rule. Using the insert option inserts the new rule prior to the existing one. The existing precedence 4 rule’s precedence changes to 5, and the change cascades down the list of rules within the ACL. That means rule 5 becomes rule 6, and rule 6 becomes rule 7.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxinsert [deny|permit] <PARAMETERS> (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}Parameters• insert [deny|permit] <PARAMETERS> (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}NOTE: NOT using insert when creating a new rule having the same precedence as an existing rule, overwrites the existing rule.[deny|permit] Inserts a deny or a permit rule within an IP ACL<PARMETERS> Provide the match criteria for this deny/permit rule. Packets will be filtered based on the criteria set here.For more information on the deny rule, see deny.For more information on the permit rule, see permit.log After specifying the match criteria, specify the action taken for filtered packetsLogs all deny/permit events matching this entry. If a source and/or destination IP address is matched an event is logged.mark [8021p <0-7>|dscp <0-63>]Specifies packets to mark• 8021p <0-7> – Marks packets by modifying 802.1.p VLAN user priority• dscp <0-63> – Marks packets by modifying DSCP TOS bits in the header](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-388.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 2211.1.4 noip-access-listRemoves a deny, permit, or disable ruleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [deny|disable|permit]no [deny|permit] [<NETWORK-SERVICE-ALIAS-NAME>|dns-name|icmp|ip|proto|tcp|udp] <RULE-PARAMETERS>no disable [deny|permit] [<NETWORK-SERVICE-ALIAS-NAME>|dns-name|icmp|ip|proto|tcp|udp] <RULE-PARAMETERS>Parameters• no <PARAMETERS>Usage GuidelinesRemoves an access list control entry. Provide the rule-precedence value when using the no command.ExampleThe following example shows the ACL ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-ip-acl-test)#show contextip access-list test deny proto vrrp any any log rule-precedence 600 deny proto ospf any any log rule-precedence 650rfs6000-37FABE(config-ip-acl-test)#rfs6000-37FABE(config-ip-acl-test)#no deny proto vrrp any any rule-precedence 600rfs6000-37FABE(config-ip-acl-test)#no deny proto ospf any any rule-precedence 650The following example shows the ACL ‘test’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-ip-acl-test)#show contextip access-list testrfs6000-37FABE(config-ip-acl-test)#no <PARAMETERS> Removes a deny, permit, or disable rule](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-390.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 2311.1.5 permitip-access-listCreates a permit rule that marks packets (from a specified source IP and/or to a specified destination IP) for forwarding. You can also use this command to modify an existing permit rule.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpermit [<NETWORK-SERVICE-ALIAS-NAME>|dns-name|icmp|ip|proto|tcp|udp]permit <NETWORK-SERVICE-ALIAS-NAME> [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|any|host <DEST-HOST-IP>|<NETWORK-GROUP-ALIAS-NAME>] (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}permit dns-name [contains|exact|suffix]permit dns-name [contains|exact|suffix] <WORD> (log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit dns-name exact <WORD> (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}permit icmp [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (<ICMP-TYPE> <ICMP-CODE>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit ip [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igmp|igp|ospf|vrrp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit [tcp|udp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|eq <SOURCE-PORT>|host <DEST-HOST-IP>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}NOTE: Use a decimal value representation to implement a permit/deny designation for a packet. The command set for IP ACLs provides the hexadecimal values for each listed EtherType. Use the decimal equivalent of the EtherType listed for any other EtherType.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-391.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 24Parameters• permit <NETWORK-SERVICE-ALIAS-NAME> [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|any|host <DEST-HOST-IP>|<NETWORK-GROUP-ALIAS-NAME>] (log,mark [8021p <0-7>|dscp <0-63>],rule-precedence <1-5000>) {(rule-description <LINE>)}<NETWORK-SERVICE-ALIAS-NAME>Applies this permit rule to packets based on service protocols and ports specified in the network-service alias• <NETWORK-SERVICE-ALIAS-NAME> – Specify the network-service alias name (should be existing and configured).A network-service alias defines service protocols and ports to match. When used with an ACL, the network-service alias defines the service-specific components of the ACL permit rule.Note: For more information on configuring network-service alias, see alias.<SOURCE-IP/MASK>Specifies the source IP address and mask (A.B.C.D/M) to match. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified network are permitted.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. Packets, matching the service protocols and ports specified in the network-service alias, received from the addresses identified by the network-group alias are permitted.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).A network-group alias defines a single or a range of addresses of devices, hosts, and networks. When used with an ACL, the network-group alias defines the network-specific component of the ACL rule (permit/deny).any Specifies the source as any source IP address. Packets, matching the service protocols and ports specified in the network-service alias, received from any source are permitted.from-vlan <VLAN-ID>Specifies a single VLAN or a range of VLANs as the match criteria. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified VLAN(s) are permitted.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLANs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified host are permitted.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> Specifies the destination IP address and mask (A.B.C.D/M) to match. Packets, matching the service protocols and ports specified in the network-service alias, addressed to the specified network are permitted.any Specifies the destination as any destination IP address. Packets, matching the service protocols and ports specified in the network-service alias, addressed to any destination are permitted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-392.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 25• permit dns-name [contains|exact (mark)|suffix] <WORD> (log,rule-precedence <1-5000>) {(rule-description <LINE>)}host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. Packets, matching the service protocols and ports specified in the network-service alias, addressed to the specified host are permitted.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the destination IP addresses. Packets, matching the service protocols and ports specified in the network-service alias, destined for the addresses identified by the network-group alias are permitted.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).log Logs all permit events matching this entry. If a source and/or destination IP address is matched (i.e. if any specified type of packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.mark [8021p <0-7>|dscp <0-63>]Specifies packets to mark• 8021p <0-7> – Marks packets by modifying 802.1.p VLAN user priority• dscp <0-63> – Marks packets by modifying DSCP TOS bits in the headerrule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this permit rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).dns-name Applies this permit rule to packets based on dns-names specified in the network-servicecontains Matches any hostname which has this DNS label. (for example, *.test.*)exact Matches an exact hostname as specified in the network-servicesuffix Matches any hostname as suffix (for example, *.test)<WORD> Identifies a specific host (as the source to match) by its domain name. Packets, matching the service protocols and ports specified in the network-service alias, received from the specified host are forwarded.log Logs all permit events matching this dns entry. If a dns-name is matched an event is logged.mark [8021p <0-7>|dscp <0-63>]Specifies packets to mark• 8021p <0-7> – Marks packets by modifying 802.1.p VLAN user priority• dscp <0-63> – Marks packets by modifying DSCP TOS bits in the header](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-393.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 26• permit icmp [<SOURCE-IP/MASK>|<NETWORK-GROUP-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-NAME>|any|host <DEST-HOST-IP>] (<ICMP-TYPE> <ICMP-CODE>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128characters in length).icmp Applies this permit rule to ICMP packets only<SOURCE-IP/MASK>Specifies the source IP address and mask (A.B.C.D/M) to match. ICMP packets received from the specified sources are permitted.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. ICMP packets received from the addresses identified by the network-group alias are permitted.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).any Specifies the source as any source IP address. ICMP packets received from any source are permitted.from-vlan <VLAN-ID>Specifies a single VLAN or a range of VLANs as the match criteria. ICMP packets received from the VLANs identified here are permitted.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLANs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. ICMP packets received from the specified host are permitted.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> Specifies the destination IP address and mask (A.B.C.D/M) to match. ICMP packets addressed to specified destinations are permitted.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the destination IP addresses. ICMP packets destined for addresses identified by the network-group alias are permitted.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).any Specifies the destination as any destination IP address. ICMP packets addressed to any destination are permitted.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. ICMP packets addressed to the specified host are permitted.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-394.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 27• permit ip [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}<ICMP-TYPE> Defines the ICMP packet typeFor example, an ICMP type 0 indicates it is an ECHO REPLY, and type 8 indicates it is an ECHO.<ICMP-CODE> Defines the ICMP message typeFor example, an ICMP code 3 indicates “Destination Unreachable”, code 1 indicates “Host Unreachable”, and code 3 indicates “Port Unreachable.”Note: After specifying the source and destination IP address(es), the ICMP message type, and the ICMP code, specify the action taken in case of a match.log Logs all permit events matching this entry. If a source and/or destination IP address is matched (i.e. a ICMP packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this permit rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).ip Applies this permit rule to IP packets only<SOURCE-IP/MASK>Specifies the source IP address and mask (A.B.C.D/M) to match. IP packets received from the specified networks are permitted.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. IP packets received from the addresses identified by the network-group alias are permitted.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).any Specifies the source as any source IP address. IP packets received from any source are permitted.from-vlan <VLAN-ID>Specifies a single VLAN or a range of VLANs as the match criteria. IP packets received from the specified VLANs are permitted.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLAN IDs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. IP packets received from the specified host are permitted.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> Specifies the destination IP address and mask (A.B.C.D/M) to match. IP packets addressed to the specified networks are permitted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-395.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 28• permit proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igmp|igp|ospf|vrrp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID>|host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|host <DEST-HOST-IP>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}any Specifies the destination as any destination IP address. IP packets addressed to any destination are permitted.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. IP packets addressed to the specified host are permitted.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the source IP addresses. IP packets destined for addresses identified by the network-group alias are permitted.• <NETWORK-GROUP-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).log Logs all permit events matching this entry. If a source and/or destination IP address is matched (i.e. a IP packet is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this permit rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).proto Configures the ACL for additional protocolsAdditional protocols (other than IP, ICMP, TCP, and UDP) must be configured using this parameter.<PROTOCOL-NUMBER>Filters protocols using their IANA protocol number• <PROTOCOL-NUMBER> – Specify the protocol number.<PROTOCOL-NAME>Filters protocols using their IANA protocol name• <PROTOCOL-NAME> – Specify the protocol name.eigrp Identifies the EIGRP protocol (number 88)EIGRP enables routers to maintain copies of neighbors’ routing tables. Routers use this information to determine the fastest route to a destination. When a router fails to find a route in its stored route tables, it sends a query to neighbors who in turn query their neighbors till a route is found. EIGRP also enables routers to inform neighbors of changes in their routing tables.gre Identifies the GRE protocol (number 47)GRE is a tunneling protocol that enables transportation of protocols (IP, IPX, DEC net, etc.) over an IP network. GRE encapsulates the packet at the source and removes the encapsulation at the destination.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-396.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 30• permit [tcp|udp] [<SOURCE-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|from-vlan <VLAN-ID> |host <SOURCE-HOST-IP>] [<DEST-IP/MASK>|<NETWORK-GROUP-ALIAS-NAME>|any|eq <SOURCE-PORT> |host <DEST-HOST-IP>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}any Specifies the destination as any destination IP address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to any destination are permitted.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addresses to the specified host are permitted.• <SOURCE-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>Applies a network-group alias to identify the destination IP addresses. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to the destinations identified in the network-group alias are permitted.• <NETWORK-ALIAS-NAME> – Specify the network-group alias name (should be existing and configured).Note: After specifying the source and destination IP address(es), specify the action taken in case of a match.log Logs all deny events matching this entry. If a source and/or destination IP address is matched (i.e. a packet (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) is received from a specified IP address and/or is destined for a specified IP address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this permit rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).tcp Applies this permit rule to TCP packets onlyudp Applies this deny rule to UDP packets only<SOURCE-IP/MASK>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the source IP address and mask (A.B.C.D/M) to match. TCP/UDP packets received from the specified sources are permitted.<NETWORK-GROUP-ALIAS-NAME>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Applies a network-group alias to identify the source IP addresses. TCP/UDP packets received from the VLANs identified here are permitted.• <NETWORK-ALIAS-GROUP-NAME> – Specify the network-group alias name (should be existing and configured).After specifying the source and destination IP address(es), specify the action taken in case of a match.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-398.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 31any This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the source as any source IP address. TCP/UDP packets received from any source are permitted.from-vlan <VLAN-ID>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies a single VLAN or a range of VLANs as the match criteria. TCP/UDP packets received from the VLANs identified here are permitted.• <VLAN-ID> – Specify the VLAN ID. To configure a range of VLANs, enter the start and end VLAN IDs separated by a hyphen (for example, 12-20).Note: Use this option with WLANs and port ACLs.host <SOURCE-HOST-IP>Identifies a specific host (as the source to match) by its IP address. TCP/UDP packets received from the specified host are permitted.• <SOURCE-HOST-IP> – Specify the source host’s exact IP address in the A.B.C.D format.<DEST-IP/MASK> This keyword is common to the ‘tcp’ and ‘udp’ parameters.Sets the destination IP address and mask (A.B.C.D/M) to match. TCP/UDP packets addressed to the specified destinations are permitted.any This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the destination as any destination IP address. TCP/UDP packets received from any destination are permitted.eq <SOURCE-PORT>Identifies a specific source port• <SOURCE-PORT> – Specify the exact source port.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IP address. TCP/UDP packets addressed to the specified host are permitted.• <DEST-HOST-IP> – Specify the destination host’s exact IP address in the A.B.C.D format.<NETWORK-GROUP-ALIAS-NAME>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Applies a network-group alias to identify the destination IP addresses. TCP/UDP packets destined to the addresses identified in the network-group alias are permitted.• <NETWORK-ALIAS-GROUP-NAME> – Specify the network-group alias name (should be existing and configured).range <START-PORT> <END-PORT>Specifies a range of source ports• <START-PORT> – Specify the first port in the range.• <END-PORT> – Specify the last port in the range.eq [<1-65535>|<SERVICE-NAME>||bgp|dns|ftp|ftp-data|gropher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]Identifies a specific destination or protocol port to match• <1-65535> – The destination port is designated by its number• <SERVICE-NAME> – Specifies the service name• bgp – The designated Border Gateway Protocol (BGP) protocol port (179)• dns – The designated Domain Name System (DNS) protocol port (53)• ftp – The designated File Transfer Protocol (FTP) protocol port (21)Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-399.png)


![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 3511.2.1 denymac-access-listCreates a deny rule that marks packets (from a specified source MAC and/or to a specified destination MAC) for rejection. You can also use this command to modify an existing deny rule.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}Parameters• deny [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}NOTE: Use a decimal value representation to implement a permit/deny designation for a packet. The command set for MAC ACLs provide the hexadecimal values for each listed EtherType. Use the decimal equivalent of the EtherType listed for any other EtherType.<SOURCE-MAC> <SOURCE-MAC-MASK>Configures the source MAC address and mask to match• <SOURCE-MAC> – Specify the source MAC address to match.• <SOURCE-MAC-MASK> – Specify the source MAC address mask.Packets received from the specified MAC addresses are dropped.any Identifies all devices as the source to deny access. Packets received from any source are dropped.host <SOURCE-HOST-MAC>Identifies a specific host as the source to deny access• <SOURCE-HOST-MAC> – Specify the source host’s exact MAC address to match. Packets received from the specified host are dropped.<DEST-MAC> <DEST-MAC-MASK>Configures the destination MAC address and mask to match• <DEST-MAC> – Specify the destination MAC address to match. • <DEST-MAC-MASK> – Specify the destination MAC address mask to match.Packets addressed to the specified MAC addresses are dropped.any Identifies all devices as the destination to deny access. Packets addressed to any destination are dropped.host <DEST-HOST-MAC>Identifies a specific host as the destination to deny access• <DEST-HOST-MAC> – Specify the destination host’s exact MAC address to match. Packets addressed to the specified host are dropped.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-403.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 36Usage GuidelinesThe deny command disallows traffic based on layer 2 (data-link layer) data. The MAC access list denies traffic from a particular source MAC address or any MAC address. It can also disallow traffic from a list of MAC addresses based on the source mask.The MAC access list can disallow traffic based on the VLAN and EtherType.•ARP•WISP•IP•802.1qdotp1p <0-7> Configures the 802.1p priority value. Sets the service classes for traffic handling• <0-7> – Specify 802.1p priority from 0 - 7.type [8021q|<1-65535>|aarp|appletalk| arp|ip|ipv6|ipx|mint|rarp|wisp]Configures the EtherType valueAn EtherType is a two-octet field in an Ethernet frame that indicates the protocol encapsulated in the payload of the frame. The EtherType values are:• 8021q – Indicates a 802.1q payload (0x8100)• <1-65535> – Indicates the EtherType protocol number• aarp – Indicates the Appletalk Address Resolution Protocol (ARP) payload (0x80F3)• appletalk – Indicates the Appletalk Protocol payload (0x809B)• arp – Indicates the ARP payload (0x0806)• ip – Indicates the Internet Protocol, Version 4 (IPv4) payload (0x0800)• ipv6 – Indicates the Internet Protocol, Version 6 (IPv6) payload (0x86DD)• ipx – Indicates the Novell’s IPX payload (0x8137)• mint – Indicates the MiNT protocol payload (0x8783)• rarp – Indicates the reverse Address Resolution Protocol (ARP) payload (0x8035)• wisp – Indicates the Wireless Internet Service Provider (WISP) payload (0x8783)vlan <1-4095> Configures the VLAN where the traffic is received• <1-4095> – Specify the VLAN ID from 1 - 4095.log Logs all deny events matching this entry. If a source and/or destination MAC address is matched (i.e. a packet is received from a specified MAC address or is destined for a specified MAC address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).NOTE: MAC ACLs always take precedence over IP based ACLs.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-404.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 3811.2.2 disablemac-access-listDisables a MAC deny or permit rule without removing it from the ACL. A disabled rule is inactive and is not used to filter packets.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdisable [deny|insert|permit]disable [deny|permit] [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,mark [8021p <0-7>|dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>) log (rule-precedence <1-5000>) {(rule-description <LINE>)}disable insert [deny|permit]Parameters• disable [deny|permit] [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,mark [8021p <0-7>|dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>) log (rule-precedence <1-5000>) {(rule-description <LINE>)}disable [deny|insert|permit]Disables a deny, insert or permit access rule without removing it from the MAC ACLNote: Provide the exact values used to configure the deny or permit rule that is to be disabled.<SOURCE-MAC> <SOURCE-MAC-MASK>Specifies the source MAC address and mask to match• <SOURCE-MAC> – Specify the source MAC address to match.• <SOURCE-MAC-MASK> – Specify the source MAC address mask.any Select ‘any’ if the rule is applicable to any source MAC addresshost <SOURCE-HOST-MAC>Specify the source host’s exact MAC address<DEST-MAC> <DEST-MAC-MASK>Specifies the destination MAC address and mask to match• <DEST-MAC> – Specify the destination MAC address.• <DEST-MAC-MASK> – Specify the destination MAC address mask.any Select ‘any’ if the rule is applicable to any destination MAC addresshost <DEST-HOST-MAC>Specify the destination host’s exact MAC addresslog The following keyword defines the action taken when a packet matches any or all of the above specified criteria• log – Logs a record. when a packet matches the specified criteria](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-406.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 39ExampleThe following example shows the MAC access list ‘test’ settings before the ‘disable’ command is executed:rfs4000-229D58(config-mac-acl-test)#show contextmac access-list test deny 41-85-45-89-66-77 FF-FF-FF-00-00-00 any vlan 1 rule-precedence 1 deny host 00-01-AE-00-22-11 any rule-precedence 2rfs4000-229D58(config-mac-acl-test)#rfs4000-229D58(config-mac-acl-test)#disable deny host 00-01-AE-00-22-11 any rule-precedence 2The following example shows the MAC access list ‘test’ settings after the ‘disable’ command is executed:rfs4000-229D58(config-mac-acl-test)#show contextmac access-list test deny 41-85-45-89-66-77 FF-FF-FF-00-00-00 any vlan 1 rule-precedence 1 disable deny host 00-01-AE-00-22-11 any rule-precedence 2rfs4000-229D58(config-mac-acl-test)#Related Commandsdotp1p <0-7> Specify the 802.1p priority from 0 - 7.mark [8021p <0-7>|dscp <0-63>]Marks/modifies packets that match the criteria specified here• 8021p <0-7> – Modifies 802.1p VLAN user priority from 0 - 7• dscp <0-63> – Modifies DSCP TOS bits in the IP header from 0 - 63Note: This option is applicable only to the disable > permit MAC ACL rule.type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp]Use the available options to specify the EtherType value.vlan <1-4095> Specify the VLAN ID(s)log Select log, if the rule has been configured to log records in case of a match.rule-precedence <1-5000> {(rule-description <LINE>)}The following keywords are recursive and common to all of the above parameters:• rule-precedence – Provide the precedence assigned to this deny or permit rule.• <1-5000> – Specify a value from 1 - 5000. The rule with the specified precedence isremoved form the MAC ACL.• rule-description <LINE> – Optional. Enter the description configured for this denyor permit rule.no Enables a disabled deny or permit ruledeny Creates a new deny access rule or modifies an existing rulepermit Creates a new permit access rule or modifies an existing rule](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-407.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 4011.2.3 ex3500mac-access-listCreates a MAC ACL deny and/or permit rule, applicable only to the EX3500 switchEach deny or permit rule consists of a set of match criteria and an associated action, which is deny access for the deny rule and allow access for the permit rule. When applied to layer 2 traffic (between a EX3500 switch and the WiNG managed service platform or a WiNG VM interface) every packet is matched against the configured match criteria and in case of a match the packet is dropped or forwarded depending on the rule type.EX3500 devices (EX3524 and EX3548) are layer 2 Gigabit Ethernet switches with either 24 or 48 10/100/1000-BASE-T ports, and four SFP transceiver slots for fiber connectivity. Each 10/100/1000 Mbps port supports both the IEEE 802.3af and IEEE 802.3at-2009 PoE standards. An EX3500 switch has an SNMP-based management agent that provides both in-band and out-of-band management access. The EX3500 switch utilizes an embedded HTTP Web agent and command line interface (CLI), which in spite of being different from that of the WiNG operating system provides WiNG controllers PoE and port management resources.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxex3500 [deny|permit] [all|tagged-eth2|untagged-eth2]ex3500 [deny|permit] [all|tagged-eth2|untagged-eth2] [any |host <SOURCE-MAC>|network <SOURCE-MAC> <SOURCE-MAC-MASK>] [any|host <DEST-MAC>|network <DEST-MAC> <DEST-MAC-MASK>] [ethertype <0-65535|ethertype-mask <0-65535>|ex3500-time-range <TIME-RANGE-NAME>|rule-precedence <1-128>|vlan <1-4094>|vlan-mask <1-4095>]Parameters• ex3500 [deny|permit] [all|tagged-eth2|untagged-eth2] [any|host <SOURCE-MAC>|network <SOURCE-MAC> <SOURCE-MAC-MASK>] [any|host <DEST-MAC>|network <DEST-MAC> <DEST-MAC-MASK>] [ethertype <0-65535|ethertype-mask <0-65535>|ex3500-time-range <TIME-RANGE-NAME>|rule-precedence <1-128>|vlan <1-4094>|vlan-mask <1-4095>]NOTE: To implement the EX3500 MAC ACL rule, apply the MAC ACL directly to a EX3500 device, or to an EX35XX profile. For more information, see access-group.[deny|permit] Creates a deny or permit MAC ACL rule and configures the rule parametersEvery EX3500 MAC ACL rule provides a set of match criteria against which incoming and outgoing packets (to and from an EX3500 device) are matched. In case of a match, the packet is dropped or forwarded depending on the rule type. The packet is dropped in case of a deny rule, and forwarded for an permit rule.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-408.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 41[all|tagged-eth2|untagged-eth2]Specifies the packet type• all – Applies this deny/permit rule to all packets• tagged-eth2 – Applies this deny/permit rule only to tagged Ethernet-2 packets• untagged-eth2 – Applies this deny/permit rule only to untagged Ethernet-2 packetsAfter specifying the packet type, configure the source and/or EX3500 MAC addresses to match.[any|host <SOURCE-MAC>|network <SOURCE-MAC> <SOURCE-MAC-MASK>]Enter the Source MAC addresses• any – Identifies all EX3500 devices as a source to match• host <SOURCE-MAC> – Identifies a specific EX3500 host as the source to match• <SOURCE-MAC> – Specify the source host’s exact MAC address• network <SOURCE-MAC> <SOURCE-MAC-MASK> – Configures a range of MAC addresses as the source to match. Packets received from any of these MAC addresses are dropped.• <SOURCE-MAC> – Specify the source MAC address to match.• <SOURCE-MAC-MASK> – Specify the source MAC bit mask.For a deny rule, packets received from EX3500 device(s) matching the specified MAC address(es) are dropped.For a permit rule, packets received from EX3500 device(s) matching the specified MAC address(es) are forwarded.[any|host <DEST-MAC>|network <DEST-MAC> <DEST-MAC-MASK>]Enter the Destination MAC addresses• any – Identifies all EX3500 devices as a destination to match• host <SOURCE-MAC> – Identifies a specific EX3500 host as the destination to match• <SOURCE-MAC> – Specify the destination host’s exact MAC address• network <SOURCE-MAC> <SOURCE-MAC-MASK> – Configures a range of MAC addresses as the destination to match. Packets addressed to any of these MAC addresses are dropped.• <SOURCE-MAC> – Specify the destination MAC address to match.• <SOURCE-MAC-MASK> – Specify the destination MAC bit mask.For a deny rule, packets addressed to EX3500 device(s) matching the specified MAC address(es) are dropped.For a permit rule, packets addressed to EX3500 device(s) matching the specified MAC address(es) are forwarded.ether-type <0-65535>Configures the Ethertype protocol number. The ether type is a two-octet field within an Ethernet frame. It indicates the protocol encapsulated in the payload of an Ethernet frame.• <0-65535> – Specify the value from 0 - 65535. The default value is 1.ethertype-mask <0-65535>Configures the Ethertype mask• <0-65535> – Specify the value from 0 - 65535. The default value is 1.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-409.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 4311.2.4 insertmac-access-listEnables the insertion of a rule in an MAC ACL without overwriting or replacing an existing rule having the same precedenceThe insert option allows a new rule to be inserted within a MAC ACL. Consider an MAC ACL consisting of rules having precedences 1, 2, 3, 4, 5, and 6. You want to insert a new rule with precedence 4, without overwriting the existing precedence 4 rule. Using the insert option inserts the new rule prior to the existing one. The existing precedence 4 rule’s precedence changes to 5, and the change cascades down the list of rules within the ACL. That means rule 5 becomes rule 6, and rule 6 becomes rule 7.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxinsert [deny|permit] <PARAMETERS> (dot1p <0-7>,mark [8021p <0-7>|dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}Parameters• insert [deny|permit] <PARAMETERS> (dot1p <0-7>,mark [8021p <0-7>|dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>,log,rule-precedence <1-5000>) {(rule-description <LINE>)}NOTE: NOT using insert when creating a new rule having the same precedence as an existing rule, overwrites the existing rule.insert [deny|permit] Inserts a deny or permit rule within an MAC ACL<PARAMETERS> Provide the match criteria for this deny/permit rule. Packets will be filtered based on the criteria set here.For more information on the deny rule, see deny.For more information on the permit rule, see permit.dot1p <0-7> Configures the 802.1p priority value. Sets the service classes for traffic handling• <0-7> – Specify 802.1p priority from 0 - 7.mark [8021p <0-7>|dscp <0-63>]Marks/modifies packets that match the criteria specified here• 8021p <0-7> – Modifies 802.1p VLAN user priority from 0 - 7• dscp <0-63> – Modifies DSCP TOS bits in the IP header from 0 - 63Note: This option is applicable only to the insert > permit MAC ACL rule.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-411.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 44Examplerfs4000-229D58(config-mac-acl-test1)#deny 11-22-33-44-55-66 11-22-33-44-55-77 any rule-precedence 1rfs4000-229D58(config-mac-acl-test1)#deny host B4-C7-99-6D-CD-9B any rule-precedence 2rfs4000-229D58(config-mac-acl-test1)#show contextmac access-list test1 deny 11-22-33-44-55-66 11-22-33-44-55-77 any rule-precedence 1 deny host B4-C7-99-6D-CD-9B any rule-precedence 2rfs4000-229D58(config-mac-acl-test1)#In the following example a new rule is inserted between the rules having precedences 1 and 2. The precedence of the existing precedence ‘2’ rule changes to precedence 3.rfs4000-229D58(config-mac-acl-test1)#insert permit host B4-C7-99-6D-B5-D6 host B4-C7-99-6D-CD-9B rule-precedence 2rfs4000-229D58(config-mac-acl-test1)#show contextmac access-list test1 deny 11-22-33-44-55-66 11-22-33-44-55-77 any rule-precedence 1 permit host B4-C7-99-6D-B5-D6 host B4-C7-99-6D-CD-9B rule-precedence 2 deny host B4-C7-99-6D-CD-9B any rule-precedence 3rfs4000-229D58(config-mac-acl-test1)#type [8021q|<1-65535>|aarp|appletalk| arp|ip|ipv6|ipx|mint|rarp|wisp]Configures the EtherType valueAn EtherType is a two-octet field in an Ethernet frame that indicates the protocol encapsulated in the payload of the frame. The EtherType values are:• 8021q – Indicates a 802.1q payload (0x8100)• <1-65535> – Indicates the EtherType protocol number• aarp – Indicates the Appletalk ARP payload (0x80F3)• appletalk – Indicates the Appletalk Protocol payload (0x809B)• arp – Indicates the ARP payload (0x0806)• ip – Indicates the IPv4 payload (0x0800)• ipv6 – Indicates the IPv6 payload (0x86DD)• ipx – Indicates the Novell’s IPX payload (0x8137)• mint – Indicates the MiNT protocol payload (0x8783)• rarp – Indicates the reverse ARP payload (0x8035)• wisp – Indicates the WISP payload (0x8783)vlan <1-4095> Configures the VLAN where the traffic is received• <1-4095> – Specify the VLAN ID from 1 - 4095.log Logs all deny/permit events matching this entry. If a source and/or destination MAC address is matched (i.e. a packet is received from a specified MAC address or is destined for a specified MAC address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this deny rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-412.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 4511.2.5 nomac-access-listNegates a command or sets its defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [deny|disable|permit]no [deny|permit] [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,mark [8021p <0-7>|dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>) log (rule-precedence <1-5000>) {(rule-description <LINE>)}no disable [deny|permit] <RULE-PARAMETERS>Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-mac-acl-test)#show contextmac access-list test permit host 11-22-33-44-55-66 any log mark 8021p 3 rule-precedence 600 permit host 22-33-44-55-66-77 host 11-22-33-44-55-66 type ip log rule-precedence 610deny any host 33-44-55-66-77-88 log rule-precedence 700rfs6000-37FABE(config-mac-acl-test)#no deny any host 33-44-55-66-77-88 log rule-precedence 700rfs6000-37FABE(config-mac-acl-test)#show contextmac access-list test permit host 11-22-33-44-55-66 any log mark 8021p 3 rule-precedence 600 permit host 22-33-44-55-66-77 host 11-22-33-44-55-66 type ip log rule-precedence 610no <PARAMETERS> Removes a deny or permit rule from the MAC ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-413.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 4611.2.6 permitmac-access-listCreates a permit rule that marks packets (from a specified source MAC and/or to a specified destination MAC) for forwarding. You can also use this command to modify an existing permit rule.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpermit [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,mark [8021p <0-7>,dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>) log (rule-precedence <1-5000>) {(rule-description <LINE>)}Parameters• permit [<SOURCE-MAC> <SOURCE-MAC-MASK>|any|host <SOURCE-HOST-MAC>] [<DEST-MAC> <DEST-MAC-MASK>|any|host <DEST-HOST-MAC>] (dot1p <0-7>,mark [8021p <0-7>,dscp <0-63>],type [8021q|<1-65535>|aarp|appletalk|arp|ip|ipv6|ipx|mint|rarp|wisp],vlan <1-4095>) log (rule-precedence <1-5000>) {(rule-description <LINE>)}NOTE: Use a decimal value representation to implement a permit/deny designation for a packet. The command set for MAC ACLs provide the hexadecimal values for each listed EtherType. Use the decimal equivalent of the EtherType listed for any other EtherType.<SOURCE-MAC> <SOURCE-MAC-MASK>Configures the source MAC address and mask to match• <SOURCE-MAC> – Specify the source MAC address to match.• <SOURCE-MAC-MASK> – Specify the source MAC address mask.Packets addressed to the specified MAC addresses are forwarded.any Identifies all devices as the source to permit access. Packets addressed from any source are forwarded.host <SOURCE-HOST-MAC>Identifies a specific host as the source to permit access• <SOURCE-HOST-MAC> – Specify the source host’s exact MAC address to match. Packets addressed to the specified host are forwarded.<DEST-MAC> <DEST-MAC-MASK>Configures the destination MAC address and mask to match• <DEST-MAC> – Specify the destination MAC address to match. • <DEST-MAC-MASK> – Specify the destination MAC address mask to match.Packets addressed to the specified MAC addresses are forwarded.DEST-MAC-MASK Specifies the destination MAC address mask to matchany Identifies all devices as the destination to permit access. Packets addressed to any destination are forwarded.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-414.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 47host <DEST-HOST-MAC>Identifies a specific host as the destination to permit access• <DEST-HOST-MAC> – Specify the destination host’s exact MAC address to match. Packets addressed to the specified host are forwarded.dotp1p <0-7> Configures the 802.1p priority value. Sets the service classes for traffic handling• <0-7> – Specify 802.1p priority from 0 - 7.mark [8021p <0-7>,dscp <0-63>]Marks/modifies packets that match the criteria specified here• 8021p <0-7> – Modifies 802.1p VLAN user priority from 0 - 7• dscp <0-63> – Modifies DSCP TOS bits in the IP header from 0 - 63Note: This option is applicable only to the MAC ACL permit rule.type [8021q|<1-65535>|aarp|appletalk| arp|ip|ipv6|ipx|mint|rarp|wisp]Configures the EtherType valueAn EtherType is a two-octet field in an Ethernet frame that indicates the protocol encapsulated in the payload of the frame. The EtherType values are:• 8021q – Indicates a 802.1q payload (0x8100)• <1-65535> – Indicates the EtherType protocol number• aarp – Indicates the Appletalk Address Resolution Protocol (ARP) payload (0x80F3)• appletalk – Indicates the Appletalk Protocol payload (0x809B)• arp – Indicates the ARP payload (0x0806)• ip – Indicates the Internet Protocol, Version 4 (IPv4) payload (0x0800)• ipv6 – Indicates the Internet Protocol, Version 6 (IPv6) payload (0x86DD)• ipx – Indicates the Novell’s IPX payload (0x8137)• mint – Indicates the MiNT protocol payload (0x8783)• rarp – Indicates the reverse Address Resolution Protocol (ARP) payload (0x8035)• wisp – Indicates the Wireless Internet Service Provider (WISP) payload (0x8783)vlan <1-4095> Configures the VLAN ID• <1-4095> – Specify the VLAN ID from 1 - 4095.log Logs all permit events matching this entry. If a source and/or destination MAC address is matched (i.e. a packet is addressed to a specified MAC address or is destined for a specified MAC address), an event is logged.rule-precedence <1-5000> rule-description <LINE>The following keywords are recursive and common to all of the above parameters:• rule-precedence – Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.• rule-description – Optional. Configures a description for this permit rule. Provide adescription that uniquely identifies the purpose of this rule (should not exceed 128characters in length).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-415.png)


![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 5011.3.1 denyipv6-access-listCreates a deny rule that rejects packets from a specified IPv6 source and/or to a specified IPv6 destination. You can also use this command to modify an existing deny rule.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny [icmpv6|ipv6|proto|tcp|udp]deny icmpv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] [code [eq <ICMPv6-CODE>|range <STARTING-ICMPv6-CODE> <ENDING-ICMPv6-CODE>]|type [eq <ICMPV6-TYPE>|range <STARTING-ICMPv6-TYPE> <ENDING-ICMPv6-TYPE>]] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny ipv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igp|ospf|vrrp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}deny [tcp|udp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|eq <SOURCE-PORT>|host <DEST-HOST-IPv6>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}Parameters• deny icmpv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] [code [eq <ICMPv6-CODE>|range <STARTING-ICMPv6-CODE> <ENDING-ICMPv6-CODE>]|type [eq <ICMPV6-TYPE>|range <STARTING-ICMPv6-TYPE> <ENDING-ICMPv6-TYPE>]] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}icmpv6 Applies this deny rule to ICMPv6 packets only<SOURCE-IPv6/MASK>Specifies a range of IPv6 source address (network) to match. ICMPv6 packets received from any source in the specified network are dropped.any Specifies the source as any IPv6 address. ICMPv6 packets received from any source are dropped.host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. ICMPv6 packets received from the specified host are dropped.• <SOURCE-HOST-IPv6> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> Specifies a range of IPv6 destination address (network) to match. ICMPv6 packets addressed to any destination within the specified network are dropped.any Specifies the destination as any IPv6 address. ICMPv6 packets addressed to any destination are dropped.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-418.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 51• deny ipv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. ICMPv6 packets addressed to the specified host are dropped.• <DEST-HOST-IPv6> – Specify the destination host’s exact IPv6 address.<ICMPv6-TYPE> [eq|range]Defines the ICMPv6 type field filter• eq – Configures a specific ICMPv6 type. Specify the ICMPv6 type value.• range – Configures a range of ICMPv6 types. Specify the starting and ending ICMPv6 type values.Note: ICMPv6 packets with type field value matching the values specified here are dropped.<ICMPv6-CODE> Defines the ICMPv6 code field filter• eq – Configures a specific ICMPv6 code. Specify the ICMPv6 code value.• range – Configures a range of ICMPv6 code. Specify the starting and ending ICMPv6 code values.Note: ICMPv6 packets with code field value matching the values specified here are dropped.log Logs all deny events matching this entryrule-precedence <1-5000>Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.rule-description <LINE>Optional. Configures a description for this deny rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).ipv6 Applies this deny rule to IPv6 packets only<SOURCE-IPv6/MASK>Specifies a range of IPv6 source address (network) to match. IPv6 packets received from any source in the specified network are dropped.any Specifies the source as any IPv6 address. IPv6 packets received from any source are dropped.host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. IPv6 packets received from the specified host are dropped.• <SOURCE-HOST-IPv6> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> Specifies a range of IPv6 destination address (network) to match. IPv6 packets addressed to any destination within the specified network are dropped.any Specifies the destination as any IPv6 address. IPv6 packets addressed to any destination are dropped.host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. IPv6 packets addressed to the specified host are dropped.• <DEST-HOST-IPv6> – Specify the destination host’s exact IPv6 address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-419.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 52• deny proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igp|ospf|vrrp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}log Logs all deny events matching this entryrule-precedence <1-5000>Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.rule-description <LINE>Optional. Configures a description for this deny rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).proto Configures the ACL for additional protocolsAdditional protocols (other than IP, ICMP, TCP, and UDP) must be configured using this parameter.<PROTOCOL-NUMBER>Filters protocols using their Internet Assigned Numbers Authority (IANA) protocol number• <PROTOCOL-NUMBER> – Specify the protocol number.<PROTOCOL-NAME>Filters protocols using their IANA protocol name• <PROTOCOL-NAME> – Specify the protocol name.eigrp Identifies the EIGRP protocol (number 88)EIGRP enables routers to maintain copies of neighbors’ routing tables. Routers use this information to determine the fastest route to a destination. When a router fails to find a route in its stored route tables, it sends a query to neighbors who in turn query their neighbors till a route is found. EIGRP also enables routers to inform neighbors of changes in their routing tables.gre Identifies the GRE protocol (number 47)GRE is a tunneling protocol that enables transportation of protocols (IP, IPX, DEC net, etc.) over an IP network. GRE encapsulates the packet at the source and removes the encapsulation at the destination.igp Identifies any private internal gateway (primarily used by CISCO for their IGRP) (number 9)IGP enables exchange of information between hosts and routers within a managed network. The most commonly used IGP protocols are: RIP and OSPF.ospf Identifies the OSPF protocol (number 89)OSPF is a link-state IGP. OSPF routes IP packets within a single routing domain (autonomous system), like an enterprise LAN. OSPF gathers link state information from neighbor routers and constructs a network topology. The topology determines the routing table presented to the Internet Layer which makes routing decisions based solely on the destination IP address found in IP packets.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-420.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 53• deny [tcp|udp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|eq <SOURCE-PORT>|host <DEST-HOST-IPv6>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}vrrp Identifies the VRRP protocol (number 112)VRRP allows a pool of routers to be advertized as a single virtual router. This virtual router is configured by hosts as their default gateway. VRRP elects a master router, from this pool, and assigns it a virtual IP address. The master router routes and forwards packets to hosts on the same subnet. When the master router fails, one of the backup routers is elected as the master and its IP address is mapped to the virtual IP address.<SOURCE-IPv6/MASK>Specifies a range of IPv6 source address (network) to match. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) received from any source in the specified network are dropped.any Specifies the source as any IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) received from any source are dropped.host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) received from the specified host are dropped.• <SOURCE-HOST-IP> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> Specifies a range of IPv6 destination address (network) to match. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to any destination within the specified network are dropped.any Specifies the destination as any IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to any destination are dropped.host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to the specified host are dropped.• <DEST-HOST-IPv6> – Specify the destination host’s exact IPv6 address.log Logs all deny events matching this entryrule-precedence <1-5000>Assigns a precedence for this deny rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.rule-description <LINE>Optional. Configures a description for this deny rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).tcp Applies this deny rule to TCP packets onlyudp Applies this deny rule to UDP packets only<SOURCE-IPv6/MASK>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies a range of IPv6 source address (network) to match. TCP/UDP packets received from any source in the specified network are dropped.any This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the source as any IPv6 address. TCP/UDP packets received from any source are dropped.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-421.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 54host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. TCP/UDP packets received from the specified host are dropped.• <SOURCE-HOST-IP> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies a range of IPv6 destination address (network) to match. TCP/UDP packets addressed to any destination within the specified network are dropped.any This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the destination as any destination IPv6 address. TCP/UDP packets received from any destination are dropped.eq <SOURCE-PORT>Identifies a specific source port• <SOURCE-PORT> – Specify the exact source port.host <DEST-HOST-IP>Identifies a specific host (as the destination to match) by its IPv6 address. TCP/UDP packets addressed to the specified host are dropped.• <DEST-HOST-IP> – Specify the destination host’s exact IP address.range <START-PORT> <END-PORT>Specifies a range of source ports• <START-PORT> – Specify the first port in the range.• <END-PORT> – Specify the last port in the range.eq [<1-65535>|<SERVICE-NAME>||bgp|dns|ftp|ftp-data|gropher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]Identifies a specific destination or protocol port to match• <1-65535> – The destination port is designated by its number• <SERVICE-NAME> – Specifies the service name• bgp – The designated BGP protocol port (179)• dns – The designated DNS protocol port (53)• ftp – The designated FTP protocol port (21)• ftp-data – The designated FTP data port (20)• gropher – The designated GROPHER protocol port (70)• https – The designated HTTPS protocol port (443)• ldap – The designated LDAP protocol port (389)• nntp – The designated NNTP protocol port (119)• ntp – The designated NTP protocol port (123)• pop3 – The designated POP3 protocol port (110)• sip – The designated SIP protocol port (5060)• smtp – The designated SMTP protocol port (25)• ssh – The designated SSH protocol port (22)• telnet – The designated Telnet protocol port (23)• tftp – The designated TFTP protocol port (69)• www – The designated www protocol port (80)range <START-PORT> <END-PORT>Specifies a range of destination ports• <START-PORT> – Specify the first port in the range.• <END-PORT> – Specify the last port in the range.log Logs all deny events matching this entry](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-422.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 5611.3.2 noipv6-access-listRemoves a deny or permit ruleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [deny|permit]no [deny|permit] [icmpv6|ipv6|proto|tcp|udp] <RULE-PARAMETERS> {(rule-description <LINE>)}Parameters• no <PARAMETERS>ExampleThe following example shows the ACL ‘test’ settings before the ‘no’ commands are executed:rfs6000-81742D(config-ipv6-acl-test)#show contextipv6 access-list test deny icmpv6 any any type eq destination-unreachable code eq router-renumbering-command log rule-precedence 1 permit proto gre any any log rule-precedence 2rfs6000-81742D(config-ipv6-acl-test)#rfs6000-81742D(config-ipv6-acl-test)#no deny icmpv6 any any type eq 1 log rule-precedence 1rfs6000-81742D(config-ipv6-acl-test)#show contextipv6 access-list test permit proto gre any any log rule-precedence 2rfs6000-81742D(config-ipv6-acl-test)#no <PARAMETERS> Removes a deny or permit rule from the selected IPv6 access list](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-424.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 5711.3.3 permitipv6-access-listCreates a permit rule that accepts packets from a specified IPv6 source and/or to a specified IPv6 destination. You can also use this command to modify an existing permit rule.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpermit [icmpv6|ipv6|proto|tcp|udp]permit icmpv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] [code [eq <ICMPv6-CODE>|range <STARTING-ICMPv6-CODE> <ENDING-ICMPv6-CODE>]|type [eq <ICMPV6-TYPE>|range <STARTING-ICMPv6-TYPE> <ENDING-ICMPv6-TYPE>]] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit ipv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igp|ospf|vrrp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}permit [tcp|udp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|eq <SOURCE-PORT>|host <DEST-HOST-IPv6>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}Parameters• permit icmpv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] [code [eq <ICMPv6-CODE>|range <STARTING-ICMPv6-CODE> <ENDING-ICMPv6-CODE>]|type [eq <ICMPV6-TYPE>|range <STARTING-ICMPv6-TYPE> <ENDING-ICMPv6-TYPE>]] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}icmpv6 Applies this permit rule to ICMPv6 packets only<SOURCE-IPv6/MASK>Specifies a range of IPv6 source address (network) to match. ICMPv6 packets received from any source in the specified network are accepted.any Specifies the source as any IPv6 address. ICMPv6 packets received from any source are accepted.host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. ICMPv6 packets received from the specified host are accepted.• <SOURCE-HOST-IPv6> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> Specifies a range of IPv6 destination address (network) to match. ICMPv6 packets addressed to any destination within the specified network are accepted.any Specifies the destination as any IPv6 address. ICMPv6 packets addressed to any destination are accepted.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-425.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 58• permit ipv6 [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. ICMPv6 packets addressed to the specified host are accepted.• <DEST-HOST-IPv6> – Specify the destination host’s exact IPv6 address.<ICMPv6-TYPE> [eq|range]Defines the ICMPv6 type field filter• eq – Configures a specific ICMPv6 type. Specify the ICMPv6 type value.• range – Configures a range of ICMPv6 types. Specify the starting and ending ICMPv6 type values.Note: ICMPv6 packets with type field value matching the values specified here are forwarded.<ICMPv6-CODE> Defines the ICMPv6 code field filter• eq – Configures a specific ICMPv6 code. Specify the ICMPv6 code value.• range – Configures a range of ICMPv6 code. Specify the starting and ending ICMPv6 code values.Note: ICMPv6 packets with code field value matching the values specified here are forwarded.log Logs all permit events matching this entryrule-precedence <1-5000>Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.rule-description <LINE>Optional. Configures a description for this permit rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).ipv6 Applies this permit rule to IPv6 packets only<SOURCE-IPv6/MASK>Specifies a range of IPv6 source address (network) to match. IPv6 packets received from any source in the specified network are forwarded.any Specifies the source as any IPv6 address. IPv6 packets received from any source are forwarded.host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. IPv6 packets received from the specified host are forwarded.• <SOURCE-HOST-IPv6> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> Specifies a range of IPv6 destination address (network) to match. IPv6 packets addressed to any destination within the specified network are forwarded.any Specifies the destination as any IPv6 address. IPv6 packets addressed to any destination are forwarded.host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. IPv6 packets addressed to the specified host are forwarded.• <DEST-HOST-IPv6> – Specify the destination host’s exact IPv6 address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-426.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 59• permit proto [<PROTOCOL-NUMBER>|<PROTOCOL-NAME>|eigrp|gre|igp|ospf|vrrp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|host <DEST-HOST-IPv6>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}log Logs all permit events matching this entryrule-precedence <1-5000>Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.rule-description <LINE>Optional. Configures a description for this permit rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).proto Configures the ACL for additional protocolsAdditional protocols (other than IP, ICMP, TCP, and UDP) must be configured using this parameter.<PROTOCOL-NUMBER>Filters protocols using their Internet Assigned Numbers Authority (IANA) protocol number• <PROTOCOL-NUMBER> – Specify the protocol number.<PROTOCOL-NAME>Filters protocols using their IANA protocol name• <PROTOCOL-NAME> – Specify the protocol name.eigrp Identifies the EIGRP protocol (number 88)EIGRP enables routers to maintain copies of neighbors’ routing tables. Routers use this information to determine the fastest route to a destination. When a router fails to find a route in its stored route tables, it sends a query to neighbors who in turn query their neighbors till a route is found. EIGRP also enables routers to inform neighbors of changes in their routing tables.gre Identifies the GRE protocol (number 47)GRE is a tunneling protocol that enables transportation of protocols (IP, IPX, DEC net, etc.) over an IP network. GRE encapsulates the packet at the source and removes the encapsulation at the destination.igp Identifies any private internal gateway (primarily used by CISCO for their IGRP) (number 9)IGP enables exchange of information between hosts and routers within a managed network. The most commonly used IGP protocols are: RIP and OSPF.ospf Identifies the OSPF protocol (number 89)OSPF is a link-state IGP. OSPF routes IP packets within a single routing domain (autonomous system), like an enterprise LAN. OSPF gathers link state information from neighbor routers and constructs a network topology. The topology determines the routing table presented to the Internet Layer which makes routing decisions based solely on the destination IP address found in IP packets.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-427.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 60• permit [tcp|udp] [<SOURCE-IPv6/MASK>|any|host <SOURCE-HOST-IPv6>] [<DEST-IPv6/MASK>|any|eq <SOURCE-PORT>|host <DEST-HOST-IPv6>|range <START-PORT> <END-PORT>] [eq [<1-65535>|<SERVICE-NAME>|bgp|dns|ftp|ftp-data|gopher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]|range <START-PORT> <END-PORT>] (log,rule-precedence <1-5000>) {(rule-description <LINE>)}vrrp Identifies the VRRP protocol (number 112)VRRP allows a pool of routers to be advertized as a single virtual router. This virtual router is configured by hosts as their default gateway. VRRP elects a master router, from this pool, and assigns it a virtual IP address. The master router routes and forwards packets to hosts on the same subnet. When the master router fails, one of the backup routers is elected as the master and its IP address is mapped to the virtual IP address.<SOURCE-IPv6/MASK>Specifies a range of IPv6 source address (network) to match. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) received from any source in the specified network are forwarded.any Specifies the source as any IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) received from any source are forwarded.host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) received from the specified host are forwarded.• <SOURCE-HOST-IPv6> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> Specifies a range of IPv6 destination address (network) to match. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to any destination within the specified network are forwarded.any Specifies the destination as any IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to any destination are forwarded.host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. Packets (EIGRP, GRE, IGMP, IGP, OSPF, or VRRP) addressed to the specified host are forwarded.• <DEST-HOST-IPv6> – Specify the destination host’s exact IPv6 address.log Logs all permit events matching this entryrule-precedence <1-5000>Assigns a precedence for this permit rule• <1-5000> – Specify a value from 1 - 5000.Note: Lower the precedence higher is the priority. A rule with precedence 3 gets priority over a rule with precedence 10.rule-description <LINE>Optional. Configures a description for this permit rule. Provide a description that uniquely identifies the purpose of this rule (should not exceed 128 characters in length).tcp Applies this permit rule to TCP packets onlyudp Applies this permit rule to UDP packets only<SOURCE-IPv6/MASK>This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies a range of IPv6 source address (network) to match. TCP/UDP packets received from any source in the specified network are forwarded.any This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the source as any IPv6 address. TCP/UDP packets received from any source are forwarded.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-428.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 61host <SOURCE-HOST-IPv6>Identifies a specific host (as the source to match) by its IPv6 address. TCP/UDP packets received from the specified host are forwarded.• <SOURCE-HOST-IPv6> – Specify the source host’s exact IPv6 address.<DEST-IPv6/MASK> This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies a range of IPv6 destination address (network) to match. TCP/UDP packets addressed to any destination within the specified network are forwarded.any This keyword is common to the ‘tcp’ and ‘udp’ parameters.Specifies the destination as any destination IPv6 address. TCP/UDP packets received from any destination are forwarded.eq <SOURCE-PORT>Identifies a specific source port• <SOURCE-PORT> – Specify the exact source port.host <DEST-HOST-IPv6>Identifies a specific host (as the destination to match) by its IPv6 address. TCP/UDP packets addressed to the specified host are forwarded.• <DEST-HOST-IPv6> – Specify the destination host’s exact IP address.range <START-PORT> <END-PORT>Specifies a range of source ports• <START-PORT> – Specify the first port in the range.• <END-PORT> – Specify the last port in the range.eq [<1-65535>|<SERVICE-NAME>||bgp|dns|ftp|ftp-data|gropher|https|ldap|nntp|ntp|pop3|sip|smtp|ssh|telnet|tftp|www]Identifies a specific destination or protocol port to match• <1-65535> – The destination port is designated by its number• <SERVICE-NAME> – Specifies the service name• bgp – The designated BGP protocol port (179)• dns – The designated DNS protocol port (53)• ftp – The designated FTP protocol port (21)• ftp-data – The designated FTP data port (20)• gropher – The designated GROPHER protocol port (70)• https – The designated HTTPS protocol port (443)• ldap – The designated LDAP protocol port (389)• nntp – The designated NNTP protocol port (119)• ntp – The designated NTP protocol port (123)• pop3 – The designated POP3 protocol port (110)• sip – The designated SIP protocol port (5060)• smtp – The designated SMTP protocol port (25)• ssh – The designated SSH protocol port (22)• telnet – The designated Telnet protocol port (23)• tftp – The designated TFTP protocol port (69)• www – The designated www protocol port (80)range <START-PORT> <END-PORT>Specifies a range of destination ports• <START-PORT> – Specify the first port in the range.• <END-PORT> – Specify the last port in the range.log Logs all permit events matching this entry](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-429.png)

![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 6411.4.1 denyip-snmp-access-listCreates a deny SNMP MIB object traffic rule. Use this command to specify the match criteria based on which SNMP traffic is deniedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdeny [<IP/M>|any|host <IP>]Parameters• deny [<IP/M>|any|host <IP>]Examplerfs6000-81742D(config-ip-snmp-acl-test)#deny 192.168.13.0/24rfs6000-81742D(config-ip-snmp-acl-test)#show contextip snmp-access-list test deny 192.168.13.0/24rfs6000-81742D(config-ip-snmp-acl-test)#Related Commandsdeny [<IP/M>|any|host <IP>]Configures the match criteria for this deny rule• <IP/M> – Specifies a network address and mask in the A.B.C.D/M format. Packets received or destined for this network are dropped• any – Specifies the match criteria as any. Packets received or destined from any address are dropped• host <IP> – Identifies a host by its IP address. Packets received or destined for this host are droppedno Removes this deny rule form the IP SNMP ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-432.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 6511.4.2 permitip-snmp-access-listCreates a permit SNMP MIB object traffic rule. Use this command to specify the match criteria based on which SNMP traffic is permitted.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpermit [<IP/M>|any|host <IP>]Parameters• permit [<IP/M>|any|host <IP>]Examplerfs6000-81742D(config-ip-snmp-acl-test)#permit host 192.168.13.13rfs6000-81742D(config-ip-snmp-acl-test)#show contextip snmp-access-list test permit host 192.168.13.13 deny 192.168.13.0/24rfs6000-81742D(config-ip-snmp-acl-test)#Related Commandspermit [<IP/M>|any|host <IP>]Configures the match criteria for this permit rule• <IP/M> – Specifies a network address and mask in the A.B.C.D/M format. Packets received or destined for this network are forwarded• any – Specifies the match criteria as any. Packets received or destined from any address are forwarded• host <IP> – Identifies a host by its IP address. Packets received or destined for this host are forwardedno Removes this permit rule form the IP SNMP ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-433.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 6611.4.3 noip-snmp-access-listRemoves a deny or permit rule from the IP SNMP ACL. Use this command to remove IP SNMP ACL as they become obsolete for filtering network access permissions.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [deny|permit] [<IP/M>|any|host <IP>]Parameters• no <PARAMETERS>Examplerfs6000-81742D(config-ip-snmp-acl-test)#show contextip snmp-access-list test permit host 192.168.13.13 deny 192.168.13.0/24rfs6000-81742D(config-ip-snmp-acl-test)#rfs6000-81742D(config-ip-snmp-acl-test)#no permit host 192.168.13.13rfs6000-81742D(config-ip-snmp-acl-test)#show contextip snmp-access-list test deny 192.168.13.0/24rfs6000-81742D(config-ip-snmp-acl-test)#no <PARAMETERS> Removes deny and/or permit access rule from this IP SNMP ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-434.png)

![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 6811.5.1 denyex3500-ext-access-listCreates a deny ACL rule that filters packets based on the source and/or destination IPv4 address, and other specified criteria. You can also use this command to modify an existing deny rule.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxdeny [<0-255>|tcp|udp] [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] [<DEST-NETWORK-IP/MASK>|any|host <DEST-HOST-IP>] [control-flag <0-63>|destination-port <0-65535>|destination-port-bitmark <0-65535>|dscp <0-63>|ex3500-time-range <TIME-RANGE-NAME>|ip-precedence <0-63>|rule-precedence <1-128>|source-port <0-65535>|source-port-bitmark <0-65535>]Parameters• deny [<0-255>|tcp|udp] [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] [<DEST-NETWORK-IP/MASK>|any|host <DEST-HOST-IP>] [control-flag <0-63>|destination-port <0-65535>|destination-port-bitmark <0-65535>|dscp <0-63>|ex3500-time-range <TIME-RANGE-NAME>|ip-precedence <0-63>|rule-precedence <1-128>|source-port <0-65535>|source-port-bitmark <0-65535>]deny [<0-255>|tcp|udp]Creates a deny rule and identifies the protocol type. This deny rule is applied only to packets matching the protocol specified here.• <0-255> – Identifies the protocol from its number. Specify the protocol number from 0 - 255.• tcp – Configures the protocol as TCP• udp – Configures the protocol as UDP[<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>]Specifies the source IP address as any, host, or network• <SOURCE-NETWORK-IP/MASK> – Configures a network as the source. Provide the network’s IPv4 address along with the mask.• host <SOURCE-HOST-IP> – Configures a single device as the source. Provide the host device’s IPv4 address.• any – Specifies that the source can be any device[<DEST-NETWORK-IP/MASK>|any|host <DEST-HOST-IP>]Specifies the destination IP address as any, host, or network. • <DEST-NETWORK-IP/MASK> – Configures a network as the destination. Provide the network’s IPv4 address along with the mask• host <DEST-HOST-IP> – Configures a single device as the destination. Provide the host device’s IPv4 address• any – Specifies that the destination can be any devicecontrol-flag <0-63> Configures the decimal number (representing a bit string) that specifies the control flag bits in byte 14 of the TCP header<0-63> – Specify a value from 0 - 63.Note: Control flags can be used only in ACLs designed to filter TCP traffic.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-436.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 7111.5.2 permitex3500-ext-access-listCreates a permit ACL rule that filters packets based on the source and/or destination IPv4 address, and other specified criteria. You can also use this command to modify an existing permit rule.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxpermit [<0-255>|tcp|udp] [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] [<DEST-NEWORK-IP/MASK>|any|host <DEST-HOST-IP>] [control-flag <0-63>|destination-port <0-65535>|destination-port-bitmark <0-65535>|dscp <0-63>|ex3500-time-range <TIME-RANGE-NAME>|ip-precedence <0-63>|rule-precedence <1-128>|source-port <0-65535>|source-port-bitmark <0-65535>]Parameters• permit [<0-255>|tcp|udp] [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] [<DEST-NEWORK-IP/MASK>|any|host <DEST-HOST-IP>] [control-flag <0-63>|destination-port <0-65535>|destination-port-bitmark <0-65535>|dscp <0-63>|ex3500-time-range <TIME-RANGE-NAME>|ip-precedence <0-63>|rule-precedence <1-128>|source-port <0-65535>|source-port-bitmark <0-65535>]permit [<0-255>|tcp|udp]Creates a permit rule and identifies the protocol type. This permit rule is applied only to packets matching the protocol specified here.• <0-255> – Identifies the protocol from its number. Specify the protocol number from 0 - 255.• tcp – Configures the protocol as TCP• udp – Configures the protocol as UDP[<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>]Specifies the source IP address as any, host, or network. • <SOURCE-NETWORK-IP/MASK> – Configures a network as the source. Provide the network’s IPv4 address along with the mask.• host <SOURCE-HOST-IP> – Configures a single device as the source. Provide the host device’s IPv4 address.• any – Specifies that the source can be any device[<DEST-NETWORK-IP/MASK>|any|host <DEST-HOST-IP>]Specifies the destination IP address as any, host, or network. • <DEST-NETWORK-IP/MASK> – Configures a network as the destination. Provide the network’s IPv4 address along with the mask.• host <DEST-HOST-IP> – Configures a single device as the destination. Provide the host device’s IPv4 address.• any – Specifies that the destination can be any device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-439.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 7411.5.3 noex3500-ext-access-listRemoves a deny or permit access rule from this IPv4 EX3500 extended ACLSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxno [deny|permit] [<0-255>|tcp|udp] [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] [<DEST-NETWORK-IP/MASK>|any|host <DEST-HOST-IP>] [control-flag <0-63>|destination-port <0-65535>|destination-port-bitmark <0-65535>|dscp <0-63>|ex3500-time-range <TIME-RANGE-NAME>|ip-precedence <0-63>|rule-precedence <1-128>|source-port <0-65535>|source-port-bitmark <0-65535>]Parameters• no <PARAMETERS>Usage GuidelinesThe keyword ‘control-flag <0-63>’ is only applicable to ACL rules filtering TCP traffic.ExampleThe following example shows the IPv4 EX3500 extended ACL ‘test’ settings before the ‘no’ commands are executed:nx9500-6C8809(config-ip-ex3500-ext-acl-test)#show contextip ex3500-ext-access-list test deny tcp 192.168.14.0/24 host 192.168.13.13 rule-precedence 1 permit tcp 192.168.14.0/24 any control-flag 16 rule-precedence 2nx9500-6C8809(config-ip-ex3500-ext-acl-test)#nx9500-6C8809(config-ip-ex3500-ext-acl-test)#no permit tcp 192.168.14.0/24 any control-flag 16 rule-precedence 2The following example shows the IPv4 EX3500 extended ACL ‘test’ settings after the ‘no’ commands are executed:nx9500-6C8809(config-ip-ex3500-ext-acl-test)#show contextip ex3500-ext-access-list test deny tcp 192.168.14.0/24 host 192.168.13.13 rule-precedence 1nx9500-6C8809(config-ip-ex3500-ext-acl-test)#no <PARAMETERS> Removes a deny or permit access rule based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-442.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 7611.6.1 denyex3500-std-access-listCreates a deny rule that rejects packets from a specified source or sources. The source can be a single device or a range of devices within a specified network. Use this command to also edit an existing deny rule.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxdeny [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] {ex3500-time-range <TIME-RANGE-NAME>}Parameters• deny [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] {ex3500-time-range <TIME-RANGE-NAME>}Examplenx9500-6C8809(config-ip-ex3500-std-acl-test)#deny 192.168.14.0/24nx9500-6C8809(config-ip-ex3500-std-acl-test)#show contextip ex3500-std-access-list test deny 192.168.13.0/24nx9500-6C8809(config-ip-ex3500-std-acl-test)#Related Commandsdeny [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>]Creates a deny rule that rejects packets from a specified source or a network. Use one of the following options to specify the source: any, host, or network.• <SOURCE-NETWORK-IP/MASK> – Configures a network as the source. Provide the network’s IPv4 address along with the mask.• host <SOURCE-HOST-IP> – Configures a single device as the source. Provide the host device’s IPv4 address.• any – Specifies that the source can be any deviceex3500-time-range <TIME-RANGE-NAME>Optional. Applies a periodic or absolute time range to this deny rule• <TIME-RANGE-NAME> – Specify the time range name (should be existing and configured). The ACL is triggered during the time period configured in the specified EX3500 time range. For information on configuring EX3500 time-range, see ex3500.no Removes a specified deny access rule from this IPv4 EX3500 standard ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-444.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 7711.6.2 permitex3500-std-access-listCreates a permit rule that allows packets from a specified source or sources. The source can be a single device or a range of devices within a specified network. Use this command to also edit an existing permit rule.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxpermit [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] {ex3500-time-range <TIME-RANGE-NAME>}Parameters• permit [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>] {ex3500-time-range <TIME-RANGE-NAME>}Examplenx9500-6C8809(config-ip-ex3500-std-acl-test)#permit host 192.168.13.13 ex3500-time-range EX3500_TimeRange_01nx9500-6C8809(config-ip-ex3500-std-acl-test)#show contextip ex3500-std-access-list test deny 192.168.14.0/24 permit host 192.168.13.13 ex3500-time-range EX3500_TimeRange_01nx9500-6C8809(config-ip-ex3500-std-acl-test)#Related Commandspermit [<SOURCE-NETWORK-IP/MASK>|any|host <SOURCE-HOST-IP>]Creates a permit rule that allows packets from a specified source or a network. Use one of the following options to specify the source: any, host, or network.• <SOURCE-NETWORK-IP/MASK> – Configures a network as the source. Provide the network’s IPv4 address along with the mask.• host <SOURCE-HOST-IP> – Configures a single device as the source. Provide the host device’s IPv4 address.• any – Specifies that the source can be any deviceex3500-time-range <TIME-RANGE-NAME>Optional. Applies a periodic or absolute time range to this deny rule• <TIME-RANGE-NAME> – Specify the time range name (should be existing and configured). The ACL is triggered during the time period configured in the specified EX3500 time range. For information on configuring EX3500 time-range, see ex3500.no Removes a specified permit access rule from this IPv4 EX3500 standard ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-445.png)
![ACCESS-LISTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 11 - 7811.6.3 noex3500-std-access-listRemoves a deny or permit access rule from this IPv4 EX3500 standard ACLSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510Syntaxno [deny|permit] [<SOURCE-IP/MASK>|any|host <IP>] {ex3500-time-range <TIME-RANGE-NAME>}Parameters• no <PARAMETERS>ExampleThe following example shows the IPv4 EX3500 standard ACL ‘test’ settings before the ‘no’ commands are executed:nx9500-6C8809(config-ip-ex3500-std-acl-test)#show contextip ex3500-std-access-list test deny 192.168.14.0/24 permit host 192.168.13.13 ex3500-time-range EX3500_TimeRange_01nx9500-6C8809(config-ip-ex3500-std-acl-test)#nx9500-6C8809(config-ip-ex3500-std-acl-test)#no deny 192.168.14.0/24The following example shows the IPv4 EX3500 standard ACL ‘test’ settings after the ‘no’ commands are executed:nx9500-6C8809(config-ip-ex3500-std-acl-test)#show contextip ex3500-std-access-list test permit host 192.168.13.13 ex3500-time-range EX3500_TimeRange_01nx9500-6C8809(config-ip-ex3500-std-acl-test)#no <PARAMETERS> Removes a deny or permit access rule based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-446.png)



![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 912.1.2.2.2 nodhcp-class-mode commandsRemoves this DHCP user class policy’s settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [multiple-user-class|option]no option user-class <VALUE>Parameters• no <PARAMETERS>ExampleThe following example shows the DHCP class settings before the ‘no’ commands are executed:rfs6000-37FABE(config-dhcp-policy-test-class-dhcpclass1)#show context dhcp-class dhcpclass1 option user-class hex multiple-user-classrfs6000-37FABE(config-dhcp-policy-test-class-dhcpclass1)#rfs6000-37FABE(config-dhcp-policy-test-class-class1)#no multiple-user-classrfs6000-37FABE(config-dhcp-policy-test-class-dhcpclass1)#no option user-class hexThe following example shows the DHCP class settings after the ‘no’ commands are executed:rfs6000-37FABE(config-dhcp-policy-test-class-dhcpclass1)#show context dhcp-class dhcpclass1rfs6000-37FABE(config-dhcp-policy-test-class-dhcpclass1)#no <PARAMETERS> Disables multiple user class options on this DHCP user class policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-455.png)



