ZyXEL Communications MAX200HW2 WiMAX Router User Manual UserMan I88MAX200HW2 revised
ZyXEL Communications Corporation WiMAX Router UserMan I88MAX200HW2 revised
Contents
- 1. User manual revised 1
- 2. User manual revised 2
- 3. User manual revised 3
- 4. User manal revised 3
User manual revised 2
Chapter 12SIP
MAX-200HW2 Series User s Guide 153
12.1.7.2 Use NAT
If you know the NAT router!s public IP address and SIP port number, you can use the Use
NAT feature to manually configure the ZyXEL Device to use a them in the SIP messages. This
eliminates the need for STUN or a SIP ALG.
You must also configure the NAT router to forward traffic with this port number to the ZyXEL Device.
12.1.7.3 STUN
STUN (Simple Traversal of User Datagram Protocol (UDP) through Network Address
Translators) allows the ZyXEL Device to find the presence and types of NAT routers and/or
firewalls between it and the public Internet. STUN also allows the ZyXEL Device to find the
public IP address that NAT assigned, so the ZyXEL Device can embed it in the SIP data
stream. STUN does not work with symmetric NAT routers or firewalls. See RFC 3489 for
details on STUN.
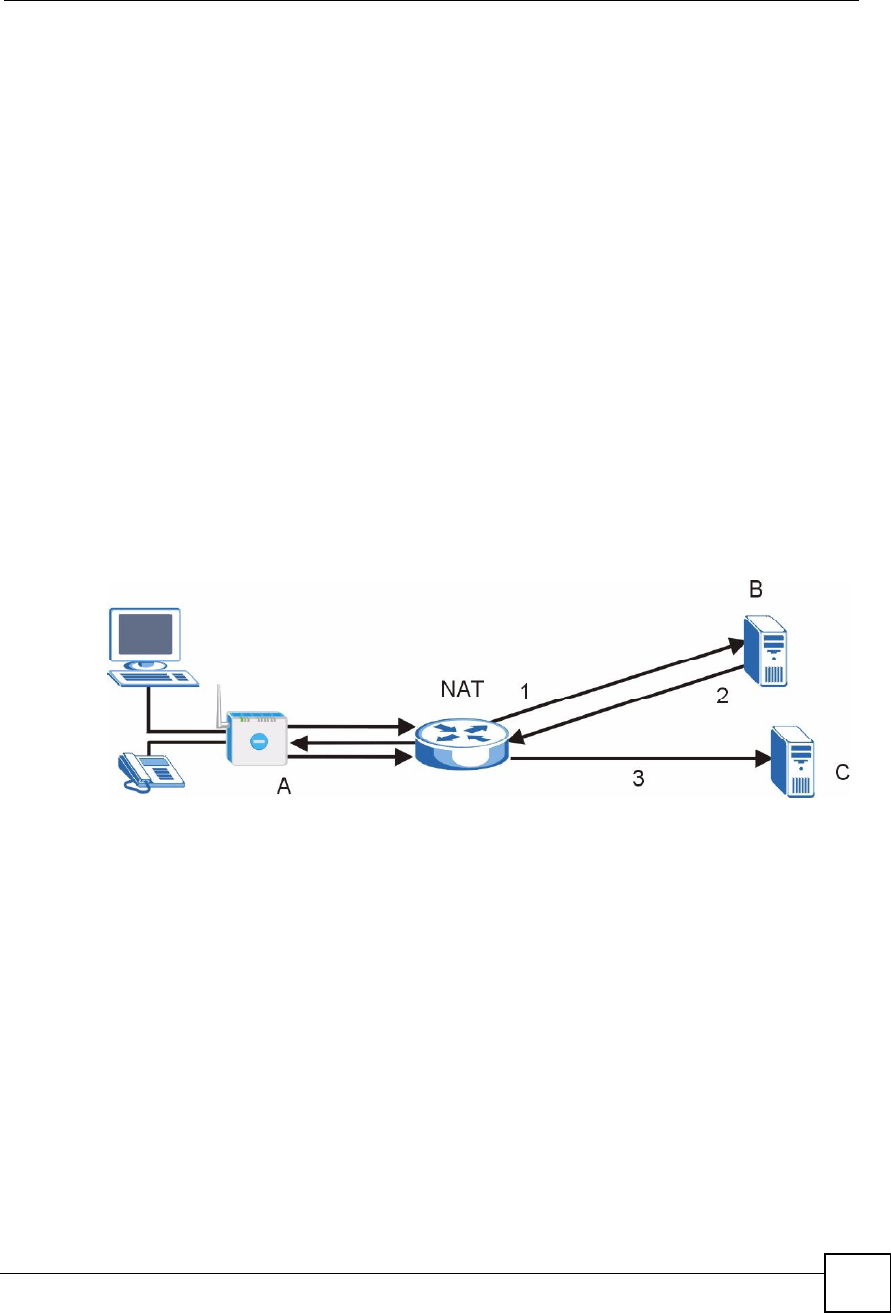
The following figure shows how STUN works.
1The ZyXEL Device (A) sends SIP packets to the STUN server (B).
2The STUN server (B) finds the public IP address and port number that the NAT router
used on the ZyXEL Device!s SIP packets and sends them to the ZyXEL Device.
3The ZyXEL Device uses the public IP address and port number in the SIP packets that it
sends to the SIP server (C).
Figure 102 STUN
12.1.7.4 Outbound Proxy
Your VoIP service provider may host a SIP outbound proxy server to handle all of the ZyXEL
Device!s VoIP traffic. This allows the ZyXEL Device to work with any type of NAT router and
eliminates the need for STUN or a SIP ALG. Turn off a SIP ALG on a NAT router in front of
the ZyXEL Device to keep it from retranslating the IP address (since this is already handled by
the outbound proxy server).
12.1.8 Voice Coding
A codec (coder/decoder) codes analog voice signals into digital signals and decodes the digital
signals back into voice signals. The ZyXEL Device supports the following codecs.
G.711 is a Pulse Code Modulation (PCM) waveform codec. PCM measures analog signal
amplitudes at regular time intervals (sampling) and converts them into digital bits
(quantization). Quantization "reads# the analog signal and then "writes# it to the nearest
digital value. For this reason, a digital sample is usually slightly different from its analog
original (this difference is known as "quantization noise#).

Chapter 12SIP
MAX-200HW2 Series User s Guide
154
G.711 provides excellent sound quality but requires 64kbps of bandwidth.
G.723 is an Adaptive Differential Pulse Code Modulation (ADPCM) waveform codec.
Differential (or Delta) PCM is similar to PCM, but encodes the audio signal based on the
difference between one sample and a prediction based on previous samples, rather than
encoding the sample!s actual quantized value. Many thousands of samples are taken each
second, and the differences between consecutive samples are usually quite small, so this
saves space and reduces the bandwidth necessary.
However, DPCM produces a high quality signal (high signal-to-noise ratio or SNR) for
high difference signals (where the actual signal is very different from what was predicted)
but a poor quality signal (low SNR) for low difference signals (where the actual signal is
very similar to what was predicted). This is because the level of quantization noise is the
same at all signal levels. Adaptive DPCM solves this problem by adapting the difference
signal!s level of quantization according to the audio signal!s strength. A low difference
signal is given a higher quantization level, increasing its signal-to-noise ratio. This
provides a similar sound quality at all signal levels.
G.723 provides high quality sound and requires 20 or 40 kbps.
G.729 is an Analysis-by-Synthesis (AbS) hybrid waveform codec. It uses a filter based on
information about how the human vocal tract produces sounds. The codec analyzes the
incoming voice signal and attempts to synthesize it using its list of voice elements. It tests
the synthesized signal against the original and, if it is acceptable, transmits details of the
voice elements it used to make the synthesis. Because the codec at the receiving end has
the same list, it can exactly recreate the synthesized audio signal.
G.729 provides good sound quality and reduces the required bandwidth to 8kbps.
12.1.9 PSTN Call Setup Signaling
PSTNs (Public Switched Telephone Networks) use DTMF or pulse dialing to set up telephone
calls.
Dual-Tone Multi-Frequency (DTMF) signaling uses pairs of frequencies (one lower frequency
and one higher frequency) to set up calls. It is also known as Touch Tone? Each of the keys
on a DTMF telephone corresponds to a different pair of frequencies.
Pulse dialing sends a series of clicks to the local phone office in order to dial numbers.3
12.1.10 MWI (Message Waiting Indication)
Enable Message Waiting Indication (MWI) enables your phone to give you a message%waiting
(beeping) dial tone when you have one or more voice messages. Your VoIP service provider
must have a messaging system that sends message-waiting-status SIP packets as defined in
RFC 3842.
3.The ZyXEL Device supports DTMF at the time of writing.
Chapter 12SIP
MAX-200HW2 Series User s Guide 155
12.1.11 Custom Tones (IVR)
IVR (Interactive Voice Response) is a feature that allows you to use your telephone to interact
with the ZyXEL Device. The ZyXEL Device allows you to record custom tones for the Caller
Ringing Tone and On Hold Tone functions. The same recordings apply to both the caller
ringing and on hold tones.
12.1.11.1 Recording Custom Tones
Use the following steps if you would like to create new tones or change your tones:
1Pick up the phone and press **** on your phone!s keypad and wait for the message that
says you are in the configuration menu.
2Press a number from 1101~1108 on your phone followed by the # key.
3Play your desired music or voice recording into the receiver!s mouthpiece. Press the #
key.
4You can continue to add, listen to, or delete tones, or you can hang up the receiver when
you are done.
12.1.11.2 Listening to Custom Tones
Do the following to listen to a custom tone:
1Pick up the phone and press **** on your phone!s keypad and wait for the message that
says you are in the configuration menu.
2Press a number from 1201~1208 followed by the # key to listen to the tone.
3You can continue to add, listen to, or delete tones, or you can hang up the receiver when
you are done.
12.1.11.3 Deleting Custom Tones
Do the following to delete a custom tone:
1Pick up the phone and press **** on your phone!s keypad and wait for the message that
says you are in the configuration menu.
2Press a number from 1301~1308 followed by the # key to delete the tone of your choice.
Press 14 followed by the # key if you wish to clear all your custom tones.
3You can continue to add, listen to, or delete tones, or you can hang up the receiver when
you are done.
12.1.12 Quality of Service (QoS)
Quality of Service (QoS) refers to both a network's ability to deliver data with minimum delay
and the networking methods used to provide bandwidth for real-time multimedia applications.
Table 58 Custom Tones Details
LABEL DESCRIPTION
Total Time for All Tones128 seconds for all custom tones combined
Maximum Time per
Individual Tone
20 seconds
Total Number of Tones
Recordable
8
You can record up to eight different custom tones but the total time must
be 128 seconds or less.
Chapter 12SIP
MAX-200HW2 Series User s Guide
156
12.1.12.1 Type Of Service (ToS)
Network traffic can be classified by setting the ToS (Type Of Service) values at the data source
(for example, at the ZyXEL Device) so a server can decide the best method of delivery, that is
the least cost, fastest route and so on.
12.1.12.2 DiffServ
DiffServ is a class of service (CoS) model that marks packets so that they receive specific per-
hop treatment at DiffServ-compliant network devices along the route based on the application
types and traffic flow. Packets are marked with DiffServ Code Points (DSCPs) indicating the
level of service desired. This allows the intermediary DiffServ-compliant network devices to
handle the packets differently depending on the code points without the need to negotiate paths
or remember state information for every flow. In addition, applications do not have to request
a particular service or give advanced notice of where the traffic is going.4
12.1.12.3 DSCP and Per-Hop Behavior
DiffServ defines a new DS (Differentiated Services) field to replace the Type of Service (TOS)
field in the IP header. The DS field contains a 2-bit unused field and a 6-bit DSCP field which
can define up to 64 service levels. The following figure illustrates the DS field.
Figure 103 DiffServ: Differentiated Service Field
DSCP is backward compatible with the three precedence bits in the ToS octet so that non-
DiffServ compliant, ToS-enabled network device will not conflict with the DSCP mapping.
The DSCP value determines the forwarding behavior, the PHB (Per-Hop Behavior), that each
packet gets across the DiffServ network. Based on the marking rule, different kinds of traffic
can be marked for different priorities of forwarding. Resources can then be allocated
according to the DSCP values and the configured policies.
12.1.12.4 VLAN
Virtual Local Area Network (VLAN) allows a physical network to be partitioned into multiple
logical networks. Only stations within the same group can communicate with each other.
Your ZyXEL Device can add IEEE 802.1Q VLAN ID tags to voice frames that it sends to the
network. This allows the ZyXEL Device to communicate with a SIP server that is a member of
the same VLAN group. Some ISPs use the VLAN tag to identify voice traffic and give it
priority over other traffic.
4.The ZyXEL Device does not support DiffServ at the time of writing.
DSCP
(6-bit)
Unused
(2-bit)
Chapter 12SIP
MAX-200HW2 Series User s Guide 157
12.2 SIP Screens
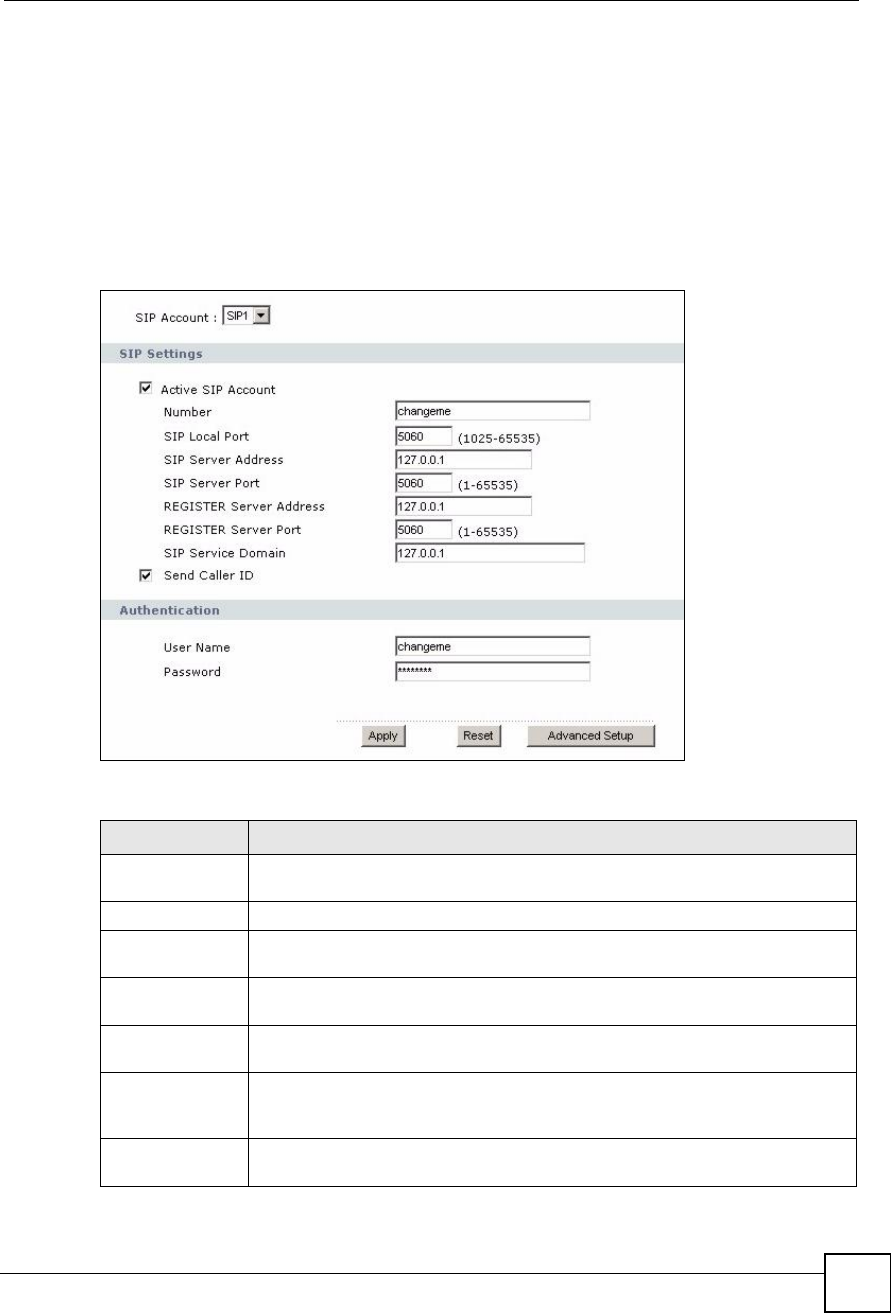
12.2.1 SIP Settings Screen
Use this screen to maintain basic information about each SIP account. Your VoIP service
provider (the company that lets you make phone calls over the Internet) should provide this.
You can also enable and disable each SIP account. To access this screen, click VoIP > SIP >
SIP Settings.
Figure 104 VoIP > SIP > SIP Settings
Each field is described in the following table.
Table 59 VoIP > SIP > SIP Settings
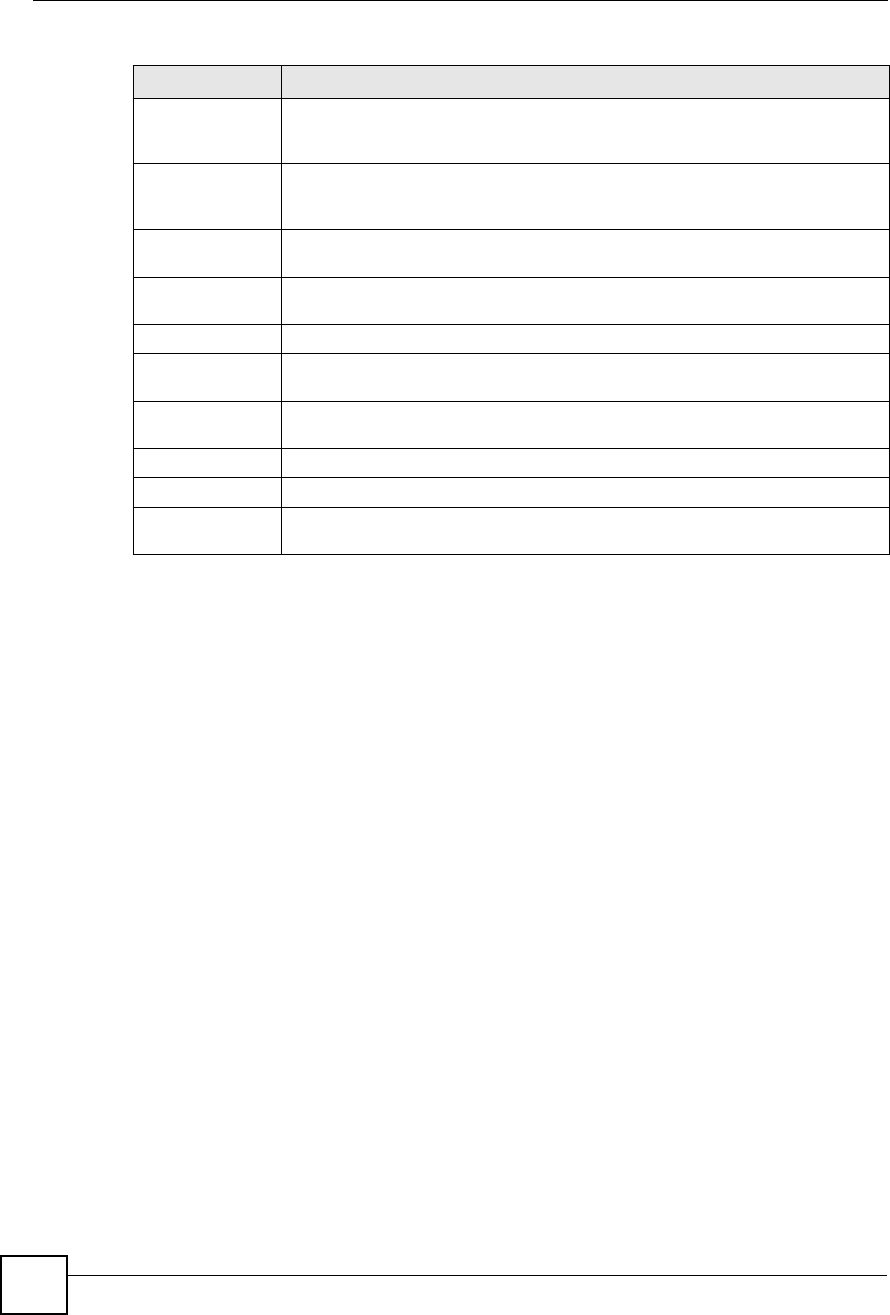
LABEL DESCRIPTION
SIP Account Select the SIP account you want to see in this screen. If you change this field, the
screen automatically refreshes.
SIP Settings
Active SIP
Account
Select this if you want the ZyXEL Device to use this account. Clear it if you do not
want the ZyXEL Device to use this account.
NumberEnter your SIP number. In the full SIP URI, this is the part before the @ symbol.
You can use up to 127 printable ASCII characters.
SIP Local PortEnter the ZyXEL Device s listening port number, if your VoIP service provider gave
you one. Otherwise, keep the default value.
SIP Server
Address
Enter the IP address or domain name of the SIP server provided by your VoIP
service provider. You can use up to 95 printable ASCII characters. It does not
matter whether the SIP server is a proxy, redirect or register server.
SIP Server PortEnter the SIP server s listening port number, if your VoIP service provider gave
you one. Otherwise, keep the default value.
Chapter 12SIP
MAX-200HW2 Series User s Guide
158
12.2.2 Advanced SIP Setup Screen
Use this screen to maintain advanced settings for each SIP account. To access this screen, click
Advanced Setup in VoIP > SIP > SIP Settings.
REGISTER
Server Address
Enter the IP address or domain name of the SIP register server, if your VoIP
service provider gave you one. Otherwise, enter the same address you entered in
the SIP Server Address field. You can use up to 95 printable ASCII characters.
REGISTER
Server Port
Enter the SIP register server s listening port number, if your VoIP service provider
gave you one. Otherwise, enter the same port number you entered in the SIP
Server Port field.
SIP Service
Domain
Enter the SIP service domain name. In the full SIP URI, this is the part after the @
symbol. You can use up to 127 printable ASCII Extended set characters.
Send Caller IDSelect this if you want to send identification when you make VoIP phone calls.
Clear this if you do not want to send identification.
Authentication
User NameEnter the user name for registering this SIP account, exactly as it was given to
you. You can use up to 95 printable ASCII characters.
PasswordEnter the user name for registering this SIP account, exactly as it was given to
you. You can use up to 95 printable ASCII Extended set characters.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Advanced Setup Click this to edit the advanced settings for this SIP account. The Advanced SIP
Setup screen appears.
Table 59 VoIP > SIP > SIP Settings
LABEL DESCRIPTION
Chapter 12SIP
MAX-200HW2 Series User s Guide 159
Figure 105 VoIP > SIP > SIP Settings > Advanced
Chapter 12SIP
MAX-200HW2 Series User s Guide
160
Each field is described in the following table.
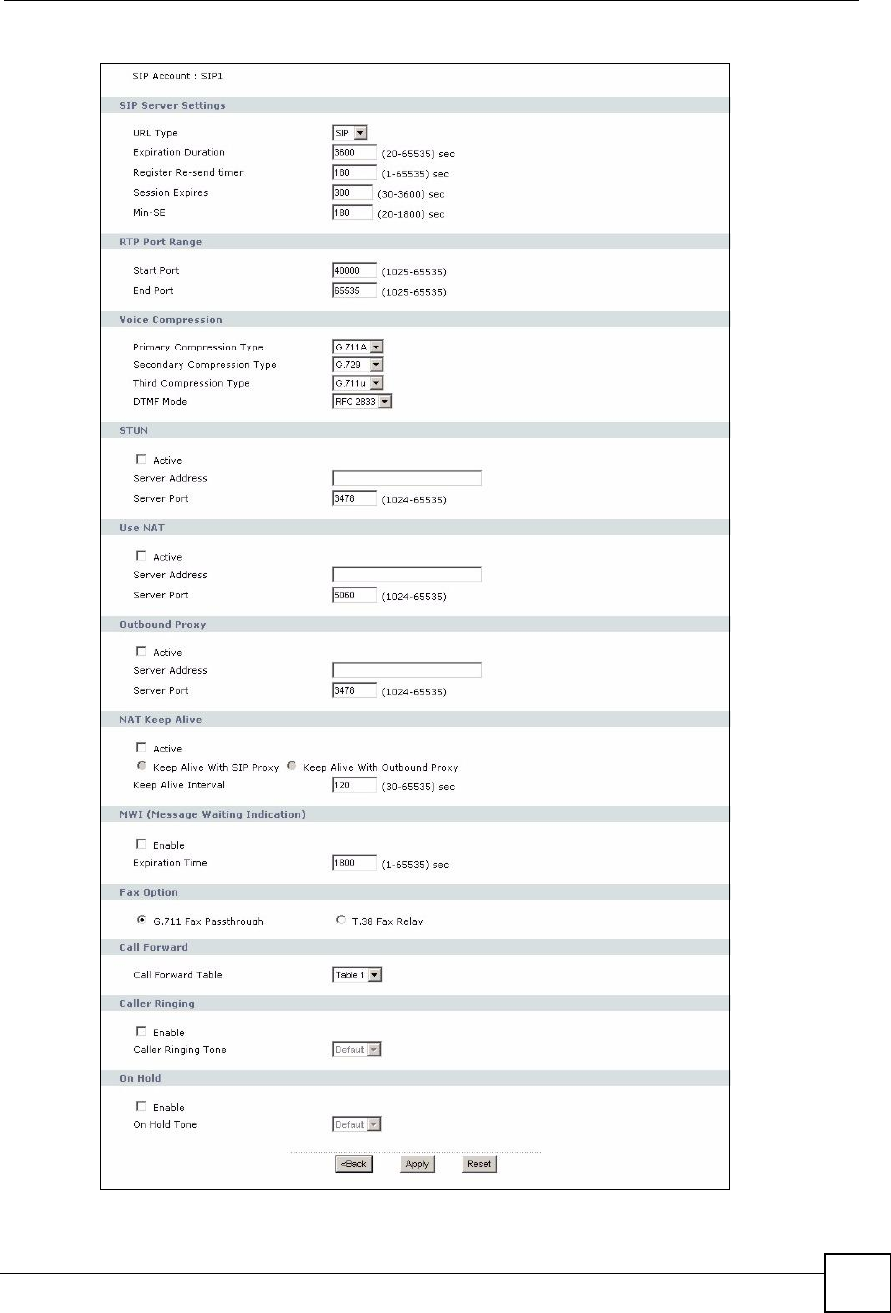
Table 60 VoIP > SIP > SIP Settings > Advanced
LABEL DESCRIPTION
SIP AccountThis field displays the SIP account you see in this screen.
SIP Server
Settings
URL TypeSelect whether or not to include the SIP service domain name when the ZyXEL
Device sends the SIP number.
SIP - include the SIP service domain name
TEL - do not include the SIP service domain name
Expiration
Duration
Enter the number of seconds your SIP account is registered with the SIP register
server before it is deleted. The ZyXEL Device automatically tries to re-register
your SIP account when one-half of this time has passed. (The SIP register server
might have a different expiration.)
Register Re-send
timer
Enter the number of seconds the ZyXEL Device waits before it tries again to
register the SIP account, if the first try failed or if there is no response.
Session ExpiresEnter the number of seconds the conversation can last before the call is
automatically disconnected. Usually, when one-half of this time has passed, the
ZyXEL Device or the other party updates this timer to prevent this from happening.
Min-SEEnter the minimum number of seconds the ZyXEL Device accepts for a session
expiration time when it receives a request to start a SIP session. If the request has
a shorter time, the ZyXEL Device rejects it.
RTP Port Range
Start Port
End Port
Enter the listening port number(s) for RTP traffic, if your VoIP service provider
gave you this information. Otherwise, keep the default values.
To enter one port number, enter the port number in the Start Port and End Port
fields.
To enter a range of ports,
#enter the port number at the beginning of the range in the Start Port field
#enter the port number at the end of the range in the End Port field.
Voice
Compression
Select the type of voice coder/decoder (codec) that you want the ZyXEL Device to
use.
G.711 provides high voice quality but requires more bandwidth (64 kbps).
#G.711A is typically used in Europe.
#G.711u is typically used in North America and Japan.
G.723 provides good voice quality, and requires 20 or 40 kbps.
In contrast, G.729 requires only 8 kbps.
The ZyXEL Device must use the same codec as the peer. When two SIP devices
start a SIP session, they must agree on a codec.
Primary
Compression
Type
Select the ZyXEL Device s first choice for voice coder/decoder.
Secondary
Compression
Type
Select the ZyXEL Device s second choice for voice coder/decoder. Select None if
you only want the ZyXEL Device to accept the first choice.
Third
Compression
Type
This field is disabled if Secondary Compression Type is None.
Select the ZyXEL Device s third choice for voice coder/decoder. Select None if
you only want the ZyXEL Device to accept the first or second choice.
Chapter 12SIP
MAX-200HW2 Series User s Guide 161
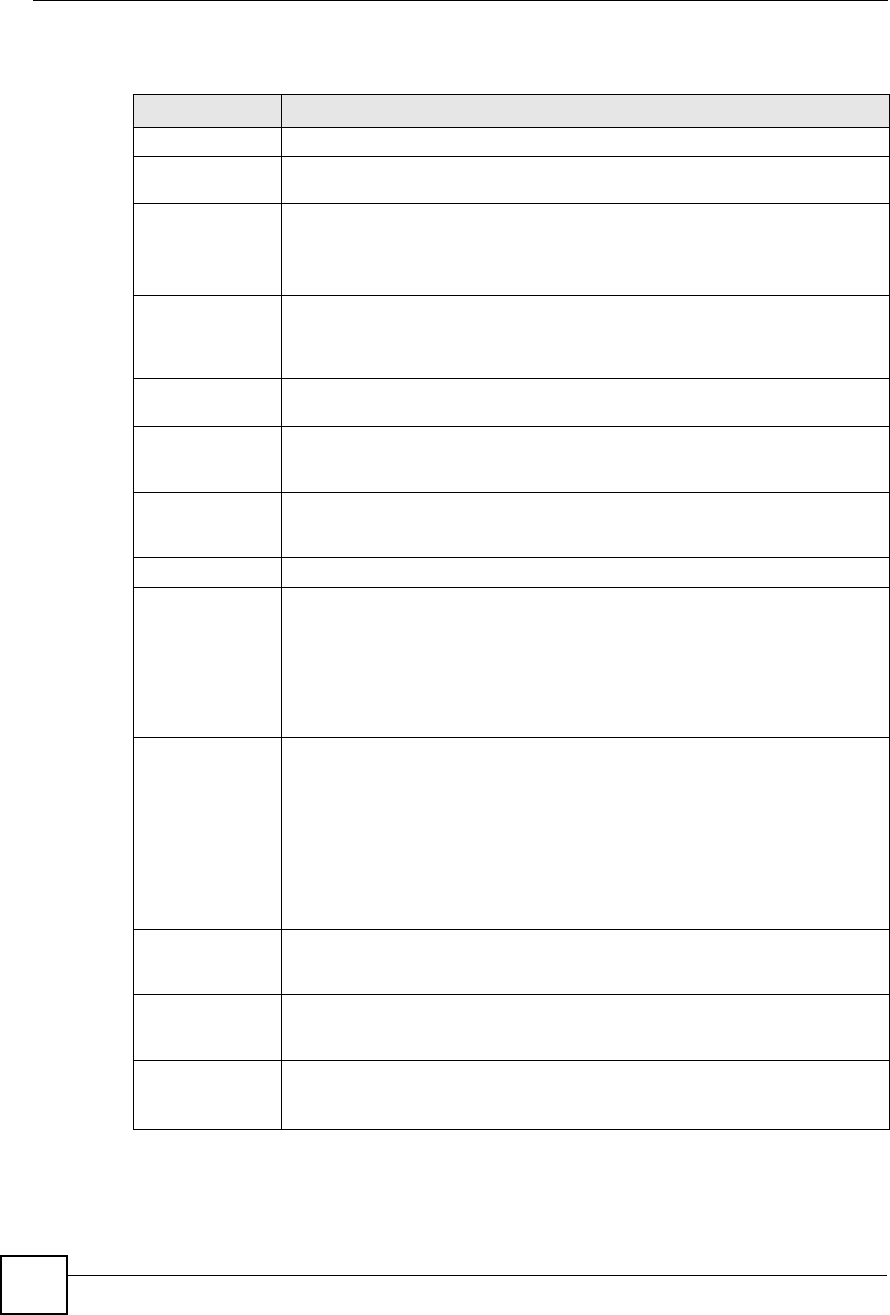
DTMF Mode Control how the ZyXEL Device handles the tones that your telephone makes
when you push its buttons. You should use the same mode your VoIP service
provider uses.
RFC 2833 - send the DTMF tones in RTP packets
PCM - send the DTMF tones in the voice data stream. This method works best
when you are using a codec that does not use compression (like G.711). Codecs
that use compression (like G.729) can distort the tones.
SIP INFO - send the DTMF tones in SIP messages
STUN
ActiveSelect this if all of the following conditions are satisfied.
#There is a NAT router between the ZyXEL Device and the SIP server.
#The NAT router is not a SIP ALG.
#Your VoIP service provider gave you an IP address or domain name for a
STUN server.
Otherwise, clear this field.
Server AddressEnter the IP address or domain name of the STUN server provided by your VoIP
service provider.
Server PortEnter the STUN server s listening port, if your VoIP service provider gave you one.
Otherwise, keep the default value.
Use NAT
ActiveSelect this if you want the ZyXEL Device to send SIP traffic to a specific NAT
router. You must also configure the NAT router to forward traffic with the specified
port to the ZyXEL Device. This eliminates the need for STUN or a SIP ALG.
Server AddressEnter the public IP address or domain name of the NAT router.
Server PortEnter the port number that your SIP sessions use with the public IP address of the
NAT router.
Outbound Proxy
ActiveSelect this if your VoIP service provider has a SIP outbound server to handle voice
calls. This allows the ZyXEL Device to work with any type of NAT router and
eliminates the need for STUN or a SIP ALG. Turn off any SIP ALG on a NAT router
in front of the ZyXEL Device to keep it from retranslating the IP address (since this
is already handled by the outbound proxy server).
Server AddressEnter the IP address or domain name of the SIP outbound proxy server.
Server PortEnter the SIP outbound proxy server s listening port, if your VoIP service provider
gave you one. Otherwise, keep the default value.
NAT Keep Alive
ActiveSelect this to stop NAT routers between the ZyXEL Device and SIP server (a SIP
proxy server or outbound proxy server) from dropping the SIP session. The ZyXEL
Device does this by sending SIP notify messages to the SIP server based on the
specified interval.
Keep Alive with
SIP Proxy
Select this if the SIP server is a SIP proxy server.
Keep Alive with
Outbound Proxy
Select this if the SIP server is an outbound proxy server. You must enable
Outbound Proxy to use this.
Keep Alive
Interval
Enter how often (in seconds) the ZyXEL Device should send SIP notify messages
to the SIP server.
MWI (Message
Waiting
Indication)
Table 60 VoIP > SIP > SIP Settings > Advanced
LABEL DESCRIPTION
Chapter 12SIP
MAX-200HW2 Series User s Guide
162
12.2.3 SIP QoS Screen
Use this screen to maintain ToS and VLAN settings for the ZyXEL Device. To access this
screen, click VoIP > SIP > QoS.
EnableSelect this if you want to hear a waiting (beeping) dial tone on your phone when
you have at least one voice message. Your VoIP service provider must support
this feature.
Expiration TimeKeep the default value, unless your VoIP service provider tells you to change it.
Enter the number of seconds the SIP server should provide the message waiting
service each time the ZyXEL Device subscribes to the service. Before this time
passes, the ZyXEL Device automatically subscribes again.
Fax OptionThis field controls how the ZyXEL Device handles fax messages.
G.711 Fax
Passthrough
Select this if the ZyXEL Device should use G.711 to send fax messages. The peer
devices must also use G.711.
T.38 Fax RelaySelect this if the ZyXEL Device should send fax messages as UDP or TCP/IP
packets through IP networks. This provides better quality, but it may have inter-
operability problems. The peer devices must also use T.38.
Call Forward
Call Forward
Table
Select which call forwarding table you want the ZyXEL Device to use for incoming
calls. You set up these tables in VoIP > Phone Book > Incoming Call Policy.
Caller Ringing
EnableCheck this box if you want people to hear a customized recording when they call
you.
Caller Ringing
Tone
Select the tone you want people to hear when they call you. See Section 12.1.11
on page 155 for information on how to record these tones.
On Hold
EnableCheck this box if you want people to hear a customized recording when you put
them on hold.
On Hold ToneSelect the tone you want people to hear when you put them on hold. See Section
12.1.11 on page 155 for information on how to record these tones.
<BackClick this to return to the SIP Settings screen without saving your changes.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Table 60 VoIP > SIP > SIP Settings > Advanced
LABEL DESCRIPTION
Chapter 12SIP
MAX-200HW2 Series User s Guide 163
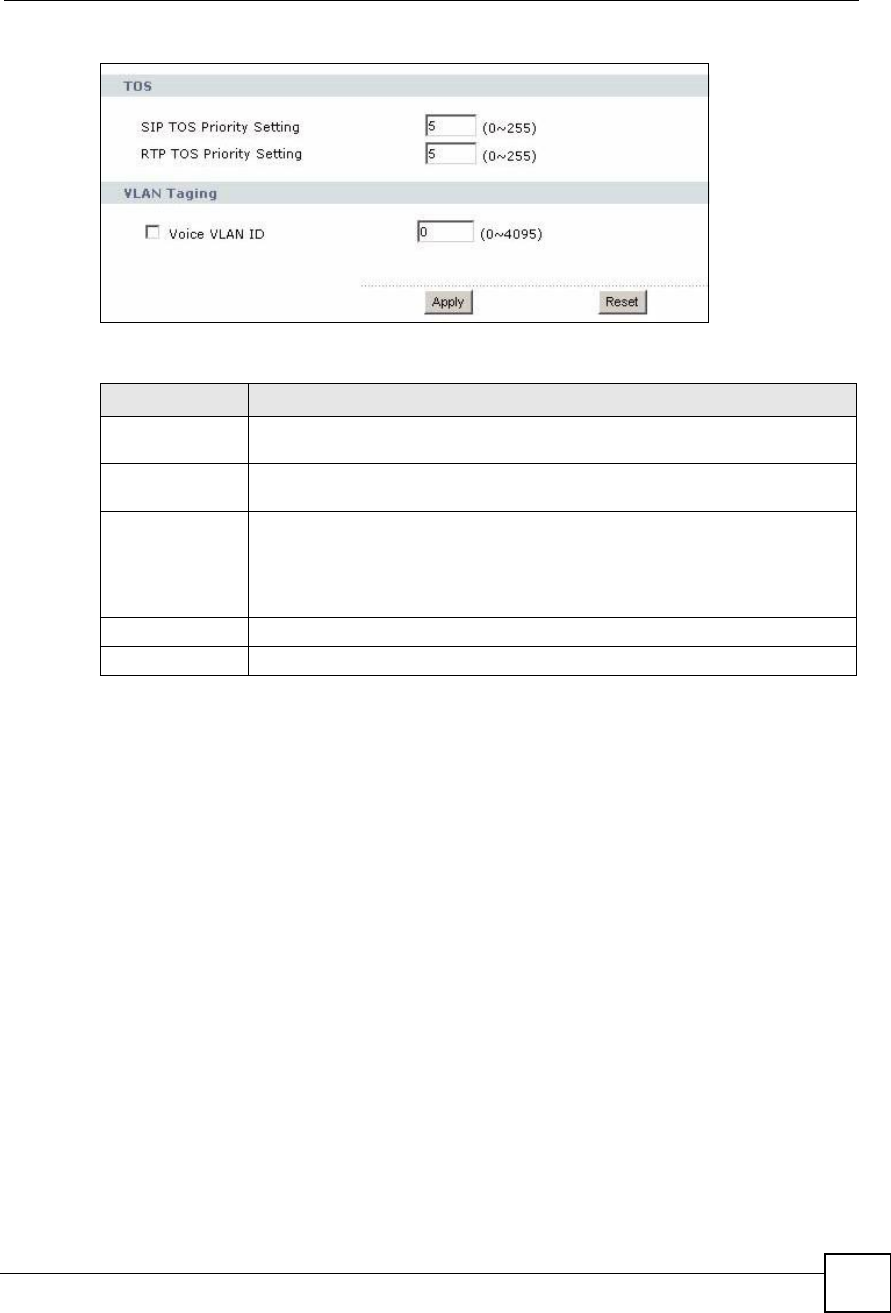
Figure 106 VoIP > SIP > QoS
Each field is described in the following table.
Table 61 VoIP > SIP > QoS
LABEL DESCRIPTION
SIP TOS Priority
Setting
Enter the priority for SIP voice transmissions. The ZyXEL Device creates Type of
Service priority tags with this priority to voice traffic that it transmits.
RTP TOS Priority
Setting
Enter the priority for RTP voice transmissions. The ZyXEL Device creates Type of
Service priority tags with this priority to RTP traffic that it transmits.
Voice VLAN IDSelect this if the ZyXEL Device has to be a member of a VLAN to communicate
with the SIP server. Ask your network administrator, if you are not sure. Enter the
VLAN ID provided by your network administrator in the field on the right. Your LAN
and gateway must be configured to use VLAN tags.
Otherwise, clear this field.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.

