ZyXEL Communications USG20W-VPN VPN Firewall User Manual Book
ZyXEL Communications Corporation VPN Firewall Book
Contents
- 1. Users Manual Part 1
- 2. Users Manual Part 2
- 3. Users Manual Part 3
- 4. Users Manual Part 4
- 5. Users Manual Part 5
Users Manual Part 2

USG20(W)-VPN Series User’s Guide
140
CHAPTER 9
Interfaces
9.1 Interface Overview
Use the Interface screens to configure the USG’s interfaces. You can also create interfaces on top
of other interfaces.
•Ports are the physical ports to which you connect cables.
•Interfaces are used within the system operationally. You use them in configuring various
features. An interface also describes a network that is directly connected to the USG. For
example, You connect the LAN network to the LAN interface.
•Zones are groups of interfaces used to ease security policy configuration.
9.1.1 What You Can Do in this Chapter
•Use the Port Role screen (Section 9.2 on page 145) to create port groups and to assign physical
ports and port groups to Ethernet interfaces.
•Use the Ethernet screens (Section 9.3 on page 146) to configure the Ethernet interfaces.
Ethernet interfaces are the foundation for defining other interfaces and network policies. RIP and
OSPF are also configured in these interfaces.
•Use the PPP screens (Section 9.4 on page 166) for PPPoE or PPTP Internet connections.
•Use the Cellular screens (Section 9.5 on page 173) to configure settings for interfaces for
Internet connections through an installed mobile broadband card.
•Use the Tunnel screens (Section 9.6 on page 182) to configure tunnel interfaces to be used in
Generic Routing Encapsulation (GRE), IPv6 in IPv4, and 6to4 tunnels.
•Use the VLAN screens (Section 9.7 on page 188) to divide the physical network into multiple
logical networks. VLAN interfaces receive and send tagged frames. The USG automatically adds
or removes the tags as needed. Each VLAN can only be associated with one Ethernet interface.
•Use the Bridge screens (Section 9.8 on page 201) to combine two or more network segments
into a single network.
•Use the Auxiliary screens (Section 9.9 on page 213) to configure the USG’s auxiliary interface to
use an external modem.
•Use the Virtual Interface screen (Section 9.9.1 on page 213) to create virtual interfaces on top
of Ethernet interfaces to tell the USG where to route packets. You can create virtual Ethernet
interfaces, virtual VLAN interfaces, and virtual bridge interfaces.
•Use the Trunk screens (Section 9.11 on page 218) to configure load balancing.

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
141
9.1.2 What You Need to Know
Interface Characteristics
Interfaces generally have the following characteristics (although not all characteristics apply to each
type of interface).
• An interface is a logical entity through which (layer-3) packets pass.
• An interface is bound to a physical port or another interface.
• Many interfaces can share the same physical port.
• An interface belongs to at most one zone.
• Many interfaces can belong to the same zone.
• Layer-3 virtualization (IP alias, for example) is a kind of interface.
Types of Interfaces
You can create several types of interfaces in the USG.
• Setting interfaces to the same port role forms a port group. Port groups creates a hardware
connection between physical ports at the layer-2 (data link, MAC address) level. Port groups are
created when you uUse the Interface > Port Roles or Interface > Port Groups screen to set
multiple physical ports to be part of the same interface.
•Ethernet interfaces are the foundation for defining other interfaces and network policies. RIP
and OSPF are also configured in these interfaces.
•Tunnel interfaces send IPv4 or IPv6 packets from one network to a specific network through
the Internet or a public network.
•VLAN interfaces receive and send tagged frames. The USG automatically adds or removes the
tags as needed. Each VLAN can only be associated with one Ethernet interface.
•Bridge interfaces create a software connection between Ethernet or VLAN interfaces at the
layer-2 (data link, MAC address) level. Unlike port groups, bridge interfaces can take advantage
of some security features in the USG. You can also assign an IP address and subnet mask to the
bridge.
•PPP interfaces support Point-to-Point Protocols (PPP). ISP accounts are required for PPPoE/PPTP
interfaces.
•Cellular interfaces are for mobile broadband WAN connections via a connected mobile
broadband device.
•Virtual interfaces provide additional routing information in the USG. There are three types:
virtual Ethernet interfaces, virtual VLAN interfaces, and virtual bridge interfaces.
•Trunk interfaces manage load balancing between interfaces.
Port groups and trunks have a lot of characteristics that are specific to each type of interface. The
other types of interfaces--Ethernet, PPP, cellular, VLAN, bridge, and virtual--have a lot of similar
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
142
characteristics. These characteristics are listed in the following table and discussed in more detail
below.
Note: - * The format of interface names other than the Ethernet and ppp interface
names is strict. Each name consists of 2-4 letters (interface type), followed by a
number (x). For most interfaces, x is limited by the maximum number of the type
of interface. For VLAN interfaces, x is defined by the number you enter in the VLAN
name field. For example, Ethernet interface names are wan1, wan2, lan1, lan2,
dmz; VLAN interfaces are vlan0, vlan1, vlan2, ...; and so on.
** - The names of virtual interfaces are derived from the interfaces on which they
are created. For example, virtual interfaces created on Ethernet interface wan1 are
called wan1:1, wan1:2, and so on. Virtual interfaces created on VLAN interface
vlan2 are called vlan2:1, vlan2:2, and so on. You cannot specify the number after
the colon(:) in the Web Configurator; it is a sequential number. You can specify the
number after the colon if you use the CLI to set up a virtual interface.
Relationships Between Interfaces
In the USG, interfaces are usually created on top of other interfaces. Only Ethernet interfaces are
created directly on top of the physical ports or port groups. The relationships between interfaces
are explained in the following table.
Table 60 Ethernet, PPP, Cellular, VLAN, Bridge, and Virtual Interface Characteristics
CHARACTERISTICS ETHERNET ETHERNET PPP CELLULAR VLAN BRIDGE VIRTUAL
Name* wan1, wan2 lan1, lan2,
dmz
pppxcellularx vlanxbrx**
Configurable Zone No No Yes Yes Yes Yes No
IP Address Assignment
Static IP address Yes Yes Yes Yes Yes Yes Yes
DHCP client Yes No Yes Yes Yes Yes No
Routing metric Yes Yes Yes Yes Yes Yes Yes
Interface Parameters
Bandwidth
restrictions Yes Yes Yes Yes Yes Yes Yes
Packet size (MTU) Yes Yes Yes Yes Yes Yes No
DHCP
DHCP server No Yes No No Yes Yes No
DHCP relay No Yes No No Yes Yes No
Connectivity Check Yes No Yes Yes Yes Yes No
Table 61 Relationships Between Different Types of Interfaces
INTERFACE REQUIRED PORT / INTERFACE
Ethernet interface physical port
VLAN interface Ethernet interface
bridge interface Ethernet interface*
VLAN interface*
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
143
Note: * You cannot set up a PPP interface, virtual Ethernet interface or virtual VLAN
interface if the underlying interface is a member of a bridge. You also cannot add
an Ethernet interface or VLAN interface to a bridge if the member interface has a
virtual interface or PPP interface on top of it.
IPv6 Overview
IPv6 (Internet Protocol version 6), is designed to enhance IP address size and features. The
increase in IPv6 address size to 128 bits (from the 32-bit IPv4 address) allows up to 3.4 x 1038 IP
addresses.
IPv6 Addressing
An 128-bit IPv6 address is written as eight 16-bit hexadecimal blocks separated by colons (:). This
is an example IPv6 address 2001:0db8:1a2b:0015:0000:0000:1a2f:0000.
IPv6 addresses can be abbreviated in two ways:
• Leading zeros in a block can be omitted. So 2001:0db8:1a2b:0015:0000:0000:1a2f:0000 can
be written as 2001:db8:1a2b:15:0:0:1a2f:0.
• Any number of consecutive blocks of zeros can be replaced by a double colon. A double colon can
only appear once in an IPv6 address. So 2001:0db8:0000:0000:1a2f:0000:0000:0015 can be
written as 2001:0db8::1a2f:0000:0000:0015, 2001:0db8:0000:0000:1a2f::0015,
2001:db8::1a2f:0:0:15 or 2001:db8:0:0:1a2f::15.
Prefix and Prefix Length
Similar to an IPv4 subnet mask, IPv6 uses an address prefix to represent the network address. An
IPv6 prefix length specifies how many most significant bits (start from the left) in the address
PPP interface Ethernet interface*
VLAN interface*
bridge interface
WAN1, WAN2, OPT*
virtual interface
(virtual Ethernet interface)
(virtual VLAN interface)
(virtual bridge interface)
Ethernet interface*
VLAN interface*
bridge interface
trunk Ethernet interface
Cellular interface
VLAN interface
bridge interface
PPP interface
Table 61 Relationships Between Different Types of Interfaces (continued)
INTERFACE REQUIRED PORT / INTERFACE
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
144
compose the network address. The prefix length is written as “/x” where x is a number. For
example,
2001:db8:1a2b:15::1a2f:0/32
means that the first 32 bits (2001:db8) from the left is the network prefix.
Link-local Address
A link-local address uniquely identifies a device on the local network (the LAN). It is similar to a
“private IP address” in IPv4. You can have the same link-local address on multiple interfaces on a
device. A link-local unicast address has a predefined prefix of fe80::/10. The link-local unicast
address format is as follows.
Subnet Masking
Both an IPv6 address and IPv6 subnet mask compose of 128-bit binary digits, which are divided
into eight 16-bit blocks and written in hexadecimal notation. Hexadecimal uses four bits for each
character (1 ~ 10, A ~ F). Each block’s 16 bits are then represented by four hexadecimal
characters. For example, FFFF:FFFF:FFFF:FFFF:FC00:0000:0000:0000.
Stateless Autoconfiguration
With stateless autoconfiguration in IPv6, addresses can be uniquely and automatically generated.
Unlike DHCPv6 (Dynamic Host Configuration Protocol version six) which is used in IPv6 stateful
autoconfiguration, the owner and status of addresses don’t need to be maintained by a DHCP
server. Every IPv6 device is able to generate its own and unique IP address automatically when
IPv6 is initiated on its interface. It combines the prefix and the interface ID (generated from its own
Ethernet MAC address) to form a complete IPv6 address.
When IPv6 is enabled on a device, its interface automatically generates a link-local address
(beginning with fe80).
When the USG’s WAN interface is connected to an ISP with a router and the USG is set to
automatically obtain an IPv6 network prefix from the router for the interface, it generates another
address which combines its interface ID and global and subnet information advertised from the
router. (In IPv6, all network interfaces can be associated with several addresses.) This is a routable
global IP address.
Prefix Delegation
Prefix delegation enables an IPv6 router (the USG) to use the IPv6 prefix (network address)
received from the ISP (or a connected uplink router) for its LAN. The USG uses the received IPv6
prefix (for example, 2001:db2::/48) to generate its LAN IP address. Through sending Router
Advertisements (RAs) regularly by multicast, the router passes the IPv6 prefix information to its
LAN hosts. The hosts then can use the prefix to generate their IPv6 addresses.
Table 62 Link-local Unicast Address Format
1111 1110 10 0 Interface ID
10 bits 54 bits 64 bits

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
145
IPv6 Router Advertisement
An IPv6 router sends router advertisement messages periodically to advertise its presence and
other parameters to the hosts in the same network.
DHCPv6
The Dynamic Host Configuration Protocol for IPv6 (DHCPv6, RFC 3315) is a server-client protocol
that allows a DHCP server to assign and pass IPv6 network addresses, prefixes and other
configuration information to DHCP clients. DHCPv6 servers and clients exchange DHCP messages
using UDP.
Each DHCP client and server has a unique DHCP Unique IDentifier (DUID), which is used for
identification when they are exchanging DHCPv6 messages. The DUID is generated from the MAC
address, time, vendor assigned ID and/or the vendor's private enterprise number registered with
the IANA. It should not change over time even after you reboot the device.
9.1.3 What You Need to Do First
For IPv6 settings, go to the Configuration > System > IPv6 screen to enable IPv6 support on the
USG first.
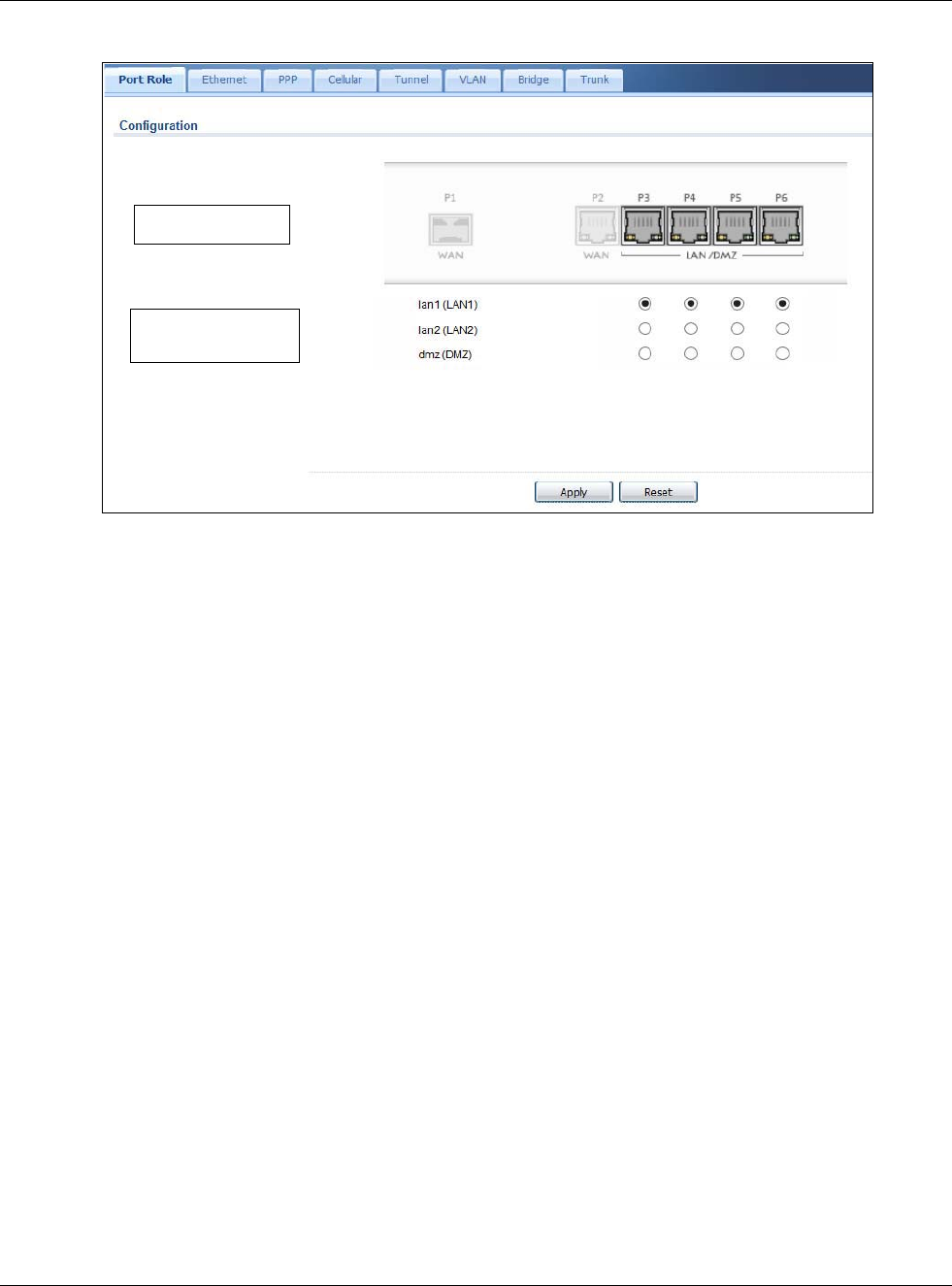
9.2 Port Role Screen
To access this screen, click Configuration > Network > Interface > Port Role. Use the Port
Role screen to set the USG’s flexible ports as part of the lan1, lan2, or dmz interfaces. This
creates a hardware connection between the physical ports at the layer-2 (data link, MAC address)
level. This provides wire-speed throughput but no security.
Note the following if you are configuring from a computer connected to a lan1, lan2, or dmz port
and change the port's role:
• A port's IP address varies as its role changes, make sure your computer's IP address is in the
same subnet as the USG's lan1, lan2, or dmz IP address.
• Use the appropriate lan1, lan2, or dmz IP address to access the USG.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
146
Figure 118 Configuration > Network > Interface > Port Role
The physical Ethernet ports are shown at the top and the Ethernet interfaces and zones are shown
at the bottom of the screen. Use the radio buttons to select for which interface (network) you want
to use each physical port. For example, select a port’s LAN radio button to use the port as part of
the LAN interface. The port will use the USG’s LAN IP address and MAC address.
When you assign more than one physical port to a network, you create a port group. Port groups
have the following characteristics:
• There is a layer-2 Ethernet switch between physical ports in the port group. This provides wire-
speed throughput but no security.
• It can increase the bandwidth between the port group and other interfaces.
• The port group uses a single MAC address.
Click Apply to save your changes and apply them to the USG.
Click Reset to change the port groups to their current configuration (last-saved values).
9.3 Ethernet Summary Screen
This screen lists every Ethernet interface and virtual interface created on top of Ethernet interfaces.
If you enabled IPv6 in the Configuration > System > IPv6 screen, you can also configure
Ethernet interfaces used for your IPv6 networks on this screen. To access this screen, click
Configuration > Network > Interface > Ethernet.
Unlike other types of interfaces, you cannot create new Ethernet interfaces nor can you delete any
of them. If an Ethernet interface does not have any physical ports assigned to it, the Ethernet
interface is effectively removed from the USG, but you can still configure it.
Physical Ports
Default
interface (ZONE)
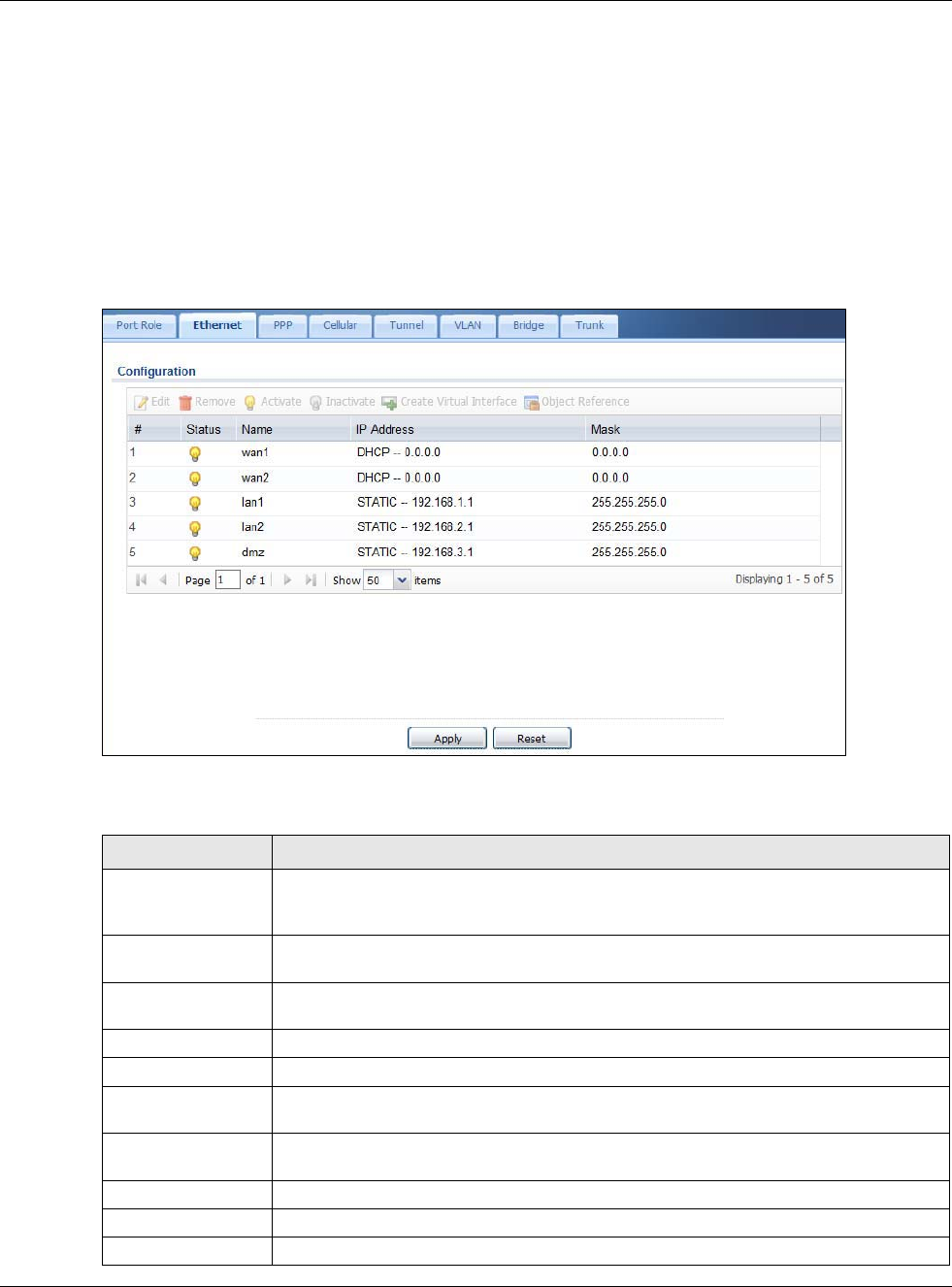
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
147
Ethernet interfaces are similar to other types of interfaces in many ways. They have an IP address,
subnet mask, and gateway used to make routing decisions. They restrict the amount of bandwidth
and packet size. They can provide DHCP services, and they can verify the gateway is available.
Use Ethernet interfaces to control which physical ports exchange routing information with other
routers and how much information is exchanged through each one. The more routing information is
exchanged, the more efficient the routers should be. However, the routers also generate more
network traffic, and some routing protocols require a significant amount of configuration and
management. The USG supports two routing protocols, RIP and OSPF. See Chapter 10 on page 238
for background information about these routing protocols.
Figure 119 Configuration > Network > Interface > Ethernet
Each field is described in the following table.
Table 63 Configuration > Network > Interface > Ethernet
LABEL DESCRIPTION
Configuration / IPv6
Configuration
Use the Configuration section for IPv4 network settings. Use the IPv6
Configuration section for IPv6 network settings if you connect your USG to an IPv6
network. Both sections have similar fields as described below.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove a virtual interface, select it and click Remove. The USG confirms you want
to remove it before doing so.
Activate To turn on an interface, select it and click Activate.
Inactivate To turn off an interface, select it and click Inactivate.
Create Virtual
Interface
To open the screen where you can create a virtual Ethernet interface, select an
Ethernet interface and click Create Virtual Interface.
Object References Select an entry and click Object Reference to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
# This field is a sequential value, and it is not associated with any interface.
Status This icon is lit when the entry is active and dimmed when the entry is inactive.
Name This field displays the name of the interface.

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
148
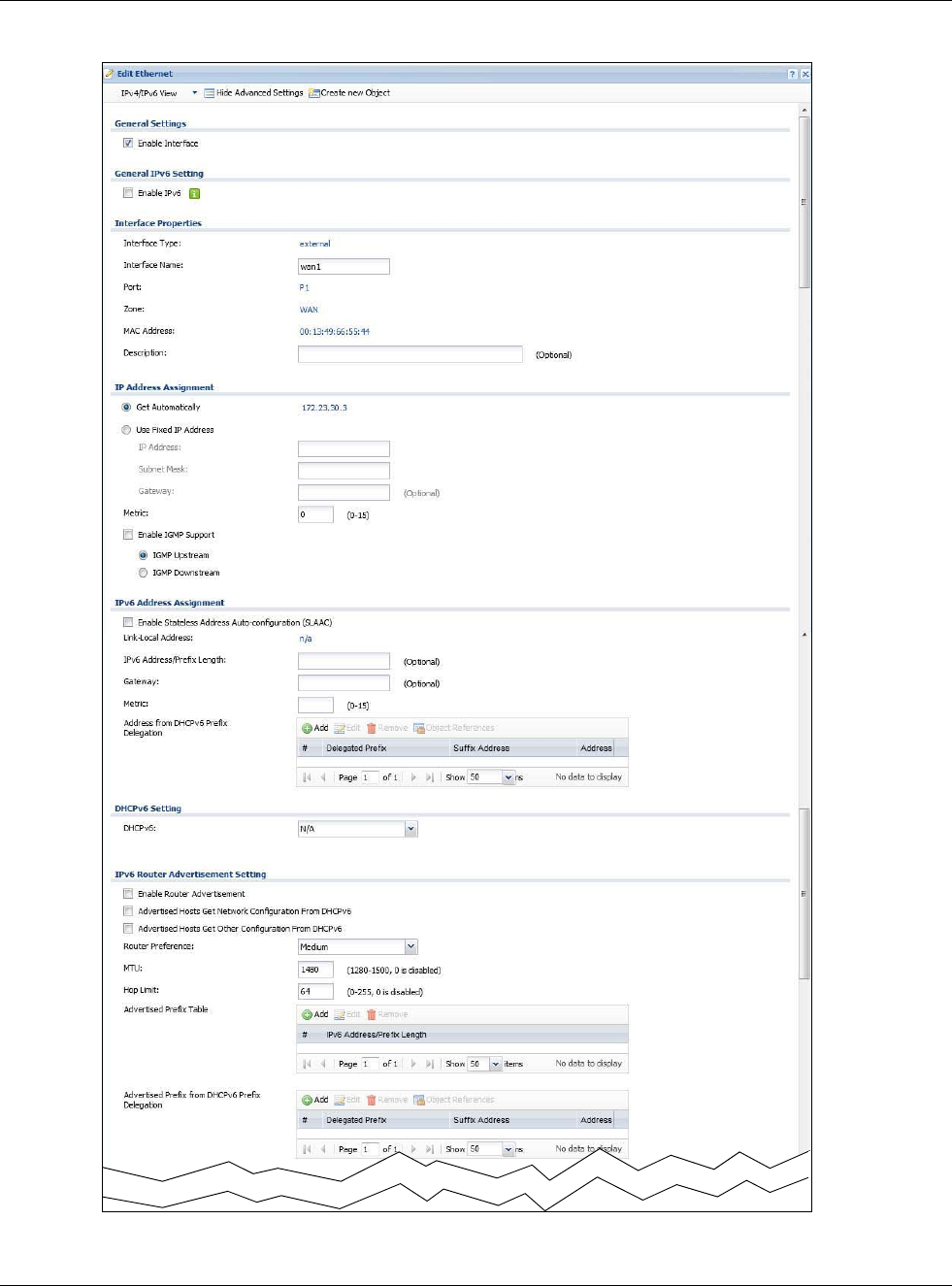
9.3.1 Ethernet Edit
The Ethernet Edit screen lets you configure IP address assignment, interface parameters, RIP
settings, OSPF settings, DHCP settings, connectivity check, and MAC address settings. To access
this screen, click an Edit icon in the Ethernet Summary screen. (See Section 9.3 on page 146.)
The OPT interface’s Edit > Configuration screen is shown here as an example. The screens for
other interfaces are similar and contain a subset to the OPT interface screen’s fields.
Note: If you create IP address objects based on an interface’s IP address, subnet, or
gateway, the USG automatically updates every rule or setting that uses the object
whenever the interface’s IP address settings change. For example, if you change
the LAN’s IP address, the USG automatically updates the corresponding interface-
based, LAN subnet address object.
With RIP, you can use Ethernet interfaces to do the following things.
• Enable and disable RIP in the underlying physical port or port group.
• Select which direction(s) routing information is exchanged - The USG can receive routing
information, send routing information, or do both.
• Select which version of RIP to support in each direction - The USG supports RIP-1, RIP-2, and
both versions.
• Select the broadcasting method used by RIP-2 packets - The USG can use subnet broadcasting or
multicasting.
With OSPF, you can use Ethernet interfaces to do the following things.
• Enable and disable OSPF in the underlying physical port or port group.
• Select the area to which the interface belongs.
• Override the default link cost and authentication method for the selected area.
• Select in which direction(s) routing information is exchanged - The USG can receive routing
information, send routing information, or do both.
IP Address This field displays the current IP address of the interface. If the IP address is 0.0.0.0 (in
the IPv4 network) or :: (in the IPv6 network), the interface does not have an IP
address yet.
In the IPv4 network, this screen also shows whether the IP address is a static IP
address (STATIC) or dynamically assigned (DHCP). IP addresses are always static in
virtual interfaces.
In the IPv6 network, this screen also shows whether the IP address is a static IP
address (STATIC), link-local IP address (LINK LOCAL), dynamically assigned
(DHCP), or an IPv6 StateLess Address AutoConfiguration IP address (SLAAC). See
Section 9.1.2 on page 141 for more information about IPv6.
Mask This field displays the interface’s subnet mask in dot decimal notation.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
Table 63 Configuration > Network > Interface > Ethernet (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
149
Set the priority used to identify the DR or BDR if one does not exist.
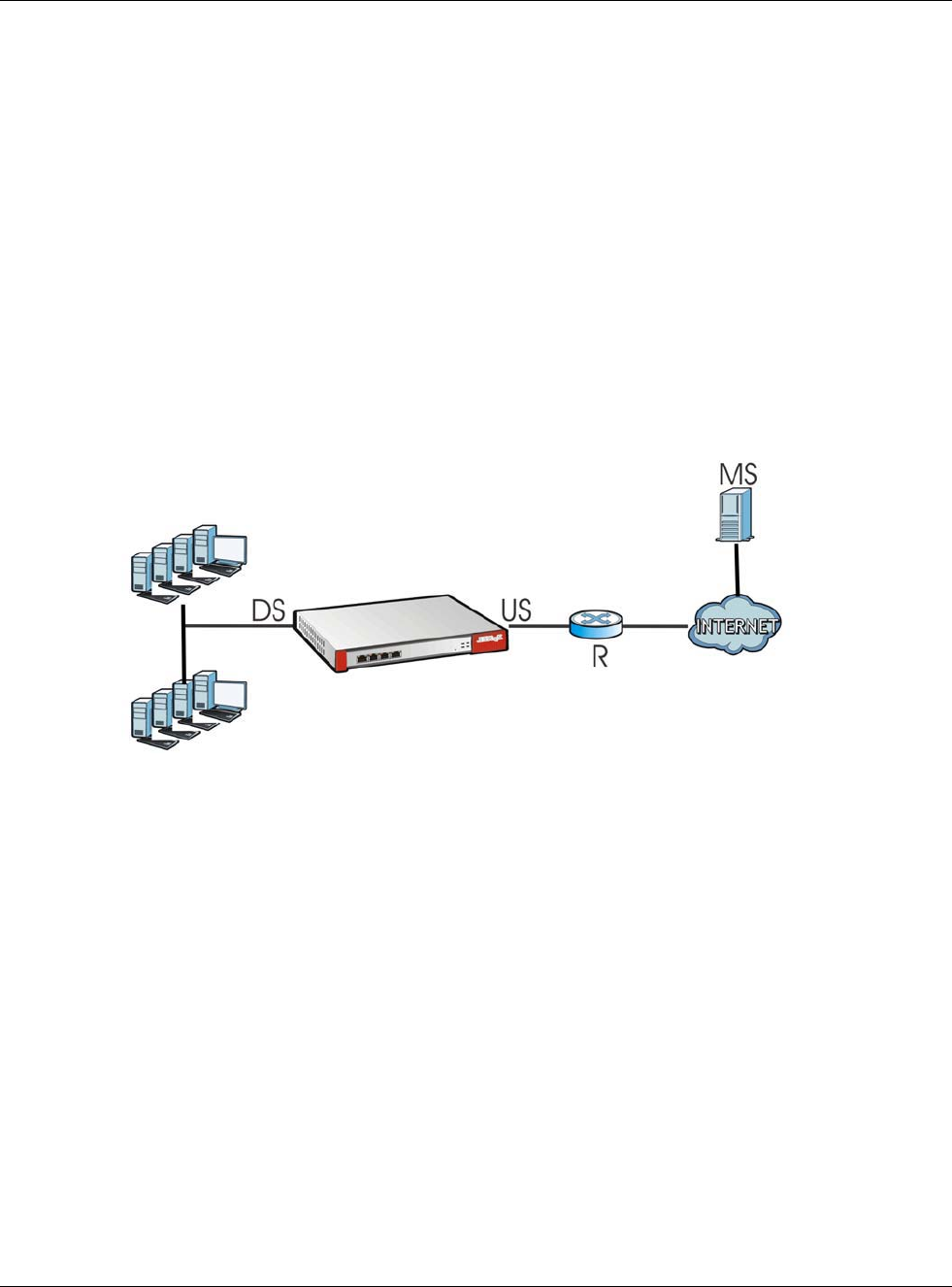
IGMP Proxy
Internet Group Management Protocol (IGMP) proxy is used for multicast routing. IGMP proxy enables the USG
to issue IGMP host messages on behalf of hosts that the USG discovered on its IGMP-enabled interfaces. The
USG acts as a proxy for its hosts. Refer to the following figure.
• DS: Downstream traffic
• US: Upstream traffic
•R: Router
• MS: Multicast Server
• Enable IGMP Upstream (US) on the USG interface that connects to a router (R) running IGMP
that is closer to the multicast server (MS).
• Enable IGMP Downstream on the USG interface which connects to the multicast hosts.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
150
• Configuration > Network > Interface > Ethernet > Edit (External Type)
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
151
Configuration > Network > Interface > Ethernet > Edit (External Type
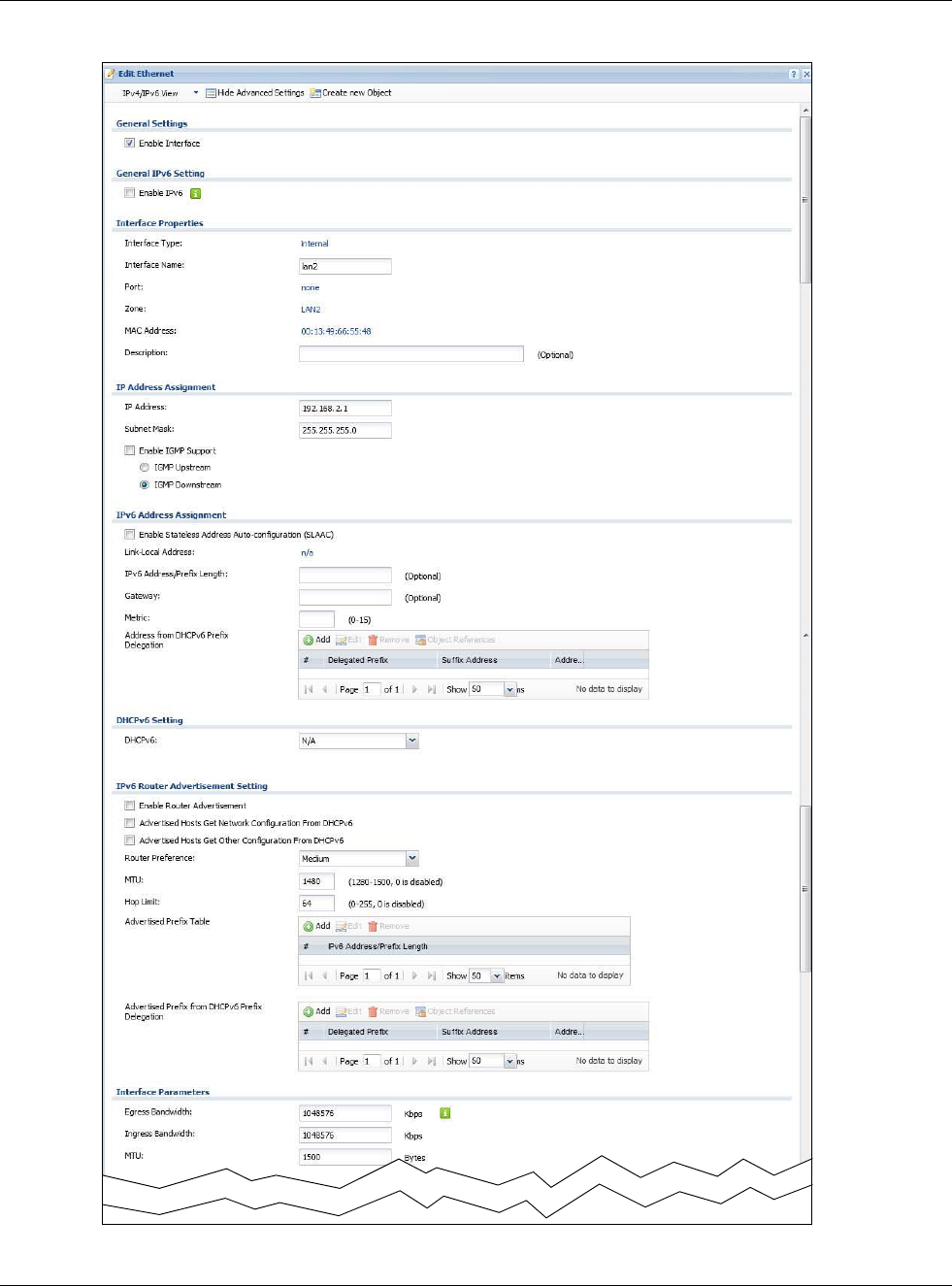
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
152
Figure 120 Configuration > Network > Interface > Ethernet > Edit (Internal Type)
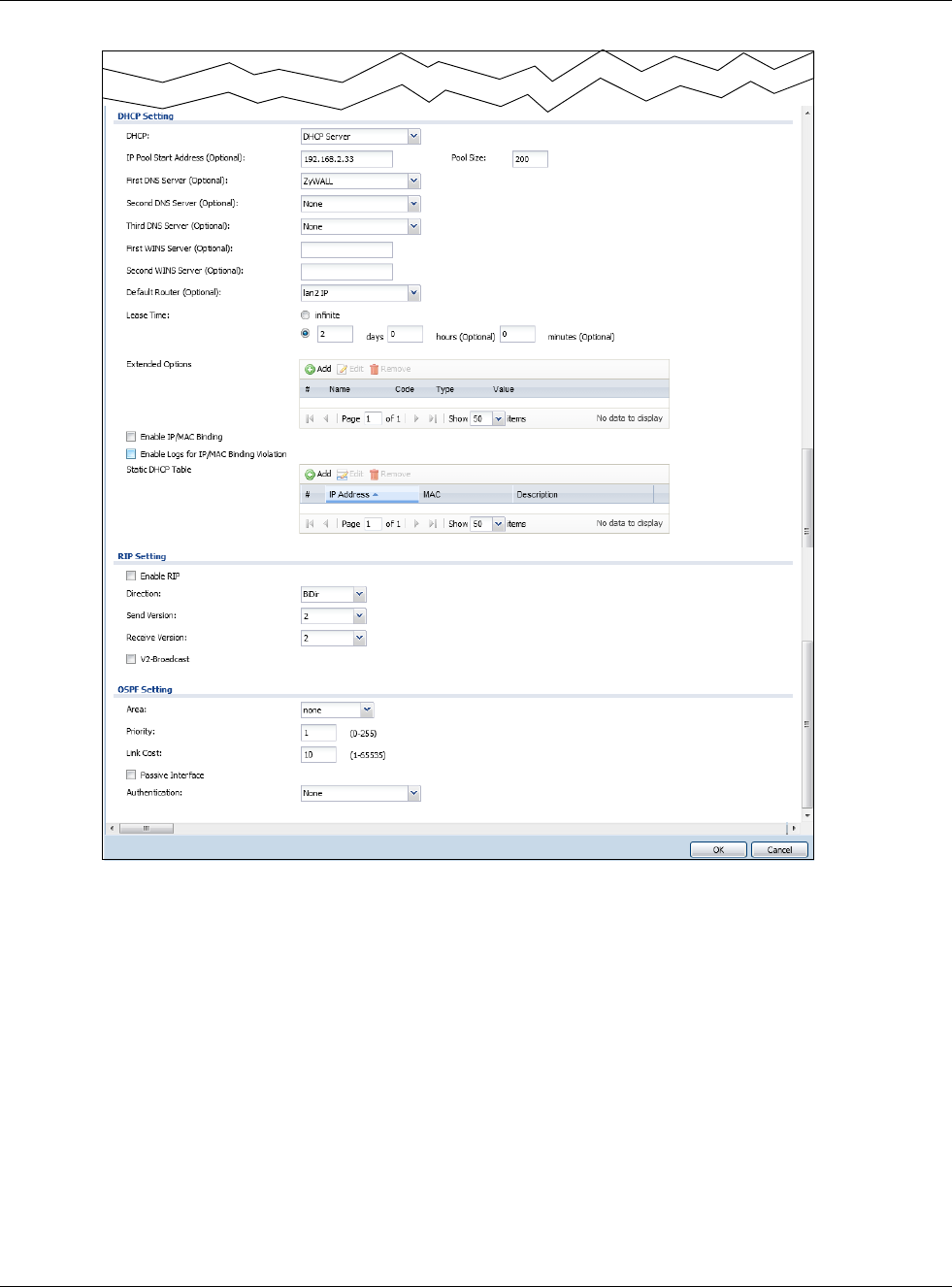
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
153
Configuration > Network > Interface > Ethernet > Edit (Internal Type)
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
154
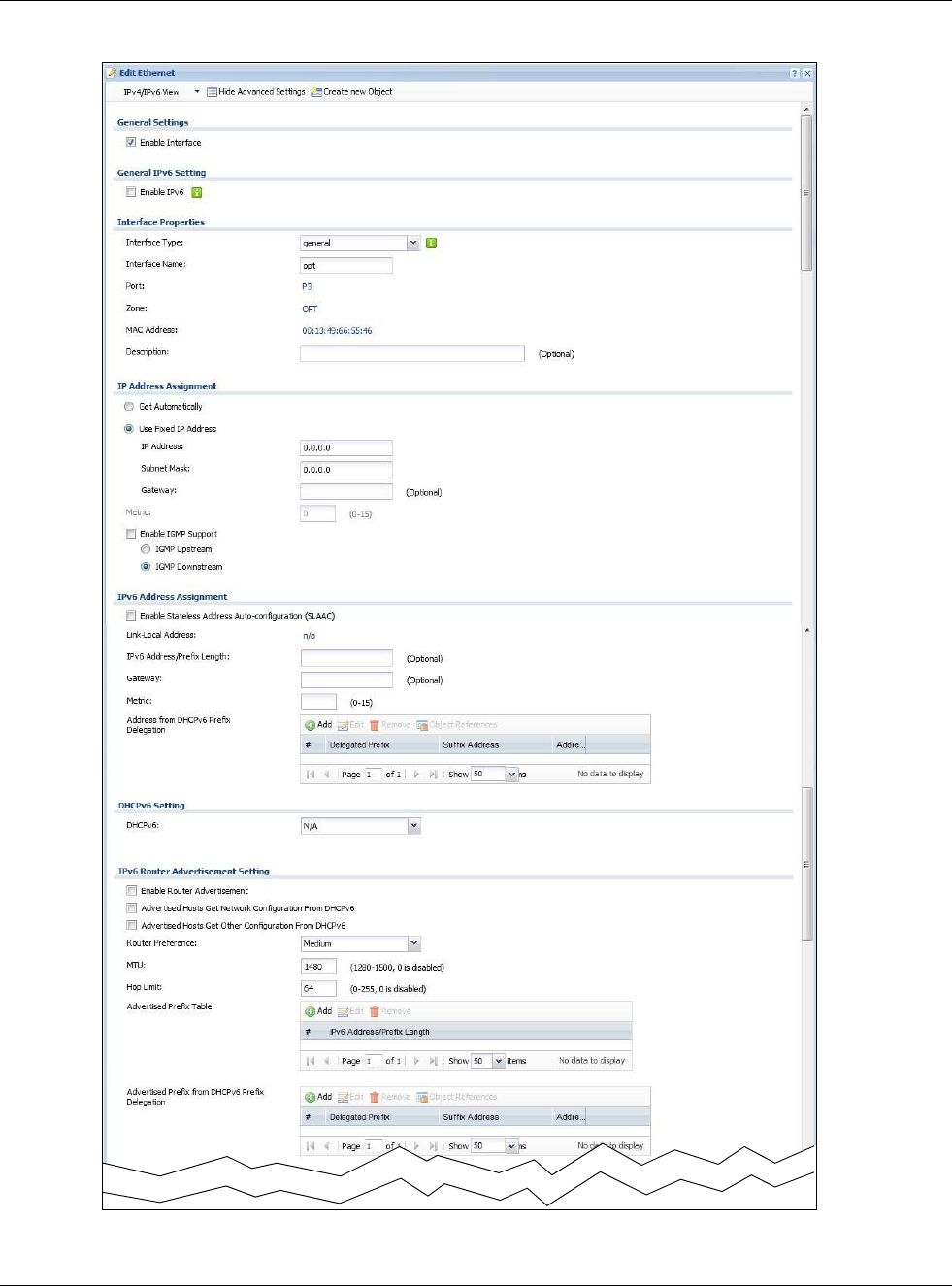
Figure 121 Configuration > Network > Interface > Ethernet > Edit (OPT)
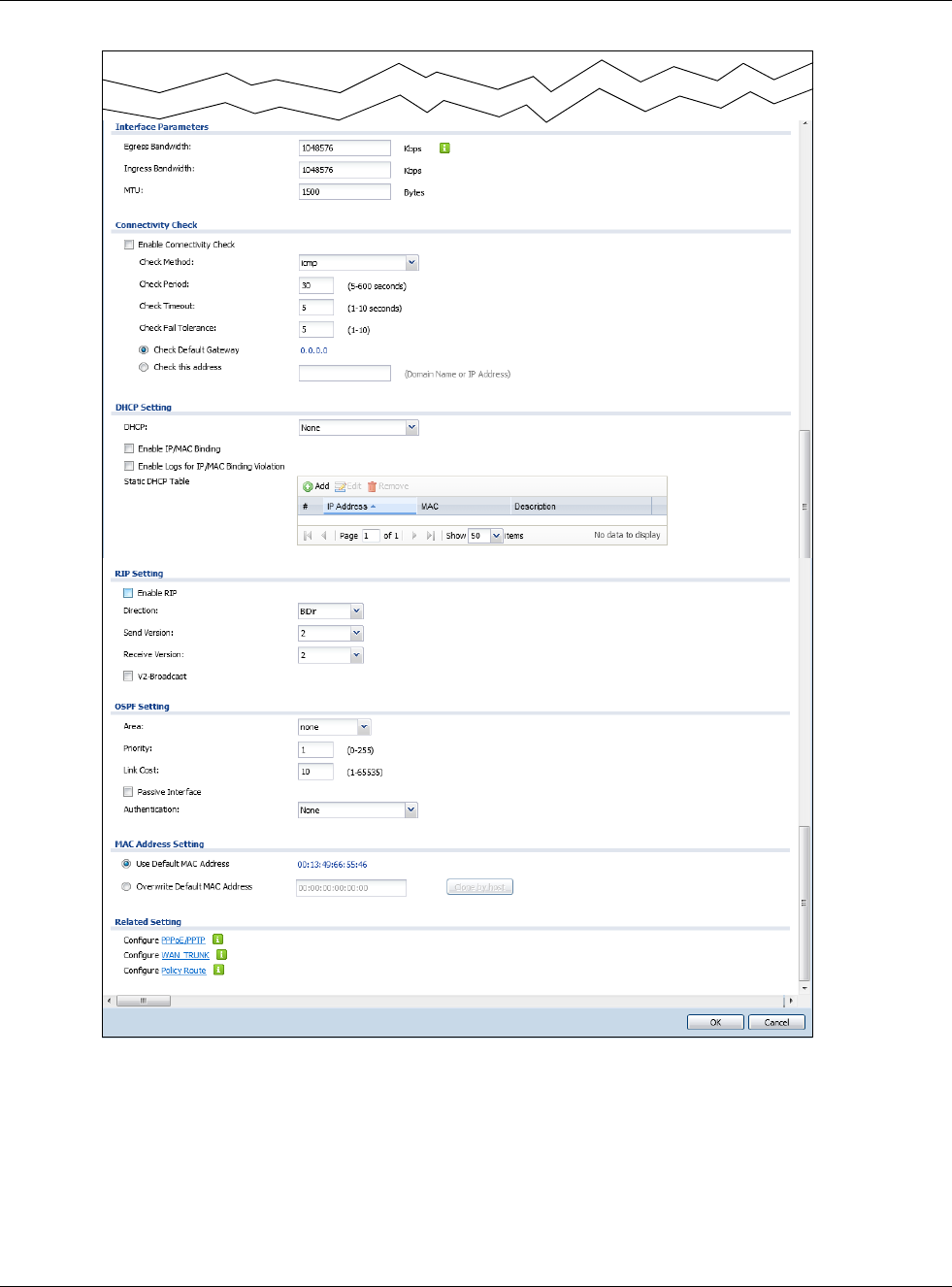
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
155
Configuration > Network > Interface > Ethernet > Edit (OPT)

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
156
This screen’s fields are described in the table below.