![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 1512.1.3.2.1 addressdhcp-pool-mode commandsAdds IP addresses to the DHCP address pool. These IP addresses are assigned to each device joining the network.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaddress [<IP>|<HOST-ALIAS-NAME>|range]address [<IP>|<HOST-ALIAS-NAME>|range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]] {class <DHCP-CLASS-NAME>}Parameters• address [<IP>|<HOST-ALIAS-NAME>|range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]] {class <DHCP-CLASS-NAME>}<IP> Adds a single IP address to the DHCP address pool<HOST-ALIAS-NAME> Adds a single host mapped to the specified host alias. The host alias should be existing and configured.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]Adds a range of IP addresses to the DHCP address pool. Use one of the following options to provide the first IP address in the range:• <START-IP> – Specifies the first IP address in the range• <START-HOST-ALIAS-NAME> – Specifies a host alias, mapped to the first IP address in the rangeUse one of the following options to provide the last IP address in the range:• <END-IP> – Specifies the last IP address in the range• <END-HOST-ALIAS-NAME> – Specifies a host alias, mapped to the last IP ad-dress in the rangeThe host aliases should be existing and configured.class <DHCP-CLASS-NAME>Optional. Applies additional DHCP options, or a modified set of options to those available to wireless clients. For more information, see dhcp-class.• <DHCP-CLASS-NAME> – Sets the DHCP class.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-461.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 1812.1.3.2.3 ddnsdhcp-pool-mode commandsConfigures Dynamic Domain Name Service (DDNS) parameters. Dynamic DNS provides a way to access an individual device in a DHCP serviced network using a static device name.Depending on the DHCP server’s configuration, the IP address of a device changes periodically. To ensure continuous accessibility to a device (having a dynamic IP address), the device’s current IP address is published to a DDNS server that resolves the static device name (used to access the device) with a changing IP address.The DDNS server must be accessible from outside the network and must be configured as an address resolver.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxddns [domainname|multiple-user-class|server|ttl]ddns domainname <DDNS-DOMAIN-NAME>ddns multiple-user-classddns server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}ddns ttl <1-864000>Parameters• ddns domainname <DDNS-DOMAIN-NAME>• ddns multiple-user-class• ddns server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}domainname <DDNS-DOMAIN-NAME>Sets the domain name used for DNS updatesThe controller uses DNS to convert human readable host names into IP addresses. Host names are not case sensitive and can contain alphabetic or numeric letters or a hyphen. A Fully Qualified Domain Name (FQDN) consists of a host name plus a domain name. For example, computername.domain.com.multiple-user-class Enables the multiple user class options with this DDNS domainserver Configures the DDNS server used by this DHCP profile[<IP>|<HOST-ALIAS-NAME>]Configures the primary DDNS server. This is the default server.Use one of the following options to specify the primary DDNS server:• <IP> – Specifies the primary DDNS server’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary DDNS server’s IP address. The host alias should be existing and configured.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-464.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 2012.1.3.2.4 default-routerdhcp-pool-mode commandsConfigures a default router or gateway IP address for a network poolAfter a DHCP client has booted, the client begins sending packets to its default router. Set the IP address of one or a group of routers the controller uses to map host names into IP addresses available to DHCP supported clients. Up to 8 default router IP addresses are supported.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdefault-router [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Parameters• default-router [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Usage GuidelinesThe IP address of the router should be on the same subnet as the client subnet.Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#default-router 192.168.13.8 192.168.13.9rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool address 192.168.13.4 class dhcpclass1 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class bootfile test.txt default-router 192.168.13.8 192.168.13.9rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#[<IP>|<HOST-ALIAS-NAME>]Configures the primary default router, using one of the following options:• <IP> – Specifies the primary default router’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary default router’s IP address{<IP1>|<HOST-ALIAS-NAME1>}Optional. Configures the secondary default router, using one of the following options:• <IP1> – Specifies the secondary default router’s IP address• <HOST-ALIAS-NAME1> – Specifies a host alias, mapped to the secondary default router’s IP address. If the primary default router is unavailable, the secondary router is used.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.A maximum of 8 default routers can be configured.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-466.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 2212.1.3.2.5 dns-serverdhcp-pool-mode commandsConfigures a network’s DNS server. The DNS server supports all clients connected to networks supported by the DHCP server.For DHCP clients, the DNS server’s IP address maps the hostname to an IP address. DHCP clients use the DNS server’s IP address based on the order (sequence) configured.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdns-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Parameters• dns-server [<IP>|<HOST-ALIAS-NAME>] {<IP1> <HOST-ALIAS-NAME1>}[<IP>|<HOST-ALIAS-NAME>]Configures the primary DNS server, using one of the following options:• <IP> – Specifies the primary DNS server’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary DNS server’s IP addressA maximum of 8 DNS servers can be configured.To enable redirection of DNS queries to OpenDNS it is necessary that the DNS server IP addresses provided here should point to the OpenDNS resolver (208.67.220.220 or 208.67.222.222). OpenDNS is a proxy DNS server that provides additional functionality, such as Web filtering, reporting, and performance enhancements in addition to DNS services. When configured on a WLAN, DNS queries from wireless clients are redirected to OpenDNS. The following example illustrates the configuration:dhcp-server-policy dhcppolicy dhcp-pool dhcppool network 192.168.1.0/24 address range 192.168.1.160 192.168.1.200 default-router 192.168.1.105 dns-server 208.67.220.220Note, the above example shows the OpenDNS server as being 208.67.2202.220. The alternative IP address 208.67.222.222 can also be used.For more information on the entire configuration that needs to be done to integrate WiNG access point, controllers, and service platform with OpenDNS , see opendns.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-468.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 2512.1.3.2.7 excluded-addressdhcp-pool-mode commandsIdentifies a single IP address or a range of IP addresses, included in the DHCP address pool, that cannot be assigned to clients by the DHCP serverSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxexcluded-address [<IP>|<HOST-ALIAS-NAME>|range]excluded-address <IP>excluded-address <HOST-ALIAS-NAME>excluded-address range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]Parameters• excluded-address <IP>• excluded-address <HOST-ALIAS-NAME>• excluded-address range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]<IP> Adds a single IP address to the excluded address list<HOST-ALIAS-NAME> Adds a host alias. The host alias is mapped to a host’s IP address. The host identified by the host alias is added to the excluded address list. The host alias should be existing and configured.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>] Adds a range of IP addresses to the excluded address list. Use one of the following options to provide the first IP address in the range:• <START-IP> – Specifies the first IP address in the range• <START-HOST-ALIAS-NAME> – Specifies a host alias, mapped to the first IP address in the rangeUse one of the following options to provide the last IP address in the range:• <END-IP> – Specifies the last IP address in the range• <END-HOST-ALIAS-NAME> – Specifies a host alias, mapped to the last IP ad-dress in the rangeThe host aliases should be existing and configured.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-471.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 2712.1.3.2.8 leasedhcp-pool-mode commandsA lease is the duration a DHCP issued IP address is valid. Once a lease expires, and if the lease is not renewed, the IP address is revoked and is available for reuse. Generally, before an IP lease expires, the client tries to get the same IP address issued for the next lease period. This feature is enabled by default, with a lease period of 24 hours (1 day).Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlease [<0-365>|infinite]lease infinitelease <0-365> {0-23} {0-59} {0-59}Parameters• lease infinite• lease <0-365> {<0-23>} {<0-59>} {<0-59>}Usage GuidelinesIf lease parameter is not configured on the DHCP pool, the default is used. The default is 24 hours.Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#lease 100 23 59 59rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool network 192.168.13.0/24 address 192.168.13.4 class dhcpclass1 lease 100 23 59 59 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 domain-name documentation bootfile test.txt default-router 192.168.13.8 192.168.13.9 dns-server 192.168.13.19rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#infinite The lease never expires (equal to a static IP address assignment)<0-365> Configures the lease duration in daysNote: Days may be 0 only when hours and/or minutes are greater than 0.<0-23> Optional. Sets the lease duration in hours<0-59> Optional. Sets the lease duration in minutes<0-59> Optional. Sets the lease duration in seconds](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-473.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 2912.1.3.2.9 netbios-name-serverdhcp-pool-mode commandsConfigures the NetBIOS (WINS) name server’s IP address. This server is used to resolve NetBIOS host names.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnetbios-name-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Parameters• netbios-name-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#netbios-name-server 192.168.13.25rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool network 192.168.13.0/24 address 192.168.13.4 class dhcpclass1 lease 100 23 59 59 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 domain-name documentation bootfile test.txt default-router 192.168.13.8 192.168.13.9 dns-server 192.168.13.19 netbios-name-server 192.168.13.25rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#Related Commands[<IP>|<HOST-ALIAS-NAME>]Configures the primary NetBIOS name server, using one of the following options:• <IP> – Specifies the primary NetBIOS name server’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary NetBIOS name server’s IP address{<IP1>|<HOST-ALIAS-NAME1>}Optional. Configures the secondary NetBIOS name server, using one of the following options:• <IP1> – Specifies the secondary NetBIOS name server’s IP address• <HOST-ALIAS-NAME1> – Specifies a host alias, mapped to the secondary NetBIOS name server’s IP address. If the primary NetBIOS name server is unavailable, the secondary server is used.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Removes the NetBIOS name server settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-475.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 3012.1.3.2.10 netbios-node-typedhcp-pool-mode commandsDefines the predefined NetBIOS node type. The NetBIOS node type resolves NetBIOS names to IP addresses.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnetbios-node-type [b-node|h-node|m-node|p-node]Parameters• netbios-node-type [b-node|h-node|m-node|p-node]Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#netbios-node-type b-noderfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool network 192.168.13.0/24 address 192.168.13.4 class dhcpclass1 lease 100 23 59 59 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 domain-name documentation netbios-node-type b-node bootfile test.txt default-router 192.168.13.8 192.168.13.9 dns-server 192.168.13.19 netbios-name-server 192.168.13.25rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#Related Commands[b-node|h-node|m-node|p-node]Defines the netbios node type• b-node – Sets the node type as broadcast. Uses broadcasts to query nodes on the network for the owner of a NetBIOS name.• h-node – Sets the node type as hybrid. Uses a combination of two or more nodes.• m-node – Sets the node type as mixed. A mixed node uses broadcast queries to find a node, and failing that, queries a known p-node name server for the address.• p-node – Sets the node type as peer-to-peer. Uses directed calls to communicate with a known NetBIOS name server (such as a WINS server), for the IP address of a NetBIOS machine.no Removes the NetBIOS node type settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-476.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 3112.1.3.2.11 networkdhcp-pool-mode commandsConfigures the DHCP server’s network settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnetwork [<IP/M>|<NETWORK-ALIAS-NAME>]Parameters• network [<IP/M>|<NETWORK-ALIAS-NAME>]Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#network 192.168.13.0/24rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool network 192.168.13.0/24 address 192.168.13.4 class dhcpclass1 lease 100 23 59 59 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 domain-name documentation netbios-node-type b-node bootfile test.txt default-router 192.168.13.8 192.168.13.9 dns-server 192.168.13.19 netbios-name-server 192.168.13.25rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#Related Commands<IP/M> Configures the network number and mask (for example, 192.168.13.0/24)<NETWORK-ALIAS-NAME>Configures a network alias to identify the network number and mask• <NETWORK-ALIAS-NAME> – Specify the network alias name. It should be existing and configured.A network alias defines a single network address. For example, ‘alias network $NET 1.1.1.0/24’. In this example, the network alias name is: $NET and the network it is mapped to is: 1.1.1.0/24. For more information, see alias.no Removes the network number and mask configured for this DHCP pool](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-477.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 3212.1.3.2.12 next-serverdhcp-pool-mode commandsConfigures the next server in the boot processSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnext-server [<IP>|<HOST-ALIAS-NAME>]Parameters• next-server [<IP>|<HOST-ALIAS-NAME>]Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#next-server 192.168.13.26rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool network 192.168.13.0/24 address 192.168.13.4 class dhcpclass1 lease 100 23 59 59 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 domain-name documentation netbios-node-type b-node bootfile test.txt default-router 192.168.13.8 192.168.13.9 dns-server 192.168.13.19 netbios-name-server 192.168.13.25 next-server 192.168.13.26rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#Related Commands<IP> Configures the next server’s (the first server in the boot process) IP address<HOST-ALIAS-NAME> Configures a host alias, mapped to the next server’s IP address• <HOST-ALIAS-NAME> – Specify the host alias name. It should be existing and configured.A host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Removes the next server configuration settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-478.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 3312.1.3.2.13 nodhcp-pool-mode commandsRemoves or resets this DHCP user pool’s settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [address|bootfile|ddns|default-router|dns-server|domain-name|excluded-address|lease|netbios-name-server|netbios-node-type|network|next-server|option|respond-via-unicast|static-binding|static-route|update]no [bootfile|default-router|dns-server|domain-name|lease|netbios-name-server|netbios-node-type|next-server|network|respond-via-unicast]no address [<IP>|<HOST-ALIAS-NAME>|all]no address range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]no ddns [domainname|multiple-user-class|server|ttl]no excluded-address [<IP>|<HOST-ALIAS-NAME>]no excluded-address range [<START-IP>|<START-HOST-ALIAS-NAME>] [<END-IP>|<END-HOST-ALIAS-NAME>]no option <OPTION-NAME>no static-binding client-identifier <CLIENT-IDENTIFIER>no static-binding hardware-address <MAC>no static-route <IP/MASK> <GATEWAY-IP>no update dns {override}Parameters• no <PARAMETERS>ExampleThe following example shows the DHCP pool settings before the ‘no’ commands are executed:rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool network 192.168.13.0/24 address 192.168.13.4 class dhcpclass1 lease 100 23 59 59 ddns server 192.168.13.9 ddns domainname WID ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 domain-name documentation netbios-node-type b-node bootfile test.txtno <PARAMETERS> Removes or resets this DHCP user pool’s settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-479.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 3512.1.3.2.14 optiondhcp-pool-mode commandsConfigures raw DHCP options. The DHCP option must be configured under the DHCP server policy. The options configured under the DHCP pool/DHCP server policy can also be used in static-bindings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoption <OPTION-NAME> [<DHCP-OPTION-IP>|<DHCP-OPTION-ASCII>]Parameters• option <OPTION-NAME> [<DHCP-OPTION-IP>|<DHCP-OPTION-ASCII>]Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#option option1 157.235.208.80rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool address 192.168.13.4 class dhcpclass1 ddns server 192.168.13.9 ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 netbios-node-type b-node dns-server 192.168.13.19 netbios-name-server 192.168.13.25 option option1 157.235.208.80rfs4000-229D58(config-dhcp-policy-test-pool-testPool)#Related Commands<OPTION-NAME> Sets the name of the DHCP option<DHCP-OPTION-IP> Sets DHCP option as an IP address<DHCP-OPTION-ASCII> Sets DHCP option as an ASCII stringNOTE: An option name in ASCII format accepts backslash (\) as an input but is not displayed in the output (Use show runnig config to view the output). Use a double backslash to represent a single backslash.no Resets values or disables the DHCP pool option settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-481.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 4012.1.3.3.1 static-bindingstatic-bindingConfigures static address bindingsA static address binding is a collection of configuration parameters, including an IP address, associated with, or bound to, a DHCP client. Bindings are managed by DHCP servers. DHCP bindings automatically map a device MAC address to an IP address using a pool of DHCP supplied addresses. Static bindings assign IP addresses without creating numerous host pools with manual bindings. Static host bindings use a text file the DHCP server reads. It eliminates the need for a lengthy configuration file and reduces the space required to maintain address pools.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxstatic-binding [client-identifier <CLIENT>|hardware-address <MAC>]Parameters• static-binding [client-identifier <CLIENT>|hardware-address <MAC>]Examplerfs4000-229D58(config-dhcp-policy-test-pool-testPool)#static-binding client-identifier testrfs4000-229D58(config-dhcp-policy-test-pool-testPool)#show context dhcp-pool testPool address 192.168.13.4 class dhcpclass1 update dns override ddns server 192.168.13.9 ddns multiple-user-class excluded-address range 192.168.13.25 192.168.13.28 netbios-node-type b-node dns-server 192.168.13.19 netbios-name-server 192.168.13.25 option option1 157.235.208.80 respond-via-unicast static-route 192.168.13.0/24 192.168.13.7 static-binding client-identifier testrfs4000-229D58(config-dhcp-policy-test-pool-testPool)#client-identifier <CLIENT>Enables a static binding configuration for a client based on its client identifier (as provided by DHCP option 61 and its key value)• <CLIENT> – Specify the client identifier (DHCP option 61).hardware-address <MAC>Enables a static binding configuration for a client based on its MAC address• <MAC> – Specify the MAC address of the client.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-486.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 4512.1.3.3.5 default-routerstatic-binding-mode commandsConfigures a default router or gateway IP address for the static binding configurationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdefault-router [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Parameters• default-router [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Usage GuidelinesThe IP address of the router should be on the same subnet as the client subnet.Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#default-router 172.16.10.8 172.16.10.9rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test client-name RFID bootfile test.txt default-router 172.16.10.8 172.16.10.9rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#Related Commands[<IP>|<HOST-ALIAS-NAME>]Configures the primary default router, using one of the following options:• <IP> – Specifies the primary default router’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary default router’s IP address{<IP1>|<HOST-ALIAS-NAME1>}Optional. Configures the secondary default router, using one of the following options:• <IP1> – Specifies the secondary default router’s IP address• <HOST-ALIAS-NAME1> – Specifies a host alias, mapped to the secondary default router’s IP address. If the primary default router is unavailable, the secondary router is used.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Resets values or disables DHCP pool static binding settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-491.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 4612.1.3.3.6 dns-serverstatic-binding-mode commandsConfigures the DNS server for this static binding configuration. This DNS server supports the client for which the static binding has been configured.For this client, the DNS server’s IP address maps the host name to an IP address. DHCP clients use the DNS server’s IP address based on the order (sequence) configured.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdns-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Parameters• dns-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#dns-server 172.16.10.7rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test client-name RFID bootfile test.txt default-router 172.16.10.8 172.16.10.9 dns-server 172.16.10.7rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#Related Commands[<IP>|<HOST-ALIAS-NAME>]Configures the primary DNS server, using one of the following options:• <IP> – Specifies the primary DNS server’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary DNS server’s IP address{<IP1>|<HOST-ALIAS-NAME1>}Optional. Configures the secondary DNS server, using one of the following options:• <IP1> – Specifies the secondary DNS server’s IP address• <HOST-ALIAS-NAME1> – Specifies a host alias, mapped to the secondary DNS server’s IP address. If the primary DNS server is unavailable, the secondary DNS server is used.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Resets values or disables DHCP pool static binding settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-492.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 4812.1.3.3.8 ip-addressstatic-binding-mode commandsConfigures a fixed IP address for a hostSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip-address [<IP>|<HOST-ALIAS-NAME>]Parameters• ip-address [<IP>|<HOST-ALIAS-NAME>]Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#ip-address 172.16.10.9rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test ip-address 172.16.10.9 client-name RFID domain-name documentation bootfile test.txt default-router 172.16.10.8 172.16.10.9 dns-server 172.16.10.7rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#Related Commands<IP> Configures a fixed IP address (in dotted decimal format) of the client using this host pool<HOST-ALIAS-NAME> Configures a host alias identifying the fixed IP address of the client using this host poolA network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Resets values or disables DHCP pool static binding settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-494.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 4912.1.3.3.9 netbios-name-serverstatic-binding-mode commandsConfigures the NetBIOS (WINS) name server’s IP address. This server is used to resolve NetBIOS host names.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnetbios-name-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Parameters• netbios-name-server [<IP>|<HOST-ALIAS-NAME>] {<IP1>|<HOST-ALIAS-NAME1>}Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#netbios-name-server 172.16.10.23rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test ip-address 172.16.10.9 client-name RFID domain-name documentation bootfile test.txt default-router 172.16.10.8 172.16.10.9 dns-server 172.16.10.7 netbios-name-server 172.16.10.23rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#Related Commands[<IP>|<HOST-ALIAS-NAME>]Configures the primary NetBIOS server, using one of the following options:• <IP> – Specifies the primary NetBIOS name server’s IP address• <HOST-ALIAS-NAME> – Specifies a host alias, mapped to the primary NetBIOS name server’s IP address{<IP1>|<HOST-ALIAS-NAME1>}Optional. Configures the secondary NetBIOS name server, using one of the following options:• <IP1> – Specifies the secondary NetBIOS name server’s IP address• <HOST-ALIAS-NAME1> – Specifies a host alias, mapped to the secondary NetBIOS name server’s IP address. If the primary NetBIOS name server is unavailable, the secondary server is used.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Resets values or disables DHCP pool static binding settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-495.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5012.1.3.3.10 netbios-node-typestatic-binding-mode commandsConfigures different predefined NetBIOS node types. The NetBIOS node defines the way a device resolves NetBIOS names to IP addresses.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnetbios-node-type [b-node|h-mode|m-node|p-node]Parameters• netbios-node-type [b-node|h-node|m-node|p-node]Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#netbios-node-type b-noderfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test ip-address 172.16.10.9 client-name RFID domain-name documentation netbios-node-type b-node bootfile test.txt default-router 172.16.10.8 172.16.10.9 dns-server 172.16.10.7 netbios-name-server 172.16.10.23rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#Related Commands[b-node|h-mode|m-node|p-node]Defines the netbios node type• b-node – Sets the node type as broadcast. Uses broadcasts to query nodes on the network for the owner of a NetBIOS name.• h-node – Sets the node type as hybrid. Uses a combination of two or more nodes.• m-node – Sets the node type as mixed. A mixed node uses broadcast queries to find a node, and failing that, queries a known p-node name server for the address.• p-node – Sets the node type as peer-to-peer. Uses directed calls to communicate with a known NetBIOS name server (such as a WINS server), for the IP address of a NetBIOS machine.no Resets values or disables DHCP pool static binding settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-496.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5112.1.3.3.11 next-serverstatic-binding-mode commandsConfigures the next server utilized in the boot processSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnext-server [<IP>|<HOST-ALIAS-NAME>]Parameters• next-server [<IP>|<HOST-ALIAS-NAME>]Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#next-server 172.16.10.24rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test ip-address 172.16.10.9 client-name RFID domain-name documentation netbios-node-type b-node bootfile test.txt default-router 172.16.10.8 172.16.10.9 dns-server 172.16.10.7 netbios-name-server 172.16.10.23 next-server 172.16.10.24rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#Related Commands<IP> Configures the next server’s (the first server in the boot process) IP address<HOST-ALIAS-NAME> Configures a host alias, mapped to the next server’s IP address• <HOST-ALIAS-NAME> – Specify the host alias name. It should be existing and configured.A network host alias maps a name to a single network host. For example, ‘alias host $HOST 1.1.1.100’. In this example the host alias is ‘$HOST’ and it maps to a single host ‘1.1.1.100’. For more information, see alias.no Resets values or disables DHCP pool static binding settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-497.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5212.1.3.3.12 nostatic-binding-mode commandsNegates or reverts static binding settings for the selected DHCP server policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [bootfile|client-name|default-router|dns-server|domain-name|ip-address|netbios-name-server|netbios-node-type|next-server|option|respond-via-unicast|static-route]no option <OPTION-NAME>no static-route <IP/MASK> <GATEWAY-IP>Parameters• no <PARAMETERS>ExampleThe following example shows the DHCP pool static binding settings before the ‘no’ commands are executed:rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test ip-address 172.16.10.9 client-name RFID domain-name documentation netbios-node-type b-node bootfile test.txt default-router 172.16.10.8 172.16.10.9 dns-server 172.16.10.7 netbios-name-server 172.16.10.23 next-server 172.16.10.24rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#no bootfilerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#no ip-addressrfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#no default-routerrfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#no dns-serverThe following example shows the DHCP pool static binding settings after the ‘no’ commands are executed:rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test client-name RFID domain-name documentation netbios-node-type b-node netbios-name-server 172.16.10.23 next-server 172.16.10.24rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#no <PARAMETERS> Negates or reverts static binding settings for the selected DHCP server policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-498.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5312.1.3.3.13 optionstatic-binding-mode commandsConfigures the raw DHCP options in the DHCP policy. The DHCP options can be used only in static bindings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoption <OPTION-NAME> [<DHCP-OPTION-IP>|<DHCP-OPTION-ASCII>]Parameters• option <OPTION-NAME> [<DHCP-OPTION-IP>|<DHCP-OPTION-ASCII>]Usage GuidelinesDefines non standard DHCP option codes (0-254)Examplerfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#option option1 172.16.10.10rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#show context static-binding client-identifier test client-name RFID domain-name documentation netbios-node-type b-node netbios-name-server 172.16.10.23 next-server 172.16.10.24 option option1 172.16.10.10rfs6000-37FABE(config-dhcp-policy-test-pool-pool1-binding-test)#<OPTION-NAME> Sets the DHCP option name<DHCP-OPTION-IP> Sets the DHCP option as an IP address<DHCP-OPTION-ASCII> Sets the DHCP option as an ASCII stringNOTE: An option name in ASCII format accepts a backslash (\) as an input, but is not displayed in the output (Use show running config to view the output). Use a double backslash to represent a single backslash.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-499.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5612.1.4 dhcp-serverdhcp-server-policyConfigures the activation-criteria (run-criteria) that triggers dynamic activation of DHCP service running on a redundancy deviceIn a managed wireless network, when the primary, active DHCP server fails (is unreachable), network clients are unable to access DHCP services, such as new IP address leasing and renewal of existing IP address leases. In such a scenario, the activation-criteria, when configured, triggers dynamic activation of the secondary DHCP server, allowing network clients to continue accessing DHCP services. The WiNG implementation provides activation-criteria options specific to a RF Domain, cluster setup, and a Virtual Router Redundancy Protocol (VRRP) master/client setup.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdhcp-server activation-criteria [cluster-master|rf-domain-manager|vrrp-master]Parameters• dhcp-server activation-criteria [cluster-master|rf-domain-manager|vrrp-master]dhcp-server Enables dynamic activation of the DHCP server, running on a redundancy device, based on the activation criteria specifiedactivation-criteria [cluster-master|rf-domain-manager|vrrp-master]Configures the activation criteria. Specify one of the following options as the activation criteria:• cluster-master – Configures the cluster-master criteria in a cluster setup. Within a cluster, DHCP service is enabled on the cluster master. While it remains disabled on the other cluster members. In case of the cluster master failing, the cluster-master activation criteria, when configured, triggers dynamic activation of DHCP service on the new cluster master.• rf-domain-manger – Configures the rf-domain-manager criteria on an RF Domain. Within a RF Domain, DHCP service is enabled on the RF Domain manager. While it remains disabled on the other devices within the RF Domain. In case of the RF Domain manager failing, the rf-domain-manager activation criteria, when configured, triggers dynamic activation of DHCP service on the new RF Domain manager.• vrrp-master – Configures the vrrp-master criteria within a VRRP master/client setup. In such a setup, the DHCP service is enabled on the VRRP master. While it remains disabled on the other members. In case of the VRRP master failing, the vrrp-master activation criteria, when configured, triggers dynamic activation of DHCP service on the new VRRP master.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-502.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5812.1.5 nodhcp-server-policyNegates a command or sets its default. When used in the DHCP server configuration context, the ‘no’ command resets or reverts the DHCP server policy settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [bootp|dhcp-class|dhcp-pool|dhcp-server|option|ping]no bootp ignoreno dhcp-class <DHCP-CLASS-NAME>no dhcp-pool <DHCP-POOL-NAME>no dhcp-server activation-criteriano option <DHCP-OPTION>no ping timeoutParameters• no <PARAMETERS>ExampleThe following example shows the DHCP policy ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-dhcp-policy-test)#show contextdhcp-server-policy test bootp ignore dhcp-class dhcpclass1 dhcp-pool pool1 address 1.2.3.4 class dhcpclass1 update dns override --More--rfs6000-37FABE(config-dhcp-policy-test)#rfs6000-37FABE(config-dhcp-policy-test)#no bootp ignorerfs6000-37FABE(config-dhcp-policy-test)#no dhcp-class dhcpclass1rfs6000-37FABE(config-dhcp-policy-test)#no dhcp-pool pool1The following example shows the DHCP policy ‘test’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-dhcp-policy-test)#show contextdhcp-server-policy testrfs6000-37FABE(config-dhcp-policy-test)#no <PARAMETERS> Negates a command or sets its default. When used in the DHCP server configuration context, the ‘no’ command resets or reverts the DHCP server policy settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-504.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 5912.1.6 optiondhcp-server-policyConfigures raw DHCP options. The DHCP option has to be configured in the DHCP server policy. The options configured in the DHCP pool/DHCP server policy can also be used in static bindings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoption <OPTION-NAME> <0-254> [ascii|hexstring|ip]Parameters• option <OPTION-NAME> <0-254> [ascii|hexstring|ip]Usage GuidelinesDefines non standard DHCP option codes (0-254)Examplerfs6000-37FABE(config-dhcp-policy-test)#option option1 200 asciirfs6000-37FABE(config-dhcp-policy-test)#show contextdhcp-server-policy test option option1 200 asciirfs6000-37FABE(config-dhcp-policy-test)#Related Commands<OPTION-NAME> Configures the option name<0-254> Configures the DHCP option code from 0 - 254ascii Configures the DHCP option as an ASCII stringhexstring Configures the DHCP option as a hexadecimal stringip Configures the DHCP option as an IP addressNOTE: An option name in ASCII format accepts a backslash (\) as an input, but is not displayed in the output (Use show running config to view the output). Use a double backslash to represent a single backslash.no Removes DHCP server options](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-505.png)





![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 6812.2.1.2.3 networkdhcpv6-pool-mode commandsConfigures this DHCPv6 pool’s network. Use this command to configure the address of the network on which this DHCP server is deployed.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnetwork [<IPv6/M>|<NETWORK-ALIAS-NAME>]Parameters• network [<IPv6/M>|<NETWORK-ALIAS-NAME>]Examplerfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#network 2002::0/64rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#show context dhcpv6-pool DHCPv6Pool1 network 2002::/64 domain-name TechPubs dns-server 2002::1rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#Related Commands<IPv6/M> Specify this DHCPv6 pool network’s IPv6 address and mask (for example, 1:2::1:0/96)<NETWORK-ALIAS-NAME>Specify this DHCPv6 pool network’s alias nameno Removes the network IPv6 address and mask configured for this DHCPv6 pool](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-514.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 6912.2.1.2.4 nodhcpv6-pool-mode commandsNegates a command or sets its default. When used in the DHCPv6 pool configuration context, the ‘no’ command resets or reverts the DHCPv6 pool’s settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [dns-server|domain-name|network|option|refresh-time|sip]Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#show context dhcpv6-pool DHCPv6Pool1 network 2002::/64 refresh-time 1000 domain-name TechPubs sip domain-name TechPubsSIP dns-server 2002::1 option DHCPv6Pool1Option 60rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#no option DHCPv6Pool1Optionrfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#no refresh-timerfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#show context dhcpv6-pool DHCPv6Pool1 network 2002::/64 domain-name TechPubs sip domain-name TechPubsSIP dns-server 2002::1rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#no <PARAMETERS> Negates a command or sets its default. When used in the DHCPv6 pool configuration context, the ‘no’ command resets or reverts the DHCPv6 pool’s settings.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-515.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 7012.2.1.2.5 optiondhcpv6-pool-mode commandsConfigures this DHCPv6 pool’s raw DHCPv6 options. This is the vendor-specific option used in this DHCPv6 pool.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoption <OPTION-NAME> [<DHCPv6-OPTION-IP>|<DHCPv6-OPTION-ASCII>]Parameters• option <OPTION-NAME> [<DHCPv6-OPTION-IP>|<DHCPv6-OPTION-ASCII>]Examplerfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#option DHCPv6Pool1Option 60rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#show context dhcpv6-pool DHCPv6Pool1 network 2002::/64 domain-name TechPubs dns-server 2002::1 option DHCPv6Pool1Option 60rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#Related Commands<OPTION-NAME> Sets the name of the DHCPv6 option<DHCPv6-OPTION-IP> Sets DHCPv6 option as an IPv6 address<DHCPv6-OPTION-ASCII> Sets DHCPv6 option as an ASCII stringNOTE: An option name in ASCII format accepts backslash (\) as an input but is not displayed in the output (Use show running config to view the output). Use a double backslash to represent a single backslash.no Removes this DHCPv6 pool’s DHCP option settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-516.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 7212.2.1.2.7 sipdhcpv6-pool-mode commandsConfigures this DHCPv6 pool’s Session Initiation Protocol (SIP) server settingConfigures the domain name or domain names associated with the SIP servers. The SIP server is used to prioritize voice and video traffic on the network. SIP is an application-layer control protocol that can establish, modify and terminate multimedia sessions or calls. A SIP system has several components (user agents, proxy servers, redirect servers, and registrars). User agents can contain SIP clients; proxy servers always contain SIP clients.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsip [address <IPv6>|domain-name <DOMAIN-NAME>]Parameters• sip [address <IPv6>|domain-name <DOMAIN-NAME>]Examplerfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#sip domain-name TechPubsSIPrfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#show context dhcpv6-pool DHCPv6Pool1 network 2002::/64 refresh-time 1000 domain-name TechPubs sip domain-name TechPubsSIP dns-server 2002::1 option DHCPv6Pool1Option 60rfs6000-37FABE(config-dhcpv6-server-policy-test-pool-DHCPv6Pool1)#Related Commandssip [address <IPv6>|domain-name <DOMAIN-NAME>]Configures the SIP server’s setting, such as address and/or domain nameno Removes this DHCPv6 pool’s SIP server setting](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-518.png)
![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 7312.2.2 optiondhcpv6-server-policyConfigures this DHCPv6 server policy’s DHCP option settings, such enterprise (vendor) IDDHCPv6 services are available for specific IP interfaces. A pool (or range) of IPv6 network addresses and DHCPv6 options can be created for each IPv6 interface defined. This range of addresses can be made available to DHCPv6 enabled devices on either a permanent or leased basis. DHCPv6 options are provided to each client with a DHCPv6 response and provide DHCPv6 clients information required to access network resources (default gateway, domain name, DNS server and WINS server configuration). An option exists to identify the vendor and functionality of a DHCPv6 client. The information is a variable-length string of characters (or octets) with a meaning specified by the vendor of the DHCPv6 client.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxoption <OPTION-NAME> <0-254> [ascii|hexstring|ipv6] <1-4294967295>Parameters• option <OPTION-NAME> <0-254> [ascii|hexstring|ipv6] <1-4294967295>option <OPTION-NAME>Specify a unique name for this DHCP option. The name should describe option's function.<0-254> Specify a DHCP option code for this option.• <0-254> – Specify a value from 0 -254. The system allows only one code, of the same value, for each DHCP option used in each DHCPv6 server policy.ascii Specifies the option type as ASCII (sends an ASCII compliant string to the client)hexstring Specifies the option type as a string of hexadecimal characters (sends a hexadecimal string to the client)ipv6 Specifies the option type as IPv6 address (sends an IPv6 compatible address to the client)<1-4294967295> This parameter is common to all option types.• <1-4294967295> – Specifies the enterprise (vendor) ID. Specify a value from 1 - 4294967295. The option code (1) is reserved for subnet-mask and cannot be used.Each vendor should have a unique vendor ID used by the DHCP server to issue vendor-specific DHCP options.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-519.png)

![DHCP-SERVER-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 12 - 7712.2.5 nodhcpv6-server-policyNegates or reverts this DHCPv6 server policy’s settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [dhcpv6-pool|option|restrict-vendor-options|server-preference]Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-dhcpv6-server-policy-test)#show contextdhcpv6-server-policy test option DHCPServerOption1 10 ascii 50 dhcpv6-pool DHCPv6Pool1 network 2002::/64 domain-name TechPubs sip domain-name TechPubsSIP dns-server 2002::1 server-preference 1 restrict-vendor-optionsrfs6000-37FABE(config-dhcpv6-server-policy-test)#rfs6000-37FABE(config-dhcpv6-server-policy-test)#no restrict-vendor-optionsrfs6000-37FABE(config-dhcpv6-server-policy-test)#no server-preferencerfs6000-37FABE(config-dhcpv6-server-policy-test)#show contextdhcpv6-server-policy test option DHCPServerOption1 10 ascii 50 dhcpv6-pool DHCPv6Pool1 network 2002::/64 domain-name TechPubs sip domain-name TechPubsSIP dns-server 2002::1rfs6000-37FABE(config-dhcpv6-server-policy-test)#no <PARAMETERS> Negates or reverts this DHCPv6 server policy’s settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-523.png)

![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 513.1.2 algfirewall-policyEnables traffic filtering at the application layer using the Application Layer Gateway (ALG) featureSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxalg [dns|facetime|ftp|pptp|sccp|sip|tftp]Parameters• alg [dns|facetime|ftp|pptp|sccp|sip|tftp]alg Enables traffic filtering at the application layer. The ALG provides filters for the fol lowi n g common p rotocols : DNS , Face time, F TP, PPTP, S CCP, S IP, an d TFTP.dns Allows Domain Name System (DNS) traffic through the firewall using its default ports. This option is enabled by default.When enabled, you can easily permit or deny traffic based on a packet’s DNS name, instead of the IP address. Use this option when configuring ACLs allowing or denying traffic for Web sites that have a single domain name resolving to any one of multiple IP addresses.facetime Allows Apple’s FaceTime video calling traffic through the firewall using its default ports. This option is disabled by default.ftp Allows File Transfer Protocol (FTP) traffic through the firewall using its default ports. This option is enabled by default.pptp Allows Point-to-Point Tunneling Protocol (PPTP) traffic through the firewall using its default ports. PPTP, a network protocol, enables secure transfer of data from a remote client to an enterprise server by encapsulating PPP packets into IP datagrams for transmission over the Internet or other public TCP/IP-based networks. This option is enabled by defaultsccp Allows Signalling Connection Control Part (SCCP) traffic through the firewall using its default ports. This option is disabled by default.SCCP is a network protocol that provides routing, flow control and error correction in telecommunication networks.sip Allows Session Initiation Protocol (SIP) traffic through the firewall using its default ports. This option is enabled by default.tftp Enables the Trivial File Transfer Protocol (TFTP) algorithm. When enabled, allows TFTP traffic through the firewall using its default ports. This option is enabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-528.png)




![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 1113.1.7 flowfirewall-policyDefines the session flow timeout interval for different packet typesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxflow [dhcp|timeout]flow dhcp statefulflow timeout [icmp|other|tcp|udp]flow timeout [icmp|other] <1-32400>flow timeout udp <15-32400>flow timeout tcp [close-wait|reset|setup|stateless-fin-or-reset|stateless-general] <1-32400>flow timeout tcp established <15-32400>Parameters• flow dhcp stateful• flow timeout [icmp|other] <1-32400>• flow timeout udp <15-32400>• flow timeout tcp [close-wait|reset|setup|stateless-fin-or-reset|stateless-general] <1-32400>dhcp Configures DHCP packet flowstateful Performs a stateful check on DHCP packets. This feature is enabled by default.timeout Configures a packet timeouticmp Configures the timeout for ICMP packets. The default is 30 seconds.other Configures the timeout for packets other than ICMP, TCP, or UDP. The default is 30 seconds.<1-32400> Configures the timeout from 1 - 32400 secondstimeout Configures a packet timeoutudp Configures the timeout for UDP packets. The default is 30 seconds.<15-32400> Configures the timeout from 15 - 32400 secondstimeout Configures a packet timeouttcp Configures the timeout for TCP packetsclose-wait Configures the closed TCP flow timeout. The default is 10 seconds.reset Configures the reset TCP flow timeout. The default is 10 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-534.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 1313.1.8 ipfirewall-policyConfigures Internet Protocol (IP) componentsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip [dos|tcp]ip dos {ascend|broadcast-multicast-icmp|chargen|fraggle|ftp-bounce|invalid-protocol|ip-ttl-zero|ipspoof|land|option-route|router-advt|router-solicit|smurf|snork|tcp-bad-sequence|tcp-fin-scan|tcp-intercept|tcp-max-incomplete|tcp-null-scan|tcp-post-syn|tcp-sequence-past-window|tcp-xmas-scan|tcphdrfrag|twinge|udp-short-hdr|winnuke}ip dos {ascend|broadcast-multicast-icmp|chargen|fraggle|ftp-bounce|invalid-protocol|ip-ttl-zero|ipsproof|land|option-route|router-advt|router-solicit|smurf|snork|tcp-bad-sequence|tcp-fin-scan|tcp-intercept|tcp-null-scan|tcp-post-scan|tcp-sequence-past-window|tcp-xmas-scan|tcphdrfrag|twinge|udp-short-hdr|winnuke} [log-and-drop|log-only] log-level [<0-7>|alerts|critical|debugging|emergencies|errors|informational|notifications|warnings]ip dos {ascend|broadcast-multicast-icmp|chargen|fraggle|ftp-bounce|invalid-protocol|ip-ttl-zero|ipsproof|land|option-route|router-advt|router-solicit|smurf|snork|tcp-bad-sequence|tcp-fin-scan|tcp-intercept|tcp-null-scan|tcp-post-scan|tcp-sequence-past-window|tcp-xmas-scan|tcphdrfrag|twinge|udp-short-hdr|winnuke} [drop-only]ip dos tcp-max-incomplete [high|low] <1-1000>ip tcp [adjust-mss|optimize-unnecessary-resends|recreate-flow-on-out-of-state-syn|validate-icmp-unreachable|validate-rst-ack-number|validate-rst-seq-number]ip tcp adjust-mss <472-1460>ip tcp [optimize-unnecessary-resends|recreate-flow-on-out-of-state-syn|validate-icmp-unreachable|validate-rst-ack-number|validate-rst-seq-number]Parameters• ip dos {ascend|broadcast-multicast-icmp|chargen|fraggle|ftp-bounce|invalid-protocol|ip-ttl-zero|ipsproof|land|option-route|router-advt|router-solicit|smurf|snork|tcp-bad-sequence|tcp-fin-scan|tcp-intercept|tcp-null-scan|tcp-post-scan|tcp-sequence-past-window|tcp-xmas-scan|tcphdrfrag|twinge|udp-short-hdr|winnuke} [log-and-drop|log-only] log-level [<0-7>|alerts|critical|debug|emergencies|errors|informational|notifications|warnings]dos Identifies IP events as DoS eventsascend Optional. Detects ASCEND DoS attacksAscend DoS attacks target known vulnerabilities in various versions of Ascend routers. Ascend routers listen on UDP port 9 for packets from Ascend's Java Configurator. Sending a formatted packet to this port can cause an Ascend router to crash.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-536.png)

![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 17• ip dos {ascend|broadcast-multicast-icmp|chargen|fraggle|ftp-bounce|invalid-protocol|ip-ttl-zero|ipsproof|land|option-route|router-advt|router-solicit|smurf|snork|tcp-bad-sequence|tcp-fin-scan|tcp-intercept|tcp-null-scan|tcp-post-scan|tcp-sequence-past-window|tcp-xmas-scan|tcphdrfrag|twinge|udp-short-hdr|winnuke} [drop-only]udp-short-hdr Optional. Enables the identification of truncated UDP headers and UDP header length fieldswinnuke Optional. This DoS attack is specific to Windows™ 95 and Windows™ NT.The WINNUKE DoS attack sends a large amount of data to UDP port 137 to crash the NETBIOS service on windows and results in high CPU utilization on the target machine.log-and-drop Logs the event and drops the packetlog-only Logs the event only, the packet is not droppedlog-level Configures the log level<0-7> Sets the numeric logging levelemergencies Numerical severity 0. System is unusablealerts Numerical severity 1. Indicates a condition where immediate action is requiredcritical Numerical severity 2. Indicates a critical conditionerrors Numerical severity 3. Indicates an error conditionwarnings Numerical severity 4. Indicates a warning conditionnotification Numerical severity 5. Indicates a normal but significant conditioninformational Numerical severity 6. Indicates a informational conditiondebugging Numerical severity 7. Debugging messagesdos Identifies IP events as DoS eventsascend Optional. Enables an ASCEND DoS check. Ascend routers listen on UDP port 9 for packets from Ascend's Java Configurator. Sending a formatted packet to this port can cause an Ascend router to crash.broacast-multicast-icmpOptional. Detects broadcast or multicast ICMP packets as an attackchargen Optional. The Character Generation Protocol (chargen) is an IP suite service primarily used for testing and debugging networks. It is also used as a source of generic payload for bandwidth and QoS measurements.fraggle Optional. A Fraggle DoS attack checks for UDP packets to or from port 7 or 19ftp-bounce Optional. A FTP bounce attack is a MIM attack that enables an attacker to open a port on a different machine using FTP. FTP requires that when a connection is requested by a client on the FTP port (21), another connection must open between the server and the client. To confirm, the PORT command has the client specify an arbitrary destination machine and port for the data connection. This is exploited by the attacker to gain access to a device that may not be the originating client.invalid-protocol Optional. Enables a check for invalid protocol numberip-ttl-zero Optional. Enables a check for the TCP/IP TTL field having a value of zero (0)ipsproof Optional. Enables a check for IP spoofing DoS attack](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-540.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 18• ip dos tcp-max-incomplete [high|low] <1-1000>land Optional. A Local Area Network Denial (LAND) is a DoS attack where IP packets are spoofed and sent to a device where the source IP and destination IP of the packet are the target device’s IP, and similarly, the source port and destination port are open ports on the same device. This causes the attacked device to reply to itself continuously.option-route Optional. Enables an IP Option Record Route DoS checkrouter-advt Optional. This is an attack, where a default route entry is added remotely to a device. This route entry is given preference, and thereby exposes an attack vector.router-solicit Optional. Router solicitation messages are sent to locate routers as a form of network scanning. This information can then be used to attack a device.smurf Optional. In this attack, a large number of ICMP echo packets are sent with a spoofed source address. This causes the device with the spoofed source address to be flooded with a large number of replies.snork Optional. This attack causes a remote Windows™ NT to consume 100% of the CPU’s resources. This attack uses a UDP packtet with a destination port of 135 and a source port of 7, 9, or 135. This attack can also be exploited as a bandwidth consuming attack.tcp-bad-sequence Optional. A DoS attack that uses a specially crafted TCP packet to cause the targeted device to drop all subsequent network traffic for a specific TCP connectiontcp-fin-scan Optional. A FIN scan finds services on ports. A closed port returns a RST. This allows the attacker to identify open ports.tcp-intercept Optional. Prevents TCP intercept attacks by using TCP SYN cookiestcp-null-scan Optional. A TCP null scan finds services on ports. A closed port returns a RST. This allows the attacker to identify open portstcp-post-syn Optional. Enables a TCP post SYN DoS attacktcp-sequence-past-windowOptional. Enables a TCP SEQUENCE PAST WINDOW DoS attack check. Disable this check to work around a bug in Windows XP's TCP stack which sends data past the window when conducting a selective ACK.tcp-xmas-scan Optional. A TCP XMAS scan finds services on ports. A closed port returns a RST. This allows the attacker to identify open ports.tcphdrfrag Optional. A DoS attack where the TCP header spans IP fragmentstwinge Optional. A twinge attack is a flood of false ICMP packets to try and slow down a systemudp-short-hdr Optional. Enables the identification of truncated UDP headers and UDP header length fieldswinnuke Optional. This DoS attack is specific to Windows™ 95 and Windows™ NT, causing devices to crash with a blue screendrop-only Optional. Drops a packet without loggingdos Identifies IP events as DoS eventstcp-max-incomplete Sets the limits for the maximum number of incomplete TCP connectionshigh Sets the upper limit for the maximum number of incomplete TCP connectionslow Sets the lower limit for the maximum number of incomplete TCP connections<1-1000> Sets the range limit from 1 - 1000 connections](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-541.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 19• ip tcp adjust-mss <472-1460>• ip tcp [optimize-unnecessary-resends|recreate-flow-on-out-of-state-syn|validate-icmp-unreachable|validate-rst-ack-number|validate-rst-seq-number]Examplerfs6000-37FABE(config-rw-policy-test)#ip dos fraggle drop-onlyrfs6000-37FABE(config-rw-policy-test)#ip dos tcp-max-incomplete high 600rfs6000-37FABE(config-rw-policy-test)#ip dos tcp-max-incomplete low 60rfs6000-37FABE(config-fw-policy-test)#ip dos tcp-sequence-past-window drop-onlyrfs6000-37FABE(config-fw-policy-test)#show contextfirewall-policy test ip dos fraggle drop-only ip dos tcp-sequence-past-window drop-only ip dos tcp-max-incomplete high 600 ip dos tcp-max-incomplete low 60 flow timeout icmp 16000 flow timeout udp 10000 flow timeout tcp established 1500 flow timeout other 16000 dhcp-offer-convert dns-snoop entry-timeout 35rfs6000-37FABE(config-fw-policy-test)#Related Commandstcp Identifies and configures TCP events and configuration itemsadjust-mss Adjusts the TCP Maximum Segment Size (MSS). Use this option to adjust the MSS for TCP segments on the router.<472-1460> Sets the TCP MSS value from 472 - 1460 bytes. The default is 472 bytes.tcp Identifies and configures TCP events and configuration itemsoptimize-unnecessary-resendsEnables the validation of unnecessary TCP packetsrecreate-flow-on-out-of-state-syncAllows a TCP SYN packet to delete an old flow in TCP_FIN_FIN_STATE, and TCP_CLOSED_STATE states and create a new flowvalidate-icmp-unreachableEnables the validation of the sequence number in ICMP unreachable error packets, which abort an established TCP flowvalidate-rst-ack-number Enables the validation of the acknowledgment number in RST packets, which abort a TCP flowvalidate-rst-seq-number Enables the validation of the sequence number in RST packets, which abort an established TCP flowno Resets firewall policy IP components](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-542.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 2013.1.9 ip-macfirewall-policyDefines an action based on the device IP MAC table, and also detects conflicts between IP addresses and MAC addressesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxip-mac [conflict|routing]ip-mac conflict drop-onlyip-mac conflict [log-and-drop|log-only] log-level [<0-7>|alerts|critical|debug|emergencies|errors|informational|notifications|warnings]ip-mac routing conflict drop-onlyip-mac routing [log-and-drop|log-only] log-level [<0-7>|alerts|critical|debug|emergencies|errors|informational|notifications|warnings]Parameters• ip-mac conflict drop-only• ip-mac conflict [log-and-drop|log-only] log-level [<0-7>|alerts|critical|debug|emergencies|errors|informational|notifications|warnings]conflict Action performed when a conflict exists between the IP address and MAC address. This option is enabled by default.drop-only Drops a packet without loggingconflict Action performed when a conflict exists between the IP address and MAC address. This option is enabled by default.log-and-drop Logs the event and drops the packet. This is the default setting.log-only Logs the event only, the packet is not droppedlog-level Configures the log level<0-7> Sets the numeric logging levelalerts Numerical severity 1. Indicates a condition where immediate action is requiredcritical Numerical severity 2. Indicates a critical conditiondebugging Numerical severity 7. Debugging messagesemergencies Numerical severity 0. System is unusableerrors Numerical severity 3. Indicates an error conditioninformational Numerical severity 6. Indicates a informational conditionnotification Numerical severity 5. Indicates a normal but significant conditionwarnings Numerical severity 4. Indicates a warning condition. This is the default setting](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-543.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 21• ip-mac routing conflict drop-only• ip-mac routing [log-and-drop|log-only] log-level [<0-7>|alerts|critical|debug|emergencies|errors|informational|notifications|warnings]Examplerfs6000-37FABE(config-rw-policy-test)#ip-mac conflict drop-onlyrfs6000-37FABE(config-rw-policy-test)#ip-mac routing conflict log-and-drop log-level notificationsrfs6000-37FABE(config-fw-policy-test)#show contextfirewall-policy test ip dos fraggle drop-only ip dos tcp-sequence-past-window drop-only ip dos tcp-max-incomplete high 600 ip dos tcp-max-incomplete low 60 ip-mac conflict drop-only ip-mac routing conflict log-only log-level notifications flow timeout icmp 16000 flow timeout udp 10000 flow timeout tcp established 1500 flow timeout other 16000 dhcp-offer-convert dns-snoop entry-timeout 35rfs6000-37FABE(config-fw-policy-test)#Related Commandsrouting Enables IPMAC routing conflict detection. This is also known as a Hole-196 attack in the network. This feature helps to detect if the client is sending routed packets to the correct router-mac-address.conflict Defines the action performed when a routing table conflict is detected. This option is enabled by default.drop-only Drops a packet without loggingrouting Defines a routing table based actionconflict Action performed when a conflict exists in the routing table. This option is enabled by default.log-and-drop Logs the event and drops the packet. This is the default setting.log-only Logs the event only, the packet is not droppedlog-level Configures the log level to log this event under<0-7> Sets the numeric logging levelalerts Numerical severity 1. Indicates a condition where immediate action is requiredcritical Numerical severity 2. Indicates a critical conditiondebugging Numerical severity 7. Debugging messagesemergencies Numerical severity 0. System is unusableerrors Numerical severity 3. Indicates an error conditioninformational Numerical severity 6. Indicates a informational conditionnotification Numerical severity 5. Indicates a normal but significant conditionwarnings Numerical severity 4. Indicates a warning condition. This is the default setting.no Disables actions based on device IP MAC table, IP address, and MAC address conflict detection](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-544.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 2213.1.10 ipv6firewall-policyConfigures IPv6 components on this firewall policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 [dos|duplicate-options|firewall|option|rewrite-flow-label|routing-type|strict-ext-hdr-check|unknown-options]ipv6 dos {hop-limit-zero|multicast-icmpv6|tcp-intercept-mobility} [drop-only|log-and-drop|log-only]ipv6 [duplicate-options|routing-type [one|two]|strict-ext-hdr-check|unknown-options] [drop-only|log-and-drop|log-only]ipv6 option {endpoint-identification|network-service-access-point|router-alert|strict-hao-opt-alert|strict-padding} [drop-only|log-and-drop|log-only]ipv6 [firewall enable|rewrite-flow-label]Parameters• ipv6 dos {hop-limit-zero|multicast-icmpv6|tcp-intercept-mobility} [drop-only|log-and-drop|log-only]dos Identifies IPv6 events as DoS eventshop-limit-zero Optional. Enables checking of IPv6 hop limit field. If the IPv6 hop limit field is ZERO (0) it is considered as attack. This option is enabled by default.multicast-icmpv6 Optional. Enables detection of multicast ICMPv6 traffic as attack. This option is applicable only to ICMPv6 Echo request or reply packets. This option is enabled by default.tcp-intercept-mobility Optional. Enables detection of IPv6 TCP packets with mobility option "HAO(Home-Address-Option)" or "RH(Routing Header) type two". When enabled, this option also detects the “don't generate TCP syn cookies” for such packets. This option is enabled by default.drop-only This parameter is common to all of the above keywords.Drops all packets. Drops the specified packet type (hop-limit-zero, multicast-icmpv6, and tcp-intercept-mobility).log-and-drop Logs the event and drops the packet. Drops the specified packet type (hop-limit-zero, multicast-icmpv6, and tcp-intercept-mobility) and logs an event.log-only Logs the event only, the packet is not dropped. Does not drop the specified packet type (hop-limit-zero, multicast-icmpv6, and tcp-intercept-mobility). But, an event is logged.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-545.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 23• ipv6 [duplicate-options|routing-type [one|two]|strict-ext-hdr-check|unknown-options] [drop-only|log-and-drop|log-only]log-level If selecting the “log-and-drop” and “log-only” action type, specify the log level. The options are:• <0-7> – Sets the numeric logging level• alerts – Numerical severity 1. Indicates a condition where immediate action is required• critical – Numerical severity 2. Indicates a critical condition• debugging – Numerical severity 7. Debugging messages• emergencies – Numerical severity 0. System is unusable• errors – Numerical severity 3. Indicates an error condition• informational – Numerical severity 6. Indicates a informational condition• notifications – Numerical severity 5. Indicates a normal but significant condition• warnings – Numerical severity 4. Indicates a warning condition. This is the default setting.duplicate-options Enables handling of duplicate options in hop-by-hop and destination option extension headers. This configuration excludes HAO handling. This option is enabled by default.routing-type [one|two] Enables checking of the following IPv6 routing types:• one – Routing Type 1(Nimrod routing). This option is disabled by default.• two – Routing Type 2(Mobile IP). This option is disabled by default.strict-ext-hdr-check Enables strict checking for out of order and number of occurrences of extension header. This option is enabled by default.unknown-options Enables handling unknown options in hop-by-hop and destination option extension headers. This option is enabled by default.drop-only This parameter is common to all of the above keywords.Drops all packets. Drops the packet if matching any of the above specified types.log-and-drop Logs the event and drops the packet. Drops the packet, if matching any of the above specified types, and logs an event.log-only Logs the event only, the packet is not dropped. Does not drop the packet, if matching any of the above specified types. But an event is logged.log-level If selecting the “log-and-drop” and “log-only” action type, specify the log level. The options are:• <0-7> – Sets the numeric logging level• alerts – Numerical severity 1. Indicates a condition where immediate action is required• critical – Numerical severity 2. Indicates a critical condition• debugging – Numerical severity 7. Debugging messages• emergencies – Numerical severity 0. System is unusable• errors – Numerical severity 3. Indicates an error condition• informational – Numerical severity 6. Indicates a informational condition• notifications – Numerical severity 5. Indicates a normal but significant condition• warnings – Numerical severity 4. Indicates a warning condition. This is the default setting.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-546.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 24• ipv6 option {endpoint-identification|network-service-access-point|router-alert|strict-hao-opt-alert|strict-padding} [drop-only|log-and-drop|log-only]• ipv6 [firewall enable|rewrite-flow-label]Examplenx4500-5CFA2B(config-fw-policy-test)#ipv6 dos hop-limit-zero drop-onlynx4500-5CFA2B(config-fw-policy-test)#ipv6 routing-type two log-and-drop log-level warningsnx4500-5CFA2B(config-fw-policy-test)#show contextfirewall-policy test no ip dos tcp-sequence-past-window ipv6 routing-type two log-and-drop log-level warnings ipv6 dos hop-limit-zero drop-onlynx4500-5CFA2B(config-fw-policy-test)#option Enables checking for the following ipv6 extension header options: • End point identification option (disabled by default)• Network service access point address option (disabled by default)• Router alert option (disabled by default)• Home address option in destination option extension header (enabled by default)• Pad1 and PadN options validating (enabled by default)All of these are optional parameters. If no option is specified, the system enables checks as per the default values.drop-only This parameter is common to all of the above keywords.Drops all packets. Drops the packet if matching any of the above specified “option” types.log-and-drop Logs the event and drops the packet. Drops the packet, if matching any of the above specified “option” types, and logs an event.log-only Logs the event only, the packet is not dropped. Does not drop the packet, if matching any of the above specified “option” types. But an event is logged.log-level If selecting the “log-and-drop” and “log-only” action type, specify the log level. The options are:• <0-7> – Sets the numeric logging level• alerts – Numerical severity 1. Indicates a condition where immediate action is required• critical – Numerical severity 2. Indicates a critical condition• debugging – Numerical severity 7. Debugging messages• emergencies – Numerical severity 0. System is unusable• errors – Numerical severity 3. Indicates an error condition• informational – Numerical severity 6. Indicates a informational condition• notifications – Numerical severity 5. Indicates a normal but significant condition• warnings – Numerical severity 4. Indicates a warning condition. This is the default setting. firewall enable Enables IPv6 firewall. This option is enabled by default.rewrite-flow-label Rewrites the IPv6 flow label field of every packet. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-547.png)

![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 2613.1.11 ipv6-macfirewall-policyDefines an action based on conflicts detected in a device’s IPv6 and MAC addressesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6-mac [conflict|routing]ipv6-mac conflict [drop-only|log-and-drop|log-only]ipv6-mac routing conflict [drop-only|log-and-drop|log-only]Parameters• ipv6-mac conflict [drop-only|log-and-drop|log-only]• ipv6-mac routing conflict [drop-only|log-and-drop|log-only]conflict Enables detection of conflict between a device’s IPv6 and MAC addresses. This option is enabled by default.This command also specifies the action to be performed when a such a conflict is detected. The options are: drop-only, log-and-drop, and log-onlydrop-only Drops a packet (with conflicting IPv6 and MAC address) without logginglog-and-drop Logs the event and drops the packet. This is the default setting.log-only Logs the event only, the packet is not droppedlog-level If selecting the “log-and-drop” and “log-only” action type, specify the log level. The options are: • <0-7> – Sets the numeric logging level• alerts – Numerical severity 1. Indicates a condition where immediate action is required• critical – Numerical severity 2. Indicates a critical condition• debugging – Numerical severity 7. Debugging messages• emergencies – Numerical severity 0. System is unusable• errors – Numerical severity 3. Indicates an error condition• informational – Numerical severity 6. Indicates a informational condition• notifications – Numerical severity 5. Indicates a normal but significant condition• warnings – Numerical severity 4. Indicates a warning condition. This is the default setting.routing conflict Enables detection of conflict between the next-hop’s IPv6 and MAC addresses. This option is enabled by default.This command also specifies the action to be performed when a such a conflict is detected. The options are: drop-only, log-and-drop, and log-only](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-549.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 2813.1.12 loggingfirewall-policyConfigures enhanced firewall loggingSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlogging [icmp-all|icmp-packet-drop|malformed-packet-drop|verbose]logging icmp-alllogging verboselogging [icmp-packet-drop|malformed-packet-drop] [all|rate-limited]Parameters• logging icmp-all• logging verbose• logging [icmp-packet-drop|malformed-packet-drop] [all|rate-limited]logging Configures enhanced firewall logging parametersicmp-all Enables logging of all ICMPv4/v6 packets allowed by the firewall. This option is disabled by default.logging Configures enhanced firewall logging parameters. This option is disabled by default.verbose Enables verbose logginglogging Configures enhanced firewall logging parametersicmp-packet-drop Drops ICMP (ICMPv4 and ICMPv6) packets that do not pass sanity checks. The default is none.malformed-packet-drop Drops raw IP (IPv4 and IPv6) packets that do not pass sanity checks. The default is none.all Logs all messagesrate-limited Enables rate-limited logging. This option sets the rate limit for log messages to one message every 20 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-551.png)

![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 3013.1.13 nofirewall-policyNegates a command or sets the default for firewall policy commandsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [acl-logging|alg|clamp|dhcp-offer-convert|dns-snoop|firewall|flow|ip|ip-mac|ipv6|ipv6-mac|logging|proxy-arp|proxy-nd|stateful-packet-inspection-l2|storm-control|virtual-defragmentation]no [acl-logging|dhcp-offer-convert|proxy-arp|proxy-nd|stateful-packet-inspection-l2]no alg [dns|facetime|ftp|pptp|sccp|sip|tftp]no clamp tcp-mssno dns-snoop entry-timeoutno firewall enableno flow dhcp statefulno flow timeout [icmp|other|udp]no flow timeout tcp [closed-wait|established|reset|setup|stateless-fin-or-reset|stateless-general]no ip dos {ascend|broadcast-multicast-icmp|chargen|fraggle|ftp-bounce|invalid-protocol|ip-ttl-zero|ipsproof|land|option-route|router-advt|router-solicit|smurf|snork|tcp-bad-sequence|tcp-fin-scan|tcp-intercept|tcp-null-scan|tcp-post-syn|tcp-sequence-past-window|tcp-xmas-scan|tcphdrfrag|twinge|udp-short-hdr|winnuke}no ip tcp [adjust-mss|optimize-unnecessary-resends|recreate-flow-on-out-of-state-syn|validate-icmp-unreachable|validate-rst-ack-number|validate-rst-seq-number]no ip-mac conflictno ip-mac routing conflictno ipv6 [dos|duplicate-options|firewall|option|rewrite-flow-label|routing-type|strict-ext-hdr-check|unknown-options]no ipv6 dos {hop-limit-zero|multicast-icmpv6|tcp-intercept-mobility}no ipv6 [duplicate-options|routing-type [one|two]|strict-ext-hdr-check|unknown-options]no ipv6 option {endpoint-identification|network-service-access-point|router-alert|strict-hao-opt-alert|strict-padding}no ipv6 [firewall enable|rewrite-flow-label]no logging [icmp-all|icmp-packet-drop|verbose|malformed-packet-drop]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-553.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 31no storm-control [arp|broadcast|multicast|unicast] {fe <1-4>|ge <1-8>|log|port-channel <1-8>|up1|wlan <WLAN-NAME>}no virtual-defragmentation {maximum-fragments-per-datagram|minimum-first-fragment-length|maximum-defragmentation-per-host|timeout}Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-fw-policy-test)#show contextfirewall-policy test ip dos fraggle drop-only no ip dos tcp-sequence-past-window ip dos tcp-max-incomplete high 600 ip dos tcp-max-incomplete low 60 storm-control broadcast level 20000 ge 4 storm-control arp log warnings ip-mac conflict drop-only ip-mac routing conflict log-and-drop log-level notifications flow timeout icmp 16000 flow timeout udp 10000 flow timeout tcp established 1500 flow timeout other 16000 dhcp-offer-convert logging icmp-packet-drop rate-limited logging malformed-packet-drop all logging verbose dns-snoop entry-timeout 35rfs6000-37FABE(config-fw-policy-test)#rfs6000-37FABE(config-fw-policy-test)#no ip dos fragglerfs6000-37FABE(config-fw-policy-test)#no storm-control arp logrfs6000-37FABE(config-fw-policy-test)#no dhcp-offer-convertrfs6000-37FABE(config-fw-policy-test)#no logging malformed-packet-droprfs6000-37FABE(config-fw-policy-test)#show contextfirewall-policy test no ip dos fraggle no ip dos tcp-sequence-past-window ip dos tcp-max-incomplete high 600 ip dos tcp-max-incomplete low 60 storm-control broadcast level 20000 ge 4 storm-control arp log none ip-mac conflict drop-only ip-mac routing conflict log-and-drop log-level notifications flow timeout icmp 16000 flow timeout udp 10000 flow timeout tcp established 1500 flow timeout other 16000 logging icmp-packet-drop rate-limited logging verbose dns-snoop entry-timeout 35rfs6000-37FABE(config-fw-policy-test)#no <PARAMETERS> Negates a command or sets the default for firewall policy commands.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-554.png)

![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 3513.1.17 storm-controlfirewall-policyEnables storm control on the firewall policyStorms are packet bombardments that exceed the high threshold value configured for an interface. During a storm, packets are throttled until the rate falls below the configured rate, severely impacting performance for the RF Domain manager interface.Storm control limits multicast, unicast and broadcast frames accepted and forwarded by a device. Messages are logged based on their severity level.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxstorm-control [arp|broadcast|multicast|unicast]storm-control [arp|broadcast|multicast|unicast] [level|log]storm-control [arp|broadcast|multicast|unicast] level <1-1000000> [fe <1-4>|ge <1-8>|port-channel <1-8>|up1|wlan <WLAN-NAME>]storm-control [arp|broadcast|multicast|unicast] log [<0-7>|alerts|critical|debugging|emergencies|errors|informational|none|notifications|warnings]Parameters• storm-control [arp|broadcast|multicast|unicast] level <1-1000000> [fe <1-4>|ge <1-8>|port-channel <1-8>|up1|wlan <WLAN-NAME>]arp Configures storm control for ARP packetsbroadcast Configures storm control for broadcast packetsmulticast Configures storm control for multicast packetsunicast Configures storm control for unicast packetslevel <1-1000000> Configures the allowed number of packets received per second before storm control begins• <1-1000000> – Sets the number of packets received per secondfe <1-4> Sets the FastEthernet port for storm control from 1 - 4ge <1-8> Sets the GigabitEthernet port for storm control from 1 - 8port-channel <1-8> Sets the port channel for storm control from 1- 8up1 Sets the uplink interfacewlan <WLAN-NAME> Configures the WLAN• <WLAN-NAME> – Sets the WLAN ID for the storm control configuration](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-558.png)
![FIREWALL-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 13 - 36• storm-control [arp|bcast|multicast|unicast] log [<0-7>|alerts|critical|debugging|emergencies|errors|informational|none|notifications|warnings]Examplerfs6000-37FABE(config-fw-policy-test)#storm-control arp log warningrfs6000-37FABE(config-fw-policy-test)#storm-control broadcast level 20000 ge 4rfs6000-37FABE(config-fw-policy-test)#show contextfirewall-policy test ip dos fraggle drop-only no ip dos tcp-sequence-past-window ip dos tcp-max-incomplete high 600 ip dos tcp-max-incomplete low 60 storm-control broadcast level 20000 ge 4 storm-control arp log warnings ip-mac conflict drop-only ip-mac routing conflict log-and-drop log-level notifications flow timeout icmp 16000 flow timeout udp 10000 flow timeout tcp established 1500 flow timeout other 16000 dhcp-offer-convert logging icmp-packet-drop rate-limited logging malformed-packet-drop all logging verbose dns-snoop entry-timeout 35rfs6000-37FABE(config-fw-policy-test)#Related Commandsarp Configures storm control for ARP packetsbroadcast Configures storm control for broadcast packetsmulticast Configures storm control for multicast packetsunicast Configures storm control for unicast packetslog Configures the storm control log level for storm control events<0-7> Sets the numeric logging level from 0 - 7alerts Numerical severity 1. Indicates a condition where immediate action is requiredcritical Numerical severity 2. Indicates a critical conditiondebugging Numerical severity 7. Debugging messagesemergencies Numerical severity 0. System is unusableerrors Numerical severity 3. Indicates an error conditioninformational Numerical severity 6. Indicates a informational conditionnone Disables storm control loggingnotification Numerical severity 5. Indicates a normal but significant conditionwarnings Numerical severity 4. Indicates a warning condition. This is the default setting.no Disables storm control limits on multicast, unicast, and broadcast frames accepted and forwarded by a device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-559.png)