Chapter 12SIP
MAX-200HW2 Series User s Guide
164

MAX-200HW2 Series User s Guide 165
CHAPTER 13
Phone
Use these screens to configure the phone you use to make phone calls with the ZyXEL Device.
13.1 Phone Overview
You can configure the volume, echo cancellation, VAD settings and custom tones for the
phone port on the ZyXEL Device. You can also select which SIP account to use for making
outgoing calls.
13.1.1 Voice Activity Detection/Silence Suppression/Comfort Noise
Voice Activity Detection (VAD) detects whether or not speech is present. This lets the ZyXEL
Device reduce the bandwidth that a call uses by not transmitting "silent packets# when you are
not speaking.
When using VAD, the ZyXEL Device generates comfort noise when the other party is not
speaking. The comfort noise lets you know that the line is still connected as total silence could
easily be mistaken for a lost connection.
13.1.2 Echo Cancellation
G.168 is an ITU-T standard for eliminating the echo caused by the sound of your voice
reverberating in the telephone receiver while you talk.
13.1.3 Supplementary Phone Services Overview
Supplementary services such as call hold, call waiting, call transfer, etc. are generally
available from your VoIP service provider. The ZyXEL Device supports the following
services:
Call Hold
Call Waiting
Making a Second Call
Call Transfer
Call Forwarding
Three-Way Conference
Internal Calls
Caller ID
CLIP (Calling Line Identification Presentation)
Chapter 13Phone
MAX-200HW2 Series User s Guide
166
CLIR (Calling Line Identification Restriction)
To take full advantage of the supplementary phone services available though
the ZyXEL Device's phone port, you may need to subscribe to the services
from your VoIP service provider.
13.1.3.1 The Flash Key
Flashing means to press the hook for a short period of time (a few hundred milliseconds)
before releasing it. On newer telephones, there should be a "flash" key (button) that generates
the signal electronically. If the flash key is not available, you can tap (press and immediately
release) the hook by hand to achieve the same effect. However, using the flash key is preferred
since the timing is much more precise. The ZyXEL Device may interpret manual tapping as
hanging up if the duration is too long
You can invoke all the supplementary services by using the flash key.
13.1.3.2 Europe Type Supplementary Phone Services
This section describes how to use supplementary phone services with the Europe TypeCall
Service Mode. Commands for supplementary services are listed in the table below.
After pressing the flash key, if you do not issue the sub-command before the default sub-
command timeout (2 seconds) expires or issue an invalid sub-command, the current operation
will be aborted.
13.1.3.2.1 European Call Hold
Call hold allows you to put a call (A) on hold by pressing the flash key.
If you have another call, press the flash key and then "2# to switch back and forth between
caller A and B by putting either one on hold.
Press the flash key and then "0# to disconnect the call presently on hold and keep the current
call on line.
Table 62 European Type Flash Key Commands
COMMAND SUB-COMMAND DESCRIPTION
Flash Put a current call on hold to place a second call.
Switch back to the call (if there is no second call).
Flash0Drop the call presently on hold or reject an incoming call which is
waiting for answer.
Flash1Disconnect the current phone connection and answer the
incoming call or resume with caller presently on hold.
Flash21. Switch back and forth between two calls.
2. Put a current call on hold to answer an incoming call.
3. Separate the current three-way conference call into two
individual calls (one is on-line, the other is on hold).
Flash3Create three-way conference connection.
Flash *98#Transfer the call to another phone.

Chapter 13Phone
MAX-200HW2 Series User s Guide 167
Press the flash key and then "1# to disconnect the current call and resume the call on hold.
If you hang up the phone but a caller is still on hold, there will be a remind ring.
13.1.3.2.2 European Call Waiting
This allows you to place a call on hold while you answer another incoming call on the same
telephone (directory) number.
If there is a second call to a telephone number, you will hear a call waiting tone. Take one of
the following actions.
Reject the second call.
Press the flash key and then press "0#.
Disconnect the first call and answer the second call.
Either press the flash key and press "1#, or just hang up the phone and then answer the
phone after it rings.
Put the first call on hold and answer the second call.
Press the flash key and then "2#.
13.1.3.2.3 European Call Transfer
Do the following to transfer an incoming call (that you have answered) to another phone.
1Press the flash key to put the caller on hold.
2When you hear the dial tone, dial "*98## followed by the number to which you want to
transfer the call. to operate the Intercom.
3After you hear the ring signal or the second party answers it, hang up the phone.
13.1.3.2.4 European Three-Way Conference
Use the following steps to make three-way conference calls.
1When you are on the phone talking to someone, place the flash key to put the caller on
hold and get a dial tone.
2Dial a phone number directly to make another call.
3When the second call is answered, press the flash key and press "3# to create a three-way
conversation.
4Hang up the phone to drop the connection.
5If you want to separate the activated three-way conference into two individual
connections (one is on-line, the other is on hold), press the flash key and press "2#.
13.1.3.3 USA Type Supplementary Services
This section describes how to use supplementary phone services with the USA TypeCall
Service Mode. Commands for supplementary services are listed in the table below.
Chapter 13Phone
MAX-200HW2 Series User s Guide
168
After pressing the flash key, if you do not issue the sub-command before the default sub-
command timeout (2 seconds) expires or issue an invalid sub-command, the current operation
will be aborted.
13.1.3.3.1 USA Call Hold
Call hold allows you to put a call (A) on hold by pressing the flash key.
If you have another call, press the flash key to switch back and forth between caller A and B
by putting either one on hold.
If you hang up the phone but a caller is still on hold, there will be a remind ring.
13.1.3.3.2 USA Call Waiting
This allows you to place a call on hold while you answer another incoming call on the same
telephone (directory) number.
If there is a second call to your telephone number, you will hear a call waiting tone.
Press the flash key to put the first call on hold and answer the second call.
13.1.3.3.3 USA Call Transfer
Do the following to transfer an incoming call (that you have answered) to another phone.
1Press the flash key to put the caller on hold.
2When you hear the dial tone, dial "*98## followed by the number to which you want to
transfer the call. to operate the Intercom.
3After you hear the ring signal or the second party answers it, hang up the phone.
13.1.3.3.4 USA Three-Way Conference
Use the following steps to make three-way conference calls.
1When you are on the phone talking to someone, place the flash key to put the caller on
hold and get a dial tone.
2Dial a phone number directly to make another call.
3When the second call is answered, press the flash key, wait for the sub-command tone
and press "3# to create a three-way conversation.
4Hang up the phone to drop the connection.
5If you want to separate the activated three-way conference into two individual
connections (one is on-line, the other is on hold), press the flash key, wait for the sub-
command tone and press "2#.
Table 63 USA Type Flash Key Commands
COMMAND SUB-COMMAND DESCRIPTION
Flash Put a current call on hold to place a second call. After the second
call is successful, press the flash key again to have a three-way
conference call.
Put a current call on hold to answer an incoming call.
Flash *98#Transfer the call to another phone.
Chapter 13Phone
MAX-200HW2 Series User s Guide 169
13.2 Phone Screens
13.2.1 Analog Phone Screen
Use this screen to control which SIP accounts and PSTN line each phone uses. To access this
screen, click VoIP > Phone > Analog Phone.
Figure 107 VoIP > Phone > Analog Phone
Each field is described in the following table.
Table 64 VoIP > Phone > Analog Phone
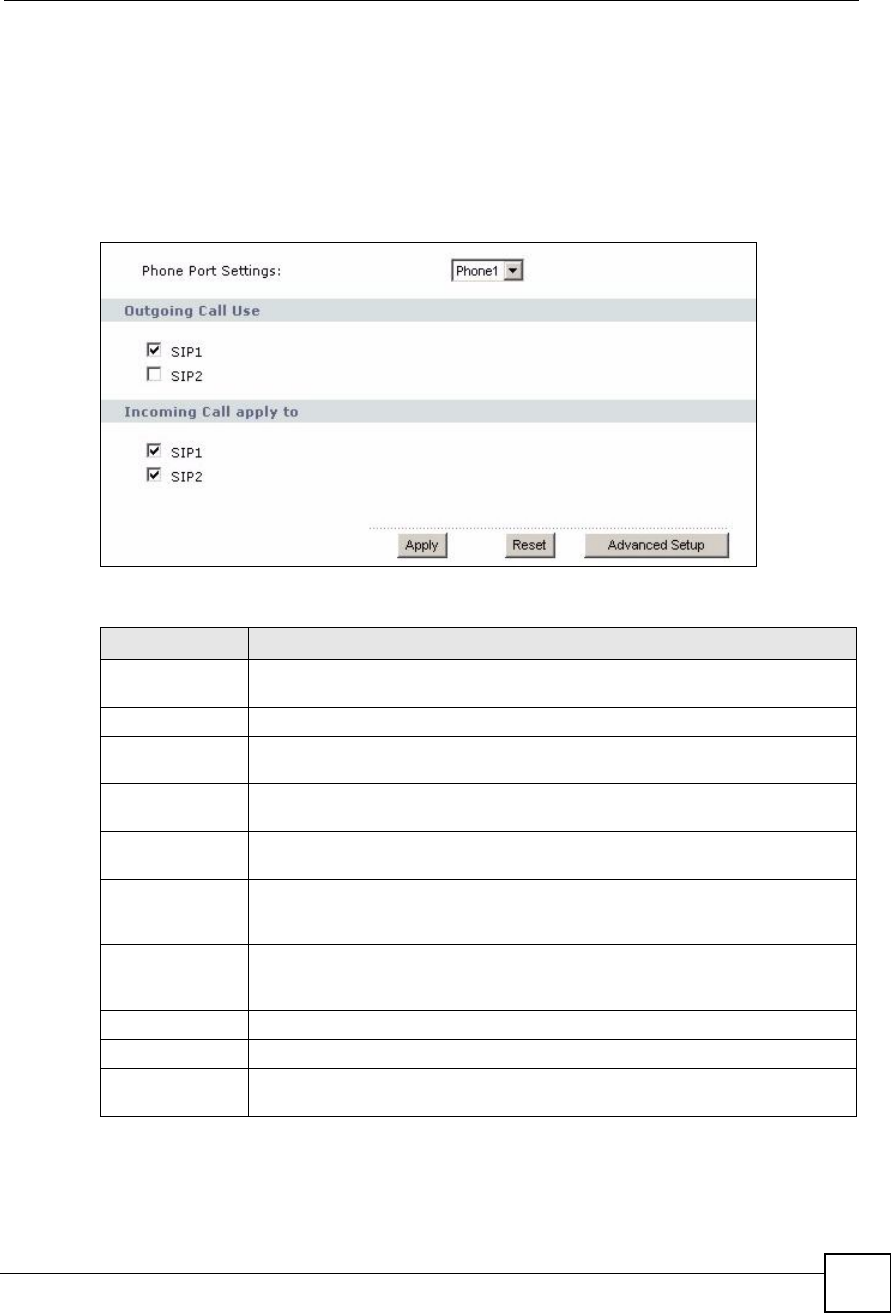
LABEL DESCRIPTION
Phone Port
Settings
Select the phone port you want to see in this screen. If you change this field, the
screen automatically refreshes.
Outgoing Call Use
SIP1Select this if you want this phone port to use the SIP1 account when it makes
calls. If you select both SIP accounts, the ZyXEL Device tries to use SIP2 first.
SIP2Select this if you want this phone port to use the SIP2 account when it makes
calls. If you select both SIP accounts, the ZyXEL Device tries to use SIP2 first.
Incoming Call
apply to
SIP1Select this if you want to receive phone calls for the SIP1 account on this phone
port. If you select more than one source for incoming calls, there is no way to
distinguish between them when you receive phone calls.
SIP2Select this if you want to receive phone calls for the SIP2 account on this phone
port. If you select more than one source for incoming calls, there is no way to
distinguish between them when you receive phone calls.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Advanced Setup Click this to edit the advanced settings for this phone port. The Advanced Analog
Phone Setup screen appears.
Chapter 13Phone
MAX-200HW2 Series User s Guide
170
13.2.2 Advanced Analog Phone Setup Screen
Use this screen to edit advanced settings for each phone port. To access this screen, click
Advanced Setup in VoIP > Phone > Analog Phone.
Figure 108 VoIP > Phone > Analog Phone > Advanced
Each field is described in the following table.
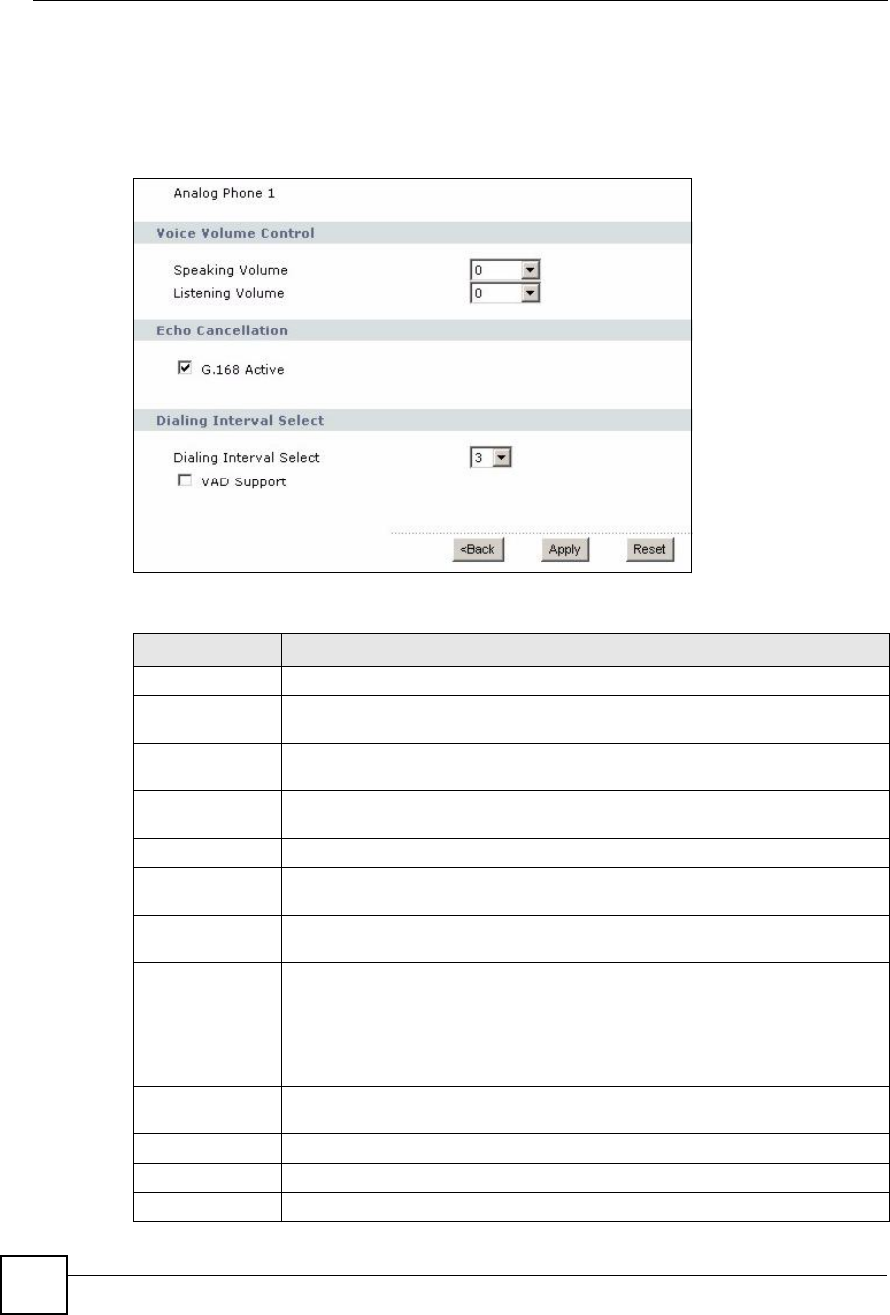
Table 65 VoIP > Phone > Analog Phone > Advanced
LABEL DESCRIPTION
Analog Phone This field displays the phone port you see in this screen.
Voice Volume
Control
Speaking VolumeEnter the loudness that the ZyXEL Device uses for speech that it sends to the
peer device. -1 is the quietest, and 1 is the loudest.
Listening VolumeEnter the loudness that the ZyXEL Device uses for speech that it receives from
the peer device. -1 is the quietest, and 1 is the loudest.
Echo Cancellation
G.168 ActiveSelect this if you want to eliminate the echo caused by the sound of your voice
reverberating in the telephone receiver while you talk.
Dialing Interval
Select
Dialing Interval
Select
Enter the number of seconds the ZyXEL Device should wait after you stop dialing
numbers before it makes the phone call. The value depends on how quickly you
dial phone numbers.
If you select Active Immediate Dial in VoIP > Phone > Common, you can press
the pound key (#) to tell the ZyXEL Device to make the phone call immediately,
regardless of this setting.
VAD SupportSelect this if the ZyXEL Device should stop transmitting when you are not
speaking. This reduces the bandwidth the ZyXEL Device uses.
<BackClick this to return to the Analog Phone screen without saving your changes.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its last-saved value.
Chapter 13Phone
MAX-200HW2 Series User s Guide 171
13.2.3 Common Phone Settings Screen
Use this screen to activate and deactivate immediate dialing. To access this screen, click VoIP
> Phone > Common.
Figure 109 VoIP > Phone > Common
Each field is described in the following table.
13.2.4 Phone Region Screen
Use this screen to maintain settings that often depend on which region of the world the ZyXEL
Device is in. To access this screen, click VoIP > Phone > Region.
Figure 110 VoIP > Phone > Region
Each field is described in the following table.
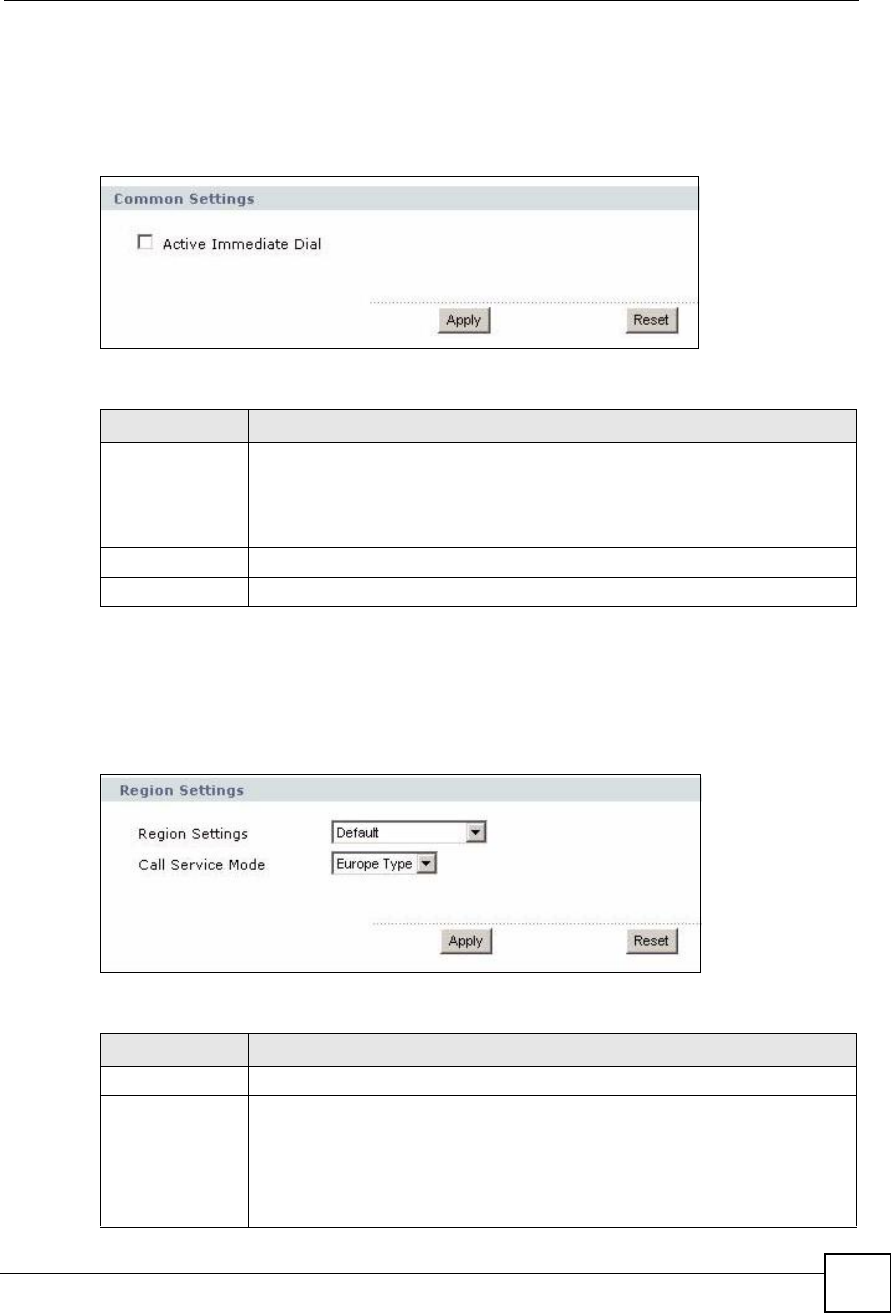
Table 66 VoIP > Phone > Common
LABEL DESCRIPTION
Active Immediate
Dial
Select this if you want to use the pound key (#) to tell the ZyXEL Device to make
the phone call immediately, instead of waiting the number of seconds you selected
in the Dialing Interval Select in VoIP > Phone > Analog Phone.
If you select this, dial the phone number, and then press the pound key if you do
not want to wait. The ZyXEL Device makes the call immediately.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Table 67 VoIP > Phone > Region
LABEL DESCRIPTION
Region Settings Select the place in which the ZyXEL Device is located. Do not select Default.
Call Service Mode Select the mode for supplementary phone services (call hold, call waiting, call
transfer and three-way conference calls) that your VoIP service provider supports.
Europe Type - use supplementary phone services in European mode
USA Type - use supplementary phone services American mode
You might have to subscribe to these services to use them. Contact your VoIP
service provider.