Table 64 Configuration > Network > Interface > Ethernet > Edit
LABEL DESCRIPTION
IPv4/IPv6 View /
IPv4 View / IPv6
View
Use this button to display both IPv4 and IPv6, IPv4-only, or IPv6-only configuration
fields.
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Create New Object Click this button to create a DHCPv6 lease or DHCPv6 request object that you may use
for the DHCPv6 settings in this screen.
General Settings
Enable Interface Select this to enable this interface. Clear this to disable this interface.
General IPv6
Setting
Enable IPv6 Select this to enable IPv6 on this interface. Otherwise, clear this to disable it.
Interface Properties
Interface Type This field is configurable for the OPT interface only. Select to which type of network
you will connect this interface. When you select internal or external the rest of the
screen’s options automatically adjust to correspond. The USG automatically adds
default route and SNAT settings for traffic it routes from internal interfaces to external
interfaces; for example LAN to WAN traffic.
internal is for connecting to a local network. Other corresponding configuration
options: DHCP server and DHCP relay. The USG automatically adds default SNAT
settings for traffic flowing from this interface to an external interface.
external is for connecting to an external network (like the Internet). The USG
automatically adds this interface to the default WAN trunk.
For general, the rest of the screen’s options do not automatically adjust and you must
manually configure a policy route to add routing and SNAT settings for the interface.
Interface Name Specify a name for the interface. It can use alphanumeric characters, hyphens, and
underscores, and it can be up to 11 characters long.
Port This is the name of the Ethernet interface’s physical port.
Zone Select the zone to which this interface is to belong. You use zones to apply security
settings such as security policy, and remote management.
MAC Address This field is read-only. This is the MAC address that the Ethernet interface uses.
Description Enter a description of this interface. It is not used elsewhere. You can use
alphanumeric and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters
long.
IP Address
Assignment
These IP address fields configure an IPv4 IP address on the interface itself. If you
change this IP address on the interface, you may also need to change a related
address object for the network connected to the interface. For example, if you use this
screen to change the IP address of your LAN interface, you should also change the
corresponding LAN subnet address object.
Get
Automatically This option appears when Interface Type is external or general. Select this to make
the interface a DHCP client and automatically get the IP address, subnet mask, and
gateway address from a DHCP server.
Use Fixed IP
Address This option appears when Interface Type is external or general. Select this if you
want to specify the IP address, subnet mask, and gateway manually.
IP Address Enter the IP address for this interface.
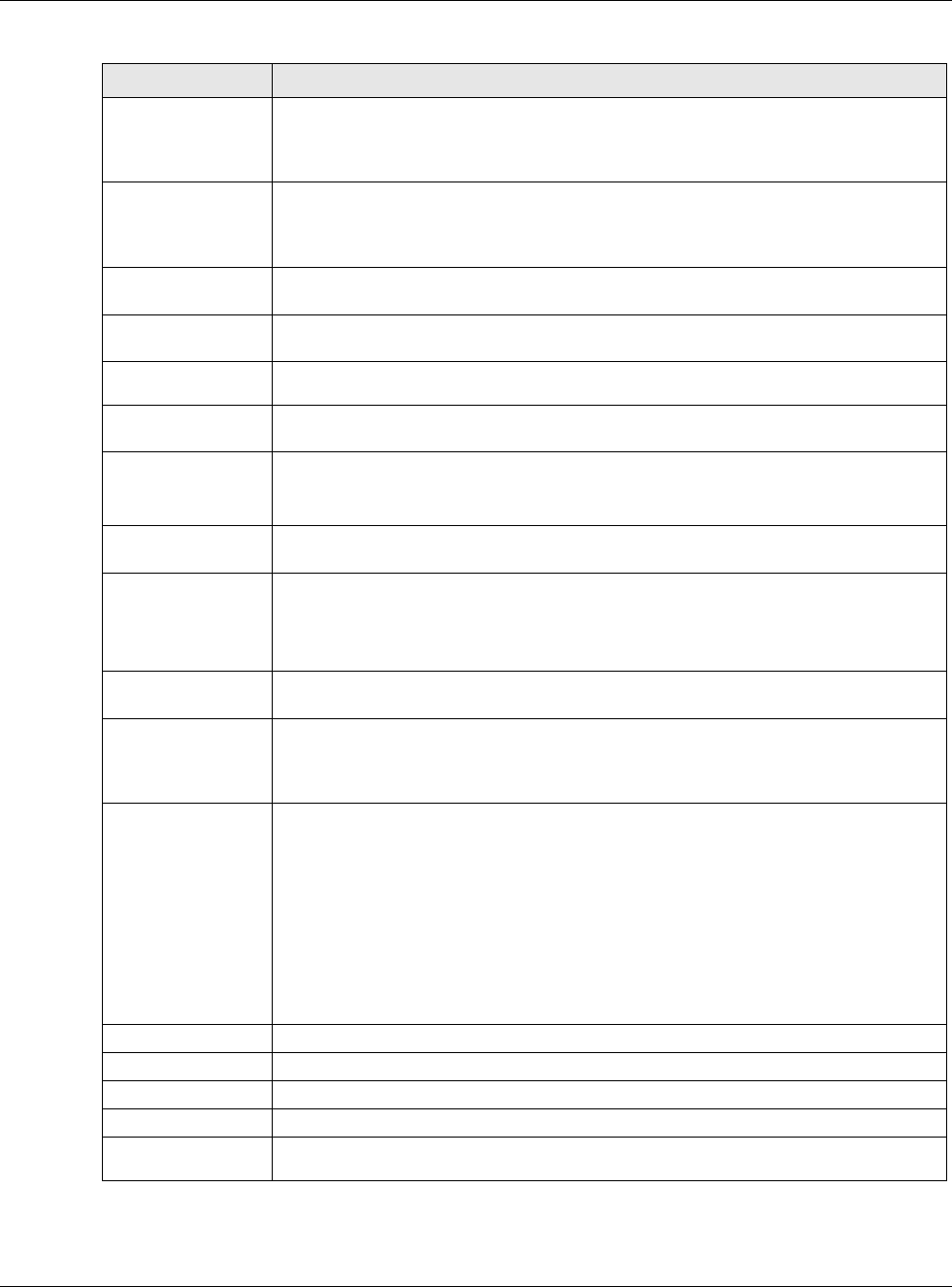
Subnet Mask Enter the subnet mask of this interface in dot decimal notation. The subnet mask
indicates what part of the IP address is the same for all computers in the network.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
157
Gateway This option appears when Interface Type is external or general. Enter the IP
address of the gateway. The USG sends packets to the gateway when it does not know
how to route the packet to its destination. The gateway should be on the same network
as the interface.
Metric This option appears when Interface Type is external or general. Enter the priority
of the gateway (if any) on this interface. The USG decides which gateway to use based
on this priority. The lower the number, the higher the priority. If two or more gateways
have the same priority, the USG uses the one that was configured first.
Enable IGMP
Support
Select this to allow the USG to act as an IGMP proxy for hosts connected on the IGMP
downstream interface.
IGMP Upstream Enable IGMP Upstream on the interface which connects to a router running IGMP that
is closer to the multicast server.
IGMP
Downstream Enable IGMP Downstream on the interface which connects to the multicast hosts.
IPv6 Address
Assignment
These IP address fields configure an IPv6 IP address on the interface itself.
Enable Stateless
Address Auto-
configuration
(SLAAC)
Select this to enable IPv6 stateless auto-configuration on this interface. The interface
will generate an IPv6 IP address itself from a prefix obtained from an IPv6 router in the
network.
Link-Local
address This displays the IPv6 link-local address and the network prefix that the USG generates
itself for the interface.
IPv6 Address/
Prefix Length Enter the IPv6 address and the prefix length for this interface if you want to use a
static IP address. This field is optional.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Gateway Enter the IPv6 address of the default outgoing gateway using colon (:) hexadecimal
notation.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Address from
DHCPv6 Prefix
Delegation
Use this table to have the USG obtain an IPv6 prefix from the ISP or a connected uplink
router for an internal network, such as the LAN or DMZ. You have to also enter a suffix
address which is appended to the delegated prefix to form an address for this
interface. See Prefix Delegation on page 144 for more information.
To use prefix delegation, you must:
• Create at least one DHCPv6 request object before configuring this table.
• The external interface must be a DHCPv6 client. You must configure the DHCPv6
request options using a DHCPv6 request object with the type of prefix-delegation.
• Assign the prefix delegation to an internal interface and enable router
advertisement on that interface.
Add Click this to create an entry.
Edit Select an entry and click this to change the settings.
Remove Select an entry and click this to delete it from this table.
# This field is a sequential value, and it is not associated with any entry.
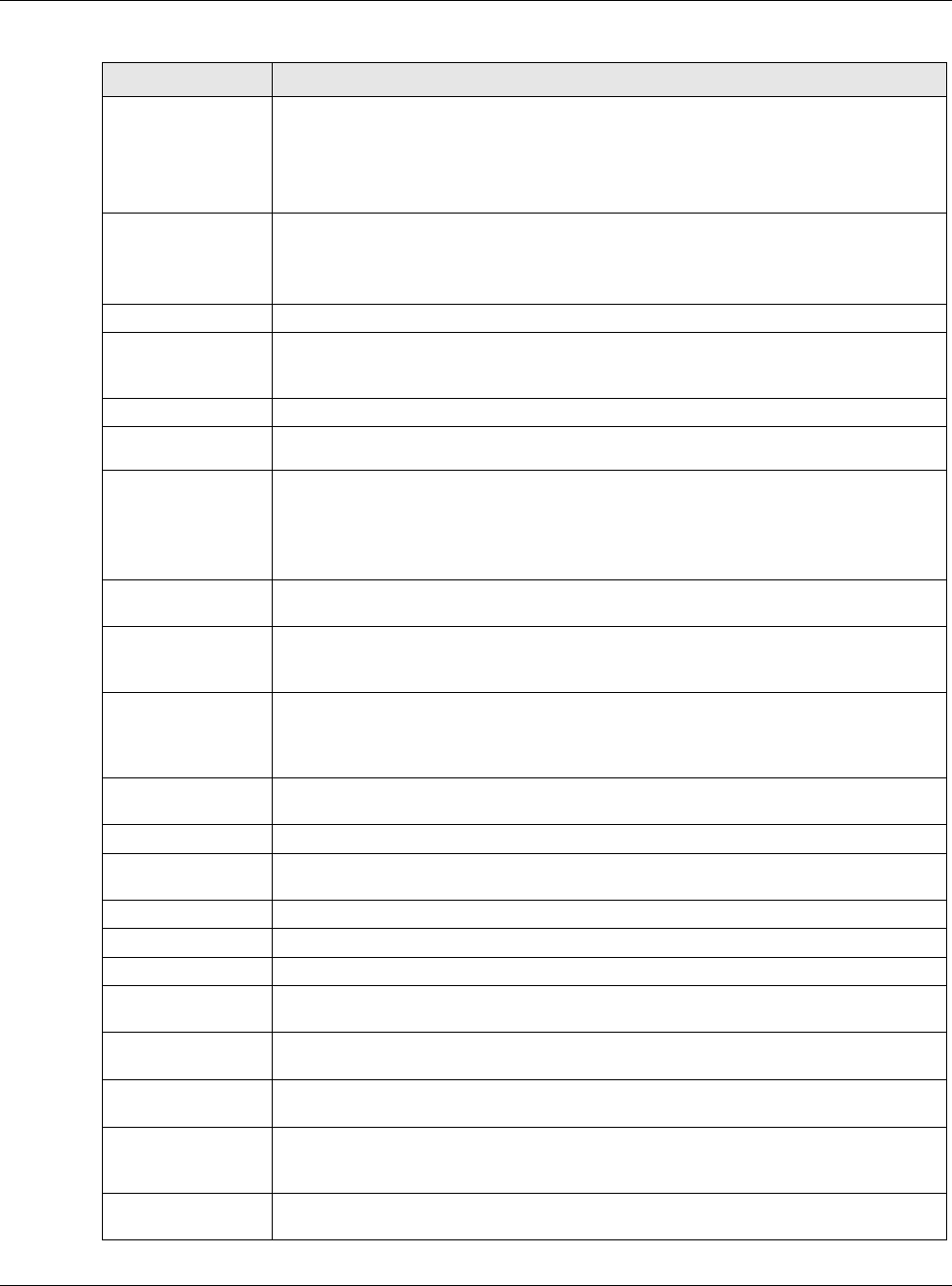
Delegated
Prefix Select the DHCPv6 request object to use from the drop-down list.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
158
Suffix
Address Enter the ending part of the IPv6 address, a slash (/), and the prefix length. The USG
will append it to the delegated prefix.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to configure
an IP address of 2003:1234:5678:1111::1/128 for this interface, then enter
::1111:0:0:0:1/128 in this field.
Address This field displays the combined IPv6 IP address for this interface.
Note: This field displays the combined address after you click OK and reopen this
screen.
DHCPv6 Setting
DUID This field displays the DHCP Unique IDentifier (DUID) of the interface, which is unique
and used for identification purposes when the interface is exchanging DHCPv6
messages with others. See DHCPv6 on page 145 for more information.
DUID as MAC Select this if you want the DUID is generated from the interface’s default MAC address.
Customized
DUID If you want to use a customized DUID, enter it here for the interface.
Enable Rapid
Commit Select this to shorten the DHCPv6 message exchange process from four to two steps.
This function helps reduce heavy network traffic load.
Note: Make sure you also enable this option in the DHCPv6 clients to make rapid commit
work.
Information
Refresh Time Enter the number of seconds a DHCPv6 client should wait before refreshing information
retrieved from DHCPv6.
Request Address This field is available if you set this interface to DHCPv6 Client. Select this to get an
IPv6 IP address for this interface from the DHCP server. Clear this to not get any IP
address information through DHCPv6.
DHCPv6 Request
Options /
DHCPv6 Lease
Options
If this interface is a DHCPv6 client, use this section to configure DHCPv6 request
settings that determine what additional information to get from the DHCPv6 server. If
the interface is a DHCPv6 server, use this section to configure DHCPv6 lease settings
that determine what additional information to offer to the DHCPv6 clients.
Add Click this to create an entry in this table. See Section 9.3.3 on page 164 for more
information.
Remove Select an entry and click this to delete it from this table.
Object
Reference Select an entry and click Object Reference to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
# This field is a sequential value, and it is not associated with any entry.
Name This field displays the name of the DHCPv6 request or lease object.
Type This field displays the type of the object.
Value This field displays the IPv6 prefix that the USG obtained from an uplink router (Server
is selected) or will advertise to its clients (Client is selected).
Interface When Relay is selected, select this check box and an interface from the drop-down list
if you want to use it as the relay server.
Relay Server When Relay is selected, select this check box and enter the IP address of a DHCPv6
server as the relay server.
IPv6 Router
Advertisement
Setting
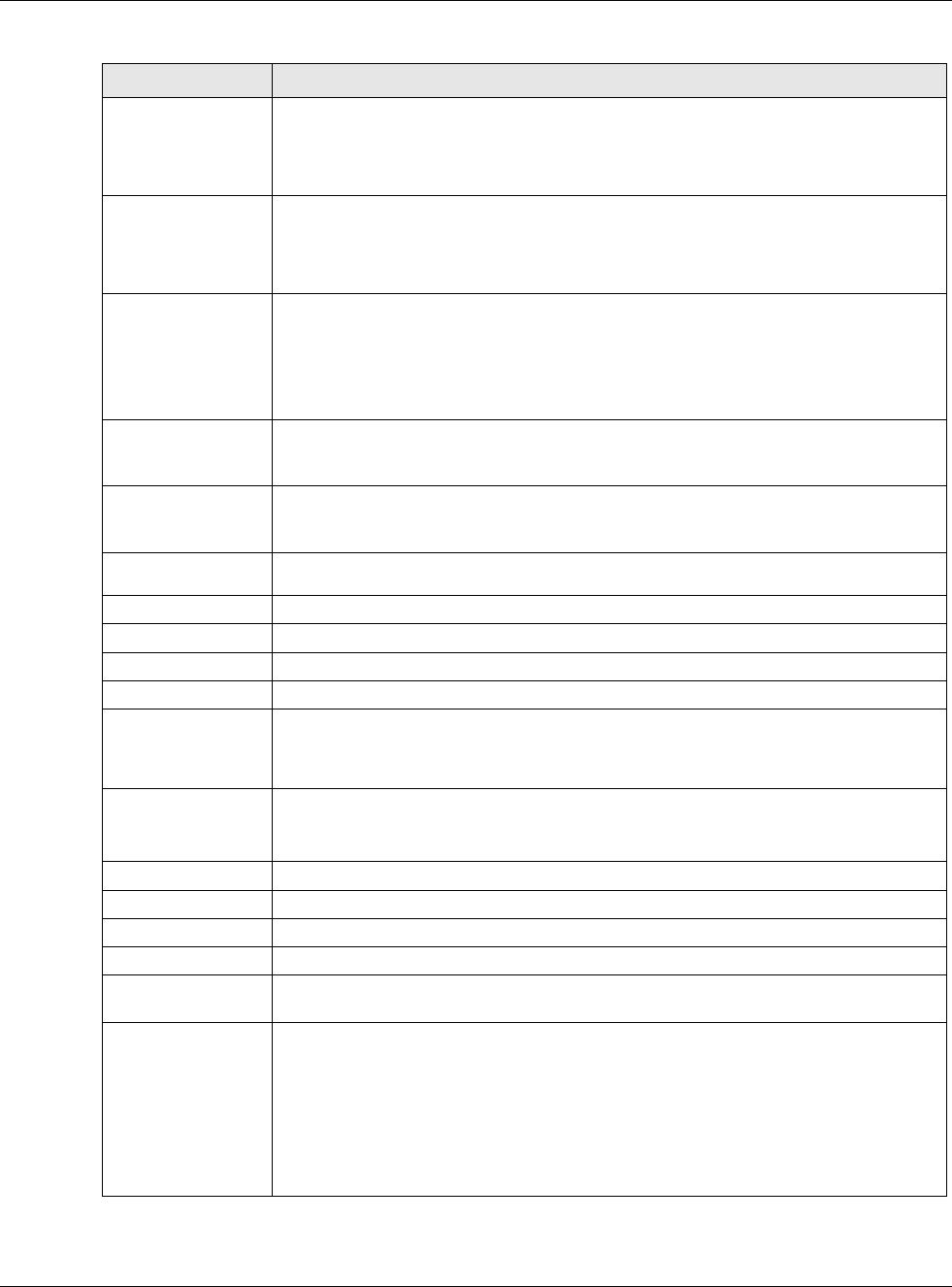
Enable Router
Advertisement Select this to enable this interface to send router advertisement messages periodically.
See IPv6 Router Advertisement on page 145 for more information.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
159
Advertised Hosts
Get Network
Configuration
From DHCPv6
Select this to have the USG indicate to hosts to obtain network settings (such as prefix
and DNS settings) through DHCPv6.
Clear this to have the USG indicate to hosts that DHCPv6 is not available and they
should use the prefix in the router advertisement message.
Advertised Hosts
Get Other
Configuration
From DHCPv6
Select this to have the USG indicate to hosts to obtain DNS information through
DHCPv6.
Clear this to have the USG indicate to hosts that DNS information is not available in
this network.
Router
Preference Select the router preference (Low, Medium or High) for the interface. The interface
sends this preference in the router advertisements to tell hosts what preference they
should use for the USG. This helps hosts to choose their default router especially when
there are multiple IPv6 router in the network.
Note: Make sure the hosts also support router preference to make this function work.
MTU The Maximum Transmission Unit. Type the maximum size of each IPv6 data packet, in
bytes, that can move through this interface. If a larger packet arrives, the USG
discards the packet and sends an error message to the sender to inform this.
Hop Limit Enter the maximum number of network segments that a packet can cross before
reaching the destination. When forwarding an IPv6 packet, IPv6 routers are required to
decrease the Hop Limit by 1 and to discard the IPv6 packet when the Hop Limit is 0.
Advertised
Prefix Table Configure this table only if you want the USG to advertise a fixed prefix to the network.
Add Click this to create an IPv6 prefix address.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
IPv6
Address/
Prefix Length
Enter the IPv6 network prefix address and the prefix length.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Advertised
Prefix from
DHCPv6 Prefix
Delegation
This table is available when the Interface Type is internal. Use this table to
configure the network prefix if you want to use a delegated prefix as the beginning part
of the network prefix.
Add Click this to create an entry in this table.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
Delegated
Prefix Select the DHCPv6 request object to use for generating the network prefix for the
network.
Suffix
Address Enter the ending part of the IPv6 network address plus a slash (/) and the prefix
length. The USG will append it to the selected delegated prefix. The combined address
is the network prefix for the network.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to divide it
into 2003:1234:5678:1111/64 for this interface and 2003:1234:5678:2222/64 for
another interface. You can use ::1111/64 and ::2222/64 for the suffix address
respectively. But if you do not want to divide the delegated prefix into subnetworks,
enter ::0/48 here, which keeps the same prefix length (/48) as the delegated prefix.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
160
Address This is the final network prefix combined by the delegated prefix and the suffix.
Note: This field displays the combined address after you click OK and reopen this
screen.
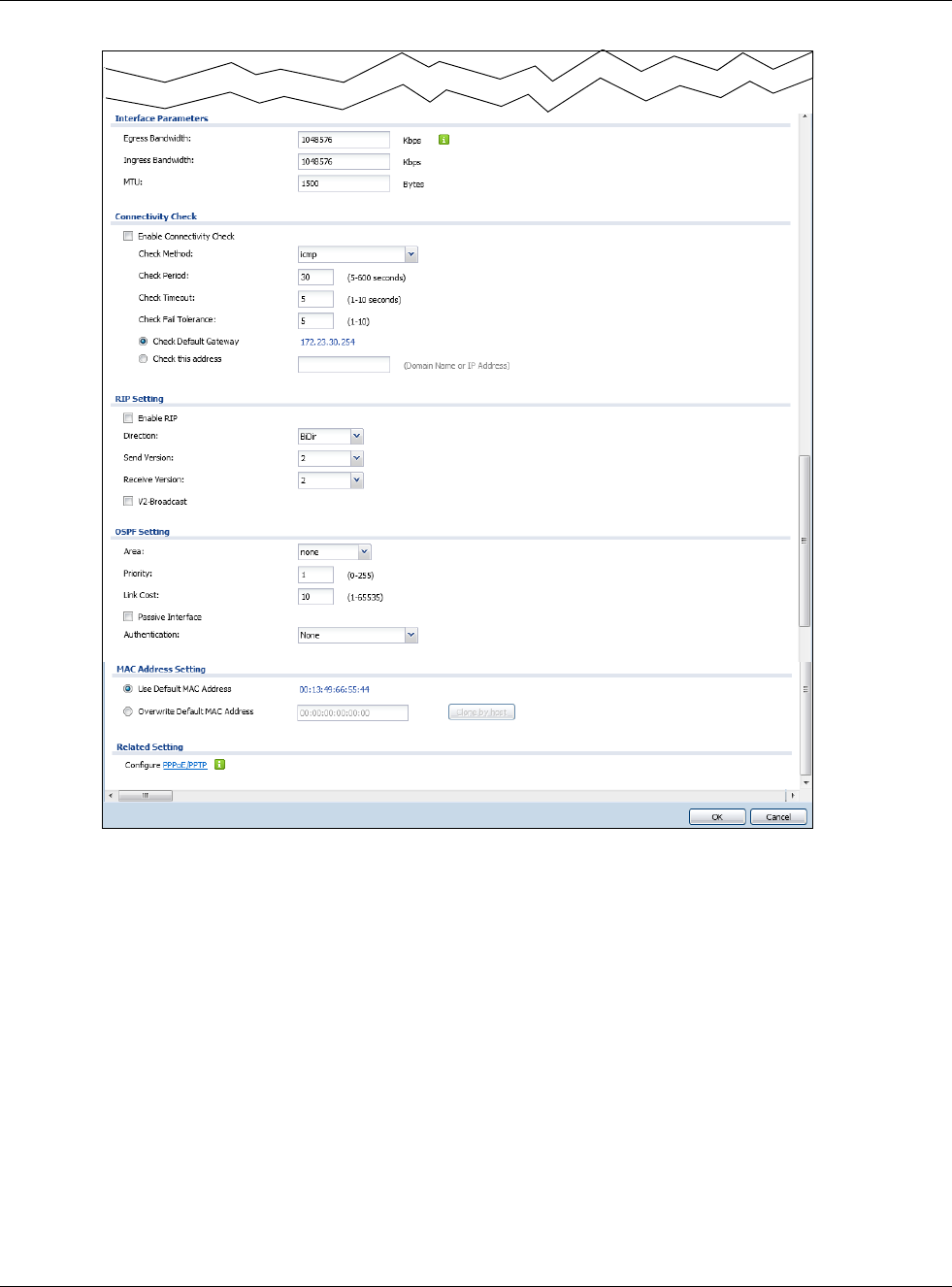
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send through
the interface to the network. Allowed values are 0 - 1048576.
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
MTU Maximum Transmission Unit. Type the maximum size of each data packet, in bytes,
that can move through this interface. If a larger packet arrives, the USG divides it into
smaller fragments. Allowed values are 576 - 1500. Usually, this value is 1500.
Connectivity Check These fields appear when Interface Properties is External or General.
The interface can regularly check the connection to the gateway you specified to make
sure it is still available. You specify how often the interface checks the connection, how
long to wait for a response before the attempt is a failure, and how many consecutive
failures are required before the USG stops routing to the gateway. The USG resumes
routing to the gateway the first time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance Enter the number of consecutive failures before the USG stops routing through the
gateway.
Check Default
Gateway Select this to use the default gateway for the connectivity check.
Check this
address Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
Check Port This field only displays when you set the Check Method to tcp. Specify the port
number to use for a TCP connectivity check.
DHCP Setting This section appears when Interface Type is internal or general.
DHCP Select what type of DHCP service the USG provides to the network. Choices are:
None - the USG does not provide any DHCP services. There is already a DHCP server
on the network.
DHCP Relay - the USG routes DHCP requests to one or more DHCP servers you
specify. The DHCP server(s) may be on another network.
DHCP Server - the USG assigns IP addresses and provides subnet mask, gateway,
and DNS server information to the network. The USG is the DHCP server for the
network.
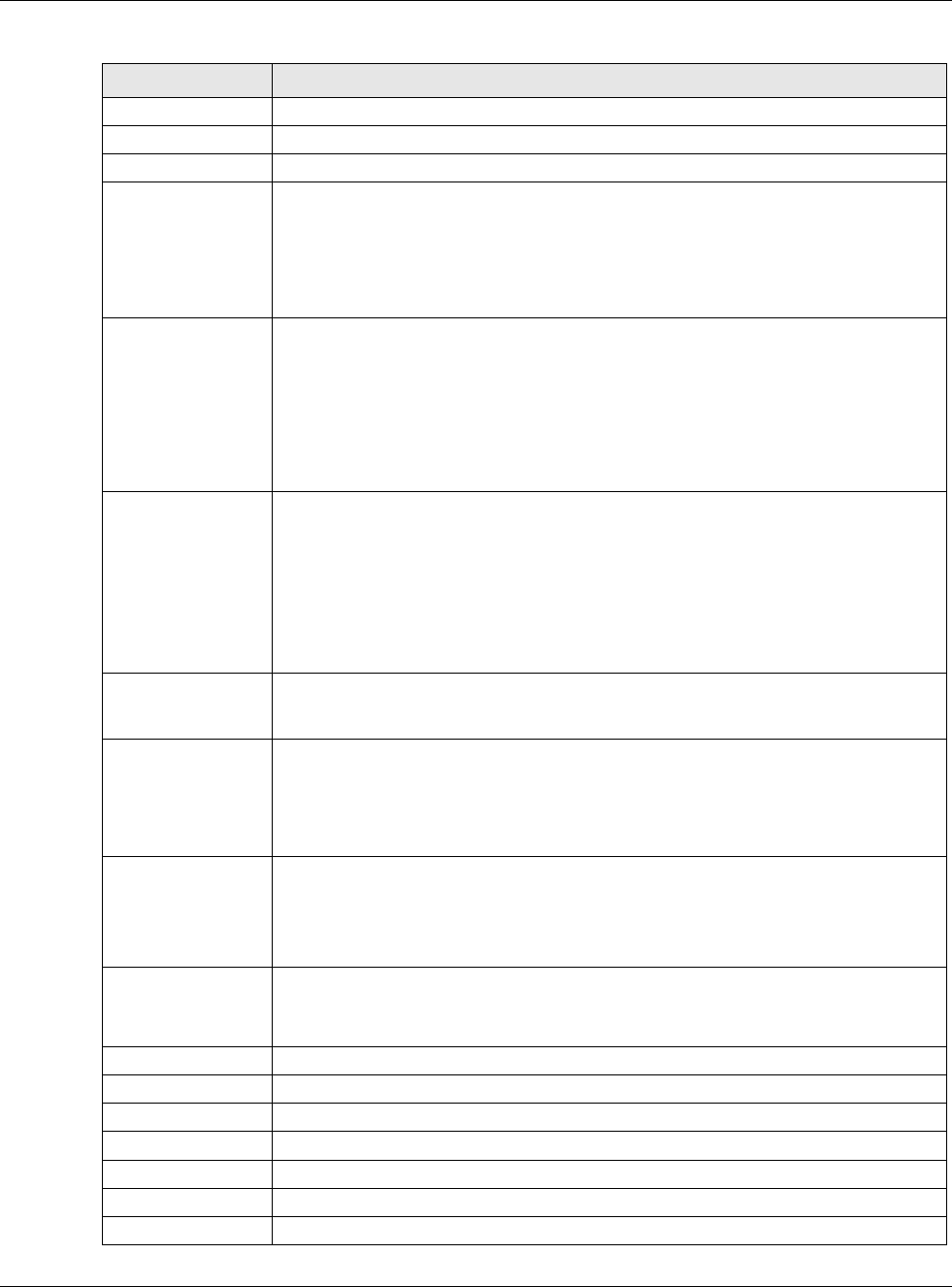
These fields appear if the USG is a DHCP Relay.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
161
Relay Server 1 Enter the IP address of a DHCP server for the network.
Relay Server 2 This field is optional. Enter the IP address of another DHCP server for the network.
These fields appear if the USG is a DHCP Server.
IP Pool Start
Address Enter the IP address from which the USG begins allocating IP addresses. If you want to
assign a static IP address to a specific computer, use the Static DHCP Table.
If this field is blank, the Pool Size must also be blank. In this case, the USG can assign
every IP address allowed by the interface’s IP address and subnet mask, except for the
first address (network address), last address (broadcast address) and the interface’s IP
address.
Pool Size Enter the number of IP addresses to allocate. This number must be at least one and is
limited by the interface’s Subnet Mask. For example, if the Subnet Mask is
255.255.255.0 and IP Pool Start Address is 10.10.10.10, the USG can allocate
10.10.10.10 to 10.10.10.254, or 245 IP addresses.
If this field is blank, the IP Pool Start Address must also be blank. In this case, the
USG can assign every IP address allowed by the interface’s IP address and subnet
mask, except for the first address (network address), last address (broadcast address)
and the interface’s IP address.
First DNS
Server, Second
DNS Server,
Third DNS
Server
Specify the IP addresses up to three DNS servers for the DHCP clients to use. Use one
of the following ways to specify these IP addresses.
Custom Defined - enter a static IP address.
From ISP - select the DNS server that another interface received from its DHCP
server.
USG - the DHCP clients use the IP address of this interface and the USG works as a
DNS relay.
First WINS
Server, Second
WINS Server
Type the IP address of the WINS (Windows Internet Naming Service) server that you
want to send to the DHCP clients. The WINS server keeps a mapping table of the
computer names on your network and the IP addresses that they are currently using.
Default Router If you set this interface to DHCP Server, you can select to use either the interface’s IP
address or another IP address as the default router. This default router will become the
DHCP clients’ default gateway.
To use another IP address as the default router, select Custom Defined and enter the
IP address.
Lease time Specify how long each computer can use the information (especially the IP address)
before it has to request the information again. Choices are:
infinite - select this if IP addresses never expire.
days, hours, and minutes - select this to enter how long IP addresses are valid.
Extended
Options This table is available if you selected DHCP server.
Configure this table if you want to send more information to DHCP clients through
DHCP packets.
Add Click this to create an entry in this table. See Section 9.3.4 on page 165.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
Name This is the name of the DHCP option.
Code This is the code number of the DHCP option.
Type This is the type of the set value for the DHCP option.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
162
Value This is the value set for the DHCP option.
Enable IP/MAC
Binding Select this option to have this interface enforce links between specific IP addresses and
specific MAC addresses. This stops anyone else from manually using a bound IP
address on another device connected to this interface. Use this to make use only the
intended users get to use specific IP addresses.
Enable Logs for
IP/MAC Binding
Violation
Select this option to have the USG generate a log if a device connected to this interface
attempts to use an IP address that is bound to another device’s MAC address.
Static DHCP
Table Configure a list of static IP addresses the USG assigns to computers connected to the
interface. Otherwise, the USG assigns an IP address dynamically using the interface’s
IP Pool Start Address and Pool Size.
Add Click this to create a new entry.
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
# This field is a sequential value, and it is not associated with a specific entry.
IP Address Enter the IP address to assign to a device with this entry’s MAC address.
MAC Enter the MAC address to which to assign this entry’s IP address.
Description Enter a description to help identify this static DHCP entry. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
RIP Setting See Section 10.6 on page 238 for more information about RIP.
Enable RIP Select this to enable RIP in this interface.
Direction This field is effective when RIP is enabled. Select the RIP direction from the drop-down
list box.
BiDir - This interface sends and receives routing information.
In-Only - This interface receives routing information.
Out-Only - This interface sends routing information.
Send Version This field is effective when RIP is enabled. Select the RIP version(s) used for sending
RIP packets. Choices are 1, 2, and 1 and 2.
Receive Version This field is effective when RIP is enabled. Select the RIP version(s) used for receiving
RIP packets. Choices are 1, 2, and 1 and 2.
V2-Broadcast This field is effective when RIP is enabled. Select this to send RIP-2 packets using
subnet broadcasting; otherwise, the USG uses multicasting.
OSPF Setting See Section 10.7 on page 240 for more information about OSPF.
Area Select the area in which this interface belongs. Select None to disable OSPF in this
interface.
Priority Enter the priority (between 0 and 255) of this interface when the area is looking for a
Designated Router (DR) or Backup Designated Router (BDR). The highest-priority
interface identifies the DR, and the second-highest-priority interface identifies the
BDR. Set the priority to zero if the interface can not be the DR or BDR.
Link Cost Enter the cost (between 1 and 65,535) to route packets through this interface.
Passive
Interface Select this to stop forwarding OSPF routing information from the selected interface. As
a result, this interface only receives routing information.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
163
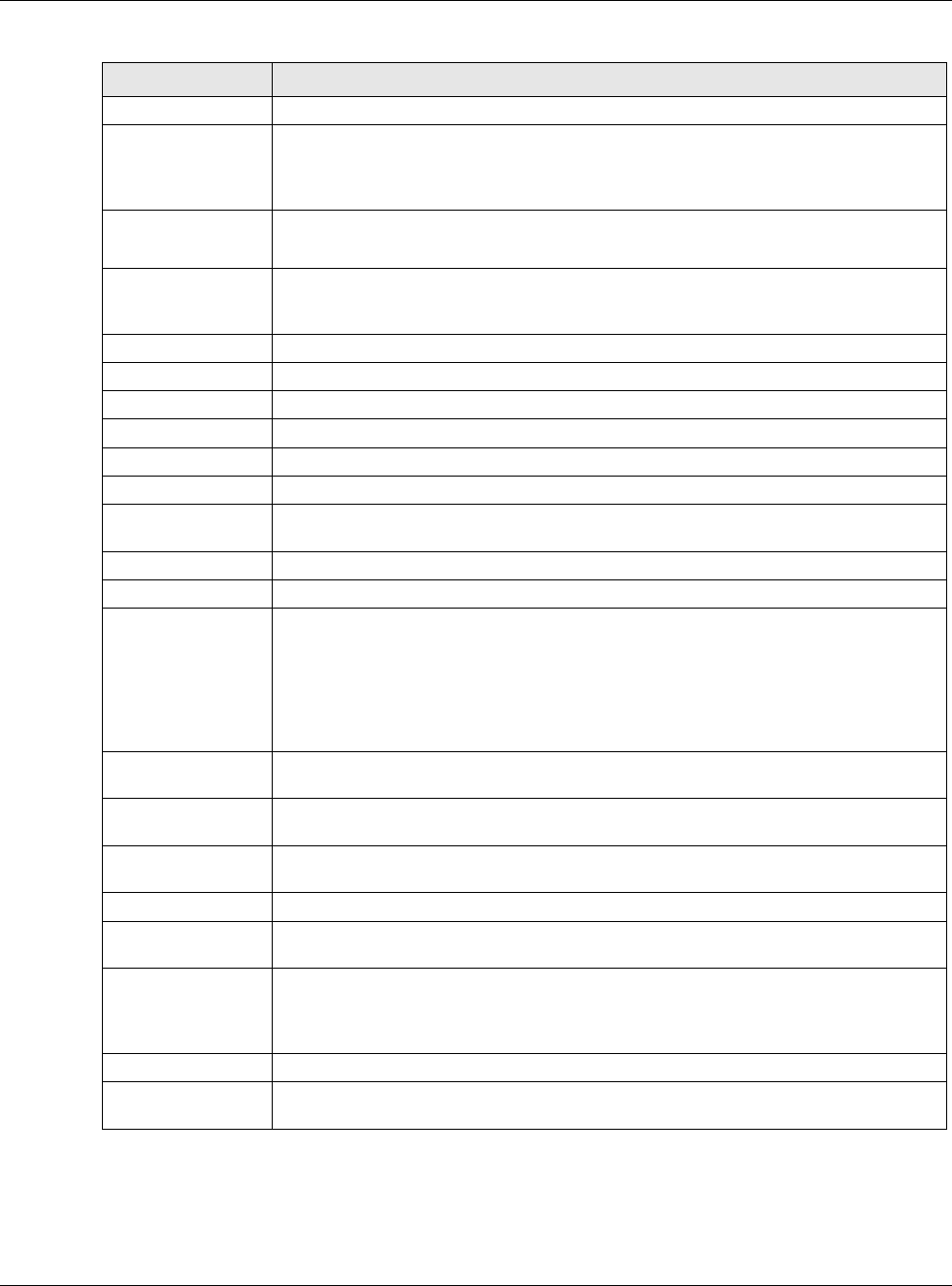
9.3.2 Object References
When a configuration screen includes an Object Reference icon, select a configuration object and
click Object Reference to open the Object References screen. This screen displays which
configuration settings reference the selected object. The fields shown vary with the type of object.
Authentication Select an authentication method, or disable authentication. To exchange OSPF routing
information with peer border routers, you must use the same authentication method
that they use. Choices are:
Same-as-Area - use the default authentication method in the area
None - disable authentication
Text - authenticate OSPF routing information using a plain-text password
MD5 - authenticate OSPF routing information using MD5 encryption
Text
Authentication
Key
This field is available if the Authentication is Text. Type the password for text
authentication. The key can consist of alphanumeric characters and the underscore,
and it can be up to 16 characters long.
MD5
Authentication
ID
This field is available if the Authentication is MD5. Type the ID for MD5
authentication. The ID can be between 1 and 255.
MD5
Authentication
Key
This field is available if the Authentication is MD5. Type the password for MD5
authentication. The password can consist of alphanumeric characters and the
underscore, and it can be up to 16 characters long.
MAC Address
Setting
This section appears when Interface Properties is External or General. Have the
interface use either the factory assigned default MAC address, a manually specified
MAC address, or clone the MAC address of another device or computer.
Use Default MAC
Address Select this option to have the interface use the factory assigned default MAC address.
By default, the USG uses the factory assigned MAC address to identify itself.
Overwrite
Default MAC
Address
Select this option to have the interface use a different MAC address. Either enter the
MAC address in the fields or click Clone by host and enter the IP address of the device
or computer whose MAC you are cloning. Once it is successfully configured, the
address will be copied to the configuration file. It will not change unless you change the
setting or upload a different configuration file.
Related Setting
Configure
PPPoE/PPTP Click PPPoE/PPTP if this interface’s Internet connection uses PPPoE or PPTP.
Configure VLAN Click VLAN if you want to configure a VLAN interface for this Ethernet interface.
Configure WAN
TRUNK Click WAN TRUNK to go to a screen where you can set this interface to be part of a
WAN trunk for load balancing.
Configure Policy
Route Click Policy Route to go to the policy route summary screen where you can manually
associate traffic with this interface.
You must manually configure a policy route to add routing and SNAT settings for an
interface with the Interface Type set to general. You can also configure a policy
route to override the default routing and SNAT behavior for an interface with an
Interface Type of internal or external.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 64 Configuration > Network > Interface > Ethernet > Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
164
Figure 122 Object References
The following table describes labels that can appear in this screen.
9.3.3 Add/Edit DHCPv6 Request/Release Options
When you configure an interface as a DHCPv6 server or client, you can additionally add DHCPv6
request or lease options which have the USG to add more information in the DHCPv6 packets. To
open the screen, click Configuration > Network > Interface > Ethernet > Edit, select
DHCPv6 Server or DHCPv6 Client in the DHCPv6 Setting section, and then click Add in the
DHCPv6 Request Options or DHCPv6 Lease Options table.
Figure 123 Configuration > Network > Interface > Ethernet > Edit > Add DHCPv6 Request/Lease
Options
Table 65 Object References
LABEL DESCRIPTION
Object Name This identifies the object for which the configuration settings that use it are displayed.
Click the object’s name to display the object’s configuration screen in the main window.
# This field is a sequential value, and it is not associated with any entry.
Service This is the type of setting that references the selected object. Click a service’s name to
display the service’s configuration screen in the main window.
Priority If it is applicable, this field lists the referencing configuration item’s position in its list,
otherwise N/A displays.
Name This field identifies the configuration item that references the object.
Description If the referencing configuration item has a description configured, it displays here.
Refresh Click this to update the information in this screen.
Cancel Click Cancel to close the screen.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
165
Select a DHCPv6 request or lease object in the Select one object field and click OK to save it.
Click Cancel to exit without saving the setting.
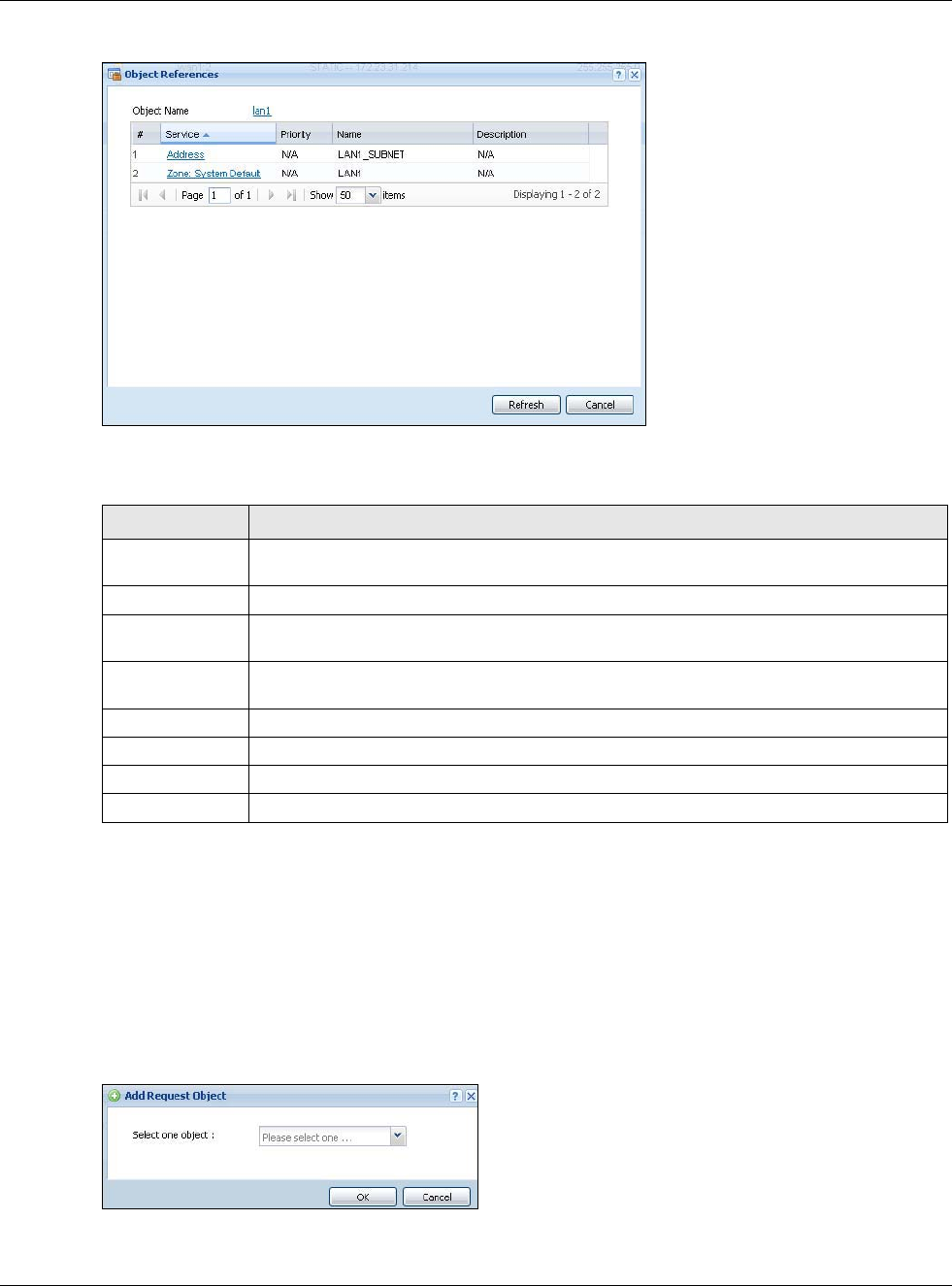
9.3.4 Add/Edit DHCP Extended Options
When you configure an interface as a DHCPv4 server, you can additionally add DHCP extended
options which have the USG to add more information in the DHCP packets. The available fields vary
depending on the DHCP option you select in this screen. To open the screen, click Configuration >
Network > Interface > Ethernet > Edit, select DHCP Server in the DHCP Setting section, and
then click Add or Edit in the Extended Options table.
