Moxa WAPN008 MOXA IEEE 802.11 a/b/g/n User Manual AirWorks AWK 3131A RCC User s Manual
Moxa Inc. MOXA IEEE 802.11 a/b/g/n AirWorks AWK 3131A RCC User s Manual
Moxa >
Contents
- 1. Users Manual
- 2. (AWK-4131A-XXXXX) UserMan
- 3. (AWK-11xyz-p-t) UserMan
- 4. (AWK-3131A) UserMan
- 5. (TAP-213-XX-CT-T) UserMan 12-29
- 6. TAP-213_UM_e1
- 7. WAPN008- UserMan_0816
- 8. WAPN008- UserMan_AWK-3131A-M12-RCC_20180820
- 9. WAPN008- UserMan_AWK-3131A-M12-RTG_20180820
- 10. WAPN008- UserMan_AWK-3131A-SSC-RTG_20180820
- 11. WAPN008- UserMan_20180911
WAPN008- UserMan_AWK-3131A-M12-RCC_20180820

AirWorks AWK-3131A-M12-RCC
User’s Manual
The software described in this manual is furnished under a license agreement and may be used only in accordance with
the terms of that agreement.
Copyright Notice
© 2018 Moxa Inc. All rights reserved.
Trademarks
The MOXA logo is a registered trademark of Moxa Inc.
All other trademarks or registered marks in this manual belong to their respective manufacturers.
Disclaimer
Information in this document is subject to change without notice and does not represent a commitment on the part of
Moxa.
Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited
to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the
products and/or the programs described in this manual, at any time.
Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for
its use, or for any infringements on the rights of third parties that may result from its use.
This product might include unintentional technical or typographical errors. Changes are periodically made to the
information herein to correct such errors, and these changes are incorporated into new editions of the publication.
Technical Support Contact Information
www.moxa.com/support
Moxa Americas
Toll-free: 1-888-669-2872
Tel: +1-714-528-6777
Fax: +1-714-528-6778
Moxa China (Shanghai office)
Toll-free: 800-820-5036
Tel: +86-21-5258-9955
Fax: +86-21-5258-5505
Moxa Europe
Tel: +49-89-3 70 03 99-0
Fax: +49-89-3 70 03 99-99
Moxa Asia-Pacific
Tel: +886-2-8919-1230
Fax: +886-2-8919-1231
Moxa India
Tel: +91-80-4172-9088
Fax: +91-80-4132-1045
Table of Contents
1. Introduction ...................................................................................................................................... 1-1
Overview ........................................................................................................................................... 1-2
Package Checklist ............................................................................................................................... 1-2
Product Features ................................................................................................................................ 1-2
Product Specifications ......................................................................................................................... 1-3
Functional Design ............................................................................................................................... 1-8
LAN Port .................................................................................................................................... 1-8
LED Indicators ............................................................................................................................ 1-9
Beeper ..................................................................................................................................... 1-10
Reset Button ............................................................................................................................. 1-10
Relay (Digital Output) ................................................................................................................ 1-11
2. Getting Started .................................................................................................................................. 2-1
First-Time Installation and Configuration ............................................................................................... 2-2
Communication Testing ....................................................................................................................... 2-3
Function Map ..................................................................................................................................... 2-5
3. Web Console Configuration ............................................................................................................... 3-1
Web Browser Configuration .................................................................................................................. 3-3
Overview ........................................................................................................................................... 3-4
Basic Settings .................................................................................................................................... 3-5
System Info Settings ................................................................................................................... 3-5
Network Settings ......................................................................................................................... 3-6
Time Settings ............................................................................................................................. 3-7
Wireless Settings ................................................................................................................................ 3-8
Operation Mode .................................................................................................................................. 3-9
Basic Wireless Settings ........................................................................................................................ 3-9
WLAN Security Settings .............................................................................................................. 3-13
Advanced Wireless Settings ........................................................................................................ 3-21
WLAN Certification Settings (For EAP-TLS in Client/Slave Mode Only) ............................................... 3-23
Extended Control Settings (AP Mode Only) ................................................................................... 3-24
Advanced Settings ............................................................................................................................ 3-25
Using Virtual LAN ...................................................................................................................... 3-26
Configuring Virtual LAN .............................................................................................................. 3-27
DHCP Server (For AP Mode Only)................................................................................................. 3-28
Packet Filters ............................................................................................................................ 3-29
RSTP Settings (for AP/Master/ACC mode only) .............................................................................. 3-31
SNMP Agent .............................................................................................................................. 3-33
Link Fault Pass-Through (for Client/Slave mode only) .................................................................... 3-35
Auto Warning Settings....................................................................................................................... 3-35
System Log .............................................................................................................................. 3-36
Syslog ..................................................................................................................................... 3-37
E-mail ...................................................................................................................................... 3-38
Relay ....................................................................................................................................... 3-39
Trap ........................................................................................................................................ 3-40
Status ............................................................................................................................................. 3-41
Wireless Status ......................................................................................................................... 3-41
Associated Client List (For AP/Master/ACC Mode Only) ................................................................... 3-42
AP Throughput .......................................................................................................................... 3-42
DHCP Client List (For AP Mode Only) ............................................................................................ 3-42
System Log .............................................................................................................................. 3-43
Relay Status ............................................................................................................................. 3-44
DI and Power Status .................................................................................................................. 3-44
RSTP Status .............................................................................................................................. 3-44
LAN Status ............................................................................................................................... 3-45
Maintenance .................................................................................................................................... 3-45
Console Settings ....................................................................................................................... 3-45
Ping ......................................................................................................................................... 3-45
Firmware Upgrade ..................................................................................................................... 3-46
Config Import Export ................................................................................................................. 3-46
Load Factory Default .................................................................................................................. 3-47
Username/Password .................................................................................................................. 3-47
Locate Device ........................................................................................................................... 3-48
Misc. Settings ........................................................................................................................... 3-48
Save Configuration ........................................................................................................................... 3-48
Restart ............................................................................................................................................ 3-49
Logout............................................................................................................................................. 3-50
4. Software Installation and Configuration ........................................................................................... 4-1
Overview ........................................................................................................................................... 4-2
AWK Search Utility .............................................................................................................................. 4-2
Installing AWK Search Utility ......................................................................................................... 4-2
Configuring AWK Search Utility ..................................................................................................... 4-5
5. Other Console Considerations ........................................................................................................... 5-1
RS-232 Console Configuration (115200, None, 8, 1, VT100)..................................................................... 5-2
Configuring Through Telnet and SSH Consoles ....................................................................................... 5-4
Configuring HTTPS/SSL Secure Access Through a Web Browser ................................................................ 5-5
Disabling Telnet and Browser Access ..................................................................................................... 5-6
A. References ........................................................................................................................................ A-1
Beacon ..............................................................................................................................................A-2
DTIM.................................................................................................................................................A-2
Fragment...........................................................................................................................................A-2
RTS Threshold ....................................................................................................................................A-2
STP and RSTP ....................................................................................................................................A-2
The STP/RSTP Concept ................................................................................................................A-2
Differences between RSTP and STP................................................................................................A-3
B. Supporting Information .................................................................................................................... B-1
Firmware Recovery .............................................................................................................................B-2
DoC (Declaration of Conformity) ...........................................................................................................B-6
Federal Communication Commission Interference Statement ............................................................B-6
Antenna Gain and RF Radiated Power ............................................................................................B-6
R&TTE Compliance Statement .......................................................................................................B-8

1
Introduction
The AWK-3131A-M12-RCC Series consists of 3-in-1 industrial AP/bridge/client devices designed specifically for
rail carriage-to-carriage communication and can provide up to 300 Mbps with IEEE 802.11n technology. The
new operation mode in the AWK-3131A-M12-RCC, Auto Carriage Connection (ACC), enables automatic
wireless connections between two adjacent train carriages. The AWK-3131A-M12-RCC is rated to operate at
temperatures ranging from -25 to 60°C for standard models and -40 to 75°C for wide-temperature models, and
is rugged enough for any harsh industrial environment.
The following topics are covered in this chapter:
Overview
Package Checklist
Product Features
Product Specifications
Functional Design
LAN Port
LED Indicators
Beeper
Reset Button
Relay (Digital Output)

AWK-3131A-M12-RCC
Introduction
1-2
Overview
The AWK-3131A-M12-RCC is 802.11n compliant to deliver speed, range, and reliability to support even the
most bandwidth-intensive applications. The 802.11n standard incorporates multiple technologies, including
Spatial Multiplexing MIMO (Multi-In, Multi-Out), 20 and 40 MHz channels, and dual bands (2.4 GHz and 5 GHz)
to generate enough speeds, while still being able to communicate with legacy 802.11a/b/g devices.
The AWK-3131A-M12-RCC is compliant with EN 50155, covering operating temperature, power input voltage,
surge, ESD, and vibration. Installation of the AWK is easy using DIN-rail mounting or distribution boxes, and
with its wide operating temperature range, IP30-rated housing with LED indicators, and DIN-rail mounting it is
a convenient yet reliable solution for all types of industrial wireless applications.
Package Checklist
Before installing the AWK-3131A-M12-RCC, ensure that the package contains the following items. If any of
these items is missing or damaged, please contact your customer service representative for assistance.
• 1 AWK-3131A-M12-RCC
• Cable holder with 1 screw
• 2 plastic RJ45 protective caps for console port
• DIN-rail kit
• Quick installation guide (printed)
• Warranty card
NOTE
Antennas are not included and should be purchased separately.
Product Features
• Designed specifically for rail carriage-to-carriage communication
• Compliant with EN 50155
• IEEE802.11a/b/g/n compliant
• Three-in-one design (AP/ACC/Client)
• Advanced wireless security
64-bit and 128-bit WEP/WPA/WPA2
SSID Hiding/IEEE 802.1X/RADIUS
Packet access control & filtering
• STP/RSTP support for network system redundancy
• Long-distance transmission support
• Turbo Roaming enables rapid handover (Client mode)
• ABC-01 for configuration import/export
• RS-232 console management
• 2DI+1DO for on-site monitoring and alerts
• Wide -40 to 75°C operating temperature range (-T model)
• Redundant 24 VDC power inputs or IEEE802.3af Power-over-Ethernet
• DIN-rail and wall mounting options
• IP30-rated protection and high-strength metal housing

AWK-3131A-M12-RCC
Introduction
1-3
Functional Design
LAN Port
The AWK-3131A-M12-RCC comes standard with 1 M12 Gigabit port. The LAN LED will light up when the LAN
cable is inserted.
Patent http://www.moxa.com/doc/operations/Moxa_Patent_Marking.pdf
ATTENTION
Do not use the PoE Injector. Instead, use an IEEE 802.3af or IEEE 802.3at compliant PSE (Power Sourcing
Equipment) for the PoE (Power over Ethernet) device.
ATTENTION
•The AWK-3131A-M12-RCC is NOT a portable mobile device and should be located at least 20 cm away
from the human body.
•The AWK-3131A-M12-RCC is NOT designed for the general public. A well-trained technician should be
enlisted to ensure safe deployment of AWK-3131A-M12-RCC units, and to establish a wireless network.
AWK-3131A-M12-RCC
Introduction
1-4
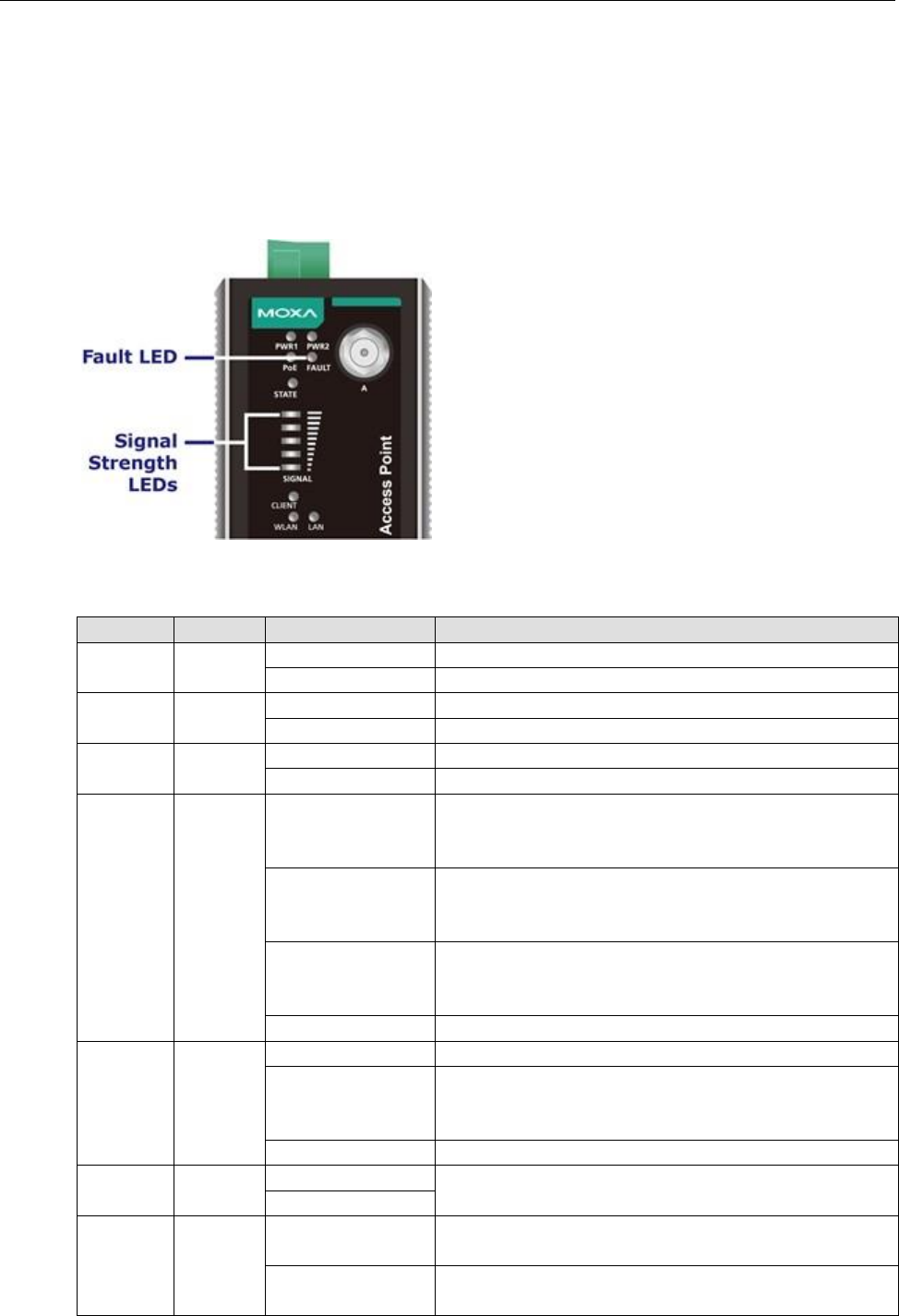
LED Indicators
The LEDs on the front panel of the AWK-3131A-M12-RCC provide a quick and easy means of determining the
current operational status and wireless settings.
The FAULT LED indicates system failures and user-configured events. If the AWK-3131A-M12-RCC cannot
retrieve the IP address from a DHCP server, the FAULT LED will blink at one second intervals. The SIGNAL
LEDs indicate signal strength, and only operate in Client mode.
The following table summarizes how to read the device’s wireless settings from the LED displays. More
information is available in Chapter 3 in the Basic Wireless Settings section.
LED
Color
State
Description
PWR1
Green
On
Power is being supplied from power input 1
Off
Power is not being supplied from power input 1
PWR2
Green
On
Power is being supplied from power input 2
Off
Power is not being supplied from power input 2
PoE
Amber
On
Power is being supplied via PoE
Off
Power is not being supplied via PoE
FAULT
Red
On
System is booting or
A system configuration error exists or
A relay event has occurred
Blinking
(slowly at 1-sec
intervals)
Cannot get an IP address from the DHCP server
Blinking
(fast at 0.5-sec
intervals)
IP address conflict
Off
Error condition does not exist
STATE
Green/
Red
Green
System is ready
Green
Blinking at 1-sec
intervals
The AWK has been located by the AWK Search Utility
Red
Booting error condition
SIGNAL
(5 LEDs)
Green
On
Signal level (for Client/Slave/ACC Slave mode only)
Off
CLIENT
Green
On
WLAN is in Client/Slave mode or ACC Slave mode with
connection established
Off
AP/Master/Sniffer/ACC Master mode or connection is NOT
established in ACC Slave mode
AWK-3131A-M12-RCC
Introduction
1-10
LED
Color
State
Description
WLAN
Amber
Amber On
WLAN is in AP/Master mode
WLAN is in Client/Slave/ACC Master/ACC Slave mode with
connection established
Amber/Blinking
Traffic in AP/Client/Master/Slave/ACC mode.
Off
WLAN is in Sniffer mode.
WLAN is in Client/Slave/ACC Master/ACC Slave mode without
a connection being established or WLAN is not working
properly.
LAN
Green
Green
LAN port’s 10/100/1000 Mbps link is active.
Green/Blinking
Data traffic at the LAN port.
Green Off
LAN port is disconnected.
Beeper
The beeper emits two short beeps when the system is ready.
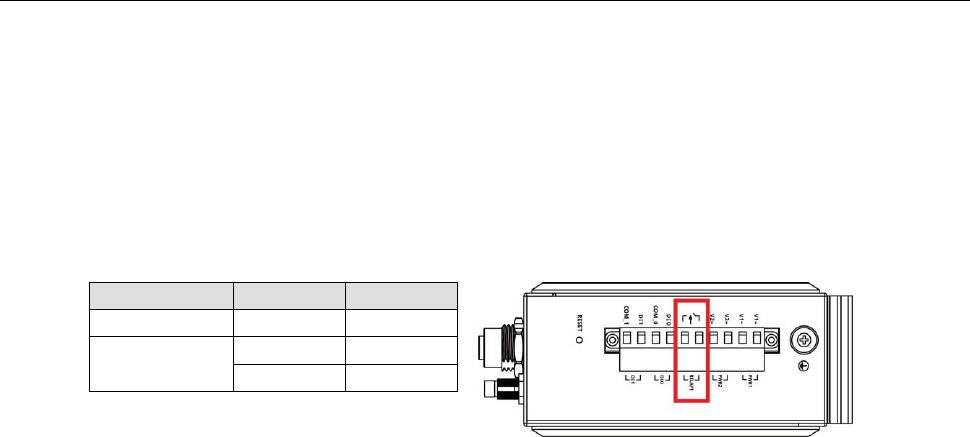
Reset Button
The RESET button is located on the top panel of the AWK-3131A-M12-RCC. You can reboot the
AWK-3131A-M12-RCC or reset it to factory default settings by pressing the RESET button with a pointed object
such as an unfolded paper clip.
• System reboot: Hold the RESET button down for under 5 seconds and then release it.
• Reset to factory default: Hold the RESET button down for over 5 seconds until the STATE LED starts
blinking green. Release the button to reset the AWK-3131A-M12-RCC.
ATTENTION
When the system fails to boot, the LEDs for STATE (Green), FAULT, and WLAN will all light up
simultaneously and blink at one-second intervals. This may be due to improper operation or other issues,
such as an unexpected shutdown while updating the firmware. To recover the firmware, refer to the Firmware
Recovery section in Appendix B Supporting Information.
AWK-3131A-M12-RCC
Introduction
1-11
Relay (Digital Output)
The AWK-3131A-M12-RCC has one relay output consisting of the 2 terminal block contacts on the top panel, as
shown below. These relay contacts are used to forward system failures and user-configured events.
The two wires attached to the relay contacts form an open circuit when a user-configured event is triggered. If
a user-configured event does not occur, the relay circuit will remain closed. For safety reasons, the relay circuit
is kept open when the AWK-3131A-M12-RCC is not powered up.
Summary of the AWK-3131A-M12-RCC’s Relay Status
Power Status
Event
Relay
Off
–
Open
On
Yes
Open
No
Short

2
Getting Started
This chapter explains how to install Moxa’s AirWorks AWK-3131A-M12-RCC for the first time, and quickly set up
your wireless network and test whether the connection is running well. The Function Map discussed in the third
section provides a convenient means of determining which functions you need to use.
The following topics are covered in this chapter:
First-Time Installation and Configuration
Communication Testing
Function Map
AWK-3131A-M12-RCC
Getting Started
2-2
First-Time Installation and Configuration
Before installing the AWK-3131A-M12-RCC, make sure that all items in the Package Checklist are in the box.
You will need access to a notebook computer or PC equipped with an Ethernet port. The AWK-3131A-M12-RCC
has a default IP address that must be used when connecting to the device for the first time.
• Step 1: Select the power source.
The AWK-3131A-M12-RCC can be powered by a DC power input or PoE (Power over Ethernet). The
AWK-3131A-M12-RCC will use whichever power source you choose.
• Step 2: Connect the AWK-3131A-M12-RCC to a notebook or PC.
Since the AWK-3131A-M12-RCC supports MDI/MDI-X auto-sensing, you can use either a straight-through
cable or crossover cable to connect the AWK-3131A-M12-RCC to a computer. The LED indicator on the
AWK-3131A-M12-RCC’s LAN port will light up when a connection is established.
• Step 3: Set up the computer’s IP address.
Choose an IP address on the same subnet as the AWK-3131A-M12-RCC. Since the AWK-3131A-M12-RCC’s
default IP address is 192.168.127.253, and the subnet mask is 255.255.255.0, you should set the IP
address of the computer to 192.168.127.xxx.
NOTE
After you select Maintenance Load Factory Default and click the Submit button, the
AWK-3131A-M12-RCC will be reset to factory default settings and the IP address will be reset to
192.168.127.253.
• Step 4: Use the web-based manager to configure the AWK-3131A-M12-RCC
Open your computer’s web browser and type http://192.168.127.253 in the address field to access the
homepage of the web-based Network Manager. Before the homepage opens, you will need to enter the user
name and password as shown in the following figure. For first-time configuration, enter the default user
name and password and then click on the Login button:
NOTE
Default user name and password:
User Name: admin
Password: moxa
For security reasons, we strongly recommend changing the default password. To do so, select Maintenance
Password, and then follow the on-screen instructions to change the password.

AWK-3131A-M12-RCC
Getting Started
3-2
NOTE
After you click Submit to apply changes the web page will refresh (Updated) will appear on the page and a
blinking reminder will be shown on the upper-right corner of the web page:
To activate the changes click Restart and then Save and Restart after you change the settings. About 30
seconds are needed for the AWK-3131A-M12-RCC to complete the reboot procedure.
• Step 5: Select the AWK-3131A-M12-RCC operation mode.
By default, the AWK-3131A-M12-RCC’s operation mode is set to AP. You can change to Client mode in
Wireless Settings Operation Mode. Detailed information about configuring the
AWK-3131A-M12-RCC’s operation can be found in Chapter 3.
• Step 6: Test communications.
In the following sections we describe two test methods that can be used to ensure that a network
connection has been established.
Communication Testing
After installing the AWK-3131A-M12-RCC you can run a sample test to make sure the AWK-3131A-M12-RCC
and wireless connection are functioning normally. Two testing methods are described below. Use the first
method if you are using only one AWK-3131A-M12-RCC device, and use the second method if you are using two
or more AWK-3131A-M12-RCC units.
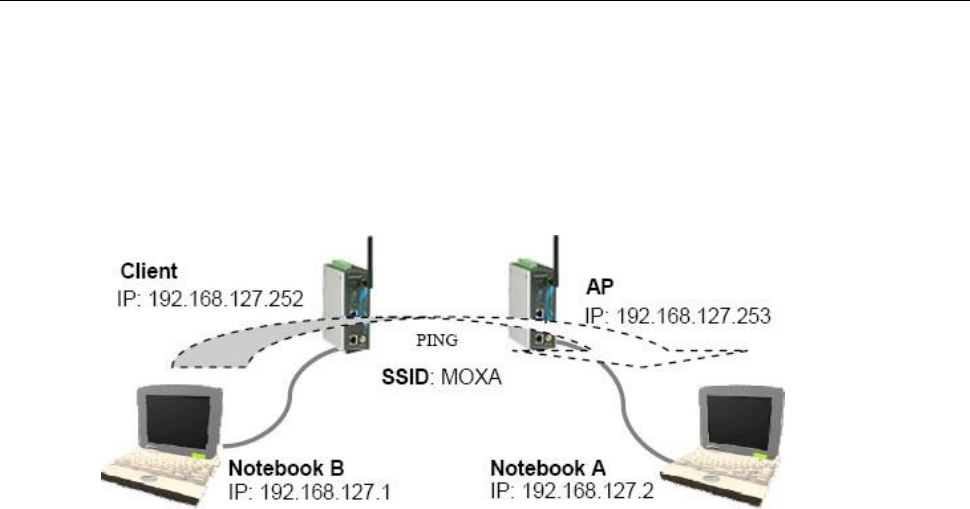
How to Test One AWK-3131A-M12-RCC
If you are only using one AWK-3131A-M12-RCC, you will need a second notebook computer equipped with a
WLAN card. Configure the WLAN card to connect to the AWK-3131A-M12-RCC (NOTE: the default SSID is
MOXA), and change the IP address of the second notebook (Notebook B) so that it is on the same subnet as
the first notebook (Notebook A), which is connected to the AWK-3131A-M12-RCC.
After configuring the WLAN card, establish a wireless connection with the AWK-3131A-M12-RCC and open the
Windows Command Prompt on Notebook B. At the prompt, type
ping <IP address of notebook A>
and then press Enter (see the figure below). A “Reply from IP address …” response means the communication
was successful. A “Request timed out.” response means the communication failed. In this case, recheck the
configuration to make sure the connections are correct.
AWK-3131A-M12-RCC
Getting Started
4-2
How to Test Two or More AWK-3131A-M12-RCC Units
If you have two or more AWK-3131A-M12-RCC units, you will need a second notebook computer (Notebook B)
equipped with an Ethernet port. Use the default settings for the first AWK-3131A-M12-RCC connected to
notebook A and change the second or third AWK-3131A-M12-RCC connected to notebook B to Client mode, and
then configure the notebooks and AWK-3131A-M12-RCC units properly.
After setting up the testing environment, open the Windows Command Prompt on notebook B. At the prompt,
type:
ping <IP address of notebook A>
and then press Enter. A “Reply from IP address …” response means the communication was successful. A
“Request timed out” response means the communication failed. In this case, recheck the configuration to make
sure the connections are correct.
AWK-3131A-M12-RCC
Getting Started
5-2
Function Map