Chapter 13Phone
MAX-200HW2 Series User s Guide
172
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its last-saved value.
Table 67 VoIP > Phone > Region
LABEL DESCRIPTION

MAX-200HW2 Series User s Guide 173
CHAPTER 14
Phone Book
Use these screens to maintain call-forwarding rules and speed-dial settings.
14.1 Phone Book Overview
Speed dial provides shortcuts for dialing frequently used (VoIP) phone numbers. It is also
required if you want to make peer-to-peer calls. In peer-to-peer calls, you call another VoIP
device directly without going through a SIP server. In the ZyXEL Device, you must set up a
speed dial entry in the phone book in order to do this. Select Non-Proxy (Use IP or URL) in
the Type column and enter the callee!s IP address or domain name. The ZyXEL Device sends
SIP INVITE requests to the peer VoIP device when you use the speed dial entry.
You do not need to configure a SIP account in order to make a peer-to-peer VoIP call.
14.2 Phone Book Screens
14.2.1 Incoming Call Policy Screen
Use this screen to maintain rules for handling incoming calls. You can block, redirect, or
accept them. To access this screen, click VoIP > Phone Book > Incoming Call Policy.
Chapter 14Phone Book
MAX-200HW2 Series User s Guide
174
Figure 111 VoIP > Phone Book > Incoming Call Policy
You can create two sets of call-forwarding rules. Each one is stored in a call-forwarding table.
Each field is described in the following table.
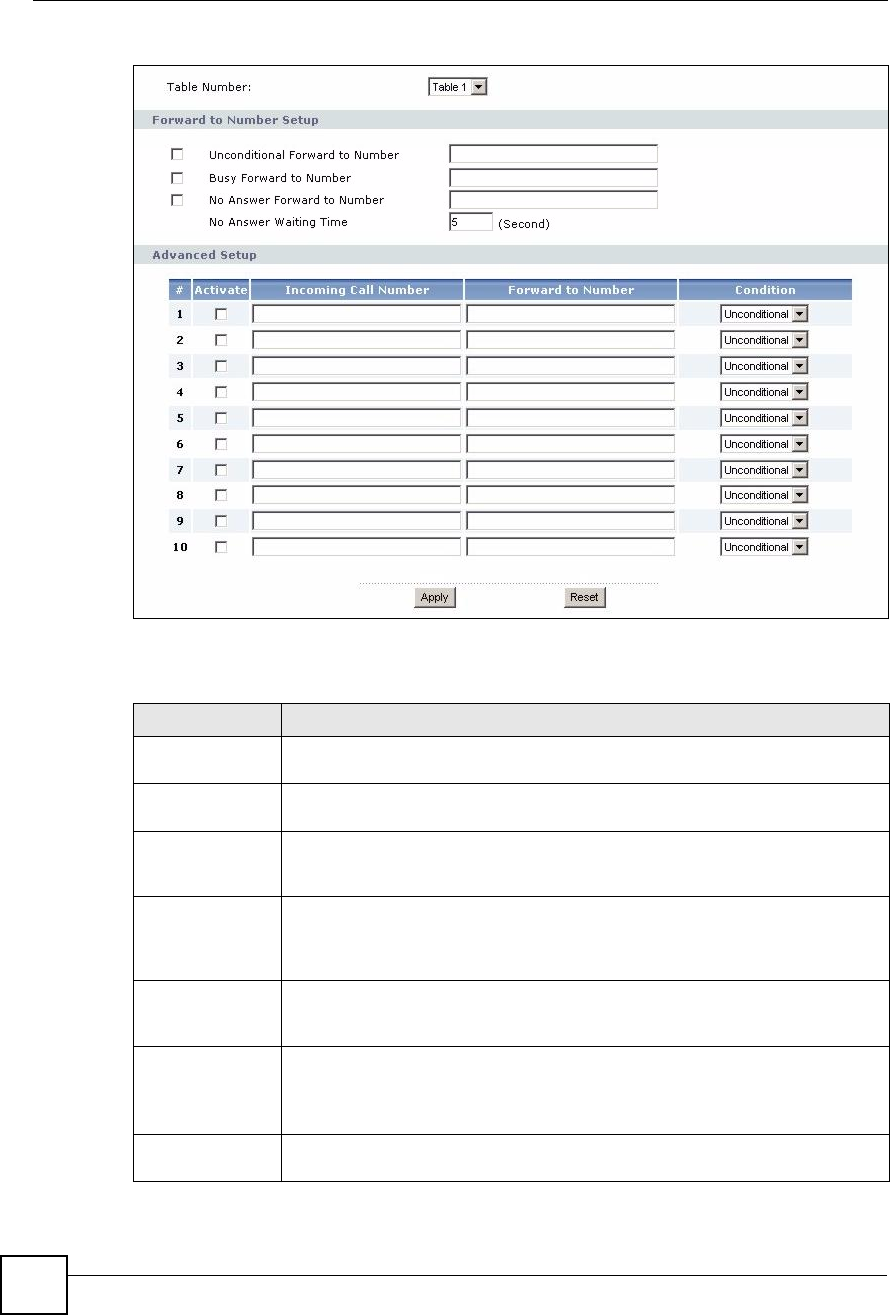
Table 68 VoIP > Phone Book > Incoming Call Policy
LABEL DESCRIPTION
Table Number Select the call-forwarding table you want to see in this screen. If you change this
field, the screen automatically refreshes.
Forward to
Number Setup
The ZyXEL Device checks these rules, in the order in which they appear, after it
checks the rules in the Advanced Setup section.
Unconditional
Forward to
Number
Select this if you want the ZyXEL Device to forward all incoming calls to the
specified phone number, regardless of other rules in the Forward to Number
section. Specify the phone number in the field on the right.
Busy Forward to
Number
Select this if you want the ZyXEL Device to forward incoming calls to the specified
phone number if the phone port is busy. Specify the phone number in the field on
the right. If you have call waiting, the incoming call is forwarded to the specified
phone number if you reject or ignore the second incoming call.
No Answer
Forward to
Number
Select this if you want the ZyXEL Device to forward incoming calls to the specified
phone number if the call is unanswered. (See No Answer Waiting Time.) Specify
the phone number in the field on the right.
No Answer
Waiting Time
This field is used by the No Answer Forward to Number feature and No Answer
conditions below.
Enter the number of seconds the ZyXEL Device should wait for you to answer an
incoming call before it considers the call is unanswered.
Advanced SetupThe ZyXEL Device checks these rules before it checks the rules in the Forward to
Number section.

Chapter 14Phone Book
MAX-200HW2 Series User s Guide 175
14.2.2 Speed Dial Screen
You have to create speed-dial entries if you want to make peer-to-peer calls or call SIP
numbers that use letters. You can also create speed-dial entries for frequently-used SIP phone
numbers. Use this screen to add, edit, or remove speed-dial entries. To access this screen, click
VoIP > Phone Book > Speed Dial.
#This field is a sequential value, and it is not associated with a specific rule. The
sequence is important, however. The ZyXEL Device checks each rule in order,
and it only follows the first one that applies.
ActivateSelect this to enable this rule. Clear this to disable this rule.
Incoming Call
Number
Enter the phone number to which this rule applies.
Forward to
Number
Enter the phone number to which you want to forward incoming calls from the
Incoming Call Number. You may leave this field blank, depending on the
Condition.
ConditionSelect the situations in which you want to forward incoming calls from the
Incoming Call Number, or select an alternative action.
Unconditional - The ZyXEL Device immediately forwards any calls from the
Incoming Call Number to the Forward to Number.
Busy - The ZyXEL Device forwards any calls from the Incoming Call Number to
the Forward to Number when your SIP account already has a call connected.
No Answer - The ZyXEL Device forwards any calls from the Incoming Call
Number to the Forward to Number when the call is unanswered. (See No
Answer Waiting Time.)
Block - The ZyXEL Device rejects calls from the Incoming Call Number.
Accept - The ZyXEL Device allows calls from the Incoming Call Number. You
might create a rule with this condition if you do not want incoming calls from
someone to be forwarded by rules in the Forward to Number section.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its last-saved value.
Table 68 VoIP > Phone Book > Incoming Call Policy
LABEL DESCRIPTION
Chapter 14Phone Book
MAX-200HW2 Series User s Guide
176
Figure 112 VoIP > Phone Book > Speed Dial
Each field is described in the following table.
Table 69 VoIP > Phone Book > Speed Dial
LABEL DESCRIPTION
Speed Dial Use this section to create or edit speed-dial entries.
Speed Dial Select the speed-dial number you want to use for this phone number.
NumberEnter the SIP number you want the ZyXEL Device to call when you dial the speed-
dial number.
NameEnter a name to identify the party you call when you dial the speed-dial number.
You can use up to 127 printable ASCII characters.
TypeSelect Use Proxy if you want to use one of your SIP accounts to call this phone
number.
Select Non-Proxy (Use IP or URL) if you want to use a different SIP server or if
you want to make a peer-to-peer call. In this case, enter the IP address or domain
name of the SIP server or the other party in the field below.
AddClick this to use the information in the Speed Dial section to update the Speed
Dial Phone Book section.
Speed Dial Phone
Book
Use this section to look at all the speed-dial entries and to erase them.
Speed DialThis field displays the speed-dial number you should dial to use this entry. You
should dial the numbers the way they appear in the screen.
NumberThis field displays the SIP number the ZyXEL Device calls when you dial the
speed-dial number.
NameThis field displays the name of the party you call when you dial the speed-dial
number.
DestinationThis field is blank, if the speed-dial entry uses one of your SIP accounts.
Otherwise, this field shows the IP address or domain name of the SIP server or
other party. (This field corresponds with the Type field in the Speed Dial section.)

Chapter 14Phone Book
MAX-200HW2 Series User s Guide 177
ModifyUse this field to edit or erase the speed-dial entry.
Click the Edit icon to copy the information for this speed-dial entry into the Speed
Dial section, where you can change it.
Click the Remove icon to erase this speed-dial entry.
Clear Click this to erase all the speed-dial entries.
Reset Click this to set every field in this screen to its last-saved value.
Table 69 VoIP > Phone Book > Speed Dial
LABEL DESCRIPTION

Chapter 14Phone Book
MAX-200HW2 Series User s Guide
178

MAX-200HW2 Series User s Guide 179
CHAPTER 15
Firewall
Use these screens to enable, configure and disable the firewall that protects your ZyXEL
Device and your LAN from unwanted or malicious traffic.
15.1 Firewall Overview
Originally, the term firewall referred to a construction technique designed to prevent the
spread of fire from one room to another. The networking term "firewall" is a system or group
of systems that enforces an access-control policy between two networks. It may also be
defined as a mechanism used to protect a trusted network from an untrusted network. Of
course, firewalls cannot solve every security problem. A firewall is one of the mechanisms
used to establish a network security perimeter in support of a network security policy. It should
never be the only mechanism or method employed. For a firewall to guard effectively, you
must design and deploy it appropriately. This requires integrating the firewall into a broad
information-security policy. In addition, specific policies must be implemented within the
firewall itself.
15.1.1 Stateful Inspection Firewall.
Stateful inspection firewalls restrict access by screening data packets against defined access
rules. They make access control decisions based on IP address and protocol. They also
"inspect" the session data to assure the integrity of the connection and to adapt to dynamic
protocols. These firewalls generally provide the best speed and transparency; however, they
may lack the granular application level access control or caching that some proxies support.
Firewalls, of one type or another, have become an integral part of standard security solutions
for enterprises.
15.1.2 About the ZyXEL Device Firewall
The ZyXEL Device firewall is a stateful inspection firewall and is designed to protect against
Denial of Service attacks when activated. The ZyXEL Device's purpose is to allow a private
Local Area Network (LAN) to be securely connected to the Internet. The ZyXEL Device can
be used to prevent theft, destruction and modification of data, as well as log events, which may
be important to the security of your network.
The ZyXEL Device is installed between the LAN and a WiMAX base station connecting to
the Internet. This allows it to act as a secure gateway for all data passing between the Internet
and the LAN.
Chapter 15Firewall
MAX-200HW2 Series User s Guide
180
The ZyXEL Device has one Ethernet (LAN) port. The LAN (Local Area Network) port
attaches to a network of computers, which needs security from the outside world. These
computers will have access to Internet services such as e-mail, FTP and the World Wide Web.
However, "inbound access# is not allowed (by default) unless the remote host is authorized to
use a specific service.
15.1.3 Guidelines For Enhancing Security With Your Firewall
1Change the default password via web configurator.
2Think about access control before you connect to the network in any way.
3Limit who can access your router.
4Don't enable any local service (such as telnet or FTP) that you don't use. Any enabled
service could present a potential security risk. A determined hacker might be able to find
creative ways to misuse the enabled services to access the firewall or the network.
5For local services that are enabled, protect against misuse. Protect by configuring the
services to communicate only with specific peers, and protect by configuring rules to
block packets for the services at specific interfaces.
6Protect against IP spoofing by making sure the firewall is active.
7Keep the firewall in a secured (locked) room.
15.1.4 The Firewall, NAT and Remote Management
Figure 113 Firewall Rule Directions
15.1.4.1 LAN-to-WAN rules
LAN-to-WAN rules are local network to Internet firewall rules. The default is to forward all
traffic from your local network to the Internet.
You can block certain LAN-to-WAN traffic in the Services screen (click the Services tab). All
services displayed in the Blocked Services list box are LAN-to-WAN firewall rules that block
those services originating from the LAN.
Blocked LAN-to-WAN packets are considered alerts. Alerts are "higher priority logs# that
include system errors, attacks and attempted access to blocked web sites. Alerts appear in red
in the View Log screen. You may choose to have alerts e-mailed immediately in the Log
Settings screen.
Chapter 15Firewall
MAX-200HW2 Series User s Guide 181
LAN-to-LAN/ZyXEL Device means the LAN to the ZyXEL Device LAN interface. This is
always allowed, as this is how you manage the ZyXEL Device from your local computer.
15.1.4.2 WAN-to-LAN rules
WAN-to-LAN rules are Internet to your local network firewall rules. The default is to block
all traffic from the Internet to your local network.
How can you forward certain WAN to LAN traffic? You may allow traffic originating from the
WAN to be forwarded to the LAN by:
Configuring NAT port forwarding rules.
Configuring One-to-One and Many-One-to-One NAT mapping rules in the SMT NAT
menus.
Configuring WAN or LAN & WAN access for services in the Remote Management
screens or SMT menus. When you allow remote management from the WAN, you are
actually configuring WAN-to-WAN/ZyXEL Device firewall rules. WAN-to-WAN/ZyXEL
Device firewall rules are Internet to the ZyXEL Device WAN interface firewall rules. The
default is to block all such traffic. When you decide what WAN-to-LAN packets to log,
you are in fact deciding what WAN-to-LAN and WAN-to-WAN/ZyXEL Device packets
to log.
Forwarded WAN-to-LAN packets are not considered alerts.
15.2 Triangle Route
When the firewall is on, your ZyXEL Device acts as a secure gateway between your LAN and
the Internet. In an ideal network topology, all incoming and outgoing network traffic passes
through the ZyXEL Device to protect your LAN against attacks.
Figure 114 Ideal Firewall Setup
15.2.1 The "Triangle Route# Problem
A traffic route is a path for sending or receiving data packets between two Ethernet devices.
You may have more than one connection to the Internet (through one or more ISPs). If an
alternate gateway is on the LAN (and its IP address is in the same subnet as the ZyXEL
Device!s LAN IP address), the "triangle route# (also called asymmetrical route) problem may
occur. The steps below describe the "triangle route# problem.
1A computer on the LAN initiates a connection by sending out a SYN packet to a
receiving server on the WAN.
2The ZyXEL Device reroutes the SYN packet through Gateway Aon the LAN to the
WAN.
Chapter 15Firewall
MAX-200HW2 Series User s Guide
182
3The reply from the WAN goes directly to the computer on the LAN without going
through the ZyXEL Device.
As a result, the ZyXEL Device resets the connection, as the connection has not been
acknowledged.
Figure 115 !Triangle Route" Problem
15.2.2 Solving the "Triangle Route# Problem
If you have the ZyXEL Device allow triangle route sessions, traffic from the WAN can go
directly to a LAN computer without passing through the ZyXEL Device and its firewall
protection.
Another solution is to use IP alias. IP alias allows you to partition your network into logical
sections over the same Ethernet interface. Your ZyXEL Device supports up to three logical
LAN interfaces with the ZyXEL Device being the gateway for each logical network.
It!s like having multiple LAN networks that actually use the same physical cables and ports.
By putting your LAN and Gateway A in different subnets, all returning network traffic must
pass through the ZyXEL Device to your LAN. The following steps describe such a scenario.
1A computer on the LAN initiates a connection by sending a SYN packet to a receiving
server on the WAN.
2The ZyXEL Devicereroutes the packet to Gateway A, which is in Subnet 2.
3The reply from the WAN goes to the ZyXEL Device.
4The ZyXEL Device then sends it to the computer on the LAN in Subnet 1.
Figure 116 IP Alias
Chapter 15Firewall
MAX-200HW2 Series User s Guide 183
15.3 Firewall Screens
15.3.1 General Firewall Screen
Use this screen to configure the basic settings for your firewall. To access this screen, click
Security > Firewall > General.
Figure 117 Security > Firewall > General
Each field is described in the following table.
15.3.2 Firewall Services Screen
Use this screen to enable service blocking, to set up the date and time service blocking is
effective, and to maintain the list of services you want to block. To access this screen, click
Security > Firewall > Services.
Table 70 Security > Firewall > General
LABEL DESCRIPTION
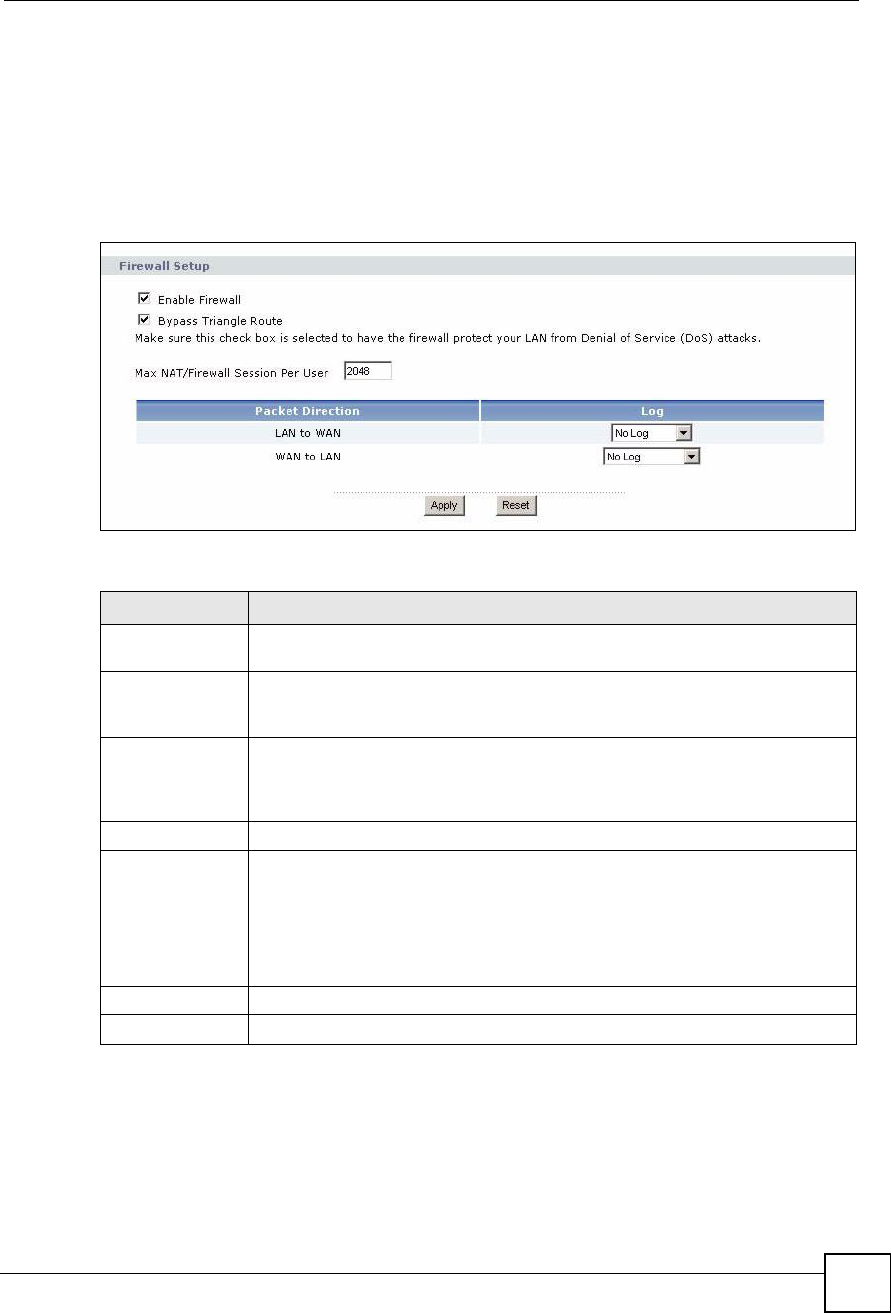
Enable Firewall Select this to activate the firewall. The ZyXEL Device controls access and protects
against Denial of Service (DoS) attacks when the firewall is activated.
Bypass Triangle
Route
Select this if you want to let some traffic from the WAN go directly to a computer in
the LAN without passing through the ZyXEL Device. See the appendices for more
information about triangle route topology.
Max NAT/Firewall
Session Per User
Select the maximum number of NAT rules and firewall rules the ZyXEL Device
enforces at one time. The ZyXEL Device automatically allocates memory for the
maximum number of rules, regardless of whether or not there is a rule to enforce.
This is the same number you enter in Network > NAT > General.
Packet Direction This field displays each direction that packets pass through the ZyXEL Device.
Log Select the situations in which you want to create log entries for firewall events.
No Log - do not create any log entries
Log Blocked - (LAN to WAN only) create log entries when packets are blocked
Log Forwarded - (WAN to LAN only) create log entries when packets are
forwarded
Log All - create log entries for every packet
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Chapter 15Firewall
MAX-200HW2 Series User s Guide
184
Figure 118 Security > Firewall > Services
Each field is described in the following table.
Table 71 Security > Firewall > Services
LABEL DESCRIPTION
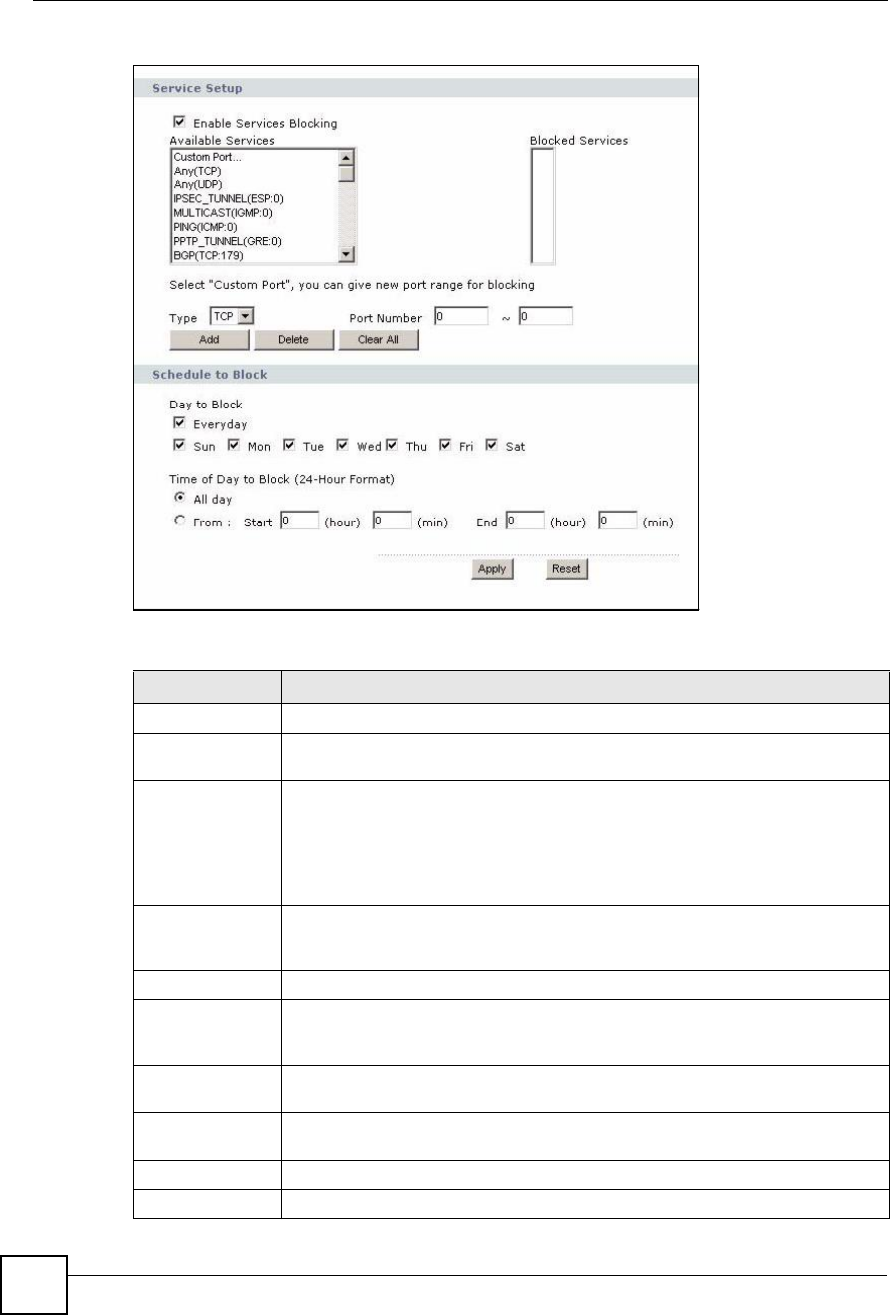
Service Setup
Enable Services
Blocking
Select this to activate service blocking. The Schedule to Block section controls
what days and what times service blocking is actually effective, however.
Available
Services
This is a list of pre-defined services (destination ports) you may prohibit your LAN
computers from using. Select the port you want to block, and click Add to add the
port to the Blocked Services field.
A custom port is a service that is not available in the pre-defined Available
Services list. You must define it using the Type and Port Number fields. See
Appendix F on page 333 for some examples of services.
Blocked Services This is a list of services (ports) that are inaccessible to computers on your LAN
when service blocking is effective. To remove a service from this list, select the
service, and click Delete.
Type Select TCP or UDP, based on which one the custom port uses.
Port Number Enter the range of port numbers that defines the service. For example, suppose
you want to define the Gnutella service. Select TCP type and enter a port range of
6345-6349.
Add Click this to add the selected service in Available Services to the Blocked
Services list.
Delete Select a service in the Blocked Services, and click this to remove the service
from the list.
Clear All Click this to remove all the services in the Blocked Services list.
Schedule to Block
Chapter 15Firewall
MAX-200HW2 Series User s Guide 185
Day to Block Select which days of the week you want the service blocking to be effective.
Time of Day to
Block
Select what time each day you want service blocking to be effective. Enter times in
24-hour format; for example, 3:00pm should be entered as 15:00.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Table 71 Security > Firewall > Services
LABEL DESCRIPTION

Chapter 15Firewall
MAX-200HW2 Series User s Guide
186

MAX-200HW2 Series User s Guide 187
CHAPTER 16
Certificates
This chapter gives background information about public-key certificates and explains how to
use the Certificates screens.
16.1 Certificates Overview
The ZyXEL Device can use certificates (also called digital IDs) to authenticate users.
Certificates are based on public-private key pairs. A certificate contains the certificate owner!s
identity and public key. Certificates provide a way to exchange public keys for use in
authentication.
A Certification Authority (CA) issues certificates and guarantees the identity of each
certificate owner. There are commercial certification authorities like CyberTrust or VeriSign
and government certification authorities. You can use the ZyXEL Device to generate
certification requests that contain identifying information and public keys and then send the
certification requests to a certification authority.
When using public-key cryptology for authentication, each host has two keys. One key is
public and can be made openly available. The other key is private and must be kept secure.
These keys work like a handwritten signature (in fact, certificates are often referred to as
"digital signatures#). Only you can write your signature exactly as it ought to look. When
people know what your signature ought to look like, they can verify whether something was
signed by you, or by someone else. In the same way, your private key "writes# your digital
signature and your public key allows people to verify whether data was signed by you, or by
someone else. This process works as follows.
1Tim wants to send a message to Jenny. He needs her to be sure that it comes from him,
and that the message content has not been altered by anyone else along the way. Tim
generates a public key pair (one public key and one private key).
2Tim keeps the private key and makes the public key openly available. This means that
anyone who receives a message seeming to come from Tim can read it and verify
whether it is really from him or not.
3Tim uses his private key to sign the message and sends it to Jenny.
4Jenny receives the message and uses Tim!s public key to verify it. Jenny knows that the
message is from Tim, and she knows that although other people may have been able to
read the message, no-one can have altered it (because they cannot re-sign the message
with Tim!s private key).
5Additionally, Jenny uses her own private key to sign a message and Tim uses Jenny!s
public key to verify the message.