Figure 124 Configuration > Network > Interface > Ethernet > Edit > Add/Edit Extended Options
The following table describes labels that can appear in this screen.
Table 66 Configuration > Network > Interface > Ethernet > Edit > Add/Edit Extended Options
LABEL DESCRIPTION
Option Select which DHCP option that you want to add in the DHCP packets sent through the
interface. See the next table for more information.
Name This field displays the name of the selected DHCP option. If you selected User Defined in
the Option field, enter a descriptive name to identify the DHCP option. You can enter up
to 16 characters (“a-z”, “A-Z, “0-9”, “-”, and “_”) with no spaces allowed. The first
character must be alphabetical (a-z, A-Z).
Code This field displays the code number of the selected DHCP option. If you selected User
Defined in the Option field, enter a number for the option. This field is mandatory.
Type This is the type of the selected DHCP option. If you selected User Defined in the Option
field, select an appropriate type for the value that you will enter in the next field. Only
advanced users should configure User Defined. Misconfiguration could result in interface
lockout.
Value Enter the value for the selected DHCP option. For example, if you selected TFTP Server
Name (66) and the type is TEXT, enter the DNS domain name of a TFTP server here. This
field is mandatory.
First IP Address,
Second IP
Address, Third IP
Address
If you selected Time Server (4), NTP Server (41), SIP Server (120), CAPWAP AC
(138), or TFTP Server (150), you have to enter at least one IP address of the
corresponding servers in these fields. The servers should be listed in order of your
preference.
First Enterprise
ID, Second
Enterprise ID
If you selected VIVC (124) or VIVS (125), you have to enter at least one vendor’s 32-
bit enterprise number in these fields. An enterprise number is a unique number that
identifies a company.
First Class,
Second Class
If you selected VIVC (124), enter the details of the hardware configuration of the host on
which the client is running, or of industry consortium compliance.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
166
The following table lists the available DHCP extended options (defined in RFCs) on the USG. See
RFCs for more information.
9.4 PPP Interfaces
Use PPPoE/PPTP interfaces to connect to your ISP. This way, you do not have to install or manage
PPPoE/PPTP software on each computer in the network.
First
Information,
Second
Information
If you selected VIVS (125), enter additional information for the corresponding enterprise
number in these fields.
OK Click this to close this screen and update the settings to the previous Edit screen.
Cancel Click Cancel to close the screen.
Table 67 DHCP Extended Options
OPTION NAME CODE DESCRIPTION
Time Offset 2 This option specifies the offset of the client's subnet in seconds from
Coordinated Universal Time (UTC).
Time Server 4 This option specifies a list of Time servers available to the client.
NTP Server 42 This option specifies a list of the NTP servers available to the client by IP
address.
TFTP Server Name 66 This option is used to identify a TFTP server when the “sname” field in the
DHCP header has been used for DHCP options. The minimum length of the
value is 1.
Bootfile 67 This option is used to identify a bootfile when the “file” field in the DHCP
header has been used for DHCP options. The minimum length of the value is
1.
SIP Server 120 This option carries either an IPv4 address or a DNS domain name to be used
by the SIP client to locate a SIP server.
VIVC 124 Vendor-Identifying Vendor Class option
A DHCP client may use this option to unambiguously identify the vendor that
manufactured the hardware on which the client is running, the software in
use, or an industry consortium to which the vendor belongs.
VIVS 125 Vendor-Identifying Vendor-Specific option
DHCP clients and servers may use this option to exchange vendor-specific
information.
CAPWAP AC 138 CAPWAP Access Controller addresses option
The Control And Provisioning of Wireless Access Points Protocol allows a
Wireless Termination Point (WTP) to use DHCP to discover the Access
Controllers to which it is to connect. This option carries a list of IPv4
addresses indicating one or more CAPWAP ACs available to the WTP.
TFTP Server 150 The option contains one or more IPv4 addresses that the client may use. The
current use of this option is for downloading configuration from a VoIP server
via TFTP; however, the option may be used for purposes other than
contacting a VoIP configuration server.
Table 66 Configuration > Network > Interface > Ethernet > Edit > Add/Edit Extended Options
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
167
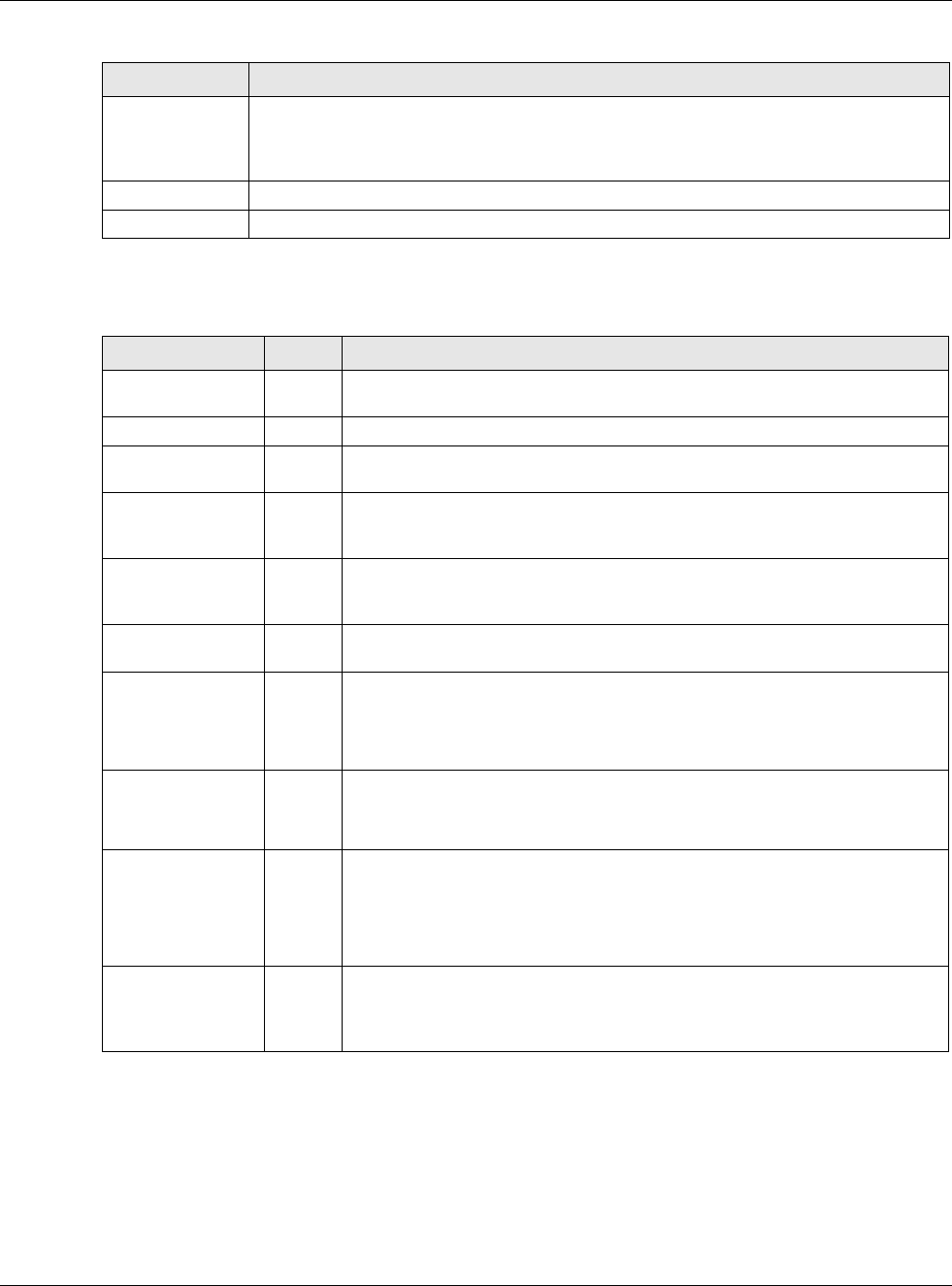
Figure 125 Example: PPPoE/PPTP Interfaces
PPPoE/PPTP interfaces are similar to other interfaces in some ways. They have an IP address,
subnet mask, and gateway used to make routing decisions; they restrict bandwidth and packet
size; and they can verify the gateway is available. There are two main differences between PPPoE/
PPTP interfaces and other interfaces.
• You must also configure an ISP account object for the PPPoE/PPTP interface to use.
Each ISP account specifies the protocol (PPPoE or PPTP), as well as your ISP account information.
If you change ISPs later, you only have to create a new ISP account, not a new PPPoE/PPTP
interface. You should not have to change any network policies.
• You do not set up the subnet mask or gateway.
PPPoE/PPTP interfaces are interfaces between the USG and only one computer. Therefore, the
subnet mask is always 255.255.255.255. In addition, the USG always treats the ISP as a
gateway.
9.4.1 PPP Interface Summary
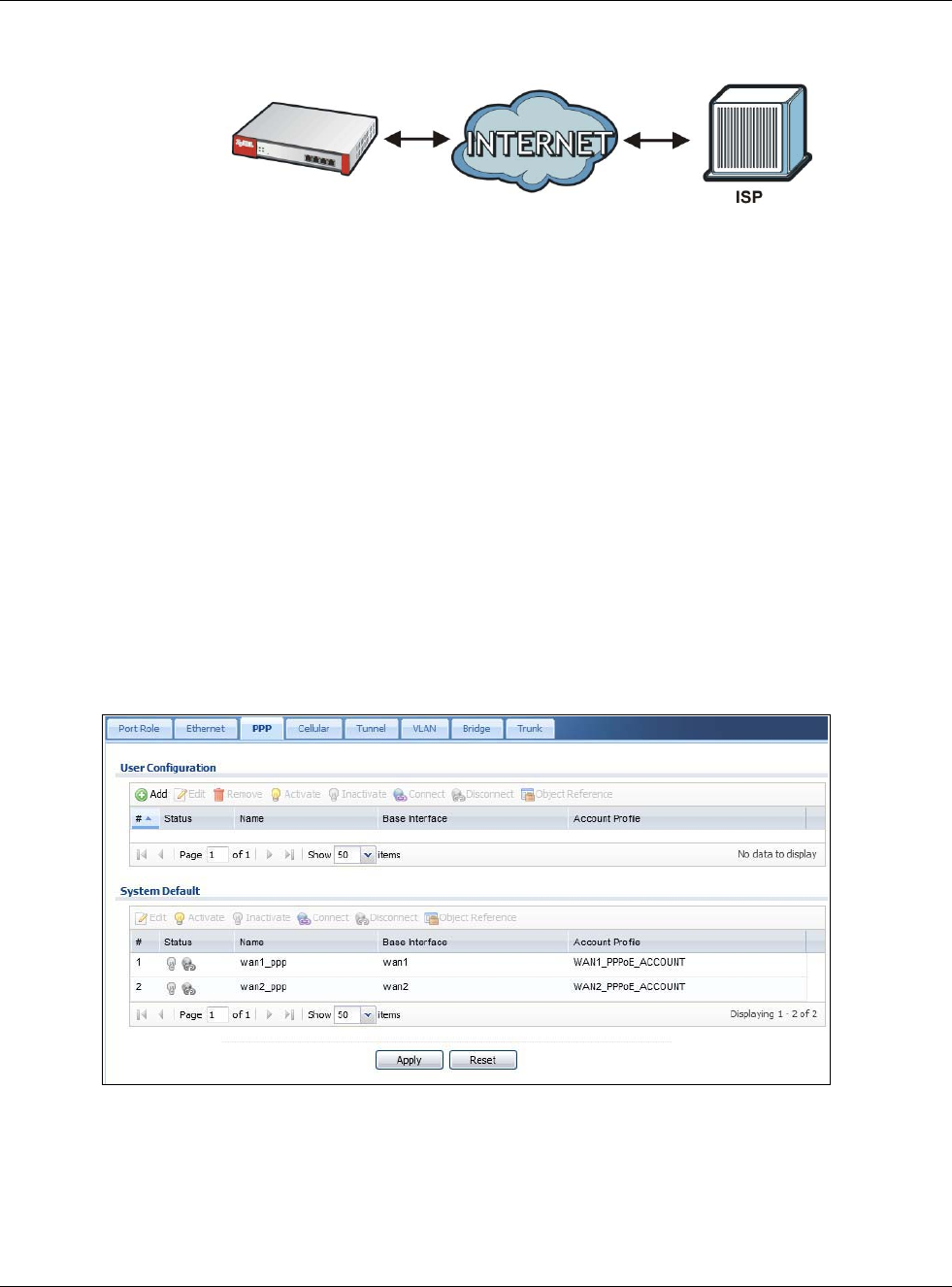
This screen lists every PPPoE/PPTP interface. To access this screen, click Configuration >
Network > Interface > PPP.
Figure 126 Configuration > Network > Interface > PPP

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
168
Each field is described in the table below.
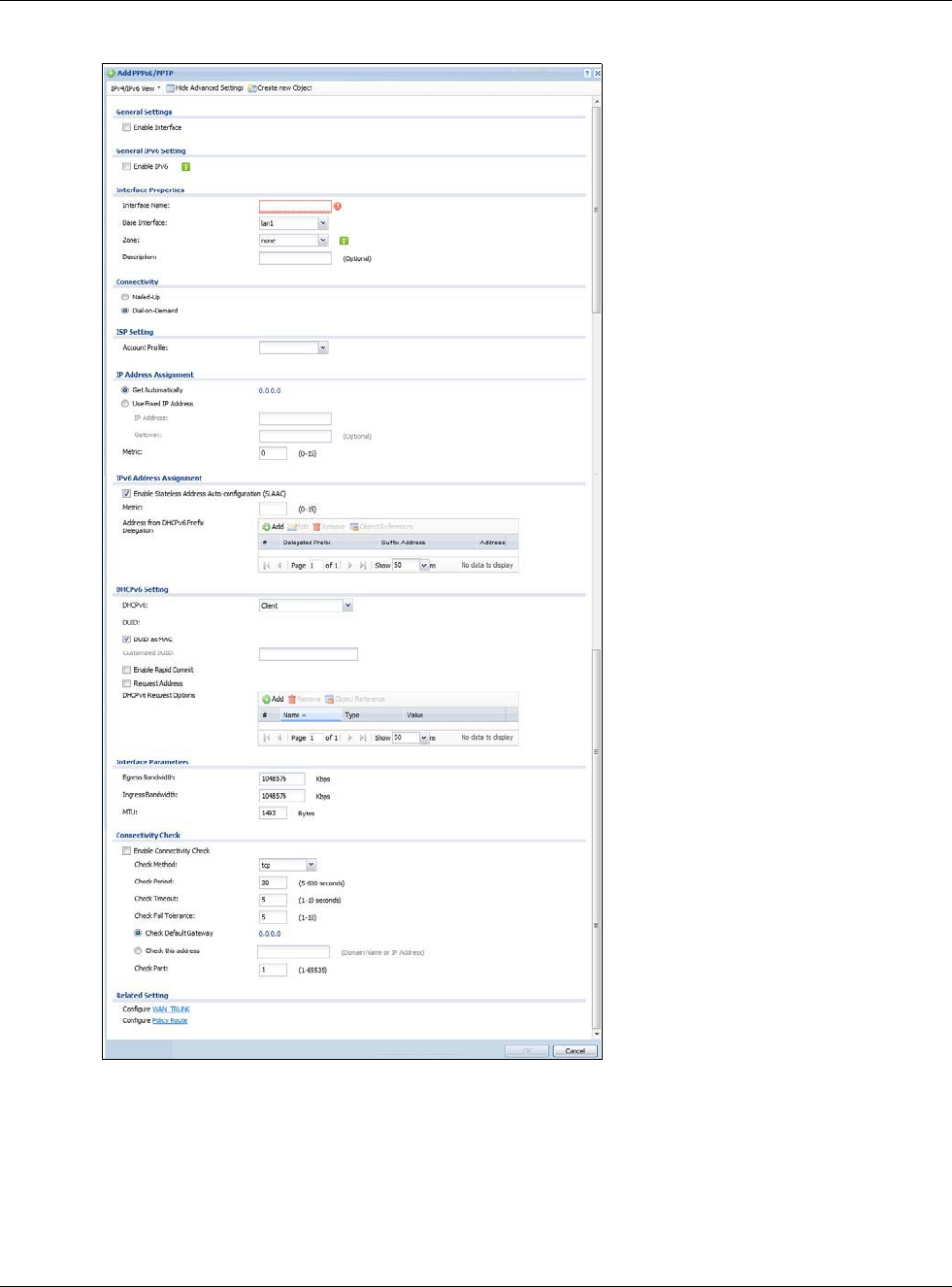
9.4.2 PPP Interface Add or Edit
Note: You have to set up an ISP account before you create a PPPoE/PPTP interface.
This screen lets you configure a PPPoE or PPTP interface. If you enabled IPv6 in the Configuration
> System > IPv6 screen, you can also configure PPP interfaces used for your IPv6 networks on
this screen. To access this screen, click the Add icon or an Edit icon in the PPP Interface screen.
Table 68 Configuration > Network > Interface > PPP
LABEL DESCRIPTION
User Configuration /
System Default
The USG comes with the (non-removable) System Default PPP interfaces pre-
configured. You can create (and delete) User Configuration PPP interfaces. System
Default PPP interfaces vary by model.
Add Click this to create a new user-configured PPP interface.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove a user-configured PPP interface, select it and click Remove. The USG
confirms you want to remove it before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Connect To connect an interface, select it and click Connect. You might use this in testing the
interface or to manually establish the connection for a Dial-on-Demand PPPoE/PPTP
interface.
Disconnect To disconnect an interface, select it and click Disconnect. You might use this in testing
the interface.
Object References Select an entry and click Object Reference to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
#This field is a sequential value, and it is not associated with any interface.
Status The activate (light bulb) icon is lit when the entry is active and dimmed when the entry
is inactive.
The connect icon is lit when the interface is connected and dimmed when it is
disconnected.
Name This field displays the name of the interface.
Base Interface This field displays the interface on the top of which the PPPoE/PPTP interface is.
Account Profile This field displays the ISP account used by this PPPoE/PPTP interface.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
169
Figure 127 Configuration > Network > Interface > PPP > Add
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
170
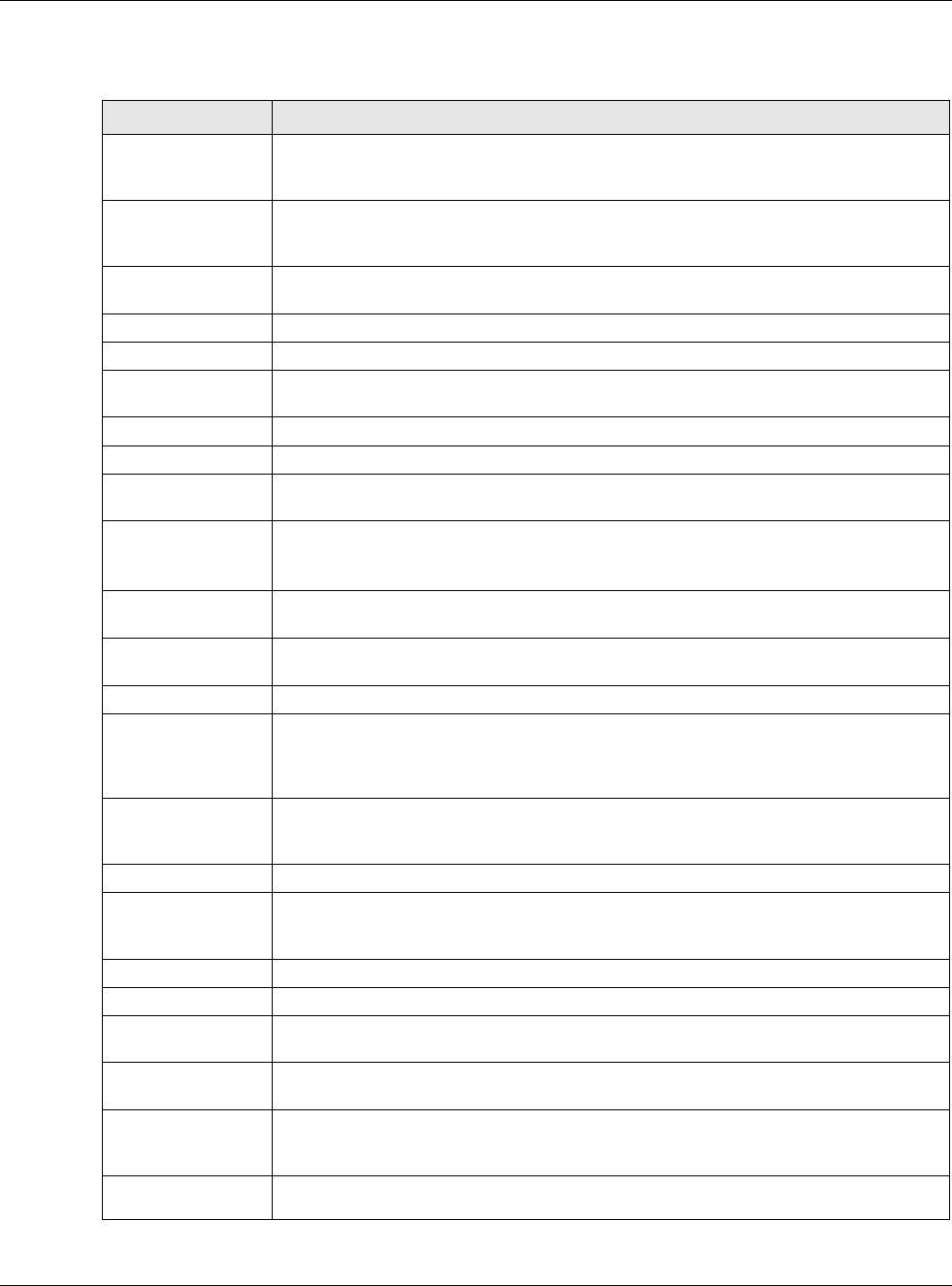
Each field is explained in the following table.
Table 69 Configuration > Network > Interface > PPP > Add
LABEL DESCRIPTION
IPv4/IPv6 View /
IPv4 View / IPv6
View
Use this button to display both IPv4 and IPv6, IPv4-only, or IPv6-only configuration
fields.
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Create New Object Click this button to create an ISP Account or a DHCPv6 request object that you may
use for the ISP or DHCPv6 settings in this screen.
General Settings
Enable Interface Select this to enable this interface. Clear this to disable this interface.
General IPv6
Setting
Enable IPv6 Select this to enable IPv6 on this interface. Otherwise, clear this to disable it.
Interface Properties
Interface Name Specify a name for the interface. It can use alphanumeric characters, hyphens, and
underscores, and it can be up to 11 characters long.
Base Interface Select the interface upon which this PPP interface is built.
Note: Multiple PPP interfaces can use the same base interface.
Zone Select the zone to which this PPP interface belongs. The zone determines the security
settings the USG uses for the interface.
Description Enter a description of this interface. It is not used elsewhere. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
Connectivity
Nailed-Up Select this if the PPPoE/PPTP connection should always be up. Clear this to have the
USG establish the PPPoE/PPTP connection only when there is traffic. You might use this
option if a lot of traffic needs to go through the interface or it does not cost extra to
keep the connection up all the time.
Dial-on-Demand Select this to have the USG establish the PPPoE/PPTP connection only when there is
traffic. You might use this option if there is little traffic through the interface or if it
costs money to keep the connection available.
ISP Setting
Account Profile Select the ISP account that this PPPoE/PPTP interface uses. The drop-down box lists
ISP accounts by name. Use Create new Object if you need to configure a new ISP
account (see Chapter 29 on page 528 for details).
Protocol This field is read-only. It displays the protocol specified in the ISP account.
User Name This field is read-only. It displays the user name for the ISP account.
Service Name This field is read-only. It displays the PPPoE service name specified in the ISP account.
This field is blank if the ISP account uses PPTP.
IP Address
Assignment
Click Show Advanced Settings to display more settings. Click Hide Advanced
Settings to display fewer settings.
Get
Automatically Select this if this interface is a DHCP client. In this case, the DHCP server configures
the IP address automatically. The subnet mask and gateway are always defined
automatically in PPPoE/PPTP interfaces.
Use Fixed IP
Address Select this if you want to specify the IP address manually.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
171
IP Address This field is enabled if you select Use Fixed IP Address.
Enter the IP address for this interface.
Metric Enter the priority of the gateway (the ISP) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
IPv6 Address
Assignment
These IP address fields configure an IPv6 IP address on the interface itself.
Enable Stateless
Address Auto-
configuration
(SLAAC)
Select this to enable IPv6 stateless auto-configuration on this interface. The interface
will generate an IPv6 IP address itself from a prefix obtained from an IPv6 router in the
network.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Address from
DHCPv6 Prefix
Delegation
Use this table to have the USG obtain an IPv6 prefix from the ISP or a connected uplink
router for an internal network, such as the LAN or DMZ. You have to also enter a suffix
address which is appended to the delegated prefix to form an address for this interface.
See Prefix Delegation on page 144 for more information.
To use prefix delegation, you must:
• Create at least one DHCPv6 request object before configuring this table.
• The external interface must be a DHCPv6 client. You must configure the DHCPv6
request options using a DHCPv6 request object with the type of prefix-delegation.
• Assign the prefix delegation to an internal interface and enable router
advertisement on that interface.
Add Click this to create an entry.
Edit Select an entry and click this to change the settings.
Remove Select an entry and click this to delete it from this table.
# This field is a sequential value, and it is not associated with any entry.
Delegated
Prefix Select the DHCPv6 request object to use from the drop-down list.
Suffix
Address Enter the ending part of the IPv6 address, a slash (/), and the prefix length. The USG
will append it to the delegated prefix.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to configure
an IP address of 2003:1234:5678:1111::1/128 for this interface, then enter
::1111:0:0:0:1/128 in this field.
Address This field displays the combined IPv6 IP address for this interface.
Note: This field displays the combined address after you click OK and reopen this
screen.
DHCPv6 Setting
DHCPv6 Select Client to obtain an IP address and DNS information from the service provider
for the interface. Otherwise, select N/A to diable the function.
DUID This field displays the DHCP Unique IDentifier (DUID) of the interface, which is unique
and used for identification purposes when the interface is exchanging DHCPv6
messages with others. See DHCPv6 on page 145 for more information.
DUID as MAC Select this if you want the DUID is generated from the interface’s default MAC address.
Customized
DUID If you want to use a customized DUID, enter it here for the interface.
Table 69 Configuration > Network > Interface > PPP > Add (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
172
Enable Rapid
Commit Select this to shorten the DHCPv6 message exchange process from four to two steps.
This function helps reduce heavy network traffic load.
Note: Make sure you also enable this option in the DHCPv6 clients to make rapid commit
work.
Request Address Select this to get an IPv6 IP address for this interface from the DHCP server. Clear this
to not get any IP address information through DHCPv6.
DHCPv6 Request
Options Use this section to configure DHCPv6 request settings that determine what additional
information to get from the DHCPv6 server.
Add Click this to create an entry in this table. See Section 9.3.4 on page 165 for more
information.
Remove Select an entry and click this to delete it from this table.
Object
Reference Select an entry and click Object Reference to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
# This field is a sequential value, and it is not associated with any entry.
Name This field displays the name of the DHCPv6 request object.
Type This field displays the type of the object.
Value This field displays the IPv6 prefix that the USG will advertise to its clients.
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send through
the interface to the network. Allowed values are 0 - 1048576.
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
MTU Maximum Transmission Unit. Type the maximum size of each data packet, in bytes,
that can move through this interface. If a larger packet arrives, the USG divides it into
smaller fragments. Allowed values are 576 - 1492. Usually, this value is 1492.
Connectivity Check The interface can regularly check the connection to the gateway you specified to make
sure it is still available. You specify how often the interface checks the connection, how
long to wait for a response before the attempt is a failure, and how many consecutive
failures are required before the USG stops routing to the gateway. The USG resumes
routing to the gateway the first time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance Enter the number of consecutive failures before the USG stops routing through the
gateway.
Check Default
Gateway Select this to use the default gateway for the connectivity check.
Check this
address Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
Table 69 Configuration > Network > Interface > PPP > Add (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
173
9.5 Cellular Configuration Screen
Mobile broadband is a digital, packet-switched wireless technology. Bandwidth usage is optimized
as multiple users share the same channel and bandwidth is only allocated to users when they send
data. It allows fast transfer of voice and non-voice data and provides broadband Internet access to
mobile devices.
Note: The actual data rate you obtain varies depending on the mobile broadband device
you use, the signal strength to the service provider’s base station, and so on.
You can configure how the USG’s mobile broadband device connects to a network (refer to Section
9.5.1 on page 176):
• You can set the mobile broadband device to connect only to the home network, which is the
network to which you are originally subscribed.
• You can set the mobile broadband device to connect to other networks if the signal strength of
the home network is too low or it is unavailable.
3G
3G (Third Generation) is a digital, packet-switched wireless technology. Bandwidth usage is
optimized as multiple users share the same channel and bandwidth is only allocated to users when
they send data. It allows fast transfer of voice and non-voice data and provides broadband Internet
access to mobile devices.
4G
4G is the fourth generation of the mobile telecommunications technology and a successor of 3G.
Both the WiMAX and Long Term Evolution (LTE) standards are the 4G candidate systems. 4G only
supports all-IP-based packet-switched telephony services and is required to offer gigabit speed
access.
Note: Note: The actual data rate you obtain varies depending on your mobile
environment. The environmental factors may include the number of mobile devices
which are currently connected to the mobile network, the signal strength to the
mobile network, and so on.
Check Port This field only displays when you set the Check Method to tcp. Specify the port
number to use for a TCP connectivity check.
Related Setting
Configure WAN
TRUNK Click WAN TRUNK to go to a screen where you can configure the interface as part of a
WAN trunk for load balancing.
Policy Route Click Policy Route to go to the screen where you can manually configure a policy
route to associate traffic with this interface.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 69 Configuration > Network > Interface > PPP > Add (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
174
See the following table for a comparison between 2G, 2.5G, 2.75G, 3G and 4G wireless
technologies.
To change your mobile broadband WAN settings, click Configuration > Network > Interface >
Cellular.
Note: Install (or connect) a compatible mobile broadband USB device to use a cellular
connection.
Note: The WAN IP addresses of a USG with multiple WAN interfaces must be on different
subnets.
Table 70 2G, 2.5G, 2.75G, 3G, 3.5G and 4G Wireless Technologies
NAME TYPE MOBILE PHONE AND DATA STANDARDS DATA
SPEED
GSM-BASED CDMA-BASED
2G Circuit-
switched
GSM (Global System for Mobile
Communications), Personal Handy-
phone System (PHS), etc.
Interim Standard 95 (IS-95), the first CDMA-
based digital cellular standard pioneered by
Qualcomm. The brand name for IS-95 is
cdmaOne. IS-95 is also known as TIA-EIA-95.
Slow
2.5G Packet-
switched
GPRS (General Packet Radio Services),
High-Speed Circuit-Switched Data
(HSCSD), etc.
CDMA2000 is a hybrid 2.5G / 3G protocol of
mobile telecommunications standards that use
CDMA, a multiple access scheme for digital radio.
CDMA2000 1xRTT (1 times Radio Transmission
Technology) is the core CDMA2000 wireless air
interface standard. It is also known as 1x, 1xRTT,
or IS-2000 and considered to be a 2.5G or 2.75G
technology.
2.75G Packet-
switched
Enhanced Data rates for GSM Evolution
(EDGE), Enhanced GPRS (EGPRS), etc.
3G Packet-
switched
UMTS (Universal Mobile
Telecommunications System), a third-
generation (3G) wireless standard
defined in ITU specification, is
sometimes marketed as 3GSM. The
UMTS uses GSM infrastructures and W-
CDMA (Wideband Code Division
Multiple Access) as the air interface.
The International Telecommunication
Union (ITU) is an international
organization within which governments
and the private sector coordinate
global telecom networks and services.
CDMA2000 EV-DO (Evolution-Data Optimized,
originally 1x Evolution-Data Only), also referred
to as EV-DO, EVDO, or just EV, is an evolution of
CDMA2000 1xRTT and enables high-speed
wireless connectivity. It is also denoted as IS-856
or High Data Rate (HDR).
3.5G Packet-
switched
HSDPA (High-Speed Downlink Packet
Access) is a mobile telephony protocol,
used for UMTS-based 3G networks and
allows for higher data transfer speeds.
4G/LTE Packet-
switched
The LTE (Long Term Evolution)
standard is based on the GSM and
UMTS network technologies. Fast
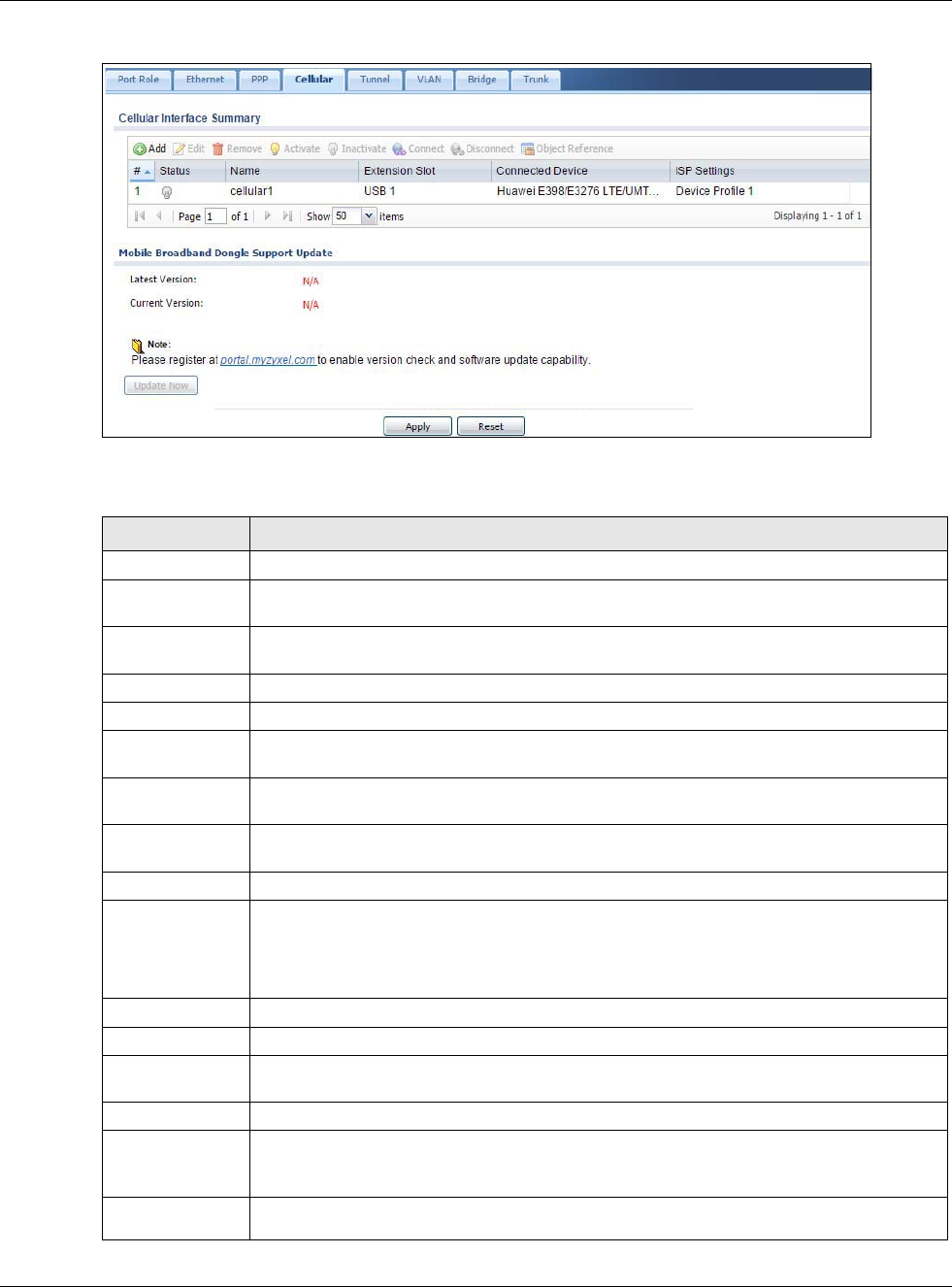
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
175
Figure 128 Configuration > Network > Interface > Cellular
The following table describes the labels in this screen.
Table 71 Configuration > Network > Interface > Cellular
LABEL DESCRIPTION
Add Click this to create a new cellular interface.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to remove it
before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Connect To connect an interface, select it and click Connect. You might use this in testing the
interface or to manually establish the connection.
Disconnect To disconnect an interface, select it and click Disconnect. You might use this in testing
the interface.
Object
References
Select an entry and click Object Reference to open a screen that shows which settings
use the entry. See Section 9.3.2 on page 163 for an example.
# This field is a sequential value, and it is not associated with any interface.
Status The activate (light bulb) icon is lit when the entry is active and dimmed when the entry is
inactive.
The connect icon is lit when the interface is connected and dimmed when it is
disconnected.
Name This field displays the name of the interface.
Extension Slot This field displays where the entry’s cellular card is located.
Connected
Device
This field displays the name of the cellular card.
ISP Settings This field displays the profile of ISP settings that this cellular interface is set to use.
Mobile
Broadband
Dongle Support
You should have registered your USG at myzyxel.com. Myzyxel.com hosts a list of
supported mobile broadband dongle devices. You should have an Internet connection to
access this website.
Latest
Version This displays the latest supported mobile broadband dongle list version number.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
176
9.5.1 Cellular Choose Slot
To change your mobile broadband settings, click Configuration > Network > Interface >
Cellular > Add (or Edit). In the pop-up window that displays, select the slot that contains the
mobile broadband device, then the Add Cellular configuration screen displays.
9.5.2 Add / Edit Cellular Configuration
This screen displays after you select the slot that contains the mobile broadband device in the
previous pop-up window.
Current
Version This displays the currently supported (by the USG) mobile broadband dongle list version
number.
Update Now If the latest version number is greater than the current version number, then click this
button to download the latest list of supported mobile broadband dongle devices to the
USG.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
Table 71 Configuration > Network > Interface > Cellular (continued)
LABEL DESCRIPTION
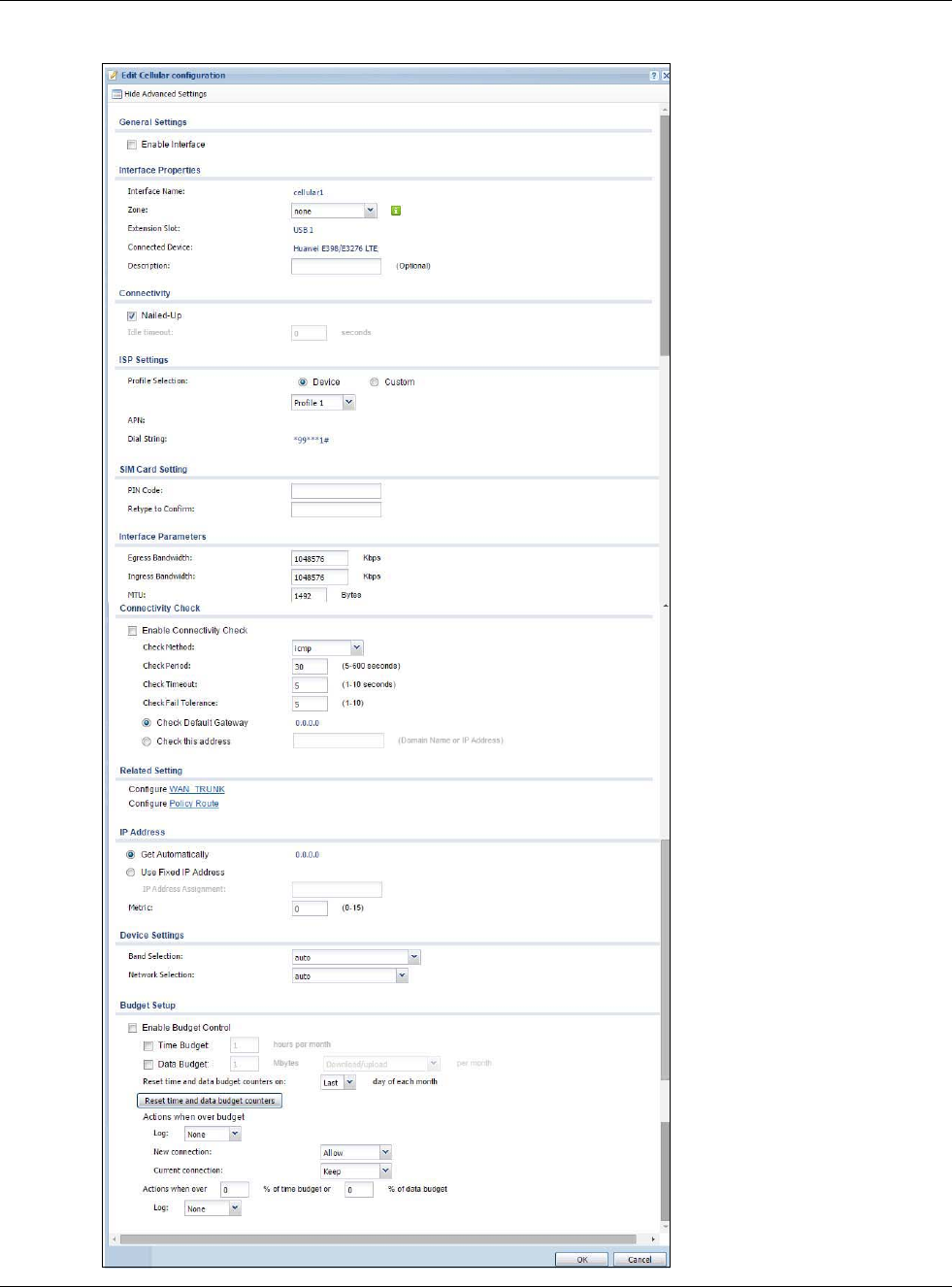
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
177
Figure 129 Configuration > Network > Interface > Cellular > Add / Edit
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
178
The following table describes the labels in this screen.
Table 72 Configuration > Network > Interface > Cellular > Add / Edit
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
General Settings
Enable Interface Select this option to turn on this interface.
Interface Properties
Interface Name Select a name for the interface.
Zone Select the zone to which you want the cellular interface to belong. The zone
determines the security settings the USG uses for the interface.
Extension Slot This is the USB slot that you are configuring for use with a mobile broadband card.
Connected
Device This displays the manufacturer and model name of your mobile broadband card if you
inserted one in the USG. Otherwise, it displays none.
Description Enter a description of this interface. It is not used elsewhere. You can use
alphanumeric and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters
long.
Connectivity
Nailed-Up Select this if the connection should always be up. Clear this to have the USG to
establish the connection only when there is traffic. You might not nail up the
connection if there is little traffic through the interface or if it costs money to keep the
connection available.
Idle timeout This value specifies the time in seconds (0~360) that elapses before the USG
automatically disconnects from the ISP’s server. Zero disables the idle timeout.
ISP Settings
Profile Selection Select Device to use one of the mobile broadband device’s profiles of device settings.
Then select the profile (use Profile 1 unless your ISP instructed you to do otherwise).
Select Custom to configure your device settings yourself.
APN This field is read-only if you selected Device in the profile selection. Select Custom in
the profile selection to be able to manually input the APN (Access Point Name)
provided by your service provider. This field applies with a GSM or HSDPA mobile
broadband card. Enter the APN from your service provider. Connections with different
APNs may provide different services (such as Internet access or MMS (Multi-Media
Messaging Service)) and charge method.
You can enter up to 63 ASCII printable characters. Spaces are allowed.
Dial String Enter the dial string if your ISP provides a string, which would include the APN, to
initialize the mobile broadband card.
You can enter up to 63 ASCII printable characters. Spaces are allowed.
This field is available only when you insert a GSM mobile broadband card.
Authentication
Type The USG supports PAP (Password Authentication Protocol) and CHAP (Challenge
Handshake Authentication Protocol). CHAP is more secure than PAP; however, PAP is
readily available on more platforms.
Use the drop-down list box to select an authentication protocol for outgoing calls.
Options are:
None: No authentication for outgoing calls.
CHAP - Your USG accepts CHAP requests only.
PAP - Your USG accepts PAP requests only.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
179
User Name This field displays when you select an authentication type other than None. This field
is read-only if you selected Device in the profile selection. If this field is configurable,
enter the user name for this mobile broadband card exactly as the service provider
gave it to you.
You can use 1 ~ 64 alphanumeric and #:%-_@$./ characters. The first character must
be alphanumeric or -_@$./. Spaces are not allowed.
Password This field displays when you select an authentication type other than None. This field
is read-only if you selected Device in the profile selection and the password is included
in the mobile broadband card’s profile. If this field is configurable, enter the password
for this SIM card exactly as the service provider gave it to you.
You can use 0 ~ 63 alphanumeric and `~!@#$%^&*()_-+={}|;:'<,>./ characters.
Spaces are not allowed.
Retype to
Confirm This field displays when you select an authentication type other than None. This field
is read-only if you selected Device in the profile selection and the password is included
in the mobile broadband card’s profile. If this field is configurable, re-enter the
password for this SIM card exactly as the service provider gave it to you.
SIM Card Setting
PIN Code This field displays with a GSM or HSDPA mobile broadband card. A PIN (Personal
Identification Number) code is a key to a mobile broadband card. Without the PIN
code, you cannot use the mobile broadband card.
Enter the 4-digit PIN code (0000 for example) provided by your ISP. If you enter the
PIN code incorrectly, the mobile broadband card may be blocked by your ISP and you
cannot use the account to access the Internet.