3
Web Console Configuration
In this chapter, we explain all aspects of web-based console configuration. Moxa’s easy-to-use management
functions help you set up your AWK-3131A-M12-RCC and make it easy to establish and maintain your wireless
network.
The following topics are covered in this chapter:
Web Browser Configuration
Overview
Basic Settings
System Info Settings
Network Settings
Time Settings
Wireless Settings
Operation Mode
Basic Wireless Settings
WLAN Security Settings
Advanced Wireless Settings
WLAN Certification Settings (For EAP-TLS in Client/Slave Mode Only)
Extended Control Settings (AP Mode Only)
Advanced Settings
Using Virtual LAN
Configuring Virtual LAN
DHCP Server (For AP Mode Only)
Packet Filters
RSTP Settings (for AP/Master/ACC mode only)
SNMP Agent
Link Fault Pass-Through (for Client/Slave mode only)
Auto Warning Settings
System Log
Syslog
E-mail
Relay
Trap
Status
Wireless Status
Associated Client List (For AP/Master/ACC Mode Only)
AP Throughput
DHCP Client List (For AP Mode Only)
System Log
Relay Status
AWK-3131A-M12-RCC
Web Console Configuration
3-3
Web Browser Configuration
Moxa AWK-3131A-M12-RCC’s web browser interface provides a convenient way to modify its configuration and
access the built-in monitoring and network administration functions.
NOTE
To use the AWK-3131A-M12-RCC’s management and monitoring functions from a PC host connected to the
same LAN as the AWK-3131A-M12-RCC, you must make sure that the PC host and the AWK-3131A-M12-RCC
are on the same logical subnet. Similarly, if the AWK-3131A-M12-RCC is configured for other VLAN settings,
you must make sure your PC host is on the management VLAN.
The Moxa AWK-3131A-M12-RCC’s default IP is 192.168.127.253.
Follow these steps to access the AWK-3131A-M12-RCC’s web-based console management interface.
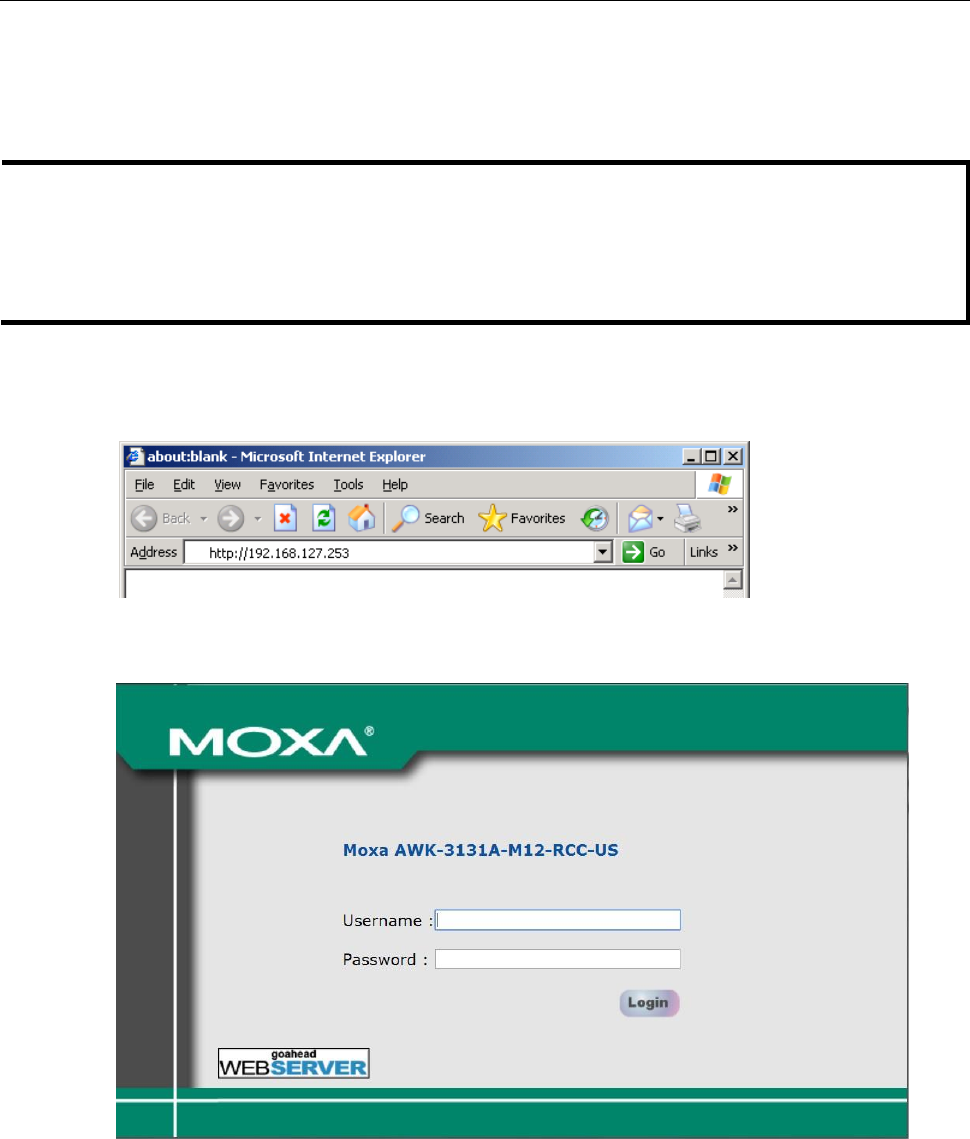
1. Open your web browser (e.g., Internet Explorer) and type the AWK-3131A-M12-RCC’s IP address in the
address field. Press Enter to establish the connection.
2. The Web Console Login page will open. Enter the password (default Username = admin; default Password
= moxa) and then click Login to continue.
3. You may need to wait a few moments for the web page to download to your computer. Note that the Model
name and IP address of your AWK-3131A-M12-RCC are both shown in the title bar of the web page. This
information can be used to help you identify multiple AWK-3131A-M12-RCC units.
AWK-3131A-M12-RCC
Web Console Configuration
3-4
4. Use the menu tree on the left side of the window to open the function pages to access each of the
AWK-3131A-M12-RCC’s functions.
In the following paragraphs, we describe each AWK-3131A-M12-RCC management function in detail. A quick
overview is available in this manual in the “Function Map” section of Chapter 2.
NOTE
The model name of the AWK-3131A-M12-RCC is shown as AWK-3131A-M12-RCC-XX, where XX indicates the
country code. The country code indicates the AWK-3131A-M12-RCC version and which bandwidth it uses. We
use AWK-3131A-M12-RCC-US as an example in the following figures. (The country code and model name
that appears on your computer screen may be different than the one shown here.)
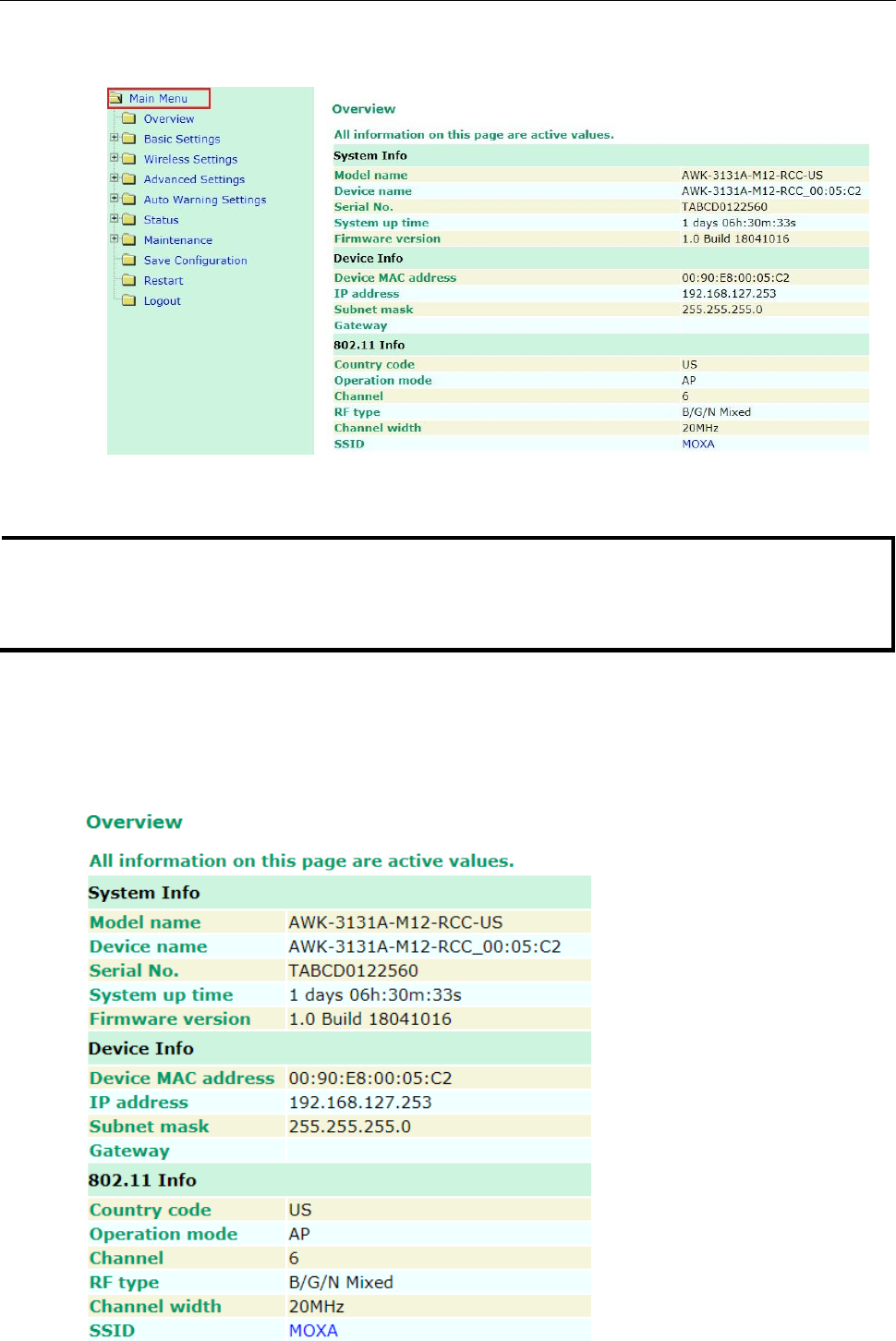
Overview
The Overview page summarizes the AWK-3131A-M12-RCC’s current status. The information is categorized
into several groups: System info, Device info, and 802.11 info.
AWK-3131A-M12-RCC
Web Console Configuration
3-5
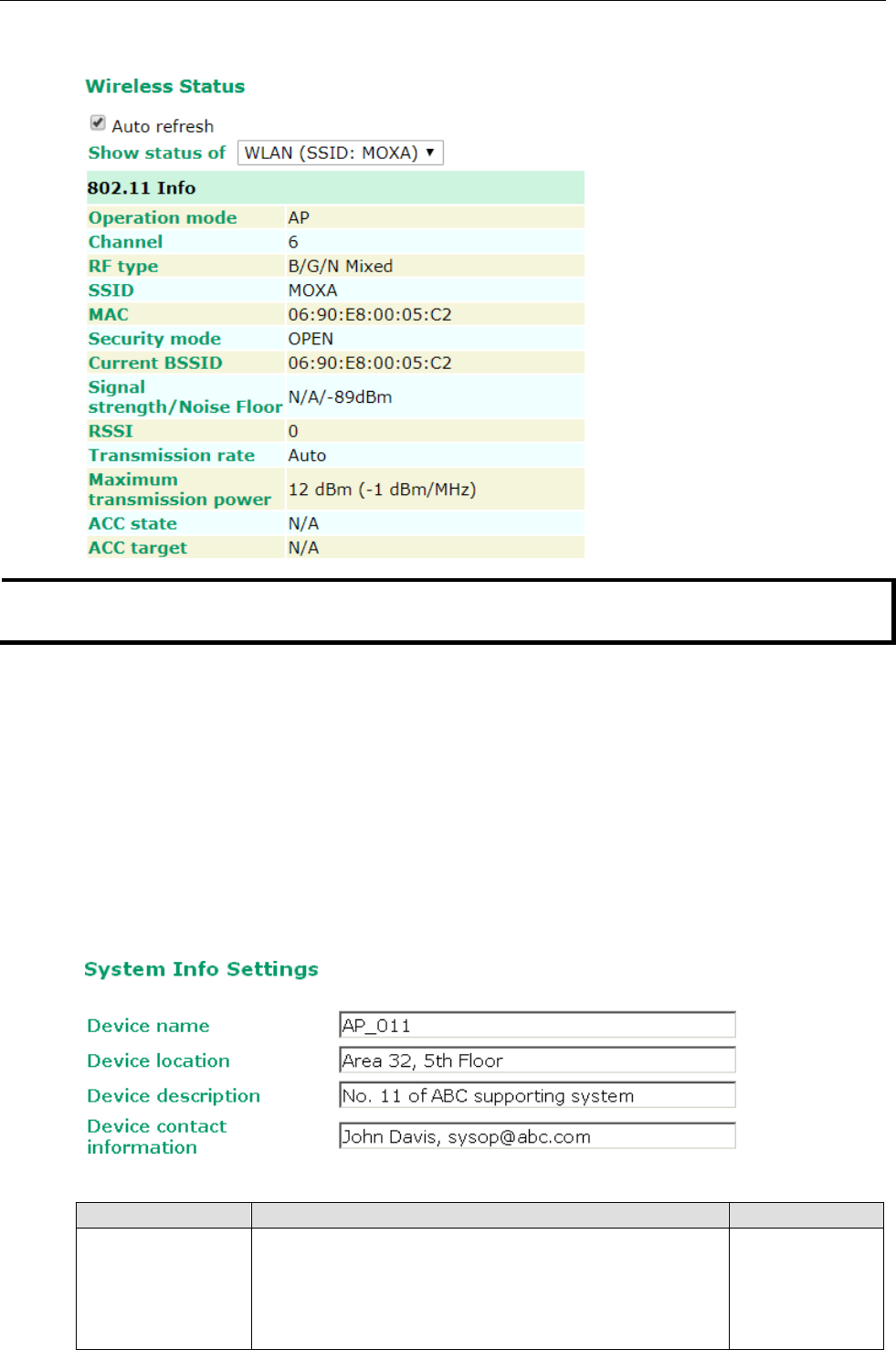
Click on SSID for more detailed 802.11 information, as shown in the following figure.
NOTE
The 802.11 info that is displayed may be different for different operation modes. For example, “Current
BSSID” is not available in Client mode, and “Signal strength” is not available in AP mode.
Basic Settings
The Basic Settings group includes the most commonly used settings required by administrators to maintain and
control the AWK-3131A-M12-RCC.
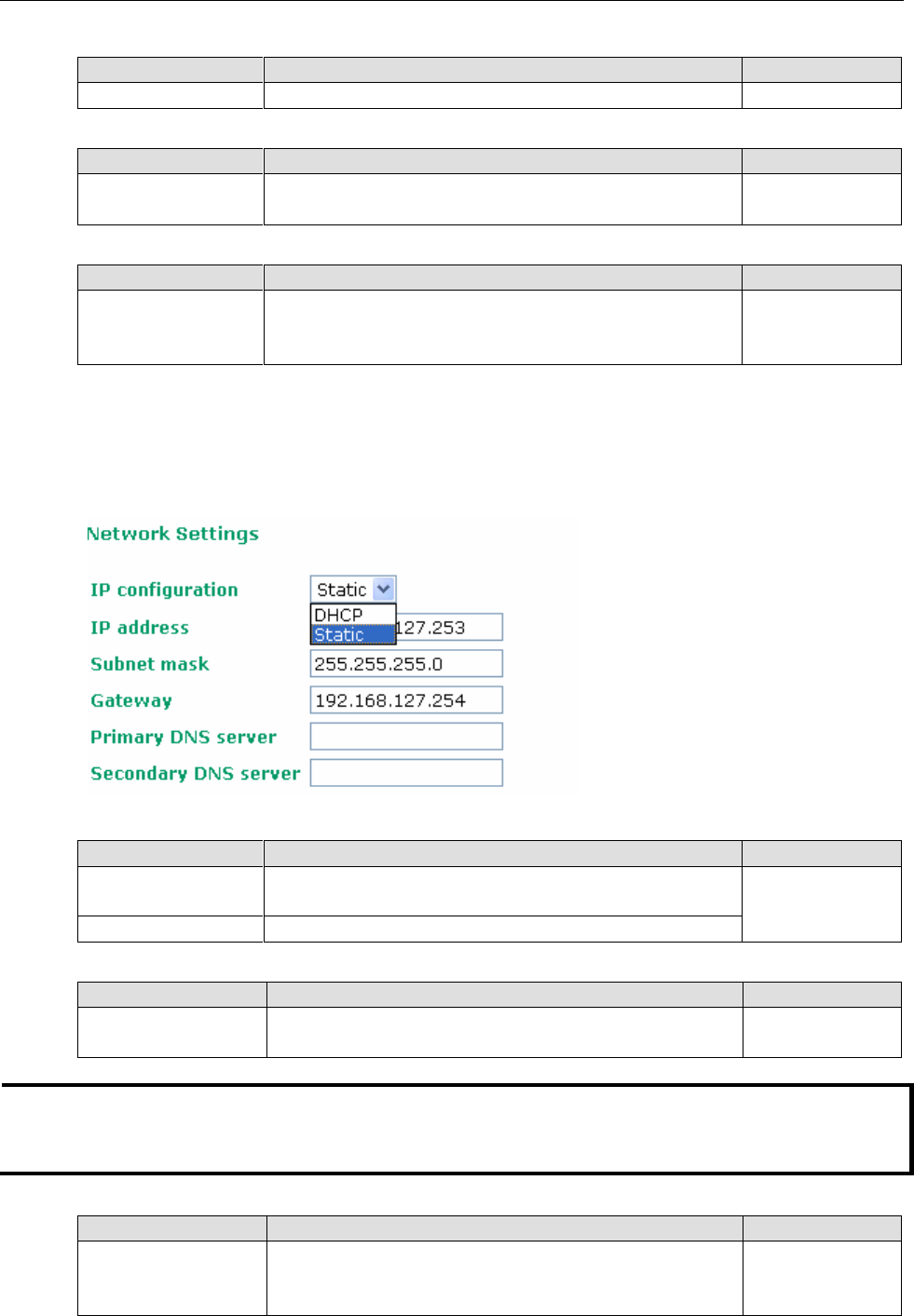
System Info Settings
The System Info items, especially Device name and Device description, are displayed and included on the
Overview page, in SNMP information, and in alarm emails. Setting System Info items makes it easier to
identify the different AWK-3131A-M12-RCC units connected to your network.
Device name
Setting
Description
Factory Default
Max. 31 of characters
This option is useful for specifying the role or application of
different AWK-3131A-M12-RCC units.
AWK-3131A-M12-R
CC_<Last 3 bytes
of this
AWK-3131A-M12-R
CC>
AWK-3131A-M12-RCC
Web Console Configuration
3-6
Device location
Setting
Description
Factory Default
Max. of 31 characters
Specifies the location of different AWK-3131A-M12-RCC units.
None
Device description
Setting
Description
Factory Default
Max. of 31 characters
Use this space to record a more detailed description of the
AWK-3131A-M12-RCC
None
Device contact information
Setting
Description
Factory Default
Max. of 31 characters
Provides information about whom to contact in order to resolve
problems. Use this space to record contact information of the
person responsible for maintaining this AWK-3131A-M12-RCC.
None
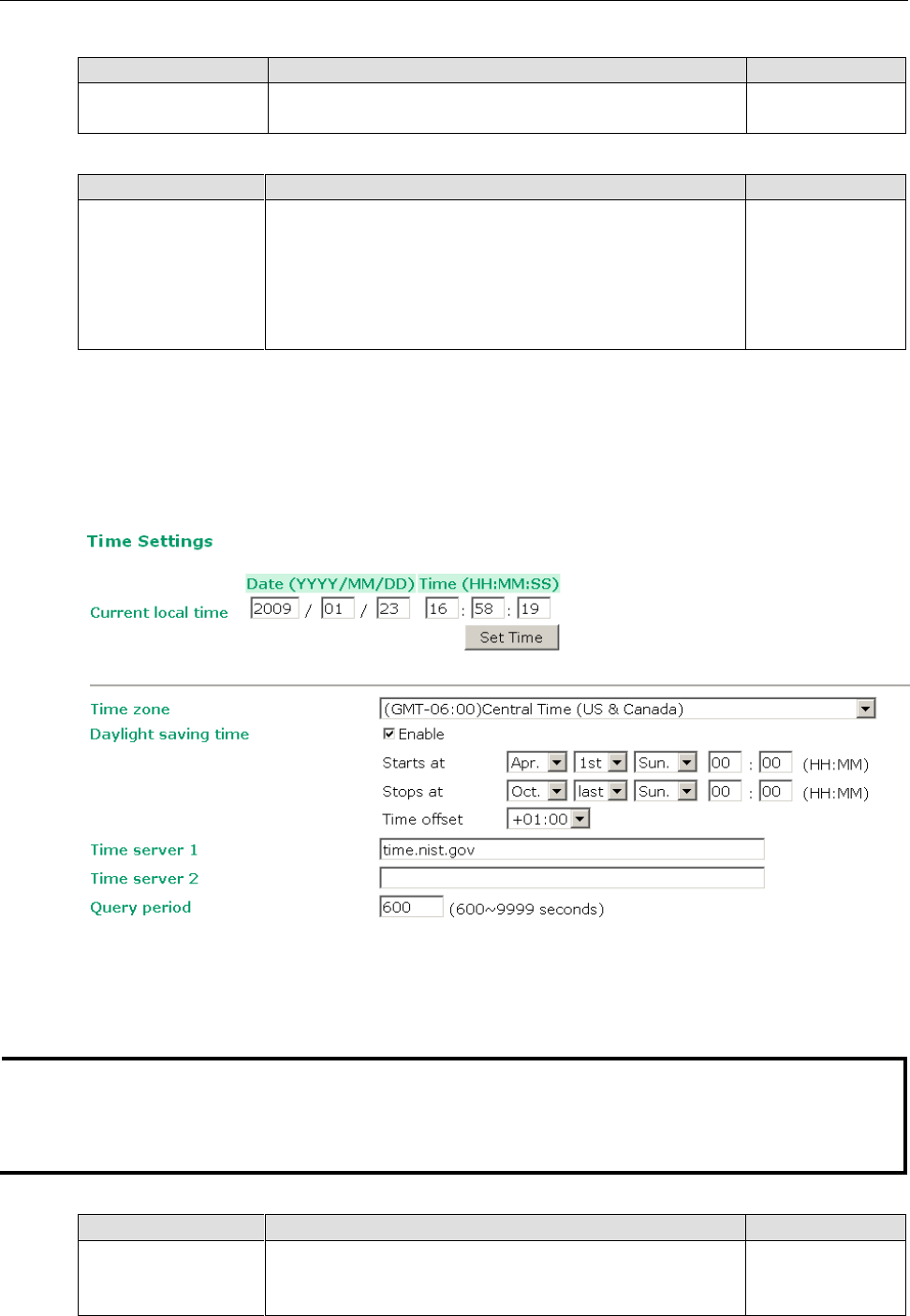
Network Settings
The Network Settings configuration panel allows you to modify the usual TCP/IP network parameters. An
explanation of each configuration item is given below.
IP configuration
Setting
Description
Factory Default
DHCP
The AWK-3131A-M12-RCC’s IP address will be assigned
automatically by the network’s DHCP server
Static
Static
Set up the AWK-3131A-M12-RCC’s IP address manually.
IP address
Setting
Description
Factory Default
AWK-3131A-M12-RCC’s
IP address
Identifies the AWK-3131A-M12-RCC on a TCP/IP network.
192.168.127.253
NOTE
DO NOT set the local subnet IP or the broadcast IP as the AWK-3131A-M12-RCC's IP address. For example,
192.168.127.0 and 192.168.127.255 cannot be assigned to the AWK-3131A-M12-RCC if the subnet mask is
set to 255.255.255.0.
Subnet mask
Setting
Description
Factory Default
AWK-3131A-M12-RCC’s
subnet mask
Identifies the type of network to which the
AWK-3131A-M12-RCC is connected (e.g., 255.255.0.0 for a
Class B network, or 255.255.255.0 for a Class C network).
255.255.255.0
AWK-3131A-M12-RCC
Web Console Configuration
3-7
Gateway
Setting
Description
Factory Default
AWK-3131A-M12-RCC’s
default gateway
The IP address of the router that connects the LAN to an
outside network.
None
Primary/ Secondary DNS server
Setting
Description
Factory Default
IP address of the
Primary/Secondary
DNS server
The IP address of the DNS Server used by your network. After
entering the DNS Server’s IP address, you can input the
AWK-3131A-M12-RCC’s URL (e.g., http://ap11.abc.com) in
your browser’s address field instead of entering the IP address.
The Secondary DNS server will be used if the Primary DNS
server fails to connect.
None
Time Settings
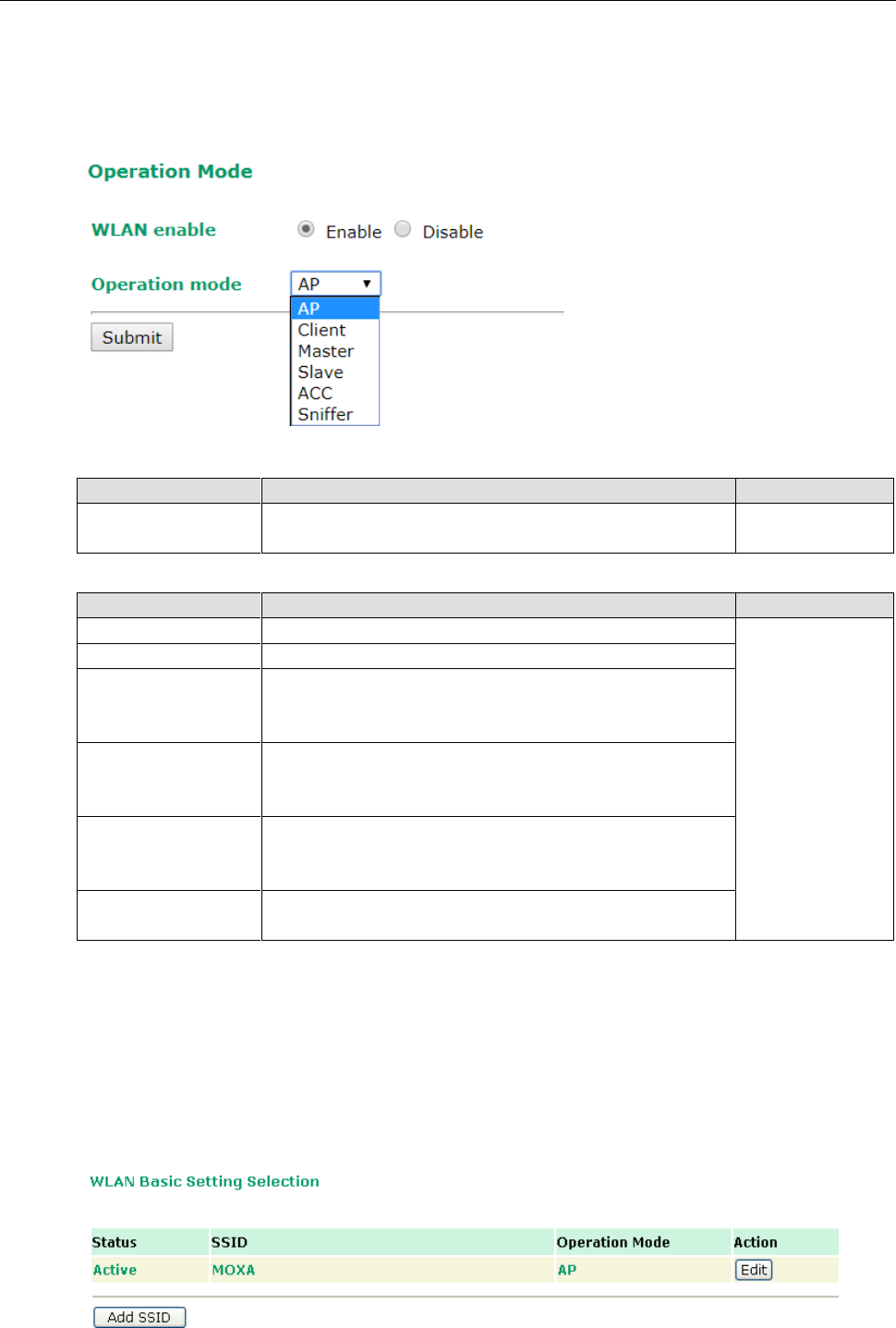
The AWK-3131A-M12-RCC has a time calibration function based on information from an NTP server or user
specified Date and Time information. Functions such as Auto warning can add real-time information to the
message.
The Current local time shows the AWK-3131A-M12-RCC’s system time when you open this web page. You
can click on the Set Time button to activate the updated date and time parameters. An “(Updated)” string will
appear to indicate that the change is complete. Local time settings will be immediately activated in the system
without running Save and Restart.
NOTE
The AWK-3131A-M12-RCC has a built-in real time clock (RTC). It is strongly recommended that users update
the Local time for the AWK-3131A-M12-RCC after the initial setup or a long-term shutdown, especially when
the network does not have an Internet connection for accessing the NTP server or there is no NTP server on
the LAN.
Current local time
Setting
Description
Factory Default
User adjustable time
The date and time parameters allow configuration of the local
time, with immediate activation.
Use 24-hour format: yyyy/mm/dd hh:mm:ss
None

AWK-3131A-M12-RCC
Web Console Configuration
3-8
Time zone
Setting
Description
Factory Default
User selectable time
zone
The time zone setting allows conversion from GMT (Greenwich
Mean Time) to local time.
GMT (Greenwich
Mean Time)
Daylight saving time
Setting
Description
Factory Default
Enable/ Disable
Daylight saving time (also known as DST or summer time)
involves advancing clocks (usually 1 hour) during the summer
time to provide an extra hour of daylight in the afternoon.
Disable
When Daylight saving time is enabled, the following parameters will be shown:
• Starts at: The date that daylight saving time begins.
• Stops at: The date that daylight saving time ends.
• Time offset: Indicates how many hours forward the clock should be advanced.
Time server 1/2
Setting
Description
Factory Default
IP/Name of Time
Server ½
IP or Domain name of the NTP time server. The 2nd NTP server
will be used if the 1st NTP server fails to connect.
Time.nist.gov
Query period
Setting
Description
Factory Default
Query period time
(1 to 9999 seconds)
This parameter determines how often the time is updated from
the NTP server.
600 (seconds)
Wireless Settings
The essential settings for wireless networks are presented in this function group. Settings must be properly set
before establishing your wireless network. Familiarize yourself with the following terms before starting the
configuration process:
AP: In a wireless local area network (WLAN), an access point is a station that transmits and receives data.
Client: When the AWK-3131A-M12-RCC is configured for Client mode, it can be used as an
Ethernet-to-wireless (or LAN-to-WLAN) network adaptor. For example, a notebook computer equipped with an
Ethernet adaptor but no wireless card can be connected to this device with an Ethernet cable to provide
wireless connectivity to another AP.
ATTENTION
Changing the time zone will automatically adjust the Current local time. You should configure the Time
zone before setting the Current local time.
AWK-3131A-M12-RCC
Web Console Configuration
3-9
Operation Mode
The AWK-3131A-M12-RCC supports five main operation modes—AP, Client, Master, Slave, and ACC—each of
which plays a distinct role on the wireless network.
Wireless Enable
Setting
Description
Factory Default
Enable/Disable
The RF (Radio Frequency) module can be manually turned on or
off. This function is available in AP operation mode only.
Enable
Operation Mode
Setting
Description
Factory Default
AP
The AWK-3131A-M12-RCC plays the role of wireless AP
AP
Client
The AWK-3131A-M12-RCC plays the role of wireless AP Client
Master
This mode collocates with AWK-5232/6232’s Wireless bridge
mode. The AWK-3131A-M12-RCC plays the role of wireless
Master.
Slave
This mode collocates with AWK-5232/6232’s Wireless bridge
mode. The AWK-3131A-M12-RCC plays the role of wireless
Slave.
ACC
This mode collocates with another AWK-3131A-M12-RCC’s ACC
mode to form an ACC link. Both AWK-3131A-M12-RCCs must
have the same basic wireless settings and security settings.
Sniffer
Turns the device into a remote Wireshark interface to capture
802.11 packets for analysis.
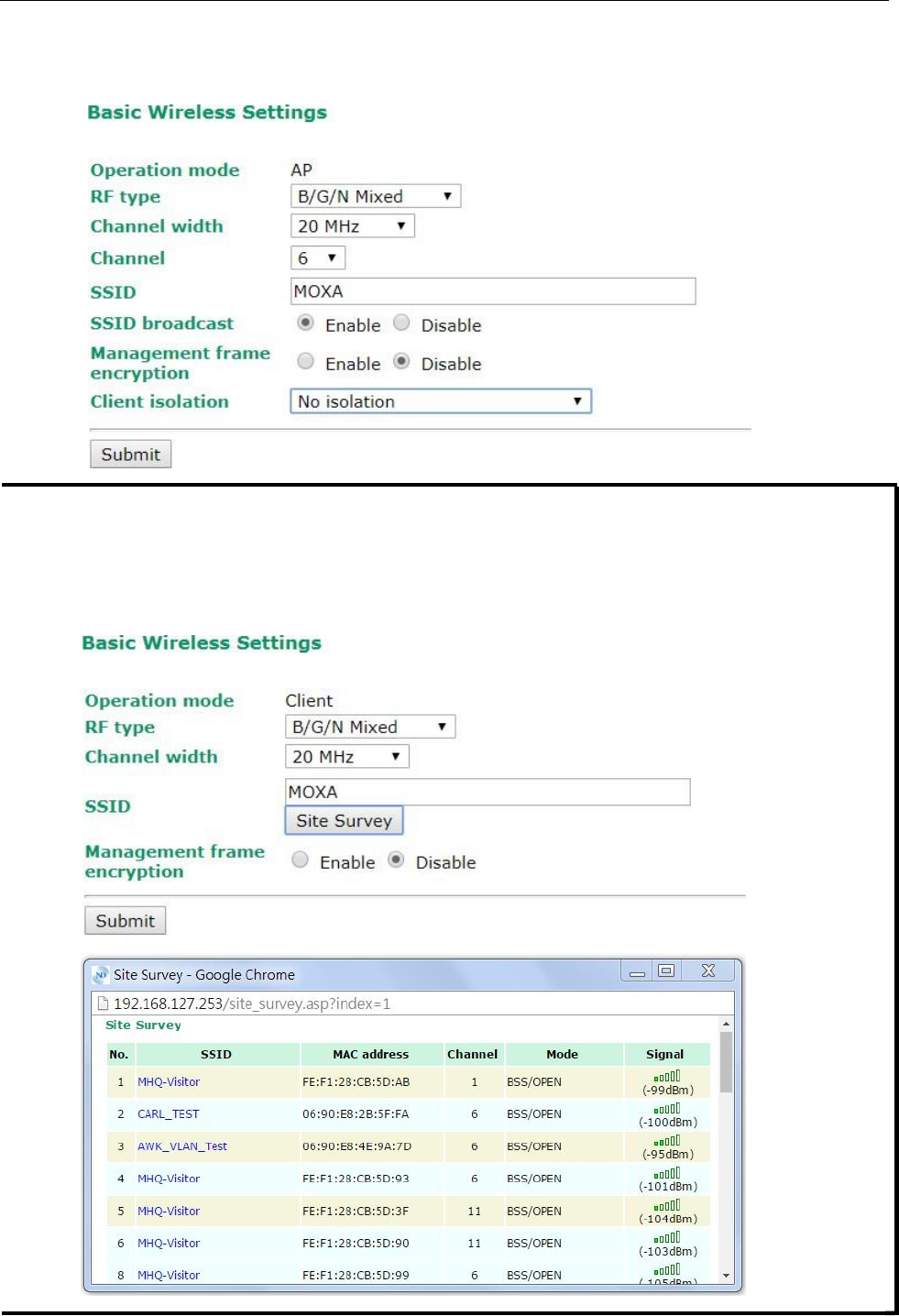
Basic Wireless Settings
The “WLAN Basic Setting Selection” panel is used to add and edit SSIDs. An SSID is a unique identifier that
wireless networking devices use to establish and maintain wireless connectivity. Multiple access points on a
network or sub-network can use the same SSIDs. You can configure your AWK to use up to 9 SSIDs, and
configure each SSID differently. All of the SSIDs are active at the same time; that is, client devices can use any
of the SSIDs to associate with the access point.
Click on Add SSID to create more SSIDs.
AWK-3131A-M12-RCC
Web Console Configuration
3-10
Click on Edit to assign different configuration settings to each SSID. The configuration panel appears as
follows:
NOTE
When you switch to Client mode, a Site Survey button will be available on the Basic Wireless Settings panel.
Click the “Site Survey” button to view information about available APs, as shown in the following figure. You can
click on the SSID of an entity and bring the value of its SSID onto the SSID field of the Basic Wireless Settings
page. Click the Refresh button to re-scan and update the table. If this client is connecting to an AP, a brief
disconnection will occur during site survey.