Chapter 16Certificates
MAX-200HW2 Series User s Guide
188
The ZyXEL Device uses certificates based on public-key cryptology to authenticate users
attempting to establish a connection, not to encrypt the data that you send after establishing a
connection. The method used to secure the data that you send through an established
connection depends on the type of connection. For example, a VPN tunnel might use the triple
DES encryption algorithm.
The certification authority uses its private key to sign certificates. Anyone can then use the
certification authority!s public key to verify the certificates.
A certification path is the hierarchy of certification authority certificates that validate a
certificate. The ZyXEL Device does not trust a certificate if any certificate on its path has
expired or been revoked.
Certification authorities maintain directory servers with databases of valid and revoked
certificates. A directory of certificates that have been revoked before the scheduled expiration
is called a CRL (Certificate Revocation List). The ZyXEL Device can check a peer!s
certificate against a directory server!s list of revoked certificates. The framework of servers,
software, procedures and policies that handles keys is called PKI (public-key infrastructure).
16.1.1 Advantages of Certificates
Certificates offer the following benefits.
The ZyXEL Device only has to store the certificates of the certification authorities that
you decide to trust, no matter how many devices you need to authenticate.
Key distribution is simple and very secure since you can freely distribute public keys and
you never need to transmit private keys.
16.2 Self-signed Certificates
You can have the ZyXEL Device act as a certification authority and sign its own certificates.
16.3 Factory Default Certificate
The ZyXEL Device generates its own unique self-signed certificate when you first turn it on.
This certificate is referred to in the GUI as the factory default certificate.
16.3.1 Certificate File Formats
Any certificate that you want to import has to be in one of these file formats:
Binary X.509: This is an ITU-T recommendation that defines the formats for X.509
certificates.
PEM (Base-64) encoded X.509: This Privacy Enhanced Mail format uses lowercase
letters, uppercase letters and numerals to convert a binary X.509 certificate into a printable
form.
Chapter 16Certificates
MAX-200HW2 Series User s Guide 189
Binary PKCS#7: This is a standard that defines the general syntax for data (including
digital signatures) that may be encrypted. A PKCS #7 file is used to transfer a public key
certificate. The private key is not included. The ZyXEL Device currently allows the
importation of a PKS#7 file that contains a single certificate.
PEM (Base-64) encoded PKCS#7: This Privacy Enhanced Mail (PEM) format uses
lowercase letters, uppercase letters and numerals to convert a binary PKCS#7 certificate
into a printable form.
Be careful to not convert a binary file to text during the transfer process. It is
easy for this to occur since many programs use text files by default.
16.4 Certificate Configuration Screens Summary
This section summarizes how to manage certificates on the ZyXEL Device.
Use the My Certificate screens to generate and export self-signed certificates or certification
requests and import the ZyXEL Device!s CA-signed certificates.
Use the Trusted CAs screens to save CA certificates and trusted remote host certificates to the
ZyXEL Device. The ZyXEL Device will trust any valid certificate that you have imported as a
trusted certificate. It will also trust any valid certificate signed by any of the certificates that
you have imported as a trusted certificate.
16.5 Verifying a Certificate
Before you import a certificate into the ZyXEL Device, you should verify that you have the
correct certificate. This is especially true of trusted certificates since the ZyXEL Device also
trusts any valid certificate signed by any of the imported trusted certificates.
16.5.1 Checking the Fingerprint of a Certificate on Your Computer
A certificate!s fingerprints are message digests calculated using the MD5 or SHA1 algorithms.
The following procedure describes how to check a certificate!s fingerprint to verify that you
have the actual certificate.
1Browse to where you have the certificate saved on your computer.
2Make sure that the certificate has a ".cer# or ".crt# file name extension.
Figure 119 Remote Host Certificates
Chapter 16Certificates
MAX-200HW2 Series User s Guide
190
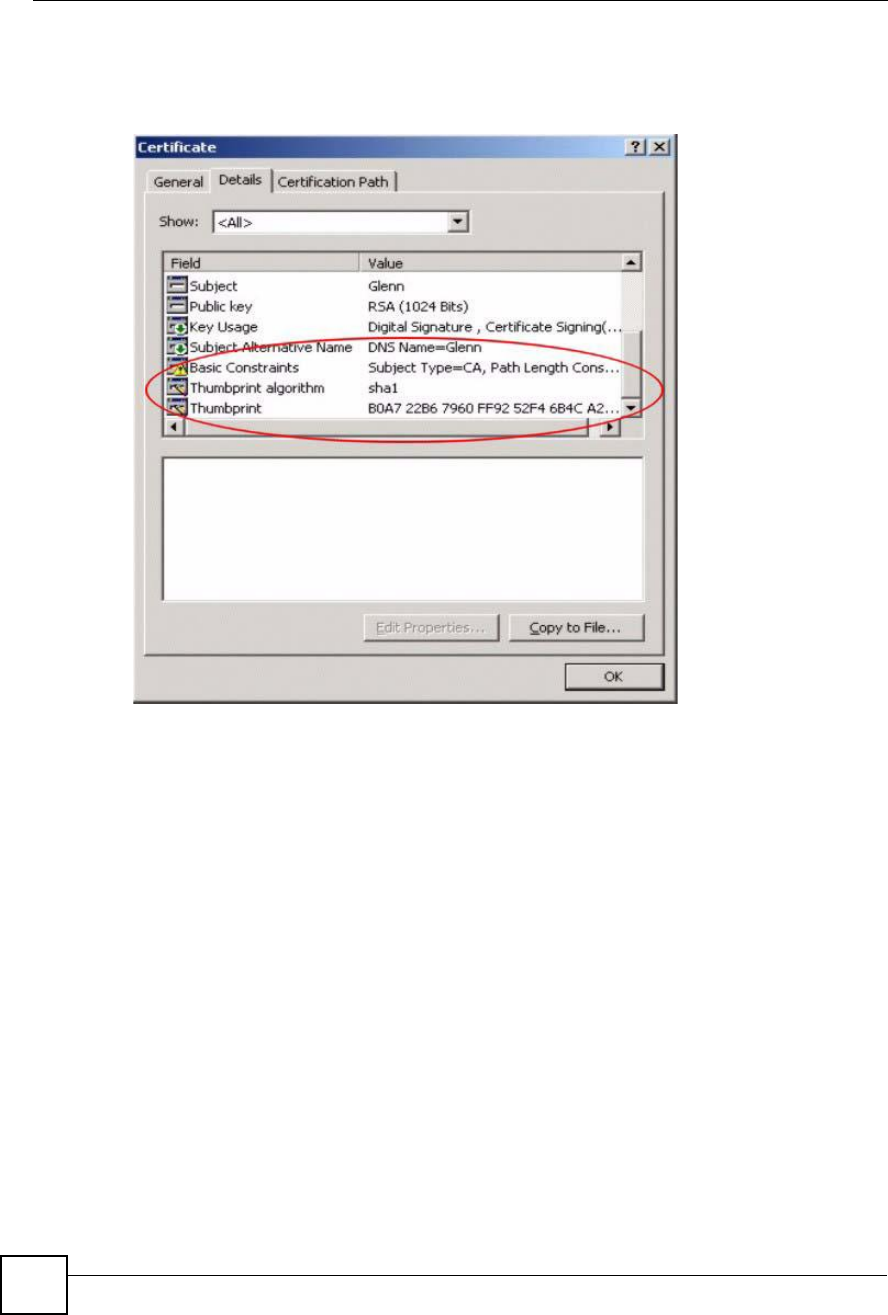
3Double-click the certificate!s icon to open the Certificate window. Click the Details tab
and scroll down to the Thumbprint Algorithm and Thumbprint fields.
Figure 120 Certificate Details
4Use a secure method to verify that the certificate owner has the same information in the
Thumbprint Algorithm and Thumbprint fields. The secure method may very based
on your situation. Possible examples would be over the telephone or through an HTTPS
connection.
16.6 My Certificates Screen
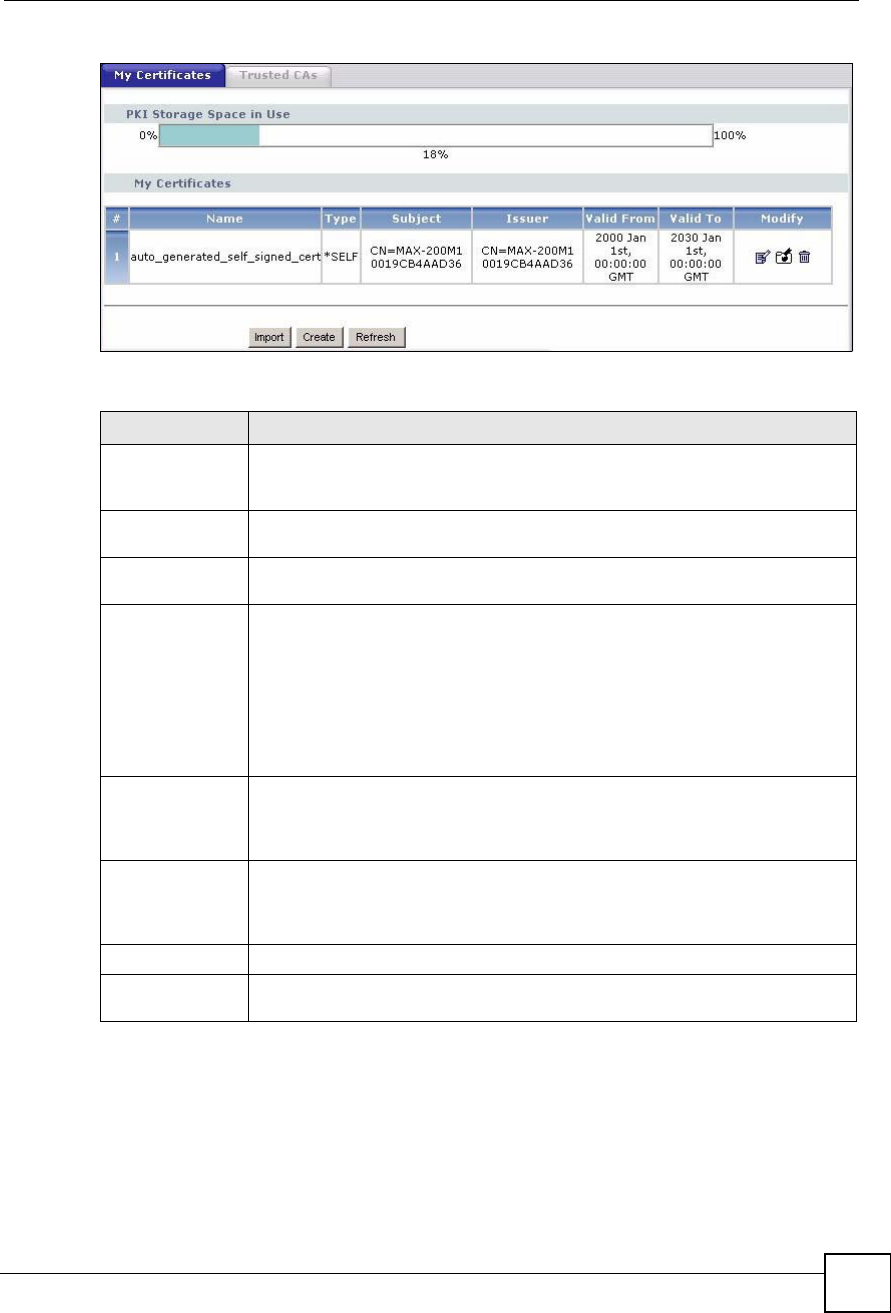
Click Security > Certificates > My Certificates to open the My Certificates screen. This is
the ZyXEL Device!s summary list of certificates and certification requests.
Chapter 16Certificates
MAX-200HW2 Series User s Guide 191
Figure 121 Security > Certificates > My Certificates
The following table describes the labels in this screen.
Table 72 Security > Certificates > My Certificates
LABEL DESCRIPTION
PKI Storage
Space in Use
This bar displays the percentage of the ZyXEL Device s PKI storage space that is
currently in use. When the storage space is almost full, you should consider
deleting expired or unnecessary certificates before adding more certificates.
#This field displays the certificate index number. The certificates are listed in
alphabetical order.
NameThis field displays the name used to identify this certificate. It is recommended that
you give each certificate a unique name.
TypeThis field displays what kind of certificate this is.
REQ represents a certification request and is not yet a valid certificate. Send a
certification request to a certification authority, which then issues a certificate. Use
the My Certificate Import screen to import the certificate and replace the request.
SELF represents a self-signed certificate.
*SELF represents the default self-signed certificate which signs the imported
remote host certificates.
CERT represents a certificate issued by a certification authority.
SubjectThis field displays identifying information about the certificate s owner, such as CN
(Common Name), OU (Organizational Unit or department), O (Organization or
company) and C (Country). It is recommended that each certificate have unique
subject information.
IssuerThis field displays identifying information about the certificate s issuing certification
authority, such as a common name, organizational unit or department,
organization or company and country. With self-signed certificates, this is the
same information as in the Subject field.
Valid FromThis field displays the date that the certificate becomes applicable.
Valid ToThis field displays the date that the certificate expires. The text displays in red and
includes an Expired! message if the certificate has expired.
Chapter 16Certificates
MAX-200HW2 Series User s Guide
192
16.6.1 My Certificates Create Screen
Click Security > Certificates > My Certificates and then the Create icon to open the My
Certificates Create screen. Use this screen to have the ZyXEL Device create a self-signed
certificate, enroll a certificate with a certification authority or generate a certification request.
ModifyClick the Details icon to open a screen with an in-depth list of information about
the certificate.
Click the Export icon to save a copy of the certificate without its private key.
Browse to the location you want to use and click Save.
Click the Remove icon to delete a certificate. A window displays asking you to
confirm that you want to delete the certificate. Subsequent certificates move up by
one when you take this action.
The ZyXEL Device keeps all of your certificates unless you specifically delete
them. Uploading new firmware or default configuration file does not delete your
certificates.
You cannot delete certificates that any of the ZyXEL Device s features are
configured to use.
ImportClick Import to open a screen where you can save a certificate to the ZyXEL
Device.
CreateClick Create to go to the screen where you can have the ZyXEL Device generate
a certificate or a certification request.
RefreshClick Refresh to display the current validity status of the certificates.
Table 72 Security > Certificates > My Certificates (continued)
LABEL DESCRIPTION
Chapter 16Certificates
MAX-200HW2 Series User s Guide 193
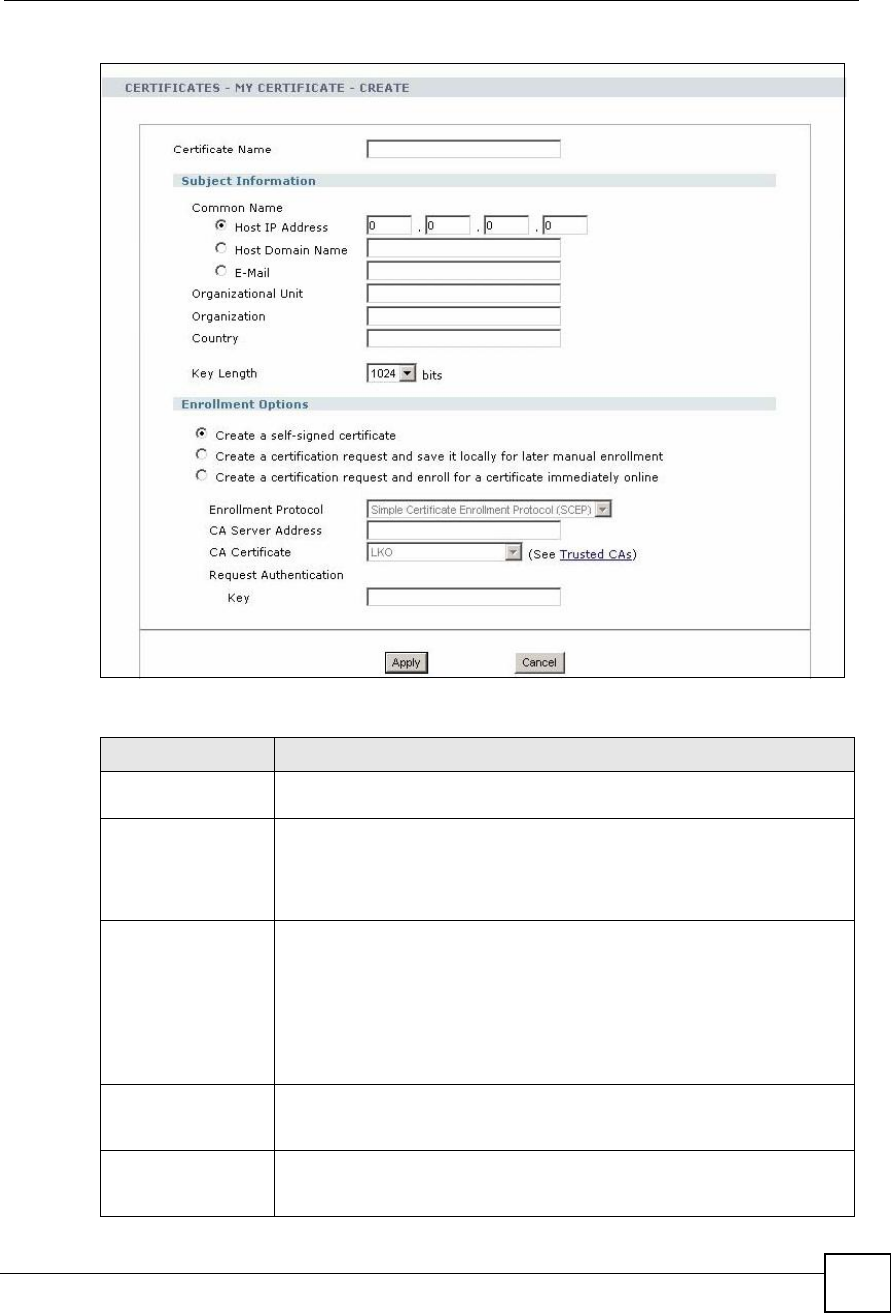
Figure 122 Security > Certificates > My Certificates > Create
The following table describes the labels in this screen.
Table 73 Security > Certificates > My Certificates > Create
LABEL DESCRIPTION
Certificate NameType a name to identify this certificate. You can use up to 31 alphanumeric
and ;$~!@#$%^&()_+[]{} ,.=- characters.
Subject InformationUse these fields to record information that identifies the owner of the
certificate. You do not have to fill in every field, although the Common Name
is mandatory. The certification authority may add fields (such as a serial
number) to the subject information when it issues a certificate. It is
recommended that each certificate have unique subject information.
Common Name Select a radio button to identify the certificate s owner by IP address, domain
name or e-mail address. Type the IP address (in dotted decimal notation),
domain name or e-mail address in the field provided. The domain name or e-
mail address is for identification purposes only and can be any string.
A domain name can be up to 255 characters. You can use alphanumeric
characters, the hyphen and periods.
An e-mail address can be up to 63 characters. You can use alphanumeric
characters, the hyphen, the @ symbol, periods and the underscore.
Organizational UnitIdentify the organizational unit or department to which the certificate owner
belongs. You can use up to 63 characters. You can use alphanumeric
characters, the hyphen and the underscore.
OrganizationIdentify the company or group to which the certificate owner belongs. You can
use up to 63 characters. You can use alphanumeric characters, the hyphen
and the underscore.
Chapter 16Certificates
MAX-200HW2 Series User s Guide
194
CountryIdentify the state in which the certificate owner is located. You can use up to
31 characters. You can use alphanumeric characters, the hyphen and the
underscore.
Key LengthSelect a number from the drop-down list box to determine how many bits the
key should use (512 to 2048). The longer the key, the more secure it is. A
longer key also uses more PKI storage space.
Enrollment OptionsThese radio buttons deal with how and when the certificate is to be generated.
Create a self-signed
certificate
Select Create a self-signed certificate to have the ZyXEL Device generate
the certificate and act as the Certification Authority (CA) itself. This way you do
not need to apply to a certification authority for certificates.
Create a certification
request and save it
locally for later
manual enrollment
Select Create a certification request and save it locally for later manual
enrollment to have the ZyXEL Device generate and store a request for a
certificate. Use the My Certificate Details screen to view the certification
request and copy it to send to the certification authority.
Copy the certification request from the My Certificate Details screen (see
Section 16.6.2 on page 195) and then send it to the certification authority.
Create a certification
request and enroll for
a certificate
immediately online
Select Create a certification request and enroll for a certificate
immediately online to have the ZyXEL Device generate a request for a
certificate and apply to a certification authority for a certificate.
You must have the certification authority s certificate already imported in the
Trusted CAs screen.
When you select this option, you must select the certification authority s
enrollment protocol and the certification authority s certificate from the drop-
down list boxes and enter the certification authority s server address. You also
need to fill in the Reference Number and Key if the certification authority
requires them.
Enrollment ProtocolThis field applies when you select Create a certification request and enroll
for a certificate immediately online. Select the certification authority s
enrollment protocol from the drop-down list box.
Simple Certificate Enrollment Protocol (SCEP) is a TCP-based enrollment
protocol that was developed by VeriSign and Cisco.
Certificate Management Protocol (CMP) is a TCP-based enrollment
protocol that was developed by the Public Key Infrastructure X.509 working
group of the Internet Engineering Task Force (IETF) and is specified in RFC
2510.
CA Server Address This field applies when you select Create a certification request and enroll
for a certificate immediately online. Enter the IP address (or URL) of the
certification authority server.
For a URL, you can use up to 511 of the following characters. a-zA-Z0-9'()+,/
:.=?;!*#@$_%-
CA CertificateThis field applies when you select Create a certification request and enroll
for a certificate immediately online. Select the certification authority s
certificate from the CA Certificate drop-down list box.
You must have the certification authority s certificate already imported in the
Trusted CAs screen. Click Trusted CAs to go to the Trusted CAs screen
where you can view (and manage) the ZyXEL Device's list of certificates of
trusted certification authorities.
Table 73 Security > Certificates > My Certificates > Create
LABEL DESCRIPTION
Chapter 16Certificates
MAX-200HW2 Series User s Guide 195
If you configured the My Certificate Create screen to have the ZyXEL Device enroll a
certificate and the certificate enrollment is not successful, you see a screen with a Return
button that takes you back to the My Certificate Create screen. Click Return and check your
information in the My Certificate Create screen. Make sure that the certification authority
information is correct and that your Internet connection is working properly if you want the
ZyXEL Device to enroll a certificate online.
16.6.2 My Certificate Details Screen
Click Security > Certificates > My Certificates and then the Details iconto open the My
Certificate Details screen. You can use this screen to view in-depth certificate information
and change the certificate!s name.
Request
Authentication
When you select Create a certification request and enroll for a certificate
immediately online, the certification authority may want you to include a
reference number and key to identify you when you send a certification
request.
Fill in both the Reference Number and the Key fields if your certification
authority uses CMP enrollment protocol. Just the Key field displays if your
certification authority uses the SCEP enrollment protocol.
For the reference number, use 0 to 99999999.
For the key, use up to 31 of the following characters. a-zA-Z0-
9;|`~!@#$%^&*()_+\{}':,./<>=-
ApplyClick Apply to begin certificate or certification request generation.
CancelClick Cancel to quit and return to the My Certificates screen.
Table 73 Security > Certificates > My Certificates > Create
LABEL DESCRIPTION
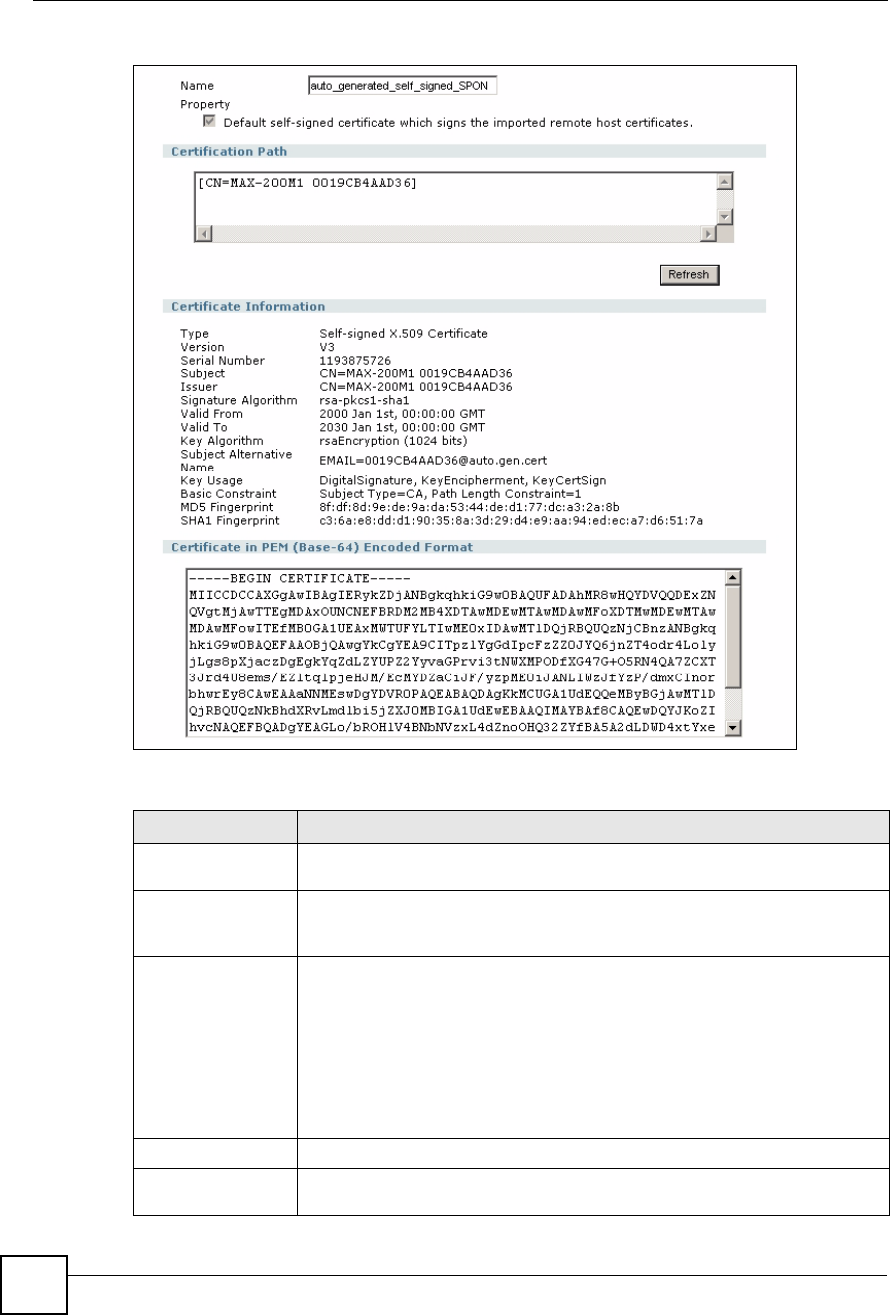
Chapter 16Certificates
MAX-200HW2 Series User s Guide
196
Figure 123 Security > Certificates > My Certificates > Details
The following table describes the labels in this screen.
Table 74 Security > Certificates > My Certificates > Details
LABEL DESCRIPTION
NameThis field displays the identifying name of this certificate. You can use up to 31
alphanumeric and ;$~!@#$%^&()_+[]{} ,.=- characters.
PropertySelect Default self-signed certificate which signs the imported remote host
certificates to use this certificate to sign the remote host certificates you upload
in the Security > Certificates > Trusted CAs screen.
Certification PathThis field displays for a certificate, not a certification request.
Click the Refresh button to have this read-only text box display the hierarchy of
certification authorities that validate the certificate (and the certificate itself).
If the issuing certification authority is one that you have imported as a trusted
certification authority, it may be the only certification authority in the list (along
with the certificate itself). If the certificate is a self-signed certificate, the
certificate itself is the only one in the list. The ZyXEL Device does not trust the
certificate and displays !Not trusted" in this field if any certificate on the path has
expired or been revoked.
RefreshClick Refresh to display the certification path.
Certificate
Information
These read-only fields display detailed information about the certificate.
Chapter 16Certificates
MAX-200HW2 Series User s Guide 197
TypeThis field displays general information about the certificate. CA-signed means
that a Certification Authority signed the certificate. Self-signed means that the
certificate s owner signed the certificate (not a certification authority). !X.509"
means that this certificate was created and signed according to the ITU-T X.509
recommendation that defines the formats for public-key certificates.
VersionThis field displays the X.509 version number. !
Serial NumberThis field displays the certificate s identification number given by the certification
authority or generated by the ZyXEL Device.
SubjectThis field displays information that identifies the owner of the certificate, such as
Common Name (CN), Organizational Unit (OU), Organization (O) and Country
(C).
IssuerThis field displays identifying information about the certificate s issuing
certification authority, such as Common Name, Organizational Unit,
Organization and Country.
With self-signed certificates, this is the same as the Subject Name field.
!none" displays for a certification request.
Signature AlgorithmThis field displays the type of algorithm that was used to sign the certificate. The
ZyXEL Device uses rsa-pkcs1-sha1 (RSA public-private key encryption
algorithm and the SHA1 hash algorithm). Some certification authorities may use
rsa-pkcs1-md5 (RSA public-private key encryption algorithm and the MD5 hash
algorithm).
Valid FromThis field displays the date that the certificate becomes applicable. !none"
displays for a certification request.
Valid ToThis field displays the date that the certificate expires. The text displays in red
and includes an Expired! message if the certificate has expired. !none" displays
for a certification request.
Key AlgorithmThis field displays the type of algorithm that was used to generate the
certificate s key pair (the ZyXEL Device uses RSA encryption) and the length of
the key set in bits (1024 bits for example).
Subject Alternative
Name
This field displays the certificate owner$s IP address (IP), domain name (DNS)
or e-mail address (EMAIL).
Key UsageThis field displays for what functions the certificate s key can be used. For
example, !DigitalSignature" means that the key can be used to sign certificates
and !KeyEncipherment" means that the key can be used to encrypt text.
Basic ConstraintThis field displays general information about the certificate. For example,
Subject Type=CA means that this is a certification authority s certificate and
!Path Length Constraint=1" means that there can only be one certification
authority in the certificate s path. This field does not display for a certification
request.
MD5 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
the MD5 algorithm.
SHA1 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
the SHA1 algorithm.
Table 74 Security > Certificates > My Certificates > Details
LABEL DESCRIPTION
Chapter 16Certificates
MAX-200HW2 Series User s Guide
198
16.6.3 My Certificate Import Screen
Click Security > Certificates > My Certificates > Import to open the My Certificate
Import screen. Follow the instructions in this screen to upload an existing certificate to the
ZyXEL Device.
You can import a certificate that matches a corresponding certification request
that was generated by the ZyXEL Device.
The certificate you import replaces the corresponding request in the My Certificates screen.
You must remove any spaces from the certificate!s filename before you can import it.
Certificate in PEM
(Base-64) Encoded
Format
This read-only text box displays the certificate or certification request in Privacy
Enhanced Mail (PEM) format. PEM uses lowercase letters, uppercase letters
and numerals to convert the binary certificate into a printable form.
You can copy and paste a certification request into a certification authority s web
page, an e-mail that you send to the certification authority or a text editor and
save the file on a management computer for later manual enrollment.
You can copy and paste a certificate into an e-mail to send to friends or
colleagues or you can copy and paste a certificate into a text editor and save the
file on a management computer for later distribution (via floppy disk for
example).
ApplyClick Apply to save your changes back to the ZyXEL Device. You can only
change the name.
CancelClick Cancel to quit and return to the My Certificates screen.
Table 74 Security > Certificates > My Certificates > Details
LABEL DESCRIPTION