If your ISP disabled PIN code authentication, enter an arbitrary number.
Retype to
Confirm Type the PIN code again to confirm it.
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send
through the interface to the network. Allowed values are 0 - 1048576. This setting is
used in WAN load balancing and bandwidth management.
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
MTU Maximum Transmission Unit. Type the maximum size of each data packet, in bytes,
that can move through this interface. If a larger packet arrives, the USG divides it into
smaller fragments. Allowed values are 576 - 1492. Usually, this value is 1492.
Connectivity Check The interface can regularly check the connection to the gateway you specified to make
sure it is still available. You specify how often the interface checks the connection, how
long to wait for a response before the attempt is a failure, and how many consecutive
failures are required before the USG stops routing to the gateway. The USG resumes
routing to the gateway the first time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Table 72 Configuration > Network > Interface > Cellular > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
180
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance Enter the number of consecutive failures before the USG stops routing through the
gateway.
Check Default
Gateway Select this to use the default gateway for the connectivity check.
Check this
address Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
Check Port This field only displays when you set the Check Method to tcp. Specify the port
number to use for a TCP connectivity check.
Related Setting
Configure WAN
TRUNK Click WAN TRUNK to go to a screen where you can configure the interface as part of
a WAN trunk for load balancing.
Configure Policy
Route Click Policy Route to go to the policy route summary screen where you can configure
a policy route to override the default routing and SNAT behavior for the interface.
IP Address
Assignment
Get
Automatically Select this option If your ISP did not assign you a fixed IP address. This is the default
selection.
Use Fixed IP
Address Select this option If the ISP assigned a fixed IP address.
IP Address
Assignment Enter the cellular interface’s WAN IP address in this field if you selected Use Fixed IP
Address.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Device Settings
Band Selection This field appears if you selected a mobile broadband device that allows you to select
the type of network to use. Select the type of mobile broadband service for your
mobile broadband connection. If you are unsure what to select, check with your mobile
broadband service provider to find the mobile broadband service available to you in
your region.
Select auto to have the card connect to an available network. Choose this option if you
do not know what networks are available.
You may want to manually specify the type of network to use if you are charged
differently for different types of network or you only have one type of network
available to you.
Select GPRS / EDGE (GSM) only to have this interface only use a 2.5G or 2.75G
network (respectively). If you only have a GSM network available to you, you may
want to select this so the USG does not spend time looking for a WCDMA network.
Select UMTS / HSDPA (WCDMA) only to have this interface only use a 3G or 3.5G
network (respectively). You may want to do this if you want to make sure the interface
does not use the GSM network.
Select LTE only to have this interface only use a 4G LTE network. This option only
appears when a USB dongle for 4G technology is inserted.
Table 72 Configuration > Network > Interface > Cellular > Add / Edit (continued)
LABEL DESCRIPTION
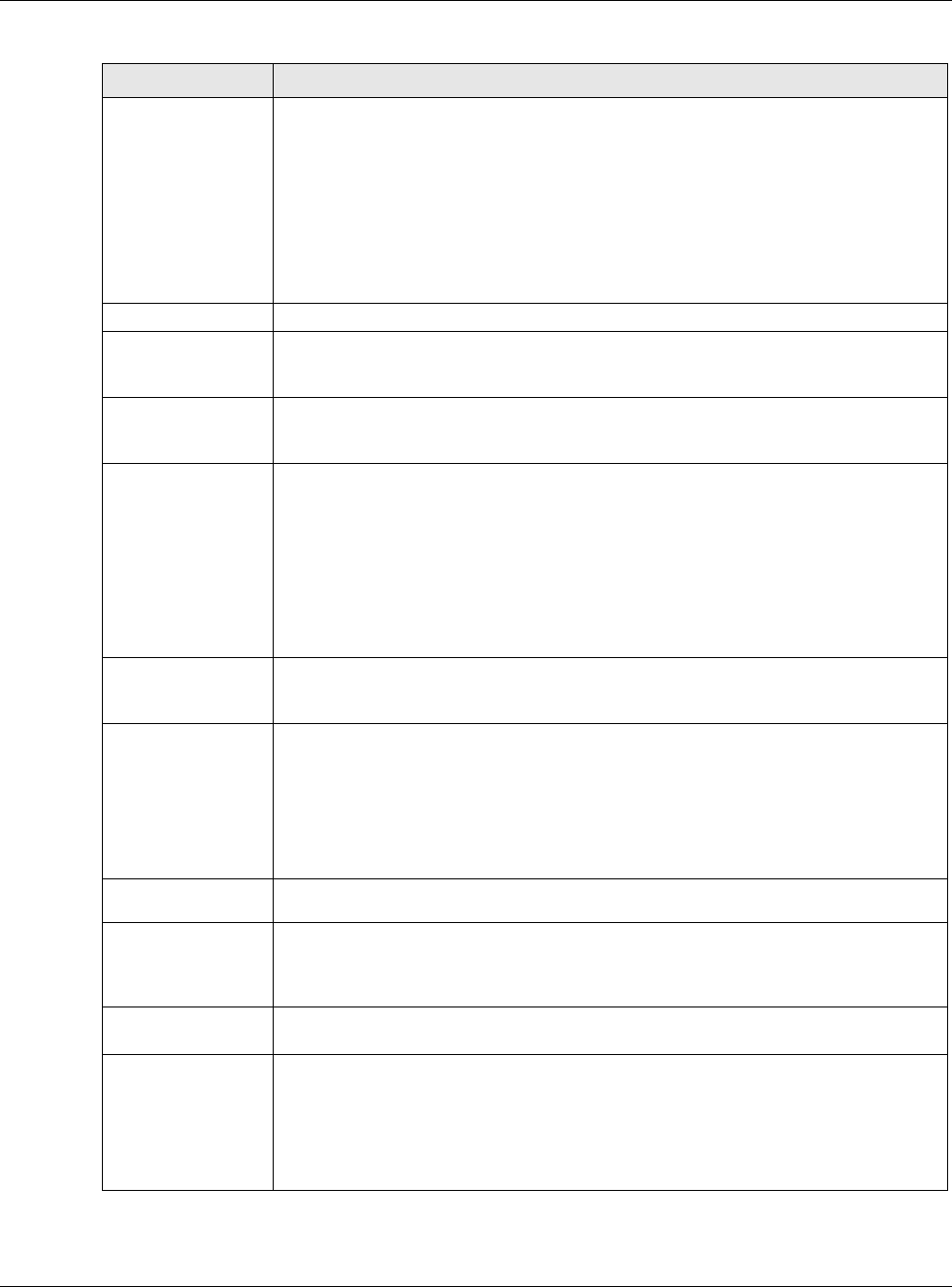
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
181
Network
Selection Home network is the network to which you are originally subscribed.
Select Home to have the mobile broadband device connect only to the home network.
If the home network is down, the USG’s mobile broadband Internet connection is also
unavailable.
Select Auto (Default) to allow the mobile broadband device to connect to a network to
which you are not subscribed when necessary, for example when the home network is
down or another mobile broadband base station's signal is stronger. This is
recommended if you need continuous Internet connectivity. If you select this, you may
be charged using the rate of a different network.
Budget Setup
Enable Budget
Control Select this to set a monthly limit for the user account of the installed mobile broadband
card. You can set a limit on the total traffic and/or call time. The USG takes the actions
you specified when a limit is exceeded during the month.
Time Budget Select this and specify the amount of time (in hours) that the mobile broadband
connection can be used within one month. If you change the value after you configure
and enable budget control, the USG resets the statistics.
Data Budget Select this and specify how much downstream and/or upstream data (in Mega bytes)
can be transmitted via the mobile broadband connection within one month.
Select Download to set a limit on the downstream traffic (from the ISP to the USG).
Select Upload to set a limit on the upstream traffic (from the USG to the ISP).
Select Download/Upload to set a limit on the total traffic in both directions.
If you change the value after you configure and enable budget control, the USG resets
the statistics.
Reset time and
data budget
counters on
Select the date on which the USG resets the budget every month. If the date you
selected is not available in a month, such as 30th or 31st, the USG resets the budget
on the last day of the month.
Reset time and
data budget
counters
This button is available only when you enable budget control in this screen.
Click this button to reset the time and data budgets immediately. The count starts over
with the mobile broadband connection’s full configured monthly time and data
budgets. This does not affect the normal monthly budget restart; so if you configured
the time and data budget counters to reset on the second day of the month and you
use this button on the first, the time and data budget counters will still reset on the
second.
Actions when
over budget Specify the actions the USG takes when the time or data limit is exceeded.
Log Select None to not create a log, Log to create a log, or Log-alert to create an alert
log. If you select Log or Log-alert you can also select recurring every to have the
USG send a log or alert for this event periodically. Specify how often (from 1 to 65535
minutes) to send the log or alert.
New connection Select Allow to permit new mobile broadband connections or Disallow to drop/block
new mobile broadband connections.
Current
connection Select Keep to maintain an existing mobile broadband connection or Drop to
disconnect it. You cannot set New connection to Allow and Current connection to
Drop at the same time.
If you set New connection to Disallow and Current connection to Keep, the USG
allows you to transmit data using the current connection, but you cannot build a new
connection if the existing connection is disconnected.
Table 72 Configuration > Network > Interface > Cellular > Add / Edit (continued)
LABEL DESCRIPTION
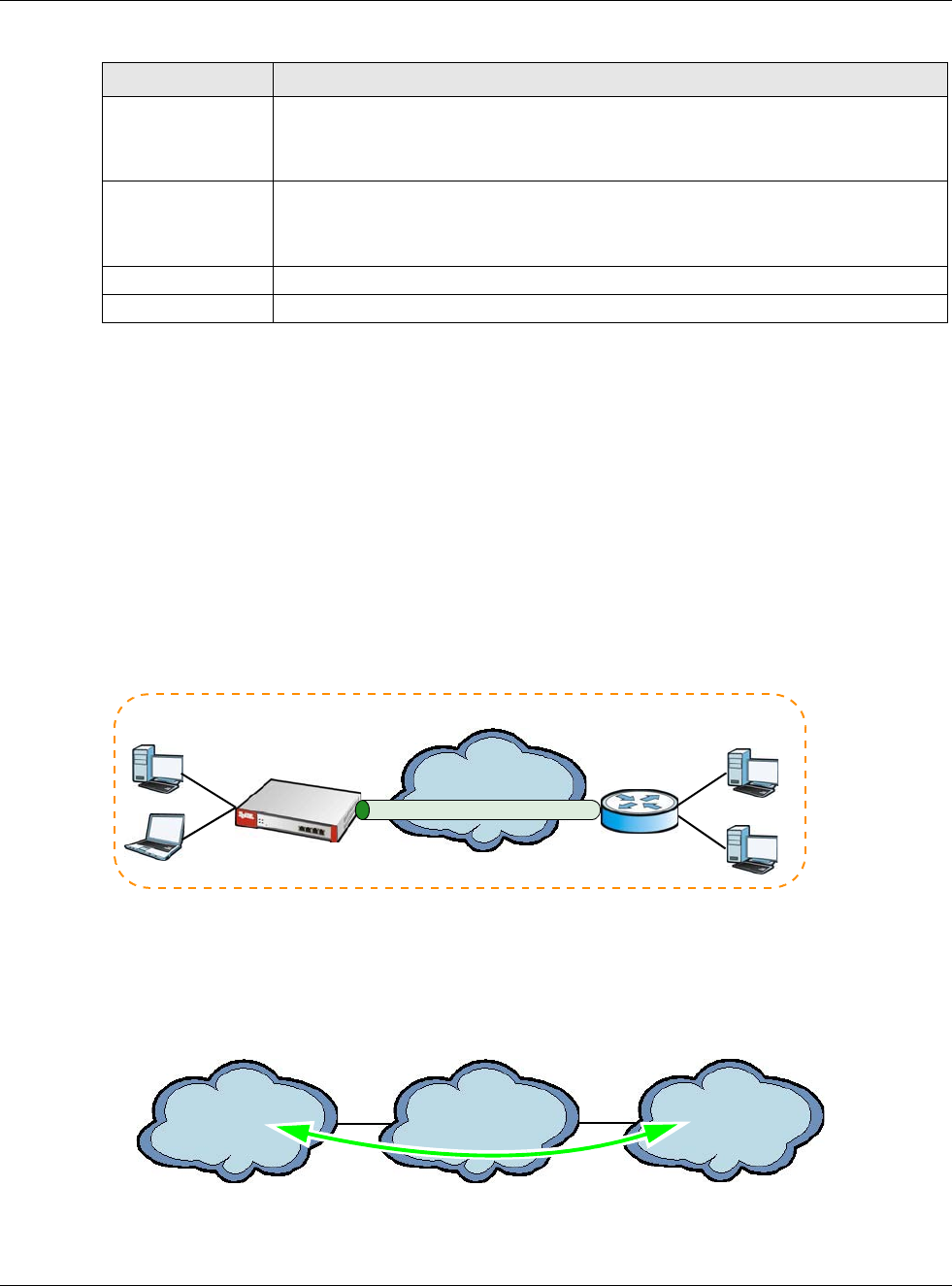
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
182
9.6 Tunnel Interfaces
The USG uses tunnel interfaces in Generic Routing Encapsulation (GRE), IPv6 in IPv4, and 6to4
tunnels.
GRE Tunneling
GRE tunnels encapsulate a wide variety of network layer protocol packet types inside IP tunnels. A
GRE tunnel serves as a virtual point-to-point link between the USG and another router over an IPv4
network. At the time of writing, the USG only supports GRE tunneling in IPv4 networks.
Figure 130 GRE Tunnel Example
IPv6 Over IPv4 Tunnels
To route traffic between two IPv6 networks over an IPv4 network, an IPv6 over IPv4 tunnel has to
be used.
Figure 131 IPv6 over IPv4 Network
On the USG, you can either set up a manual IPv6-in-IPv4 tunnel or an automatic 6to4 tunnel. The
following describes each method:
Actions when over
% of time budget or
% of data budget
Specify the actions the USG takes when the specified percentage of time budget or
data limit is exceeded. Enter a number from 1 to 99 in the percentage fields. If you
change the value after you configure and enable budget control, the USG resets the
statistics.
Log Select None to not create a log when the USG takes this action, Log to create a log, or
Log-alert to create an alert log. If you select Log or Log-alert you can also select
recurring every to have the USG send a log or alert for this event periodically.
Specify how often (from 1 to 65535 minutes) to send the log or alert.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 72 Configuration > Network > Interface > Cellular > Add / Edit (continued)
LABEL DESCRIPTION
Internet
IPv4
IPv4
IPv6 IPv6
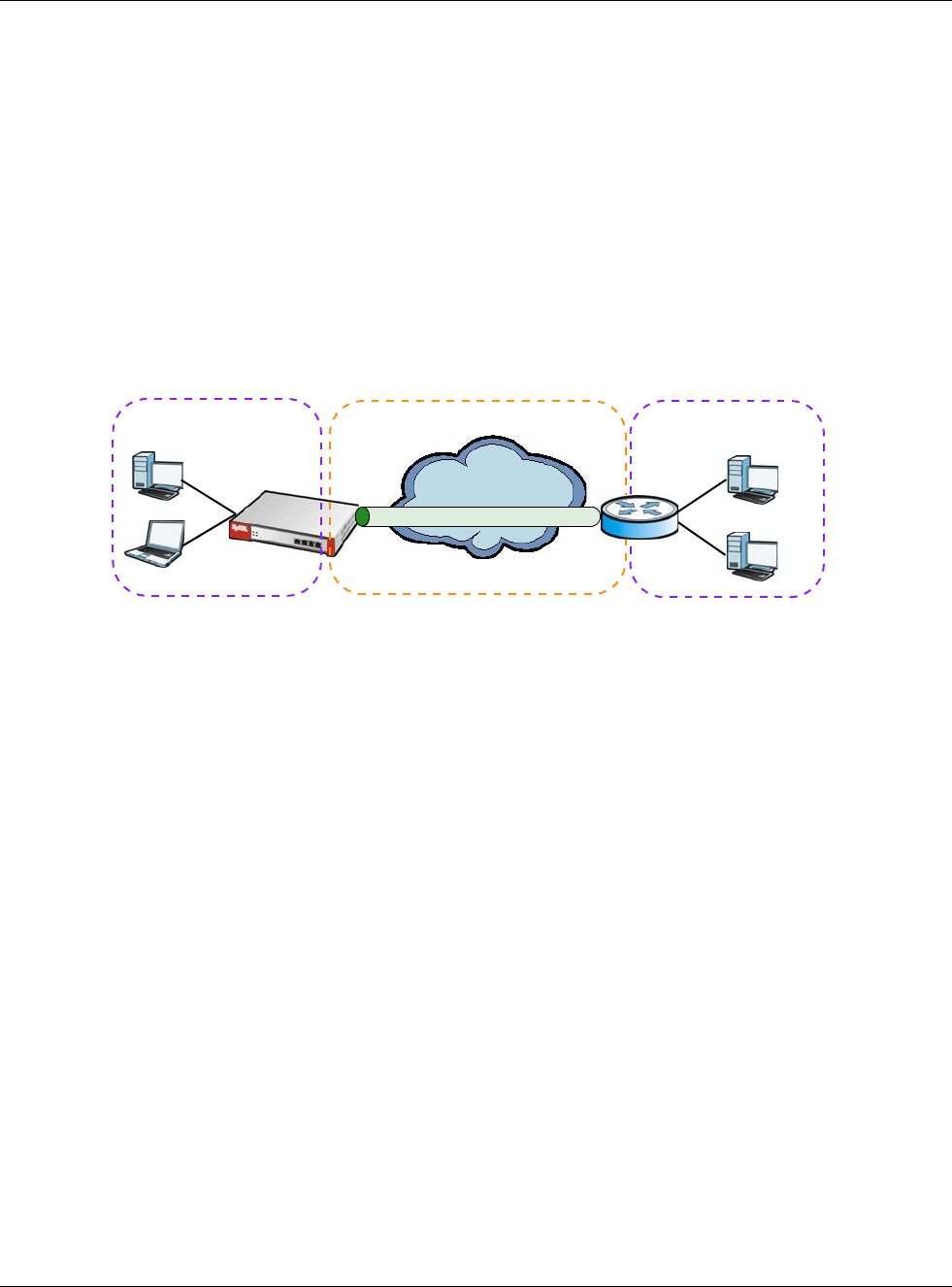
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
183
IPv6-in-IPv4 Tunneling
Use this mode on the WAN of the USG if
• your USG has a public IPv4 IP address given from your ISP,
and
• you want to transmit your IPv6 packets to one and only one remote site whose LAN network is
also an IPv6 network.
With this mode, the USG encapsulates IPv6 packets within IPv4 packets across the Internet. You
must know the WAN IP address of the remote gateway device. This mode is normally used for a
site-to-site application such as two branch offices.
Figure 132 IPv6-in-IPv4 Tunnel
In the USG, you must also manually configure a policy route for an IPv6-in-IPv4 tunnel to make the
tunnel work.
6to4 Tunneling
This mode also enables IPv6 packets to cross IPv4 networks. Unlike IPv6-in-IPv4 tunneling, you do
not need to configure a policy route for a 6to4 tunnel. Through your properly pre-configuring the
destination router’s IP address in the IP address assignments to hosts, the USG can automatically
forward 6to4 packets to the destination they want to go. A 6to4 relay router is required to route
6to4 packets to a native IPv6 network if the packet’s destination do not match your specified
criteria.
In this mode, the USG should get a public IPv4 address for the WAN. The USG adds an IPv4 IP
header to an IPv6 packet when transmitting the packet to the Internet. In reverse, the USG
removes the IPv4 header from an IPv6 packet when receiving it from the Internet.
An IPv6 address using the 6to4 mode consists of an IPv4 address, the format is as the following:
2002:[a public IPv4 address in hexadecimal]::/48
For example, a public IPv4 address is 202.156.30.41. The converted hexadecimal IP string is
ca.9c.1Ee.29. The IPv6 address prefix becomes 2002:ca9c:1e29::/48.
IPv6
IPv4
IPv6
Internet
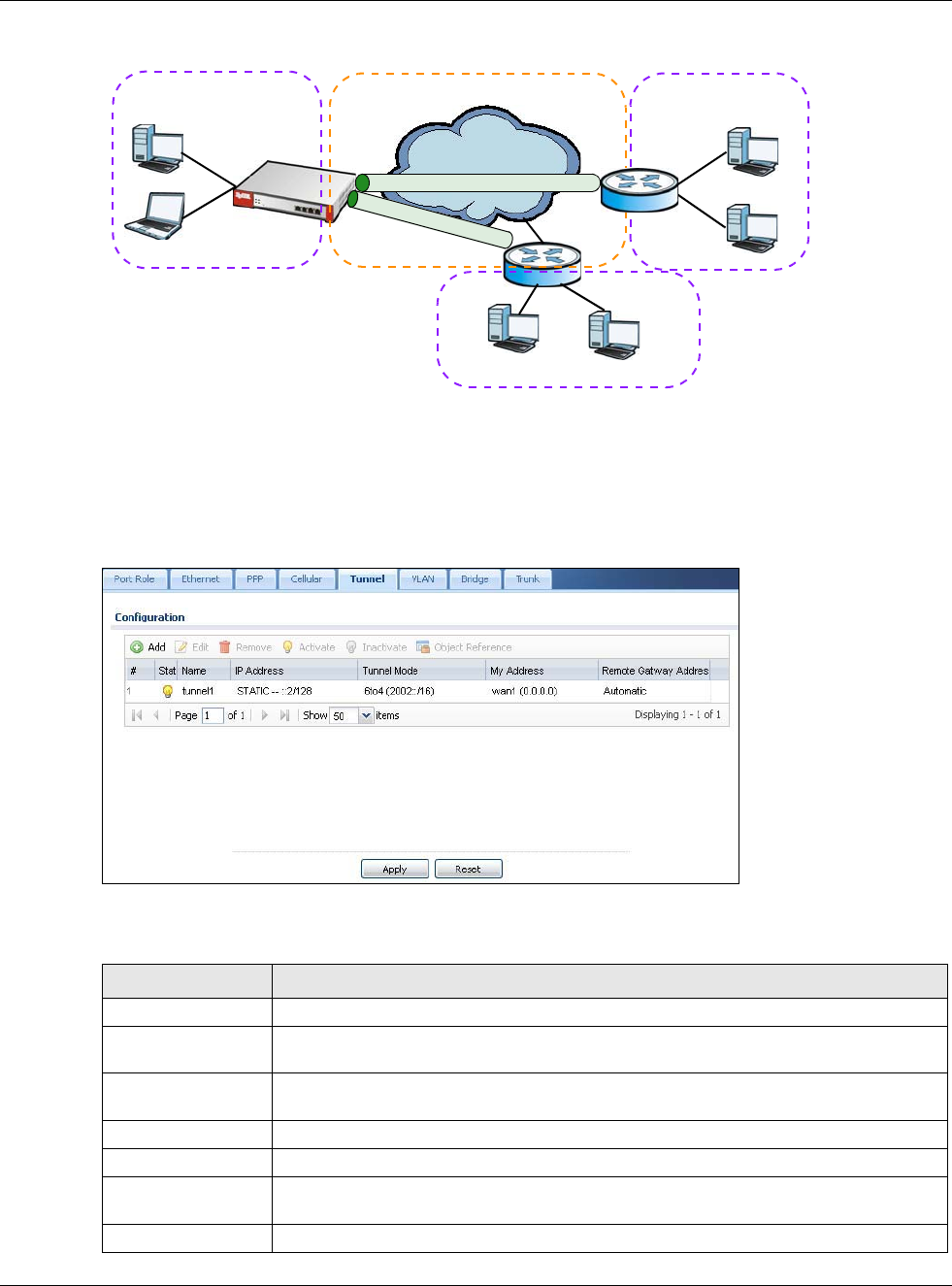
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
184
Figure 133 6to4 Tunnel
9.6.1 Configuring a Tunnel
This screen lists the USG’s configured tunnel interfaces. To access this screen, click Network >
Interface > Tunnel.
Figure 134 Network > Interface > Tunnel
Each field is explained in the following table.
Internet
IPv6
IPv4
IPv6
IPv6
Table 73 Network > Interface > Tunnel
LABEL DESCRIPTION
Add Click this to create a new GRE tunnel interface.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to remove
it before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Object References Select an entry and click Object Reference to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
#This field is a sequential value, and it is not associated with any interface.
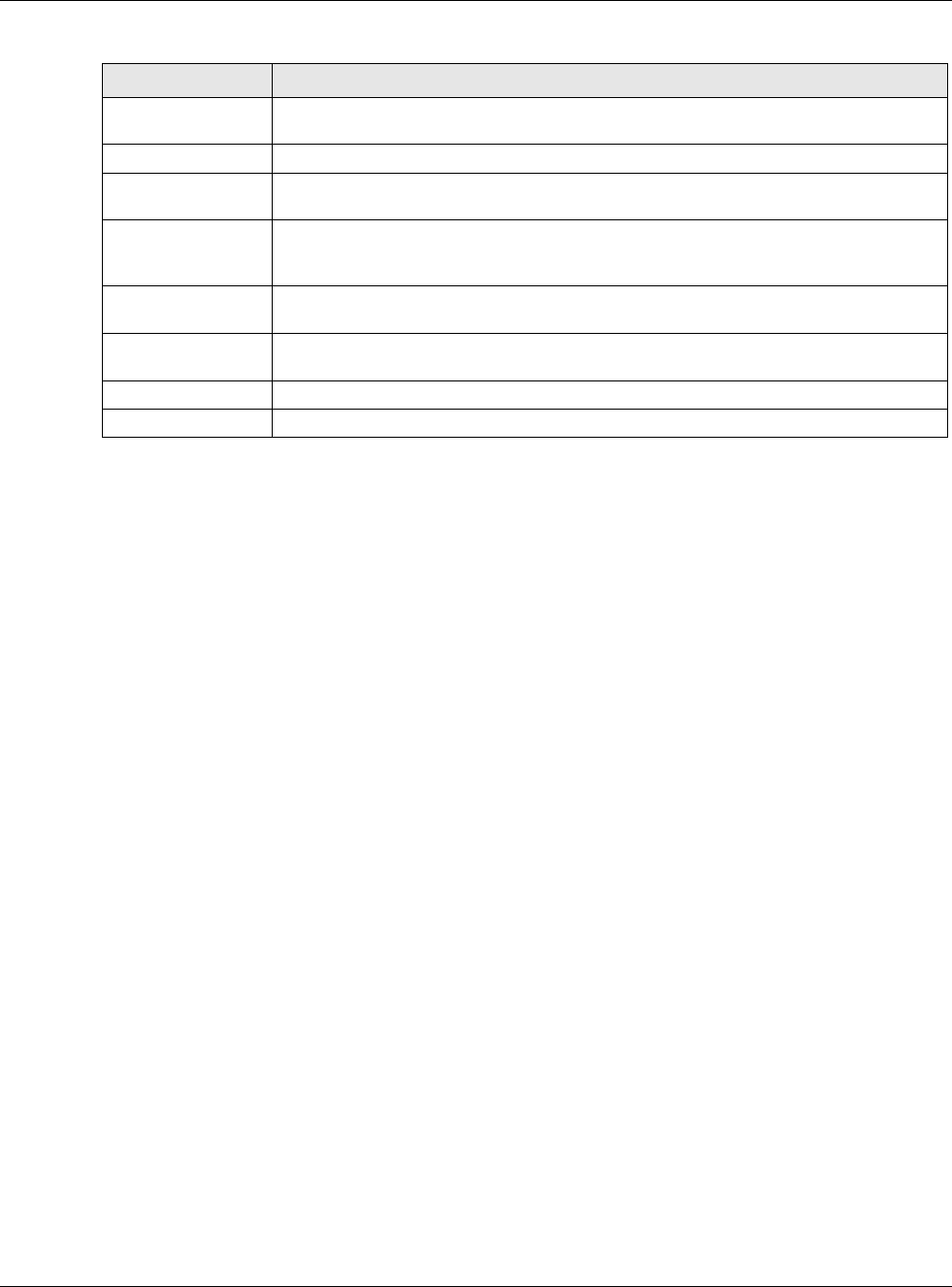
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
185
9.6.2 Tunnel Add or Edit Screen
This screen lets you configure a tunnel interface. Click Configuration > Network > Interface >
Tunnel > Add (or Edit) to open the following screen.
Status The activate (light bulb) icon is lit when the entry is active and dimmed when the entry
is inactive.
Name This field displays the name of the interface.
IP Address This is the IP address of the interface. If the interface is active (and connected), the
USG tunnels local traffic sent to this IP address to the Remote Gateway Address.
Tunnel Mode This is the tunnel mode of the interface (GRE, IPv6-in-IPv4 or 6to4). This field also
displays the interface’s IPv4 IP address and subnet mask if it is a GRE tunnel.
Otherwise, it displays the interface’s IPv6 IP address and prefix length.
My Address This is the interface or IP address uses to identify itself to the remote gateway. The
USG uses this as the source for the packets it tunnels to the remote gateway.
Remote Gateway
Address
This is the IP address or domain name of the remote gateway to which this interface
tunnels traffic.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to begin configuring this screen afresh.
Table 73 Network > Interface > Tunnel (continued)
LABEL DESCRIPTION
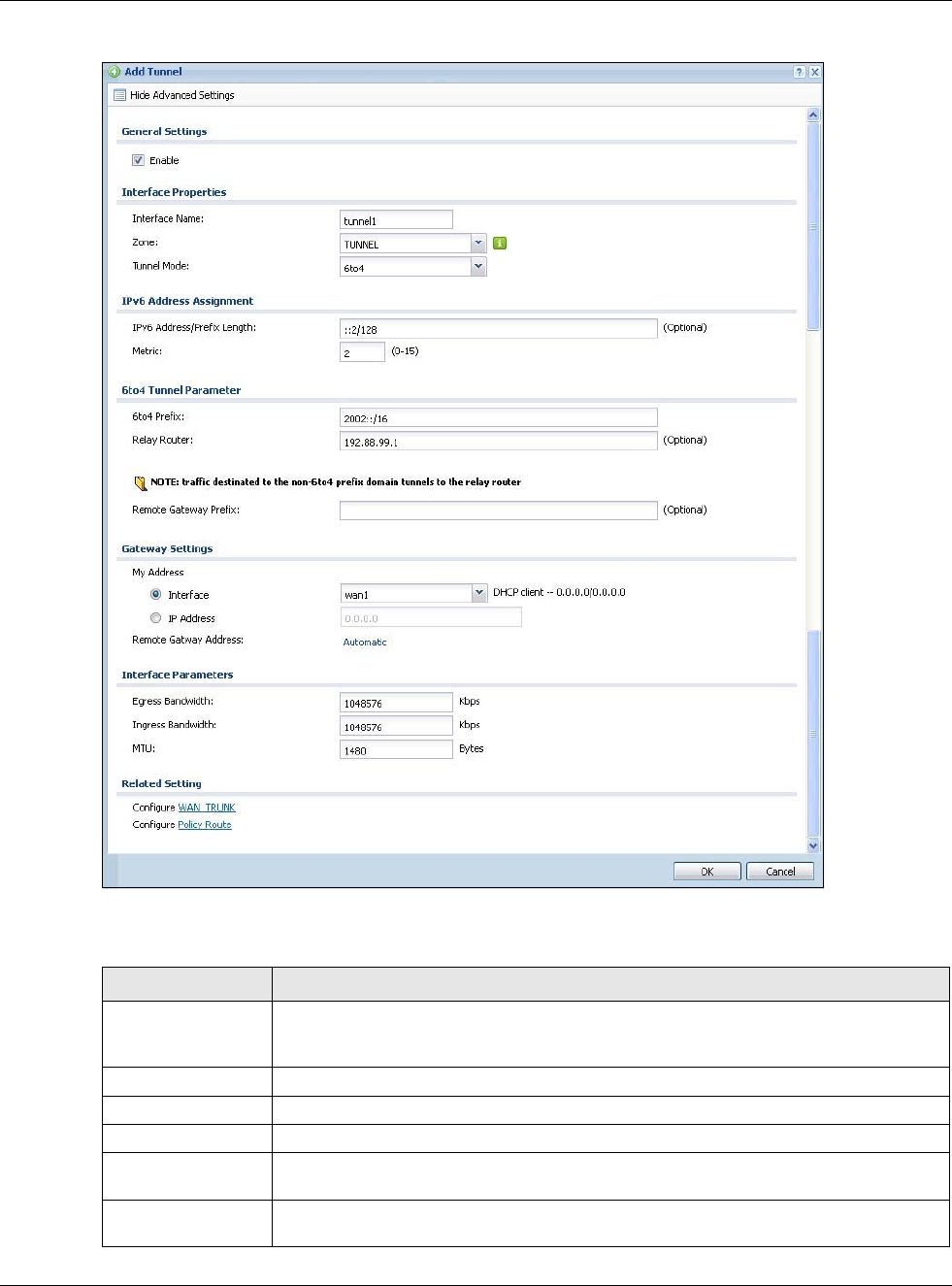
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
186
Figure 135 Network > Interface > Tunnel > Add/Edit
Each field is explained in the following table.
Table 74 Network > Interface > Tunnel > Add/Edit
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
General Settings
Enable Select this to enable this interface. Clear this to disable this interface.
Interface Properties
Interface Name This field is read-only if you are editing an existing tunnel interface. Enter the name of
the tunnel interface. The format is tunnelx, where x is 0 - 3. For example, tunnel0.
Zone Use this field to select the zone to which this interface belongs. This controls what
security settings the USG applies to this interface.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
187
Tunnel Mode Select the tunneling protocol of the interface (GRE, IPv6-in-IPv4 or 6to4). See
Section 9.6 on page 182 for more information.
IP Address
Assignment
This section is available if you are configuring a GRE tunnel.
IP Address Enter the IP address for this interface.
Subnet Mask Enter the subnet mask of this interface in dot decimal notation. The subnet mask
indicates what part of the IP address is the same for all computers in the network.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
IPv6 Address
Assignment
This section is available if you are configuring an IPv6-in-IPv4 or a 6to4 tunnel.
IPv6 Address/
Prefix Length Enter the IPv6 address and the prefix length for this interface if you want to use a static
IP address. This field is optional.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
6to4 Tunnel
Parameter
This section is available if you are configuring a 6to4 tunnel which encapsulates IPv6 to
IPv4 packets.
6to4 Prefix Enter the IPv6 prefix of a destination network. The USG forwards IPv6 packets to the
hosts in the matched network.
If you enter a prefix starting with 2002, the USG will forward the matched packets to
the IPv4 IP address converted from the packets’ destination address. The IPv4 IP
address can be converted from the next 32 bits after the prefix you specified in this
field. See 6to4 Tunneling on page 183 for an example. The USG forwards the
unmatched packets to the specified Relay Router.
Relay Router Enter the IPv4 address of a 6to4 relay router which helps forward packets between
6to4 networks and native IPv6 networks.
Remote
Gateway Prefix Enter the IPv4 network address and network bits of a remote 6to4 gateway, for
example, 14.15.0.0/16.
This field works if you enter a 6to4 Prefix not starting with 2002 (2003 for example).
The USG forwards the matched packets to a remote gateway with the network address
you specify here, and the bits converted after the 6to4 Prefix in the packets.
For example, you configure the 6to4 prefix to 2003:A0B::/32 and the remote gateway
prefix to 14.15.0.0/16. If a packet’s destination is 2003:A0B:1011:5::8, the USG
forwards the packet to 14.15.16.17, where the network address is 14.15.0.0 and the
host address is the remain bits converted from 1011 after the packet’s 6to4 prefix
(2003:A0B).
Gateway Settings
My Address Specify the interface or IP address to use as the source address for the packets this
interface tunnels to the remote gateway. The remote gateway sends traffic to this
interface or IP address.
Remote
Gateway
Address
Enter the IP address or domain name of the remote gateway to which this interface
tunnels traffic.
Automatic displays in this field if you are configuring a 6to4 tunnel. It means the 6to4
tunnel will help forward packets to the corresponding remote gateway automatically by
looking at the packet’s destination address.
Table 74 Network > Interface > Tunnel > Add/Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
188
9.7 VLAN Interfaces
A Virtual Local Area Network (VLAN) divides a physical network into multiple logical networks. The
standard is defined in IEEE 802.1q.
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send through
the interface to the network. Allowed values are 0 - 1048576. This setting is used in
WAN load balancing and bandwidth management.
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
MTU Maximum Transmission Unit. Type the maximum size of each data packet, in bytes,
that can move through this interface. If a larger packet arrives, the USG divides it into
smaller fragments. Allowed values are 576 - 1500. Usually, this value is 1500.
Connectivity Check This section is available if you are configuring a GRE tunnel.
The interface can regularly check the connection to the gateway you specified to make
sure it is still available. You specify how often the interface checks the connection, how
long to wait for a response before the attempt is a failure, and how many consecutive
failures are required before the USG stops routing to the gateway. The USG resumes
routing to the gateway the first time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance Enter the number of consecutive failures before the USG stops routing through the
gateway.
Check Default
Gateway Select this to use the default gateway for the connectivity check.
Check this
address Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
Check Port This field displays when you set the Check Method to tcp. Specify the port number to
use for a TCP connectivity check.
Related Setting
WAN TRUNK Click this link to go to a screen where you can configure WAN trunk load balancing.
Policy Route Click this link to go to the screen where you can manually configure a policy route to
associate traffic with this interface.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 74 Network > Interface > Tunnel > Add/Edit (continued)
LABEL DESCRIPTION
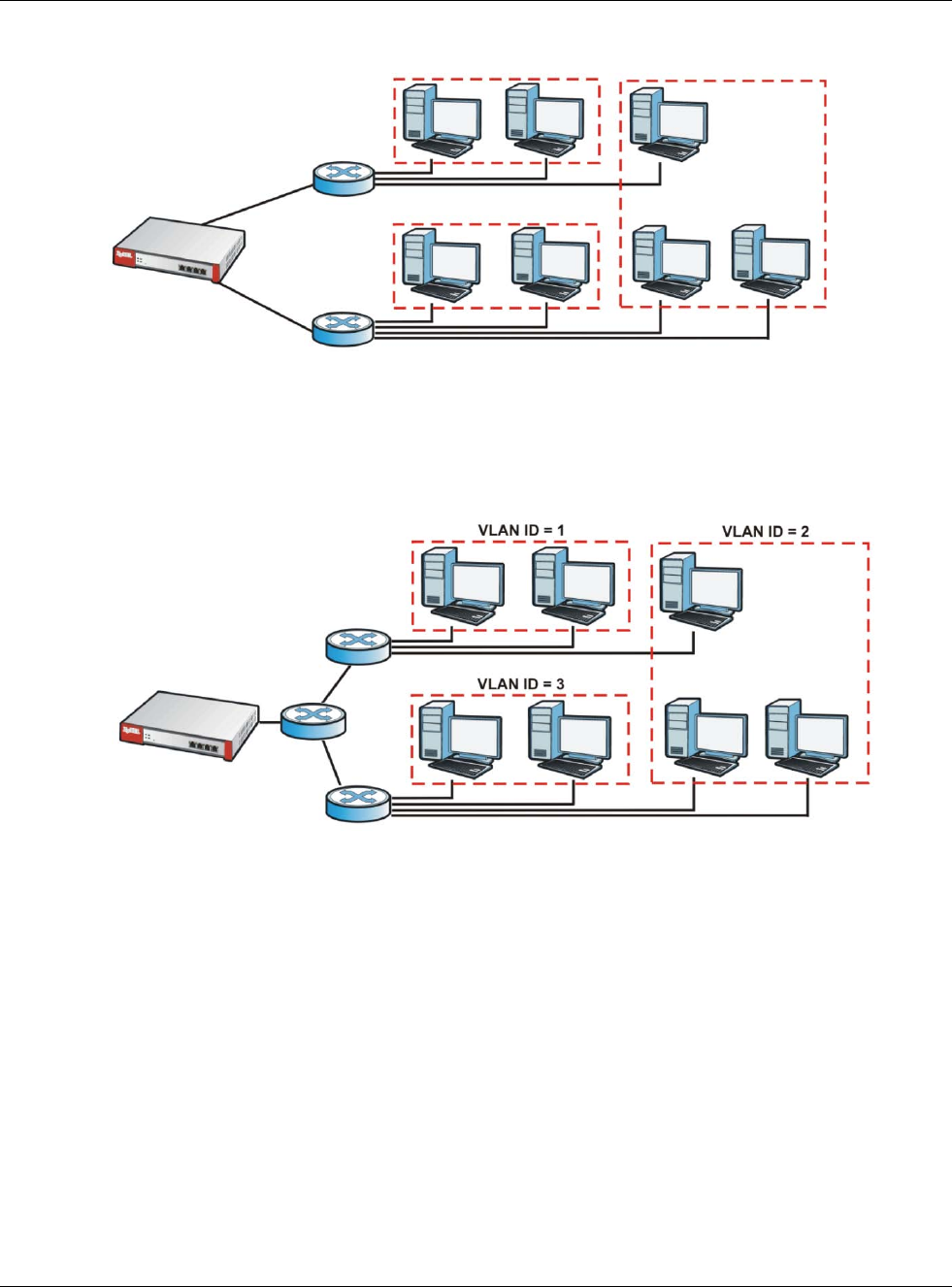
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
189
Figure 136 Example: Before VLAN
In this example, there are two physical networks and three departments A, B, and C. The physical
networks are connected to hubs, and the hubs are connected to the router.
Alternatively, you can divide the physical networks into three VLANs.
Figure 137 Example: After VLAN
Each VLAN is a separate network with separate IP addresses, subnet masks, and gateways. Each
VLAN also has a unique identification number (ID). The ID is a 12-bit value that is stored in the
MAC header. The VLANs are connected to switches, and the switches are connected to the router.
(If one switch has enough connections for the entire network, the network does not need switches
A and B.)
• Traffic inside each VLAN is layer-2 communication (data link layer, MAC addresses). It is handled
by the switches. As a result, the new switch is required to handle traffic inside VLAN 2. Traffic is
only broadcast inside each VLAN, not each physical network.
• Traffic between VLANs (or between a VLAN and another type of network) is layer-3
communication (network layer, IP addresses). It is handled by the router.
This approach provides a few advantages.
• Increased performance - In VLAN 2, the extra switch should route traffic inside the sales
department faster than the router does. In addition, broadcasts are limited to smaller, more
logical groups of users.
AB
C
A
B

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
190
• Higher security - If each computer has a separate physical connection to the switch, then
broadcast traffic in each VLAN is never sent to computers in another VLAN.
• Better manageability - You can align network policies more appropriately for users. For example,
you can create different content filtering rules for each VLAN (each department in the example
above), and you can set different bandwidth limits for each VLAN. These rules are also
independent of the physical network, so you can change the physical network without changing
policies.
In this example, the new switch handles the following types of traffic:
•Inside VLAN 2.
• Between the router and VLAN 1.
• Between the router and VLAN 2.
• Between the router and VLAN 3.
VLAN Interfaces Overview
In the USG, each VLAN is called a VLAN interface. As a router, the USG routes traffic between VLAN
interfaces, but it does not route traffic within a VLAN interface. All traffic for each VLAN interface
can go through only one Ethernet interface, though each Ethernet interface can have one or more
VLAN interfaces.
Note: Each VLAN interface is created on top of only one Ethernet interface.
Otherwise, VLAN interfaces are similar to other interfaces in many ways. They have an IP address,
subnet mask, and gateway used to make routing decisions. They restrict bandwidth and packet
size. They can provide DHCP services, and they can verify the gateway is available.
9.7.1 VLAN Summary Screen
This screen lists every VLAN interface and virtual interface created on top of VLAN interfaces. If you
enabled IPv6 in the Configuration > System > IPv6 screen, you can also configure VLAN
interfaces used for your IPv6 networks on this screen. To access this screen, click Configuration >
Network > Interface > VLAN.
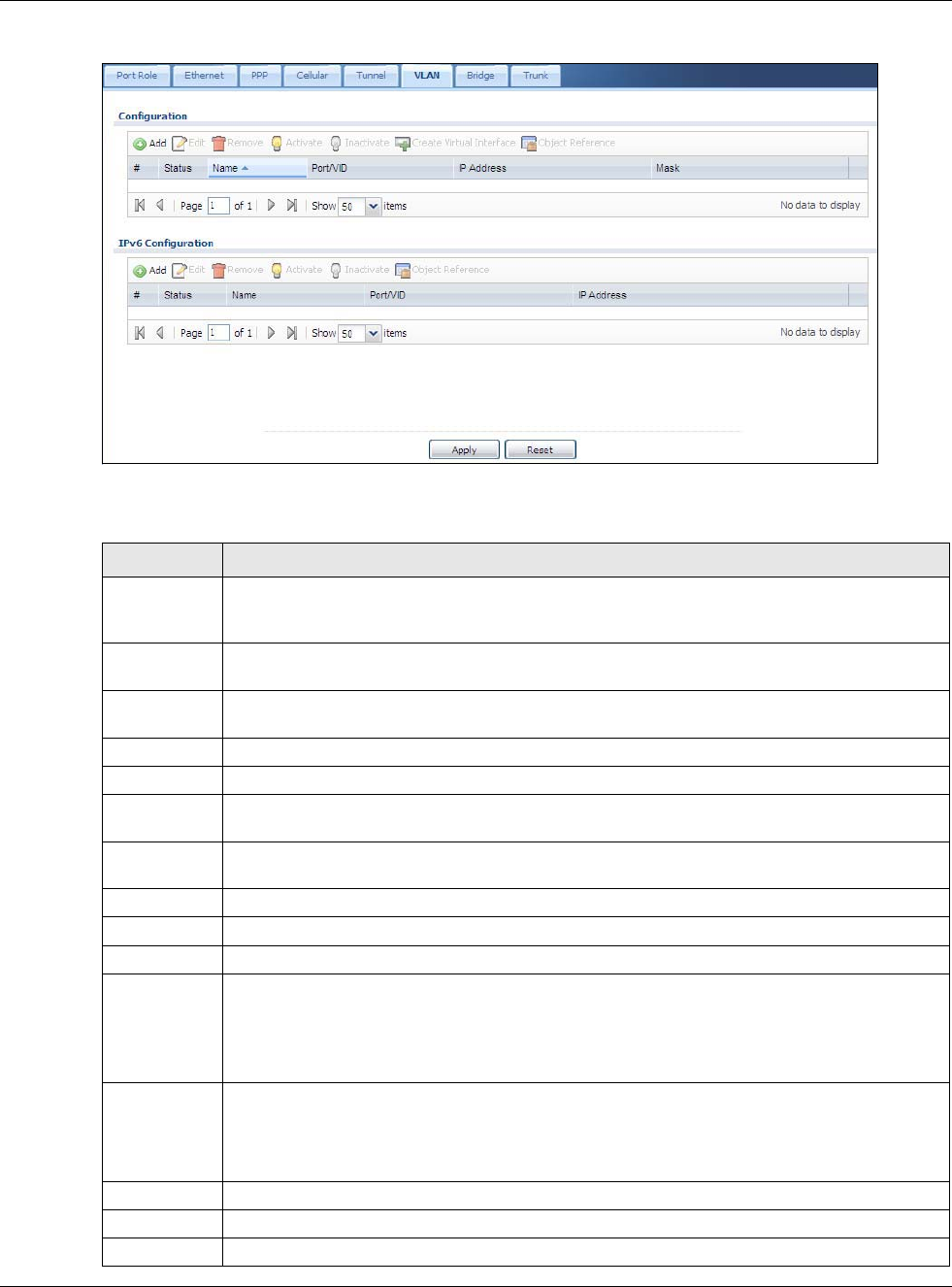
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
191
Figure 138 Configuration > Network > Interface > VLAN
Each field is explained in the following table.
