ZyXEL Communications MAX200HW2 WiMAX Router User Manual UserMan I88MAX200HW2 revised
ZyXEL Communications Corporation WiMAX Router UserMan I88MAX200HW2 revised
Contents
- 1. User manual revised 1
- 2. User manual revised 2
- 3. User manual revised 3
- 4. User manal revised 3
User manual revised 3
Chapter 22Logs
MAX-200HW2 Series User s Guide 253
Table 116 FSM Logs: Callee Side
LOG MESSAGE DESCRIPTION
VoIP Call Start from
SIP[SIP Port Number]
A VoIP phone call came to the ZyXEL Device from the listed SIP
number.
VoIP Call Established
Ph[Phone Port] <-
Outgoing Call Number
A VoIP phone call was set up from the listed SIP number to the
ZyXEL Device.
VoIP Call End
Phone[Phone Port]
A VoIP phone call that came into the ZyXEL Device has terminated.
Table 117 Lifeline Logs
LOG MESSAGE DESCRIPTION
PSTN Call Start A PSTN call has been initiated.
PSTN Call End A PSTN call has terminated.
PSTN Call Established A PSTN call has been set up.

Chapter 22Logs
MAX-200HW2 Series User s Guide
254
MAX-200HW2 Series User s Guide 255
CHAPTER 23
Tools
Use these screens to upload new firmware, back up and restore the configuration, and restart
the ZyXEL Device.
23.1 Tools Overview
23.1.1 Firmware
Contact your service provider for information on available firmware upgrades.
Firmware files (usually) use the system model name with a "*.bin" extension, e.g., "ZyXEL
Device.bin". The upload process uses HTTP (Hypertext Transfer Protocol) and may take up to
two minutes. After a successful upload, the system will reboot.
Only use firmware for your ZyXEL Device s specific model. Refer to the label
on the back of your ZyXEL Device.
23.2 Tools Screens
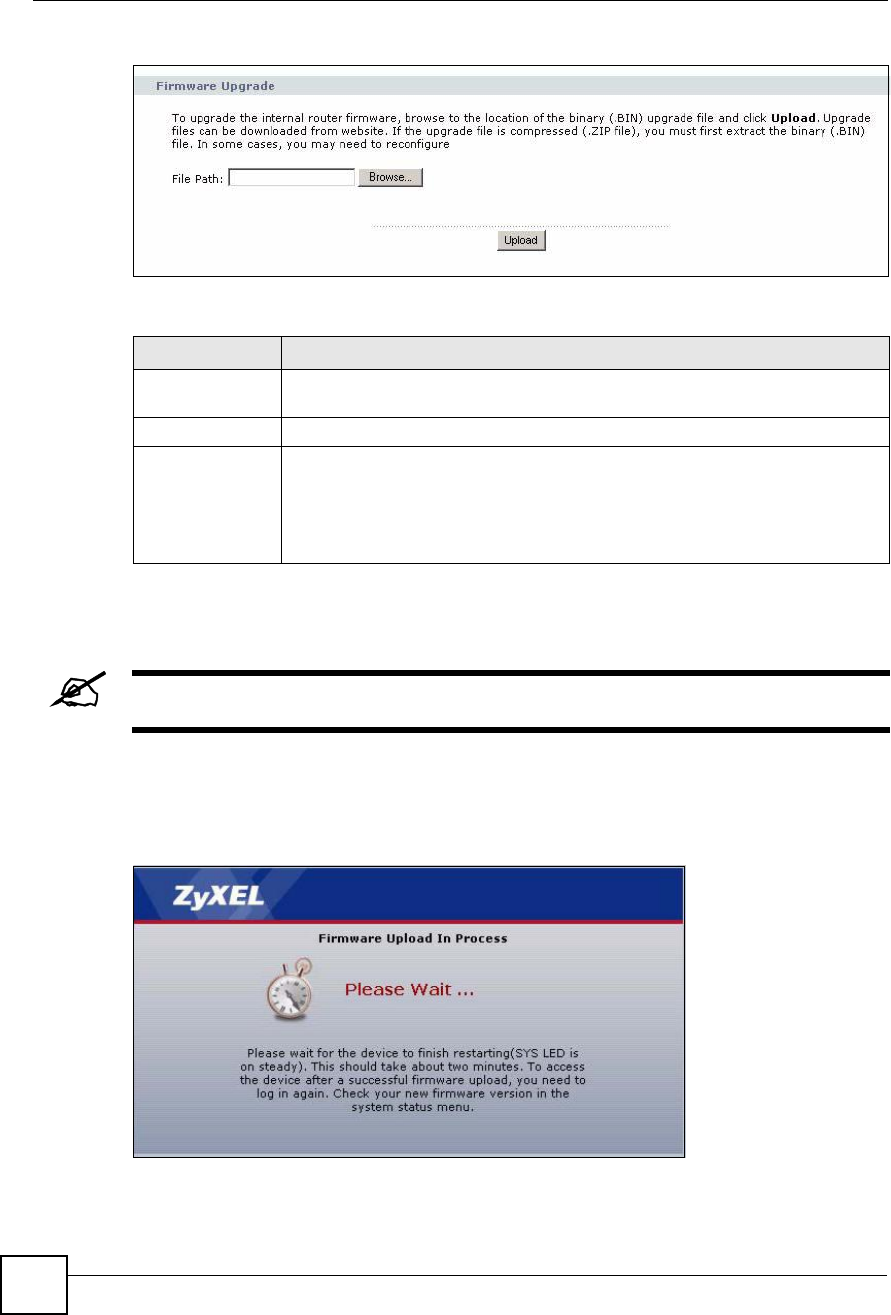
23.2.1 Firmware Screen
Use this screen to upload new firmware to the ZyXEL Device. To access this screen, click
Maintenance > Tools > Firmware.
Only use firmware for your ZyXEL Device s specific model. Refer to the label
on the bottom of your ZyXEL Device.
Chapter 23Tools
MAX-200HW2 Series User s Guide
256
Figure 160 Maintenance > Tools > Firmware
Each field is described in the following table.
23.2.2 Firmware Upload Screens
Do not turn off the device while firmware upload is in progress!
When the ZyXEL Device starts to upload firmware, the Firmware Upload in Process screen
appears.
Figure 161 Firmware Upload In Process
Table 118 Maintenance > Tools > Firmware
LABEL DESCRIPTION
File Path Enter the location of the .bin file you want to upload, or click Browse... to find it.
You must decompress compressed (.zip) files before you can upload them.
Browse... Click this to find the .bin file you want to upload.
Upload Click this to begin uploading the selected file. This may take up to two minutes.
See Section 23.2.2 on page 256 for more information about this process.
Note: Do not turn off the device while firmware upload is in
progress!
Chapter 23Tools
MAX-200HW2 Series User s Guide 257
The process usually takes about two minutes. The device automatically restarts in this time.
This causes a temporary network disconnect. In some operating systems, you may see the
following icon on your desktop.
Figure 162 Network Temporarily Disconnected
After two minutes, log in again, and check your new firmware version in the Status screen.
You might have to open a new browser window to log in.
If the upload is not successful, the following screen appears.
Figure 163 Firmware Upload Error
Click Return to go back to the Firmware screen.
23.2.3 Configuration Screen
Use this screen to back up or restore the configuration of the ZyXEL Device. You can also use
this screen to reset the ZyXEL Device to the factory default settings. To access this screen,
click Maintenance > Tools > Configuration.
Figure 164 Maintenance > Tools > Configuration

Chapter 23Tools
MAX-200HW2 Series User s Guide
258
Each field is described in the following table.
23.2.4 Restore Configuration Screens
Do not turn off the device while configuration file upload is in progress.
When the ZyXEL Device has finished restoring the selected configuration file, the following
screen appears.
Figure 165 Configuration Upload Successful
The device now automatically restarts. This causes a temporary network disconnect. In some
operating systems, you may see the following icon on your desktop.
Table 119 Maintenance > Tools > Configuration
LABEL DESCRIPTION
Backup
Configuration
Backup Click this to save the ZyXEL Device s current configuration to a file on your
computer. Once your device is configured and functioning properly, it is highly
recommended that you back up your configuration file before making configuration
changes. The backup configuration file is useful if you need to return to your
previous settings.
Restore
Configuration
File PathEnter the location of the file you want to upload, or click Browse... to find it.
BrowseClick this to find the file you want to upload.
UploadClick this to restore the selected configuration file. See Section 23.2.4 on page
258 for more information about this.
Note: Do not turn off the device while configuration file upload is in
progress.
Back to Factory
Defaults
Reset Click this to clear all user-entered configuration information and return the ZyXEL
Device to its factory defaults. There is no warning screen.
Chapter 23Tools
MAX-200HW2 Series User s Guide 259
Figure 166 Network Temporarily Disconnected
If the ZyXEL Device!s IP address is different in the configuration file you selected, you may
need to change the IP address of your computer to be in the same subnet as that of the default
management IP address (192.168.5.1). See your Quick Start Guide or the appendices for
details on how to set up your computer!s IP address.
You might have to open a new browser to log in again.
If the upload was not successful, a Configuration Upload Error screen appears.
Figure 167 Configuration Upload Error
Click Return to go back to the Configuration screen.
23.2.5 Restart Screen
Use this screen to reboot the ZyXEL Device without turning the power off. To access this
screen, click Maintenance > Tools > Restart.
Figure 168 Maintenance > Tools > Restart
This does not affect the ZyXEL Device!s configuration. When you click Restart, the
following screen appears.

Chapter 23Tools
MAX-200HW2 Series User s Guide
260
Figure 169 Maintenance > Tools > Restart > In Progress
Wait one minute for the device to finish restarting. Then, you can log in again.

261
PART IV
Troubleshooting
and Specifications
Troubleshooting (263)
Product Specifications (269)

262

MAX-200HW2 Series User s Guide 263
CHAPTER 24
Troubleshooting
This chapter offers some suggestions to solve problems you might encounter. The potential
problems are divided into the following categories.
Power, Hardware Connections, and LEDs
ZyXEL Device Access and Login
Internet Access
Phone Calls and VoIP
Reset the ZyXEL Device to Its Factory Defaults
Wireless LAN Troubleshooting
24.1 Power, Hardware Connections, and LEDs
The ZyXEL Device does not turn on. None of the LEDs turn on.
1Make sure you are using the power adaptor or cord included with the ZyXEL Device.
2Make sure the power adaptor or cord is connected to the ZyXEL Device and plugged in
to an appropriate power source. Make sure the power source is turned on.
3Disconnect and re-connect the power adaptor or cord to the ZyXEL Device.
4If the problem continues, contact the vendor.
One of the LEDs does not behave as expected.
1Make sure you understand the normal behavior of the LED. See Section 1.2.1 on page
35.
2Check the hardware connections. See the Quick Start Guide and Section 1.2 on page 35.
3Inspect your cables for damage. Contact the vendor to replace any damaged cables.
4Disconnect and re-connect the power adaptor to the ZyXEL Device.
5If the problem continues, contact the vendor.
Chapter 24Troubleshooting
MAX-200HW2 Series User s Guide
264
24.2 ZyXEL Device Access and Login
I forgot the IP address for the ZyXEL Device.
1The default IP address is 192.168.1.1.
2If you changed the IP address and have forgotten it, you might get the IP address of the
ZyXEL Device by looking up the IP address of the default gateway for your computer.
To do this in most Windows computers, click Start > Run, enter cmd, and then enter
ipconfig. The IP address of the Default Gateway might be the IP address of the ZyXEL
Device (it depends on the network), so enter this IP address in your Internet browser.
3If this does not work, you have to reset the ZyXEL Device to its factory defaults. See
Section 24.1 on page 263.
I forgot the password.
1The default password is 1234.
2If this does not work, you have to reset the ZyXEL Device to its factory defaults. See
Section 23.2.3 on page 257.
I cannot see or access the Login screen in the web configurator.
1Make sure you are using the correct IP address.
The default IP address is 192.168.1.1.
If you changed the IP address (Section 9.2.1 on page 122), use the new IP address.
If you changed the IP address and have forgotten it, see the troubleshooting
suggestions for I forgot the IP address for the ZyXEL Device.
2Check the hardware connections, and make sure the LEDs are behaving as expected. See
the Quick Start Guide and Section 1.2.1 on page 35.
3Make sure your Internet browser does not block pop-up windows and has JavaScripts
and Java enabled. See Appendix C on page 301.
4If there is a DHCP server on your network, make sure your computer is using a dynamic
IP address. Your ZyXEL Device is a DHCP server by default.
If there is no DHCP server on your network, make sure your computer!s IP address is in
the same subnet as the ZyXEL Device. See Appendix D on page 309.
5Reset the ZyXEL Device to its factory defaults, and try to access the ZyXEL Device
with the default IP address. See Section 23.2.3 on page 257.
6If the problem continues, contact the network administrator or vendor, or try one of the
advanced suggestions.

Chapter 24Troubleshooting
MAX-200HW2 Series User s Guide 265
Advanced Suggestions
Try to access the ZyXEL Device using another service, such as Telnet. If you can access
the ZyXEL Device, check the remote management settings and firewall rules to find out
why the ZyXEL Device does not respond to HTTP.
If your computer is connected wirelessly, use a computer that is connected to a LAN/
ETHERNET port.
I can see the Login screen, but I cannot log in to the ZyXEL Device.
1Make sure you have entered the user name and password correctly. The default user
name is admin, and the default password is 1234. These fields are case-sensitive, so
make sure [Caps Lock] is not on.
2You cannot log in to the web configurator while someone is using Telnet to access the
ZyXEL Device. Log out of the ZyXEL Device in the other session, or ask the person
who is logged in to log out.
3Disconnect and re-connect the power adaptor or cord to the ZyXEL Device.
4If this does not work, you have to reset the ZyXEL Device to its factory defaults. See
Section 23.2.3 on page 257.
I cannot Telnet to the ZyXEL Device.
See the troubleshooting suggestions for I cannot see or access the Login screen in the web
configurator. Ignore the suggestions about your browser.
24.3 Internet Access
I cannot access the Internet.
1Check the hardware connections, and make sure the LEDs are behaving as expected. See
the Quick Start Guide and Section 1.2.1 on page 35.
2Make sure you entered your ISP account information correctly in the wizard. These
fields are case-sensitive, so make sure [Caps Lock] is not on.
3Check your security settings. In the web configurator, go to the Status screen. Click the
Details... link next to Profile in the WiMAX Information box and make sure that you
are using the correct security settings for your Internet account.
4Check your WiMAX settings. The ZyXEL Device may have been set to search the
wrong frequencies for a wireless connection. In the web configurator, go to the Status
screen. Click the Details... link next to Site Information in the WiMAX Information

Chapter 24Troubleshooting
MAX-200HW2 Series User s Guide
266
box and ensure that the values are correct. If the values are incorrect, enter the correct
frequency settings in the Network > WAN > WiMAX Frequency screen. If you are
unsure of the correct values, contact your service provider.
5If you are trying to access the Internet wirelessly, make sure the wireless settings in the
wireless client are the same as the settings in the AP.
6Disconnect all the cables from your ZyXEL Device, and follow the directions in the
Quick Start Guide again.
7If the problem continues, contact your ISP.
I cannot access the Internet anymore. I had access to the Internet (with the
ZyXEL Device), but my Internet connection is not available anymore.
1Check the hardware connections, and make sure the LEDs are behaving as expected. See
the Quick Start Guide and Section 1.2.1 on page 35.
2Disconnect and re-connect the power adaptor to the ZyXEL Device.
3If the problem continues, contact your ISP.
The Internet connection is slow or intermittent.
1The quality of the ZyXEL Device!s wireless connection to the base station may be poor.
Poor signal reception may be improved by moving the ZyXEL Device away from thick
walls and other obstructions, or to a higher floor in your building.
2There may be radio interference caused by nearby electrical devices such as microwave
ovens and radio transmitters. Move the ZyXEL Device away or switch the other devices
off. Weather conditions may also affect signal quality.
3As well as having an external antenna connector, the MAX-210HW2 is equipped with an
internal directional antenna. If you know the location of the base station, orient the front
of the ZyXEL Device (the side with the LEDs) towards the base station. If you do not
know the location of the base station, experiment by moving the ZyXEL Device while
observing the SIGNAL LEDs for an increase in received signal strength. The MAX-
200HW2 and MAX-230HW2 do not have internal antennas.
4There might be a lot of traffic on the network. Look at the LEDs, and check Section 1.2.1
on page 35. If the ZyXEL Device is sending or receiving a lot of information, try closing
some programs that use the Internet, especially peer-to-peer applications.
5Disconnect and re-connect the power adaptor to the ZyXEL Device.
6If the problem continues, contact the network administrator or vendor, or try one of the
advanced suggestions.
The Internet connection disconnects.

Chapter 24Troubleshooting
MAX-200HW2 Series User s Guide 267
Check your WiMAX link and signal strength using the LINK and SIGNAL LEDs on the device. See the
following section if signal strength is poor or the ZyXEL Device has no link to a base station.
Contact your ISP if the problem persists.
24.4 Phone Calls and VoIP
The telephone port won t work or the telephone lacks a dial tone.
1Check the telephone connections and telephone wire.
2Make sure you have the VoIP SIP Settings screen properly configured.
I can access the Internet, but cannot make VoIP calls.
1Make sure you have the VoIP SIP Settings screen properly configured.
2The VoIP LED should come on. Make sure that your telephone is connected to the
LINE port.
3You can also check the VoIP status in the Status screen.
4If the VoIP settings are correct, use speed dial to make peer-to-peer calls. If you cannot
make a call using speed dial, there may be something wrong with the SIP server. Contact
your VoIP service provider.
Problems With Multiple SIP Accounts
You can set up two SIP accounts on your ZyXEL Device. By default your ZyXEL Device uses
SIP account 1 for outgoing calls, and it uses SIP accounts 1 and 2 for incoming calls. With this
setting, you always use SIP account 1 for your outgoing calls and you cannot distinguish
which SIP account the calls are coming in through. If you want to control the use of different
dialing plans for accounting purposes or other reasons, you need to configure your phone port
in order to control which SIP account you are using when placing or receiving calls.
24.5 Reset the ZyXEL Device to Its Factory Defaults
If you reset the ZyXEL Device, you lose all of the changes you have made. The ZyXEL
Device re-loads its default settings, and the password resets to 1234. You have to make all of
your changes again.
Chapter 24Troubleshooting
MAX-200HW2 Series User s Guide
268
You will lose all of your changes when you push the RESET button.
To reset the ZyXEL Device,
1Make sure the PWR LED is on and not blinking.
2Press and hold the RESET button for five to ten seconds. Release the RESET button
when the PWR LED begins to blink. The default settings have been restored.
If the ZyXEL Device restarts automatically, wait for the ZyXEL Device to finish restarting,
and log in to the web configurator. The password is "1234#.
If the ZyXEL Device does not restart automatically, disconnect and reconnect the ZyXEL
Device!s power. Then, follow the directions above again.
24.5.1 Pop-up Windows, JavaScripts and Java Permissions
Please see Section Appendix C on page 301.
24.6 Wireless LAN Troubleshooting
I cannot access the ZyXEL Device orping any computer from the WLAN
1Make sure the wireless LAN is enabled on the ZyXEL Device
2Make sure the wireless adapter on the wireless station is working properly.
3Make sure the wireless adapter (installed on your computer) is IEEE 802.11 compatible
and supports the same wireless standard as the ZyXEL Device.
4Make sure your computer (with a wireless adapter installed) is within the transmission
range of the ZyXEL Device.
5Check that both the ZyXEL Device and your wireless station are using the same wireless
and wireless security settings.
6Make sure traffic between the WLAN and the LAN is not blocked by the firewall on the
ZyXEL Device.
7Make sure you allow the ZyXEL Device to be remotely accessed through the WLAN
interface. Check your remote management settings.
MAX-200HW2 Series User s Guide 269
CHAPTER 25
Product Specifications
This chapter gives details about your ZyXEL Device!s hardware and firmware features.
Table 120 Product Specifications
PHYSICAL AND ENVIRONMENTAL
Product Name WIMAX-200HW2/WIMAX-210HW2/WIMAX-230HW2
Ethernet InterfaceFour auto-negotiating, auto-MDI/MDI-X 10/100 Mbps RJ-45
Ethernet ports
WLAN InterfaceWiFi (54 Mbps) interface (801.11g, 802.16b backward compatible)
Telephony InterfaceTwo analog interfaces for standard telephones through RJ-11
connectors
StandardsIEEE 802.16e-2005
Antenna MAX-210HW2:
Built-in patch antenna (WiMAX): 6dBi, 70?azimuth, 30?elevation
WiMAX SMA antenna connector, equipped by default with 2dBi omni
antenna, 60
WiFi SMA antenna connector, equipped by default with 2dBi omni
antenna, 60
MAX-200HW2/MAX-230HW2:
WiFi SMA antenna connector, equipped by default with 2dBi omni
antenna, 60
Panel Directional Antenna
Operating Temperature 0蚓 to 45蚓
Storage Temperature -25蚓 to 55蚓
Operating Humidity10% ~ 90% (non-condensing)
Storage Humidity 10% to 95%
Power Supply18 V DC 1A
Power consumptionWorst-case-scenario 10W, peak 15W
Weight600g
Dimensions216 x 164 x 52mm
RADIO SPECIFICATIONS
Media Access ProtocolIEEE 802.16e
WiMAX BandwidthMAX-200HW2: 2.5 - 2.7 GHz
MAX-210HW2: 3.4 ~ 3.6 GHz
MAX-230HW2: 2.3 ~ 2.4 GHz
Data RateDownlink:
Maximum 5 Mbps
Uplink:
Maximum 2 Mbps
Chapter 25Product Specifications
MAX-200HW2 Series User s Guide
270
ModulationQPSK (uplink and downlink)
16-QAM (uplink and downlink)
64-QAM (downlink only)
Output Power27dBm (+/- 1dB)
Duplex modeTime Division Duplex (TDD)
SOFTWARE SPECIFICATIONS
SecurityPKMv2
EAP
CCMP, 128-bit AES
Table 121 Physical Features
FEATUREDESCRIPTION
Auto-crossover 10/100 Mbps
Ethernet Interface
This interface automatically adjusts to either a crossover or straight-
through Ethernet cable.
External Antenna The MAX-210HW2 is equipped with WiFi and WiMAX omnidirectional
antennas.
The MAX-200HW2 and MAX-230HW2 are equippped with a WiFi
omnidirectional antenna and a WiMAX panel directional antenna.
Telephone Port Connect analog telephones to the ZyXEL Device s 2 LINE ports (RJ-
11 connector) to take advantage of its Voice over IP (VoIP) features.
Reset ButtonThe reset button is built into the rear panel. Use this button to restore
the factory default password to 1234; IP address to 192.168.1.1,
subnet mask to 255.255.255.0 and DHCP server enabled with a pool
of 32 IP addresses starting at 192.168.1.33.
Table 122 Non-Physical Features
FEATUREDESCRIPTION
High Speed Wireless Internet
Access
The ZyXEL Device is ideal for high-speed wireless Internet browsing.
WiMAX (Worldwide Interoperability for Microwave Access) is a
wireless networking standard providing high-bandwidth, wide-range
secured wireless service. The ZyXEL Device is a WiMAX mobile
station (MS) compatible with the IEEE 802.16e standard.
WiFi FunctionalityAllow the IEEE 802.11b and/or IEEE 802.11g wireless clients to
connect to the ZyXEL Device wirelessly. Enable wireless security
(WEP, WPA(2), WPA(2)-PSK) and/or MAC filtering to protect your
wireless network.
FirewallThe ZyXEL Device is a stateful inspection firewall with DoS (Denial of
Service) protection. By default, when the firewall is activated, all
incoming traffic from the WAN to the LAN is blocked unless it is
initiated from the LAN. The ZyXEL Device s firewall supports TCP/
UDP inspection, DoS detection and prevention, real time alerts,
reports and logs.
Content FilteringThe ZyXEL Device can block access to web sites containing specified
keywords. You can define time periods and days during which content
filtering is enabled and include or exclude a range of users on the LAN
from content filtering.
Auto ProvisioningYour Internet service provider can automatically update your device s
configuration via an auto-provisioning server.
Table 120 Product Specifications (continued)
Chapter 25Product Specifications
MAX-200HW2 Series User s Guide 271
Auto Firmware UpgradeYour device gives you the option to upgrade to a newer firmware
version if it finds one during auto-provisioning. Your VoIP service
provider must have an auto-provisioning server and a server set up
with firmware in order for this feature to work.
Network Address Translation
(NAT)
Network Address Translation (NAT) allows the translation of an
Internet protocoladdress used within one network (for example a
private IP address used in a local network) to a different IP address
known withinanother network (for example a public IP address used
on the Internet).
Universal Plug and Play
(UPnP)
Your device and other UPnP enabled devices can use the standard
TCP/IP protocol to dynamically join a network, obtain an IP address
and convey their capabilities to each other.
Dynamic DNS SupportWith Dynamic DNS support, you can have a static hostname alias for
a dynamic IP address, allowing the host to be more easily accessible
from various locations on the Internet. You must register for this
service with a Dynamic DNS service provider.
DHCPDHCP (Dynamic Host Configuration Protocol) allows the individual
clients (computers) to obtain the TCP/IP configuration at start-up from
a centralized DHCP server. Your device has built-in DHCP server
capability enabled by default. It can assign IP addresses, an IP default
gateway and DNS servers to DHCP clients. Your device can also act
as a surrogate DHCP server (DHCP Relay) where it relays IP address
assignment from the actual real DHCP server to the clients.
Multiple PVC (Permanent
Virtual Circuits) Support
Your device supports up to 8 Permanent Virtual Circuits (PVCs).
IP AliasIP alias allows you to partition a physical network into logical networks
over the same Ethernet interface. Your device supports three logical
LAN interfaces via its single physical Ethernet interface with the your
device itself as the gateway for each LAN network.
IP Policy Routing (IPPR)Traditionally, routing is based on the destination address only and the
router takes the shortest path to forward a packet. IP Policy Routing
(IPPR) provides a mechanism to override the default routing behavior
and alter the packet forwarding based on the policy defined by the
network administrator.
RENA Ringer Equivalence Number (REN) is used to determine the number
of devices (like telephones or fax machines) that may be connected to
the telephone line. Your device has a REN of three, so it can support
three devices per telephone port.
Multiple SIP AccountsYou can configure multiple voice (SIP) accounts.
SIP ALGYour device is a SIP Application Layer Gateway (ALG). It allows VoIP
calls to pass through NAT for devices behind it (such as a SIP-based
VoIP software application on a computer).
Dynamic Jitter BufferThe built-in adaptive buffer helps to smooth out the variations in delay
(jitter) for voice traffic. This helps ensure good voice quality for your
conversations.
Voice Activity Detection/
Silence Suppression
Voice Activity Detection (VAD) reduces the bandwidth that a call uses
by not transmitting when you are not speaking.
Comfort Noise GenerationYour device generates background noise to fill moments of silence
when the other device in a call stops transmitting because the other
party is not speaking (as total silence could easily be mistaken for a
lost connection).
Table 122 Non-Physical Features
FEATUREDESCRIPTION

Chapter 25Product Specifications
MAX-200HW2 Series User s Guide
272
Echo Cancellation You device supports G.168, an ITU-T standard for eliminating the echo
caused by the sound of your voice reverberating in the telephone
receiver while you talk.
QoS (Quality of Service) Quality of Service (QoS) mechanisms help to provide better service on
a per-flow basis. Your device supports Type of Service (ToS) tagging.
This allows the device to tag voice frames so they can be prioritized
over the network.
Packet FiltersYour device s packet filtering function allows added network security
and management.
Table 122 Non-Physical Features
FEATUREDESCRIPTION

273
PART V
Appendices and
Index
WiMAX Security (275)
Setting up Your Computer!s IP Address (279)
Pop-up Windows, JavaScripts and Java Permissions (301)
IP Addresses and Subnetting (309)
Wireless LANs (319)
Common Services (333)
Legal Information (337)
Customer Support (341)
Index (347)

274

MAX-200HW2 Series User s Guide 275
APPENDIX A
WiMAX Security
Wireless security is vital to protect your wireless communications. Without it, information
transmitted over the wireless network would be accessible to any networking device within
range.
User Authentication and Data Encryption
The WiMAX (IEEE 802.16) standard employs user authentication and encryption to ensure
secured communication at all times.
User authentication is the process of confirming a user!s identity and level of authorization.
Data encryption is the process of encoding information so that it cannot be read by anyone
who does not know the code.
WiMAX uses PKMv2 (Privacy Key Management version 2) for authentication, and CCMP
(Counter Mode with Cipher Block Chaining Message Authentication Protocol) for data
encryption.
WiMAX supports EAP (Extensible Authentication Protocol, RFC 2486) which allows
additional authentication methods to be deployed with no changes to the base station or the
mobile or subscriber stations.
PKMv2
PKMv2 is a procedure that allows authentication of a mobile or subscriber station and
negotiation of a public key to encrypt traffic between the MS/SS and the base station. PKMv2
uses standard EAP methods such as Transport Layer Security (EAP-TLS) or Tunneled TLS
(EAP-TTLS) for secure communication.
In cryptography, a $key! is a piece of information, typically a string of random numbers and
letters, that can be used to $lock! (encrypt) or $unlock! (decrypt) a message. Public key
encryption uses key pairs, which consist of a public (freely available) key and a private
(secret) key. The public key is used for encryption and the private key is used for decryption.
You can decrypt a message only if you have the private key. Public key certificates (or $digital
IDs!) allow users to verify each other!s identity.
RADIUS
RADIUS is based on a client-server model that supports authentication, authorization and
accounting. The base station is the client and the server is the RADIUS server. The RADIUS
server handles the following tasks:

Appendix AWiMAX Security
MAX-200HW2 Series User s Guide
276
Authentication
Determines the identity of the users.
Authorization
Determines the network services available to authenticated users once they are connected
to the network.
Accounting
Keeps track of the client!s network activity.
RADIUS is a simple package exchange in which your base station acts as a message relay
between the MS/SS and the network RADIUS server.
Types of RADIUS Messages
The following types of RADIUS messages are exchanged between the base station and the
RADIUS server for user authentication:
Access-Request
Sent by an base station requesting authentication.
Access-Reject
Sent by a RADIUS server rejecting access.
Access-Accept
Sent by a RADIUS server allowing access.
Access-Challenge
Sent by a RADIUS server requesting more information in order to allow access. The base
station sends a proper response from the user and then sends another Access-Request
message.
The following types of RADIUS messages are exchanged between the base station and the
RADIUS server for user accounting:
Accounting-Request
Sent by the base station requesting accounting.
Accounting-Response
Sent by the RADIUS server to indicate that it has started or stopped accounting.
In order to ensure network security, the access point and the RADIUS server use a shared
secret key, which is a password they both know. The key is not sent over the network. In
addition to the shared key, password information exchanged is also encrypted to protect the
network from unauthorized access.
Diameter
Diameter (RFC 3588) is a type of AAA server that provides several improvements over
RADIUS in efficiency, security, and support for roaming.
Security Association
The set of information about user authentication and data encryption between two computers
is known as a security association (SA). In a WiMAX network, the process of security
association has three stages.