Chapter 16Certificates
MAX-200HW2 Series User s Guide 199
Figure 124 Security > Certificates > My Certificates > Import
The following table describes the labels in this screen.
16.7 Trusted CAs
Click Security > Certificates > Trusted CAs to open the Trusted CAs screen. This screen
displays a summary list of certificates of the certification authorities that you have set the
ZyXEL Device to accept as trusted. The ZyXEL Device accepts any valid certificate signed by
a certification authority on this list as being trustworthy; thus you do not need to import any
certificate that is signed by one of these certification authorities.
Table 75 Security > Certificates > My Certificates > Import
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Browse to find it.
You cannot import a certificate with the same name as a certificate that is already in the
ZyXEL Device.
Browse Click Browse to find the certificate file you want to upload.
ApplyClick Apply to save the certificate on the ZyXEL Device.
CancelClick Cancel to quit and return to the My Certificates screen.
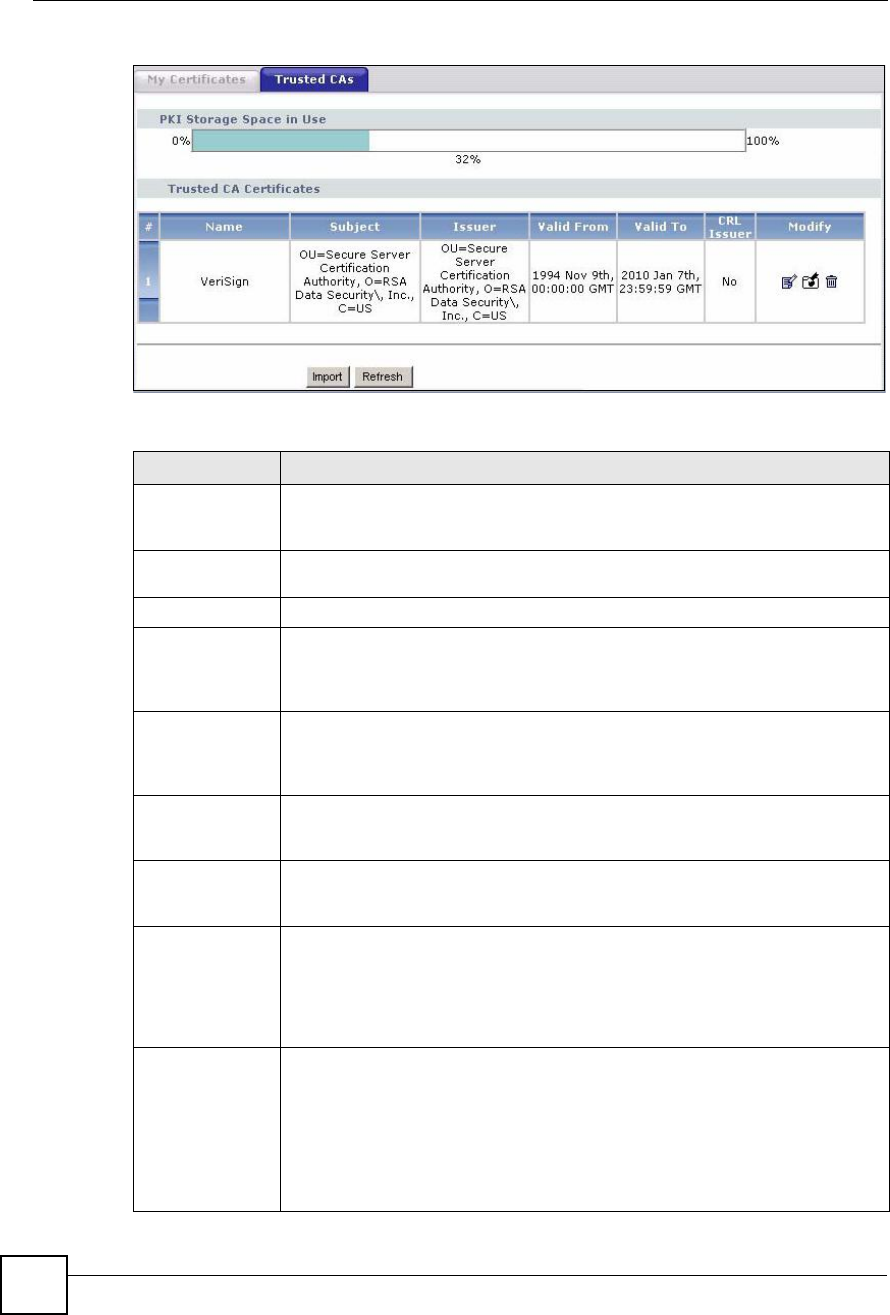
Chapter 16Certificates
MAX-200HW2 Series User s Guide
200
Figure 125 Security > Certificates > Trusted CAs
The following table describes the labels in this screen.
Table 76 Security > Certificates > Trusted CAs
LABEL DESCRIPTION
PKI Storage
Space in Use
This bar displays the percentage of the ZyXEL Device s PKI storage space that is
currently in use. When the storage space is almost full, you should consider
deleting expired or unnecessary certificates before adding more certificates.
#This field displays the certificate index number. The certificates are listed in
alphabetical order.
NameThis field displays the name used to identify this certificate.
SubjectThis field displays identifying information about the certificate s owner, such as CN
(Common Name), OU (Organizational Unit or department), O (Organization or
company) and C (Country). It is recommended that each certificate have unique
subject information.
IssuerThis field displays identifying information about the certificate s issuing certification
authority, such as a common name, organizational unit or department,
organization or company and country. With self-signed certificates, this is the
same information as in the Subject field.
Valid FromThis field displays the date that the certificate becomes applicable. The text
displays in red and includes a Not Yet Valid! message if the certificate has not yet
become applicable.
Valid ToThis field displays the date that the certificate expires. The text displays in red and
includes an Expiring! or Expired! message if the certificate is about to expire or
has already expired.
CRL IssuerThis field displays Yes if the certification authority issues CRL (Certificate
Revocation Lists) for the certificates that it has issued and you have selected the
Check incoming certificates issued by this CA against a CRL check box in the
certificate s details screen to have the ZyXEL Device check the CRL before
trusting any certificates issued by the certification authority. Otherwise the field
displays No.
ModifyClick the Details icon to open a screen with an in-depth list of information about
the certificate.
Use the Export icon to save the certificate to a computer. Click the icon and then
Save in the File Download screen. The Save As screen opens, browse to the
location that you want to use and click Save.
Click the Remove icon to delete the certificate. A window displays asking you to
confirm that you want to delete the certificate. Note that subsequent certificates
move up by one when you take this action.
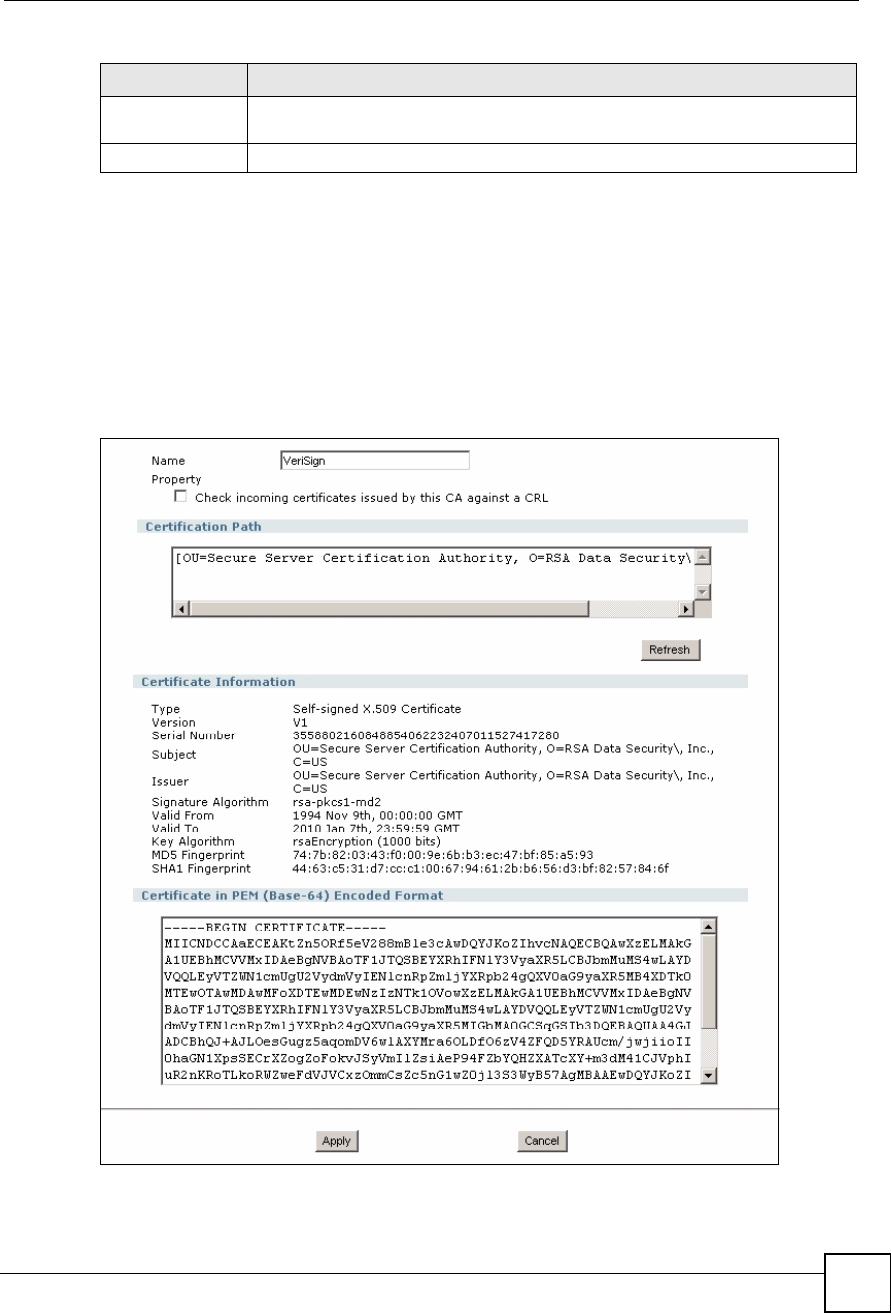
Chapter 16Certificates
MAX-200HW2 Series User s Guide 201
16.8 Trusted CA Details
Click Security > Certificates > Trusted CAs to open the Trusted CAs screen. Click the
details icon to open the Trusted CA Details screen. Use this screen to view in-depth
information about the certification authority!s certificate, change the certificate!s name and set
whether or not you want the ZyXEL Device to check a certification authority!s list of revoked
certificates before trusting a certificate issued by the certification authority.
Figure 126 Security > Certificates > Trusted CAs > Details
ImportClick Import to open a screen where you can save the certificate of a certification
authority that you trust, from your computer to the ZyXEL Device.
RefreshClick this button to display the current validity status of the certificates.
Table 76 Security > Certificates > Trusted CAs (continued)
LABEL DESCRIPTION
Chapter 16Certificates
MAX-200HW2 Series User s Guide
202
The following table describes the labels in this screen.
Table 77 Security > Certificates > Trusted CAs > Details
LABEL DESCRIPTION
NameThis field displays the identifying name of this certificate. If you want to change
the name, type up to 31 characters to identify this key certificate. You may use
any character (not including spaces).
Property
Check incoming
certificates issued
by this CA against a
CRL
Select this check box to have the ZyXEL Device check incoming certificates that
are issued by this certification authority against a Certificate Revocation List
(CRL).
Clear this check box to have the ZyXEL Device not check incoming certificates
that are issued by this certification authority against a Certificate Revocation List
(CRL).
Certification PathClick the Refresh button to have this read-only text box display the end entity s
certificate and a list of certification authority certificates that shows the hierarchy
of certification authorities that validate the end entity s certificate. If the issuing
certification authority is one that you have imported as a trusted certification
authority, it may be the only certification authority in the list (along with the end
entity s own certificate). The ZyXEL Device does not trust the end entity s
certificate and displays !Not trusted" in this field if any certificate on the path has
expired or been revoked.
RefreshClick Refresh to display the certification path.
Certificate
Information
These read-only fields display detailed information about the certificate.
TypeThis field displays general information about the certificate. CA-signed means
that a Certification Authority signed the certificate. Self-signed means that the
certificate s owner signed the certificate (not a certification authority). X.509
means that this certificate was created and signed according to the ITU-T X.509
recommendation that defines the formats for public-key certificates.
VersionThis field displays the X.509 version number.
Serial NumberThis field displays the certificate s identification number given by the certification
authority.
SubjectThis field displays information that identifies the owner of the certificate, such as
Common Name (CN), Organizational Unit (OU), Organization (O) and Country
(C).
IssuerThis field displays identifying information about the certificate s issuing
certification authority, such as Common Name, Organizational Unit,
Organization and Country.
With self-signed certificates, this is the same information as in the Subject
Name field.
Signature AlgorithmThis field displays the type of algorithm that was used to sign the certificate.
Some certification authorities use rsa-pkcs1-sha1 (RSA public-private key
encryption algorithm and the SHA1 hash algorithm). Other certification
authorities may use rsa-pkcs1-md5 (RSA public-private key encryption
algorithm and the MD5 hash algorithm).
Valid FromThis field displays the date that the certificate becomes applicable. The text
displays in red and includes a Not Yet Valid! message if the certificate has not
yet become applicable.
Valid ToThis field displays the date that the certificate expires. The text displays in red
and includes an Expiring! or Expired! message if the certificate is about to expire
or has already expired.
Key AlgorithmThis field displays the type of algorithm that was used to generate the
certificate s key pair (the ZyXEL Device uses RSA encryption) and the length of
the key set in bits (1024 bits for example).
Chapter 16Certificates
MAX-200HW2 Series User s Guide 203
16.9 Trusted CA Import
Click Security > Certificates > Trusted CAs to open the Trusted CAs screen and then click
Import to open the Trusted CA Import screen. Follow the instructions in this screen to save
a trusted certification authority!s certificate from a computer to the ZyXEL Device. The
ZyXEL Device trusts any valid certificate signed by any of the imported trusted CA
certificates.
You must remove any spaces from the certificate s filename before you can
import the certificate.
MD5 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
the MD5 algorithm. You can use this value to verify with the certification
authority (over the phone for example) that this is actually their certificate.
SHA1 FingerprintThis is the certificate s message digest that the ZyXEL Device calculated using
the SHA1 algorithm. You can use this value to verify with the certification
authority (over the phone for example) that this is actually their certificate.
Certificate in PEM
(Base-64) Encoded
Format
This read-only text box displays the certificate or certification request in Privacy
Enhanced Mail (PEM) format. PEM uses lowercase letters, uppercase letters
and numerals to convert the binary certificate into a printable form.
You can copy and paste the certificate into an e-mail to send to friends or
colleagues or you can copy and paste the certificate into a text editor and save
the file on a management computer for later distribution (via floppy disk for
example).
ApplyClick Apply to save your changes back to the ZyXEL Device. You can only
change the name and/or set whether or not you want the ZyXEL Device to
check the CRL that the certification authority issues before trusting a certificate
issued by the certification authority.
CancelClick Cancel to quit and return to the Trusted CAs screen.
Table 77 Security > Certificates > Trusted CAs > Details (continued)
LABEL DESCRIPTION
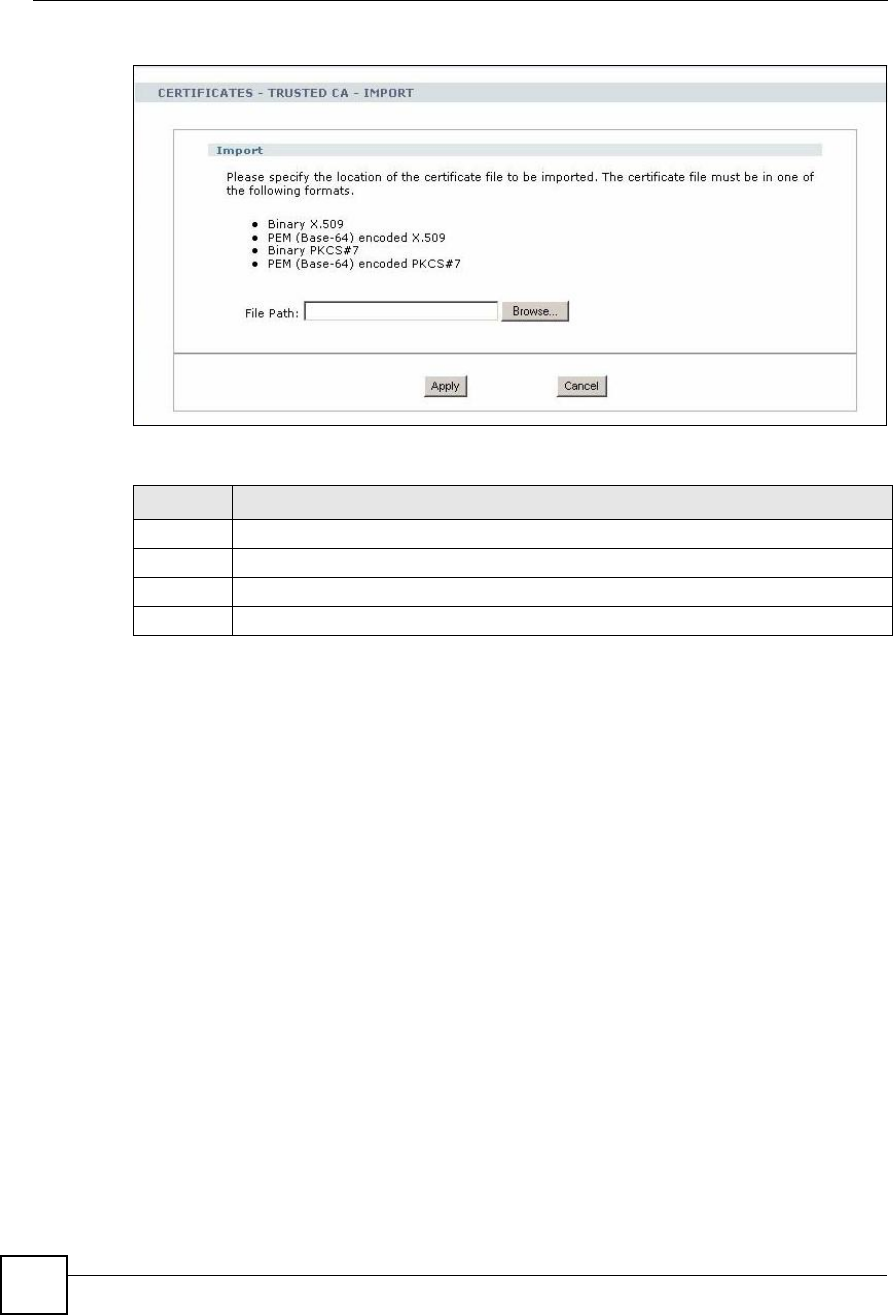
Chapter 16Certificates
MAX-200HW2 Series User s Guide
204
Figure 127 Security > Certificates > Trusted CAs > Import
The following table describes the labels in this screen.
Table 78 Security > Certificates > Trusted CAs Import
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Browse to find it.
Choose... Click Choose... to find the certificate file you want to upload.
ApplyClick Apply to save the certificate on the ZyXEL Device.
CancelClick Cancel to quit and return to the Trusted CAs screen.

MAX-200HW2 Series User s Guide 205
CHAPTER 17
Content Filter
Use these screens to create and enforce policies that restrict access to the Internet based on
content.
17.1 Content Filtering Overview
Internet content filtering allows you to create and enforce Internet access policies tailored to
their needs. Content filtering is the ability to block certain web features or specific URL
keywords.
The ZyXEL Device can block web features such as ActiveX controls, Java applets, cookies
and disable web proxies. The ZyXEL Device also allows you to define time periods and days
during which the ZyXEL Device performs content filtering.
17.2 Content Filtering Screens
17.2.1 Content Filter Screen
Use this screen to set up a trusted IP address, which web features are restricted, and which
keywords are blocked when content filtering is effective. To access this screen, click Security
> Content Filter > Filter.
Chapter 17Content Filter
MAX-200HW2 Series User s Guide
206
Figure 128 Security > Content Filter > Filter
Each field is described in the following table.
Table 79 Security > Content Filter > Filter
LABEL DESCRIPTION
Trusted IP Setup
Trusted Computer
IP Address
You can allow a specific computer to access all Internet resources without the
restrictions you set in these screens. Enter the IP address of the trusted computer.
Restrict Web
Features
Select the web features you want to disable. If a user downloads a page with a
restricted feature, that part of the web page appears blank or grayed out.
ActiveX - This is a tool for building dynamic and active Web pages and distributed
object applications. When you visit an ActiveX Web site, ActiveX controls are
downloaded to your browser, where they remain in case you visit the site again.
Java - This is used to build downloadable Web components or Internet and
intranet business applications of all kinds.
Cookies - This is used by Web servers to track usage and to provide service
based on ID.
Web Proxy - This is a server that acts as an intermediary between a user and the
Internet to provide security, administrative control, and caching service. When a
proxy server is located on the WAN, it is possible for LAN users to avoid content
filtering restrictions.
Keyword Blocking
Enable URL
Keyword Blocking
Select this if you want the ZyXEL Device to block Web sites based on words in the
web site address. For example, if you block the keyword bad,http://
www.website.com/bad.html is blocked.
Keyword Type a keyword you want to block in this field. You can use up to 64 printable
ASCII characters. There is no wildcard character, however.
Add Click this to add the specified Keyword to the Keyword List. You can enter up to
64 keywords.
Keyword List This field displays the keywords that are blocked when Enable URL Keyword
Blocking is selected. To delete a keyword, select it, click Delete, and click Apply.
Chapter 17Content Filter
MAX-200HW2 Series User s Guide 207
17.2.2 Content Filter Schedule Screen
Use this screen to set up the schedule when content filtering is effective. To access this screen,
click Security > Content Filter > Schedule.
Figure 129 Security > Content Filter > Schedule
Each field is described in the following table.
Delete Click Delete to remove the selected keyword in the Keyword List. The keyword
disappears after you click Apply.
Clear All Click this button to remove all of the keywords in the Keyword List.
Denied Access
Message
Enter the message that is displayed when the ZyXEL Device s content filter
feature blocks access to a web site.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Cancel Click this to set every field in this screen to its last-saved value.
Table 79 Security > Content Filter > Filter
LABEL DESCRIPTION
Table 80 Security > Content Filter > Schedule
LABEL DESCRIPTION
Day to Block Select which days of the week you want content filtering to be effective.
Time of Day to
Block
Select what time each day you want content filtering to be effective. Enter times in
24-hour format; for example, 3:00pm should be entered as 15:00.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.

Chapter 17Content Filter
MAX-200HW2 Series User s Guide
208
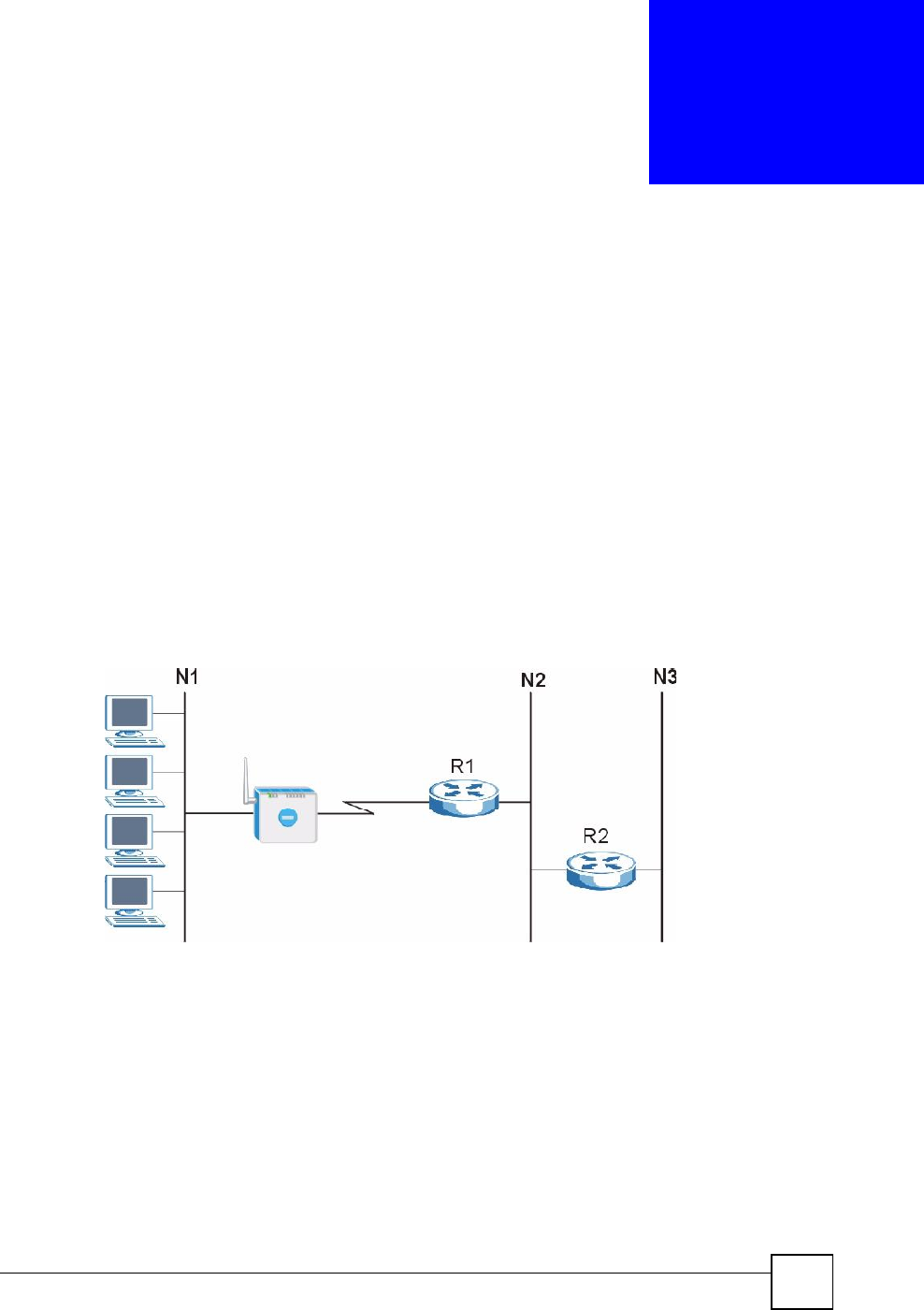
MAX-200HW2 Series User s Guide 209
CHAPTER 18
Static Route
Use these screens to configure static routes on the ZyXEL Device.
18.1 Static Route Overview
Each remote node specifies only the network to which the gateway is directly connected, and
the ZyXEL Device has no knowledge of the networks beyond. For instance, the ZyXEL
Device knows about network N2 in the following figure through remote node Router 1.
However, the ZyXEL Device is unable to route a packet to network N3 because it doesn't
know that there is a route through the same remote node Router 1 (via gateway Router 2). The
static routes are for you to tell the ZyXEL Device about the networks beyond the remote
nodes.
Figure 130 Example of Static Routing Topology
18.2 Static Route Screens
18.2.1 IP Static Route Screen
Use this screen to look at static routes in the ZyXEL Device. To access this screen, click
Management > Static Route > IP Static Route.
Chapter 18Static Route
MAX-200HW2 Series User s Guide
210
The first static route is the default route and cannot be modified or deleted.
Figure 131 Management > Static Route > IP Static Route
Each field is described in the following table.
18.2.2 IP Static Route Edit Screen
Use this screen to edit a static route in the ZyXEL Device. To access this screen, click an Edit
icon in Management > Static Route > IP Static Route.
Table 81 Management > Static Route > IP Static Route
LABEL DESCRIPTION
#This field is a sequential value, and it is not associated with a specific rule. The
sequence is important, however. The ZyXEL Device checks each rule in order,
and it follows only the first one that applies.
Name This field displays the name that describes the static route.
Active This field shows whether this static route is active (Yes) or not (No).
Destination This field displays the destination IP address(es) that this static route affects.
Gateway This field displays the IP address of the gateway to which the ZyXEL Device
should send packets for the specified Destination. The gateway is a router or a
switch on the same network segment as the device's LAN or WAN port. The
gateway helps forward packets to their destinations.
Modify Use this field to edit or erase the static route.
Click the Edit icon to open the IP Static Route Edit screen for this static route.
Click the Remove icon to erase this static route.

Chapter 18Static Route
MAX-200HW2 Series User s Guide 211
Figure 132 Management > Static Route > IP Static Route > Edit
Each field is described in the following table.
Table 82 Management > Static Route > IP Static Route > Edit
LABEL DESCRIPTION
Route Name Enter the name of the static route.
Active Select this if you want the static route to be used. Clear this if you do not want the
static route to be used.
Private Select this if you do not want the ZyXEL Device to tell other routers about this
static route. For example, you might select this if the static route is in your LAN.
Clear this if you want the ZyXEL Device to tell other routers about this static route.
Destination IP
Address
Enter one of the destination IP addresses that this static route affects.
IP Subnet Mask Enter the subnet mask that defines the range of destination IP addresses that this
static route affects. If this static route affects only one IP address, enter
255.255.255.255.
Gateway IP
Address
Enter the IP address of the gateway to which the ZyXEL Device should send
packets for the specified Destination. The gateway is a router or a switch on the
same network segment as the device's LAN or WAN port. The gateway helps
forward packets to their destinations.
Metric Usually, you should keep the default value. This field is related to RIP. See
Chapter 9 on page 119 for more information.
The metric represents the "cost of transmission". A router determines the best
route for transmission by choosing a path with the lowest "cost". The smaller the
metric, the lower the "cost". RIP uses hop count as the measurement of cost,
where 1 is for a directly-connected network. The metric must be 1-15; if you use a
value higher than 15, the routers assume the link is down.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Cancel Click this to return to the previous screen without saving your changes.