AWK-3131A-M12-RCC
Web Console Configuration
3-11
RF type
Setting
Description
Factory Default
2.4 GHz
B
Only supports the IEEE 802.11b standard
B/G/N Mixed
G
Only supports the IEEE 802.11g standard
B/G Mixed
Supports IEEE 802.11b/g standards, but 802.11g may operate
at a slower speed if when 802.11b clients are on the network
G/N Mixed
Supports IEEE 802.11g/n standards, but 802.11n may operate
at a slower speed if 802.11g clients are on the network
B/G/N Mixed
Supports IEEE 802.11b/g/n standards, but 802.11g/n may
operate at a slower speed if 802.11b clients are on the network
N Only (2.4GHz)
Only supports the 2.4 GHz IEEE 802.11n standard
5 GHz
A
Only supports the IEEE 802.11a standard
A/N Mixed
Supports IEEE 802.11a/n standards, but 802.11n may operate
at a slower speed if 802.11a clients are on the network
N Only (5GHz)
Only supports the 5 GHz IEEE 802.11n standard
Channel Width (for any 11N RF type only)
Setting
Description
Factory Default
20 MHz
Select your channel width, If you are not sure which option to
use, select 20/ 40MHz (Auto)
20 MHz
20/40 MHz
Channel bonding
If 20/40 MHz only is the Channel Width setting, this channel bonding will auto set the channel based on your
channel setting.
Channel (for AP/Master/ACC mode only)
Setting
Description
Factory Default
Available channels vary
with RF type
The AWK-3131A-M12-RCC plays the role of wireless AP,
Master, or ACC.
6 (in B/G/N Mixed
mode)
SSID
Setting
Description
Factory Default
Max. of 31 characters
The SSID of a client and the SSID of the AP must be identical for
the client and AP to be able to communicate with each other.
MOXA
SSID broadcast (for AP/Master/ACC mode only)
Setting
Description
Factory Default
Enable/ Disable
SSID can be broadcast or not
Enable
Management frame encryption
Setting
Description
Factory Default
Enable/ Disable
Enables management frame encryption to protect your wireless
network from DoS attacks. This function only works with
Moxa's Wireless device such as TAP, AWK-RCC, and RTG series
devices.
Disable
NOTE
Product models such as the AWK-3131A-M12-RCC-EU Series use EU bands that are under ETSI regulation.
Users must disable the SSID broadcast setting in these models when they use 5 GHz channels 36, 40, 44, 48,
52, 56, 60, 64, 100, 104, 108, 112, 116, 120, 124, 128, 132, 136, and 140.
Client Isolation (for AP mode only)
Client isolation is used to isolate the associated wireless clients connected to one or more APs. Isolated clients
cannot communicate with each other, so the level of security is increased. Depending on the type of client
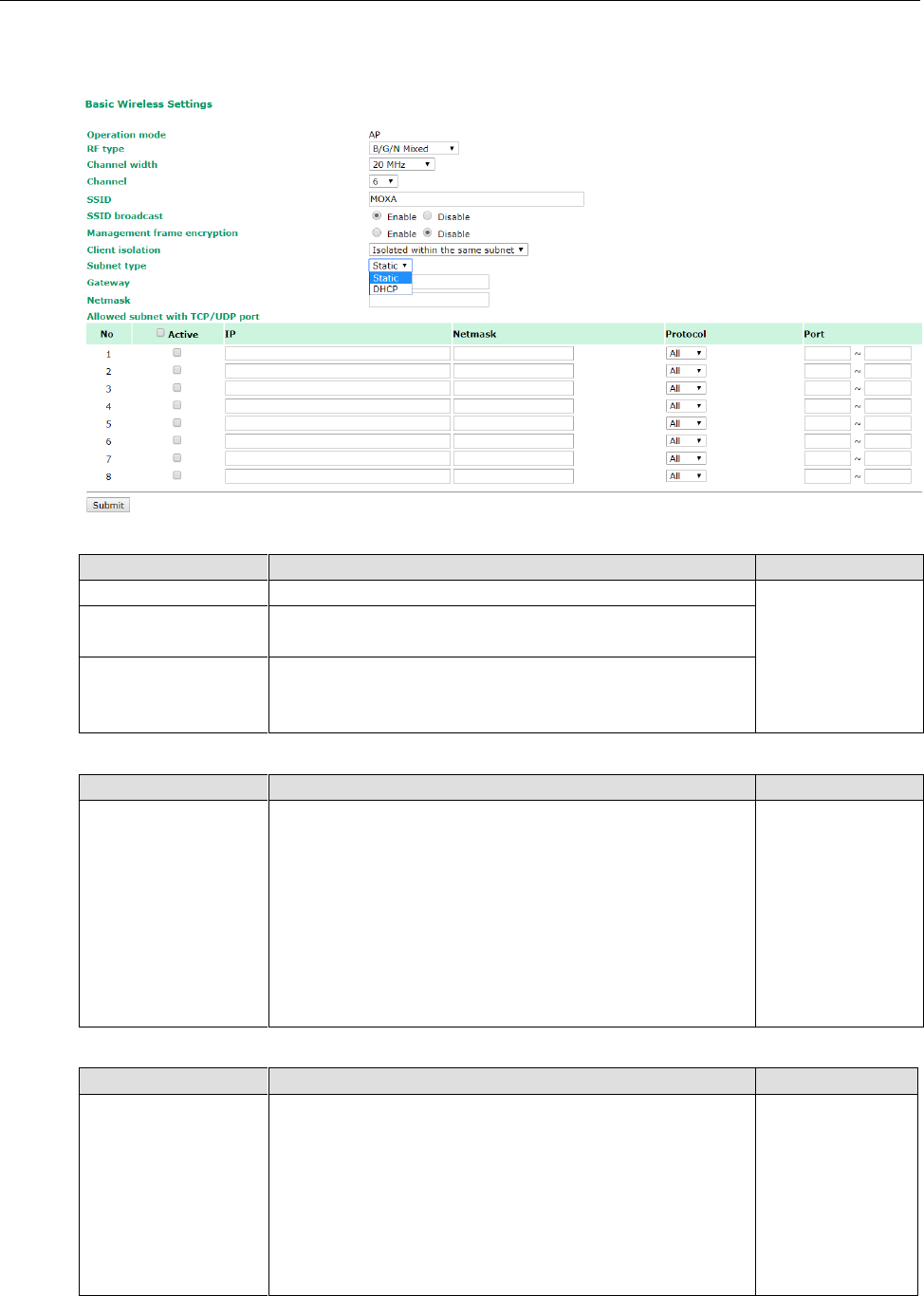
AWK-3131A-M12-RCC
Web Console Configuration
3-12
isolation used, you can specify exceptions (for clients) within the isolation network. This function can be, for
example, used in the case of an enterprise server service.
Client Isolation
Setting
Description
Factory Default
No isolation
No isolation is applied.
No isolation
Isolated within the
same AP
All clients associated to this AP will be isolated from each other.
Isolated within the
same subnet
All clients in the specified subnet will be isolated from each
other. The subnet is defined by the following two parameters,
gateway and netmask.
Subnet type
Setting
Description
Factory Default
Static/DHCP
This setting can be used to specify the subnet type when the
Isolated within the same subnet option is selected.
For applications that use a fixed IP address use the Static
value. For example, maintenance of hand held devices or
tablets that already have a fixed IP in the same subnet as the
AP. If your application requires wireless clients to retrieve new
IP addresses from the onboard DHCP server (or from the
build-in DHCP server) each time the clients connect to an AP,
select the DHCP option.
Static
Gateway
Setting
Description
Factory Default
Gateway for client
isolation function
This setting can be used when the Isolated within the same
subnet option is selected. The gateway setting along with the
netmask is used to define the network in which wireless clients
will be isolated from each other.
If the Subnet Type is set to Static, this setting must be
applied. If the Subnet Type is set to DHCP, this field can be left
blank and the gateway address will be assigned by the DHCP
server.
None
AWK-3131A-M12-RCC
Web Console Configuration
3-13
Netmask
Setting
Description
Factory Default
Netmask for client
isolation function
This setting can be used when the Isolated within the same
subnet option is selected.
If the Subnet Type is set to Static, this setting must be
applied. If the Subnet Type is set to DHCP, this field can be left
blank and the gateway address will be assigned by the DHCP
server.
None
The Allowed subnet with TCP/UDP port setting is used to specify the exceptions (subnets or hosts) when
the Isolated within the same subnet option is selected. Up to eight subnets or hosts can be included in the
list.
Active
Setting
Description
Factory Default
Enable/Disable
This checkbox enables or disables the rule for allowed subnet
settings.
Disable
IP
Setting
Description
Factory Default
IP address for allowed
subnet definition
The IP address of the subnet definition. Hosts in this subnet can
be accessed by other hosts or wireless clients in the same
subnet.
None
Netmask
Setting
Description
Factory Default
Netmask for allowed
subnet definition
The netmask of the subnet definition. Hosts in this subnet can
be accessed by other hosts or wireless clients in the same
subnet. You can also define the exception host by entering
255.255.255.255 in this field.
None
Protocol
Setting
Description
Factory Default
Protocol for allowed
subnet definition
The protocol of the subnet definition. Hosts in this subnet can
be accessed by other hosts or wireless clients in the same
subnet.
All
Port
Setting
Description
Factory Default
Port for allowed subnet
definition
The port range of the subnet definition. Hosts in this subnet can
be accessed by other hosts or wireless clients in the same
subnet.
None
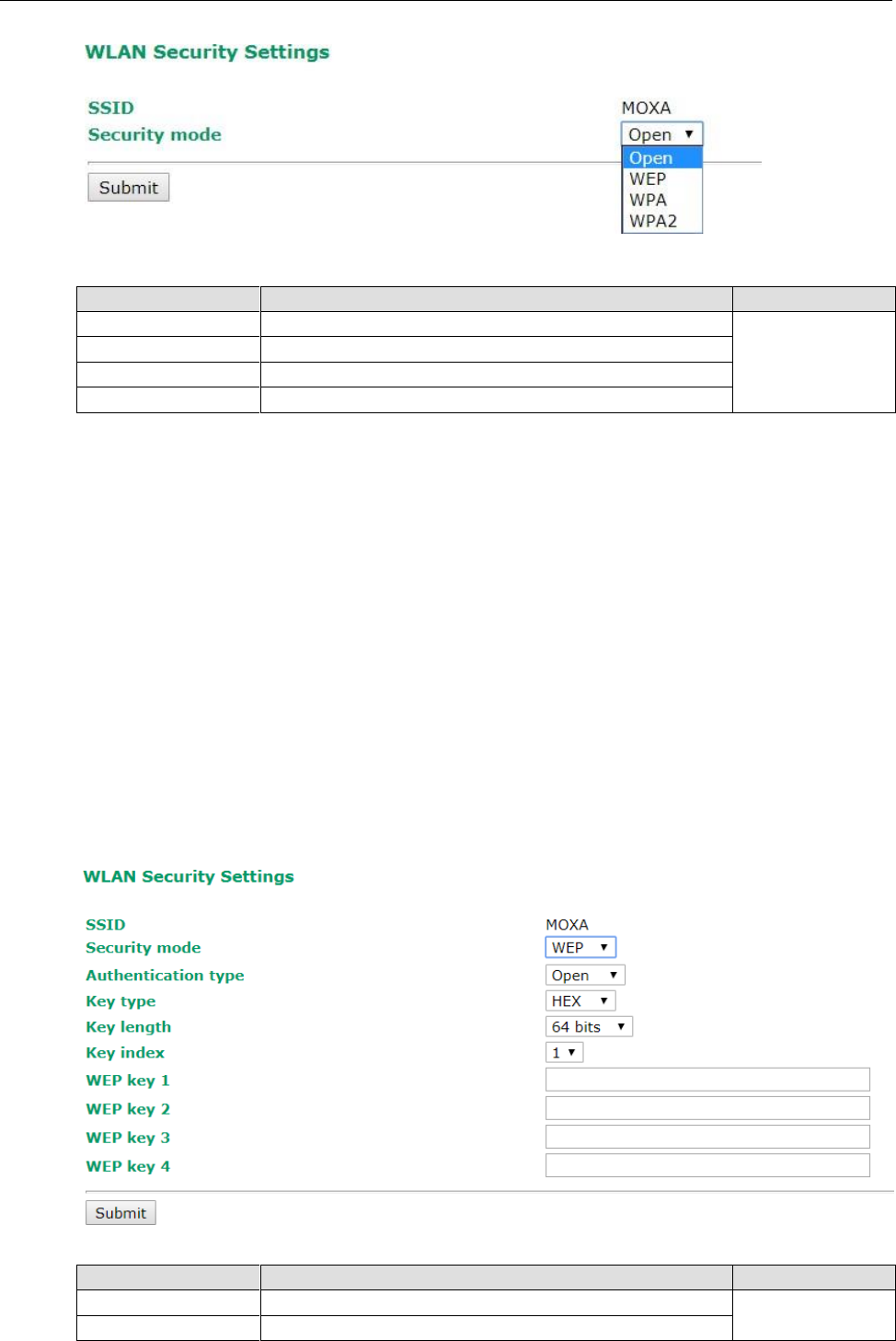
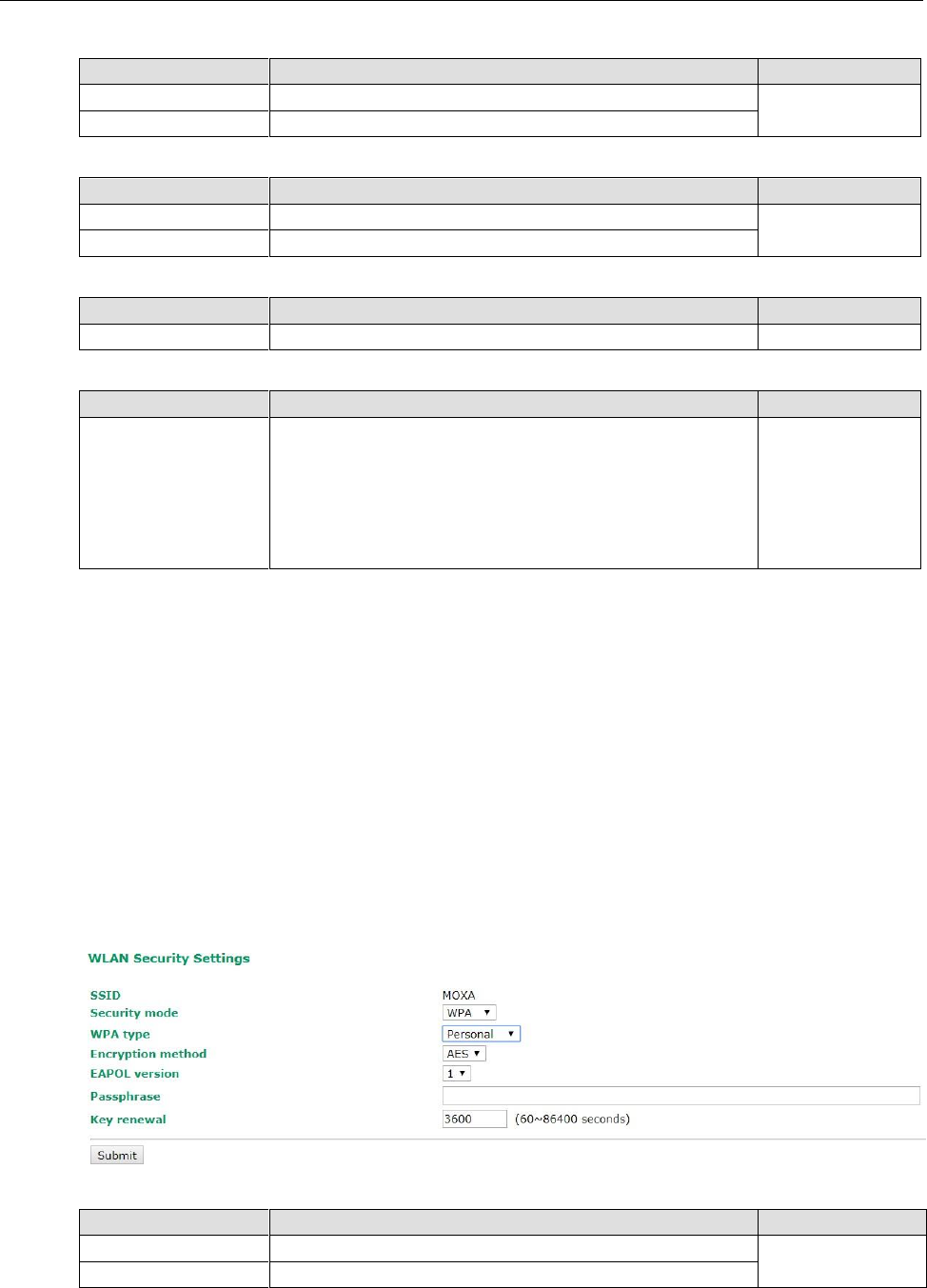
WLAN Security Settings
The AWK-3131A-M12-RCC provides four standardized wireless security modes: Open, WEP (Wired Equivalent
Privacy), WPA (Wi-Fi Protected Access), and WPA2. Several security modes are available in the
AWK-3131A-M12-RCC by selecting Security mode and WPA type:
• Open: No authentication, no data encryption.
• WEP: Static WEP (Wired Equivalent Privacy) keys must be configured manually.
• WPA/WPA2-Personal: Also known as WPA/WPA2-PSK. You will need to specify the Pre-Shared Key in the
Passphrase field, which will be used by the TKIP or AES engine as a master key to generate keys that
actually encrypt outgoing packets and decrypt incoming packets.
• WPA/WPA2-Enterprise: Also called WPA/WPA2-EAP (Extensible Authentication Protocol). In addition to
device-based authentication, WPA/WPA2-Enterprise enables user-based authentication via IEEE802.1X.
The AWK-3131A-M12-RCC can support three EAP methods: EAP-TLS, EAP-TTLS, and EAP-PEAP.
AWK-3131A-M12-RCC
Web Console Configuration
3-14
Security mode
Setting
Description
Factory Default
Open
No authentication
Open
WEP
Static WEP is used
WPA*
WPA is used
WPA2*
Fully supports IEEE802.11i with “TKIP/AES + 802.1X”
Open
For security reasons, you should NOT set security mode to Open System, since authentication and data
encryption are NOT performed in Open System mode.
WEP
According to the IEEE802.11 standard, WEP can be used for authentication and data encryption to maintain
confidentiality. Shared (or Shared Key) authentication type is used if WEP authentication and data encryption
are both needed. Normally, Open (or Open System) authentication type is used when WEP data encryption is
run with authentication.
When WEP is enabled as a security mode, the length of a key (so-called WEP seed) can be specified as 64/128
bits, which is actually a 40/104-bit secret key with a 24-bit initialization vector. The AWK-3131A-M12-RCC
provides 4 entities of WEP key settings that can be selected to use with Key index. The selected key setting
specifies the key to be used as a send-key for encrypting traffic from the AP side to the wireless client side. All
4 WEP keys are used as receive-keys to decrypt traffic from the wireless client side to the AP side.
The WEP key can be presented in two Key types, HEX and ASCII. Each ASCII character has 8 bits, so a 40-bit
(or 64-bit) WEP key contains 5 characters, and a 104-bit (or 128-bit) key has 13 characters. In hex, each
character uses 4 bits, so a 40-bit key has 10 hex characters, and a 128-bit key has 26 characters.
Authentication type
Setting
Description
Factory Default
Open
Data encryption is enabled, but without authentication
Open
Shared
Data encryption and authentication are both enabled.
AWK-3131A-M12-RCC
Web Console Configuration
3-15
Key type
Setting
Description
Factory Default
HEX
Specifies WEP keys in hex-decimal number form
HEX
ASCII
Specifies WEP keys in ASCII form
Key length
Setting
Description
Factory Default
64 bits
Uses 40-bit secret keys with 24-bit initialization vector
64 bits
128 bits
Uses 104-bit secret key with 24-bit initialization vector
Key index
Setting
Description
Factory Default
1-4
Specifies which WEP key is used
Open
WEP key 1-4
Setting
Description
Factory Default
ASCII type:
64 bits: 5 chars
128 bits: 13chars
HEX type:
64 bits: 10 hex chars
128 bits: 26 hex chars
A string that can be used as a WEP seed for the RC4 encryption
engine.
None
WPA/WPA2-Personal
WPA (Wi-Fi Protected Access) and WPA2 represent significant improvements over the WEP encryption method.
WPA is a security standard based on 802.11i draft 3, while WPA2 is based on the fully ratified version of 802.11i.
The initial vector is transmitted, encrypted, and enhanced with its 48 bits, twice as long as WEP. The key is
regularly changed so that true session is secured.
Even though AES encryption is only included in the WPA2 standard, it is widely available in the WPA security
mode of some wireless APs and clients as well. The AWK-3131A-M12-RCC also supports AES algorithms in WPA
and WPA2 for better compatibility.
Personal versions of WPA/WPA2, also known as WPA/WPA-PSK (Pre-Shared Key), provide a simple way of
encrypting a wireless connection for high confidentiality. A Passphrase is used as a basis for encryption
methods (or cipher types) in a WLAN connection. The passphrases should be complicated and as long as
possible. There must be at least 8 ASCII characters in the Passphrase, and it could go up to 63. For security
reasons, this passphrase should only be disclosed to users who need it, and it should be changed regularly.
WPA type
Setting
Description
Factory Default
Personal
Provides Pre-Shared Key-enabled WPA and WPA2
Personal
Enterprise
Provides enterprise-level security for WPA and WPA2
3-16
AWK-3131A-M12-RCC
Web Console Configuration
Encryption method
Setting
Description
Factory Default
TKIP*
Temporal Key Integrity Protocol is enabled
AES
AES
Advance Encryption System is enabled
Mixed**
Provides TKIP broadcast key and TKIP+AES unicast key for
some legacy AP clients. This option is rarely used.
*This option is only available with 802.11a/b/g standard
**This option is only available for legacy mode in APs and does not support AES-enabled clients.
Passphrase
Setting
Description
Factory Default
8 to 63 characters
Master key to generate keys for encryption and decryption
None
Key renewal (for AP/Master mode only)
Setting
Description
Factory Default
60 to 86400 seconds
(1 minute to 1 day)
Specifies the time period of group key renewal
3600 (seconds)
NOTE
The key renewal value dictates how often the wireless AP encryption keys should be changed. The security
level is generally higher if you set the key renewal value to a shorter number, which forces the encryption keys
to be changed more frequently. The default value is 3600 seconds (6 minutes). Longer time periods can be
considered if the line is not very busy.
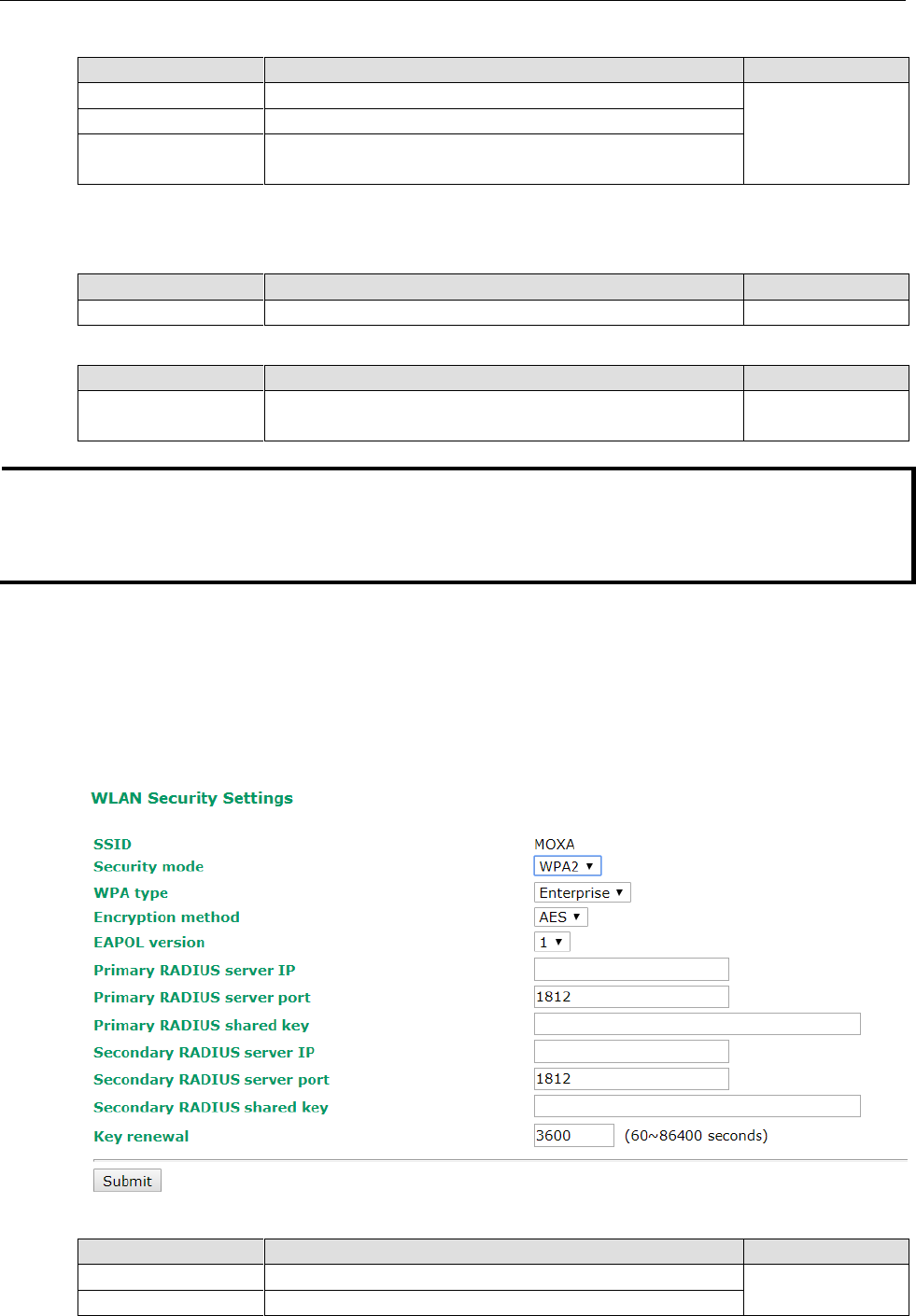
WPA/WPA2-Enterprise (for AP/Master mode)
By setting WPA type to Enterprise, you can use EAP (Extensible Authentication Protocol), a framework
authentication protocol used by 802.1X to provide network authentication. In these Enterprise-level security
modes, a back-end RADIUS (Remote Authentication Dial-In User Service) server is needed if IEEE 802.1X
functionality is enabled in WPA /WPA2. The IEEE 802.1X protocol also offers the possibility of carrying out an
efficient connection authentication on a large-scale network. It is not necessary to exchange keys or
passphrases.
WPA type
Setting
Description
Factory Default
Personal
Provides Pre-Shared Key-enabled WPA and WPA2
Personal
Enterprise
Provides enterprise-level security for WPA and WPA2
3-17
AWK-3131A-M12-RCC
Web Console Configuration
Encryption method
Setting
Description
Factory Default
TKIP*
Temporal Key Integrity Protocol is enabled
AES
AES
Advance Encryption System is enabled
Mixed**
Provides TKIP broadcast key and TKIP+AES unicast key for
some legacy AP clients. This option is rarely used.
*This option is only available with 802.11a/b/g standard
**This option is available only for legacy mode in APs and does not support AES-enabled clients.
Primary/Secondary RADIUS server IP
Setting
Description
Factory Default
The IP address of
RADIUS server
Specifies the delegated RADIUS server for EAP
None
Primary/Secondary RADIUS port
Setting
Description
Factory Default
Port number
Specifies the port number of the delegated RADIUS server
1812
Primary/ Secondary RADIUS shared key
Setting
Description
Factory Default
Max. of 31 characters
The secret key shared between AP and RADIUS server
None
Key renewal
Setting
Description
Factory Default
60 to 86400 seconds
(1 minute to 1 year)
Specifies the time period of group key renewal
3600 (seconds)
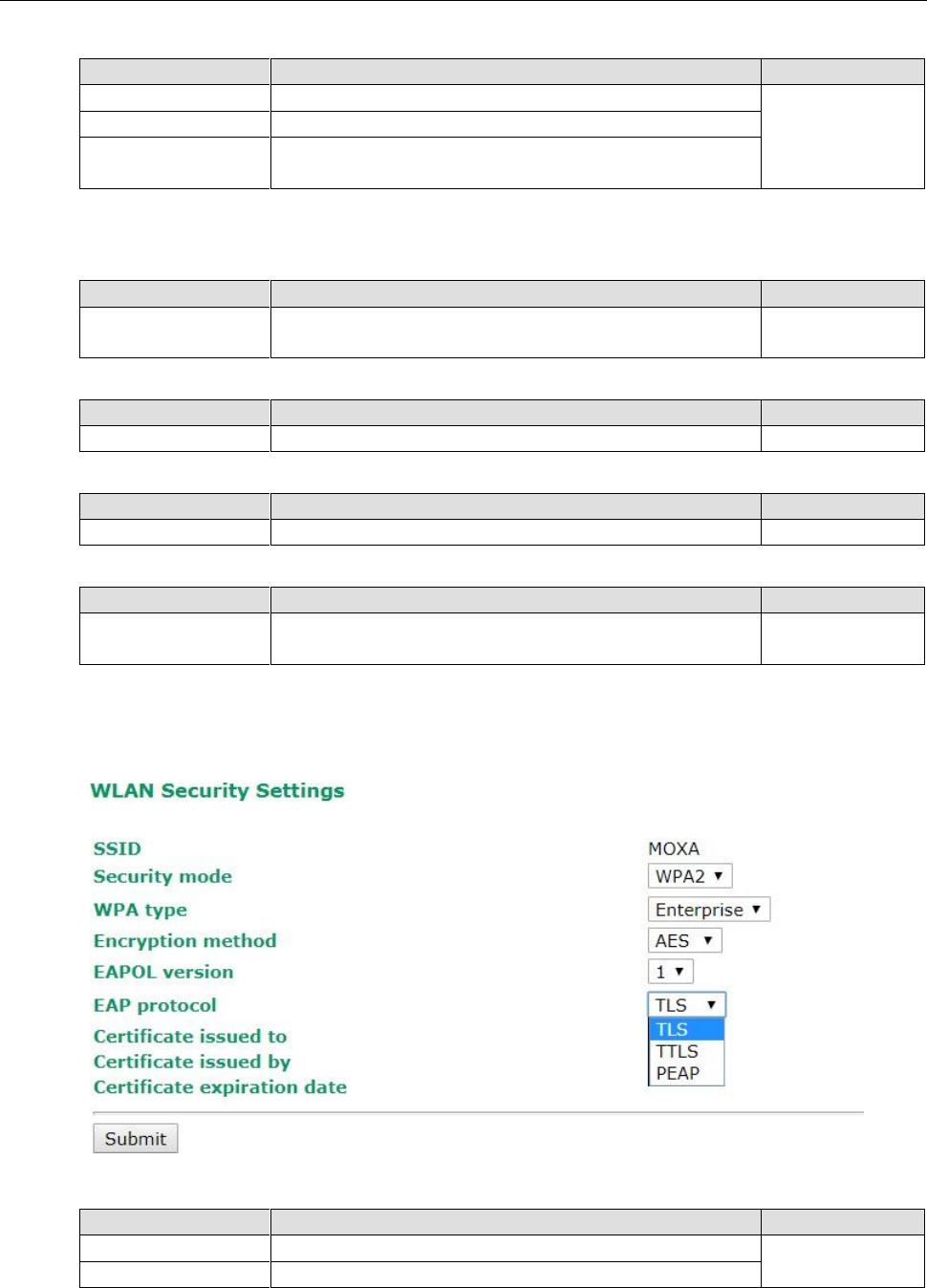
WPA/WPA2-Enterprise (for Client/Slave mode)
When used as a client, the AWK-3131A-M12-RCC can support three EAP methods (or EAP protocols):
EAP-TLS, EAP-TTLS, and EAP-PEAP, corresponding to WPA/WPA-Enterprise settings on the AP side.
Encryption method
Setting
Description
Factory Default
TKIP
Temporal Key Integrity Protocol is enabled
AES
AES
Advance Encryption System is enabled
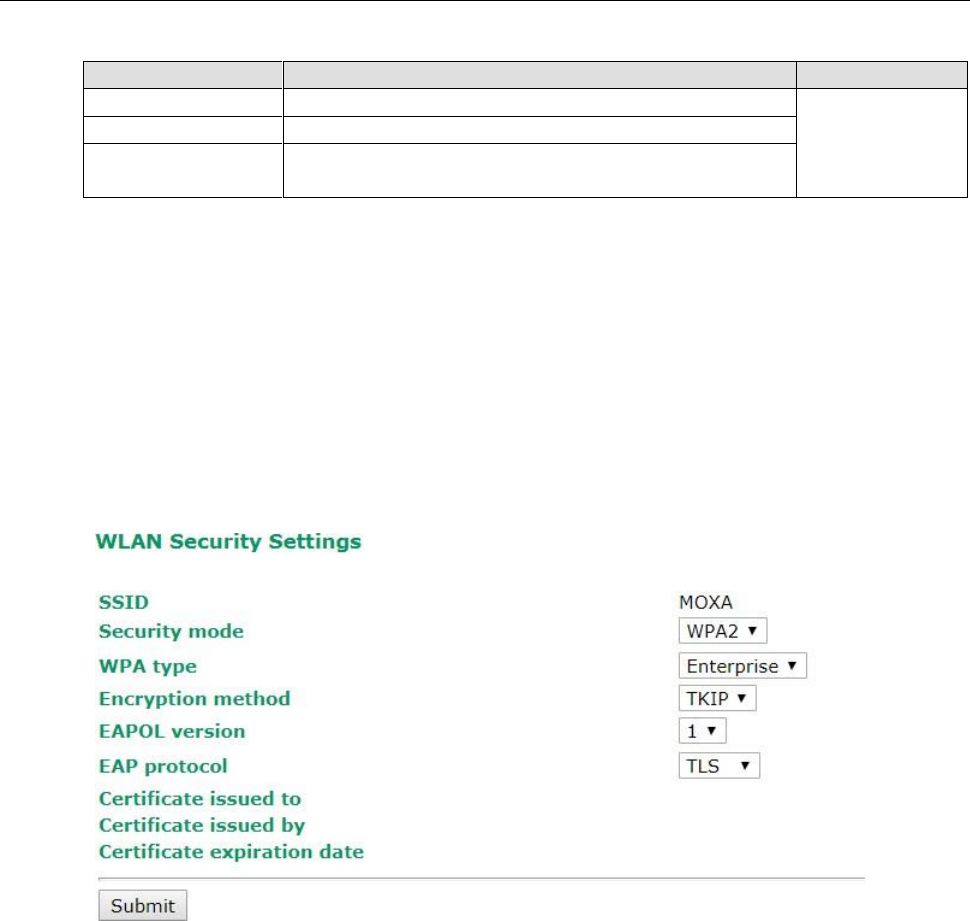
3-18
AWK-3131A-M12-RCC
Web Console Configuration
EAP Protocol
Setting
Description
Factory Default
TLS
Specifies Transport Layer Security protocol
TLS
TTLS
Specifies Tunneled Transport Layer Security
PEAP
Specifies Protected Extensible Authentication Protocol, or
Protected EAP
Before choosing the EAP protocol for your WPA/WPA2-Enterpise settings on the client end, please contact the
network administrator to make sure the system supports the protocol on the AP end. Detailed information on
these three popular EAP protocols is presented in the following sections.
EAP-TLS
TLS is the standards-based successor to Secure Socket Layer (SSL). It can establish a trusted communication
channel over a distrusted network. TLS provides mutual authentication through certificate exchange. EAP-TLS
is also secure to use. You are required to submit a digital certificate to the authentication server for validation,
but the authentication server must also supply a certificate.
You can use Basic Wireless Settings WLAN Certificate Settings to import your WLAN certificate and
enable EAP-TLS on the client end.
You can check the current certificate status in Current Status if it is available.
• Certificate issued to: Shows the certificate user
• Certificate issued by: Shows the certificate issuer
• Certificate expiration date: Indicates when the certificate has expired
EAP-TTLS
It is usually much easier to re-use existing authentication systems, such as a Windows domain or Active
Directory, LDAP directory, or Kerberos realm, rather than creating a parallel authentication system. As a result,
TTLS (Tunneled TLS) and PEAP (Protected EAP) are used to support the use of so-called “legacy authentication
methods.”
TTLS and PEAP work in a similar way. First, they establish a TLS tunnel (EAP-TLS for example), and validate
whether the network is trustworthy with digital certificates on the authentication server. This step establishes
a tunnel that protects the next step (or “inner” authentication), and consequently is sometimes referred to as
“outer” authentication. The TLS tunnel is then used to encrypt an older authentication protocol that
authenticates the user for the network.
As you can see, digital certificates are still needed for outer authentication in a simplified form. Only a small
number of certificates are required, which can be generated by a small certificate authority. Certificate
reduction makes TTLS and PEAP much more popular than EAP-TLS.
3-19
AWK-3131A-M12-RCC
Web Console Configuration
The AWK-3131A-M12-RCC provides some non-cryptographic EAP methods, including PAP, CHAP, MS-CHAP,
and MS-CHAP-V2. These EAP methods are not recommended for direct use on wireless networks. However,
they may be useful as inner authentication methods with TTLS and PEAP.
Because the inner and outer authentications can use distinct user names in TTLS and PEAP, you can use an
anonymous user name for the outer authentication, with the true user name only shown through the encrypted
channel. Keep in mind that not all client software supports anonymous alteration. Confirm this with the network
administrator before you enable identity hiding in TTLS and PEAP.
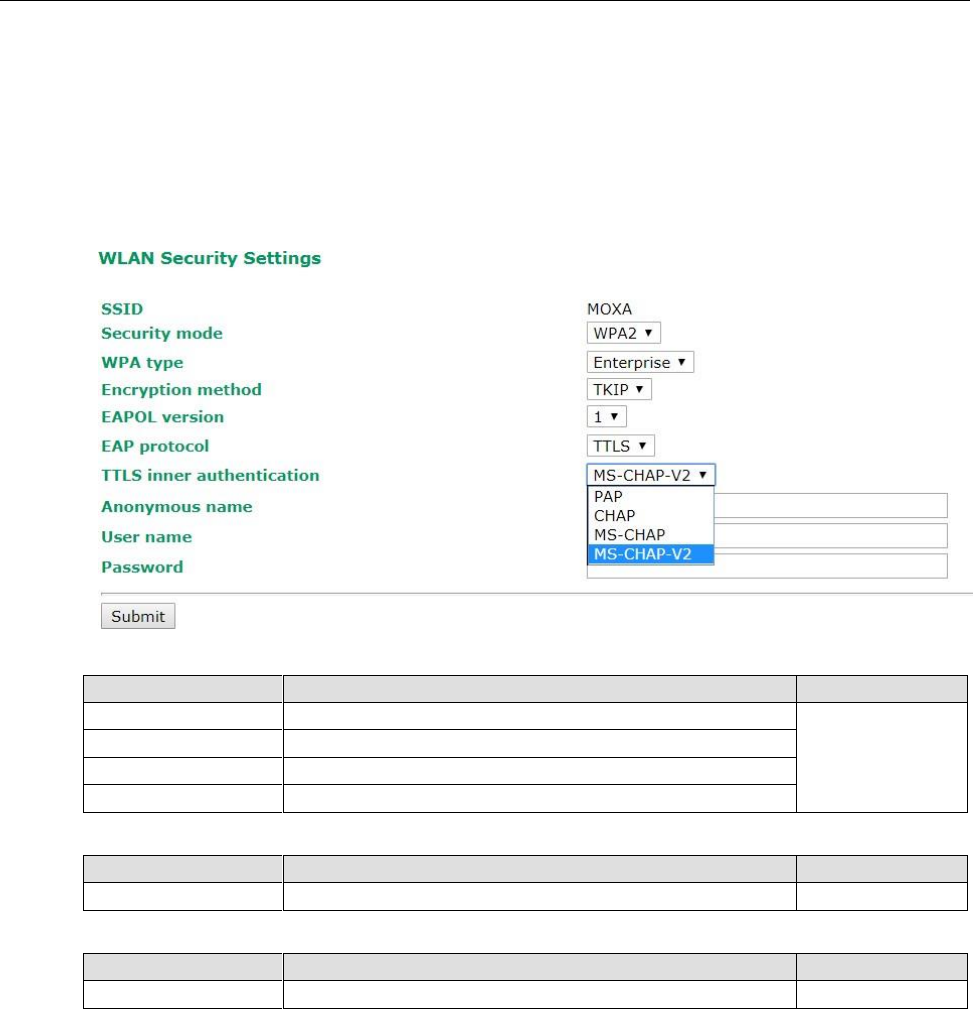
TTL Inner Authentication
Setting
Description
Factory Default
PAP
Password Authentication Protocol is used
MS-CHAP-V2
CHAP
Challenge Handshake Authentication Protocol is used
MS-CHAP
Microsoft CHAP is used
MS-CHAP-V2
Microsoft CHAP version 2 is used
Anonymous
Setting
Description
Factory Default
Max. of 31 characters
A distinct name used for outer authentication
None
User name & Password
Setting
Description
Factory Default
User name and password used in inner authentication
None
AWK-3131A-M12-RCC
Web Console Configuration
3-20
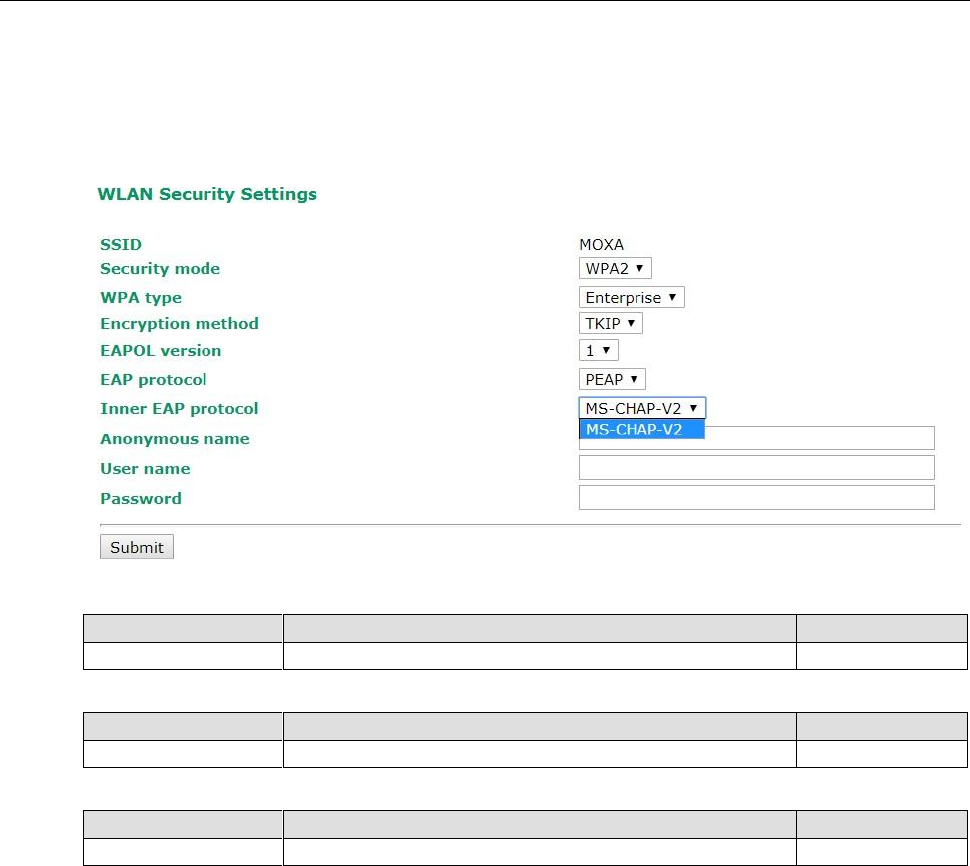
PEAP
There are a few differences in the TTLS and PEAP inner authentication procedures. TTLS uses the encrypted
channel to exchange attribute-value pairs (AVPs), while PEAP uses the encrypted channel to start a second EAP
exchange inside of the tunnel. The AWK-3131A-M12-RCC provides MS-CHAP-V2 merely as an EAP method for
inner authentication.
Inner EAP protocol
Setting
Description
Factory Default
MS-CHAP-V2
Microsoft CHAP version 2 is used
MS-CHAP-V2
Anonymous
Setting
Description
Factory Default
Max. of 31 characters
A distinct name used for outer authentication
None
User name & Password
Setting
Description
Factory Default
User name and password used in inner authentication
None
AWK-3131A-M12-RCC
Web Console Configuration
3-21
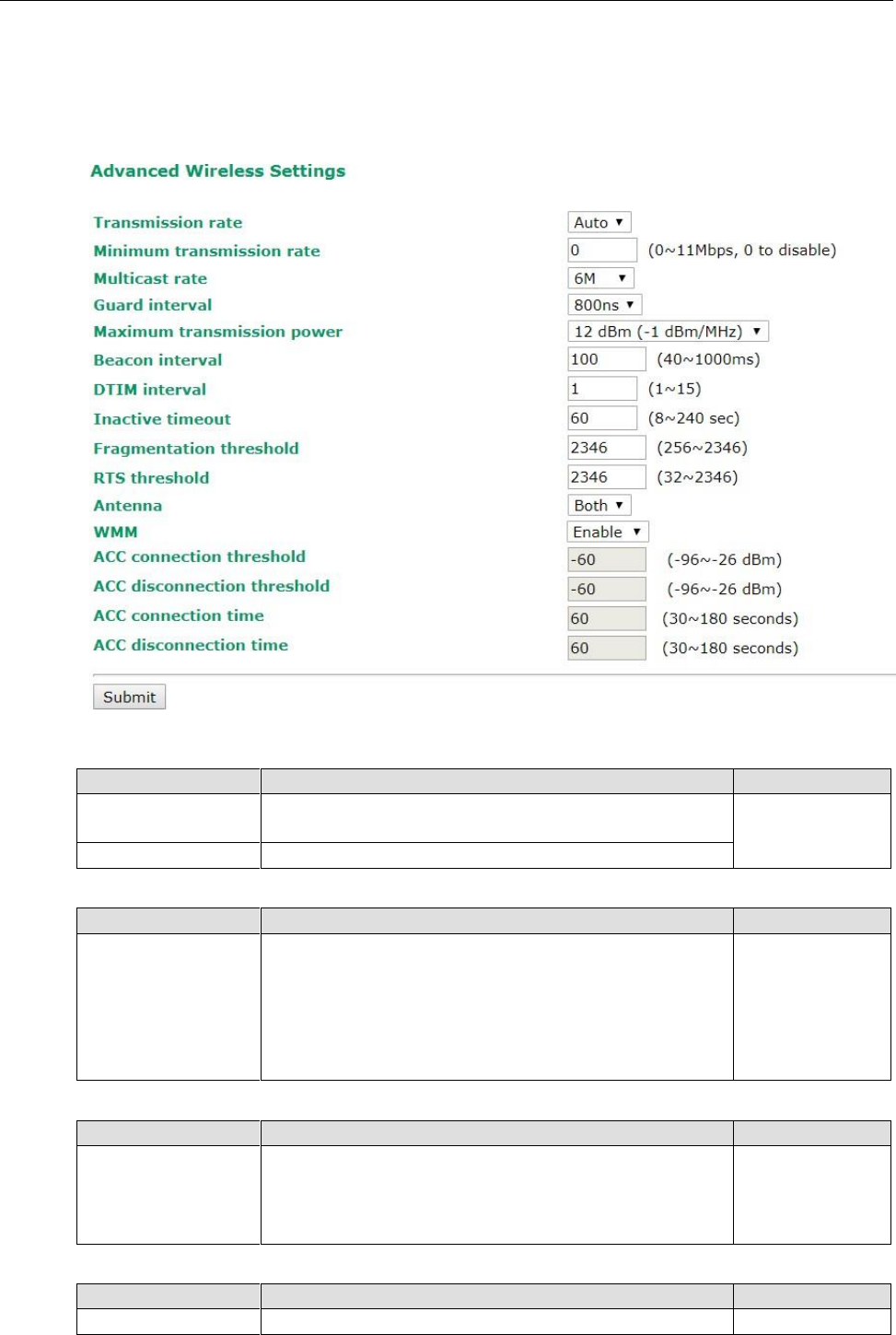
Advanced Wireless Settings
Additional wireless-related parameters are presented in this section to help you set up your wireless network
in detail.
Transmission Rate
Setting
Description
Factory Default
Auto
The AWK-3131A-M12-RCC senses and adjusts the data rate
automatically
Auto
Available rates
Users can manually select a target transmission data rate
Multicast Rate (for AP/Master/ACC mode only)
Setting
Description
Factory Default
Multicast rate
(6M ~ 54M)
You can set a fixed multicast rate for the transmission of
broadcast and multicast packets on a per-radio basis. This
parameter can be useful in an environment where multicast
video streaming is occurring in the wireless medium, provided
that the wireless clients are capable of handling the configured
rate.
6M
Guarding Interval
Setting
Description
Factory Default
Guarding Interval
Guarding interval is used to ensure that distinct transmissions
do not interfere with one another. You can select the guarding
interval manually for Wireless-N connections. The two options
are Short (400ns) and Long (800ns).
800 ns.
Maximum transmission Power
Setting
Description
Factory Default
Transmission Power
Specifies transmission power for the radio in the unit of dBm.
12 dBm