Table 75 Configuration > Network > Interface > VLAN
LABEL DESCRIPTION
Configuration
/ IPv6
Configuration
Use the Configuration section for IPv4 network settings. Use the IPv6 Configuration
section for IPv6 network settings if you connect your USG to an IPv6 network. Both sections
have similar fields as described below.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify the
entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to remove it
before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Create Virtual
Interface
To open the screen where you can create a virtual interface, select an interface and click
Create Virtual Interface.
Object
References
Select an entry and click Object Reference to open a screen that shows which settings use
the entry. See Section 9.3.2 on page 163 for an example.
#This field is a sequential value, and it is not associated with any interface.
Status This icon is lit when the entry is active and dimmed when the entry is inactive.
Name This field displays the name of the interface.
Port/VID For VLAN interfaces, this field displays
• the Ethernet interface on which the VLAN interface is created
• the VLAN ID
For virtual interfaces, this field is blank.
IP Address This field displays the current IP address of the interface. If the IP address is 0.0.0.0, the
interface does not have an IP address yet.
This screen also shows whether the IP address is a static IP address (STATIC) or dynamically
assigned (DHCP). IP addresses are always static in virtual interfaces.
Mask This field displays the interface’s subnet mask in dot decimal notation.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
192
9.7.2 VLAN Add/Edit
Select an existing entry in the previous scrren and click Edit or click Add to create a new entry. The
following screen appears.
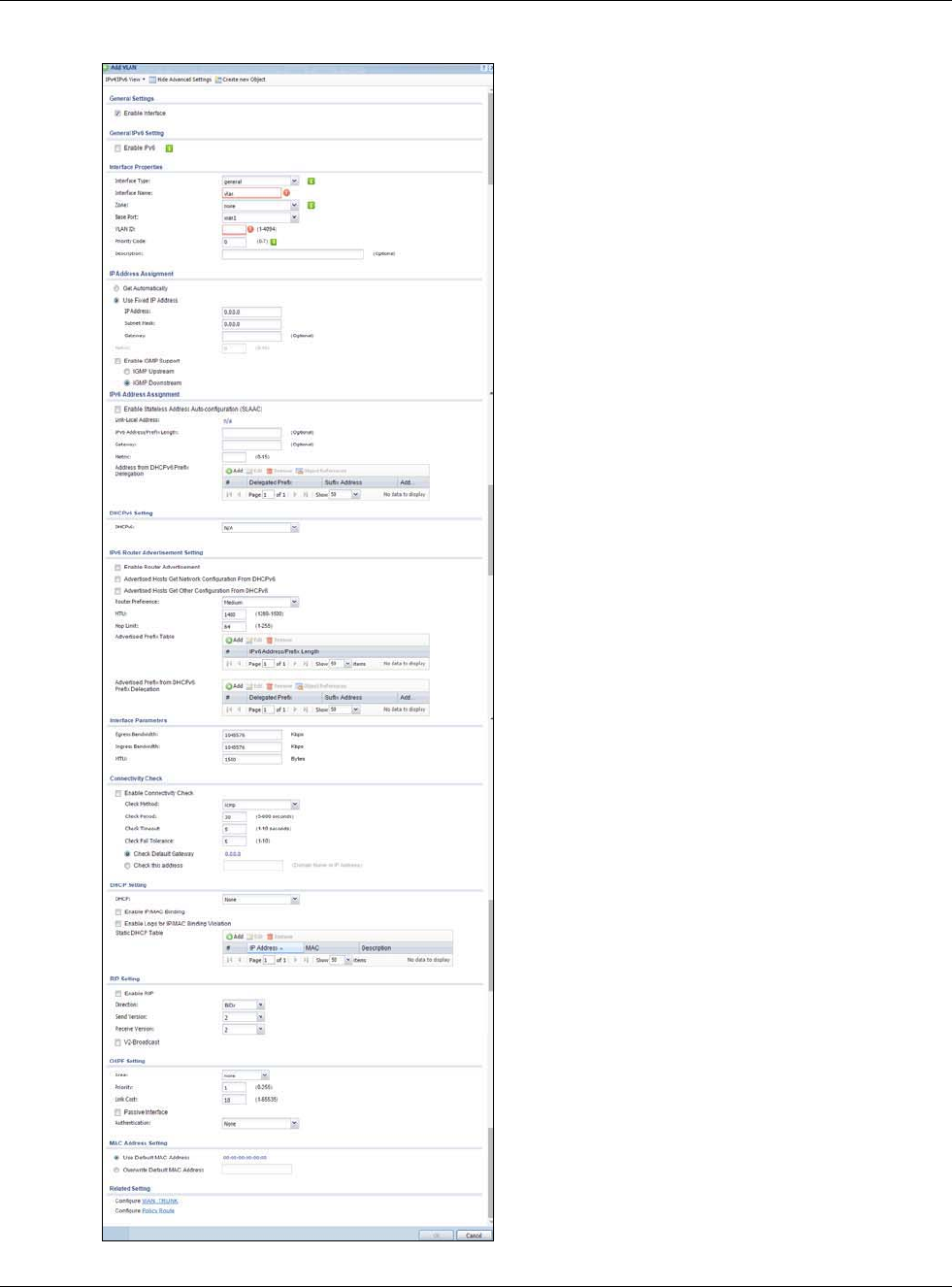
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
193
Figure 139 Configuration > Network > Interface > VLAN > Add /Edit
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
194
Each field is explained in the following table.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit
LABEL DESCRIPTION
IPv4/IPv6 View /
IPv4 View / IPv6
View
Use this button to display both IPv4 and IPv6, IPv4-only, or IPv6-only configuration
fields.
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Create New Object Click this button to create a DHCPv6 lease or DHCPv6 request object that you may use
for the DHCPv6 settings in this screen.
General Settings
Enable Interface Select this to turn this interface on. Clear this to disable this interface.
General IPv6
Setting
Enable IPv6 Select this to enable IPv6 on this interface. Otherwise, clear this to disable it.
Interface Properties
Interface Type Select one of the following option depending on the type of network to which the USG
is connected or if you want to additionally manually configure some related settings.
internal is for connecting to a local network. Other corresponding configuration
options: DHCP server and DHCP relay. The USG automatically adds default SNAT
settings for traffic flowing from this interface to an external interface.
external is for connecting to an external network (like the Internet). The USG
automatically adds this interface to the default WAN trunk.
For general, the rest of the screen’s options do not automatically adjust and you must
manually configure a policy route to add routing and SNAT settings for the interface.
Interface Name This field is read-only if you are editing an existing VLAN interface. Enter the number of
the VLAN interface. You can use a number from 0~4094. For example, use vlan0,
vlan8, and so on. The total number of VLANs you can configure on the USG depends on
the model.
Zone Select the zone to which the VLAN interface belongs.
Base Port Select the Ethernet interface on which the VLAN interface runs.
VLAN ID Enter the VLAN ID. This 12-bit number uniquely identifies each VLAN. Allowed values
are 1 - 4094. (0 and 4095 are reserved.)
Priority Code This is a 3-bit field within a 802.1Q VLAN tag that’s used to prioritize associated
outgoing VLAN traffic. "0" is the lowest priority level and "7" is the highest. See Table
158 on page 407. The setting configured in Configuration > BWM overwrites the
priority setting here.
Description Enter a description of this interface. It is not used elsewhere. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
IP Address
Assignment
Get
Automatically Select this if this interface is a DHCP client. In this case, the DHCP server configures
the IP address, subnet mask, and gateway automatically.
You should not select this if the interface is assigned to a VRRP group.
Use Fixed IP
Address Select this if you want to specify the IP address, subnet mask, and gateway manually.
IP Address This field is enabled if you select Use Fixed IP Address.
Enter the IP address for this interface.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
195
Subnet Mask This field is enabled if you select Use Fixed IP Address.
Enter the subnet mask of this interface in dot decimal notation. The subnet mask
indicates what part of the IP address is the same for all computers in the network.
Gateway This field is enabled if you select Use Fixed IP Address.
Enter the IP address of the gateway. The USG sends packets to the gateway when it
does not know how to route the packet to its destination. The gateway should be on the
same network as the interface.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Enable IGMP
Support
Select this to allow the USG to act as an IGMP proxy for hosts connected on the IGMP
downstream interface.
IGMP Upstream Enable IGMP Upstream on the interface which connects to a router running IGMP that
is closer to the multicast server.
IGMP
Downstream Enable IGMP Downstream on the interface which connects to the multicast hosts.
IPv6 Address
Assignment
These IP address fields configure an IPv6 IP address on the interface itself.
Enable Stateless
Address Auto-
configuration
(SLAAC)
Select this to enable IPv6 stateless auto-configuration on this interface. The interface
will generate an IPv6 IP address itself from a prefix obtained from an IPv6 router in the
network.
Link-Local
address This displays the IPv6 link-local address and the network prefix that the USG generates
itself for the interface.
IPv6 Address/
Prefix Length Enter the IPv6 address and the prefix length for this interface if you want to configure a
static IP address for this interface. This field is optional.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Gateway Enter the IPv6 address of the default outgoing gateway using colon (:) hexadecimal
notation.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Address from
DHCPv6 Prefix
Delegation
Use this table to have the USG obtain an IPv6 prefix from the ISP or a connected uplink
router for an internal network, such as the LAN or DMZ. You have to also enter a suffix
address which is appended to the delegated prefix to form an address for this interface.
See Prefix Delegation on page 144 for more information.
To use prefix delegation, you must:
• Create at least one DHCPv6 request object before configuring this table.
• The external interface must be a DHCPv6 client. You must configure the DHCPv6
request options using a DHCPv6 request object with the type of prefix-delegation.
• Assign the prefix delegation to an internal interface and enable router
advertisement on that interface.
Add Click this to create an entry.
Edit Select an entry and click this to change the settings.
Remove Select an entry and click this to delete it from this table.
# This field is a sequential value, and it is not associated with any entry.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
196
Delegated
Prefix Select the DHCPv6 request object to use from the drop-down list.
Suffix
Address Enter the ending part of the IPv6 address, a slash (/), and the prefix length. The USG
will append it to the delegated prefix.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to configure
an IP address of 2003:1234:5678:1111::1/128 for this interface, then enter
::1111:0:0:0:1/128 in this field.
Address This field displays the combined IPv6 IP address for this interface.
Note: This field displays the combined address after you click OK and reopen this
screen.
DHCPv6 Setting
DUID This field displays the DHCP Unique IDentifier (DUID) of the interface, which is unique
and used for identification purposes when the interface is exchanging DHCPv6
messages with others. See DHCPv6 on page 145 for more information.
DUID as MAC Select this to have the DUID generated from the interface’s default MAC address.
Customized
DUID If you want to use a customized DUID, enter it here for the interface.
Enable Rapid
Commit Select this to shorten the DHCPv6 message exchange process from four to two steps.
This function helps reduce heavy network traffic load.
Note: Make sure you also enable this option in the DHCPv6 clients to make rapid commit
work.
Information
Refresh Time Enter the number of seconds a DHCPv6 client should wait before refreshing information
retrieved from DHCPv6.
Request Address This field is available if you set this interface to DHCPv6 Client. Select this to get an
IPv6 IP address for this interface from the DHCP server. Clear this to not get any IP
address information through DHCPv6.
DHCPv6 Request
Options /
DHCPv6 Lease
Options
If this interface is a DHCPv6 client, use this section to configure DHCPv6 request
settings that determine what additional information to get from the DHCPv6 server.
If this interface is a DHCPv6 server, use this section to configure DHCPv6 lease settings
that determine what to offer to the DHCPv6 clients.
Add Click this to create an entry in this table. See Section 9.3.3 on page 164 for more
information.
Remove Select an entry and click this to change the settings.
Object
Reference Select an entry and click this to delete it from this table.
# This field is a sequential value, and it is not associated with any entry.
Name This field displays the name of the DHCPv6 request or lease object.
Type This field displays the type of the object.
Value This field displays the IPv6 prefix that the USG obtained from an uplink router (Server
is selected) or will advertise to its clients (Client is selected).
Interface When Relay is selected, select this check box and an interface from the drop-down list
if you want to use it as the relay server.
Relay Server When Relay is selected, select this check box and enter the IP address of a DHCPv6
server as the relay server.
IPv6 Router
Advertisement
Setting
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
197
Enable Router
Advertisement Select this to enable this interface to send router advertisement messages periodically.
See IPv6 Router Advertisement on page 145 for more information.
Advertised Hosts
Get Network
Configuration
From DHCPv6
Select this to have the USG indicate to hosts to obtain network settings (such as prefix
and DNS settings) through DHCPv6.
Clear this to have the USG indicate to hosts that DHCPv6 is not available and they
should use the prefix in the router advertisement message.
Advertised Hosts
Get Other
Configuration
From DHCPv6
Select this to have the USG indicate to hosts to obtain DNS information through
DHCPv6.
Clear this to have the USG indicate to hosts that DNS information is not available in this
network.
Router
Preference Select the router preference (Low, Medium or High) for the interface. The interface
sends this preference in the router advertisements to tell hosts what preference they
should use for the USG. This helps hosts to choose their default router especially when
there are multiple IPv6 router in the network.
Note: Make sure the hosts also support router preference to make this function work.
MTU The Maximum Transmission Unit. Type the maximum size of each IPv6 data packet, in
bytes, that can move through this interface. If a larger packet arrives, the USG divides
it into smaller fragments.
Hop Limit Enter the maximum number of network segments that a packet can cross before
reaching the destination. When forwarding an IPv6 packet, IPv6 routers are required to
decrease the Hop Limit by 1 and to discard the IPv6 packet when the Hop Limit is 0.
Advertised
Prefix Table Configure this table only if you want the USG to advertise a fixed prefix to the network.
Add Click this to create an IPv6 prefix address.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
IPv6
Address/
Prefix Length
Enter the IPv6 network prefix address and the prefix length.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Advertised
Prefix from
DHCPv6 Prefix
Delegation
Use this table to configure the network prefix if you want to use a delegated prefix as
the beginning part of the network prefix.
Add Click this to create an entry in this table.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
Delegated
Prefix Select the DHCPv6 request object to use for generating the network prefix for the
network.
Suffix
Address Enter the ending part of the IPv6 network address plus a slash (/) and the prefix
length. The USG will append it to the selected delegated prefix. The combined address
is the network prefix for the network.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to divide it
into 2003:1234:5678:1111/64 for this interface and 2003:1234:5678:2222/64 for
another interface. You can use ::1111/64 and ::2222/64 for the suffix address
respectively. But if you do not want to divide the delegated prefix into subnetworks,
enter ::0/48 here, which keeps the same prefix length (/48) as the delegated prefix.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
198
Address This is the final network prefix combined by the delegated prefix and the suffix.
Note: This field displays the combined address after you click OK and reopen this
screen.
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send through
the interface to the network. Allowed values are 0 - 1048576.
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
MTU Maximum Transmission Unit. Type the maximum size of each data packet, in bytes,
that can move through this interface. If a larger packet arrives, the USG divides it into
smaller fragments. Allowed values are 576 - 1500. Usually, this value is 1500.
Connectivity Check The USG can regularly check the connection to the gateway you specified to make sure
it is still available. You specify how often to check the connection, how long to wait for a
response before the attempt is a failure, and how many consecutive failures are
required before the USG stops routing to the gateway. The USG resumes routing to the
gateway the first time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance Enter the number of consecutive failures before the USG stops routing through the
gateway.
Check Default
Gateway Select this to use the default gateway for the connectivity check.
Check this
address Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
Check Port This field only displays when you set the Check Method to tcp. Specify the port
number to use for a TCP connectivity check.
DHCP Setting The DHCP settings are available for the OPT, LAN and DMZ interfaces.
DHCP Select what type of DHCP service the USG provides to the network. Choices are:
None - the USG does not provide any DHCP services. There is already a DHCP server
on the network.
DHCP Relay - the USG routes DHCP requests to one or more DHCP servers you
specify. The DHCP server(s) may be on another network.
DHCP Server - the USG assigns IP addresses and provides subnet mask, gateway, and
DNS server information to the network. The USG is the DHCP server for the network.
These fields appear if the USG is a DHCP Relay.
Relay Server 1 Enter the IP address of a DHCP server for the network.
Relay Server 2 This field is optional. Enter the IP address of another DHCP server for the network.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
199
These fields appear if the USG is a DHCP Server.
IP Pool Start
Address Enter the IP address from which the USG begins allocating IP addresses. If you want to
assign a static IP address to a specific computer, click Add Static DHCP.
If this field is blank, the Pool Size must also be blank. In this case, the USG can assign
every IP address allowed by the interface’s IP address and subnet mask, except for the
first address (network address), last address (broadcast address) and the interface’s IP
address.
Pool Size Enter the number of IP addresses to allocate. This number must be at least one and is
limited by the interface’s Subnet Mask. For example, if the Subnet Mask is
255.255.255.0 and IP Pool Start Address is 10.10.10.10, the USG can allocate
10.10.10.10 to 10.10.10.254, or 245 IP addresses.
If this field is blank, the IP Pool Start Address must also be blank. In this case, the
USG can assign every IP address allowed by the interface’s IP address and subnet
mask, except for the first address (network address), last address (broadcast address)
and the interface’s IP address.
First DNS Server
Second DNS
Server
Third DNS
Server
Specify the IP addresses up to three DNS servers for the DHCP clients to use. Use one
of the following ways to specify these IP addresses.
Custom Defined - enter a static IP address.
From ISP - select the DNS server that another interface received from its DHCP server.
USG - the DHCP clients use the IP address of this interface and the USG works as a
DNS relay.
First WINS
Server, Second
WINS Server
Type the IP address of the WINS (Windows Internet Naming Service) server that you
want to send to the DHCP clients. The WINS server keeps a mapping table of the
computer names on your network and the IP addresses that they are currently using.
Default Router If you set this interface to DHCP Server, you can select to use either the interface’s IP
address or another IP address as the default router. This default router will become the
DHCP clients’ default gateway.
To use another IP address as the default router, select Custom Defined and enter the
IP address.
Lease time Specify how long each computer can use the information (especially the IP address)
before it has to request the information again. Choices are:
infinite - select this if IP addresses never expire
days, hours, and minutes - select this to enter how long IP addresses are valid.
Extended
Options This table is available if you selected DHCP server.
Configure this table if you want to send more information to DHCP clients through
DHCP packets.
Add Click this to create an entry in this table. See Section 9.3.4 on page 165.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
Name This is the option’s name.
Code This is the option’s code number.
Type This is the option’s type.
Value This is the option’s value.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
200
Enable IP/MAC
Binding Select this option to have the USG enforce links between specific IP addresses and
specific MAC addresses for this VLAN. This stops anyone else from manually using a
bound IP address on another device connected to this interface. Use this to make use
only the intended users get to use specific IP addresses.
Enable Logs for
IP/MAC Binding
Violation
Select this option to have the USG generate a log if a device connected to this VLAN
attempts to use an IP address that is bound to another device’s MAC address.
Static DHCP
Table Configure a list of static IP addresses the USG assigns to computers connected to the
interface. Otherwise, the USG assigns an IP address dynamically using the interface’s
IP Pool Start Address and Pool Size.
Add Click this to create a new entry.
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
# This field is a sequential value, and it is not associated with a specific entry.
IP Address Enter the IP address to assign to a device with this entry’s MAC address.
MAC Address Enter the MAC address to which to assign this entry’s IP address.
Description Enter a description to help identify this static DHCP entry. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
RIP Setting See Section 10.6 on page 238 for more information about RIP.
Enable RIP Select this to enable RIP on this interface.
Direction This field is effective when RIP is enabled. Select the RIP direction from the drop-down
list box.
BiDir - This interface sends and receives routing information.
In-Only - This interface receives routing information.
Out-Only - This interface sends routing information.
Send Version This field is effective when RIP is enabled. Select the RIP version(s) used for sending
RIP packets. Choices are 1, 2, and 1 and 2.
Receive Version This field is effective when RIP is enabled. Select the RIP version(s) used for receiving
RIP packets. Choices are 1, 2, and 1 and 2.
V2-Broadcast This field is effective when RIP is enabled. Select this to send RIP-2 packets using
subnet broadcasting; otherwise, the USG uses multicasting.
OSPF Setting See Section 10.7 on page 240 for more information about OSPF.
Area Select the area in which this interface belongs. Select None to disable OSPF in this
interface.
Priority Enter the priority (between 0 and 255) of this interface when the area is looking for a
Designated Router (DR) or Backup Designated Router (BDR). The highest-priority
interface identifies the DR, and the second-highest-priority interface identifies the BDR.
Set the priority to zero if the interface can not be the DR or BDR.
Link Cost Enter the cost (between 1 and 65,535) to route packets through this interface.
Passive
Interface Select this to stop forwarding OSPF routing information from the selected interface. As
a result, this interface only receives routing information.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
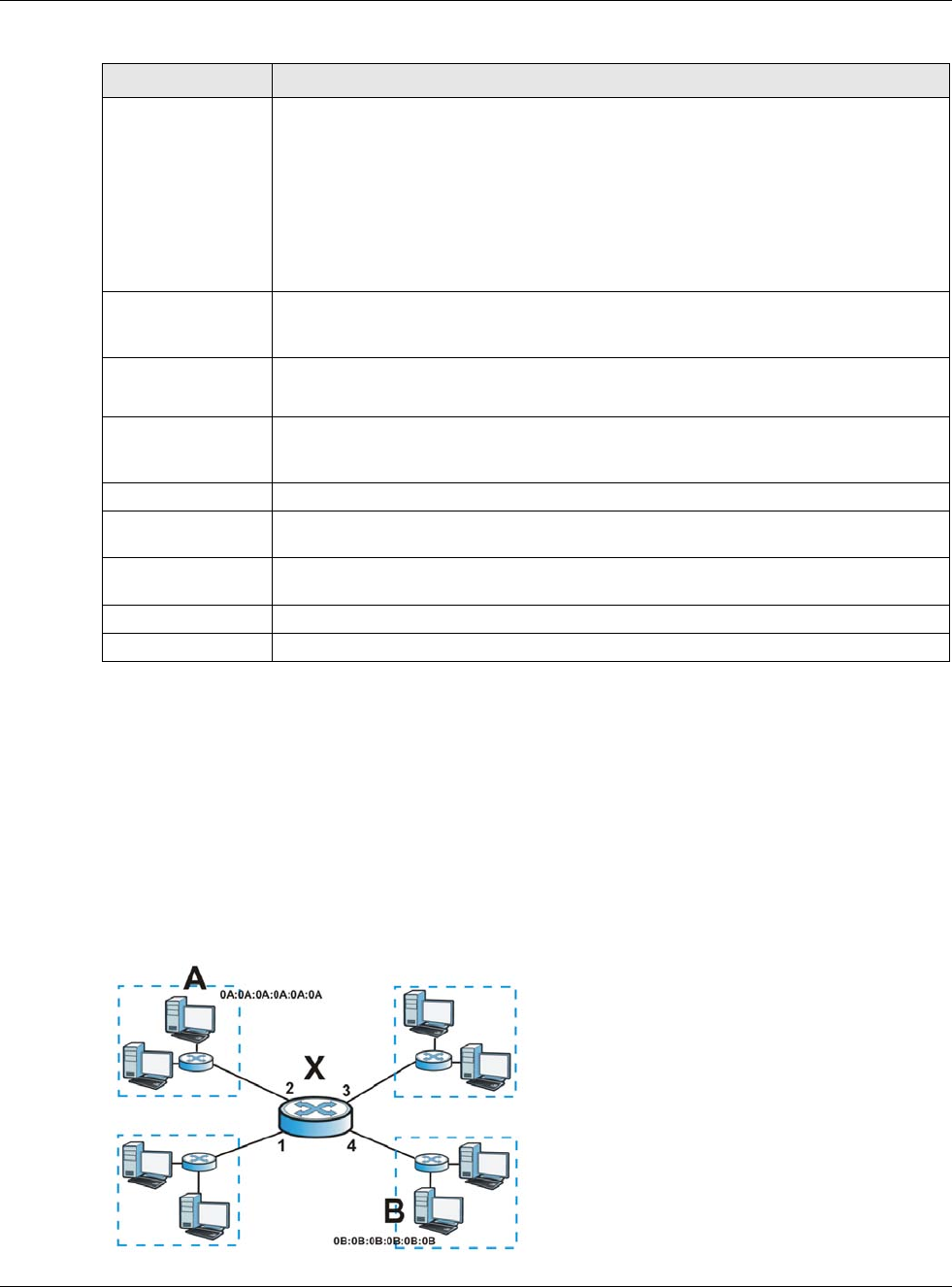
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
201
9.8 Bridge Interfaces
This section introduces bridges and bridge interfaces and then explains the screens for bridge
interfaces.
Bridge Overview
A bridge creates a connection between two or more network segments at the layer-2 (MAC
address) level. In the following example, bridge X connects four network segments.
Authentication Select an authentication method, or disable authentication. To exchange OSPF routing
information with peer border routers, you must use the same authentication method
that they use. Choices are:
Same-as-Area - use the default authentication method in the area
None - disable authentication
Text - authenticate OSPF routing information using a plain-text password
MD5 - authenticate OSPF routing information using MD5 encryption
Text
Authentication
Key
This field is available if the Authentication is Text. Type the password for text
authentication. The key can consist of alphanumeric characters and the underscore,
and it can be up to 16 characters long.
MD5
Authentication
ID
This field is available if the Authentication is MD5. Type the ID for MD5
authentication. The ID can be between 1 and 255.
MD5
Authentication
Key
This field is available if the Authentication is MD5. Type the password for MD5
authentication. The password can consist of alphanumeric characters and the
underscore, and it can be up to 16 characters long.
Related Setting
Configure WAN
TRUNK Click WAN TRUNK to go to a screen where you can set this VLAN to be part of a WAN
trunk for load balancing.
Configure Policy
Route Click Policy Route to go to the screen where you can manually configure a policy
route to associate traffic with this VLAN.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 76 Configuration > Network > Interface > VLAN > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
202
When the bridge receives a packet, the bridge records the source MAC address and the port on
which it was received in a table. It also looks up the destination MAC address in the table. If the
bridge knows on which port the destination MAC address is located, it sends the packet to that port.
If the destination MAC address is not in the table, the bridge broadcasts the packet on every port
(except the one on which it was received).
In the example above, computer A sends a packet to computer B. Bridge X records the source
address 0A:0A:0A:0A:0A:0A and port 2 in the table. It also looks up 0B:0B:0B:0B:0B:0B in the
table. There is no entry yet, so the bridge broadcasts the packet on ports 1, 3, and 4.
If computer B responds to computer A, bridge X records the source address 0B:0B:0B:0B:0B:0B
and port 4 in the table. It also looks up 0A:0A:0A:0A:0A:0A in the table and sends the packet to
port 2 accordingly.
Bridge Interface Overview
A bridge interface creates a software bridge between the members of the bridge interface. It also
becomes the USG’s interface for the resulting network.
Unlike the device-wide bridge mode in ZyNOS-based USGs, this USG can bridge traffic between
some interfaces while it routes traffic for other interfaces. The bridge interfaces also support more
functions, like interface bandwidth parameters, DHCP settings, and connectivity check. To use the
whole USG as a transparent bridge, add all of the USG’s interfaces to a bridge interface.
A bridge interface may consist of the following members:
• Zero or one VLAN interfaces (and any associated virtual VLAN interfaces)
• Any number of Ethernet interfaces (and any associated virtual Ethernet interfaces)
When you create a bridge interface, the USG removes the members’ entries from the routing table
and adds the bridge interface’s entries to the routing table. For example, this table shows the
routing table before and after you create bridge interface br0 (250.250.250.0/23) between lan1
and vlan1.
Table 77 Example: Bridge Table After Computer A Sends a Packet to Computer B
MAC ADDRESS PORT
0A:0A:0A:0A:0A:0A 2
Table 78 Example: Bridge Table After Computer B Responds to Computer A
MAC ADDRESS PORT
0A:0A:0A:0A:0A:0A 2
0B:0B:0B:0B:0B:0B 4
Table 79 Example: Routing Table Before and After Bridge Interface br0 Is Created
IP ADDRESS(ES) DESTINATION IP ADDRESS(ES) DESTINATION
210.210.210.0/24 lan1 221.221.221.0/24 vlan0
210.211.1.0/24 lan1:1 230.230.230.192/26 wan2
221.221.221.0/24 vlan0 241.241.241.241/32 dmz
222.222.222.0/24 vlan1 242.242.242.242/32 dmz
230.230.230.192/26 wan2 250.250.250.0/23 br0
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
203
In this example, virtual Ethernet interface lan1:1 is also removed from the routing table when lan1
is added to br0. Virtual interfaces are automatically added to or remove from a bridge interface
when the underlying interface is added or removed.
9.8.1 Bridge Summary
This screen lists every bridge interface and virtual interface created on top of bridge interfaces. If
you enabled IPv6 in the Configuration > System > IPv6 screen, you can also configure bridge
interfaces used for your IPv6 network on this screen. To access this screen, click Configuration >
Network > Interface > Bridge.
Figure 140 Configuration > Network > Interface > Bridge
Each field is described in the following table.
241.241.241.241/32 dmz
242.242.242.242/32 dmz
Table 79 Example: Routing Table Before and After Bridge Interface br0 Is Created (continued)
IP ADDRESS(ES) DESTINATION IP ADDRESS(ES) DESTINATION
Table 80 Configuration > Network > Interface > Bridge
LABEL DESCRIPTION
Configuration / IPv6
Configuration
Use the Configuration section for IPv4 network settings. Use the IPv6
Configuration section for IPv6 network settings if you connect your USG to an IPv6
network. Both sections have similar fields as described below.
Add Click this to create a new entry.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to remove
it before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Create Virtual
Interface
To open the screen where you can create a virtual interface, select an interface and
click Create Virtual Interface.

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
204
9.8.2 Bridge Add/Edit
This screen lets you configure IP address assignment, interface bandwidth parameters, DHCP
settings, and connectivity check for each bridge interface. To access this screen, click the Add or
Edit icon in the Bridge Summary screen. The following screen appears.
Object References Select an entry and click Object Reference to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
#This field is a sequential value, and it is not associated with any interface.
Status This icon is lit when the entry is active and dimmed when the entry is inactive.
Name This field displays the name of the interface.
IP Address This field displays the current IP address of the interface. If the IP address is 0.0.0.0,
the interface does not have an IP address yet.
This screen also shows whether the IP address is a static IP address (STATIC) or
dynamically assigned (DHCP). IP addresses are always static in virtual interfaces.
Member This field displays the Ethernet interfaces and VLAN interfaces in the bridge interface. It
is blank for virtual interfaces.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
Table 80 Configuration > Network > Interface > Bridge (continued)
LABEL DESCRIPTION
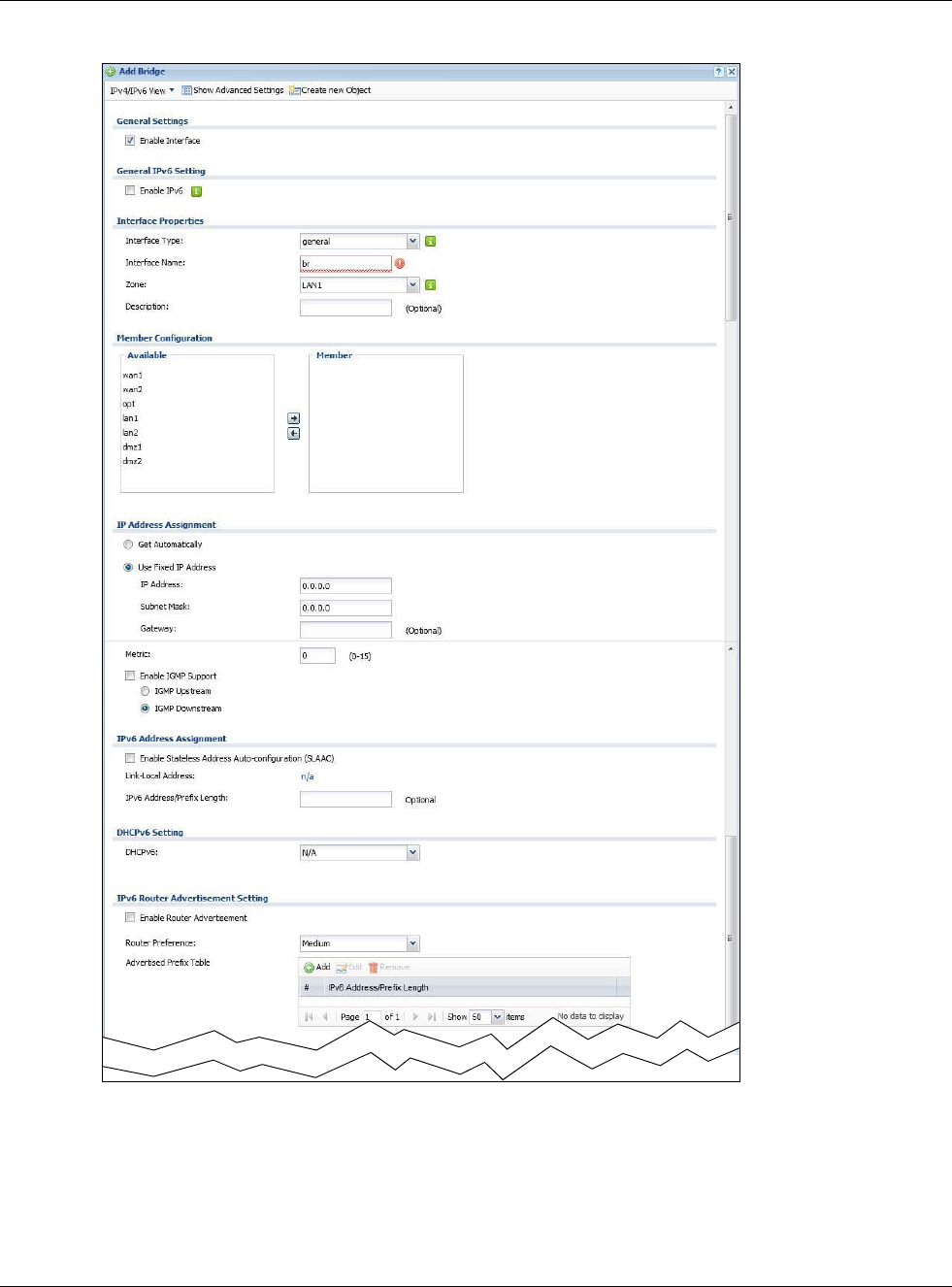
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
205
Figure 141 Configuration > Network > Interface > Bridge > Add / Edit
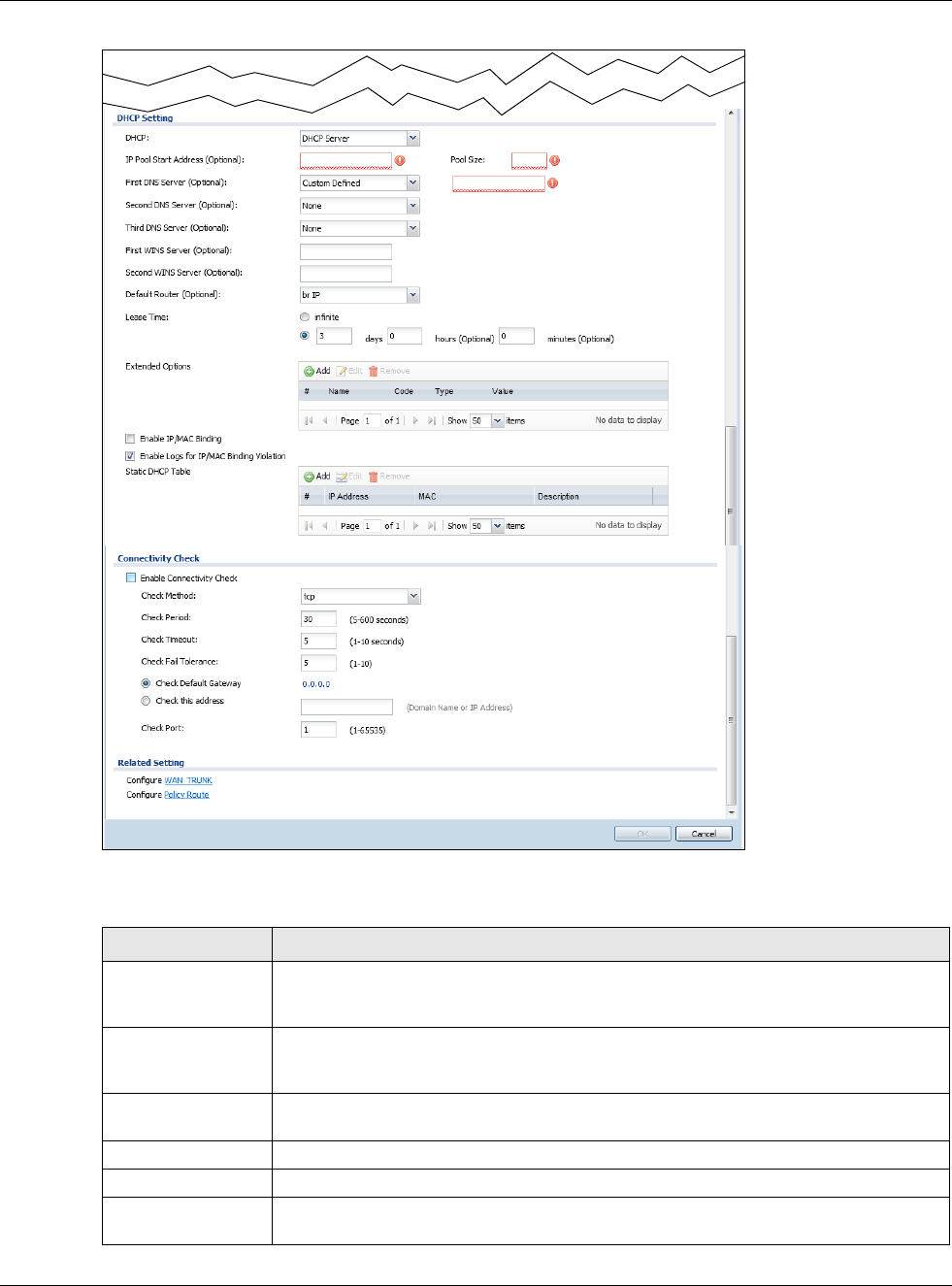
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
206
Configuration > Network > Interface > Bridge > Add
Each field is described in the table below.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit
LABEL DESCRIPTION
IPv4/IPv6 View /
IPv4 View / IPv6
View
Use this button to display both IPv4 and IPv6, IPv4-only, or IPv6-only configuration
fields.
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Create New Object Click this button to create a DHCPv6 lease or DHCPv6 request object that you may use
for the DHCPv6 settings in this screen.
General Settings
Enable Interface Select this to enable this interface. Clear this to disable this interface.
General IPv6
Setting
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
207
Enable IPv6 Select this to enable IPv6 on this interface. Otherwise, clear this to disable it.
Interface Properties
Interface Type Select one of the following option depending on the type of network to which the USG
is connected or if you want to additionally manually configure some related settings.
internal is for connecting to a local network. Other corresponding configuration
options: DHCP server and DHCP relay. The USG automatically adds default SNAT
settings for traffic flowing from this interface to an external interface.
external is for connecting to an external network (like the Internet). The USG
automatically adds this interface to the default WAN trunk.
For general, the rest of the screen’s options do not automatically adjust and you must
manually configure a policy route to add routing and SNAT settings for the interface.
Interface Name This field is read-only if you are editing the interface. Enter the name of the bridge
interface. The format is brx, where x is 0 - 11. For example, br0, br3, and so on.
Zone Select the zone to which the interface is to belong. You use zones to apply security
settings such as security policy and remote management.
Description Enter a description of this interface. It is not used elsewhere. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
Member
Configuration
Available This field displays Ethernet interfaces and VLAN interfaces that can become part of the
bridge interface. An interface is not available in the following situations:
• There is a virtual interface on top of it
• It is already used in a different bridge interface
Select one, and click the >> arrow to add it to the bridge interface. Each bridge
interface can only have one VLAN interface.
Member This field displays the interfaces that are part of the bridge interface. Select one, and
click the << arrow to remove it from the bridge interface.
IP Address
Assignment
Get
Automatically Select this if this interface is a DHCP client. In this case, the DHCP server configures
the IP address, subnet mask, and gateway automatically.
Use Fixed IP
Address Select this if you want to specify the IP address, subnet mask, and gateway manually.
IP Address This field is enabled if you select Use Fixed IP Address.
Enter the IP address for this interface.
Subnet Mask This field is enabled if you select Use Fixed IP Address.
Enter the subnet mask of this interface in dot decimal notation. The subnet mask
indicates what part of the IP address is the same for all computers in the network.
Gateway This field is enabled if you select Use Fixed IP Address.
Enter the IP address of the gateway. The USG sends packets to the gateway when it
does not know how to route the packet to its destination. The gateway should be on the
same network as the interface.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Enable IGMP
Support
Select this to allow the USG to act as an IGMP proxy for hosts connected on the IGMP
downstream interface.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
208
IGMP Upstream Enable IGMP Upstream on the interface which connects to a router running IGMP that
is closer to the multicast server.
IGMP
Downstream Enable IGMP Downstream on the interface which connects to the multicast hosts.
IPv6 Address
Assignment
These IP address fields configure an IPv6 IP address on the interface itself.
Enable Stateless
Address Auto-
configuration
(SLAAC)
Select this to enable IPv6 stateless auto-configuration on this interface. The interface
will generate an IPv6 IP address itself from a prefix obtained from an IPv6 router in the
network.
Link-Local
address This displays the IPv6 link-local address and the network prefix that the USG generates
itself for the interface.
IPv6 Address/
Prefix Length Enter the IPv6 address and the prefix length for this interface if you want to use a static
IP address. This field is optional.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Gateway Enter the IPv6 address of the default outgoing gateway using colon (:) hexadecimal
notation.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Address from
DHCPv6 Prefix
Delegation
Use this table to have the USG obtain an IPv6 prefix from the ISP or a connected uplink
router for an internal network, such as the LAN or DMZ. You have to also enter a suffix
address which is appended to the delegated prefix to form an address for this interface.
See Prefix Delegation on page 144 for more information.
To use prefix delegation, you must:
• Create at least one DHCPv6 request object before configuring this table.
• The external interface must be a DHCPv6 client. You must configure the DHCPv6
request options using a DHCPv6 request object with the type of prefix-delegation.
• Assign the prefix delegation to an internal interface and enable router
advertisement on that interface.
Add Click this to create an entry.
Edit Select an entry and click this to change the settings.
Remove Select an entry and click this to delete it from this table.
# This field is a sequential value, and it is not associated with any entry.
Delegated
Prefix Select the DHCPv6 request object to use from the drop-down list.
Suffix
Address Enter the ending part of the IPv6 address, a slash (/), and the prefix length. The USG
will append it to the delegated prefix.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to configure
an IP address of 2003:1234:5678:1111::1/128 for this interface, then enter
::1111:0:0:0:1/128 in this field.
Address This field displays the combined IPv6 IP address for this interface.
Note: This field displays the combined address after you click OK and reopen this
screen.
DHCPv6 Setting
DUID This field displays the DHCP Unique IDentifier (DUID) of the interface, which is unique
and used for identification purposes when the interface is exchanging DHCPv6
messages with others. See DHCPv6 on page 145 for more information.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
209
DUID as MAC Select this if you want the DUID is generated from the interface’s default MAC address.
Customized
DUID If you want to use a customized DUID, enter it here for the interface.
Enable Rapid
Commit Select this to shorten the DHCPv6 message exchange process from four to two steps.
This function helps reduce heavy network traffic load.
Note: Make sure you also enable this option in the DHCPv6 clients to make rapid commit
work.
Information
Refresh Time Enter the number of seconds a DHCPv6 client should wait before refreshing information
retrieved from DHCPv6.
Request Address This field is available if you set this interface to DHCPv6 Client. Select this to get an
IPv6 IP address for this interface from the DHCP server. Clear this to not get any IP
address information through DHCPv6.
DHCPv6 Request
Options /
DHCPv6 Lease
Options
If this interface is a DHCPv6 client, use this section to configure DHCPv6 request
settings that determine what additional information to get from the DHCPv6 server.
If the interface is a DHCPv6 server, use this section to configure DHCPv6 lease settings
that determine what to offer to the DHCPv6 clients.
Add Click this to create an entry in this table. See Section 9.3.3 on page 164 for more
information.
Remove Select an entry and click this to change the settings.
Object
Reference Select an entry and click this to delete it from this table.
# This field is a sequential value, and it is not associated with any entry.
Name This field displays the name of the DHCPv6 request or lease object.
Type This field displays the type of the object.
Value This field displays the IPv6 prefix that the USG obtained from an uplink router (Server
is selected) or will advertise to its clients (Client is selected).
Interface When Relay is selected, select this check box and an interface from the drop-down list
if you want to use it as the relay server.
Relay Server When Relay is selected, select this check box and enter the IP address of a DHCPv6
server as the relay server.
IPv6 Router
Advertisement
Setting
Enable Router
Advertisement Select this to enable this interface to send router advertisement messages periodically.
See IPv6 Router Advertisement on page 145 for more information.
Advertised Hosts
Get Network
Configuration
From DHCPv6
Select this to have the USG indicate to hosts to obtain network settings (such as prefix
and DNS settings) through DHCPv6.
Clear this to have the USG indicate to hosts that DHCPv6 is not available and they
should use the prefix in the router advertisement message.
Advertised Hosts
Get Other
Configuration
From DHCPv6
Select this to have the USG indicate to hosts to obtain DNS information through
DHCPv6.
Clear this to have the USG indicate to hosts that DNS information is not available in this
network.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
210
Router
Preference Select the router preference (Low, Medium or High) for the interface. The interface
sends this preference in the router advertisements to tell hosts what preference they
should use for the USG. This helps hosts to choose their default router especially when
there are multiple IPv6 router in the network.
Note: Make sure the hosts also support router preference to make this function work.
MTU The Maximum Transmission Unit. Type the maximum size of each IPv6 data packet, in
bytes, that can move through this interface. If a larger packet arrives, the USG divides
it into smaller fragments.
Hop Limit Enter the maximum number of network segments that a packet can cross before
reaching the destination. When forwarding an IPv6 packet, IPv6 routers are required to
decrease the Hop Limit by 1 and to discard the IPv6 packet when the Hop Limit is 0.