Chapter 18Static Route
MAX-200HW2 Series User s Guide
212

MAX-200HW2 Series User s Guide 213
CHAPTER 19
Remote MGMT
Use these screens to control which computers can use which services to access the ZyXEL
Device on each interface.
19.1 Remote Management Overview
Remote management allows you to determine which services/protocols can access which
ZyXEL Device interface (if any) from which computers.
You may manage your ZyXEL Device from a remote location via:
To disable remote management of a service, select Disable in the corresponding Server
Access field.
You may only have one remote management session running at a time. The ZyXEL Device
automatically disconnects a remote management session of lower priority when another
remote management session of higher priority starts. The priorities for the different types of
remote management sessions are as follows.
1Telnet
2HTTP
19.1.1 Remote Management Limitations
Remote management over LAN or WAN will not work when:
1A filter in SMT menu 3.1 (LAN) or in menu 11.5 (WAN) is applied to block a Telnet,
FTP or Web service.
2You have disabled that service in one of the remote management screens.
3The IP address in the Secured Client IP field does not match the client IP address. If it
does not match, the ZyXEL Device will disconnect the session immediately.
4There is already another remote management session with an equal or higher priority
running. You may only have one remote management session running at one time.
19.1.2 Remote Management and NAT
When NAT is enabled:
Table 83
#Internet (WAN only) #ALL (LAN and WAN)
#LAN only #Neither (Disable).
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide
214
Use the ZyXEL Device!s WAN IP address when configuring from the WAN.
Use the ZyXEL Device!s LAN IP address when configuring from the LAN.
19.1.3 System Timeout
There is a default system management idle timeout of five minutes (three hundred seconds).
The ZyXEL Device automatically logs you out if the management session remains idle for
longer than this timeout period. The management session does not time out when a statistics
screen is polling. You can change the timeout period in the Maintenance > System > General
screen.
19.2 Remote Management Screens
19.2.1 WWW Screen
Use this screen to control HTTP access to your ZyXEL Device. To access this screen, click
Management > Remote MGMT > WWW.
Figure 133 Management > Remote MGMT > WWW
Each field is described in the following table.
19.2.2 Telnet Screen
Use this screen to control Telnet access to your ZyXEL Device. To access this screen, click
Management > Remote MGMT > Telnet.
Table 84 Management > Remote MGMT > WWW
LABEL DESCRIPTION
Server Port Enter the port number this service can use to access the ZyXEL Device. The
computer must use the same port number.
Server Access Select the interface(s) through which a computer may access the ZyXEL Device
using this service.
Secured Client IP
Address
Select All to allow any computer to access the ZyXEL Device using this service.
Select Selected to only allow the computer with the IP address that you specify to
access the ZyXEL Device using this service.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its default value.
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide 215
Figure 134 Management > Remote MGMT > Telnet
Each field is described in the following table.
19.2.3 FTP Screen
Use this screen to control FTP access to your ZyXEL Device. To access this screen, click
Management > Remote MGMT > FTP.
Figure 135 Management > Remote MGMT > FTP
Each field is described in the following table.
Table 85 Management > Remote MGMT > Telnet
LABEL DESCRIPTION
Server Port Enter the port number this service can use to access the ZyXEL Device. The
computer must use the same port number.
Server Access Select the interface(s) through which a computer may access the ZyXEL Device
using this service.
Secured Client IP
Address
Select All to allow any computer to access the ZyXEL Device using this service.
Select Selected to only allow the computer with the IP address that you specify to
access the ZyXEL Device using this service.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its default value.
Table 86 Management > Remote MGMT > FTP
LABEL DESCRIPTION
Server Port Enter the port number this service can use to access the ZyXEL Device. The
computer must use the same port number.
Server Access Select the interface(s) through which a computer may access the ZyXEL Device
using this service.
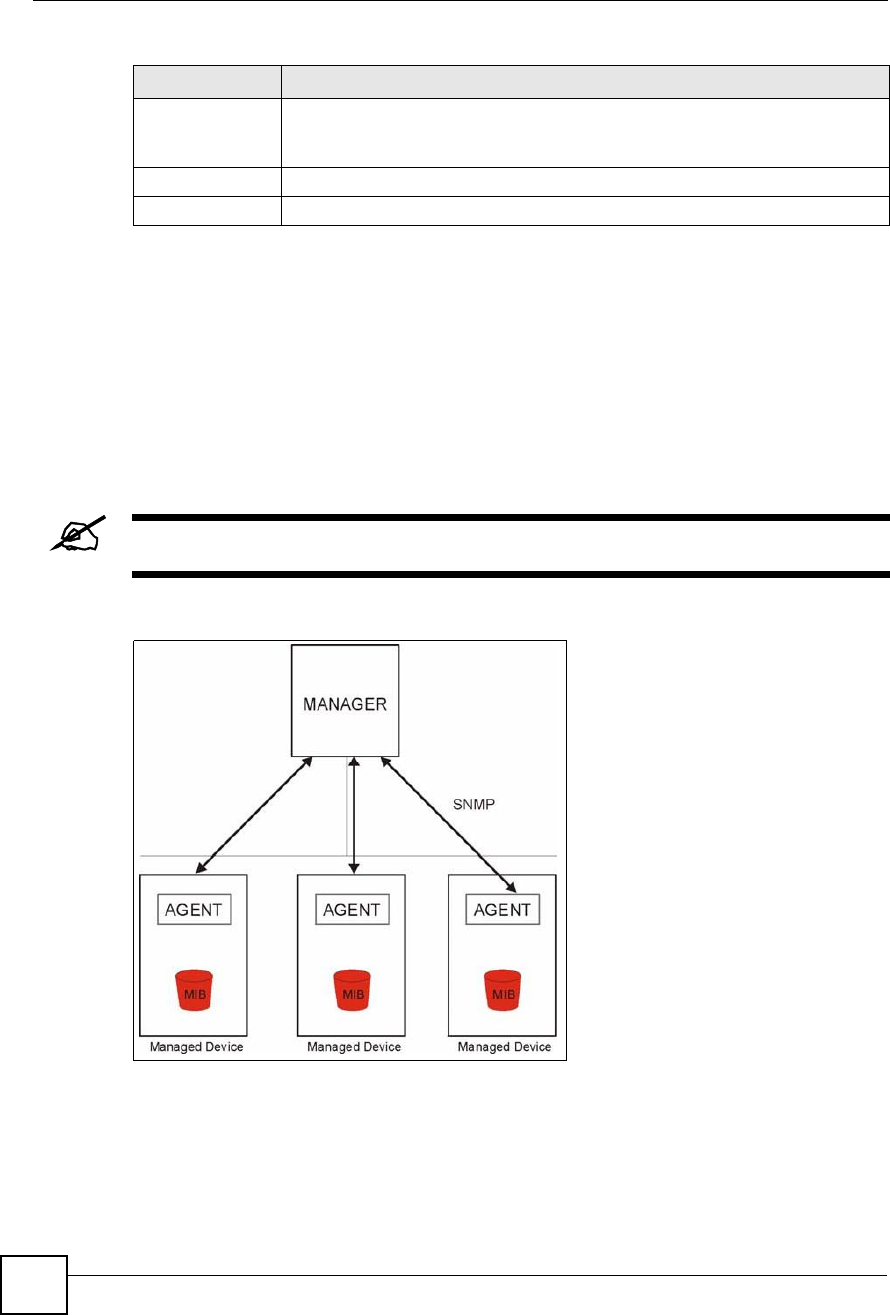
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide
216
19.3 SNMP
Simple Network Management Protocol (SNMP) is a protocol used for exchanging
management information between network devices. SNMP is a member of the TCP/IP
protocol suite. Your ZyXEL Device supports SNMP agent functionality, which allows a
manager station to manage and monitor the ZyXEL Device through the network. The ZyXEL
Device supports SNMP version one (SNMPv1) and version two (SNMPv2). The next figure
illustrates an SNMP management operation.
SNMP is only available if TCP/IP is configured.
Figure 136 SNMP Management Model
An SNMP managed network consists of two main types of component: agents and a manager.
An agent is a management software module that resides in a managed device (the ZyXEL
Device). An agent translates the local management information from the managed device into
a form compatible with SNMP. The manager is the console through which network
administrators perform network management functions. It executes applications that control
and monitor managed devices.
Secured Client IP
Address
Select All to allow any computer to access the ZyXEL Device using this service.
Select Selected to only allow the computer with the IP address that you specify to
access the ZyXEL Device using this service.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its default value.
Table 86 Management > Remote MGMT > FTP
LABEL DESCRIPTION
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide 217
The managed devices contain object variables/managed objects that define each piece of
information to be collected about a device. Examples of variables include such as number of
packets received, node port status etc. A Management Information Base (MIB) is a collection
of managed objects. SNMP allows a manager and agents to communicate for the purpose of
accessing these objects.
SNMP itself is a simple request/response protocol based on the manager/agent model. The
manager issues a request and the agent returns responses using the following protocol
operations:
Get - Allows the manager to retrieve an object variable from the agent.
GetNext - Allows the manager to retrieve the next object variable from a table or list
within an agent. In SNMPv1, when a manager wants to retrieve all elements of a table
from an agent, it initiates a Get operation, followed by a series of GetNext operations.
Set - Allows the manager to set values for object variables within an agent.
Trap - Used by the agent to inform the manager of some events.
19.3.1 Supported MIBs
The ZyXEL Device supports MIB II that is defined in RFC-1213 and RFC-1215. The focus of
the MIBs is to let administrators collect statistical data and monitor status and performance.
19.3.2 SNMP Traps
The ZyXEL Device will send traps to the SNMP manager when any one of the following
events occurs:
19.3.3 Configuring SNMP
To change your ZyXEL Device!s SNMP settings, click Advanced > Remote MGMT >
SNMP. The screen appears as shown.
Use this screen to control FTP access to your ZyXEL Device. To access this screen, click
Management > Remote MGMT > SNMP.
Table 87 SNMP Traps
TRAP # TRAP NAME DESCRIPTION
0coldStart (defined in RFC-1215)A trap is sent after booting (power on).
1warmStart (defined in RFC-1215)A trap is sent after booting (software reboot).
4authenticationFailure (defined in
RFC-1215)
A trap is sent to the manager when receiving any
SNMP get or set requirements with the wrong
community (password).
6whyReboot (defined in ZYXEL-
MIB)
A trap is sent with the reason of restart before
rebooting when the system is going to restart (warm
start).
6a For intentional reboot: A trap is sent with the message "System reboot by
user!" if reboot is done intentionally, (for example,
download new files, CI command "sys reboot", etc.).
6b For fatal error: A trap is sent with the message of the fatal code if the
system reboots because of fatal errors.
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide
218
Figure 137 Management > Remote MGMT > SNMP
The following table describes the labels in this screen.
19.3.4 DNS Screen
Use this screen to control DNS access to your ZyXEL Device. To access this screen, click
Management > Remote MGMT > DNS.
Table 88 Remote Management: SNMP
LABEL DESCRIPTION
SNMP Configuration
Get Community Enter the Get Community, which is the password for the incoming Get and
GetNext requests from the management station. The default is public and
allows all requests.
Set Community Enter the Set community, which is the password for incoming Set requests
from the management station. The default is public and allows all requests.
Trap Community Enter the trap community, which is the password sent with each trap to the
SNMP manager. The default is public and allows all requests.
Trap Destination Enter the IP address of the station to send your SNMP traps to.
SNMP
Port You may change the server port number for a service if needed, however you
must use the same port number in order to use that service for remote
management.
Access Status Select the interface(s) through which a computer may access the ZyXEL Device
using this service.
Secured Client IP A secured client is a !trusted" computer that is allowed to communicate with the
ZyXEL Device using this service.
Select All to allow any computer to access the ZyXEL Device using this service.
Choose Selected to just allow the computer with the IP address that you specify
to access the ZyXEL Device using this service.
Apply Click this button to save your customized settings and exit this screen.
Reset Click this button to set each field in this screen to its default value.
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide 219
Figure 138 Management > Remote MGMT > DNS
Each field is described in the following table.
19.3.5 Security Screen
Use this screen to control how your ZyXEL Device responds to other types of requests. To
access this screen, click Management > Remote MGMT > Security.
Figure 139 Management > Remote MGMT > Security
Table 89 Management > Remote MGMT > DNS
LABEL DESCRIPTION
Server Port This field is read-only. This field displays the port number this service uses to
access the ZyXEL Device. The computer must use the same port number.
Server Access Select the interface(s) through which a computer may access the ZyXEL Device
using this service.
Secured Client IP
Address
Select All to allow any computer to access the ZyXEL Device using this service.
Select Selected to only allow the computer with the IP address that you specify to
access the ZyXEL Device using this service.
Apply Click this to save your changes.
Reset Click this to set every field in this screen to its last-saved value.
Chapter 19Remote MGMT
MAX-200HW2 Series User s Guide
220
Each field is described in the following table.
Table 90 Management > Remote MGMT > Security
LABEL DESCRIPTION
Respond to Ping
on
Select the interface(s) on which the ZyXEL Device should respond to incoming
ping requests.
Disable - the ZyXEL Device does not respond to any ping requests.
LAN - the ZyXEL Device only responds to ping requests received from the LAN.
WAN - the ZyXEL Device only responds to ping requests received from the WAN.
LAN & WAN - the ZyXEL Device responds to ping requests received from the
LAN or the WAN.
Do not respond to
requests for
unauthorized
services
Select this to prevent outsiders from discovering your ZyXEL Device by sending
requests to unsupported port numbers. If an outside user attempts to probe an
unsupported port on your ZyXEL Device, an ICMP response packet is
automatically returned. This allows the outside user to know the ZyXEL Device
exists. Your ZyXEL Device supports anti-probing, which prevents the ICMP
response packet from being sent. This keeps outsiders from discovering your
ZyXEL Device when unsupported ports are probed.
If you clear this, your ZyXEL Device replies with an ICMP Port Unreachable
packet for a port probe on unused UDP ports and with a TCP Reset packet for a
port probe on unused TCP ports.
Apply Click this to save your changes.
Cancel Click this to set every field in this screen to its default value.

MAX-200HW2 Series User s Guide 221
CHAPTER 20
UPnP
Use this screen to set up UPnP.
20.1 Introducing Universal Plug and Play
Universal Plug and Play (UPnP) is a distributed, open networking standard that uses TCP/IP
for simple peer-to-peer network connectivity between devices. A UPnP device can
dynamically join a network, obtain an IP address, convey its capabilities and learn about other
devices on the network. In turn, a device can leave a network smoothly and automatically
when it is no longer in use.
20.1.1 How do I know if I'm using UPnP?
UPnP hardware is identified as an icon in the Network Connections folder (Windows XP).
Each UPnP compatible device installed on your network will appear as a separate icon.
Selecting the icon of a UPnP device will allow you to access the information and properties of
that device.
20.1.2 NAT Traversal
UPnP NAT traversal automates the process of allowing an application to operate through NAT.
UPnP network devices can automatically configure network addressing, announce their
presence in the network to other UPnP devices and enable exchange of simple product and
service descriptions. NAT traversal allows the following:
Dynamic port mapping
Learning public IP addresses
Assigning lease times to mappings
Windows Messenger is an example of an application that supports NAT traversal and UPnP.
See Chapter 10 on page 129 for further information about NAT.
20.1.3 Cautions with UPnP
The automated nature of NAT traversal applications in establishing their own services and
opening firewall ports may present network security issues. Network information and
configuration may also be obtained and modified by users in some network environments.
All UPnP-enabled devices may communicate freely with each other without additional
configuration. Disable UPnP if this is not your intention.
Chapter 20UPnP
MAX-200HW2 Series User s Guide
222
20.1.4 UPnP and ZyXEL
ZyXEL has achieved UPnP certification from the Universal Plug and Play Forum Creates
UPnP& Implementors Corp. (UIC). ZyXEL's UPnP implementation supports IGD 1.0
(Internet Gateway Device). At the time of writing ZyXEL's UPnP implementation supports
Windows Messenger 4.6 and 4.7 while Windows Messenger 5.0 and Xbox are still being
tested.
The ZyXEL Device only sends UPnP multicasts to the LAN.
See later sections for examples of installing UPnP in Windows XP and Windows Me as well as
an example of using UPnP in Windows.
20.2 UPnP Examples
20.2.1 Installing UPnP in Windows Example
This section shows how to install UPnP in Windows Me and Windows XP.
20.2.1.1 Installing UPnP in Windows Me
Follow the steps below to install the UPnP in Windows Me.
1Click Start and Control Panel. Double-click Add/Remove Programs.
2Click on the Windows Setup tab and select Communication in the Components
selection box. Click Details.
Figure 140 Add/Remove Programs: Windows Setup: Communication
Chapter 20UPnP
MAX-200HW2 Series User s Guide 223
3In the Communications window, select the Universal Plug and Play check box in the
Components selection box.
Figure 141 Add/Remove Programs: Windows Setup: Communication Components
4Click OK to go back to the Add/Remove Programs Properties window and click Next.
5Restart the computer when prompted.
20.2.1.2 Installing UPnP in Windows XP
Follow the steps below to install the UPnP in Windows XP.
1Click Start and Control Panel.
2Double-click Network Connections.
3In the Network Connections window, click Advanced in the main menu and select
Optional Networking Components .
Figure 142 Network Connections
4The Windows Optional Networking Components Wizard window displays. Select
Networking Service in the Components selection box and click Details.
Chapter 20UPnP
MAX-200HW2 Series User s Guide
224
Figure 143 Windows Optional Networking Components Wizard
5In the Networking Services window, select the Universal Plug and Play check box.
Figure 144 Networking Services
6Click OK to go back to the Windows Optional Networking Component Wizard
window and click Next.
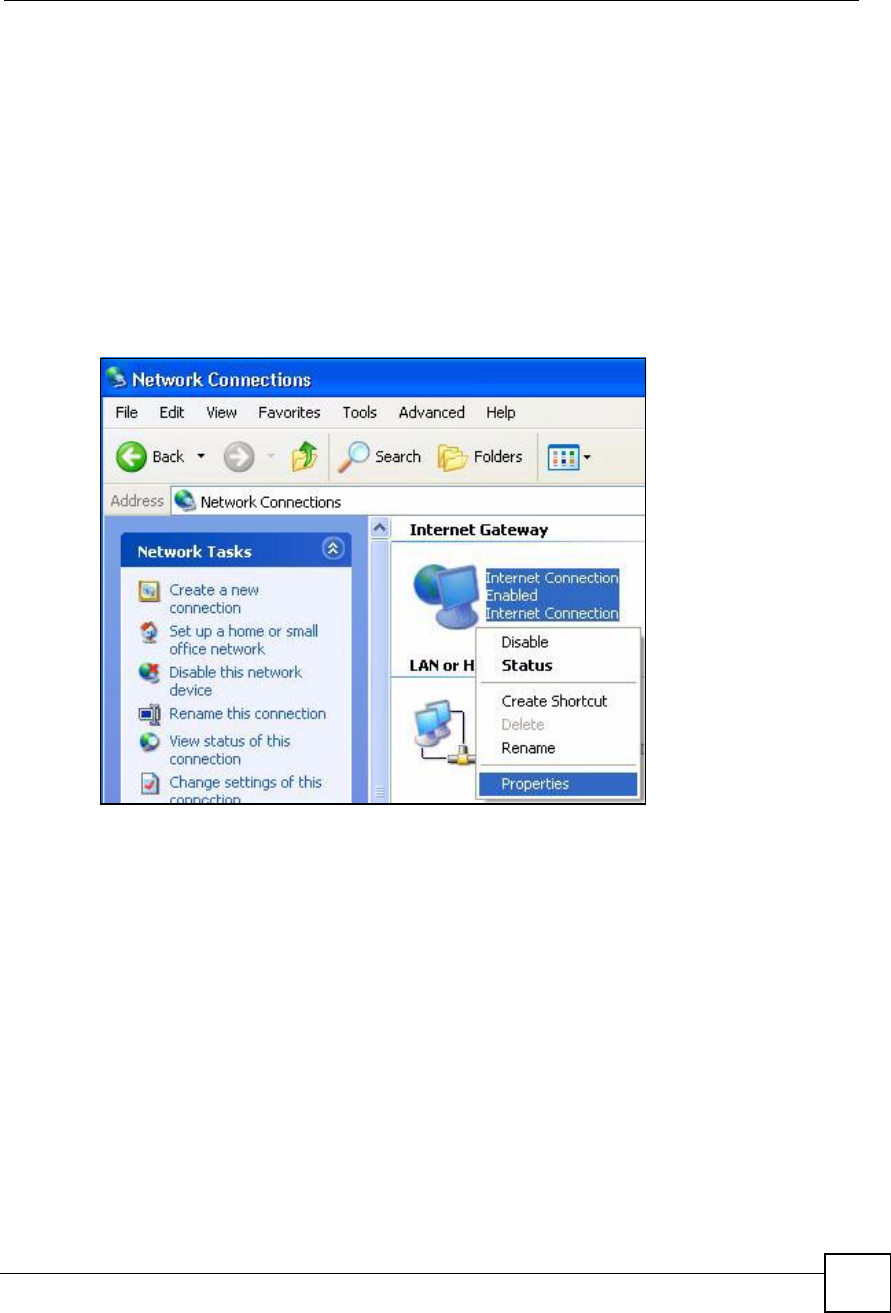
Chapter 20UPnP
MAX-200HW2 Series User s Guide 225
20.2.2 Using UPnP in Windows XP Example
This section shows you how to use the UPnP feature in Windows XP. You must already have
UPnP installed in Windows XP and UPnP activated on the ZyXEL Device.
Make sure the computer is connected to a LAN port of the ZyXEL Device. Turn on your
computer and the ZyXEL Device.
20.2.2.1 Auto-discover Your UPnP-enabled Network Device
1Click Start and Control Panel. Double-click Network Connections. An icon displays
under Internet Gateway.
2Right-click the icon and select Properties.
Figure 145 Network Connections
3In the Internet Connection Properties window, click Settings to see the port mappings
there were automatically created.
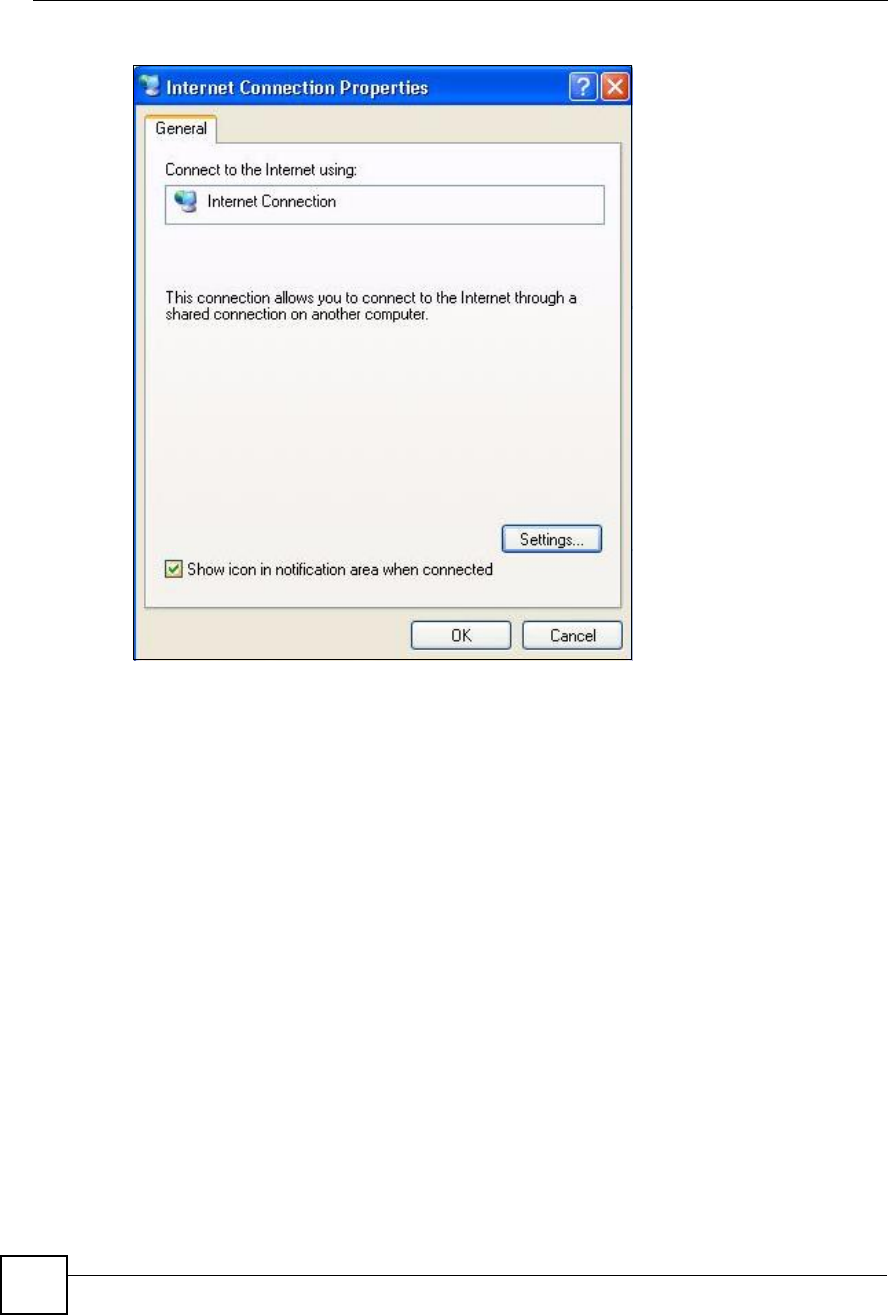
Chapter 20UPnP
MAX-200HW2 Series User s Guide
226
Figure 146 Internet Connection Properties
4You may edit or delete the port mappings or click Add to manually add port mappings.
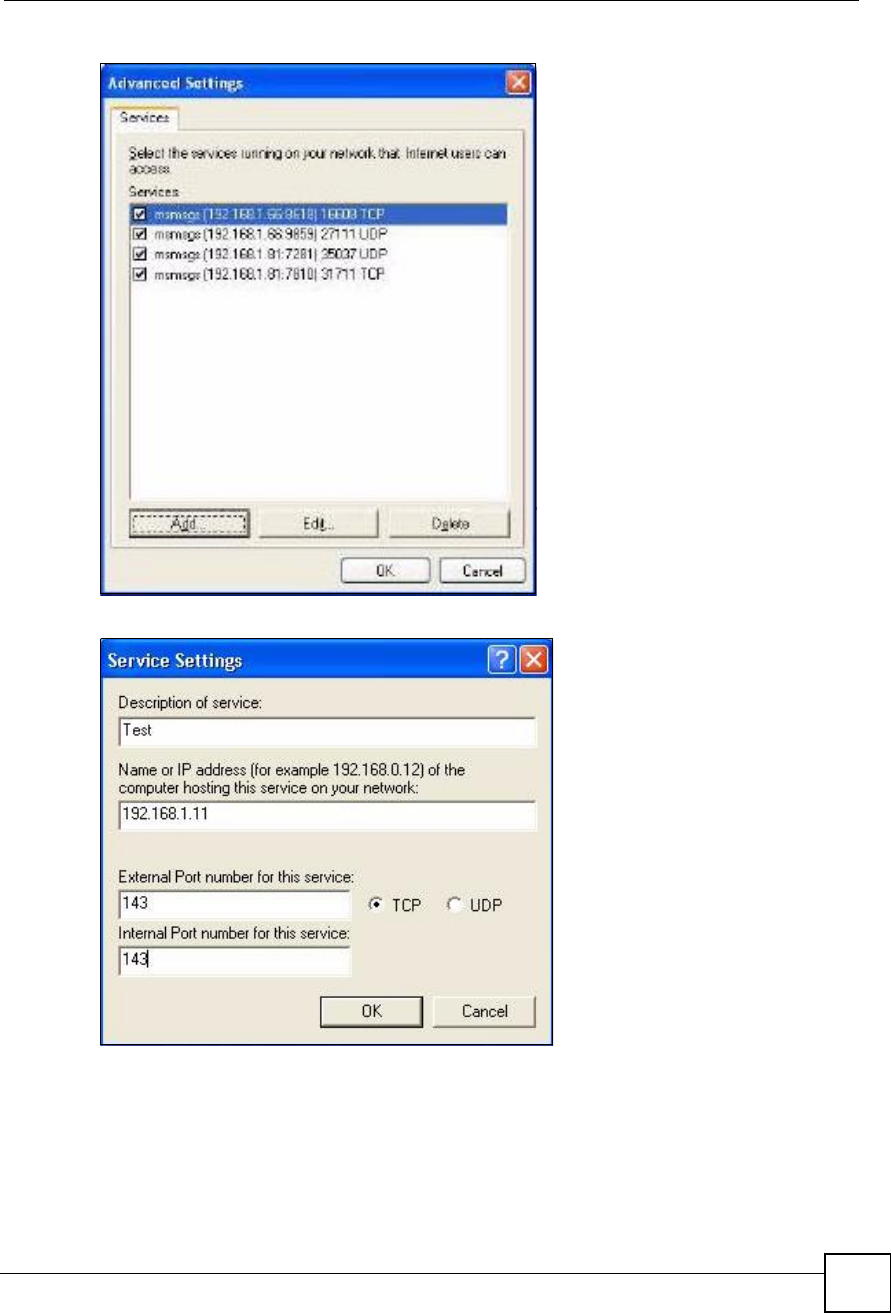
Chapter 20UPnP
MAX-200HW2 Series User s Guide 227
Figure 147 Internet Connection Properties: Advanced Settings
Figure 148 Internet Connection Properties: Advanced Settings: Add
5When the UPnP-enabled device is disconnected from your computer, all port mappings
will be deleted automatically.
6Select Show icon in notification area when connected option and click OK. An icon
displays in the system tray.
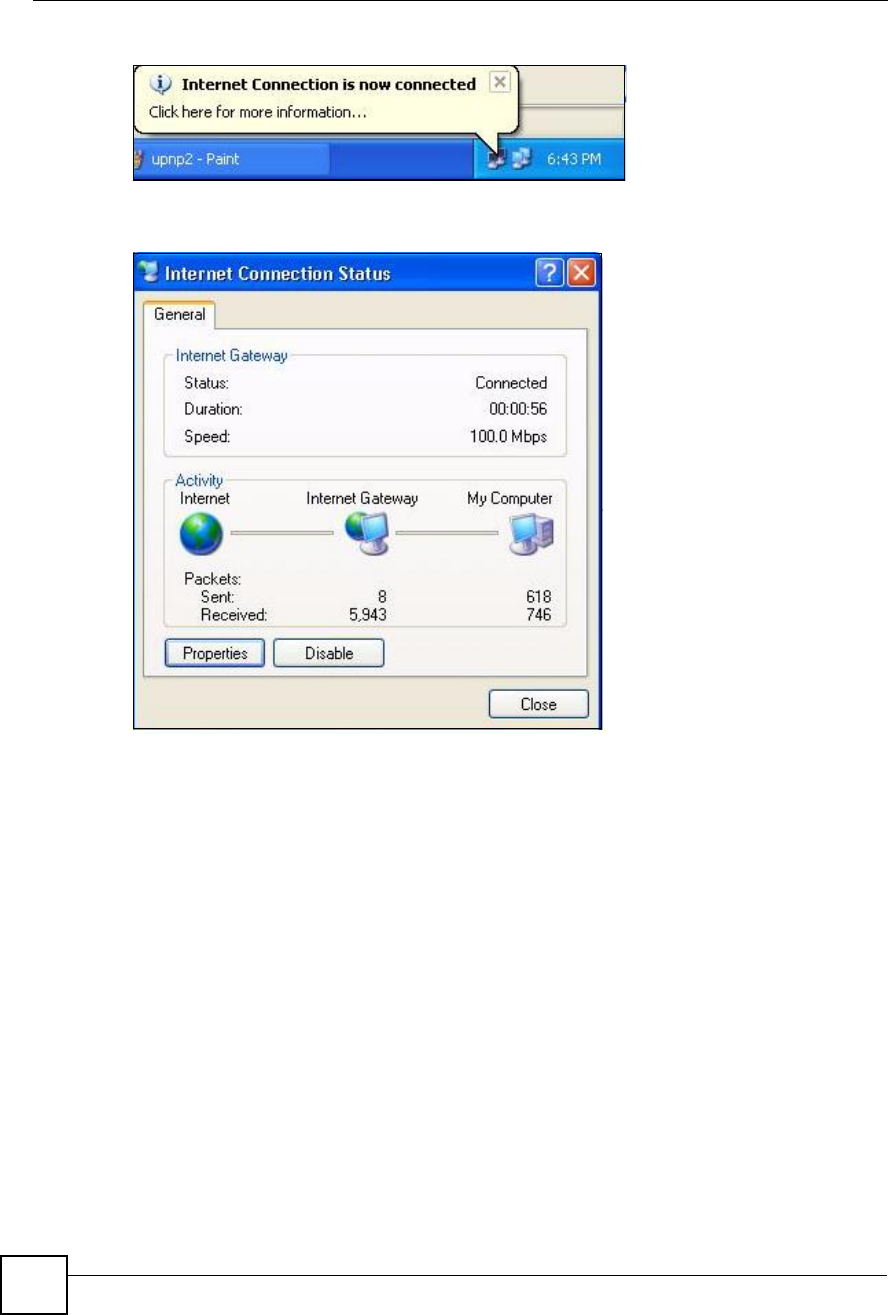
Chapter 20UPnP
MAX-200HW2 Series User s Guide
228
Figure 149 System Tray Icon
7Double-click on the icon to display your current Internet connection status.
Figure 150 Internet Connection Status
20.2.2.2 Web Configurator Easy Access
With UPnP, you can access the web-based configurator on the ZyXEL Device without finding
out the IP address of the ZyXEL Device first. This becomes helpful if you do not know the IP
address of the ZyXEL Device.
Follow the steps below to access the web configurator.
1Click Start and then Control Panel.
2Double-click Network Connections.
3Select My Network Places under Other Places.
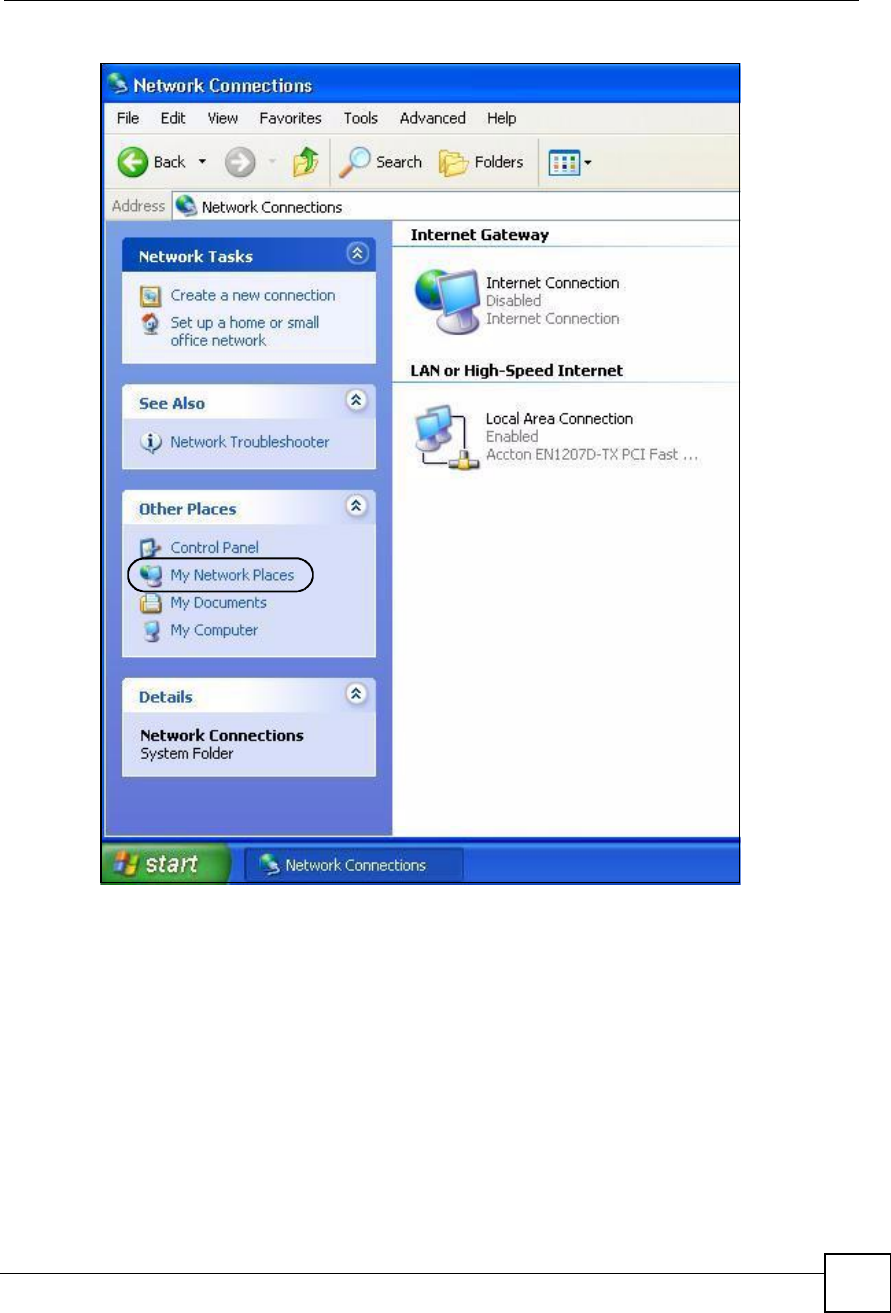
Chapter 20UPnP
MAX-200HW2 Series User s Guide 229
Figure 151 Network Connections
4An icon with the description for each UPnP-enabled device displays under Local
Network.
5Right-click on the icon for your ZyXEL Device and select Invoke. The web configurator
login screen displays.
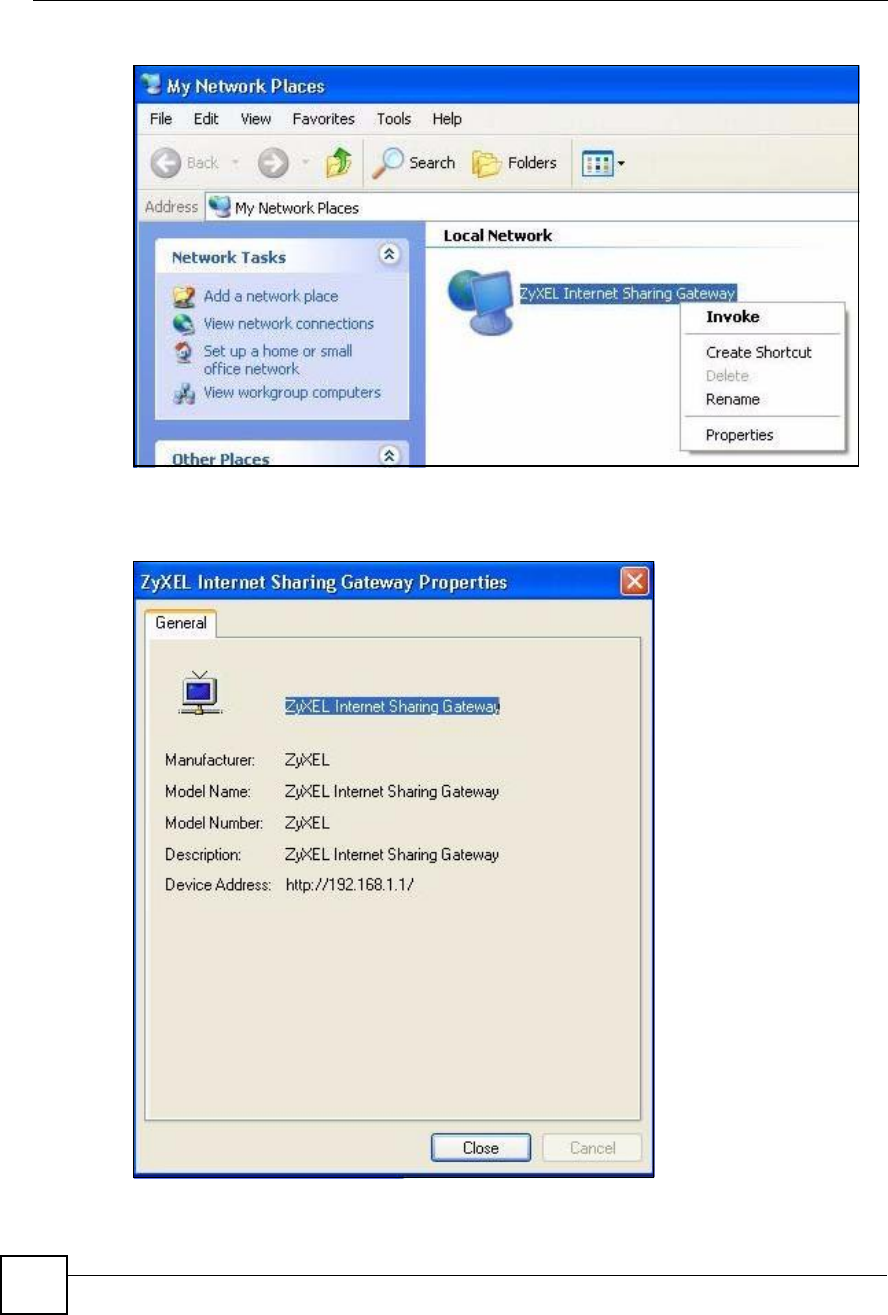
Chapter 20UPnP
MAX-200HW2 Series User s Guide
230
Figure 152 Network Connections: My Network Places
6Right-click on the icon for your ZyXEL Device and select Properties. A properties
window displays with basic information about the ZyXEL Device.
Figure 153 Network Connections: My Network Places: Properties: Example
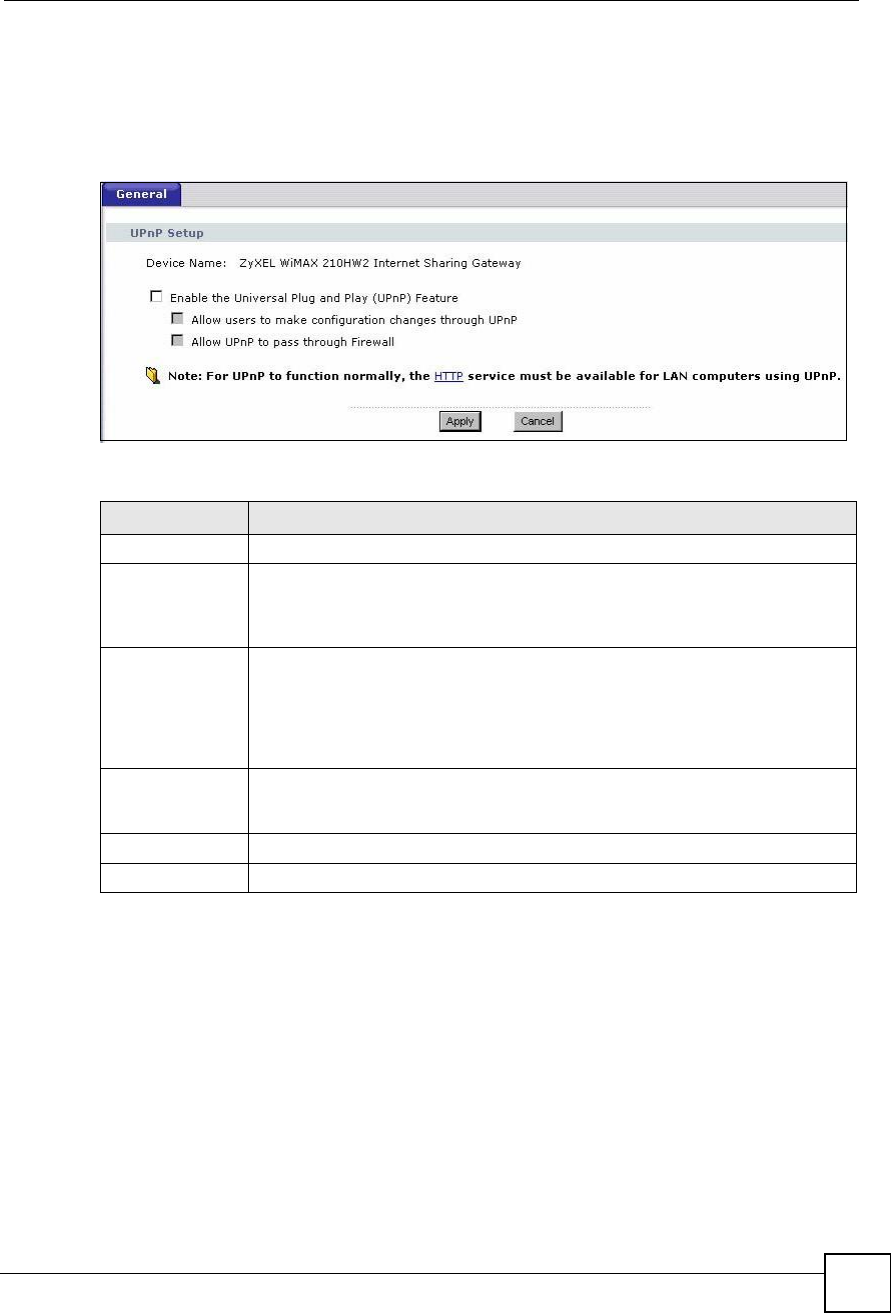
Chapter 20UPnP
MAX-200HW2 Series User s Guide 231
20.3 UPnP Screen
Use this screen to set up UPnP in your ZyXEL Device. To access this screen, click
Management > UPnP.
Figure 154 Management > UPnP
Each field is described in the following table.
Table 91 Management > UPnP
LABEL DESCRIPTION
Device Name This field identifies your device in UPnP applications.
Enable the
Universal Plug
and Play (UPnP)
Feature
Select this to activate UPnP. Be aware that anyone could use a UPnP application
to open the web configurator's login screen without entering the ZyXEL Device's
IP address. You still have to enter the password, however.
Allow users to
make
configuration
changes through
UPnP
Select this to allow UPnP-enabled applications to automatically configure the
ZyXEL Device so that they can communicate through the ZyXEL Device. For
example, using NAT traversal, UPnP applications automatically reserve a NAT
forwarding port in order to communicate with another UPnP enabled device; this
eliminates the need to manually configure port forwarding for the UPnP enabled
application.
Allow UPnP to
pass through
Firewall
Select this to allow traffic from UPnP-enabled applications to bypass the firewall.
Clear this if you want the firewall to check UPnP application packets (for example,
MSN packets).
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Cancel Click this to set every field in this screen to its default value.