![MINT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 14 - 814.1.6 nomint-policyNegates a command or reverts values to their default. When used in the config MiNT policy mode, the no command resets or reverts the following global MiNT policy parameters: routing level, MTU, router packet priority, and UDP or IP encapsulation settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [level|lsp|mtu|router|udp]no level 2 area-idno lsp checksumno mtuno router packet priorityno udp port <LINE-SINK>Parameters• no <PARAMETERS>ExampleThe following example shows the global Mint Policy parameters before the ‘no’ commands are executed:rfs6000-37FABE(config-mint-policy-global-default)#show contextmint-policy global-default udp port 1024 mtu 996 level 2 area-id 2000 sign-unknown-device security-level control-and-data rejoin-timeout 1000rfs6000-37FABE(config-mint-policy-global-default)#rfs6000-37FABE(config-mint-policy-global-default)#no level 2 area-idrfs6000-37FABE(config-mint-policy-global-default)#no mturfs6000-37FABE(config-mint-policy-global-default)#no udp portThe following example shows the global Mint Policy parameters after the ‘no’ commands are executed:rfs6000-37FABE(config-mint-policy-global-default)#show contextmint-policy global-default sign-unknown-device security-level control-and-data rejoin-timeout 1000rfs6000-37FABE(config-mint-policy-global-default)#no <PARAMETERS> The no command resets or reverts the following global MiNT policy parameters: routing level, MTU, router packet priority, and UDP or IP encapsulation settings.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-568.png)



![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 515.1.1 aaa-loginmanagement-policyConfigures Authentication, Authorization and Accounting (AAA) authentication mode used with this management policy. The different modes are: local authentication and external RADIUS server authentication.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaaa-login [local|radius|tacacs]aaa-login localaaa-login radius [external|fallback|policy]aaa-login radius [external|fallback|policy <AAA-POLICY-NAME>]aaa-login tacacs [accounting|authentication|authorization|fallback|policy]aaa-login tacacs [accounting|authentication|authorization|fallback|policy <AAA-TACACS-POLICY-NAME>]Parameters• aaa-login local• aaa-login radius [external|fallback|policy <AAA-POLICY-NAME>]local Sets local as the preferred authentication mode. Local authentication uses the local username database to authenticate a user.Note: The AP6511 and AP6521 platforms do not support local RADIUS resource.radius Configures the RADIUS server parametersNote: If local authentication is disabled, use this command to specify if the RADIUS server used is external, fallback, or specified by a AAA policy.external Configures external RADIUS server as the preferred authentication modefallback Configures RADIUS server authentication as the primary authentication modeWhen RADIUS server authentication fails, the system uses local authentication. This command configures local authentication as a backup mode.policy <AAA-POLICY-NAME>Associates a specified AAA policy with this management policy. The AAA policy determines if a client is granted access to the network.• <AAA-POLICY-NAME> – Specify the AAA policy name (should be existing and configured).Note: For more information on configuring AAA policy, see AAA-POLICY.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-573.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 6• aaa-login tacacs [accounting|authentication|authorization|fallback|policy <AAA-TACACS-POLICY-NAME>]Usage GuidelinesUse AAA login to determine whether management user authentication must be performed against a local user database or an external RADIUS server.Examplerfs6000-37FABE(config-management-policy-test)#aaa-login radius externalrfs6000-37FABE(config-management-policy-test)#aaa-login radius policy testrfs6000-37FABE(config-management-policy-test)#show contextmanagement-policy test http server no ssh aaa-login radius external aaa-login radius policy testrfs6000-37FABE(config-management-policy-test)#Related Commandstacacs Configures Terminal Access Control Access-Control System (TACACS) server parametersaccounting Configures TACACS accountingauthentication Configures TACACS authenticationauthorization Configures TACACS authorizationfallback Configures TACACS as the primary authentication mode. When TACACS authentication fails, the system uses local authentication. This command configures local authentication as a backup mode.policy <AAA-TACACS-POLICY-NAME>Associates a specified AAA TACACS policy with this management policy. TACACS policies control user access to devices and network resources while providing separate accounting, authentication, and authorization services.• <AAA-TACACS-POLICY-NAME> – Specify the TACACS policy name (should be existing and configured).Note: For more information on configuring AAA TACACS policy, see AAA-TACACS-POLICY.no Removes the TACACS server settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-574.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 715.1.2 allowed-locationsmanagement-policyConfigures a user-role based access control to RF Domains and locations with respect to the NSight user interface (UI). When configured, this access control is enforced only on the NSight UI. The WiNG and NSight applications may have the same users with different permissions defined in each application. Various user roles are supported in WiNG (superuser, system-admin, network-admin, security-admin, device-provisioning-admin, helpdesk and monitor). With NSight, a user logging into the NSight UI should also have an access control restriction based on the role they’re assigned. For example, a WiNG user with helpdesk privileges should have access to only the site (RF Domain) in which the helpdesk is situated, and the location tree should contain only one RF Domain. Similarly, when a user responsible for a set of sites logs in NSight, their location tree needs to contain the RF Domains for which they’re responsible.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxallowed-locations <WORD> locations [NONE|ALL|<LIST-OF-LOCATIONS>]Parameters• allowed-locations <WORD> locations [NONE|ALL|<LIST-OF-LOCATIONS>]NOTE: For more information on NSight-policy configuration, see nsight-policy.allowed-locations <WORD>Configures a location tag and associates a list locations with the tag<WORD> – Provide a location tag not exceeding 32 characters in length.locations [NONE|ALL|<LIST-OF-LOCATIONS>]Associates locations with the above created location tag• NONE – When specified, states that none of the locations are to be allowed access.• ALL – When specified, states that all the locations are to be allowed access.• <LIST-OF-LOCATIONS> – Specifies a list of locations or individual RF Domains. When specified, states that the specified list of locations or RF Domain are allowed access.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-575.png)

![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 1015.1.4 ftpmanagement-policyEnables File Transfer Protocol (FTP) on this management policy. FTP is the standard protocol for transferring files over a TCP/IP network. FTP requires administrators enter a valid username and password authenticated locally. FTP access is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxftp {password|rootdir|username}ftp {password [1 <ENCRYPTED-PASSWORD>|<PASSWORD>]}ftp {rootdir <DIR>}ftp {username <USERNAME> password [1 <ENCRYPTED-PASSWORD>|<PASSWORD>] rootdir <DIR>}Parameters• ftp {password [1 <ENCRYPTED-PASSWORD>|<PASSWORD>]}• ftp {rootdir <DIR>}• ftp {username <USERNAME> password [1 <ENCRYPTED-PASSWORD>|<PASSWORD>] rootdir <DIR>}ftp password Optional. Configures the FTP server password1 <ENCRYPTED-PASSWORD>Configures an encrypted password. Use this option when copy pasting the password from another device.• <ENCRYPTED-PASSWORD> – Specify the password. The password should not exceed 63 characters in length.<PASSWORD> Configures a clear text passwordftp rootdir <DIR> Optional. Configures the root directory for FTP logins• <DIR> – Specify the root directory path. By default the root directory is set to flash:/ftp username <USERNAME>Optional. Configures a new user account on the FTP server. The FTP user file lists users with FTP server access.• <USERNAME> – Specify the username. The username should not exceed 32 characters in length.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-578.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 11Usage GuidelinesThe string size of an encrypted password (option 1, password is encrypted with a SHA1 algorithm) must be exactly 40 characters.Examplerfs6000-37FABE(config-management-policy-test)#ftp username superuser password test@123 rootdir dirrfs6000-37FABE(config-management-policy-test)#show contextmanagement-policy test http server ftp username superuser password 1 f617ca50c59fb47028f96db4baab5f3d8f03c03ab257960b0fd127c69f02cd7e rootdir dir no ssh aaa-login radius external aaa-login radius policy test banner motd "Have a Good Day"rfs6000-37FABE(config-management-policy-test)#Related Commandspassword 1 [<ENCRYPTED-PASSWORD>|<PASSWORD>]Configures an encrypted password• <ENCRYPTED-PASSWORD> – Specifies an encrypted password (use this option if copy pasting from another device). The password should not exceed 63 characters in length.• <PASSWORD> – Configures a clear text passwordrootdir <DIR> After specifying the password, configure the FTP root directory.• rootdir <DIR> – Configures the root directory for FTP logins. Specify the root directory path.no Disables FTP and its settings, such as the server password, root directory, and users](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-579.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 1315.1.6 httpsmanagement-policyEnables Hyper Text Transport Protocol Secure (HTTPS) on this management policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxhttps [server|sslv3|use-secure-ciphers-only]Parameters• https [server|sslv3|use-secure-ciphers-only]Examplerfs6000-37FABE(config-management-policy-test)#https serverrfs6000-37FABE(config-management-policy-test)#show contextmanagement-policy test http server https server ftp username superuser password 1 f617ca50c59fb47028f96db4baab5f3d8f03c03ab257960b0fd127c69f02cd7e rootdir dir no ssh aaa-login radius external aaa-login radius policy test banner motd "Have a Good Day"rfs6000-37FABE(config-management-policy-test)#NOTE: If the a RADIUS server is not reachable, HTTPS management access to the controller or access point may be denied. RADIUS support is available locally on controllers and access points, with the exception of AP6511 and AP6522 models, which require an external RADIUS resource.https Configures secure HTTP related parameters on this management policyserver Enables HTTPS on this management policy. HTTPS provides both authentication and data encryption as opposed to just authentication. This option is enabled by default.sslv3 Enables the use of SSLv3 protocol to connect to a Web page. When enabled, SSLv2 Web authentication is disabled, and enforces the use of Web browsers supporting SSLv3, which is a more secure protocol. This option is disabled by default.use-secure-ciphers-onlyEnables the use of TLS v1.2 ciphers to secure client-server network communications. When enabled, for HTTPS connections the TLS v1.2 protocol is used, instead of the less secure TLS v1.0 or TLS v1.1 protocols. This option is enabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-581.png)

![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 1615.1.8 ipv6management-policyRestricts management access to specified hosts and/or subnets based on their IPv6 addresses and prefixes respectivelySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxipv6 restrict-access [host|ipv6-access-list|subnet]ipv6 restrict-access host <IPv6> {log|subnet}ipv6 restrict-access host <IPv6> {log [all|denied-only]}ipv6 restrict-access host <IPv6> {subnet <IPv6-PREFIX> {log [all|denied-only]}}ipv6 restrict-access ipv6-access-list <IPv6-ACCESS-LIST-NAME>ipv6 restrict-access subnet <IPv6-PREFIX> {host|log}ipv6 restrict-access subnet <IPv6-PREFIX> {log [all|denied-only]}ipv6 restrict-access subnet <IPv6-PREFIX> {host <IPv6> {log [all|denied-only]}}Parameters• ipv6 restrict-access host <IPv6> {log [all|denied-only]}• ipv6 restrict-access host <IPv6> {subnet <IPv6-PREFIX> {log [all|denied-only]}}host <IPv6> Restricts management access to a specified host, based on the host’s IPv6 address• <IPv6> – Specify the host’s IPv6 address.log [all|denied-only] Optional. Configures a logging policy for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when a host is denied access)host <IPv6> Restricts management access to a specified host, based on the host’s IPv6 address.• <IPv6> – Specify the host’s IPv6 address.subnet <IPv6-PREFIX> Optional. Restricts access to the host on a specified IPv6 subnet• <IPv6-PREFIX> – Specify the subnet’s IPv6 prefix in the X:X::X:X/M format.log [all|denied-only] Optional. Configures a logging policy for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when a host/subnet is denied access)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-584.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 17• ipv6 restrict-access ipv6-access-list <IPv6-ACCESS-LIST-NAME>• ipv6 restrict-access subnet <IPv6-PREFIX> {log [all|denied-only]}• ipv6 restrict-access subnet <IPv6-PREFIX> {host <IPv6> {log [all|denied-only]}}Examplerfs6000-37FABE(config-management-policy-test)#ipv6 restrict-access host 2001:fdbc:06cf:0011::13 subnet 2001:fdbc:06cf:0011::0/64 log allrfs6000-37FABE(config-management-policy-test)#show contextmanagement-policy test http server no ssh ipv6 restrict-access host 2001:fdbc:06cf:0011::13 subnet 2001:fdbc:06cf:0011::0/64 log allrfs6000-37FABE(config-management-policy-test)#Related Commandsipv6-access-list <IPv6-ACCESS-LIST-NAME>Uses an IPv6 Access Control List (ACL) to filter access requests. IPv6 ACLs filter/mark packets based on the IPv6 address from which they arrive. IPv6 hosts configure themselves automatically when connected to an IPv6 network using the neighbor discovery (ND) protocol via ICMPv6 router discovery messages. These hosts require firewall packet protection unique to IPv6 traffic, as IPv6 addresses are composed of eight groups of four hexadecimal digits separated by colons. An existing IPv6 ACL can be created and used in the management policy context to permit or deny access to specific hosts and/or subnets.• <IPv6-ACCESS-LIST-NAME> – Specify the IPv6 ACL name.subnet <IPv6-PREFIX>Restricts management access to a specified IPv6 subnet• <IPv6-PREFIX> – Specify the subnet’s IPv6 prefix in the X:X::X:X/M format.log [all|denied-only] Optional. Configures a logging policy for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when a host/subnet is denied access)subnet <IPv6-PREFIX>Restricts management access to a specified IPv6 subnet• <IPv6-PREFIX> – Specify the subnet’s IPv6 prefix in the X:X::X:X/M format.host <IPv6> Optional. Restricts management access to a specific host within the specified subnet• <IPv6> – Specify the host’s IPv6 address.log [all|denied-only] Optional. Configures a logging policy for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when a host/subnet is denied access)no Removes management access restriction settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-585.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 1815.1.9 nomanagement-policyNegates a command or reverts values to their default. When used in the config management policy mode, the no command negates or reverts management policy settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [aaa-login|allowed-locations|banner|ftp|http|https|idle-session-timeout|ipv6|passwd-entry|privilege-mode-password|rest-server|restrict-access|snmp-server|ssh|t5|telnet|user|service]no aaa-login tacacs [accounting|authentication|authorization|fallback|policy]no allowed-location <LOCATION-TAG>no banner motdno ftp {password|rootdir}no http serverno https [server|sslv3|use-secure-ciphers-only]no passwd-entry role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|vendor-admin|web-user-admin]no [idle-session-timeout|privilege-mode-password|rest-server|restrict-access]no ipv6 restrict-accessno snmp-server [community|display-vlan-info-per-radio|enable|host|manager|max-pending-requests|request-timeout|suppress-security-configuration-level|throttle|user]no snmp-server [community <WORD>|display-vlan-info-per-radio|enable traps|host <IP> {<1-65535>}|manager [all|v1|v2|v3]|max-pending-requests|request-timeout|suppress-security-configuration-level|throttle|user [snmpmanager|snmpoperator|snmptrap]]no ssh {login-grace-time|port|use-key}no t5 snmp-server [community|enable|host]no [telnet|user <USERNAME>]no service prompt crash-infoParameters• no <PARAMETERS>no <PARAMETERS> Removes or reverts this Management policy settings based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-586.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 2015.1.10 passwd-entrymanagement-policyConfigures user-account lockout and unlock parameters. Use this option to configure the maximum number of consecutive, failed login attempts allowed before an account is locked out, and the duration of lockout.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpasswd-entry role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|vendor-admin|web-user-admin] max-fail <1-100> lockout-time <<0-600>Parameters• passwd-entry role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|vendor-admin|web-user-admin] max-fail <1-100> lockout-time <0-600>passwd-entry role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|vendor-admin|web-user-admin] max-fail <1-100> lockout-time <<0-600>Configures user-role based account lockout criteria• role – Select the user-role. The options are:• device-provisioning-admin•helpdesk• monitor•network-admin•security-admin• system-admin• vendor-admin• web-user-admin] • max-fail <1-100> – Specify the maximum number of consecutive, failed at-tempts allowed before an account is locked. Specify a value from 1 - 100. • lockout-time <<0-600> – Specify the maximum time, in minutes, forwhich an account remains locked. The value ‘0’ indicates that the ac-count is permanently locked. Specify a value from 0 - 600 minutes.When configured, the lockout is individually applied to each account within the specified role/roles. For example, consider the ‘monitor’ role having two users: ‘user1’ and ‘user2’. The max-fail and lockout-time is set at ‘5’ attempts and ‘10’ minutes respectively. In this scenario, user2 makes 5 consecutive, failed login attempts, and the user2 account is locked out for 10 minutes. However, during this lockout time the user1 account remains active.Note: Note, in the event-system-policy context, enable ‘login-lockout’ and ‘login-unlocked’ event notification to trigger e-mail or syslog notification to users on occurrence of the login-lockout and login-unlock events. For more information, see event.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-588.png)

![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 23Follow the steps below to configure a hashed-string alias and use it as a privilege mode password:1 In the global-configuration context, create a hashed-string alias.nx9500-6C8809(config)#alias hashed-string $PriMode Test12345nx9500-6C8809(config)#show context | include aliasalias vlan $BLR-01 1alias string $IN-Blr-EcoSpace-Floor-4 IBEF4alias encrypted-string $READ 0 publicalias encrypted-string $WRITE 0 privatealias hashed-string $PriMode 1 faffdde27cb49ad634ea20df4f7c8ef2685894d10ffcb1b2efba054112ecfc75nx9500-6C8809(config)#2 In the management-policy context, configure the hashed-string alias created in step 1 as the privilege mode password.nx9500-6C8809(config-management-policy-test)#privilege-mode-password $PrivModenx9500-6C8809(config-management-policy-default)#show contextmanagement-policy defaulthttps server rest-server ssh user admin password 1 ad4d8797f007444ccdda3788b9ee0e8b46f3facb4308e045239eb7771e127ed5 role superuser access all snmp-server community 0 $WRITE rw snmp-server community 0 $READ ro snmp-server user snmptrap v3 encrypted des auth md5 2 yqr96yyVzmD4ZbU2I7Eh/QAAAAjWNKa4KXF95pruUCSnhOiT snmp-server user snmpmanager v3 encrypted des auth md5 2 NOf8+2+AY2r4ZbU2I7Eh/QAAAAgc0l8ahJYo3AjHo9wXzYGo t5 snmp-server community public ro 192.168.0.1 t5 snmp-server community private rw 192.168.0.1 privilege-mode-password $PriModenx9500-6C8809(config-management-policy-default)#3 Confirm, if the privilege mode is password protected.nx9500-6C8809 login: adminPassword:Feb 07 14:40:47 2017: %AUTH-6-INFO: login[28768]: user 'admin' on 'ttyS0' from 'Console' logged inFeb 07 14:40:47 2017: nx9500-6C8809 : %SYSTEM-5-LOGIN: Successfully logged in user 'admin' with privilege 'superuser' from 'ttyS0'nx9500-6C8809>enPassword:Related Commandsno Removes the configured CLI privilege mode access password](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-591.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 2515.1.13 restrict-accessmanagement-policyRestricts management access to a set of hosts or subnetsRestricting remote access to a controller or service platform ensures only trusted hosts can communicate with enabled management services. This ensures only trusted hosts can perform management tasks and provide protection from brute force attacks from hosts attempting to break into the controller or service platform managed network.Administrators can permit management connections to be established on any IP interface on the controller or service platform (including IP interfaces used to provide captive portal guest access). Administrators can restrict management access by limiting access to a specific host (IP address), subnet, or ACL on the controller or service platform.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrestrict-access [host|ip-access-list|subnet]restrict-access host <IP> {log|subnet}restrict-access host <IP> {log [all|denied-only]}restrict-access host <IP> {subnet <IP/M> {log [all|denied-only]}}restrict-access ip-access-list <IP-ACCESS-LIST-NAME>restrict-access subnet <IP/M> {host|log}restrict-access subnet <IP/M> {log [all|denied-only]}restrict-access subnet <IP/M> {host <IP> {log [all|denied-only]}}Parameters• restrict-access host <IP> {log [all|denied-only]}• restrict-access host <IP> {subnet <IP/M> {log [all|denied-only]}}host <IP> Restricts management access to a specified host, based on the host’s IPv4 address• <IP> – Specify the host’s IPv4 address.log [all|denied-only] Optional. Configures a logging policy for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access (when an access request is received from a host denied access, a record is logged)host <IP> Restricts management access to a specified host, based on the host’s IPv4 address• <IP> – Specify the host’s IPv4 address.subnet <IP/M> Optional. Restricts access to the host on a specified subnet• <IP/M> – Specify the subnet’s IPv4 address and mask in the A.B.C.D/M format.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-593.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 26• restrict-access ip-access-list <IP-ACCESS-LIST-NAME>• restrict-access subnet <IP/M> {log [all|denied-only]}• restrict-access subnet <IP/M> {host <IP> {log [all|denied-only]}}log [all|denied-only] Optional. Configures a logging policy for access requests.• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when access request received from a host is denied)ip-access-list Uses an IPv4 ACL to filter access requestsIPv4 ACLs filter/mark packets based on the IPv4 address from which they arrive. IP and non-IP traffic, on the same layer 2 interface, can be filtered by applying an IPv4 ACL. Each IPv4 ACL contains a set of deny and/or permit rules. Each rule is specific to source and destination IPv4 addresses and the unique rules and precedence definitions assigned. When the network traffic matches the criteria specified in one of these rules, the action defined in that rule is used to determine whether the traffic is allowed or denied.<IP-ACCESS-LIST-NAME>Specify the IPv4 ACL name.subnet <IP/M> Restricts management access to a specified subnet• <IP/M> – Specify the subnet’s IPv4 address and mask in the A.B.C.D/M format.log [all|denied-only] Optional. Configures a logging policy for access requests. Sets the log type generated for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when access request received from a subnet is denied)subnet <IP/M> Restricts management access to a specified subnet• <IP/M> – Specify the subnet’s IPv4 address and mask in the A.B.C.D/M formathost <IP> Optional. Uses the host IP address as a second filter• <IP> – Specify the host’s IPv4 address.log [all|denied-only] Optional. Configures a logging policy for access requests. Sets the log type generated for access requests• all – Logs all access requests, both denied and permitted• denied-only – Logs only denied access events (when access request received from a host within the specified subnet is denied)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-594.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 2815.1.14 snmp-servermanagement-policyConfigures the Simple Network Management Protocol (SNMP) engine settings. SNMP is an application layer protocol that facilitates the exchange of management information between the controller and a managed device. SNMP enabled devices listen on port 162 (by default) for SNMP packets from the controller’s management server. SNMP uses read-only and read-write community strings as an authentication mechanism to monitor and configure supported devices. The read-only community string gathers statistics and configuration parameters from a supported wireless device. The read-write community string is used by a management server to set device parameters. SNMP is generally used to monitor a system’s performance and other parameters.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsnmp-server [community|enable|display-vlan-info-per-radio|host|manager|max-pending-requests|request-timeout|suppress-security-configuration-level|throttle|user]snmp-server community [0 <WORD>|2 <WORD>|<WORD>] [ro|rw] {ip-snmp-access-list <IP-SNMP-ACL-NAME>}snmp-server enable trapssnmp-server host <IP> [v1|v2c|v3] {<1-65535>}snmp-server manager [all|v1|v2|v3]snmp-server [max-pending-requests {<64-1024>}|request-timeout {<2-720>}]snmp-server [display-vlan-info-per-radio|throttle <1-100>|suppress-security-configuration-level [0|1]]snmp-server user [snmpmanager|snmpoperator|snmptrap]snmp-server user [snmpmanager|snmpoperator|snmptrap] v3 [auth|encrypted]snmp-server user [snmpmanager|snmpoperator|snmptrap] v3 auth md5 [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]snmp-server user [snmpmanager|snmpoperator|snmptrap] v3 encrypted [auth md5|des auth md5] [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-596.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 29Parameters• snmp-server community [0 <WORD>|2 <WORD>|<WORD>] [ro|rw] {ip-snmp-access-list <IP-SNMP-ACL-NAME>}• snmp-server enable traps• snmp-server host <IP> [v1|v2c|v3] {<1-65535>}community [0 <WORD>|2 <WORD>|<WORD>]Sets the community string and associated access privileges. Define a public or private community designation. By default, SNMPv2 community strings on most devices are set to public for the read-only community string, and private for the read-write community string.• 0 <WORD> – Sets a clear text SNMP community string• 2 <WORD> – Sets an encrypted SNMP community string• <WORD> – Sets the SNMP community string[ro|rw] After configuring the SNMP community string, set the access permission for each community string used by devices to retrieve or modify information. Available options include• ro – Assigns read-only access to the specified SNMP community (allows a remote device to retrieve information)• rw – Assigns read and write access to the specified SNMP community (allows a remote device to modify settings)ip-snmp-access-list <IP-SNMP-ACL-NAME>Optional. Associates an IP SNMP access list (should be existing and configured). The IP SNMP ACL sets the SNMP management station’s IP address. SNMP trap information is received at this address.enable traps Enables trap generation (using the trap receiver configuration defined). This feature is disabled by default. Enabling this feature ensures the dispatch of SNMP notifications to all hosts.In a managed network, the controller uses SNMP trap receivers to notify faults. SNMP traps are unsolicited notifications triggered by thresholds (or actions) on devices and are therefore an important fault management tool.A SNMP trap receiver is the destination of SNMP messages (external to the controller). A trap is like a Syslog message, just over another protocol (SNMP). A trap is generated when a device consolidates event information and transmits the information to an external repository. The trap contains several standard items, such as the SNMP version, community, etc.SNMP trap notifications exist for most controller operations, but not all are necessary for day-to-day operation.host <IP> Configures a host’s IP address. This is the external server resource dedicated to receiving SNMP traps on behalf of the controller.[v1|v2c|v3] Configures the SNMP version used to send the traps• v1 – Uses SNMP version 1. This option is disabled by default.• v2c – Uses SNMP version 2c. This option is disabled by default.• v3 – Uses SNMP version 3. This option is enabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-597.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 30• snmp-server manager [all|v1|v2|v3]• snmp-server [max-pending-requests {<64-1024>}|request-timeout {<2-720>}]• snmp-server [display-vlan-info-per-radio|throttle <1-100>|suppress-security-configuration-level [0|1]]<1-65535> Optional. Configures the virtual port of the server resource dedicated to receiving SNMP traps• <1-65535> – Optional. Specify a value from 1 - 65535. The default port is 162.manager [all|v2|v3] Enables SNMP manager and specifies the SNMP version• all – Enables SNMP manager version v2 and v3• v1 – Enables SNMP manager version v1 only. SNMPv1 uses a simple password (“community string”). Data is unencrypted (clear text). Consequently it provides limited security, and should be used only inside LANs behind firewalls, not in WANs.• v2 – Enables SNMP manager version v2 only. SNMPv2 provides device management using a hierarchical set of variables. SNMPv2 uses Get, GetNext, and Set operations for data management. SNMPv2 is enabled by default.• v3 – Enables SNMP manager version v3 only. SNMPv3 adds security and remote configuration capabilities to previous versions. The SNMPv3 architecture introduces the User-based Security Model (USM) for message security and the View-based Access Control Model (VACM) for access control. The architecture supports the concurrent use of different security, access control and message processing techniques. SNMPv3 is enabled by default.max-pending-requests {<64-1024>}Sets the maximum number of requests that can be pending at any given time• <64-1024> – Optional. Specify a value from 64 - 1024. The default is 128.request-timeout{<2-720>}Sets the interval, in seconds, after which an error message is returned for a pending request• <2-720> – Optional. Specify a value from 2 - 720 seconds. The default is 240 seconds.display-vlan-info-per-radioEnables the display of the VLAN ID along with the radio interface IDthrottle <1-100> Sets CPU usage for SNMP activities. Use this command to set the CPU usage from 1 - 100.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-598.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 31• snmp-server user [snmpmanager|snmpoperator|snmptrap] v3 auth md5 [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]• snmp-server user [snmpmanager|snmpoperator|snmptrap] v3 encrypted [auth md5|des auth md5] [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]suppress-security-configuration-level [0|1]Sets the level of suppression of SNMP security configuration information• 0 – If this option is selected, an empty string is returned for the SNMP request for security configuration information. Security configuration information consists of:•Passwords•Keys• Shared secretsThe default setting is 0.• 1 – Suppresses the display of the policy, IP ACL, passwords, keys and shared secrets. If this option is selected, in addition to suppression from ‘Level 0’, an empty string is returned for a SNMP request on following items:• Management policies•IP ACL• Tables containing user names and community stringsuser [snmpmanager|snmpoperator|snmptrap]Defines user access to the SNMP engine• snmpmanager – Sets user as a SNMP manager• snmpoperator – Sets user as a SNMP operator• snmptrap – Sets user as a SNMP trap userv3 auth md5 Uses SNMP version 3 as the security model• auth – Uses an authentication protocol• md5 – Uses HMAC-MD5 algorithm for authentication[0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]Configures password using one of the following options:• 0 <PASSWORD> – Configures clear text password• 2 <ENCRYPTED - PASSWORD> – Configures encrypted password• <PASSWORD> – Specifies a password for authentication and privacy protocolsuser [snmpmanager|snmpoperator|snmptrap]Defines user access to the SNMP engine• snmpmanager – Sets user as a SNMP manager• snmpoperator – Sets user as a SNMP operator• snmptrap – Sets user as a SNMP trap userv3 encrypted Uses SNMP version 3 as the security model• encrypted – Uses encrypted privacy protocolauth md5 Uses authentication protocol• auth – Sets authentication parameters• md5 – Uses HMAC-MD5 algorithm for authenticationdes auth md5 Uses privacy protocol for user privacy• des – Uses CBC-DES for privacyAfter specifying the privacy protocol, specify the authentication mode.• auth – Sets user authentication parameters• md5 – Uses HMAC-MD5 algorithm for authentication](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-599.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 32Examplerfs6000-37FABE(config-management-policy-test)#snmp-server community snmp1 rorfs6000-37FABE(config-management-policy-test)#snmp-server host 172.16.10.23 v3 162rfs6000-37FABE(config-management-policy-test)#commitrfs6000-37FABE(config-management-policy-test)#snmp-server user snmpmanager v3 auth md5 test@123rfs6000-37FABE(config-management-policy-test)#show contextmanagement-policy test no http server https server ftp username superuser password 1 f617ca50c59fb47028f96db4baab5f3d8f03c03ab257960b0fd127c69f02cd7e rootdir dir no ssh snmp-server community snmp1 ro snmp-server user snmpmanager v3 encrypted des auth md5 0 test@123 snmp-server host 172.16.10.23 v3 162 aaa-login radius external aaa-login radius policy test idle-session-timeout 0 restrict-access host 172.16.10.2 log allrfs6000-37FABE(config-management-policy-test)#Related Commands[0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]The following are common to both the auth and des parameters:Configures password using one of the following options:• 0 <PASSWORD> – Configures a clear text password• 2 <ENCRYPTED - PASSWORD> – Configures an encrypted password• <PASSWORD> – Specifies a password for authentication and privacy protocolsno Disables or resets the SNMP server settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-600.png)

![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 3415.1.16 t5management-policyConfigures SNMP server settings for T5 devices on this management policyA T5 controller is an external device that can be adopted and managed by a WiNG controller. When enabled as a supported external device, a T5 controller can provide data to WiNG to assist in it’s management within a WiNG supported subnet.This command enables SNMP to communicate with T5 devices within the network. SNMP facilitates the exchange of management information between the controller or service platform and the T5 device. For more information, see snmp-server.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510Syntaxt5 snmp-server [community|contact|enable|host|location]t5 snmp-server community <COMMUNITY-NAME> [ro|rw] <SNMP-STATION-IP>t5 snmp-server contact <LINE>t5 snmp-server enable [server|traps]t5 snmp-server host <IP>t5 snmp-server location <LINE>Parameters• t5 snmp-server community <COMMUNITY-NAME> [ro|rw] <SNMP-STATION-IP>• t5 snmp-server contact <LINE>community <COMMUNITY-NAME> [ro|rw]Defines a public or private community designation. By default, SNMPv2 community strings on most devices are set to public, for the read-only community string, and private for the read-write community string.• <COMMUNITY-NAME> – Specify the SNMP community name, and configure the access permission for this community string (used by devices to retrieve or modify information).• ro – Allows a remote device to retrieve information only• rw – Allows a remote device to retrieve information and modify settings<SNMP-STATION-IP> Specify the SNMP management station IP address for receiving trap informationcontact <LINE> Configures the administrator of SNMP trap events for the T5 controller.• <LINE> – Specify the administrator’s name (should not exceed 64 characters).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-602.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 35• t5 snmp-server enable [server|traps]• t5 snmp-server host <IP>• t5 snmp-server location <LINE>Examplenx9500-6C8809(config-management-policy-test)#t5 snmp-server community lab rw 192.168.13.7nx9500-6C8809(config-management-policy-test)#show contextmanagement-policy test http server no ssh t5 snmp-server community lab rw 192.168.13.7nx9500-6C8809(config-management-policy-test)#Related Commandsenable [server|traps] Enables the following:• server – Enables the SNMP server. When enabled, the system accepts SNMP management data. This is enabled by default.• traps – Enables SNMP traps. When enabled, the system generates SNMP traps. This is enabled by default.host <IP> Configures the T5 SNMP host’s IP address. The SNMP host receives the SNMP notifications.• <IP> – Specify the SNMP host’s IP address.location <LINE> Configures the system location for SNMP traps.• <LINE> – Specify the SNMP trap location (should not exceed 64 characters).no Removes or reverts SNMP server configuration for T5 devices](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-603.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 3715.1.18 usermanagement-policyAdds new user account. Use this option to add a new user, and define the role, access type, and allowed locations assigned to the user.Management services like Telnet, SSHv2, HTTP, HTTPs and FTP require users (administrators) enter a valid username and password, which is authenticated locally or centrally on a RADIUS server. SNMPv3 also requires a valid username and password, which is authenticated by the SNMPv3 module. For CLI users, the controller or service platform also requires user role information to know what permissions to assign.• If local authentication is used, associated role information is defined on the controller or service platform when the user account is created.• If RADIUS is used, role information is supplied by RADIUS using vendor-specific return attributes. If no role information is supplied by RADIUS, the controller or service platform applies default read-only permissions.Administrators can limit users to specific management interfaces. During authentication, the controller or service platform looks at the user’s access assignment to determine if the user has permissions to access an interface:• If local authentication is used, role information is defined on the controller or service platform when the user account is created.• If RADIUS is used, role information is supplied by RADIUS using vendor-specific return attributes.The controller or service platform authenticates users using the integrated local database. When user credentials are presented the controller or service platform validates the username and password against the local database and assigns permissions based on the associated roles assigned. The controller or service platform can also deny the authentication request if the user is attempting to access a management interface not specified in the account’s access mode list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuser <USERNAME> password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>] role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|vendor-admin|web-user-admin]user <USERNAME> password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>] role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|web-user-admin] access [all|console|ssh|telnet|web] ({allowed-locations <ALLOWED-LOCATIONS>})user <USERNAME> password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>] role vendor-admin group <VENDOR-GROUP-NAME>](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-605.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 38Parameters• user <USERNAME> password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>] role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|web-user-admin] access [all|console|ssh|telnet|web] ({allowed-locations <ALLOWED-LOCATIONS>})user <USERNAME> Adds a new user account to this management policy• <USERNAME> – Sets the username. This is a mandatory field and cannot exceed 32 characters. Assign a name representative of the user and the intended role.password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>]Configures a password• 0 <PASSWORD> – Sets a clear text password• 1 <SHA1-PASSWORD> – Sets the SHA1 hash of the password• <PASSWORD> – Sets the passwordrole Configures the user role. The options are:• device-provisioning-admin – Device provisioning administrator. Has privileges to update (provision) device configuration files or firmware. Such updates run the risk of overwriting and losing a devices existing configuration unless the configuration is properly archived.• helpdesk – Helpdesk administrator. Performs troubleshooting tasks, such as run troubleshooting utilities (like a sniffer), view/retrieve logs, clear statistics, reboot, create and copy technical support dumps. The helpdesk administrator can also create a guest user account and password for registration. However, the helpdesk admin cannot execute controller or service platform reloads.• monitor – Monitor. Has read-only access to the system. Can view configuration and statistics except for secret information.• network-admin – Network administrator. Manages layer 2, layer 3, Wireless, RADIUS server, DHCP server, and Smart RF• security-admin – Security administrator. Modifies WLAN keys and passphrases• superuser – Superuser. Has full access, including halt and delete startup-config• system-admin – System administrator. Upgrades image, boot partition, time, and manages admin access• web-user-admin – Web user administrator. This role is used to create guest users and credentials. The Web user admin can access only the custom GUI screen and does not have access to the normal CLI and GUI.access [all|console|ssh|telnet|web]Configures the access type• all – Allows all types of access: console, SSH, Telnet, and Web• console – Allows console access only• ssh – Allows SSH access only• telnet – Allows Telnet access only• web – Allows Web access onlyallowed-locations <ALLOWED-LOCATIONS>Optional. This keyword is recursive and optional. It configures a list of locations (either as a path or a RF Domain) to which this user is allowed access.• <ALLOWED-LOCATIONS> – Specify the allowed locations.Note: Use this option to configure a list of RF Domains or its tree nodes to which this user is allowed access with respect to the Nsight policy.Note: This option is not applicable to the user role ‘web-user-admin’.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-606.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 39• user <USERNAME> password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>] role vendor-admin group <VENDOR-GROUP-NAME>Examplerfs6000-37FABE(config-management-policy-test)#user TESTER password test123 rolesuperuser access allrfs6000-37FABE(config-management-policy-test)#show contextmanagement-policy test telnet port 200 no http server https server ftp username superuser password 1 f617ca50c59fb47028f96db4baab5f3d8f03c03ab257960b0fd127c69f02cd7e rootdir dir ssh port 162 user TESTER password 1 b6b37c51405f4e93c67fe8af82d450c9fd6af69324cd56a55055cefe695b6a14 role superuser access all snmp-server community snmp1 ro snmp-server user snmpmanager v3 encrypted des auth md5 0 test@123 snmp-server host 172.16.10.23 v3 162user <USERNAME> Adds a new user account to this management policy• <USERNAME> – Sets the username. This is a mandatory field and cannot exceed 32 characters. Assign a name representative of the user and the intended role.password [0 <PASSWORD>|1 <SHA1-PASSWORD>|<PASSWORD>]Configures a password• 0 <PASSWORD> – Sets a clear text password• 1 <SHA1-PASSWORD> – Sets the SHA1 hash of the password• <PASSWORD> – Sets the passwordrole vendor-admin Configures this user’s role as vendor-admin. Once created, the vendor-admin can access the online device-registration portal to add devices to the RADIUS vendor group to which he/she belongs. Vendor-admins have only Web access to the device registration portal.The WiNG software allows multiple vendors to securely on-board their devices through a single SSID. Each vendor has a ‘vendor-admin’ user who is assigned a unique, username/password credential for RADIUS server validation. Successfully validated vendor-admins can on-board their devices, which are, on completion of the on-boarding process, immediately placed on the vendor-allowed VLAN. On subsequent associations with this SSID, registered devices are dynamically placed into the vendor-allowed VLAN.If assigning the vendor-admin role, provide the vendor's group name for RADIUS authentication. The vendor's group takes precedence over the statically configured group for device registration.Note: Use the service > show > wireless > credential-cache command to view on-boarded device’s VLAN assignment.Note: Ensure that the REST server is enabled, to allow vendor users access to the online device registration portal. Note, by default the REST server is enabled. For more information, see rest-server.group <VENDOR-GROUP-NAME>Associates this vendor-admin user with a vendor group, required for RADIUS authentication. The vendor group should be existing and configured in the RADIUS group policy. For more information on configuring RADIUS groups, see radius-group.• <VENDOR-GROUP-NAME> – Provide the vendor group name. In case of multiple allowed groups, provide a list of comma-separated group names.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-607.png)
![MANAGEMENT-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 15 - 4115.1.19 servicemanagement-policyInvokes service commandsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxservice [prompt|show]service [prompt crash-info|show cli]Parameters• service [prompt crash-info|show cli]Examplerfs6000-37FABE(config-management-policy-test)#service show cliManagement Mode mode:+-help [help] +-search +-WORD [help search WORD (|detailed|only-show|skip-show|skip-no)] +-detailed [help search WORD (|detailed|only-show|skip-show|skip-no)] +-only-show [help search WORD (|detailed|only-show|skip-show|skip-no)] +-skip-show [help search WORD (|detailed|only-show|skip-show|skip-no)] +-skip-no [help search WORD (|detailed|only-show|skip-show|skip-no)]+-show +-commands [show commands] +-simulate +-stats [show simulate stats] +-eval +-WORD [show eval WORD] +-debugging [show debugging (|(on DEVICE-OR-DOMAIN-NAME))] +-cfgd [show debugging cfgd] +-on +-DEVICE-OR-DOMAIN-NAME [show debugging (|(on DEVICE-OR-DOMAIN-NAME))] +-fib [show debugging fib(|(on DEVICE-NAME))] +-on +-DEVICE-NAME [show debugging fib(|(on DEVICE-NAME))] +-wireless [show debugging wireless (|(on DEVICE-OR-DOMAIN-NAME))] +-on--More--Related Commandsservice promptcrash-infoUpdates CLI prompt settings• crash-info – Includes an asterix at the end of the prompt if the device has crash files in the flash:/crashinfo folderservice show cli Displays running system information• cli – Displays the current mode’s CLI treeno Disables the inclusion of an asterix indicator notifying the presence of crash files](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-609.png)


![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 516.1.2 policyradius-groupSets a RADIUS group’s authorization settings, such as access day/time, WLANs, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpolicy [access|day|inactivity-timeout|role|session-time|ssid|time|vlan]policy vlan <1-4094>policy access [all|console|ssh|telnet|web]policy access [all|console|ssh|telnet|web] {(all|console|ssh|telnet|web)}policy day [all|fr|mo|sa|su|th|tu|we|weekdays] {(fr|mo|sa|su|th|tu|we|weekdays)}policy inactivity-timeout <60-86400>policy role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|web-user-admin]policy session-time <5-144000>policy ssid <SSID>policy time start <HH:MM> end <HH:MM>Parameters• policy vlan <1-4094>NOTE: A user-based VLAN is effective only if dynamic VLAN authorization is enabled for the WLAN.NOTE: Access and role settings are applicable only to a management group. They cannot be configured for a RADIUS non-management group.vlan <1-4094> Sets the guest RADIUS group’s VLAN ID from 1 - 4094. The VLAN ID is representative of the shared SSID each group member (user) employs to interoperate within the network (once authenticated by the local RADIUS server).This option applicable to a guest user group, which has guest access and temporary permissions to the local RADIUS server. The terms of the guest access can be set uniquely for each group. Guest user groups cannot be made management groups with unique access and role permissions.Enable dynamic VLAN assignment for the WLAN for the VLAN assignment to take effect.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-614.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 6• policy access [all|console|ssh|telnet|web] {(all|console|ssh|telnet|web)}• policy role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|web-user-admin]• policy inactivity-timeout <60-86400>access Configures access type for a management group. Management groups can be assigned unique access and role permissions.• all – Allows all access. Wireless client access to the console, ssh, telnet, and/or Web• console – Allows console access only• ssh – Allows SSH access only• telnet – Allows Telnet access only•web – Allows Web access onlyThese parameters are recursive, and you can provide access to more than one component.role [device-provisioning-admin|helpdesk|monitor|network-admin|security-admin|superuser|system-admin|web-user-admin]Configures the role assigned to a management RADIUS group. If a group is listed as a management group, it may also have a unique role assigned. Available roles include:• device-provisioning-admin – Device provisioning administrator. Has privileges to update (provision) device configuration files or firmware. Such updates run the risk of overwriting and losing a devices existing configuration unless the configuration is properly archived.• helpdesk – Helpdesk administrator. Performs troubleshooting tasks, such as clear statistics, reboot, create and copy tech support dumps. The helpdesk administrator can also create a guest user account and password for registration. These details can be e-mailed or sent as SMS to a mobile phone.• monitor – Monitor. Has read-only access to the network. Can view configuration and statistics except for secret information• network-admin – Network administrator. has wired and wireless access to the network. Manages layer 2, layer 3, Wireless, RADIUS server, DHCP server, and Smart RF• security-admin – Security administrator. Has full read/write access to the network. Modifies WLAN keys and passphrases• superuser – Superuser. Has full access, including halt and delete startup config• system-admin – System administrator. Upgrades image, boot partition, time, and manages admin access• web-user-admin – Web user administrator. This role is used to create guest users and credentials. The web-user-admin can access only the custom GUI screen and does not have access to the normal CLI and GUI.inactivity-timeout <60-86400>Configures the inactivity time for this RADIUS group users. If a frame is not received from a client for the specified period, then the client’s session is removed. When defined, this value is used instead of the captive-portal inactivity timeout. If the inactivity timeout is not configured in the radius-group context or the captive-portal context, the default timeout (60 seconds) is applied.• <60-86400> – Specify a value from 60 - 86400 seconds. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-615.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 7• policy session-time <5-144000>• policy ssid <SSID>• policy day [all|fr|mo|sa|su|th|tu|we|weekdays] {(fr|mo|sa|su|th|tu|we|weekdays)}• policy time start <HH:MM> end <HH:MM>Usage GuidelinesA management group access policy provides:• access details•user roles• policy’s start and end timeThe SSID, day, and VLAN settings are not applicable to a management user group.session-time <5-144000>Configures the session duration for client’s belonging to a specific vendor group. Once configured, this is the duration for which over-the-air, on-boarded, successfully authenticated devices, belonging to a vendor group, get online access. The session is removed on completion of this duration. The vendor’s RADIUS group takes precedence over statically configured group for device registration.• <5-144000> – Specify a value from 5 - 144000 minutes. This option is disabled by default.For more information, see configuring device registration with dynamic VLAN assignment.ssid <SSID> Sets the Service Set Identifier (SSID) for this guest RADIUS group. Use this command to assign SSIDs that users within this RADIUS group are allowed to associate. Assign SSIDs of those WLANs only that the guest users need to access. This option is not available for a management group.• <SSID> – Specify a case-sensitive alphanumeric SSID, not exceeding 32 characters.day [all|fr|mo|sa|su|th|tu|we|weekdays]Configures the days on which this guest RADIUS group members can access the local RADIUS resources. The options are recursive, and you can provide access on multiple days.• fr – Allows access on Friday only• mo – Allows access on Mondays only• sa – Allows access on Saturdays only• su – Allows access on Sundays only• th – Allows access on Thursdays only• tu – Allows access on Tuesdays only• we – Allows access on Wednesdays only• weekdays – Allows access on weekdays only (Monday to Friday)time start<HH:MM> end <HH:MM>Configures the time when this RADIUS group can access the network• start <HH:MM> – Sets the start time in the HH:MM format (for example, 13:30 means the user can login only after 1:30 PM). Specifies the time users, within each listed group, can access the local RADIUS resources.• end <HH:MM> – Sets the end time in the HH:MM format (for example, 17:30 meansthe user is allowed to remain logged in until 5:30 PM). Specifies the time users, within each listed group, lose access to the local RADIUS resources.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-616.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 916.1.3 rate-limitradius-groupSets the rate limit for the guest RADIUS server groupSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrate-limit [from-air|to-air] <100-1000000>Parameters• rate-limit [from-air|to-air] <100-1000000>Examplerfs6000-37FABE(config-radius-group-test)#rate-limit to-air 200rfs6000-37FABE(config-radius-group-test)#show contextradius-group test guest policy vlan 1 policy ssid test policy day mo policy day tu policy day we policy day th policy day fr policy day sa policy day su rate-limit to-air 200 policy time start 13:30 end 17:30rfs6000-37FABE(config-radius-group-test)#Related CommandsNOTE: The rate-limit setting is not applicable to a management group.to-air <100-1000000> Sets the rate limit in the downlink direction, from the network to the wireless client• <100-1000000> – Specify the rate from 100 - 1000000 Kbps.from-air <100-1000000>Sets the rate limit in the uplink direction, from the wireless client to the network• <100-1000000> – Specify the rate from 100 - 1000000 Kbps.no Removes the RADIUS guest group’s rate limits](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-618.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 1016.1.4 noradius-groupNegates a command or sets its default. Removes or modifies the RADIUS group policy settings. When used in the config RADIUS group mode, the no command removes or modifies the following settings: access type, access days, role type, VLAN ID, and SSID.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [guest|policy|rate-limit]no policy [access|day|inactivity-timeout|role|session-time|ssid|time|vlan]no policy access [all|console|ssh|telnet|web]no policy day [all|fr|mo|sa|su|th|tu|we|weekdays]no policy session-timeno policy ssid [<SSID>|all]no policy [inactivity-timeout|role|time|vlan]no rate-limit [from-air|to-air]Parameters• no <PARAMETERS>ExampleThe following example shows the RADIUS guest group ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-radius-group-test)#show contextradius-group test guest policy vlan 1 policy ssid test policy day mo policy day tu policy day we policy day th policy day fr policy day sa policy day su rate-limit to-air 200 policy time start 13:30 end 17:30rfs6000-37FABE(config-radius-group-test)#rfs6000-37FABE(config-radius-group-test)#no guestrfs6000-37FABE(config-radius-group-test)#no rate-limit to-airrfs6000-37FABE(config-radius-group-test)#no policy day allno <PARAMETERS> Negates a command or sets its default. Removes or modifies the RADIUS group policy settings. When used in the config RADIUS group mode, the no command removes or modifies the following settings: access type, access days, role type, VLAN ID, and SSID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-619.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 1416.2.1 authenticationradius-server-policySpecifies the RADIUS datasource used for user authentication. Options include local for the local user database or LDAP for a remote LDAP resource.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthentication [data-source|eap-auth-type]authentication data-source [ldap|local]authentication data-source [ldap {fallack}|local] {(ssid <SSID> precedence <1-5000>)}authentication eap-auth-type [all|peap-gtc|peap-mschapv2|tls|ttls-md5|ttls-mschapv2|ttls-pap]Parameters• authentication data-source [ldap {fallback}|local] {(ssid <SSID> precedence <1-5000>)}data-source The RADIUS sever can either use the local database or an external LDAP server to authenticate a user. It is necessary to specify the data source. The options are: LDAP and local.ldap fallback Uses a remote LDAP server as the data source• fallback – Optional. Enables fallback to local authentication. This feature ensures that if the designated external LDAP resource were to fail or become unavailable, the client is authenticated against the local RADIUS resource. This option is disabled by default.When using LDAP as the authentication external source, PEAP-MSCHAPv2 authentication type can be used only if the LDAP server returns the password as plain-text. PEAP-MSCHAPv2 authentication is not supported if the LDAP server returns encrypted passwords. This restriction does not apply for Microsoft's Active Directory server.local Uses the local user database to authenticate a user. This is the default setting.ssid <SSID> precedence <1-5000>The following keywords are recursive and common to both ‘ldap’ and ‘local’ parameters:• ssid – Optional. Associates the data source, selected in the previous step, with a SSID• <SSID> – Specify the SSID for this authentication data source. The SSID is case sen-sitive and should not exceed 32 characters in length. Do not use any of the followingcharacters (< > | " & \ ? ,).Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-623.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 15• authentication eap-auth-type [all|peap-gtc|peap-mschapv2|tls|ttls-md5|ttls-mschapv2|ttls-pap]Examplerfs6000-37FABE(config-radius-server-policy-test)#authentication eap-auth-type tlsrfs6000-37FABE(config-radius-server-policy-test)#show contextradius-server-policy test authentication eap-auth-type tlsrfs6000-37FABE(config-radius-server-policy-test)#Related Commands• precedence <SSID> – Sets the precedence for this authentication rule. The pre-cedence value allows systematic evaluation and application of rules. Rules withthe lowest precedence receive the highest priority.• <1-5000> – Specify a precedence from 1- 5000.Specifying the SSID allows the RADIUS server to use the SSID attribute in access requests to determine the data source to use. This option is applicable to onboard RADIUS servers only.eap-auth-type Uses Extensible Authentication Protocol (EAP), with this RADIUS server policy, for user authenticationThe EAP authentication types supported by the local RADIUS server are: all, peap-gtc, peap-mschapv2, tls, ttls-md5, ttls-mschapv2, ttls-pap.all Enables both TTLS and PEAP authentication. This is the default setting.peap-gtc Enables PEAP with default authentication using GTCpeap-mschapv2 Enables PEAP with default authentication using MSCHAPv2When using LDAP as the authentication external source, PEAP-MSCHAPv2 authentication type can be used only if the LDAP server returns the password as plain-text. PEAP-MSCHAPv2 authentication is not supported if the LDAP server returns encrypted passwords. This restriction does not apply for Microsoft's Active Directory server.tls Enables TLS as the EAP typettls-md5 Enables TTLS with default authentication using md5ttls-mschapv2 Enables TTLS with default authentication using MSCHAPv2ttls-pap Enables TTLS with default authentication using PAPno Removes the RADIUS authentication settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-624.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 1616.2.2 bypassradius-server-policyEnables bypassing a CRL check. When enabled, this feature bypasses checks for missing and expired CRLs. This option is enabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxbypass [crl-check|expired-crl]Parameters• bypass [crl-check|expired-crl]Examplenx9500-6C8809(config-radius-server-policy-test)#bypass crl-checknx9500-6C8809(config-radius-server-policy-test)#no bypass crl-checknx9500-6C8809(config-radius-server-policy-test)#show contextradius-server-policy test no bypass crl-checknx9500-6C8809(config-radius-server-policy-test)#Related Commandsbypass [crl-check|expired-crl]Bypasses CRL check based on the parameters passed• crl-check – Bypasses CRL check of missing CRLs• expired-crl – Bypasses CRL check of expired CRLsNote: A CRL is a list of certificates that have been revoked or are no longer valid.no Disables bypassing of checking for missing CRLs or expired CRLs](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-625.png)


![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 1916.2.5 ldap-agentradius-server-policyConfigures the LDAP agent’s settings in the RADIUS server policy contextWhen a user's credentials are stored on an external LDAP server, the local RADIUS server cannot successfully conduct PEAP-MSCHAPv2 authentication, since it is not aware of the user's credentials maintained on the external LDAP server resource. Therefore, up to two LDAP agents can be provided locally so remote LDAP authentication can be successfully accomplished on the remote LDAP resource (using credentials maintained locally).This feature is available to all controller, service platforms and access point models, with the exception of AP6511 and AP6521 models running in standalone AP or virtual controller AP mode. However, this feature is supported by dependent mode AP6511 and AP6521 model access points when adopted and managed by a controller or service platform.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxldap-agent [join|join-retry-timeout|primary|secondary]ldap-agent [join {on <DEVICE-NAME>}|join-retry-timeout <60-300>]ldap-agent [primary|secondary] domain-name <LDAP-DOMAIN-NAME> domain-admin-user <ADMIN-USER-NAME> domain-admin-password [0 <WORD>|2 <WORD>]Parameters• ldap-agent [join {on <DEVICE-NAME>}|join-retry-timeout <60-300>]ldap-agent Configures the LDAP agent’s settingsjoin {on <DEVICE-NAME>}Initiates the join process, which binds the RADIUS server with the LDAP server’s (Windows) domain. When successful, the hostname (name of the AP, wireless controller, or service platform) is added to the LDAP server’s Active Directory.• on <DEVICE-NAME> – Optional. Specifies the device name• <DEVICE-NAME> – Specify the name of the AP, wireless controller, or serviceplatform.To confirm the join status of a controller, use the show > ldap-agent > join-status command.join-retry-timeout <60-300>If the join process fails (i.e. the RADIUS server fails to join the LADP server’s domain), the process is retried after a specified interval. This command configures the interval (in seconds) between two successive join attempts.• <60-300> – Set the timeout value from 60 - 300 seconds. The default is 60 seconds.A retry timer is initiated as soon as the join process starts, which tracks the time lapse in case of a failure.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-628.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 20• ldap-agent [primary|secondary] domain-name <LDAP-DOMAIN-NAME> domain-admin-user <ADMIN-USER-NAME> domain-admin-password [0 <WORD>|2 <WORD>]Examplerfs4000-229D58(config-radius-server-policy-test)#ldap-agent primary domain-nametest domain-admin-user Administrator domain-admin-password 0 test@123rfs4000-229D58(config-radius-server-policy-test)#rfs4000-229D58(config-radius-server-policy-test)#show contextradius-server-policy test ldap-agent primary domain-name test domain-admin-user Administrator domain-admin-password 0 test@123rfs4000-229D58(config-radius-server-policy-test)#Related Commandsldap-agent Configures the LDAP agent’s settingsprimary Configures the primary LDAP server details, such as domain name, user name, and password. The RADIUS server uses these credentials to bind with the primary LDAP server.secondary Configures the secondary LDAP server details, such as domain name, user name, and password. The RADIUS server uses these credentials to bind with the secondary LDAP server.domain-name <LDAP-DOMAIN-NAME>This keyword is common to both the ‘primary’ and ‘secondary’ parameters.• domain-name – Configures the primary or secondary LDAP server’s domain name• <LDAP-DOMAIN-NAME> – Specify the domain name.domain-admin-user <ADMIN-USER-NAME>This keyword is common to both the ‘primary’ and ‘secondary’ parameters.• domain-admin-user – Configures the primary or secondary LDAP server’s admin user name• <ADMIN-USER-NAME> – Specify the admin user’s name.domain-admin-password [0 <WORD>|2 <WORD>]This keyword is common to both the ‘primary’ and ‘secondary’ parameters.• domain-admin-password – Configures the primary or secondary LDAP server’s admin user password• 0 <WORD> – Specifies the password in the unencrypted format• 2 <WORD> – Specifies the password in the encrypted formatno Removes LDAP agent settings from this RADIUS server policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-629.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 2216.2.7 ldap-serverradius-server-policyConfigures the LDAP server’s settings. Configuring LDAP server allows users to login and authenticate from anywhere on the network.Administrators have the option of using the local RADIUS server to authenticate users against an external LDAP server resource. Using an external LDAP user database allows the centralization of user information and reduces administrative user management overhead making RADIUS authorization more secure and efficient.RADIUS is not just a database. It is a protocol for asking intelligent questions to a user database (like LDAP). LDAP however is just a database of user credentials used optionally with the local RADIUS server to free up resources and manage user credentials from a secure remote location. It is the local RADIUS resources that provide the tools to perform user authentication and authorize users based on complex checks and logic. A LDAP user database alone cannot perform such complex authorization checks.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxldap-server [dead-period|primary|secondary]ldap-server dead-period <0-600>ldap-server [primary|secondary] host <IP> port <1-65535> login <LOGIN-NAME> bind-dn <BIND-DN> base-dn <BASE-DN> passwd [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>] passwd-attr <ATTR> group-attr <ATTR> group-filter <FILTER> group-membership <WORD> {net-timeout <1-10>|start-tls net-timeout <1-10>|tls-mode net-timeout <1-10>}Parameters• ldap-server dead-period <0-600>• ldap-server [primary|secondary] host <IP> port <1-65535> login <LOGIN-NAME> bind-dn <BIND-DN> base-dn <BASE-DN> passwd [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>] passwd-attr <ATTR> group-attr <ATTR> group-filter <FILTER> group-membership <WORD> {net-timeout <1-10>|start-tls net-timeout <1-10>|tls-mode net-timeout <1-10>}}dead-period <0-600> Sets an interval, in seconds, during which the local server will not contact its LDAP server resource once its been defined as unavailable. A dead period is only implemented when additional LDAP servers are configured and available.• <0-600> – Specify a value from 0 - 600 seconds. The default is 300 seconds.ldap primary Configures the primary LDAP server settingsldap secondary Configures the secondary LDAP server settingshost <IP> Specifies the LDAP host’s IP address• <IP> – Specify the LDAP server’s IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-631.png)
![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 23port <1-65535> Configures the LDAP server port• <1-65535> – Specify a port between 1 - 65535.login <LOGIN-NAME> Configures the login name of a user to access the LDAP server• <LOGIN-NAME> – Specify a login ID (should not exceed 127 characters).bind-dn <BIND-DN> Configures a distinguished bind name. This is the distinguished name (DN) used to bind with the LDAP server. The DN is the name that uniquely identifies an entry in the LDAP directory. A DN is made up of attribute value pairs, separated by commas.• <BIND-DN> – Specify a bind name (should not exceed 127 characters).base-dn <BASE-DN> Configures a distinguished base name. This is the DN that establishes the base object for the search. The base object is the point in the LDAP tree at which to start searching. LDAP DNs begin with a specific attribute (usually some sort of name), and continue with progressively broader attributes, often ending with a country attribute. The first component of the DN is referred to as the Relative Distinguished Name (RDN). It identifies an entry distinctly from any other entries that have the same parent• <BASE-DN> – Specify a base name (should not exceed 127 characters).passwd [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]Sets a valid password for the LDAP server.• 0 <PASSWORD> – Sets an UNENCRYPTED password• 2 <ENCRYPTED-PASSWORD> – Sets an ENCRYPTED password• <PASSWORD> – Sets the LDAP server bind password, specified UNENCRYPTED, with a maximum size of 31 characterspasswd-attr <ATTR> Specify the LDAP server password attribute (should not exceed 63 characters).group-attr <ATTR> Specify a name to configure group attributes (should not exceed 31 characters).LDAP systems have the facility to poll dynamic groups. In an LDAP dynamic group an administrator can specify search criteria. All users matching the search criteria are considered a member of this dynamic group. Specify a group attribute used by the LDAP server. An attribute could be a group name, group ID, password or group membership name.group-filter <FILTER> Specify a name for the group filter attribute (should not exceed 255 characters).This filter is typically used for security role-to-group assignments and specifies the property to look up groups in the directory service.group-membership <WORD>Specify a name for the group membership attribute (should not exceed 63 characters).This attribute is sent to the LDAP server when authenticating users.net-time <1-10> Optional. Select a value from 1 - 10 to configure the network timeout (number of seconds to wait for a response from the target primary or secondary LDAP server). The default is 10 seconds.start-tls net-timeout <1-10>Optional. Select a value from 1 - 10 to configure the network timeout for secure communication using start_tls support on the external LDAP server.tls-mode net-timeout <1-10>Optional. Select a value from 1 - 10 to configure the network timeout for secure communication using tls_mode support on the external LDAP server.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-632.png)

![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 2616.2.9 nasradius-server-policyConfigures the key sent to a RADIUS clientA RADIUS client is a mechanism to communicate with a central server to authenticate users and authorize access to the controller, service platform or Access Point managed network.The client and server share a secret (a password). That shared secret followed by the request authenticator is put through a MD5 hash algorithm to create a 16 octet value which is XORed with the password entered by the user. If the user password is greater than 16 octets, additional MD5 calculations are performed, using the previous ciphertext instead of the request authenticator. The server receives a RADIUS access request packet and verifies the server possesses a shared secret for the client. If the server does not possess a shared secret for the client, the request is dropped. If the client received a verified access accept packet, the username and password are considered correct, and the user is authenticated. If the client receives a verified access reject message, the username and password are considered to be incorrect, and the user is not authenticated.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnas <IP/M> secret [0|2|<LINE>]nas <IP/M> secret [0 <LINE>|2 <LINE>|<LINE>]Parameters• nas <IP/M> secret [0 <LINE>|2<LINE>]Examplerfs6000-37FABE(config-radius-server-policy-test)#nas 172.16.10.10/24 secret 0 wirelesswellrfs6000-37FABE(config-radius-server-policy-test)#show contextradius-server-policy test authentication eap-auth-type tls crl-check nas 172.16.10.10/24 secret 0 wirelesswell local realm realm1 ldap-server primary host 172.16.10.19 port 162 login "test" bind-dn "bind-dn1" base-dn "base-dn1" passwd 0 test@123 passwd-attr test123 group-attr group1 group-filter "groupfilter1" group-membership groupmembership1 net-timeout 2 ldap-server dead-period 100rfs6000-37FABE(config-radius-server-policy-test)#<IP/M> Sets the RADIUS client’s IP address• <IP/M> – Sets the RADIUS client’s IP address in the A.B.C.D/M formatsecret [0 <LINE>|2 <LINE>|<LINE>]Sets the RADIUS client’s shared secret. Use one of the following options:• 0 <LINE> – Sets an UNENCRYPTED secret• 2 <LINE> – Sets an ENCRYPTED secret• <LINE> – Defines the secret (client shared secret) up to 64 characters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-635.png)

![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 2816.2.10 noradius-server-policyNegates a command or reverts back to default settings. When used with in the config RADIUS server policy mode, the no command removes settings, such as crl-check, LDAP group verification, RADIUS client, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [authentication|bypass|chase-referral|clr-check|ldap-agent|ldap-group-verification|ldap-server|local|nas|proxy|session-resumption|termination|use]no bypass [crl-check|expired-crl]no authentication [data-source|eap]no authentication [data-source {ldap {fallback}|local|ssid}|eap configuration]no [chase-referral|clr-check|ldap-group-verification|nas <IP/M>|session-resumption]no ldap-agent [join-retry-timeout|primary|secondary]no local realm [<REALM-NAME>|all]no proxy [realm <REALM-NAME>|retry-count|retry-delay]no ldap-server [dead-period|primary|secondary]no terminationno use [radius-group [<RAD-GROUP-NAME>|all]|radius-user-pool-policy [<RAD-USER-POOL-NAME>|all]]Parameters• no <PARAMETERS>ExampleThe following example shows the RADIUS server policy ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-radius-server-policy-test)#show contextradius-server-policy test authentication eap-auth-type tls crl-check nas 172.16.10.10/24 secret 0 wirelesswell local realm realm1 ldap-server primary host 172.16.10.19 port 162 login "test" bind-dn "bind-dn1" base-dn "bas-dn1" passwd 0 test@123 passwd-attr test123 group-attr group1 group-filter "groupfilter1" group-membership groupmembership1 net-timeout 2 ldap-server dead-period 100no <PARAMETERS> Negates a command or reverts back to default settings. When used with in the config RADIUS server policy mode, the no command removes settings, such as crl-check, LDAP group verification, RADIUS client etc](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-637.png)

![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 3016.2.11 proxyradius-server-policyConfigures a proxy RADIUS server based on the realm/suffix. The realm identifies where the RADIUS server forwards AAA requests for processing.A user’s access request is sent to a proxy RADIUS server if it cannot be authenticated by the local RADIUS resources. The proxy server checks the information in the user access request and either accepts or rejects the request. If the proxy server accepts the request, it returns configuration information specifying the type of connection service required to authenticate the user.The RADIUS proxy appears to act as a RADIUS server to NAS, whereas the proxy appears to act as a RADIUS client to the RADIUS server.When the proxy server receives a request for a user name with a realm, the server references a table of realms. If the realm is known, the server proxies the request to the RADIUS server.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxproxy [realm|retry-count|retry-delay]proxy realm <REALM-NAME> server <IP> port <1024-65535> secret [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]proxy retry-count <3-6>proxy retry-delay <5-10>Parameters• proxy realm <REALM-NAME> server <IP> port <1024-65535> secret [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]proxy realm <REALM-NAME>Configures the realm name• <REALM-NAME> – Specify the realm name. The name should not exceed 50 characters.server <IP> Configures the proxy server’s IP address. This is the address of server checking the information in the user access request and either accepting or rejecting the request on behalf of the local RADIUS server.• <IP> – Sets the proxy server’s IP addressport <1024-65535> Configures the proxy server’s port. This is the TCP/IP port number for the server that acts as a data source for the proxy server.• <1024-65535> – Sets the proxy server’s port from 1024 - 65535 (default port is 1812)secret [0 <PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>Sets the proxy server secret string. The options are:• 0 <PASSWORD> – Sets an UNENCRYPTED password• 2 <ENCRYPTED-PASSWORD> – Sets an ENCRYPTED password• <PASSWORD> – Sets the proxy server shared secret value](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-639.png)