Advertised
Prefix Table Configure this table only if you want the USG to advertise a fixed prefix to the network.
Add Click this to create an IPv6 prefix address.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
IPv6
Address/
Prefix Length
Enter the IPv6 network prefix address and the prefix length.
The prefix length indicates what the left-most part of the IP address is the same for all
computers in the network, that is, the network address.
Advertised
Prefix from
DHCPv6 Prefix
Delegation
Use this table to configure the network prefix if you want to use a delegated prefix as
the beginning part of the network prefix.
Add Click this to create an entry in this table.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
Delegated
Prefix Select the DHCPv6 request object to use for generating the network prefix for the
network.
Suffix
Address Enter the ending part of the IPv6 network address plus a slash (/) and the prefix
length. The USG will append it to the selected delegated prefix. The combined address
is the network prefix for the network.
For example, you got a delegated prefix of 2003:1234:5678/48. You want to divide it
into 2003:1234:5678:1111/64 for this interface and 2003:1234:5678:2222/64 for
another interface. You can use ::1111/64 and ::2222/64 for the suffix address
respectively. But if you do not want to divide the delegated prefix into subnetworks,
enter ::0/48 here, which keeps the same prefix length (/48) as the delegated prefix.
Address This is the final network prefix combined by the selected delegated prefix and the
suffix.
Note: This field displays the combined address after you click OK and reopen this
screen.
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send through
the interface to the network. Allowed values are 0 - 1048576.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
211
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
MTU Maximum Transmission Unit. Type the maximum size of each data packet, in bytes,
that can move through this interface. If a larger packet arrives, the USG divides it into
smaller fragments. Allowed values are 576 - 1500. Usually, this value is 1500.
DHCP Setting
DHCP Select what type of DHCP service the USG provides to the network. Choices are:
None - the USG does not provide any DHCP services. There is already a DHCP server
on the network.
DHCP Relay - the USG routes DHCP requests to one or more DHCP servers you
specify. The DHCP server(s) may be on another network.
DHCP Server - the USG assigns IP addresses and provides subnet mask, gateway, and
DNS server information to the network. The USG is the DHCP server for the network.
These fields appear if the USG is a DHCP Relay.
Relay Server 1 Enter the IP address of a DHCP server for the network.
Relay Server 2 This field is optional. Enter the IP address of another DHCP server for the network.
These fields appear if the USG is a DHCP Server.
IP Pool Start
Address Enter the IP address from which the USG begins allocating IP addresses. If you want to
assign a static IP address to a specific computer, click Add Static DHCP.
If this field is blank, the Pool Size must also be blank. In this case, the USG can assign
every IP address allowed by the interface’s IP address and subnet mask, except for the
first address (network address), last address (broadcast address) and the interface’s IP
address.
Pool Size Enter the number of IP addresses to allocate. This number must be at least one and is
limited by the interface’s Subnet Mask. For example, if the Subnet Mask is
255.255.255.0 and IP Pool Start Address is 10.10.10.10, the USG can allocate
10.10.10.10 to 10.10.10.254, or 245 IP addresses.
If this field is blank, the IP Pool Start Address must also be blank. In this case, the
USG can assign every IP address allowed by the interface’s IP address and subnet
mask, except for the first address (network address), last address (broadcast address)
and the interface’s IP address.
First DNS Server
Second DNS
Server
Third DNS
Server
Specify the IP addresses up to three DNS servers for the DHCP clients to use. Use one
of the following ways to specify these IP addresses.
Custom Defined - enter a static IP address.
From ISP - select the DNS server that another interface received from its DHCP server.
USG - the DHCP clients use the IP address of this interface and the USG works as a
DNS relay.
First WINS
Server, Second
WINS Server
Type the IP address of the WINS (Windows Internet Naming Service) server that you
want to send to the DHCP clients. The WINS server keeps a mapping table of the
computer names on your network and the IP addresses that they are currently using.
Default Router If you set this interface to DHCP Server, you can select to use either the interface’s IP
address or another IP address as the default router. This default router will become the
DHCP clients’ default gateway.
To use another IP address as the default router, select Custom Defined and enter the
IP address.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
212
Lease time Specify how long each computer can use the information (especially the IP address)
before it has to request the information again. Choices are:
infinite - select this if IP addresses never expire
days, hours, and minutes - select this to enter how long IP addresses are valid.
Extended
Options This table is available if you selected DHCP server.
Configure this table if you want to send more information to DHCP clients through
DHCP packets.
Add Click this to create an entry in this table. See Section 9.3.4 on page 165.
Edit Select an entry in this table and click this to modify it.
Remove Select an entry in this table and click this to delete it.
# This field is a sequential value, and it is not associated with any entry.
Name This is the option’s name.
Code This is the option’s code number.
Type This is the option’s type.
Value This is the option’s value.
Enable IP/MAC
Binding Select this option to have this interface enforce links between specific IP addresses and
specific MAC addresses. This stops anyone else from manually using a bound IP
address on another device connected to this interface. Use this to make use only the
intended users get to use specific IP addresses.
Enable Logs for
IP/MAC Binding
Violation
Select this option to have the USG generate a log if a device connected to this interface
attempts to use an IP address that is bound to another device’s MAC address.
Static DHCP
Table Configure a list of static IP addresses the USG assigns to computers connected to the
interface. Otherwise, the USG assigns an IP address dynamically using the interface’s
IP Pool Start Address and Pool Size.
Add Click this to create a new entry.
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
# This field is a sequential value, and it is not associated with a specific entry.
IP Address Enter the IP address to assign to a device with this entry’s MAC address.
MAC Address Enter the MAC address to which to assign this entry’s IP address.
Description Enter a description to help identify this static DHCP entry. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
Connectivity Check The interface can regularly check the connection to the gateway you specified to make
sure it is still available. You specify how often the interface checks the connection, how
long to wait for a response before the attempt is a failure, and how many consecutive
failures are required before the USG stops routing to the gateway. The USG resumes
routing to the gateway the first time the gateway passes the connectivity check.
Enable
Connectivity
Check
Select this to turn on the connection check.
Check Method Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Check Period Enter the number of seconds between connection check attempts.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
213
9.9 Virtual Interfaces
Use virtual interfaces to tell the USG where to route packets. Virtual interfaces can also be used in
VPN gateways (see Chapter 21 on page 332).
Virtual interfaces can be created on top of Ethernet interfaces, VLAN interfaces, or bridge
interfaces. Virtual VLAN interfaces recognize and use the same VLAN ID. Otherwise, there is no
difference between each type of virtual interface. Network policies (for example, security policies)
that apply to the underlying interface automatically apply to the virtual interface as well.
Like other interfaces, virtual interfaces have an IP address, subnet mask, and gateway used to
make routing decisions. However, you have to manually specify the IP address and subnet mask;
virtual interfaces cannot be DHCP clients. Like other interfaces, you can restrict bandwidth through
virtual interfaces, but you cannot change the MTU. The virtual interface uses the same MTU that the
underlying interface uses. Unlike other interfaces, virtual interfaces do not provide DHCP services,
and they do not verify that the gateway is available.
9.9.1 Virtual Interfaces Add/Edit
This screen lets you configure IP address assignment and interface parameters for virtual
interfaces. To access this screen, click the Create Virtual Interface icon in the Ethernet, VLAN, or
bridge interface summary screen.
Check Timeout Enter the number of seconds to wait for a response before the attempt is a failure.
Check Fail
Tolerance Enter the number of consecutive failures before the USG stops routing through the
gateway.
Check Default
Gateway Select this to use the default gateway for the connectivity check.
Check this
address Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
Check Port This field only displays when you set the Check Method to tcp. Specify the port
number to use for a TCP connectivity check.
Related Setting
Configure WAN
TRUNK Click WAN TRUNK to go to a screen where you can configure the interface as part of a
WAN trunk for load balancing.
Configure Policy
Route Click Policy Route to go to the screen where you can manually configure a policy
route to associate traffic with this bridge interface.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 81 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL DESCRIPTION
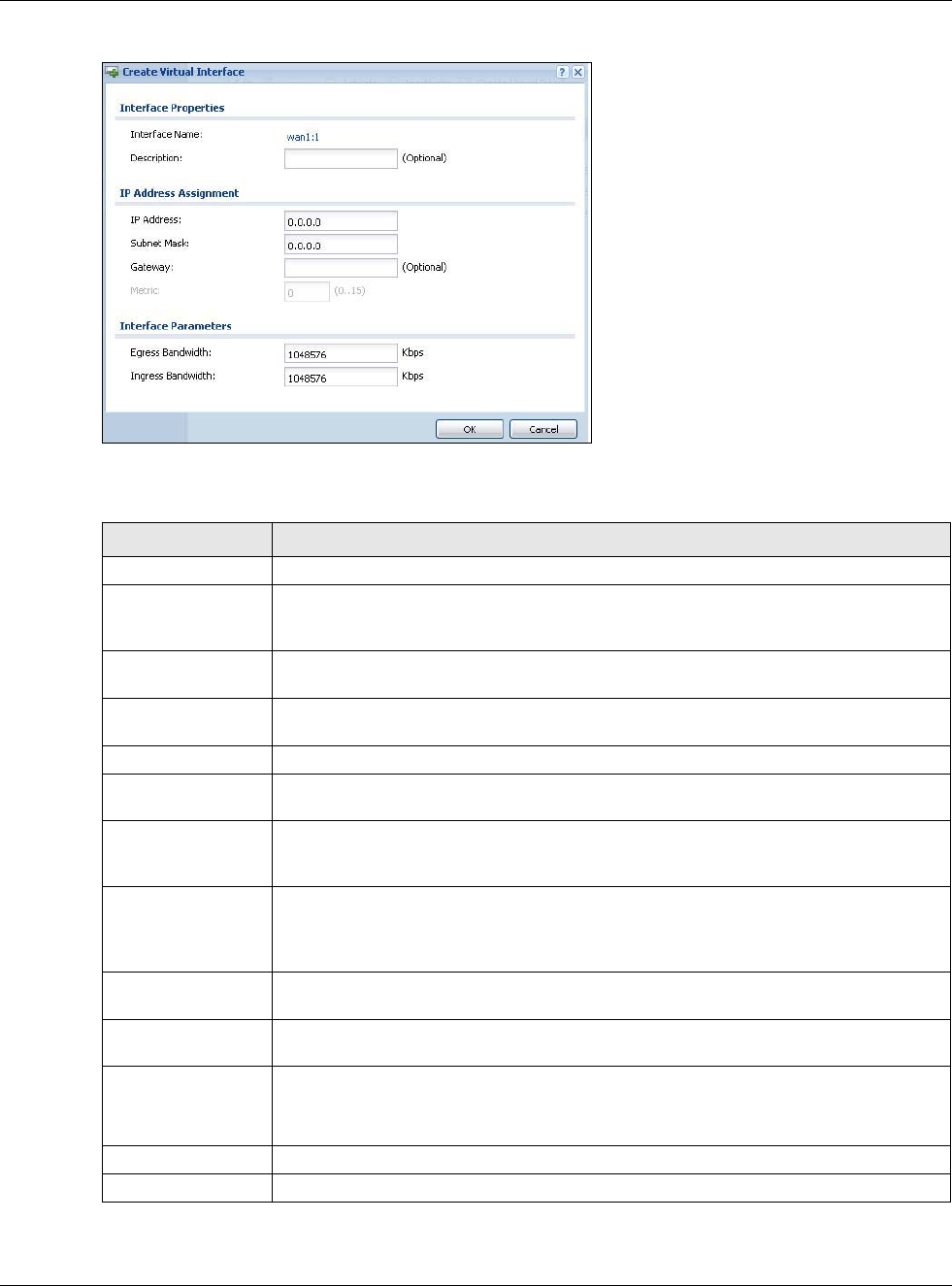
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
214
Figure 142 Configuration > Network > Interface > Create Virtual Interface
Each field is described in the table below.
Table 82 Configuration > Network > Interface > Create Virtual Interface
LABEL DESCRIPTION
Interface Properties
Interface Name This field is read-only. It displays the name of the virtual interface, which is
automatically derived from the underlying Ethernet interface, VLAN interface, or bridge
interface.
Description Enter a description of this interface. It is not used elsewhere. You can use alphanumeric
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
IP Address
Assignment
IP Address Enter the IP address for this interface.
Subnet Mask Enter the subnet mask of this interface in dot decimal notation. The subnet mask
indicates what part of the IP address is the same for all computers in the network.
Gateway Enter the IP address of the gateway. The USG sends packets to the gateway when it
does not know how to route the packet to its destination. The gateway should be on the
same network as the interface.
Metric Enter the priority of the gateway (if any) on this interface. The USG decides which
gateway to use based on this priority. The lower the number, the higher the priority. If
two or more gateways have the same priority, the USG uses the one that was
configured first.
Interface
Parameters
Egress
Bandwidth Enter the maximum amount of traffic, in kilobits per second, the USG can send through
the interface to the network. Allowed values are 0 - 1048576.
Ingress
Bandwidth This is reserved for future use.
Enter the maximum amount of traffic, in kilobits per second, the USG can receive from
the network through the interface. Allowed values are 0 - 1048576.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
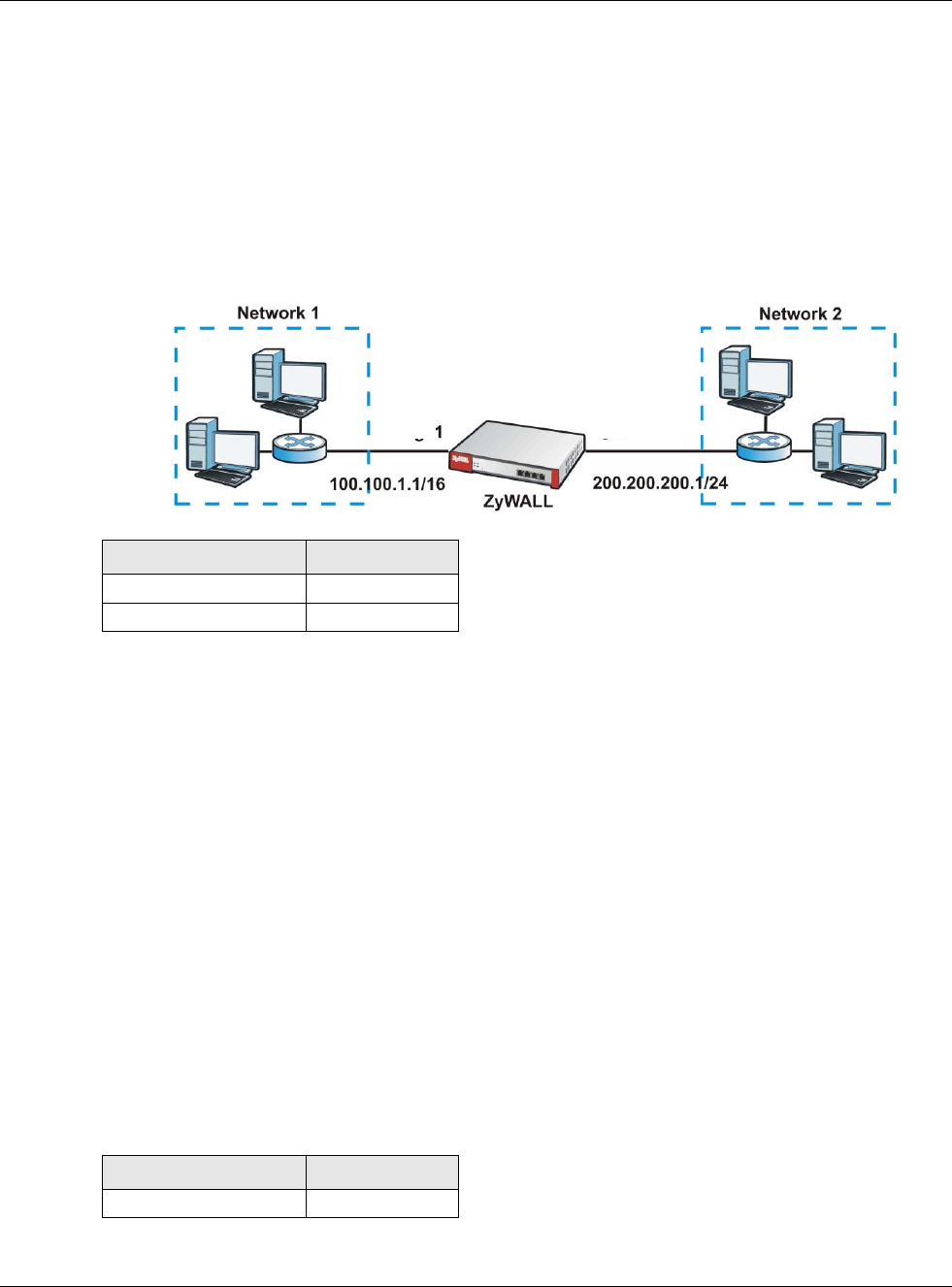
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
215
9.10 Interface Technical Reference
Here is more detailed information about interfaces on the USG.
IP Address Assignment
Most interfaces have an IP address and a subnet mask. This information is used to create an entry
in the routing table.
Figure 143 Example: Entry in the Routing Table Derived from Interfaces
For example, if the USG gets a packet with a destination address of 100.100.25.25, it routes the
packet to interface lan1. If the USG gets a packet with a destination address of 200.200.200.200, it
routes the packet to interface wan1.
In most interfaces, you can enter the IP address and subnet mask manually. In PPPoE/PPTP
interfaces, however, the subnet mask is always 255.255.255.255 because it is a point-to-point
interface. For these interfaces, you can only enter the IP address.
In many interfaces, you can also let the IP address and subnet mask be assigned by an external
DHCP server on the network. In this case, the interface is a DHCP client. Virtual interfaces,
however, cannot be DHCP clients. You have to assign the IP address and subnet mask manually.
In general, the IP address and subnet mask of each interface should not overlap, though it is
possible for this to happen with DHCP clients.
In the example above, if the USG gets a packet with a destination address of 5.5.5.5, it might not
find any entries in the routing table. In this case, the packet is dropped. However, if there is a
default router to which the USG should send this packet, you can specify it as a gateway in one of
the interfaces. For example, if there is a default router at 200.200.200.100, you can create a
gateway at 200.200.200.100 on ge2. In this case, the USG creates the following entry in the
routing table.
Table 83 Example: Routing Table Entries for Interfaces
IP ADDRESS(ES) DESTINATION
100.100.1.1/16 lan1
200.200.200.1/24 wan1
Table 84 Example: Routing Table Entry for a Gateway
IP ADDRESS(ES) DESTINATION
0.0.0.0/0 200.200.200.100
lan1 wan1

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
216
The gateway is an optional setting for each interface. If there is more than one gateway, the USG
uses the gateway with the lowest metric, or cost. If two or more gateways have the same metric,
the USG uses the one that was set up first (the first entry in the routing table). In PPPoE/PPTP
interfaces, the other computer is the gateway for the interface by default. In this case, you should
specify the metric.
If the interface gets its IP address and subnet mask from a DHCP server, the DHCP server also
specifies the gateway, if any.
Interface Parameters
The USG restricts the amount of traffic into and out of the USG through each interface.
• Egress bandwidth sets the amount of traffic the USG sends out through the interface to the
network.
• Ingress bandwidth sets the amount of traffic the USG allows in through the interface from the
network.At the time of writing, the USG does not support ingress bandwidth management.
If you set the bandwidth restrictions very high, you effectively remove the restrictions.
The USG also restricts the size of each data packet. The maximum number of bytes in each packet
is called the maximum transmission unit (MTU). If a packet is larger than the MTU, the USG divides
it into smaller fragments. Each fragment is sent separately, and the original packet is re-assembled
later. The smaller the MTU, the more fragments sent, and the more work required to re-assemble
packets correctly. On the other hand, some communication channels, such as Ethernet over ATM,
might not be able to handle large data packets.
DHCP Settings
Dynamic Host Configuration Protocol (DHCP, RFC 2131, RFC 2132) provides a way to automatically
set up and maintain IP addresses, subnet masks, gateways, and some network information (such
as the IP addresses of DNS servers) on computers in the network. This reduces the amount of
manual configuration you have to do and usually uses available IP addresses more efficiently.
In DHCP, every network has at least one DHCP server. When a computer (a DHCP client) joins the
network, it submits a DHCP request. The DHCP servers get the request; assign an IP address; and
provide the IP address, subnet mask, gateway, and available network information to the DHCP
client. When the DHCP client leaves the network, the DHCP servers can assign its IP address to
another DHCP client.
In the USG, some interfaces can provide DHCP services to the network. In this case, the interface
can be a DHCP relay or a DHCP server.
As a DHCP relay, the interface routes DHCP requests to DHCP servers on different networks. You
can specify more than one DHCP server. If you do, the interface routes DHCP requests to all of
them. It is possible for an interface to be a DHCP relay and a DHCP client simultaneously.
As a DHCP server, the interface provides the following information to DHCP clients.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
217
• IP address - If the DHCP client’s MAC address is in the USG’s static DHCP table, the interface
assigns the corresponding IP address. If not, the interface assigns IP addresses from a pool,
defined by the starting address of the pool and the pool size.
The USG cannot assign the first address (network address) or the last address (broadcast
address) in the subnet defined by the interface’s IP address and subnet mask. For example, in
the first entry, if the subnet mask is 255.255.255.0, the USG cannot assign 50.50.50.0 or
50.50.50.255. If the subnet mask is 255.255.0.0, the USG cannot assign 50.50.0.0 or
50.50.255.255. Otherwise, it can assign every IP address in the range, except the interface’s IP
address.
If you do not specify the starting address or the pool size, the interface the maximum range of IP
addresses allowed by the interface’s IP address and subnet mask. For example, if the interface’s
IP address is 9.9.9.1 and subnet mask is 255.255.255.0, the starting IP address in the pool is
9.9.9.2, and the pool size is 253.
• Subnet mask - The interface provides the same subnet mask you specify for the interface. See IP
Address Assignment on page 215.
• Gateway - The interface provides the same gateway you specify for the interface. See IP Address
Assignment on page 215.
• DNS servers - The interface provides IP addresses for up to three DNS servers that provide DNS
services for DHCP clients. You can specify each IP address manually (for example, a company’s
own DNS server), or you can refer to DNS servers that other interfaces received from DHCP
servers (for example, a DNS server at an ISP). These other interfaces have to be DHCP clients.
It is not possible for an interface to be the DHCP server and a DHCP client simultaneously.
WINS
WINS (Windows Internet Naming Service) is a Windows implementation of NetBIOS Name Server
(NBNS) on Windows. It keeps track of NetBIOS computer names. It stores a mapping table of your
network’s computer names and IP addresses. The table is dynamically updated for IP addresses
assigned by DHCP. This helps reduce broadcast traffic since computers can query the server instead
of broadcasting a request for a computer name’s IP address. In this way WINS is similar to DNS,
although WINS does not use a hierarchy (unlike DNS). A network can have more than one WINS
server. Samba can also serve as a WINS server.
PPPoE/PPTP Overview
Point-to-Point Protocol over Ethernet (PPPoE, RFC 2516) and Point-to-Point Tunneling Protocol
(PPTP, RFC 2637) are usually used to connect two computers over phone lines or broadband
connections. PPPoE is often used with cable modems and DSL connections. It provides the following
advantages:
• The access and authentication method works with existing systems, including RADIUS.
• You can access one of several network services. This makes it easier for the service provider to
offer the service
Table 85 Example: Assigning IP Addresses from a Pool
START IP ADDRESS POOL SIZE RANGE OF ASSIGNED IP ADDRESS
50.50.50.33 5 50.50.50.33 - 50.50.50.37
75.75.75.1 200 75.75.75.1 - 75.75.75.200
99.99.1.1 1023 99.99.1.1 - 99.99.4.255
120.120.120.100 100 120.120.120.100 - 120.120.120.199

Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
218
• PPPoE does not usually require any special configuration of the modem.
PPTP is used to set up virtual private networks (VPN) in unsecure TCP/IP environments. It sets up
two sessions.
1The first one runs on TCP port 1723. It is used to start and manage the second one.
2The second one uses Generic Routing Encapsulation (GRE, RFC 2890) to transfer information
between the computers.
PPTP is convenient and easy-to-use, but you have to make sure that firewalls support both PPTP
sessions.
9.11 Trunk Overview
Use trunks for WAN traffic load balancing to increase overall network throughput and reliability.
Load balancing divides traffic loads between multiple interfaces. This allows you to improve quality
of service and maximize bandwidth utilization for multiple ISP links.
Maybe you have two Internet connections with different bandwidths. You could set up a trunk that
uses spillover or weighted round robin load balancing so time-sensitive traffic (like video) usually
goes through the higher-bandwidth interface. For other traffic, you might want to use least load
first load balancing to even out the distribution of the traffic load.
Suppose ISP A has better connections to Europe while ISP B has better connections to Australia.
You could use policy routes and trunks to have traffic for your European branch office primarily use
ISP A and traffic for your Australian branch office primarily use ISP B.
Or maybe one of the USG's interfaces is connected to an ISP that is also your Voice over IP (VoIP)
service provider. You can use policy routing to send the VoIP traffic through a trunk with the
interface connected to the VoIP service provider set to active and another interface (connected to
another ISP) set to passive. This way VoIP traffic goes through the interface connected to the VoIP
service provider whenever the interface’s connection is up.
•Use the Trunk summary screen (Section 9.12 on page 221) to view the list of configured trunks
and which load balancing algorithm each trunk uses.
•Use the Add Trunk screen (Section 9.12.1 on page 222) to configure the member interfaces for
a trunk and the load balancing algorithm the trunk uses.
•Use the Add System Default screen (Section 9.12.2 on page 224) to configure the load
balancing algorithm for the system default trunk.
9.11.1 What You Need to Know
• Add WAN interfaces to trunks to have multiple connections share the traffic load.
• If one WAN interface’s connection goes down, the USG sends traffic through another member of
the trunk.
• For example, you connect one WAN interface to one ISP and connect a second WAN interface to
a second ISP. The USG balances the WAN traffic load between the connections. If one interface's
connection goes down, the USG can automatically send its traffic through another interface.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
219
You can also use trunks with policy routing to send specific traffic types through the best WAN
interface for that type of traffic.
• If that interface’s connection goes down, the USG can still send its traffic through another
interface.
• You can define multiple trunks for the same physical interfaces.
1LAN user A logs into server B on the Internet. The USG uses wan1 to send the request to server B.
2The USG is using active/active load balancing. So when LAN user A tries to access something on the
server, the request goes out through wan2.
3The server finds that the request comes from wan2’s IP address instead of wan1’s IP address and
rejects the request.
If link sticking had been configured, the USG would have still used wan1 to send LAN user A’s
request to the server and server would have given the user A access.
Load Balancing Algorithms
The following sections describe the load balancing algorithms the USG can use to decide which
interface the traffic (from the LAN) should use for a session. In the load balancing section, a session
may refer to normal connection-oriented, UDP or SNMP2 traffic. The available bandwidth you
configure on the USG refers to the actual bandwidth provided by the ISP and the measured
bandwidth refers to the bandwidth an interface is currently using.
Least Load First
The least load first algorithm uses the current (or recent) outbound bandwidth utilization of each
trunk member interface as the load balancing index(es) when making decisions about to which
interface a new session is to be distributed. The outbound bandwidth utilization is defined as the
measured outbound throughput over the available outbound bandwidth.
Here the USG has two WAN interfaces connected to the Internet. The configured available outbound
bandwidths for WAN 1 and WAN 2 are 512K and 256K respectively.
Figure 144 Least Load First Example
The outbound bandwidth utilization is used as the load balancing index. In this example, the
measured (current) outbound throughput of WAN 1 is 412K and WAN 2 is 198K. The USG calculates
the load balancing index as shown in the table below.
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
220
Since WAN 2 has a smaller load balancing index (meaning that it is less utilized than WAN 1), the
USG will send the subsequent new session traffic through WAN 2.
Weighted Round Robin
Round Robin scheduling services queues on a rotating basis and is activated only when an interface
has more traffic than it can handle. A queue is given an amount of bandwidth irrespective of the
incoming traffic on that interface. This queue then moves to the back of the list. The next queue is
given an equal amount of bandwidth, and then moves to the end of the list; and so on, depending
on the number of queues being used. This works in a looping fashion until a queue is empty.
The Weighted Round Robin (WRR) algorithm is best suited for situations when the bandwidths set
for the two WAN interfaces are different. Similar to the Round Robin (RR) algorithm, the Weighted
Round Robin (WRR) algorithm sets the USG to send traffic through each WAN interface in turn. In
addition, the WAN interfaces are assigned weights. An interface with a larger weight gets more
chances to transmit traffic than an interface with a smaller weight.
For example, in the figure below, the configured available bandwidth of WAN1 is 1M and WAN2 is
512K. You can set the USG to distribute the network traffic between the two interfaces by setting
the weight of wan1 and wan2 to 2 and 1 respectively. The USG assigns the traffic of two sessions to
wan1 and one session's traffic to wan2 in each round of 3 new sessions.
Figure 145 Weighted Round Robin Algorithm Example
Spillover
The spillover load balancing algorithm sends network traffic to the first interface in the trunk
member list until the interface’s maximum allowable load is reached, then sends the excess
network traffic of new sessions to the next interface in the trunk member list. This continues as
long as there are more member interfaces and traffic to be sent through them.
Suppose the first trunk member interface uses an unlimited access Internet connection and the
second is billed by usage. Spillover load balancing only uses the second interface when the traffic
load exceeds the threshold on the first interface. This fully utilizes the bandwidth of the first
interface to reduce Internet usage fees and avoid overloading the interface.
In this example figure, the upper threshold of the first interface is set to 800K. The USG sends
network traffic of new sessions that exceed this limit to the secondary WAN interface.
Table 86 Least Load First Example
INTERFACE OUTBOUND LOAD BALANCING INDEX
(M/A)
AVAILABLE (A) MEASURED (M)
WAN 1 512 K 412 K 0.8
WAN 2 256 K 198 K 0.77
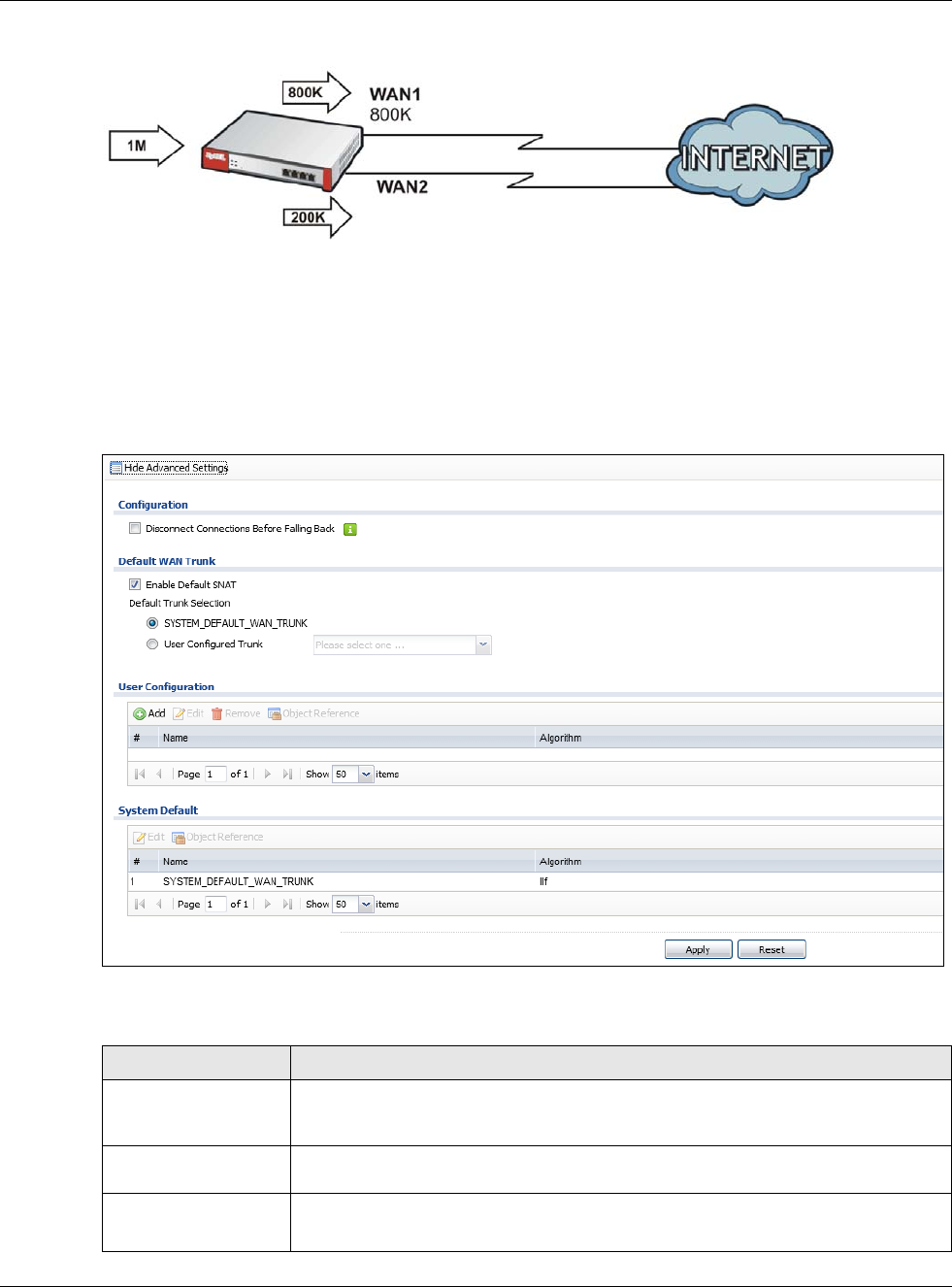
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
221
Figure 146 Spillover Algorithm Example
9.12 The Trunk Summary Screen
Click Configuration > Network > Interface > Trunk to open the Trunk screen. This screen lists
the configured trunks and the load balancing algorithm that each is configured to use.
Figure 147 Configuration > Network > Interface > Trunk
The following table describes the items in this screen.
Table 87 Configuration > Network > Interface > Trunk
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Configuration Configure what to do with existing passive mode interface connections when an
interface set to active mode in the same trunk comes back up.
Disconnect
Connections
Before Falling Back
Select this to terminate existing connections on an interface which is set to passive
mode when any interface set to active mode in the same trunk comes back up.
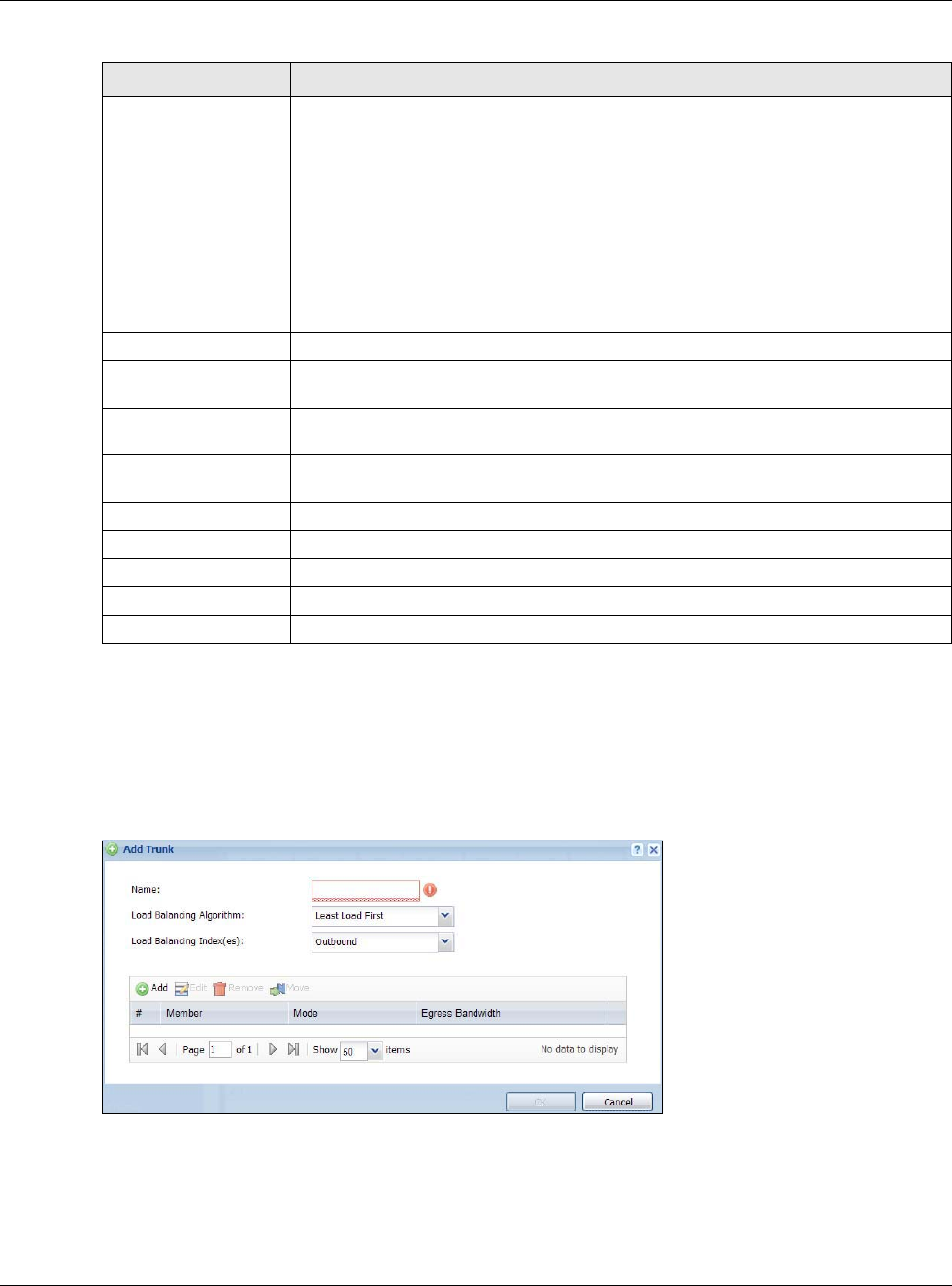
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
222
9.12.1 Configuring a User-Defined Trunk
Click Configuration > Network > Interface > Trunk, in the User Configuration table click the
Add (or Edit) icon to open the following screen. Use this screen to create or edit a WAN trunk
entry.
Figure 148 Configuration > Network > Interface > Trunk > Add (or Edit)
Enable Default SNAT Select this to have the USG use the IP address of the outgoing interface as the
source IP address of the packets it sends out through its WAN trunks. The USG
automatically adds SNAT settings for traffic it routes from internal interfaces to
external interfaces.
Default Trunk
Selection
Select whether the USG is to use the default system WAN trunk or one of the user
configured WAN trunks as the default trunk for routing traffic from internal interfaces
to external interfaces.
User Configuration /
System Default
The USG automatically adds all external interfaces into the pre-configured system
default SYSTEM_DEFAULT_WAN_TRUNK. You cannot delete it. You can create
your own User Configuration trunks and customize the algorithm, member
interfaces and the active/passive mode.
Add Click this to create a new user-configured trunk.
Edit Double-click an entry or select it and click Edit to open a screen where you can
modify the entry’s settings.
Remove To remove a user-configured trunk, select it and click Remove. The USG confirms
you want to remove it before doing so.
Object References Select an entry and click Object References to open a screen that shows which
settings use the entry. See Section 9.3.2 on page 163 for an example.
# This field is a sequential value, and it is not associated with any interface.
Name This field displays the label that you specified to identify the trunk.
Algorithm This field displays the load balancing method the trunk is set to use.
Apply Click this button to save your changes to the USG.
Reset Click this button to return the screen to its last-saved settings.
Table 87 Configuration > Network > Interface > Trunk (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
223
Each field is described in the table below.
Table 88 Configuration > Network > Interface > Trunk > Add (or Edit)
LABEL DESCRIPTION
Name This is read-only if you are editing an existing trunk. When adding a new trunk, enter a
descriptive name for this trunk. You may use 1-31 alphanumeric characters,
underscores (_), or dashes (-), but the first character cannot be a number. This value is
case-sensitive.
Load Balancing
Algorithm
Select a load balancing method to use from the drop-down list box.
Select Weighted Round Robin to balance the traffic load between interfaces based on
their respective weights. An interface with a larger weight gets more chances to
transmit traffic than an interface with a smaller weight. For example, if the weight ratio
of wan1 and wan2 interfaces is 2:1, the USG chooses wan1 for 2 sessions’ traffic and
wan2 for 1 session’s traffic in each round of 3 new sessions.
Select Least Load First to send new session traffic through the least utilized trunk
member.
Select Spillover to send network traffic through the first interface in the group
member list until there is enough traffic that the second interface needs to be used
(and so on).
Load Balancing
Index(es)
This field is available if you selected to use the Least Load First or Spillover method.
Select Outbound, Inbound, or Outbound + Inbound to set the traffic to which the
USG applies the load balancing method. Outbound means the traffic traveling from an
internal interface (ex. LAN) to an external interface (ex. WAN). Inbound means the
opposite.
The table lists the trunk’s member interfaces. You can add, edit, remove, or move
entries for user configured trunks.
Add Click this to add a member interface to the trunk. Select an interface and click Add to
add a new member interface after the selected member interface.
Edit Select an entry and click Edit to modify the entry’s settings.
Remove To remove a member interface, select it and click Remove. The USG confirms you
want to remove it before doing so.
Move To move an interface to a different number in the list, click the Move icon. In the field
that appears, specify the number to which you want to move the interface.
# This column displays the priorities of the group’s interfaces. The order of the interfaces
in the list is important since they are used in the order they are listed.
Member Click this table cell and select an interface to be a group member.
If you select an interface that is part of another Ethernet interface, the USG does not
send traffic through the interface as part of the trunk. For example, if you have physical
port 5 in the ge2 representative interface, you must select interface ge2 in order to
send traffic through port 5 as part of the trunk. If you select interface ge5 as a member
here, the USG will not send traffic through port 5 as part of the trunk.
Mode Click this table cell and select Active to have the USG always attempt to use this
connection.
Select Passive to have the USG only use this connection when all of the connections
set to active are down. You can only set one of a group’s interfaces to passive mode.
Weight This field displays with the weighted round robin load balancing algorithm. Specify the
weight (1~10) for the interface. The weights of the different member interfaces form a
ratio. This ratio determines how much traffic the USG assigns to each member
interface. The higher an interface’s weight is (relative to the weights of the interfaces),
the more sessions that interface should handle.
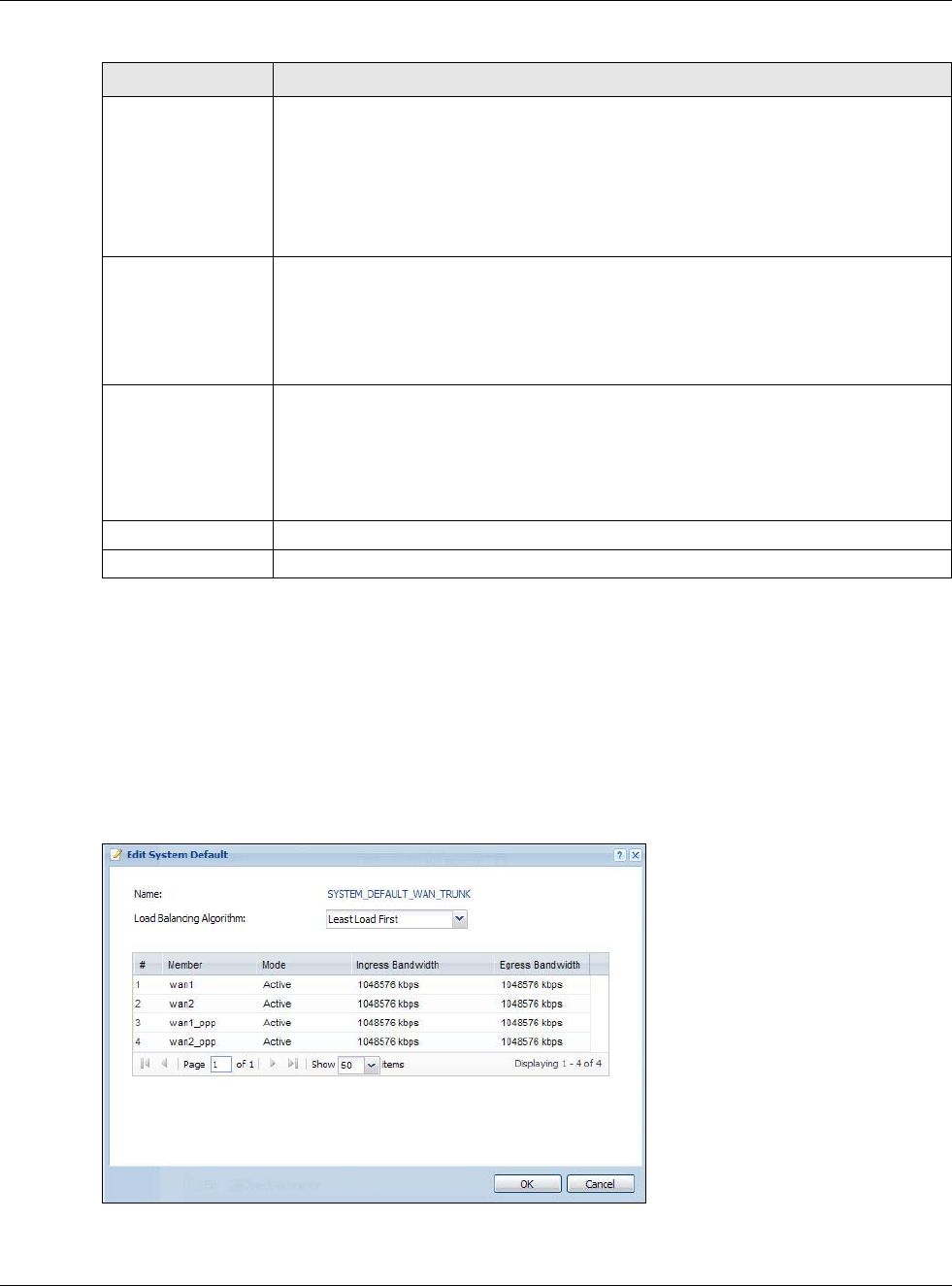
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
224
9.12.2 Configuring the System Default Trunk
In the Configuration > Network > Interface > Trunk screen and the System Default section,
select the default trunk entry and click Edit to open the following screen. Use this screen to
change the load balancing algorithm and view the bandwidth allocations for each member interface.
Note: The available bandwidth is allocated to each member interface equally and is not
allowed to be changed for the default trunk.
Figure 149 Configuration > Network > Interface > Trunk > Edit (System Default)
Ingress Bandwidth This is reserved for future use.
This field displays with the least load first load balancing algorithm. It displays the
maximum number of kilobits of data the USG is to allow to come in through the
interface per second.
Note: You can configure the bandwidth of an interface in the corresponding interface edit
screen.