Appendix AWiMAX Security
MAX-200HW2 Series User s Guide 277
Authorization request and reply
The MS/SS presents its public certificate to the base station. The base station verifies the
certificate and sends an authentication key (AK) to the MS/SS.
Key request and reply
The MS/SS requests a transport encryption key (TEK) which the base station generates
and encrypts using the authentication key.
Encrypted traffic
The MS/SS decrypts the TEK (using the authentication key). Both stations can now
securely encrypt and decrypt the data flow.
CCMP
All traffic in a WiMAX network is encrypted using CCMP (Counter Mode with Cipher Block
Chaining Message Authentication Protocol). CCMP is based on the 128-bit Advanced
Encryption Standard (AES) algorithm.
$Counter mode! refers to the encryption of each block of plain text with an arbitrary number,
known as the counter. This number changes each time a block of plain text is encrypted.
Counter mode avoids the security weakness of repeated identical blocks of encrypted text that
makes encrypted data vulnerable to pattern-spotting.
$Cipher Block Chaining Message Authentication! (also known as CBC-MAC) ensures
message integrity by encrypting each block of plain text in such a way that its encryption is
dependent on the block before it. This series of $chained! blocks creates a message
authentication code (MAC or CMAC) that ensures the encrypted data has not been tampered
with.
Authentication
The ZyXEL Device supports EAP-TTLS authentication.
EAP-TTLS (Tunneled Transport Layer Service)
EAP-TTLS is an extension of the EAP-TLS authentication that uses certificates for only the
server-side authentications to establish a secure connection (with EAP-TLS digital
certifications are needed by both the server and the wireless clients for mutual authentication).
Client authentication is then done by sending username and password through the secure
connection, thus client identity is protected. For client authentication, EAP-TTLS supports
EAP methods and legacy authentication methods such as PAP, CHAP, MS-CHAP and MS-
CHAP v2.

Appendix AWiMAX Security
MAX-200HW2 Series User s Guide
278
MAX-200HW2 Series User s Guide 279
APPENDIX B
Setting up Your Computer s IP
Address
The purpose of this appendix is to show you how to configure an IP address
on your computer depending on what operating system you have. It does NOT
mean that your ZyXEL Device supports all these operating systems.
All computers must have a 10M or 100M Ethernet adapter card and TCP/IP installed.
Windows 95/98/Me/NT/2000/XP/Vista, Macintosh OS 7 and later operating systems and all
versions of UNIX/LINUX include the software components you need to install and use TCP/
IP on your computer. Windows 3.1 requires the purchase of a third-party TCP/IP application
package.
TCP/IP should already be installed on computers using Windows NT/2000/XP, Macintosh OS
7 and later operating systems.
After the appropriate TCP/IP components are installed, configure the TCP/IP settings in order
to "communicate" with your network.
If you manually assign IP information instead of using dynamic assignment, make sure that
your computers have IP addresses that place them in the same subnet as the ZyXEL Device!s
LAN port.
Windows 95/98/Me
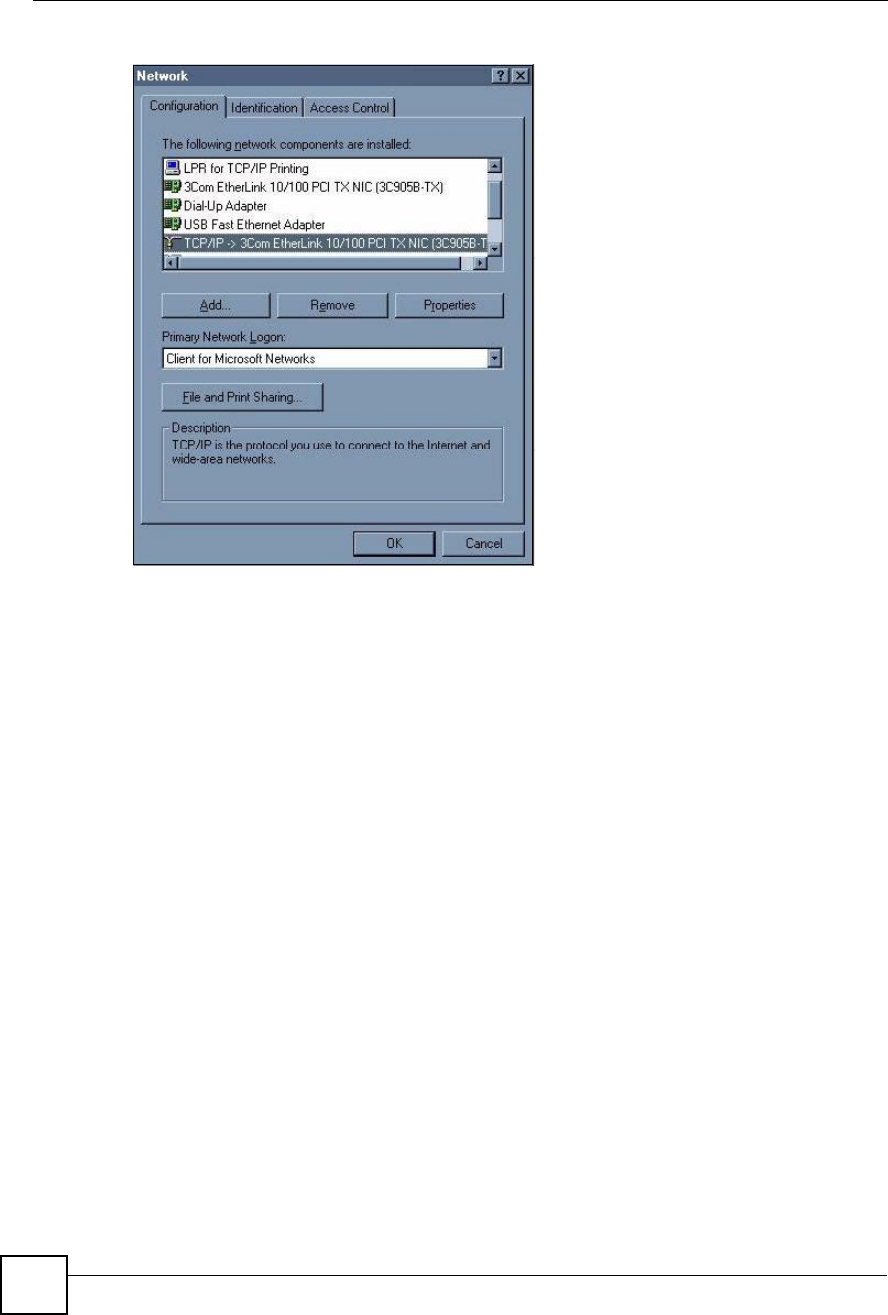
Click Start,Settings,Control Panel and double-click the Network icon to open the Network
window.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
280
Figure 170 WIndows 95/98/Me: Network: Configuration
Installing Components
The Network window Configuration tab displays a list of installed components. You need a
network adapter, the TCP/IP protocol and Client for Microsoft Networks.
If you need the adapter:
1In the Network window, click Add.
2Select Adapter and then click Add.
3Select the manufacturer and model of your network adapter and then click OK.
If you need TCP/IP:
1In the Network window, click Add.
2Select Protocol and then click Add.
3Select Microsoft from the list of manufacturers.
4Select TCP/IP from the list of network protocols and then click OK.
If you need Client for Microsoft Networks:
1Click Add.
2Select Client and then click Add.
3Select Microsoft from the list of manufacturers.
4Select Client for Microsoft Networks from the list of network clients and then click
OK.
5Restart your computer so the changes you made take effect.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 281
Configuring
1In the Network window Configuration tab, select your network adapter's TCP/IP entry
and click Properties
2Click the IP Address tab.
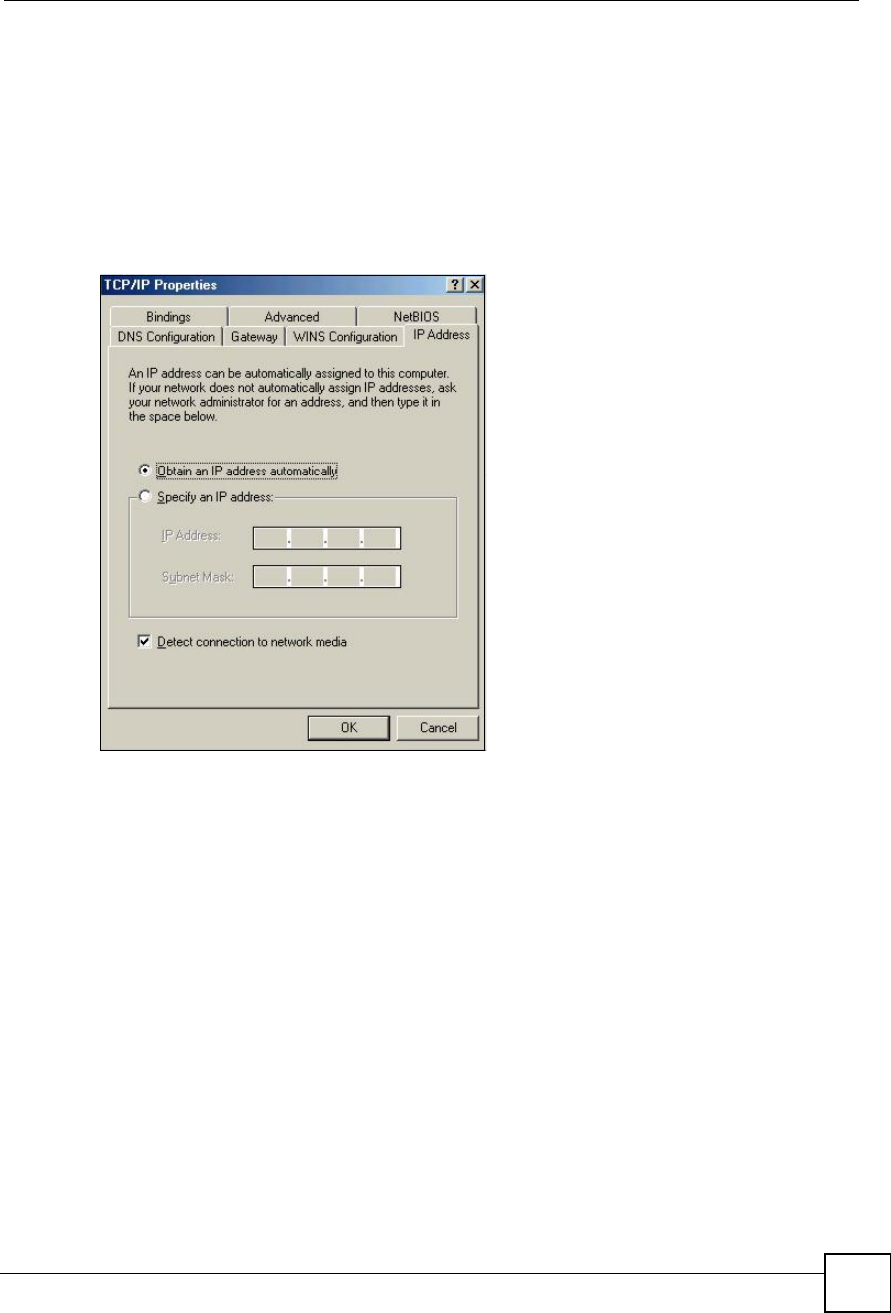
If your IP address is dynamic, select Obtain an IP address automatically.
If you have a static IP address, select Specify an IP address and type your
information into the IP Address and Subnet Mask fields.
Figure 171 Windows 95/98/Me: TCP/IP Properties: IP Address
3Click the DNS Configuration tab.
If you do not know your DNS information, select Disable DNS.
If you know your DNS information, select Enable DNS and type the information in
the fields below (you may not need to fill them all in).

Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
282
Figure 172 Windows 95/98/Me: TCP/IP Properties: DNS Configuration
4Click the Gateway tab.
If you do not know your gateway!s IP address, remove previously installed gateways.
If you have a gateway IP address, type it in the New gateway field and click Add.
5Click OK to save and close the TCP/IP Properties window.
6Click OK to close the Network window. Insert the Windows CD if prompted.
7Turn on your ZyXEL Device and restart your computer when prompted.
Verifying Settings
1Click Start and then Run.
2In the Run window, type "winipcfg" and then click OK to open the IP Configuration
window.
3Select your network adapter. You should see your computer's IP address, subnet mask
and default gateway.
Windows 2000/NT/XP
The following example figures use the default Windows XP GUI theme.
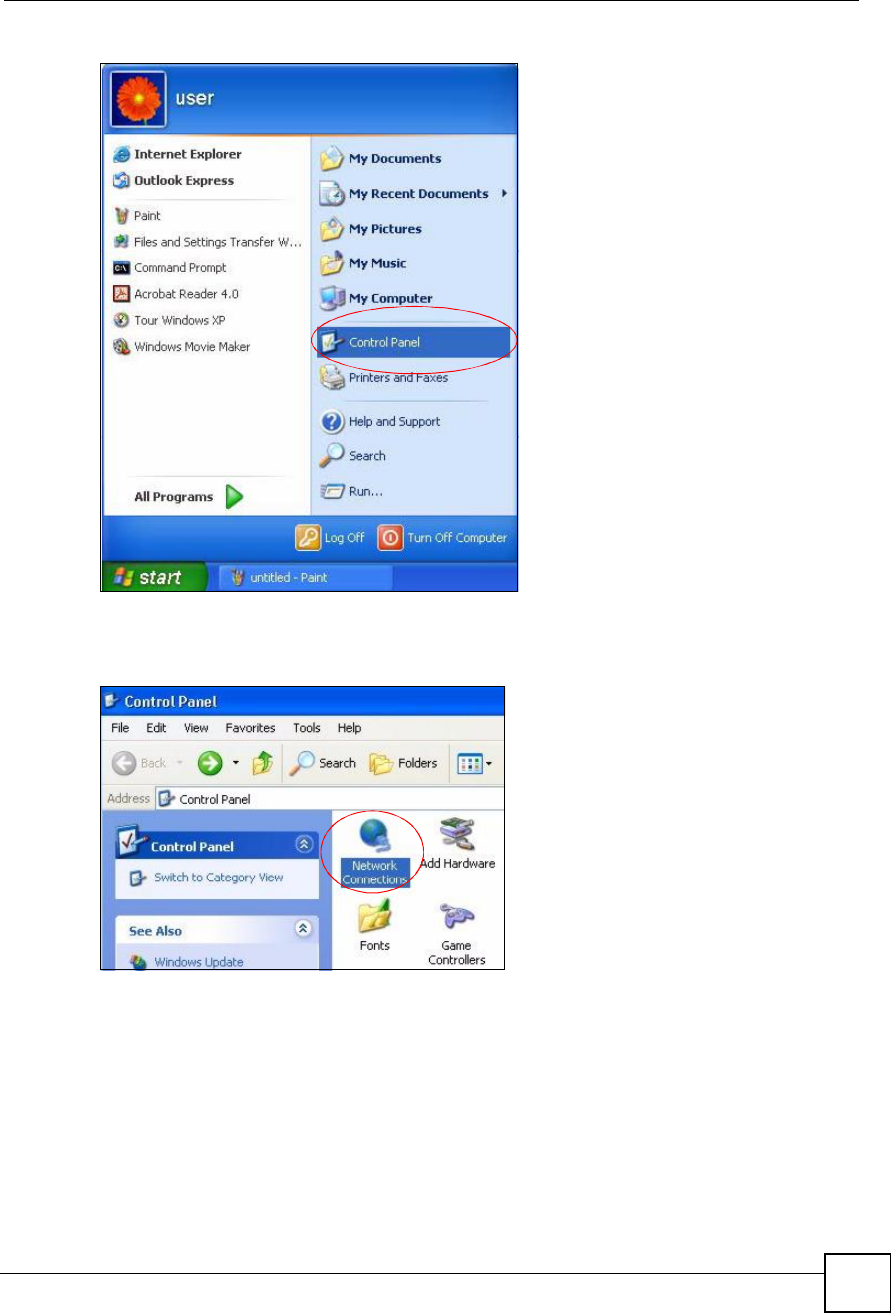
1Click start (Start in Windows 2000/NT), Settings,Control Panel.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 283
Figure 173 Windows XP: Start Menu
2In the Control Panel, double-click Network Connections (Network and Dial-up
Connections in Windows 2000/NT).
Figure 174 Windows XP: Control Panel
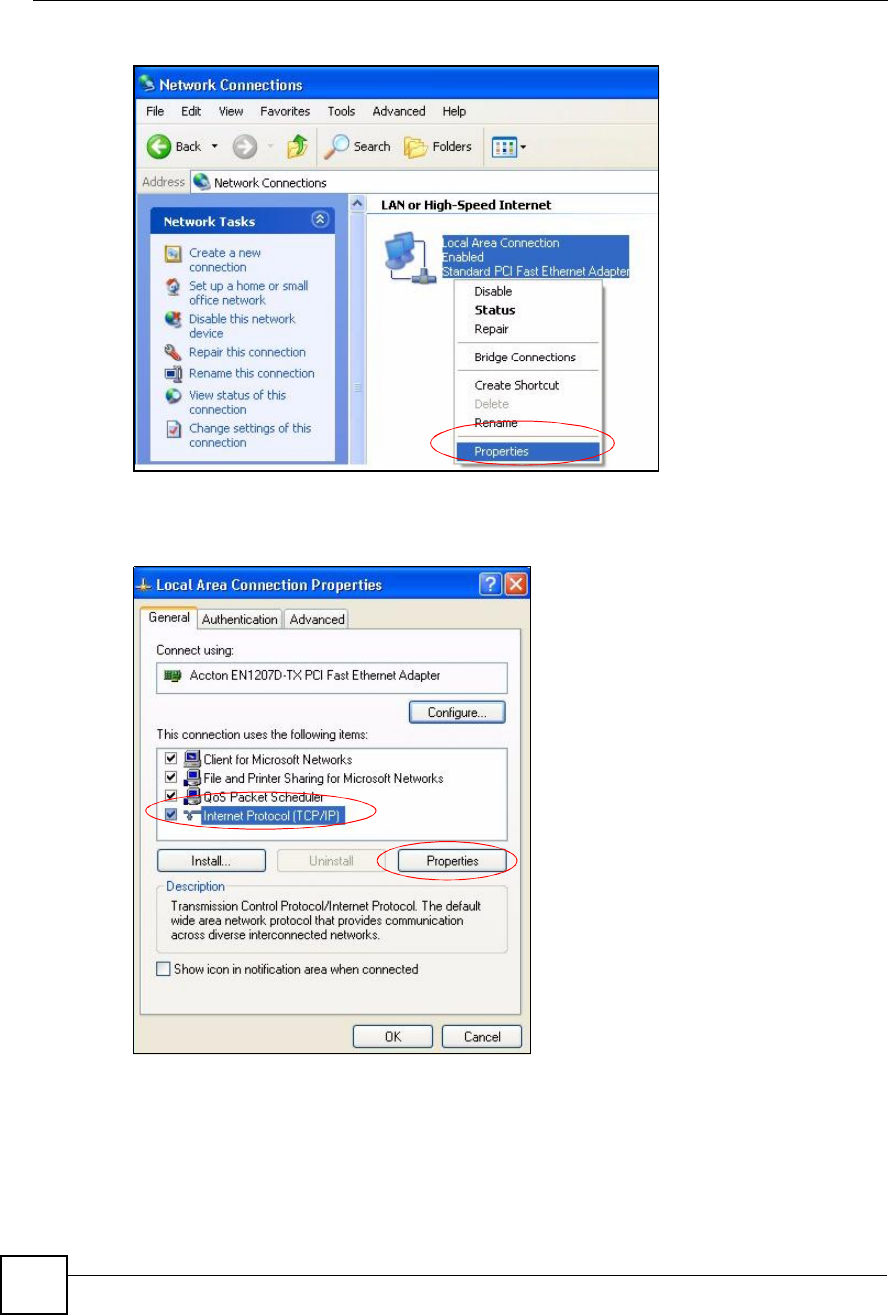
3Right-click Local Area Connection and then click Properties.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
284
Figure 175 Windows XP: Control Panel: Network Connections: Properties
4Select Internet Protocol (TCP/IP) (under the General tab in Win XP) and then click
Properties.
Figure 176 Windows XP: Local Area Connection Properties
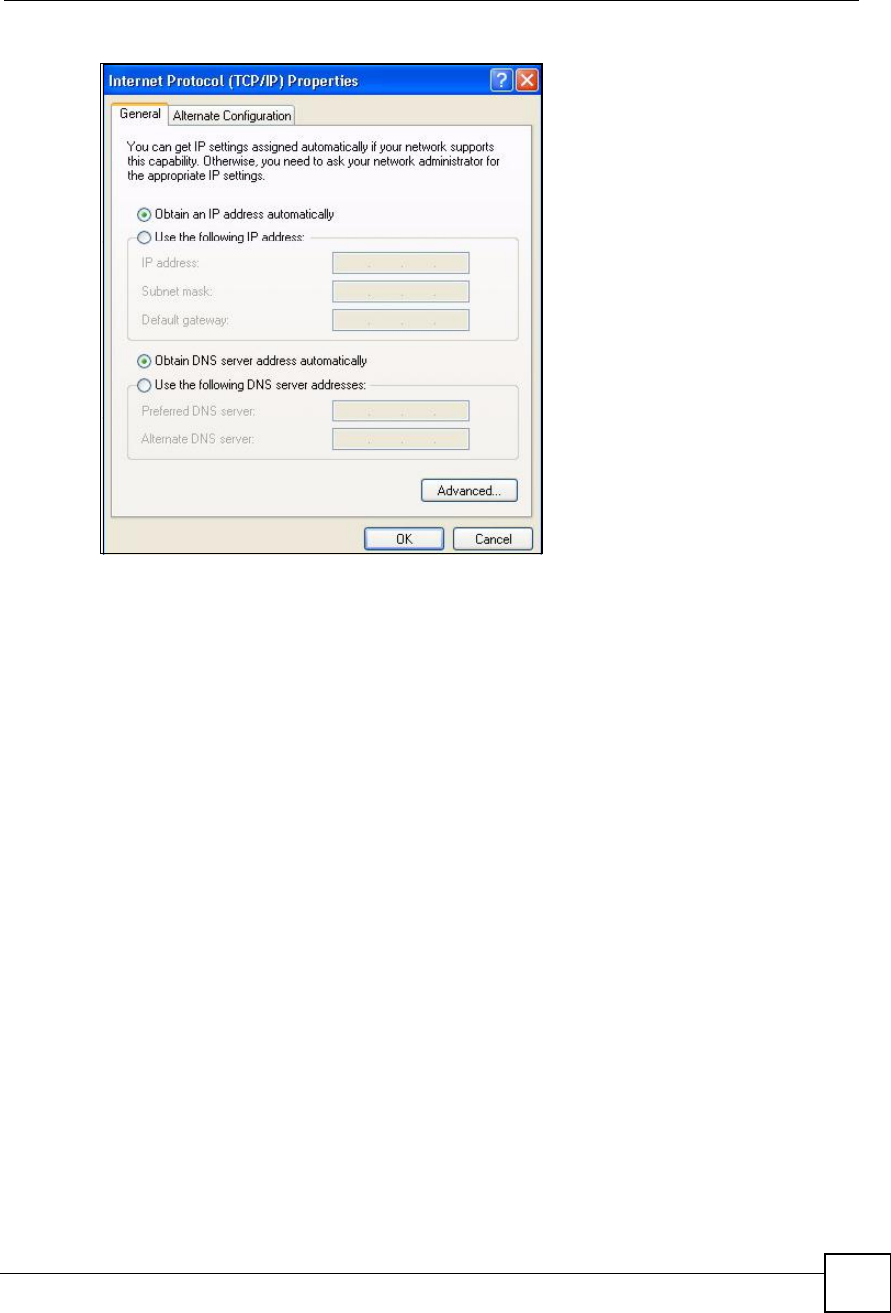
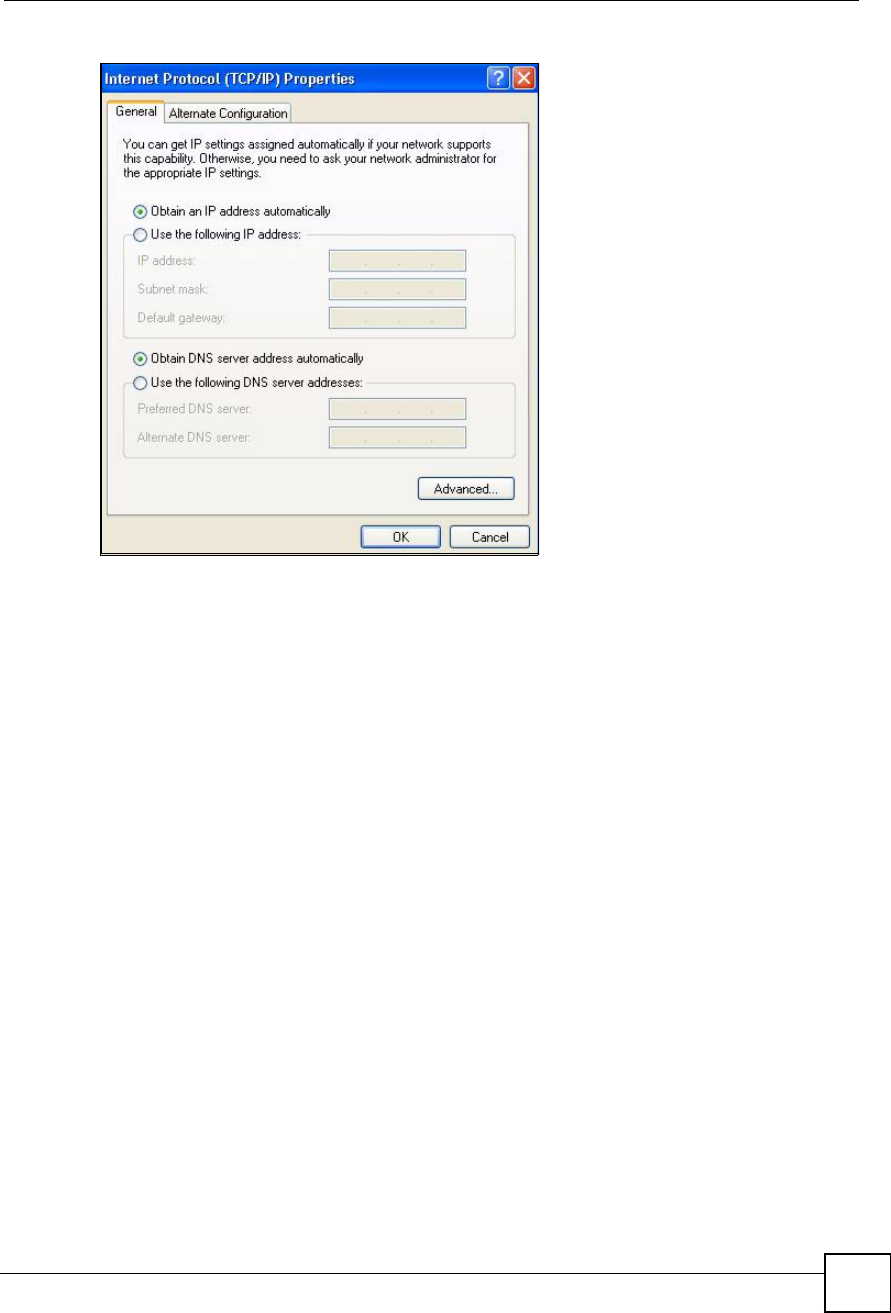
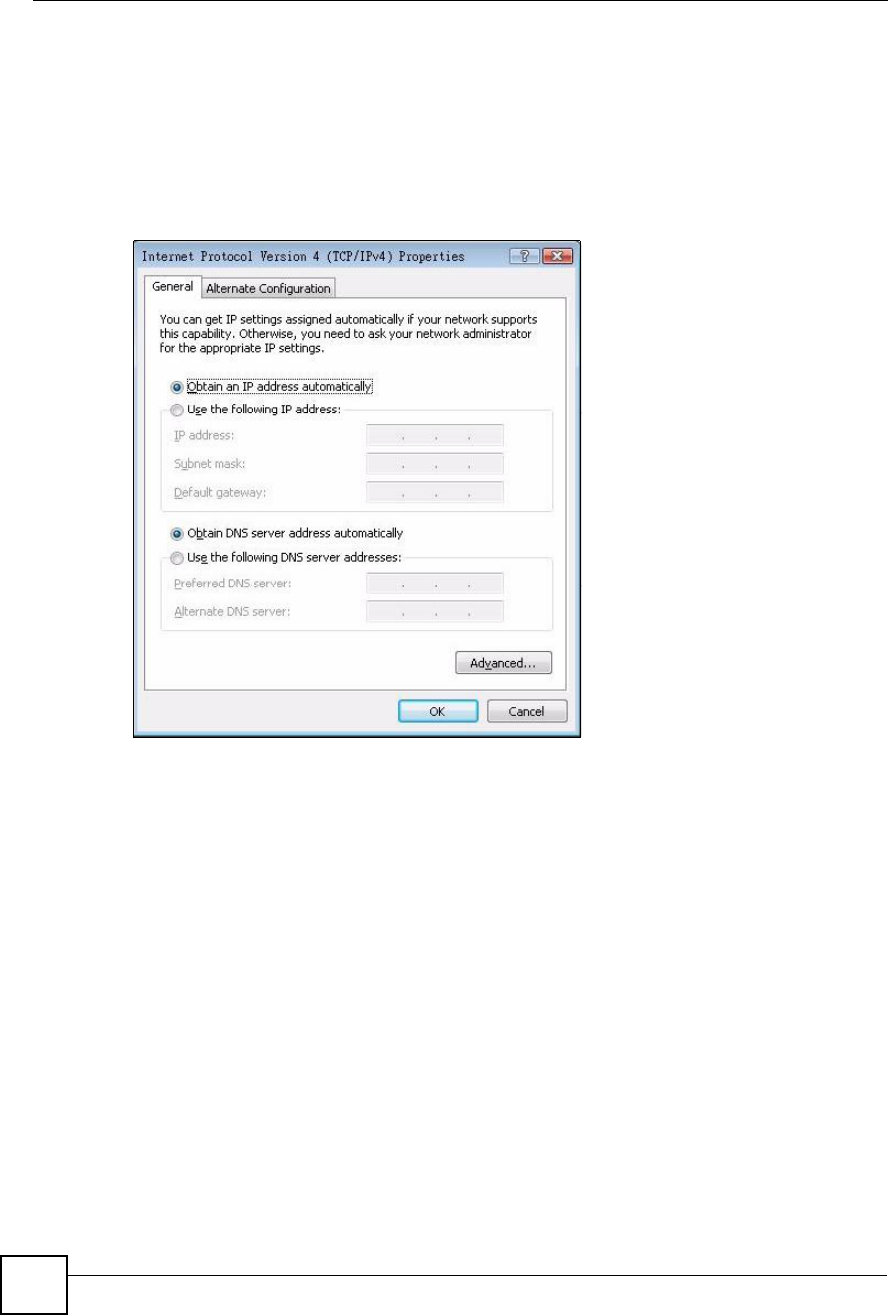
5The Internet Protocol TCP/IP Properties window opens (the General tab in Windows
XP).
If you have a dynamic IP address click Obtain an IP address automatically.
If you have a static IP address click Use the following IP Address and fill in the IP
address,Subnet mask, and Default gateway fields.
Click Advanced.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 285
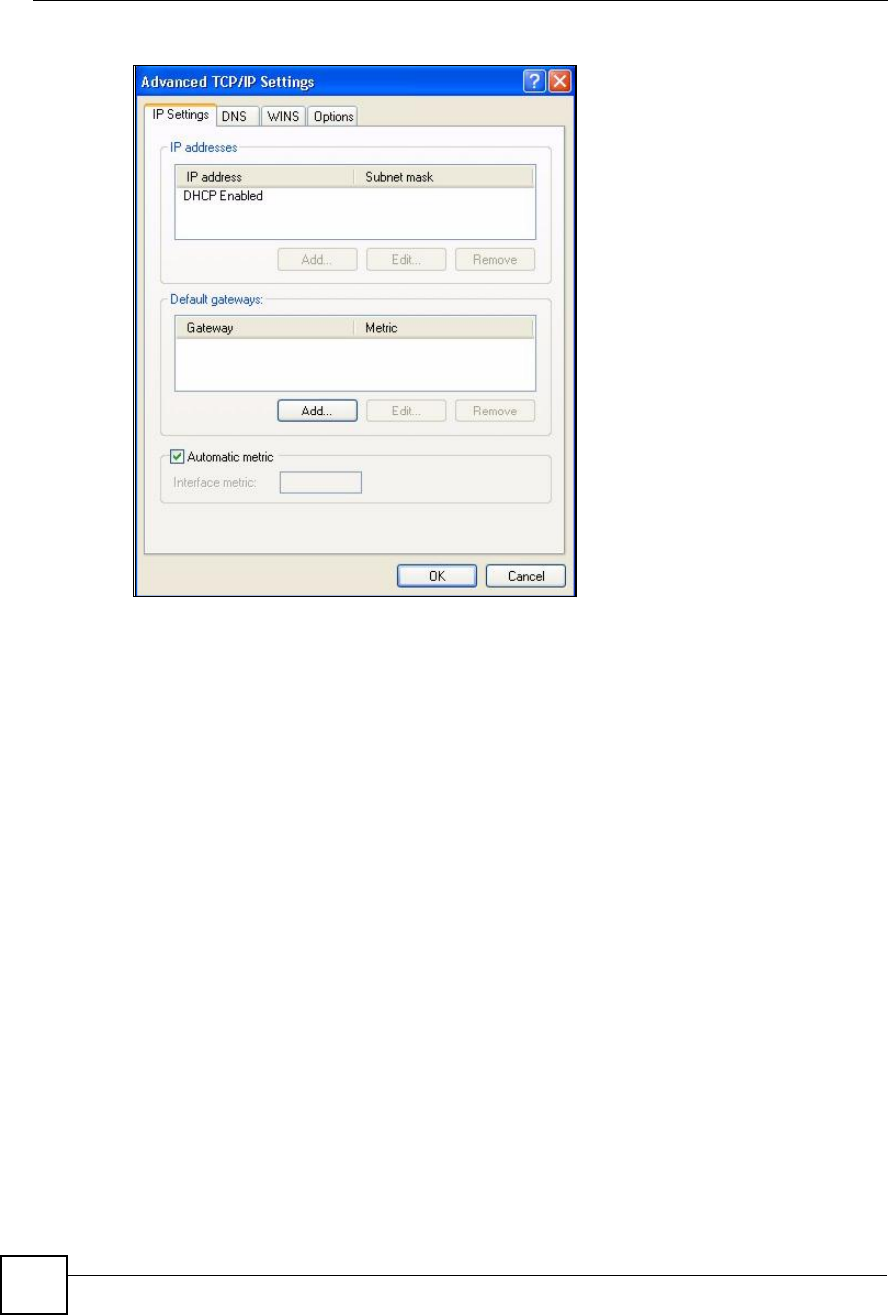
Figure 177 Windows XP: Internet Protocol (TCP/IP) Properties
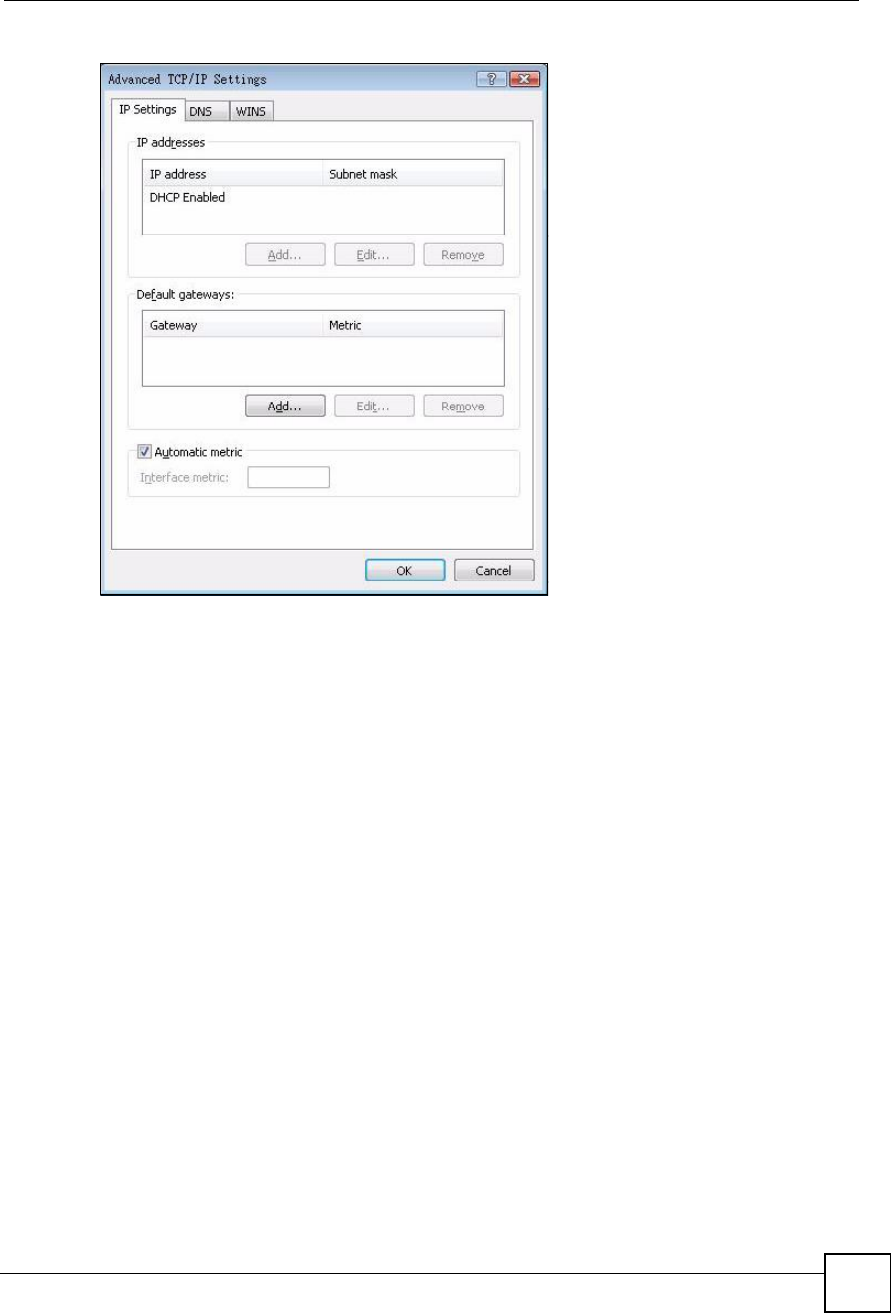
6 If you do not know your gateway's IP address, remove any previously installed
gateways in the IP Settings tab and click OK.
Do one or more of the following if you want to configure additional IP addresses:
In the IP Settings tab, in IP addresses, click Add.
In TCP/IP Address, type an IP address in IP address and a subnet mask in Subnet
mask, and then click Add.
Repeat the above two steps for each IP address you want to add.
Configure additional default gateways in the IP Settings tab by clicking Add in
Default gateways.
In TCP/IP Gateway Address, type the IP address of the default gateway in Gateway.
To manually configure a default metric (the number of transmission hops), clear the
Automatic metric check box and type a metric in Metric.
Click Add.
Repeat the previous three steps for each default gateway you want to add.
Click OK when finished.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
286
Figure 178 Windows XP: Advanced TCP/IP Properties
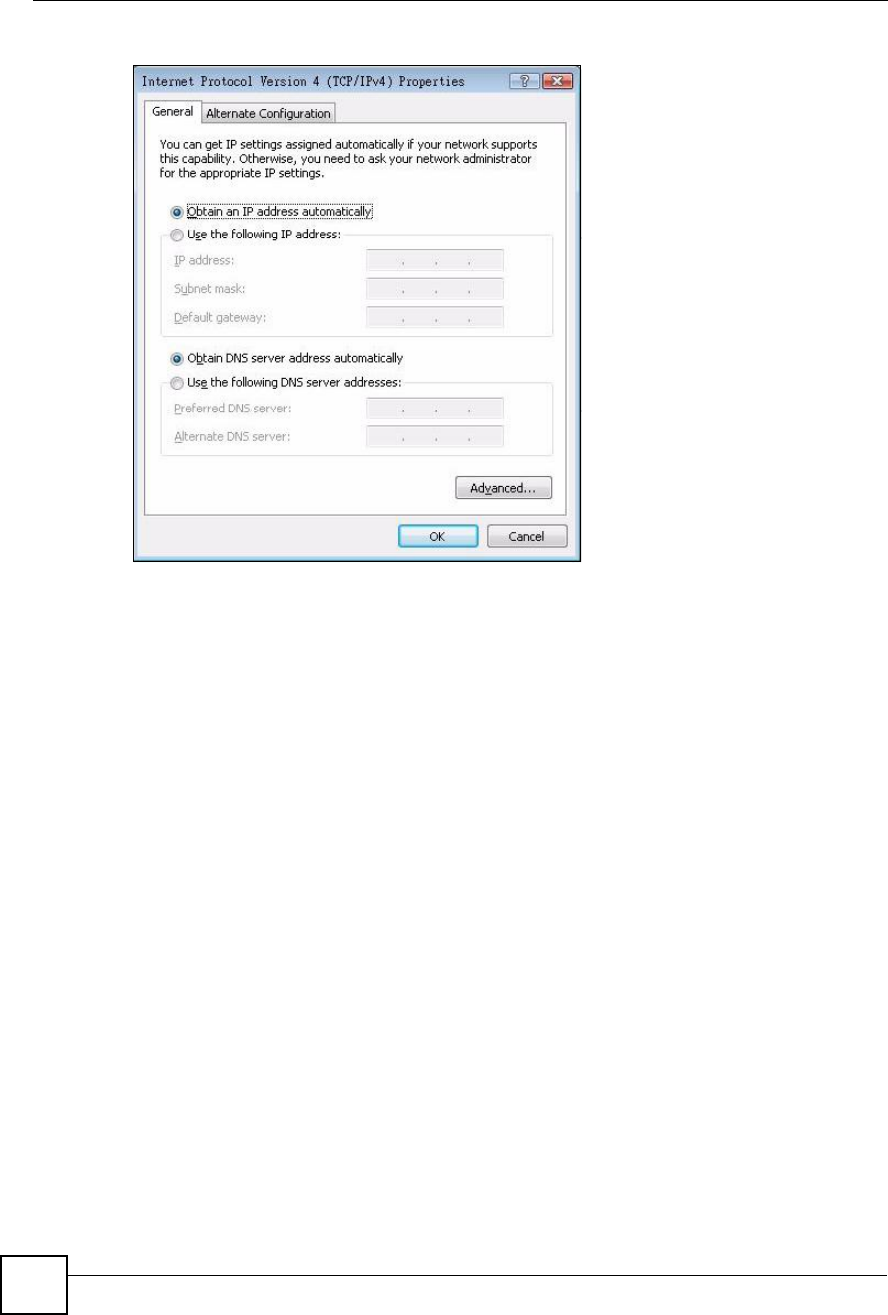
7In the Internet Protocol TCP/IP Properties window (the General tab in Windows
XP):
Click Obtain DNS server address automatically if you do not know your DNS
server IP address(es).
If you know your DNS server IP address(es), click Use the following DNS server
addresses, and type them in the Preferred DNSserver and Alternate DNS server
fields.
If you have previously configured DNS servers, click Advanced and then the DNS
tab to order them.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 287
Figure 179 Windows XP: Internet Protocol (TCP/IP) Properties
8Click OK to close the Internet Protocol (TCP/IP) Properties window.
9Click Close (OK in Windows 2000/NT) to close the Local Area Connection
Properties window.
10 Close the Network Connections window (Network and Dial-up Connections in
Windows 2000/NT).
11 Turn on your ZyXEL Device and restart your computer (if prompted).
Verifying Settings
1Click Start,All Programs,Accessories and then Command Prompt.
2In the Command Prompt window, type "ipconfig" and then press [ENTER]. You can
also open Network Connections, right-click a network connection, click Status and
then click the Support tab.
Windows Vista
This section shows screens from Windows Vista Enterprise Version 6.0.
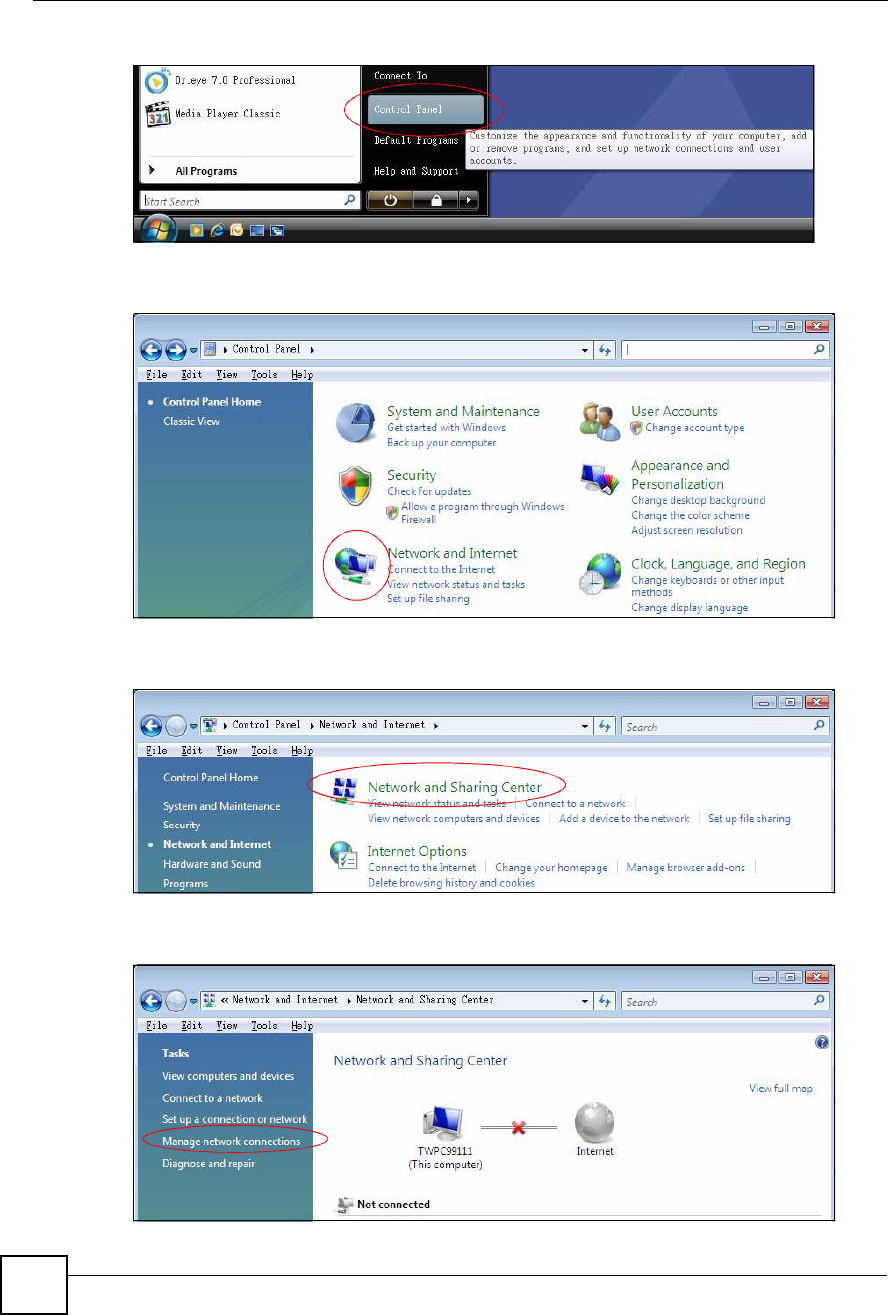
1Click the Start icon, Control Panel.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
288
Figure 180 Windows Vista: Start Menu
2In the Control Panel, double-click Network and Internet.
Figure 181 Windows Vista: Control Panel
3Click Network and Sharing Center.
Figure 182 Windows Vista: Network And Internet
4Click Manage network connections.
Figure 183 Windows Vista: Network and Sharing Center
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 289
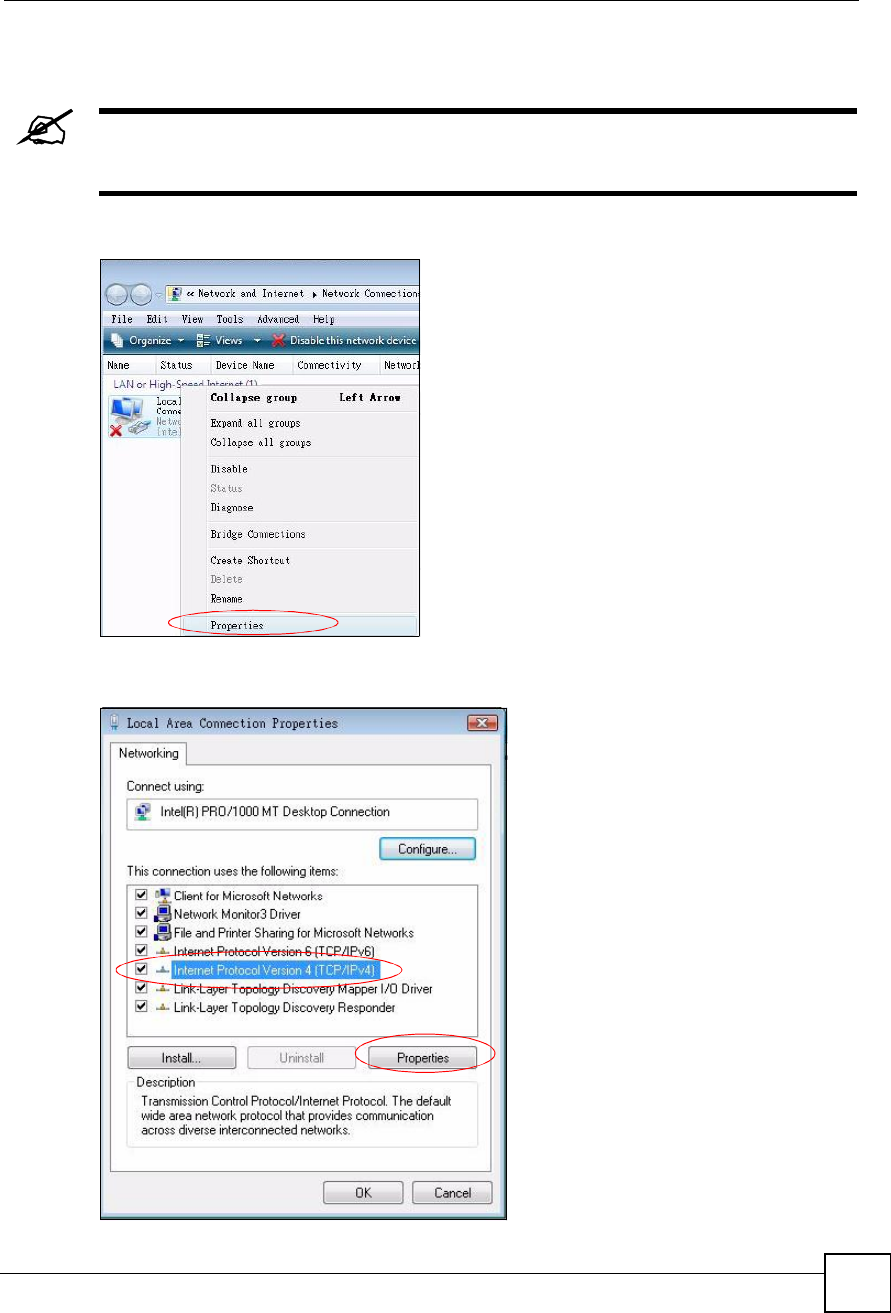
5Right-click Local Area Connection and then click Properties.
During this procedure, click Continue whenever Windows displays a screen
saying that it needs your permission to continue.
Figure 184 Windows Vista: Network and Sharing Center
6Select Internet Protocol Version 4 (TCP/IPv4) and click Properties.
Figure 185 Windows Vista: Local Area Connection Properties
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
290
7The Internet Protocol Version 4 (TCP/IPv4) Properties window opens (the General
tab).
If you have a dynamic IP address click Obtain an IP address automatically.
If you have a static IP address click Use the following IP address and fill in the IP
address,Subnet mask, and Default gateway fields.
Click Advanced.
Figure 186 Windows Vista: Internet Protocol Version 4 (TCP/IPv4) Properties
8 If you do not know your gateway's IP address, remove any previously installed
gateways in the IP Settings tab and click OK.
Do one or more of the following if you want to configure additional IP addresses:
In the IP Settings tab, in IP addresses, click Add.
In TCP/IP Address, type an IP address in IP address and a subnet mask in Subnet
mask, and then click Add.
Repeat the above two steps for each IP address you want to add.
Configure additional default gateways in the IP Settings tab by clicking Add in
Default gateways.
In TCP/IP Gateway Address, type the IP address of the default gateway in Gateway.
To manually configure a default metric (the number of transmission hops), clear the
Automatic metric check box and type a metric in Metric.
Click Add.
Repeat the previous three steps for each default gateway you want to add.
Click OK when finished.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 291
Figure 187 Windows Vista: Advanced TCP/IP Properties
9In the Internet Protocol Version 4 (TCP/IPv4) Properties window, (the General tab):
Click Obtain DNS server address automatically if you do not know your DNS
server IP address(es).
If you know your DNS server IP address(es), click Use the following DNS server
addresses, and type them in the Preferred DNSserver and Alternate DNS server
fields.
If you have previously configured DNS servers, click Advanced and then the DNS
tab to order them.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
292
Figure 188 Windows Vista: Internet Protocol Version 4 (TCP/IPv4) Properties
10 Click OK to close the Internet Protocol Version 4 (TCP/IPv4) Properties window.
11 Click Close to close the Local Area Connection Properties window.
12 Close the Network Connections window.
13 Turn on your ZyXEL Device and restart your computer (if prompted).
Verifying Settings
1Click Start,All Programs,Accessories and then Command Prompt.
2In the Command Prompt window, type "ipconfig" and then press [ENTER]. You can
also open Network Connections, right-click a network connection, click Status and
then click the Support tab.
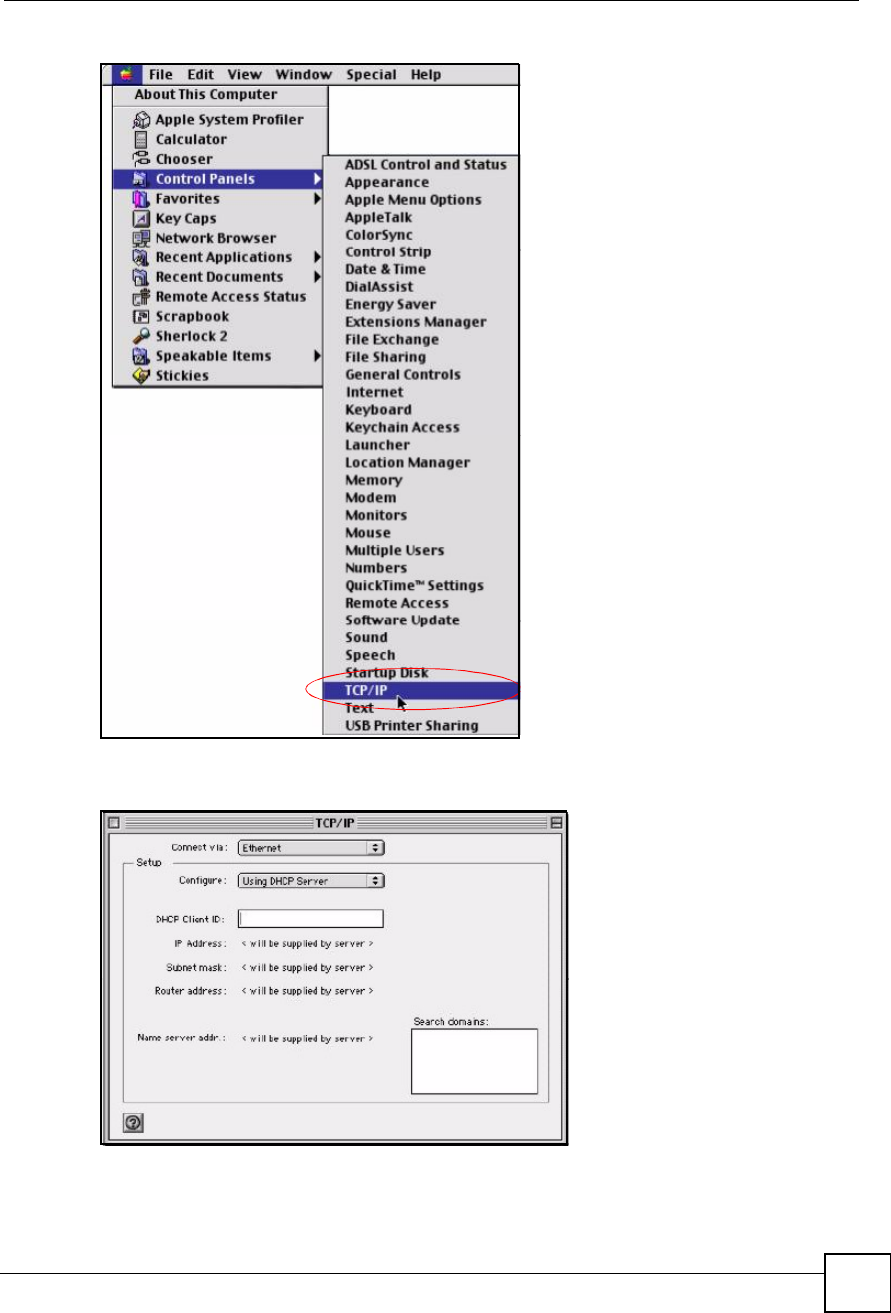
Macintosh OS 8/9
1Click the Apple menu, Control Panel and double-click TCP/IP to open the TCP/IP
Control Panel.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 293
Figure 189 Macintosh OS 8/9: Apple Menu
2Select Ethernet built-in from the Connect via list.
Figure 190 Macintosh OS 8/9: TCP/IP
3For dynamically assigned settings, select Using DHCP Server from the Configure: list.
4For statically assigned settings, do the following:
From the Configure box, select Manually.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
294
Type your IP address in the IP Address box.
Type your subnet mask in the Subnet mask box.
Type the IP address of your ZyXEL Device in the Router address box.
5Close the TCP/IP Control Panel.
6Click Save if prompted, to save changes to your configuration.
7Turn on your ZyXEL Device and restart your computer (if prompted).
Verifying Settings
Check your TCP/IP properties in the TCP/IP Control Panel window.
Macintosh OS X
1Click the Apple menu, and click System Preferences to open the System Preferences
window.
Figure 191 Macintosh OS X: Apple Menu
2Click Network in the icon bar.
Select Automatic from the Location list.
Select Built-in Ethernet from the Show list.
Click the TCP/IP tab.
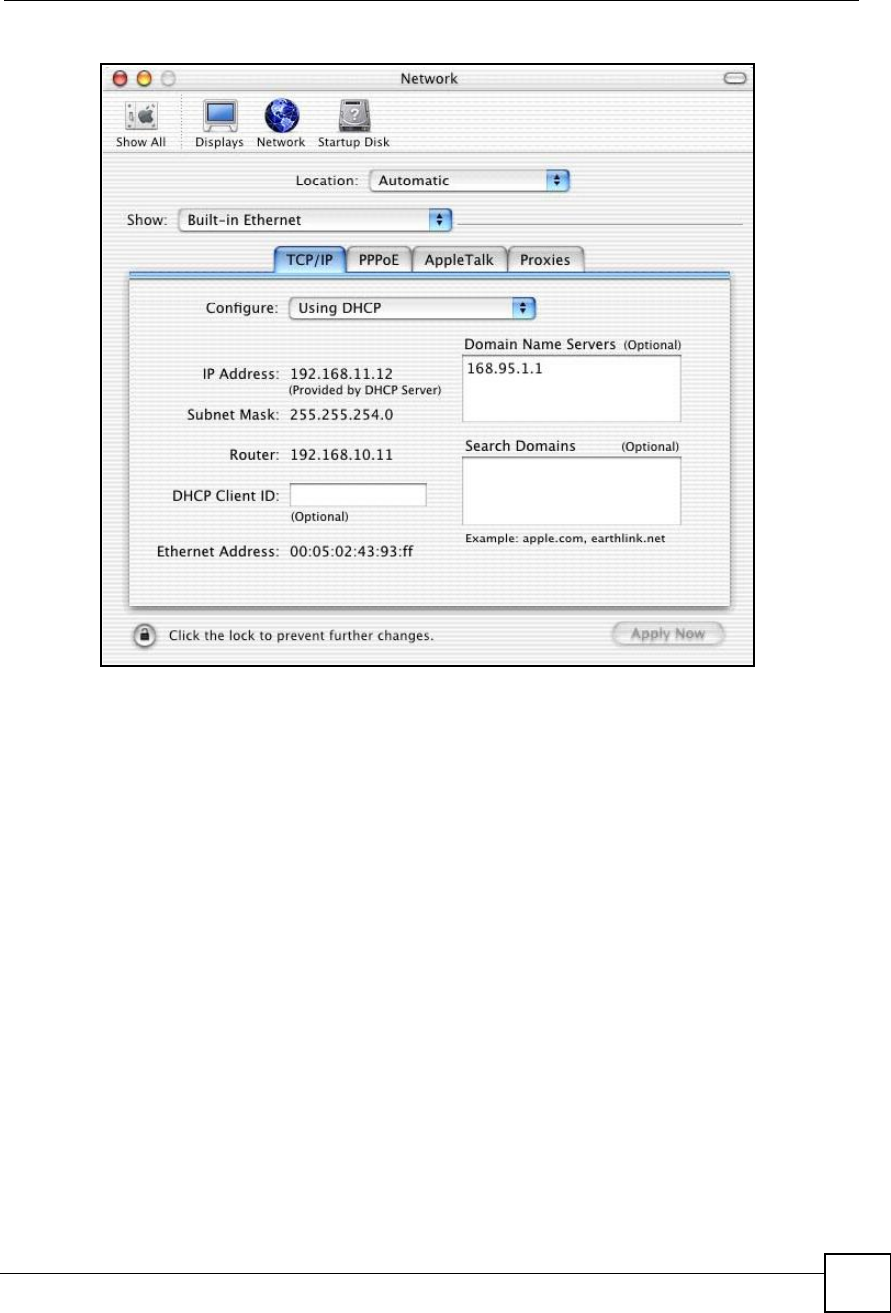
3For dynamically assigned settings, select Using DHCP from the Configure list.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 295
Figure 192 Macintosh OS X: Network
4For statically assigned settings, do the following:
From the Configure box, select Manually.
Type your IP address in the IP Address box.
Type your subnet mask in the Subnet mask box.
Type the IP address of your ZyXEL Device in the Router address box.
5Click Apply Now and close the window.
6Turn on your ZyXEL Device and restart your computer (if prompted).
Verifying Settings
Check your TCP/IP properties in the Network window.
Linux
This section shows you how to configure your computer!s TCP/IP settings in Red Hat Linux
9.0. Procedure, screens and file location may vary depending on your Linux distribution and
release version.
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
296
Make sure you are logged in as the root administrator.
Using the K Desktop Environment (KDE)
Follow the steps below to configure your computer IP address using the KDE.
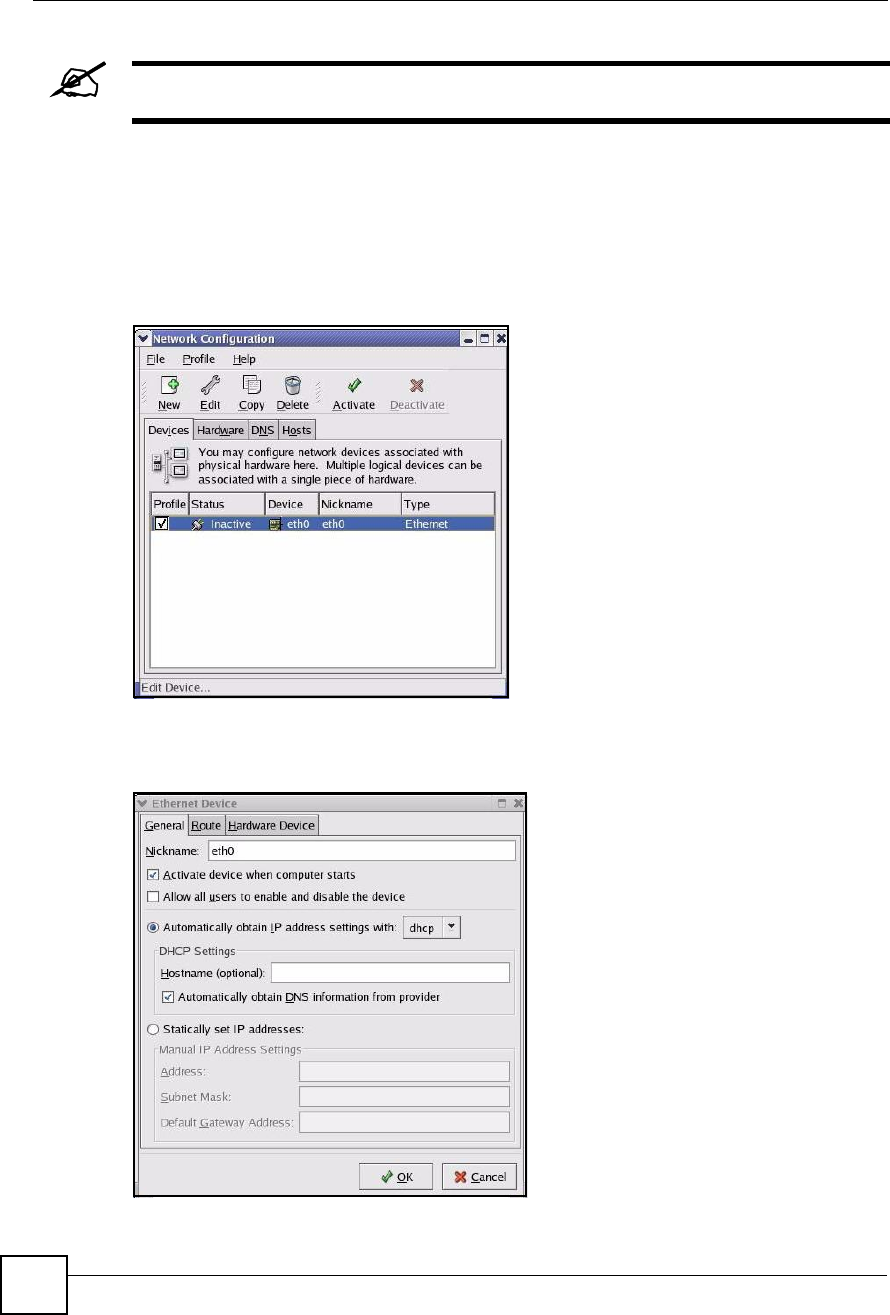
1Click the Red Hat button (located on the bottom left corner), select System Setting and
click Network.
Figure 193 Red Hat 9.0: KDE: Network Configuration: Devices
2Double-click on the profile of the network card you wish to configure. The Ethernet
Device General screen displays as shown.
Figure 194 Red Hat 9.0: KDE: Ethernet Device: General
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 297
If you have a dynamic IP address, click Automatically obtain IP address settings
with and select dhcp from the drop down list.
If you have a static IP address, click Statically set IP Addresses and fill in the
Address,Subnet mask, and Default Gateway Address fields.
3Click OK to save the changes and close the Ethernet Device General screen.
4If you know your DNS server IP address(es), click the DNS tab in the Network
Configuration screen. Enter the DNS server information in the fields provided.
Figure 195 Red Hat 9.0: KDE: Network Configuration: DNS
5Click the Devices tab.
6Click the Activate button to apply the changes. The following screen displays. Click Yes
to save the changes in all screens.
Figure 196 Red Hat 9.0: KDE: Network Configuration: Activate
7After the network card restart process is complete, make sure the Status is Active in the
Network Configuration screen.
Using Configuration Files
Follow the steps below to edit the network configuration files and set your computer IP
address.
1Assuming that you have only one network card on the computer, locate the ifconfig-
eth0 configuration file (where eth0 is the name of the Ethernet card). Open the
configuration file with any plain text editor.
If you have a dynamic IP address, enter dhcp in the BOOTPROTO= field. The
following figure shows an example.

Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
298
Figure 197 Red Hat 9.0: Dynamic IP Address Setting in ifconfig-eth0
If you have a static IP address, enter static in the BOOTPROTO= field. Type
IPADDR= followed by the IP address (in dotted decimal notation) and type NETMASK=
followed by the subnet mask. The following example shows an example where the
static IP address is 192.168.1.10 and the subnet mask is 255.255.255.0.
Figure 198 Red Hat 9.0: Static IP Address Setting in ifconfig-eth0
2If you know your DNS server IP address(es), enter the DNS server information in the
resolv.conf file in the /etc directory. The following figure shows an example where
two DNS server IP addresses are specified.
Figure 199 Red Hat 9.0: DNS Settings in resolv.conf
3After you edit and save the configuration files, you must restart the network card. Enter
./network restart in the /etc/rc.d/init.d directory. The following figure
shows an example.
Figure 200 Red Hat 9.0: Restart Ethernet Card
DEVICE=eth0
ONBOOT=yes
BOOTPROTO=dhcp
USERCTL=no
PEERDNS=yes
TYPE=Ethernet
DEVICE=eth0
ONBOOT=yes
BOOTPROTO=static
IPADDR=192.168.1.10
NETMASK=255.255.255.0
USERCTL=no
PEERDNS=yes
TYPE=Ethernet
nameserver 172.23.5.1
nameserver 172.23.5.2
[root@localhost init.d]# network restart
Shutting down interface eth0: [OK]
Shutting down loopback interface: [OK]
Setting network parameters: [OK]
Bringing up loopback interface: [OK]
Bringing up interface eth0: [OK]
Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide 299
Verifying Settings
Enter ifconfig in a terminal screen to check your TCP/IP properties.
Figure 201 Red Hat 9.0: Checking TCP/IP Properties
[root@localhost]# ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:BA:72:5B:44
inet addr:172.23.19.129 Bcast:172.23.19.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:717 errors:0 dropped:0 overruns:0 frame:0
TX packets:13 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:730412 (713.2 Kb) TX bytes:1570 (1.5 Kb)
Interrupt:10 Base address:0x1000
[root@localhost]#

Appendix BSetting up Your Computer s IP Address
MAX-200HW2 Series User s Guide
300
MAX-200HW2 Series User s Guide 301
APPENDIX C
Pop-up Windows, JavaScripts
and Java Permissions
In order to use the web configurator you need to allow:
Web browser pop-up windows from your device.
JavaScripts (enabled by default).
Java permissions (enabled by default).
Internet Explorer 6 screens are used here. Screens for other Internet Explorer
versions may vary.
Internet Explorer Pop-up Blockers
You may have to disable pop-up blocking to log into your device.
Either disable pop-up blocking (enabled by default in Windows XP SP (Service Pack) 2) or
allow pop-up blocking and create an exception for your device!s IP address.
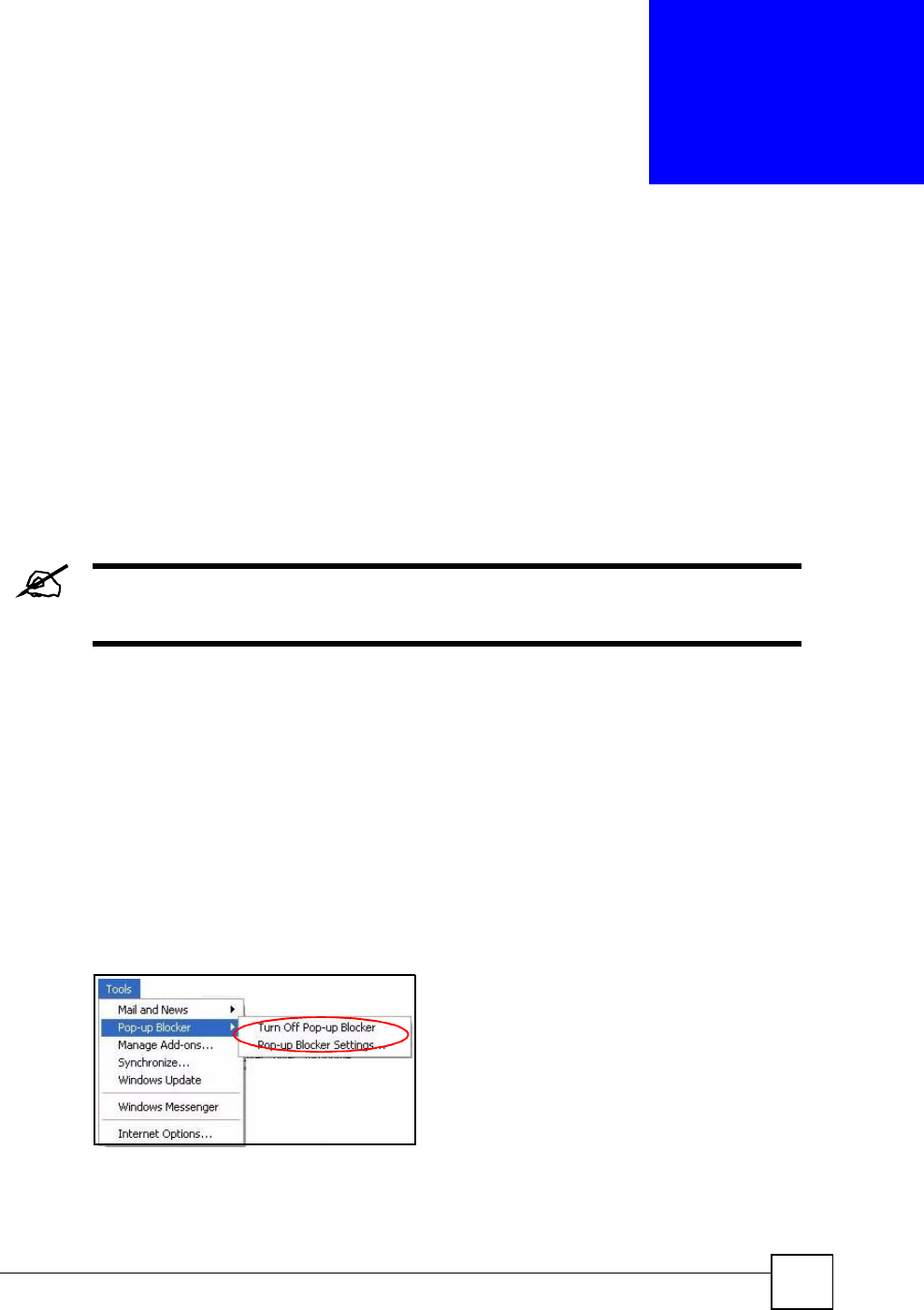
Disable Pop-up Blockers
1In Internet Explorer, select Tools,Pop-up Blocker and then select Turn Off Pop-up
Blocker.
Figure 202 Pop-up Blocker
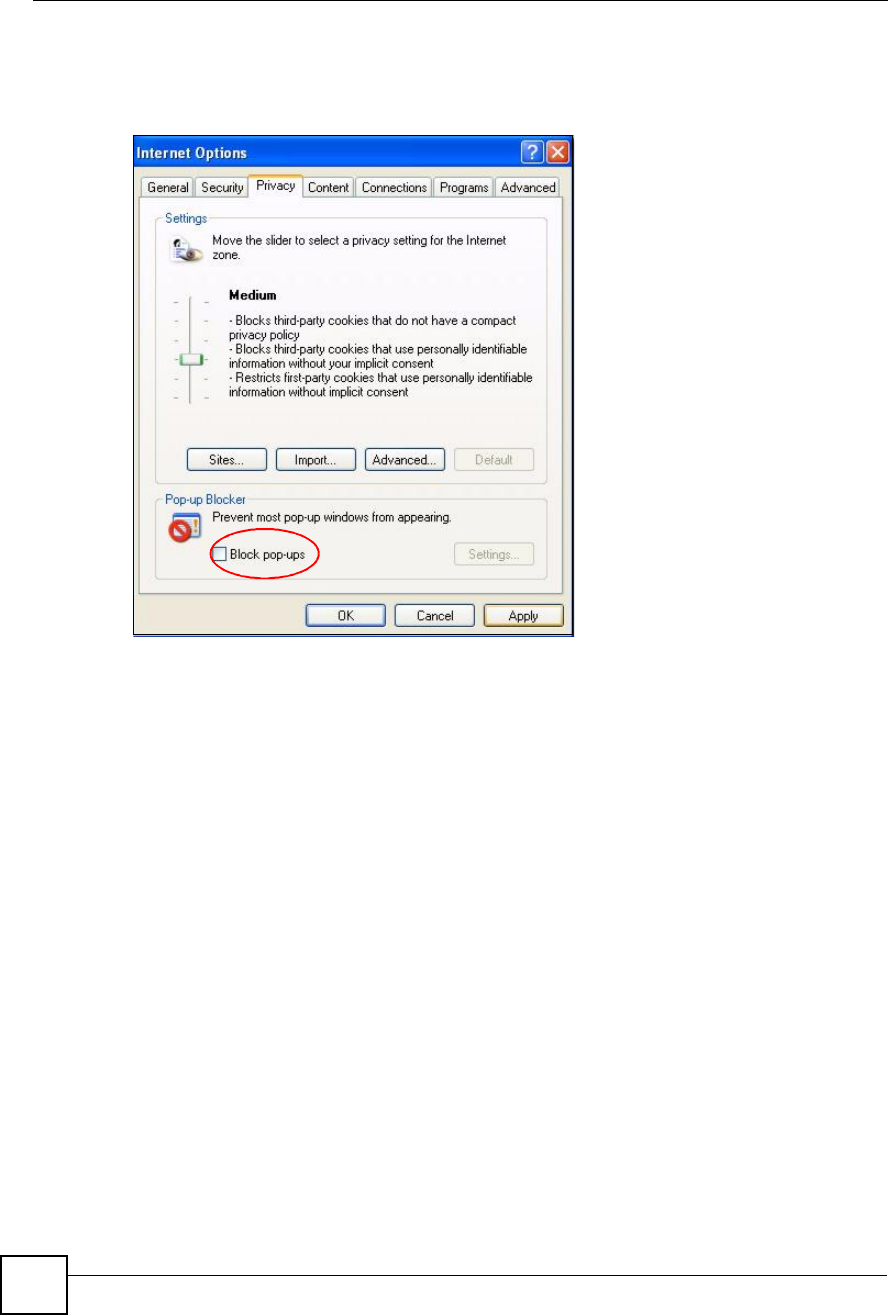
You can also check if pop-up blocking is disabled in the Pop-up Blocker section in the
Privacy tab.
1In Internet Explorer, select Tools,Internet Options,Privacy.
Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide
302
2Clear the Block pop-ups check box in the Pop-up Blocker section of the screen. This
disables any web pop-up blockers you may have enabled.
Figure 203 Internet Options: Privacy
3Click Apply to save this setting.
Enable Pop-up Blockers with Exceptions
Alternatively, if you only want to allow pop-up windows from your device, see the following
steps.
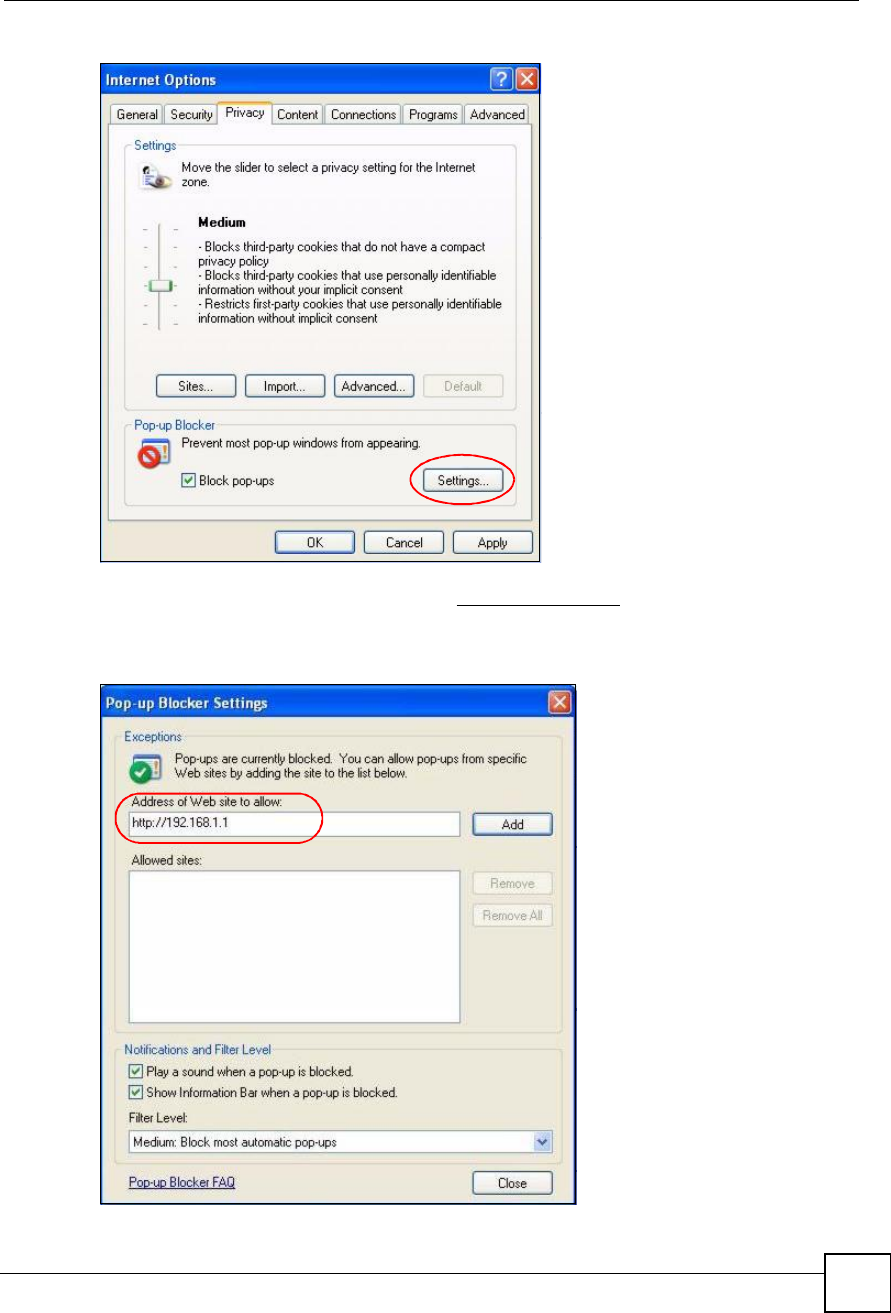
1In Internet Explorer, select Tools,Internet Options and then the Privacy tab.
2Select Settings to open the Pop-up Blocker Settings screen.
Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide 303
Figure 204 Internet Options: Privacy
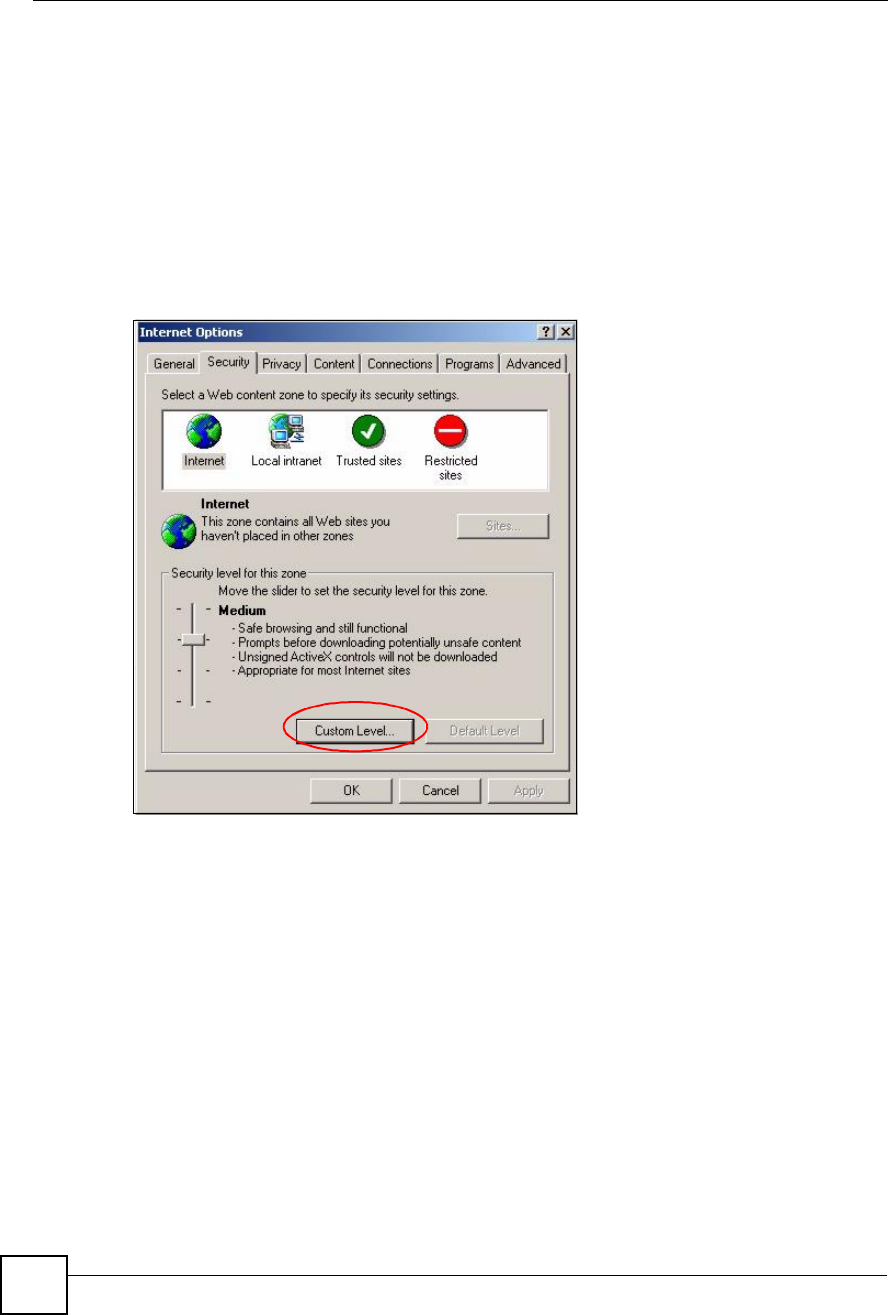
3Type the IP address of your device (the web page that you do not want to have blocked)
with the prefix "http://#. For example, http://192.168.167.1.
4Click Add to move the IP address to the list of Allowed sites.
Figure 205 Pop-up Blocker Settings
Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide
304
5Click Close to return to the Privacy screen.
6Click Apply to save this setting.
JavaScripts
If pages of the web configurator do not display properly in Internet Explorer, check that
JavaScripts are allowed.
1In Internet Explorer, click Tools,Internet Options and then the Security tab.
Figure 206 Internet Options: Security
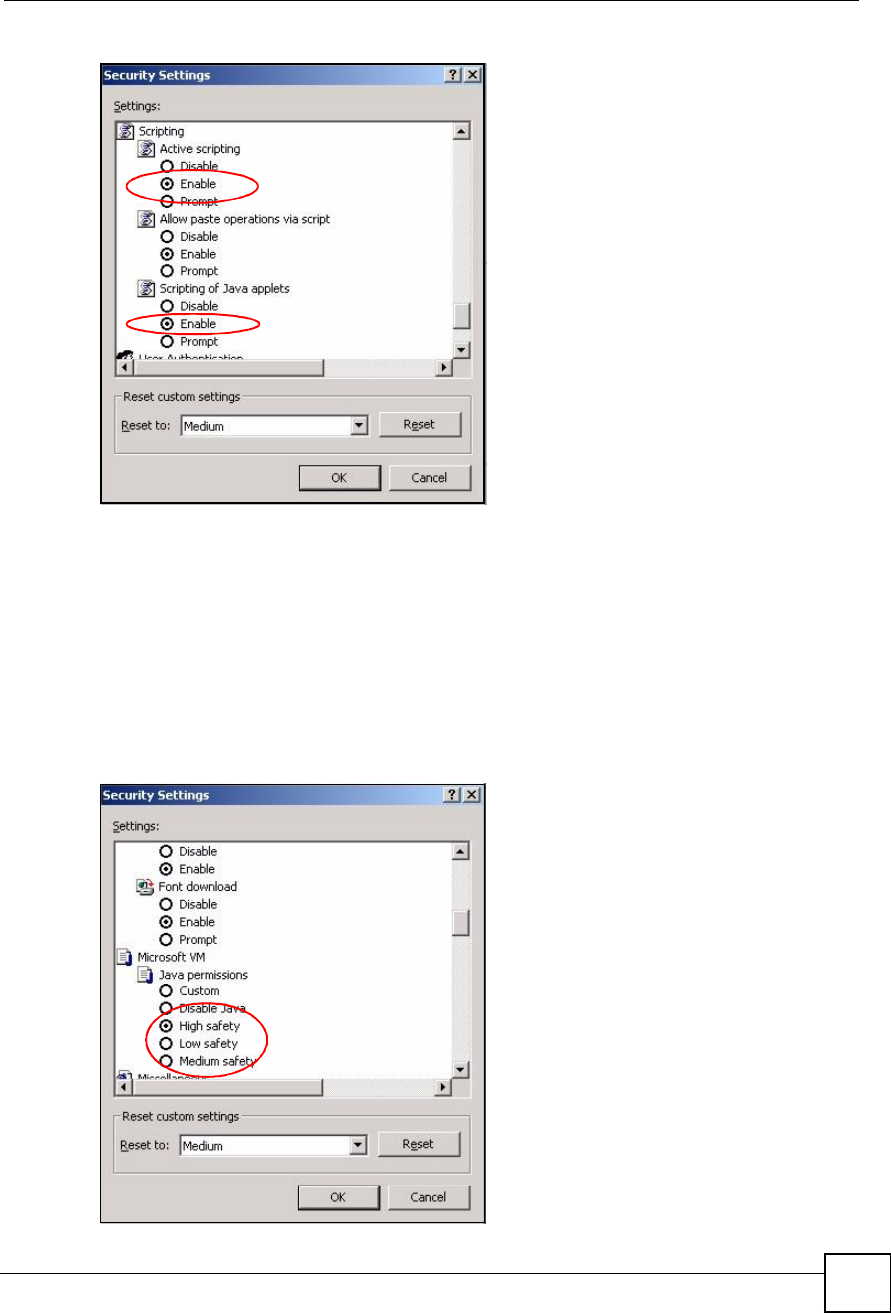
2Click the Custom Level... button.
3Scroll down to Scripting.
4Under Active scripting make sure that Enable is selected (the default).
5Under Scripting of Java applets make sure that Enable is selected (the default).
6Click OK to close the window.
Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide 305
Figure 207 Security Settings - Java Scripting
Java Permissions
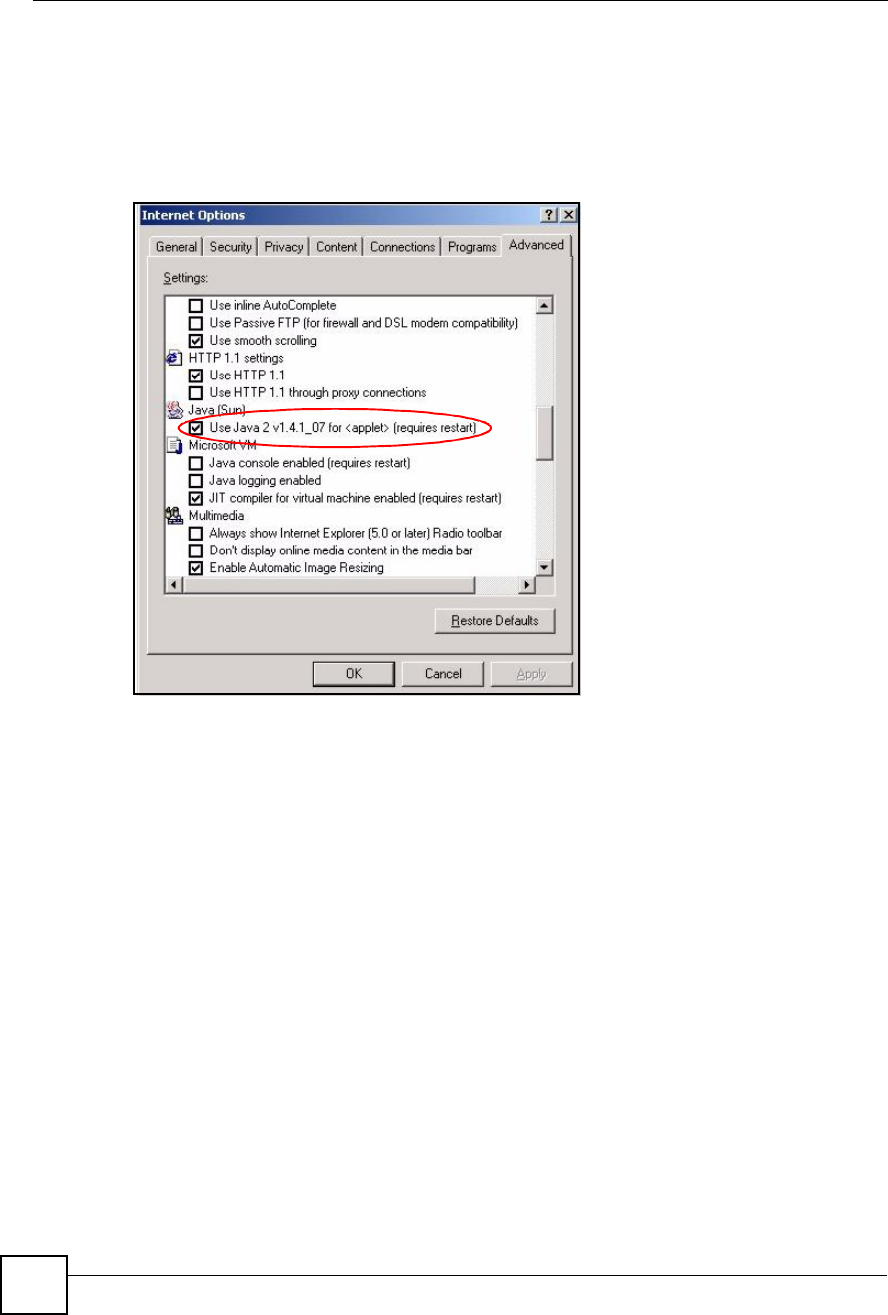
1From Internet Explorer, click Tools,Internet Options and then the Security tab.
2Click the Custom Level... button.
3Scroll down to Microsoft VM.
4Under Java permissions make sure that a safety level is selected.
5Click OK to close the window.
Figure 208 Security Settings - Java
Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide
306
JAVA (Sun)
1From Internet Explorer, click Tools,Internet Options and then the Advanced tab.
2Make sure that Use Java 2 for <applet> under Java (Sun) is selected.
3Click OK to close the window.
Figure 209 Java (Sun)
Mozilla Firefox
Mozilla Firefox 2.0 screens are used here. Screens for other versions may vary.
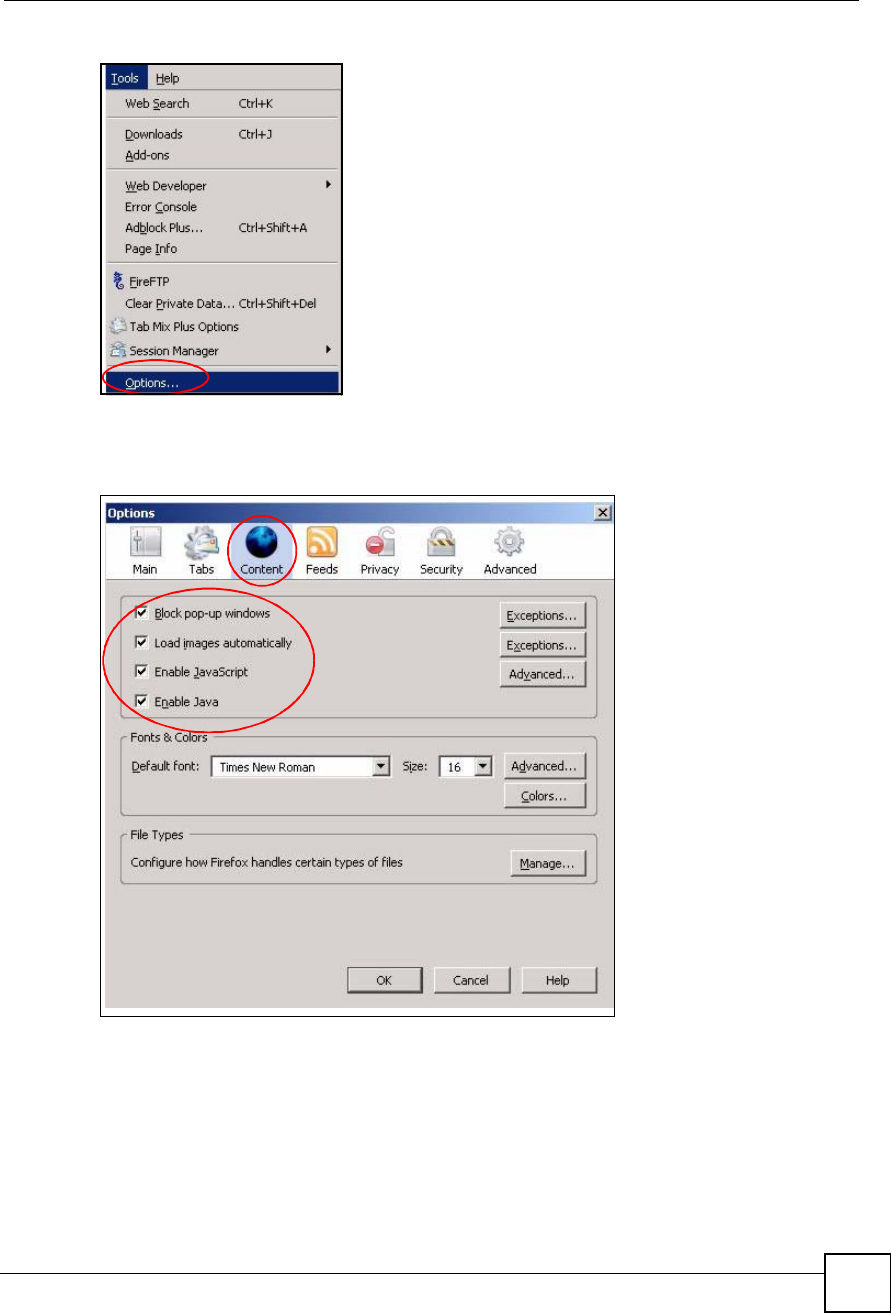
You can enable Java, Javascripts and pop-ups in one screen. Click Tools, then click Options in
the screen that appears.
Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide 307
Figure 210 Mozilla Firefox: Tools > Options
Click Content.to show the screen below. Select the check boxes as shown in the following
screen.
Figure 211 Mozilla Firefox Content Security