![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 3416.2.14 useradius-server-policyDefines settings used with the RADIUS server policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [radius-group <RAD-GROUP-NAME1> {RAD-GROUP-NAME2}|radius-user-pool-policy <RAD-USER-POOL-NAME>]Parameters• use [radius-group <RAD-GROUP-NAME1> {RAD-GROUP-NAME2}|radius-user-pool-policy <RAD-USER-POOL-NAME>]Examplerfs6000-37FABE(config-radius-server-policy-test)#use radius-group testrfs6000-37FABE(config-radius-server-policy-test)#show contextradius-server-policy test proxy retry-delay 8 proxy retry-count 4 proxy realm test1 server 172.16.10.7 port 1025 secret 0 test1123 ldap-server primary host 172.16.10.19 port 162 login "test" bind-dn "bind-dn1" base-dn "bas-dn1" passwd 0 test@123 passwd-attr test123 group-attr group1 group-filter "groupfilter1" group-membership groupmembership1 net-timeout 2 use radius-group test session-resumption lifetime 10 max-entries 11rfs6000-37FABE(config-radius-server-policy-test)#Related Commandsradius-group <RAD-GROUP-NAME1> {RAD-GROUP-NAME2}Associates a specified RADIUS group (for LDAP users) with this RADIUS server policyYou can optionally associate two RADIUS groups with one RADIUS server policy.radius-user-pool-policy <RAD-USER-POOL-NAME>Associates a specified RADIUS user pool with this RADIUS server policy. Specify a user pool name.no Disassociates a RADIUS group or a RADIUS user pool policy from this RADIUS server policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-643.png)


![RADIUS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 16 - 3716.3.2 userradius-user-pool-policyConfigures RADIUS user parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuser <USERNAME> password [0 <UNECRYPTED-PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>] {group <RAD-GROUP-NAME>} {guest}user <USERNAME> password [0 <UNECRYPTED-PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>] {group <RAD-GROUP-NAME>} {guest expiry-time <HH:MM> expiry-date <MM/DD/YYYY> {access-duration <0-525600>|data-limit|email-id <EMAIL-ID>|start-time <HH:MM> start-date <MM/DD/YYY>|telephone <TELEPHONE-NUMBER>}}user <USERNAME> password [0 <UNECRYPTED-PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>] {group <RAD-GROUP-NAME>} {guest expiry-time <HH:MM> expiry-date <MM/DD/YYYY> {access-duration <0-525600>|data-limit <1-102400> committed-downlink <100-1000000> committed-uplink <100-1000000> reduced-downlink <100-1000000> reduced-uplink <100-1000000>|email-id <EMAIL-ID>|start-time <HH:MM> start-date <MM/DD/YYY>|telephone <TELEPHONE-NUMBER>}} Parameters• user <USERNAME> password [0 <UNECRYPTED-PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>] {group <RAD-GROUP-NAME>} {guest expiry-time <HH:MM> expiry-date <MM:DD:YYY> {access-duration <0-525600>|data-limit <1-102400> committed-downlink <100-1000000> committed-uplink <100-1000000> reduced-downlink <100-1000000> reduced-uplink <100-1000000>|email-id <EMAIL-ID>|start-time <HH:MM> start-date <MM/DD/YYY>|telephone <TELEPHONE-NUMBER>}}user <USERNAME> Adds a new RADIUS user to the RADIUS user pool• <USERNAME> – Specify the name of the user. The username should not exceed 64 characters.Note: The username is a unique alphanumeric string identifying this user, and cannot be modified with the rest of the configuration.passwd [0 <UNENCRYPTED-PASSWORD>|2 <ENCRYPTED-PASSWORD>|<PASSWORD>]Configures the user password (provide a password unique to this user)• 0 <UNENCRYPTED-PASSWORD> – Sets an unencrypted password• 2 <ENCRYPTED-PASSWORD> – Sets an encrypted password• <PASSWORD> – Sets a password (specified unencrypted) up to 21 charactersgroup <RAD-GROUP-NAME>Optional. Configures the RADIUS server group of which this user is a member• <RAD-GROUP-NAME> – Specify the group name in the local database.If the user is a guest, assign the user a group with temporary access privileges.guest Optional. Specifies that this user is a guest user. Guest users have restricted access. After enabling a guest user account, specify the expiry time and date for this account.A guest user can be assigned only to a guest user group.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-646.png)



![RADIO-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 17 - 517.1.1 accelerated-multicastradio-qos-policyConfigures multicast streams for acceleration. Multicasting allows group transmission of data streams.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccelerated-multicast [client-timeout|max-client-streams|max-streams|overflow-policy|stream-threshold]accelerated-multicast [client-timeout <5-6000>|max-client-streams <1-4>|max-streams <0-256>|overflow-policy [reject|revert]|stream-threshold <1-500>]Parameters• accelerated-multicast [client-timeout <5-6000>|max-client-streams <1-4>|max-streams <0-256>|overflow-policy [reject|revert]|stream-threshold <1-500>]Examplerfs6000-37FABE(config-radio-qos-test)#accelerated-multicast client-timeout 500rfs6000-37FABE(config-radio-qos-test)#accelerated-multicast stream-threshold 15rfs6000-37FABE(config-radio-qos-test)#show contextradio-qos-policy test accelerated-multicast stream-threshold 15 accelerated-multicast client-timeout 500rfs6000-37FABE(config-radio-qos-test)#Related Commandsclient-timeout <5-6000>Configures a timeout period in seconds for wireless clients• <5-6000> – Specify a value from 5 - 6000 seconds. The default is 60 seconds.max-client-streams <1-4>Configures the maximum number of accelerated multicast streams per client• <1-4> – Specify a value from 1 - 4. The default is 2.max-streams <0-256> Configures the maximum number of accelerated multicast streams per radio• <0-256> – Specify a value from 0 - 256. The default is 25.overflow-policy [reject|revert]Specifies the policy in case too many clients register simultaneously. The radio QOS policy can be configured to follow one of the following courses of action:• reject – Rejects new clients. The default overflow policy is reject.• revert – Reverts to regular multicast deliveryWhen the number of wireless clients using accelerated multicast exceeds the configured value (max-streams), the radio can either reject new wireless clients or revert existing clients to a non-accelerated state.stream-threshold <1-500>Configures the number of multicast packets per second threshold value. Once this threshold is crossed, the system triggers streams to accelerate.• <1-500> – Specify a value from 1 - 500. The default is 25 packets per second.no Reverts accelerated multicasting settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-654.png)
![RADIO-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 17 - 617.1.2 admission-controlradio-qos-policyEnables admission control across all radios for one or more access categories. Enabling admission control for an access category, ensures clients associated to an access point and complete WMM admission control before using that access category.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxadmission-control [background|best-effort|firewall-detected-traffic|implicit-tspec|video|voice]admission-control [firewall-detected-traffic|implicit-tspec]admission-control [background|best-effort|video|voice] {max-airtime-percent|max-clients|max-roamed-clients|reserved-for-roam-percent}admission-control [background|best-effort|video|voice] {max-airtime-percent <0-150>|max-clients <0-256>|max-roamed-clients <0-256>|reserved-for-roam-percent <0-150>}Parameters• admission-control [firewall-detected-traffic|implicit-tspec]• admission-control [background|best-effort|video|voice] {max-airtime-percent <0-150>|max-clients <0-256>|max-roamed-clients <0-256>|reserved-for-roam-percent <0-150>}admission-control firewall-detected-trafficEnforces admission control for traffic whose access category is detected by the firewall ALG. For example, SIP voice calls. This feature is enabled by default.When enabled, the firewall simulates reception of frames for voice traffic when the voice traffic was originated via SIP or SCCP control traffic. If a client exceeds configured values, the call is stopped and/or received voice frames are forwarded at the next non admission controlled traffic class priority. This applies to clients that do not send TSPEC frames only.admission-control implicit-tspecEnables implicit traffic specifiers for clients that do not support WMM TSPEC, but are accessing admission-controlled access categories. This feature is enabled by default.This feature requires wireless clients to send their traffic specifications to an access point before they can transmit or receive data. If enabled, this setting applies to this radio QoS policy. When enabled, the access point simulates the reception of frames for any traffic class by looking at the amount of traffic the client is receiving and sending. If the client sends more traffic than has been configured for an admission controlled traffic class, the traffic is forwarded at the priority of the next non admission controlled traffic class. This applies to clients that do not send TSPEC frames only.admission-control backgroundConfigures background access category admission control parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-655.png)


![RADIO-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 17 - 1017.1.3 noradio-qos-policyNegates a command or resets configured settings to their default. When used in the radio QOS policy mode, the no command enables the resetting of accelerated multicast parameters, admission control parameters, and MultiMedia parameters.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [accelerated-multicast|admission-control|smart-aggregation|wmm|service]no accelerated-multicast [client-timeout|max-client-streams|max-streams|overflow-policy|stream-threshold]no admission-control [firewall-detected-traffic|implicit-tspec|background|best-effort|video|voice]no admission-control [firewall-detected-traffic|implicit-tspec]no admission-control [background|best-effort|video|voice] {max-airtime-percent|max-clients|max-roamed-clients|reserved-for-roam-percent}no smart-aggregation {delay|max-mesh-hops|min-aggregation-limit}no smart-aggregation {delay [background|best-effort|streaming-video|video-conferencing|voice]|max-mesh-hops|min-aggregation-limit}no wmm [background|best-effort|video|voice] [aifsn|cw-max|cw-min|txop-limit]no service admission-control across-reassocParameters• no <PARAMETERS>ExampleThe following example shows the Radio-qos-policy ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-radio-qos-test)#show contextradio-qos-policy test admission-control voice max-airtime-percent 9 admission-control voice reserved-for-roam-percent 8 admission-control best-effort max-clients 200 accelerated-multicast stream-threshold 15 accelerated-multicast client-timeout 500rfs6000-37FABE(config-radio-qos-test)#rfs6000-37FABE(config-radio-qos-test)#no admission-control best-effort max-clientsrfs6000-37FABE(config-radio-qos-test)#no accelerated-multicast client-timeoutno <PARAMETERS> Negates a command or resets configured settings to their default. When used in the radio QOS policy mode, the no command enables the resetting of accelerated multicast parameters, admission control parameters, and MultiMedia parameters.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-659.png)
![RADIO-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 17 - 1217.1.4 smart-aggregationradio-qos-policyConfigures smart aggregation parameters on this Radio QoS policy. Smart aggregation is disabled by default.Smart aggregation enhances frame aggregation by dynamically selecting the time when the aggregated frame is transmitted. In a frame’s typical aggregation, an aggregated frame is sent when:• A pre-configured number of aggregated frames is reached• An administrator-defined interval has elapsed since the first frame (of a set of frames to be aggregated) was received• An administrator-defined interval has elapsed since the last frame (not necessarily the final frame) of a set of frames to be aggregated was receivedWith this enhancement, an aggregation delay is set uniquely for each traffic class. For example, voice traffic might not be aggregated, but sent immediately. Whereas, background data traffic is set a delay for aggregating frames, and these aggregated frames are sent.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsmart-aggregation {delay|max-mesh-hops|min-aggregation-limit}smart-aggregation {delay [background|best-effort|streaming-video|video-conferencing|voice] <0-1000>}smart-aggregation {max-mesh-hops <1-10>}smart-aggregation {min-aggregation-limit <0-64>}Parameters• smart-aggregation {delay [background|best-effort|streaming-video|video-conferencing|voice] <0-1000>}delay Optional. Configures the maximum delay parameter for each traffic typeThis is the maximum delay, in milliseconds, in the transmission of the first frame received.background Configures the maximum delay parameter, in milliseconds, for background traffic (250 msec)best-effort Configures the maximum delay parameter, in milliseconds, for best effort traffic (150 msec)streaming-video Configures the maximum delay parameter, in milliseconds, for streaming video traffic (150 msec)video-conferencing Configures the maximum delay parameter, in milliseconds, for video conference traffic (40 msec)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-661.png)
![RADIO-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 17 - 1417.1.5 serviceradio-qos-policyInvokes service commands in the radio QoS configuration modeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxservice [admission-control|show]service admission-control across-reassocservice show cliParameters• service admission-control across-reassoc• service show cliExamplerfs4000-229D58(config-radio-qos-test)#service admission-control across-reassocrfs4000-229D58(config-radio-qos-test)#show contextradio-qos-policy test service admission-control across-reassocrfs4000-229D58(config-radio-qos-test)#rfs4000-229D58(config-radio-qos-test)#service show cliRadio QoS Mode mode:+-help [help] +-search +-WORD [help search WORD (|detailed|only-show|skip-show|skip-no)] +-detailed [help search WORD (|detailed|only-show|skip-show|skip-no)] +-only-show [help search WORD (|detailed|only-show|skip-show|skip-no)] +-skip-show [help search WORD (|detailed|only-show|skip-show|skip-no)] +-skip-no [help search WORD (|detailed|only-show|skip-show|skip-no)]+-show +-commands [show commands] +-adoption +-log --More--]service Invokes service commandsadmission-control across-reassocRetains previously negotiated TSPEC parameters across re-associations on the radioFor more information on admission-control parameters, see admission-control.service show cli Displays running system information• cli – Displays the Radio QoS mode’s CLI tree](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-663.png)

![RADIO-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 17 - 1617.1.6 wmmradio-qos-policyConfigures 802.11e wireless multimedia (wmm) parametersSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwmm [background|best-effort|video|voice]wmm [background|best-effort|video|voice] [aifsn <1-15>|cw-max <0-15>|cw-min <0-15>|txop-limit <0-65535>]Parameters• wmm [background|best-effort|video|voice] [aifsn <1-15>|cw-max <0-15>|cw-min <0-15>|txop-limit <0-65535>]wmm background Configures background access category wireless multimedia settingswmm best-effort Configures best effort access category wireless multimedia settingswmm video Configures video access category wireless multimedia settingswmm voice Configures voice access category wireless multimedia settingsaifsn <1-15> Configures Arbitrary Inter-Frame Space Number (AIFSN) as the wait time between data frames derived from the AIFSN and slot time• background – Sets the current AIFSN for low (background) traffic. The default is 7.• best-effort – Sets the current AIFSN for normal (best-effort) traffic. The default is 3.• video – Set the current AIFSN for video traffic. Higher-priority traffic video categories should have lower AIFSNs than lower-priority traffic categories. This causes lower-priority traffic to wait longer before attempting access. The default is 1.• voice – Sets the current AIFSN for voice traffic. Higher-priority traffic voice categories should have lower AIFSNs than lower-priority traffic categories. This causes lower-priority traffic to wait longer before attempting access. The default is 1.The following keyword is common to all of the above traffic types:• <1-15> – Sets a value from 1 - 15cw-max <0-15> Clients pick a number between 0 and the min contention window to wait before retransmission. Clients then double their wait time on a collision, until it reaches the maximum contention window.• background – Sets CW Max for low (background) traffic. The default is 10.• best-effort – Sets CW Max for normal (best effort) traffic. The default is 6.Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-665.png)



![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 318.1.1 default-rolerole-policyAssigns a default role to a wireless client that fails to match any of the user-defined rolesWhen a wireless client accesses a network, the client’s details, retrieved from the LDAP server, are matched against all user-defined roles within the role policy. If the client fails to match any of these user-defined role filters, the client is assigned the default role. The action taken (permit or deny access) is determined by the IP and/or MAC ACL associated with the default role.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdefault-role use [ip-access-list|ipv6-access-list|mac-access-list]default-role use [ip-access-list|ipv6-access-list|mac-access-list] [in|out] <IP/IPv6/MAC-ACCESS-LIST-NAME> precedence <1-100>Parameters• default-role use [ip-access-list|ipv6-access-list|mac-access-list] [in|out] <IP/IPv6/MAC-ACCESS-LIST-NAME> precedence <1-100>default-role use Enables default role configuration. This role is applied to a wireless client not matching any of the user-defined roles.• Use – Associates an IP, IPv6, or MAC access list with the default role[ip-access-list|ipv6-access-list|mac-access-list] [in|out] <IP/IPv6/MAC-ACCESS-LIST-NAME>Associates an IP access list, IPv6 access list, or a MAC access list with this default role• in – Applies the rule (IP, IPv6, or MAC) to incoming packets• out – Applies the rule (IP, IPv6, or MAC) to outgoing packetsIP and MAC access control lists (ACLs) act as firewalls by blocking and/or permitting data traffic in both directions (inbound and outbound) within a managed network. IP ACLs use IP addresses for matching operations. Whereas, MAC ACLs use MAC addresses for matching operations, In case of a match (i.e. if a packet is received from or is destined for a specified IP or MAC address), an action is taken. This action is a typical allow, deny or mark designation to controller packet traffic. For more information on ACLs, see AAA-POLICY.• <IP/IPv6/MAC-ACCESS-LIST-NAME> – Specify the access list name.The ACL applied determines the action applied to a client assigned the default role.precedence <1-100>The following keyword is common to the all of the above parameters:• precedence – Assigns a precedence value to the ACL identified in the previous step.• <1-100> – Specify a precedence from 1 - 100.ACLs are applied in increasing order of their precedence. Rules with lower precedence are given priority.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-670.png)


![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 618.1.3 ldap-queryrole-policyEnables LDAP service and specifies the LDAP server query modeConfiguring the LDAP server query mode automatically enables LDAP service on this role policy. By default LDAP service is disabled.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxldap-query [self|through-controller]Parameters• ldap-query [self|through-controller]Examplerfs6000-37FABE(config-role-policy-test)#ldap-query selfrfs6000-37FABE(config-role-policy-test)#show contextrole-policy test default-role use ip-access-list in test precedence 1 ldap-query self ldap-deadperiod 100rfs6000-37FABE(config-role-policy-test)#Related Commandsself Configures LDAP query mode as self. The AP directly queries the LDAP server for user information. Select ‘self’ to use local LDAP server resources configured using the ldap-server command.through-controller Configures LDAP query mode as through-controller. The AP queries the LDAP server, for user information, through the controller.Use this option when the AP is layer 2 adopted to the controller.no Disables LDAP service on this role policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-673.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 718.1.4 ldap-serverrole-policyAssociates a specified LDAP server with this role policy. Use this command to configure the credentials needed to bind with the LDAP server.When enabled, LDAP service allows the AP or controller to bind with the LDAP server and retrieve user details. This information is matched with the user-defined roles within the role policy. If a match is made, the user is assigned the role and allowed or denied access to the controller managed network.You can associate two LDAP servers with a role policy, allowing failover in case the primary server is unreachable.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxldap-server <1-2> host [<IP>|<FQDN>] bind-dn <BIND-DN> base-dn <BASE-DN> bind-password <PASSWORD> {port <1-65535>} {(server-type [active-directory|openldap])}Parameters• ldap-server <1-2> host [<IP>|<HOSTNAME>] bind-dn <BIND-DN> base-dn <BASE-DN> bind-password <PASSWORD> {port <1-65535>} {(server-type [active-directory|openldap])}Usage GuidelinesUse the ldap-query command to enable LDAP service on a role policy.Use the show > role > ldap-stats command to view LDAP server status and state.ldap-server <1-2> Specify the LDAP server ID from 1 - 2.The primary LDAP server (ID 1) is used to bind and query. The secondary LDAP server (ID 2) is for failover.host [<IP>|<FQDN>] Specify the LDAP server’s IP address or Fully Qualified Domain Name (FQDN).bind-dn <BIND-DN> Specify the bind distinguished name (used for binding with the server).base-dn <BASE-DN> Specify the base distinguished name (used for searching). This should not exceed 127 characters.bind-password <PASSWORD>Specify the LDAP server password associated with the bind DN.port <1-65535> Optional. Specify the LDAP server port from 1 - 65535. (default is 389).server-type [active-directory|openldap]The following keywords are common to the ‘port’ parameter:• server-type – Optional. Specifies the LDAP server type• active-directory – Enables support for active directory attribute search. This is thedefault setting.• openldap – Enables support for openLDAP attribute search](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-674.png)

![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 1018.1.6 norole-policyNegates a command or resets settings to their default. When used in the config role policy mode, the no command removes or resets the role policy settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [default-role|ldap-deadperiod|ldap-query|ldap-server <1-2>|ldap-timeout|user-role]no [ldap-deadperiod|ldap-query|ldap-server <1-2>|ldap-timeout]no default-role use [ip-access-list|ipv6-access-list|mac-access-list]no default-role use [ip-access-list|ipv6-access-list|mac-access-list] [in|out] <IP/IPv6/MAC-ACCESS-LIST-NAME> precedence <1-100>no user-role <ROLE-NAME>Parameters• no <PARAMETERS>ExampleThe following example shows the role policy ‘test’ setting before the ‘no’ commands are executed:rfs6000-37FABE(config-role-policy-test)#show contextrole-policy test default-role use ip-access-list in test precedence 1 ldap-query self ldap-timeout 1 ldap-deadperiod 100 ldap-server 1 host 192.168.13.7 bind-dn CN=Adminstrator,CN=Users,DC=TechPub,DC=com base-dn CN=Administrator,CN=Users,DC=com bind-password 0 superuser port 2rfs6000-37FABE(config-role-policy-test)#rfs6000-37FABE(config-role-policy-test)#no ldap-deadperiodrfs6000-37FABE(config-role-policy-test)#no ldap-timeoutrfs6000-37FABE(config-role-policy-test)#no ldap-server 1The following example shows the role policy ‘test’ setting after the ‘no’ commands are executed:rfs6000-37FABE(config-role-policy-test)#show contextrole-policy test default-role use ip-access-list in test precedence 1 ldap-query selfrfs6000-37FABE(config-role-policy-test)#no <PARAMETERS> Negates a command or resets settings to their default. When used in the config role policy mode, the no command removes or resets the role policy settings.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-677.png)


![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 1518.1.7.2.1 ap-locationuser-role commandsConfigures an AP’s deployment location based filter for this user-defined roleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxap-location [any|contains|exact|not-contains]ap-location anyap-location [contains|exact|not-contains] <WORD>Parameters• ap-location any• ap-location [contains|exact|not-contains] <WORD>Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#ap-location contains officerfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 ap-location contains officerfs6000-37FABE(config-role-policy-test-user-role-testing)#Related Commandsap-location any Specifies the AP location to match (in a RF Domain) or the AP’s resident configuration• any – Defines an AP’s location as anyap-location Specifies the AP location to match (in a RF Domain) or the AP’s resident configuration. Select one of the following filter options: contains, exact, or not-contains.contains <WORD> Applies role if the associating AP’s location contains the location string specified in the role.• <WORD> – Specify the location string to match.exact <WORD> Applies role if the associating AP’s location exactly matches the string specified in the role.• <WORD> – Specify the exact location string to match.not-contains <WORD> Applies role if the associating AP’s location does not contain the location string specified in the role.• <WORD> – Specify the location string not to match.no Removes an AP’s deployment location string from this user-defined role](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-682.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 1618.1.7.2.2 assignuser-role commandsConfigures upstream/downstream rate limits and VLAN ID. Clients matching this user-defined role filters are associated with the specified VLAN, and assigned the specified data rates.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxassign [rate-limit|VLAN]assign rate-limit [from-client|to-client] <1-65536>assign vlan <1-4094>Parameters• assign rate-limit [from-client|to-client] <1-65536>• assign vlan <1-4094>Usage GuidelinesACLs can only be used with tunnel or isolated-tunnel modes. They do not work with the local and automatic modes.In case of bridge VLAN, the default bridging mode is ‘auto’. Change the bridging mode to ‘tunnel’. This extends the controller’s existing VLAN onto the AP and ensures that wireless clients are served IP addresses.assign rate-limit [from-client|to-client] <1-65536>Assigns an upstream and downstream traffic rate limit• from-client – Assigns a rate limit, in Kbps, for the upstream (from client) traffic• to-client – Assigns a rate limit, in Kbps, for the downstream (to client) traffic• <1-65536> – Specify upstream and/or downstream rate limits from 1 - 65536 Kbps.Wireless clients matching this user-defined role are assigned the configured rate limits.assign vlan <1-4094> Assigns a VLAN (identified by VLAN’s ID). Clients matching this user-defined role are associated with the specified VLAN. The VLAN ID represents the shared SSID each user employs to interoperate within the network (once authenticated by the local RADIUS server).This feature is disabled by default.• <1-4094> – Specify the VLAN ID from 1 - 4094.A wireless client that fails to match any user-defined role is assigned to the default role (configured as a role policy setting) and is mapped to the default VLAN under the WLAN.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-683.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 1818.1.7.2.3 authentication-typeuser-role commandsConfigures the authentication type based filter for this user-defined roleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthentication-type [any|eq|neq]authentication-type anyauthentication-type [eq|neq] [eap|kerberos|mac-auth|none]{(eap|kerberos|mac-auth|none)}Parameters• authentication-type any• authentication-type [eq|neq] [eap|kerberos|mac-auth|none] {(eap|kerberos|mac-auth|none)}Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#authentication-type eq kerberosrfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 authentication-type eq kerberos ap-location contains officerfs6000-37FABE(config-role-policy-test-user-role-testing)#any The authentication type is any (eq or neq). This is the default setting.eq [eap|kerberos|mac-auth|none]The role is applied only when the authentication type matches (equals) one or more than one of the following types:• eap – Extensible authentication protocol• kerberos – Kerberos authentication• mac-auth – MAC authentication protocol• none – no authentication usedThese parameters are recursive, and you can configure more than one unique authentication type for this user-defined role.neq [eap|kerberos|mac-auth|none]The role is applied only when the authentication type does not match (not equals) any of the following types:• eap – Extensible authentication protocol• kerberos – Kerberos authentication• mac-auth – MAC authentication protocol• none – no authentication usedThese parameters are recursive, and you can configure more than one unique ‘not equal to’ authentication type for this user-defined role.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-685.png)

![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 2018.1.7.2.4 captive-portaluser-role commandsConfigures a captive portal based filter for this user-defined role. A captive portal is a guest access policy that provides temporary and restrictive access to the wireless network. When applied to a WLAN, a captive portal policy ensures secure guest access.This command defines user-defined role filters based on a wireless client’s state of authentication.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcaptive-portal authentication-state [any|post-login|pre-login]Parameters• captive-portal authentication-state [any|post-login|pre-login]Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#captive-portal authentication-state pre-loginrfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 authentication-type eq kerberos ap-location contains office captive-portal authentication-state pre-loginrfs6000-37FABE(config-role-policy-test-user-role-testing)#Related Commandsauthentication-state Defines the authentication state of a client connecting to a captive portalany Specifies any authentication state (authenticated and pending authentication). This is the default setting.This option makes no distinction on whether authentication is conducted before or after the wireless client has logged in.post-login Specifies authentication is completed successfullyThis option requires the wireless client to share authentication credentials after logging into the managed network.pre-login Specifies authentication is pendingThis option enables captive portal client authentication before the client is logged into the controller.no Removes the captive portal based role filter settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-687.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 2118.1.7.2.5 cityuser-role commandsConfigures a wireless client filter based on the city nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcity [any|contains|exact|not-contains]city [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• city [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#city exact SanJoserfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 authentication-type eq kerberos ap-location contains office captive-portal authentication-state pre-login city exact SanJoserfs6000-37FABE(config-role-policy-test-user-role-testing)#Related Commandscity Specifies a wireless client filter based on how the ‘city’ name, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-contain.any No specific city associated with this user-defined role. This role can be applied to any wireless client from any city.contains <WORD> The role is applied only when the city name, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the city name returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the city name, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the city name returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the city name, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the city name returned by the RADIUS server). It should not contain the provided expression.no Removes the city name configured with this user-defined role](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-688.png)

![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 2318.1.7.2.7 companyuser-role commandsConfigures a wireless client filter based on the company nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcompany [any|contains|exact|not-contains]company [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• company [any|exact <WORD>|contains <WORD>|not-contains <WORD>]company Specifies a wireless client filter based on how the ‘company’ name, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-containsany No specific company associated with this user-defined role. This role is applied to any wireless client from any company (no strings to match). This is the default setting.contains <WORD> The role is applied only when the company name, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the company name returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the company name, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the company name returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the company name, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the company name returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-690.png)
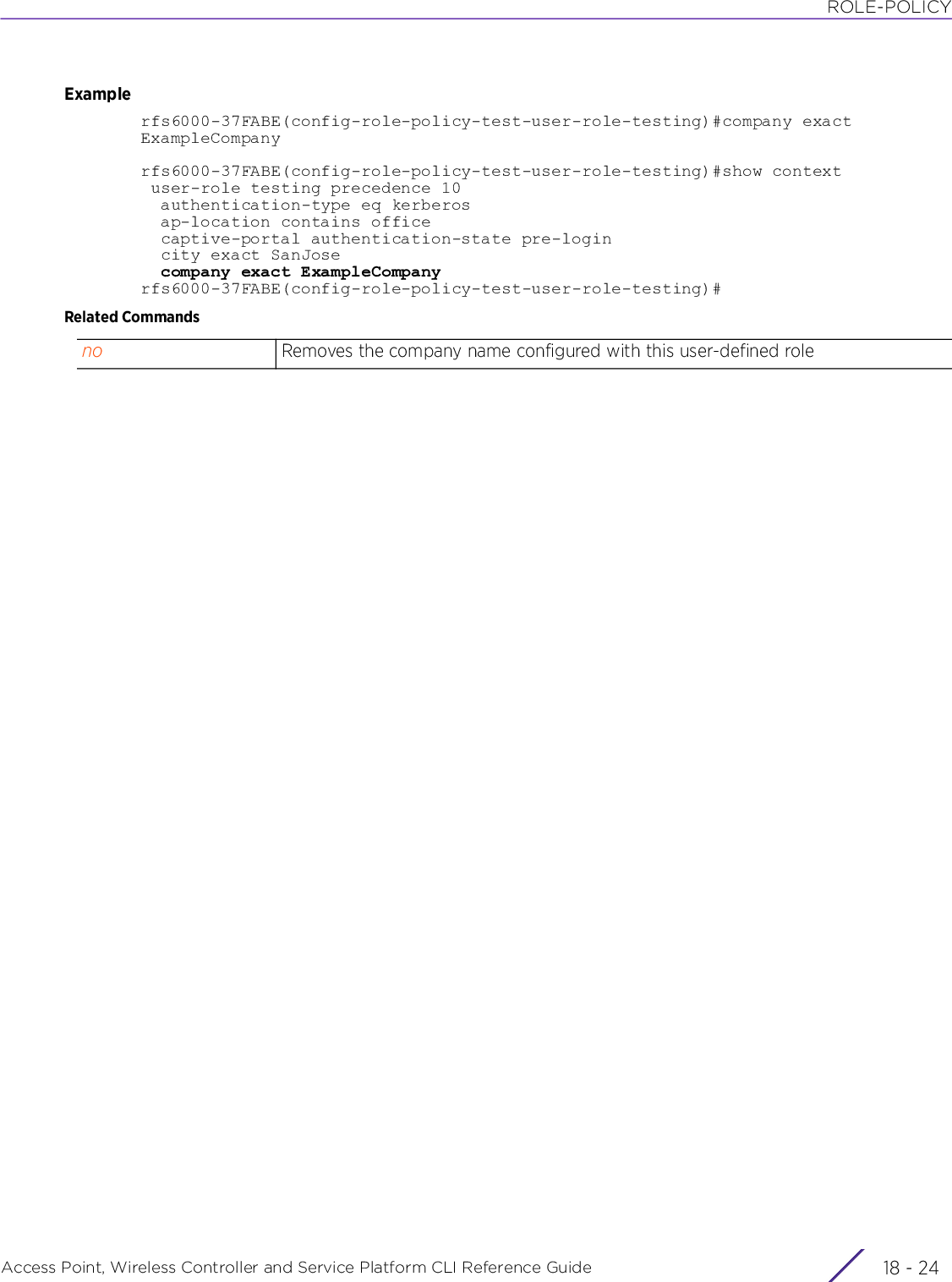
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 2518.1.7.2.8 countryuser-role commandsConfigures a wireless client filter based on the country nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcountry [any|contains|exact|not-contains]country [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• country [any|exact <WORD>|contains <WORD>|not-contains <WORD>]country Specifies a wireless client filter based on how the ‘country’ name, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-containsany No specific country associated with this user-defined role. This role is applied to any wireless client from any country (no strings to match). This is the default setting.contains <WORD> The role is applied only when the country name, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the country name returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the country name, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the country name returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the country name, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the country name returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-692.png)
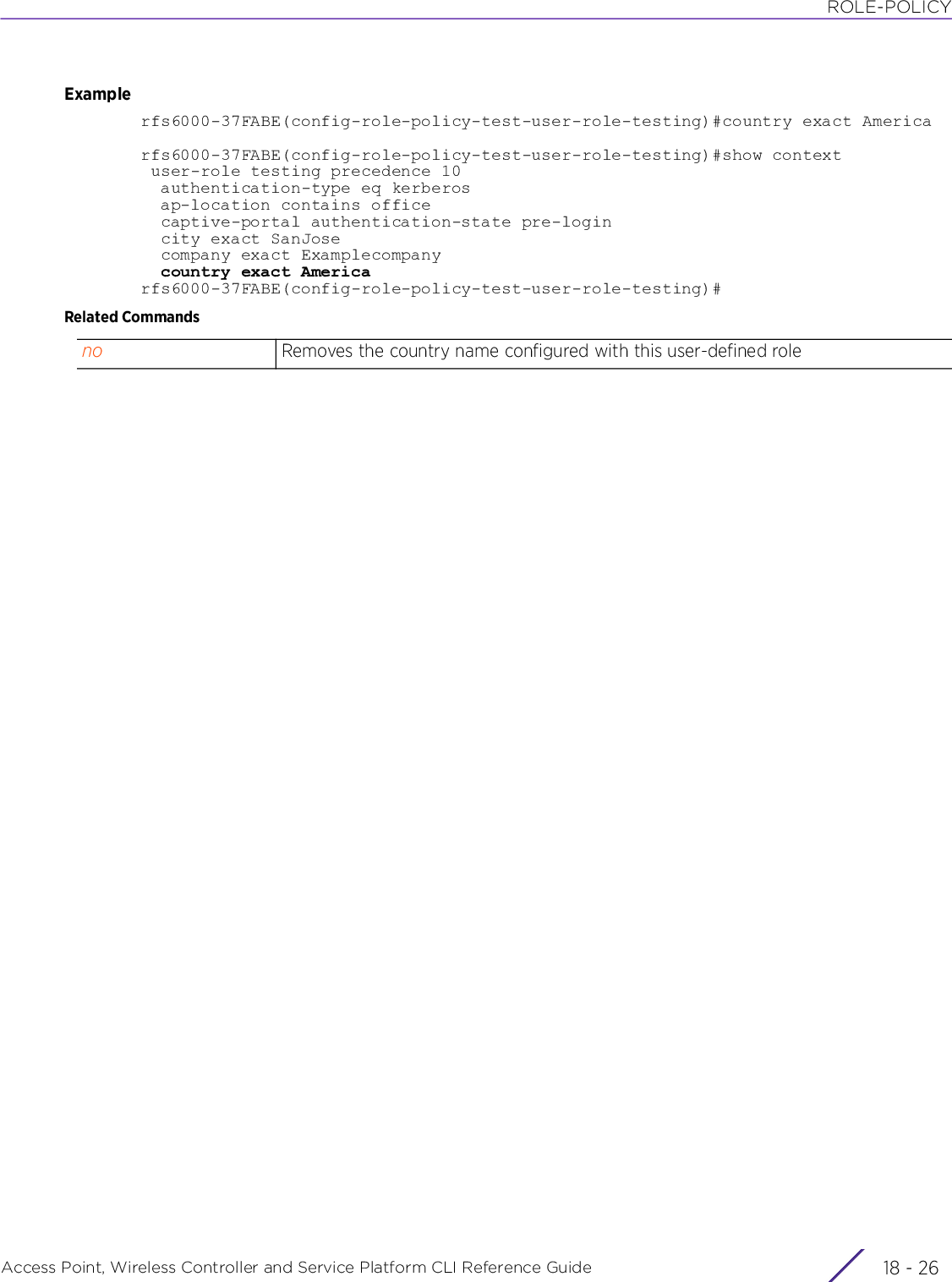
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 2718.1.7.2.9 departmentuser-role commandsConfigures a wireless client filter based on the department nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdepartment [any|contains|exact|not-contains]department [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• department [any|exact <WORD>|contains <WORD>|not-contains <WORD>]department Specifies a wireless client filter based on how the ‘department’ name, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-containsany No specific department associated with this user-defined role. This role can be applied to any wireless client from any department (no strings to match). This is the default setting.contains <WORD> The role is applied only when the department name, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the department name returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the department name, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the department name returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the department name, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the department name returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-694.png)
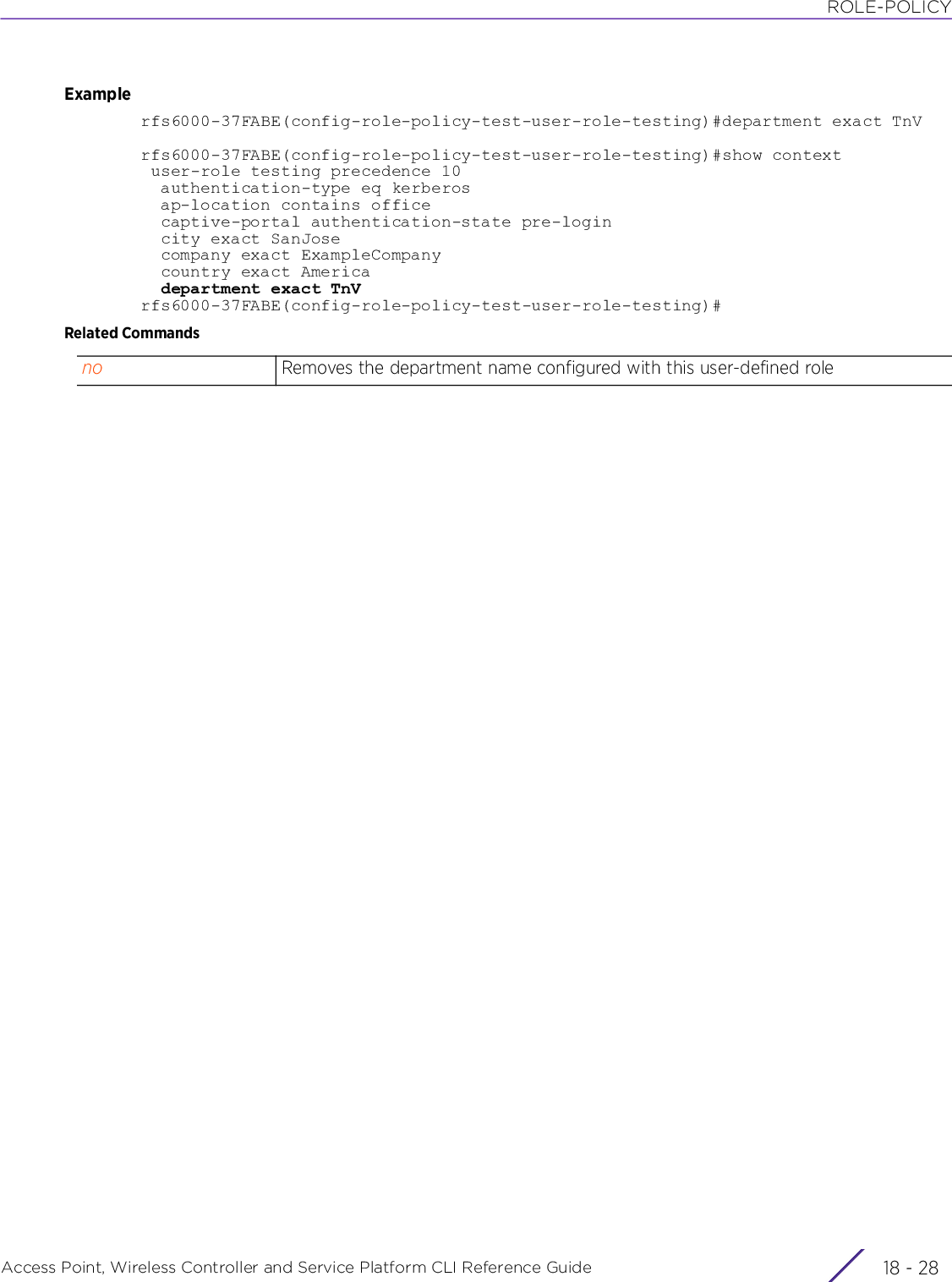
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 2918.1.7.2.10 emailiduser-role commandsConfigures a wireless client filter based on the e-mail IDSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxemailid [any|contains|exact|not-contains]emailid [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• emailid [any|exact <WORD>|contains <WORD>|not-contains <WORD>]emailid Specifies a wireless client filter based on how the ‘e-mail ID’, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-containsany No specific e-mail ID associated with this user-defined role. This role can be applied to any wireless client having any e-mail ID (no strings to match). This is the default setting.contains <WORD> The role is applied only when the e-mail ID, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the e-mail ID returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the e-mail ID, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the e-mail ID returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the e-mail ID, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the e-mail ID returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-696.png)
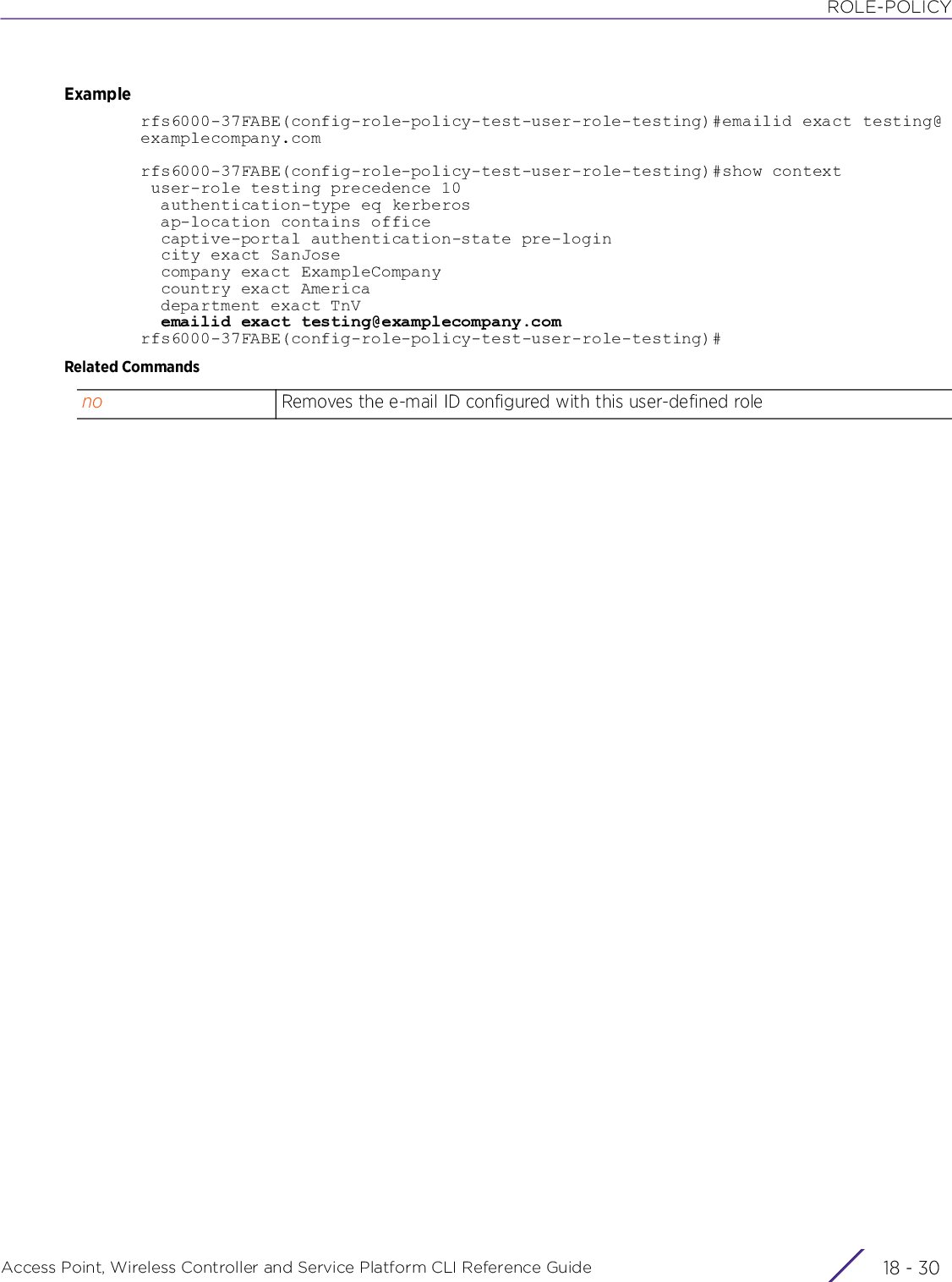
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 3118.1.7.2.11 employee-typeuser-role commandsConfigures a wireless client filter based on the employee typeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxemployee-type [any|contains|exact|not-contains]employee-type [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• employee-type [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Examplerfs4000-229D58(config-role-policy-test-user-role-test1)#employee-type exact consultantrfs4000-229D58(config-role-policy-test-user-role-user1)#show context user-role user1 precedence 1 employee-type exact consultantrfs4000-229D58(config-role-policy-test-user-role-user1)#Related Commandsemployee-type Specifies a wireless client filter based on how the ‘employee type’, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-contains.any No specific employee type associated with this user-defined role. This role can be applied to any wireless client having any employee type (no strings to match). This is the default setting.contains <WORD> The role is applied only when the employee type, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the employee type returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the employee type, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the employee type returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the employee type, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the employee type returned by the RADIUS server). It should not contain the provided expression.no Removes the employee type filter configured with this user-defined role](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-698.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 3218.1.7.2.12 employeeiduser-role commandsConfigures a wireless client filter based on the employee IDSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxemployeeid [any|contains|exact|not-contains]employeeid [any|exact <WORD>|contains <WORD>|not-contains <WORD>]Parameters• employeeid [any|exact <WORD>|contains <WORD>|not-contains <WORD>]employeeid Specifies a wireless client filter based on how the ‘employee ID’, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-contains.any No specific employee ID associated with this user-defined role. This role can be applied to any wireless client having any employee ID (no strings to match). This is the default setting.contains <WORD> The role is applied only when the employee ID, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the employee ID returned by the RADIUS server). It should contain the provided expression.exact The role is applied only when the employee ID, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the employee ID returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the employee ID, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the employee ID returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-699.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 3418.1.7.2.13 encryption-typeuser-role commandsSelects the encryption type for this user-defined role. Encryption ensures privacy between access points and wireless clients. There are various modes of encrypting communication on a WLAN, such as Counter-model CBC-MAC Protocol (CCMP), Wired Equivalent Privacy (WEP), keyguard, Temporal Key Integrity Protocol (TKIP), etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxencryption-type [any|eq|neq]encryption-type anyencryption-type [eq|neq] [ccmp|keyguard|none|tkip|wep128|wep64] (ccmp|keyguard|none|tkip|tkip-ccmp|wep128|wep64)}Parameters• encryption-type any• encryption-type [eq|neq] [ccmp|keyguard|none|tkip|wep128|wep64] {(ccmp|keyguard|none|tkip|tkip-ccmp|wep128|wep64)}any The encryption type can be any one of the listed options (ccmp|keyguard|tkip|wep128|wep64). This is the default setting.eq [ccmp|keyguard|none|tkip|wep128|wep64]The role is applied only if the encryption type equals to one of the following options:• ccmp – Encryption mode is CCMP• keyguard – Encryption mode is keyguard. Keyguard encryption shields the master encryption keys from being discovered.• none – No encryption mode specified• tkip – Encryption mode is TKIP• wep128 – Encryption mode is WEP128• wep64 – Encryption mode is WEP64These parameters are recursive, and you can configure more than one encryption type for this user-defined role.neq [ccmp|keyguard|none|tkip|wep128|wep64]The role is applied only if encryption type is not equal to any of the following options:• ccmp – Encryption mode is not equal to CCMP• keyguard – Encryption mode is not equal to keyguard• none: Encryption mode is not equal to none• tkip – Encryption mode is not equal to TKIPContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-701.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 3618.1.7.2.14 groupuser-role commandsConfigures a wireless client filter based on the RADIUS group nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxgroup [any|contains|exact|not-contains]group [any|contains <WORD>|exact <WORD>|not-contains <WORD>]Parameters• group [any|contains <WORD>|exact <WORD>|not-contains <WORD>]group Specifies a wireless client filter based on how the RADIUS group name matches the provided expression. Select one of the following options: any, contains, exact, or not-containsany This user-defined role can fit into any group (no strings to match). This is the default setting.contains <WORD> The role is applied only when the RADIUS group name contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the group name returned by the RADIUS server). It should contain the provided expression.exact <WORD> The role is applied only when the RADIUS group name exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the group name returned by the RADIUS server). It should be an exact match.not-contains <WORD>The role is applied only when the RADIUS group name does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the group name returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-703.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 3918.1.7.2.16 mu-macuser-role commandsConfigures a MAC address and mask based filter for this role policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmu-mac [<MAC>|any]mu-mac anymu-mac <MAC> {mask <MAC>}Parameters• mu-mac any• mu-mac <MAC> {mask <MAC>}Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#mu-mac 11-22-33-44-55-66rfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 authentication-type eq kerberos encryption-type eq wep128 ap-location contains office mu-mac 11-22-33-44-55-66 group contains testgroup captive-portal authentication-state pre-login city exact SanJose company exact ExampleCompany country exact America department exact TnV emailid exact testing@examplecompany.com employeeid contains TnVTest1rfs6000-37FABE(config-role-policy-test-user-role-testing)#Related Commandsany Applies role to any wireless client (no MAC address to match). This is the default setting.<MAC> Applies role to the wireless client having specified MAC address• <MAC> – Sets the MAC address in the AA-BB-CC-DD-EE-FF formatmask <MAC> Optional. After specifying the client’s MAC address, specify the mask in the AA-BB-CC-DD-EE-FF format. The role is applied to the wireless client exactly matching the specified MAC address and MAC mask.no Removes the MAC address and mask for this user-defined role](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-706.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 4018.1.7.2.17 nouser-role commandsNegates a command or resets configured settings to their default. When used in the config role policy user-defined role mode, the no command removes or resets settings, such as AP location, authentication type, encryption type, captive portal, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [ap-location|assign|authentication-type|captive-portal|city|client-identity|company|country|department|emailid|employee-type|employeeid|encryption-type|group|memberOf|mu-mac|radius-user|ssid|state|title|use|user-defined]no [ap-location|assign|authentication-type|city|client-identity|company|country|department|emailid|employee-type|employeeid|encryption-type|group|mu-mac|memberOf|ssid|radius-user|state|title|user-defined]no captive-portal authentication-stateno use [application-policy|bonjour-gw-discovery-policy|ip-access-list|ipv6-access-list|mac-access-list|url-filter]no use [ip-access-list|ipv6-access-list|mac-access-list] [in|out] <IP/IPv6/MAC-ACCESS-LIST-NAME> precedence <1-100>no use [application-policy|bonjour-gw-discovery-policy|url-filter]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.no <PARAMETERS> Negates a command or resets configured settings to their default. When used in the config role policy user-defined role mode, the no command removes or resets settings, such as AP location, authentication type, encryption type, captive portal, etc.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-707.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 4218.1.7.2.18 radius-useruser-role commandsConfigures a wireless client filter based on the RADIUS user nameSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxradius-user [any|contains|ends-with|exact|not-contains|starts-with]Parameters• radius-user [any|contains|ends-with|exact|not-contains|starts-with]radius-user Specifies a wireless client filter based on how the ‘radius-user’ name, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-contains.any No specific RADIUS user name associated with this user-defined role. This role can be applied to any wireless client (no strings to match). This is the default setting.contains <WORD> The role is applied only when the ‘radius-user’ name, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the ‘radius-user’ name returned by the RADIUS server). It should contain the provided expression.You can use the realm or any sub-string of the user name.ends-with <WORD> Enables role assignment on the basis of the wireless client’s “department” and/or “group”• <WORD> – Specify the string (could be department/group code). For example: 1005000002. In this the last three digits represent the department/group code. The remaining digits represent user’s badge number.The role is applied only when the ‘radius-user’ name, returned by the RADIUS server, ends with the string specified here.exact <WORD> The role is applied only when the ‘radius-user’ name, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the ‘radius-user’ name returned by the RADIUS server). It should be an exact match.Provide the complete user name along with the realm.not-contains <WORD> The role is applied only when the ‘radius-user’ name, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the ‘radius-user’ name returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-709.png)

![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 4418.1.7.2.19 ssiduser-role commandsConfigures a SSID based filterSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxssid [any|exact|contains|not-contains]ssid anyssid [exact|contains|not-contains] <WORD>Parameters• ssid any• ssid [exact|contains|not-contains] <WORD>ssid any Specifies a wireless client filter based on how the SSID is specified in a WLAN• any – The role is applied to any SSID location. This is the default setting.ssid Specifies a wireless client filter based on how the SSID is specified in a WLAN. This options are: contains, exact, or not-containsexact <WORD> The role is applied only when the SSID, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the SSID string to match. The SSID is case sensitive and is compared against the SSID configured for the WLAN.contains <WORD> The role is applied only when the SSID, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the SSID string to match. The SSID is case sensitive and is compared against the SSID configured for the WLAN.not-contains <WORD> The role is applied only when the SSID, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the SSID string not to match. The SSID is case sensitive and is compared against the SSID configured for the WLAN.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-711.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 45Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#ssid not-contains DevUserrfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 ssid not-contains DevUser captive-portal authentication-state pre-login city exact SanJose company exact ExampleCompany country exact America department exact TnV emailid exact testing@examplecompany.comrfs6000-37FABE(config-role-policy-test-user-role-testing)#]Related Commandsno Removes the SSID configured for a user-defined role](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-712.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 4618.1.7.2.20 stateuser-role commandsConfigures a user role state to match with this user-defined roleSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxstate [any|contains|exact|not-contains]state [any|contains <WORD>|exact <WORD>|not-contains <WORD>]Parameters• state [any|contains <WORD>|exact <WORD>|not-contains <WORD>]state Specifies a wireless client filter option based on how the RADIUS state matches the provided expression. Select one of the following options: any, contains, exact, or not-contains.any This user role can fit any wireless client irrespective of the state (no strings to match).contains <WORD> The user role is applied only when the RADIUS state contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the state returned by the RADIUS server). It should contain the provided expression.exact <WORD> The role is applied only when the RADIUS state exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the state returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the RADIUS state does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the state returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-713.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 4818.1.7.2.21 titleuser-role commandsConfigures a ‘title’ string to matchSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtitle [any|contains|exact|not-contains]title [any|contains <WORD>|exact <WORD>|not-contains <WORD>]Parameters• title [any|contains <WORD>|exact <WORD>|not-contains <WORD>]Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#title anyRelated Commandstitle Specifies a wireless client filter based on how the title string, returned by the RADIUS server, matches the provided expression. Select one of the following options: any, contains, exact, or not-contains.any This user role can fit any wireless client irrespective of the title (no strings to match).contains <WORD> The user role is applied only when the title string, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the title returned by the RADIUS server). It should contain the provided expression.exact <WORD> The role is applied only when the title string, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the title returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the title string, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the title returned by the RADIUS server). It should not contain the provided expression.no Removes the ‘title’ filter string configured with a user role](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-715.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 4918.1.7.2.22 useuser-role commandsConfigures an access list based firewall with this user roleA firewall is a mechanism enforcing access control, and is considered a first line of defense in protecting proprietary information within the network. The means by which this is accomplished varies, but in principle, firewalls are mechanisms both blocking and permitting data traffic based on inbound and outbound IP and MAC rules.IP based firewall rules are specific to source and destination IP addresses and the unique rules and precedence orders assigned. Both IP and non-IP traffic on the same layer 2 interface can be filtered by applying both an IP ACL and a MAC.A MAC firewall rule uses source and destination MAC addresses for matching operations, where the result is a typical allow, deny or mark designation to packet traffic.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [application-policy|bonjour-gw-discovery-policy|ip-access-list|ipv6-access-list|mac-access-list|url-filter]use bonjour-gw-discovery-policy <POLICY-NAME>use [ip-access-list|ipv6-access-list] [in|out] <IP/ipv6-ACCESS-LIST-NAME> precedence <1-100>use mac-access-list [in|out] <MAC-ACCESS-LIST-NAME> precedence <1-100>use url-filter <URL-FILTER-NAME>Parameters• use application-policy|bonjour-gw-discovery-policy] <POLICY-NAME>application-policy <POLICY-NAME>Uses an existing Application policy with a user role. When associated, the Application policy enforces application assurance for all users using this role.• <POLICY-NAME> – Specify the Application policy name (should be existing and configured).For more information on Application policy, see application-policy.bonjour-gw-discovery-policy <POLICY-NAME>Uses an existing Bonjour GW Discovery policy with a user role. When associated, the Bonjour GW Discovery policy is applied for the Bonjour requests coming from this specific user roles.• <POLICY-NAME> – Specify the Bonjour GW Discovery policy name (should be existing and configured).For more information on Bonjour GW Discovery policy, see bonjour-gw-discovery-policy.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-716.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 50• use [ip-access-list|ipv6-access-list] [in|out] <IP/IPv6-ACCESS-LIST-NAME> precedence <1-100>• use mac-access-list [in|out] <MAC-ACCESS-LIST-NAME> precedence <1-100>• use url-filter <URL-FILTER-NAME>Examplerfs6000-37FABE(config-role-policy-test-user-role-testing)#use ip-access-list intest precedence 9rfs6000-37FABE(config-role-policy-test-user-role-testing)#show context user-role testing precedence 10 ssid not-contains DevUser captive-portal authentication-state pre-login city exact SanJose company exact ExampleCompany country exact America department exact TnV emailid exact testing@examplecompany.com state exact active use ip-access-list in test precedence 9rfs6000-37FABE(config-role-policy-test-user-role-testing)#rfs6000-37FABE(config-role-policy-bonjour_test-user-role-bonjour_user1)#use bonjour-gw-discovery-policy role2rfs6000-37FABE(config-role-policy-bonjour_test-user-role-bonjour_user1)#show context user-role bonjour_user1 precedence 2 use bonjour-gw-discovery-policy role2rfs6000-37FABE(config-role-policy-bonjour_test-user-role-bonjour_user1)#ip-access-list [in|out] Uses an IPv4 or IPv6 ACL with this user role• in – Applies the rule to incoming packets• out – Applies the rule to outgoing packets<IPv4/IPv6-ACCESS-LIST-NAME>Specify the IPv4/IPv6 access list name.precedence <1-100> After specifying the name of the access list, specify the precedence applied to it. Based on the packets received, a lower precedence value is evaluated first.• <1-100> – Sets a precedence from 1 - 100mac-access-list [in|out] Uses a MAC access list with this user role• in – Applies the rule to incoming packets• out – Applies the rule to outgoing packets<MAC-ACCESS-LIST-NAME>Specify the MAC access list name.precedence <1-100> After specifying the name of the access list, specify the precedence applied to it. Based on the packets received, a lower precedence value is evaluated first• <1-100> – Sets a precedence from 1 - 100use url-filter <URL-FILTER-NAME>Uses an existing URL filter that acts as a Web content filter firewall rule.• <POLICY-NAME> – Specify the URL filter name (should be existing and configured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-717.png)
![ROLE-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 18 - 5218.1.7.2.23 user-defineduser-role commandsEnables you to define a filter based on an attribute defined in the Active Directory or the OpenLDAP serverSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuser-defined <ATTR-STRING> [any|contains|exact|not-contains]user-defined <ATTR-STRING> [any|contains <WORD>|exact <WORD>|not-contains <WORD>]Parameters• user-defined <ATTR-STRING> [any|exact <WORD>|contains <WORD>|not-contains <WORD>]user-defined <ATTR-STRING>Specify a filter based on an attribute defined in the AD or OpenLDAP server.• <ATTR-NAME> – Specify the attribute string.After specifying the attribute name, specify the match type.any No specific string to match. This role can be applied to any wireless client. This is the default setting.contains <WORD> The role is applied only when the user-defined attribute value, returned by the RADIUS server, contains the string specified in the role.• <WORD> – Specify the string to match (this is case sensitive, and is compared against the value returned by the RADIUS server). It should contain the provided expression.exact <WORD> The role is applied only when the user-defined attribute value, returned by the RADIUS server, exactly matches the string specified in the role.• <WORD> – Specify the exact string to match (this is case sensitive, and is compared against the value returned by the RADIUS server). It should be an exact match.not-contains <WORD> The role is applied only when the user-defined attribute value, returned by the RADIUS server, does not contain the string specified in the role.• <WORD> – Specify the string not to match (this is case sensitive, and is compared against the value returned by the RADIUS server). It should not contain the provided expression.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-719.png)

![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 419.1.1 areasmart-rf-policyConfigures the channel list and power for a specified areaSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxarea <AREA-NAME/STRING-ALIAS> channel-list [2.4GHz|5GHz] <CHANNEL-LIST>Parameters• area <AREA-NAME/STRING-ALIAS> channel-list [2.4GHz|5GHz] <CHANNEL-LIST>Examplerfs6000-37FABE(config-smart-rf-policy-test)#area test channel-list 2.4GHz 1,2,3rfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3rfs6000-37FABE(config-smart-rf-policy-test)#nx9500-6C8809(config)#alias string $AREA Ecospacenx9500-6C8809(config)#commitnx9500-6C8809(config-smart-rf-policy-test)#exitnx9500-6C8809(config-smart-rf-policy-Ecospace)#area $AREA channel-list 5GHz 36,44nx9500-6C8809(config-smart-rf-policy-Ecospace)#show contextsmart-rf-policy Ecospace area $AREA channel-list 5GHz 36,44nx9500-6C8809(config-smart-rf-policy-Ecospace)#Related Commandsarea <AREA-NAME/STRING-ALIAS>Specifies the area name• <AREA-NAME/STRING-ALIAS> – Specify the area name as clear text. Alternately, use a string-alias to specify the area name. If using a string-alias, ensure that the string-alias is existing and configured.channel-list [2.4GHz|5GHZ] <CHANNEL-LIST>Selects the channels for the specified area in the 2.4 GHz or 5.0 GHz band• 2.4GHz – Selects the channels for the specified area in the 2.4 GHz band• 5GHz – Selects the channels for the specified area in the 5.0 GHz bandThe following keyword is common to the 2.4 GHz and 5.0 GHz bands:• <CHANNEL-LIST> – Enter a comma-separated list of channels for the selectedband.no Removes channel list/power configuration for an area](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-724.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 519.1.2 assignable-powersmart-rf-policyConfigures the Smart RF power settings over both 2.4 GHZ and 5.0 GHZ radiosSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxassignable-power [2.4GHz|5GHz] [max|min] <1-20>Parameters• assignable-power [2.4GHz|5GHz] [max|min] <1-20>Examplerfs6000-37FABE(config-smart-rf-policy-test)#assignable-power 5GHz max 20rfs6000-37FABE(config-smart-rf-policy-test)#assignable-power 5GHz min 8rfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3 assignable-power 5GHz min 8 assignable-power 5GHz max 20rfs6000-37FABE(config-smart-rf-policy-test)#Related Commands2.4GHz [max|min] <1-20>Assigns a power range on the 2.4 GHz band• max <1-20> – Sets the upper limit in the range from 1 dBm - 20 dBm (default is 17 dBm)• min <1-20> – Sets the lower limit in the range from 1 dBm - 20 dBm (default is 4 dBm)5GHz [max|min] <1-20>Assigns a power range on the 5.0 GHz band• max <1-20> – Sets the upper limit in the range from 1 dBm - 20 dBm (default is 17 dBm)• min <1-20> – Sets the lower limit in the range from 1 dBm - 20 dBm (default is 4 dBm)no Resets assignable power to its default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-725.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 619.1.3 avoidance-timesmart-rf-policyAllows Smart-RF enabled radios to avoid channels with high levels of interference and channels where radar has been detectedThis command configures the interval for which a channel is avoided on detection of interference or radar, and is applicable only if the channel selection mode is set to Smart and a Smart-RF policy is applied to the access point’s RF Domain. For more information on configuring a radio’s channel of operation, see channel.Certain 5.0 GHz channels are subject to FCC / ETSI DFS regulations that require channels transmitting critical radar signals to be free of interference from radio signals. Consequently, DFS-enabled 5.0 GHz radios scan and switch channels if radar is detected on their current channel of operation. If radar-free channels are not available, the radio stops transmitting until it identifies a radar-free channel.Adaptivity is a new European Union (EU) stipulation that requires access points to monitor interference levels on their current channel of operation, and stop functioning on channels with interference levels exceeding ETSI-specified threshold values. When enabled, this feature ensures recovery by switching the radio to a new channel with less interference.Once adaptivity or DFS is triggered, the radio’s channel is switched based on the channel selection mode specified. If the channel is fixed, the radio attempts to come back to its specified channel of operation after the DFS/adaptivity channel evacuation period has expired.On the other hand, if the radio’s channel selection mode is set to Smart or ACS, once adaptivity or DFS is triggered, the channel is avoided until the avoidance-time, specified here, expires. Once the evacuation period has expired, the channel is free for use by both Smart-RF and ACS.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxavoidance-time [adaptivity|dfs] <30-3600>NOTE: To optionally disable the radio from switching back to its original channel of operation, execute the no > dfs-rehome command in the radio interface configuration mode of the access point’s profile or device. For more information, see dfs-rehome.NOTE: For radio’s having channel selection mode set to ACS, Random, or Fixed adaptivity timeout can be configured in the access point’s radio interface mode. For more information, see adaptivity.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-726.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 7Parameters• avoidance-time [adaptivity|dfs] <30-3600>Examplenx4500-5CFA2B(config-smart-rf-policy-test)#avoidance-time adaptivity 200nx4500-5CFA2B(config-smart-rf-policy-test)#avoidance-time dfs 300nx4500-5CFA2B(config-smart-rf-policy-test)#show contextsmart-rf-policy test avoidance-time dfs 300 avoidance-time adaptivity 200nx4500-5CFA2B(config-smart-rf-policy-test)#nx4500-5CFA2B(config-smart-rf-policy-test)#no avoidance-time adaptivitynx4500-5CFA2B(config-smart-rf-policy-test)#show context include-factory | include avoidance-time avoidance-time dfs 300 avoidance-time adaptivity 90nx4500-5CFA2B(config-smart-rf-policy-test)#Related Commandsavoidance-time [adaptivity|dfs]Configures the time for which a channel is avoided after dfs or adaptivity is triggered• adaptivity – Sets the time, in minutes, for which a radio avoids an adaptivity-regulated channel detected with interference• dfs – Sets the time, in minutes, for which a radio avoids a DFS-regulated channel detected with radar• <30-3600> – Specify a value from 30 - 3600 minutes. The default for both parameters is 90 minutes.no Reverts the DFS/adaptivity regulated channel avoidance time to default (90 minutes)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-727.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 819.1.4 channel-listsmart-rf-policyAssigns a list of channels, for the selected frequency, used in Smart RF scansSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxchannel-list [2.4GHz|5GHz] <WORD>Parameters• channel-list [2.4GHz|5GHz] <WORD>Examplerfs6000-37FABE(config-smart-rf-policy-test)#channel-list 2.4GHz 1,12rfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3 assignable-power 5GHz min 8 assignable-power 5GHz max 20 channel-list 2.4GHz 1,12rfs6000-37FABE(config-smart-rf-policy-test)#Related Commands2.4GHz <WORD> Assigns a channel list for the 2.4 GHz band• <WORD> – Specify a comma separated list of channels5GHz <WORD> Assigns a channel list for the 5.0 GHz band• <WORD> – Specify a comma separated list of channelsno Removes the channel list for the selected frequency](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-728.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 919.1.5 channel-widthsmart-rf-policySelects the channel width for Smart RF configurationSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxchannel-width [2.4GHz|5GHz]channel-width 2.4GHz [20MHz|40MHz|auto]channel-width 5GHz [20MHz|40MHz|80MHz|auto]Parameters• channel-width 2.4GHz [20MHz|40MHz|auto]• channel-width 5GHz [20MHz|40MHz|auto]Usage GuidelinesThe 20/40 MHz operation allows the access point to receive packets from clients using 20 MHz, and transmit using 40 MHz. This mode is supported for 802.11n users on both the 2.4 GHz and 5.0 GHz radios. If an 802.11n user selects two channels (a primary and secondary channel), the system is configured for dynamic 20/40 operation. When 20/40 is selected, clients can take advantage of wider channels. 802.11n clients experience improved throughput using 40 MHz while legacy clients (either 802.11a or 802.11b/g depending on the radio selected) can still be serviced without interruption using 20 MHz. Select auto to enable automatic assignment of channels to working radios to avoid channel overlap and avoid interference from external RF sources.NOTE: In addition to 20 MHz and 40 MHz, AP82XX also provides support for 80 MHz channels.2.4GHz [20MHz|40MHz|auto]Assigns the channel width for the 2.4 GHz band• 20MHz – Assigns the 20 MHz channel width. This is the default setting.• 40MHz – Assigns the 40 MHz channel width• auto – Assigns the best possible channel in the 20 MHz or 40 MHz channel width5GHz [20MHz|40MHz|80MHz|auto]Assigns the channel width for the 5.0 GHz band• 20MHz – Assigns the 20 MHz channel width• 40MHz – Assigns the 40 MHz channel width. This is the default setting.• 80MHz – Assigns the 80 MHz channel width (supported only on AP8232)• auto – Assigns the best possible channel in the 20 MHz, 40 MHz, or 80 MHz channel width](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-729.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 1119.1.6 coverage-hole-recoverysmart-rf-policyEnables recovery from coverage hole errors detected by Smart RF. Use this command to configure the coverage hole recovery settings.When coverage hole recovery is enabled, on detection of a coverage hole, Smart RF first determines the power increase needed based on the signal-to-noise ratio (SNR) for a client as seen by the access point radio. If a client’s SNR is above the specified threshold, the transmit power is increased until the SNR falls below the threshold.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcoverage-hole-recovery {client-threshold|coverage-interval|interval|snr-threshold}coverage-hole-recovery {client-threshold [2.4GHz|5GHz] <1-255>}coverage-hole-recovery {coverage-interval|interval} [2.4GHz|5GHz] <1-120>coverage-hole-recovery {snr-threshold [2.4Ghz|5Ghz] <1-75>}Parameters• coverage-hole-recovery {client-threshold [2.4GHz|5GHz] <1-255>}• coverage-hole-recovery {coverage-interval|interval} [2.4GHz|5GHz] <1-120>NOTE: The coverage-hole-recovery parameters can be modified only if the sensitivity level is set to ‘custom’. For more information, see sensitivity.client-threshold Optional. Specifies the minimum number of clients associated to a radio in order to trigger coverage hole recovery.2.4GHz <1-255> Specifies the minimum number of clients on the 2.4 GHz band• <1-255> – Sets a value from 1 - 255. The default is 1.5GHz <1-255> Specifies the minimum number of clients on the 5.0 GHz band• <1-255> – Sets a value from 1 - 255. The default is 1.coverage-interval Optional. Specifies the interval between the discovery of a coverage hole and the initiation of coverage hole recoveryinterval Optional. Specifies the interval at which coverage hole recovery is performed even before a coverage hole is detected](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-731.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 12• coverage-hole-recovery {snr-threshold} [2.4Ghz|5Ghz] <1-75>Examplerfs6000-37FABE(config-smart-rf-policy-test)#coverage-hole-recovery snr-threshold 5GHz 1rfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3 sensitivity custom assignable-power 5GHz min 8 assignable-power 5GHz max 20 channel-list 2.4GHz 1,12 channel-width 5GHz auto coverage-hole-recovery snr-threshold 5GHz 1rfs6000-37FABE(config-smart-rf-policy-test)#Related Commands2.4GHz <1-120> The following keywords are common to the ‘coverage-interval’ and ‘interval’ parameters:• 2.4GHz <1-120> – Specifies the coverage hole recovery interval on the 2.4 GHz band• <1-120> – Specify a value from 1 - 120 seconds.Note: coverage-interval – The default is 10 seconds.Note: interval – The default is 30 seconds.5GHz <1-120> The following keywords are common to the ‘coverage-interval’ and ‘interval’ parameters:• 5GHz <1-120> – Specifies a coverage hole recovery interval on the 5.0 GHz band• <1-120> – Specify a value from 1 - 120 seconds.Note: coverage-interval – The default is 10 seconds.Note: interval – The default is 30 seconds.snr-threshold Optional. Specifies the SNR threshold. This value is the SNR threshold for an associated client as seen by its associated AP radio. When the SNR threshold is exceeded, the radio increases its transmit power to increase coverage for the associated client.2.4GHz <1-75> Specifies SNR threshold on the 2.4 GHz band• <1-75> – Sets a value from 1 dB - 75 dB. The default is 20 dB.5GHz <1-75> Specifies SNR threshold on the 5.0 GHz band• <1-75> – Sets a value from 1 - 75. The default is 20 dB.no Disables recovery from coverage hole errors](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-732.png)