Egress Bandwidth This field displays with the least load first or spillover load balancing algorithm. It
displays the maximum number of kilobits of data the USG is to send out through the
interface per second.
Note: You can configure the bandwidth of an interface in the corresponding interface edit
screen.
Spillover This field displays with the spillover load balancing algorithm. Specify the maximum
bandwidth of traffic in kilobits per second (1~1048576) to send out through the
interface before using another interface. When this spillover bandwidth limit is
exceeded, the USG sends new session traffic through the next interface. The traffic of
existing sessions still goes through the interface on which they started.
The USG uses the group member interfaces in the order that they are listed.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 88 Configuration > Network > Interface > Trunk > Add (or Edit) (continued)
LABEL DESCRIPTION
Chapter 9 Interfaces
USG20(W)-VPN Series User’s Guide
225
Each field is described in the table below.
Table 89 Configuration > Network > Interface > Trunk > Edit (System Default)
LABEL DESCRIPTION
Name This field displays the name of the selected system default trunk.
Load Balancing
Algorithm
Select the load balancing method to use for the trunk.
Select Weighted Round Robin to balance the traffic load between interfaces based
on their respective weights. An interface with a larger weight gets more chances to
transmit traffic than an interface with a smaller weight. For example, if the weight
ratio of wan1 and wan2 interfaces is 2:1, the USG chooses wan1 for 2 sessions’ traffic
and wan2 for 1 session’s traffic in each round of 3 new sessions.
Select Least Load First to send new session traffic through the least utilized trunk
member.
Select Spillover to send network traffic through the first interface in the group
member list until there is enough traffic that the second interface needs to be used
(and so on).
The table lists the trunk’s member interfaces. This table is read-only.
# This column displays the priorities of the group’s interfaces. The order of the
interfaces in the list is important since they are used in the order they are listed.
Member This column displays the name of the member interfaces.
Mode This field displays Active if the USG always attempt to use this connection.
This field displays Passive if the USG only use this connection when all of the
connections set to active are down. Only one of a group’s interfaces can be set to
passive mode.
Weight This field displays with the weighted round robin load balancing algorithm. Specify the
weight (1~10) for the interface. The weights of the different member interfaces form
a ratio. s
Ingress Bandwidth This is reserved for future use.
This field displays with the least load first load balancing algorithm. It displays the
maximum number of kilobits of data the USG is to allow to come in through the
interface per second.
Egress Bandwidth This field displays with the least load first or spillover load balancing algorithm. It
displays the maximum number of kilobits of data the USG is to send out through the
interface per second.
Spillover This field displays with the spillover load balancing algorithm. Specify the maximum
bandwidth of traffic in kilobits per second (1~1048576) to send out through the
interface before using another interface. When this spillover bandwidth limit is
exceeded, the USG sends new session traffic through the next interface. The traffic of
existing sessions still goes through the interface on which they started.
The USG uses the group member interfaces in the order that they are listed.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
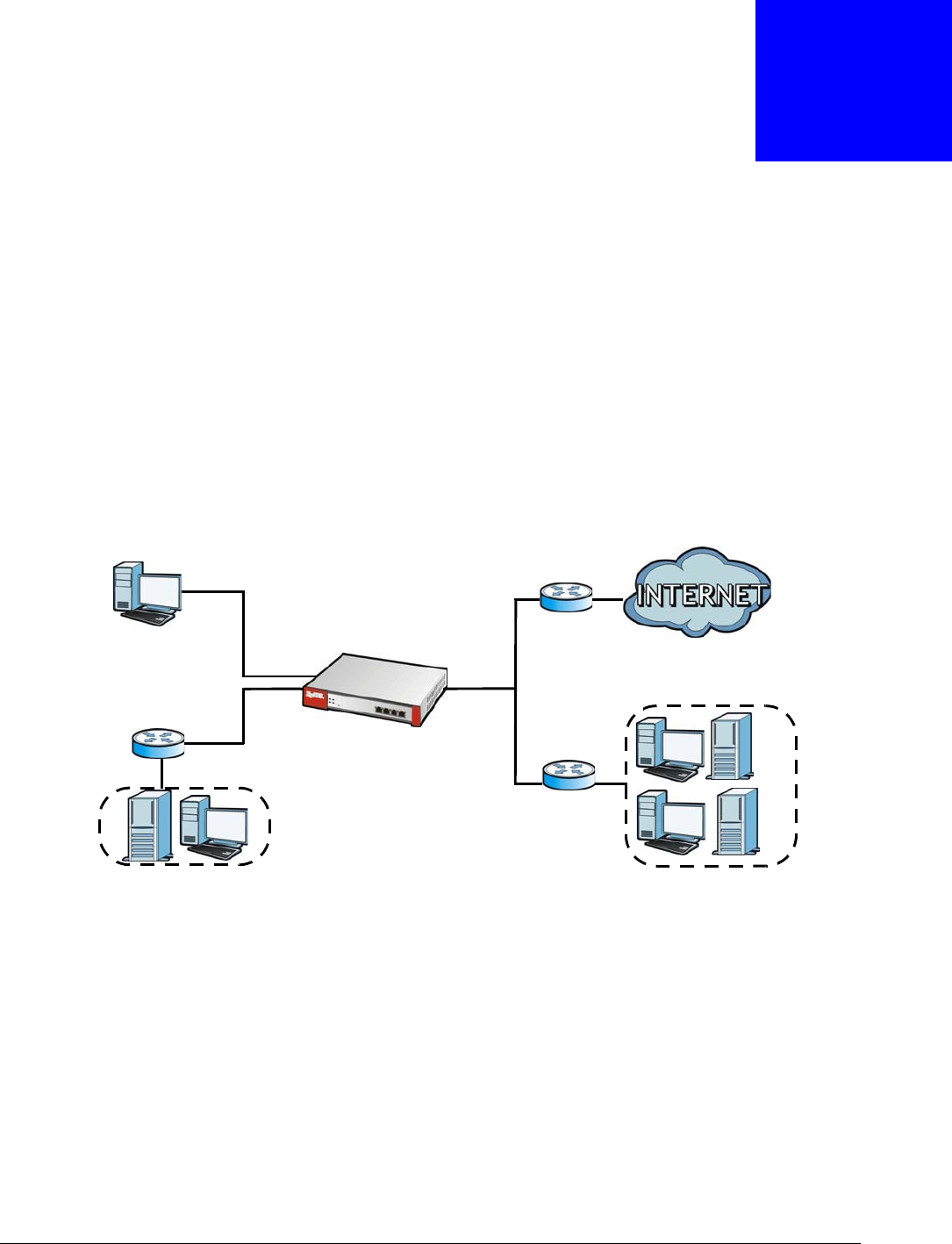
USG20(W)-VPN Series User’s Guide
226
CHAPTER 10
Routing
10.1 Policy and Static Routes Overview
Use policy routes and static routes to override the USG’s default routing behavior in order to send
packets through the appropriate interface or VPN tunnel.
For example, the next figure shows a computer (A) connected to the USG’s LAN interface. The USG
routes most traffic from Ato the Internet through the USG’s default gateway (R1). You create one
policy route to connect to services offered by your ISP behind router R2. You create another policy
route to communicate with a separate network behind another router (R3) connected to the LAN.
Figure 150 Example of Policy Routing Topology
Note: You can generally just use policy routes. You only need to use static routes if you
have a large network with multiple routers where you use RIP or OSPF to
propagate routing information to other routers.
10.1.1 What You Can Do in this Chapter
•Use the Policy Route screens (see Section 10.2 on page 228) to list and configure policy routes.
•Use the Static Route screens (see Section 10.3 on page 235) to list and configure static routes.
WAN
R1
R2
A
R3
LAN

Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
227
10.1.2 What You Need to Know
Policy Routing
Traditionally, routing is based on the destination address only and the USG takes the shortest path
to forward a packet. IP Policy Routing (IPPR) provides a mechanism to override the default routing
behavior and alter the packet forwarding based on the policy defined by the network administrator.
Policy-based routing is applied to incoming packets on a per interface basis, prior to the normal
routing.
How You Can Use Policy Routing
• Source-Based Routing – Network administrators can use policy-based routing to direct traffic
from different users through different connections.
• Bandwidth Shaping – You can allocate bandwidth to traffic that matches routing policies and
prioritize traffic. You can also use policy routes to manage other types of traffic (like ICMP traffic)
and send traffic through VPN tunnels.
• Cost Savings – IPPR allows organizations to distribute interactive traffic on high-bandwidth, high-
cost paths while using low-cost paths for batch traffic.
• Load Sharing – Network administrators can use IPPR to distribute traffic among multiple paths.
• NAT - The USG performs NAT by default for traffic going to or from the WAN interfaces. A routing
policy’s SNAT allows network administrators to have traffic received on a specified interface use a
specified IP address as the source IP address.
Note: The USG automatically uses SNAT for traffic it routes from internal interfaces to
external interfaces. For example LAN to WAN traffic.
Static Routes
The USG usually uses the default gateway to route outbound traffic from computers on the LAN to
the Internet. To have the USG send data to devices not reachable through the default gateway, use
static routes. Configure static routes if you need to use RIP or OSPF to propagate the routing
information to other routers. See Chapter 10 on page 238 for more on RIP and OSPF.
Policy Routes Versus Static Routes
• Policy routes are more flexible than static routes. You can select more criteria for the traffic to
match and can also use schedules, NAT, and bandwidth management.
• Policy routes are only used within the USG itself. Static routes can be propagated to other routers
using RIP or OSPF.
• Policy routes take priority over static routes. If you need to use a routing policy on the USG and
propagate it to other routers, you could configure a policy route and an equivalent static route.
DiffServ
QoS is used to prioritize source-to-destination traffic flows. All packets in the same flow are given
the same priority. CoS (class of service) is a way of managing traffic in a network by grouping
similar types of traffic together and treating each type as a class. You can use CoS to give different
priorities to different packet types.
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
228
DiffServ (Differentiated Services) is a class of service (CoS) model that marks packets so that they
receive specific per-hop treatment at DiffServ-compliant network devices along the route based on
the application types and traffic flow. Packets are marked with DiffServ Code Points (DSCPs)
indicating the level of service desired. This allows the intermediary DiffServ-compliant network
devices to handle the packets differently depending on the code points without the need to
negotiate paths or remember state information for every flow. In addition, applications do not have
to request a particular service or give advanced notice of where the traffic is going.
DSCP Marking and Per-Hop Behavior
DiffServ defines a new DS (Differentiated Services) field to replace the Type of Service (TOS) field
in the IP header. The DS field contains a 2-bit unused field and a 6-bit DSCP field which can define
up to 64 service levels. The following figure illustrates the DS field.
DSCP is backward compatible with the three precedence bits in the ToS octet so that non-DiffServ
compliant, ToS-enabled network device will not conflict with the DSCP mapping.
The DSCP value determines the forwarding behavior, the PHB (Per-Hop Behavior), that each packet
gets across the DiffServ network. Based on the marking rule, different kinds of traffic can be
marked for different kinds of forwarding. Resources can then be allocated according to the DSCP
values and the configured policies.
10.2 Policy Route Screen
Click Configuration > Network > Routing to open the Policy Route screen. Use this screen to
see the configured policy routes and turn policy routing based bandwidth management on or off.
A policy route defines the matching criteria and the action to take when a packet meets the criteria.
The action is taken only when all the criteria are met. The criteria can include the user name,
source address and incoming interface, destination address, schedule, IP protocol (ICMP, UDP, TCP,
etc.) and port.
The actions that can be taken include:
• Routing the packet to a different gateway, outgoing interface, VPN tunnel, or trunk.
• Limiting the amount of bandwidth available and setting a priority for traffic.
IPPR follows the existing packet filtering facility of RAS in style and in implementation.
If you enabled IPv6 in the Configuration > System > IPv6 screen, you can also configure policy
routes used for your IPv6 networks on this screen.
Click on the icons to go to the OneSecurity.com website where there is guidance on configuration
walkthroughs, troubleshooting, and other information.
DSCP (6 bits) Unused (2 bits)
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
229
Figure 151 Configuration > Network > Routing > Policy Route
The following table describes the labels in this screen.
Table 90 Configuration > Network > Routing > Policy Route
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Enable BWM This is a global setting for enabling or disabling bandwidth management on the USG.
You must enable this setting to have individual policy routes apply bandwidth
management.
IPv4 Configuration /
IPv6 Configuration
Use the IPv4 Configuration section for IPv4 network settings. Use the IPv6
Configuration section for IPv6 network settings if you connect your USG to an IPv6
network. Both sections have similar fields as described below.
Use IPv4/IPv6 Policy
Route to Override
Direct Route
Select this to have the USG forward packets that match a policy route according to
the policy route instead of sending the packets directly to a connected network.
Add Click this to create a new entry. Select an entry and click Add to create a new entry
after the selected entry.
Edit Double-click an entry or select it and click Edit to open a screen where you can
modify the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to
remove it before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Move To change a rule’s position in the numbered list, select the rule and click Move to
display a field to type a number for where you want to put that rule and press
[ENTER] to move the rule to the number that you typed.
The ordering of your rules is important as they are applied in order of their
numbering.
#This is the number of an individual policy route.
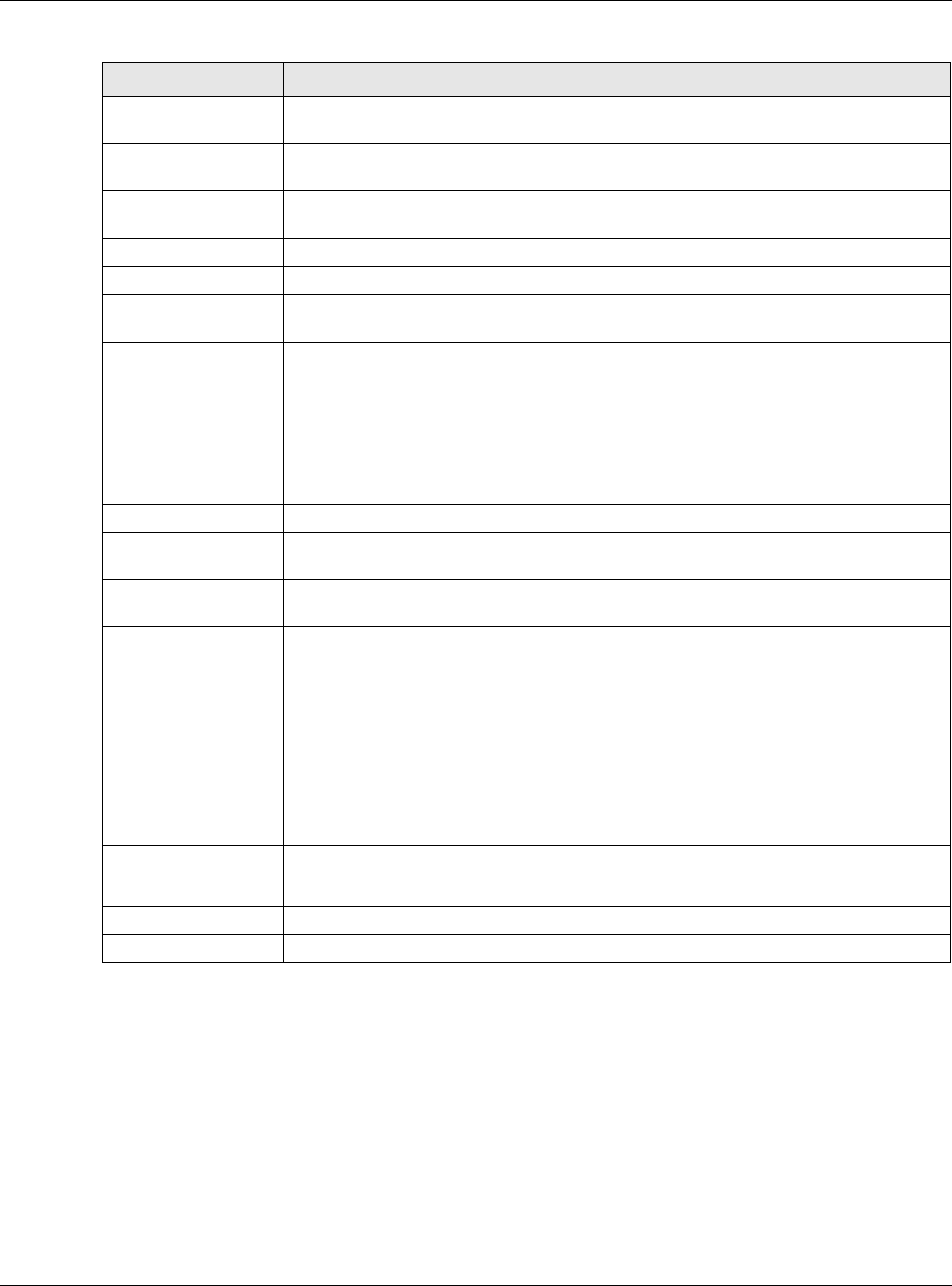
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
230
10.2.1 Policy Route Edit Screen
Click Configuration > Network > Routing to open the Policy Route screen. Then click the Add
or Edit icon in the IPv4 Configuration or IPv6 Configuration section. The Add Policy Route or
Policy Route Edit screen opens. Use this screen to configure or edit a policy route. Both IPv4 and
IPv6 policy route have similar settings except the Address Translation (SNAT) settings.
Status This icon is lit when the entry is active, red when the next hop’s connection is down,
and dimmed when the entry is inactive.
User This is the name of the user (group) object from which the packets are sent. any
means all users.
Schedule This is the name of the schedule object. none means the route is active at all times if
enabled.
Incoming This is the interface on which the packets are received.
Source This is the name of the source IP address (group) object. any means all IP addresses.
Destination This is the name of the destination IP address (group) object. any means all IP
addresses.
DSCP Code This is the DSCP value of incoming packets to which this policy route applies.
any means all DSCP values or no DSCP marker.
default means traffic with a DSCP value of 0. This is usually best effort traffic
The “af” entries stand for Assured Forwarding. The number following the “af”
identifies one of four classes and one of three drop preferences. See Assured
Forwarding (AF) PHB for DiffServ on page 237 for more details.
Service This is the name of the service object. any means all services.
Source Port This is the name of a service object. The USG applies the policy route to the packets
sent from the corresponding service port. any means all service ports.
Next-Hop This is the next hop to which packets are directed. It helps forward packets to their
destinations and can be a router, VPN tunnel, outgoing interface or trunk.
DSCP Marking This is how the USG handles the DSCP value of the outgoing packets that match this
route. If this field displays a DSCP value, the USG applies that DSCP value to the
route’s outgoing packets.
preserve means the USG does not modify the DSCP value of the route’s outgoing
packets.
default means the USG sets the DSCP value of the route’s outgoing packets to 0.
The “af” choices stand for Assured Forwarding. The number following the “af”
identifies one of four classes and one of three drop preferences. See Assured
Forwarding (AF) PHB for DiffServ on page 237 for more details.
SNAT This is the source IP address that the route uses.
It displays none if the USG does not perform NAT for this route.
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
Table 90 Configuration > Network > Routing > Policy Route (continued)
LABEL DESCRIPTION
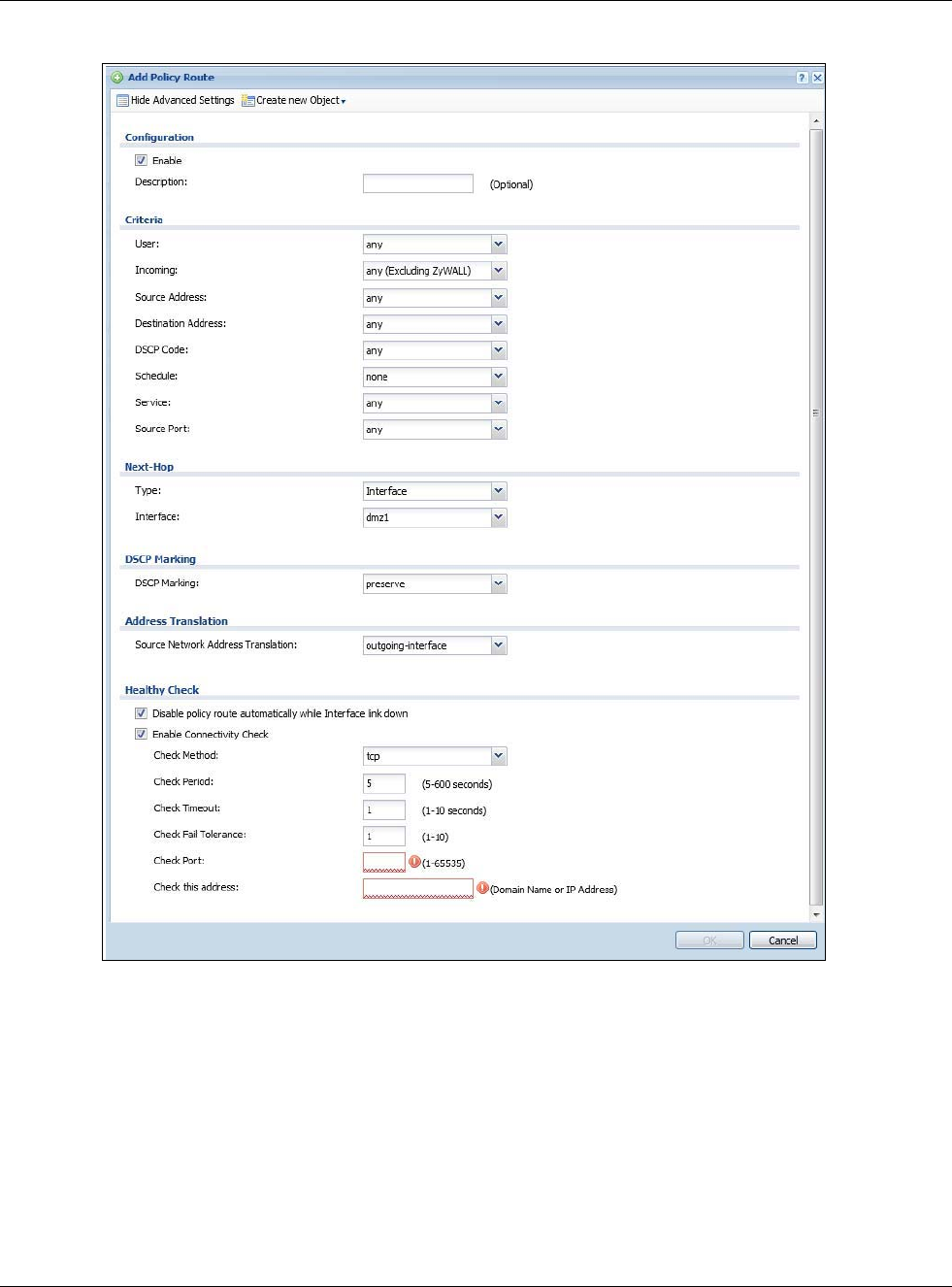
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
231
Figure 152 Configuration > Network > Routing > Policy Route > Add/Edit (IPv4 Configuration)
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
232
Figure 153 Configuration > Network > Routing > Policy Route > Add/Edit (IPv6 Configuration)
The following table describes the labels in this screen.
Table 91 Configuration > Network > Routing > Policy Route > Add/Edit
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Create new Object Use this to configure any new settings objects that you need to use in this screen.
Configuration
Enable Select this to activate the policy.
Description Enter a descriptive name of up to 31 printable ASCII characters for the policy.
Criteria
User Select a user name or user group from which the packets are sent.
Incoming Select where the packets are coming from; any, an interface, a tunnel, an SSL VPN, or
the USG itself. For an interface, a tunnel, or an SSL VPN, you also need to select the
individual interface, VPN tunnel, or SSL VPN connection.
Source Address Select a source IP address object from which the packets are sent.
Destination Address Select a destination IP address object to which the traffic is being sent. If the next hop
is a dynamic VPN tunnel and you enable Auto Destination Address, the USG uses
the local network of the peer router that initiated an incoming dynamic IPSec tunnel as
the destination address of the policy instead of your configuration here.
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
233
DSCP Code Select a DSCP code point value of incoming packets to which this policy route applies
or select User Define to specify another DSCP code point. The lower the number the
higher the priority with the exception of 0 which is usually given only best-effort
treatment.
any means all DSCP value or no DSCP marker.
default means traffic with a DSCP value of 0. This is usually best effort traffic
The “af” choices stand for Assured Forwarding. The number following the “af”
identifies one of four classes and one of three drop preferences. See Assured
Forwarding (AF) PHB for DiffServ on page 237 for more details.
User-Defined
DSCP Code Use this field to specify a custom DSCP code point when you select User Define in the
previous field.
Schedule Select a schedule to control when the policy route is active. none means the route is
active at all times if enabled.
Service Select a service or service group to identify the type of traffic to which this policy route
applies.
Source Port Select a service or service group to identify the source port of packets to which the
policy route applies.
Next-Hop
Type Select Auto to have the USG use the routing table to find a next-hop and forward the
matched packets automatically.
Select Gateway to route the matched packets to the next-hop router or switch you
specified in the Gateway field. You have to set up the next-hop router or switch as a
HOST address object first.
Select VPN Tunnel to route the matched packets via the specified VPN tunnel.
Select Trunk to route the matched packets through the interfaces in the trunk group
based on the load balancing algorithm.
Select Interface to route the matched packets through the specified outgoing
interface to a gateway (which is connected to the interface).
Gateway This field displays when you select Gateway in the Type field. Select a HOST address
object. The gateway is an immediate neighbor of your USG that will forward the packet
to the destination. The gateway must be a router or switch on the same segment as
your USG's interface(s).
VPN Tunnel This field displays when you select VPN Tunnel in the Type field. Select a VPN tunnel
through which the packets are sent to the remote network that is connected to the
USG directly.
Auto Destination
Address This field displays when you select VPN Tunnel in the Type field. Select this to have
the USG use the local network of the peer router that initiated an incoming dynamic
IPSec tunnel as the destination address of the policy.
Leave this cleared if you want to manually specify the destination address.
Trunk This field displays when you select Trunk in the Type field. Select a trunk group to
have the USG send the packets via the interfaces in the group.
Interface This field displays when you select Interface in the Type field. Select an interface to
have the USG send traffic that matches the policy route through the specified interface.
Table 91 Configuration > Network > Routing > Policy Route > Add/Edit (continued)
LABEL DESCRIPTION
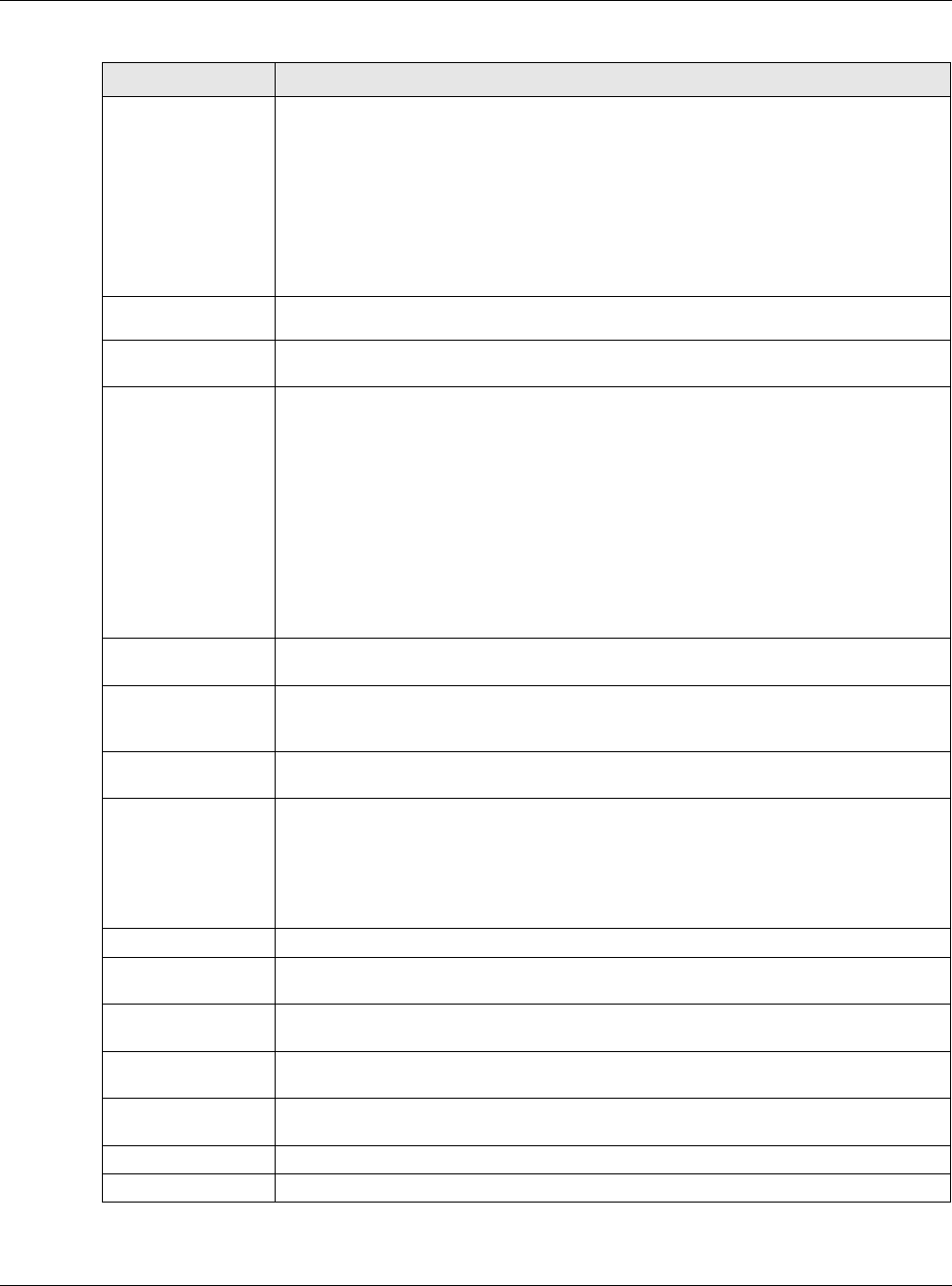
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
234
DSCP Marking Set how the USG handles the DSCP value of the outgoing packets that match this
route.
Select one of the pre-defined DSCP values to apply or select User Define to specify
another DSCP value. The “af” choices stand for Assured Forwarding. The number
following the “af” identifies one of four classes and one of three drop preferences. See
Assured Forwarding (AF) PHB for DiffServ on page 237 for more details.
Select preserve to have the USG keep the packets’ original DSCP value.
Select default to have the USG set the DSCP value of the packets to 0.
User-Defined
DSCP Code Use this field to specify a custom DSCP value.
Address Translation Use this section to configure NAT for the policy route. This section does not apply to
policy routes that use a VPN tunnel as the next hop.
Source Network
Address Translation
Select none to not use NAT for the route.
Select outgoing-interface to use the IP address of the outgoing interface as the
source IP address of the packets that matches this route.
To use SNAT for a virtual interface that is in the same WAN trunk as the physical
interface to which the virtual interface is bound, the virtual interface and physical
interface must be in different subnets.
Otherwise, select a pre-defined address (group) to use as the source IP address(es) of
the packets that match this route.
Use Create new Object if you need to configure a new address (group) to use as the
source IP address(es) of the packets that match this route.
Healthy Check Use this part of the screen to configure a route connectivity check and disable the
policy if the interface is down.
Disable policy route
automatically while
Interface link down
Select this to disable the policy if the interface is down or disabled. This is available for
Interface and Trunk in the Type field above.
Enable Connectivity
Check
Select this to turn on the connection check. This is available for Interface and
Gateway in the Type field above.
Check Method: Select the method that the gateway allows.
Select icmp to have the USG regularly ping the gateway you specify to make sure it is
still available.
Select tcp to have the USG regularly perform a TCP handshake with the gateway you
specify to make sure it is still available.
Check Period: Enter the number of seconds between connection check attempts (5-600 seconds).
Check Timeout: Enter the number of seconds to wait for a response before the attempt is a failure (1-
10 seconds).
Check Fail
Tolerance:
Enter the number of consecutive failures before the USG stops routing using this policy
(1-10).
Check Port: This field only displays when you set the Check Method to tcp. Specify the port number
to use for a TCP connectivity check (1-65535).
Check this address: Select this to specify a domain name or IP address for the connectivity check. Enter
that domain name or IP address in the field next to it.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 91 Configuration > Network > Routing > Policy Route > Add/Edit (continued)
LABEL DESCRIPTION
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
235
10.3 IP Static Route Screen
Click Configuration > Network > Routing > Static Route to open the Static Route screen.
This screen displays the configured static routes. Configure static routes to be able to use RIP or
OSPF to propagate the routing information to other routers. If you enabled IPv6 in the
Configuration > System > IPv6 screen, you can also configure static routes used for your IPv6
networks on this screen.
Figure 154 Configuration > Network > Routing > Static Route
The following table describes the labels in this screen.
10.3.1 Static Route Add/Edit Screen
Select a static route index number and click Add or Edit. The screen shown next appears. Use this
screen to configure the required information for a static route.
Table 92 Configuration > Network > Routing > Static Route
LABEL DESCRIPTION
IPv4 Configuration /
IPv6 Configuration
Use the IPv4 Configuration section for IPv4 network settings. Use the IPv6
Configuration section for IPv6 network settings if you connect your USG to an IPv6
network. Both sections have similar fields as described below.
Add Click this to create a new static route.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to remove
it before doing so.
#This is the number of an individual static route.
Destination This is the destination IP address.
Subnet Mask This is the IP subnet mask.
Prefix This is the IPv6 prefix for the destination IP address.
Next-Hop This is the IP address of the next-hop gateway or the interface through which the traffic
is routed. The gateway is a router or switch on the same segment as your USG's
interface(s). The gateway helps forward packets to their destinations.
Metric This is the route’s priority among the USG’s routes. The smaller the number, the higher
priority the route has.
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
236
Figure 155 Configuration > Network > Routing > Static Route > Add (IPv4 Configuration)
Figure 156 Configuration > Network > Routing > Static Route > Add (IPv6 Configuration)
The following table describes the labels in this screen.
Table 93 Configuration > Network > Routing > Static Route > Add
LABEL DESCRIPTION
Destination IP This parameter specifies the IP network address of the final destination. Routing is
always based on network number.
If you need to specify a route to a single host, enter the specific IP address here and use
a subnet mask of 255.255.255.255 (for IPv4) in the Subnet Mask field or a prefix of 128
(for IPv6) in the Prefix Length field to force the network number to be identical to the
host ID.
For IPv6, if you want to send all traffic to the gateway or interface specified in the
Gateway IP or Interface field, enter :: in this field and 0 in the Prefix Length field.
Subnet Mask Enter the IP subnet mask here.
Prefix Length Enter the number of left-most digits in the destination IP address, which indicates the
network prefix. Enter :: in the Destination IP field and 0 in this field if you want to send
all traffic to the gateway or interface specified in the Gateway IP or Interface field.
Gateway IP Select the radio button and enter the IP address of the next-hop gateway. The gateway is
a router or switch on the same segment as your USG's interface(s). The gateway helps
forward packets to their destinations.
Interface Select the radio button and a predefined interface through which the traffic is sent.
Metric Metric represents the “cost” of transmission for routing purposes. IP routing uses hop
count as the measurement of cost, with a minimum of 1 for directly connected networks.
Enter a number that approximates the cost for this link. The number need not be precise,
but it must be 0~127. In practice, 2 or 3 is usually a good number.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
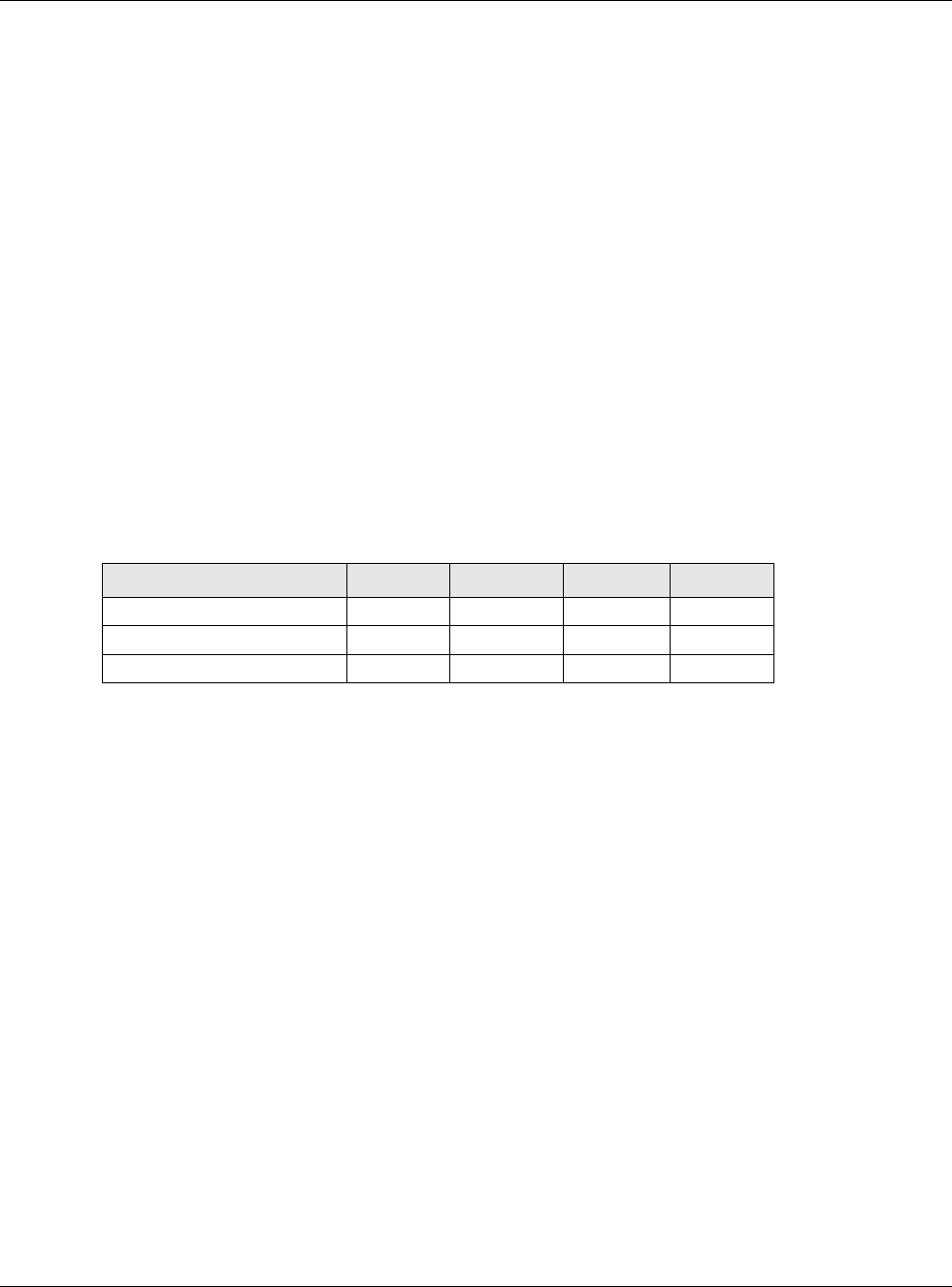
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
237
10.4 Policy Routing Technical Reference
Here is more detailed information about some of the features you can configure in policy routing.
NAT and SNAT
NAT (Network Address Translation - NAT, RFC 1631) is the translation of the IP address in a packet
in one network to a different IP address in another network. Use SNAT (Source NAT) to change the
source IP address in one network to a different IP address in another network.
Assured Forwarding (AF) PHB for DiffServ
Assured Forwarding (AF) behavior is defined in RFC 2597. The AF behavior group defines four AF
classes. Inside each class, packets are given a high, medium or low drop precedence. The drop
precedence determines the probability that routers in the network will drop packets when
congestion occurs. If congestion occurs between classes, the traffic in the higher class (smaller
numbered class) is generally given priority. Combining the classes and drop precedence produces
the following twelve DSCP encodings from AF11 through AF43. The decimal equivalent is listed in
brackets.
Maximize Bandwidth Usage
The maximize bandwidth usage option allows the USG to divide up any available bandwidth on the
interface (including unallocated bandwidth and any allocated bandwidth that a policy route is not
using) among the policy routes that require more bandwidth.
When you enable maximize bandwidth usage, the USG first makes sure that each policy route gets
up to its bandwidth allotment. Next, the USG divides up an interface’s available bandwidth
(bandwidth that is unbudgeted or unused by the policy routes) depending on how many policy
routes require more bandwidth and on their priority levels. When only one policy route requires
more bandwidth, the USG gives the extra bandwidth to that policy route.
When multiple policy routes require more bandwidth, the USG gives the highest priority policy
routes the available bandwidth first (as much as they require, if there is enough available
bandwidth), and then to lower priority policy routes if there is still bandwidth available. The USG
distributes the available bandwidth equally among policy routes with the same priority level.
Table 94 Assured Forwarding (AF) Behavior Group
CLASS 1 CLASS 2 CLASS 3 CLASS 4
Low Drop Precedence AF11 (10) AF21 (18) AF31 (26) AF41 (34)
Medium Drop Precedence AF12 (12) AF22 (20) AF32 (28) AF42 (36)
High Drop Precedence AF13 (14) AF23 (22) AF33 (30) AF43 (38)
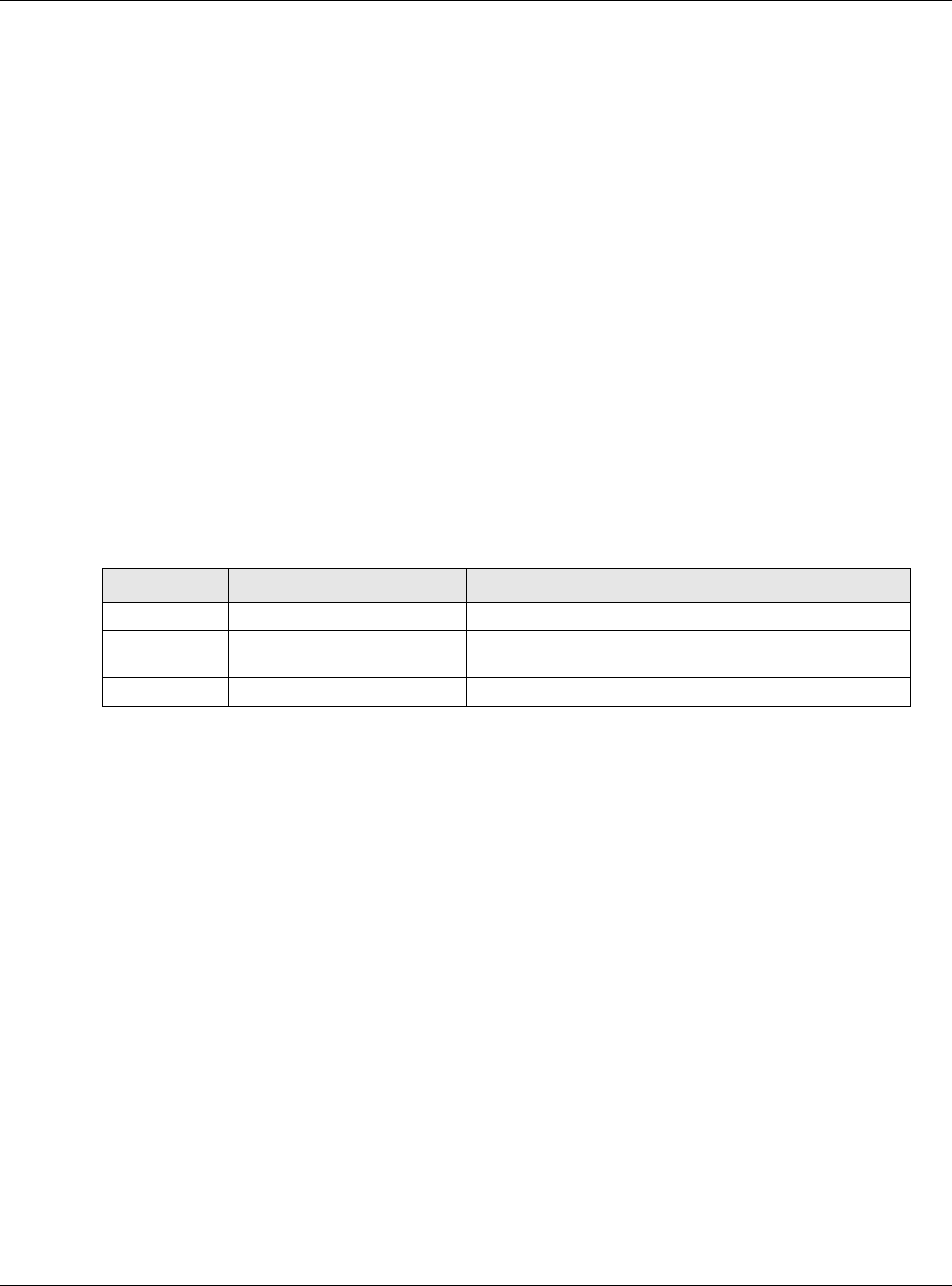
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
238
10.5 Routing Protocols Overview
Routing protocols give the USG routing information about the network from other routers. The USG
stores this routing information in the routing table it uses to make routing decisions. In turn, the
USG can also use routing protocols to propagate routing information to other routers.
Routing protocols are usually only used in networks using multiple routers like campuses or large
enterprises.
•Use the RIP screen (see Section 10.6 on page 238) to configure the USG to use RIP to receive
and/or send routing information.
•Use the OSPF screen (see Section 10.7 on page 240) to configure general OSPF settings and
manage OSPF areas.
•Use the OSPF Area Add/Edit screen (see Section 10.7.2 on page 244) to create or edit an OSPF
area.
10.5.1 What You Need to Know
The USG supports two standards, RIP and OSPF, for routing protocols. RIP and OSPF are compared
here and discussed further in the rest of the chapter.
Finding Out More
See Section 10.8 on page 247 for background information on routing protocols.
10.6 The RIP Screen
RIP (Routing Information Protocol, RFC 1058 and RFC 1389) allows a device to exchange routing
information with other routers. RIP is a vector-space routing protocol, and, like most such
protocols, it uses hop count to decide which route is the shortest. Unfortunately, it also broadcasts
its routes asynchronously to the network and converges slowly. Therefore, RIP is more suitable for
small networks (up to 15 routers).
• In the USG, you can configure two sets of RIP settings before you can use it in an interface.
•First, the Authentication field specifies how to verify that the routing information that is
received is the same routing information that is sent. This is discussed in more detail in
Authentication Types on page 247.
• Second, the USG can also redistribute routing information from non-RIP networks, specifically
OSPF networks and static routes, to the RIP network. Costs might be calculated differently,
however, so you use the Metric field to specify the cost in RIP terms.
• RIP uses UDP port 520.
Table 95 RIP vs. OSPF
RIP OSPF
Network Size Small (with up to 15 routers) Large
Metric Hop count Bandwidth, hop count, throughput, round trip time and
reliability.