AWK-3131A-M12-RCC
Web Console Configuration
3-22
Beacon Interval (for AP/Master/ACC mode only)
Setting
Description
Factory Default
Beacon Interval
(40 to 1000 ms)
Indicates the frequency interval of the beacon
100 (ms)
DTIM Interval (for AP/Master/ACC mode only)
Setting
Description
Factory Default
Data Beacon Rate
(1 to 15)
Indicates how often the AWK-3131A-M12-RCC sends out a
Delivery Traffic Indication Message
1
Fragmentation threshold
Setting
Description
Factory Default
Fragment Length
(256 to 2346)
Specifies the maximum size a data packet before splitting and
creating another new packet
2346
RTS threshold
Setting
Description
Factory Default
RTS/CTS Threshold
(256 to 2346)
Determines how large a packet can be before the Access Point
coordinates transmission and reception to ensure efficient
communication
2346
NOTE
Most countries define a limit for the Equivalent Isotropically Radiated Power (EIRP) for an RF transmitting
system. The EIRP should not exceed the permitted limit for the country of operation. EIRP = transmission
power + antenna gain (dBi).
NOTE
Transmission power indicates the maximum value of transmission power which the user plans. However, the
real transmitted power depends on the radio module and some facts, such as country, regulatory limitations
and data rate. Please check the Transmission power in Status > Wireless Status for a real and updated value
of transmission power, which the AWK is currently using.
You can refer to the related glossaries in the reference section for detailed information about the
above-mentioned settings. By setting these parameters properly, you can better tune the performance of your
wireless network.
Antenna
Setting
Description
Factory Default
A/B/Both
Specifies the output antenna port. Setting Antenna to Both
allows 2x2 MIMO communication under 802.11n and 2T2R
communication in legacy 802.11a/b/g modes.
Both
WMM
Setting
Description
Factory Default
Enable/Disable
WMM is a QoS standard for WLAN traffic. Voice and video data
will be given priority bandwidth when enabled with WMM
supported wireless clients.
Disable
ACC Connection Threshold
Setting
Description
Factory Default
ACC Connection
Threshold
If the signal strength of an AWK-3131A-M12-RCC can be above
this value for the period of time specified in the “ACC
Connection Time” field, this AWK-3131A-M12-RCC will be
considered as a connecting candidate.
-60dBm
AWK-3131A-M12-RCC
Web Console Configuration
3-23
ACC Disconnection Threshold
Setting
Description
Factory Default
ACC Disconnection
Threshold
If the signal strength of the AWK-3131A-M12-RCC is below this
threshold value for the period of time specified in the “ACC
Disconnection Time” field, the ACC link will be brought down.
-60dBm
ACC Connection Time
Setting
Description
Factory Default
ACC Connection
Time
This is the period of time for an AWK-3131A-M12-RCC to be
considered as a connecting candidate.
60 seconds
ACC Disconnection Time
Setting
Description
Factory Default
ACC Disconnection
Time
This is the period of time for an ACC link to be considered as a
poor connection. The ACC link will be brought down after the
specified time period.
60 seconds
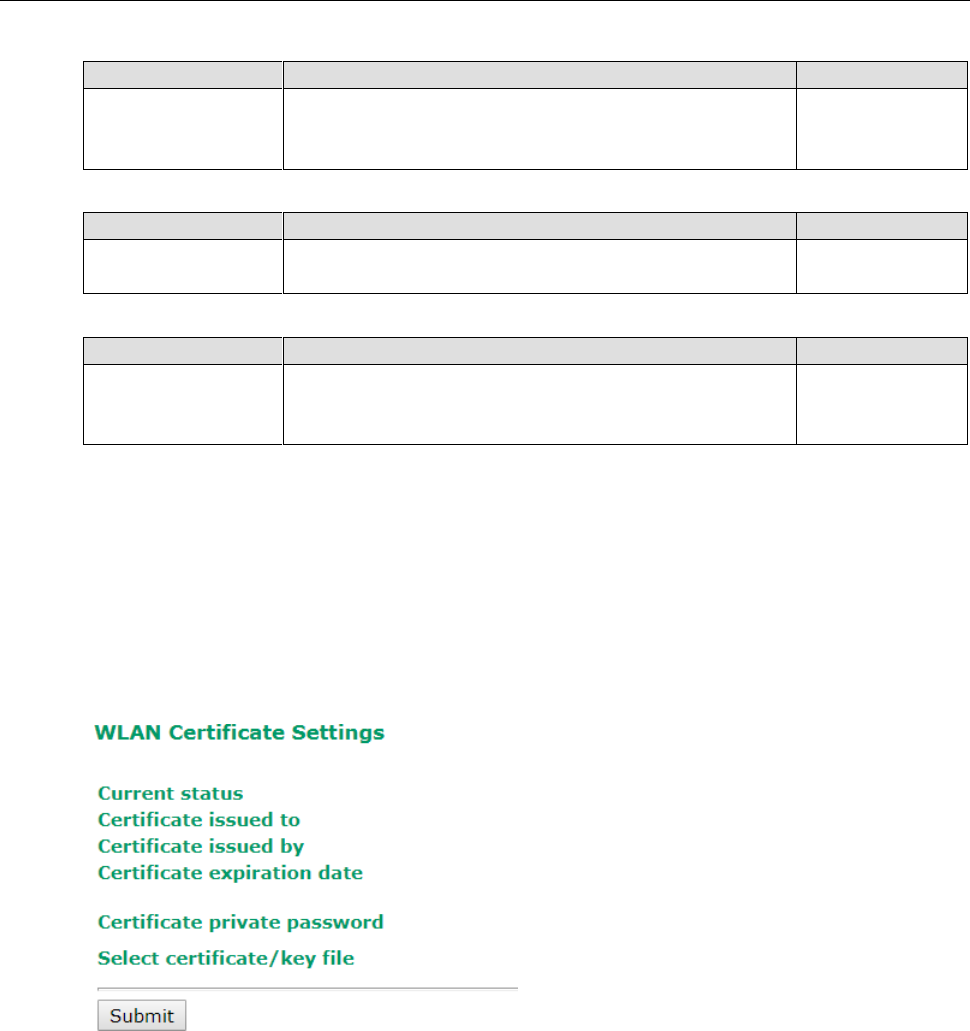
WLAN Certification Settings (For EAP-TLS in Client/Slave
Mode Only)
When EAP-TLS is used, a WLAN Certificate will be required at the client end to support WPA/WPA2-Enterprise.
The AWK-3131A-M12-RCC can support the PKCS #12, also known as Personal Information Exchange Syntax
Standard, certificate formats that define file formats commonly used to store private keys with accompanying
public key certificates, protected with a password-based symmetric key.
Current Status displays information for the current WLAN certificate, which has been imported into the
AWK-3131A-M12-RCC. Nothing will be shown if a certificate is not available.
Certificate issued to: Shows the certificate user
Certificate issued by: Shows the certificate issuer
Certificate expiration date: Indicates when the certificate has expired
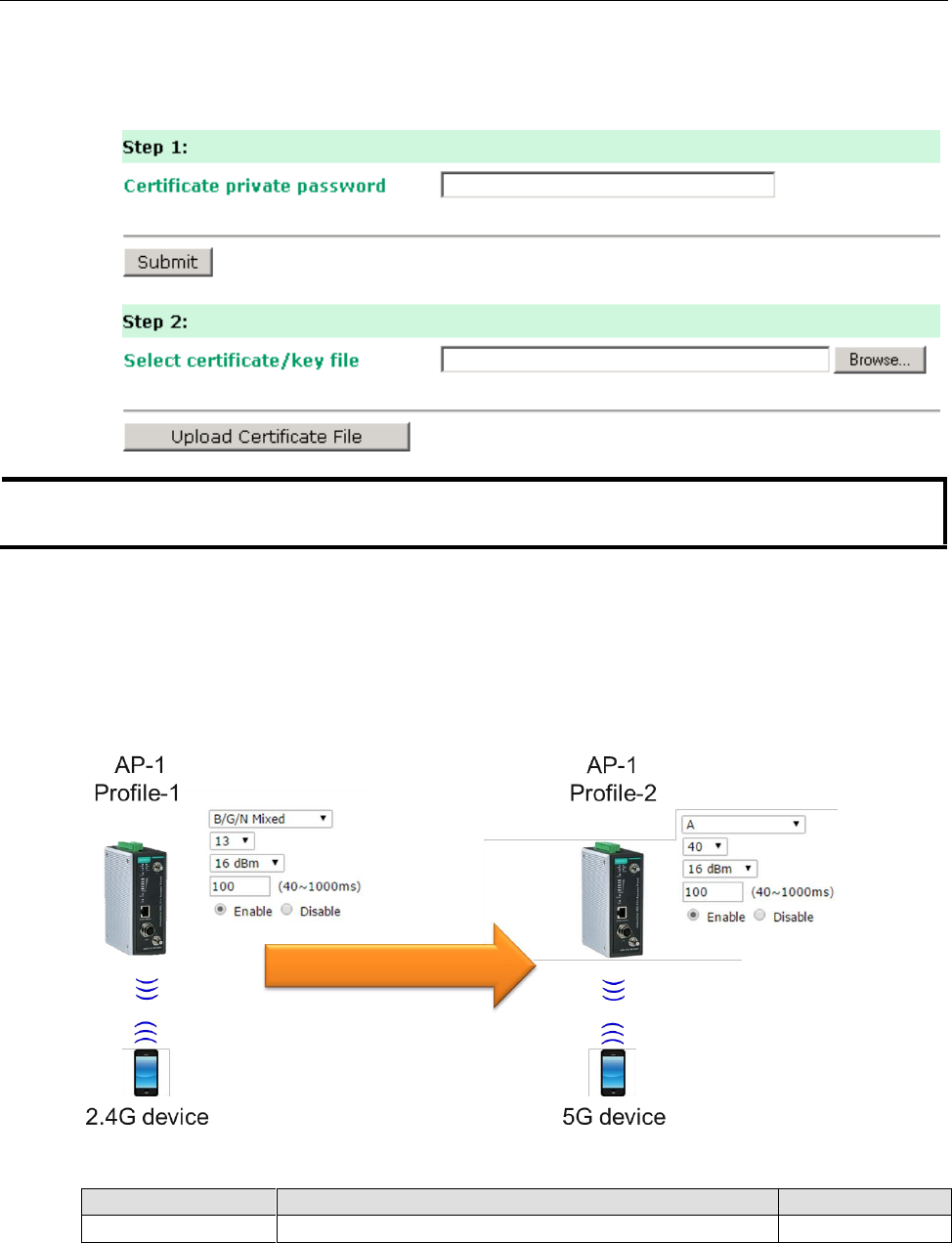
You can import a new WLAN certificate in Import WLAN Certificate by following these steps, in order:
1. Input the corresponding password (or key) in the Certificate private password field and then click
Submit to set the password.
2. The password will be displayed in the Certificate private password field. Click on the Browse button in
Select certificate/key file and select the certificate file.
AWK-3131A-M12-RCC
Web Console Configuration
3-24
3. Click Upload Certificate File to import the certificate file. If the import succeeds, you can see the
information uploaded in Current Certificate. If it fails, you may need to return to step 1 to set the
password correctly and then import the certificate file again.
NOTE
The WLAN certificate will remain after the AWK-3131A-M12-RCC reboots. Even though it is expired, it can still
be seen on the Current Certificate.
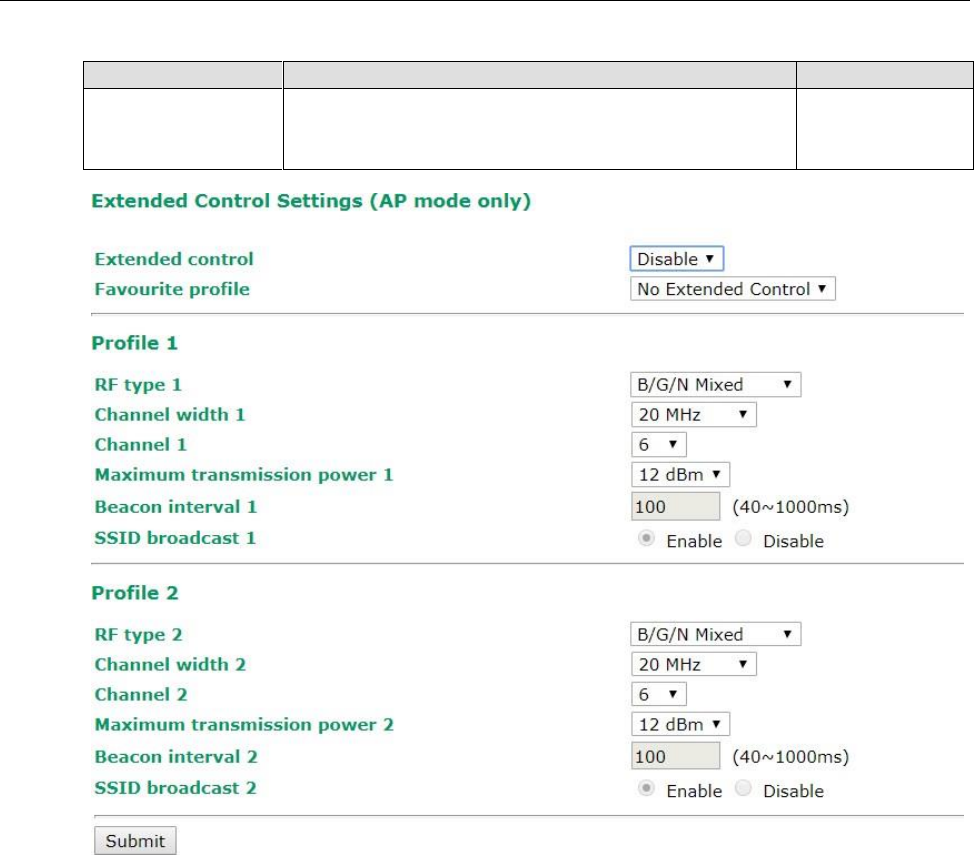
Extended Control Settings (AP Mode Only)
Use this function to quickly switch to your favorite profiles recorded in the device. The function allows you to
easily demo or change the settings in your device.
In the following example, we demonstrate how to quickly change from the 2.4G band to the 5G band.
Extended Control Setting (AP mode only)
Setting
Description
Factory Default
Enable/Disable
Enable the function to quickly switch to your favorite profile.
Disable
AWK-3131A-M12-RCC
Web Console Configuration
3-25
Favorite Profile
Setting
Description
Factory Default
Profile 1/
Profile 2
Choose your favorite profile to quickly switch RF type, channel,
transmission power, beacon interval, and beacon broadcast
status.
No Extended Control
Advanced Settings
Several advanced functions are available to increase the functionality of your AWK-3131A-M12-RCC and
wireless network system. A VLAN is a collection of clients and hosts grouped together as if they were connected
to the broadcast domains in a layer 2 network. The DHCP server helps you deploy wireless clients efficiently.
Packet filters provide security mechanisms, such as firewalls, in different network layers. Moreover, the
AWK-3131A-M12-RCC can support STP/RSTP protocol to increase reliability across the entire network, and
SNMP support can make network management easier.

AWK-3131A-M12-RCC
Web Console Configuration
3-26
Using Virtual LAN
Setting up Virtual LANs (VLANs) on your AWK series increases the efficiency of your network by dividing the
LAN into logical segments, as opposed to physical segments. In general, VLANs are easier to manage.
The Virtual LAN (VLAN) Concept
What is a VLAN?
A virtual LAN, commonly known as a VLAN, is a group of hosts with a common set of requirements that
communicate as if they were attached to the same broadcast domain, regardless of their physical location. A
VLAN has the same attributes as a physical LAN, but it allows for end stations to be grouped together even if
they are not located on the same network switch. Network reconfiguration can be done through software
instead of physically relocating devices.
VLANs now extend as far as the reach of the access point signal. Clients can be segmented into wireless
sub-networks via SSID and VLAN assignment. A Client can access the network by connecting to an AP
configured to support its assigned SSID/VLAN.
Benefits of VLANs
VLANs are used to conveniently, efficiently, and easily manage your network in the following ways:
• Manage adds, moves, and changes from a single point of contact
• Define and monitor groups
• Reduce broadcast and multicast traffic to unnecessary destinations
• Improve network performance and reduce latency
• Increase security
• Secure network restricts members to resources on their own VLAN
• Clients roam without compromising security
VLAN Workgroups and Traffic Management
The AP assigns clients to a VLAN based on a Network Name (SSID). The AP can support up to 9 SSIDs per radio
interface, with a unique VLAN configurable per SSID.
The AP matches packets transmitted or received to a network name with the associated VLAN. Traffic received
by a VLAN is only sent on the wireless interface associated with that same VLAN. This eliminates unnecessary
traffic on the wireless LAN, conserving bandwidth and maximizing throughput.
In addition to enhancing wireless traffic management, the VLAN-capable AP supports easy assignment of
wireless users to workgroups. In a typical scenario, each user VLAN represents a department workgroup; for
example, one VLAN could be used for a marketing department and the other for a human resource department.
In this scenario, the AP would assign every packet it accepted to a VLAN. Each packet would then be identified
as marketing or human resource, depending on which wireless client received it. The AP would insert VLAN
headers or “tags” with identifiers into the packets transmitted on the wired backbone to a network switch.
Finally, the switch would be configured to route
packets from the marketing department to the
appropriate corporate resources such as printers
and servers. Packets from the human resource
department could be restricted to a gateway that
allowed access to only the Internet. A member of
the human resource department could send and
receive e-mail and access the Internet, but would
be prevented from accessing servers or hosts on
the local corporate network.
AWK-3131A-M12-RCC
Web Console Configuration
3-27
Configuring Virtual LAN
VLAN Settings
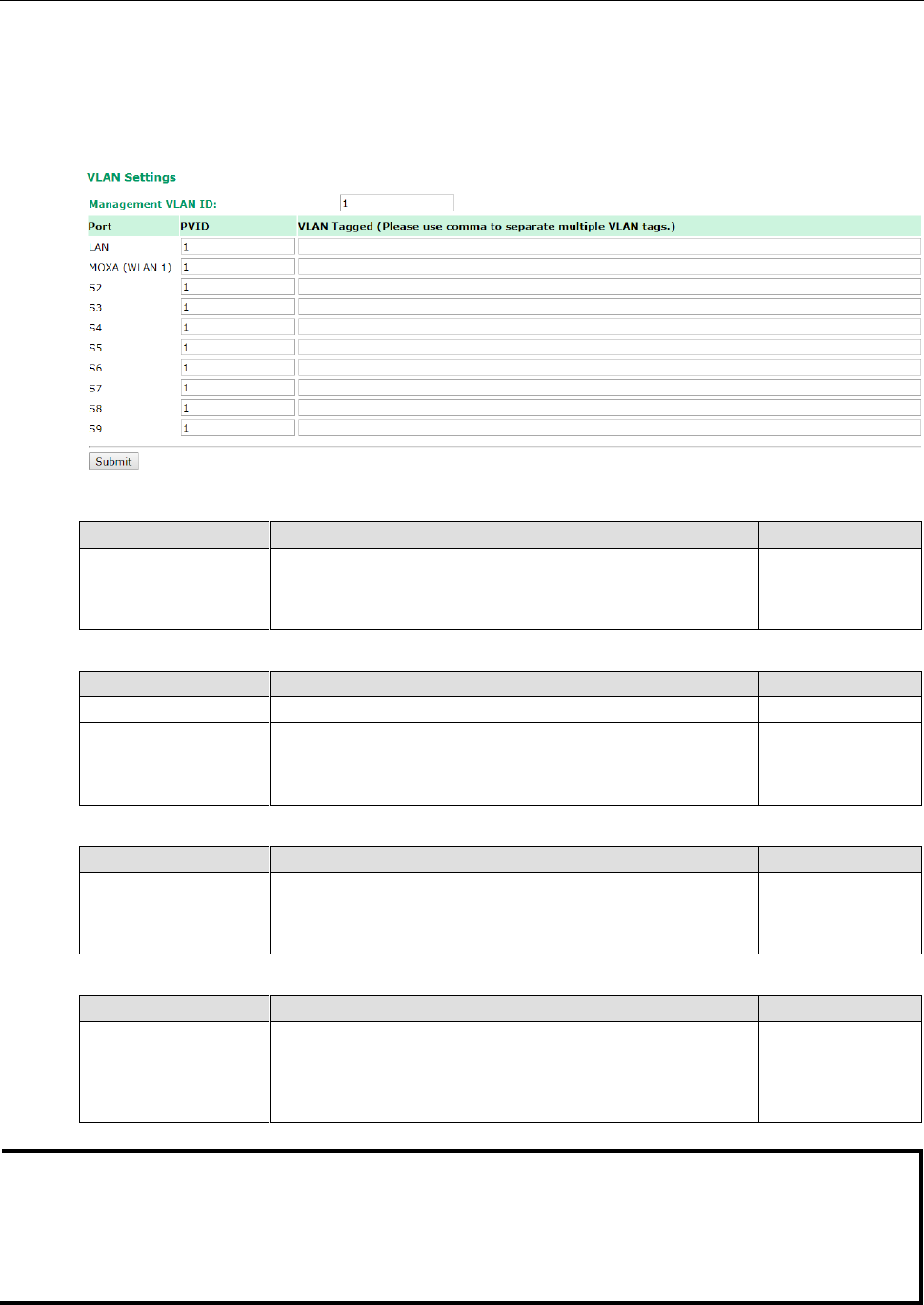
To configure the AWK’s VLAN, use the VLAN Setting page to configure the ports.
Management VLAN ID
Setting
Description
Factory Default
VLAN ID
ranges from
1 to 4094
Set the management VLAN of this AWK.
1
Port
Type
Description
Trunk Port
LAN
This port is the LAN port on the AWK.
Yes
WLAN
This is a wireless port for the specific SSID. This field will refer
to the SSID that you have created. If more SSIDs have been
created, new rows will be added.
Port PVID
Setting
Description
Factory Default
VLAN ID ranging from 1
to 4094
Set the port’s VLAN ID for devices that connect to the port. The
port can be a LAN port or WLAN ports.
1
VLAN Tagged
Setting
Description
Factory Default
A comma-separated list
of VLAN IDs. Each of
the VLAN IDs range
from 1 to 4094.
Specify which VLANs can communicate with this specific VLAN.
(Empty)
NOTE
The VLAN feature can allow wireless clients to manage the AP. If the VLAN Management ID matches a VLAN
ID, then those wireless clients who are members of that VLAN will have AP management access.
CAUTION: Once a VLAN Management ID is configured and is equivalent to one of the VLAN IDs on the AP, all
members of that User VLAN will have management access to the AP. Be careful to restrict VLAN membership
to those with legitimate access to the AP.
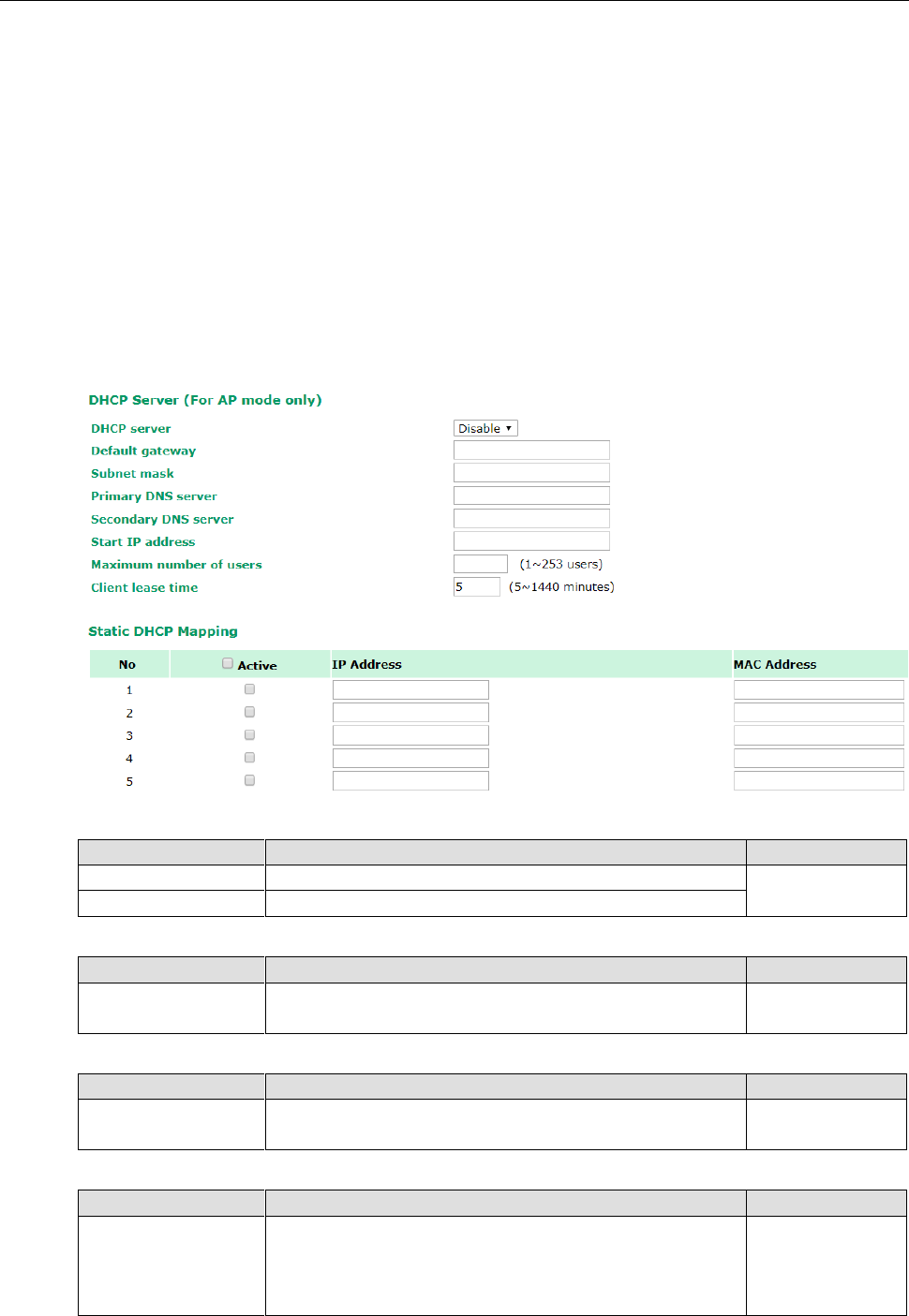
AWK-3131A-M12-RCC
Web Console Configuration
3-28
DHCP Server (For AP Mode Only)
DHCP (Dynamic Host Configuration Protocol) is a networking protocol that allows administrators to assign
temporary IP addresses to network computers by “leasing” an IP address to a user for a limited amount of time,
instead of assigning permanent IP addresses.
The AWK-3131A-M12-RCC can act as a simplified DHCP server and easily assign IP addresses to your DHCP
clients by responding to the DHCP requests from the client ends. The IP-related parameters you set on this
page will also be sent to the client.
You can also assign a static IP address to a specific client by entering its MAC address. The
AWK-3131A-M12-RCC provides a Static DHCP mapping list with up to 16 entities. Be reminded to check the
Active check box for each entity to activate the setting.
You can check the IP assignment status under Status DHCP Client List.
DHCP server
Setting
Description
Factory Default
Enable
Enables AWK-3131A-M12-RCC as a DHCP server
Disable
Disable
Disable DHCP server function
Default gateway
Setting
Description
Factory Default
IP address of a default
gateway
The IP address of the router that connects to an outside
network
None
Subnet mask
Setting
Description
Factory Default
subnet mask
Identifies the type of sub-network (e.g., 255.255.0.0 for a
Class B network, or 255.255.255.0 for a Class C network)
None
Primary/ Secondary DNS server
Setting
Description
Factory Default
IP address of Primary/
Secondary DNS server
The IP address of the DNS Server used by your network. After
entering the DNS Server’s IP address, you can use URL as well.
The Secondary DNS server will be used if the Primary DNS
server fails to connect.
None
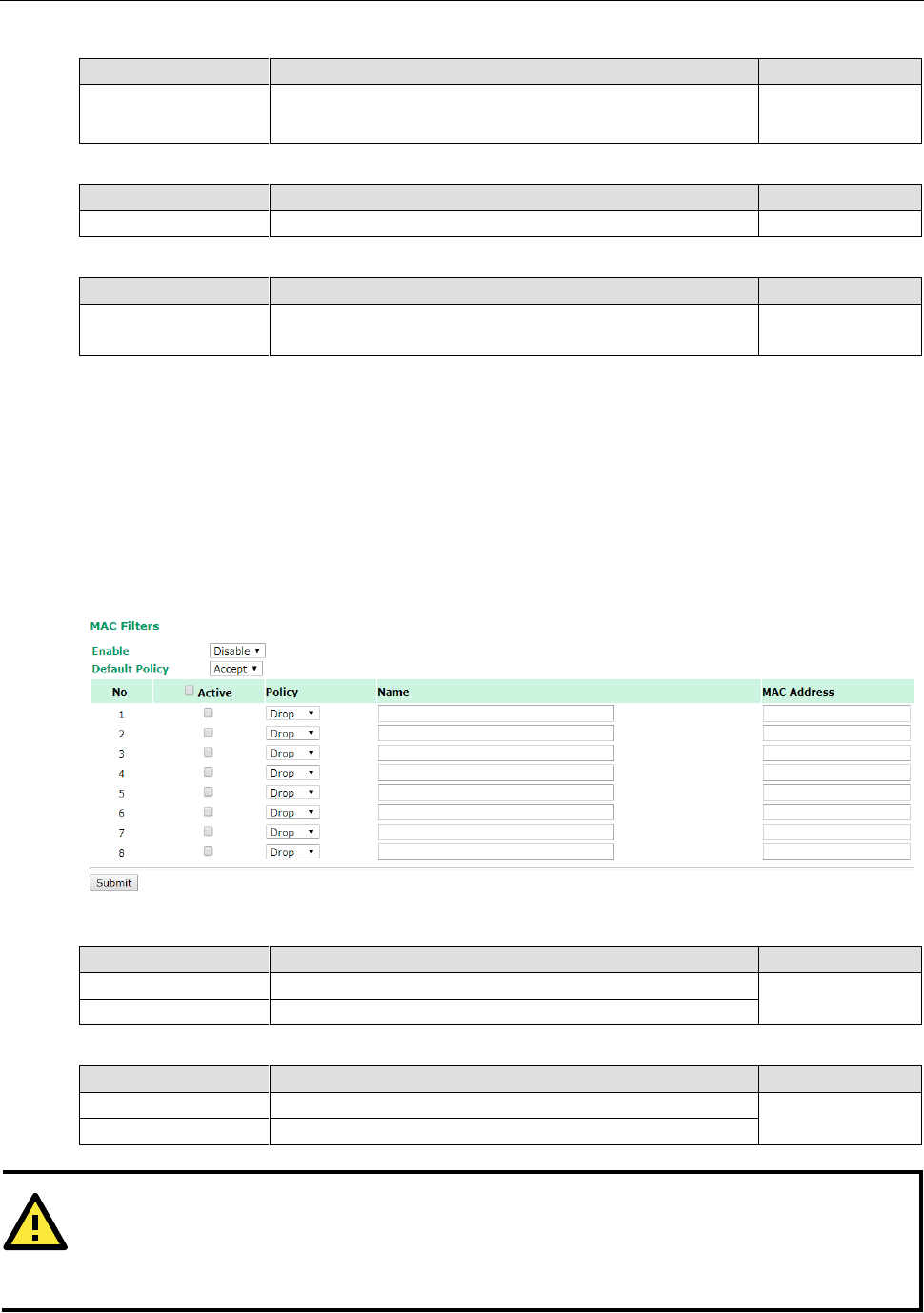
AWK-3131A-M12-RCC
Web Console Configuration
3-29
Start IP address
Setting
Description
Factory Default
IP address
Indicates the IP address which AWK-3131A-M12-RCC can start
assigning
None
Maximum number of users
Setting
Description
Factory Default
1 – 253
Specifies how many IP address can be assigned continuously
None
Client lease time
Setting
Description
Factory Default
5 – 1440 minutes
The lease time for which an IP address is assigned. The IP
address may go expired after the lease time is reached.
5 (minutes)
Packet Filters
The AWK-3131A-M12-RCC includes various filters for IP-based packets going through LAN and WLAN
interfaces. You can set these filters as a firewall to help enhance network security.
MAC Filter
The AWK-3131A-M12-RCC’s MAC filter is a policy-based filter that can allow or filter out IP-based packets with
specified MAC addresses. The AWK-3131A-M12-RCC provides 8 entities for setting MAC addresses in your
filtering policy. Remember to check the Active check box for each entity to activate the setting.
Enable
Setting
Description
Factory Default
Enable
Enables MAC filter
Disable
Disable
Disables MAC filter
Policy
Setting
Description
Factory Default
Accept
Only the packets fitting the entities on list can be allowed.
Accept
Drop
Any packet fitting the entities on list will be denied.
ATTENTION
Be careful when you enable the filter function:
Drop + “no entity on list is activated” = all packets are allowed
Accept + “no entity on list is activated” = all packets are denied