![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 1419.1.8 group-bysmart-rf-policyEnables grouping of APs on the basis of their location in a building (floor) or an areaWithin a large RD Domain, grouping of APs (within an area or on the same floor in a building) facilitates statistics gathering and troubleshooting.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxgroup-by [area|floor]Parameters• group-by [area|floor]Examplerfs6000-37FABE(config-smart-rf-policy-test)#group-by floorrfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3 group-by floor sensitivity custom assignable-power 5GHz min 8 assignable-power 5GHz max 20 channel-list 2.4GHz 1,12 channel-width 5GHz auto coverage-hole-recovery snr-threshold 5GHz 1rfs6000-37FABE(config-smart-rf-policy-test)#Related Commandsarea Groups radios based on their area of locationfloor Groups radios based on their floor locationBoth options are disabled by default.no Removes Smart RF group settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-734.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 1519.1.9 interference-recoverysmart-rf-policyEnables interference recovery from neighboring radios and other sources of WiFi and non-WiFi interference. Interference is the excess noise detected within the Smart RF supported radio coverage area. Smart RF provides mitigation from interfering sources by monitoring the noise levels and other RF parameters on an access point radio’s current channel. When a noise threshold is exceeded, Smart RF selects an alternative channel with less interference. To avoid channel flapping a hold timer is defined, which disables interference avoidance for a specific period of time upon detection. Interference recovery is enabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxinterference-recovery {channel-hold-time|channel-switch-delta|client-threshold|interference|neighbor-offset|noise|noise-factor}interference-recovery {channel-switch-delta [2.4GHz|5GHZ] <5-35>}interference-recovery {channel-hold-time <0-86400>|client-threshold <1-255>|interference|neighbor-offset <3-10>|noise|noise-factor <1.0-3.0>}Parameters• interference-recovery {channel-switch-delta [2.4GHz|5GHZ] <5-35>}• interference-recovery {channel-hold-time <0-86400>|client-threshold <1-255>|interference|neighbor-offset <3-10>|noise|noise-factor <1.0-3.0>}NOTE: The interference-recovery parameters can be modified only if the sensitivity level is set to ‘custom’. For more information, see sensitivity.channel-switch-delta Optional. Configures a threshold value for the difference between interference levels on the current channel and the prospective channel needed to trigger a channel change. If the difference in noise levels on the current channel and the prospective channel is below the configured threshold, the channel is not changed.[2.4GHz|5GHz] Selects the band• 2.4GHz – Selects the 2.4 GHz band• 5GHz – Selects the 5.0 GHz band<5-35> Specifies the threshold value for the difference between the current and prospective channel interference levels• <5-35> – Sets a value from 5 dBm - 35 dBm. The default setting is 20 dBm for both 2.4 GHz and 5.0 GHz bands.channel-hold-time <0-86400> Optional. Defines the minimum time between two channel change recoveries• <0-86400> – Sets the time, in seconds, between channel change assignments based on interference or noise. The default is 7,200 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-735.png)

![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 1719.1.10 neighbor-recoverysmart-rf-policyEnables recovery from errors due to faulty neighboring radios. Enabling neighbor recovery ensures automatic recovery from failed radios within the radio coverage area. Smart RF instructs neighboring access points to increase their transmit power to compensate for the failed radio. Neighbor recovery is enabled by default when the sensitivity setting is medium.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxneighbor-recovery {dynamic-sampling|power-hold-time|power-threshold}neighbor-recovery {dynamic-sampling} {retries <1-10>|threshold <1-30>}neighbor-recovery {power-hold-time <0-3600>}neighbor-recovery {power-threshold [2.4Ghz|5Ghz] <-85--55>}Parameters• neighbor-recovery {dynamic-sampling} {retries <1-10>|threshold <1-30>}• neighbor-recovery {power-hold-time <0-3600>}NOTE: The neighbor-recovery parameters can be modified only if the sensitivity level is set to ‘custom’. For more information, see sensitivity.dynamic-sampling Optional. Enables dynamic sampling on this Smart RF policy. Dynamic sampling allows you to define how Smart RF adjustments are triggered by locking the ‘retry’ and ‘threshold’ values. Dynamic sampling is disabled by default.retries <1-10> Optional. Specifies the number of retries before allowing a power level adjustments to compensate for a potential coverage hole.• <1-10> – Sets the number of retries from 1 - 10. The default is 3.threshold <1-30> Optional. Specifies the minimum number of sample reports before which a power change requires dynamic sampling• <1-30> – Sets the minimum number of reports from 1 - 30. The default is 5.power-hold-time Optional. Specifies the minimum time, in seconds, between two power changes on a radio during neighbor-recovery<0-3600> Sets the time from 0 - 3600 sec. The default is 0 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-737.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 18• neighbor-recovery {power-threshold [2.4Ghz|5Ghz] <-85--55>}Examplerfs6000-37FABE(config-smart-rf-policy-test)#neighbor-recovery power-threshold 2.4GHz -82rfs6000-37FABE(config-smart-rf-policy-test)#neighbor-recovery power-threshold 5GHz -65rfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3 group-by floor sensitivity custom assignable-power 5GHz min 8 assignable-power 5GHz max 20 channel-list 2.4GHz 1,12 channel-width 5GHz auto interference-recovery channel-switch-delta 5GHz 5 neighbor-recovery power-threshold 5GHz -65 neighbor-recovery power-threshold 2.4GHz -82 coverage-hole-recovery snr-threshold 5GHz 1rfs6000-37FABE(config-smart-rf-policy-test)#Related Commandspower-threshold Optional. Specifies the power threshold based on which recovery is performedThe 2.4 GHz/5.0 GHz radio uses the value specified here as the maximum power increase threshold if the radio is required to increase its output power to compensate for a failed radio within its coverage area.[2.4GHz|5GHz] Selects the band• 2.4GHz – Selects the 2.4 GHz band• 5GHz – Selects the 5.0 GHz band<-85--55> Specify the threshold value• <-85--55> – Sets the power threshold from -85 dBm - -55 dBm. The default is -70 dBm for both the 2.4 GHz and 5.0 GHz bands.no Disables recovery from faulty neighbor radios](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-738.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 1919.1.11 nosmart-rf-policyNegates a command or sets its default. When used in the config Smart RF policy mode, the no command disables or resets Smart RF settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [area|assignable-power|avoidance-time|channel-list|channel-width|coverage-hole-recovery|enable|group-by|interference-recovery|neighbor-recovery|smart-ocs-monitoring]no area <AREA-NAME> channel-list [2.4GHZ|5GHZ]no assignable-power [2.4GHZ|5GHZ] [max|min]no [channel-list|channel-width] [2.4GHZ|5GHZ]no coverage-hole-recovery [client-threshold|coverage-interval|interval|snr-threshold] [2.4GHZ|5GHZ]no avoidance-time [adaptivity|dfs]no enableno group-by [area|floor]no interference-recovery {channel-hold-time|channel-switch-delta [2.4GHZ|5GHZ]|client-threshold|interference|neighbor-offset|noise|noise-factor}no neighbor-recovery {dynamic-sampling {retries|threshold}|power-hold-time|power-threshold [2.4GHZ|5GHZ]}no smart-rf-monitoring {awareness-override [schedule <1-3>|threshold]|client-aware [2.4GHZ|5GHZ]|extended-scan-frequency [2.4GHZ|5GHZ]|frequency [2.4GHZ|5GHZ]|off-channel-duration [2.4GHZ|5GHZ]|power-save-aware [2.4GHZ|5GHZ]|sample-count [2.4GHZ|5GHZ]|voice-aware [2.4GHZ|5GHZ]}Parameters• no <PARAMETERS>no <PARAMETERS> Negates a command or sets its default. When used in the config Smart RF policy mode, the no command disables or resets the Smart RF policy settings.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-739.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 2119.1.12 sensitivitysmart-rf-policyConfigures Smart RF sensitivity level. The sensitivity level determines Smart RF scanning and sampling aggressiveness. For example, a low sensitivity level indicates a less aggressive Smart-RF policy. This translates to fewer samples taken during off-channel scanning and short off-channel durations. When the sensitivity level is set to high, Smart-RF collects more samples, and remains off-channel longer.The Smart RF sensitivity level options include low, medium, high, and custom. Medium, is the default setting. The custom option allows an administrator to adjust the parameters and thresholds for interference recovery, coverage hole recovery, and neighbor recovery. However, the low, medium, and high settings still allow utilization of these features.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsensitivity [custom|high|low|medium]Parameters• sensitivity [custom|high|low|medium]Usage GuidelinesTo enable the power and channel setting parameters, set sensitivity to custom or medium.To enable the monitoring and scanning parameters, set sensitivity to custom.To enable the neighbor recovery, interference and coverage hole recovery parameters, set sensitivity to custom.sensitivity Configures Smart RF sensitivity levels. The options available are: custom, high, low, and medium.custom Enables custom interference recovery, coverage hole recovery, and neighbor recovery as additional Smart RF optionshigh High sensitivitylow Low sensitivitymedium Medium sensitivity. This is the default setting.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-741.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 2319.1.13 smart-ocs-monitoringsmart-rf-policyApplies smart Off Channel Scanning (OCS) instead of dedicated detectorsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsmart-ocs-monitoring {awareness-override|client-aware|extended-scan-frequency|frequency|off-channel-duration|power-save-aware|sample-count|tx-load-aware|voice-aware}smart-ocs-monitoring {awareness-override [schedule|threshold]}smart-ocs-monitoring {awareness-override schedule <1-3> <START-TIME> <END-TIME> <DAY>}smart-ocs-monitoring {awareness-override threshold <10-10000>}smart-ocs-monitoring {client-aware [2.4GHz|5GHz] <1-255>}smart-ocs-monitoring {extended-scan-frequency [2.4GHz|5GHz] <0-50>}smart-ocs-monitoring {frequency [2.4GHz|5GHz] <1-120>}smart-ocs-monitoring {off-channel-duration [2.4GHz|5GHz] <20-150>}smart-ocs-monitoring {power-save-aware [2.4GHz|5GHz] [disable|dynamic|strict]}smart-ocs-monitoring {sample-count [2.4GHz|5GHz] <1-15>}smart-ocs-monitoring {tx-load-aware [2.4GHz|5GHz] <1-100>}smart-ocs-monitoring {voice-aware [2.4GHz|5GHz] [disable|dynamic|strict]}Parameters• smart-ocs-monitoring {awareness-override schedule <1-3> <START-TIME> <END-TIME> <DAY>}awareness-override Optional. Use this parameter to configure client awareness settings overridesschedule <1-3> <START-TIME> <END-TIME> {<DAY>}Configures a time and day schedule when awareness settings are overridden• <1-3> – Sets the awareness override schedule index. A maximum of three overrides can be configured.• <START-TIME> – Sets the override start time in HH:MM format• <END-TIME> – Sets the override end time in HH:MM format• DAY – Optional. Set the day when the override is active. Use one of the follow-ing formats:• all – Override is active on all days• sun – Override is active only on Sundays• mon – Override is active only on MondaysContd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-743.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 24• smart-ocs-monitoring {awareness-override threshold <10-10000>}• smart-ocs-monitoring {client-aware [2.4GHz|5GHz] <1-255>}• smart-ocs-monitoring {extended-scan-frequency [2.4GHz|5GHz] <0-50>}• smart-ocs-monitoring {frequency [2.4GHz|5GHz] <1-120>}• tue – Override is active only on Tuesdays• wed – Override is active only on Wednesdays• thu – Override is active only on Thursdays• fri – Override is active only on Fridays• sat – Override is active only on Saturdaysawareness-override threshold <10-10000>Optional. Use this parameter to configure client awareness settings overrides• threshold – Specifies the threshold after which client awareness settings are overridden. When the specified threshold is reached, awareness settings are overridden.• <10-10000> – Specify a threshold value from 10 -10000. The default is 10.client-aware Optional. Enables client aware scanning on this Smart RF policyUse this parameter to configure a client threshold number. When the number of clients connected to a radio equals this threshold number, the radio avoids channel scanning.This feature is disabled by default.2.4GHz <1-255> Enables client aware scanning on the 2.4 GHz bandAvoids radio scanning when a specified minimum number of clients are present• <1-255> – Sets the minimum number of clients from 1 - 255. The default is 1 client.5GHz <1-255> Enables client aware scanning on the 5.0 GHz bandAvoids radio scanning when a specified minimum number of clients are present• <1-255> – Sets the minimum number of clients from 1 - 255. The default is 1 client.extended-scan-frequencyOptional. Enables an extended scan, as opposed to a neighbor only scan, on this Smart RF policy. This is the frequency radios use to scan for non-peer radios.2.4GHz <0-50> Enables extended scan on the 2.4 GHz band• <0-50> – Sets the number of trails from 0 - 50. The default is 5.5GHz <0-50> Enables extended scan on the 5.0 GHz band• <0-50> – Sets the number of trails from 0 - 50. The default is 5.frequency Optional. Specifies the scan frequency. This is the frequency, in seconds, in which smart-ocs-monitoring changes channels for an off channel scan.2.4GHz <1-120> Selects the 2.4 GHz band• <1-120> – Sets a scan frequency from 1 - 120 sec. The default is 6 seconds.5GHz <1-120> Selects the 5.0 GHz band• <1-120> – Sets a scan frequency from 1 - 120 sec. The default is 6 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-744.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 25• smart-ocs-monitoring {off-channel-duration [2.4GHz|5GHz] <20-150>}• smart-ocs-monitoring {power-save-aware [2.4GHz|5GHz] [disable|dynamic|strict]}• smart-ocs-monitoring {sample-count [2.4GHz|5GHz] <1-15>}• smart-ocs-monitoring {tx-load-aware [2.4GHz|5GHz] <1-100>}off-channel-duration Optional. Specifies the duration to scan off channelThis is the duration access point radios use to monitor devices within the network and, if necessary, perform self healing and neighbor recovery to compensate for coverage area losses within a RF Domain.2.4GHz <20-150> Selects the 2.4 GHz band (in milliseconds)• <20-150> – Sets the off channel duration from 20 - 150 msec. The default is 50 milliseconds.5GHz <20-150> Selects the 5.0 GHz band (in milliseconds)• <20-150> – Sets the off channel duration from 20 - 150 msec. The default is 50 milliseconds.power-save-aware Optional. Enables power save awareness scanning mode on this Smart RF policy. The options are: disable, dynamic, and strict.This setting allows Smart RF to detect power save clients and take them into consideration when performing off channel scans.Strict disables smart monitoring as long as a power save capable client is associated to a radio. Dynamic disables smart monitoring as long as there is data buffered for a power save client at the radio.2.4GHz [disable|dynamic|strict]Sets power save awareness scanning mode on the 2.4 GHz band• disable – Disables power save awareness scanning• dynamic – Dynamically avoids scanning based on traffic for power save (PSP) clients• strict – Strictly avoids scanning when PSP clients are presentThe default is dynamic.5GHz [disable|dynamic|strict]Sets power save awareness scanning mode on the 5.0 GHz band• disable – Disables power save awareness scanning• dynamic – Dynamically avoids scanning based on traffic for PSP clients• strict – Strictly avoids scanning when PSP clients are presentThe default is dynamic.sample-count Optional. Specifies the number of samples to collect before reporting an issue to the Smart RF master2.4GHz <1-15> Selects the 2.4 GHz band• <1-15> – Specifies the number of samples to collect from 1 - 15. The default is 10.5GHz <1-15> Selects the 5.0 GHz band• <1-15> – Specifies the number of samples to collect from 1 - 15. The default is 5.tx-load-aware Optional. Specifies a transmit load percentage that serves as a threshold before scanning is avoided for an access point’s 2.4 GHz or 5.0 GHz band. This option is disabled for both 2.4 GHz and 5.0 GHz bands.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-745.png)
![SMART-RF-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 19 - 26• smart-ocs-monitoring {voice-aware [2.4GHz|5GHz] [disable|dynamic|strict]}Examplerfs6000-37FABE(config-smart-rf-policy-test)#smart-ocs-monitoring extended-scan-frequency 2.4GHz 9rfs6000-37FABE(config-smart-rf-policy-test)#smart-ocs-monitoring sample-count 2.4GHz 3rfs6000-37FABE(config-smart-rf-policy-test)#show contextsmart-rf-policy test area test channel-list 2.4GHz 1,2,3 group-by floor sensitivity custom channel-list 2.4GHz 1,12 channel-width 5GHz auto smart-ocs-monitoring off-channel-duration 2.4GHz 25 smart-ocs-monitoring frequency 5GHz 3 smart-ocs-monitoring frequency 2.4GHz 3 smart-ocs-monitoring sample-count 5GHz 3 smart-ocs-monitoring sample-count 2.4GHz 3 smart-ocs-monitoring extended-scan-frequency 5GHz 0 smart-ocs-monitoring extended-scan-frequency 2.4GHz 9 root-recovery root-path-metric-threshold 800--More--rfs6000-37FABE(config-smart-rf-policy-test)#Related Commands2.4GHz <1-100> Selects the 2.4 GHz band• <1-100> – Specify a transmit load percentage from 1 - 100%. When enabled, the default is 1%.5GHz <1-100> Selects the 5.0 GHz band• <1-100> – Specify a transmit load percentage from 1 - 100%. When enabled, the default is 1%.voice-aware Optional. Enables voice awareness scanning mode on this Smart RF policy. The options are: disable, dynamic, and strict.Strict disables smart monitoring as long as a voice client is associated to a radio. Dynamic disables smart monitoring as long as there is data buffered for a voice client at the radio.2.4GHz [disable|dynamic|strict]Specifies the scanning mode on the 2.4 GHz band• disable – Disables voice awareness scanning• dynamic – Dynamically avoids scanning based on traffic for voice clients• strict – Strictly avoids scanning when voice clients are presentNote: The default is dynamic.5GHz [disable|dynamic|strict]Specifies the scanning mode on the 5.0 GHz band• disable – Disables voice awareness scanning• dynamic – Dynamically avoids scanning based on traffic for voice clients• strict – Strictly avoids scanning when voice clients are present.Note: The default is dynamic.no Disables off channel monitoring](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-746.png)




![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 520.1.1 ap-detectionwips-policyEnables the detection of unauthorized or unsanctioned APs. Unauthorized APs are untrusted access points connected to an access point managed network. These untrusted APs accept wireless client associations. It is important to detect such rogue APs and declare them unauthorized. Rogue AP detection is disabled by default.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxap-detection {ageout|air-termination|interferer-threshold|recurring-event-interval|wait-time}ap-detection {ageout <30-86400>|interferer-threshold <-100--10>|recurring-event-interval <0-10000>|wait-time <10-600>}ap-detection air-termination {allow-channel-switch|mode [auto|manual]}Parameters• ap-detection {ageout <30-86400>|interferer-threshold <-100--10>|recurring-event-interval <0-10000>|wait-time <10-600>}ap-detection Enables detection of unauthorized or unsanctioned APsageout <30-86400>Optional. Configures the unauthorized AP ageout interval. The WIPS policy uses this value to ageout unauthorized APs.• <30-86400> – Sets an ageout interval from 30 - 86400 seconds. The default is 5 minutes (300 seconds).recurring-event-interval <0-10000>Configures recurring event interval help of unauthorized APs• <0-10000> – Configures the recurring interval between 0 - 10000 seconds. The default is 300 seconds.interferer-threshold <-100--10>Configures RSSI threshold value to determine if an unsanctioned ap is an interferer or not• <-100--10> – Configures the rssi threshold between -100 - -10 dBm. The default is -75 dBm.wait-time <10-600>Optional. Configures the wait time before a detected AP is declared as unauthorized and potentially removed• <10-600> – Sets a wait time from 10 - 600 seconds. The default is 1 minute (60 seconds).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-751.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 6• ap-detection air-termination {allow-channel-switch|mode [auto|manual]}Examplerfs6000-37FABE(config-wips-policy-test)#ap-detection wait-time 15rfs6000-37FABE(config-wips-policy-test)#ap-detection age-out 50rfs6000-37FABE(config-wips-policy-test)#show contextwips-policy test ap-detection-age-out 50 ap-detection-wait-time 15rfs6000-37FABE(config-wips-policy-test)#nx9500-6C8809(config-wips-policy-test)#ap-detection recurring-event-interval 10nx9500-6C8809(config-wips-policy-test)#show contextwips-policy test ap-detection recurring-event-interval 10nx9500-6C8809(config-wips-policy-test)#Related Commandsap-detection Enables detection of unauthorized or unsanctioned APsair-termination {allow-channel-switch|mode [auto|manual]}Enables air termination of unauthorized APs. This option is disabled by default.• allow-channel-switch – Optional. Allows channel switch of unauthorized APs based on the channel mode. This option is disabled by default.• mode [auto|manual] – Optional. Select the mode as auto or manual to configure. The default setting is manual.no Resets unauthorized or unsanctioned AP detection settings to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-752.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 820.1.3 eventwips-policyConfigures events, filters and threshold values for this WIPS policy. Events are grouped into three categories, AP anomaly, client anomaly, and excessive. WLANs are baselined for matching criteria. Any deviation from this baseline is considered an anomaly and logged as an event.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxevent [ap-anomaly|client-anomaly|enable-all-events|excessive]event ap-anomaly [ad-hoc-violation|airjack|ap-ssid-broadcast-in-beacon|asleap|impersonation-attack|null-probe-response|transmitting-device-using-invalid-mac|unencrypted-wired-leakage|wireless-bridge]event client-anomaly [dos-broadcast-deauth|fuzzing-all-zero-macs|fuzzing-invalid-frame-type|fuzzing-invalid-mgmt-frames|fuzzing-invalid-seq-num|identical-src-and-dest-addr|invalid-8021x-frames|netstumbler-generic|non-conforming-data|wellenreiter] {filter-ageout <0-86400>}event enable-all-eventsevent excessive [80211-replay-check-failure|aggressive-scanning|auth-server-failures|decryption-failures|dos-assoc-or-auth-flood|dos-eapol-start-storm|dos-unicast-deauth-or-disassoc|eap-flood|eap-nak-flood|frames-from-unassoc-station] {filter-ageout <0-86400>|threshold-client <0-65535>|threshold-radio <0-65535>}Parameters• event ap-anomaly [ad-hoc-violation|airjack|ap-ssid-broadcast-in-beacon|asleap|impersonation-attack|null-probe-response|transmitting-device-using-invalid-mac|unencrypted-wired-leakage|wireless-bridge]NOTE: By default all event monitoring is disabled.ap-anomaly Enables AP anomaly event trackingAn AP anomaly event refers to suspicious frames sent by neighboring APs. An administrator enables the filtering of each listed event and sets the thresholds for the generation of event notification and filtering.ad-hoc-violation Tracks ad-hoc network violationsairjack Tracks AirJack attacksap-ssid-broadcast-in-beaconTracks AP SSID broadcasts in beacon eventsasleap Tracks ASLEAP attacks. These attacks break Lightweight Extensible Authentication Protocol (LEAP) passwordsimpersonation-attack Tracks impersonation attacks. These are also referred to as spoofing attacks, where the attacker assumes the address of an authorized device.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-754.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 9• event client-anomaly [dos-broadcast-deauth|fuzzing-all-zero-macs|fuzzing-invalid-frame-type|fuzzing-invalid-mgmt-frames|fuzzing-invalid-seq-num|identical-src-and-dest-addr|invalid-8021x-frames|netstumbler-generic|non-conforming-data|wellenreiter] {filter-ageout <0-86400>}• event enable-all-eventsnull-probe-response Tracks null probe response attackstransmitting-device-using-invalid-macTracks the transmitting device using an invalid MAC attacksunencrypted-wired-leakageTracks unencrypted wired leakagewireless-bridge Tracks wireless bridge (WDS) framesclient-anomaly Enables client anomaly event trackingThese are suspicious events performed by wireless clients compromising the security of the network. An administrator can enable or disable filtering of each listed event and set the thresholds required for the generation of the event notification and filtering action applied.dos-broadcast-deauth Tracks DoS broadcast deauthentication eventsfuzzing-all-zero-macs Tracks Fuzzing: All zero MAC addresses observedfuzzing-invalid-frame-typeTracks Fuzzing: Invalid frame type detectedfuzzing-invalid-mgmt-framesTracks Fuzzing: Invalid management frame detectedfuzzing-invalid-seq-num Tracks Fuzzing: Invalid sequence number detectedidentical-src-and-dest-addrTracks identical source and destination addresses detectioninvalid-8021x-frames Tracks Fuzzing: Invalid 802.1x frames detectednetstumbler-generic Tracks Netstumbler (v3.2.0, 3.2.3, 3.3.0) eventsnon-conforming-data Tracks non conforming data packetswellenreiter Tracks Wellenreiter eventsfilter-ageout <0-86400> The following keywords are common to all of the above client anomaly events:• filter-ageout <0-86400> – Optional. Configures the filter expiration interval in seconds• <0-86400> – Sets the filter ageout interval from 0 - 86400 seconds. The defaultis 0 seconds.Note: For each violation define a filter time in seconds, which determines how long the packets (received from an attacking device) are ignored once a violation has been triggered. Ignoring frames from an attacking device minimizes the effectiveness of the attack and the impact to the site until permanent mitigation can be performed.The filter ageout value is applicable across the entire RF Domain using this WIPS policy. If an MU is detected performing an attack and is filtered by one of the APs, the information is passed on to all APs and controllers within the RF Domain through the domain manager. Consequently the MU is filtered, for the specified period of time, across all devices.enable-all-events Enables tracking of all intrusion events (client anomaly and excessive events)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-755.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 10• event excessive [80211-replay-check-failure|aggressive-scanning|auth-server-failures|decryption-failures|dos-assoc-or-auth-flood|dos-eapol-start-storm|dos-unicast-deauth-or-disassoc|eap-flood|eap-nak-flood|frames-from-unassoc-station] {filter-ageout [<0-86400>]|threshold-client [<0-5535>]|threshold-radio <0-65535>}excessive Enables the tracking of excessive events. Excessive events are actions performed continuously and repetitively. These events can impact the performance of the controller managed network. DoS attacks come under this category.80211-replay-check-failureTracks 802.11replay check failureaggressive-scanning Tracks aggressive scanning eventsauth-server-failures Tracks failures reported by authentication serversdecryption-failures Tracks decryption failuresdos-assoc-or-auth-flood Tracks DoS association or authentication floodsdos-eapol-start-storm Tracks DoS EAPOL start stormsdos-unicast-deauth-or-disassocTracks DoS dissociation or deauthentication floodseap-flood Tracks EAP floodseap-nak-flood Tracks EAP NAK floodsframes-from-unassoc-stationTracks frames from unassociated clientsfilter-ageout <0-86400> The following keywords are common to all excessive events:• filter-ageout <0-86400> – Optional. Configures a filter expiration interval in seconds. It sets the duration for which the client is filtered. The client is added to a ACL as a special entry and frames received from this client are dropped.• <0-86400> – Sets a filter ageout interval from 0 - 86400 seconds. The default is 0 seconds.Note: This value is applicable across the RF Domain. If a client is detected performing an attack and is filtered by one of the APs, the information is passed to the domain controller. The domain controller then propagates this information to all APs and wireless controllers in the RF Domain.threshold-client <0-65535>The following keywords are common to all excessive events:• threshold-client <0-65535> – Optional. Configures a client threshold value after which the filter is triggered and an event is recorded• <0-65535> – Sets a wireless client threshold value from 0 - 65535 secondsthreshold-radio <0-65535>The following keywords are common to all excessive events:• threshold-radio <0-65535> – Optional. Configures a radio threshold value after which the filter is triggered and an event is recorded• <0-65535> – Sets a radio threshold value from 0 - 65535 seconds](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-756.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 1320.1.5 interference-eventwips-policySpecifies events contributing to the Smart RF WiFi interference calculationsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxinterference-event [non-conforming-data|wireless-bridge]Parameters• interference-event [non-conforming-data|wireless-bridge]Examplerfs6000-37FABE(config-wips-policy-test)#interference-event non-conforming-datarfs6000-37FABE(config-wips-policy-test)#show contextwips-policy test history-throttle-duration 77 event excessive 80211-replay-check-failure threshold-client 10 threshold-radio 99 filter-ageout 9 event client-anomaly wellenreiter filter-ageout 99 interference-event non-conforming-data ap-detection-ageout 50 ap-detection-wait-time 15rfs6000-37FABE(config-wips-policy-test)#Related Commandsnon-conforming-data Considers non conforming data packets when calculating Smart RF interferencewireless-bridge Considers Wireless Bridge (WDS) frames when calculating Smart RF interferenceno Disables this WIPS policy signature as a Smart RF interference source](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-759.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 1420.1.6 nowips-policyNegates a command or resets configured settings to their default. When used in the config WIPS policy mode, the no command negates or resets filters and thresholds.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [ap-detection|enable|event|history-throttle-duration|interference-event|signature|use]no [enable|history-throttle-duration]no ap-detection {ageout {<LINE-SINK>}|air-termination|interferer-threshold <-100--10>|recurring-event-interval <0-10000>wait-time {<LINE-SINK>}} no event [ap-anomaly|client-anomaly|enable-all-events|excessive]no event ap-anomaly [ad-hoc-violation|airjack|ap-ssid-broadcast-in-beacon|asleap|impersonation-attack|null-porbe-response|transmitting-device-using-invalid-mac|unencrypted-wired-leakage|wireless-bridge]no event client-anomaly [dos-broadcast-deauth|fuzzing-all-zero-macs|fuzzing-invalid-frame-type|fuzzing-invalid-mgmt-frames|fuzzing-invalid-seq-num|identical-src-and-dest-addr|invalid-8021x-frames|netstumbler-generic|non-conforming-data|wellenreiter] {filter-ageout <0-86400>}no event excessive [80211-replay-check-failure|aggressive-scanning|auth-server-failures|decryption-failures|dos-assoc-or-auth-flood|dos-eapol-start-storm|dos-unicast-deauth-or-disassoc|eap-flood|eap-nak-flood|frames-from-unassoc-station] {filter-ageout <0-86400>|threshold-client <0-65535>|threshold-radio <0-65535>}no interference-event [non-conforming-data|wireless-bridge]no signature <WIPS-SIGNATURE>no use device-categorizationParameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.no <PARAMETERS> Negates a command or resets configured settings to their default. When used in the config WIPS policy mode, the no command negates or resets filters and thresholds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-760.png)





![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 2320.1.7.2.4 frame-typesignature mode commandsConfigures the frame type used for matching with this WIPS policy signatureSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxframe-type [all|assoc|auth|beacon|data|deauth|disassoc|mgmt|probe-req|probe-resp|reassoc]Parameters• frame-type [all|assoc|auth|beacon|data|deauth|disassoc|mgmt|probe-req|probe-resp|reassoc]Usage GuidelinesThe frame type configured determines the SSID match type configured. To configure the SSID match type as SSID, the frame type must be beacon, probe-req or probe-resp.Examplerfs6000-37FABE(config-test-signature-test)#frame-type reassocrfs6000-37FABE(config-test-signature-test)#show context signature test bssid 11-22-33-44-55-66 dst-mac 55-66-77-88-99-00 frame-type reassoc filter-ageout 8rfs6000-37FABE(config-test-signature-test)#Related Commandsframe-type Configures the frame type used for matchingall Configures all frame type matchingassoc Configures association frame matchingauth Configures authentication frame matchingbeacon Configures beacon frame matchingdata Configures data frame matchingdeauth Configures deauthentication frame matchingdisassoc Configures disassociation frame matchingmgmt Configures management frame matchingprobe-req Configures probe request frame matchingprobe-resp Configures probe response frame matchingreassoc Configures re-association frame matchingno Resets a WIPS signature frame type](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-769.png)


![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 2820.1.7.2.9 ssid-matchsignature mode commandsConfigures the SSID (and its character length) used for matchingSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxssid-match [ssid|ssid-len]ssid-match [ssid <SSID>|ssid-len <0-32>]Parameters• ssid-match [ssid <SSID>|ssid-len <0-32>]Examplerfs6000-37FABE(config-test-signature-test)#ssid-match ssid PrinterLanrfs6000-37FABE(config-test-signature-test)#show context signature test bssid 11-22-33-44-55-66 src-mac 00-1E-E5-EA-1D-60 dst-mac 55-66-77-88-99-00 frame-type beacon ssid-match ssid PrinterLan filter-ageout 8 payload 1 pattern test offset 1rfs6000-37FABE(config-test-signature-test)#Related Commandsssid <SSID> Specifies the SSID match string• <SSID> – Specify the SSID string.Note: Specify the correct SSID to ensure proper filtering.ssid-len <0-32> Specifies the length of the SSID• <0-32> – Specify the SSID length from 0 - 32 characters.no Removes the configured SSID](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-774.png)
![WIPS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 20 - 3120.1.7.2.12 nosignature mode commandsNegates a command or resets settings to their default. When used in the config WIPS policy signature mode, the no command resets or removes WIPS signature settings.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [bssid|dst-mac|filter-ageout|frame-type|interference-event|mode|payload|src-mac|ssid-match|threshold-client|threshold-radio]no [bssid|dts-mac|filter-ageout|frame-type|interference-event|mode enable|payload <1-3>|src-mac|ssid-match [ssid|ssid-len]|threshold-client|threshold-radio]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.ExampleThe following is the WIPS signature ‘test’ settings before the execution of the ‘no’ command:rfs6000-37FABE(config-test-signature-test)#show context signature test bssid 11-22-33-44-55-66 src-mac 00-1E-E5-EA-1D-60 dst-mac 55-66-77-88-99-00 frame-type beacon ssid-match ssid PrinterLan filter-ageout 8 threshold-client 88 threshold-radio 88 payload 1 pattern test offset 1rfs6000-37FABE(config-test-signature-test)#no <PARAMETERS> Negates a command or resets settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-777.png)

![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 321.1.1 accelerated-multicastwlan-qos-policyConfigures the accelerated multicast stream address and forwarding QoS classification settingsEnabling this option allows the system to automatically detect and convert multicast streams to unicast streams. When a stream is converted and queued up for transmission, there are a number of classification mechanisms that can be applied to the stream. Use the classification options to specify the traffic type to prioritize.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccelerated-multicast [<IP>|autodetect]accelerated-multicast [<IP>|autodetect] {classification [background|best-effort|trust|video|voice]}Parameters• accelerated-multicast [<IP>|autodetect] {classification [background|best-effort|trust|video|voice]}accelerated-multicast Configures the accelerated multicast stream address and forwarding QoS classification<IP> Configures a multicast IP address in the A.B.C.D format. The system can configure up to 32 IP addresses for each WLAN QoS policyautodetect Allows the system to automatically detect multicast streams to be accelerated. This parameter allows the system to convert multicast streams to unicast, or to specify multicast streams converted to unicast.classification Optional. Configures the QoS classification (traffic class) settings. When the stream is converted and queued for transmission, specify the type of classification applied to the stream. The options are: background, best-effort, trust, voice, and video.background Forwards streams with background (low) priority. This parameter is common to both <IP> and auto detect.best-effort Forwards streams with best effort (normal) priority. This parameter is common to both <IP> and autodetect.trust No change to the streams forwarding traffic class. This parameter is common to both <IP> and autodetect.video Forwards streams with video traffic priority. This parameter is common to both <IP> and autodetect.voice Forwards streams with voice traffic priority. This parameter is common to both <IP> and autodetect.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-782.png)

![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 521.1.2 classificationwlan-qos-policySpecifies how traffic on this WLAN is classified. This classification is based on relative prioritization on the radio.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxclassification [low|non-unicast|non-wmm|normal|video|voice|wmm]classification [low|normal|video|voice|wmm]classification non-unicast [voice|video|normal|low|default]classification non-wmm [voice|video|normal|low]Parameters• classification [low|normal|video|voice|wmm]• classification non-unicast [voice|video|normal|low|default]low Optimized for background traffic. Implies all traffic on this WLAN is low priority on the radionormal Optimized for best effort traffic. Implies all traffic on this WLAN is prioritized as best effort traffic on the radiovideo Optimized for video traffic. Implies all traffic on this WLAN is prioritized as video traffic on the radiovoice Optimized for voice traffic. Implies all traffic on this WLAN is prioritized as voice traffic on the radiowmm Uses WMM based classification, using DSCP or 802.1p tags, to classify traffic into different queuesImplies WiFi Multimedia QoS extensions are enabled on this radio. This allows different traffic streams between the wireless client and the access point to be prioritized according to the type of traffic (voice, video etc). The WMM classification supports high throughput data rates required for 802.11n device support. This is the default setting.non-unicast Optimized for non-unicast traffic. Implies all traffic on this WLAN is designed for broadcast or multiple destinationsvideo Optimized for non-unicast video traffic. Implies all WLAN non-unicast traffic is classified and treated as video packetsvoice Optimized for non-unicast voice traffic. Implies all WLAN non-unicast traffic is classified and treated as voice packetsnormal Optimized for non-unicast best effort traffic. Implies all WLAN non-unicast traffic is classified and treated as normal priority packets (best effort).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-784.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 6• classification non-wmm [voice|video|normal|low]Examplerfs6000-37FABE(config-wlan-qos-test)#classification wmmrfs6000-37FABE(config-wlan-qos-test)#classification non-wmm videorfs6000-37FABE(config-wlan-qos-test)#classification non-unicast normalrfs6000-37FABE(config-wlan-qos-test)#show contextwlan-qos-policy test classification non-wmm video classification non-unicast normal qos trust dscp qos trust wmm accelerated-multicast autodetect classification voicerfs6000-37FABE(config-wlan-qos-test)#low Optimized for non-unicast background traffic. Implies all WLAN non-unicast traffic is classified and treated as low priority packets (background)default Uses the default classification mode (same as unicast classification if WMM is disabled, normal if unicast classification is WMM). This is the default setting.non-wmm Specifies how traffic from non-WMM clients is classifiedvoice Optimized for non-WMM voice traffic. Implies all WLAN non-WMM client traffic is classified and treated as voice packetsvideo Optimized for non-WMM video traffic. Implies all WLAN non-WMM client traffic is classified and treated as video packetsnormal Optimized for non-WMM best effort traffic. Implies all WLAN non-WMM client traffic is classified and treated as normal priority packets (best effort). This is the default setting.low Optimized for non-WMM background traffic. Implies all WLAN non-WMM client traffic is classified and treated as low priority packets (background)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-785.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 721.1.3 multicast-maskwlan-qos-policyConfigures an egress prioritization multicast mask for this WLAN QoS policyNormally all multicast and broadcast packets are buffered until the periodic DTIM interval (indicated in the 802.11 beacon frame), when clients in power save mode wake to check for frames. However, for certain applications and traffic types, the administrator may want the frames transmitted immediately, without waiting for the DTIM interval. By configuring a primary or secondary prioritization multicast mask, the network administrator can indicate which packets are transmitted immediately.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmulticast-mask [primary|secondary] <MAC/MASK>Parameters• multicast-mask [primary|secondary] <MAC/MASK>Examplerfs6000-37FABE(config-wlan-qos-test)#multicast-mask primary 11-22-33-44-55-66/22-33-44-55-66-77rfs6000-37FABE(config-wlan-qos-test)#show contextwlan-qos-policy test classification non-wmm video multicast-mask primary 11-22-33-44-55-66/22-33-44-55-66-77 classification non-unicast normal qos trust dscp qos trust wmm accelerated-multicast autodetect classification voicerfs6000-37FABE(config-wlan-qos-test)#primary <MAC/MASK> Configures the primary egress prioritization multicast mask• <MAC/MASK> – Provide the MAC address and the mask in the AA-BB-CC-DD-EE-FF /XX-XX-XX-XX-XX-XX-XX format. The default value is 00-00-00-00-00-00/FF-FF-FF-FF-FF-FF.Note: Setting masks is optional and only needed if there are traffic types requiring special handling.secondary <MAC/MASK>Configures the secondary egress prioritization multicast mask• <MAC/MASK> – Provide the MAC address and the mask in the AA-BB-CC-DD-EE-FF /XX-XX-XX-XX-XX-XX-XX format. The default value is 00-00-00-00-00-00/FF-FF-FF-FF-FF-FF.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-786.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 821.1.4 nowlan-qos-policyNegates a command or resets settings to their defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [accelerated-multicast|classification|multicast-mask|qos|rate-limit|svp-prioritization|voice-prioritization|wmm]no [accelerated-multicast [<IP>|autodetect]|classification {non-unicast|non-wmm}|multicast-mask [primary|secondary]|qos trust [dscp|wmm]|svp-prioritization|voice-prioritization]no rate-limit [client|wlan] [from-air|to-air] {max-burst-size|rate|red-threshold}no rate-limit [client|wlan] [from-air|to-air] {max-burst-size|rate|red-threshold [background|best-effort|video|voice]}no wmm [background|best-effort|power-save|qbss-load-element|video|voice]no wmm [power-save|qbss-load-element]no wmm [backgorund|best-effort|video|voice] [aifsn|cw-max|cw-min|txop-limit]Parameters• no <PARAMETERS>ExampleThe following example shows the WLAN QoS Policy ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-wlan-qos-test)#show contextwlan-qos-policy test classification non-wmm video multicast-mask primary 11-22-33-44-55-66/22-33-44-55-66-77 classification non-unicast normal qos trust dscp qos trust wmm accelerated-multicast autodetect classification voicerfs6000-37FABE(config-wlan-qos-test)#rfs6000-37FABE(config-wlan-qos-test)#no classification non-wmmrfs6000-37FABE(config-wlan-qos-test)#no multicast-mask primaryrfs6000-37FABE(config-wlan-qos-test)#no qos trust dscpThe following example shows the WLAN QoS Policy ‘test’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-wlan-qos-test)#show contextwlan-qos-policy test classification non-unicast normal no qos trust dscp qos trust wmm accelerated-multicast autodetect classification voicerfs6000-37FABE(config-wlan-qos-test)#no <PARAMETERS> Negates a command or resets settings to their default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-787.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 921.1.5 qoswlan-qos-policyEnables QoS on this WLANSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxqos trust [dscp|wmm]Parameters• qos trust [dscp|wmm]Examplerfs6000-37FABE(config-wlan-qos-test)#qos trust wmmrfs6000-37FABE(config-wlan-qos-test)#qos trust dscprfs6000-37FABE(config-wlan-qos-test)#show contextwlan-qos-policy test classification non-unicast normal qos trust dscp qos trust wmm accelerated-multicast autodetect classification voicerfs6000-37FABE(config-wlan-qos-test)#trust [dscp|wmm] Trusts the QoS values of ingressing packets. Both these options are enabled by default.• dscp – Trusts the IP DSCP values of ingressing packets• wmm – Trusts the 802.11 WMM QoS values of ingressing packets](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-788.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 1021.1.6 rate-limitwlan-qos-policyConfigures the WLAN traffic rate limits using the WLAN QoS policyExcessive traffic causes performance issues or brings down the network entirely. Excessive traffic can be caused by numerous sources including network loops, faulty devices or malicious software such as a worm or virus that has infected one or more devices at the branch. Rate limiting limits the maximum rate sent to or received from the wireless network (and WLAN) per wireless client. It prevents any single user from overwhelming the wireless network. It can also provide differential service for service providers. The uplink and downlink rate limits are usually configured on a RADIUS server using vendor specific attributes. Rate limits are extracted from the RADIUS server’s response. When such attributes are not present, settings defined on the controller (access point, wireless controller, or service platform) are applied. An administrator can set separate QoS rate limits for upstream (data transmitted from the managed network) and downstream (data transmitted to the managed network).Before defining rate limit thresholds for WLAN upstream and downstream traffic, it is recommended that you define the normal number of ARP, broadcast, multicast and unknown unicast packets that typically transmit and receive from each supported WMM access category. If thresholds are defined too low, normal network traffic (required by end-user devices) are dropped resulting in intermittent outages and performance problems.Connected wireless clients can also have QoS rate limit settings defined in both the upstream and downstream direction.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrate-limit [client|wlan] [from-air|to-air] {max-burst-size|rate|red-threshold}rate-limit [client|wlan] [from-air|to-air] {max-burst-size <2-1024>|rate <50-1000000>}rate-limit [client|wlan] [from-air|to-air] {red-threshold [background <0-100>|best-effort <0-100>|video <0-100>|voice <0-100>]}Parameters• rate-limit [client|wlan] [from-air|to-air] {max-burst-size <2-1024>|rate <50-1000000>}rate-limit Configures traffic rate limit parametersclient Configures traffic rate limiting parameters on a per-client basiswlan Configures traffic rate limiting parameters on a per-WLAN basisfrom-air Configures traffic rate limiting from a wireless client to the networkto-air Configures the traffic rate limit from the network to a wireless client](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-789.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 11• rate-limit [client|wlan] [from-air|to-air] {red-threshold [background <0-100>|best-effort <0-100>|video <0-100>|voice <0-100>]}max-burst-size <2-1024>Optional. Sets the maximum burst size from 2 - 1024 kbytes. The chances of the upstream or downstream packet transmission getting congested for the WLAN’s client destination are reduced for smaller burst sizes. The default values are:- WLAN ‘to-air’ and ‘from-air’: 320 kbytes- Client ‘to-air’ and ‘from-air’: 64 kbytesSmaller the burst, lesser are the chances of upstream packet transmission resulting in congestion for the WLAN’s client destinations. By trending the typical number of ARP, broadcast, multicast and unknown unicast packets over a period of time, the average rate for each access category can be obtained. Once a baseline is obtained, administrators should then add a 10% margin (minimally) to allow for traffic bursts at the site.rate <50-1000000> Optional. Sets the traffic rate from 50 - 1000000 Kbps. This limit is the threshold value for the maximum number of packets received or transmitted over the WLAN from all access categories. Any traffic that exceeds the specified rate is dropped and a log message is generated. The default values are:- WLAN ‘to-air’ and ‘from-air’: 5000 kbytes- Client ‘to-air’ and ‘from-air’: 1000 kbytesrate-limit Configures traffic rate limit parametersclient Configures traffic rate limiting parameters on a per-client basiswlan Configures traffic rate limiting parameters on a per-WLAN basisfrom-air Configures traffic rate limiting from a wireless client to the networkto-air Configures the traffic rate limit from the network to a wireless clientred-threshold Configures random early detection threshold values for a designated traffic classbackground <0-100> Optional. Sets the maximum burst size from 2 - 1024 kbytes. The chances of the upstream or downstream packet transmission getting congested for the WLAN’s client destination are reduced for smaller burst sizes. The default values are:- WLAN ‘to-air’ and ‘from-air’: 320 kbytes- Client ‘to-air’ and ‘from-air’: 64 kbytesSmaller the burst, lesser are the chances of upstream packet transmission resulting in congestion for the WLAN’s client destinations. By trending the typical number of ARP, broadcast, multicast and unknown unicast packets over a period of time, the average rate for each access category can be obtained. Once a baseline is obtained, administrators should then add a 10% margin (minimally) to allow for traffic bursts at the site.best-effort <0-100> The following is common to the ‘from-air’ and ‘to-air’ parameters:Optional. Sets a percentage value for best effort traffic in the upstream or downstream direction. Best effort traffic exceeding the defined threshold is dropped and a log message is generated. The default threshold values are:- WLAN ‘to-air’ and ‘from-air’: 50%- Client ‘to-air’ and ‘from-air’: 50%](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-790.png)

![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 1521.1.9 wmmwlan-qos-policyConfigures 802.11e/Wireless Multimedia (WMM) parameters for this WLAN QoS policyWMM makes it possible for both home networks and Enterprises to decide which data streams are most important and assign them a higher traffic priority.WMM’s prioritization capabilities are based on the four access categories (background, best-effort, video, and voice). Higher the Access Category (AC) higher is the transmission probability over the controller managed WLAN. ACs correspond to the 802.1d priorities, facilitating interoperability with QoS policy management mechanisms. WMM enabled controllers coexist with legacy devices (not WMM-enabled).Packets not assigned to a specific access category are categorized as best effort by default. Applications assign each data packet to a given access category. Categorized packets are added to one of four independent transmit queues (one per access category). The client has an internal collision resolution mechanism to address collision among different queues, which selects the frames with the highest priority to transmit.The same mechanism deals with external collision, to determine which client should be granted the Opportunity to Transmit (TXOP). The collision resolution algorithm responsible for traffic prioritization is probabilistic and depends on two timing parameters that vary for each access category. These parameters are:• The minimum interframe space, or Arbitrary Inter-Frame Space Number (AIFSN)• The contention window, sometimes referred to as the random back off waitBoth values are smaller for high-priority traffic. The value of the contention window varies through time. Initially the contention window is set to a value that depends on the AC. As frames with the highest AC tend to have the lowest back off values, they are more likely to get a TXOP.After each collision the contention window is doubled until a maximum value (also dependent on the AC) is reached. After successful transmission, the contention window is reset to its initial, AC dependant value. The AC with the lowest back off value gets the TXOP.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwmm [background|best-effort|power-save|qbss-load-element|video|voice]wmm [power-save|qbss-load-element]wmm [background|best-effort|video|voice] [aifsn <2-15>|cw-max <0-15>|cw-min <0-15>|txop-limit <0-65535>]Parameters• wmm [power-save|qbss-load-element]wmm Configures 802.11e/wireless multimedia parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-794.png)
![WLAN-QOS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 21 - 16• wmm [background|best-effort|video|voice] [aifsn <2-15>|cw-max <0-15>|cw-min <0-15>|txop-limit <0-65535>]power-save Enables support for the WMM-Powersave mechanism. This mechanism, also known as Unscheduled Automatic Power Save Delivery (U-APSD), is specifically designed for WMM voice devices. This feature is enabled by default.qbss-load-element Enables support for the QOS Basic Service Set (QBSS) load information element in beacons and probe response packets advertised by access packets. This feature is enabled by default.wmm Configures 802.11e/wireless multimedia parameters. This parameter enables the configuration of four access categories. Applications assign each data packet to one of these four access categories and queues them for transmission.background Configures background access category parametersbest-effort Configures best effort access category parameters. Packets not assigned to any particular access category are categorized by default as having best effort priorityvideo Configures video access category parametersvoice Configures voice access category parametersaifsn <2-15> Configures Arbitrary Inter-Frame Space Number (AIFSN) from 2 - 15. AIFSN is the wait time between data frames. This parameter is common to background, best effort, video and voice.The default for traffic voice categories is 2The default for traffic video categories is 2The default for traffic best effort (normal) categories is 3The default for traffic background (low) categories is 7• <2-15> – Sets a value from 2 - 15cw-max <0-15> Configures the maximum contention window. Wireless clients pick a number between 0 and the minimum contention window to wait before retransmission. Wireless clients then double their wait time on a collision, until it reaches the maximum contention window. This parameter is common to background, best effort, video and voice.The default for traffic voice categories is 3The default for traffic video categories is 4The default for traffic best effort (normal) categories 10The default for traffic background (low) categories is 10• <0-15> – ECW: the contention window. The actual value used is (2^ECW - 1). Set a value from 0 - 15.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-795.png)



![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 522.1.1 cookie-sizel2tpv3-policy-commandsConfigures the size of the cookie field present in each L2TPv3 data packet. L2TPv3 data packets contain a session cookie that identifies the session (pseudowire) corresponding to it. In a tunnel, the cookie is a 4-byte or 8-byte signature shared between the two tunnel endpoints. This signature is configured at both the source and destination routers. If the signature at both ends do not match, the data is dropped. All sessions within a tunnel have the same session cookie size.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcookie-size [0|4|8]Parameters• cookie-size [0|4|8]Examplerfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#cookie-size 8rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#show contextl2tpv3 policy L2TPV3Policy1 cookie-size 8rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#Related Commandscookie-size [0|4|8] Configures the cookie-field size for each data packet. Select one of the following options:• 0 – No cookie field present in each L2TPv3 data message (this is the default setting)• 4 – 4 byte cookie field present in each L2TPv3 data message• 8 – 8 byte cookie field present in each L2TPv3 data messageno Resets the cookie-field size to its default (0 - no cookie field present in each L2TPv3 data packet)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-801.png)

![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 922.1.5 nol2tpv3-policy-commandsNegates or reverts L2TPv3 policy settings to defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [cookie-size|failover-delay|force-l2-path-recovery|hello-interval|reconnect-attempts|reconnect-interval|retry-attempts|retry-interval|rx-window-size|tx-window-size]Parameters• no <PARAMETERS>ExampleThe following example shows the l2tpv3 policy ‘L2TPV3Policy1’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#show contextl2tpv3 policy L2TPV3Policy1 hello-interval 200 retry-attempts 10 retry-interval 30 cookie-size 8 reconnect-interval 100 reconnect-attempts 50rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no hello-intervalrfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no reconnect-attemptsrfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no reconnect-intervalrfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no retry-attemptsrfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no retry-intervalrfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no cookie-sizeThe following example shows the l2tpv3 policy ‘L2TPV3Policy1’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#show contextl2tpv3 policy L2TPV3Policy1rfs6000-37FABE(config-l2tpv3-policy-L2TPV3Policy1)#no <PARAMETERS> Negates or reverts L2TPv3 policy settings to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-805.png)



![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 1722.2.1 establishment-criterial2tpv3-tunnel-commandsConfigures L2TPv3 tunnel establishment criteriaA L2TPv3 tunnel is established from the current device to the NOC controller when the current device becomes the VRRP master, cluster master, or RF Domain manager. Similarly, the L2TPv3 tunnel is closed when the current device switches to standby or backup mode.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxestablishment-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]Parameters• establishment-criteria [always|cluster-master|rf-domain-manager|vrrp-master <1-255>]always Always establishes a L2TPv3 tunnel from the current device to the NOC controller. This is the default setting.The ‘always’ option indicates the device need not be a cluster-master, rf-domain-manager, or vrrp-master to establish a tunnel.cluster-master Establishes a L2TPv3 tunnel from the current device to the NOC controller, only when the current device becomes the cluster masterNote: The L2TPv3 tunnel is closed when the current device switches back the standby or backup mode.rf-domain-manager Establishes a L2TPv3 tunnel from the current device to the NOC controller, only when the current device becomes the RF Domain managerNote: The L2TPv3 tunnel is closed when the current device switches back the standby or backup mode.vrrp-master <1-255> Establishes a L2TPv3 tunnel from the current device to the NOC controller, only when the current device becomes the VRRP master• <1-255> – Specify the VRRP group number from 1 - 255.Note: The L2TPv3 tunnel is closed when the current device switches back the standby or backup mode.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-813.png)




![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 2322.2.6 nol2tpv3-tunnel-commandsNegates or reverts a L2TPv3 tunnel settings to defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [establishment-criteria|fast-failover|hostname|local-ip-address|mtu|peer <1-2>|router-id|session|use]Parameters• no <PARAMETERS>ExampleThe tunnel settings before the ‘no’ command is executed:rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#show context l2tpv3 tunnel Tunnel1 local-ip-address 172.16.10.2 mtu 1280 hostname TunnelHost1 establishment-criteria cluster-masterrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#The tunnel settings after the ‘no’ command is executed:rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#no local-ip-addressrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#no mturfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#no hostnamerfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#show context l2tpv3 tunnel Tunnel1 establishment-criteria cluster-masterrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#no <PARAMETERS> Negates or reverts a L2TPv3 tunnel settings to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-819.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 2422.2.7 peerl2tpv3-tunnel-commandsConfigures the L2TPv3 tunnel’s peers. At least one peer must be specified.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxpeer <1-2> {hostname|ip-address|ipsec-secure|router-id|udp}peer <1-2> {hostname [<HOSTNAME>|any]} {ipsec-secure|router-id|udp}peer <1-2> {ip-address <IP>} {hostname|ipsec-secure|router-id|udp}peer <1-2> {ipsec-secure} {gw [<IP>|<WORD>]}peer <1-2> {router-id [<IP>|<WORD>|any]} {ipsec-secure|udp}peer <1-2> {udp} {ipsec-secure|port <1-65535>}Parameters• peer <1-2> {hostname [<HOSTNAME>|any]} {ipsec-secure|router-id|udp}peer <1-2> Configures the tunnel’s peer ID• <1-2> – Specify the ID from 1 - 2. The peer ID identifies the primary (ID 1) secondary (ID 2) peers. The L2TPv3 tunnel is established with the primary peer. The secondary peer is used for tunnel failover. If the peer is not specified, tunnel establishment does not occur.Note: At any time the tunnel is established with only one peer, unless fast-failover support is configured on the L2TPv3 tunnel. For more information, see fast-failover.hostname [<HOSTNAME>|any]Optional. Configures the peers’ hostname. The hostname options are:• <HOSTNAME> – Specifies the hostname as Fully Qualified Domain Name (FQDN) or partial DN or any other name• any – Peer name is not specified. If the hostname is ‘any’ this tunnel is considered as responder only and will allow incoming connection from any host.ipsec-secure {gw [<IP>|<WORD>]}After specifying the peer hostname, optionally specify the IPSec settings:• ipsec-secure – Optional. Enables auto IPSec on the L2TPv3 tunnel• gw – Optional. Configures the IPSec gateway. Use one of the following options toconfigure the IPSec gateway:• <IP> – Configures IPSec gateway’s IP address• <WORD> – Configures IPSec gateway’s hostnamerouter-id [<IP>|<WORD>|any]After specifying the peer hostname, optionally specify router ID settings:• router-id – Optional. Configures the peer’s router ID in one of the following formats:• <IP> – Peer router ID in the IP address (A.B.C.D) format• <WORD> – Peer router ID range (for example, 100-120)• any – Peer router ID is not specified. This allows incoming connection from anyrouter ID.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-820.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 25• peer <1-2> {ip-address <IP>} {hostname|ipsec-secure|router-id|udp}• peer <1-2> {ipsec-secure} {gw [<IP>|<WORD>]}udp {ipsec-secure gw|port <1-65535> {ipsec-secure}}After specifying the peer hostname, optionally specify UDP settings:The UDP option configures the encapsulation mode for this tunnel.• UDP – Optional. Configures UDP encapsulation (default encapsulation is IP)• ipsec-secure gw – Optional. Enables auto IPSec• port <1-65535> {ipsec-secure} – Optional. Configures the peer’s UDP port run-ning the L2TPv3 service from 1 - 65535. After specifying the peer UDP port, option-ally configure the IPSec settings.peer <1-2> Configures the tunnel’s peer ID from 1 - 2. At any time the tunnel is established with only one peer.ip-address <IP> Optional. Configures the peer’s IP address in the A.B.C.D format• <IP> – Specify the peer’s IP address.hostname [<FQDN>|any]After specifying the peer IP address, optionally specify the peer’s hostname:• hostname – Optional. Configures the peers’ hostname. The hostname options are:• <FQDN> – Specifies the hostname as FQDN or partial DN• any – Peer name is not specified. If the hostname is ‘any’ this tunnel is consideredas responder only and will allow incoming connection from any host.ipsec-secure {gw [<IP>|<WORD>]}After specifying the peer IP address, optionally specify the IPSec settings:• ipsec-secure – Optional. Enables auto IPSec• gw – Optional. Configures the IPSec gateway. Use one of the following options toconfigure the IPSec gateway:• <IP> – Configures IPSec gateway’s IP address• <WORD> – Configures IPSec gateway’s hostnamerouter-id [<A.B.C.D>|<WORD>|any]After specifying the peer IP address, optionally specify the router ID using one of the following options:• router-id – Optional. Configures the peer’s router-id in one of the following formats:• <A.B.C.D> – Peer router ID in the IP address (A.B.C.D) format• <WORD> – Peer router ID range (for example, 100-120)• any – Peer router ID is not specified. This allows incoming connection from anyrouter ID.udp {ipsec-secure gw|port <1-65535> {ipsec-secure}}After specifying the peer IP address, optionally specify the peer’s UDP port settings:The UDP option configures the encapsulation mode for this tunnel.• UDP – Optional. Configures UDP encapsulation (default encapsulation is IP)• ipsec-secure gw – Optional. Enables auto IPSec• port <1-65535> – Optional. Configures the peer’s UDP port running the L2TPv3service from 1 - 65535. After specifying the peer UDP port, optionally configure theIPSec settings.peer <1-2> Configures the tunnel’s peer ID from 1 - 2. At any time the tunnel is established with only one peer.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-821.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 26• peer <1-2> {router-id [<IP>|<WORD>|any]} {ipsec-secure|udp}• peer <1-2> {udp} {ipsec-secure|port <1-65535>}ipsec-secure {gw [<IP>|<WORD>]}Optional. Enables auto IPSec for this peer• gw – Optional. Configures the IPSec gateway. Use one of the following options to configure the IPSec gateway:• <IP> – Configures IPSec gateway’s IP address• <WORD> – Configures IPSec gateway’s hostnamepeer <1-2> Configures the tunnel peer ID from 1 - 2. At any time the tunnel is established with only one peer.router-id [<A.B.C.D>|<WORD>|any]Optional. Configures the peer’s router-id in one of the following formats:• <A.B.C.D> – Peer router ID in the IP address (A.B.C.D) format• <WORD> – Peer router ID range (for example, 100-120)• any – Peer router ID is not specified. This allows incoming connection from any router ID.ipsec-secure {gw [<IP>|<WORD>]}After specifying the peer’s router ID, optionally specify the IPSec settings.• ipsec-secure – Optional. Enables auto IPSec• gw – Optional. Configures the IPSec gateway. Use one of the following optionsto configure the IPSec gateway:• <IP> – Configures IPSec gateway’s IP address• <WORD> – Configures IPSec gateway’s hostnameudp {ipsec-secure gw|port <1-65535> {ipsec-secure}}After specifying the peer’s router ID, optionally specify the IPSec settings.The UDP option configures the encapsulation mode for this tunnel.• UDP – Optional. Configures UDP encapsulation (default encapsulation is IP)• ipsec-secure gw – Optional. Enables auto IPSec• port <1-65535> – Optional. Configures the peer’s UDP port running the L2TPv3service from 1 - 65535. After specifying the peer UDP port, optionally configure theIPSec settings.peer <1-2> Configures the tunnel peer ID from 1 - 2. At any time the tunnel is established with only one peer.udp {ipsec-secure|port <1-65535> {ipsec-secure}}Optional. Configures UDP encapsulation for this tunnel’s pee (default encapsulation is IP)• ipsec-secure – Optional. Configures IPSec gateway on this peer UDP port• port <1-65535> – Optional. Configures the peer’s UDP port running the L2TPv3 service from 1 - 65535. After specifying the peer UDP port, optionally configure the IPSec settings.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-822.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 2822.2.8 router-idl2tpv3-tunnel-commandsConfigures the tunnel’s local router IDSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrouter-id [<1-4294967295>|<IP>]Parameters• router-id [<1-4294967295>|<IP>]Examplerfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#router-id 2000rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#show context l2tpv3 tunnel Tunnel1 peer 2 hostname tunnel1peer1 udp port 100 router-id 2000 establishment-criteria cluster-masterrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#Related Commandsrouter-id [<1-4294967295>|<IP>]Configures the tunnel’s local router ID in one of the following formats:• <1-4294967295> – Router ID in the number format (from1 - 4294967295)• <IP> – Router ID in IP address format (A.B.C.D)no Removes the tunnel’s router ID](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-824.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 2922.2.9 sessionl2tpv3-tunnel-commandsConfigures a session’s pseudowire ID, which describes the session’s purpose. The session established message sends this pseudowire ID to the L2TPv3 peer.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsession <L2TPV3-SESSION-NAME> [pseudowire-id|rate-limit]session <L2TPV3-SESSION-NAME> pseudowire-id <1-4294967295> traffic-source vlan <VLAN-ID-RANGE> {native-vlan <1-4094>}session <L2TPV3-SESSION-NAME> rate-limit [egress|ingress] rate <50-1000000> max-burst-size <2-1024>Parameters• session <L2TPV3-SESSION-NAME> pseudowire-id <1-4294967295> traffic-source vlan <VLAN-ID-RANGE> {native-vlan <1-4094>}• session <L2TPV3-SESSION-NAME> rate-limit [egress|ingress] rate <50-1000000> max-burst-size <2-1024>session <L2TPV3-SESSION-NAME>Configures this session’s name• <L2TPV3-SESSION-NAME> – Specify the L2TPV3 session name (should not exceed 31 characters in length). A tunnel is usable only if it has one or more session(s) (having specific session names) configured. The L2TPv3 tunnel has no idle timeout, it closes when the last tunnel session is closed.pseudowire-id <1-4294967295>Configures the pseudowire ID for this session from 1- 4204067295A pseudowire is an emulation of a layer 2 point-to-point connection over a packet-switching network (PSN). A pseudowire is needed to encapsulate and tunnel layer 2 protocols across a layer 3 network.traffic-source vlan <VLAN-ID-RANGE>Configures VLAN as the traffic source for this tunnel• <VLAN-ID-RANGE> – Configures VLAN range list of traffic source. Specify the VLAN IDs as a range (for example, 10-20, 25, 30-35).native-vlan <1-4094> Optional – Configures the native VLAN ID for this session, which is not tagged• <1-4094> – Specify the native VLAN ID from 1- 4094.session <L2TPV3-SESSION-NAME>Configures this session’s name• <L2TPV3-SESSION-NAME> – Specify the L2TPV3 session name (should not exceed 31 characters in length). A tunnel is usable only if it has one or more session(s) (having specific session names) configured. The L2TPv3 tunnel has no idle timeout, it closes when the last tunnel session is closed.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-825.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 30Usage GuidelinesThe working status of a pseudowire is reflected by the state of the L2TPv3 session. If the corresponding session is L2TPv3 down, the pseudowire associated with it must be shut down.Examplerfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#session tunnel1peer1session1 pseudowire-id 5000 traffic-source vlan 10-20 native-vlan 1rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#show context l2tpv3 tunnel Tunnel1 peer 2 hostname tunnel1peer1 udp port 100 session tunnel1peer1session1 pseudowire-id 5000 traffic-source vlan 10-20 native-vlan 1 router-id 2000 establishment-criteria cluster-masterrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#Related Commandsrate-limit [egress|ingress]Configures a rate for incoming and/or outgoing traffic on this L2TPv3 tunnel. When configured, this option limits the rate at which data is sent to or received from L2TPv3 tunnel members.• egress – Applies the specified rate to outbound traffic, from the L2TPv3 tunnel (going out from access points, wireless controllers, and service platforms) to the network• ingress – Applies the specified rate to inbound traffic, from the network to the L2TPV3 tunnel (coming in to access points, wireless controllers, and service platforms) rate <50-1000000> Specify the data rate, in kilobits per second, for the incoming and/or outgoing traffic• <50-1000000> – Specify a value from 50 - 1000000 kbps. The default is 5000 Kbps.max-burst-size <2-1024> Configures the maximum burst size, in kilobytes, for incoming/outgoing traffic rate limiting (depending on the direction selected) on a L2TPv3 tunnel.• <2-1024> – Specify the maximum burst size from 2 - 1024 kbytes. Smaller the burst size, lesser are the chances of the upstream packet transmission resulting in congestion of the L2TPv3 tunnel traffic. The default setting is 320 kbytes.no Removes a session](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-826.png)
![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 3122.2.10 usel2tpv3-tunnel-commandsConfigures a tunnel to use a specified L2TPv3 tunnel policy and specified critical resourcesSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [critical-resource|l2tpv3-policy]use critical-resource <CRM-NAME1> {<CRM-NAME2>} <CRM-NAME3>} <CRM-NAME4>}use l2tpv3-policy <L2TPV3-POLICY-NAME>Parameters• use critical-resource <CRM-NAME1> {<CRM-NAME2>} {<CRM-NAME3>} {<CRM-NAME4>}• use l2tpv3-policy <L2TPV3-POLICY-NAME>Examplerfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#use l2tpv3-policy L2TPV3Policy1rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#show context l2tpv3 tunnel Tunnel1 peer 2 hostname tunnel1peer1 udp port 100 use l2tpv3-policy L2TPV3Policy1 session tunnel1peer1session1 pseudowire-id 5000 traffic-source vlan 10-20 native-vlan 1 router-id 2000 establishment-criteria cluster-masterrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-tunnel-Tunnel1)#Related Commandsuse critical-resource<CRM-NAME1> {<CRM-NAME2>}{<CRM-NAME3>}{<CRM-NAME4>}Specifies the critical resource(s) to use with this tunnel• <CRM1-NAME> – Specify the first critical resource name (should be existing).• <CRM-NAME2/3/4> – Optional. Specify the second/third/fourth critical resourcenames. Maximum of four critical resources can be monitored.Note: In case of tunnel initiator, L2TPv3 tunnel is established only if the critical resources identified by the <CRM-NAME1>.................. <CRM-NAME4> arguments are available at the time of tunnel establishment.Note: In case of L2TPv3 tunnel termination, all incoming tunnel establishment requests are rejected if the critical resources specified by the <CRM-NAME1>.............. <CRM-NAME4> arguments are not available.use l2tpv3-policy <L2TPV3-POLICY-NAME>Associates a specified L2TPv3 policy with this tunnel• <L2TPV3-POLICY-NAME> – Specify the policy name (should be existing and configured).no Removes the L2TPv3 policy configured with a tunnel and reverts to the default tunnel policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-827.png)