Appendix CPop-up Windows, JavaScripts and Java Permissions
MAX-200HW2 Series User s Guide
308

MAX-200HW2 Series User s Guide 309
APPENDIX D
IP Addresses and Subnetting
This appendix introduces IP addresses and subnet masks.
IP addresses identify individual devices on a network. Every networking device (including
computers, servers, routers, printers, etc.) needs an IP address to communicate across the
network. These networking devices are also known as hosts.
Subnet masks determine the maximum number of possible hosts on a network. You can also
use subnet masks to divide one network into multiple sub-networks.
Introduction to IP Addresses
One part of the IP address is the network number, and the other part is the host ID. In the same
way that houses on a street share a common street name, the hosts on a network share a
common network number. Similarly, as each house has its own house number, each host on the
network has its own unique identifying number - the host ID. Routers use the network number
to send packets to the correct network, while the host ID determines to which host on the
network the packets are delivered.
Structure
An IP address is made up of four parts, written in dotted decimal notation (for example,
192.168.1.1). Each of these four parts is known as an octet. An octet is an eight-digit binary
number (for example 11000000, which is 192 in decimal notation).
Therefore, each octet has a possible range of 00000000 to 11111111 in binary, or 0 to 255 in
decimal.
The following figure shows an example IP address in which the first three octets (192.168.1)
are the network number, and the fourth octet (16) is the host ID.
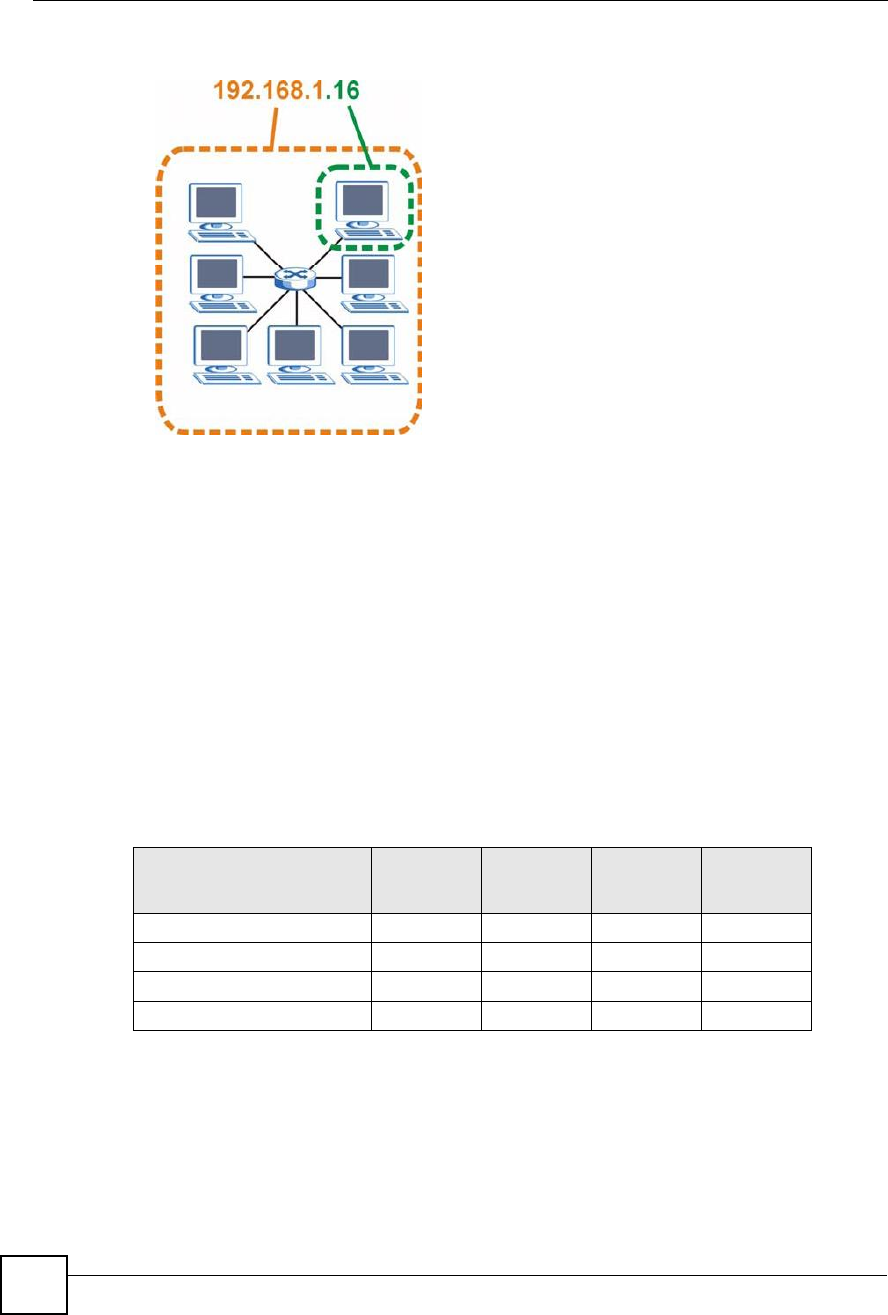
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide
310
Figure 212 Network Number and Host ID
How much of the IP address is the network number and how much is the host ID varies
according to the subnet mask.
Subnet Masks
A subnet mask is used to determine which bits are part of the network number, and which bits
are part of the host ID (using a logical AND operation). The term "subnet# is short for "sub-
network#.
A subnet mask has 32 bits. If a bit in the subnet mask is a "1# then the corresponding bit in the
IP address is part of the network number. If a bit in the subnet mask is "0# then the
corresponding bit in the IP address is part of the host ID.
The following example shows a subnet mask identifying the network number (in bold text)
and host ID of an IP address (192.168.1.2 in decimal).
By convention, subnet masks always consist of a continuous sequence of ones beginning from
the leftmost bit of the mask, followed by a continuous sequence of zeros, for a total number of
32 bits.
Subnet masks can be referred to by the size of the network number part (the bits with a "1#
value). For example, an "8-bit mask# means that the first 8 bits of the mask are ones and the
remaining 24 bits are zeroes.
Table 123 IP Address Network Number and Host ID Example
1ST OCTET:
(192)
2ND
OCTET:
(168)
3RD
OCTET:
(1)
4TH OCTET
(2)
IP Address (Binary)11000000101010000000000100000010
Subnet Mask (Binary) 111111111111111111111111 00000000
Network Number 110000001010100000000001
Host ID00000010
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide 311
Subnet masks are expressed in dotted decimal notation just like IP addresses. The following
examples show the binary and decimal notation for 8-bit, 16-bit, 24-bit and 29-bit subnet
masks.
Network Size
The size of the network number determines the maximum number of possible hosts you can
have on your network. The larger the number of network number bits, the smaller the number
of remaining host ID bits.
An IP address with host IDs of all zeros is the IP address of the network (192.168.1.0 with a
24-bit subnet mask, for example). An IP address with host IDs of all ones is the broadcast
address for that network (192.168.1.255 with a 24-bit subnet mask, for example).
As these two IP addresses cannot be used for individual hosts, calculate the maximum number
of possible hosts in a network as follows:
Notation
Since the mask is always a continuous number of ones beginning from the left, followed by a
continuous number of zeros for the remainder of the 32 bit mask, you can simply specify the
number of ones instead of writing the value of each octet. This is usually specified by writing
a "/# followed by the number of bits in the mask after the address.
For example, 192.1.1.0 /25 is equivalent to saying 192.1.1.0 with subnet mask
255.255.255.128.
The following table shows some possible subnet masks using both notations.
Table 124 Subnet Masks
BINARY
DECIMAL
1ST
OCTET
2ND
OCTET
3RD
OCTET 4TH OCTET
8-bit mask 11111111 00000000 00000000 00000000 255.0.0.0
16-bit mask 11111111 11111111 00000000 00000000 255.255.0.0
24-bit mask 11111111 11111111 11111111 00000000 255.255.255.0
29-bit mask 11111111 11111111 11111111 11111000 255.255.255.248
Table 125 Maximum Host Numbers
SUBNET MASK HOST ID SIZE MAXIMUM NUMBER OF HOSTS
8 bits255.0.0.024 bits2
24 % 216777214
16 bits255.255.0.016 bits2
16 % 265534
24 bits255.255.255.08 bits2
8
% 2254
29 bits255.255.255.2483 bits2
3
% 26
Table 126 Alternative Subnet Mask Notation
SUBNET MASK ALTERNATIVE
NOTATION
LAST OCTET
(BINARY)
LAST OCTET
(DECIMAL)
255.255.255.0 /24 0000 0000 0
255.255.255.128 /25 1000 0000 128
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide
312
Subnetting
You can use subnetting to divide one network into multiple sub-networks. In the following
example a network administrator creates two sub-networks to isolate a group of servers from
the rest of the company network for security reasons.
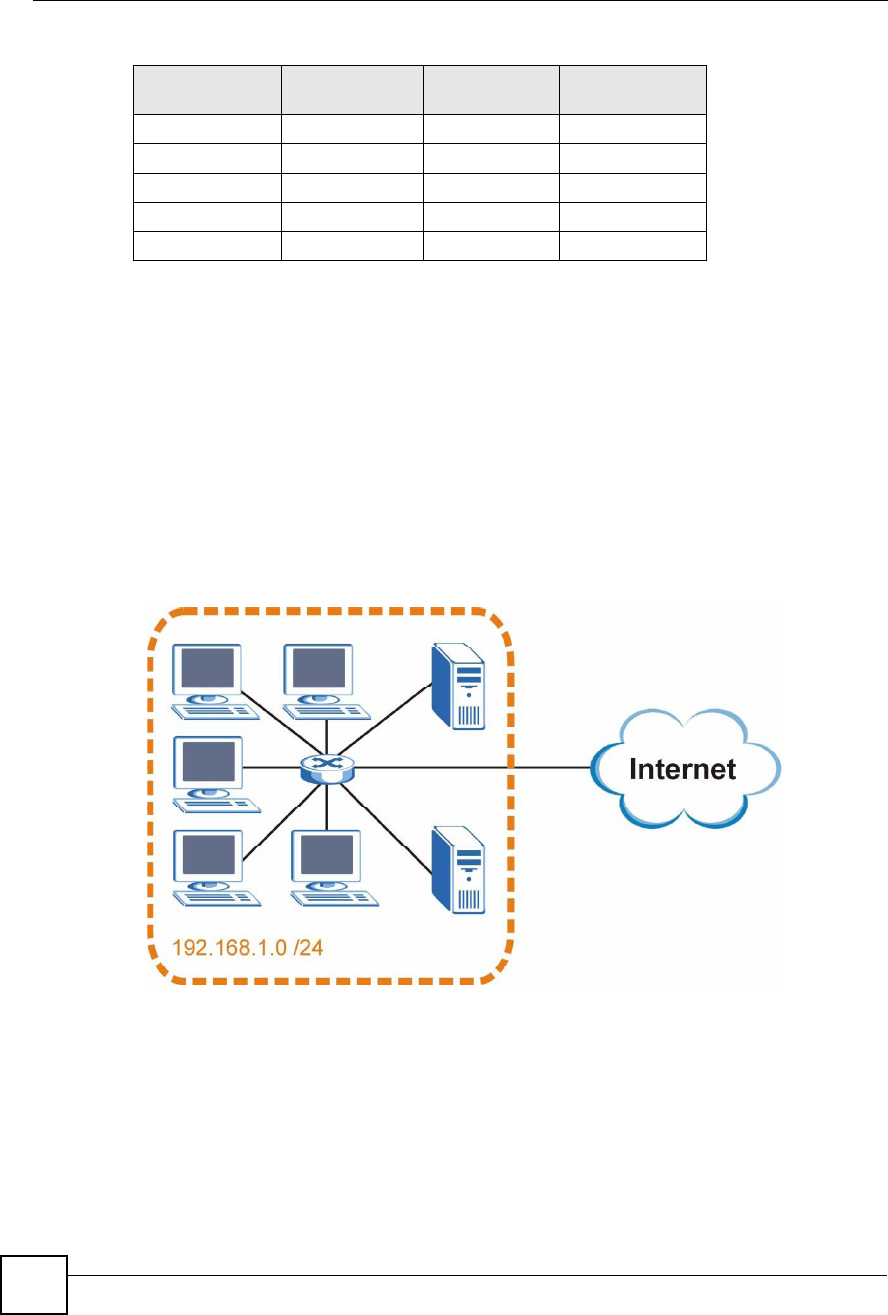
In this example, the company network address is 192.168.1.0. The first three octets of the
address (192.168.1) are the network number, and the remaining octet is the host ID, allowing a
maximum of 28 % 2 or 254 possible hosts.
The following figure shows the company network before subnetting.
Figure 213 Subnetting Example: Before Subnetting
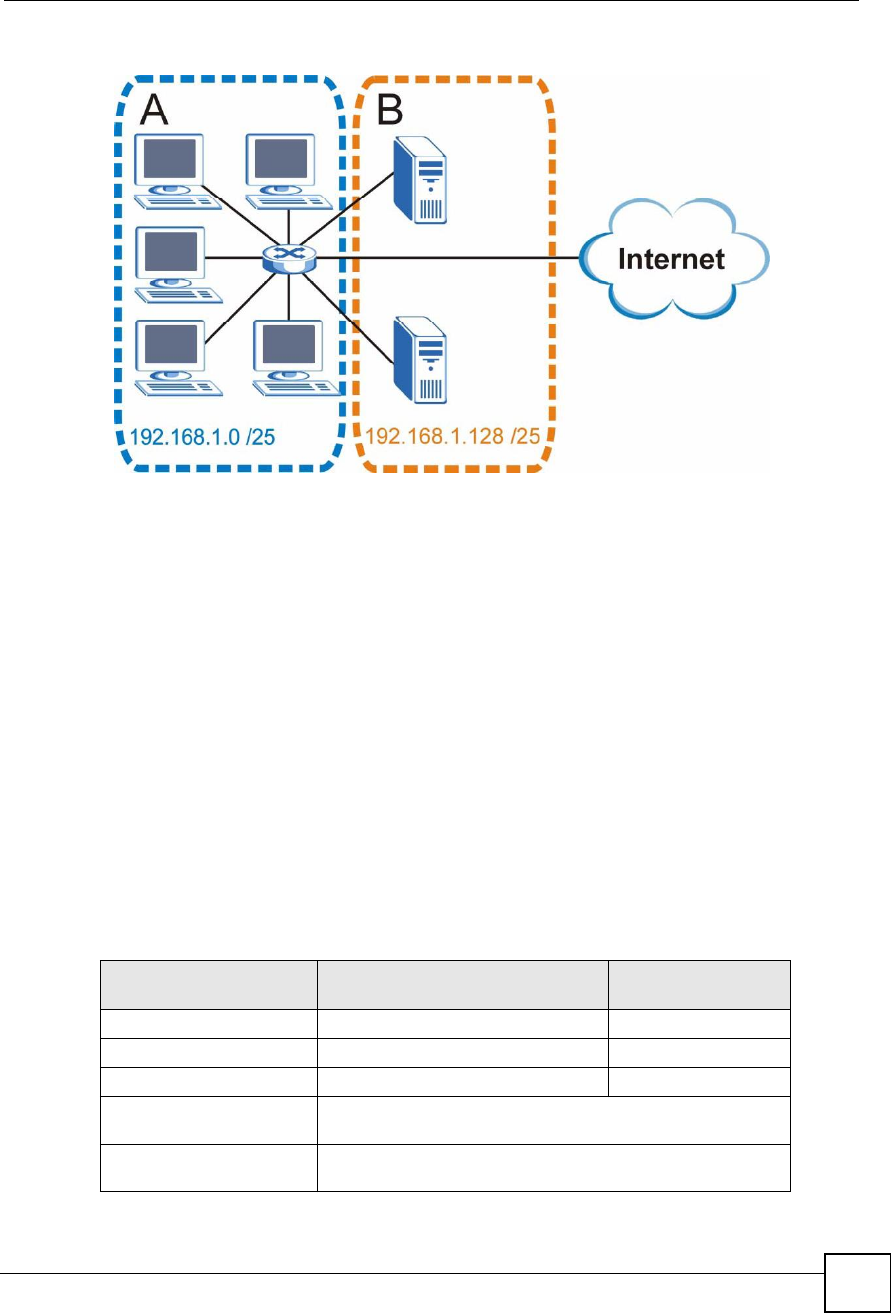
You can "borrow# one of the host ID bits to divide the network 192.168.1.0 into two separate
sub-networks. The subnet mask is now 25 bits (255.255.255.128 or /25).
The "borrowed# host ID bit can have a value of either 0 or 1, allowing two subnets;
192.168.1.0 /25 and 192.168.1.128 /25.
The following figure shows the company network after subnetting. There are now two sub-
networks, A and B.
255.255.255.192 /26 1100 0000 192
255.255.255.224 /27 1110 0000 224
255.255.255.240 /28 1111 0000 240
255.255.255.248 /29 1111 1000 248
255.255.255.252 /30 1111 1100 252
Table 126 Alternative Subnet Mask Notation (continued)
SUBNET MASK ALTERNATIVE
NOTATION
LAST OCTET
(BINARY)
LAST OCTET
(DECIMAL)
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide 313
Figure 214 Subnetting Example: After Subnetting
In a 25-bit subnet the host ID has 7 bits, so each sub-network has a maximum of 27 % 2 or 126
possible hosts (a host ID of all zeroes is the subnet!s address itself, all ones is the subnet!s
broadcast address).
192.168.1.0 with mask 255.255.255.128 is subnet A itself, and 192.168.1.127 with mask
255.255.255.128 is its broadcast address. Therefore, the lowest IP address that can be assigned
to an actual host for subnet A is 192.168.1.1 and the highest is 192.168.1.126.
Similarly, the host ID range for subnet B is 192.168.1.129 to 192.168.1.254.
Example: Four Subnets
The previous example illustrated using a 25-bit subnet mask to divide a 24-bit address into two
subnets. Similarly, to divide a 24-bit address into four subnets, you need to "borrow# two host
ID bits to give four possible combinations (00, 01, 10 and 11). The subnet mask is 26 bits
(11111111.11111111.11111111.11000000) or 255.255.255.192.
Each subnet contains 6 host ID bits, giving 26 - 2 or 62 hosts for each subnet (a host ID of all
zeroes is the subnet itself, all ones is the subnet!s broadcast address).
Table 127 Subnet 1
IP/SUBNET MASK NETWORK NUMBER LAST OCTET BIT
VALUE
IP Address (Decimal) 192.168.1. 0
IP Address (Binary) 11000000.10101000.00000001. 00000000
Subnet Mask (Binary) 11111111.11111111.11111111. 11000000
Subnet Address:
192.168.1.0
Lowest Host ID: 192.168.1.1
Broadcast Address:
192.168.1.63
Highest Host ID: 192.168.1.62
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide
314
Example: Eight Subnets
Similarly, use a 27-bit mask to create eight subnets (000, 001, 010, 011, 100, 101, 110 and
111).
The following table shows IP address last octet values for each subnet.
Table 128 Subnet 2
IP/SUBNET MASK NETWORK NUMBER LAST OCTET BIT
VALUE
IP Address 192.168.1. 64
IP Address (Binary) 11000000.10101000.00000001. 01000000
Subnet Mask (Binary) 11111111.11111111.11111111. 11000000
Subnet Address:
192.168.1.64
Lowest Host ID: 192.168.1.65
Broadcast Address:
192.168.1.127
Highest Host ID: 192.168.1.126
Table 129 Subnet 3
IP/SUBNET MASK NETWORK NUMBER LAST OCTET BIT
VALUE
IP Address 192.168.1. 128
IP Address (Binary) 11000000.10101000.00000001. 10000000
Subnet Mask (Binary) 11111111.11111111.11111111. 11000000
Subnet Address:
192.168.1.128
Lowest Host ID: 192.168.1.129
Broadcast Address:
192.168.1.191
Highest Host ID: 192.168.1.190
Table 130 Subnet 4
IP/SUBNET MASK NETWORK NUMBER LAST OCTET BIT
VALUE
IP Address 192.168.1. 192
IP Address (Binary) 11000000.10101000.00000001. 11000000
Subnet Mask (Binary) 11111111.11111111.11111111. 11000000
Subnet Address:
192.168.1.192
Lowest Host ID: 192.168.1.193
Broadcast Address:
192.168.1.255
Highest Host ID: 192.168.1.254
Table 131 Eight Subnets
SUBNET SUBNET
ADDRESS FIRST ADDRESS LAST
ADDRESS
BROADCAST
ADDRESS
1 0 1 30 31
2 32 33 62 63
3 64 65 94 95
4 96 97 126 127
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide 315
Subnet Planning
The following table is a summary for subnet planning on a network with a 24-bit network
number.
The following table is a summary for subnet planning on a network with a 16-bit network
number.
5128 129 158 159
6 160 161 190 191
7 192 193 222 223
8 224 225 254 255
Table 131 Eight Subnets (continued)
SUBNET SUBNET
ADDRESS FIRST ADDRESS LAST
ADDRESS
BROADCAST
ADDRESS
Table 132 24-bit Network Number Subnet Planning
NO. "BORROWED#
HOST BITS SUBNET MASK NO. SUBNETS NO. HOSTS PER
SUBNET
1255.255.255.128 (/25) 2 126
2 255.255.255.192 (/26) 4 62
3 255.255.255.224 (/27) 8 30
4 255.255.255.240 (/28) 16 14
5 255.255.255.248 (/29) 32 6
6 255.255.255.252 (/30) 64 2
7 255.255.255.254 (/31) 128 1
Table 133 16-bit Network Number Subnet Planning
NO. "BORROWED#
HOST BITS SUBNET MASK NO. SUBNETS NO. HOSTS PER
SUBNET
1255.255.128.0 (/17) 2 32766
2 255.255.192.0 (/18) 4 16382
3 255.255.224.0 (/19) 8 8190
4 255.255.240.0 (/20) 16 4094
5 255.255.248.0 (/21) 32 2046
6 255.255.252.0 (/22) 64 1022
7 255.255.254.0 (/23) 128 510
8 255.255.255.0 (/24) 256 254
9 255.255.255.128 (/25) 512 126
10 255.255.255.192 (/26) 1024 62
11 255.255.255.224 (/27) 2048 30
12 255.255.255.240 (/28) 4096 14
13 255.255.255.248 (/29) 8192 6

Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide
316
Configuring IP Addresses
Where you obtain your network number depends on your particular situation. If the ISP or
your network administrator assigns you a block of registered IP addresses, follow their
instructions in selecting the IP addresses and the subnet mask.
If the ISP did not explicitly give you an IP network number, then most likely you have a single
user account and the ISP will assign you a dynamic IP address when the connection is
established. If this is the case, it is recommended that you select a network number from
192.168.0.0 to 192.168.255.0. The Internet Assigned Number Authority (IANA) reserved this
block of addresses specifically for private use; please do not use any other number unless you
are told otherwise. You must also enable Network Address Translation (NAT) on the ZyXEL
Device.
Once you have decided on the network number, pick an IP address for your ZyXEL Device
that is easy to remember (for instance, 192.168.1.1) but make sure that no other device on your
network is using that IP address.
The subnet mask specifies the network number portion of an IP address. Your ZyXEL Device
will compute the subnet mask automatically based on the IP address that you entered. You
don't need to change the subnet mask computed by the ZyXEL Device unless you are
instructed to do otherwise.
Private IP Addresses
Every machine on the Internet must have a unique address. If your networks are isolated from
the Internet (running only between two branch offices, for example) you can assign any IP
addresses to the hosts without problems. However, the Internet Assigned Numbers Authority
(IANA) has reserved the following three blocks of IP addresses specifically for private
networks:
10.0.0.0 ' 10.255.255.255
172.16.0.0 ' 172.31.255.255
192.168.0.0 ' 192.168.255.255
You can obtain your IP address from the IANA, from an ISP, or it can be assigned from a
private network. If you belong to a small organization and your Internet access is through an
ISP, the ISP can provide you with the Internet addresses for your local networks. On the other
hand, if you are part of a much larger organization, you should consult your network
administrator for the appropriate IP addresses.
Regardless of your particular situation, do not create an arbitrary IP address; always follow the
guidelines above. For more information on address assignment, please refer to RFC 1597,
Address Allocation for Private Internets and RFC 1466, Guidelines for Management of IP
Address Space.
14 255.255.255.252 (/30) 16384 2
15 255.255.255.254 (/31) 32768 1
Table 133 16-bit Network Number Subnet Planning (continued)
NO. "BORROWED#
HOST BITS SUBNET MASK NO. SUBNETS NO. HOSTS PER
SUBNET
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide 317
IP Address Conflicts
Each device on a network must have a unique IP address. Devices with duplicate IP addresses
on the same network will not be able to access the Internet or other resources. The devices may
also be unreachable through the network.
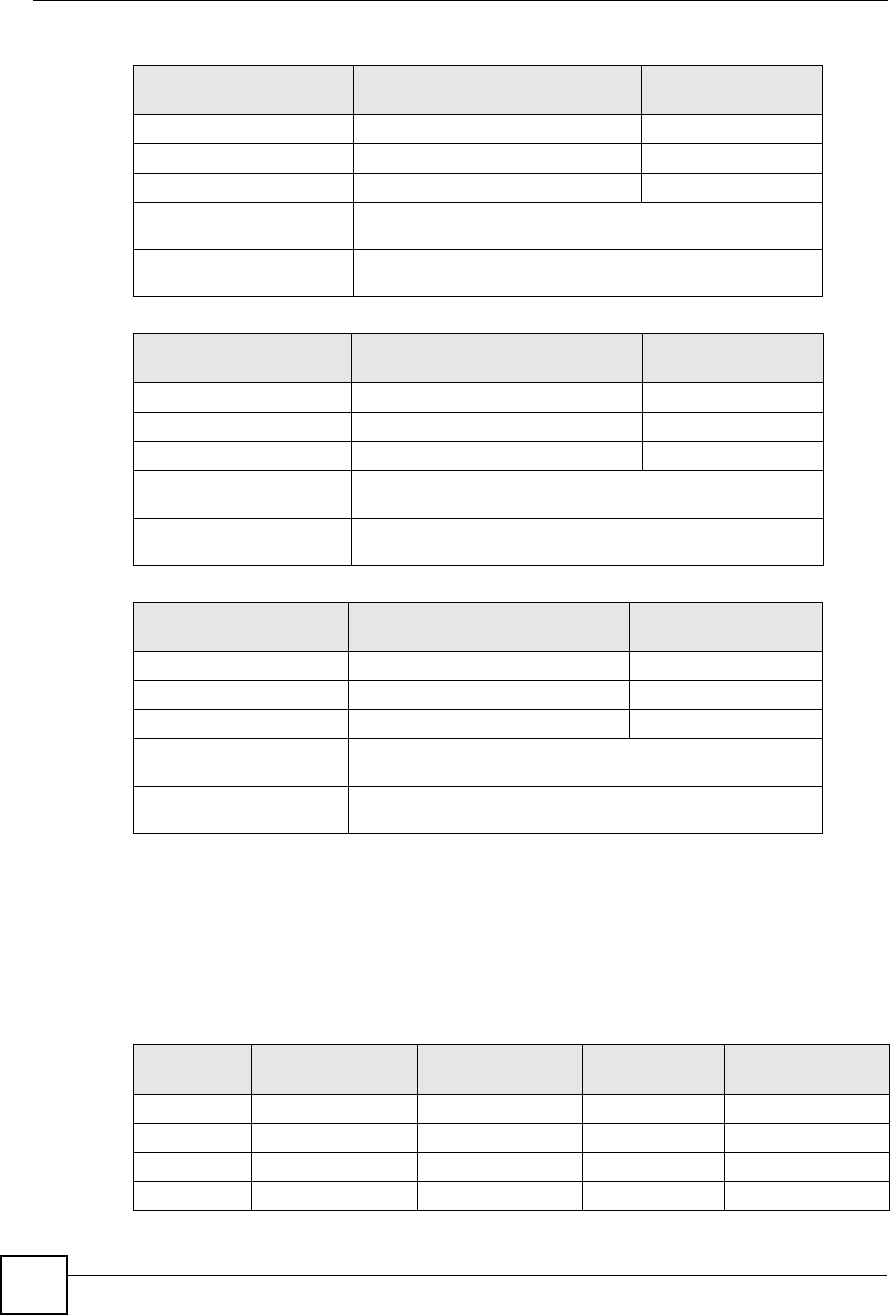
Conflicting Computer IP Addresses Example
More than one device can not use the same IP address. In the following example computer A
has a static (or fixed) IP address that is the same as the IP address that a DHCP server assigns
to computer B which is a DHCP client. Neither can access the Internet. This problem can be
solved by assigning a different static IP address to computer A or setting computer A to obtain
an IP address automatically.
Figure 215 Conflicting Computer IP Addresses Example
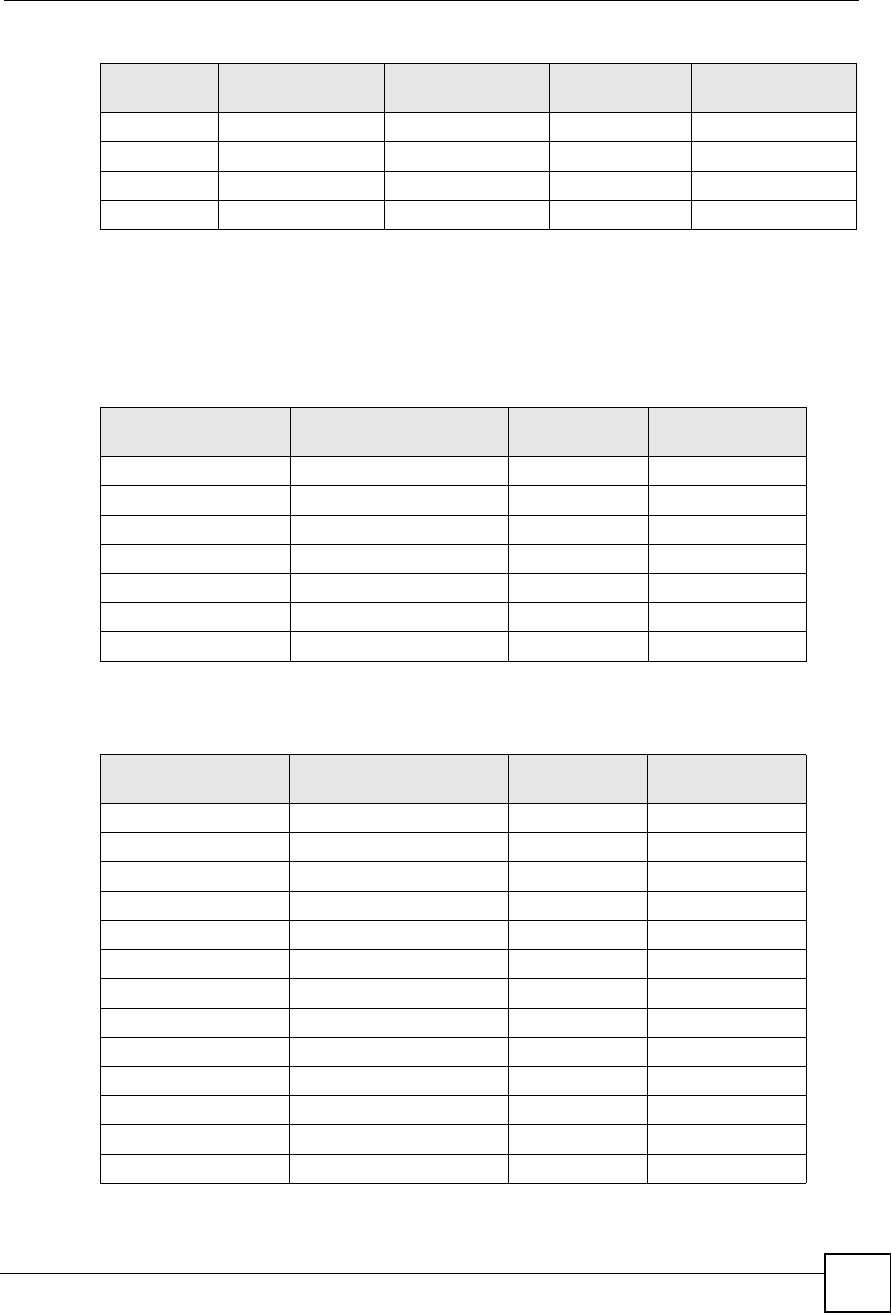
Conflicting Router IP Addresses Example
Since a router connects different networks, it must have interfaces using different network
numbers. For example, if a router is set between a LAN and the Internet (WAN), the router!s
LAN and WAN addresses must be on different subnets. In the following example, the LAN
and WAN are on the same subnet. The LAN computers cannot access the Internet because the
router cannot route between networks.
Figure 216 Conflicting Computer IP Addresses Example
Appendix DIP Addresses and Subnetting
MAX-200HW2 Series User s Guide
318
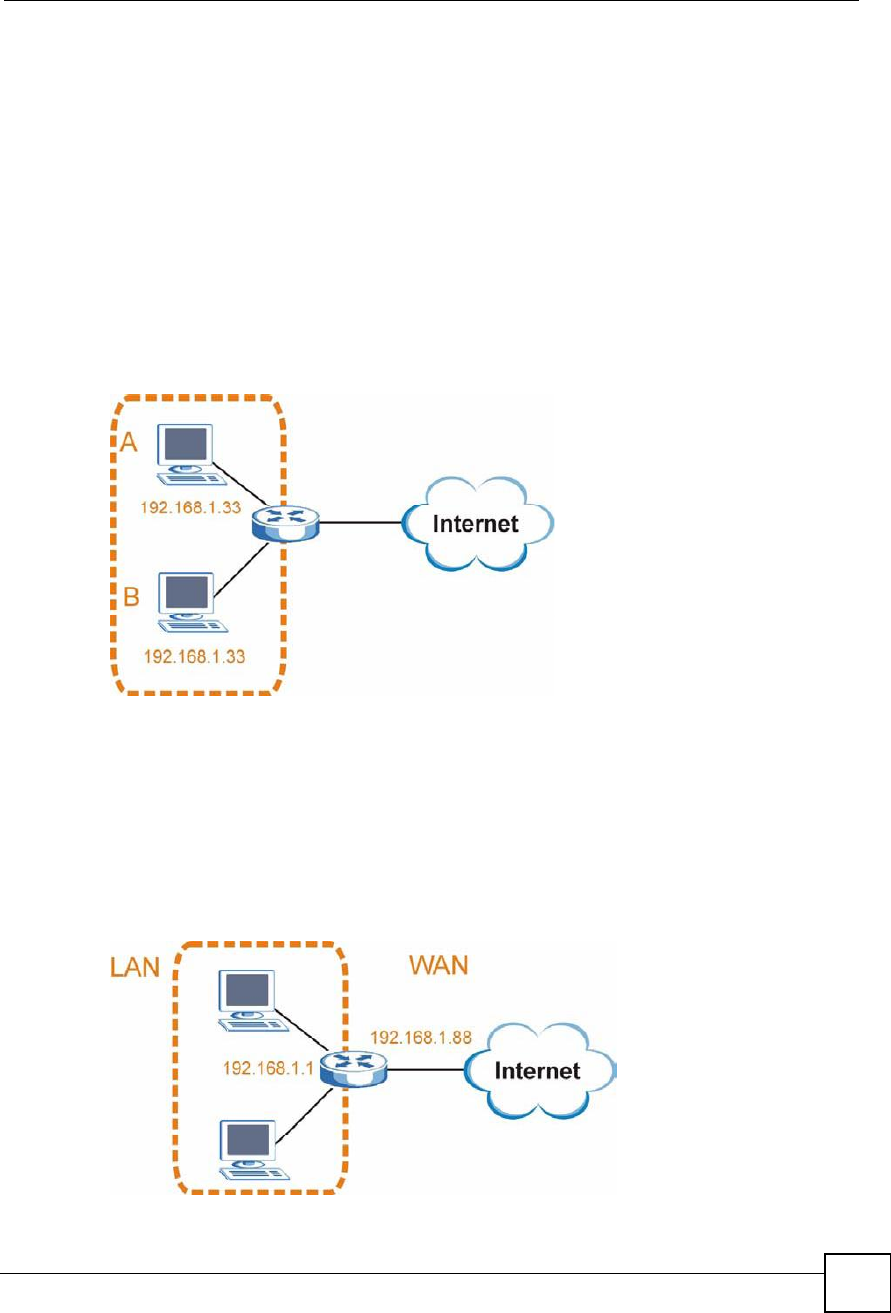
Conflicting Computer and Router IP Addresses Example
More than one device can not use the same IP address. In the following example, the computer
and the router!s LAN port both use 192.168.1.1 as the IP address. The computer cannot access
the Internet. This problem can be solved by assigning a different IP address to the computer or
the router!s LAN port.
Figure 217 Conflicting Computer and Router IP Addresses Example

MAX-200HW2 Series User s Guide 319
APPENDIX E
Wireless LANs
Wireless LAN Topologies
This section discusses ad-hoc and infrastructure wireless LAN topologies.
Ad-hoc Wireless LAN Configuration
The simplest WLAN configuration is an independent (Ad-hoc) WLAN that connects a set of
computers with wireless adapters (A, B, C). Any time two or more wireless adapters are within
range of each other, they can set up an independent network, which is commonly referred to as
an ad-hoc network or Independent Basic Service Set (IBSS). The following diagram shows an
example of notebook computers using wireless adapters to form an ad-hoc wireless LAN.
Figure 218 Peer-to-Peer Communication in an Ad-hoc Network
BSS
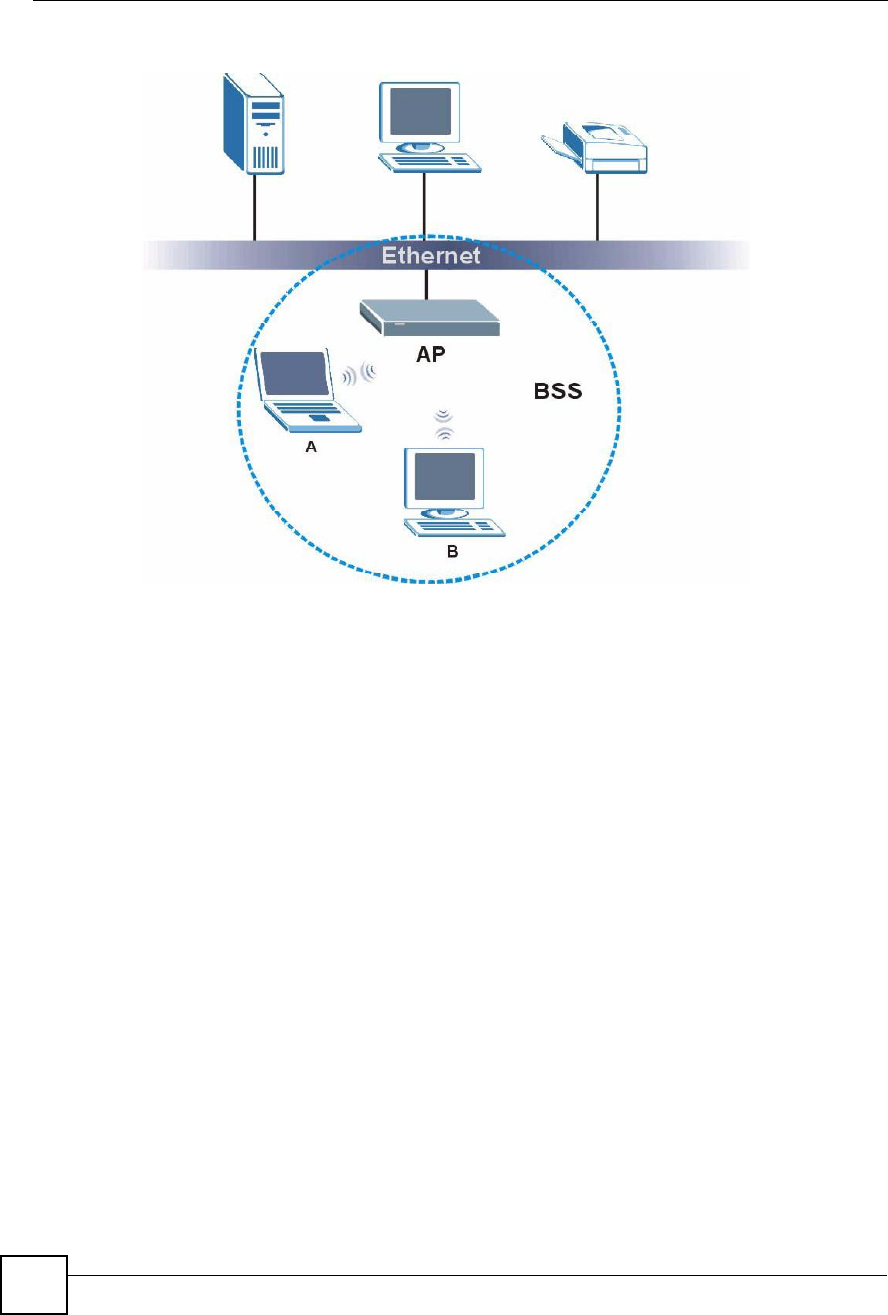
A Basic Service Set (BSS) exists when all communications between wireless clients or
between a wireless client and a wired network client go through one access point (AP).
Intra-BSS traffic is traffic between wireless clients in the BSS. When Intra-BSS is enabled,
wireless client A and B can access the wired network and communicate with each other. When
Intra-BSS is disabled, wireless client A and B can still access the wired network but cannot
communicate with each other.
Appendix EWireless LANs
MAX-200HW2 Series User s Guide
320
Figure 219 Basic Service Set
ESS
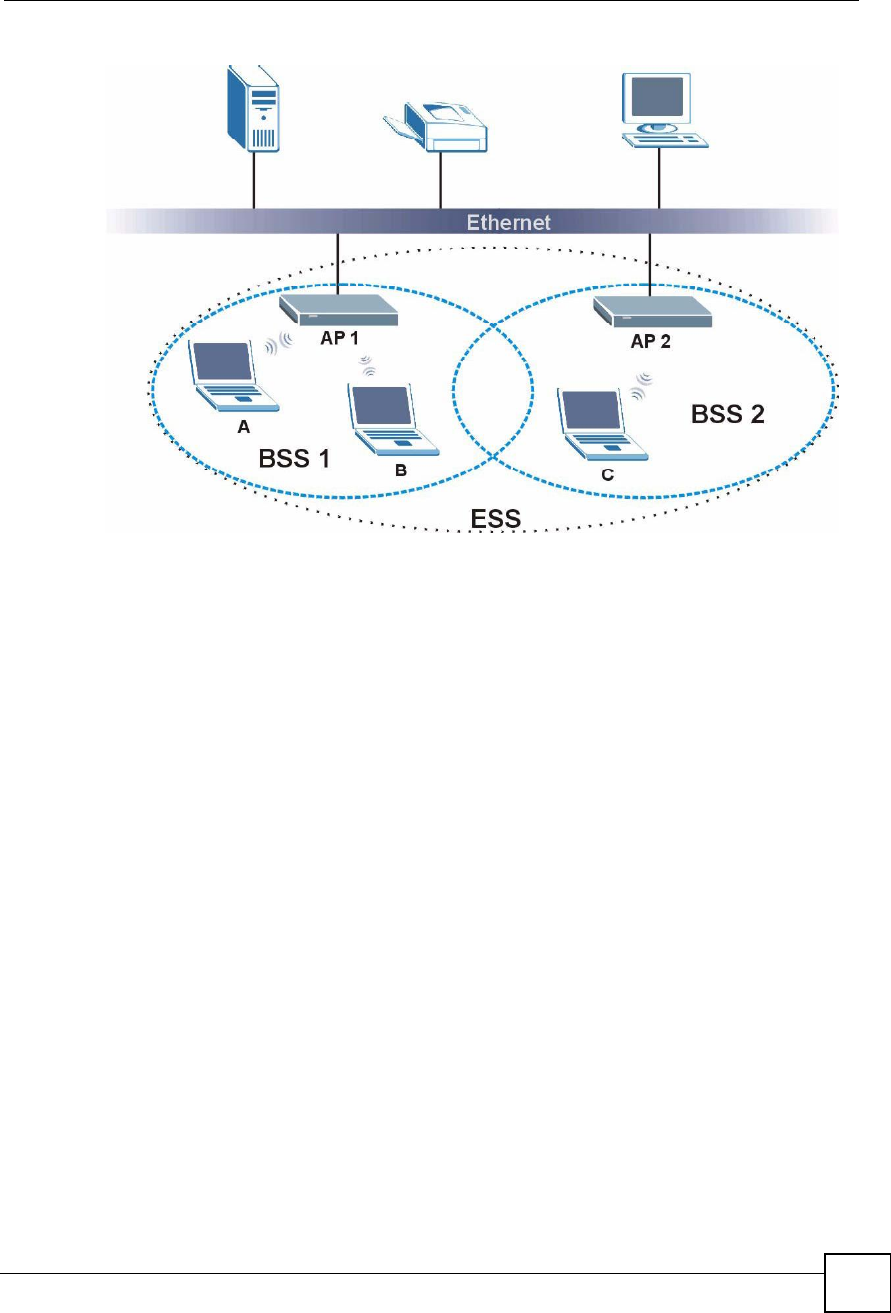
An Extended Service Set (ESS) consists of a series of overlapping BSSs, each containing an
access point, with each access point connected together by a wired network. This wired
connection between APs is called a Distribution System (DS).
This type of wireless LAN topology is called an Infrastructure WLAN. The Access Points not
only provide communication with the wired network but also mediate wireless network traffic
in the immediate neighborhood.
An ESSID (ESS IDentification) uniquely identifies each ESS. All access points and their
associated wireless clients within the same ESS must have the same ESSID in order to
communicate.
Appendix EWireless LANs
MAX-200HW2 Series User s Guide 321
Figure 220 Infrastructure WLAN
Channel
A channel is the radio frequency(ies) used by wireless devices to transmit and receive data.
Channels available depend on your geographical area. You may have a choice of channels (for
your region) so you should use a channel different from an adjacent AP (access point) to
reduce interference. Interference occurs when radio signals from different access points
overlap causing interference and degrading performance.
Adjacent channels partially overlap however. To avoid interference due to overlap, your AP
should be on a channel at least five channels away from a channel that an adjacent AP is using.
For example, if your region has 11 channels and an adjacent AP is using channel 1, then you
need to select a channel between 6 or 11.
RTS/CTS
A hidden node occurs when two stations are within range of the same access point, but are not
within range of each other. The following figure illustrates a hidden node. Both stations (STA)
are within range of the access point (AP) or wireless gateway, but out-of-range of each other,
so they cannot "hear" each other, that is they do not know if the channel is currently being
used. Therefore, they are considered hidden from each other.
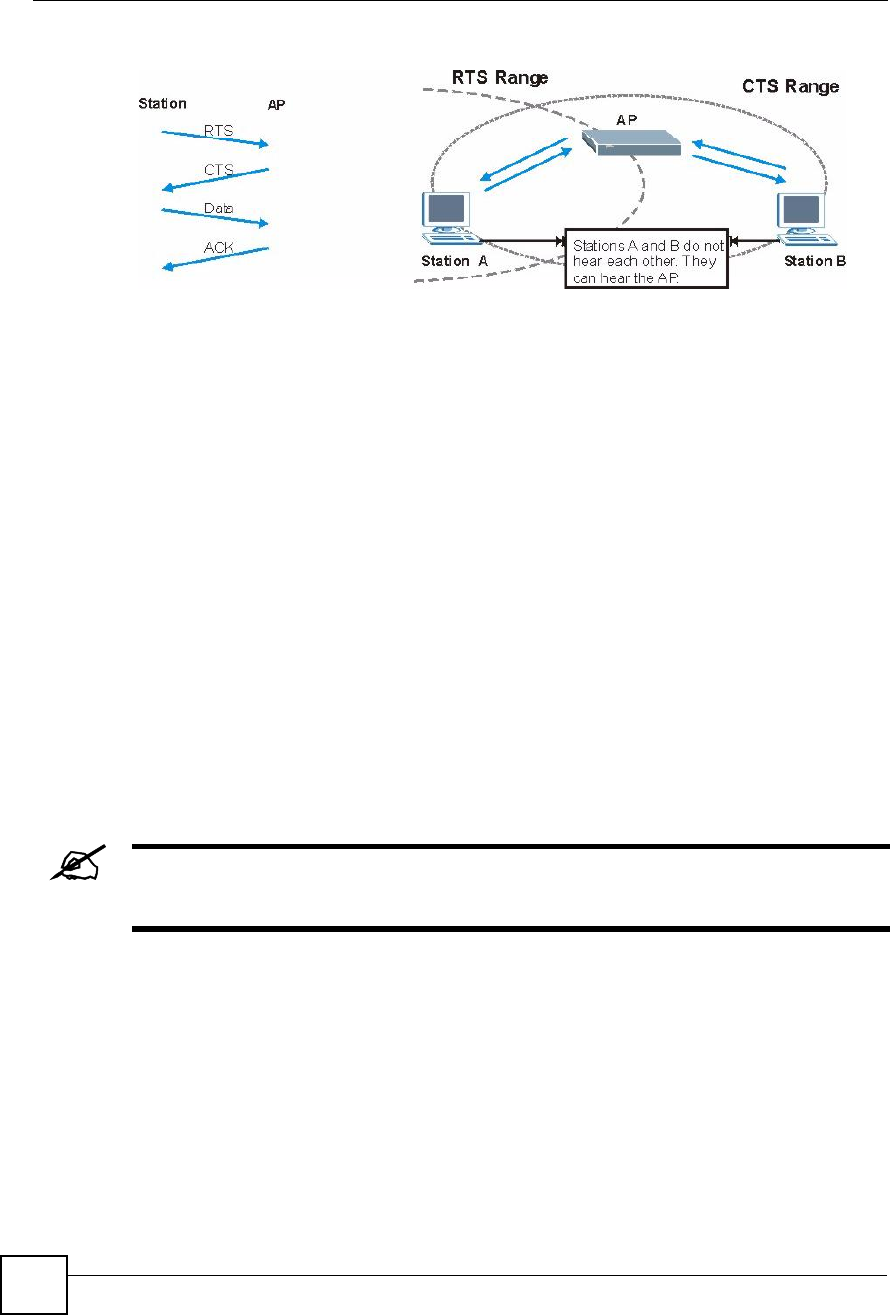
Appendix EWireless LANs
MAX-200HW2 Series User s Guide
322
Figure 221 RTS/CTS
When station A sends data to the AP, it might not know that the station B is already using the
channel. If these two stations send data at the same time, collisions may occur when both sets
of data arrive at the AP at the same time, resulting in a loss of messages for both stations.
RTS/CTS is designed to prevent collisions due to hidden nodes. An RTS/CTS defines the
biggest size data frame you can send before an RTS (Request To Send)/CTS (Clear to Send)
handshake is invoked.
When a data frame exceeds the RTS/CTS value you set (between 0 to 2432 bytes), the station
that wants to transmit this frame must first send an RTS (Request To Send) message to the AP
for permission to send it. The AP then responds with a CTS (Clear to Send) message to all
other stations within its range to notify them to defer their transmission. It also reserves and
confirms with the requesting station the time frame for the requested transmission.
Stations can send frames smaller than the specified RTS/CTS directly to the AP without the
RTS (Request To Send)/CTS (Clear to Send) handshake.
You should only configure RTS/CTS if the possibility of hidden nodes exists on your network
and the "cost" of resending large frames is more than the extra network overhead involved in
the RTS (Request To Send)/CTS (Clear to Send) handshake.
If the RTS/CTS value is greater than the Fragmentation Threshold value (see next), then the
RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as data frames will
be fragmented before they reach RTS/CTS size.
Enabling the RTS Threshold causes redundant network overhead that could
negatively affect the throughput performance instead of providing a remedy.
Fragmentation Threshold
AFragmentation Threshold is the maximum data fragment size (between 256 and 2432
bytes) that can be sent in the wireless network before the AP will fragment the packet into
smaller data frames.
A large Fragmentation Threshold is recommended for networks not prone to interference
while you should set a smaller threshold for busy networks or networks that are prone to
interference.
Appendix EWireless LANs
MAX-200HW2 Series User s Guide 323
If the Fragmentation Threshold value is smaller than the RTS/CTS value (see previously)
you set then the RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as
data frames will be fragmented before they reach RTS/CTS size.
Preamble Type
Preamble is used to signal that data is coming to the receiver. Short and long refer to the length
of the synchronization field in a packet.
Short preamble increases performance as less time sending preamble means more time for
sending data. All IEEE 802.11 compliant wireless adapters support long preamble, but not all
support short preamble.
Use long preamble if you are unsure what preamble mode other wireless devices on the
network support, and to provide more reliable communications in busy wireless networks.
Use short preamble if you are sure all wireless devices on the network support it, and to
provide more efficient communications.
Use the dynamic setting to automatically use short preamble when all wireless devices on the
network support it, otherwise the ZyXEL Device uses long preamble.
The wireless devices MUSTuse the same preamble mode in order to
communicate.
IEEE 802.11g Wireless LAN
IEEE 802.11g is fully compatible with the IEEE 802.11b standard. This means an IEEE
802.11b adapter can interface directly with an IEEE 802.11g access point (and vice versa) at
11 Mbps or lower depending on range. IEEE 802.11g has several intermediate rate steps
between the maximum and minimum data rates. The IEEE 802.11g data rate and modulation
are as follows:
Wireless Security Overview
Wireless security is vital to your network to protect wireless communication between wireless
clients, access points and the wired network.
Table 134 IEEE 802.11g
DATA RATE (MBPS) MODULATION
1DBPSK (Differential Binary Phase Shift Keyed)
2DQPSK (Differential Quadrature Phase Shift Keying)
5.5 / 11CCK (Complementary Code Keying)
6/9/12/18/24/36/48/54OFDM (Orthogonal Frequency Division Multiplexing)
Appendix EWireless LANs
MAX-200HW2 Series User s Guide
324
Wireless security methods available on the ZyXEL Device are data encryption, wireless client
authentication, restricting access by device MAC address and hiding the ZyXEL Device
identity.
The following figure shows the relative effectiveness of these wireless security methods
available on your ZyXEL Device.
You must enable the same wireless security settings on the ZyXEL Device and
on all wireless clients that you want to associate with it.
IEEE 802.1x
In June 2001, the IEEE 802.1x standard was designed to extend the features of IEEE 802.11 to
support extended authentication as well as providing additional accounting and control
features. It is supported by Windows XP and a number of network devices. Some advantages
of IEEE 802.1x are:
User based identification that allows for roaming.
Support for RADIUS (Remote Authentication Dial In User Service, RFC 2138, 2139) for
centralized user profile and accounting management on a network RADIUS server.
Support for EAP (Extensible Authentication Protocol, RFC 2486) that allows additional
authentication methods to be deployed with no changes to the access point or the wireless
clients.
RADIUS
RADIUS is based on a client-server model that supports authentication, authorization and
accounting. The access point is the client and the server is the RADIUS server. The RADIUS
server handles the following tasks:
Authentication
Determines the identity of the users.
Authorization
Table 135 Wireless Security Levels
SECURITY
LEVEL SECURITY TYPE
Least
Secure
Most Secure
Unique SSID (Default)
Unique SSID with Hide SSID Enabled
MAC Address Filtering
WEP Encryption
IEEE802.1x EAP with RADIUS Server Authentication
Wi-Fi Protected Access (WPA)
WPA2