Chapter 20UPnP
MAX-200HW2 Series User s Guide
232

MAX-200HW2 Series User s Guide 233
CHAPTER 21
System
Use this screen to set up general system settings, change the system mode, change the
password, configure the DDNS server settings, and set the current date and time.
21.1 System Features Overview
21.1.1 System Name
System Name is for identification purposes. However, because some ISPs check this name
you should enter your computer's "Computer Name".
In Windows 95/98 click Start, Settings, Control Panel, Network. Click the
Identification tab, note the entry for the Computer Name field and enter it as the System
Name.
In Windows 2000, click Start, Settings and Control Panel and then double-click System.
Click the Network Identification tab and then the Properties button. Note the entry for
the Computer name field and enter it as the System Name.
In Windows XP, click Start, My Computer, View system information and then click the
Computer Name tab. Note the entry in the Full computer name field and enter it as the
ZyXEL Device System Name.
21.1.2 Domain Name
The Domain Name entry is what is propagated to the DHCP clients on the LAN. If you leave
this blank, the domain name obtained by DHCP from the ISP is used. While you must enter
the host name (System Name) on each individual computer, the domain name can be assigned
from the ZyXEL Device via DHCP.
21.1.3 DNS Server Address Assignment
Use DNS (Domain Name System) to map a domain name to its corresponding IP address and
vice versa, for instance, the IP address of www.zyxel.com is 204.217.0.2. The DNS server is
extremely important because without it, you must know the IP address of a computer before
you can access it.
The ZyXEL Device can get the DNS server addresses in the following ways.
1The ISP tells you the DNS server addresses, usually in the form of an information sheet,
when you sign up. If your ISP gives you DNS server addresses, enter them in the DNS
Server fields in the SYSTEM General screen.

Chapter 21System
MAX-200HW2 Series User s Guide
234
2If the ISP did not give you DNS server information, leave the DNS Server fields in the
SYSTEM General screen set to 0.0.0.0 for the ISP to dynamically assign the DNS
server IP addresses.
21.1.4 Dynamic DNS
Dynamic DNS allows you to update your current dynamic IP address with one or many
dynamic DNS services so that anyone can contact you (in NetMeeting, CU-SeeMe, etc.). You
can also access your FTP server or Web site on your own computer using a domain name (for
instance myhost.dhs.org, where myhost is a name of your choice) that will never change
instead of using an IP address that changes each time you reconnect. Your friends or relatives
will always be able to call you even if they don't know your IP address.
First of all, you need to have registered a dynamic DNS account with www.dyndns.org. This is
for people with a dynamic IP from their ISP or DHCP server that would still like to have a
domain name. The Dynamic DNS service provider will give you a password or key.
Enabling the wildcard feature for your host causes *.yourhost.dyndns.org to be aliased to the
same IP address as yourhost.dyndns.org. This feature is useful if you want to be able to use,
for example, www.yourhost.dyndns.org and still reach your hostname.
If you have a private WAN IP address, then you cannot use Dynamic DNS.
21.1.5 Pre-defined NTP Time Servers List
The ZyXEL Device uses the following pre-defined list of NTP time servers if you do not
specify a time server or it cannot synchronize with the time server you specified.
The ZyXEL Device can use this pre-defined list of time servers regardless of
the Time Protocol you select.
When the ZyXEL Device uses the pre-defined list of NTP time servers, it randomly selects
one server and tries to synchronize with it. If the synchronization fails, then the ZyXEL
Device goes through the rest of the list in order from the first one tried until either it is
successful or all the pre-defined NTP time servers have been tried.
Table 92 Pre-defined NTP Time Servers
ntp1.cs.wisc.edu
ntp1.gbg.netnod.se
ntp2.cs.wisc.edu
tock.usno.navy.mil
ntp3.cs.wisc.edu
ntp.cs.strath.ac.uk
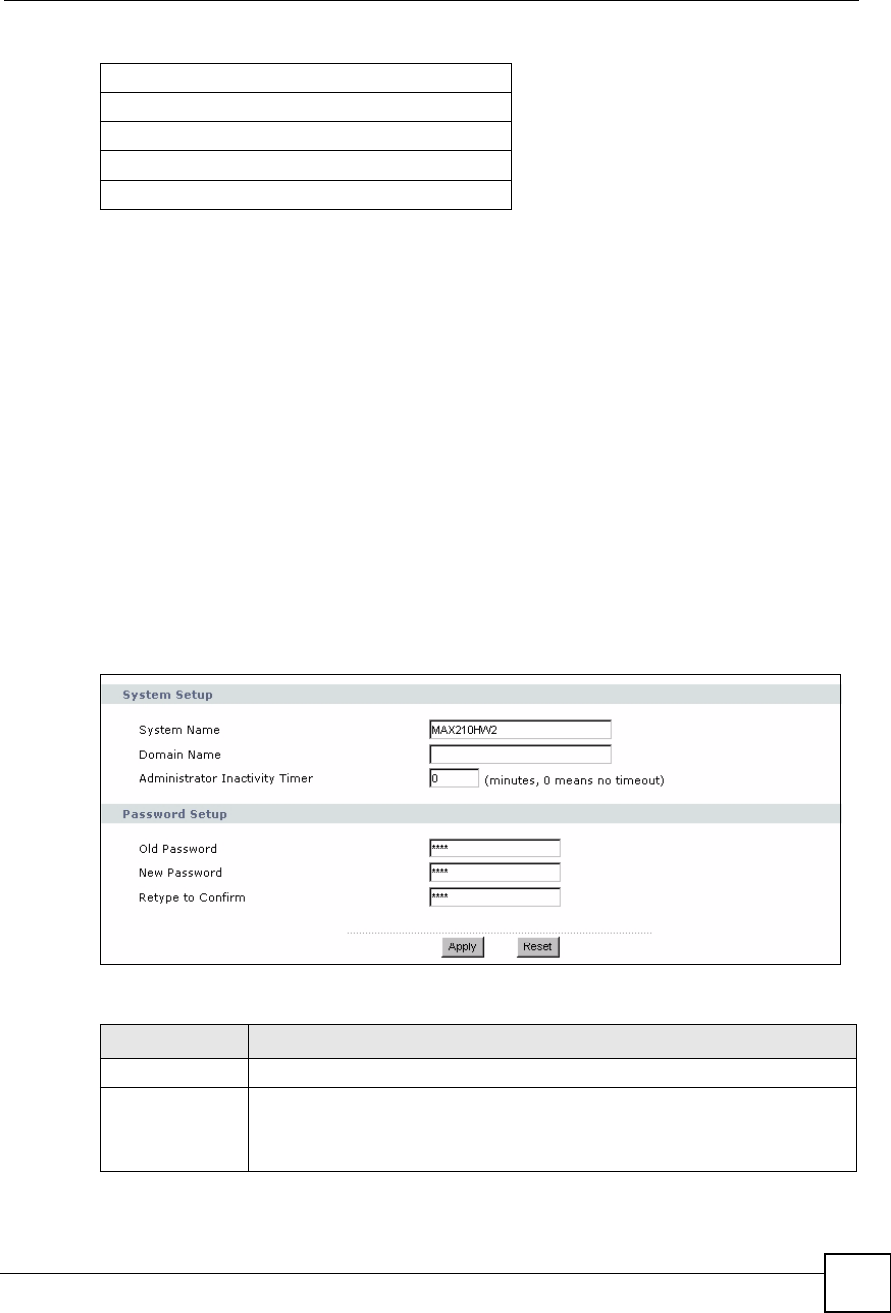
Chapter 21System
MAX-200HW2 Series User s Guide 235
21.1.6 Resetting the Time
The ZyXEL Device resets the time in the following instances:
When the ZyXEL Device starts up.
When you click Apply in the Time Setting Screen.
24-hour intervals after starting.
21.2 System Screens
21.2.1 General System Screen
Use this screen to change the ZyXEL Device!s mode, set up the ZyXEL Device!s system
name, domain name, idle timeout, and administrator password. To access this screen, click
Maintenance > System > General.
Figure 155 Maintenance > System > General
Each field is described in the following table.
ntp1.sp.se
time1.stupi.se
tick.stdtime.gov.tw
tock.stdtime.gov.tw
time.stdtime.gov.tw
Table 92 Pre-defined NTP Time Servers
Table 93 Maintenance > System > General
LABEL DESCRIPTION
System Setup
System NameEnter your computer's "Computer Name". This is for identification purposes, but
some ISPs also check this field. This name can be up to 30 alphanumeric
characters long. Spaces are not allowed, but dashes !-" and underscores "_" are
accepted.
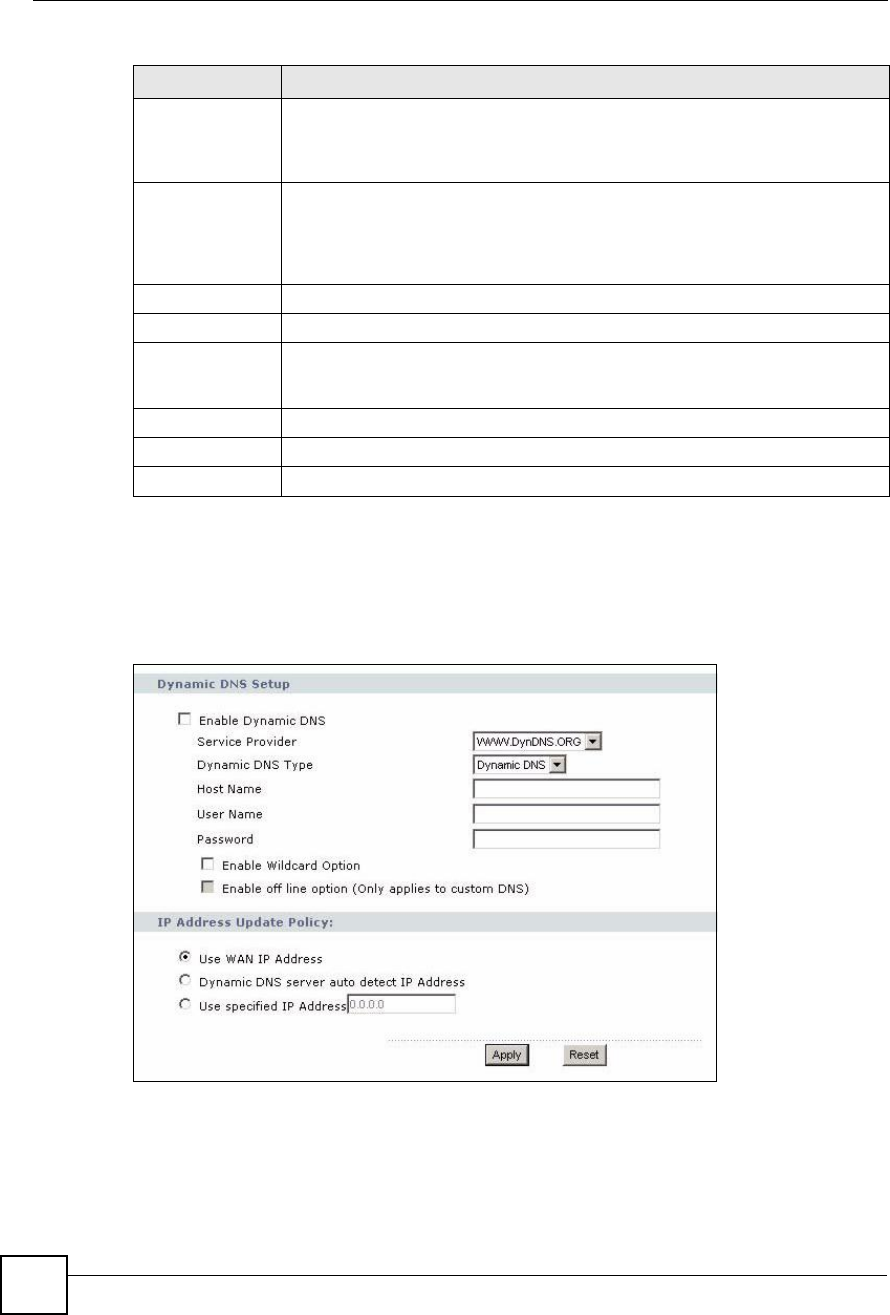
Chapter 21System
MAX-200HW2 Series User s Guide
236
21.2.2 Dynamic DNS Screen
Use this screen to set up the ZyXEL Device as a dynamic DNS client. To access this screen,
click Maintenance > System > Dynamic DNS.
Figure 156 Maintenance > System > Dynamic DNS
Domain NameEnter the domain name entry that is propagated to DHCP clients on the LAN. If
you leave this blank, the domain name obtained from the ISP is used. Use up to
38 alphanumeric characters. Spaces are not allowed, but dashes !-" and periods
"." are accepted.
Administrator
Inactivity Timer
Enter the number of minutes a management session can be left idle before the
session times out. After it times out, you have to log in again. A value of "0" means
a management session never times out, no matter how long it has been left idle.
This is not recommended. Long idle timeouts may have security risks. The default
is five minutes.
Password Setup
Old PasswordEnter the current password you use to access the ZyXEL Device.
New PasswordEnter the new password for the ZyXEL Device. You can use up to 30 characters.
As you type the password, the screen displays an asterisk (*) for each character
you type.
Retype to ConfirmEnter the new password again.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its default value.
Table 93 Maintenance > System > General
LABEL DESCRIPTION

Chapter 21System
MAX-200HW2 Series User s Guide 237
Each field is described in the following table.
21.2.3 Time Setting Screen
Use this screen to set the date, time, and time zone in the ZyXEL Device. To access this
screen, click Maintenance > System > Time Setting.
Table 94 Maintenance > System > Dynamic DNS
LABEL DESCRIPTION
Dynamic DNS
Setup
Enable Dynamic
DNS
Select this to use dynamic DNS.
Service Provider Select the name of your Dynamic DNS service provider.
Dynamic DNS
Type
Select the type of service that you are registered for from your Dynamic DNS
service provider.
Host Name Enter the host name. You can specify up to two host names, separated by a
comma (",").
User Name Enter your user name.
Password Enter the password assigned to you.
Enable Wildcard
Option
Select this to enable the DynDNS Wildcard feature.
Enable offline
option
This field is available when CustomDNS is selected in the DDNS Type field.
Select this if your Dynamic DNS service provider redirects traffic to a URL that you
can specify while you are off line. Check with your Dynamic DNS service provider.
IP Address
Update Policy
Use WAN IP
Address
Select this if you want the ZyXEL Device to update the domain name with the
WAN port's IP address.
Dynamic DNS
server auto detect
IP address
Select this if you want the DDNS server to update the IP address of the host
name(s) automatically. Select this optionwhen there are one or more NAT routers
between the ZyXEL Device and the DDNS server.
Note: The DDNS server may not be able to detect the proper IP
address if there is an HTTP proxy server between the ZyXEL
Device and the DDNS server.
Use specified IP
address
Select this if you want to use the specified IP address with the host name(s). Then,
specify the IP address. Use this option if you have a static IP address.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its default value.
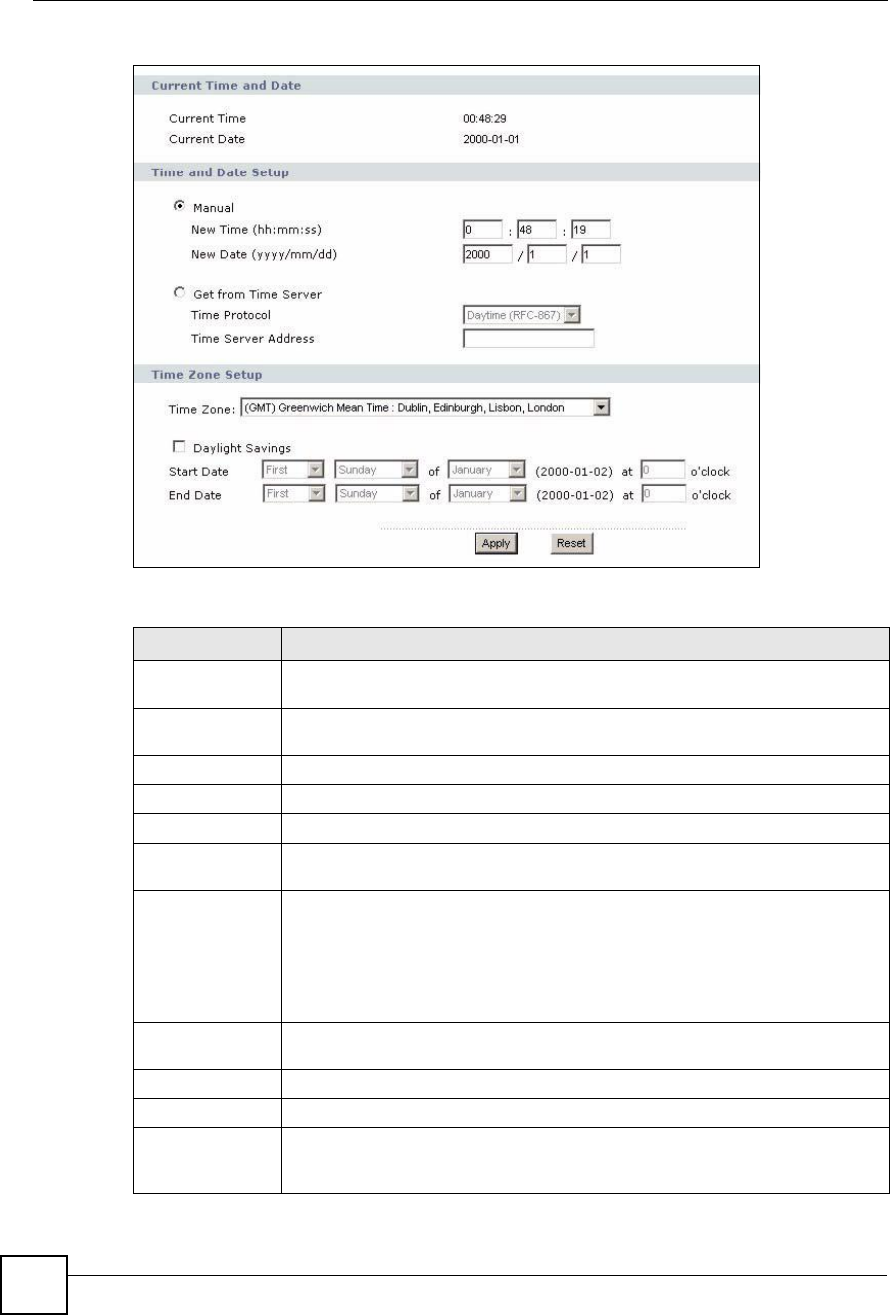
Chapter 21System
MAX-200HW2 Series User s Guide
238
Figure 157 Maintenance > System > Time Setting
Each field is described in the following table.
Table 95 Maintenance > System > Time Setting
LABEL DESCRIPTION
Current Time and
Date
This section displays the current date and time.
Time and Date
Setup
Manual Select this if you want to specify the current date and time in the fields below.
New Time Enter the new time in this field, and click Apply.
New Date Enter the new date in this field, and click Apply.
Get from Time
Server
Select this if you want to use a time server to update the current date and time in
the ZyXEL Device.
Time ProtocolSelect the time service protocol that your time server uses.Check with your ISP or
network administrator, or use trial-and-error to find a protocol that works.
Daytime (RFC 867) - This format is day/month/year/time zone.
Time (RFC 868) - This format displays a 4-byte integer giving the total number of
seconds since 1970/1/1 at 0:0:0.
NTP (RFC 1305) - This format is similar to Time (RFC 868).
Time Server
Address
Enter the IP address or URL of your time server. Check with your ISP or network
administrator if you are unsure of this information.
Time Zone Setup
Time ZoneSelect the time zone at your location.
Daylight SavingsSelect this if your location uses daylight savings time. Daylight savings is a period
from late spring to early fall when many places set their clocks ahead of normal
local time by one hour to give more daytime light in the evening.