![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 3422.3.1 local-cookiel2tpv3-manual-session-commandsConfigures the local cookie field size for the manual sessionSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxlocal-cookie size [4|8] <1-4294967295> {<1-4294967295>}Parameters• local-cookie size [4|8] <1-4294967295> {<1-4294967295>}Examplerfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#local-cookie size 8 200 300rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#show context l2tpv3 manual-session test local-cookie size 8 200 300rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#Related Commandslocal-cookie size [4|8] Configures the local cookie field size for this manual session. The options are:• 4 – 4 byte local cookie field• 8 – 8 byte local cookie field<1-4294967295> Configures the local cookie value first word. Applies to both the 4 byte and 8 byte local cookies<1-4294967295> Optional – Configures the local cookie value second word. Applicable to only 8 byte cookies. This parameter is ignored for 4 byte cookies.no Removes the local cookie size configured for a manual session](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-830.png)



![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 3822.3.5 nol2tpv3-manual-session-commandsNegates or reverts L2TPv3 manual session settings to defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [local-cookie|local-ip-address|local-session-id|mtu|peer|remote-cookie|remote-session-id|traffic-source]Parameters• no <PARAMETERS>ExampleThe following example shows the manual session ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#show context l2tpv3 manual-session test local-ip-address 1.2.3.4 peer ip-address 5.6.7.8 udp port 150 traffic-source vlan 50-60 native-vlan 2 local-session-id 1 remote-session-id 200 remote-cookie size 8 400 700rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#no local-ip-addressrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#no local-session-idrfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#no remote-session-idThe following example shows the manual session ‘test’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#show context l2tpv3 manual-session test peer ip-address 5.6.7.8 udp port 150 traffic-source vlan 50-60 native-vlan 2 remote-cookie size 8 400 700rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#no <PARAMETERS> Negates or reverts L2TPv3 manual session settings to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-834.png)

![L2TPV3-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 22 - 4022.3.7 remote-cookiel2tpv3-manual-session-commandsConfigures the manual session’s remote cookie field sizeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxremote-cookie size [4|8] <1-4294967295> {<1-4294967295>}Parameters• remote-cookie size [4|8] <1-4294967295> {<1-4294967295>}Examplerfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#remote-cookie size 8 400 700rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#show context l2tpv3 manual-session test local-ip-address 1.2.3.4 peer ip-address 5.6.7.8 udp port 150 mtu 200 local-session-id 1 remote-cookie size 8 400 700rfs6000-37FABE(config-profile default-rfs7000-l2tpv3-manual-session-test)#Related Commandsremote-cookie size [4|8]Configures the remote cookie field size for this manual session. The options are:• 4 – 4 byte remote cookie field• 8 – 8 byte remote cookie field<1-4294967295> Configures the remote cookie value first word. Applies to both the 4 byte and 8 byte local cookies<1-4294967295> Optional – Configures the remote cookie value second word. Applicable to only 8 byte cookies. This parameter is ignored for 4 byte cookies.no Removes the manual session’s remote cookie field size](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-836.png)


![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 423.1.1.1 areaareaConfigures OSPF network areas (OSPF enables interfaces)An OSPF network can be subdivided into routing areas to simplify administration and optimize traffic utilization. Areas are logical groupings of hosts and networks, including routers having interfaces connected to an included network. Each area maintains a separate link state database whose information may be summarized towards the rest of the network by the connecting router. Areas are identified by 32-bit IDs, expressed either in decimal, or octet-based dot-decimal notation. Areas can defined as: stub area, totally-stub, non-stub, nssa, totally nssa. Each of these area types have been discussed further in the area-type section of this chapter.At least one default area, bearing number ‘0’, should be configured for every OSPF network. In case of multiple areas, the default area 0 forms the backbone of the network. The default area 0 is used as a link to the other areas. Each area has its own link-state database.A router running OSPF sends hello packets to discover neighbors and elect a designated router. The hello packet includes link state information and list of neighbors. OSPF is savvy with layer 2 topologies. If on a point-to-point link, OSPF knows it is sufficient, and the link stays up. If on a broadcast link, the router waits for election before determining if the link is functional.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxarea [<0-4294967295>|<IP>]Parameters• area [<0-4294967295>|<IP>]Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf)#area 4 ?rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.4)#?Router OSPF Area Mode commands: area-type OSPF area type authentication Authentication scheme for OSPF area no Negate a command or set its defaults range Routes matching this range are considered for summarization (ABR only) clrscr Clears the display screen commit Commit all changes made in this session do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous modearea Defines an OSPF area<0-4294967295> Defines an OSPF area in the form of a 32 bit integer• <0-4294967295> – Specify the value from 0 - 4294967295.<IP> Defines an OSPF area in the form of an IP address• <IP> – Specify the IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-842.png)

![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 723.1.1.2.1 area-typeOSPF-area-modeConfigures a particular OSPF area type as STUB, Totally STUB, NSSA or Totally NSSAAreas can be defined as:• stub area - Is an area that does not receive route advertisements external to the autonomous system (AS), and routing from within the area is based entirely on a default route.• totally-stub - Is an area that does not allow summary routes and external routes. A default route is the only way to route traffic outside of the area. When there is only one route out of the area, fewer routing decisions are needed, lowering system resource utilization.• non-stub - Is an area that imports autonomous system external routes and forwards to other areas. However. it still cannot receive external routes from other areas.• nssa - A Not-So-Stubby Area (NSSA) is an extension of a stub that allows the injection of limited external routes into a stub area. If selecting NSSA, no external routes, except a default route, enter the area.• totally-nssa - Is a NSSA using 3 and 4 summary routes are not flooded into this type of area. It is also possible to declare an area both totally stubby and not-so-stubby, which means that the area will receive only the default route from area 0.0.0.0, but can also contain an Autonomous System Boundary Router (ASBR) that accepts external routing information and injects it into the local area, and from the local area into area 0.0.0.0.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxarea-type [nssa|stub]area-type nssa {default-cost|no-summary|translate-always|translate-candidate|translate-never}area-type nssa {default-cost <0-16777215> {no-summary}|no-summary {default-cost <0-16777215>}}area-type nssa {translate-always|translate-candidate|translate-never} {(default-cost <0-16777215>|no-summary)}area-type stub {default-cost <0-16777215> {no-summary}|no-summary {default-cost <0-16777215>}}Parameters• area-type [nssa|stub]{default-cost|no-summary|translate-always|translate-candidate|translate-never}area-type Configures a particular OSPF area type as STUB, Totally STUB, NSSA or Totally NSSAnssa Configures the OSPF area as NSSAstub Configures the OSPF area as Stubby Area (STUB)default-cost <0-16777215>Specifies the default summary cost that will be advertised, if the OSPF area is a STUB or NSSA• <0-16777215> – Specify the default summary cost value from 0 - 16777215.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-845.png)

![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 923.1.1.2.2 authenticationOSPF-area-modeSpecifies an authentication scheme used for an OSPF area used with the OSPF dynamic routeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxauthentication [message-digest|simple-password]Parameters• authentication [message-digest|simple-password]Usage GuidelinesOSPF packet authentication enables routers to use predefined passwords and participate within a routing domain. The two authentication modes are:• MD-5 – MD-5 authentication is a cryptographic authentication mode, where every router has a key (password) and key-id configured on it. This key and key-id together form the message digest that is appended to the OSPF packet.• Simple Password – Simple password authentication allows a password (key) to be configured per area. Routers in the same area and participating in the routing domain have to be configured with the same key.Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#authentication simple-passwordrfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#show context area 0.0.0.1 authentication simple-password area-type stub default-cost 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#Related Commandsmessage-digest Configures the message-digest (MD-5) authentication schemesimple-password Configures the simple password authentication schemeno Removes the authentication scheme](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-847.png)

![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 1123.1.1.2.4 noOSPF-area-modeNegates a command or set its defaultsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxno [area-type|authentication|range]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated. ExampleThe following example shows the OSPF router settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#show context area 0.0.0.1 authentication simple-password range 172.16.10.0/24 area-type stub default-cost 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#no authenticationrfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#no range 172.16.10.0/24The following example shows the OSPF router settings after the ‘no’ commands are executed:rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#show context area 0.0.0.1 area-type stub default-cost 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf-area-0.0.0.1)#no <PARAMETERS> Negates a command or set its defaults](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-849.png)

![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 1323.1.3 default-informationrouter-modeControls the distribution of default route information. Use the default-information > originate command to advertise a default route in the routing table.This option is disabled by default. When enabled, the default route becomes a distributed route.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxdefault-information originate {always|metric|metric-type}default-information originate {always|metric <0-16777214>|metric-type [1|2]} {(metric <0-16777214>|metric-type [1|2])}Parameters• default-information originate {always|metric <0-16777214>|metric-type [1|2]} {(metric <0-16777214>|metric-type [1|2])}Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf)#default-information originate metric-type 2 metric 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf area 0.0.0.4 auto-cost reference-bandwidth 1 default-information originate metric 1 metric-type 2rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#Related Commandsoriginate Originates default route information. Enabling this feature makes the default route a distributed route. This option is disabled by default.always Optional. Always distributes default route information (will continue to advertise default route information even if that information has been removed from the routing table for some reason). This option is disabled by default.metric <0-16777214> This is a recursive parameter and can be optionally configured along with the metric-type option.• metric <0-16777214> – Optional. Specifies OSPF metric value for redistributed routes (this value is used to generate the default route)• <0-16777214> – Specify a value from 0 - 16777214.metric-type [1|2] This is a recursive parameter and can be optionally configured along with the metric option.• metric-type [1|2] – Optional. Sets OSPF exterior metric type for redistributed routes (this information is advertised with the OSPF routing domain)• 1 – Sets OSPF external type 1 metrics• 2 – Sets OSPF external type 2 metricsno Disables advertising of default route information available in the routing table](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-851.png)

![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 1523.1.5 networkrouter-modeAssigns networks to specified areas (defines the OSPF interfaces and their associated area IDs)Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxnetwork <IP/M> area [<0-4294967295>|<IP>]Parameters• network <IP/M> area [<0-4294967295>|<IP>]Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf)#network 1.2.3.0/24 area 4.5.6.7rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf network 1.2.3.0/24 area 4.5.6.7 area 0.0.0.4 auto-cost reference-bandwidth 1 default-information originate metric 1 metric-type 2 ip default-gateway priority 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#Related Commands<IP/M> Specifies an OSPF network address/mask value. Defines networks (IP addresses and mask) participating in OSPF.area [<0-4294967295>|<IP>]Specifies an OSPF area, associated with the OSPF address range, in one of the following formats:• <0-4294967295> – Specifies a 32 bit OSPF area ID from 0 - 4294967295• <IP> – Defines an OSPF area ID in the form of an IPv4 addressno Removes the OSPF network to area ID association](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-853.png)
![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 1723.1.7 passiverouter-modeConfigures specified OSPF interface as passive. This option is disabled by default.A passive interface receives routing updates, but does not transmit them.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxpassive [<WORD>|all|vlan <1-4094>]Parameters• passive [<WORD>|all|vlan <1-4094>]Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf)#passive vlan 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf ospf enable network 1.2.3.0/24 area 4.5.6.7 area 0.0.0.4 auto-cost reference-bandwidth 1 default-information originate metric 1 metric-type 2 passive vlan1 ip default-gateway priority 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#Related Commands<WORD> Enables the OSPF passive mode on the interface specified by the <WORD> parameterall Enables the OSPF passive mode on all the L3 interfacesvlan <1-4094> Enables the OSPF passive mode on the specified VLAN interface• <1-4094> – Specify the VLAN interface ID from 1 - 4094.no Disables the OSPF passive mode on a specified interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-855.png)
![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 1823.1.8 redistributerouter-modeSpecifies the route types redistributed by OSPFSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxredistribute [bgp|connected|kernel|static] {metric <0-16777214>|metric-type [1|2]}Parameters• redistribute [connected|kernel|static] {metric <0-16777214>|metric-type [1|2]}Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf)#redistribute static metric-type 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf ospf enable network 1.2.3.0/24 area 4.5.6.7 area 0.0.0.4 auto-cost reference-bandwidth 1 default-information originate metric 1 metric-type 2 redistribute static metric-type 1 passive vlan1 ip default-gateway priority 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#Related Commandsbgp Redistributes all BGP routes by OSPFconnected Redistributes all connected interface routes by OSPFkernel Redistributes all routes that are neither connected, static, dynamic, nor bgpstatic Redistributes static routes by OSPFmetric <0-16777214> The following keywords are common to the ‘bgp’, ‘connected’, ‘kernel’, and ‘static’ parameters:• metric <0-16777214> – Optional. Specifies the OSPF metric value for redistributed routes. • <0-16777214> – Specify a value from 0 - 16777214.metric-type [1|2] The following keywords are common to the ‘connected’, ‘kernel’, and ‘static’ parameters:• metric-type [1|2] – Optional. Sets the OSPF exterior metric type for redistributed routes• 1 – Sets the OSPF external type 1 metrics• 2 – Sets the OSPF external type 2 metricsno Removes the OSPF redistribution of various route types](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-856.png)
![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 1923.1.9 route-limitrouter-modeLimits the number of routes managed by OSPF. The maximum limit supported by the platform is the default configuration defined under the router-ospf context.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxroute-limit [num-routes|reset-time|retry-count|retry-timeout]route-limit [num-routes <DYNAMIC-ROUTE-LIMIT>|reset-time <1-86400>|retry-count <1-32>|retry-timeout <1-3600>] {(num-routes|reset-time|retry-count|retry-timeout)}Parameters• route-limit [num-routes <DYNAMIC-ROUTE-LIMIT>|reset-time <1-86400>|retry-count <1-32>|retry-timeout <1-3600>] {(num-routes|reset-time|retry-count|retry-timeout)}Examplerfs6000-37FABE(config-profile default-rfs7000-router-ospf)#route-limit num-routes 10 retry-count 5 retry-timeout 60 reset-time 10rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf ospf enable network 1.2.3.0/24 area 4.5.6.7 area 0.0.0.4 auto-cost reference-bandwidth 1 default-information originate metric 1 metric-type 2 redistribute static metric-type 1 passive vlan1 route-limit num-routes 10 retry-count 5 retry-timeout 60 reset-time 10 ip default-gateway priority 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#num-routes <DYNAMIC-ROUTE-LIMIT>Specifies the maximum number of non self-generated LSAs this process can receive• <DYNAMIC-ROUTE-LIMIT> – Specify the dynamic route limit.reset-time <1-86400> Specifies the time, in seconds, after which the retry-count is reset to zero<1-86400> – Specify a value from 1 - 86400 seconds. The default is 360 seconds.retry-count <1-32> Specifies the maximum number of times adjacencies can be suppressed. Each time OSPF gets into an ignore state, a counter increments. If the counter exceeds the timeout configured by the retry-count parameter, OSPF stays in the same ignore state. Manual intervention is required to get OSPF out of the ignore state. • <1-32> – Specify a value from 1 - 32. The default is 5.retry-timeout <1-3600> Specifies the retry time in seconds. During this time, OSPF remains in ignore state and all adjacencies are suppressed.• <1-3600> – Specify a value from 1 - 3600 seconds. The default is 60 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-857.png)


![ROUTER-MODE COMMANDSAccess Point, Wireless Controller and Service Platform CLI Reference Guide 23 - 2223.1.11 norouter-modeNegates a command or reverts settings to their defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7622, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000Syntaxno [area|auto-cost|default-information|ip|network|ospf|passive|redistribute|route-limit|router-id]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.ExampleThe following example shows the OSPF router interface settings before the ‘no’ commands are executed:rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf network 1.2.3.0/24 area 4.5.6.7 area 0.0.0.4 auto-cost reference-bandwidth 1 default-information originate metric 1 metric-type 2 redistribute static metric-type 1 passive vlan1 route-limit num-routes 10 reset-time 10 ip default-gateway priority 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#no area 4rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#no auto-cost reference-bandwidthrfs6000-37FABE(config-profile default-rfs7000-router-ospf)#no network 1.2.3.0/24 area 4.5.6.7The following example shows the OSPF router interface settings after the ‘no’ commands are executed:rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#show context router ospf default-information originate metric 1 metric-type 2 redistribute static metric-type 1 passive vlan1 route-limit num-routes 10 reset-time 10 ip default-gateway priority 1rfs6000-37FABE(config-profile default-rfs7000-router-ospf)#no <PARAMETERS> Negates a command or set its defaults](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-860.png)






![ROUTING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 24 - 924.1.4.1 default-next-hoproute-map-modeSets the default next hop for packets satisfying match criteriaIf a packet, subjected to PBR, does not have an explicit route to the destination, the configured default next hop is used. This value is set as either the IP address of the next hop or the outgoing interface. Only one default next hop can be defined. The difference between the next hop and the default next-hop is: in case of the former, PBR occurs first, then destination-based routing. In case of the latter, the order is reverse. Use this command to set either the default next hop IP address or define either a WWAN1, PPPoE1, or VLAN interface.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7562, AP7602, AP7612, AP7622, AP7632, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdefault-next-hop [<IP>|<ROUTER-IF-NAME>|pppoe1|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwan1]Parameters• default-next-hop [<IP>|<ROUTER-IF-NAME>|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|pppoe1|vlan <1-4094>|wwan1]Examplerfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#default-next-hop wwan1rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#show context route-map 1 default-next-hop wwan1rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#Related Commandsdefault-next-hop Sets the next hop router to which packets are sent in case the next hop is not the adjacent router<IP> Specifies next hop router’s IP address<ROUTER-IF-NAME> Specifies the outgoing interface name (router interface name)pppoe1 Specifies the PPPoE interfaceserial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>Specifies the serial interface’s slot, port, and channel group IDsvlan <1-4094> Specifies a VLAN interface ID • <1-4094> – Specify a value from 1 - 4094.wwan1 Specifies the WAN interfaceno Removes default next hop router settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-869.png)


![ROUTING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 24 - 1224.1.4.4 matchroute-map-modeSets the match clausesEach route map entry has a set of match clauses used to segregate and filter packets. Packets can be segregated using any one of the following criteria:•IP Access List - A typical IP ACL can be used for routing traffic. The mark and log actions in ACL rules however are neglected. Route-map entries have separate logging. Only one ACL can be configured per route map entry.ACL rules configured under route map entries merge to create a single ACL. Route map precedence values determine the prioritization of the rules in this merged ACL. An IP DSCP value is also added to the ACL rules.-IP DSCP - Packet filtering can be performed by traffic class, as determined from the IP Differentiated Services Code Point (DSCP) field. One DSCP value can be configured per route map entry. If IP ACLs on a WLAN, ports or SVI mark packets, the new/marked DSCP value is used for matching.-Incoming WLAN - Packets can be filtered on the basis of the incoming WLAN. Depending on whether the receiving device has an onboard radio or not, the following two scenarios are possible:•Device with an onboard radio: If a device having an onboard radio and capable of PBR receives a packet on a local WLAN, this WLAN is used for selection.•Device without an onboard radio: If a device, without an onboard radio, capable of PBR receives a packet from an extended VLAN, it passes the WLAN information in the MiNT packet to the PBR router. The PBR router uses this information as match criteria.-Client role - The client role can be used as match criteria, similar to a WLAN. Each device has to agree on a unique identifier for role definition and pass the same MINT tunneled packets.-Incoming SVI - A source IP address qualifier in an ACL typically satisfies filter requirements. But if the source host (where the packet originates) is multiple hops away, the incoming SVI can be used as match criteria. In this context the SVI refers to the device interface performing PBR, and not to the source device.The action taken for filtered packets is determined by the mark (action) clauses. If no action is defined, the default is to fallback to destination-based routing for packets satisfying the match criteria. For more information on configuring mark clauses, see mark. And for more information on fallback action, see fallback.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxmatch [incoming-interface|ip|ip-access-list|wireless-client-role|wlan]match incoming-interface [<ROUTER-IF-NAME>|pppoe1|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwan1]match ip dscp <0-63>](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-872.png)
![ROUTING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 24 - 13match ip-access-list <IP-ACCESS-LIST-NAME>match wireless-client-role <ROLE-POLICY-NAME> <ROLE-NAME>match wlan <WLAN-NAME>Parameters• match incoming-interface [<ROUTER-IF-NAME>|pppoe1|serial<SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwan1]• match ip dscp <0-63>• match ip-access-list <IP-ACCESS-LIST-NAME>• match wireless-client-role <ROLE-POLICY-NAME> <ROLE-NAME>• match wlan <WLAN-NAME>incoming-interface Sets the incoming SVI match clause. Specify an interface name.<ROUTER-IF-NAME> Specifies the layer 3 interface name (route interface)pppoe1 Specifies the PPP over Ethernet interfaceserial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>Specifies the serial interface’s slot, port, and channel group IDs.vlan <1-4094> Specifies the VLAN interface ID• <1-4094> – Specify a VLAN ID from 1 - 4094.wwan1 Specifies the WAN interface nameip dscp <0-63> Sets the DSCP match clause• <0-63> – Specify a value from 0 - 63. The defined DSCP value is used as a matching clause for this route map.ip-access-list <IP-ACCESS-LIST-NAME>Sets the match clause using a pre-configured IP access list• <IP-ACCESS-LIST-NAME> – Specify a pre-configured IP access list name.wireless-client-role <ROLE-POLICY-NAME> <ROLE-NAME>Sets the wireless client role match clause• <ROLE-POLICY-NAME> – Specify a pre-configured role policy.• <ROLE-NAME> – Specify a pre-configured role within it.wlan <WLAN-NAME> Sets the incoming WLAN match clause• <WLAN-NAME> – Specify a WLAN name.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-873.png)

![ROUTING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 24 - 1524.1.4.5 next-hoproute-map-modeSets the next hop for packets satisfying match criteriaThis command allows you to configure the primary and secondary hop priority requests.Define the primary and secondary hop settings. When defined, the primary hop resource is used with no additional considerations when ever it is available.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxnext-hop [<IP>|<ROUTER-IF-NAME>|pppoe1|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwlan1] {<IP>|<ROUTER-IF-NAME>|pppoe1|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwlan1}Parameters• next-hop [<IP>|<ROUTER-IF-NAME>|pppoe1|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwlan1] {<IP>|<ROUTER-IF-NAME>|pppoe1|serial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>|vlan <1-4094>|wwlan1}next-hop Sets the next hop (primary and secondary) for packets satisfying match criteriaIt is not mandatory to define the secondary hop interface. The secondary hop is used in case the primary hop is unavailable.<IP> Specifies the primary and secondary next hop router’s IP address<WORD> Specifies the layer 3 Interface name (router interface)pppoe1 Specifies the PPP over Ethernet interfaceserial <SLOT-ID> <PORT-ID> <CHANNEL-GROUP-ID>Specifies the serial interface’s slot, port, and channel group IDs.vlan <1-4094> Specifies the VLAN interface ID• <1-4094> – Specify a VLAN ID from 1 - 4094. The VLAN interface should be a DHCP client.wwan1 Specifies the WAN interface](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-875.png)
![ROUTING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 24 - 1724.1.4.6 noroute-map-modeNegates a command or sets its defaultsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [default-next-hop|fallback|mark|match|next-hop]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated.ExampleThe following example shows the route-map ‘1’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#show context route-map 1 match incoming-interface pppoe1 next-hop vlan1 default-next-hop wwan1 mark ip dscp 7rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#no default-next-hoprfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#no next-hopThe following example shows the route-map ‘1’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#show context route-map 1 match incoming-interface pppoe1 mark ip dscp 7rfs6000-37FABE(config-routing-policy-testpolicy-route-map-1)#no <PARAMETERS> Negates a command or set its defaults](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-877.png)

![ROUTING-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 24 - 1924.1.6 norouting-policy-commandsNegates a command or sets its defaultsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [apply-to-local-packets|logging|route-map|use]Parameters• no <PARAMETERS>Usage GuidelinesThe no command negates any command associated with it. Wherever required, use the same parameters associated with the command getting negated. ExampleThe following example shows the routing policy ‘testpolicy’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-routing-policy-testpolicy)#show contextrouting-policy testpolicy logging route-map 1 match incoming-interface pppoe1 default-next-hop wwan1 mark ip dscp 7rfs6000-37FABE(config-routing-policy-testpolicy)#rfs6000-37FABE(config-routing-policy-testpolicy)#no loggingrfs6000-37FABE(config-routing-policy-testpolicy)#no route-map 1rfs6000-37FABE(config-routing-policy-testpolicy)#no apply-to-local-packetsThe following example shows the routing policy ‘testpolicy’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-routing-policy-testpolicy)#show contextrouting-policy testpolicy no apply-to-local-packetsrfs6000-37FABE(config-routing-policy-testpolicy)#no <PARAMETERS> Negates a command or set its defaults](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-879.png)

![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 325.1.1 accountingaaa-tacacs-policyConfigures the server type and interval at which interim accounting updates are sent to the server. Up to 2 accounting servers can be configured.This feature tracks user activities on the network, and provides information such as, resources used and usage time. This information can be used for audit and billing purposes.TACACS accounting tracks user activity and is useful for security audit purposes.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccounting [access-method|auth-fail|commands|server|session]accounting access-method [all|console|ssh|telnet] {(console|ssh|telnet)}accounting [auth-fail|commands|session]accounting server [<1-2>|preference]accounting server preference [authenticated-server-host|authenticated-server-number|authorized-server-host|authorized-server-number|none]accounting server <1-2> [host|retry-timeout-factor <50-200>|timeout]accounting server <1-2> host <IP/HOSTNAME> {secret [0 <SECRET>|2 <SECRET>|<SECRET>]} {port <1-65535>}accounting server <1-2> timeout <3-5> {attempts <1-3>}Parameters• accounting access-method [all|console|ssh|telnet] {(console|ssh|telnet)}• accounting [auth-fail|commands|session]access-method Configures TACACS accounting access mode. The options are: console, SSH, Telnet, and all.all Configures TACACS accounting for all access modesconsole Configures TACACS accounting for console access onlyssh Configures TACACS accounting for SSH access onlytelnet Configures TACACS accounting for Telnet access onlyauth-fail Enables accounting for authentication fail details. This option is disabled by default.commands Enables accounting of commands executed. This option is disabled by default.session Enables accounting for session start and stop details. This option is disabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-882.png)
![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 4• accounting server preference [authenticated-server-host|authenticated-server-number|authorized-server-host|authorized-server-number|none]• accounting server <1-2> retry-timeout-factor <50-200>• accounting server <1-2> host <IP/HOSTNAME> {secret [0 <SECRET>|2 <SECRET>|<SECRET>]} {port <1-65535>}server Configures a TACACS accounting serverpreference Configures the accounting server preference (specifies the method of selecting a server, from the pool, to send the request)authenticated-server-hostSets the authentication server as the accounting server. This is the default setting.This parameter indicates the same server is used for authentication and accounting. The server is referred to by its hostname.authenticated-server-numberSets the authentication server as the accounting serverThis parameter indicates the same server is used for authentication and accounting. The server is referred to by its index or number.authorized-server-host Sets the authorization server as the accounting serverThis parameter indicates the same server is used for authorization and accounting. The server is referred to by its hostname.authorized-server-numberSets the authorized server as the accounting serverThis parameter indicates the same server is used for authorization and accounting. The server is referred to by its index number.none Indicates the accounting server is independent of the authentication and authorization serversserver <1-2> Configures an accounting server. Up to 2 accounting servers can be configuredretry-timeout-factor <50-200>Sets the scaling factor for retry timeouts• <50-200> – Specify a value from 50 - 200. The default is 100.A value of 100 indicates the time gap between two consecutive retires remains the same irrespective of the number of retries.A value lesser than 100 indicates the time gap between two consecutive retries reduces with each successive retry.A value greater than 100 indicates the time gap between two consecutive retries increases with each successive retry.server <1-2> Configures an accounting server. Up to 2 accounting servers can be configuredhost <IP/HOSTNAME> Configures the accounting server’s IP address or hostnamesecret [0 <SECRET>|2 <SECRET>|<SECRET>]Optional. Configures a common secret key used to authenticate with the accounting server• 0 <SECRET> – Configures a clear text secret key• 2 <SECRET> – Configures an encrypted secret key• <SECRET> – Specify the secret key. This shared secret should not exceed 127 characters.port <1-65535> Optional. Configures the accounting server port (the port used to connect to the accounting server)• <1-65535> – Specify the TCP accounting port number from 1 - 65535. The default port is 49.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-883.png)

![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 625.1.2 authenticationaaa-tacacs-policyConfigures user authentication parameters. Users are allowed or denied access to the network based on the authentication parameters set.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthentication [access-method|directed-request|server|service]authentication access-method [all|console|ssh|telnet|web] {(console|ssh|telnet|web)}authentication directed-requestauthentication server <1-2> [host|retry-timeout-factor|timeout]authentication server <1-2> host <IP/HOSTNAME> {secret [0 <SECRET>|2 <SECRET>|<SECRET>]} {port <1-65535>}authentication server <1-2> retry-timeout-factor <50-200>authentication server <1-2> timeout <3-60> {attempts <1-10>}authentication service <SERVICE-NAME> {protocol <AUTHENTICATION-PROTO-NAME>}Parameters• authentication access-method [all|console|ssh|telnet|web] {(console|ssh|telnet)}• authentication directed-request• authentication server <1-2> host <IP/HOSTNAME> {secret [0 <SECRET>|2 <SECRET>|<SECRET>]} {port <1-65535>}access-method Configures access modes for TACACS authentication. The options are: console, SSH, Telnet, Web, and all.all Authenticates users using all access modes (console, SSH, and Telnet)console Authenticates users using console access onlyssh Authenticates users using SSH access onlytelnet Authenticates users using Telnet access onlyweb Authenticates users using Web interface onlydirected-request Enables user to specify TACACS server to use with `@server'. This option is disabled by default.The specified server should be present in the configured servers list.server <1-2> Configures a TACACS authentication server. Up to 2 TACACS servers can be configured• <1-2> – Specify the TACACS server index from 1 - 2.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-885.png)
![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 7• authentication server <1-2> retry-timeout-factor <50-200>• authentication server <1-2> timeout <3-60> {attempts <1-10>}• authentication service <SERVICE-NAME> {protocol <AUTHENTICATION-PROTO-NAME>}host <IP/HOSTNAME> Sets the TACACS server’s IP address or hostnamesecret [0 <SECRET>|2 <SECRET>|<SECRET>]Configures the secret key used to authenticate with the TACACS server• 0 <SECRET> – Configures a clear text secret• 2 <SECRET> – Configures an encrypted secret• <SECRET> – Specify the secret key. The shared key should not exceed 127 characters.port <1-65535> Optional. Specifies the port used to connect to the TACACS server• <1-65535> – Specify a value for the TCP authentication port from 1 - 65535. The default port is 49.server <1-2> Configures a TACACS authentication server. Up to 2 TACACS servers can be configured• <1-2> – Specify the TACACS server index from 1 - 2.retry-timeout-factor <50-200>Configures timeout scaling between two consecutive TACACS authentication retries• <50-200> – Specify the scaling factor from 50 - 200. The default is 100.A value of 100 indicates the interval between consecutive retires remains the same irrespective of the number of retries.A value lesser than 100 indicates the interval between consecutive retries reduces with each successive retry.A value greater than 100 indicates the interval between consecutive retries increases with each successive retry.server <1-2> Configures a TACACS authentication server. Up to 2 TACACS servers can be configured• <1-2> – Specify the TACACS server index from 1- 2.timeout <3-60> Configures the timeout, in seconds, for each request sent to the TACACS server. This is the time allowed to elapse before another request is sent to the TACACS server. If a response is received from the TACACS server within this time, no retry is attempted.• <3-60> – Specify a value from 3- 60 seconds. The default is 3 seconds.attempts <1-10> Optional. Indicates the number of retry attempts to make before giving up• <1-10> – Specify a value from 1 -10. The default is 3.service <SERVICE-NAME>Configures the TACACS authentication service nameprotocol <AUTHENTICATION-PROTO-NAME>Optional. Specify the authentication protocol used with this TACACS policy.A maximum of five entries is allowed.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-886.png)
![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 925.1.3 authorizationaaa-tacacs-policyConfigures authorization parametersThis feature allows network administrators to limit user accessibility and configure varying levels of accessibility for different users.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxauthorization [access-method|allow-privileged-commands|server]authorization access-method [all|console|telnet|ssh] {(console|ssh|telnet)}authorization server [<1-2>|preference]authorization server <1-2> [host|retry-timeout-factor|timeout]authorizationserver <1-2> host <IP/HOSTNAME> {secret [0 <SECRET>|2 <SECRET>|<SECRET>]} {port <1-65535>}authorization server <1-2> retry-timeout-factor <50-200>authorization server <1-2> timeout <3-5> {attempts <1-3>}authorization server preference [authenticated-server-host|authenticated-server-number|none]Parameters• authorization access-method [all|console|telnet|ssh] {(console|ssh|telnet)}• authorization allow-privileged-commands• authorization server <1-2> host <IP/HOSTNAME> {secret [0 <SECRET>|2 <SECRET>|<SECRET>]} {port <1-65535>}access-method Configures the access method for command authorizationall Authorizes commands from all access methodsconsole Authorizes commands from the console onlytelnet Authorizes commands from Telnet onlyssh Authorizes commands from SSH only{console|ssh|telnet} Optional. Configures more than one access method for command authorizationallow-privileged-commandsAllows privileged commands execution without command authorization. This option is disabled by default.server <1-2> Configures a TACACS authorization server. Up to 2 TACACS servers can be configured• <1-2> – Specify the TACACS server index from 1 - 2.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-888.png)
![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 10• authorization server <1-2> retry-timeout-factor <50-200>• authorization server <1-2> timeout <3-5> {attempts <1-3>}• authorization server preference [authenticated-server-host|authenticated-server-number|none]host <IP/HOSTNAME> Sets the TACACS server’s IP address or hostnamesecret [0 <SECRET>|2 <SECRET>|<SECRET>]Optional. Configures the secret used to authorize with the TACACS server• 0 <SECRET> – Configures a clear text secret• 2 <SECRET> – Configures an encrypted secret• <SECRET> – Specify the secret key. The shared key should not exceed 127 characters.port <1-65535> Optional. Specifies the port used to connect to the TACACS server• <1-65535> – Specify a value for the TCP authorization port from 1 - 65535. The default port is 49.server <1-2> Configures a TACACS authorization server. Up to 2 TACACS servers can be configured• <1-2> – Specify the TACACS server index from 1 - 2.retry-timeout-factor <50-200>Configures the scaling of timeouts between consecutive TACACS authorization retries• <50-200> – Specify the scaling factor from 50 - 200. The default is 100.A value of 100 indicates the interval between consecutive retires remains the same irrespective of the number of retries.A value lesser than 100 indicates the interval between consecutive retries reduces with each successive retry.A value greater than 100 indicates the interval between consecutive retries increases with each successive retry.server <1-2> Configures a TACACS authorization server. Up to 2 TACACS servers can be configured• <1-2> – Specify the TACACS server’s index from 1- 2.timeout <3-5> Configures the timeout, in seconds, for each request sent to the TACACS server. This is the time allowed to elapse before another request is sent to the TACACS server. If a response is received from the TACACS server within this time, no retry is attempted.• <3-5> – Specify a value from 3 - 5 seconds. The default is 3 seconds.attempts <1-3> Optional. Indicates the number of retry attempts to make before giving up• <1-3> – Specify a value from 1 - 3. The default is 3.preference Configures the authorization server preferenceauthenticated-server-hostSets the authentication server as the authorization serverThis parameter indicates the same server is used for authentication and authorization. The server is referred to by its hostname.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-889.png)
![AAA-TACACS-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 25 - 1225.1.4 noaaa-tacacs-policyNegates a AAA TACACS policy command or sets its defaultSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622,, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [accounting|authentication|authorization]Parameters• no <PARAMETERS>ExampleThe following example shows the AAA-TACACS policy ‘test’ settings before the ‘no’ commands are executed:rfs6000-37FABE(config-aaa-tacacs-policy-test)#show contextaaa-tacacs-policy test authentication directed-request accounting server preference authorized-server-number authorization allow-privileged-commands accounting auth-fail accounting commandsrfs6000-37FABE(config-aaa-tacacs-policy-test)#rfs6000-37FABE(config-aaa-tacacs-policy-test)#no authentication directed-requestrfs6000-37FABE(config-aaa-tacacs-policy-test)#no accounting auth-failrfs6000-37FABE(config-aaa-tacacs-policy-test)#no authorization allow-privileged-commandsThe following example shows the AAA-TACACS policy ‘test’ settings after the ‘no’ commands are executed:rfs6000-37FABE(config-aaa-tacacs-policy-test)#show contextaaa-tacacs-policy test accounting server preference authorized-server-number accounting commandsrfs6000-37FABE(config-aaa-tacacs-policy-test)#Related Commandsno <PARAMETERS> Provide the parameters needed to reset or disable the desired AAA-TACACS policy setting.accounting Configures TACACS accounting parametersauthentication Configures TACACS authentication parametersauthorization Configures TACACS authorization parameters](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-891.png)

![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 426.1.1 allowed-vlansmeshpoint-config-instanceDefines VLANs allowed to pass traffic on the mesh network. Use this command to add and remove VLANs from the list of allowed VLANs.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxallowed-vlans [<VLAN-ID>|add <VLAN-ID>|remove <VLAN-ID>]Parameters• allowed-vlans [<VLAN-ID>|add <VLAN-ID>|remove <VLAN-ID>]Examplerfs6000-37FABE(config-meshpoint-test)#allowed-vlans 1rfs6000-37FABE(config-meshpoint-test)#allowed-vlans add 10-23rfs6000-37FABE(config-meshpoint-test)#allowed-vlans remove 17rfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test meshid test beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 security-mode none no rootrfs6000-37FABE(config-meshpoint-test)#Related Commandsallowed-vlans Defines VLANs allowed access on the mesh network<VLAN-ID> The VLAN ID or the range of IDs to be managed.A single VLAN or multiple VLANs can be added to the list of allowed VLANs. When adding multiple VLANs, specify the range (for example, 10-20, 25, 30-35). Use this command to create a VLAN list on a new meshpoint.add <VLAN-ID> Adds a single VLAN or a range of VLANs to the list of allowed VLANs. To specify a range of VLANs, specify the first and last VLAN ID in the range separated by a hyphen (for example, 1-10).• <VLAN-ID> – Specify the VLAN ID or the range of IDs to add.remove <VLAN-ID> Removes a single VLAN or a range of VLANs from the list of allowed VLANs• <VLAN-ID> – Specify the VLAN ID or the range of IDs to remove.no Clears the list of VLANs allowed access to the mesh network](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-895.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 526.1.2 beacon-formatmeshpoint-config-instanceConfigures the beacon transmission format for this meshpoint. Beacons are transmitted periodically to advertise that a wireless network is available. It contains all the required information for a device to connect to the network.The beacon format advertises how a mesh capable AP7161 acts. APs can act either as an access point or a meshpoint.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxbeacon-format [access-point|mesh-point]Parameters• beacon-format [access-point|mesh-point]Examplerfs6000-37FABE(config-meshpoint-test)#beacon-format mesh-pointrfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test meshid test beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 security-mode none no rootrfs6000-37FABE(config-meshpoint-test)#Related Commandsbeacon-format Configures how a mesh capable AP71XX acts in a mesh networkaccess-point Uses access point style beaconsmesh-point Uses meshpoint style beacons (this is the default setting)no Resets the beacon format for this meshpoint to its default (mesh-point)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-896.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 626.1.3 control-vlanmeshpoint-config-instanceConfigures a VLAN as the dedicated control VLANMesh management traffic can be sent over a dedicated VLAN. This dedicated VLAN is known as the control VLAN, and should be configured in the backhaul port of all the access points configured as meshpont roots. Once configured, the control VLAN enables communication between meshpoint’s root APs.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcontrol-vlan [<1-4094>|<VLAN-ALIAS-NAME>]Parameters• control-vlan [<1-4094>|<VLAN-ALIAS-NAME>]Examplerfs6000-37FABE(config-meshpoint-test)#control-vlan 1rfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test meshid test beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 security-mode none no rootrfs6000-37FABE(config-meshpoint-test)#Related Commandscontrol-vlan Configures a VLAN as a dedicated carrier of mesh management traffic[<1-4094>|<VLAN-ALIAS-NAME>]Configures the control VLAN• <1-4094> – Specify the control VLAN from 1 - 4094. The default is VLAN 1.• <VLAN-ALIAS-NAME> – Uses a vlan-alias to specify the control vlan. If using a vlan-alias, ensure that it is existing and configured.If VLAN 1 is configured as the control VLAN, ensure that the VLAN is configured in the wired port of all access points belonging to same meshpoint.Note: Control VLAN need not necessarily be added in the allowed VLAN list.no Resets the control VLAN for this meshpoint to its default of 1](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-897.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 726.1.4 data-ratesmeshpoint-config-instanceConfigures individual data rates for the 2.4 GHz and 5.0 GHz frequency bands. In Mesh network, a mesh point is a virtual mesh networking instance on a device, similar to a WLAN AP. On each device, up to 4 mesh points can be created and 2 can be created per radio. Each mesh point radio can have carefully administrated radio rates specific to the 2.4 or 5 GHz band. Use this command to configure these radio rates.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxdata-rates [2.4GHz|5GHz]data-rates 2.4GHz [b-only|bg|bgn|default|g-only|gn]data-rates 2.4GHz custom (1|11|12|18|2|24|36|48|5.5|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|mcs0-15|mcs0-7|mcs8-15|basic-mcs0-7)data-rates 5GHz [a-only|an|default]data-rates 5GHz custom (12|18|24|36|48|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|mcs0-15|mcs0-7|mcs8-15|basic-mcs0-7)Parameters• data-rates 2.4GHz [b-only|bg|bgn|default|g-only|gn]• data-rates 2.4GHz custom (1|11|12|18|2|24|36|48|5.5|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|mcs0-15|mcs0-7|mcs8-15|basic-mcs0-7)NOTE: Ensure that the basic data rates configured on a meshpoint’s root and non-root access points is the same.data-rates 2.4GHz Configures preset data rates for the 2.4 GHz frequency.b-only Configures data rate for the meshpoint using 802.11b only rates.bg Configures data rate for the meshpoint using 802.11b and 802.11g rates.default Configures data rate for the meshpoint at a pre-configured default rate for this frequency.g-only Configures data rate for the meshpoint using 802.11g only rates.gn Configures data rate for the meshpoint using 802.11g and 802.11n rates.data-rates 2.4GHz Configures the preset data rates for the 2.4 GHz frequencyDefine both minimum Basic and optimal Supported rates as required for the 802.11b rates, 802.11g rates and 802.11n rates supported by the 2.4 GHz band. Contd..](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-898.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 8• data-rates 5GHz [a-only|an|default]These are the rates wireless client traffic is supported within this mesh point. If supporting 802.11n, select a supported MCS index.Set a Modulation and Coding Scheme (MCS) in respect to the radio's channel width and guard interval. A MCS defines (based on RF channel conditions) an optimal combination of 8 data rates, bonded channels, multiple spatial streams, different guard intervals and modulation types.Meshpoints can communicate as long as they support the same basic MCS (as well as non-802.11n basic rates). The selected rates apply to associated client traffic within this mesh point only.custom (1|11|12|18|2|24|36|48|5.5|54|6|9|basic-1|basic-11|basic-12|basic-18|basic-2|basic-24|basic-36|basic-48|basic-5.5|basic-54|basic-6|basic-9|mcs0-15|mcs0-7|mcs8-15|basic-mcs0-7)Configures custom rates• 1 – Configures the available rate at 1 Mbps• 2 – Configures the available rate at 2 Mbps• 5.5 – Configures the available rate at 5.5 Mbps• 6 – Configures the available rate at 6 Mbps• 9 – Configures the available rate at 9 Mbps• 11 – Configures the available rate at 11 Mbps• 12 – Configures the available rate at 12 Mbps• 18 – Configures the available rate at 18 Mbps• 24 – Configures the available rate at 24 Mbps• 36 – Configures the available rate at 36 Mbps• 48 – Configures the available rate at 48 Mbps• 54 – Configures the available rate at 54 Mbps• basic-1 – Configures the available rate at a basic rate of 1 Mbps• basic-2 – Configures the available rate at a basic rate of 2 Mbps• basic-5.5 – Configures the available rate at a basic rate of 5.5 Mbps• basic-6 – Configures the available rate at a basic rate of 6 Mbps• basic-9 – Configures the available rate at a basic rate of 9 Mbps• basic-11 – Configures the available rate at a basic rate of 11 Mbps• basic-12 – Configures the available rate at a basic rate of 12 Mbps• basic-18 – Configures the available rate at a basic rate of 18 Mbps• basic-24 – Configures the available rate at a basic rate of 24 Mbps• basic-36 – Configures the available rate at a basic rate of 36 Mbps• basic-48 – Configures the available rate at a basic rate of 48 Mbps• basic-54 – Configures the available rate at a basic rate of 54 Mbps• basic-mcs0-7 – Configures the MCS index range of 0 - 7 for basic rate• mcs0-7 – Configures the MCS index range of 0-7 as the data rate• mcs0-15 – Configures the MCS index range of 0-15 as the data rate• msc8-15 – Configures the MCS index range of 8-15 as the data rateMultiple choices can be made from the above list of rates.data-rates 5GHz Configures the preset data rates for the 5.0 GHz frequencya-only Configures the data rate for the meshpoint using 802.11a only ratesbn Configures the data rate for the meshpoint using 802.11a and 802.11n rates](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-899.png)




![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 1526.1.9 nomeshpoint-config-instanceNegates meshpoint commands or resets their values to defaultSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [allowed-vlans|beacon-format|control-vlan|description|force|meshid|root|security-mode|shutdown]no data-rates [2.4GHz|5GHz]no force peer-paths-through-rootno neighbor inactivity-timeoutno use [aaa-policy|meshpoint-qos-policy]no wpa2 [eap|key-rotation|psk]no wpa2 eap [auth-type|identity|peap-mschapv2|tls trustpoint]no wpa2 key-rotation [broadcast|unicast]no wpa2 pskno service allow-ht-onlyParameters• no <PARAMETERS>Examplerfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test description "This is an example of a meshpoint description" meshid TestingMeshPoint shutdown beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 neighbor inactivity-timeout 300 data-rates 2.4GHz bgn data-rates 5GHz an security-mode psk wpa2 psk 0 Test Company wpa2 key-rotation unicast 1200 wpa2 key-rotation broadcast 600 rootrfs6000-37FABE(config-meshpoint-test)#rfs6000-37FABE(config-meshpoint-test)#no allowed-vlansrfs6000-37FABE(config-meshpoint-test)#no beacon-formatrfs6000-37FABE(config-meshpoint-test)#no control-vlanrfs6000-37FABE(config-meshpoint-test)#no descriptionrfs6000-37FABE(config-meshpoint-test)#no meshidrfs6000-37FABE(config-meshpoint-test)#no rootrfs6000-37FABE(config-meshpoint-test)#no security-modeno <PARAMETERS> Removes or reverts this meshpoint settings to default based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-906.png)

![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 1926.1.11 security-modemeshpoint-config-instanceConfigures the security mode for this meshpointSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxsecurity-mode [eap|none|psk]Parameters• security-mode [eap|none|psk]ExampleThe following example shows root meshpoint configuration with PSK authentication enabled:rfs6000-37FABE(config-meshpoint-test)#security-mode pskrfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test description "This is an example of a meshpoint description" meshid TestingMeshPoint beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 neighbor inactivity-timeout 300 data-rates 2.4GHz bgn data-rates 5GHz an security-mode psk rootrfs6000-37FABE(config-meshpoint-test)#The following example shows root meshpoint configuration with EAP authentication enabled:rfs6000-37FABE(config-meshpoint-root)#show contextmeshpoint test meshid test beacon-format mesh-point control-vlan 101 allowed-vlans 101,103 use aaa-policy test security-mode eap rootrfs6000-37FABE(config-meshpoint-test)#Related Commandssecurity-mode Configures the security mode for this meshpointeap Uses 802.1X/EAP as the security mode. When using this option, use the wpa2 command to specify the EAP authentication type and related parameters.none No security is configured for this meshpointpsk Uses Pre Shared Key (PSK) as the security mode. When using this option, use the wpa2 command to enter a 64 character HEX or an 8-63 ASCII character passphrase used for authentication on the mesh point.no Resets the security configuration for this meshpoint to “none”. This indicates that no security is configured for this meshpoint.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-910.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 2026.1.12 servicemeshpoint-config-instanceUse this command to allow only those neighbors who are capable of 802.11n data rates to associate with this meshpoint.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxservice [allow-ht-only|show cli]Parameters• service [allow-ht-only|show cli]Examplerfs6000-37FABE(config-meshpoint-test)#service allow-ht-onlyrfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test description "This is an example of a meshpoint description" meshid TestingMeshPoint shutdown beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 neighbor inactivity-timeout 300 data-rates 2.4GHz bgn data-rates 5GHz an security-mode psk wpa2 psk 0 Test Company wpa2 key-rotation unicast 1200 wpa2 key-rotation broadcast 600 root service allow-ht-onlyrfs6000-37FABE(config-meshpoint-test)#Related Commandsservice allow-ht-only Allows only those neighbors who are capable of high throughput data rates (802.11n data rates) to associate with the meshpointservice show cli Displays running system configurationno Removes the restriction that only 802.11n capable neighbor devices can associate with this meshpointservice Invokes service commands to troubleshoot or debug](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-911.png)

![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 2226.1.14 usemeshpoint-config-instanceUses a Quality of Service (QoS) policy defined specifically for meshpoints. To use this QoS policy, it must be defined. To define a meshpoint QoS policy, see meshpoint-qos-policy-config-instance.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxuse [aaa-policy <AAA-POLICY-NAME>|meshpoint-qos-policy <MESHPOINT-QOS-POLICY-NAME>]Parameters• use [aaa-policy <AAA-POLICY-NAME>|meshpoint-qos-policy <MESHPOINT-QOS-POLICY-NAME>]Examplerfs6000-37FABE(config-meshpoint-test)#use meshpoint-qos-policy testrfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test description "This is an example of a meshpoint description" meshid TestingMeshPoint shutdown beacon-format mesh-point control-vlan 1 allowed-vlans 1,10-16,18-23 neighbor inactivity-timeout 300 data-rates 2.4GHz bgn data-rates 5GHz an security-mode psk root use meshpoint-qos-policy testrfs6000-37FABE(config-meshpoint-test)#Related Commandsuse meshpoint-qos-policy <MESHPOINT-QOS-POLICY-NAME>Configures this meshpoint to use a predefined meshpoint QoS policy• <MESHPOINT-QOS-POLICY-NAME> – Specify the meshpoint QoS policy name (should be existing and configured).use aaa-policy <AAA-POLICY-NAME>Configures this meshpoint to use a predefined aaa-policy• <AAA-POLICY-NAME> – Specify the aaa-policy name (should be existing and configured).no Removes the meshpoint QoS policy associated with this meshpointmeshpoint-qos-policy-config-instanceCreates and configures a meshpoint QoS policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-913.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 2326.1.15 wpa2meshpoint-config-instanceUse this command to configure the parameters of authentication mode specified using the ‘security-mode’ keyword. This command also allows you to set a unicast and broadcast key rotation interval.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxwpa2 [eap|psk|key-rotation]wpa2 key-rotation [broadcast|unicast] <30-86400>wpa2 psk [0 <SECRET>|2 <SECRET>|<SECRET>]wpa2 eap [auth-type|identity|peap-mschapv2|tls]wpa2 eap [auth-type [peap-mschapv2|tls]|identity <WORD>]wpa2 eap peap-mschapv2 user <USER-NAME> password [0 <WORD>|2 <WORD>|<WORD>] {trustpoint <TRUSTPOINT-NAME>}wpa2 eap tls trustpoint <TRUSTPOINT-NAME>Parameters• wpa2 key-rotation [broadcast|unicast] <30-86400>• wpa2 psk [0 <SECRET>|2 <SECRET>|<SECRET>]wpa2 key-rotation Enables periodic rotation of encryption keys used for broadcast and unicast trafficbroadcast Configures key rotation interval for broadcast and multicast traffic. This option is disabled by default.When enabled, the key indices used for encrypting/decrypting broadcast traffic is alternatively rotated based on the defined interval. Key rotation enhances the broadcast traffic security on the WLAN.unicast Configures key rotation interval for unicast traffic. This option is disabled by default.<30-86400> Configures key rotation interval from 30 - 86400 seconds for unicast or broadcast transmissionwpa2 psk Configures the shared key for authentication mode PSK. If the security mode is set as ‘psk’ using the ‘security-mode’ keyword, use this command to configure the pre-shared key.secret [0 <SECRET>|2 <SECRET>|<SECRET>]Configures the PSK used to authenticate this meshpoint with other meshpoints in the network• 0 <SECRET> – Configures a clear text secret• 2 <SECRET> – Configures an encrypted secret• <SECRET> – Specify the secret key. The pre-shared key can be in ASCII (8 to 63 characters in length) or Hexadecimal (not exceeding 64 characters in length) formats.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-914.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 24• wpa2 eap [auth-type [peap-mschapv2|tls]|identity <WORD>]• wpa2 eap peap-mschapv2 user <USER-NAME> password [0 <WORD>|2 <WORD>|<WORD>] {trustpoint <TRUSTPOINT-NAME>}• wpa2 eap tls trustpoint <TRUSTPOINT-NAME>Examplerfs6000-37FABE(config-meshpoint-test)#wpa2 key-rotation broadcast 600rfs6000-37FABE(config-meshpoint-test)#wpa2 key-rotation unicast 1200rfs6000-37FABE(config-meshpoint-test)#wpa2 psk Test Companyrfs6000-37FABE(config-meshpoint-test)#show contextmeshpoint test description "This is an example of a meshpoint description" meshid TestingMeshPointwpa2 eap Configures the 802.1X/EAP based authentication type for this meshpoint. If the security mode is set as ‘eap’ using the ‘security-mode’ keyword, use this command to specify the EAP type. The options are: peap-mschapv2 and tls.auth-type [peap-mschapv2|tls]Specifies the EAP authentication type. The options are:• peap-mschapv2 – Configures EAP authentication type as Protected Extensible Authentication Protocol (PEAP) with default auth type MSCHAPv2. This is the default setting. If using auth-type as ‘peap-mschapv2’, use the ‘peap-mschapv2’ keyword to configure user credentials and trustpoint details.• tls – Configures EAP authentication type as Transport Layer Security (TLS)If using auth-type as ‘tls’, use the ‘tls’ keyword to configure trustpoint details.Note: The certificate should be issued from an Enterprise or public certificate authority to allow 802.1X clients to validate the identity of the authentication server prior to forwarding credentials.identity <WORD> Configures identity to be used during phase1 authentication• <WORD> – Enter a string up to 256 characters in length (this should not be actual identity of user but some anonymous/bogus username)wpa2 eap peap-mschapv2 Configures PEAP-related user credentials and trustpoint detailsuser <USER-NAME> password [0 <WORD>|2 <WORD>|<WORD>]Specify the user credentials used for authentication• user <USER-NAME> – Specify the user name.• password [0 <WORD>|2 <WORD>|<WORD>] – Specify the password associated with the specified user.trustpoint <TRUSTPOINT-NAME>Optional. Associates a trustpoint used for installing CA certificate and verifying server certificate• <TRUSTPOINT-NAME> – Specify the trustpoint name (should be existing and configured).wpa2 eap tls Configures TLS client related parameterstrustpoint <TRUSTPOINT-NAME>Configures trustpoint details• trustpoint <TRUSTPOINT-NAME> – Assigns a trustpoint to be used for installing TLS client certificate, client private key, and CA certificate• <TRUSTPOINT-NAME> – Specify the trustpoint name (should be existing and configured)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-915.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 2726.2.1 accelerated-multicastmeshpoint-qos-policy-config-instanceConfigures the accelerated multicast stream’s address and forwarding QoS classificationSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaccelerated-multicast [<MULTICAST-IP>|autodetect] {classification [background|best-effort|trust|video|voice]}Parameters• accelerated-multicast [<MULTICAST-IP>|autodetect] {classification [background|best-effort|trust|video|voice]}NOTE: For accelerated multicast feature to work, IGMP querier must be enabled. When a user joins a multicast stream, an entry is created in the device’s (AP or wireless controller) snoop table and the entry is set to expire after a set time period. Multicast packets are forwarded to the appropriate wireless LAN or mesh until this entry is available in the snoop table. Snoop querier keeps the snoop table current by updating entries that are set to expire. It also keeps an entry for each multicast stream till there are users registered for the stream.accelerated-multicast Configures the accelerated multicast stream address and forwarding QoS classification<MULTICAST-IP> Specify a list of multicast addresses and classifications. Packets are accelerated when the destination address matches.autodetect Lets the system to automatically detect multicast streams to be acceleratedThis option allows the administrator to convert multicast packets to unicast in order to provide better overall airtime utilization and performance. The system can be configured to automatically detect multicast streams and convert them to unicast, or specify which multicast streams are to be converted to unicast. When the stream is converted and being queued up for transmission, there are a number of classification mechanisms applied to the stream and the administrator can select what type of classification they would want. Classification types are trust, voice, video, best effort, and background.classification Optional. Defines the QoS classification to apply to a multicast stream. The following options are available:•background• best effort•trust•video•voice](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-918.png)

![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 2926.2.2 nomeshpoint-qos-policy-config-instanceNegates the commands for meshpoint QoS policy or resets their values to their defaultSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [accelerated-multicast|rate-limit]no accelerated-multicast [<MULTICAST-IP>|autodetect]no rate-limit [meshpoint|neighbor] [from-air|to-air] {max-burst-size|rate}no rate-limit [meshpoint|neighbor] [from-air|to-air] {red-threshold [background|best-effort|video|voice]}Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-meshpoint-qos-test)#show contextmeshpoint-qos-policy test rate-limit meshpoint from-air rate 80000 rate-limit meshpoint from-air red-threshold video 80 rate-limit meshpoint from-air red-threshold voice 70 accelerated-multicast 224.0.0.1 classification videorfs6000-37FABE(config-meshpoint-qos-test)#no rate-limit meshpoint from-air raterfs6000-37FABE(config-meshpoint-qos-test)#no rate-limit meshpoint from-air red-threshold video 80rfs6000-37FABE(config-meshpoint-qos-test)#no rate-limit meshpoint from-air red-threshold voice 70rfs6000-37FABE(config-meshpoint-qos-test)#show contextmeshpoint-qos-policy test accelerated-multicast 224.0.0.1 classification videorfs6000-37FABE(config-meshpoint-qos-test)#no <PARAMETERS> Removes or reverts this meshpoint QoS policy settings to default based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-920.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 3026.2.3 rate-limitmeshpoint-qos-policy-config-instanceConfigures the rate limiting of traffic on a per meshpoint or per neighbor basisExcessive traffic can cause performance issues or bring down the network entirely. Excessive traffic, bombardments and interference are caused by numerous sources, such as network loops, faulty devices, or malicious software (such as a worm or virus) that has infected one or more branch-level devices. Rate limiting limits the maximum rate sent to or received from the wireless network (and meshpoint) per neighbor. It prevents any single user from overwhelming the wireless network. It also provides differential service for service providers. An administrator can set separate QoS rate limit configurations for data transmitted from the network and data transmitted from a mesh point's neighbor.Before defining rate limit thresholds for meshpoint transmit and receive traffic, it is recommended that you define the normal number of ARP, broadcast, multicast, and unknown unicast packets that typically transmit and receive from each supported WMM access category. If thresholds are defined too low, normal network traffic (required by end-user devices) is dropped, resulting in intermittent outages and performance problems.A connected neighbor can also have QoS rate limit settings defined in both the transmit and receive direction.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XX• Wireless Controllers — RFS6000• Service Platforms — NX6524, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxrate-limit [meshpoint|neighbor]rate-limit [meshpoint|neighbor] [from-air|to-air] {max-burst-size <2-1024>|rate <50-1000000>}rate-limit [meshpoint|neighbor] [from-air|to-air] {red-threshold [background <0-100>|best-effort <0-100>|video <0-100>|voice <0-100>]}Parameters• rate-limit [meshpoint|neighbor] [from-air|to-air] {max-burst-size <2-1024>|rate <50-1000000>}meshpoint Configures rate limit parameters for all data received from any meshpoint in the mesh network. This option is disabled by default.neighbor Configures rate limit parameters for neighboring meshpoint devices. Enables rate limiting for data transmitted from the client to its associated access point radio and connected controller. This option is disabled by default.from-air Configures rate limits for traffic from the wireless neighbor to the network.to-air Configures rate limits for traffic from the network to the wireless neighbor.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-921.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 31• rate-limit [meshpoint|neighbor] [from-air|to-air] {red-threshold [background <0-100>|best-effort <0-100>|video <0-100>|voice <0-100>]}max-burst-size <2-1024> Optional. Configures the maximum burst size in kilobytes.• <2-1024> – Set a value from 2 - 1024 kbytes.For a meshpoint: The smaller the burst, the less likely that the transmit packet transmission results in congestion for the meshpoint's client destinations. By trending the typical number of ARP, broadcast, multicast and unknown unicast packets over a period of time, the average rate for each access category can be obtained. Once a baseline is obtained, administrators should then add a 10% margin (minimally) to allow for traffic bursts at the site. The default burst size is 320 kbytes.For a neighbor: The smaller the burst, the less likely the transmit packet transmission will result in congestion for the wireless client. The default burst size is 64 kbytes.rate <50-1000000> Optional. Defines a receive or transmit rate limit in kilobytes per second• <50-1000000> – Set a value from 50 - 1000000 kbps.For a meshpoint: This limit constitutes a threshold for the maximum number of packets transmitted or received over the meshpoint (from all access categories). Traffic that exceeds the defined rate is dropped and a log message is generated. The default setting is 5000 kbps.For a neighbor: This limit constitutes a threshold for the maximum the number of packets transmitted or received (from all access categories). Traffic that exceeds the defined rate is dropped by the client and a log message is generated. The default rate is 1,000 kbps.meshpoint Configures rate limit parameters for a meshpointneighbor Configures rate limit parameters for neighboring meshpoint devicesfrom-air Configures rate limits for traffic from the wireless neighbor to the networkto-air Configures rate limit value for traffic from the network to the wireless neighborred-threshold Optional. Configures random early detection threshold (RED threshold) for traffic classbackground <0-100> The following keyword is applicable to the ‘from-air’ and ‘to-air’ traffics.• background <0-100> – Configures the threshold for low priority (background) traffic• <0-100> – Specify a value from 0 - 100.For a meshpoint: This is a percentage of the maximum burst size for low priority traffic. Background traffic exceeding the defined threshold is dropped and a log message is generated. Background traffic consumes the least bandwidth of any access category, so this value can be set to a lower value once a general transmit rate is known by the network administrator (using a time trend analysis). The default threshold is 50%.For a neighbor: This is a percentage of the maximum burst size for low priority traffic. Background traffic exceeding the defined threshold is dropped by the client and a log message is generated. The default threshold is 50%.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-922.png)