Appendix EWireless LANs
MAX-200HW2 Series User s Guide 325
Determines the network services available to authenticated users once they are connected
to the network.
Accounting
Keeps track of the client!s network activity.
RADIUS is a simple package exchange in which your AP acts as a message relay between the
wireless client and the network RADIUS server.
Types of RADIUS Messages
The following types of RADIUS messages are exchanged between the access point and the
RADIUS server for user authentication:
Access-Request
Sent by an access point requesting authentication.
Access-Reject
Sent by a RADIUS server rejecting access.
Access-Accept
Sent by a RADIUS server allowing access.
Access-Challenge
Sent by a RADIUS server requesting more information in order to allow access. The
access point sends a proper response from the user and then sends another Access-Request
message.
The following types of RADIUS messages are exchanged between the access point and the
RADIUS server for user accounting:
Accounting-Request
Sent by the access point requesting accounting.
Accounting-Response
Sent by the RADIUS server to indicate that it has started or stopped accounting.
In order to ensure network security, the access point and the RADIUS server use a shared
secret key, which is a password, they both know. The key is not sent over the network. In
addition to the shared key, password information exchanged is also encrypted to protect the
network from unauthorized access.
Types of EAP Authentication
This section discusses some popular authentication types: EAP-MD5, EAP-TLS, EAP-TTLS,
PEAP and LEAP. Your wireless LAN device may not support all authentication types.
EAP (Extensible Authentication Protocol) is an authentication protocol that runs on top of the
IEEE 802.1x transport mechanism in order to support multiple types of user authentication. By
using EAP to interact with an EAP-compatible RADIUS server, an access point helps a
wireless station and a RADIUS server perform authentication.
The type of authentication you use depends on the RADIUS server and an intermediary AP(s)
that supports IEEE 802.1x. .

Appendix EWireless LANs
MAX-200HW2 Series User s Guide
326
For EAP-TLS authentication type, you must first have a wired connection to the network and
obtain the certificate(s) from a certificate authority (CA). A certificate (also called digital IDs)
can be used to authenticate users and a CA issues certificates and guarantees the identity of
each certificate owner.
EAP-MD5 (Message-Digest Algorithm 5)
MD5 authentication is the simplest one-way authentication method. The authentication server
sends a challenge to the wireless client. The wireless client $proves! that it knows the password
by encrypting the password with the challenge and sends back the information. Password is
not sent in plain text.
However, MD5 authentication has some weaknesses. Since the authentication server needs to
get the plaintext passwords, the passwords must be stored. Thus someone other than the
authentication server may access the password file. In addition, it is possible to impersonate an
authentication server as MD5 authentication method does not perform mutual authentication.
Finally, MD5 authentication method does not support data encryption with dynamic session
key. You must configure WEP encryption keys for data encryption.
EAP-TLS (Transport Layer Security)
With EAP-TLS, digital certifications are needed by both the server and the wireless clients for
mutual authentication. The server presents a certificate to the client. After validating the
identity of the server, the client sends a different certificate to the server. The exchange of
certificates is done in the open before a secured tunnel is created. This makes user identity
vulnerable to passive attacks. A digital certificate is an electronic ID card that authenticates the
sender!s identity. However, to implement EAP-TLS, you need a Certificate Authority (CA) to
handle certificates, which imposes a management overhead.
EAP-TTLS (Tunneled Transport Layer Service)
EAP-TTLS is an extension of the EAP-TLS authentication that uses certificates for only the
server-side authentications to establish a secure connection. Client authentication is then done
by sending username and password through the secure connection, thus client identity is
protected. For client authentication, EAP-TTLS supports EAP methods and legacy
authentication methods such as PAP, CHAP, MS-CHAP and MS-CHAP v2.
PEAP (Protected EAP)
Like EAP-TTLS, server-side certificate authentication is used to establish a secure connection,
then use simple username and password methods through the secured connection to
authenticate the clients, thus hiding client identity. However, PEAP only supports EAP
methods, such as EAP-MD5, EAP-MSCHAPv2 and EAP-GTC (EAP-Generic Token Card),
for client authentication. EAP-GTC is implemented only by Cisco.
LEAP
LEAP (Lightweight Extensible Authentication Protocol) is a Cisco implementation of IEEE
802.1x.

Appendix EWireless LANs
MAX-200HW2 Series User s Guide 327
Dynamic WEP Key Exchange
The AP maps a unique key that is generated with the RADIUS server. This key expires when
the wireless connection times out, disconnects or reauthentication times out. A new WEP key
is generated each time reauthentication is performed.
If this feature is enabled, it is not necessary to configure a default encryption key in the
wireless security configuration screen. You may still configure and store keys, but they will
not be used while dynamic WEP is enabled.
EAP-MD5 cannot be used with Dynamic WEP Key Exchange
For added security, certificate-based authentications (EAP-TLS, EAP-TTLS and PEAP) use
dynamic keys for data encryption. They are often deployed in corporate environments, but for
public deployment, a simple user name and password pair is more practical. The following
table is a comparison of the features of authentication types.
WPA and WPA2
WPA is a subset of the IEEE 802.11i standard. WPA2 (IEEE 802.11i) is a wireless security
standard that defines stronger encryption, authentication and key management than WPA.
Key differences between WPA or WPA2 and WEP are improved data encryption and user
authentication.
If both an AP and the wireless clients support WPA2 and you have an external RADIUS
server, use WPA2 for stronger data encryption. If you don't have an external RADIUS server,
you should use WPA2-PSK (WPA2-Pre-Shared Key) that only requires a single (identical)
password entered into each access point, wireless gateway and wireless client. As long as the
passwords match, a wireless client will be granted access to a WLAN.
If the AP or the wireless clients do not support WPA2, just use WPA or WPA-PSK depending
on whether you have an external RADIUS server or not.
Select WEP only when the AP and/or wireless clients do not support WPA or WPA2. WEP is
less secure than WPA or WPA2.
Table 136 Comparison of EAP Authentication Types
EAP-MD5 EAP-TLS EAP-TTLS PEAP LEAP
Mutual Authentication No Yes Yes Yes Yes
Certificate % Client No Yes Optional Optional No
Certificate % Server No Yes Yes Yes No
Dynamic Key Exchange No Yes Yes Yes Yes
Credential Integrity None Strong Strong Strong Moderate
Deployment Difficulty Easy Hard Moderate Moderate Moderate
Client Identity Protection No No Yes Yes No

Appendix EWireless LANs
MAX-200HW2 Series User s Guide
328
Encryption
Both WPA and WPA2 improve data encryption by using Temporal Key Integrity Protocol
(TKIP), Message Integrity Check (MIC) and IEEE 802.1x. WPA and WPA2 use Advanced
Encryption Standard (AES) in the Counter mode with Cipher block chaining Message
authentication code Protocol (CCMP) to offer stronger encryption than TKIP.
TKIP uses 128-bit keys that are dynamically generated and distributed by the authentication
server. AES (Advanced Encryption Standard) is a block cipher that uses a 256-bit
mathematical algorithm called Rijndael. They both include a per-packet key mixing function,
a Message Integrity Check (MIC) named Michael, an extended initialization vector (IV) with
sequencing rules, and a re-keying mechanism.
WPA and WPA2 regularly change and rotate the encryption keys so that the same encryption
key is never used twice.
The RADIUS server distributes a Pairwise Master Key (PMK) key to the AP that then sets up
a key hierarchy and management system, using the PMK to dynamically generate unique data
encryption keys to encrypt every data packet that is wirelessly communicated between the AP
and the wireless clients. This all happens in the background automatically.
The Message Integrity Check (MIC) is designed to prevent an attacker from capturing data
packets, altering them and resending them. The MIC provides a strong mathematical function
in which the receiver and the transmitter each compute and then compare the MIC. If they do
not match, it is assumed that the data has been tampered with and the packet is dropped.
By generating unique data encryption keys for every data packet and by creating an integrity
checking mechanism (MIC), with TKIP and AES it is more difficult to decrypt data on a Wi-Fi
network than WEP and difficult for an intruder to break into the network.
The encryption mechanisms used for WPA(2) and WPA(2)-PSK are the same. The only
difference between the two is that WPA(2)-PSK uses a simple common password, instead of
user-specific credentials. The common-password approach makes WPA(2)-PSK susceptible to
brute-force password-guessing attacks but it!s still an improvement over WEP as it employs a
consistent, single, alphanumeric password to derive a PMK which is used to generate unique
temporal encryption keys. This prevent all wireless devices sharing the same encryption keys.
(a weakness of WEP)
User Authentication
WPA and WPA2 apply IEEE 802.1x and Extensible Authentication Protocol (EAP) to
authenticate wireless clients using an external RADIUS database. WPA2 reduces the number
of key exchange messages from six to four (CCMP 4-way handshake) and shortens the time
required to connect to a network. Other WPA2 authentication features that are different from
WPA include key caching and pre-authentication. These two features are optional and may not
be supported in all wireless devices.
Key caching allows a wireless client to store the PMK it derived through a successful
authentication with an AP. The wireless client uses the PMK when it tries to connect to the
same AP and does not need to go with the authentication process again.
Pre-authentication enables fast roaming by allowing the wireless client (already connecting to
an AP) to perform IEEE 802.1x authentication with another AP before connecting to it.
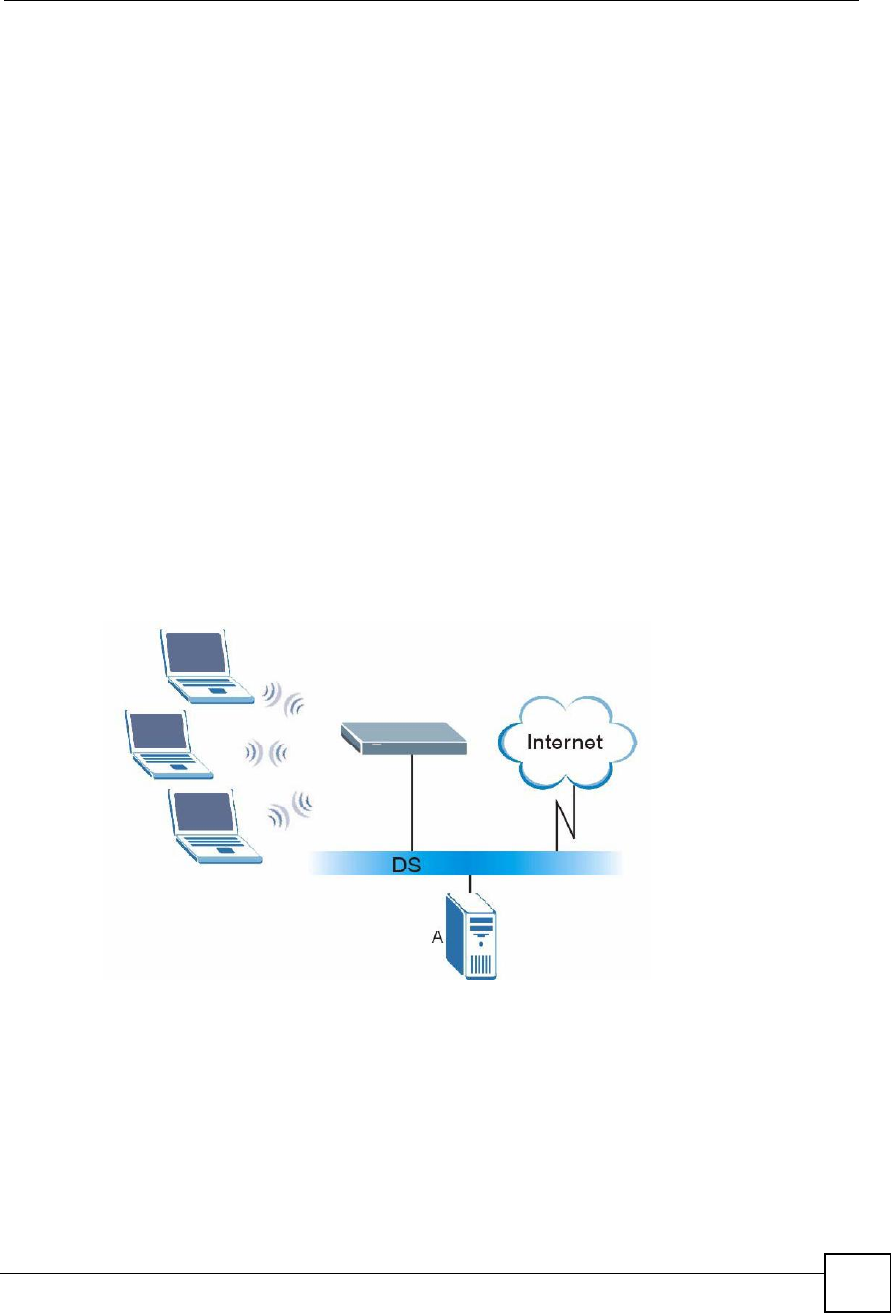
Appendix EWireless LANs
MAX-200HW2 Series User s Guide 329
Wireless Client WPA Supplicants
A wireless client supplicant is the software that runs on an operating system instructing the
wireless client how to use WPA. At the time of writing, the most widely available supplicant is
theWPA patch for Windows XP, Funk Software's Odyssey client.
The Windows XP patch is a free download that adds WPA capability to Windows XP's built-in
"Zero Configuration" wireless client. However, you must run Windows XP to use it.
WPA(2) with RADIUS Application Example
To set up WPA(2), you need the IP address of the RADIUS server, its port number (default is
1812), and the RADIUS shared secret. A WPA(2) application example with an external
RADIUS server looks as follows. "A" is the RADIUS server. "DS" is the distribution system.
1The AP passes the wireless client's authentication request to the RADIUS server.
2The RADIUS server then checks the user's identification against its database and grants
or denies network access accordingly.
3A 256-bit Pairwise Master Key (PMK) is derived from the authentication process by the
RADIUS server and the client.
4The RADIUS server distributes the PMK to the AP. The AP then sets up a key hierarchy
and management system, using the PMK to dynamically generate unique data encryption
keys. The keys are used to encrypt every data packet that is wirelessly communicated
between the AP and the wireless clients.
Figure 222 WPA(2) with RADIUS Application Example
WPA(2)-PSK Application Example
A WPA(2)-PSK application looks as follows.
1First enter identical passwords into the AP and all wireless clients. The Pre-Shared Key
(PSK) must consist of between 8 and 63 ASCII characters or 64 hexadecimal characters
(including spaces and symbols).
2The AP checks each wireless client's password and allows it to join the network only if
the password matches.
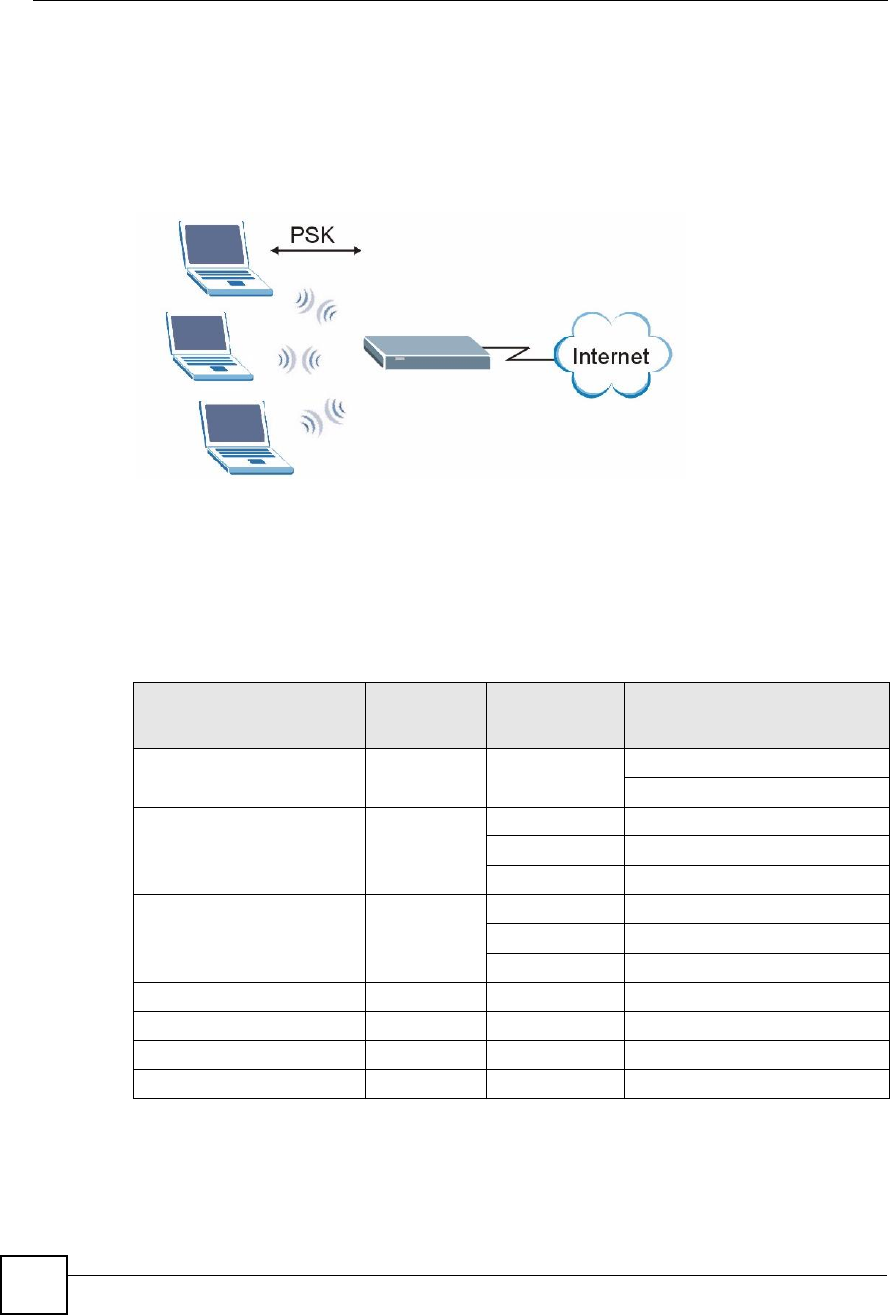
Appendix EWireless LANs
MAX-200HW2 Series User s Guide
330
3The AP and wireless clients generate a common PMK (Pairwise Master Key). The key
itself is not sent over the network, but is derived from the PSK and the SSID.
4The AP and wireless clients use the TKIP or AES encryption process, the PMK and
information exchanged in a handshake to create temporal encryption keys. They use
these keys to encrypt data exchanged between them.
Figure 223 WPA(2)-PSK Authentication
Security Parameters Summary
Refer to this table to see what other security parameters you should configure for each
authentication method or key management protocol type. MAC address filters are not
dependent on how you configure these security features.
Table 137 Wireless Security Relational Matrix
AUTHENTICATION
METHOD/ KEY
MANAGEMENT PROTOCOL
ENCRYPTIO
N METHOD
ENTER
MANUAL KEY IEEE 802.1X
OpenNoneNoDisable
Enable without Dynamic WEP Key
Open WEP No Enable with Dynamic WEP Key
Yes Enable without Dynamic WEP Key
Yes Disable
Shared WEP No Enable with Dynamic WEP Key
Yes Enable without Dynamic WEP Key
Yes Disable
WPA TKIP/AES No Enable
WPA-PSK TKIP/AES Yes Disable
WPA2 TKIP/AES No Enable
WPA2-PSK TKIP/AES Yes Disable

Appendix EWireless LANs
MAX-200HW2 Series User s Guide 331
Antenna Overview
An antenna couples RF signals onto air. A transmitter within a wireless device sends an RF
signal to the antenna, which propagates the signal through the air. The antenna also operates in
reverse by capturing RF signals from the air.
Positioning the antennas properly increases the range and coverage area of a wireless LAN.
Antenna Characteristics
Frequency
An antenna in the frequency of 2.4GHz (IEEE 802.11b and IEEE 802.11g) or 5GHz (IEEE
802.11a) is needed to communicate efficiently in a wireless LAN
Radiation Pattern
A radiation pattern is a diagram that allows you to visualize the shape of the antenna!s
coverage area.
Antenna Gain
Antenna gain, measured in dB (decibel), is the increase in coverage within the RF beam width.
Higher antenna gain improves the range of the signal for better communications.
For an indoor site, each 1 dB increase in antenna gain results in a range increase of
approximately 2.5%. For an unobstructed outdoor site, each 1dB increase in gain results in a
range increase of approximately 5%. Actual results may vary depending on the network
environment.
Antenna gain is sometimes specified in dBi, which is how much the antenna increases the
signal power compared to using an isotropic antenna. An isotropic antenna is a theoretical
perfect antenna that sends out radio signals equally well in all directions. dBi represents the
true gain that the antenna provides.
Types of Antennas for WLAN
There are two types of antennas used for wireless LAN applications.
Omni-directional antennas send the RF signal out in all directions on a horizontal plane.
The coverage area is torus-shaped (like a donut) which makes these antennas ideal for a
room environment. With a wide coverage area, it is possible to make circular overlapping
coverage areas with multiple access points.
Directional antennas concentrate the RF signal in a beam, like a flashlight does with the
light from its bulb. The angle of the beam determines the width of the coverage pattern.
Angles typically range from 20 degrees (very directional) to 120 degrees (less directional).
Directional antennas are ideal for hallways and outdoor point-to-point applications.