AWK-3131A-M12-RCC
Web Console Configuration
3-30
IP Protocol Filter
The AWK-3131A-M12-RCC’s IP protocol filter is a policy-based filter that can allow or filter out IP-based packets
with specified IP protocol and source/destination IP addresses.
The AWK-3131A-M12-RCC provides 8 entities for setting IP protocol and source/destination IP addresses in
your filtering policy. Four IP protocols are available: All, ICMP, TCP, and UDP. You must specify either the
Source IP or the Destination IP. By combining IP addresses and netmasks, you can specify a single IP address
or a range of IP addresses to accept or drop. For example, “IP address 192.168.1.1 and netmask
255.255.255.255” refers to the sole IP address 192.168.1.1. “IP address 192.168.1.1 and netmask
255.255.255.0” refers to the range of IP addresses from 192.168.1.1 to 192.168.255. Remember to check the
Active check box for each entity to activate the setting.
Enable
Setting
Description
Factory Default
Enable
Enables IP protocol filter
Disable
Disable
Disables IP protocol filter
Policy
Setting
Description
Factory Default
Accept
Only the packets fitting the entities on the list can be allowed
Accept
Drop
Any packet fitting the entities on the list will be denied
TCP/UDP Port Filter
The AWK-3131A-M12-RCC’s TCP/UDP port filter is a policy-based filter that can allow or filter out
TCP/UDP-based packets with a specified source or destination port.
The AWK-3131A-M12-RCC provides 8 entities for setting the range of source/destination ports of a specific
protocol. In addition to selecting TCP or UDP protocol, you can set either the source port, destination port, or
both. The end port can be left empty if only a single port is specified. Of course, the end port cannot be larger
than the start port.
The Application name is a text string that describes the corresponding entity with up to 31 characters.
Remember to check the Active check box for each entity to activate the setting.
Enable
Setting
Description
Factory Default
Enable
Enables TCP/UDP port filter
Disable
Disable
Disables TCP/UDP port filter
ATTENTION
Be careful when you enable the filter function:
Drop + “no entity on list is activated” = all packets are allowed.
Accept + “no entity on list is activated” = all packets are denied.
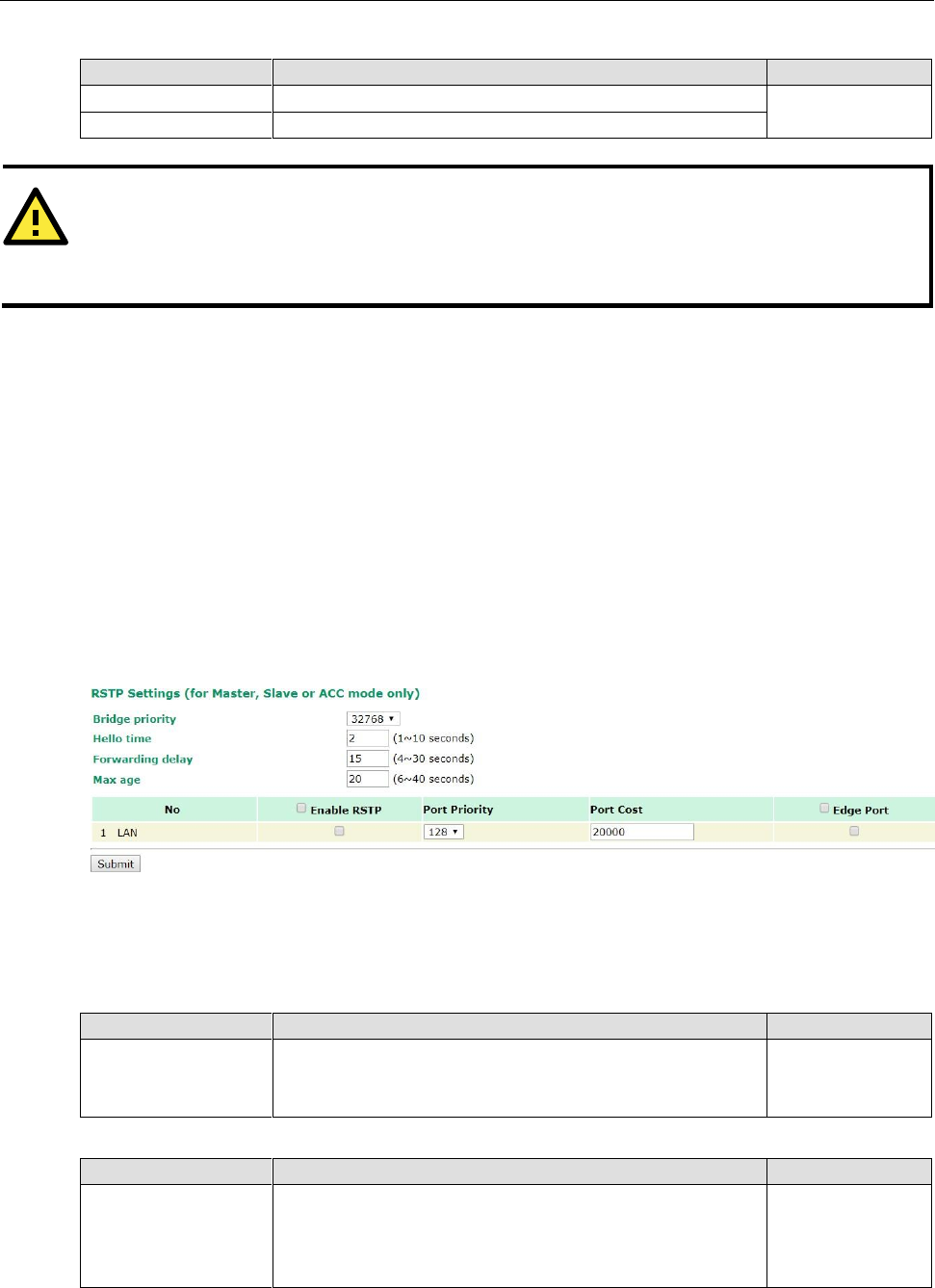
AWK-3131A-M12-RCC
Web Console Configuration
3-31
Policy
Setting
Description
Factory Default
Accept
Only the packets fitting the entities on list can be allowed.
Accept
Drop
Any packet fitting the entities on list will be denied.
RSTP Settings (for AP/Master/ACC mode only)
AWK-3131A-M12-RCC supports IEEE802.1D Spanning Tree Protocol and IEEE802.1w Rapid STP standards. In
addition to eliminating unexpected path looping, STP/RSTP can provide a backup path recovery if a wired/
wireless path fails accidentally. The reliability and availability can increase because this fail-over function.
AWK-3131A-M12-RCC’s STP/RSTP feature is disabled by default. To be completely effective, you must enable
RSTP/STP on every AWK-3131A-M12-RCC connected to your network. If AWK-3131A-M12-RCC plays a Client
role, which is connected to a device (PLC, RTU, etc.) as opposed to network switch equipment, it is not
necessary to enable STP/RSTP. The reason is that it will cause unnecessary negotiation.
AWK-3131A-M12-RCCs support STP/RSTP in AP mode only.
The following figures indicate which Spanning Tree Protocol parameters can be configured. A more detailed
explanation of each parameter is given below the figure.
RSTP status
This field will appear only when selected to operate STP/RSTP. It indicates whether this AWK-3131A-M12-RCC
is the Root of the Spanning Tree (the root is determined automatically) or not.
Bridge priority
Setting
Description
Factory Default
Numerical value
selected
by user
You can increase the bridge priority by selecting a lower
number. A higher bridge priority brings a greater chance of
being established as the root of the Spanning Tree topology.
32768
Hello time
Setting
Description
Factory Default
Numerical value input
by user
(1 – 10 seconds)
The root of the Spanning Tree topology periodically sends out a
“hello” message to other devices on the network to check if the
topology is healthy. Hello time indicates how often the root
sends hello messages.
2 (seconds)
ATTENTION
Be careful when you enable the filter function:
Drop + “no entity on list is activated” = all packets are allowed
Accept + “no entity on list is activated” = all packets are denied

AWK-3131A-M12-RCC
Web Console Configuration
3-32
Forwarding delay
Setting
Description
Factory Default
Numerical value input
by user
(4 – 30 seconds)
The amount of time this device waits before checking to see if it
should change to a different topology.
15 (seconds)
Max. age
Setting
Description
Factory Default
Numerical value input
by user
(6 – 40 seconds)
As a non-root role, if the device has not received a hello
message from the root longer than Max. age, it will reconfigure
itself as a root. Once two or more devices on the network are
recognized as a root, the devices will renegotiate to set up a
new Spanning Tree topology.
20 (seconds)
Enable RSTP
Setting
Description
Factory Default
Enable/ disable
Enables or disables the port as a node on the Spanning Tree
topology.
Disable
(unchecked)
Port priority
Setting
Description
Factory Default
Numerical value
selected by user
Increase this port’s priority as a node on the Spanning Tree
topology by inputting a lower number.
128
Port cost
Setting
Description
Factory Default
Enable/ Disable
Input a higher cost to indicate that this port is less suitable as a
node for the Spanning Tree topology
2000000
Edge port
Setting
Description
Factory Default
Checked/ unchecked
Sets a port, which no BPDU expectedly goes through, as an
edge port
unchecked, except
AP port
NOTE
We recommend you set an edge port for the port, which is connected to a non-STP/RSTP sub-network or an
end device (PLC, RTU, etc.) as opposed to network equipment. This can prevent unnecessary waiting and
negotiation of STP/RSTP protocol, and accelerate system initialization. When an edge port receives BPDUs, it
can still function as an STP/RSTP port and start negotiation.
Setting an edge port is different from disabling STP/RSTP on a port. If you disable STP/RSTP, a port will not
deal with STP/RSTP BPDUs at all.
Port Status
Port Status indicates the current Spanning Tree status of this port. Use Forwarding for normal transmission,
or Blocking to block transmission.