![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 3826.3.2.1 acsmeshpoint-device-commandsEnables Automatic Channel Selection (ACS) on this meshpoint device (access point). When enabled, this feature automatically selects the best channel for a meshpoint-device radio based on the device configuration, channel conditions, and network layout.In a wireless network deployment, it is advantageous for network devices to have the ability to operate in multiple channels and not be limited to only a single channel. Multiple channels increase the bandwidth and throughput of the wireless network. In such a scenario, each network device must have a mechanism to dynamically select a suitable channel of operation. ACS provides the required mechanism for a MCX enabled device.Use this command to configure the ACS settings and override the default meshpoint configurations.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxacs [channel-hold-time|channel-switch-delta|channel-width|ocs-duration|ocs-frequency|path-min|path-threshold|preferred-interface-tolerance-period|preferred-radio-interface|priority-meshpoint|sample-count|snr-delta|signal-threshold|tolerance-period]acs channel-hold-time [2.4GHz|5GHz] <0-86400>acs channel-switch-delta [2.4GHz|5GHz] <5-35>acs channel-width [2.4GHz|5GHz] [20MHz|40MHz|80MHz|auto]acs ocs-duration [2.4GHz|5GHz] <20-250>acs ocs-frequency [2.4GHz|5GHz] <1-60>acs path-min [2.4GHz|5GHz] <100-20000>acs path-threshold [2.4GHz|5GHz] <800-65535>acs preferred-interface-tolerance-period [2.4GHz|5GHz] <10-600>acs preferred-radio-interface [2.4GHz|5GHz] <0-2>acs priority-meshpoint [2.4GHz|5GHz] <MESHPOINT-NAME>acs sample-count [2.4GHz|5GHz] <1-10>acs snr-delta [2.4GHz|5GHz] <1-100>acs signal-threshold [2.4GHz|5GHz] <-100-0>acs tolerance-period [2.4GHz|5GHz] <10-600>Parameters• acs channel-hold-time [2.4GHz|5GHz] <0-86400>acs Configures ACS settings and overrides on the selected meshpoint-device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-929.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 39• acs channel-switch-delta [2.4GHz|5GHz] <5-35>• acs channel-width [2.4GHz|5GHz] [20MHz|40MHz|80MHz|auto]• acs ocs-duration [2.4GHz|5GHz] <20-250>• acs ocs-frequency [2.4GHz|5GHz] <1-60>channel-hold-time [2.4GHz|5GHz] <0-86400>Configures the minimum time, in seconds, before a periodic scan, to assess channel conditions for a meshpoint root, is triggered.• 2.4GHz – Configures the channel hold interval for the 2.4GHz radio band• 5.0GHz – Configures the channel hold interval for the 5.0GHz radio bandThe following keyword is common to the ‘2.4GHz’ and ‘5.0GHz’ bands:• <0-86400> – Specify a value from 0 - 86400 seconds. The default is 1800seconds.A value of ‘0’ disables periodic channel assessment.acs Configures ACS settings and overrides on the selected meshpoint-devicechannel-switch-delta [2.4GHz|5GHz] <5-35>Configures the difference in interference between the current and best channel needed to trigger a channel change. Once the difference in the current channel and the best channel interference equals the configured value, a channel change is triggered.• 2.4GHz – Configures the channel switch delta for the 2.4GHz radio band• 5.0GHz – Configures the channel switch delta for the 5.0GHz radio bandThe following keyword is common to the ‘2.4GHz’ and ‘5.0GHz’ bands:• <5-35> – Specify a value from 5 - 35 dBm. The default is 10 dBm.acs Configures ACS settings and overrides on the selected meshpoint-devicechannel-width [2.4GHz|5GHz] [20MHz|40MHz|80MHz|auto]Configures the channel width that meshpoint auto channel selection assigns to the radio• 2.4 GHz – Configures the operating channel width for the 2.4 GHz radio band• 5.0 GHz – Configures the operating channel width for the 5.0 GHz radio bandThe following keywords are common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• 20 MHz – Assigns the 20 MHz channel width to the radio• 40 MHz – Assigns the 40 MHz channel width to the radio• 80 MHz – Assigns the 80 MHz channel width to the radio• auto – Selects and assigns the best possible channel from the 20/40/80 MHzwidth. This is the default setting.acs Configures ACS settings and overrides on the selected meshpoint-deviceocs-duration [2.4GHz|5GHz] <20-250>Configures the duration, in milliseconds, of off -channel scans (OCSs) • 2.4 GHz – Configures the ocs-duration for the 2.4 GHz radio band• 5.0 GHz – Configures the ocs-duration for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <20-250> – Specify a value from 20 - 250 milliseconds. The default value is50 milliseconds.acs Configures ACS settings and overrides on the selected meshpoint-device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-930.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 40• acs path-min [2.4GHz|5GHz] <100-20000>• acs path-threshold [2.4GHz|5GHz] <800-65535>• acs preferred-interface-tolerance-period [2.4GHz|5GHz] <10-600>• acs preferred-radio-interface [2.4GHz|5GHz] <0-2>ocs-frequency [2.4GHz|5GHz] <1-60>Configures the interval, in seconds, at which off-channel scan is performed. An ocs-frequency of 10 seconds means that an off-channel scan will be performed once every 10 seconds.• 2.4 GHz – Configures the ocs-frequency for the 2.4 GHz radio band• 5.0 GHz – Configures the ocs-frequency for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <1-60> – Specify a value form 1 - 60 seconds. The default is 6 seconds.acs Configures ACS settings and overrides on the selected meshpoint-devicepath-min [2.4GHz|5GHz] <100-20000>Configures the minimum root path metric needed for auto channel selection. This is the acceptance root path metric value to consider a root as a possible candidate mesh node.• 2.4 GHz – Configures the minimum root path metric for the 2.4 GHz radio band• 5.0 GHz – Configures the minimum root path metric for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <100-20000> – Specify a value from 100 - 20000. The default is 1000.acs Configures ACS settings and overrides on the selected meshpoint-devicepath-threshold [2.4GHz|5GHz] <800-65535>Configures the root path metric threshold for auto channel selection. This is the acceptance root path metric threshold beyond which the root bound to is considered as bad.• 2.4 GHz – Configures the root path metric threshold for the 2.4 GHz radio band• 5.0 GHz – Configures the root path metric threshold for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <800-65535> – Specify a value from 800 - 65535. The default is 1500.acs Configures ACS settings and overrides on the selected meshpoint-devicepreferred-interface-tolerance-period [2.4GHz|5GHz] <10-600>Configures the maximum tolerance period, in seconds, for low root metrics on the preferred interface. This is the duration to wait before triggering an automatic channel selection for the next mesh-hop on the preferred interface.• 2.4 GHz – Configures the maximum tolerance period for the 2.4 GHz radio band• 5.0 GHz – Configures the maximum tolerance period for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <800-65535> – Specify a value from 10 - 600 seconds.acs Configures ACS settings and overrides on the selected meshpoint-device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-931.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 41• acs priority-meshpoint [2.4GHz|5GHz] <MESHPOINT-NAME>• acs sample-count [2.4GHz|5GHz] <1-10>• acs snr-delta [2.4GHz|5GHz] <1-100>• acs signal-threshold [2.4GHz|5GHz] <-100-0>preferred-radio-interface [2.4GHz|5GHz] <0-2>Configures the preferred radio interface on dual band APs• 2.4 GHz – Configures the preferred radio interface for the 2.4 GHz radio band• 5.0 GHz – Configures the preferred radio interface for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <0-2> – Specify a value form 0 - 2. A value of 0 (zero) indicates no preferred radio.acs Configures ACS settings and overrides on the selected meshpoint-devicepriority-meshpoint [2.4GHz|5GHz] <MESHPOINT-NAME>Configures the priority meshpoint. Configuring a priority meshpoint overrides automatic meshpoint configuration.• 2.4 GHz – Configures the priority meshpoint for the 2.4 GHz radio band• 5.0 GHz – Configures the priority meshpoint for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <MESHPOINT-NAME> – Specify the meshpoint name for the selected radioband.acs Configures ACS settings and overrides on the selected meshpoint-devicesample-count [2.4GHz|5GHz] <1-10>Configures the minimum number of scan cycle samples to consider for auto channel selection• 2.4 GHz – Configures the sample count for the 2.4 GHz radio band• 5.0 GHz – Configures the sample count for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <1-10> – Specify a value from 1 -10. The default is 5 samples.acs Configures ACS settings and overrides on the selected meshpoint-devicesnr-delta [2.4GHz|5GHz] <1-100>Configures the channel SNR delta. A meshpoint on a candidate channel must have a SNR of a greater delta than the next hop on the current channel.• 2.4 GHz – Configures the snr-delta for the 2.4 GHz radio band• 5.0 GHz – Configures the snr-delta for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <1-100> – Specify a value from 1 - 100 dB. The default is 5 dB.acs Configures ACS settings and overrides on the selected meshpoint-devicesignal-threshold [2.4GHz|5GHz] <-100-0>Configures the signal strength threshold. If the signal strength of the next hop drops below the configured signal-threshold, a scan is triggered.• 2.4 GHz – Configures the signal-threshold for the 2.4 GHz radio band• 5.0 GHz – Configures the signal-threshold for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <-100-0> – Specify a value from -100 - 0 dB. The default is -65 dB.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-932.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 42• acs tolerance-period [2.4GHz|5GHz] <10-600>Examplerfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#acs channel-hold-time 2.4GHz 2500rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#acs ocs-duration 2.4GHz 30rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#acs ocs-frequency 2.4GHz 1rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#show context meshpoint-device test acs ocs-frequency 2.4GHz 1 acs osc-duration 2.4GHz 30 acs channel-hold-time 2.4GHz 2500rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#Related Commandsacs Configures ACS settings and overrides on the selected meshpoint-devicetolerance-period [2.4GHz|5GHz] <10-600>Configures the maximum tolerance period in seconds. This is the interval to wait for the root bound to recovery from a bad link.• 2.4 GHz – Configures the tolerance-period for the 2.4 GHz radio band• 5.0 GHz – Configures the tolerance-period for the 5.0 GHz radio bandThe following keyword is common to the ‘2.4 GHz’ and ‘5.0 GHz’ bands:• <10-600> – Specify a value from 10 - 600 seconds. the default is 60 seconds.no Reverts the configured ACS settings to default](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-933.png)

![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 4426.3.2.3 hysteresismeshpoint-device-commandsConfigures path selection SNR hysteresis values on this meshpoint-device (access point). These are settings that facilitate dynamic path selection. Configuring hysteresis prevents frequent re-ranking of the shortest path cost.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxhysteresis [min-threshold|period|root-sel-snr-delta|snr-delta]hysteresis [min-threshold <-100-0>|period <0-600>|root-sel-snr-delta <1-100>|snr-delta <1-100>]Parameters• hysteresis [min-threshold <-100-0>|period <0-600>|root-sel-snr-delta <1-100>|snr-delta <1-100>]Examplerfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#hysteresis period 15rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#hysteresis root-sel-snr-delta 12rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#hysteresis snr-delta 3rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#hysteresis min-threshold -65rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#show context meshpoint-device test hysteresis period 15 hysteresis snr-delta 3 hysteresis min-threshold -65 hysteresis root-sel-snr-delta 12rfs4000-229D58(config-profile-testAP71XX-meshpoint-test)#min-threshold <-100-0> Configures the minimum signal strength that a device should have to be considered a likely candidate in the mesh route (to the mesh root node) selection process.• <-100-0> – Specify a value from -100 - 0 dB. The default is 0 dB.period <0-600> Configures the interval, in seconds, for which a likely candidate’s path method hysteresis is sustained. In other words a device capable of sustaining the signal strength for the specified period of time is a likely candidate in the mesh route (to the mesh root node) selection process.• <0-600> – Specify a value from 0 - 600 seconds. The default is 1 second.root-sel-snr-delta <1-100>Configures the signal strength, in dB, that a device has to sustain, within the delta range, to be considered a likely candidate in the mesh route (to the mesh root node) selection process.• <1-100> – Specify a value from 1 - 100 dB.snr-delta <1-100> Configures the SNR delta. The device with must have a SNR of a greater delta than its current neighbor to be considered a likely candidate in the mesh route (to the mesh root) selection process.• <1-100> – Specify a value from 1 - 100 dB. The default is 1 dB.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-935.png)

![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 4626.3.2.4 monitormeshpoint-device-commandsEnables monitoring of critical resource and primary port links. It also configures the action taken in case a critical resource goes down or a primary port link is lost.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxmonitor [critical-resource|primary-port-link-loss] action no-rootParameters• monitor [critical-resource|primary-port-link-loss] action no-rootExamplerfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#monitor critical-resource action no-rootrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#show context meshpoint-device test name test monitor critical-resource action no-rootrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#Related Commandscritical-resource Enables critical resource down event monitoringprimary-port-link-loss Enables primary port link loss event monitoringaction no-root The following are common to all of the above:• action – Sets the action taken if a critical resource goes down or if a primary port link is lost• no-root – Changes the meshpoint to be non root (this is the action taken incase any of the above mentioned two events occur)no Disables monitoring of critical resource and primary port links.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-937.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 4726.3.2.5 path-methodmeshpoint-device-commandsConfigures the path selection method used on a meshpoint device. This is the method used to select the route to the root node within a mesh network.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxpath-method [bound-pair|mobile-snr-leaf|snr-leaf|uniform]Parameters• path-method [bound-pair|mobile-snr-leaf|snr-leaf|uniform]Examplerfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#path-method mobile-snr-leafrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#show context meshpoint-device TEST name TEST path-method mobile-snr-leafrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#Related Commandspath-method Sets the method used to select the path to the root node in a mesh networkbound-pair Enables a meshpoint to form an exclusive path with only one other meshpoint. Select this option to bind one mesh point connection at a time. Once established, other mesh point connenction requests are denied.mobile-snr-leaf Configures the path selection method as mobile-snr-leaf. When selected, the path to the root node is selected based on the Signal-to-Noise Ratio (SNR) to a neighboring device. This option allows meshpoint devices to select a neighbor with the strongest SNR. Meshpoint devices using the mobile-snr-leaf method are non-forwarding nodes in the meshpoint traffic.Note: Select this option for Vehicular Mounted Modem (VMM) access points or other mobile devices.Note: VMM is supported only on the AP7161 model access point.snr-leaf This option allows meshpoints to select a neighbor with the strongest SNR. It is similar to the mobile-snr-leaf option, but is not applicable to mobile devices, such as VMMs.uniform Indicates the path selection method is uniform. When selected, two paths will be considered equivalent if the average goodput is the same for both paths. This is the default setting.Note: Select this option for infrastructure devices.no Resets the path selection method on a meshpoint device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-938.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 4826.3.2.6 preferredmeshpoint-device-commandsConfigures the preferred path parameters for this meshpoint deviceSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxpreferred [neighbor <MAC>|root <MAC>|interface [2.4GHz|4.9GHz|5GHz]]Parameters• preferred [neighbor <MAC>|root <MAC>|interface [2.4GHz|4.9GHz|5GHz]]Examplerfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#preferred neighbor 11-22-33-44-55-66rfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#preferred root 22-33-44-55-66-77rfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#preferred interface 5GHzrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#show context meshpoint-device test name test preferred root 22-33-44-55-66-77 preferred neighbor 11-22-33-44-55-66 preferred interface 5GHz monitor critical-resource action no-rootrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#Related Commandspreferred Configures the preferred path parametersneighbor <MAC> Adds the MAC address of a neighbor meshpoint as a preferred neighborroot <MAC> Adds the MAC address of a root meshpoint as a preferred rootinterface [2.4GHz|4.9GHz|5GHz]Sets the preferred interfaceno Removes the configuration of preferred paths for this meshpoint device](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-939.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 4926.3.2.7 rootmeshpoint-device-commandsConfigures this meshpoint device as the root meshpointYou can optionally use the select-method option to enable dynamic mesh selection. When enabled, this option overrides root or no-root configuration and uses the selection method.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxroot {select-method [auto-mint|auto-proximity]}Parameters• root {select-method [auto-mint|auto-proximity]}root Configures this meshpoint device as the root meshpointselect-method auto-mintOptional. Enables dynamic mesh selection. When enabled, this option overrides root or no-root configuration and chooses the selection method.• auto-mint – Enables dynamic root selection using Auto-MiNT (based on path cost)The Auto-Mint or Cost Method dynamically determines the root/non-root configuration of a meshpoint by:• Monitoring and ranking the signal strength and path cost of neighboring meshpoints.• Setting the configuration to:• non-root: If the link with the shortest path to the cost-root mesh device is a MCXmeshpoint link• root: If the link with the shortest path to the cost-root mesh device is a non MCXmeshpoint link (wired link).• This requires that the meshpoint device, in the brain car, be configured as the‘cost root’ and the ‘cost root’ meshpoint-device be the l2 gateway to the controller.Use the root-select > cost-root command to configure a meshpoint-device as ‘cost-root’.• Using signal strength of neighboring meshpoint as the sole metric to determinethe next mesh hop to the root.• Loop detection with both meshpoints in a car select non-root and form a meshlink with the same root• auto-proximity – Enables dynamic root selection using meshpoint proximity. When auto-proximity is selected, root selection is based on signal strength of candidate roots.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-940.png)
![MESHPOINTAccess Point, Wireless Controller and Service Platform CLI Reference Guide 26 - 5226.3.2.9 nomeshpoint-device-commandsNegates the commands for a meshpoint device or resets values to defaultSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7522, AP7532, AP7562, AP81XXSyntaxno [acs|exclude|hysteresis|monitor|path-method|preferred|root|root-select]no acs [channel-hold-time|channel-switch-delta|channel-width|ocs-duration|ocs-frequency|path-min|path-threshold|preferred-interface-tolerance-period|preferred-radio-interface|priority-meshpoint|sample-count|snr-delta|signal-threshold|tolerance-period] [2.4GHZ|5GHz]no exclude wired-peer mint-level-1no hysteresis [min-threshold|period|root-sel-snr-delta|snr-delta]no monitor [critical-resource|primary-port-link-loss]no [path-method|root {select-method}]no root-select cost-rootno preferred [interface|root|neighbor]Parameters• no <PARAMETERS>Examplerfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#show context meshpoint-device test name test root preferred root 22-33-44-55-66-77 preferred neighbor 11-22-33-44-55-66 preferred interface 5GHz monitor critical-resource action no-rootrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#rfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#no monitor critical-resourcerfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#no preferred neighborrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#no rootrfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#no preferred interfacerfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#show context meshpoint-device test name test no root preferred root 22-33-44-55-66-77rfs6000-37FABE(config-profile-AP71XXTestProfile-meshpoint-test)#no <PARAMETERS> Removes or reverts this meshpoint device settings to default based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-943.png)

![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 427.1.2 access-network-typepasspoint-policyConfigures the access network type for this hotspot. The beacons and probe responses communicate the type of hotspot (public, private, guest-use, emergency, etc.) to clients seeking access.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxaccess-network-type [chargeable-public|emergency-services|experimental|free-public|personal-device|private|private-guest|wildcard]Parameters• access-network-type [chargeable-public|emergency-services|experimental|free-public|personal-device|private|private-guest|wildcard]Examplerfs4000-229D58(config-passpoint-policy-test)#access-network-type chargeable-publicrfs4000-229D58(config-passpoint-policy-test)#show contexthotspot2-policy test access-network-type chargeable-public 3gpp mcc 310 mnc 970 3gpp mcc 505 mnc 14rfs4000-229D58(config-passpoint-policy-test)#Related Commandsaccess-network-type Select the access network type for this hotspot. The options are:• chargeable-public – The network type is a chargeable public network• emergency-services – The network is used to provide emergency services only• experimental – The network is used for test or experimental purposes only• free-public – The network type is a free public• personal-device – The network is used for personal devices only• private – The network is a private network • private-guest – The network is a private network with guest access (default setting)• wildcard – Includes all access network typesIf the network type is set to chargeable-public, probe responses advertise this hotspot as a chargeable-public hotspot.no Reverts to the default access network type setting (private)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-947.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 527.1.3 connection-capabilitypasspoint-policyConfigures the connection capability element in this passpoint policy. When configured, it communicates which ports are open or closed on the Hotspot, in response to an ANQP query.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxconnection-capability [ftp|http|icmp|ip-protocol|ipsec-vpn|pptp-vpn|sip|ssh|tls-vpn]connection-capability [ftp|http|icmp|ipsec-vpn|pptp-vpn|sip|ssh|tls-vpn] [closed|open|unknown]connection-capability ip-protocol <0-255> port <0-65535> [closed|open|unknown]Parameters• connection-capability [ftp|http|icmp|ipsec-vpn|pptp-vpn|sip|ssh|tls-vpn] [closed|open|unknown]• connection-capability ip-protocol <0-255> port <0-65535> [closed|open|unknown]connection-capability Configures the connection capability element in this passpoint policyftp Specifies the protocol type as FTP. Configures TCP port 20.http Specifies the protocol type as HTTP. Configures TCP port 80.icmp Specifies the protocol type as ICMPipsec-vpn Specifies the protocol type as IPSEC VPN. Configures ESP and UDP ports 500 and 4500.pptp-vpn Specifies the protocol type as PPTP VPN. Configures TCP port 1723.sip Specifies the protocol type as SIP. Configures TCP port 5060 and UDP port 5060.ssh Specifies the protocol type as SSH. Configures TCP port 20tls-vpn Specifies the protocol type as TLS VPN. Configures TCP port 443.port <0-65535> [closed|open|unknownAfter specifying the protocol type, specify the port (associated with the selected protocol) and its status.• closed – Specifies that the port(s) is/are closed• open – Specifies that the port(s) is/are open• unknown – Specifies that the port(s) status is not knownWhen the connection capability element is not configured, the hotspot does not return the element in an ANQP capability request and ignores any ANQP query for the element.connection-capability Configures the connection capability element in this passpoint policyip-protocol <0-255> Identifies the IP protocol by the protocol’s number. For example, for simple message protocol (SMP) specify 121.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-948.png)

![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 1027.1.7 ip-address-typepasspoint-policyAdvertises the IP address type used in this hotspot. This information is returned in response to ANQP queries.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxip-address-type [ipv4|ipv6]ip-address-type ipv4 [double-nat|not-available|port-restricted|port-restricted-double-nat|port-restricted-single-nat|public|single-nat|unknown]ip-address-type ipv6 [available|not-available|unknown]Parameters• ip-address-type ipv4 [double-nat|not-available|port-restricted|port-restricted-double-nat|port-restricted-single-nat|public|single-nat|unknown]• ip-address-type ipv6 [available|not-available|unknown]ip-address-type ipv4 Configures the as IPv4 address type availability informationdouble-nat Specifies double NATed private IPv4 address is availablenot-available Specifies IPv4 address is not availableport-restricted Specifies port-restricted IPV4 address is availableport-restricted-double-natSpecifies port-restricted IPv4 address and double NATed IPv4 address is availableport-restricted-single-natSpecifies port-restricted IPv4 address and single NATed IPv4 address is availablepublic Specifies public IPv4 address is availablesingle-nat Specifies single NATed IPv4 address is availableunknown Specifies no information configured regarding the IPv4 address availabilityip-address-type ipv6 Configures the IPv6 address type availability informationavailable Specifies IPv6 address is availablenot-available Specifies IPv6 address is not availableunknown Specifies no information configured regarding the IPv6 address availability](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-953.png)


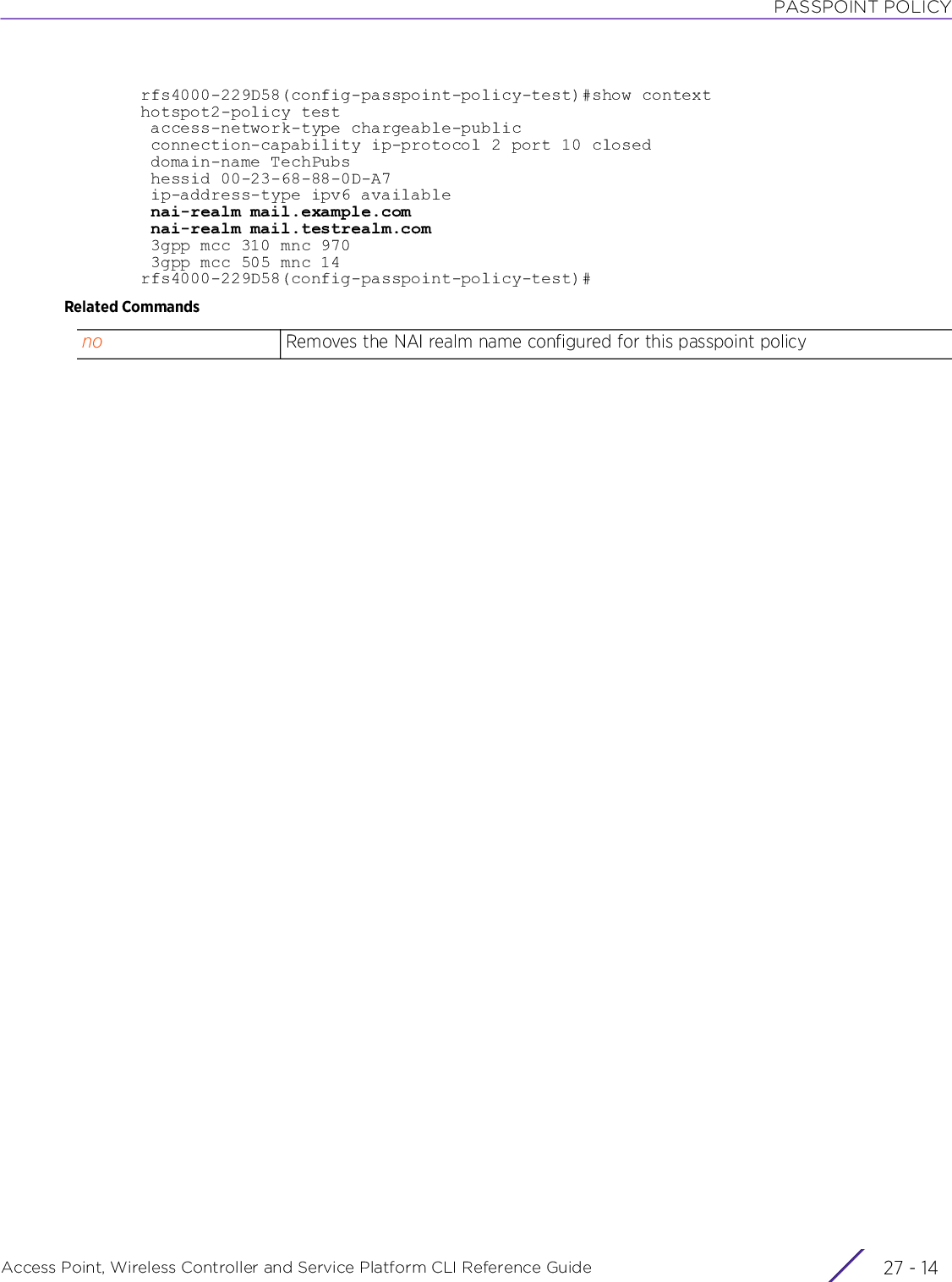

![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 1627.1.8.2.1 eap-methodnai-realm-config-mode commandsSpecifies the EAP authentication mechanisms supported by each of the service providers associated with this passpoint policySupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxeap-method <1-10> [<1-255>|fast|gtc|identity|ikev2|ms-auth|mschapv2|otp|peap|psk|rsa-public-key|sim|tls|ttls] auth-param [credential|expanded-eap|expanded-inner-eap|inner-eap|non-eap-inner|tunn-eap-credential|vendor] [cert|hw-token|nfc-secure-elem|none|sim|soft-token|username-password|usim|vendor]Parameters• eap-method <1-10> [<1-255>|fast|gtc|identity|ikev2|ms-auth|mschapv2|otp|peap|psk|rsa-public-key|sim|tls|ttls] auth-param [credential|expanded-eap|expanded-inner-eap|inner-eap|non-eap-inner|tunn-eap-credential|vendor][cert|hw-token|nfc-secure-elem|none|sim|soft-token|username-password|usim|vendor]eap-method <1-10> Creates an EAP authentication method and assigns it an index number• <1-10> – Specify a identifier for this EAP method from 1 - 10.A maximum of 10 (ten) authentication methods can be specified for every NAI realm. After creating the EAP authentication method, specify the associated authentication mechanisms (method types).<1-255> Identifies the EAP authentication method type from the corresponding Internet Assigned Numbers Authority (IANA) number<1-255> – Specify the IANA identity number for the authentication protocol from 1 -255.fast Specifies the EAP authentication method type as Flexible Authentication via Secure Tunneling (FAST)gtc Specifies the EAP authentication method type as Generic Token Card (GTC)identity Specifies the EAP authentication method type as Identificationikev2 Specifies the EAP authentication method type as Internet Key Exchange Protocol version 2 (IKEv2)ms-auth Specifies the EAP authentication method type as Microsoft Authentication (MS-Auth)mschapv2 Specifies the EAP authentication method type as Microsoft Challenge Handshake Authentication Protocol version 2(MSCHAPv2)opt Specifies the EAP authentication method type as One Time Password (OTP)peap Specifies the EAP authentication method type as Protected Extensible Authentication Protocol (PEAP)psk Specifies the EAP authentication method type as Pre-shared Key (PSK)rsa-public-key Specifies the EAP authentication method type as RSA public key protocolsim Specifies the EAP authentication method type as GSM Subscriber Identity Module (SIM)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-959.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 17ExampleThe following examples show four EAP authentication methods associated with the NAI realm ‘mail.example.com’. Each method supports a different EAP authentication mechanism:rfs4000-229D58(config-passpoint-policy-test-nai-realm-mail.example.com)#eap-method 1 ttls auth-param vendor hex 00001Erfs4000-229D58(config-passpoint-policy-test-nai-realm-mail.example.com)#eap-method 2 rsa-public-key auth-param credential certrfs4000-229D58(config-passpoint-policy-test-nai-realm-mail.example.com)#eap-method 4 peap auth-param credential certrfs4000-229D58(config-passpoint-policy-test-nai-realm-mail.example.com)#show context nai-realm mail.example.com eap-method 1 ttls auth-param vendor hex 00121F eap-method 2 rsa-public-key auth-param credential cert eap-method 3 otp auth-param credential username-password eap-method 4 peap auth-param credential certrfs4000-229D58(config-passpoint-policy-test-nai-realm-mail.example.com)#tls Specifies the EAP authentication method type as Transport Layer Security (TLS)ttls Specifies the EAP authentication method type as Tunneled Transport Layer Security (TTLS)auth-param After specifying the EAP authentication method type, specify the authentication parameters. These parameters depend on the EAP authentication mechanism selected.[cert|hw-token|nfc-secure-elem|none|sim|soft-token|username-password|usim|vendor]The following parameters are common to all the above authentication parameters:• cert – Certificate• hw-token – Hardware token• nfc-secure-elem – NFC secure element• none – No credential• sim – Subscriber identity module• soft-token – Soft token• username-password – Username and password• usim – Universal subscriber identity module• vendor – Vendor specific credential](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-960.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 1827.1.9 net-auth-typepasspoint-policyConfigures the network authentication type used in this hotspot. The details configured are returned in response to an ANQP query.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxnet-auth-type [accept-terms|dns-redirect|http-redirect|online-enroll] {url <URL>}Parameters• net-authtype [accept-terms|dns-redirect|http-redirect|online-enroll] {url <URL>}Examplerfs4000-229D58(config-passpoint-policy-test)#net-auth-type accept-terms url "www.test.com"rfs4000-229D58(config-passpoint-policy-test)#rfs4000-229D58(config-passpoint-policy-test)#show contexthotspot2-policy test access-network-type chargeable-public connection-capability ip-protocol 2 port 10 closed domain-name TechPubs hessid 00-23-68-88-0D-A7 ip-address-type ipv6 available nai-realm mail.example.com eap-method 1 ttls auth-param vendor hex 00001E eap-method 2 rsa-public-key auth-param credential cert eap-method 3 otp auth-param credential username-password eap-method 4 peap auth-param credential cert nai-realm mail.testrealm.com net-auth-type accept-terms url www.test.com 3gpp mcc 310 mnc 970 3gpp mcc 505 mnc 14rfs4000-229D58(config-passpoint-policy-test)#Related Commandsnet-auth-type Specifies the network authentication type used with this passpoint policy. The options are: accept-terms, dns-redirect, http-redirect, and online-enrollaccept-terms Enables user acceptance of terms and conditionsdns-redirect Enables DNS redirection of userhttp-redirect Enables HTTP redirection of useronline-enroll Enables online user enrolmenturl <URL> Optional. Specify the location for each of above network authentication types.no Removes the network authentication type configured with this passpoint policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-961.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 1927.1.10 nopasspoint-policyRemoves or reverts the passpoint policy settingsSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxno [3gpp|access-network-type|connection-capability|domain-name|hessid|internet|ip-address-type|nai-realm|net-auth-type|operator|osu|roam-consortium|venue|wan-metrics]Parameters• no <PARAMETERS>ExampleThe following example shows the passpoint policy ‘test’ settings before the ‘no’ commands are executed:rfs4000-229D58(config-passpoint-policy-test)#show contexthotspot2-policy test access-network-type chargeable-public connection-capability ip-protocol 2 port 10 closed domain-name TechPubs hessid 00-23-68-88-0D-A7 ip-address-type ipv6 available nai-realm mail.example.com eap-method 1 ttls auth-param vendor hex 00001E eap-method 2 rsa-public-key auth-param credential cert eap-method 3 otp auth-param credential username-password eap-method 4 peap auth-param credential cert nai-realm mail.testrealm.com net-auth-type accept-terms url www.test.com 3gpp mcc 310 mnc 970 3gpp mcc 505 mnc 14rfs4000-229D58(config-passpoint-policy-test)#rfs4000-229D58(config-passpoint-policy-test)#no access-network-typerfs4000-229D58(config-passpoint-policy-test)#no hessidrfs4000-229D58(config-passpoint-policy-test)#no nai-realm mail.example.comrfs4000-229D58(config-passpoint-policy-test)#no 3gpp mcc 310 mnc 970rfs4000-229D58(config-passpoint-policy-test)#no internetrfs4000-229D58(config-passpoint-policy-test)#show contexthotspot2-policy test connection-capability ip-protocol 2 port 10 closed domain-name TechPubs no internet ip-address-type ipv6 available nai-realm mai.testrealm.com net-auth-type accept-terms url www.test.com 3gpp mcc 505 mnc 14rfs4000-229D58(config-passpoint-policy-test)#no <PARAMETERS> Removes or reverts the passpoint policy settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-962.png)


![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 2227.1.12.1 osuosuAdds an online sign up (OSU) SSID (WLAN)/OSU provider and enters its configuration modeSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxosu [provider <PASSPOINT-OSU-PROVIDER>|ssid <SSID>]Parameters• osu [provider <PASSPOINT-OSU-PROVIDER>|ssid <SSID>]Examplenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#?Passpoint OSU Provider Mode commands: description Configure the english description of the online signup provider icon Add an icon for the online signup provider method Specify the online signup method supported by provider nai Configure the NAI for the online signup provider name Configure the english name of the online signup provider no Negate a command or set its defaults server-url Configure the signup url for the online signup provider clrscr Clears the display screen commit Commit all changes made in this session do Run commands from Exec mode end End current mode and change to EXEC mode exit End current mode and down to previous mode help Description of the interactive help system revert Revert changes service Service Commands show Show running system information write Write running configuration to memory or terminalnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#Related Commandsosu Use this command to configure an online sign up (OSU) SSID/OSU provider. In the OSU SSID/provider configuration mode, specify OSU details, such as names, descriptions, servers, methods, and icons available. This information is returned in response to a station’s Hotspot 2.0 query. When configured, this option enables a station to obtain credentials for an Hotspot 2.0 enabled SSID.provider <PASSPOINT-OSU-PROVIDER>Creates an OSU provider for this passpoint and enters its configuration mode• <PASSPOINT-OSU-PROVIDER> – Specify an identification for this OSU passpoint provider.ssid <SSID> Configures an OSU WLAN’s SSID. This is the open authentication SSID that a user can use to obtain credentials for the passpoint SSID.• <SSID> – Specify the SSID.no Removes the OSU WLAN/provider configured with this passpoint policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-965.png)
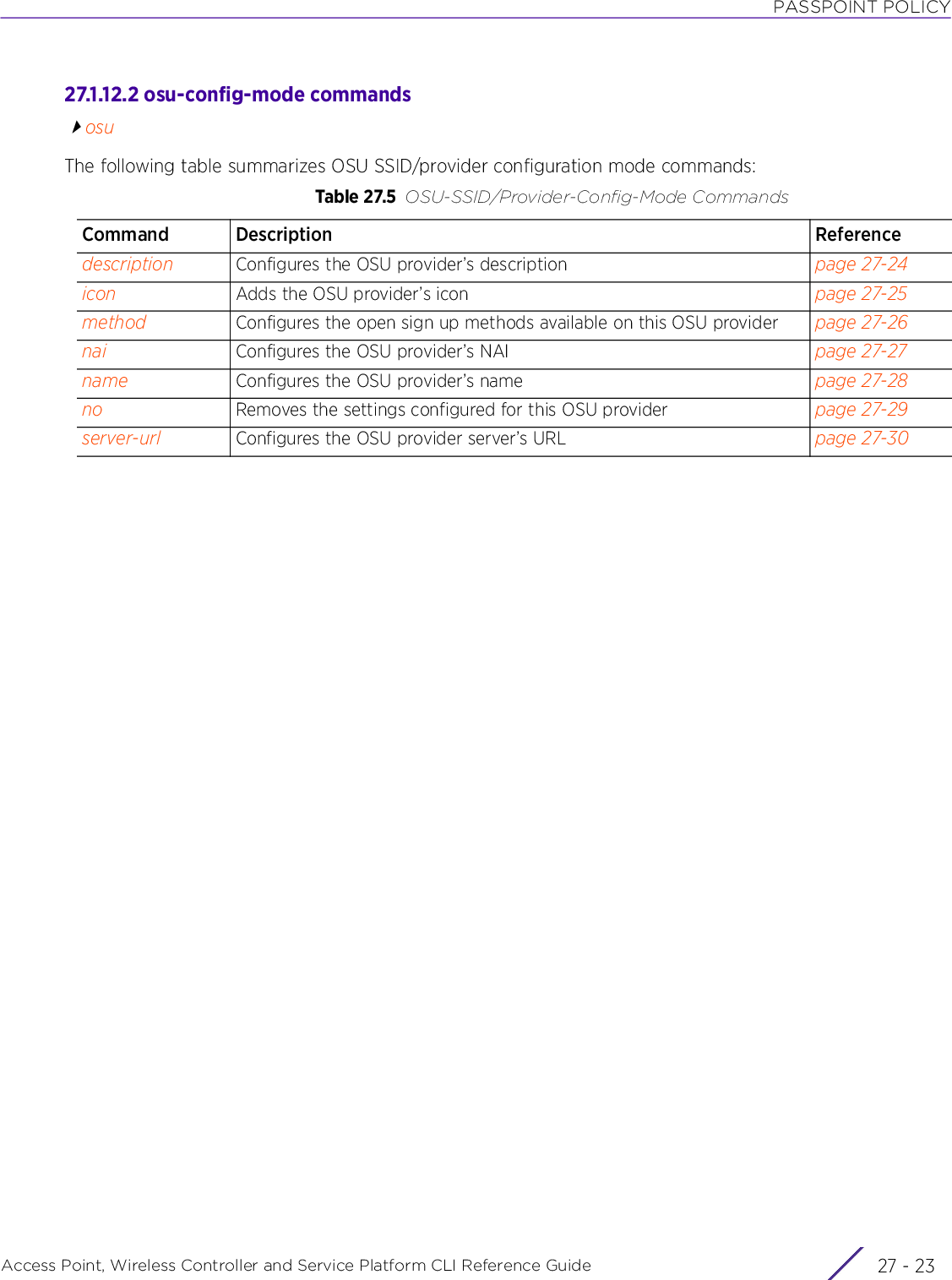
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 2427.1.12.2.2 descriptionosu-config-mode commandsConfigures the OSU SSID/provider’s description. This value is returned in the ANQP OSU providers list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxdescription [<DESCRIPTION>|iso-lang <ISO-LANG-CODE>]Parameters• description [<DESCRIPTION>|iso-lang <ISO-LANG-CODE>]Examplenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#description "Provides free service for testing purposes"nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#show context osu provider WiFi description "Provides free service for testing purposes"nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#Related Commands<DESCRIPTION> Provides a description for the OSU provider. It should not exceed 253 characters in length.• <DESCRIPTION> – Specify the description in one or more languages. By default the system configures the name in English.iso-lang <ISO-LANG-CODE>Identifies the language by its ISO 639 language code (for example, ‘chi-chinese’ or ‘spa-spanish’). By default the language is set to English. If specifying the description in any language other than English, specify the ISO language code.no Removes this OSU provider’s description](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-967.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 2527.1.12.2.3 iconosu-config-mode commandsAdds the OSU provider’s icon. This value is returned in the ANQP OSU providers list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxicon iso-lang <ISO-LANG-CODE> width <0-65535> height <0-65535> mime-type <FILE-MIME-TYPE> file [<IMAGE-FILE-NAME/PATH>|<FILE-NAME>]Parameters• icon iso-lang <ISO-LANG-CODE> width <0-65535> height <0-65535> mime-type <FILE-MIME-TYPE> file [<IMAGE-FILE-NAME/PATH>|<FILE-NAME>]Examplenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#icon iso-lang engwidth 128 height 128 mime-type image/png file flash:/wifi_iconnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#show context osu provider WiFi description "Provides free service for testing purposes" icon iso-lang eng width 128 height 128 mime-type image/png file flash:/wifi_iconnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#Related Commandsicon iso-lang <ISO-LANG-CODE>Configures an icon representing the OSU provider• iso-lang <ISO-LANG-CODE> – Identifies the language by its ISO 639 language code (for example, ‘chi-chinese’ or ‘spa-spanish’). By default the language is set to English. If specifying the image file name and path in any language other than English, specify the ISO language code.width <0-65535> Configures the icon’s width in pixels• <0-65535> – Specify a value from 0 - 65535 pixels.height <0-65535> Configures the icon’s height in pixels• <0-65535> – Specify a value from 0 - 65535 pixels.mime-type <FILE-MIME-TYPE>Configures a string describing the icon’s standard mime type. For example, image/png• <FILE-MIME-TYPE> – Specify the icon’s mime type.file [<IMAGE-FILE-NAME/PATH>|<FILE-NAME>]Configures the location and name of the image file• <IMAGE-FILE-NAME/PATH> – Specify the path and filename. For example, flash:/icon.png• <FILE-NAME> – Use this option to specify the filename in the flash:/ directoryno Removes this OSU provider’s icon](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-968.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 2627.1.12.2.4 methodosu-config-mode commandsConfigures the open sign up methods available on this OSU provider. This value is returned, in the specified order of precedence, in the ANQP OSU providers list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxmethod [oma-dm|soap-xml-spp] priority <1-2>Parameters• method [oma-dm|soap-xml-spp] priority <1-2>Examplenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#method soap-xml-spp priority 1nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#show context osu provider WiFi description "Provides free service for testing purposes" icon iso-lang eng width 128 height 128 mime-type image/png file flash:/wifi_icon method soap-xml-spp priority 1nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#Related Commandsmethod [oma-dm|soap-xml-spp] priority <1-2>Configures the online sign up methods supported by this OSU provider• oma-dm – Configures the OSU method used as Open Mobile Alliance (OMA) device management• soap-xml-spp – Configures the OSU method used as Soap-xml subscription provisioning protocol• priority <1-2> – Sets the priority of the specified method. Select a value from 1 - 2. Thedefault is one (1).no Removes the online sign up methods configured on this OSU provider](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-969.png)

![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 2827.1.12.2.6 nameosu-config-mode commandsConfigures the OSU provider’s name. This value is returned in the ANQP OSU providers list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxname [<NAME>|iso-lang <ISO-LANG-CODE>]Parameters• name [<NAME>|iso-lang <ISO-LANG-CODE>]Examplenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#name "WIFI Alliance OSU"nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#show context osu provider WiFI name "WIFI Alliance OSU" description "Provides free service for testing purposes" icon iso-lang eng width 128 height 128 mime-type image/png file flash:/wifi_icon method soap-xml-spp priority 1 nai wifi.orgnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#Related Commands<NAME> Configures the OSU provider’s name. It should not exceed 253 characters in length.• <NAME> – Specify the name in one or more languages. By default the system configures the name in English.iso-lang <ISO-LANG-CODE>Identifies the language by its ISO 639 language code (for example, ‘chi-chinese’ or ‘spa-spanish’). By default the language is set to English. If specifying the name in any language other than English, specify the ISO language code.no Removes this OSU provider’s name](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-971.png)
![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 2927.1.12.2.7 noosu-config-mode commandsRemoves the settings configured for this OSU provider. Once removed the information is not included in the ANQP providers list.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxno [description|icon|method|nai|name|server-url]no [description|icon|name] {iso-lang <ISO-LANG-CODE>}no [nai|server-url]no method [oma-dm|soap-xml-spp]Parameters• no <PARAMETERS>Examplenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#show context osu provider WiFi name "WIFI Alliance OSU" description "Provides free service for testing purposes" icon iso-lang eng width 128 height 128 mime-type image/png file flash:/wifi_icon method soap-xml-spp priority 1 nai wifi.org server-url osu-server.wifi.orgnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#nx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#no descriptionnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#no icon iso-lang engnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#no namenx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#show context osu provider WiFi method soap-xml-spp priority 1 nai wifi.org server-url osu-server.wifi.orgnx9500-6C8809(config-passpoint-policy-test-osu-provider-WiFi)#no <PARAMETERS> Removes the settings configured for this OSU provider](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-972.png)


![PASSPOINT POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 27 - 3227.1.14 venuepasspoint-policyConfigures the venue where this hotspot is located. The hotspot venue configuration informs prospective clients about the hotspot’s nature of activity, such as educational, institutional, residential, etc.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms —NX7500, NX7510, NX7520, NX7530, NX95XX, NX9600, VX9000Syntaxvenue [group|name]venue group [assembly|business|educational|industrial|institutional|mercantile|outdoor|residential|storage|unspecified|utility-and-misc|vehicular] typevenue name [<VENUE-NAME>|iso-lang]venue name <VENUE-NAME>venue name iso-lang <ISO-LANG-CODE> <VENUE-NAME>Parameters• venue group [assembly|business|educational|industrial|institutional|mercantile|outdoor|residential|storageunspecified|utility-and-misc|vehicular] typevenue group Configures the venue group associated with this hotspotassembly type Configures the venue group as assembly (1). This hotspot type is applicable to public assembly venues.• type – Specifies the venue type for this group. The options are:• <0-255> – Specifies an unlisted venue type number from 0 -255• amphitheater – Specifies the venue type as amphitheater (4)• amusement-park – Specifies the venue type as amusement park (5)• arena – Specifies the venue type as arena (1)• bar – Specifies the venue type as bar (12)• coffee-shop – Specifies the venue type as a coffee shop (13)• convention-centre – Specifies the venue type as a convention center (7)• emergency-coordination-center – Specifies the venue type as a emergency coordination center (15)• library – Specifies the venue type as a library (8)• museum – Specifies the venue type as a museum (9)• passenger-terminal – Specifies the venue type as a passenger terminal (3)• place-of-worship – Specifies the venue type as a place of worship (6)• restaurant – Specifies the venue type as a restaurant (10)• stadium – Specifies the venue type as a stadium (2)• theater – Specifies the venue type as a theater (11)• unspecified – Specifies the venue type as not specified (0)• zoo – Specifies the venue type as a zoo (14)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-975.png)
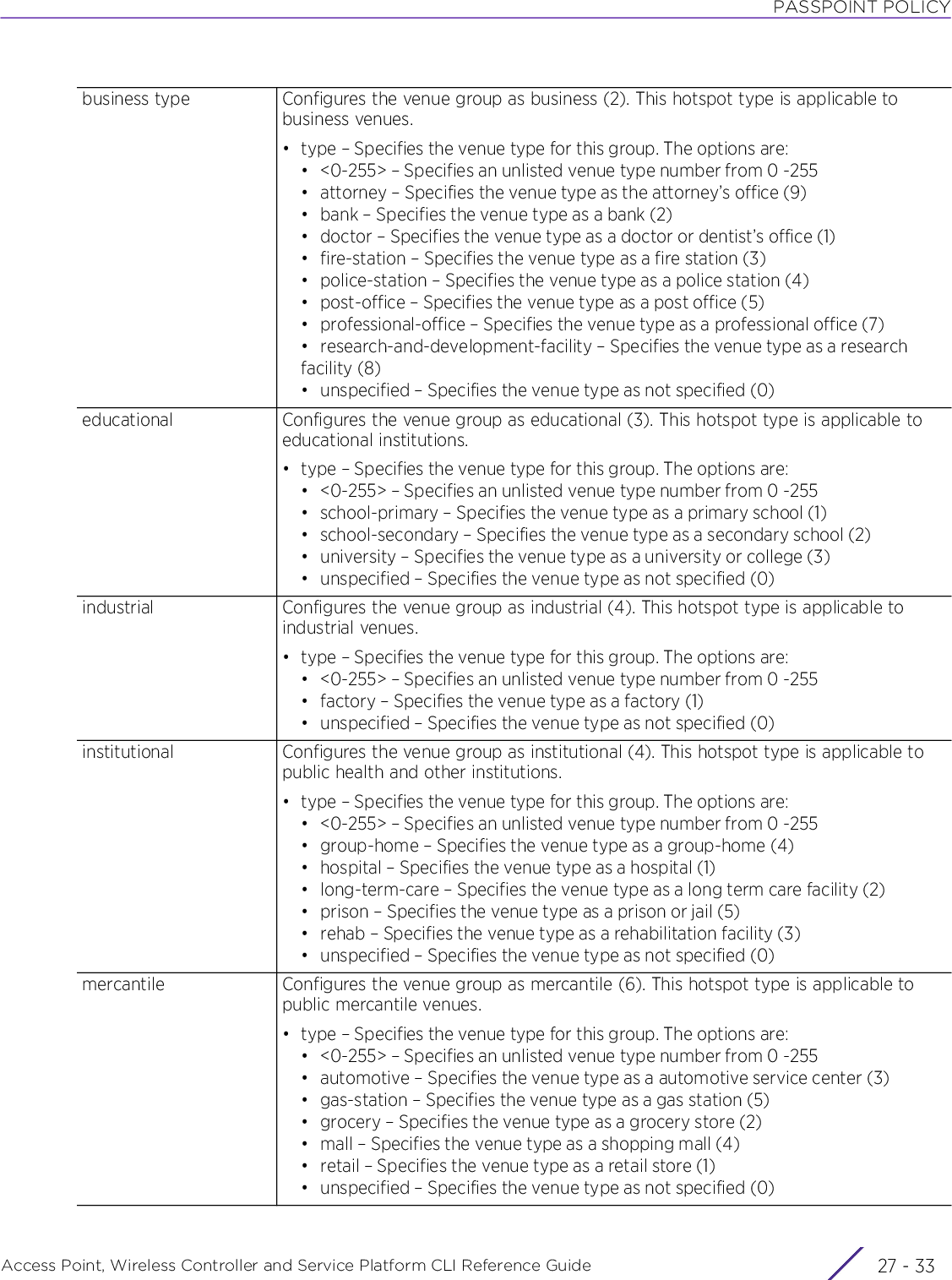

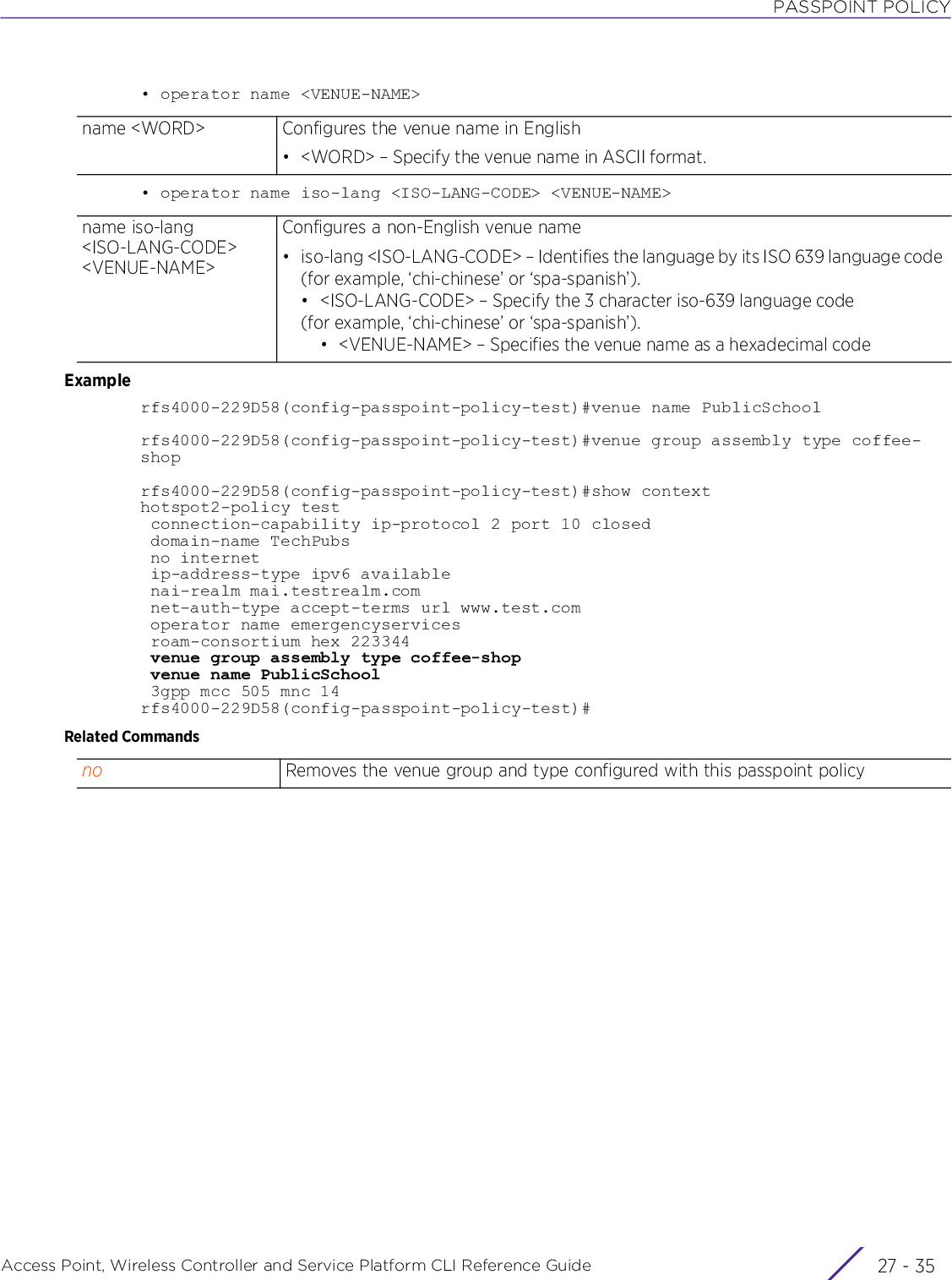



![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 428.1.1 denybgp-ip-prefix-list-config commandsCreates and configures a deny prefix-list rule. The deny rule specifies match criteria based on which prefixes received from (or transmitted to) a BGP neighbor are filtered. A deny action is applied on these filtered prefixes. For example, in the BGP router neighbor context a filter is applied using a IP prefix list. The list contains a deny rule with a prefix to match as 192.168.13.0/24. All prefixes received from the neighbor matching this prefix are denied.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxdeny prefix-list <1-4292967294> [<PREFIX-TO-MATCH/MASK>|any]deny prefix-list <1-4292967294> [<PREFIX-TO-MATCH/MASK> {ge <0-32>|le <0-32>}|any]Parameters• deny prefix-list <1-4292967294> [<PREFIX-TO-MATCH/MASK> {ge <0-32>|le <0-32>}|any]Examplenx9500-6C8809(config-bgp-ip-prefix-list-test)#deny prefix-list 1 168.192.13.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#show contextbgp ip-prefix-list test deny prefix-list 1 168.192.13.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#Related Commandsdeny prefix-list <1-4294967295> [<PREFIX-TO-MATCH/MASK>|any]Creates and configures a deny prefix-list rule• <1-4294967295> – Configures a sequence number for this deny rule. Specify a value from 1 - 4294967295. Within a prefix list, rules are applied in an ascending order of their sequence number. Rules with lower sequence number are applied first.• <PREFIX-TO-MATCH/MASK> – Specify the prefix to match. For example 10.0.0.0/8or 192.168.13.0/24. Routes matching the specified prefix are filtered.• ge <0-32> – Optional. Specifies a greater than or equal to value for the IP prefixlength (subnet mask)• le <0-32> – Optional. Specifies a less than or equal to value for the IP prefix lengthThe ‘ge’ and ‘le’ options specify a IP prefix length range. Use these options to specify a more specific (granular) prefix match criteria.• any – Sets the prefix match criteria to any. When selected, all routes are filtered, andthe action applied is deny. At the backend, this option sets the match criteria to0.0.0.0/0 le 32.no Removes a deny prefix-list rule from this IP prefix list](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-983.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 528.1.2 permitbgp-ip-prefix-list-config commandsCreates and configures a permit prefix-list rule. The permit rule specifies match criteria based on which prefixes received from (or transmitted to) a BGP neighbor are filtered. A permit action is applied on these filtered prefixes. For example, in the BGP router neighbor context a filter is applied using a IP prefix list. The list contains a permit rule with a prefix to match as 172.168.10.0/24. All prefixes received from the neighbor matching this prefix are permitted.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxpermit prefix-list <1-4294967295> [<PREFIX-TO-MATCH/MASK>|any]Parameters• permit prefix-list <1-4294967295> [<PREFIX-TO-MATCH/MASK>|any]Examplenx9500-6C8809(config-bgp-ip-prefix-list-test)#permit prefix-list 2 172.122.10.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#show contextbgp ip-prefix-list test deny prefix-list 1 168.192.13.0/24 permit prefix-list 2 172.122.10.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#Related Commandsdeny prefix-list <1-4294967295> [<PREFIX-TO-MATCH/MASK>|any]Creates and configures a permit prefix-list rule• <1-4294967295> – Configures a sequence number for this permit rule. Specify a value from 1 - 4294967295. Within a prefix list, rules are applied in an ascending order of their sequence number. Rules with lower sequence number are applied first.• <PREFIX-TO-MATCH/MASK> – Specify the prefix to match. For example 10.0.0.0/8or 192.168.13.0/24. Routes matching the specified prefix are filtered.• ge – Optional. Specifies a greater than or equal to value for the IP prefix length(subnet mask)• le – Optional. Specifies a less than or equal to value for the IP prefix lengthUse the ‘ge’ and ‘le’ options to specify a IP prefix length range. Use these options to specify a more specific (granular) prefix match criteria.• any – Sets the prefix match criteria to any. When selected, all routes are filtered, andthe action applied is permit. At the backend, this option sets the match criteria to0.0.0.0/0 le 32.no Removes a permit prefix rule from this IP prefix list](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-984.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 628.1.3 nobgp-ip-prefix-list-config commandsRemoves the specified deny or permit prefix-list rule from this IP prefix listSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno [deny|permit]no [deny|permit] prefix-list <1-4294967295> {<PREFIX-TO-MATCH/MASK>|any}Parameters• no <PARATMETERS>ExampleThe following example shows the IP prefix list ‘test’ settings before the ‘no’ command is executed:nx9500-6C8809(config-bgp-ip-prefix-list-test)#show contextbgp ip-prefix-list test deny prefix-list 1 168.192.13.0/24 permit prefix-list 2 172.122.10.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#The following example shows the IP prefix list ‘test’ settings after the ‘no’ command is executed:nx9500-6C8809(config-bgp-ip-prefix-list-test)#no deny prefix-list 1 168.192.13.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#show contextbgp ip-prefix-list test permit prefix-list 2 172.122.10.0/24nx9500-6C8809(config-bgp-ip-prefix-list-test)#no <PARAMETERS> Removes a deny or permit rule from this IP prefix list](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-985.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 828.2.1 denybgp-ip-access-list-config commandsCreates and configures a deny entry for this BGP IP ACLSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxdeny access-list [<PREFIX-TO-MATCH/MASK> {exact-match}|any]Parameters• deny access-list [<PREFIX-TO-MATCH/MASK> {exact-match}|any]Examplenx9500-6C8809(config-bgp-ip-access-list-test)#deny access-list 192.168.13.0/24 exact-matchnx9500-6C8809(config-bgp-ip-access-list-test)#show contextbgp ip-access-list test deny access-list 192.168.13.0/24 exact-matchnx9500-6C8809(config-bgp-ip-access-list-test)#Related Commandsdeny access-list [<PREFIX-TO-MATCH/MASK> {exact-match}|any]Creates and configures a deny entry for this BGP IP ACL• <PREFIX-TO-MATCH/MASK> – Specify the prefix to match.• exact-match – Optional. Enables an exact match of the prefix provided in the pre-vious step. When configured, the route is denied only in case of an exact match.• any – Specifies the prefix to match as ‘any’. no Removes the specified the deny entry in this IP BGP ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-987.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 928.2.2 permitbgp-ip-access-list-config commandsCreates and configures a permit entry for this BGP IP ACLSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxpermit access-list [<PREFIX-TO-MATCH/MASK> {exact-match}|any]Parameters• permit access-list [<PREFIX-TO-MATCH/MASK> {exact-match}|any]Examplenx9500-6C8809(config-bgp-ip-access-list-test)#permit access-list 172.168.10.0/24nx9500-6C8809(config-bgp-ip-access-list-test)#show contextbgp ip-access-list test permit access-list 172.168.10.0/24 deny access-list 192.168.13.0/24 exact-matchnx9500-6C8809(config-bgp-ip-access-list-test)#Related Commandspermit access-list [<PREFIX-TO-MATCH/MASK> {exact-match}|any]Creates and configures a permit entry for this BGP IP ACL• <PREFIX-TO-MATCH/MASK> – Specify the prefix to match.• exact-match – Optional. Enables an exact match of the prefix provided in the pre-vious step. When configured, the route is permitted only in case of an exact match.• any – Specifies the prefix to match as ‘any’. no Removes the specified the permit entry in this IP BGP ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-988.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 1028.2.3 nobgp-ip-access-list-config commandsRemoves a deny or permit entry from this BGP IP ACLSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno [deny|permit]no [deny|permit] access-list [<PREFIX-TO-MATCH/MASK>|any]Parameters• no <PARAMETERS>ExampleThe following example shows the BGP IP ACL ‘test’ settings before the ‘no’ command is executed:nx9500-6C8809(config-bgp-ip-access-list-test)#show contextbgp ip-access-list test permit access-list 172.168.10.0/24 deny access-list 192.168.13.0/24 exact-matchnx9500-6C8809(config-bgp-ip-access-list-test)#nx9500-6C8809(config-bgp-ip-access-list-test)#no permit access-list 172.168.10.0/24The following example shows the BGP IP ACL ‘test’ settings after the ‘no’ command is executed:nx9500-6C8809(config-bgp-ip-access-list-test)#show contextbgp ip-access-list test deny access-list 192.168.13.0/24 exact-matchnx9500-6C8809(config-bgp-ip-access-list-test)#no <PARAMETERS> Removes a deny or permit entry from this BGP IP ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-989.png)

![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 1428.3.3 nobgp-as-path-list-config commandsRemoves a deny or permit rule from this AS path ACLSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno as-path-list [deny|permit] <REG-EXP>Parameters• no <PARAMETERS>Examplenx9500-6C8809(config-bgp-as-path-list-test)#show contextbgp as-path-list test deny as-path ^100$ permit as-path _323_ permit as-path _200_nx9500-6C8809(config-bgp-as-path-list-test)#nx9500-6C8809(config-bgp-as-path-list-test)#no permit as-path _323_nx9500-6C8809(config-bgp-as-path-list-test)#show contextbgp as-path-list test deny as-path ^100$ permit as-path _200_nx9500-6C8809(config-bgp-as-path-list-test)#no <PARAMETERS> Removes a deny or permit rule from this AS path ACL](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-993.png)

![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 1728.4.1 denybgp-community-list-config commandsCreates and configures a deny community (expanded or standard) ruleStandard community lists specify known communities and community numbers. Expanded community lists filter communities using a regular expression that specifies patterns to match the attributes of different communities.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxdeny community [expanded|standard]deny community expanded <LINE>deny community standard [AA:NN|internet|local-AS|no-advertise|no-export]Parameters• deny community expanded <LINE>• deny community standard [AA:NN|internet|local-AS|no-advertise|no-export]deny community expanded <LINE>Configures a deny expanded community list entry and associates it with a regular expression to match. The regular expression represents the patterns to match in the community attributes.• <LINE> – Provide the regular expression.deny community standard [AA:NN|internet|local-AS|no-advertise|no-export]Configures a deny standard community list entry and associates it with a predefined, globally used, known community or community number. The options are:• aa:nn - Configures the community number. The first part (aa) represents the AS number. The second part (nn) represents a 2-byte number.• internet – Advertises this route to the internet community• local-AS – Prevents transmission of this route outside the local AS• no-advertise – Prevents advertisement of this route to any peer (internal or external• no-export – Prevents advertisement of this route to external BGP peers (keeping this route within an AS)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-996.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 1928.4.2 permitbgp-community-list-config commandsCreates and configures a permit community (expanded or standard) ruleStandard community lists specify known communities and community numbers. Expanded community lists filter communities using a regular expression that specifies patterns to match the attributes of different communities.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxpermit community [expanded|standard]permit community expanded <LINE>permit community standard [AA:NN|internet|local-AS|no-advertise|no-export]Parameters• permit community expanded <LINE>• permit community standard [AA:NN|internet|local-AS|no-advertise|no-export]Examplenx9500-6C8809(config-bgp-community-list-test)#permit community expanded 300nx9500-6C8809(config-bgp-community-list-test)# show contextbgp community-list test permit community expanded 300 deny community expanded 100nx9500-6C8809(config-bgp-community-list-test)#nx9500-6C8809(config-bgp-community-list-test1)#permit community standard no-exportnx9500-6C8809(config-bgp-community-list-test1)#show contextbgp community-list test1 permit community standard no-exportnx9500-6C8809(config-bgp-community-list-test1)#permit community expanded <LINE>Configures a permit expanded community list entry and associates it with a regular expression to match. The regular expression represents the patterns to match in the community attributes.• <LINE> – Provide the regular expression.permit community standard [AA:NN|internet|local-AS|no-advertise|no-export]Configures a permit standard community list entry and associates it with a predefined, globally used, known community or community number. The options are:• aa:nn – Configures the community number. The first part (aa) represents the AS number. The second part (nn) represents a 2-byte number.• internet – Advertises this route to the internet community• local-AS – Prevents transmission of this route outside the local AS• no-advertise – Prevents advertisement of this route to any peer (internal or external• no-export – Prevents advertisement of this route to external BGP peers (keeping this route within an AS)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-998.png)

![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 2128.4.3 nobgp-community-list-config commandsRemoves a deny or permit community rule from this community listSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno [deny|permit] community expanded <LINE>no [deny|permit] community standard [AA:NN|internet|local-AS|no-advertise|no-export]Parameters• no <PARAMETERS>ExampleThe following example shows the settings of the community list ‘test’ before the ‘no’ command is executed:nx9500-6C8809(config-bgp-community-list-test)#show contextbgp community-list test permit community expanded 300 deny community expanded 100nx9500-6C8809(config-bgp-community-list-test)#nx9500-6C8809(config-bgp-community-list-test)#no deny community expanded 100The following example shows the settings of the community list ‘test’ after the ‘no’ command is executed:nx9500-6C8809(config-bgp-community-list-test)#show contextbgp community-list test permit community expanded 300nx9500-6C8809(config-bgp-community-list-test)#no <PARAMETERS> Removes a deny or permit expanded community rule from this community list• <LINE> – Specify the regular expression associated with the rule.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1000.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 2328.5.1 denybgp-extcommunity-list-config commandsCreates and configures a deny extended community (expanded or standard) ruleSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxdeny extcommunity [expanded|standard]deny extcommunity expanded <LINE>deny extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Parameters• deny extcommunity expanded <LINE>• deny extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Examplenx9500-6C8809(config-bgp-extcommunity-list-test)#deny extcommunity standard rt 200:12nx9500-6C8809(config-bgp-extcommunity-list-test)#show contextbgp extcommunity-list test deny extcommunity standard rt 200:12nx9500-6C8809(config-bgp-extcommunity-list-test)#nx9500-6C8809(config)#show context!! Configuration of NX9500 version 5.9.1.0-026R!!version 2.5!......................................................!bgp community-list test1 permit community standard no-export!bgp extcommunity-list test deny extcommunity standard rt 200:12!--More--nx9500-6C8809(config)#deny extcommunity expanded <LINE>Configures a deny expanded named extended community list entry and associates it with a regular expression to match. The regular expression represents the patterns to match in the extended community attributes.• <LINE> – Provide the regular expression.deny extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Configures a deny standard named extended community list entry. and associates it with the target or origin community attributes.• rt – Configures the route target (RT) extended community attribute• soo – Configures the site-of-origin (SOO) extended community attribute• <COMMUNITY-NUMBER> – Specify the community number in one of the followingformats: AA:NN or A.B.C.D:NN](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1002.png)