Chapter 21System
MAX-200HW2 Series User s Guide 239
Start DateEnter which hour on which day of which week of which month daylight-savings
time starts.
End DateEnter which hour on the which day of which week of which month daylight-savings
time ends.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Reset Click this to set every field in this screen to its last-saved value.
Table 95 Maintenance > System > Time Setting
LABEL DESCRIPTION

Chapter 21System
MAX-200HW2 Series User s Guide
240

MAX-200HW2 Series User s Guide 241
CHAPTER 22
Logs
Use these screens to look at log entries and alerts and to configure the ZyXEL Device!s log
and alert settings.
22.1 Logs Overview
For a list of log messages, see Section 22.3 on page 245.
22.1.1 Alerts
An alert is a type of log that warrants more serious attention. Some categories such as System
Errors consist of both logs and alerts.
22.1.2 Syslog Logs
There are two types of syslog: event logs and traffic logs. The device generates an event log
when a system event occurs, for example, when a user logs in or the device is under attack.
The device generates a traffic log when a "session" is terminated. A traffic log summarizes the
session's type, when it started and stopped the amount of traffic that was sent and received and
so on. An external log analyzer can reconstruct and analyze the traffic flowing through the
device after collecting the traffic logs.
Chapter 22Logs
MAX-200HW2 Series User s Guide
242
The following table shows RFC-2408 ISAKMP payload types that the log displays. Please
refer to the RFC for detailed information on each type.
Table 96 Syslog Logs
LOG MESSAGE DESCRIPTION
Event Log: <Facility*8 + Severity>Mon
dd hr:mm:ss hostname
src="<srcIP:srcPort>"
dst="<dstIP:dstPort>" msg="<msg>"
note="<note>" devID="<mac address>"
cat="<category>"
This message is sent by the system ("RAS" displays as the
system name if you haven t configured one) when the
router generates a syslog. The facility is defined in the Log
Settings screen. The severity is the log s syslog class. The
definition of messages and notes are defined in the various
log charts throughout this appendix. The !devID" is the
MAC address of the router s LAN port. The !cat" is the
same as the category in the router s logs.
Traffic Log: <Facility*8 + Severity>Mon
dd hr:mm:ss hostname
src="<srcIP:srcPort>"
dst="<dstIP:dstPort>" msg="Traffic Log"
note="Traffic Log" devID="<mac
address>" cat="Traffic Log"
duration=seconds sent=sentBytes
rcvd=receiveBytes dir="<from:to>"
protoID=IPProtocolID
proto="serviceName" trans="IPSec/
Normal"
This message is sent by the device when the connection
(session) is closed. The facility is defined in the Log
Settings screen. The severity is the traffic log type. The
message and note always display "Traffic Log". The "proto"
field lists the service name. The "dir" field lists the incoming
and outgoing interfaces ("LAN:LAN", "LAN:WAN",
"LAN:DEV" for example).
Table 97 RFC-2408 ISAKMP Payload Types
LOG DISPLAY PAYLOAD TYPE
SA Security Association
PROP Proposal
TRANS Transform
KE Key Exchange
ID Identification
CER Certificate
CER_REQ Certificate Request
HASH Hash
SIG Signature
NONCE Nonce
NOTFY Notification
DEL Delete
VID Vendor ID
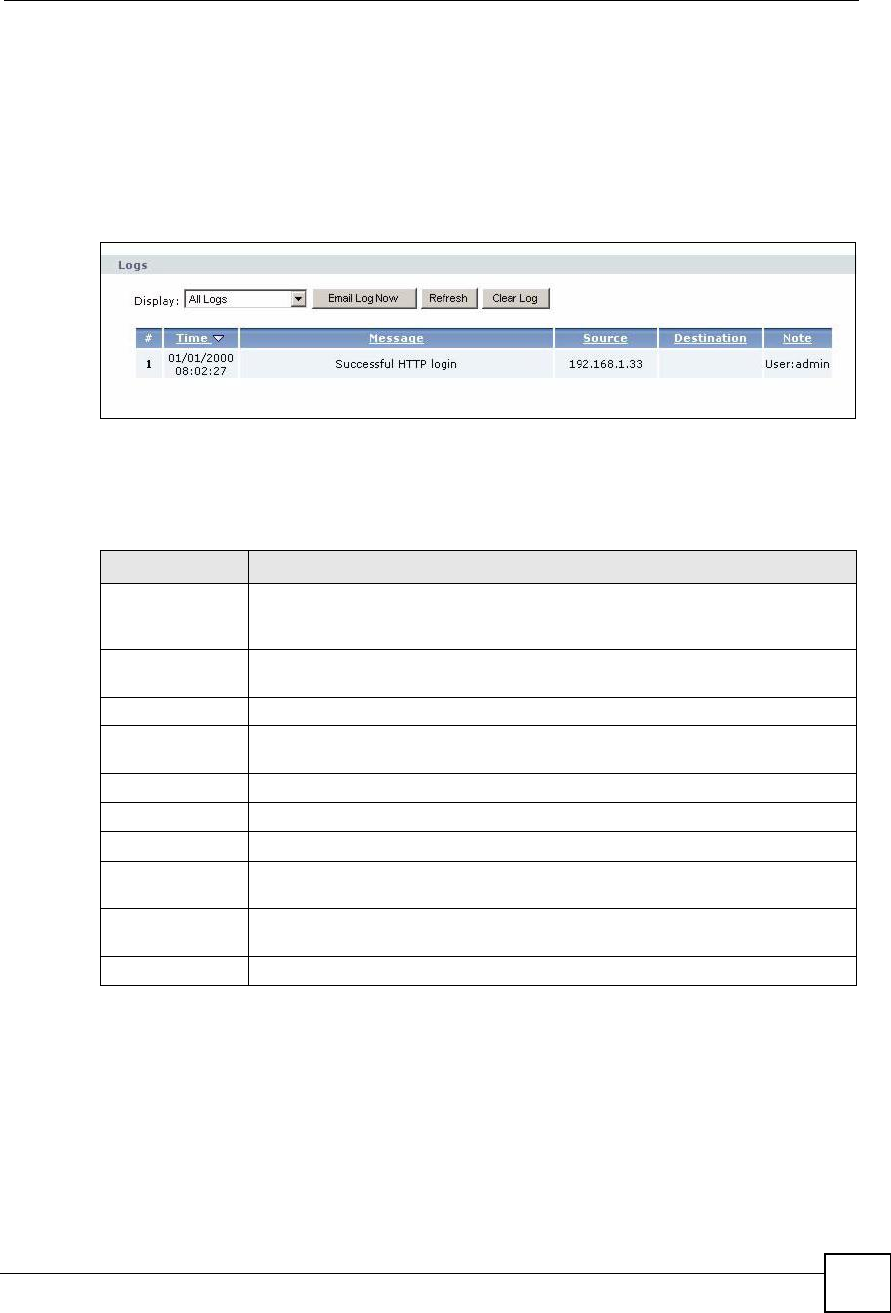
Chapter 22Logs
MAX-200HW2 Series User s Guide 243
22.2 Logs Screens
22.2.1 Log Viewer Screen
Use this screen to look at log entries and alerts. Alerts are written in red. To access this screen,
click Maintenance > Logs > View Log.
Figure 158 Maintenance > Logs > View Log
Click a column header to sort log entries in descending (later-to-earlier) order. Click again to
sort in ascending order. The small triangle next to a column header indicates how the table is
currently sorted (pointing downward is descending; pointing upward is ascending). Each field
is described in the following table.
22.2.2 Log Settings Screen
Use this screen to configure where the ZyXEL Device sends logs and alerts, the schedule for
sending logs, and which logs and alerts are sent or recorded.
To access this screen, click Maintenance > Logs > Log Settings.
Table 98 Maintenance > Logs > View Log
LABEL DESCRIPTION
Display Select a category whose log entries you want to view. To view all logs, select All
Logs. The list of categories depends on what log categories are selected in the
Log Settings page.
Email Log Now Click this to send the log screen to the e-mail address specified in the Log
Settings page.
Refresh Click Refresh to renew the log screen.
Clear Log Click Clear Log to clear all the log entries, regardless of what is shown on the log
screen.
#This field is a sequential value, and it is not associated with a specific log entry.
Time This field displays the time the log entry was recorded.
Message This field displays the reason for the log entry. See Section 22.3 on page 245.
Source This field displays the source IP address and the port number of the incoming
packet. In many cases, some or all of this information may not be available.
Destination This field lists the destination IP address and the port number of the incoming
packet. In many cases, some or all of this information may not be available.
Note This field displays additional information about the log entry.
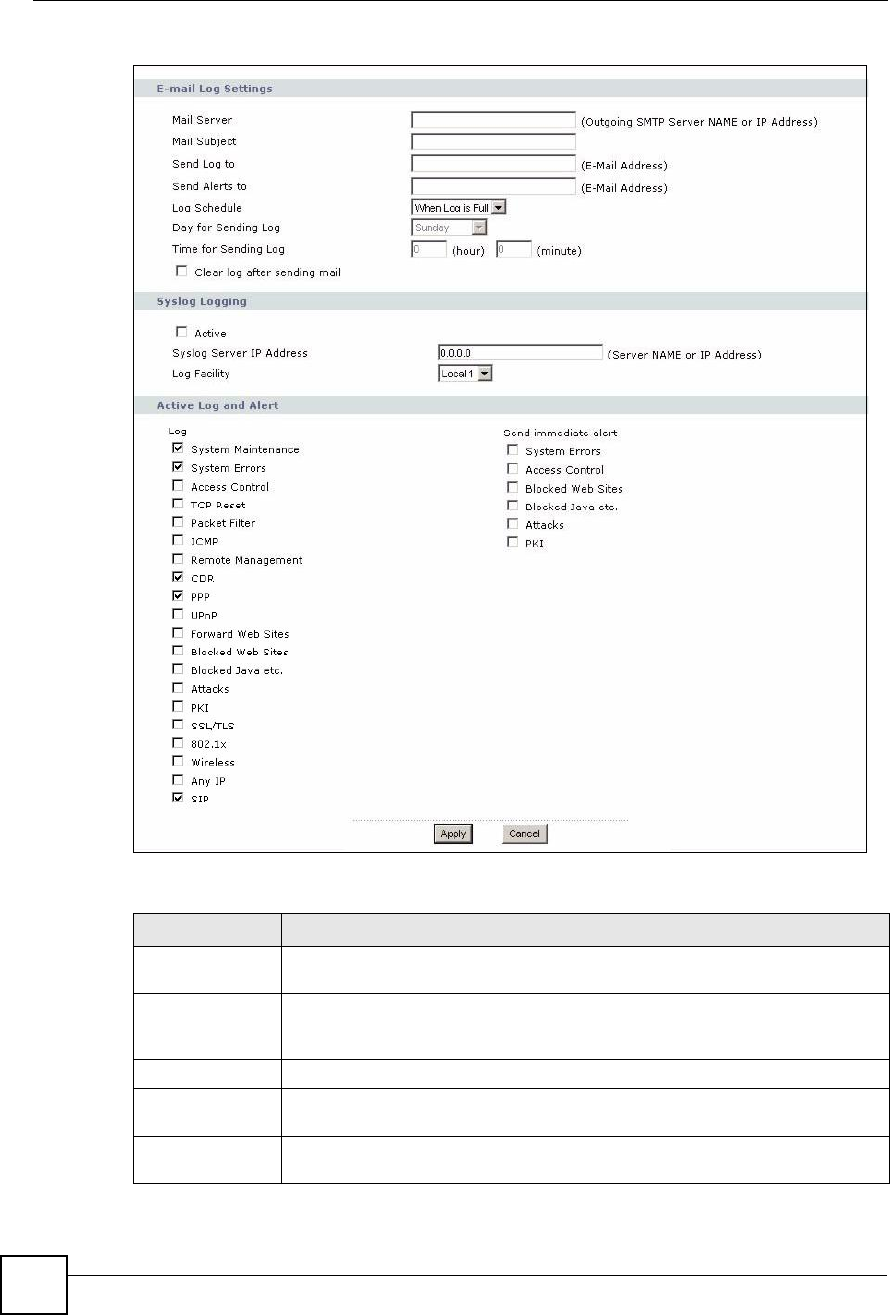
Chapter 22Logs
MAX-200HW2 Series User s Guide
244
Figure 159 Maintenance > Logs > Log Settings
Each field is described in the following table.
Table 99 Maintenance > Logs > Log Settings
LABEL DESCRIPTION
E-mail Log
Settings
Mail Server Enter the server name or the IP address of the mail server the ZyXEL Device
should use to e-mail logs and alerts. Leave this field blank if you do not want to
send logs or alerts by e-mail.
Mail Subject Enter the subject line used in e-mail messages the ZyXEL Device sends.
Send Log to Enter the e-mail address to which log entries are sent by e-mail. Leave this field
blank if you do not want to send logs by e-mail.
Send Alerts to Enter the e-mail address to which alerts are sent by e-mail. Leave this field blank if
you do not want to send alerts by e-mail.
Chapter 22Logs
MAX-200HW2 Series User s Guide 245
22.3 Log Message Descriptions
The following tables provide descriptions of example log messages.
Log Schedule Select the frequency with which the ZyXEL Device should send log messages by
e-mail.
#Daily
#Weekly
#Hourly
#When Log is Full
#None.
If the Weekly or the Daily option is selected, specify a time of day when the E-mail
should be sent. If the Weekly option is selected, then also specify which day of the
week the E-mail should be sent. If the When Log is Full option is selected, an
alert is sent when the log fills up. If you select None, no log messages are sent.
Day for Sending
Log
This field is only available when you select Weekly in the Log Schedule field.
Select which day of the week to send the logs.
Time for Sending
Log
This field is only available when you select Daily or Weekly in the Log Schedule
field.
Enter the time of day in 24-hour format (for example 23:00 equals 11:00 pm) to
send the logs.
Clear log after
sending mail
Select this to clear all logs and alert messages after logs are sent by e-mail.
Syslog Logging Syslog logging sends a log to an external syslog server used to store logs.
Active Select this to enable syslog logging.
Syslog Server IP
Address
Enter the server name or IP address of the syslog server that logs the selected
categories of logs.
Log Facility Select a location. The log facility allows you to log the messages in different files in
the syslog server. See the documentation of your syslog for more details.
Active Log and
Alert
Log Select the categories of logs that you want to record.
Send immediate
alert
Select the categories of alerts that you want the ZyXEL Device to send
immediately.
Apply Click this to save your changes and to apply them to the ZyXEL Device.
Cancel Click this to set every field in this screen to its last-saved value.
Table 99 Maintenance > Logs > Log Settings
LABEL DESCRIPTION
Table 100 System Error Logs
LOG MESSAGE DESCRIPTION
WAN connection is down. The WAN connection is down. You cannot access the network
through this interface.
%s exceeds the max.
number of session per
host!
This attempt to create a NAT session exceeds the maximum
number of NAT session table entries allowed to be created per
host.
Chapter 22Logs
MAX-200HW2 Series User s Guide
246
Table 101 System Maintenance Logs
LOG MESSAGE DESCRIPTION
Time calibration is
successful
The device has adjusted its time based on information from
the time server.
Time calibration failed The device failed to get information from the time server.
WAN interface gets IP: %s The WAN interface got a new IP address from the DHCP or
PPPoE server.
DHCP client gets %s A DHCP client got a new IP address from the DHCP server.
DHCP client IP expired A DHCP client's IP address has expired.
DHCP server assigns %s The DHCP server assigned an IP address to a client.
Successful WEB login Someone has logged on to the device's web configurator
interface.
WEB login failed Someone has failed to log on to the device's web configurator
interface.
TELNET Login Successfully Someone has logged on to the router via telnet.
TELNET Login Fail Someone has failed to log on to the router via telnet.
Successful FTP login Someone has logged on to the device via ftp.
FTP login failed Someone has failed to log on to the device via ftp.
NAT Session Table is Full! The maximum number of NAT session table entries has been
exceeded and the table is full.
Time initialized by Daytime
Server
The device got the time and date from the Daytime server.
Time initialized by Time
server
The device got the time and date from the time server.
Time initialized by NTP
server
The device got the time and date from the NTP server.
Connect to Daytime server
fail
The device was not able to connect to the Daytime server.
Connect to Time server fail The device was not able to connect to the Time server.
Connect to NTP server fail The device was not able to connect to the NTP server.
Too large ICMP packet has
been dropped
The device dropped an ICMP packet that was too large.
Configuration Change: PC =
0x%x, Task ID = 0x%x
The device is saving configuration changes.
Table 102 Access Control Logs
LOG MESSAGE DESCRIPTION
Firewall default policy: [ TCP |
UDP | IGMP | ESP | GRE | OSPF ]
<Packet Direction>
Attempted TCP/UDP/IGMP/ESP/GRE/OSPF access
matched the default policy and was blocked or forwarded
according to the default policy s setting.
Firewall rule [NOT] match:[ TCP
| UDP | IGMP | ESP | GRE | OSPF
] <Packet Direction>, <rule:%d>
Attempted TCP/UDP/IGMP/ESP/GRE/OSPF access
matched (or did not match) a configured firewall rule
(denoted by its number) and was blocked or forwarded
according to the rule.
Chapter 22Logs
MAX-200HW2 Series User s Guide 247
Triangle route packet forwarded:
[ TCP | UDP | IGMP | ESP | GRE |
OSPF ]
The firewall allowed a triangle route session to pass
through.
Packet without a NAT table entry
blocked: [ TCP | UDP | IGMP |
ESP | GRE | OSPF ]
The router blocked a packet that didn't have a
corresponding NAT table entry.
Router sent blocked web site
message: TCP
The router sent a message to notify a user that the router
blocked access to a web site that the user requested.
Exceed maximum sessions per host (%d).The device blocked a session because the host's
connections exceeded the maximum sessions per host.
Firewall allowed a packet that matched a
NAT session: [ TCP | UDP ]
A packet from the WAN (TCP or UDP) matched a cone
NAT session and the device forwarded it to the LAN.
Table 103 TCP Reset Logs
LOG MESSAGE DESCRIPTION
Under SYN flood attack,
sent TCP RST
The router sent a TCP reset packet when a host was under a SYN
flood attack (the TCP incomplete count is per destination host.)
Exceed TCP MAX
incomplete, sent TCP RST
The router sent a TCP reset packet when the number of TCP
incomplete connections exceeded the user configured threshold.
(the TCP incomplete count is per destination host.)
Peer TCP state out of
order, sent TCP RST
The router sent a TCP reset packet when a TCP connection state
was out of order.Note: The firewall refers to RFC793 Figure 6 to
check the TCP state.
Firewall session time
out, sent TCP RST
The router sent a TCP reset packet when a dynamic firewall
session timed out.
The default timeout values are as follows:
ICMP idle timeout: 3 minutes
UDP idle timeout: 3 minutes
TCP connection (three way handshaking) timeout: 270 seconds
TCP FIN-wait timeout: 2 MSL (Maximum Segment Lifetime set in
the TCP header).
TCP idle (established) timeout (s): 150 minutes
TCP reset timeout: 10 seconds
Exceed MAX incomplete,
sent TCP RST
The router sent a TCP reset packet when the number of
incomplete connections (TCP and UDP) exceeded the user-
configured threshold. (Incomplete count is for all TCP and UDP
connections through the firewall.)Note: When the number of
incomplete connections (TCP + UDP) > !Maximum Incomplete
High", the router sends TCP RST packets for TCP connections
and destroys TOS (firewall dynamic sessions) until incomplete
connections < !Maximum Incomplete Low".
Access block, sent TCP
RST
The router sends a TCP RST packet and generates this log if you
turn on the firewall TCP reset mechanism (via CI command: sys
firewall tcprst).
Table 102 Access Control Logs (continued)
LOG MESSAGE DESCRIPTION
Chapter 22Logs
MAX-200HW2 Series User s Guide
248
For type and code details, see Table 112 on page 251.
Table 104 Packet Filter Logs
LOG MESSAGE DESCRIPTION
[ TCP | UDP | ICMP | IGMP |
Generic ] packet filter
matched (set: %d, rule: %d)
Attempted access matched a configured filter rule (denoted
by its set and rule number) and was blocked or forwarded
according to the rule.
Table 105 ICMP Logs
LOG MESSAGE DESCRIPTION
Firewall default policy: ICMP
<Packet Direction>, <type:%d>,
<code:%d>
ICMP access matched the default policy and was
blocked or forwarded according to the user's setting.
Firewall rule [NOT] match: ICMP
<Packet Direction>, <rule:%d>,
<type:%d>, <code:%d>
ICMP access matched (or didn t match) a firewall rule
(denoted by its number) and was blocked or forwarded
according to the rule.
Triangle route packet forwarded:
ICMP
The firewall allowed a triangle route session to pass
through.
Packet without a NAT table entry
blocked: ICMP
The router blocked a packet that didn t have a
corresponding NAT table entry.
Unsupported/out-of-order ICMP:
ICMP
The firewall does not support this kind of ICMP packets
or the ICMP packets are out of order.
Router reply ICMP packet: ICMP The router sent an ICMP reply packet to the sender.
Table 106 CDR Logs
LOG MESSAGE DESCRIPTION
board %d line %d channel %d,
call %d, %s C01 Outgoing Call
dev=%x ch=%x %s
The router received the setup requirements for a call. !call" is
the reference (count) number of the call. !dev" is the device
type (3 is for dial-up, 6 is for PPPoE). "channel" or !ch" is the
call channel ID.For example, "board 0 line 0 channel 0, call 3,
C01 Outgoing Call dev=6 ch=0 "Means the router has dialed
to the PPPoE server 3 times.
board %d line %d channel %d,
call %d, %s C02 OutCall
Connected %d %s
The PPPoE or dial-up call is connected.
board %d line %d channel %d,
call %d, %s C02 Call
Terminated
The PPPoE or dial-up call was disconnected.
Table 107 PPP Logs
LOG MESSAGE DESCRIPTION
ppp:LCP Starting The PPP connection s Link Control Protocol stage has started.
ppp:LCP Opening The PPP connection s Link Control Protocol stage is opening.
ppp:CHAP Opening The PPP connection s Challenge Handshake Authentication Protocol stage is
opening.
ppp:IPCP
Starting
The PPP connection s Internet Protocol Control Protocol stage is starting.
Chapter 22Logs
MAX-200HW2 Series User s Guide 249
For type and code details, see Table 112 on page 251.
ppp:IPCP Opening The PPP connection s Internet Protocol Control Protocol stage is opening.
ppp:LCP Closing The PPP connection s Link Control Protocol stage is closing.
ppp:IPCP Closing The PPP connection s Internet Protocol Control Protocol stage is closing.
Table 108 UPnP Logs
LOG MESSAGE DESCRIPTION
UPnP pass through Firewall UPnP packets can pass through the firewall.
Table 109 Content Filtering Logs
LOG MESSAGE DESCRIPTION
%s: Keyword blocking The content of a requested web page matched a user defined
keyword.
%s: Not in trusted web
list
The web site is not in a trusted domain, and the router blocks all traffic
except trusted domain sites.
%s: Forbidden Web site The web site is in the forbidden web site list.
%s: Contains ActiveX The web site contains ActiveX.
%s: Contains Java
applet
The web site contains a Java applet.
%s: Contains cookie The web site contains a cookie.
%s: Proxy mode
detected
The router detected proxy mode in the packet.
%s: Trusted Web site The web site is in a trusted domain.
%s When the content filter is not on according to the time schedule.
Waiting content filter
server timeout
The external content filtering server did not respond within the timeout
period.
DNS resolving failed The ZyXEL Device cannot get the IP address of the external content
filtering via DNS query.
Creating socket failed The ZyXEL Device cannot issue a query because TCP/IP socket
creation failed, port:port number.
Connecting to content
filter server fail
The connection to the external content filtering server failed.
License key is invalid The external content filtering license key is invalid.
Table 110 Attack Logs
LOG MESSAGE DESCRIPTION
attack [ TCP | UDP | IGMP
| ESP | GRE | OSPF ]
The firewall detected a TCP/UDP/IGMP/ESP/GRE/OSPF attack.
attack ICMP (type:%d,
code:%d)
The firewall detected an ICMP attack.
land [ TCP | UDP | IGMP |
ESP | GRE | OSPF ]
The firewall detected a TCP/UDP/IGMP/ESP/GRE/OSPF land
attack.
Table 107 PPP Logs (continued)
LOG MESSAGE DESCRIPTION
Chapter 22Logs
MAX-200HW2 Series User s Guide
250
land ICMP (type:%d,
code:%d)
The firewall detected an ICMP land attack.
ip spoofing - WAN [ TCP |
UDP | IGMP | ESP | GRE |
OSPF ]
The firewall detected an IP spoofing attack on the WAN port.
ip spoofing - WAN ICMP
(type:%d, code:%d)
The firewall detected an ICMP IP spoofing attack on the WAN
port.
icmp echo : ICMP
(type:%d, code:%d)
The firewall detected an ICMP echo attack.
syn flood TCP The firewall detected a TCP syn flood attack.
ports scan TCP The firewall detected a TCP port scan attack.
teardrop TCP The firewall detected a TCP teardrop attack.
teardrop UDP The firewall detected an UDP teardrop attack.
teardrop ICMP (type:%d,
code:%d)
The firewall detected an ICMP teardrop attack.
illegal command TCP The firewall detected a TCP illegal command attack.
NetBIOS TCP The firewall detected a TCP NetBIOS attack.
ip spoofing - no routing
entry [ TCP | UDP | IGMP
| ESP | GRE | OSPF ]
The firewall classified a packet with no source routing entry as an
IP spoofing attack.
ip spoofing - no routing
entry ICMP (type:%d,
code:%d)
The firewall classified an ICMP packet with no source routing
entry as an IP spoofing attack.
vulnerability ICMP
(type:%d, code:%d)
The firewall detected an ICMP vulnerability attack.
traceroute ICMP (type:%d,
code:%d)
The firewall detected an ICMP traceroute attack.
ports scan UDPThe firewall detected a UDP port scan attack.
Firewall sent TCP packet in
response to DoS attack TCP
The firewall sent TCP packet in response to a DoS attack
ICMP Source Quench ICMPThe firewall detected an ICMP Source Quench attack.
ICMP Time Exceed ICMPThe firewall detected an ICMP Time Exceed attack.
ICMP Destination Unreachable
ICMP
The firewall detected an ICMP Destination Unreachable attack.
ping of death. ICMPThe firewall detected an ICMP ping of death attack.
smurf ICMPThe firewall detected an ICMP smurf attack.
Table 111 Remote Management Logs
LOG MESSAGE DESCRIPTION
Remote Management: FTP deniedAttempted use of FTP service was blocked according to
remote management settings.
Remote Management: TELNET deniedAttempted use of TELNET service was blocked according
to remote management settings.
Table 110 Attack Logs (continued)
LOG MESSAGE DESCRIPTION
Chapter 22Logs
MAX-200HW2 Series User s Guide 251
Remote Management: HTTP or UPnP
denied
Attempted use of HTTP or UPnP service was blocked
according to remote management settings.
Remote Management: WWW deniedAttempted use of WWW service was blocked according to
remote management settings.
Remote Management: HTTPS deniedAttempted use of HTTPS service was blocked according to
remote management settings.
Remote Management: SSH deniedAttempted use of SSH service was blocked according to
remote management settings.
Remote Management: ICMP Ping
response denied
Attempted use of ICMP service was blocked according to
remote management settings.
Remote Management: DNS deniedAttempted use of DNS service was blocked according to
remote management settings.
Table 112 ICMP Notes
TYPE CODE DESCRIPTION
0Echo Reply
0Echo reply message
3Destination Unreachable
0Net unreachable
1Host unreachable
2Protocol unreachable
3Port unreachable
4A packet that needed fragmentation was dropped because it was set to Don't
Fragment (DF)
5Source route failed
4Source Quench
0A gateway may discard internet datagrams if it does not have the buffer space
needed to queue the datagrams for output to the next network on the route to
the destination network.
5Redirect
0Redirect datagrams for the Network
1Redirect datagrams for the Host
2Redirect datagrams for the Type of Service and Network
3Redirect datagrams for the Type of Service and Host
8Echo
0Echo message
11 Time Exceeded
0Time to live exceeded in transit
1Fragment reassembly time exceeded
12 Parameter Problem
0Pointer indicates the error
Table 111 Remote Management Logs
LOG MESSAGE DESCRIPTION
Chapter 22Logs
MAX-200HW2 Series User s Guide
252
13 Timestamp
0Timestamp request message
14 Timestamp Reply
0Timestamp reply message
15 Information Request
0Information request message
16 Information Reply
0Information reply message
Table 113 SIP Logs
LOG MESSAGE DESCRIPTION
SIP Registration Success
by SIP:SIP Phone Number
The listed SIP account was successfully registered with a SIP
register server.
SIP Registration Fail by
SIP:SIP Phone Number
An attempt to register the listed SIP account with a SIP register
server was not successful.
SIP UnRegistration
Success by SIP:SIP Phone
Number
The listed SIP account s registration was deleted from the SIP
register server.
SIP UnRegistration Fail
by SIP:SIP Phone Number
An attempt to delete the listed SIP account s registration from the
SIP register server failed.
Table 114 RTP Logs
LOG MESSAGE DESCRIPTION
Error, RTP init fail The initialization of an RTP session failed.
Error, Call fail: RTP
connect fail
A VoIP phone call failed because the RTP session could not be
established.
Error, RTP connection
cannot close
The termination of an RTP session failed.
Table 115 FSM Logs: Caller Side
LOG MESSAGE DESCRIPTION
VoIP Call Start Ph[Phone
Port Number] <- Outgoing
Call Number
Someone used a phone connected to the listed phone port to
initiate a VoIP call to the listed destination.
VoIP Call Established
Ph[Phone Port] ->
Outgoing Call Number
Someone used a phone connected to the listed phone port to
make a VoIP call to the listed destination.
VoIP Call End Phone[Phone
Port]
A VoIP phone call made from a phone connected to the listed
phone port has terminated.
Table 112 ICMP Notes (continued)
TYPE CODE DESCRIPTION