Convergence Slow Fast
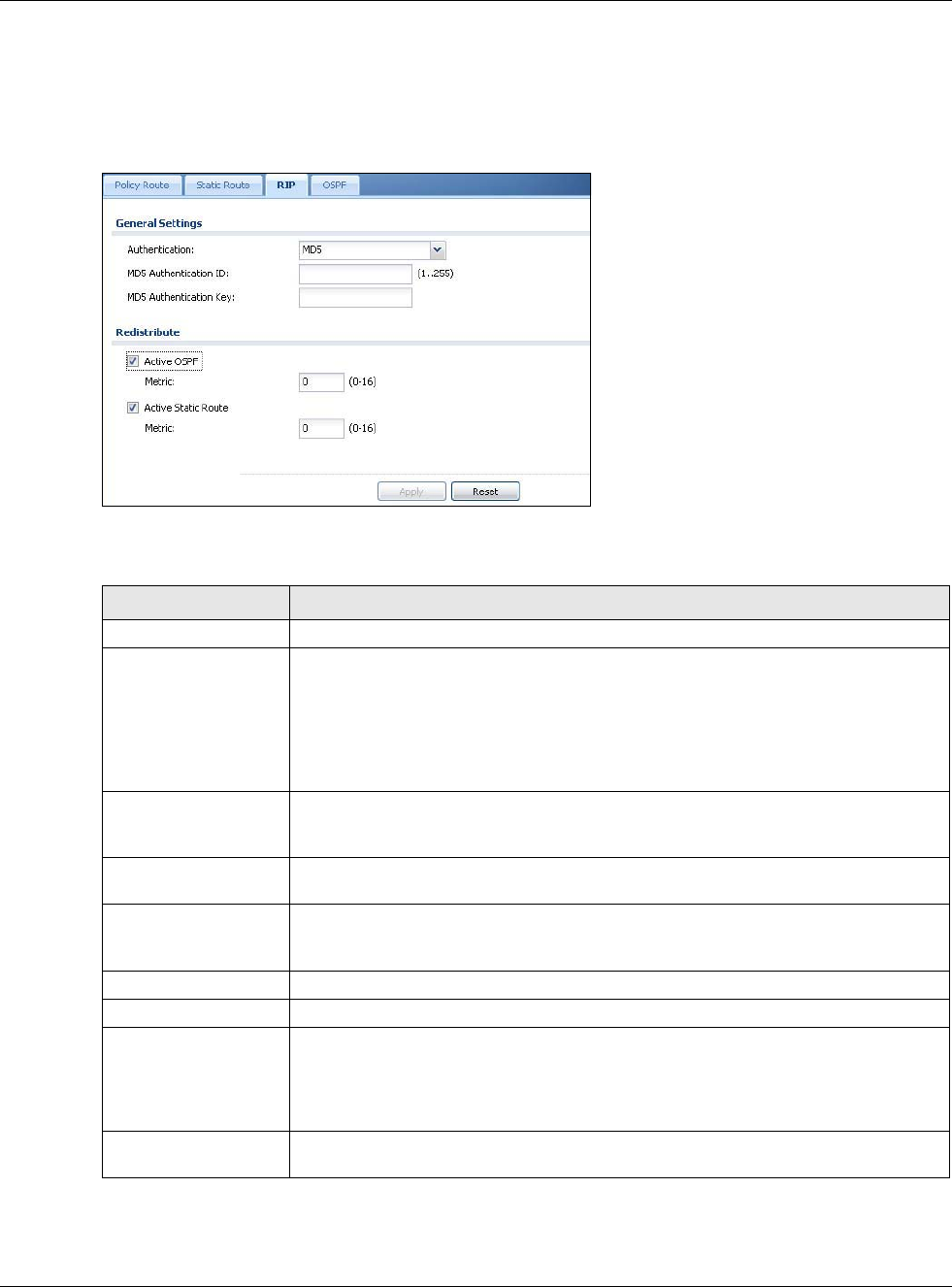
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
239
Use the RIP screen to specify the authentication method and maintain the policies for
redistribution.
Click Configuration > Network > Routing > RIP to open the following screen.
Figure 157 Configuration > Network > Routing > RIP
The following table describes the labels in this screen.
Table 96 Configuration > Network > Routing Protocol > RIP
LABEL DESCRIPTION
Authentication
Authentication Select the authentication method used in the RIP network. This authentication
protects the integrity, but not the confidentiality, of routing updates.
None uses no authentication.
Text uses a plain text password that is sent over the network (not very secure).
MD5 uses an MD5 password and authentication ID (most secure).
Text
Authentication Key This field is available if the Authentication is Text. Type the password for text
authentication. The key can consist of alphanumeric characters and the underscore,
and it can be up to 16 characters long.
MD5
Authentication ID This field is available if the Authentication is MD5. Type the ID for MD5
authentication. The ID can be between 1 and 255.
MD5
Authentication Key This field is available if the Authentication is MD5. Type the password for MD5
authentication. The password can consist of alphanumeric characters and the
underscore, and it can be up to 16 characters long.
Redistribute
Active OSPF Select this to use RIP to advertise routes that were learned through OSPF.
Metric Type the cost for routes provided by OSPF. The metric represents the “cost” of
transmission for routing purposes. RIP routing uses hop count as the measurement
of cost, with 1 usually used for directly connected networks. The number does not
have to be precise, but it must be between 0 and 16. In practice, 2 or 3 is usually
used.
Active Static Route Select this to use RIP to advertise routes that were learned through the static route
configuration.

Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
240
10.7 The OSPF Screen
OSPF (Open Shortest Path First, RFC 2328) is a link-state protocol designed to distribute routing
information within a group of networks, called an Autonomous System (AS). OSPF offers some
advantages over vector-space routing protocols like RIP.
• OSPF supports variable-length subnet masks, which can be set up to use available IP addresses
more efficiently.
• OSPF filters and summarizes routing information, which reduces the size of routing tables
throughout the network.
• OSPF responds to changes in the network, such as the loss of a router, more quickly.
• OSPF considers several factors, including bandwidth, hop count, throughput, round trip time, and
reliability, when it calculates the shortest path.
• OSPF converges more quickly than RIP.
Naturally, OSPF is also more complicated than RIP, so OSPF is usually more suitable for large
networks.
OSPF uses IP protocol 89.
OSPF Areas
An OSPF Autonomous System (AS) is divided into one or more areas. Each area represents a group
of adjacent networks and is identified by a 32-bit ID. In OSPF, this number may be expressed as an
integer or as an IP address.
There are several types of areas.
• The backbone is the transit area that routes packets between other areas. All other areas are
connected to the backbone.
• A normal area is a group of adjacent networks. A normal area has routing information about the
OSPF AS, any networks outside the OSPF AS to which it is directly connected, and any networks
outside the OSPF AS that provide routing information to any area in the OSPF AS.
• A stub area has routing information about the OSPF AS. It does not have any routing information
about any networks outside the OSPF AS, including networks to which it is directly connected. It
relies on a default route to send information outside the OSPF AS.
• A Not So Stubby Area (NSSA, RFC 1587) has routing information about the OSPF AS and
networks outside the OSPF AS to which the NSSA is directly connected. It does not have any
routing information about other networks outside the OSPF AS.
Metric Type the cost for routes provided by the static route configuration. The metric
represents the “cost” of transmission for routing purposes. RIP routing uses hop
count as the measurement of cost, with 1 usually used for directly connected
networks. The number does not have to be precise, but it must be between 0 and 16.
In practice, 2 or 3 is usually used.
Apply Click this button to save your changes to the USG.
Reset Click this button to return the screen to its last-saved settings.
Table 96 Configuration > Network > Routing Protocol > RIP (continued)
LABEL DESCRIPTION
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
241
Each type of area is illustrated in the following figure.
Figure 158 OSPF: Types of Areas
This OSPF AS consists of four areas, areas 0-3. Area 0 is always the backbone. In this example,
areas 1, 2, and 3 are all connected to it. Area 1 is a normal area. It has routing information about
the OSPF AS and networks X and Y. Area 2 is a stub area. It has routing information about the OSPF
AS, but it depends on a default route to send information to networks X and Y. Area 3 is a NSSA. It
has routing information about the OSPF AS and network Y but not about network X.
OSPF Routers
Every router in the same area has the same routing information. They do this by exchanging Hello
messages to confirm which neighbor (layer-3) devices exist, and then they exchange database
descriptions (DDs) to create a synchronized link-state database. The link-state database contains
records of router IDs, their associated links and path costs. The link-state database is then
constantly updated through Link State Advertisements (LSA). Each router uses the link state
database and the Dijkstra algorithm to compute the least cost paths to network destinations.
Like areas, each router has a unique 32-bit ID in the OSPF AS, and there are several types of
routers. Each type is really just a different role, and it is possible for one router to play multiple
roles at one time.
• An internal router (IR) only exchanges routing information with other routers in the same area.
• An Area Border Router (ABR) connects two or more areas. It is a member of all the areas to
which it is connected, and it filters, summarizes, and exchanges routing information between
them.
• An Autonomous System Boundary Router (ASBR) exchanges routing information with routers in
networks outside the OSPF AS. This is called redistribution in OSPF.
• A backbone router (BR) has at least one interface with area 0. By default, every router in area 0
is a backbone router, and so is every ABR.
Table 97 OSPF: Redistribution from Other Sources to Each Type of Area
SOURCE \ TYPE OF AREA NORMAL NSSA STUB
Static routes Yes Yes No
RIP Yes Yes Yes
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
242
Each type of router is illustrated in the following example.
Figure 159 OSPF: Types of Routers
In order to reduce the amount of traffic between routers, a group of routers that are directly
connected to each other selects a designated router (DR) and a backup designated router (BDR).
All of the routers only exchange information with the DR and the BDR, instead of exchanging
information with all of the other routers in the group. The DR and BDR are selected by priority; if
two routers have the same priority, the highest router ID is used.
The DR and BDR are selected in each group of routers that are directly connected to each other. If
a router is directly connected to several groups, it might be a DR in one group, a BDR in another
group, and neither in a third group all at the same time.
Virtual Links
In some OSPF AS, it is not possible for an area to be directly connected to the backbone. In this
case, you can create a virtual link through an intermediate area to logically connect the area to the
backbone. This is illustrated in the following example.
Figure 160 OSPF: Virtual Link
In this example, area 100 does not have a direct connection to the backbone. As a result, you
should set up a virtual link on both ABR in area 10. The virtual link becomes the connection
between area 100 and the backbone.
You cannot create a virtual link to a router in a different area.
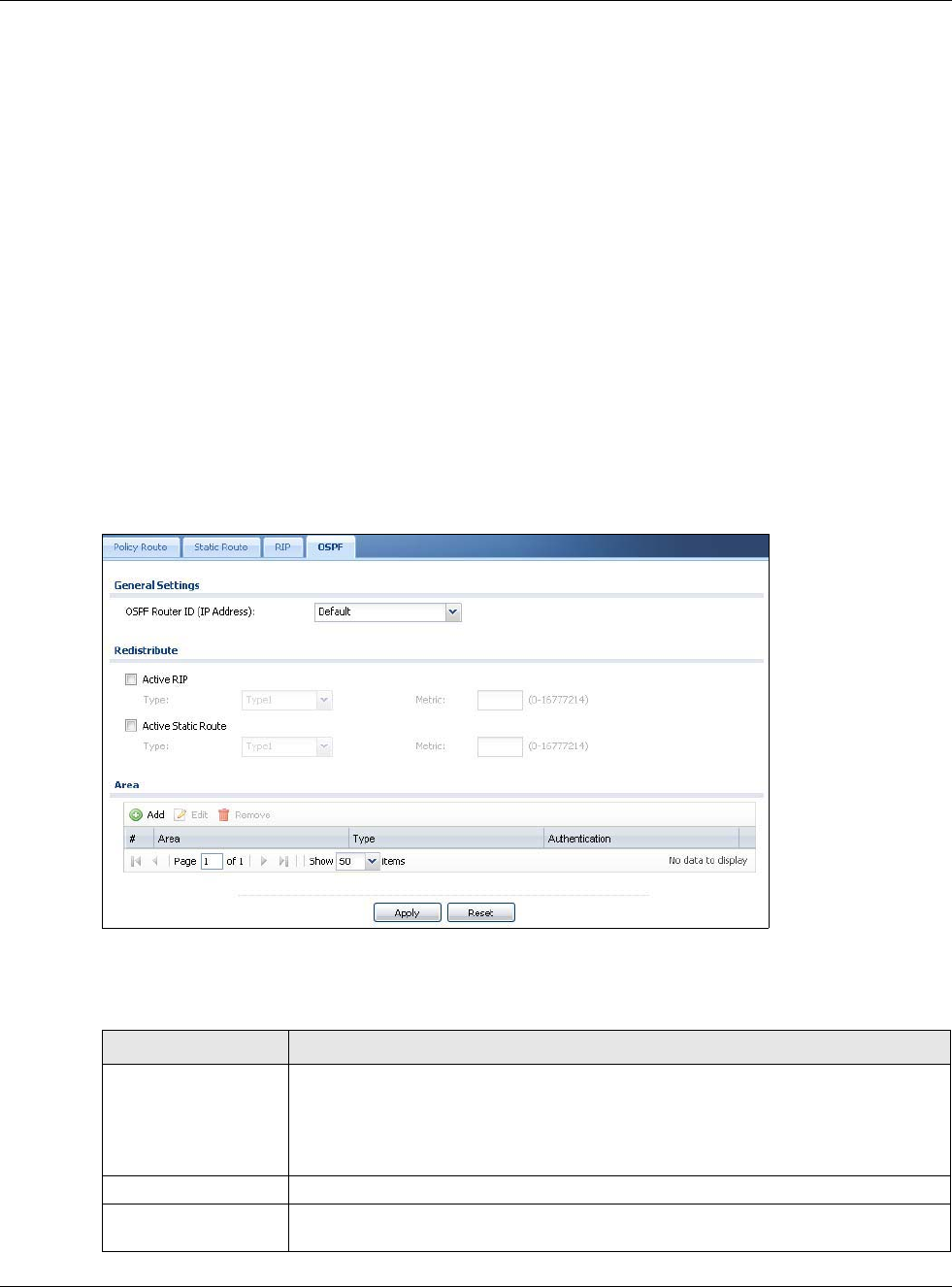
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
243
OSPF Configuration
Follow these steps when you configure OSPF on the USG.
1Enable OSPF.
2Set up the OSPF areas.
3Configure the appropriate interfaces. See Section 9.3.1 on page 148.
4Set up virtual links, as needed.
10.7.1 Configuring the OSPF Screen
Use the first OSPF screen to specify the OSPF router the USG uses in the OSPF AS and maintain the
policies for redistribution. In addition, it provides a summary of OSPF areas, allows you to remove
them, and opens the OSPF Add/Edit screen to add or edit them.
Click Configuration > Network > Routing > OSPF to open the following screen.
Figure 161 Configuration > Network > Routing > OSPF
The following table describes the labels in this screen. See Section 10.7.2 on page 244 for more
information as well.
Table 98 Configuration > Network > Routing Protocol > OSPF
LABEL DESCRIPTION
OSPF Router ID Select the 32-bit ID the USG uses in the OSPF AS.
Default - the first available interface IP address is the USG’s ID.
User Defined - enter the ID (in IP address format) in the field that appears when
you select User Define.
Redistribute
Active RIP Select this to advertise routes that were learned from RIP. The USG advertises
routes learned from RIP to Normal and NSSA areas but not to Stub areas.
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
244
10.7.2 OSPF Area Add/Edit Screen
The OSPF Area Add/Edit screen allows you to create a new area or edit an existing one. To access
this screen, go to the OSPF summary screen (see Section 10.7 on page 240), and click either the
Add icon or an Edit icon.
Type Select how OSPF calculates the cost associated with routing information from RIP.
Choices are: Type 1 and Type 2.
Type 1 - cost = OSPF AS cost + external cost (Metric)
Type 2 - cost = external cost (Metric); the OSPF AS cost is ignored.
Metric Type the external cost for routes provided by RIP. The metric represents the “cost” of
transmission for routing purposes. The way this is used depends on the Type field.
This value is usually the average cost in the OSPF AS, and it can be between 1 and
16777214.
Active Static Route Select this to advertise routes that were learned from static routes. The USG
advertises routes learned from static routes to all types of areas.
Type Select how OSPF calculates the cost associated with routing information from static
routes. Choices are: Type 1 and Type 2.
Type 1 - cost = OSPF AS cost + external cost (Metric)
Type 2 - cost = external cost (Metric); the OSPF AS cost is ignored.
Metric Type the external cost for routes provided by static routes. The metric represents the
“cost” of transmission for routing purposes. The way this is used depends on the
Type field. This value is usually the average cost in the OSPF AS, and it can be
between 1 and 16777214.
Area This section displays information about OSPF areas in the USG.
Add Click this to create a new OSPF area.
Edit Double-click an entry or select it and click Edit to open a screen where you can
modify the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to
remove it before doing so.
# This field is a sequential value, and it is not associated with a specific area.
Area This field displays the 32-bit ID for each area in IP address format.
Type This field displays the type of area. This type is different from the Type field above.
Authentication This field displays the default authentication method in the area.
Apply Click this button to save your changes to the USG.
Reset Click this button to return the screen to its last-saved settings.
Table 98 Configuration > Network > Routing Protocol > OSPF (continued)
LABEL DESCRIPTION
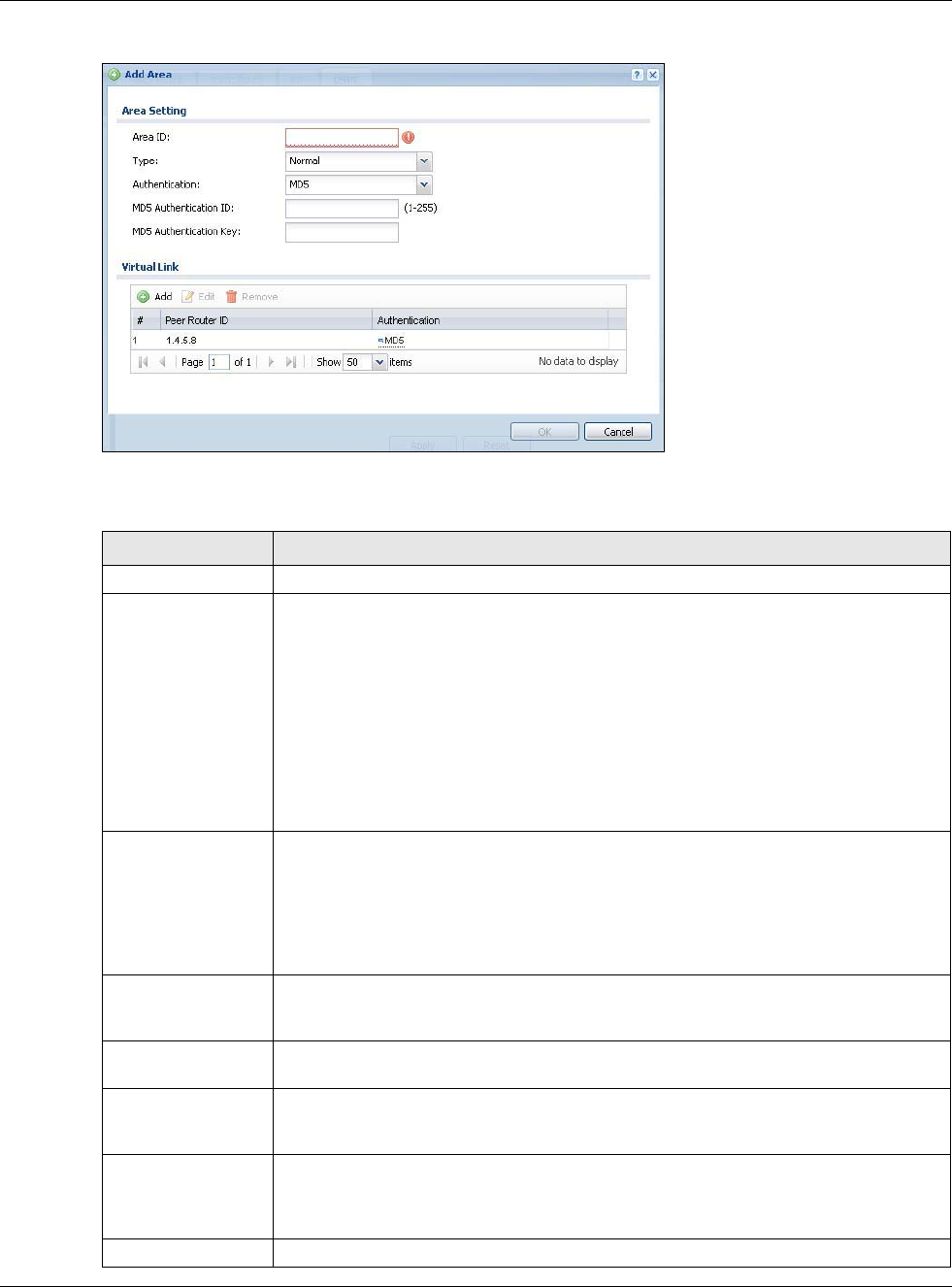
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
245
Figure 162 Configuration > Network > Routing > OSPF > Add
The following table describes the labels in this screen.
Table 99 Configuration > Network > Routing > OSPF > Add
LABEL DESCRIPTION
Area ID Type the unique, 32-bit identifier for the area in IP address format.
Type Select the type of OSPF area.
Normal - This area is a normal area. It has routing information about the OSPF AS and
about networks outside the OSPF AS.
Stub - This area is an stub area. It has routing information about the OSPF AS but not
about networks outside the OSPF AS. It depends on a default route to send information
outside the OSPF AS.
NSSA - This area is a Not So Stubby Area (NSSA), per RFC 1587. It has routing
information about the OSPF AS and networks that are outside the OSPF AS and are
directly connected to the NSSA. It does not have information about other networks
outside the OSPF AS.
Authentication Select the default authentication method used in the area. This authentication protects
the integrity, but not the confidentiality, of routing updates.
None uses no authentication.
Text uses a plain text password that is sent over the network (not very secure).
MD5 uses an MD5 password and authentication ID (most secure).
Text Authentication
Key
This field is available if the Authentication is Text. Type the password for text
authentication. The key can consist of alphanumeric characters and the underscore,
and it can be up to 16 characters long.
MD5 Authentication
ID
This field is available if the Authentication is MD5. Type the default ID for MD5
authentication in the area. The ID can be between 1 and 255.
MD5 Authentication
Key
This field is available if the Authentication is MD5. Type the default password for MD5
authentication in the area. The password can consist of alphanumeric characters and
the underscore, and it can be up to 16 characters long.
Virtual Link This section is displayed if the Type is Normal. Create a virtual link if you want to
connect a different area (that does not have a direct connection to the backbone) to
the backbone. You should set up the virtual link on the ABR that is connected to the
other area and on the ABR that is connected to the backbone.
Add Click this to create a new virtual link.
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
246
10.7.3 Virtual Link Add/Edit Screen
The Virtual Link Add/Edit screen allows you to create a new virtual link or edit an existing one.
When the OSPF add or edit screen (see Section 10.7.2 on page 244) has the Type set to Normal, a
Virtual Link table displays. Click either the Add icon or an entry and the Edit icon to display a
screen like the following.
Figure 163 Configuration > Network > Routing > OSPF > Add > Add
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to remove
it before doing so.
# This field is a sequential value, and it is not associated with a specific area.
Peer Router ID This is the 32-bit ID (in IP address format) of the other ABR in the virtual link.
Authentication This is the authentication method the virtual link uses. This authentication protects the
integrity, but not the confidentiality, of routing updates.
None uses no authentication.
Text uses a plain text password that is sent over the network (not very secure). Hover
your cursor over this label to display the password.
MD5 uses an MD5 password and authentication ID (most secure). Hover your cursor
over this label to display the authentication ID and key.
Same as Area has the virtual link also use the Authentication settings above.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 99 Configuration > Network > Routing > OSPF > Add (continued)
LABEL DESCRIPTION
Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
247
The following table describes the labels in this screen.
10.8 Routing Protocol Technical Reference
Here is more detailed information about RIP and OSPF.
Authentication Types
Authentication is used to guarantee the integrity, but not the confidentiality, of routing updates. The
transmitting router uses its key to encrypt the original message into a smaller message, and the
smaller message is transmitted with the original message. The receiving router uses its key to
encrypt the received message and then verifies that it matches the smaller message sent with it. If
the received message is verified, then the receiving router accepts the updated routing information.
The transmitting and receiving routers must have the same key.
The USG supports three types of authentication for RIP and OSPF routing protocols:
•None - no authentication is used.
•Text – authentication using a plain text password, and the (unencrypted) password is sent over
the network. This method is usually used temporarily to prevent network problems.
•MD5 – authentication using an MD5 password and authentication ID.
MD5 is an authentication method that produces a 128-bit checksum, called a message-digest, for
each packet. It also includes an authentication ID, which can be set to any value between 1 and
255. The USG only accepts packets if these conditions are satisfied.
• The packet’s authentication ID is the same as the authentication ID of the interface that received
it.
Table 100 Configuration > Network > Routing > OSPF > Add > Add
LABEL DESCRIPTION
Peer Router ID Enter the 32-bit ID (in IP address format) of the other ABR in the virtual link.
Authentication Select the authentication method the virtual link uses. This authentication protects the
integrity, but not the confidentiality, of routing updates.
None uses no authentication.
Text uses a plain text password that is sent over the network (not very secure).
MD5 uses an MD5 password and authentication ID (most secure).
Same as Area has the virtual link also use the Authentication settings above.
Text Authentication
Key
This field is available if the Authentication is Text. Type the password for text
authentication. The key can consist of alphanumeric characters and the underscore,
and it can be up to 16 characters long.
MD5 Authentication
ID
This field is available if the Authentication is MD5. Type the default ID for MD5
authentication in the area. The ID can be between 1 and 255.
MD5 Authentication
Key
This field is available if the Authentication is MD5. Type the default password for
MD5 authentication in the area. The password can consist of alphanumeric characters
and the underscore, and it can be up to 16 characters long.
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.

Chapter 10 Routing
USG20(W)-VPN Series User’s Guide
248
• The packet’s message-digest is the same as the one the USG calculates using the MD5 password.
For RIP, authentication is not available in RIP version 1. In RIP version 2, you can only select one
authentication type for all interfaces. For OSPF, the USG supports a default authentication type by
area. If you want to use this default in an interface or virtual link, you set the associated
Authentication Type field to Same as Area. As a result, you only have to update the
authentication information for the area to update the authentication type used by these interfaces
and virtual links. Alternatively, you can override the default in any interface or virtual link by
selecting a specific authentication method. Please see the respective interface sections for more
information.
USG20(W)-VPN Series User’s Guide
249
CHAPTER 11
DDNS
11.1 DDNS Overview
Dynamic DNS (DDNS) services let you use a domain name with a dynamic IP address.
11.1.1 What You Can Do in this Chapter
•Use the DDNS screen (see Section 11.2 on page 250) to view a list of the configured DDNS
domain names and their details.
•Use the DDNS Add/Edit screen (see Section 11.2.1 on page 251) to add a domain name to the
USG or to edit the configuration of an existing domain name.
11.1.2 What You Need to Know
DNS maps a domain name to a corresponding IP address and vice versa. Similarly, Dynamic DNS
(DDNS) maps a domain name to a dynamic IP address. As a result, anyone can use the domain
name to contact you (in NetMeeting, CU-SeeMe, etc.) or to access your FTP server or Web site,
regardless of the current (dynamic) IP address.
Note: You must have a public WAN IP address to use Dynamic DNS.
You must set up a dynamic DNS account with a supported DNS service provider before you can use
Dynamic DNS services with the USG. When registration is complete, the DNS service provider gives
you a password or key. At the time of writing, the USG supports the following DNS service
providers. See the listed websites for details about the DNS services offered by each.
Note: Record your DDNS account’s user name, password, and domain name to use to
configure the USG.
After you configure the USG, it automatically sends updated IP addresses to the DDNS service
provider, which helps redirect traffic accordingly.
Table 101 DDNS Service Providers
PROVIDER SERVICE TYPES SUPPORTED WEBSITE
DynDNS Dynamic DNS, Static DNS, and Custom DNS www.dyndns.com
Dynu Basic, Premium www.dynu.com
No-IP No-IP www.no-ip.com
Peanut Hull Peanut Hull www.oray.cn
3322 3322 Dynamic DNS, 3322 Static DNS www.3322.org
Selfhost Selfhost selfhost.de
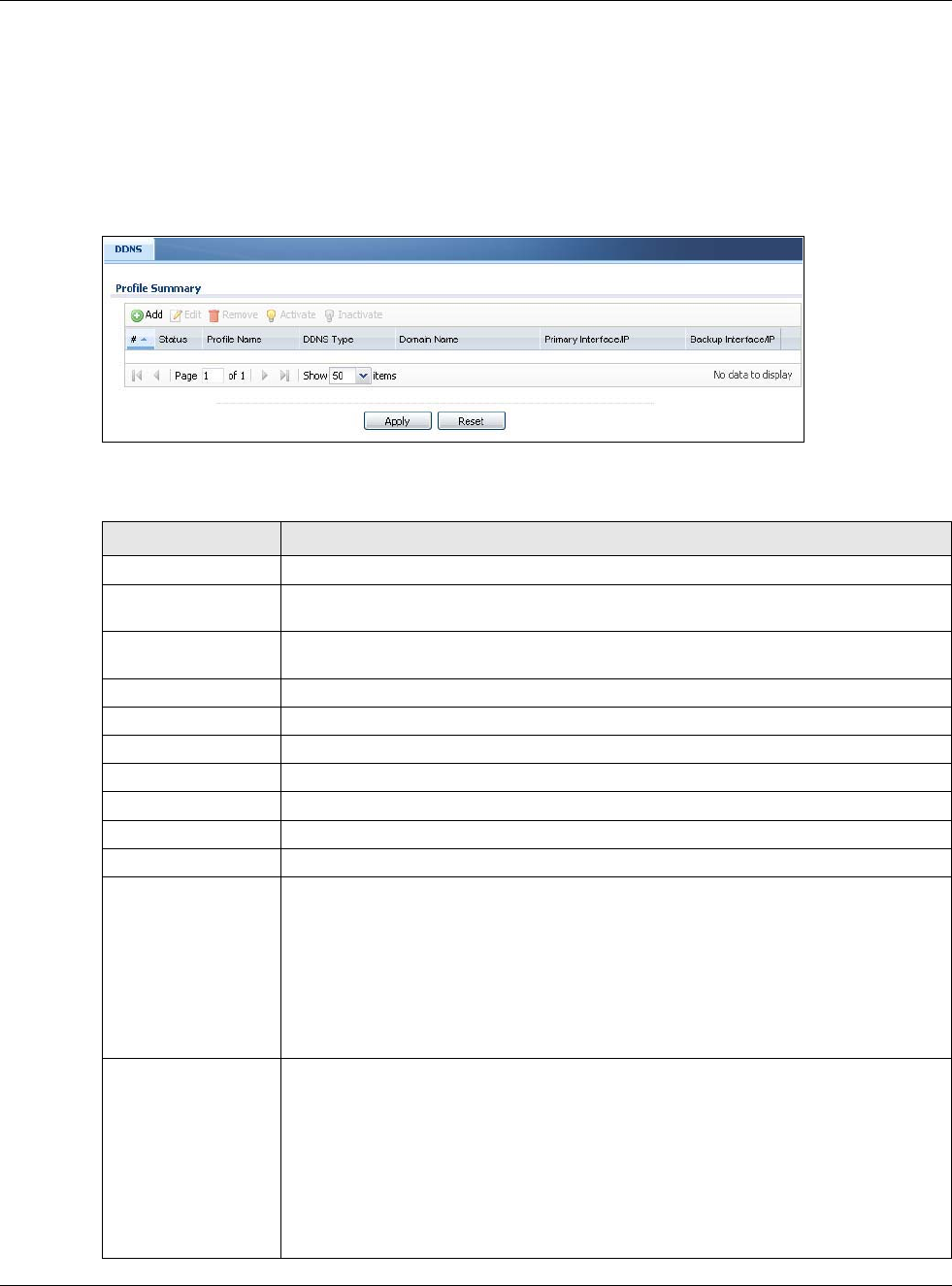
Chapter 11 DDNS
USG20(W)-VPN Series User’s Guide
250
11.2 The DDNS Screen
The DDNS screen provides a summary of all DDNS domain names and their configuration. In
addition, this screen allows you to add new domain names, edit the configuration for existing
domain names, and delete domain names. Click Configuration > Network > DDNS to open the
following screen.
Figure 164 Configuration > Network > DDNS
The following table describes the labels in this screen.
Table 102 Configuration > Network > DDNS
LABEL DESCRIPTION
Add Click this to create a new entry.
Edit Double-click an entry or select it and click Edit to open a screen where you can modify
the entry’s settings.
Remove To remove an entry, select it and click Remove. The USG confirms you want to
remove it before doing so.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
#This is the number of an individual DDNS profile.
Status This icon is lit when the entry is active and dimmed when the entry is inactive.
Profile Name This field displays the descriptive profile name for this entry.
DDNS Type This field displays which DDNS service you are using.
Domain Name This field displays each domain name the USG can route.
Primary Interface/IP This field displays the interface to use for updating the IP address mapped to the
domain name followed by how the USG determines the IP address for the domain
name.
from interface - The IP address comes from the specified interface.
auto detected -The DDNS server checks the source IP address of the packets from
the USG for the IP address to use for the domain name.
custom - The IP address is static.
Backup Interface/IP This field displays the alternate interface to use for updating the IP address mapped to
the domain name followed by how the USG determines the IP address for the domain
name. The USG uses the backup interface and IP address when the primary interface
is disabled, its link is down or its connectivity check fails.
from interface - The IP address comes from the specified interface.
auto detected -The DDNS server checks the source IP address of the packets from
the USG for the IP address to use for the domain name.
custom - The IP address is static.
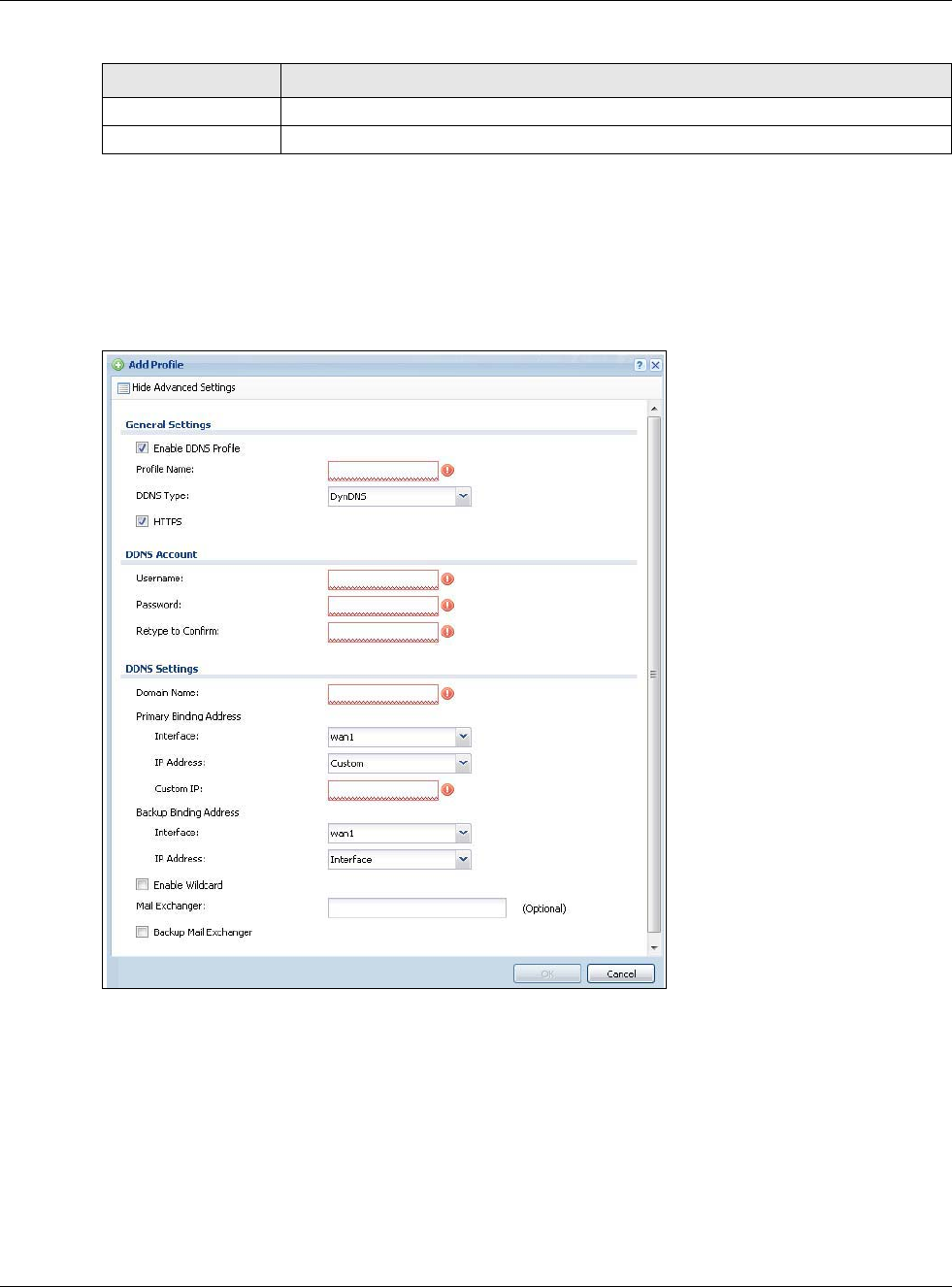
Chapter 11 DDNS
USG20(W)-VPN Series User’s Guide
251
11.2.1 The Dynamic DNS Add/Edit Screen
The DDNS Add/Edit screen allows you to add a domain name to the USG or to edit the
configuration of an existing domain name. Click Configuration > Network > DDNS and then an
Add or Edit icon to open this screen.
Figure 165 Configuration > Network > DDNS > Add
Apply Click this button to save your changes to the USG.
Reset Click this button to return the screen to its last-saved settings.
Table 102 Configuration > Network > DDNS (continued)
LABEL DESCRIPTION
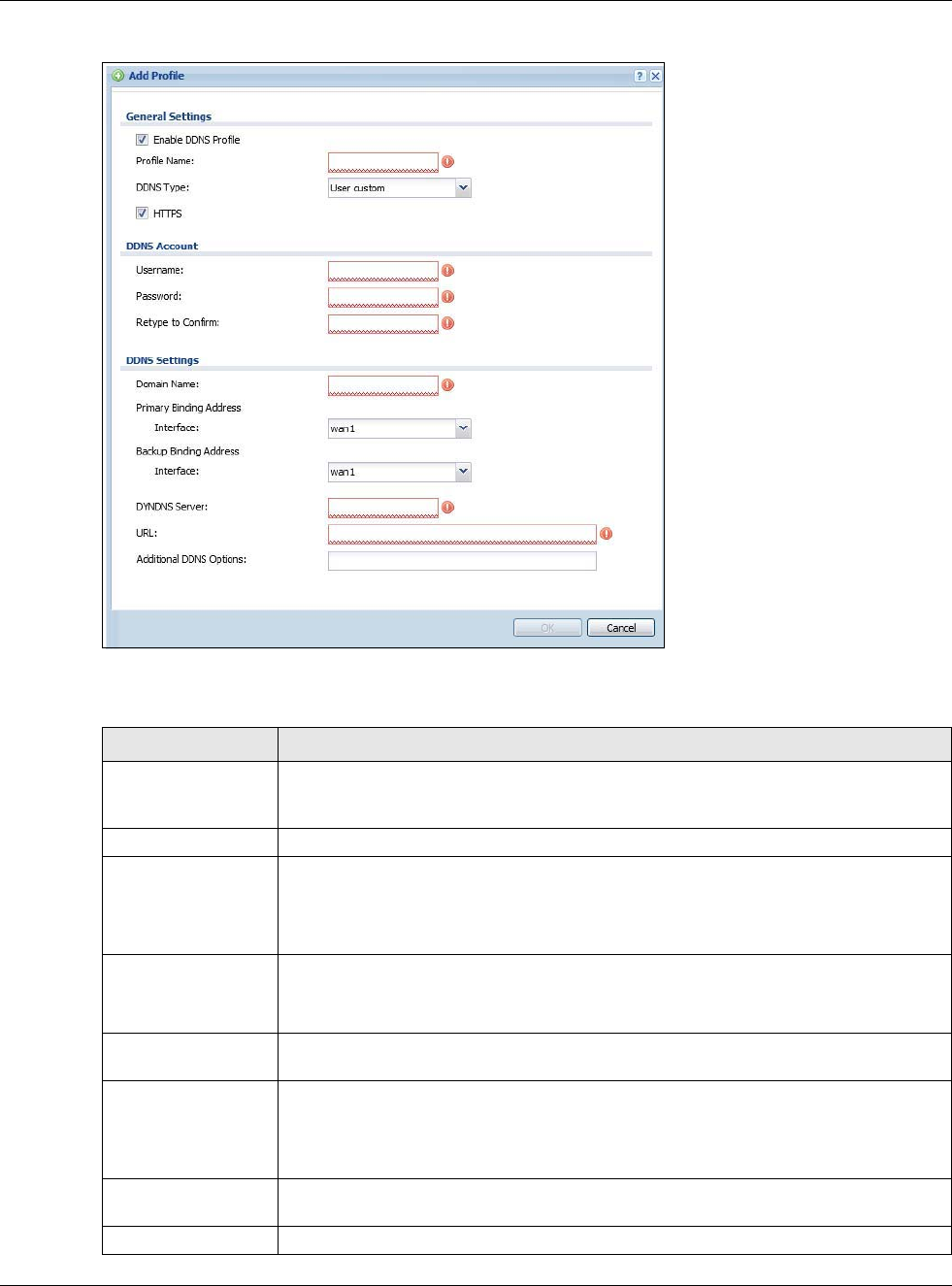
Chapter 11 DDNS
USG20(W)-VPN Series User’s Guide
252
Figure 166 Configuration > Network > DDNS > Add - Custom
The following table describes the labels in this screen.
Table 103 Configuration > Network > DDNS > Add
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Enable DDNS Profile Select this check box to use this DDNS entry.
Profile Name When you are adding a DDNS entry, type a descriptive name for this DDNS entry in the
USG. You may use 1-31 alphanumeric characters, underscores(_), or dashes (-), but
the first character cannot be a number. This value is case-sensitive.
This field is read-only when you are editing an entry.
DDNS Type Select the type of DDNS service you are using.
Select User custom to create your own DDNS service and configure the DYNDNS
Server, URL, and Additional DDNS Options fields below.
HTTPS Select this to encrypt traffic using SSL (port 443), including traffic with username and
password, to the DDNS server. Not all DDNS providers support this option.
Username Type the user name used when you registered your domain name. You can use up to
31 alphanumeric characters and the underscore. Spaces are not allowed.
For a Dynu DDNS entry, this user name is the one you use for logging into the service,
not the name recorded in your personal information in the Dynu website.
Password Type the password provided by the DDNS provider. You can use up to 64 alphanumeric
characters and the underscore. Spaces are not allowed.
Retype to Confirm Type the password again to confirm it.
Chapter 11 DDNS
USG20(W)-VPN Series User’s Guide
253
DDNS Settings
Domain name Type the domain name you registered. You can use up to 255 characters.
Primary Binding
Address
Use these fields to set how the USG determines the IP address that is mapped to your
domain name in the DDNS server. The USG uses the Backup Binding Address if the
interface specified by these settings is not available.
Interface Select the interface to use for updating the IP address mapped to the domain name.
Select Any to let the domain name be used with any interface.
IP Address The options available in this field vary by DDNS provider.
Interface -The USG uses the IP address of the specified interface. This option appears
when you select a specific interface in the Primary Binding Address Interface field.
Auto - If the interface has a dynamic IP address, the DDNS server checks the source
IP address of the packets from the USG for the IP address to use for the domain name.
You may want to use this if there are one or more NAT routers between the USG and
the DDNS server.
Note: The USG may not determine the proper IP address if there is an HTTP proxy
server between the USG and the DDNS server.
Custom - If you have a static IP address, you can select this to use it for the domain
name. The USG still sends the static IP address to the DDNS server.
Custom IP This field is only available when the IP Address is Custom. Type the IP address to use
for the domain name.
Backup Binding
Address
Use these fields to set an alternate interface to map the domain name to when the
interface specified by the Primary Binding Interface settings is not available.
Interface Select the interface to use for updating the IP address mapped to the domain name.
Select Any to let the domain name be used with any interface. Select None to not use
a backup address.
IP Address The options available in this field vary by DDNS provider.
Interface -The USG uses the IP address of the specified interface. This option appears
when you select a specific interface in the Backup Binding Address Interface field.
Auto -The DDNS server checks the source IP address of the packets from the USG for
the IP address to use for the domain name. You may want to use this if there are one
or more NAT routers between the USG and the DDNS server.
Note: The USG may not determine the proper IP address if there is an HTTP proxy
server between the USG and the DDNS server.
Custom - If you have a static IP address, you can select this to use it for the domain
name. The USG still sends the static IP address to the DDNS server.
Custom IP This field is only available when the IP Address is Custom. Type the IP address to use
for the domain name.
Enable Wildcard This option is only available with a DynDNS account.
Enable the wildcard feature to alias subdomains to be aliased to the same IP address
as your (dynamic) domain name. This feature is useful if you want to be able to use,
for example, www.yourhost.dyndns.org and still reach your hostname.
Table 103 Configuration > Network > DDNS > Add (continued)
LABEL DESCRIPTION
Chapter 11 DDNS
USG20(W)-VPN Series User’s Guide
254
Mail Exchanger This option is only available with a DynDNS account.
DynDNS can route e-mail for your domain name to a mail server (called a mail
exchanger). For example, DynDNS routes e-mail for john-doe@yourhost.dyndns.org to
the host record specified as the mail exchanger.
If you are using this service, type the host record of your mail server here. Otherwise
leave the field blank.
See www.dyndns.org for more information about mail exchangers.
Backup Mail
Exchanger
This option is only available with a DynDNS account.
Select this check box if you are using DynDNS’s backup service for e-mail. With this
service, DynDNS holds onto your e-mail if your mail server is not available. Once your
mail server is available again, the DynDNS server delivers the mail to you. See
www.dyndns.org for more information about this service.
DYNDNS Server This field displays when you select User custom from the DDNS Type field above.
Type the IP address of the server that will host the DDSN service.
URL This field displays when you select User custom from the DDNS Type field above.
Type the URL that can be used to access the server that will host the DDSN service.
Additional DDNS
Options
This field displays when you select User custom from the DDNS Type field above.
These are the options supported at the time of writing:
• dyndns_system to specify the DYNDNS Server type - for example,
dyndns@dyndns.org
• ip_server_name which should be the URL to get the server’s public IP address - for
example, http://myip.easylife.tw/
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving.
Table 103 Configuration > Network > DDNS > Add (continued)
LABEL DESCRIPTION