AWK-3131A-M12-RCC
Web Console Configuration
3-33
SNMP Agent
The AWK-3131A-M12-RCC supports SNMP V1/V2c/V3. SNMP V1 and SNMP V2c use a community string match
for authentication, which means that SNMP servers access all objects with read-only or read/write permissions
using the community string public/private (default value). SNMP V3, which requires you to select an
authentication level of MD5 or SHA, is the most secure protocol. You can also enable data encryption to
enhance data security.
The AWK-3131A-M12-RCC’s MIB can be found in the software CD and supports reading the attributes via SNMP.
(Only get method is supported.)
SNMP security modes and security levels supported by the AWK-3131A-M12-RCC are shown in the following
table. Select the security mode and level that will be used to communicate between the SNMP agent and
manager.
Protocol
Version
Setting on
UI web page
Authentication
Type
Data
Encryption
Method
SNMP
V1, V2c
V1, V2c
Read
Community
Community string
No
Use a community string match for
authentication
V1, V2c
Write/Read
Community
Community string
No
Use a community string match for
authentication
SNMP V3
No-Auth
No
No
Use account with admin or user to access
objects
MD5 or SHA
Authentication
based on MD5 or
SHA
No
Provides authentication based on HMAC-MD5,
or HMAC-SHA algorithms. 8-character
passwords are the minimum requirement for
authentication.
MD5 or SHA
Authentication
based on MD5 or
SHA
Data
encryption
key
Provides authentication based on HMAC-MD5
or HMAC-SHA algorithms, and data encryption
key. 8-character passwords and a data
encryption key are the minimum requirements
for authentication and encryption.
The following parameters can be configured on the SNMP Agent page. A more detailed explanation of each
parameter is given below the following figure.
AWK-3131A-M12-RCC
Web Console Configuration
3-34
Enable
Setting
Description
Factory Default
Enable
Enables SNMP Agent
Disable
Disable
Disables SNMP Agent
Remote Management
Setting
Description
Factory Default
Enable
Allow remote management via SNMP agent
Disable
Disable
Disallow remote management via SNMP agent
Read community (for V1, V2c)
Setting
Description
Factory Default
V1, V2c Read
Community
Use a community string match with a maximum of 31
characters for authentication. This means that the SNMP agent
can access all objects with read-only permissions using this
community string.
public
Write community (for V1, V2c)
Setting
Description
Factory Default
V1, V2c Read /Write
Community
Use a community string match with a maximum of 31
characters for authentication. This means that the SNMP agent
can accesses all objects with read/write permissions using this
community string.
private
SNMP agent version
Setting
Description
Factory Default
V1, V2c, V3, or
V1, V2c, or V3 only
Select the SNMP protocol version used to manage the switch.
V1, V2c
Admin auth type (for V1, V2c, V3, and V3 only)
Setting
Description
Factory Default
No Auth
Use admin account to access objects. No authentication
No Auth
MD5
Provide authentication based on the HMAC-MD5 algorithms.
8-character passwords are the minimum requirement for
authentication.
SHA
Provides authentication based on
HMAC-SHA algorithms. 8-character passwords are the
minimum requirement for authentication.
Admin private key (for V1, V2c, V3, and V3 only)
Setting
Description
Factory Default
Disable
No data encryption
Disable
DES
DES-based data encryption
AES
AES-based data encryption
Private key
A data encryption key is the minimum requirement for data encryption (maximum of 63 characters)
Private MIB Information Device Object ID
Also known as OID. This is the AWK-3131A-M12-RCC’s enterprise value. It is fixed.
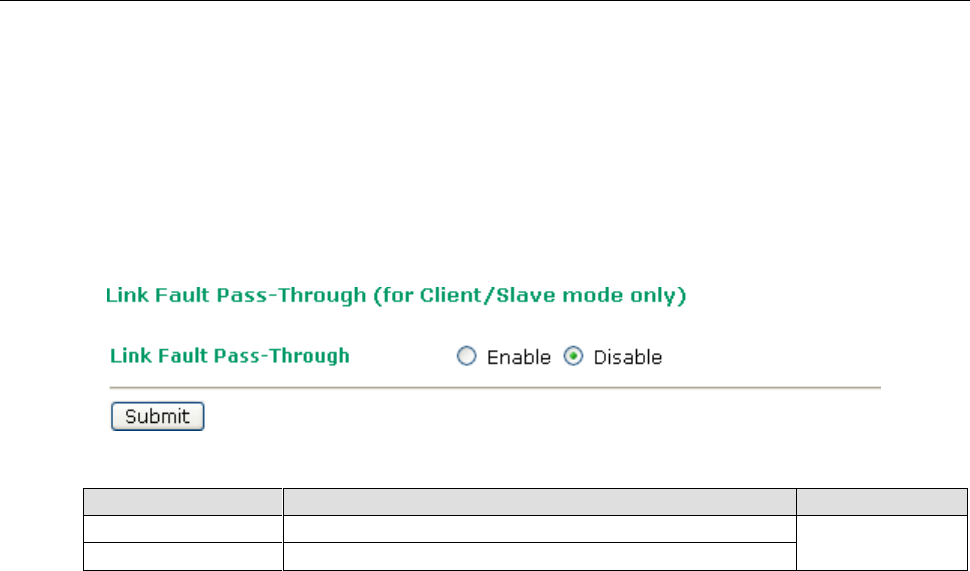
AWK-3131A-M12-RCC
Web Console Configuration
3-35
Link Fault Pass-Through (for Client/Slave mode only)
This function means if Ethernet port is link down, wireless connection will be forced to disconnect. Once
Ethernet link is recovered, AWK will try to connect to AP.
If wireless is disconnected, AWK restarts auto-negotiation on Ethernet port but always stays in the link failure
state. Once the wireless connection is recovered, AWK will try to recover the Ethernet link.
System log will indicate the link fault pass through events in addition to the original link up/down events.
Link Fault Pass-Through
Setting
Description
Factory Default
Enable
Enables Link Fault Pass-Through
Disable
Disable
Disables Link Fault Pass-Through
Auto Warning Settings
Since industrial-grade devices are often located at the endpoints of a system, these devices will not always
know what is happening elsewhere on the network. This means that these devices, including wireless APs or
clients, must provide system maintainers with real-time alarm messages. Even when system administrators
are out of the control room for an extended period, they can still be informed of the status of devices almost
instantaneously when exceptions occur.
In addition to logging these events, the AWK-3131A-M12-RCC supports different approaches to warn
engineers automatically, such as SNMP trap, e-mail, and relay output. It also supports two digital inputs to
integrate sensors into your system to automate alarms by email and relay output.
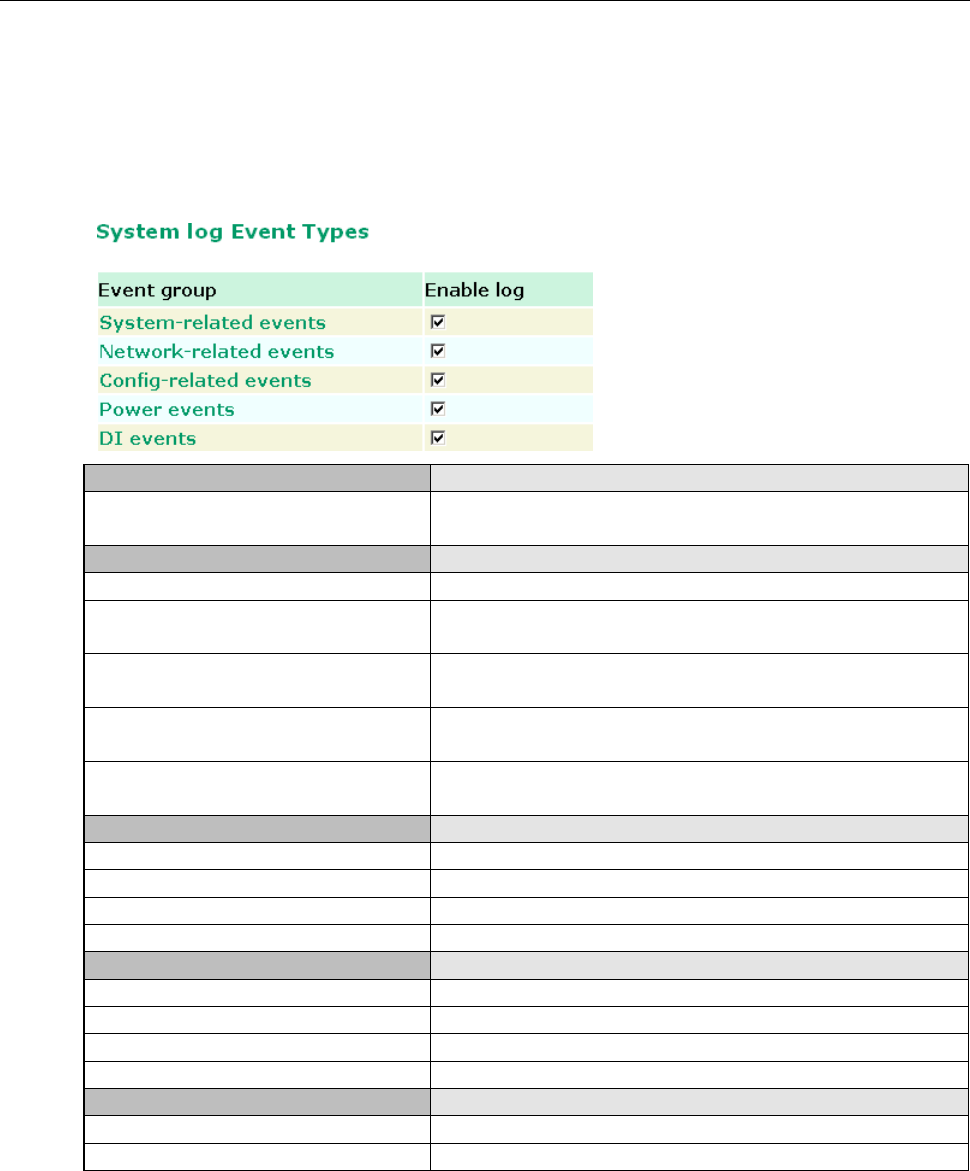
AWK-3131A-M12-RCC
Web Console Configuration
3-36
System Log
System Log Event Types
Detail information for grouped events is shown in the following table. You can check the box for Enable log to
enable the grouped events. All default values are enabled (checked). The log for system events can be seen in
Status System Log.
System-related events
Event is triggered when…
System restart (warm start)
The AWK-3131A-M12-RCC is rebooted, such as when its settings
are changed (IP address, subnet mask, etc.).
Network-related events
Event is triggered when…
LAN link on
The LAN port is connected to a device or network.
LAN link off
The port is disconnected (e.g., the cable is pulled out, or the
opposing device shuts down).
Client joined/ left
(for AP/Master mode)
A wireless client is associated or disassociated.
WLAN connected to AP
(for Client/Slave mode)
The AWK-3131A-M12-RCC is associated with an AP.
WLAN disconnected
(for Client/Slave mode)
The AWK-3131A-M12-RCC is disassociated from an AP.
Config-related events
Event is triggered when…
Configuration Changed
A configuration item has been changed.
Configuration file import via Web Console
The configuration file is imported to the AWK-3131A-M12-RCC.
Console authentication failure
An incorrect password is entered.
Firmware upgraded
The AWK-3131A-M12-RCC’s firmware is updated.
Power events
Event is triggered when…
Power 1/2 transition (On -> Off)
The AWK-3131A-M12-RCC is powered down in PWR1/2.
PoE transition (On -> Off)
The AWK-3131A-M12-RCC is powered down in PoE.
Power 1/2 transition (Off -> On)
The AWK-3131A-M12-RCC is powered via PWR1/2.
PoE transition (Off -> On)
The AWK-3131A-M12-RCC is powered via PoE.
DI events
Event is triggered when…
DI0/1 transition (On -> Off)
Digital Input 0/1 is triggered by on to off transition
DI0/1 transition (Off -> On)
Digital Input 0/1 is triggered by off to on transition
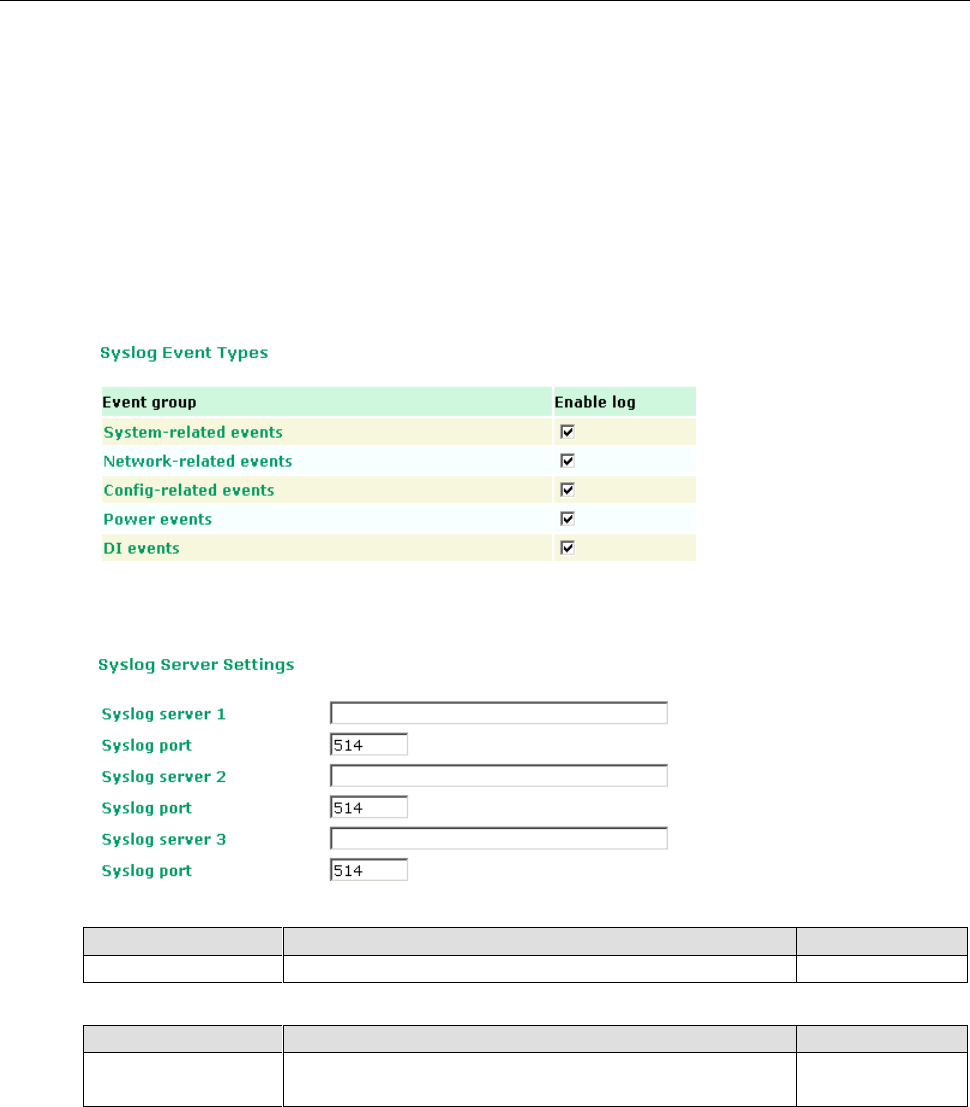
AWK-3131A-M12-RCC
Web Console Configuration
3-37
Syslog
This function provide event logs for the Syslog server. Up to three configurable Syslog servers and Syslog
server UDP port numbers are supported. When an event occurs, the event will be sent as a Syslog UDP packet
to the specified Syslog server.
Syslog Event Types
Detail information for the grouped events is shown in the following table. By default, the logs for all event
groups are enabled (checked). If you want to enable logging for a specific event group, check the
corresponding box under Enable log. Additional details on the event groups are available in the System log
Event Types table above.
Syslog Server Settings
You can configure the parameters for your Syslog servers in this page.
Syslog server 1/ 2/ 3
Setting
Description
Factory Default
IP address
Enter the IP address of the 1st/ 2nd/ 3rd Syslog Server
None
Syslog port
Setting
Description
Factory Default
Port destination
(1 to 65535)
Enter the UDP port of the corresponding Syslog server
514
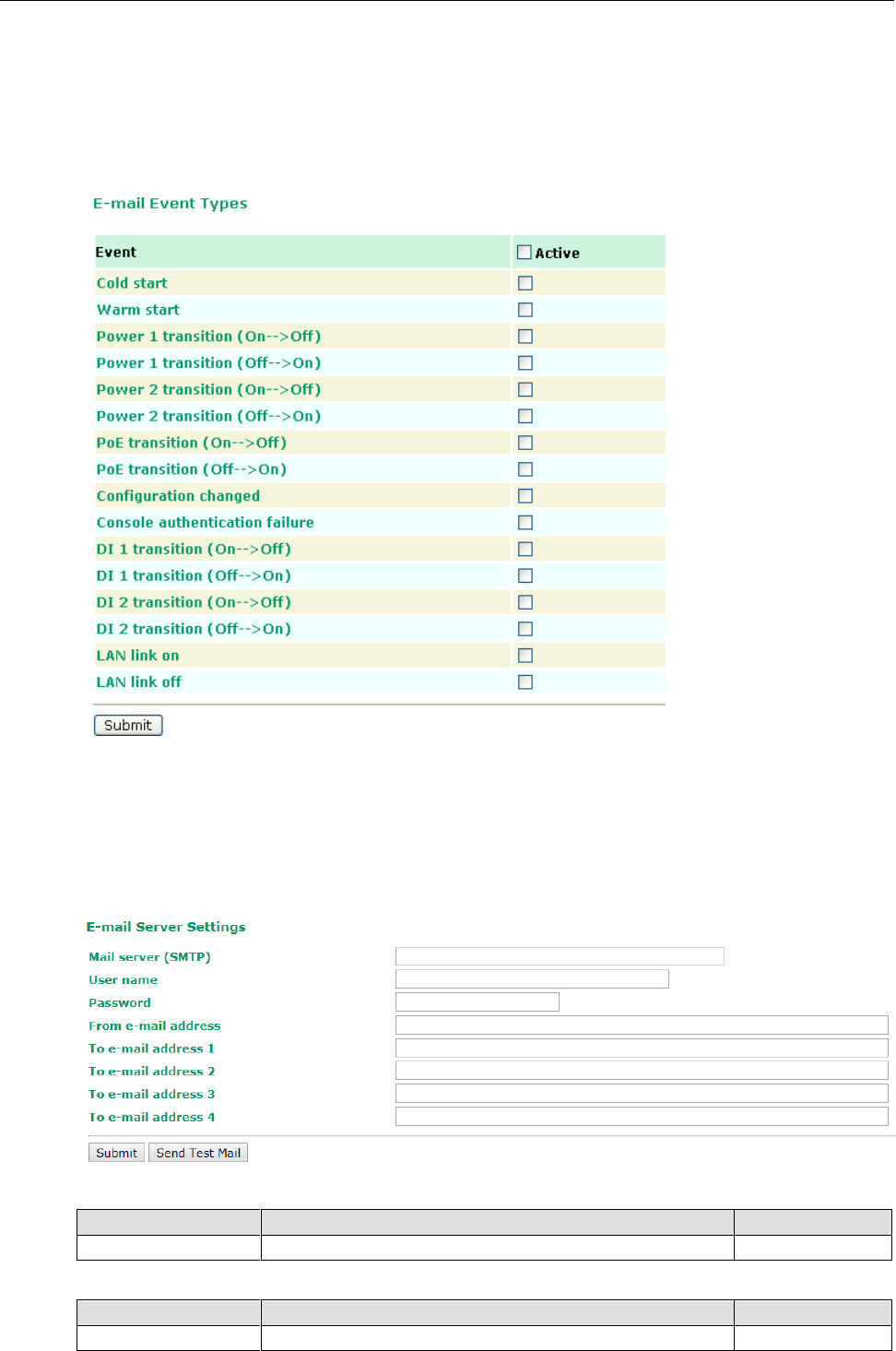
AWK-3131A-M12-RCC
Web Console Configuration
3-38
E-mail
E-mail Event Types
Check the box for Active to enable the event items. All default values are deactivated (unchecked). Details for
each event item can be found on the “System log Event Types” table on page 3-31.
E-mail Server Settings
You can set up to 4 e-mail addresses to receive alarm emails from the AWK-3131A-M12-RCC. The following
parameters can be configured on the E-mail Server Settings page. In addition, a Send Test Mail button can
be used to test whether the Mail server and e-mail addresses work well. More detailed explanations about these
parameters are given after the following figure.
Mail server (SMTP)
Setting
Description
Factory Default
IP address
The IP Address of your email server.
None
User name & Password
Setting
Description
Factory Default
User name and password used in the SMTP server
None
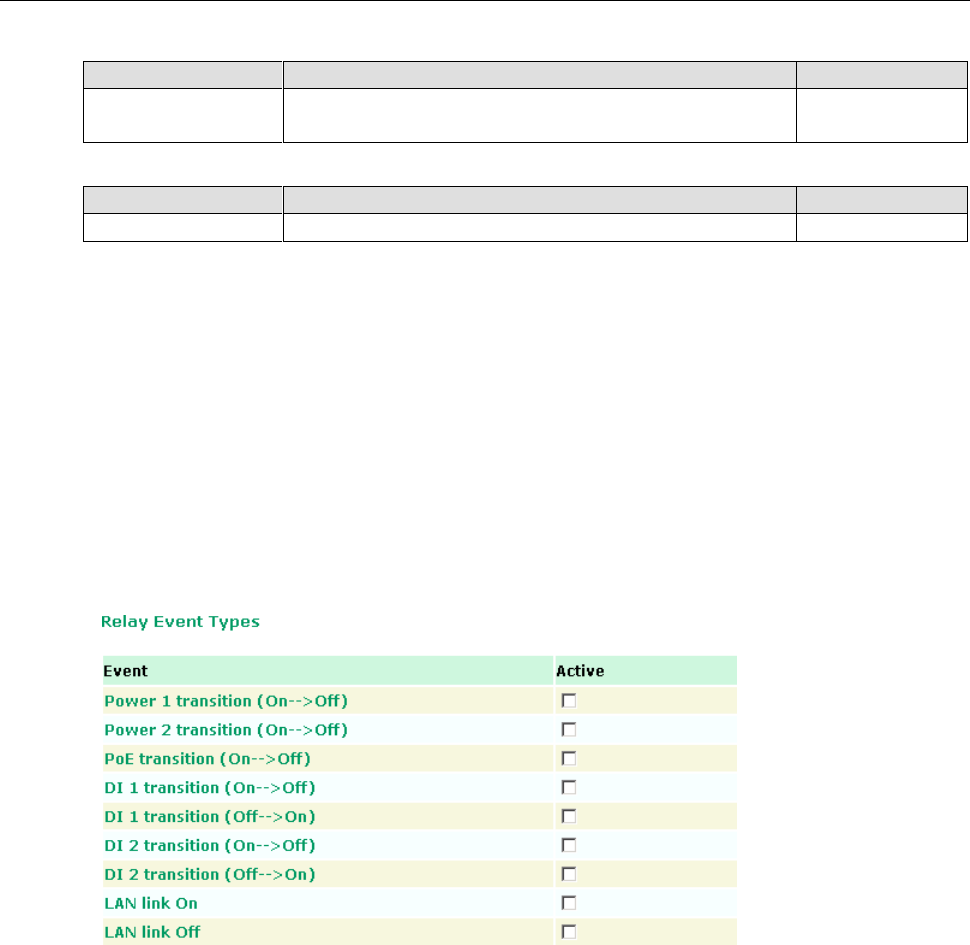
AWK-3131A-M12-RCC
Web Console Configuration
3-39
From e-mail address
Setting
Description
Factory Default
Max. 63 characters
Enter the administrator’s e-mail address which will be shown in
the “From” field of a warning e-mail.
None
To E-mail address 1/ 2/ 3/ 4
Setting
Description
Factory Default
Max. 63 characters
Enter the receivers’ e-mail addresses.
None
Relay
The AWK-3131A-M12-RCC has one relay output, which consists of 2 terminal block contacts on the
AWK-3131A-M12-RCC’s top panel. These relay contacts are used to indicate user-configured events and
system failure.
The two wires attached to the relay contacts form an open circuit when a user-configured event is triggered. If
a user-configured event does not occur, the relay circuit will remain closed. For safety reasons, the relay circuit
is kept open when the AWK-3131A-M12-RCC is not powered.
Relay Event Types
You can check the box for Active to enable the event items. All default values are deactivated (unchecked).
Details for each event item can be found in the “System log Event Types” table on page 3-31.
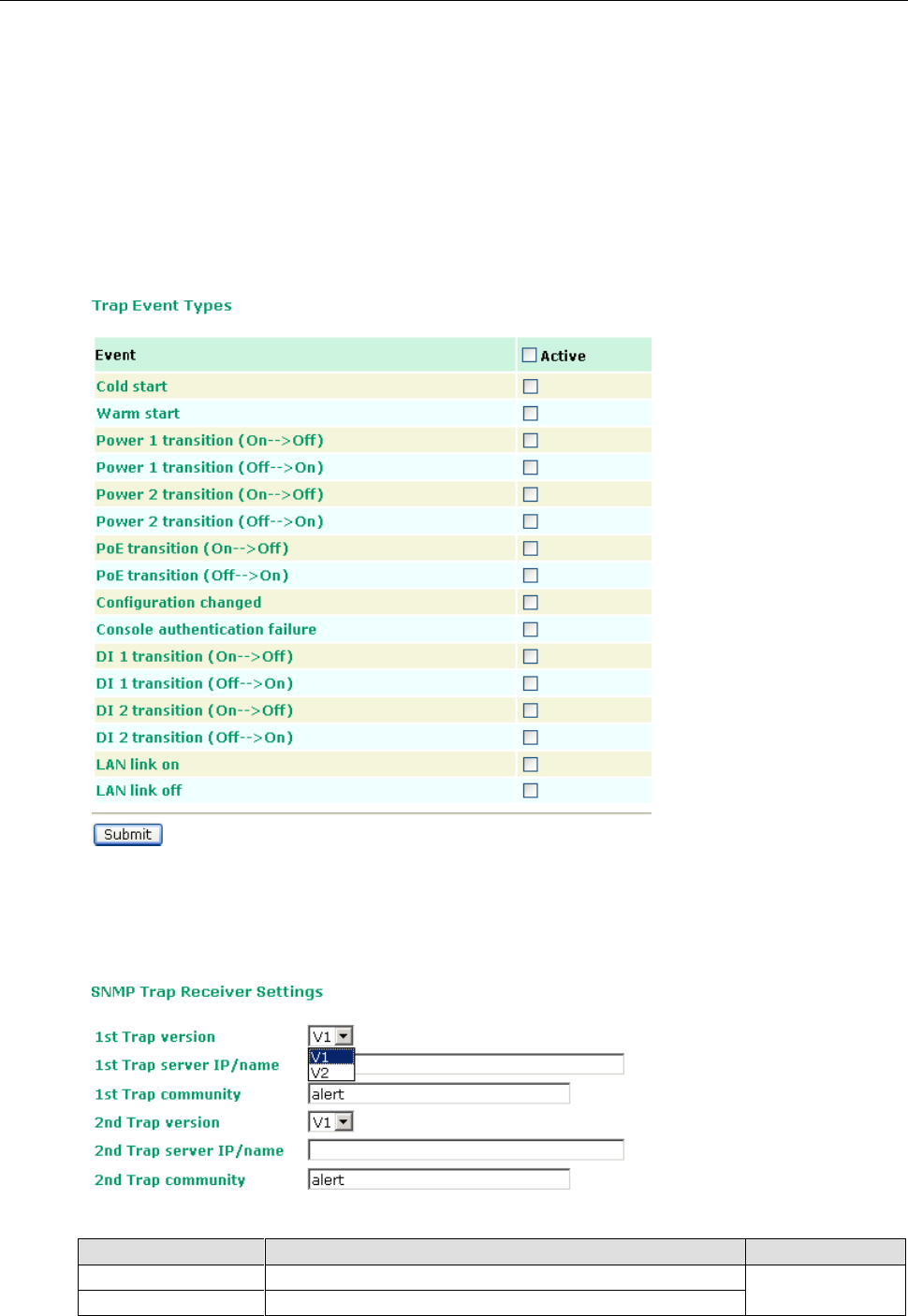
AWK-3131A-M12-RCC
Web Console Configuration
3-40
Trap
Traps can be used to signal abnormal conditions (notifications) to a management station. This trap-driven
notification can make your network more efficient.
Because a management station usually takes care of a large number of devices that have a large number of
objects, it will be overloading for the management station to poll or send requests to query every object on
every device. It would be better if the managed device agent could notify the management station by sending
a message known as a trap for the event.
Trap Event Types
SNMP Trap Receiver Settings
SNMP traps are defined in SMIv1 MIBs (SNMPv1) and SMIv2 MIBs (SNMPv2c). The two styles are basically
equivalent, and it is possible to convert between the two. You can set the parameters for SNMP trap receivers
through the web page.
1st / 2nd Trap version
Setting
Description
Factory Default
V1
SNMP trap defined in SNMPv1
V1
V2
SNMP trap defined in SNMPv2
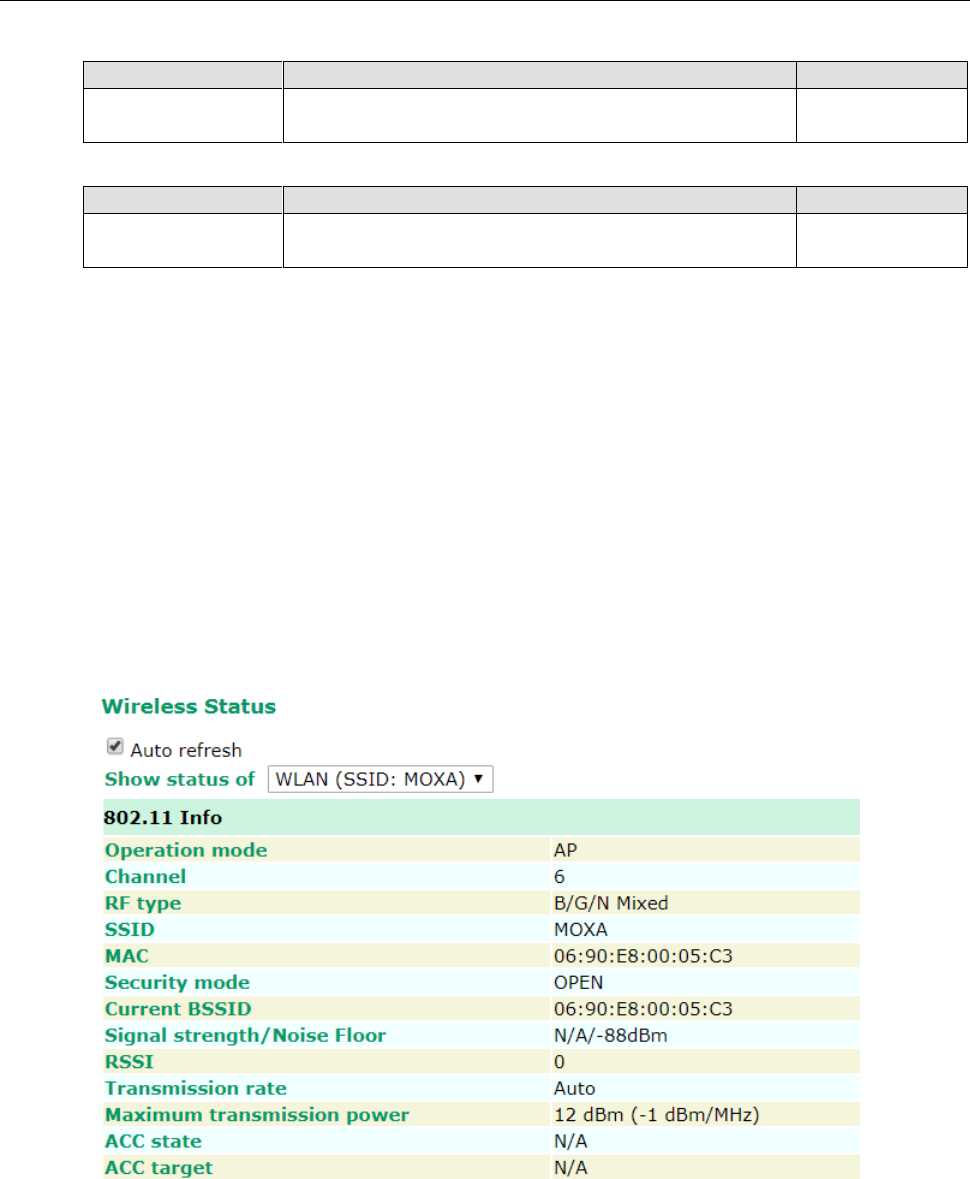
AWK-3131A-M12-RCC
Web Console Configuration
3-41
1st / 2nd Trap server IP/name
Setting
Description
Factory Default
IP address or host
name
Enter the IP address or name of the trap server used by your
network.
None
1st / 2nd Trap community
Setting
Description
Factory Default
Max. of 31 characters
Use a community string match with a maximum of 31
characters for authentication.
alert
Status
Wireless Status
The status for 802.11 info parameters, such as Operation mode and Channel, are shown on the Wireless
Status page. The status will refresh every 5 seconds if the Auto refresh box is checked.
Certain values for 802.11 info may not show up due to different operation modes. As a result, Current BSSID
and Signal strength are not available in AP mode.
It is helpful to use the continuously updated information on this page, such as Signal strength, to monitor the
signal strength of the AWK-3131A-M12-RCC in Client, Slave, or ACC mode.
The transmission power indicated is the current transmission power being updated periodically.
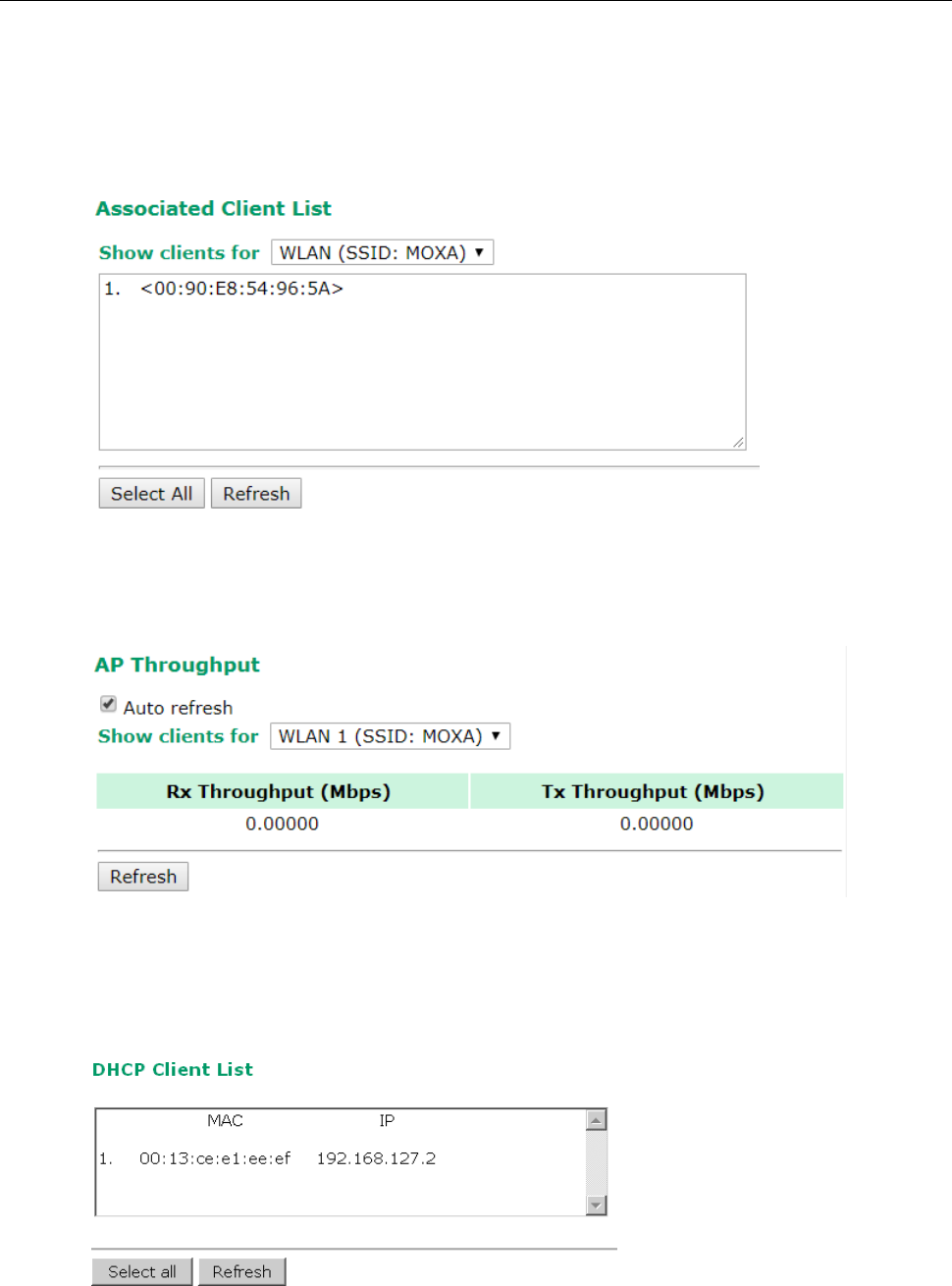
AWK-3131A-M12-RCC
Web Console Configuration
3-42
Associated Client List (For AP/Master/ACC Mode Only)
Associated Client List shows all the clients that are currently associated to a particular AWK-3131A-M12-RCC.
You can click Select all to select all the content in the list for further editing. You can click Refresh to refresh
the list.
AP Throughput
Per radio interface, the AP throughput page shows the overall throughput continuously.
DHCP Client List (For AP Mode Only)
The DHCP Client List shows all the clients that require and have successfully received IP assignments. You can
click the Refresh button to refresh the list.
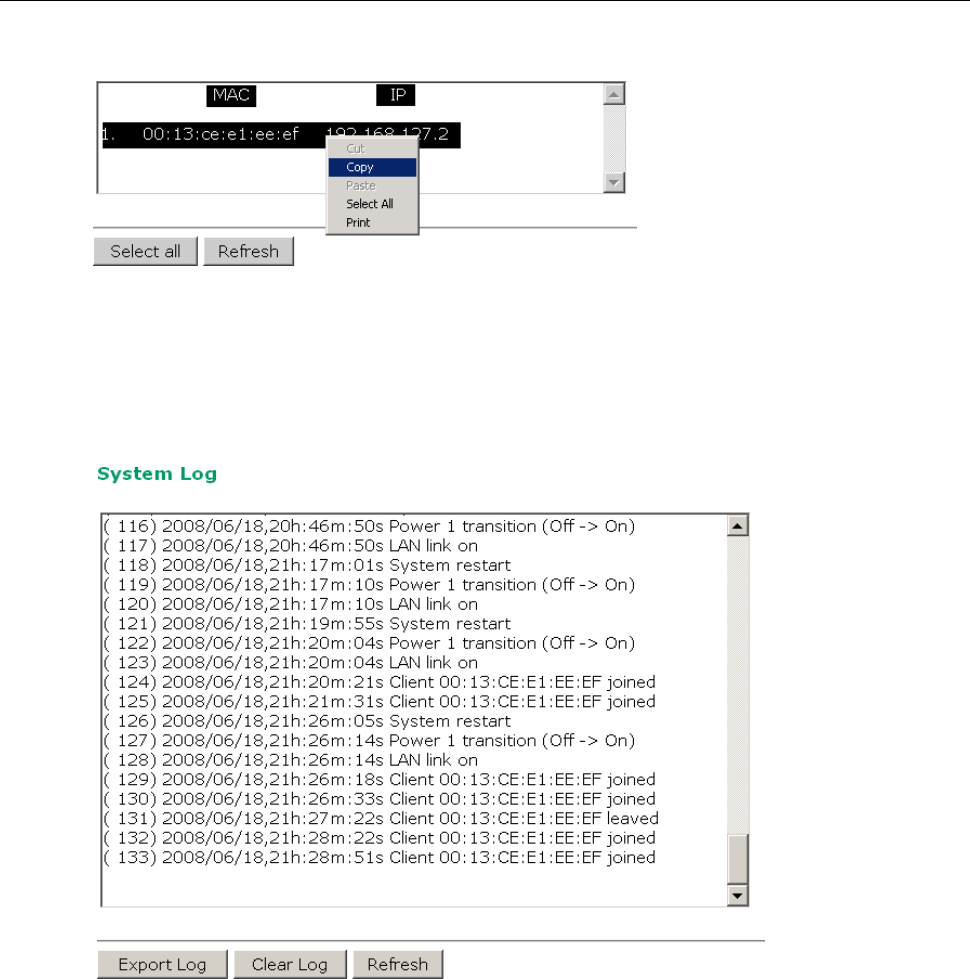
AWK-3131A-M12-RCC
Web Console Configuration
3-43
You can press Select all button to select all content in the list for further editing.
System Log
Triggered events are recorded in System Log. You can export the log contents to an available viewer by clicking
Export Log. You can use the Clear Log button to clear the log contents and the Refresh button to refresh the
log.
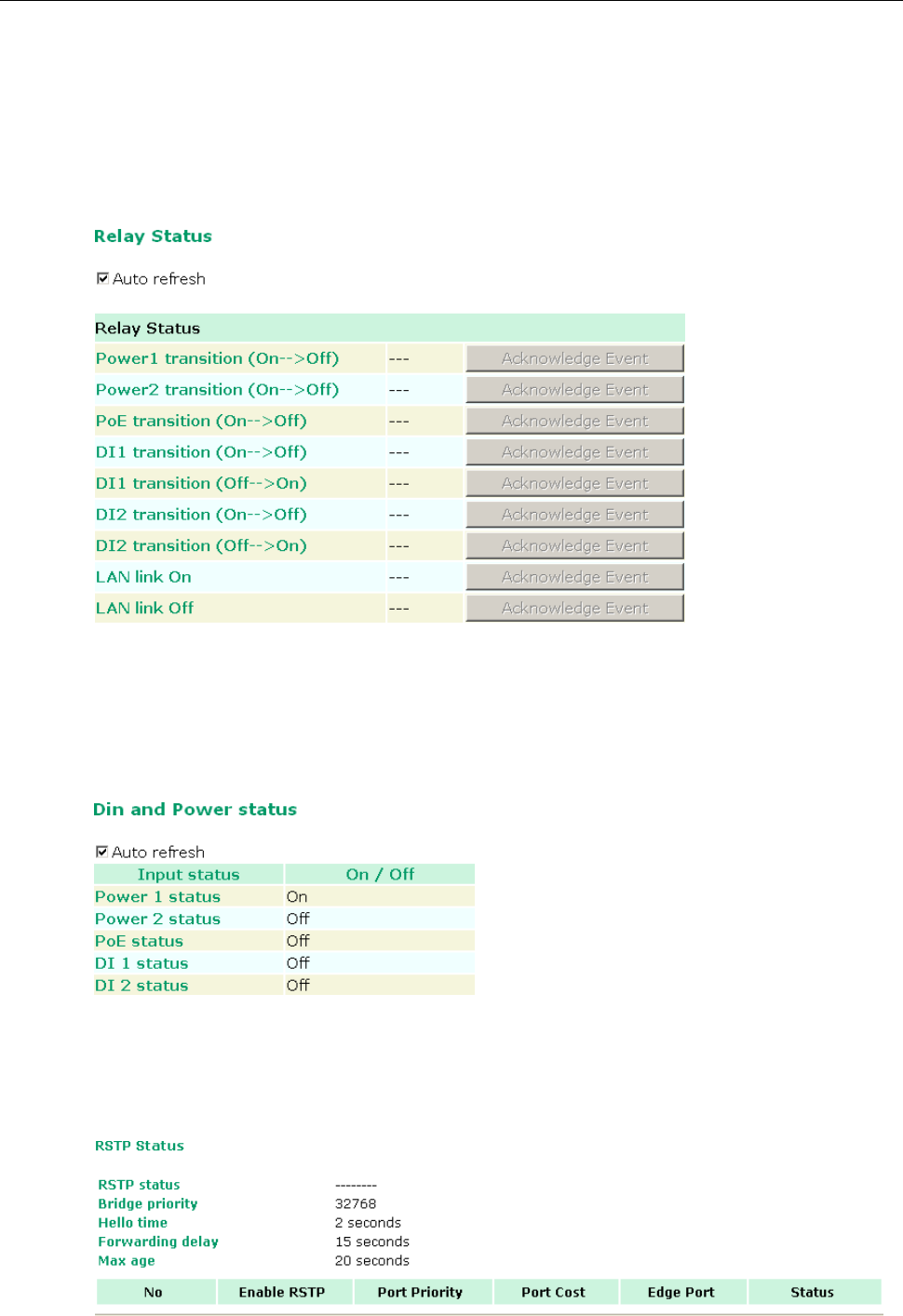
AWK-3131A-M12-RCC
Web Console Configuration
3-44
Relay Status
The status of user-configurable events can be found under Relay Status. The status will refresh every 5
seconds if the Auto refresh box is checked.
If an event is triggered, it will be noted on this list. System administrators can click Acknowledge Event when
he has acknowledged the event and addressed it.
DI and Power Status
The status of power inputs and digital inputs is shown on this web page. The status will refresh every 5 seconds
if the Auto refresh box is checked.
RSTP Status
The following figures indicate the status which Spanning Tree Protocol parameters have been configured.
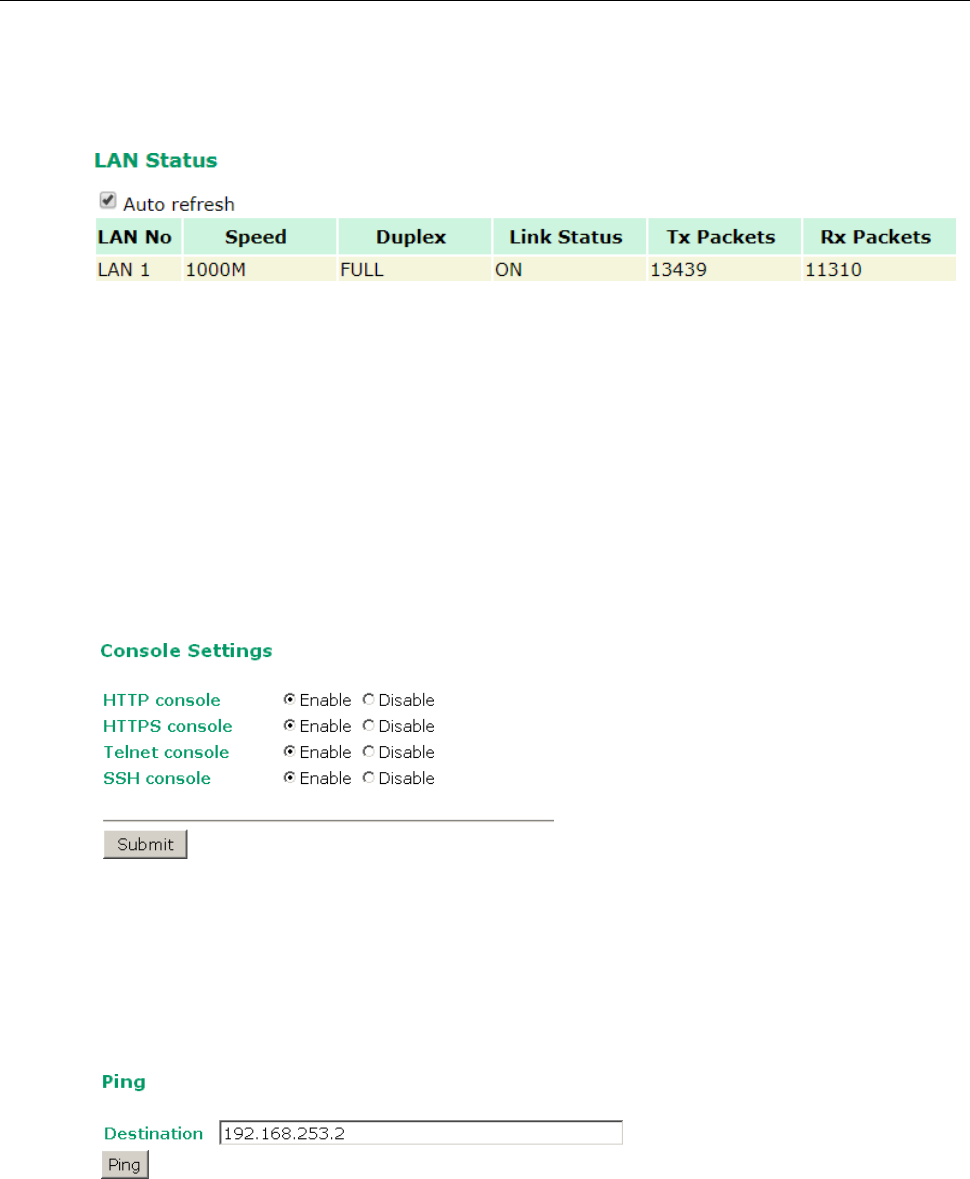
AWK-3131A-M12-RCC
Web Console Configuration
3-45
LAN Status
This page shows the LAN information, which includes speed, duplex, link status, and packet status.
Maintenance
Maintenance functions provide the administrator with tools to manage the AWK-3131A-M12-RCC and
wired/wireless networks.
Console Settings
You can enable or disable access permission for the following consoles: HTTP, HTTPS, Telnet and SSH
connections. For more security, we recommend you only allow access to the two secured consoles, HTTPS and
SSH.
Ping
Ping helps to diagnose the integrity of wired or wireless networks. By inputting a node’s IP address in the
Destination field, you can use the ping command to make sure it exists and whether or not the access path
is available.
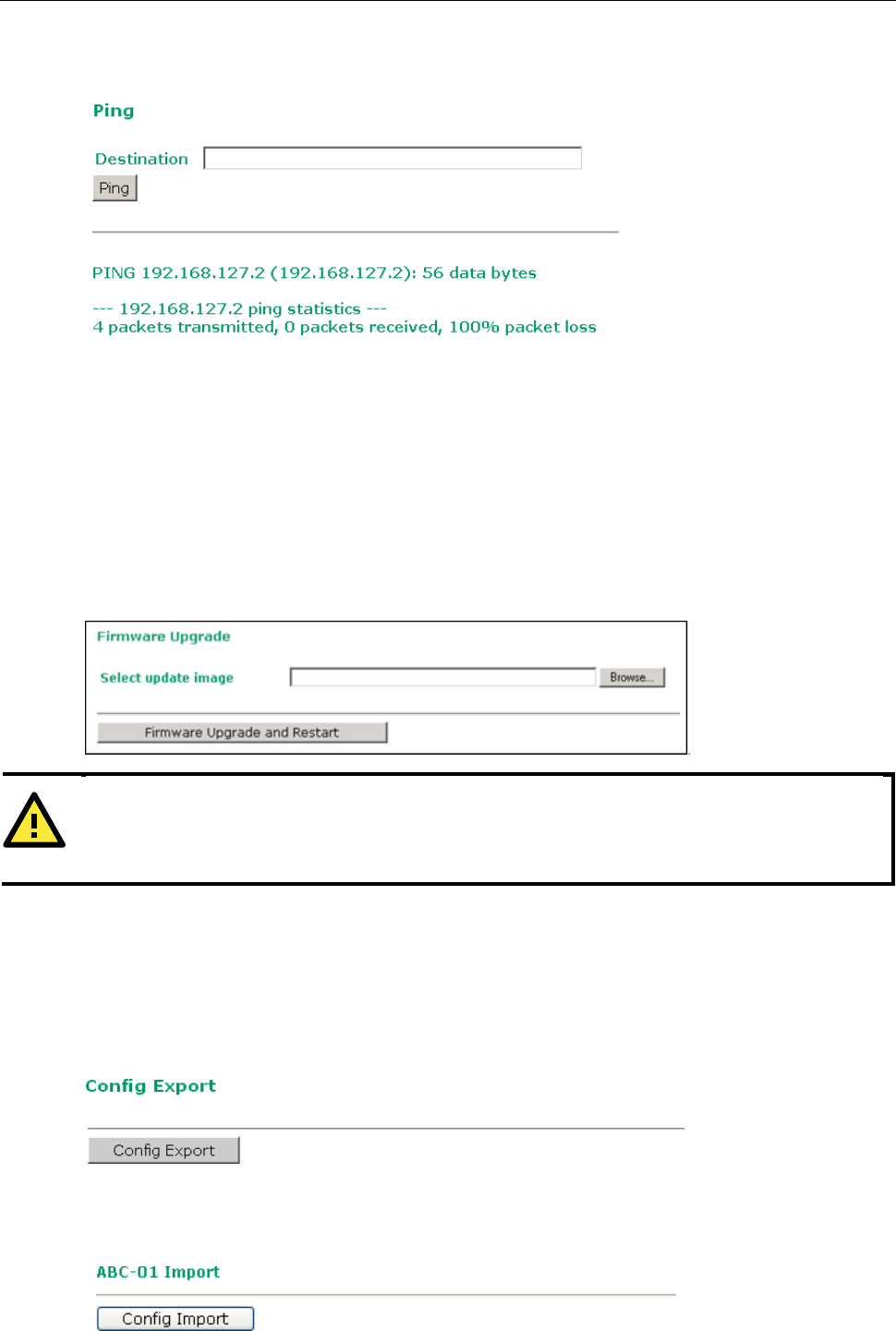
AWK-3131A-M12-RCC
Web Console Configuration
3-46
If the node and access path are available, you will see that all packets were successfully transmitted with no
loss. Otherwise, some, or even all, packets may get lost, as shown in the following figure.
Firmware Upgrade
The AWK-3131A-M12-RCC can be enhanced with more value-added functions by installing firmware upgrades.
The latest firmware is available at Moxa’s download center.
Before running a firmware upgrade, make sure the AWK-3131A-M12-RCC is off-line. Click the Browse button
to specify the firmware image file and click Firmware Upgrade and Restart to start the firmware upgrade.
After the progress bar reaches 100%, the AWK-3131A-M12-RCC will reboot itself.
When upgrading your firmware, the AWK-3131A-M12-RCC’s other functions are forbidden.
Config Import Export
You can back up or restore the AWK-3131A-M12-RCC’s configuration with Config Import Export.
In the Config Import section, click Browse to specify the configuration file and click Config Import button
to begin importing the configuration.
You can also back up or restore the ABC-01 (HW Rev. 1.1 support only) configuration with Config Import
Export.
ATTENTION
Please make sure the power source is stable when you upgrade your firmware. An unexpected power breakup
may damage your AWK-3131A-M12-RCC.
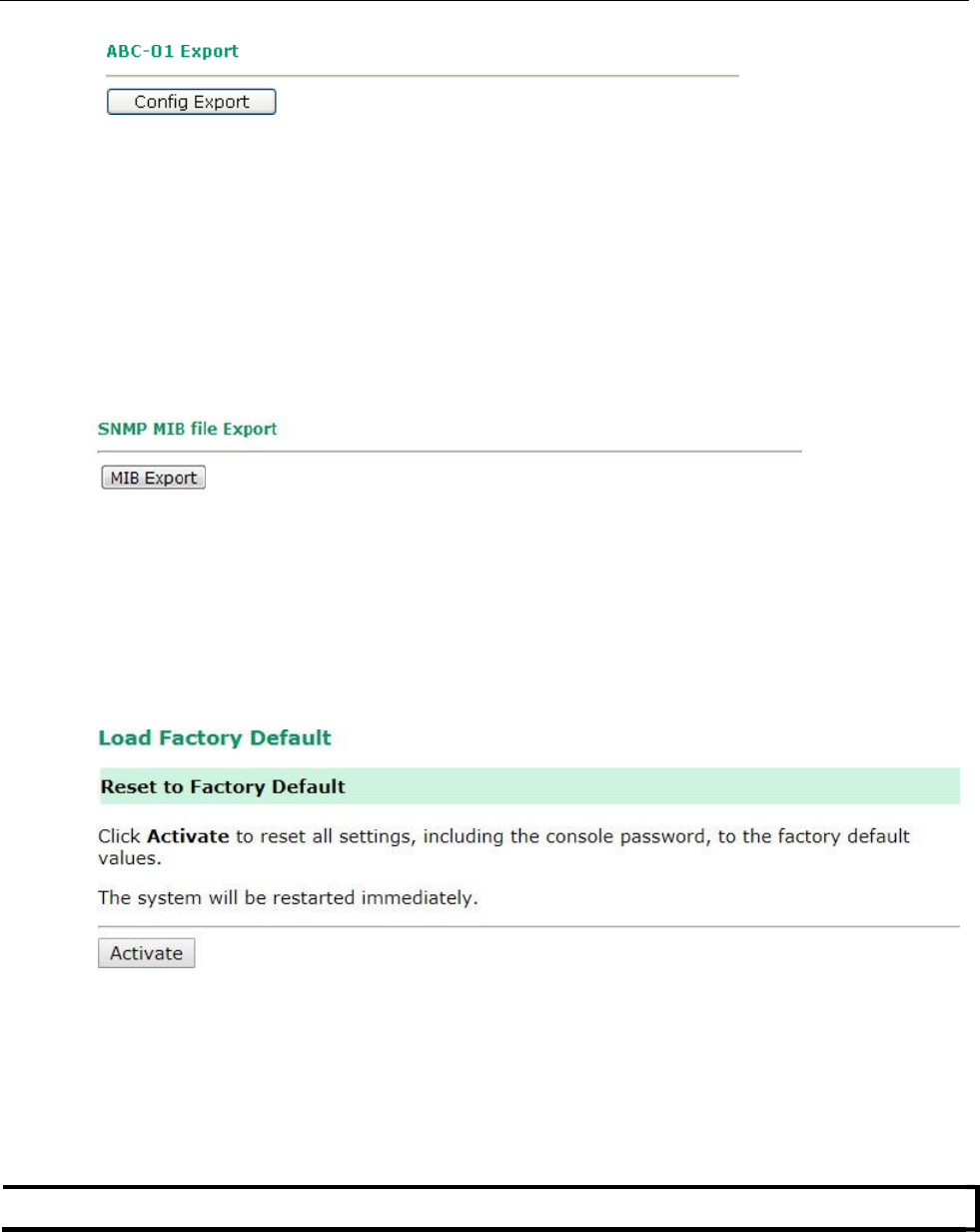
AWK-3131A-M12-RCC
Web Console Configuration
3-47
To download the configuration to the AWK:
1. Turn off the AWK.
2. Plug in the ABC-01 to the AWK’s RS-232 console.
3. Turn on AWK.
4. AWK will detect ABC-01 during boot-up, and download the configuration from the ABC-01 to the AWK
automatically. Once the configuration downloads and if configuration format is correct, the AWK will emit
three short beeps, then continue the boot up.
5. Once the AWK has booted up successfully, it will emit the normal two beeps, and the ready LED will turn to
solid green.
SNMP MIB file for AWK-3131A-M12-RCC is embedded in the device. To export the MIB file, simply click on the
“MIB Export” button and save it to your local drive.
Load Factory Default
Use this function to reset the AWK-3131A-M12-RCC and roll all settings back to the factory default values. You
can also reset the hardware by pressing the reset button on the top panel of the AWK-3131A-M12-RCC.
Username/Password
You can change the administration password for each of the AWK-3131A-M12-RCC’s console managers on this
page. Before you set up a new password, you must input the current password and reenter the new password
for confirmation. For your security, do not use the default password moxa, and remember to change the
administration password regularly.
NOTE
Default password: moxa
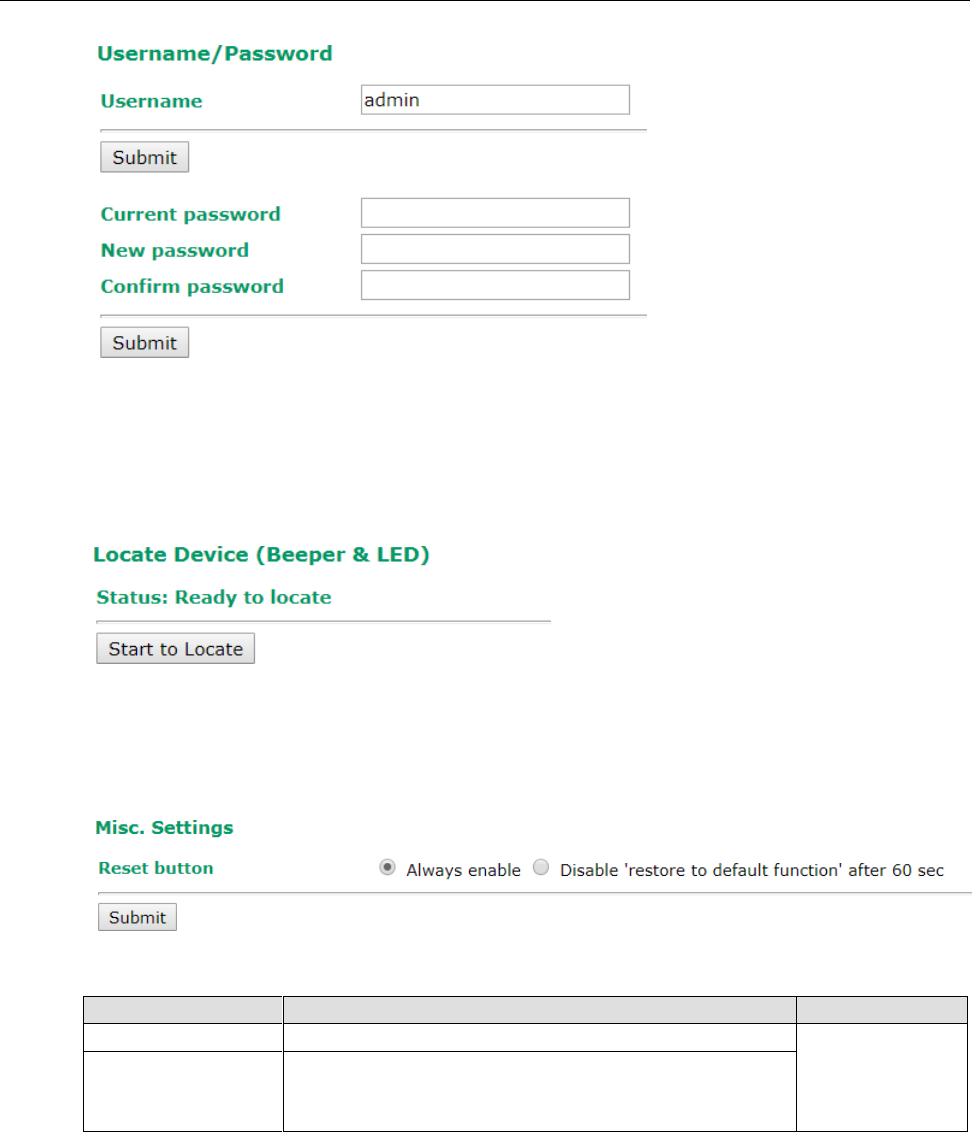
AWK-3131A-M12-RCC
Web Console Configuration
3-48
Locate Device
When you click on the Start to Locate button, the AP will beep and the AP’s LED will flash making it easy to
identify the AP. To stop the beeping, click on the Stop locating button.
Misc. Settings
Additional settings to help you manage your AWK-3131A-M12-RCC, are available on this page.
Reset button
Setting
Description
Factory Default
Always enable
The AWK-3131A-M12-RCC’s Reset button works normally.
Always enable
Disable ‘restore to
default function’ after
60 sec
The AWK-3131A-M12-RCC’s reset to default function will be
inactive 60 seconds after the AWK-3131A-M12-RCC finishes
booting up.
Save Configuration
The following figure shows how the AWK-3131A-M12-RCC stores the setting changes into volatile and
non-volatile memory. All data stored in volatile memory will disappear when the AWK-3131A-M12-RCC is
shutdown or rebooted unless they are y. Because the AWK-3131A-M12-RCC starts up and initializes with the
settings stored in flash memory, all new changes must be saved to flash memory before restarting the
AWK-3131A-M12-RCC. This also means the new changes will not work unless you run either the Save
Configuration function or the Restart function.
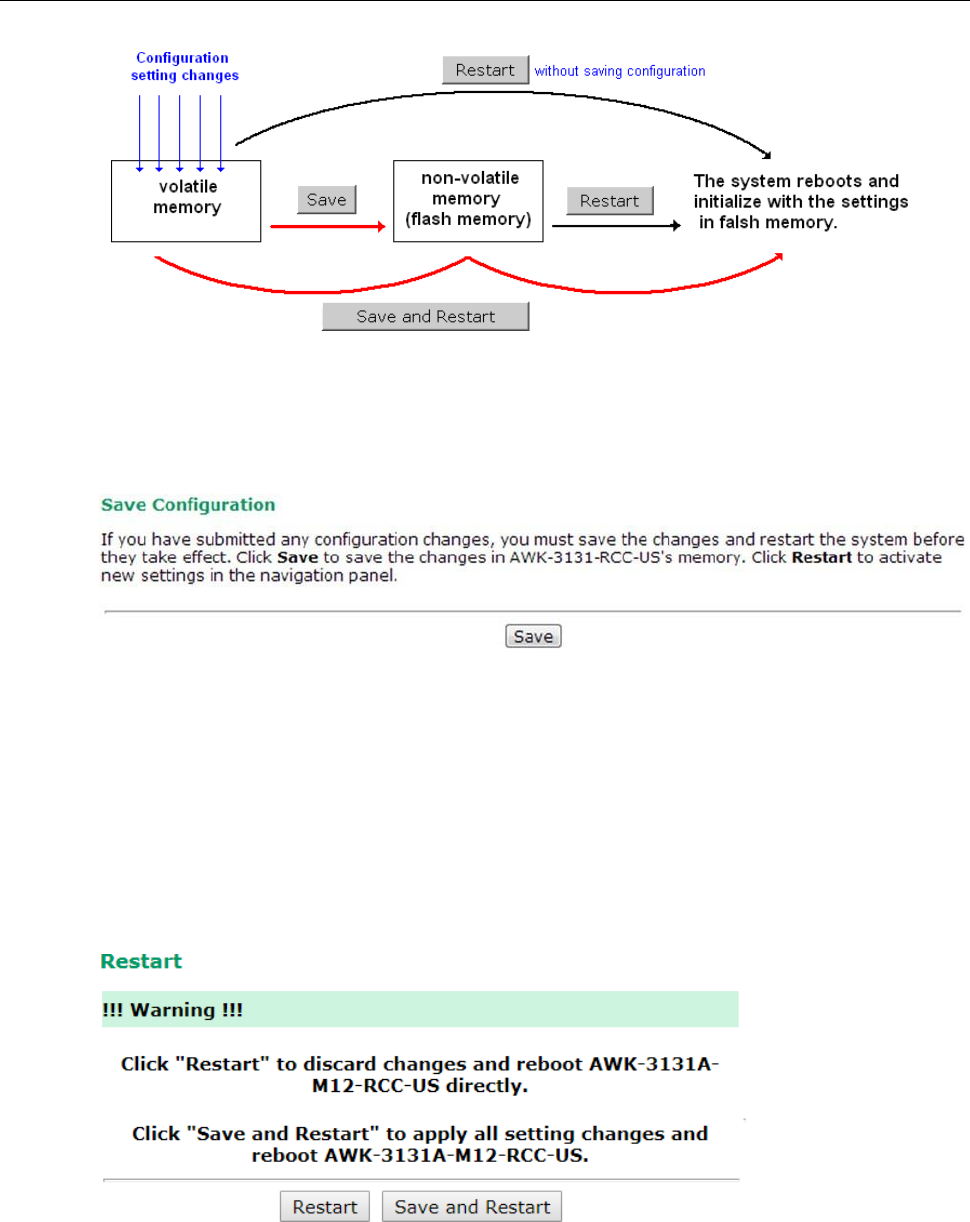
AWK-3131A-M12-RCC
Web Console Configuration
3-49
After you click on Save Configuration in the left menu box, the following screen will appear. Click Save if you
wish to update the configuration settings in the flash memory at this time. Alternatively, you may choose to run
other functions and put off saving the configuration until later. However, the new setting changes will remain
in the non-volatile memory until you save the configurations.
Restart
If you submitted configuration changes, you will find a blinking string in the upper right corner of the screen.
After making all your changes, click the Restart function in the left menu box. One of two different screens will
appear.
If you made changes recently but did not save, you will be given two options. Clicking the Restart button here
will reboot the AWK-3131A-M12-RCC directly, and all setting changes will be ignored. Clicking the Save and
Restart button will apply all setting changes and then reboot the AWK-3131A-M12-RCC.
If you run the Restart function without changing any configurations or saving all your changes, you will see
just one Restart button on your screen.
AWK-3131A-M12-RCC
Web Console Configuration
3-50
You will not be able to run any of the AWK-3131A-M12-RCC’s functions while the system is rebooting.
Logout
Logout helps users disconnect the current HTTP or HTTPS session and go to the Login page. For security
reasons, we recommend you logout before quitting the console manager.
AWK-3131A-M12-RCC
Software Installation and Configuration
4-2
Overview
The Documentation & Software CD included with your AWK-3131A-M12-RCC is designed to make the
installation and configuration procedure easy and straightforward. This auto-run CD includes AWK Search
Utility (to broadcast search for all AWK’s accessible over the network), the AWK-3131A-M12-RCC User’s
Manual, and Quick Installation Guide.
AWK Search Utility
Installing AWK Search Utility
1. Download the Windows AWK Search Utility from Moxa’s website: https://www.moxa.com/support/.
Extract the contents of the zip file and double-click on the WirelessSearchUtility_x.x_Build_xxxxxxxx file to
run the utility.
2. Click Next to install program files to the default directory, or click Browse to select an alternate location.
AWK-3131A-M12-RCC
Software Installation and Configuration
4-3
3. Click Next to create the program’s shortcut files to the default directory, or click Browse to select an
alternate location.
4. Click Next to select additional tasks.
AWK-3131A-M12-RCC
Software Installation and Configuration
4-4
5. Click Next to proceed with the installation.
The installer displays a summary of the installation options selected.
6. Click Install to begin the installation. The setup window will report the progress of the installation. To
change the installation settings, click Back and navigate to the previous screen.
7. Click Finish to complete the installation of the AWK Search Utility.
AWK-3131A-M12-RCC
Software Installation and Configuration
4-5
Configuring AWK Search Utility
The Broadcast Search function is used to locate all AWK-3131A-M12-RCC APs that are connected to the same
LAN as your computer (host). After locating an AWK-3131A-M12-RCC, you will be able to change its IP address.
Since the Broadcast Search function searches by TCP packet and not IP address, it doesn’t matter if the
AWK-3131A-M12-RCC is configured as an AP or Client. In either case, APs and Clients connected to the LAN will
be located, regardless of whether or not they are part of the same subnet as the host.
First-time installation of the AWK Search Utility requires you to key in the management password. For security
reasons, be sure to have a system administrator install the AWK Search Utility on your computer.
NOTE
The default management password for the AWK Search Utility is moxa.
1. Start the AWK Search Utility program. When the Login page appears, select the “Search AWK only”
option to search for AWKs and to view each AWK’s configuration. Select the “AWK management” option to
assign IPs, upgrade firmware, and locate devices.
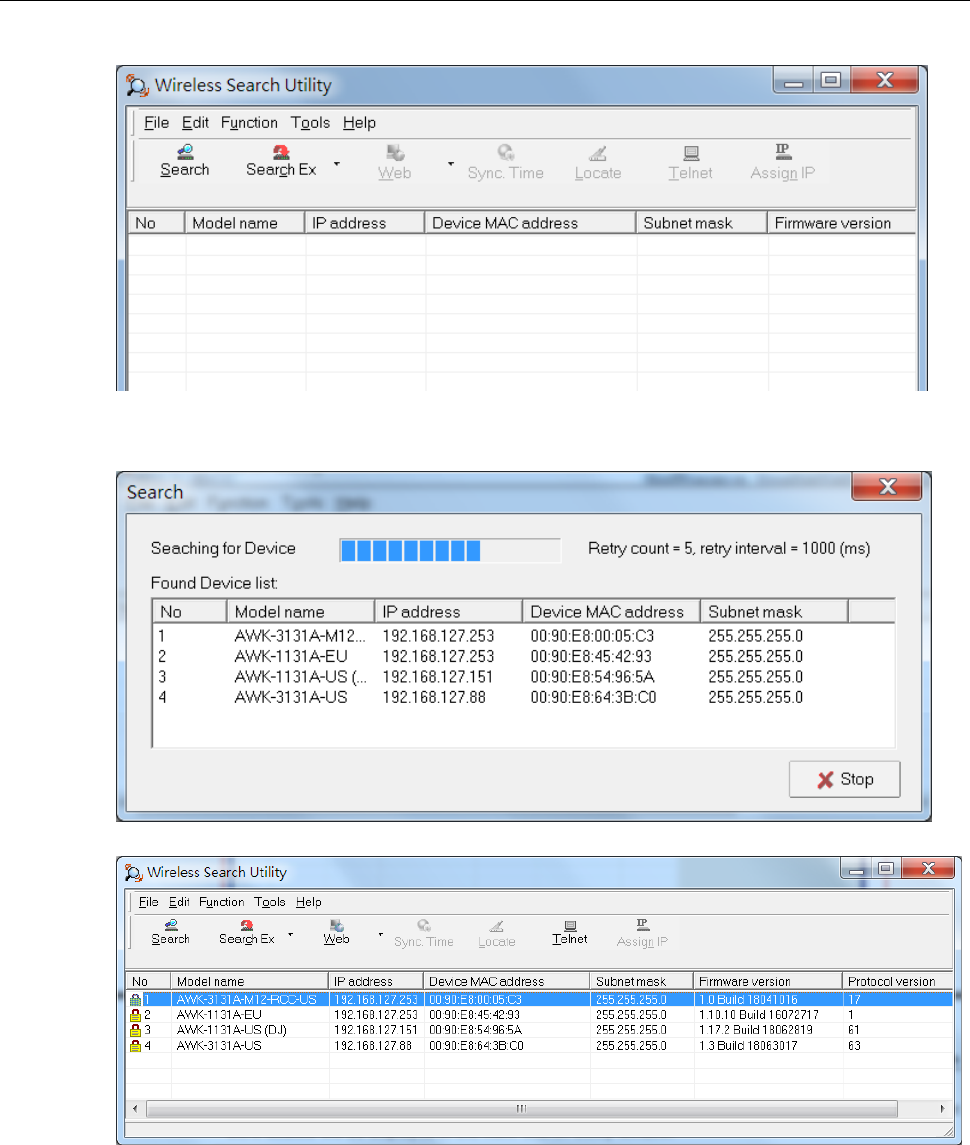
AWK-3131A-M12-RCC
Software Installation and Configuration
4-6
2. Open the AWK Search Utility and then click the Search icon.
3. The “Searching” window indicates the progress of the search. When the search is complete, all AWKs that
were located will be displayed in the AWK Search Utility window.
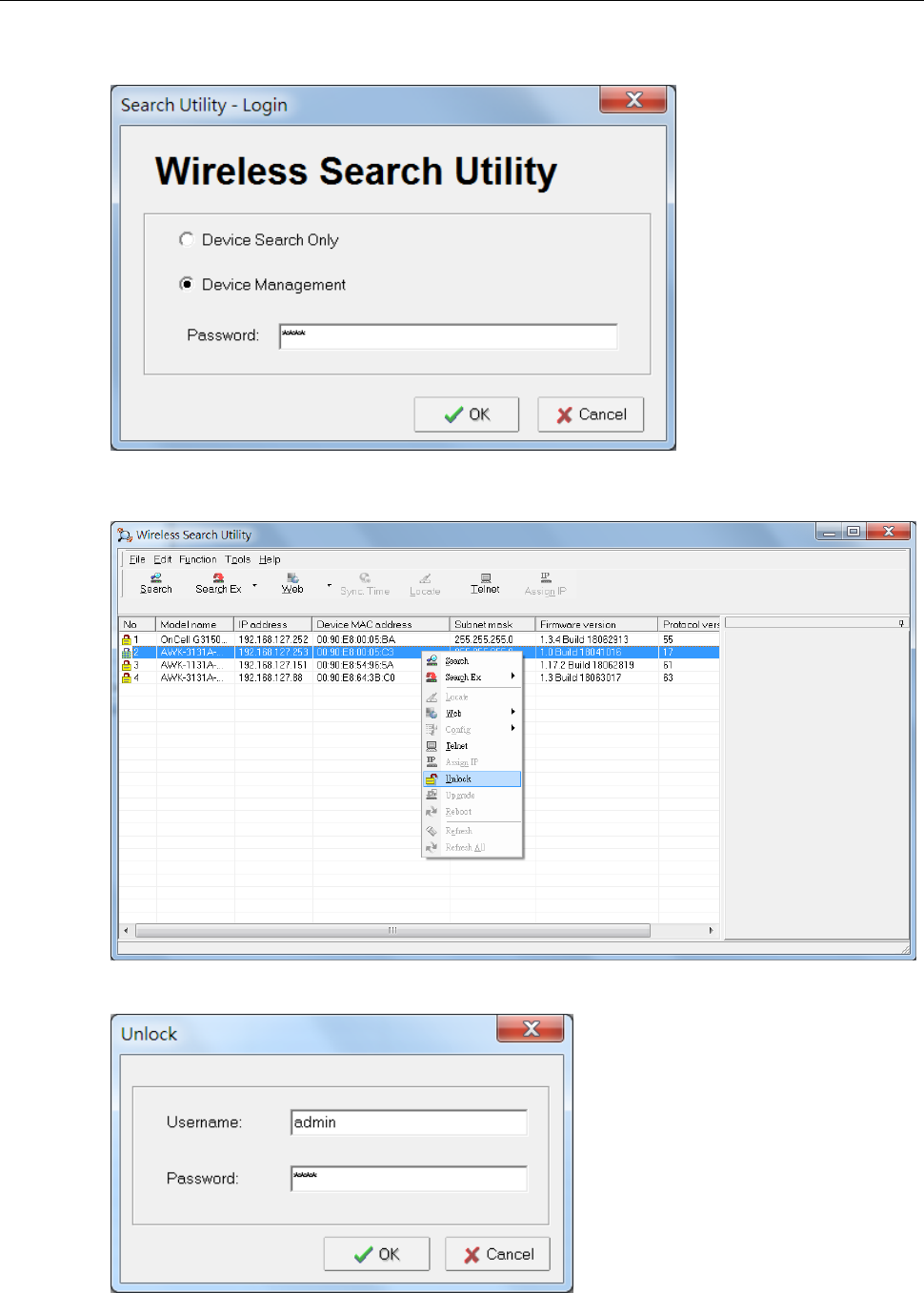
AWK-3131A-M12-RCC
Software Installation and Configuration
4-7
4. To access the advanced configuration, close the AWK Search Utility and start it again.
Select the Device Management option and click OK.
5. Make sure your AWK is unlocked.
To unlock the device, right click on the device and select Unlock.
Specify the Username and Password for the device to unlock the device.
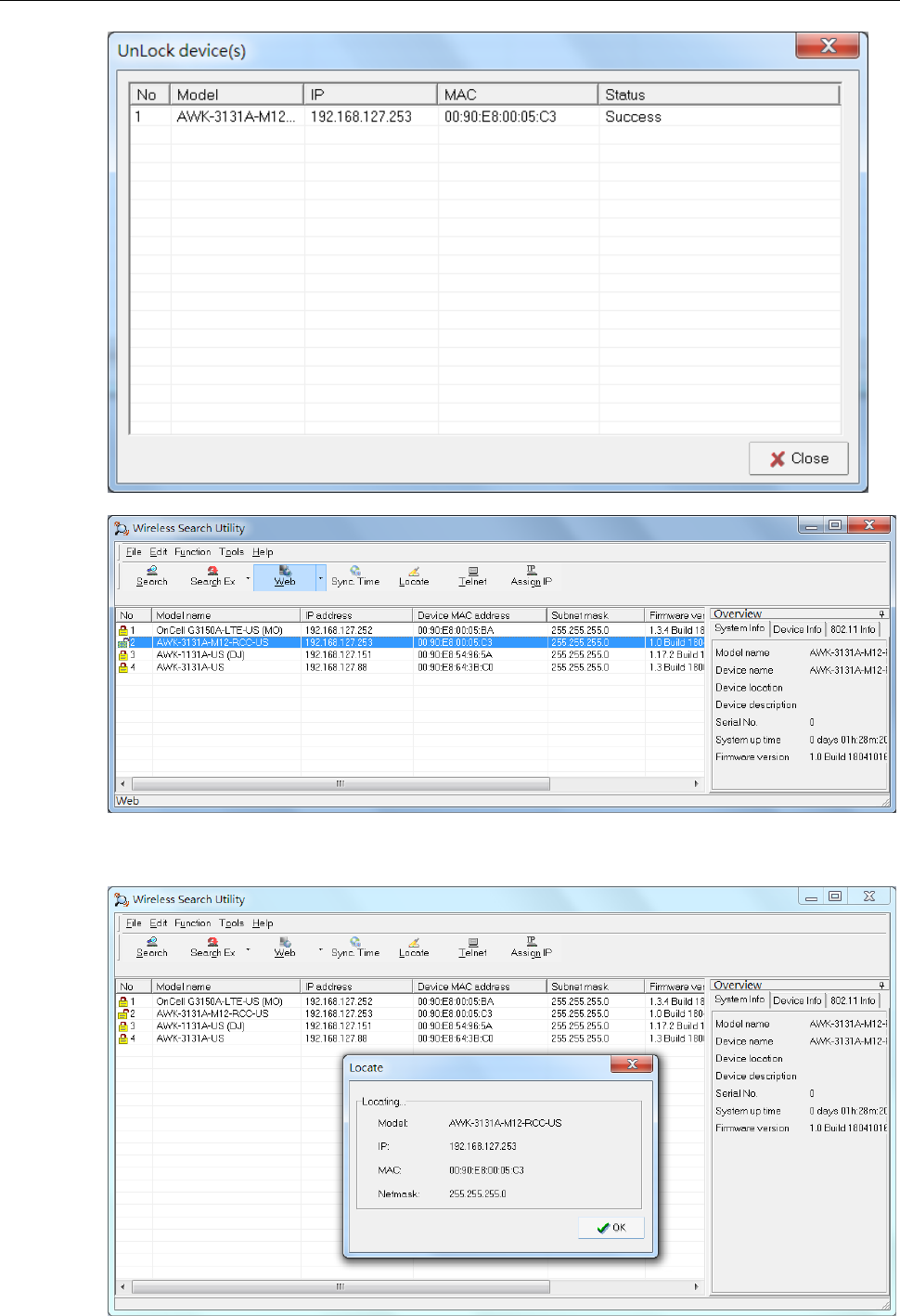
AWK-3131A-M12-RCC
Software Installation and Configuration
4-8
6. Click Locate to cause the selected device to beep. Click on the OK button for the utility to stop locating the
device.
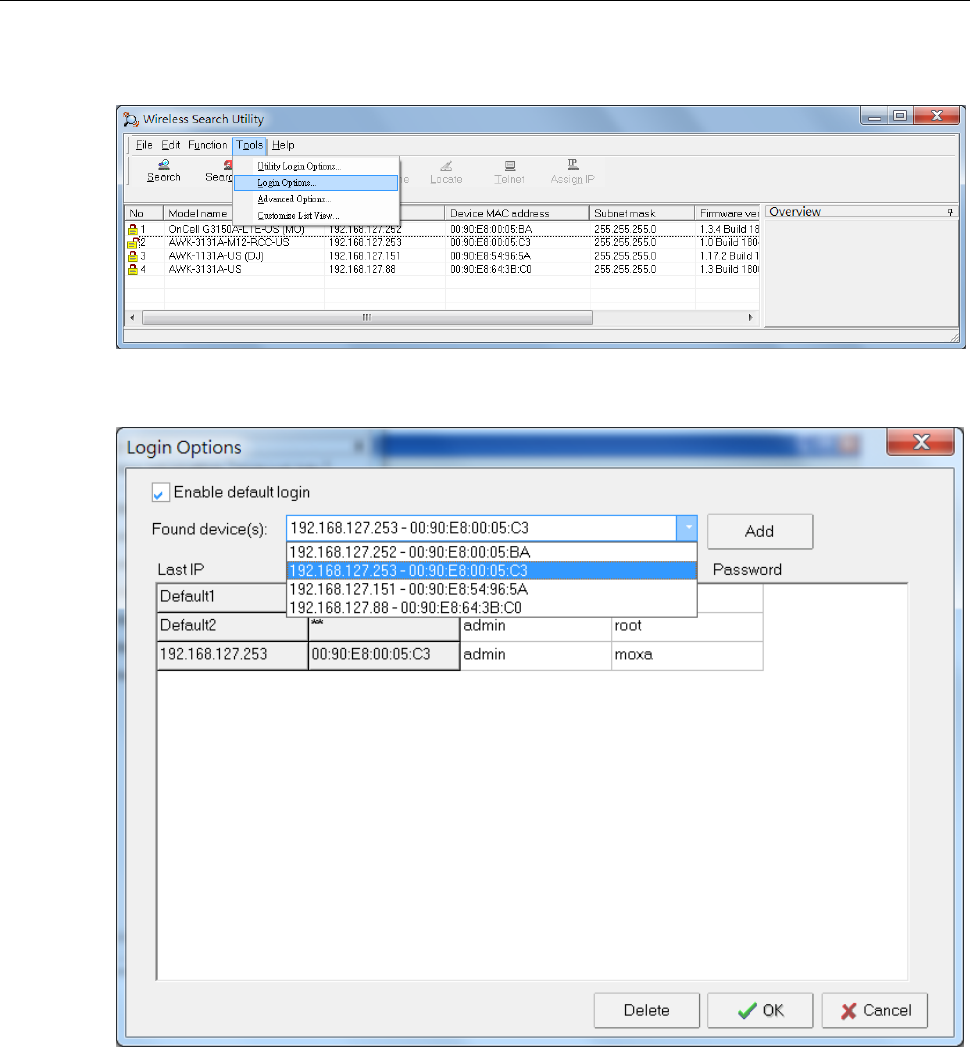
AWK-3131A-M12-RCC
Software Installation and Configuration
4-9
To unlock a specific product without requiring to enter the Username/password each time, go to Tools Login
Options to manage and unlock multiple products.
Use the scroll down list to select the MAC addresses of the AWKs that you would like to manage, and then click
Add.
Key in the password for the AWK device and then click OK to save the password.
If you return to the search page and search for the AWK device, you will find that the AWK will unlock
automatically.
AWK-3131A-M12-RCC
Software Installation and Configuration
4-10
7. To modify the configuration of the selected product, click on the Web icon to open the web UI.
For additional details, refer to Chapter 3, “Web Console Configuration” for information on how to use the
web console.
8. Click on the Telnet icon if you would like to use telnet to configure the selected device.
ATTENTION
For security purposes, we suggest that you can change the AWK search utility login password instead of using
the default.
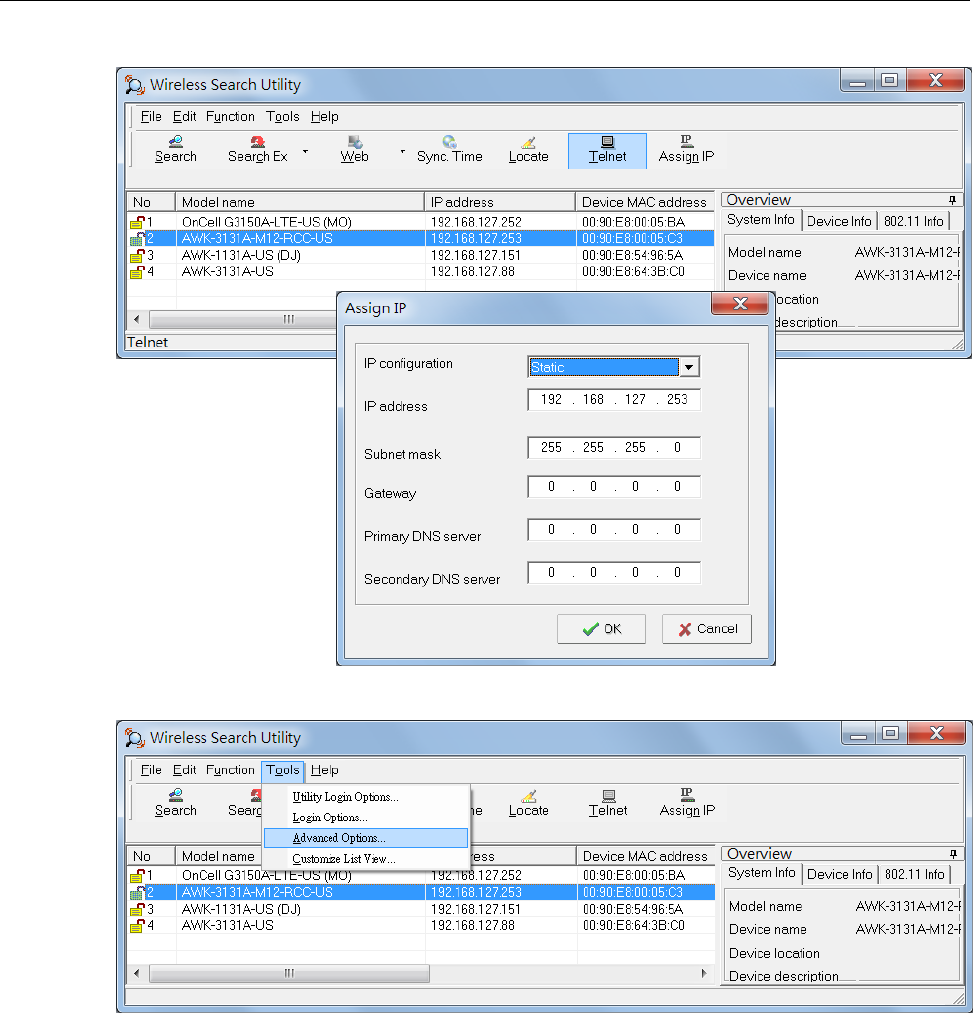
AWK-3131A-M12-RCC
Software Installation and Configuration
4-11
9. Click Assign IP to change the IP setting.
The three advanced options—Search, Connection, and Miscellaneous—are explained below:
Search
• Retry count (default=5): Indicates how many times the search will be retried automatically.
• Retry interval (ms): The time lapse between retries.
• Multicast retry (default=3): Indicates how many times the search by multicasting will be retried
automatically.
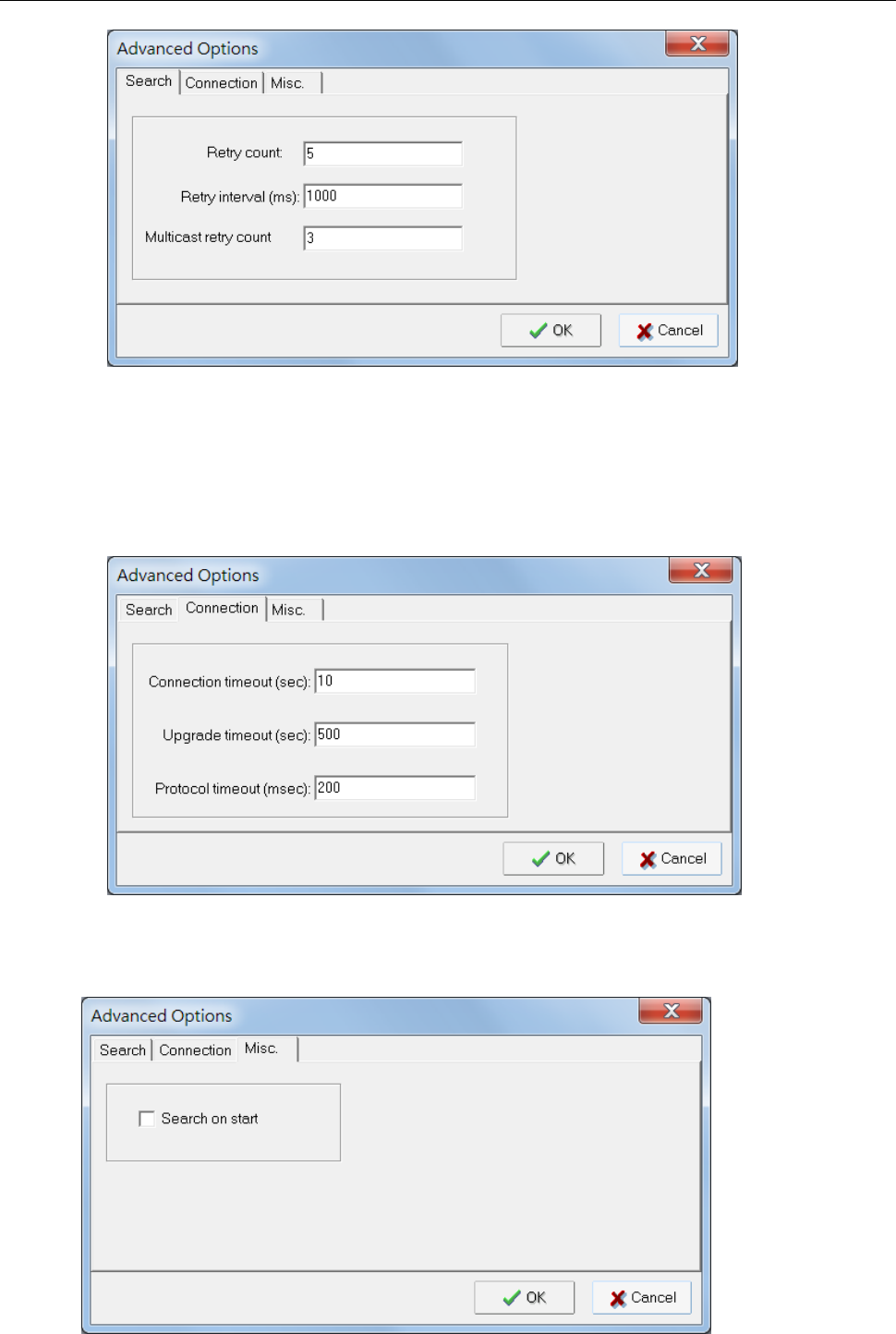
AWK-3131A-M12-RCC
Software Installation and Configuration
4-12
Connection
• Connection timeout (sec): Use this option to set the waiting time for the Default Login, Locate, Assign
IP, Upload Firmware, and Unlock to complete.
• Upgrade timeout (sec): Use this option to set the waiting time for the connection to disconnect while the
firmware is upgrading. Use this option to set the waiting time for the Firmware to write to flash.
• Protocol timeout (msec): It defines the default timeout while applying any operation, such as assigning
a new IP address to the selected product.
Misc.
Search on start: Checkmark this box if you would like the search function to start searching for devices after
you log in to the AWK search Utility.