![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 2528.5.2 permitbgp-extcommunity-list-config commandsCreates and configures a permit extended community (expanded or standard) ruleSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxpermit extcommunity [expanded|standard]permit extcommunity expanded <LINE>permit extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Parameters• permit extcommunity expanded <LINE>• permit extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Examplenx9500-6C8809(config-bgp-extcommunity-list-test)#permit extcommunity standard rt 192.168.13.13:12nx9500-6C8809(config-bgp-extcommunity-list-test)#show contextbgp extcommunity-list test permit extcommunity standard rt 192.168.13.13:12 deny extcommunity standard rt 200:12nx9500-6C8809(config-bgp-extcommunity-list-test)#nx9500-6C8809(config)#show context!! Configuration of NX9500 version 5.9.1.0-026R!!version 2.5!......................................................!bgp community-list test1 permit community standard no-export!bgp extcommunity-list test permit extcommunity standard rt 192.168.13.13:12 deny extcommunity standard rt 200:12!permit extcommunity expanded <LINE>Configures a permit expanded named extended community list entry and associates it with a regular expression to match. The regular expression represents the patterns to match in the extended community attributes.• <LINE> – Provide the regular expression.permit extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Configures a permit standard named extended community list entry. and associates it with the target or origin community attributes.• rt – Configures the RT extended community attribute• soo – Configures the SOO extended community attribute• <COMMUNITY-NUMBER> – Specify the community number in one of the followingformats: AA:NN or A.B.C.D:NN](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1004.png)

![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 2728.5.3 nobgp-extcommunity-list-config commandsRemoves an existing deny or permit extended community rule from this extcommunity listSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno [deny|permit] extcommunity expanded <LINE>no [deny|permit] extcommunity standard [rt|soo] <COMMUNITY-NUMBER>Parameters• no <PARAMETERS>ExampleThe following example shows the extended community ‘test’ settings before the ‘no’ command is executed:nx9500-6C8809(config-bgp-extcommunity-list-test)#show contextbgp extcommunity-list test permit extcommunity standard rt 192.168.13.13:12 deny extcommunity standard rt 200:12nx9500-6C8809(config-bgp-extcommunity-list-test)#nx9500-6C8809(config-bgp-extcommunity-list-test)#no permit extcommunity standard 192.168.13.13:12The following example shows the extended community ‘test’ settings after the ‘no’ command is executed:nx9500-6C8809(config-bgp-extcommunity-list-test)#show contextbgp extcommunity-list test deny extcommunity standard rt 200:12nx9500-6C8809(config-bgp-extcommunity-list-test)#no <PARAMETERS> Removes a deny or permit expanded extended community rule from this community list](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1006.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 3128.6.2 matchbgp-route-map-config commandsConfigures the match criteria associated with this deny or permit BGP route mapSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxmatch [as-path|community|extcommunity|ip-address|ip-next-hop|ip-route-source|metric|origin|tag]match [as-path <AS-PATH-LIST-NAME>|community <COMMUNITY-LIST-NAME> {exact-match}|extcommunity <EXTCOMMUNITY-LIST-NAME>]match [ip-address|ip-next-hop|ip-route-source] [BGP-IP-ACCESS-LIST <BGP-ACL-NAME>|prefix-list <PREFIX-LIST-NAME>]match metric <0-4294967295>match origin [egp|igp|incomplete]match tag <0-65535>Parameters• match [as-path <AS-PATH-LIST-NAME>|community <COMMUNITY-LIST-NAME> {exact-match}|extcommunity <EXTCOMMUNITY-LIST-NAME>]• match [ip-address|ip-next-hop|ip-route-source] [BGP-IP-ACCESS-LIST <BGP-ACL-NAME>|prefix-list <PREFIX-LIST-NAME>]as-path <AS-PATH-LIST-NAME>Configures a BGP AS path list to matchAn AS path is a list of ASs a packet traverses to reach its destination.• <AS-PATH-LIST-NAME> – Specify the AS path list name (should be existing and configured)community <COMMUNITY-LIST-NAME> {exact-match}Configures the AS community list string to match• <COMMUNITY-LIST-NAME> – Specify the AS community list name (should be existing and configured).• exact-match – Optional. Does an exact match when matching the specified AScommunity string. This option is disabled by default.extcommunity <EXTCOMMUNITY-LIST-NAME>Configures the external community list string to match• <EXTCOMMUNITY-LIST-NAME> – Specify the external community list name (should be existing and configured).match Configures match criteria used to filter BGP routes when forwarding packetsip-address [BGP-IP-ACCESS-LIST <BGP-ACL-NAME>|prefix-list <PREFIX-LIST-NAME>]Configures a string of IP addresses, in the route, to matchThe IP Address is a list of IP addresses in the route used to filter the route. Use one of the following options to provide a list of IP addresses:• BGP-IP-ACCESS-LIST <BGP-ACL-NAME> – Associates an existing BGP ACL with this BGP route map. Specify the BGP ACL name (should be existing and configured).• prefix-list <PREFIX-LIST-NAME> – Associates an existing IP address prefix list with this BGP route map. The IP Address Prefix List is a list of prefixes in the route used to filter route. Specify the prefix list name (should be existing and configured).](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1010.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 32• match metric <0-4294967295>• match origin [egp|igp|incomplete]• match tag <0-65535>ip-next-hop [BGP-IP-ACCESS-LIST <BGP-ACL-NAME>|prefix-list <PREFIX-LIST-NAME>]Configures the next-hop’s IP address to matchThe IP Next Hop is a list of IP addresses used to filter routes based on the IP address of the next-hop in the route. Use one of the following options to provide next-hop’s IP addresses:• BGP-IP-ACCESS-LIST <BGP-ACL-NAME> – Associates an existing BGP ACL with this BGP route map. Specify the BGP ACL name (should be existing and configured).• prefix-list <PREFIX-LIST-NAME> – Associates an existing IP next-hop prefix list with this BGP route map. The IP Next Hop Prefix List is a list of prefixes for the route’s next-hop determining how the route is filtered. Specify the prefix list name (should be existing and configured).ip-route-source [BGP-IP-ACCESS-LIST <BGP-ACL-NAME>|prefix-list <PREFIX-LIST-NAME>]Configures the advertised route source IP address to matchThe IP Route Source is a list of IP addresses used to filter routes based on the advertised IP address of the source. Use one of the following options to provide route-source IP addresses:• BGP-IP-ACCESS-LIST <BGP-ACL-NAME> – Associates an existing BGP ACL with this BGP route map. Specify the BGP ACL name (should be existing and configured).• prefix-list <PREFIX-LIST-NAME> – Associates an existing IP route source prefix list with this BGP route map. The IP Route Source Prefix List is a list of prefixes used to filter routes based on the prefix list used for the source. Specify the prefix list name (should be existing and configured).match metric <0-4294967295>Defines the exterior metric, used for route map distribution, to matchBGP uses a route table managed by the external metric defined. Setting a metric provides a dynamic way to load balance between routes of equal cost.• <0-4294967295> – Specify the external metric value from 0 - 4294967295.match origin [gp|igp|incomplete]Configures the source of the BGP route to match. Options include:• egp – Matches if the origin of the route is from the exterior gateway protocol (eBGP). eBGP exchanges routing table information between hosts outside an autonomous system.• igp – Matches if the origin of the route is from the interior gateway protocol (iBGP). iBGP exchanges routing table information between routers within an autonomous system.• incomplete – Matches if the origin of the route is not identifiablematch tag <0-65535> Configures the BGP route tag to matchThe Tag is a way to preserve a route’s AS path information for routers in iBGP. This option is disabled by default.• <0-65535> – Specify the iBGP route’s tag from 0 - 65535.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1011.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 3428.6.3 nobgp-route-map-config commandsRemoves or reverts the settings defined for a deny or permit route-map ruleSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno [description|match <PARAMETERS>|set <PARAMETERS>]Parameters• no <PARAMETERS>ExampleThe following example shows the ‘deny route-map rule-1’ settings before the ‘no’ commands are executed:nx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#show context deny route-map 1 description "This is a deny route map rule" match as-path FilterList_01 match ip-route-source prefix-list PrefixList_01 set aggregator-as 1 192.168.13.7 set as-path exclude 20 set ip next-hop peer-address set metric 300 set local-preference 30 set community internetnx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#nx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#no match as-pathnx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#no set aggregator-asnx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#no set metricThe following example shows the ‘deny route-map rule-1’ settings after the ‘no’ commands are executed:nx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#show context deny route-map 1 description "This is a deny route map rule" match ip-route-source prefix-list PrefixList_01 set as-path exclude 20 set ip next-hop peer-address set local-preference 30 set community internetnx9500-6C8809(config-dr-route-map-test-dr-route-map-rule-1)#The following example shows the route-map ‘test’ settings:nx9500-6C8809(config-dr-route-map-test)#show contextroute-map test deny route-map 1 description "This is a deny route map rule" match ip-route-source prefix-list PrefixList_01 set as-path exclude 20 set ip next-hop peer-address set local-preference 30 set community internet permit route-map 2 match ip-next-hop DL_01nx9500-6C8809(config-dr-route-map-test)#no <PARAMETERS> Removes the description configured for a deny or permit route-map rule](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1013.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 3528.6.4 setbgp-route-map-config commandsConfigures the values attributed to a route matching the match criteria specified in the BGP deny or permit route-map rules. These attributes are applied before the route is sent out.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxset [aggregator-as|as-path|atomic-aggregate|comm-list|community|extcommunity|ip|local-preference|metric|origin|originator-id|source-ip|tag|weight]set aggregator-as <1-4294967295> <IP>set as-path [exclude|prepend] <1-4294967295> {<1-4294967295>}set atomic-aggregateset comm-list delete <COMMUNITY-LIST-NAME>set community [<COMMUNITY-NUMBER>|none]set extcommunity [rt|soo] <EXTCOMMUNITY-NUMBER>set ip next-hop [<IP>|peer-address]set local-preference <0-4294967295>set metric <0-4294967295>set origin [egp|igp|incomplete]set originatorid <IP>set source-ip <IP>set tag <0-65535>set weight <0-4294967295>Parameters• set aggregator-as <1-4294967295> <IP>set aggregator-as <1-4294967295> <IP>Configures the BGP aggregator’s ASN and IP address. Aggregates minimize the size of routing tables. Aggregation combines the characteristics of multiple routes and advertises them as a single route. The configured BGP aggregator settings are applied to filtered routes.• <1-4294967295> – Specify the route aggregator’s ASN from 1- 4294967295. This option is disabled by default.• <IP> – Specify the route aggregator’s IP address. BGP allows the aggregation ofspecific routes into one route using an aggregate IP address.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1014.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 36• set as-path [exclude|prepend] <1-4294967295> {<1-4294967295>}• set atomic-aggregate• set comm-list delete <COMMUNITY-LIST-NAME>• set community [<COMMUNITY-NUMBER>|none]• set extcommunity [rt|soo] <EXTCOMMUNITY-NUMBER>set as-path [exclude|prepend] <1-4294967295> {<1-4294967295>}Configures the BGP transform AS path attribute to be applied to filtered routes• exclude – Configures a single AS, or a list of ASs, excluded from the AS path• prepend – Configures a single AS, or a list of ASs, prepended to the AS path• <1-4294967295> – This keyword is common to the ‘exclude’ and ‘prepend’ param-eters. Use it to specify the AS number. The ASs identified here are excluded or pre-pended depending on the option selected.You can configure multiple ASNs.set atomic-aggregate Enables BGP atomic aggregate attributesWhen a BGP enabled wireless controller or service platform receives a set of overlapping routes from a peer, or if the set of routes selects a less specific route, then the local device must set this value when propagating the route to its neighbors. This option is disabled by default.set comm-list delete <COMMUNITY-LIST-NAME>Deletes specified BGP communities. All communities matching the community list name string are deleted from the route.A BGP community is a group of routes sharing a common attribute.• <COMMUNITY-LIST-NAME> – Specify the community list name.set community [<COMMUNITY-NUMBER>|none]Configures a community attribute for this route• <COMMUNITY-NUMBER> – Specify a community attribute. Use one of the following formats:• internet - Advertises this route to the Internet. This is a global community.• local-AS - Prevents the transmit of packets outside the local AS• no-advertise - Prevents advertisement of this route to any peer, either internal orexternal• no-export - Prevents advertisement of this route to BGP peers, keeping this routewithin an AS.• aa:nn - Configures the first part (aa) representing the AS number. The second part(nn) represents a 2-byte number.• none – Specifies community attribute as noneset extcommunity [rt|soo] <EXTCOMMUNITY-NUMBER>Configures a extended community attribute for this route• rt – Identifies the route target (rt) extended community• soo – Identifies the site-of-origin (soo) community. This is the origin community associated with the route reflector.• <EXTCOMMUNITY-NUMBER> – This keyword is common to the ‘rt’ and ‘soo’ param-eters. Use it to specify the extended community number.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1015.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 37• set ip next-hop [<IP>|peer-address]• set local-preference <0-4294967295>• set metric <0-4294967295>• set origin [egp|igp|incomplete]• set originatorid <IP>• set source-ip <IP>• set tag <0-65535>• set weight <0-4294967295>set ip next-hop [<IP>|peer-address]Configures the next hop for this route. Use one of the following options to identify the next hop:• <IP> – Specify the nest hop’s IP address• peer-address – Enables the identification of the next-hop address for peer devices. This option is disabled by default set local-preference <0-4294967295>Configures the BGP local preference path attribute for this route map. When configured, enables the communication of preferred routes out of the AS between peers. This option is disabled by default• <0-4294967295> – Specify the preference value from 0 - 4294967295.set metric <0-4294967295>Configures a metric for the routeBGP uses a route table managed by the external metric defined. Setting a metric provides a dynamic way to load balance between routes of equal cost.• <0-4294967295> – Specify the metric from 0 - 4294967295.set origin [egp|igp|incomplete]Configures the origin code for this BGP route map• egp - Sets the origin of the route to eBGP• igp - Sets the origin of the route to iBGP• incomplete - Sets the origin of the route as not identifiable. Use this option if the route is from a source other than eBGP or iBGP.set originatorid <IP> Configures this route map’s originator IP addressset source-ip <IP> Configures this route map’s source IP address• <IP> – Specify the IP address in the A.B.C.D format.set tag <0-65535> Configures this route map’s tag valueThe Tag is a way to preserve a route’s AS path information for routers in iBGP. • <0-65335> – Specify a tag value from 0 - 65535.set weight <0-4294967295>Enables assignment of a weighted priority to the aggregate route• <0-4292967295> – Specify a value from 0 - 4294967295.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1016.png)


![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 4328.7.3 bgpbgp-router-config commandsConfigures BGP router parametersSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxbgp [always-compare-med|bestpath|client-to-client|cluster-id|confederation|dampening|default|deterministic-med|enable|enforce-first-as|fast-external-failover|graceful-restart|log-neighbor-changes|neighbor|network|router-id|scan-time]bgp [always-compare-med|deterministic-med|enable|enforce-first-as|fast-external-failover|log-neighbor-changes]bgp best-path [as-path [confed|ignore]|compare-router-id|med {confed {missing-as-worst}|missing-as-worst}]bgp client-to-client reflectionbgp cluster <IP>bgp confederation [identifier|peers] <1-4294967295>bgp dampening {<1-45>} {<1-20000>} <1-20000> <1-255>bgp default [ipv4-unicast|local-preference <0-4294967295>]bgp graceful-restart {stalepath-time <1-3600>}bgp neighbor <IP>bgp network import-checkbgp router-id <IP>bgp scan-time <5-60>Parameters• bgp [always-compare-med|deterministic-med|enable|enforce-first-as|fast-external-failover|log-neighbor-changes]always-compare-med Enables comparison of Multi-exit Discriminators (MEDs) received from neighbors. This option is disabled by default.MED is a value used by BGP peers to select the best route among multiple routes. When enabled, the MED value encoded in the route is always compared when selecting the best route to the host network. A route with a lower MED value is preferred over a route with a higher MED value. BGP does not discriminate between iBGP and eBGP when using MED for route selection. This option is mutually exclusive to the deterministic-med option.deterministic-med Enables selection of the best MED path from amongst all paths advertised by neighboring ASs. This option is disabled by default.MED is used by BGP peers to select the best route among multiple routes. When enabled, MED route values (from the same AS) are compared to select the best route. This best route is then compared with other routes in the BGP route table to select the best overall route. This option is mutually exclusive to the always-compare-med option.enable Starts the BGP daemon on the device (wireless controller or service platform). BGP is disabled by default.enforce-first-as Enforces the first AS for all BGP routes. This option is disabled by default.When enforced, devices deny updates received from an external neighbor that does not have the neighbor’s configured AS at the beginning of the received AS path parameter. This enhances security by not allowing traffic from an unauthorized AS.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1022.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 44• bgp best-path [as-path [confed|ignore]|compare-router-id|med {confed {missing-as-worst}|missing-as-worst}]• bgp client-to-client reflectionfast-external-failover Enables immediate resetting of BGP session on the interface once the BGP connection goes down. This option is enabled by default.When enabled, a session is reset as soon as the direct link to an external peer goes down. Normally, when a BGP connection goes down, the device waits for the expiry of the duration specified in holdtime parameter before bringing down the interface.To configure the ‘holdtime’, use the timers > bgp > <keepalive-time> > <holdtime> command in this (BGP router) configuration mode.log-neighbor-changes Enables logging of a BGP neighbor’s status change (active or not active) events. It also enables the logging of the reason for such change in status.best-path Modifies the bestpath selection algorithm. The route selection algorithm uses the following criteria when selecting the preferred route: as-path, router-id, and med.as-path [confed|ignore]Enables an AS path from being considered as a criteria for selecting the preferred route• confed – Enables comparison of path lengths (including confederation sets and sequences) when selecting a route (EXPERIMENTAL). This option is disabled by default.• ignores – Disables an AS path length from being considered as a criteria for selecting a preferred route. When, disabled the AS path length is ignored. This option is disabled by default.compare-router-id Enables the use of router ID as a selection criteria when selecting the preferred route. When enabled, the router ID is used to select the best path between two identical BGP routes. The route with the lower router ID is selected over a route with a higher router ID. This option is disabled by default.med {confed {missing-as-worst}|missing-as-worst}Enables comparison of AS path MED value when selecting the preferred routeMED is a value used by BGP peers to select the best route among multiple routes. When enabled, the MED value encoded in the route is always compared to determine the best route to the host network. A route with a lower MED value is preferred over a route with a higher MED value.• confed – Optional. Enables comparison of MED value among confederation paths (EXPERIMENTAL). When enabled, you can optionally enable the treatment of AS paths without the MED value as the least preferable route. This option is disabled by default.• missing-as-worst – Optional. Enables the treatment of AS paths without the MED value as the least preferable route. This option is disabled by default.client-to-client reflectionEnables client-to-client route reflection (EXPERIMENTAL)Route reflectors are used when all iBGP speakers are not fully meshed. If the clients are fully meshed, the route-reflectors are not required. This option is enabled by default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1023.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 45• bgp cluster <IP>• bgp confederation [identifier|peers] <1-4294967295>• bgp dampening {<1-45>} {<1-20000>} <1-20000> <1-255>• bgp default [ipv4-unicast|local-preference <0-4294967295>]cluster <IP> Enables and sets a cluster ID, in case the BGP cluster has more than one route-reflectorA cluster generally consists of a single route-reflector and its clients. The cluster is usually identified by the router ID of this single route-reflector. Sometimes, to increase redundancy, a cluster might have more than one route-reflector configured. In this case, all route-reflectors in the cluster are identified by the cluster ID (configured in the IP format).confederation [identifier|peers] <1-4294967295>Configures AS confederation (group of ASs) parameters (identifier and peers)• identifier – Enables and sets a BGP confederation identifier to allow an AS to be divided into several ASs. In other words an AS is divided into multiple ASs, and together they form a confederation. This confederation is visible to external routers as a single AS. The ASN is usually the confederation ID. Specify a value from 1 - 4294967295.Forming AS confederation reduces iBGP mesh inside an AS.• peers – Configures the maximum number of the ASs constituting this BGP confederation. Specify the AS number from 1 - 4294967295. Multiple ASs can be added to the list of confederation members.bgp dampening {<1-45>} {<1-20000>} <1-20000> <1-255>Enables dampening and configures dampening parameters. This option is disabled by default.Dampening minimizes the instability caused by route flapping. A penalty is added for every flap in the flapping route. As soon as the total penalty reaches the specified Route Suppress Limit value, the advertisement of this route is suppressed. This penalty is delayed when the time specified in Half Lifetime occurs. Once the penalty becomes lower than the value specified in Start Route Reuse, the advertisement of the route is un-suppressed.• <1-45> – Optional. Configures the half lifetime (in minutes). A penalty is imposed on a route that flaps. This is the time for the penalty to decrease to half its current value. Specify a value from 1 - 45 minutes. The default is 1 minute.• <1-20000> – Optional. Configures the route reuse value. When the penalty for a suppressed route decays below the value specified here, the route is un-suppressed (reused). Specify a value from 1 - 20000.• <1-20000> – Configures the route suppress value. When a route flaps, a penalty is added to the route. When the penalty reaches or exceeds the value specified as the ‘maximum duration to suppress a stable route’. Specify a value from 1 - 20000.The maximum duration to suppress a stable route, is the next set of value configured in this command from 1 - 255.• <1-255> – Configures the maximum duration, in minutes, a suppressed route is suppressed. This is the maximum duration for which a route remains suppressed before it is reused. Specify a value from 1 - 255 minutes.default Configures the following defaults for BGP neighbor-related parameters: IPv4 unicast and local preference](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1024.png)

![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 4828.7.4 bgp-route-limitbgp-router-config commandsConfigures the BGP route limit parametersSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxbgp-route-limit [num-routes <VALUE>|reset-time <1-86400>|retry-count <1-32>|retry-timeout <1-3600>]Parameters• bgp-route-limit [num-routes <VALUE>|reset-time <1-86400>|retry-count <1-32>|retry-timeout <1-3600>]Examplenx9500-6C8809(config-profile NX9500Profile-router-bgp)#bgp-route-limit num-routes 10nx9500-6C8809(config-profile NX9500Profile-router-bgp)#show context router bgp bgp enable asn 1 aggregate-address 116.117.118.0/24 as-set summary-only bgp neighbor 192.168.13.99 remote-as 199 maximum-prefix 9999 80 restart 50 bgp-route-limit num-routes 10nx9500-6C8809(config-profile NX9500Profile-router-bgp)#Related Commandsnum-routes <VALUE> Configures the number of routes that can be stored on this BGP router. Set this value based on the available memory on this BGP router (wireless controller or service platform).• <VALUE> – Specify a value from 1 - 4,294,967,295. The default is 9216 routes.reset-time <1-86400> Configures the reset time in seconds. This is the time after which the retry count value is set to Zero (0). • <1-86400> – Specify a value from 1- 86,400 seconds. The default is 360 seconds.retry-count <1-32> Configures the maximum number of times the BGP process is reset before being permanently shut down. Once shut down, the BGP process has to be started manually. The BGP process is reset if it is flooded with route entries that exceed the maximum number of routes configured for this device.• <1-32> – Specify a value from 1 - 32. The default is 5 routes.retry-timeout <1-3600>Configures the duration, in seconds, the BGP process is temporarily shut down, before a reset of the process is attempted.• <1-3600> – Specify a value from 1 - 3600 seconds. The default is 60 seconds.no Removes BGP route limitations configured. Use the no command to revert back to default.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1027.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 4928.7.5 distancebgp-router-config commandsConfigures administrative distance parameters. The distance parameter is a rating of the trustworthiness of a route. The higher the distance, lower is the trust rating. The distance can be set for each type of route indicating its trust rating.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxdistance [<IP/M> <1-255> <BGP-ACL-NAME>|bgp <1-255> <1-255> <1-255>]Parameters• distance [<IP/M> <1-255> <BGP-ACL-NAME>|bgp <1-255> <1-255> <1-255>]Examplenx9500-6C8809(config-profile testNX9000-router-bgp)#distance bgp 200 100 200nx9500-6C8809(config-profile testNX9000-router-bgp)#show context router bgp bgp enable asn 1 aggregate-address 116.117.118.0/24 as-set summary-only distance bgp 200 100 200 bgp neighbor 192.168.13.99 remote-as 199 maximum-prefix 9999 80 restart 50 bgp-route-limit num-routes 10nx9500-6C8809(config-profile testNX9000-router-bgp)#Related Commandsdistance <IP/M> <1-255> <BGP-ACL-NAME>Configures the default administrative distance, specified by the <1-255> parameter, when the route’s source IP address matches the specified IP prefix • <IP/M> – Specify the IP source prefix and prefix length.• <1-255> – Specify the distance from 1 - 255.• <BGP-ACL-NAME> – Optional. Specify the BGP access list name.bgp <1-255> <1-255> <1-255>Configures the default administrative distance for different route types• <1-255> – Configures the default administrative distance for routes external to this AS. Specify a value from 1 - 255.• <1-255> – Configures the default administrative distance for routes internal to thisAS. Specify a value from 1 - 255.• <1-255> – Configures the default administrative distance for local routes. Specifya value from 1 - 255.no Removes the administrative distance related configurations](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1028.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 5228.7.8 nobgp-router-config commandsRemoves the BGP router settingsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxno [aggregate-address|bgp|bgp-route-limit|distance|ip|network|route-redistribute|timers]Parameters• no <PARAMETERS>ExampleThe following example shows the BGP router settings before the ‘no’ commands have been executed:nx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#show context router bgp bgp enable asn 1 aggregate-address 116.117.118.0/24 as-set summary-only bgp neighbor 192.168.13.199 remote-as 1 use route-map UnSupMap_01 in bgp neighbor 192.168.13.99 remote-as 199 maximum-prefix 9999 80 restart 50 bgp-route-limit num-routes 10 reset-time 360nx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#nx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#no bgp neighbor 192.168.13.99nx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#no aggregate-address 116.117.118.0/24nx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#no bgp-route-limit The following example shows the BGP router settings after the ‘no’ commands have been executed:nx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#show context router bgp bgp enable asn 1 bgp neighbor 192.168.13.199 remote-as 1 use route-map UnSupMap_01 innx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp)#no <PARAMETERS> Removes the BGP router settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1031.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 5328.7.9 route-redistributebgp-router-config commandsEnables redistribution of routes learnt from other routing protocols into BGPLarge ISP networks using multiple routing protocols, need to enable redistribution of routes across routing protocols. Routing protocols differ in their basic characteristics, such as metrics, administrative distance, classful and classless capabilities, etc. When enabling redistribution, these differences have to be taken into consideration.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxroute-redistribute [connected|kernel|ospf|static] {metric <0-4294967295>|route-map <ROUTE-MAP-NAME>}Parameters• route-redistribute [connected|kernel|ospf|static] {metric <0-4294967295>|route-map <ROUTE-MAP-NAME>}route-redistribute Redistributes routes learnt from other protocolsconnected Redistributes directly connected routes• metric <0-4294967295> – Optional. Specify the metric for the redistributed routes.• route-map <ROUTE-MAP-NAME> – Optional. Specifies the route map name. The route map defines the match criteria based on which routes are filtered before redistribution. For more information on route maps, see match.kernel Redistributes kernel routes. These are routes that are neither connected, nor static, nor dynamic.• metric <0-4294967295> – Optional. Specify the metric for the redistributed routes.• route-map <ROUTE-MAP-NAME> – Optional. Specifies the route map name. The route map defines the match criteria based on which routes are filtered before redistribution. For more information on route maps, see match.ospf Redistributes OSPF routes• metric <0-4294967295> – Optional. Specify the metric for the redistributed routes.• route-map <ROUTE-MAP-NAME> – Optional. Specifies the route map name. The route map defines the match criteria based on which routes are filtered before redistribution. For more information on route maps, see match.static Redistributes static routes• metric <0-4294967295> – Optional. Specify the metric for the redistributed routes.• route-map <ROUTE-MAP-NAME> – Optional. Specifies the route map name. The route map defines the match criteria based on which routes are filtered before redistribution. For more information on route maps, see match.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1032.png)


![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 6328.8.5 capabilitybgp-neighbor-config commandsEnables the advertisement of capability (dynamic and ORF) to BGP peersSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxcapability [dynamic|orf]capability dynamiccapability orf prefix-list [both|receive|send]Parameters• capability dynamic• capability orf prefix-list [both|receive|send]Examplenx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#capability orf prefix-list bothnx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#showcontext bgp neighbor 192.168.13.99 advertisement-interval 100 allowas-in 10 attribute-unchanged as-path capability orf prefix-list bothnx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#Related Commandscapability dynamic Enables the advertisement of dynamic capabilityEnable this option to show a neighbor device’s capability to advertise or withdraw and address capability to other peers in a non-disruptive manner. This option is disabled by default.capability dynamic [both|receive|send]Enables the advertisement of Outbound Router Filtering (ORF) capability. This option is disabled by default.Enable this option to enable ORF, and advertise this capability to peer devices. ORFs send and receive capabilities to lessen the number of updates exchanged between BGP peers. By filtering updates, ORF minimizes update generation and exchange overhead.The local BGP device advertises ORF in the send mode. The peer BGP device receives the ORF capability in the receive mode. The two devices exchange updates to maintain the ORF for each router. Only a peer group or an individual BGP router can be configured to be in receive or send mode. A a peer group member cannot be configured.• both – Advertises the capability to send and receive the ORF to/from this neighbor• receive – Advertises the capability to receive the ORF from this neighbor• send – Advertises the capability to send the ORF to this neighborno Disables advertisement of capability (dynamic and ORF) to BGP peers](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1042.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 8228.8.24 send-communitybgp-neighbor-config commandsEnables sending of the community attribute to the BGP neighbor. The community attribute groups destinations in a certain community and applies routing decisions based on the community. On receiving community attribute, the BGP router announces it to the neighbor.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxsend-community [both|extended|standard]Parameters• send-community [both|extended|standard]Examplenx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#send-community bothnx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#show context bgp neighbor 192.168.13.99 remote-as 100 advertisement-interval 100 peer-group eBGPPeerGrp1 port 21 allowas-in 10 attribute-unchanged as-path capability orf prefix-list both default-originate description neighbor "This neighbor is an external AS neighbor" disable-connected-check dont-capability-negotiate ebgp-multihop 20 enforce-multihop local-as 20 no-prepend maximum-prefix 400 50 warning-only next-hop-self override-capability passive password neighbor eBGPneighbor@300 remove-private-as route-server-client send-community bothnx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#Related Commandssend-community [both|extended|standard]Enables sending of the community attributes to the BGP neighbor• both – Sends extended and standard community attributes• extended – Sends extended community attributes only• standard – Sends standard community attributes onlyno Disables sending of the community attribute to the BGP neighbor](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1061.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 8628.8.28 timersbgp-neighbor-config commandsConfigures this BGP neighbor’s keepalive and holdtime durationsSupported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxtimers [<0-65535> <0-65535>|connect <0-65535>]Parameters• timers [<0-65535> <0-65535>|connect <0-65535>]Examplenx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#timers 20 40nx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#timers connect 20nx9500-6C8809(config-profile testNX9000-router-bgp-neighbor-192.168.13.99)#show context bgp neighbor 192.168.13.99 remote-as 100 advertisement-interval 100 peer-group eBGPPeerGrp1 port 21 strict-capability-match timers connect 20 timers 20 40 allowas-in 10 attribute-unchanged as-path capability orf prefix-list both default-originate description neighbor "This neighbor is an external AS neighbor" disable-connected-check dont-capability-negotiate ebgp-multihop 20 enforce-multihopNOTE: The keepalive and holdtime settings configured at the neighbor level override those configured on the BGP router.timers <0-65535> <0-65535>Sets the keepalive and holdtime intervals• <0-65535> – Specifies the keepalive interval from 0 - 65535 seconds. It is the interval, in seconds, between two successive keepalive packets exchanged with this neighbor to keep the TCP connection alive.• <0-65535> – Specifies the holdtime interval from 0 - 65535. This is the time thisneighbor will wait without receiving a keepalive packet from its neighbor before declaring it dead. If the time since the last keepalive packet received (from its neighbor) exceeds the value set here, the neighbor is declared dead.timers connect <0-65535>Sets the BGP connect time. This is the interval, in seconds, after which BGP tries to connect to a dead peer.• <0-65535> – Specify a value from 1 - 65535 seconds.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1065.png)
![BORDER GATEWAY PROTOCOLAccess Point, Wireless Controller and Service Platform CLI Reference Guide 28 - 9028.8.31 usebgp-neighbor-config commandsConfigures filters for this neighbor. These filters are BGP IP ACL, IP prefix list, AS path list, and route map. Based on the filters used, updates received from this neighbor are filtered.Supported in the following platforms:• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX9500, NX9510, NX9600Syntaxuse [distribute-list <BGP-IP-ACL-NAME>|filter-list <AS-PATH-LIST-NAME>|prefix-list <IP-PREFIX-LIST-NAME>|route-map <BGP-ROUTE-MAP-NAME>]Parameters• use [distribute-list <BGP-IP-ACL-NAME>|filter-list <AS-PATH-LIST-NAME>|prefix-list <IP-PREFIX-LIST-NAME>|route-map <BGP-ROUTE-MAP-NAME>]Examplenx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp-neighbor-192.168.13.99)#use filter-list FilterList_01 innx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp-neighbor-192.168.13.99)#use route-map testBGPRouteMap outnx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp-neighbor-192.168.13.99)#show context bgp neighbor 192.168.13.99 remote-as 199 use filter-list FilterList_01 in maximum-prefix 9999 80 restart 50 use route-map testBGPRouteMap out unsuppress-map testnx9500-6C8809(config-device B4-C7-99-6C-88-09-router-bgp-neighbor-192.168.13.99)#Related Commandsuse [distribute-list <BGP-IP-ACL-NAME>|filter-list <AS-PATH-LIST-NAME>|prefix-list <IP-PREFIX-LIST-NAME>|route-map <BGP-ROUTE-MAP-NAME>]Uses predefined and configured filters with this neighbor• distribute-list <BGP-IP-ACL-NAME> – Uses a BGP IP ACL• <BGP-IP-ACL-NAME> – Specify the BGP IP ACL name.• filter-list <AS-PATH-LIST-NAME> – Uses an AS path list• <AS-PATH-LIST-NAME> – Specify the AS path list name.• prefix-list <IP-PREFIX-LIST-NAME> – Uses a IP prefix list• <IP-PREFIX-LIST-NAME> – Specify the IP prefix list name.• route-map <BGP-ROUTE-MAP-NAME> – Uses a route map• <BGP-ROUTE-MAP-NAME> – Specify the route map name.no Removes the filters used to filter updates received from this neighbor](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1069.png)
![CRYPTO-CMP-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 29 - 329.1.1 ca-servercrypto-cmp-policy-instanceConfigures the primary and secondary CMP CA server details.The CA is an external network authority (usually a trusted third-party server) that generates and issues digital certificates in response to requests received from network devices. Use this command to configure the primary and secondary CA server details, such as name of the device hosting the CA server, the port used to access the CA server, and the path where the certificate is stored. Once defined, devices using this CMP policy automatically send requests to the specified primary CA server, and retrieve the certificate from the specified location. If the primary CA server is not reachable, the requests are sent to the secondary CA server.Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP7602, AP7612, AP7622, AP7632, AP7662, AP82XX, AP8432, AP8533, WiMod• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxca-server [primary|secondary] host <IP> port <1-65535> path <PATH>Parameters• ca-server [primary|secondary] host <IP> port <1-65535> path <PATH>ca-server [primary|secondary]Configures the primary and secondary CMP CA server details (IPv4 address, port, and path)• primary – Configures the primary CMP CA server’s details• secondary – Configures the secondary CMP CA server’s detailsThe secondary CMP CA is used in case the primary CA server is not reachable. CA server settings are required to complete CMP requests.host <IP> Configures IPv4 address of the device hosting the primary/secondary CA server• <IP/HOSTNAME> – Specify the server’s IPv4 address.port <1-65535> Configures the port on which the primary/secondary CA server can be reached• <1-65535> – Specify the port number from 1 - 65535.path <PATH> Configures the path or filename of the primary/secondary CMP CA certificate. Enter the complete relative path to the file on the server.• <PATH> – Specify the path. Once specified, the certificate is downloaded from this location and installed on the device.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1073.png)

![CRYPTO-CMP-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 29 - 529.1.2 cert-key-sizecrypto-cmp-policy-instanceConfigures the size of the key associated with a certificate requestSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP7602, AP7612, AP7622, AP7632, AP7662, AP82XX, AP8432, AP8533, WiMod• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxcert-key-size [2048|3072|4096]Parameters• cert-key-size [2048|3072|4096]Examplenx9500-6C8809(config-cmp-policy-test)#cert-key-size 3072nx9500-6C8809(config-cmp-policy-test)#show contextcrypto-cmp-policy test cert-key-size 3072 trustpoint cmp-test subject-name "CN=ExampleCompany, O=Example Company" secret 2 osr2bwjR+0L+G64ny3wfuAAAAAtTFjeFnvOIixTHLDfgt7Bu reference-id 123456 sender-name "CN=ExampleCompany.com, O=Example Company" recipient-name "O=Example Company, CN=ExampleCompany.com"nx9500-6C8809(config-cmp-policy-test)#Related Commandscert-key-size [2048|3072|4096]Configures the certificate request key size. The options are:• 2048 – Sets the key size to 2048 bits. This is the default setting.• 3072 – Sets the key size to 3072 bits• 4096 – Sets the key size to 4096 bitsno Reverts the certificate request key size to default (2048 bits)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1075.png)


![CRYPTO-CMP-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 29 - 829.1.5 subjectAltNamecrypto-cmp-policy-instanceConfigures the subjectAltName identity for this CMP policySupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP7602, AP7612, AP7622, AP7632, AP7662, AP82XX, AP8432, AP8533, WiMod• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000SyntaxsubjectAltName [address <IP>|dn <DISTINGUISHED-NAME>|email <EMAIL-ID>|fqdn <FQDN>|string <USER-DEFINED-STRING>]Parameters• subjectAltName [address <IP>|dn <DISTINGUISHED-NAME>|email <EMAIL-ID>|fqdn <FQDN>|string <USER-DEFINED-STRING>]Exampleap6522-D8273A(config-cmp-policy-CMP)#subjectAltName dn TechPubsCAap6522-D8273A(config-cmp-policy-CMP)#show contextcrypto-cmp-policy CMP cert-update cert-renewal-timeout 60 ca-server primary host 192.168.8.74 port 8 path cmp subjectAltName dn TechPubsCAap6522-D8273A(config-cmp-policy-CMP)#Related CommandssubjectAltName [address <IP>|dn <DISTINGUISHED-NAME>|email <EMAIL-ID>|fqdn <FQDN>|string <USER-DEFINED-STRING>]Configures the subjectAltName identity using one of the following options:• address <IP> – Uses IP address as identity• <IP> – Specify the IP address.• dn <DISTINGUISHED-NAME> – Uses distinguished name as identity• <DISTINGUISHED-NAME> – Specify the DISTINGUISHED-NAME.• email <EMAIL-ID> – Uses e-mail address as identity• <EMAIL-ID> – Specify the e-mail address.• fqdn <FQDN> – Uses FQDN as identity• <FQDN> – Specify the FQDN.• string <USER-DEFINED-STRING> – Uses a user specified name as identity• <USER-DEFINED-STRING> – Specify the string to use as identity.no Removes the subjectAltName identity configured with this CMP policy](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1078.png)
![CRYPTO-CMP-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 29 - 929.1.6 trustpointcrypto-cmp-policy-instanceConfigures a trustpoint and its associated information, such as the subject name, the sender’s (device requesting certification) details, and the recipient's (CA) details. This information is needed to obtain the certificate from the CA server using CMP.Each certificate is digitally signed by a trustpoint and contains device-specific information, such as device name, IP address, serial number. It helps to uniquely identify a device. Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP7602, AP7612, AP7622, AP7632, AP7662, AP82XX, AP8432, AP8533, WiMod• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxtrustpoint <TRUSTPOINT-NAME> subject-name <WORD> secret [0 <WORD>|2 <WORD>] reference-id <WORD> sender-name <WORD> [recipient-name <WORD>|ca-psk <CERT-PATH>]Parameters• trustpoint <TRUSTPOINT-NAME> subject-name <WORD> secret [0 <WORD>|2 <WORD>] reference-id <WORD> sender-name <WORD> [recipient-name <WORD>|ca-psk <CERT-PATH>]trustpoint <TRUSTPOINT-NAME>Configures a trustpoint name (should not exceed 32 characters)• <TRUSTPOINT-NAME> – Specify the trustpoint’s name.subject-name <WORD>Configures a subject name for this trustpoint. The subject name should uniquely identify the certificate and should not exceed 512 characters in length.secret [0 <WORD>|2 <WORD>]Configures the secret used to encrypt the trustpoint. The secret should not exceed 128 characters in length.• 0 <WORD> – Configures a clear text password• 2 <WORD> – Configures an encrypted passwordreference-id <WORD>Configures the reference ID. The CA server uses this information to identify the shared secret key used.• <WORD> – Specify the reference ID.sender-name <WORD>Configures the sender’s name. The CA server uses this information to identify the shared secret key used. The sender’s name should not exceed 512 characters in length.• <WORD> – Specify the sender name.recipient-name Configures the recipient’s name. The CA server uses this information to validate the request. The recipient's name should not exceed 256 characters in length.ca-psk <CERT-PATH> Configures the certificate path for the server certificate• <CERT-PATH> – Specify the certificate path.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1079.png)

![CRYPTO-CMP-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 29 - 1229.1.8 nocrypto-cmp-policy-instanceRemoves or reverts this crypto CMP policy settingsSupported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP82XX, AP8432, AP8533, WiMod• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [ca-server <SERVER-NAME>|cert-key-size|cert-renewal-timeout|cross-cert-validate|subjectAltName|trustpoint <TRUSTPOINT-NAME>|use autogen-uniqueid]Parameters• no <PARAMETERS>Exampleap6522-D8273A(config-cmp-policy-CMP)#show context cert-update cert-renewal-timeout 60 use autogen-uniqueid ca-server primary host 192.168.8.74 port 8 path cmp trustpoint cmp-test subject-name "CN=ExampleCompany, O=Example Company" secret 0 test-secret reference-id 123456 sender-name "CN=ExampleCompany.com, O=Example Company" recipient-name "O=Example Company, CN=ExampleCompany.com" subjectAltName dn TechPubsCAap6522-D8273A(config-cmp-policy-CMP)#ap6522-D8273A(config-cmp-policy-CMP)#no cert-renewal-timeoutap6522-D8273A(config-cmp-policy-CMP)#no subjectAltNameap6522-D8273A(config-cmp-policy-CMP)#show context cert-update use autogen-uniqueid ca-server primary host 192.168.8.74 port 8 path cmp trustpoint cmp-test subject-name "CN=ExampleCompany, O=Example Company" secret 0 test-secret reference-id 123456 sender-name "CN=ExampleCompany.com, O=Example Company" recipient-name "O=Example Company, CN=ExampleCompany.com"ap6522-D8273A(config-cmp-policy-CMP)#no <PARAMETERS> Removes or reverts this crypto CMP policy settings](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1082.png)

![CRYPTO-CMP-POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 29 - 1529.2.2 showother-cmp-related-commandsDisplays current status of CMP requests in progress. This command also displays trustpoint details (CMP and non-CMP trustpoints).Supported in the following platforms:• Access Points — AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP81XX, AP7602, AP7612, AP7622, AP7632, AP7662, AP82XX, AP8432, AP8533, WiMod• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxshow crypto [cmp|pki]show crypto cmp request status {on <DEVICE-NAME>}show crypto pki trustpoints {<TRUSTPOINT-NAME>|all} {on <DEVICE-NAME>}Parameters• show crypto cmp request status {on <DEVICE-NAME>}• show crypto pki trustpoints {<TRUSTPOINT-NAME>|all} {on <DEVICE-NAME>}Exampleap6522-D8273A#show crypto pki trustpoints--------------------------------------------------------------------------------------- TRUSTPOINT KEY NAME VALID UNTIL--------------------------------------------------------------------------------------- cmp-test cmp-test-key Fri May 9 09:44:22 2014 GMT default-trustpoint default_rsa_key Fri Dec 30 00:00:40 2022 GMT---------------------------------------------------------------------------------------ap6522-D8273A#ap6522-D8273A(config)#show crypto cmp request statusCMP Request Status: cmp-completeap6522-D8273A#show crypto cmp request {on <DEVICE-NAME>}Displays the current status of all on-going CMP requests• on <DEVICE-NAME> – Optional. Optionally specify the name of the AP, wireless controller, or service platform to view CMP request status on a specified device.show pki trustpoints {<TRUSTPOINT-NAME>|all} on <DEVICE-NAME>Displays all trustpoints including CMP generated trustpoints• <TRUSTPOINT-NAME> – Optional. Specify a trustpoint name. Displays details of the trustpoint identified by the <TRUSTPOINT-NAME> parameter.• all – Optional. Displays details of all configured trustpoints• on <DEVICE-NAME> – Optional.Optionally specify the name of the AP, wireless con-troller, or service platform to view trustpoints configured on a specified device.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1085.png)
![ROAMING ASSIST POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 30 - 330.1.1 actionroaming-assist-policy-instanceSpecifies the action invoked on the client once it reaches a specified threshold value. The threshold values are configured based on the client load.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaction [assisted-roam|deauth|log]Parameters• action [assisted-roam|deauth|log]Examplerfs6000-81742D(config-roaming-assist-policy-test)#action logrfs6000-81742D(config-roaming-assist-policy-test)#Related Commandsaction [assisted-roam|deauth|log]Configures the action invoked on the client once it reaches the specified threshold value. The options are:• assisted-roam – Provides 802.11v assisted roaming facility to the client• deauth – De-authenticates the client. This is the default setting.•log – Generates a logIn all three cases an event is generated. However, the message generated differs and is based on the action specified.no Removes the configured action details](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1088.png)
![ROAMING ASSIST POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 30 - 430.1.2 aggressivenessroaming-assist-policy-instanceConfigures a roaming aggressiveness value for wireless clients. Configuring this value increases the client’s roaming capabilities in scenarios where the client’s location is likely to change drastically and suddenly. For example, when a client hops on to a train that speeds up quickly. In such a scenario, the access point receives a maximum of 2 (two) messages, from the client, having relatively low RSSI value. This results in a decaying-average, which is above the specified handover-threshold value. Consequently, the client is unable to roam.Supported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxaggressiveness [highest|lowest|medium|medium-high|medium-low]Parameters• aggressiveness [highest|lowest|medium|medium-high|medium-low]Examplenx9500-6C8809(config-roaming-assist-policy-test)#aggressiveness mediumnx9500-6C8809(config-roaming-assist-policy-test)#show contextroaming-assist-policy test aggressiveness mediumnx9500-6C8809(config-roaming-assist-policy-test)#Related Commandsaggressiveness [highest|lowest|medium|medium-high|medium-low]Configures a roaming aggressiveness value for wireless clients. The options are:• highest – De-authenticates client in case of any degradation in the client’s link quality. When selected, the access point considers only the RSSI value of the last message received from the client.• lowest – De-authenticates client only in case of significant degradation in the client’s link quality. When selected, the access point uses a weighted average [80% of decaying average + 20% of last seen RSSI] as the final reported RSSI value. This is the default setting.• medium – This is an intermediate setting between not roaming and performance• medium-high – Allows roaming even if performance goes down. When selected, the access point calculates the client’s signal strength based on average received signal as well as last received signal level, weighted towards the last received value.• medium-low – Allows roaming even if performance goes average. When selected, the access point calculates the client’s signal strength based on average received signal as well as last received signal level, weighted towards the average value.no Reverts the aggressiveness value to default (lowest)](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1089.png)
![ROAMING ASSIST POLICYAccess Point, Wireless Controller and Service Platform CLI Reference Guide 30 - 1130.1.9 noroaming-assist-policy-instanceRemoves or reverts this roaming assist policy settings based on the parameters passedSupported in the following platforms:• Access Points — AP6521, AP6522, AP6532, AP6562, AP7161, AP7502, AP7522, AP7532, AP7562, AP7602, AP7612, AP7622, AP7632, AP7662, AP81XX, AP82XX, AP8432, AP8533• Wireless Controllers — RFS4000, RFS6000• Service Platforms — NX5500, NX7500, NX7510, NX7520, NX7530, NX9500, NX9510, NX9600, VX9000Syntaxno [action|aggressiveness|detection-threshold|disassoc-time|handoff-count|handoff-threshold|monitoring-interval|sampling-interval]Parameters• no <PARAMETERS>Examplerfs6000-81742D(config-roaming-assist-policy-test)#no actionrfs6000-81742D(config-roaming-assist-policy-test)#no detection-thresholdrfs6000-81742D(config-roaming-assist-policy-test)#no handoff-thresholdrfs6000-81742D(config-roaming-assist-policy-test)#show contextroaming-assist-policy test sampling-interval 20 monitoring-interval 10rfs6000-81742D(config-roaming-assist-policy-test)#no <PARAMETERS> Removes or reverts this roaming assist policy settings to default based on the parameters passed](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1096.png)







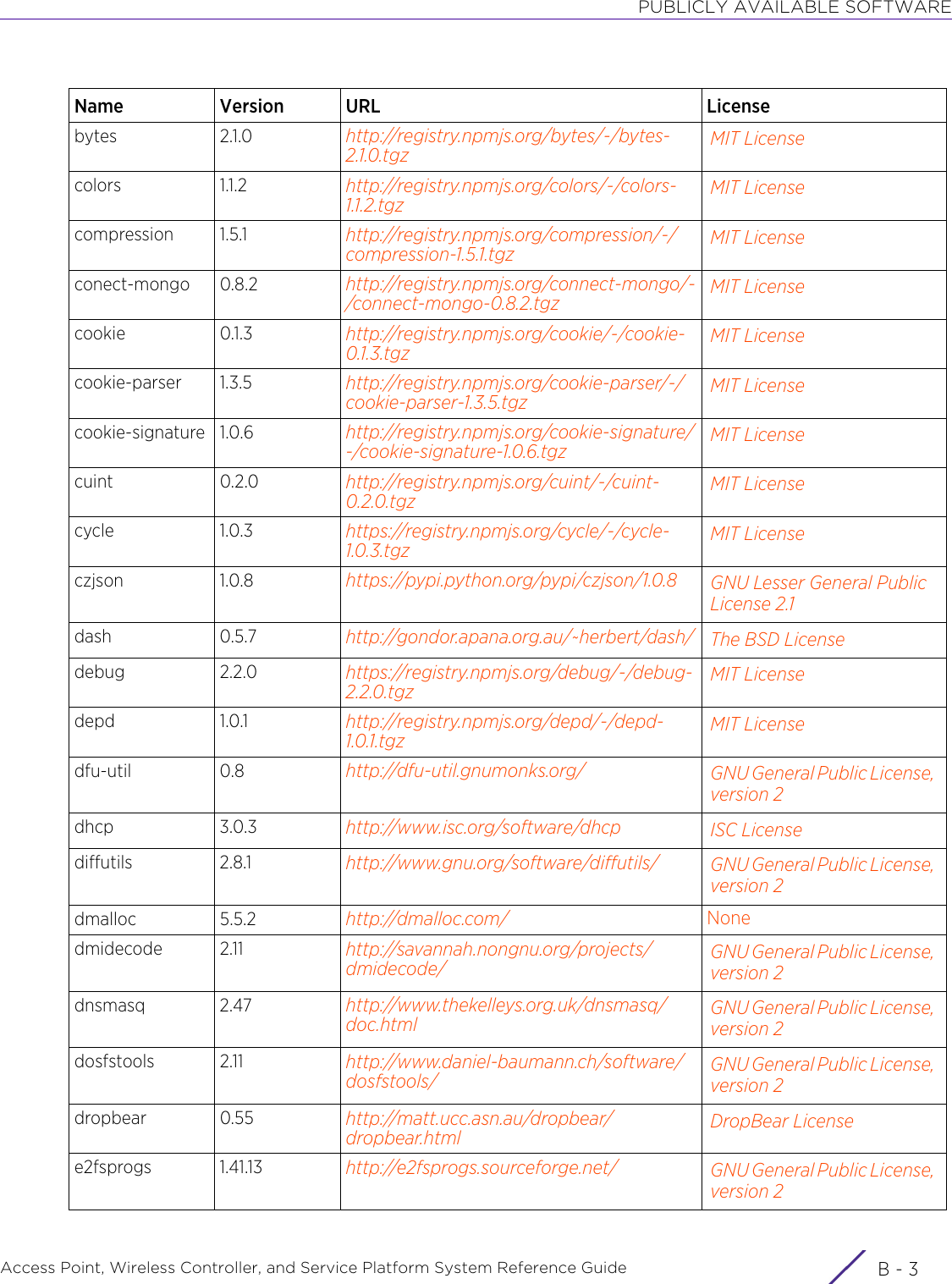
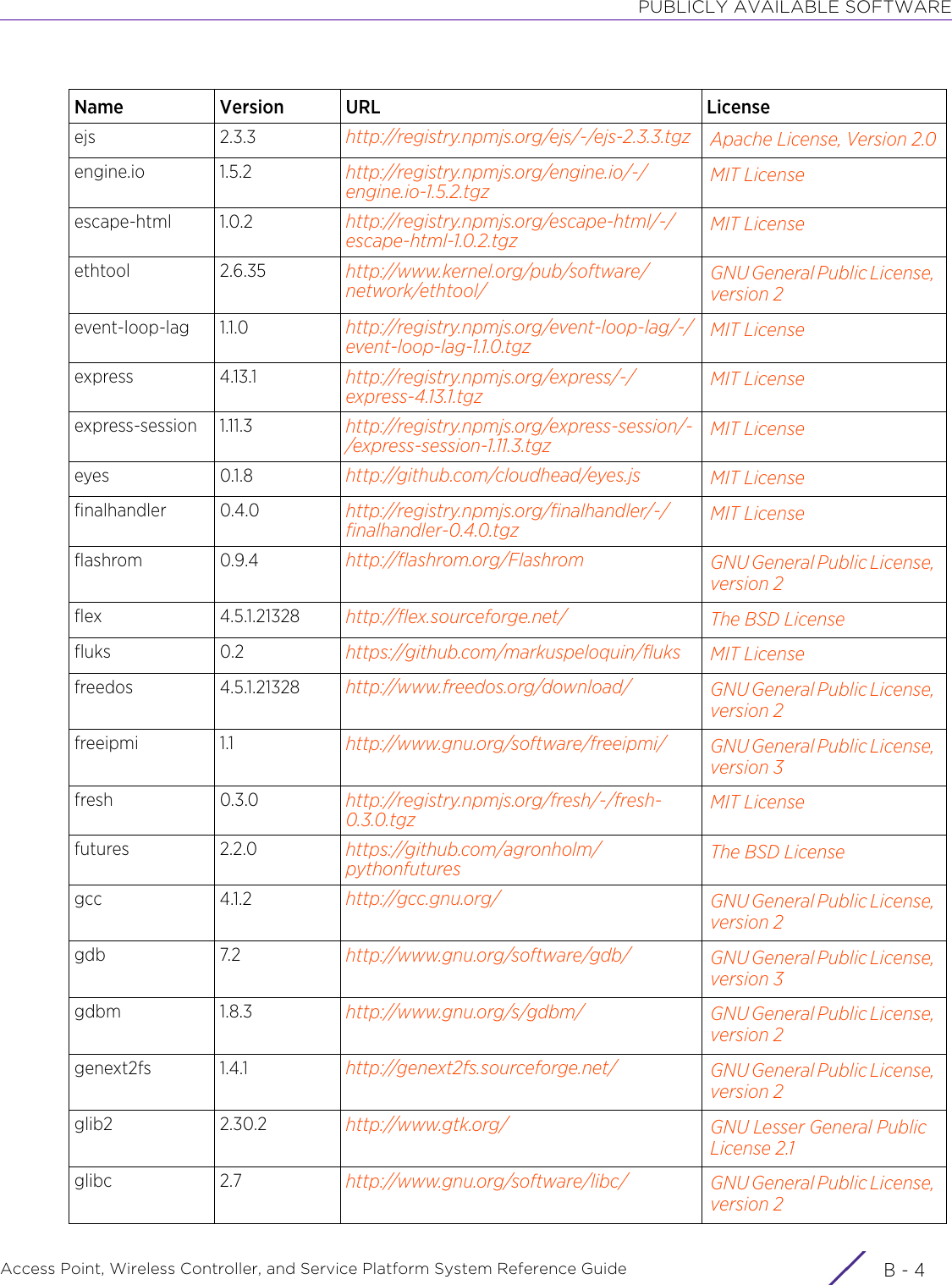
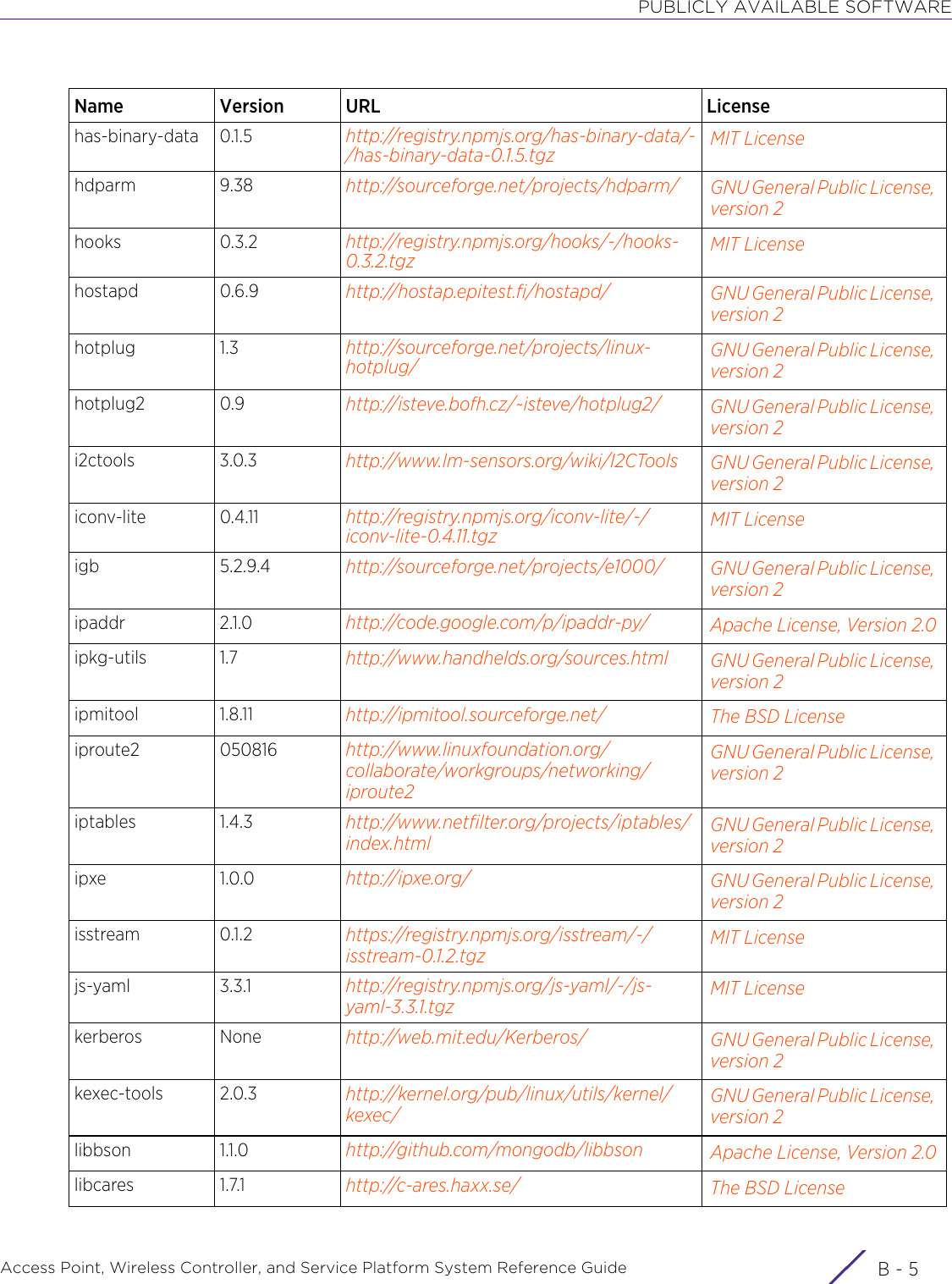
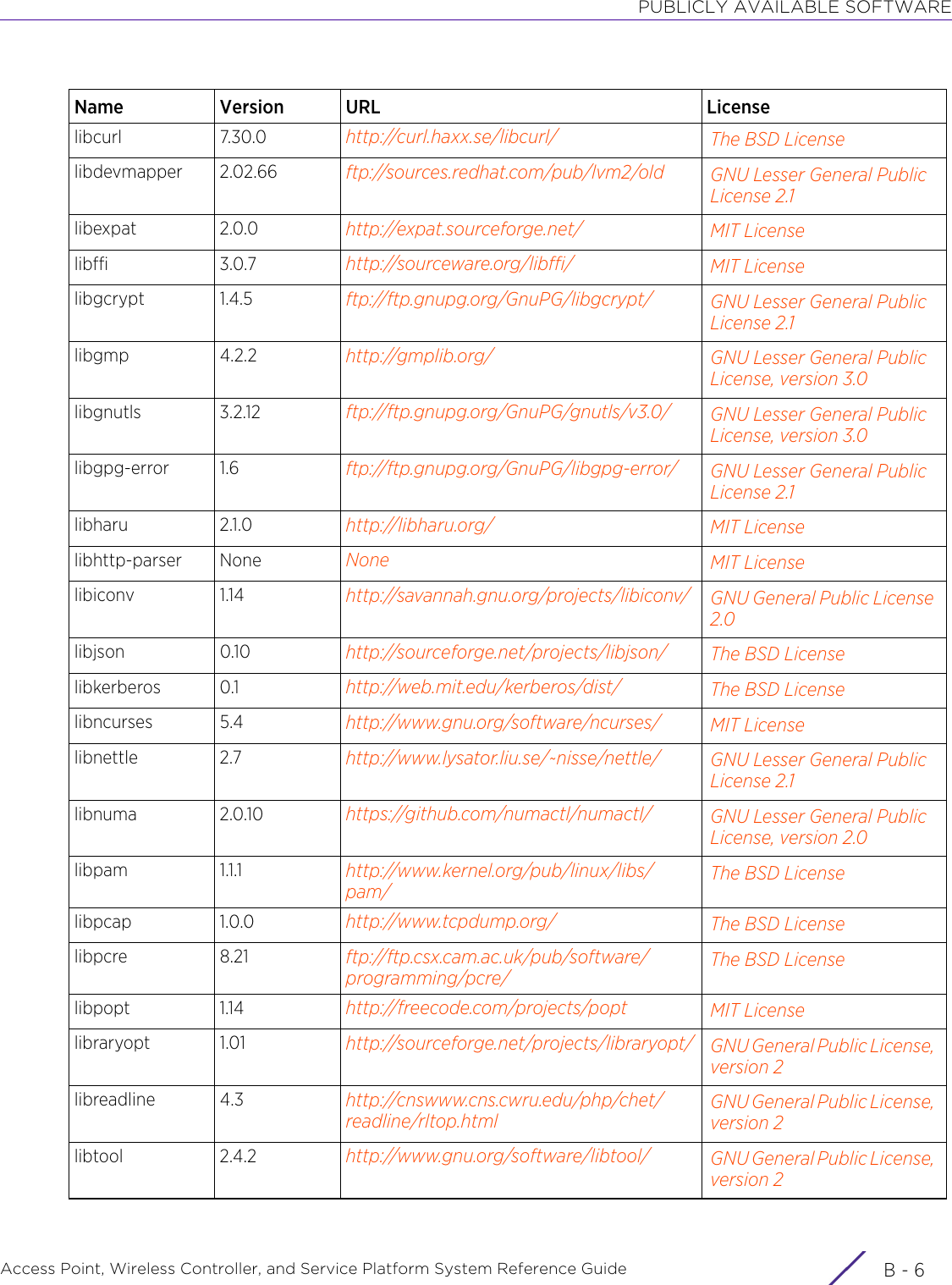






![PUBLICLY AVAILABLE SOFTWAREAccess Point, Wireless Controller, and Service Platform System Reference Guide B - 31[This is the first released version of the Lesser GPL. It also counts as the successor of the GNU Library Public License, version 2, hence the version number 2.1.]PreambleThe licenses for most software are designed to take away yourfreedom to share and change it. By contrast, the GNU General Public Licenses are intended to guarantee your freedom to share and change free software--to make sure the software is free for all its users.This license, the Lesser General Public License, applies to some specially designated software packages--typically libraries--of the Free Software Foundation and other authors who decide to use it. You can use it too, but we suggest you first think carefully about whether this license or the ordinary General Public License is the better strategy to use in any particular case, based on the explanations below.When we speak of free software, we are referring to freedom of use, not price. Our General Public Licenses are designed to make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish); that you receive source code or can get it if you want it; that you can change the software and use pieces of it in new free programs; and that you are informed that you can do these things.To protect your rights, we need to make restrictions that forbid distributors to deny you these rights or to ask you to surrender these rights. These restrictions translate to certain responsibilities for you if you distribute copies of the library or if you modify it. For example, if you distribute copies of the library, whether gratis or for a fee, you must give the recipients all the rights that we gave you. You must make sure that they, too, receive or can get the source code. If you link other code with the library, you must provide complete object files to the recipients, so that they can relink them with the library after making changes to the library and recompiling it. And you must show them these terms so they know their rights.We protect your rights with a two-step method: (1) we copyright the library, and (2) we offer you this license, which gives you legal permission to copy, distribute and/or modify the library.To protect each distributor, we want to make it very clear that there is no warranty for the free library. Also, if the library is modified by someone else and passed on, the recipients should know that what they have is not the original version, so that the original author's reputation will not be affected by problems that might be introduced by others.Finally, software patents pose a constant threat to the existence of any free program. We wish to make sure that a company cannot effectively restrict the users of a free program by obtaining a restrictive license from a patent holder. Therefore, we insist that any patent license obtained for a version of the library must be consistent with the full freedom of use specified in this license.Most GNU software, including some libraries, is covered by the ordinary GNU General Public License. This license, the GNU Lesser General Public License, applies to certain designated libraries, and is quite different from the ordinary General Public License. We use this license for certain libraries in order to permit linking those libraries into non-free programs.When a program is linked with a library, whether statically or using a shared library, the combination of the two is legally speaking a combined work, a derivative of the original library. The ordinary General Public License therefore permits such linking only if the entire combination fits its criteria of freedom. The Lesser General Public License permits more lax criteria for linking other code with the library.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1135.png)

![PUBLICLY AVAILABLE SOFTWAREAccess Point, Wireless Controller, and Service Platform System Reference Guide B - 57TO OPERATE WITH ANY OTHER SOFTWARE), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. END OF TERMS AND CONDITIONS B.3.13 GNU Lesser General Public License, version 2.0GNU LIBRARY GENERAL PUBLIC LICENSEVersion 2, June 1991Copyright (C) 1991 Free Software Foundation, Inc. 51 Franklin St, Fifth Floor, Boston, MA 02110-1301, USAEveryone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.[This is the first released version of the library GPL. It is numbered 2 because it goes with version 2 of the ordinary GPL.]PreambleThe licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU General Public Licenses are intended to guarantee your freedom to share and change free software--to make sure the software is free for all its users.This license, the Library General Public License, applies to some specially designated Free Software Foundation software, and to any other libraries whose authors decide to use it. You can use it for your libraries, too.When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish), that you receive source code or can get it if you want it, that you can change the software or use pieces of it in new free programs; and that you know you can do these things.To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to ask you to surrender the rights. These restrictions translate to certain responsibilities for you if you distribute copies of the library, or if you modify it.For example, if you distribute copies of the library, whether gratis or for a fee, you must give the recipients all the rights that we gave you. You must make sure that they, too, receive or can get the source code. If you link a program with the library, you must provide complete object files to the recipients so that they can relink them with the library, after making changes to the library and recompiling it. And you must show them these terms so they know their rights.Our method of protecting your rights has two steps: (1) copyright the library, and (2) offer you this license which gives you legal permission to copy, distribute and/or modify the library.Also, for each distributor's protection, we want to make certain that everyone understands that there is no warranty for this free library. If the library is modified by someone else and passed on, we want its recipients to know that what they have is not the original version, so that any problems introduced by others will not reflect on the original authors' reputations.](https://usermanual.wiki/Extreme-Networks/AP3917E.WiNG-5-9-1-CLI-Reference-Guide-Part-2/User-Guide-3831162-Page-1161.png)