Appendix EWireless LANs
MAX-200HW2 Series User s Guide
332
Positioning Antennas
In general, antennas should be mounted as high as practically possible and free of
obstructions. In point-to%point application, position both antennas at the same height and in a
direct line of sight to each other to attain the best performance.
For omni-directional antennas mounted on a table, desk, and so on, point the antenna up. For
omni-directional antennas mounted on a wall or ceiling, point the antenna down. For a single
AP application, place omni-directional antennas as close to the center of the coverage area as
possible.
For directional antennas, point the antenna in the direction of the desired coverage area.
MAX-200HW2 Series User s Guide 333
APPENDIX F
Common Services
The following table lists some commonly-used services and their associated protocols and port
numbers. For a comprehensive list of port numbers, ICMP type/code numbers and services,
visit the IANA (Internet Assigned Number Authority) web site.
Name: This is a short, descriptive name for the service. You can use this one or create a
different one, if you like.
Protocol: This is the type of IP protocol used by the service. If this is TCP/UDP, then the
service uses the same port number with TCP and UDP. If this is USER-DEFINED, the
Port(s) is the IP protocol number, not the port number.
Port(s): This value depends on the Protocol. Please refer to RFC 1700 for further
information about port numbers.
If the Protocol is TCP,UDP, or TCP/UDP, this is the IP port number.
If the Protocol is USER, this is the IP protocol number.
Description: This is a brief explanation of the applications that use this service or the
situations in which this service is used.
Table 138 Commonly Used Services
NAME PROTOCOL PORT(S) DESCRIPTION
AH
(IPSEC_TUNNEL)
User-Defined 51 The IPSEC AH (Authentication Header)
tunneling protocol uses this service.
AIM/New-ICQ TCP 5190 AOL s Internet Messenger service. It is also
used as a listening port by ICQ.
AUTH TCP 113 Authentication protocol used by some
servers.
BGP TCP 179 Border Gateway Protocol.
BOOTP_CLIENT UDP 68 DHCP Client.
BOOTP_SERVER UDP 67 DHCP Server.
CU-SEEME TCP
UDP
7648
24032
A popular videoconferencing solution from
White Pines Software.
DNS TCP/UDP 53 Domain Name Server, a service that
matches web names (for example
www.zyxel.com) to IP numbers.
ESP
(IPSEC_TUNNEL)
User-Defined 50 The IPSEC ESP (Encapsulation Security
Protocol) tunneling protocol uses this
service.
FINGER TCP 79 Finger is a UNIX or Internet related
command that can be used to find out if a
user is logged on.
Appendix FCommon Services
MAX-200HW2 Series User s Guide
334
FTP TCP
TCP
20
21
File Transfer Program, a program to enable
fast transfer of files, including large files
that may not be possible by e-mail.
H.323 TCP 1720 NetMeeting uses this protocol.
HTTP TCP 80 Hyper Text Transfer Protocol - a client/
server protocol for the world wide web.
HTTPS TCP 443 HTTPS is a secured http session often
used in e-commerce.
ICMP User-Defined 1 Internet Control Message Protocol is often
used for diagnostic or routing purposes.
ICQ UDP 4000 This is a popular Internet chat program.
IGMP (MULTICAST) User-Defined 2 Internet Group Management Protocol is
used when sending packets to a specific
group of hosts.
IKE UDP 500 The Internet Key Exchange algorithm is
used for key distribution and management.
IRC TCP/UDP 6667 This is another popular Internet chat
program.
MSN Messenger TCP 1863 Microsoft Networks messenger service
uses this protocol.
NEW-ICQ TCP 5190 An Internet chat program.
NEWS TCP 144 A protocol for news groups.
NFS UDP 2049 Network File System - NFS is a client/
server distributed file service that provides
transparent file sharing for network
environments.
NNTP TCP 119 Network News Transport Protocol is the
delivery mechanism for the USENET
newsgroup service.
PING User-Defined 1 Packet INternet Groper is a protocol that
sends out ICMP echo requests to test
whether or not a remote host is reachable.
POP3 TCP 110 Post Office Protocol version 3 lets a client
computer get e-mail from a POP3 server
through a temporary connection (TCP/IP or
other).
PPTP TCP 1723 Point-to-Point Tunneling Protocol enables
secure transfer of data over public
networks. This is the control channel.
PPTP_TUNNEL
(GRE)
User-Defined 47 PPTP (Point-to-Point Tunneling Protocol)
enables secure transfer of data over public
networks. This is the data channel.
RCMD TCP 512 Remote Command Service.
REAL_AUDIO TCP 7070 A streaming audio service that enables real
time sound over the web.
REXEC TCP 514 Remote Execution Daemon.
RLOGIN TCP 513 Remote Login.
RTELNET TCP 107 Remote Telnet.
Table 138 Commonly Used Services (continued)
NAME PROTOCOL PORT(S) DESCRIPTION
Appendix FCommon Services
MAX-200HW2 Series User s Guide 335
RTSP TCP/UDP 554 The Real Time Streaming (media control)
Protocol (RTSP) is a remote control for
multimedia on the Internet.
SFTP TCP 115 Simple File Transfer Protocol.
SMTP TCP 25 Simple Mail Transfer Protocol is the
message-exchange standard for the
Internet. SMTP enables you to move
messages from one e-mail server to
another.
SNMP TCP/UDP 161 Simple Network Management Program.
SNMP-TRAPS TCP/UDP 162 Traps for use with the SNMP (RFC:1215).
SQL-NET TCP 1521 Structured Query Language is an interface
to access data on many different types of
database systems, including mainframes,
midrange systems, UNIX systems and
network servers.
SSH TCP/UDP 22 Secure Shell Remote Login Program.
STRM WORKS UDP 1558 Stream Works Protocol.
SYSLOG UDP 514 Syslog allows you to send system logs to a
UNIX server.
TACACS UDP 49 Login Host Protocol used for (Terminal
Access Controller Access Control System).
TELNET TCP 23 Telnet is the login and terminal emulation
protocol common on the Internet and in
UNIX environments. It operates over TCP/
IP networks. Its primary function is to allow
users to log into remote host systems.
TFTP UDP 69 Trivial File Transfer Protocol is an Internet
file transfer protocol similar to FTP, but
uses the UDP (User Datagram Protocol)
rather than TCP (Transmission Control
Protocol).
VDOLIVE TCP 7000 Another videoconferencing solution.
Table 138 Commonly Used Services (continued)
NAME PROTOCOL PORT(S) DESCRIPTION

Appendix FCommon Services
MAX-200HW2 Series User s Guide
336

MAX-200HW2 Series User s Guide 337
APPENDIX G
Legal Information
Copyright
Copyright ?2007 by ZyXEL Communications Corporation.
The contents of this publication may not be reproduced in any part or as a whole, transcribed,
stored in a retrieval system, translated into any language, or transmitted in any form or by any
means, electronic, mechanical, magnetic, optical, chemical, photocopying, manual, or
otherwise, without the prior written permission of ZyXEL Communications Corporation.
Published by ZyXEL Communications Corporation. All rights reserved.
Disclaimers
ZyXEL does not assume any liability arising out of the application or use of any products, or
software described herein. Neither does it convey any license under its patent rights nor the
patent rights of others. ZyXEL further reserves the right to make changes in any products
described herein without notice. This publication is subject to change without notice.
Trademarks
ZyNOS (ZyXEL Network Operating System) is a registered trademark of ZyXEL
Communications, Inc. Other trademarks mentioned in this publication are used for
identification purposes only and may be properties of their respective owners.
Certifications
Federal Communications Commission (FCC) Interference Statement
The device complies with Part 15 of FCC rules. Operation is subject to the following two
conditions:
This device may not cause harmful interference.
This device must accept any interference received, including interference that may cause
undesired operations.
This device has been tested and found to comply with the limits for a Class B digital device
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable
protection against harmful interference in a residential installation. This device generates,
uses, and can radiate radio frequency energy, and if not installed and used in accordance with
the instructions, may cause harmful interference to radio communications. However, there is
no guarantee that interference will not occur in a particular installation.

Appendix GLegal Information
MAX-200HW2 Series User s Guide
338
If this device does cause harmful interference to radio/television reception, which can be
determined by turning the device off and on, the user is encouraged to try to correct the
interference by one or more of the following measures:
1Reorient or relocate the receiving antenna.
2Increase the separation between the equipment and the receiver.
3Connect the equipment into an outlet on a circuit different from that to which the
receiver is connected.
4Consult the dealer or an experienced radio/TV technician for help.
FCC Radiation Exposure Statement
The device complies with FCC RF radiation exposure limits set forth for an uncontrolled
environment, under 47 CFR 2.1093 paragraph (d)(2). End users must follow the specific
operating instructions for satisfying RF exposure compliance.To maintain compliance
with FCC RF exposure compliance requirements, please follow operation instruction as
documented in this manual.
This transmitter must not be co-located or operating in conjunction with any other antenna
or transmitter.
To comply with FCC RF exposure compliance requirements, a separation distance of at
least 20 cm must be maintained between the antenna of this device and all persons.
Notices
Changes or modifications not expressly approved by the party responsible for compliance
could void the user's authority to operate the equipment.
Viewing Certifications
1Go to http://www.zyxel.com.
2Select your product from the drop-down list box on the ZyXEL home page to go to that
product's page.
3Select the certification you wish to view from this page.

Appendix GLegal Information
MAX-200HW2 Series User s Guide 339
ZyXEL Limited Warranty
ZyXEL warrants to the original end user (purchaser) that this product is free from any defects
in materials or workmanship for a period of up to two years from the date of purchase. During
the warranty period, and upon proof of purchase, should the product have indications of failure
due to faulty workmanship and/or materials, ZyXEL will, at its discretion, repair or replace the
defective products or components without charge for either parts or labor, and to whatever
extent it shall deem necessary to restore the product or components to proper operating
condition. Any replacement will consist of a new or re-manufactured functionally equivalent
product of equal or higher value, and will be solely at the discretion of ZyXEL. This warranty
shall not apply if the product has been modified, misused, tampered with, damaged by an act
of God, or subjected to abnormal working conditions.
Note
Repair or replacement, as provided under this warranty, is the exclusive remedy of the
purchaser. This warranty is in lieu of all other warranties, express or implied, including any
implied warranty of merchantability or fitness for a particular use or purpose. ZyXEL shall in
no event be held liable for indirect or consequential damages of any kind to the purchaser.
To obtain the services of this warranty, contact ZyXEL's Service Center for your Return
Material Authorization number (RMA). Products must be returned Postage Prepaid. It is
recommended that the unit be insured when shipped. Any returned products without proof of
purchase or those with an out-dated warranty will be repaired or replaced (at the discretion of
ZyXEL) and the customer will be billed for parts and labor. All repaired or replaced products
will be shipped by ZyXEL to the corresponding return address, Postage Paid. This warranty
gives you specific legal rights, and you may also have other rights that vary from country to
country.
Registration
Register your product online to receive e-mail notices of firmware upgrades and information
at www.zyxel.com.

Appendix GLegal Information
MAX-200HW2 Series User s Guide
340

MAX-200HW2 Series User s Guide 341
APPENDIX H
Customer Support
Please have the following information ready when you contact customer support.
Required Information
Product model and serial number.
Warranty Information.
Date that you received your device.
Brief description of the problem and the steps you took to solve it.
"+# is the (prefix) number you dial to make an international telephone call.
Corporate Headquarters (Worldwide)
Support E-mail: support@zyxel.com.tw
Sales E-mail: sales@zyxel.com.tw
Telephone: +886-3-578-3942
Fax: +886-3-578-2439
Web: www.zyxel.com, www.europe.zyxel.com
FTP: ftp.zyxel.com, ftp.europe.zyxel.com
Regular Mail: ZyXEL Communications Corp., 6 Innovation Road II, Science Park,
Hsinchu 300, Taiwan
Costa Rica
Support E-mail: soporte@zyxel.co.cr
Sales E-mail: sales@zyxel.co.cr
Telephone: +506-2017878
Fax: +506-2015098
Web: www.zyxel.co.cr
FTP: ftp.zyxel.co.cr
Regular Mail: ZyXEL Costa Rica, Plaza Roble Escazú, Etapa El Patio, Tercer Piso, San
Jos? Costa Rica
Czech Republic
E-mail: info@cz.zyxel.com
Telephone: +420-241-091-350
Fax: +420-241-091-359
Web: www.zyxel.cz

Appendix HCustomer Support
MAX-200HW2 Series User s Guide
342
Regular Mail: ZyXEL Communications, Czech s.r.o., Modransk?621, 143 01 Praha 4 -
Modrany, Cesk?Republika
Denmark
Support E-mail: support@zyxel.dk
Sales E-mail: sales@zyxel.dk
Telephone: +45-39-55-07-00
Fax: +45-39-55-07-07
Web: www.zyxel.dk
Regular Mail: ZyXEL Communications A/S, Columbusvej, 2860 Soeborg, Denmark
Finland
Support E-mail: support@zyxel.fi
Sales E-mail: sales@zyxel.fi
Telephone: +358-9-4780-8411
Fax: +358-9-4780-8448
Web: www.zyxel.fi
Regular Mail: ZyXEL Communications Oy, Malminkaari 10, 00700 Helsinki, Finland
France
E-mail: info@zyxel.fr
Telephone: +33-4-72-52-97-97
Fax: +33-4-72-52-19-20
Web: www.zyxel.fr
Regular Mail: ZyXEL France, 1 rue des Vergers, Bat. 1 / C, 69760 Limonest, France
Germany
Support E-mail: support@zyxel.de
Sales E-mail: sales@zyxel.de
Telephone: +49-2405-6909-69
Fax: +49-2405-6909-99
Web: www.zyxel.de
Regular Mail: ZyXEL Deutschland GmbH., Adenauerstr. 20/A2 D-52146, Wuerselen,
Germany
Hungary
Support E-mail: support@zyxel.hu
Sales E-mail: info@zyxel.hu
Telephone: +36-1-3361649
Fax: +36-1-3259100
Web: www.zyxel.hu
Regular Mail: ZyXEL Hungary, 48, Zoldlomb Str., H-1025, Budapest, Hungary

Appendix HCustomer Support
MAX-200HW2 Series User s Guide 343
India
Support E-mail: support@zyxel.in
Sales E-mail: sales@zyxel.in
Telephone: +91-11-30888144 to +91-11-30888153
Fax: +91-11-30888149, +91-11-26810715
Web: http://www.zyxel.in
Regular Mail: India - ZyXEL Technology India Pvt Ltd., II-Floor, F2/9 Okhla Phase -1,
New Delhi 110020, India
Japan
Support E-mail: support@zyxel.co.jp
Sales E-mail: zyp@zyxel.co.jp
Telephone: +81-3-6847-3700
Fax: +81-3-6847-3705
Web: www.zyxel.co.jp
Regular Mail: ZyXEL Japan, 3F, Office T&U, 1-10-10 Higashi-Gotanda, Shinagawa-ku,
Tokyo 141-0022, Japan
Kazakhstan
Support: http://zyxel.kz/support
Sales E-mail: sales@zyxel.kz
Telephone: +7-3272-590-698
Fax: +7-3272-590-689
Web: www.zyxel.kz
Regular Mail: ZyXEL Kazakhstan, 43 Dostyk Ave., Office 414, Dostyk Business Centre,
050010 Almaty, Republic of Kazakhstan
Malaysia
Support E-mail: support@zyxel.com.my
Sales E-mail: sales@zyxel.com.my
Telephone: +603-8076-9933
Fax: +603-8076-9833
Web: http://www.zyxel.com.my
Regular Mail: ZyXEL Malaysia Sdn Bhd., 1-02 & 1-03, Jalan Kenari 17F, Bandar
Puchong Jaya, 47100 Puchong, Selangor Darul Ehsan, Malaysia
North America
Support E-mail: support@zyxel.com
Support Telephone: +1-800-978-7222
Sales E-mail: sales@zyxel.com
Sales Telephone: +1-714-632-0882
Fax: +1-714-632-0858
Web: www.zyxel.com
Appendix HCustomer Support
MAX-200HW2 Series User s Guide
344
Regular Mail: ZyXEL Communications Inc., 1130 N. Miller St., Anaheim, CA 92806-
2001, U.S.A.
Norway
Support E-mail: support@zyxel.no
Sales E-mail: sales@zyxel.no
Telephone: +47-22-80-61-80
Fax: +47-22-80-61-81
Web: www.zyxel.no
Regular Mail: ZyXEL Communications A/S, Nils Hansens vei 13, 0667 Oslo, Norway
Poland
E-mail: info@pl.zyxel.com
Telephone: +48-22-333 8250
Fax: +48-22-333 8251
Web: www.pl.zyxel.com
Regular Mail: ZyXEL Communications, ul. Okrzei 1A, 03-715 Warszawa, Poland
Russia
Support: http://zyxel.ru/support
Sales E-mail: sales@zyxel.ru
Telephone: +7-095-542-89-29
Fax: +7-095-542-89-25
Web: www.zyxel.ru
Regular Mail: ZyXEL Russia, Ostrovityanova 37a Str., Moscow 117279, Russia
Singapore
Support E-mail: support@zyxel.com.sg
Sales E-mail: sales@zyxel.com.sg
Telephone: +65-6899-6678
Fax: +65-6899-8887
Web: http://www.zyxel.com.sg
Regular Mail: ZyXEL Singapore Pte Ltd., No. 2 International Business Park, The Strategy
#03-28, Singapore 609930
Spain
Support E-mail: support@zyxel.es
Sales E-mail: sales@zyxel.es
Telephone: +34-902-195-420
Fax: +34-913-005-345
Web: www.zyxel.es
Regular Mail: ZyXEL Communications, Arte, 21 5ª planta, 28033 Madrid, Spain

Appendix HCustomer Support
MAX-200HW2 Series User s Guide 345
Sweden
Support E-mail: support@zyxel.se
Sales E-mail: sales@zyxel.se
Telephone: +46-31-744-7700
Fax: +46-31-744-7701
Web: www.zyxel.se
Regular Mail: ZyXEL Communications A/S, Sjöporten 4, 41764 Göteborg, Sweden
Thailand
Support E-mail: support@zyxel.co.th
Sales E-mail: sales@zyxel.co.th
Telephone: +662-831-5315
Fax: +662-831-5395
Web: http://www.zyxel.co.th
Regular Mail: ZyXEL Thailand Co., Ltd., 1/1 Moo 2, Ratchaphruk Road, Bangrak-Noi,
Muang, Nonthaburi 11000, Thailand.
Ukraine
Support E-mail: support@ua.zyxel.com
Sales E-mail: sales@ua.zyxel.com
Telephone: +380-44-247-69-78
Fax: +380-44-494-49-32
Web: www.ua.zyxel.com
Regular Mail: ZyXEL Ukraine, 13, Pimonenko Str., Kiev 04050, Ukraine
United Kingdom
Support E-mail: support@zyxel.co.uk
Sales E-mail: sales@zyxel.co.uk
Telephone: +44-1344-303044, 08707-555779 (UK only)
Fax: +44-1344-303034
Web: www.zyxel.co.uk
FTP: ftp.zyxel.co.uk
Regular Mail: ZyXEL Communications UK Ltd., 11 The Courtyard, Eastern Road,
Bracknell, Berkshire RG12 2XB, United Kingdom (UK)

Appendix HCustomer Support
MAX-200HW2 Series User s Guide
346

Index
MAX-200HW2 Series User s Guide 347
Index
Numerics
802.11 Mode 106
A
AAA 108
AbS 154
Access point 91
See also AP.
accounting server
see AAA
ACK message 150
activity 108
Advanced Encryption Standard
See AES.
advanced encryption standard
see AES
AES 277,328
AK 277
ALG 131,271
alternative subnet mask notation 311
analysis-by-synthesis 154
Antenna 36,117
antenna 269
directional 331
gain 331
omni-directional 331
Antenna selection 117
AP 91
See also access point.
AP (access point) 321
application layer gateway 131,152,271
Application Layer Gateway. See ALG.
authentication 68,84,108,110,275
inner 277
types 277
authentication key
see AK
authentication server
see AAA
authorization 275
authorization request and reply 277
authorization server
see AAA
auto firmware upgrade 271
auto-discovering UPnP-enabled network devices 225
automatic log out 41
auto-provisioning 270
B
base station
see BS
Basic Service Set, See BSS 319
Basic wireless security 64
BS 107
links 107
BSS 319
BYE request 150
C
CA 187,188,326
and certificates 188
call hold 166,168
call service mode 166,167
call transfer 167,168
call waiting 167,168
CBC-MAC 277
CCMP 275,277
cell 107
certificate 275
verification 277
Certificate Authority
See CA.
Certificate Management Protocol (CMP) 194
Certificate Revocation List (CRL) 188
certificates 187
advantages 188
and CA 188
certification path 188,196
expired 188
factory-default 188
file formats 188
fingerprints 197

Index
MAX-200HW2 Series User s Guide
348
importing 192
not used for encryption 188
revoked 188
self-signed 194
serial number 197
storage space 191
thumbprint algorithms 190
thumbprints 190
used for authentication 188
verifying fingerprints 189
Certification Authority. See CA.
certification requests 187,194
certifications 337
notices 338
viewing 338
chaining 277
chaining message authentication
see CCMP
change password at login 40
channel 91,321
interference 321
circuit-switched telephone networks 149
Class of Service (CoS) 156
clicks 154
client server
SIP 150
client-server protocol 150
CMAC
see MAC
code 275
codec 153
coder/decoder 153
comfort noise 165
comfort noise generation 271
computer name 233
configuration upload successful 258,259
connections 35
contact information 341
copyright 337
CoS 156
counter mode
see CCMP
coverage area 107
cryptography 275
CTS (Clear to Send) 322
customer support 341
D
data encryption 275,276
data flow 277
data rate 269
daytime RFC 867 238
decoder 153
decryption 275,277
default LAN IP address 39
device name 231
DHCP 233,234,271
DHCP client 271
DHCP clients 233
DHCP relay 271
DHCP server 271
DIAMETER 108
differentiated services 156
DiffServ 156
DiffServ Code Point (DSCP) 156
DiffServ code point (DSCP) 156
DiffServ marking rule 156
digital ID 275
dimensions 269
disclaimer 337
DL frequency 113
domain name 233
download frequency
see DL frequency
DS field 156
DSCPs 156
DTMF 154
dual-tone multi-frequency
see DTMF
duplex 270
dynamic DNS 234,271
dynamic host configuration protocol 271
dynamic jitter buffer 271
dynamic WEP key exchange 327
E
EAP 108
EAP Authentication 325
echo cancellation 165,272
encoding 275
encrypted traffic 277
encryption 93,275,276,277,328
and local (user) database 93
key 94
WPA compatible 94
environmental specifications 269
ESS 320

Index
MAX-200HW2 Series User s Guide 349
ESSID 268
ethernet 269
ethernet encapsulation 129
europe type call service mode 166
Extended Service Set, See ESS 320
Extended wireless security 65
extensible authorization protocol
see EAP
External Antenna 270
F
FCC interference statement 337
firewall 179,180
firmware upload 256
firmware upload error 257
flash key 166
flashing 166
Fragmentation Threshold 106
fragmentation threshold 322
frequency band 114
scanning 114
frequency pairs 154
frequency ranges 113
FTP 213,234
FTP restrictions 213
G
G.168 165,272
G.711 153
G.729 154
General wireless LAN screen 94
Graphical User Interface (GUI) 33
H
hardware 35
hidden node 321
hide SSID 92
HTTP 255
humidity 269
hybrid waveform codec 154
hypertext transfer protocol 255
I
IANA 316
IBSS 319
identity 108,275
idle timeout 214
IEEE 802.11g 323
IEEE 802.16 107,275
IEEE 802.16e 3,107
IEEE 802.1Q VLAN 156
IGD 1.0 222
Independent Basic Service Set
See IBSS 319
initialization vector (IV) 328
inner authentication 277
install UPnP 222
Windows Me 222
Windows XP 223
installation 35
interface 269
Internet access 108,270
Internet access wizard setup 61
Internet Assigned Numbers Authority
See IANA 316
Internet gateway device 222
Internet service provider
see ISP
Internet Telephony Service Provider 34
Internet telephony service provider 149
interoperability 107
introduction 33
IP alias 271
IP policy routing (IPPR) 271
IP-PBX 149
ISP 49
ITSP 149
ITU-T 165
J
jitter buffer 271
K
key 68,84,110,275
key request and reply 277

Index
MAX-200HW2 Series User s Guide
350
L
listening port 161
local (user) database 92
and encryption 93
log out 41
M
MAC 104,277
MAC address 92
MAC address filter 92
MAC address filtering 104
MAC filter 104
MAN 107
management information base (MIB) 217
managing the device
good habits 37
manual site survey 113
Media access control 104
media access protocol 269
message authentication code
see MAC
message integrity 277
Message Integrity Check (MIC) 328
message waiting indication 154
Metropolitan Area Network
see MAN
microwave 107
mobile station
see MS
modulation 270
MS 107
multimedia 149
multiple PVC support 271
multiple SIP accounts 271
MWI 154
My Certificates. See also certificates. 190
N
NAT 316
and remote management 213
server sets 129
NAT routers 153
NAT traversal 221
network activity 108
network address translation (NAT) 271
network address translators 153
network disconnect 257,259
network services 108
NTP RFC 1305 238
NTP time servers 234
O
OK response 150
operating humidity 269
operating temperature 269
outbound proxy 152,153
SIP 153
outbound proxy server 153
P
Pairwise Master Key (PMK) 328,330
pattern-spotting 277
PBX services 149
PCM 153
peer-to-peer calls 173
per-hop behavior 156
PHB (per-hop behavior) 156
phone book 173
phone services 165
physical specifications 269
PKMv2 68,84,108,110,275,277
plain text encryption 277
port forwarding 129
port numbers 129
services 129
port numbers 129
power 269
output 270
power supply 269
preamble mode 323
pre-defined NTP time servers list 234
preparation 33
privacy key management
see PKM
private key 275
product registration 339
proxy server
SIP 151
PSK 328

Index
MAX-200HW2 Series User s Guide 351
PSTN 154
public certificate 277
public key 68,84,110,275
Public Switched Telephone Network 154
Public-Key Infrastructure (PKI) 188
public-private key pairs 187
pulse code modulation 153
pulse dialing 154
Q
QoS 155,272
quality of service
see QoS
Quality of Service (QoS) 106
Quick Start Guide 35,39
R
radio specifications 269
RADIUS 108,275,324
message types 325
messages 325
Shared Secret Key 276
shared secret key 325
RADIUS Message Types 276
RADIUS Messages 276
RADIUS server 92
real-time transport protocol 152
redirect server
SIP 151
register server
SIP 152
registration
product 339
related documentation 3
remote management 213
remote management and NAT 213
remote management limitations 213
REN 271
required bandwidth 154
reset button 41,258
resetting the time 235
resetting your device 41
RFC 1305 238
RFC 1889 152
RFC 2510. See Certificate Management Protocol.
RFC 3489 153
RFC 3842 154
RFC 867 238
RFC 868 238
ringer equivalence number 271
Roaming 105
RTP 152
RTS (Request To Send) 322
threshold 321,322
RTS/CTS Threshold 106
S
safety warnings 6
secure communication 68,84,110,275
secure connection 108
security 270,275
security association 276
see SA
see QoS
see WAN
server, outbound proxy 153
Service Set 95
Service Set IDentification 95
Service Set IDentity. See SSID.
services 108,129
session initiation protocol
see SIP
silence suppression 165,271
silent packets 165
Simple Certificate Enrollment Protocol (SCEP) 194
SIP 149
ALG 131
authentication 74
authentication password 74
SIP account 149,271
SIP ACK message 150
SIP ALG 131,152,271
SIP application layer gateway 131,271
SIP BYE request 150
SIP call progression 150
SIP client 150
SIP client server 150
SIP identities 149
SIP INVITE request 150
SIP number 74,149
SIP OK response 150
SIP outbound proxy 153
SIP proxy server 151

Index
MAX-200HW2 Series User s Guide
352
SIP redirect server 151
SIP register server 152
SIP server address 74
SIP servers 150
SIP service domain 74,150
SIP URI 149
SIP user agent 150
SNMP 216
manager 216
MIBs 217
sound quality 154
specifications
physical and environmental 269
radio 269
speed dial 173
SS 107
SSID 91,95
hide 92
standards 269
stateful inspection 179
storage humidity 269
storage temperature 269
STUN 152,153
subnet 309
subnet mask 310
subnetting 312
subscriber station
see SS
supplementary phone services 165
syntax conventions 4
system name 233
system timeout 214
T
tampering
TDD 270
TEK 277
telephone keys 154
temperature 269
Temporal Key Integrity Protocol (TKIP) 328
TFTP restrictions 213
three-way conference 167,168
time
resetting 235
time RFC 868 238
TLS 68,84,110,275
ToS 156
Touch Tone 154
trademarks 337
transport encryption key
see TEK
transport layer security
see TLS
triangle 181
triangle route
solutions 182
trigger port forwarding 130
process 130
TTLS 68,84,110,275,277
tunneled TLS
see TTLS
Type of Service 156
U
UIC 222
unauthorized device 275
uniform resource identifier 149
Universal Plug and Play 221
application 221
security issues 221
Universal Plug and Play (UPnP) 271
Universal Plug and Play Forum 222
UPnP 221,231
auto-discovery 225
installing example 222
UPnP certification 222
USA type call service mode 167
use NAT 152,153
user agent, SIP 150
user authentication 92,275
local (user) database 92
RADIUS server 92
weaknesses 93
user ID 74
user name 237
V
VAD 165,271
verification 277
virtual local area network
see VLAN
VLAN 156
VLAN group 156
VLAN ID 156

Index
MAX-200HW2 Series User s Guide 353
VLAN ID tags 156
VLAN tags 156
voice activity detection 165,271
voice coding 153
voice mail 149
voice over IP
see VoIP
VoIP 3,149
standards compliance 271
W
WAN 107
WAN setup 107
warranty 339
note 339
waveform codec 153
web configurator 39
weight 269
WEP Encryption 97
WEP encryption 96
WEP key 96
wide area network
WiMAX 3,107,269
security 276
WiMAX Forum 107
WiMAX bandwidth 269
wireless channel 268
wireless client 91
wireless client WPA supplicants 329
Wireless Interoperability for Microwave Access
see WiMAX
Wireless LAN 91
wireless LAN 268
wireless Metropolitan Area Network
see MAN
Wireless network
basic guidelines 91
channel 91
encryption 93
example 91
MAC address filter 92
overview 91
security 92
SSID 91
wireless network 3
access 107
standard 107
Wireless security 92
overview 92
type 92
wireless security 268,270,275,323
wizard setup 61
WLAN 91
interference 321
security parameters 330
WPA 327
key caching 328
pre-authentication 328
user authentication 328
vs WPA-PSK 328
wireless client supplicant 329
with RADIUS application example 329
WPA compatible 94
WPA2 327
user authentication 328
vs WPA2-PSK 328
wireless client supplicant 329
with RADIUS application example 329
WPA2-Pre-Shared Key 327
WPA2-PSK 327,328
application example 329
WPA-PSK 327,328
application example 329
Z
ZyXEL utility 33,35

Index
MAX-200HW2 Series User s Guide
354

Index
MAX-200HW2 Series User s Guide 355

Index
MAX-200HW2 Series User s Guide
356