5
Other Console Considerations
This chapter explains how to access the AWK-3131A-M12-RCC for the first time. In addition to HTTP access,
there are four ways to access AWK-3131A-M12-RCC: serial console, Telnet console, SSH console, and HTTPS
console. The serial console connection method, which requires using a short serial cable to connect the
AWK-3131A-M12-RCC to a PC’s COM port, can be used if you do not know the AWK-3131A-M12-RCC’s IP
address. The other consoles can be used to access the AWK-3131A-M12-RCC over an Ethernet LAN, or over the
Internet.
The following topics are covered in this chapter:
RS-232 Console Configuration (115200, None, 8, 1, VT100)
Configuring Through Telnet and SSH Consoles
Configuring HTTPS/SSL Secure Access Through a Web Browser
Disabling Telnet and Browser Access
AWK-3131A-M12-RCC
Other Console Considerations
5-2
RS-232 Console Configuration (115200, None, 8,
1, VT100)
The serial console connection method, which requires using a short serial cable to connect the
AWK-3131A-M12-RCC to a PC’s COM port, can be used if you do not know the AWK-3131A-M12-RCC’s IP
address. It is also convenient to use serial console configurations when you cannot access the
AWK-3131A-M12-RCC over Ethernet LAN, such as in the case of LAN cable disconnections or broadcast
storming over the LAN.
NOTE
We recommend using Moxa PComm (Lite) Terminal Emulator, which can be downloaded free of charge
from Moxa’s website (www.moxa.com/support).
Before running the PComm Terminal Emulator program, use an RJ45 to DB9-F (or RJ45 to DB25-F) cable to
connect the AWK-3131A-M12-RCC’s RS-232 console port to your PC’s COM port (COM1 or COM2, depending on
how your system is set up). After installing the PComm Terminal Emulator, take the following steps to access
the RS-232 console utility.
1. From the Windows Start menu, select PComm (Lite) > PComm Terminal Emulator.
2. In the Port Manager menu of the emulator, click on Open.
The Property window opens up.
ATTENTION
Do not use the RS-232 console when the AWK-3131A-M12-RCC is powered by a reversed voltage.
(e.g., -48 VDC), even though reverse voltage protection is supported. If you need to connect the RS-232
console at a reverse voltage potential, ensure that the serial port on the PC/laptop is well protected before
attaching it to the AWK that is supplied by a -48 VDC system. An isolated USB-to-serial converter like Moxa
UPort 1250I is recommended to create a reliable connection with an AWK device. Alternatively, be sure to use
a serial isolator, such as Moxa TCC-82, to protect both the AWK's serial console and your serial port.
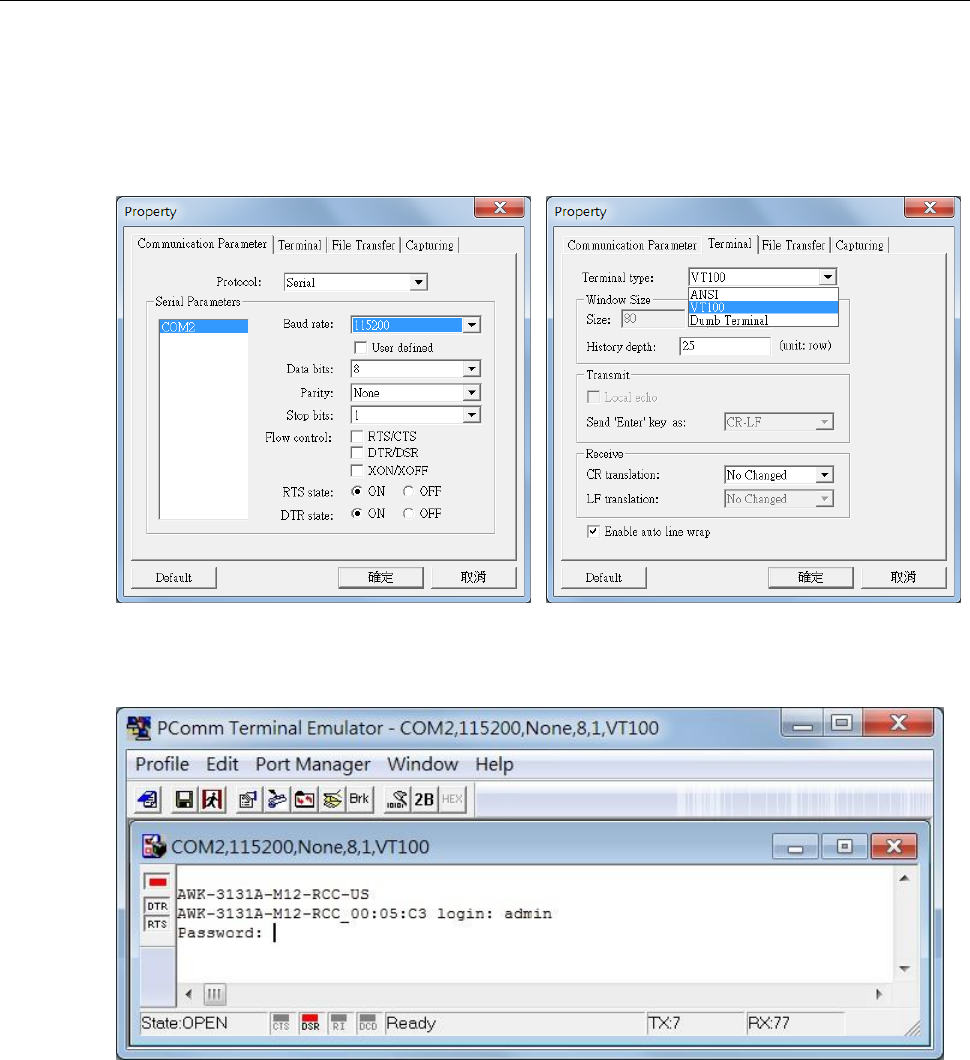
AWK-3131A-M12-RCC
Other Console Considerations
5-3
3. Configure the following settings:
In the Communication Parameter page, select the appropriate COM port for Console
Connection and set 115200 for Baud Rate, 8 for Data Bits, None for Parity, and 1 for Stop
Bits.
Click on the Terminal tab, and select VT100 (or ANSI) for the Terminal Type.
Click on OK to continue.
The Console login screen opens up.
4. Log into the RS-232 console with the login name (default: admin) and password (default: moxa, if no new
password is set).
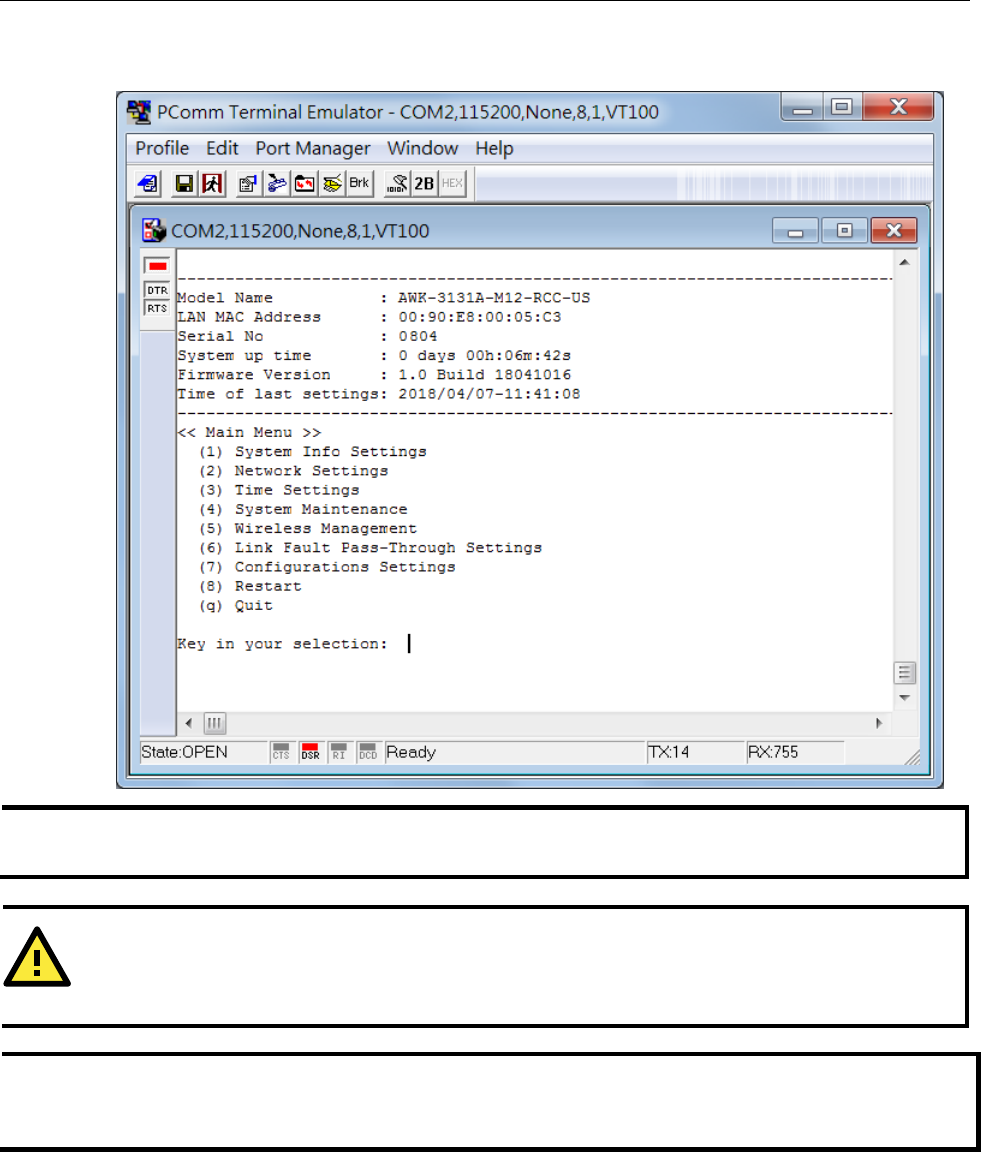
AWK-3131A-M12-RCC
Other Console Considerations
5-4
The AWK-3131A-M12-RCC’s device information and Main Menu options are displayed
5. Key in the number corresponding to the menu option that you would like to select.
NOTE
To modify the appearance of the PComm Terminal Emulator window, select Edit Font and then choose the
desired formatting options.
NOTE
The AWK's serial console needs to detect a DSR signal to activate the console output. Be sure to use a full
8-wire serial cable instead of a 3-wire (Tx/Rx/GND only). For a good connection to the AWK device we
recommend using Moxa serial console cable - CBL-RJ45F9-150.
Configuring Through Telnet and SSH Consoles
You may use Telnet or SSH client to access the AWK-3131A-M12-RCC and manage the console over a network.
To access the AWK-3131A-M12-RCC’s functions over the network from a PC host that is connected to the same
LAN as the AWK-3131A-M12-RCC, you need to make sure that the PC host and the AWK-3131A-M12-RCC are
on the same logical subnet. To do this, check your PC host’s IP address and subnet mask.
ATTENTION
If you unplug the RS-232 cable or disable the DTR signal, a disconnection event will be evoked to enforce
logout for network security. You will need to log in again to resume operation.
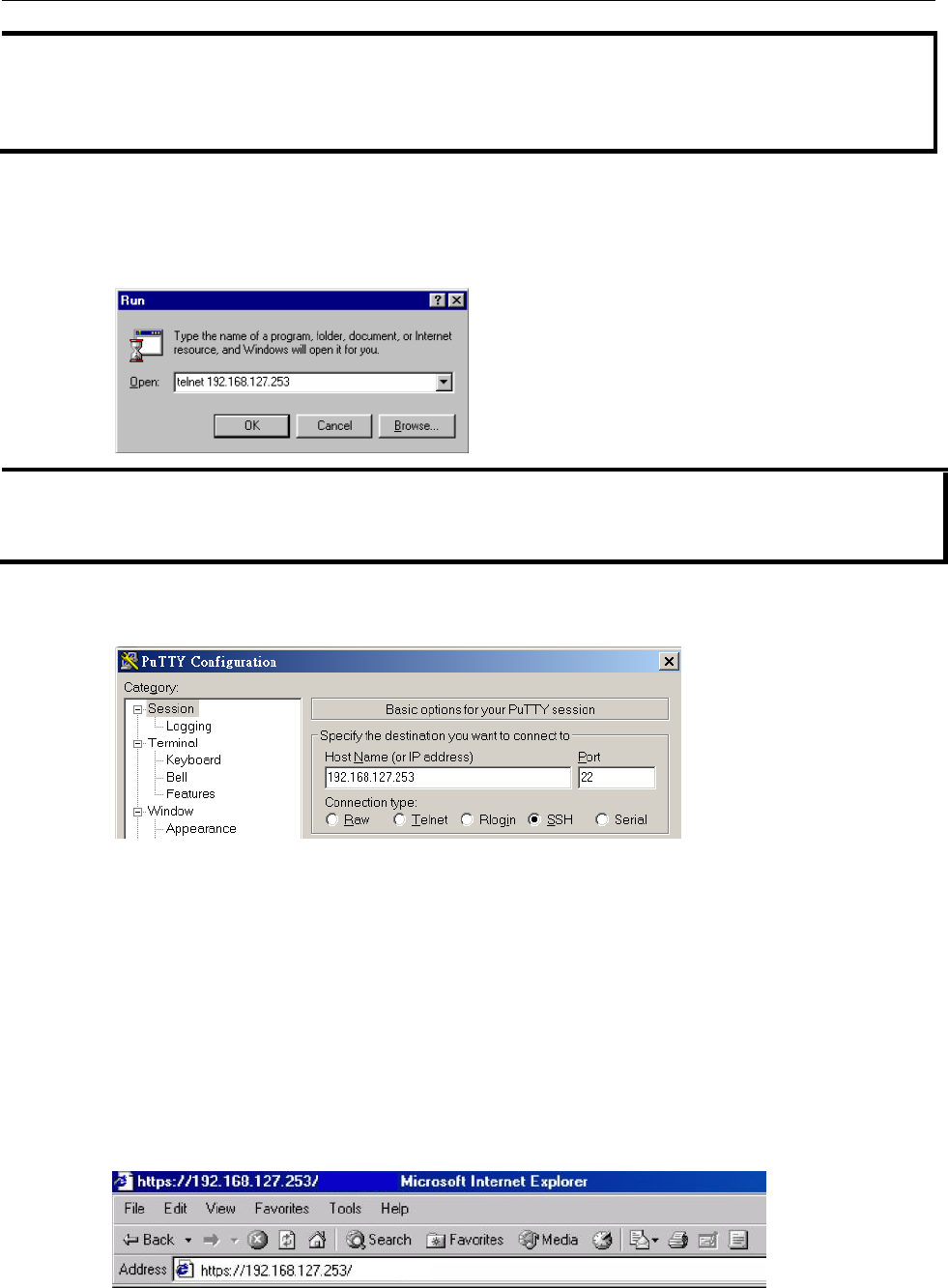
5-5
AWK-3131A-M12-RCC
Other Console Considerations
NOTE
The AWK-3131A-M12-RCC’s default IP address is 192.168.127.253 and the default subnet mask is
255.255.255.0 (for a Class C network). If you do not set these values properly, please check the network
settings of your PC host and then change the IP address to 192.168.127.xxx and subnet mask to
255.255.255.0.
Follow the steps below to access the console utility via Telnet or SSH client.
1. From Windows Desktop, run Start Run, and then use Telnet to access the AWK-3131A-M12-RCC’s IP
address from the Windows Run window (you may also issue the telnet command from the MS-DOS
prompt).
NOTE
Telnet is not a default service in Windows 7 and later versions for a PC/laptop. In order to use the telnet service,
you will need to activate it from Control Panel Programs Turn Windows features on or off. Select
Telnet Client and press OK.
2. When using the SSH client (e.g., PuTTY), run the client program and then input the AWK-3131A-M12-RCC’s
IP address, specifying 22 for the SSH connection port.
3. The Console login screen will appear. Please refer to the previous paragraph “RS-232 Console Configuration”
and for login and administration.
Configuring HTTPS/SSL Secure Access Through
a Web Browser
To secure your HTTP access, the AWK-3131A-M12-RCC supports HTTPS/SSL encryption for all HTTP traffic.
Perform the following steps to access the AWK-3131A-M12-RCC’s web browser interface via HTTPS/SSL.
1. Open your web browser and type https://<AWK-3131A-M12-RCC’s IP address> in the address field. Press
Enter to establish the connection.
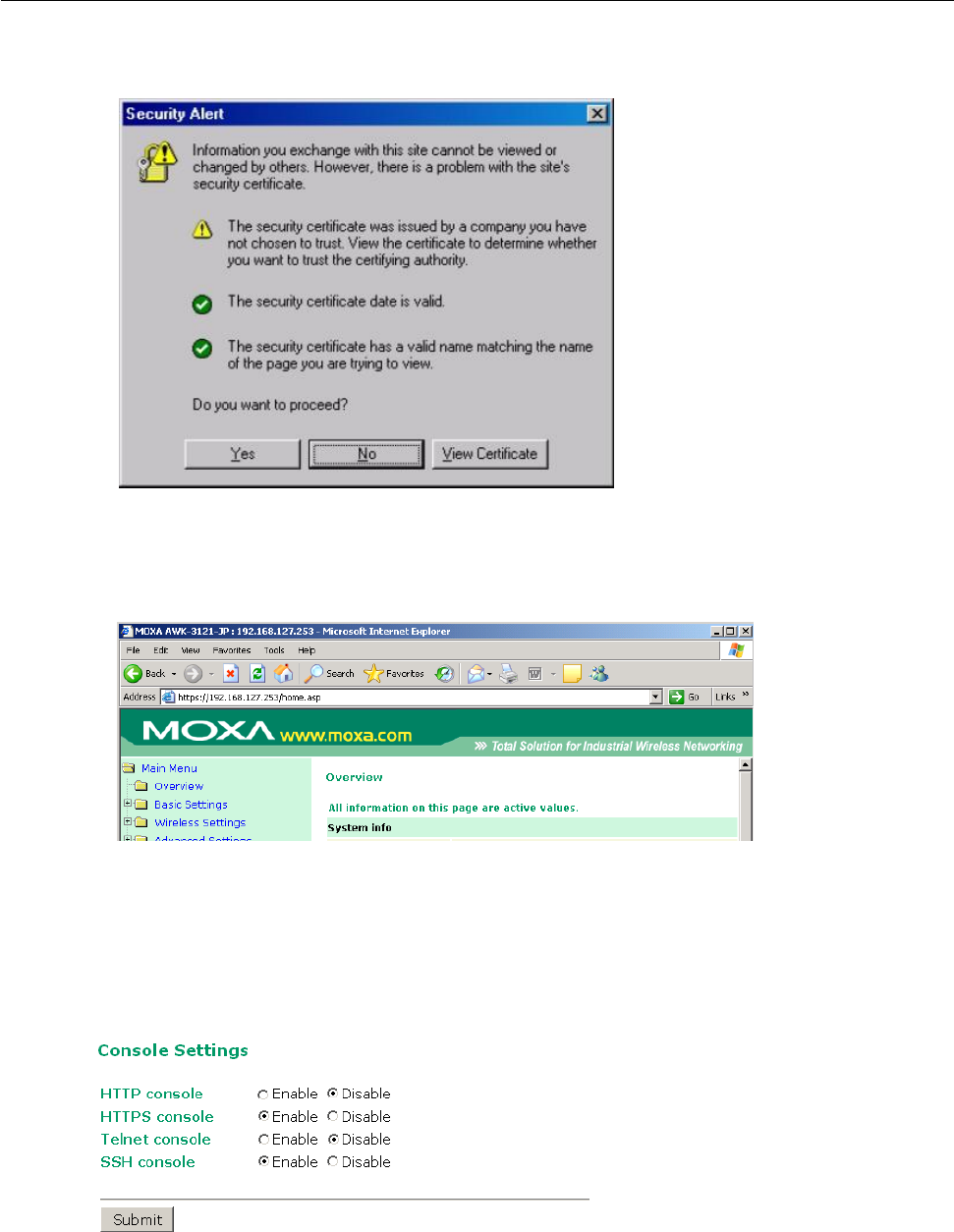
5-6
AWK-3131A-M12-RCC
Other Console Considerations
2. Warning messages will pop out to warn users that the security certificate was issued by a company they
have not chosen to trust.
3. Select Yes to accept the certificate issued by Moxa IW and then enter the AWK-3131A-M12-RCC’s web
browser interface secured via HTTPS/SSL. (You can see the protocol in URL is https.) Then you can use the
menu tree on the left side of the window to open the function pages to access each of
AWK-3131A-M12-RCC’s functions.
Disabling Telnet and Browser Access
If you are connecting the AWK-3131A-M12-RCC to a public network but do not intend to use its management
functions over the network, then we suggest disabling both Telnet Console and Web Configuration. Please run
Maintenance Console Settings to disable them, as shown in the following figure.

A
References
This chapter provides more detailed information about wireless-related technologies. The information in this
chapter can help you administer your AWK-3131A-M12-RCCs and plan your industrial wireless network better.
The following topics are covered in this appendix:
Beacon
DTIM
Fragment
RTS Threshold
STP and RSTP
The STP/RSTP Concept
Differences between RSTP and STP

AWK-3131A-M12-RCC
References
A-2
Beacon
A beacon is a packet broadcast by the AP to keep the network synchronized. A beacon includes the wireless LAN
service area, the AP address, the Broadcast destination address, a time stamp, Delivery Traffic Indicator Maps
(DTIM), and the Traffic Indicator Message (TIM). Beacon Interval indicates the frequency interval of AP.
DTIM
Delivery Traffic Indication Map (DTIM) is contained in beacon frames. It is used to indicate that broadcast and
multicast frames buffered by the AP will be delivered shortly. Lower settings result in more efficient networking,
while preventing your PC from dropping into power-saving sleep mode. Higher settings allow your PC to enter
sleep mode, thus saving power.
Fragment
A lower setting means smaller packets, which will create more packets for each transmission. If you have
decreased this value and experience high packet error rates, you can increase it again, but it will likely decrease
overall network performance. Only minor modifications of this value are recommended.
RTS Threshold
RTS Threshold (256-2346) – This setting determines how large a packet can be before the Access Point
coordinates transmission and reception to ensure efficient communication. This value should remain at its
default setting of 2,346. When you encounter inconsistent data flow, only minor modifications are
recommended.
STP and RSTP
The STP/RSTP Concept
Spanning Tree Protocol (STP) was designed to help reduce link failures in a network, and provide protection
from loops. Networks that have a complicated architecture are prone to broadcast storms caused by
unintended loops in the network. The STP protocol is part of the IEEE802.1D standard, 1998 Edition bridge
specification.
Rapid Spanning Tree Protocol (RSTP) implements the Spanning Tree Algorithm and Protocol defined by
IEEE802.1w-2001 standard. RSTP provides the following benefits:
• The topology of a bridged network will be determined much more quickly compared to STP.
• RSTP is backward compatible with STP, making it relatively easy to deploy. For example:
Defaults to sending 802.1D-style BPDUs if packets with this format are received.
STP (802.1D) and RSTP (802.1w) can operate on the LAN ports and WLAN ports (AP, Master, Slave, and
ACC modes) of the same AWK-3131A-M12-RCC.
This feature is particularly helpful when the AWK-3131A-M12-RCC connects to older equipment, such as legacy
switches.

AWK-3131A-M12-RCC
References
A-3
Differences between RSTP and STP
RSTP is similar to STP, but includes additional information in the BPDUs that allow each bridge to confirm that
it has taken action to prevent loops from forming when it decides to enable a link to a neighboring bridge.
Adjacent bridges connected via point-to-point links will be able to enable a link without waiting to ensure that
all other bridges in the network have had time to react to the change. The main benefit of RSTP is that the
configuration decision is made locally rather than network-wide, allowing RSTP to carry out automatic
configuration and restore a link faster than STP.

B
Supporting Information
This chapter presents additional information about this product. You can also learn how to contact Moxa for
technical support.
The following topics are covered in this appendix:
Firmware Recovery
DoC (Declaration of Conformity)
Federal Communication Commission Interference Statement
Antenna Gain and RF Radiated Power
R&TTE Compliance Statement
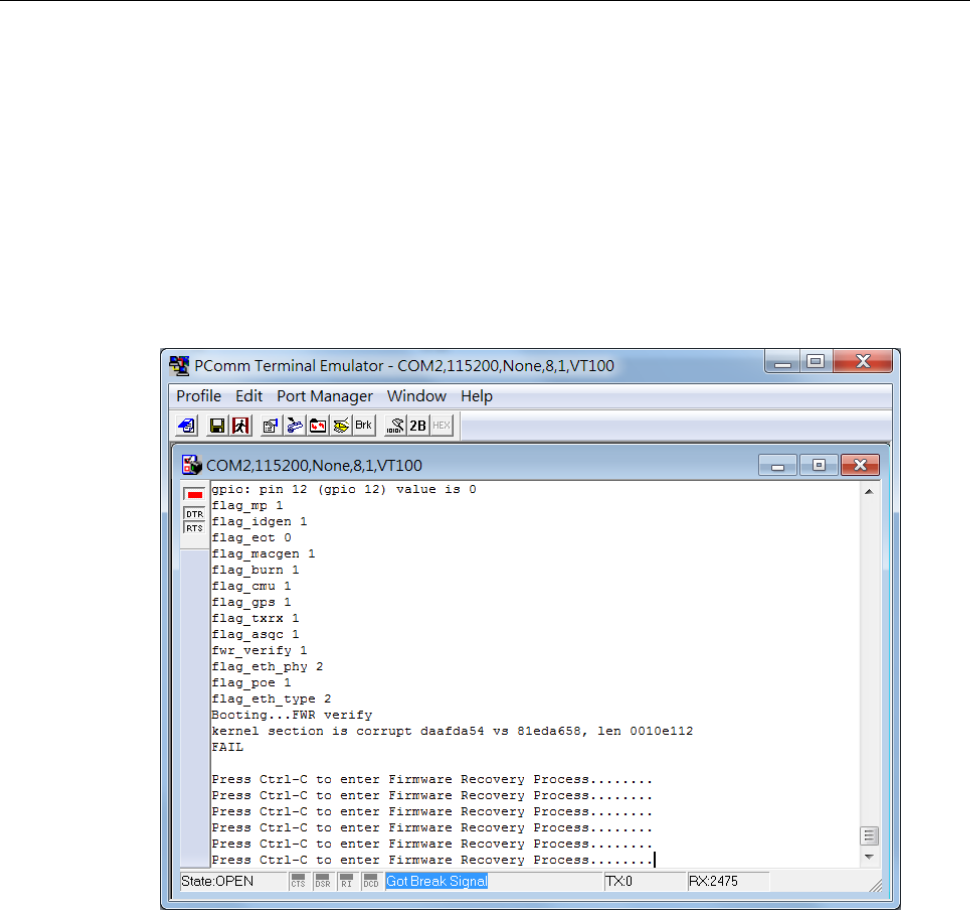
AWK-3131A-M12-RCC
Supporting Information
B-2
Firmware Recovery
If the FAULT, Signal Strength, CLIENT, BRIDGE and WLAN LEDs light up simultaneously and blink at
one-second intervals, this indicates that the system boot up has failed. Boot-up failure may result from some
wrong operation or other issues, such as an unexpected shutdown during firmware update. The
AWK-3131A-M12-RCC is designed to help administrators recover such damage and quickly resume system
operation. Refer to the following instructions to recover the firmware on an AWK-3131A-M12-RCC:
1. Connect to the AWK-3131A-M12-RCC’s RS-232 console using the setting 115200 bps, None, 8, and
1.
The following message is shown on the terminal emulator every second.
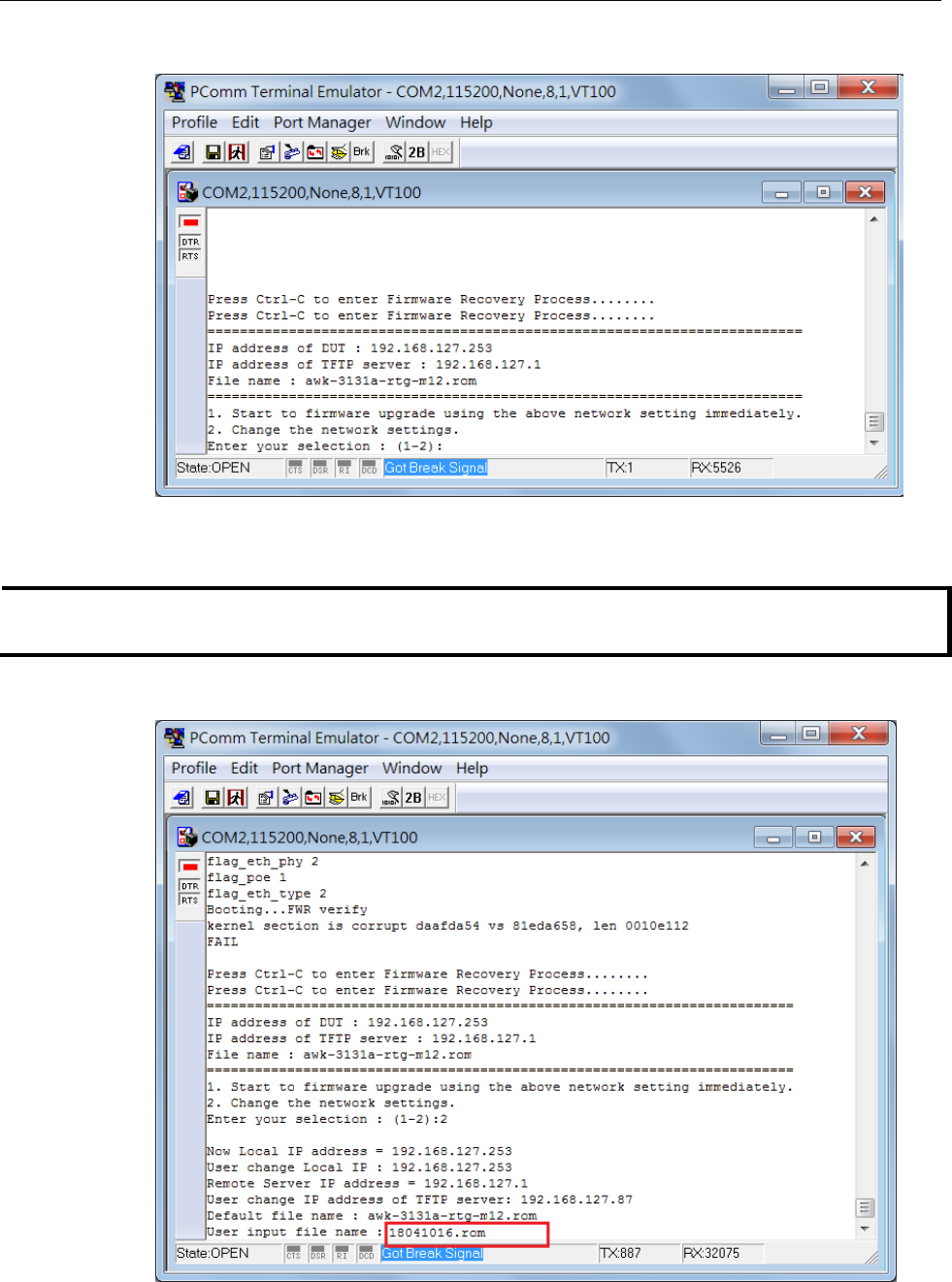
AWK-3131A-M12-RCC
Supporting Information
B-3
2. Press Ctrl - C and the following message will appear.
3. In the console terminal, select 2 and press Enter
4. Specify the IP addresses of the AWK and the TFTP Server, and the firmware filename.
NOTE
You should have the address of a TFTP server, where the correct firmware file is stored, handy before
performing this step.
5. Press Enter to proceed.
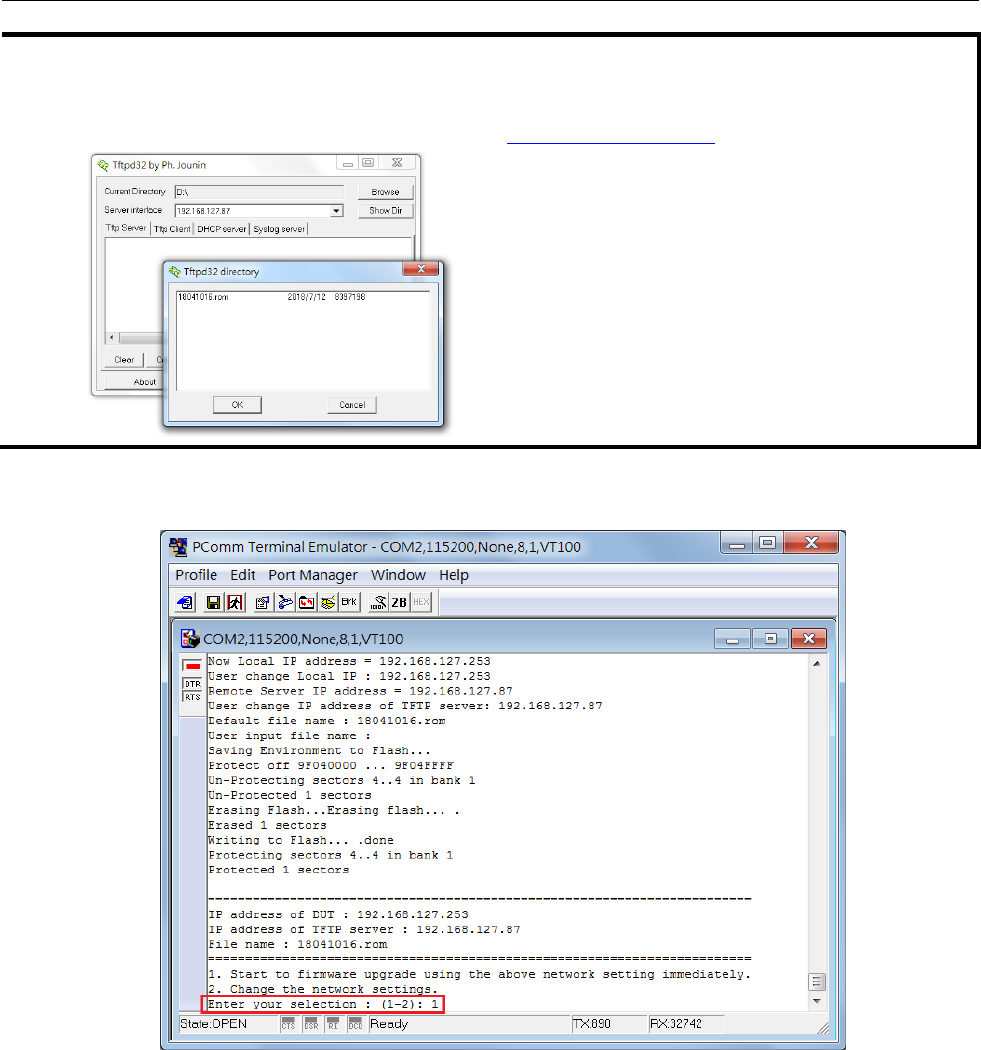
B-4
AWK-3131A-M12-RCC
Supporting Information
NOTE
The firmware file downloaded from Moxa’s website has a complex filename, which may not be convenient for
use during a firmware recovery operation. It is recommended that you rename the file to give it a short file
name, e.g.:18041016.rom, to ease the recovery process.
Here is an example that uses the shareware, tftpd (http://tftpd32.jounin.net/).
6. Confirm that the settings are correct and press 1 and then Enter to proceed.
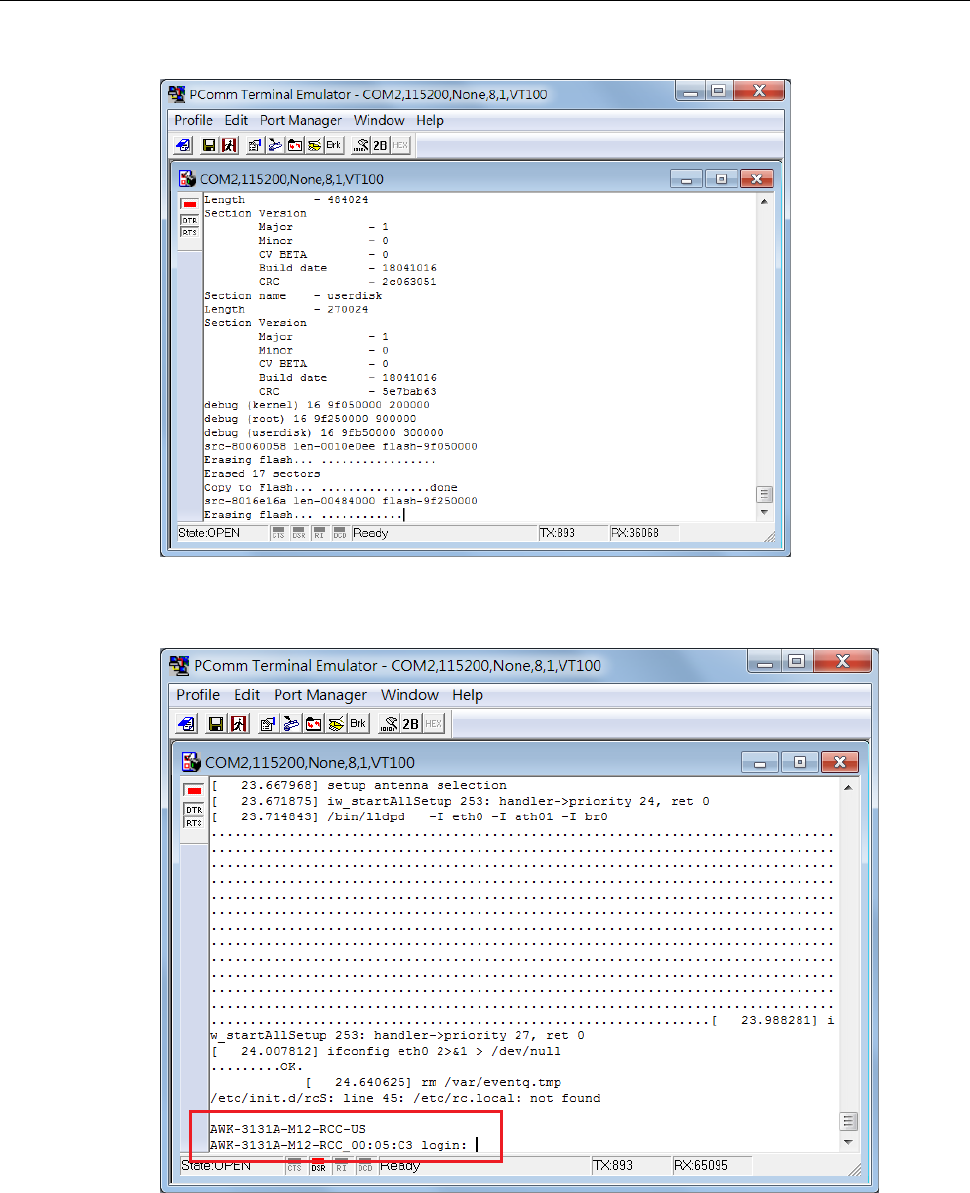
B-5
AWK-3131A-M12-RCC
Supporting Information
The following message is displayed on the console terminal.
After the firmware recovering process is successfully completed, you will hear two short beeps and the
STATE led on the device will turn green.

B-6
AWK-3131A-M12-RCC
Supporting Information
DoC (Declaration of Conformity)
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part
15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in
a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not
installed and used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a particular installation. If
this equipment does cause harmful interference to radio or television reception, which can be determined by
turning the equipment off and on, the user is encouraged to try to correct the interference by one of the
following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
Caution: Any changes or modifications not expressly approved by the grantee of this device could void the
user's authority to operate the equipment.
RF exposure warning
This equipment must be installed and operated in accordance with provided instructions and the antenna(s)
used for this transmitter must be installed to provide a separation distance of at least 20cm from all persons
and must not be co-located or operating in conjunction with any other antenna or transmitter, End-users and
installers must be provide with antenna installation instructions and transmitter. End-users and installers
must be provide with antenna installation instructions and transmitter operating conditions for satisfying RF
exposure compliance.
Antenna List
Antenna Part No.
Antenna Type
Maximum Antenna Gain
ANT-WDB-WDB-O-2-BK
Dipole Antenna
2.34 dBi for 5.25~5.35GHz
2.34 dBi for 5.47~5.725GHz
ANT-WDB-ARM-0202
Dipole Antenna
1.6 dBi for 5.25~5.35 GHz
1.8 dBi for 5.47~5.725 GHz

B-7
AWK-3131A-M12-RCC
Supporting Information
NCC (National Communication Commission)
本產品符合低功率電波輻射性電機管理辦法第十二條、第十四條等條文規定:
經型式認證合格之低功率射頻電機, 非經許可,公司, 商號或使用者均不得擅自變更頻率,加大功率或變更
原設計之特性及功能。
低功率射頻電機之使用不得影響飛航影響安全及干擾合法通信, 經發現有干擾現象時,應立即停用,並改
善至無干擾時方得繼續使用。
前項合法通信,指一電信法規定作業之無線電通信低功率射頻電機需忍受合法通信或工業,科學及醫療用
電波輻射性電機設備之干擾。

B-8
AWK-3131A-M12-RCC
Supporting Information
R&TTE Compliance Statement
Moxa declares that the apparatus AWK-3131A-RTG complies with the essential requirements and other
relevant provisions of Directive 1999/5/EC.
This equipment complies with all the requirements of DIRECTIVE 1999/5/CE OF THE EUROPEAN PARLIAMENT
AND THE COUNCIL OF 9 March 1999 on radio equipment and telecommunication terminal equipment and the
mutual recognition of their conformity (R&TTE).
The R&TTE Directive repeals and replaces in the directive 98/13/EEC (Telecommunications Terminal
Equipment and Satellite Earth Station Equipment) as of April 8, 2000.
Safety
This equipment is designed with the utmost care for the safety of those who install and use it. However, special
attention must be paid to the dangers of electric shock and static electricity when working with electrical
equipment. All guidelines of this and of the computer manufacturer must therefore be allowed at all times to
ensure the safe use of the equipment.
EU Countries Intended for Use
The ETSI version of this device is intended for home and office use in Austria, Belgium, Denmark, Finland,
France (with Frequency channel restrictions), Germany, Greece, Ireland, Italy, Luxembourg, Portugal, Spain,
Sweden, The Netherlands, and United Kingdom.
The ETSI version of this device is also authorized for use in EFTA member states Norway and Switzerland.
EU Countries Not Intended for Use
None.
Potential Restrictive Use
France: only channels 10, 11, 12, and 13.


